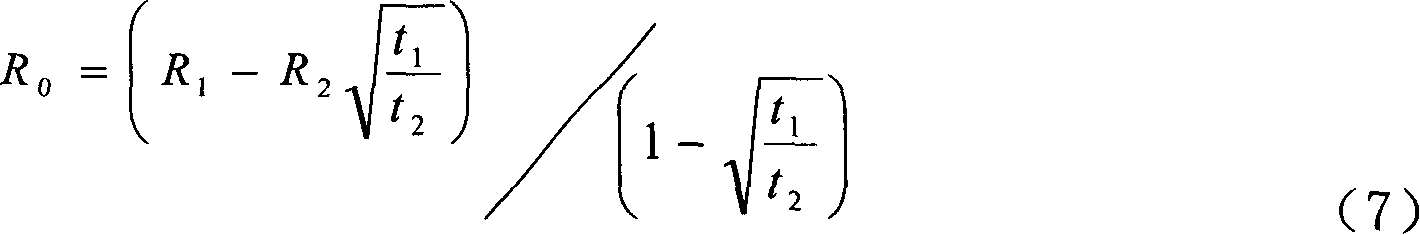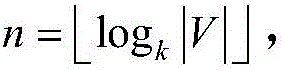Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
127 results about "Out degree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
, former Software Developer at SRM CARE. The in degree and out degree are discuss in only directed graph or tree.The in degree is defined as the number edges that comes at the particular node.However the out degree is defined as that the number of edges that leaves a particular node in the tree or graph.
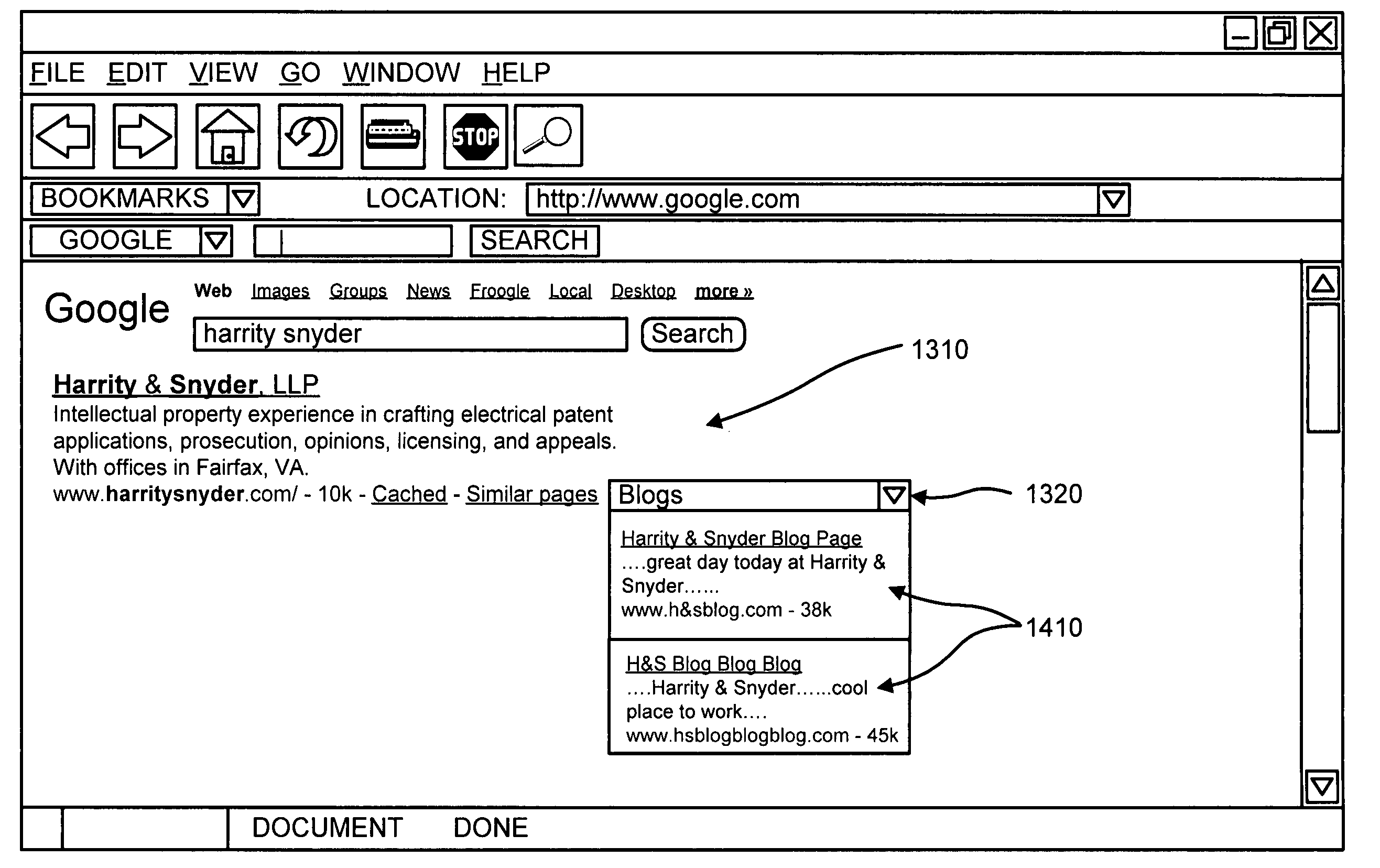
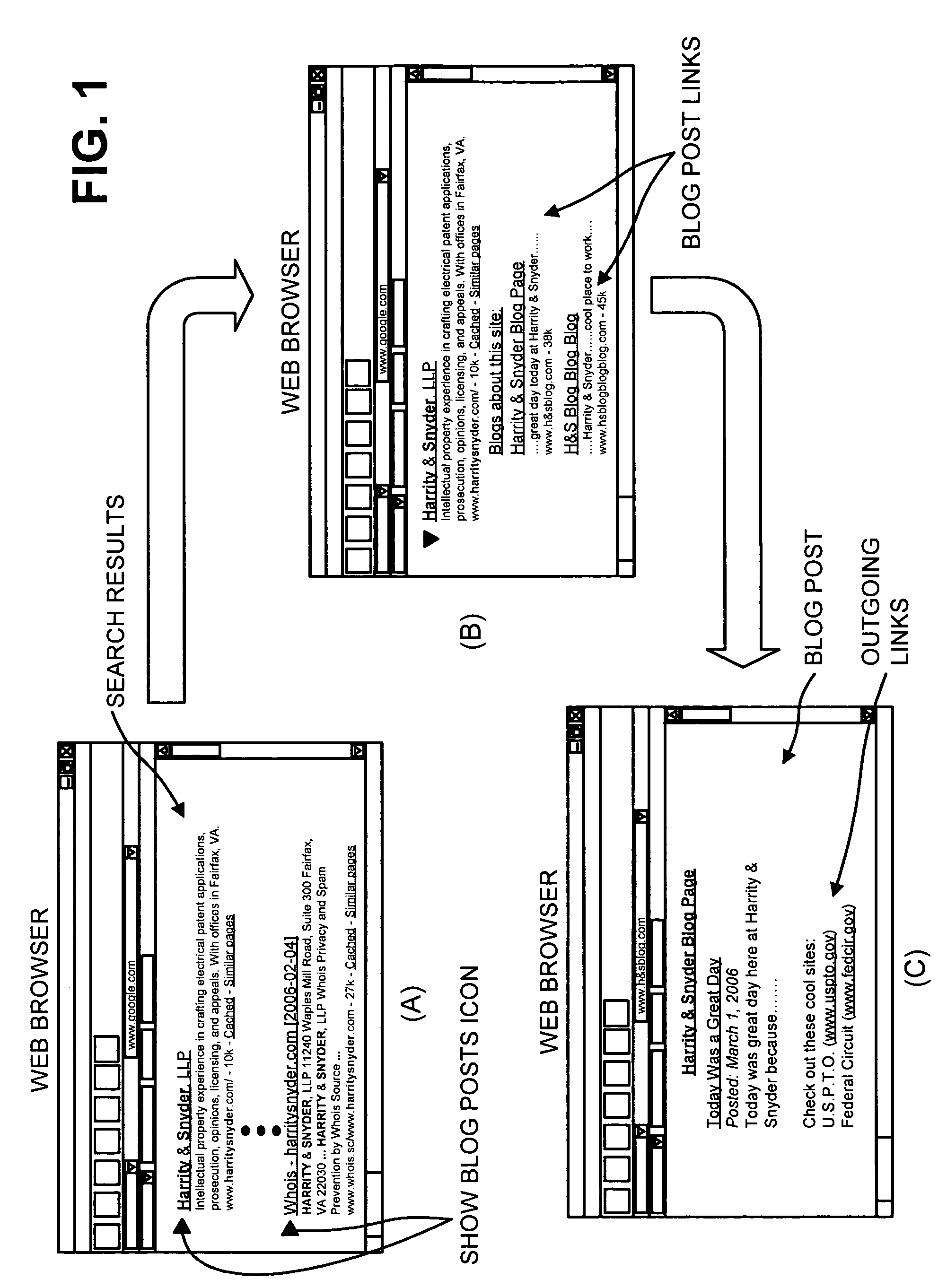
Providing blog posts relevant to search results
A device identifies a search result document based on a search query, and searches a blog post repository to identify a blog post relevant to the search result document. The device also rejects the blog post if the blog post has insufficient length, contains outgoing links located a predetermined distance from the beginning of the blog post, has a large out-degree, was created before or after a predetermined time, or has incoming links with a low link-based score. The device further provides the blog post in connection with the search result document if the blog post was not rejected.
Owner:GOOGLE LLC
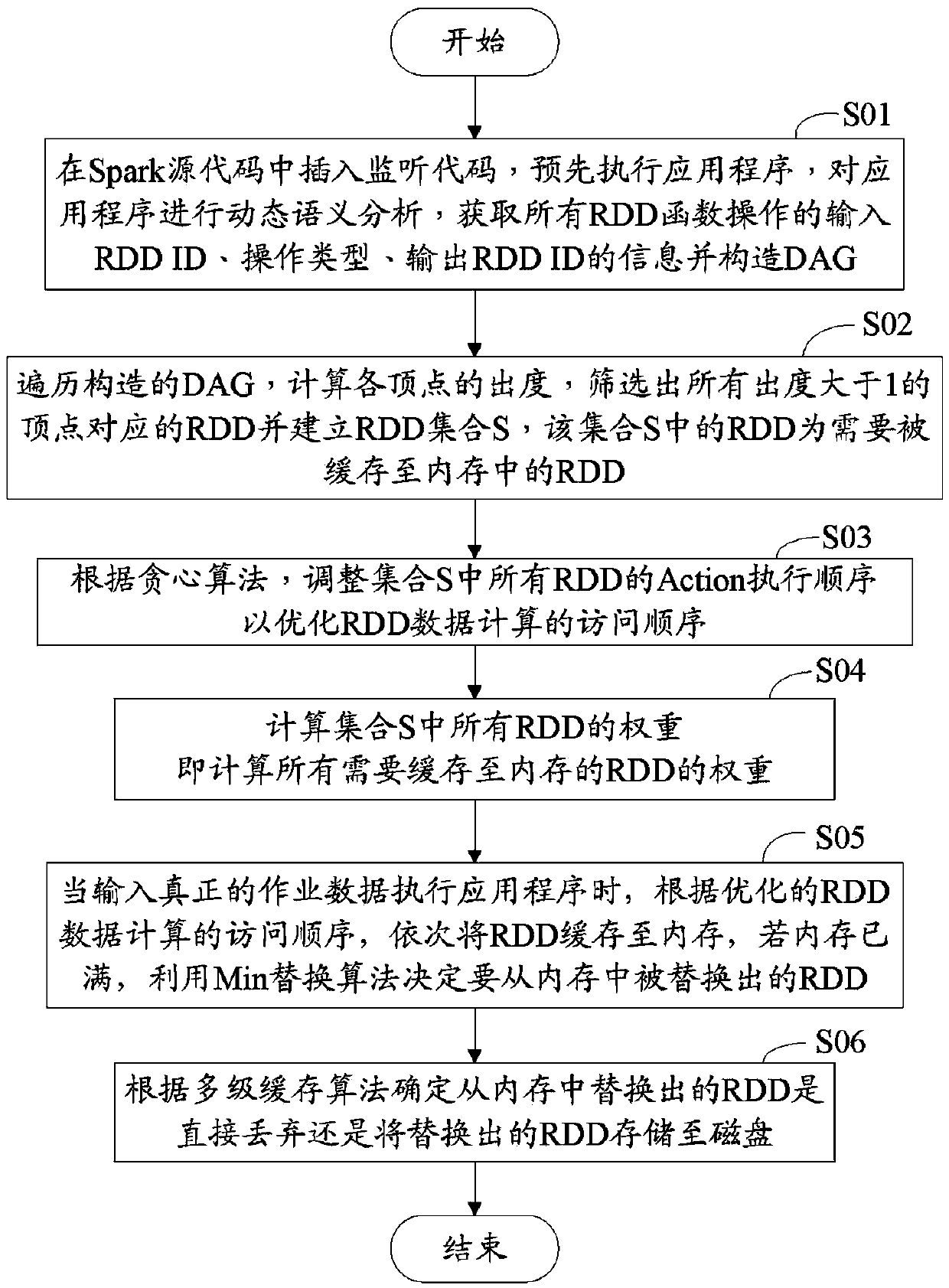
Caching optimizing method of internal storage calculation
ActiveCN103631730AIncrease profitLighten the programming burdenMemory adressing/allocation/relocationGreedy algorithmSpeed of processing
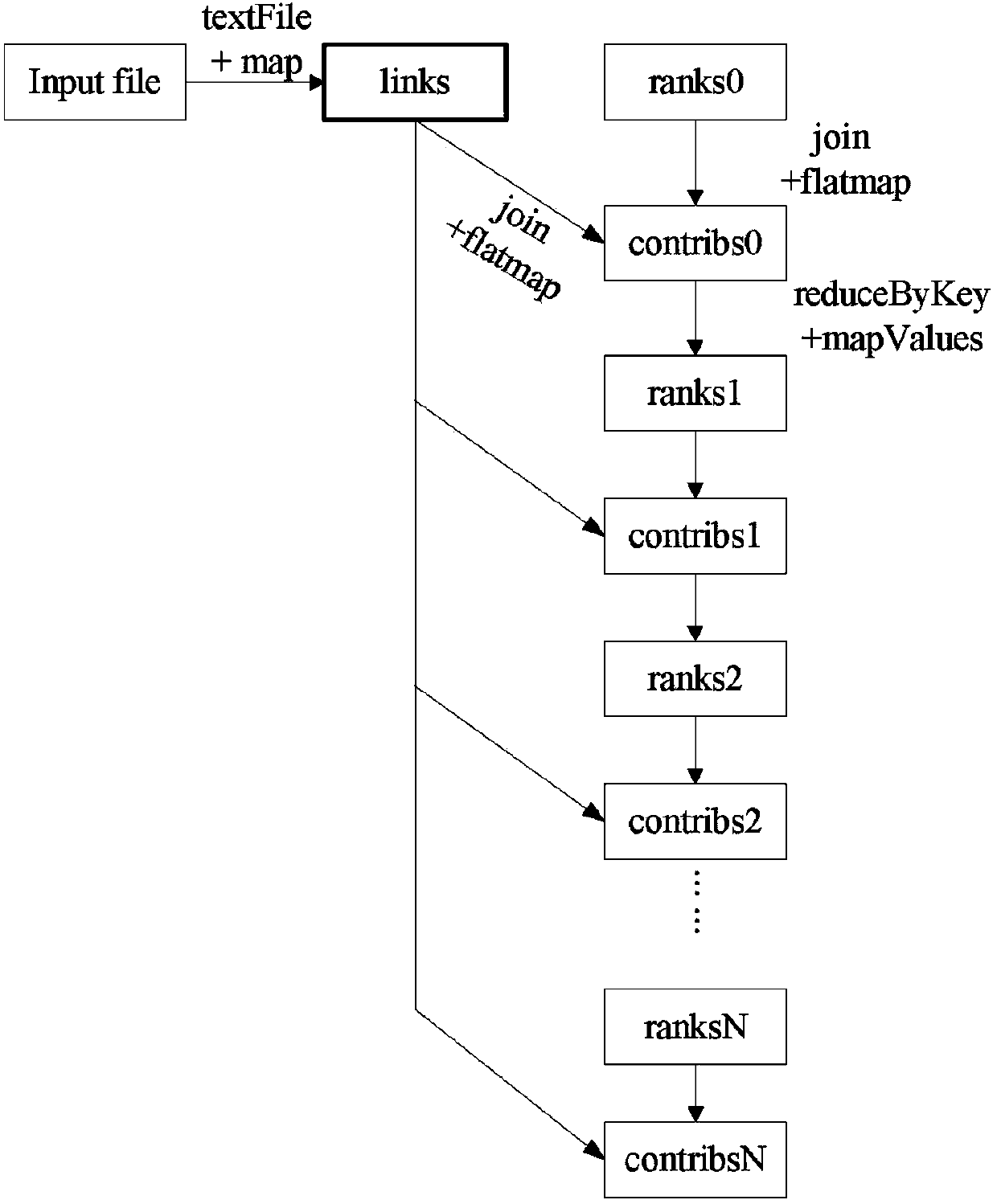
The invention provides a caching optimizing method of internal storage calculation. The method includes the steps that monitoring codes are inserted into a Spark source program, and dynamic semantic analysis is performed on an application program to construct a DAG; out-degrees of all vertexes in the DAG are calculated, RDDs of the vertexes of which the out-degrees are larger than one are screened, and the screened RDDs are RDDs needing to be cached to an internal storage; according to a greedy algorithm, the execution sequence of Action is adjusted so that the access sequence of RDD data calculation can be optimized; the weights of the RDDs are calculated, and the replaced RDDs in the internal storage are determined according to an internal storage replacement algorithm; it is determined how to process the replaced RDDs according to a multi-level caching algorithm. By the utilization of the caching optimizing method of internal storage calculation, a programmer does not need to examine and weigh internal storage using and display the RDDs of the appointed loading internal storage in the process of programming, programming loads of the programmer are reduced, meanwhile, the utilization rate of the internal storage is improved, and then the speed of processing big data is increased.
