Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
338 results about "Cloud architecture" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
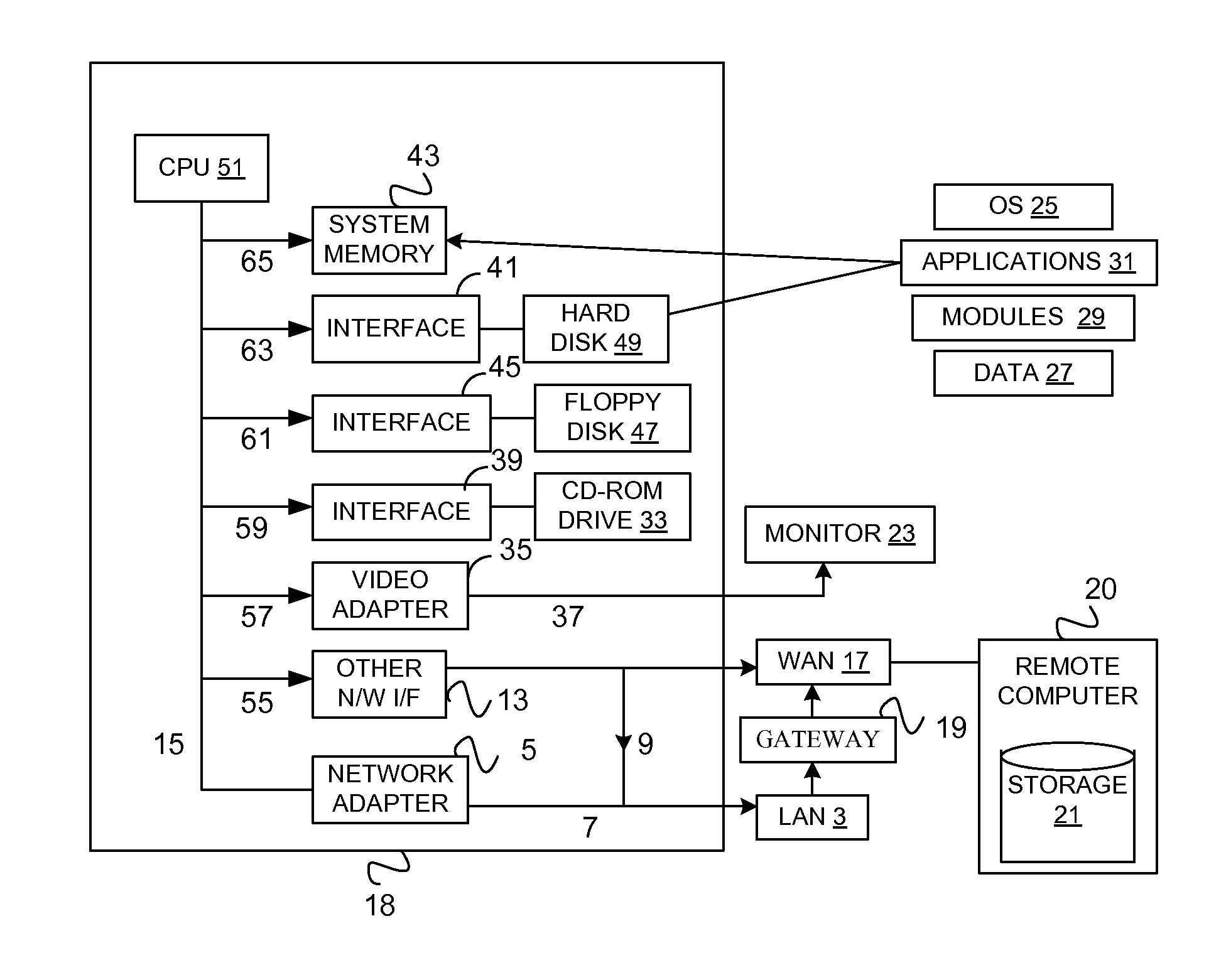
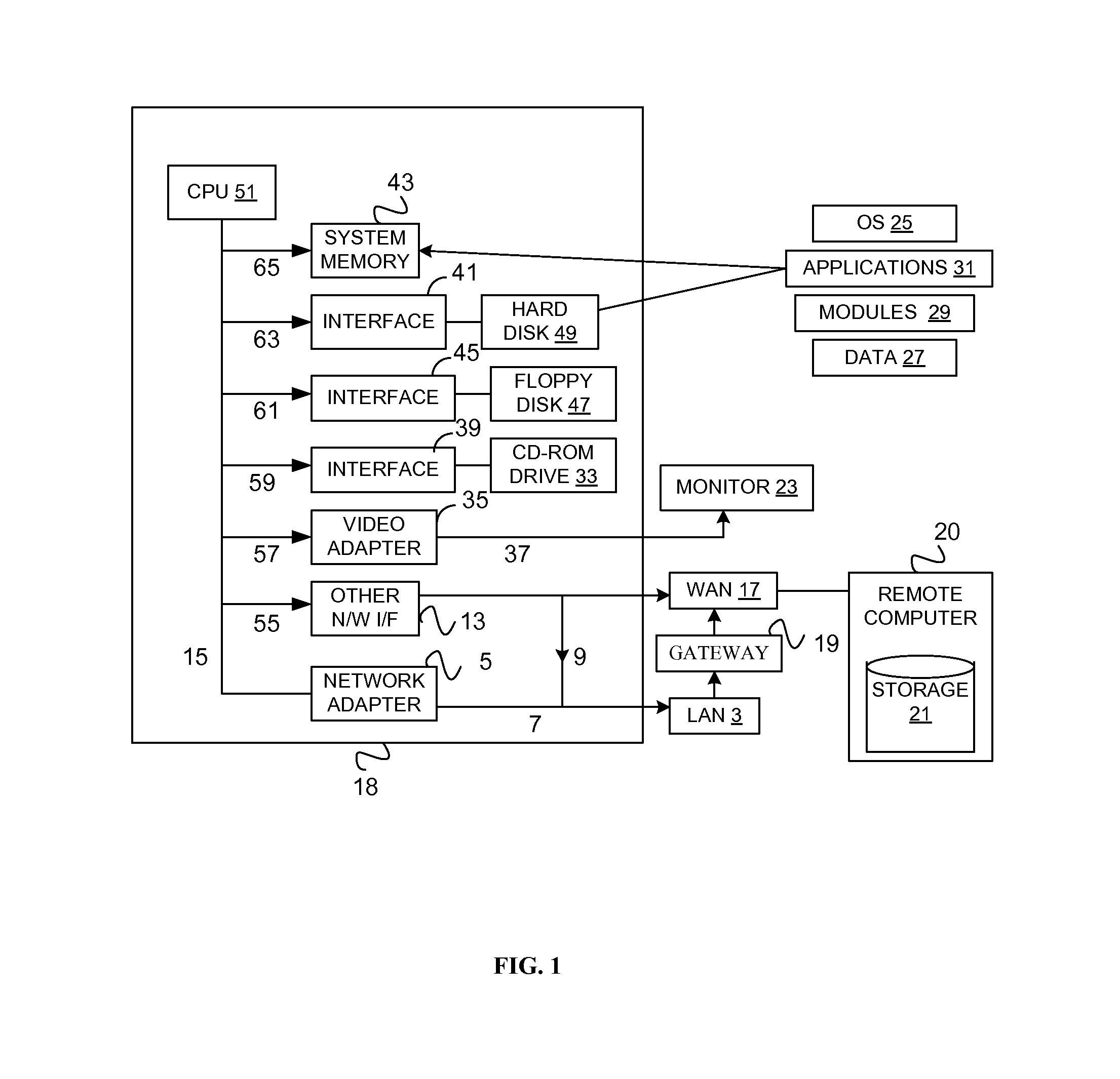
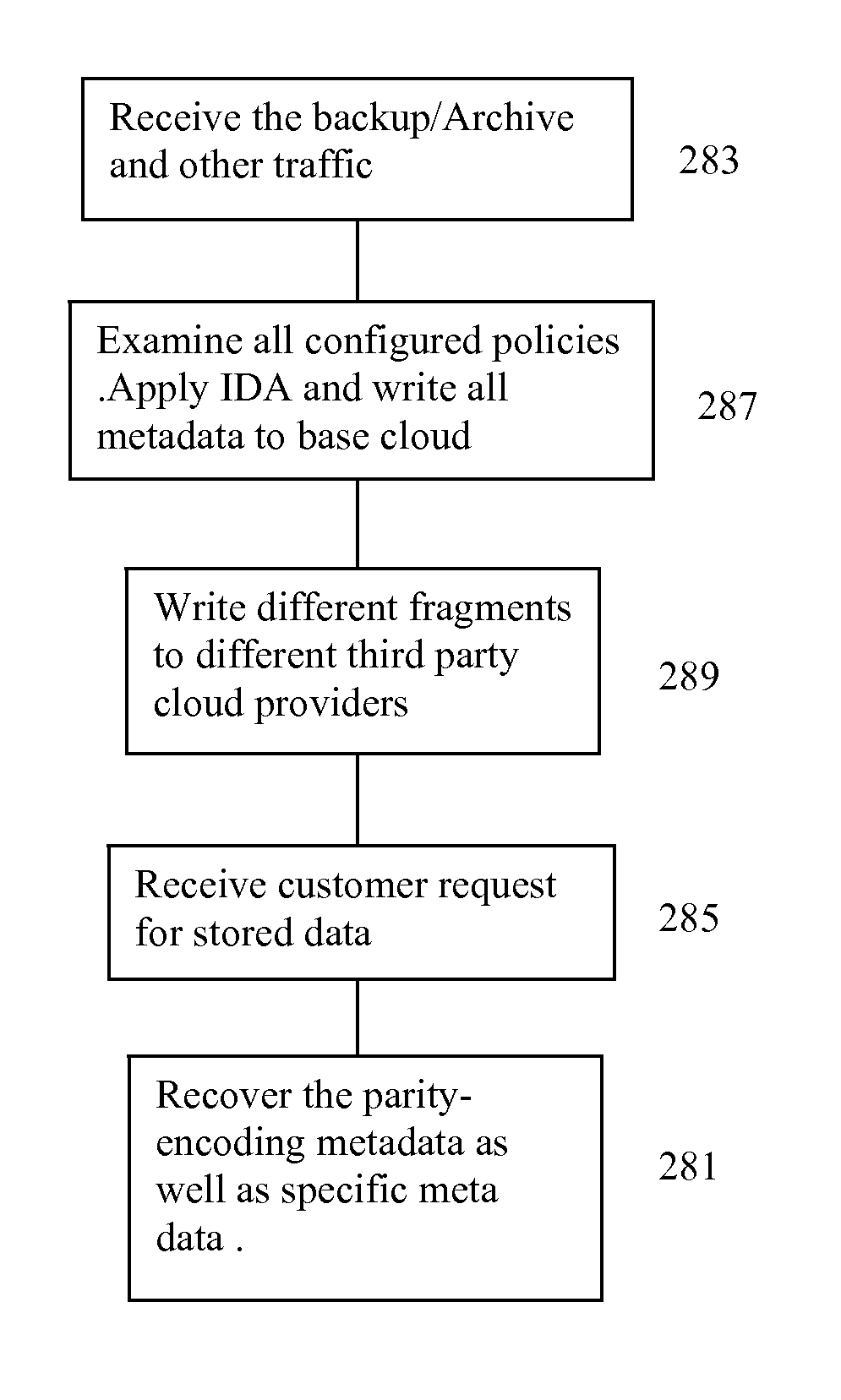
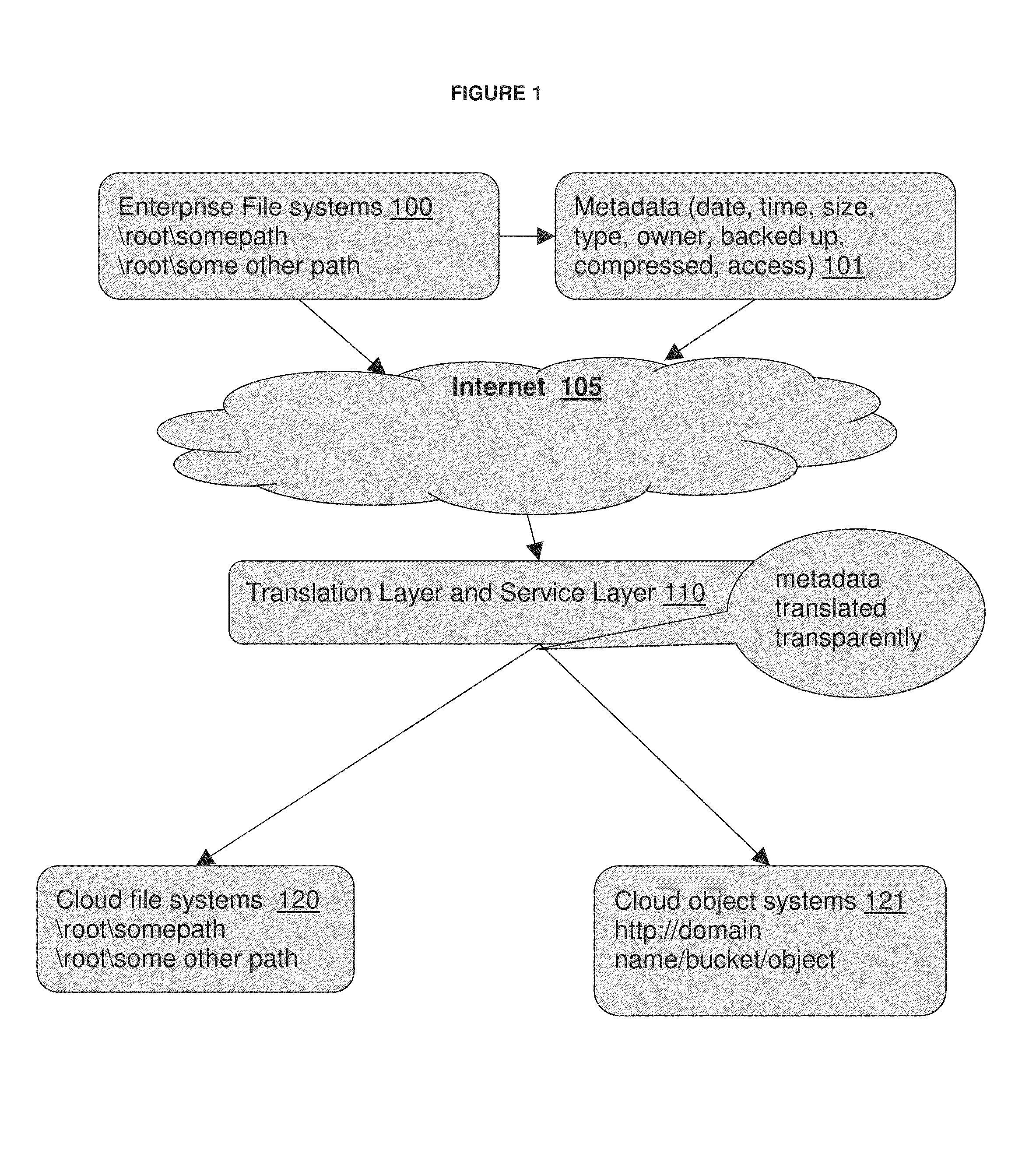
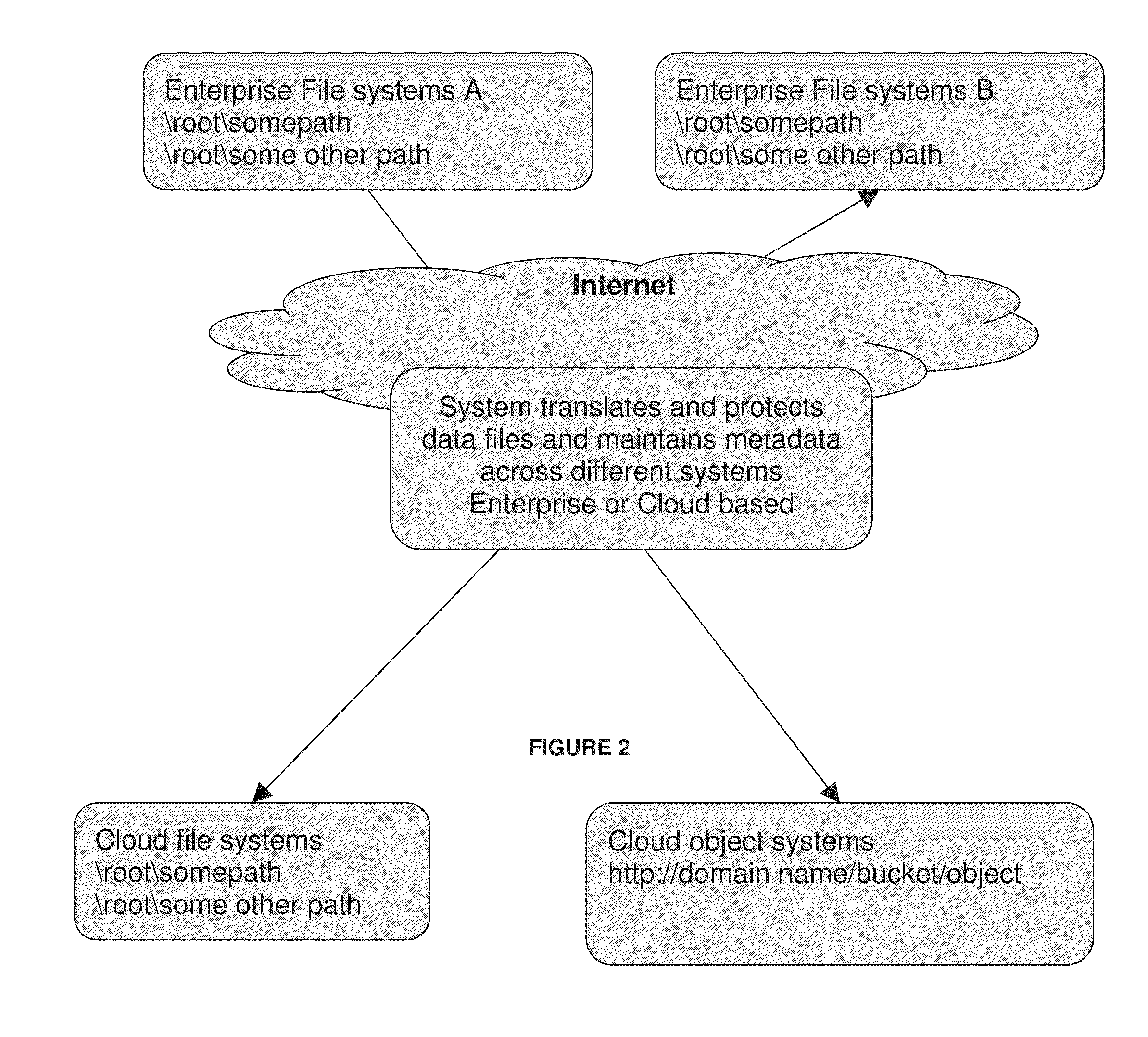
Distributed virtual storage cloud architecture and a method thereof
ActiveUS20130204849A1Prevent lockInput/output to record carriersDigital data information retrievalThird partyVirtualization
The present disclosure relates to a distributed information storage system which functions as virtual cloud storage overlay on top of physical cloud storage systems. The disclosure discloses transparently solving all the data management related security, virtualization, reliability and enables transparent cloud storage migration, cloud storage virtualization, information dispersal and integration across disparate cloud storage devices operated by different providers or on-premise storage. The cloud storage is owned or hosted by same or different third-party providers who own the information contained in the storage which eliminates cloud dependencies. This present disclosure functions as a distributed cloud storage delivery platform enabling various functionalities like cloud storage virtualization, cloud storage integration, cloud storage management and cloud level RAID.
