Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
409 results about "Storage virtualization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
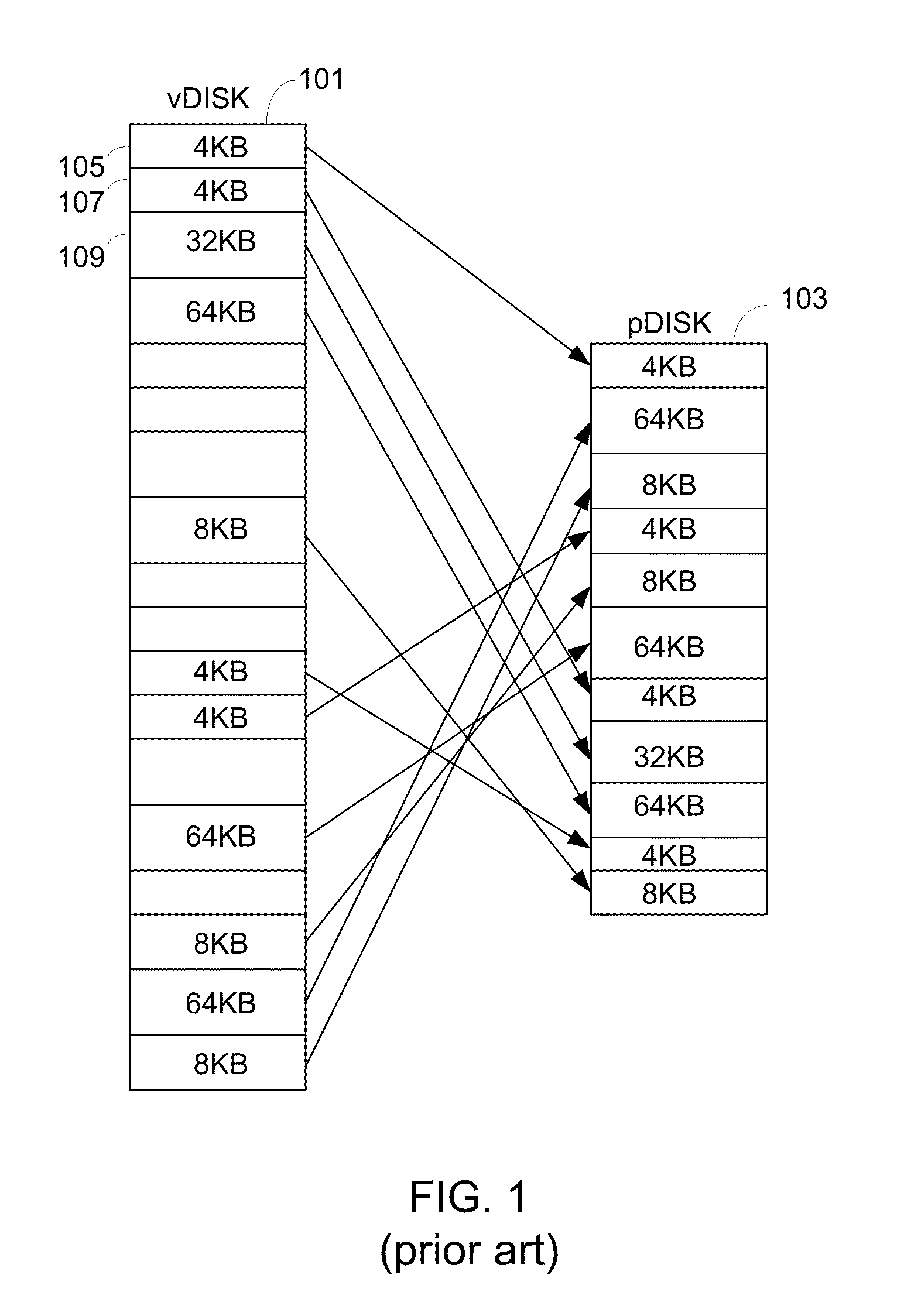
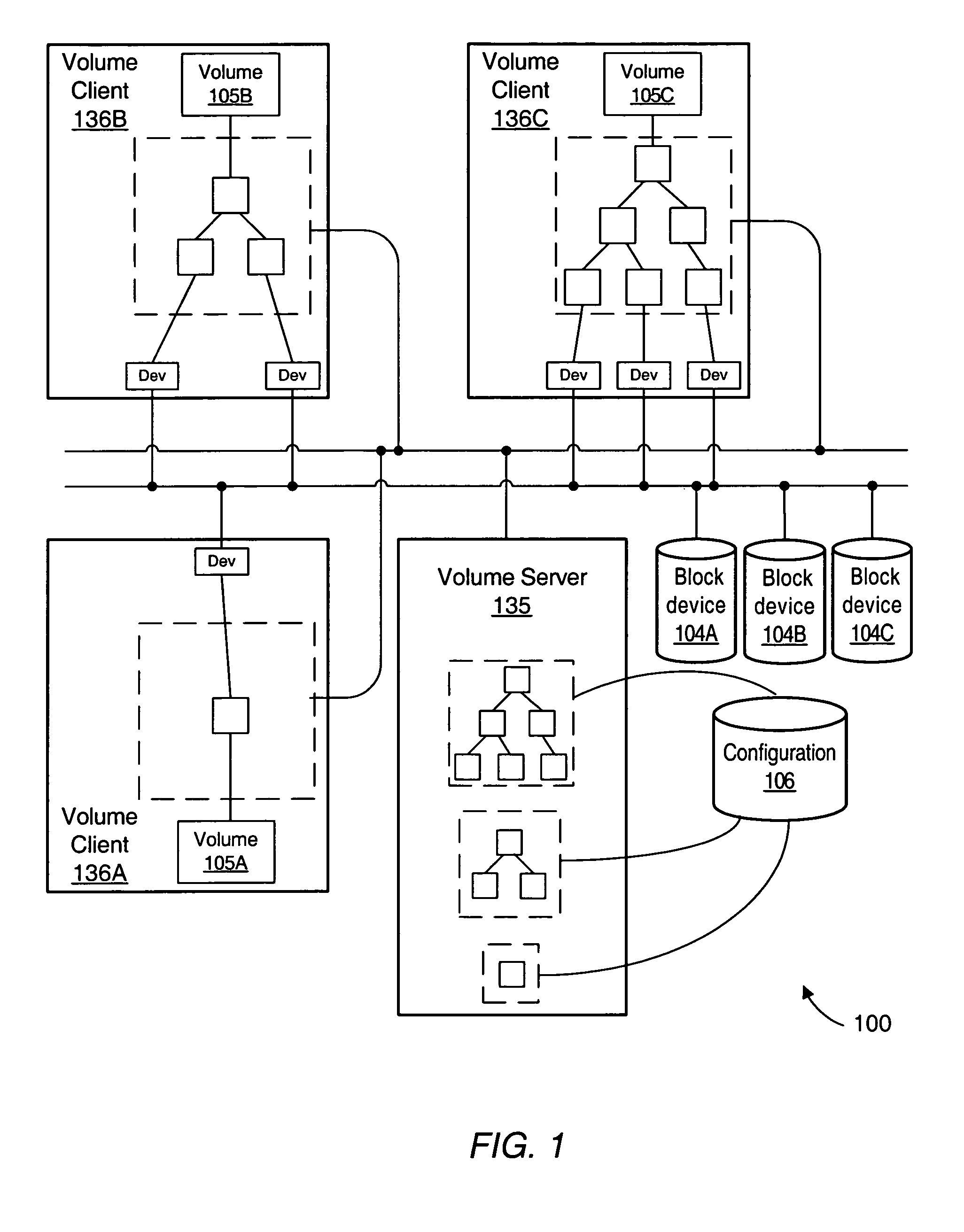
In computer science, storage virtualization is "the process of presenting a logical view of the physical storage resources to" a host computer system, "treating all storage media (hard disk, optical disk, tape, etc.) in the enterprise as a single pool of storage."
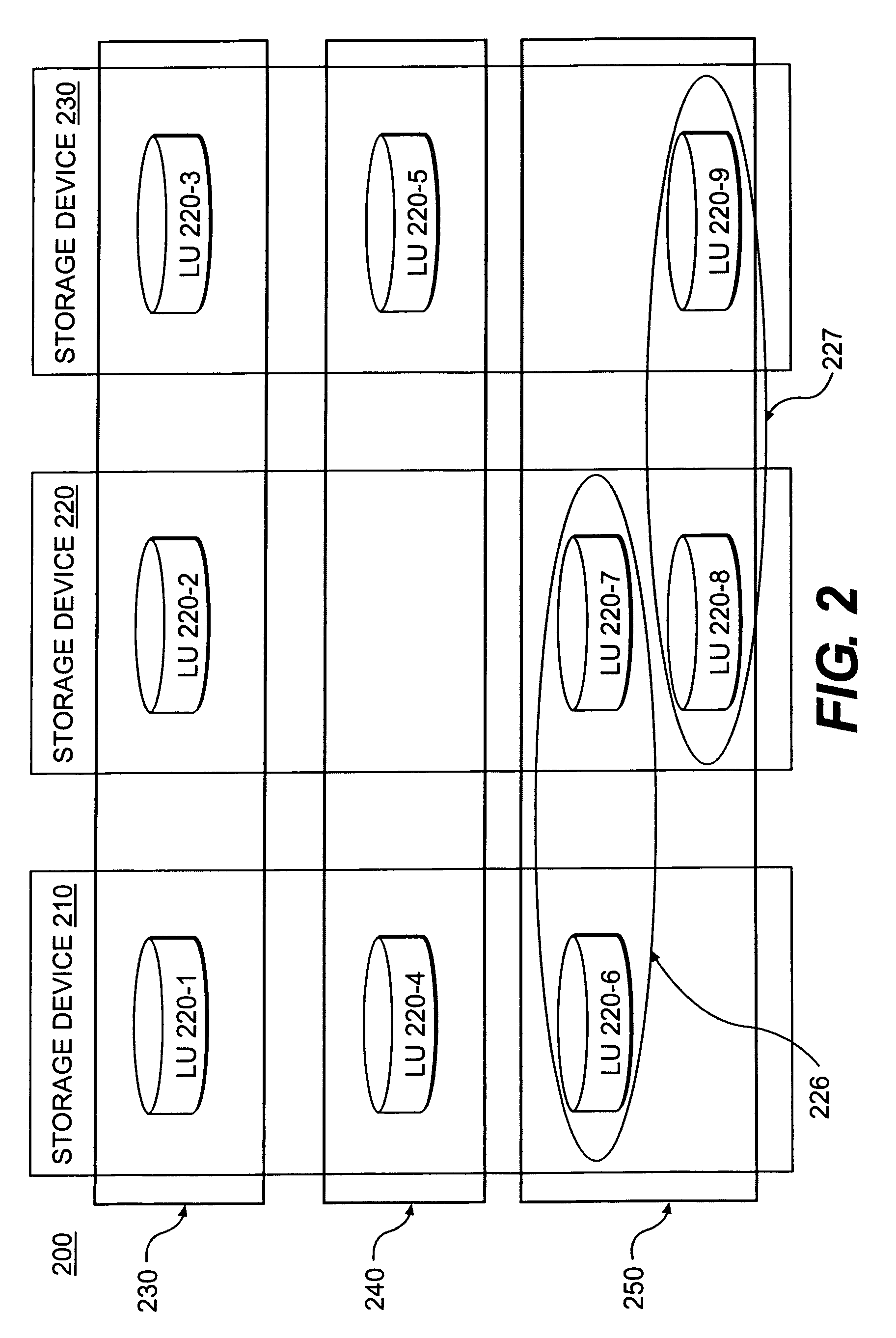
Storage virtualization system and methods
InactiveUS20050125593A1Reduce consumptionWithout impactInput/output to record carriersMemory adressing/allocation/relocationRAIDIslanding
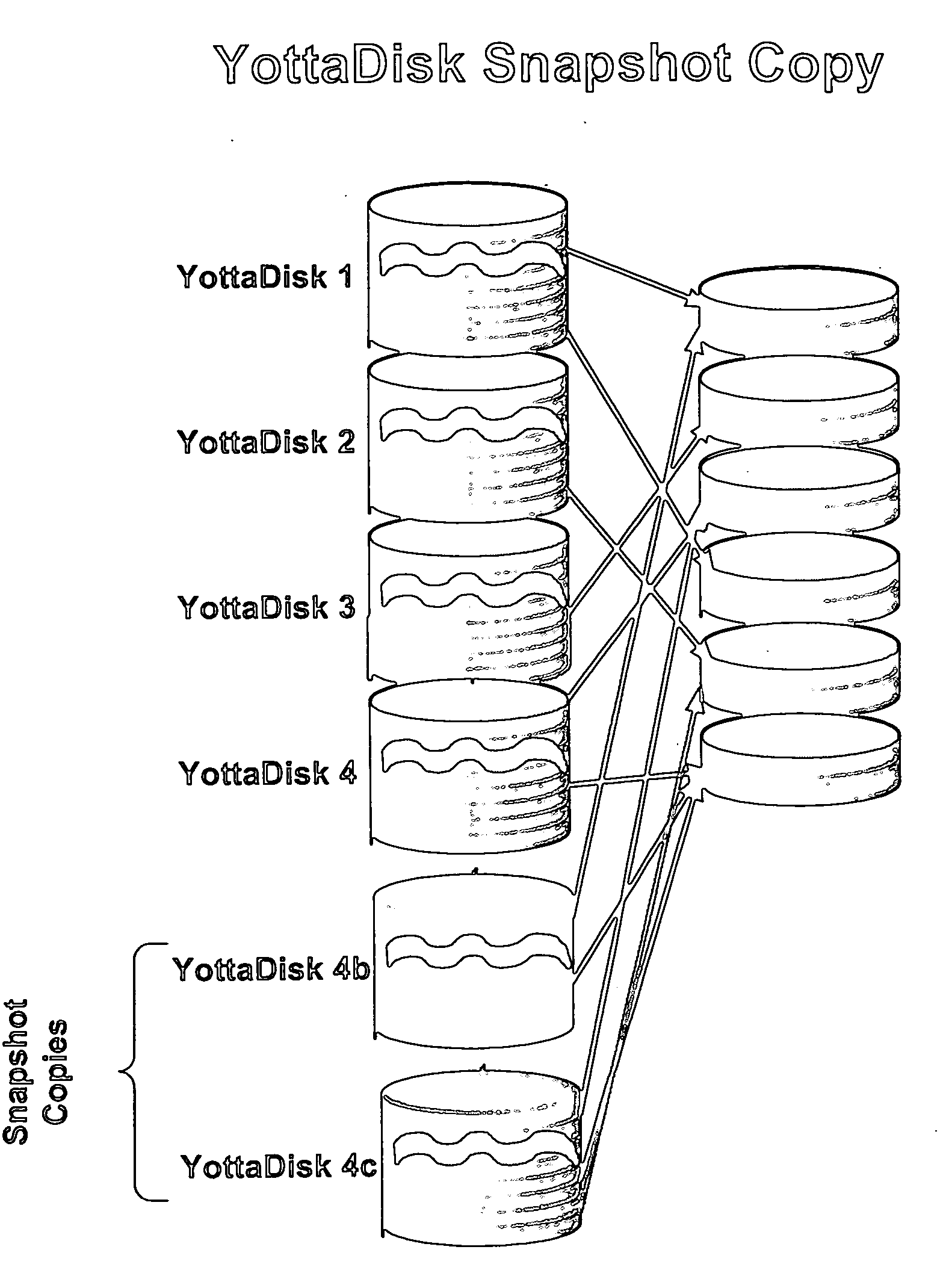
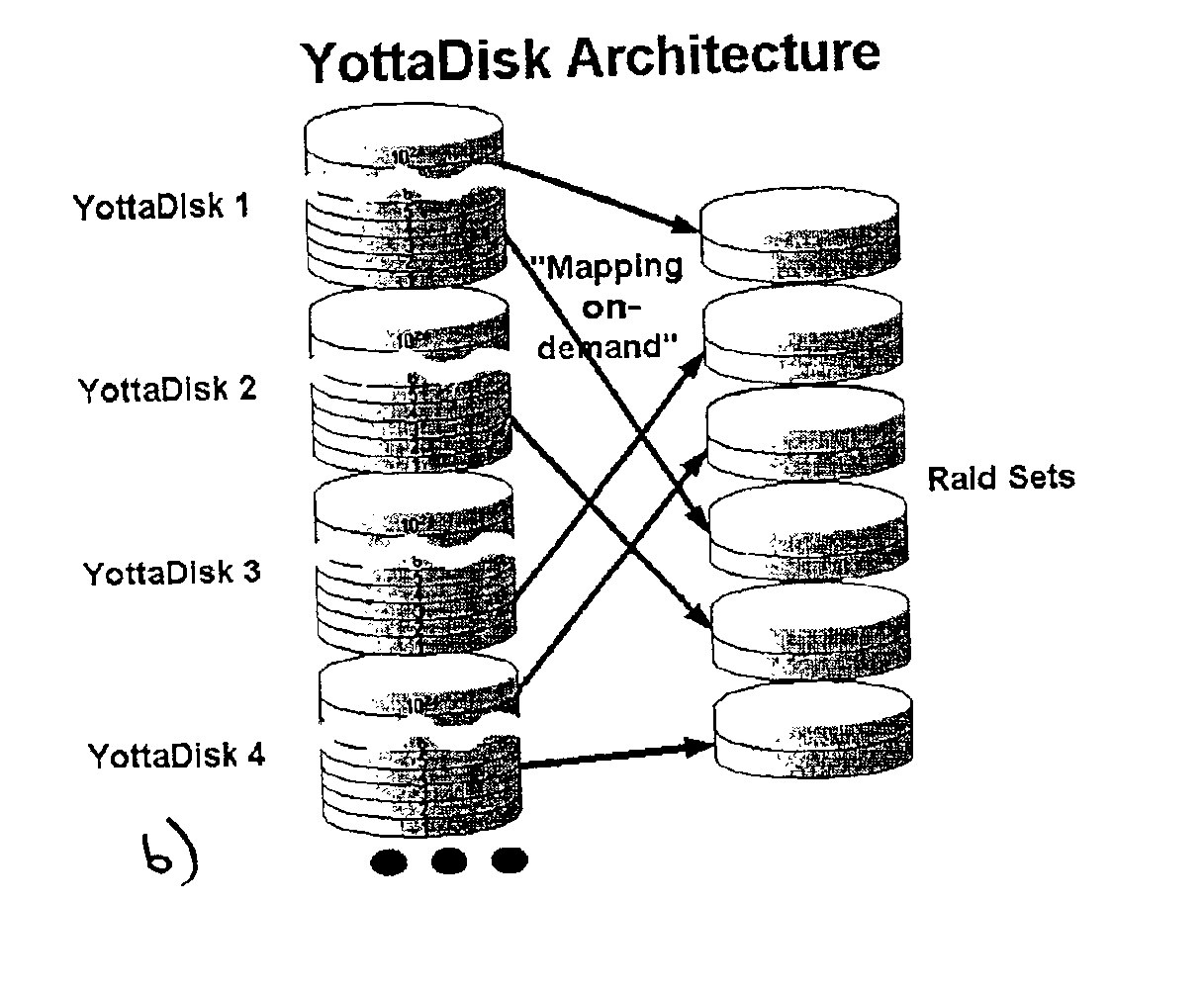
Storage virtualization systems and methods that allow customers to manage storage as a utility rather than as islands of storage which are independent of each other. A demand mapped virtual disk image of up to an arbitrarily large size is presented to a host system. The virtualization system allocates physical storage from a storage pool dynamically in response to host I / O requests, e.g., SCSI I / O requests, allowing for the amortization of storage resources-through a disk subsystem while maintaining coherency amongst I / O RAID traffic. In one embodiment, the virtualization functionality is implemented in a controller device, such as a controller card residing in a switch device or other network device, coupled to a storage system on a storage area network (SAN). The resulting virtual disk image that is observed by the host computer is larger than the amount of physical storage actually consumed.
Owner:EMC IP HLDG CO LLC
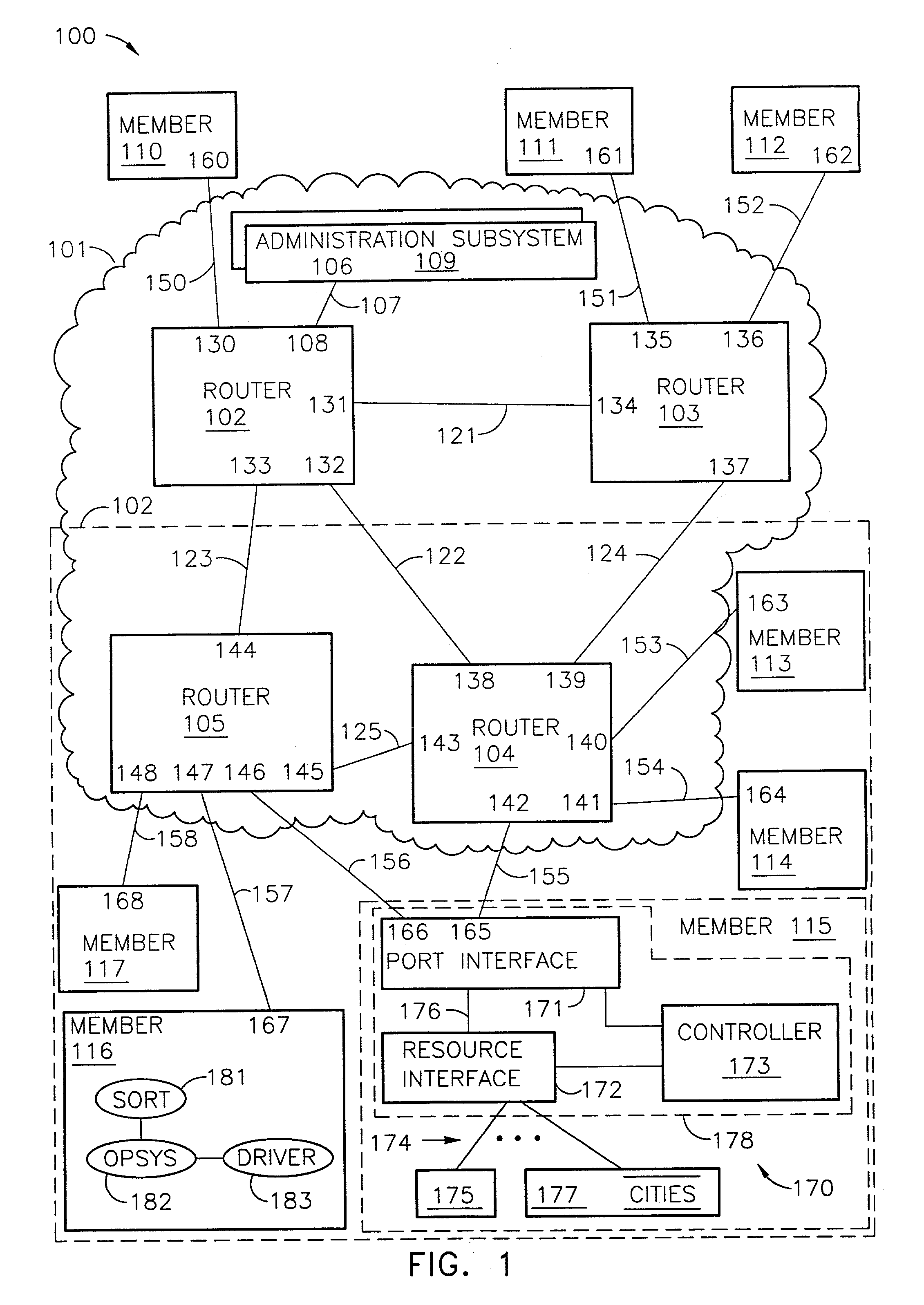
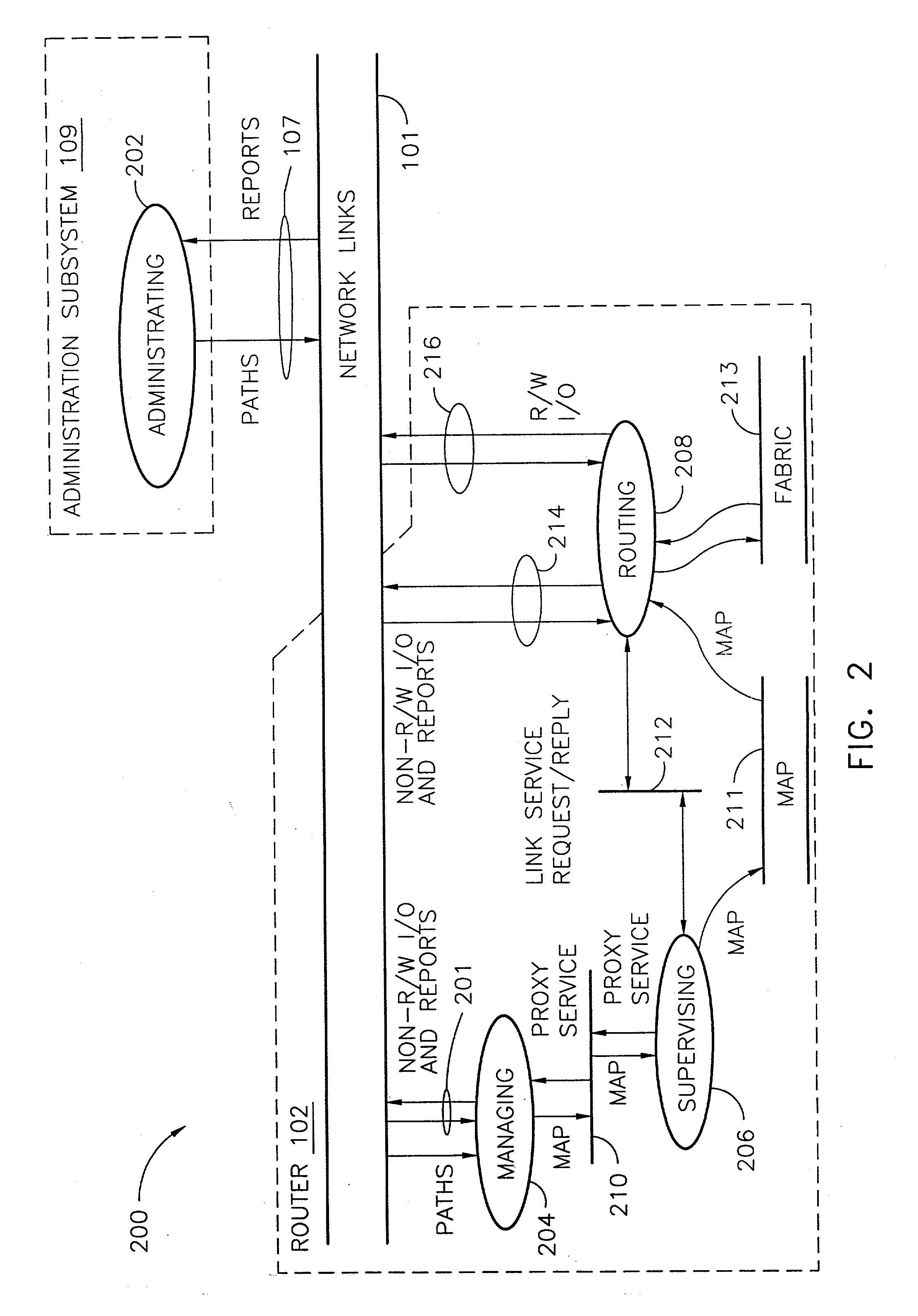
Router and methods using network addresses for virtualization
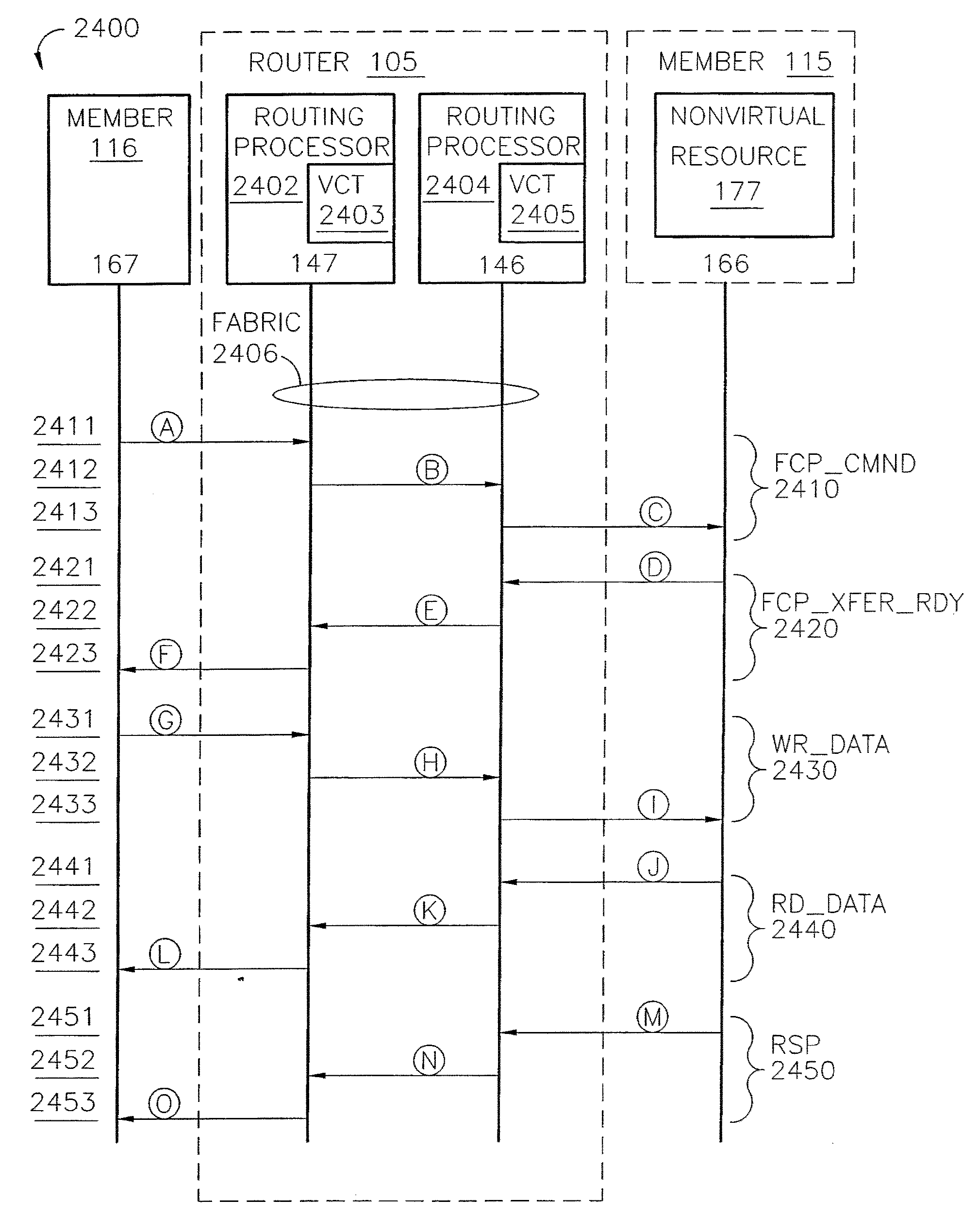
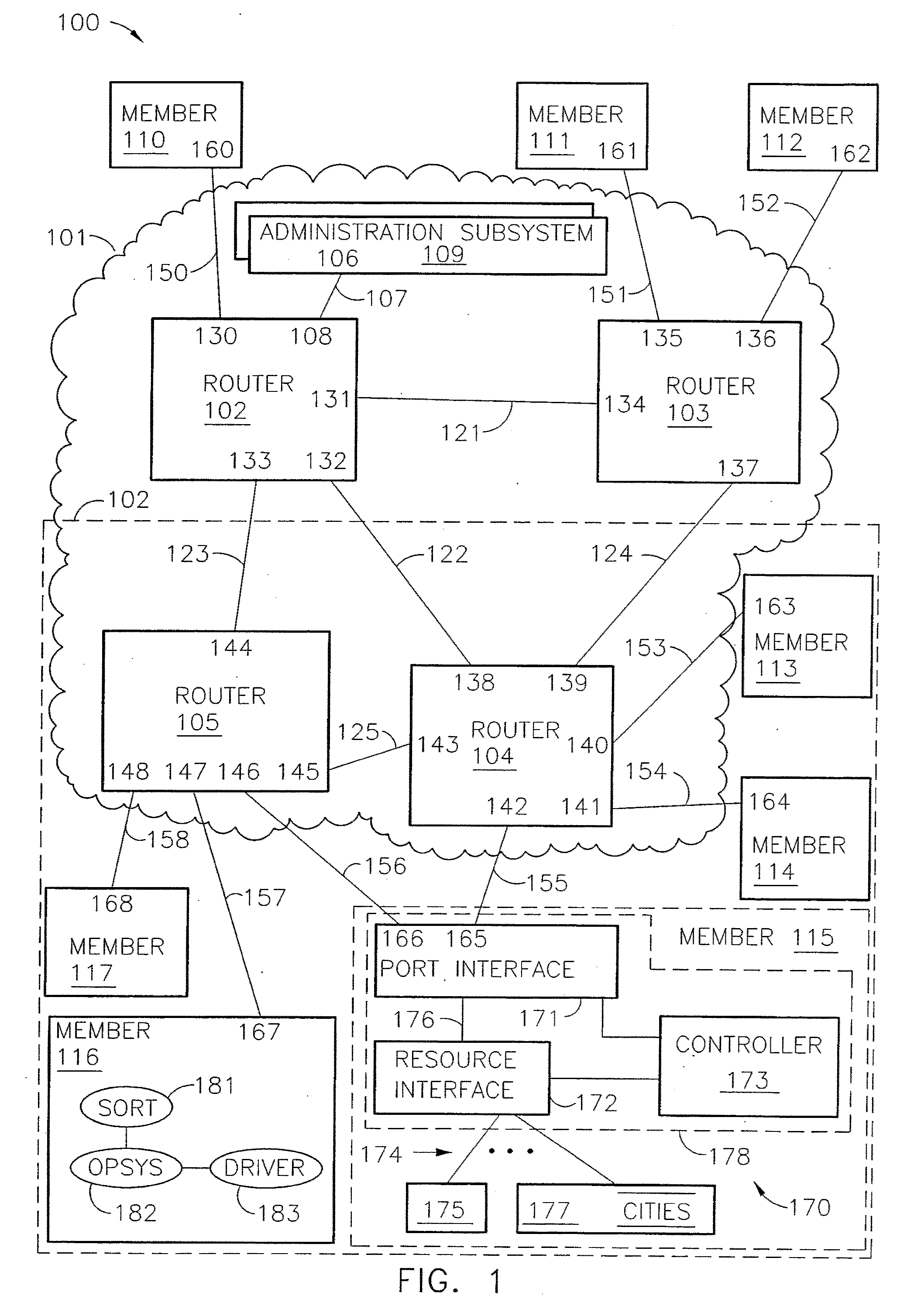
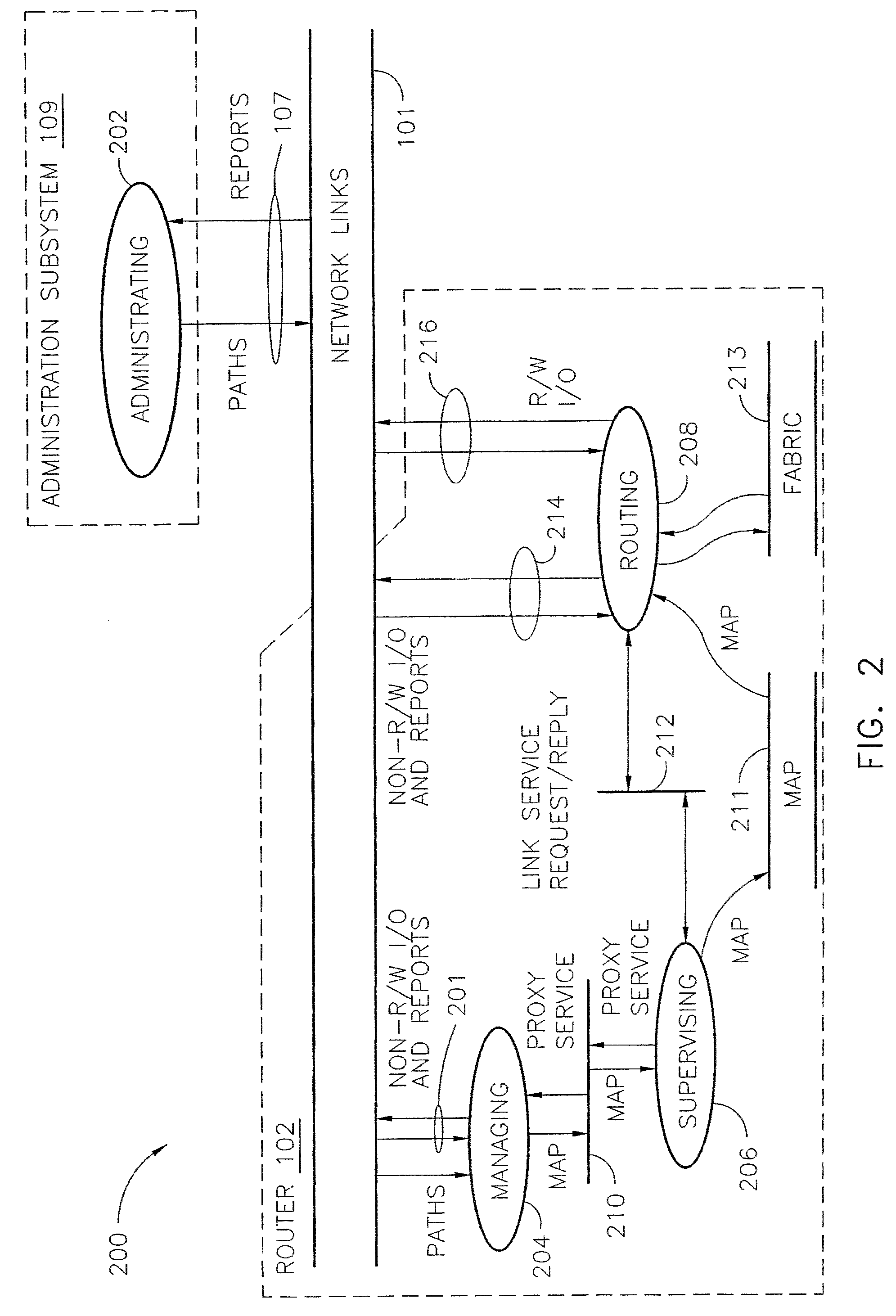
ActiveUS7200144B2Easy to operateImprove efficiency and reliabilityData switching by path configurationQuality of serviceDeficit round robin
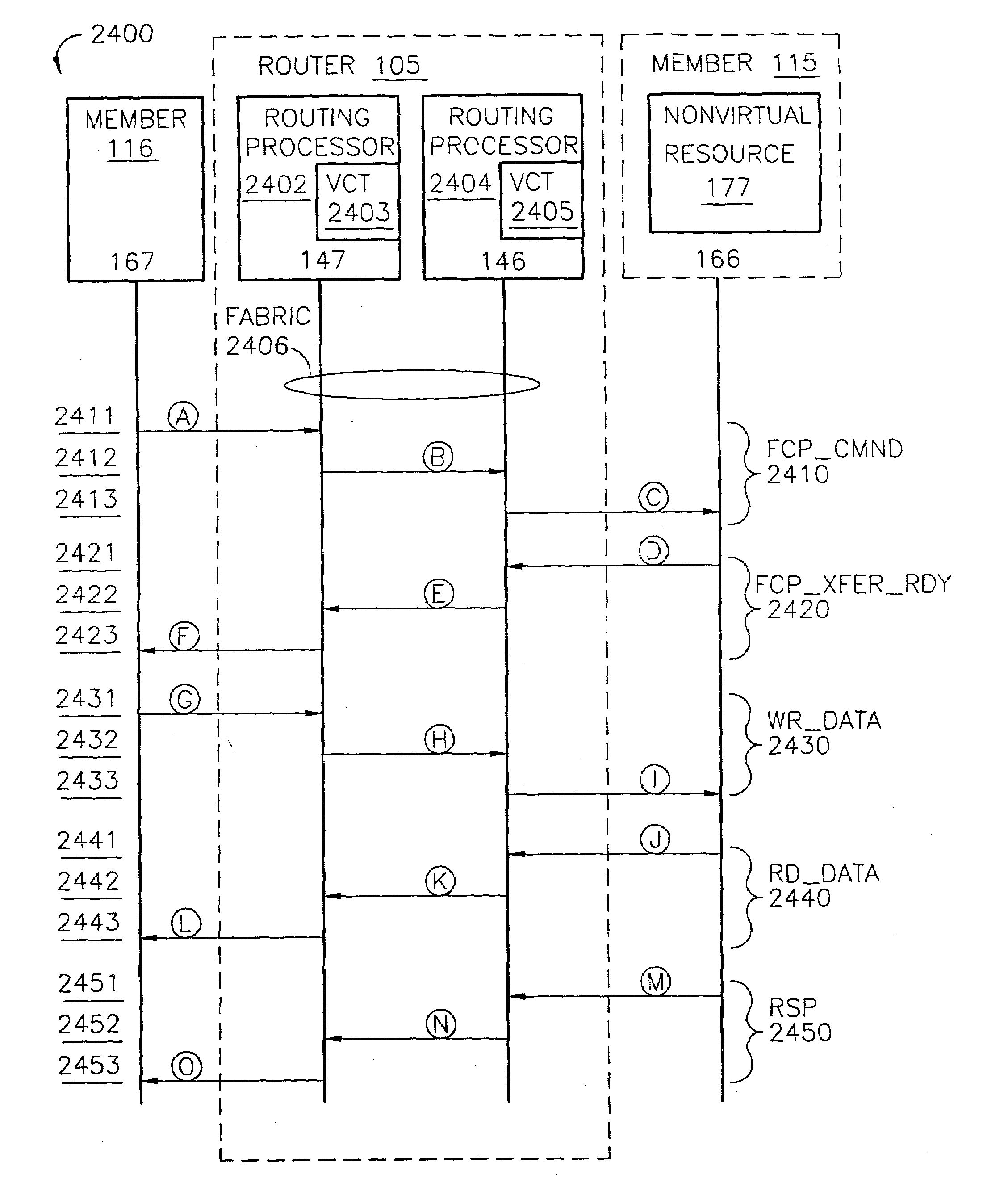
A router for use in a network includes a scalable architecture and performs methods for implementing quality of service on a logical unit behind a network port; and for implementing storage virtualization. The architecture includes a managing processor, a supervising processor; and a plurality of routing processors coupled to a fabric. The managing processor has an in-band link to a routing processor. A routing processor receives a frame from the network, determines by parsing the frame, the protocol and logical unit number, and routes the frame to a queue according to a traffic class associated with the logical unit number in routing information prepared for the processors. An arbitration scheme empties the queue in accordance with a deficit round robin technique. If a routing processor detects the frame's destination is a virtual entity, and so is part of a virtual transaction, the router conducts a nonvirtual transaction in concert with the virtual transaction. The nonvirtual transaction accomplishes the intent of the virtual transaction but operates on an actual network port, for example, a storage device.
Owner:MARVELL ASIA PTE LTD
Methods and apparatus for implementing virtualization of storage within a storage area network
ActiveUS20030172149A1Ensure integrityInput/output to record carriersMultiple digital computer combinationsStorage area networkVirtual storage
