Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
107 results about "Primitive operation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Primitive operations. In addition to the operations that IBM® Rational® Rhapsody® automatically generates, you can define your own operations for objects. Each operation has a name and return type, and might include arguments. User‑defined operations are called primitive operations in Rational Rhapsody.
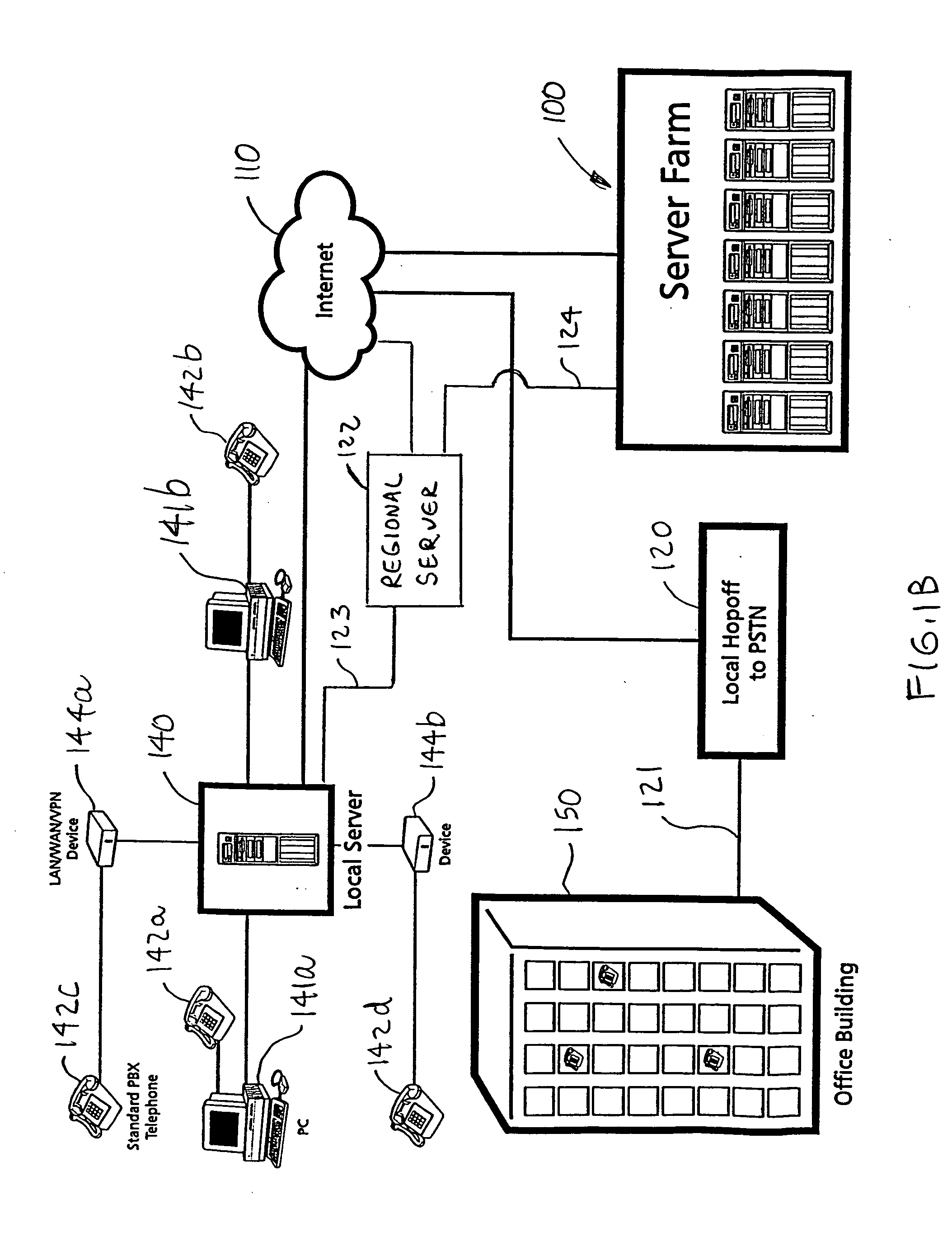
Networked computer system
InactiveUS6854009B1Multiple digital computer combinationsBootstrappingOperational systemRandom access memory
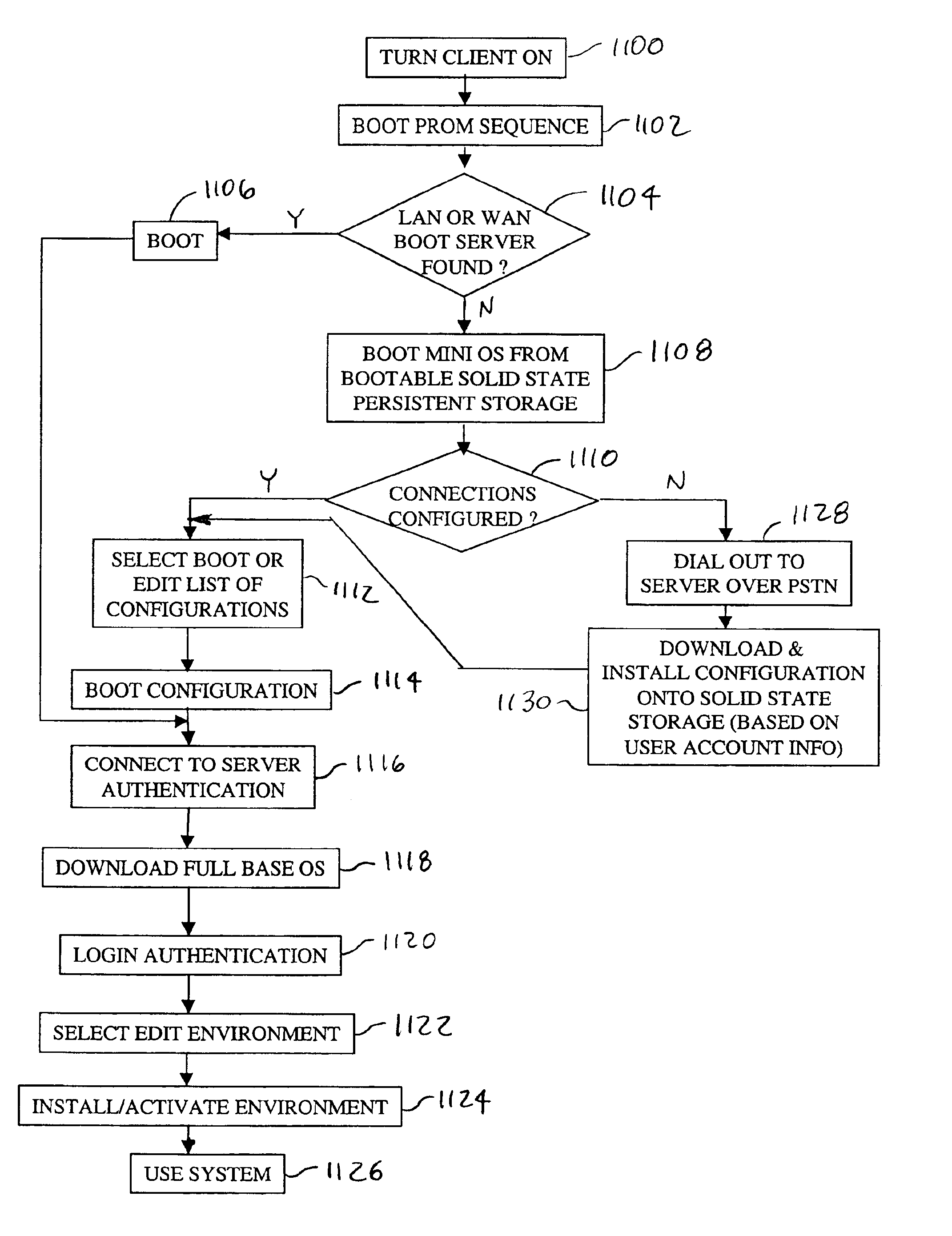
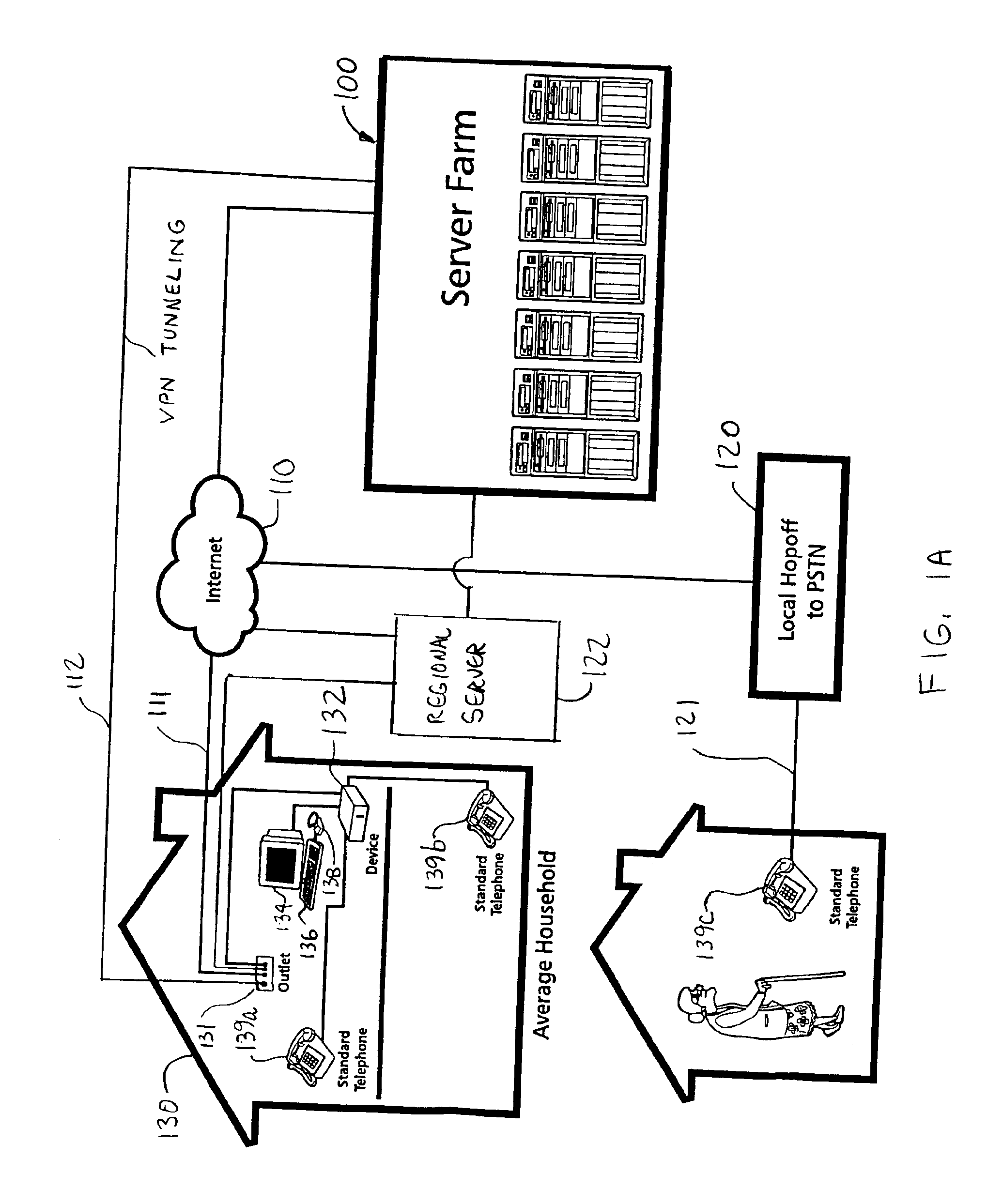
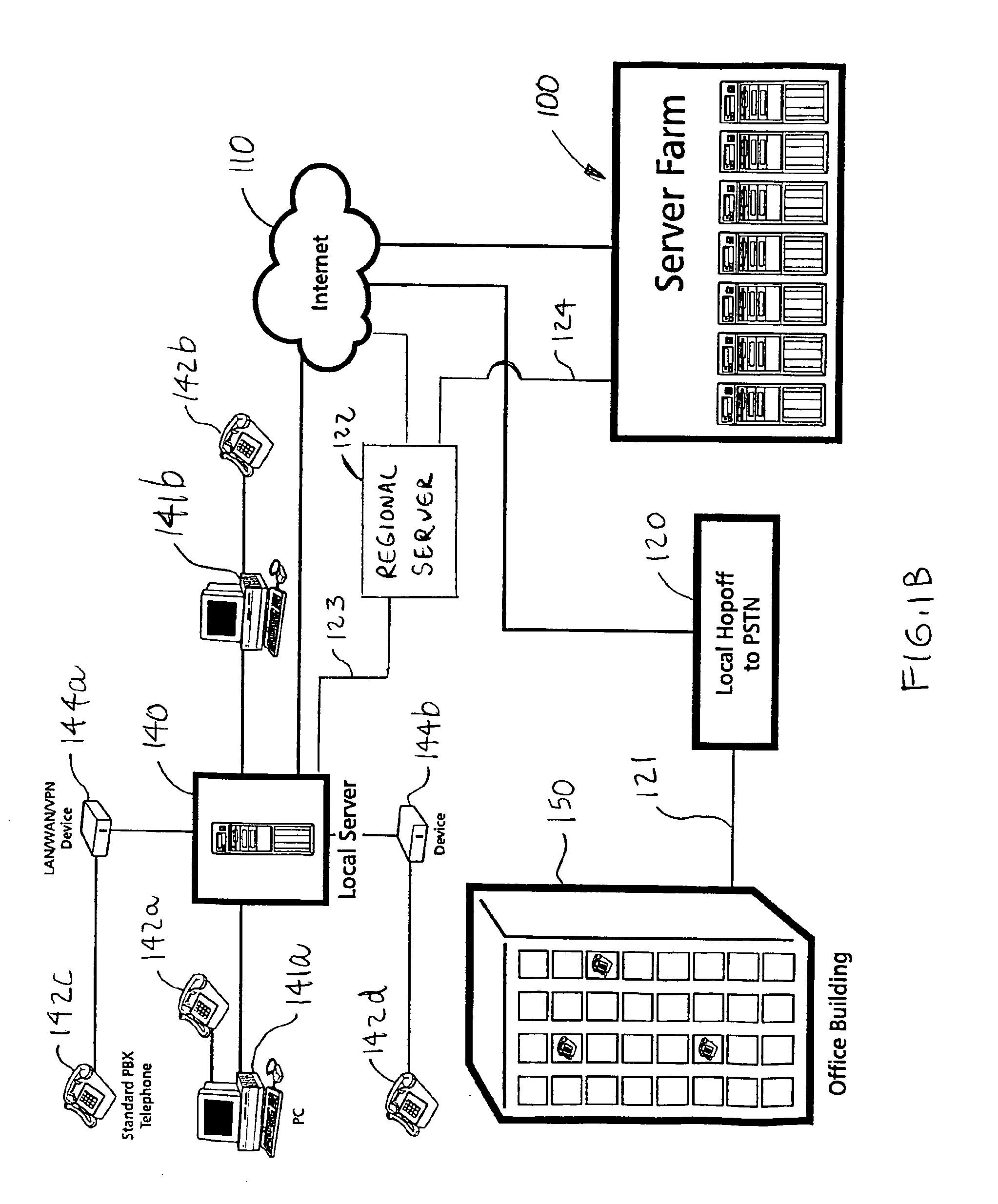
A networked computer system has a plurality of servers and a plurality of distributed clients, which may be devices or computers. Each client has a boot operating system (OS). Upon startup, the boot OS in each client automatically initiates a connection to one of the servers via the Internet. The boot OS can detect the type of medium (e.g., cable modem, DSL) to which the client is connected. The server automatically downloads a base OS and dynamically configures a suite of applications on the client without running the standard installation programs. One included application is an Internet telephony application, allowing a user to plug a standard telephone into the client appliance or computer, pick up the telephone, and automatically dial out using long distance Internet telephony. Optionally, the server may download a plurality of operating systems that are automatically initiated to run concurrently on the client. The clients use a random access memory (RAM) caching technique. A first portion of each OS or application is downloaded at startup and maintained in the client RAM, containing the files needed to launch the OS or application. If the client processes a request for an OS or application program file not in the client's RAM, the requested file is automatically downloaded from the server.
Owner:CA TECH INC
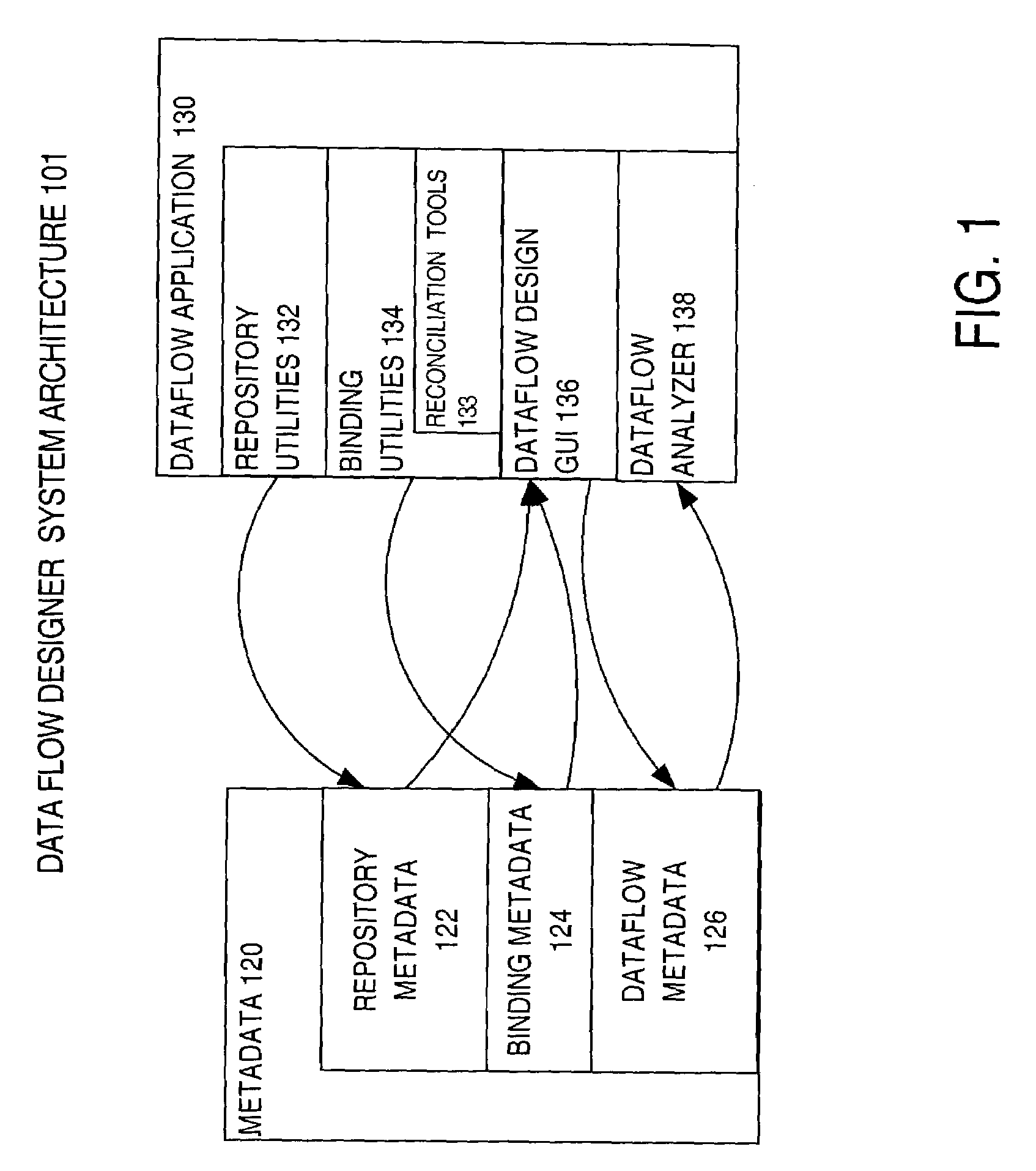
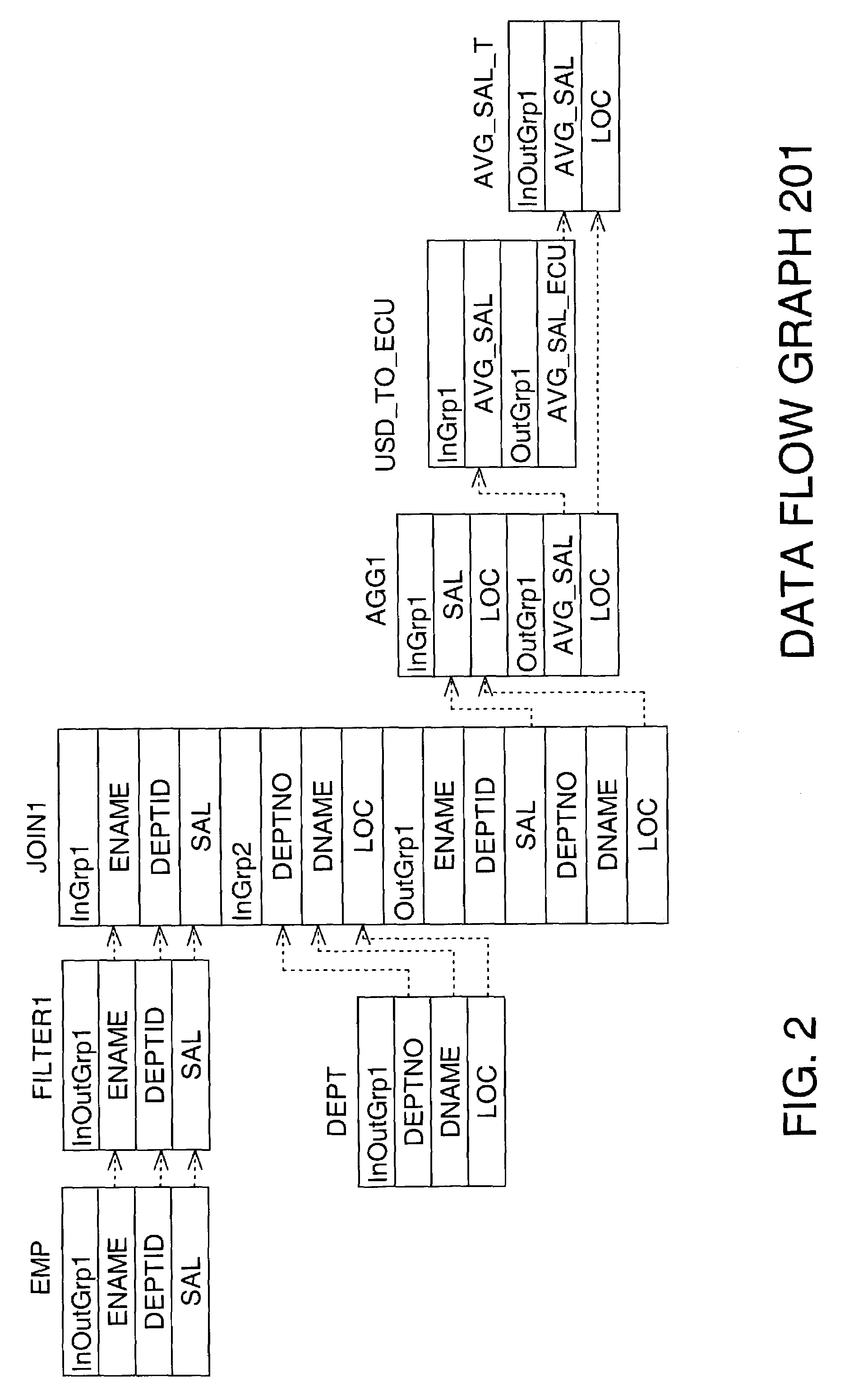
Operator approach for generic dataflow designs
ActiveUS7343585B1Digital data information retrievalSpecial data processing applicationsData warehousePrimitive operation
Described herein is an operator-based approach to representing dataflows. A dataflow is a set of one or more operations and one or more flows of data that are processed successively by the set of operations. A dataflow is described by a generic description in which operations in a dataflow are represented by operators. An operator defines a primitive operation (e.g. join, filter), specifying not only the type of operation, but the inputs and outputs, rules, and criteria that govern the operation. From the generic description, a code implementation is generated that may be completely executed on a source database system and target data warehouse, without need for an intermediate system to participate in the execution of the code implementation, such as a data movement engine.