Owner:CHACKO PETER
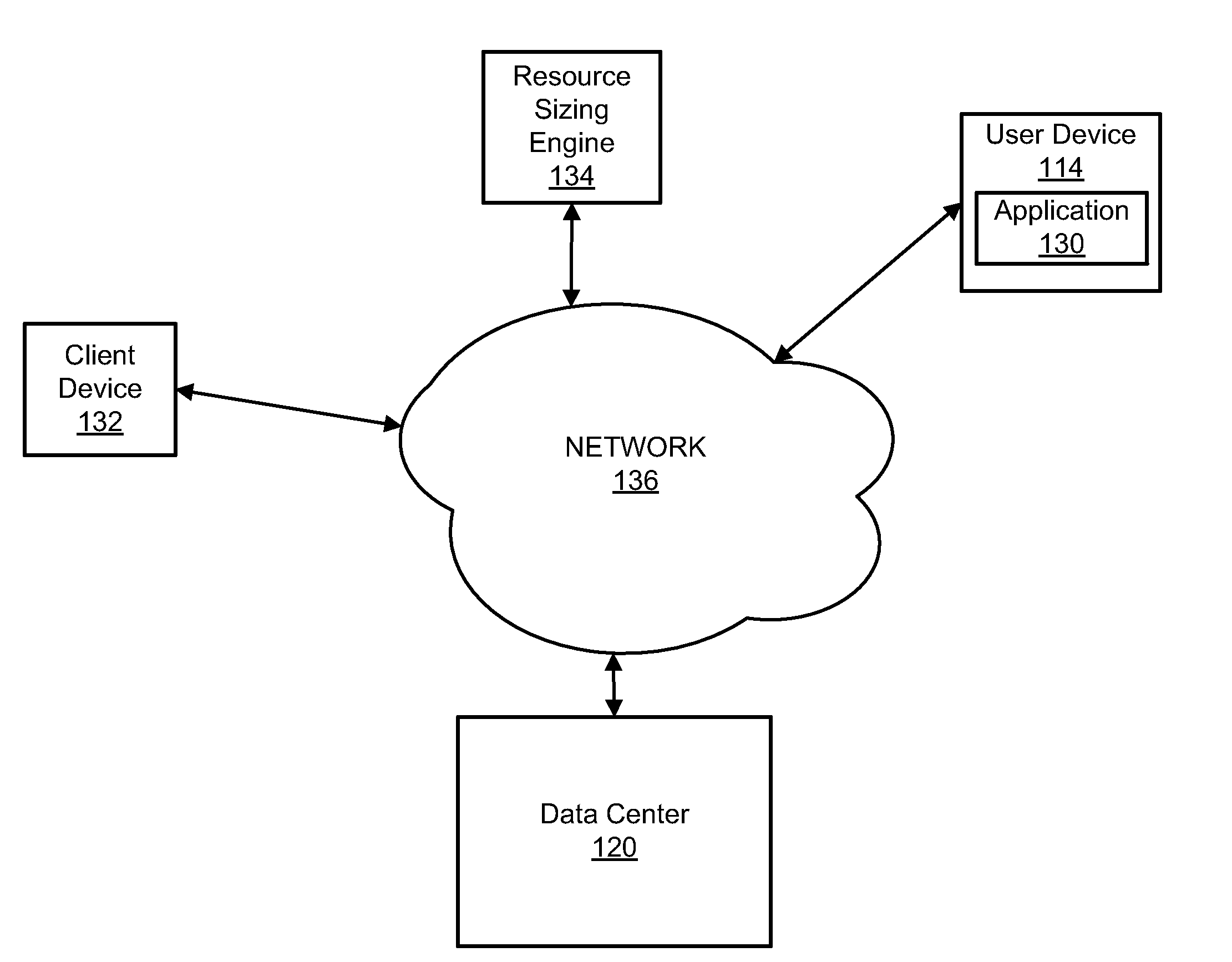
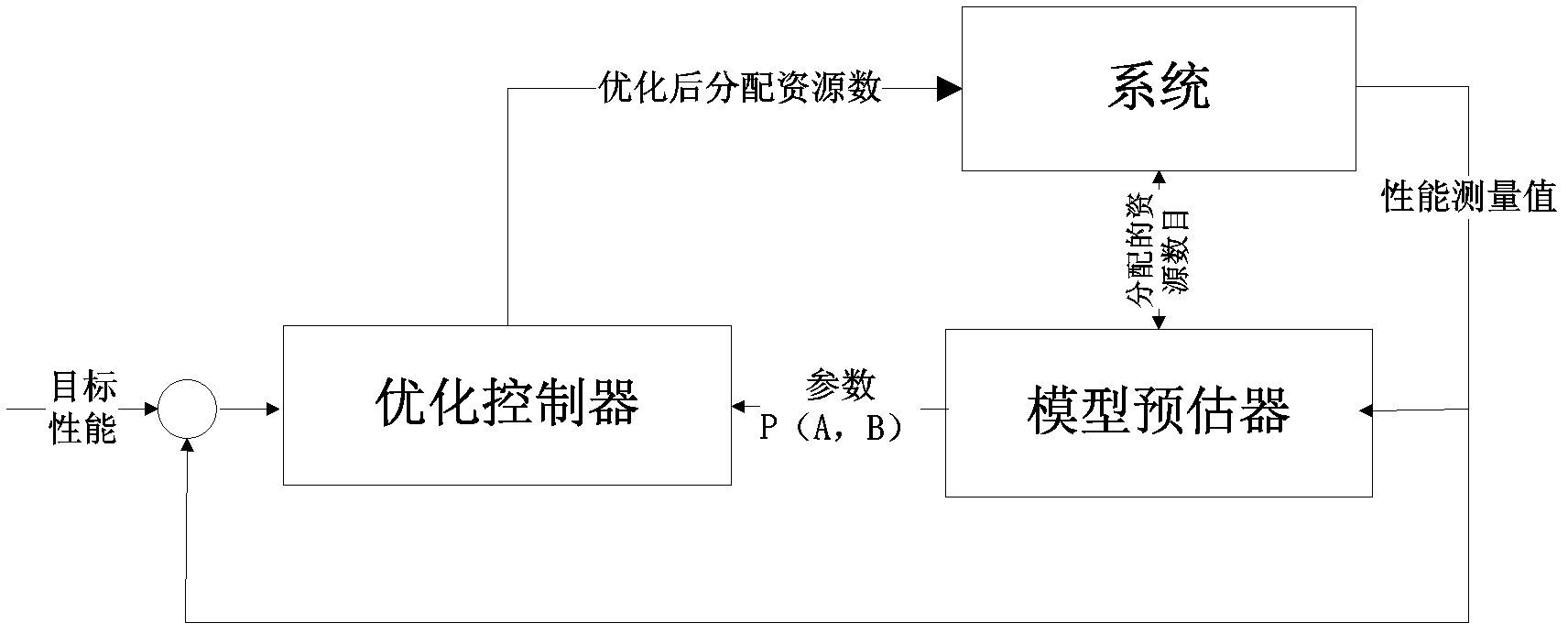
Systems and methods for sizing resources in a cloud-based environment
InactiveUS20120233315A1Well formedDigital computer detailsProgram controlQuality of serviceData center
Systems and methods for sizing resources in a cloud-based environment are provided. In an exemplary embodiment, a method includes receiving quality of service requirements and a functional description of a cloud architecture associated with the application, including application resources and relations between the application resources, performing latency analysis of data packets in a compute layer of the cloud architecture, with the latency analysis including comparing size per time metrics of the data packets, determining minimal resources to guarantee the quality of service requirements based on the latency analysis and the quality of service requirements, and providing to the data center the minimal resources.
Owner:JOYENT
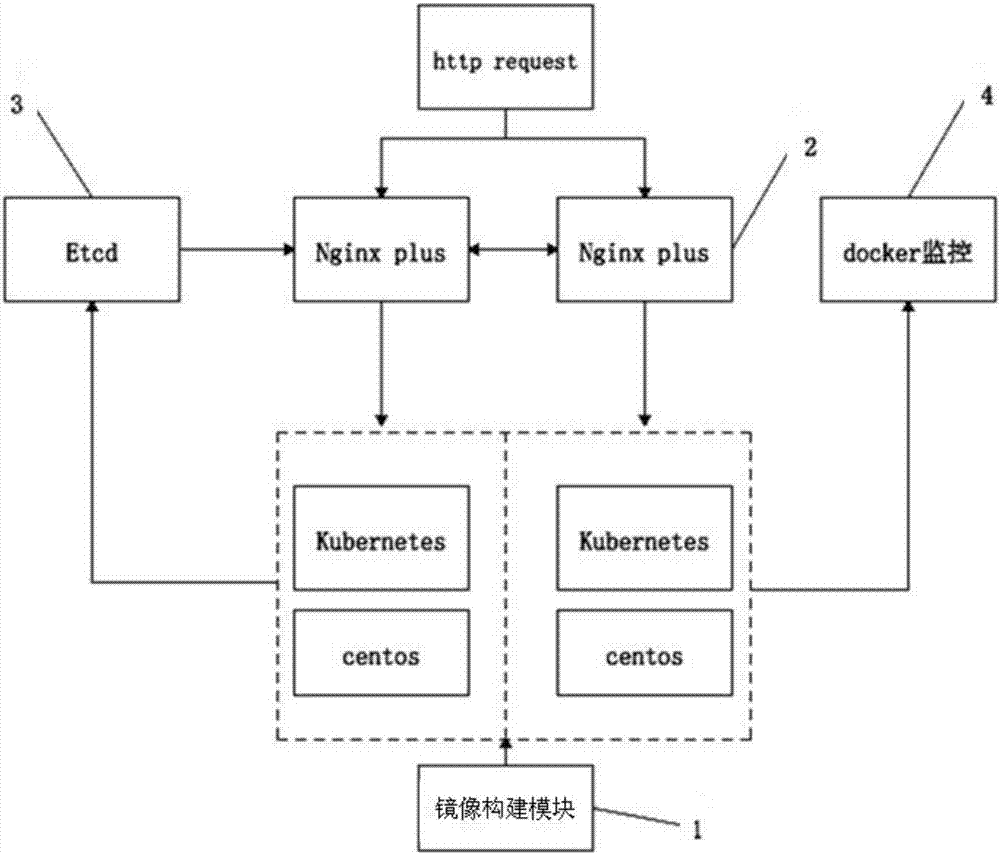
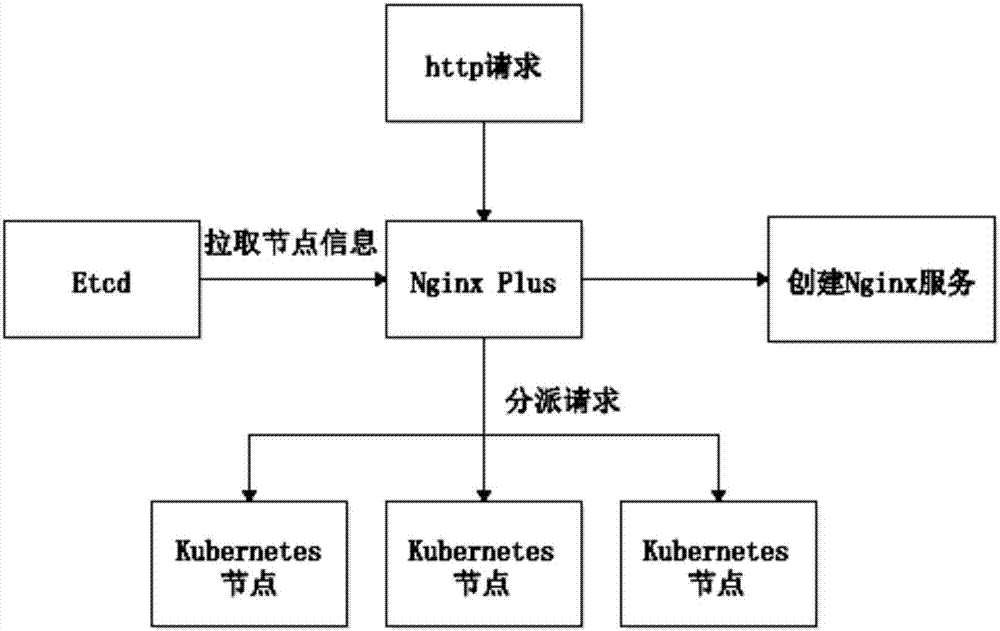
Kubernetes based capacitor cloud configuration and interaction method among modules of cloud configuration
ActiveCN106888254ASolve communication problemsEasy to createData switching networksData warehouseHigh availability
The invention discloses a Kubernetes based capacitor cloud configuration and an interaction method among modules of cloud configuration. The Kubernetes based capacitor cloud configuration comprises a processor, and a mirror image construction module, a data warehouse module, a load balancing module, a service discovery module and a container monitoring module connected with the processor; the mirror image construction module provides mirror image file making, storing and distributing services; the data warehouse module stores and processes data in a database of a cluster; the load balancing module carries out load balancing on calculating nodes in the Kubernetes cluster; the service discovery module obtains information of dynamic change of the calculating nodes in the Kubernetes cluster; and the container monitoring module collects and displays information of motion state of the calculating nodes in the Kubernetes cluster. The cloud configuration and the interaction method can be applied to container systems which need high availability and expansibility conveniently.
Owner:广州陆盛智能科技有限公司
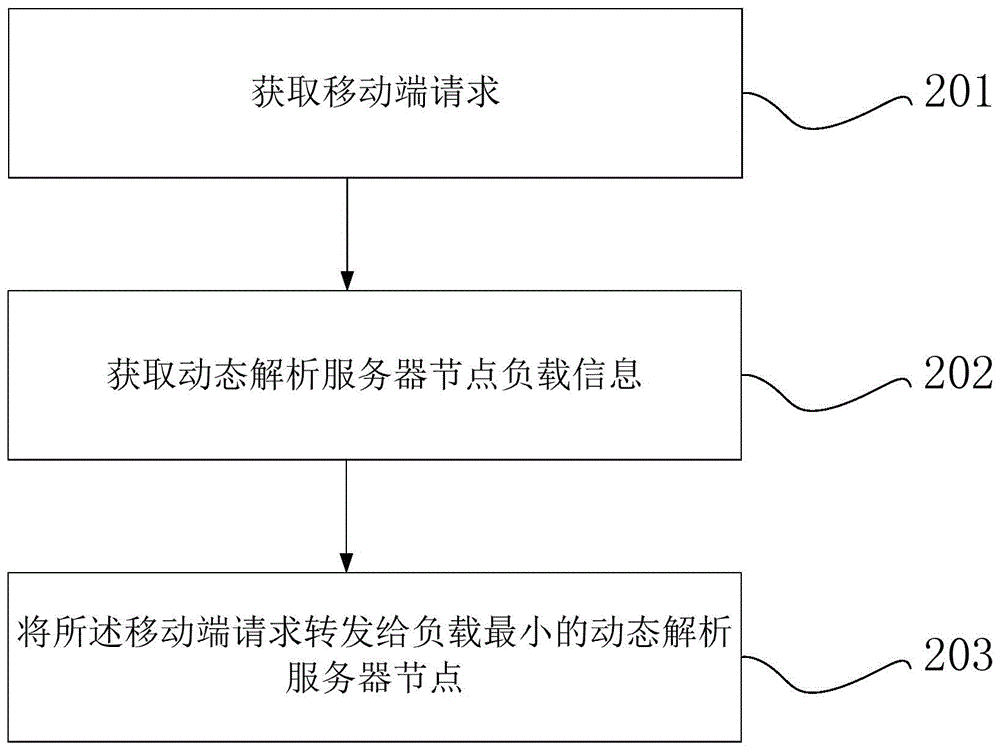
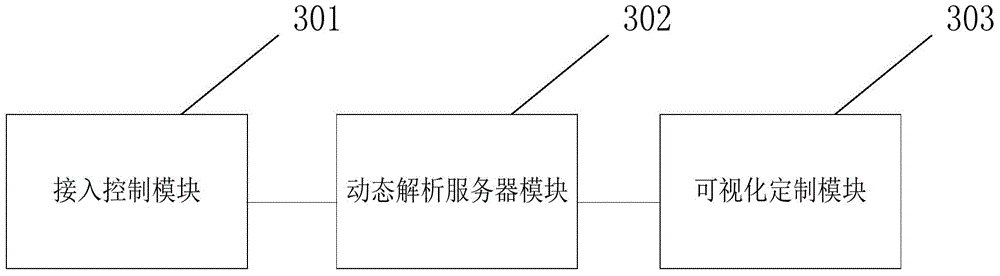
Self-adaptive method and system based on cloud architecture
The invention provides a self-adaptive method and a system based on a cloud architecture. The method comprises the following steps of obtaining a mobile terminal request, and forwarding the mobile terminal request to a dynamic analysis server; enabling the dynamic analysis server to obtain the requested network webpage data according to the mobile terminal request, and dynamically analyzing the network webpage data, so as to obtain a dynamic analysis result; utilizing the analysis result to obtain a webpage service function fragment in a network webpage, and generating network slices; regrouping the network slices, generating the regrouped network webpage data, and sending the regrouped network webpage data to a mobile terminal.
Owner:BEIJING HANDSCAPE TECH
Dynamic quality of service in edge cloud architectures
ActiveUS20190140933A1Network traffic/resource managementData switching networksQuality of serviceAccess network
A device of a service coordinating entity includes communications circuitry to communicate with a plurality of access networks via a corresponding plurality of network function virtualization (NFV) instances, processing circuitry, and a memory device. The processing circuitry is to perform operations to monitor stored performance metrics for the plurality of NFV instances. Each of the NFV instances is instantiated by a corresponding scheduler of a plurality of schedulers on a virtualization infrastructure of the service coordinating entity. A plurality of stored threshold metrics is retrieved, indicating a desired level for each of the plurality of performance metrics. A threshold condition is detected for at least one of the performance metrics for an NFV instance of the plurality of NFV instances, based on the retrieved plurality of threshold metrics. A hardware resource used by the NFV instance to communicate with an access network is adjusted based on the detected threshold condition.
Owner:INTEL CORP
Website security monitoring method based on cloud architecture
ActiveCN103685575AImprove securityReduce lossesData switching networksComplex event processingSecurity monitoring
The invention discloses a website security monitoring method based on a cloud architecture. The event is used as the drive, and the cloud architecture is used as the support, so as to support the centralized monitoring early-alarming of massive websites and the quick response processing of each event; the 24-hour security event automatic monitoring and alarming is carried out on various websites, so as to cooperate with operation and maintenance monitoring personnel to implement manual analysis and event processing on the security events. Through the 24-hour cooperation of the website security monitoring and event operation and maintenance monitoring personnel, the latest real security events in the website can be timely monitored, so a user can timely process various major security events, and reduce the loss and risk caused by various security events.
Owner:洪高颖
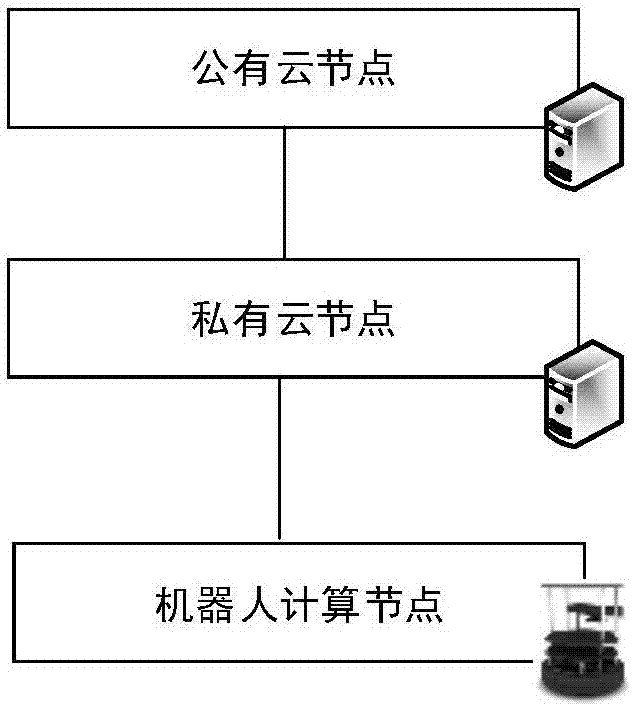
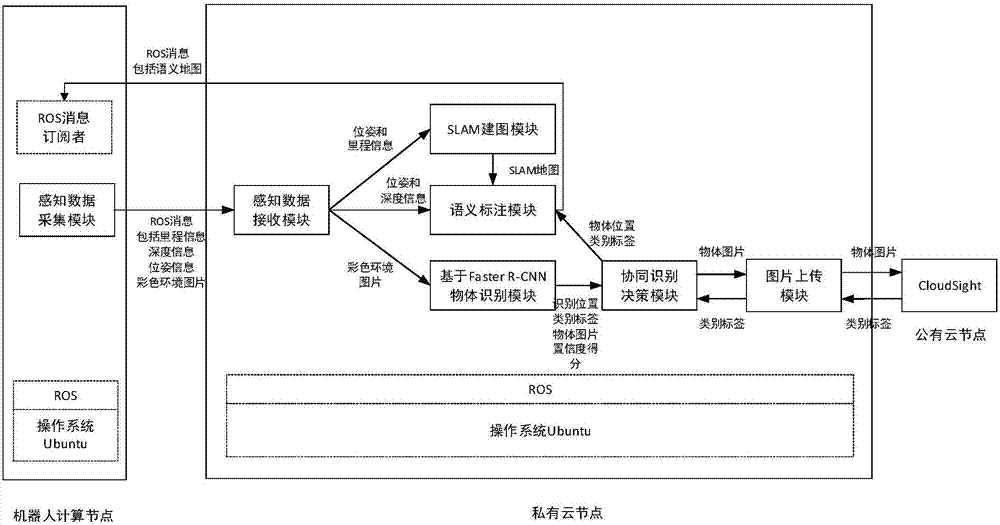
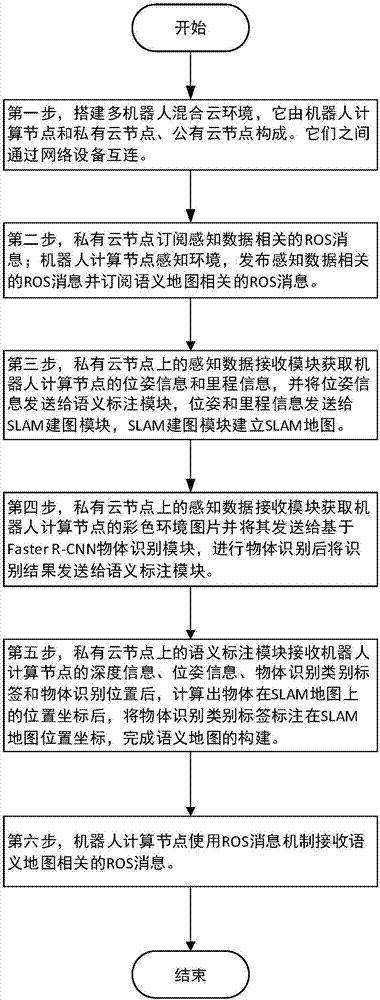
Semantic map construction method based on cloud robot mixed cloud architecture
ActiveCN107066507AReduce computing loadImprove accuracyCharacter and pattern recognitionGeographical information databasesComputer scienceSemantic map
The invention discloses a semantic map construction method based on cloud robot mixed cloud architecture, and aims to achieve a proper balance for improving object identification accuracy and shortening identification time. The technical scheme of the method is that mixed cloud consisting of a robot, a private cloud node and a public cloud node is constructed, wherein the private cloud node obtains an environment picture shot by the robot and milemeter and position data on the basis of an ROS (Read-Only-Storage) message mechanism, and SLAM (Simultaneous Location and Mapping) is used for drawing an environmental geometric map in real time on the basis of the milemeter and position data. The private cloud node carries out object identification on the basis of an environment picture, and an object which may be wrongly identified is uploaded to the public cloud node to be identified. The private cloud node maps an object category identification tag returned from the public cloud node and an SLAM map, and the corresponding position of the object category identification tag on a map finishes the construction of a semantic map. When the method is adopted, the local calculation load of the robot can be lightened, request response time is minimized, and object identification accuracy is improved.
