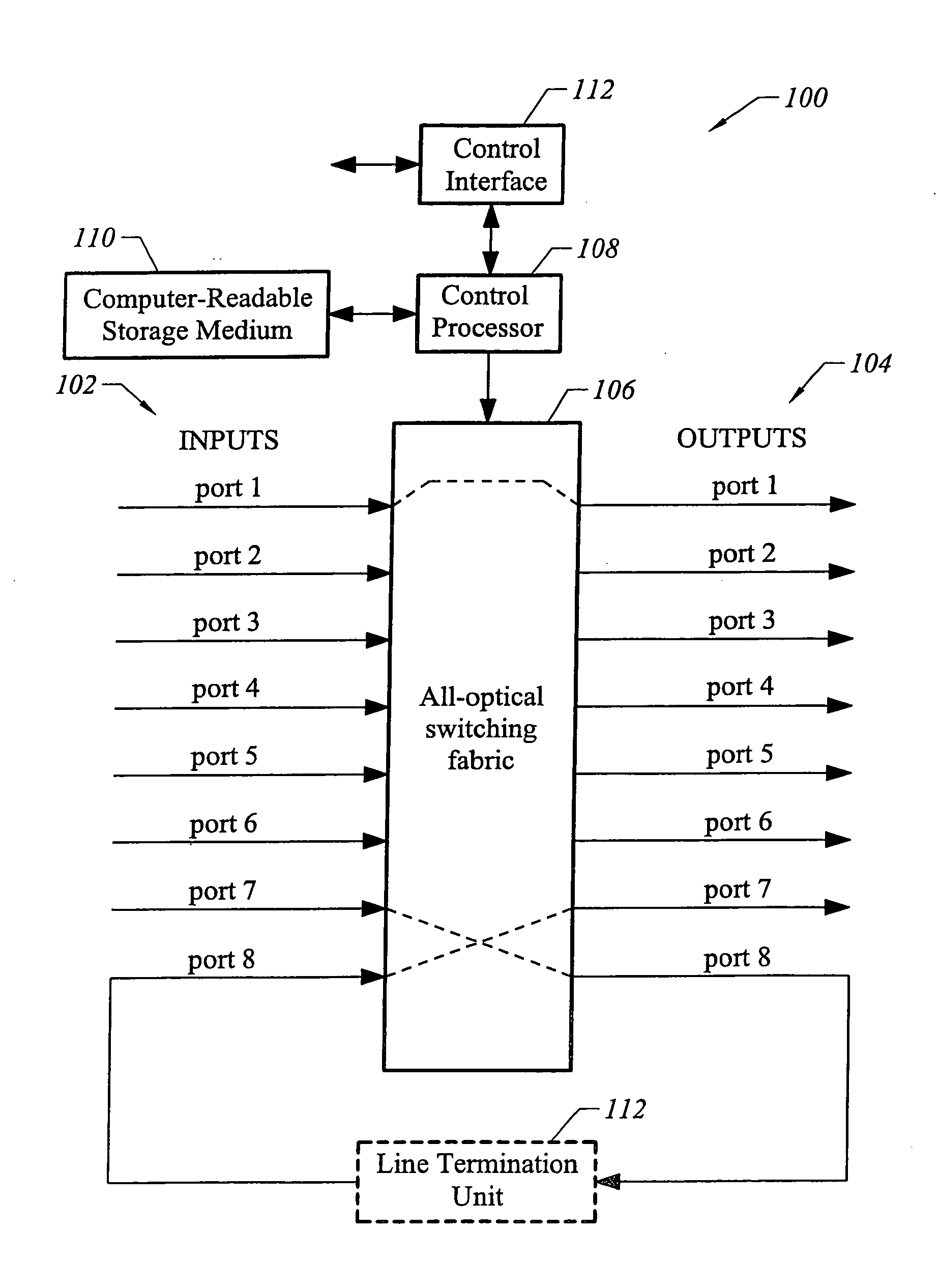
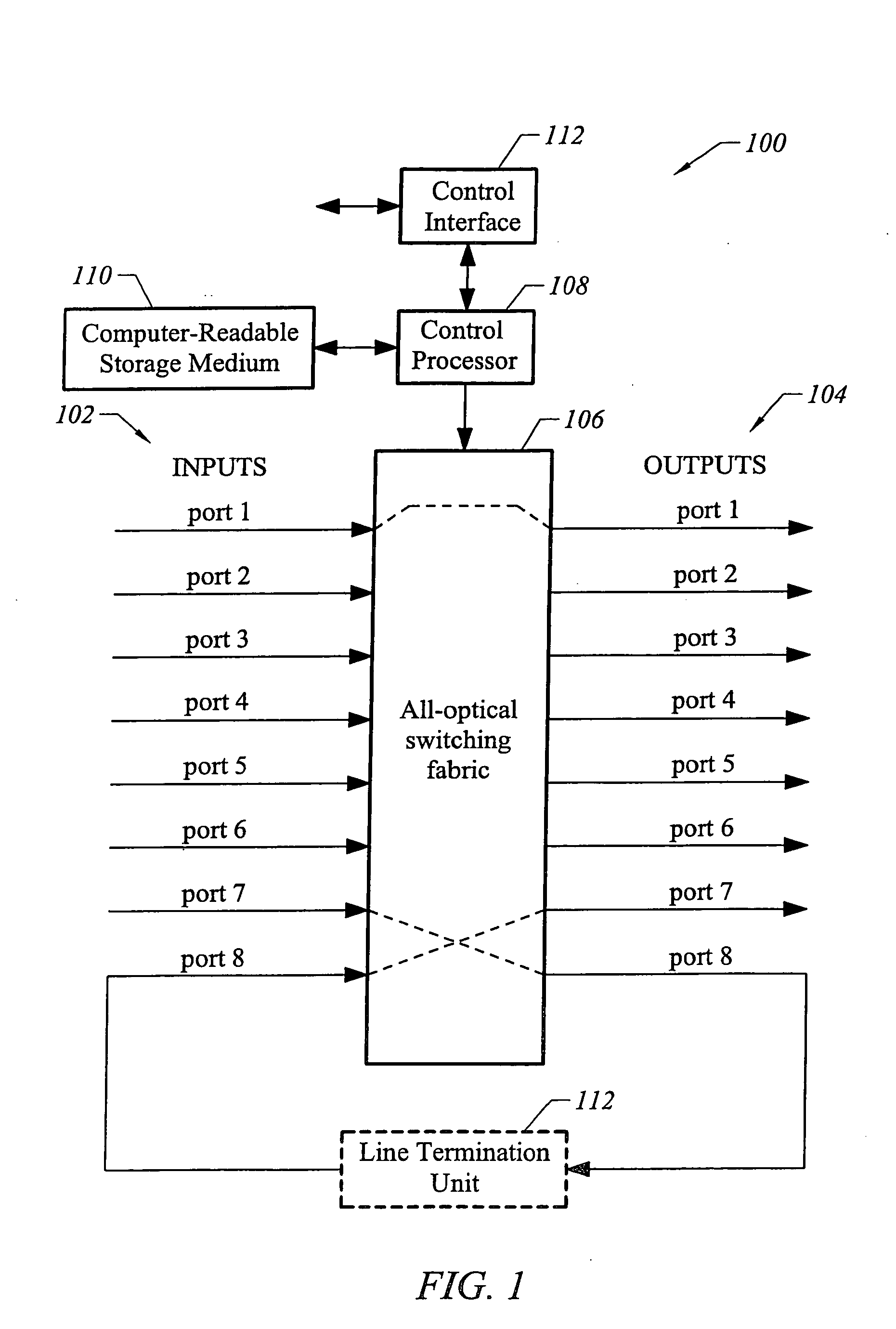
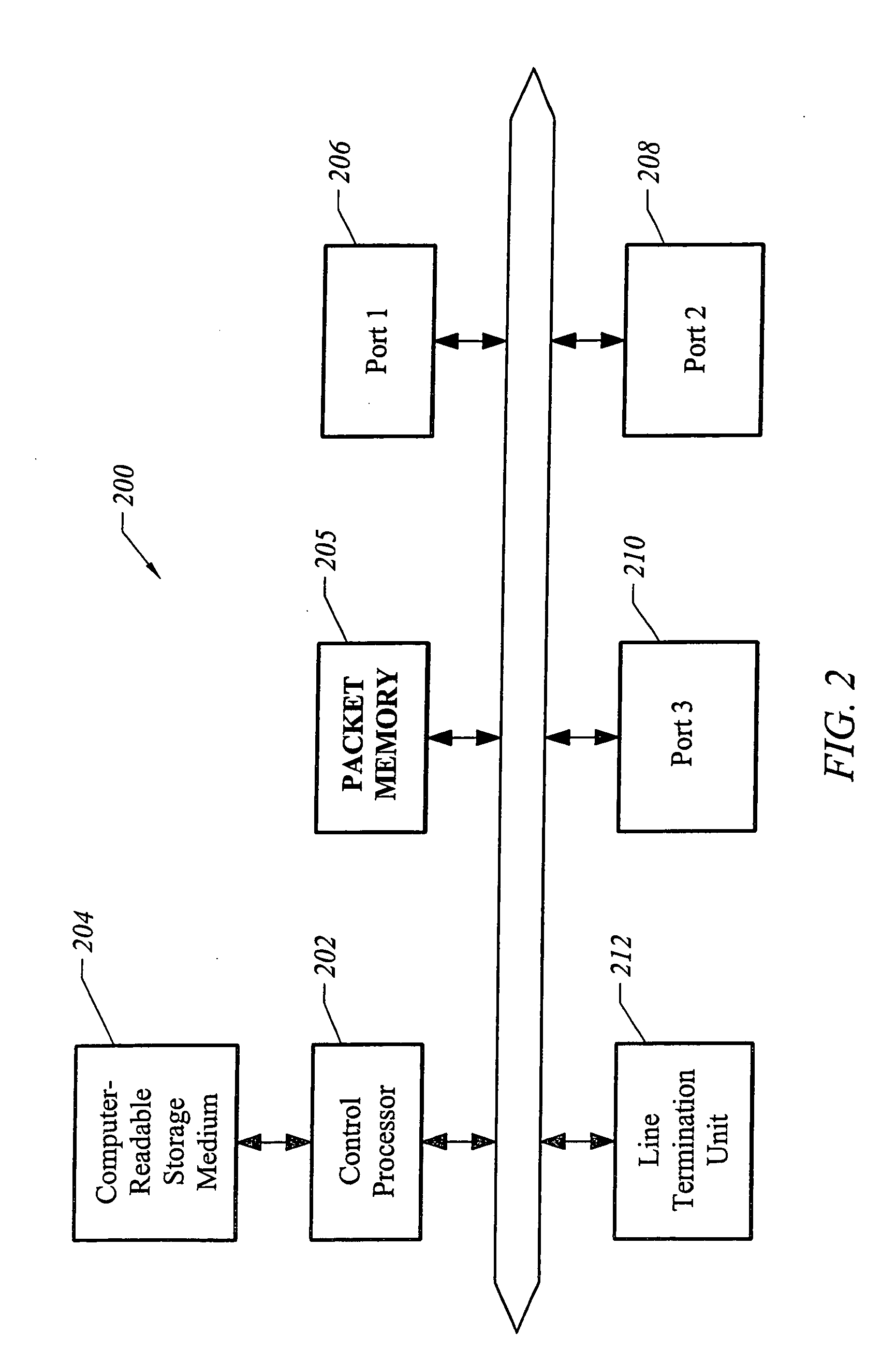
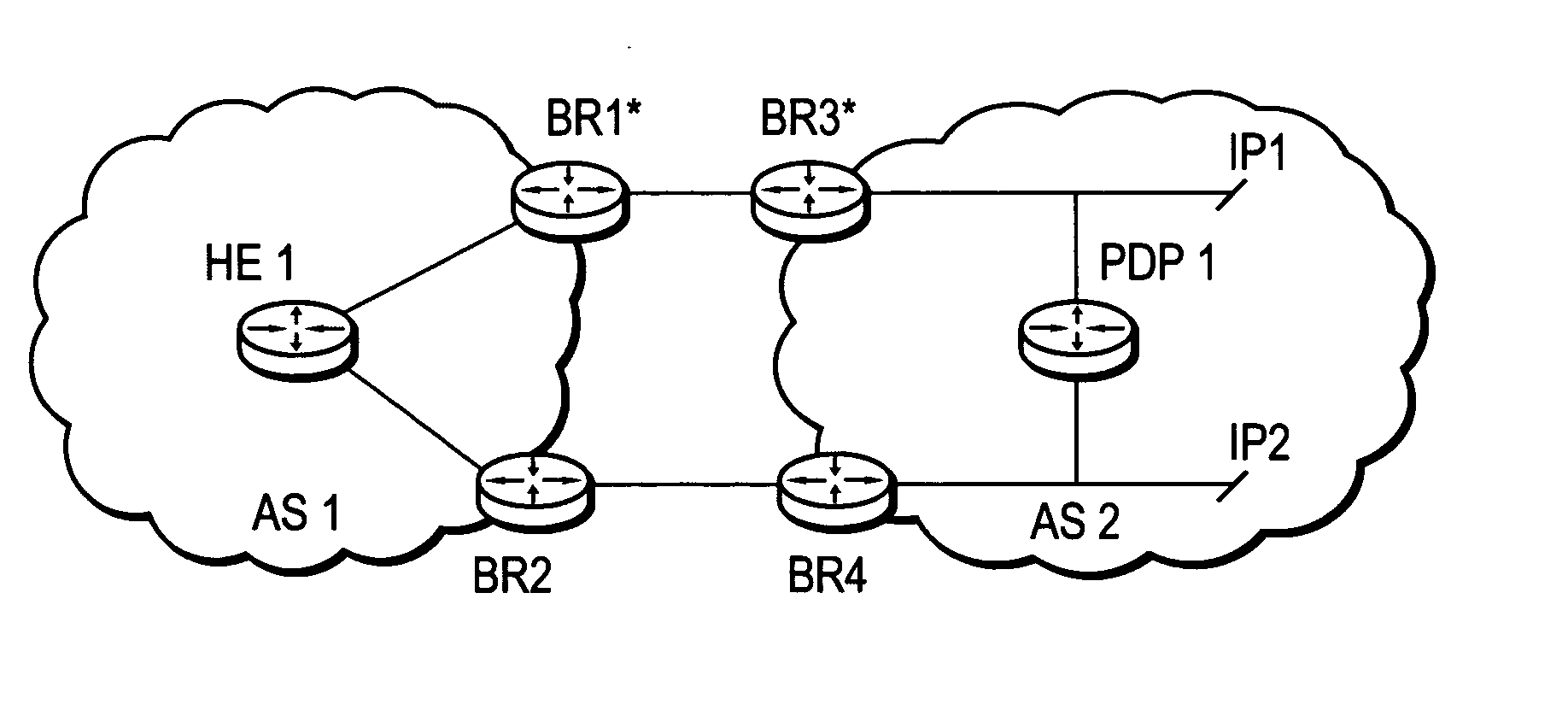
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
252 results about "Verification procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Verification and validation are independent procedures that are used together for checking that a product, service, or system meets requirements and specifications and that it fulfills its intended purpose. These are critical components of a quality management system such as ISO 9000.
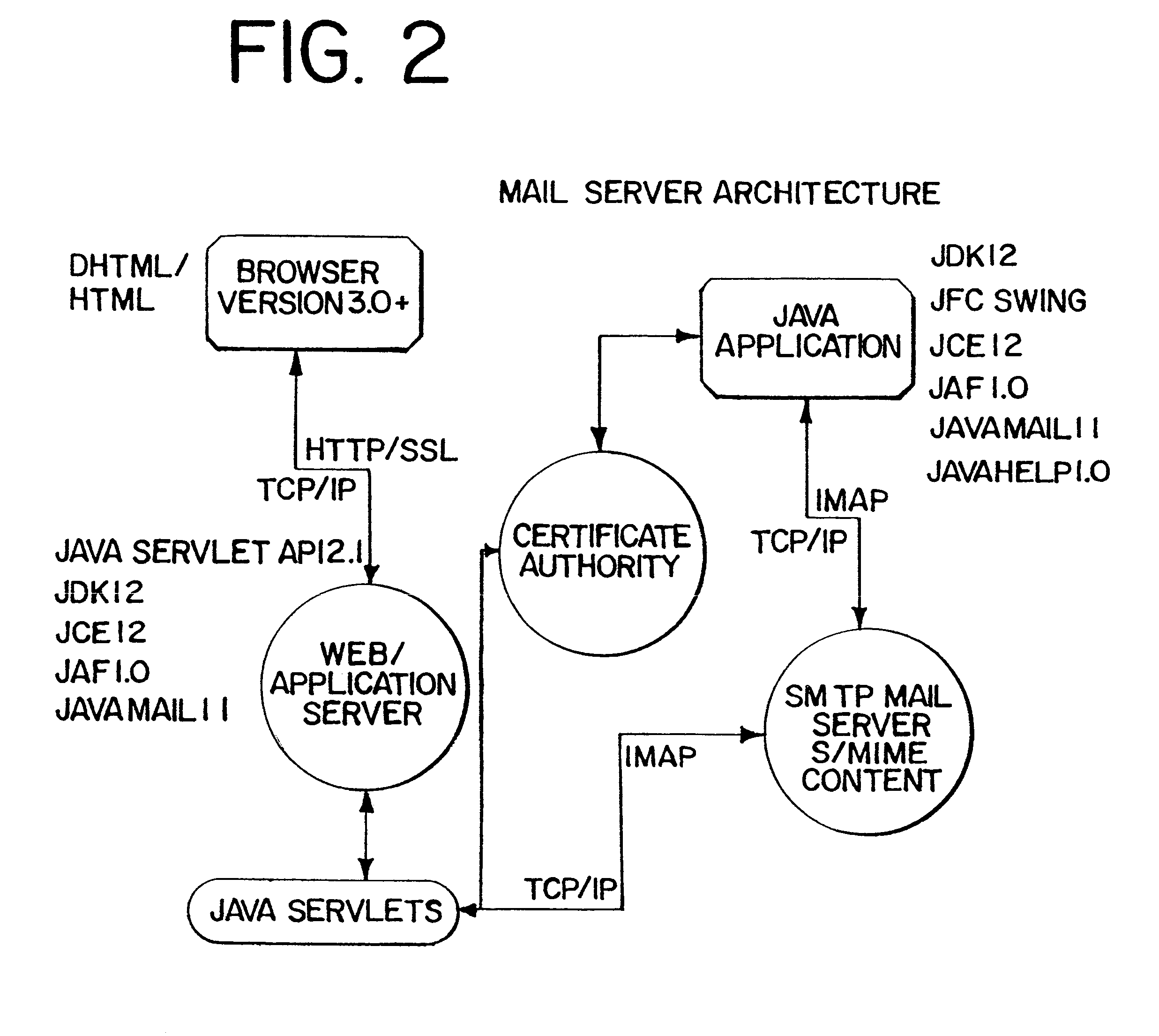
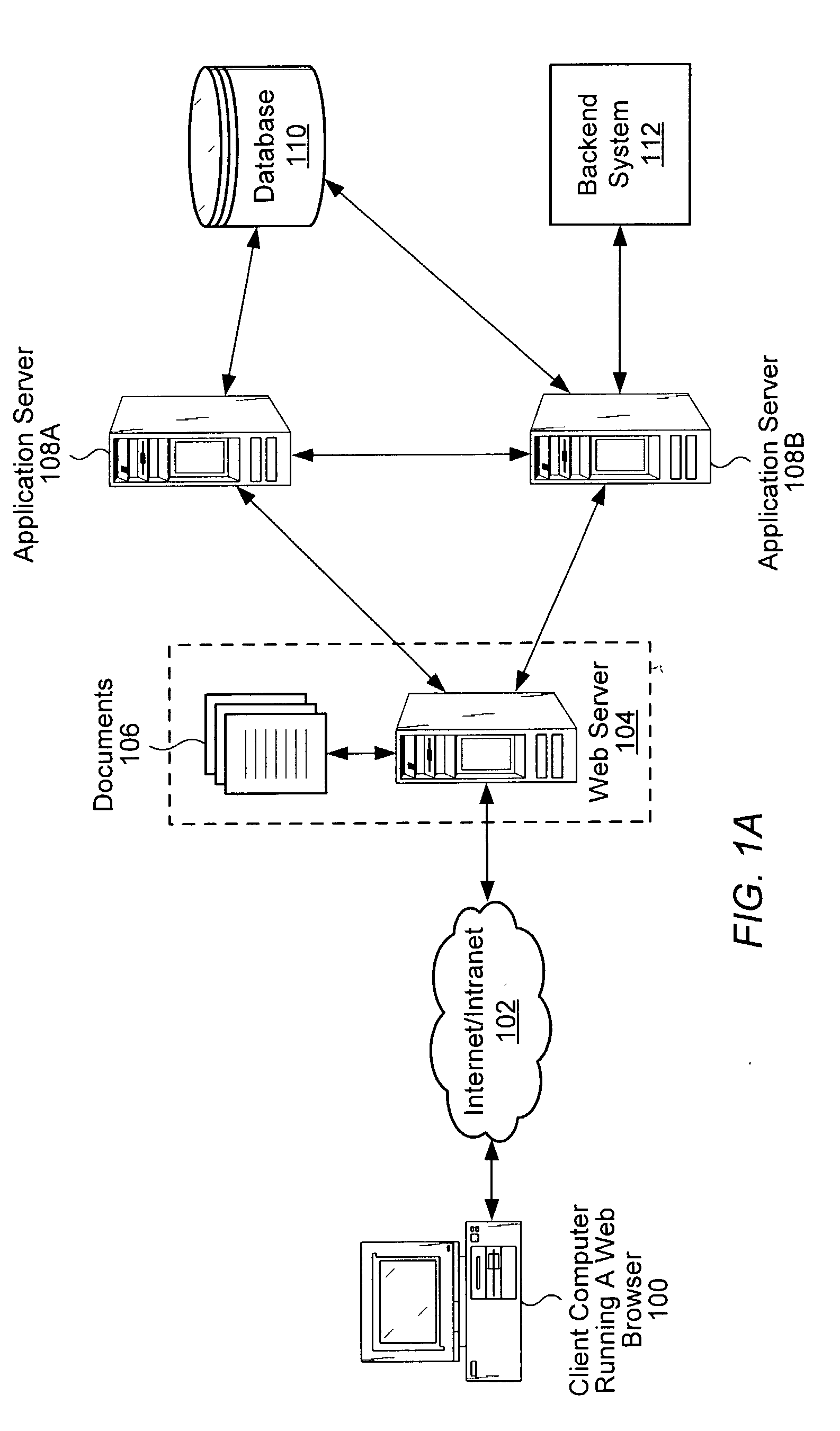
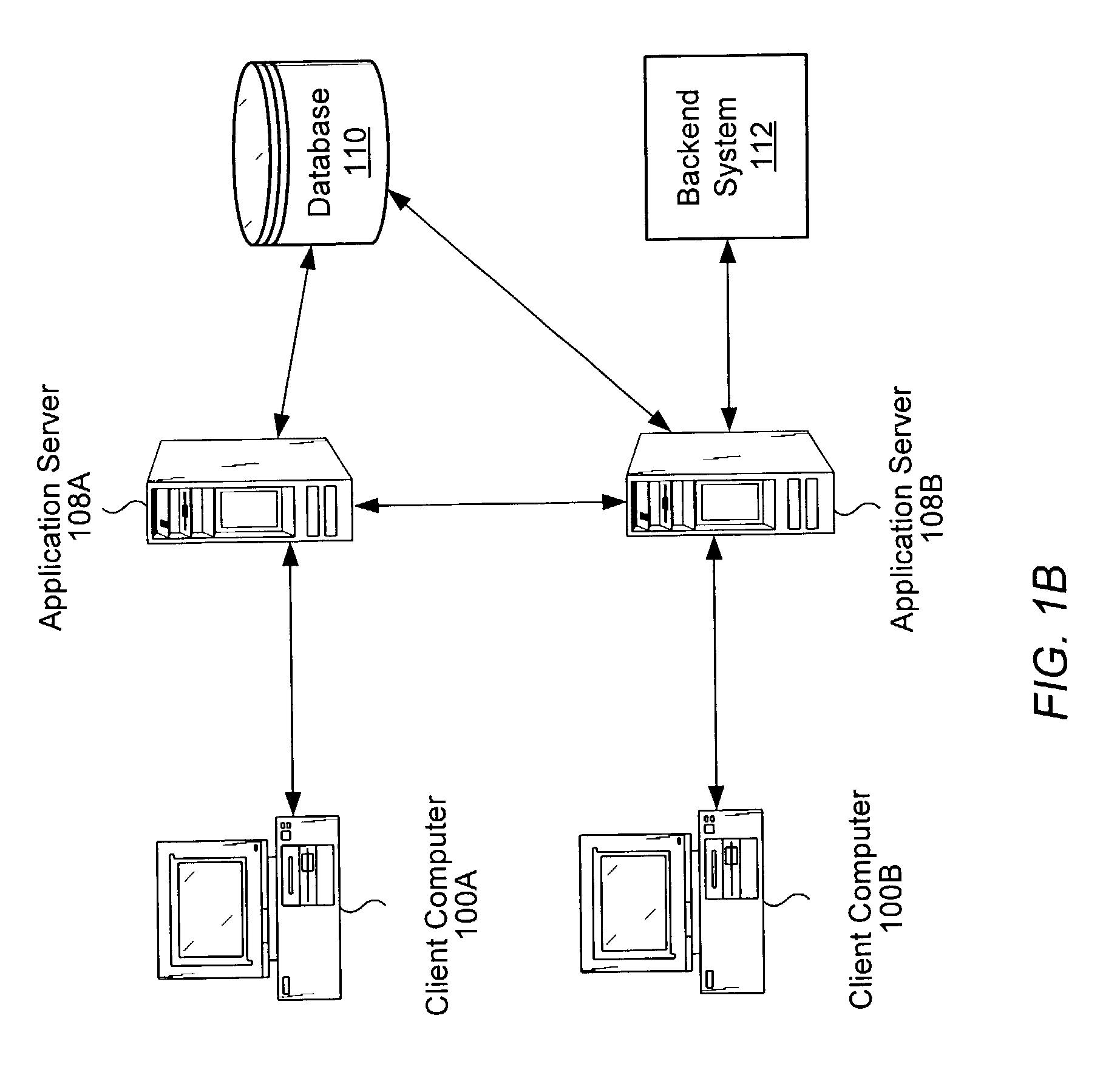
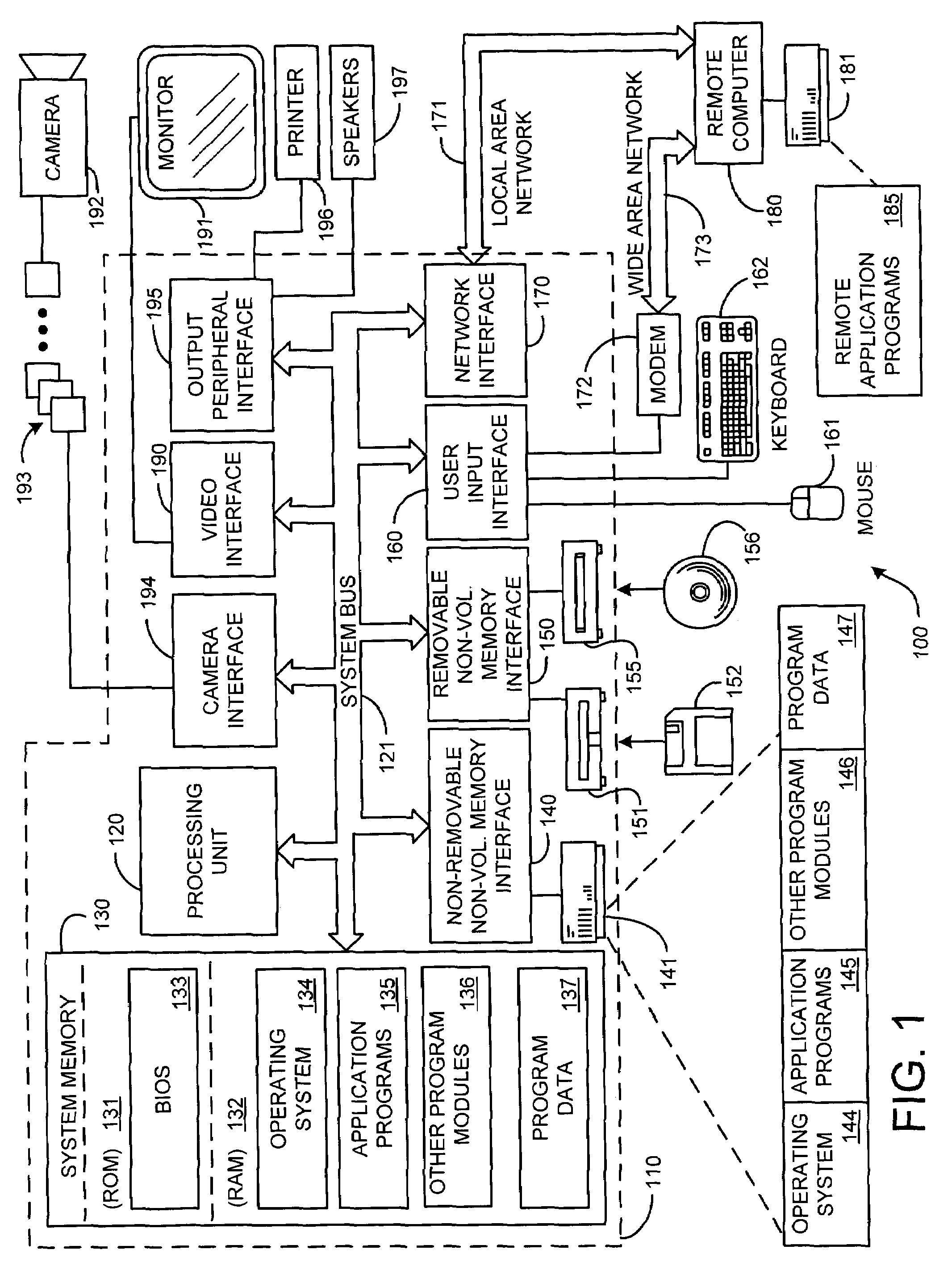
Interoperable full-featured web-based and client-side e-mail system
InactiveUS6356937B1More secure log-inMultiple digital computer combinationsOffice automationApplication softwareProprietary software
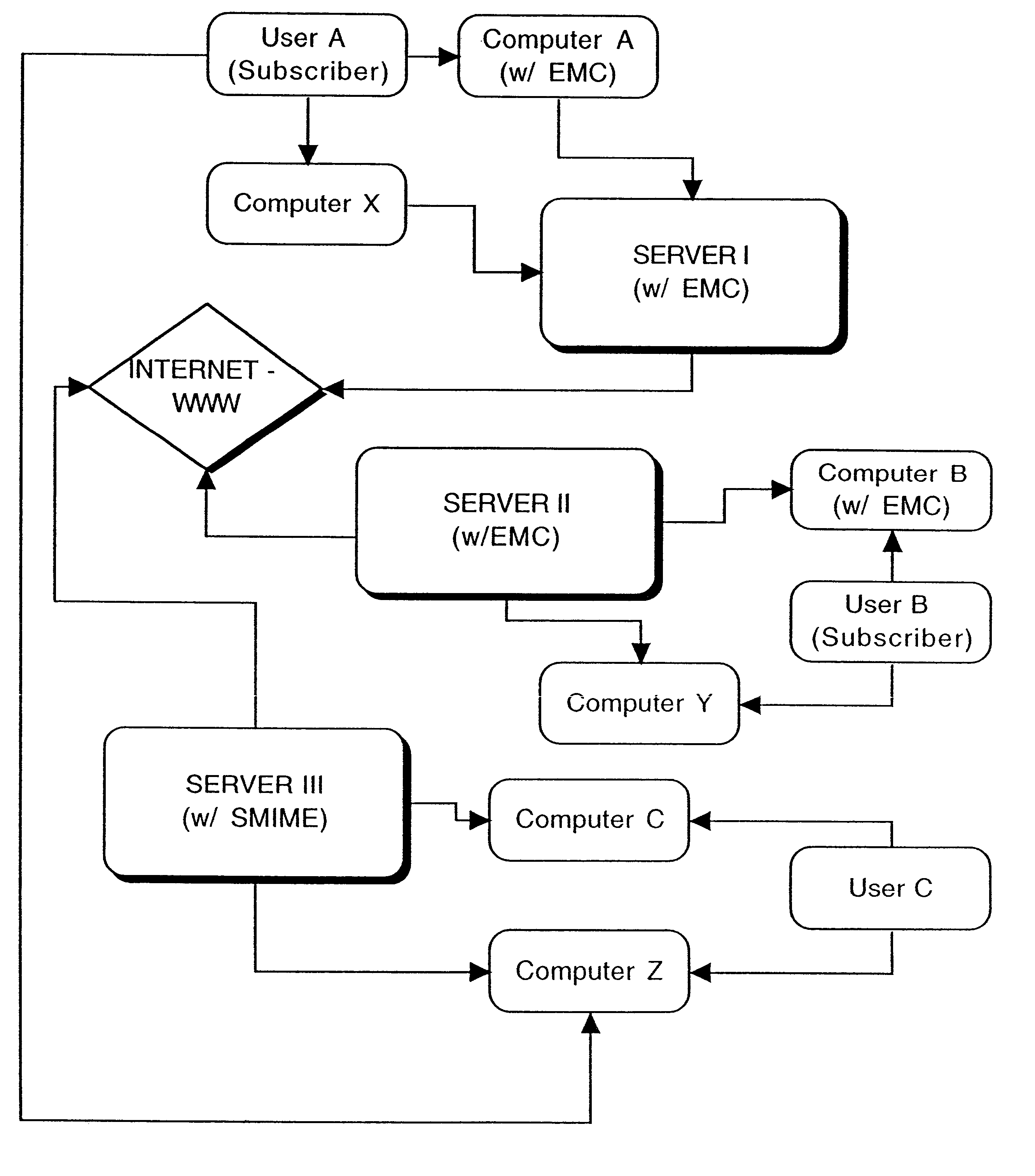
A full-featured e-mail system is used in both Internet-based and client-side (personal computer) forms. In each form, either basic e-mail service is provided to system subscribers or a secure, premium service with authentication, concealment, integrity, and non-repudiation functions for electronic messaging services is provided. In either form and at either level of service, subscribers can work off-line on their own computers with proprietary software loaded or, alternatively, on-line on any computer with an Internet connection. The system is interoperable, to preserve security, with all S / MIME compliant software applications, even for those users not subscribing to a service implementing the disclosed system. Digital certificates can be provided as a security service of the disclosed system, rather than requiring a second source with separate verification procedures. As additional optional features, the subscriber can control compression of outgoing attachment files, rather than having that function absent or operate in some automatic way. Decompression of such file attachments when received occurs automatically for subscribers, without having to invoke a different program or system. Interactive help features, book hierarchy uniformity for messages, accounts, certificates, virus warnings, and dual naming capability are also provided and available to subscribers in both the Web-based and the client-side application forms disclosed herein, and in both basic and premium service levels.
