Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
53 results about "Transparent computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Transparent computing is a computing paradigm in which services are shared. It is considered a form of persuasive computing.
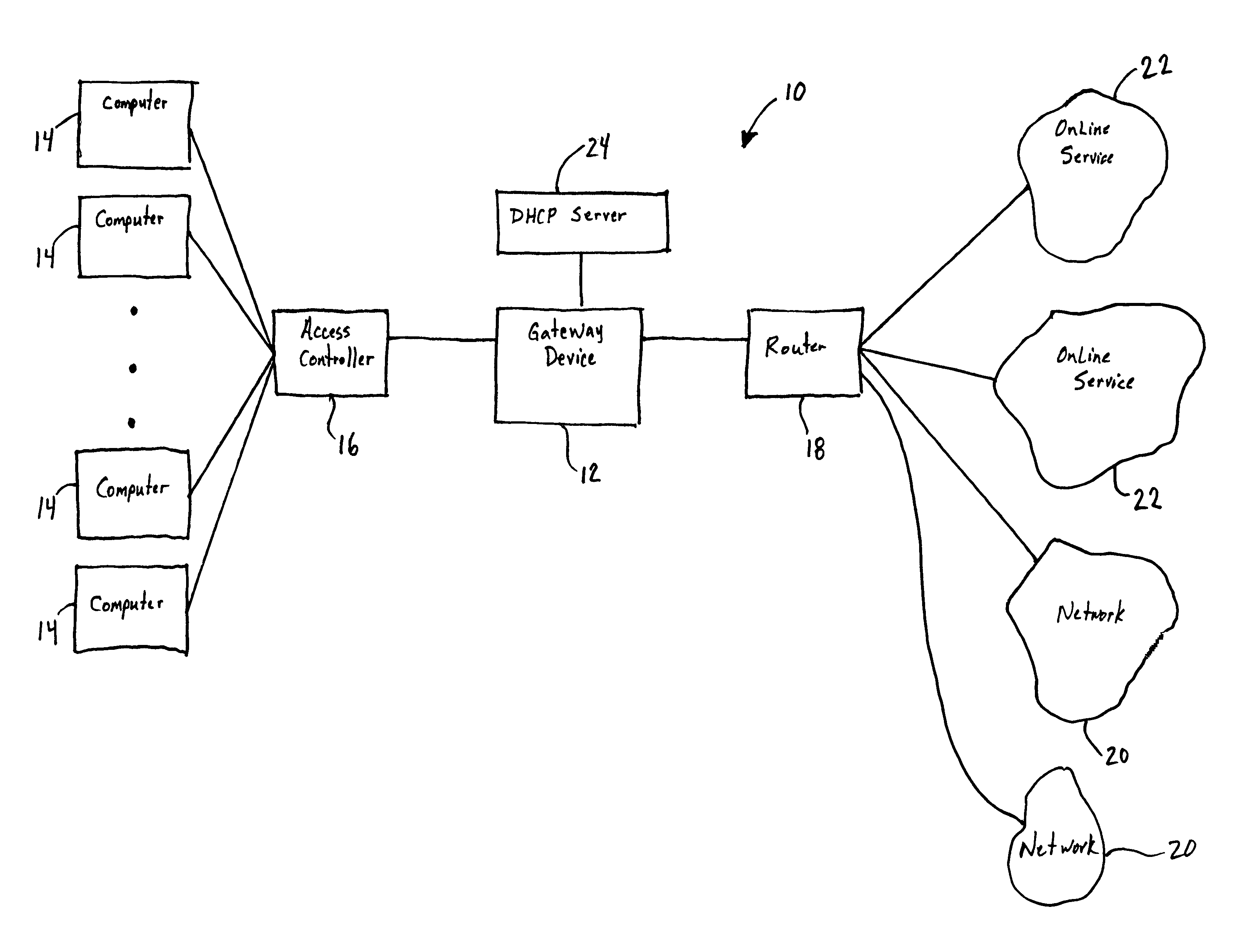
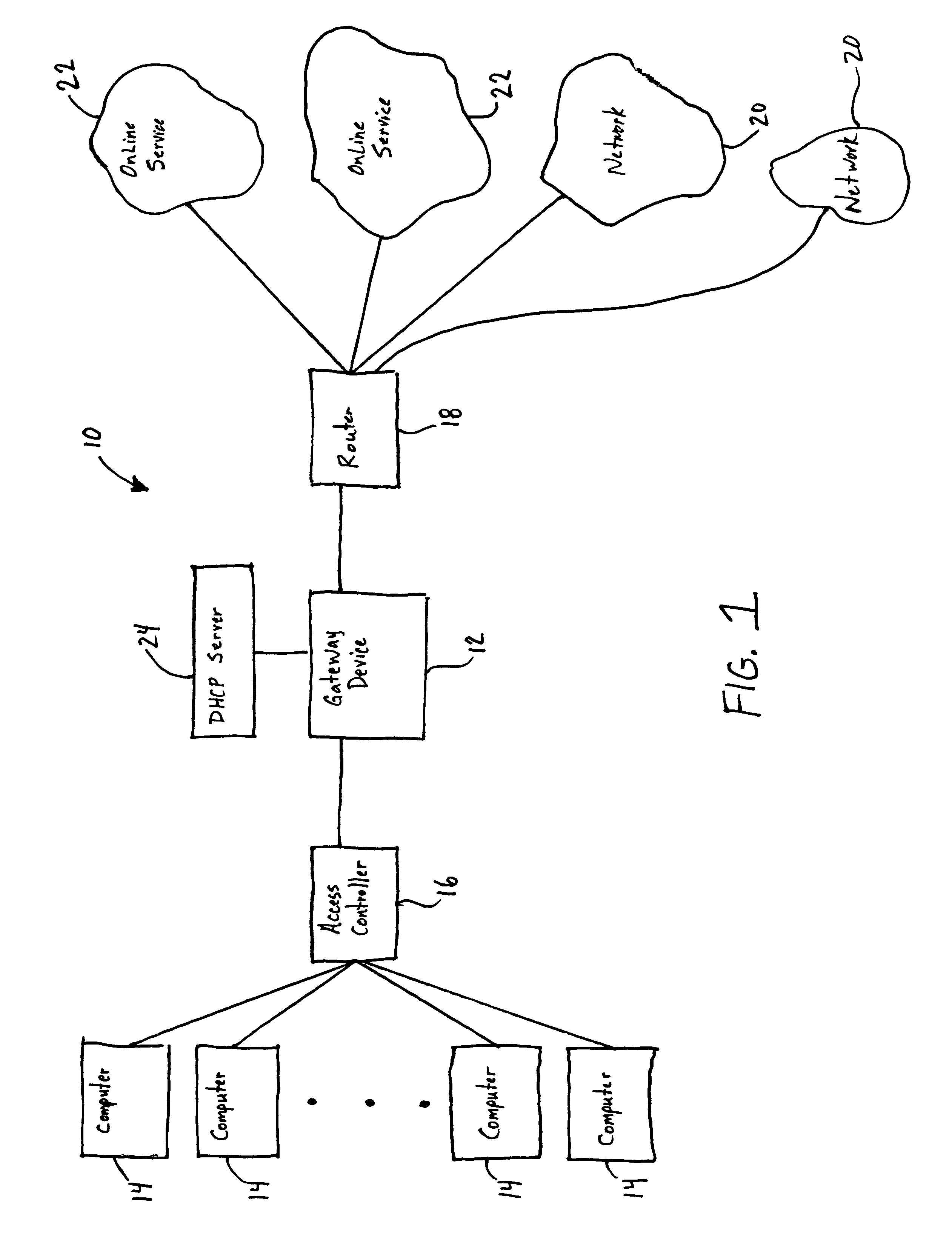
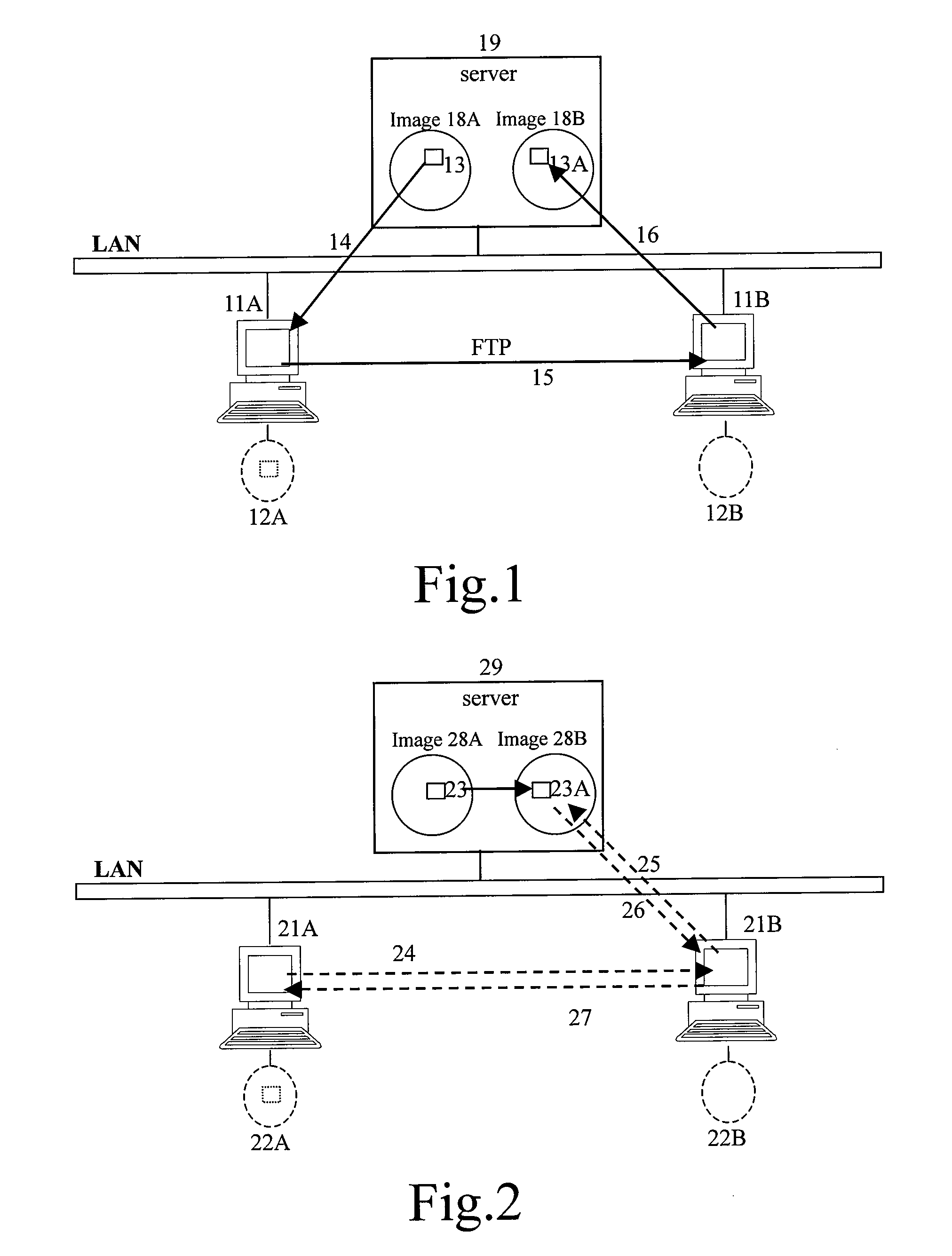
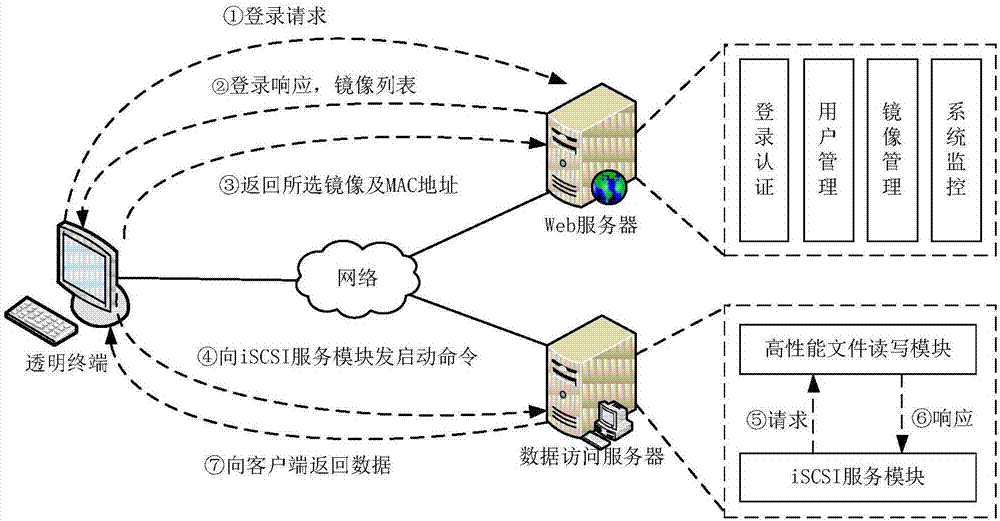
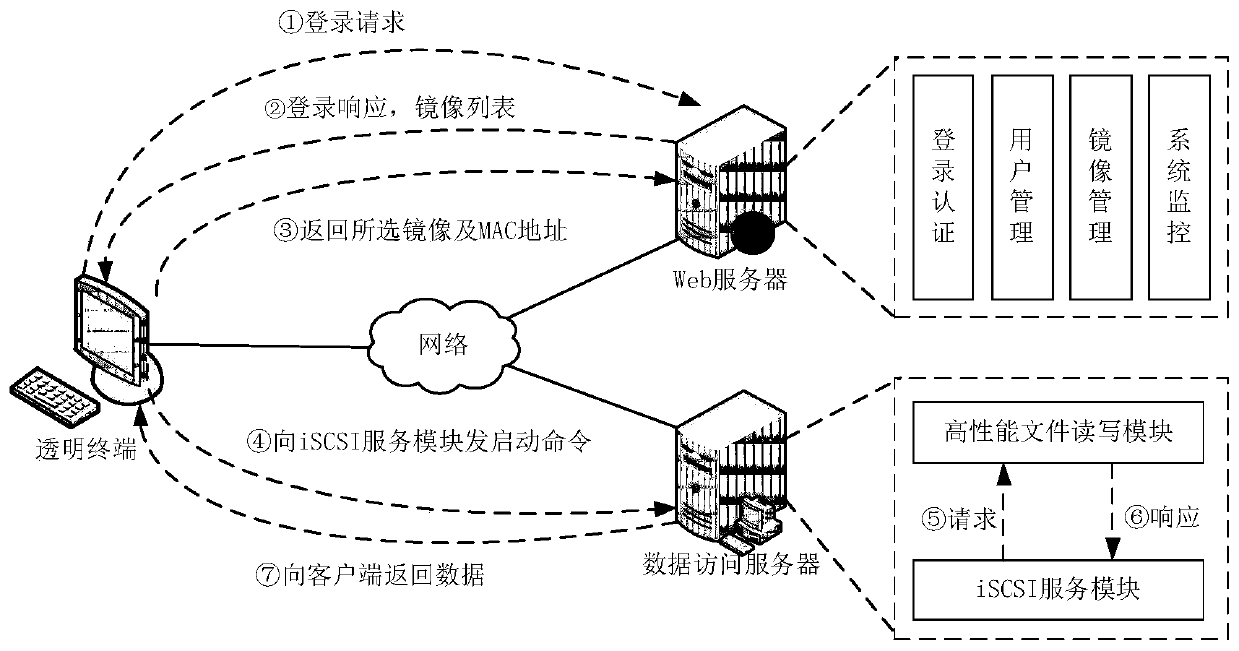
Systems and methods for authorizing, authenticating and accounting users having transparent computer access to a network using a gateway device
InactiveUS8713641B1Avoid accessDigital data processing detailsMultiple digital computer combinationsComputer networkTransparent computing
A system and method for authorizing, authenticating and accounting users having transparent access to a destination network, wherein the users otherwise have access to a home network through home network settings resident on the user's computers, and wherein the users can access the destination network without altering the home network settings and without installing software on the user's computer. The system includes a gateway device for receiving a request from a user for access to the destination network, and means for identifying an attribute associated with the user based upon a packet received by the gateway device, wherein the packet is transmitted from the user's computer, and wherein the user's computer is configured for accessing the home network.
Owner:NOMADIX INC
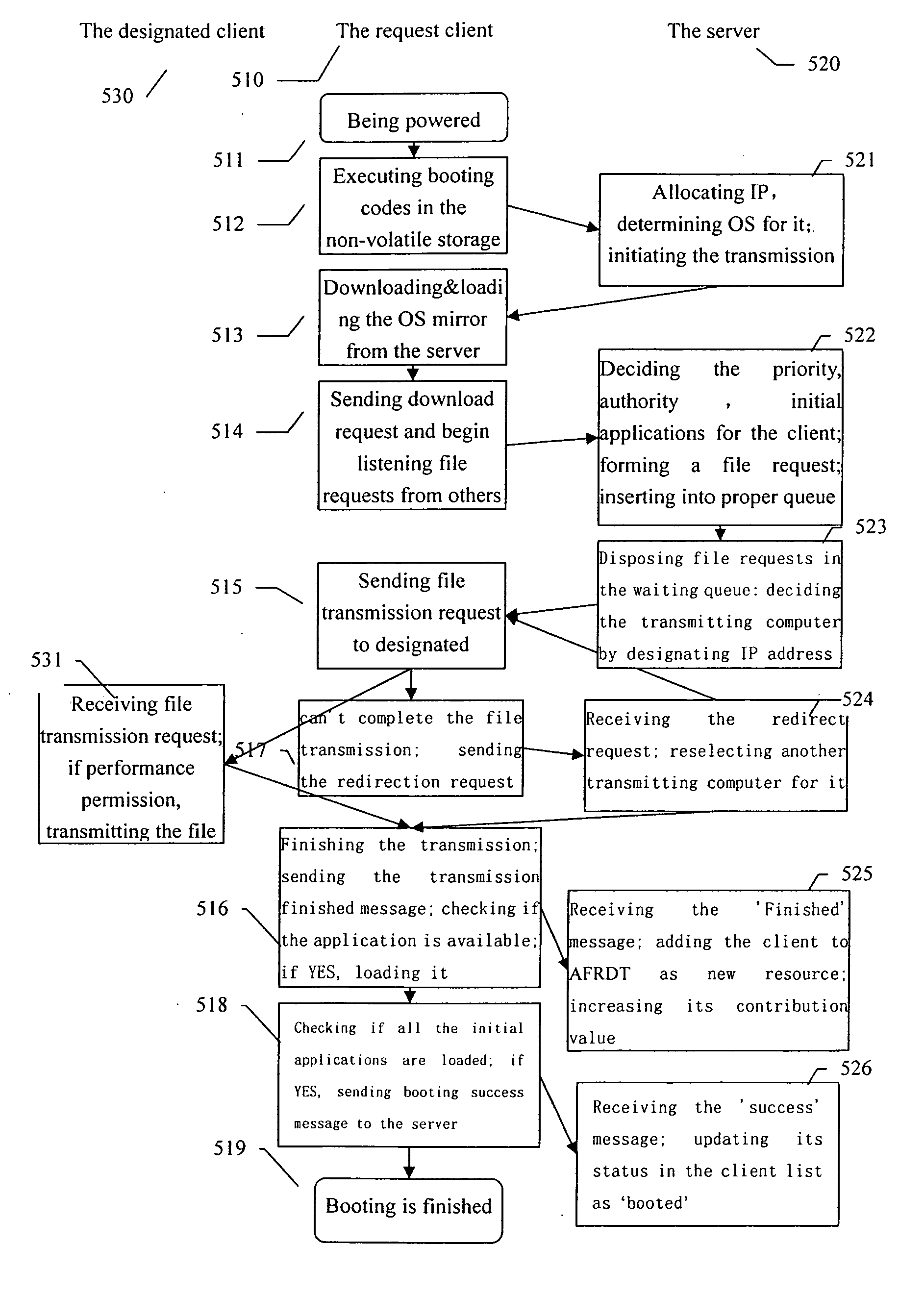
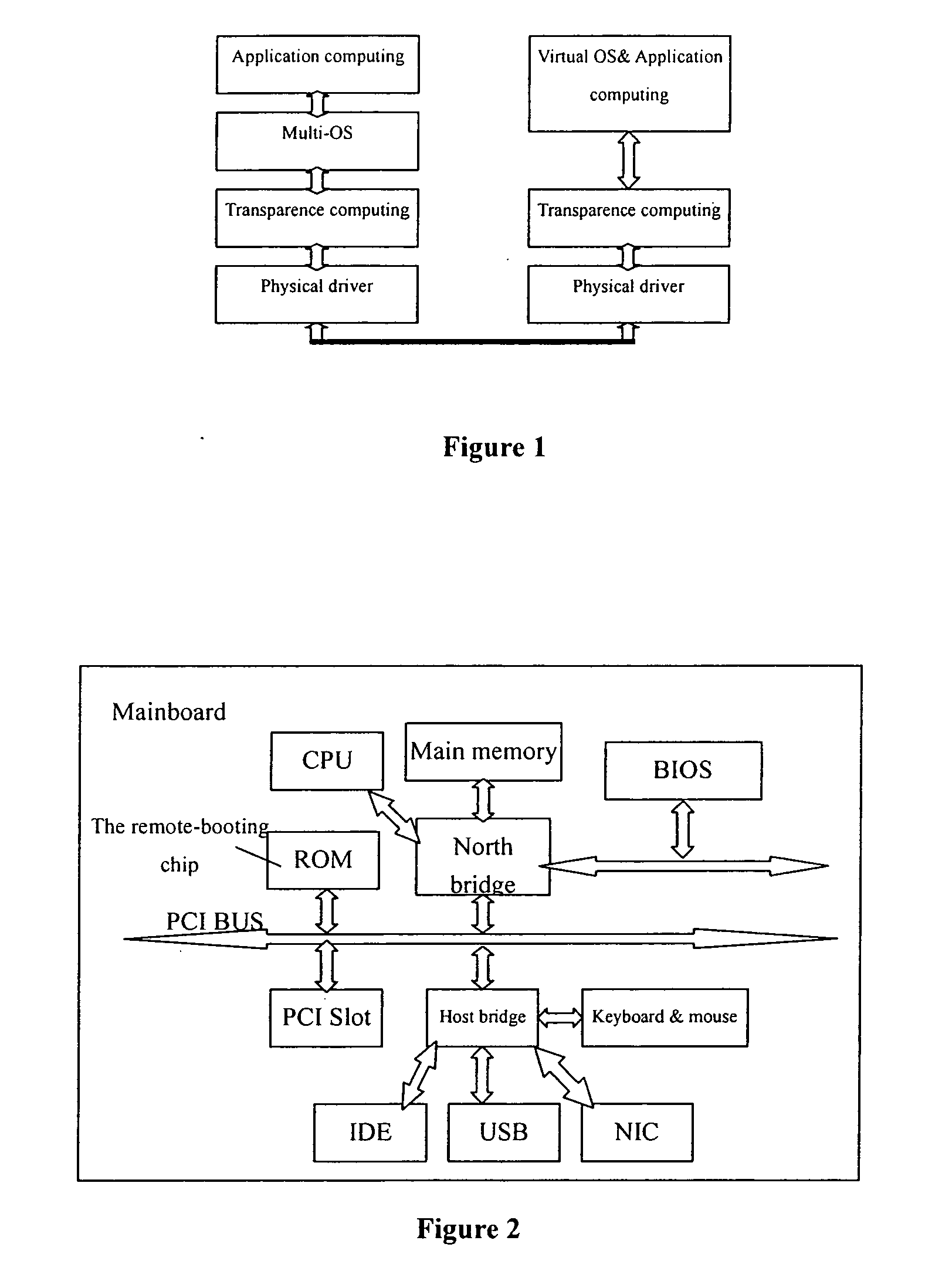
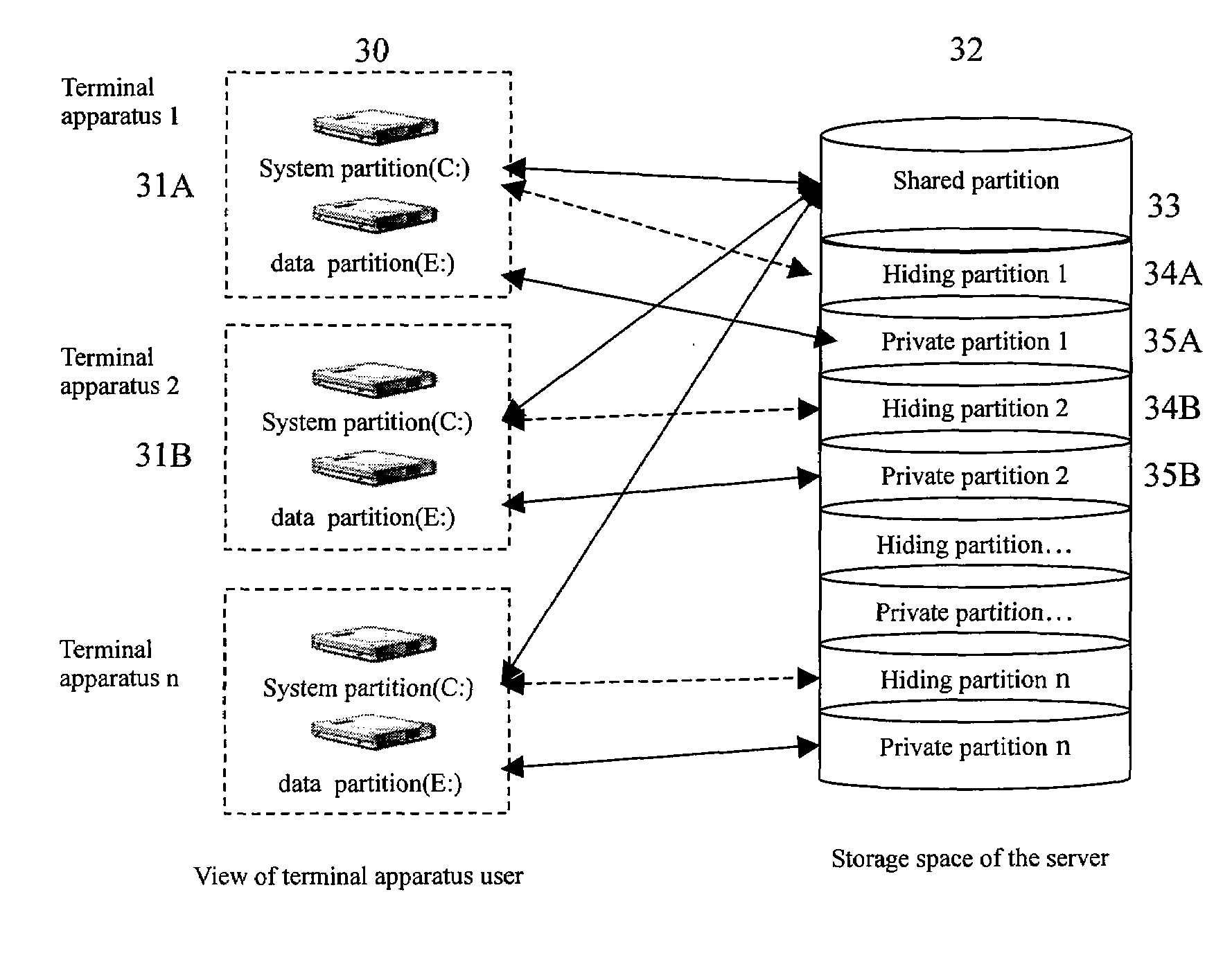