Owner:NAT UNIV OF DEFENSE TECH
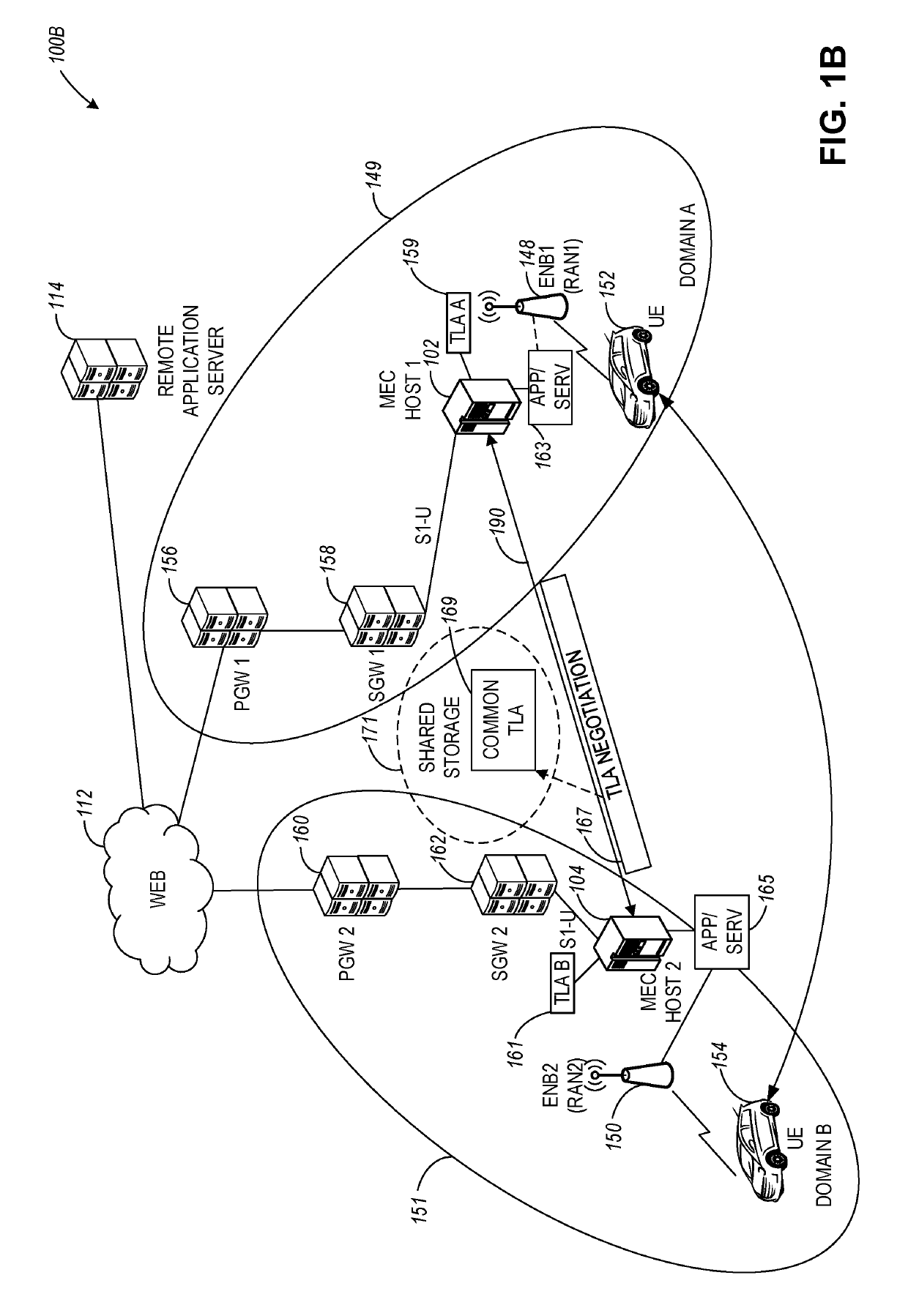
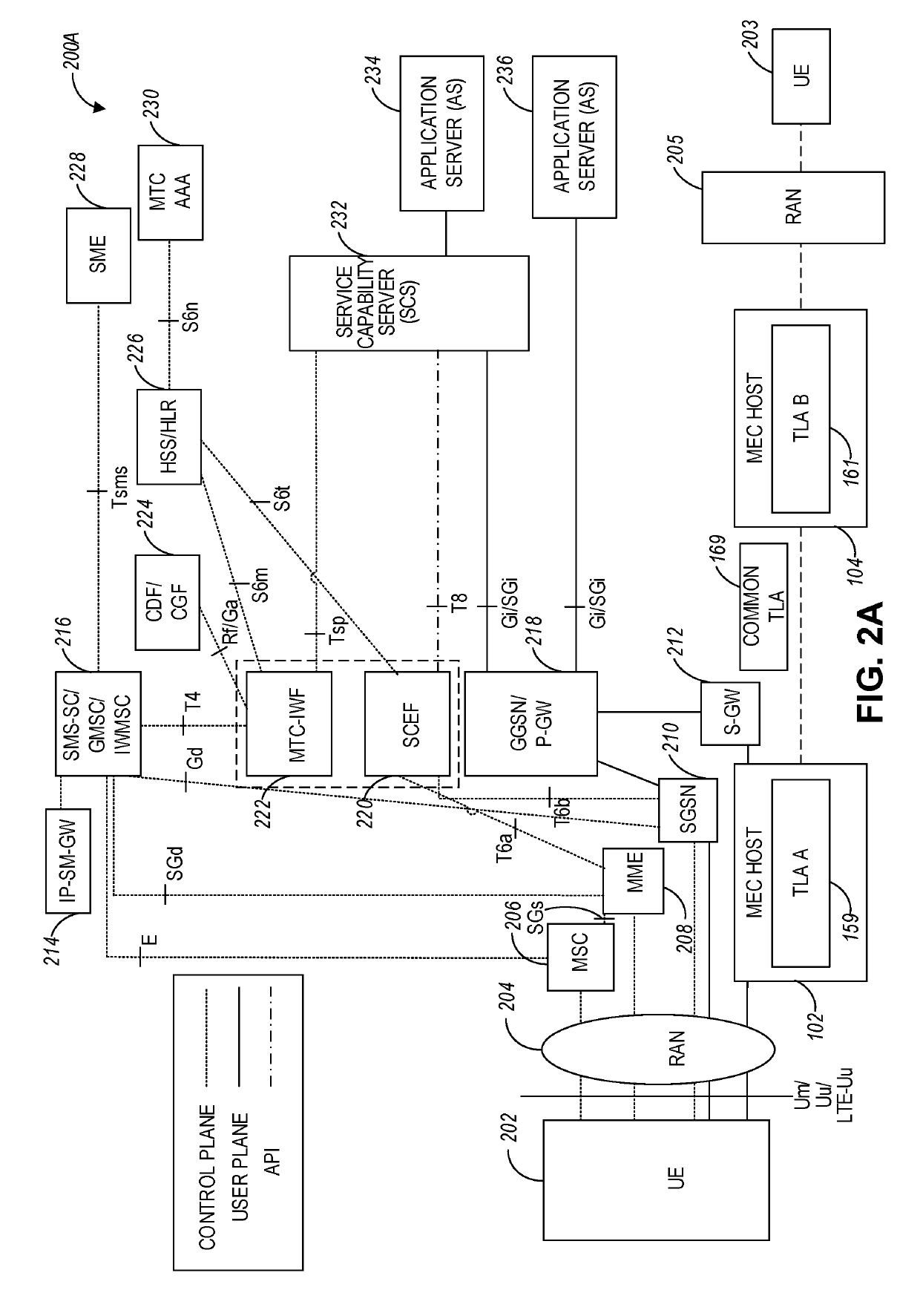
Multi-domain trust establishment in edge cloud architectures
ActiveUS20190141536A1Network traffic/resource managementParticular environment based servicesAccess networkTrust level
A service coordinating entity device includes communications circuitry to communicate with a first access network, processing circuitry, and a memory device. The processing circuitry is to perform operations to, in response to a request for establishing a connection with a user equipment (UE) in a second access network, retrieve a first Trusted Level Agreement (TLA) including trust attributes associated with the first access network. One or more exchanges of the trust attributes of the first TLA and trust attributes of a second TLA associated with the second access network are performed using a computing service executing on the service coordinating entity. A common TLA with trust attributes associated with communications between the first and second access networks is generated based on the exchanges. Data traffic is routed from the first access network to the UE in the second access network based on the trust attributes of the common TLA.
Owner:INTEL CORP
Remote industrial monitoring using a cloud infrastructure
ActiveCN103685442AMathematical modelsTesting/monitoring control systemsMessage queueIndustrial monitoring
The invention discloses a remote industrial monitoring using a cloud infrastructure. A cloud-based infrastructure facilitates gathering, transmitting, and remote storage of control and automation data using an agent-based communication channel. The infrastructure collects the industrial data from an industrial enterprise and intelligently sorts and organizes the acquired data based on selected criteria. Message queues can be configured on the cloud platform to segregate the industrial data according to priority, data type, or other criteria. Behavior assemblies stored in customer-specific manifests on the cloud platform define customer-specific preferences for processing data stored in the respective message queues. Web-based tools can deliver automated notifications to an end user device based on analysis of the stored data, and allow the user to remotely view the stored data.
Owner:ROCKWELL AUTOMATION TECH
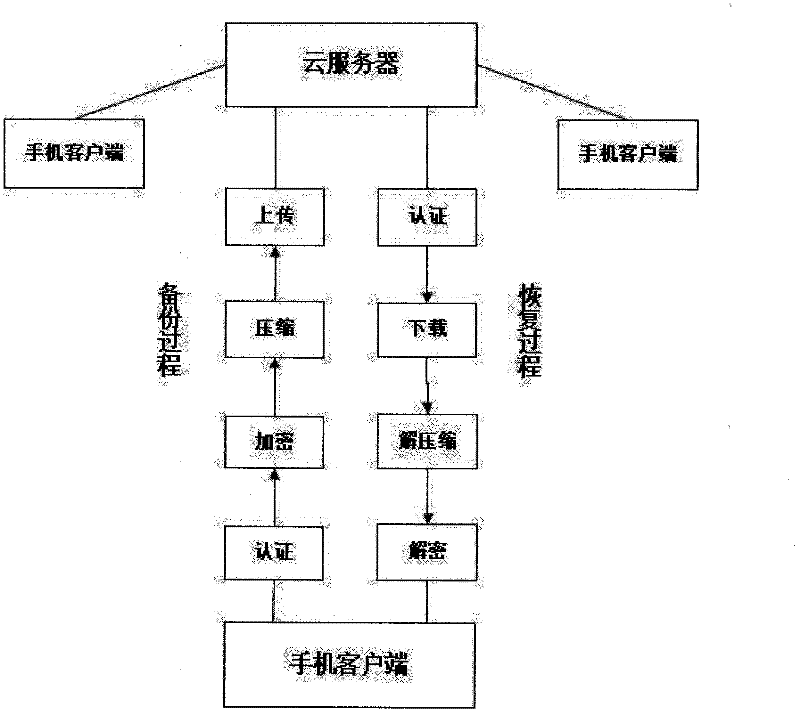
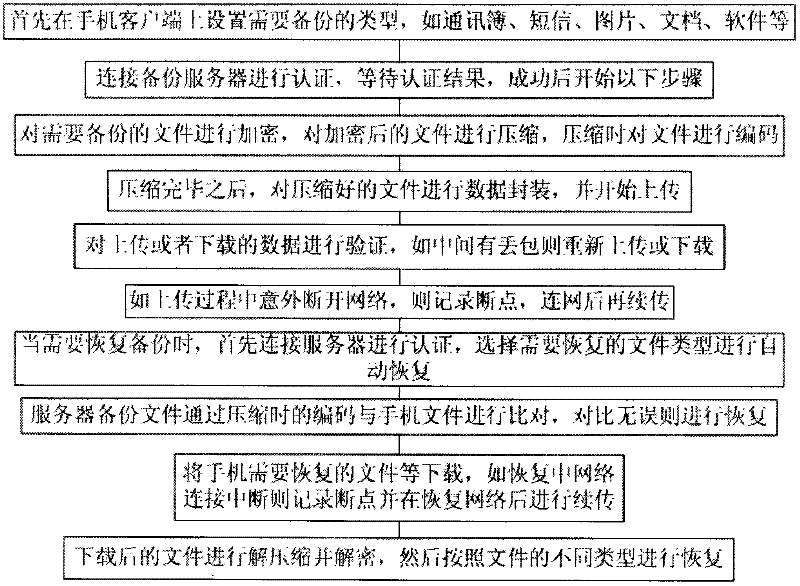
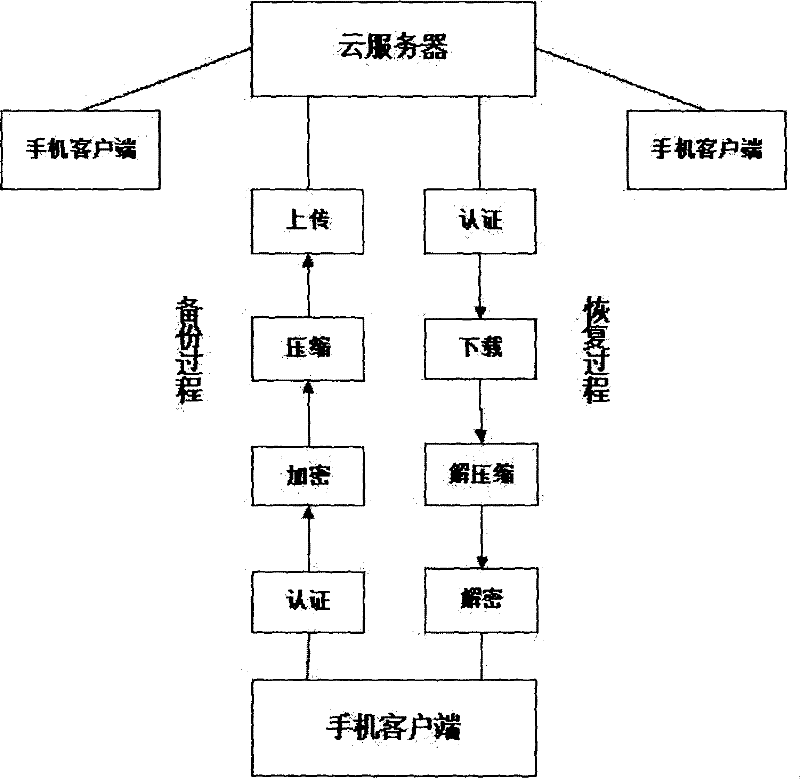
Mobile phone cloud encryption backup and recovery method based on cloud architecture
InactiveCN102638565AData transmission is completeTransmissionSecurity arrangementComputer hardwareRecovery method
The invention discloses a mobile phone cloud encryption backup and recovery method based on a cloud architecture. The method comprises the following steps of: setting a type required to be backuped on a mobile phone client; connecting a backup server for authentication, waiting for an authentication result, and if the authentication is succeeded, starting the following steps: encrypting a file to be backuped, compressing the encrypted file, and encoding the file during compression; after the compression, performing data package on the compressed file, and starting to upload; and performing comparison in advance in a subsequent uploading process or downloading process. According to the method, data are uploaded to a cloud server after being encrypted and compressed; due to the functions of compression, encryption, interruption continuation and the like, the speed of transmitting the backup data is relatively high, and the data transmission is relatively secure; and even if a network is interrupted in a data transmission process, the residual data can be still transmitted.
Owner:WUXI HUASAI INFORMATION TECH
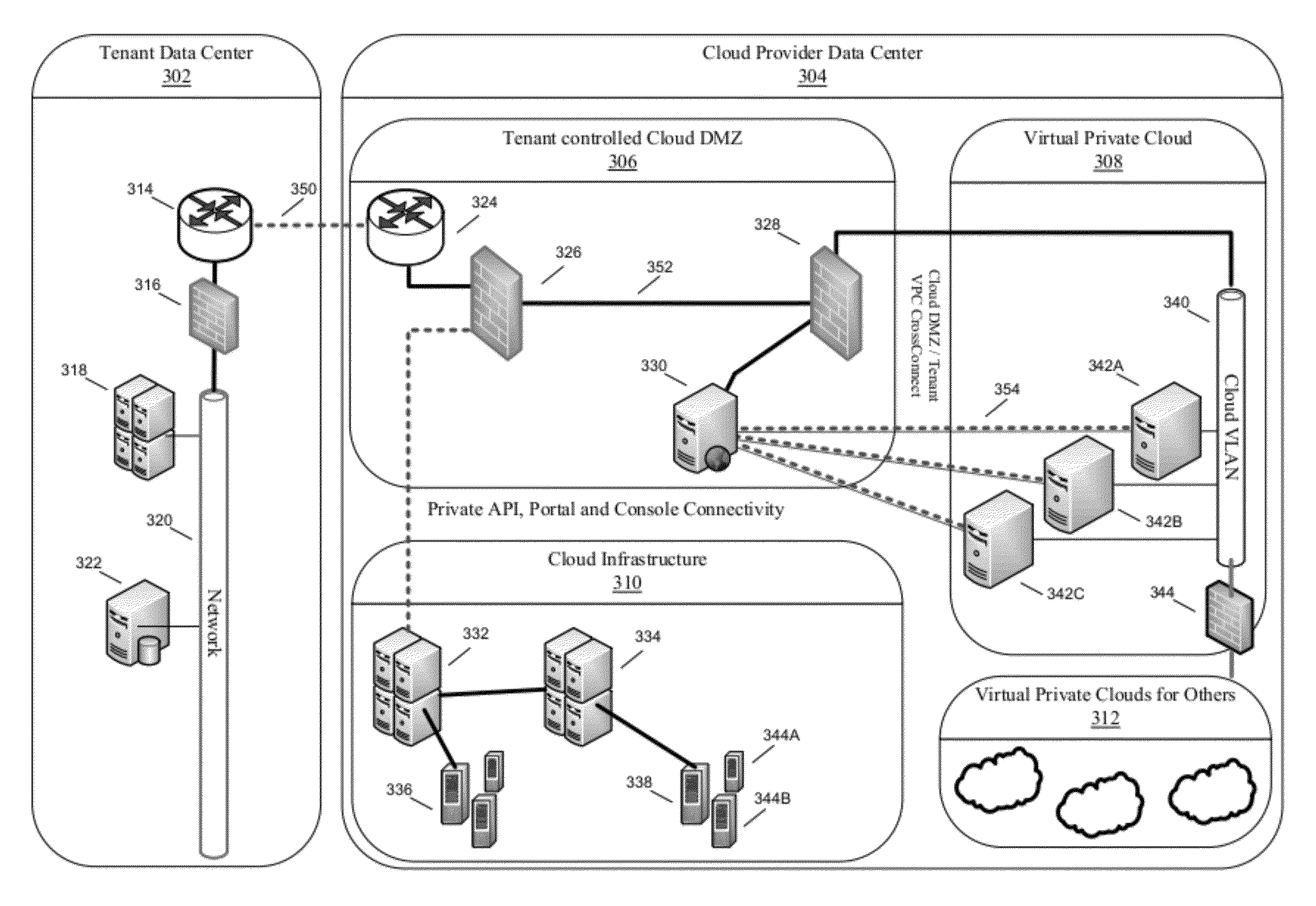
Secure network cloud architecture
ActiveUS8799997B2Digital data processing detailsMultiple digital computer combinationsSchema for Object-Oriented XMLCloud provider
Apparatuses, computer readable media, methods, and systems are described for requesting creation of virtual machine (VM) in a cloud environment comprising a virtual private cloud. Through various communications between a cloud DMZ, cloud provider, and / or company's network, a VM instance may be securely created, initialized, booted, unlocked, and / or monitored through a series of interactions building, in some examples, upon a root of trust.
