Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
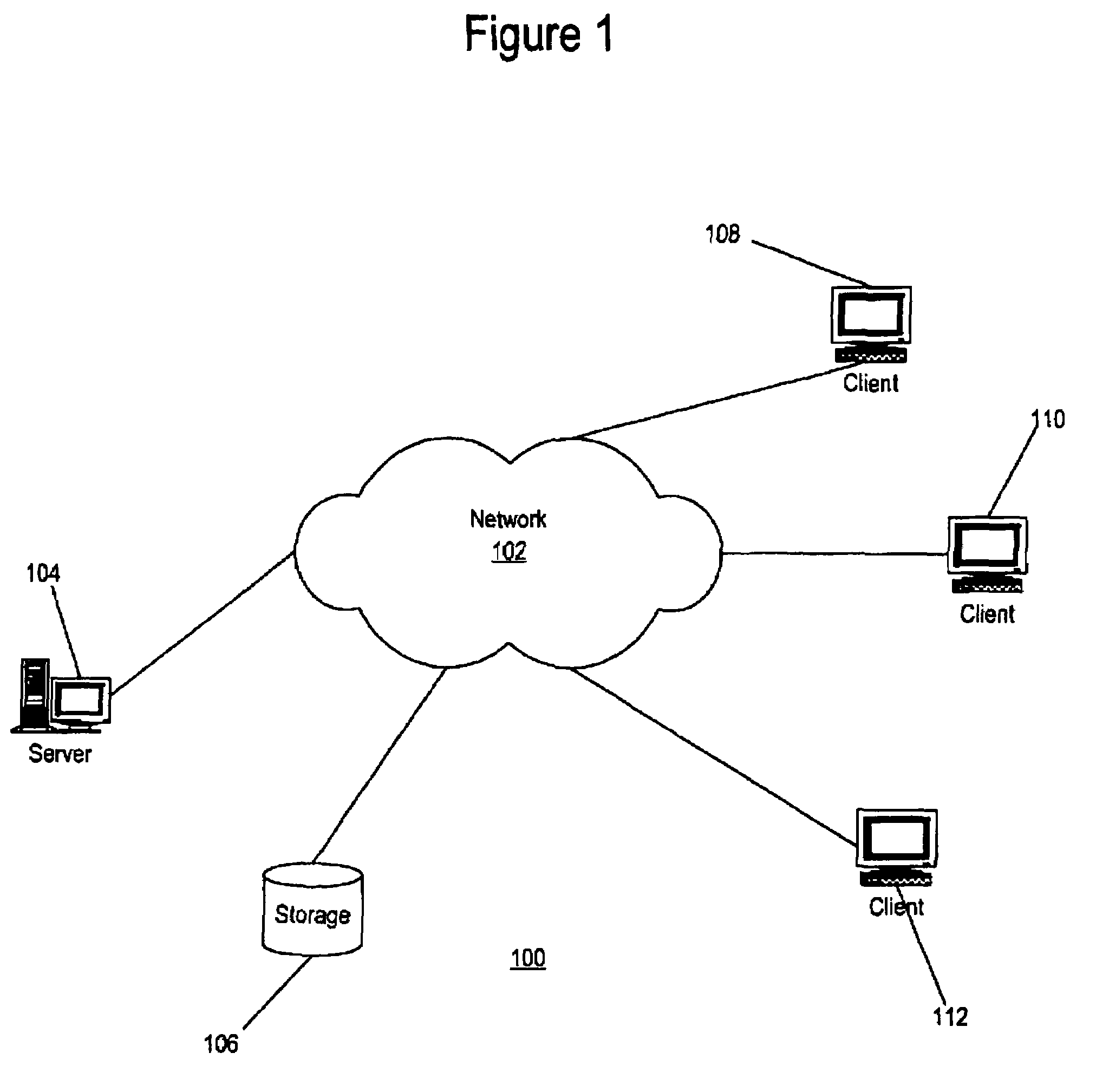
812 results about "Operating system kernel" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
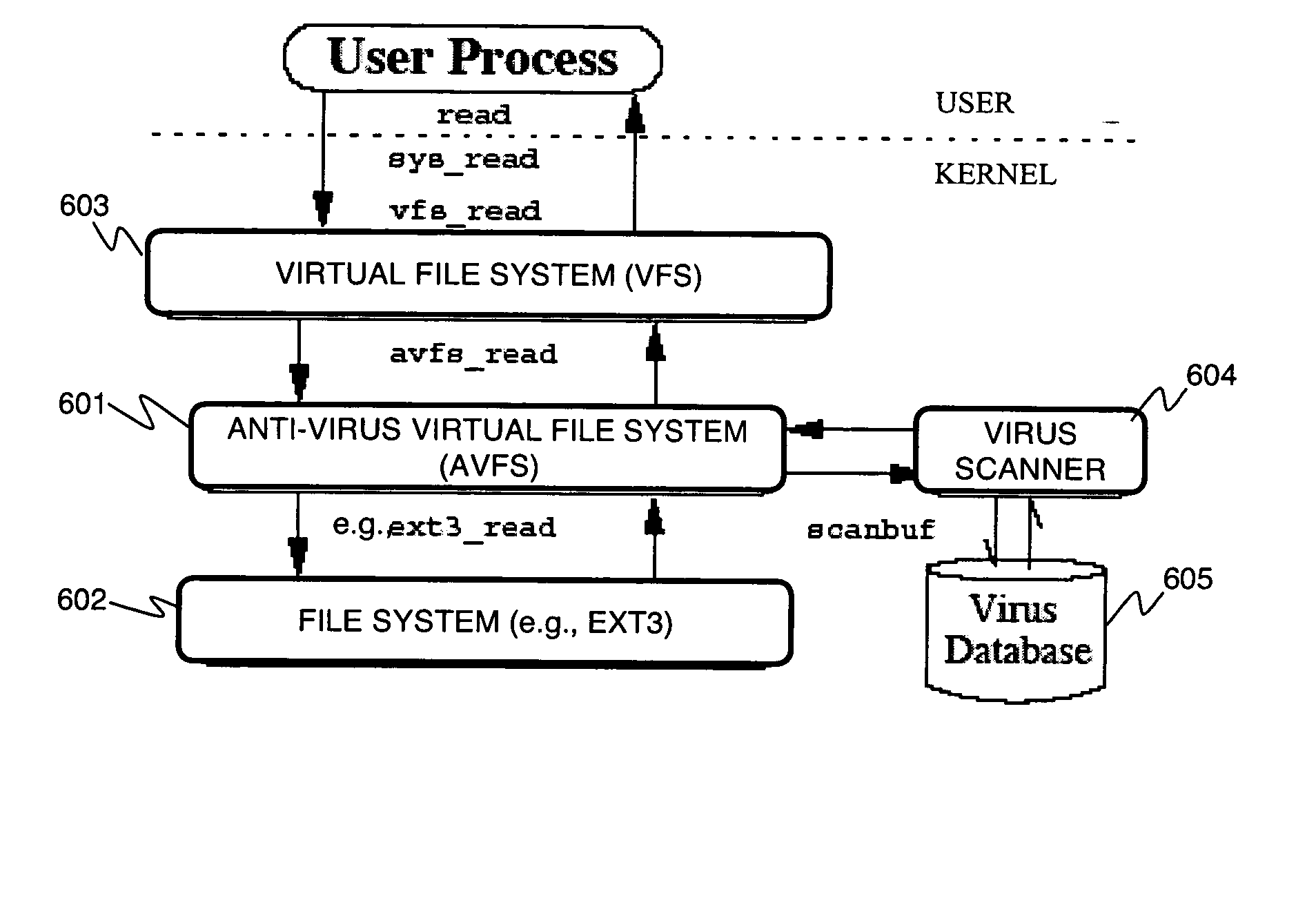
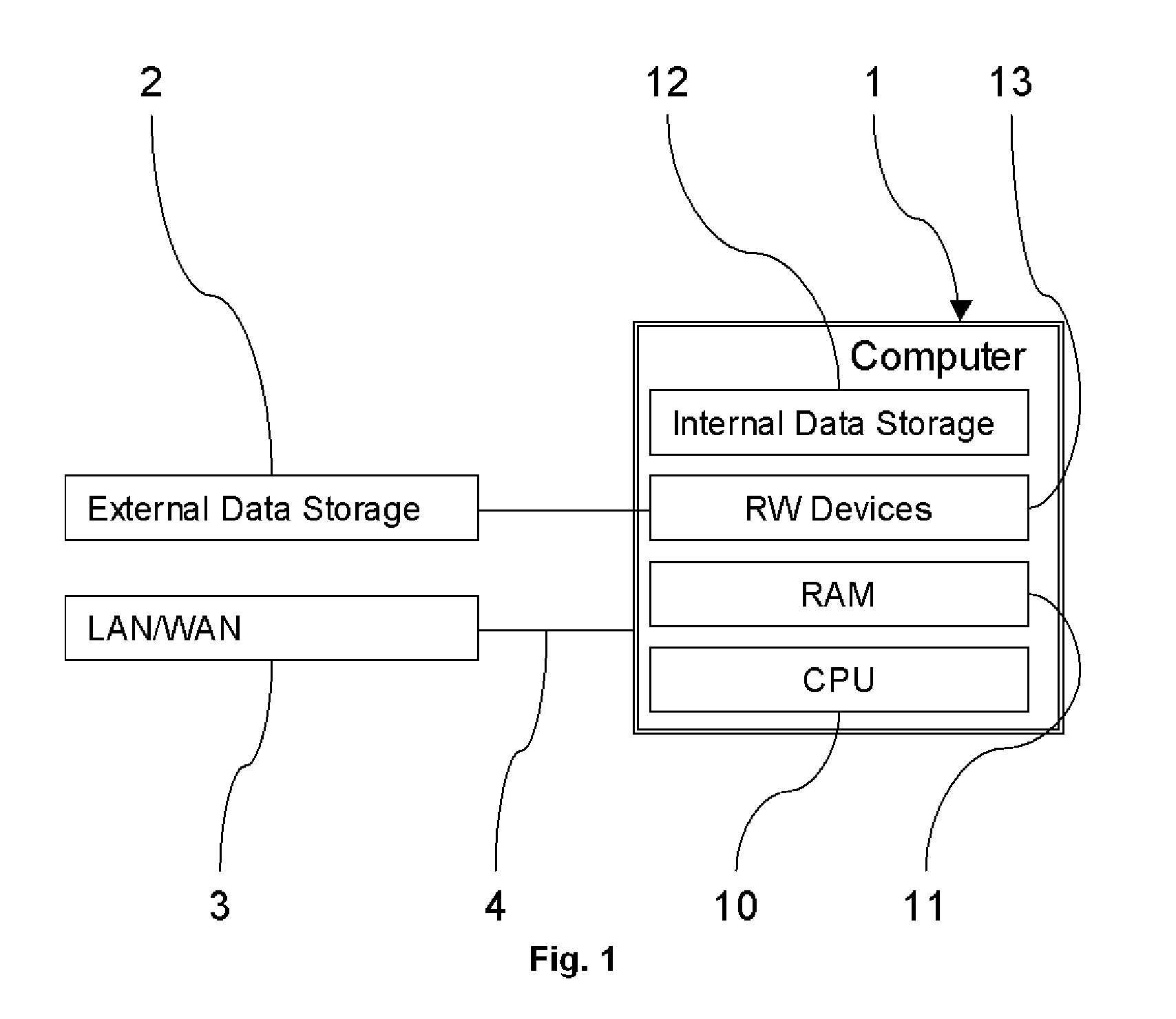
Stackable file systems and methods thereof
InactiveUS20050273858A1Memory loss protectionError detection/correctionOperational systemFile system
An operating system kernel, including a protocol stack, includes a network layer for receiving a message from a data network, a stackable file system layer coupled to the network layer for inspecting the message, wherein the stackable file system layer is coupled to a storage device, the stackable file system determining and storing file system level information determined from the message, and a wrapped file system comprising a file targeted by the message coupled to the stackable file system layer for receiving the message inspected by the stackable file system.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK +1
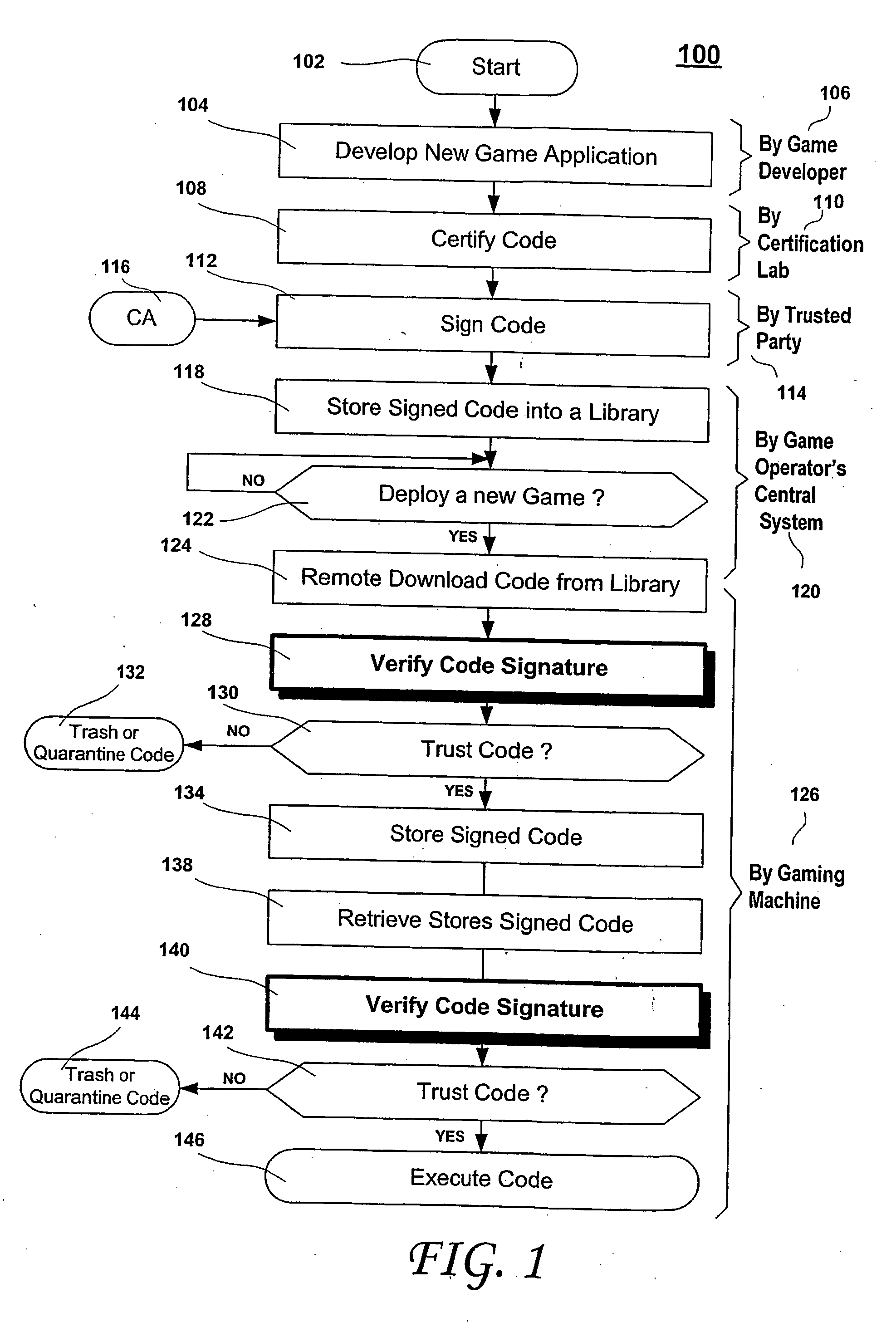
Secure game download
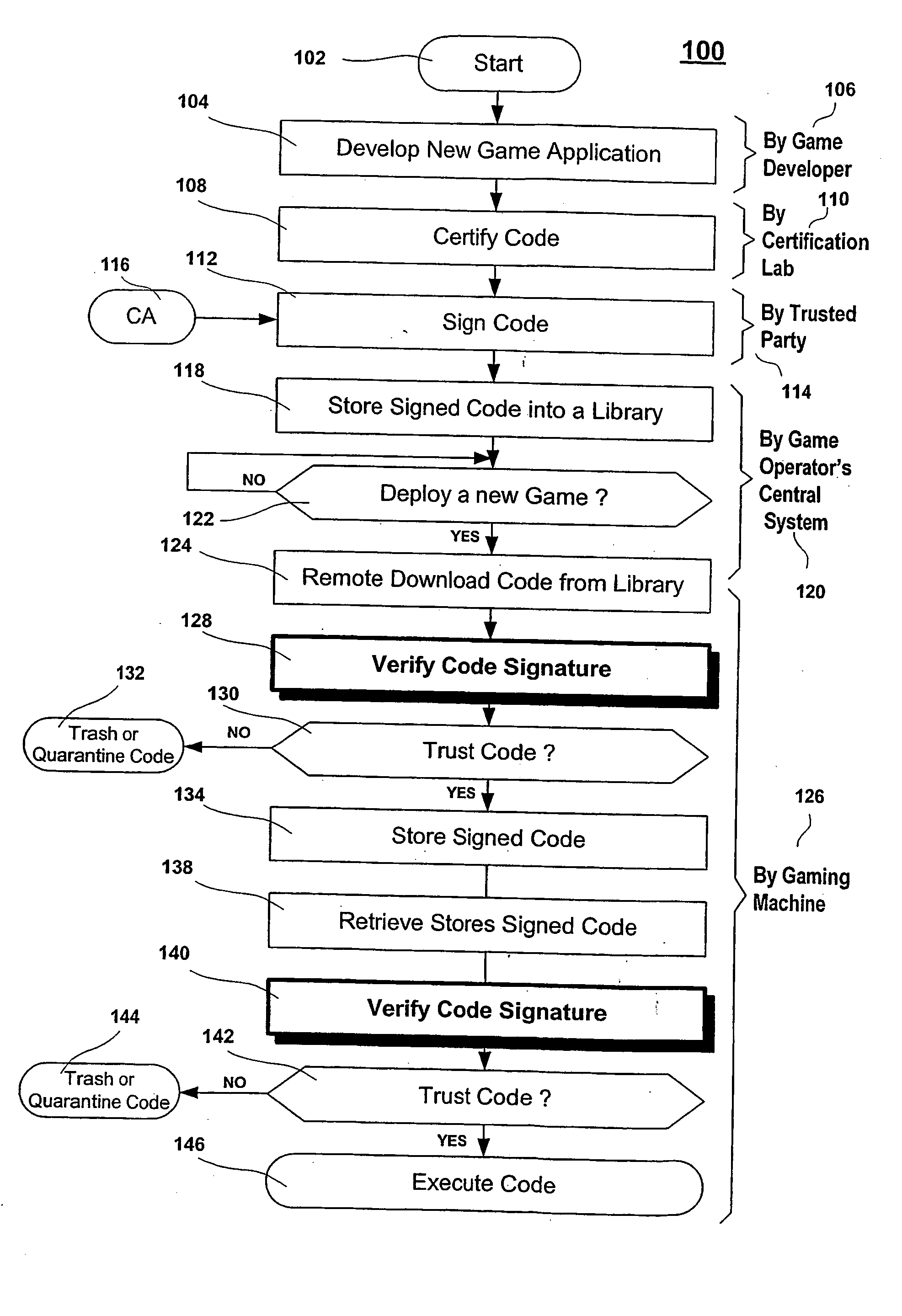
ActiveUS20060100010A1Apparatus for meter-controlled dispensingPlatform integrity maintainanceOperational systemCode signing
A method for gaming terminals, gaming kiosks and lottery terminals to ensure that the code-signing verification process of downloaded game software can be trusted. Drivers independently developed from the operating system supplier are embedded within the operating system kernel to verify that the micro-coded hardware components, the BIOS (808), the operating system components and the downloaded game software can be trusted.
Owner:IGT
Voice driven operating system for interfacing with electronic devices: system, method, and architecture
InactiveUS20150279366A1Keep users engaged in conversationNatural language data processingProgramming languages/paradigmsOperational systemSoftware architecture
A system comprising an electronic device, a means for the electronic device to receive input text, a means to generate a response wherein the means to generate the response is a software architecture organized in the form of a stack of functional elements. These functional elements comprise an operating system kernel whose blocks and elements are dedicated to natural language processing, a dedicated programming language specifically for developing programs to run on the operating system, and one or more natural language processing applications developed employing the dedicated programming language, wherein the one or more natural language processing applications may run in parallel. Moreover, one or more of these natural language processing applications employ an emotional overlay.
Owner:CUBIC ROBOTICS
Snapshot restore of application chains and applications
InactiveUS6848106B1Data processing applicationsProgram initiation/switchingOperational systemSystem call
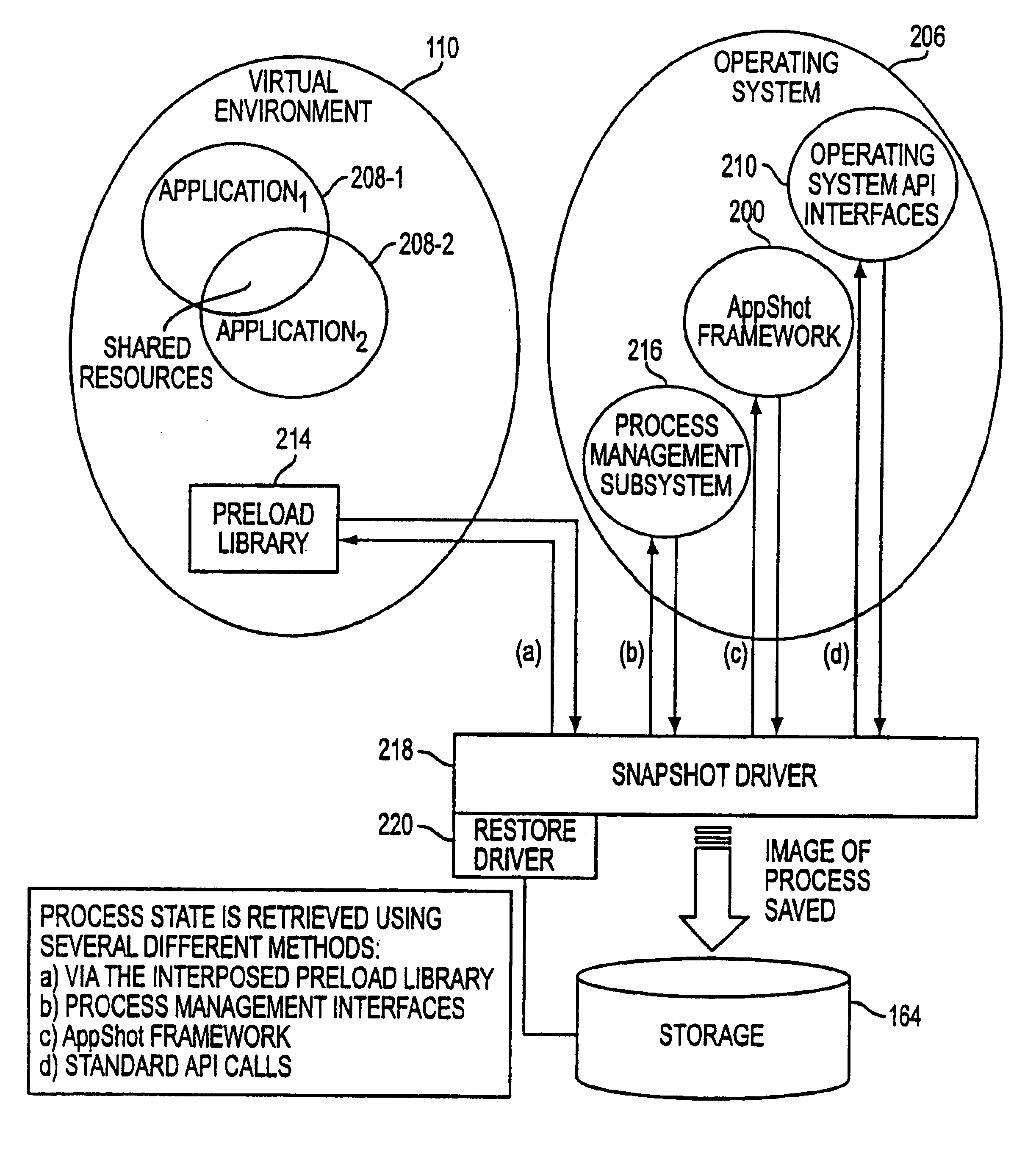
The present invention saves all process state, memory, and dependencies related to a software application to a snapshot image. Interprocess communication (IPC) mechanisms such as shared memory and semaphores must be preserved in the snapshot image as well. IPC mechanisms include any resource that is shared between two process or any communication mechanism or channel that allow two processes to communicate or interoperate is a form of IPC. Between snapshots, memory deltas are flushed to the snapshot image, so that only the modified-pages need be updated. Software modules are included to track usage of resources and their corresponding handles. At snapshot time, state is saved by querying the operating system kernel, the application snapshot / restore framework components, and the process management subsystem that allows applications to retrieve internal process-specific information not available through existing system calls. At restore time, the reverse sequence of steps for the snapshot procedure is followed and state is restored by making requests to the kernel, the application snapshot / restore framework, and the process management subsystem.