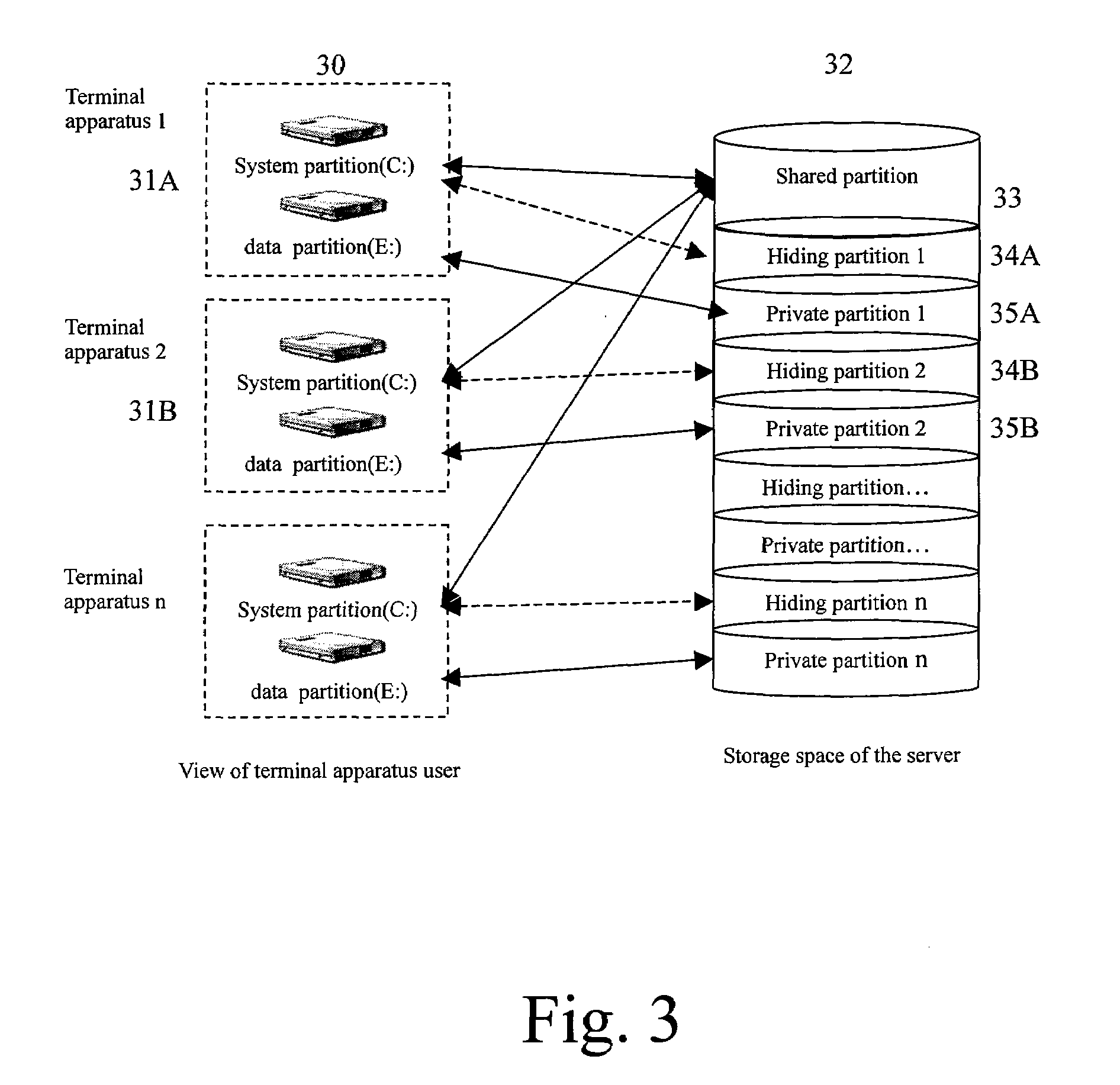
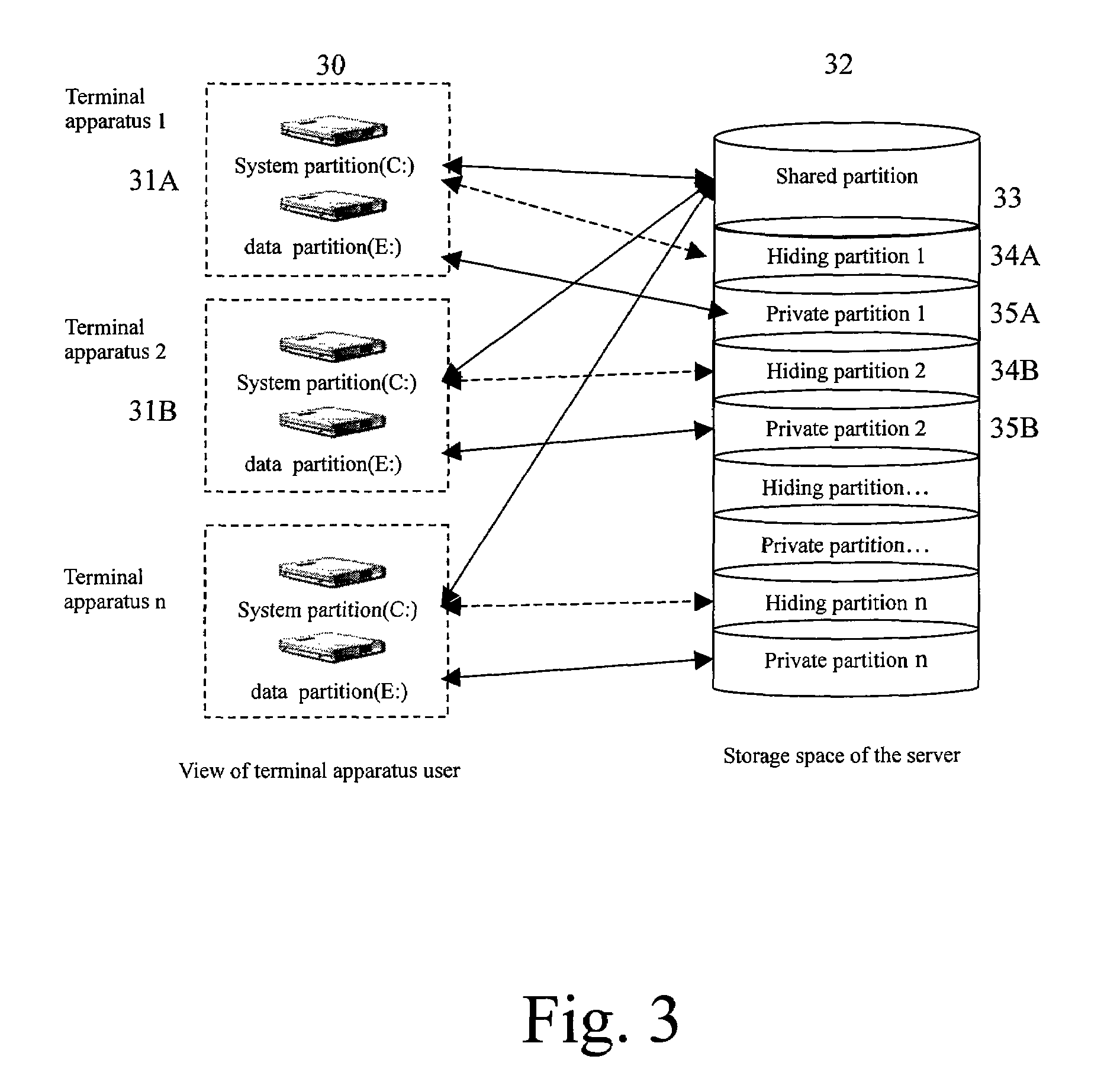
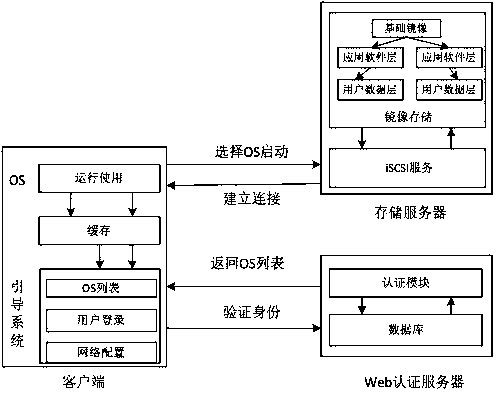
Method and computing system for transparence computing on the computer network
ActiveUS20060117172A1Improve performanceImprove availabilityDigital computer detailsData resettingOperational systemTransparent computing
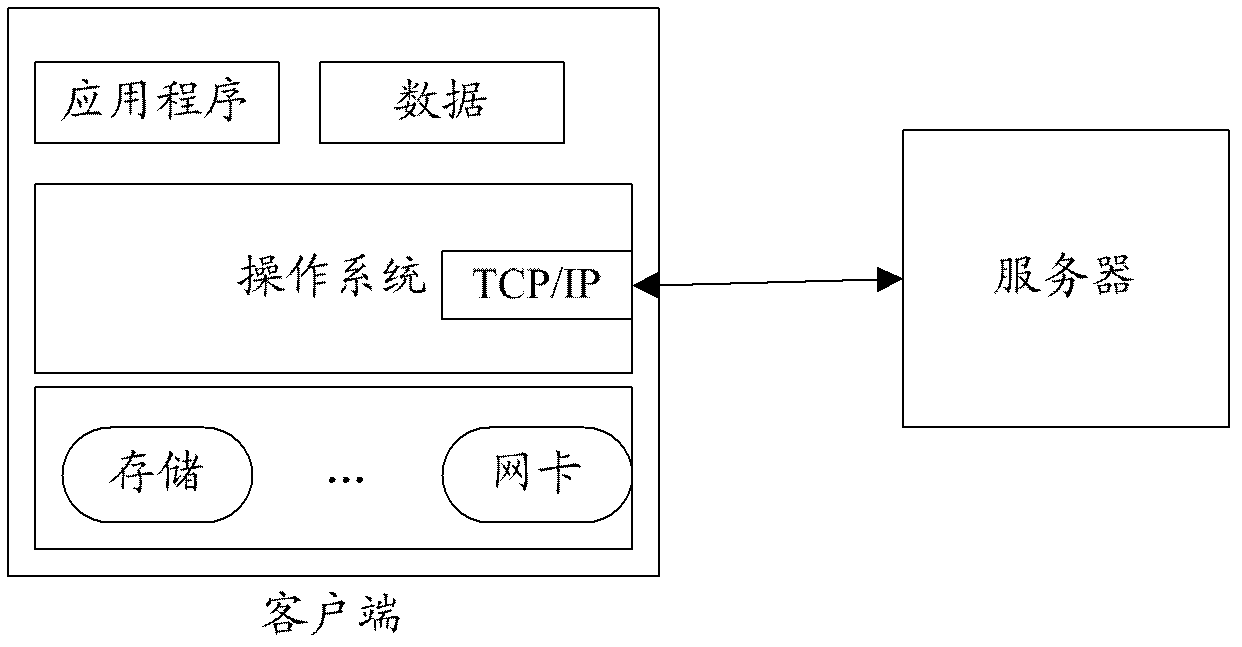
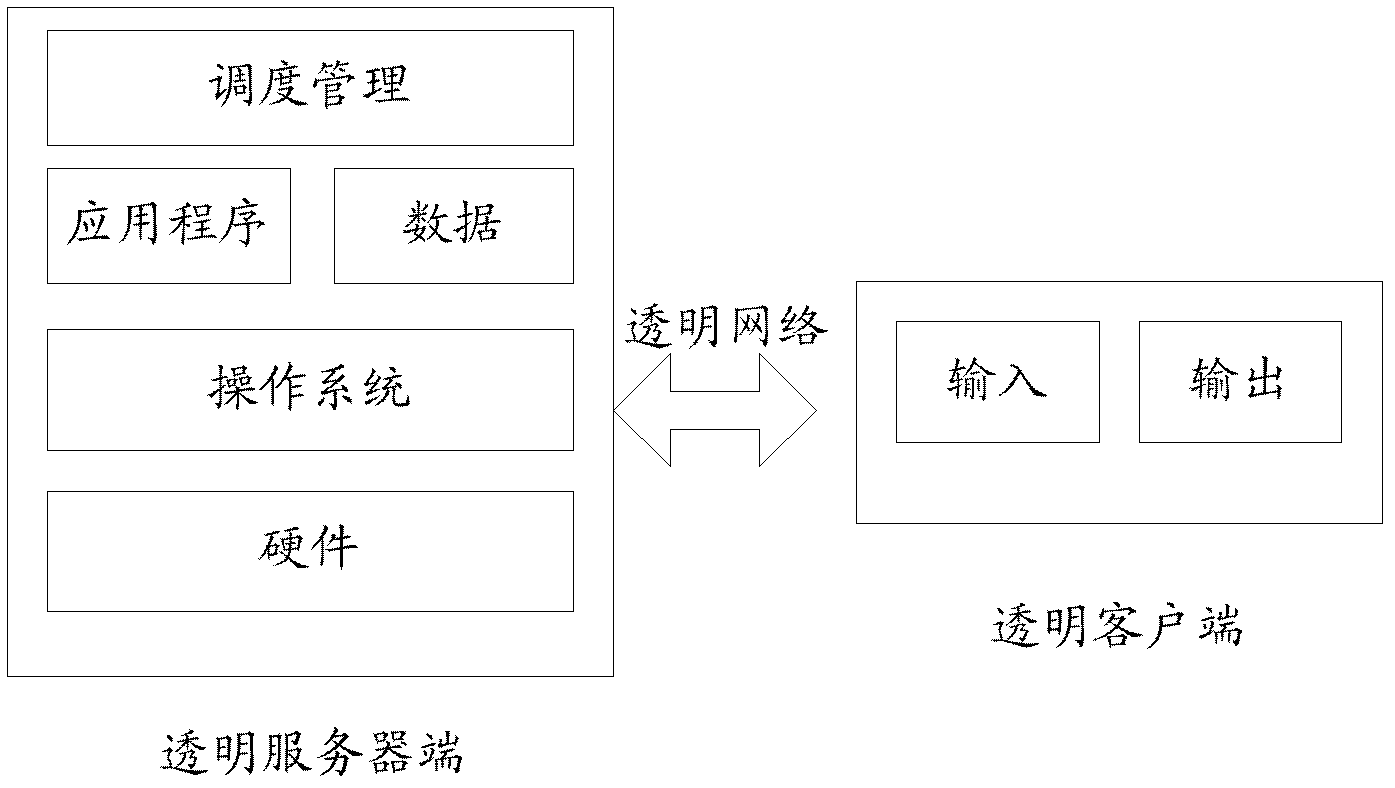
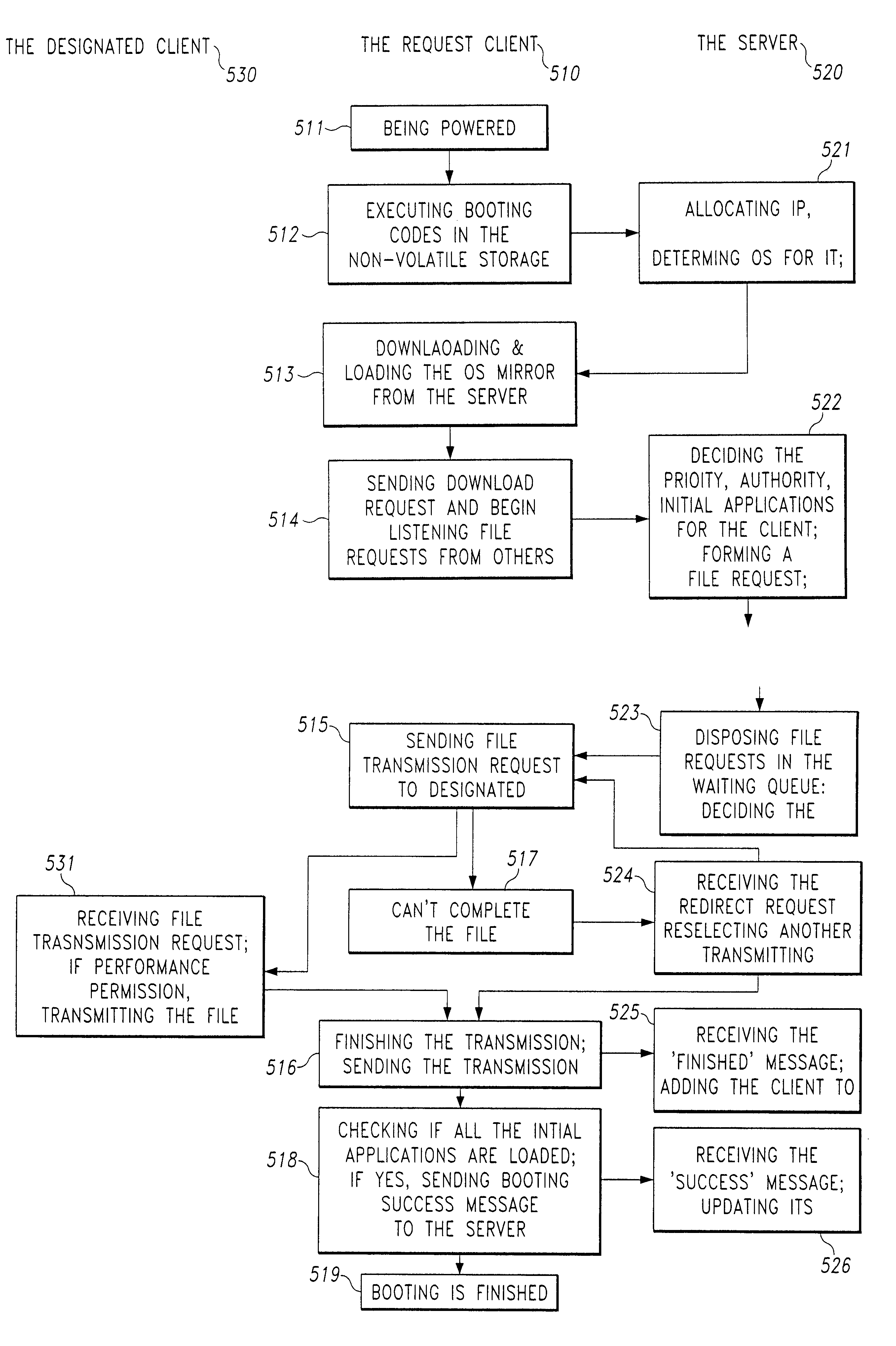
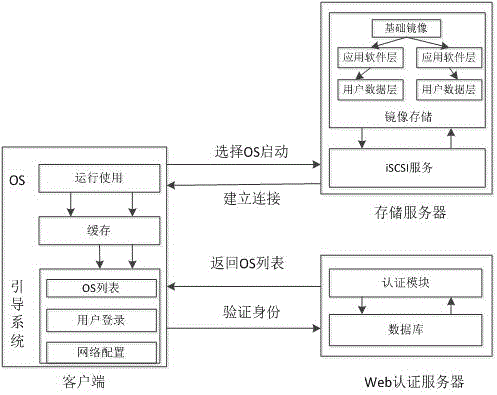
A computing system based on Transparence Computing consists of clients and a server. There is no disk and no preinstalled OS on the client; a remote booting chip is set on the client's mainboard for downloading and loading the OS. Boot-supporting services, OS kernel mirrors, and applications are preset on the server; After being powered, the client broadcasts the boot request to the network and the server allocates network parameters for it. The client downloads an OS-selecting script from the server. After the user selects the needed OS, the client downloads and loads the selected OS from the server. Hence, the client fulfills the user's computing requirements just as a normal PC. The computing work is implemented on the client-side, during which the client can acquire corresponding resources such as applications, data, and documents from the server on demand. The client can be provided with private storage across the network by presetting a service in the mirror for creating virtual disks on the server, and thus data generated during or after the computing can be persistently stored on the server's storage.