Owner:MEC MANAGEMENT LLC
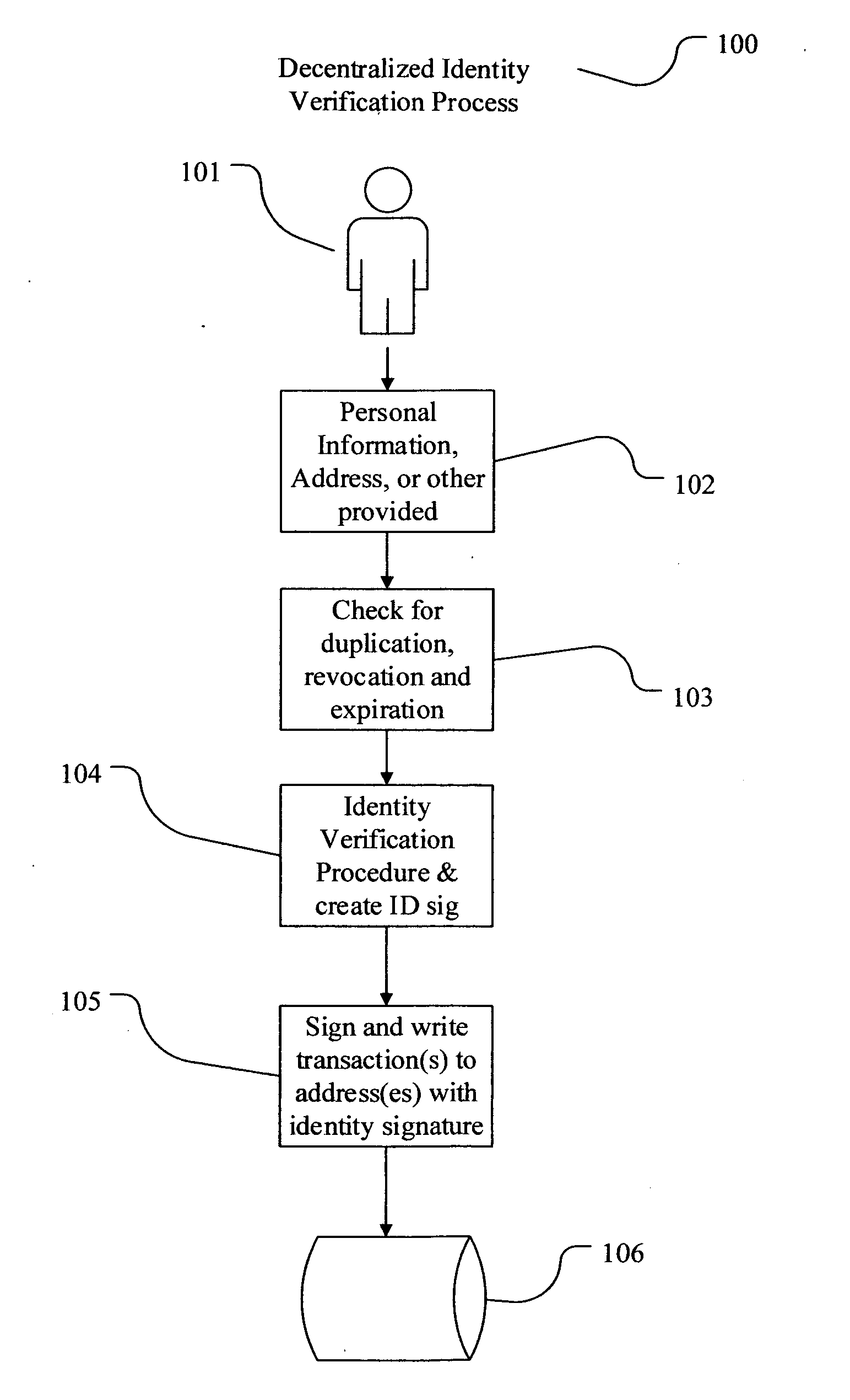
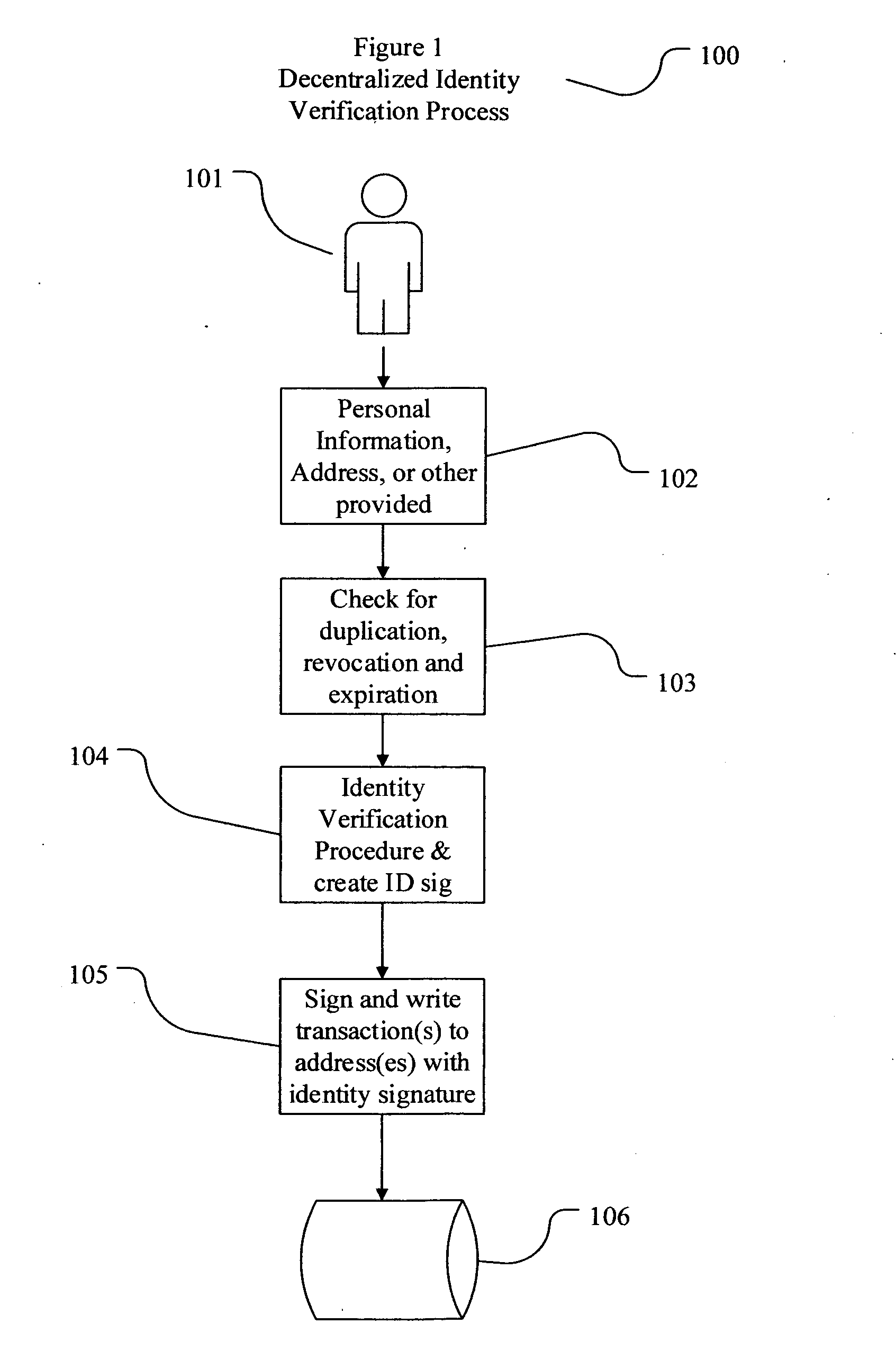
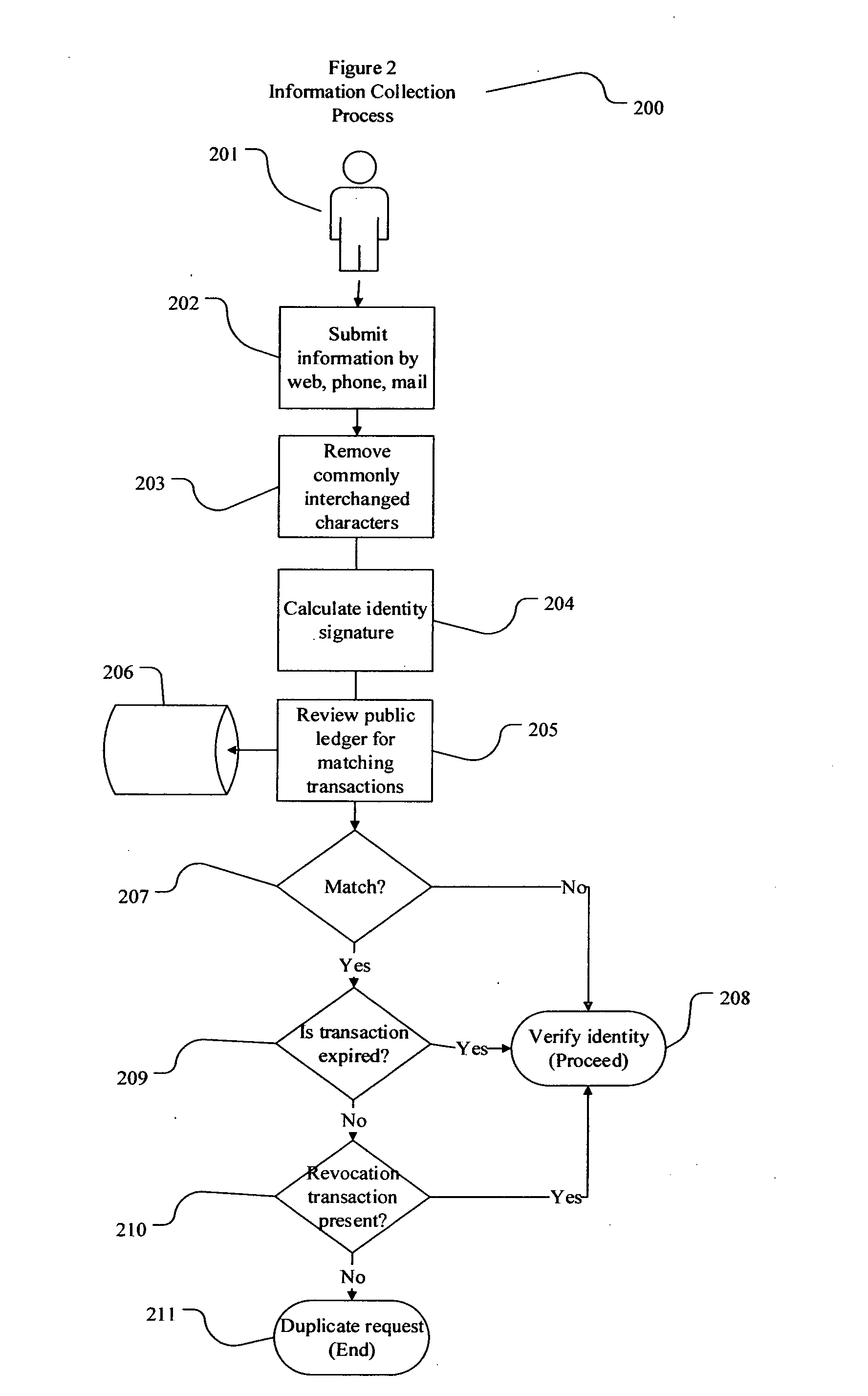
Decentralized identity verification systems and methods
InactiveUS20150356523A1Cryptography processingUser identity/authority verificationRegulatory authorityFinancial transaction
The present invention involves systems and methods that allow participants in cryptocurrency networks to exchange cryptocurrency for traditional currency legally and safely without requiring the use of a traditional exchange or online brokerage as a fiduciary. The invention accomplishes this through the use of a decentralized identity verification protocol that allows a service provider to verify the identity of a participant and then publish an identity signature on the participant's cryptocurrency address or addresses. The invention enables full compliance with Country specific customer identification program and anti-money laundering requirements, and maintains the ability to independently satisfy requests for information or data retention requirements if requested by legally authorized parties, but does not require that the participant store the private keys or access controls to their cryptocurrency on an exchange or brokerage service.The invention serves to verify a participant's identity in full compliance with US Bank Secrecy and Patriot Act provisions or similar regulations where identification may be achieved through non-documentary or documentary identity verification procedures. After passing the applicable verification procedure, the service provider stamps the participant's cryptocurrency address with a transaction containing an identity signature. This identity signature within the transaction consists of a public indicator of the participant's Country and subdivision, a compliance level code, an ID type indicator, and an identity hash. The identity hash is created from the digests of cryptographic hash functions where the participant's personal information is used as an input. The service provider signs the transaction with their authorized private key that corresponds to their publicly accessible public key. This serves as a publicly verifiable confirmation that the identity associated with the address in question was validated by the service provider authorized to act on behalf of the regulatory authority.The participant may then purchase and sell cryptographic currency from and to a third party exchange or brokerage service legally and safely when using their verified cryptocurrency address. This is because the third party is able to confirm compliance by openly referencing and verifying the identity verification transaction present on the address. Subsequent transactions where the third party sells or purchases cryptocurrency for the verified participant are similarly stamped with a transaction conforming to the identity verification protocol. This allows the third party interacting with the verified participant's address to observe any regulations limiting the amount or frequency of transactions over a variable period of time. It follows that this address could be used with any third party or participant in the cryptocurrency network that observes the decentralized identity verification protocol, all without requiring the third party or participant to collect and verify personal information redundantly. The ability to verify an identity remotely also eliminates the need for the third party to act as a fiduciary holding the private keys or access controls to the verified address. Lawful requests for information by authorized authorities are served to the service provider as digitally signed transactions that may then be linked to the participant's identity and transactions, allowing the protocol to observe subpoenas or similar lawful requests for information. The encrypted personal information may be held in escrow by the service provider indexed to the verified cryptocurrency address for such purposes. An alternate embodiment would store the encrypted personal information in a decentralized network of other participants, with the information accessible for retrieval using the public key of the verified cryptocurrency address and decryption using the corresponding private key, decentralizing the process entirely except for the identity verification step.
Owner:CHAINID
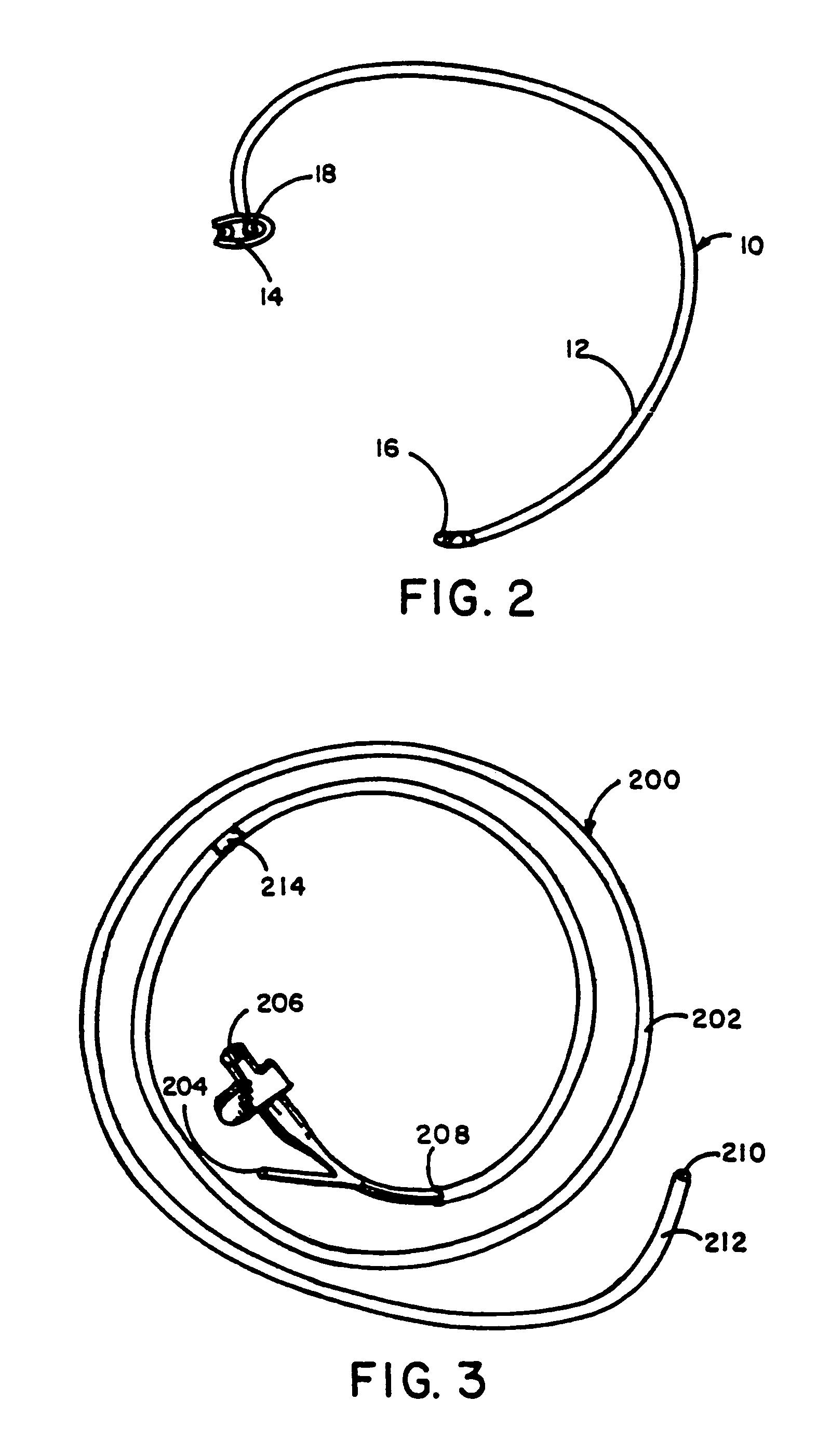
Catheter apparatus and methodology for generating a fistula on-demand between closely associated blood vessels at a pre-chosen anatomic site in-vivo
The present invention provides catheter apparatus and catheterization methodology for generating an arteriovenous fistula or a veno-venous fistula on-demand between closely associated blood vessels and at a chosen anatomic site in-vivo. The catheter apparatus is preferably employed in pairs, each catheter of the pair being suitable for percutaneous introduction into and extension through a blood vessel. The catheterization methodology employs the catheter apparatus preferably in conjunction with conventional radiological techniques in order to place, verify, and confirm a proper alignment, orientation, and positioning for the catheters in-vivo prior to activating the perforation means for generating a fistula. The invention permits the generation of arteriovenous fistulae and veno-venous fistulae anatomically anywhere in the vascular system of a patient; nevertheless, the invention is most desirably employed in the peripheral vascular system as exists in the extremities of the body to aid in the treatment of the patient under a variety of different medical ailments and pathologies.
