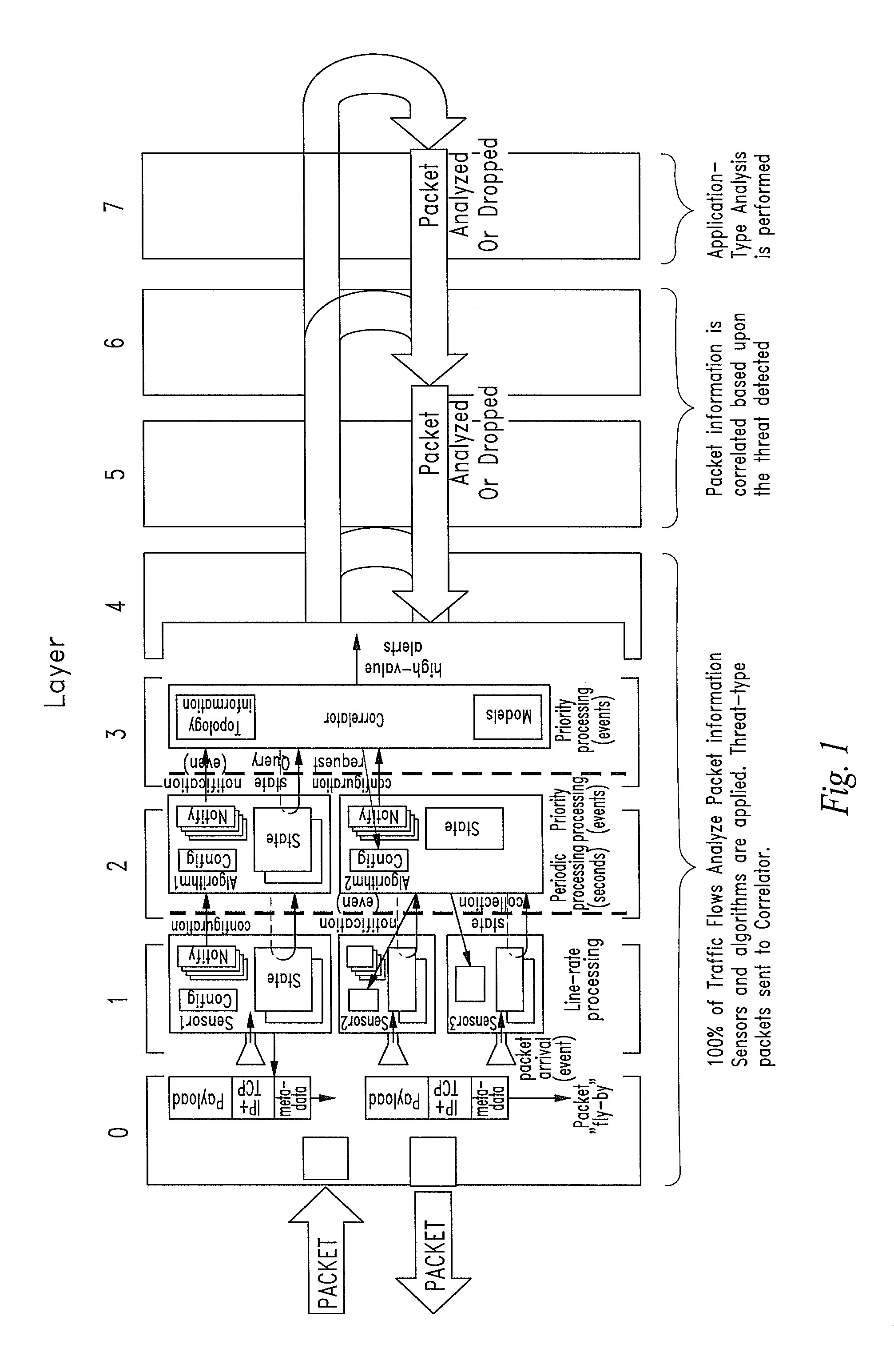
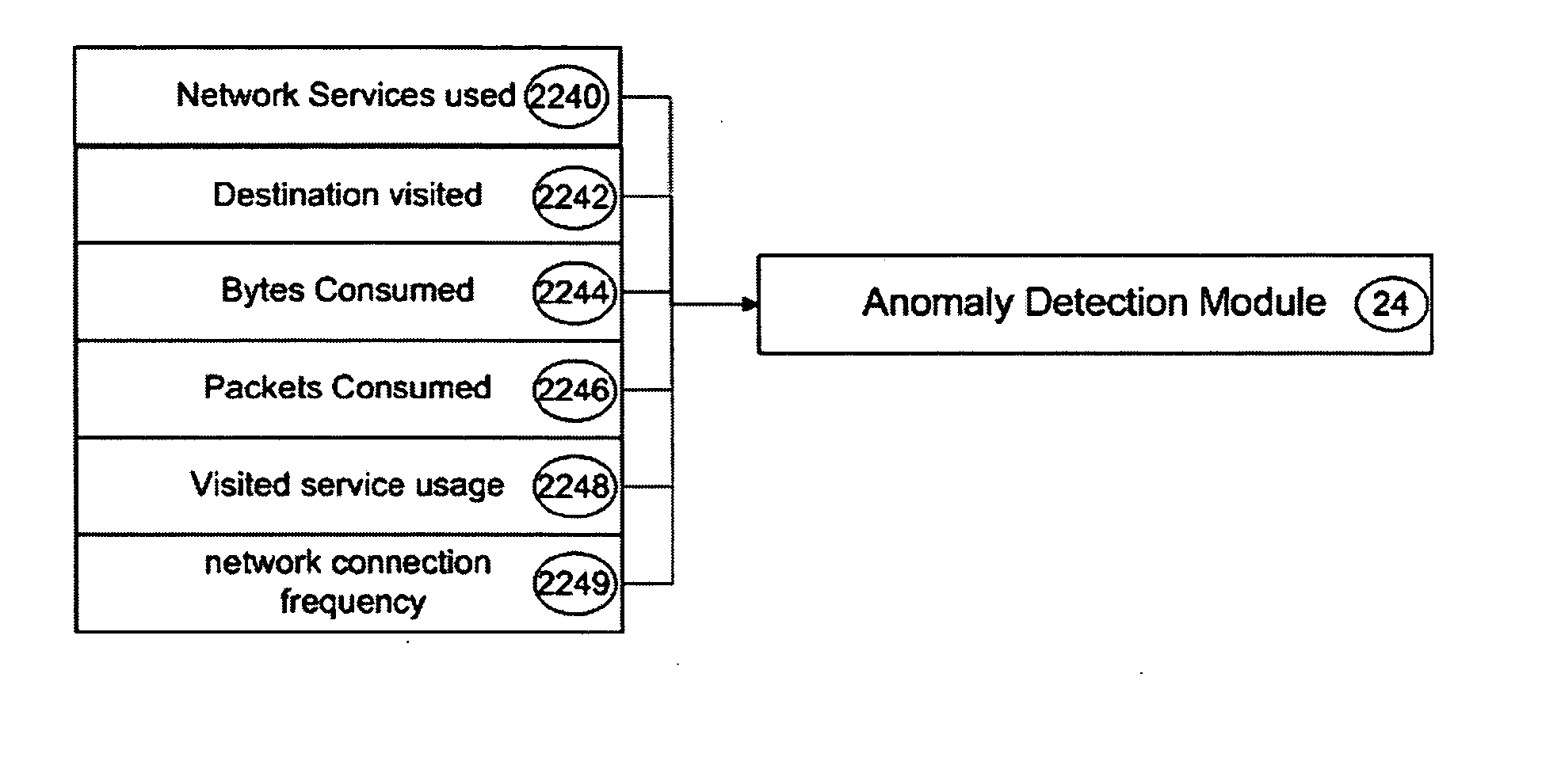
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1036 results about "Network behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network behavior analysis (NBA) is a way to enhance the security of a proprietary network by monitoring traffic and noting unusual actions or departures from normal operation.