Owner:ORACLE INT CORP
Networked computer system
A networked computer system has a plurality of servers and a plurality of distributed clients, which may be devices or computers. Each client has a boot operating system (OS). Upon startup, the boot OS in each client automatically initiates a connection to one of the servers via the Internet. The boot OS can detect the type of medium (e.g., cable modem, DSL) to which the client is connected. The server automatically downloads a base OS and dynamically configures a suite of applications on the client without running the standard installation programs. One included application is an Internet telephony application, allowing a user to plug a standard telephone into the client appliance or computer, pick up the telephone, and automatically dial out using long distance Internet telephony. Optionally, the server may download a plurality of operating systems that are automatically initiated to run concurrently on the client. The clients use a random access memory (RAM) caching technique. A first portion of each OS or application is downloaded at startup and maintained in the client RAM, containing the files needed to launch the OS or application. If the client processes a request for an OS or application program file not in the client's RAM, the requested file is automatically downloaded from the server.
Owner:HUGHES TREVOR
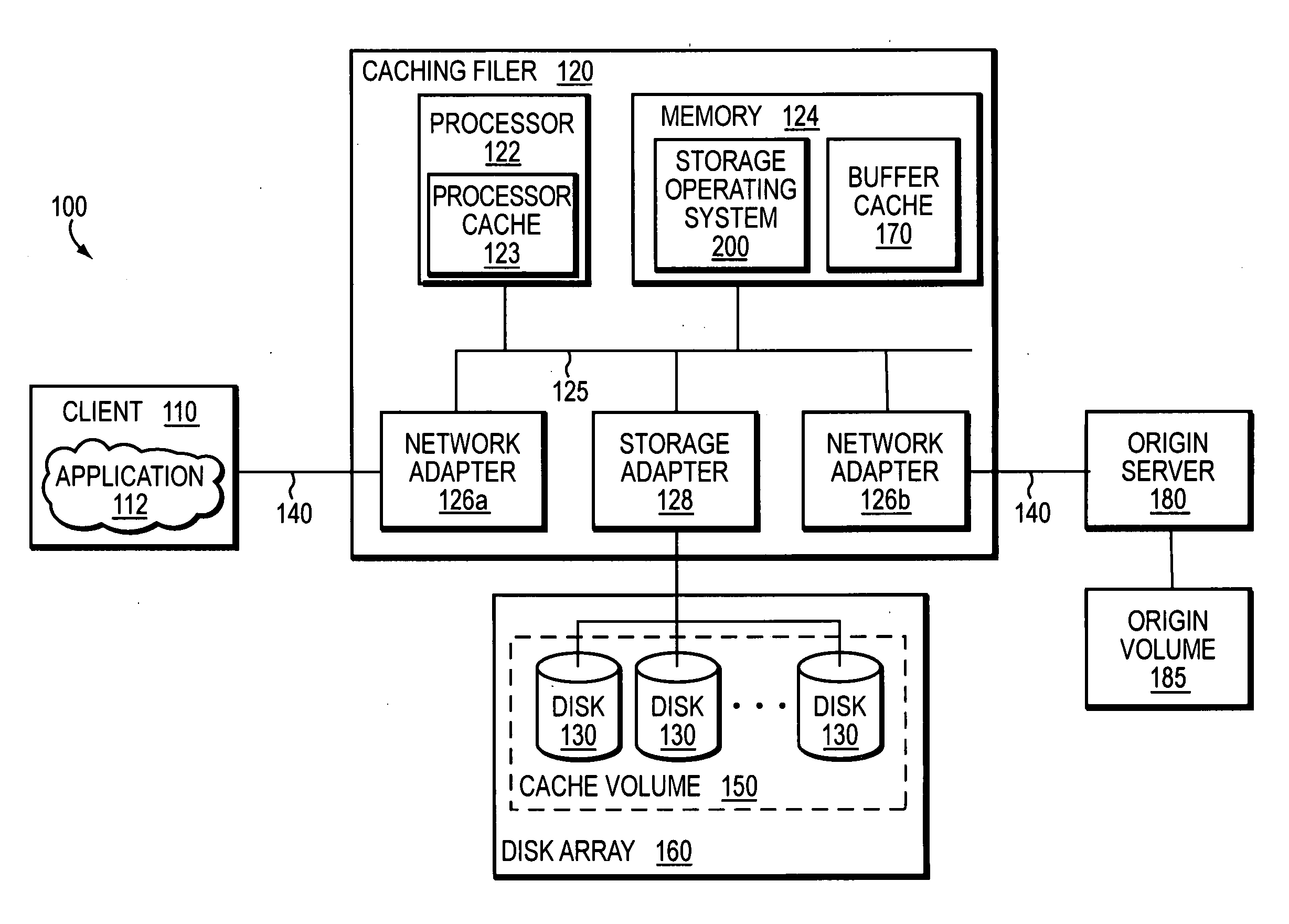
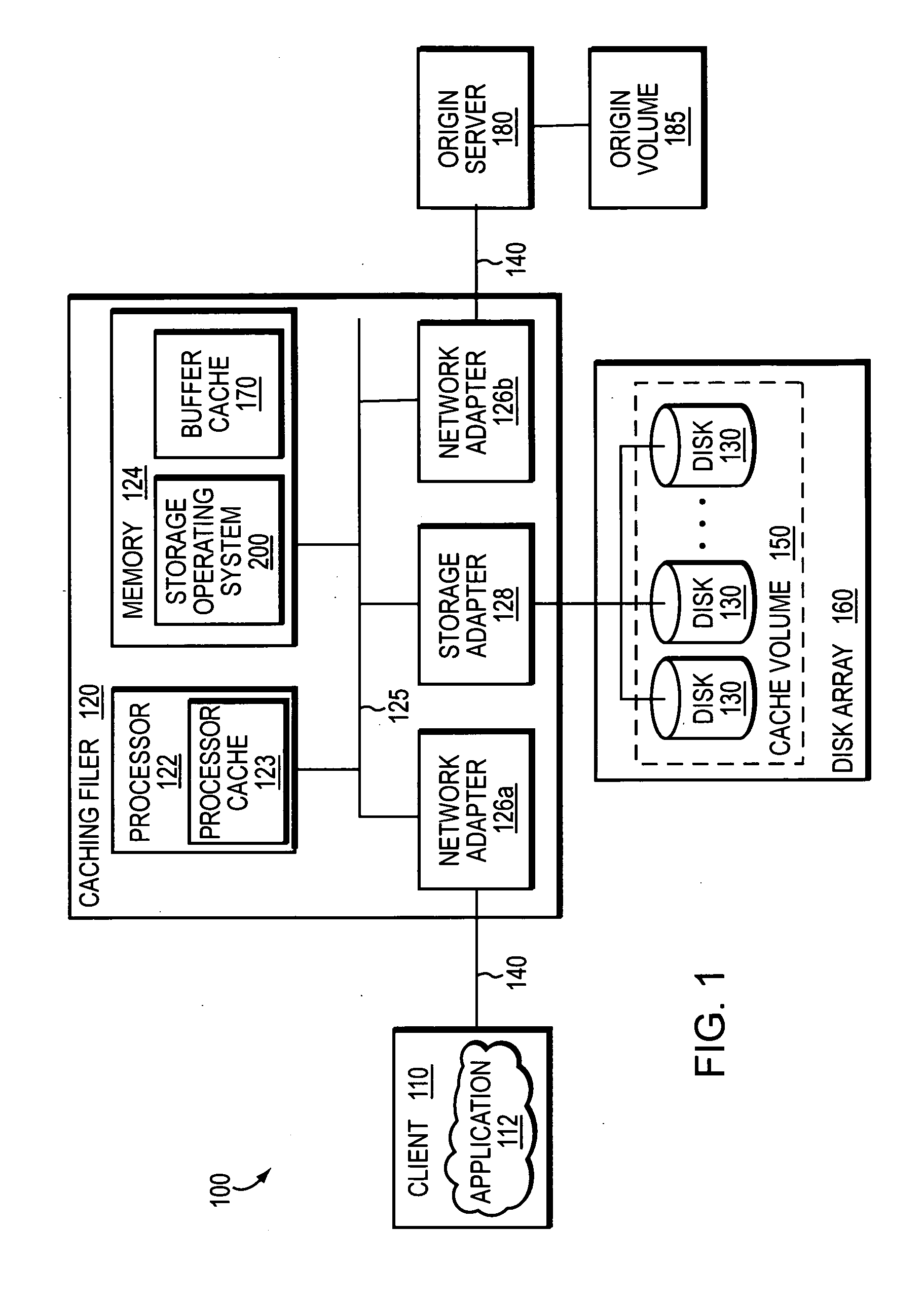
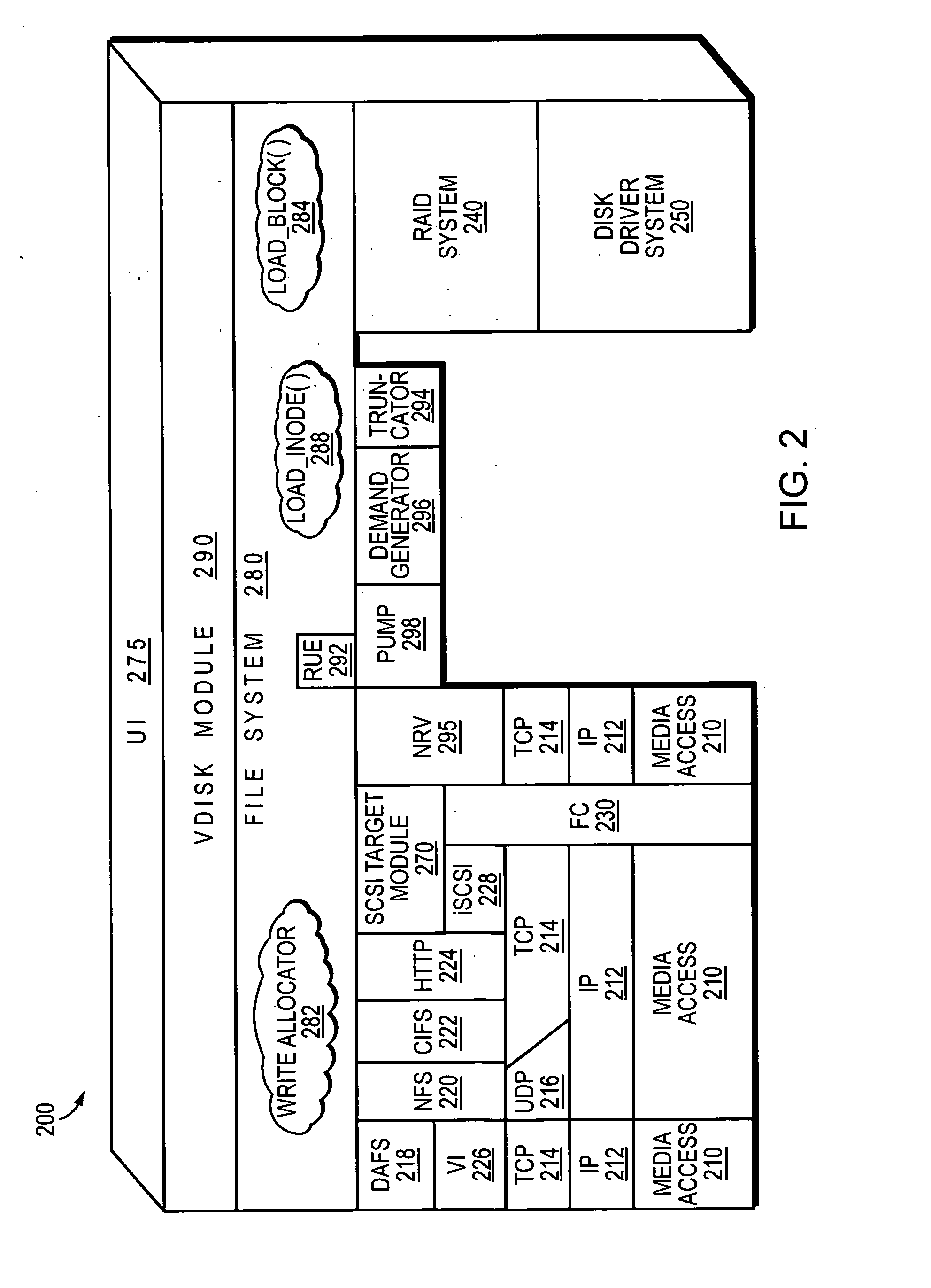
System and method for caching network file systems
ActiveUS20070250552A1Fast and efficient client accessDigital computer detailsTransmissionPrimitive operationFile system
A network caching system has a multi-protocol caching filer coupled to an origin server to provide storage virtualization of data served by the filer in response to data access requests issued by multi-protocol clients over a computer network. The multi-protocol caching filer includes a file system configured to manage a sparse volume that “virtualizes” a storage space of the data to thereby provide a cache function that enables access to data by the multi-protocol clients. To that end, the caching filer further includes a multi-protocol engine configured to translate the multi-protocol client data access requests into generic file system primitive operations executable by both the caching filer and the origin server.
Owner:NETWORK APPLIANCE INC
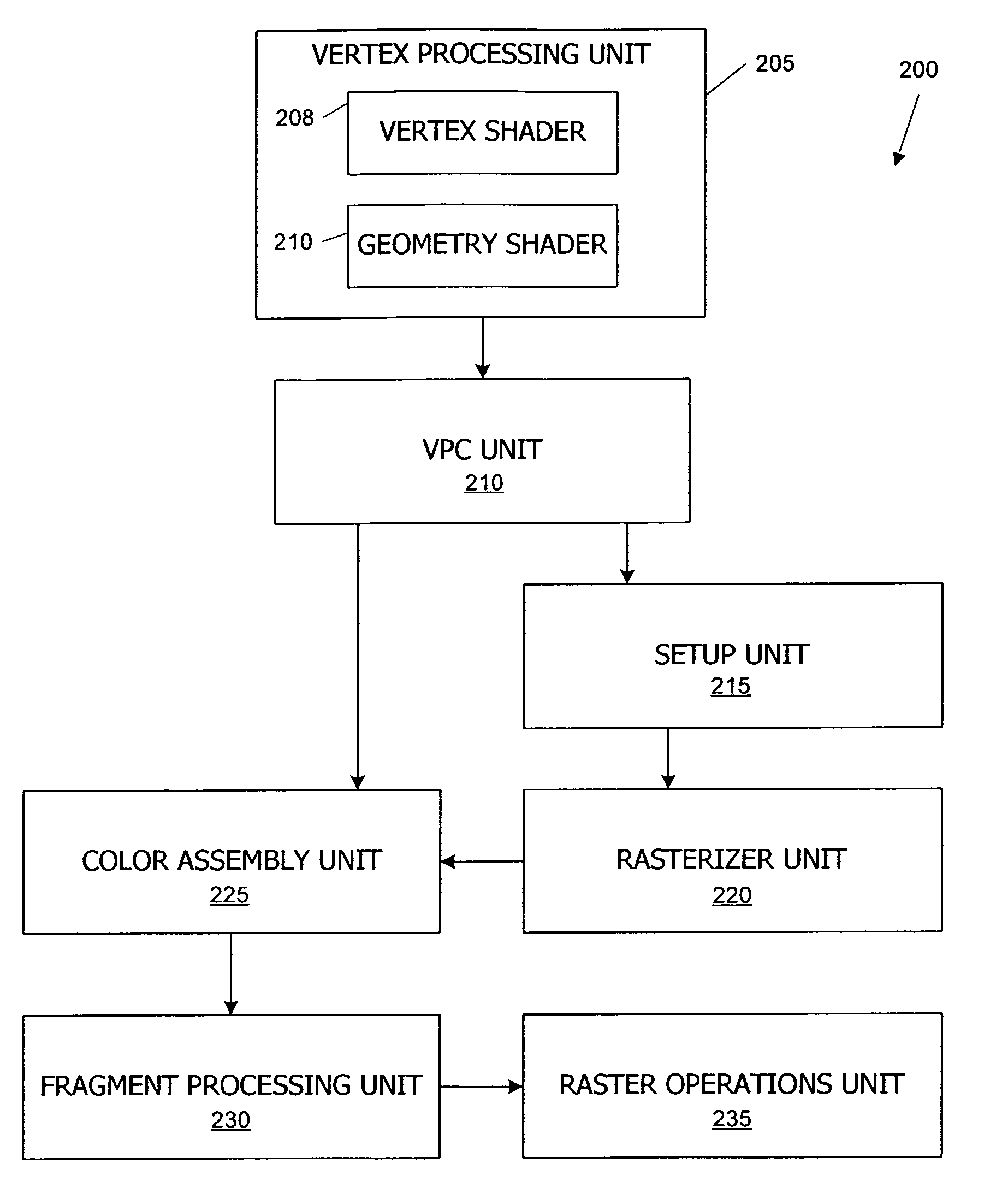
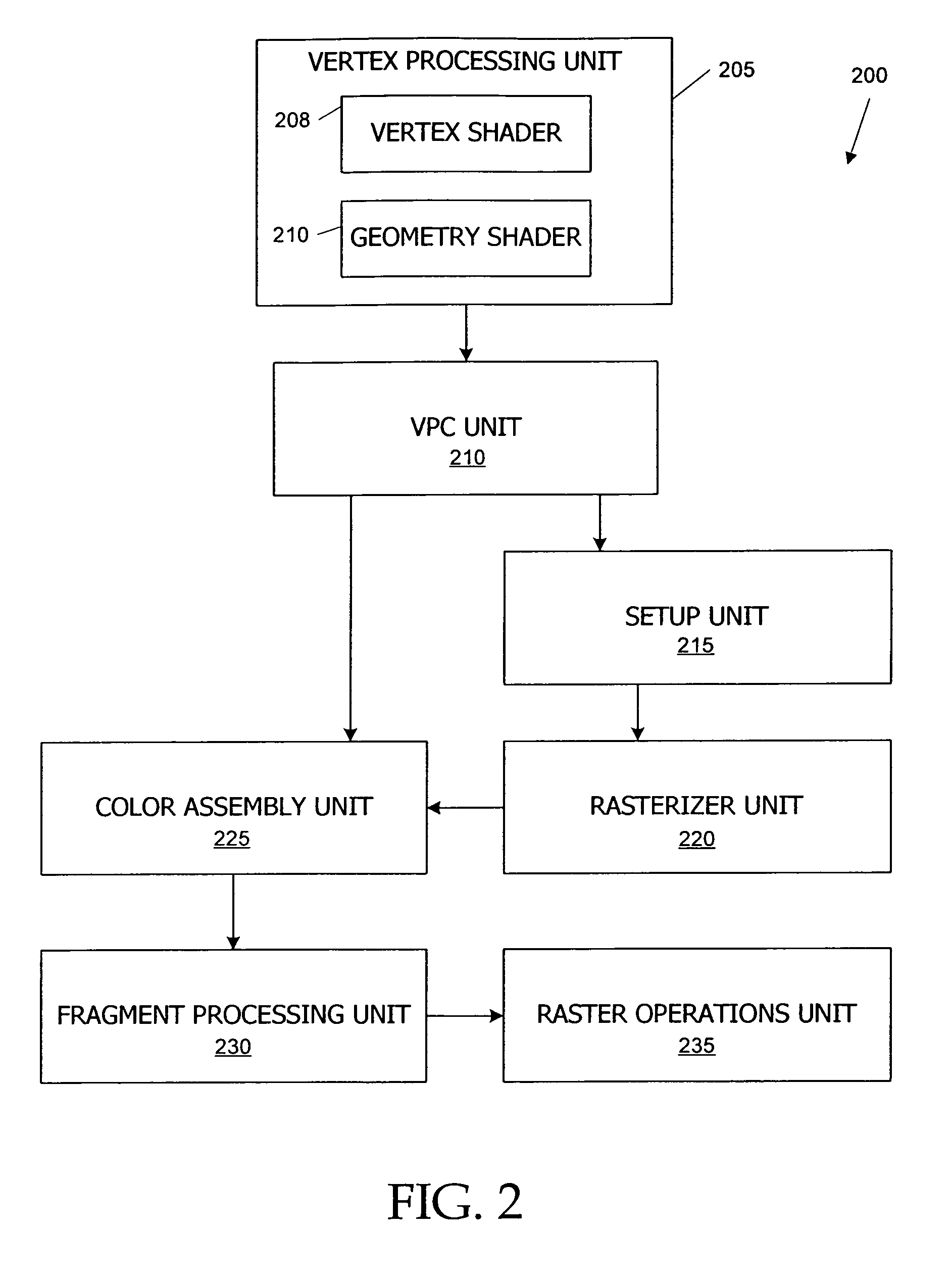
Culling in a vertex processing unit
ActiveUS7468726B1Improve throughputReduce in quantity3D-image renderingComputational sciencePrimitive operation
A graphics processor performs culling of invisible primitives in a vertex processing unit that includes a geometry shader or other processing engine that performs per-primitive operations. Primitives can be culled after clip space coordinates for the vertices have been computed and in some instances before at least one other vertex attribute has been computed. To the extent that this early culling reduces the number of vertices for which the full set of attributes is computed or reduces the number of primitives or vertices delivered to downstream units, throughput of the processor is increased.