Owner:清能艾科(深圳)能源技术有限公司
Lake-reservoir cyanobacteria water bloom recognition method based on remote sensing monitoring and evidence fusion technology improvement
ActiveCN103439472AImprove fitting accuracyResolve indicatorsTesting waterPhylum CyanobacteriaRegression analysis
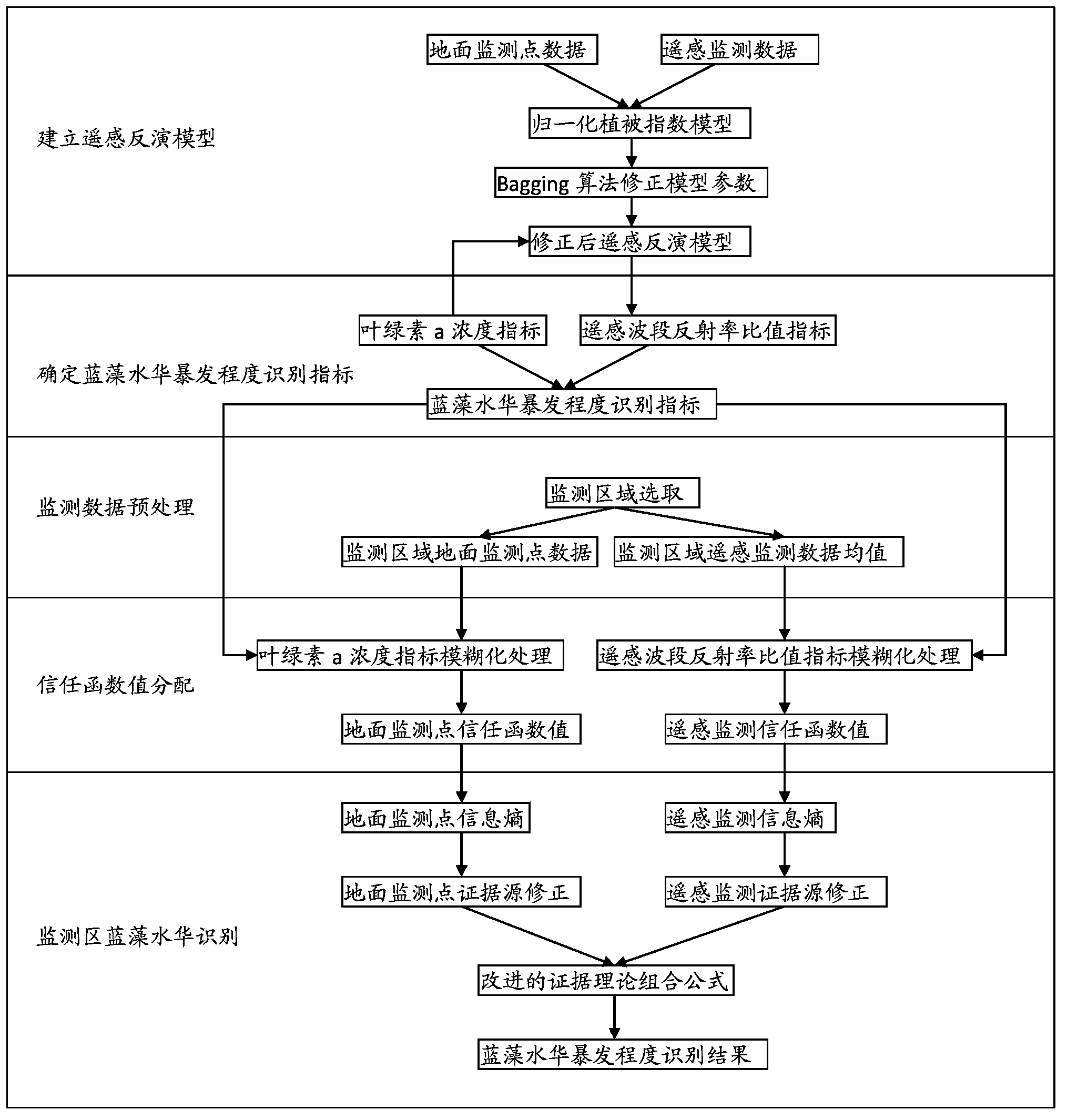
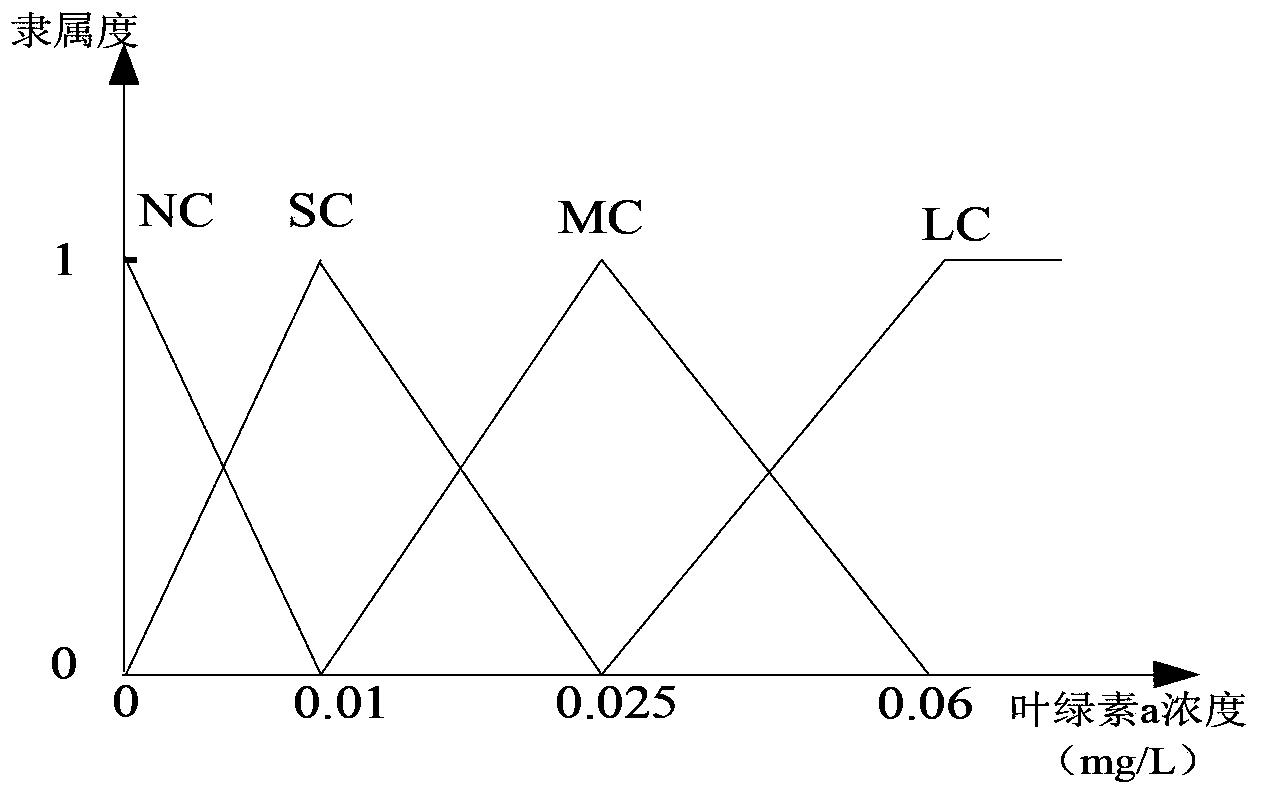
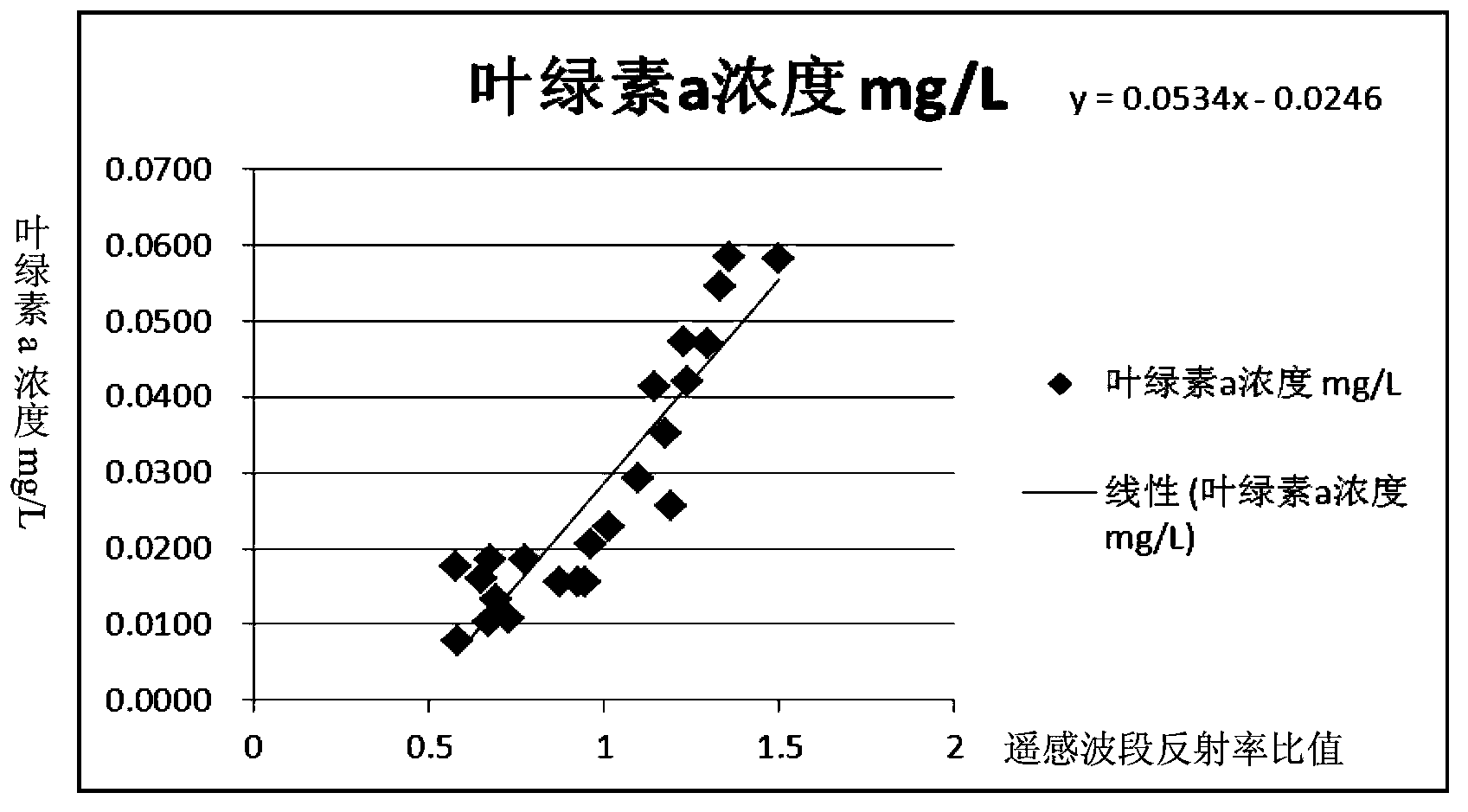
The present invention discloses a lake-reservoir cyanobacteria water bloom recognition method based on remote sensing monitoring and evidence fusion technology improvement, and belongs to the technical field of environmental projects. The method comprises: establishing a remote sensing inversion model, determining cyanobacteria water bloom breaking-out degree recognition indexes, pre-treating monitoring data, assigning belief function values, and recognizing monitoring area cyanobacteria water bloom. According to the present invention, an ensemble learning Bagging algorithm is fused into regression analysis of the remote sensing inversion model (ie., the normalization vegetation index model) to correct parameters of the model to obtain the corrected remote sensing inversion model so as to improve fitting accuracy; the problem of selection of indexes for lake-reservoir cyanobacteria water bloom recognition and value ranges thereof is solved; the problems of selection of the monitoring area and pretreatment of the monitoring data are solved; the problem of assignment of the belief function values is solved; and effective cyanobacterial water bloom recognition is achieved.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
Chinese integrated entity linking method based on graph model
InactiveCN105183770AImprove accuracyImprove efficiencySpecial data processing applicationsEntity linkingNODAL
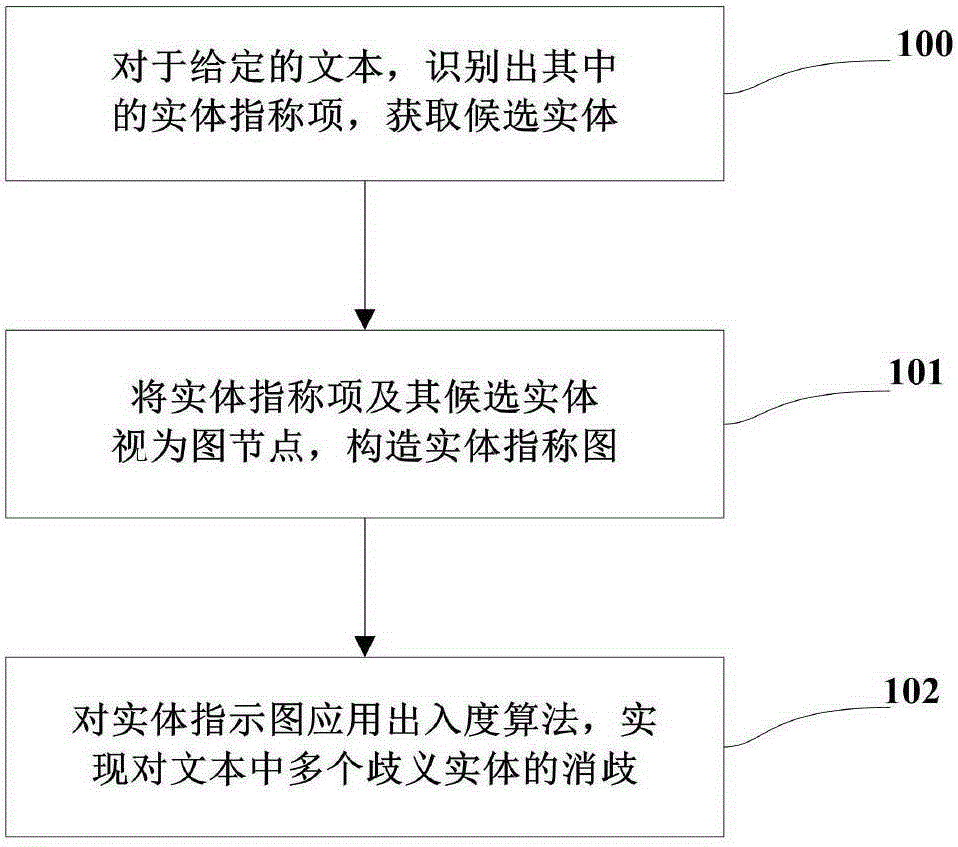
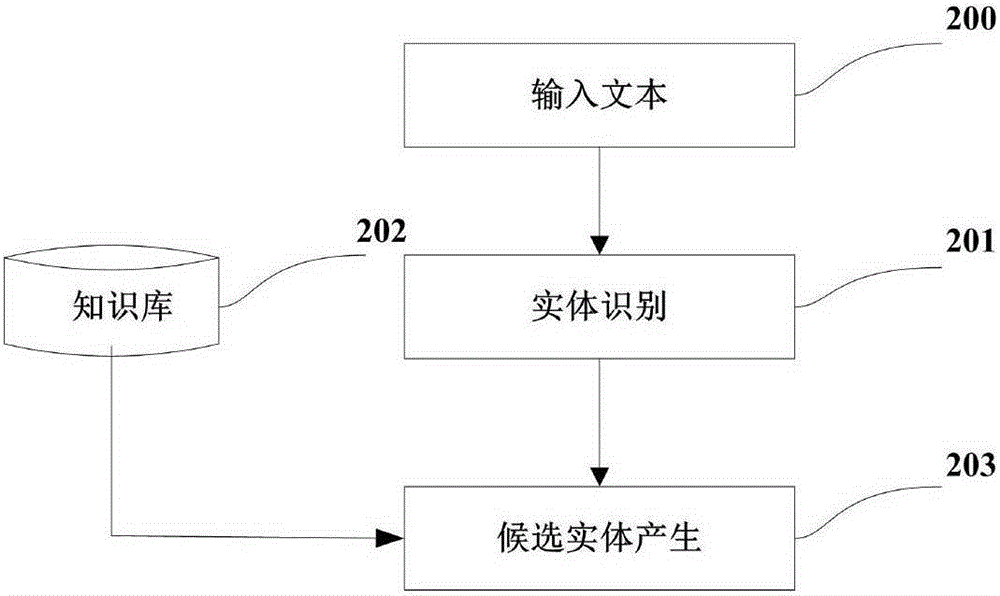
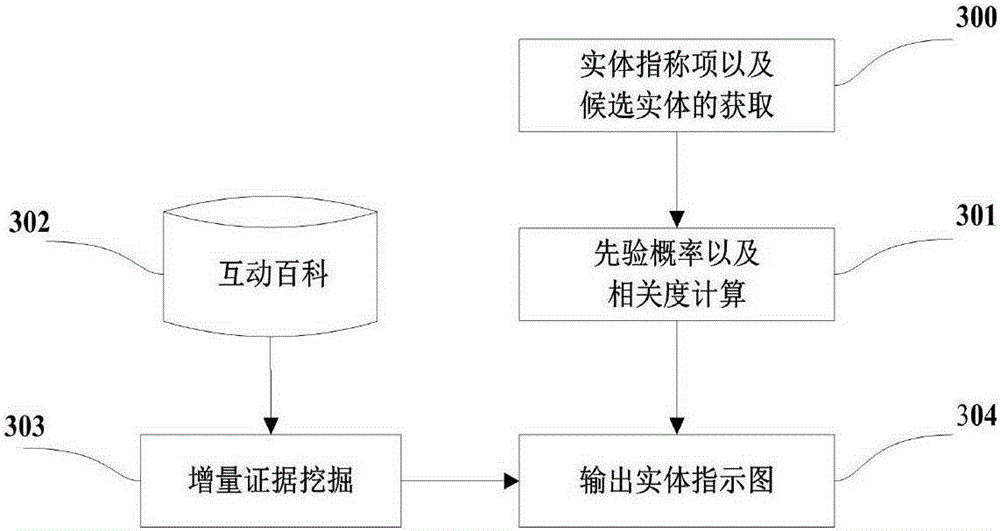
The present invention discloses a Chinese integrated entity linking method based on a graph model. An ambiguous entity in a text can be mapped into a specific entity in a real world, in order to provide aid for knowledge base expansion, information extraction and search engines. The method mainly comprises three parts of generating a candidate entity, constructing an entity indicator diagram, and disambiguating an integrated entity. For a given text, an entity referent item therein is recognized to obtain the candidate entity. The entity referent item and the candidate entity thereof are regarded as graph nodes to construct an entity referent graph. An in-degree and out-degree algorithm is applied to the entity indicator diagram for implementing disambiguation of multiple ambiguous entities in the text. The present invention does not depend on the knowledge base completely in the establishment of the entity indicator diagram, and also can implement incremental evidence mining to find evidence on an encyclopedia webpage. Dependence path analysis is employed to find the possibly related entity referent item. When the dependence path sizes of two entity referent items are within a set range, the two entity referent items are regarded as the possibly related entity referent items. Further, whether their candidate entities have relations in the real world is determined, so that the efficiency of disambiguation is greatly improved.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Passive miniature methanol fuel cell membrane electrode and its preparation method
ActiveCN102315457AImprove power densityImprove discharge stabilityCell electrodesCell membraneOxygen
The invention provides a passive miniature methanol fuel cell membrane electrode and its preparation method. The passive miniature methanol fuel cell membrane electrode is composed of a proton exchange membrane, an anode diffusion layer, an anode catalysis layer, a cathode diffusion layer and a cathode catalysis layer, wherein the cathode catalysis layer is composed of three-layer of superabsorbent nano particles in gradient distribution. The preparation method of the membrane electrode comprises the preparation of the cathode diffusion layer and the anode diffusion layer, the preparation of the anode catalysis layer, the preparation of the cathode catalysis layer and the process of forming membrane electrode by hot pressing. The passive miniature methanol fuel cell membrane electrode of the invention is capable of increasing the volumetric specific energy of a monomer battery, reducing the watered-out degree of the cathode, enhancing the mass transfer of oxygen, raising the power density and the discharge stability of the miniature methanol fuel cell. The invention has the advantages of convenient and rapid operation and easy control.
Owner:INFORMATION SCI RES INST OF CETC
Processing method and concentricity measuring tool for coaxial hole of diesel engine oil supply unit casing
ActiveCN103372666AEasy to useEasy to use for coaxial measurementMeasurement/indication equipmentsEngineeringOut degree
The invention discloses a processing method and a concentricity measuring tool for a coaxial hole of a diesel engine oil supply unit casing. The processing method comprises the steps of first adjusting the distance between a tailstock and a spindle; fixing a workpiece; installing and adjusting a boring machine, and installing a boring cutter in a first cutter groove; boring first three holes close to the machine tool spindle, enabling a working table to return, and enabling the machine tool spindle and the workpiece to be immobile; installing a lever indicator in a second cutter groove to detect the first three bored holes; installing the boring cutter in the second cutter groove to bore last three holes far away from the machine tool spindle; assembling the concentricity measuring tool in the coaxial hole of the diesel engine oil supply unit casing, and installing lever indicators to respectively detect circular run-out degrees of a first hole, a second hole, a third hole, a fourth hole, a fifth hole and a sixth hole. Processing of the six holes can be finished rapidly, concentricity errors can be measured rapidly by using the concentricity measuring tool, and the concentricity measuring tool is convenient to use, low in manufacturing cost and simple to operate and has accuracy in measurement.
Owner:KUNSHAN JIANGJIN MACHINERY
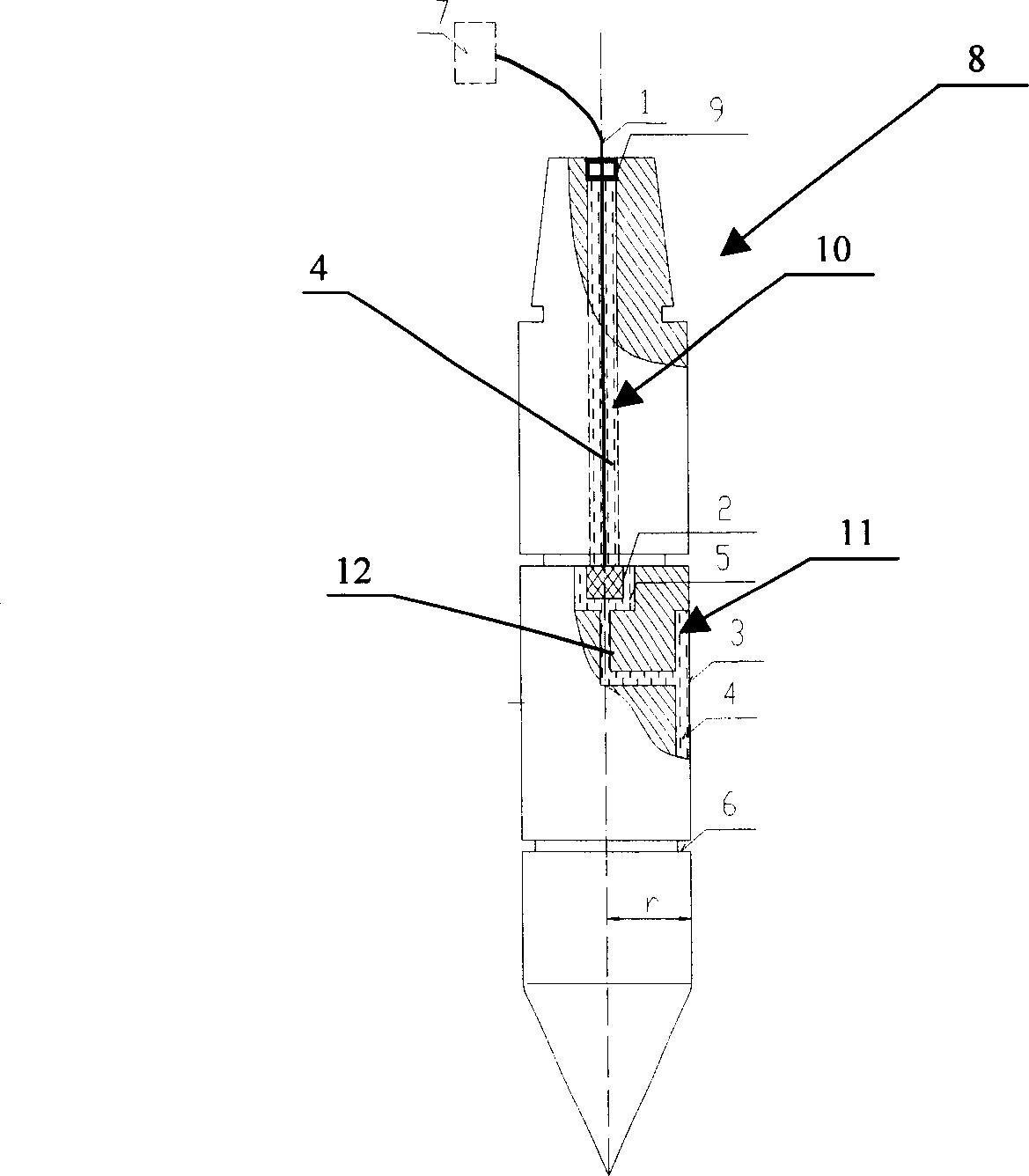
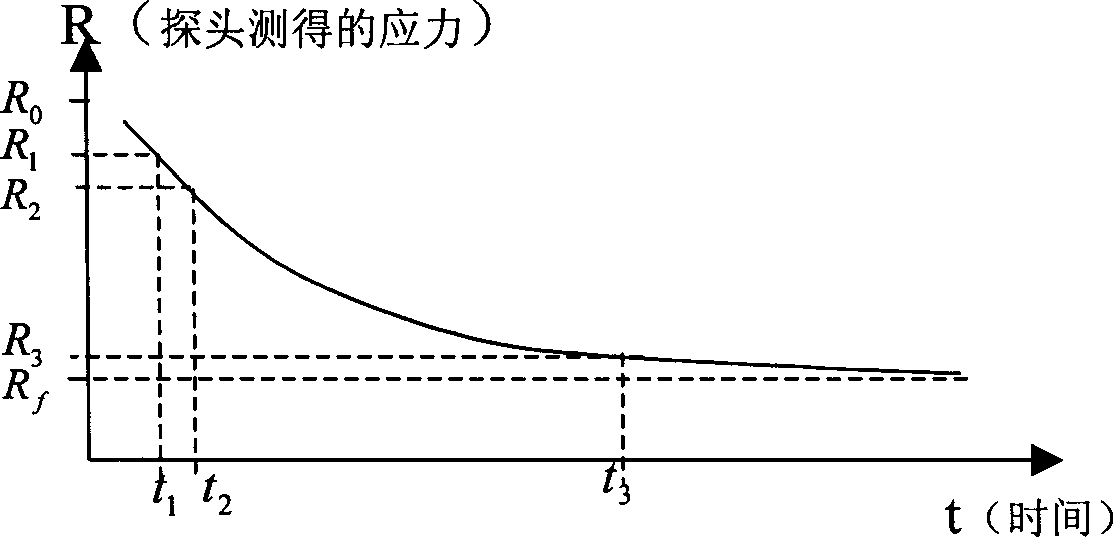
Probe for in-situ real time measuring saturated fine soil borizontal stress and measuring, calculating method
ActiveCN1793917ACompact structureWeld tightlyEarth material testingSpecial data processing applicationsHorizontal stressSoil science
A method for measuring horizontal stress of fine granulated saturation soil at original place in real time calculates out degree U of consolidation and horizontal consolidation coefficient C as well as static side pressure coefficient K by obtaining relation curve of horizontal pressure R at saturation soil layer deep position to time T and by applying three ¿C points calculation means to calculate horizontal stress R1 at initial time and horizontal stress at time of finalizing excess pore water pressure evanish . The probe for realizing said method is also disclosed.