Owner:TSINGHUA UNIV
Transparent computing method and transparent computing system based on virtualization technology
ActiveCN104166586AMeeting Mobility NeedsShort startup timeTransmissionSoftware simulation/interpretation/emulationVirtualizationOperational system
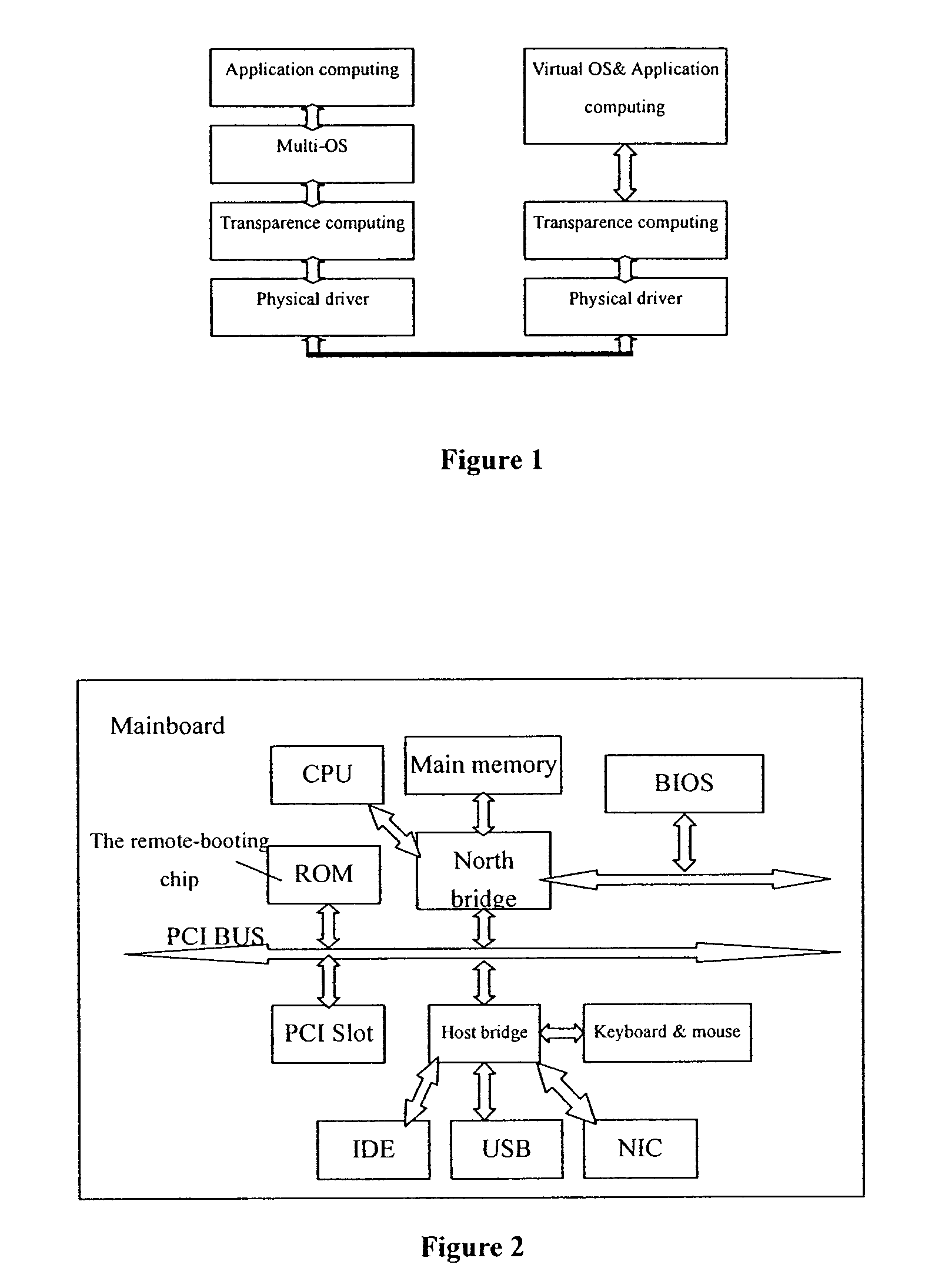
The invention discloses a transparent computing method and transparent computing system based on the virtualization technology. Through the virtualization technology, physical differences between different hardware platforms of a client are shielded, wide support for different hardware devices is provided, the mobility requirement of a user is met, application service support across terminal devices and operating systems is provided for the user, and the user does not need to worry about management of computer hardware devices and systems. The scheme is achieved in the transparent computing system based on a wide area network, a request is started by the client in the transparent computing system, legality of the request is confirmed through a management client and a transparent main server of a software resource server, connection of resources is given, instance operating systems stored in the transparent software resource server are loaded remotely and run, needed service is acquired, and the task requirement of the user is completed. The transparent computing method and transparent computing system based on the virtualization technology can adapt to different hardware platforms and operating system platforms, can be started on the wide area network faster, and is higher in safety performance and practicability.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
Method for remotely starting transparent computing system client through wireless local area network
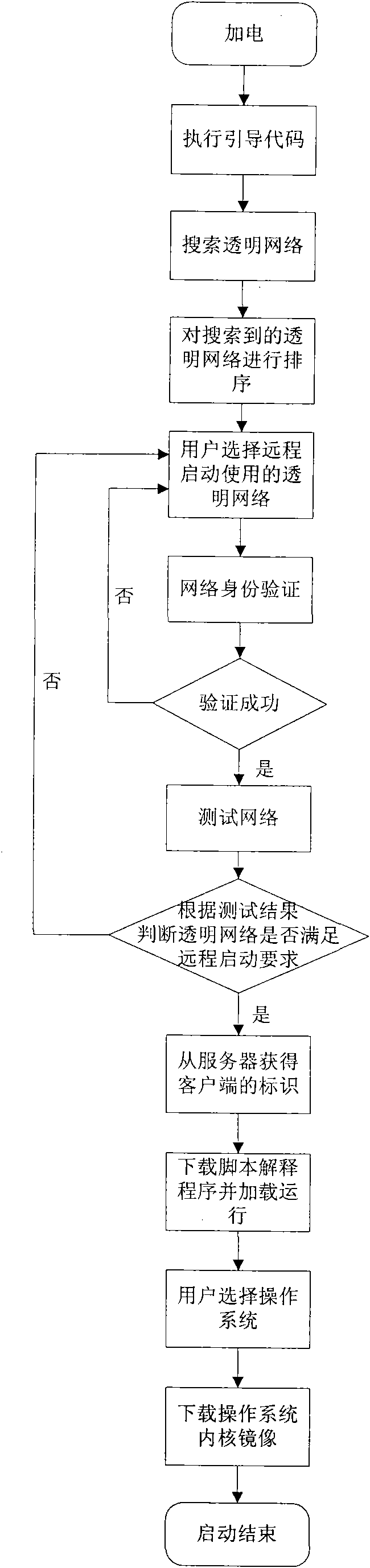
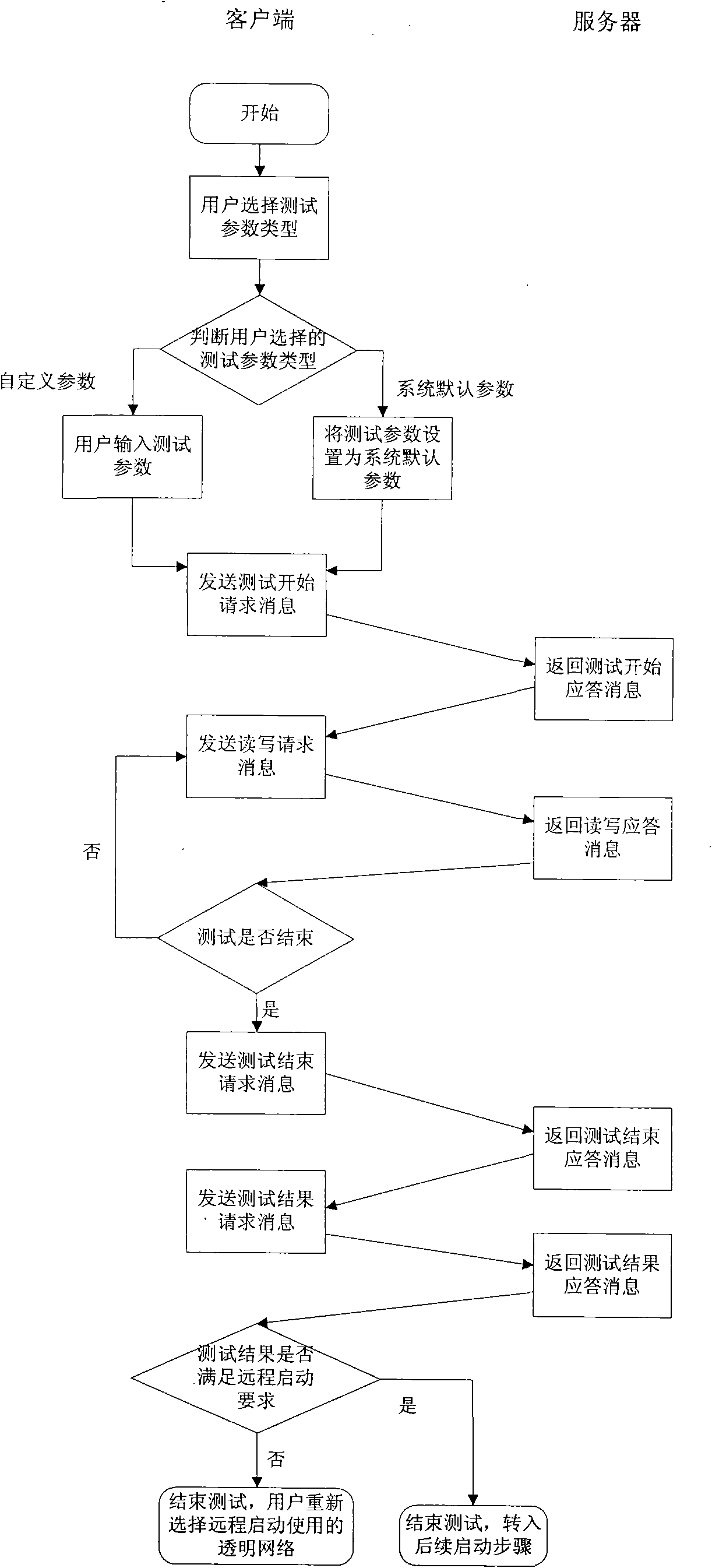
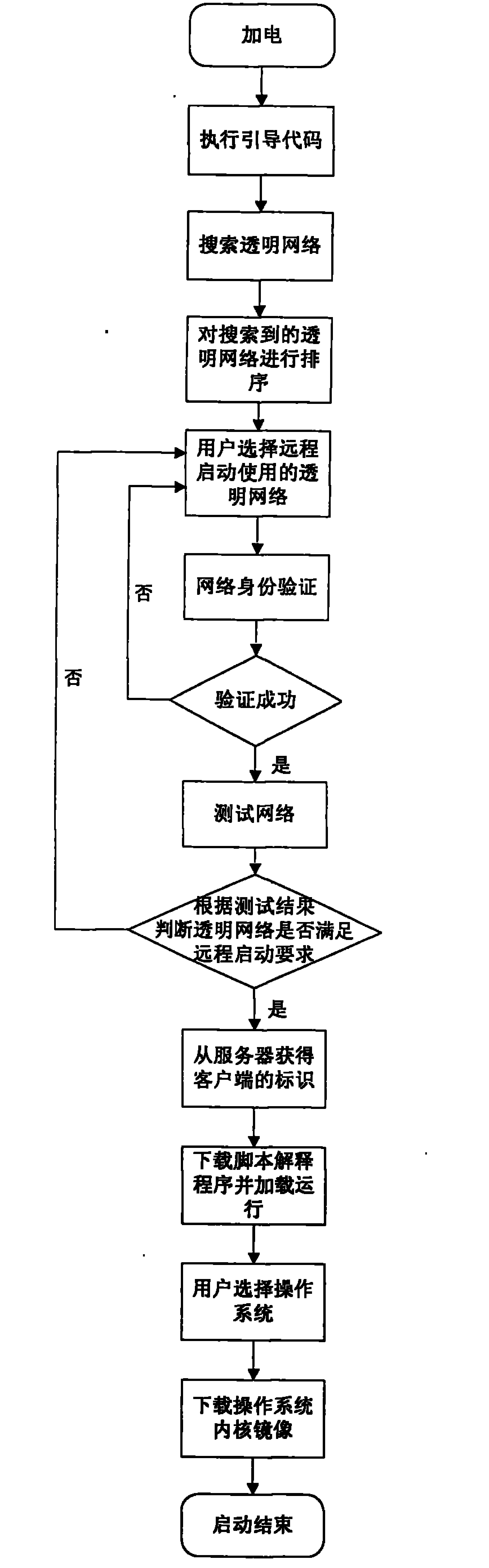
The invention relates to a method for remotely starting a transparent computing system client through a wireless local area network, which belongs to the technical field of computing systems. The method comprises that: the client executes a guide code in a guide chip and searches for transparent networks in a current region according to a preset searching period; the client sequences the searched transparent networks and displays a transparent network list obtained by the sequencing to a user; the user selects to remotely start a used transparent network, and the client performs network authentication on the transparent network selected by the user and tests the transparent network which is selected by the user and passes the authentication; a starting code of the guide chip acquires an identifier of the client from a server; and the user selects an operating system to be loaded. The method has the advantage of solving the problems that the transparent networks and non-transparent networks cannot be distinguished under the wireless network by the conventional methods for remotely starting the transparent computing system, that potential safety hazard exists in network access, that the network authentication cannot be performed, that network stability cannot be detected, and the like.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
Transparent computing system
InactiveCN102664958ASimplify hardware and software designLow hardware requirementsTransmissionOperational systemInformation resource
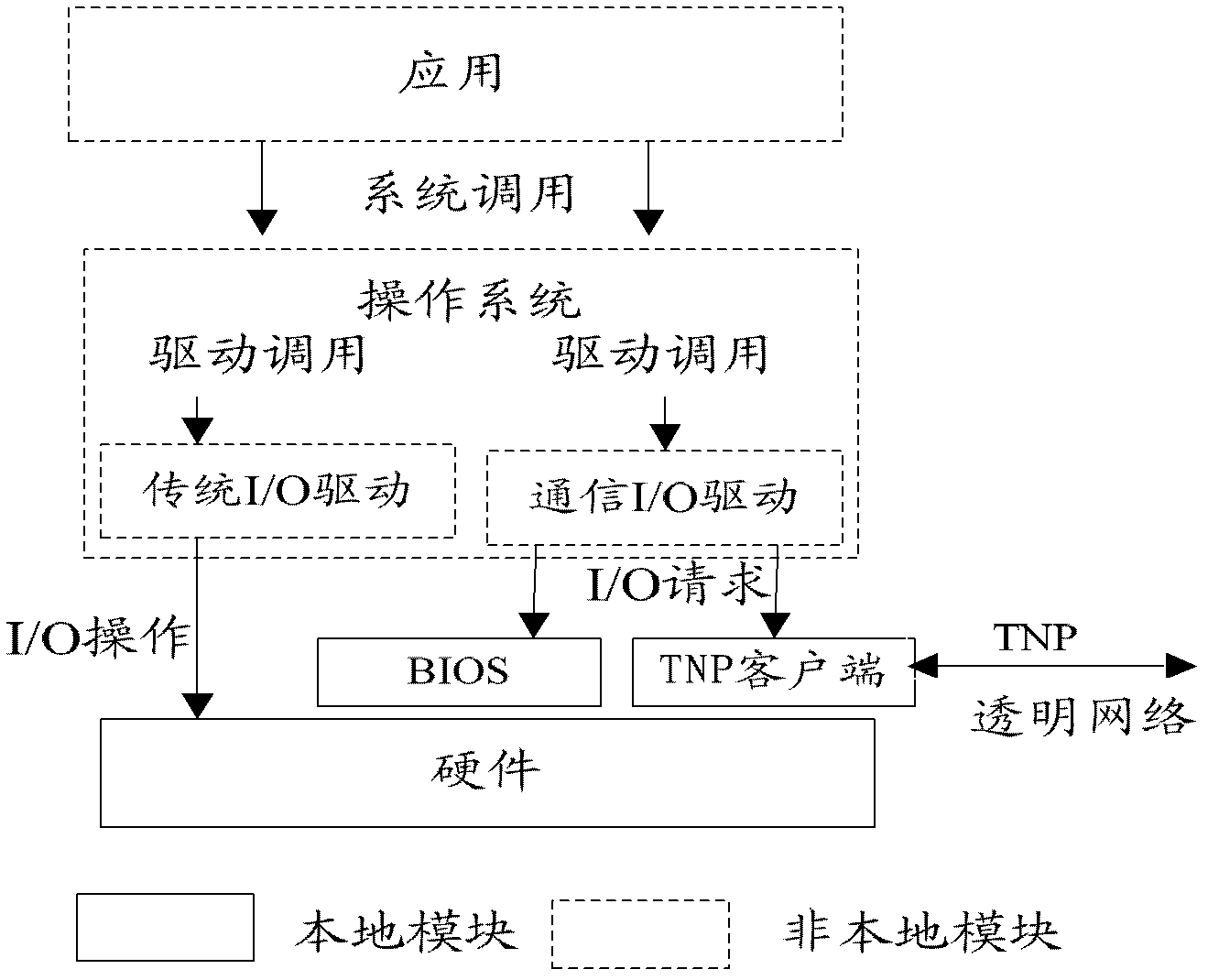
The embodiment of the invention discloses a transparent computing system, which comprises a transparent client, a transparent server and a transparent network. The transparent client comprises a hardware module, a basic input output system (BIOS), a transparent network protocol (TNP) client module, an operating system and an application program, wherein the hardware module, the BIOS and the TNP client module are fixedly arranged on the transparent client; the transparent client stores various software and information resources required by a user, and executes task scheduling, resource allocation and data transmission and management; the transparent client realizes communication connection with the transparent server through the transparent network, dynamically downloads the operating system from the transparent server, and loads the operating system; the loaded operating system interacts with the hardware of the transparent client in driving and calling way; and the application program obtains service provided by the operating system in a system calling way. The transparent computing system is high in network independence and reliable in internetworking; and the software and hardware design of the transparent client is simplified, hardware requirements are low, and cost is saved.
Owner:SUN YAT SEN UNIV
Method and computing system for transparence computing on the computer network
ActiveUS7467293B2Improve performanceImprove availabilityDigital computer detailsData resettingOperational systemTransparent computing
A computing system based on Transparence Computing consists of clients and a server. There is no disk and no preinstalled OS on the client; a remote booting chip is set on the client's mainboard for downloading and loading the OS. Boot-supporting services, OS kernel mirrors, and applications are preset on the server; After being powered, the client broadcasts the boot request to the network and the server allocates network parameters for it. The client downloads an OS-selecting script from the server. After the user selects the needed OS, the client downloads and loads the selected OS from the server. Hence, the client fulfills the user's computing requirements just as a normal PC. The computing work is implemented on the client-side, during which the client can acquire corresponding resources such as applications, data, and documents from the server on demand. The client can be provided with private storage across the network by presetting a service in the mirror for creating virtual disks on the server, and thus data generated during or after the computing can be persistently stored on the server's storage.