Owner:BANK OF AMERICA CORP
Intelligent collaborative cloud architecture based on data driving in universal network convergence scene
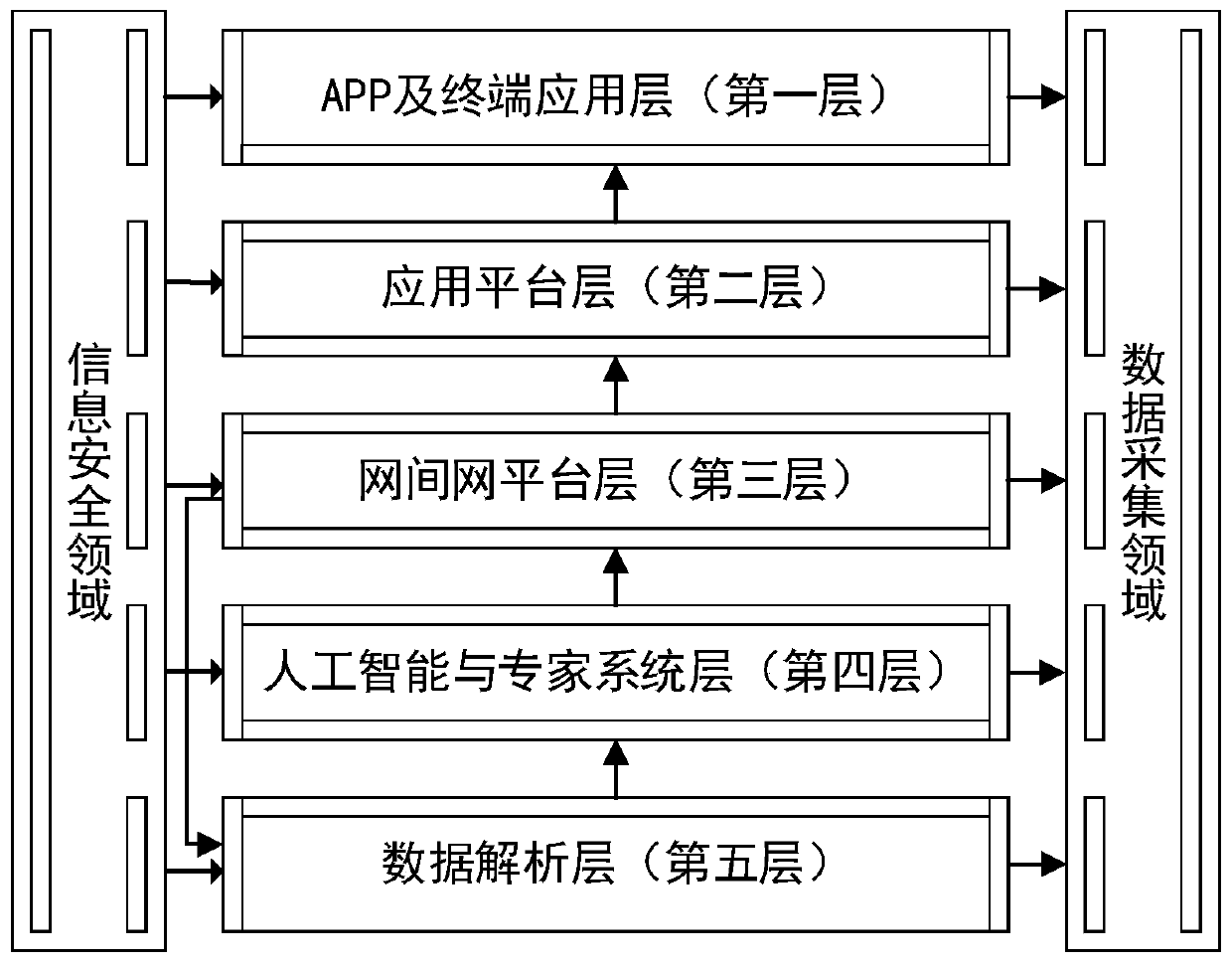
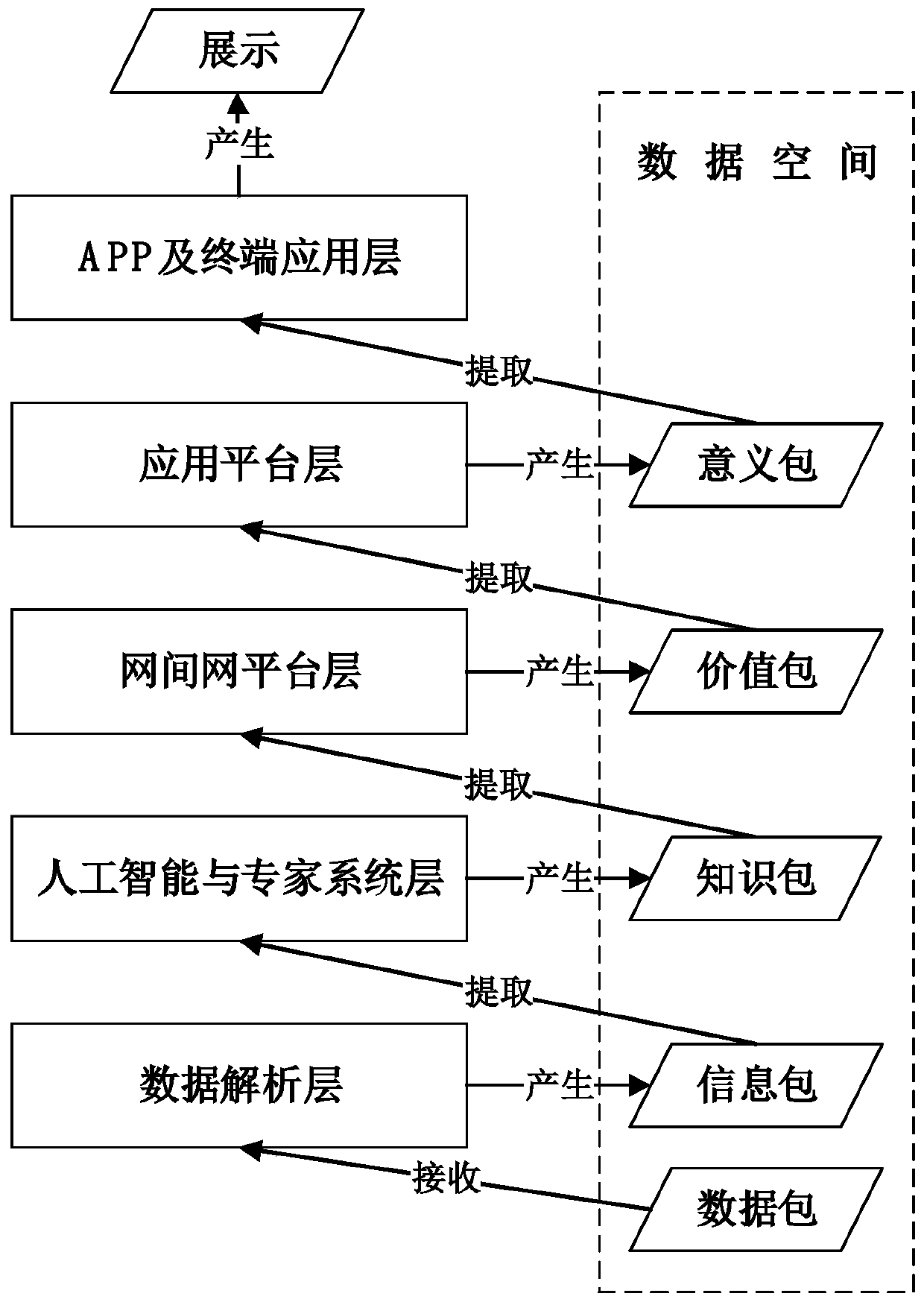
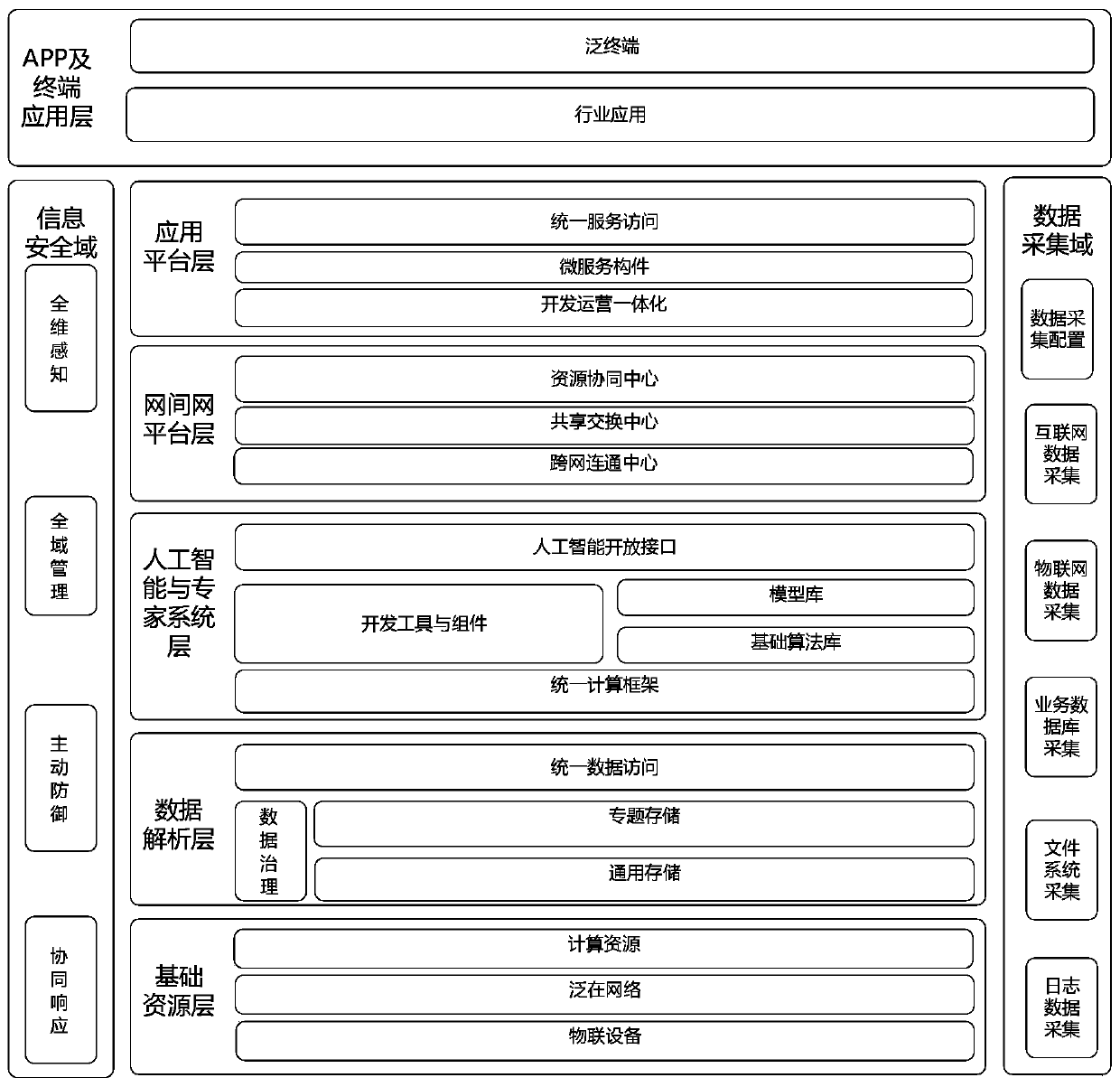
The invention relates to an intelligent collaborative cloud architecture based on data driving in a universal network convergence scene, and the architecture comprises a data analysis layer which is used for the arrangement and mining of data, and forming a primary data product for the extraction of an artificial intelligence and expert system layer; the artificial intelligence and expert system layer is used for extracting the primary data product provided by the data analysis layer and carrying out deep processing as required; the inter-network platform layer is used for providing standard specifications of data and service intercommunication; the application platform layer is used for extracting general data products from the inter-network platform layer and carrying out architecture and industry generality service support; the APP and terminal application layer is used for sending a data acquisition application to the application platform layer and acquiring a data product requiredby a user from the application platform layer; the invention relates to the field of data acquisition and is used for acquiring multivariate heterogeneous data. The intelligent collaborative cloud architecture based on data driving in the universal network integration scene can effectively solve the practical problems of cross-industry and cross-domain information resource dispersion, low utilization rate, unsmooth communication and the like.
Owner:中国长峰机电技术研究设计院
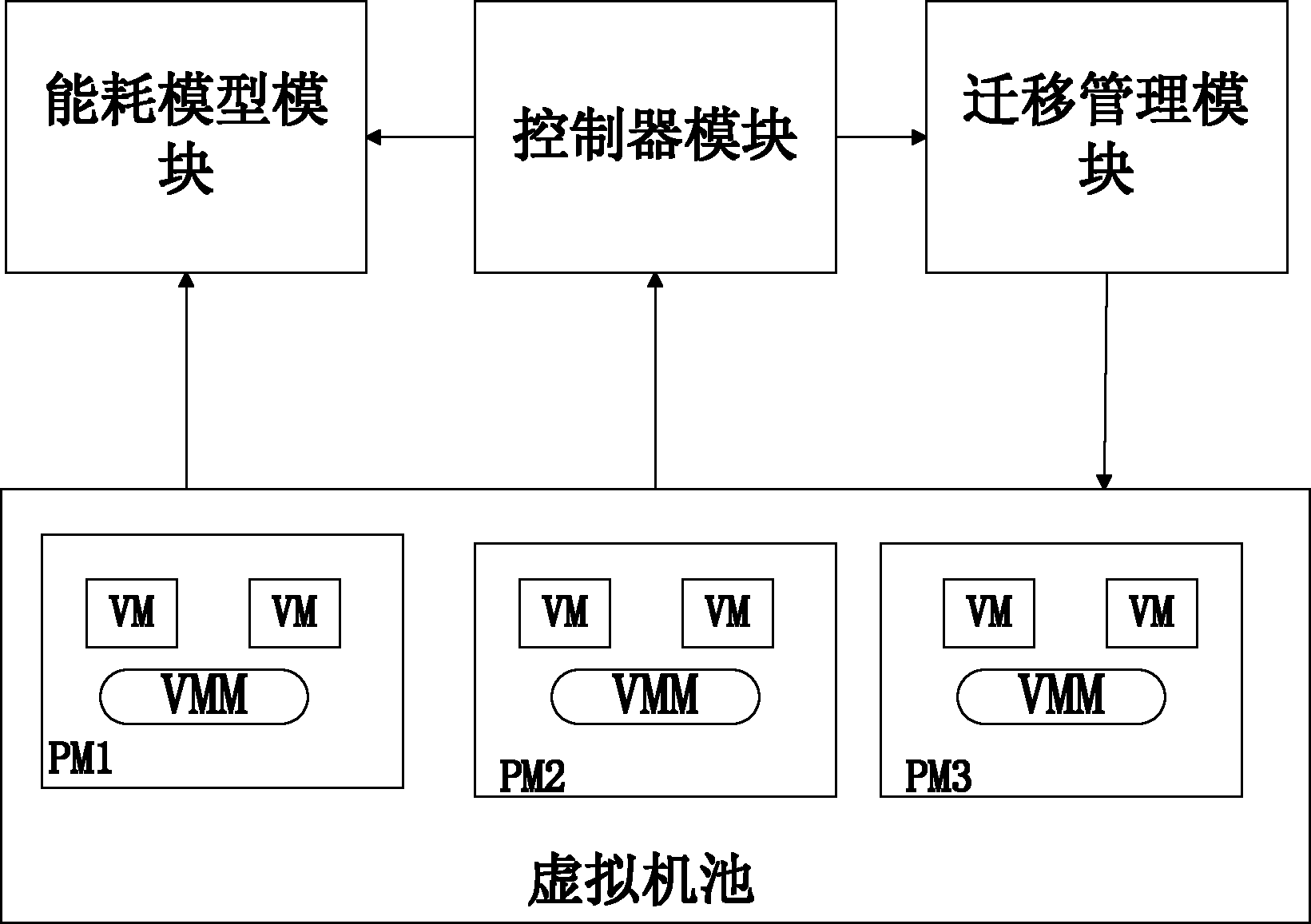
Virtual machine resource optimal control method and control system based on elastic virtual machine pool
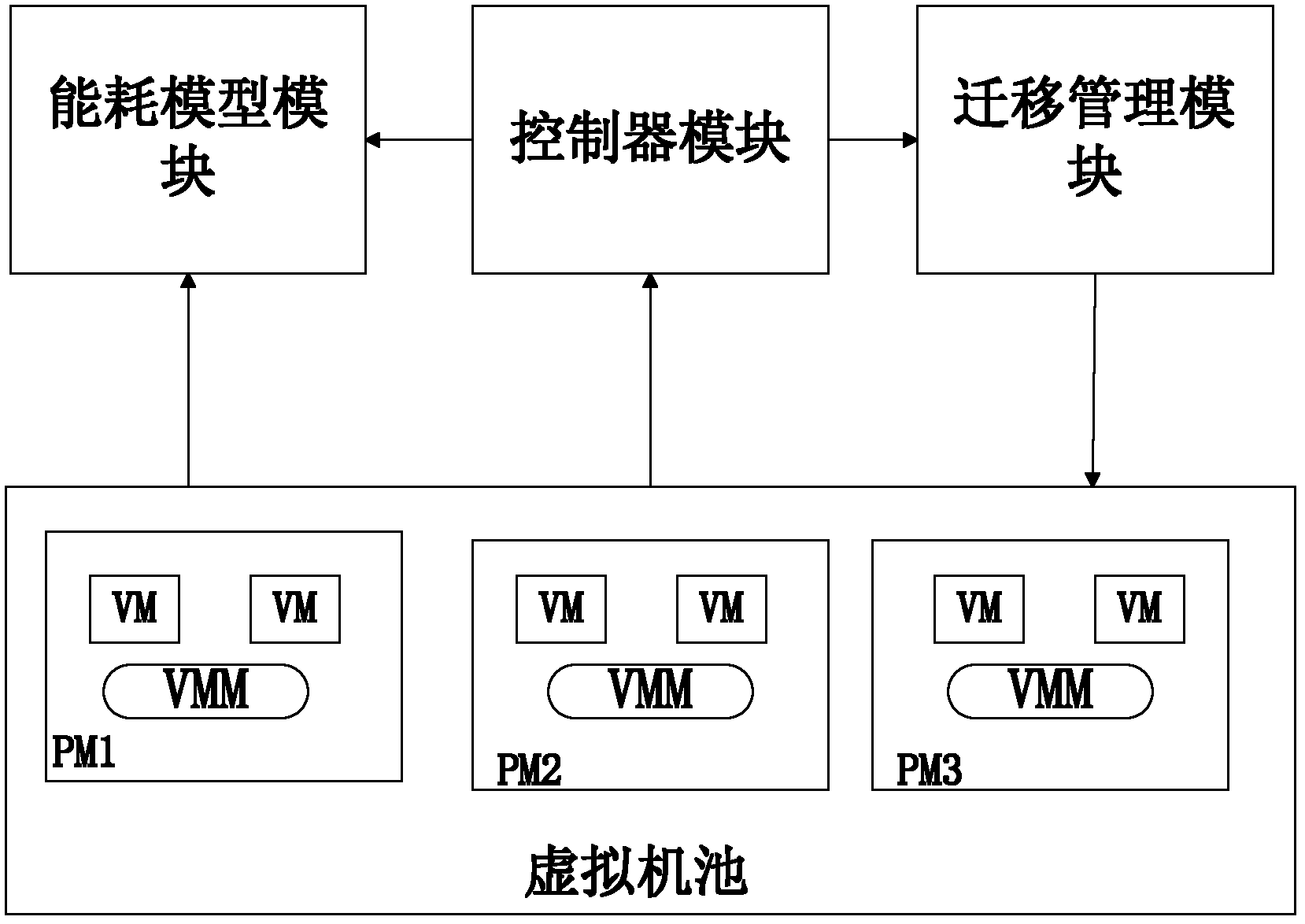
InactiveCN102662750AMigration is validSolve the problem of energy consumptionProgram initiation/switchingEnergy efficient computingResource utilizationControl system
Owner:SHANGHAI JIAO TONG UNIV
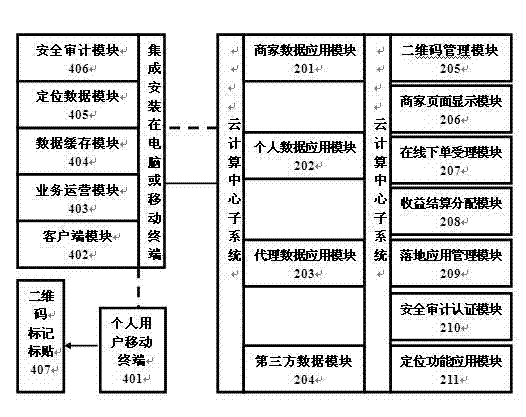
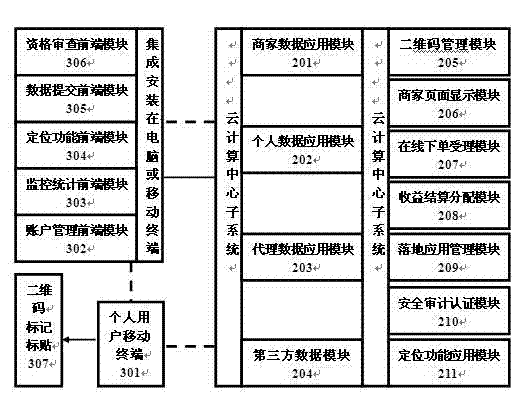
Cloud architecture system of two-dimension code application
ActiveCN103177377ARestrict popular applicationGlobalTransmissionMarketingThird partySoftware engineering
The invention discloses a cloud architecture system of two-dimension code application, relates to the relative mobile internet technology, the two-dimension code technology, the geographic positioning technology and the telecommunication technology, and provides a comprehensive cloud architecture bottom platform support and a series of solutions to two-dimension universal application. The comprehensive cloud architecture bottom platform can effectively overcome difficulties existed in current two-dimension application, and particularly solve the problems that two-dimension information data integration which cannot be realized by the prior art but is needed to be realized is effectively built up between a buyer and a user to realize combination of simple and convenient businesses. Therefore, the two-dimension code application technology can be widely applied and popularized on-line and off-line among a buyer, a user and a third-party platform.
