Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
386results about "Software metrics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
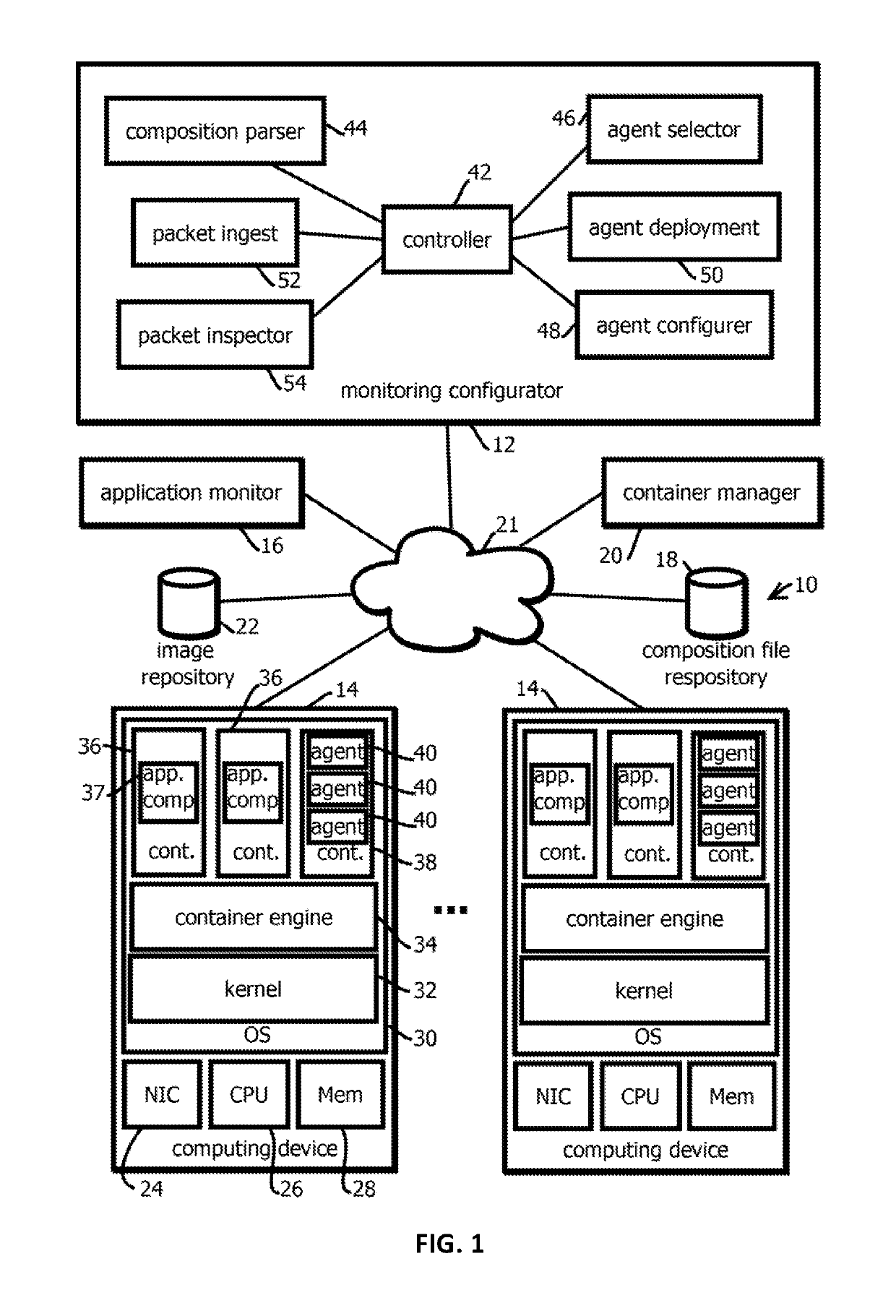
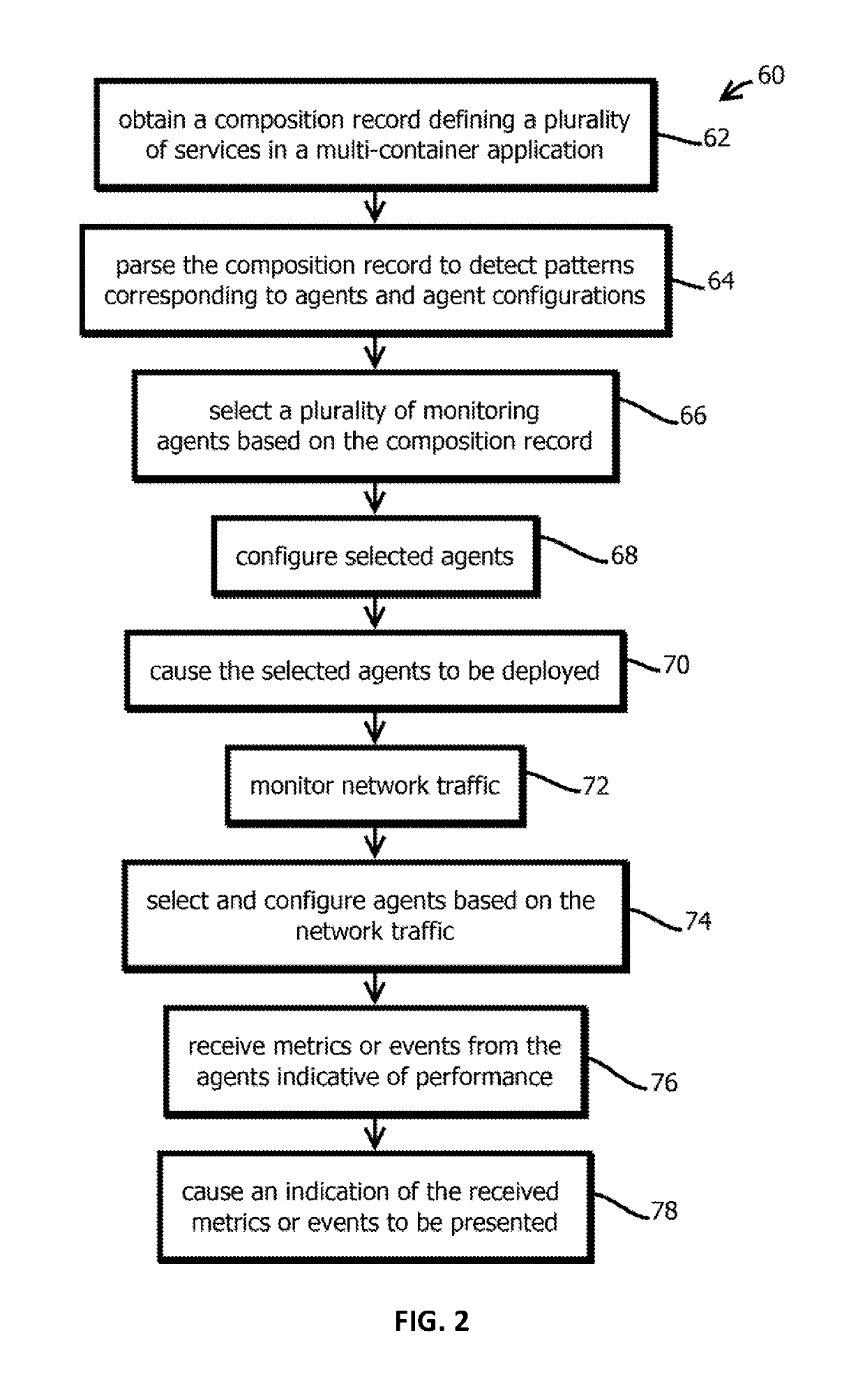
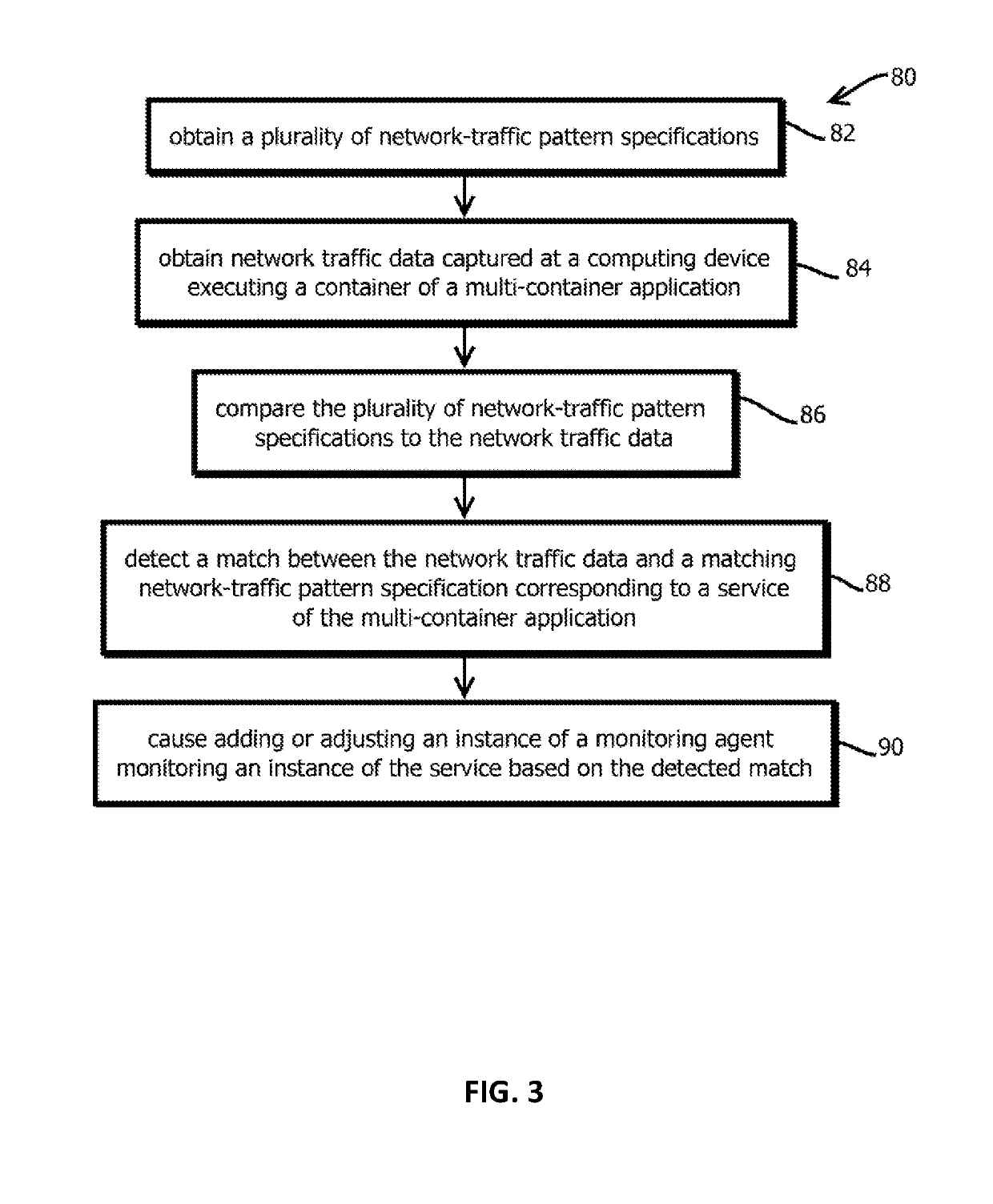
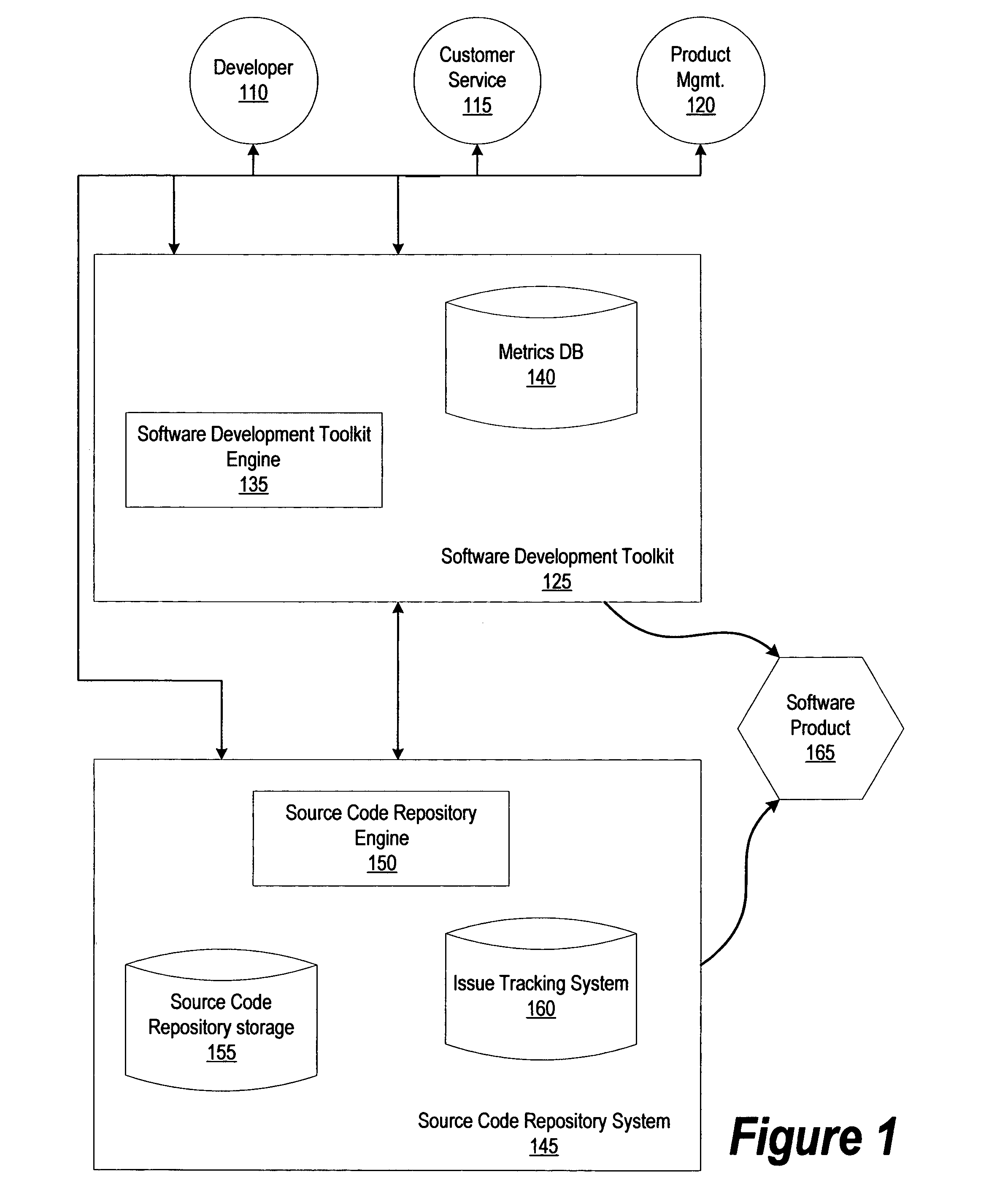
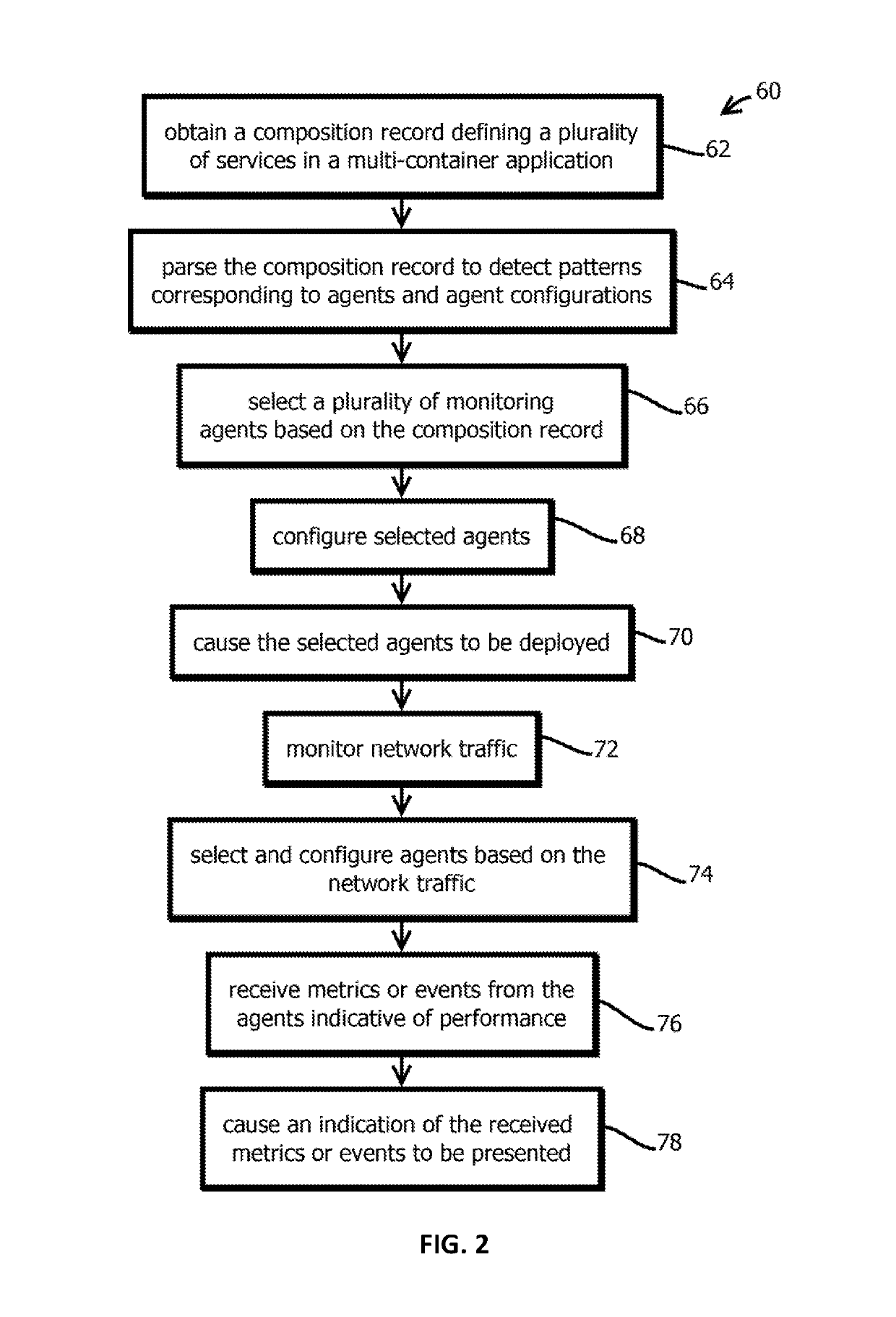
Introspection driven monitoring of multi-container applications
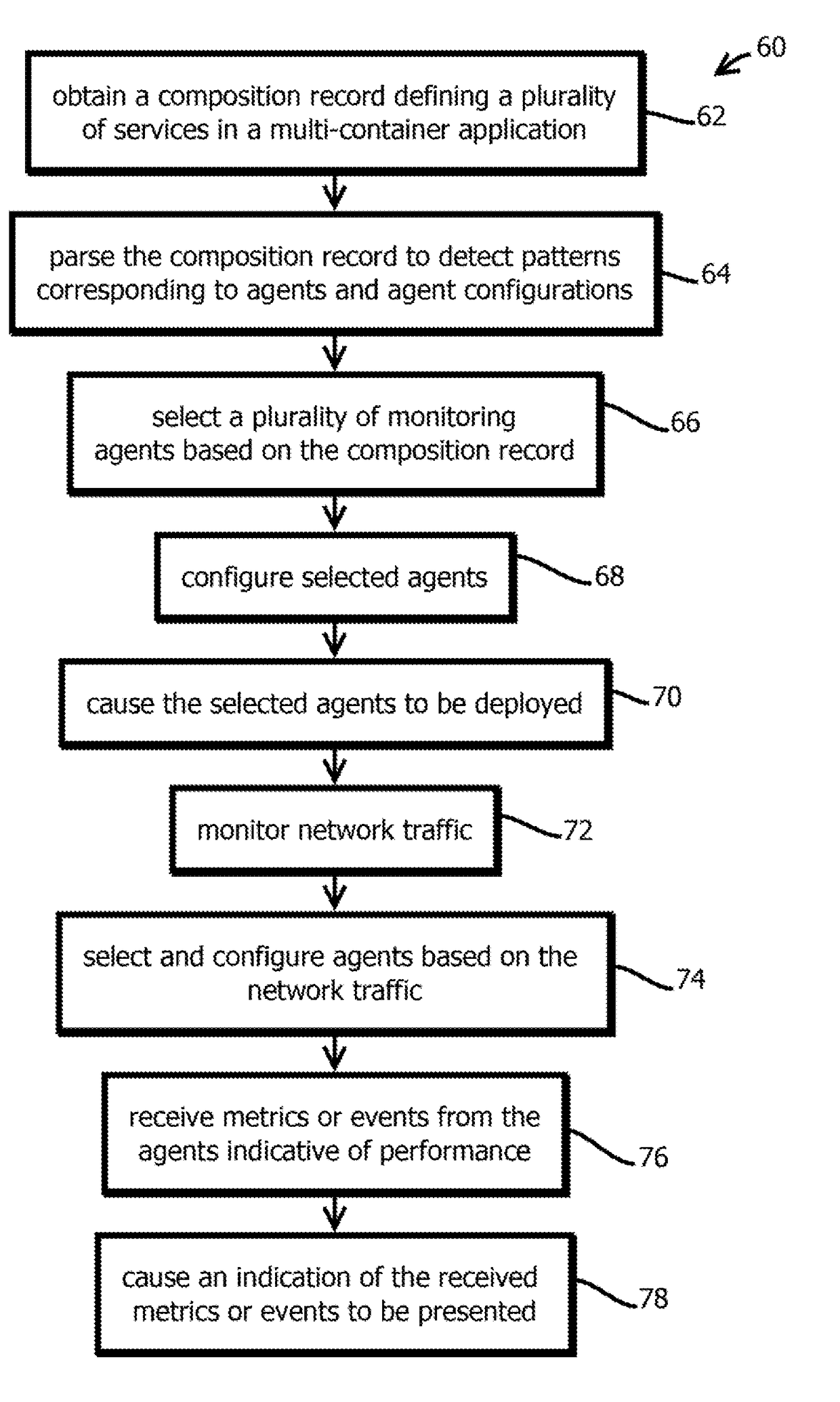
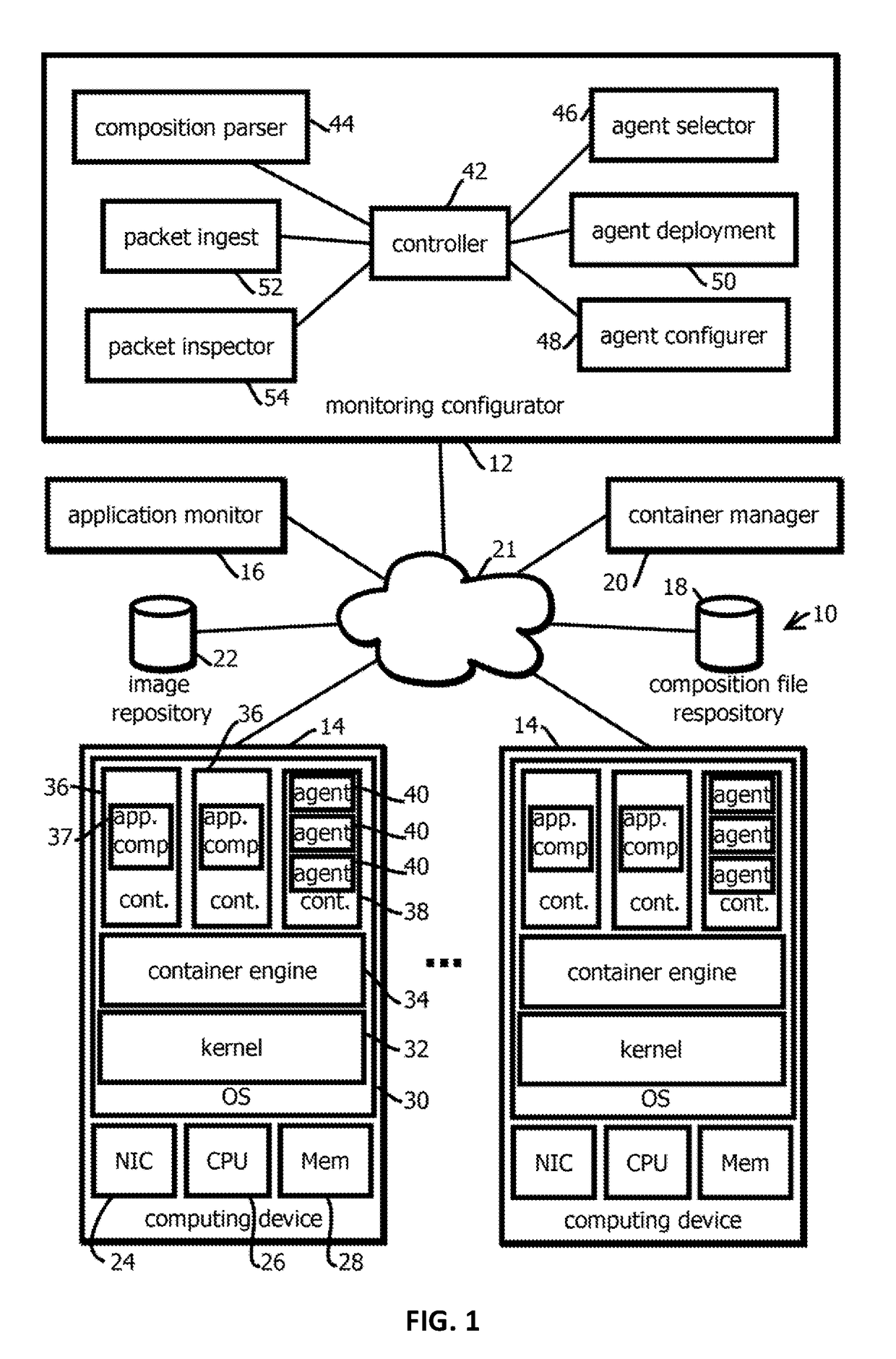
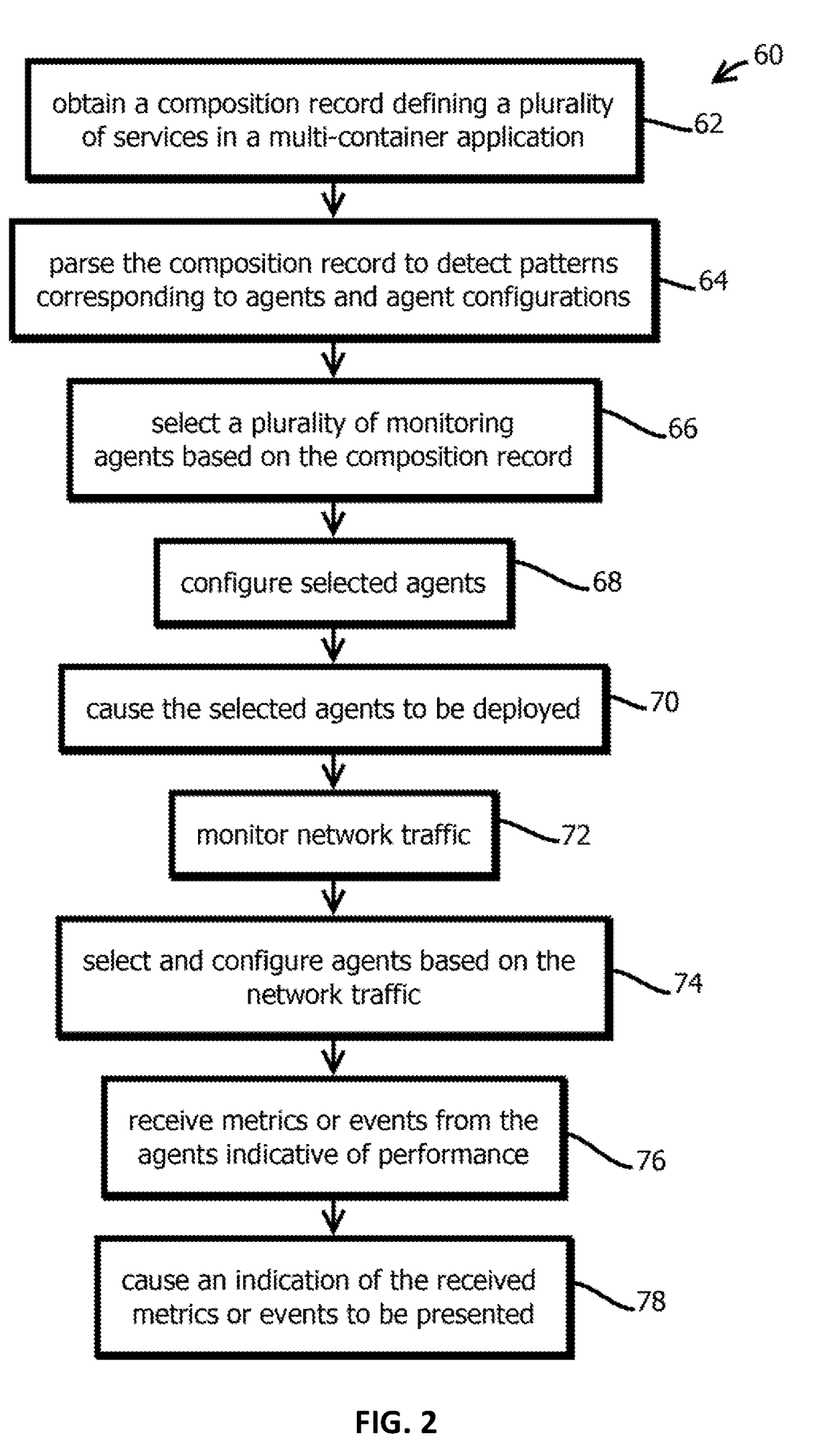
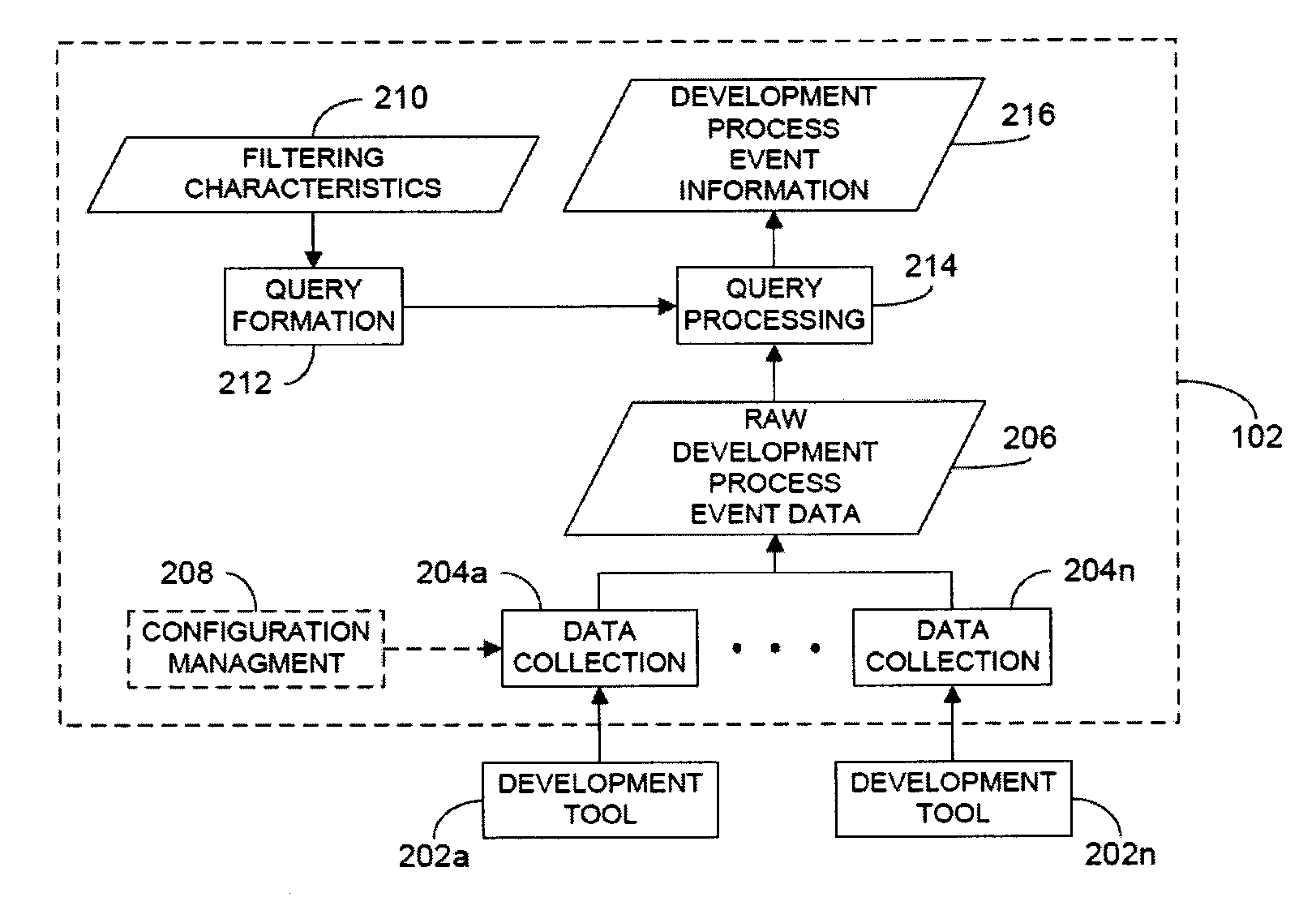
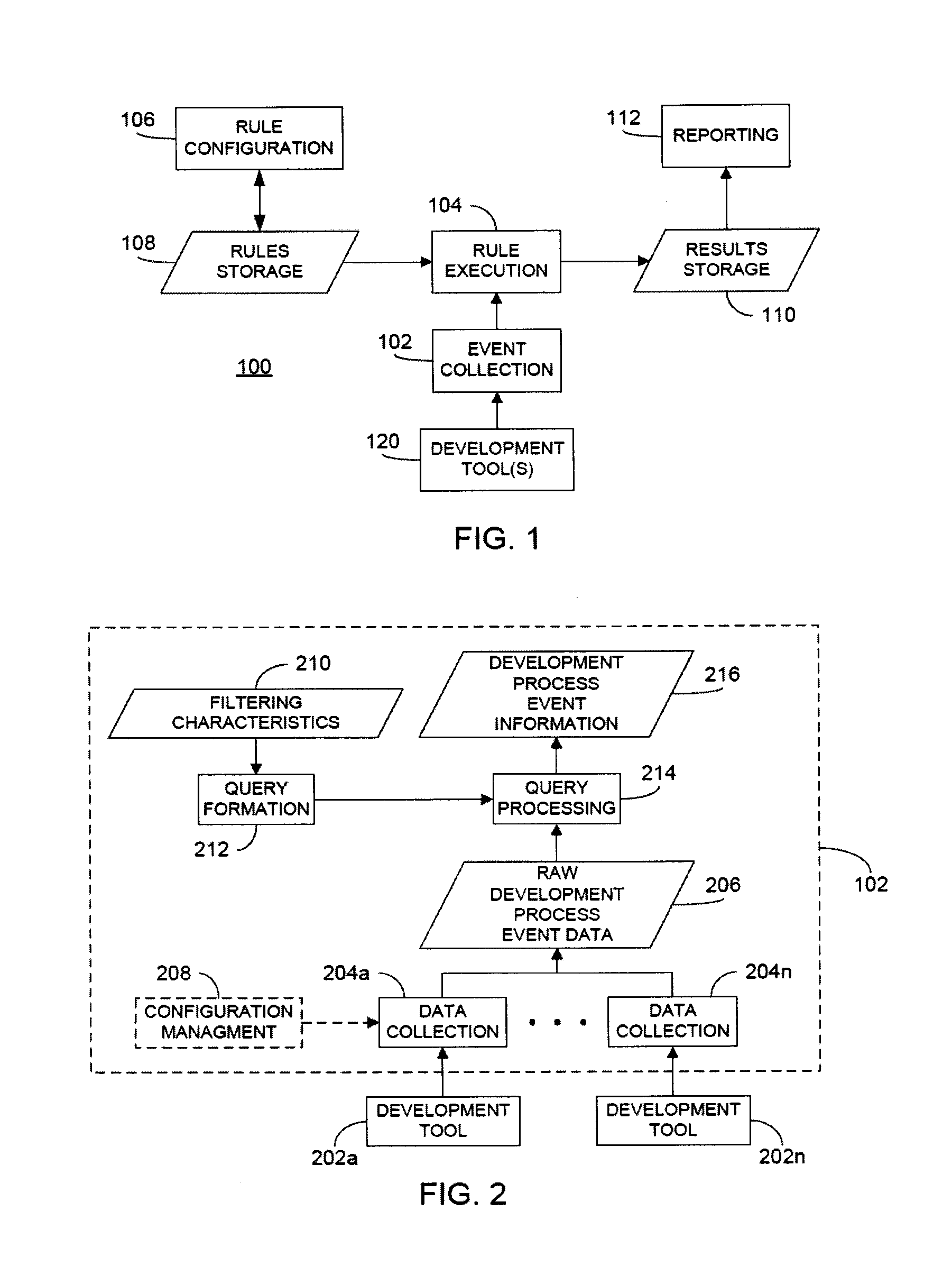
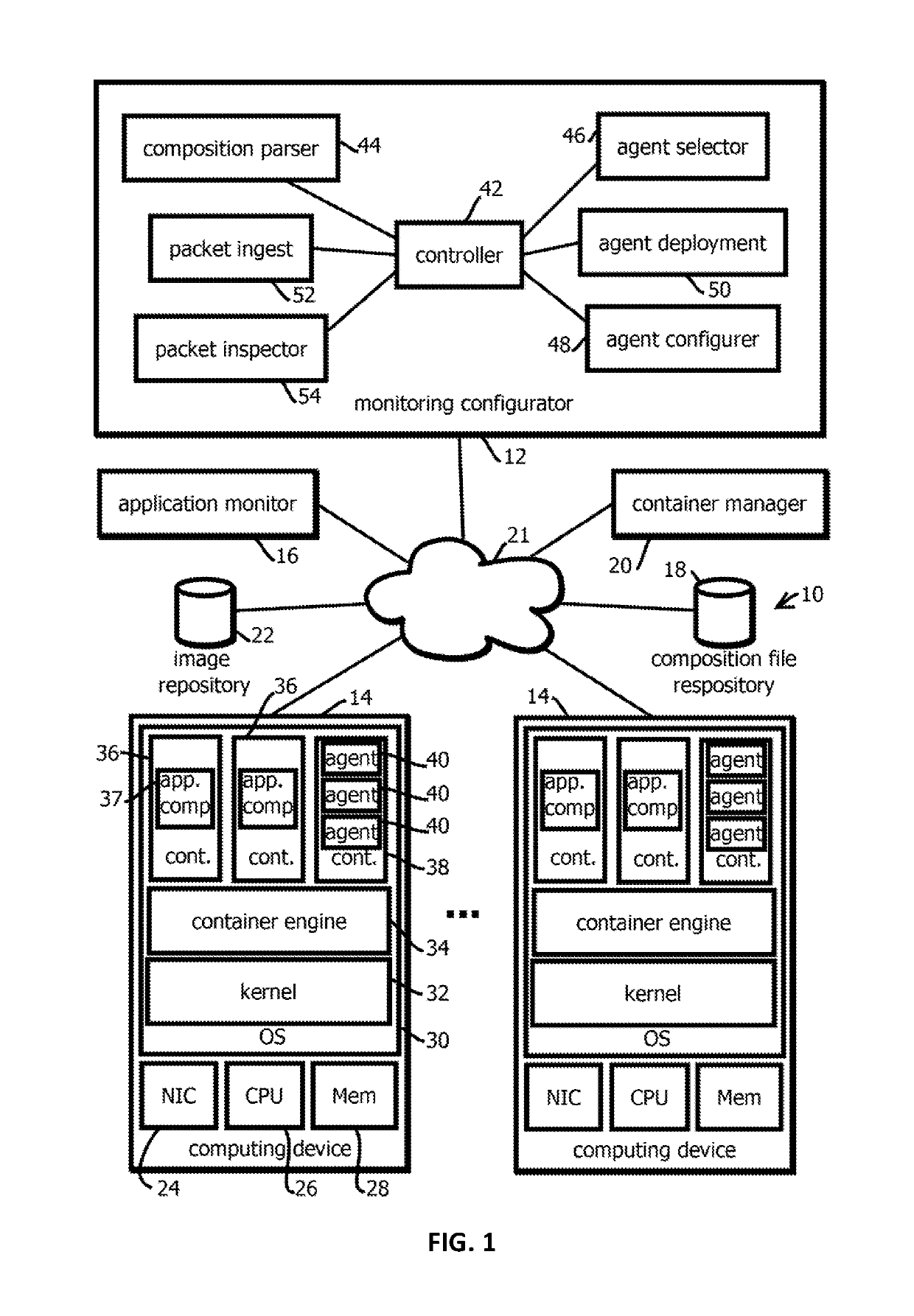
Provided is a process, including: obtaining a composition record defining at least one service of a multi-container application; selecting a plurality of infrastructure or application performance monitoring agents based on the composition record defining the multi-container application; causing the selected agents to be deployed on one or more computing devices executing the multi-container application; receiving metrics or events from the agents indicative of performance of at least part of the multi-container application or at least some of the one or more computing devices executing the multi-container application; and causing an indication of the received metrics or events to be presented.
Owner:CA TECH INC
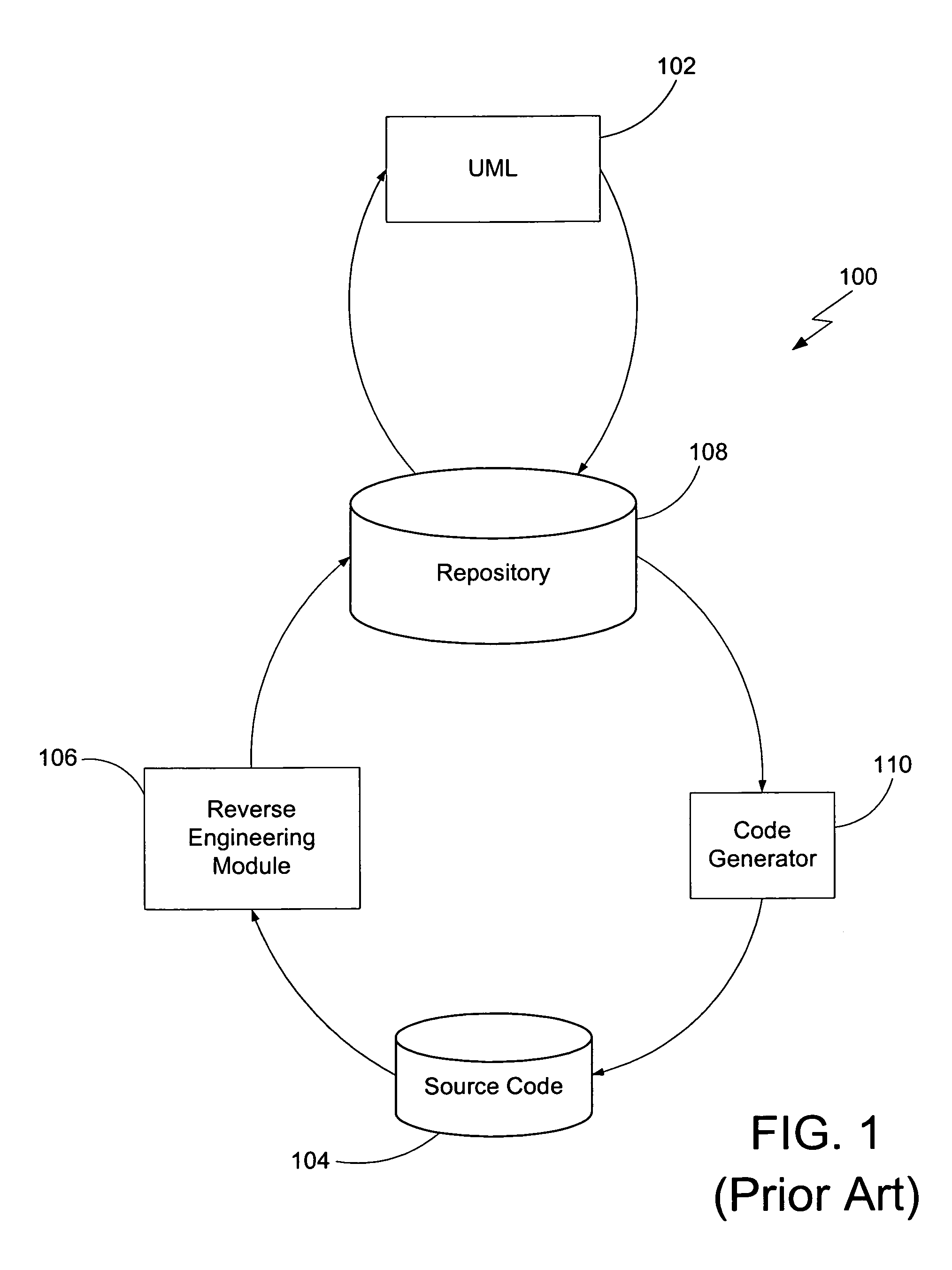
Method and system for displaying changes of source code
InactiveUS6993710B1Overcome limitationsVersion controlDigital computer detailsGraphicsSoftware development
Methods and systems consistent with the present invention provide an improved software development tool which displays versions of source code with the indications of the edits in a graphical representation, wherein the graphical representation of the source code is not merely a text representation on a user interface. Each version reflects an instance in an edit history, i.e., reflects the changes made to the source code.