Owner:TSINGHUA UNIV
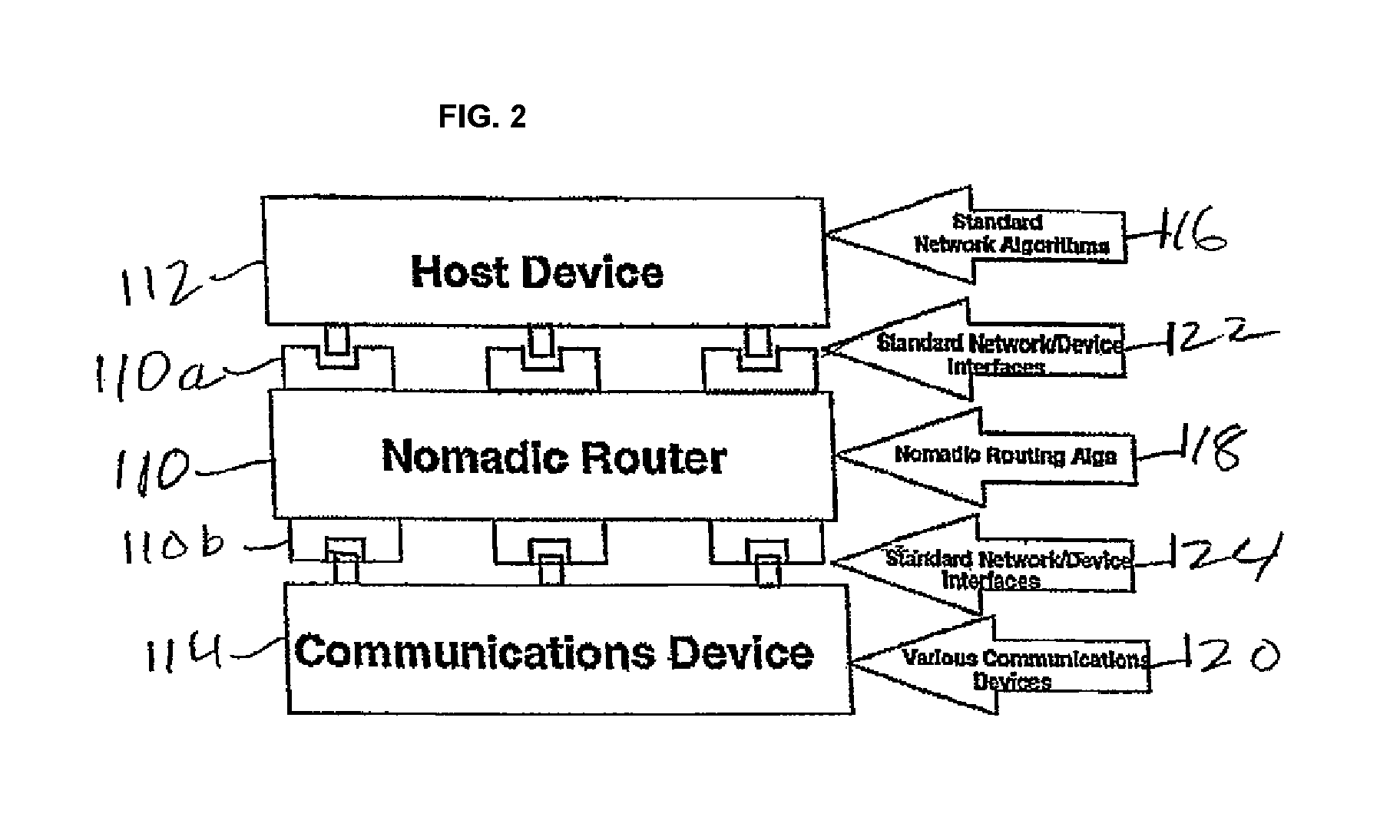
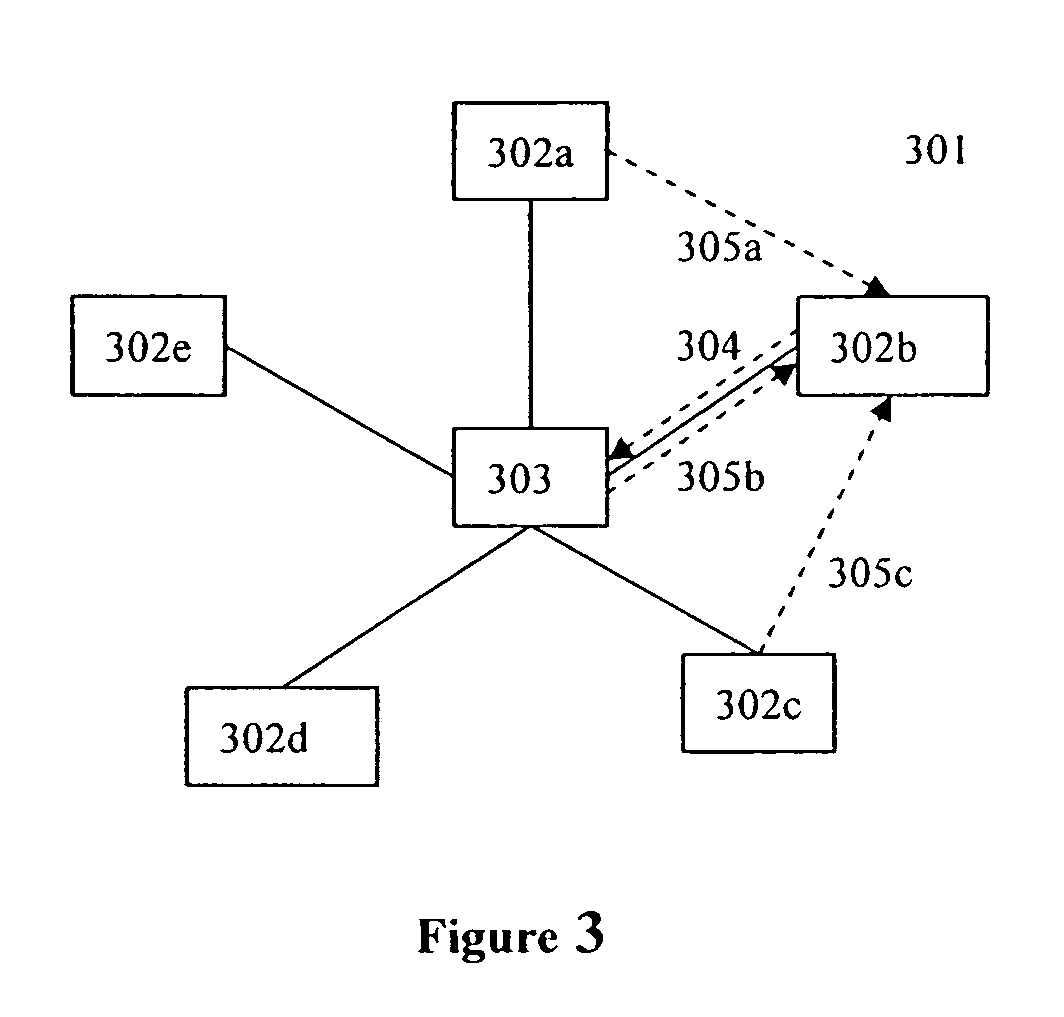
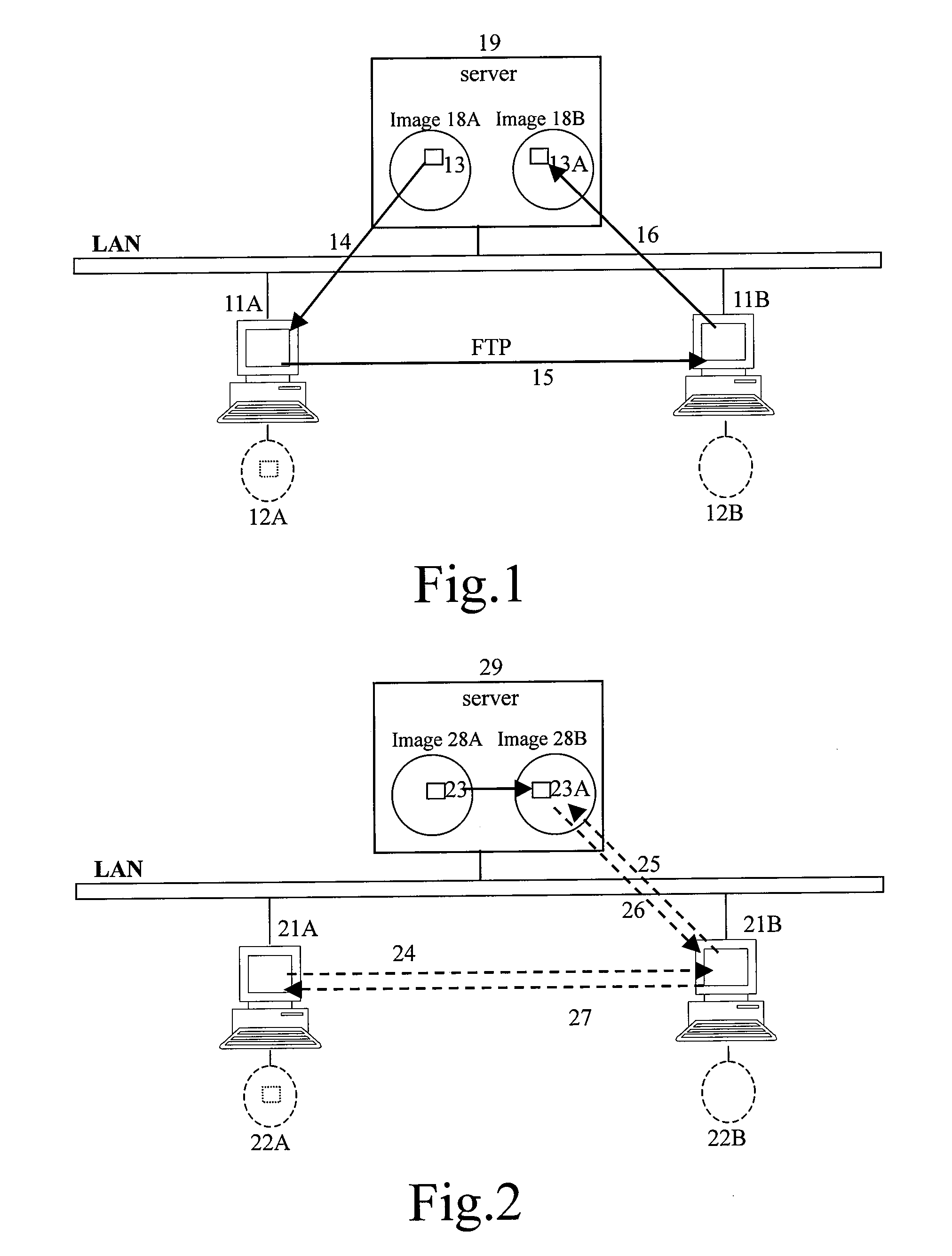
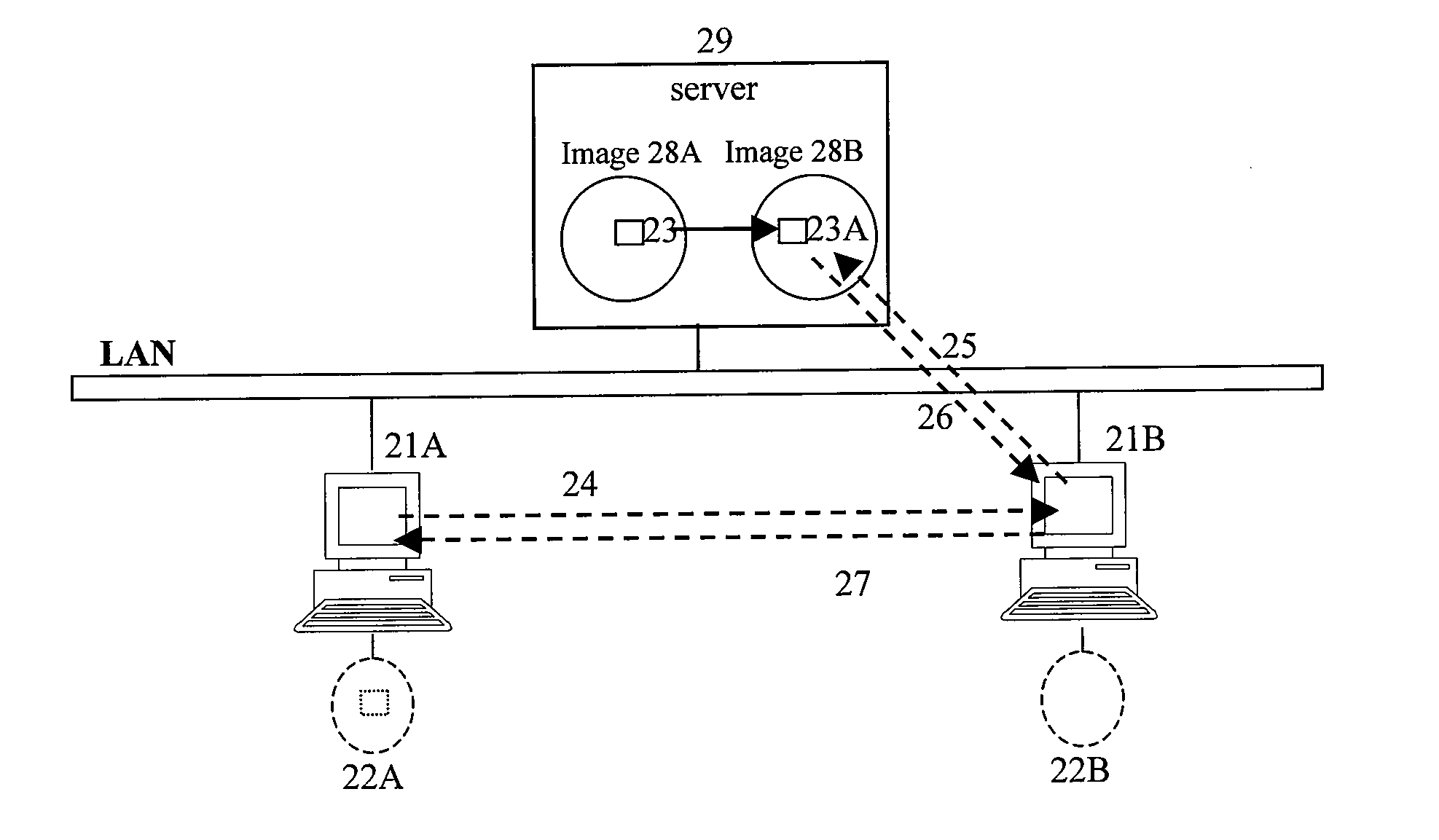
Method for transferring data between terminal apparatuses in a transparent computation system
ActiveUS20070271239A1Improve data transfer efficiencyImprove performanceDigital data information retrievalDigital computer detailsComputer hardwareTransparent computing
A method for transferring data between terminal apparatuses in a network at least comprising a server, a first terminal apparatus and a second terminal apparatus, wherein the server has a storage device at least comprising a first and a second disk images; the method comprising: generating a message of data transfer request based on the information on the data to be transferred; transferring the generated message to the second terminal apparatus; receiving the message and transferring the message to the server if the requested data transfer is allowed; and transferring date between the first disk image and the second disk image, in response to the reception of the message.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
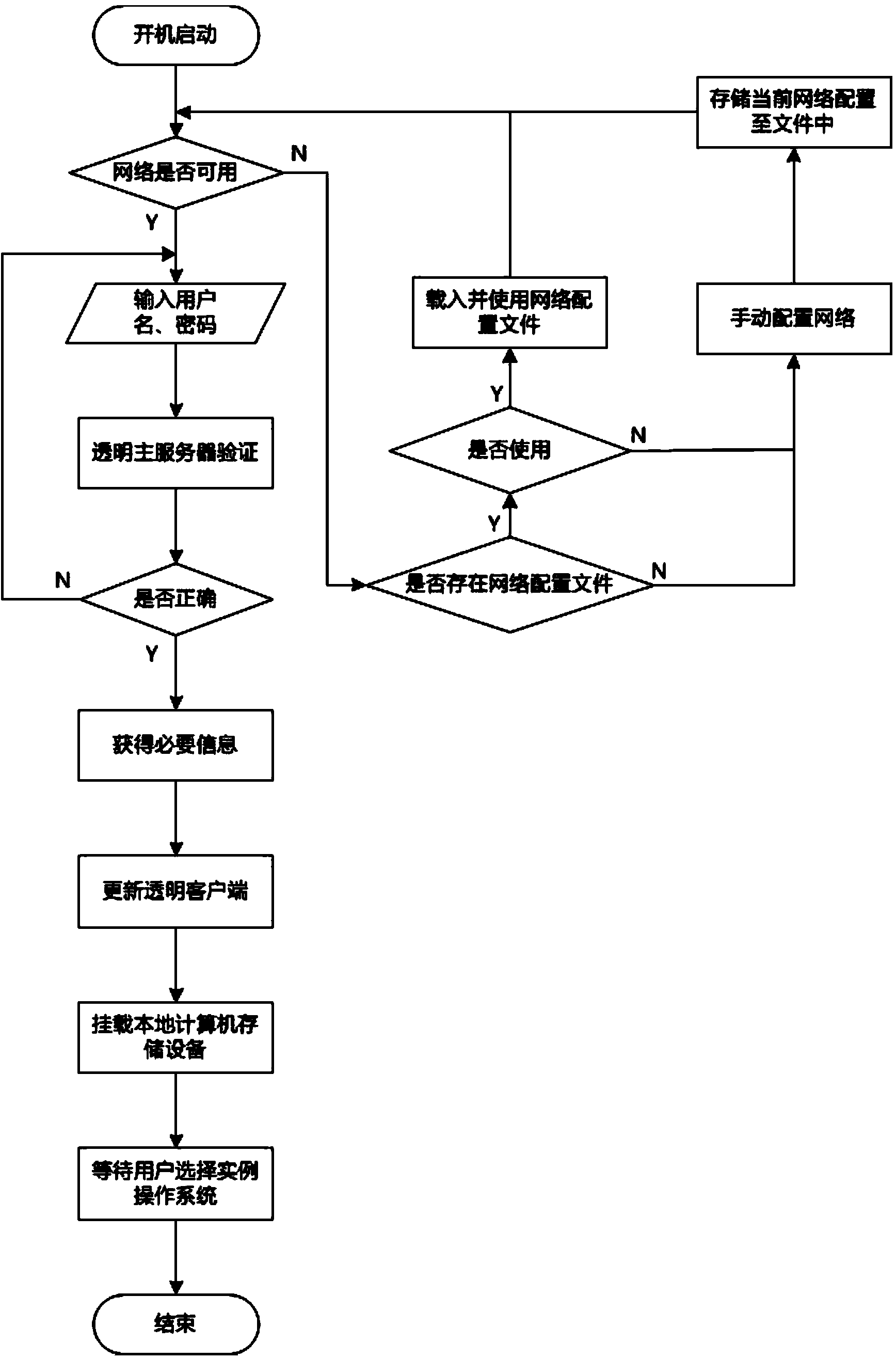
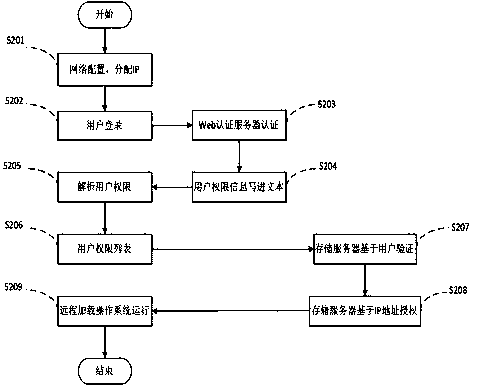
User identity authentication method suitable for transparent computing system and system configuration method
ActiveCN106549976AImprove safety and reliabilityImprove experienceTransmissionPasswordTransparent computing
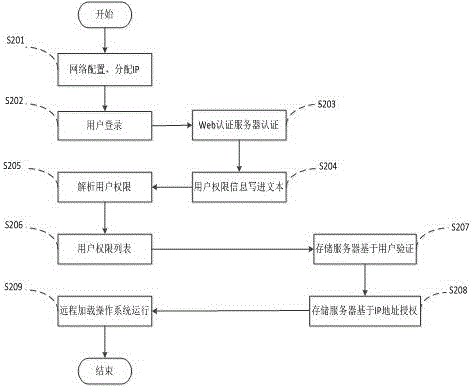
The invention discloses a user identity authentication method suitable for a transparent computing system and a system configuration method. The user identity authentication method comprises: when a user boots up and logs in, a client transmits a login requesting information to an authentication server, and the authentication server queries a background database, acquires an operating system authority list bootable by the user and transmits the list to the client; the user selects the operating system and invokes a remote loading request to a storage server; and the storage server authenticates a user name and passwords of the client, checks a mirror image configuration file of the operating system of the user after the authentication passes, and judges whether the authentication succeeds according to the IP of the client and mirror image IP settings of an operating system to be booted up. The system configuration method is used for configuring the transparent computing system using the user identity authentication method. According to the user identity authentication method suitable for the transparent computing system and the system configuration method, which are provided by the invention, the authority management of the user is achieved, a plurality of individual services can be provided, and the user experience is perfected.
Owner:CENT SOUTH UNIV
Method and system for starting intelligent terminal based on transparent computing and intelligent self-service system
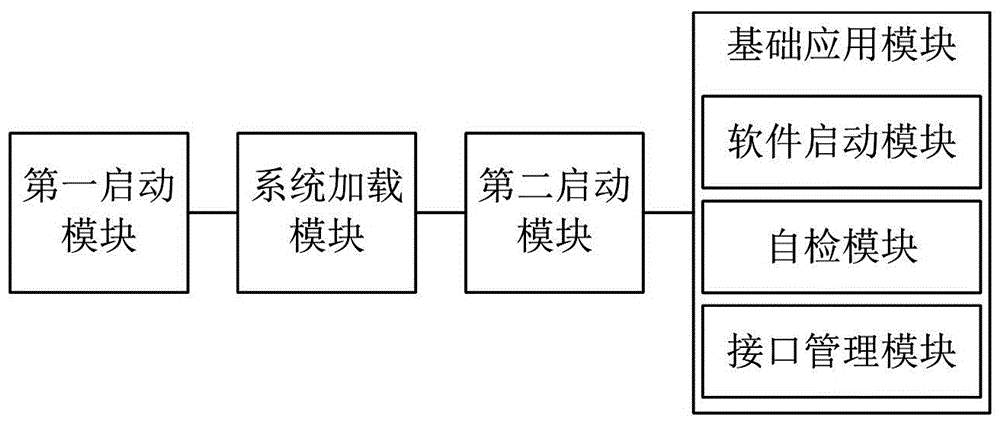
ActiveCN106250139AImprove start-up efficiencyEasy maintenanceSpecific program execution arrangementsTransparent computingApplication software
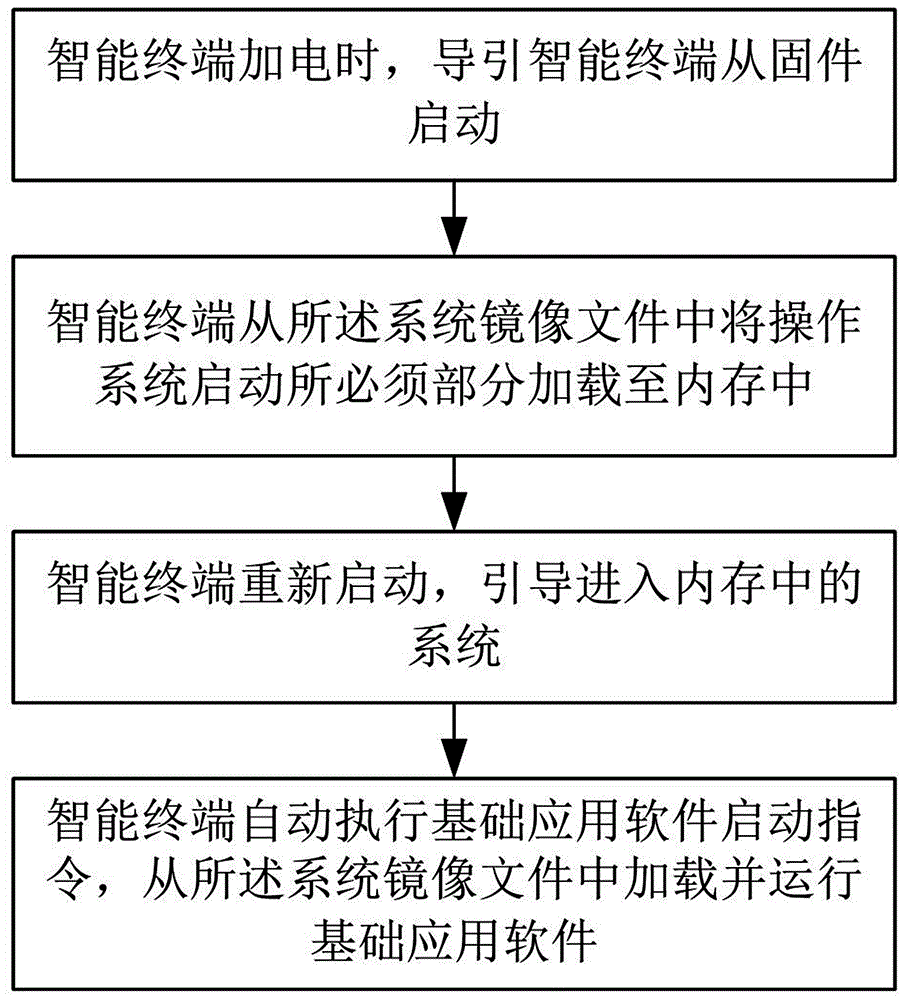
The present invention discloses a method for starting an intelligent terminal based on transparent computing, which makes various types of intelligent terminals correspond to the same system image file. The starting steps of the intelligent terminal include: S1, the intelligent terminal is booted from the firmware when the intelligent terminal is powered on; S2, the intelligent terminal loads a part of the system image files which is necessary for the operating system to boot into the memory; S3, the intelligent terminal is rebooted and the system that is in the memory is booted; S4, the intelligent terminal automatically executes a basic application software starting instruction, loads and runs the basic application software from the system image files to generate a user interface matching the intelligent terminal. The invention also discloses a starting system using the method and an intelligent self-service system. The invention has the advantages that the starting progress does not need manual duty with high starting efficiency, convenient equipment maintenance and good expansibility.
Owner:HUNAN NEW CLOUDNET TECH CO LTD +1
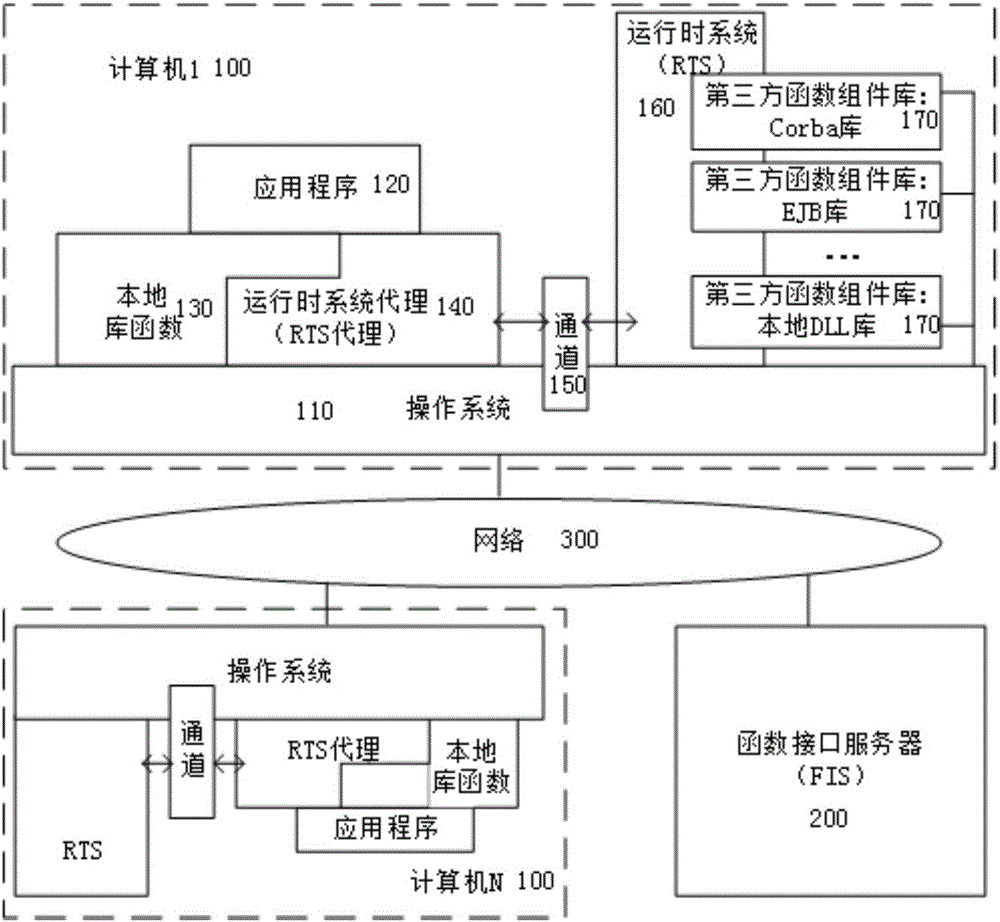
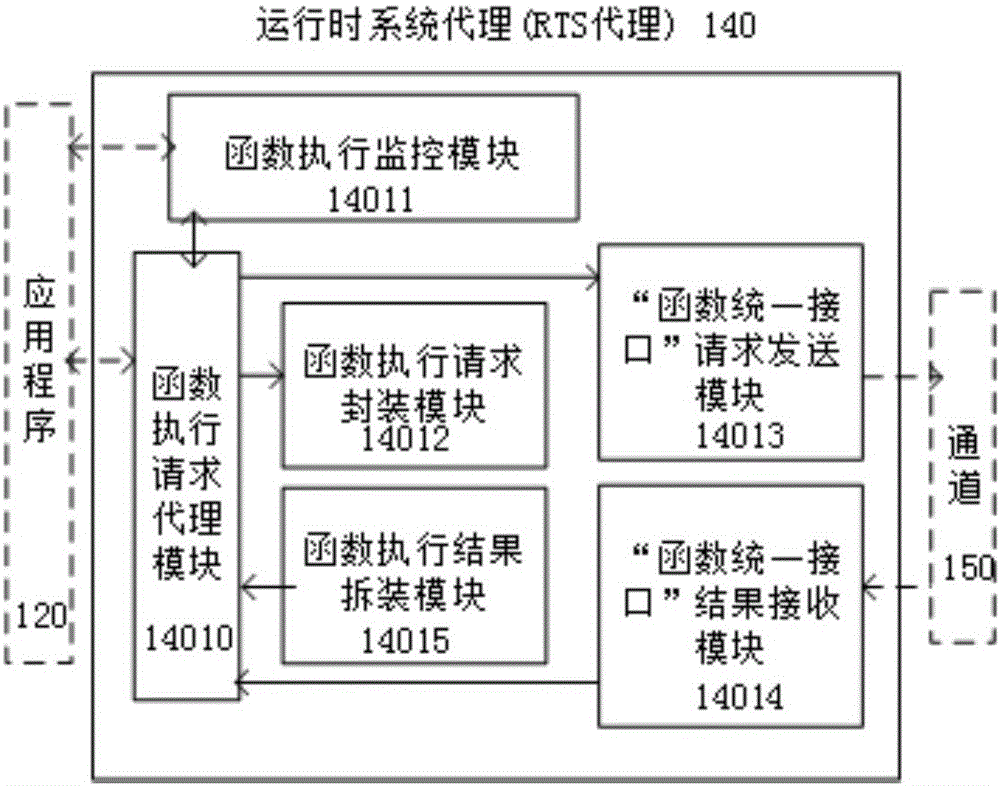
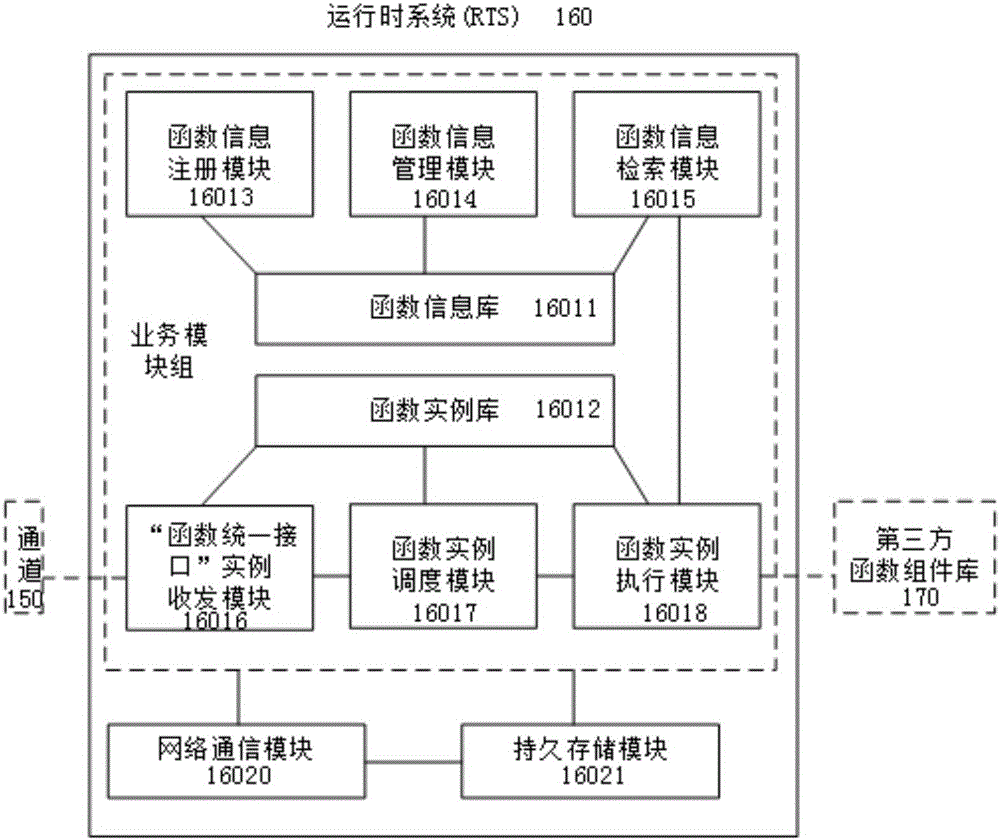
Uniform interface calling oriented runtime system and running method
ActiveCN105975261ARealize shared reuseReduce overheadProgram loading/initiatingExecution paradigmsThird partyTransparent computing
The invention discloses a uniform interface calling oriented runtime system and a running method, and belongs to the field of a computer. The runtime system comprises a runtime system agent device, a runtime system device, a function interface server device, a channel device and a network device. The running method of the runtime system comprises the steps of registering a function of a third party function component library; loading a runtime system agent by an application; delivering the function needing to be called by the application to the runtime system through the runtime system agent; finding the corresponding third party function component library by the runtime system according to function interface information, performing a function instance and returning a performing result to the runtime system agent; and returning the result to the application by the runtime system agent. According to the system and the method, through establishment of the uniform interface calling oriented runtime system, multiplexing among component libraries of different programming languages is realized, transparent computing is realized, and the application cost is reduced.