Owner:MEDTRONIC VASCULAR INC
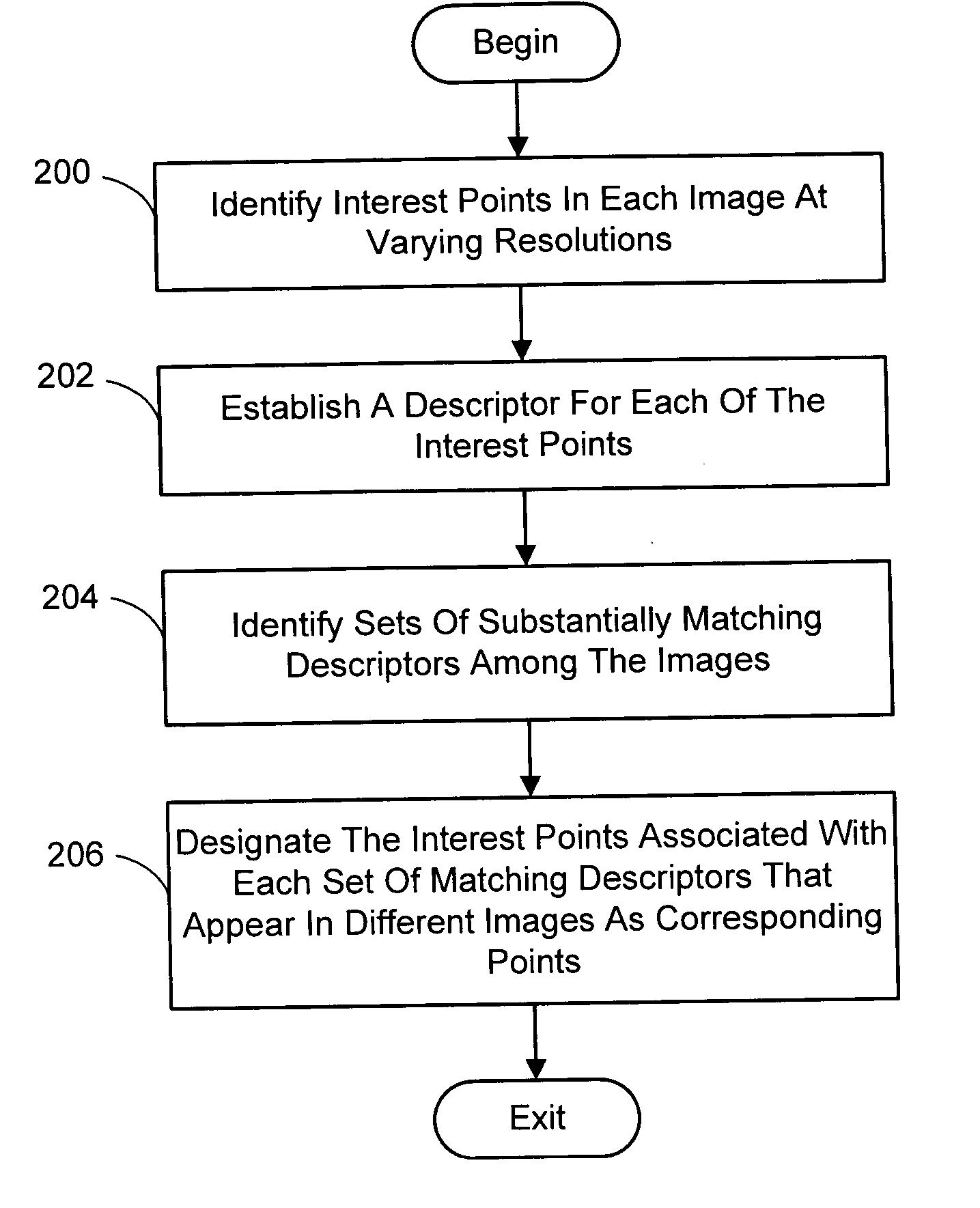
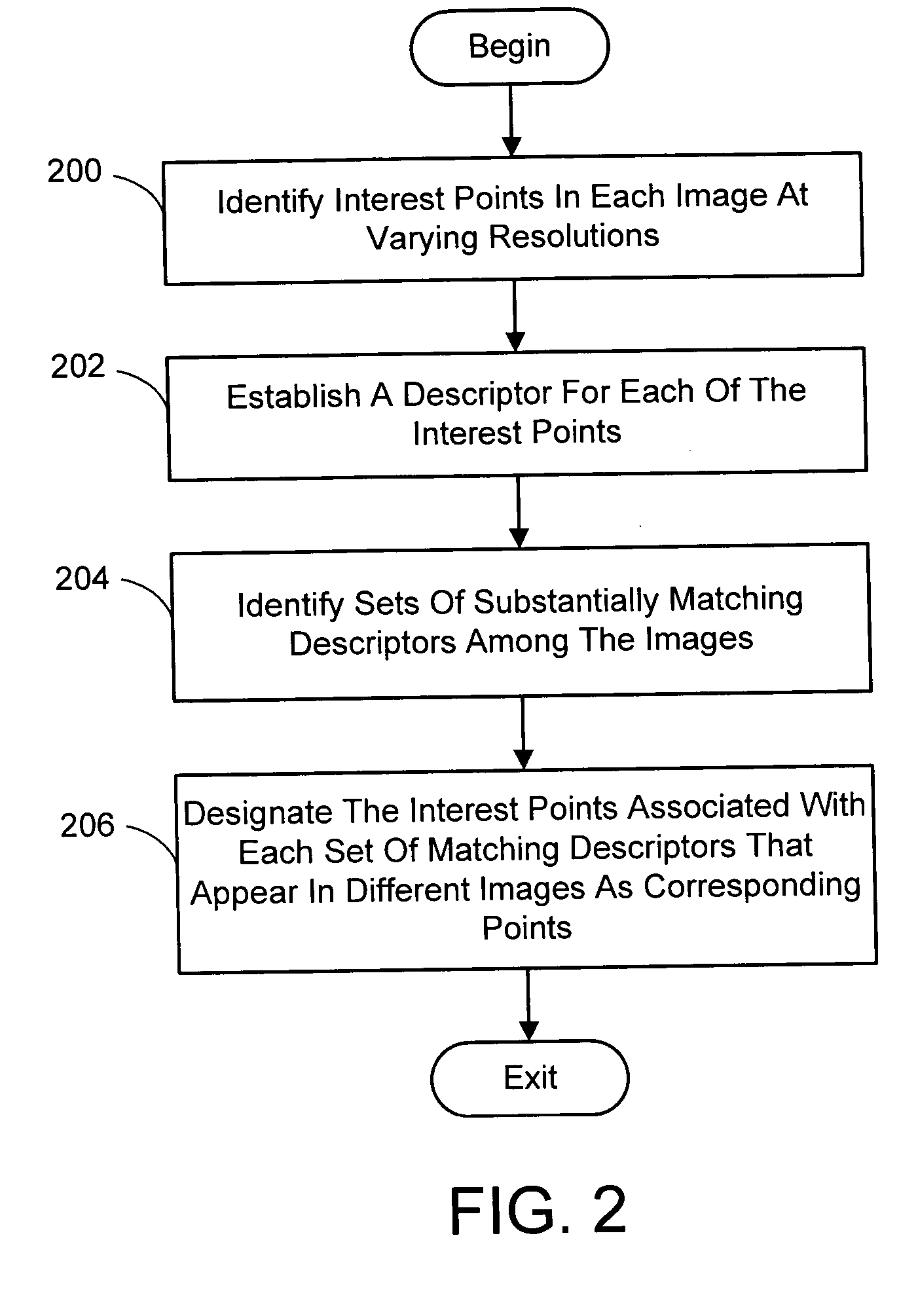
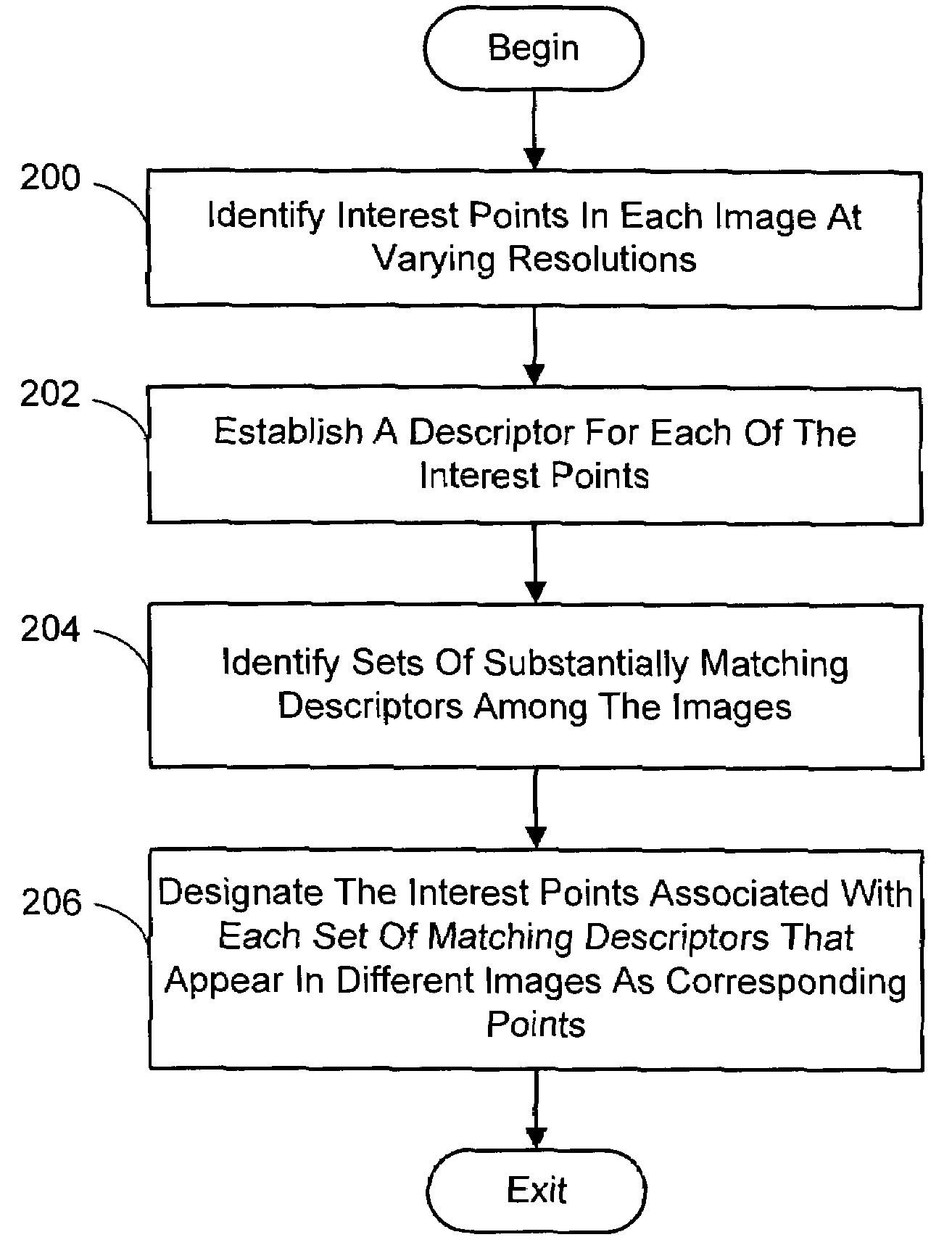
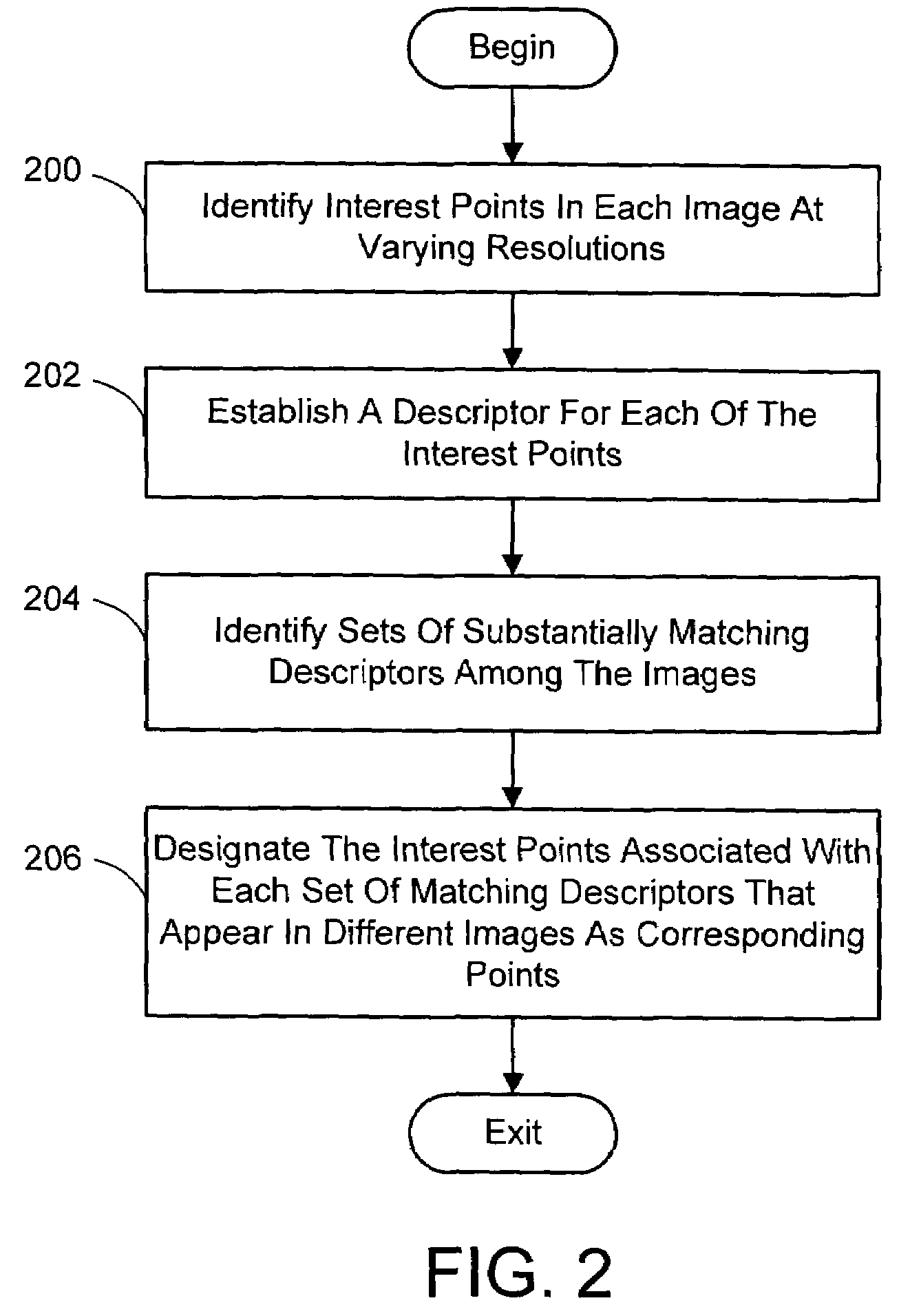
Multi-image feature matching using multi-scale oriented patches
InactiveUS20050238198A1Quick extractionEasy to liftConveyorsImage analysisPattern recognitionNear neighbor
A system and process for identifying corresponding points among multiple images of a scene is presented. This involves a multi-view matching framework based on a new class of invariant features. Features are located at Harris corners in scale-space and oriented using a blurred local gradient. This defines a similarity invariant frame in which to sample a feature descriptor. The descriptor actually formed is a bias / gain normalized patch of intensity values. Matching is achieved using a fast nearest neighbor procedure that uses indexing on low frequency Haar wavelet coefficients. A simple 6 parameter model for patch matching is employed, and the noise statistics are analyzed for correct and incorrect matches. This leads to a simple match verification procedure based on a per feature outlier distance.
Owner:MICROSOFT TECH LICENSING LLC
System for protection of goods against counterfeiting
InactiveUS6996543B1Fast informationQuick verificationOther printing matterUser identity/authority verificationPrint versionDigital image
In order to verify the authenticity of manufactured goods, a smart tag is attached to the goods containing encrypted authentication information, such as a serial number, a description of the good's physical appearance or chemical decomposition, its color, or digital images of the good etc. The encryption procedure comprises public / private key encryption with zero-knowledge protocols. Zero knowledge protocols allow a smart tag to be authenticatable and yet be duplication resistant by allowing the verifying agent to convince him / herself that the smart tag is authentic without revealing its authentication information. The verification procedure can be done using a reader at a point of sale (POS) machine equipped with the appropriate public key and zero-knowledge protocols to decrypt the authentication information. A printed version of the serial number or other authentication information may be placed on the goods in human readable form to quickly verify the information electronically read from the smart tag. With the present invention, only the manufacturer can create such smart tags with the associated data thus making it virtually impossible to pass off a counterfeit good as authentic. In addition to authenticating counterfeit goods, the present invention can be used to detect authentic goods being sold in a parallel market.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
Pluggable semantic verification and validation of configuration data
ActiveUS20040019670A1Digital computer detailsData switching networksData validationSource Data Verification
A pluggable semantic verification and syntactic validation mechanism for server configuration information. In one embodiment, the data verification and validation mechanism may be implemented as modules that may be plugged into a framework. In one embodiment, the mechanism may include a generic test case framework that may call test cases to verify and validate changes to configuration information. In one embodiment, each test case may implement an interface through which the framework calls a test case. The test case may return results, e.g. whether the test passed or failed, and may return additional information, e.g. why the test failed. If the change is valid, then the change may be made to the configuration information. If the change is not valid, the change is not made or alternatively is made with a warning. If the change is made, one or more other servers may be notified of the change.
Owner:ORACLE INT CORP
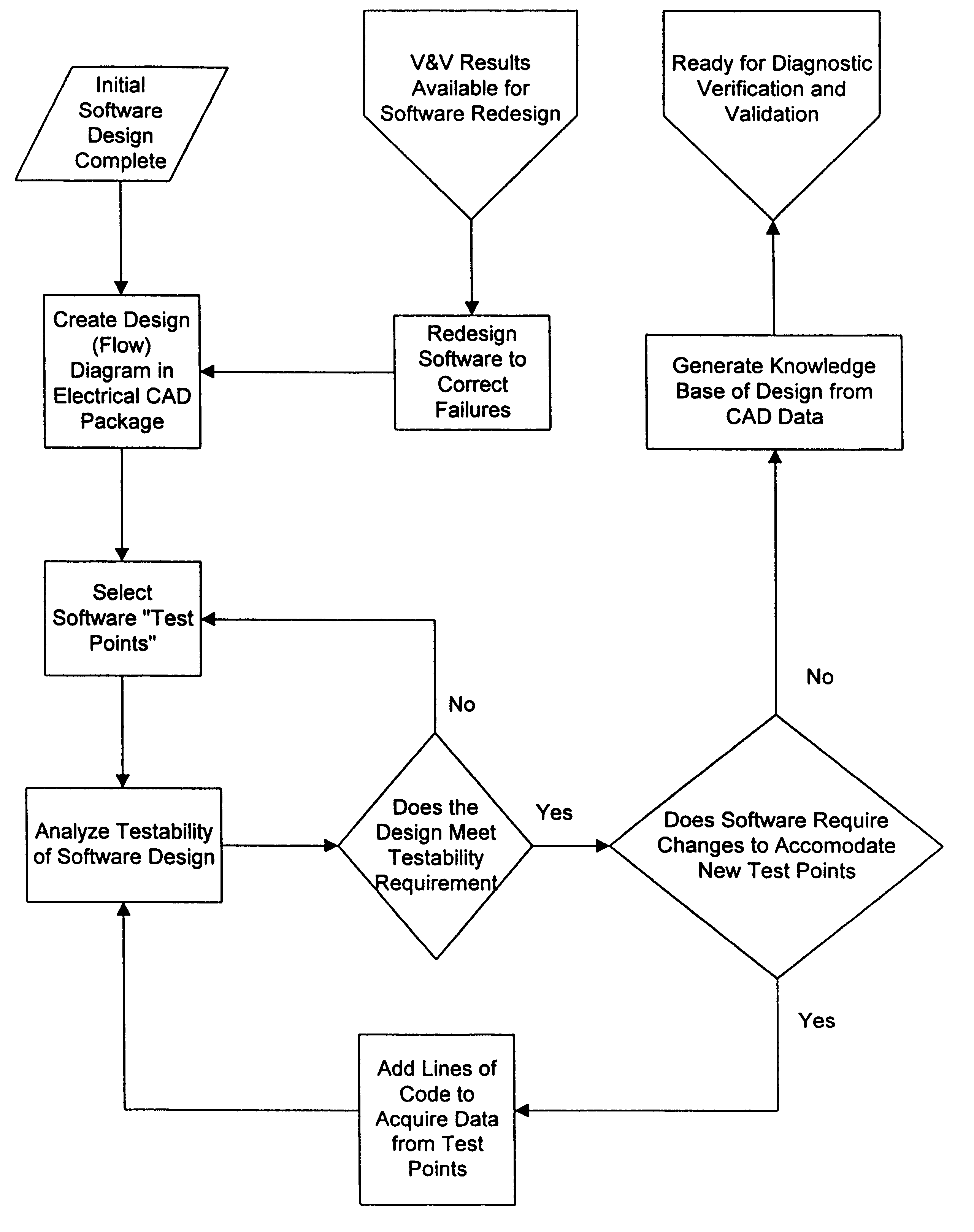
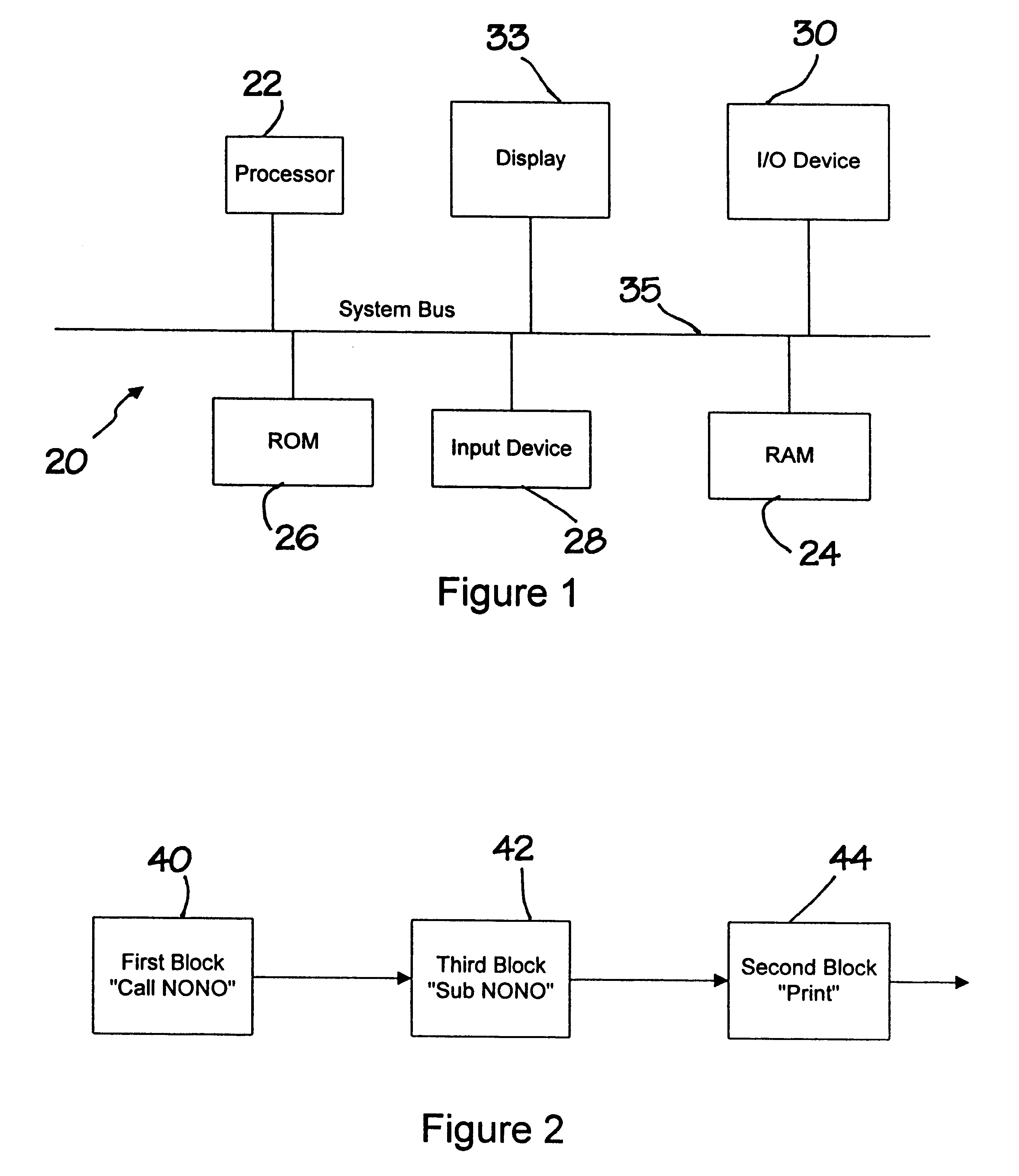
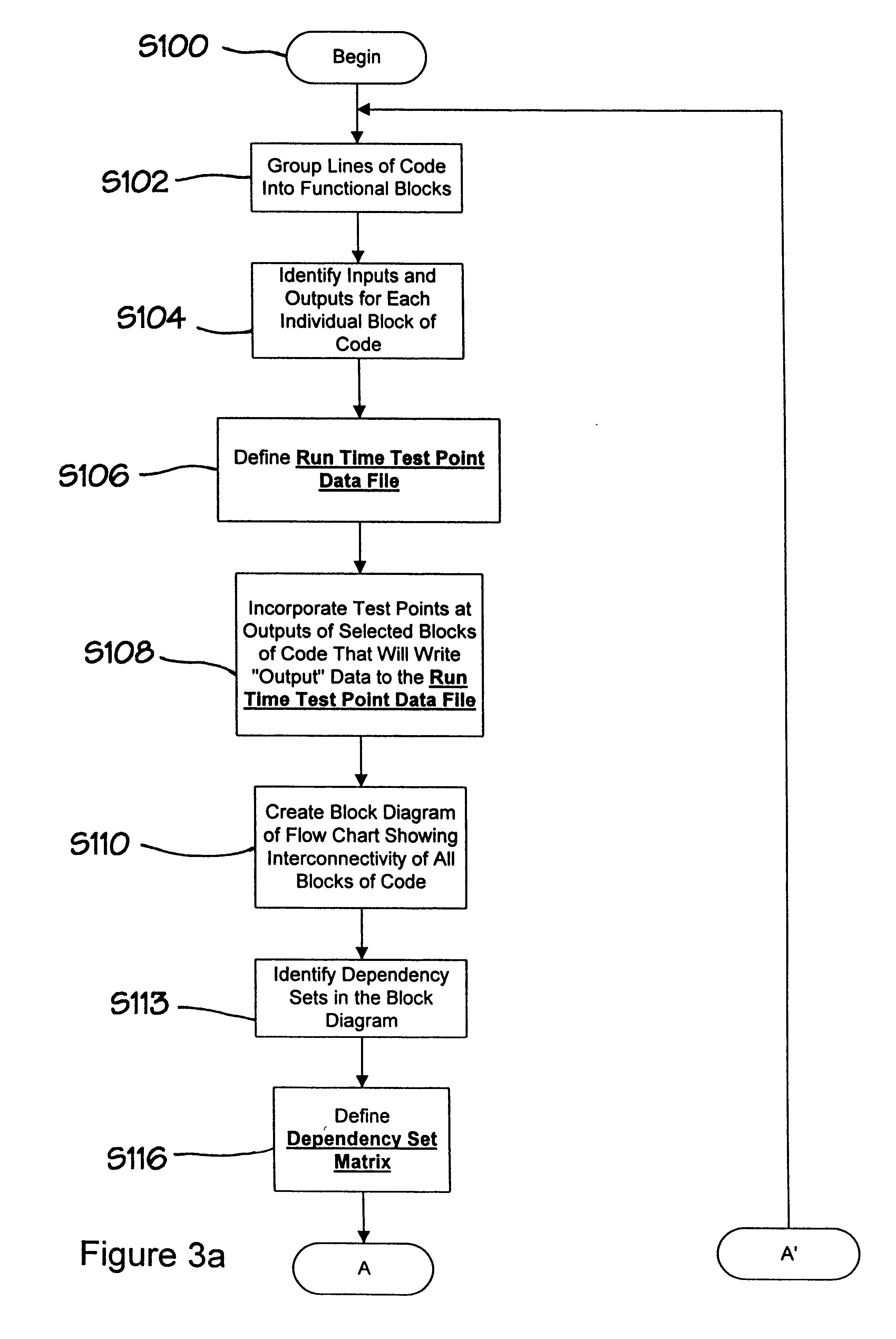
Method and apparatus for debugging, verifying and validating computer software
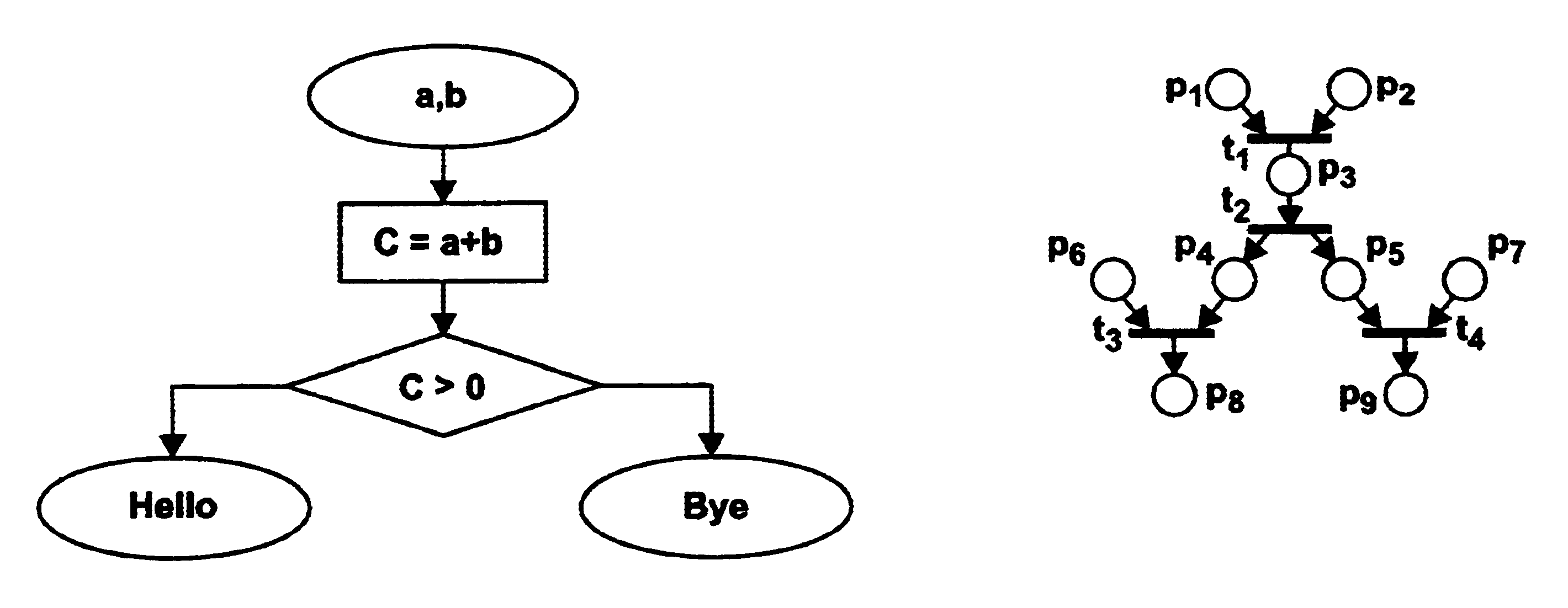
InactiveUS6173440B1Software testing/debuggingProgram loading/initiatingSoftware designVerification procedure
A new approach for software debugging, verification and validation is disclosed. The present invention utilizes a knowledge-based reasoning approach to build a functional model of the software code for identifying and isolating failures in the software code. The knowledge-based reasoning approach of the present invention uses the software design, which is preferably based upon a flow chart or block diagram representation of the software functionality, to build the functional model. The software block diagram contributes to the functional model by defining the inputs and outputs of the various blocks of code, as well as defining data interconnections between the various blocks of code. In accordance with a method of the present invention, test points are strategically inserted throughout the code, and each test point is associated with a corresponding block of code. Expected values of the test points for an expected proper-operation execution of the computer program are generated. The computer program is then executed on a computer, and the actual values of the test points from the program execution are compared with the expected values of the test points. Failed test points which do not agree with corresponding expected values are determined. The functional model, which includes information functionally relating the various test points to one another, is then used to isolate the failed test points to one or more sources of failure in the code.