Methods and apparatus for implementing storage virtualization on a network device of a storage area network are disclosed. A frame or packet is received at a port of the network device. It is then determined that the frame or packet pertains to access of a virtual storage location of a virtual storage unit representing one or more physical storage locations on one or more physical storage units of the storage area network. A virtual-physical mapping between the one or more physical storage locations and the virtual storage location is then obtained. A new or modified frame or packet is then sent to an initiator or a target specified by the virtual-physical mapping.
Owner:CISCO TECH INC
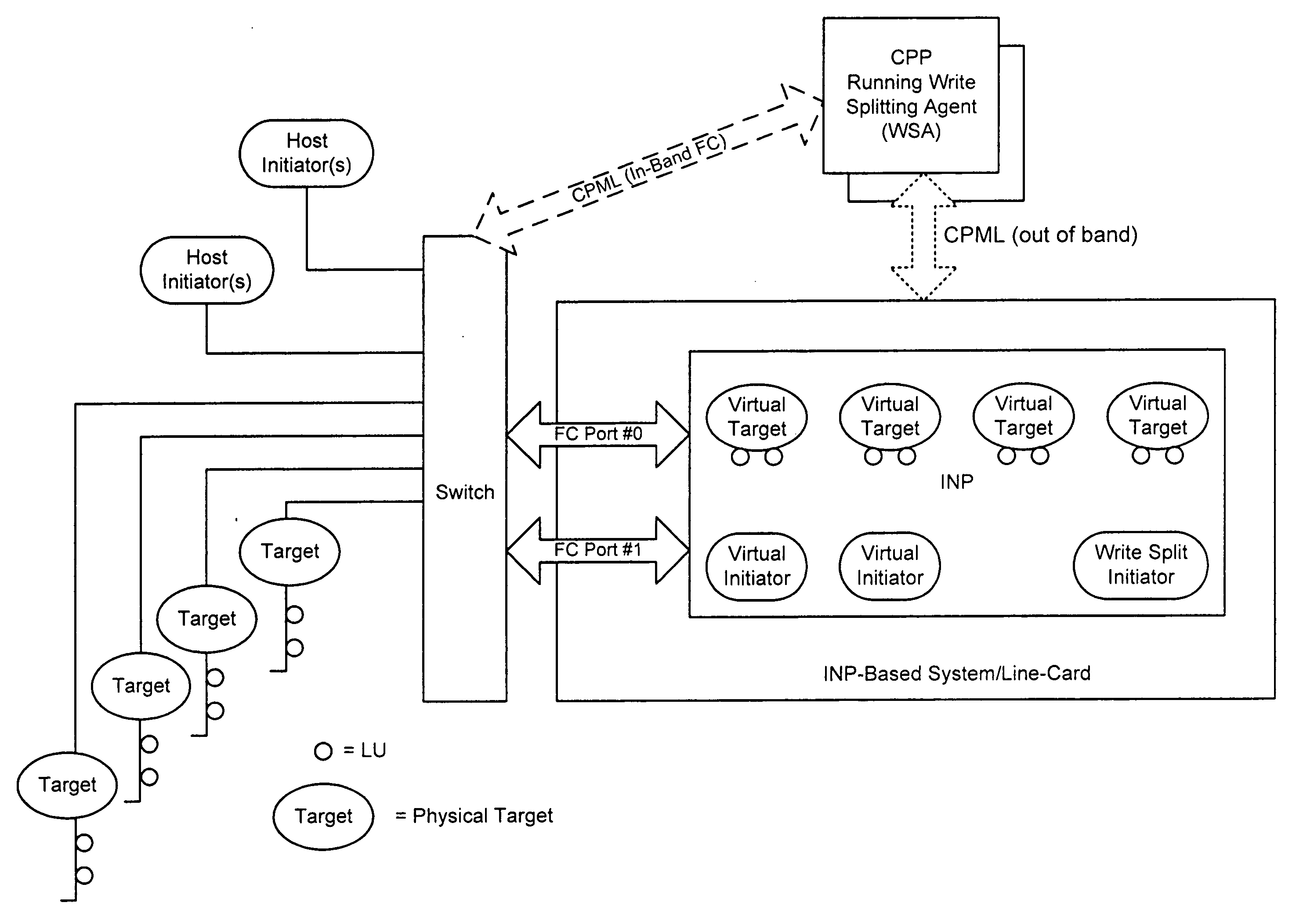
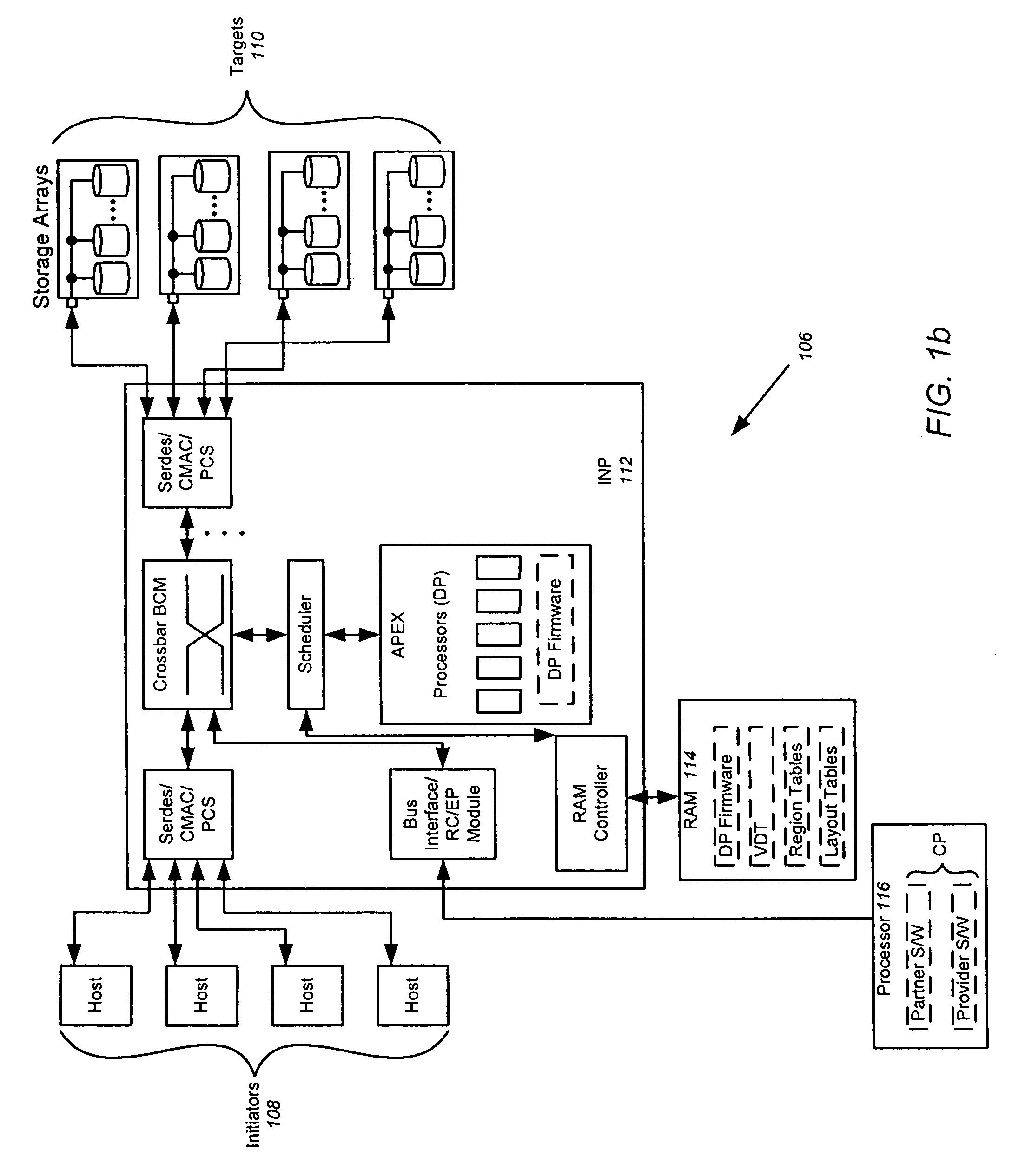
Apparatus for performing storage virtualization
ActiveUS20070239944A1Simplify writingIncrease overheadError detection/correctionMemory adressing/allocation/relocationVirtual targetData management
The splitting of storage applications and functions into a control path (CP) component and a data path (DP) component is disclosed. Reads and writes may be handled primarily in the DP. The CP may be responsible for discovery, configuration, and exception handling. The CP can also be enabled for orchestrating complex data management operations such as snapshots and migration. Storage virtualization maps a virtual I / O to one or more physical I / O. A virtual target (vTarget) in the virtual domain is associated with one physical port in the physical domain. Each vTarget may be associated with one or more virtual LUNs (vLUNs). Each vLUN includes one or more vExtents. Each vExtent may point to a region table, and each entry in the region table may contain a pointer to a region representing a portion of a pExtent, and attributes (e.g. read / write, read only, no access) for that region.
Owner:AVAGO TECH INT SALES PTE LTD
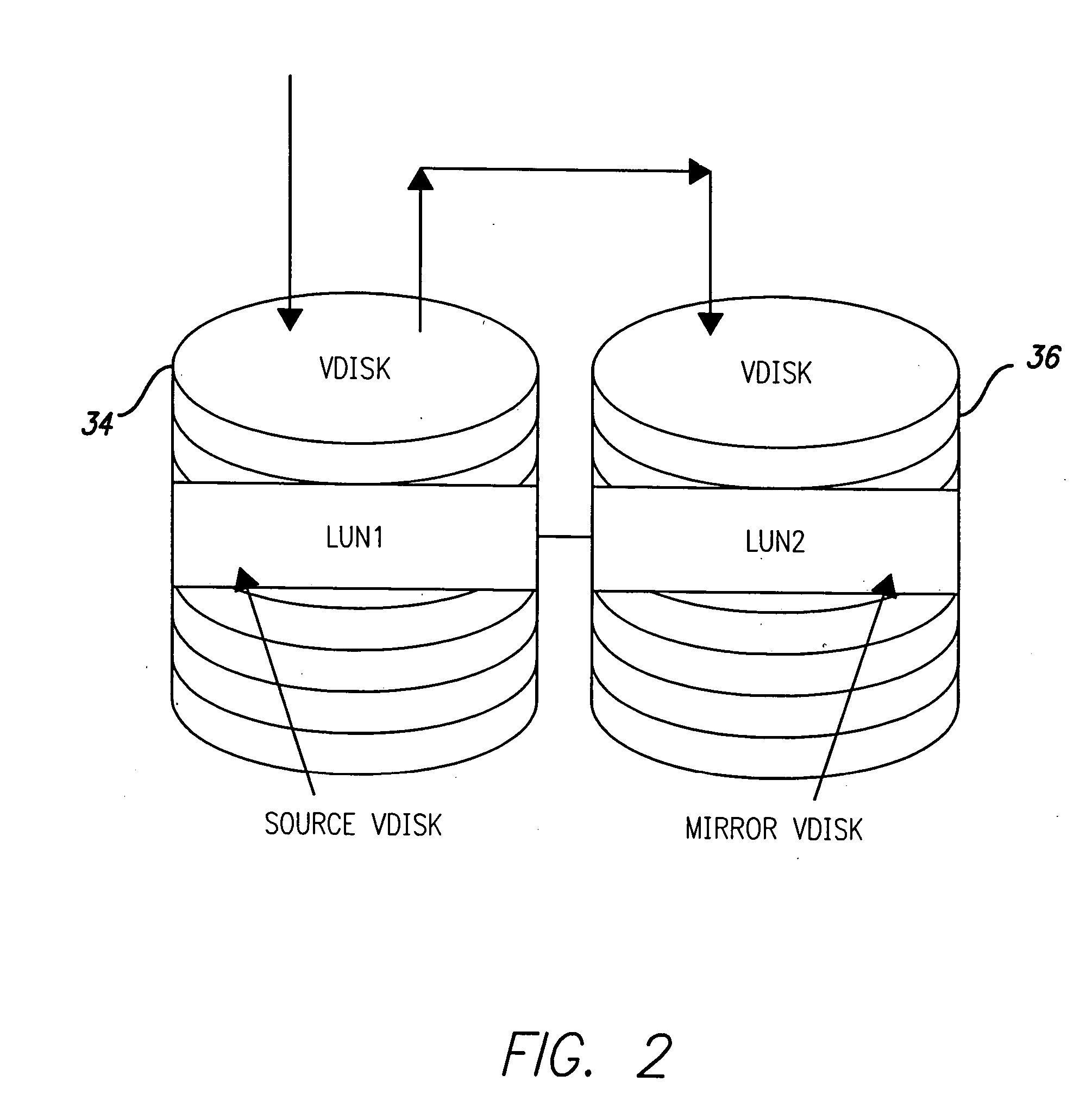
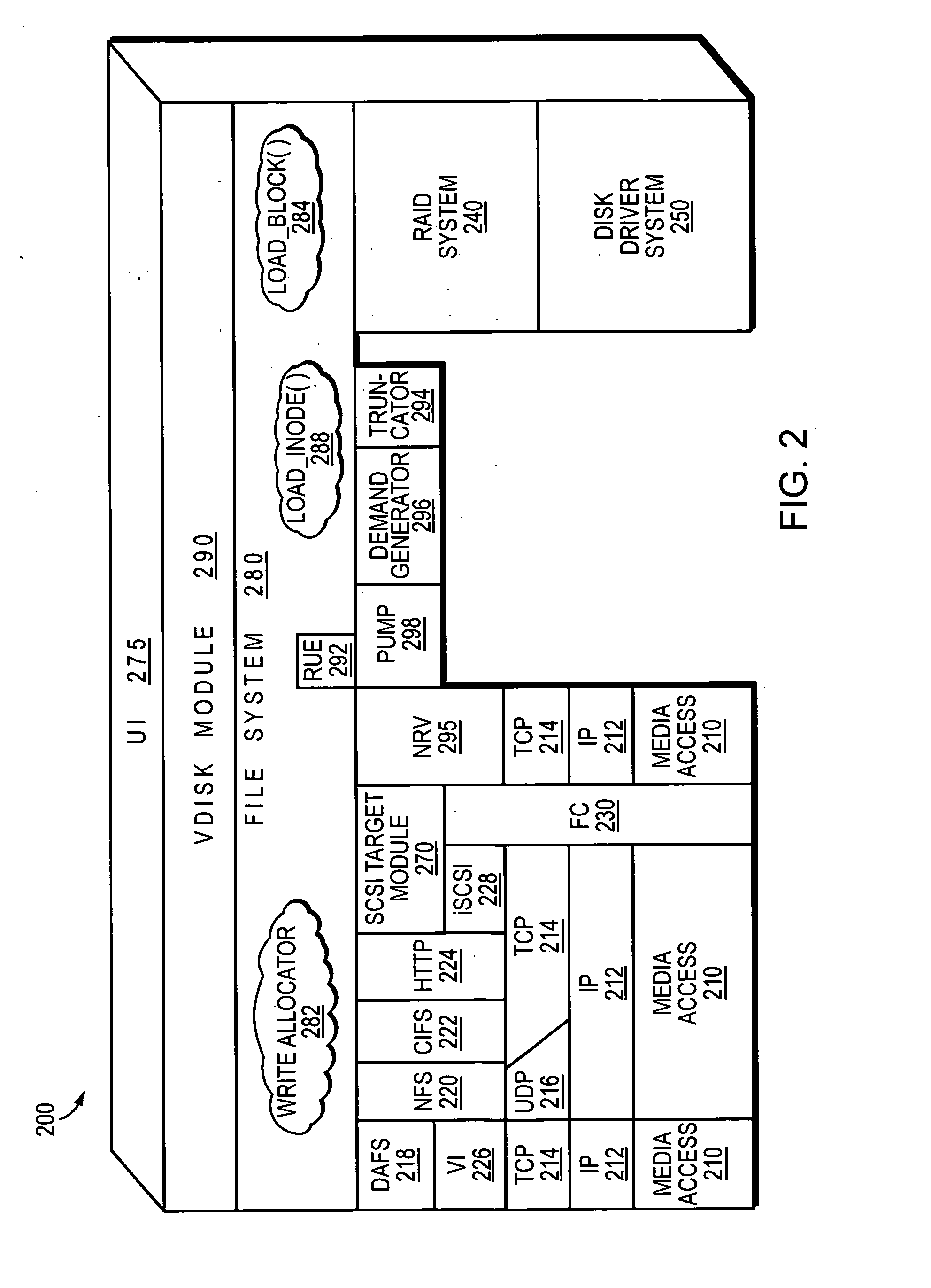
Storage virtualization by layering virtual disk objects on a file system
InactiveUS7107385B2Input/output to record carriersData processing applicationsOperational systemFile system
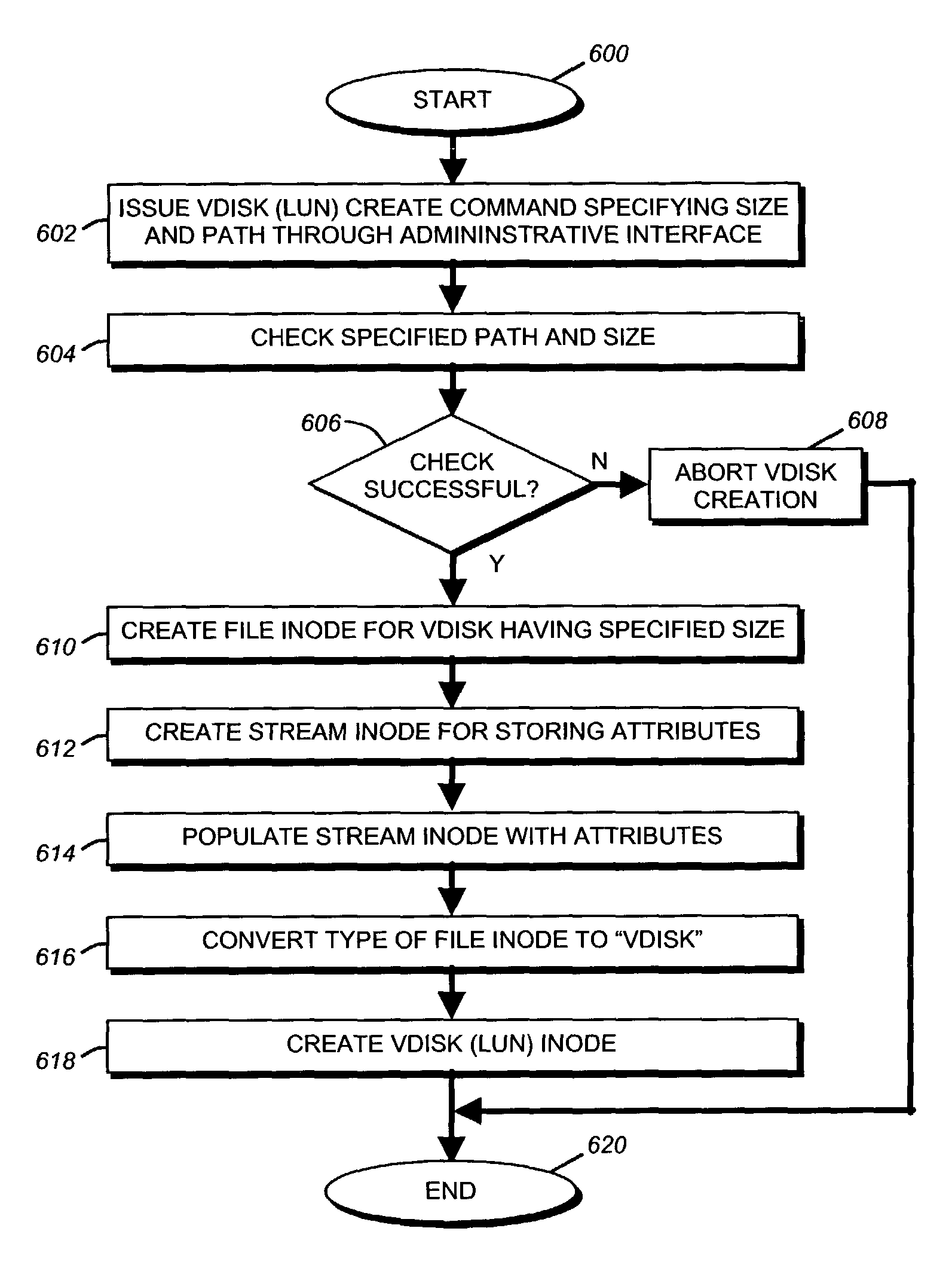
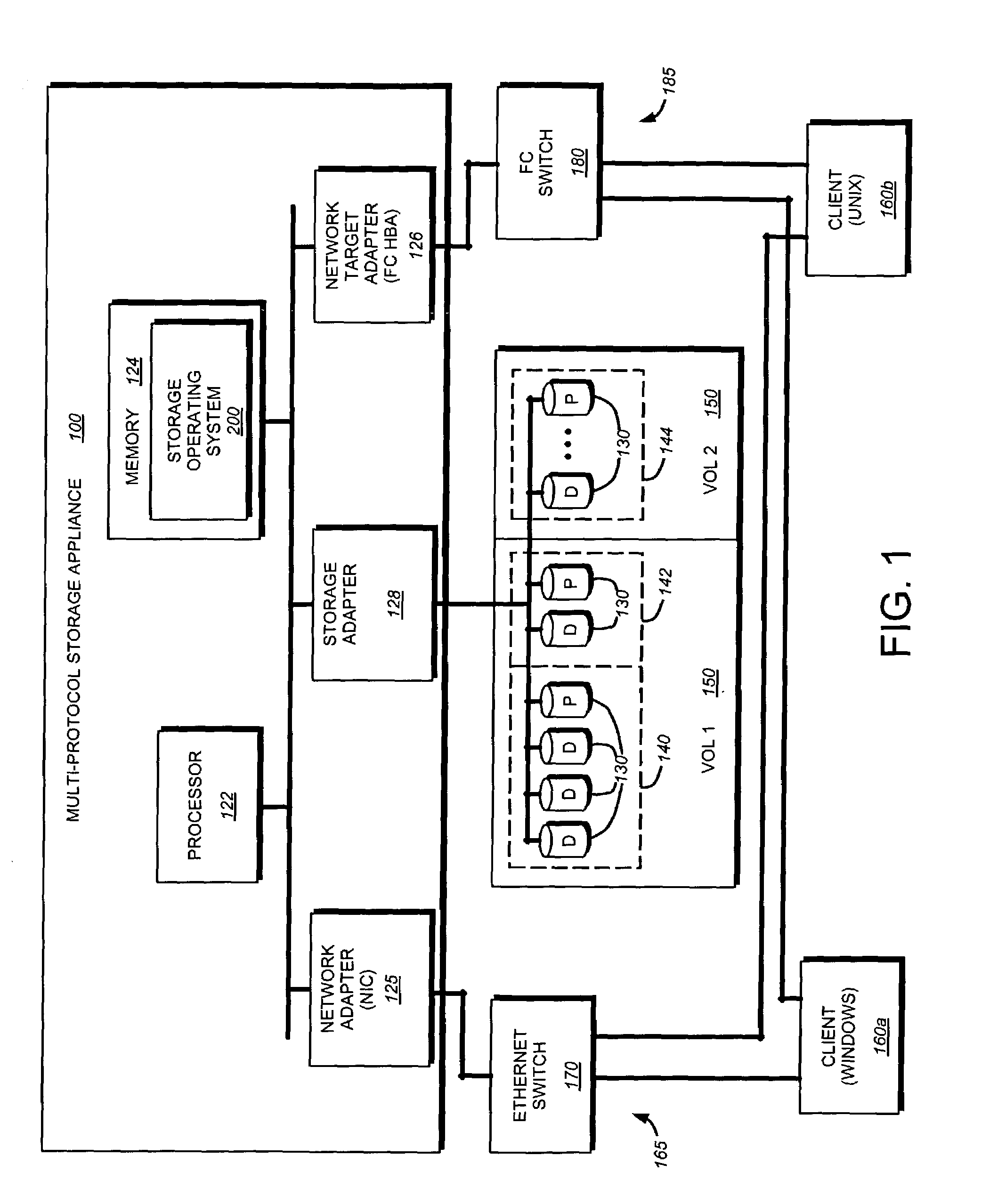
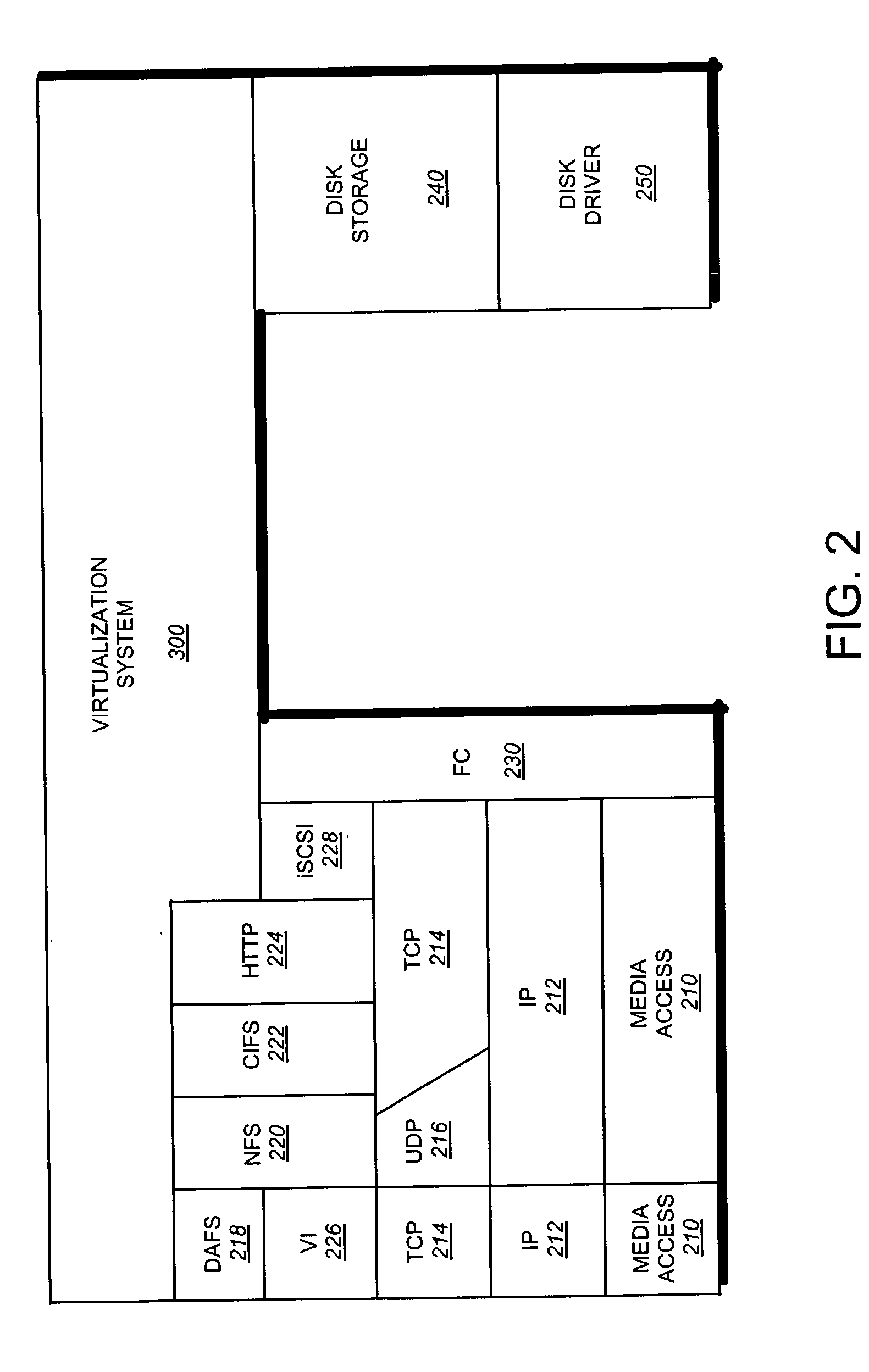
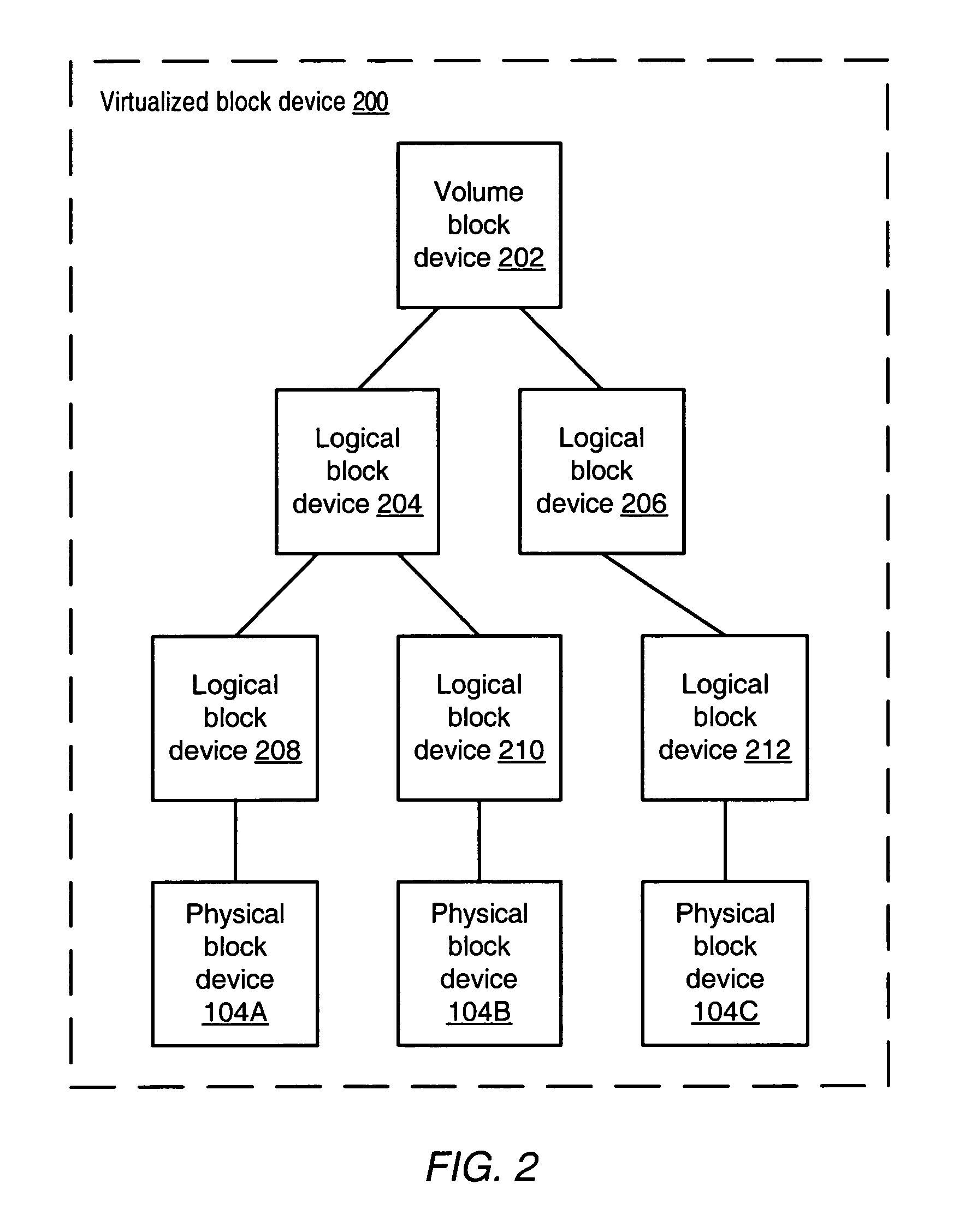
A storage virtualization selection technique “automates” a virtualization selection process to create virtual disk (vdisk) storage objects over a volume of a file system implemented by a storage operating system of a multi-protocol storage appliance. The file system provides a virtualization system that aggregates physical storage of a set of disks or portions (e.g., extents) of disks into a pool of blocks that can be dynamically allocated to form a vdisk. The file system also provides reliability guarantees for the vdisks in accordance with its underlying architecture. That is, the file system organizes its storage within volumes created among the managed disks. The vdisk is thereafter created as a storage object within a volume and, thus, inherits the underlying reliability configuration associated with that volume. The portions are aggregated and allocated as a vdisk with reliability guarantees in response to a request to create the vdisk from a user of the storage appliance and without further user involvement.
Owner:NETWORK APPLIANCE INC
End-to-end virtualization
InactiveUS20120099602A1Facilitates end-to-end virtualizationData switching by path configurationData virtualizationNetwork virtualization
One embodiment of the present invention provides a system that facilitates end-to-end virtualization. During operation, a network interface residing on an end host sets up a tunnel. The network interface then encapsulates a packet destined to a virtual machine based on a tunneling protocol. By establishing a tunnel that allows a source host to address a remote virtual machine, embodiments of the present invention facilitate end-to-end virtualization.
Owner:AVAGO TECH INT SALES PTE LTD
Method and apparatus for providing network virtualization