Owner:NANKAI UNIV
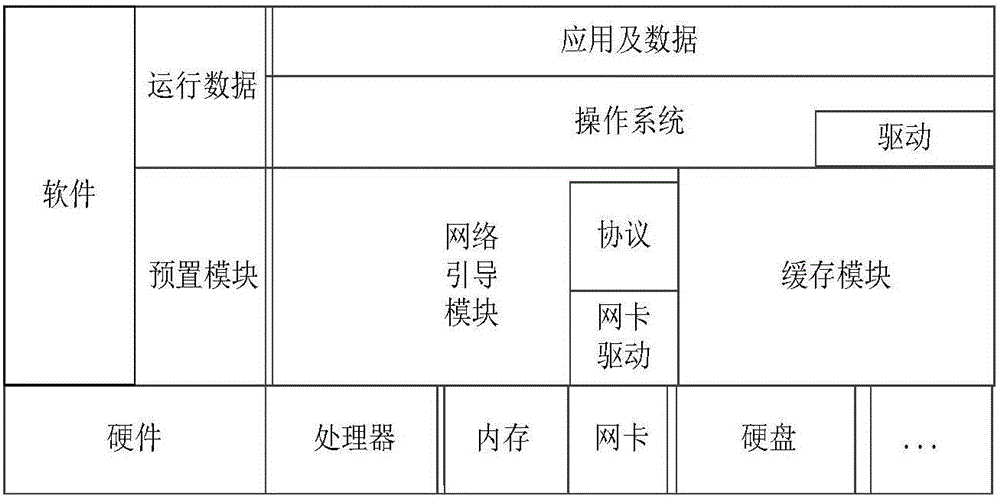
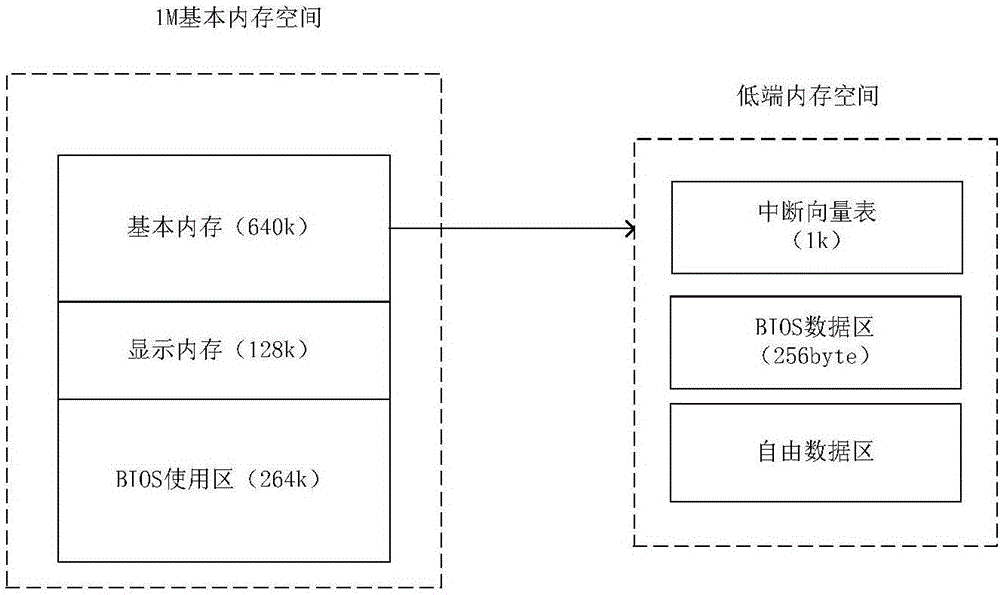
Client block level cache optimization method in mobile transparent computing environment
ActiveCN106850825AFast startupReduce loadInput/output to record carriersTransmissionCache optimizationOperational system
The invention discloses a client block level cache optimization method in a mobile transparent computing environment. A mobile client is electrified. POST self-check and hardware initialization are carried out on the client. After the self-check is carried out on the client, a network boot module is performed on a read-only memory. The network boot module obtains an allocation state of a memory, checks a BIOS data area of the memory, loads wireless network card drive and configures a network protocol stack. After a network access function is supported, a virtual disk is initialized, BIOS service is modified, and I / O redirection is carried out. A user logs in and selects a to-be-operated operating system, searches a cache and starts the operating system. According to the method, a local memory device of the mobile client is taken as a cache medium; the virtual system disk is established in the program of the network boot module; the disk in the BIOS service is modified; a processing program is interrupted; moreover, a cache mechanism is established through utilization of a client level cache module; the starting speed of the client is greatly improved; network loads are reduced; and the user experience is improved.
Owner:CENT SOUTH UNIV
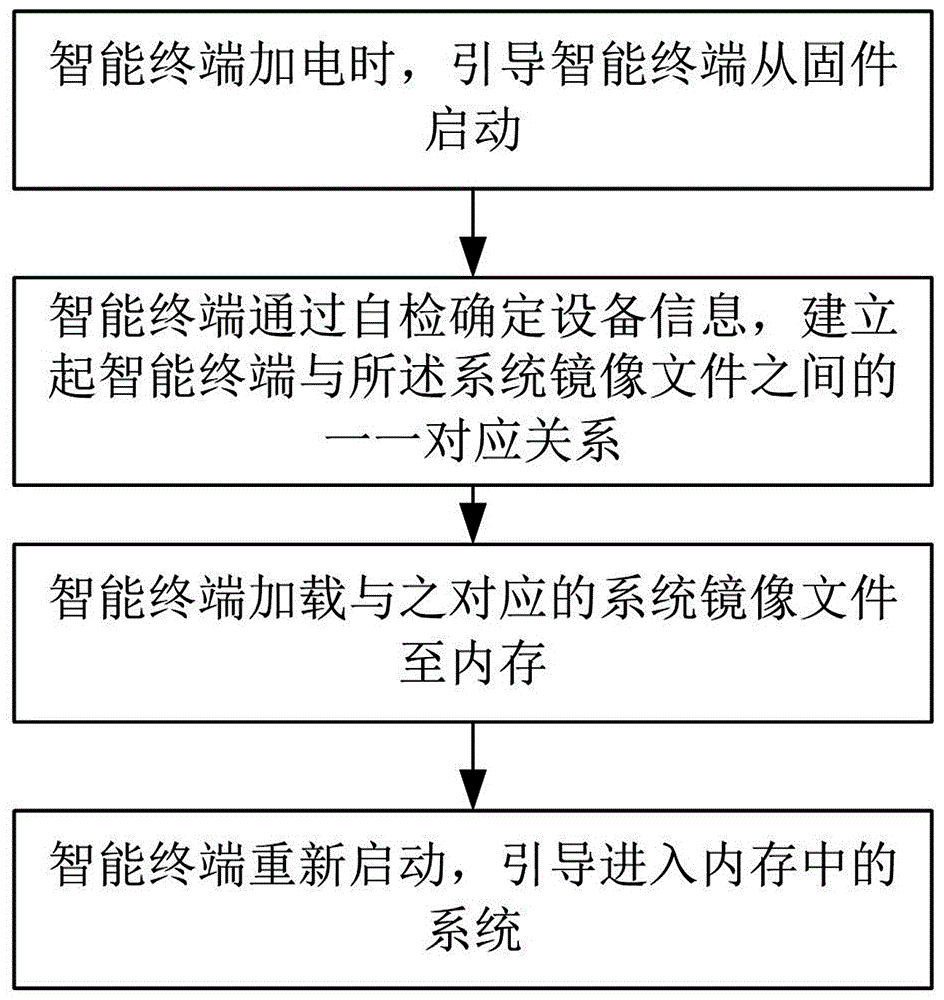
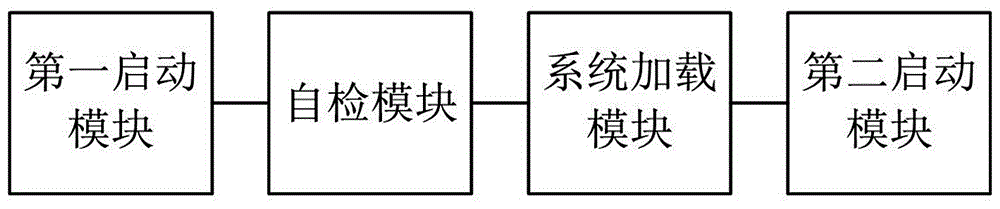
Intelligent terminal starting method, intelligent terminal starting system and intelligent self-service system based on transparent computing
ActiveCN106254638AImprove start-up efficiencyEasy maintenanceSubstation equipmentProgram loading/initiatingInternal memoryTransparent computing
The invention discloses an intelligent terminal starting method based on transparent computing. For each type of intelligent terminals, a corresponding system image file is stored. The starting process of an intelligent terminal comprises the following steps: S1, when the intelligent terminal is powered on, the intelligent terminal is guided to be started from hardware; S2, the intelligent terminal determines equipment information through self-inspection, and a one-to-one corresponding relationship between intelligent terminals and system image files is established; S3, the intelligent terminal loads a corresponding system image file to the internal memory; and S4, the intelligent terminal is restarted to guide a system entering the internal memory. The invention further discloses a starting system employing the starting method, and an intelligent self-service system. The method and the systems have the advantages of unattended starting process, high starting efficiency, convenient equipment maintenance, high scalability, and the like.
Owner:HUNAN NEW CLOUDNET TECH CO LTD +1
Transparent computing based intelligent software starting method
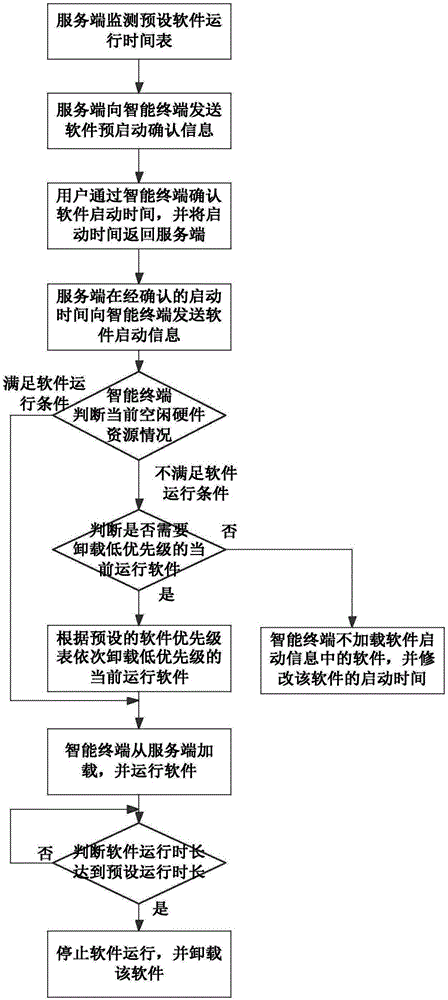
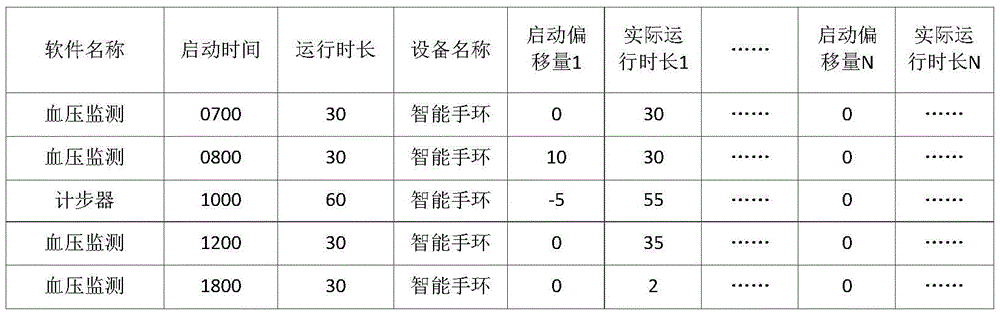
ActiveCN105511880ASupport smart boot managementDoes not occupy hardware resourcesPower supply for data processingBootstrappingTime scheduleStart time
The invention discloses a transparent computing based intelligent software starting method. A software running time table is preset by a user and comprises the name of software, the starting time and the running duration; an intelligent terminal downloads and runs corresponding software from a server in the starting time according to the software running time table, monitors the software running time and stops the software when the preset running duration is reached. The intelligent terminal only needs to receive starting information sent by a server side, hardware resources of the intelligent terminal are not occupied, energy of the intelligent terminal is not consumed, and the method has the advantages of low resource occupation, low energy consumption, multi-terminal management, learning of use habits of the user and intelligent optimization and adjustment of software starting time.
Owner:新云网科技集团股份有限公司
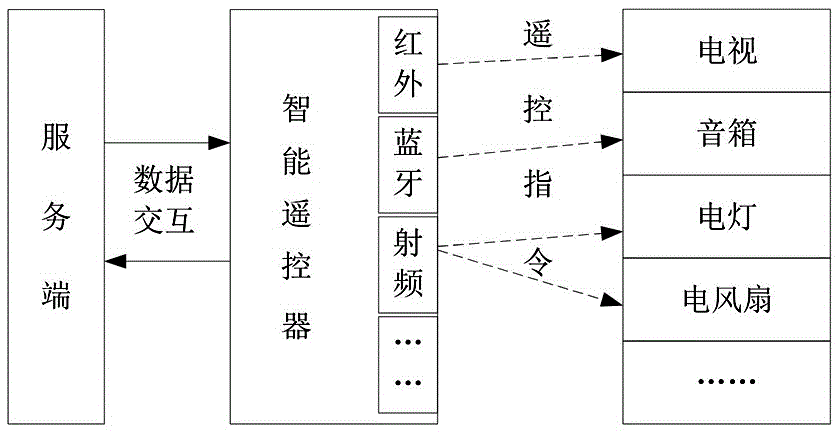
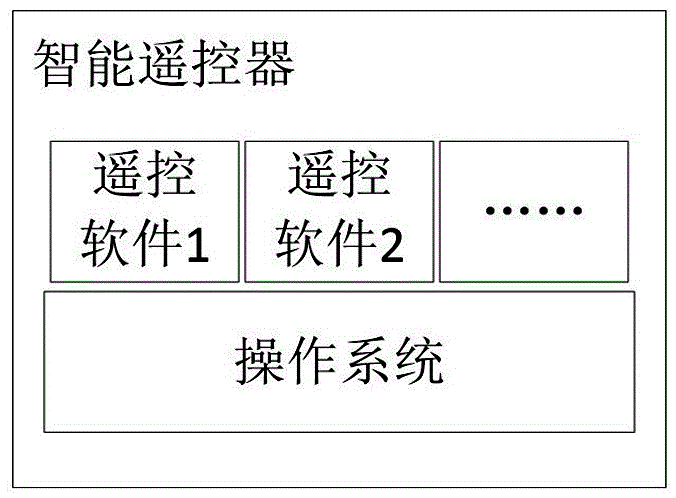
Intelligent remote controller control method based on transparence computing
InactiveCN105513317AReduce manufacturing costReduce waiting timeNon-electrical signal transmission systemsRemote controlNetwork connection
The invention discloses an intelligent remote controller control method based on transparence computing. The intelligent remote controller control method comprises the following steps: S1, establishing network connection between an intelligent remote controller and a server side; selecting types, brands and models of controlled equipment from the intelligent remote controller by a user; S2, loading remote control software from the server side by the intelligent remote controller according to the types, brands and models of the controlled equipment, and realizing remote control of the controlled equipment through the remote control software. The intelligent remote controller disclosed by the invention does not need to provide a large-capacity storage space, and abundant remote control software can be obtained and operated through the server side; the intelligent remote controller has the advantages of effectively reduced manufacturing cost, extremely great expandability and the like.
Owner:CENT SOUTH UNIV
Method for transferring data between terminal apparatuses in a transparent computation system
ActiveUS7818390B2Improve data transfer efficiencyImprove performanceDigital data information retrievalMultiple digital computer combinationsComputer hardwareTransparent computing
A method for transferring data between terminal apparatuses in a network at least comprising a server, a first terminal apparatus and a second terminal apparatus, wherein the server has a storage device at least comprising a first and a second disk images; the method comprising: generating a message of data transfer request based on the information on the data to be transferred; transferring the generated message to the second terminal apparatus; receiving the message and transferring the message to the server if the requested data transfer is allowed; and transferring date between the first disk image and the second disk image, in response to the reception of the message.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
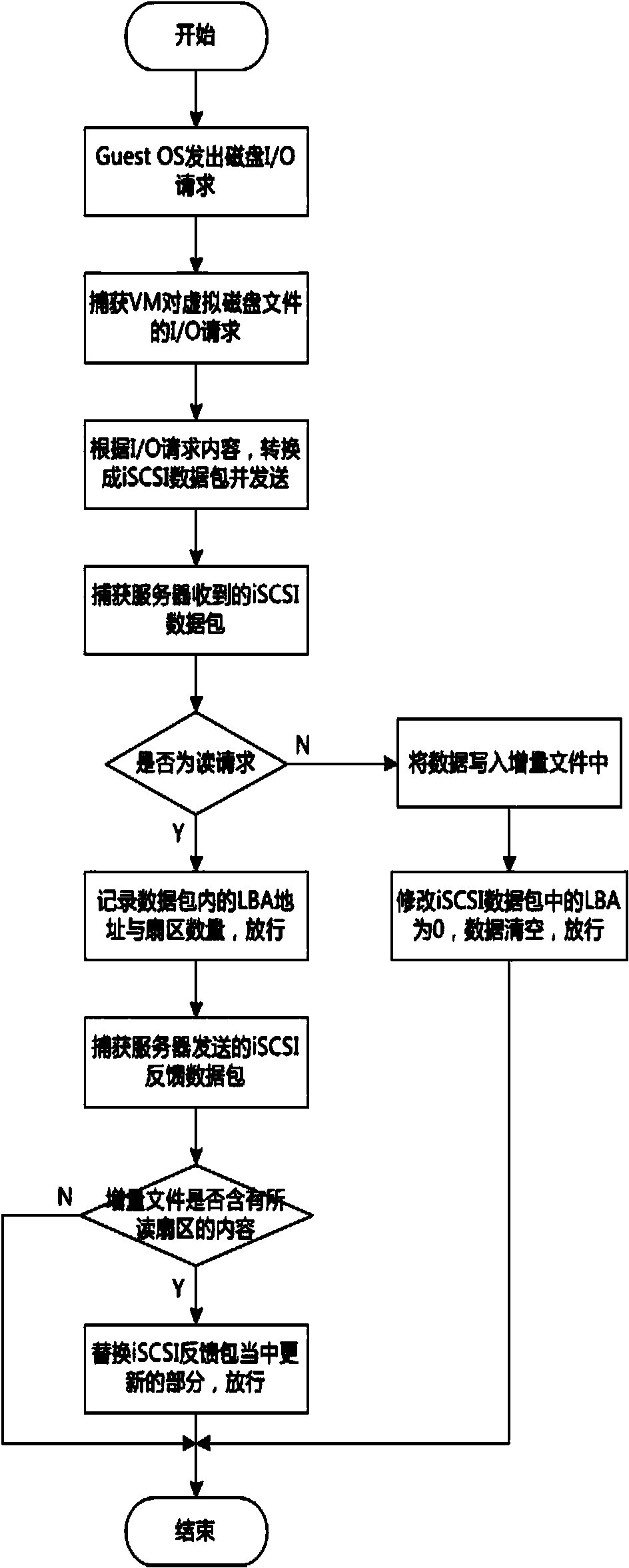
Terminal data migration method and system based on transparent computing
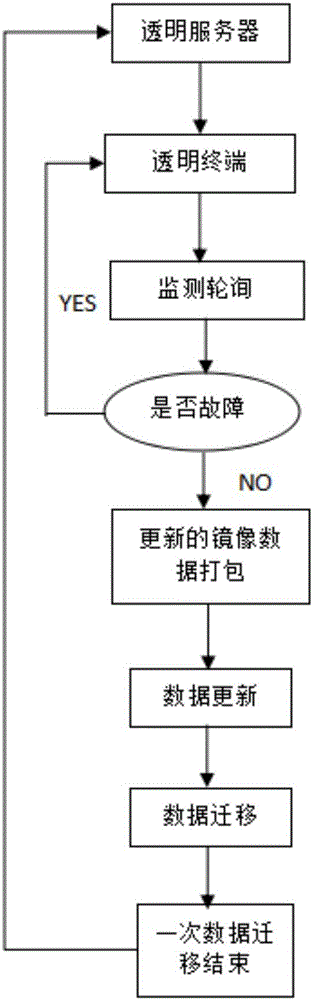