Owner:BORLAND
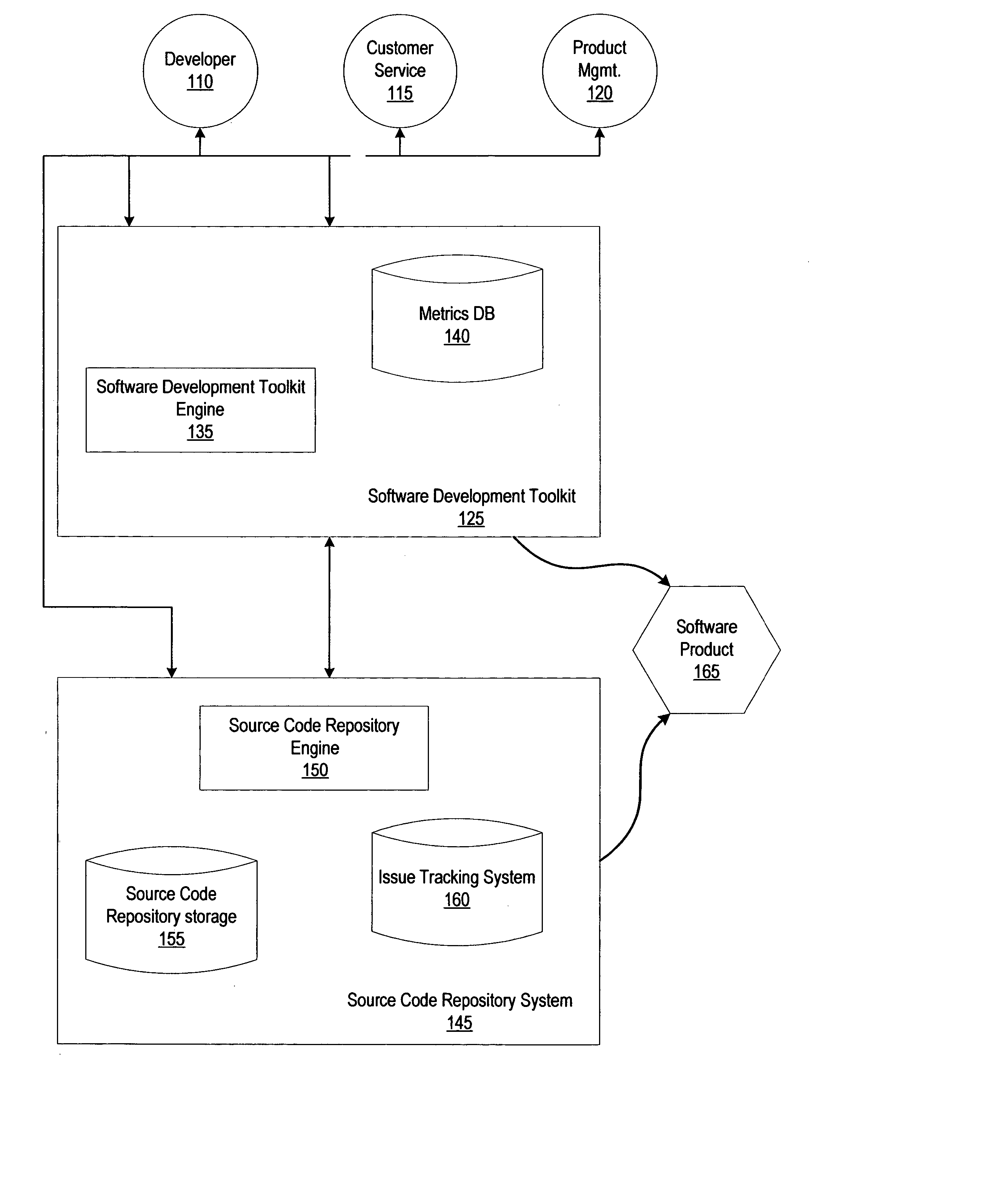
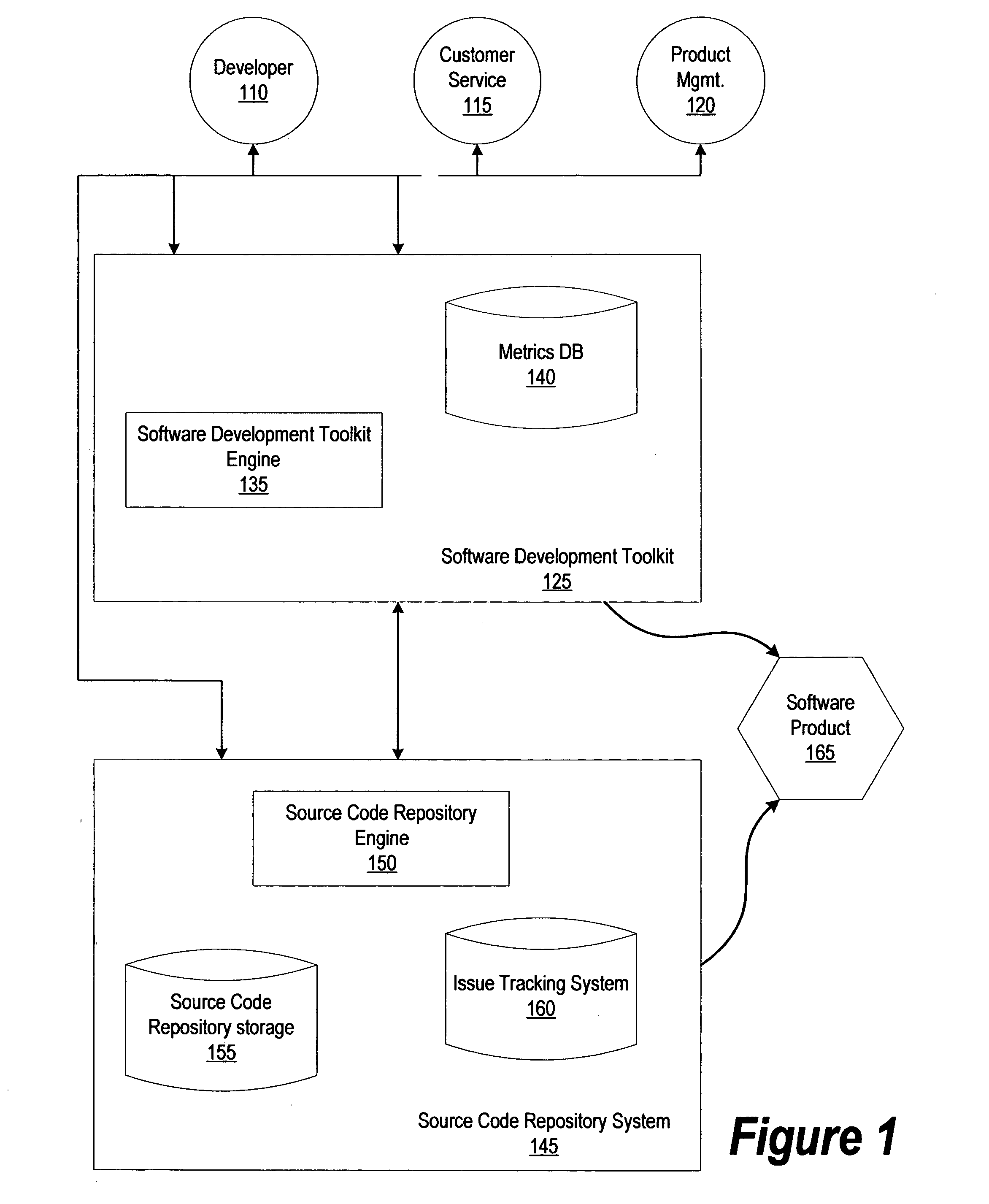
System and method for managing source code and acquiring metrics in software development
ActiveUS20040230964A1Ease of evaluationSoftware testing/debuggingSoftware metricsSoftware development processParallel computing
A method and system is described for managing the development of software source code, and in addition, collecting useful metrics about the development process. A first source code is provided in a desired state. The desired state may be the requirement that the source code can be built or the desired state may be the requirement that the source code can be built and pass one or more tests. A second source code is then received. The second source may be a modified copy of the source code. It is then determined whether the second source code is in the desired state, and the first source code is updated using the second source code in response to the second source code being in the desired state. Metrics that may be collected include: the name of a task, time to complete the task, line of code involved, etc.
Owner:WAUGH LAWRENCE TAYLOR +1
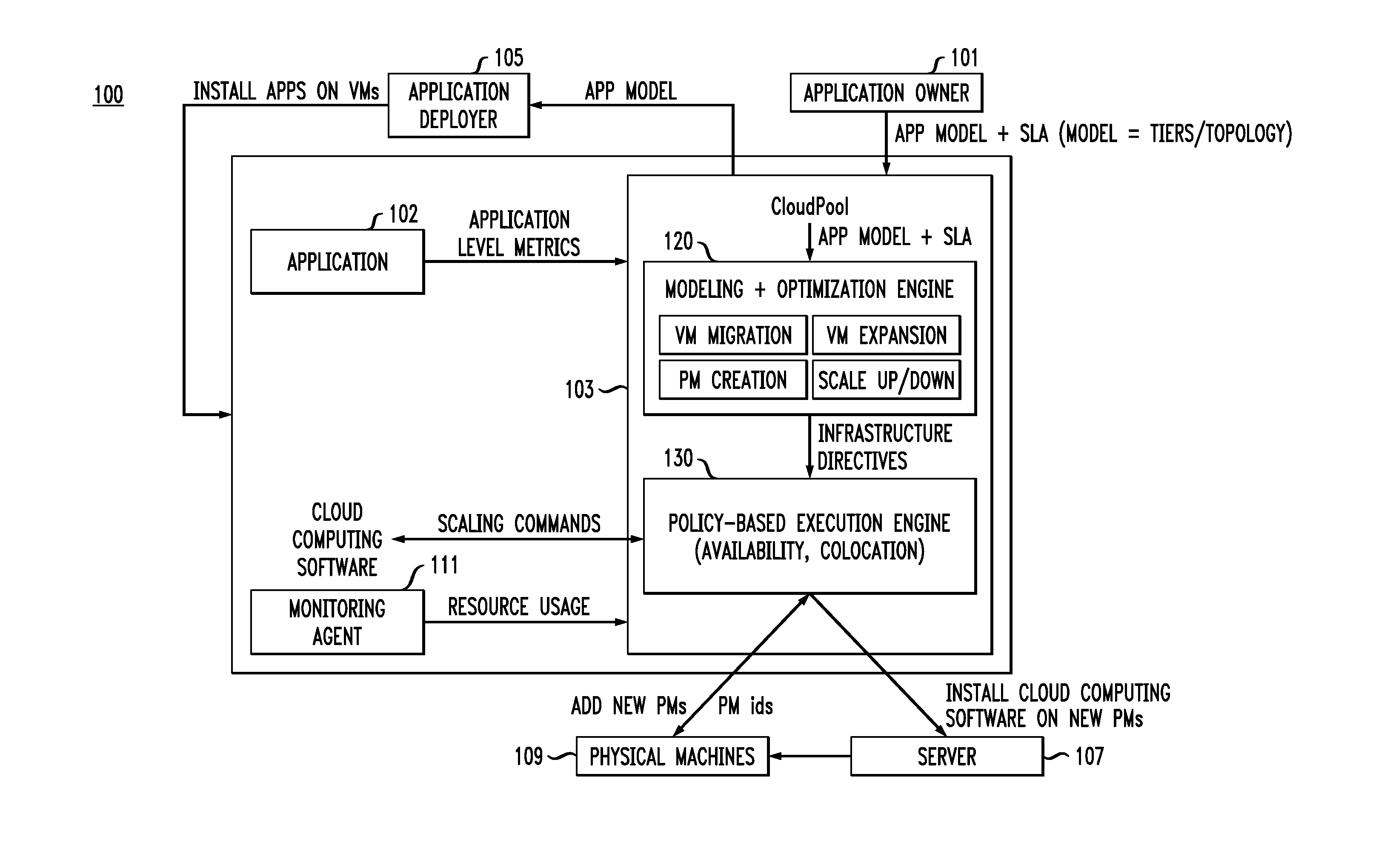
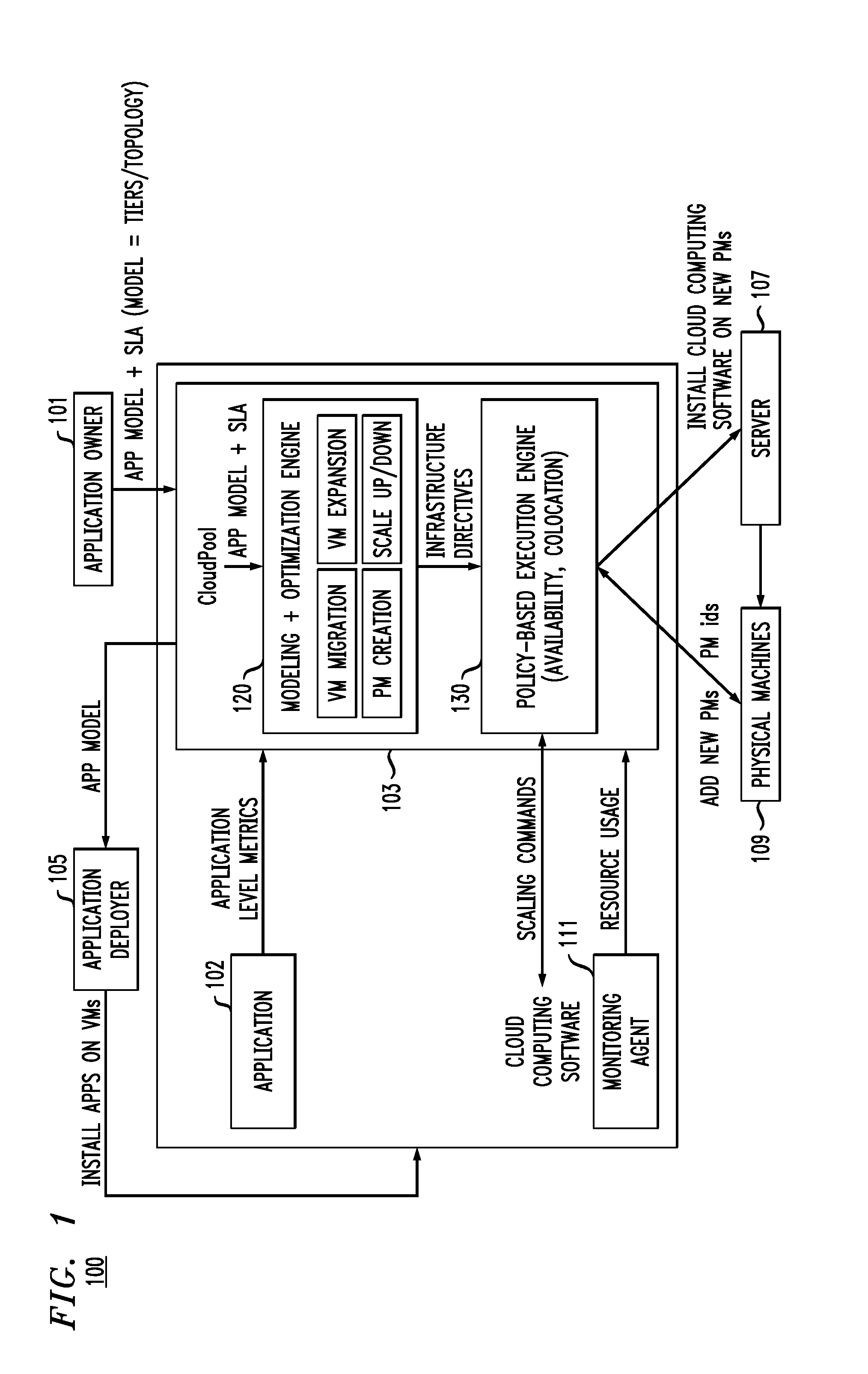
Systems and methods for scaling a cloud infrastructure
ActiveUS20150169291A1Minimizing resource consumptionRobustnessSoftware designSoftware metricsCloud service providerDistributed computing
A method for scaling a cloud infrastructure, comprises receiving at least one of resource-level metrics and application-level metrics, estimating parameters of at least one application based on the received metrics, automatically and dynamically determining directives for scaling application deployment based on the estimated parameters, and providing the directives to a cloud service provider to execute the scaling.