A method and apparatus for providing network virtualization on a packet network are disclosed. For example, the method receives a request from a user, wherein the request comprises at least one of: a feature of a network component or a network component for a virtual network. The method determines if the request can be instantiated over one or more real network resources, and then instantiates the request via the one or more real network resources, if it is determined that the request can be instantiated.
Owner:RAKUTEN GRP INC
Storage virtualization system and methods
InactiveUS6857059B2Reduce consumptionWithout impactInput/output to record carriersMemory adressing/allocation/relocationStorage area networkNetwork virtualization
Storage virtualization systems and methods that allow customers to manage storage as a utility rather than as islands of storage which are independent of each other. A demand mapped virtual disk image of up to an arbitrarily large size is presented to a host system. The virtualization system allocates physical storage from a storage pool dynamically in response to host I / O requests, e.g., SCSI I / O requests, allowing for the amortization of storage resources through a disk subsystem while maintaining coherency amongst I / O RAID traffic. In one embodiment, the virtualization functionality is implemented in a controller device, such as a controller card residing in a switch device or other network device, coupled to a storage system on a storage area network (SAN). The resulting virtual disk image that is observed by the host computer is larger than the amount of physical storage actually consumed.
Owner:EMC IP HLDG CO LLC
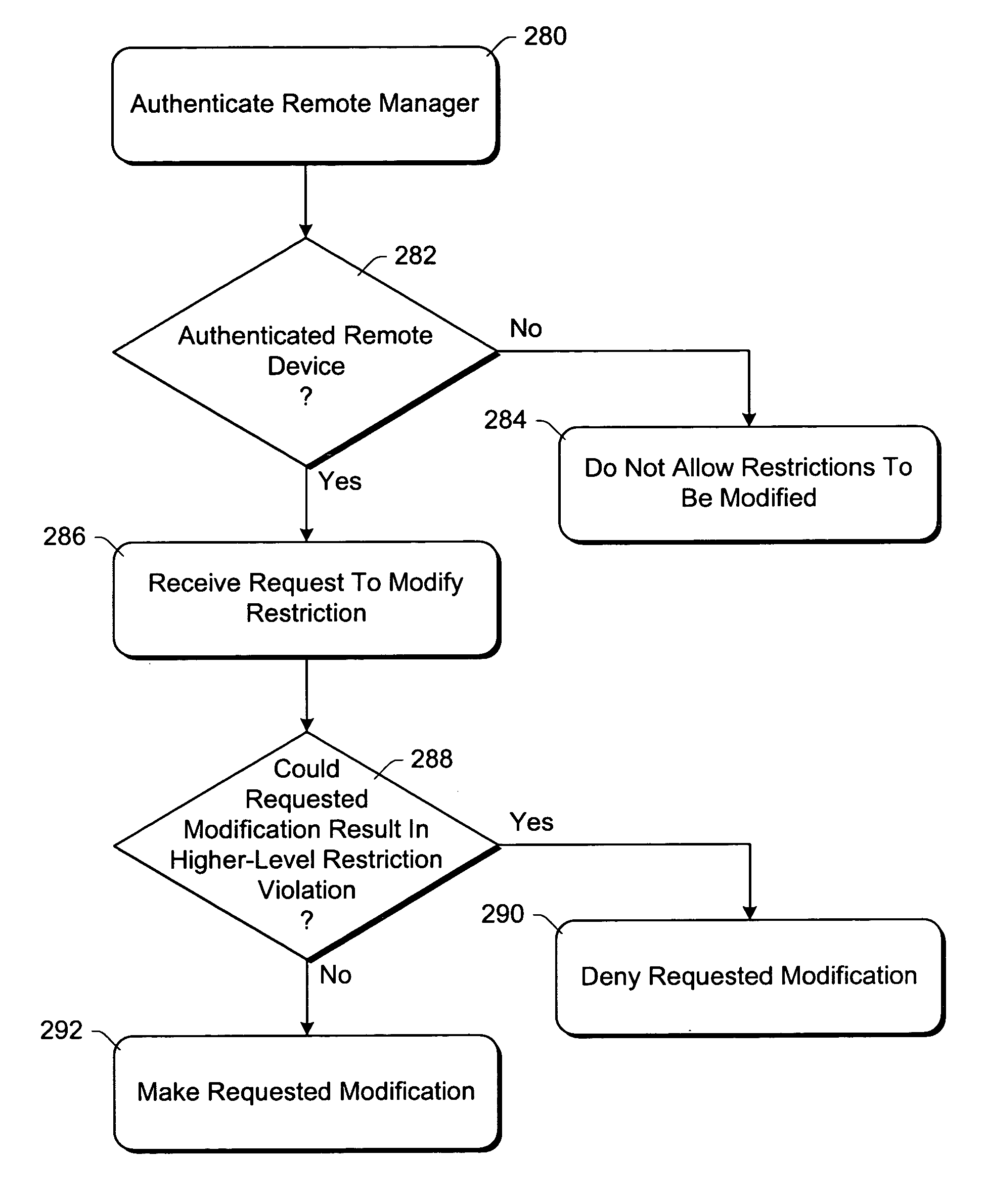
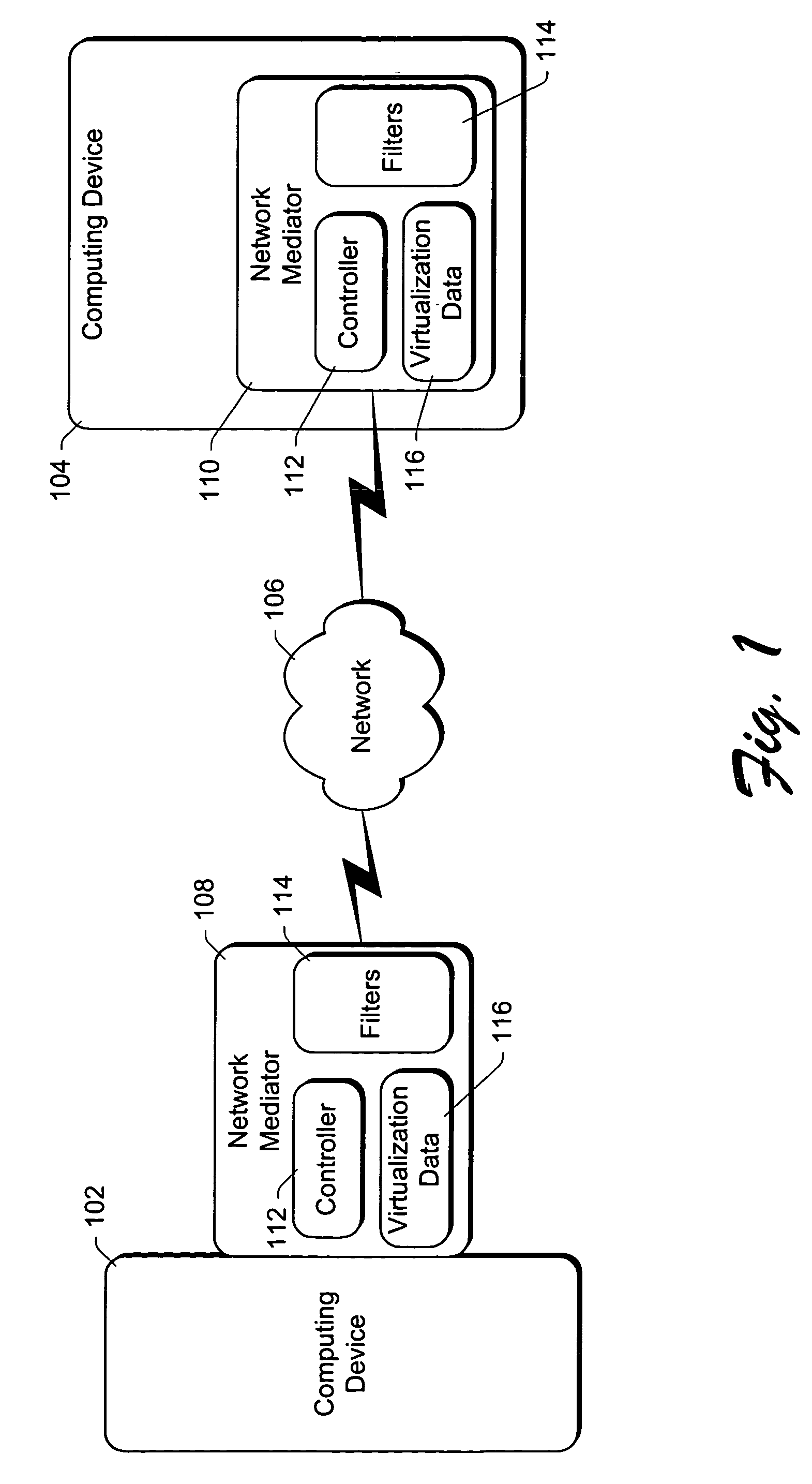
Using packet filters and network virtualization to restrict network communications
InactiveUS7093288B1Communication be restrictRandom number generatorsCharacter and pattern recognitionNetwork packetNetwork addressing
A network mediator corresponding to a computing device uses packet filters to restrict network communications. The network mediator includes a set of one or more filters, each filter having parameters that are compared to corresponding parameters of a data packet to be passed through the network mediator. The network mediator determines whether to allow the data packet through based on whether the data packet parameters match any filter parameters. The set of filters can be modified by a remote device, but cannot be modified by the computing device whose communications are being restricted. When a data packet is sent from the computing device, the data packet will include the virtual address which is changed to the network address by the network mediator prior to forwarding the packet on the network, and vice versa. By virtualizing the addresses, the computing device is restricted in accessing other devices over the network.
Owner:MICROSOFT TECH LICENSING LLC
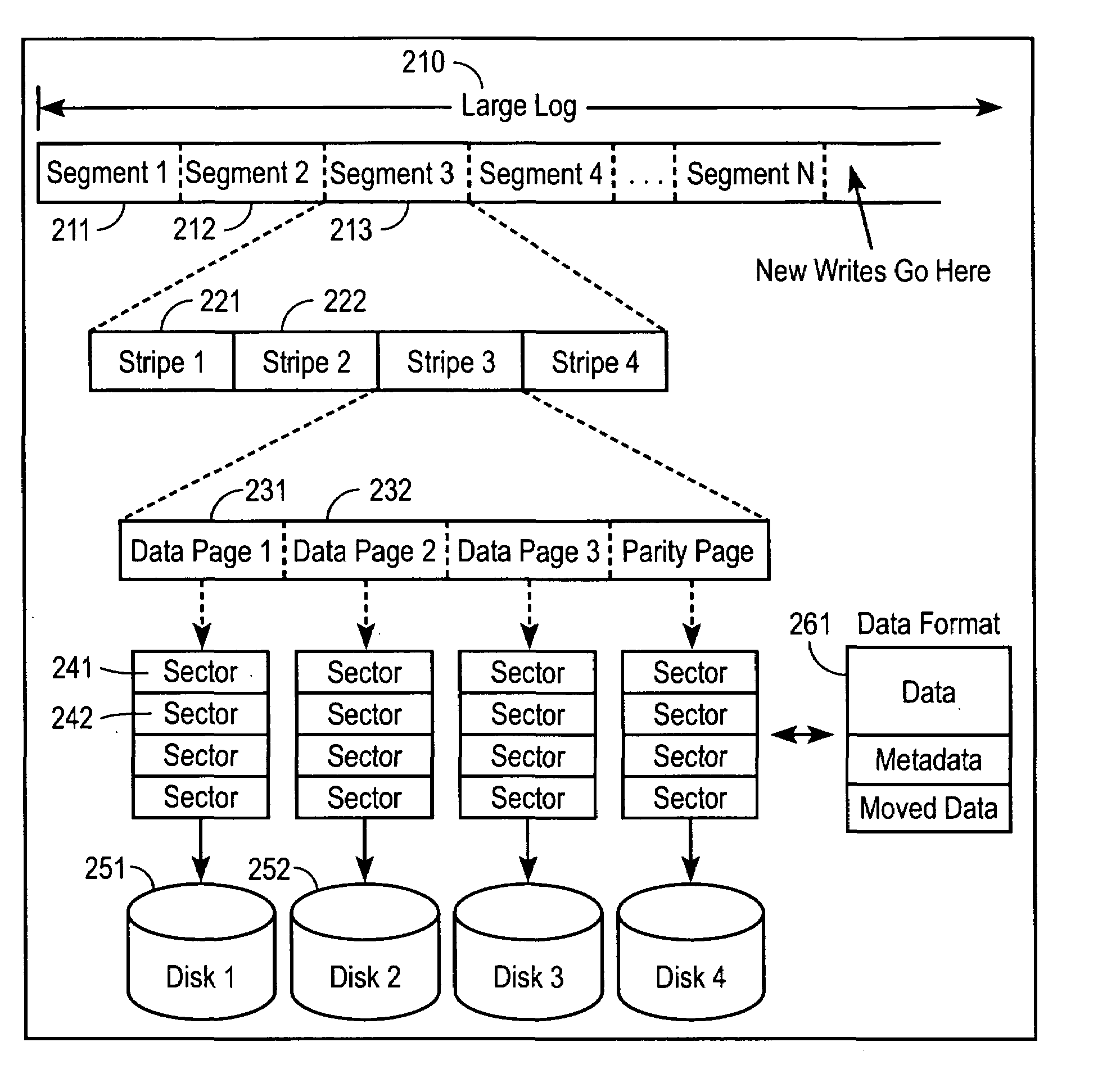
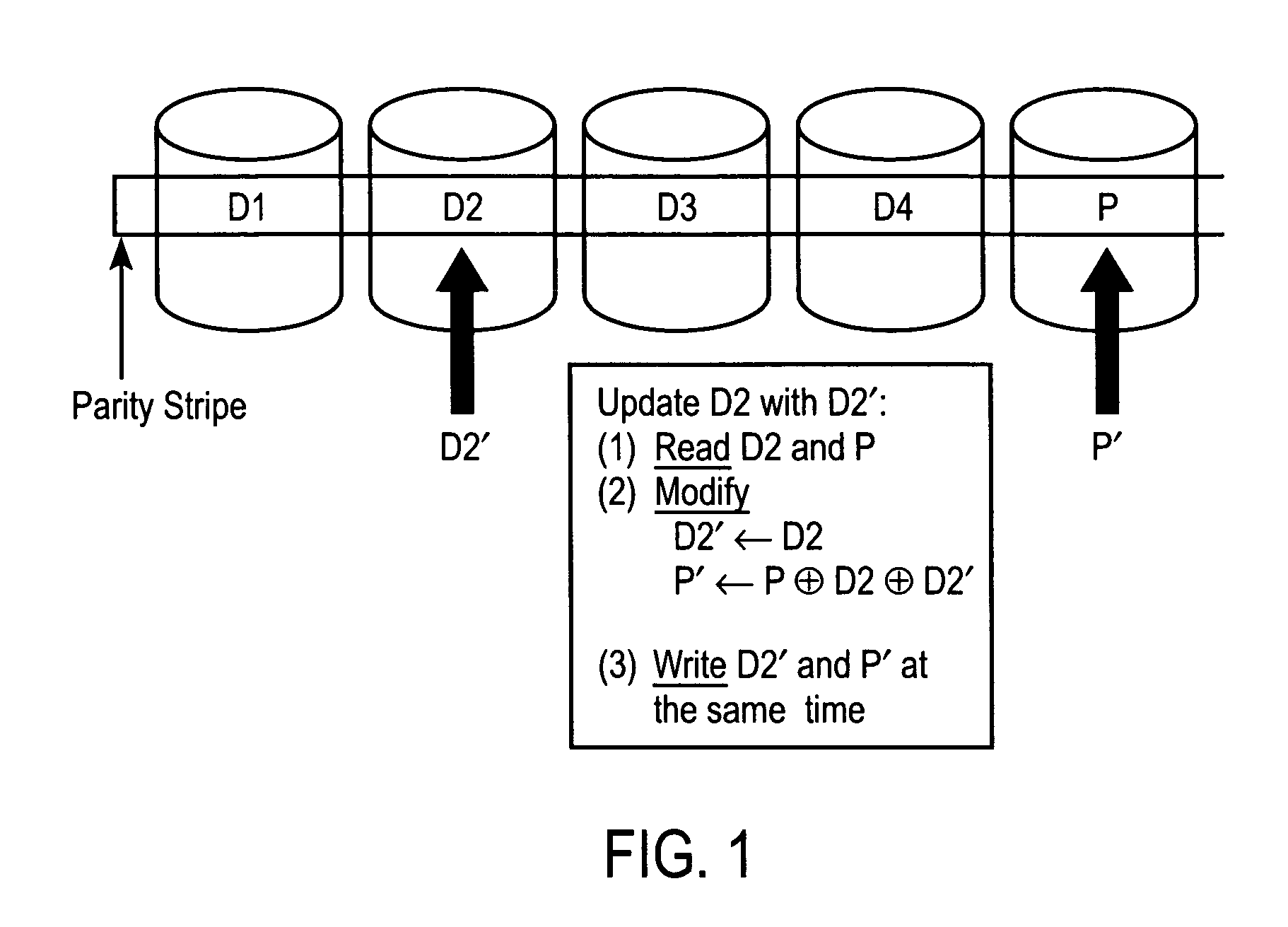
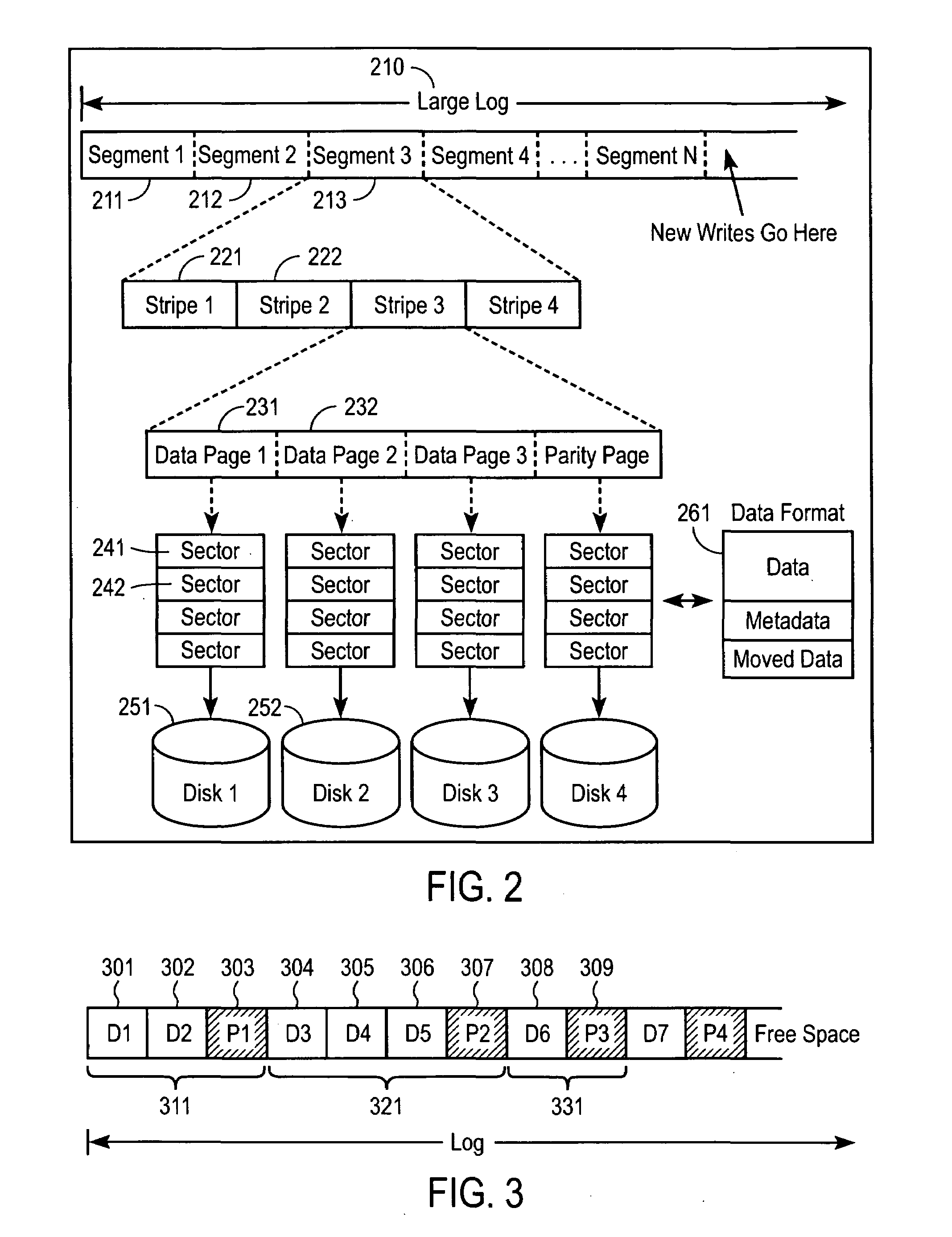
High-performance log-structured RAID
InactiveUS7047358B2Easily made atomicSmall write performanceData processing applicationsRedundant data error correctionRAIDNon-volatile memory
This invention describes a high-performance, log-structured implementation of a RAID subsystem that can be efficiently implemented in software. The methods described here allow the RAID subsystem to achieve high performance without using specialized hardware such as non-volatile memory or hardware XOR / DMA engines. Furthermore, the RAID implementation described here is well suited for supporting many functions required for advanced storage virtualization such as virtual disks, graceful addition and removal of disks, tolerating multi-disk failures, and snapshots.