Owner:MCDONNELL DOUGLAS
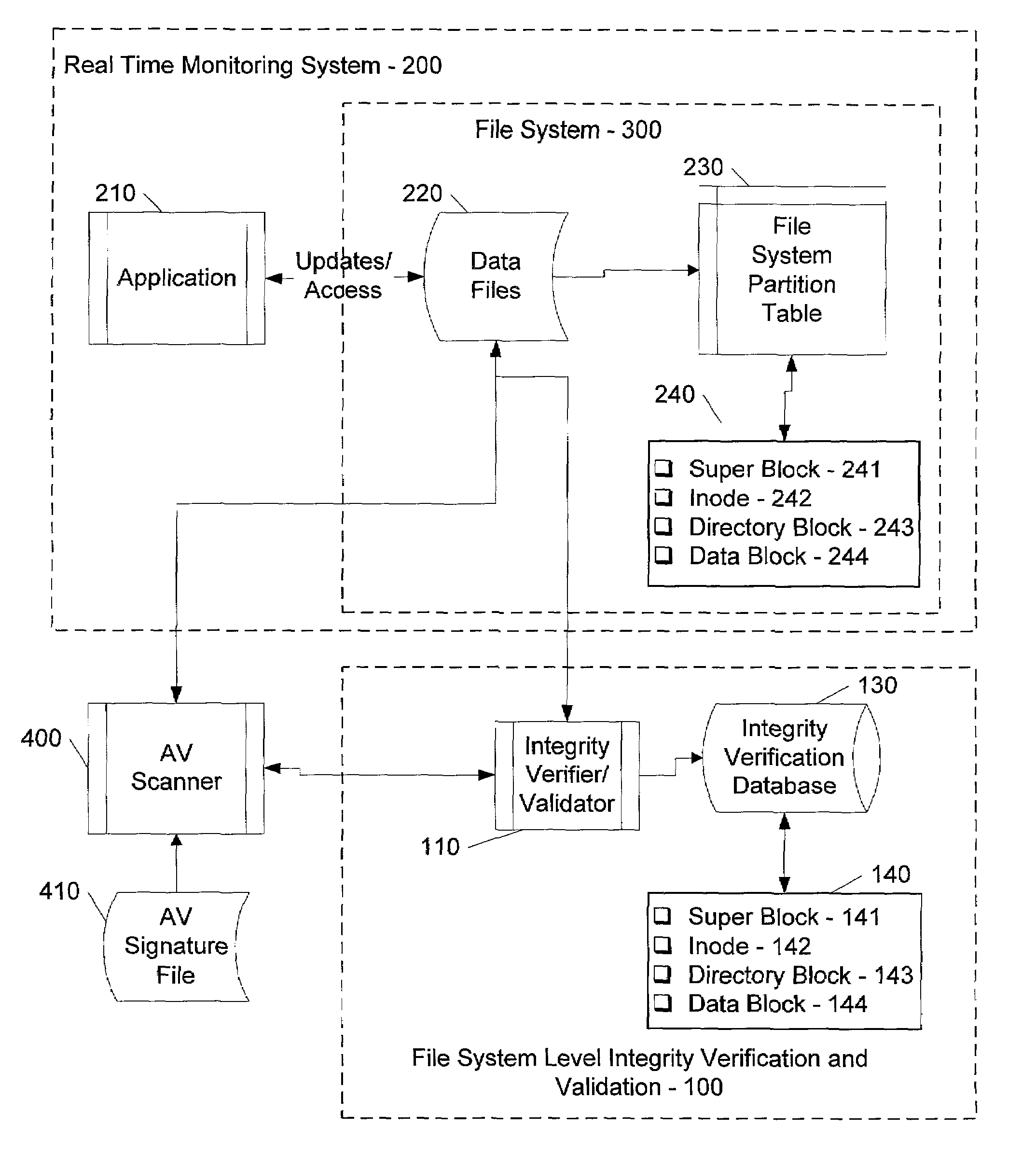
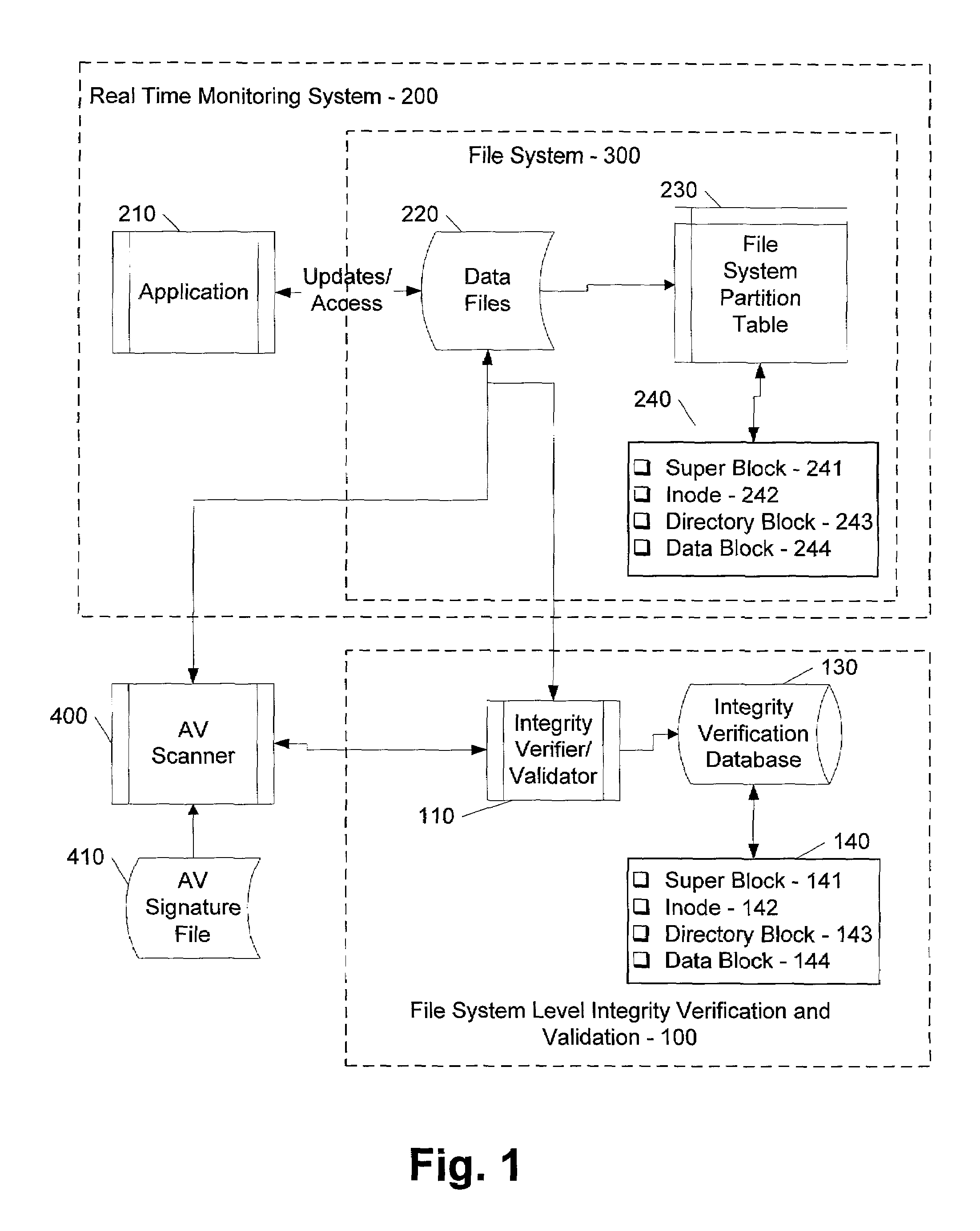
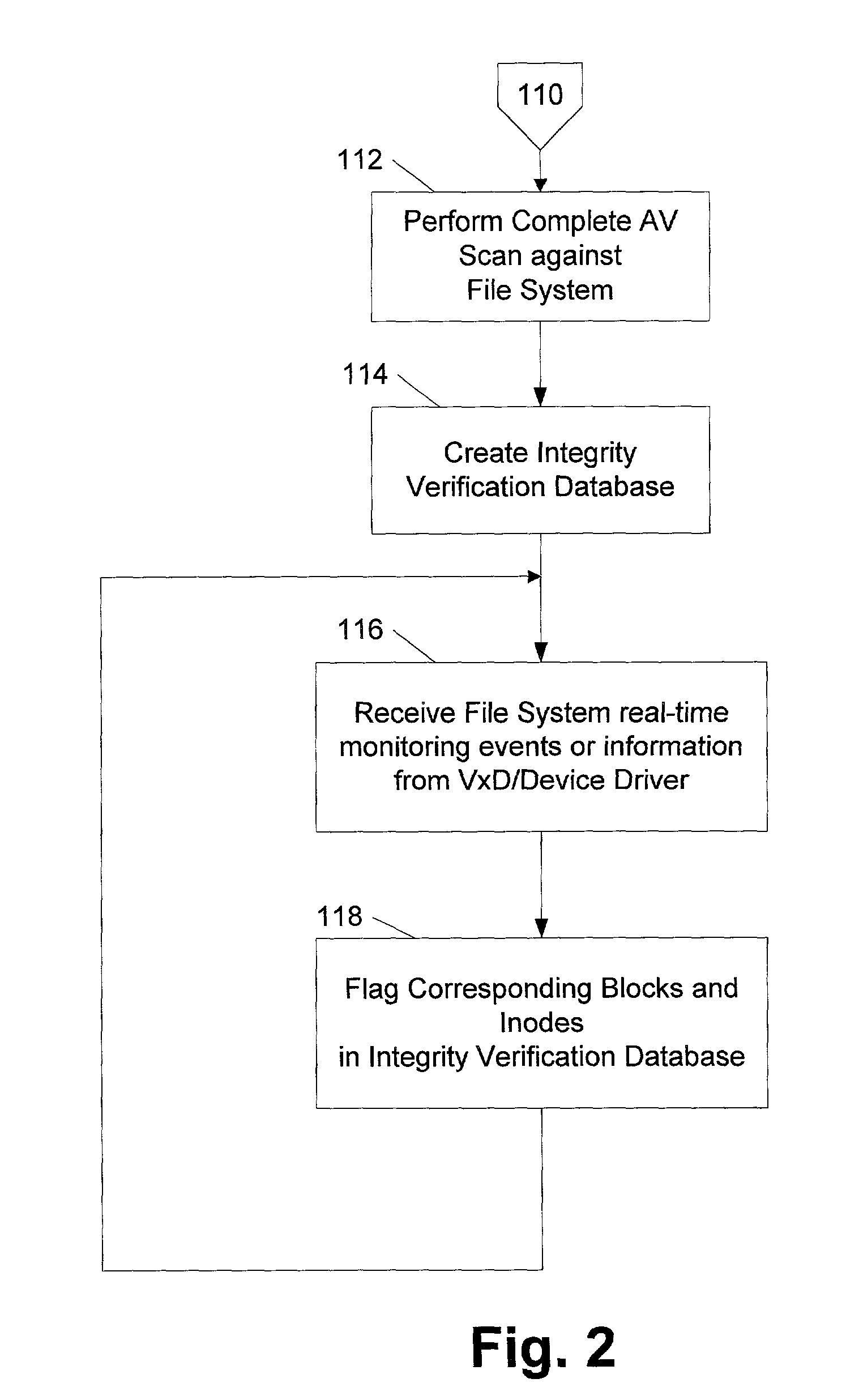
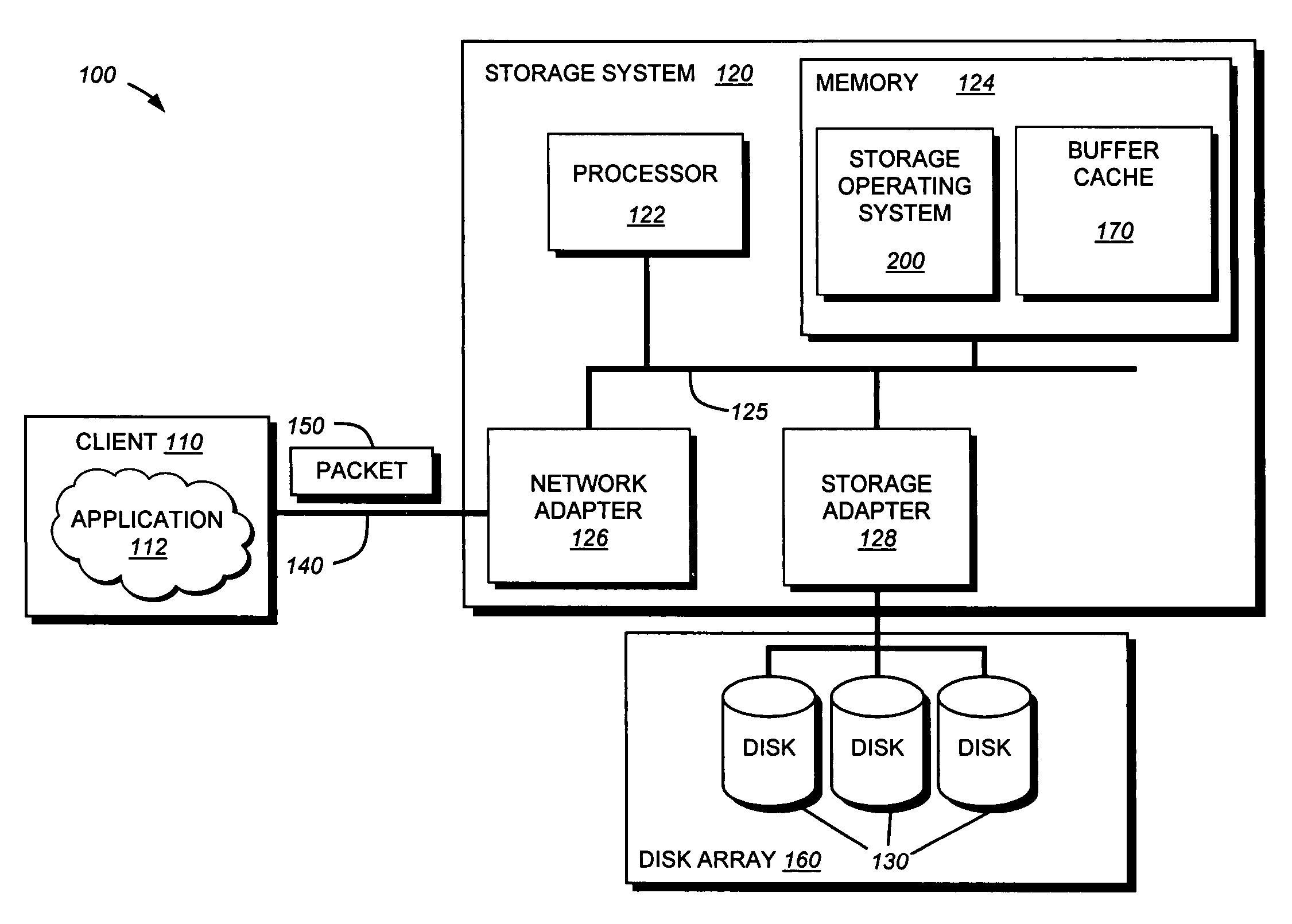
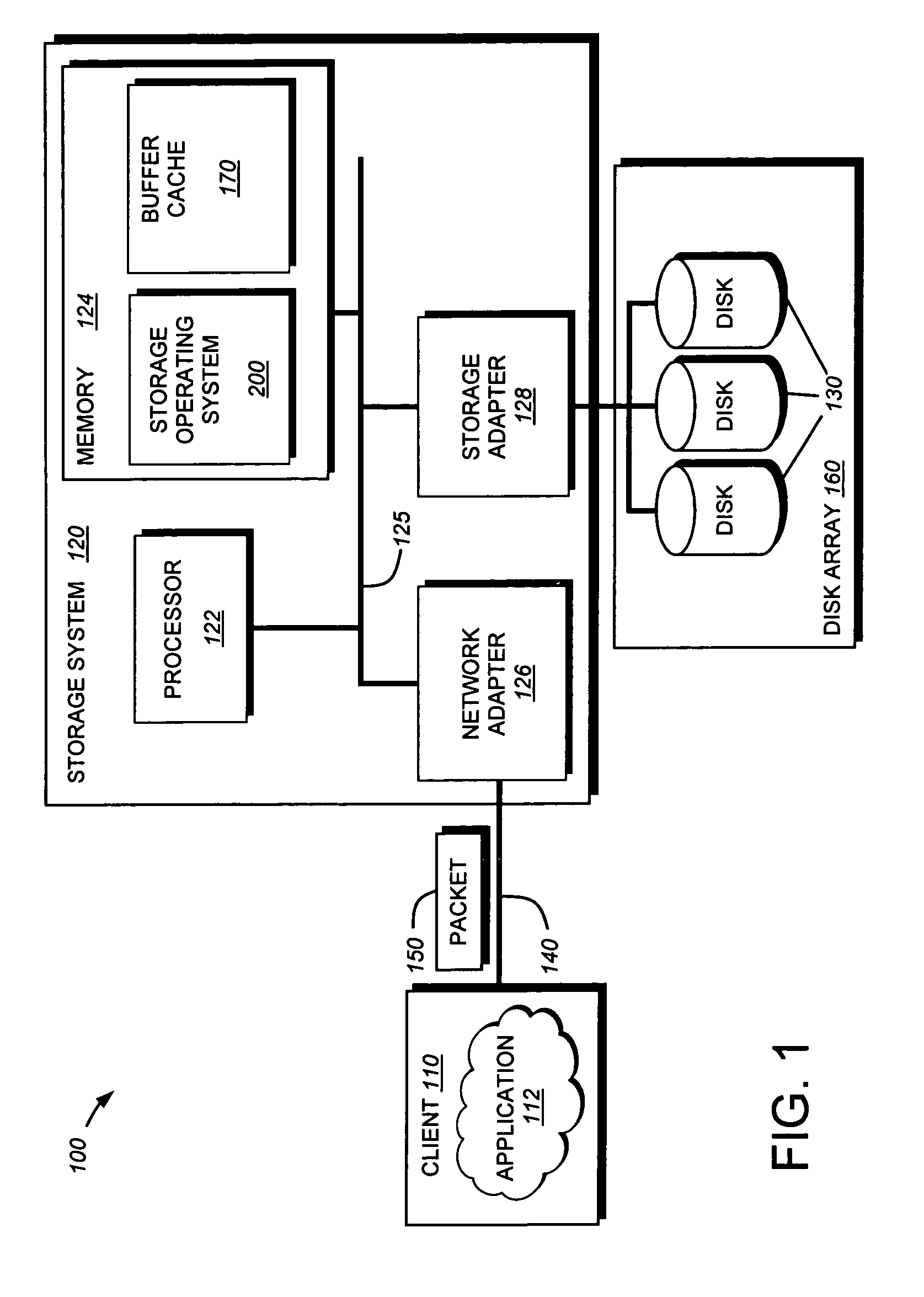
File system level integrity verification and validation
ActiveUS7069594B1Preventing rescanningGood level of efficiencyMemory loss protectionError detection/correctionAnti virusInode
An integrity verifier and validator is provided in which an initial anti-virus scan is performed against an entire file system to verify the integrity of the file system and create a corresponding file system level integrity verification database of known scanned regions of the file system. The database contains a copy of the file system's partition table referencing the range of occupied inodes and directory blocks. When new or updated content is written to the file system the integrity of the corresponding occupied inodes and directory blocks is no longer assured, and the integrity verifier flags them on the database for rescanning. Subsequent attempts to rescan any portion of the file system triggers the integrity validator to scan the database to validate whether that portion of the file system falls within any of the occupied inodes or directory blocks that have been flagged for rescanning. If they are not flagged, then rescanning of that portion of the file system is unnecessary as the integrity of at least that portion is assured. However, if they are flagged, then the anti-virus software rescans that portion of the file system for the presence of viruses.
Owner:MCAFEE LLC
Method and system for the secured distribution of multimedia titles
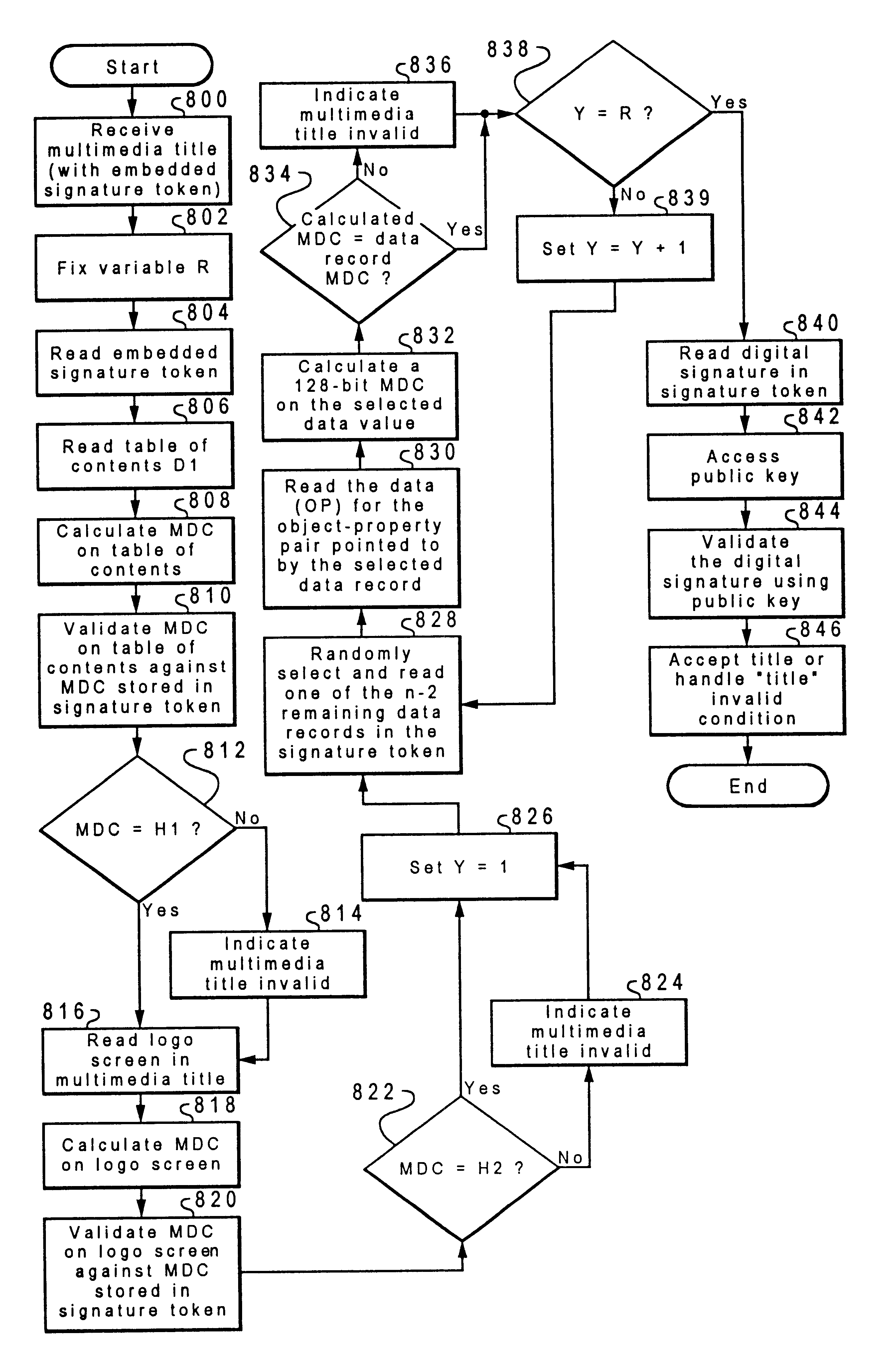
InactiveUSRE38375E1Memory loss protectionDigital data processing detailsData processing systemProgramming language
A method and system for detecting authorized programs within a data processing system. The present invention creates a validation structure for validating a program. The validation structure is embedded in the program and in response to an initiation of the program, a determination is made as to whether the program is an authorized program. The determination is made using the validation structure.
Owner:ACTIVISION PUBLISHING
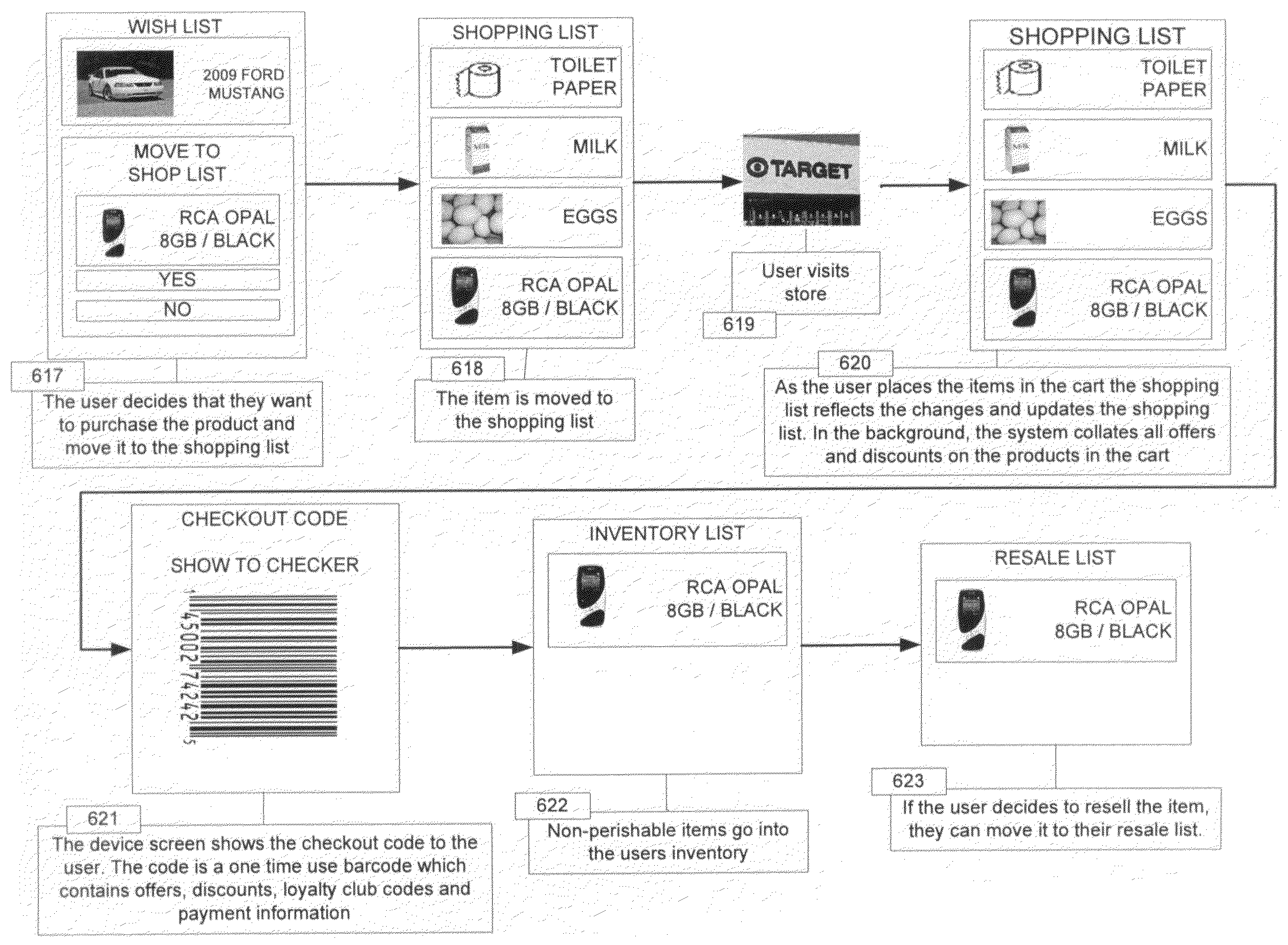
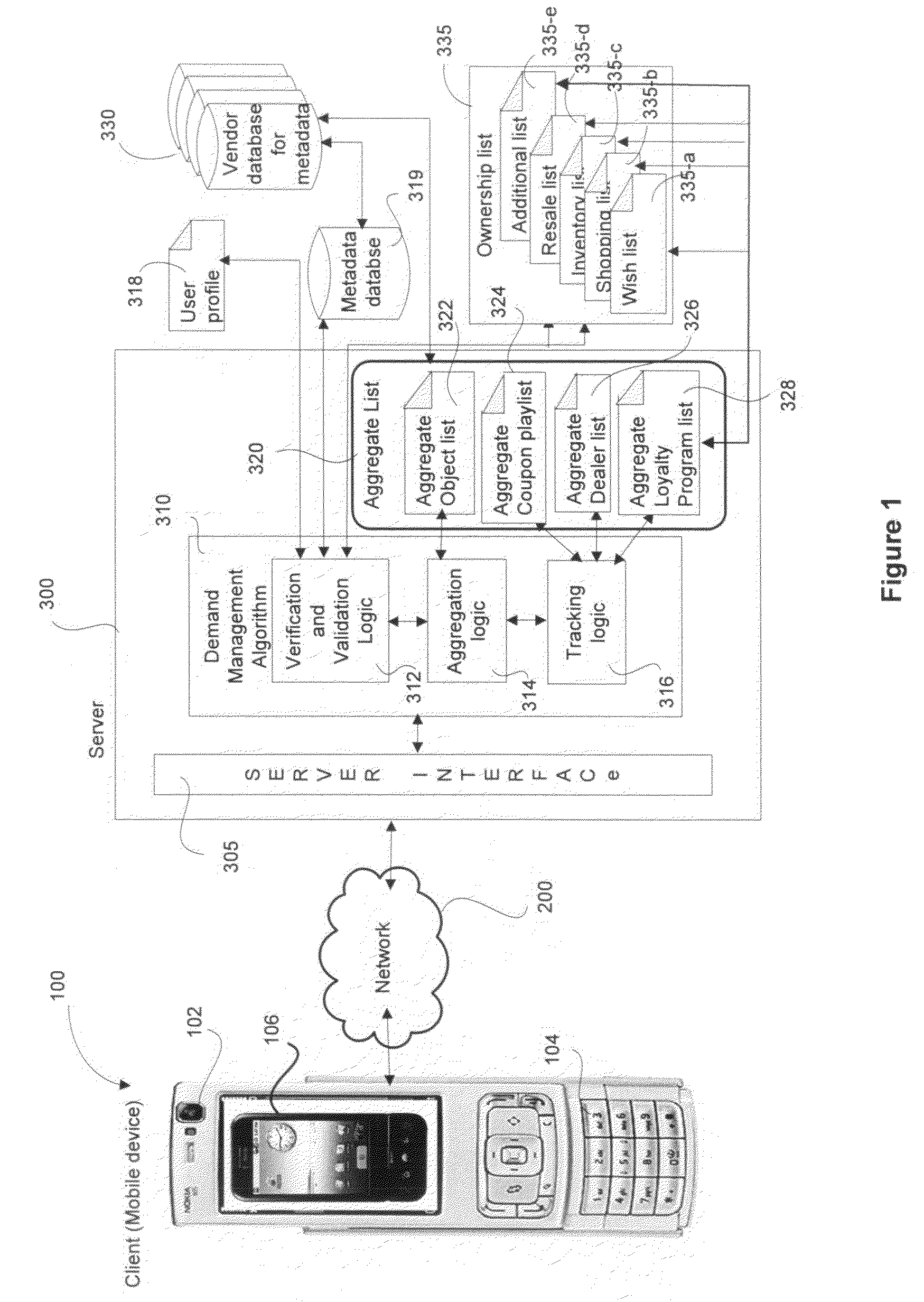
Dynamic Demand Calculation using Captured Data of Real Life Objects
ActiveUS20100179857A1Maximize utilizationAttract more usersHand manipulated computer devicesPayment architectureManagement objectSubject matter
Methods and system for managing demand for an object includes capturing information about the object through a mobile device associated with a user. The mobile device is configured to capture information about the object that include one or more of a spatial, temporal, topical and social attributes of the object. The identity of the object is verified and validated using this metadata captured by the user through the device from the real world object or its proxy. Upon successful verification and validation, the object and its metadata are automatically added to a wish list of the user. An aggregate list is generated using the attributes and metadata of the object from a plurality of users. The aggregate list defines a source of demand for the object. The object is tracked as it progresses through various phases of ownership cycle using dynamic demand calculations based on the information associated with the objects, the users and the aggregate lists.