Owner:CHONGQING ZHITAO INFORMATION TECH CENT
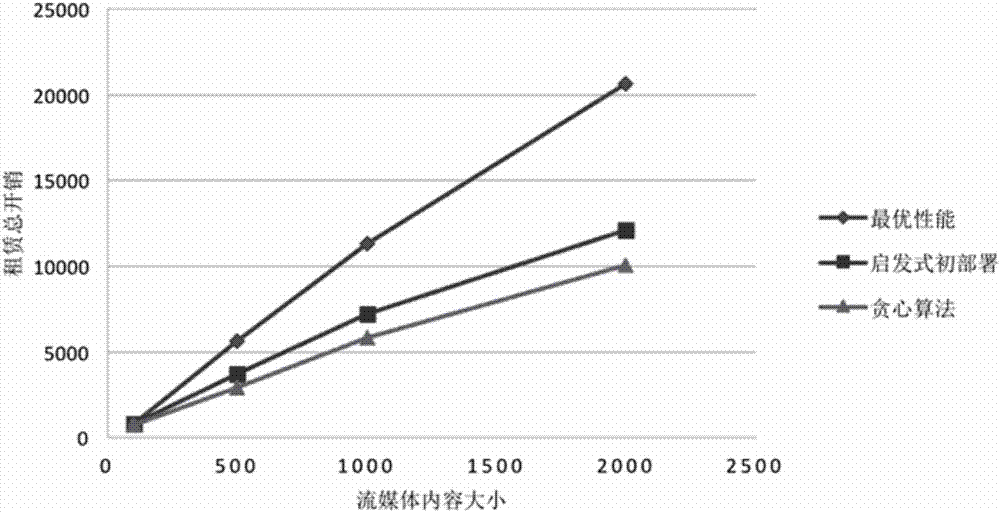
Content distribution service resource optimized dispatching method based on multi-cloud architecture
The invention belongs to the field of cloud computing and network multimedia technology, and particularly relates to a content distribution service resource optimized dispatching method based on multi-cloud architecture. The method comprises the following steps: selecting an initial deployment stage on multi-cloud, and providing a cloud selection initial deployment heuristic algorithm based on charging strategies of a plurality of candidate public service resource providers; in a multi-cloud expansion stage, providing two different multi-cloud expansion methods in a predictable ARIMA model and a cloud outburst scene; and in a multi-cloud switching stage, copying content resources in a newly started data center in batches at a delay as short as possible based on a pre-copied Precopying strategy. By adoption of the content distribution service resource optimized dispatching method, the automatic optimized deployment of a streaming media application in a multi-cloud environment is solved, when the access flow increases abruptly, the volume of the cloud architecture is smartly expanded, and when a certain private cloud data center or a certain public cloud crashes or occurs a serious bandwidth problem, how to quickly switch the cloud service is solved.
Owner:FUDAN UNIV
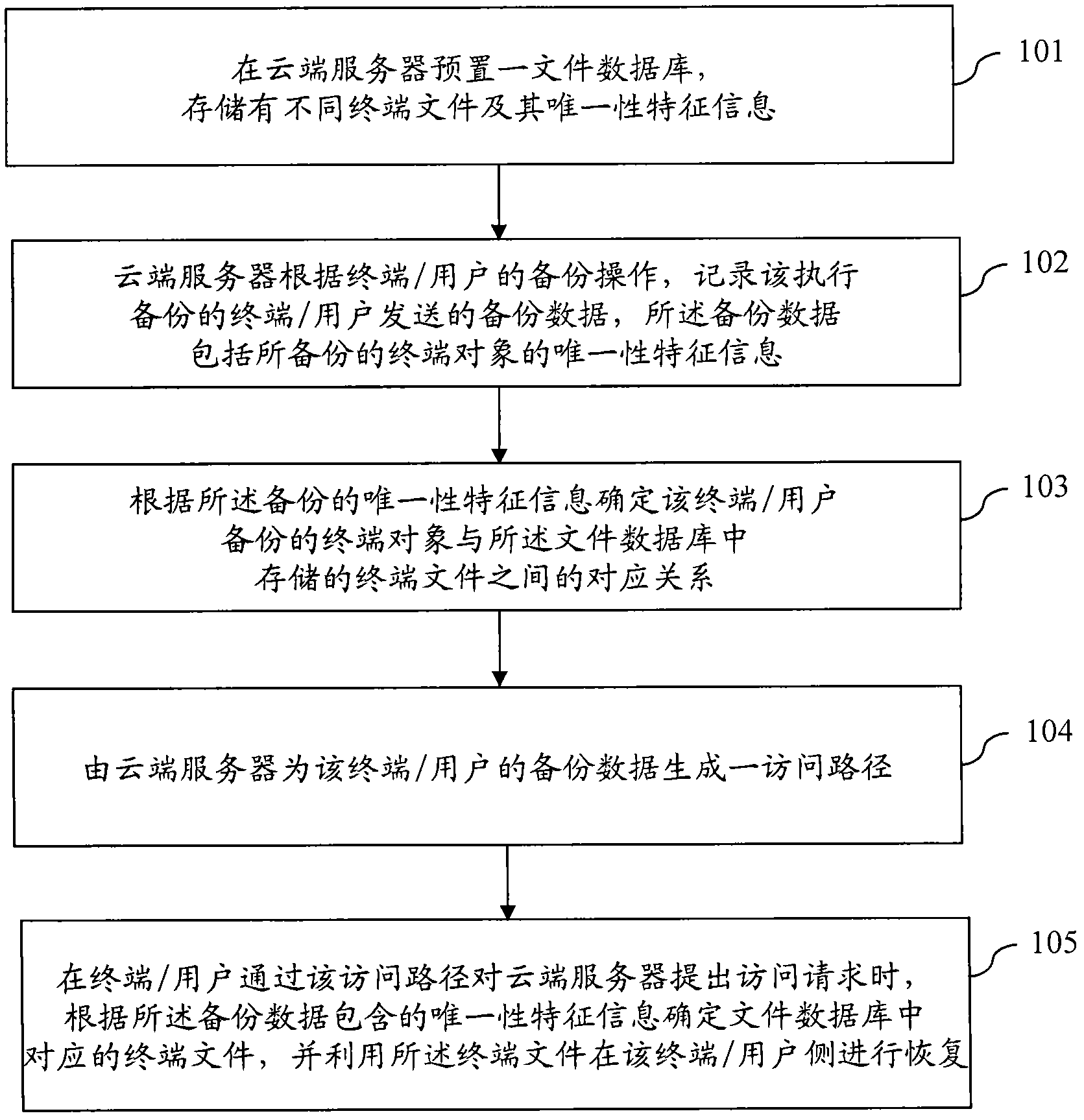
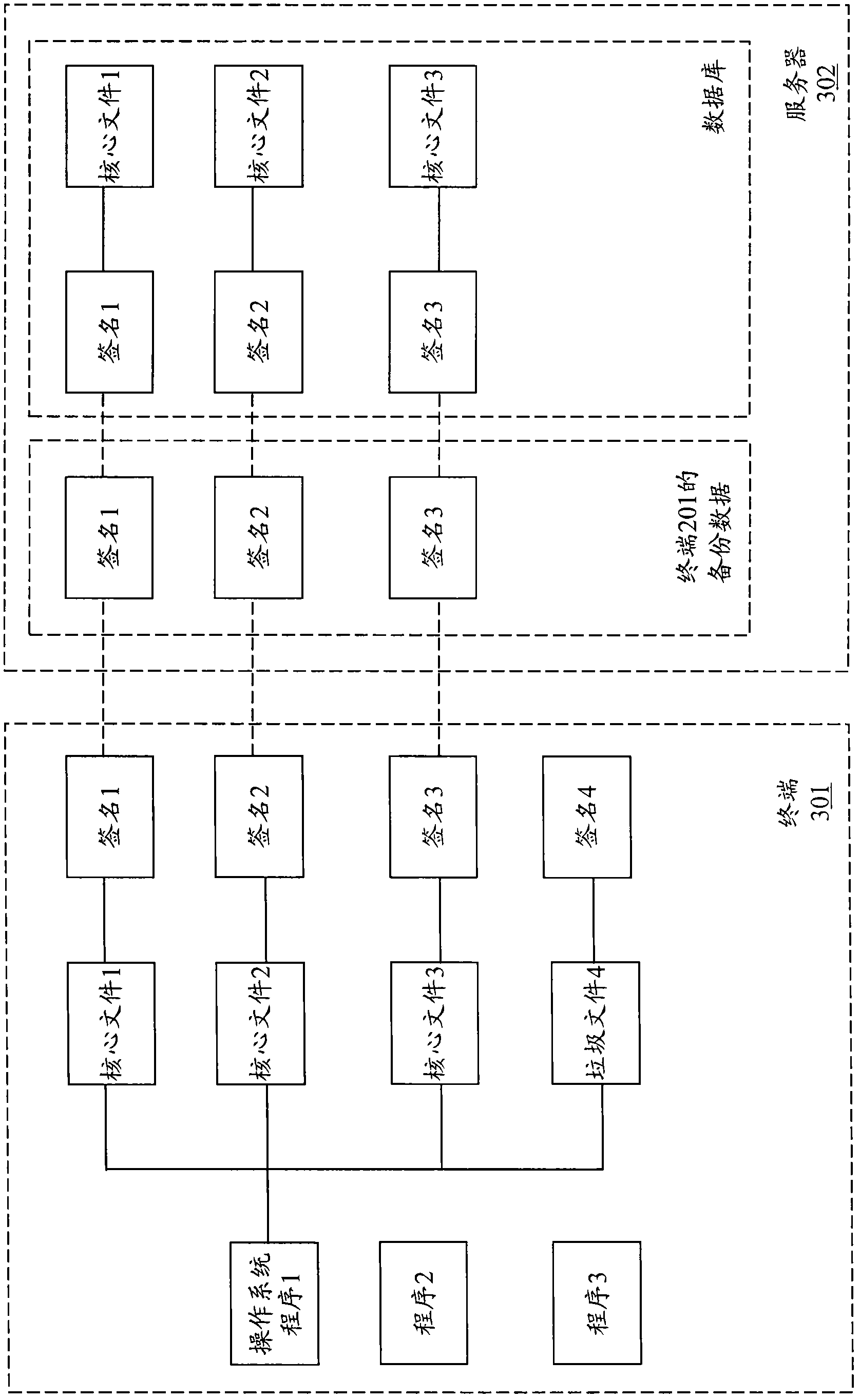
Terminal backup object sharing and recovery method based on cloud architecture
InactiveCN102360320AEasy content managementImprove backupTransmissionRedundant operation error correctionRecovery methodComputer terminal
The invention provides a terminal backup object sharing and recovery method based on a cloud architecture. The method comprises the following steps of: presetting a file database at a cloud server, wherein the file database stores different terminal files and uniqueness characteristic information of the files; recording the backup data sent by the terminal / the user and subjected to backup, by the cloud server, wherein the backup data comprise the uniqueness characteristic information of the backed up terminal object; determining the corresponding relation between the terminal object backed up by the terminal / the user and the terminal file stored in the file database according to the uniqueness characteristic information of the backup; generating an access path for the backup data of the terminal / the user by the cloud server; and when the terminal / the user makes an access request to the cloud server via the access path, determining the corresponding terminal files in the file database according to the uniqueness characteristic information contained in the backup data, and executing recovery at the terminal / the user side based on the terminal files. With the method, backup data sharing is realized, and speed of backup recovery is improved.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
Ceph-based network target range rear-end storage system design method
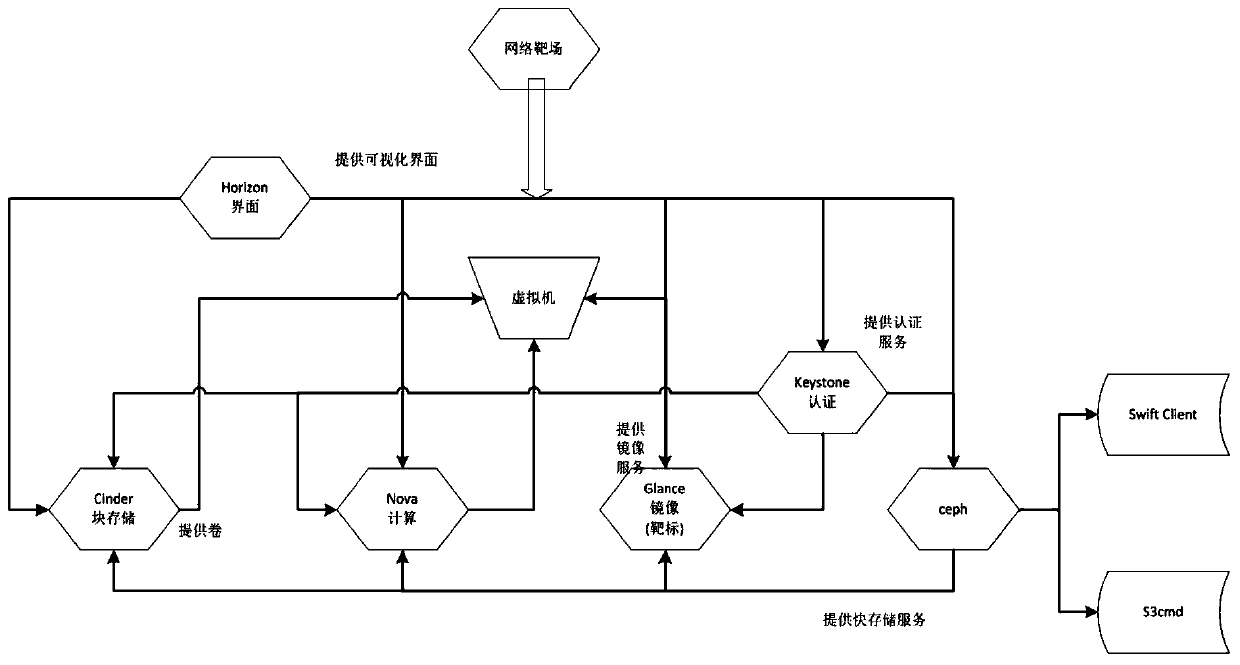
PendingCN110750334AImprove deployment efficiencyImprove storage securityInput/output to record carriersSoftware simulation/interpretation/emulationStorage securityIncremental backup
The invention relates to a Ceph-based network target range rear-end storage system design method, and relates to the technical field of information security. The invention provides a construction method of a network target range rear-end storage system under a cloud architecture in order to solve the problems existing in an existing network target range rear-end storage system. According to the method, the Ceph is combined with the OpenStack, the Ceph is used as Nova in the OpenStack; an identity authentication service Keystone of the OpenStack is bound with a Ceph object gateway at a storagerear end of a Glance, Cinder native component, and secondary development of management application is carried out based on a Ceph gateway module. The method can effectively improve the deployment efficiency and the storage security of the network target range. Therefore, the functions of second-speed starting of the virtual machine, real-time migration of the virtual machine, data fragmentation storage, data full backup, data incremental backup and the like in the network target range are achieved.
Owner:BEIJING INST OF COMP TECH & APPL
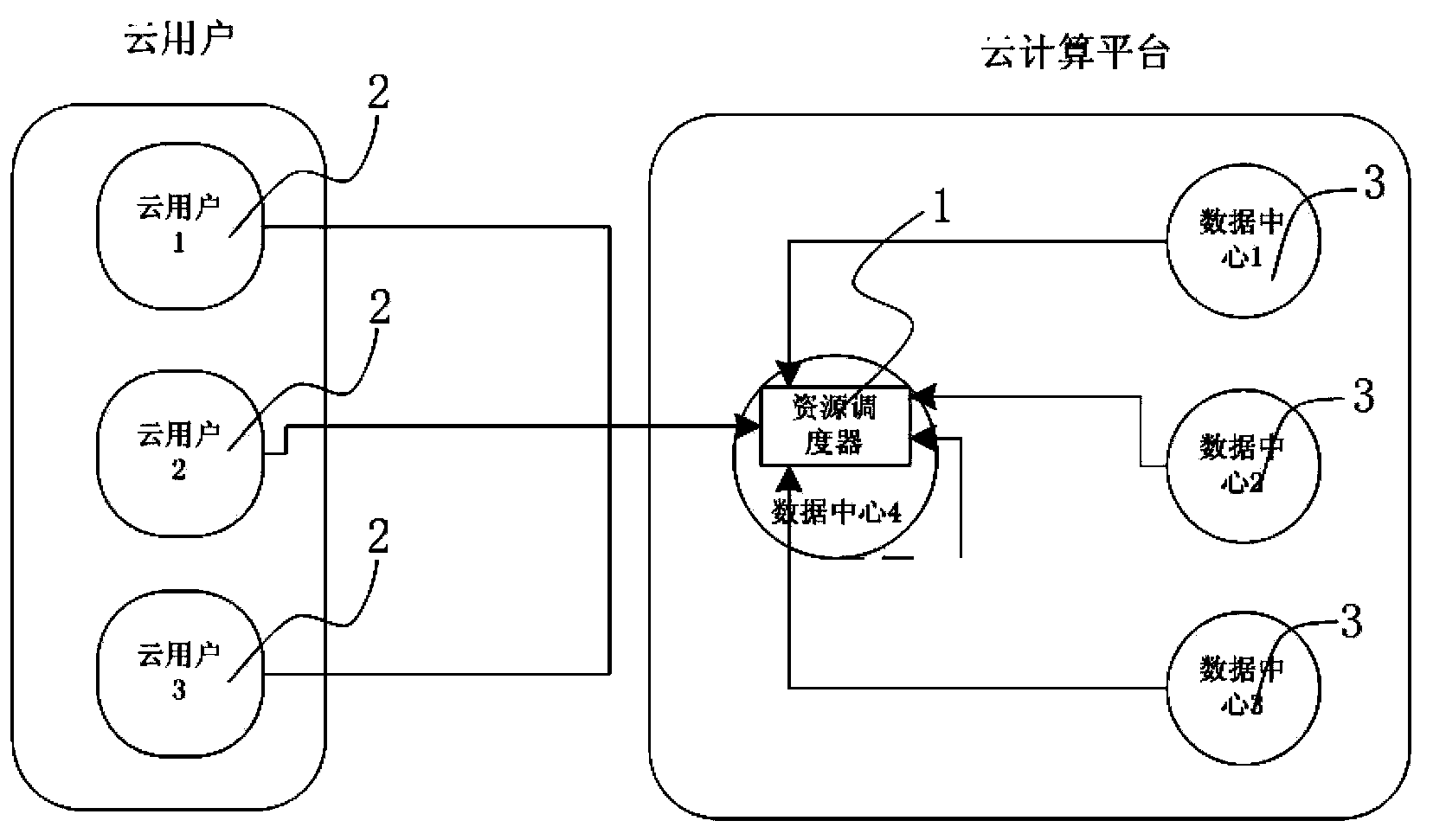
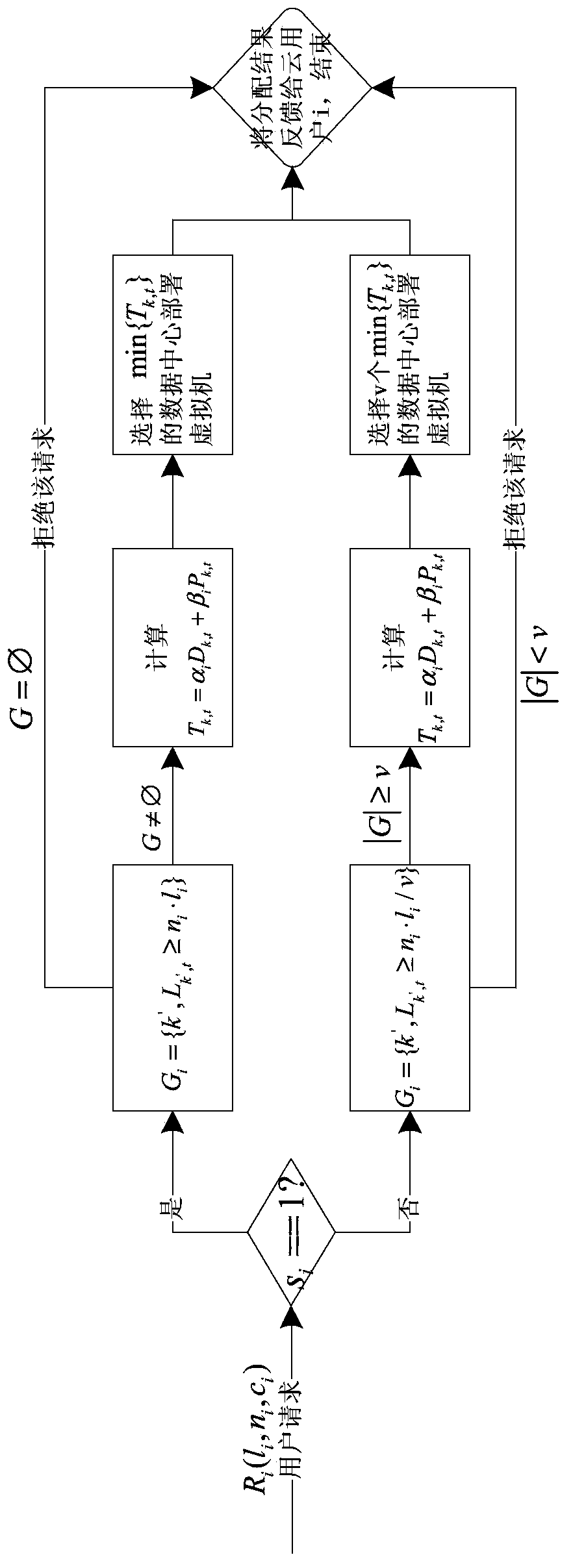
Resource distribution system based on service features under distributed cloud architecture and method thereof
The invention discloses a resource distribution system based on service features under a distributed cloud architecture and a method thereof. The method comprises the following steps: (1) establishing a cloud resource distribution system based on service features; (2) establishing an updating mechanism of a data center state list; (3) making a cloud user submit a cloud resource request to a resource dispatcher; (4) selecting to carry out step (5) or step (6) according to the service feature of the cloud user; (5) deploying a virtual machine for the cloud user by adopting a centralized way; (6) deploying a virtual machine for the cloud user by adopting a distributed way; (7) finishing the distribution of the virtual machine, and feeding back a distribution result to the cloud user through a resource manager. The resource distribution system mainly aims to solve the problem of resource distribution of cloud user services with different service features in a distributed cloud computing environment.