Owner:NVIDIA CORP
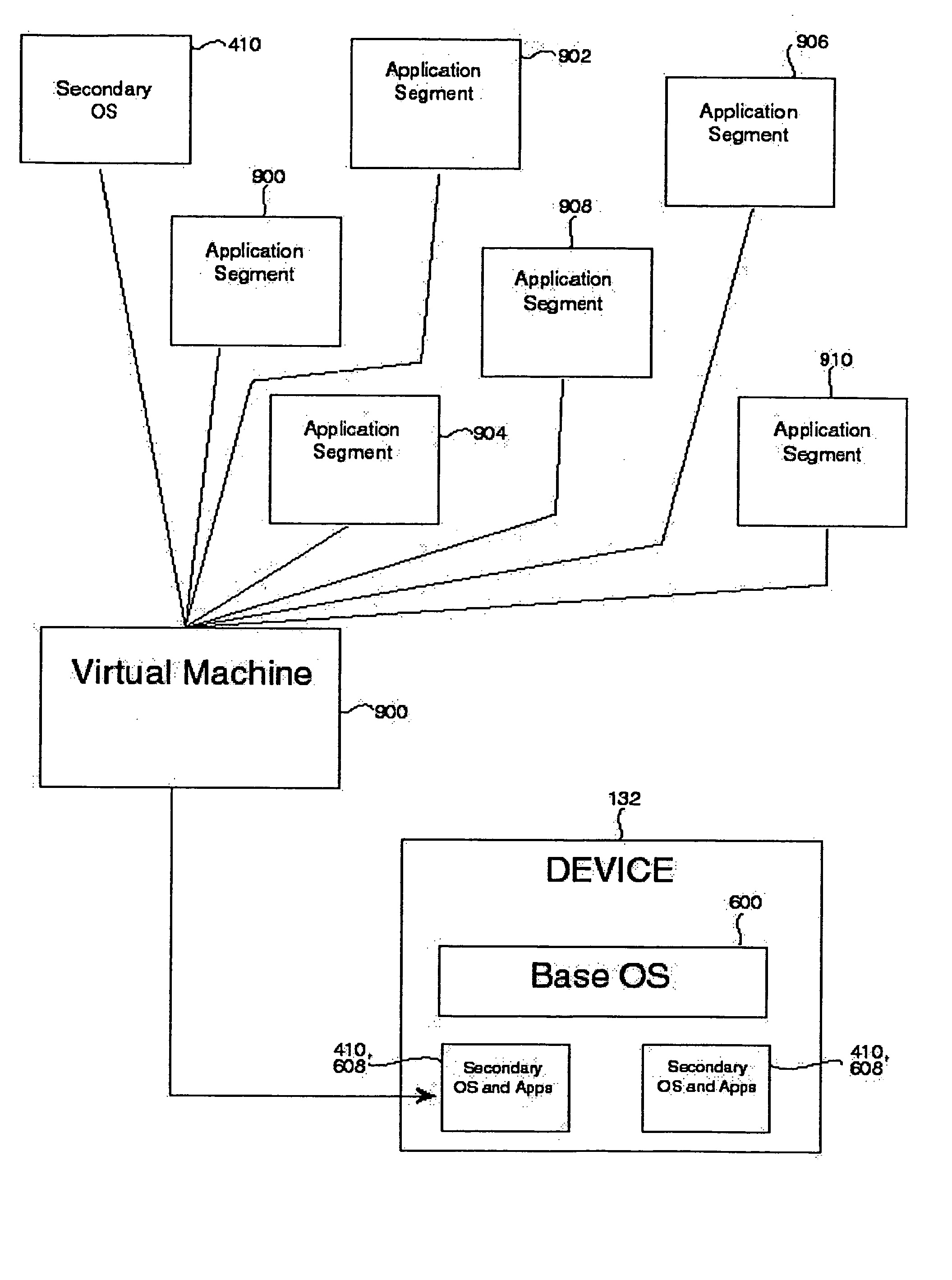
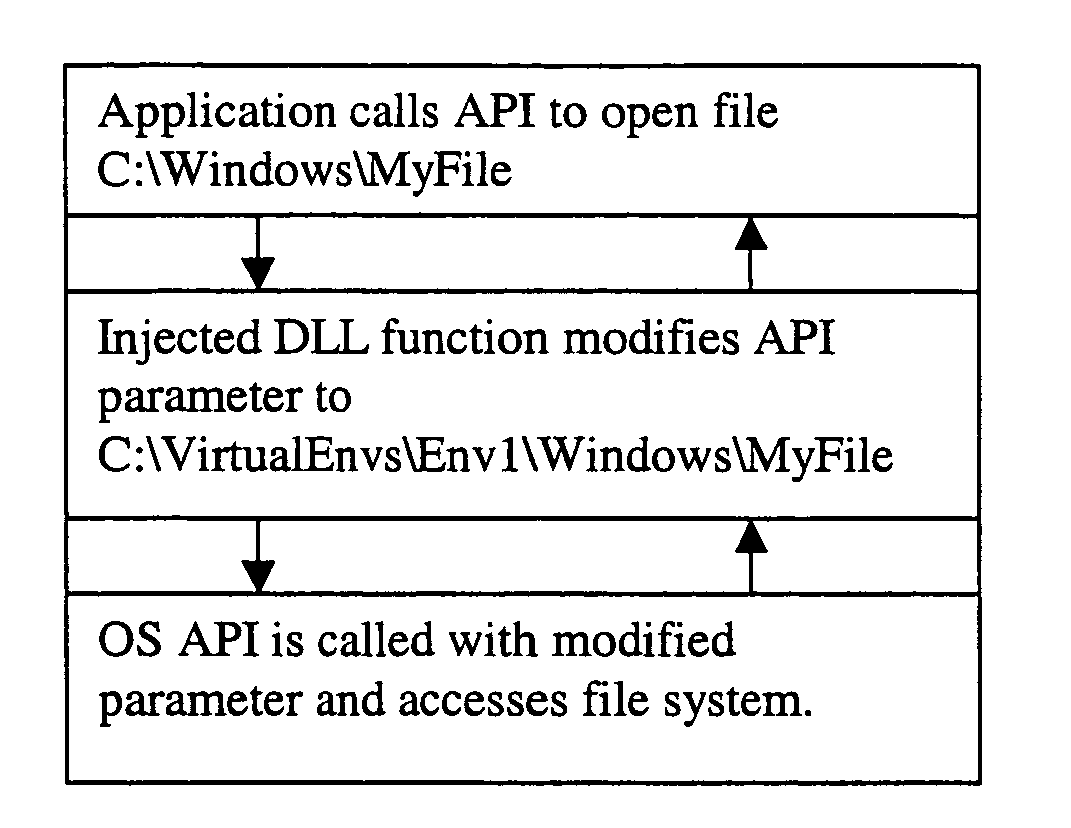
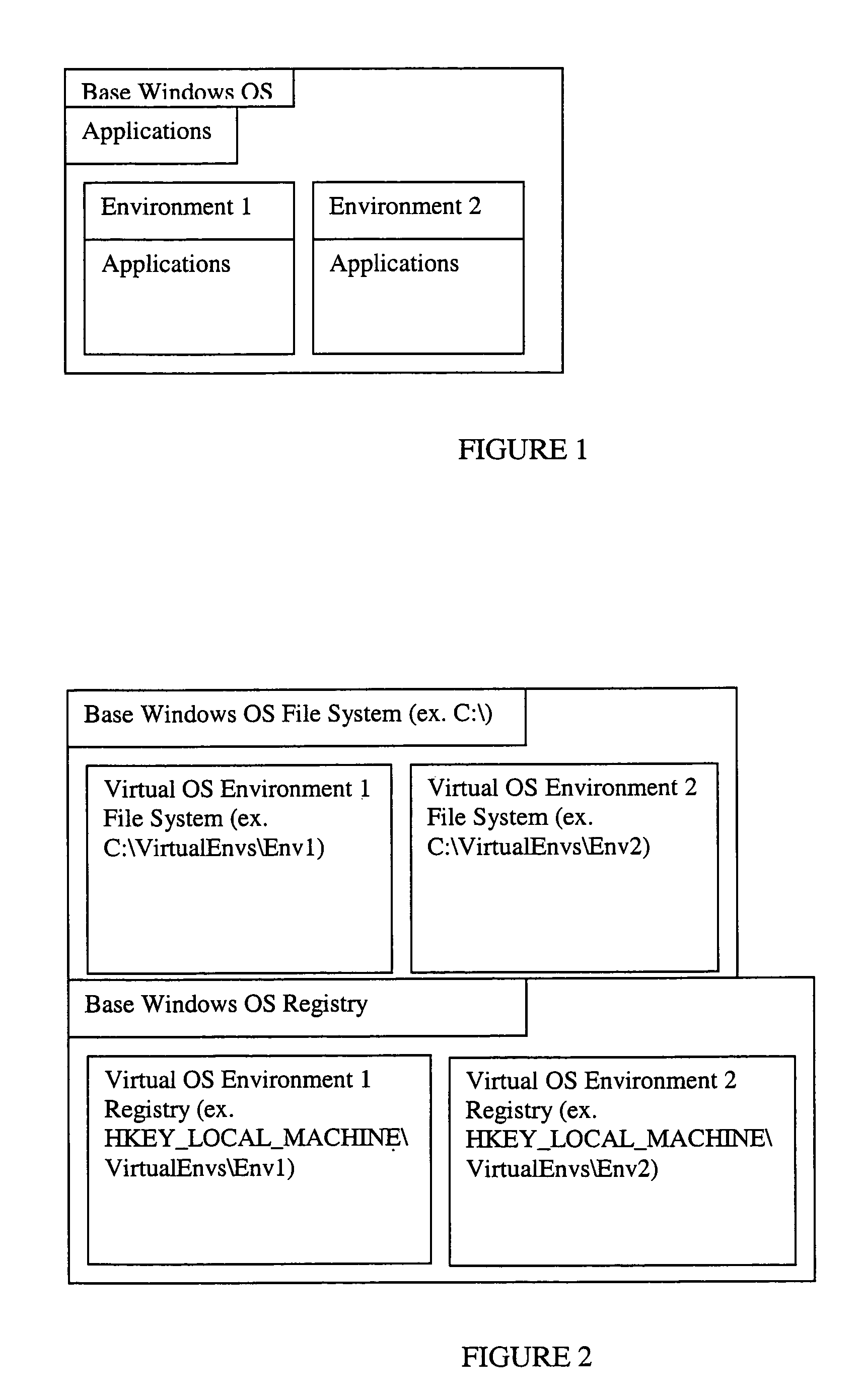
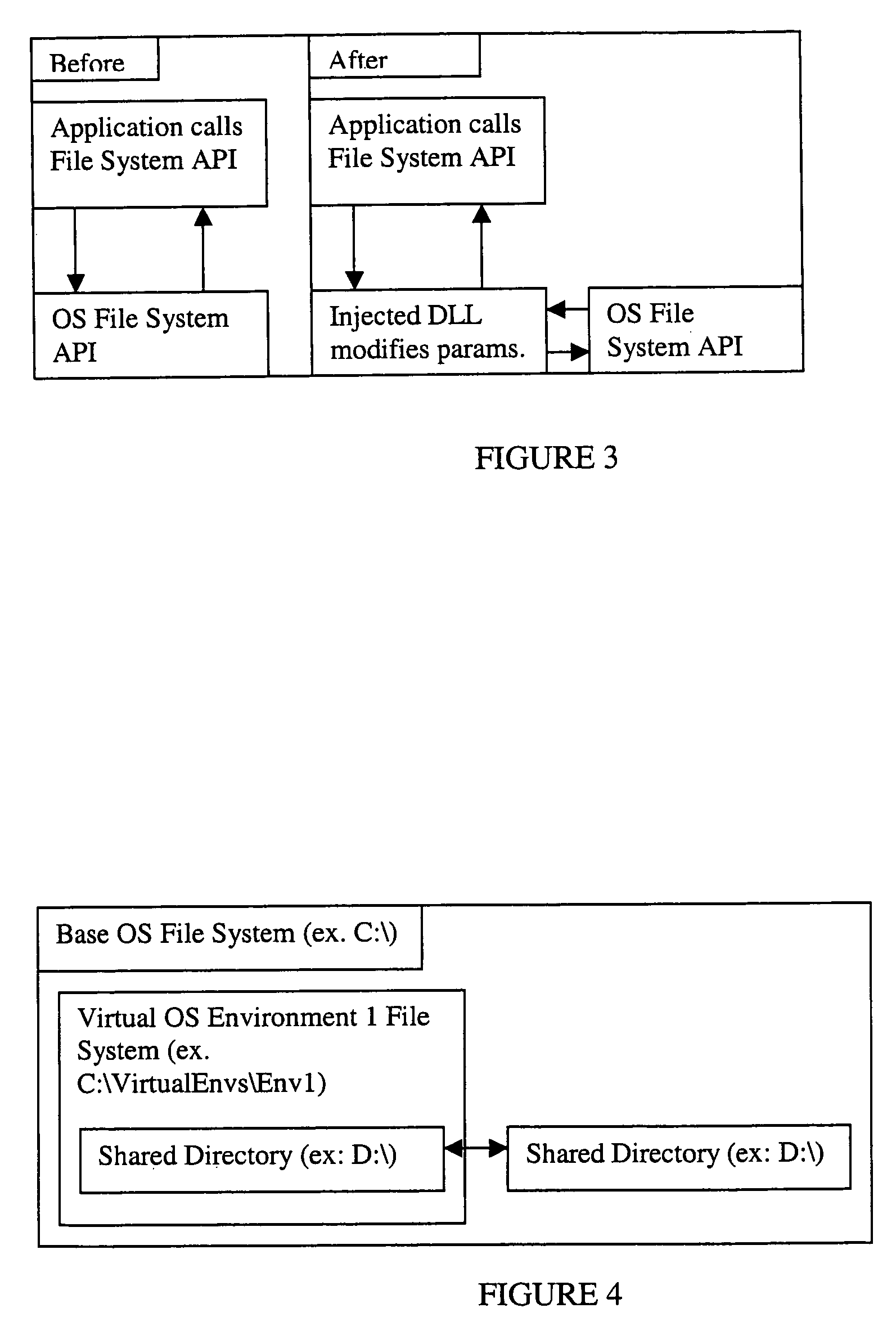
Virtual OS computing environment
InactiveUS7673308B2Software simulation/interpretation/emulationMemory systemsOperational systemFile system
Multiple, semi-independent virtual operating system (OS) environments coexist within a single (OS) such that a change made in one environment does not affect the main OS or any other environment. In this way each virtual OS environment appears to be an independent OS for the applications running within it. The file system and registry information for each environment is independent of the base OS and other environments. Each of the environments can contain a group of installed applications that will run independently of each other. Although the invention is described in terms of a Windows® environment, the approach is applicable to other operating systems through appropriate modification.
Owner:CA TECH INC
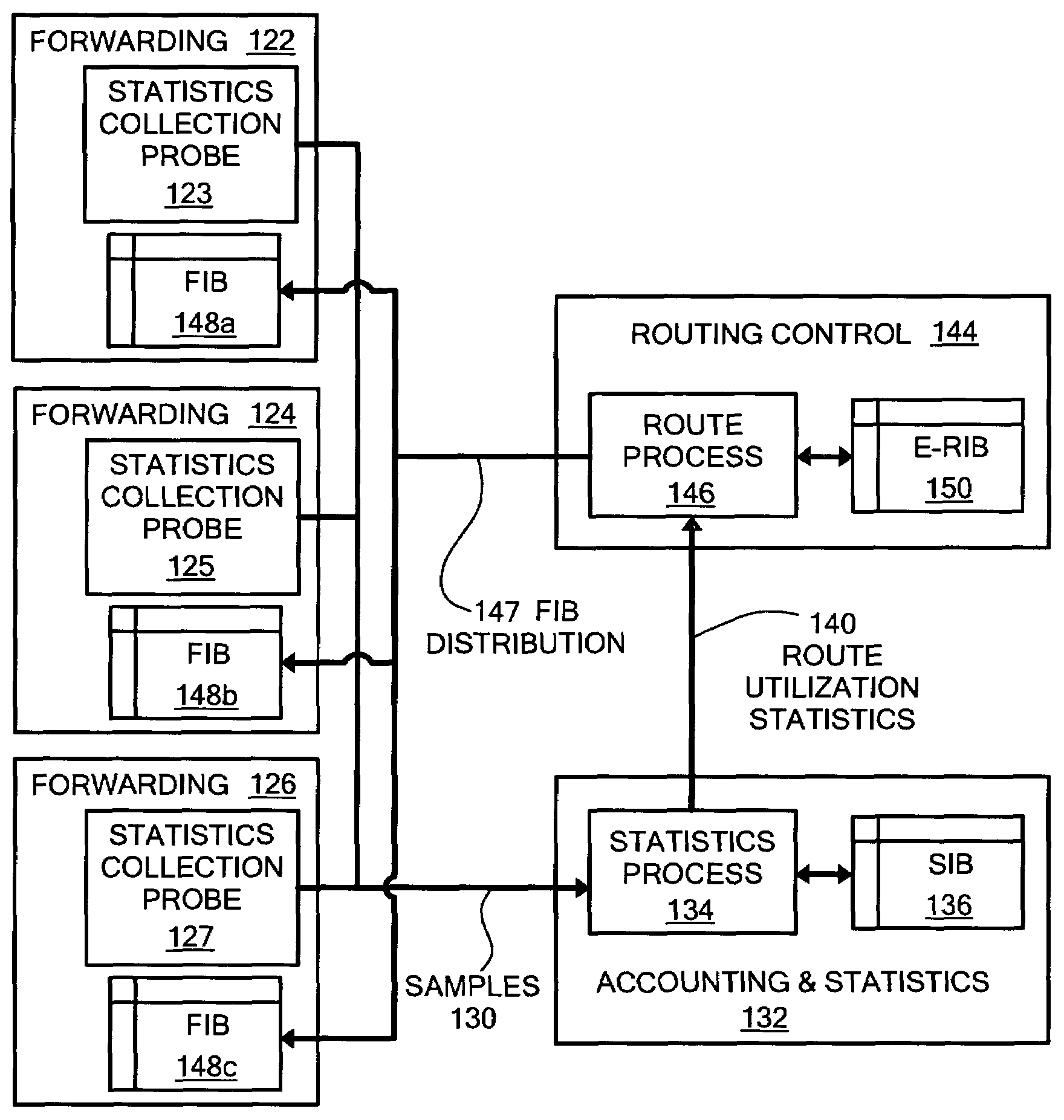
Network accounting statistics collection
InactiveUS7577736B1Improve the level ofReduce transmission bandwidthMetering/charging/biilling arrangementsError preventionPrimitive operationCollection system
A system for network accounting statistics collection including a statistics collector associated with each packet forwarding engine. Each statistics collector has one or more accounting elements, each of which includes some number of counters, such as packet and byte counters. Each statistics collector receives accounting instructions from the associated forwarding engine for packets processed by the forwarding engine, including packets that will be discarded without being forwarded. Each accounting instruction includes an identifier uniquely indicating one of the accounting elements, and information used to increment the counters within the accounting element. Upon receipt of an accounting instruction, the receiving statistics collector increments the counters in the accounting element. The accounting instruction is a relatively simple primitive operation in the disclosed system, enabling high-speed operation. Each statistics collector collects data over a fixed sampling interval that may range from a number of milliseconds to one or more minutes. Each sampling period begins with a reset of an accounting element store, and ends with at least one set of data being flushed to a management system for further processing and / or formatting.