Owner:IBM CORP
Introspection driven monitoring of multi-container applications
Owner:CA TECH INC
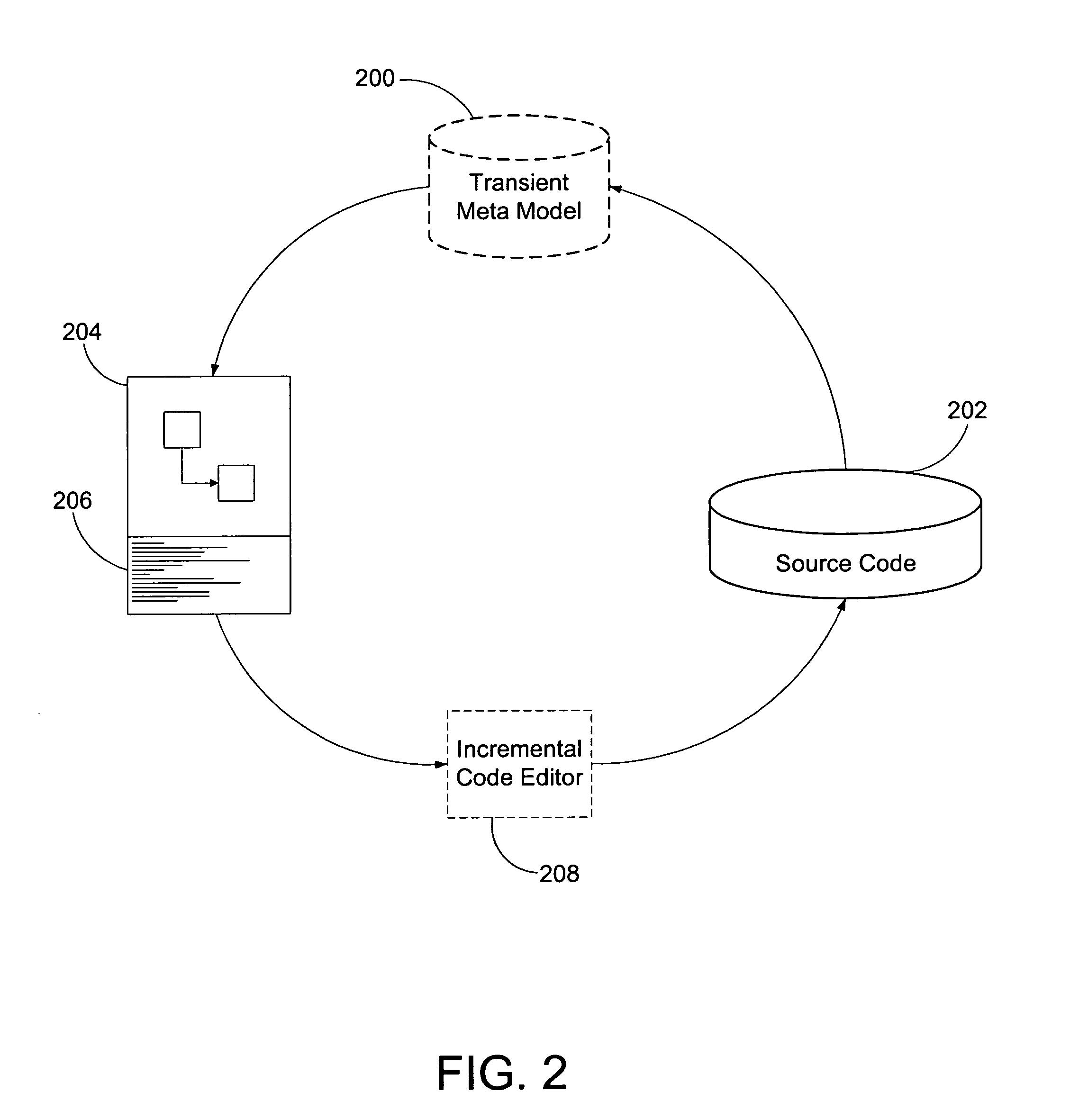
Development System with Improved Methodology for Creation and Reuse of Software Assets
ActiveUS20090210855A1Easy to createVersion controlReverse engineeringApplication softwareImproved method
A development system with improved methodology for creation and reuse of software assets is shown and described. In one embodiment, for example, in a development system, a method is described for facilitating creation of a reusable application, the method comprises steps of: during development of the application, capturing knowledge and intent of the application's original developer alongside source code created for the application; producing an archival module storing the source code for the application together with metadata capturing the knowledge and intent of the original developer, the metadata including at least one script guiding subsequent developers in use and modification of the source code for the application; and consuming the archival module by a follow-on developer, including executing the at least one script for facilitating creation of a reusable version of the application.
Owner:EMBARCADERO TECHNOLOGIES
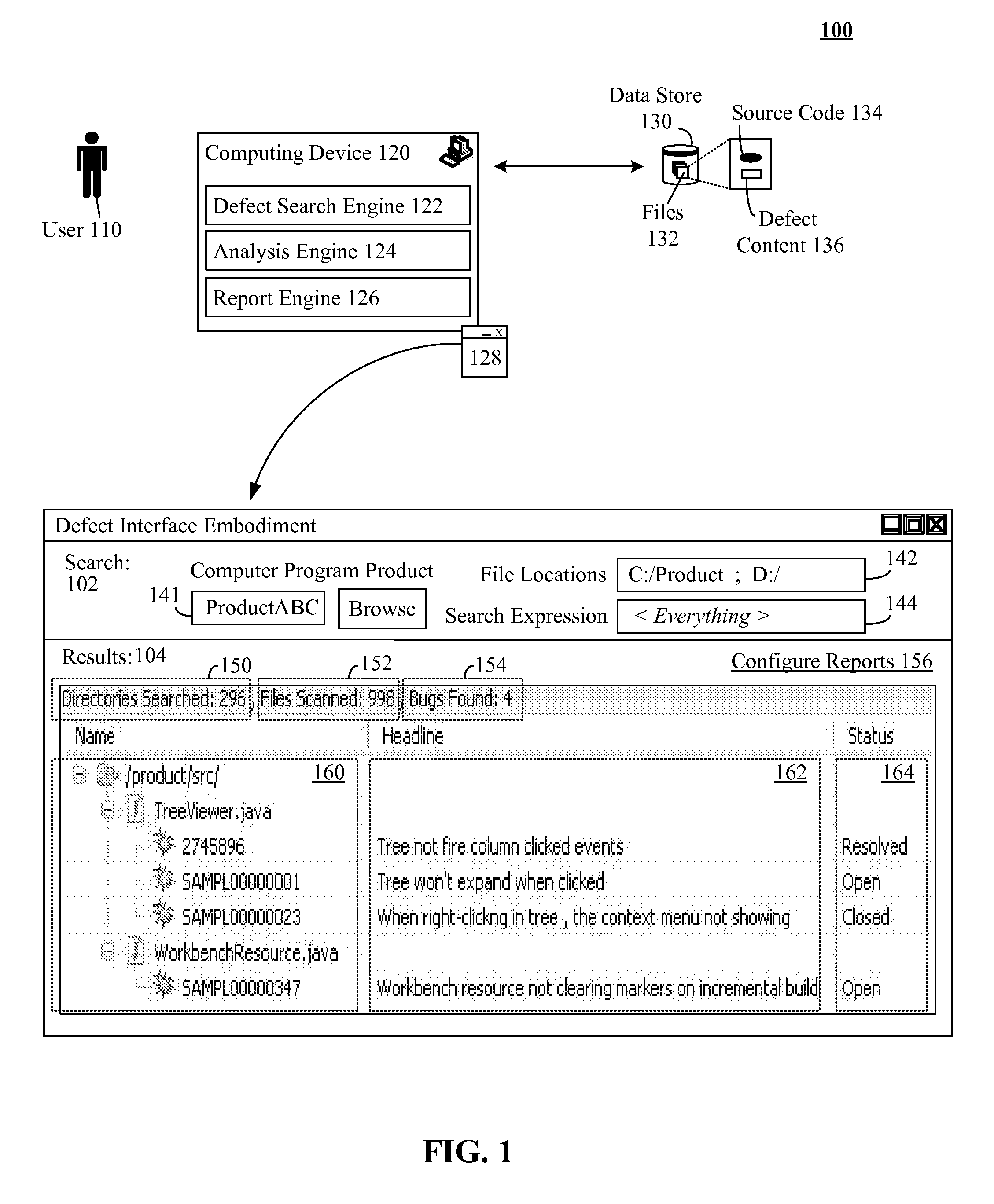
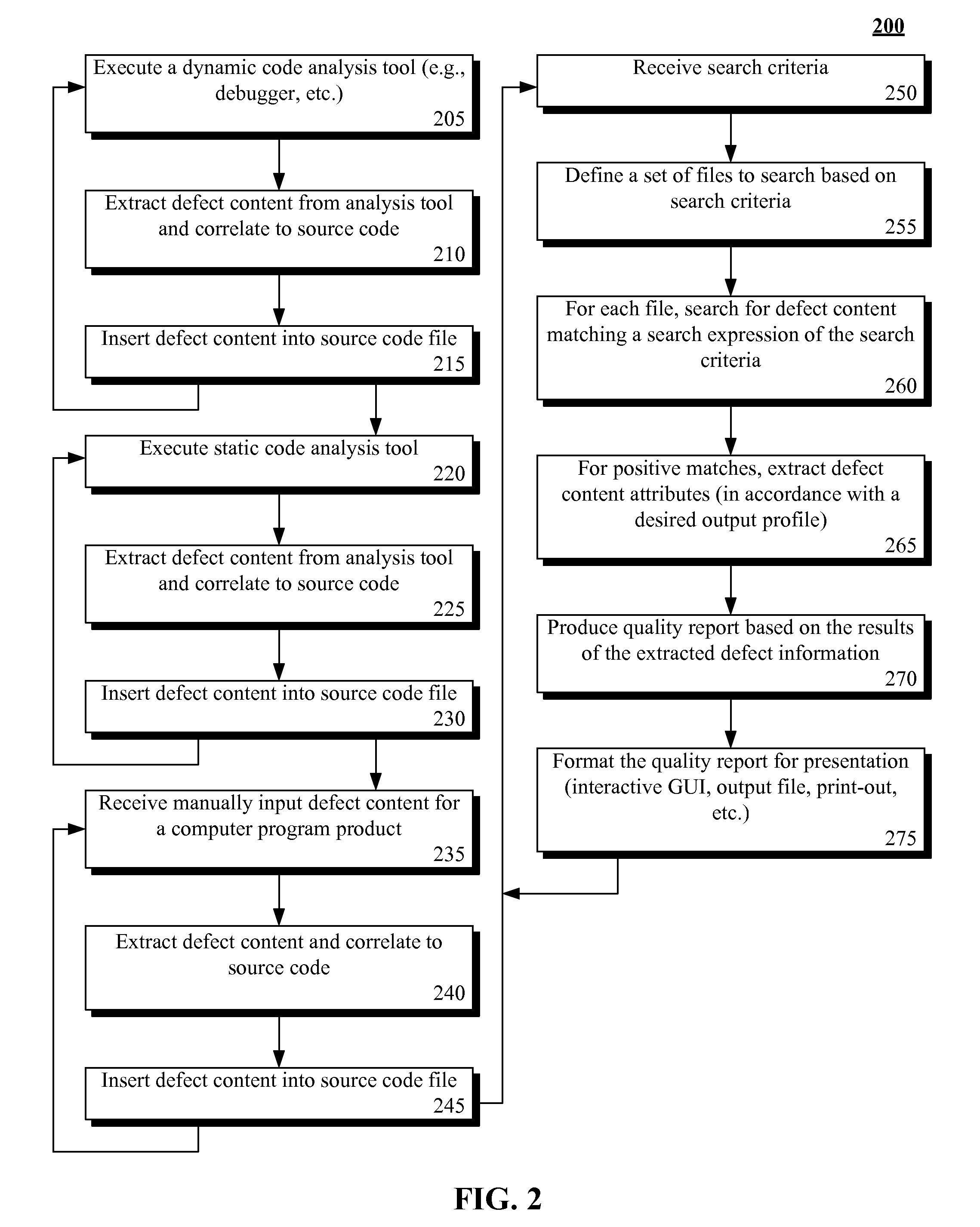
Including defect content in source code and producing quality reports from the same
InactiveUS20110161938A1Digital data processing detailsSoftware metricsGraphicsGraphical user interface
Defect content for a computer program product can be stored with source code of the computer program product. A computer program product analysis tool having a graphical user interface can be provided. Search criteria for defect content for the computer program product can be specified by a user via the graphical user interface. The stored defect content of the source code of the computer program product can be searched based on the search criteria. A computer program product quality report can be produced for the computer program product based on results of the searching of the stored defect content.
Owner:IBM CORP
Method and system for crowd-sourced algorithm development
InactiveUS20170083312A1Improve processing speedConfidenceService provisioningSoftware designComputer hardwareCrowd sourcing
A system for development of an algorithm for analysis of sensor data includes one or more wearable sensor devices, a smart device, and a cloud computing platform. The sensors in the wearable sensor device produce sensor data (e.g., physiological data) from a user that can be processed by a software algorithm in the wearable sensor device or by a connected smart device (e.g., a smartphone) via cloud computing, producing an algorithm output. The raw sensor data along with other information, such as the algorithm output and sensor data features can be sent to the cloud computing platform for storage and to enable developers to access the data in order to modify the software algorithms. The wearable sensor device can be configured to send more or less data to the cloud computing platform according to the performance of the software algorithm.
Owner:MC 10 INC
Determining Context Specific Content
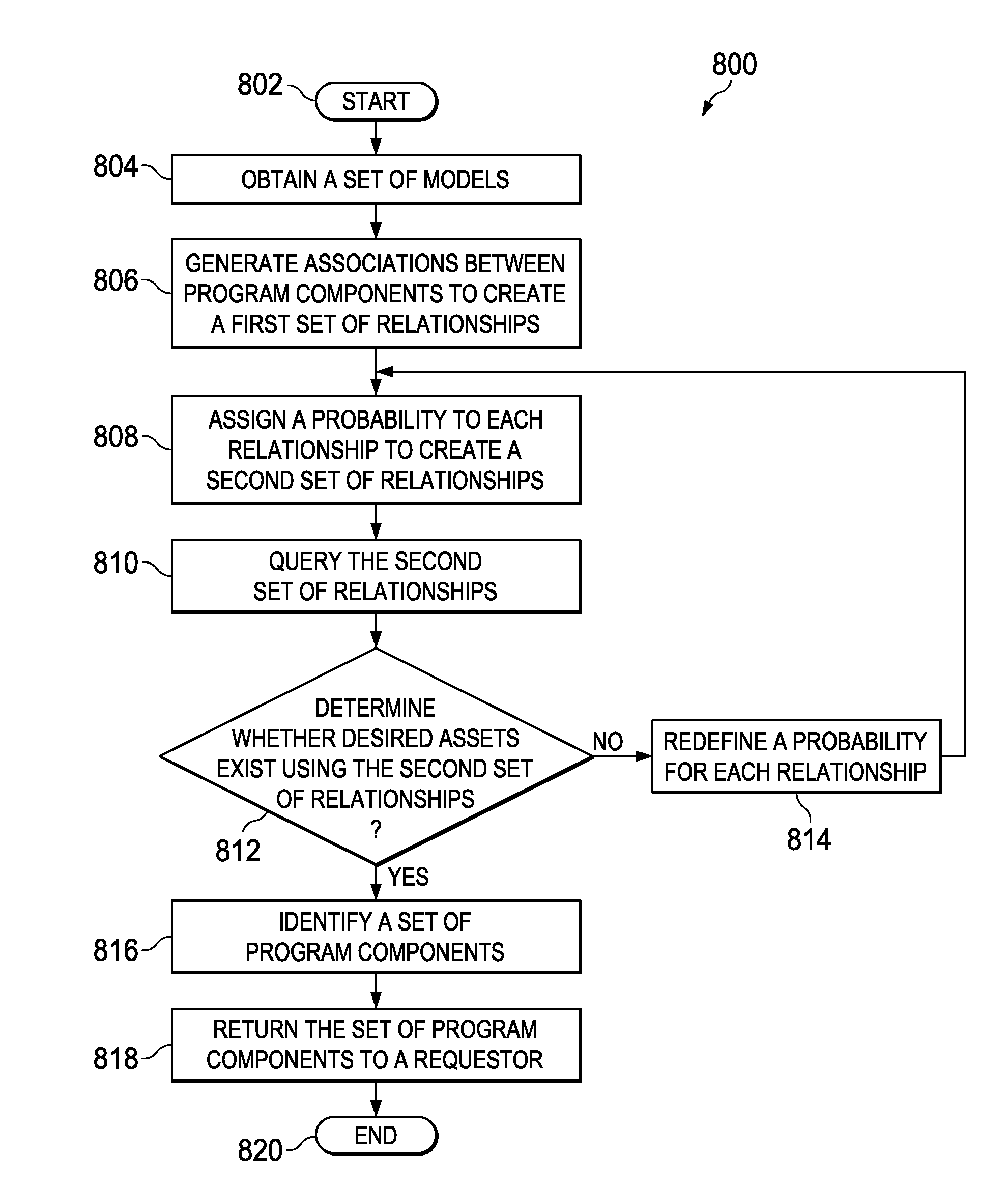
InactiveUS20110099536A1Probabilistic networksSoftware metricsProbability representationContext specific
In one illustrative embodiment, a computer-implemented method for identifying program components, generates, by a processor unit, associations between the program components stored in a computer usable storage medium to create a first set of relationships, and assigns, by the processor unit, a probability to each relationship in the first set of relationships to create a second set of relationships, wherein the probability indicates a strength of the associations between the program components.
Owner:IBM CORP
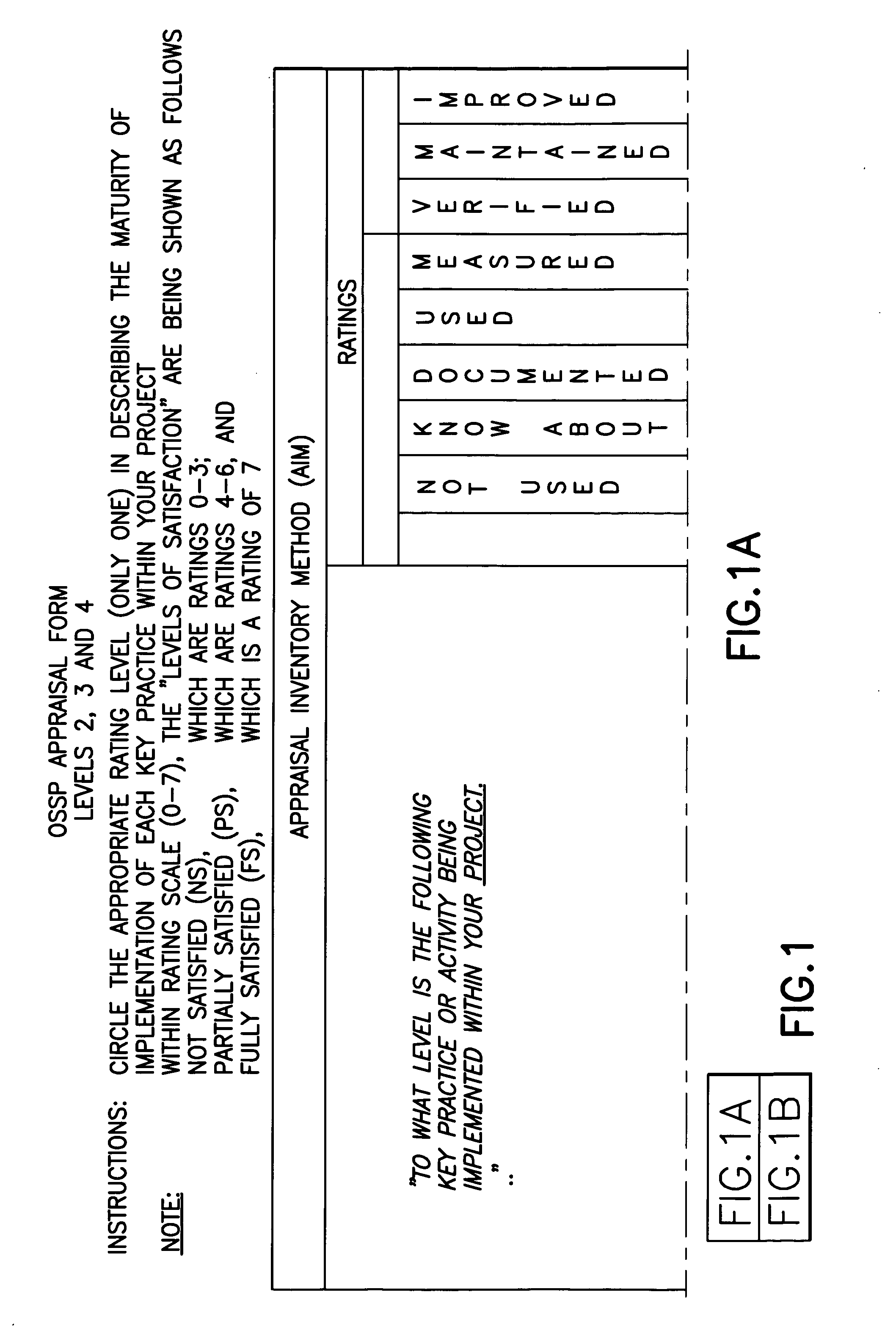
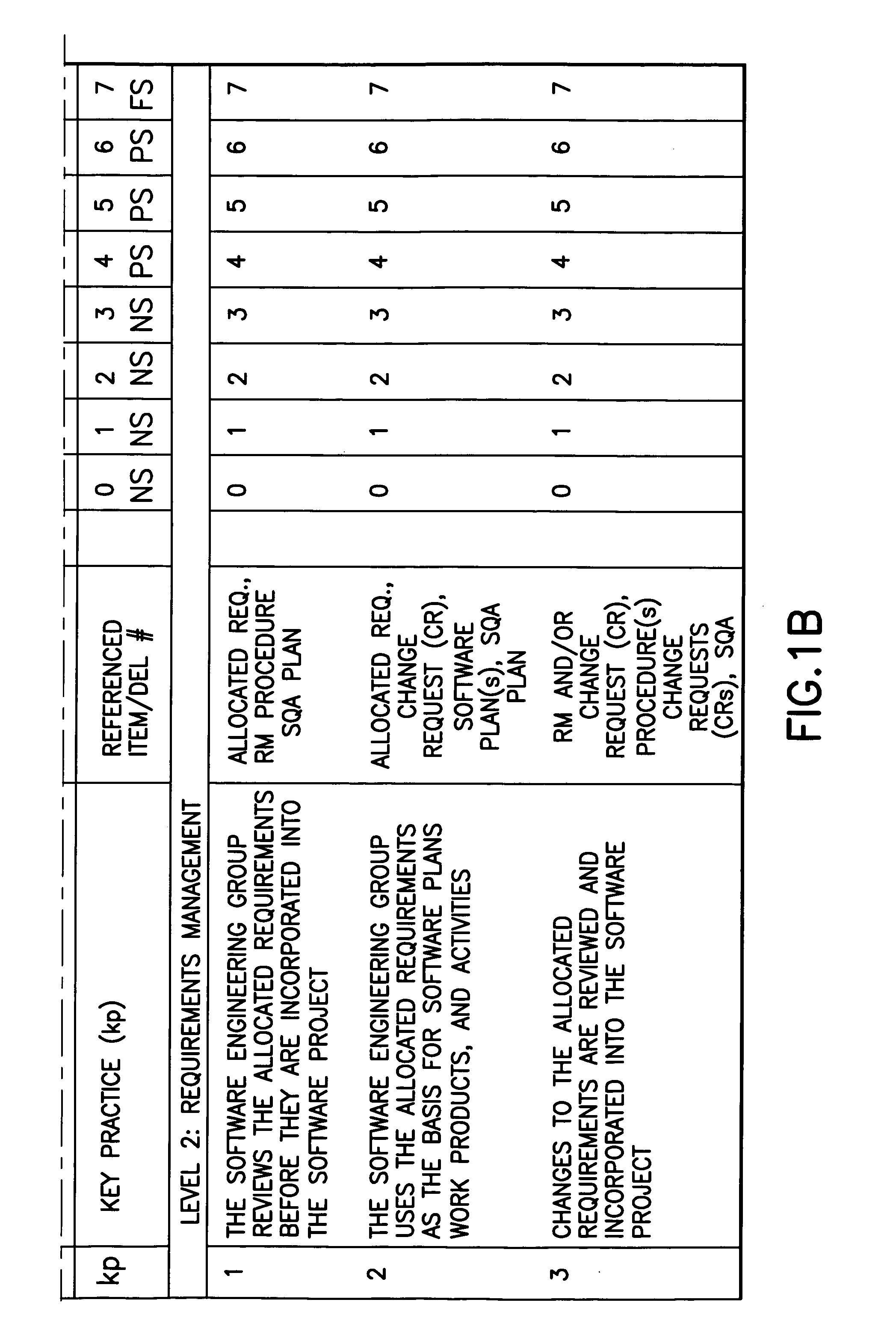
Method for validating software development maturity
InactiveUS20050125272A1Software testing/debuggingSoftware metricsSoftware engineeringSoftware development
A validation procedure for assessing the status a software engineering process for compliance, and improving the measured compliance, with the Carnegie Mellon SEI / CMM Software Maturity Model includes a validation meeting in the course of which a validation team reviews deliverables demonstrative of the process being performed and asks a structured set of questions that are structured in accordance with the CMM and correlate with the deliverables.
Owner:NOKIA SOLUTIONS & NETWORKS OY
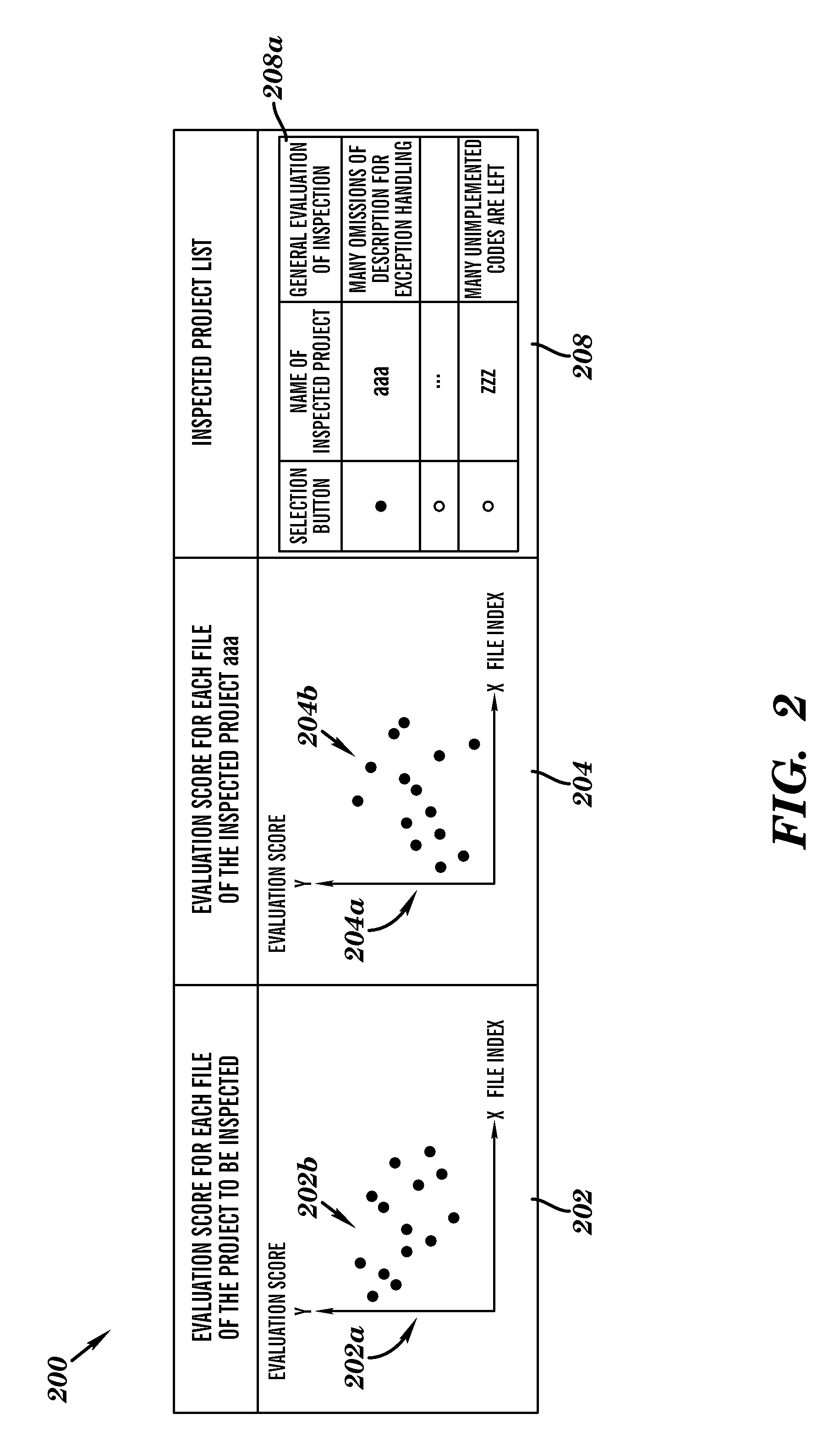
Source code inspection method and system
A source code inspection method and system. The method includes receiving by a computing system, source code files associated with a specified project. The computing system retrieves metrics data comprising software metrics associated with the source code files. The computing system generates first evaluation scores associated with the source code files. The computing system generates and presents to a user, a graph displaying the first evaluation scores. The computing system calculates parameter values associated with an evaluation function used to calculate second evaluation scores associated with the source code files. The computing system calculates the second evaluation scores by enabling the evaluation function using the parameter values. The computing system generates and presents to the user, a second graph displaying the second evaluation scores.