Owner:铁道第三勘察设计院有限公司
Method and system for converting ladder diagram program into instruction list program and compiling instruction list program
InactiveCN104267654AImprove scalabilityImprove portabilityProgramme control in sequence/logic controllersError checkingOut degree
The invention discloses a method and system for converting a ladder diagram program into an instruction list program and executing compiling and interpretation of the instruction list program. According to the ladder diagram conversion method, energy flow classes and auxiliary nodes are introduced according to the characteristics of edition and execution of a ladder diagram, the class is set on each diagram peak, and an auxiliary node is added; the serial and parallel connection relationship is judged according to the out-degree and in-degree of the class and the auxiliary node where an element is located. After the ladder diagram is converted into the instruction list, a PLC immediate compiling method combined with compiling and interpretation and a divide-and-conquer method concept are adopted, a compiling front end and an interpretation rear end are designed independently, and in combination with a GCC rear-end structure, a PLC compiling system specific to a special machine model is generated. The method and system for converting the ladder diagram program into the instruction list program and compiling the instruction list program have the advantages that the ladder diagram program with a complex logic structure can be accurately and rapidly converted into the instruction list program, and in the conversion process, grammar error checking is carried out on the program, and the common errors like an open circuit, a short circuit and a bridge circuit are excluded, so that the correctness of the generated instruction list program is guaranteed.
Owner:CENT SOUTH UNIV
Network anomaly behavior detection method based on out-degree and in-degree of host
ActiveCN104135474AReduce technical difficultyLow resource consumptionData switching networksNetwork behaviorAnomalous behavior
The invention discloses a method for detecting network anomaly behaviors based on the out-degree and in-degree of a host, and provides a host attribute determination and attack detection method from a brand new aspect. A certain quantity of types of network behavior detection and anomaly behavior monitoring can be realized under the condition of low technical difficulty and low resource consumption. A degree, the out-degree and the in-degree are defined firstly, wherein the degree is the connection quantity of quadruples; the out-degree refers to the connection quantity of quadruples transmitted by the host to other hosts; and the in-degree refers to the connection quantity of quadruples received from other hosts by the host. According to the method, detection of the network anomaly behaviors is realized according to whether the out-degree and in-degree proportions of the host surpass a known range or not; and the out-degree and in-degree proportion ranges of different service hosts are different.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Preparation method of dendrobium officinale super-micropowder
InactiveCN103191311AReasonable designPromote dissolutionPowder deliveryPlant ingredientsSolubilityAdditive ingredient
The invention belongs to the technical field of preparation of Chinese herbal medicines, in particular relates to a preparation method of dendrobium officinale and more particularly relates to a preparation method of dendrobium officinale super-micropowder. The preparation method can be used for overcoming the defects that the traditional dendrobium officinale finished-product is low in solubility and absorbance. The preparation method of the dendrobium officinale supper-micropowder comprises the following steps of: washing, cutting, liquid nitrogen freezing, refrigerative grinding, processing by using a freezer dryer, sterilizing, weighing, packaging and the like. The preparation method of the dendrobium officinale supper-micropowder is reasonable in design and simple in step; and the dendrobium officinale super-micropowder prepared by using the preparation method can be used for improving dissolving-out degree of effective ingredients and is beneficial to human body absorption and increase of bioavailability.
Owner:河南省三禾药业有限公司
Peer vehicle discovery method based on streaming large data
ActiveCN108564788AReduce complexityDetection of traffic movementCharacter and pattern recognitionStreaming dataSlide window
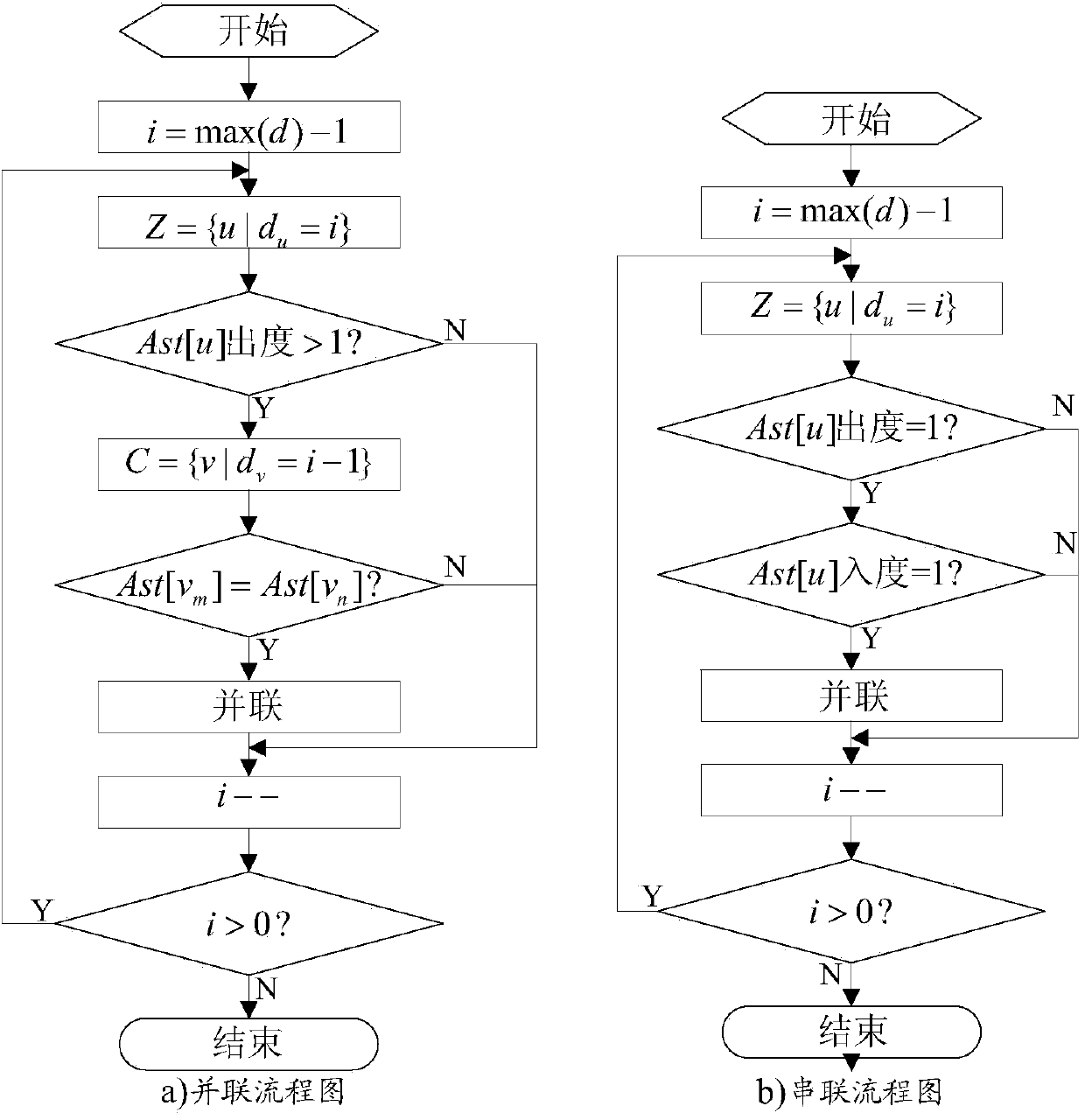
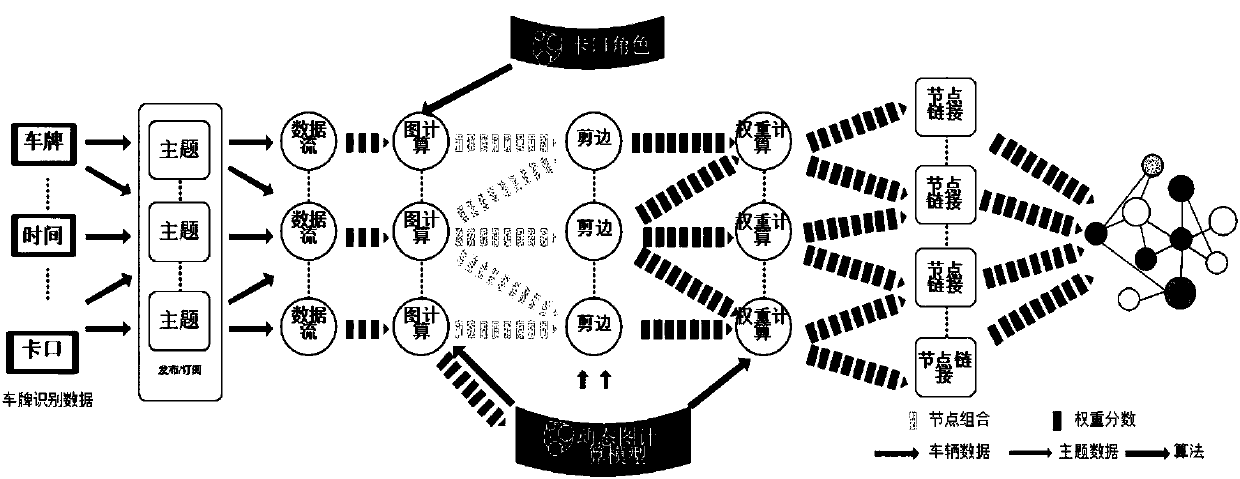
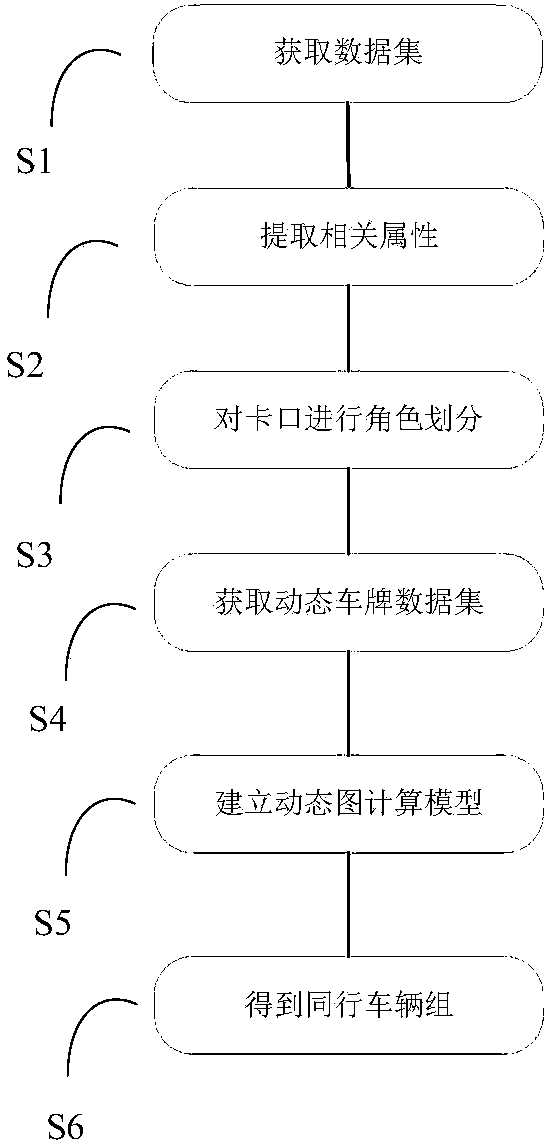
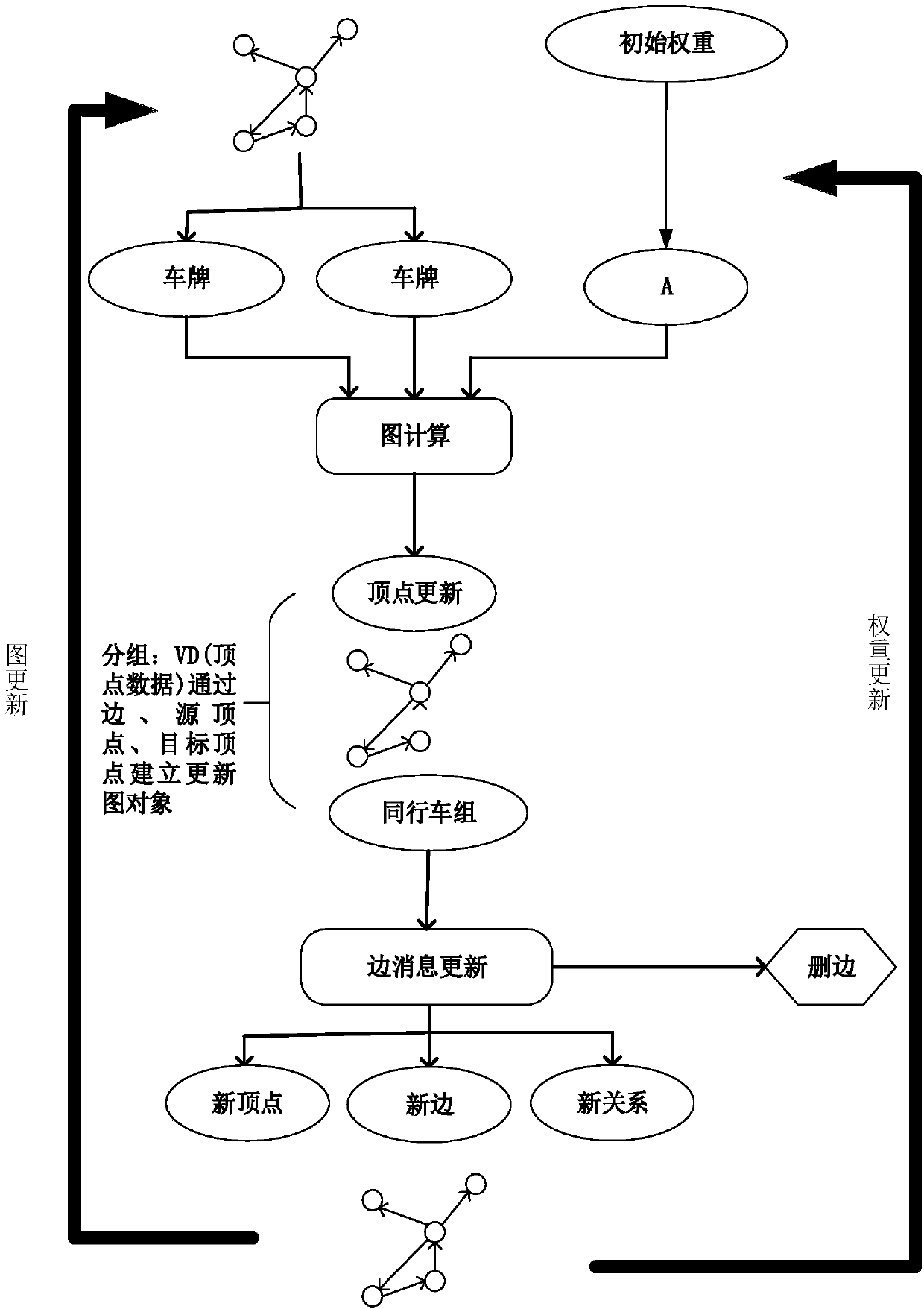
The invention claims a peer vehicle discovery method based on streaming large data. The method comprises the steps: first, clustering the bayonet traffic and the number of branches. Through the obtained bayonet clusters, the role identification of the bayonet is verified, and the power law of the bayonet traffic is verified. Secondly, the Spark streaming time sliding window is introduced on the basis of streaming data. According to the driving trajectory, the context between the vehicles is obtained, and the creation and improvement of the peer corpus is completed. Finally, the PDGC (Plate number Dynamic Graph Computing) algorithm is proposed. A dynamic relationship diagram between vehicles is established based on dynamic corpus and bayonet role identification. The bayonet role is associated with the map between the influence factor and the vehicle, and the peer train is obtained by real-time trimming of the vehicle map and calculation of the weights between the peer vehicles, effectively reducing the complexity of data processing. The method is provided with the ability to discover peer vehicle groups in real time, which is not only used for searching for similar tracks, but alsois possible to mine the tracking vehicle by calculating the out-degree and penetration of the vertices of the vehicle map.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
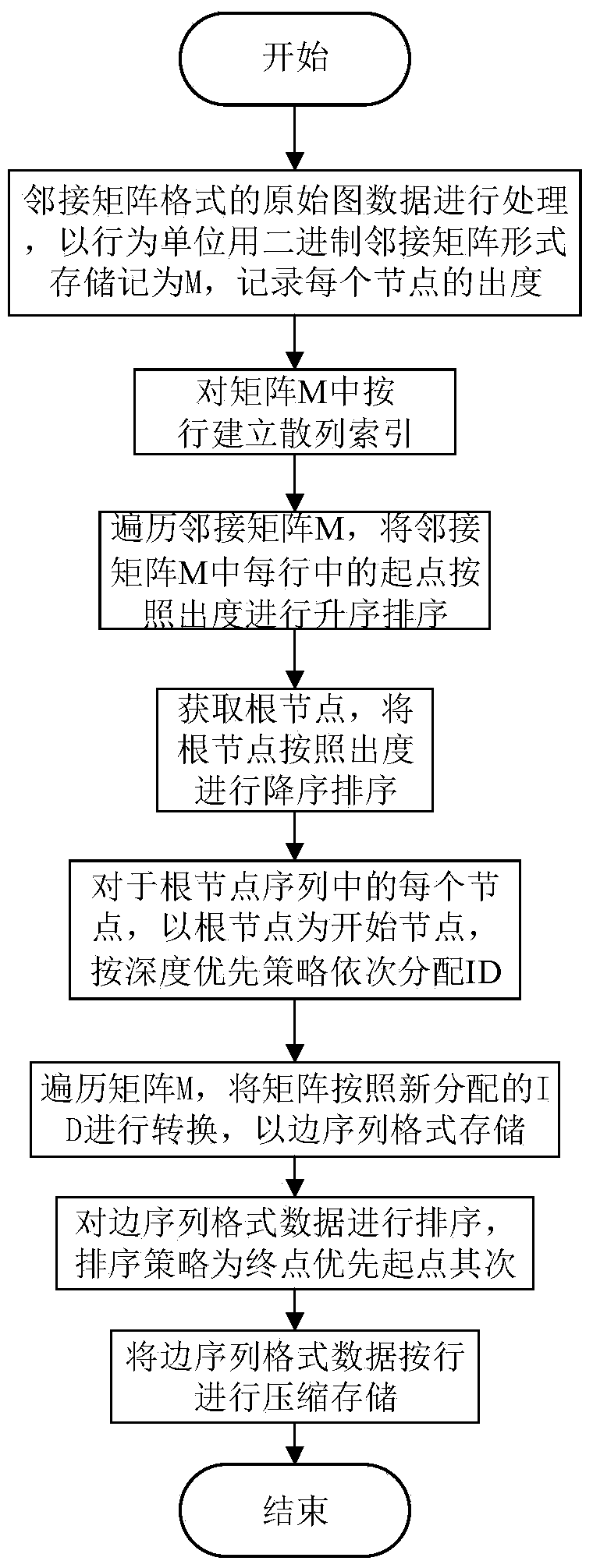