Method, a device and computer program products for protecting privacy of users from web-trackers
InactiveUS20170142158A1Protect user privacyPrivacy protectionTransmissionSecurity arrangementWeb siteNetwork behavior
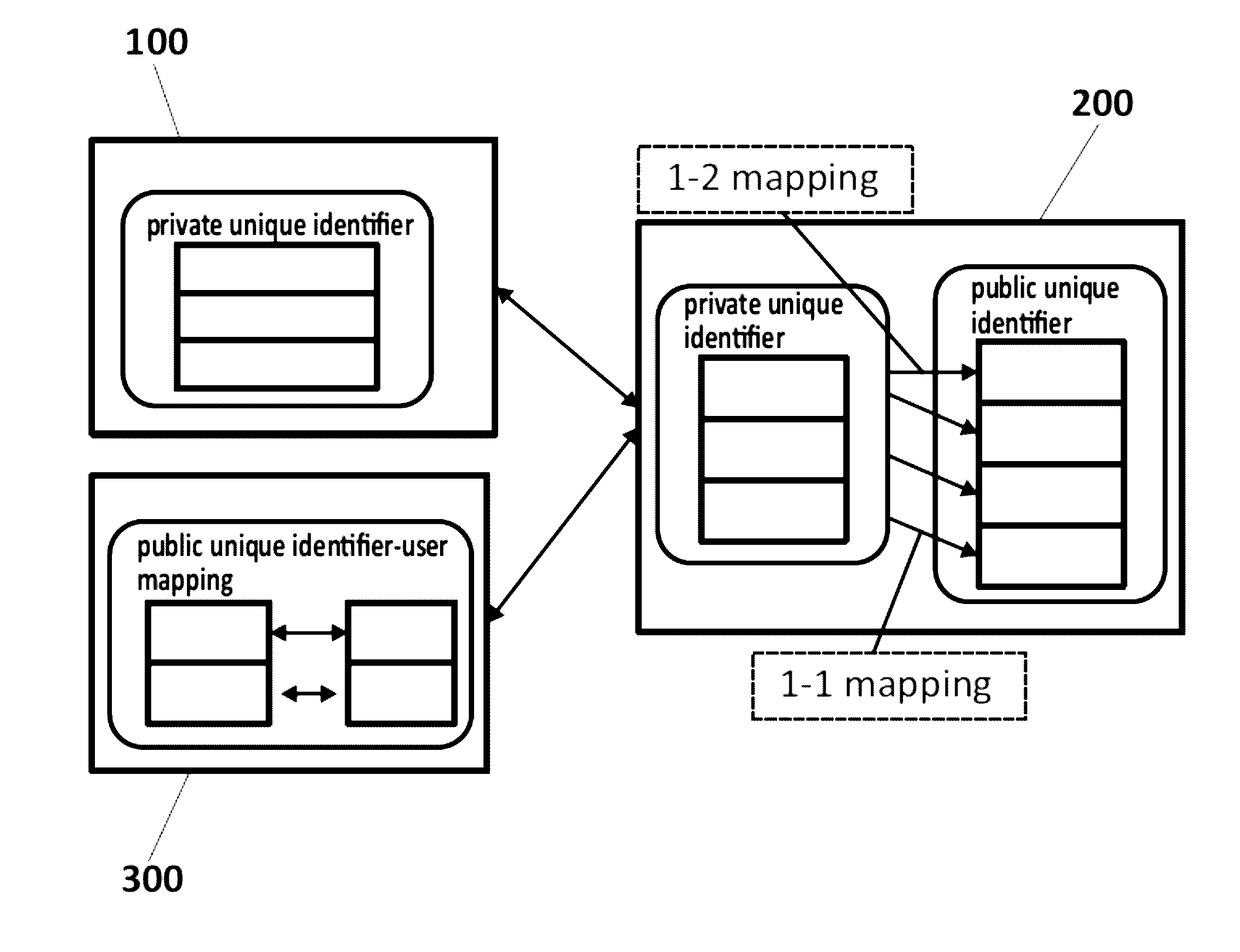
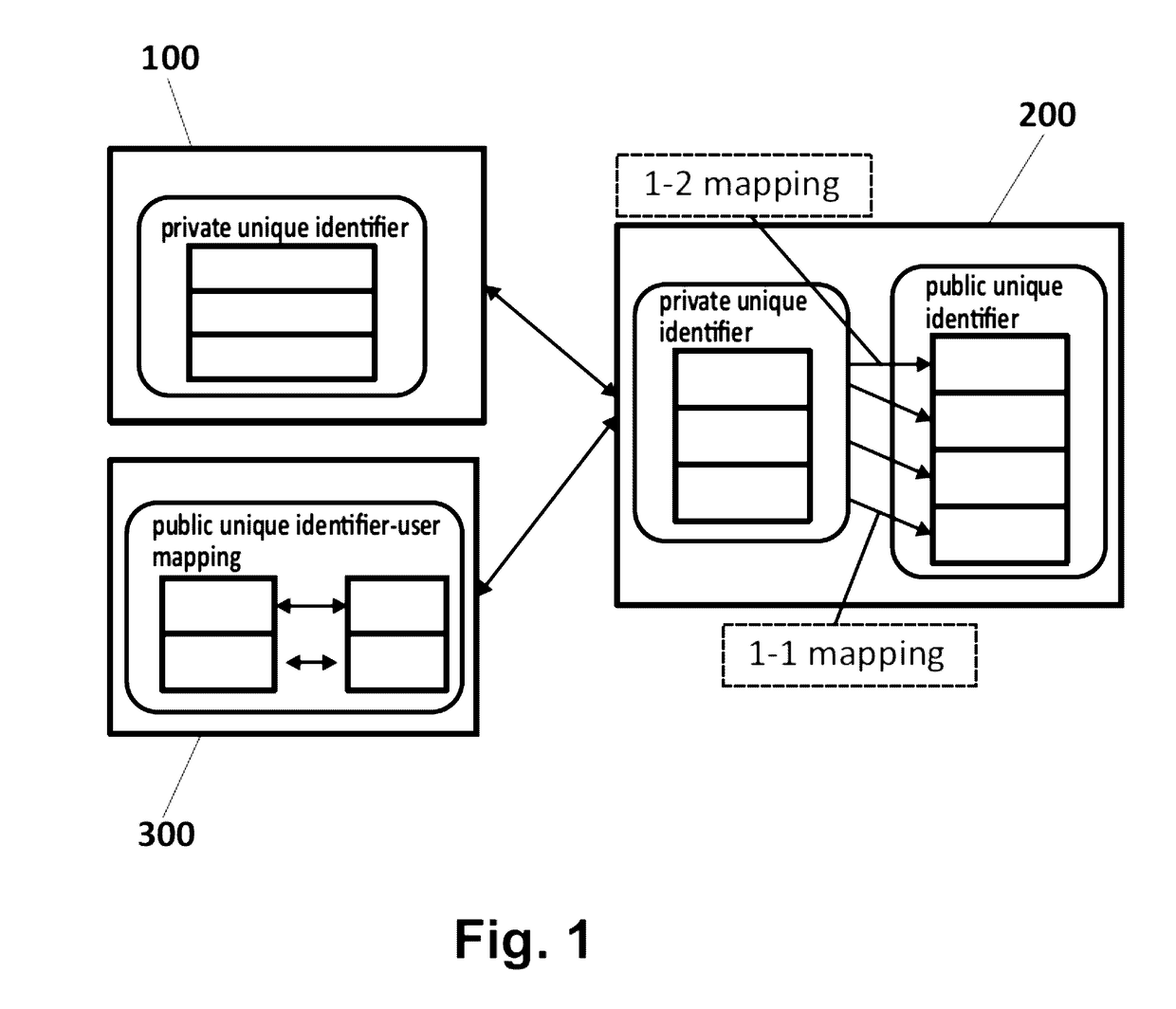
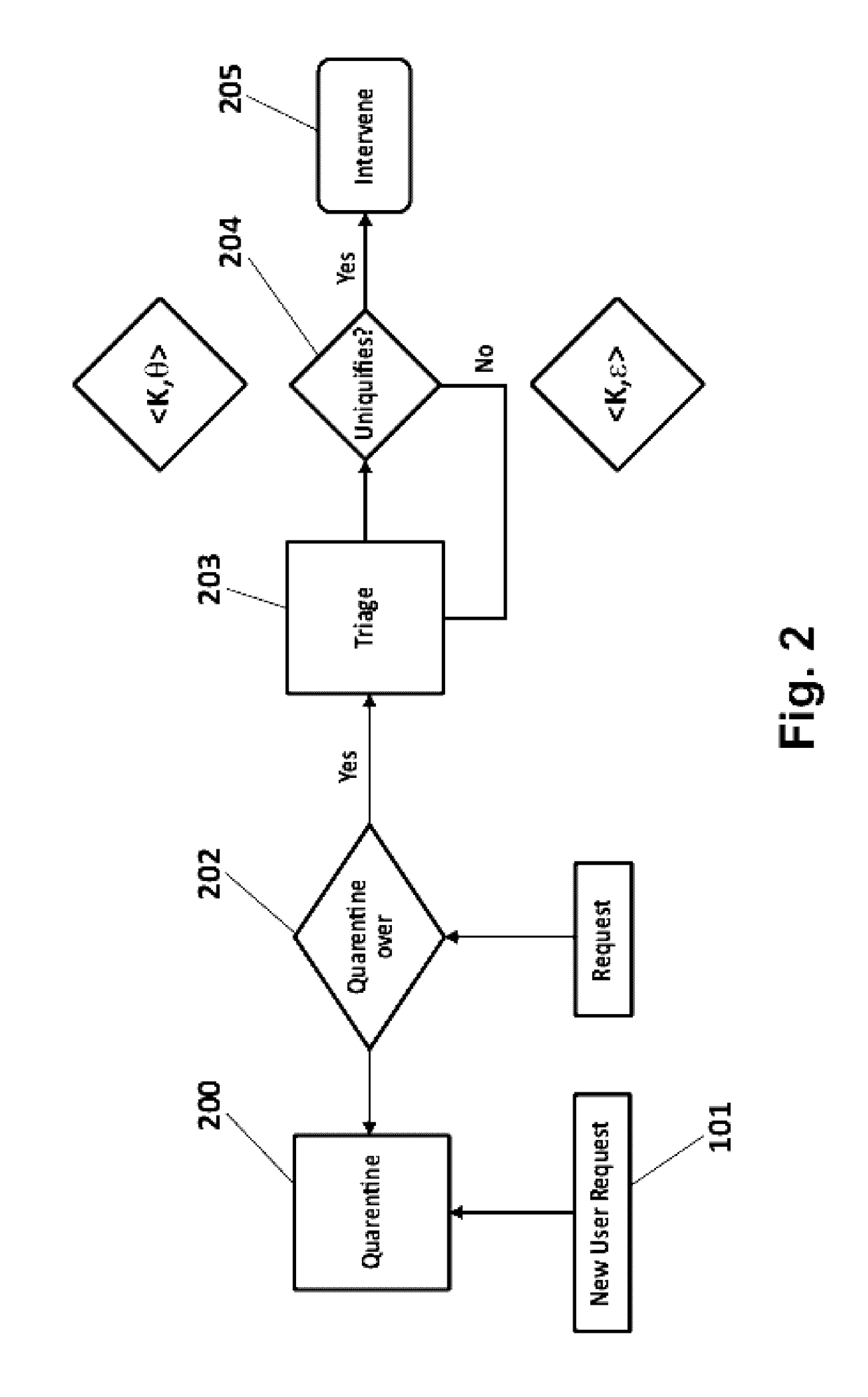
A method, a device and computer program products for protecting privacy of users from web-trackersThe method comprising:capturing and removing a public unique identifier set by a Website (300) in a computing device (100D) of a user (100);monitoring, during a first time-period, web-requests the user (100) makes to obtain a web-behavioral profile of the user (300), and storing the obtained web-behavioral profile as a first vector;tracking, during a second time-period, the web-requests to examine the effect each web-request has on assisting the de-anonymization of the user (100), obtaining a second vector;classifying, the obtained second vector taking into account a computed similarity score parameter;creating and mapping, a corresponding private unique identifier for said captured public identifier; andexecuting, based on said mapping between the private and the public unique identifiers, an intervention algorithm for said web-tracker, that considers a configured intervention policy.