InactiveCN107438110ASafe migration processQuick migrationTransmissionOperational systemTransparent computing
The invention discloses a terminal data migration method and system based on transparent computing, and the method specifically comprises the following steps: S1, starting a system, and enabling a transparent terminal to carry out the monitoring polling of all mirror data in a transparent database if the transparent terminal monitors that the original basic mirror data of an operating system in a transparent server has updates; S2, enabling the transparent terminal to package the updated mirror data if no fault is found in monitoring polling; S3, enabling the transparent terminal to transmit a data migration instruction to the transparent server after packaging, enabling a drive program to direct the reading and writing of the system to the updated mirror data, and achieving the migration of data at a time. According to the invention, the system mirror data is packaged as a body, and the method employs an incremental backup mode for data migration. Moreover, before the packaged migration of data, the transparent terminal will carry out the real-time monitoring and polling whether the mirror data has a fault or not. The method is safe, quick and unique in migration process.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
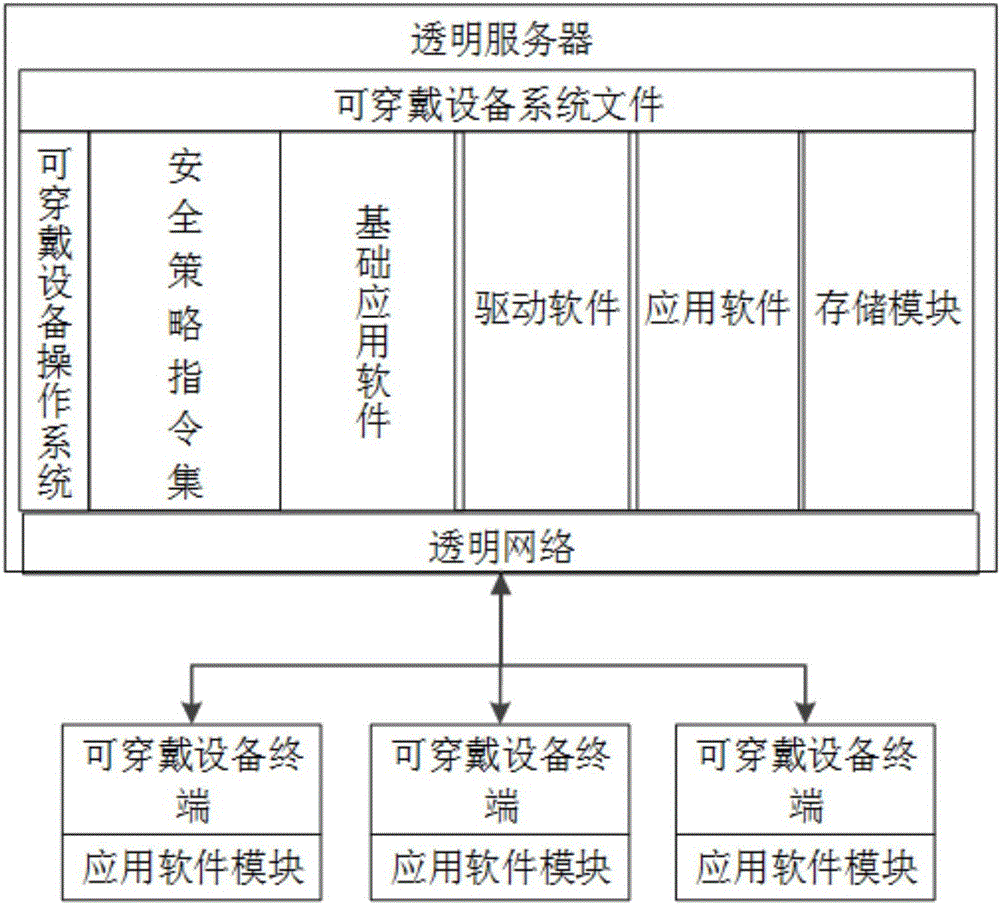
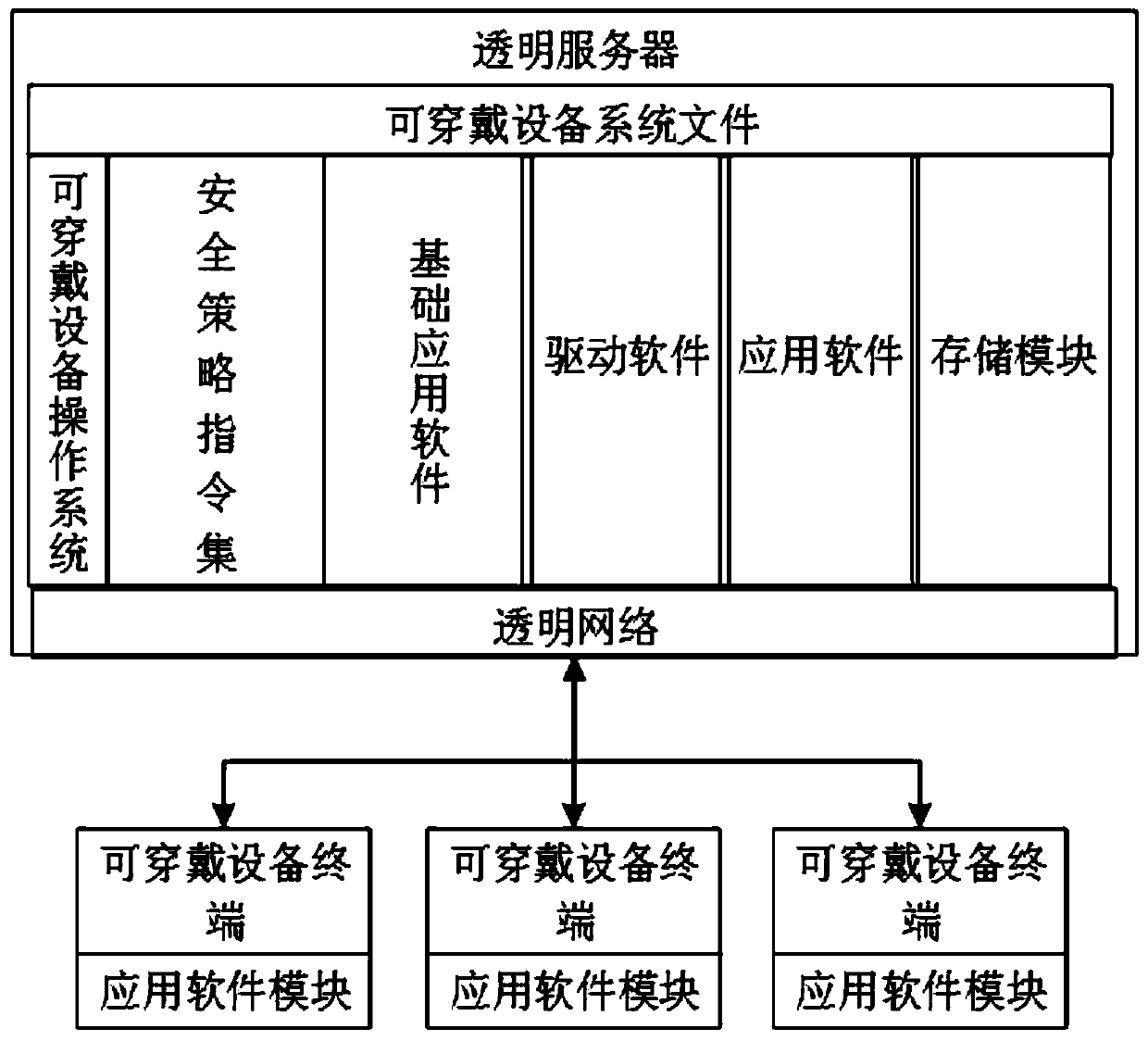
Wearable equipment safety management method, transparent server, and cloud architecture system
ActiveCN107438109AEnsure safetyGuaranteed privacyWireless commuication servicesTransmissionOperational systemTransparent computing
The invention discloses wearable equipment safety management method, a transparent server, and a cloud architecture system. The method specifically comprises the following steps: S1, classifying the application software in a wearable equipment system terminal, and specifying different data storage modes for different types of application software; S2, enabling wearable equipment to carry out the dividing of different storage regions at the transparent server for different types of application software, wherein the storage regions are provided for the corresponding type of application software for data storage; S3, enabling the transparent server to carry out the data storage according to the divided storage regions through the application software data received by a transparent network. According to the invention, an operating system of the wearable equipment terminal is mirrored and stored at the transparent server based on a transparent computing architecture, and the method can guarantee the safety of the system and data, and guarantees the privacy of a user. The method can achieve the selective storage of the background data of all application software, guarantees the data safety, selectivity, uniqueness and flexibility, and is better in expansibility and compatibility.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
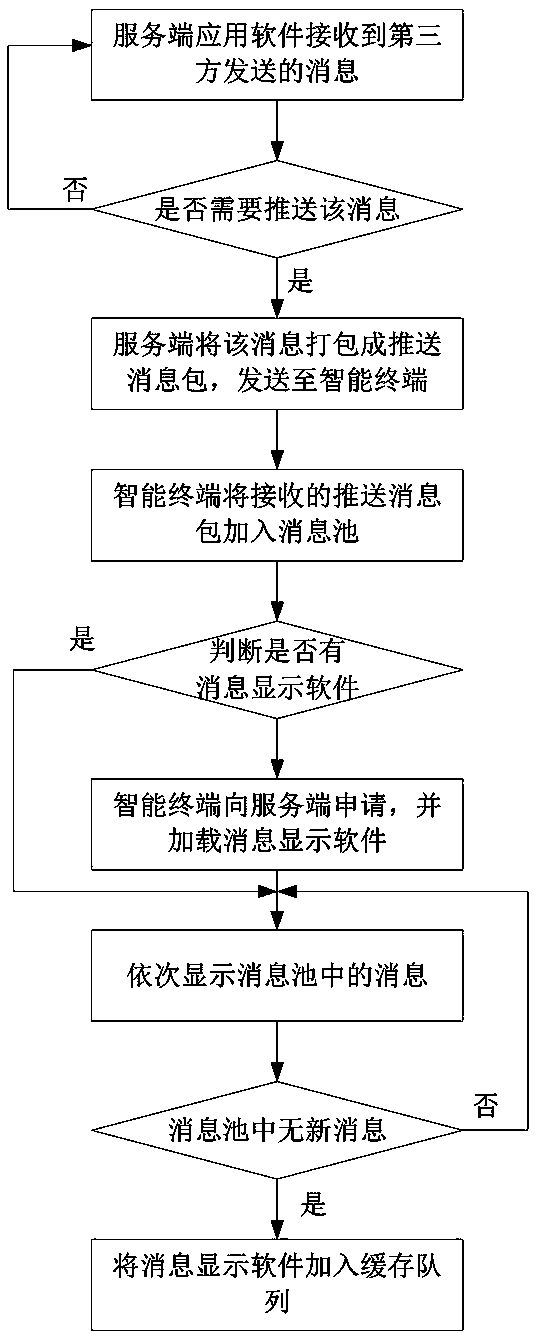
Transparence computing based method for pushing messages to intelligent terminal
The invention discloses a transparence computing based method for pushing messages to an intelligent terminal. A server receives messages sent by a third party, and sends the messages needing to be pushed to the intelligent terminal to the intelligent terminal in a manner of pushing a message packet; the intelligent terminal receives the pushed message packet, sends an application to the server, loads message display software, and displays the received messages. The method has the advantages of low requirements on hardware configuration and storage space of the intelligent terminal, few occupied resources, low energy consumption and well protection for the privacy of a user.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
Transparent computing based payment method
InactiveCN105488664AReduce the burden onTo achieve the role of decouplingFinancePayment circuitsPasswordBank account
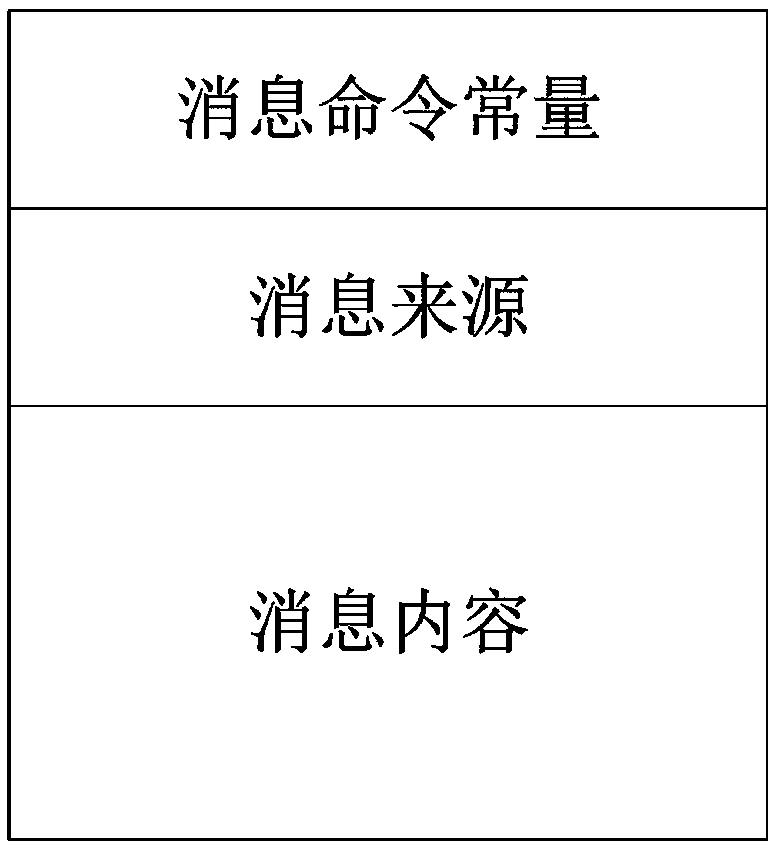
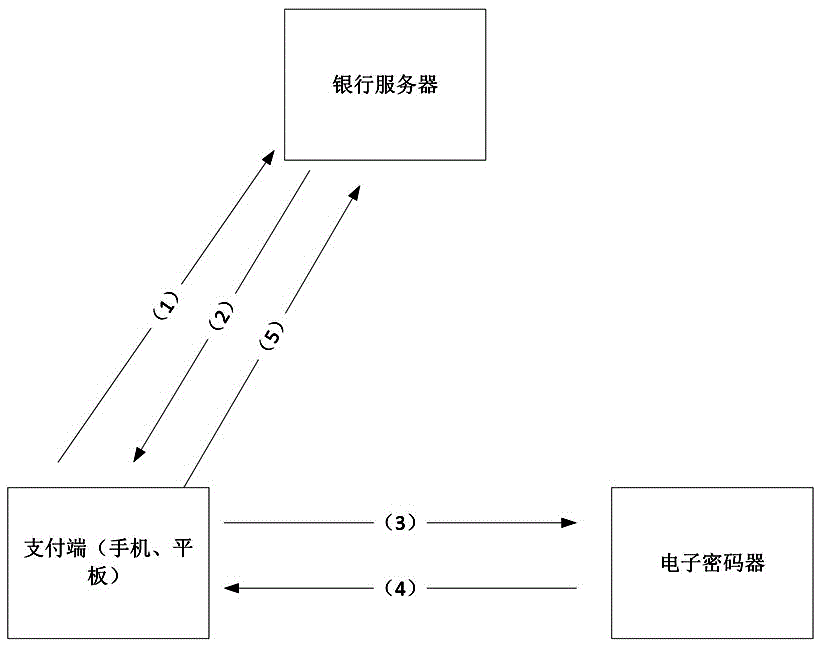
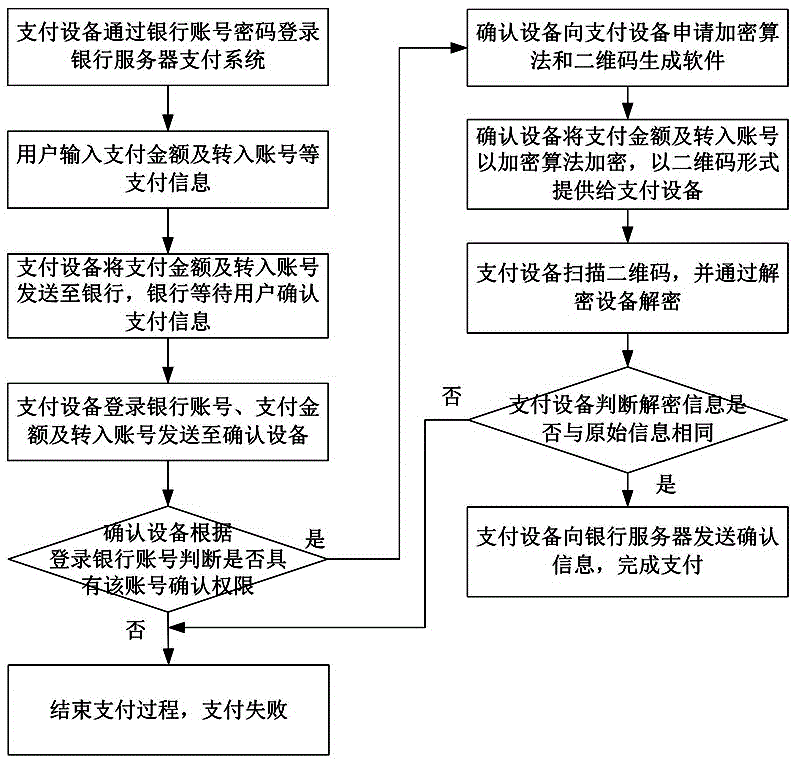
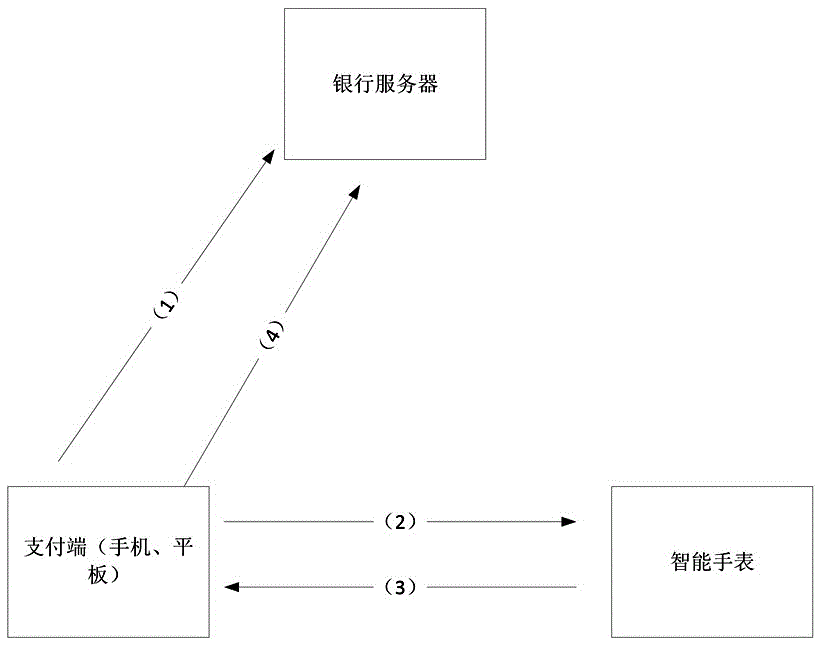
The invention discloses a transparent computing based payment method. The method comprises the steps that when a user makes a payment in a payment device, a bank account, a password and a confirmation device bound with the bank account are required at the same time necessarily, and the confirmation device is bound with the payment device; when the payment device sends payment information to a bank, the payment information is sent to the confirmation device, the confirmation device encrypts the payment information and provides the encrypted payment information to the payment device in the form of a two-dimensional code, the payment device confirms the correctness of two-dimensional code information generated by the confirmation device by scanning the two-dimensional code, and when the two-dimensional code information is determined to be consistent with the payment information, payment confirmation information is sent to a bank server to finish the payment, otherwise, the payment is failed and the payment process is ended. The method has the advantages of reducing bank data storage, reducing communication frequency and ensuring payment security.
Owner:CENT SOUTH UNIV
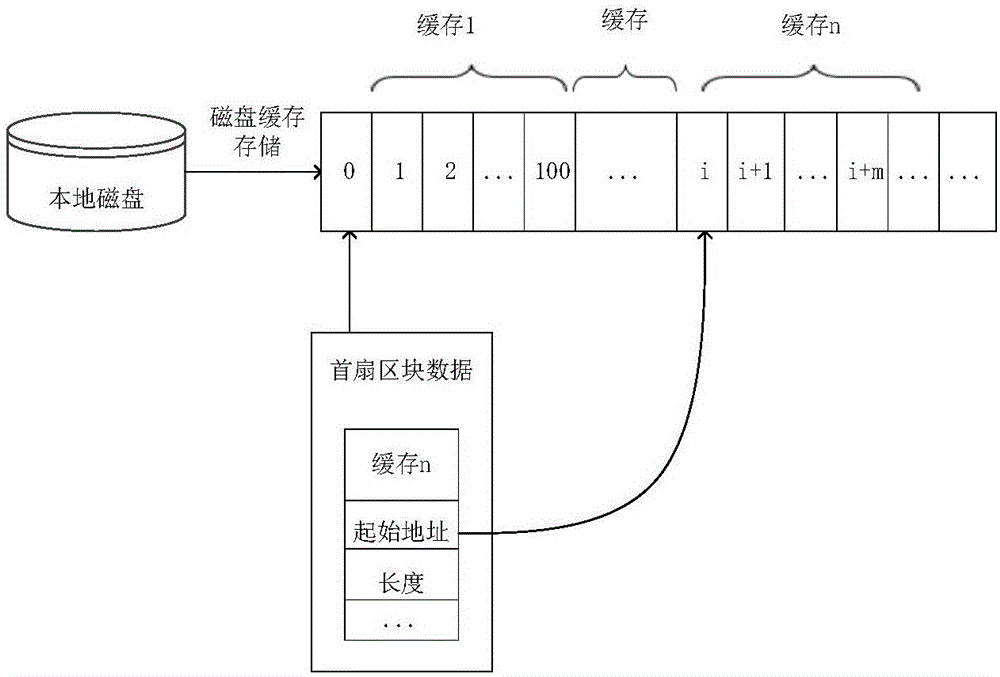
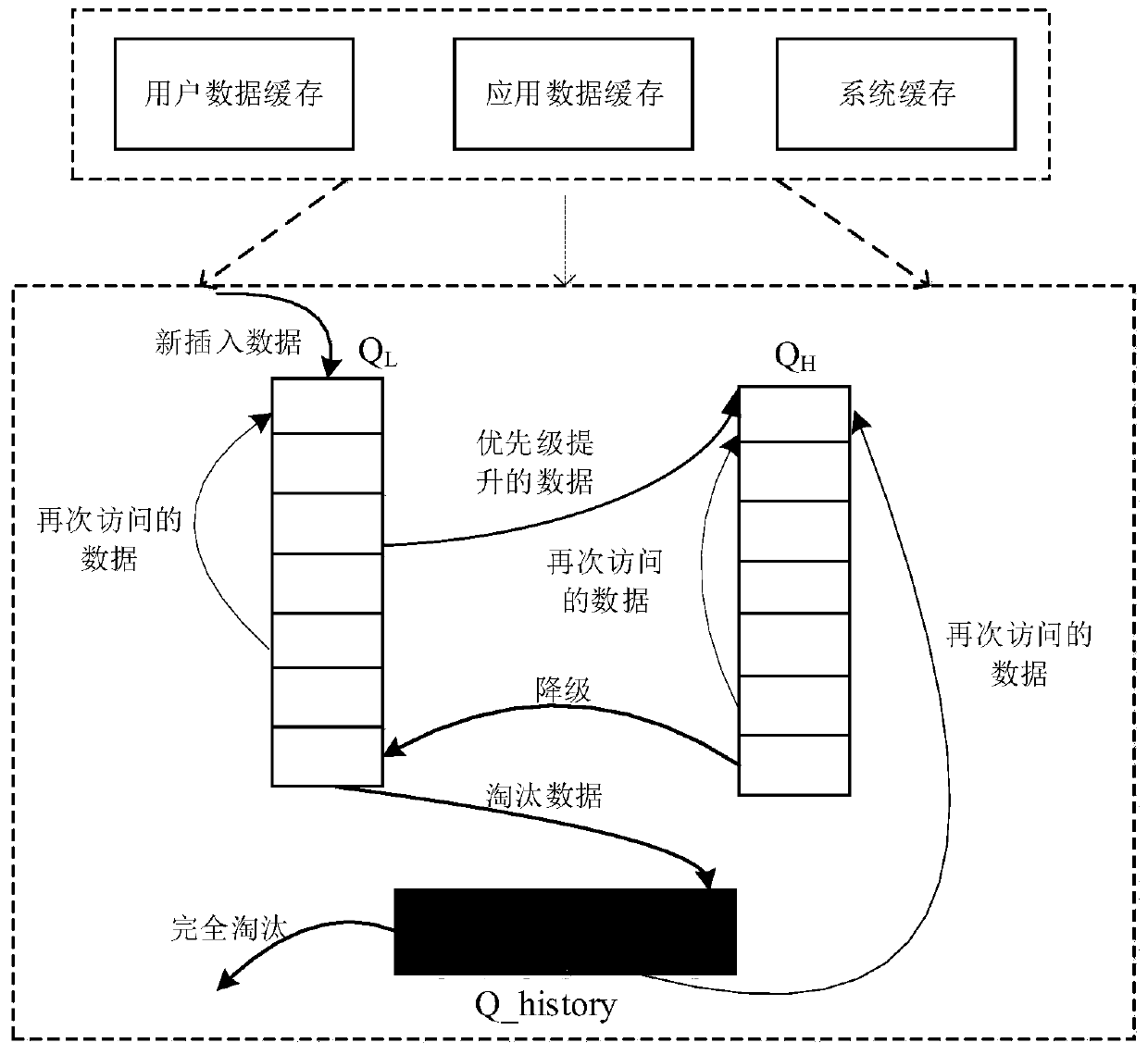
Server based on transparent service platform data access and cache optimization method thereof
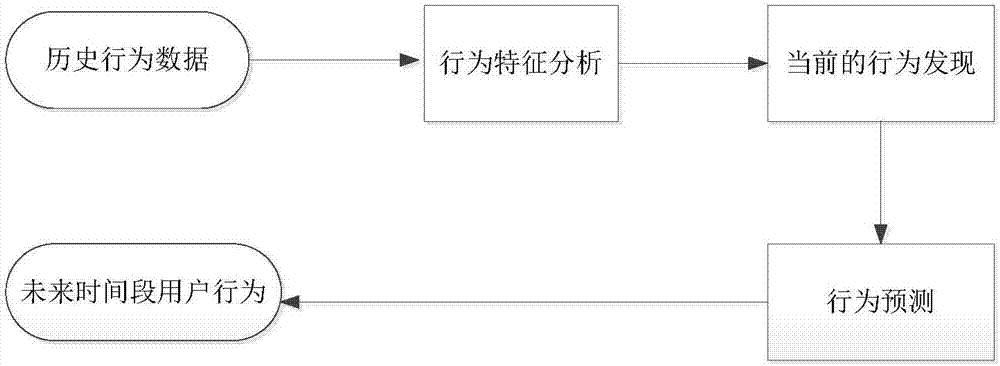
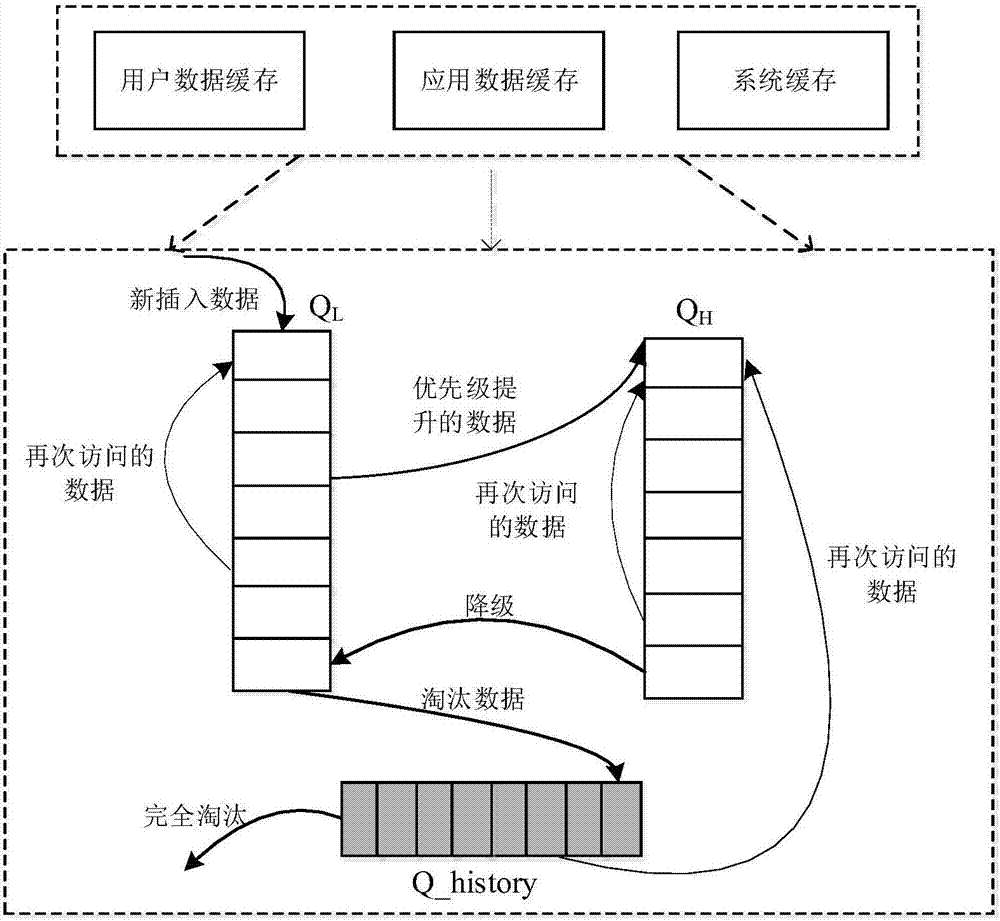
ActiveCN107370807AOptimize caching mechanismImprove hit rateTransmissionQuality of servicePrediction algorithms
The invention relates to the computer network technology, and discloses a server based on transparent service platform data access and a cache optimization method thereof, in order to improve the hit rate of cache and improve the quality of service of transparent computing. The method disclosed by the invention comprises the following steps: counting the frequency of transparent computing server data bock access behaviors of a large number of terminal users at time intervals, quantizing the data block access behaviors of the users by using information entropy, and judging whether the current user access behaviors have concentricity; when it is judged that the user access behaviors have concentricity, screening data blocks having high access frequency at present, and predicting the access frequency distribution of the screened data blocks within a period of time in the future by using an exponential smoothing prediction algorithm; and optimizing the cache of the server according to a predicted frequency distribution result.