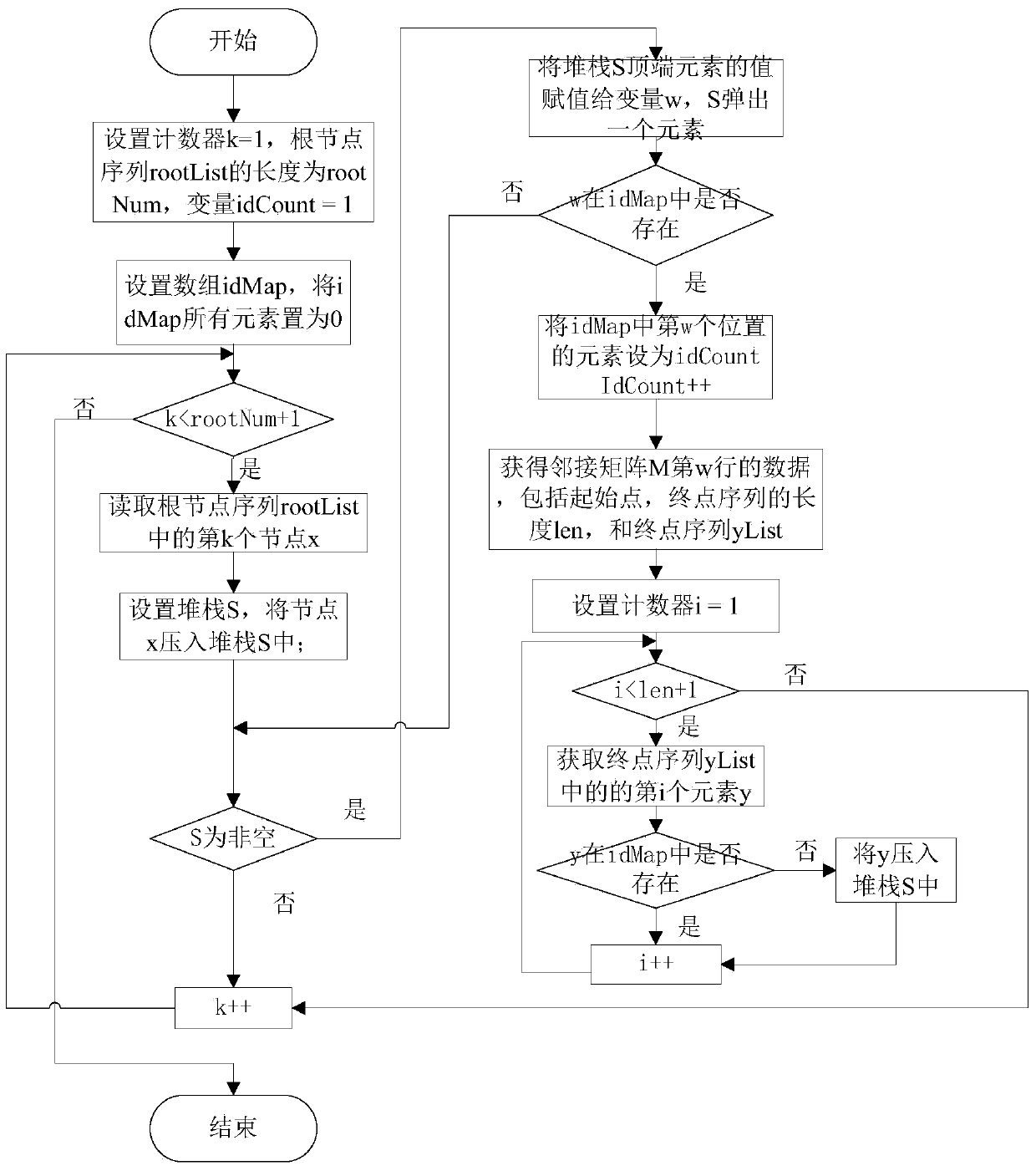
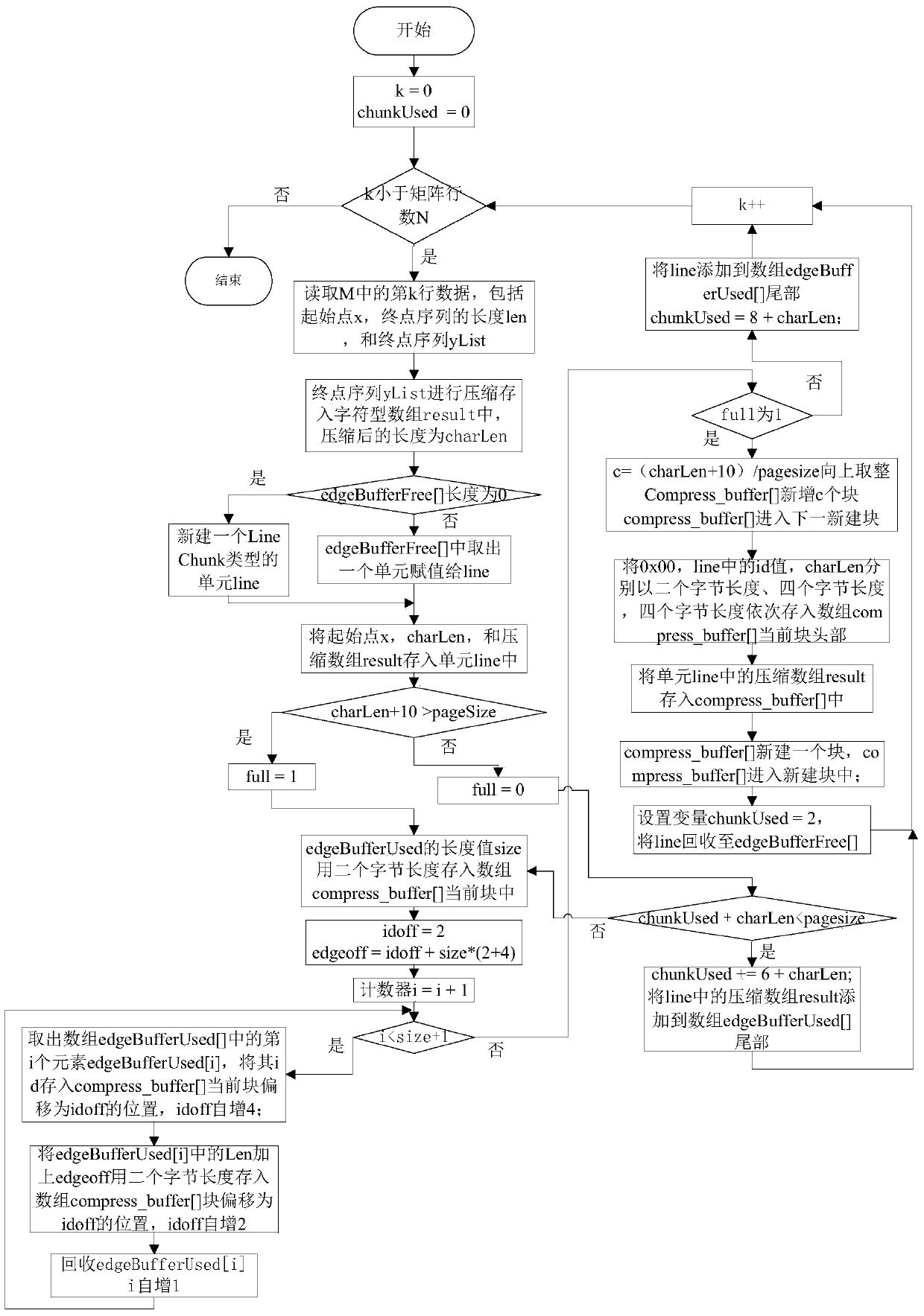
Compression and storage method for large-scale image data
The invention discloses a compression and storage method for large-scale image data. The method comprises the following steps of (1) storing the data of original images by a binary adjacent matrix M in a behavior unit; (2) according to the deviation value of each row in the adjacent matrix M, establishing a hash index; (3) ascending the starting points of each row in the adjacent matrix M according to the out-degree; (4) recording nodes with in-degree of 0 as root nodes, descending the root nodes according to the out-degree, and recording as a root node list; (5) for each node in the root node list, using each root node as the starting node, and sequentially distributing ID (identity) according to the depth-first strategy; (6) traversing the adjacent matrix M, converting the matrix according to the newly distributed ID, and storing in an edge list format; (7) sequencing the data with the edge list format; (8) compressing and storing the data with the edge list format in a line mode. The method has the advantages that the required data storage space is little, the number of random reading times is little, and the parallel degree of threads is high.
Owner:HUAZHONG UNIV OF SCI & TECH
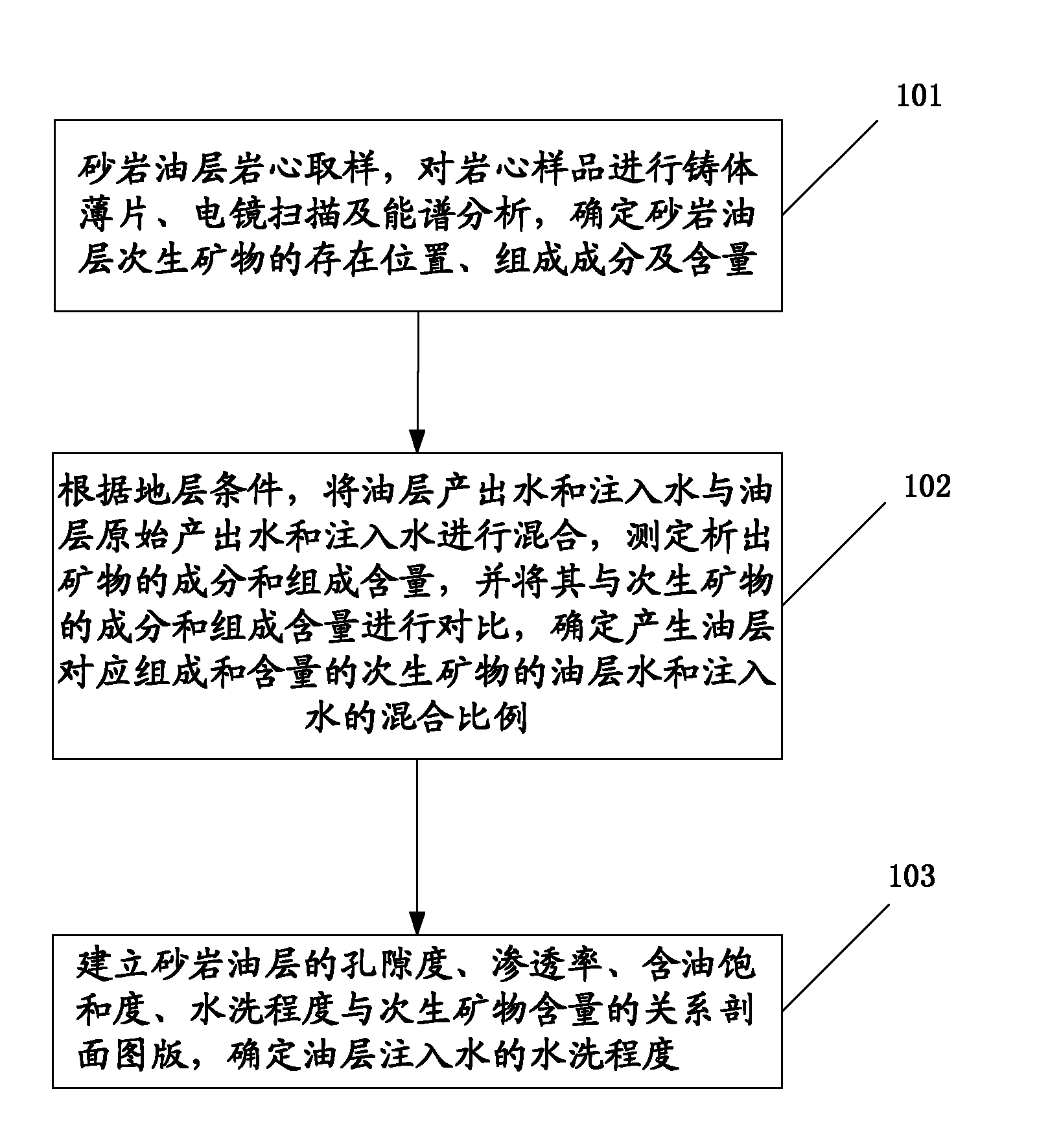
Method for evaluating watered-out degree of ultralow-permeability water-drive reservoir sandstone oil layer
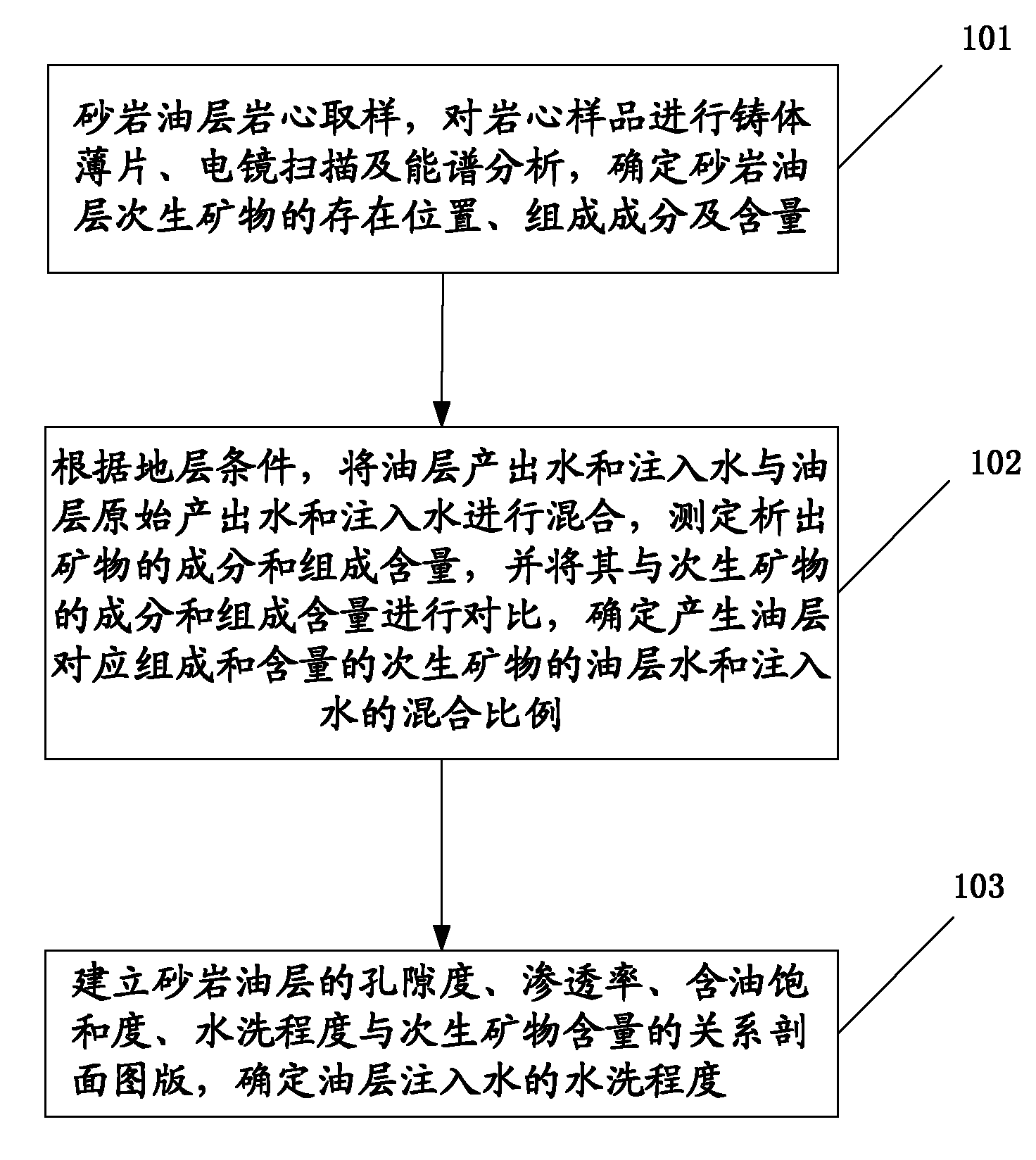
ActiveCN101942995AReflect the actual degree of washingAvoid the phenomenon of multiple washing degreesFluid removalPorosityTerra firma
The invention discloses a method for evaluating the watered-out degree of an ultralow-permeability water-drive reservoir sandstone oil layer, which belongs to the technical field of oil-field development. The method comprises the following steps: analyzing the core sample of the sandstone oil layer, and determining the position, composition and content of secondary minerals in the sandstone oil layer; according to the conditions of the stratum, mixing the output water and injected water in the oil layer with the original output water and injected water of the oil layer, and determining the mixing ratio of oil layer water, which produces secondary minerals with oil layer composition and content, to injected water; and establishing a relation sectional drawing among porosity, permeability, oil saturation, watered-out degree and secondary mineral content of the sandstone oil layer, and determining the watered-out degree of the oil layer injected water. The evaluation analysis result provided by the invention can reflect the actual watered-out degree of the analyzed oil layer, prevents one oil layer from producing multiple watered-out degrees, and lays a firm foundation for determining the principal digging direction and technique for oil-field development adjustment.
Owner:PETROCHINA CO LTD
Testing device and testing method for horizontal well subsection well completion inflow
The invention relates to a testing device and a testing method for horizontal well subsection well completion inflow, the device comprises an oil water separating pumping system, an oil water mixing inflow system, a horizontal well subsection well completion imitating well tube system and a speed reducing buffer liquid pot, the oil water separating pumping system is connected to a plurality of sets of oil water mixing inflow systems in a parallel mode through the oil water external connection pipeline, each set of oil water mixing inflow system is connected to the flow in hole of the horizontal well subsection well completion imitating well tube system through the pipeline; the horizontal well subsection well completion well completion inflow imitating well tube system, the speed reducing buffer liquid pot, the oil water separator inlet of the oil water separating pumping system are connected through the pipelines. The testing device and testing method for horizontal well subsection well completion inflow can display the different liquid producing sections, water out degree for horizontal well subsection well completion and the well tube pressure and temperature change relationship under impact of the centre tube column; the test under single factor influence can be realized as well as the test under multi-factor coupling function, the scientific base can be offered for developing the horizontal well water finding testing technology.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Processing method of irradiated chicken claw and pickled pepper product
InactiveCN102113538AEliminate residueNot soft rotten shape plumpMeat/fish preservation by irradiation/electric treatmentChicken-clawsPoultry product
The invention relates to a processing method of an irradiated chicken claw and pickled pepper product, relating to the technical fields of poultry product processing and irradiation quality assurance. The processing method sequentially comprises the processes of thawing, bleaching, boiling in water, picking, packaging and irradiating. The invention changes the traditional mode of boiling before bleaching and adopts the mode of bleaching before boiling in water, which is beneficial to eliminating bleach liquor residues in chicken claws and preventing minute bubbles in a packaging bag from influencing quality guarantee period, the addition of composite salt for preprocessing is beneficial to avoidance of the phenomenon that the boiling-out degree is difficult to grasp in the mode of bleaching before boiling in water, and the boiling temperature and time are favorably controlled to ensure that the chicken claws are not too soft and are kept to be full. In the invention, the processing technology is improved so as to effectively control the initial microbial content and anaerobe, irradiation is combined for sterilization and quality guarantee, and thus, the purposes that chicken claw products processed in an industrialized way have the characteristics of unique flavor, suitability to tastes of the mass and long quality guarantee period are achieved.