Owner:RPX CLEARINGHOUSE
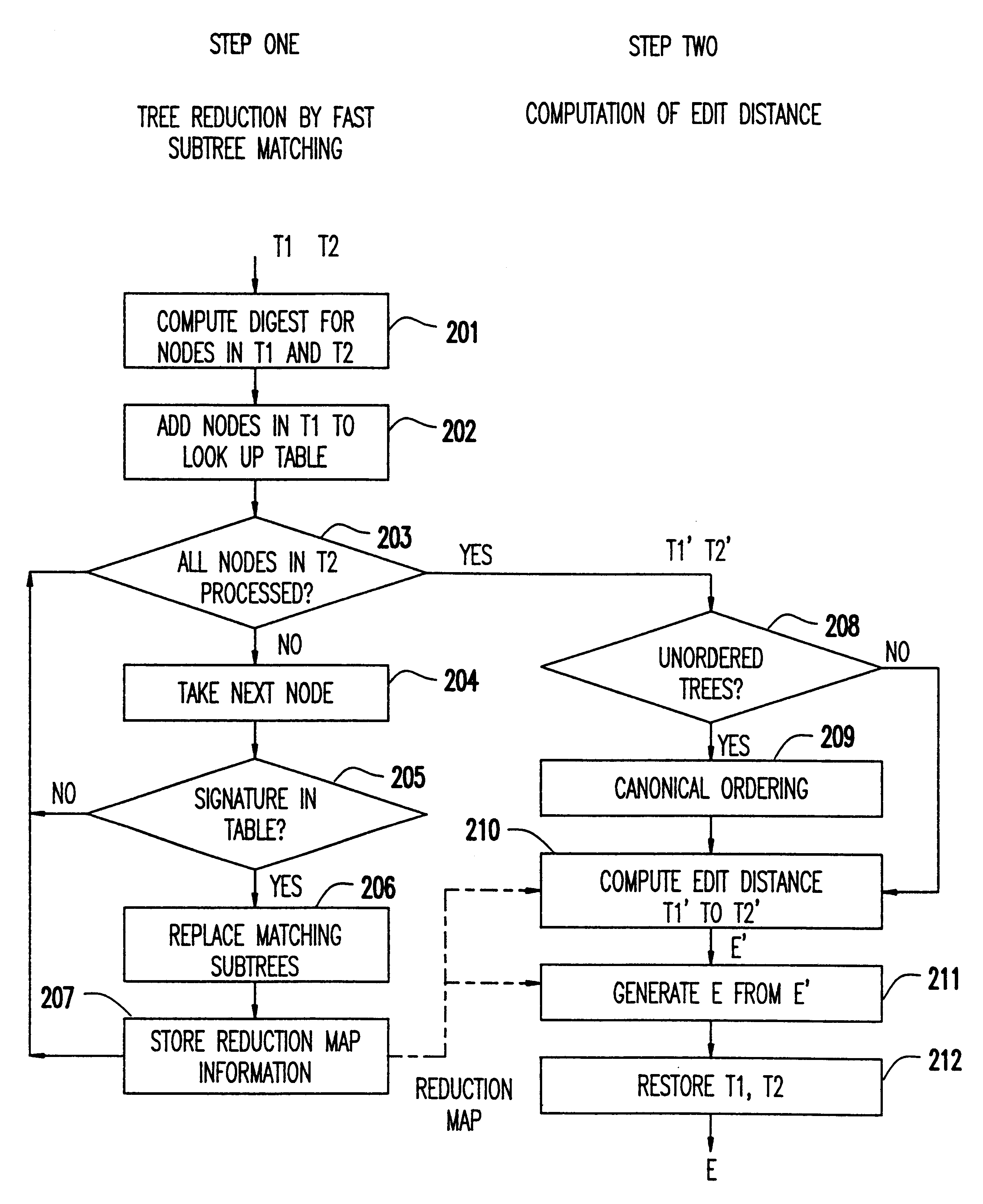
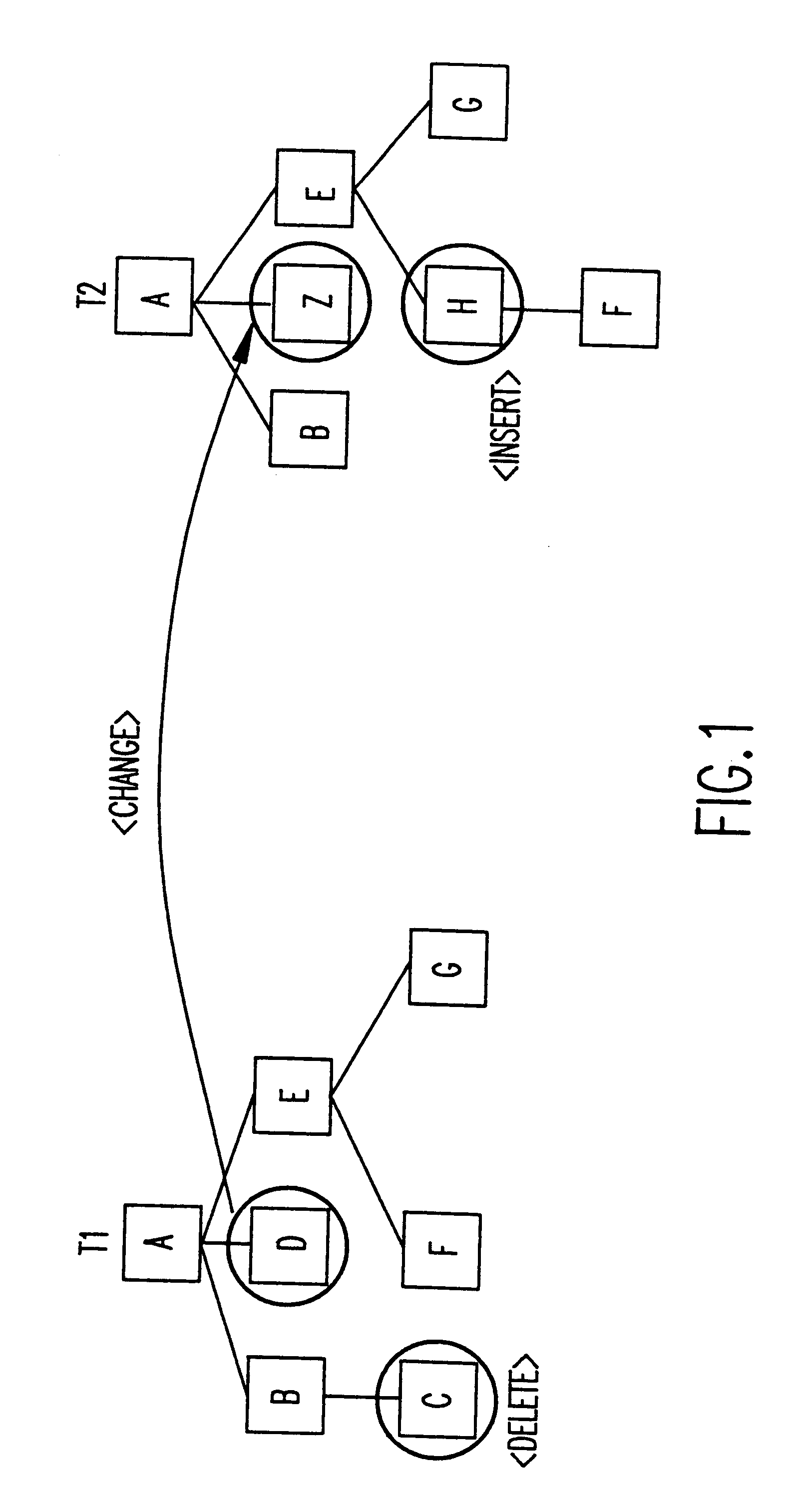
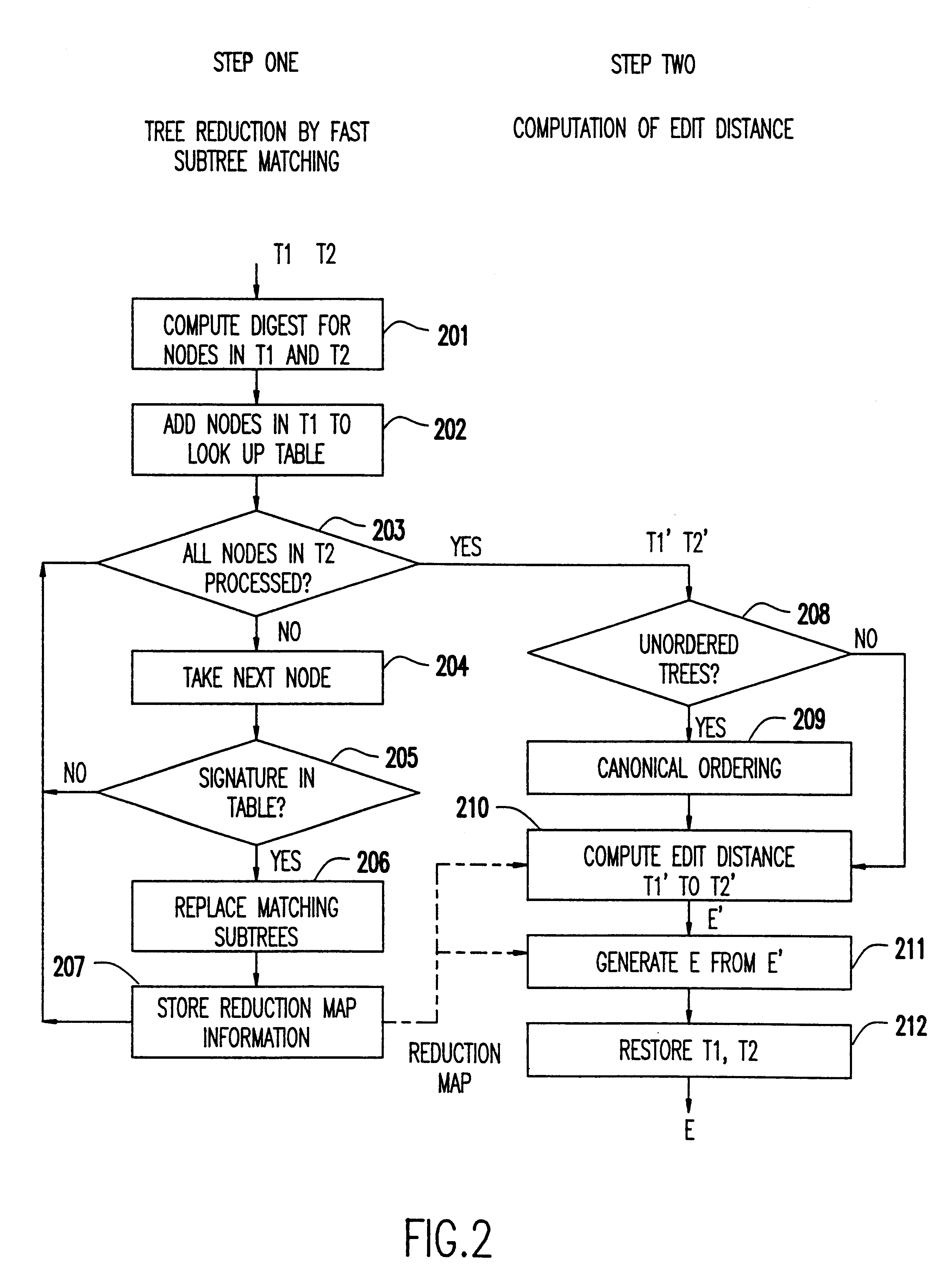
Quick difference and update for tree structure data
InactiveUS6260042B1Data processing applicationsDigital data information retrievalPrimitive operationTree structured data
Efficient differencing and update mechanisms operate directly on the native representation of the data. No irrelevant differences are introduced by the process. The difference reports generated are stated in terms of the basic operations that can be performed on a data tree, thus requiring no additional interpretation, and making it amenable to direct human inspection and understanding. This mechanism can become a central part of any version management system.
Owner:IBM CORP
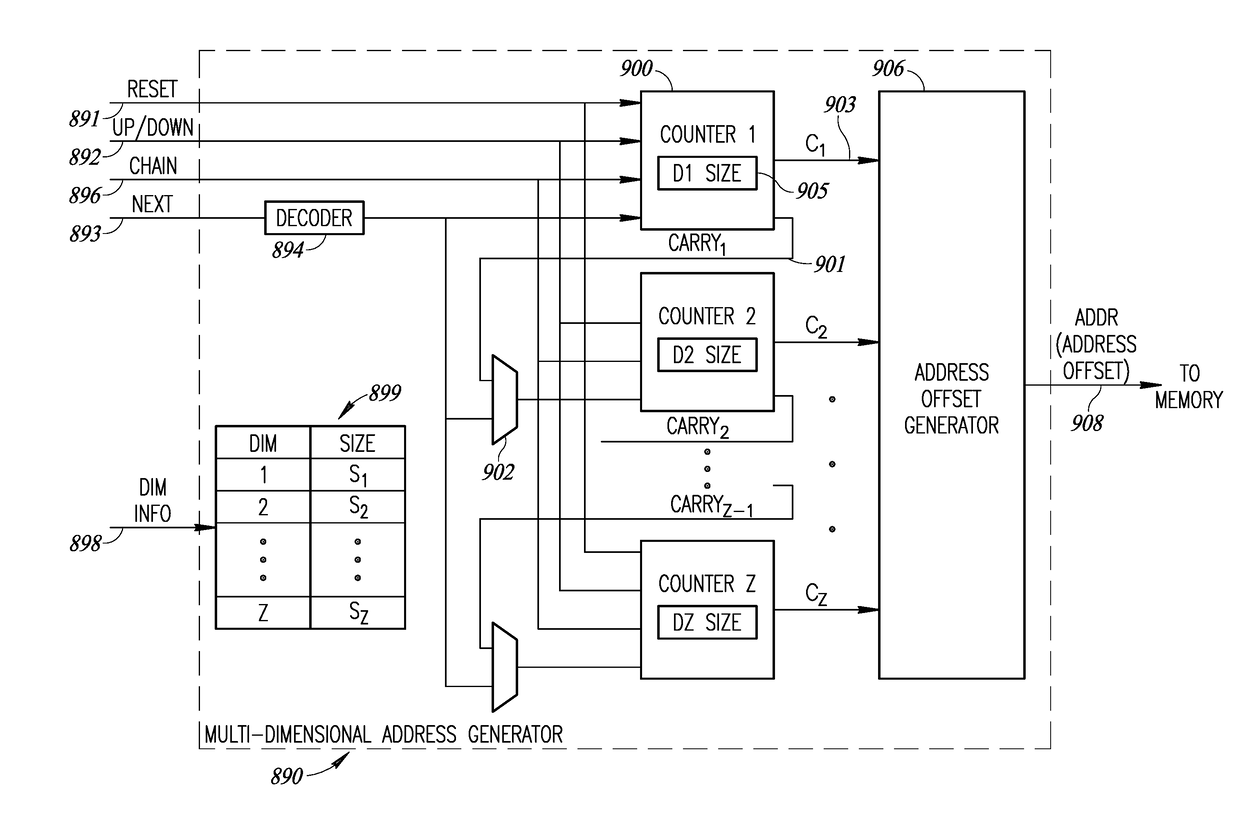
System And Method Of Memory Access Of Multi-Dimensional Data
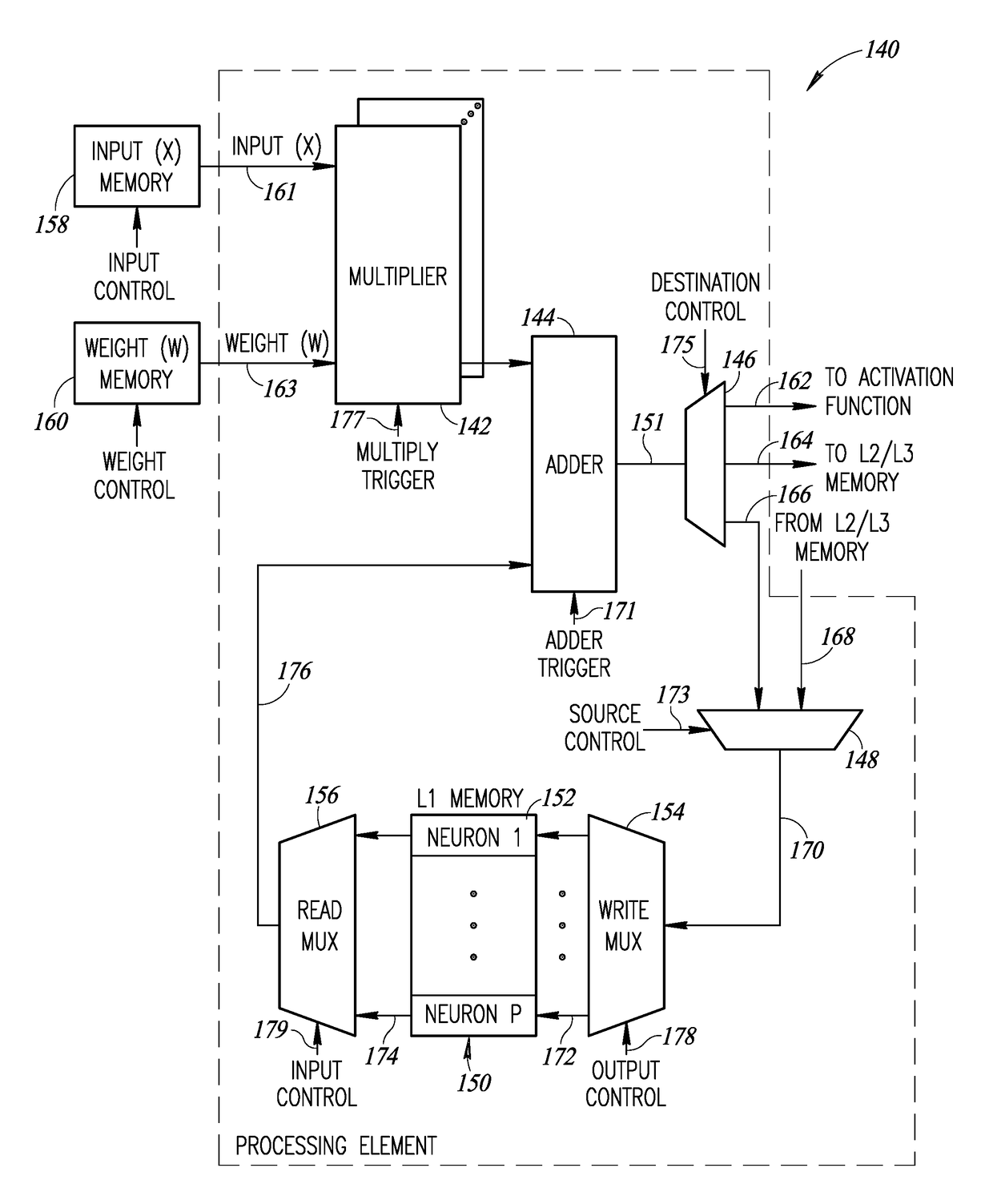
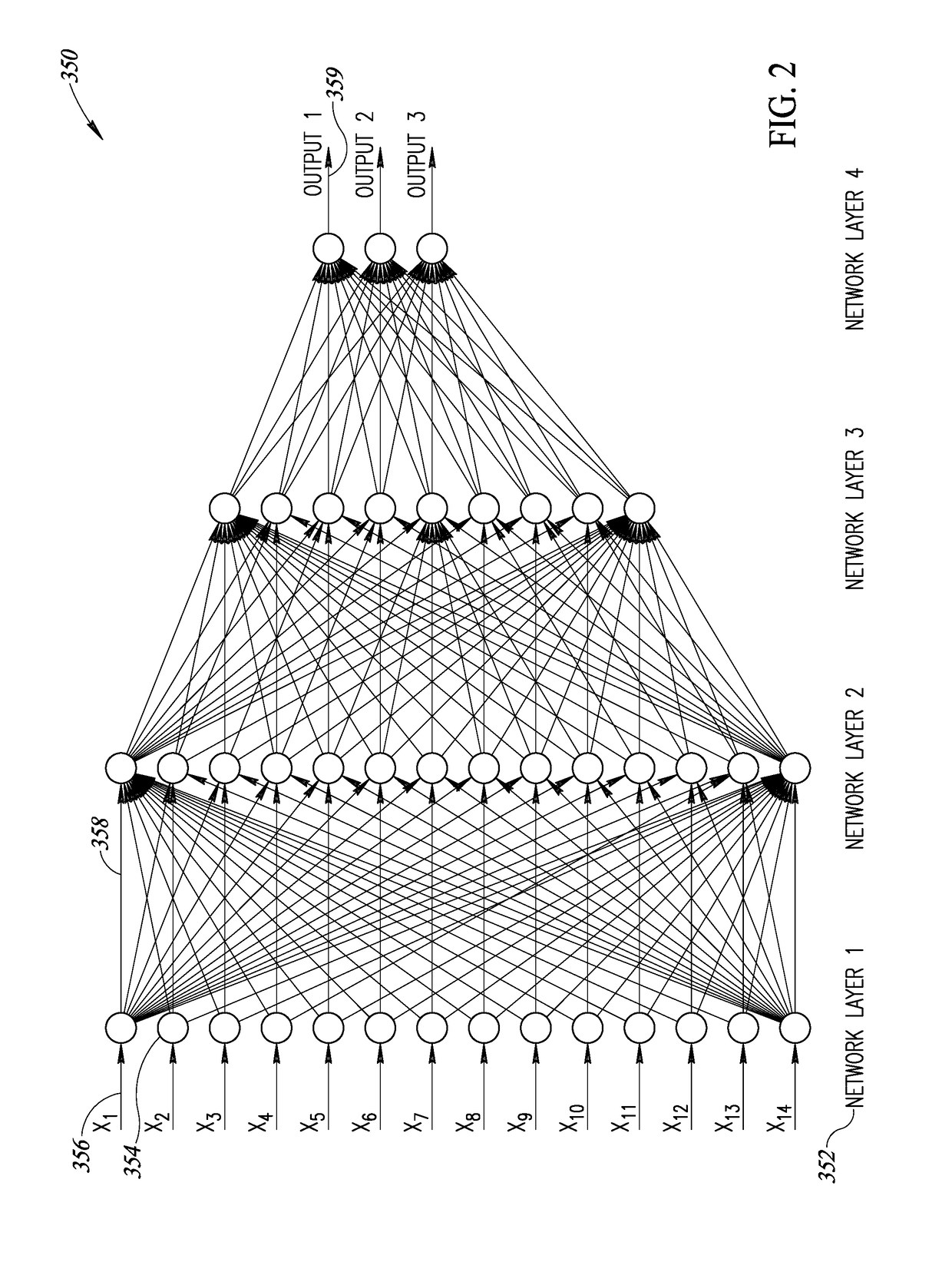
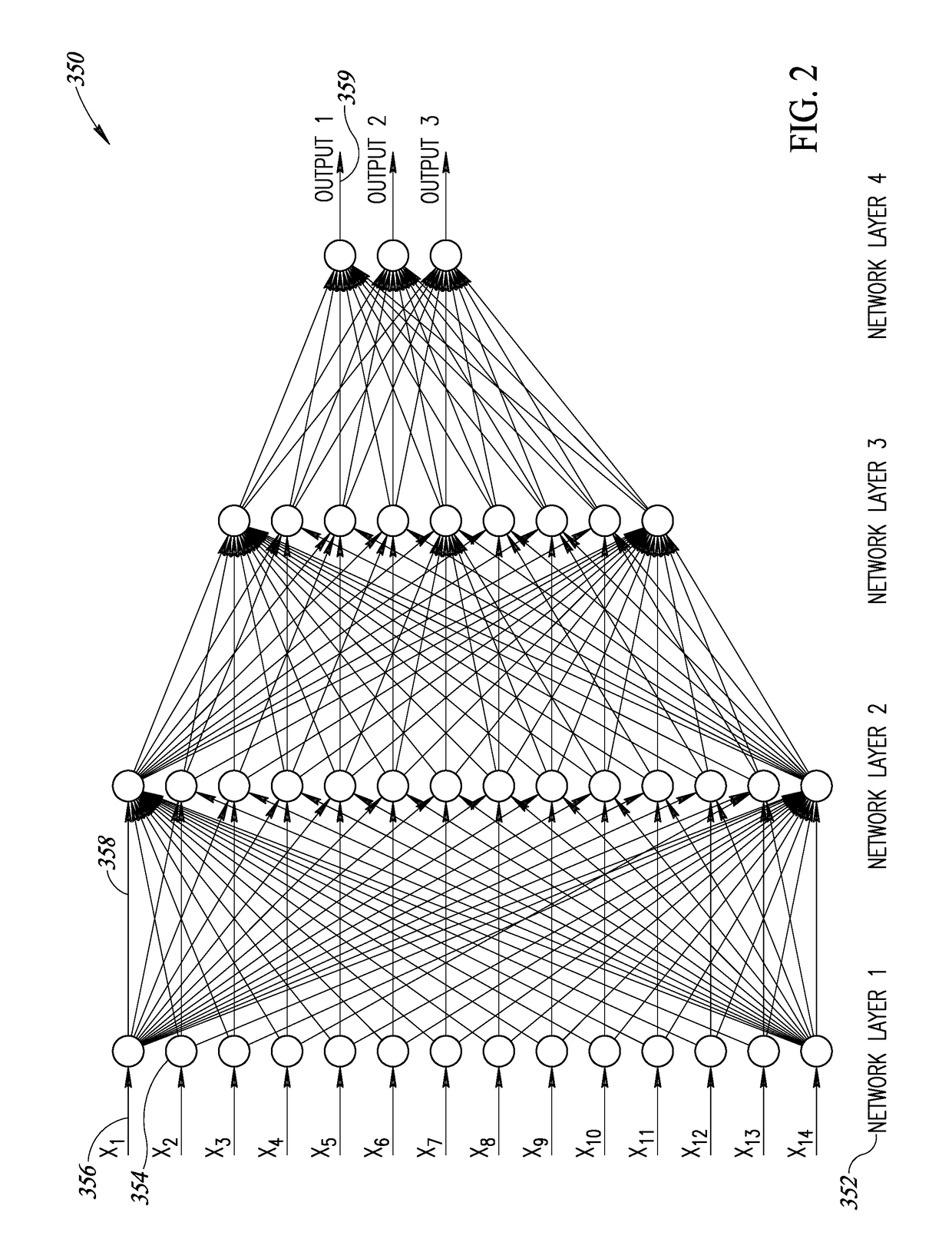
ActiveUS20180285254A1More efficientIncrease unit densityDigital data processing detailsMemory adressing/allocation/relocationLean controlNerve network
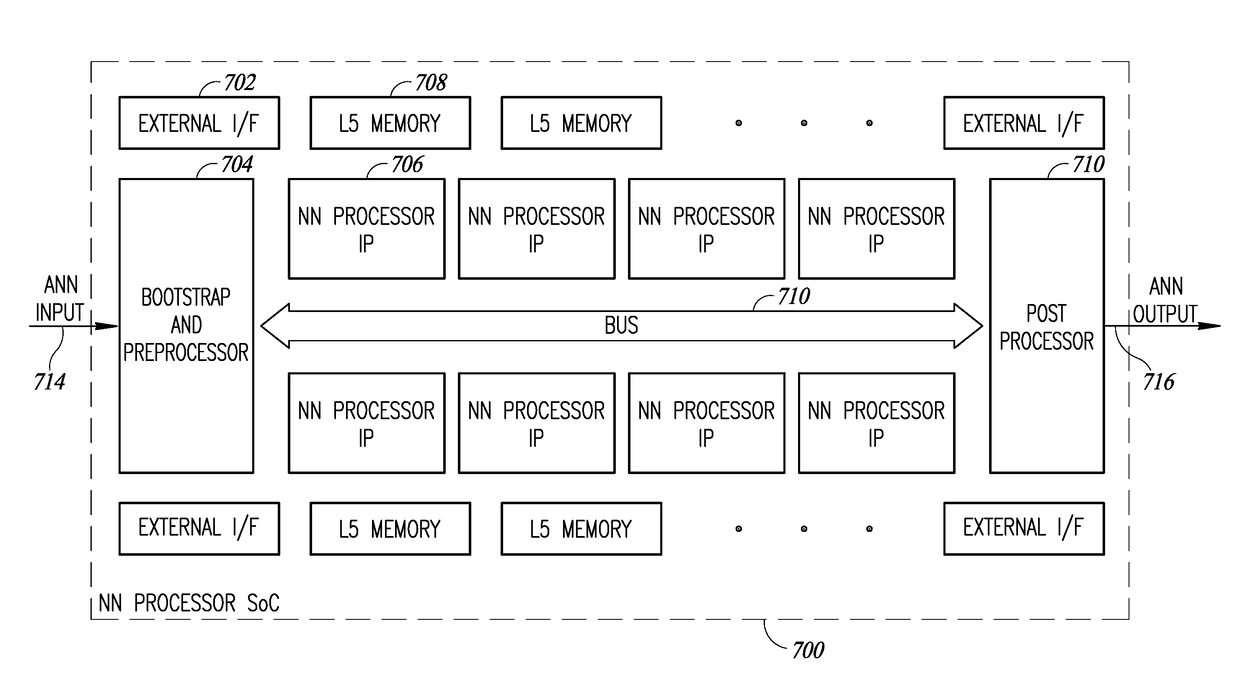
A novel and useful system and method of accessing multi-dimensional data in memory. The invention is applicable to neural network (NN) processing engines adapted to implement artificial neural networks (ANNs). The NN processor is constructed from self-contained computational units organized in a hierarchical architecture. The homogeneity enables simpler management and control of similar computational units, aggregated in multiple levels of hierarchy. Computational units are designed with minimal overhead as possible, where additional features and capabilities are aggregated at higher levels in the hierarchy. On-chip memory provides storage for content inherently required for basic operation at a particular hierarchy and is coupled with the computational resources in an optimal ratio. Lean control provides just enough signaling to manage only the operations required at a particular hierarchical level. Dynamic resource assignment agility is provided which can be adjusted as required depending on resource availability and capacity of the device.