Owner:广州市兰卡科技有限公司
Networking method of load balancing device and server and client access method
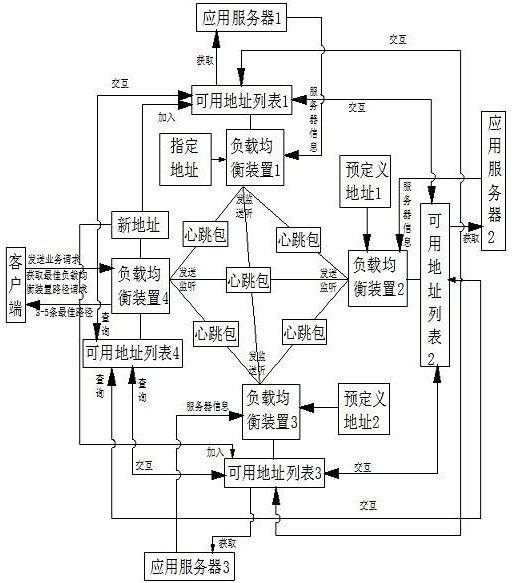
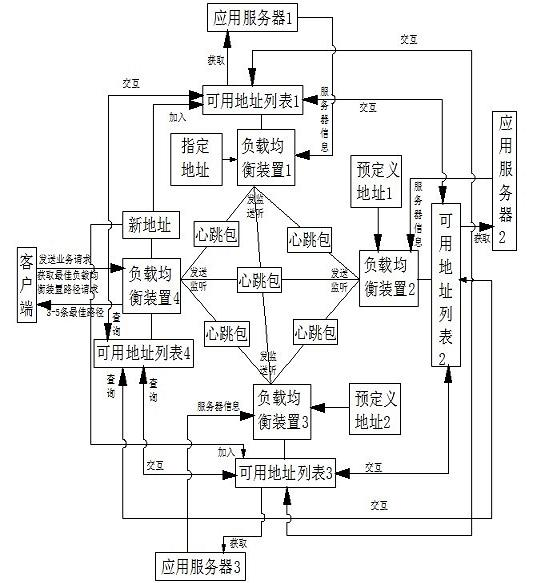
InactiveCN102281190AImprove networking efficiencyImprove accuracyData switching networksApplication serverAccess method
The present invention relates to a networking method for a cloud architecture load balancing apparatus, capable of effectively managing a load balancing apparatus cluster. The invention also relates to a method for adding a load balancing apparatus cluster to an application server, capable of acquiring the state information of the application server realtimely. Further, the invention discloses a method for accessing the application server to a client, which carries out weighted calculation based on the response time and load situation of the application server, and the network provider of the client, allocates the optimal resources automatically, and effectively shortens the response time of a request.
Owner:杭州斯凯网络科技有限公司
Self-organizing cloud architecture and optimization method and system for edge computing
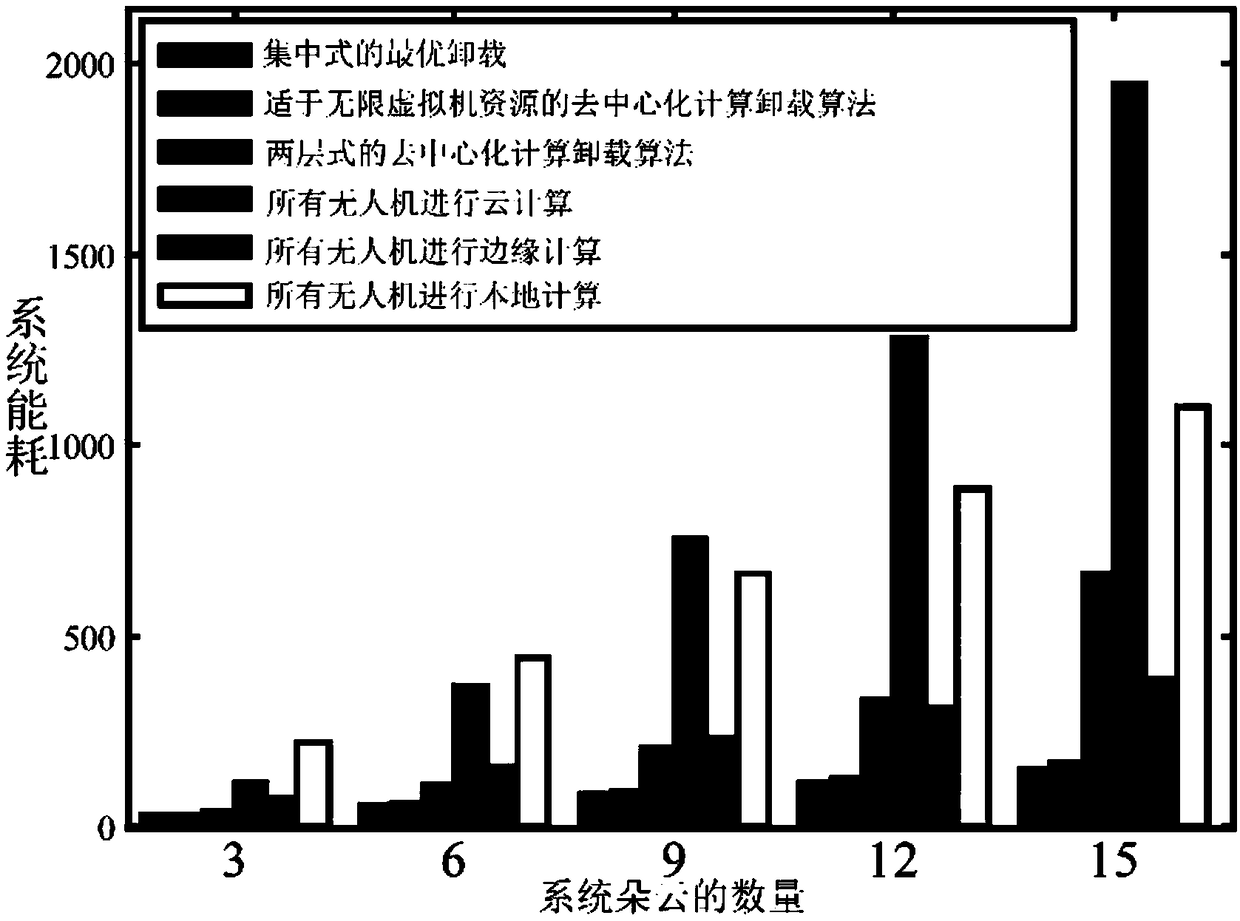
ActiveCN109302463AReduce overheadReduce energy consumptionEnergy efficient computingData switching networksEdge computingComputer terminal
The invention provides a self-organizing cloud architecture and optimization method and system for edge computing. The method comprises: a model construction step: performing model construction on a hierarchical unmanned aerial vehicle system; a decentralized computing unloading algorithm step suitable for an infinite virtual machine resource situation: respectively performing game decision according to conditions met by an unmanned aerial vehicle terminal bandwidth of the unmanned aerial vehicle system so as to achieve Nash equilibrium; and a decentralized computing unloading algorithm step suitable for a finite virtual machine resource situation: designing a decentralized computing unloading algorithm to perform algorithm computing. The invention provides a layered decentralized unloading method to reduce the communication overhead while maintaining the energy efficiency; and according to the self-organizing cloud architecture and optimization method and system provided by the invention, the energy-saving computing unloading decision problem in the hierarchical unmanned aerial vehicle system is modeled as a non-cooperative game for research, the decentralized computing unloadingalgorithm is designed for the situations of infinite virtual machine resources and finite virtual machine resources, and it is proved that the algorithm can achieve the Nash equilibrium.
Owner:SHANGHAI JIAO TONG UNIV
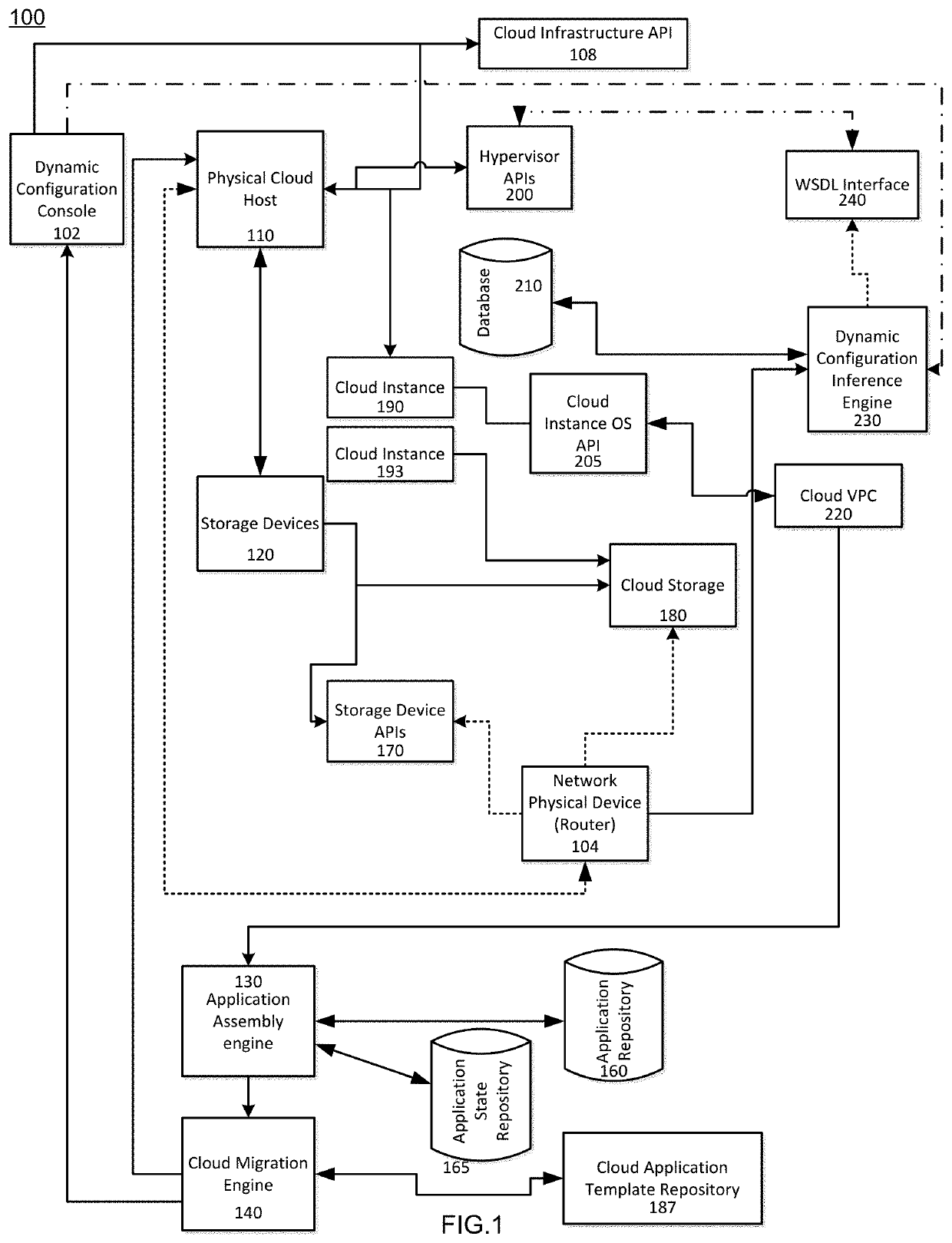
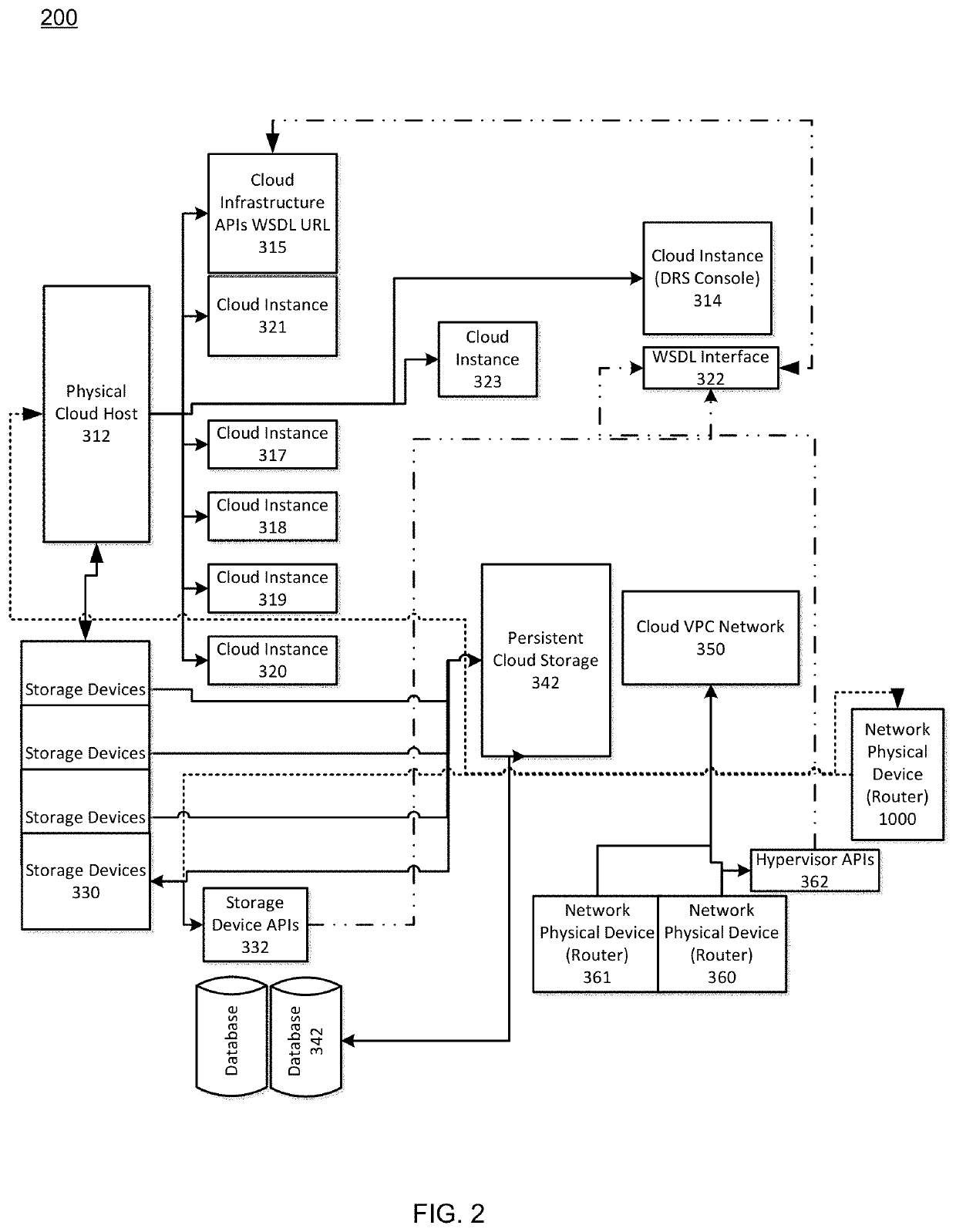
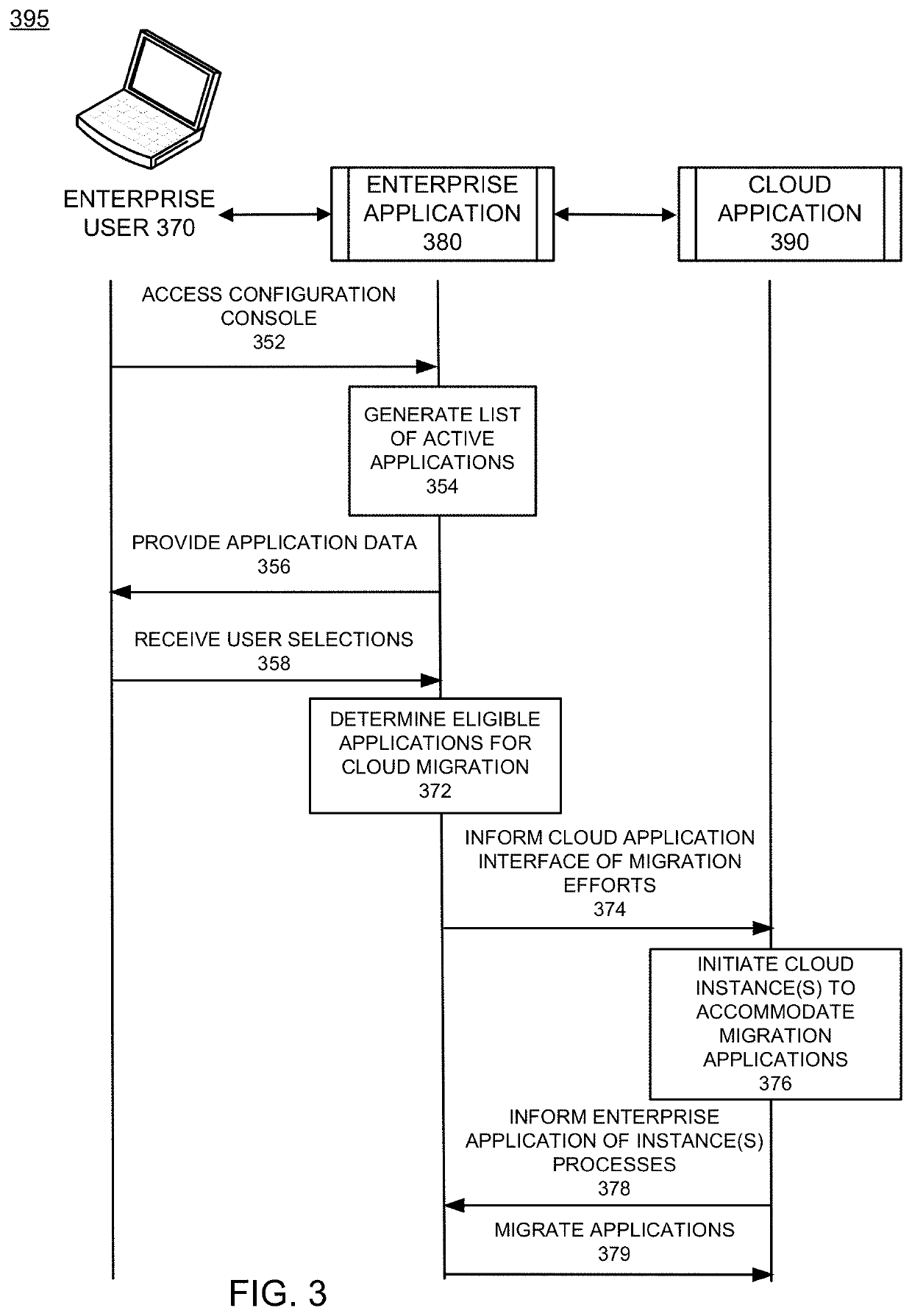
Dynamic resource allocation of cloud instances and enterprise application migration to cloud architecture
Cloud migration may be performed by identifying applications that are currently operating in the enterprise and performing certain determinations as to whether those applications are proper candidates for the migration to the cloud. One example method of operation may provide identifying at least one application operating on an enterprise network, retrieving current usage data of the at least one application, comparing the current usage data of the at least one application to a threshold amount of usage data to determine whether the application has exceeded the threshold amount of usage data. Next, the creation of an instance process may be performed on an entity operating outside the enterprise network and the application may be operated via the instance process and otherwise terminated in the enterprise network to alleviate resources.
Owner:GOOGLE LLC
Extending organizational boundaries throughout a cloud architecture
InactiveUS20140189124A1Digital computer detailsData switching networksDomain nameInformation sharing
An information sharing paradigm for a cloud computing solution enables flexible organizational boundaries with respect to cloud resources. Cloud service customers manage their own organization boundary but can extend that boundary selectively by associating cloud resources they own with sets of domain names that may be associated with requests for cloud resources that the organization may be willing to share with other organizations that are using the cloud environment, and by ensuring that any such requests for resources that are shared in this manner are associated with one or more message handling policies that have been defined by (or otherwise associated with) the resource-owning organization. Cloud resources owned by an organization (even those marked as “internal only”) may be selectively shared with one or more other organizations using the cloud environment depending on the domain names associated with the requests. Message handling policies are enforced with respect to shared resources.