Owner:TELEFONICA SA
Cyber Behavior Analysis and Detection Method, System and Architecture
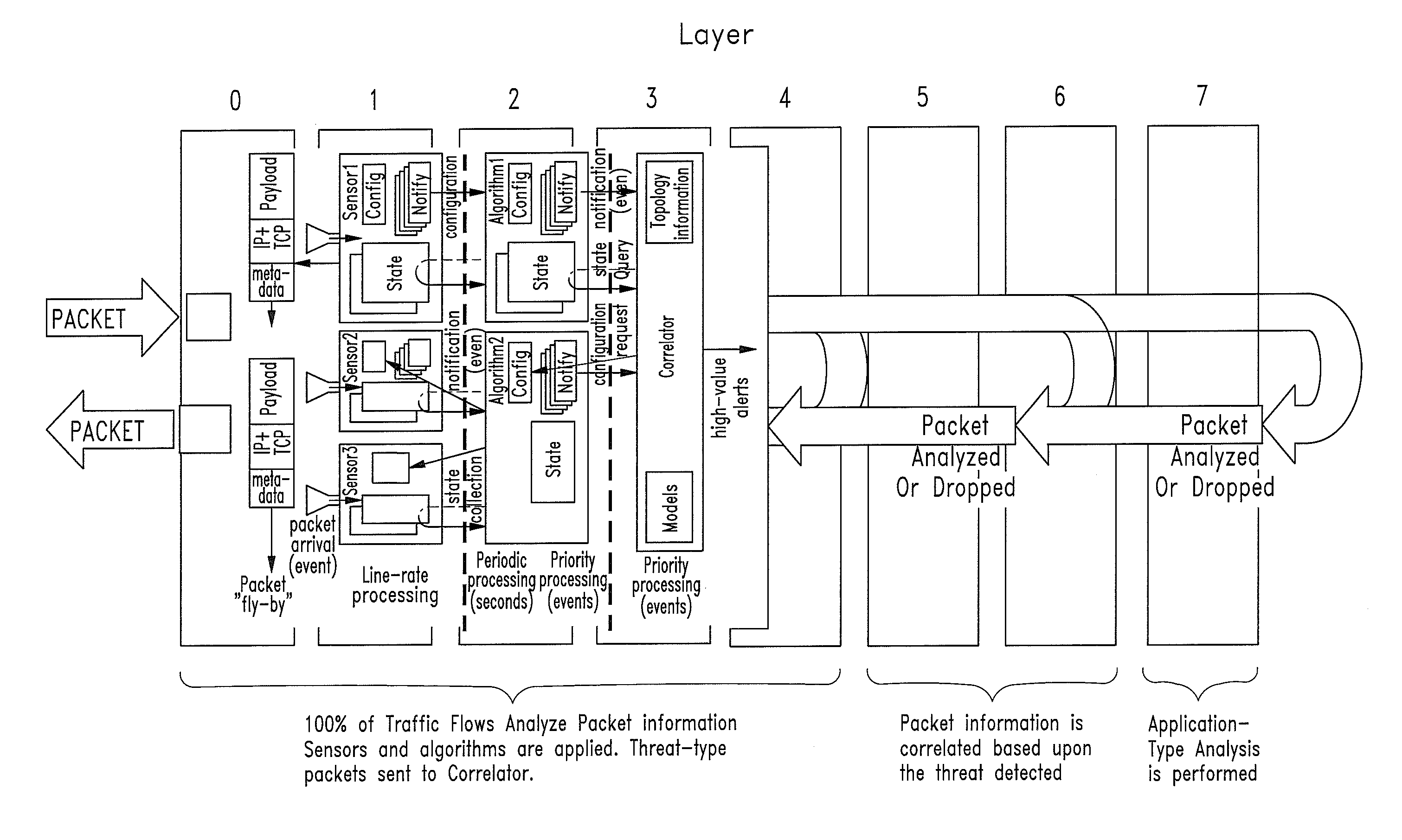
A scalable cyber-security system, method and architecture for the identification of malware and malicious behavior in a computer network. Host flow, host port usage, host information and network data at the application, transport and network layers are aggregated from within the network and correlated to identify a network behavior such as the presence of malicious code.
Owner:CYBER ADAPT INC
Method and system for user network behavioural based anomaly detection
InactiveUS20070245420A1Memory loss protectionError detection/correctionApplication softwareBehavioural analysis
A baseline can be defined using specific attributes of the network traffic. Using the established baseline, deviation can then be measured to detect anomaly on the network. The accuracy of the baseline is the most important criterion of any effective network anomaly detection technique. In a local area network (LAN) environment, the attributes change very frequently by many change agents; for example, new entities, such as users, application, and network-enabled devices, added to and removed from the LAN environment. The invention provides an improved method of establishing a baseline for network anomaly detection based on user's behaviour profiling. A user behaviour profiling is a distinct network usage pattern pertaining to a specific individual user operating on the LAN environment. No two users profiling would be the same. A group of users that have similar network usage attributes can be extrapolated using data mining technique to establish a group profiling baseline to detect network usage anomaly. By combining user and group profiling, a network anomaly detection system can measure subtle shift in network usage and as a result separate good user's network usage behaviour from the bad one. Using the said technique, a lower rate of false positives of network anomaly can be created that is suitable to operate in a highly dynamic LAN environment.