Owner:SYMANTEC OPERATING CORP
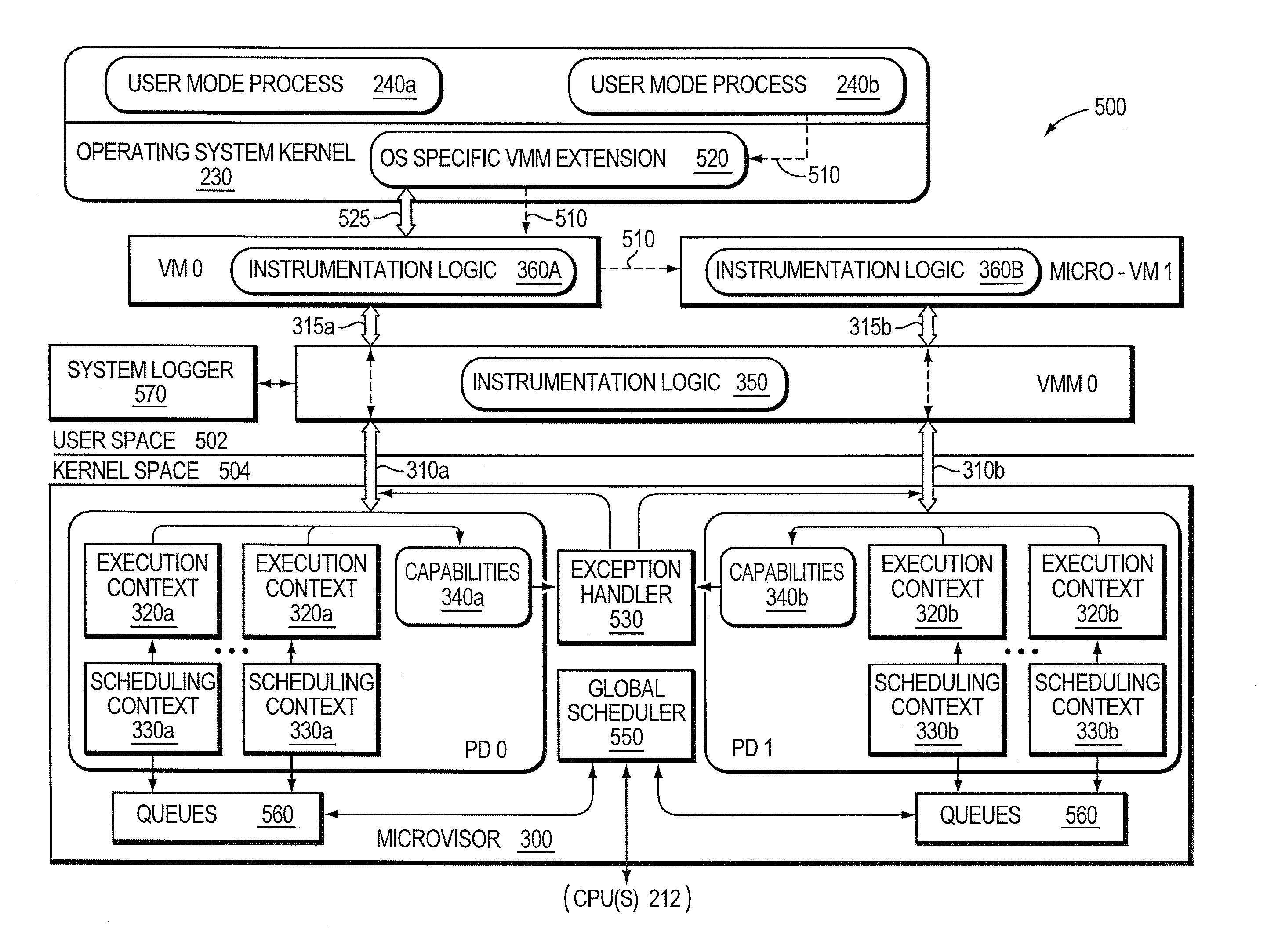
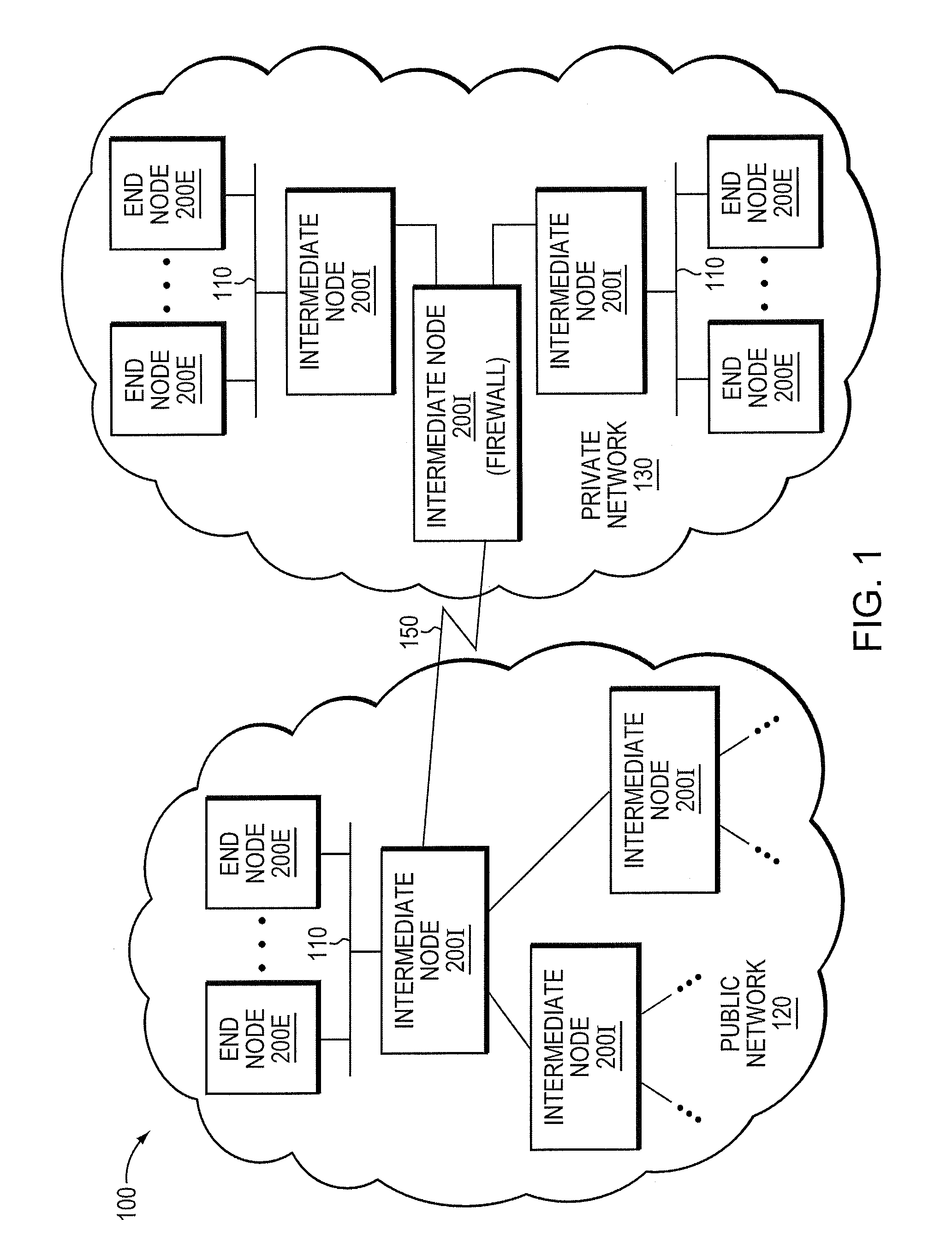
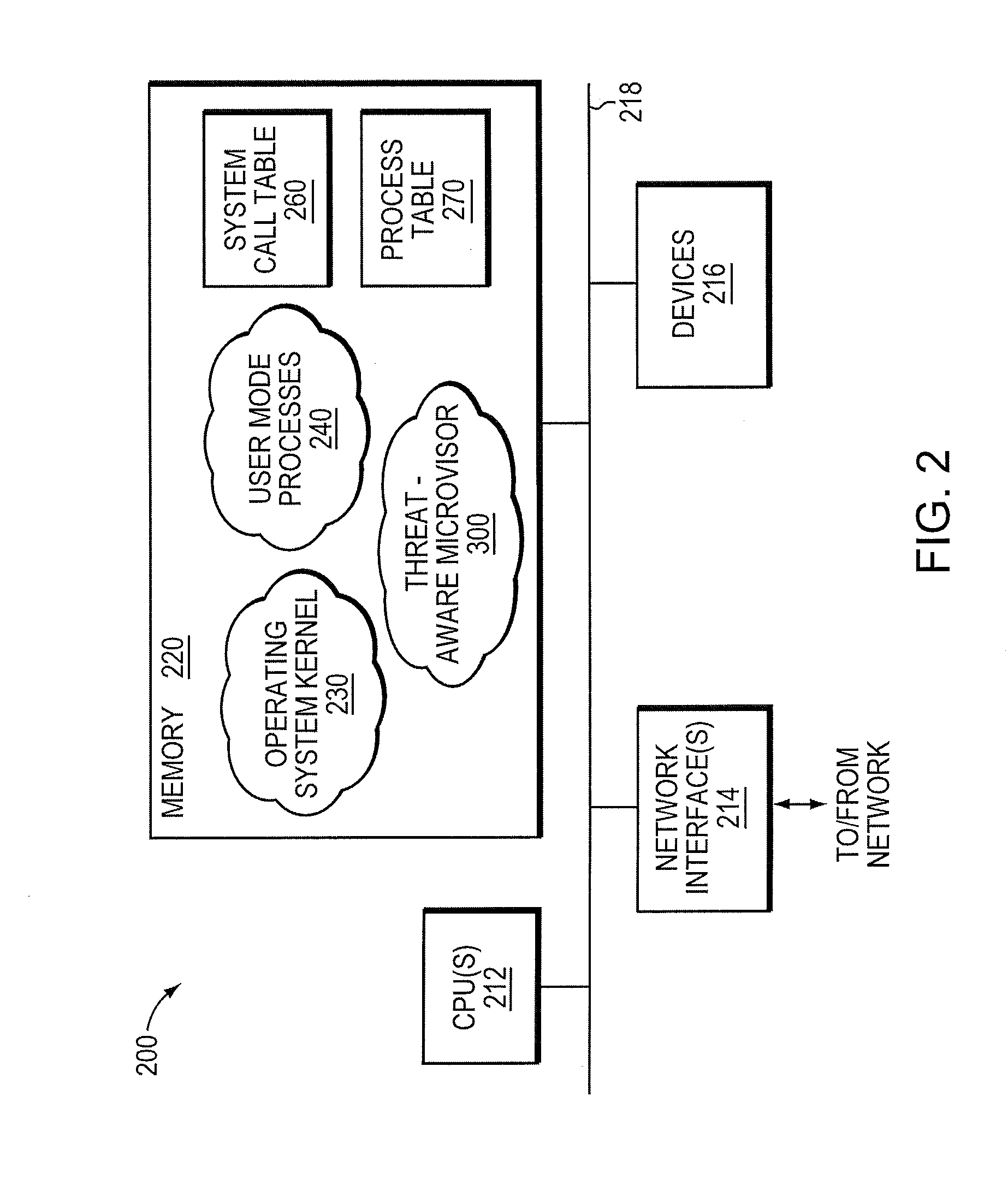
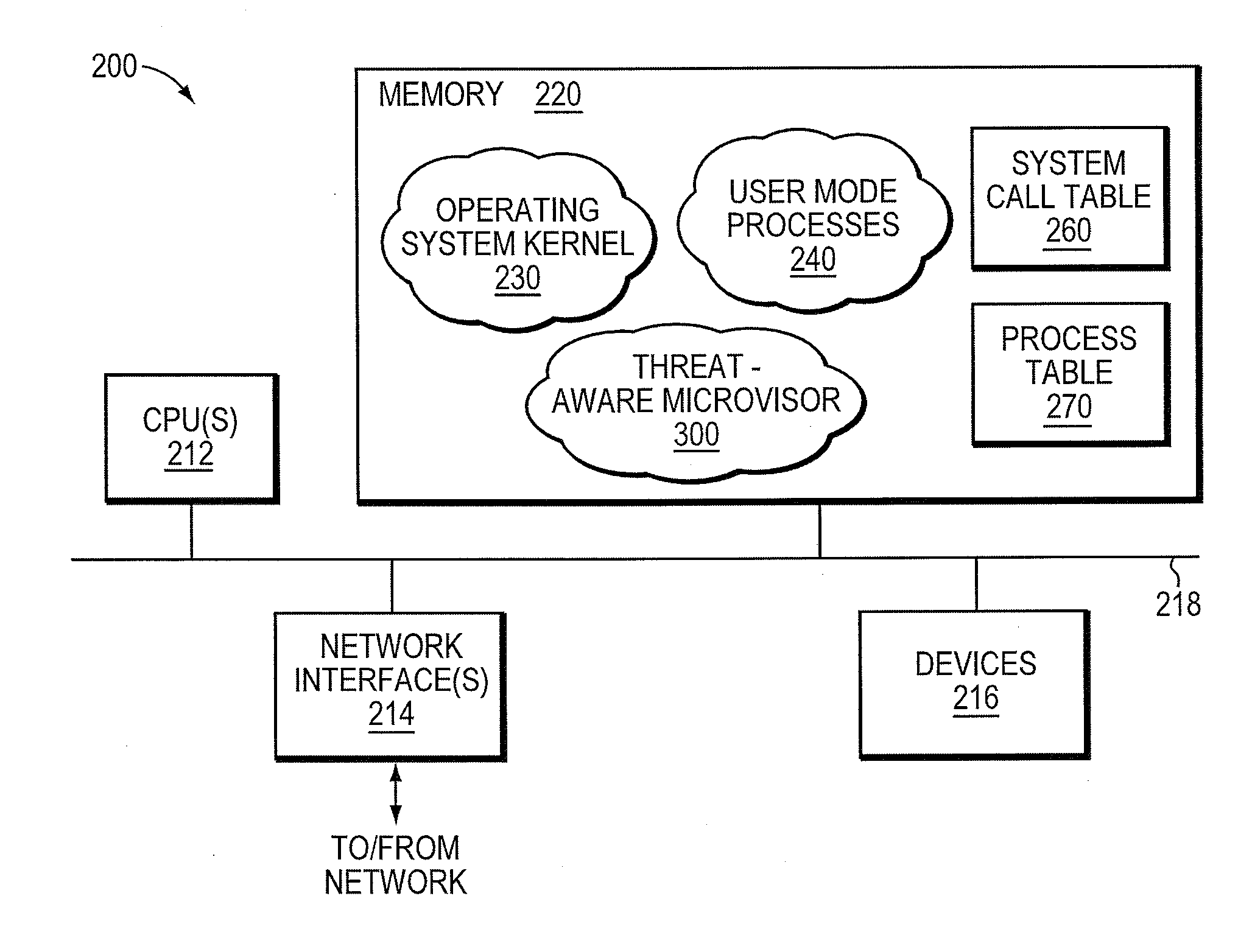
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS20150199532A1Digital data processing detailsAnalogue secracy/subscription systemsVirtualizationSecurity analysis
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
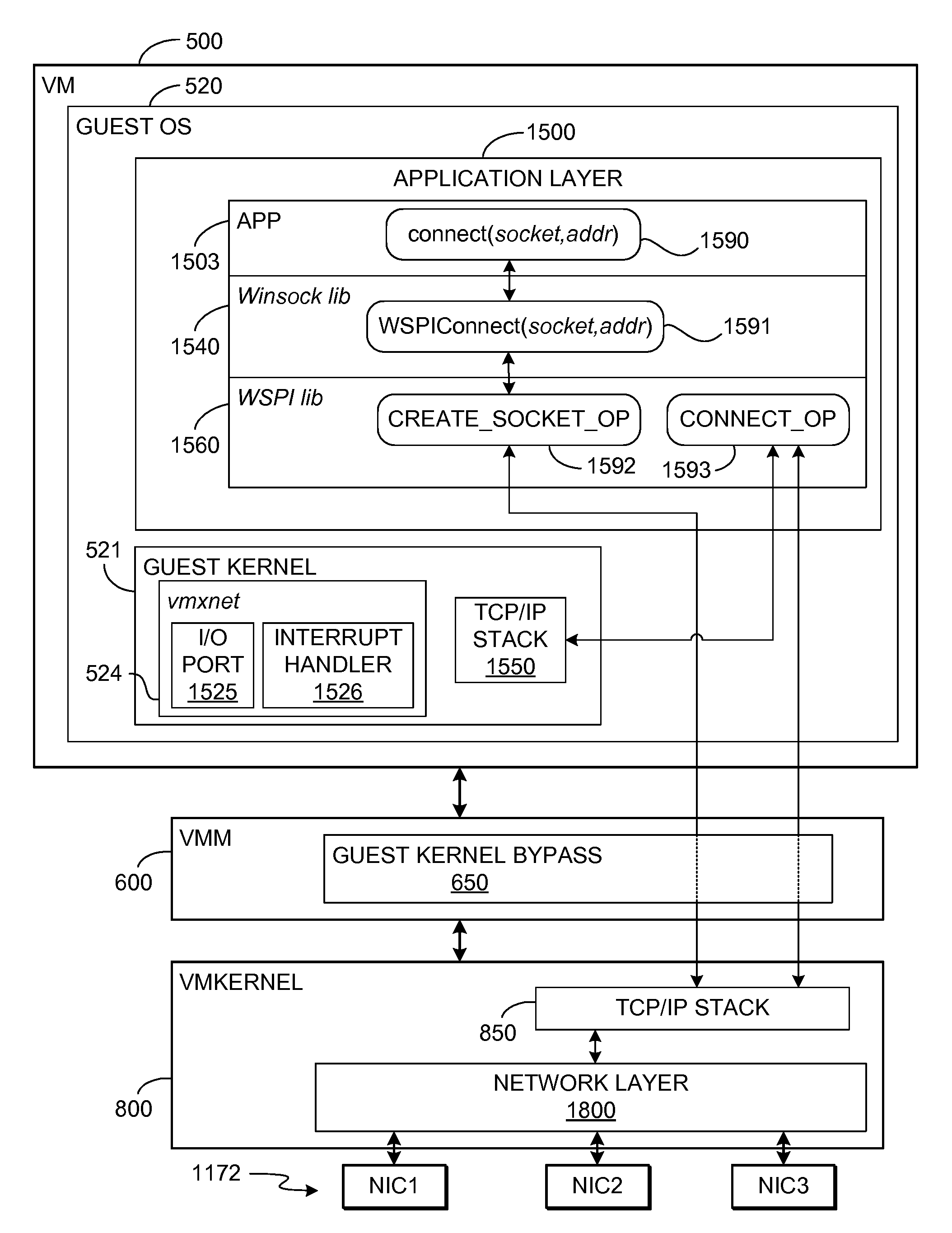
TCP/IP offloading for virtual machines
An engine (TOE) is provided in a virtualized computer system for offloading I / O tasks using any defined protocol such as TCP / IP. The system includes a virtual machine (VM), which has a guest operating system (OS) that runs via a virtual machine monitor (VMM) on a system-level software platform (vmkernel), which also forms the software interface layer to at least one physical network connection device. A TCP / IP stack is included in vmkernel. During normal I / O operation, for sockets associated with TOE, processes in an application layer in the guest OS are able to communicate directly with vmkernel's TCP / IP stack, thereby bypassing the guest OS kernel.
Owner:VMWARE INC
Method and system for providing high availability to computer applications
ActiveUS20060090097A1Improve usabilityEasy to controlHardware monitoringNon-redundant fault processingOperational systemHigh availability
A set of system-level high availability services for computer systems, including a service that functions in general terms like an extension of the operating system. By providing High Availability (HA) at the system-level, modifications to the applications or the operating system kernel are not required.
Owner:RED HAT
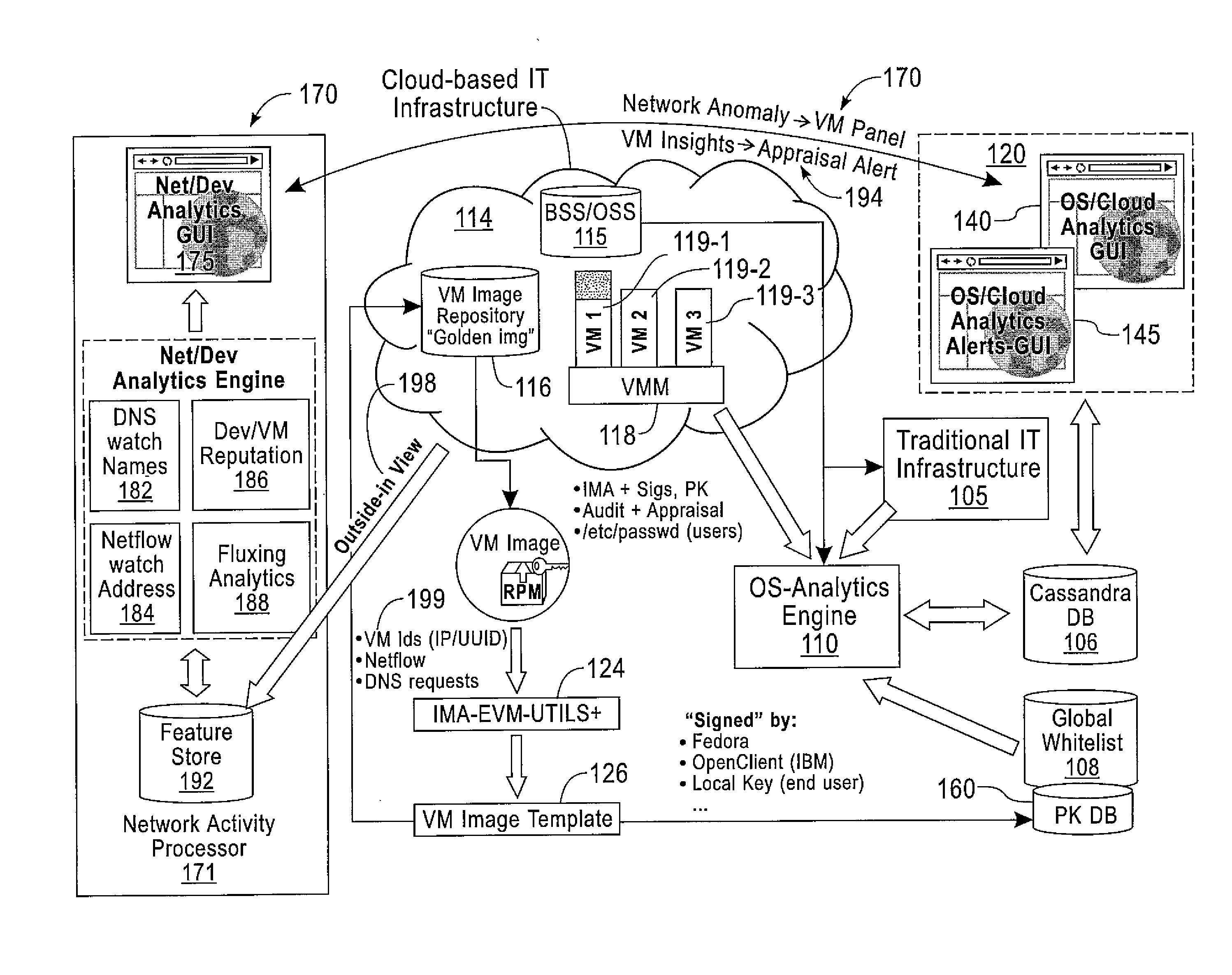
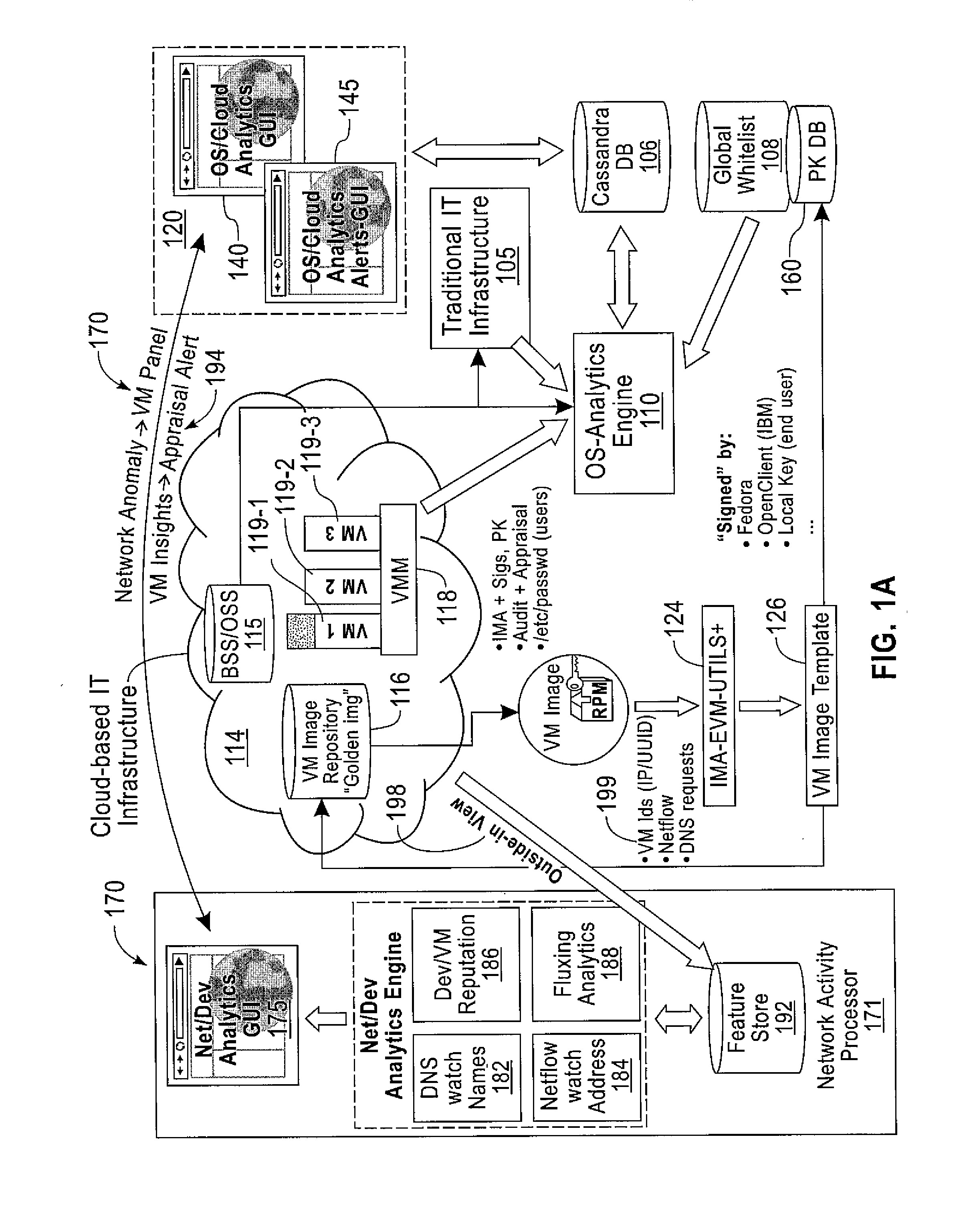
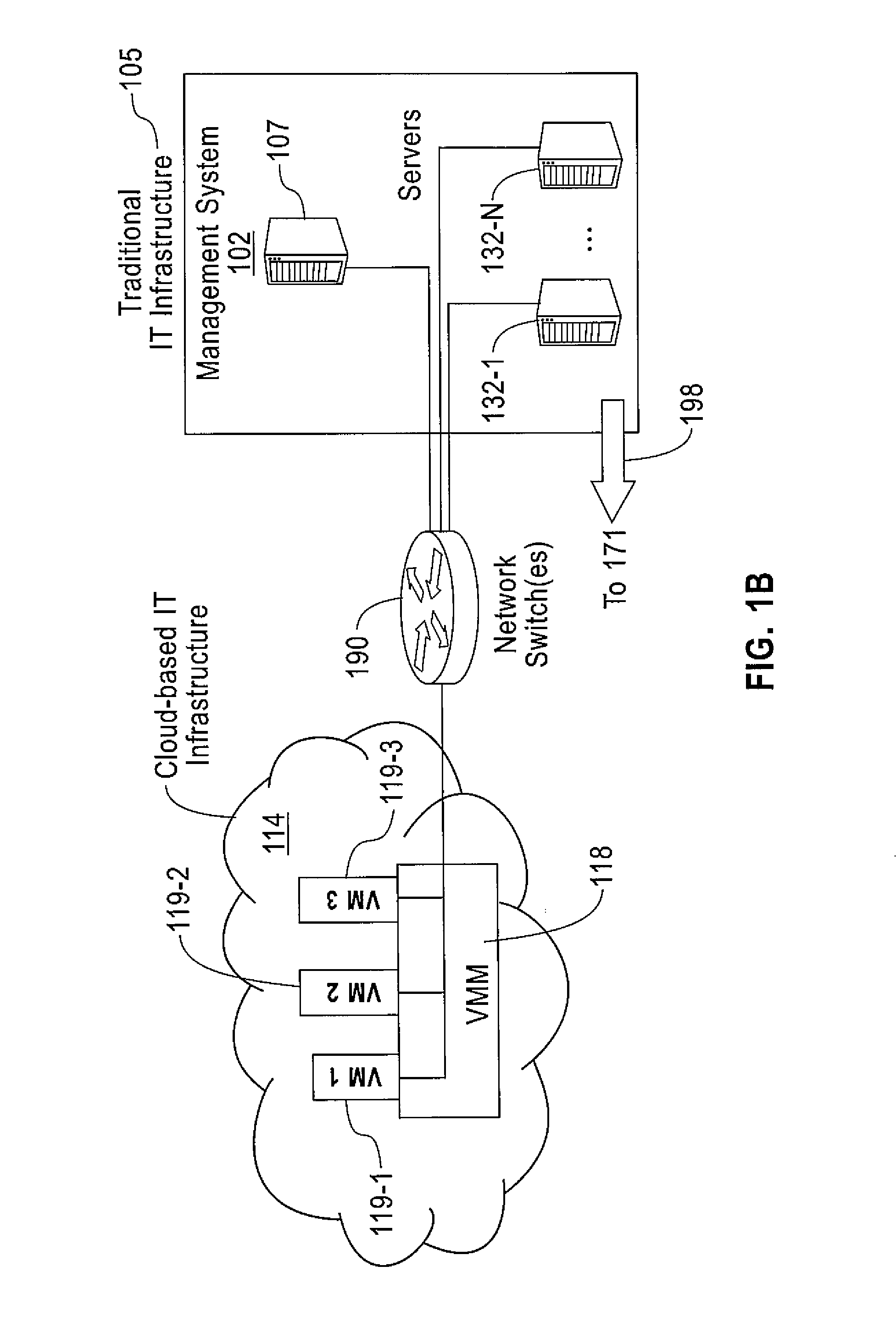
Computer Implemented Techniques for Detecting, Investigating and Remediating Security Violations to IT Infrastructure
A method includes collecting system calls and call parameters invoked by monitored applications for target computer systems. The system calls and call parameters are received from operating system kernels on the plurality of target computer systems. Sequences of systems calls and call parameters of the monitored applications are correlated among different target computer systems to deduce malicious activities. Remedial action(s) are performed in response to malicious activities being deduced as being malicious by the correlating. Another method includes determining that network activity at a specific time is deemed to be suspicious. Using IP addresses involved in the suspicious network activity, computer system(s) are determined that are sources of the suspicious network activity. Based on the specific time and the determined computer system(s), application(s) are determined that are executing on the determined computer system(s) that are causing the suspicious network activity. Remedial action(s) are performed for the determined computer system(s).