Owner:扬州扬福科技有限公司
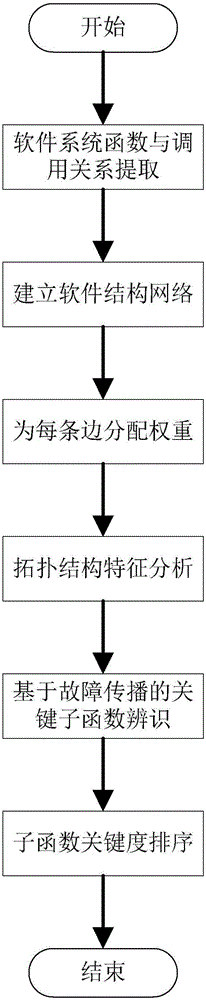
Software key function identification method based on complex network fault propagation
InactiveCN105045574ACompliant with the actual software systemGuaranteed uptimeSpecific program execution arrangementsCascading failureNODAL
The invention discloses a software key function identification method based on complex network fault propagation. The software key function identification method comprises the following steps: 1) according to a source code, carrying out subfunction and calling relation extraction on a program, and carrying out abstraction to obtain a network chart of a software structure; 2) according to a probability of calling and executing each subfunction, endowing each side with a certain weight w, wherein the weight is a failure probability of inter-function cascading faults; 3) analyzing the topological structure characteristics of software, and calculating an in-degree value and an out-degree value of each node, wherein the in-degree value of the node is a frequency that the function is called by other functions, and the out-degree value of the node is the frequency that the function calls other functions; 4) carrying out a cascading failure simulation experiment on each node of a software network, and calculating the node numbers G, i.e., the criticality, of a maximum connected subgraph of the software network after each node is subjected to stable failure; and 5) sorting the G in an increasing sequence to obtain the criticality of each function. The software key function identification method is simple and reliable. Compared with a traditional method, the software key function identification method can precisely identify a software key function.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID
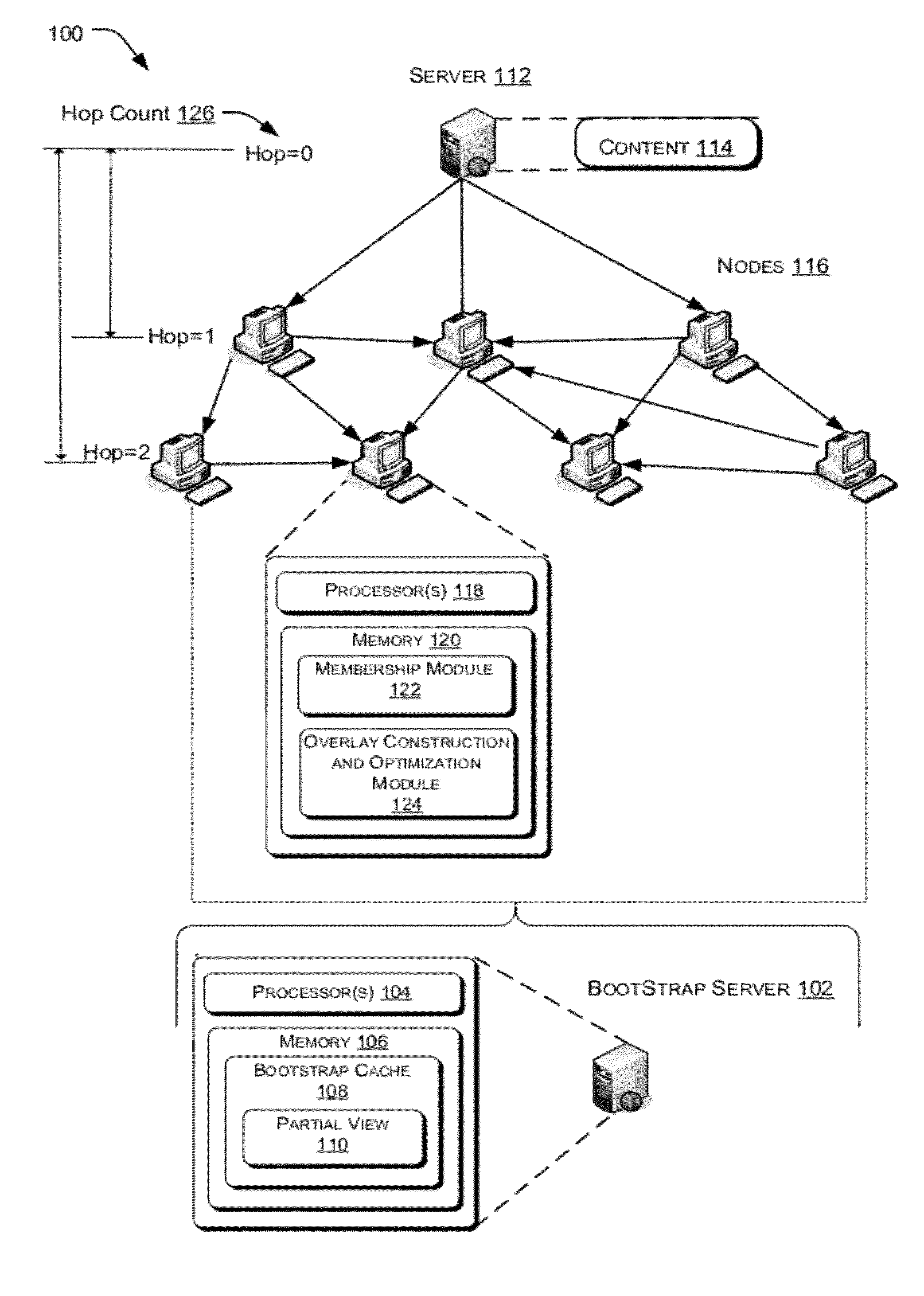
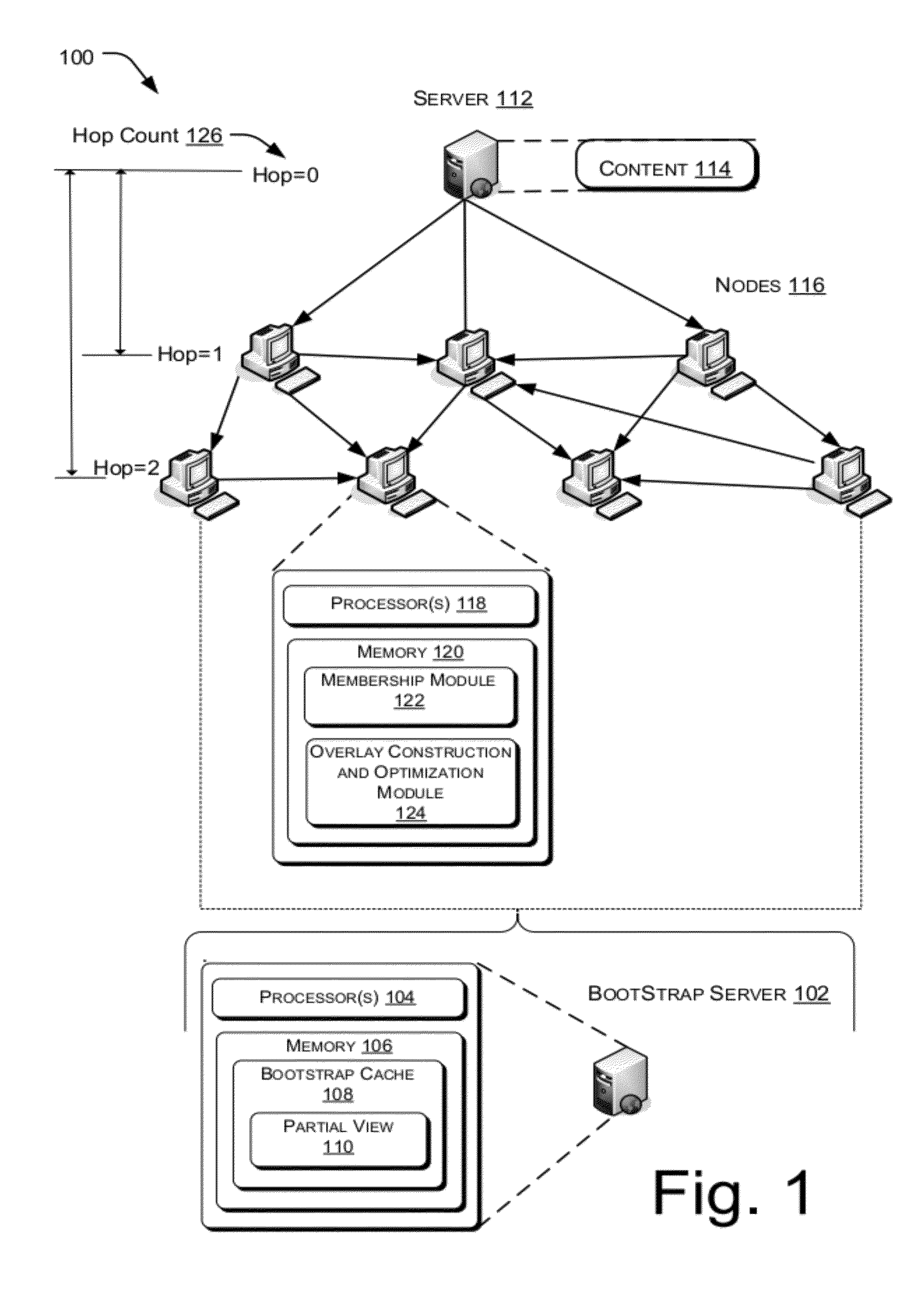
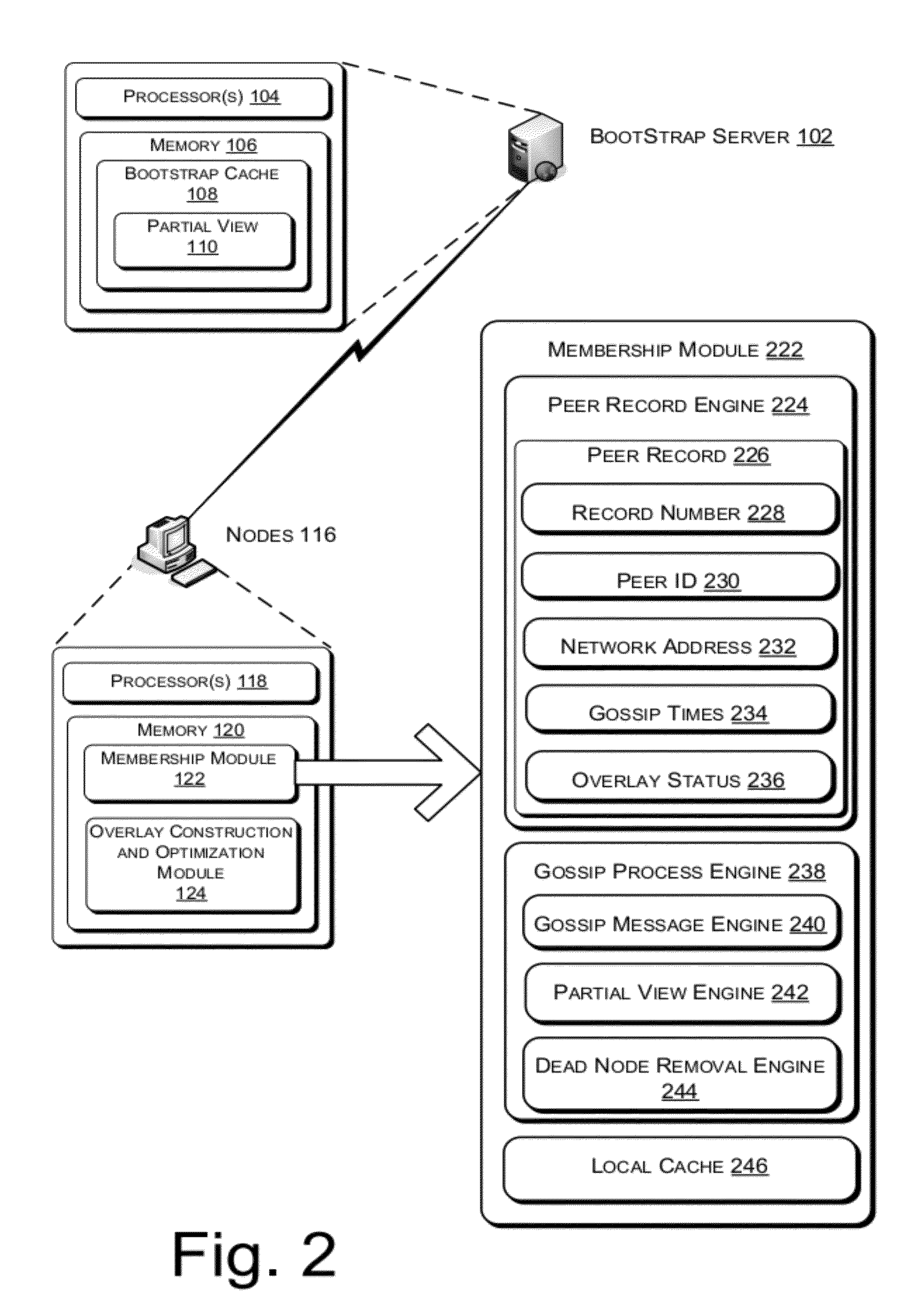
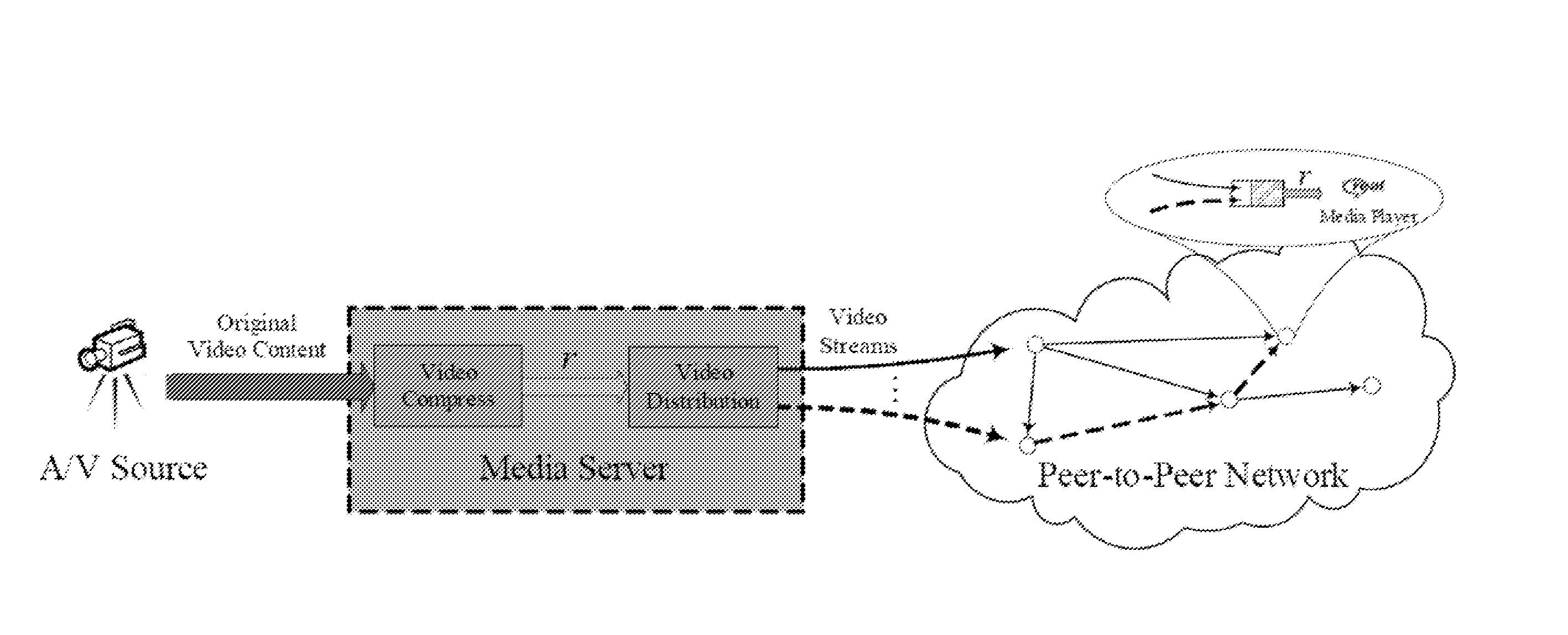
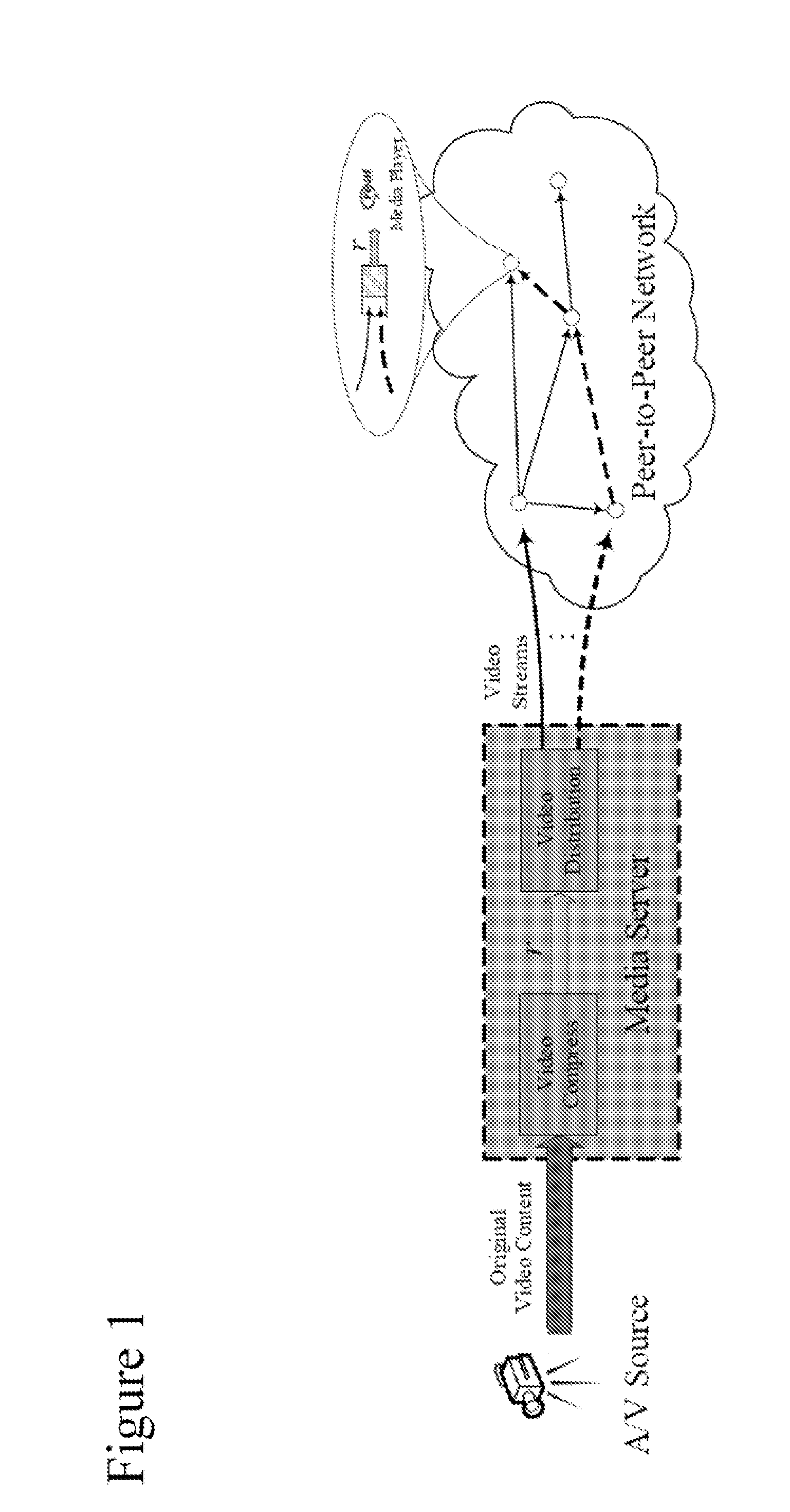
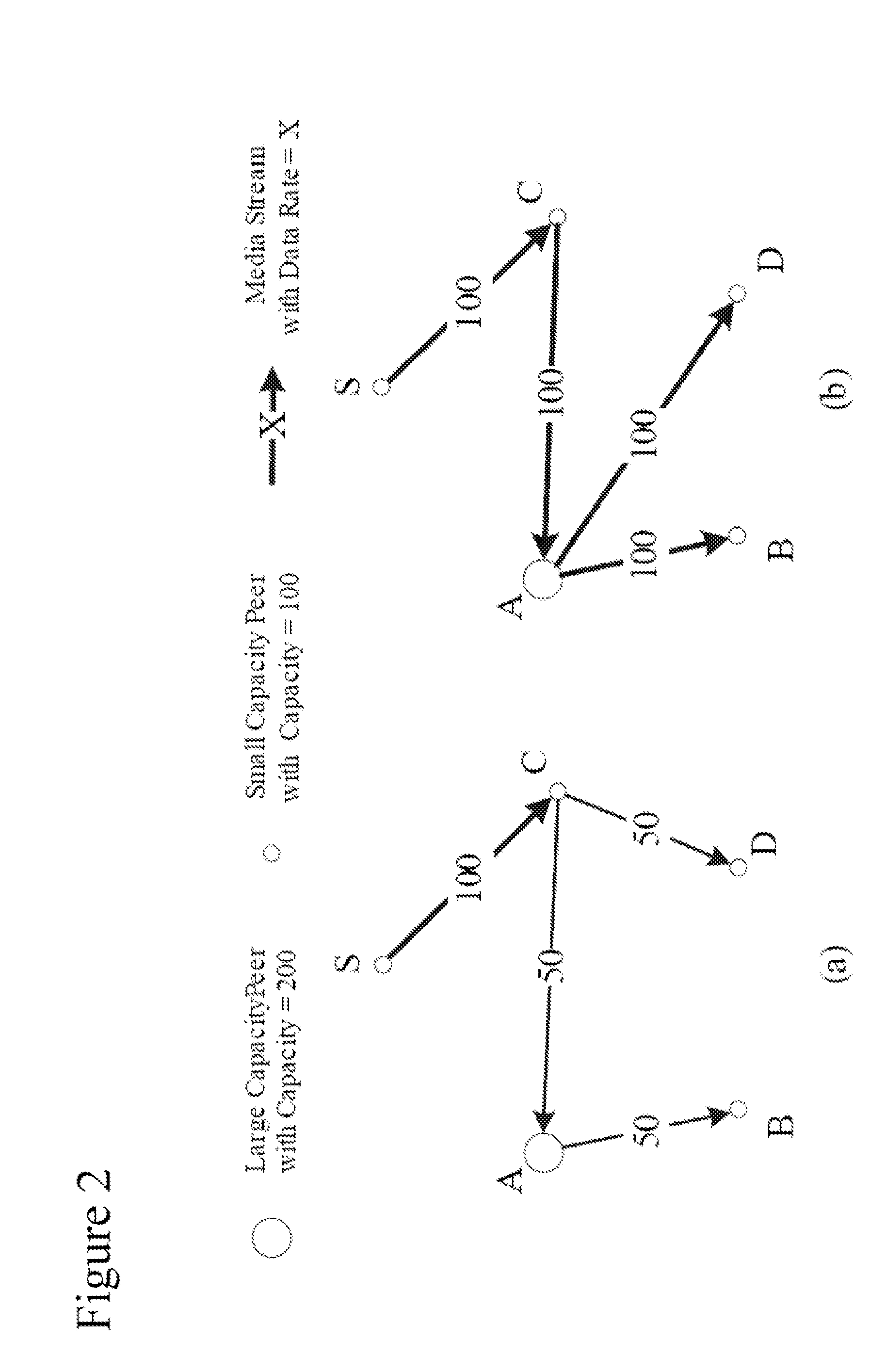
Peer-to-peer (P2P) streaming overlay construction and optimization
ActiveUS8352585B2Improved data flowSpeed up the flowMultiple digital computer combinationsTransmissionDirected graphOut degree
This document describes a directed graph model using a peer-to-peer overlay structure and a gossip-based protocol to maintain the distributed membership. A protocol suite for peers to join the live streaming session, form the P2P streaming overlay, and exchange video packets with others has also been presented. The different capabilities of the heterogeneous peers are well depicted using an adaptive out-degree mechanism. The performance of the whole system is maintained by a contribution-aware mechanism, which ensures that the peers with large contribution will get more chance to be served than those with small or no contribution.