Owner:IBM CORP
Detecting, using, and sharing it design patterns and Anti-patterns
InactiveUS20110265064A1Improve system performanceImprove performanceWeb data indexingDigital data processing detailsAnti-patternTheoretical computer science
Various embodiments described and illustrated herein include at least one of systems, methods, and software to identify, use, or share patterns and anti-patterns. Embodiments that include pattern and anti-pattern identification operate to identify candidate patterns and anti-patterns within a deployed system and to confirm or receive confirmation that the identified candidates are indeed patterns or anti-patterns. Embodiments that use patterns and anti-patterns operate to consume the identified patterns and anti-patterns to improve system performance. The embodiments that share patterns and anti-patterns include mechanisms whereby patterns and anti-patterns can be sent to and received from other systems.
Owner:CA TECH INC
Integrated System for Software Application Development
InactiveUS20180210709A1Many stepsEqually distributedProgram documentationIntelligent editorsSoftware development processPredictive modelling
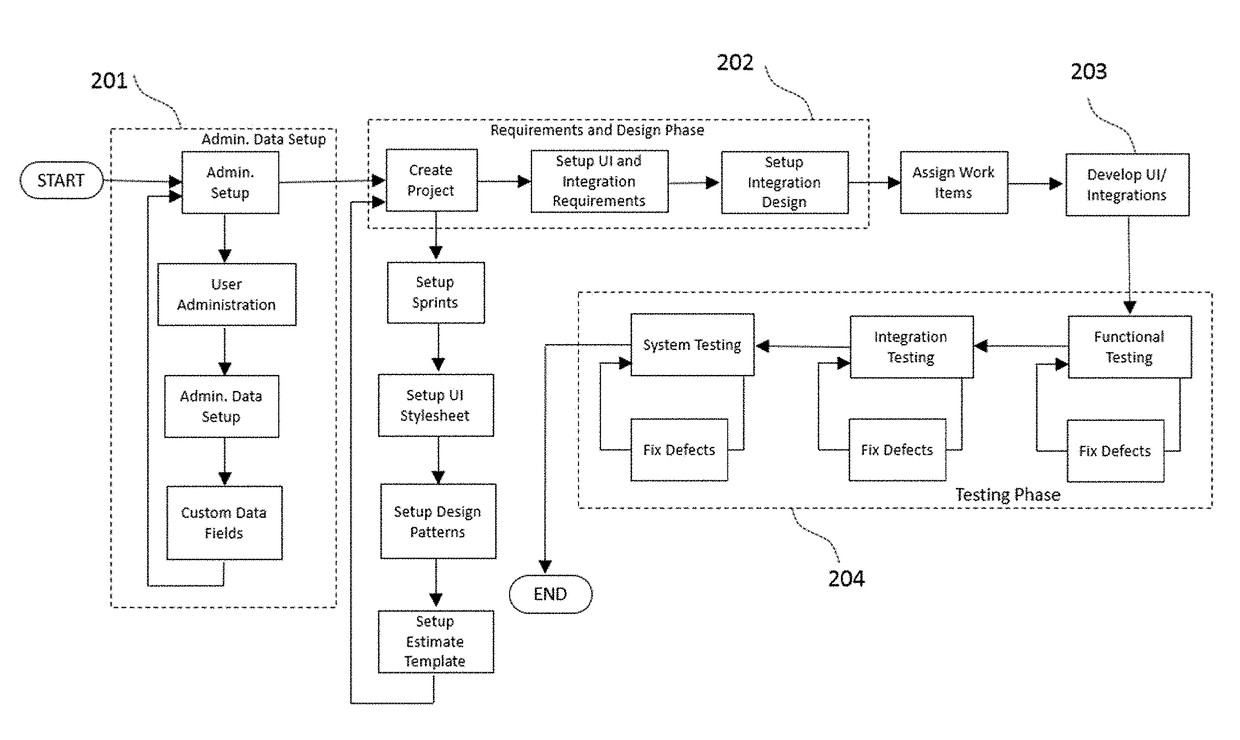
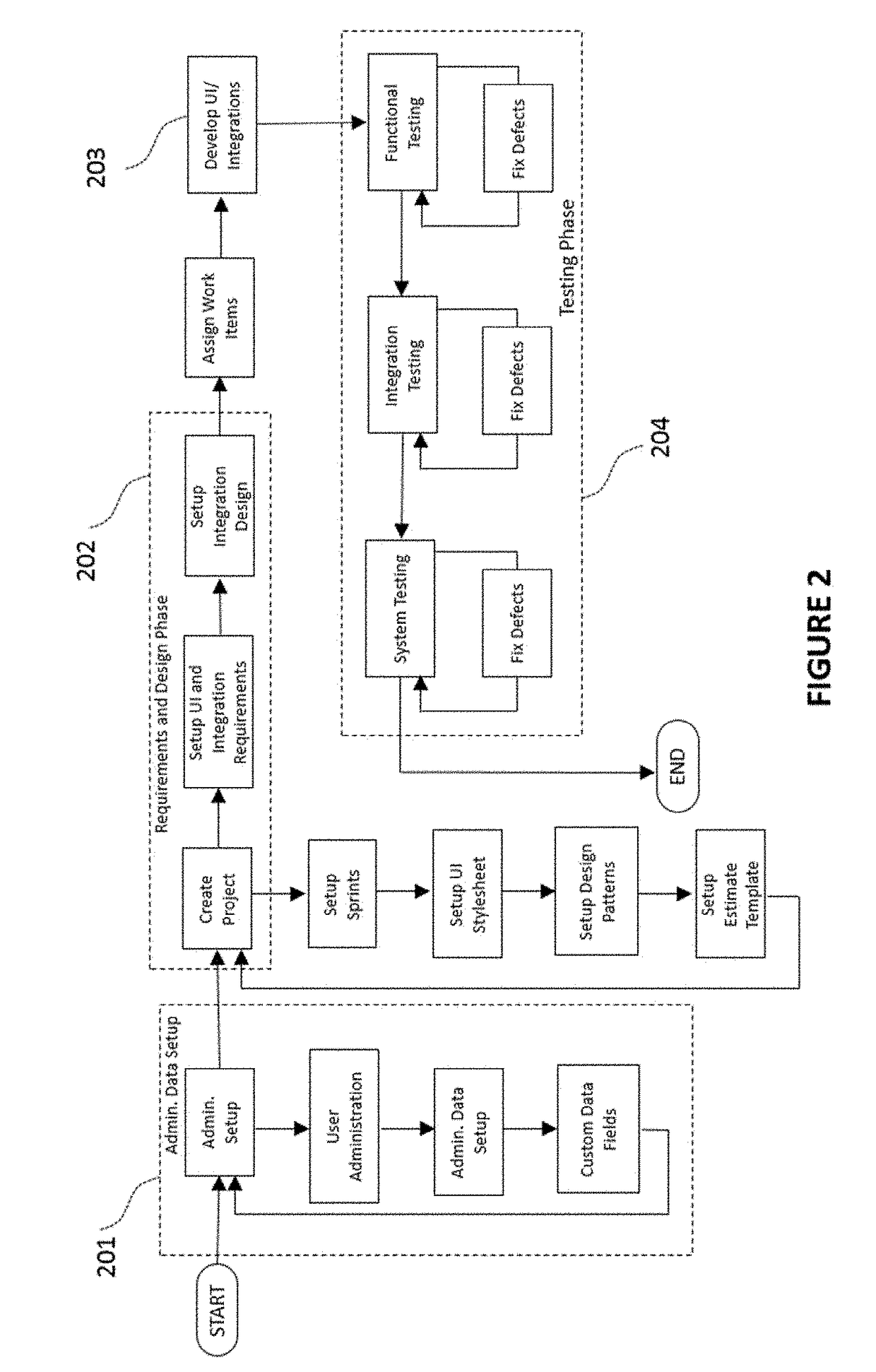
Methods and systems are disclosed for developing a software application through requirements specification, design, effort estimation, assigning and tracking work items, development, testing, collaboration and project management. The system is structured as an integrated software development system allowing for structured, systematic and user friendly set up of requirements specification (including workflow, user interface, business rules and integrations), technical design for UI features and integrations using design patterns, automated effort estimation, automated story card and task creation. The system also provides a novel, audio-video playback capability for workflow visualization. Further, the system provides visual depiction of defects and changed items side-by-side with requirements, as well as predictive modeling of defects that allows for forecasting of defect completion rate. In the preferred embodiment, the system is delivered as a multi-tenant Software as a Service.
Owner:BHARTHULWAR SHRIDHAR V
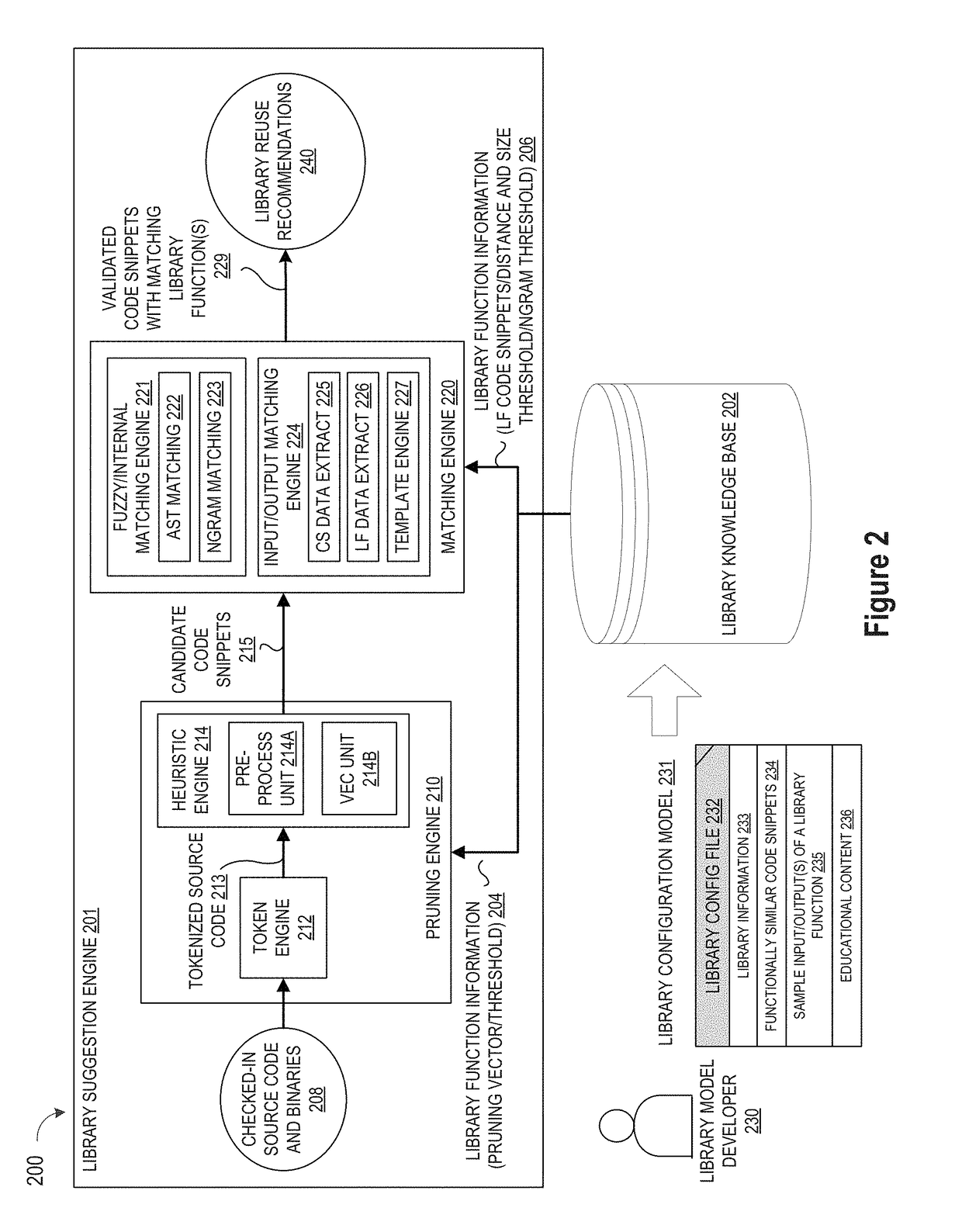
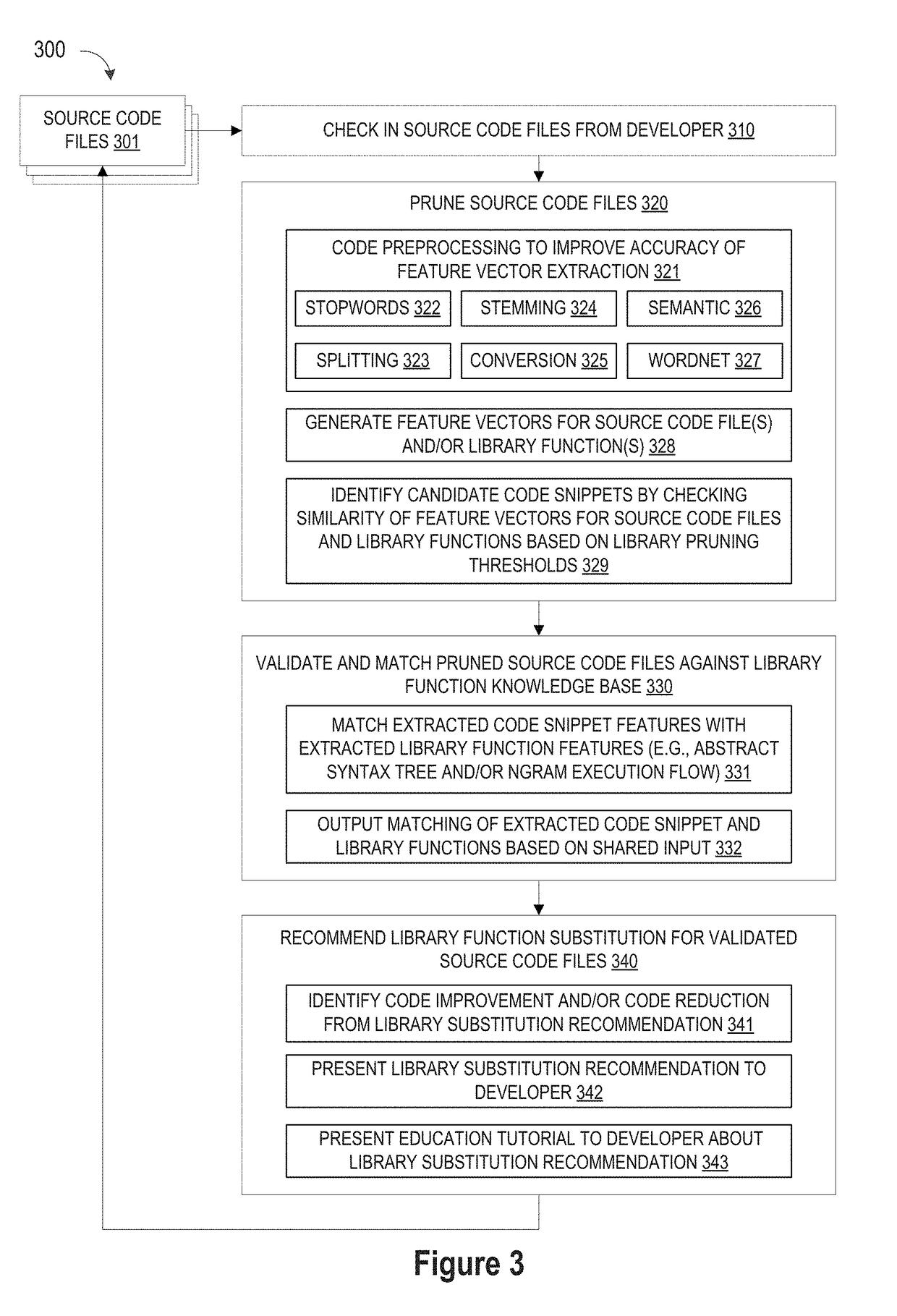
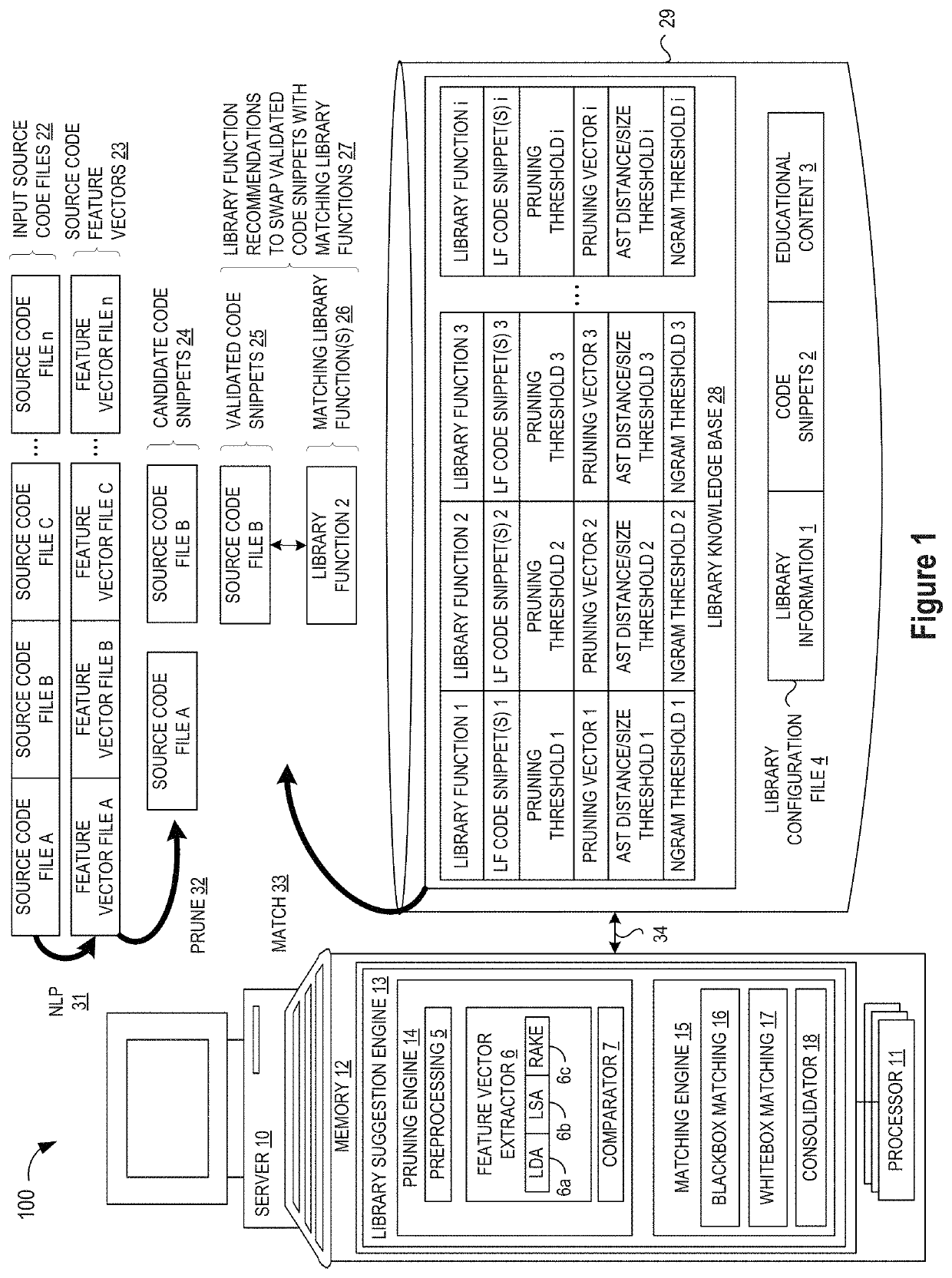
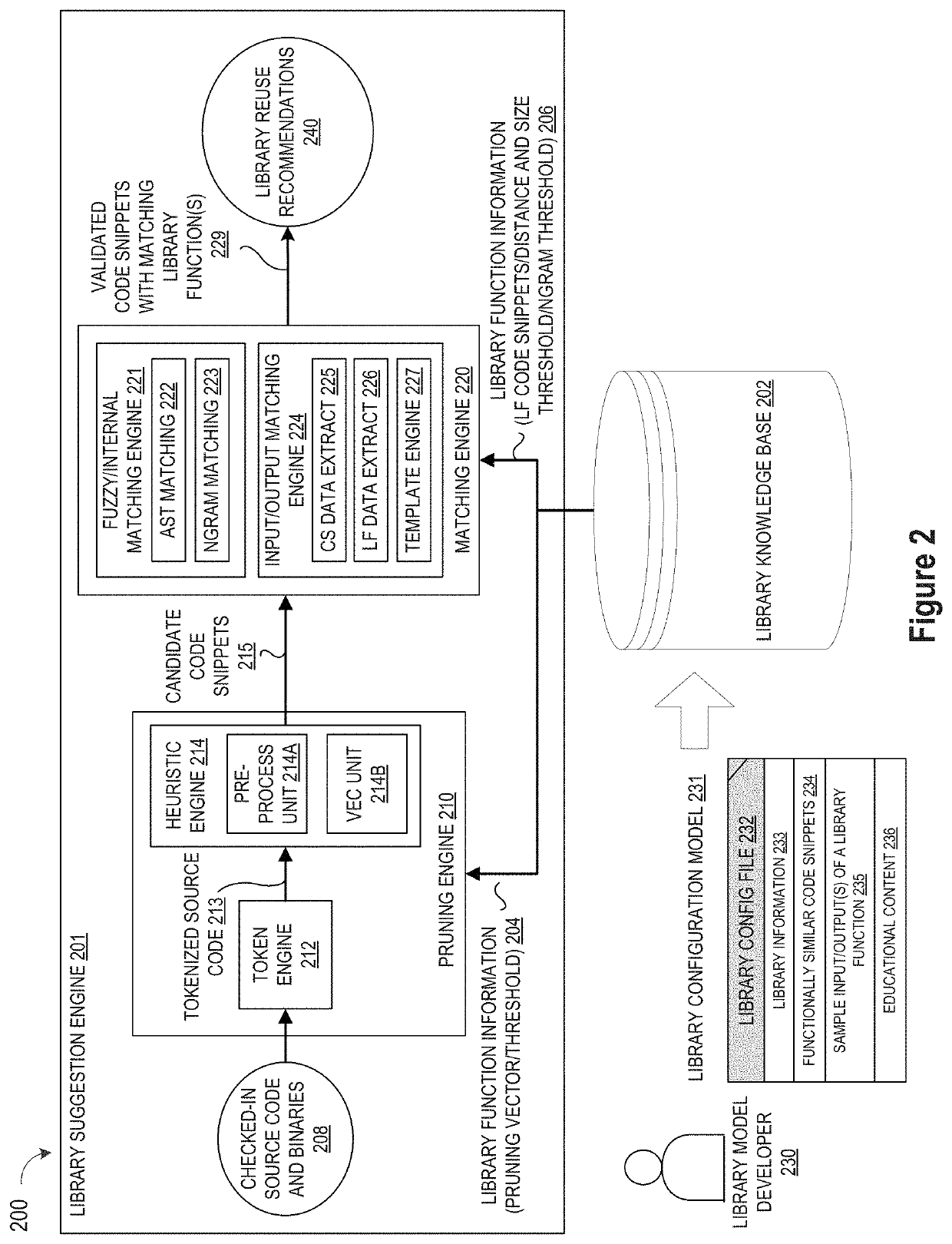
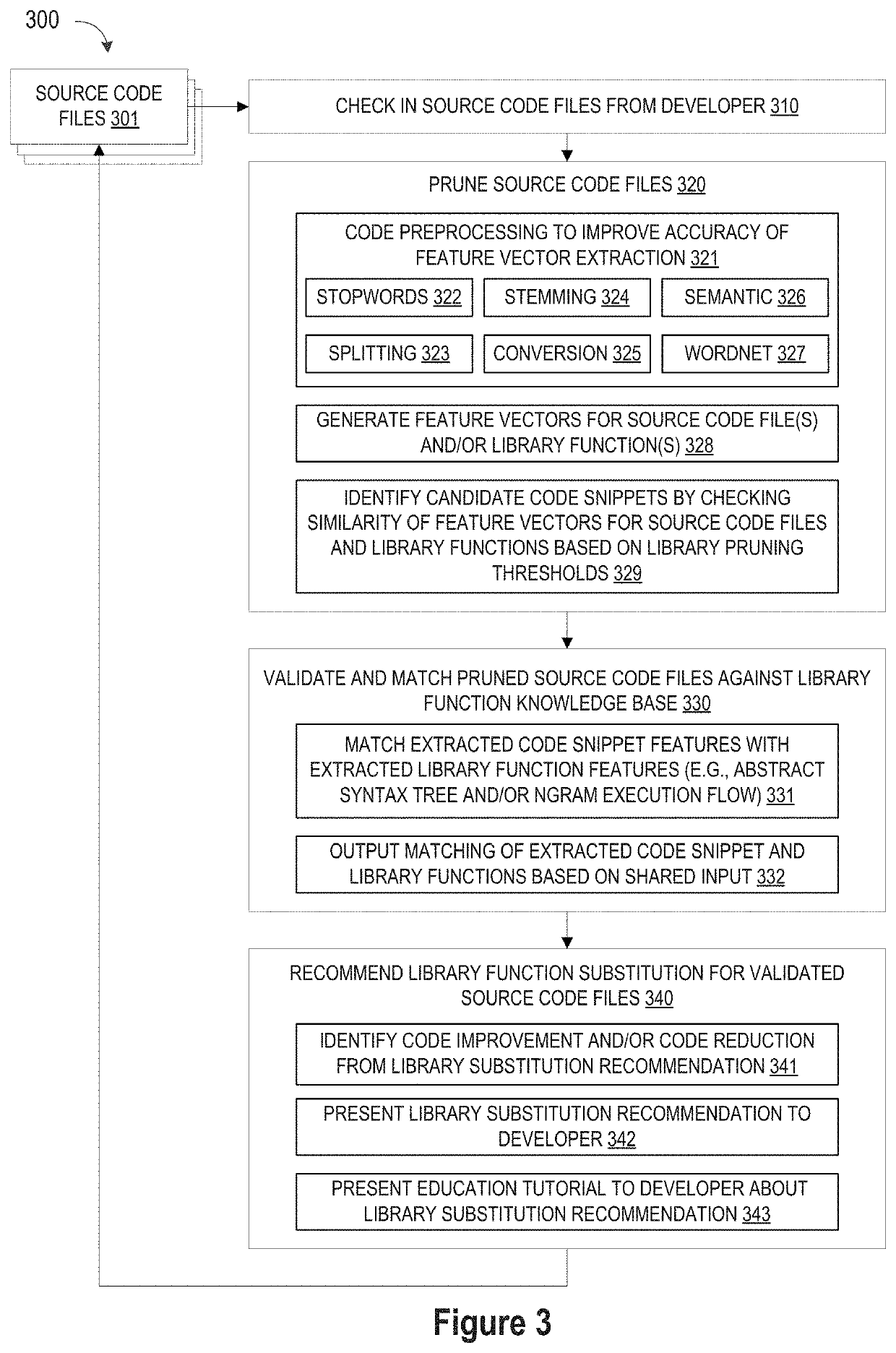
Pruning Engine
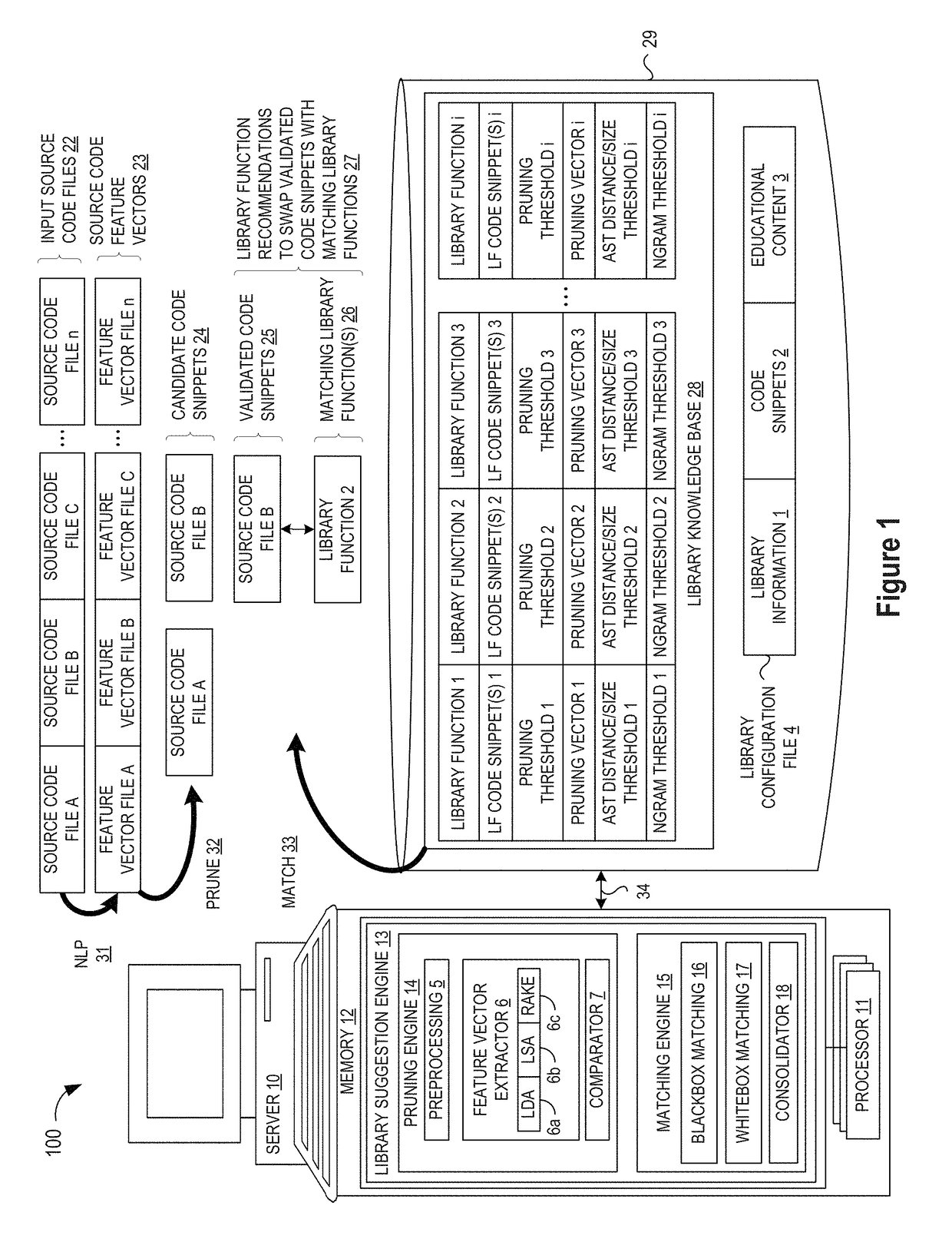
ActiveUS20190079741A1Improve code reuseImprove accuracyVersion controlCode refactoringCode snippetSource code file
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by preprocessing input source code files with codeword processing operations to generate a plurality of preprocessed input source code files, identifying candidate code snippets by pruning one or more preprocessed input source code files that do not meet a similarity threshold measure for library functions stored in the system library, and identifying at least a first validated code snippet from the one or more candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics.