Owner:HAILO TECH LTD
Method and apparatus for fundamental operations on token sequences: computing similarity, extracting term values, and searching efficiently
ActiveUS7421418B2Digital data information retrievalFuzzy logic based systemsAlgorithmPrimitive operation
Owner:NAHAVA
Method, device and sever for writing, modifying and restoring data
ActiveCN101706802AEnsure consistencyReduce the chance of data inconsistenciesSpecial data processing applicationsDistributed File SystemPrimitive operation
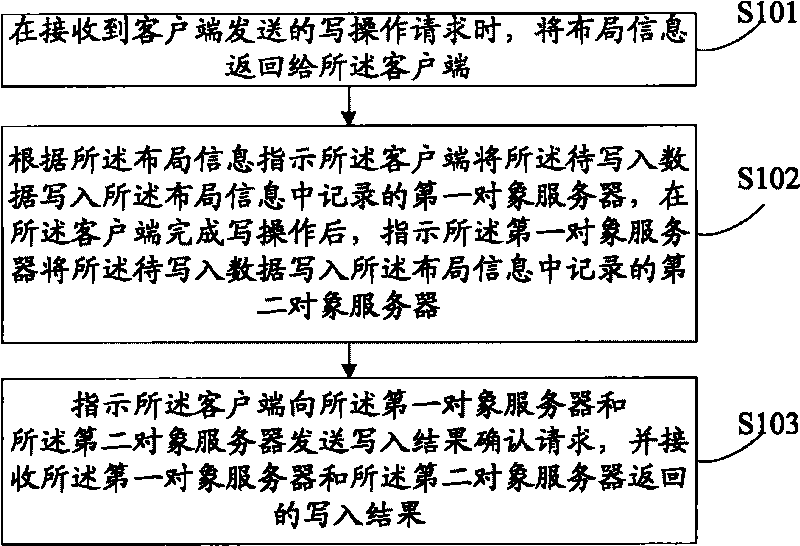
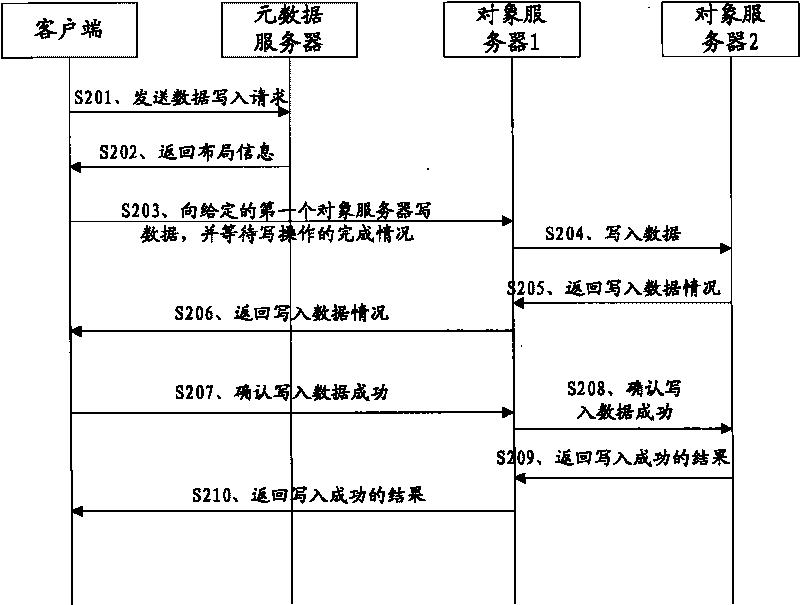
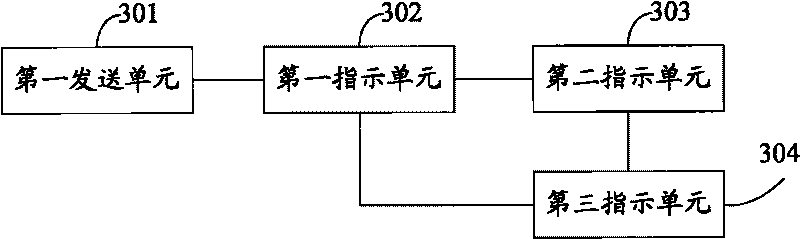
The embodiment of the invention discloses a method, a device and a sever for writing, modifying and restoring data. The scheme provided by the embodiment of the invention starts from three basic operations of writing, modifying and restoring the data on object servers respectively, and ensures the consistency when a plurality of copies of same object data are simultaneously stored on different object servers through a series of methods, thereby greatly reducing the probability of inconsistent data between the copies, fundamentally preventing the appearance of a single copy, and greatly improving the reliability of a distributed file system.
Owner:HUAWEI TECH CO LTD
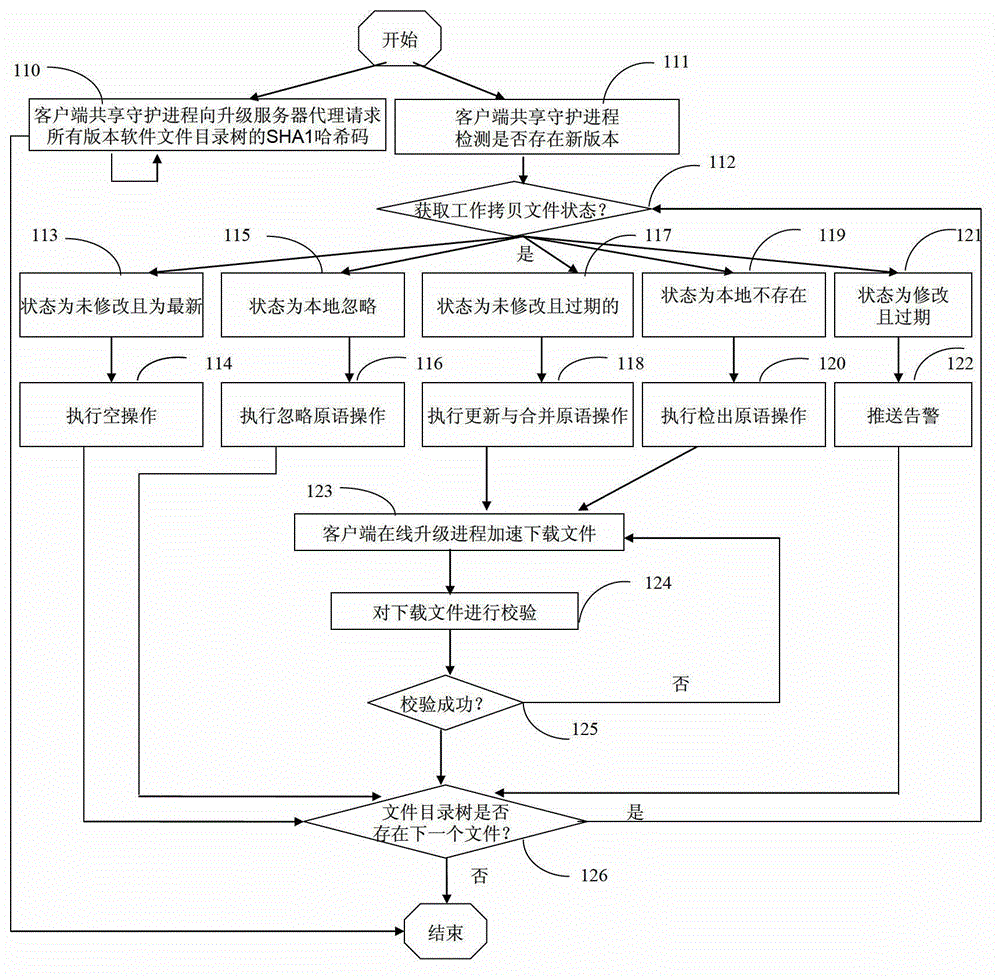
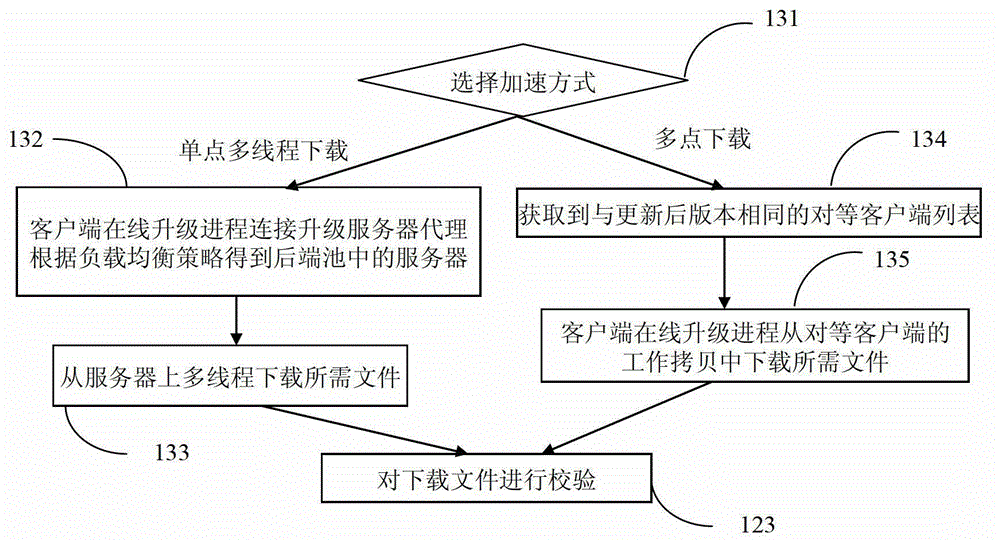
Method and device for software online updating and downloading acceleration
ActiveCN102868731AImplement addressingImplement storageProgram loading/initiatingTransmissionServer agentPrimitive operation
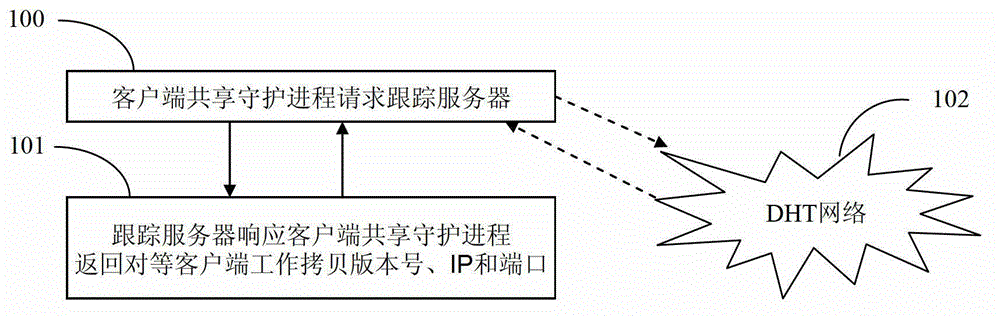
The invention relates to a method and a device for software online updating and downloading acceleration. The device comprises a client end online updating process device, a client end shared guard process device, a tracking server device, a updating server agent device and a plurality of updating server devices, stored contents in each updating server device are completely same to form an updating server pool in an annular queue, and real-time synchronization is realized via implementing a synchronizing primitive operation for version control by a version warehouse on each updating server device. The method is suitable for a situation of a large concurrency of client ends, the occupied updating server source is small, pressure of the updating servers is relieved, and the efficiency and service quality of the software online updating are improved.
Owner:UNIV OF JINAN
Neural Network Processing Element Incorporating Compute And Local Memory Elements
ActiveUS20180285727A1High computational unit densityReduce power consumptionResource allocationDigital data processing detailsLean controlNerve network
A novel and useful neural network (NN) processing core adapted to implement artificial neural networks (ANNs) and incorporating processing circuits having compute and local memory elements. The NN processor is constructed from self-contained computational units organized in a hierarchical architecture. The homogeneity enables simpler management and control of similar computational units, aggregated in multiple levels of hierarchy. Computational units are designed with minimal overhead as possible, where additional features and capabilities are aggregated at higher levels in the hierarchy. On-chip memory provides storage for content inherently required for basic operation at a particular hierarchy and is coupled with the computational resources in an optimal ratio. Lean control provides just enough signaling to manage only the operations required at a particular hierarchical level. Dynamic resource assignment agility is provided which can be adjusted as required depending on resource availability and capacity of the device.
Owner:HAILO TECH LTD
Integrated management system of geographic information data
InactiveCN106610958AEfficient integrationGuaranteed presenceDatabase management systemsGeographical information databasesPrimitive operationGeographic information system
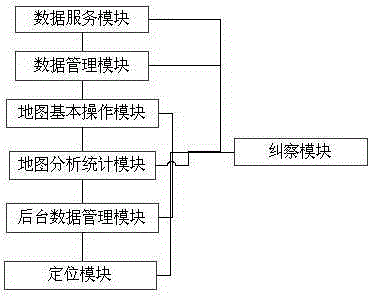
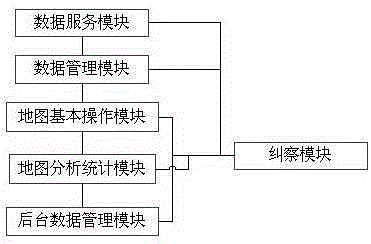
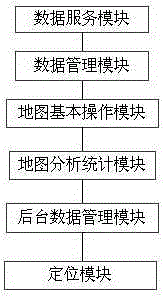
The invention discloses an integrated management system of geographic information data, and belongs to the geographic information technology. The system is characterized in comprising a data service module, a data management module, a basic operation module of a map, a map analysis and statistics module and a background data management module, wherein the data service module integrates, analyzes and transmits data of different service forms into the map; the data management module carries out graph management and fusion on two-dimensional and three-dimensional geographic information data; the basic operation module of the map carries out display control on a layer of each dimension on the basis of spatial data; on the basis of the spatial data, the map analysis and statistics module carries out overlay analysis; and the background data management module updates the spatial data in fixed time to perfect the spatial data. The integrated management system has the advantages that the multi-source data, including the spatial data, business data, attribute data, basic base map data and the like, can be effectively fused, and data processing and application can be effectively combined and applied.
Owner:星际空间(天津)科技发展有限公司
Actor system and method for analytics and processing of big data
InactiveUS20140379775A1Answered efficientlyReduce loadProgram controlTransmissionActor systemsProcedure Agents
The embodiments herein provide a system architecture, application model and methods to write Big Data programs using actor systems and asynchronous messaging middleware akka and scala language. The system comprises an actor network connected to a cloud network and to a distributed virtual machine (DVM) network. The actors are connected respectively to the DVMs based on a predefined protocol. A scheduler is provided to schedule the resources to an actor in the actor network. A stop and start mechanism is provided to change a connection between the actors and the DVMs. The system server sends a message to the actor to disconnect an actor connected to one DVM and to connect the actor to another DVM based on a load of a process agent present in each DVM to balance a load on the actor. The system server adds three fundamental operations over actor systems.