Owner:IBM CORP
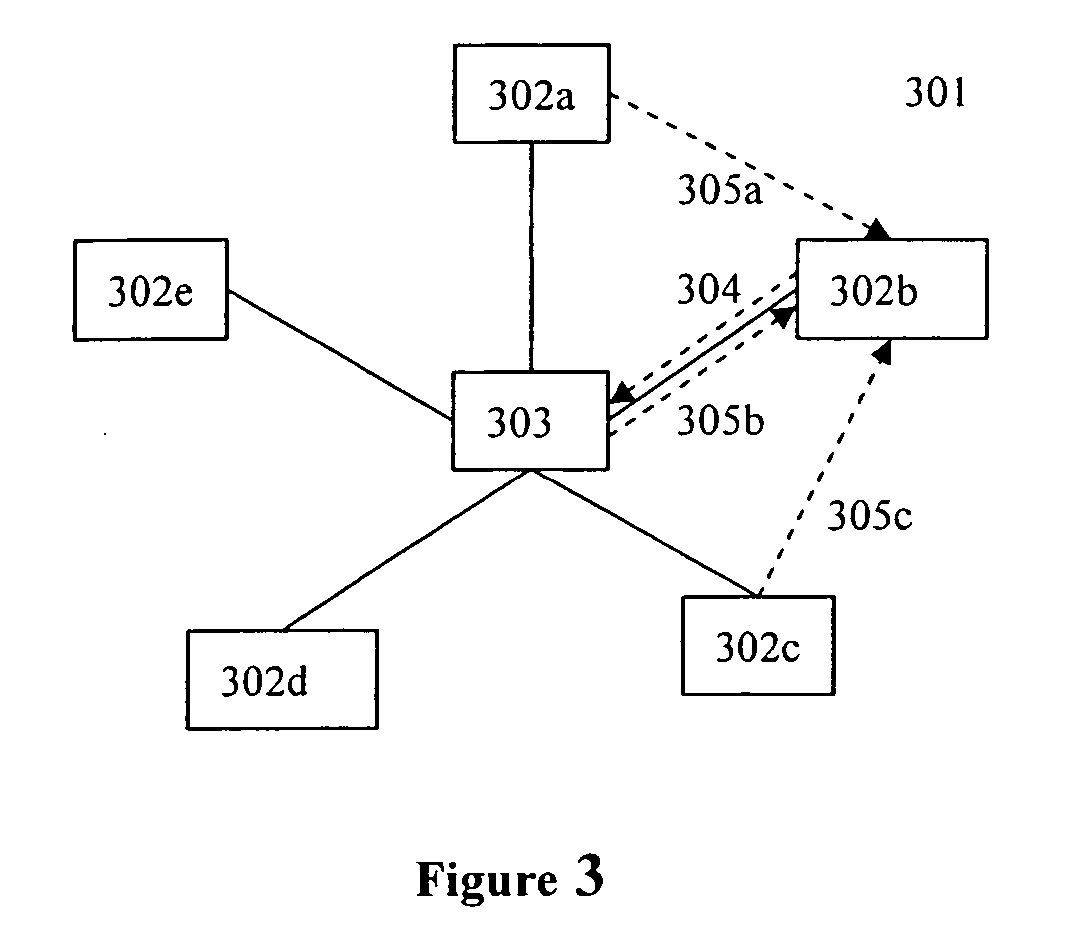
Method and system for controlling a complementary user interface on a display surface
InactiveUS6892359B1Reduce displayData processing applicationsMultiprogramming arrangementsOperational systemDisplay device
An alternate display content controller provides a technique for controlling a video display separately from and in addition to the content displayed on the operating system display surface. Where the display is a computer monitor, the alternate display content controller interacts with the computer utility operating system and hardware drivers to control allocation of display space and create and control one or more parallel graphical user interfaces in addition to the operating system desktop. An alternate display content controller may be incorporated in either hardware or software. As software, an alternate display content controller may be an application running on the computer operating system, or may include an operating system kernel of varying complexity ranging from dependent on the utility operating system for hardware system services to a parallel system independent of the utility operating system and capable of supporting dedicated applications. The alternate display content controller may also include content and operating software delivered over the Internet or any other LAN. The alternate display content controller may also be included in a television decoder / settop box to permit two or more parallel graphical user interfaces to be displayed simultaneously.
Owner:OSTENDO TECH INC
Managed distribution of digital assets
ActiveUS20050060537A1High acceptanceEasy to produceHardware monitoringComputer security arrangementsOperational systemNetwork connection
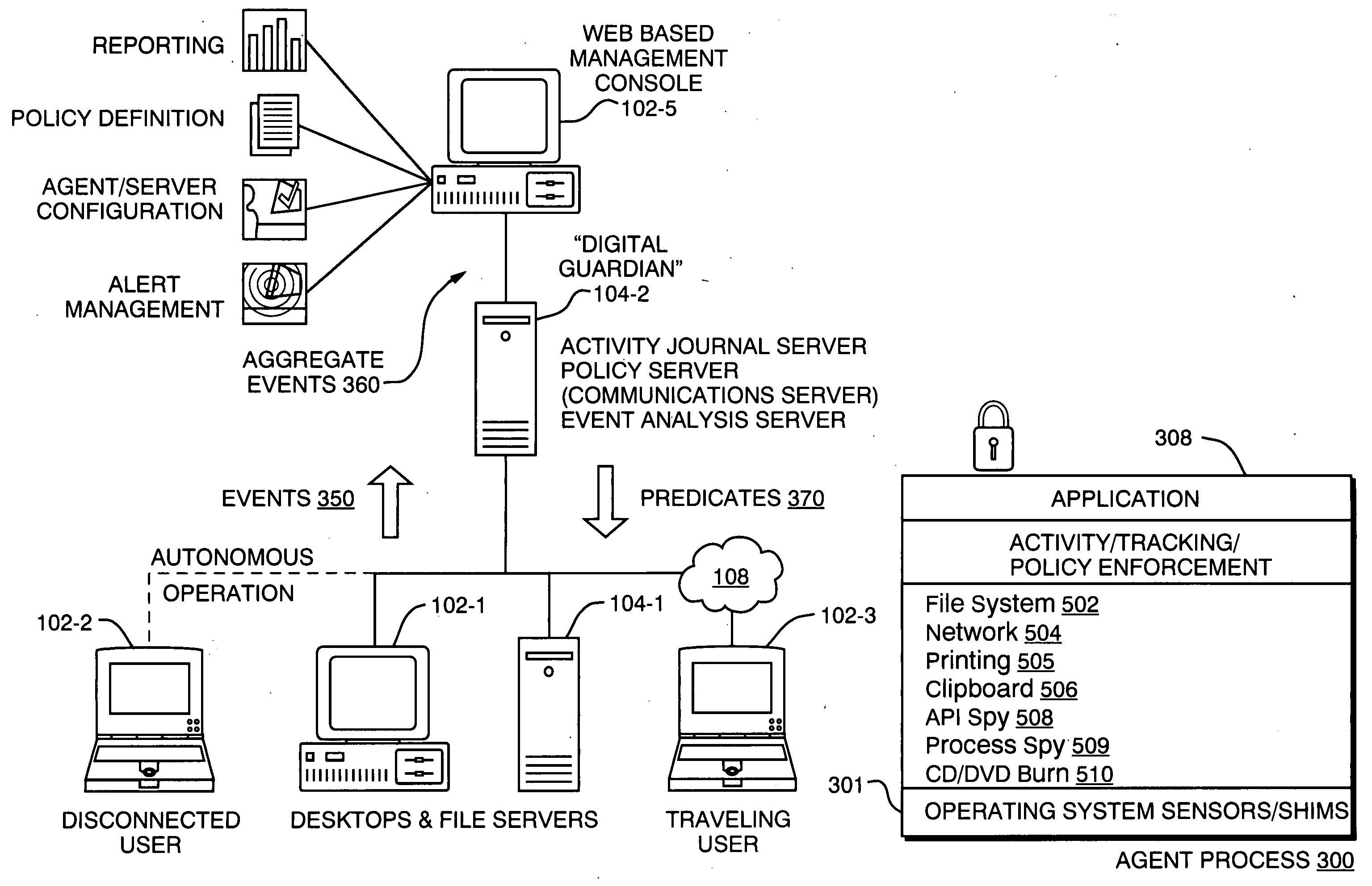
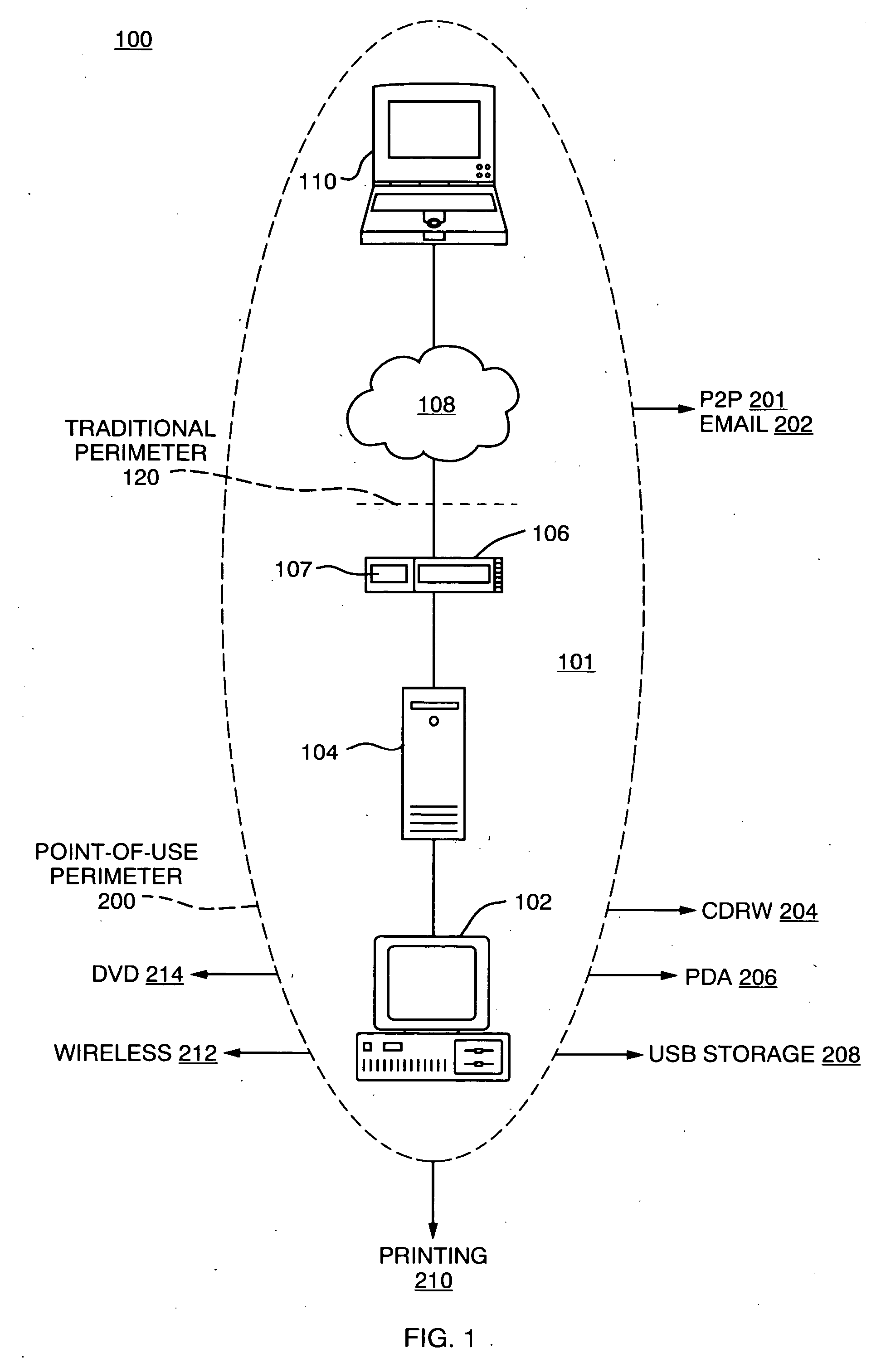
A technique for establishing usage control over digital assets such as computer files. The system model not only tracks authorized users' access to files, but monitors passage of such files to uncontrollable removable storage media or through network connections and the like which may indicate possible abuse of access rights. In accordance with a preferred embodiment, an autonomous independent agent process running at a point of use, such a background process in a client operating system kernel, interrupts requests for access to resources. The agent process senses low level system events, filters, and aggregates them. A policy engine analyzes sequences of aggregate events to determine when policy violations occur.
Owner:DIGITAL GUARDIAN LLC
Methods for describing processor features
ActiveUS20060200663A1Detect and enable and manage operationGeneral purpose stored program computerMultiprogramming arrangementsOperational systemParallel computing
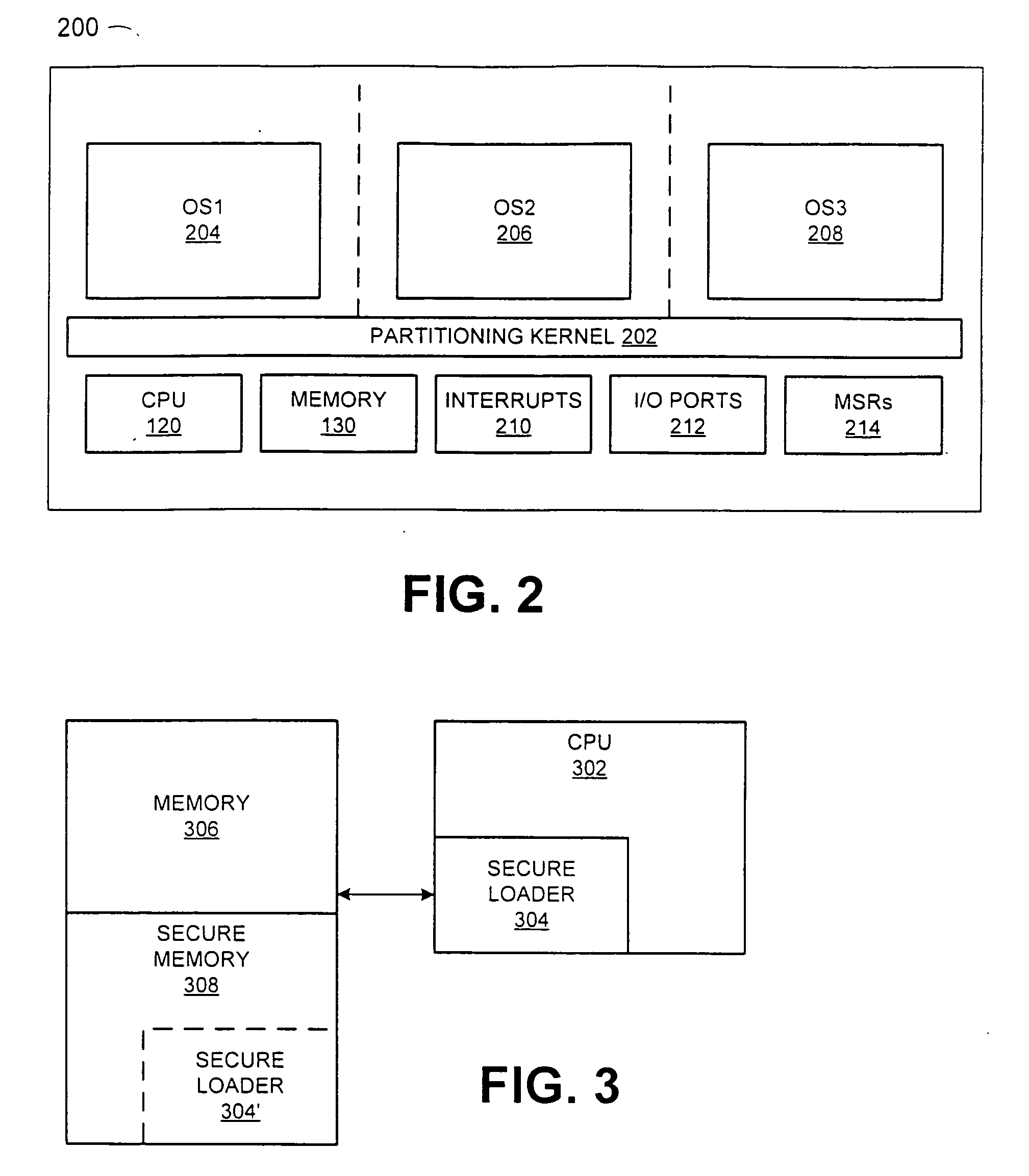
A machine readable description of a new feature of a processor is provided by a processor vendor. Control code executing on a processor, such as a traditional operating system kernel, a partitioning kernel, or the like can be programmed to receive the description of the feature and to use information provided by the description to detect, enable and manage operation of the new feature.
Owner:MICROSOFT TECH LICENSING LLC
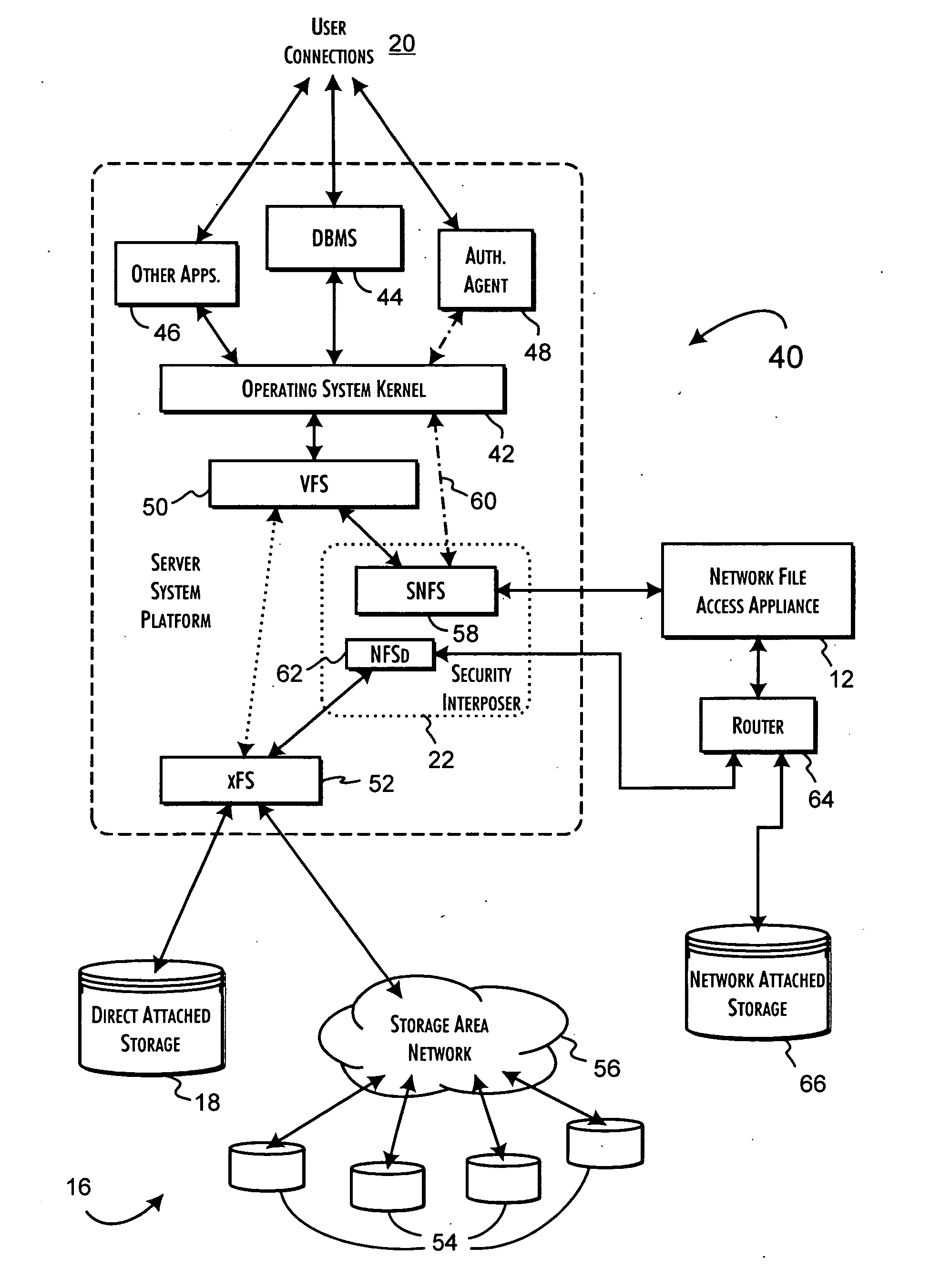
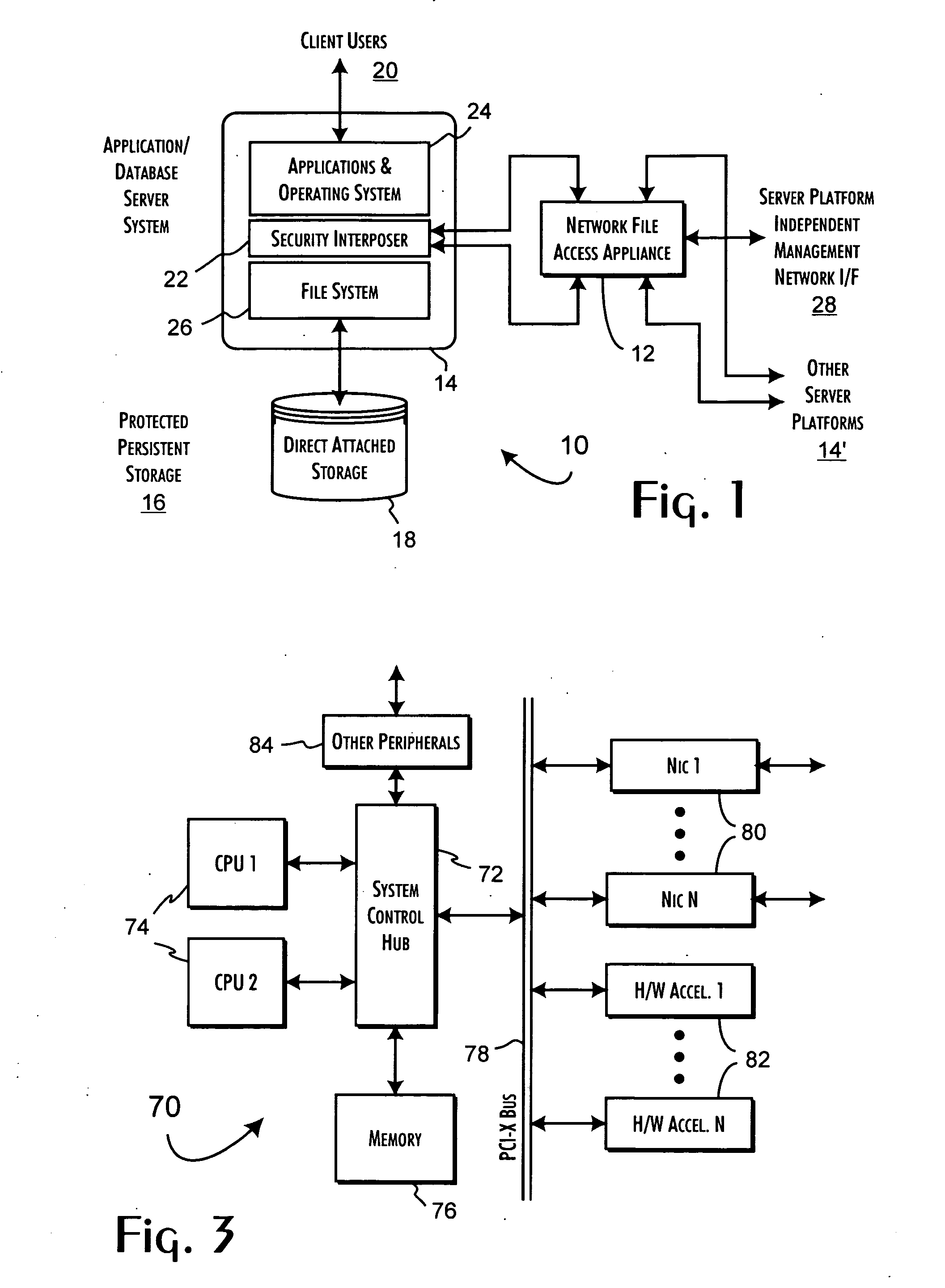
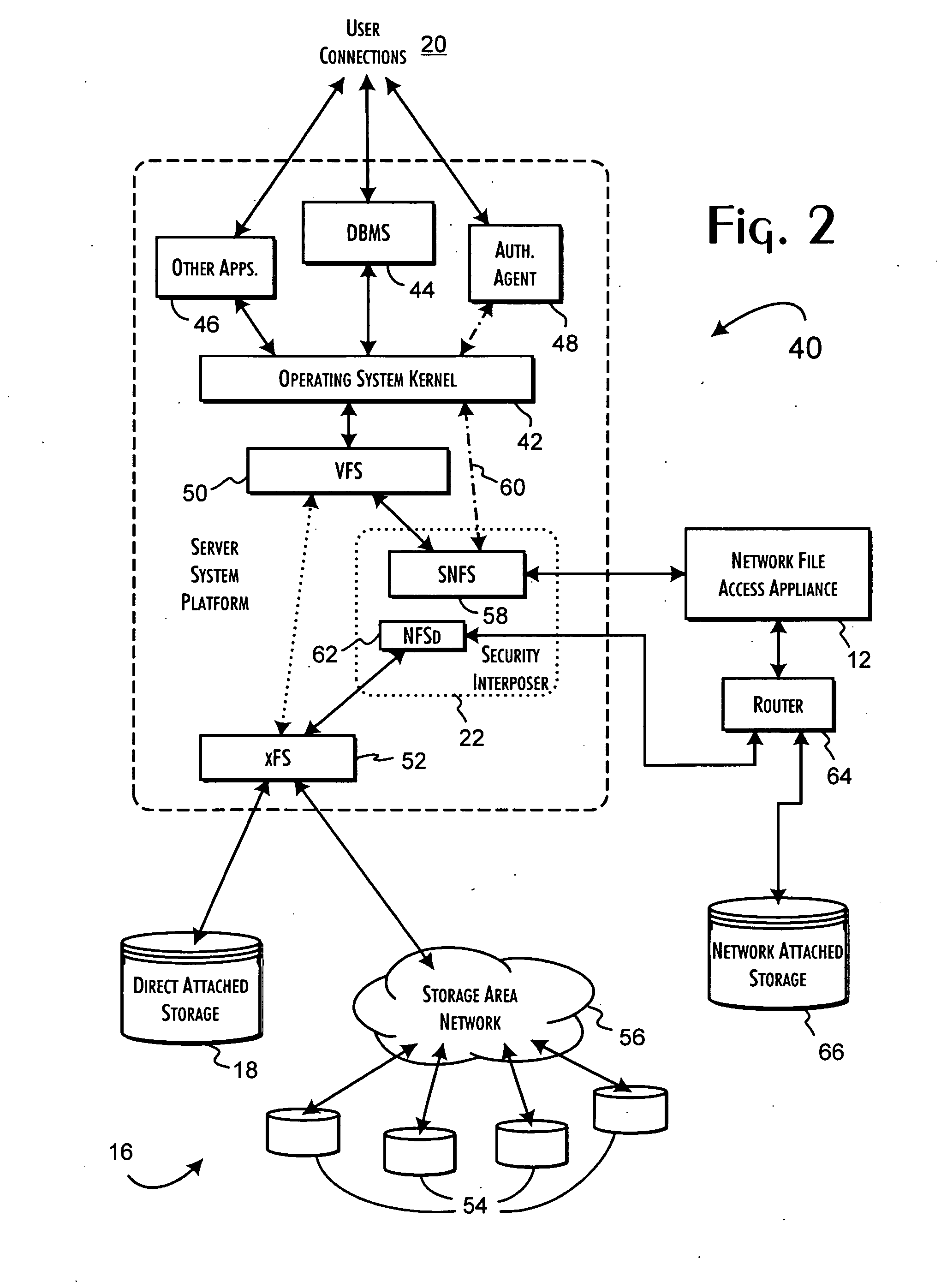
Secure file system server architecture and methods
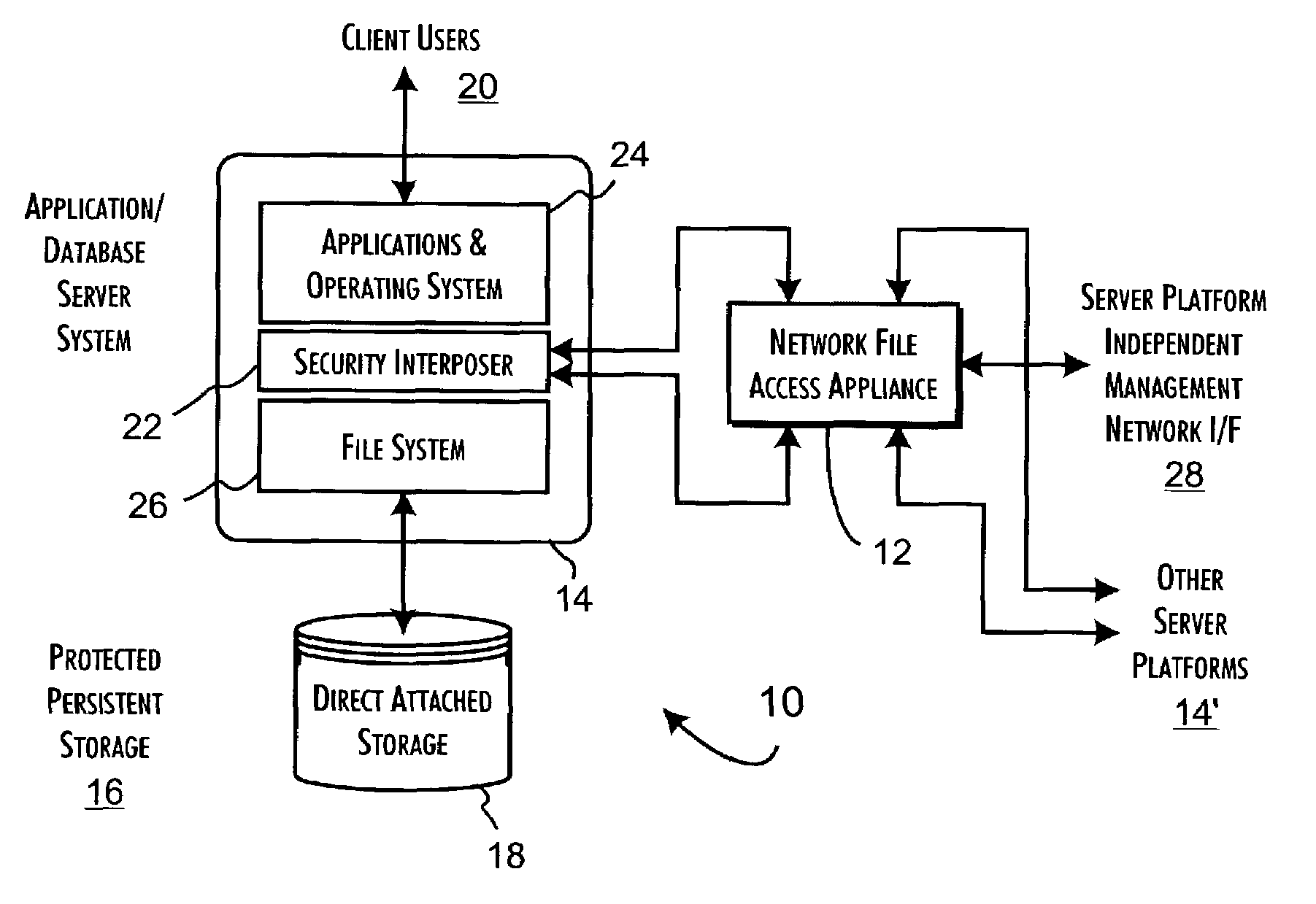
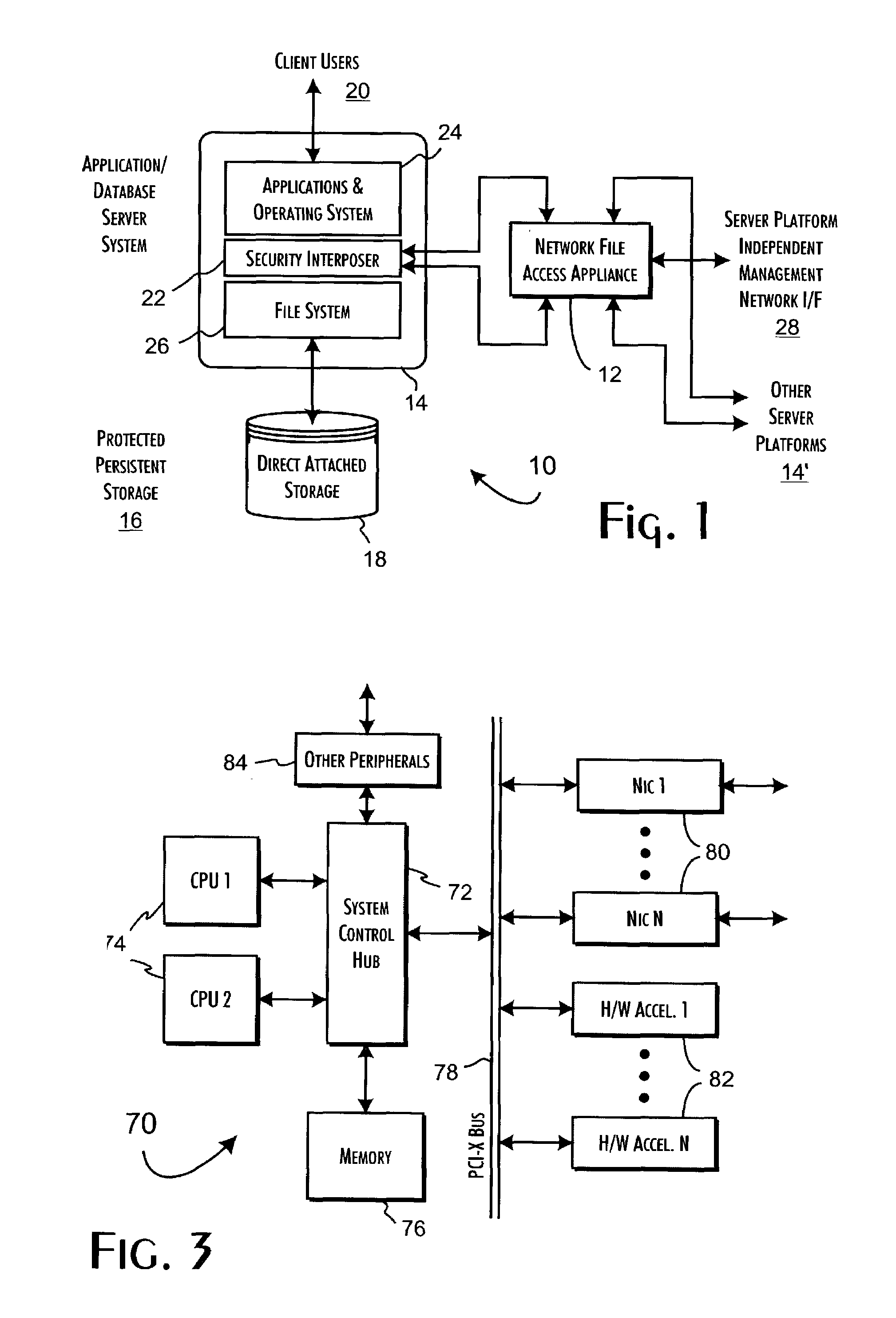
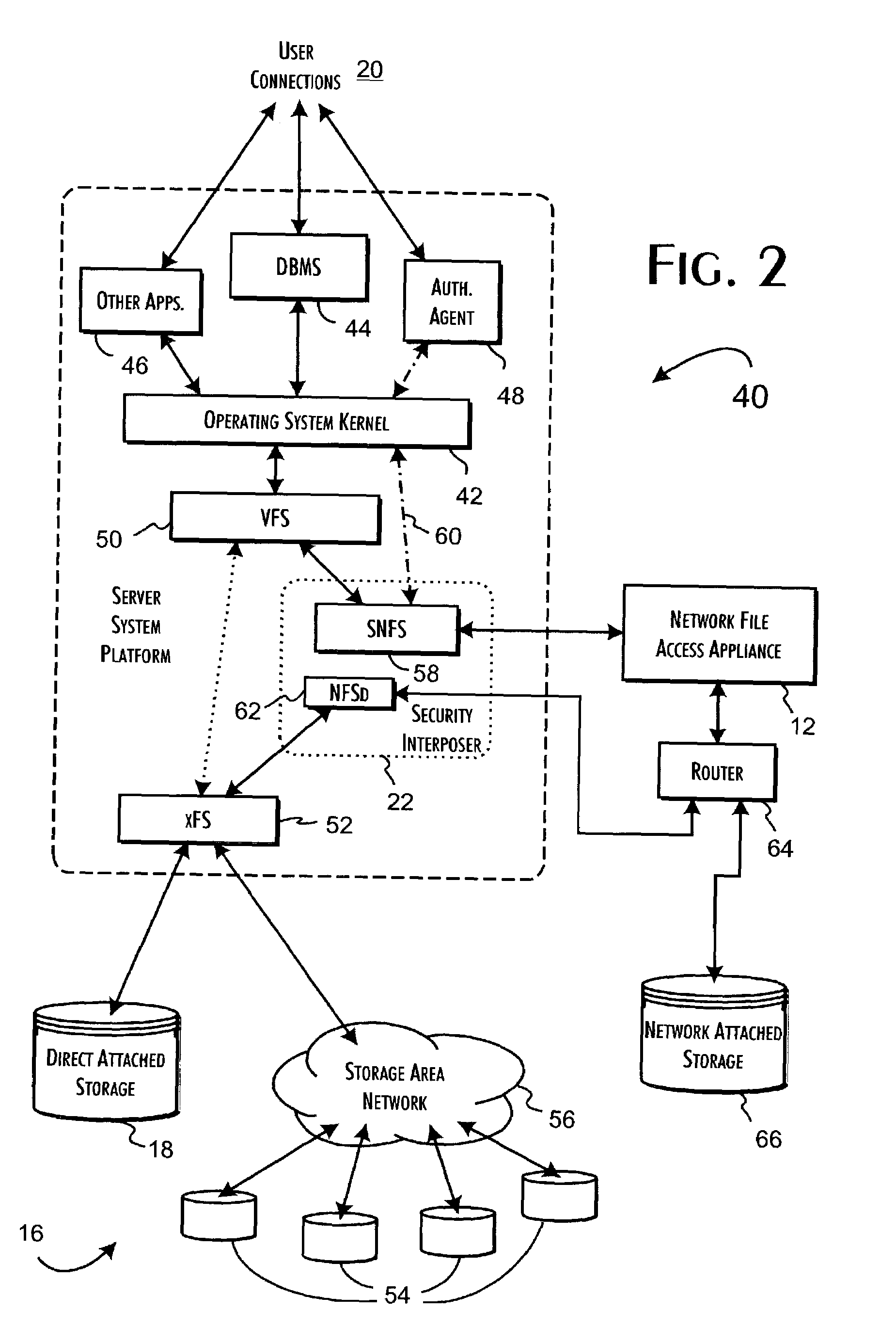
InactiveUS7143288B2Efficient collectionOperational safetyDigital data processing detailsAnalogue secracy/subscription systemsOperational systemFile system
A data server platform includes a security file system layer interposed between the platform operating system kernel and file system. The secure file system layer is structured to implement a file access control function that selectively constrains data transfer operations initiated through the operating system kernel by an application program to transfer file data through the file system with respect to a persistent data store. A file access controller, implemented independent of the operating system kernel, is coupled to the security file system layer and supports the file access control function by defining permitted file data transfers through the file system. Management of the file access controller separate from the data server platform ensures that any security breach of the platform operating system kernel cannot compromise the function of the security file system layer.