Owner:YONG YUH MING +1
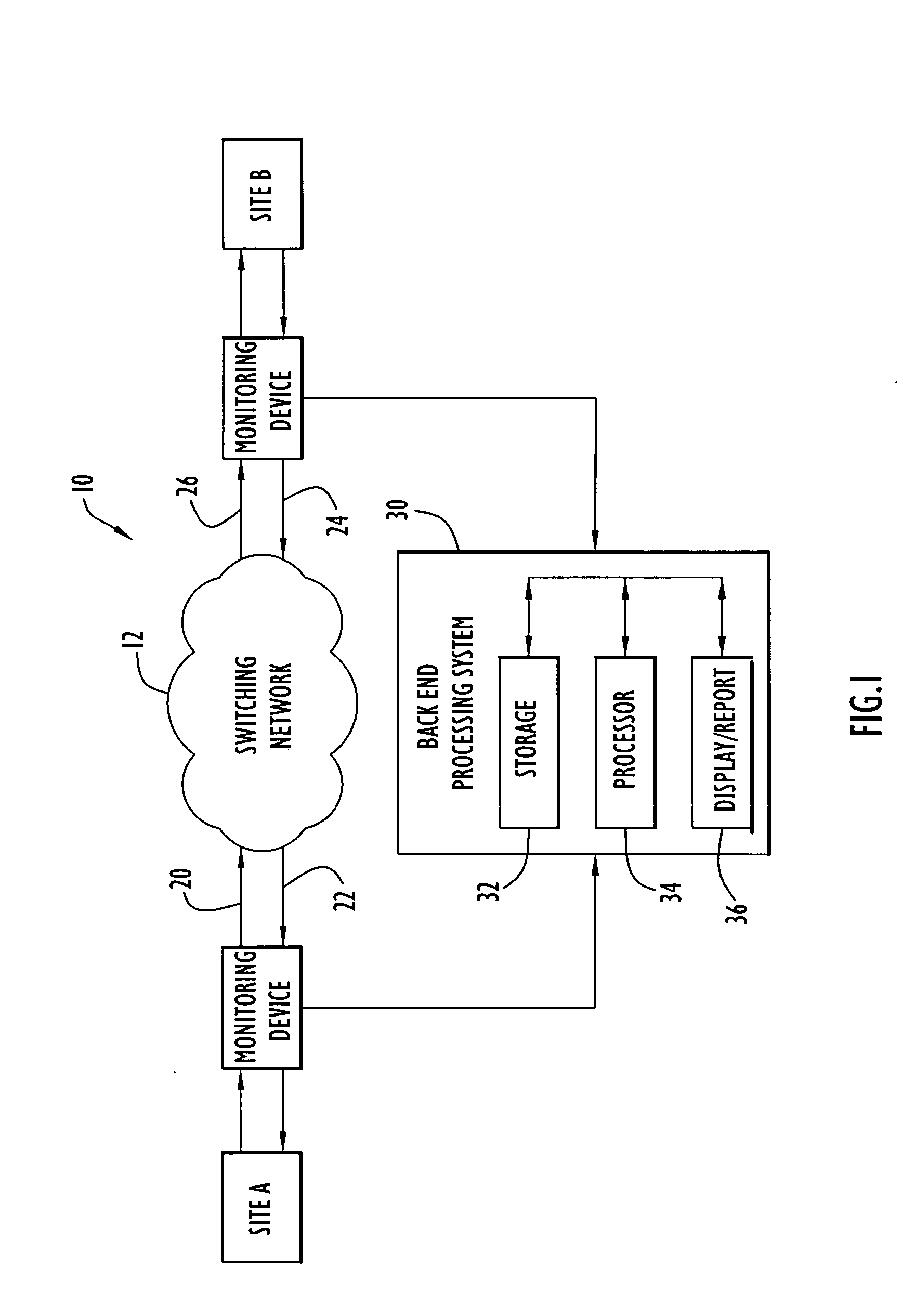
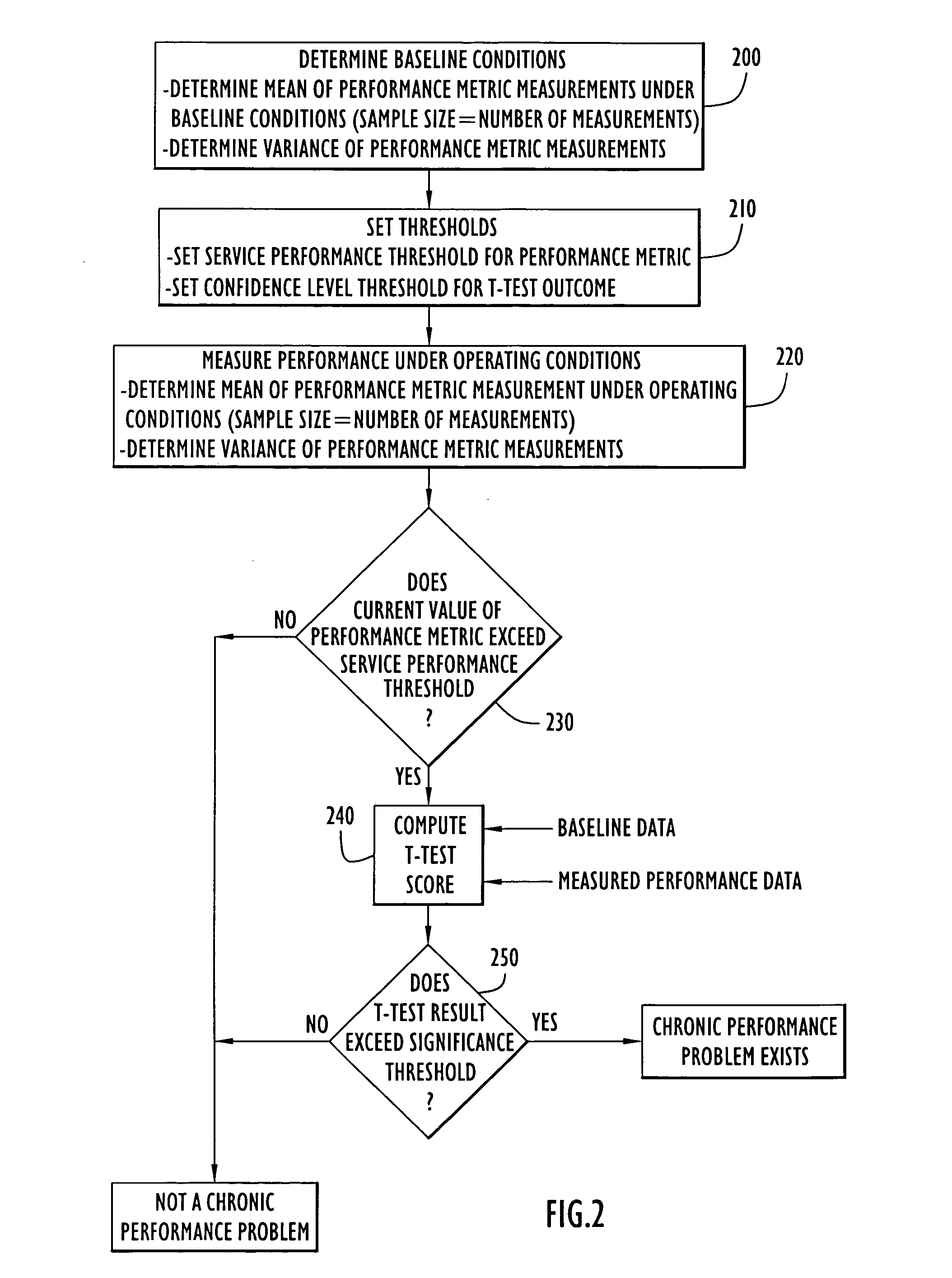
Methods and apparatus for identifying chronic performance problems on data networks
ActiveUS20060176824A1Reliable and accurate measurementError preventionFrequency-division multiplex detailsNetwork behaviorHandling system
A system for identifying chronic performance problems on data networks includes network monitoring devices that provide measurements of performance metrics such as latency, jitter, and throughput, and a processing system for analyzing measurement data to identify the onset of chronic performance problems. Network behavior is analyzed to develop a baseline performance level (e.g., computing a mean and variance of a baseline sample of performance metric measurements). An operating performance level is measured during operation of the network (e.g., computing a mean and variance of an operating sample of performance metric measurements). A chronic performance problem is identified if the operating performance level exceeds a performance threshold and a difference between the baseline performance level and the