Owner:KORANGY FRED +3
System and method for providing text descriptions to electronic databases
InactiveUS6343292B1Overcomes shortcomingMeet actual needsData processing applicationsSpecial data processing applicationsPrimitive operationDatabase
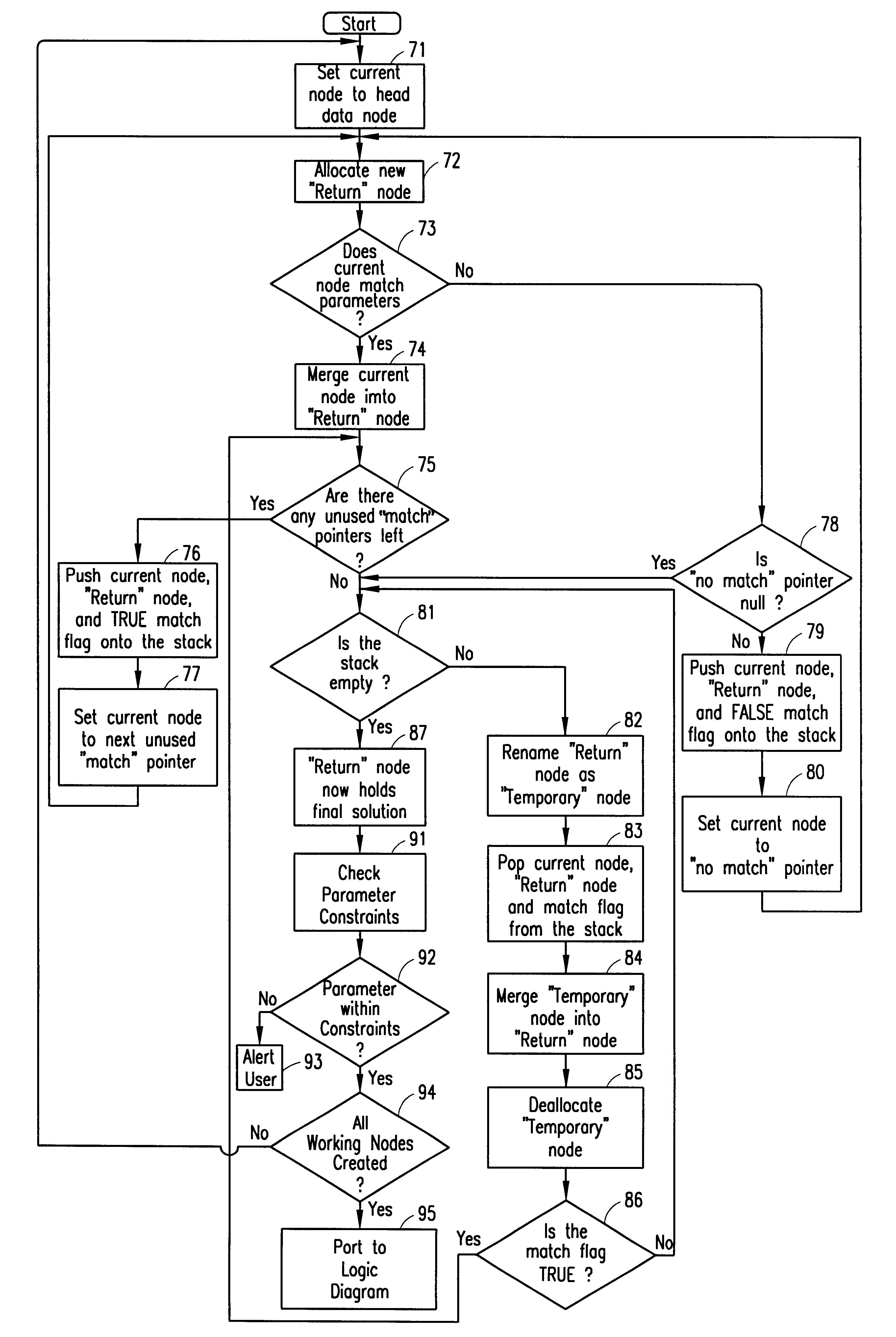
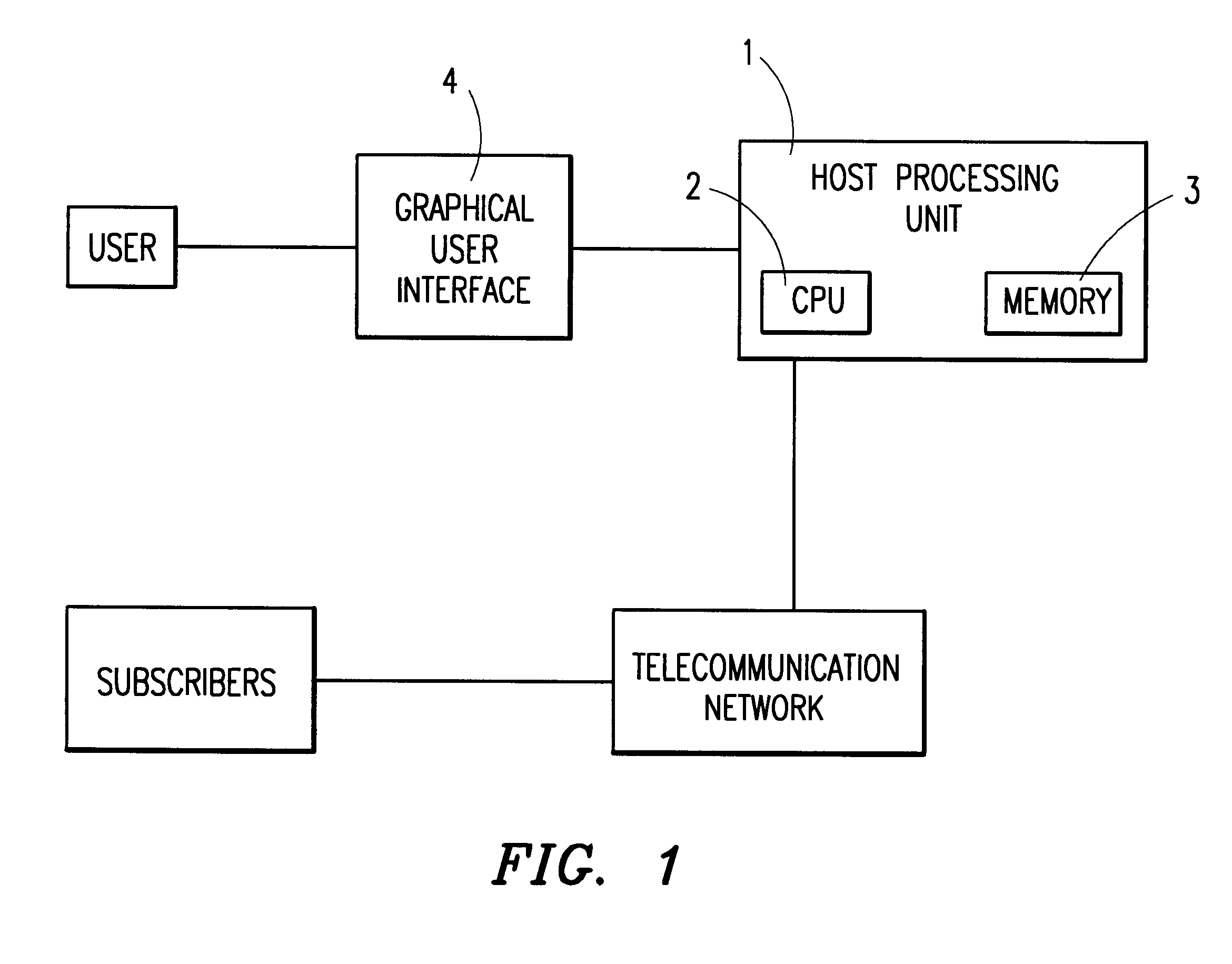
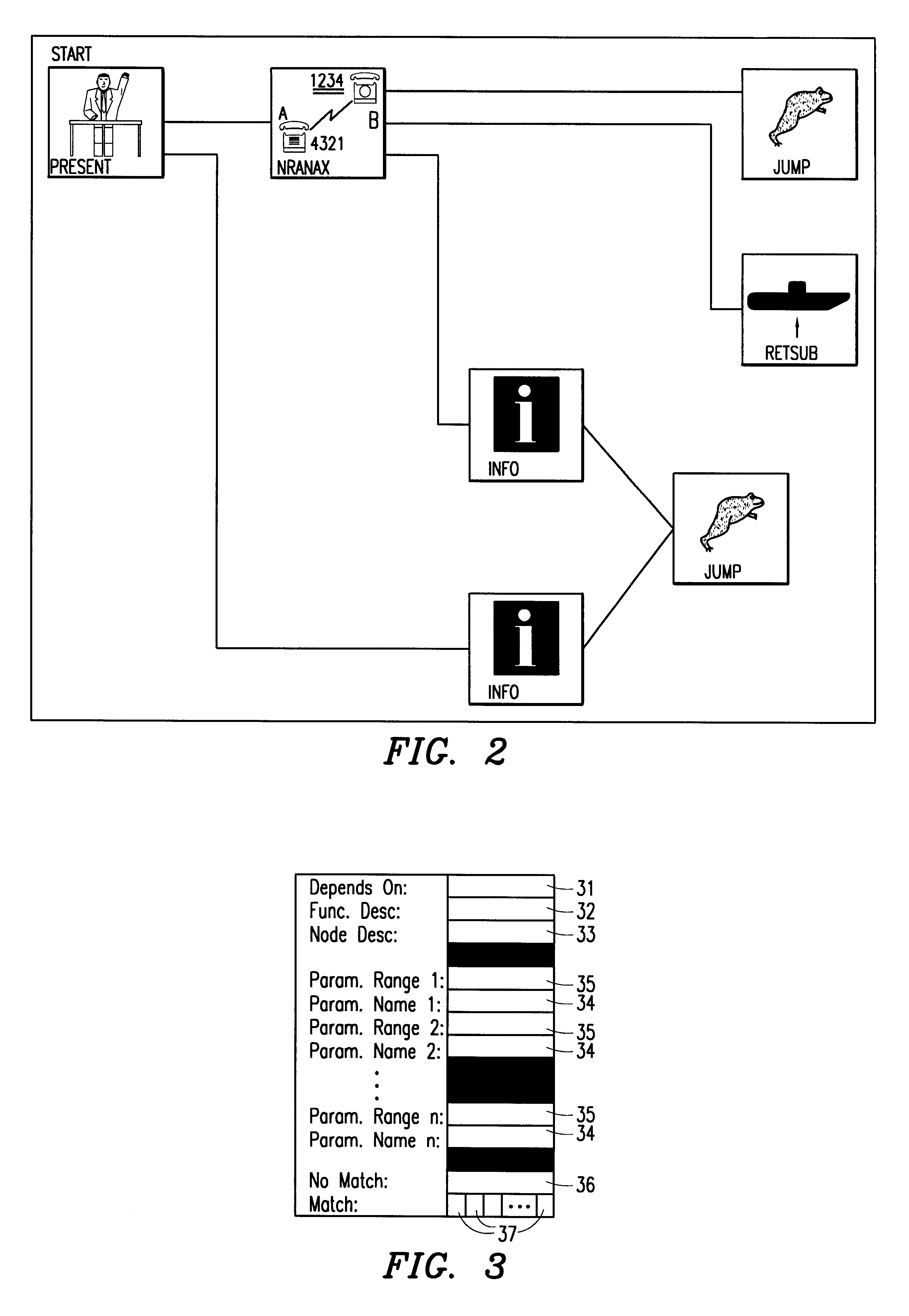
A development tool for creating telecommunication subscriber services or other operations. The tool reads a subscriber service logic diagram containing function primitives which define the service and creates data structures containing text descriptions of primitive operation and parameters pertaining thereto. The tool then examines the data structures and determines the appropriate text descriptions for the function primitives and corresponding parameters, based upon parameter values assigned by a user in creating the subscriber service logic diagram. The tool also validates parameters against available constraints. The text descriptions are then ported into the subscriber service logic diagram, thereby clarifying the operation of the subscriber service defined by the logic diagram.
Owner:ERICSSON INC
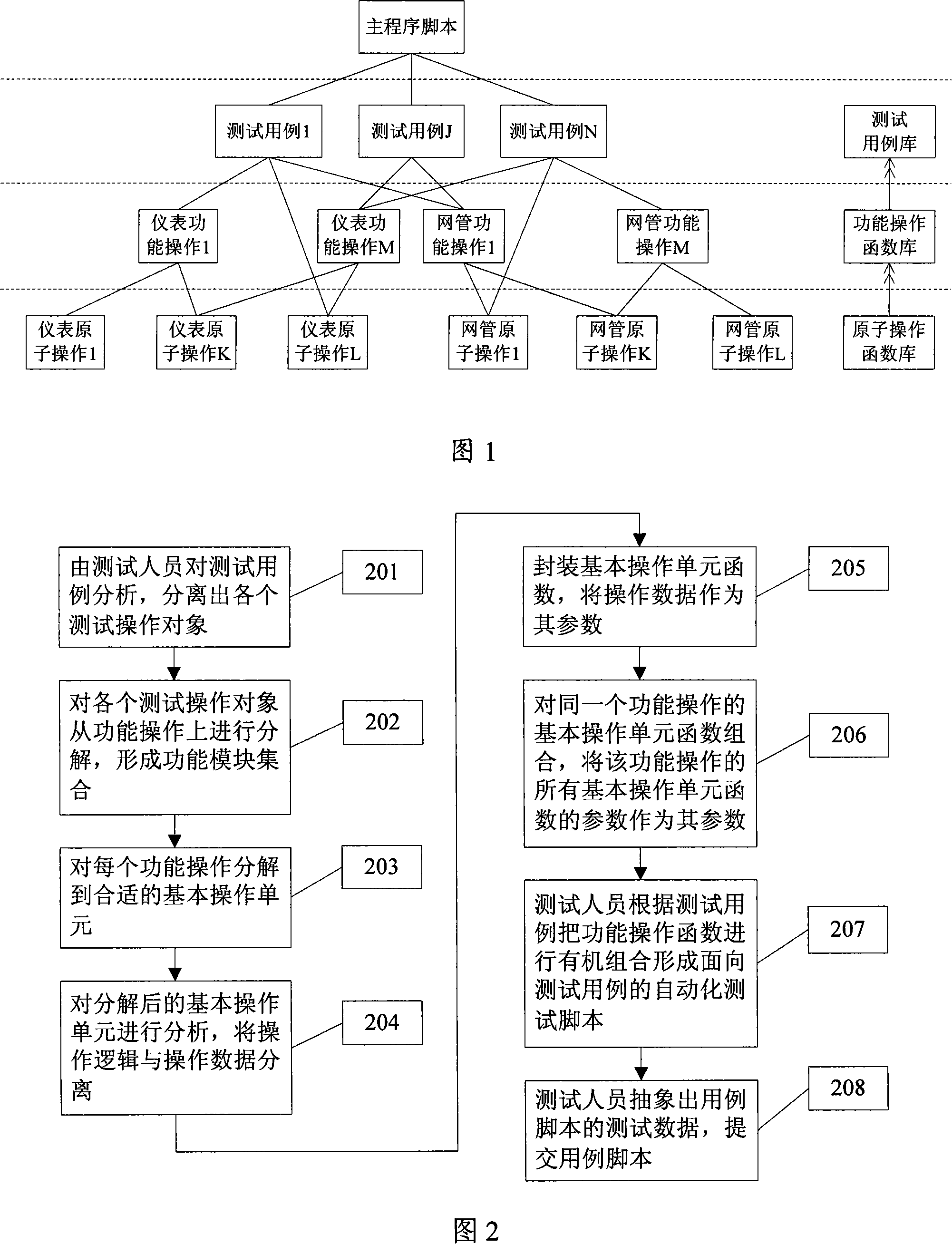
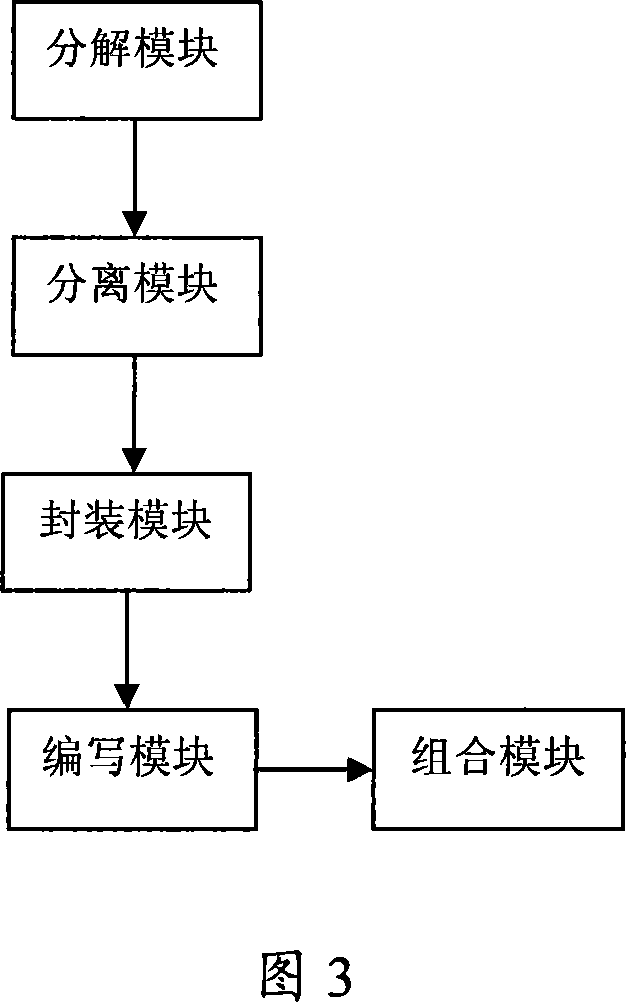
Function operation packaging based automatization test script implementing method and apparatus
InactiveCN101141319AImprove versatilityImprove test efficiencyData switching networksTest scriptPrimitive operation
The utility model discloses an automatic test script method and device based on the functional package. The method comprises the steps as follows: the test target collected from the test cases is decomposed according to the functions and each function can be decomposed into a basic operational unit; separate the operational logic from the operational data in the basic operational unit; package the basic operational unit function based on the operational data and establish the basic operational unit function bank; constitute the basic operational unit function with the same function and set the parameters of all the basic operational unit functions as the parameters of the function, so as to establish the functional bank; according to the test cases, constitute the functions into the automatic test scripts for the test cases; also, abstract the test data of the case scripts, so as to establish the automatic test scripts database. The utility model can enhance the compatibility of the case scripts and reduce the workload of script maintenance as well as the script writing difficulty.
Owner:ZTE CORP
Electronic mail system with authentication methodology for supporting relaying in a message transfer agent
InactiveUS6865671B1Multiple digital computer combinationsSecret communicationPrimitive operationInternet privacy
An electronic mail (“e-mail”) system is described that provides a methodology that allows the system to determine when it is appropriate to relay e-mail messages, particularly from “roaming” users. In basic operation, the methodology of the present invention first checks whether the client has been authenticated. If not, the decision of whether relaying is allowed may be subject to other rules in the system, such as whether the user currently resides behind the company's firewall. Of interest herein is a case where the client has been authenticated. In that case, the system can allow relaying for everyone who has a certificate (“cert”) signed by certain certificate authorities (“CAs”). Additionally, the system can require specific cert subjects.
Owner:PROOFPOINT INC
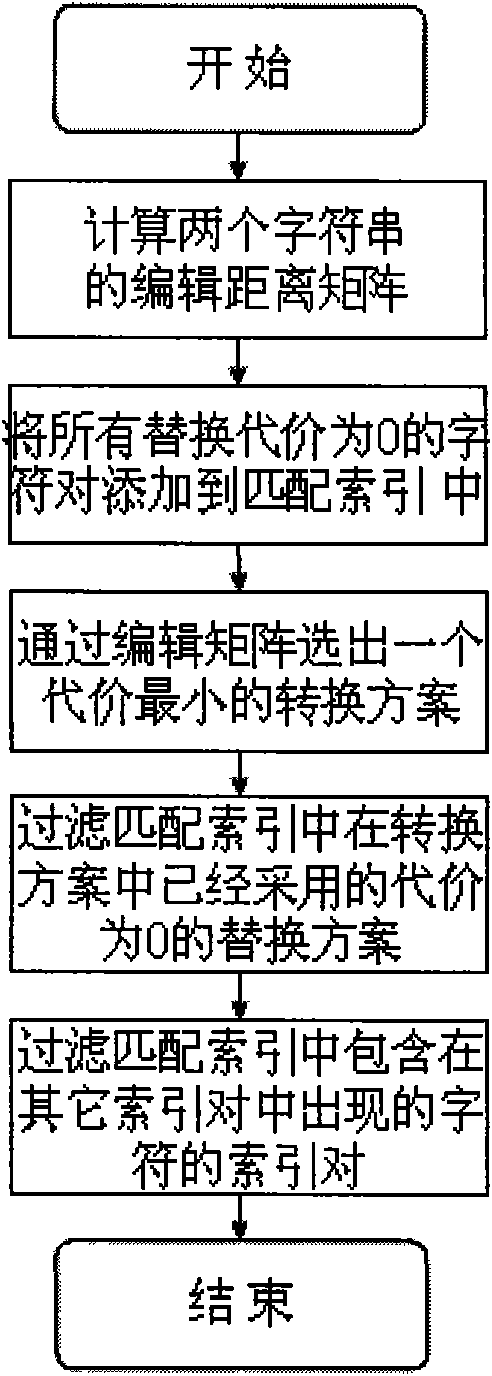
Method for analyzing similarity of character string under Web environment
InactiveCN101561813AImprove applicabilityImprove matching accuracySpecial data processing applicationsPattern recognitionDistance matrix
The invention discloses a method for analyzing the similarity of character strings under a Web environment, comprising the following steps of: firstly, defining basic operation cost; pretreating the character strings to identify first characters thereof and remove the characters without real meaning; building distance matrix to realize the optimization of an edit distance by building a match index; then judging an abbreviated word, firstly judging whether the two character strings has an abbreviation relationship, if the abbreviation relationship is ensured, the distance is optimized; wherein, the abbreviation relationship is determined by two factors: (1) judging whether the two character strings has the similarity; and (2) judging whether the first characters of the two character strings have been matched; and after that optimizing the distance of the abbreviated word, wherein, the optimization is realized by reducing the cost for decreasing continuously inserted characters and continuously cancelled characters. The method for analyzing the similarity of the character strings can well treat the situations such as omission, abbreviation and character disorder which are usually in Web, has higher application, and under a Wed unknown environment has higher matching precision.