Owner:MIDDLEFIELD VENTURES +7
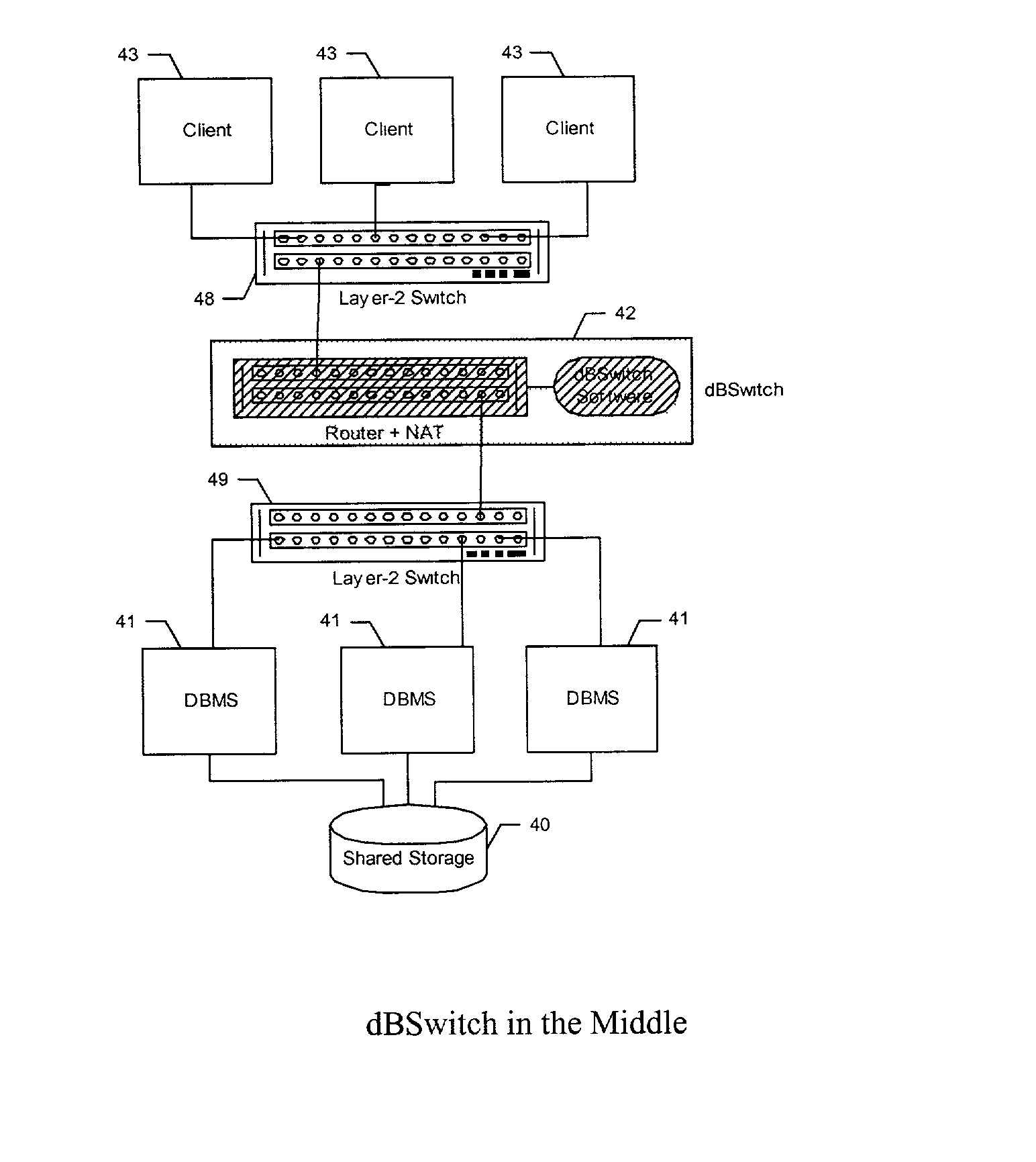
Database Switch enabling a database area network
InactiveUS20030154236A1Multiple digital computer combinationsTransmissionArea networkApplication software
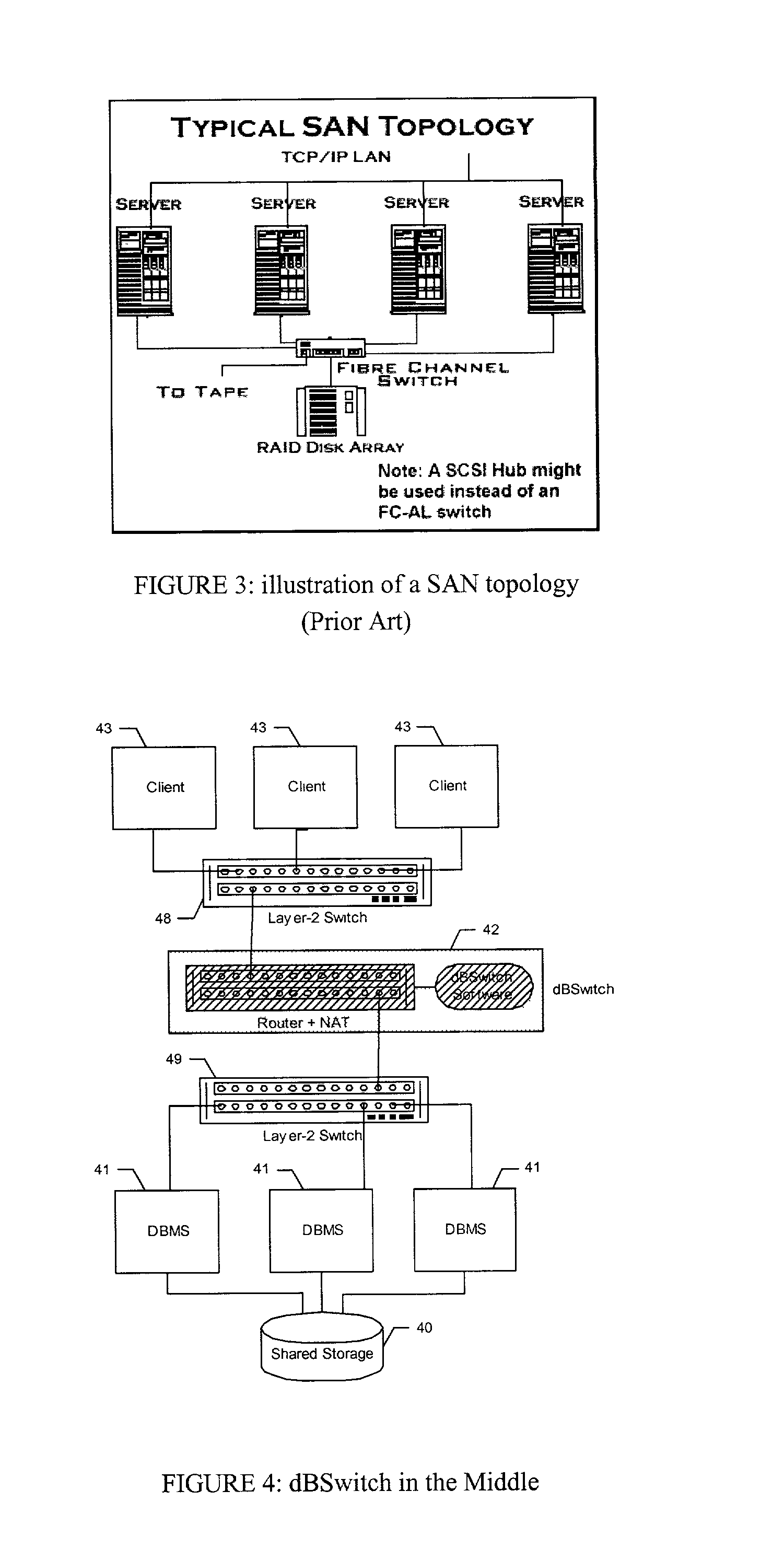
A method and system for improving utilization of the typical DBMS client-server configuration is provided. Specifically, the present invention can include a Database Switch (dBSwitch) situated between the applications and database servers in a network, capable of dynamically and transparently connecting applications to databases using standard database servers and standard protocols. The Database Switch appliance performs this database routing in real time, with high bandwidth and negligible latency. The Database Switch enables the formation of a Database Area Network (DAN) architecture, which promotes database virtualization by integrating the database servers, the shared storage, and the interconnecting network, making them appear to be one large, scalable database server. This DAN architecture yields high utilization, high availability, scalability on demand, simplified management and security, in a shared and heterogeneous application environment.
Owner:DAR SHAUL +3
Switch assisted frame aliasing for storage virtualization
InactiveUS6876656B2Reduce the burden onError preventionTransmission systemsTransaction dataData virtualization
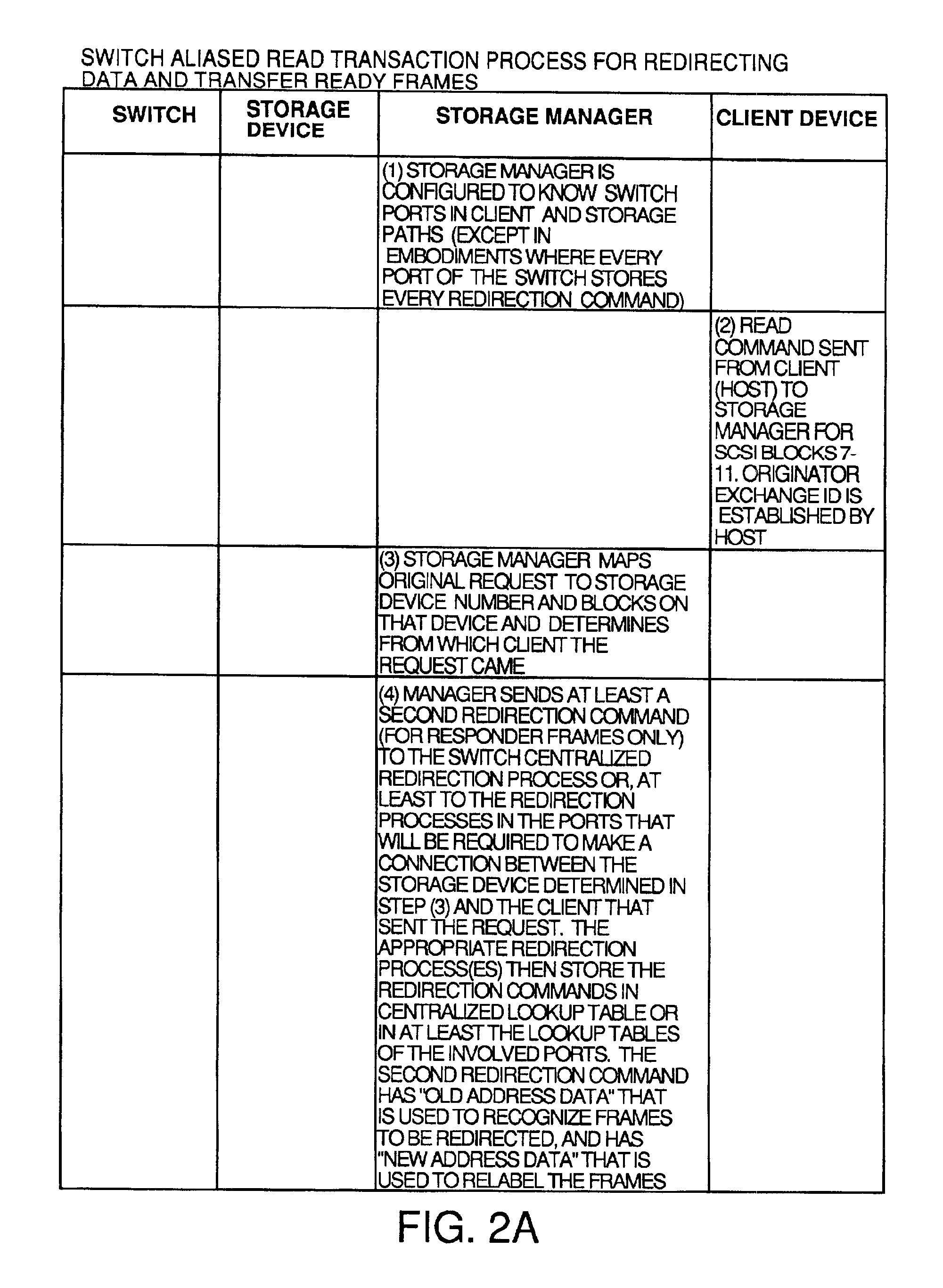
An apparatus and process for relabelling and redirecting at least some of the read transaction data frames and the write transaction write data and transfer ready frames in a network so as to bypass a storage manager and pass directly between the client and a storage device via a switch. This eliminates the storage manager as a bottleneck. Some embodiments redirect every read and write transaction, and others redirect only large transactions, or only ones not stored in cache or when latency gets too high. Redirection is accomplished by transmission from the storage manager to a switch redirection commands that contain old and new address data. When a frame to be redirected comes in, its address is compared to the old address data. If there is a match, the new address data is substituted and the frame is passed to a conventional routing process to be routed so as to bypass the storage manager.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
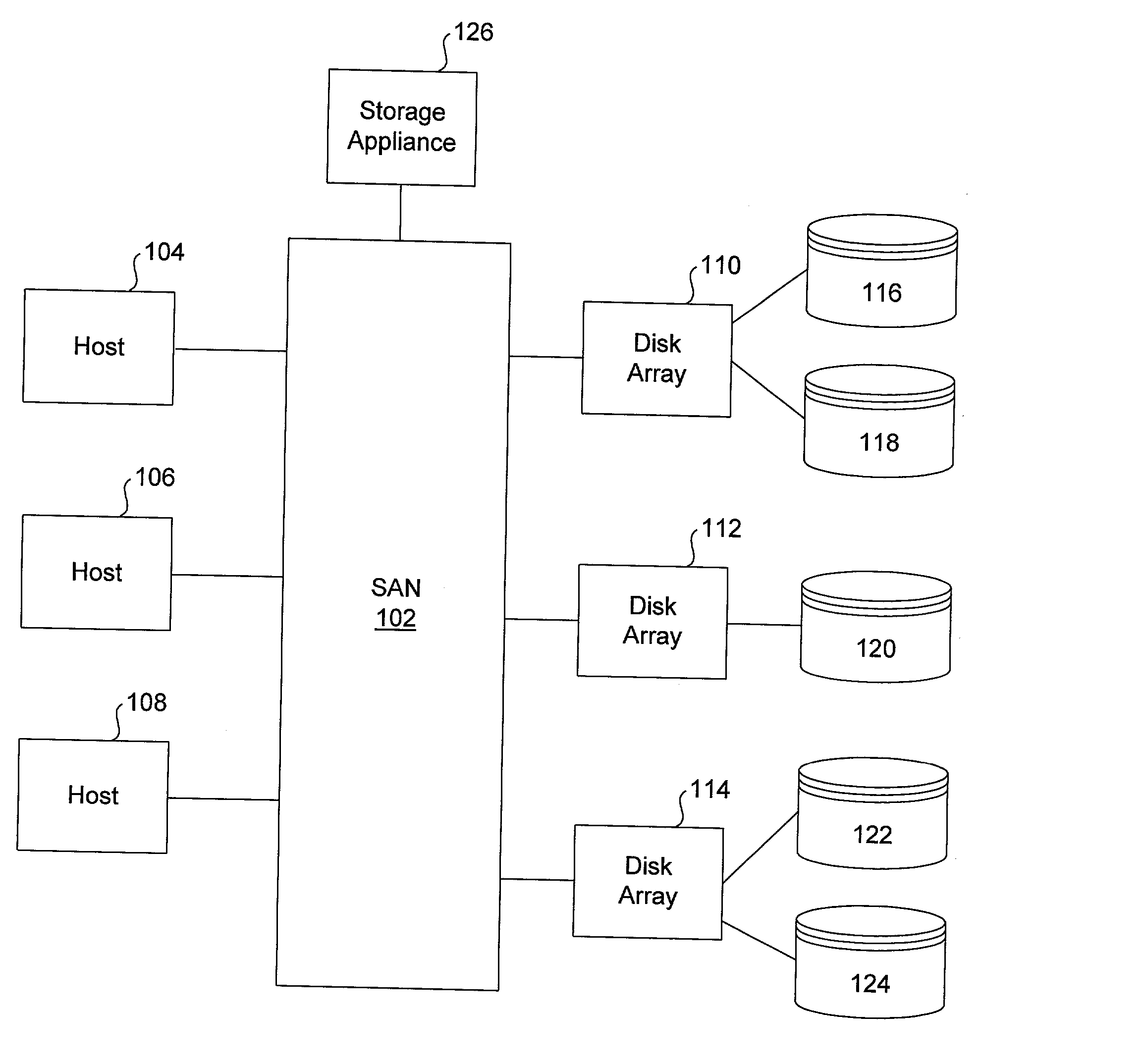
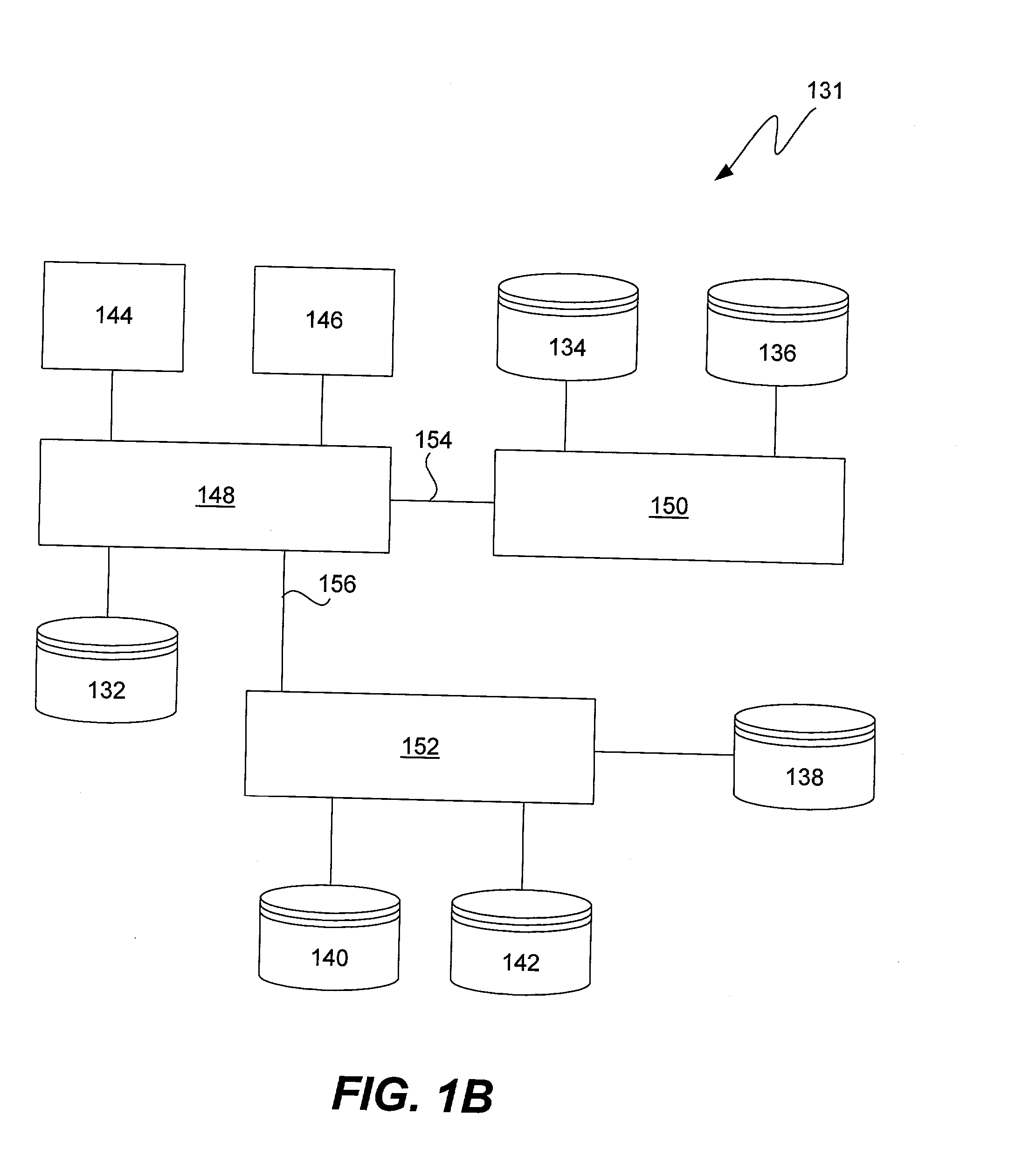
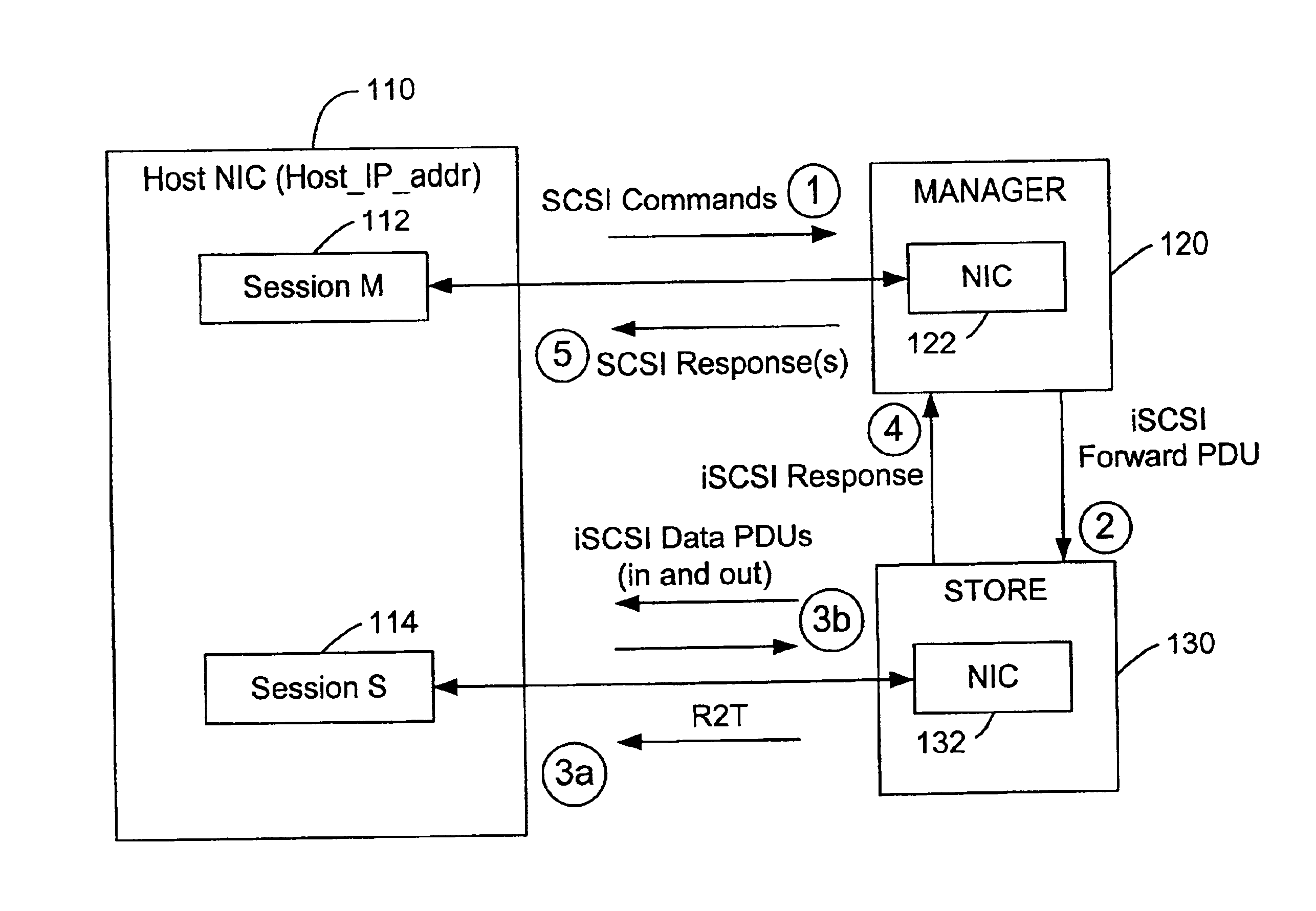
System and method for storage virtualization
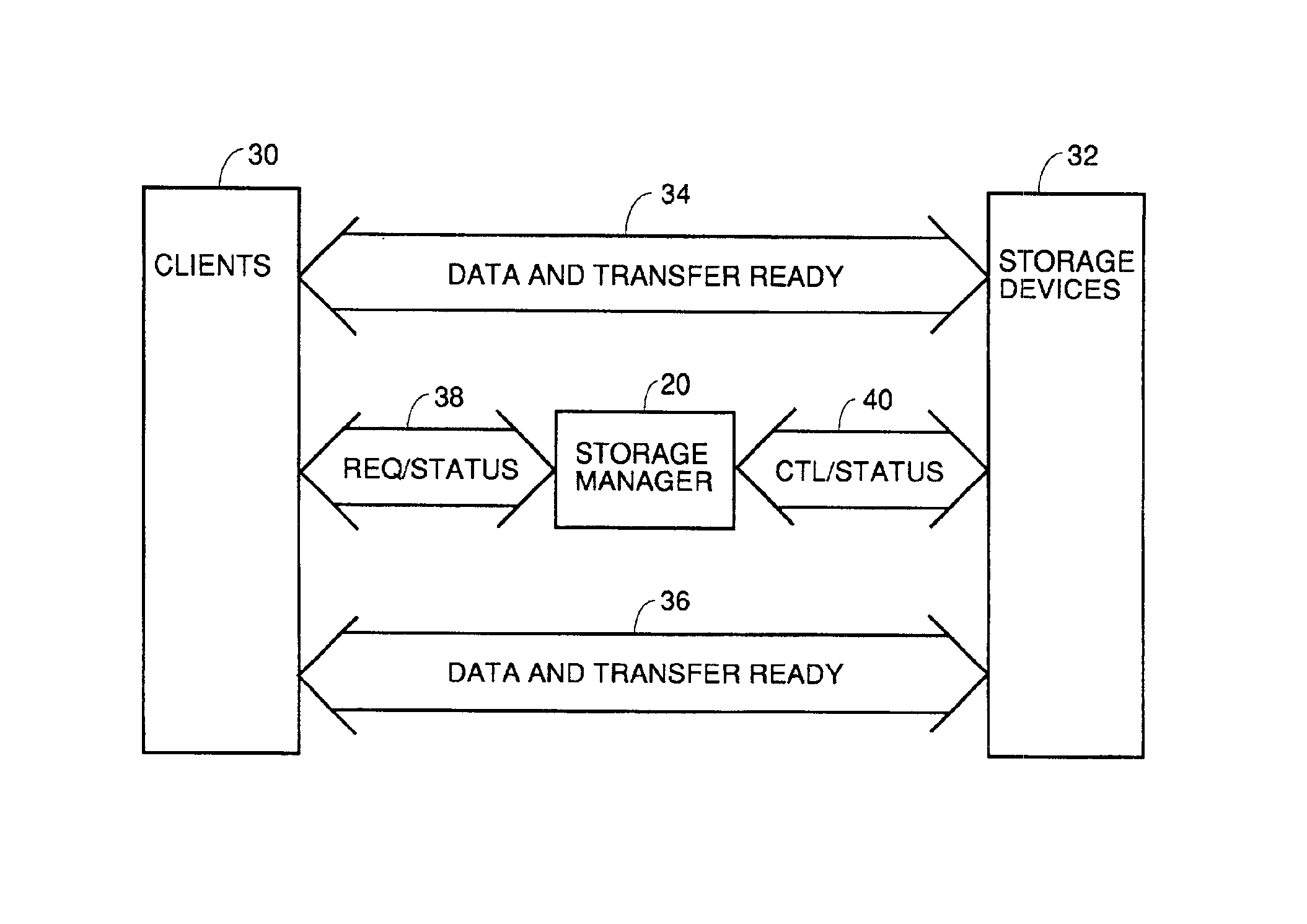
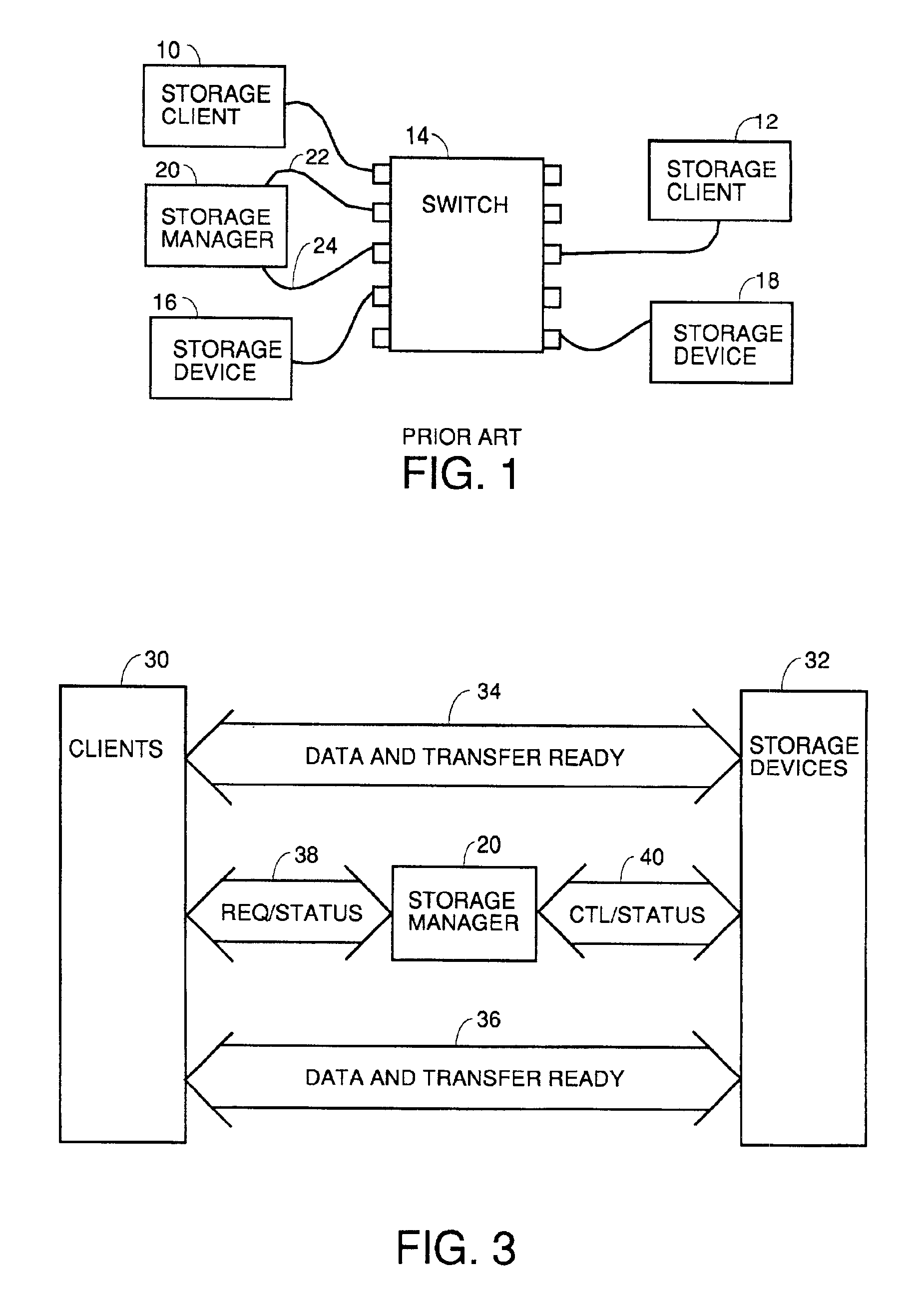
The present invention is generally directed to a system and method for virtualizing storage in a networked system. In accordance with one aspect of the invention, in a system having an initiator and at least one storage device, an inventive method determines, based upon a SCSI command received by a manager from the initiator, which of the data storage devices are implicated by the SCSI command. The method then forms an iSCSI command that is sent from the manager to each of the implicated storage devices, and receives at the manager an iSCSI response from each of implicated storage devices, after each of the storage devices has completed its implicated data transactions with the initiator. Finally, the method forms a SCSI response that is sent by the manager to the initiator. A corresponding system is also provided.