operating performance level is determined to be statistically significant. A t-test based on the baseline mean and variance and the operating mean and variance can be used to determine if this difference is significant.
Owner:NETSCOUT SYSTEMS
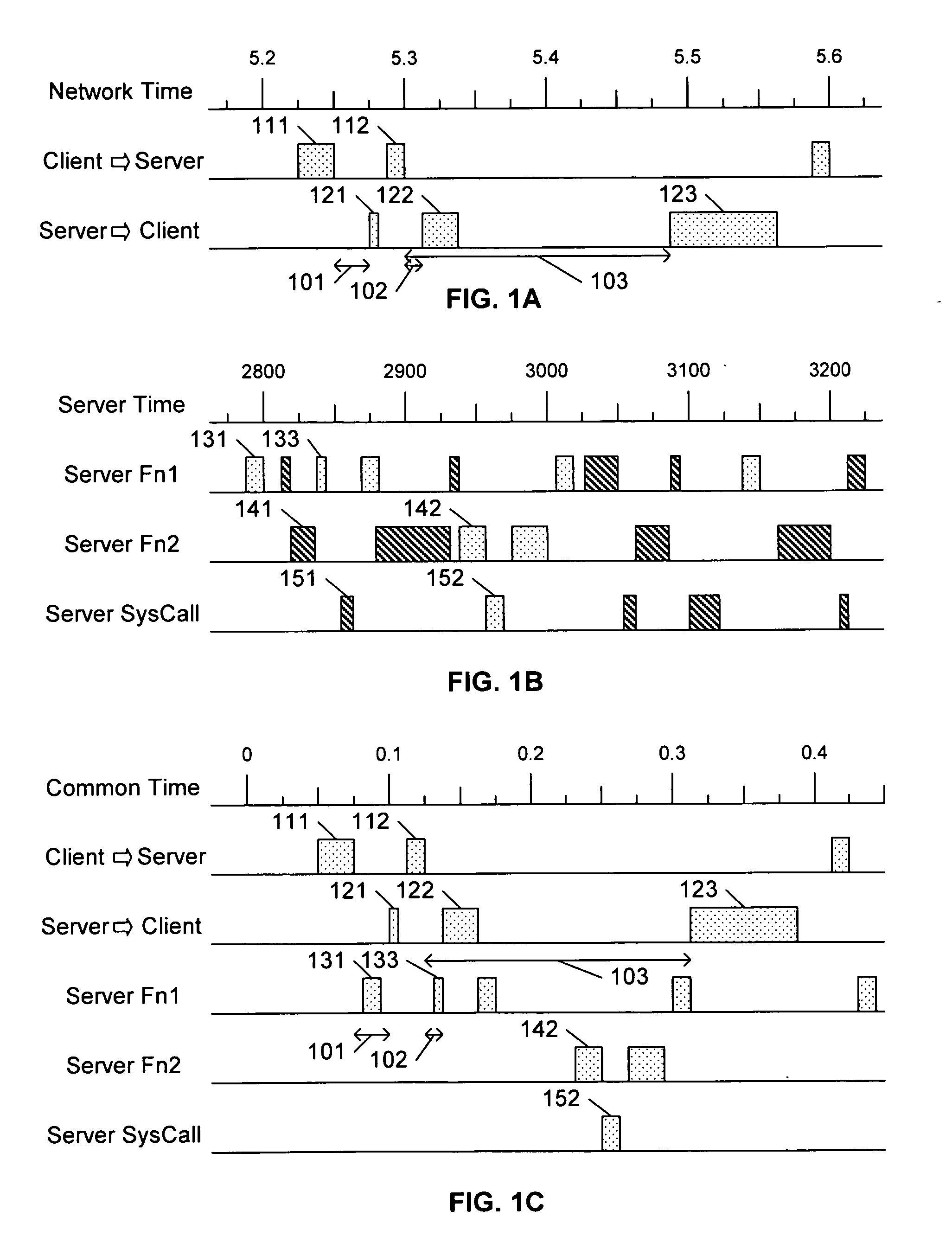
Capture, analysis, and visualization of concurrent system and network behavior of an application
A first capture system that captures network communication events related to an application, and a second capture system that captures internal processing events related to the application. A visualization system analyzes the data captured by each of the capture systems, synchronizes and correlates the data, and presents an integrated display of these communication and processing events. In a preferred embodiment, the communicated messages include an identifier of the application, and the processing components also associate an identifier of the application to each recorded processing event. To facilitate the integrated display of the events, the visualization system synchronizes the recorded communication and processing events to a common time base.