Owner:R2 SOLUTIONS
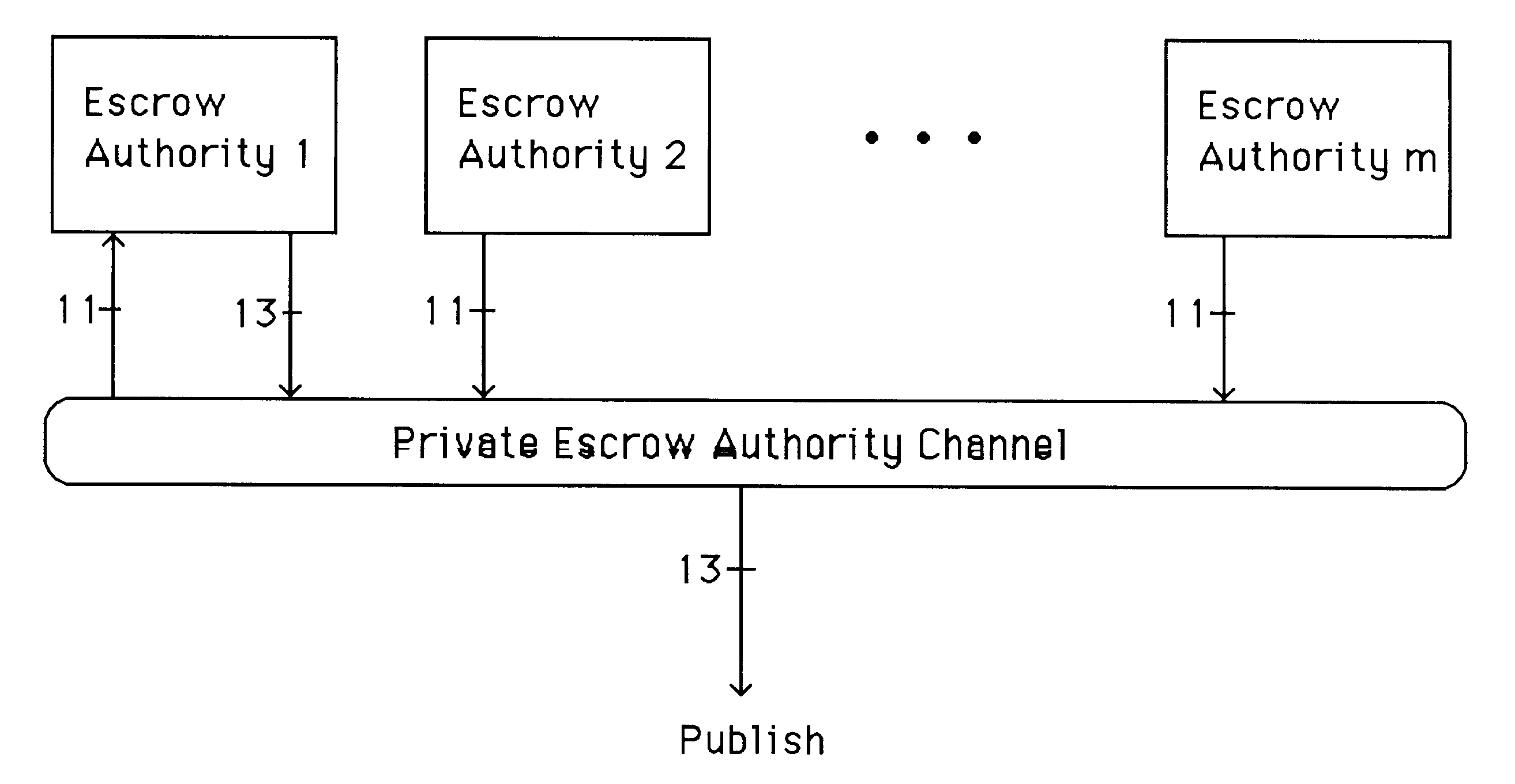
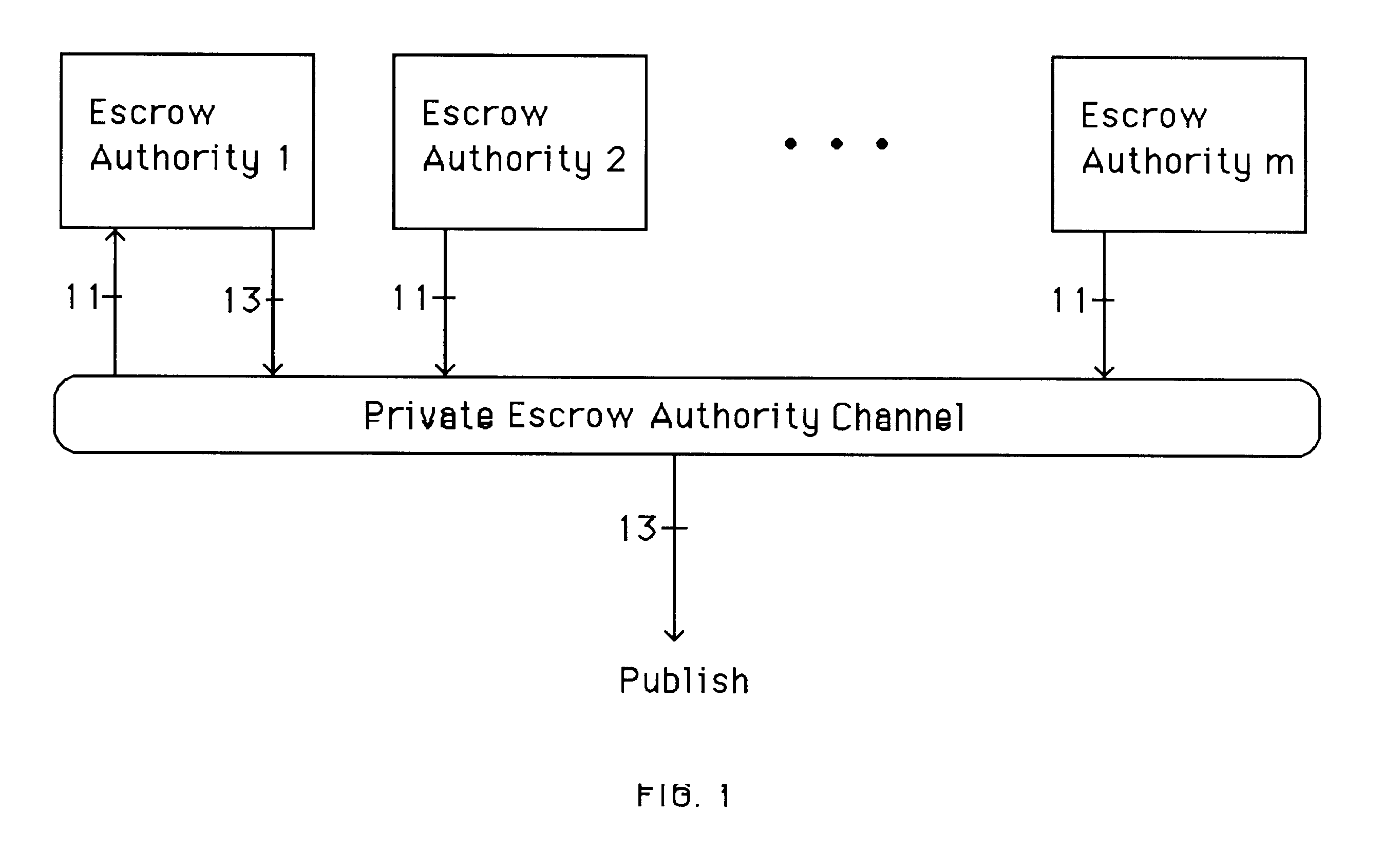
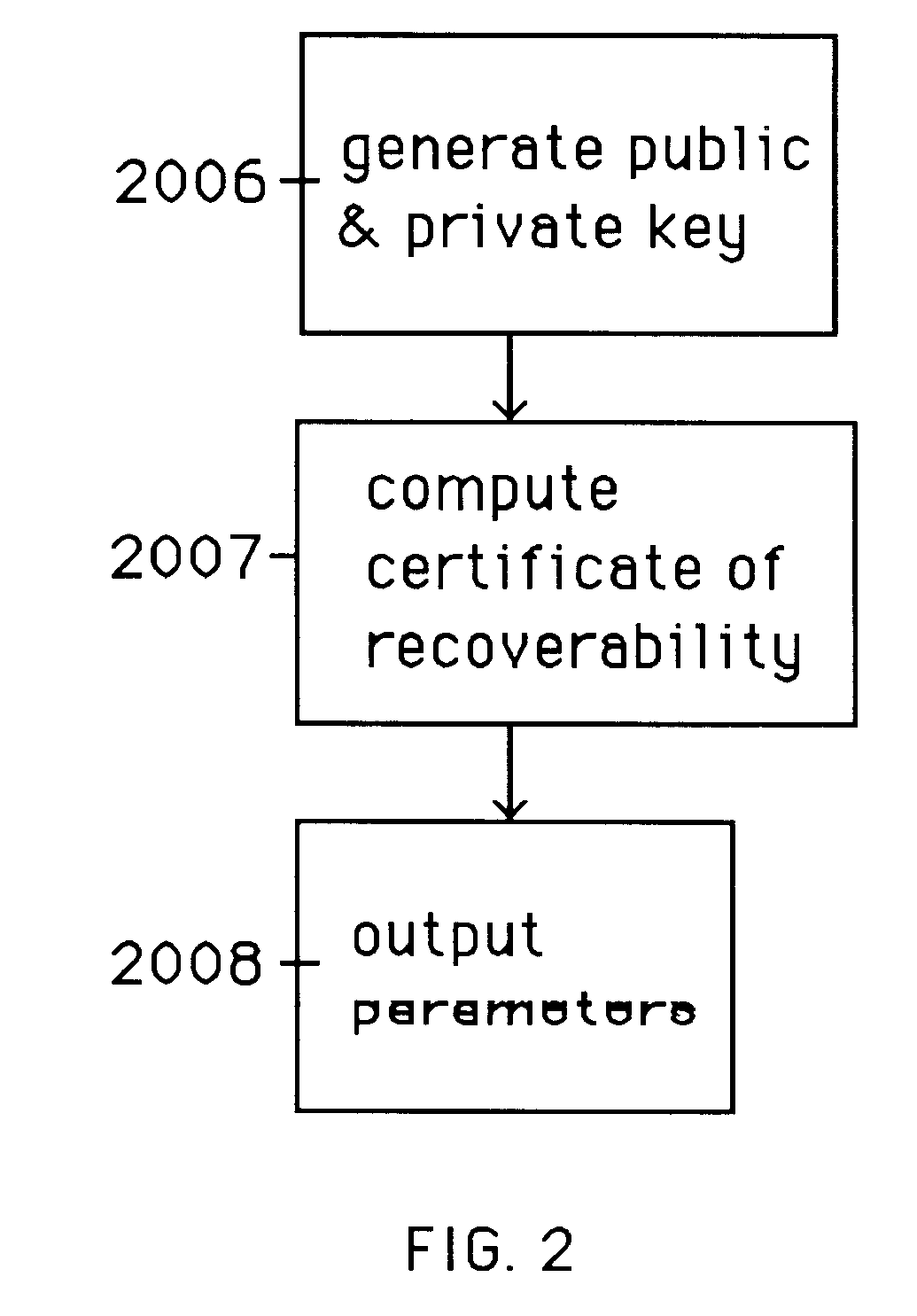
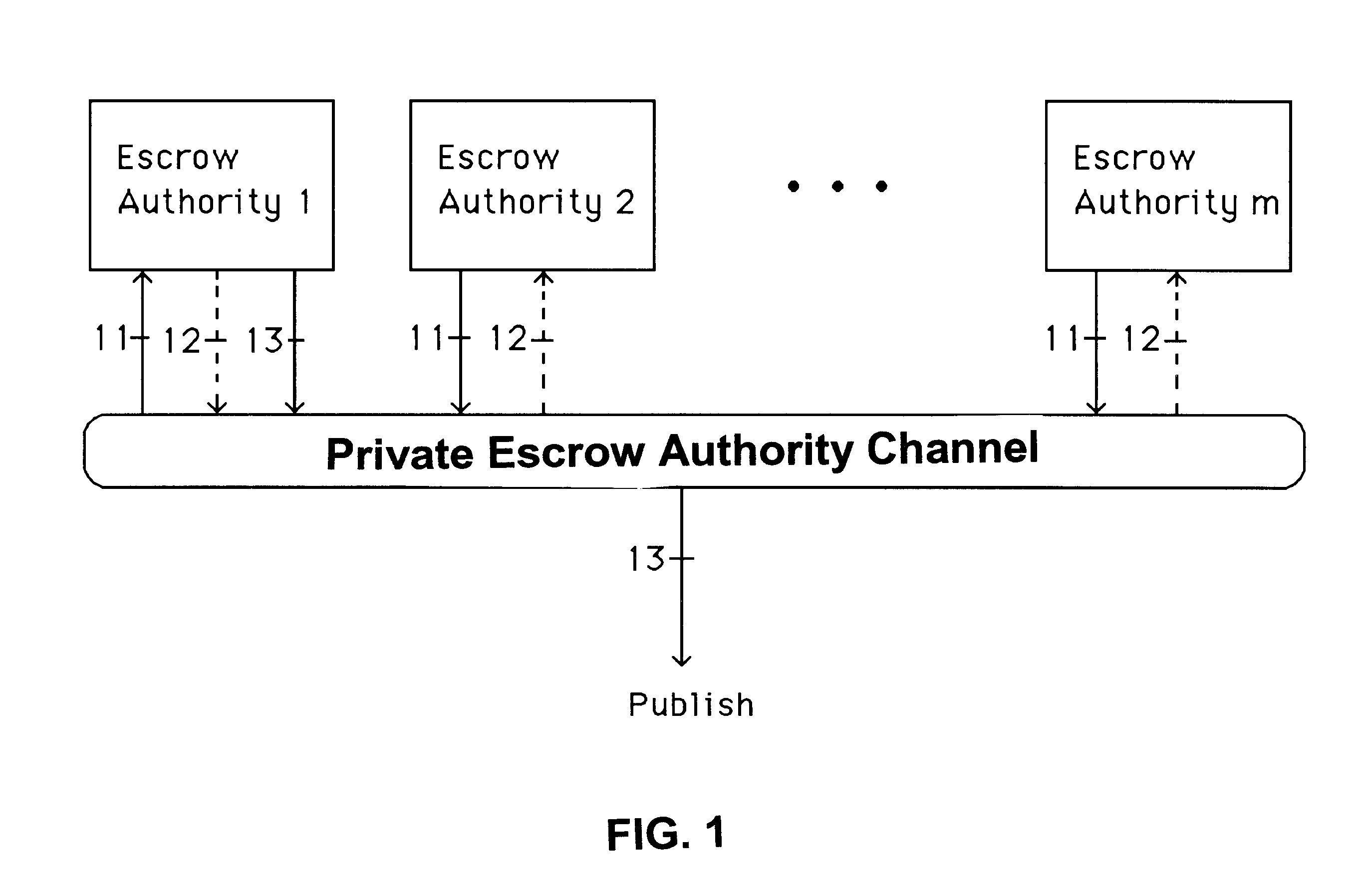
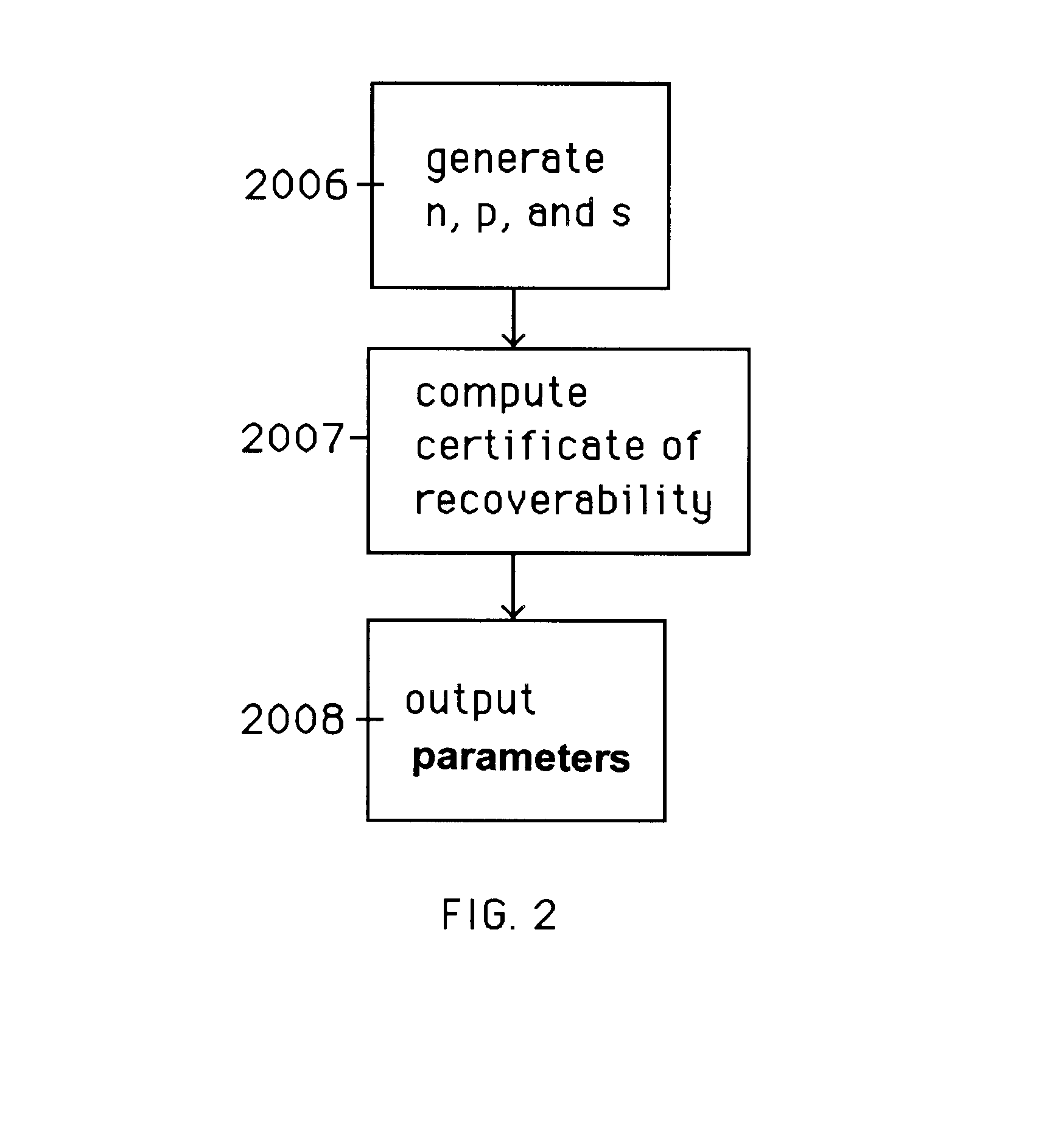
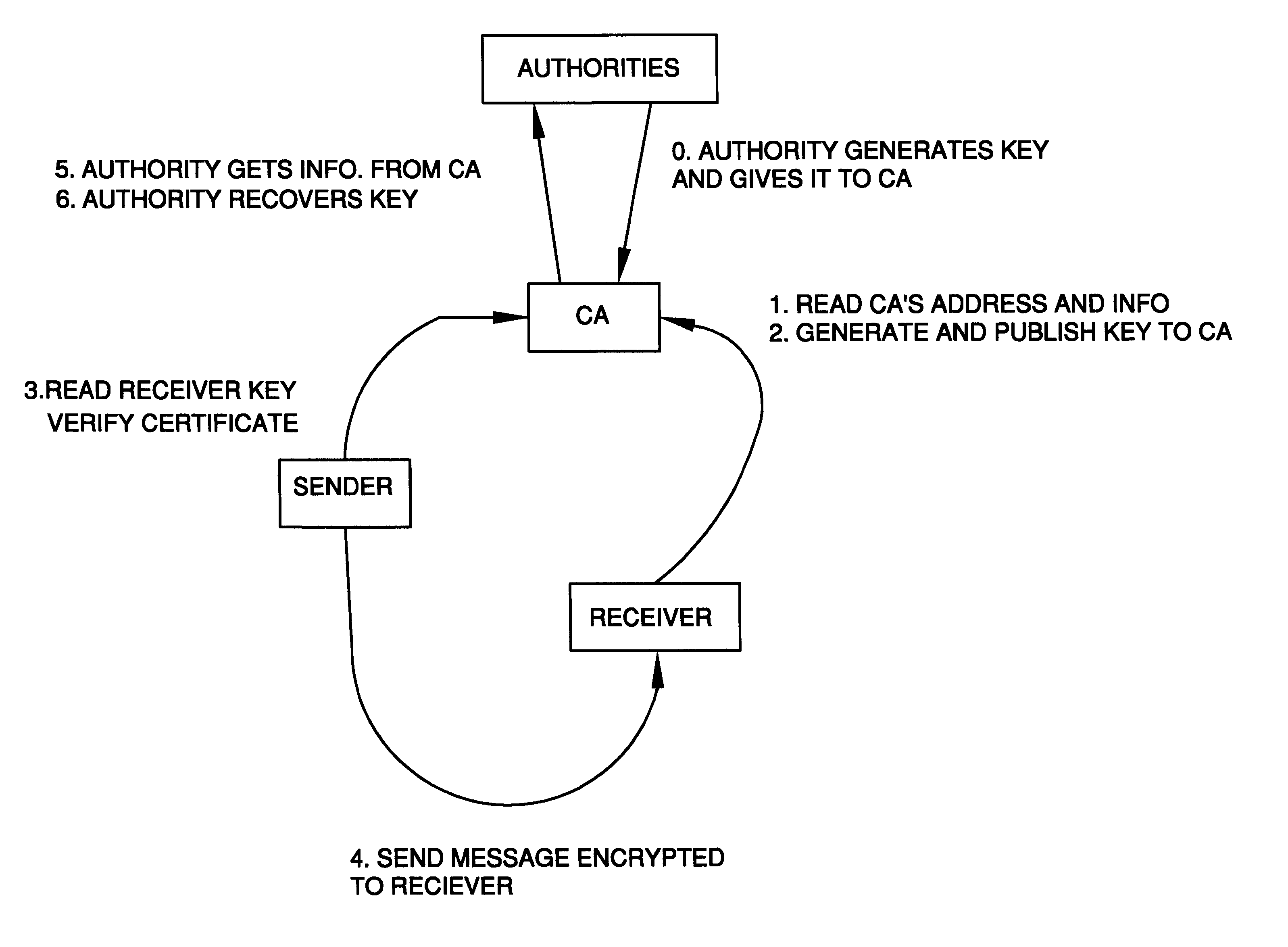
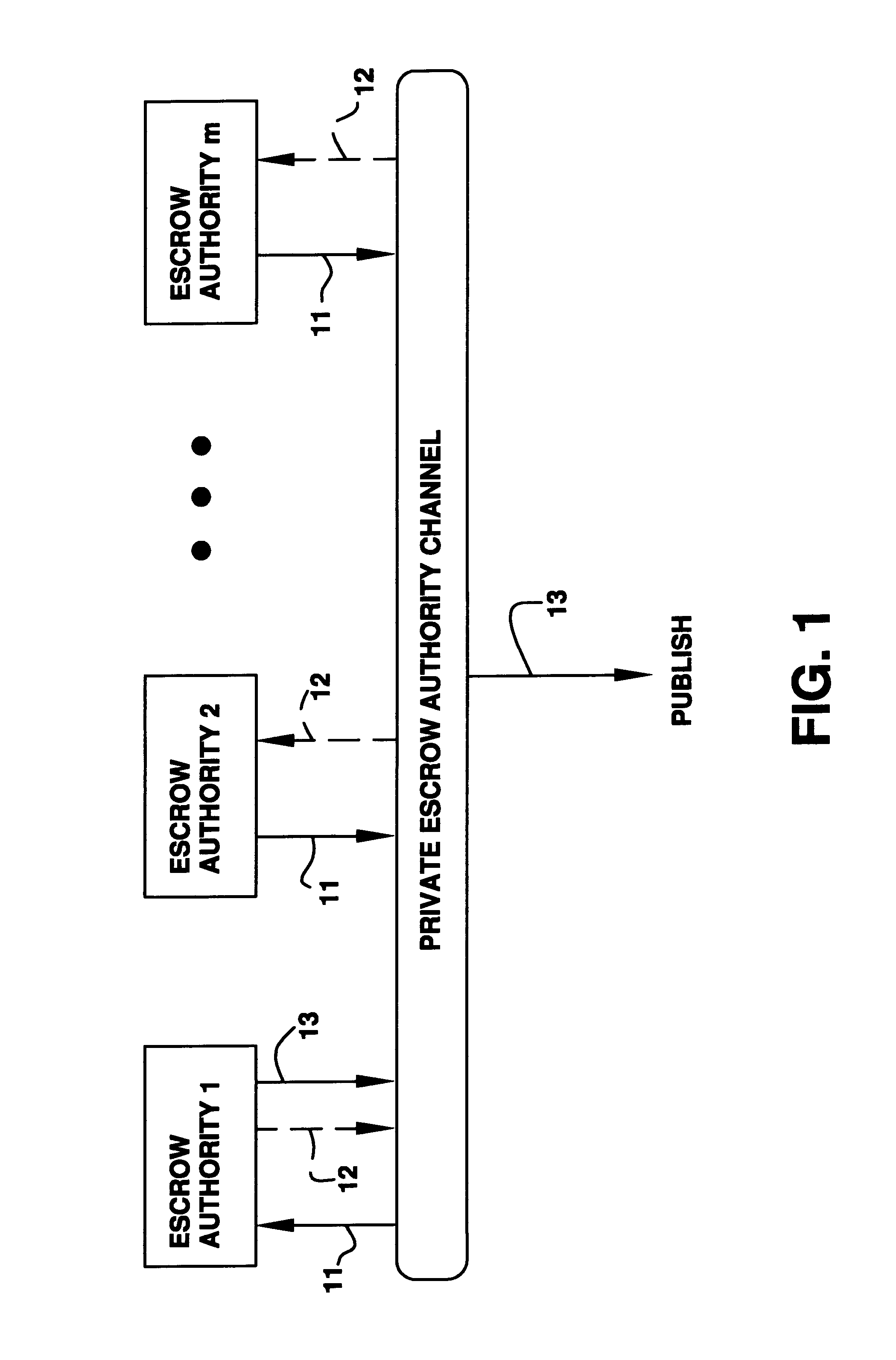
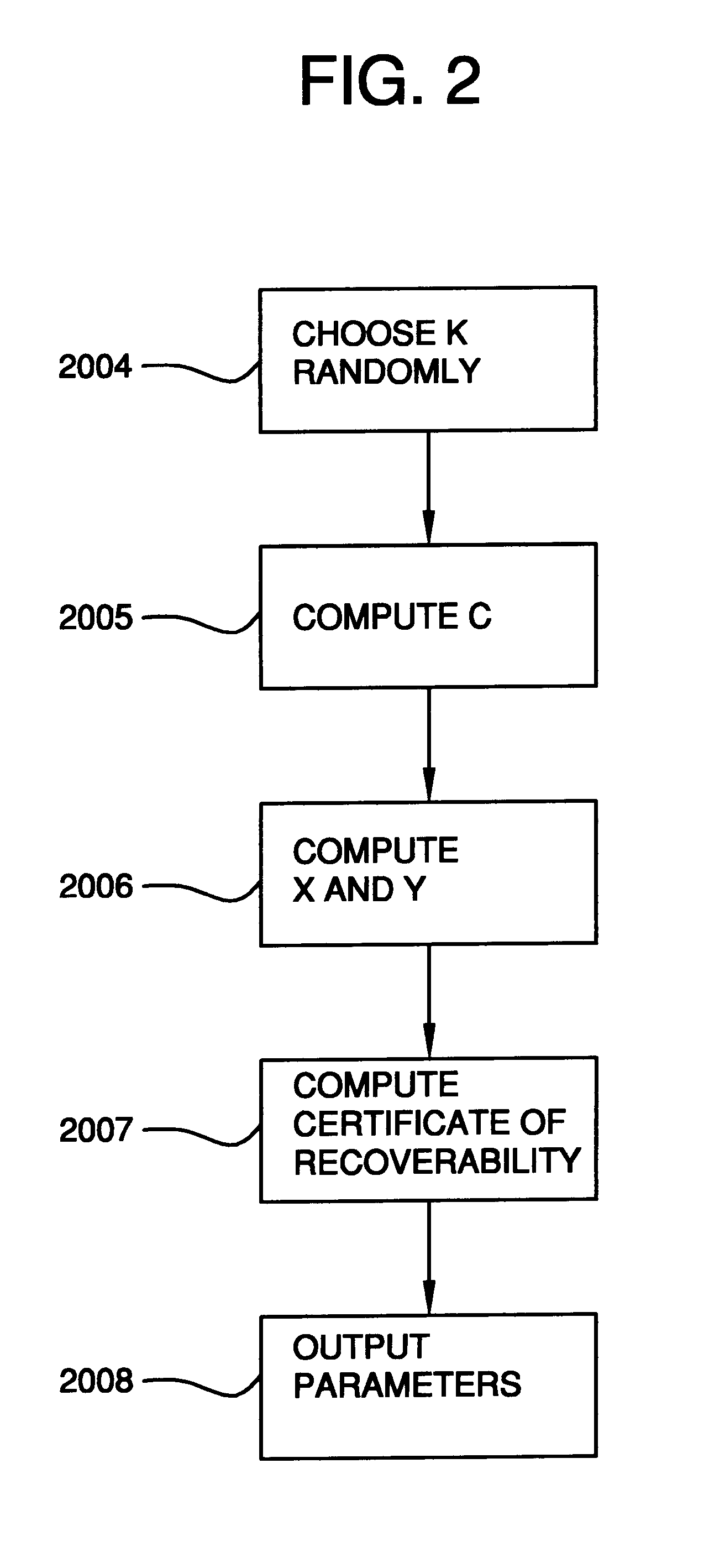
Auto-recoverable and auto-certifiable cryptostem using zero-knowledge proofs for key escrow in general exponential ciphers
InactiveUS6282295B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityValidation methods
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The proof and verification method involves one party proving to a second party that a third party can gain access to an encrypted value. In addition, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or ElGamal cryptosystem. The system is applicable for lawenforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. The system security relies solely on the security of cipher systems involved whose security has been extensively studied in the past.