Owner:THALES DIS CPL USA INC
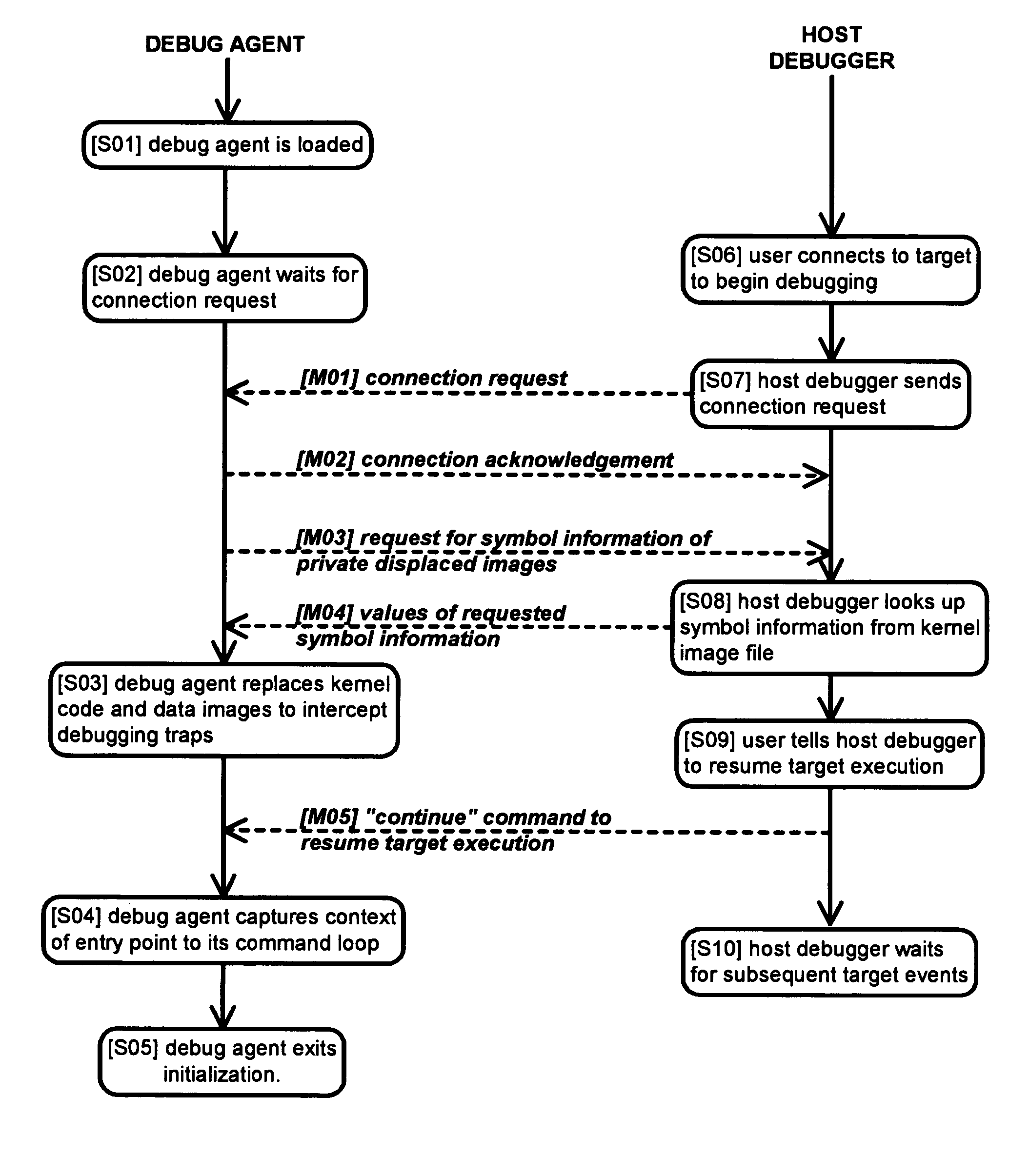
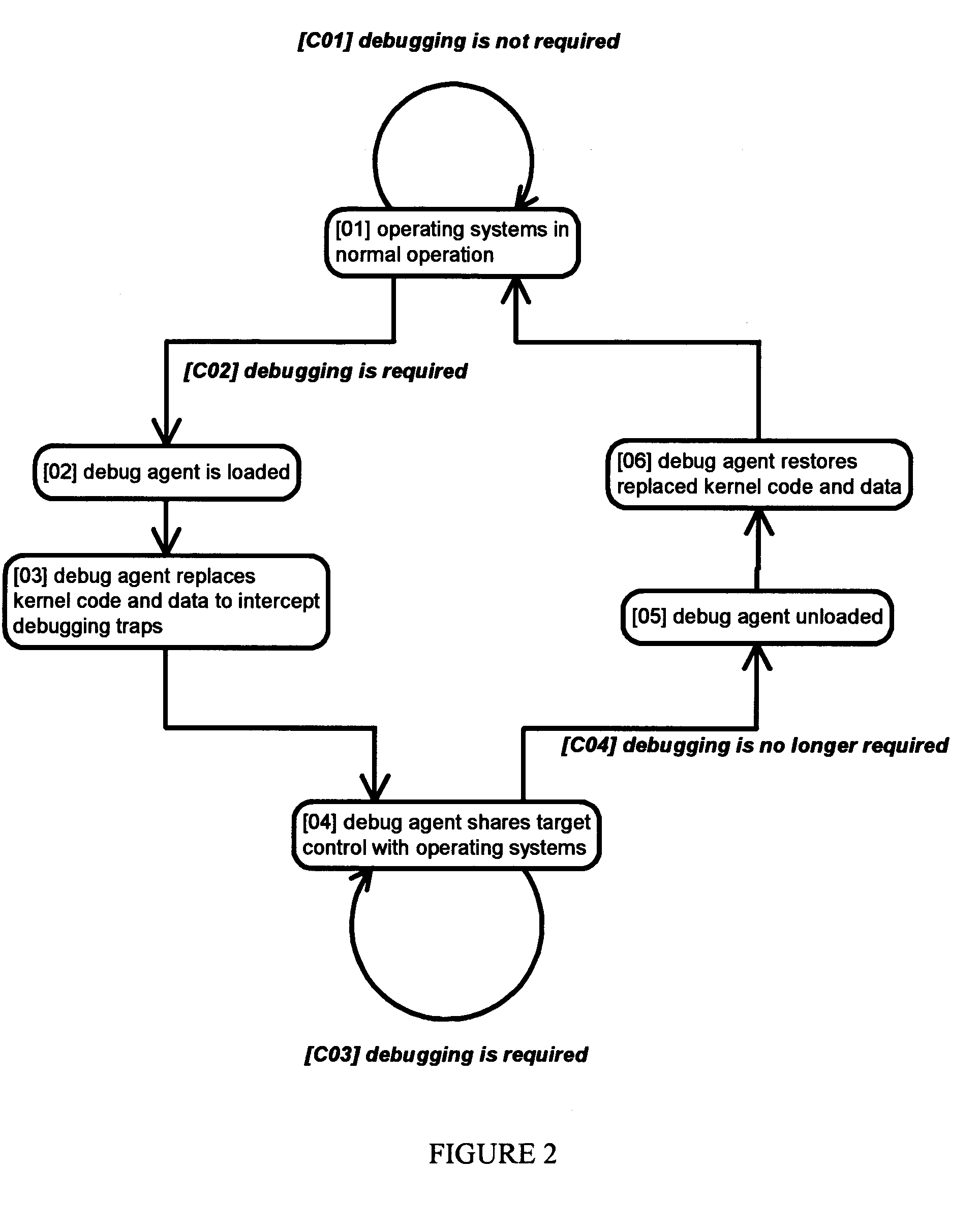
Method and apparatus for remote debugging of kernel and application software
InactiveUS20050216895A1Modified dynamicallyError detection/correctionSpecific program execution arrangementsOperational systemSystem call
A method and apparatus for debugging of OS kernel and applications software that does not require use of a hardware probe; can debug both user-mode programs and a significant body of the OS kernel code; allows the OS to continue servicing exceptions while debugging; leverages OS built-in device drivers for communicating devices to communicate with the host debugger; and can debug a production version of the OS kernel. When debugging is required, the running OS kernel dynamically loads a software-based debug agent on demand whereby such debug agent dynamically modifies the running production OS kernel code and data to intercept debugging traps and provide run-control. To provide debugging of loadable module, the debug agent implement techniques to intercept the OS module loading system call; set breakpoints in the loaded module initialization function; calculate the start address of the debugged module in memory; and asynchronously put the system under debug. By structuring command loop to execute in non-exception mode, and devising a process to transfer execution from the debug agent exception handler to the debug agent command loop and back, the debug agent can communicate with the host debugger using interrupt-driven input / output devices as well as allowing the system to service interrupts while under debug.
Owner:TRAN HIEU TRUNG
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS9292686B2Digital data protectionPlatform integrity maintainanceVirtualizationOperational system
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
Threat-aware microvisor
ActiveUS20150199513A1Memory loss protectionError detection/correctionOperational systemComputer module
A threat-aware microvisor is configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing on a node of a network environment. The microvisor may be embodied as a module disposed or layered beneath (underlying) an operating system kernel executing on the node to thereby control privileges (i.e., access permissions) to kernel resources, such as one or more central processing units (CPUs), network interfaces, memory, and / or devices, of the node. Illustratively, the microvisor may be configured to control access to one or more of the resources in response to a request by an operating system process to access the resource.
Owner:FIREEYE SECURITY HLDG US LLC
Computer protection against malware affection
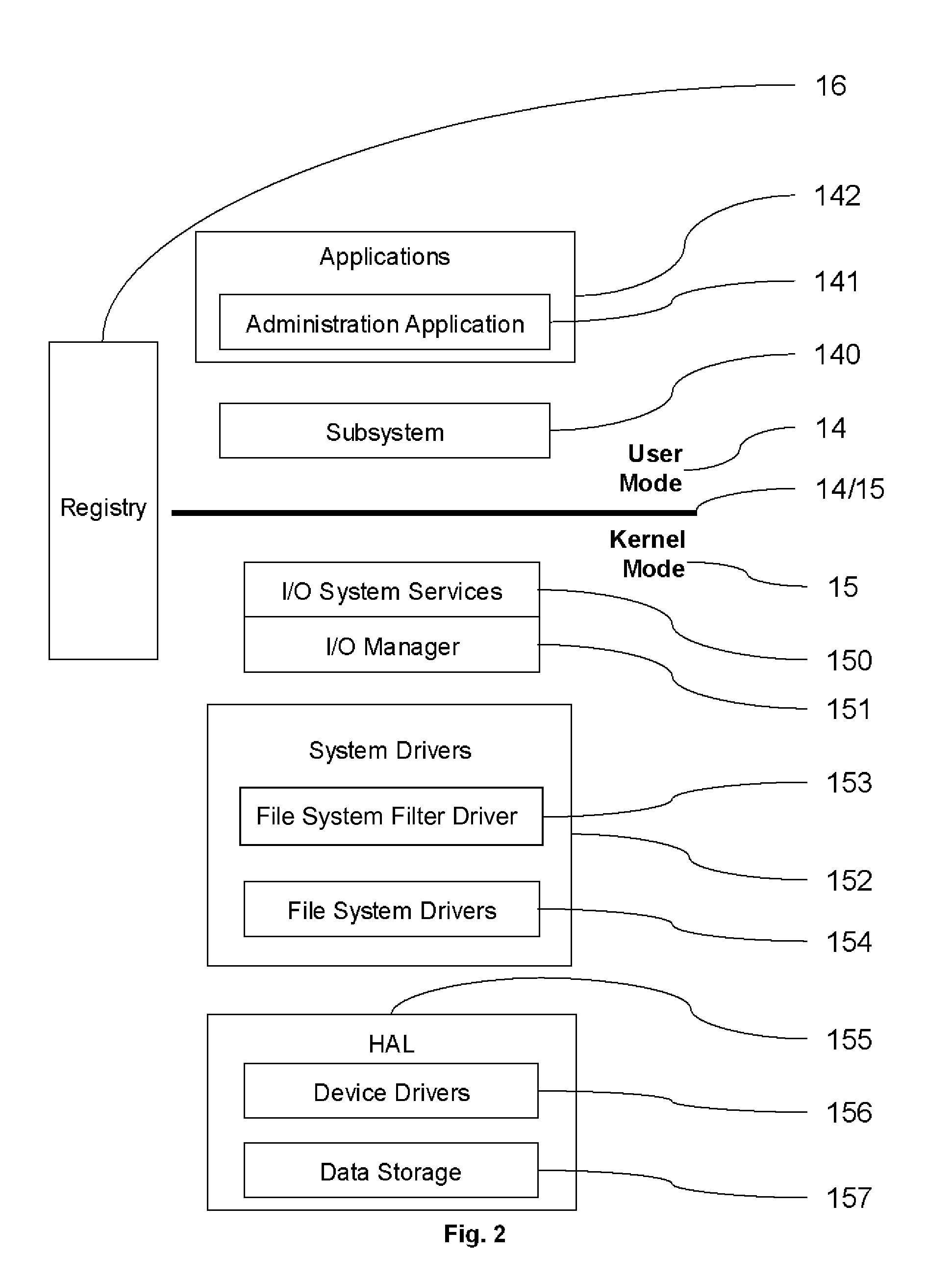
ActiveUS20100043072A1Malware can be thwartedMemory loss protectionError detection/correctionOperational systemData memory
A method is provided of protecting a computer against malware affection. The computer has a data storage and an operating system for managing the data storage. The method comprises providing a filter module in the operating system which operates to detect an attempt to store data in the data storage, to determine a data format of the data to be stored in the data storage, and to prevent storage of the data if the data format is determined to relate to a predefined type. The filter module may be provided as a file system filter driver in a kernel of the operating system. The filter module may be arranged to operate between an input / output manager of the operating system and a driver associated with the data storage. The input / output manager and driver associated with the data storage may form part of the kernel of the operating system.