Owner:NORTHEASTERN UNIV
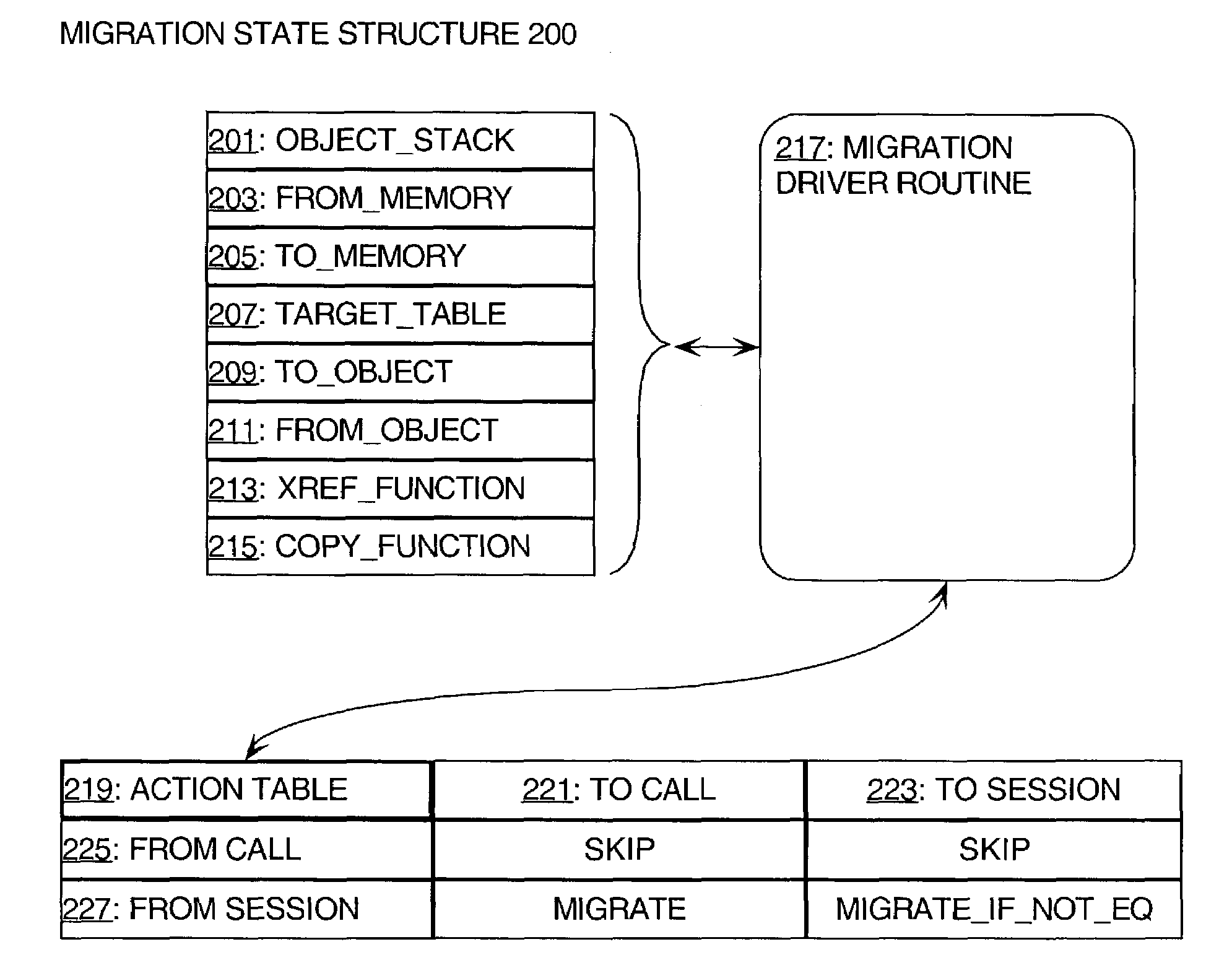
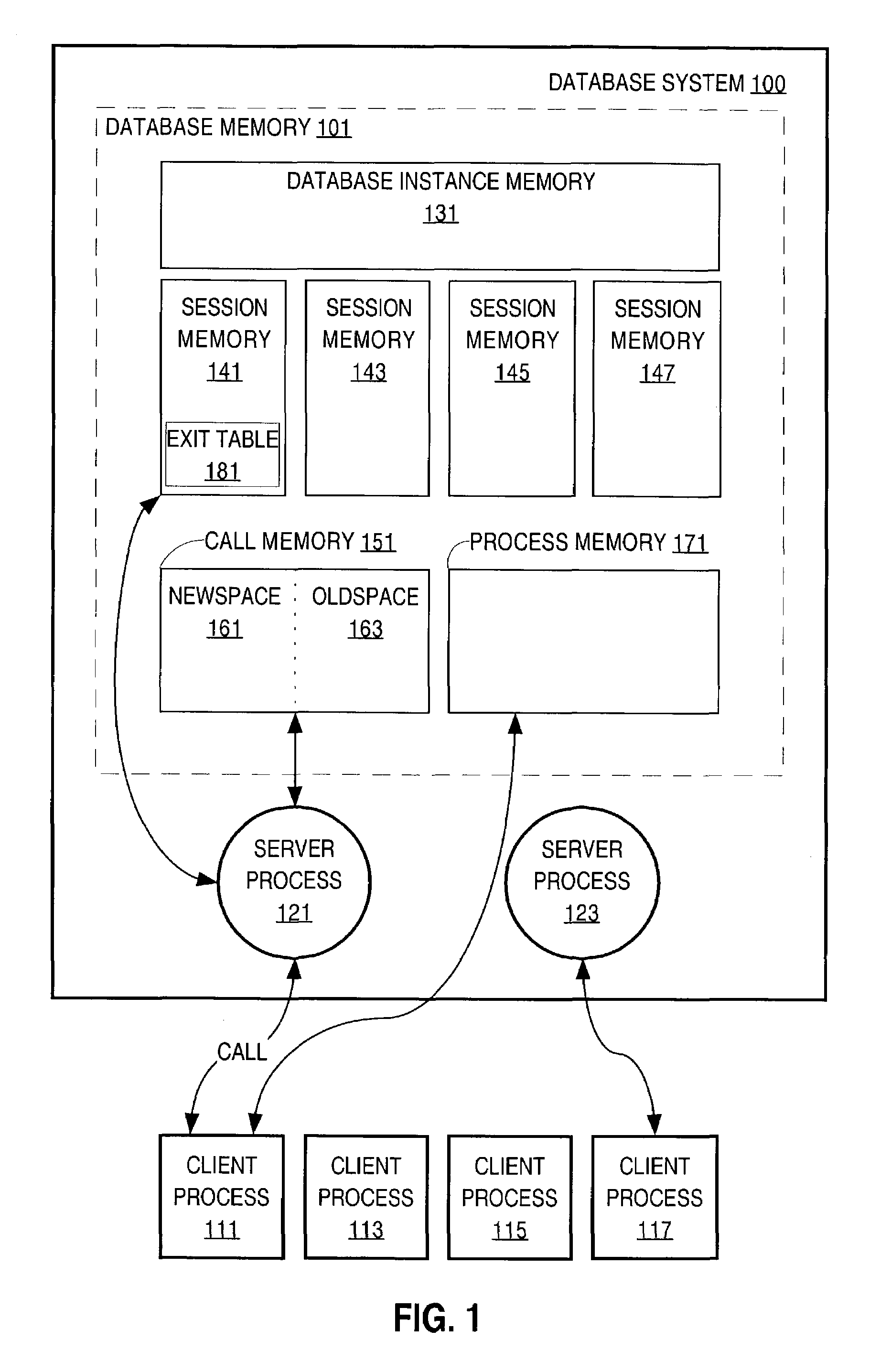
Method for performing data migration
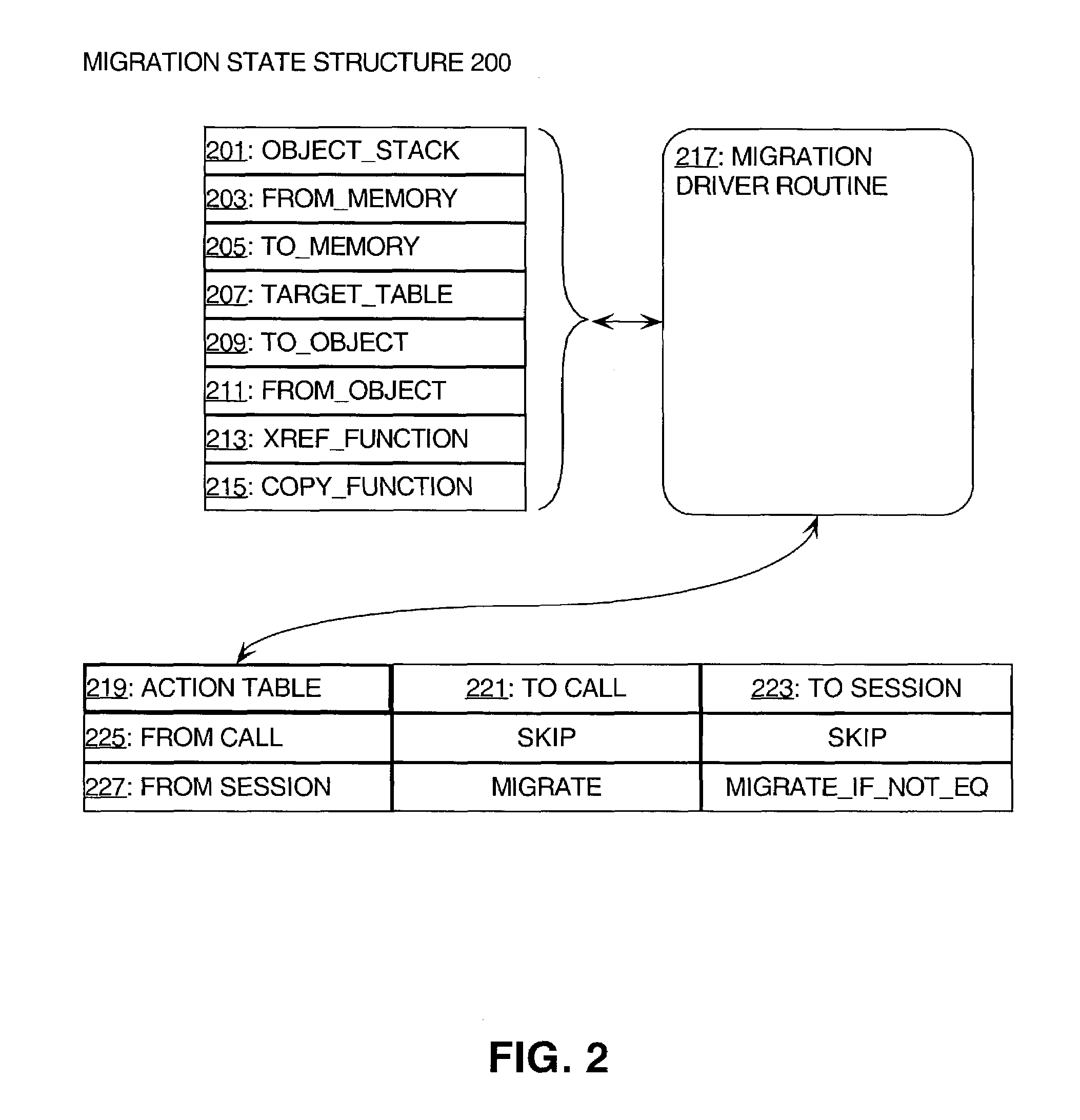
ActiveUS7072919B2Data processing applicationsDigital data processing detailsObject copyingExternal reference
A method and software for performing data migration is described in which a common data migration driver routine is provided to handle various and disparate kinds of migration operations in a conceptually unified manner. Differences between the migration operations are handled by variations in how the state of the data migration driver routine is initialized, including pointers to low-level routines. Furthermore, a table of actions can be used to direct the basic operation of object copying, external reference created, and object interning.
Owner:ORACLE INT CORP
Selective operating system patching/updating
ActiveUS20140325498A1Save storage spaceIncrease flexibilityProgram loading/initiatingMemory systemsOperational systemSoftware update
An application typically runs on top of an operating system. Some computing device have the ability to reboot and load a different operating system whenever an application or set of applications is run. If an old application requires an old operating system version, it is possible to load that OS instead. Every application can have its own version of the operating system. Only new applications or a small set of applications need to use the new OS—all the old applications may run their own older version of the OS. Patches or software updates can be applied only for particular applications. Other applications that need the same base OS but don't need the patch can skip using the patch. It is possible to determine what version the application is and selectively apply the patch based on the version of the application.
Owner:NINTENDO CO LTD
General data processing method based on multiple parallel
InactiveCN101833438ANo need for static dataSpeed upConcurrent instruction executionPrimitive operationDynamic management
The invention discloses a general data processing method based on multiple parallel, comprising the steps of: (1) dividing an application program for data processing into a plurality of execution behaviors; (2) dividing all of the execution behaviors into a plurality of tasks according to the basic operation types of data by the execution behavior; (3) dividing the data to be processed by the application program into static data and dynamic data; and (4) operating computational tasks on a GPU (Graphic Processing Unit), and operating logical judgment tasks on a CPU (Central Processing Unit) until the execution of the application program is finished. The data processing method performs specialized optimization for complex algorithm with dynamically-characterized performance behavior and irregular data structures, and can carry out dynamic management on the data according to a memory locality principle and an SIMD (Single Instruction Multiple Data) operation mechanism during data processing so as to effectively utilize the computing resources and the memory resources of hardware furthest during the data processing by the application program.
Owner:ZHEJIANG UNIV
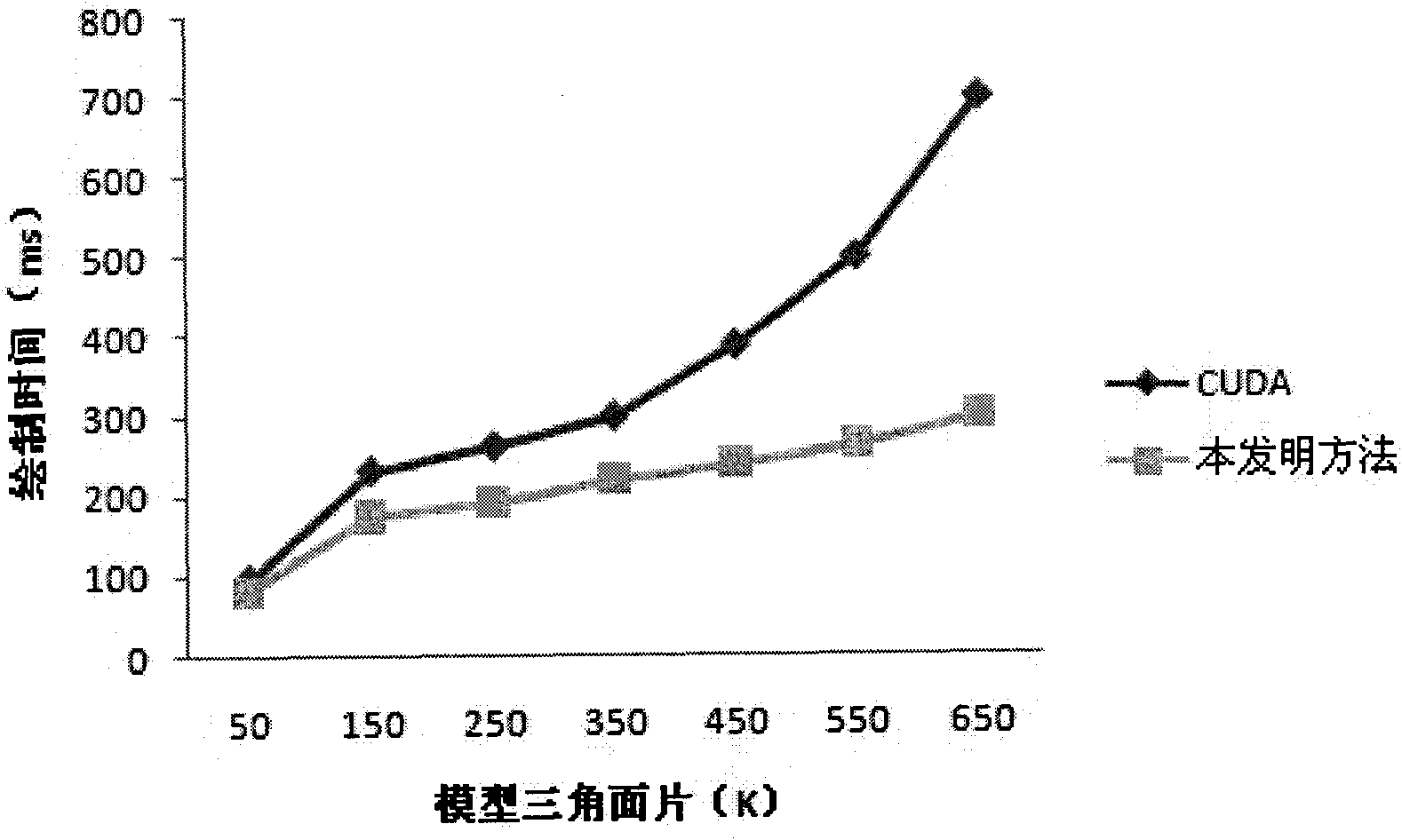
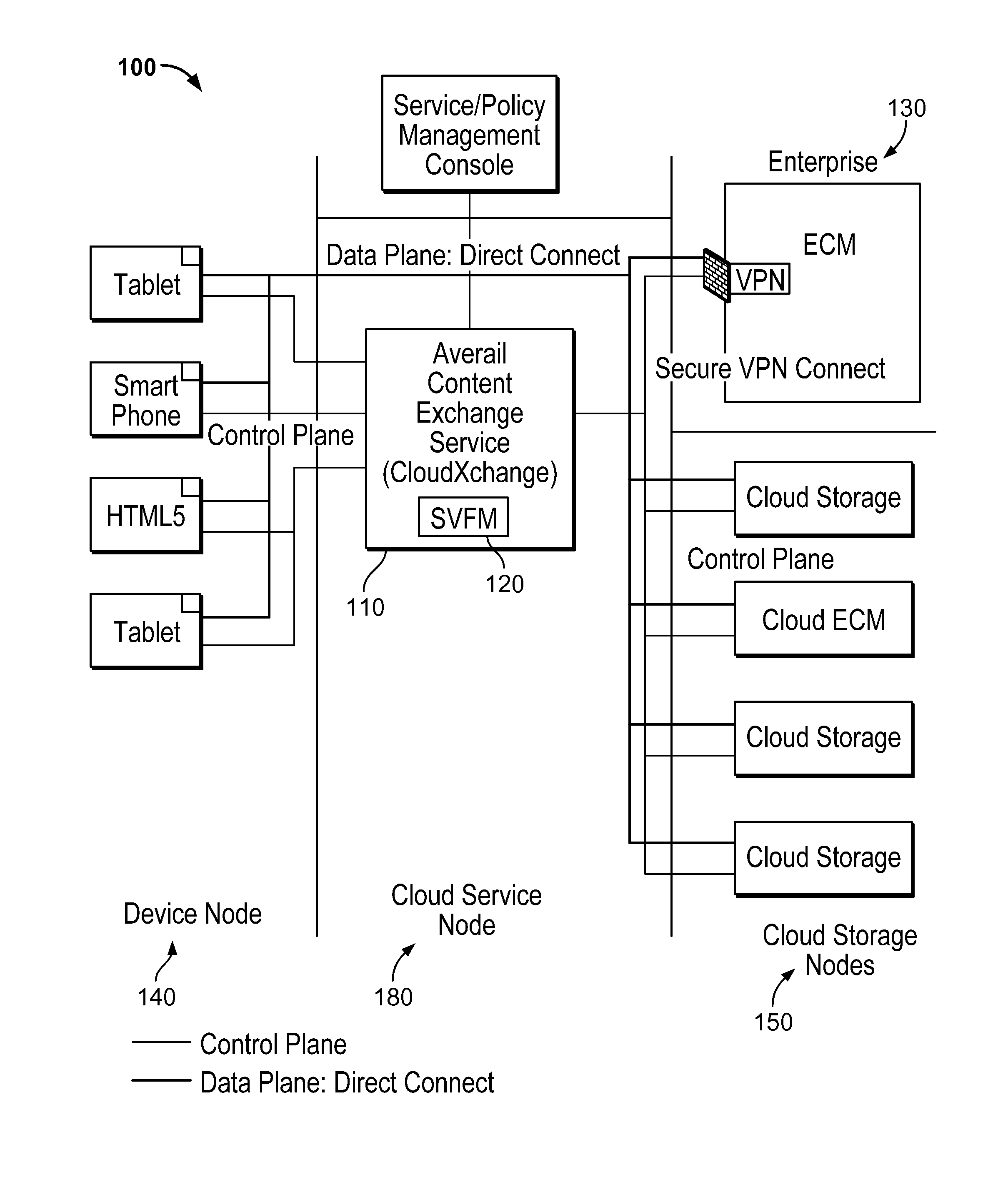
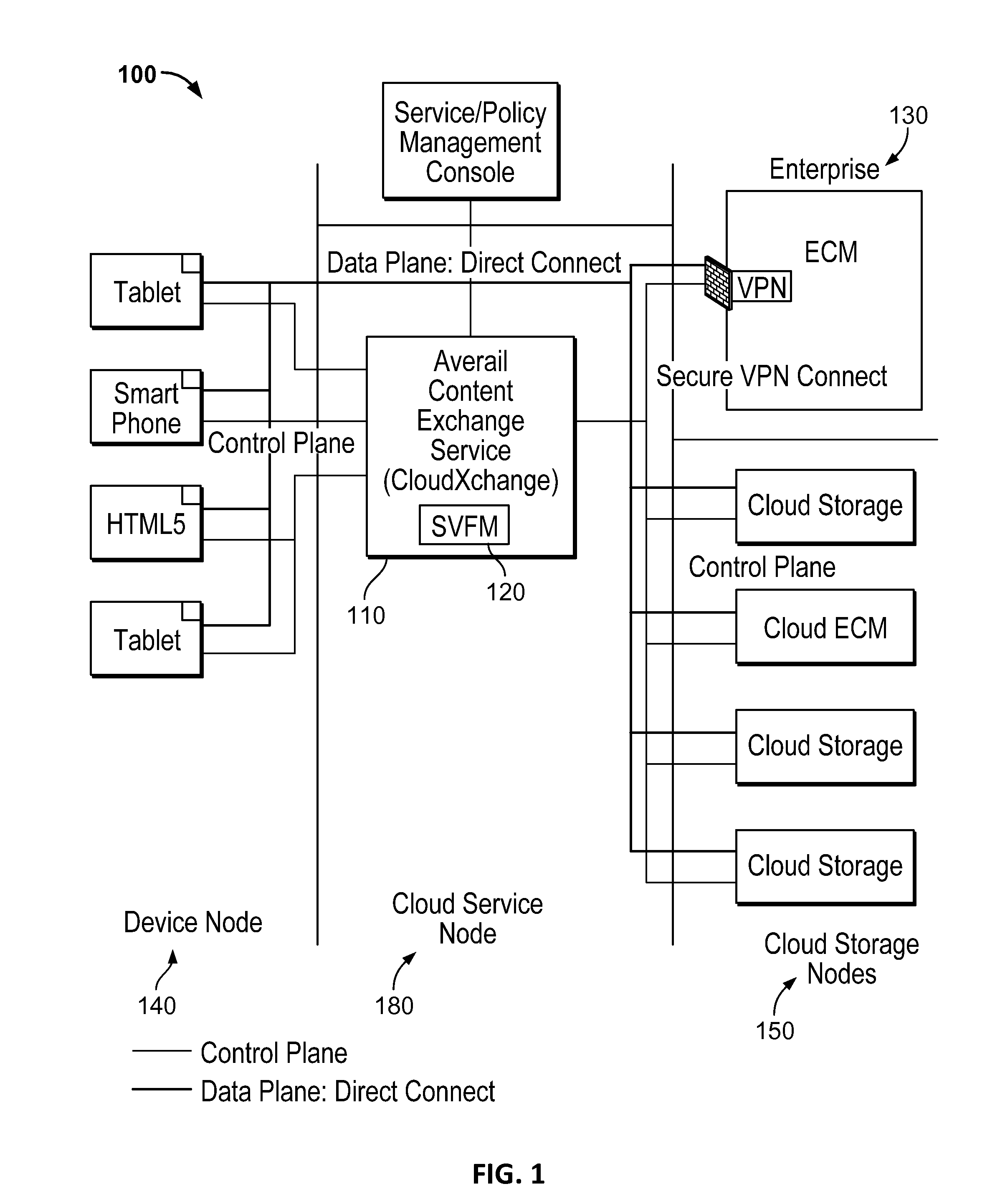
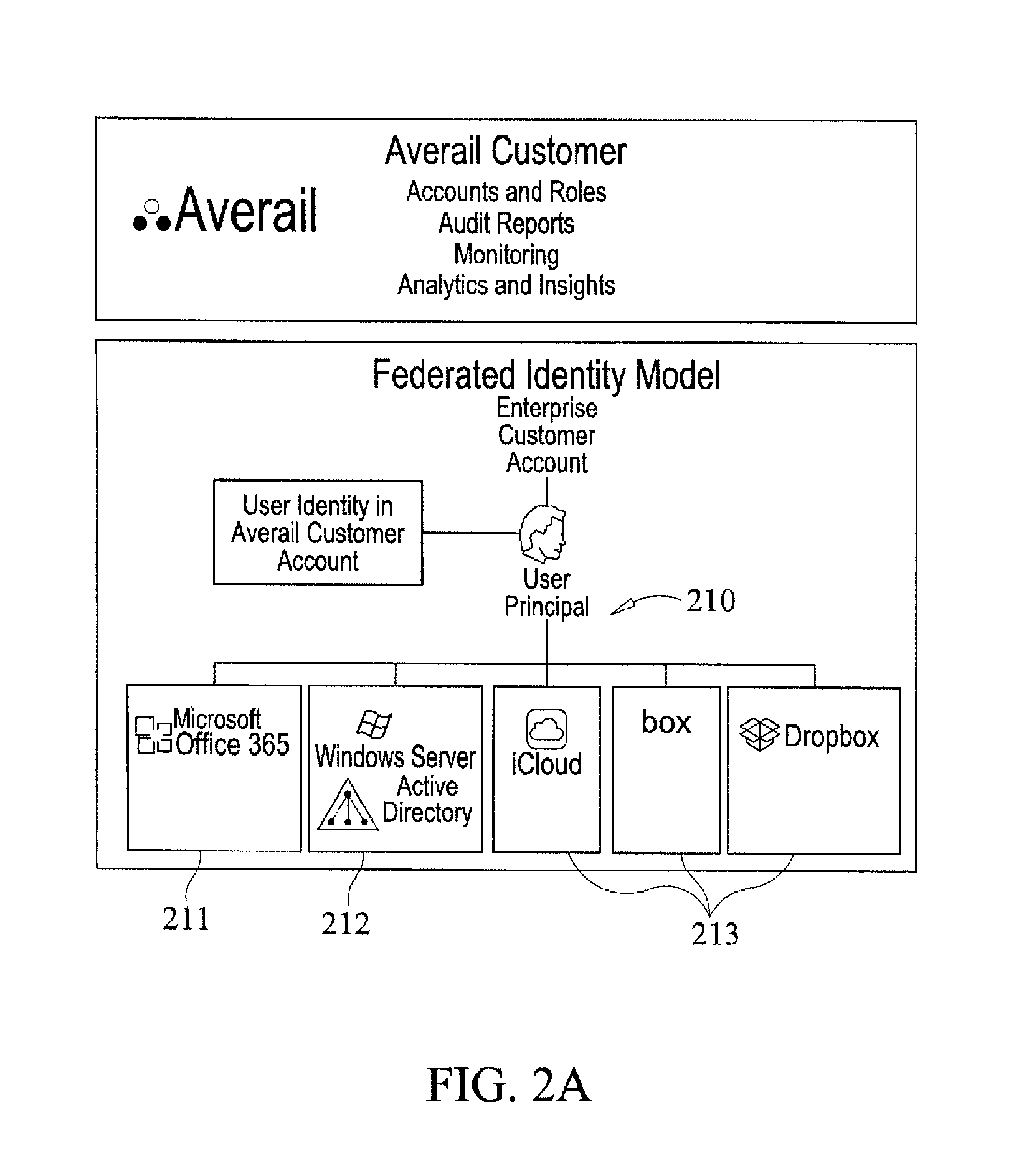
Secure virtual file management system
ActiveUS9465953B2Key distribution for secure communicationDigital data information retrievalVirtual file systemPrimitive operation
Virtual file management is disclosed. Managed content from multiple separate storage domains is organized into a virtual file system that maintains with respect to each of at least a subset of said separate storage domains information of storage domain specific file system primitives to perform primitive operations with respect to content stored in that storage domain. Policies are determined that apply to the managed content. Each policy indicates primitive operations permitted to be performed with respect to the managed content. Information comprising the virtual file system and the policies is provided to a client application on a mobile device. The client application is configured to provide access to the managed content in the virtual file system in a manner at least in part indicated in the policies, including by allowing the permitted primitive operations to be performed using said storage domain specific file system primitives.