Owner:CRYPTOPEAK SECURITY LLC
Universal verification and validation system and method of computer-aided software quality assurance and testing
InactiveUS6671874B1Eliminate degradationProgram documentationSoftware testing/debuggingDocumentation procedureSystem requirements
A method of developing a model of a computer program represents the system requirement conditions and events as a set of positions and transitions, maps the system requirements in a table of positions with position and optionally transition designations, tags one or more significant positions in the including any conditional positions, and creates a reference designation associating alternative conditions with their respective conditional positions. A universal software test development method can be applied to the model by mapping the conditions to a set of positions including a starting position which has no input, a terminal position which has no output, and intermediate positions between the starting position and the terminal position, and generating from the set of positions a table of positions, associating each positions with an expression of the position representing the corresponding system requirements. Both the model development method and the test development method can be implemented automatically by computer software, and the test development method allows for automated development of test documentation. These methods can thus be applied for the verification and validation of computer software.
Owner:SOFEA INC
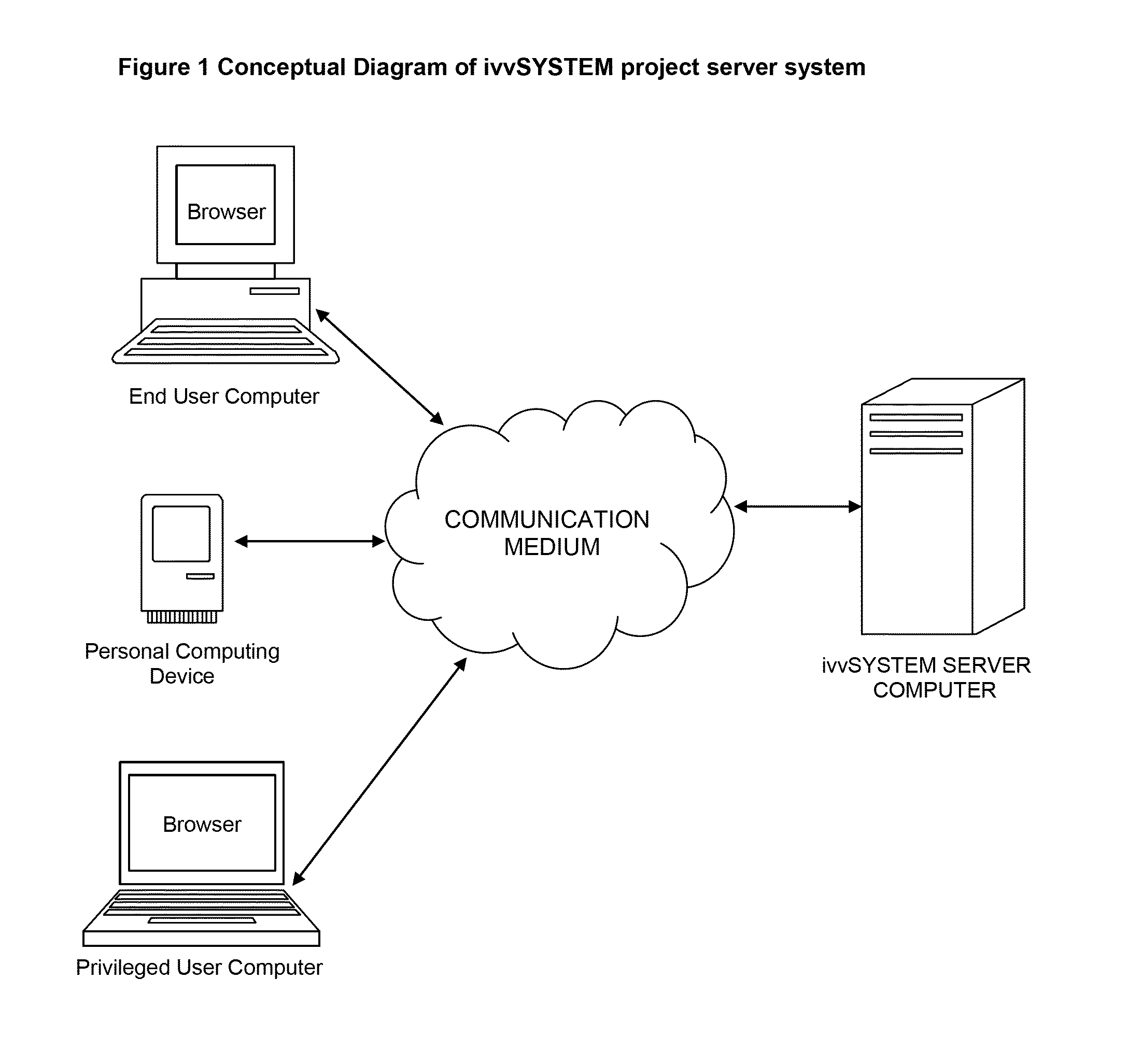
System and method for independent verification and validation
ActiveUS8543620B2Simplifies complex logisticsQuick mapDigital data processing detailsResourcesOperational systemNetwork service
This invention is to solve the high cost of IV&V by simplifying the complex logistics of project management. This is an intelligent project management system comprising a project server computer remotely accessible by a user computing device. The project server computer includes several databases: A database of electronic library which stores documents that are required by the project, a database which stores project data that reflect the state of the project, and a database which stores the user information of privileged users. Several modules are executing in the project server computer to generate the view of the project, to automatically monitor the state of the project, to verify and validate the mapping between multiple documents for requirement traceability, to automatically indicate the state of the project, to automatically provide assistance to the user, to automatically inform the stakeholder on matters related to the project, and to authenticate the privileged user. This intelligent project management system assumes that the server computer contains a standard computer operating system that includes at least a web server, an email server and a search engine facility.
Owner:APLIX RES
Multi-image feature matching using multi-scale oriented patches
InactiveUS7382897B2Quick extractionEasy to liftConveyorsImage analysisPattern recognitionNear neighbor
Owner:MICROSOFT TECH LICENSING LLC
Auto-Recoverable and Auto-certifiable cryptosystems with RSA or factoring based keys
InactiveUS6389136B1Fast and easy disseminationEasy to handleKey distribution for secure communicationPublic key for secure communicationTrusted authorityComposite number
A method is provided for an escrow cryptosystem that is essentially overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. The keys generated are based on composite numbers (like RSA keys). A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The keys generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key is recoverable by the escrow authorities. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware. The system is efficient and can be implemented as a "drop-in" replacement to an RSA or Rabin cryptosystem. The system is applicable for law-enforcement, file systems, e-mail systems, certified e-mail systems, and any scenario in which public key cryptography can be employed and where private keys or information encrypted under public keys need to be recoverable. Another aspect of the system is the possibility to organize it in a hierarchical tree structure, where each element in the tree is an escrow authority (or authorities) capable to recover keys and / or information encrypted under these keys within the subtree rooted at the authority (or authorities) and only within this subtree.
Owner:CRYPTOPEAK SECURITY LLC
Auto-escrowable and auto-certifiable cryptosystems
InactiveUS6202150B1Fast and easy disseminationEasy to handleKey distribution for secure communicationUser identity/authority verificationTrusted authorityTamper proof hardware
A method is provided for an escrow cryptosystem that is overhead-free, does not require a cryptographic tamper-proof hardware implementation (i.e., can be done in software), is publicly verifiable, and cannot be used subliminally to enable a shadow public key system. A shadow public key system is an unescrowed public key system that is publicly displayed in a covert fashion. The key generated by the method are auto-recoverable and auto-certifiable (abbrev. ARC). The ARC Cryptosystem is based on a key generation mechanism that outputs a public / private key pair, and a certificate of proof that the key was generated according to the algorithm. Each generated public / private key pair can be verified efficiently to be escrowed properly by anyone. The verification procedure does not use the private key. Hence, the general public has an efficient way of making sure that any given individual's private key is escrowed properly, and the trusted authorities will be able to access the private key if needed. Since the verification can be performed by anyone, there is no need for a special trusted entity, known in the art as a "trusted third party". The cryptosystem is overhead free since there is no additional protocol interaction between the user who generates his or her own key, and the certification authority or the escrow authorities, in comparison to what is required to submit the public key itself in regular certified public key systems. Furthermore, the system is designed so that its internals can be made publicly scrutinizable (e.g., it can be distributed in source code form). This differs from many schemes which require that the escrowing device be tamper-proof hardware.
Owner:CRYPTOPEAK SECURITY LLC
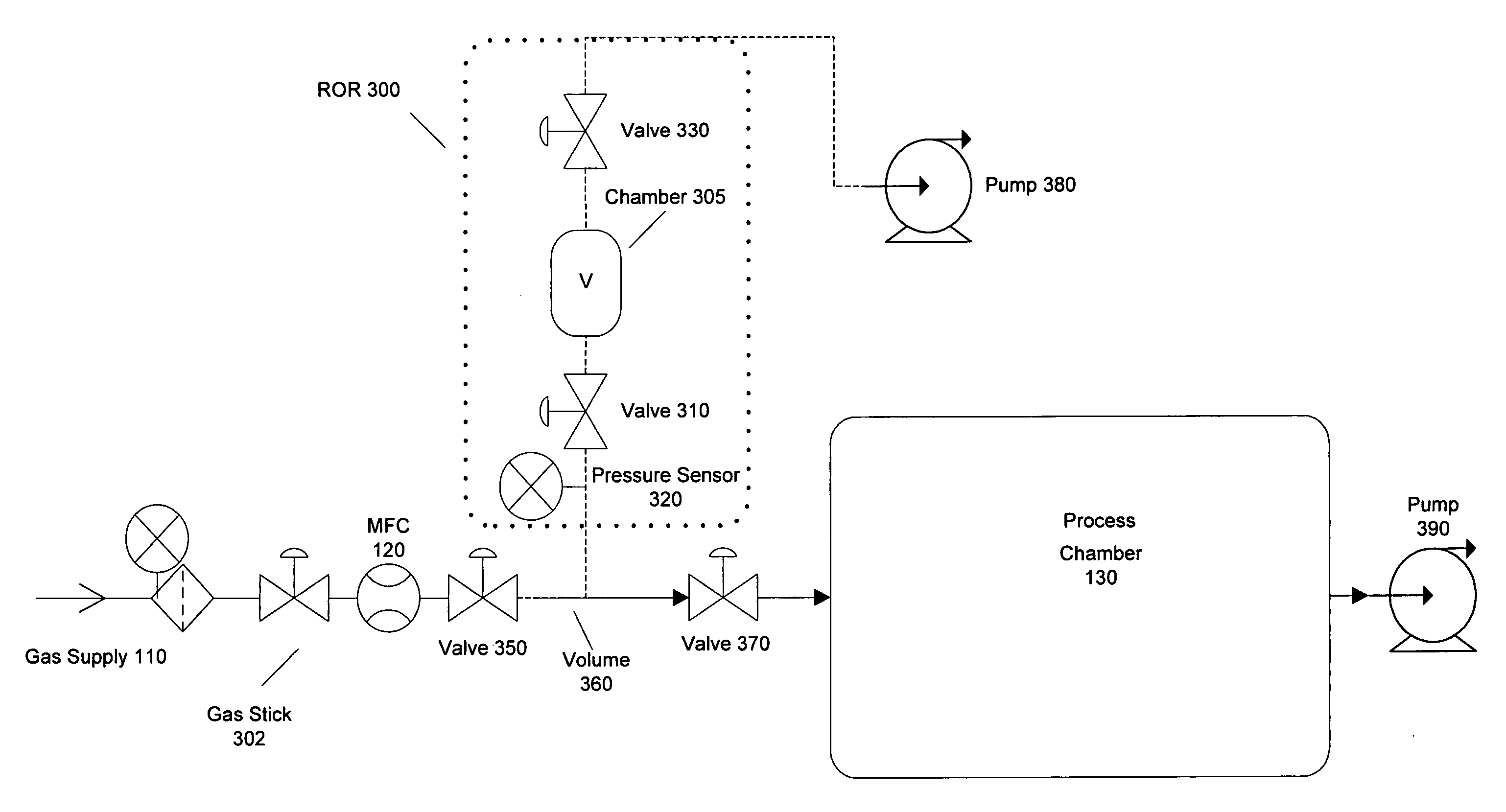
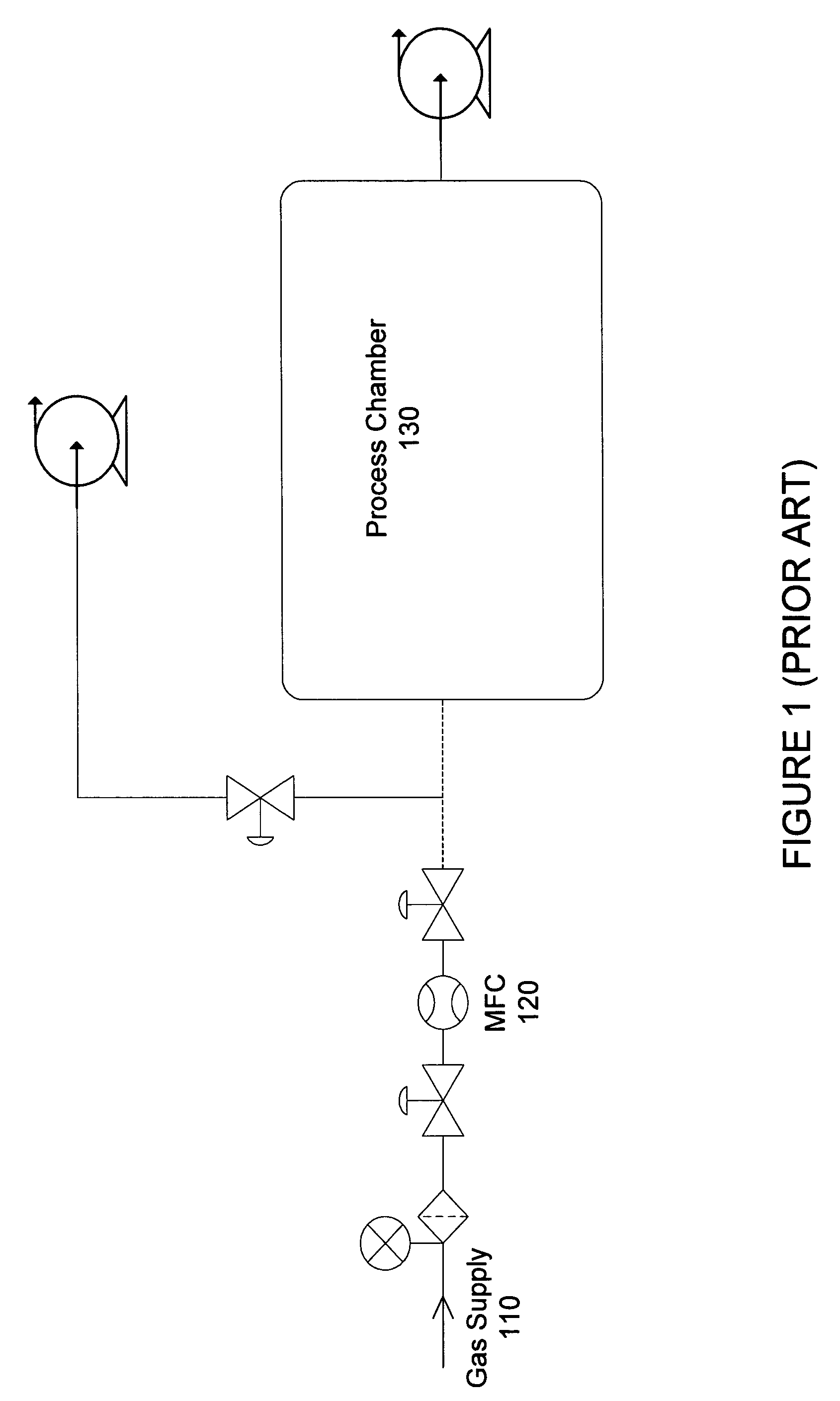
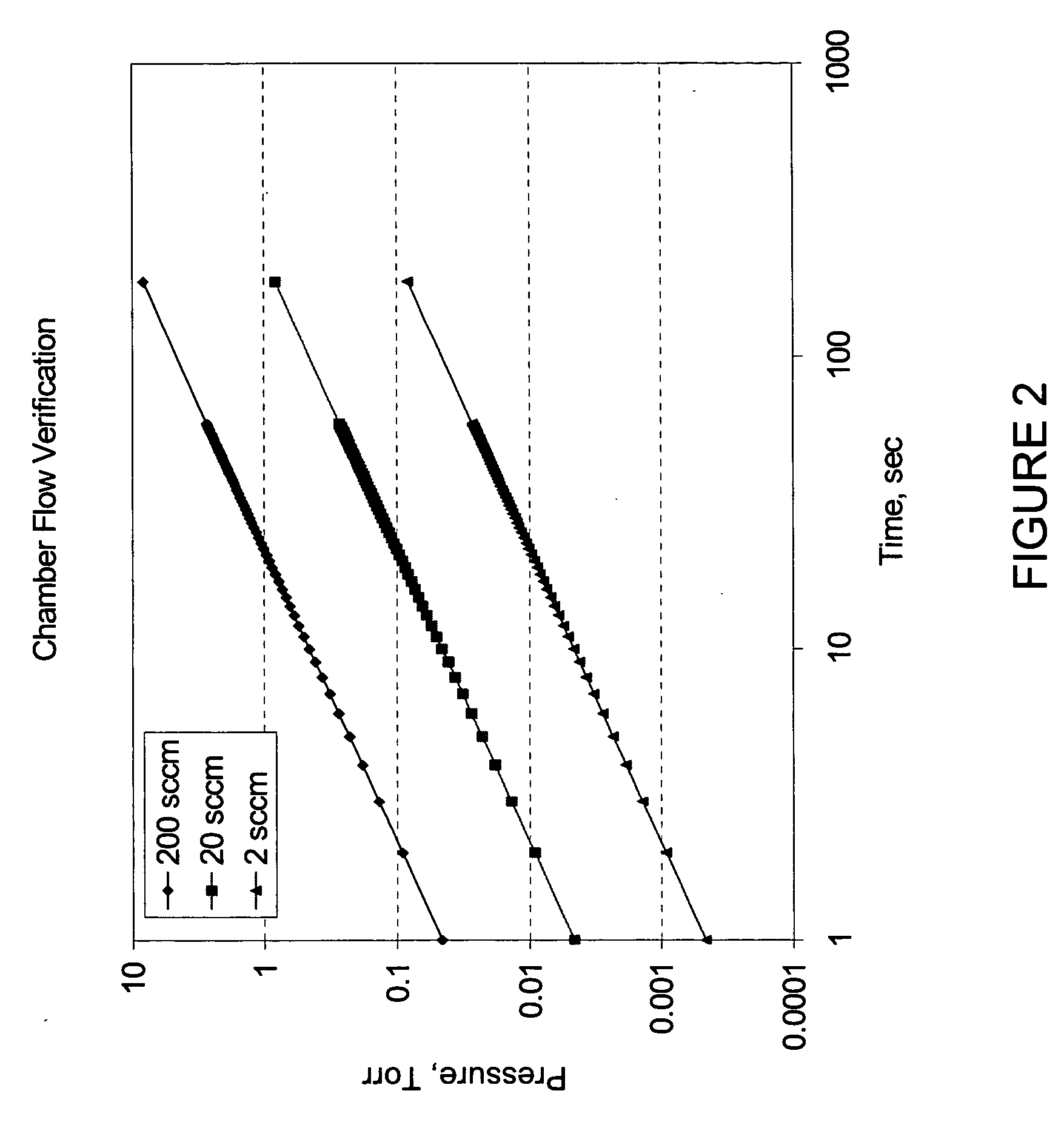
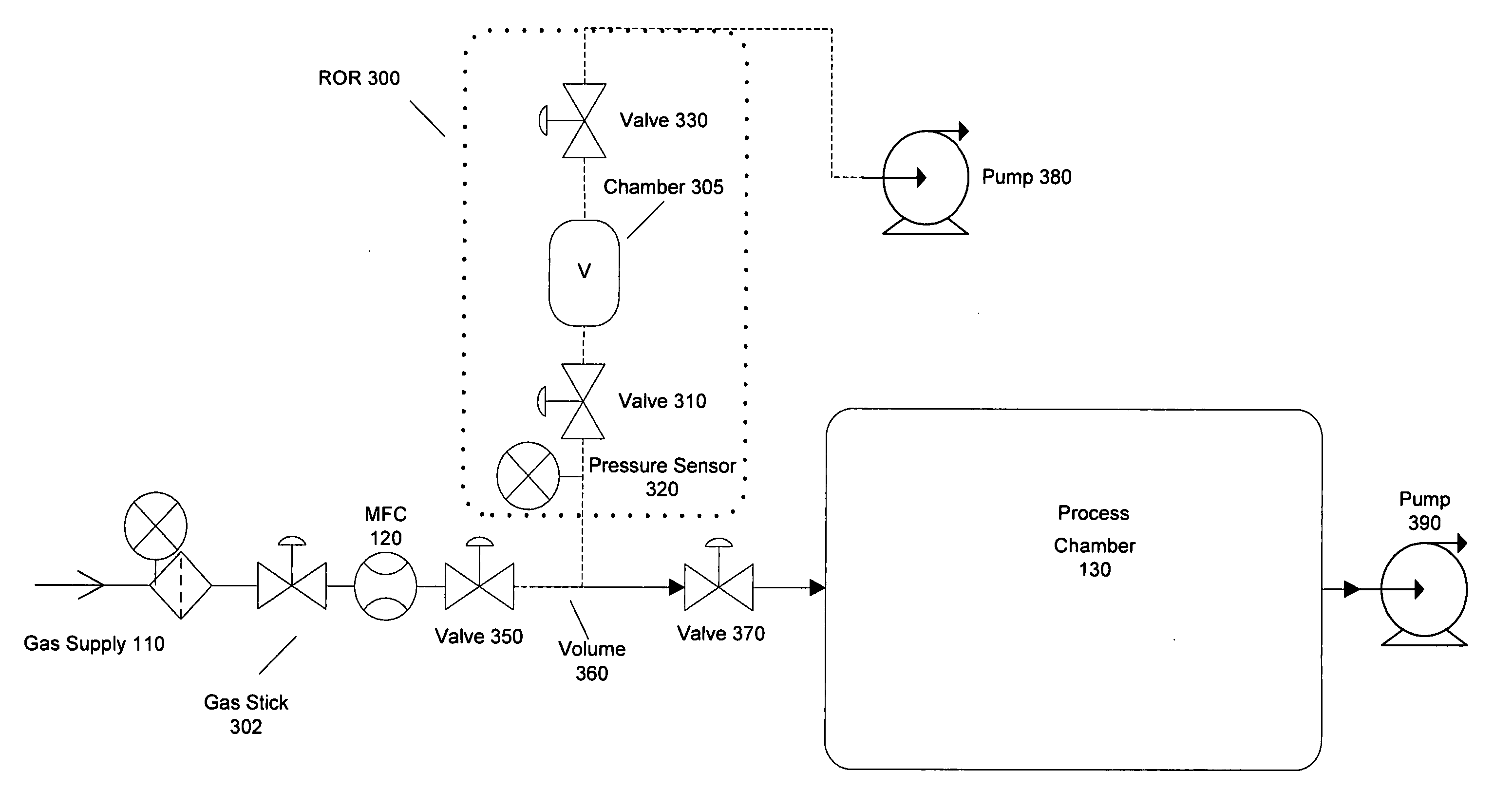
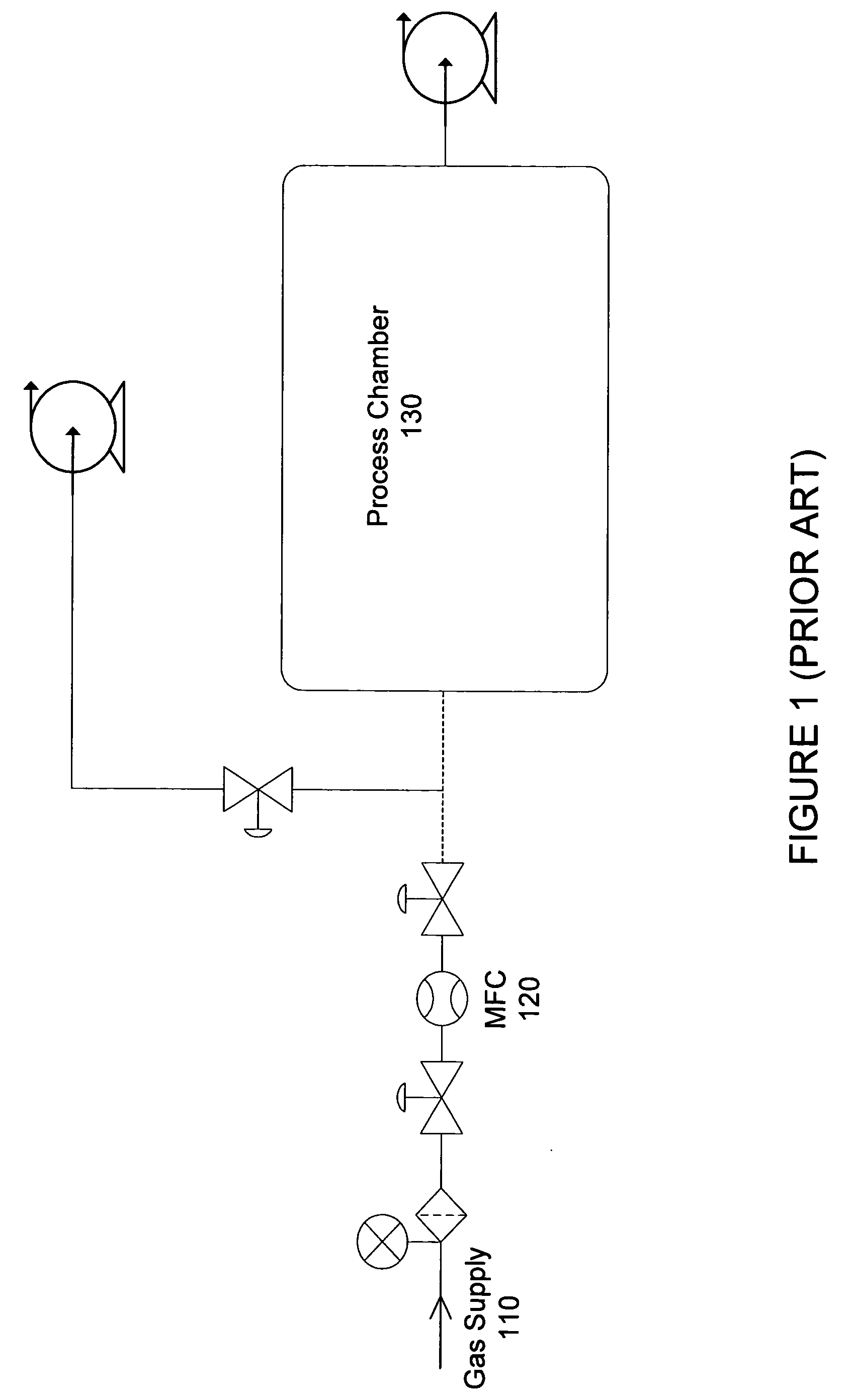
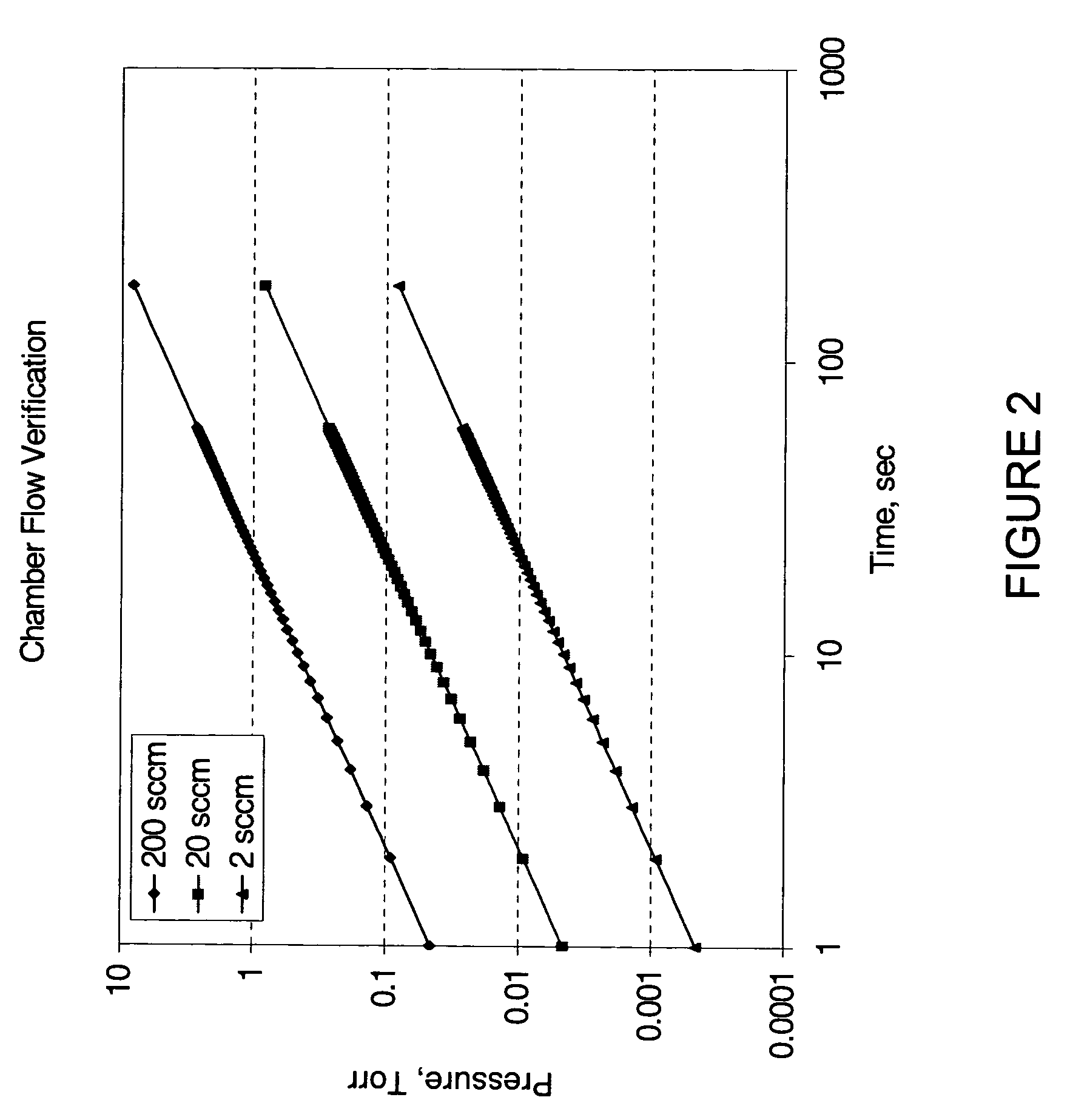
Method and system for flow measurement and validation of a mass flow controller
ActiveUS20060011237A1Operating means/releasing devices for valvesTesting/calibration apparatusEngineeringVerification and validation
Systems and methods for flow verification and validation of mass flow controllers are disclosed. A mass flow controller may be commanded to a specified flow and flow measurement commenced. During an interval, gas is accumulated in a first volume and measurements taken within this volume. The various measurements taken during the interval may then be used to calculate the flow rate. The flow rate, in turn, may be used to determine the accuracy of the mass flow controller relative to a setpoint.