Owner:CENT SOUTH UNIV
Network isolation method based on transparent computing, system, network card and application
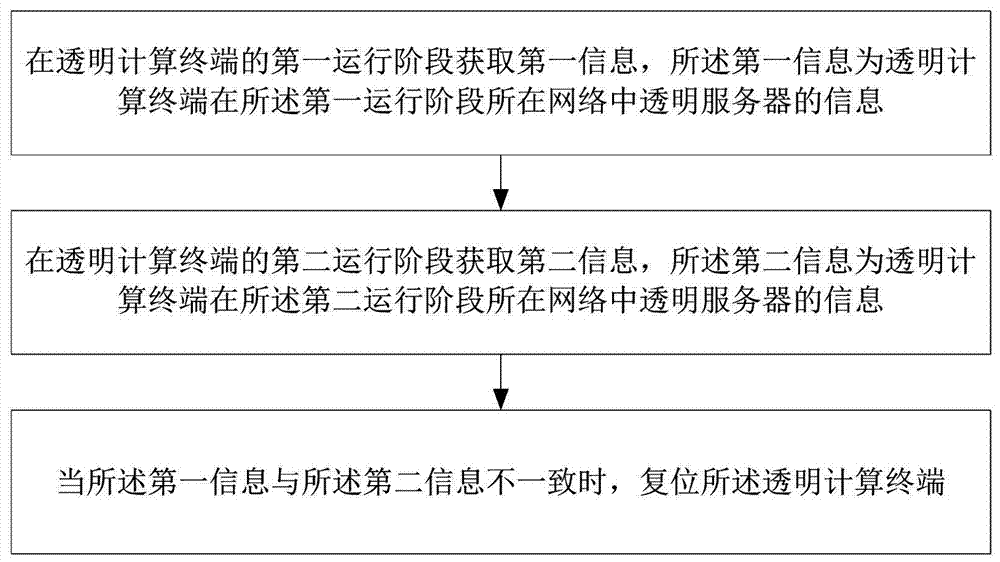
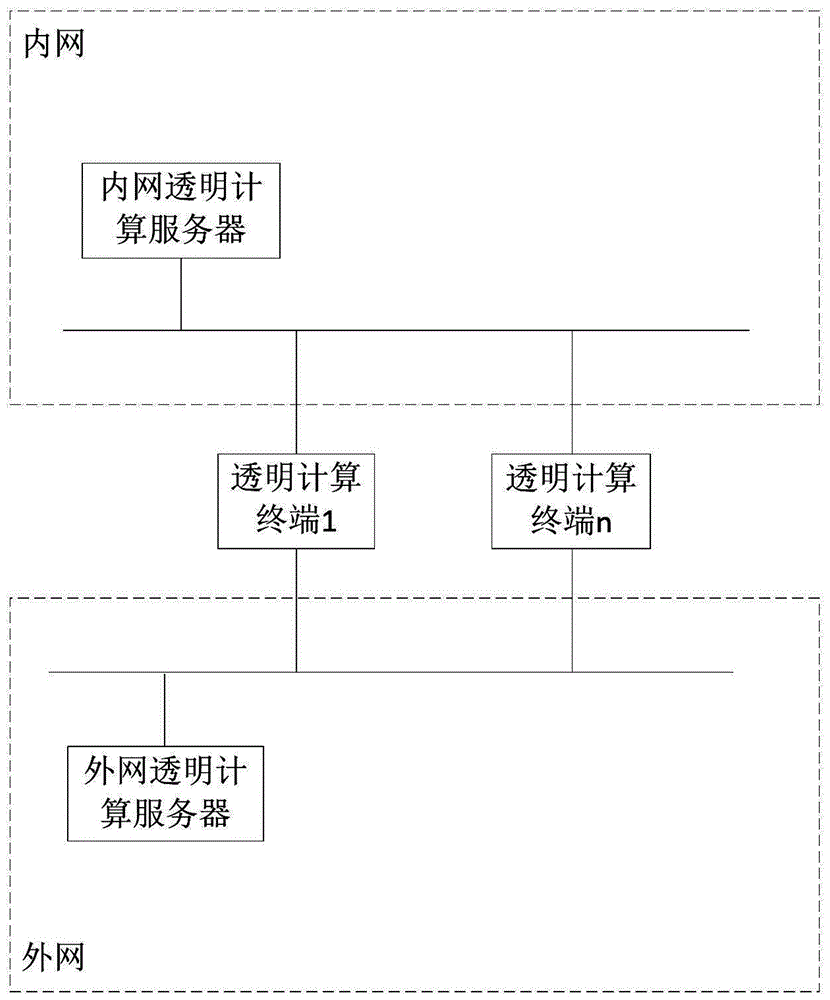
ActiveCN106856481APrevent running across the networkAvoid risk of leakageTransmissionTransparent computingNetwork isolation
The invention discloses a network isolation method based on transparent computing, a system, a network card and application. The network isolation method comprises the following steps: S1, acquiring first information in a first operation stage of a transparent computing terminal, wherein the first information is information of a transparent server in a network of the transparent computing terminal in the first operation stage; S2, acquiring second information in a second operation stage of the transparent computing terminal, wherein the second information is information of the transparent server in the network of the transparent computing terminal in the second operation stage; S3, when the first information is not accordant with the second information, resetting the transparent computing terminal. The network isolation method has the advantages that the security is high, the risk of confidence breakage caused when the transparent computing terminal is connected with different networks can be effectively reduced, and operation security of the transparent computing terminal is ensured.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
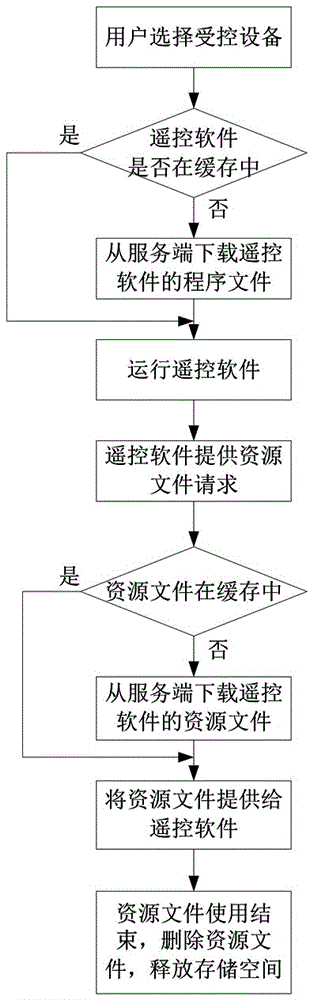
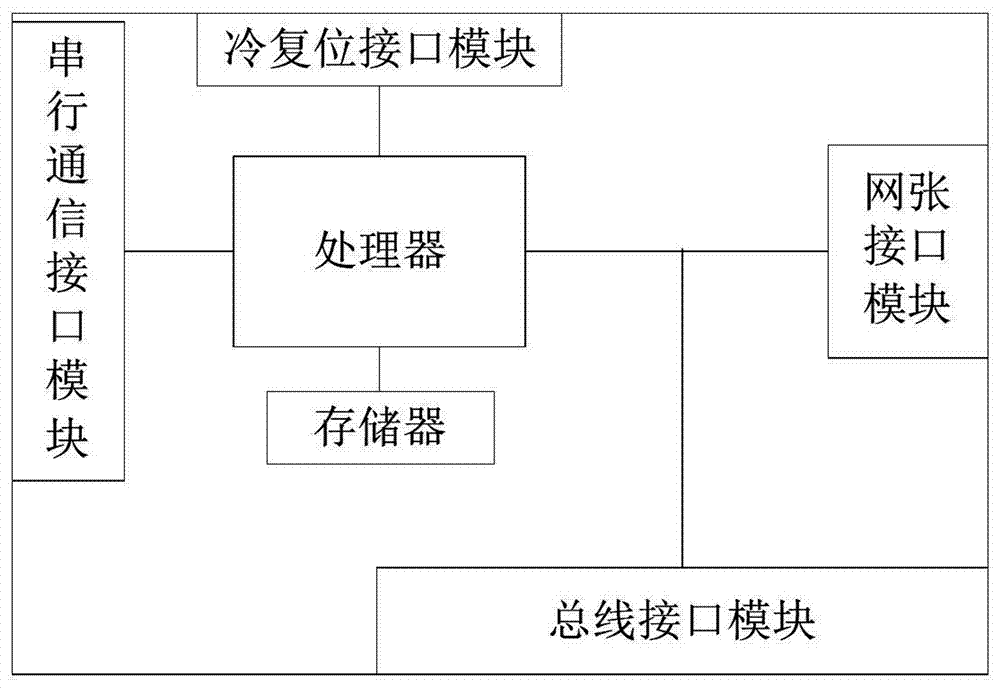
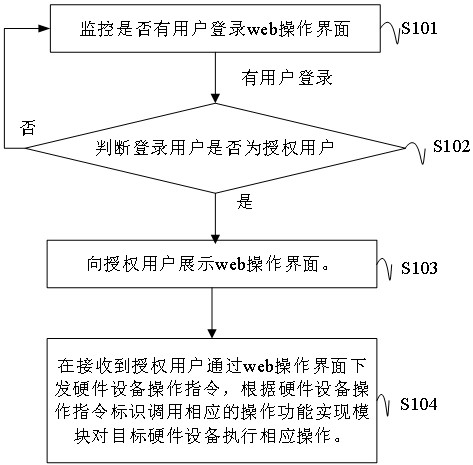
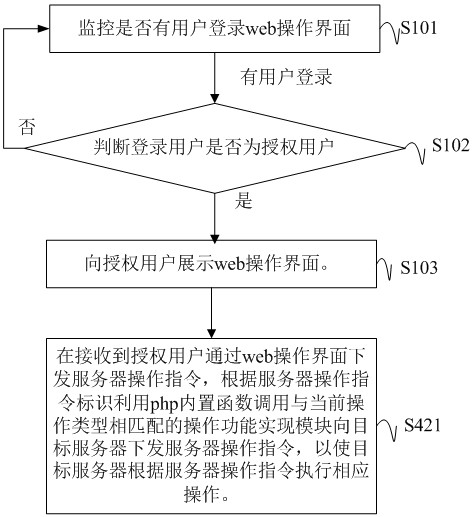
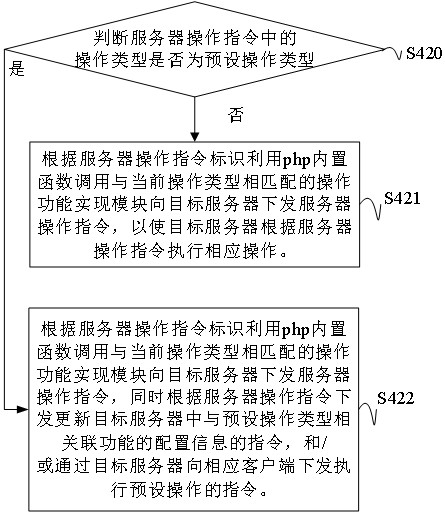
Remote control method and device for hardware equipment, storage medium and transparent computing system
The invention discloses a remote control method and device for hardware equipment, a computer readable storage medium and a transparent computing system. The method comprises the steps of: after it isverified that a current login user is an authorized user, displaying a web operation interface to the authorized user; authorizing a user to issue a hardware end and a remote operation type to be remotely controlled in a hardware equipment operation instruction form on a web operation interface, and calling a corresponding operation function implementation module by the system according to a received hardware equipment operation instruction identifier to execute corresponding remote operation on target hardware equipment corresponding to the instruction; and generating the operation functionrealization module by packaging and converting a group of operation commands for realizing a preset operation function. According to the invention, remote control of the hardware end is realized, andan operator does not need to well know the operation code of the operation to be executed.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
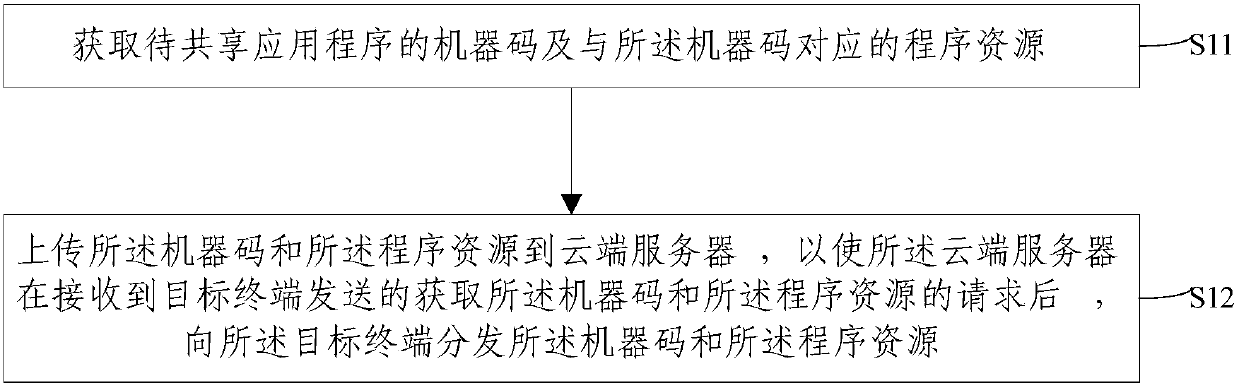
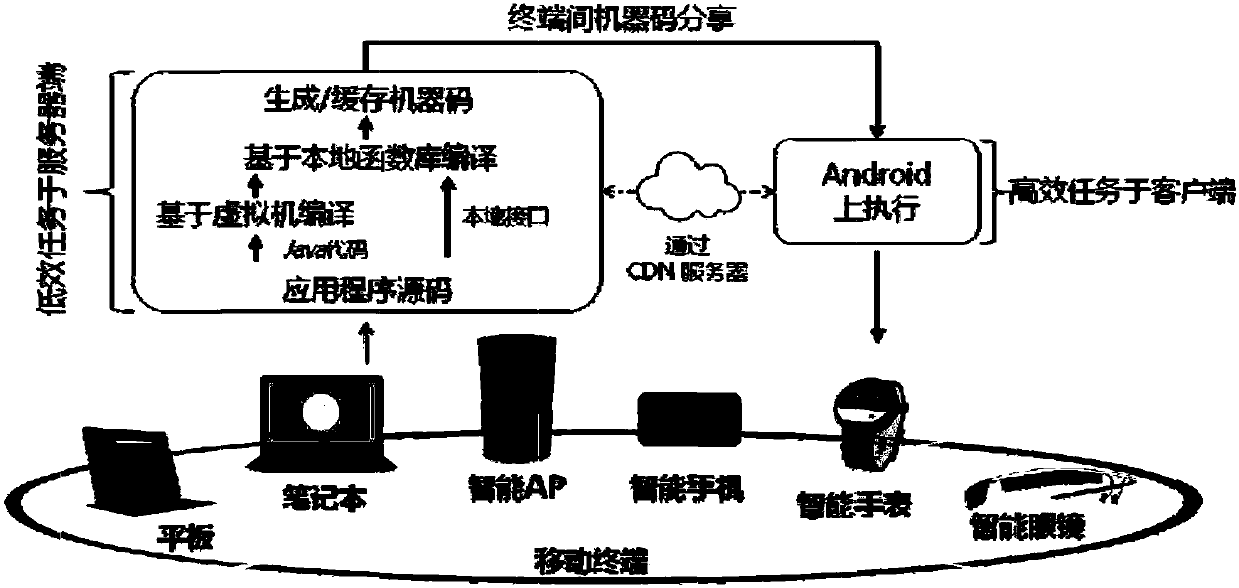
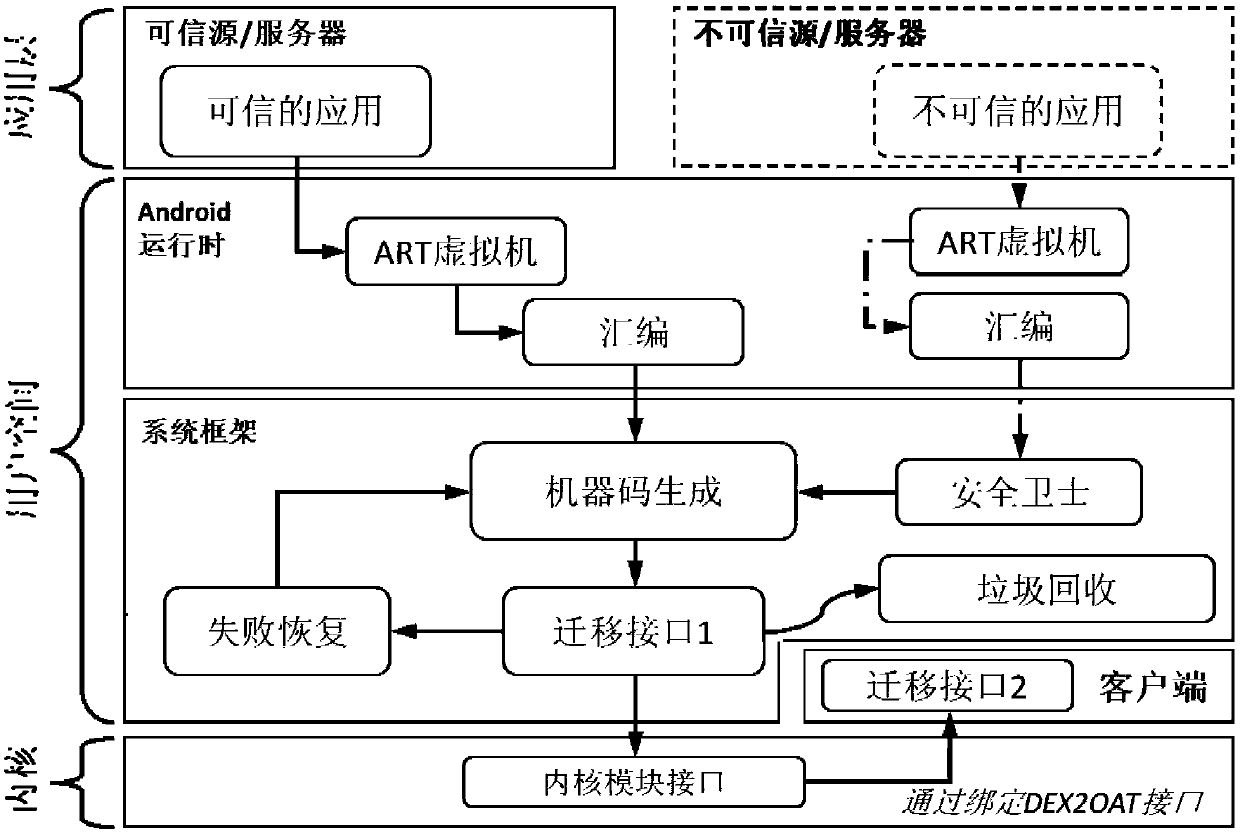
Transparent computing terminal application program synchronization sharing method and device
InactiveCN107872497ALower latencyReduce power consumptionCurrent supply arrangementsSubstation equipmentTransparent computingLatency (engineering)
The invention provides a transparent computing terminal application program synchronization sharing method and device. The method includes the steps of acquiring a machine code of an application program to be shared and a program resource corresponding to the machine code; and uploading the machine code and the program resource to a cloud server, so that after receiving a request sent by a targetterminal to acquire the machine code and the program resource, the cloud server distributes the machine code and the program resource to the target terminal and finally a corresponding application function is executed by the target terminal. The machine code of the application program is shared among the mobile terminals, so that a user can directly execute the machine code of a desired function to meet the high quality user experience requirements of the user for low latency, low power consumption, no residual files, and no special facilities of mobile applications.
Owner:TSINGHUA UNIV
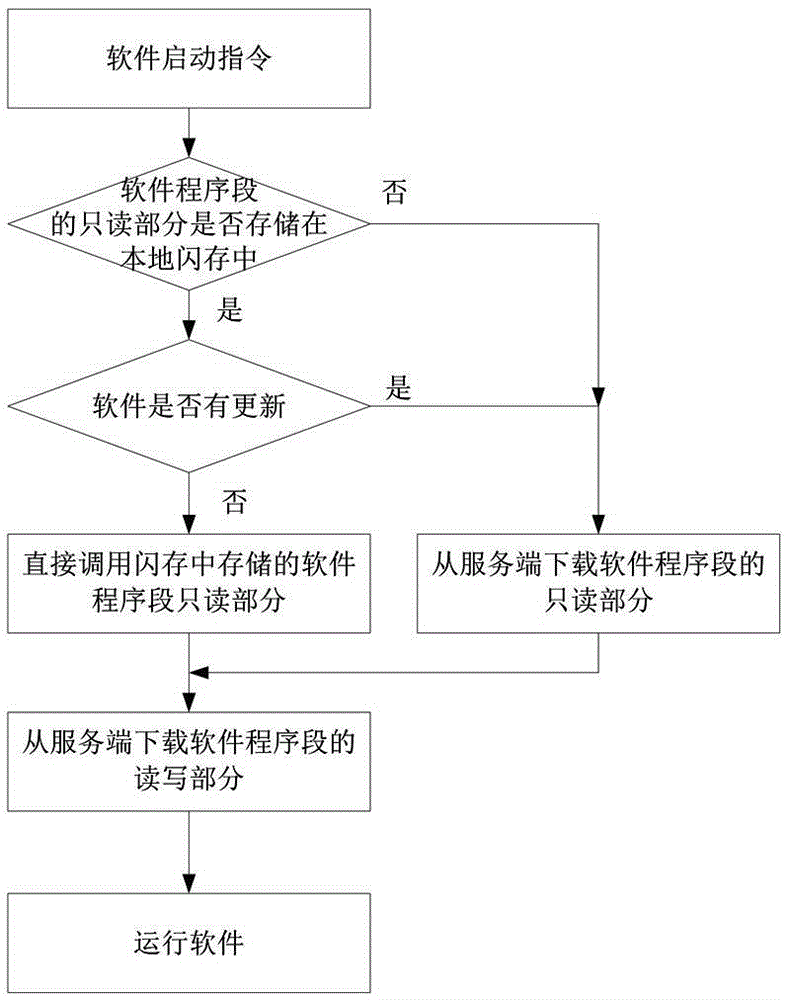
Intelligent terminal software updating method based on transparent computing
ActiveCN105426216AImprove update efficiencyProgram loading/initiatingSoftware deploymentSoftware updateSoftware engineering
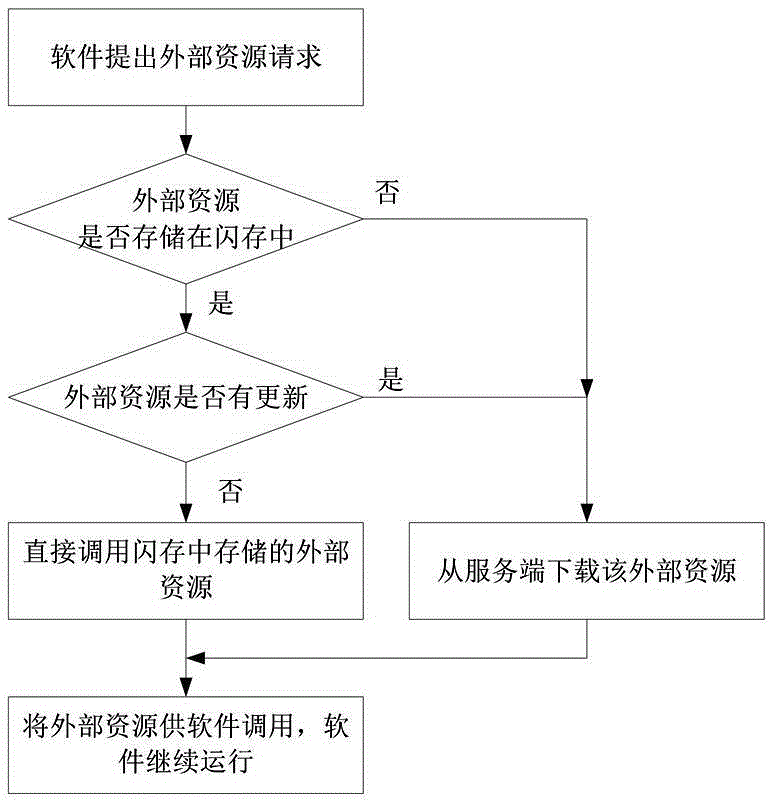
The invention discloses an intelligent terminal software updating method based on transparent computing. The method comprises the steps that S1, an intelligent terminal acquires a software enabled instruction and judges whether the read-only part of software is saved in a local flash memory, S2 is conducted if yes, and S3 is conducted if no; S2, the intelligent terminal enquires a server side about whether the software is updated, the read-only part, in the flash memory, of the software is updated, the read-write part of the software is downloaded, and the software is run to finish updating if yes, and the read-only part, in the flash memory, of the software is called directly, the read-write part of the software is downloaded and the software is run if no; S3, the intelligent terminal downloads the read-only part and the read-write part of the software from the server side and loads the read-only part and the read-write part of the software into a local memory, and the software is run. The method has the advantages of being simple, convenient, transparent to users, high in updating efficiency and the like.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
Isolation network card for transparent computing terminal as well as application and network switching method thereof
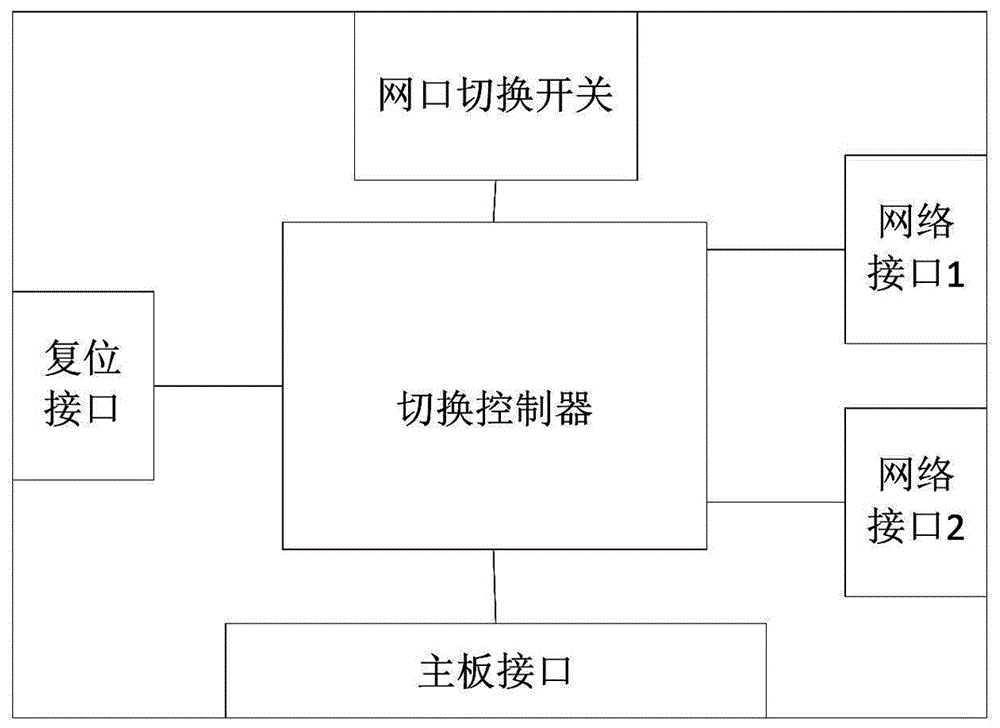
InactiveCN106790298ASimple structureRealize switchingTransmissionTransparent computingNetwork switch
The invention discloses an isolation network card for a transparent computing terminal as well as application and a network switching method thereof. The isolation network card comprises at least two network interfaces used for connecting to a network, a network interface change-over switch used for selecting the network interface to be started for use, a switching controller which is used for establishing a connection between a mainboard interface and the network interface to be started for use according to the selection of the network interface change-over switch and generating a reset signal, a reset interface used for outputting the reset signal, and the mainboard interface used for communicating with a mainboard, wherein the network interfaces, the network interface change-over switch, the reset interface and the mainboard interface are respectively connected with the switching controller. The isolation network card has the advantages of being safe, convenient and fast to switch, simple in structure, low in cost, and the like.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
The server and its cache optimization method based on transparent service platform data access
ActiveCN107370807BOptimize caching mechanismImprove hit rateTransmissionQuality of serviceCache optimization
The invention relates to computer network technology, and discloses a server based on transparent service platform data access and a caching optimization method thereof, so as to improve the hit rate of caching and improve the service quality of transparent computing. The method of the present invention includes: counting the frequency of access behaviors of a large number of terminal users to transparent computing server data blocks in time intervals, and using information entropy to quantify the user data block access behaviors to determine whether the current user access behaviors are centralized; When judging that the user's access behavior is centralized, screen out the currently accessed data blocks with high frequency, and use the exponential smoothing prediction algorithm to predict the access frequency distribution of the screened out data blocks for a period of time in the future; according to the predicted frequency The distribution results are optimized for caching on the server side.