Owner:ROTHWELL WILLIAM GRANT
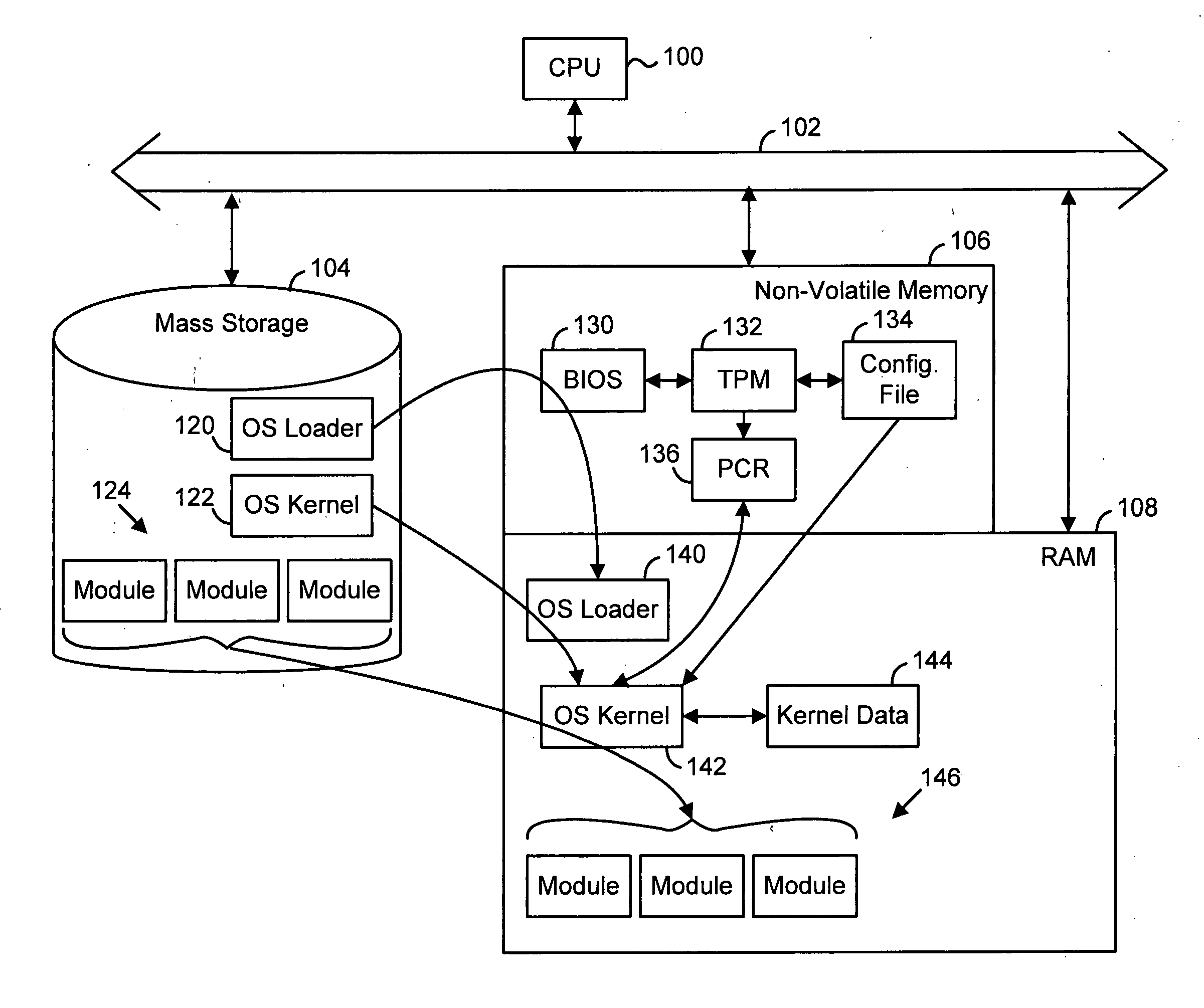
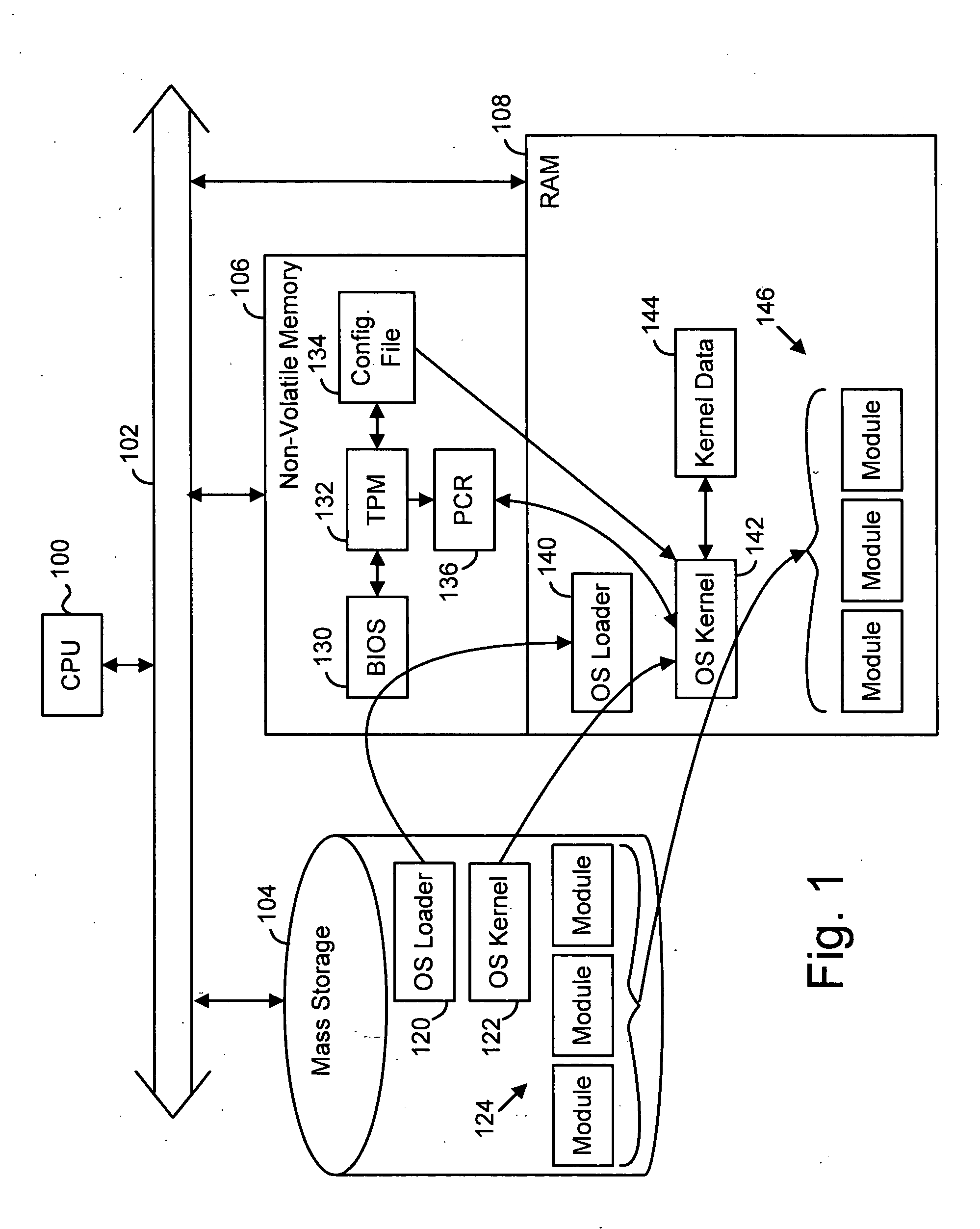
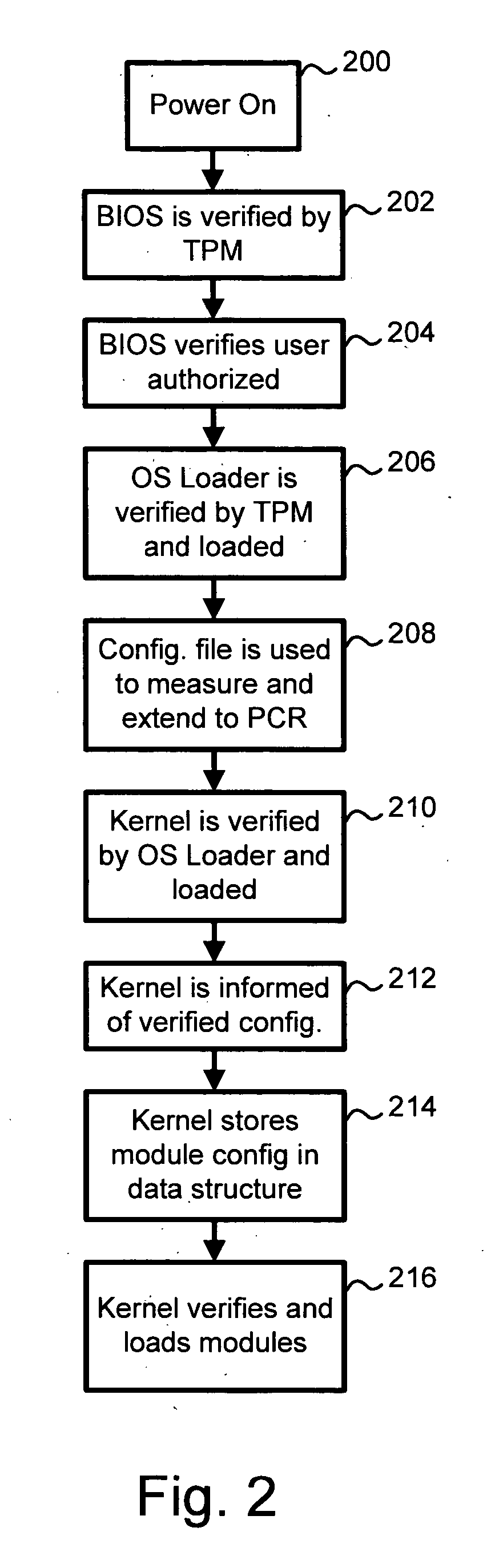
Establishing a trusted platform in a digital processing system
InactiveUS20060015717A1User identity/authority verificationUnauthorized memory use protectionDigital signal processingOperational system
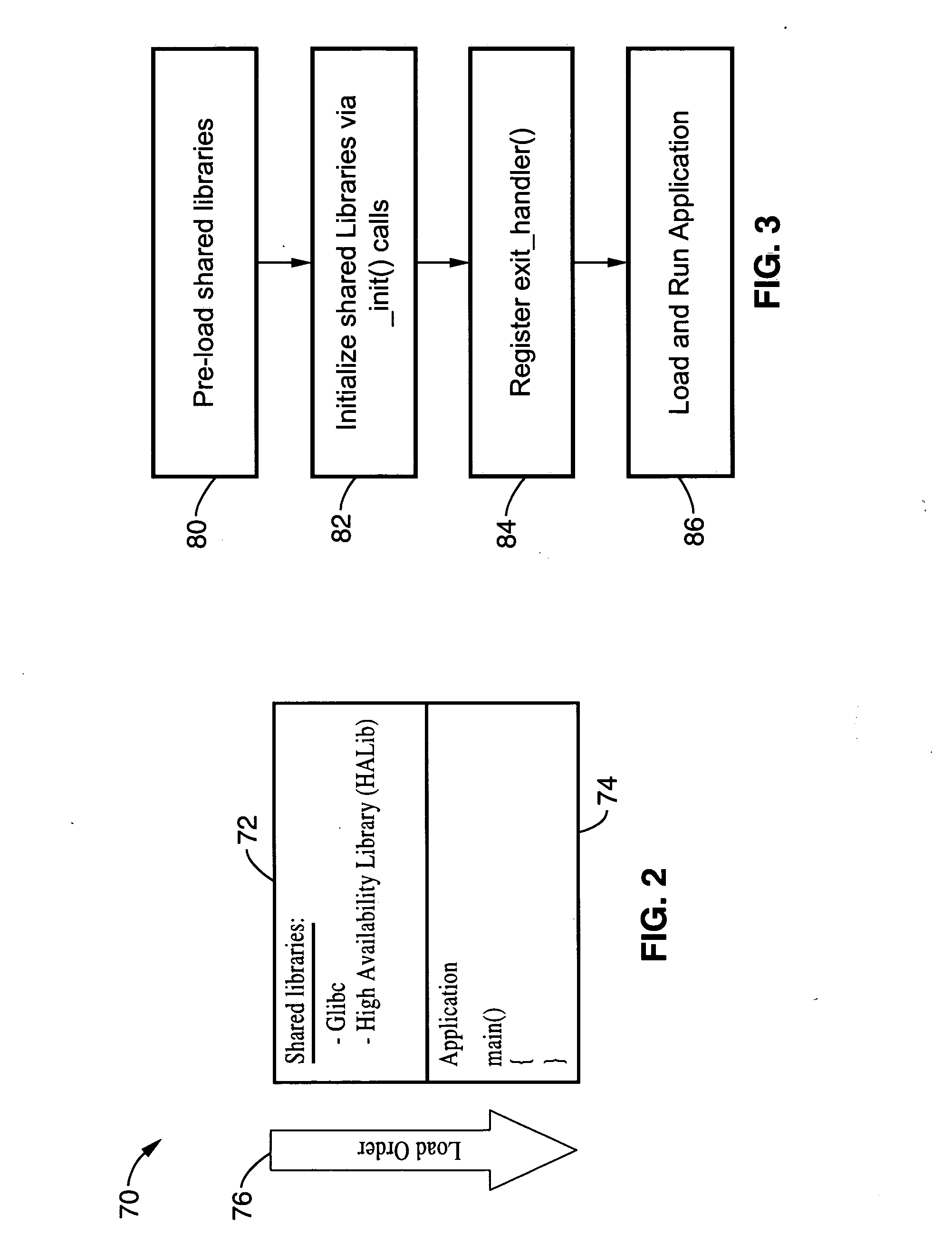
A trusted platform in a digital processing system is maintained even when modules, or other processes or data, are loaded after a boot sequence. A configuration file is used to include measurements (e.g., hash values, signatures, etc.) of modules to be loaded. After secure boot-up the operating system kernel uses the configuration file to check module integrity prior to loading and executing. If a module does not verify against the configuration file data then the system can prevent further operation, restrict certain operations, indicate the non-trusted nature of the system or take other actions. In one embodiment, if a module does not pass the integrity check then the failed measurement is extended into a specific Platform Configuration Register (PCR) within a Trusted Platform Manager (TPM) process. Subsequently, client applications can determine if the platform is trustable based on the return of the PCR value. A local application (application running in the same platform) can “seal” secrets to a trusted platform. The operation of the application relies on the secrets, which can only be revealed in a trusted platform.
Owner:SONY ELECTRONICS INC +1
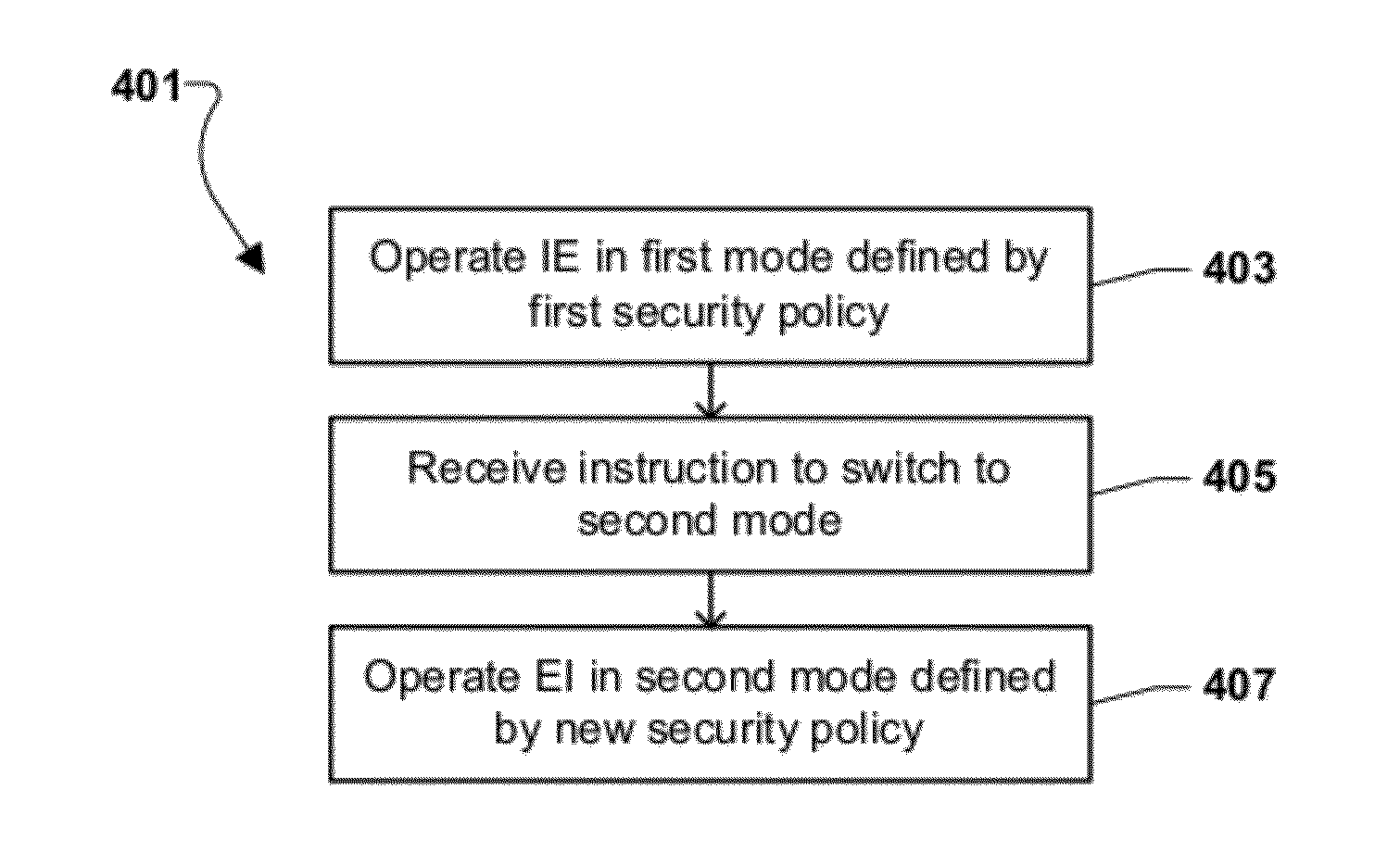
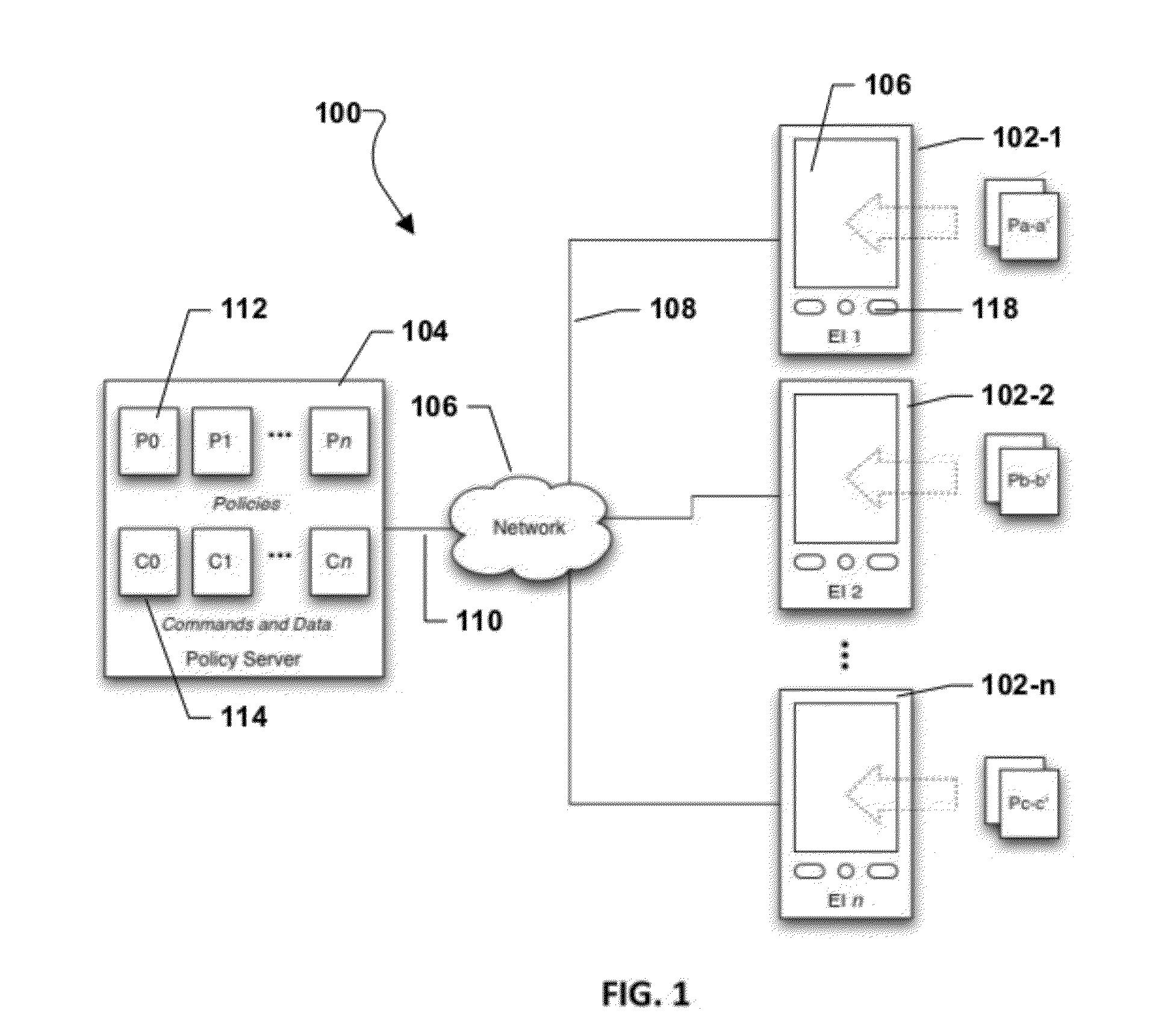
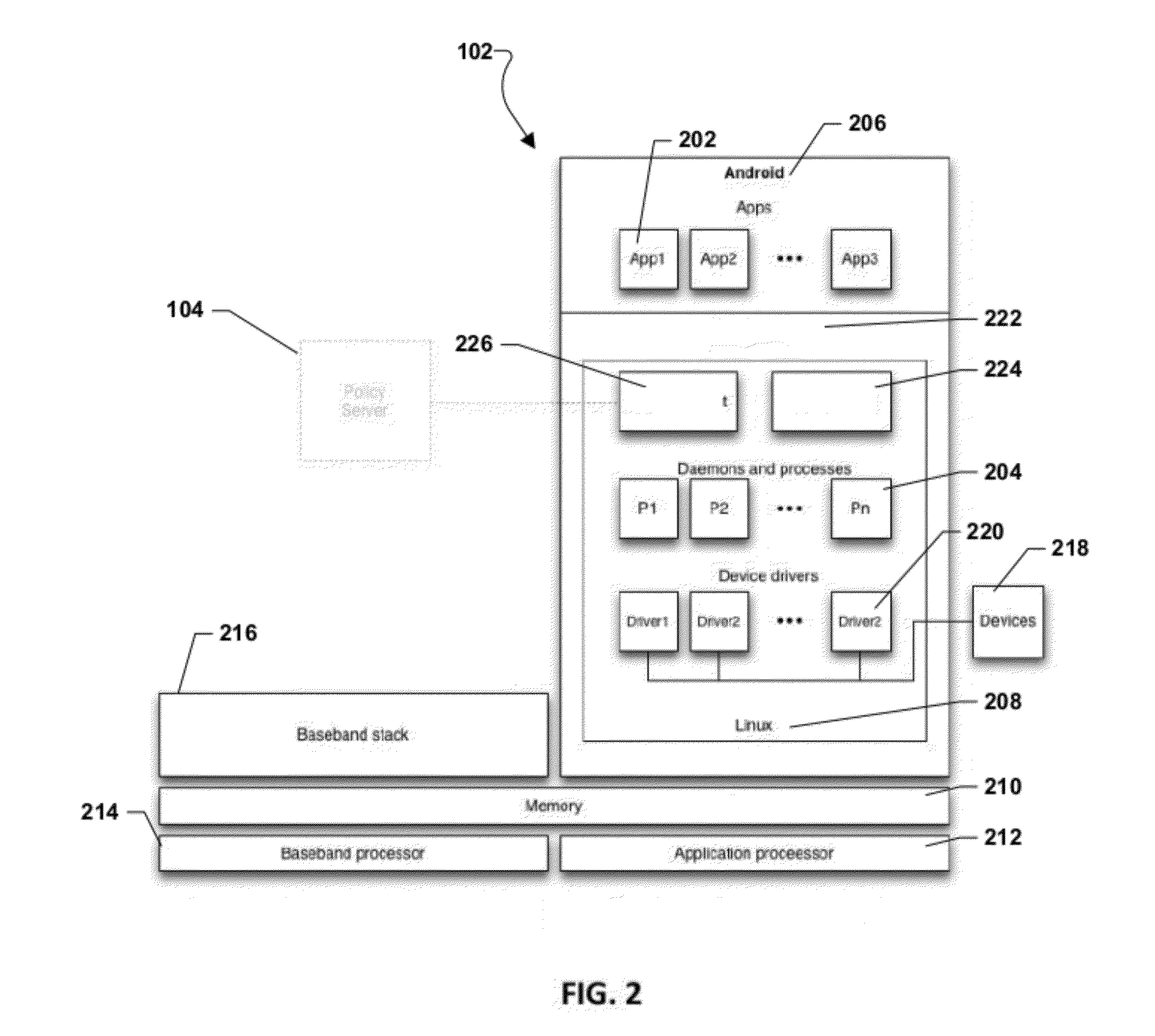
Systems and Methods for Enhanced Security in Wireless Communication
ActiveUS20120216242A1Error detection/correctionPlatform integrity maintainanceSecure communicationCommunications security
A communication system having a policy server coupled to a communications network for managing secure communication with and among end instruments (EI). The EI comprises a memory, and a processor coupled to the memory with processor-executable instructions, including instructions for an operating system kernel; and instructions for a protection core that monitors operations of the operating system kernel in accordance with a security policy for the EI. Security policies can intercept calls to an operating system kernel and for each call, determining whether the call is allowed under the security policy(ies). Policies are stored in a policy library and transmitted to an EI over a wireless communication network.