Owner:ENTEGRIS INC +1
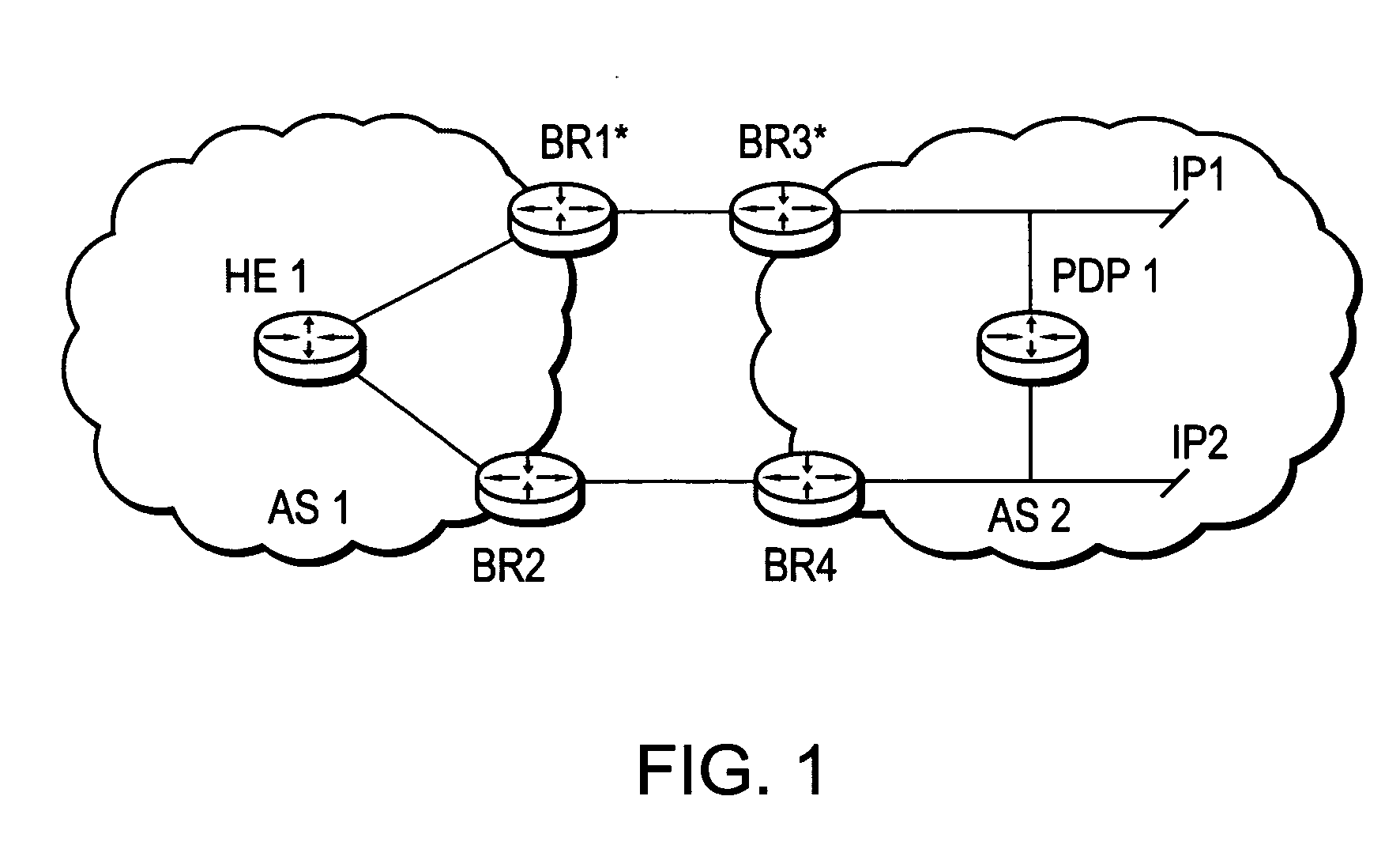
System and method for verifying and restoring the consistency of inode to pathname mappings in a filesystem
InactiveUS20070067256A1Digital data processing detailsMultiple digital computer combinationsInodeOnline document
A system and method verifies and restores the consistency of inode to pathname mappings. In a first embodiment, an off-line verification procedure is modified to verify and correct the primary name inode to pathname mapping information within inodes of a file system. In a second embodiment, an on-line file system verification process is modified to verify inode to pathname mapping information upon the loading of each inode within the file system.
Owner:NETWORK APPLIANCE INC
System and method for the configuration of an automotive vehicle with modeled sensors
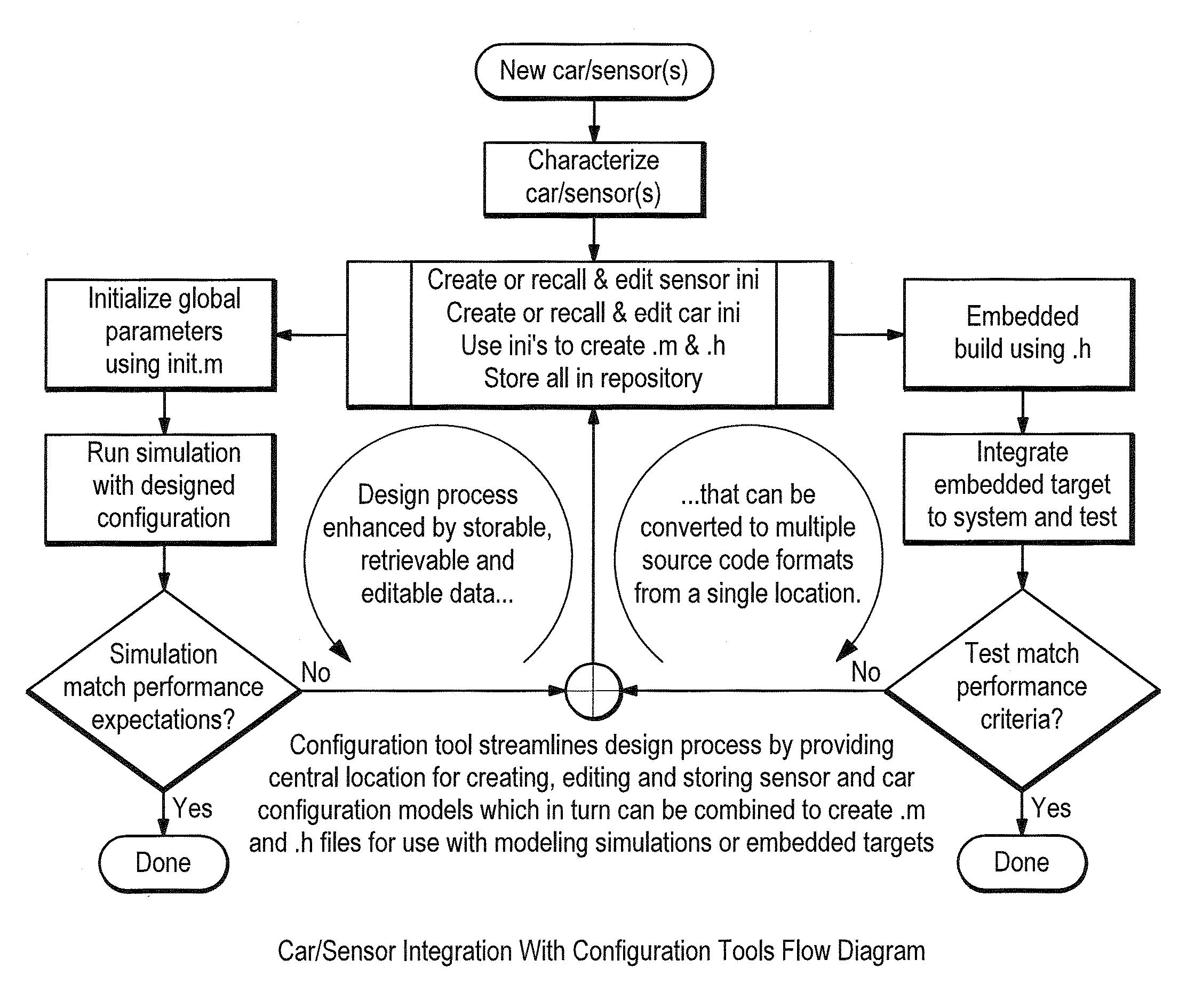
InactiveUS8417490B1Reduce process complexityProvide functionalityGeometric CADAnalogue computers for vehiclesAutomotive softwareData modeling
A system and methods are disclosed for providing integrated software development environment for the design, verification and validation of advanced automotive safety systems. The system allows automotive software to be developed on a host computer using a collection of computer programs running simultaneously as processes and synchronized by a central process. The software disclosed uses separate synchronized processes, permitting signals from disparate sources to be generated by a simulation running on the host computer or from actual sensors and data bus signals coming from and going to actual vehicle hardware which is connected to their bus counterparts in the host computer on a real-time basis. The methods disclosed are for providing an Algorithm Prototyping, Analysis and Test through an integrated framework for dynamic data modeling and application development.
Owner:AUTOBRILLIANCE LLC +1
Link discovery and verification procedure using loopback
InactiveUS20050083835A1Save implementation costMinimization requirementsLaser detailsError preventionCross connectionLoopback
Systems and methods for link discovery and verification technique that minimize the need for line termination resources that generate and interpret packets. Of two nodes verifying a link to one another, only one node need have any line termination capability. The node lacking line termination capability simply loops back packets generated by the other node thus verifying the link. Thus, an optical cross-connect can verify links to a wide variety of node types by employing a single line termination unit capable of terminating any suitable packet type. Alternatively, a router can verify connectivity to an optical cross-connect even when the optical cross-connect lacks any line termination capability at all. This saves greatly on implementation costs for optical networks.
Owner:CISCO TECH INC
Dynamic enforcement of MPLS-TE inter-domain policy and QoS
InactiveUS20070019558A1Efficient mechanismError preventionFrequency-division multiplex detailsQuality of servicePolicy decision
A technique dynamically enforces inter-domain policy and quality of service (QoS) for Traffic Engineering (TE) Label Switched Paths (LSPs) between a local domain and a remote domain in a computer network. According to the enforcement technique, a Path Computation Element (PCE) of the local domain receives a path computation request for an inter-domain TE-LSP from the remote domain, and triggers a policy verification procedure at a Policy Decision Point (PDP) of the local domain. The PDP determines whether the requested TE-LSP is allowed based on configured policy for the remote domain and previously established TE-LSPs from the remote domain. In the event the requested TE-LSP is allowed and subsequently established, a Policy Enforcement Point (PEP) along the TE-LSP, e.g., a border router of the local domain or a dedicated server, updates the PDP with the state of the TE-LSP. In response to the update, the PDP returns a QoS template indicating configured QoS guidelines the PEP must enforce for that TE-LSP. If the TE-LSP is eventually torn down, the PEP again updates the PDP with the state of the TE-LSP.
Owner:CISCO TECH INC
System and method for verifying and restoring the consistency of inode to pathname mappings in a filesystem
InactiveUS7707193B2Digital data processing detailsMultiple digital computer combinationsInodeOnline document
A system and method verifies and restores the consistency of inode to pathname mappings. In a first embodiment, an off-line verification procedure is modified to verify and correct the primary name inode to pathname mapping information within inodes of a file system. In a second embodiment, an on-line file system verification process is modified to verify inode to pathname mapping information upon the loading of each inode within the file system.
Owner:NETWORK APPLIANCE INC
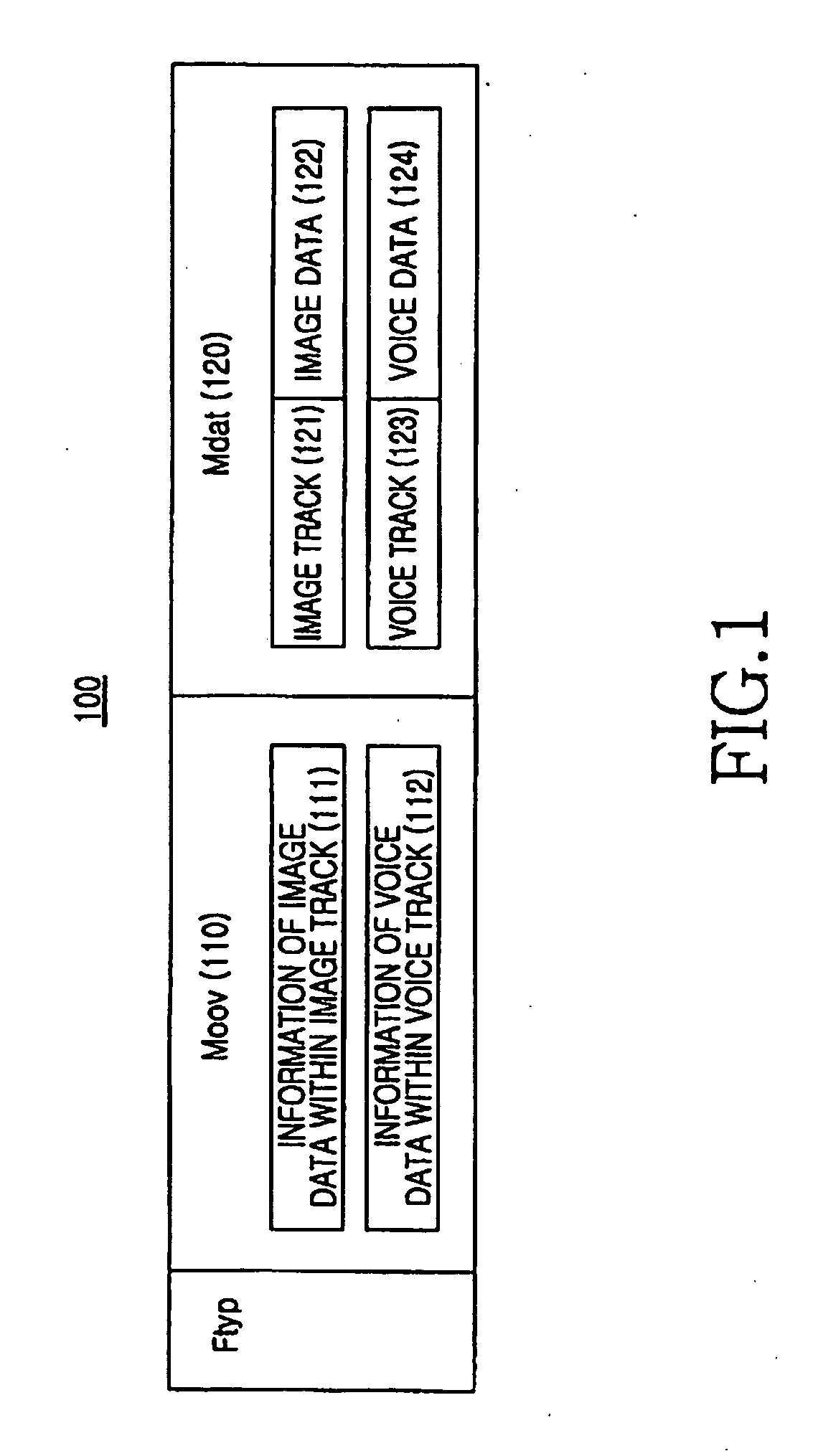
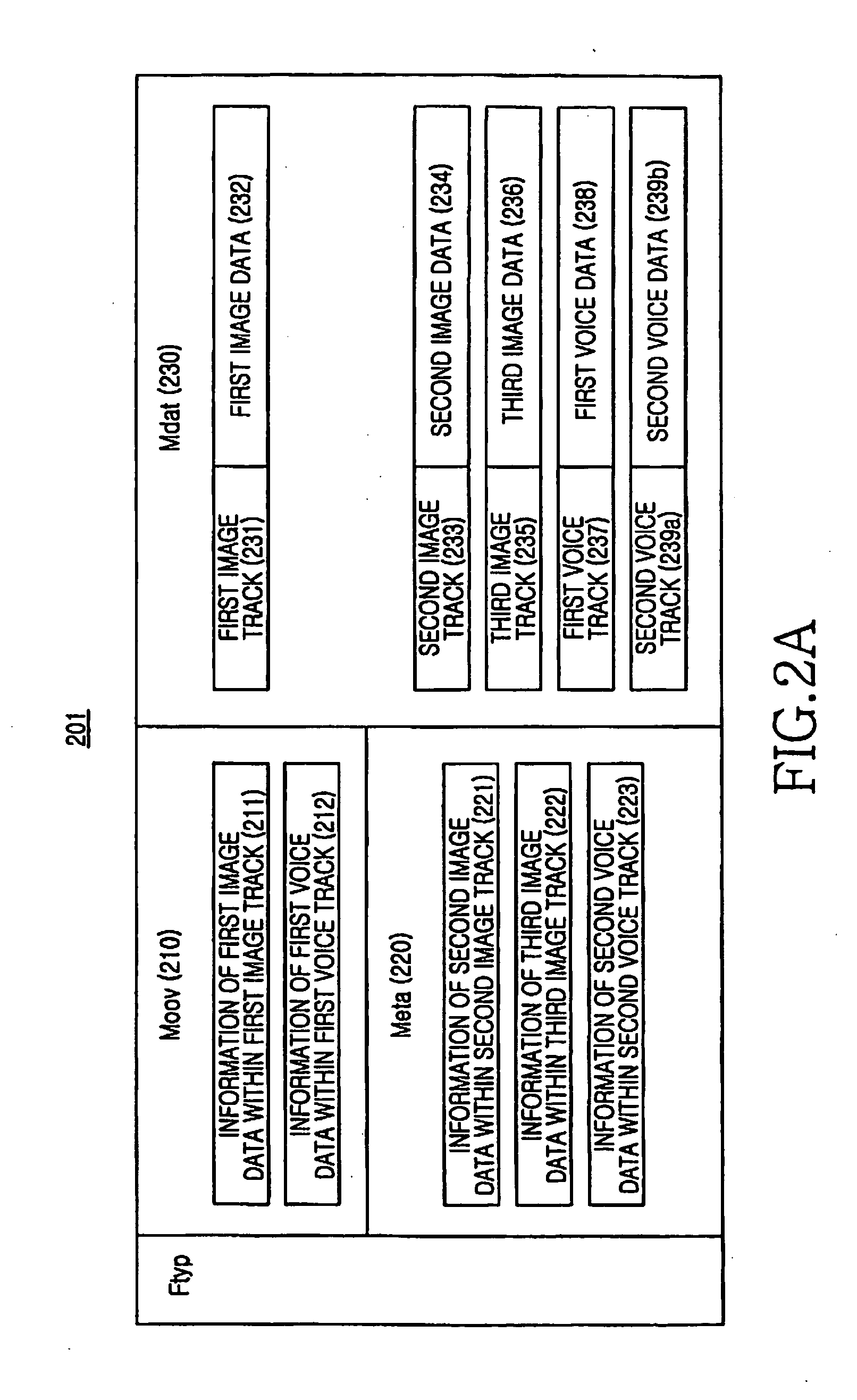
System and method for generating and reproducing 3D stereoscopic image file including 2d image
A method for controlling moving picture encoding using channel information of wireless networks is provided. By the method, it is possible to use a pre-verified standard technology in the prescription of a stereoscopic image file format, thereby simplifying a verification procedure for a new standard. Also, it is possible to use a new a stereoscopic image file format, thereby selecting, generating, and reproducing either of a 2D image file or a 3D stereoscopic image file. In particular, according to a system and a method for using a file format used to generate a 3D stereoscopic image, it is possible to reproduce and display a caption in the form of a 2D image during reproduction of the 3D stereoscopic image, thereby reducing eyestrain of a user, and additionally providing an image such as news, or an advertisement, to a user.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for flow measurement and validation of a mass flow controller
ActiveUS20060005882A1Accurately determineMinimize false flow conditionOperating means/releasing devices for valvesTesting/calibration apparatusStream flowValidation methods
Systems and methods for flow verification and validation of mass flow controllers are disclosed. A mass flow controller may be commanded to a specified flow and flow measurement commenced. Gas is accumulated in a first volume and while measurements are taken within this volume. Gas may then flow into a second volume while measurements are taken. The various measurements taken during the two intervals may then be used to calculate the flow rate. The flow rate, in turn, may be used to determine the accuracy of the mass flow controller relative to a setpoint. Additionally, these systems and methods may utilize only one volume to perform flow verification by flowing gas into this volume, taking measurements, and calculating the flow rate based only upon this set of measurements.
Owner:BROOKS INSTRUMENT +1
Identity validation and verification system and associated methods
A computer implemented system and method verify and validate a user identity for enrollment in a secure personal dataset accessing system. A personal dataset includes identifiable attributes of the user. Using a computer, authenticity of an asserted user identity includes electronically verified identifiable attributes to form the personal dataset. A biometric identifier of the user is automatically captured for validating the identifiable attributes by confirming that the asserted identity matches the identifiable attributes. A traceable e-audit trail is provided in an enterprise infrastructure and bench mark performance indicator. A digital security element is generated and results in the user electronically receiving a password and a unique electronic address is assigned to the user. The digital security element is then transmitted to the user from the computer and enables electronic access to the personal dataset relating to the user, the personal dataset having been authenticated through the verification and validation.
Owner:KRAGH JAMES F
Private network link verification procedure in free space optical communication network
InactiveUS7079551B2Multiplex system selection arrangementsError preventionTelecommunications linkVerification procedure
A system and method for verifying the integrity of a communication link in a wireless optical communication network. The system and method include monitoring the communication link on at least two levels and enabling or disabling signaling over the communication link appropriately depending on events reported through the system.