Owner:DEVFACTORY INNOVATIONS FZ LLC
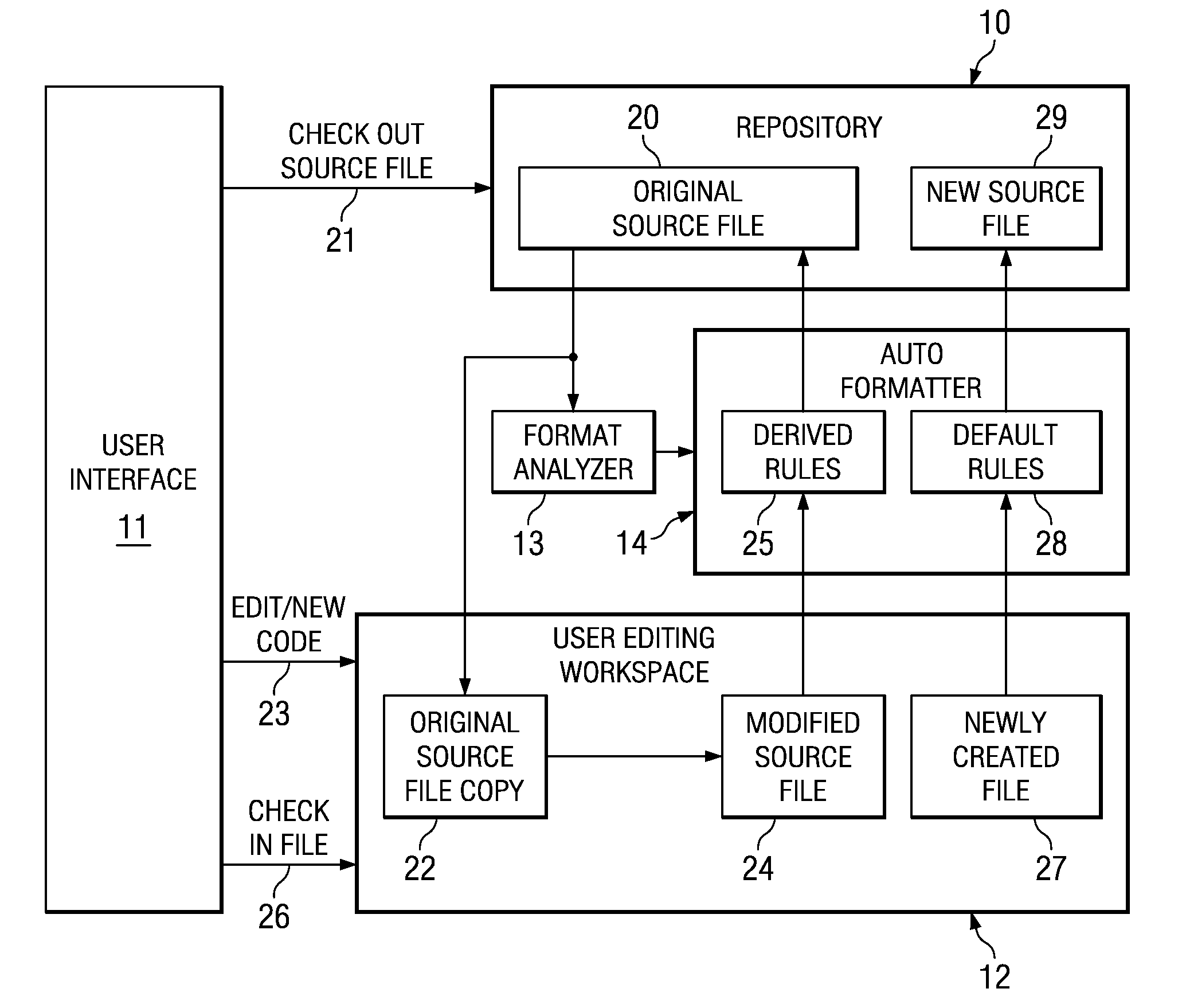
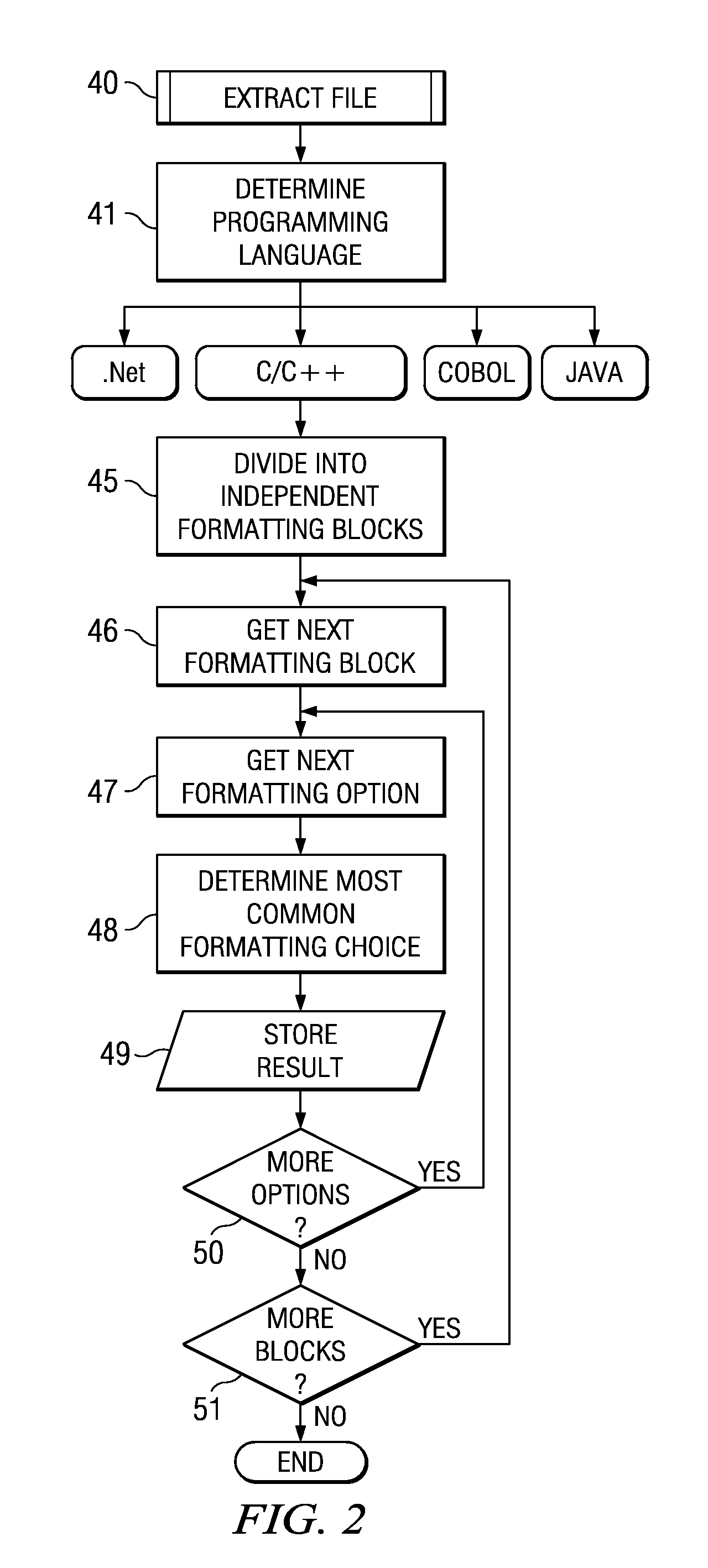
Automatic Formatting of Computer Program Source Code
ActiveUS20080229290A1Reduce the possibilityEasy to identifyError detection/correctionVersion controlDead codeUser input
A method and system is provided for auto formatting changes to computer program source code stored in a code repository. The code comprises a plurality of separately identifiable sections each of which includes non-functional formatting information which differs between at least some of the sections. In response to a user input request a selected source code section is extracted and edited via a user interface. A set of formatting rules is determined automatically from at least the code section being edited. This set of rules is one of a plurality of possible sets corresponding to the separately identifiable sections. The edited code is then formatted according to the determined set of formatting rules and stored in the code repository.
Owner:IBM CORP
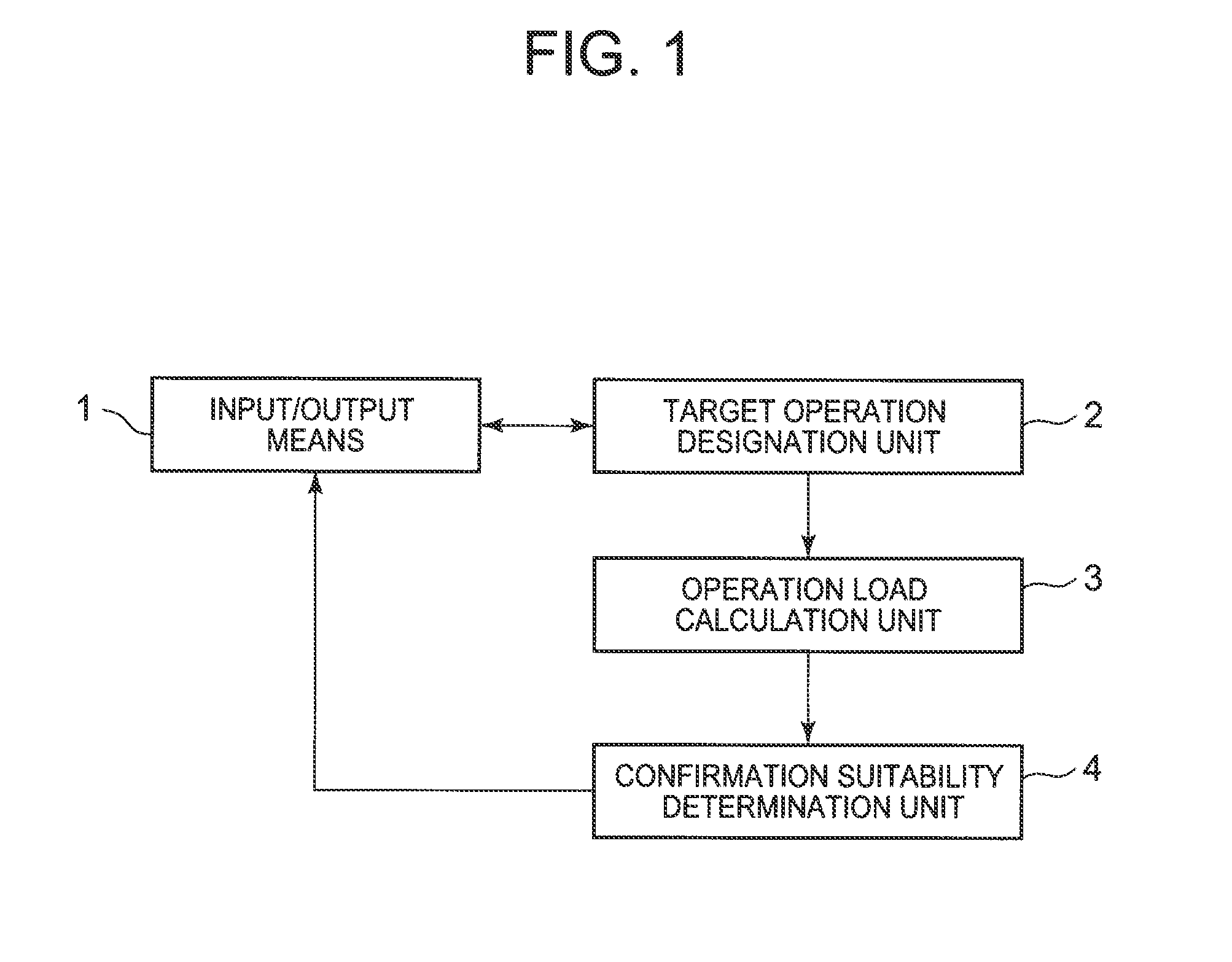
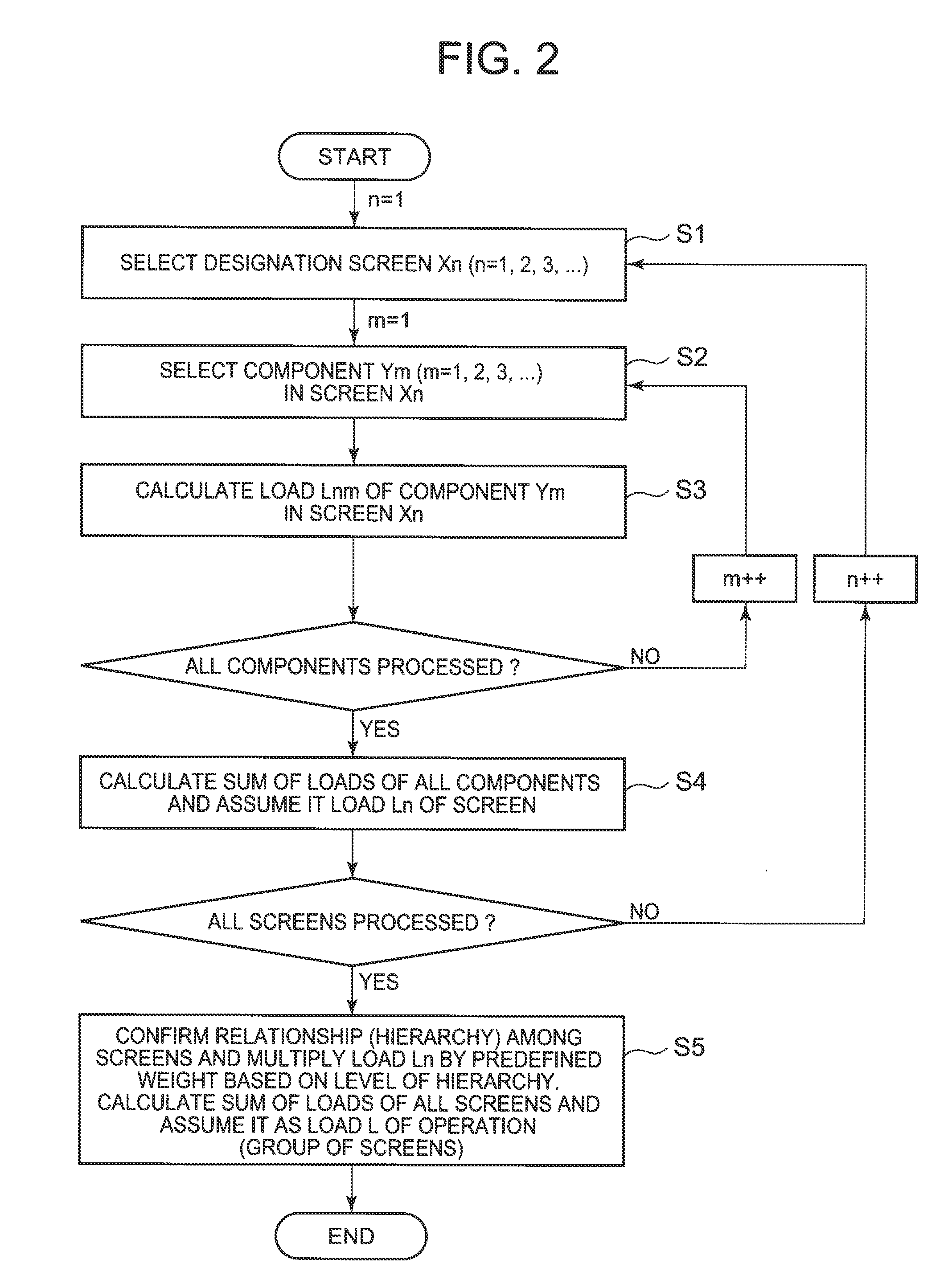
GUI evaluation system, method and program
A GUI evaluation system for evaluating GUI usability includes an operation load calculation unit which calculate a load value indicating a level of load of an operation based on attributes of UI components used for a GUI to be evaluated, and a confirmation suitability determination unit which determines suitability of a confirmation method related to the operation based on a load value calculated by the operation load calculation unit.
Owner:NEC CORP
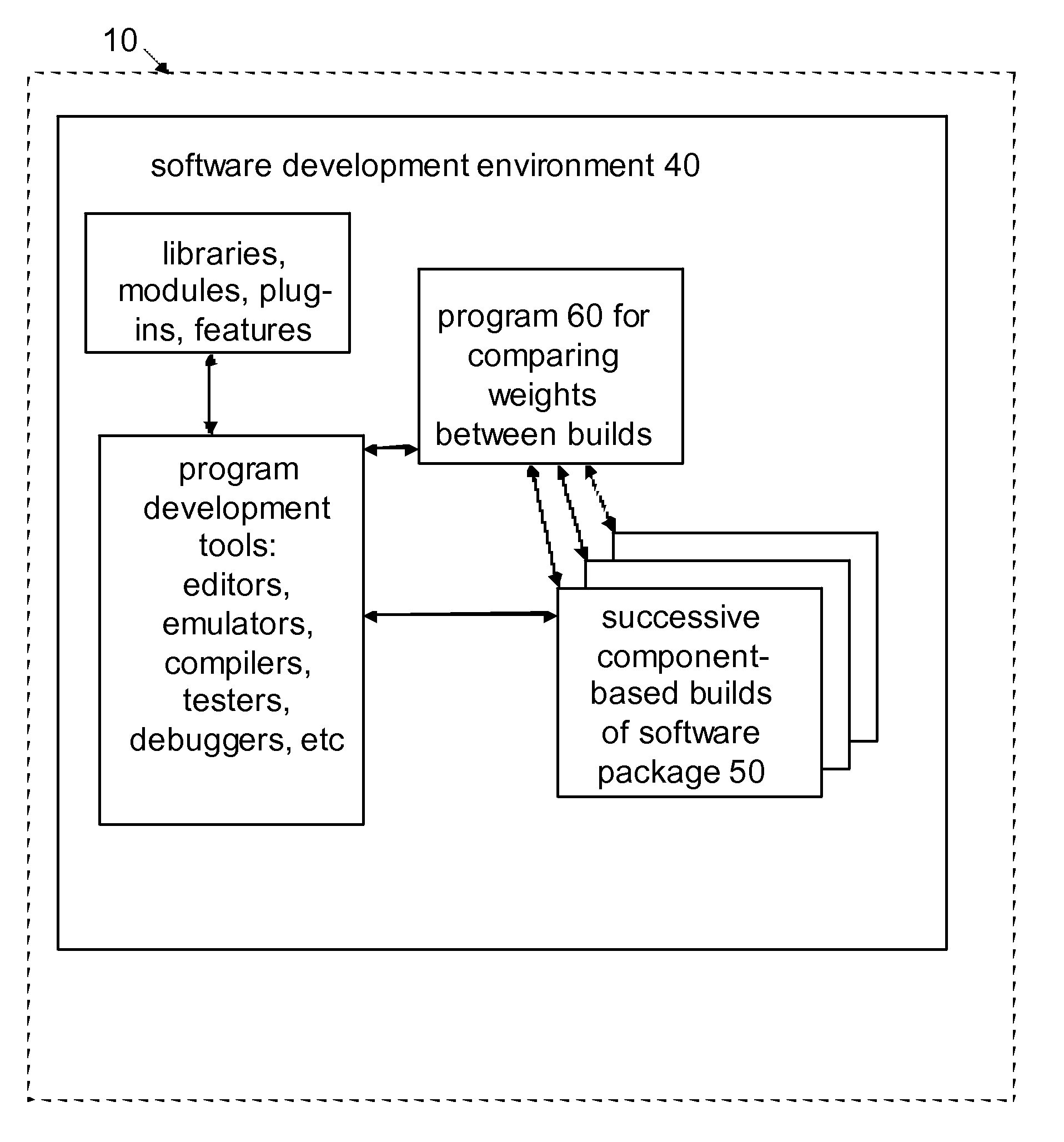
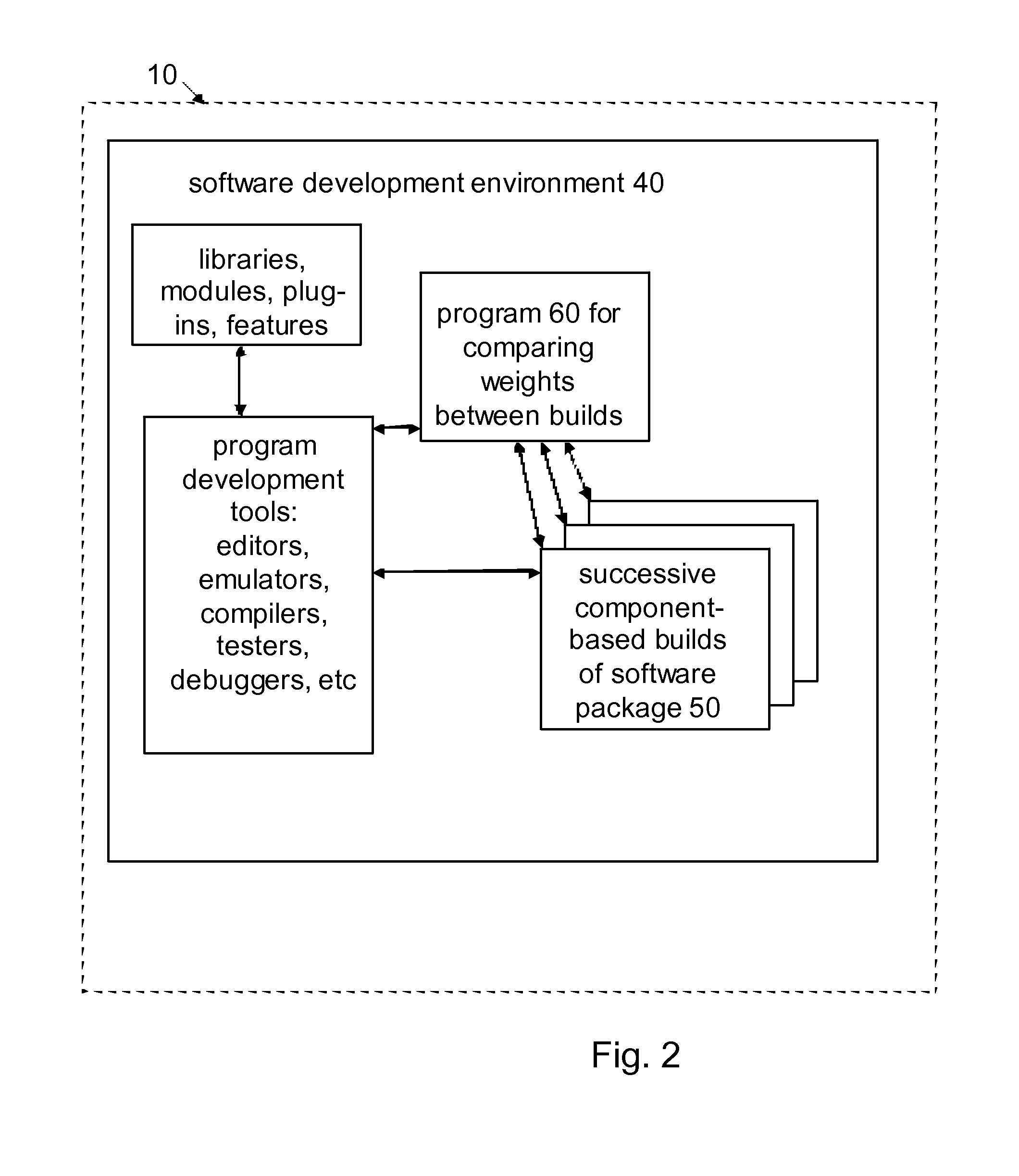
Computer system, program, and method for comparing component weights between builds
A computer system, program, or method may provide for quantifying changes in an individual component among a plurality of components in a software development environment where the components are incorporated in a build. This may include calculating a baseline weight of the individual component prior to a change; effecting, in the software development environment, the change to the individual component; calculating a modified weight of the individual component after the change; determining a threshold for a difference between the baseline weight and the modified weight of the individual component; calculating the difference between the baseline weight and the modified weight of the individual component; and providing on the software development computer a notification if the difference exceeds the threshold. The weights of the individual component may use data such as a count of other components required by the individual component, an install size, a runtime memory usage, a depth of a dependency tree, a component license type, a component category for memory location, a component code type, and / or other types of data.
Owner:IBM CORP
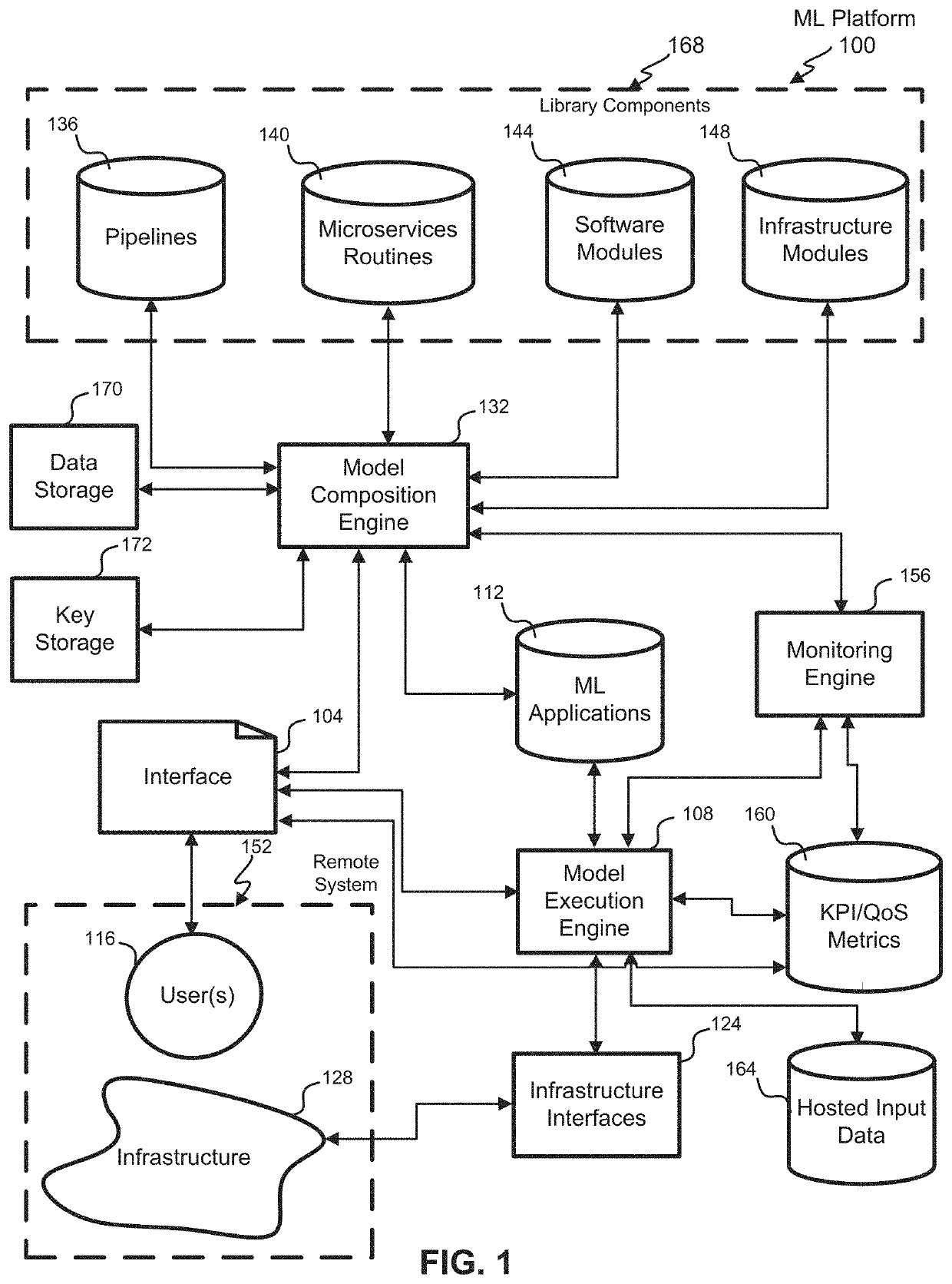
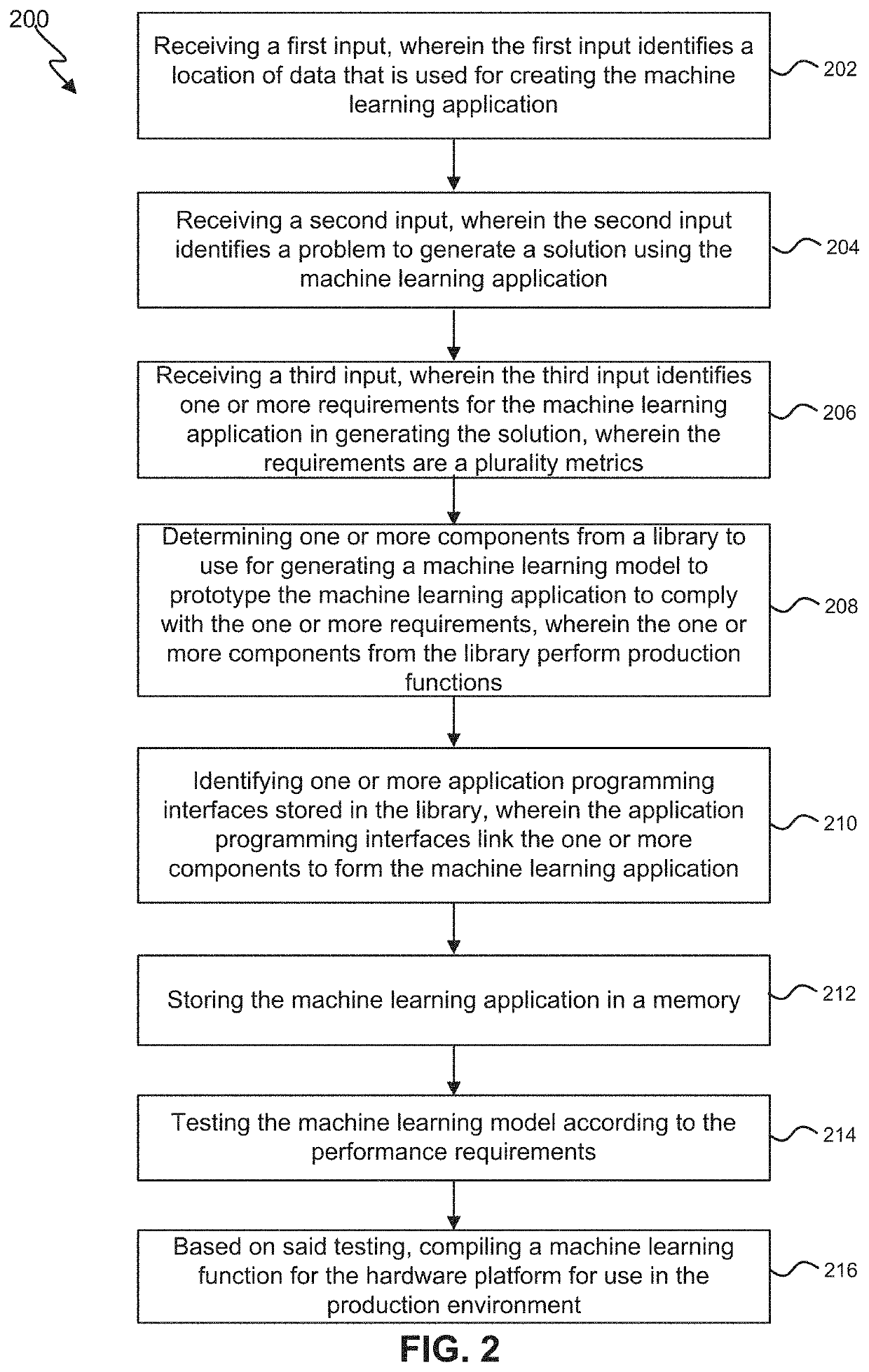
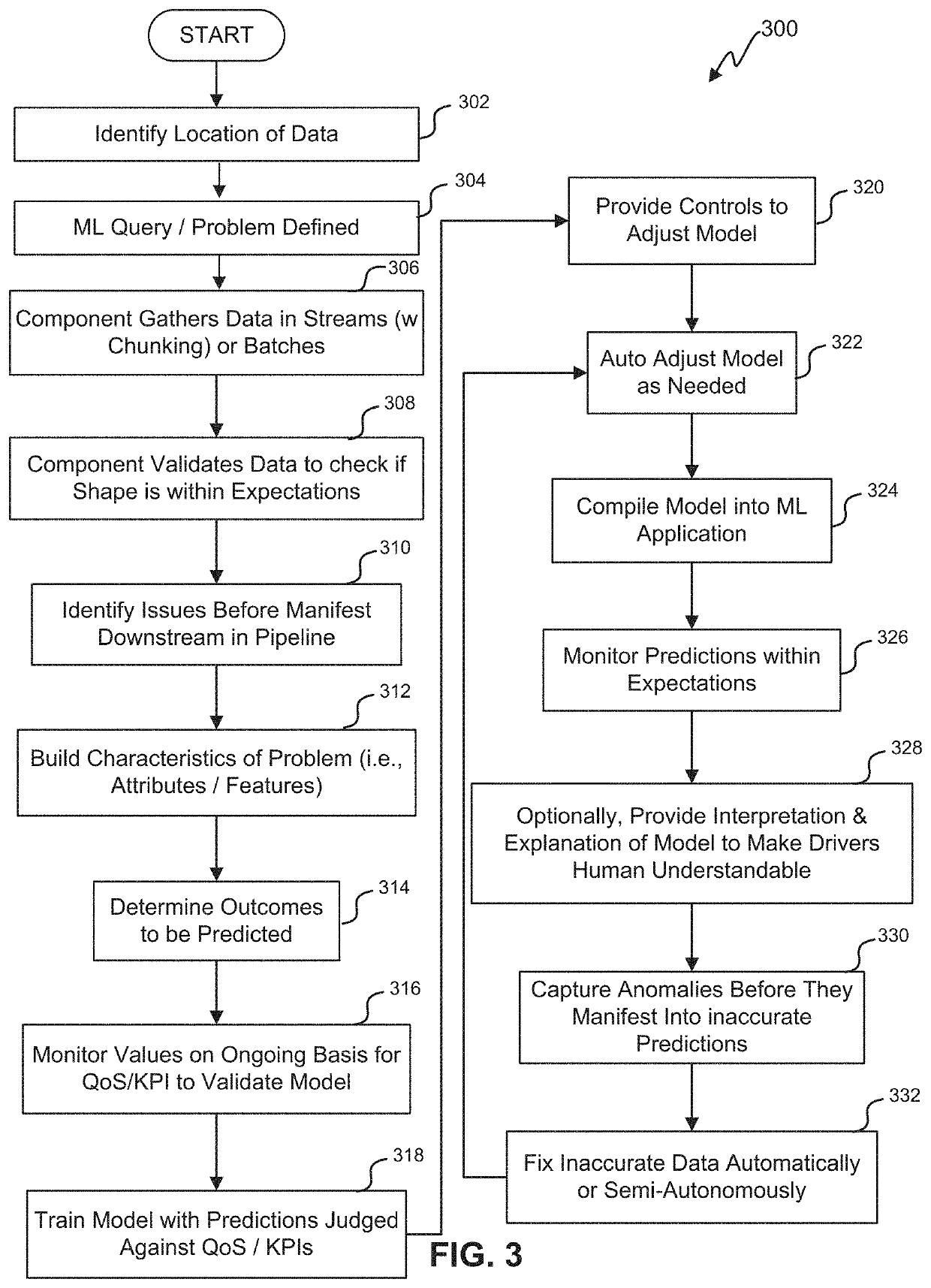
Techniques for adaptive pipelining composition for machine learning (ML)
ActiveUS20210081848A1Simple interfaceEfficient mappingEnsemble learningReverse engineeringGround truthEngineering
The present disclosure relates to systems and methods for an adaptive pipelining composition service that can identify and incorporate one or more new models into the machine learning application. The machine learning application with the new model can be tested off-line with the results being compared with ground truth data. If the machine learning application with the new model outperforms the previously used model, the machine learning application can be upgraded and auto-promoted to production. One or more parameters may also be discovered. The new parameters may be incorporated into the existing model in an off-line mode. The machine learning application with the new parameters can be tested off-line and the results can be compared with previous results with existing parameters. If the new parameters outperform the existing parameters as compared with ground-truth data, the machine learning application can be auto-promoted to production.