Owner:REDWALL TECH
By-pass and tampering protection for application wrappers
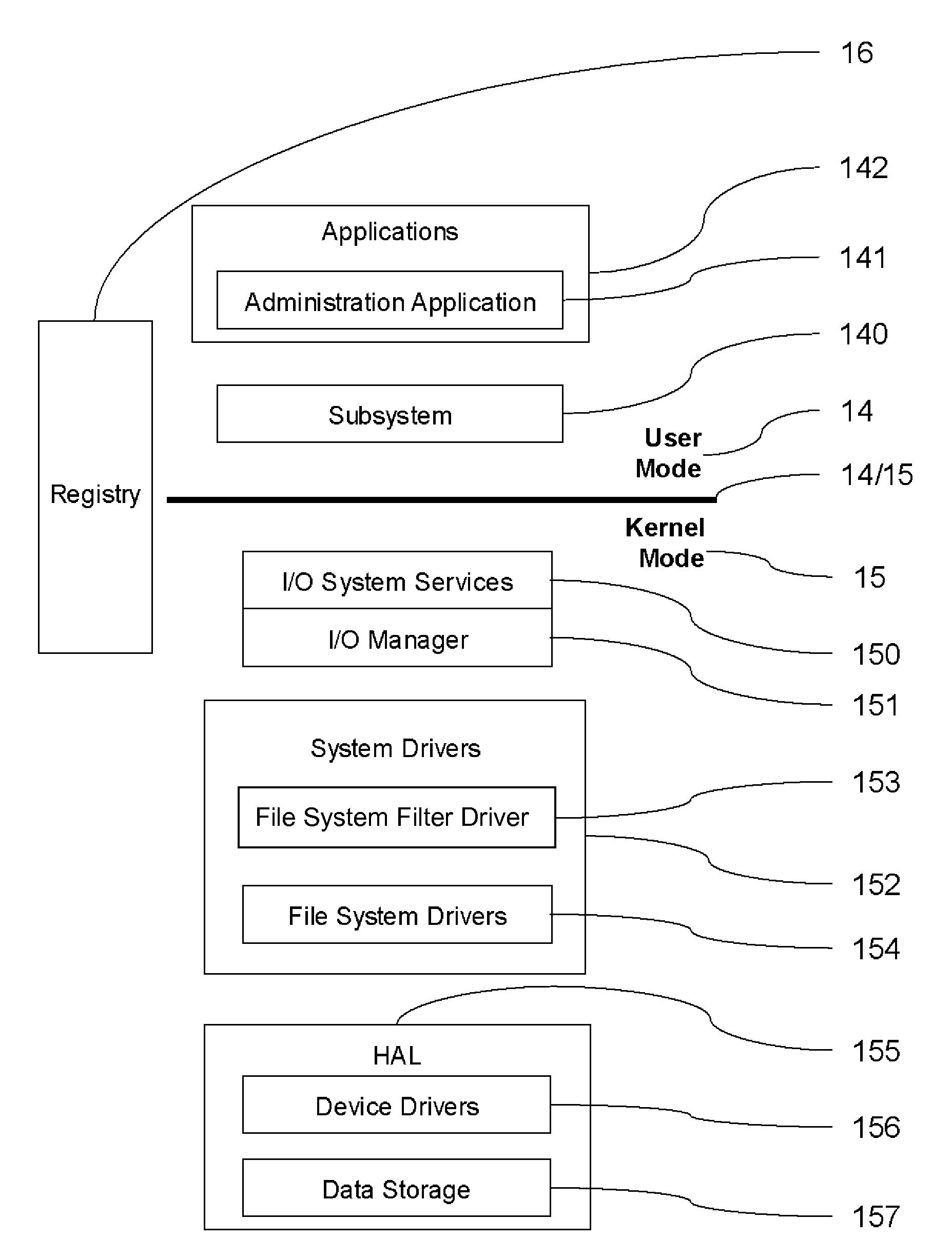
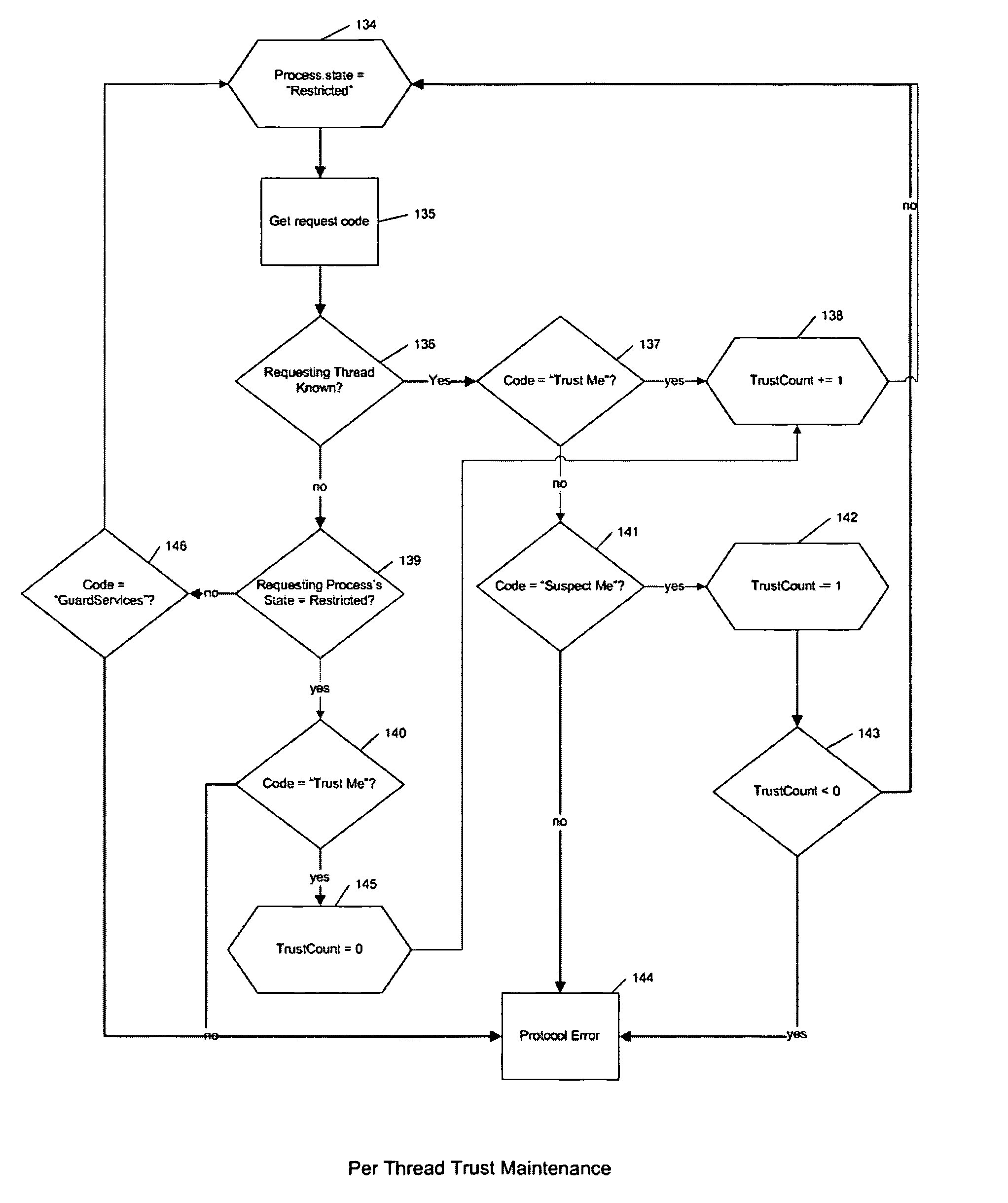
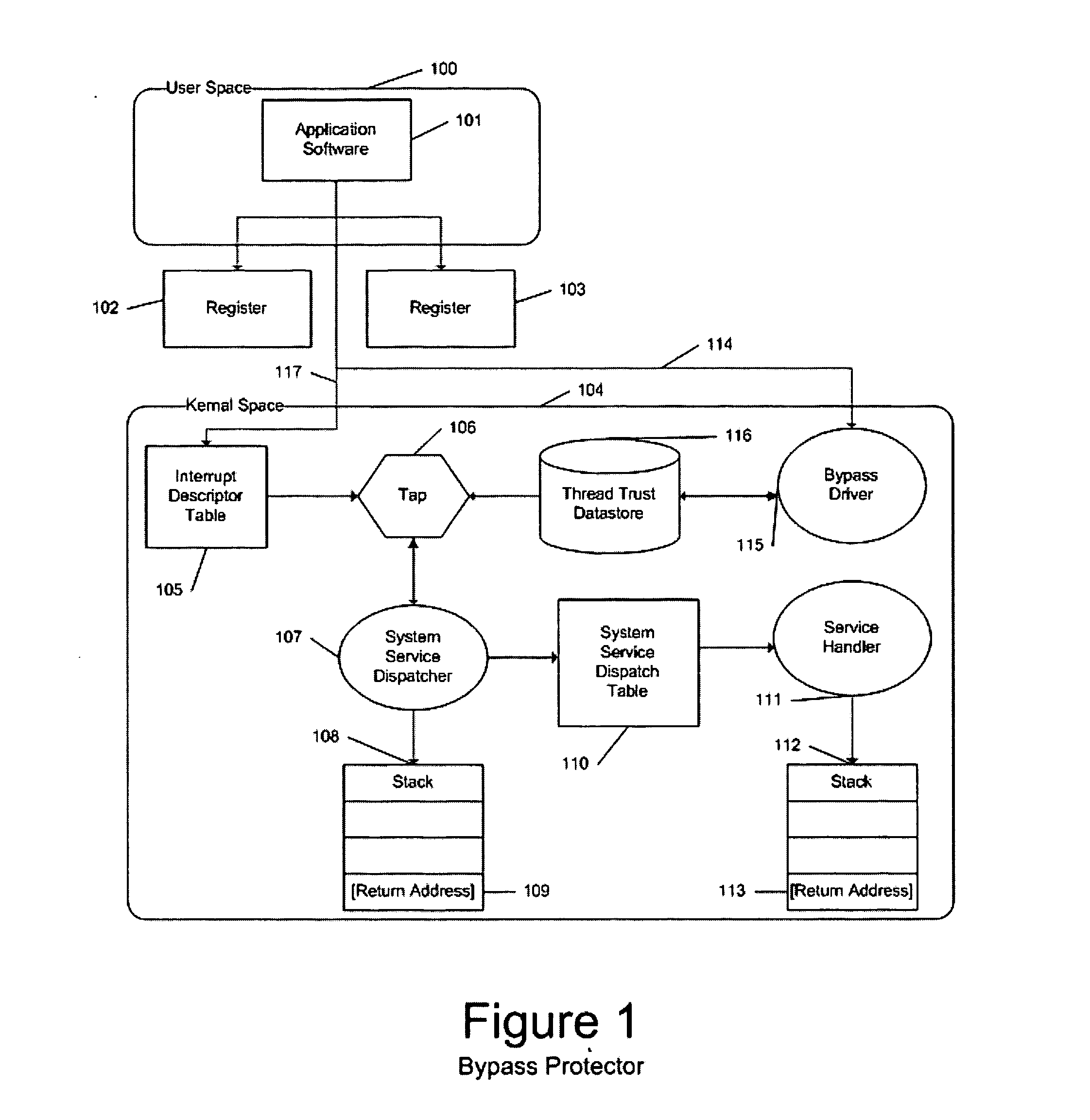
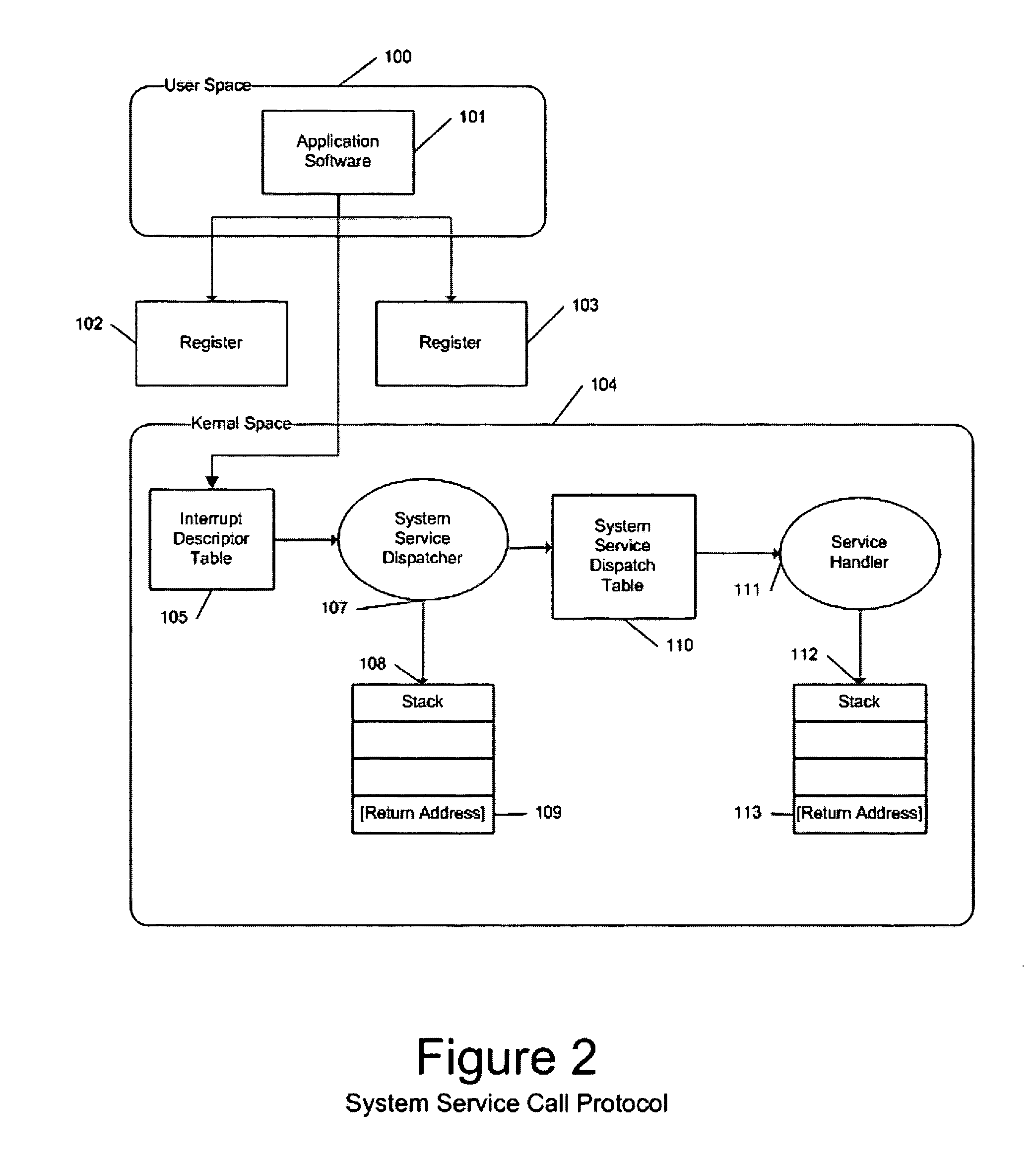
InactiveUS20050108516A1Restoration of protectionSpecific access rightsPlatform integrity maintainanceOperational systemHooking
In a computer system with an operating system that supports multiple levels of interfaces (APIs) that application programs (i.e. programs executing outside the operating system kernel in user mode) can invoke to obtain services from the operating system, and the employment of a hooking or mediation technology within a user-mode process (i.e. an instantiation of an application program) to intercept / mediate invocations of selected interfaces of some of those levels, the Tampering Protection protects the code and statically or heap allocated data of the mediators from corruption by the code of the user-mode process being mediated that resides and operates in the same address space as the code and data of the mediators (as such corruption would compromise the integrity of the mediator and could prevent it from accomplishing its intended mediation purpose). It does so by providing memory protection services that allow mediators to define data areas (both static segments and dynamic heaps) to be protected and to temporarily unprotect them during the execution of a mediator so that they can be modified during that execution, thus ensuring that the mediate application does not directly use the operating system services to override Tampering Protection management of these protected segments or protected.
Owner:BALZER ROBERT +1
Methods, systems and computer program products for server based type of service classification of a communication request
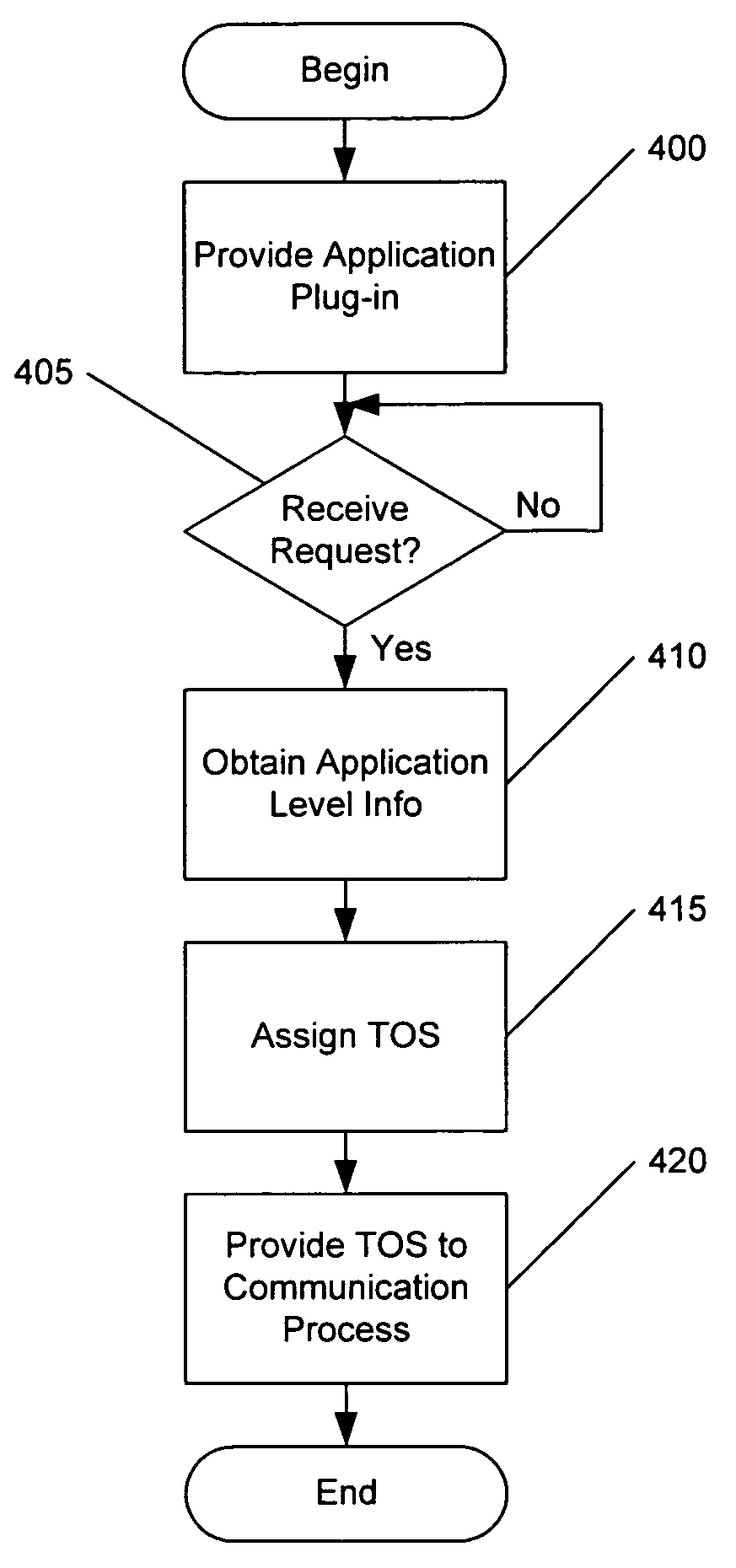
InactiveUS7089294B1Multiple digital computer combinationsData switching networksOperational systemApplication software
Methods, systems and computer program products are provided for type of service classification of a communication request for an application executing on a server. An application plug-in associated with the application is provided in an operating system kernel of the server. The application plug-in receives the communication request and obtains application level information from the received communication request. The application plug-in further assigns a type of service classification to the received communication request based on the obtained application level information and provides the assigned type of service classification information for the communication request to a process executing on the server for processing communications from the server responsive to the communication request.
Owner:IBM CORP
Method and computing system for transparence computing on the computer network
ActiveUS20060117172A1Improve performanceImprove availabilityDigital computer detailsData resettingOperational systemTransparent computing
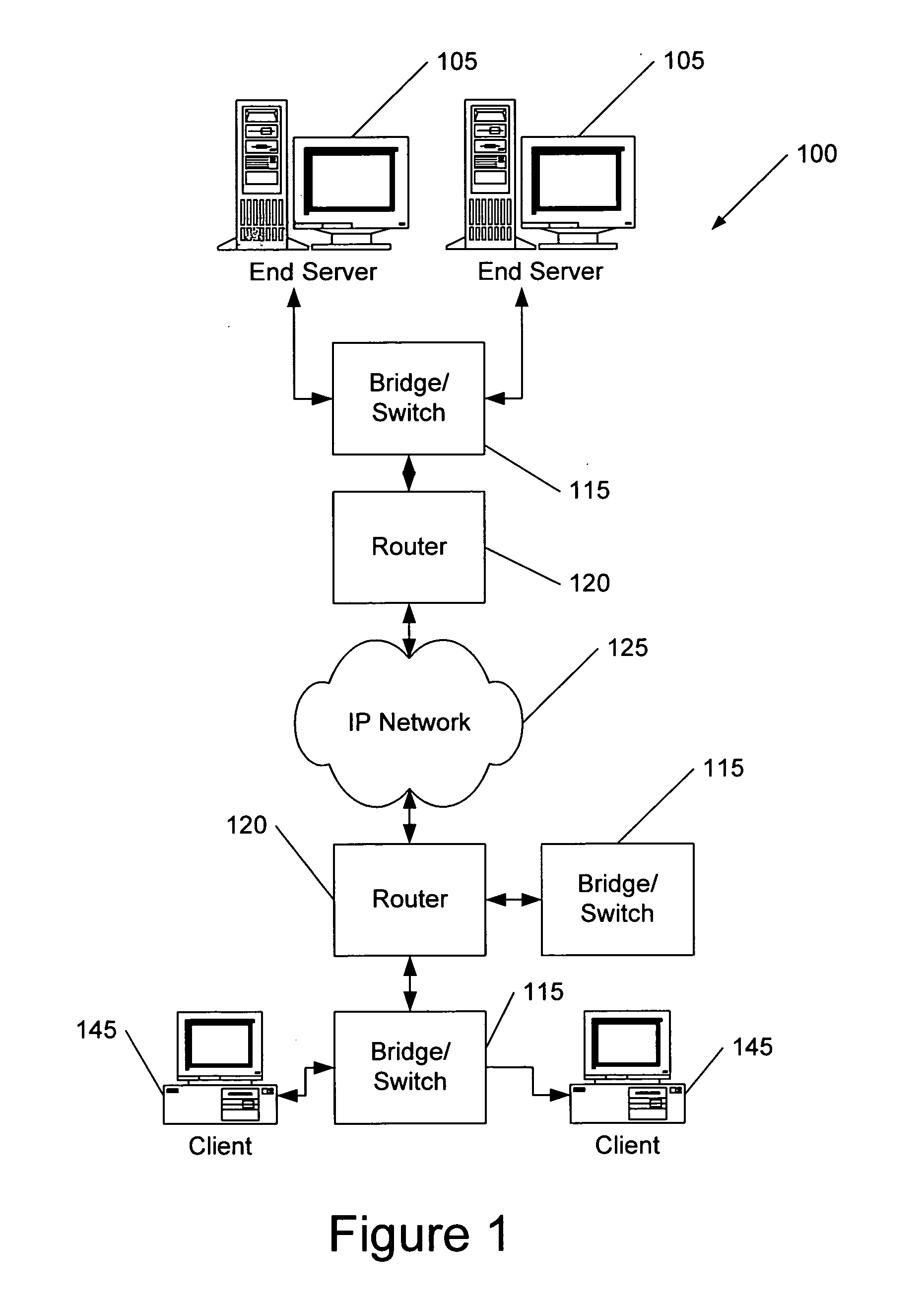
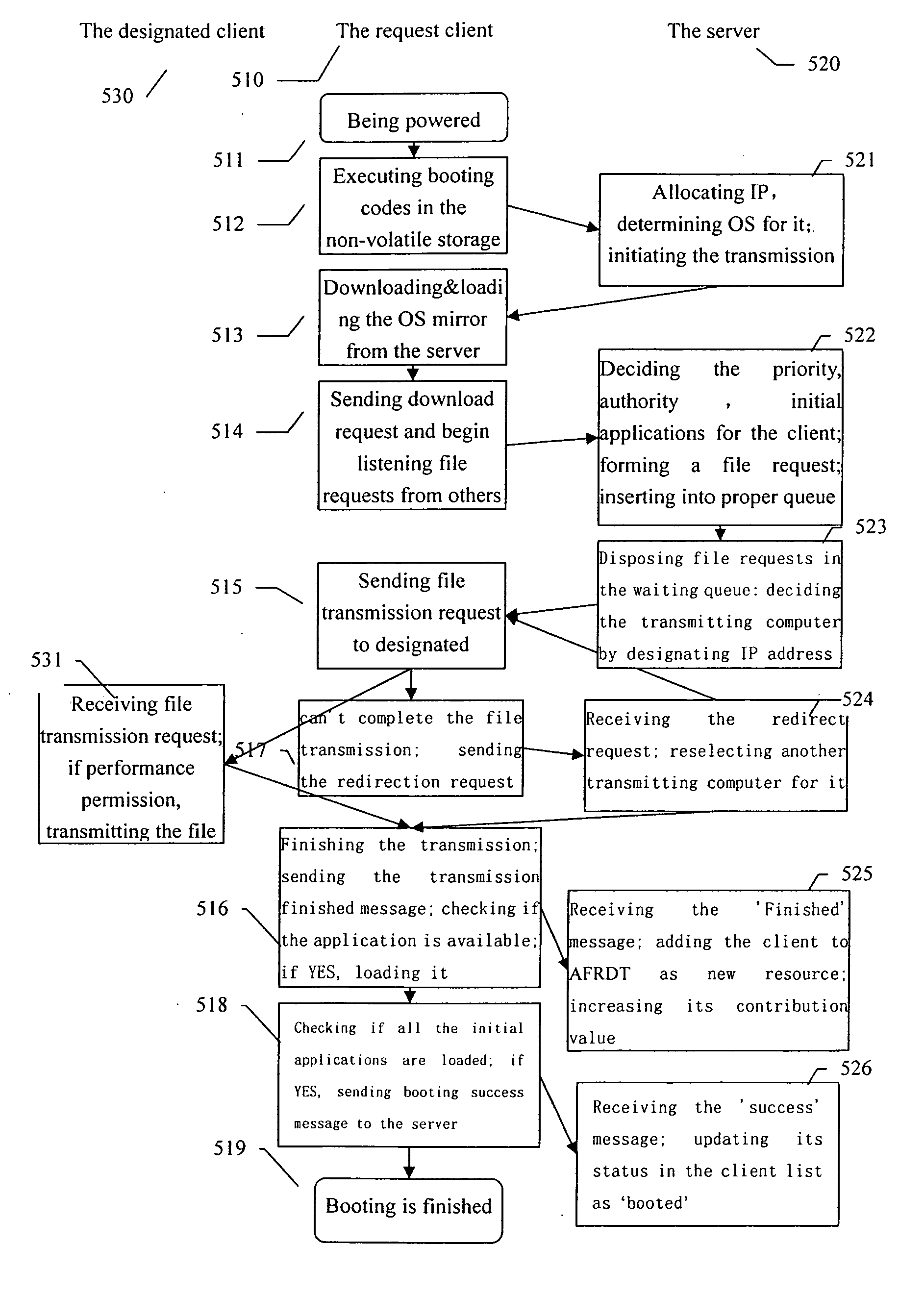
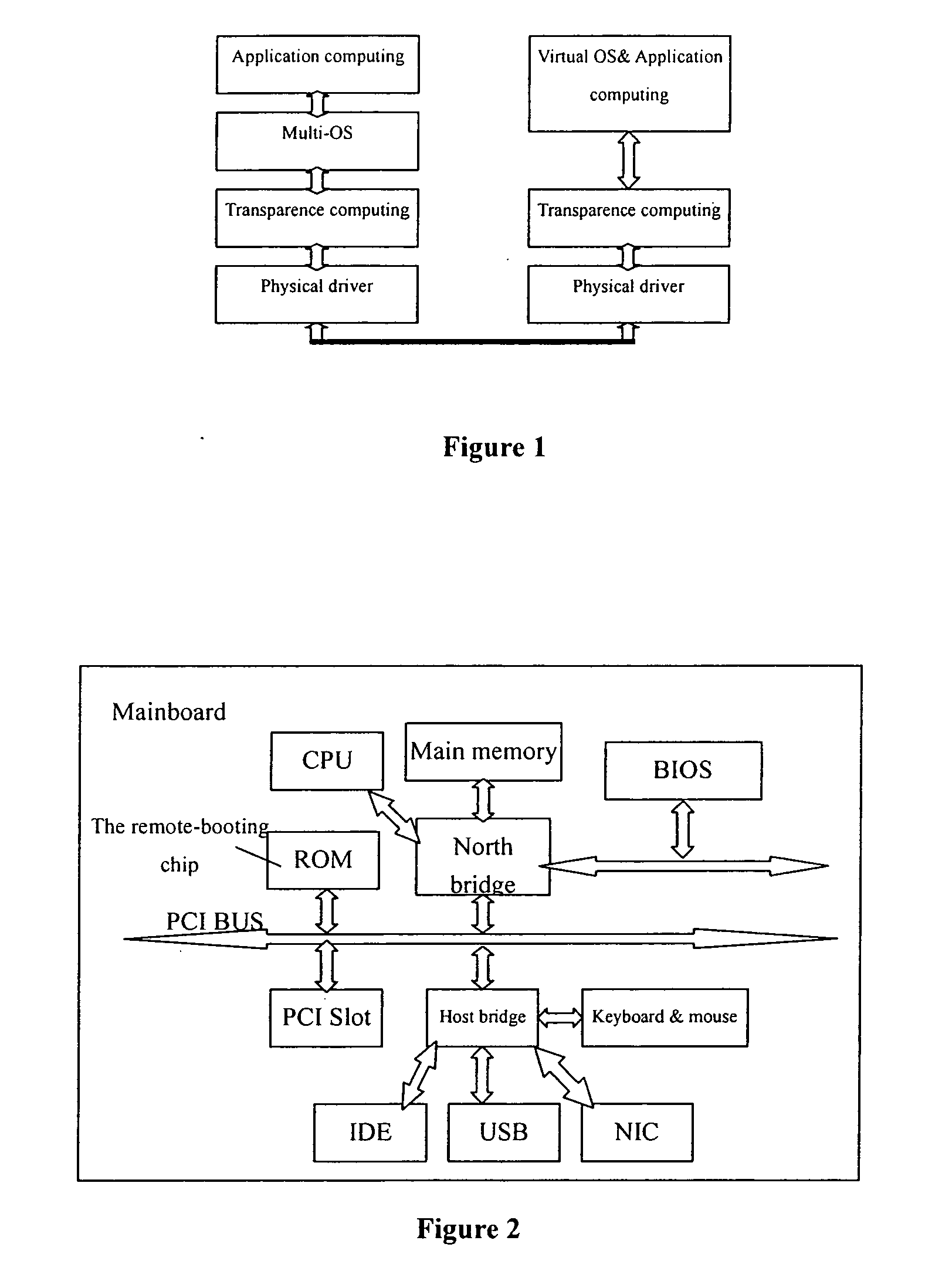
A computing system based on Transparence Computing consists of clients and a server. There is no disk and no preinstalled OS on the client; a remote booting chip is set on the client's mainboard for downloading and loading the OS. Boot-supporting services, OS kernel mirrors, and applications are preset on the server; After being powered, the client broadcasts the boot request to the network and the server allocates network parameters for it. The client downloads an OS-selecting script from the server. After the user selects the needed OS, the client downloads and loads the selected OS from the server. Hence, the client fulfills the user's computing requirements just as a normal PC. The computing work is implemented on the client-side, during which the client can acquire corresponding resources such as applications, data, and documents from the server on demand. The client can be provided with private storage across the network by presetting a service in the mirror for creating virtual disks on the server, and thus data generated during or after the computing can be persistently stored on the server's storage.
Owner:TSINGHUA UNIV
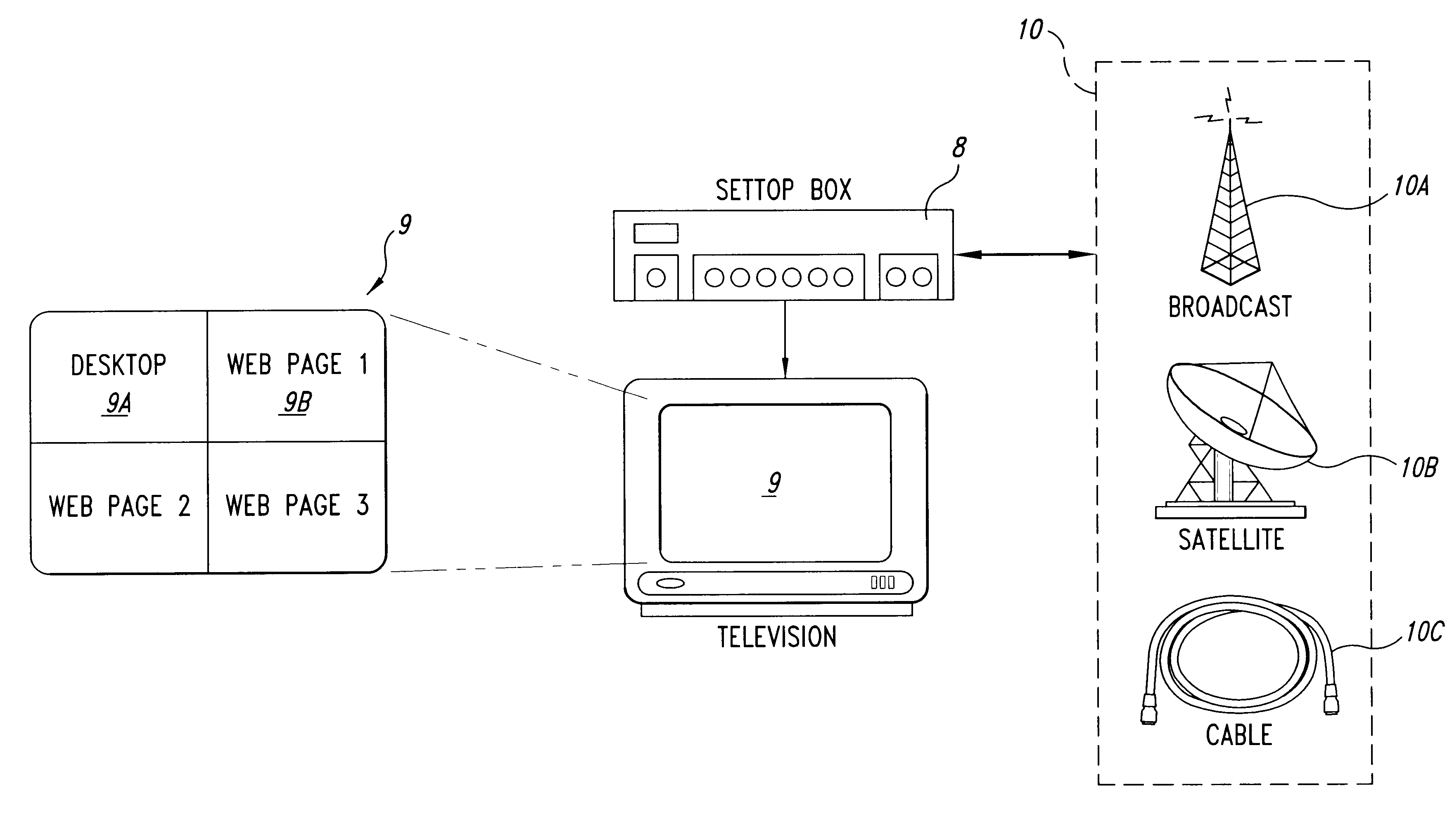
Alternate display content controller
InactiveUS6337717B1Television system detailsMemory adressing/allocation/relocationOperational systemThe Internet
An alternate display content controller provides a technique for controlling a video display separately from and in addition to the content displayed on the operating system monitor. Where the display is a computer monitor, the alternate display content controller interacts with the computer utility operating system and hardware drivers to control allocation of display space and create and control one or more parallel graphical user interfaces adjacent the operating system desktop. An alternate display content controller may be incorporated in either hardware or software. As software, an alternate display content controller may be an application running on the computer operating system, or may include an operating system kernel of varying complexity ranging from dependent on the utility operating system for hardware system services to a parallel system independent of the utility operating system and capable of supporting dedicated applications. The alternate display content controller may also include content and operating software delivered over the internet or any other LAN. The alternate display content controller may also be included in a television decoder / settop box to permit two or more parallel graphical user interfaces to be displayed simultaneously.