Owner:MICROSOFT TECH LICENSING LLC
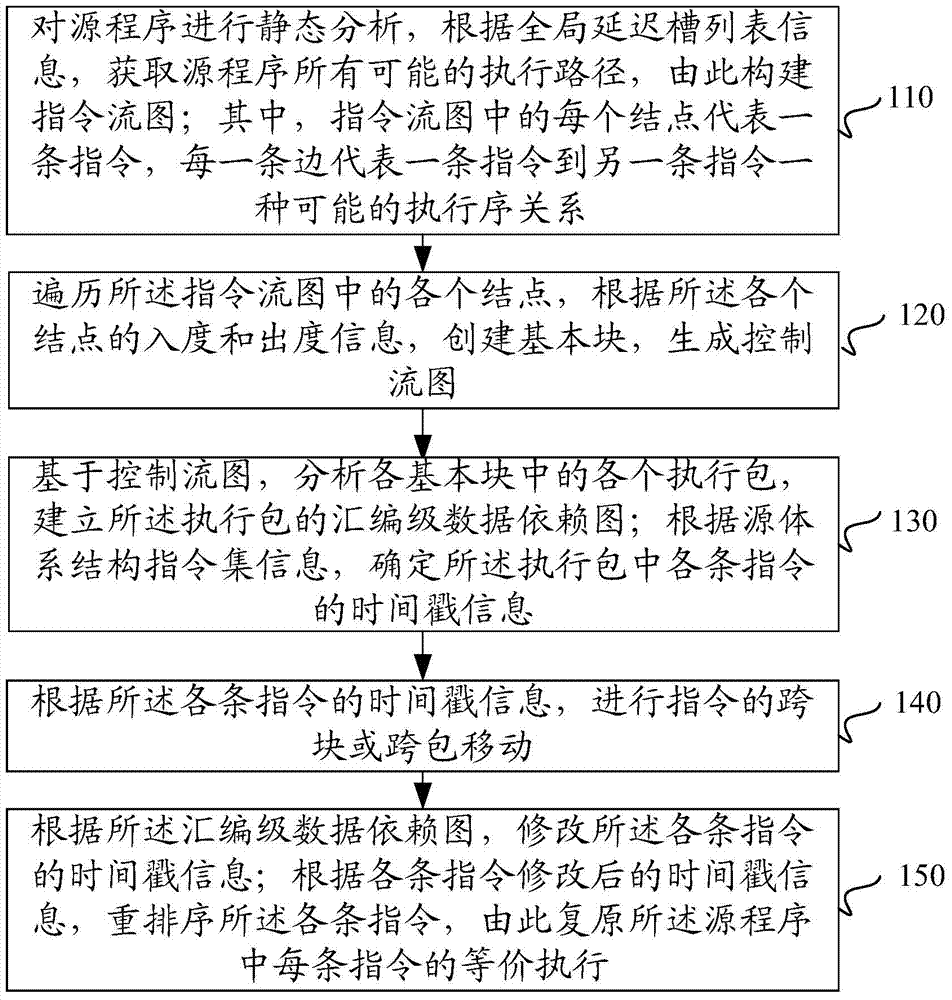
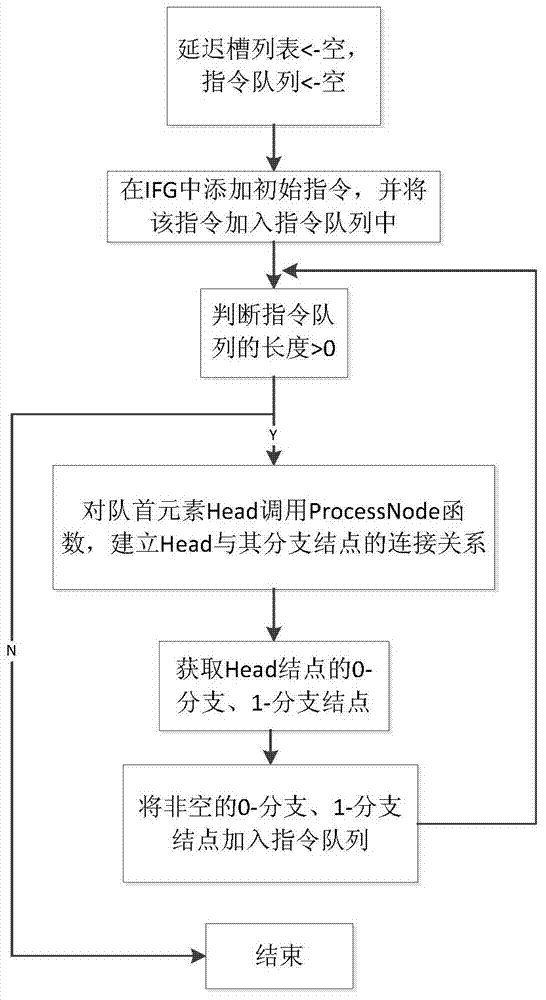
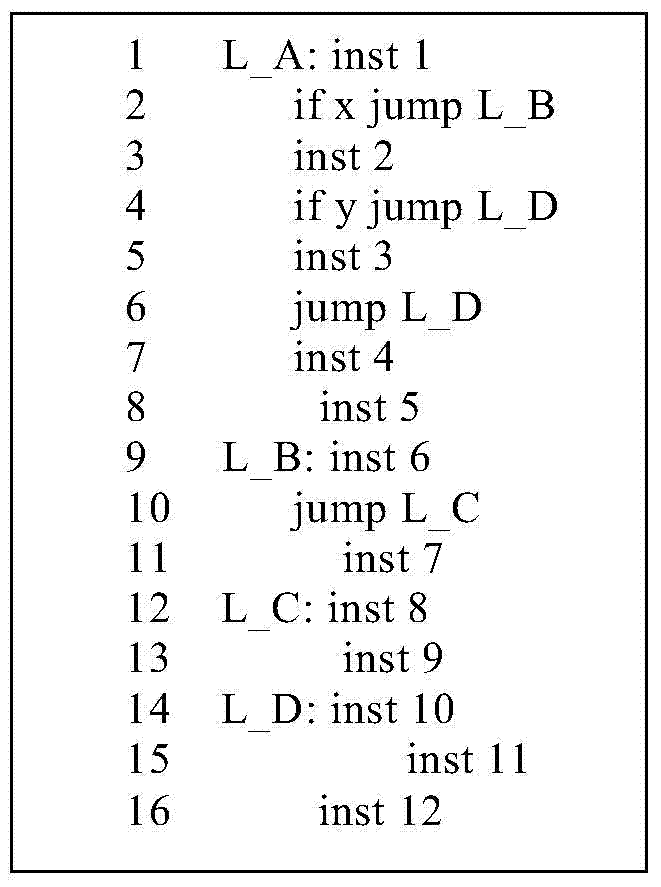
Control flow graph reconstruction method for scheduled assembly codes
InactiveCN103577242AAccurate reconstructionLess extra instructionsSpecific program execution arrangementsMemory systemsTimestampReconstruction method
The invention relates to a control flow graph reconstruction method for scheduled assembly codes. The method includes the steps that static analysis is carried out on a source program, all possible execution paths of the source program are obtained through global delay slot list information, and an instruction flow graph is built; each node in the instruction flow graph represents one instruction; all nodes in the instruction flow graph are traversed, basic blocks are built according to in-degree information and out-degree information of each node, and a control flow graph is built; on the basis of the control flow graph, each execution packet in each basic block is analyzed, and an assembly level data dependence graph is built for the execution packets; according to information of a source system structure instruction set, timestamp information of each instruction in each execution packet is determined; according to the timestamp information of each instruction, cross-block or cross-packet moving of the instructions is carried out; according to the assembly level data dependence graph, the timestamp information of each instruction is modified; according to the modified timestamp information of each instruction, the instructions are sequenced again, and therefore equivalent execution of the instructions in the source program is restored.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Large-scale graph data processing method based on k<2>-tree and multi-valued decision diagram
InactiveCN106294739ACompact structureCompact storageSpecial data processing applicationsPrimitive operationAlgorithm
The invention discloses a large-scale graph data processing method based on a k<2>-tree and a Multi-valued Decision Diagram (MDD). The method comprises the following steps: 1, performing n-bit encoding on a peak of a graph according to the rule of the k<2>-tree, FORMULA, k being greater than or equal to 2; 2, encoding an edge according to a peak code; 3, constructing an MDD structure according to an edge code to obtain a k<2>-MDD structure which corresponds to an oriented graph and contains n variables, wherein the k<2>-MDD structure has the nature of the MDD and is applicable to the simplification rule of the MDD; 4, performing the following basic operation of the graph on the obtained k<2>-MDD structure through logic operation of a symbol decision diagram: edge inquiry, outside adjacent inquiry and calculation of an out degree of the peak, inside adjacent inquiry and calculation of an in degree of the peak, as well as adding and deletion of an edge, and the like. According to the method, the MDD is used for storing graph data, so that isomorphic sub trees in the k<2>-tree are combined, the number of nodes is reduced, and the structure is more compact; the basic operation of the graph is converted into the logic operation, so that the operation is simpler.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Complex network-based object-oriented integration testing method
InactiveCN101477490AIncrease coverageReduce in quantitySoftware testing/debuggingSoftware networkIntegration testing
The invention discloses an integration test method facing objects and based on a complex network. The method comprises the following steps: (1) establishing a system structural model of detected software by adopting a unified modeling language, and stating a UML (unified modeling language) class diagram to a software network G equal to (V, E); (2) traversing the whole software network, recording the class relied by each class and the in-degree and the out-degree of the class in a tetrad; (3) first, intensively testing the class with a big in-degree and an out-degree of zero; (4) in secession, detecting the relied class utilizing the class without adding classes or a new class in each detection; and repeatedly conducting step (4) along the testing sequence relying on class hierarchy, so as to ensure that the class detected prior is superior to that detected afterwards until the system for constructing complete detected software. The invention combines complex network and the object-facing software test together, and conducts integration test to the object-facing procedures combining with the internal topology structural characteristics of the object-facing software, thereby optimizing test cases and reducing test work load.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
Network negative information impact minimization method based on topic model
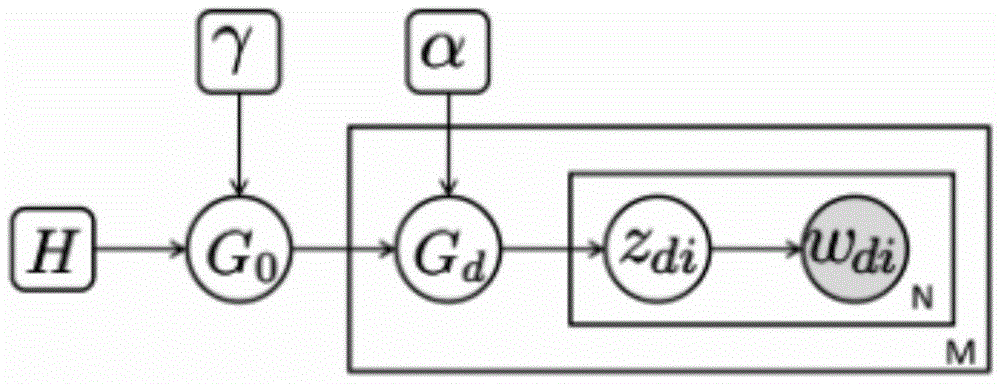
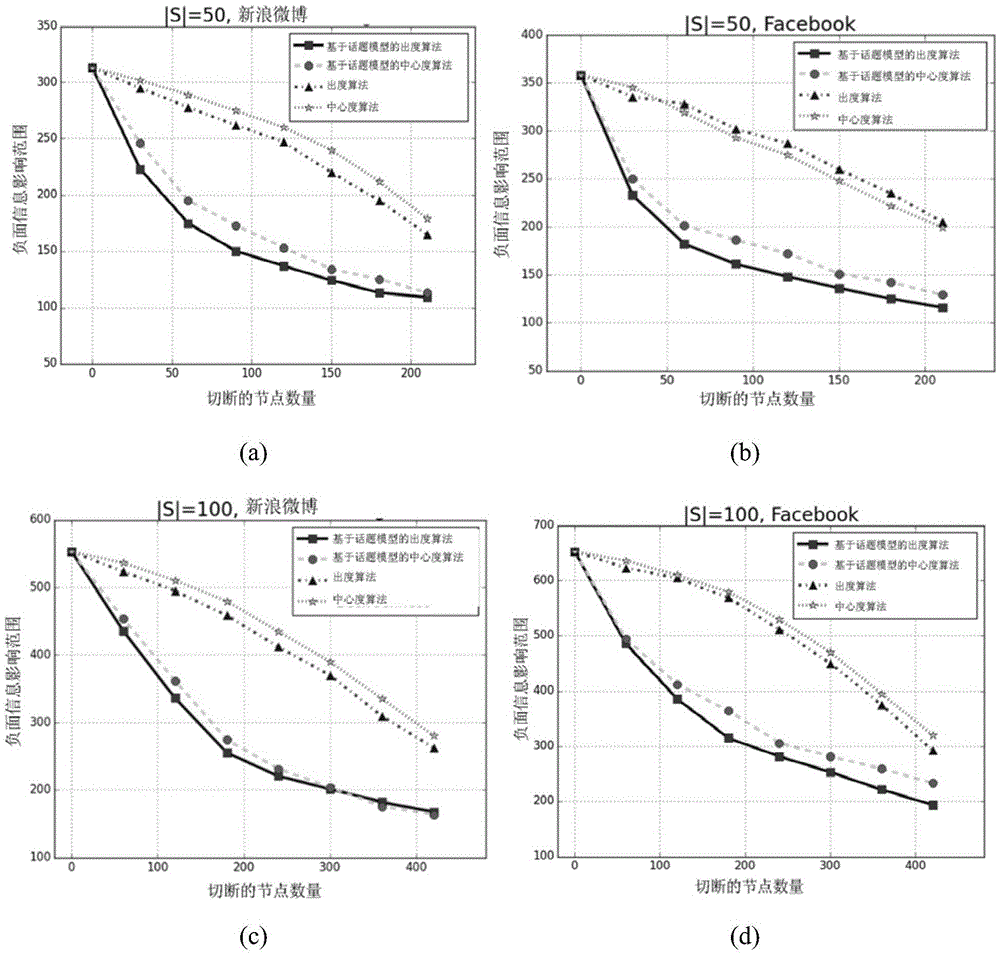
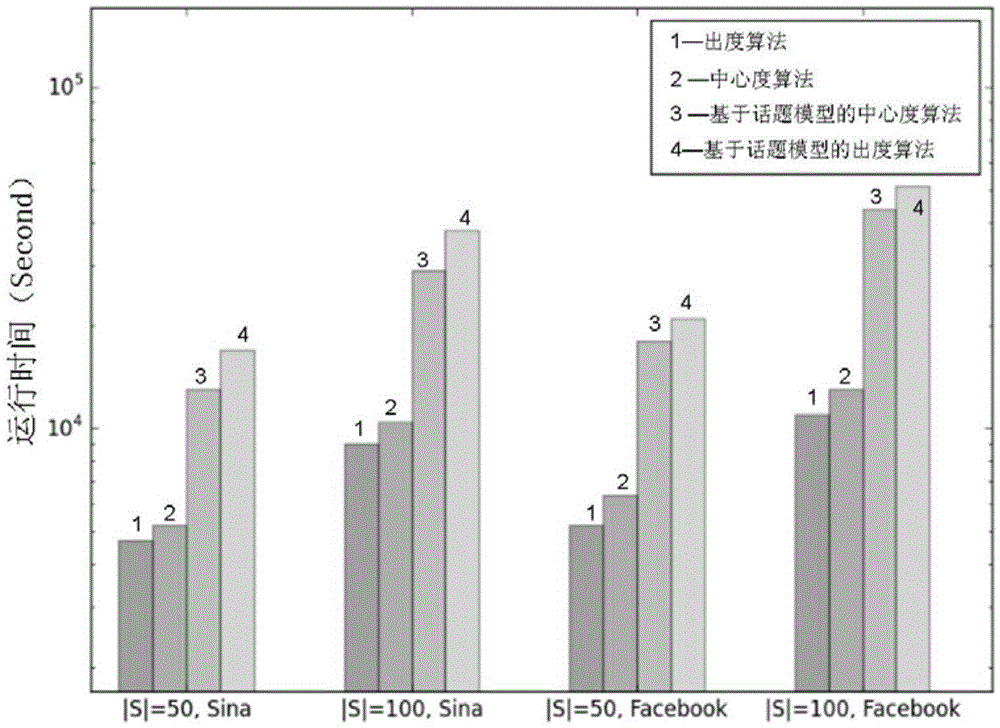
ActiveCN105468681ASmall area of influenceGood effectData processing applicationsSpecial data processing applicationsOut degreeTopic model
The invention relates to a network negative information impact minimization method based on a topic model. The network negative information impact minimization method comprises the following steps: 1) adopting a directed graph to express the propagation of information in a social network, and independently calculating the probability distribution of the negative information and the probability distribution of historical information on each edge through the topic model; 2) independently calculating a distance, i.e., KL (Kullback-Leibler) divergence d(w,i), between the probability distribution of the negative information and the probability distribution of historical information on each edge, wherein d expresses a calculation result of the KL divergence, w expresses the topic distribution of the historical information, and i expresses the topic distribution of the negative information; 3) calculating tb(w)=b(w) / d(w,i) and to(w)=o(w) / d(w,i), wherein b(w) and o(w) are independently the calculation results of a centrality algorithm and an out-degree in-degree algorithm and are sorted from big to small, and the first k nodes are removed to minimize the propagation range of the negative information. The method disclosed by the invention can effectively control the social network of which the malicious information is burst, and greatly reduces an impact range of the negative information.
Owner:INST OF INFORMATION ENG CAS
Method for realizing webpage fading-in and fading-out in browser
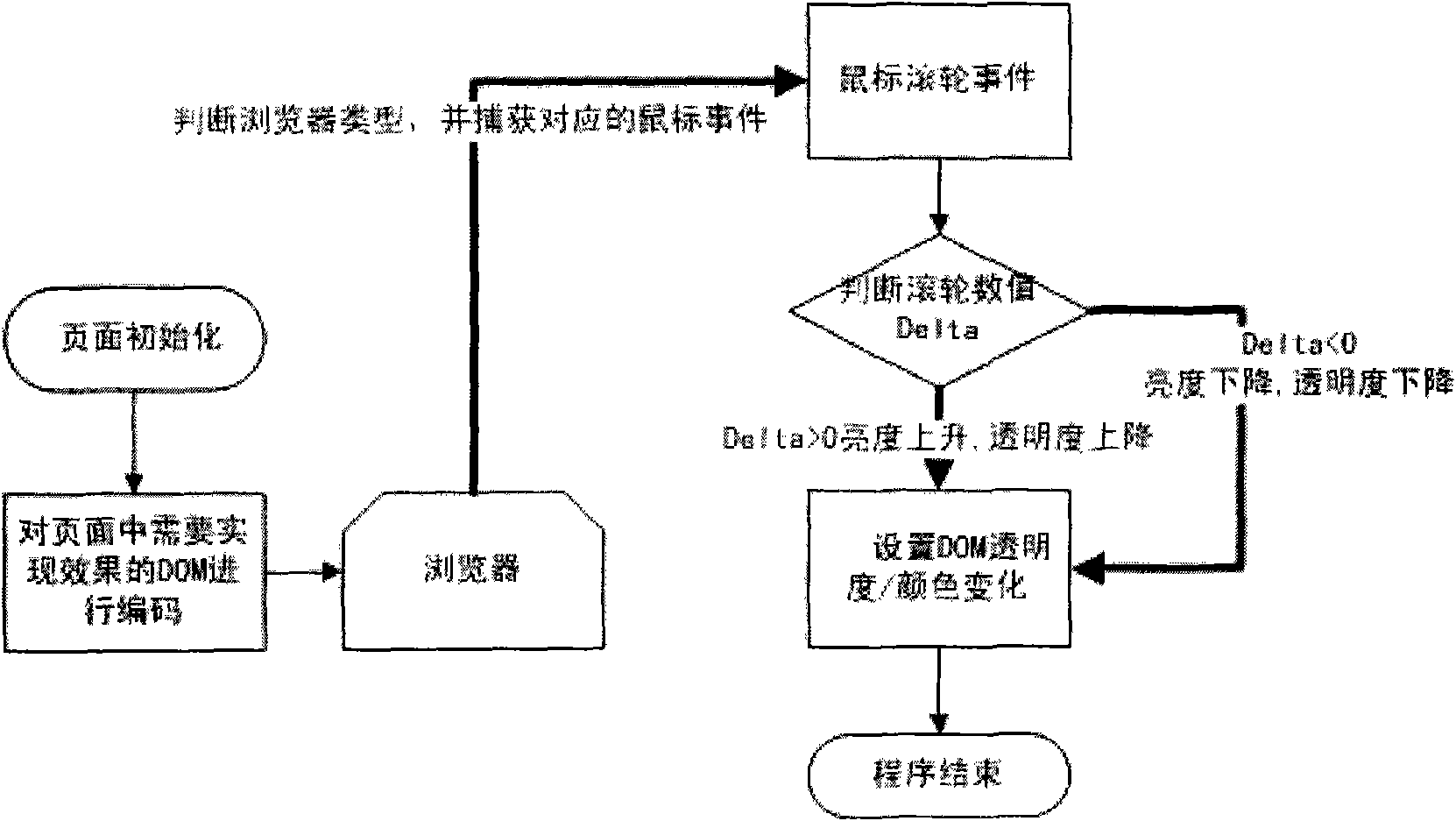
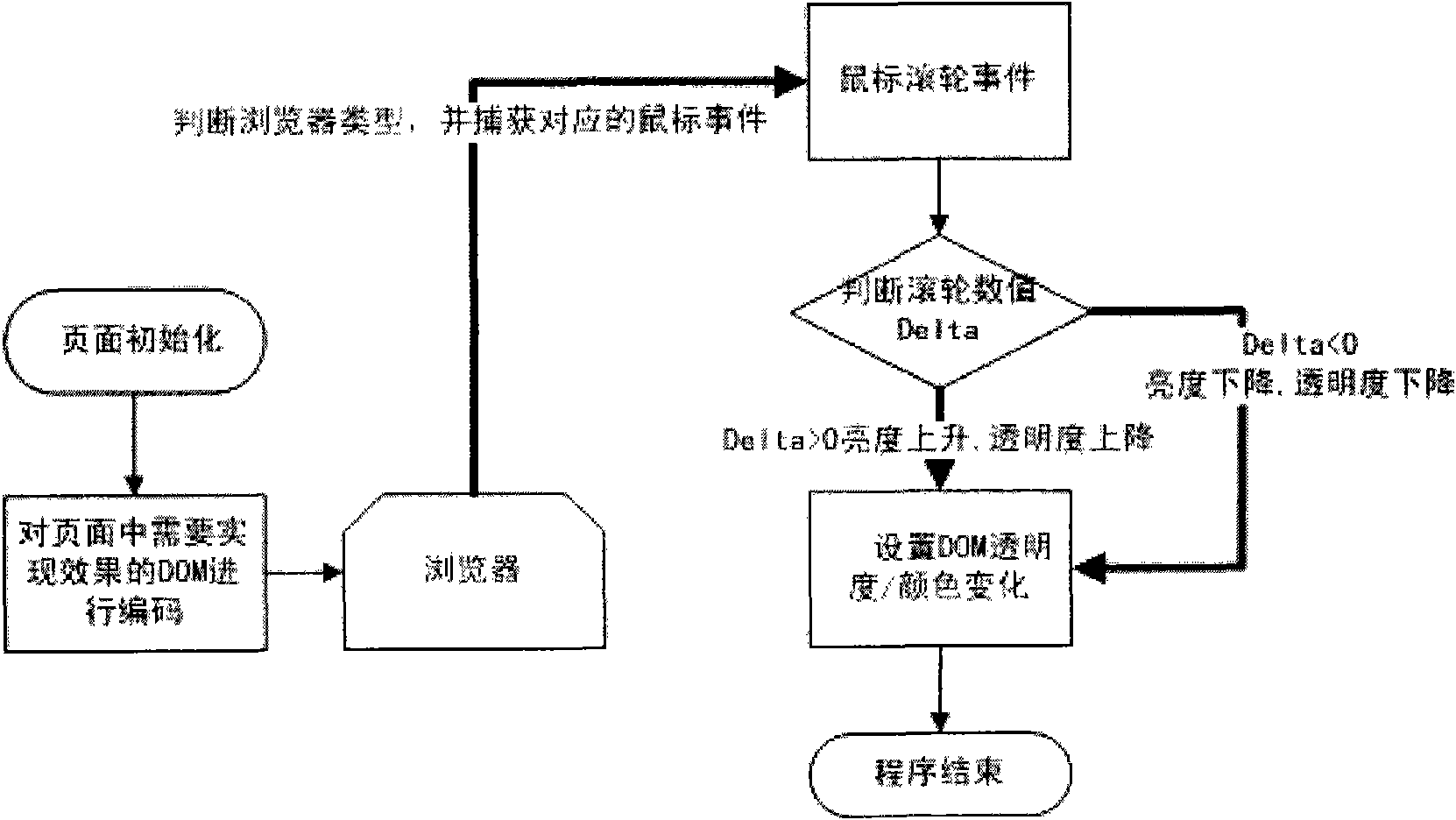
InactiveCN101794284ATo achieve the invisible effectSpecial data processing applicationsUnique identifierOut degree
The invention relates to a method for reazlizing webpage fading-in and fading-out in a browser, which comprises the following steps: coding a page element needing the effect, setting a unique identifier, and coding areas to be realized into a DOM layer in a unified way; judging the type of the browser of a terminal user, and responding to a corresponding user mouse roller event; responding to the mouse roller through JavaScript and an event handler; setting initial testing value variables of the roller and event variables; setting a parameter representing a roller rolling distance for an roller rolling event; calculating a fading-in and fading-out degree according to the roller rolling distance; calculating the value of color or transparency to be reached for the control according to the fading-in and fading-out degree to be reached; obtaining the color to be reached for the control according to the transmission value of the roller rolling event and the background color of the upper-layer page element; and changing the background color of the elements of the page into the color to be reached or changing the transparency of the element.