Owner:IBM CORP
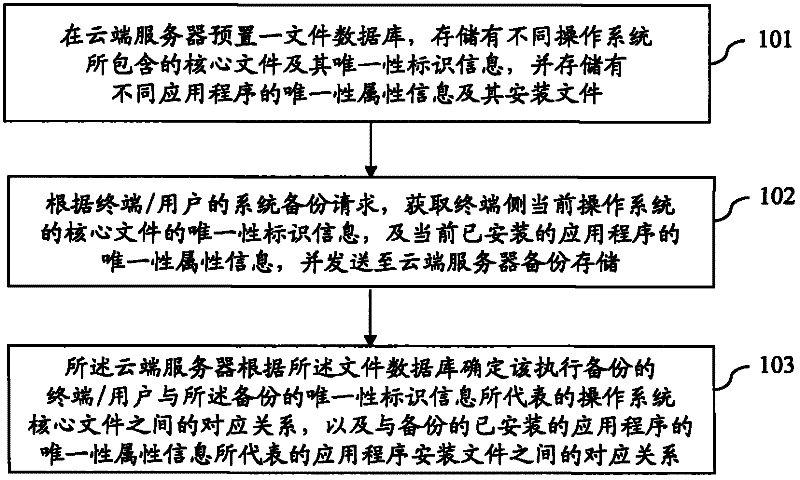
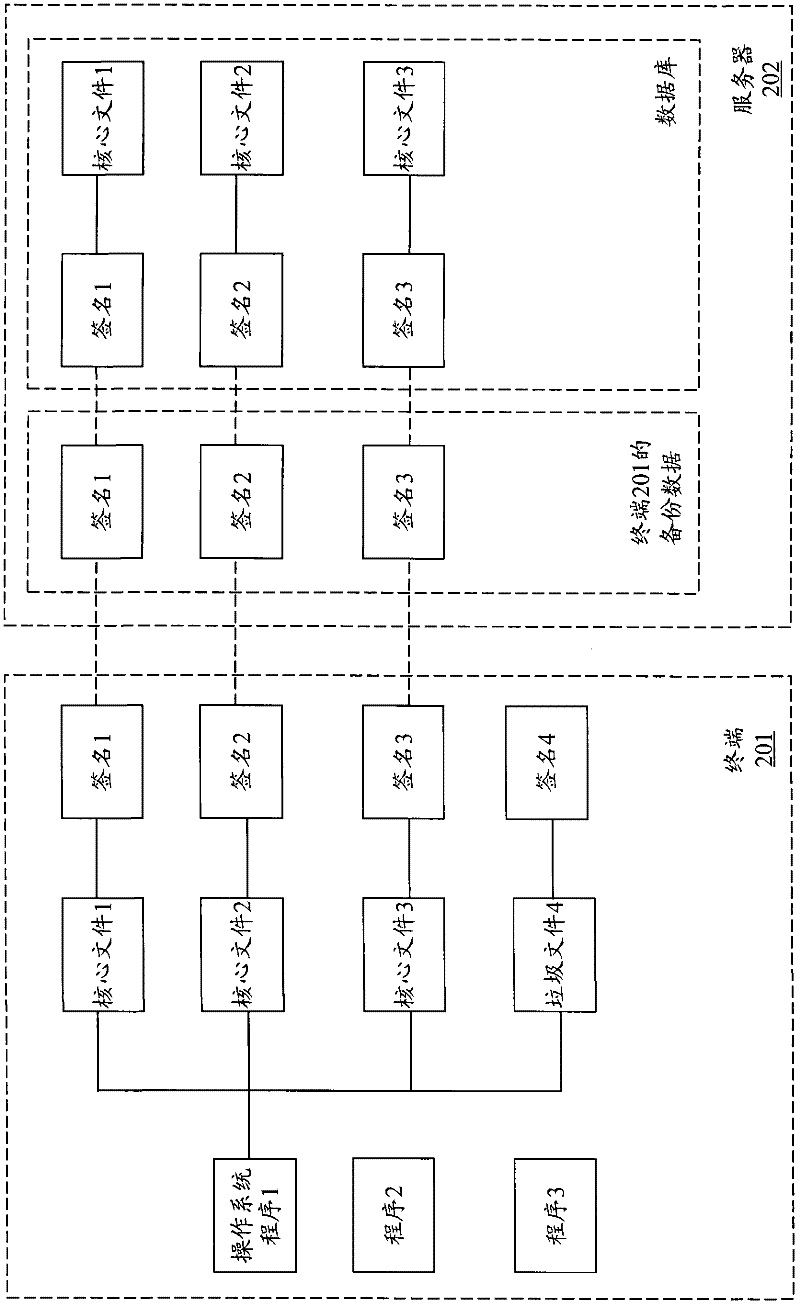
Method for backing up and restoring terminal system based on cloud architecture
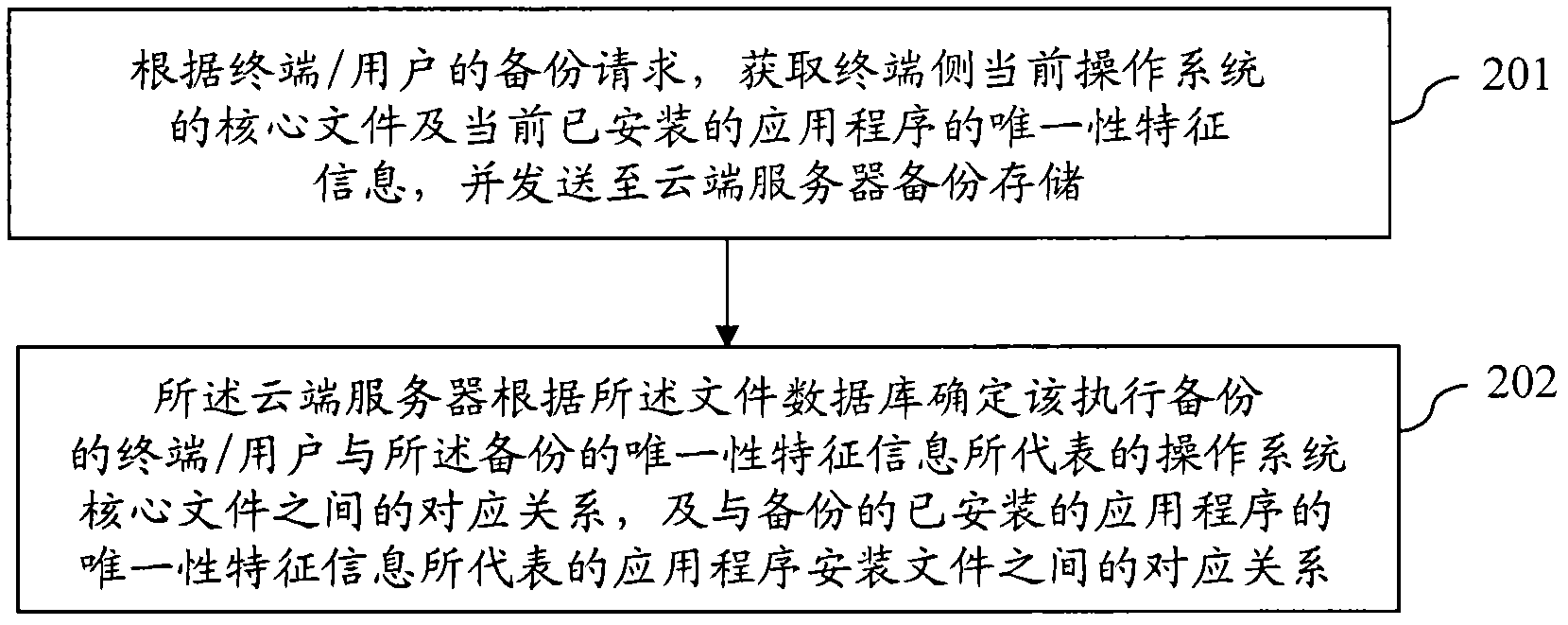
InactiveCN102508735AReduce transfer volumeImprove backupRedundant operation error correctionSpecial data processing applicationsOperational systemRestoration method
The invention provides a method for backing up and restoring a terminal system based on a cloud architecture. The method comprises the following steps of: in the process of backing up, pre-setting a file database on a cloud server, wherein core files included in different operation systems and unique identifier information of the core files, and unique attribute information of different application programs and installation files of the unique attribute information are stored in the file database; then, according to a system backup request of a terminal / user, obtaining the unique identifier information of the core file of the current operation system of a terminal side and the unique attribute information of the currently installed application program, and sending the unique identifier information and the unique attribute information to the cloud server to be backed up and stored; and determining a corresponding relation between the terminal / user for executing a backup and the core file of the operation system represented by the unique identifier information of the backup and a corresponding relation between the terminal / user for executing the backup and the installation file of the application program represented by the unique attribute information of the installed application program of the backup by the cloud server according to the file database. The method disclosed by the invention is capable of increasing speed for backing up and restoring and reducing transmission quantity.
Owner:QIZHI SOFTWARE (BEIJING) CO LTD
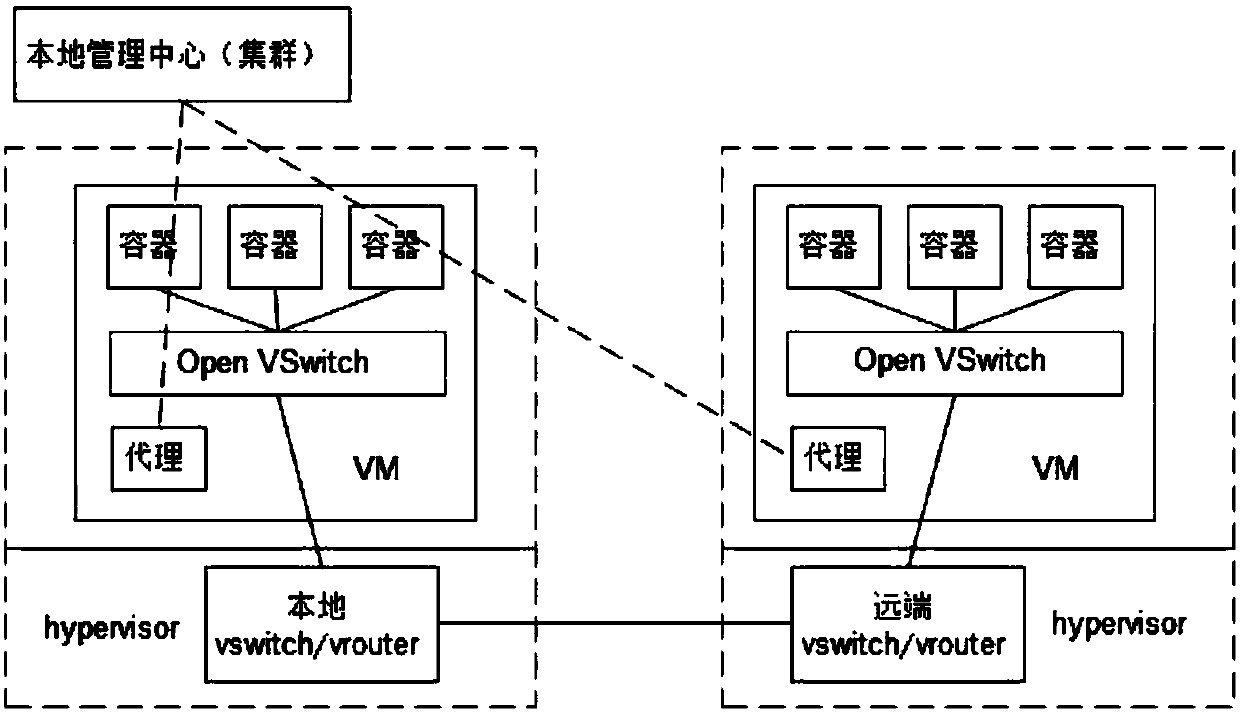
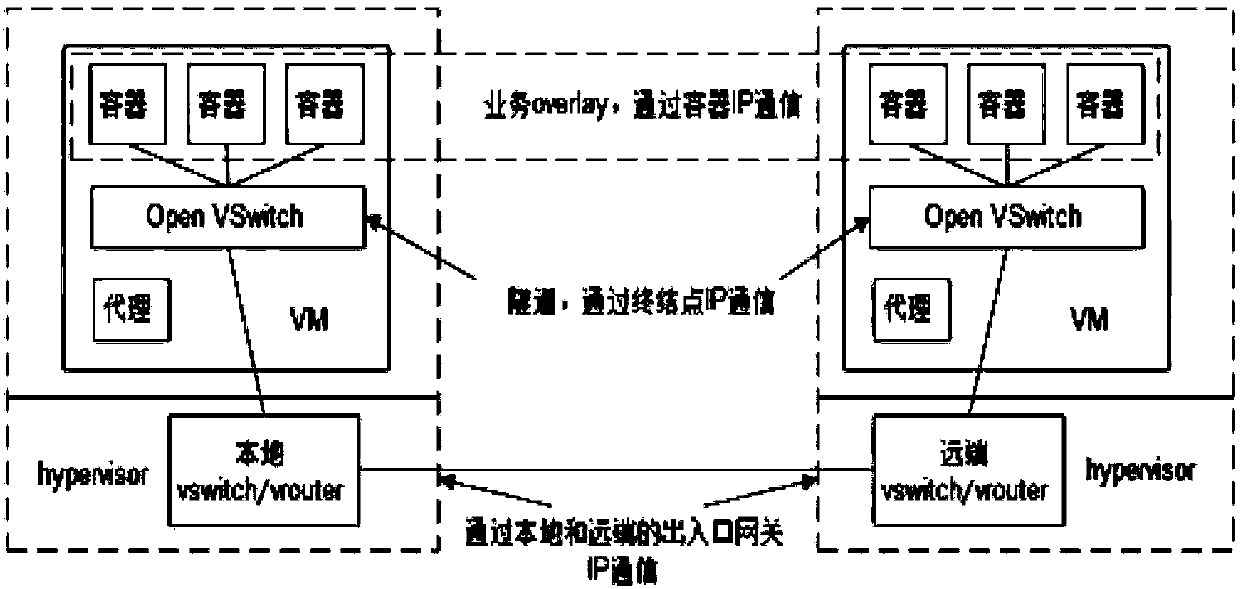
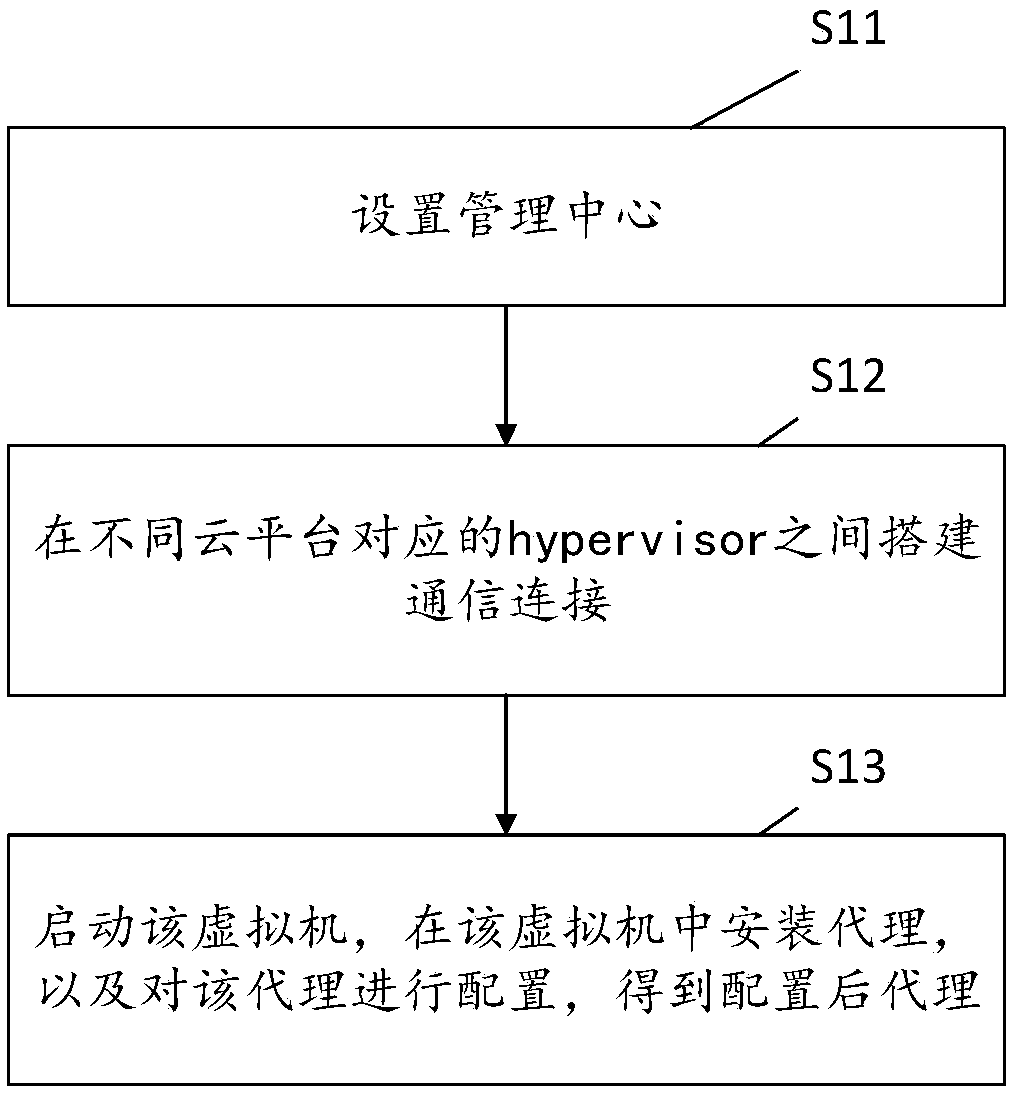
Service cross-cloud architecture and creation method and management method thereof
ActiveCN107911463AReduce difficultyImplement schedulingData switching networksCloud architectureVirtual machine
The application discloses service cross-cloud architecture. The service cross-cloud architecture comprises a management center, virtual machines respectively located on different cloud platforms, andmultiple hypervisors respectively corresponding to each cloud platform, wherein each virtual machine comprises a container, an Open vSwitch and a proxy; firstly, an access among hypervisors corresponding to different cloud platforms is constructed; the management center transmits a management command to a local hypervisor corresponding to a target virtual machine; the local Open vSwitch acquires the management command received by the local hypervisor through the local proxy, and transmits the management command to the local corresponding container, thereby performing the corresponding servicemanagement on the container by using the management command. Since the service cross-cloud architecture is based on the virtual network configuration and applies the container and the Open vSwitch, the service network and the bottom cloud platform are separated, the unified management among different cloud platforms can be directly realized, and the service cross-cloud difficulty is reduced. Correspondingly, the application further discloses the service cross-cloud architecture creation method and the management method.
Owner:SANGFOR TECH INC
Distributed virtual storage cloud architecture and a method thereof
ActiveUS9128626B2Input/output to record carriersDigital data information retrievalThird partyVirtualization
The present disclosure relates to a distributed information storage system which functions as virtual cloud storage overlay on top of physical cloud storage systems. The disclosure discloses transparently solving all the data management related security, virtualization, reliability and enables transparent cloud storage migration, cloud storage virtualization, information dispersal and integration across disparate cloud storage devices operated by different providers or on-premise storage. The cloud storage is owned or hosted by same or different third-party providers who own the information contained in the storage which eliminates cloud dependencies. This present disclosure functions as a distributed cloud storage delivery platform enabling various functionalities like cloud storage virtualization, cloud storage integration, cloud storage management and cloud level RAID.
Owner:CHACKO PETER
Method and system for metadata synchronization
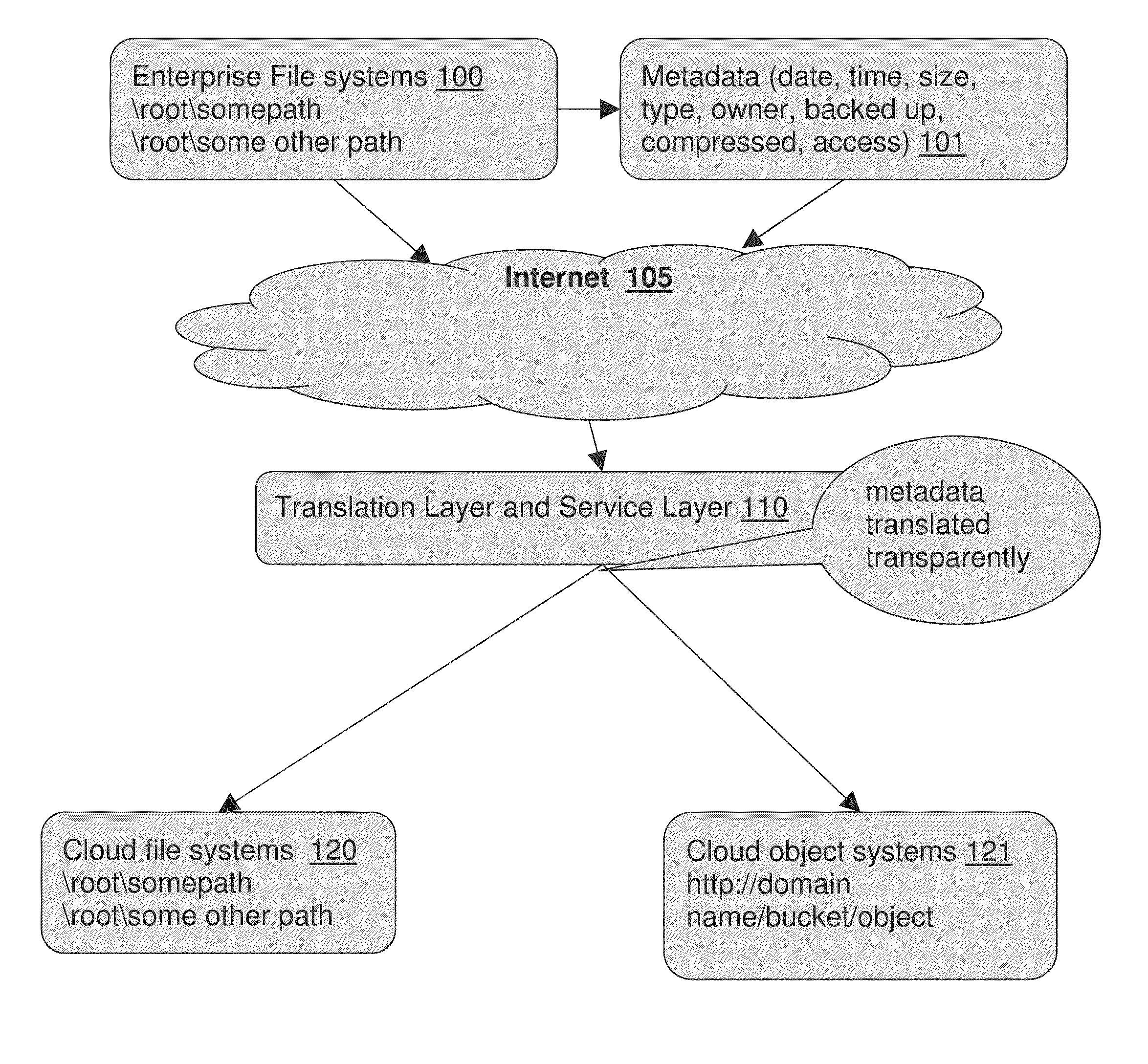
InactiveUS20160259811A1Increase ratingsDigital data information retrievalDigital data protectionDistributed computingCloud architecture
The present disclosure provides a method for providing transparent configuration metadata for file access and security between replicated copies of data using dissimilar protocols and technologies to store share and access file based data in a hybrid cloud architecture.