Owner:OSTENDO TECH INC
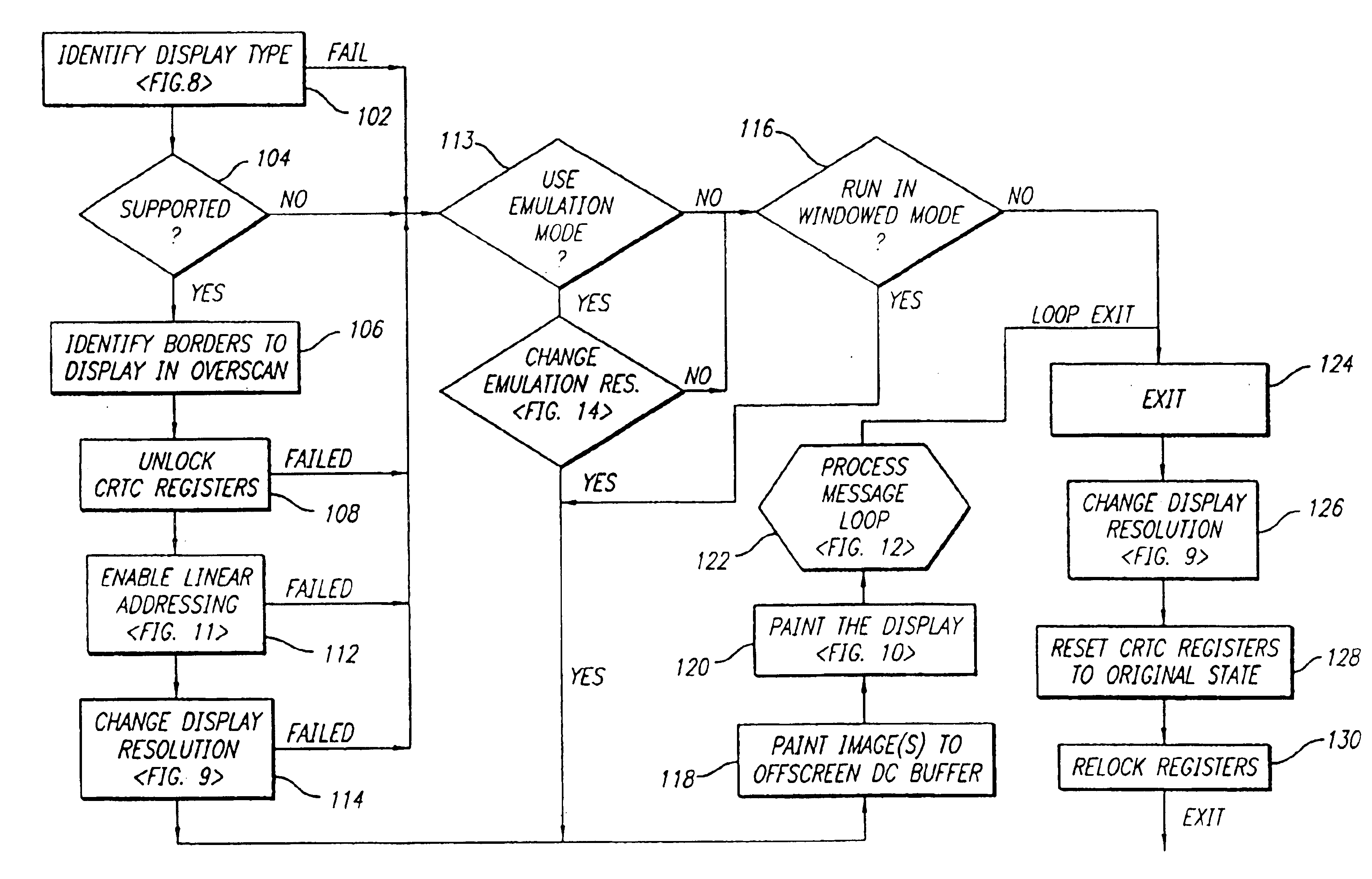
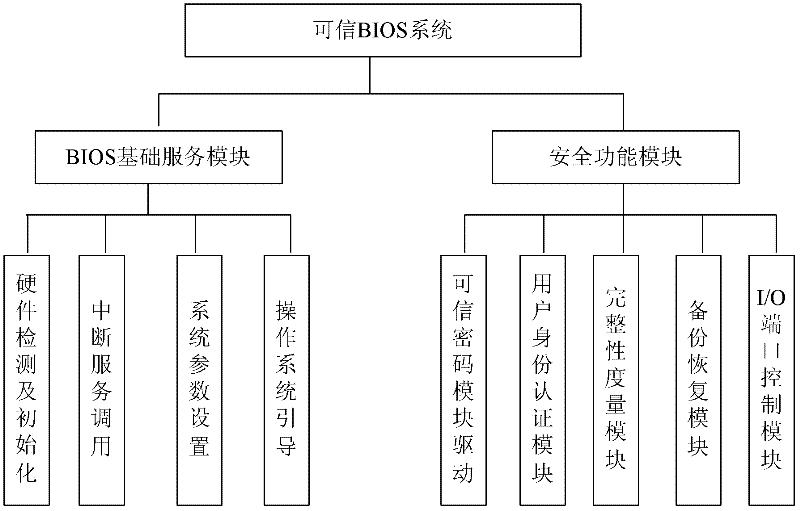
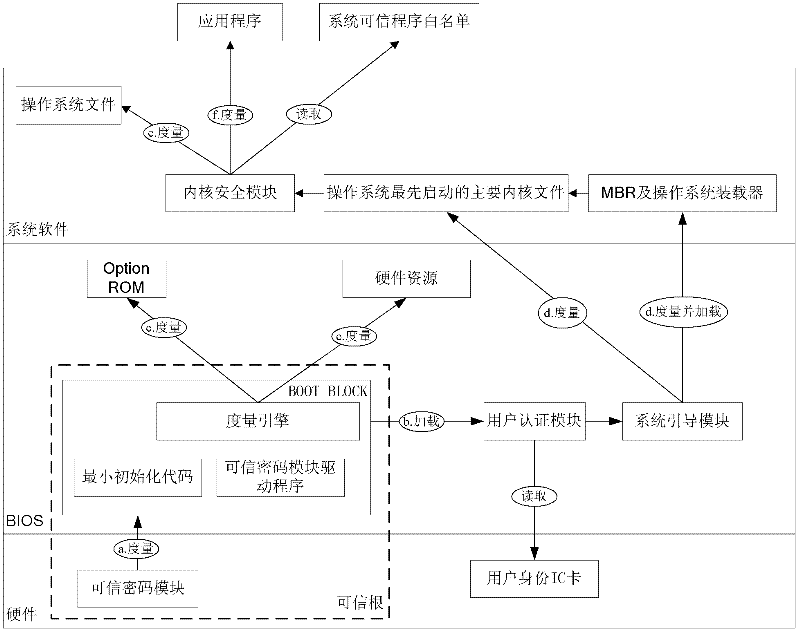
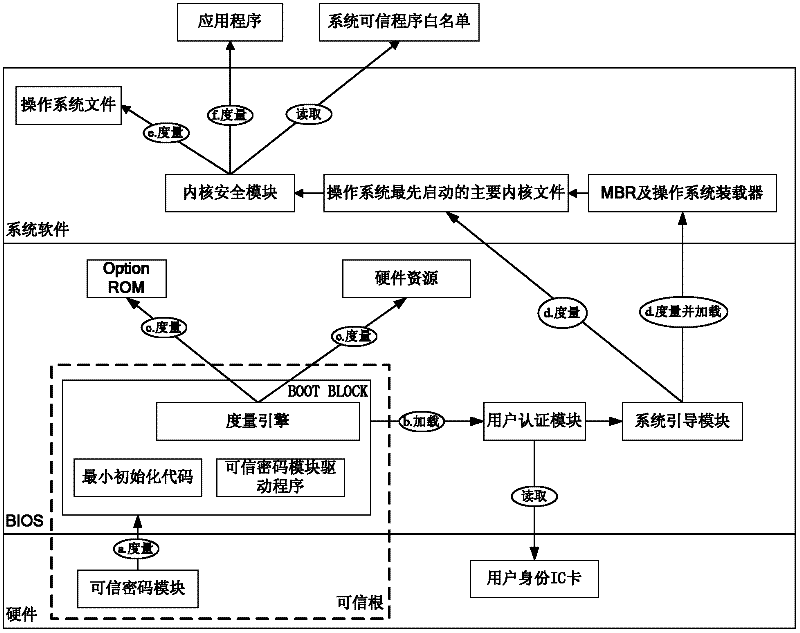
Trust chain transfer method for trusted computing platform
InactiveCN102332070ANot easy to tamper withNot easy to attackPlatform integrity maintainanceOperational systemTrusted Computing
The invention discloses a trust chain transfer method for a trusted computing platform. A trusted computing module (TCM) serving as a starting point of starting a trust chain is started and actively initiated at first to verify the trustiness of a BIOS (basic input output system) chip; after the trusted BIOS chip is started, a MAIN BLOCK of the BIOS chip performs concentrated integrity verification on key files of an MBR (master boot record), an operating system loader and an operating system kernel; in the starting process of an operating system, the starting and running of an unauthorized program are prevented in a way of combining the integrity verification based on a white list and running program control; and hashing operations for the integrity verification are finished by a hardware computing engine. When a user starts any executable program, a security module in the operating system kernel checks the integrity of the program and checks whether the program is in the trusted program white list or not, and only application programs which are in the trusted program white list of the system and have integrity measures consistent with an expected value are permitted to be run. High-efficiency and fine-grained trust chain transfer is realized, the damages of viruses to system files and program files can be prevented, and the execution of the unauthorized program can be prevented.
Owner:中国人民解放军海军计算技术研究所
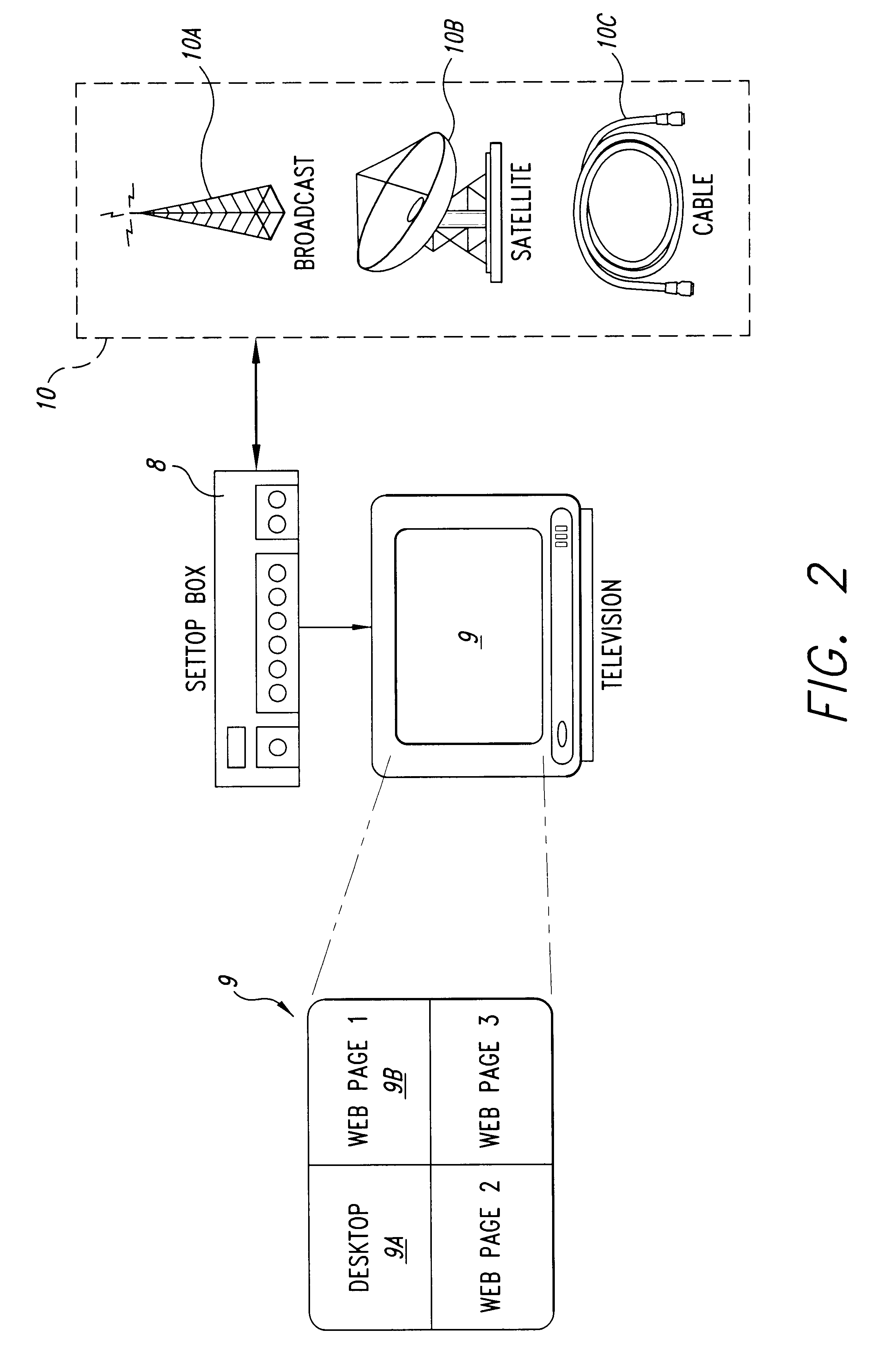
Method and system for controlling a comlementary user interface on a display surface
InactiveUS20100005396A1Reduce displayStatic indicating devicesInternal/peripheral component protectionGraphicsOperational system
An alternate display content controller provides a technique for controlling a video display separately from and in addition to the content displayed on the operating system display surface. Where the display is a computer monitor, the alternate display content controller interacts with the computer utility operating system and hardware drivers to control allocation of display space and create and control one or more parallel graphical user interfaces in addition to the operating system desktop. An alternate display content controller may be incorporated in either hardware or software. As software, an alternate display content controller may be an application running on the computer operating system, or may include an operating system kernel of varying complexity ranging from dependent on the utility operating system for hardware system services to a parallel system independent of the utility operating system and capable of supporting dedicated applications. The alternate display content controller may also include content and operating software delivered over the Internet or any other LAN. The alternate display content controller may also be included in a television decoder / settop box to permit two or more parallel graphical user interfaces to be displayed simultaneously.
Owner:NASON D DAVID +1
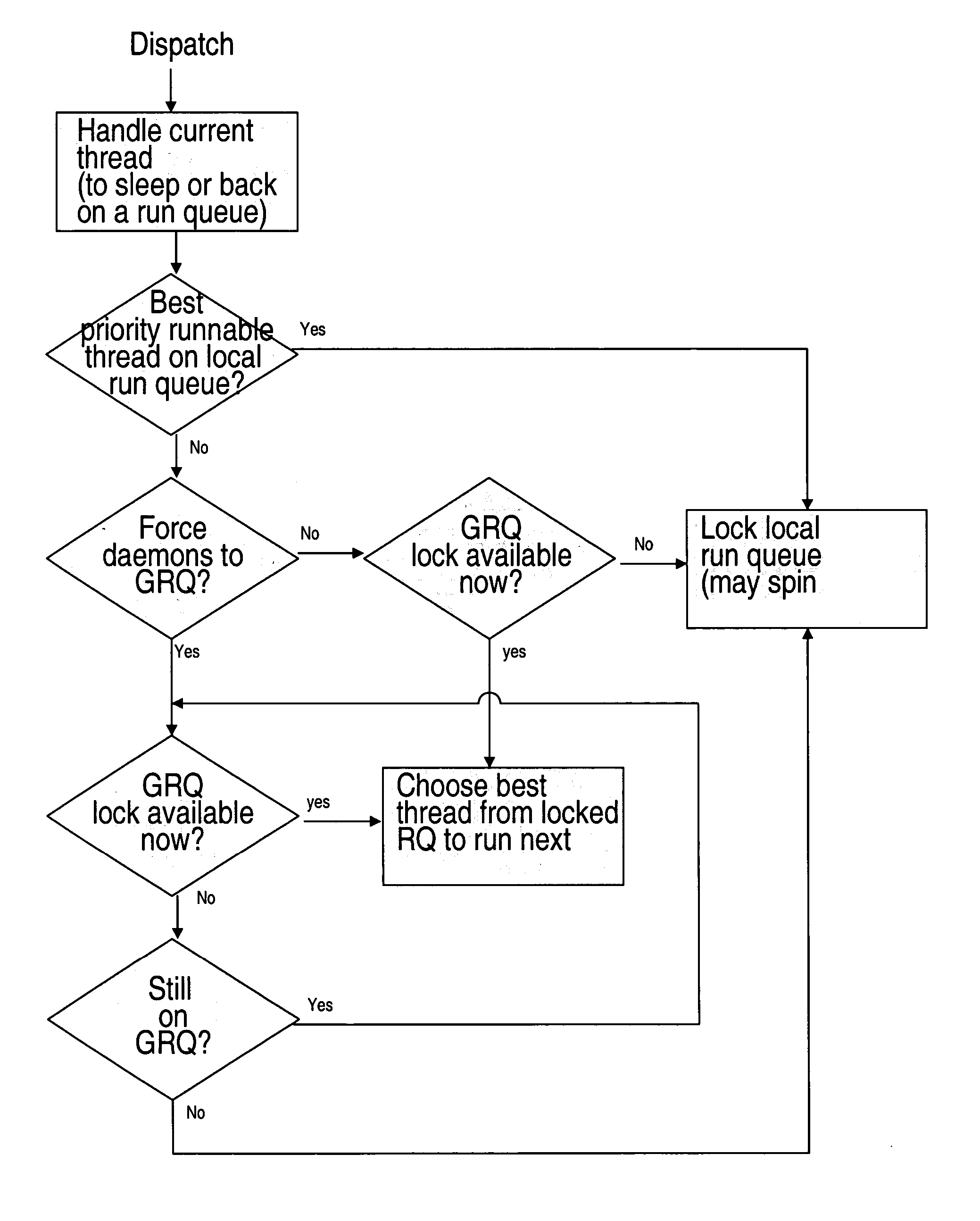
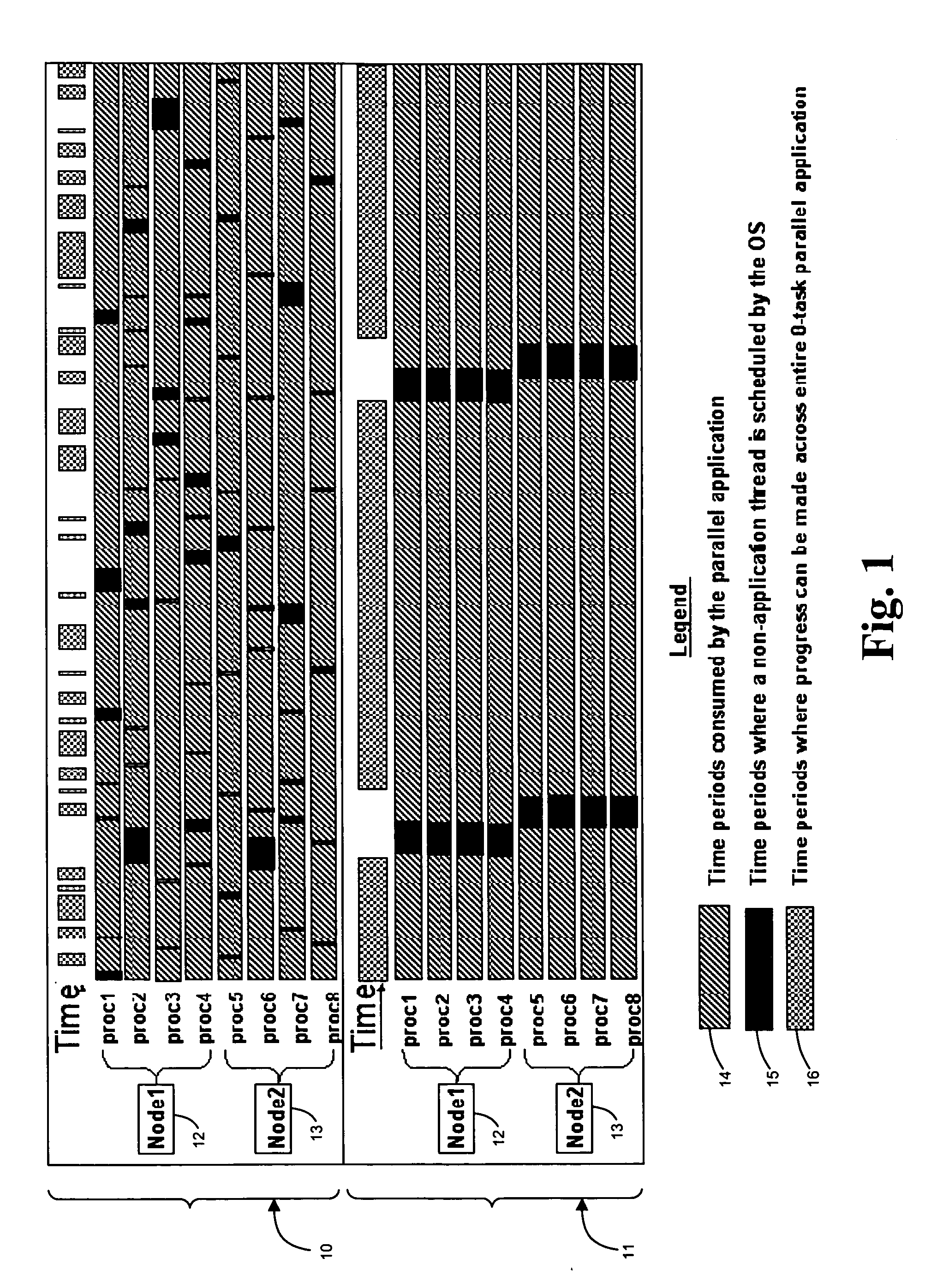
Parallel-aware, dedicated job co-scheduling method and system
InactiveUS20050131865A1Improve performanceImprove scalabilityProgram initiation/switchingSpecial data processing applicationsExtensibilityOperational system
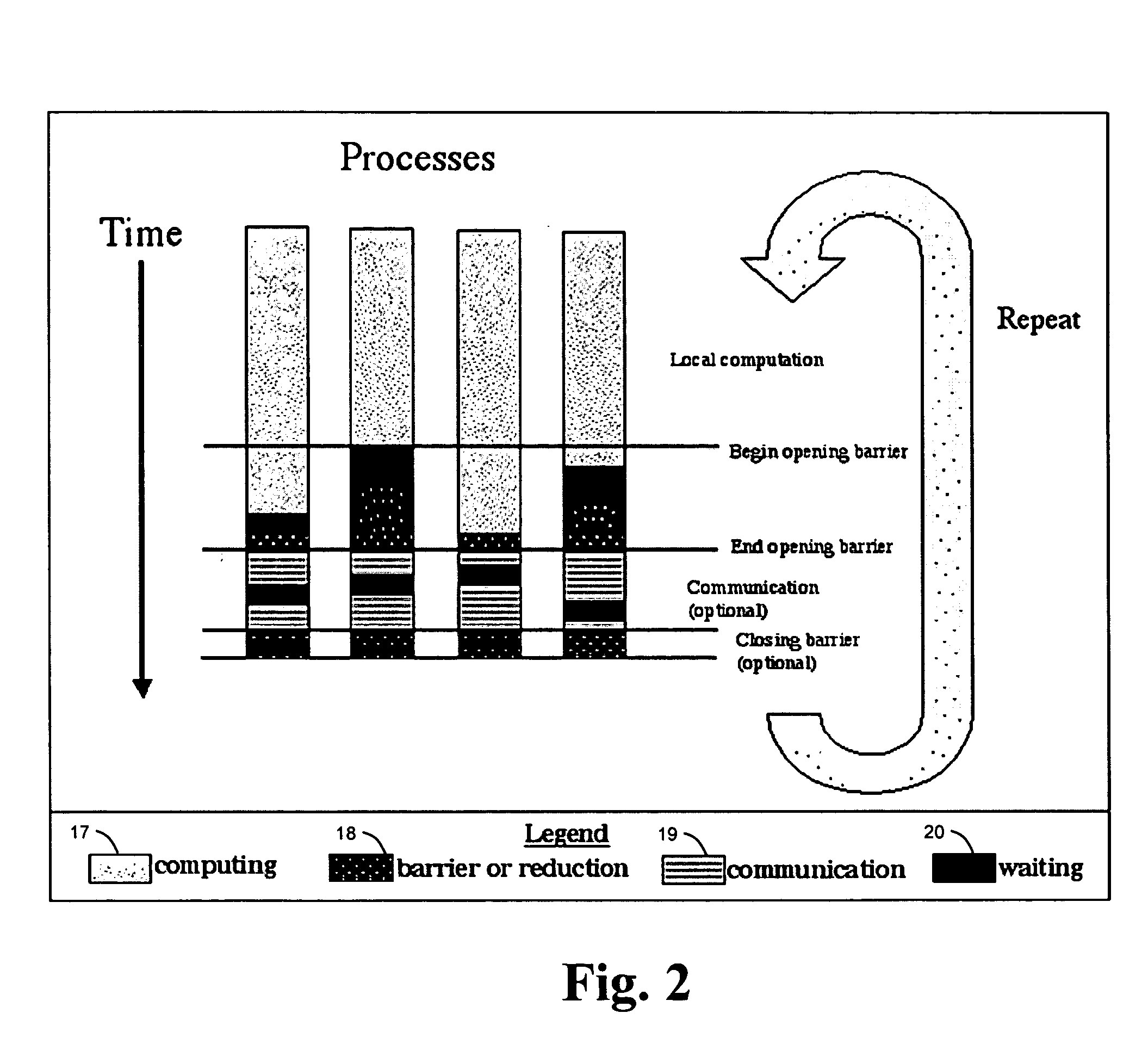
In a parallel computing environment comprising a network of SMP nodes each having at least one processor, a parallel-aware co-scheduling method and system for improving the performance and scalability of a dedicated parallel job having synchronizing collective operations. The method and system uses a global co-scheduler and an operating system kernel dispatcher adapted to coordinate interfering system and daemon activities on a node and across nodes to promote intra-node and inter-node overlap of said interfering system and daemon activities as well as intra-node and inter-node overlap of said synchronizing collective operations. In this manner, the impact of random short-lived interruptions, such as timer-decrement processing and periodic daemon activity, on synchronizing collective operations is minimized on large processor-count SPMD bulk-synchronous programming styles.