Owner:上海纽融视科技有限公司
Intelligent peer-to-peer media streaming
ActiveUS8477658B2Speed up the flowMultiple digital computer combinationsNetworks interconnectionOut degreePeer-to-peer
Owner:THE HONG KONG UNIV OF SCI & TECH
Construction method of Euler diagram and method for optimizing test sequence based on method
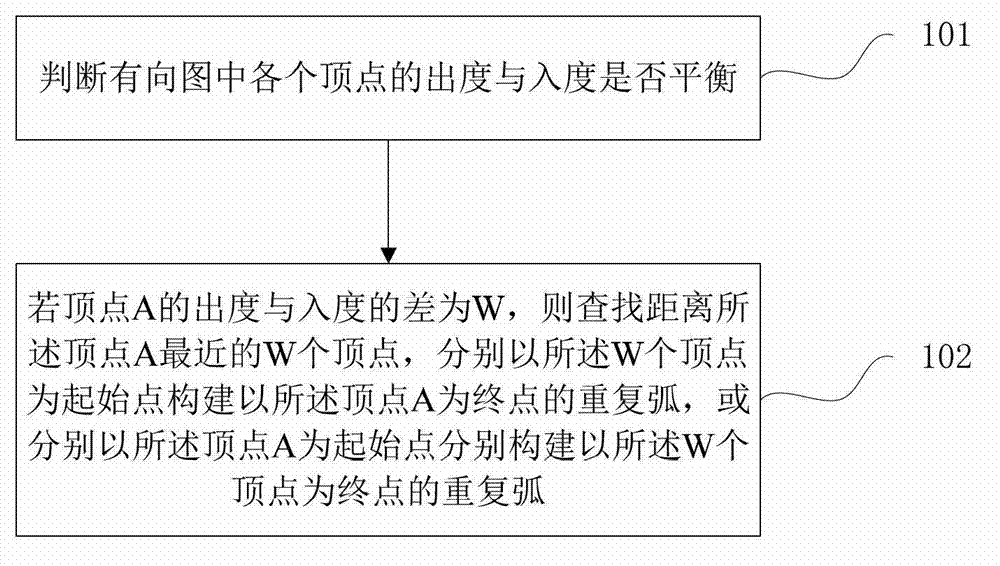
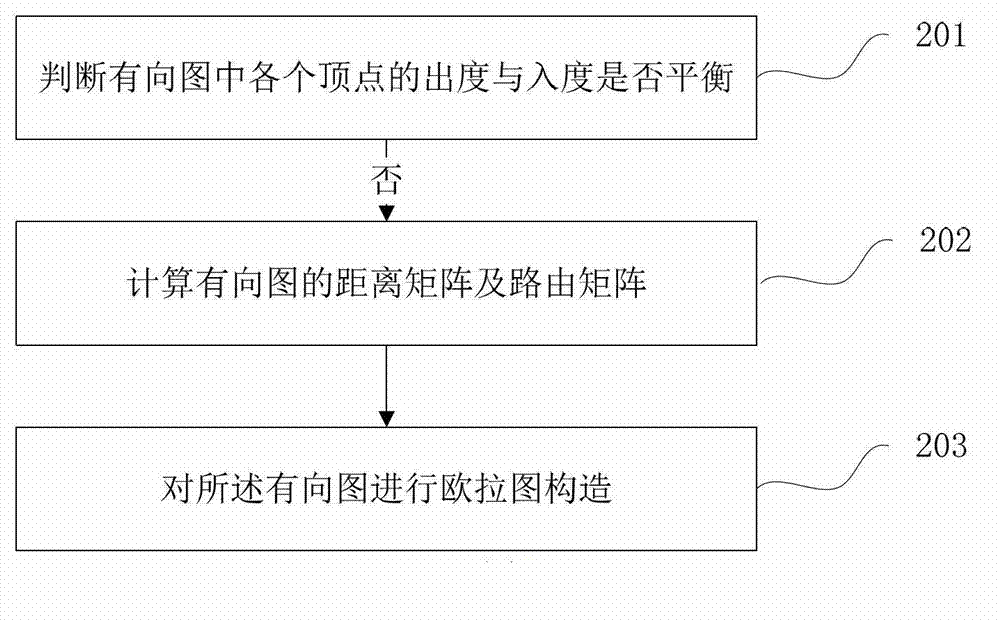
ActiveCN103049656AReduce usageImprove efficiencySpecial data processing applicationsTheoretical computer scienceOut degree
The invention discloses a construction method of Euler diagram and a method for optimizing test sequence based on the method, wherein the construction method of Euler diagram comprises the following steps: judging whether out-degree and in-degree of each peak in the digraph are balanced, wherein arcs among all peaks in the diagraph have access directions, the out-degree is total number of arcs by using the current peak as a beginning point, and the in-degree is the total number of arcs by using the current peak as an ending point; if the difference between the out-degree and the in-degree of the peak A is W, searching W peaks mostly close to the peak A, respectively using W peaks as beginning points to construct repeated arcs by using the peak A as an ending point, or respectively using the peak A as the beginning point to respectively construct repeated arcs by using W peaks as ending points. Through the method disclosed by the invention, the use of auxiliary space is reduced, and the efficiency of Euler diagram construction is improved.
Owner:CHINA ACADEMY OF RAILWAY SCI CORP LTD +3
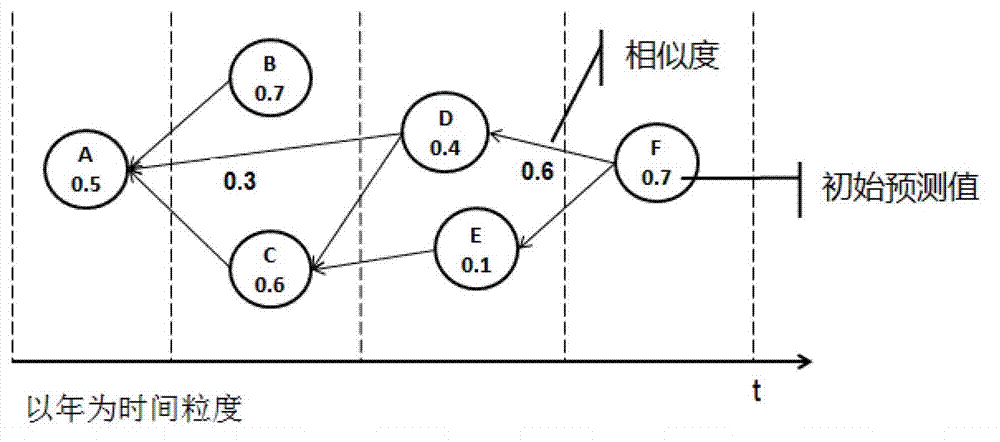
Patent introduction predicted value calculation method
The invention discloses a patent introduction predicted value calculation method. The method comprises the following steps of: firstly, extracting main characteristics influencing patent introduction, wherein the main characteristics relate to write quality, novelty, technology trend, an inventor and an agent; then constructing a classifier according to historical data and patent characteristic values, calculating an initial patent introduction predicted value, constructing a patent citation network according to the similarity of patents, initializing the patent introduction predicted value of each node, and iteratively calculating the introduction predicted value of a target patent according to the nodes citing the patent as well as the introduction predicted values, out-degrees and in-degrees of patents cited by the nodes based on an idea similar to a Hits algorithm; subsequently, acquiring an interested patent set of a user based on keyword search in combination with the patent characteristics; and finally, displaying a search result in a descending order of the introduction predicted values of the patents in the patent set, and recommending the patents with high introduction possibility to the user. The patent introduction predicted value calculation method provided by the invention has the advantages of high effectiveness and timeliness.
Owner:WUHAN UNIV
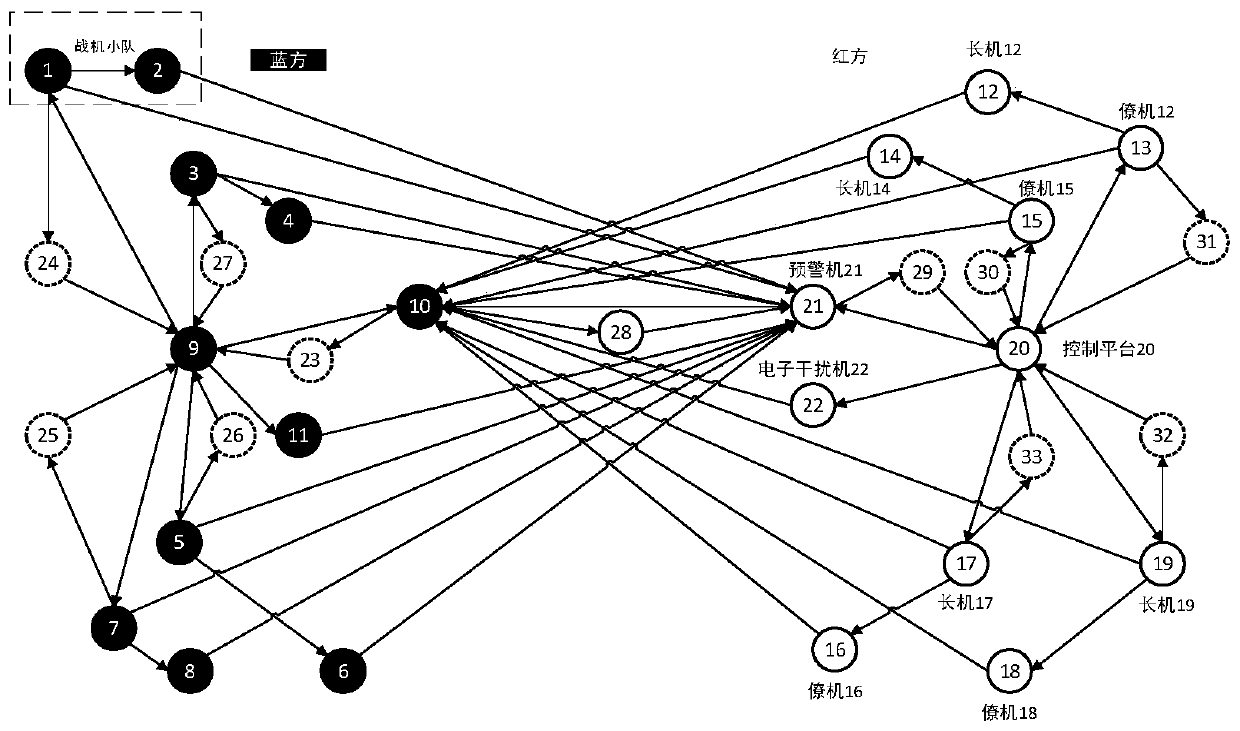
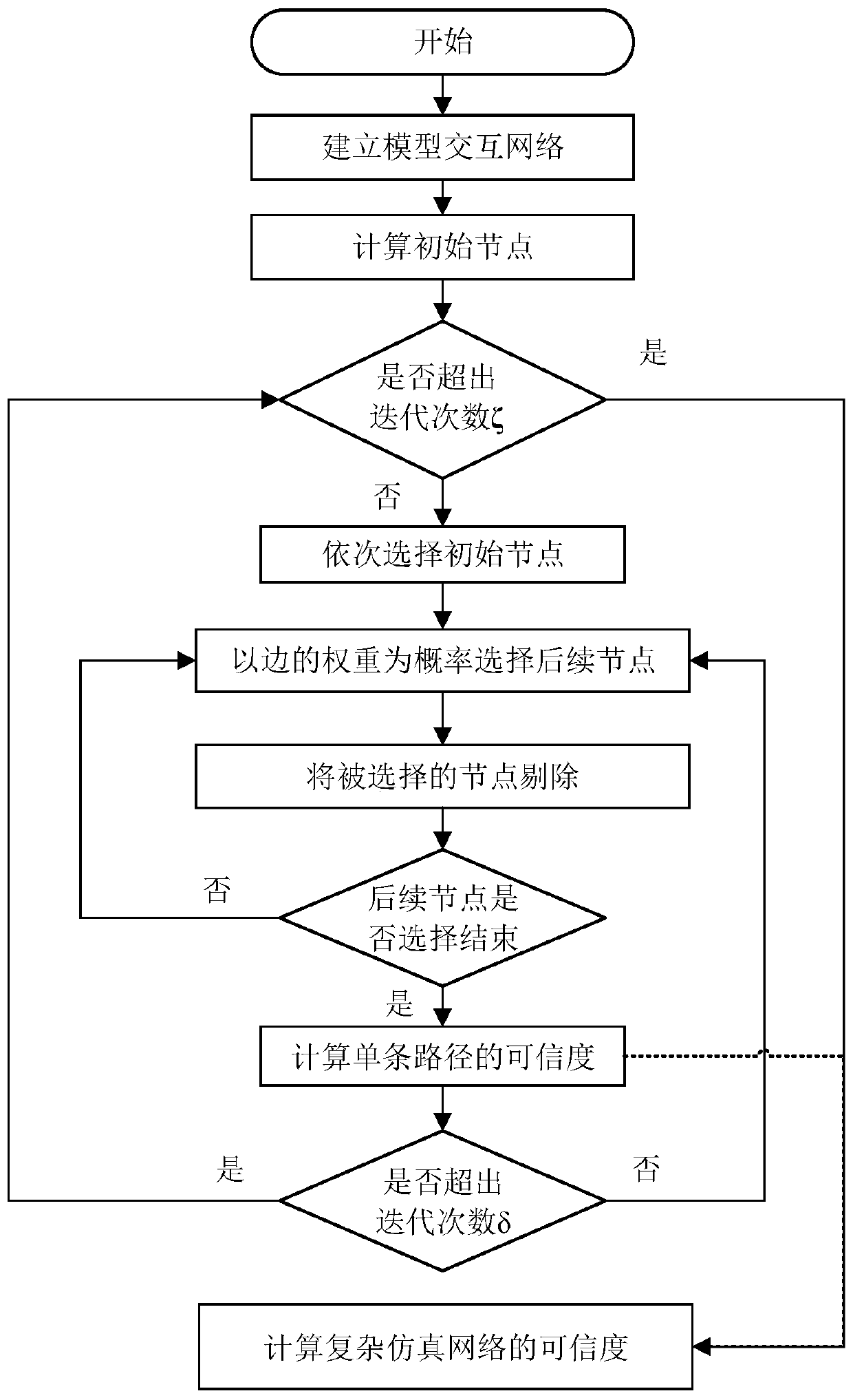
Complex simulation system credibility evaluation method based on network topology path
ActiveCN109960863AMethod objectiveSolving the problem of difficult-to-quantify credibilityDesign optimisation/simulationSpecial data processing applicationsNODALParallel computing
The invention discloses a complex simulation system credibility evaluation method based on a network topology path, and belongs to the field of system simulation. And under the condition that the nodecredibility of the single model is known, the credibility of the whole complex simulation system is quantified. The method comprises the following steps: firstly, analyzing an information interactionrelationship between component models in the complex simulation system, calculating weights of edges between nodes according to objective indexes, and abstracting the complex simulation system into adirected weighted model interaction network; and calculating the out-degree of each node in a model interaction network, selecting a node with a relatively high out-degree as an initial node, starting from the initial node, obtaining different single execution paths, calculating the credibility of the single execution path, and integrating the credibility of all the execution paths to obtain thecredibility of a simulation system. Aiming at a complex equipment simulation system with the characteristics of complex mechanism, complex input and output variables, strong uncertainty and the like,the invention solves the problem that it is difficult to carry out quantitative analysis on evaluation of the credibility of the complex equipment simulation system.