Owner:ORACLE INT CORP
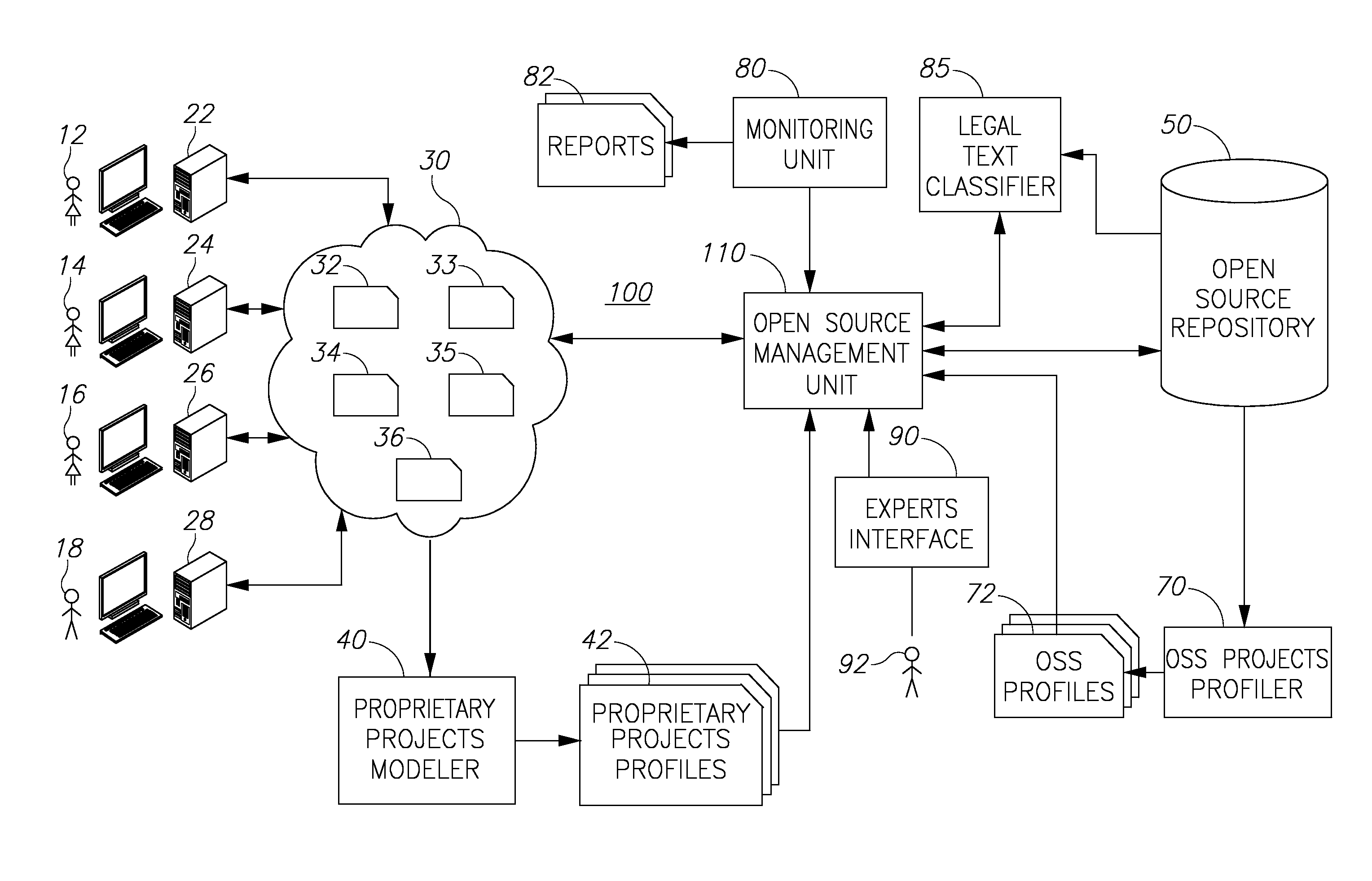
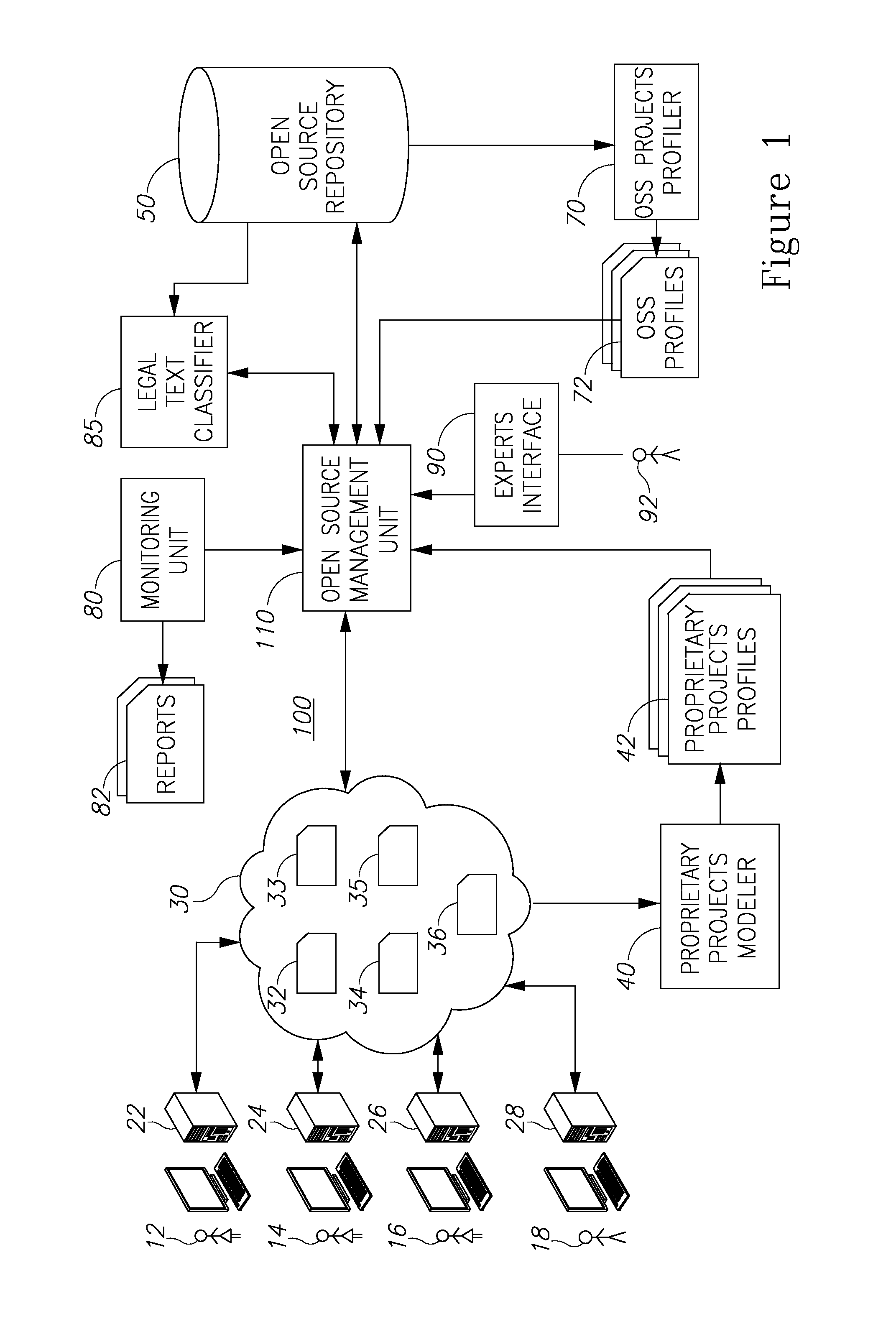
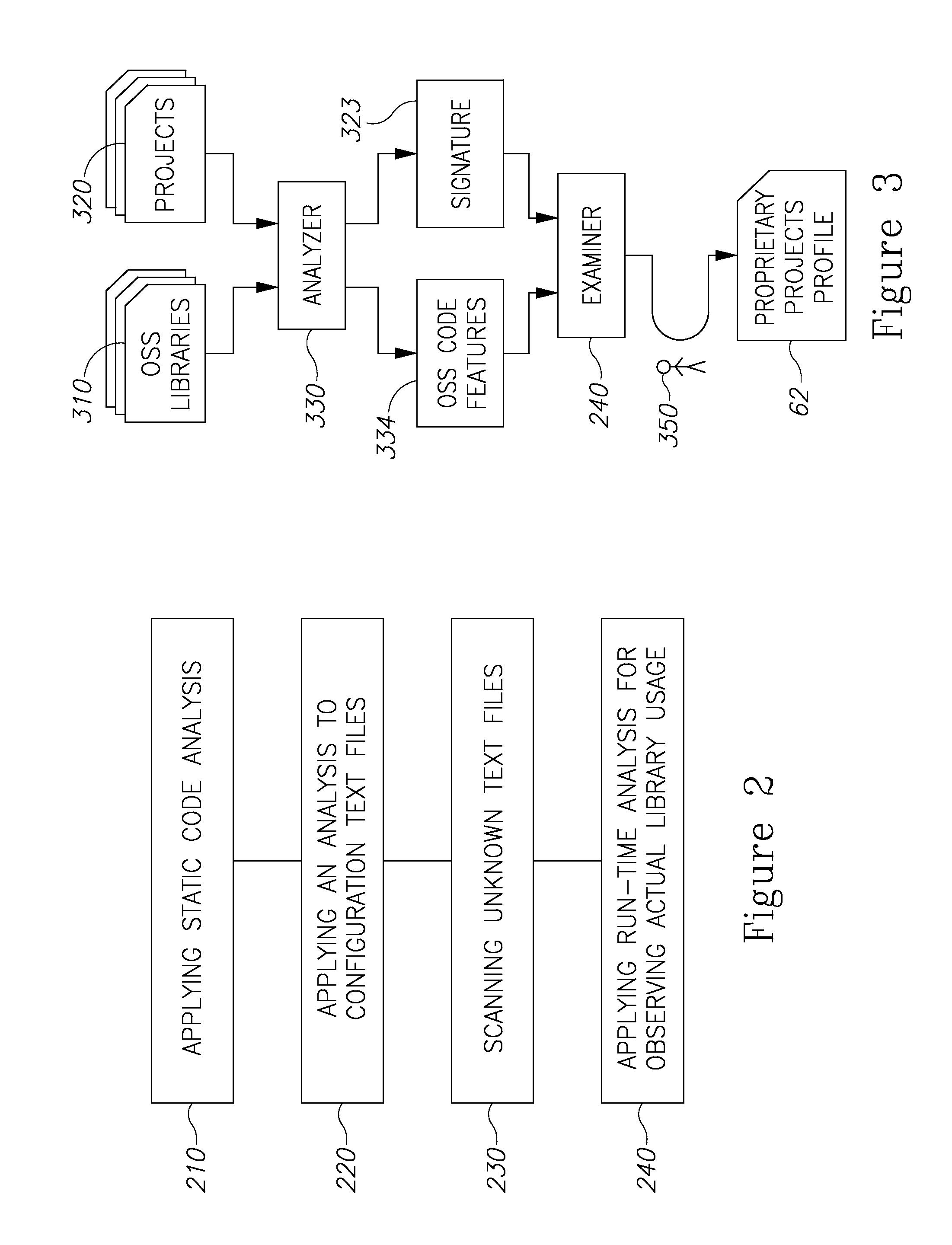
Open source management system and method
A method of controlling and managing open source software (OSS) resources used by developers in their software projects is provided herein. The method includes the following steps: analyzing the software projects, to yield a proprietary projects model that represents dependencies of source code portions of the software projects upon the OSS resources; generating and updating over time, OSS profiles for the OSS resources exhibiting technical and legal attributes; generating and updating over time, projects profiles for the software projects, based on the model and on monitoring and learning OSS resources usage by the developers; and monitoring actual OSS resources usage and providing the developers with at least one of: reports responsive to the changes the OSS; and guidance responsive to queries from the developers, wherein the reports and the guidance are based on the actual OSS usage, projects model, the projects profiles, and the OSS profiles.
Owner:WHITE SOURCE
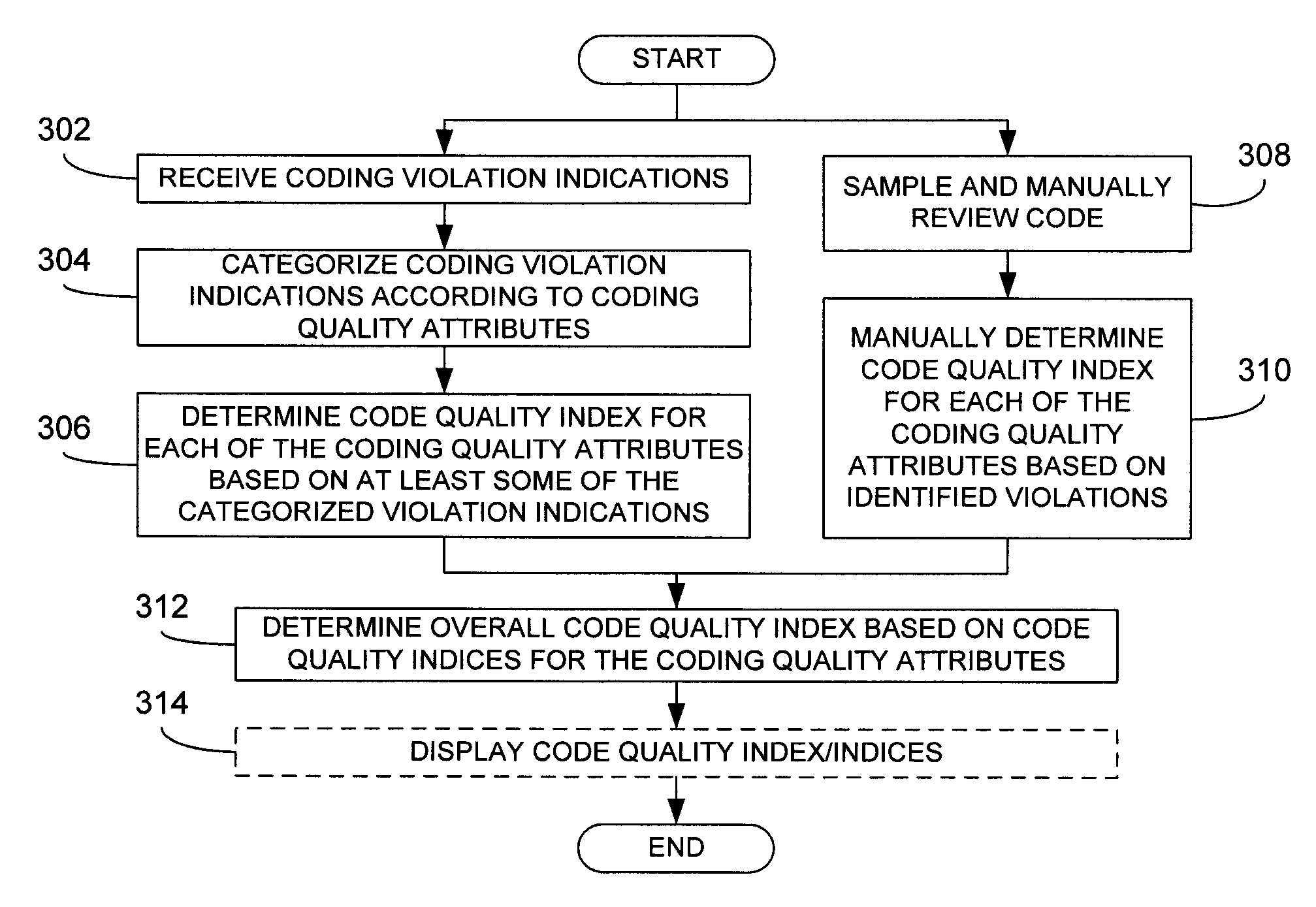
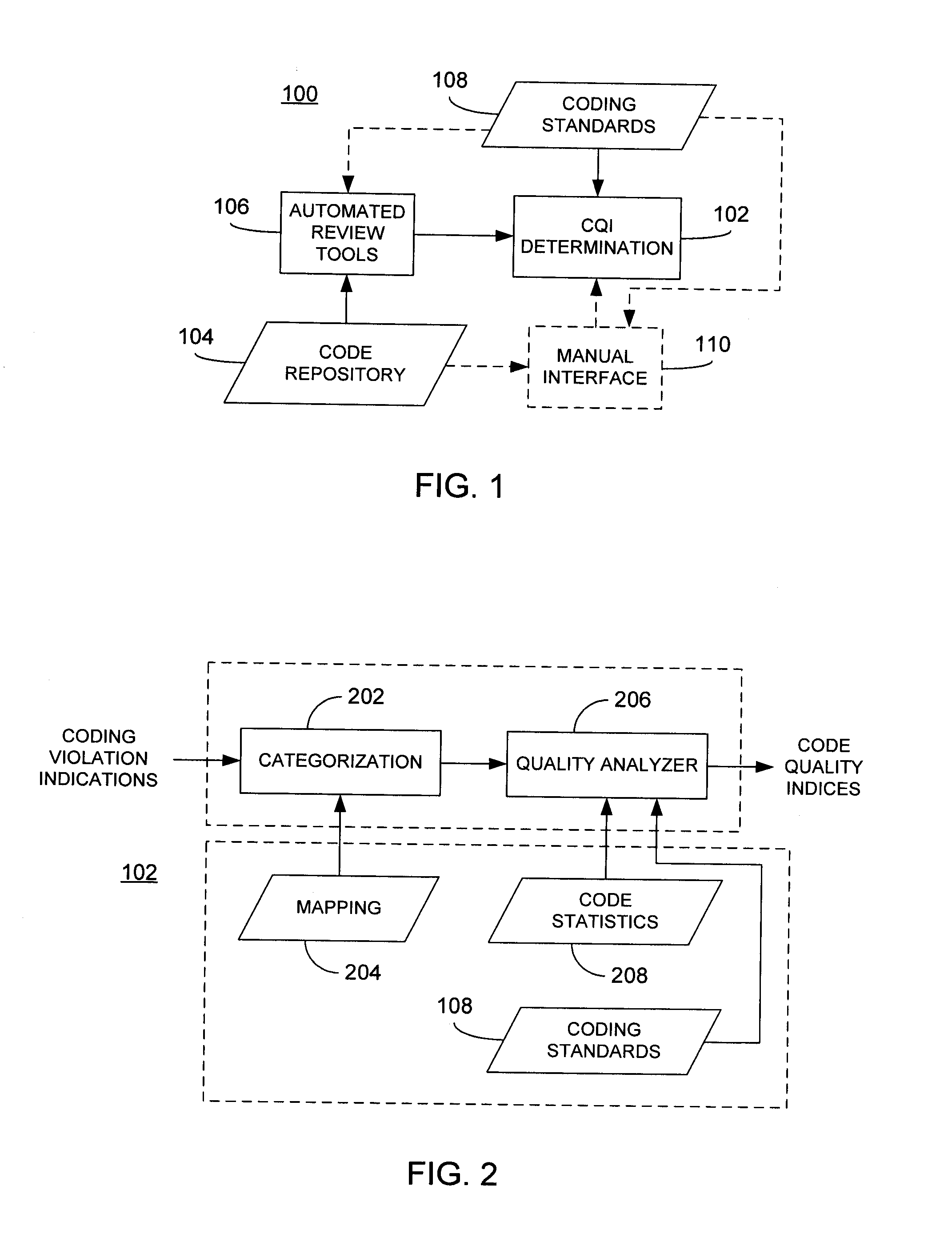
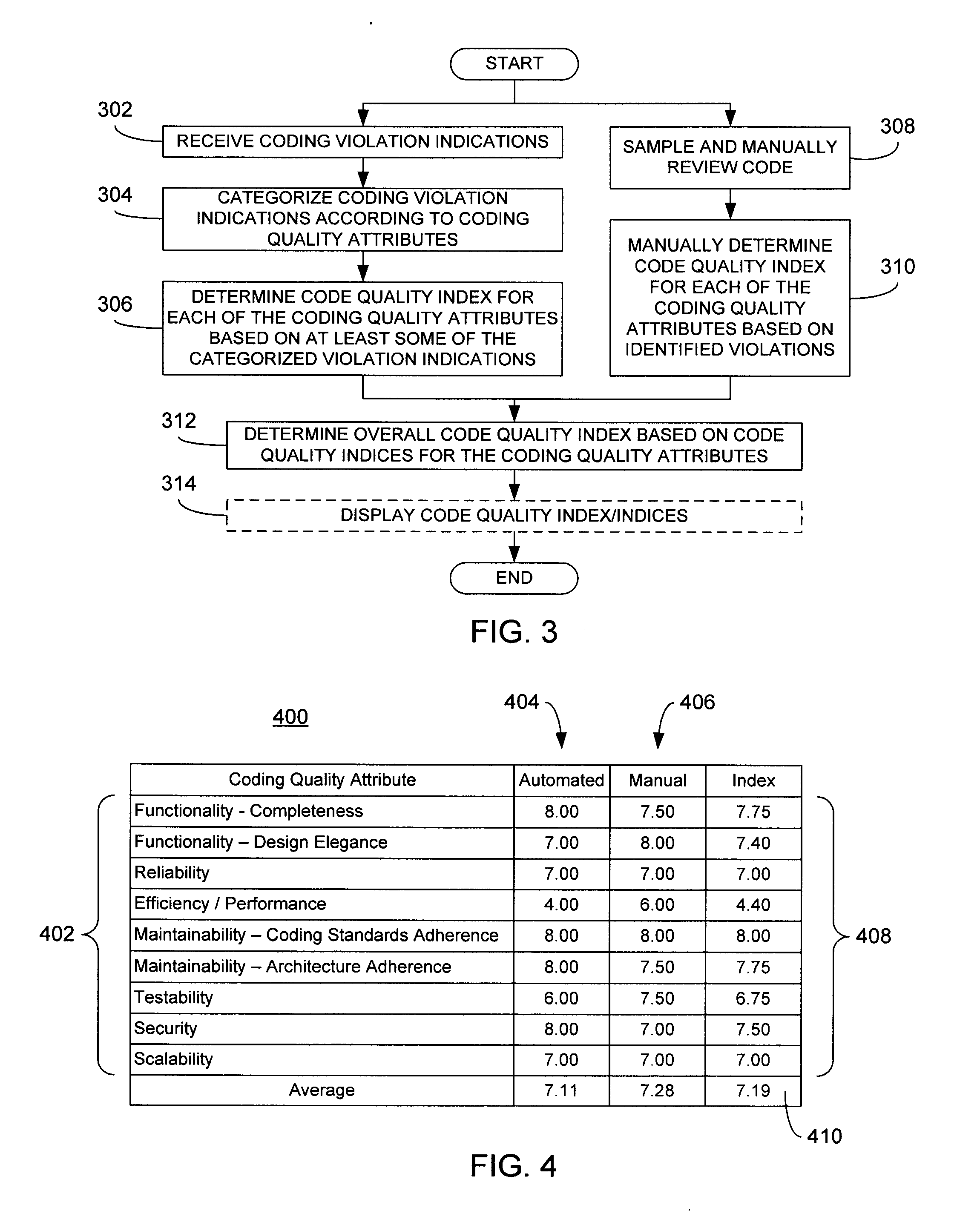
Assessment of software code quality based on coding violation indications
ActiveUS20110055798A1Overcome limitationsError detection/correctionSoftware metricsCoding qualitySoftware
A plurality of coding violation indications corresponding to software code are categorized according to a plurality of coding quality attributes. The coding violation indications may be reported via static analysis tools or via manual analysis of the software code. The categorized coding violations serve as the basis for determining a plurality of code quality indices each corresponding to a respective one of the plurality of coding quality attributes. In an embodiment, the plurality of code quality indices may be further processed to determine an overall code quality index for the software code. One or more of the resulting code quality indices may be displayed to a user. In this manner, code quality indices may be provided that are directly based on coding violations reported through static analysis.
Owner:ACCENTURE GLOBAL SERVICES LTD
Pruning engine
A method and apparatus are disclosed for enhancing operable functionality of input source code files from a software program by preprocessing input source code files with codeword processing operations to generate a plurality of preprocessed input source code files, identifying candidate code snippets by pruning one or more preprocessed input source code files that do not meet a similarity threshold measure for library functions stored in the system library, and identifying at least a first validated code snippet from the one or more candidate code snippets that matches a first library function stored in the system memory on the basis of at least first and second matching metrics.