Owner:LAWRENCE LIVERMORE NAT SECURITY LLC
Method of controlling memory access
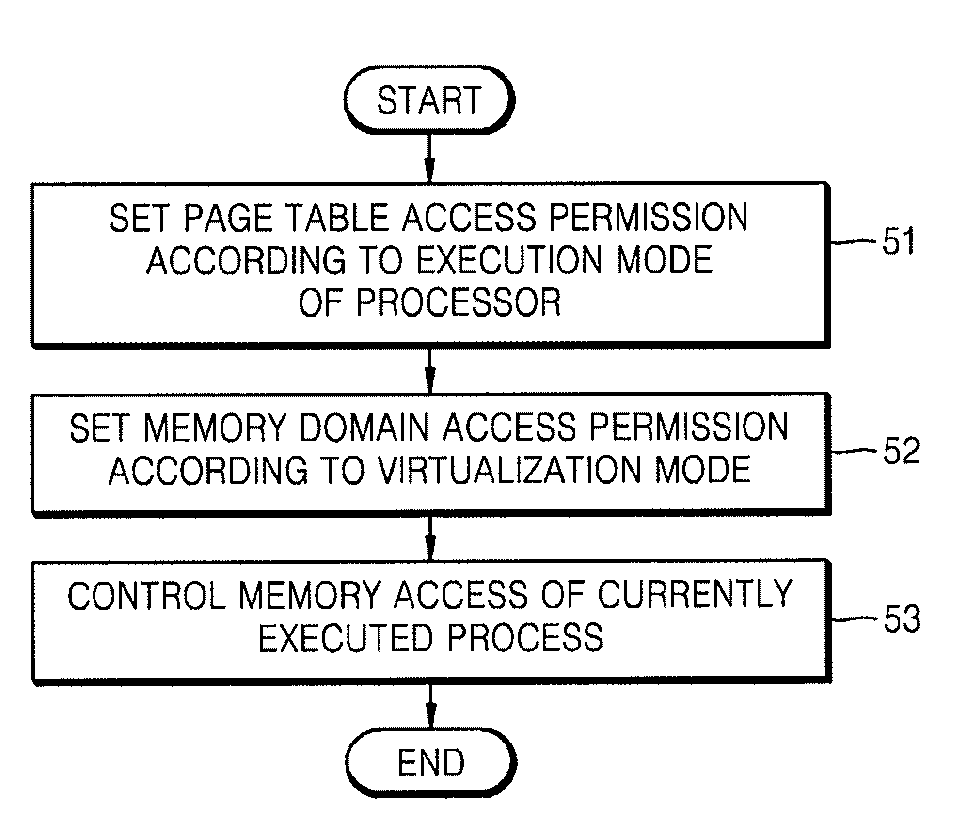
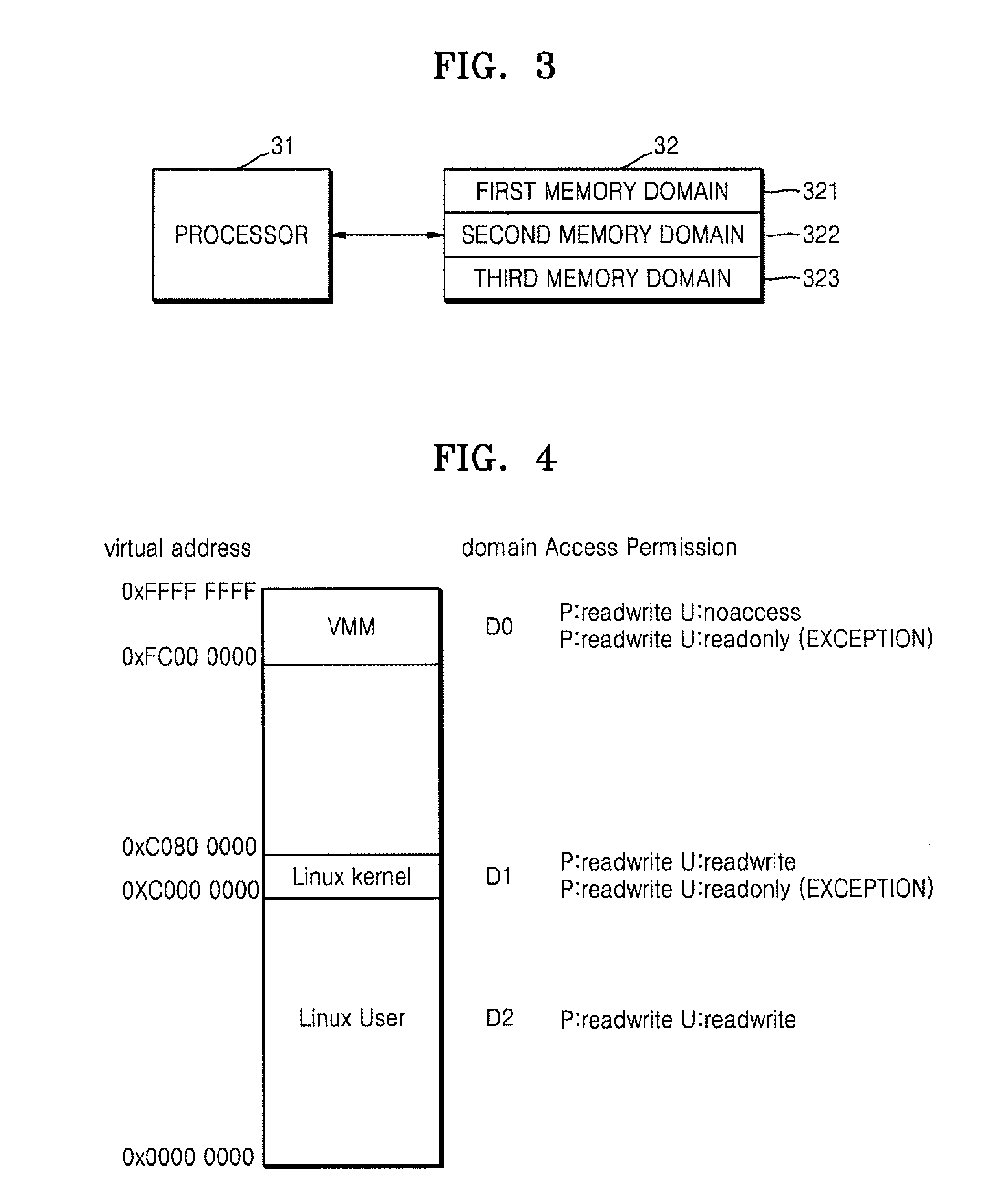
ActiveUS20080244206A1Unauthorized memory use protectionComputer security arrangementsOperational systemA domain
Provided is a method of controlling memory access. In a system including a first layer element executed in a privileged mode having a first priority of permission to access the entire region of a memory and second and third layer elements executed in an unprivileged mode having a second priority of permission to access a partial region of the memory, the method of controlling memory access determines whether the memory is accessible for each page that is an address space unit, based on which mode a layer element currently accessing the memory is executed in between the privileged mode and the unprivileged mode; and determines whether the memory is accessible based on which one of the first, second and third layer elements corresponds to a domain currently being attempted to be accessed from among a plurality of domains of the memory. Accordingly, a memory domain allocated to a guest operating system kernel is effectively protected from an application executed in the unprivileged mode in which the guest operating system kernel is executed.
Owner:SAMSUNG ELECTRONICS CO LTD
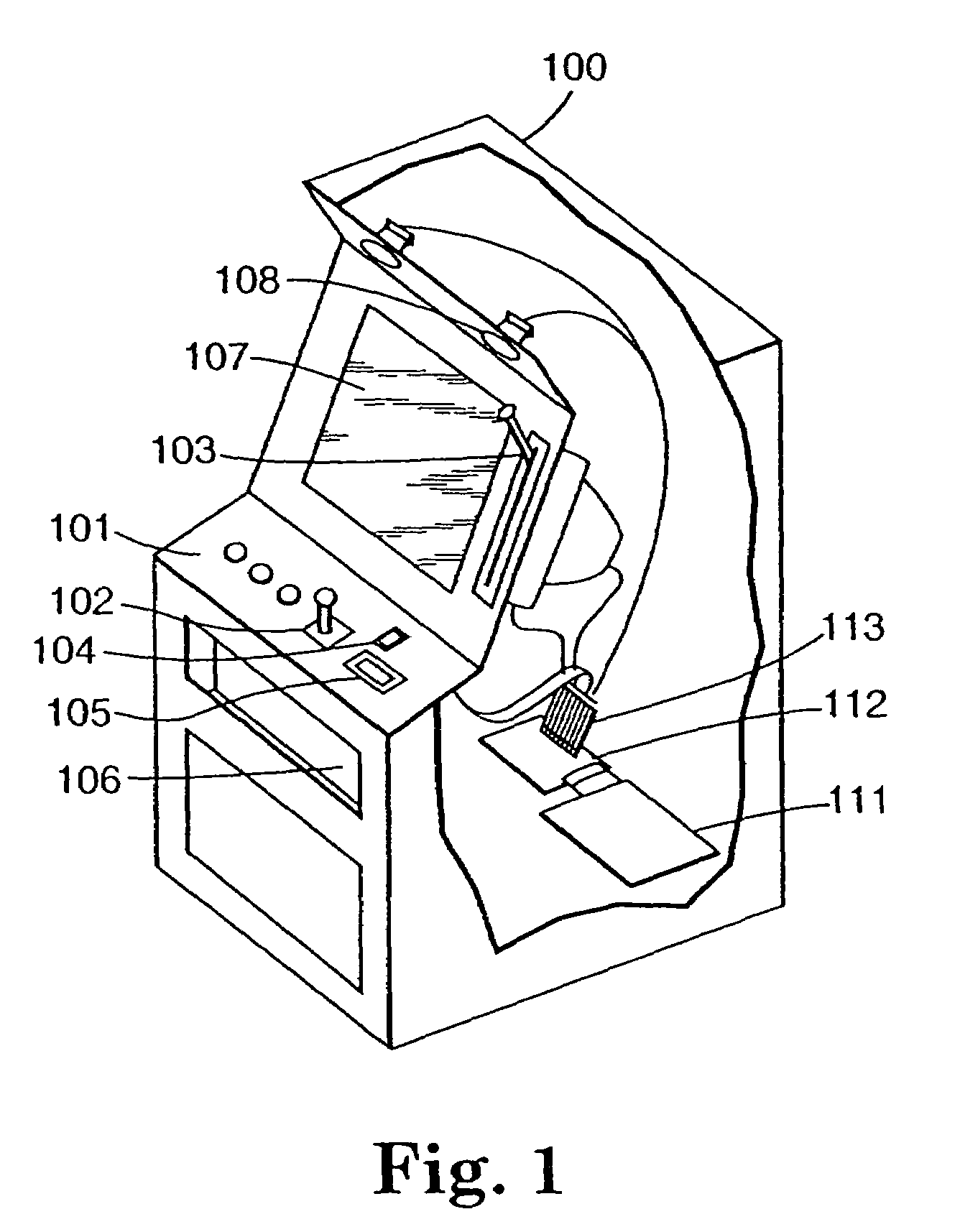
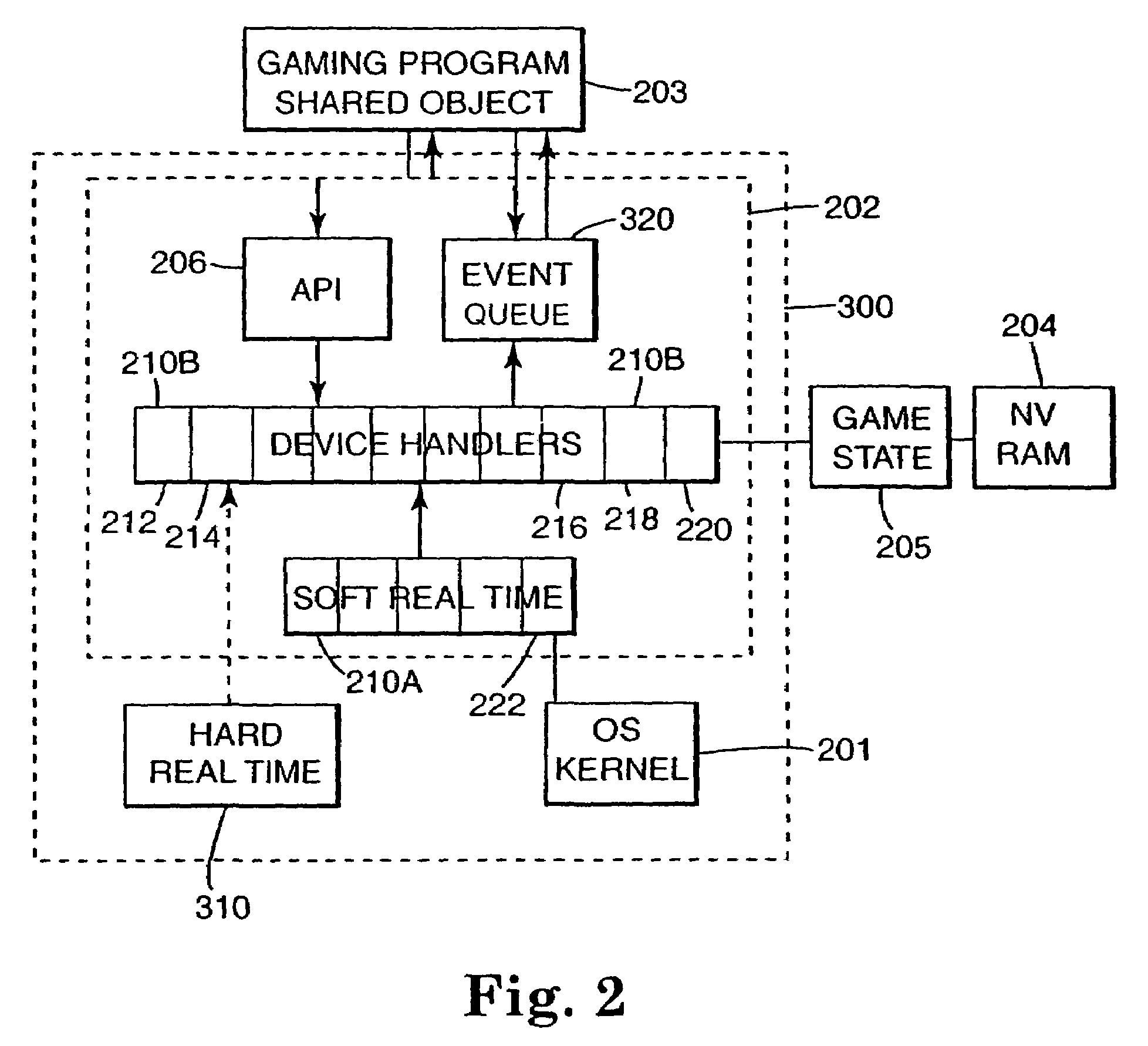
Method for developing gaming programs compatible with a computerized gaming operating system and apparatus
InactiveUS7618317B2Assured of performanceReduce approval timeMemory loss protectionComputer security arrangementsOperational systemApplication software
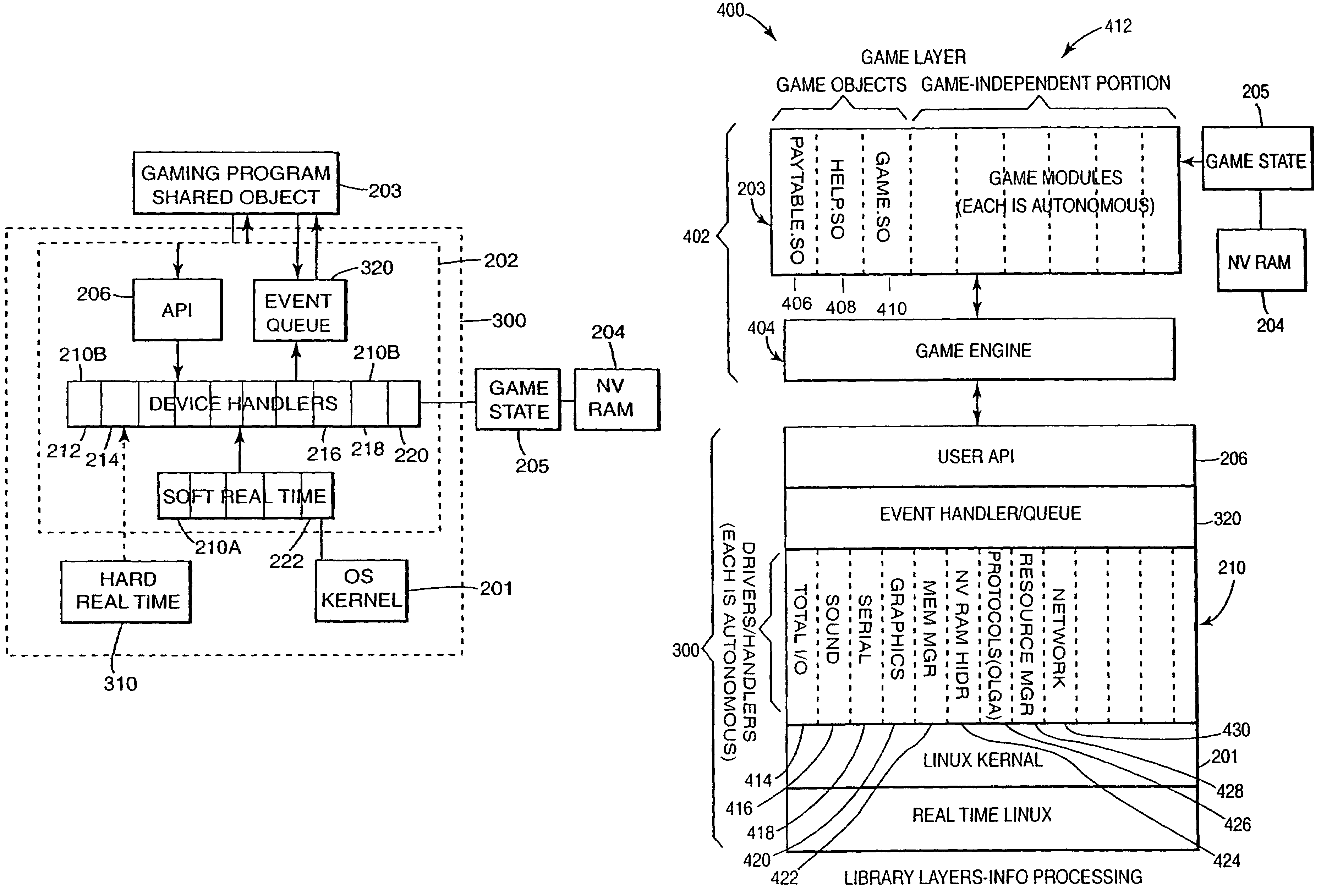
The present invention in various embodiments provides a computerized wagering game method and apparatus that features an operating system kernel, a system handler application that loads and executes gaming program shared objects and features nonvolatile storage that facilitates sharing of information between gaming program objects. The system handler of some embodiments further provides an API library of functions callable from the gaming program objects, and facilitates the use of callback functions on change of data stored in nonvolatile storage. The nonvolatile storage also provides a nonvolatile record of the state of the computerized wagering game, providing protection against loss of the game state due to power loss. The system handler application in various embodiments includes a plurality of device handlers, providing an interface to selected hardware and the ability to monitor hardware-related events.
Owner:IGT
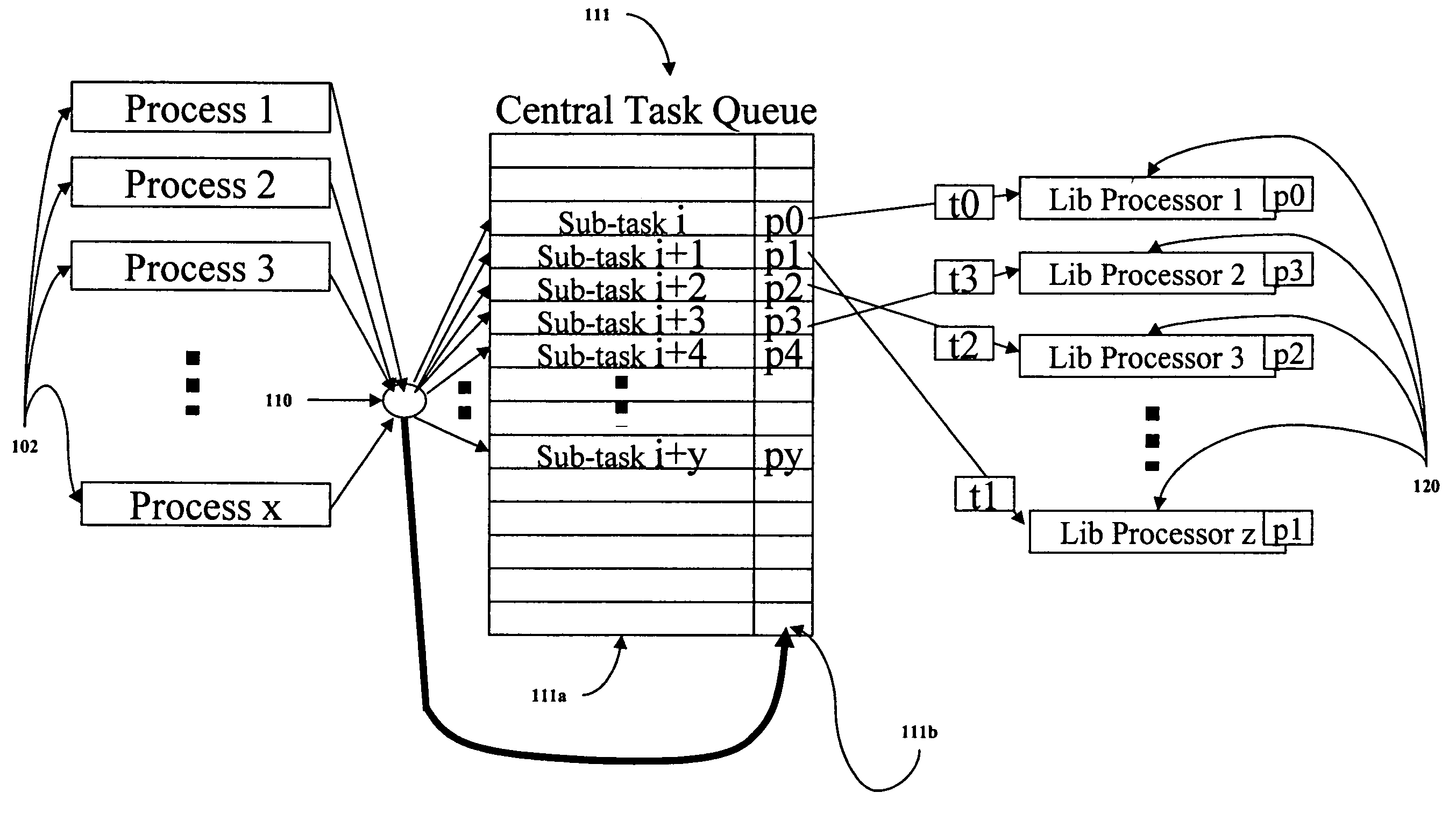
Operating system kernel-assisted, self-balanced, access-protected library framework in a run-to-completion multi-processor environment
A method for managing multiple processors in the execution of one or more processes in a task-based library platform. The one or more processes are partitioned into highly granulized sub-tasks from a library calling process, whereby each sub-task has a protection attribute associated with it. The protection attribute designates processing resources that a processor may use in the execution of the sub-task. The sub-tasks are placed in a central task queue, whereby idling processors in the multiple processor system obtain consecutive sub-tasks in the queue until all the processes have been executed. Each processor executes a sub-task using only those processing resources that have been designated as being available by the protection attribute of the sub-task. The atomic execution results of the one more sub-tasks may then be combined into an execution result for the process. Also provided is a task-based library for processor management.
Owner:TWITTER INC
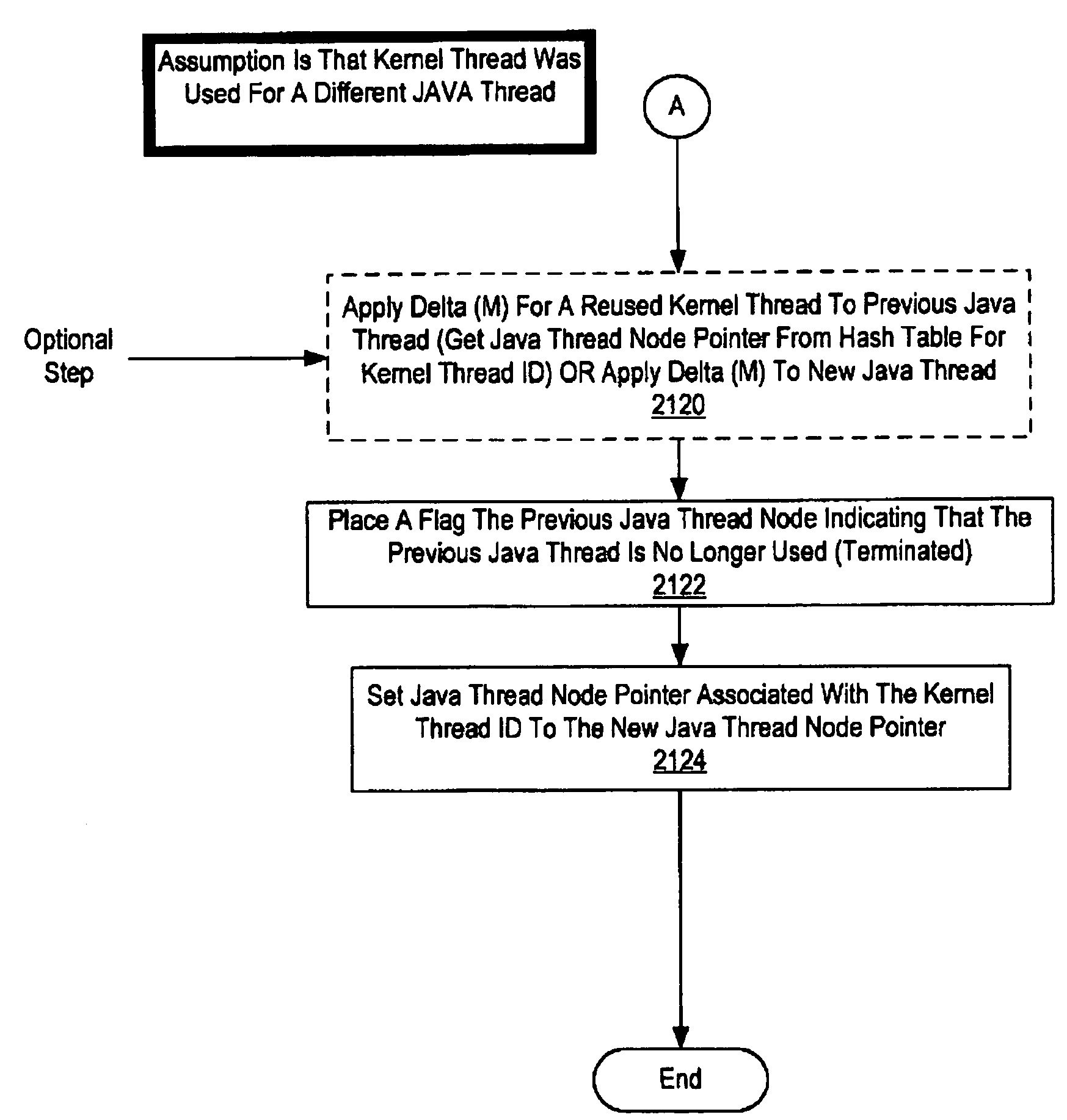
Method and system for tracing profiling information using per thread metric variables with reused kernel threads
InactiveUS7389497B1Error detection/correctionSpecific program execution arrangementsOperational systemOperating system
A method and system for tracing profiling information using per thread metric variables with reused kernel threads is disclosed. In one embodiment kernel thread level metrics are stored by the operating system kernel. A profiler request metric information for the operating system kernel in response to an event. After the kernel thread level metrics are read by the operating system for a profiler, their values are reset to zero by the operating system kernel. The profiler then applies the metric values to base metric values to appropriate Java threads that are stored in nodes in a tree structure base on the type of event and whether or not the kernel thread has been reused. In another embodiment non-zero values of thread level metrics are entered on a liked list. In response to a request from a profiler, the operating system kernel reads each kernel thread's entry in the linked list and zeros each entry. The profiler can then update the intermediate full tree snapshots of profiling information with the collection of non-zero metric variables.
Owner:IBM CORP
Secure file system server architecture and methods
InactiveUS20070050620A1Efficient collectionOperational safetyDigital data processing detailsAnalogue secracy/subscription systemsOperational systemFile system
A data server platform includes a security file system layer interposed between the platform operating system kernel and file system. The secure file system layer is structured to implement a file access control function that selectively constrains data transfer operations initiated through the operating system kernel by an application program to transfer file data through the file system with respect to a persistent data store. A file access controller, implemented independent of the operating system kernel, is coupled to the security file system layer and supports the file access control function by defining permitted file data transfers through the file system. Management of the file access controller separate from the data server platform ensures that any security breach of the platform operating system kernel cannot compromise the function of the security file system layer.
Owner:THALES ESECURITY INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com