Owner:IVANTI INC
Neural Network Processor Incorporating Inter-Device Connectivity
ActiveUS20180285726A1More efficientIncrease unit densityResource allocationDigital data processing detailsNerve networkMultiple single-level
A novel and useful neural network (NN) processing core incorporating inter-device connectivity and adapted to implement artificial neural networks (ANNs). A chip-to-chip interface spreads a given ANN model across multiple devices in a seamless manner. The NN processor is constructed from self-contained computational units organized in a hierarchical architecture. The homogeneity enables simpler management and control of similar computational units, aggregated in multiple levels of hierarchy. Computational units are designed with minimal overhead as possible, where additional features and capabilities are aggregated at higher levels in the hierarchy. On-chip memory provides storage for content inherently required for basic operation at a particular hierarchy and is coupled with the computational resources in an optimal ratio. Lean control provides just enough signaling to manage only the operations required at a particular hierarchical level. Dynamic resource assignment agility is provided which can be adjusted as required depending on resource availability and capacity of the device.
Owner:HAILO TECH LTD
Configurable And Programmable Sliding Window Based Memory Access In A Neural Network Processor
ActiveUS20180285725A1More efficientIncrease unit densityResource allocationDigital data processing detailsDynamic resourcePrimitive operation
A novel and useful neural network (NN) processing core adapted to implement artificial neural networks (ANNs) and incorporating configurable and programmable sliding window based memory access. The memory mapping and allocation scheme trades off random and full access in favor of high parallelism and static mapping to a subset of the overall address space. The NN processor is constructed from self-contained computational units organized in a hierarchical architecture. The homogeneity enables simpler management and control of similar computational units, aggregated in multiple levels of hierarchy. Computational units are designed with minimal overhead as possible, where additional features and capabilities are aggregated at higher levels in the hierarchy. On-chip memory provides storage for content inherently required for basic operation at a particular hierarchy and is coupled with the computational resources in an optimal ratio. Lean control provides just enough signaling to manage only the operations required at a particular hierarchical level. Dynamic resource assignment agility is provided which can be adjusted as required depending on resource availability and capacity of the device.
Owner:HAILO TECH LTD
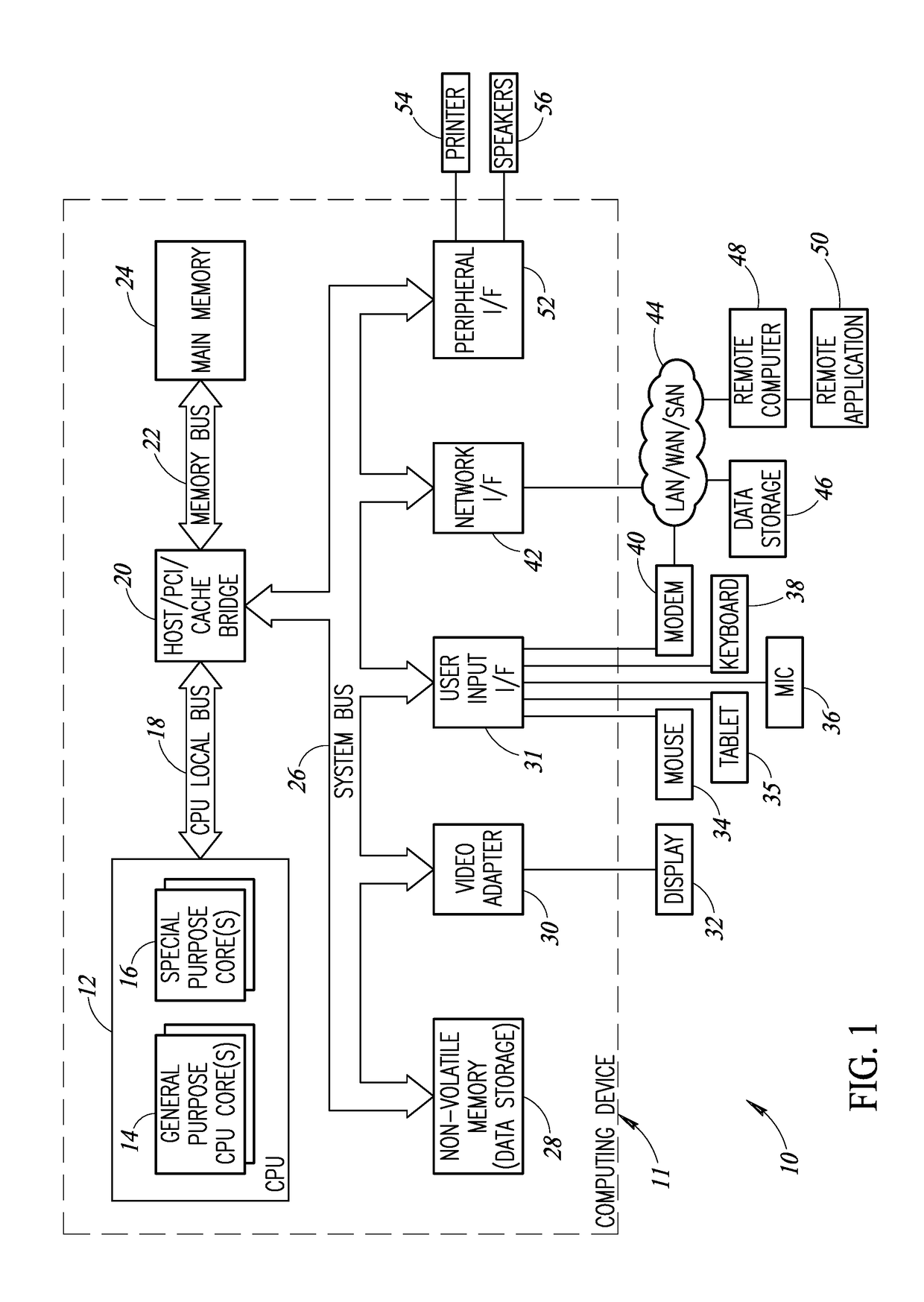
System and method for expediting and automating mainframe computer setup
ActiveUS7194737B2Digital computer detailsProgram loading/initiatingOperational systemPrimitive operation
The present invention preferably automates mainframe computer operating system upgrades by automatically installing a base operating system on the mainframe system, performing information-gathering of an existing mainframe computer system, using the information to recreate the environment settings of the existing system, and providing a series of directives typically required of a skilled mainframe computer systems programmer for an IPL. By preparing a mainframe computer system to automatically perform an IPL, and, thereafter, automating a series of configuration process to install optional products, the present invention decreases the amount of time and operator skill-level requirements for prior art mainframe computer operating system upgrades.
Owner:FRAMETECH LLC
Large-scale graph data processing method based on k<2>-tree and multi-valued decision diagram
InactiveCN106294739ACompact structureCompact storageSpecial data processing applicationsPrimitive operationAlgorithm
The invention discloses a large-scale graph data processing method based on a k<2>-tree and a Multi-valued Decision Diagram (MDD). The method comprises the following steps: 1, performing n-bit encoding on a peak of a graph according to the rule of the k<2>-tree, FORMULA, k being greater than or equal to 2; 2, encoding an edge according to a peak code; 3, constructing an MDD structure according to an edge code to obtain a k<2>-MDD structure which corresponds to an oriented graph and contains n variables, wherein the k<2>-MDD structure has the nature of the MDD and is applicable to the simplification rule of the MDD; 4, performing the following basic operation of the graph on the obtained k<2>-MDD structure through logic operation of a symbol decision diagram: edge inquiry, outside adjacent inquiry and calculation of an out degree of the peak, inside adjacent inquiry and calculation of an in degree of the peak, as well as adding and deletion of an edge, and the like. According to the method, the MDD is used for storing graph data, so that isomorphic sub trees in the k<2>-tree are combined, the number of nodes is reduced, and the structure is more compact; the basic operation of the graph is converted into the logic operation, so that the operation is simpler.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Electric power enterprise service bus realization method and device
ActiveCN102629939AAvoid paralysisImprove efficiencyData processing applicationsBus networksGuidelinePrimitive operation
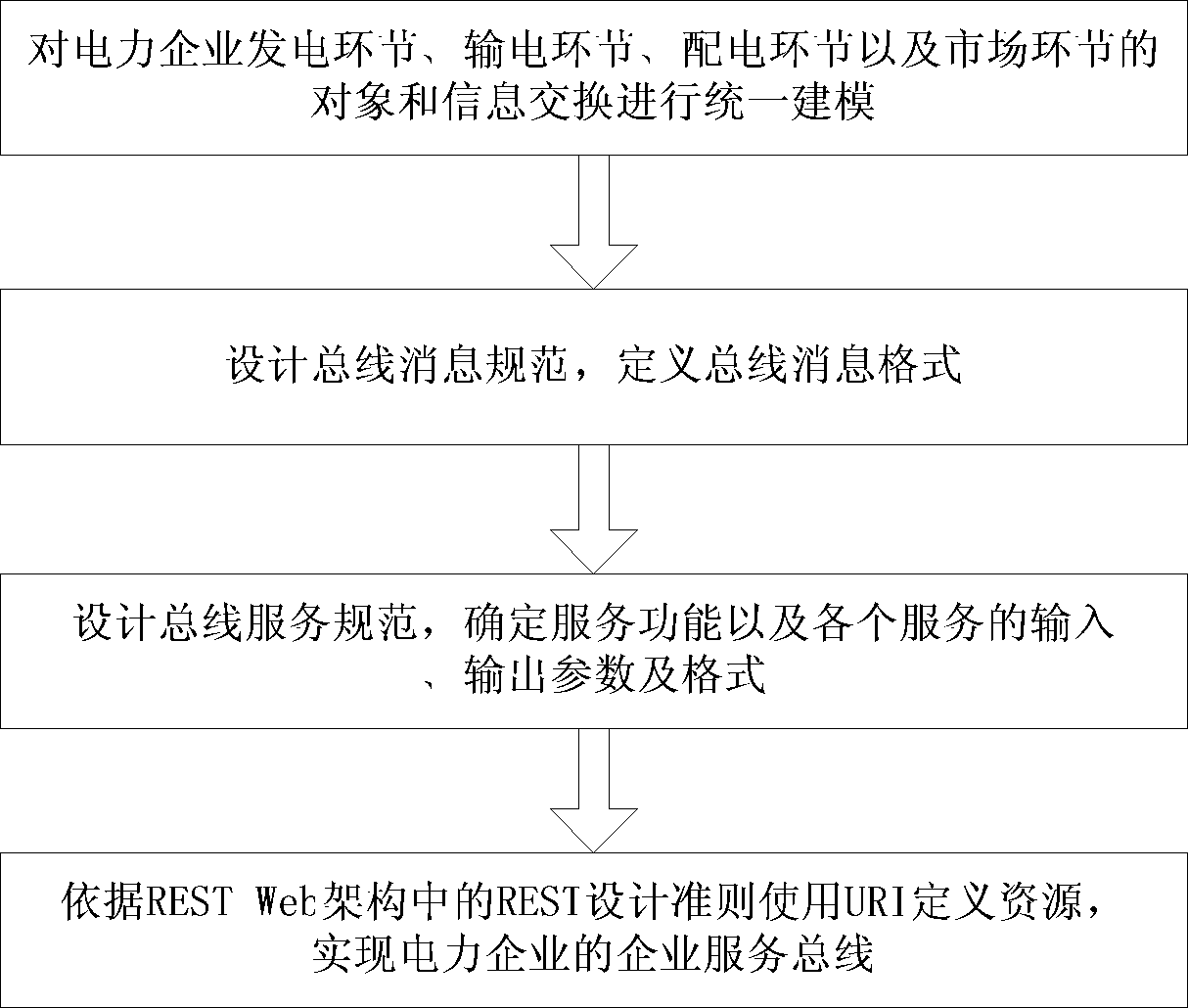
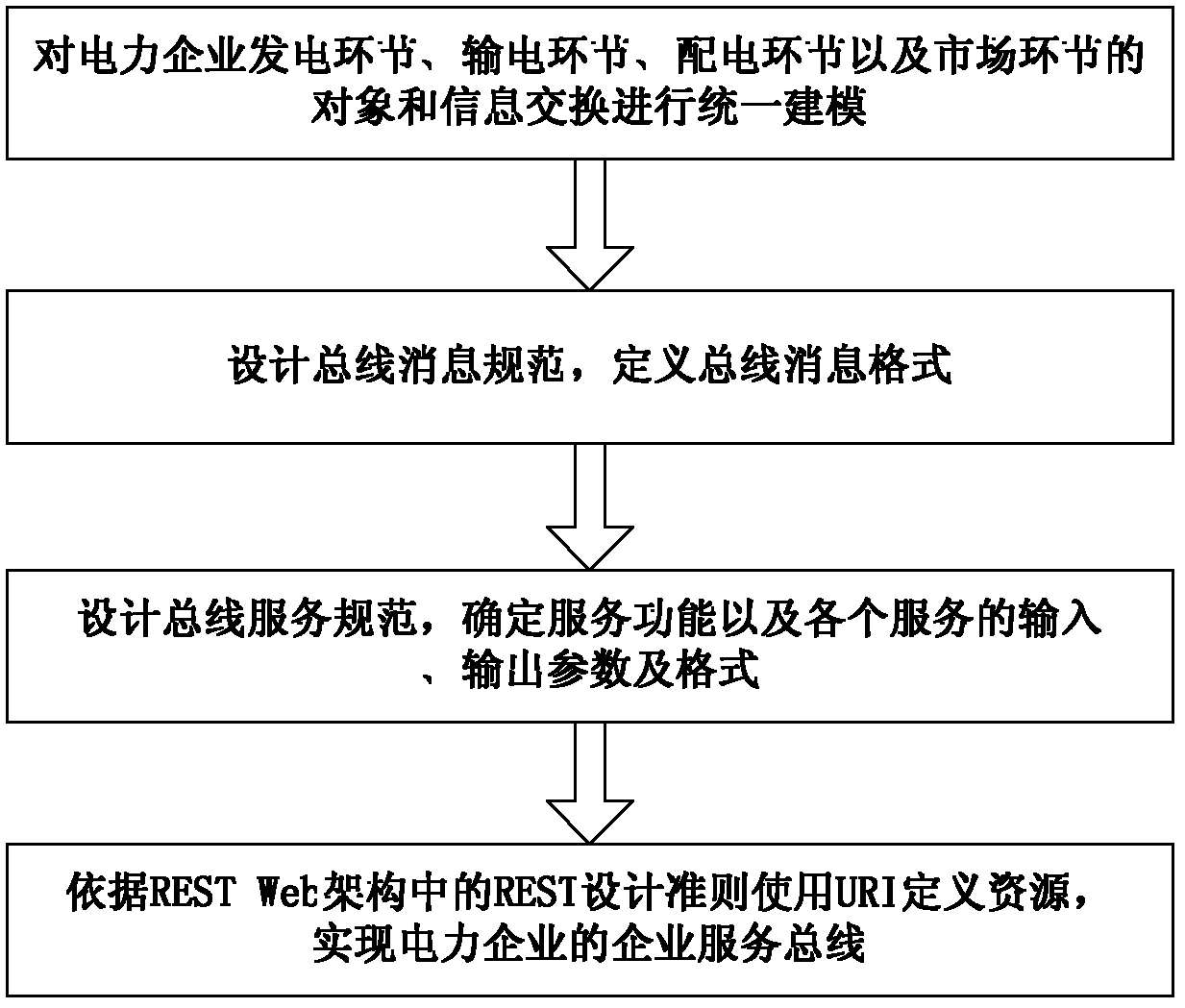
The invention provides an electric power enterprise service bus realization method and a device. The method includes the following steps of: carrying out unified modeling on objects and information exchange of an electric power enterprise power generation link, a power transmission link, a power distribution link and a market link; designing a bus message specification, and defining a total line message format; designing a bus service specification, and determining a service function and input, output parameters and formats of each service; according to a REST design guideline in a REST Web framework, using a URI to define resource, and realizing an enterprise service bus of an electric power enterprise. The method and the device are based on the REST Web framework and are directly realized on an HTTP protocol, a basic operation of the HTTP protocol can be used to realize a concrete function of the enterprise service bus, thus a problem of all services on the enterprise service bus are paralyzed caused by the change of the enterprise service bus and an associated information system is effectively avoided, and the method and the device have a good market prospect.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
System and methods for handling verification errors
ActiveUS20130254727A1Well formedCAD circuit designSpecial data processing applicationsComputer architecturePrimitive operation
Systems, apparatus and methods for handling verification violations are disclosed. In one aspect, a method stores a list of fix information in addition to geometric shapes for each layer during verification, such as design rule checking For each primitive operation step performed during verification, two tasks are performed. First, if the primitive operation is a dimensional checking operation (i.e., width, spacing or enclosure), then for each violation, the first task creates fix information containing violation edge pairs and adds the created fix information to the fix information list on the output layer. Second, for all operations and after the output shapes on the output layer are generated, a second task passes the fix information on input layers which overlap any output shape of the output layer to the output layer's fix information list. Finally, fix guides for the final violation results are generated and drawn based on the final fix information list.
Owner:SYNOPSYS INC
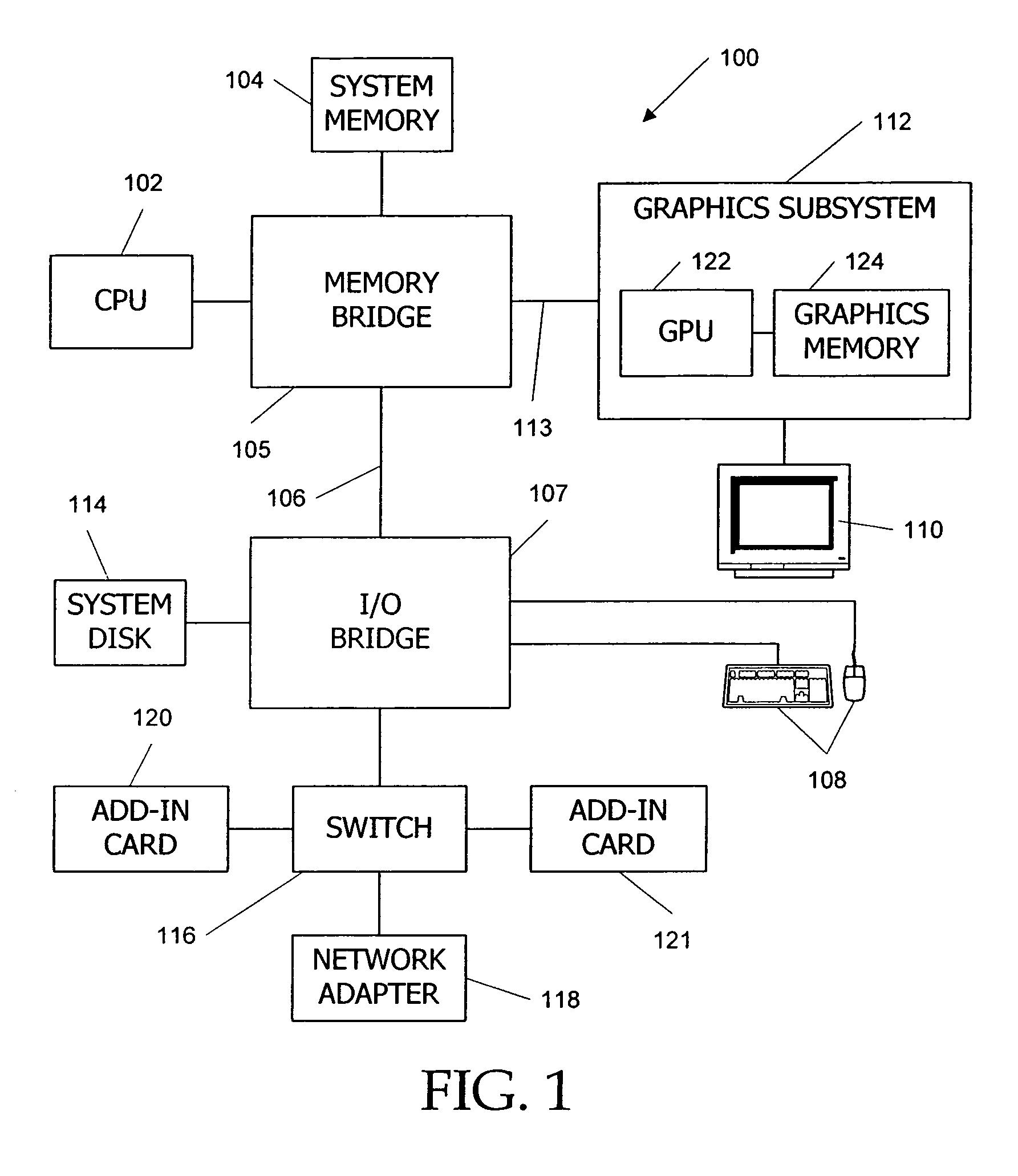
Early primitive assembly and screen-space culling for multiple chip graphics system
InactiveUS6943797B2Image memory managementProcessor architectures/configurationComputational scienceGraphics
A multi-chip system and method are disclosed for incorporating a primitive assembler in each of one or more geometry chips and one or more rasterization chips. This system may allow per-primitive operations to be performed in the geometry chips, and also allow use of a vertex data interface for sending vertex data to the rasterization chips. The primitive assemblers in the geometry chips may assemble vertices into primitives for clipping tests. The geometry chips may also test an assembled primitive against the projected boundaries of a set of screen space regions, where each region is assigned to one of the rasterization chips. Those primitives residing in more than one region may be sub-divided into two or more new primitives so that each new primitive resides in only one screen space region. The geometry chip may then send the vertex data for each primitive to the corresponding rasterization chip.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com