Owner:CENT SOUTH UNIV
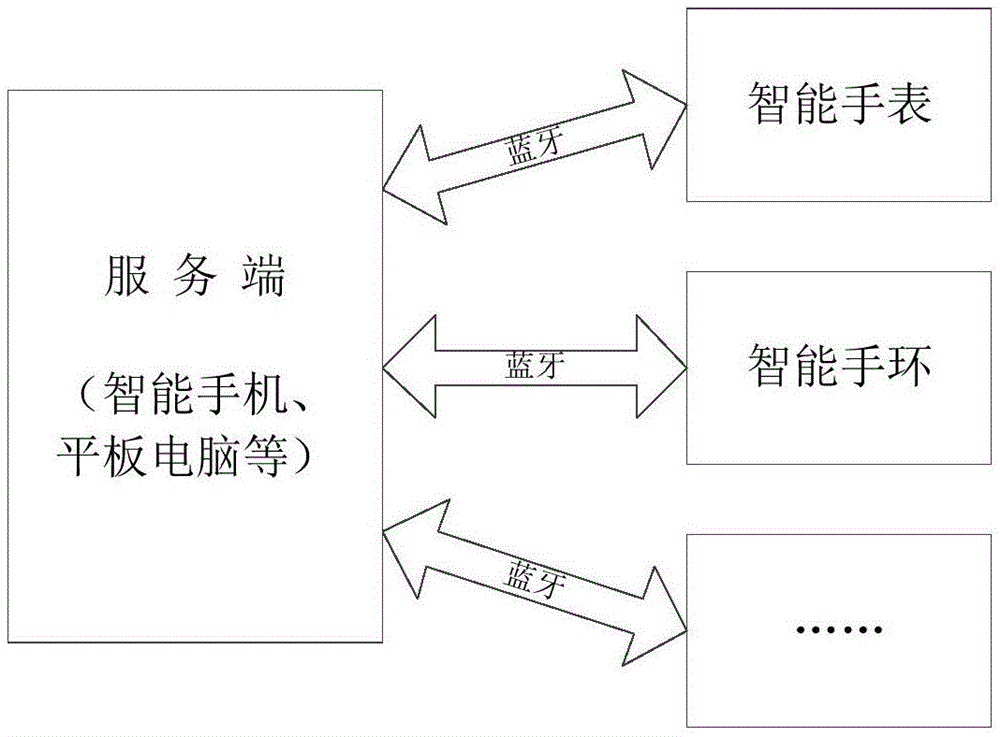
Wearable device security management method, transparent server-side and cloud architecture system
ActiveCN107438109BEnsure safetyGuaranteed privacyTransmissionMachine-to-machine/machine-type communication serviceOperational systemTransparent computing
The invention discloses wearable equipment safety management method, a transparent server, and a cloud architecture system. The method specifically comprises the following steps: S1, classifying the application software in a wearable equipment system terminal, and specifying different data storage modes for different types of application software; S2, enabling wearable equipment to carry out the dividing of different storage regions at the transparent server for different types of application software, wherein the storage regions are provided for the corresponding type of application software for data storage; S3, enabling the transparent server to carry out the data storage according to the divided storage regions through the application software data received by a transparent network. According to the invention, an operating system of the wearable equipment terminal is mirrored and stored at the transparent server based on a transparent computing architecture, and the method can guarantee the safety of the system and data, and guarantees the privacy of a user. The method can achieve the selective storage of the background data of all application software, guarantees the data safety, selectivity, uniqueness and flexibility, and is better in expansibility and compatibility.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
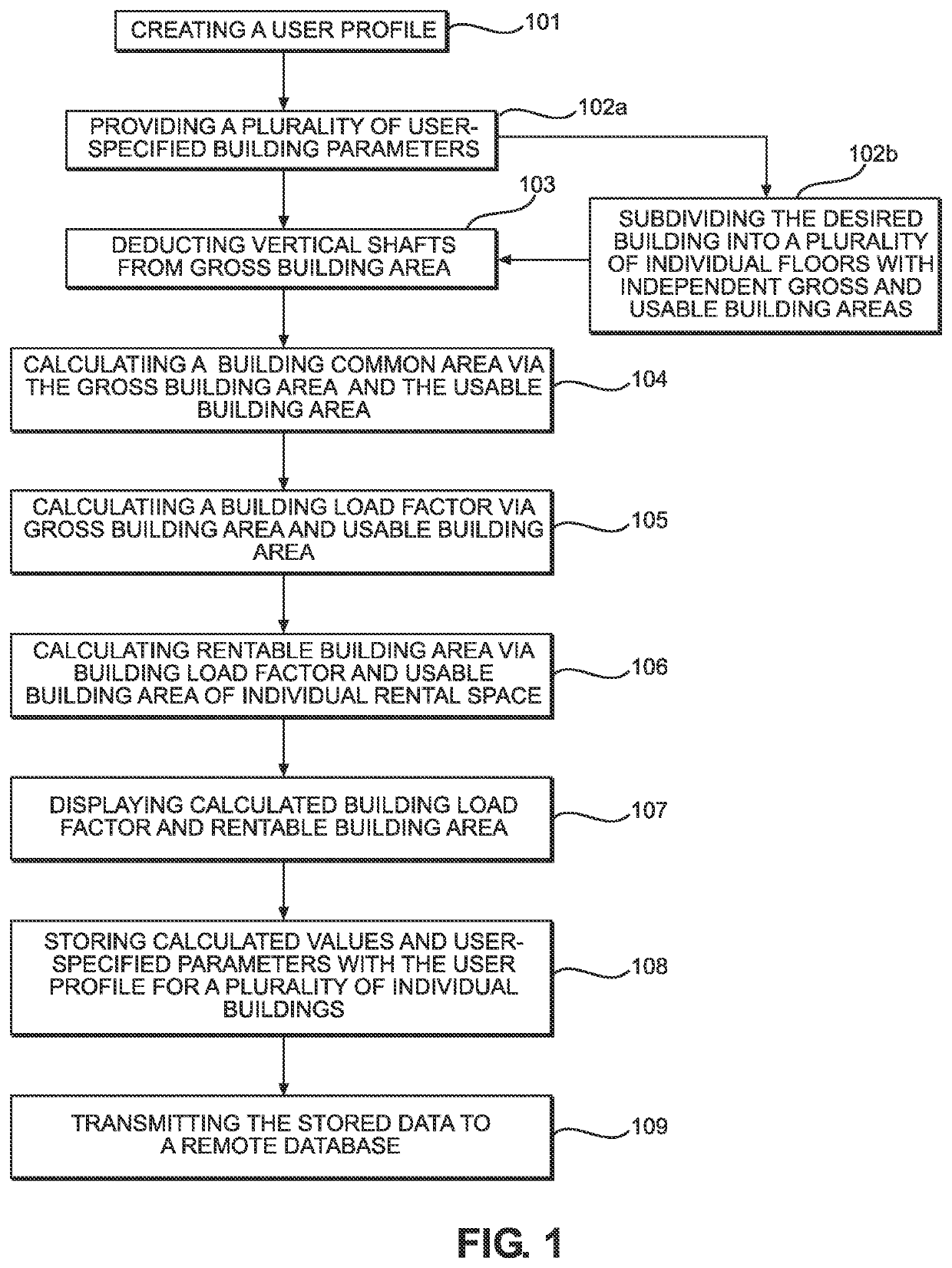
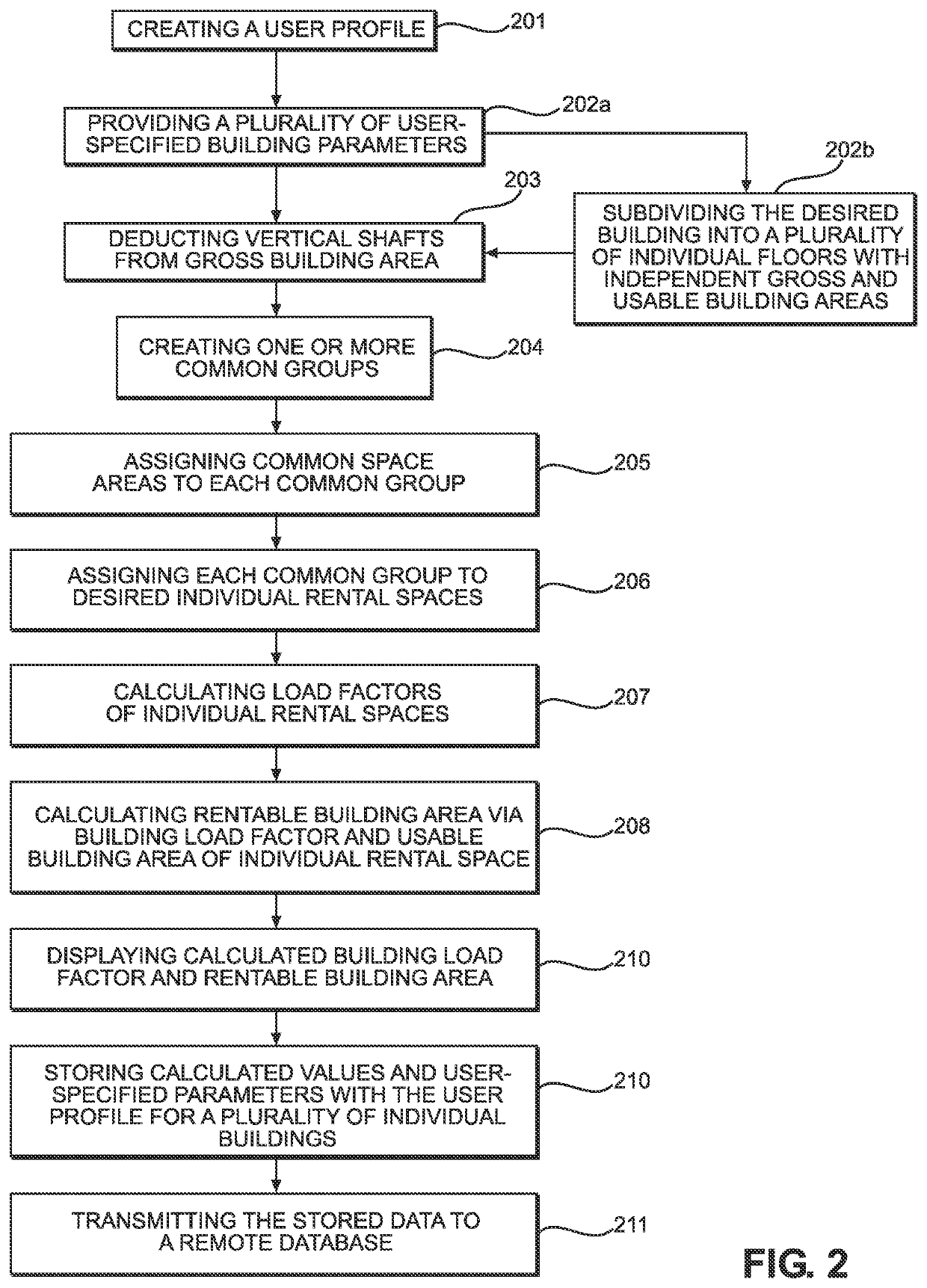
System and Method for Calculating Rentable Building Area
PendingUS20220342636A1Market predictionsDigital data processing detailsArchitectural engineeringTransparent computing
A system and method for calculating rentable building area is provided. The system includes a device having a non-transitory computer readable memory and a processor, wherein the device is in wireless communication with a remote database. The non-transitory computer readable memory includes a software application thereon, wherein the software application calculates a building load factor and a rentable building area of individual rental spaces within a desired building via a plurality of user-specified building parameters. The plurality of user-specified building parameters includes at least a gross building area and a usable building area, wherein the building load factor is calculated via the gross building area and the total usable building area. The rentable building area is then calculated via the usable building area of the individual rental space and the building load factor and displayed on a display of the device.
Owner:TORRES TERRY
A user identity authentication method and system configuration method suitable for transparent computing systems
ActiveCN106549976BImprove safety and reliabilityImprove experienceTransmissionPasswordTransparent computing
The invention discloses a user identity authentication method suitable for a transparent computing system and a system configuration method. The user identity authentication method comprises: when a user boots up and logs in, a client transmits a login requesting information to an authentication server, and the authentication server queries a background database, acquires an operating system authority list bootable by the user and transmits the list to the client; the user selects the operating system and invokes a remote loading request to a storage server; and the storage server authenticates a user name and passwords of the client, checks a mirror image configuration file of the operating system of the user after the authentication passes, and judges whether the authentication succeeds according to the IP of the client and mirror image IP settings of an operating system to be booted up. The system configuration method is used for configuring the transparent computing system using the user identity authentication method. According to the user identity authentication method suitable for the transparent computing system and the system configuration method, which are provided by the invention, the authority management of the user is achieved, a plurality of individual services can be provided, and the user experience is perfected.
Owner:CENT SOUTH UNIV
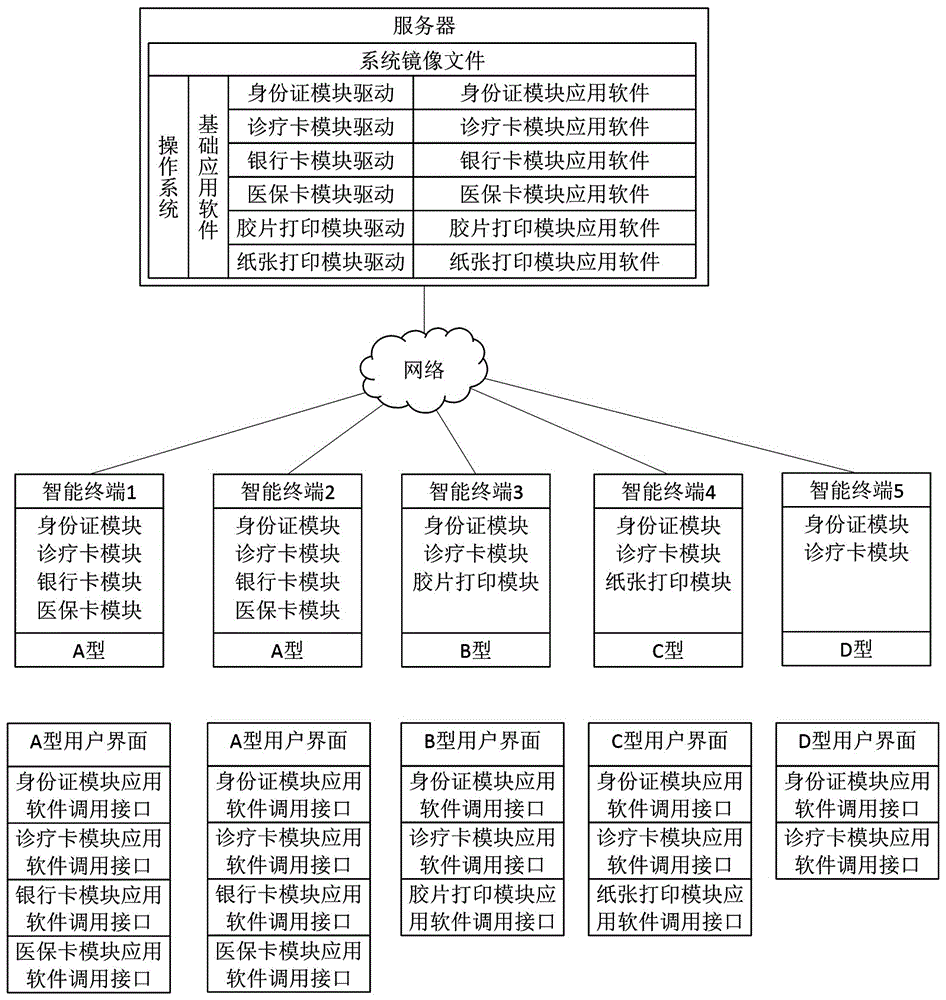
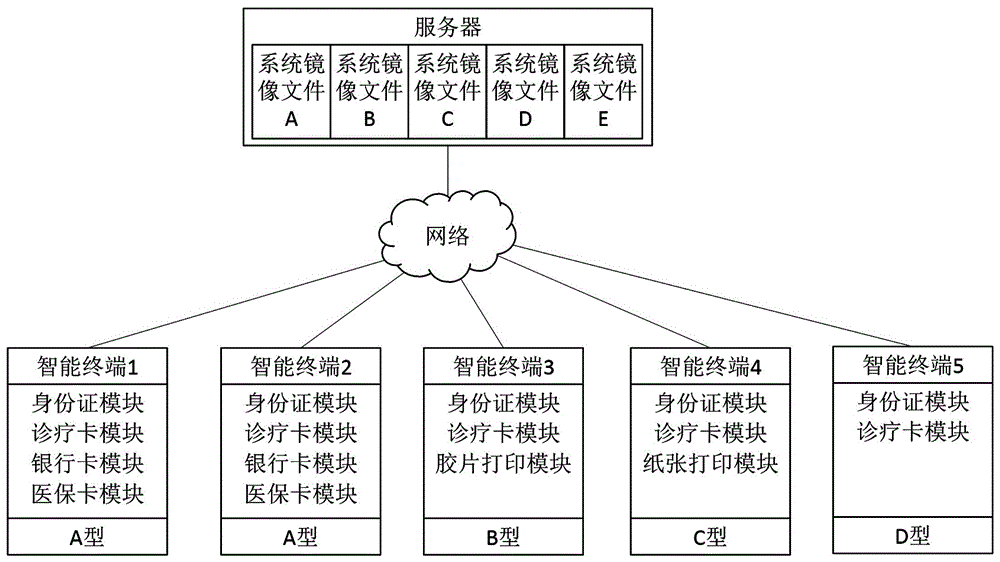
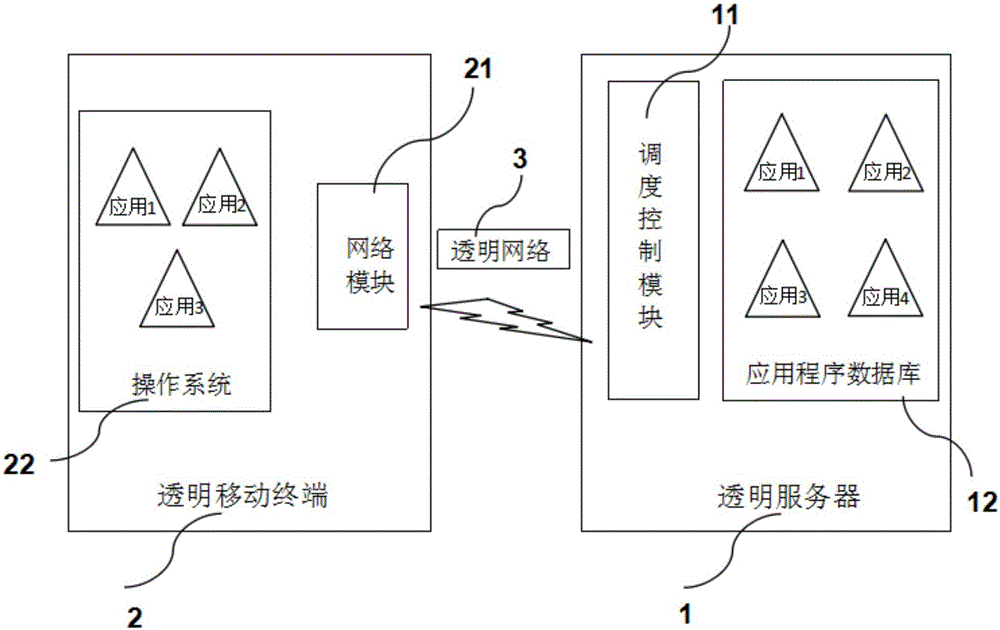
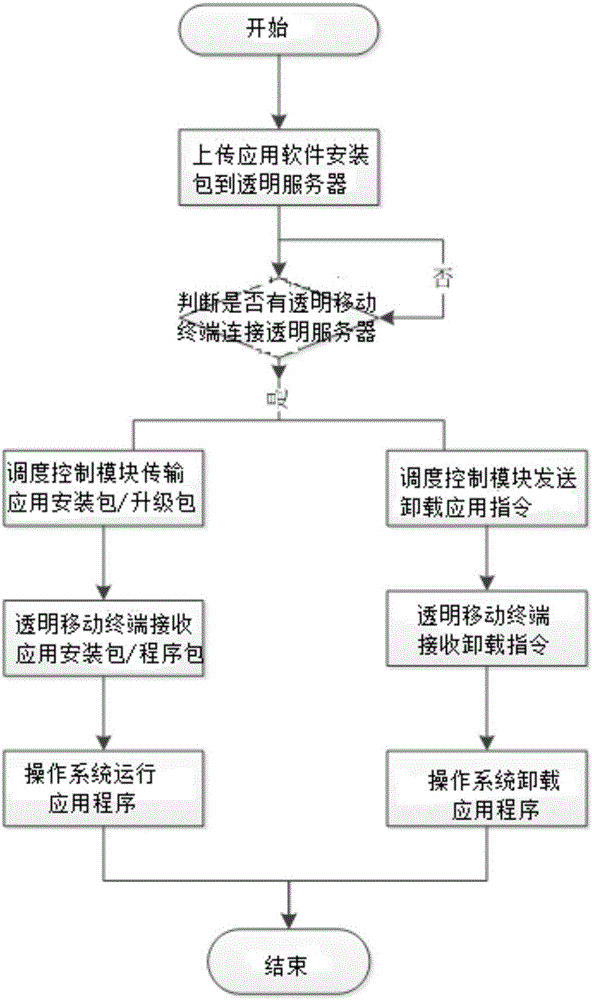
Mobile terminal application management method and system based on transparent computing
InactiveCN107528918AImprove management efficiencyImprove experienceProgram loading/initiatingTransmissionProgram managementComputer module
The invention provides a mobile terminal application management method and system based on transparent computing. The mobile terminal application management method based on the transparent computing comprises the following steps: S1, a transparent server stores the application installation package or the upgrade package in the application database through a scheduling control module; S2, the transparent server scanning transparent mobile terminals connected with the transparent server; and S3, if the transparent mobile terminal connected with the transparent server is scanned by the transparent server in the step S2, the installation, upgrading, and uninstall of the applications requiring management in the operation system of transparent mobile terminals connected with the transparent server is realized through the scheduling control module. The invention can realize the unified installation, uninstall, upgrading and other operations for the application required by the same mobile terminal in the same place through a transparent server, and the invention is based on the transparent computing framework, therefore, the management efficiency is high, and the management is convenient and quick; and the applications in the same mobile terminal is managed by a transparent server uniformly, therefore, the personnel management cost and the maintenance cost is greatly saved.
Owner:HUNAN NEW CLOUDNET TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com