Owner:INTELLECTUAL VENTURES FUND 83 LLC
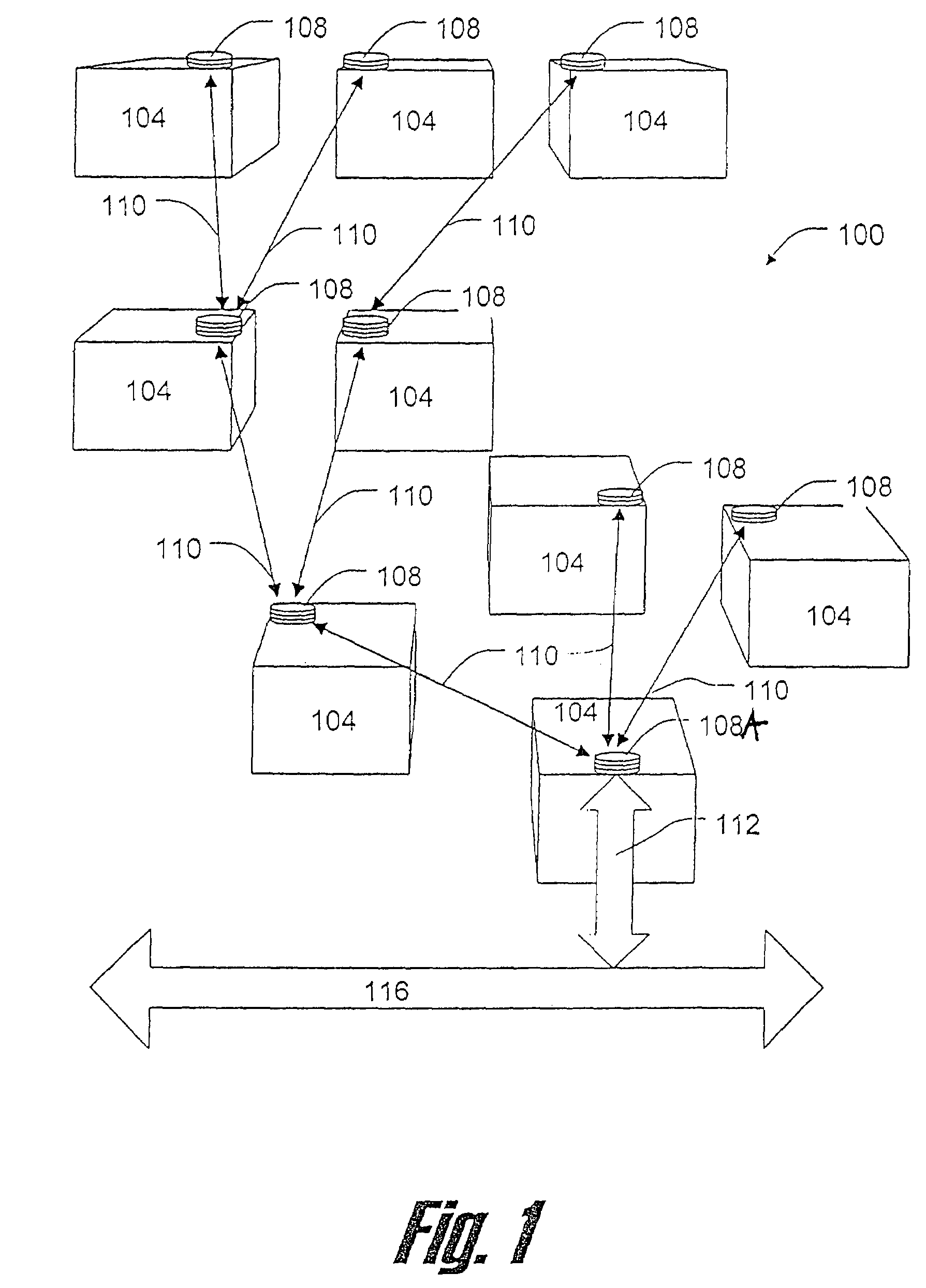
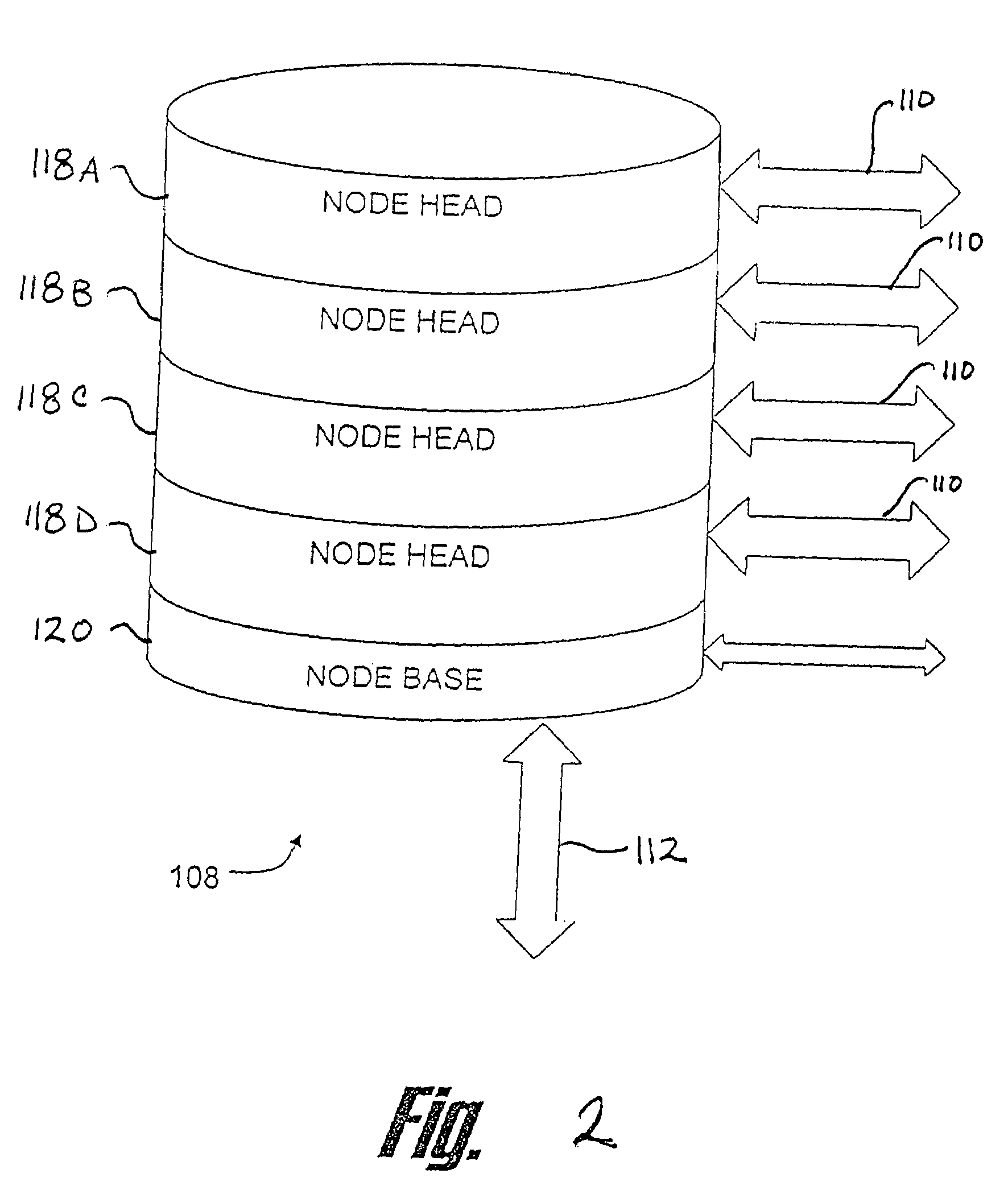
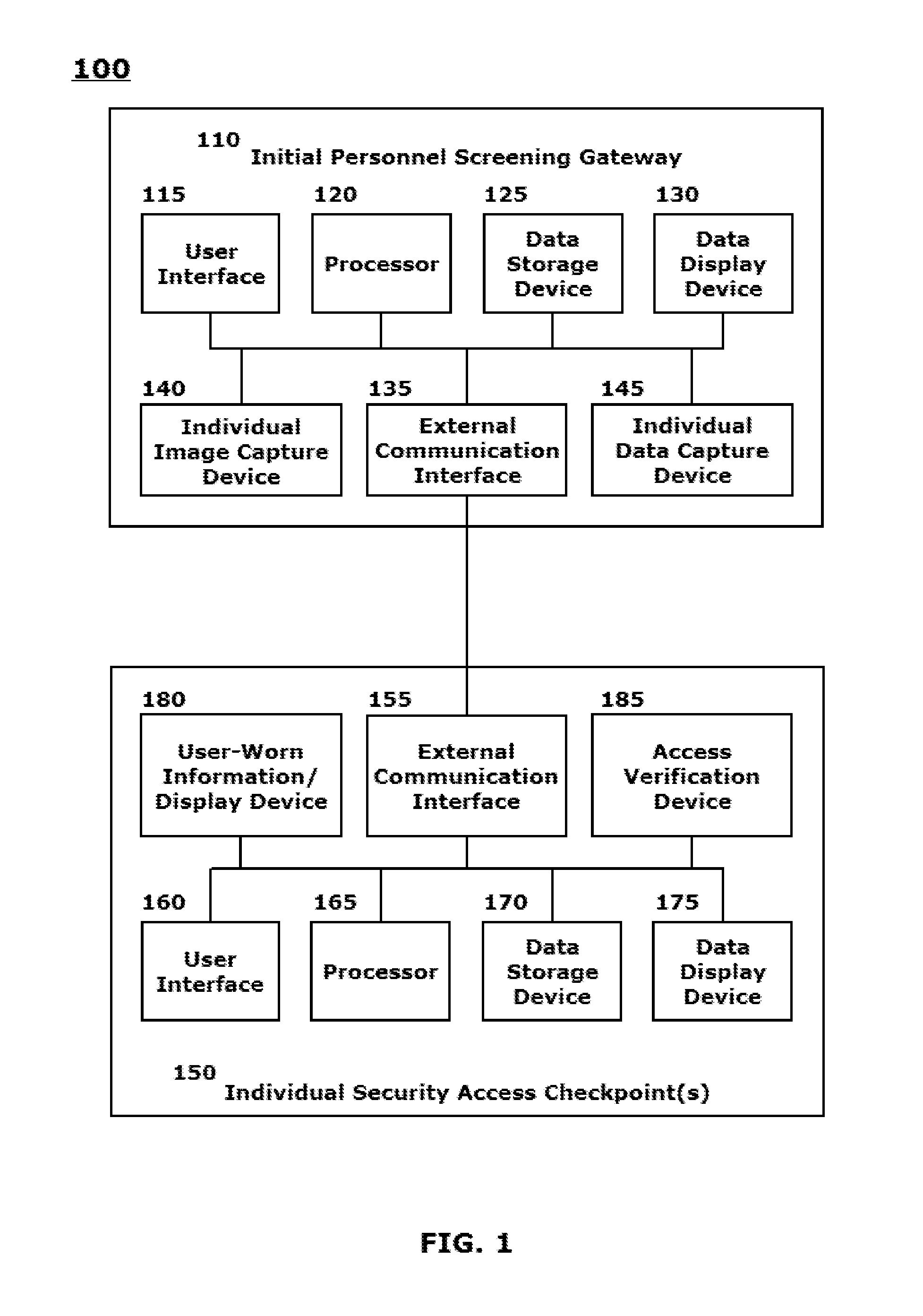
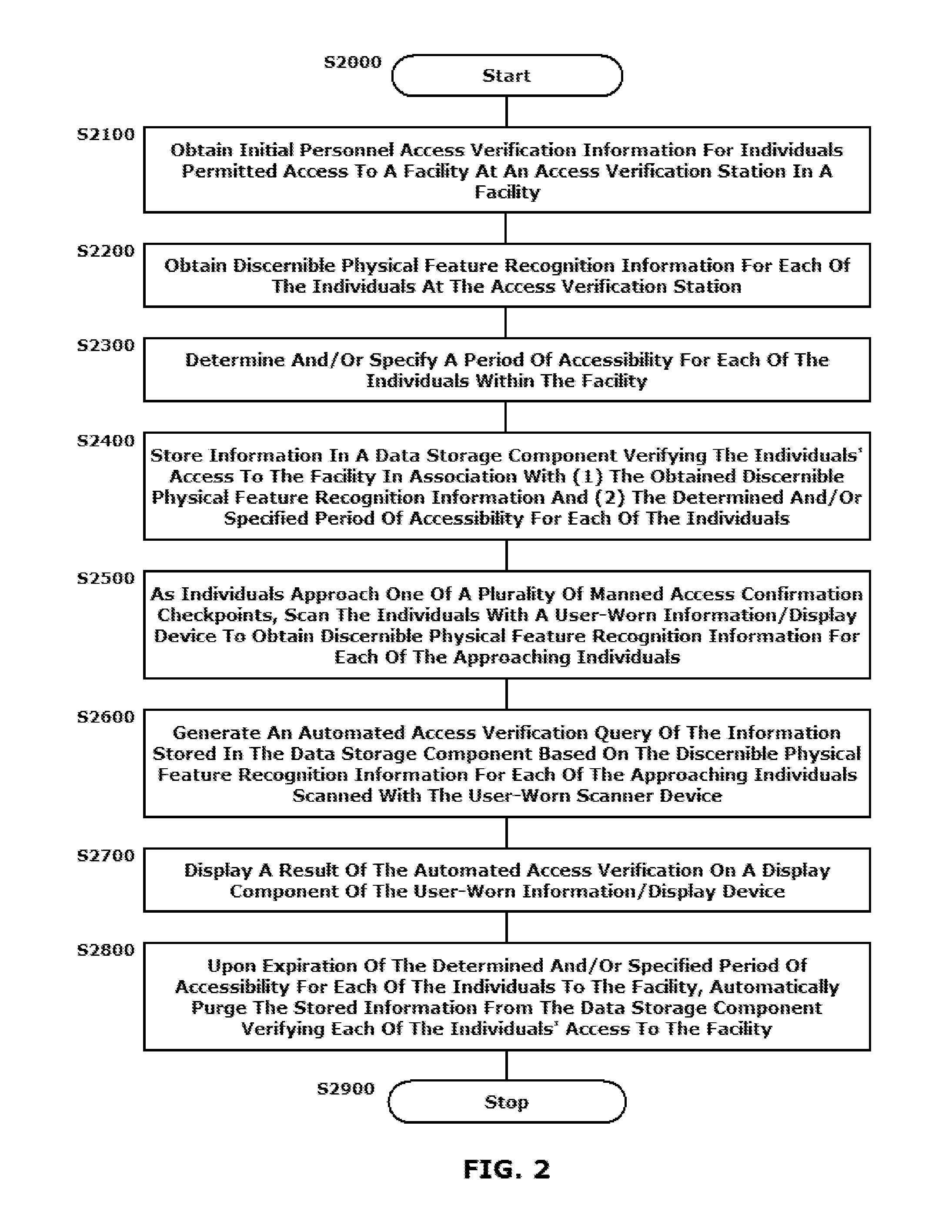
Image capture and individual verification security system integrating user-worn display components and communication technologies
ActiveUS9245175B1Improve securityReduce morbidityProgramme controlComputer controlScreening proceduresHuman interaction
A system and method are provided for integrating user-worn display components and communication technologies into image capture and individual verification security systems. User-worn input / output (I / O) devices are employed to streamline the security screening procedures that continue to require human interaction for visual identification of participating individuals entering secure areas, particularly in large numbers. Individual access credentials and / or permissions are verified for individuals initially upon entry within the facility, and discernible physical feature recognition information, including facial recognition information, to be associated with the access verification for the individuals is collected. The user-worn I / O devices are used by security and screening personnel to observe discernible physical features of individuals presenting themselves at one or more internal security or limited access checkpoints and to initiate comparison analysis of the observed discernible physical features with stored discernible physical feature recognition information to expedite clearance and / or verification procedures.
Owner:ROCKWELL COLLINS INC
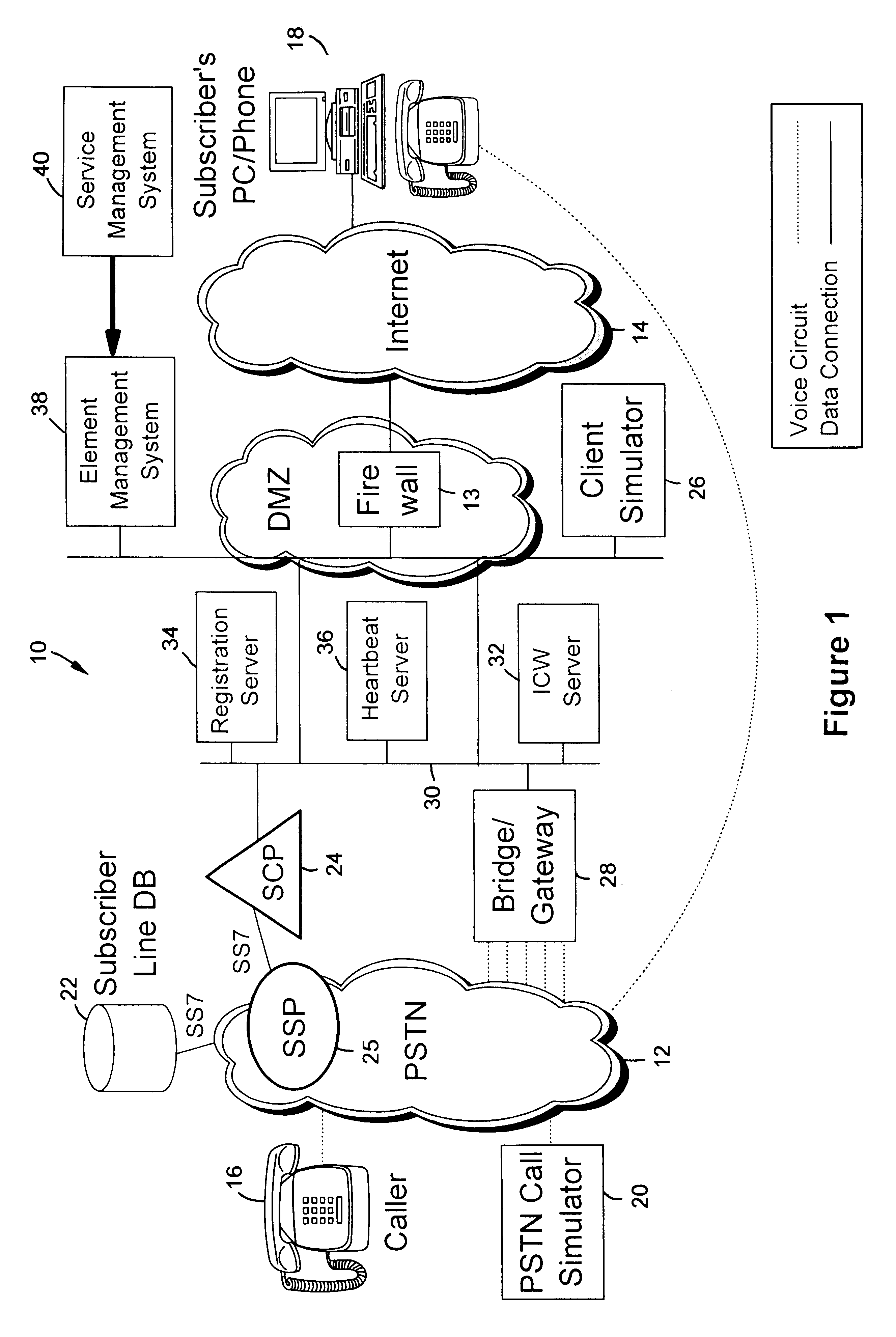
System and method of operation for verifying and validating public switch telephone networks (PSTN) to (IP) network services
A system verifies and validates PSTN to IP Network services prior to the availability of the services to a plurality of subscribers. A PSTN call generator services a plurality of callers coupled to the PSTN and to a test database. An IP client simulator is coupled to the test database and to an IP Network. A data bus couples the PSTN and the IP Network to a registration server for registering the client and a heartbeat server for tracking the system for heartbeat message. An application server processes test service calls from the PSTN call generator whereby PSTN-IP Network services can be executed for all clients or individual clients as represented by the IP Client simulator for verification and validation of PSTN services to IP Network clients prior to the availability of the services to the clients.
Owner:IBM CORP
Method for validating software development maturity
InactiveUS20050125272A1Software testing/debuggingSoftware metricsSoftware engineeringSoftware development
A validation procedure for assessing the status a software engineering process for compliance, and improving the measured compliance, with the Carnegie Mellon SEI / CMM Software Maturity Model includes a validation meeting in the course of which a validation team reviews deliverables demonstrative of the process being performed and asks a structured set of questions that are structured in accordance with the CMM and correlate with the deliverables.
Owner:NOKIA SOLUTIONS & NETWORKS OY
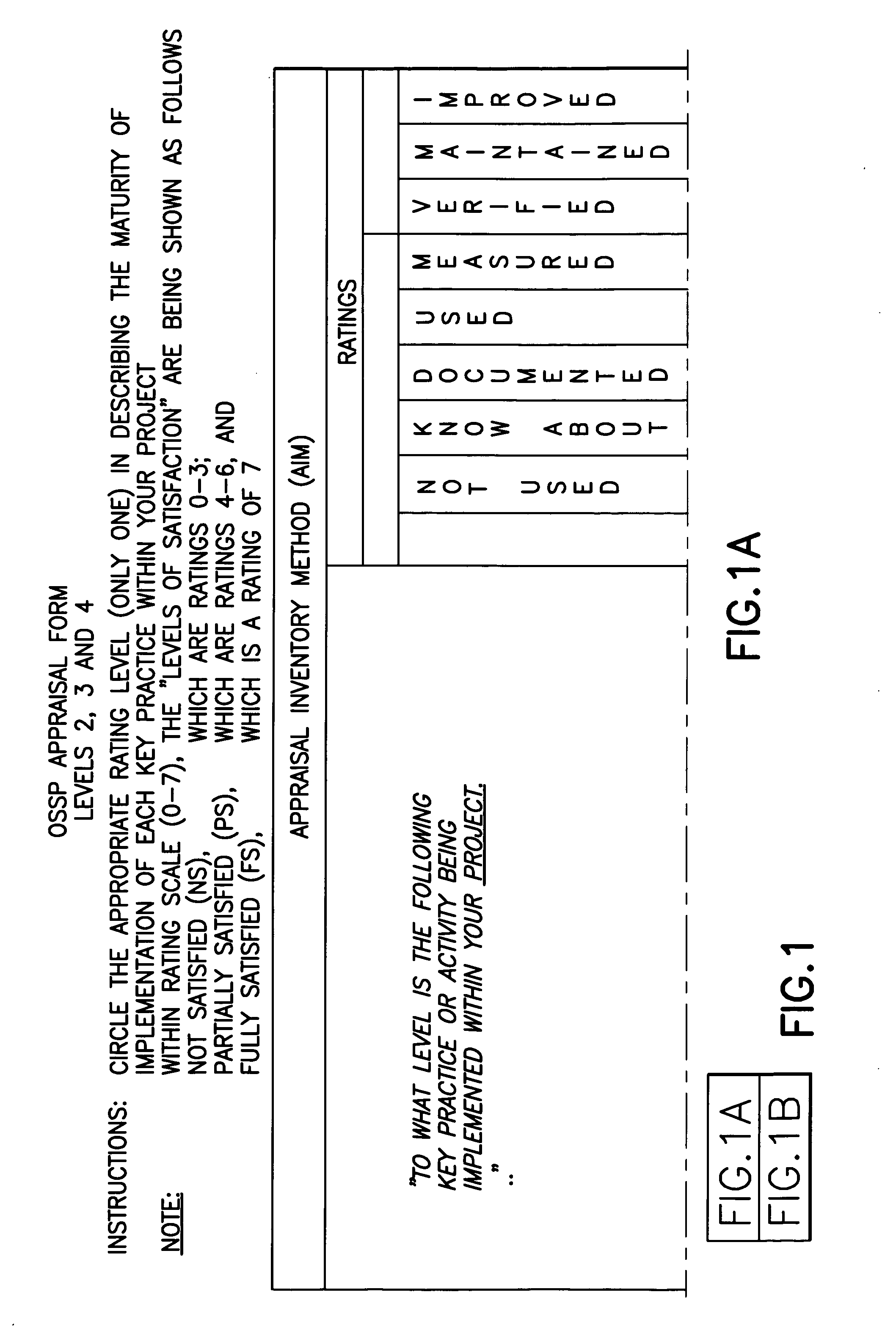
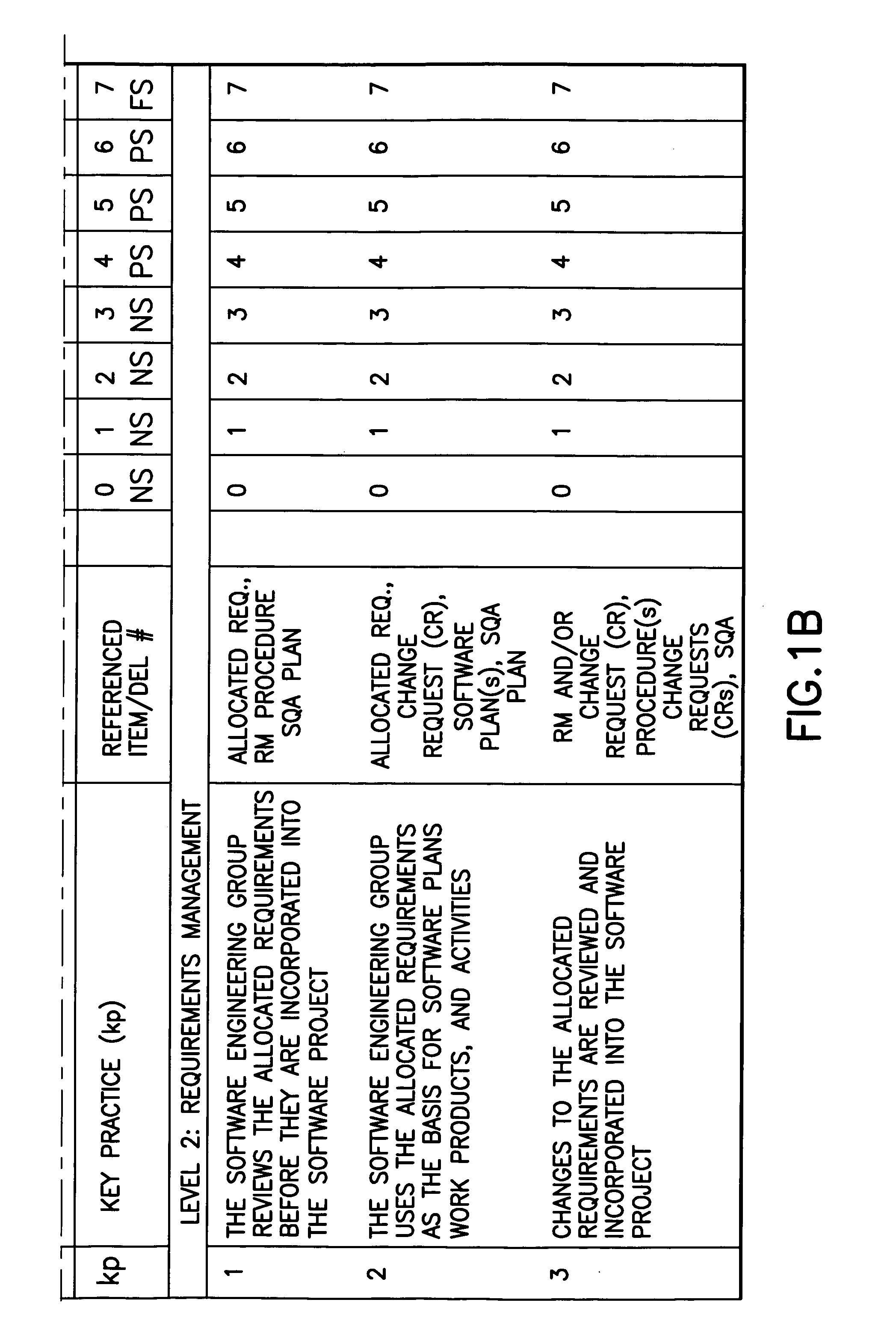
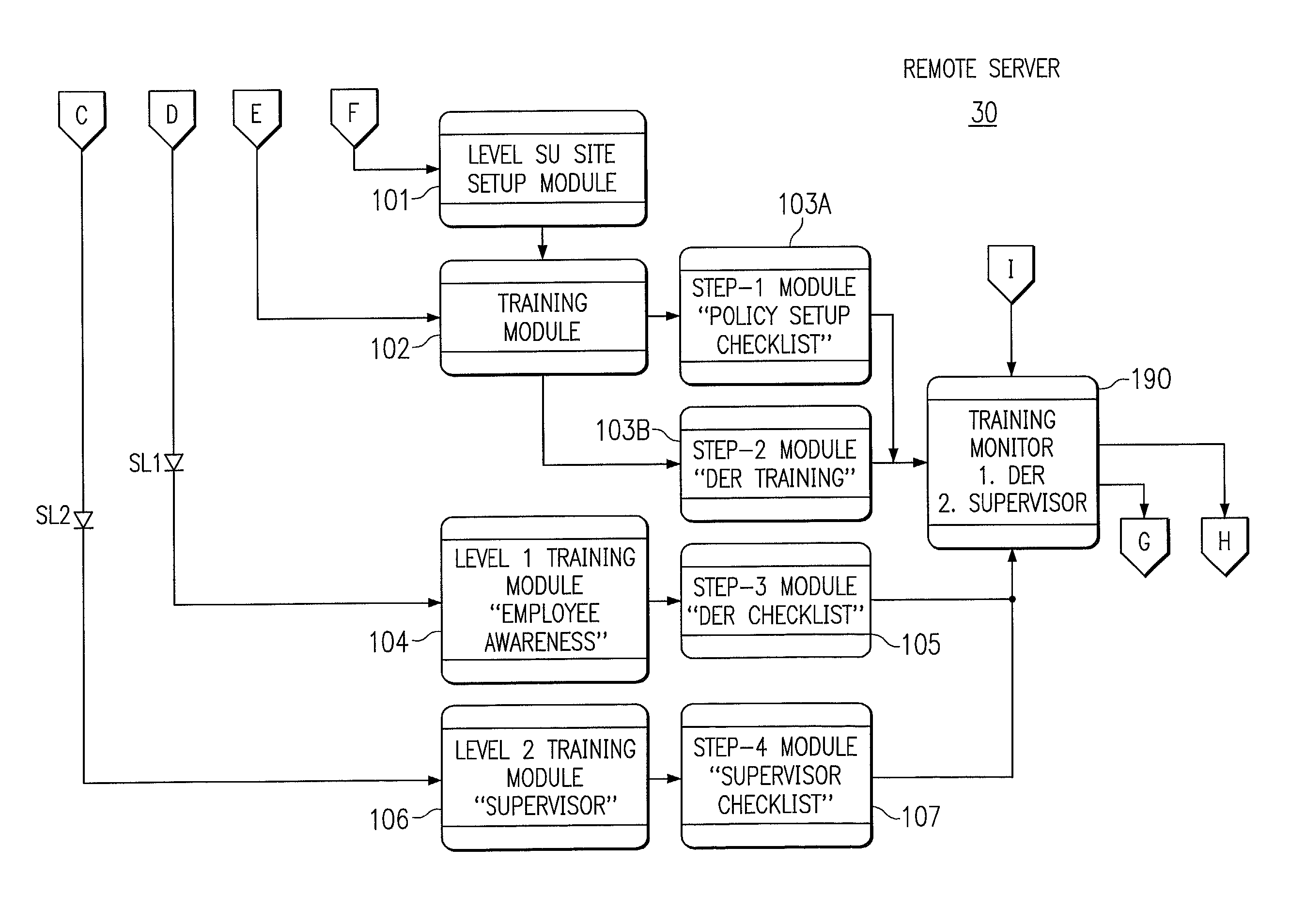
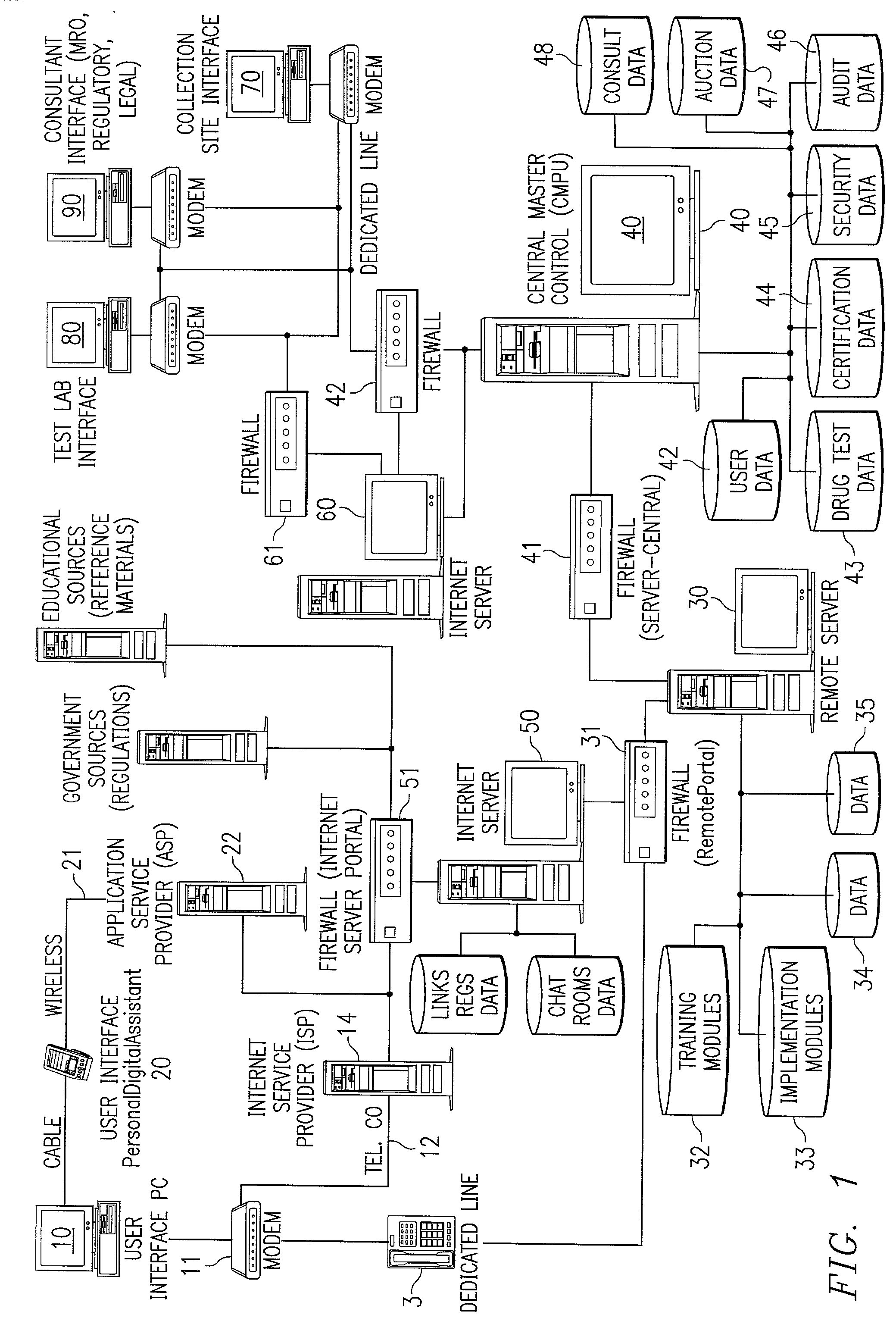
System and method for implementing an employee-rights-sensitive drug free workplace policy
InactiveUS20020198748A1Maximize employer conformanceReadily defensibleOffice automationSpecial data processing applicationsDrug-free workplaceGood practice
Owner:DRUG RISK SOLUTIONS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com