Owner:DEVFACTORY INNOVATIONS FZ LLC
System and method for managing source code and acquiring metrics in software development
ActiveUS8225302B2Ease of evaluationSoftware testing/debuggingSoftware metricsSoftware development processParallel computing
A method and system is described for managing the development of software source code, and in addition, collecting useful metrics about the development process. A first source code is provided in a desired state. The desired state may be the requirement that the source code can be built or the desired state may be the requirement that the source code can be built and pass one or more tests. A second source code is then received. The second source may be a modified copy of the source code. It is then determined whether the second source code is in the desired state, and the first source code is updated using the second source code in response to the second source code being in the desired state. Metrics that may be collected include: the name of a task, time to complete the task, line of code involved, etc.
Owner:WAUGH LAWRENCE TAYLOR +1
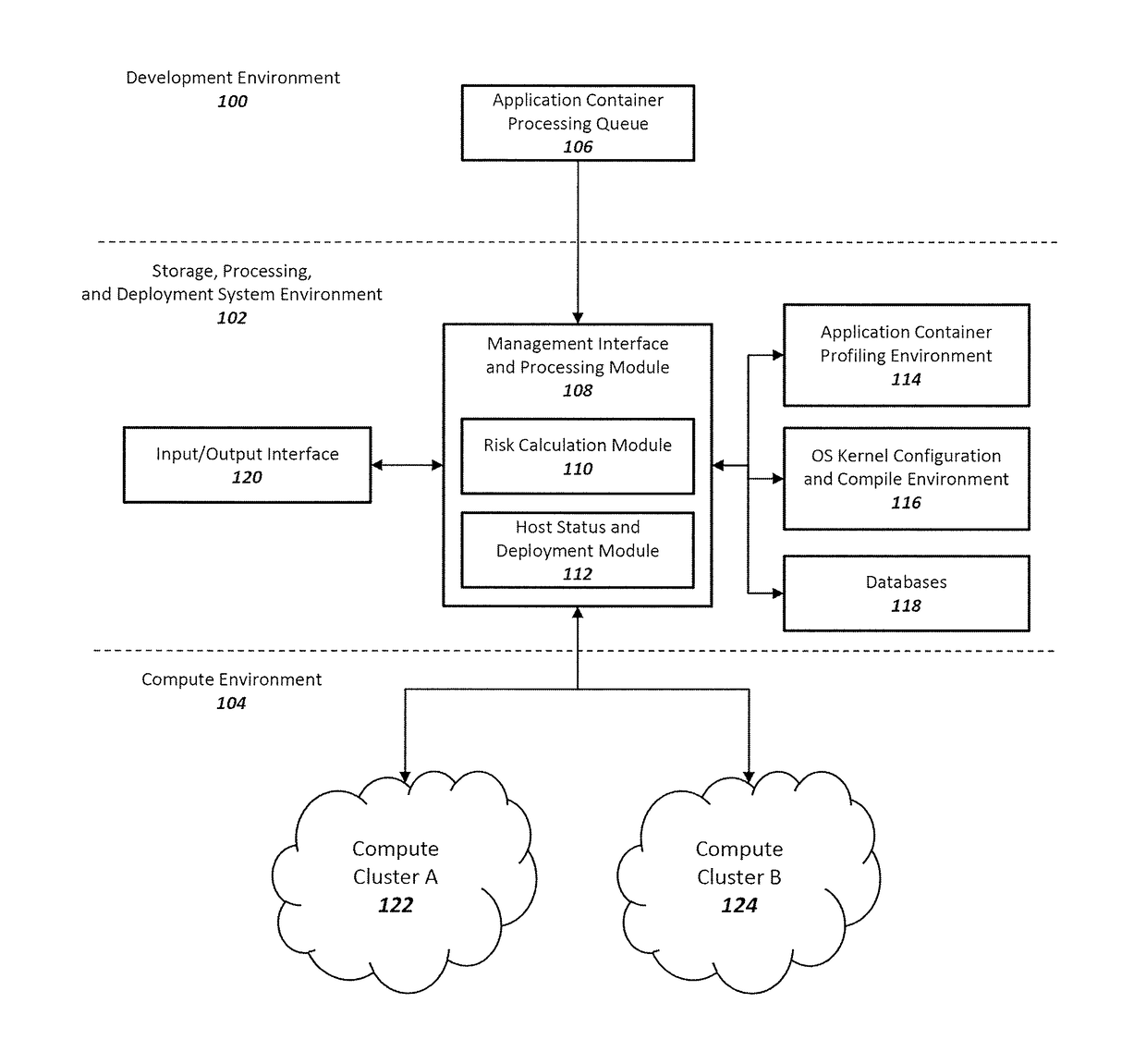
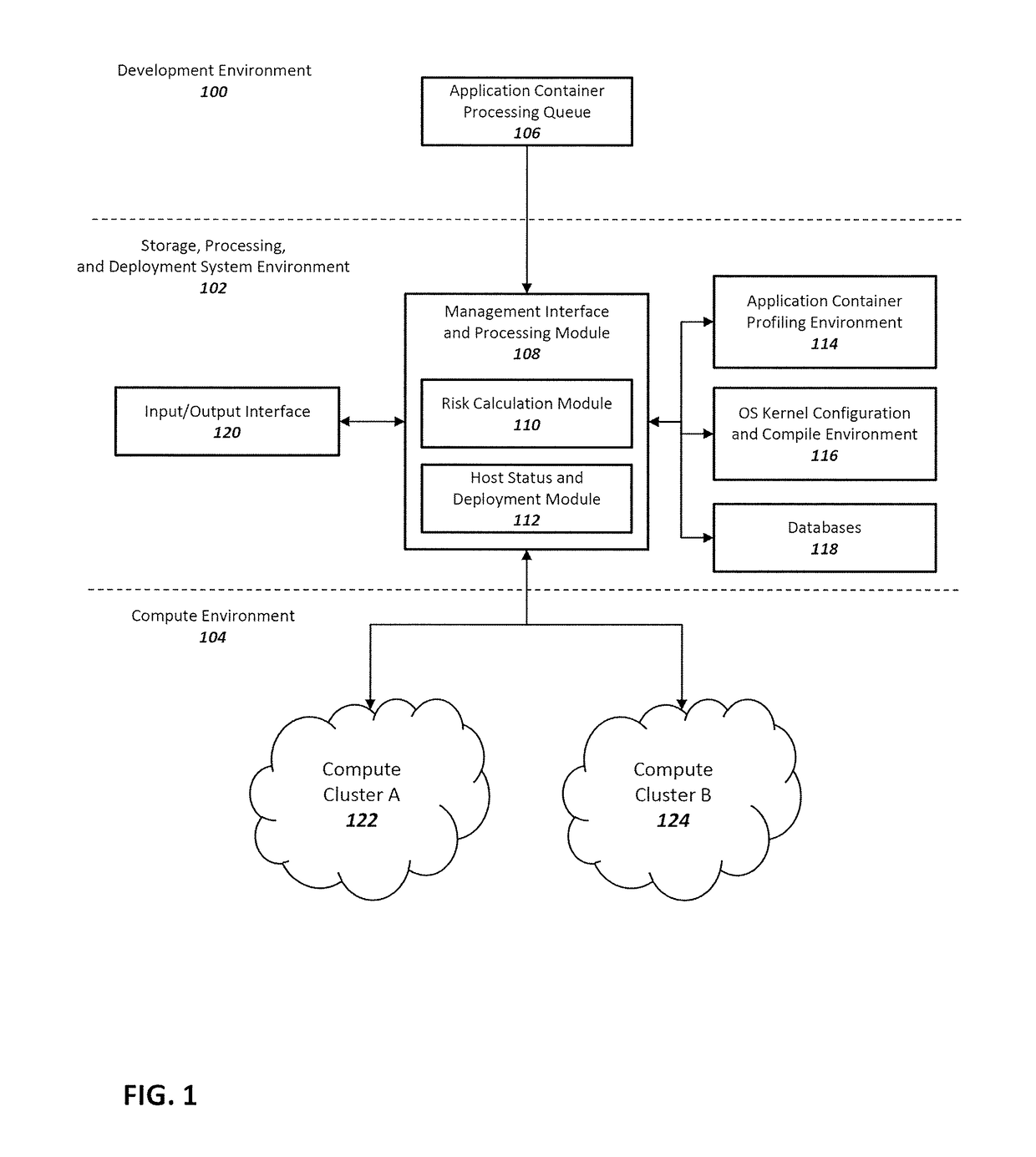
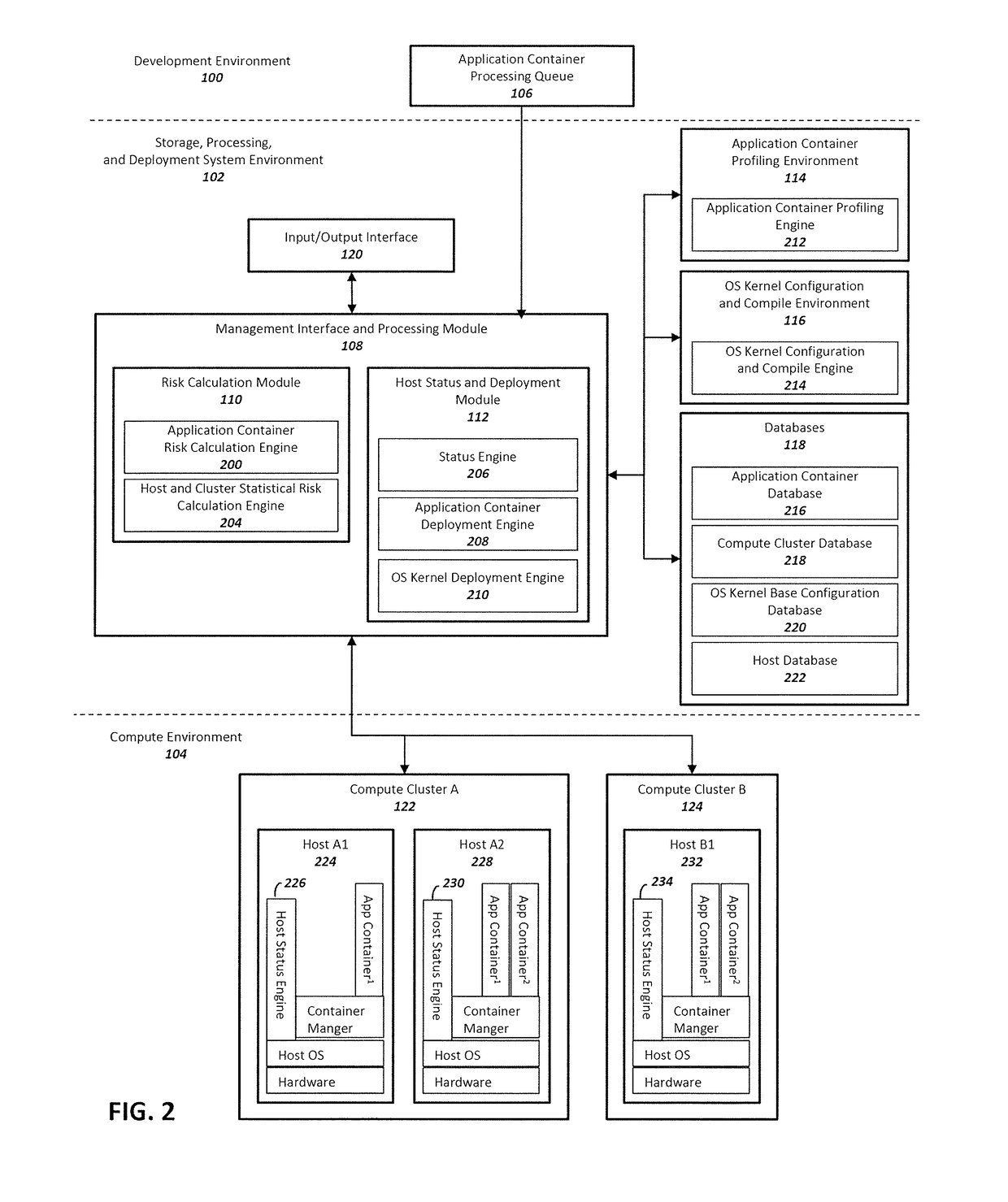
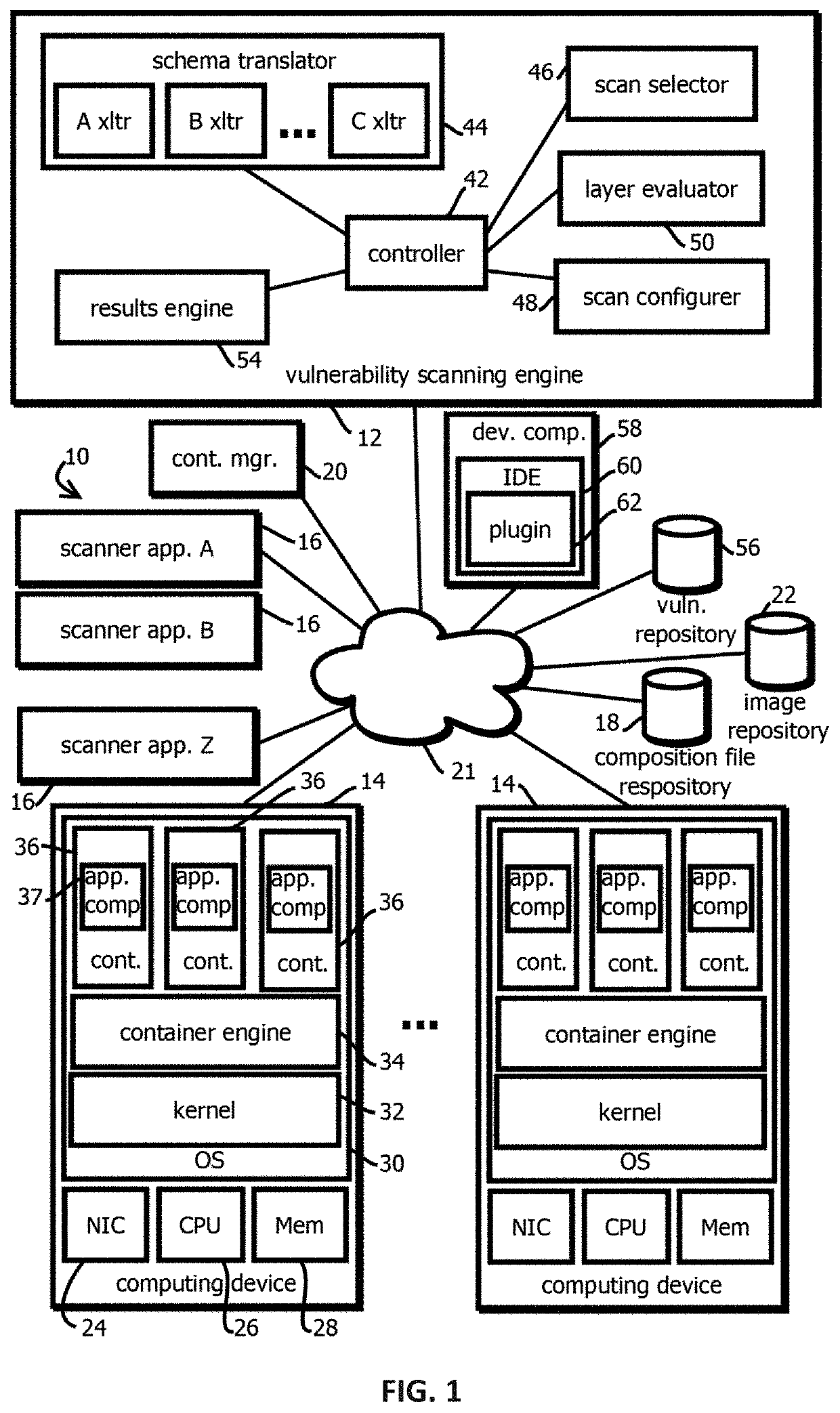
Method and system for enhancing application container and host operating system security in a multi-tenant computing environment
ActiveUS20180046457A1Reliability/availability analysisSoftware testing/debuggingOperating system securityComputerized system
A system for application container security comprising an application container processing and deployment computer system configured to receive an application container, determine operating system kernel requirements of the application container, calculate a risk value based on the operating system kernel requirements of the application container, determine availability of a host computer to host the application container, by determining if the operating system kernel of the host computer meets operational requirements of the application container. The operational requirements including the risk value for the application container. When the operating system kernel of the host computer is determined to meet the operational requirements, pair the application container with the operating system kernel of the host computer. When the operating system kernel of the host computer is determined to not meet the operational requirements, configure and compile a container-specific operating system kernel that meets the operational requirements.
Owner:MAXISIQ INC
Software application quality assessment
InactiveUS20170235662A1Reliability/availability analysisSoftware testing/debuggingApplication softwareQuality assessment
First data is accessed describing a plurality of different functional aspects of a particular software application. The first data is received from multiple different sources. Second data is accessed describing a plurality of different non-functional aspects of the particular software application, the second data received from multiple different sources. A plurality of functional scores for the particular software application is derived based on the plurality of functional aspects. A plurality of non-functional scores for the particular software application is derived based on the plurality of non-functional aspects. A quality score for the particular software application is calculated from the plurality of functional scores and the plurality of non-functional scores.
Owner:CA TECH INC
Rule merging in system for monitoring adherence by developers to a software code development process
ActiveUS20120317541A1Improve efficiencyMagnifies processing burdenNuclear monitoringDigital computer detailsSoftware development processSubject-matter expert
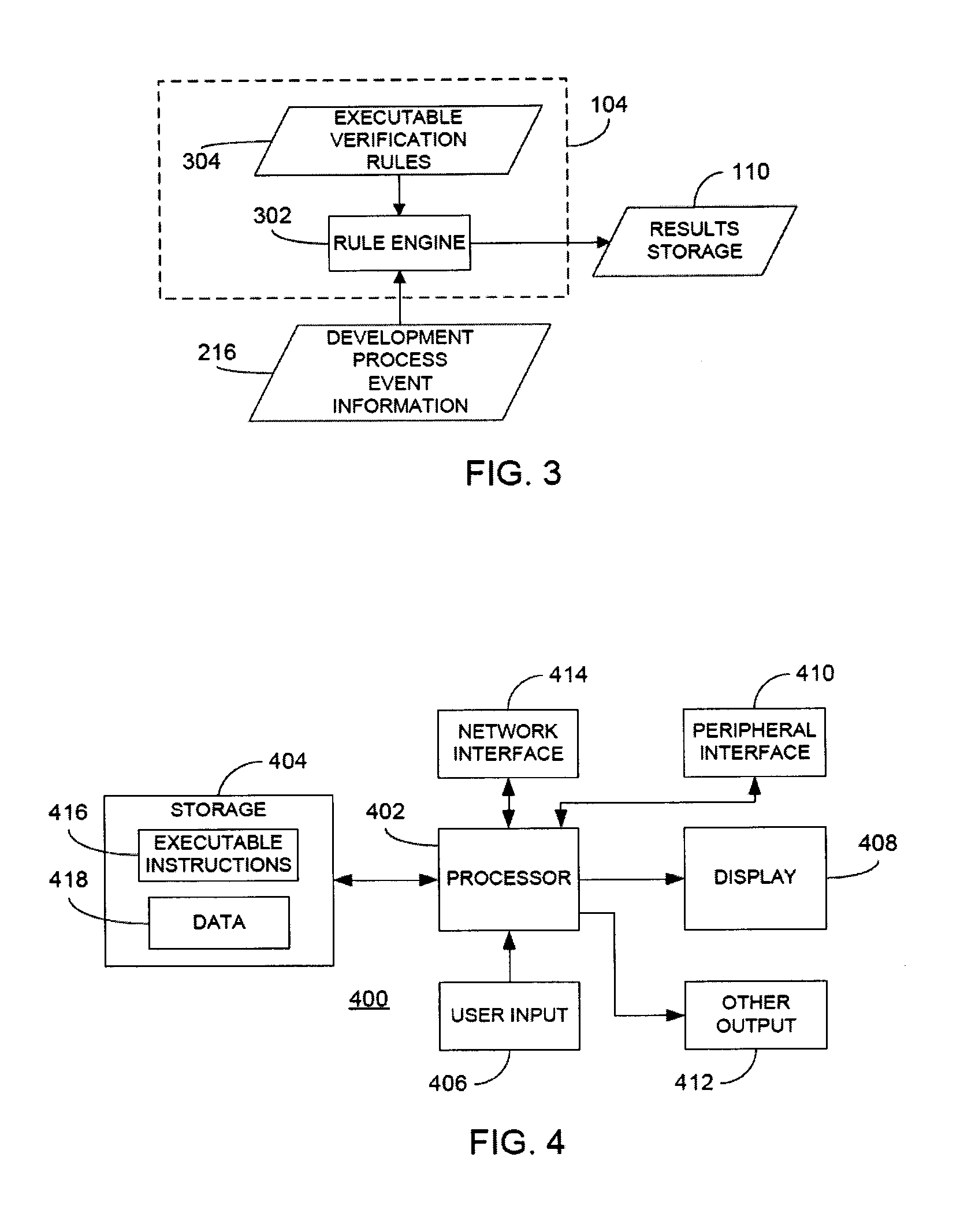
In a rule-based system for monitoring process adherence, first and second processing patterns are received and merged to provide a merged processing pattern. Each processing pattern, which may be expressed in a state graph representation, embodies at least a portion of a desired software code development process. Optionally, the merged processing pattern may be presented to a subject-matter expert to obtain feedback thereon. The merged processing pattern may then be converted into an executable process verification rule for use in monitoring process adherence. In an embodiment, development process event data is compared to the executable process verification rules. Violations of the rules result in the generation of failure indications that may be stored and subsequently reported as needed. In this manner, efficiency of automated process adherence monitoring systems may be improved when determining the level of compliance by developers with one or more software code development processes.
Owner:ACCENTURE GLOBAL SERVICES LTD
Introspection driven monitoring of multi-container applications
Owner:CA TECH INC
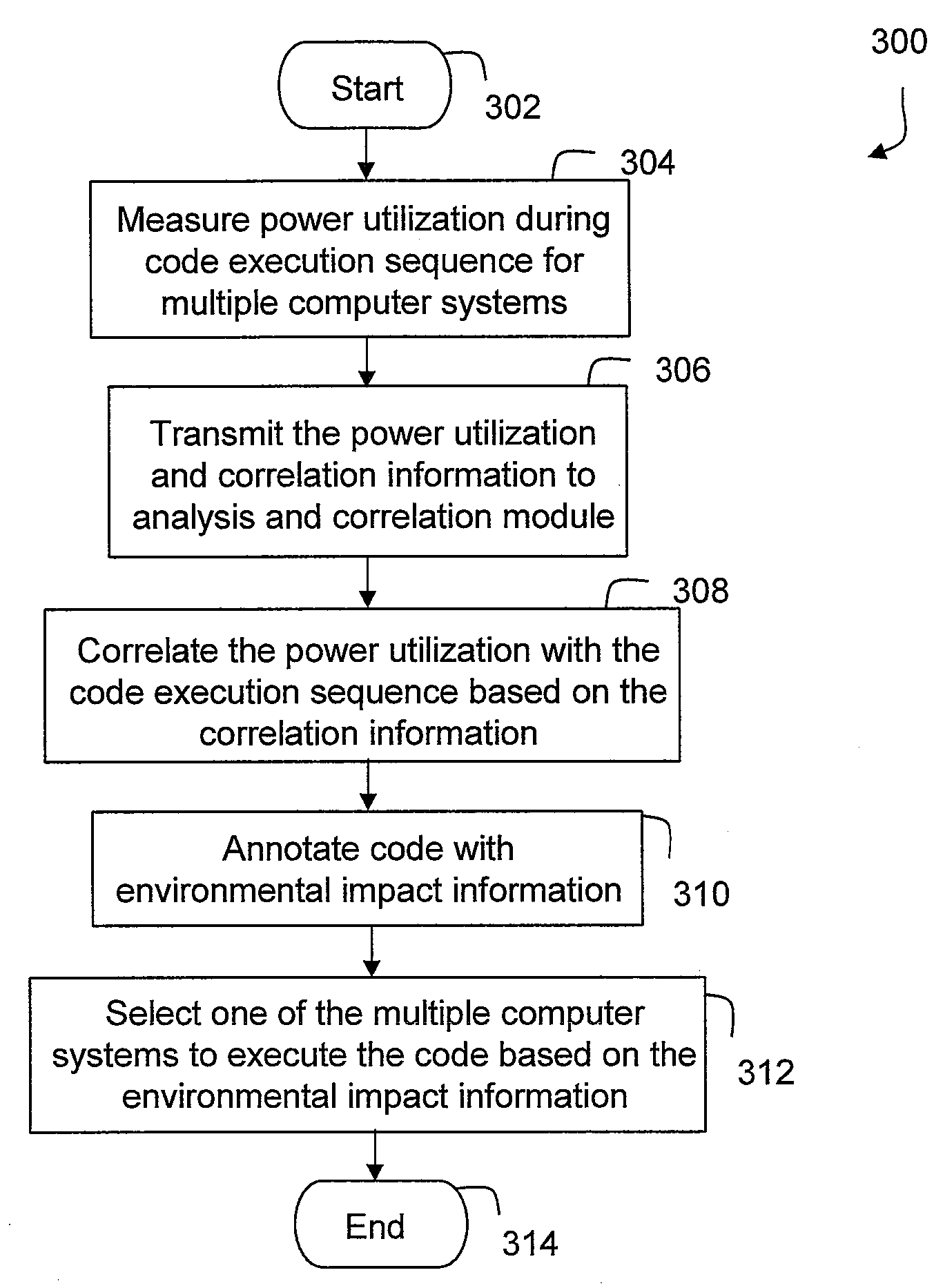
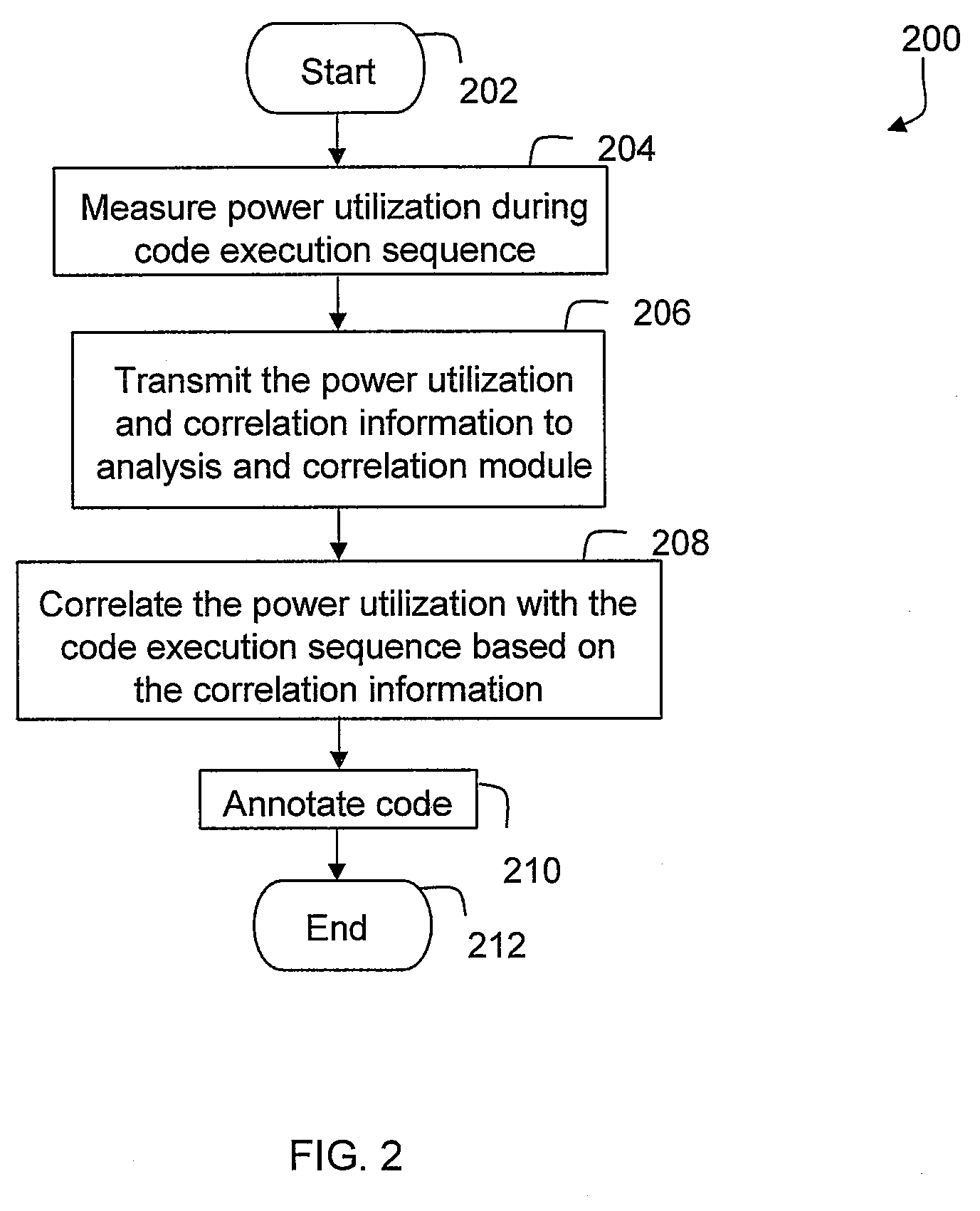
Techniques for Providing Environmental Impact Information Associated With Code
InactiveUS20100306737A1Error detection/correctionProgram documentationEnvironment effectComputer science
A technique for providing environmental impact information associated with code includes determining, based on execution of the code on a computer system, an environmental impact of a code execution sequence included in the code. A section of the code that is associated with the code execution sequence is then annotated with environmental impact information associated with the environmental impact of the code execution sequence.