Owner:QUALCOMM INC
Storage area network, data replication and storage controller, and method for replicating data using virtualized volumes
A storage area network (SAN) controller and method for storing and replicating data between sites in a storage area network in which storage controllers at each site implement storage virtualization. A storage cell is implemented at each site comprising at least one storage controller and a pool of physical storage coupled to the controller. A copy set comprising a logical unit (LUN) of storage, referred to as a member, in each of the storage cells is defined. As operational data transactions are performed against one of the members of a copy set, they are replicated, immediately or after a delay, in each other member of the copy set. As changes are made to dependent attributes such as size of one member of the copy set, the change is replicated in each other member of the copy set automatically. Changes can be made in the independent attributes such as size of each member of the copy set independently of other members of the copy set.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Coordination of quality of service in a multi-layer virtualized storage environment
ActiveUS7636801B1Digital data processing detailsMultiple digital computer combinationsQuality of serviceComputer science
A system for coordination for quality of service in multi-layer storage virtualization environments includes a first, second and third storage entity at a respective first, second and third layer of virtualized storage. The first storage entity sends a request for an I / O task to the second storage entity. In response to the request, the second storage entity may be configured to cooperate with the third storage entity to perform one or more I / O operations to satisfy one or more quality of service requirements associated with the I / O task.
Owner:SYMANTEC OPERATING CORP
Systems and methods for providing a storage virtualization environment
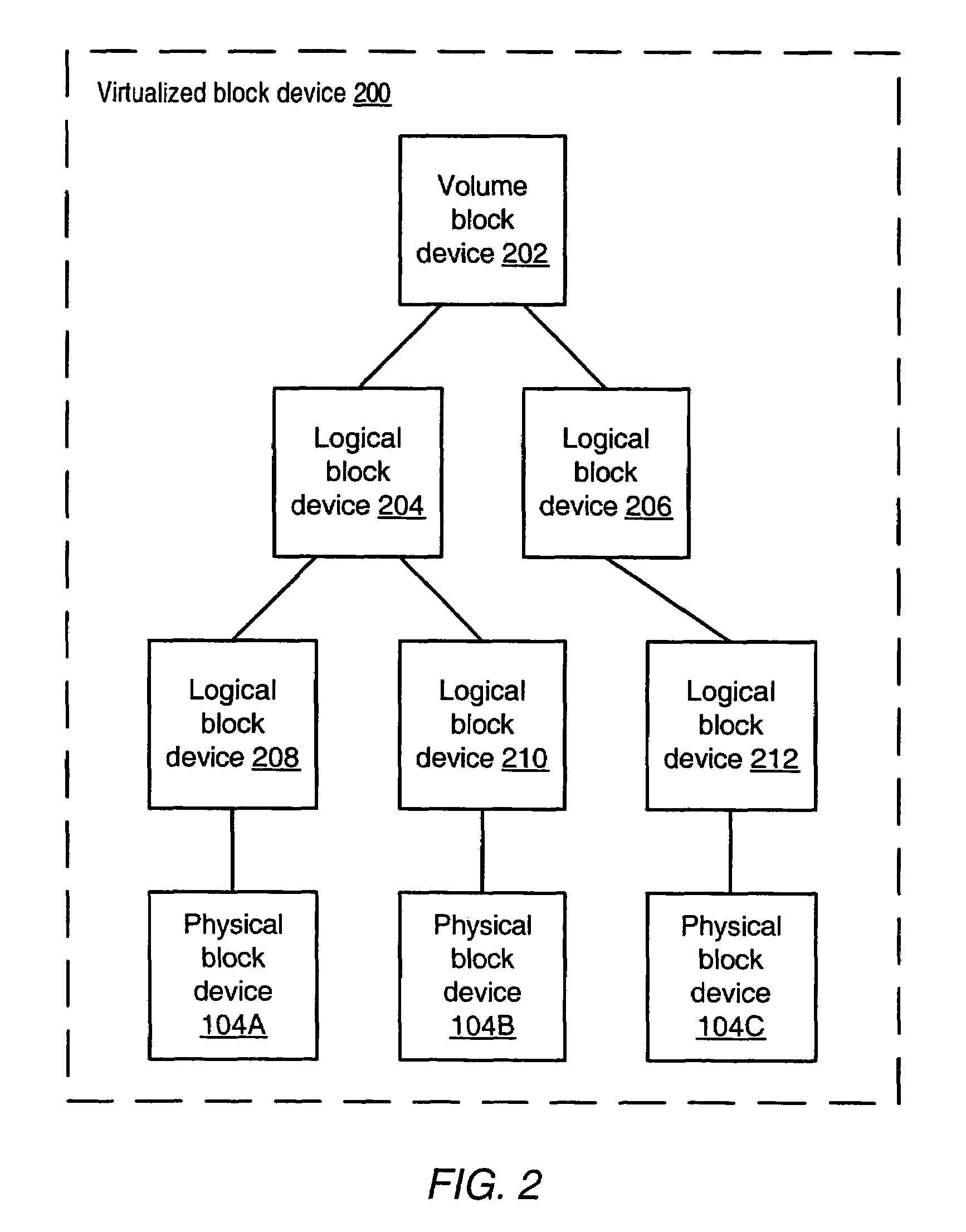
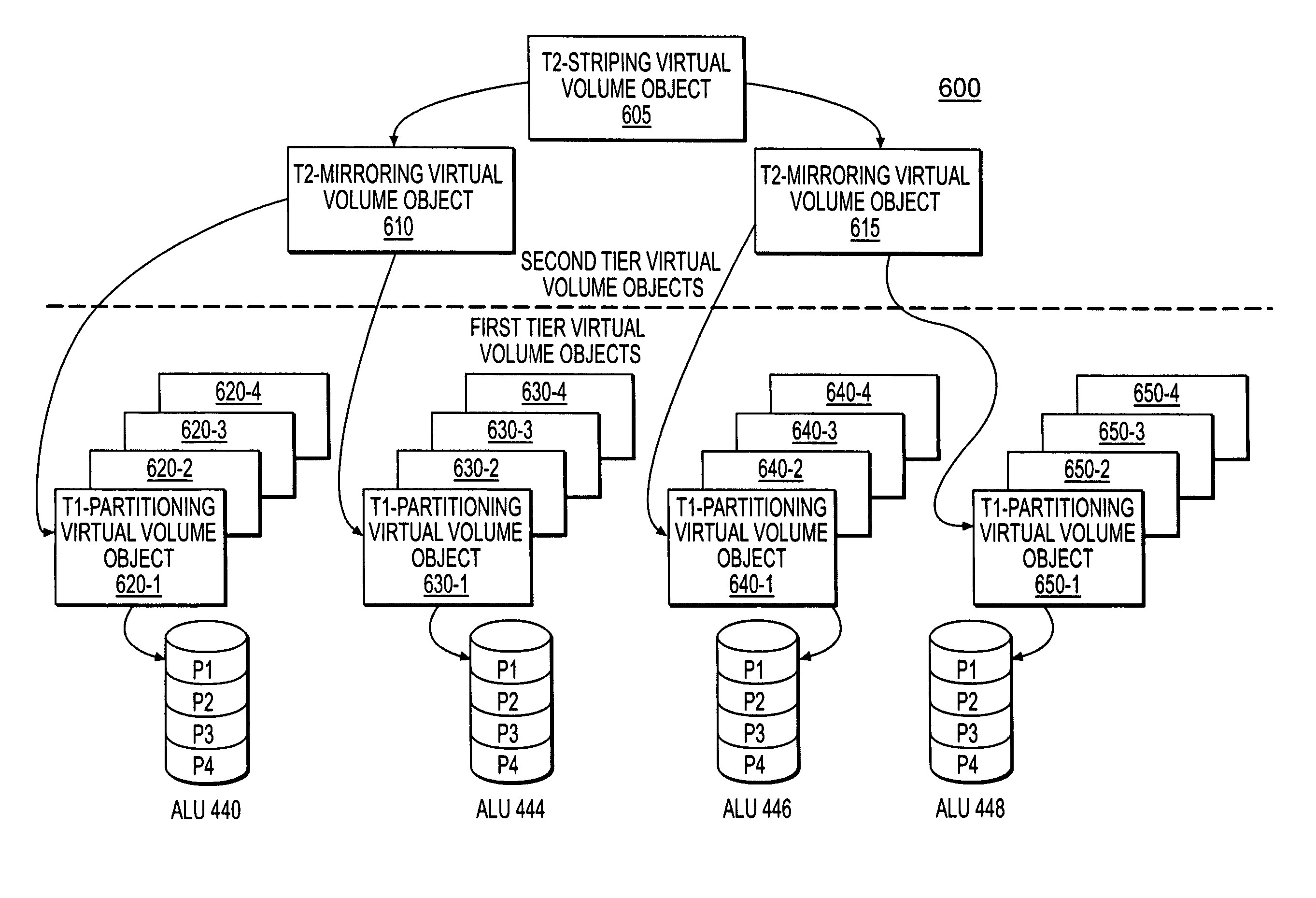
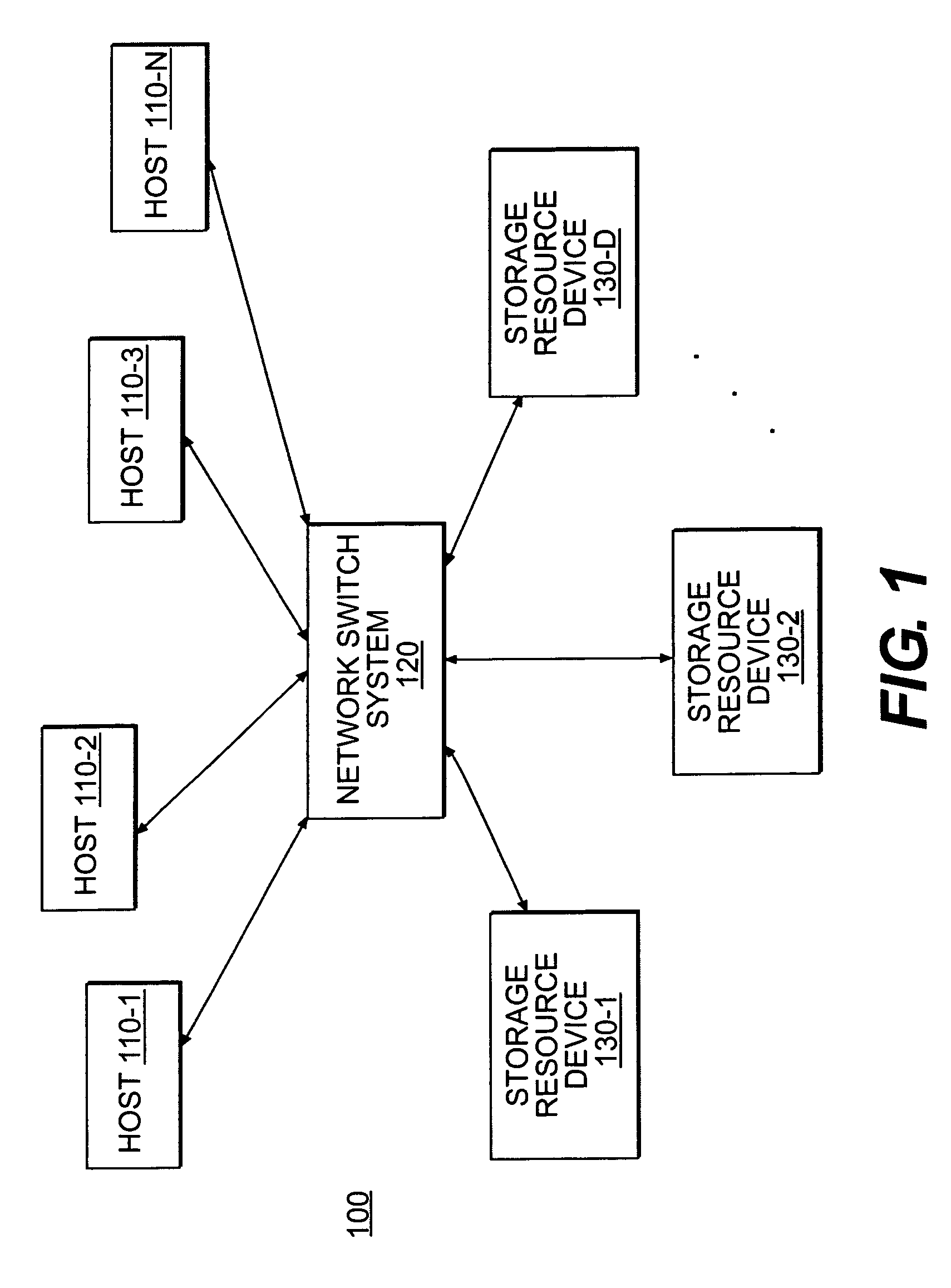
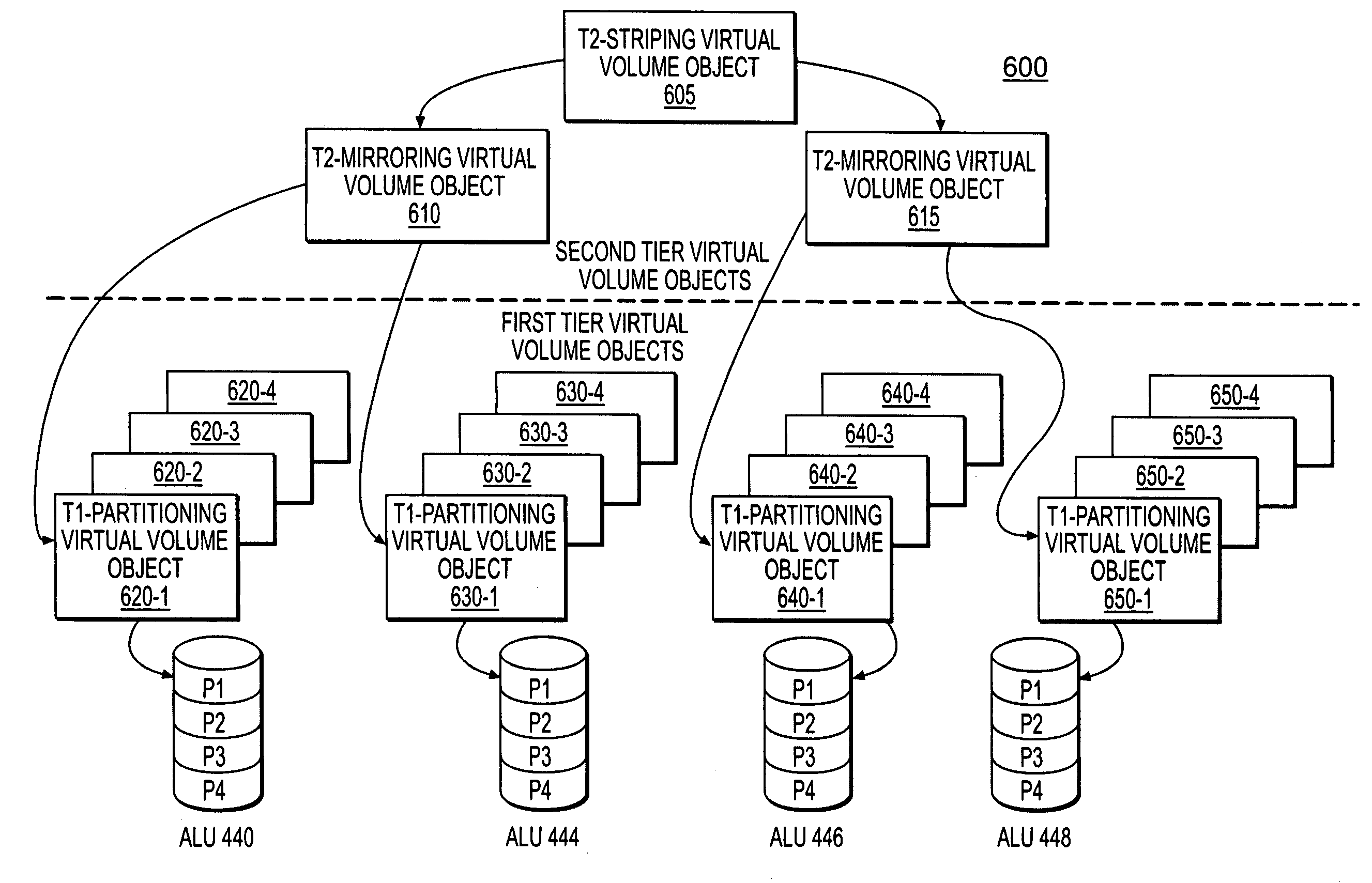
ActiveUS7236987B1Improve availabilityImprove scalabilityData processing applicationsSpecial data processing applicationsNetwork switchLogical partition
A storage virtualization environment is provided that includes a system for providing one or more virtual volumes. The system may include a host system and a set of storage devices, each of which includes physical block addresses that stores data. Further, the system includes a network switch system connecting the host system and the set of storage devices and is configured to define and manage a virtual volume associated with data distributed across the physical block addresses. The network switch system includes a first virtualization layer that maintains first tier objects including information reflecting a relationship between the physical block addresses and one or more logical partitions of virtual volume data. Moreover, the network switch system includes a second virtualization layer that maintains second tier objects including information reflecting a logical configuration of the virtual volume. The network switch system manages the virtual volume for the host system using the first and second tier objects.
Owner:ORACLE INT CORP
Systems and methods for configuring a storage virtualization environment
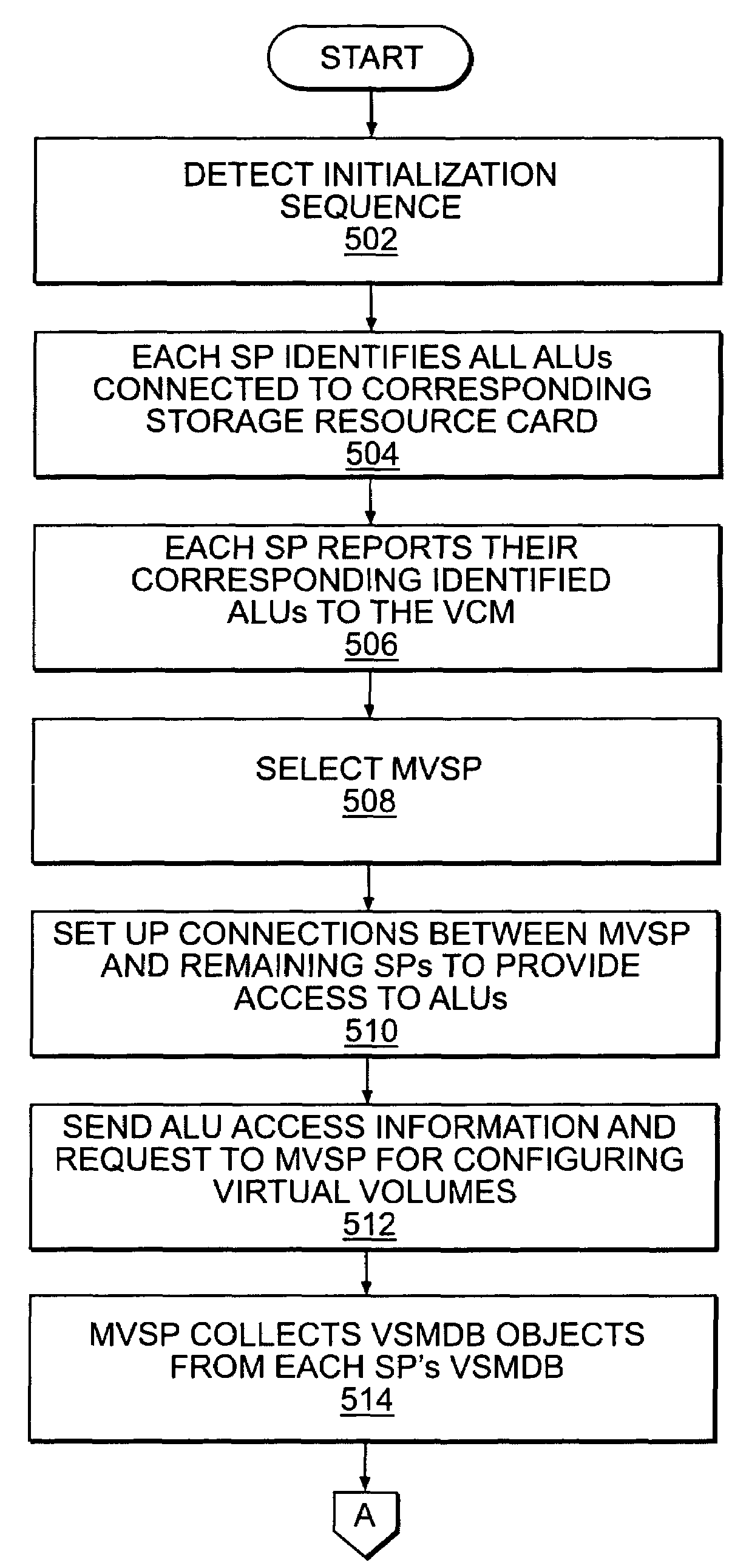
ActiveUS7383381B1Improve availabilityImprove scalabilityError detection/correctionTransmissionNetwork switchLogical tree
A storage virtualization environment is provided that includes a network switch system for initializing a virtual volume in a system including a host system, and storage devices. The network switch system includes storage processors including first and second tier storage processors and a Virtualization Coherency Manager (VCM) for receiving storage connectivity identifying which storage processors are connected to selected ones of the storage devices. Further, the network switch system includes a master storage processor for creating a logical tree based on the storage connectivity information, the logical tree reflecting a virtual volume of data distributed across the storage devices and includes (i) first tier objects representing partitions of the virtual volume data and (ii) second tier objects representing a logical configuration of the virtual volume. In one embodiment, the VCM assigns the first tier objects to selective ones of the first tier storage processors and assigns the second tier objects to selective ones of the second tier storage processors based on the logical tree. Further, each of the selective first and second tier storage processors initialize a local portion of the virtual volume to allow the host system to access the virtual volume through the network switch system.