Owner:BEIHANG UNIV
Modeling directed scale-free object relationships
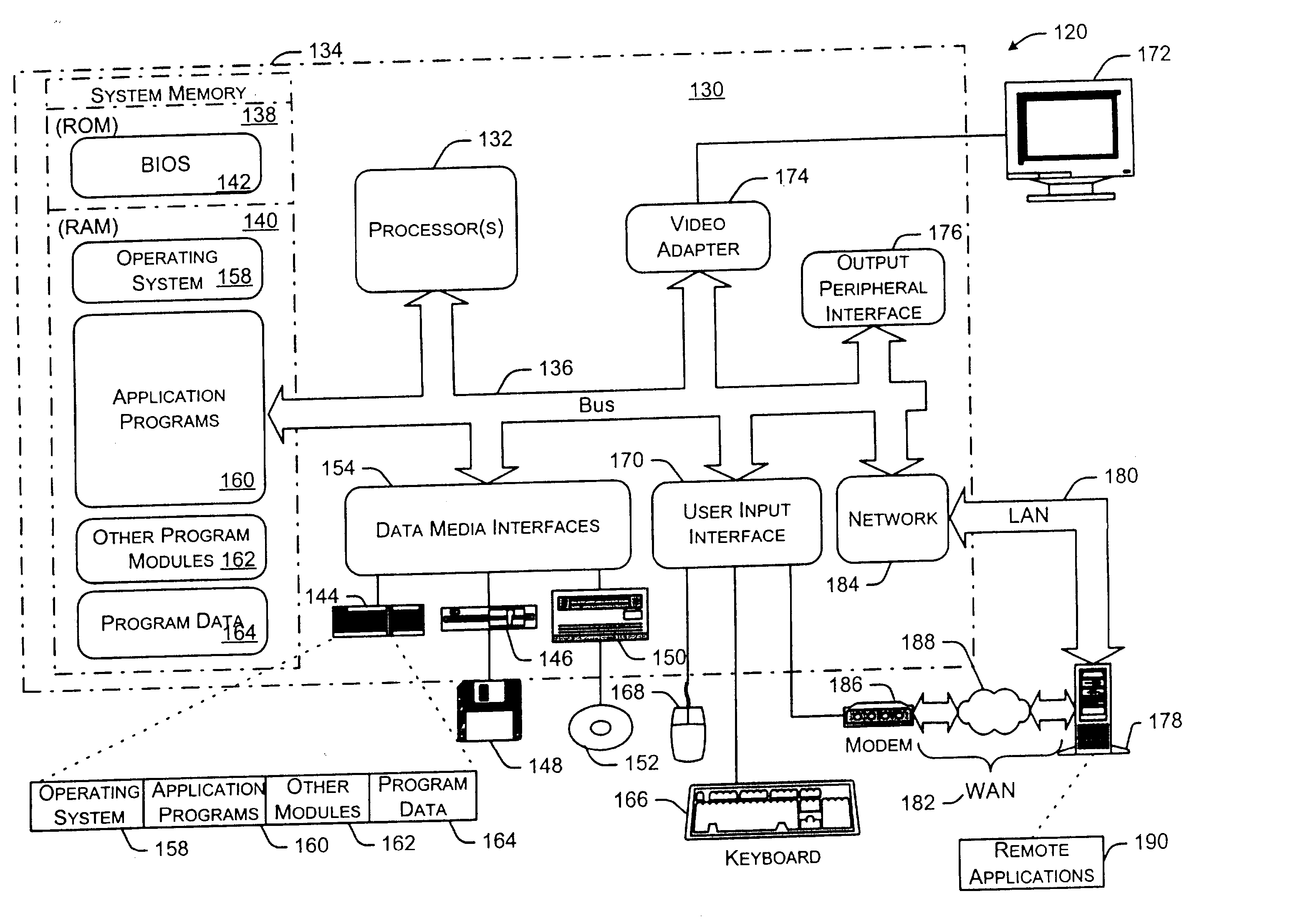
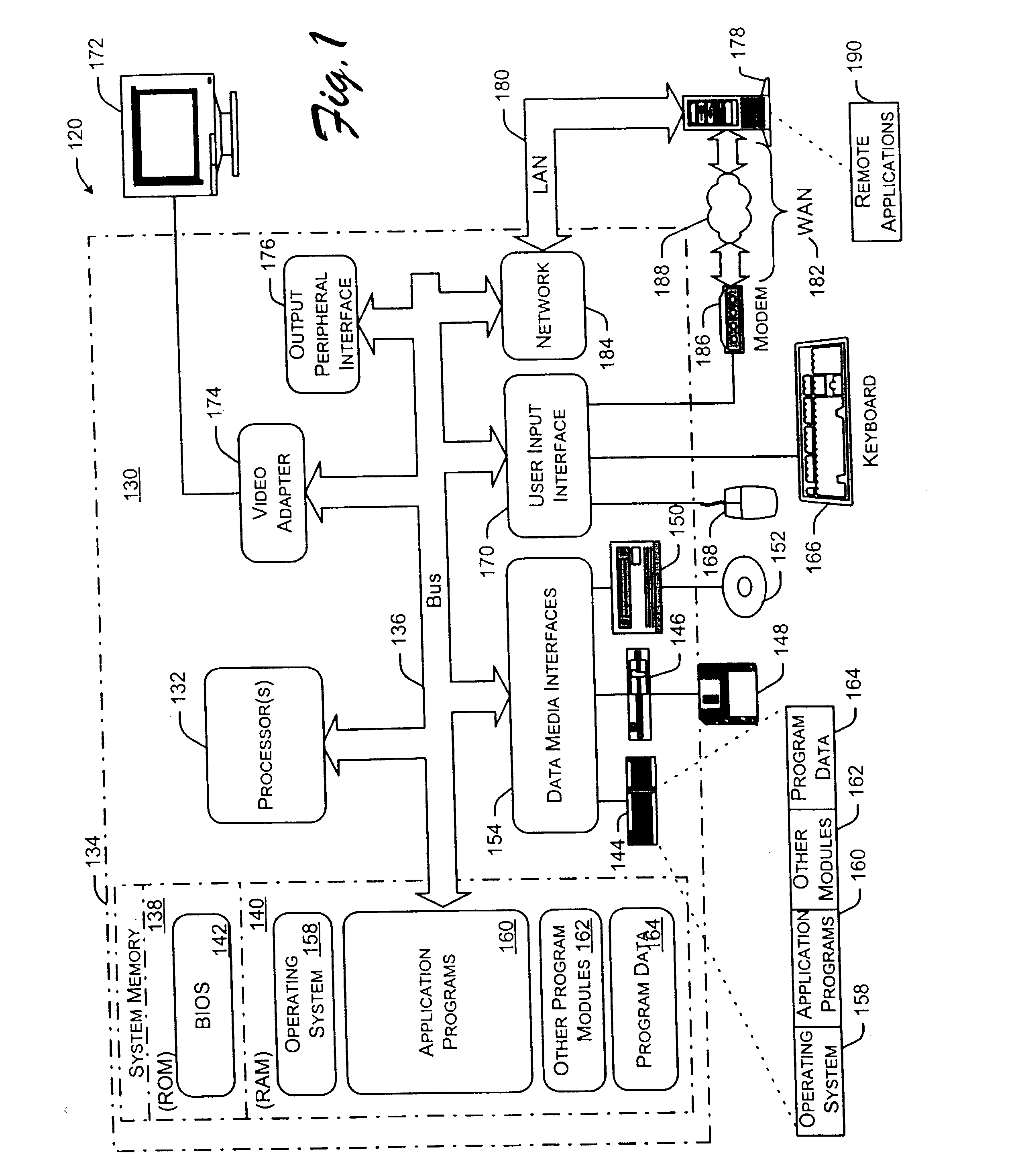
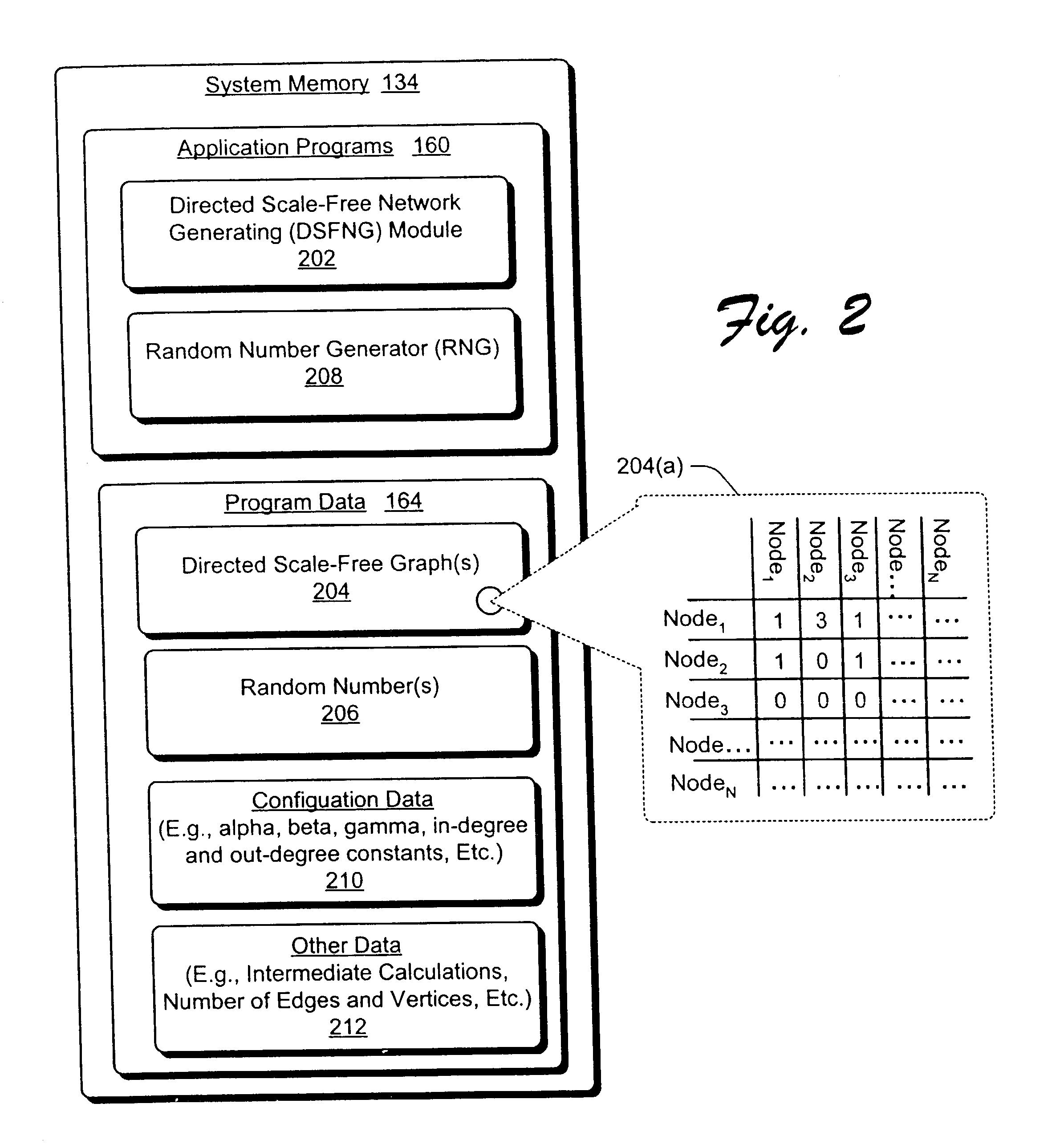
InactiveUS20050021316A1Character and pattern recognitionComputation using non-denominational number representationGraphicsAlgorithm
Systems and methods for generating models of directed scale-free object relationships are described. In one aspect, a sequence of random numbers is generated. Individual ones of these random numbers are then selected over time to generate the directed scale-free object relationships as a graph based on sequences of in-degrees and out-degrees.
Owner:MICROSOFT TECH LICENSING LLC
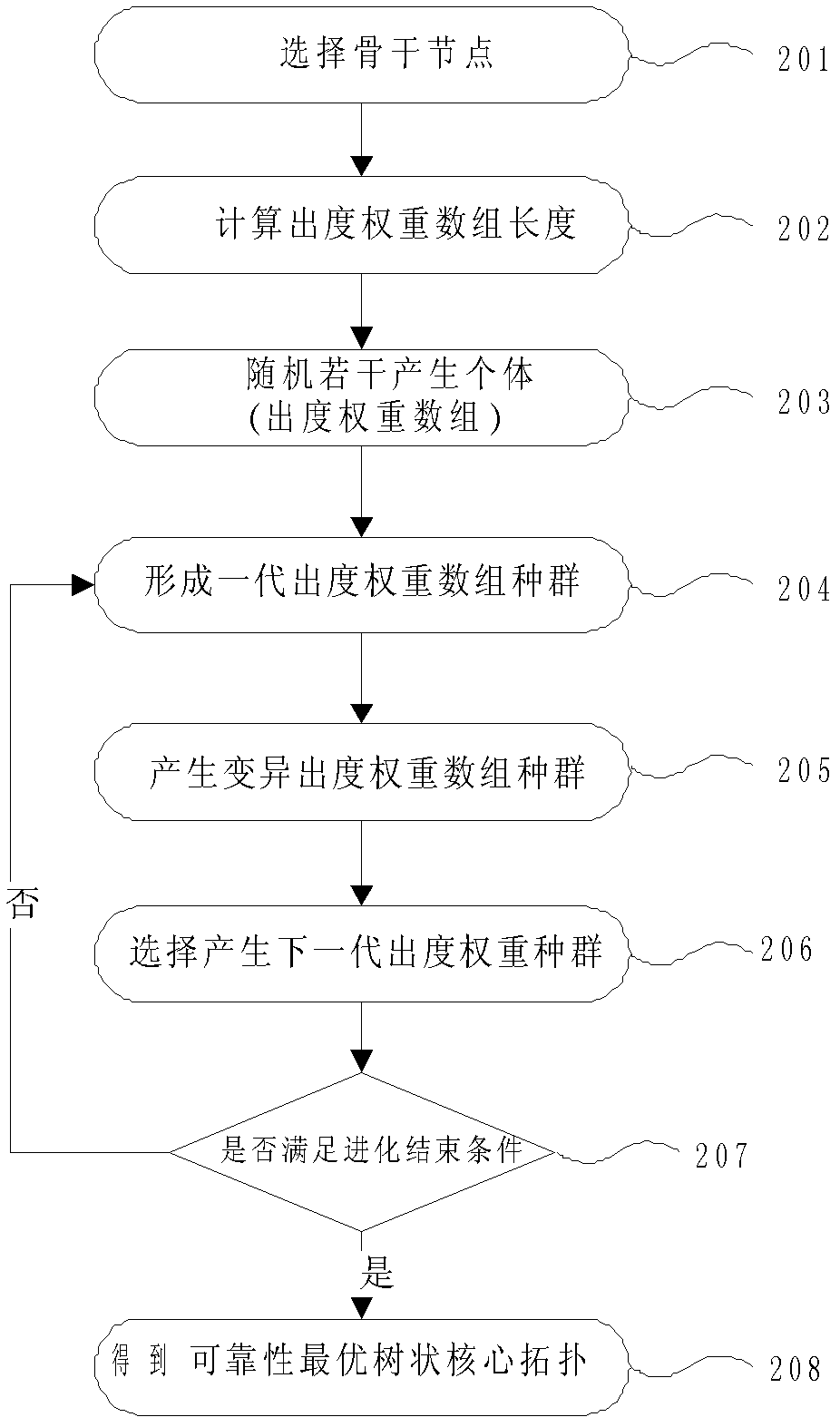
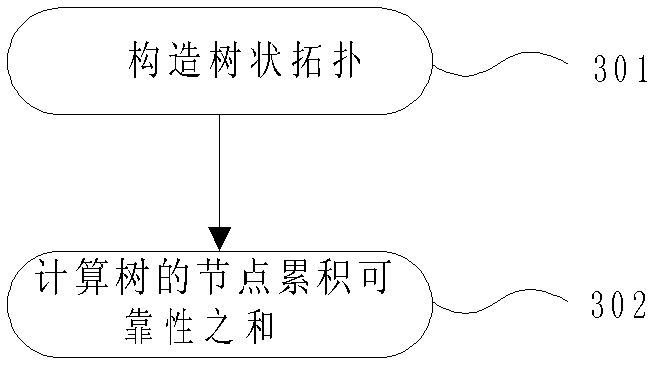
Reliability optimal tree-shaped core topological solving method of P2P live broadcast covering network
InactiveCN102624596AImprove applicabilityImprove applicability, that is, give full play to the high efficiency of tree topologyStar/tree networksArray data structureOut degree
The invention aims at providing a reliability optimal tree-shaped core topological solving method of a P2P live broadcast covering network, which comprises the steps of: converting out-degree and reliability of a backbone node of the P2P live broadcast covering network into weighting reliability through hierarchical out-degree weighting, constructing a tree-shaped core topology by layers by using the weighting reliability as a sequencing basis; optimizing a hierarchical weight set by using an evolutionary programming algorithm, and solving by using the sum of accumulated reliability of all nodes in an evolution process as an evolution index to obtain a tree topology with optimal reliability. According to the reliability optimal tree-shaped core topological solving method of the P2P live broadcast covering network, provided by the invention, the stability of the P2P live broadcast covering network is improved, and the live broadcast time delay is reduced.
Owner:ZHEJIANG UNIVERSITY OF MEDIA AND COMMUNICATIONS
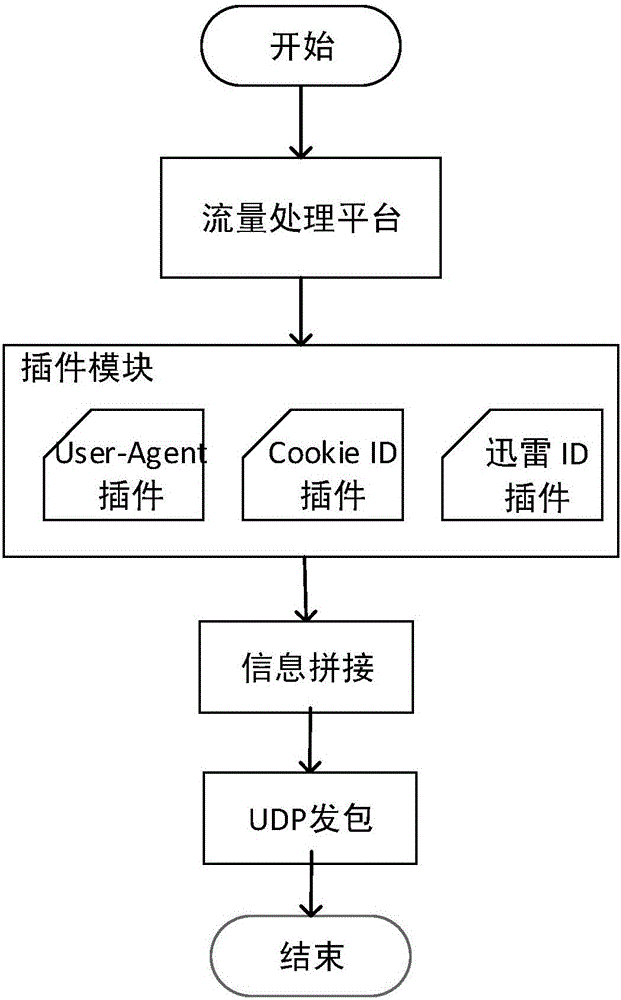
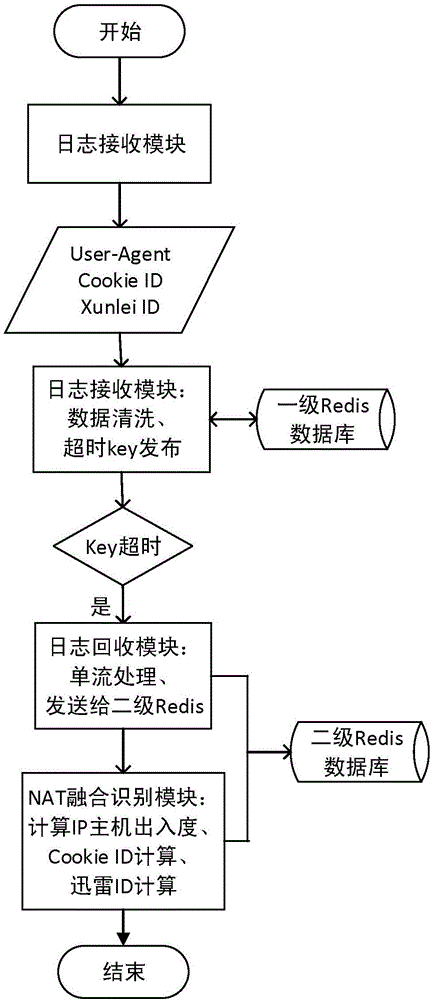
NAT detection method based on converged user behavior and Thunder ID
The invention discloses an NAT detection method based on converged user behaviors and Thunder ID. The method comprises the following steps: (1) enabling a traffic processing platform to extract the User-Agent, Cookie ID and Thunder ID information from the captured network traffic, and splicing the extracted information to an JSON string; (2) loading and balancing the JSON string to a corresponding server in the traffic processing platform for processing according to quintuples of the network traffic; and (3) enabling the server to classify the data according to the quintuples, and when determining that the TCP flow corresponding to a certain quintuple ends, on-line processing the TCP flow, wherein the on-line processing method comprises the following steps: calculating the host out-degree and host in-degree of the client IP according to the quintuples, determining the NAT attribute of the client IP, and calculating the host scale of the client IP. According to the NAT detection method disclosed by the invention, a large number of IP attributes can be calibrated, and the NAT scale can be accurately determined.
Owner:INST OF INFORMATION ENG CAS
Fountain encoding and decoding method for forward error correction of binary erasure channel
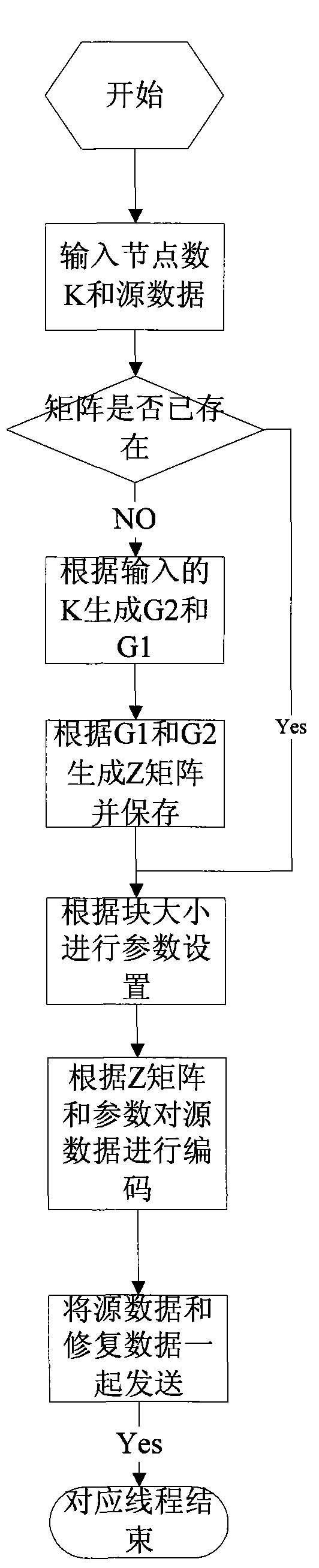
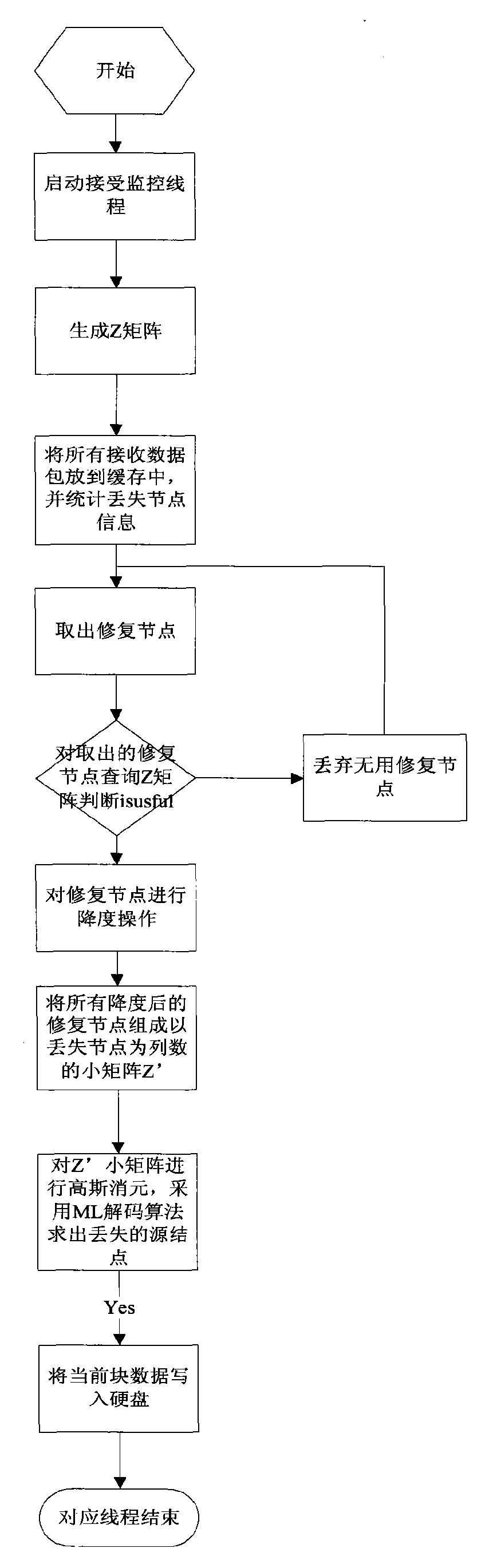
ActiveCN101630999ASmall footprintTime taken is smallError preventionCode conversionEncoding algorithmForward error correction
The invention relates to a fountain encoding and decoding method for forward error correction of a binary erasure channel, and the encoding method does not need to calculate intermediate nodes while maintaining output which is the same with the traditional Raptor Codes encoding algorithm and directly calculates check nodes through a generator matrix, thereby being high efficient and simple. The decoding method does not need to calculate the intermediate nodes while maintaining redundancy rate which is the same with the traditional Raptor Codes, and the size of a matrix Z'N'*k which is constituted by carrying out degree reduction on repair nodes is only linearly correlated with the product of the packet loss rate of the binary erasure channel and the number of source nodes, thereby being more efficient and simple in comparison of the matrix ZN*K with the size which is linearly correlated with data of the source nodes, and the matrix ZN*K needs to be processed during the traditional Raptor Codes decoding.
Owner:SPACE STAR TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com