Owner:SUPERNA INC
Cloud architecture of energy efficiency management system and operation method thereof
InactiveCN103905553AReduce the impact of installation and maintenanceLow costTransmissionDynamic load balancingData acquisition
The invention discloses a cloud architecture of an energy efficiency management system and an operation method of the cloud architecture. By introducing the cloud architecture and the operation method of the cloud architecture, fast seamless connecting-in of a newly added service module and acquired data share can be achieved by the system according to continuous expanding of client service classes, meanwhile, energy efficiency data can be acquired, processed and published by the system efficiently with dynamic load balance and high quality according to the client service scale, normal operation of user service is guaranteed, and the availability and the running efficiency of the system can be substantially improved through interior monitoring and operating mechanisms of the system.
Owner:JIANGSU LINYANG ENERGY CO LTD +1
End-side-cloud architecture-based community fire monitoring system
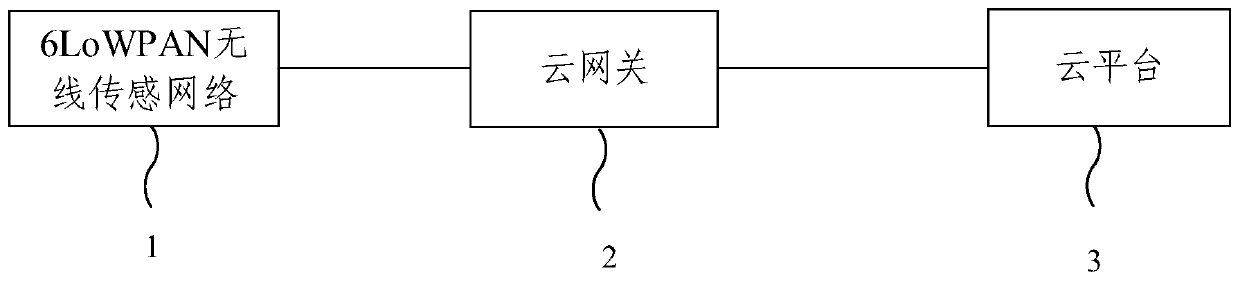
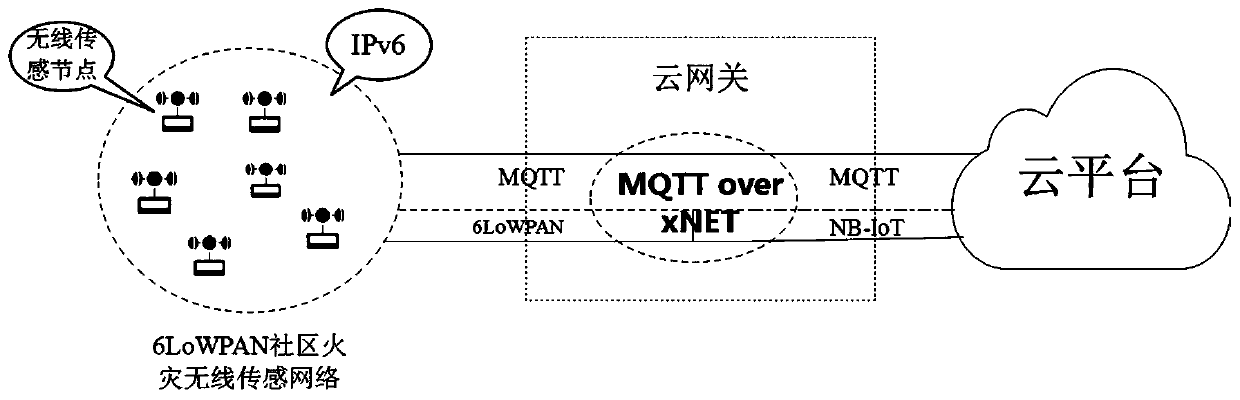
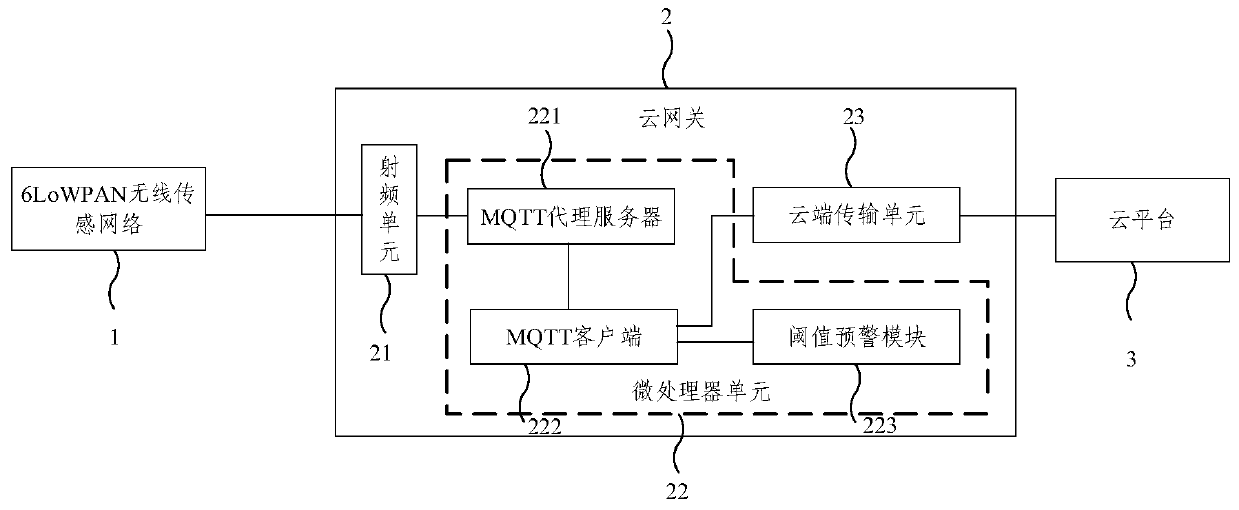
ActiveCN110807905ARealize cloudAchieve perceptionTransmission systemsNetwork topologiesNerve networkFire risk
The embodiment of the invention provides an end-side-cloud architecture-based community fire monitoring system. The community fire monitoring system comprises 6LoWPAN wireless sensing networks, cloudgateways and a cloud platform, wherein the 6LoWPAN wireless sensing networks have a fire risk sensing function; the cloud gateways are connected with the 6LoWPAN wireless sensing networks and is connected to the cloud platform through the 6LoWPAN wireless sensing networks; the cloud gateway performs data transmission based on an MQTT protocol; and the cloud platform utilizes a community fire fuzzyneural network early warning model and the edge calculation of the cloud gateway to realize real-time early warning and control of fire risk. According to the embodiment of the invention, the low-cost arrangement of the fire monitoring network is realized, the signal quality is improved, and the reliability is enhanced; the data transmission of the wireless sensing networks and the cloud platformis carried out through the single MQTT protocol, and the data transmission efficiency and the timeliness of fire early warning are improved; and the perception, transmission, analysis, early warningand control of the fire risk of the community are comprehensively realized.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
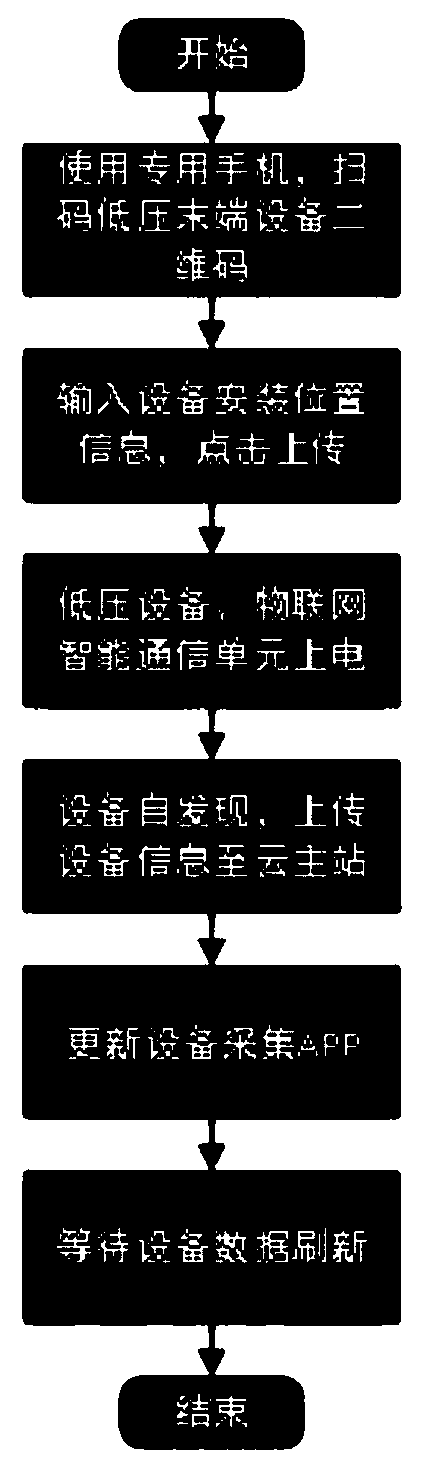
Intelligent power distribution room based on Internet of Things technology and implementation method thereof
PendingCN110518697ARealize panoramic monitoringRealize plug and playCircuit arrangementsTransmissionData displayCommunication unit
The invention relates to an intelligent power distribution room based on the Internet of Things technology, which comprises a cloud master station, a communication network, an edge computing gateway,an Internet of Things intelligent communication unit and power distribution area intelligent terminal equipment, wherein the cloud master station is a storage, display and analysis interface of powerdistribution area data, is deployed in an intranet by adopting a cloud architecture, and comprises an Internet of Things equipment access platform and a data display platform; the edge computing gateway, the Internet of Things intelligent communication unit and the power distribution area intelligent terminal equipment are installed in the power distribution room, and the edge computing gateway and the Internet of Things intelligent communication unit are internally provided with intelligent terminal equipment data acquisition APPs corresponding to each other. The invention further relates toan intelligent power distribution room implementation method based on the Internet of Things and a plug-and-play method of the terminal equipment. According to the invention, panoramic monitoring of power distribution room equipment and terminal equipment in a transformer area is realized; the plug-and-play of the terminal equipment is realized through the Internet of Things intelligent communication unit; and a special mobile phone is adopted to facilitate the operation and maintenance of field workers.
Owner:SHANDONG ELECTRICAL ENG & EQUIP GRP XINNENG TECH CO LTD
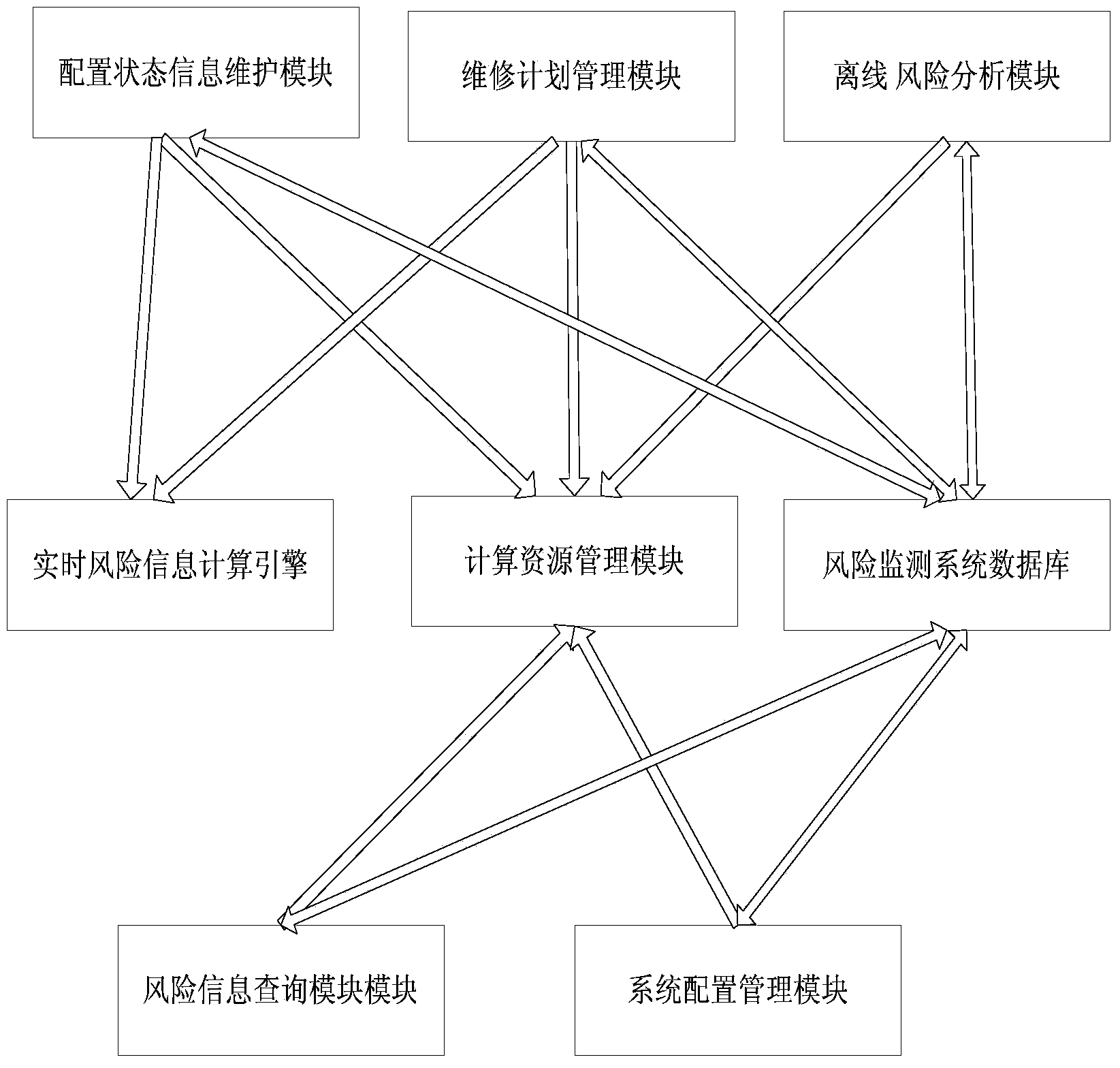
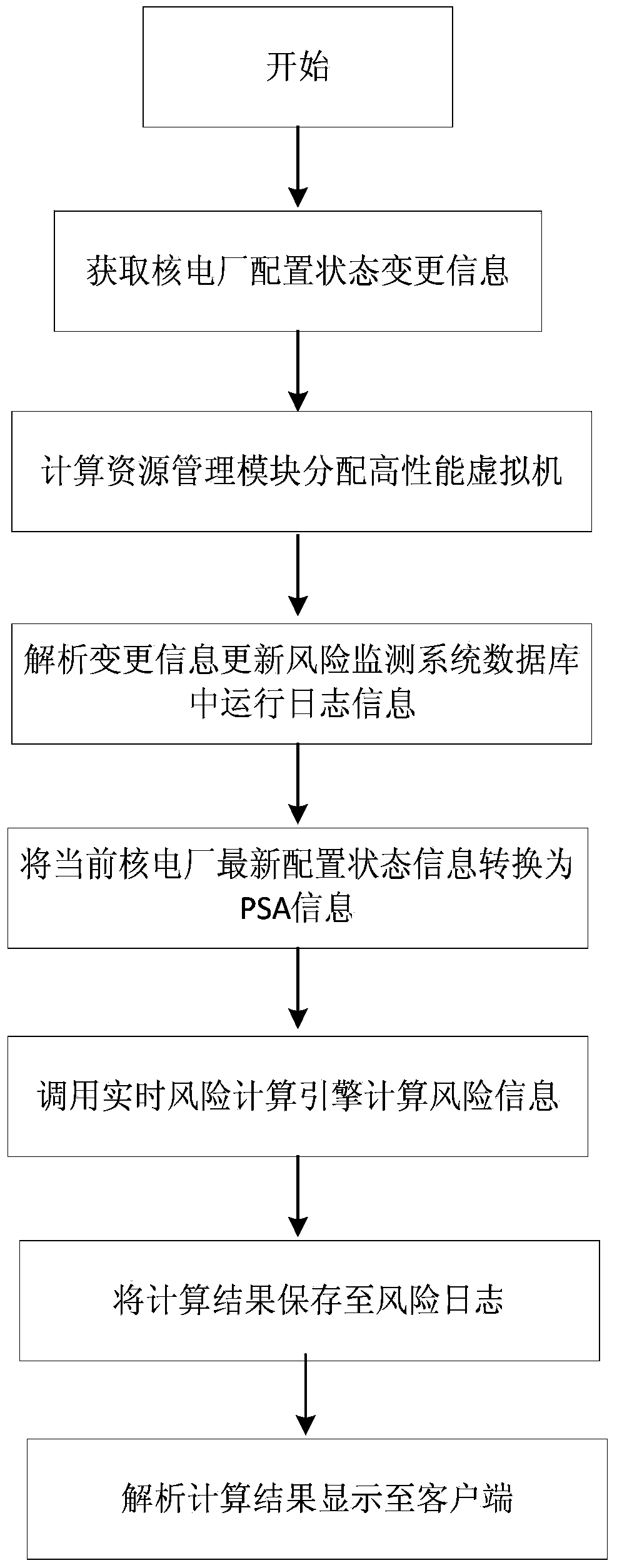
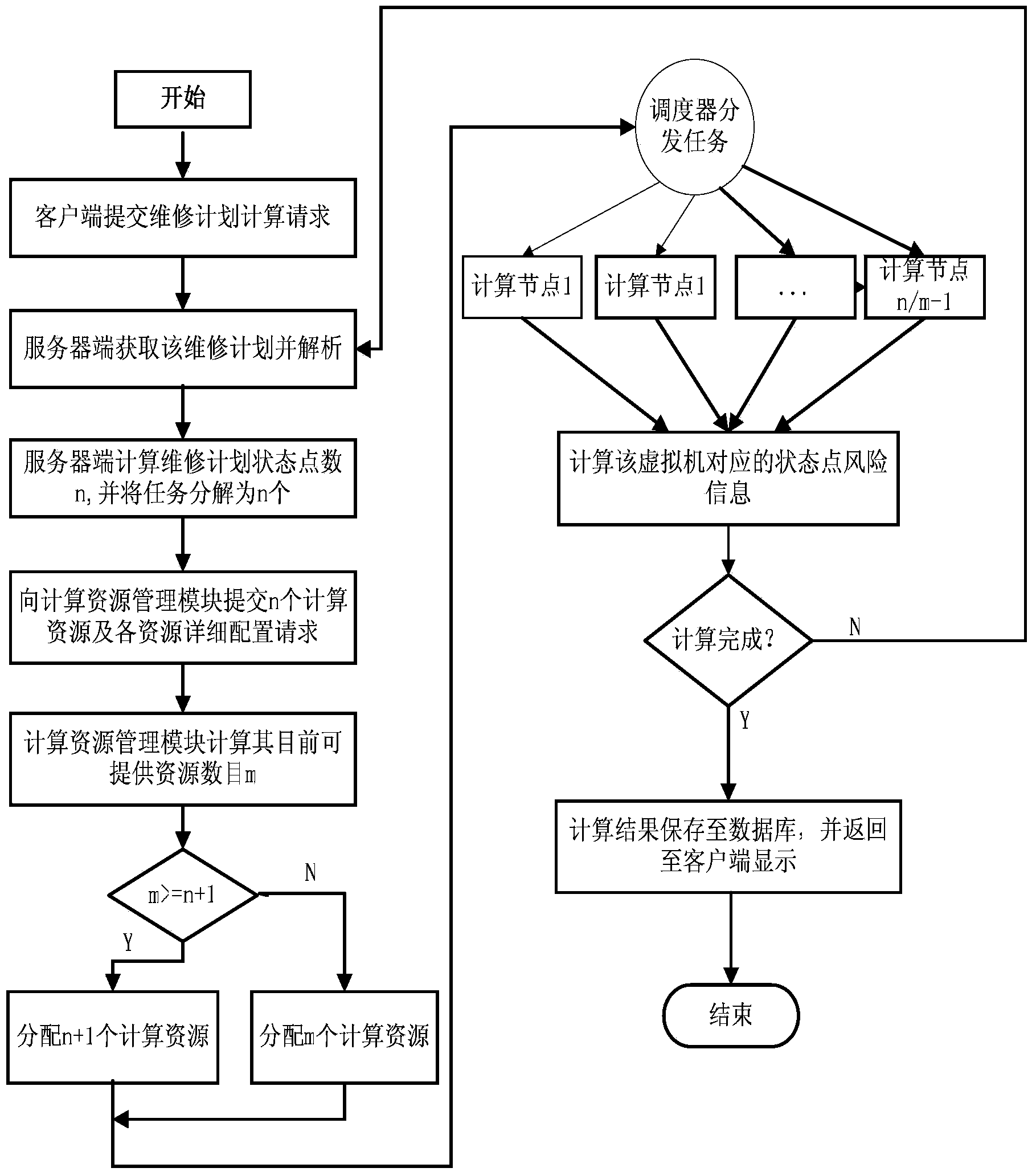
System and method for monitoring risks of nuclear power plant based on cloud architecture
ActiveCN103400246AGuaranteed uptimeReliable, stable and continuous operationTechnology managementResourcesNuclear powerProgram planning
The invention discloses a system and a method for monitoring risks of a nuclear power plant based on a cloud architecture. The system comprises eight functional modules. The system is built based on a cloud platform, and builds idle physical machines in the nuclear power plant into a virtual machine cluster through the Internet, the system can perform the automatic migration of fault nodes so as to ensure the stable, reliable and continuous running of the nodes; and by using the advantages of the combination of cloud computing and distributed computing, a problem that when a maintenance plan management module of the system for monitoring risks is used to carry out a large-scale maintenance plan, computing resources are dynamically distributed according to the number of state points of the maintenance plan, thereby solving the problem that too slow computing speed can not meet the demands of practical production management and saving the computing resources to the greatest extent.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com