Owner:ORACLE INT CORP
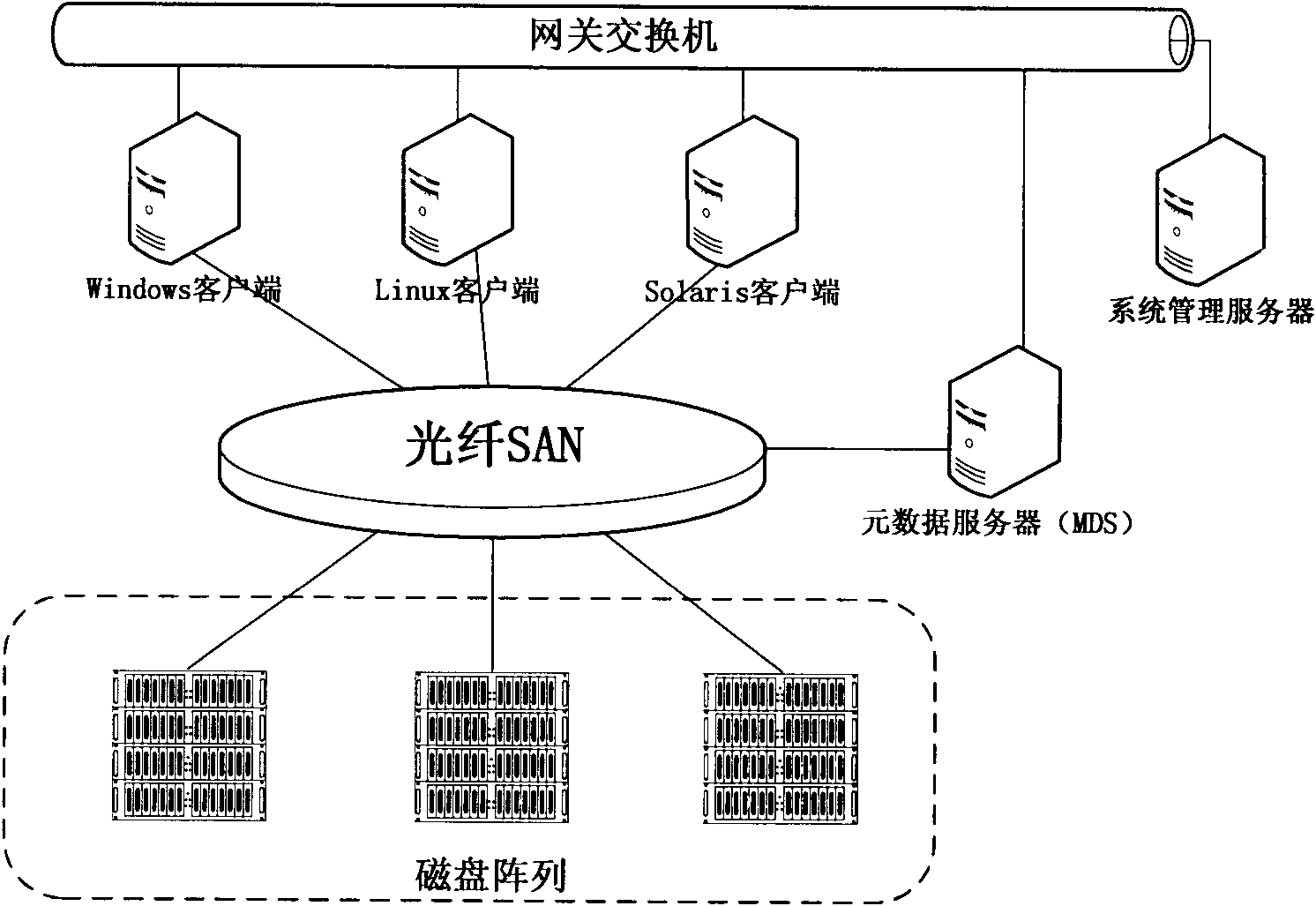
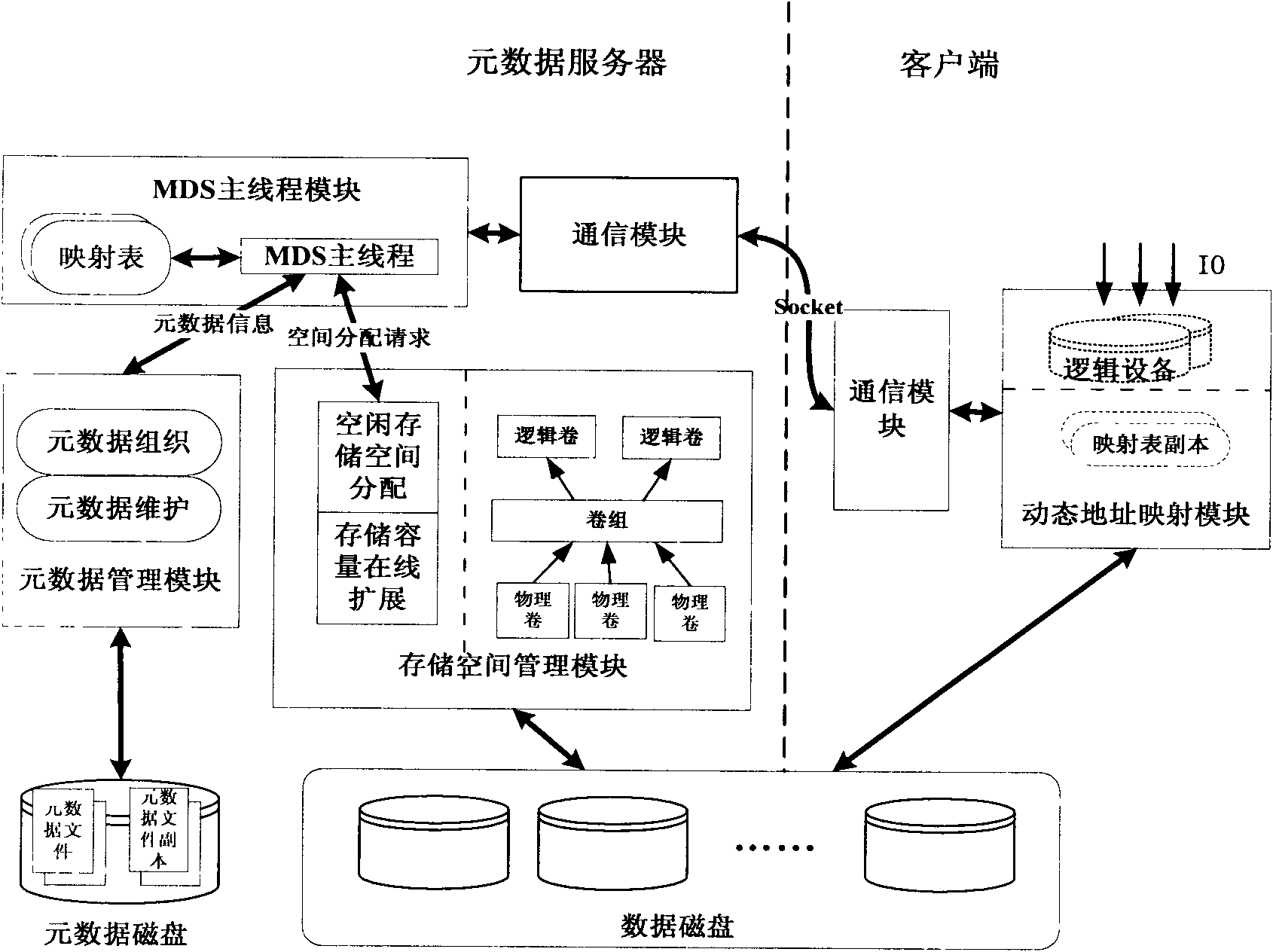
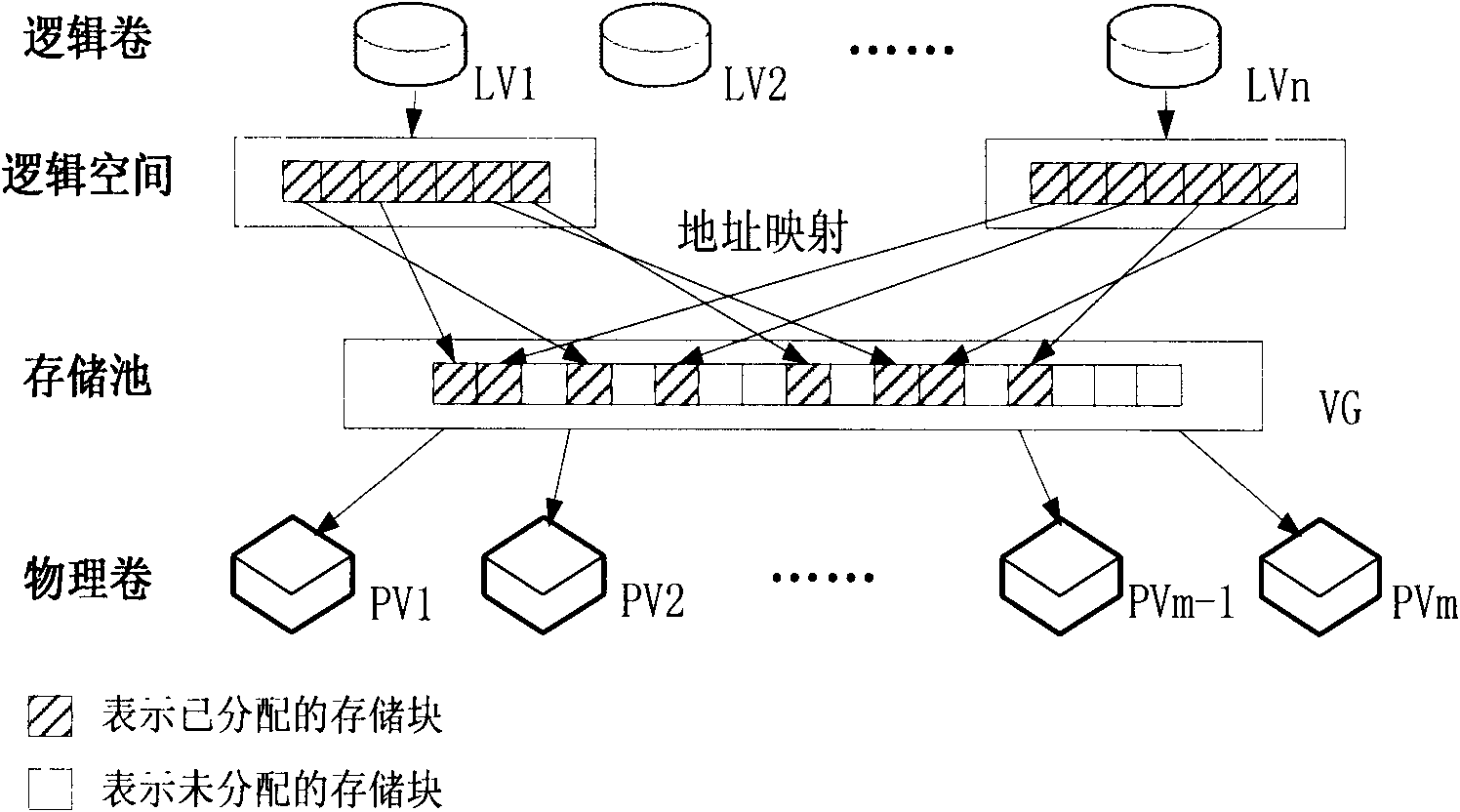
Method for allocating mass storage resources according to needs in heterogeneous SAN (Storage Area Network) environment
InactiveCN101997918AIncrease profitReduce procurement costsTransmissionMass storageApplication server
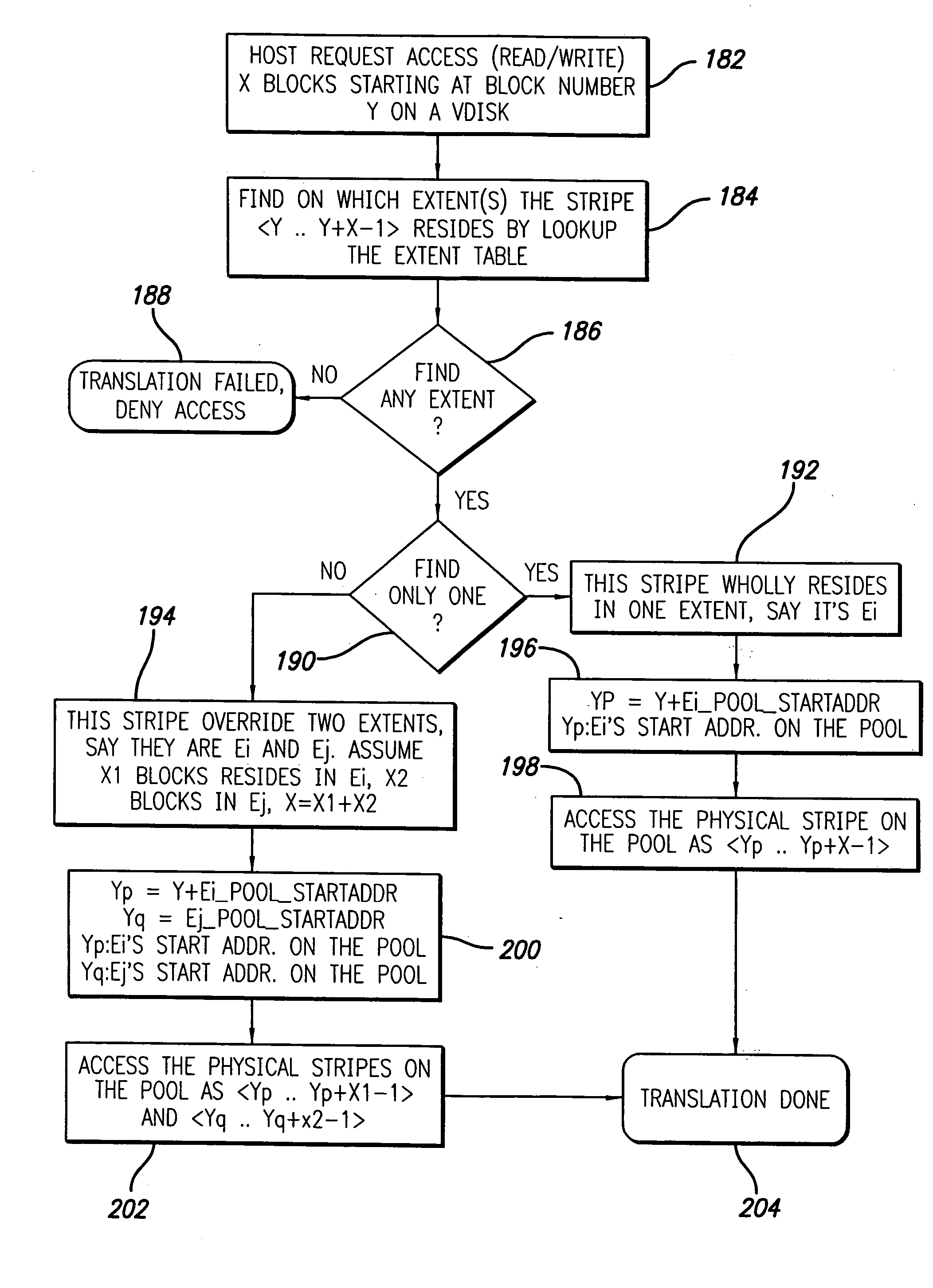
The invention relates to a method for allocating mass storage resources according to needs in a heterogeneous SAN (Storage Area Network) environment, belonging to the field of storage area networks, in particular to the technical field of storage virtualization therein. The invention is characterized by designing and realizing an out-of-band storage virtualization system aiming at a heterogeneousstorage application server and various storage devices in the SAN environment and providing a method for allocating the mass storage resources according to needs based on allocation while writing anddynamic address mapping mechanism on the basis of the system. The method can be used for allocating the storage resources according to the actual needs of applications, dynamically expanding the mapping relation between the logic storage space and the physical storage space, effectively increasing the utilization rate of the storage resources and the expandability of storage capacity, reducing the maintenance cost of the storage devices and realizing instant storage purchase.
Owner:TSINGHUA UNIV
Virtual Disk Mapping
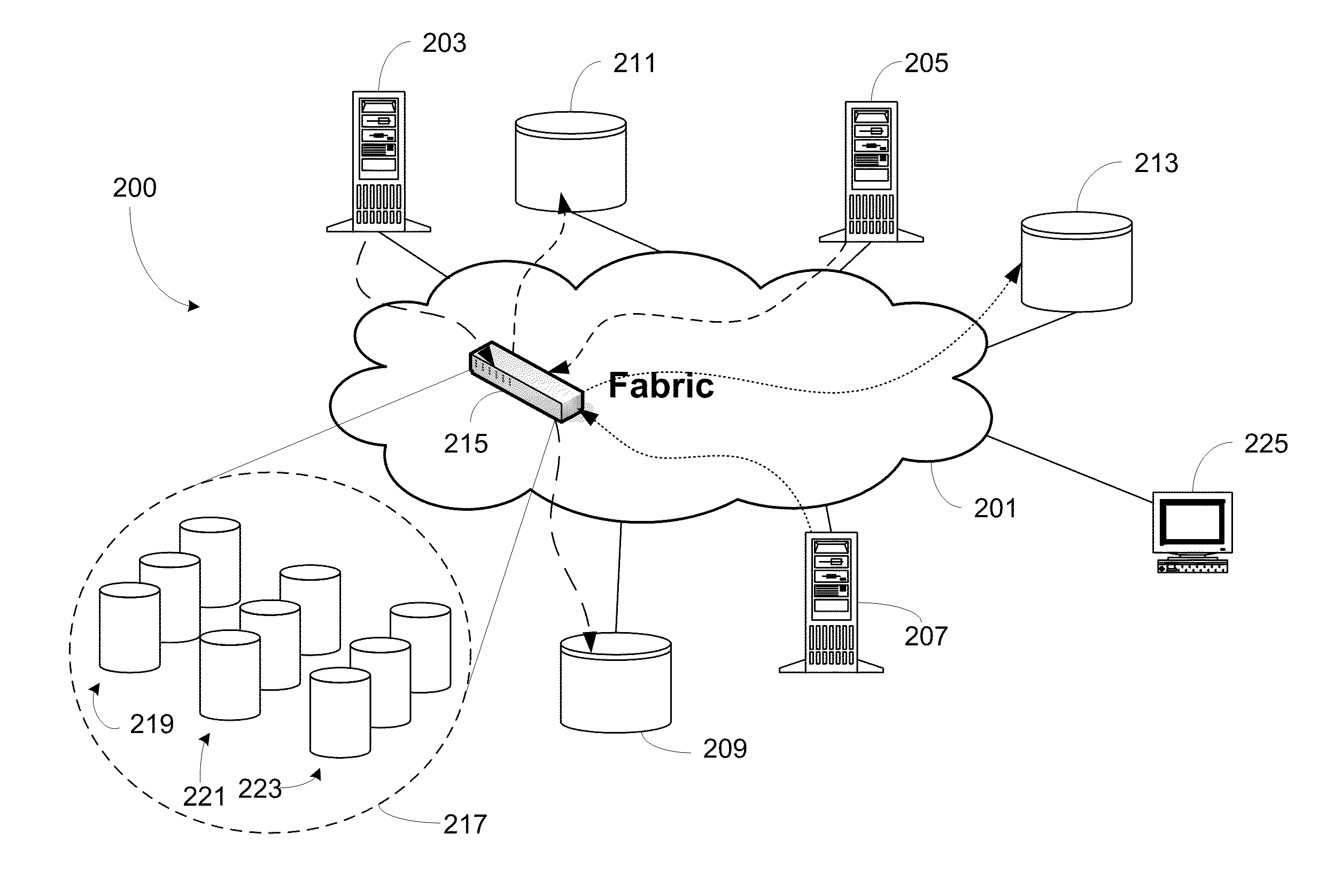
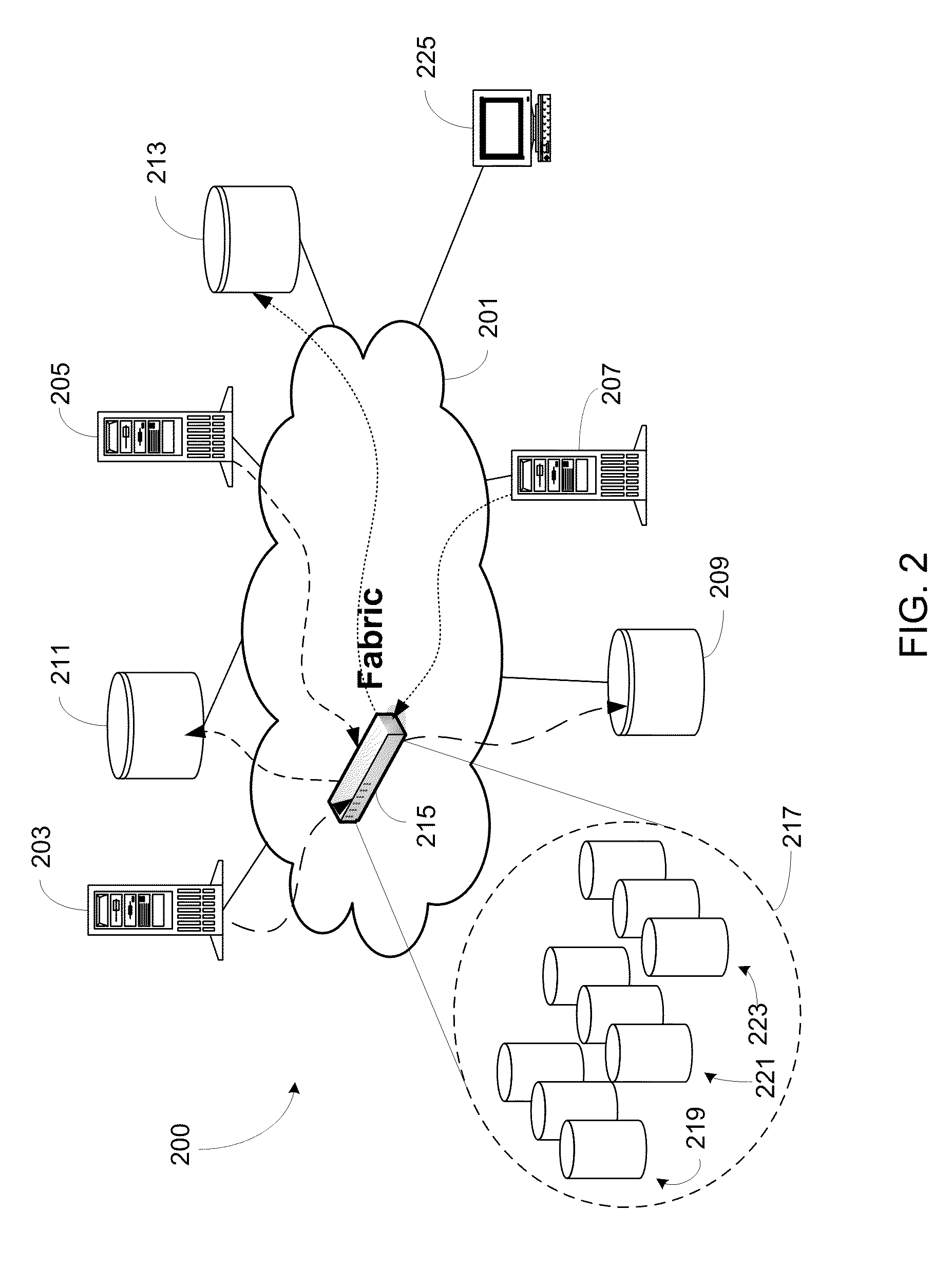
ActiveUS20110107052A1Increase storage capacityImprove performanceMemory adressing/allocation/relocationInput/output processes for data processingStorage area networkData storing
A storage area network can include a storage virtualization entity—intelligent storage application resource (iSAR)—either as a separate device in the fabric, or as an integrated module in one or more switches within the fabric. All I / O operations can be re-directed to iSAR for processing. iSAR can segment virtual storage and physical storage into units, where each unit of the virtual storage is mapped to a single unit in physical storage. Data associated with incoming I / O operation can be compressed before being stored in physical storage. iSAR includes overflow reserve storage at the block, sub-page and page level to accommodate changes in compressed data size on subsequent I / O operations. These measures can improve I / O performance and reduce fragmentation. iSAR can also employ deduplication of incoming data stored on physical storage to improve storage efficiency.
Owner:AVAGO TECH INT SALES PTE LTD
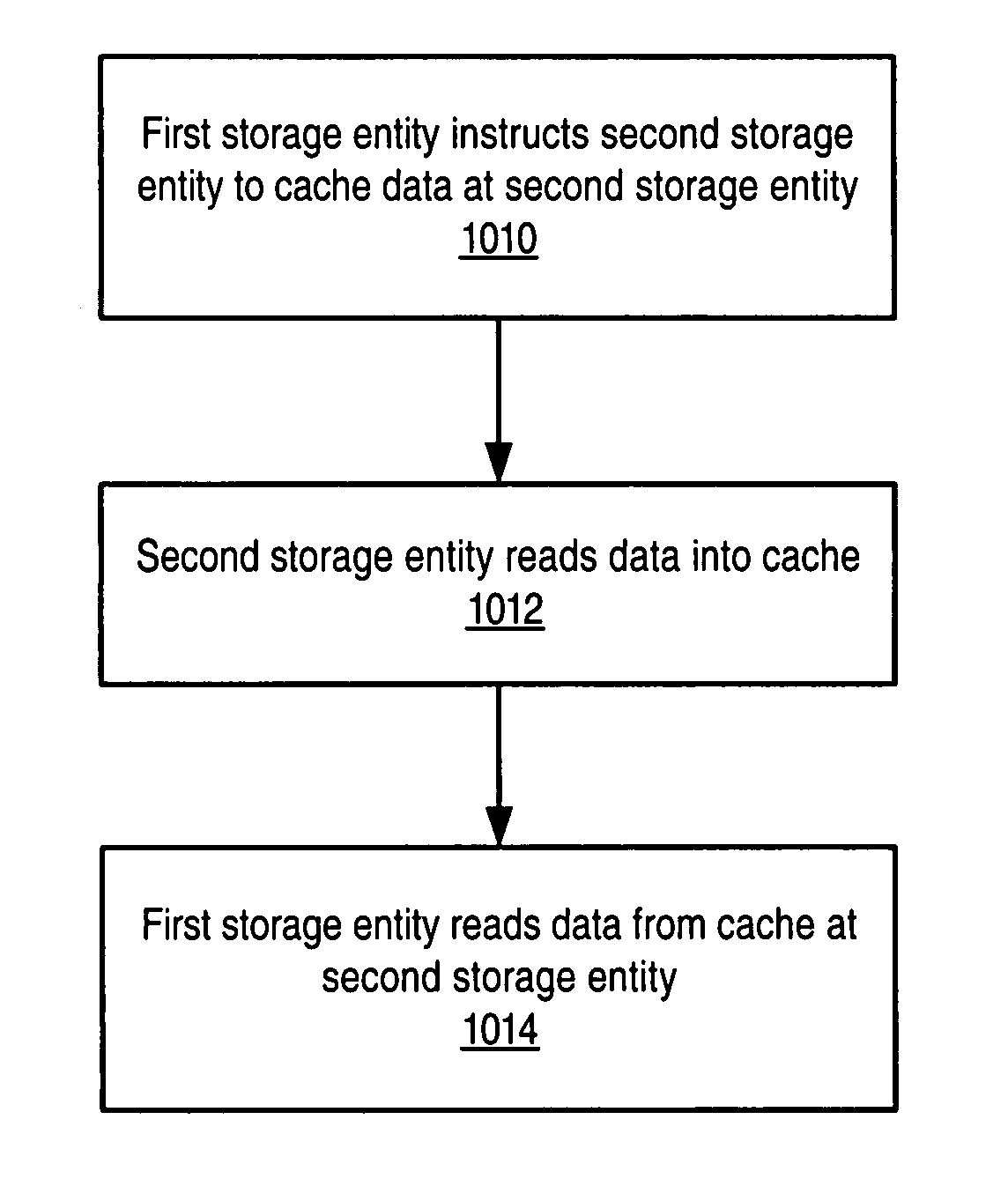
Coordination of caching and I/O management in a multi-layer virtualized storage environment
ActiveUS7386662B1Not freeMemory architecture accessing/allocationError detection/correctionApplication softwareOperating system
Systems and methods are disclosed for performing cache and I / O management in a multi-layer storage virtualization environment. Block virtualization may be implemented at various layers, each with one or more storage entities. One storage entity may coordinate and leverage the cache and the caching mechanism available with another storage entity. The storage entities may be at the same layer (horizontal cache coordination) or at different layers (vertical cache coordination). Cache coordination may include application-assisted read-ahead.
Owner:SYMANTEC OPERATING CORP
Storage virtualization
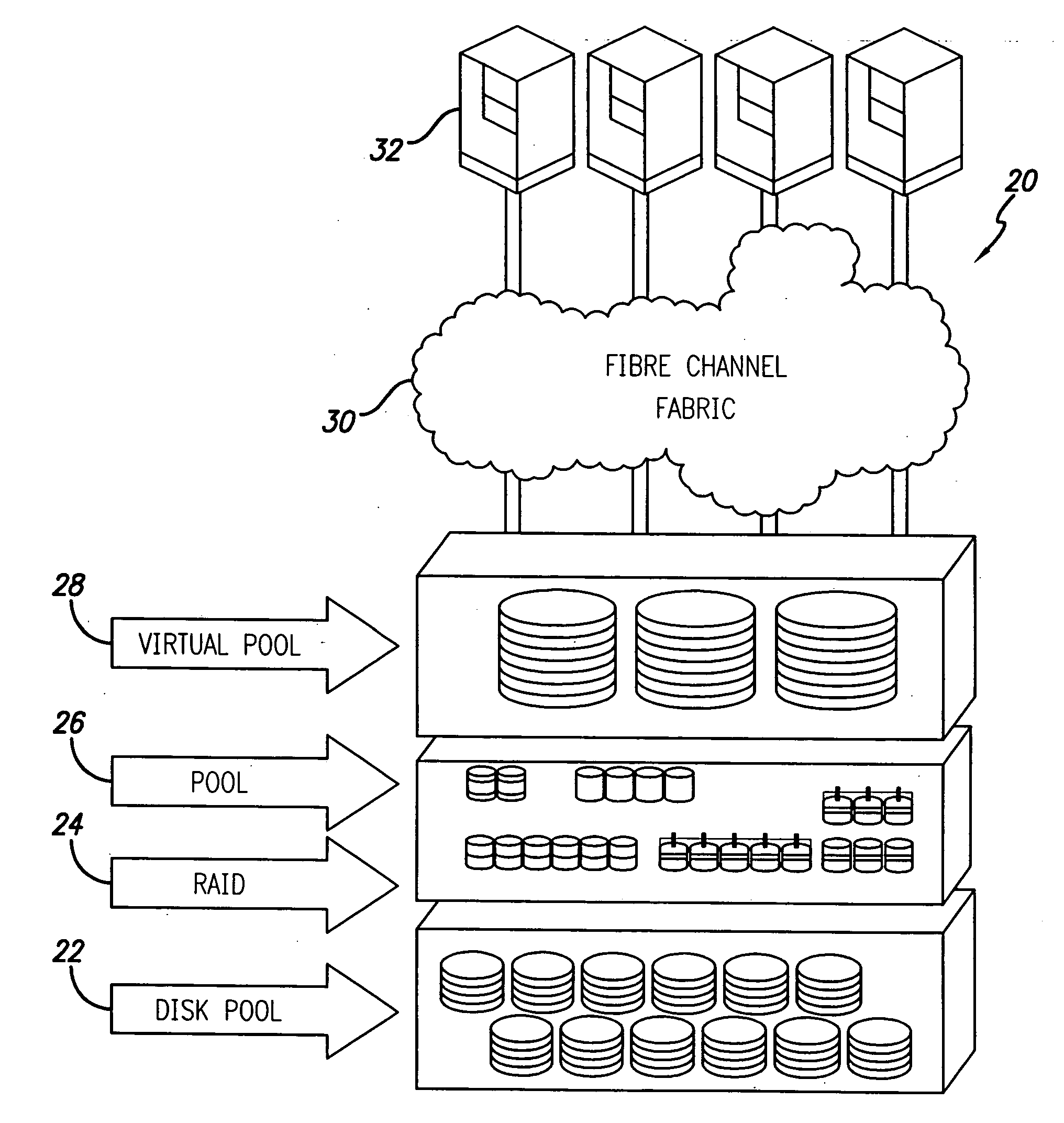
InactiveUS20060101204A1Improve abilitiesError detection/correctionMemory systemsRAIDStorage management
A storage virtualization system that follows a four-layer hierarchy model, which facilitates the ability to create storage policies to automate complex storage management issues, is provided. The four-layers are a disk pool, Redundant Arrays of Independent Disks (RAID arrays), storage pools and a virtual pool of Virtual Disks (Vdisks). The storage virtualization system creates virtual storage arrays from the RAID arrays and assigns these arrays to storage pools in which all of the arrays have identical RAID levels and underlying chunk sizes representing in abstraction very large arrays. Virtual disks are then created from these pools wherein the abstraction of a storage pool makes it possible to create storage policies for the automatic expansion of virtual disks as they fill with user files.