Owner:KYNDRYL INC
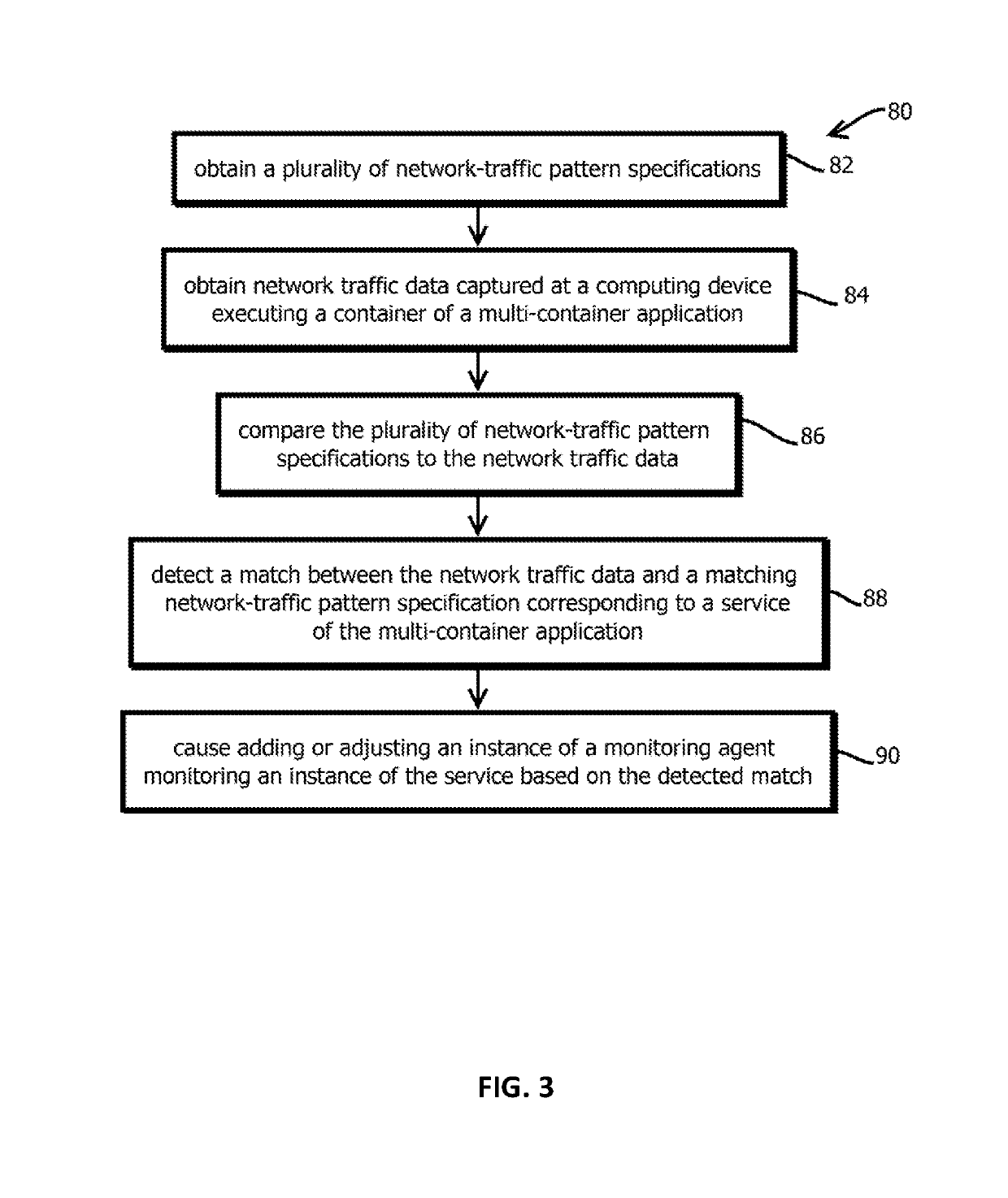
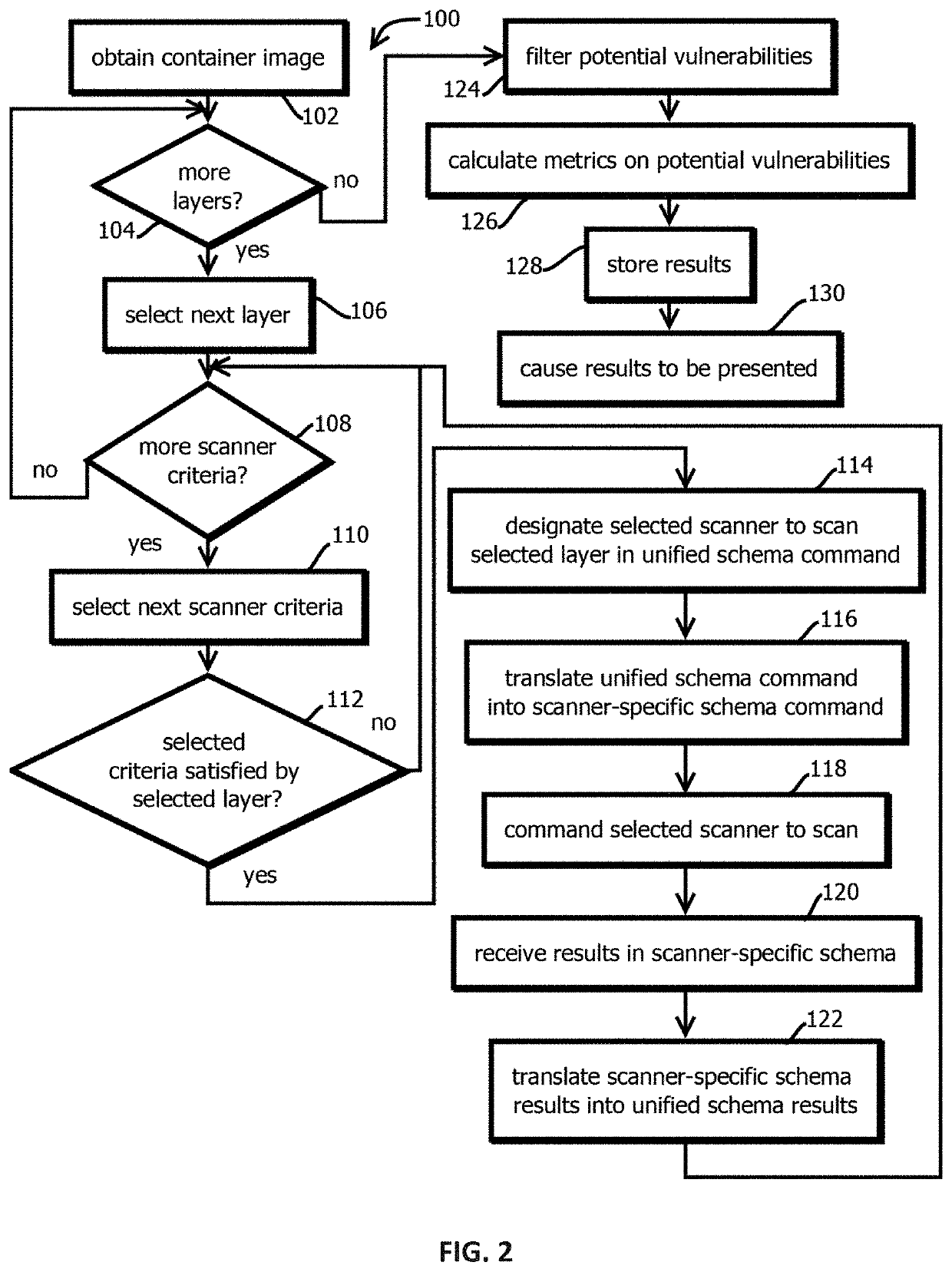
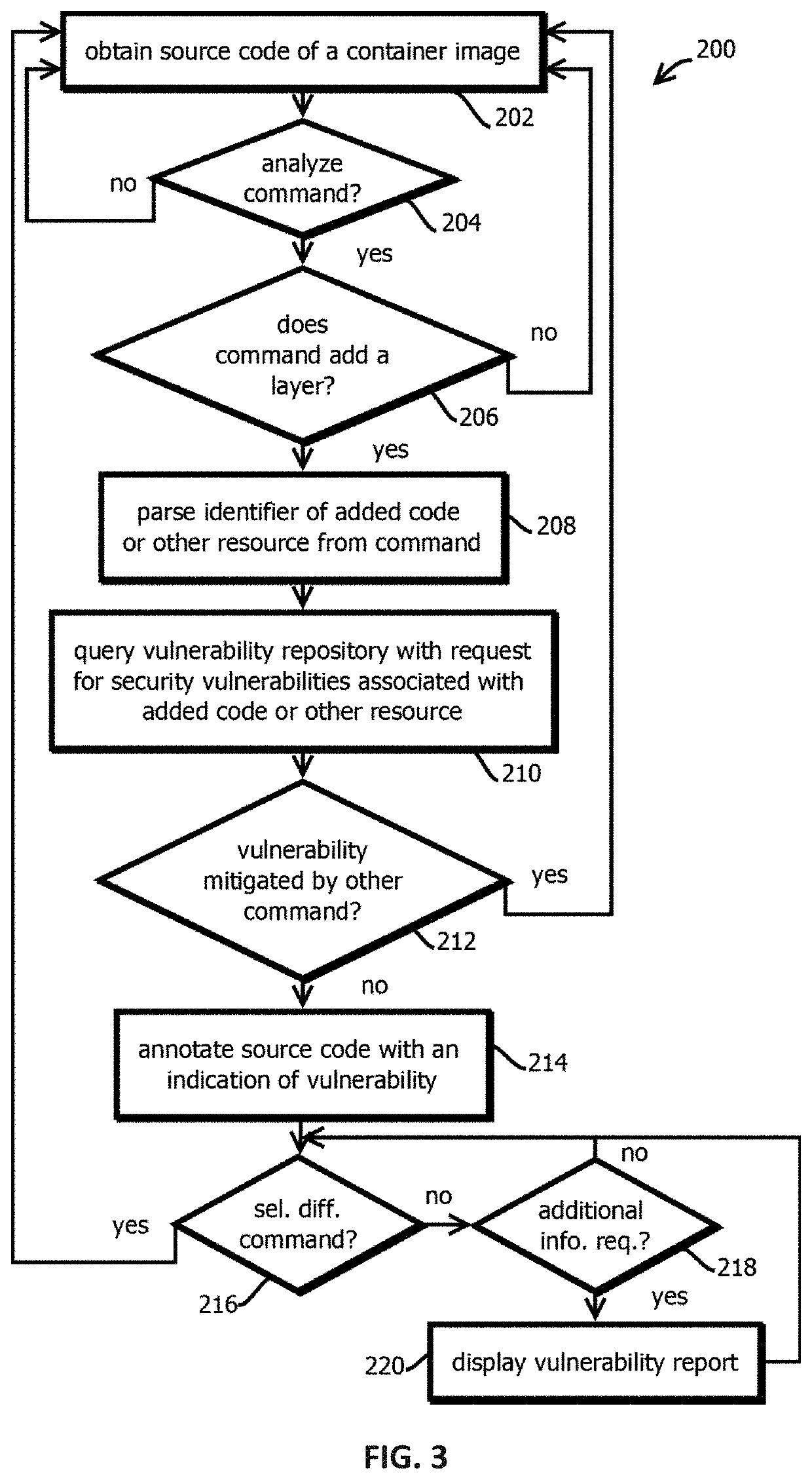
Selectively applying heterogeneous vulnerability scans to layers of container images
Provided is a process that includes obtaining a container image; for each of a plurality of the constituent images of the container image, determining, with one or more processors, whether the respective constituent image contains a vulnerability by: selecting a respective subset of scanners from among a set of a plurality of scanners by comparing respective scanner criteria to at least part of the respective constituent image, causing at least part of the respective constituent image to be scanned with the selected respective subset of scanners, and identifying potential vulnerabilities in the respective constituent image based on output of the scanning; and storing results based on at least some identified potential vulnerabilities in memory.
Owner:CA TECH INC
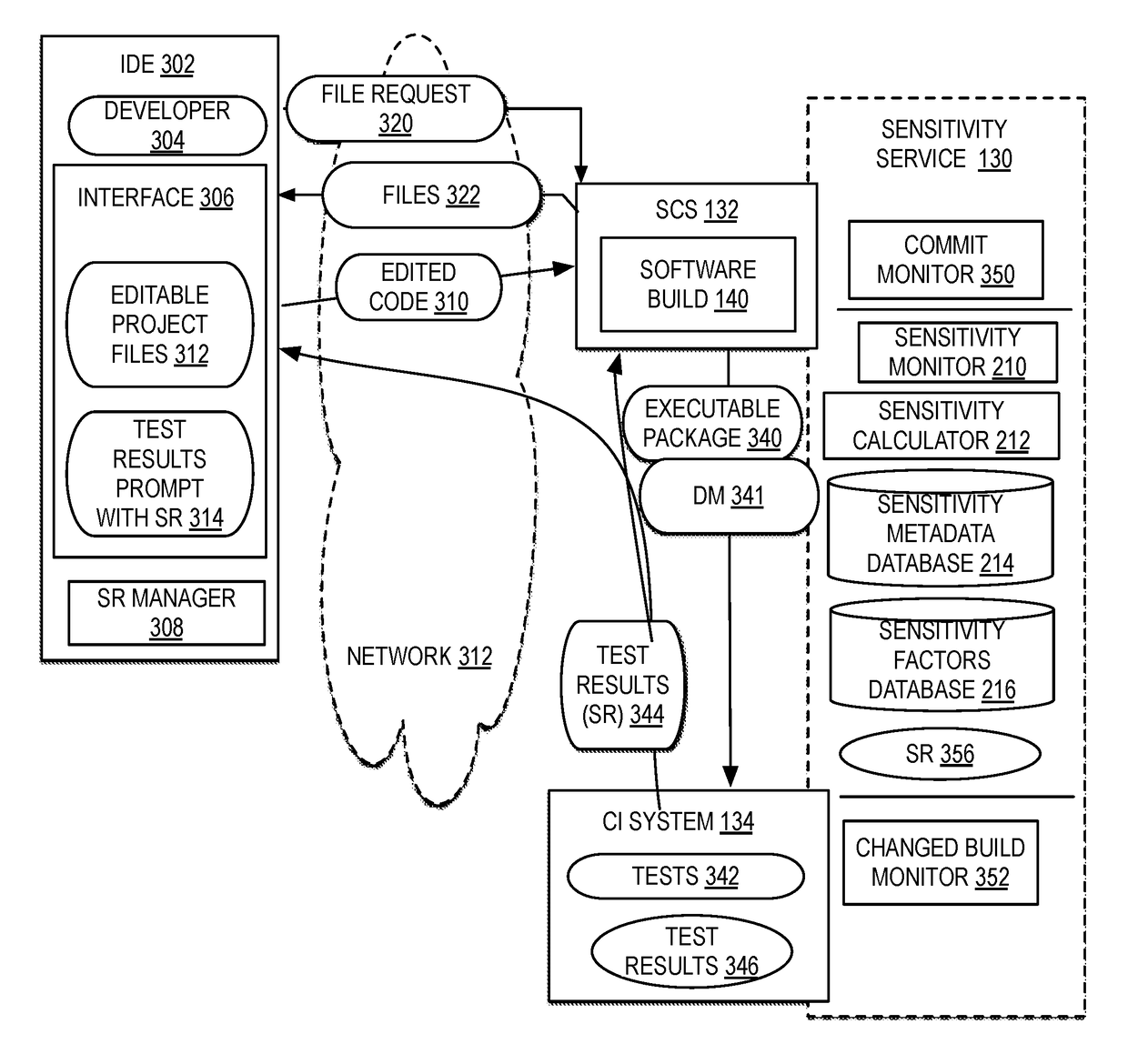
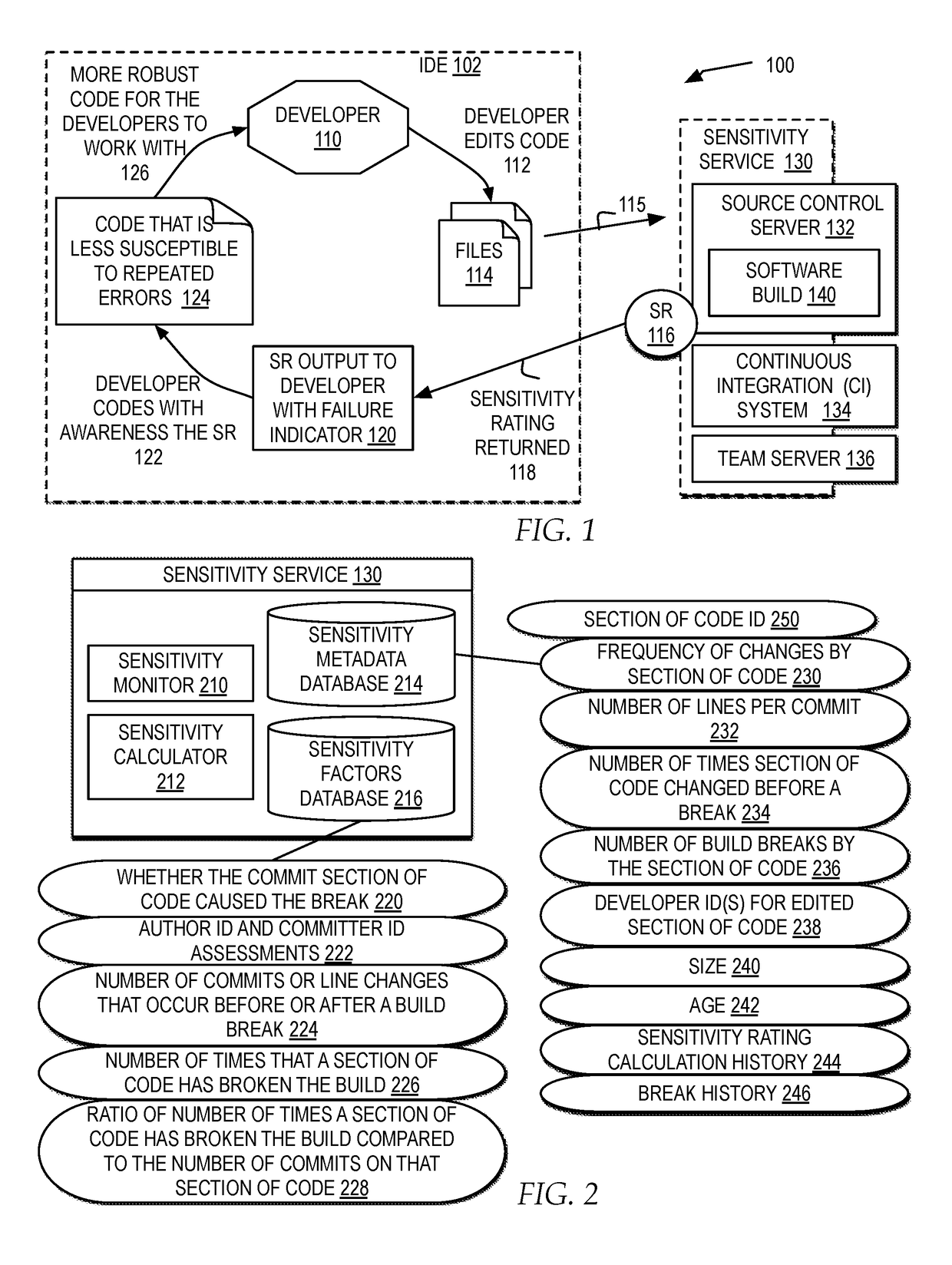
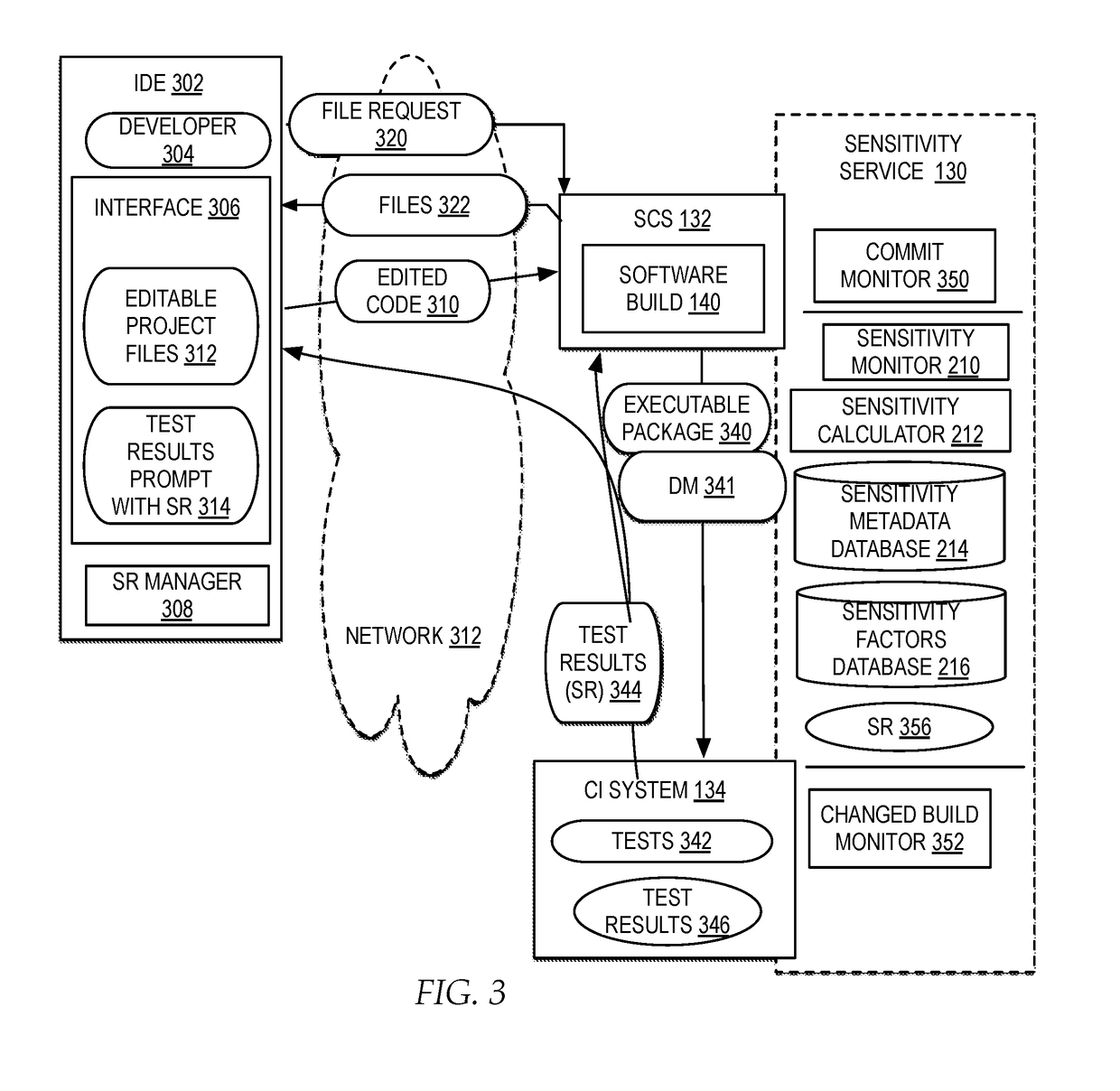
Developing software project plans based on developer sensitivity ratings detected from monitoring developer error patterns
ActiveUS20180129483A1Reduce buildMinimize timeVersion controlSoftware testing/debuggingProgram planningComputer science
A selection of one or more files for a project plan for a software build is identified. A historical assessment of one or more developers available during a build timeline for the project plan is accessed, the historical assessment comprising an assessment value calculated from one or more previously evaluated sensitivity ratings from one or more previously edited files by the one or more developers of one or more previous software builds. An optimized selection of the one or more developers is assigned to each selection of one or more files based on the historical assessment. The optimized selection of the one or more developers for each selection of one or more files in the project plan for the software build is output.
Owner:IBM CORP
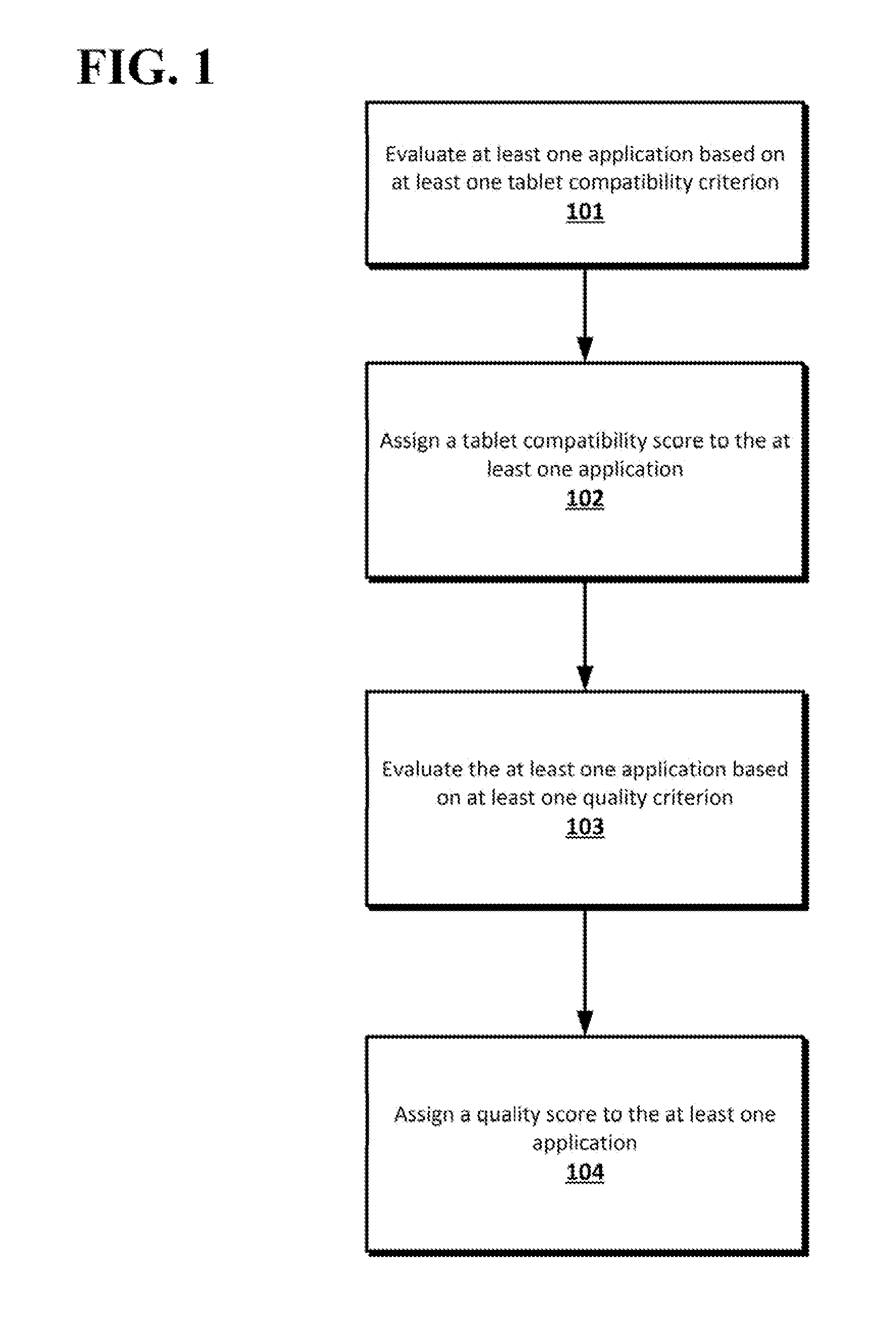
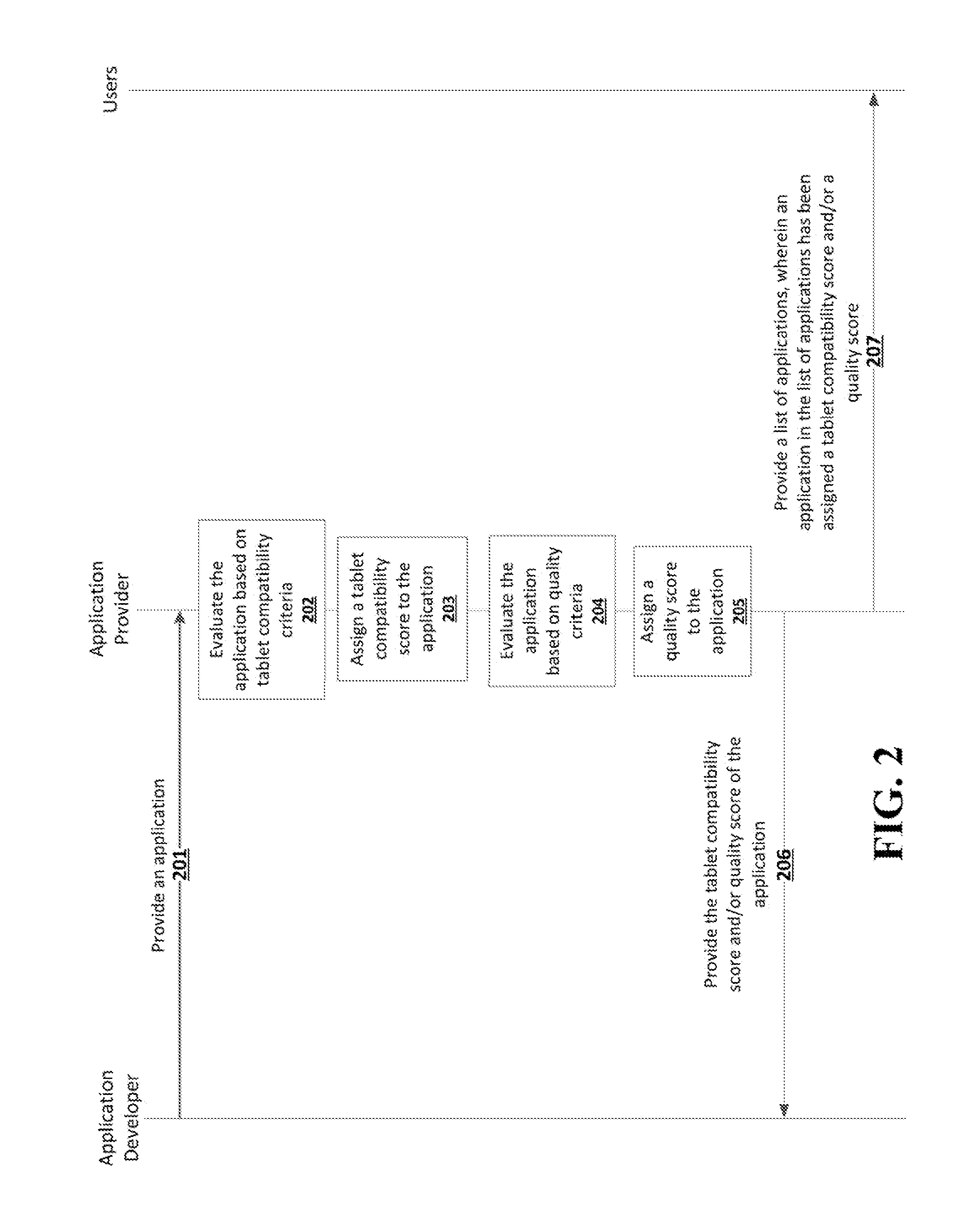
System for assessing an application for tablet compatibility and quality
InactiveUS20150106384A1Digital data information retrievalDigital data processing detailsTablet computerComputer compatibility
Applications that have been designed for a smaller format device such as a smartphone and simply ported to a larger format device such as a tablet can be discerned from applications designed specifically for the larger format device. An application can be evaluated based on tablet compatibility criteria and can be assigned a tablet compatibility score. The application can be evaluated based on quality criteria and can be assigned a quality score. The compatibility score and the quality score can be used to help find and rate any number of applications.
Owner:GOOGLE LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com