Owner:IQSTOR NETWORKS
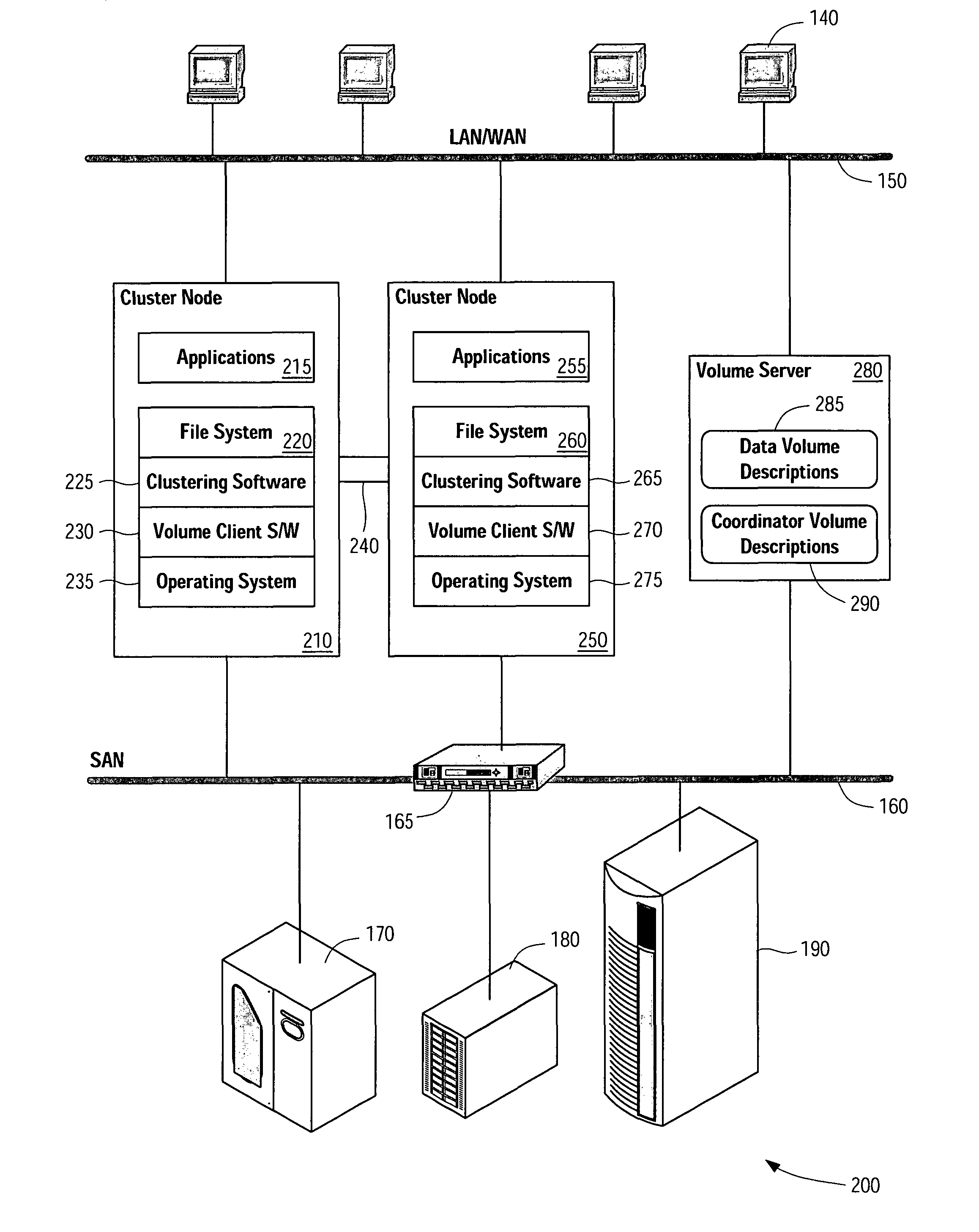
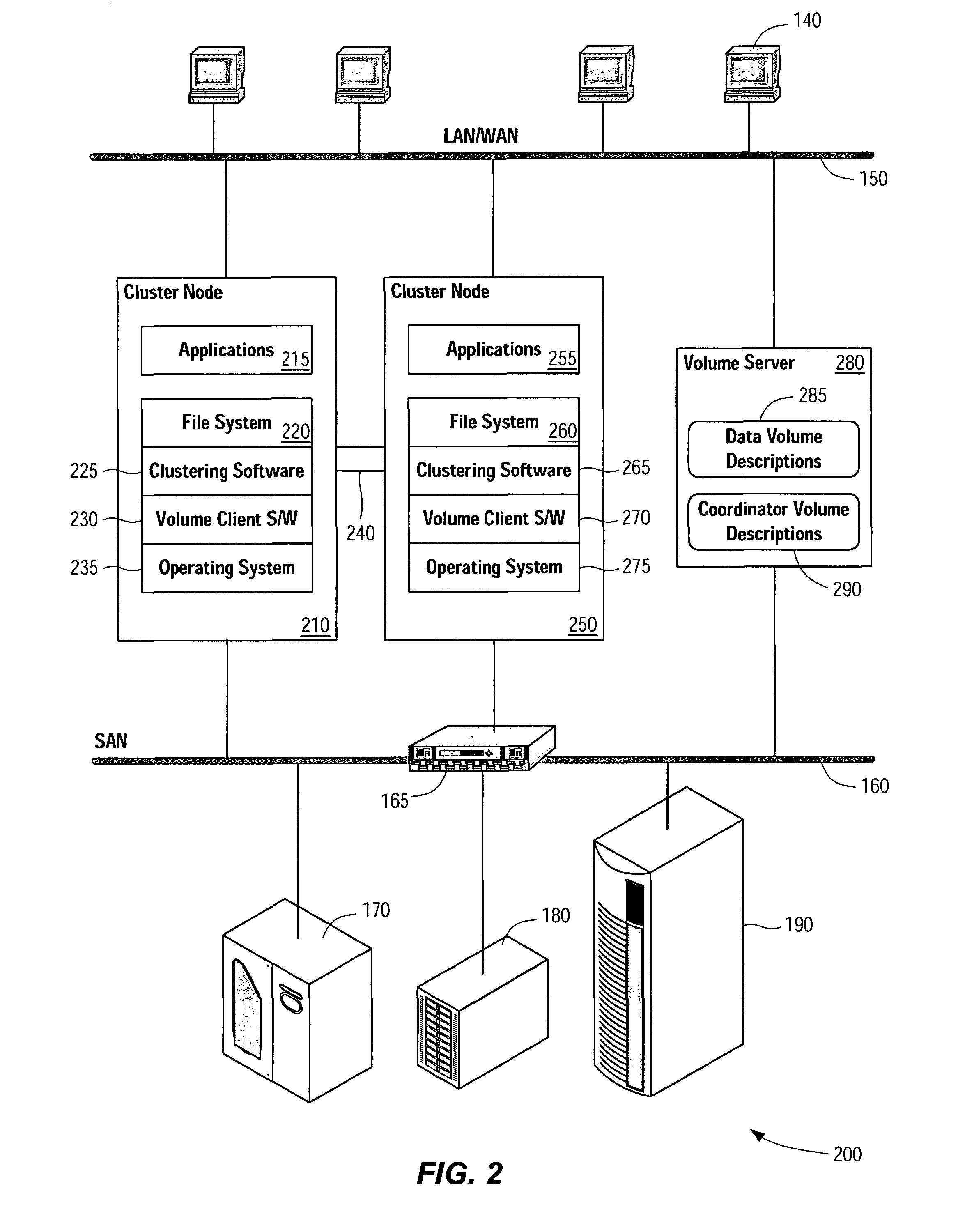
System and method for resolving cluster partitions in out-of-band storage virtualization environments
ActiveUS7739541B1Reduce failover timeImprove the problemMultiple digital computer combinationsNon-redundant fault processingSplit-brainClient-side
Systems, methods, apparatus and software can configure, support, and make use of a coordinator virtual device to determine which node or nodes of a cluster should be ejected from the cluster as a result of a cluster partition or other error event. Fencing software operating on the cluster nodes monitors the cluster for a cluster partition (split-brain) event, and when such an event occurs, software on the nodes attempts to gain control of the coordinator virtual device. A node that succeeds in gaining control of the coordinator virtual device survives. Nodes failing to gain control of the coordinator virtual device remove themselves or are removed from the cluster. The coordinator virtual device can be established by a virtual device configuration server which provides coordinator virtual device access to cluster nodes acting as virtual device configuration clients.
Owner:SYMANTEC OPERATING CORP
Systems and methods for providing a multi-path network switch system
ActiveUS7290168B1Improve availabilityImprove scalabilityDetecting faulty computer hardwareTransmissionNetwork switchMulti path
A storage virtualization environment is provided that includes a system for providing multi-path communications in a virtualization storage environment for managing a virtual volume of data. The system may include a host system connected to first and second communication fabrics and a network switch system connected to the first and second communication fabrics and to third and fourth communication fabrics / Further, the system includes a set of storage devices storing virtual volume data and connected to the third and fourth storage communication fabrics. In certain embodiments the network switch system includes a first set of storage processors having access to the host system and maintaining virtual volume objects reflecting a logical configuration of the virtual volume. Further, the network switch system includes a second set of storage processors having access to the storage devices and maintaining virtual volume objects associated with logical partitions of the virtual volume data. Also, the first and second set of storage processors are interconnected by a fifth communication fabric and the network switch system provides fault tolerant access by the host system to the virtual volume data using one of a plurality of dynamically configurable multi-communication paths traversing selective combinations of the fabrics, storage processors, and storage devices.
Owner:ORACLE INT CORP
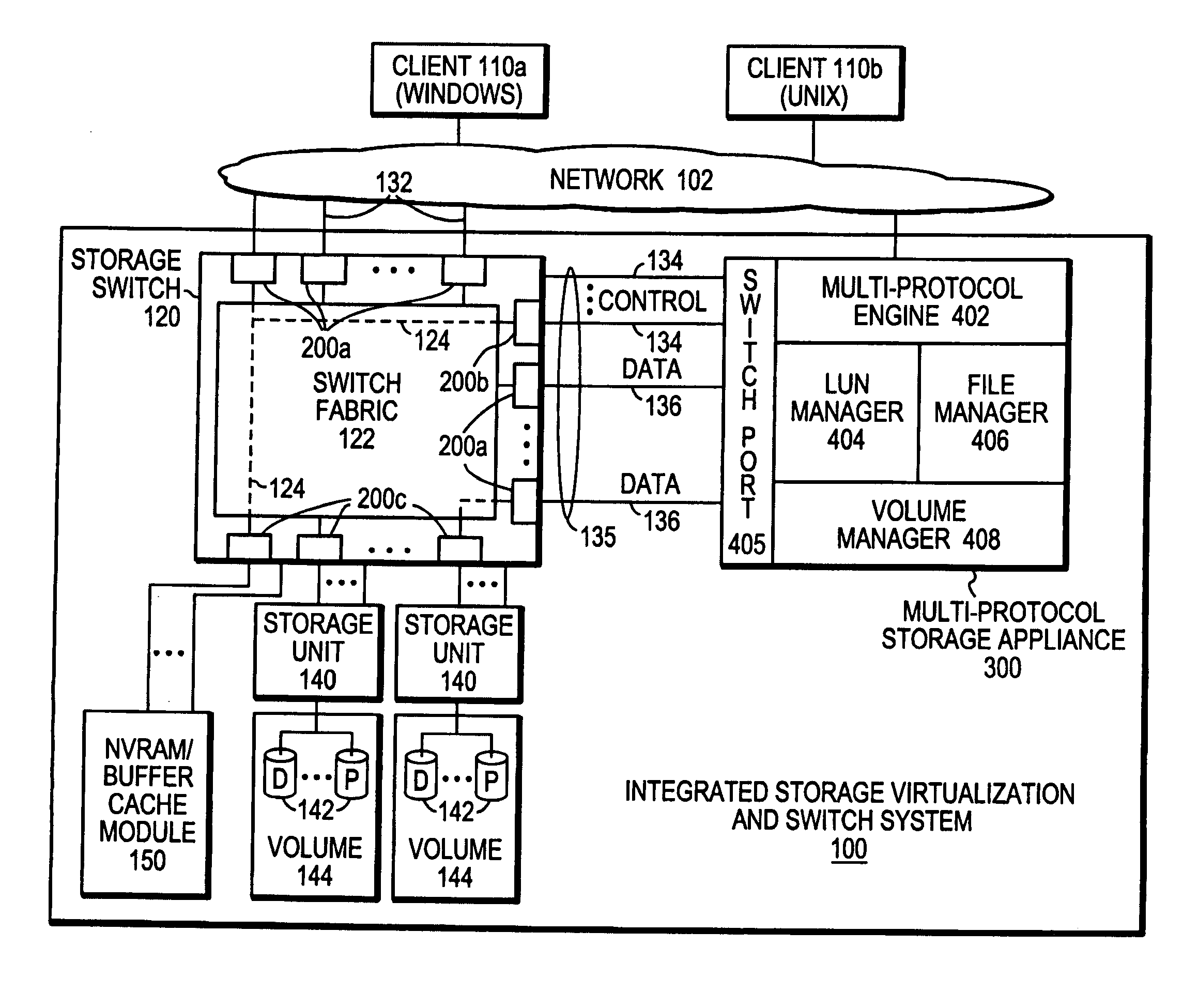
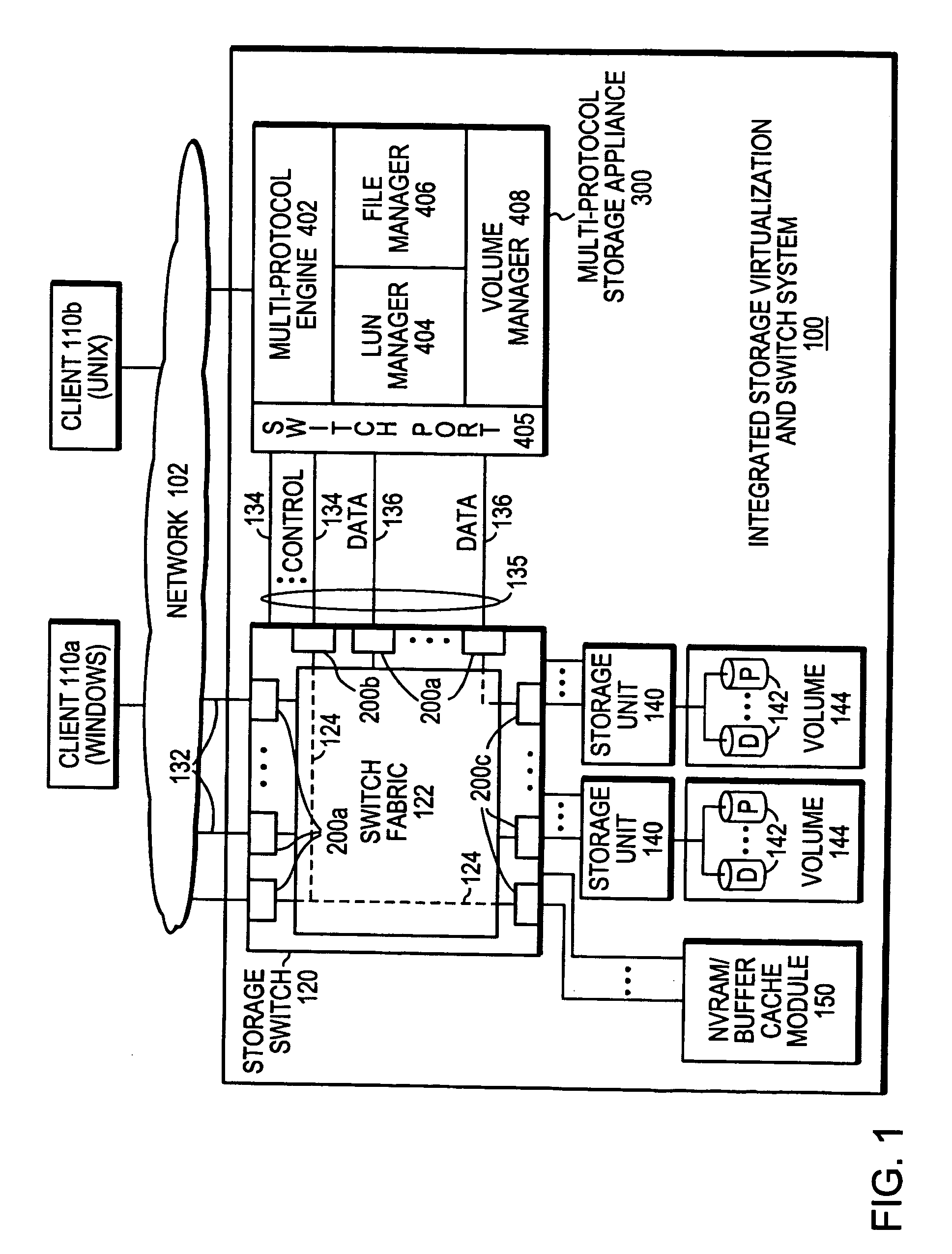
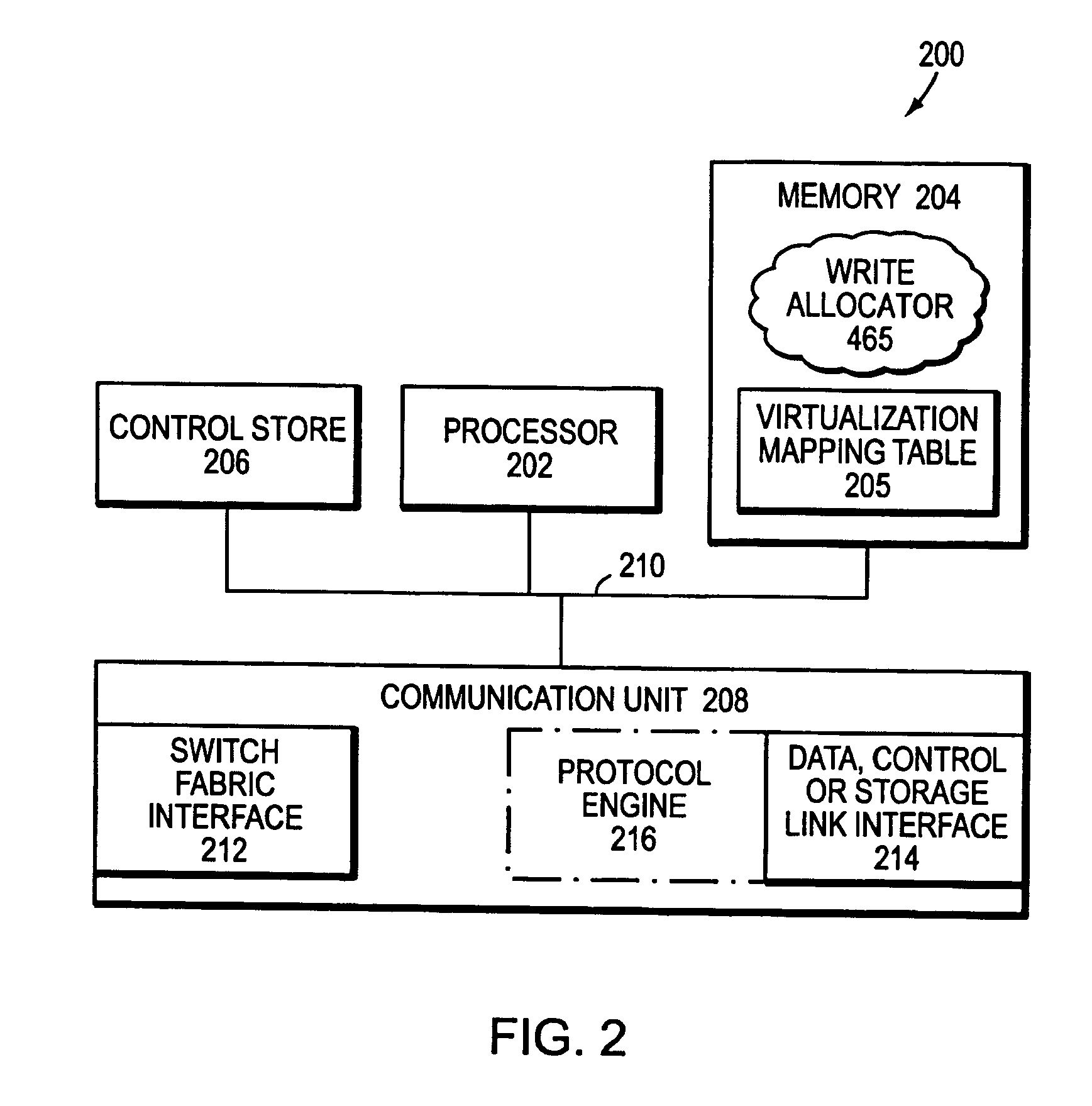
Integrated storage virtualization and switch system
ActiveUS20060206603A1Reduce sizeImprove connectivityDigital computer detailsTransmissionOperational systemFile system
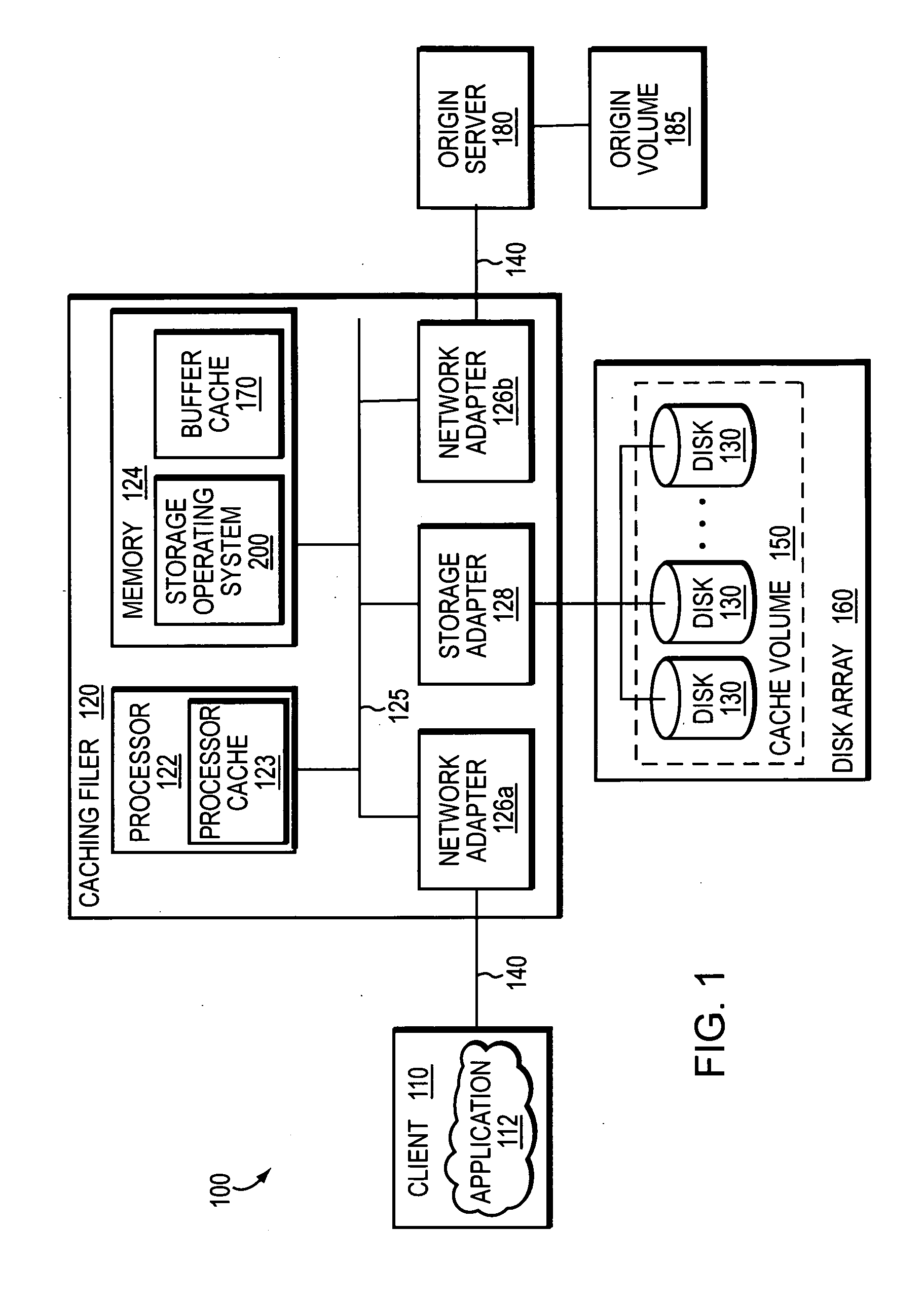
A system integrates an intelligent storage switch with a flexible virtualization system to enable efficient service of file and block protocol data access requests for information stored on the system. A storage operating system executing on a storage system coupled to the switch implements the virtualization system to provide a unified view of storage to clients by logically organizing the information as named files, directories and logical unit numbers. The virtualization system is illustratively embodied as a file system having a write allocator configured to provide a flexible block numbering policy that addresses volume management capabilities, such as storage virtualization, at a finer granularity (e.g., a single block) than that of previous non-flexible storage virtualization schemes. The flexible block numbering policy also yields substantial benefits in terms of increased write efficiency and elimination of storage “hot spots”, as well as a compelling point-in-time read-only data image (snapshot) mechanism.
Owner:NETWORK APPLIANCE INC
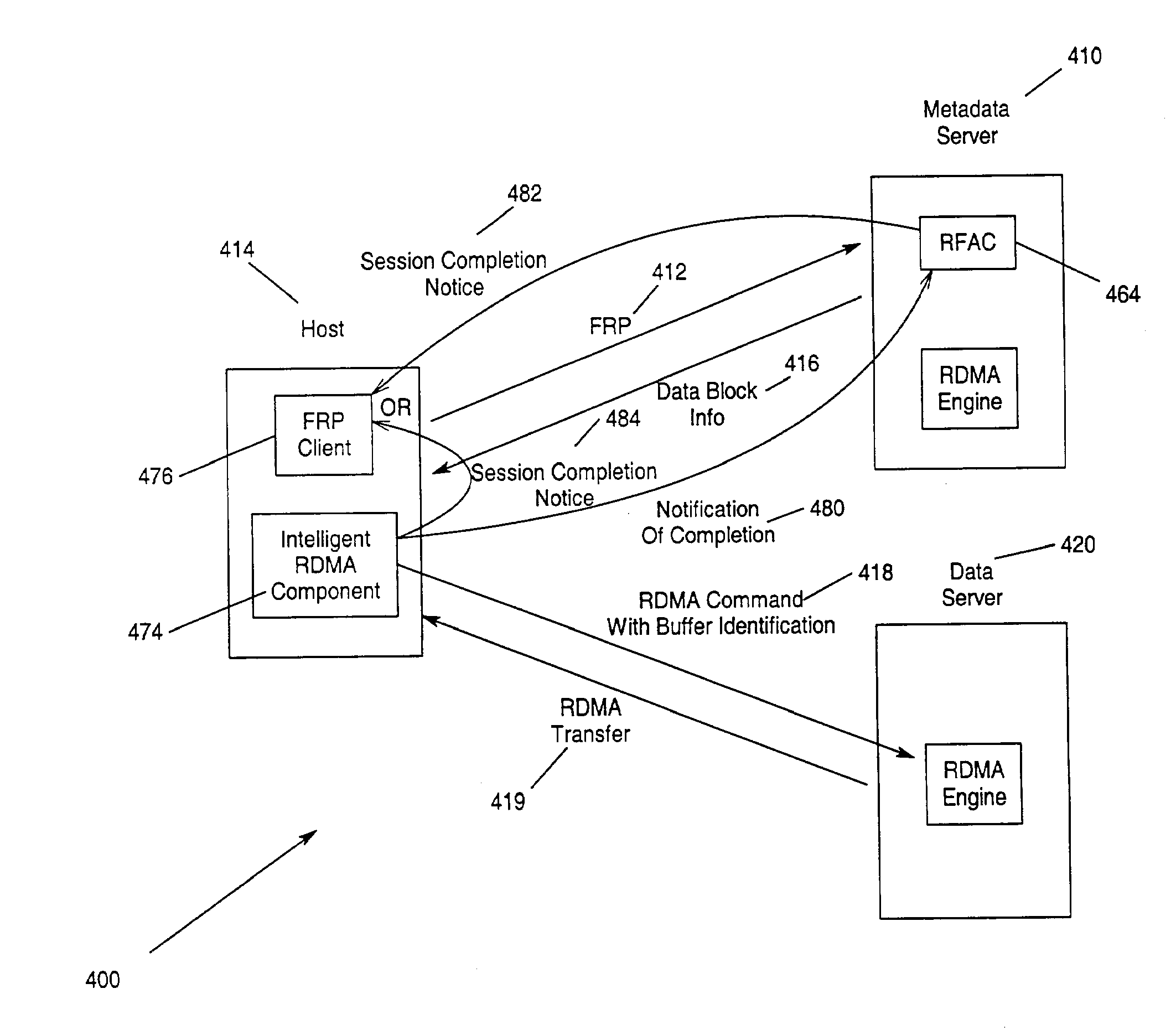
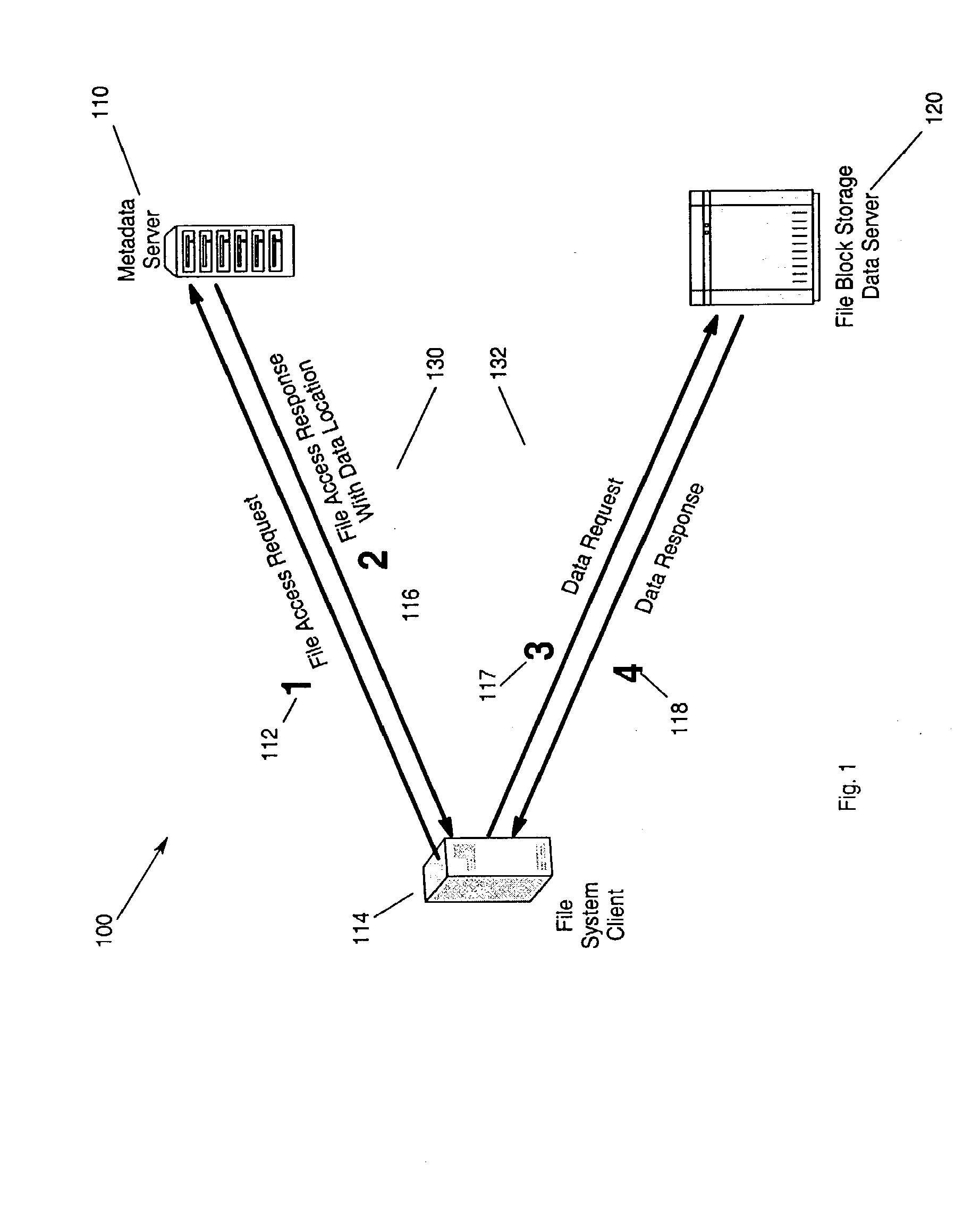
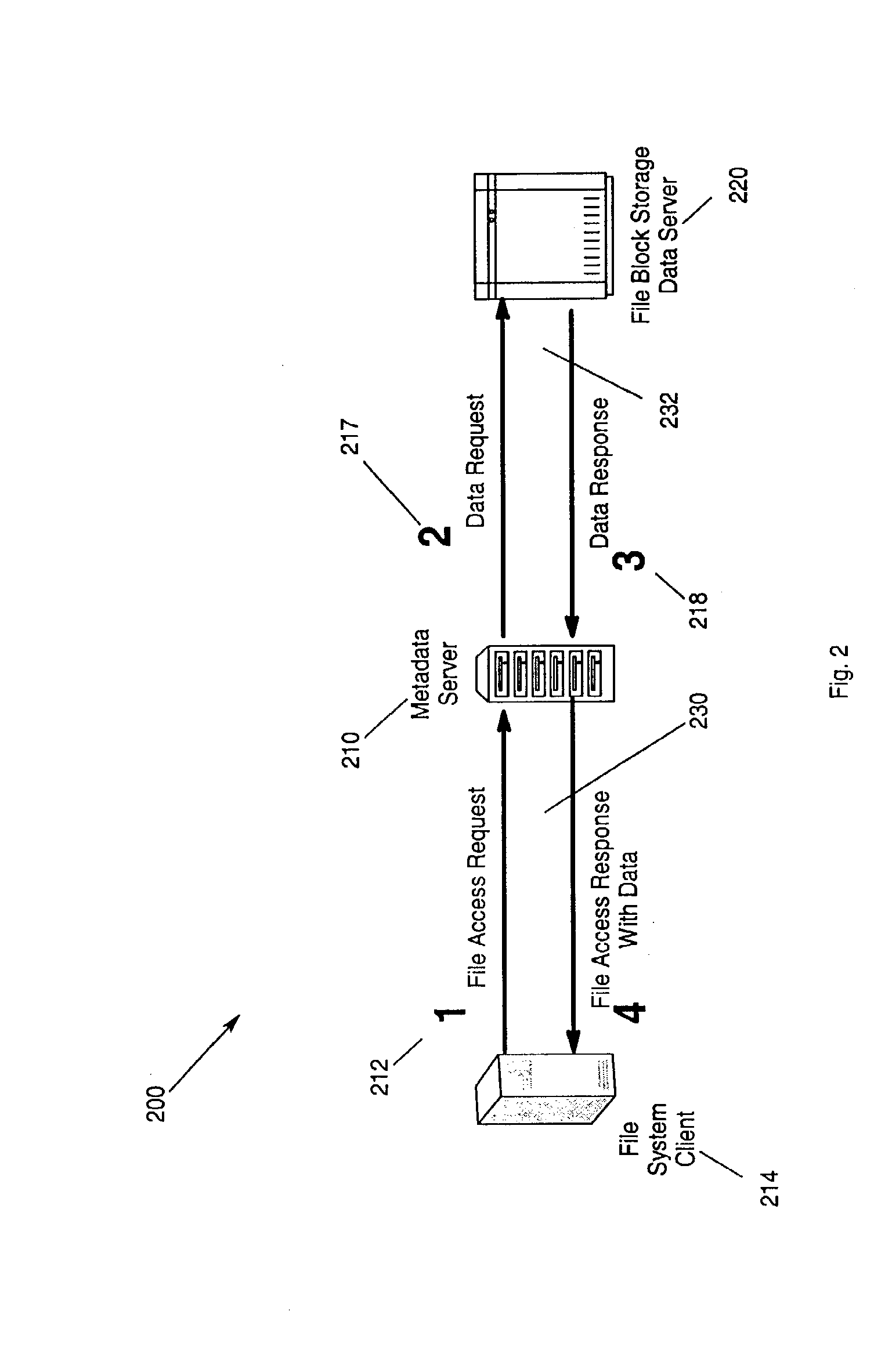
Distributed file serving architecture system with metadata storage virtualization and data access at the data server connection speed
InactiveUS20100095059A1Efficient accessSufficient operationMemory loss protectionMultiple digital computer combinationsData accessRemote direct memory access
Method, apparatus and program storage device that provides a distributed file serving architecture with metadata storage virtualization and data access at the data server connection speed is provided. A host issues a file access request including data target locations. The file access request including data target locations is processed. Remote direct memory access (RDMA) channel endpoint connection are issued in response to the processing of the file access request. An RDMA transfer of the file-block data associated with the file access request is made directly between a memory at the host and a data server.
Owner:IBM CORP
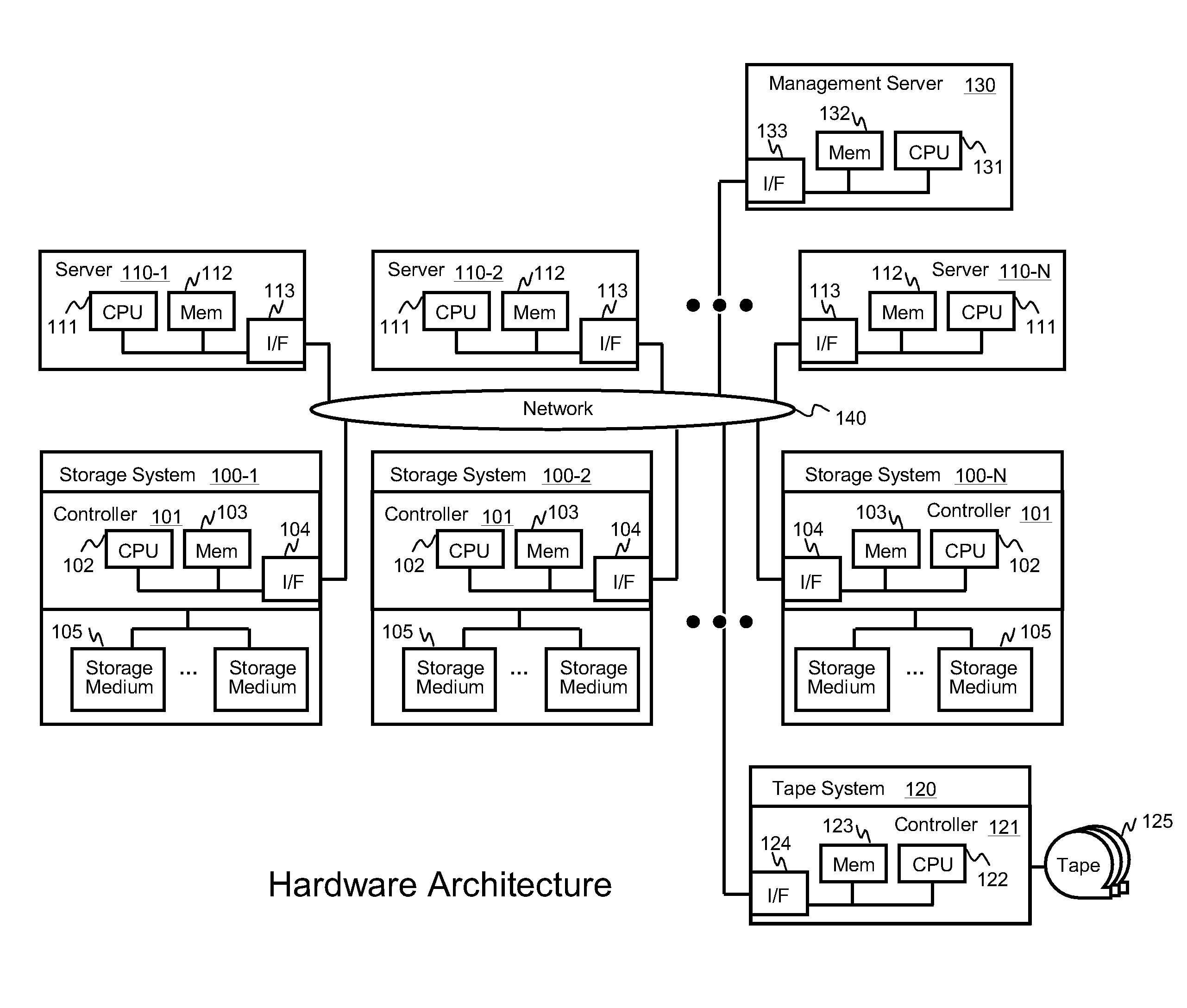
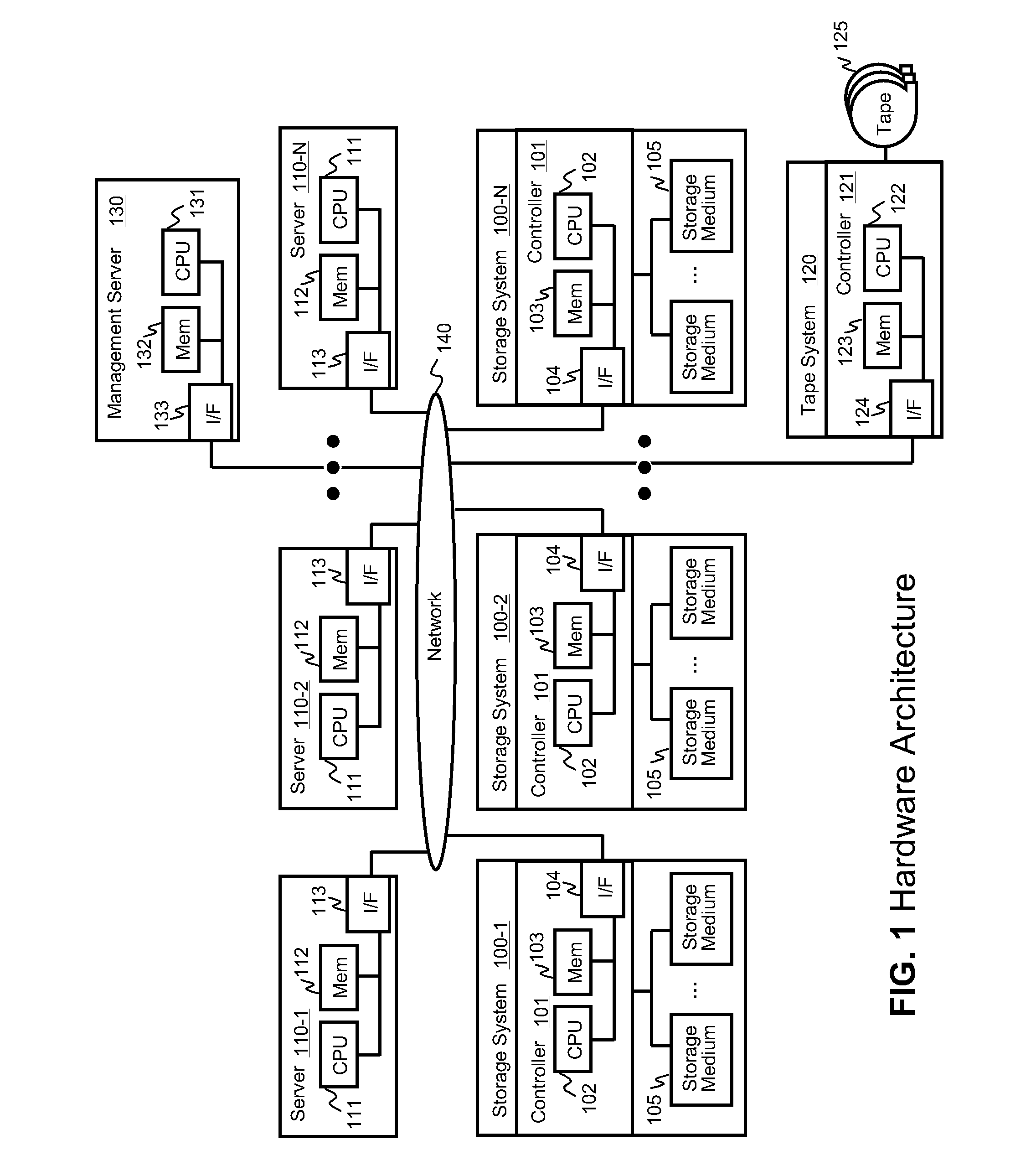
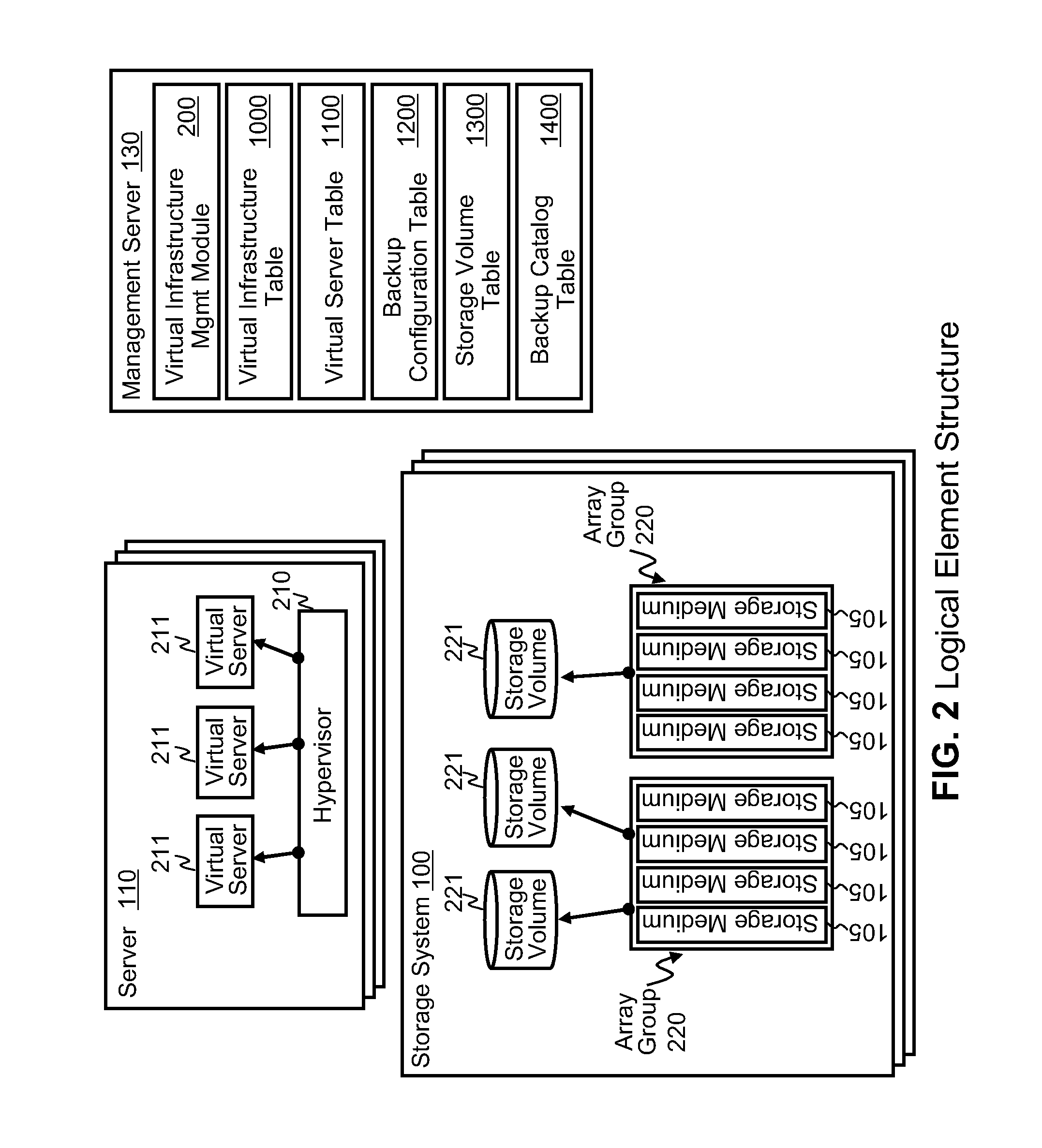
Data backup system and method for virtual infrastructure
InactiveUS20100125712A1Reduce in quantityMinimize the numberMemory loss protectionDigital data processing detailsResource poolData center
Systems for backing up the data of an IT system by utilizing server or storage virtualization technology to create and move logical IT infrastructures dynamically. A virtualized IT system provides a server resource pool and a storage resource pool composed from multiple physical devices either within a datacenter or a globally located plurality of datacenters. The virtual server and the storage volume provisioned from those pools will be paired to form the virtual infrastructure. In other words, the virtual infrastructure becomes a logical IT environment build with the required computing and storage resources needed in order to execute specific applications. The virtual infrastructure can also be migrated within / among datacenter sites.
Owner:HITACHI LTD
Router and methods using network addresses for virtualization
InactiveUS20070183421A1Improve efficiency and reliabilityEasy resource managementData switching by path configurationQuality of serviceDeficit round robin
A router for use in a network includes a scalable architecture and performs methods for implementing quality of service on a logical unit behind a network port; and for implementing storage virtualization. The architecture includes a managing processor, a supervising processor; and a plurality of routing processors coupled to a fabric. The managing processor has an in-band link to a routing processor. A routing processor receives a frame from the network, determines by parsing the frame, the protocol and logical unit number, and routes the frame to a queue according to a traffic class associated with the logical unit number in routing information prepared for the processors. An arbitration scheme empties the queue in accordance with a deficit round robin technique. If a routing processor detects the frame's destination is a virtual entity, and so is part of a virtual transaction, the router conducts a nonvirtual transaction in concert with the virtual transaction. The nonvirtual transaction accomplishes the intent of the virtual transaction but operates on an actual network port, for example, a storage device.
Owner:TERRELL WILLIAM C +9
System and method for caching network file systems
ActiveUS20070250552A1Fast and efficient client accessDigital computer detailsTransmissionPrimitive operationFile system
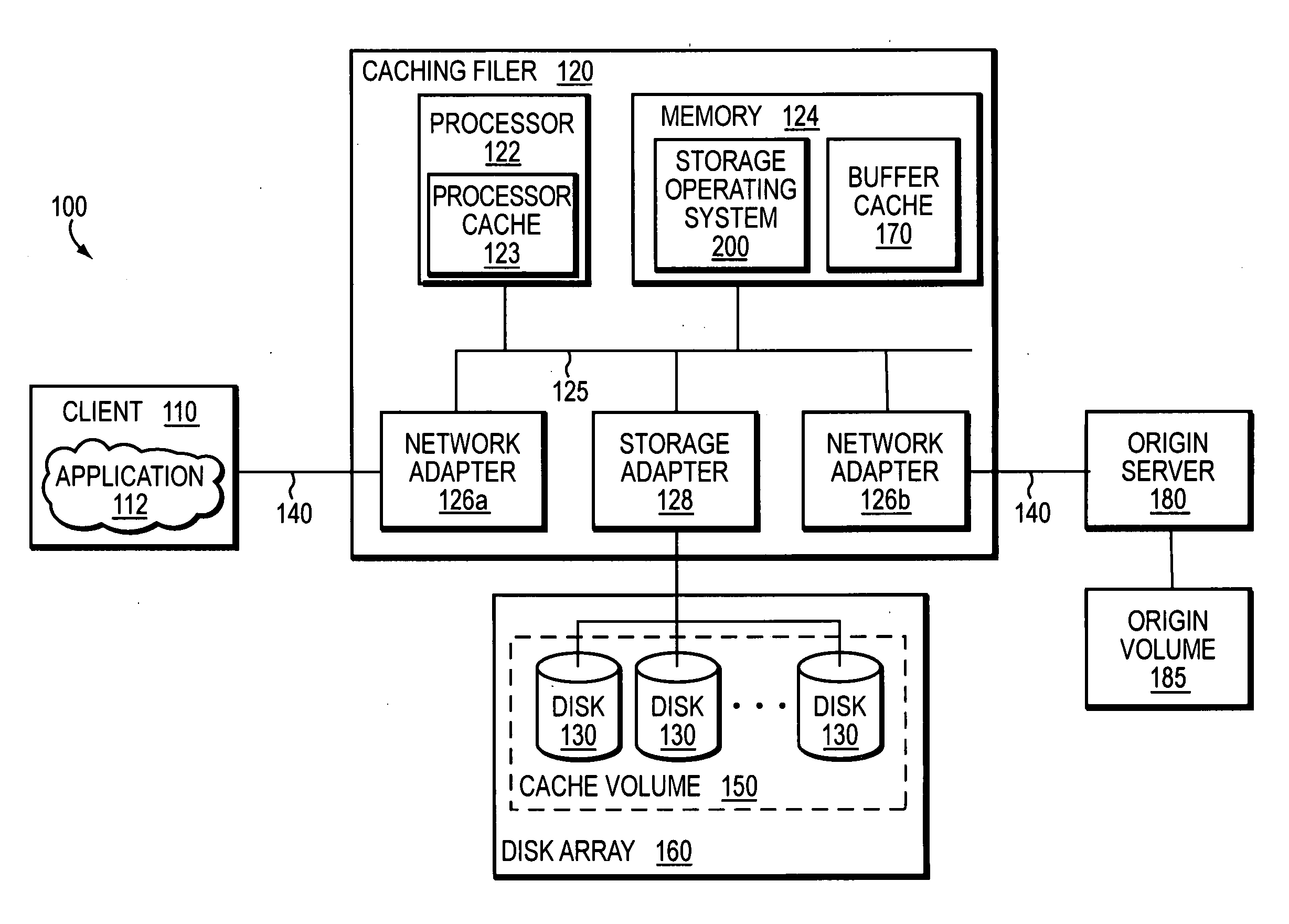
A network caching system has a multi-protocol caching filer coupled to an origin server to provide storage virtualization of data served by the filer in response to data access requests issued by multi-protocol clients over a computer network. The multi-protocol caching filer includes a file system configured to manage a sparse volume that “virtualizes” a storage space of the data to thereby provide a cache function that enables access to data by the multi-protocol clients. To that end, the caching filer further includes a multi-protocol engine configured to translate the multi-protocol client data access requests into generic file system primitive operations executable by both the caching filer and the origin server.
Owner:NETWORK APPLIANCE INC
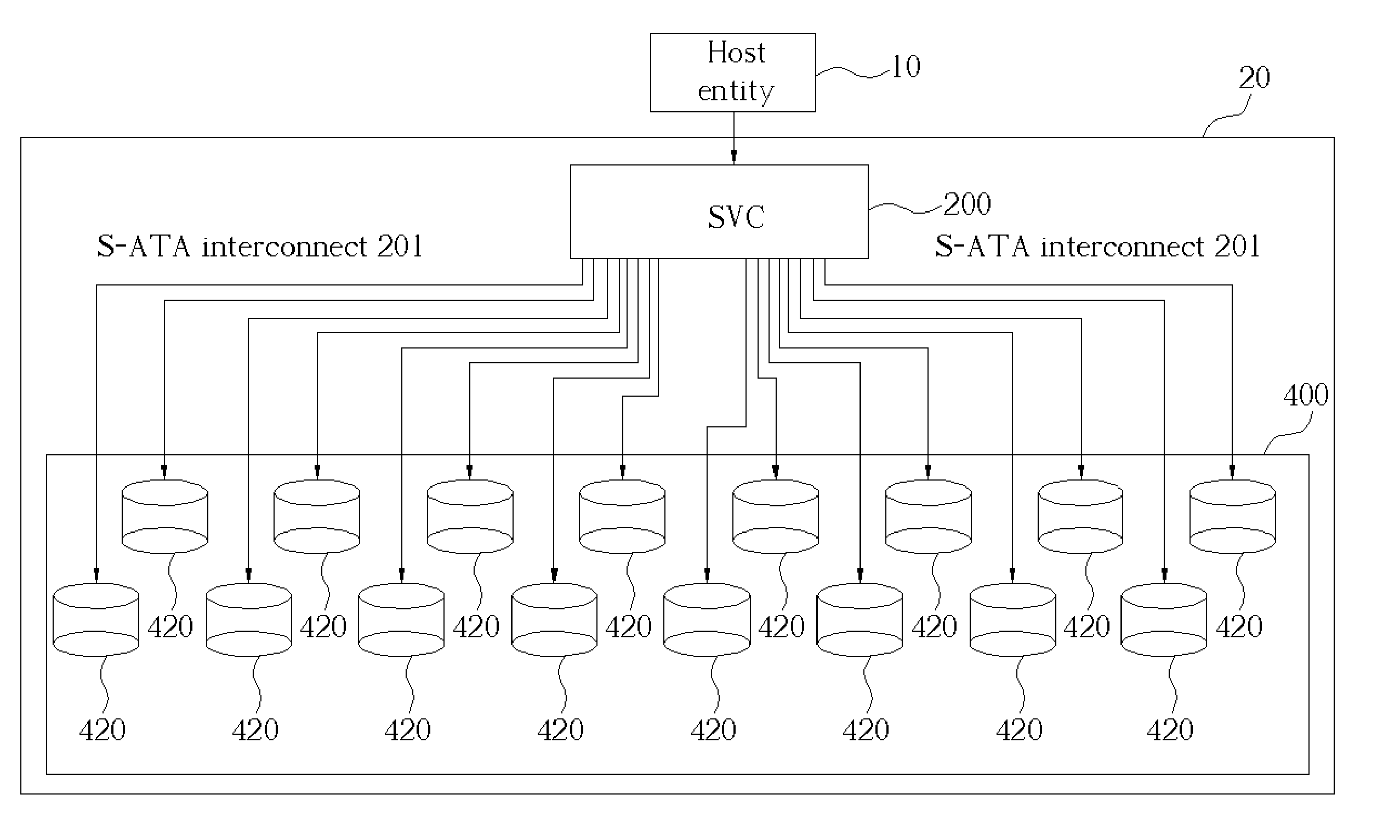
Storage virtualization computer system and external controller therefor
ActiveUS20050005044A1Input/output to record carriersMemory adressing/allocation/relocationSerial ATAHost machine
Owner:INFORTREND TECH INC
Apparatus, system and method incorporating virtualization for data storage
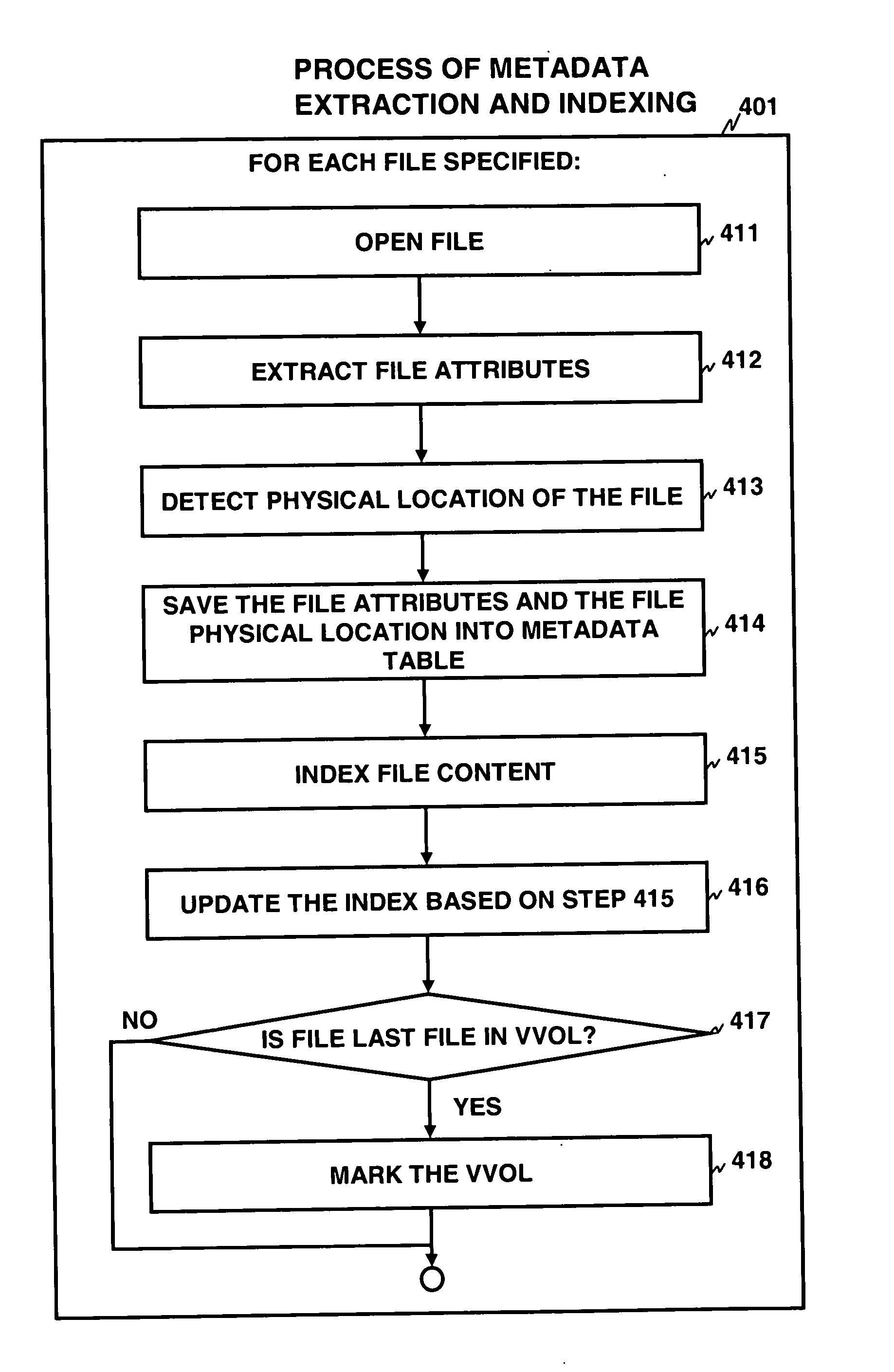
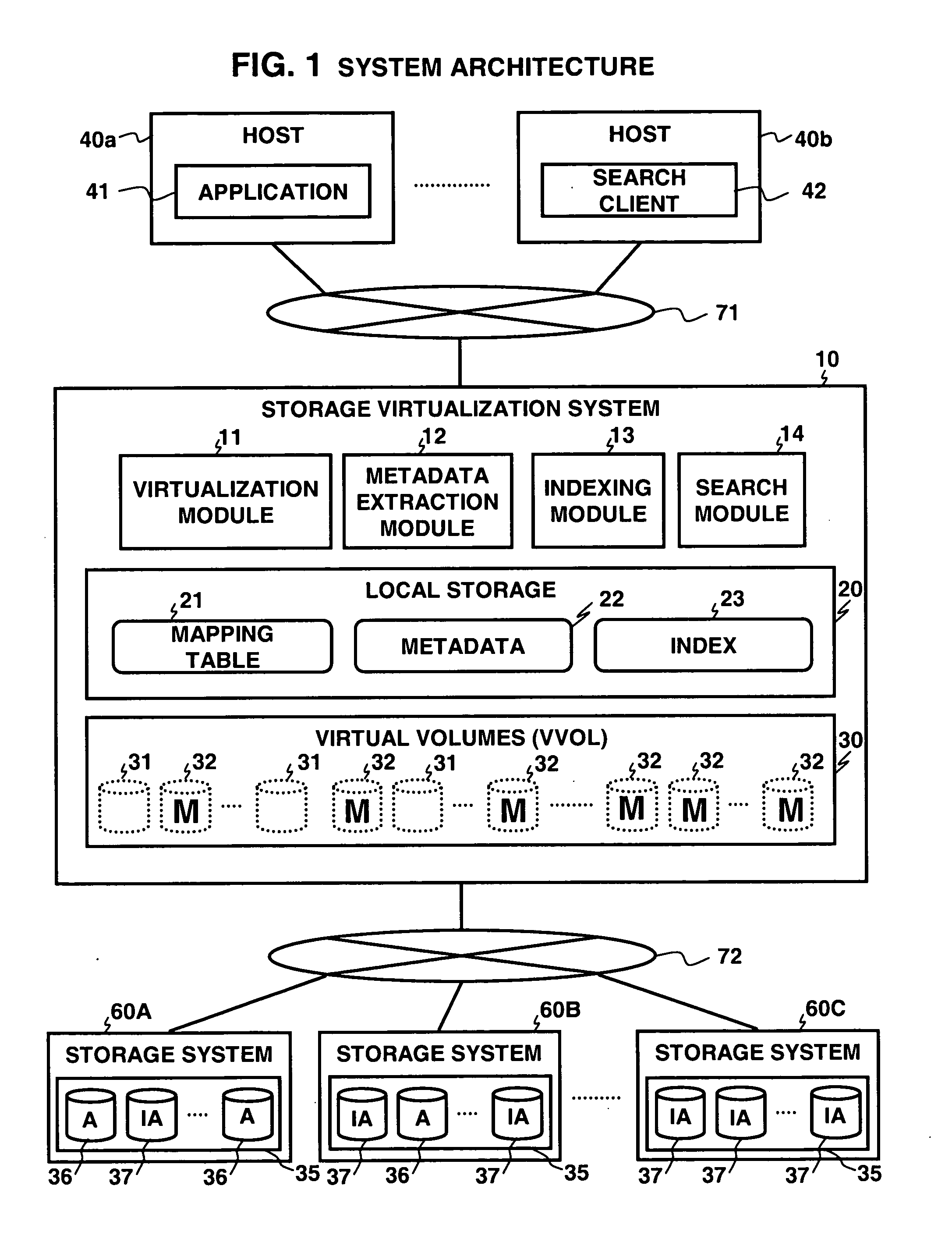
InactiveUS20070143559A1Save powerSave other management costEnergy efficient ICTFile metadata searchingData ingestionExternal storage
For long-term data preservation, a storage virtualization system contains a metadata extraction module, an indexing module, a search module, and a virtualization module. The system utilizes two types of virtual volumes: unmarked volumes and marked volumes. The metadata extraction module extracts metadata that describes the data stored in logical volumes located in external storage. The indexing module scans the data and creates an index, and the index and metadata are stored in a local storage. After metadata is extracted for all data in a volume, and all data in the volume are indexed, the virtual volume corresponding to that volume is marked and the volume is ready to be made inactive. The search module allows a user to search for desired data using the metadata and the index stored in the local storage instead having to access the external storage systems where the data is actually stored.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com