Owner:RIVERBED TECH LLC
Network intrusion detection system having application inspection and anomaly detection characteristics
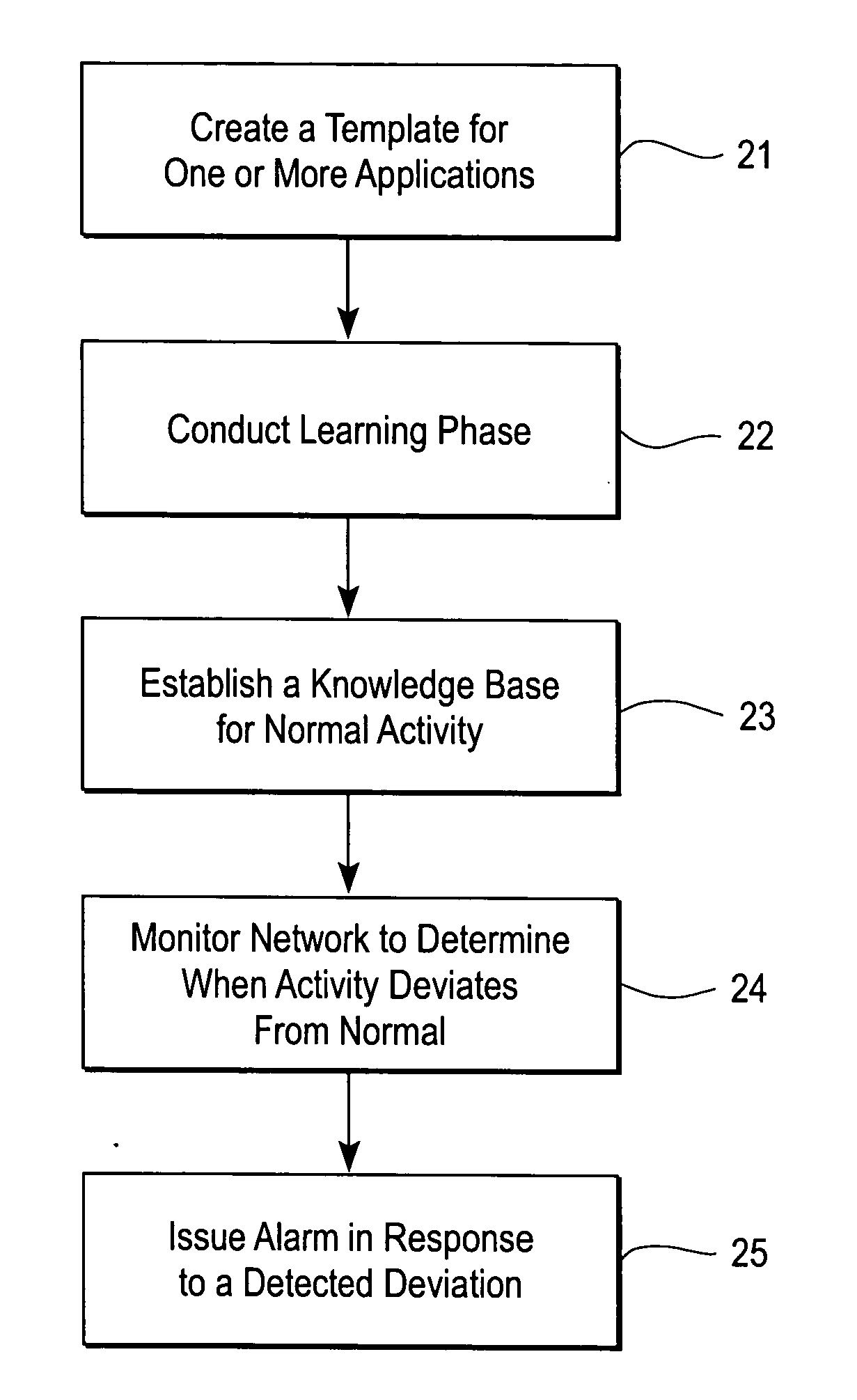
An intrusion detection system and method for a computer network includes a processor and one or more programs that run on the processor for application inspection of data packets traversing the computer network. The one or more programs also obtaining attribute information from the packets specific to a particular application and comparing the attribute information against a knowledge database that provides a baseline of normal network behavior. The processor raises an alarm whenever the attribute information exceeds a predetermined range of deviation from the baseline of normal network behavior. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:CISCO TECH INC
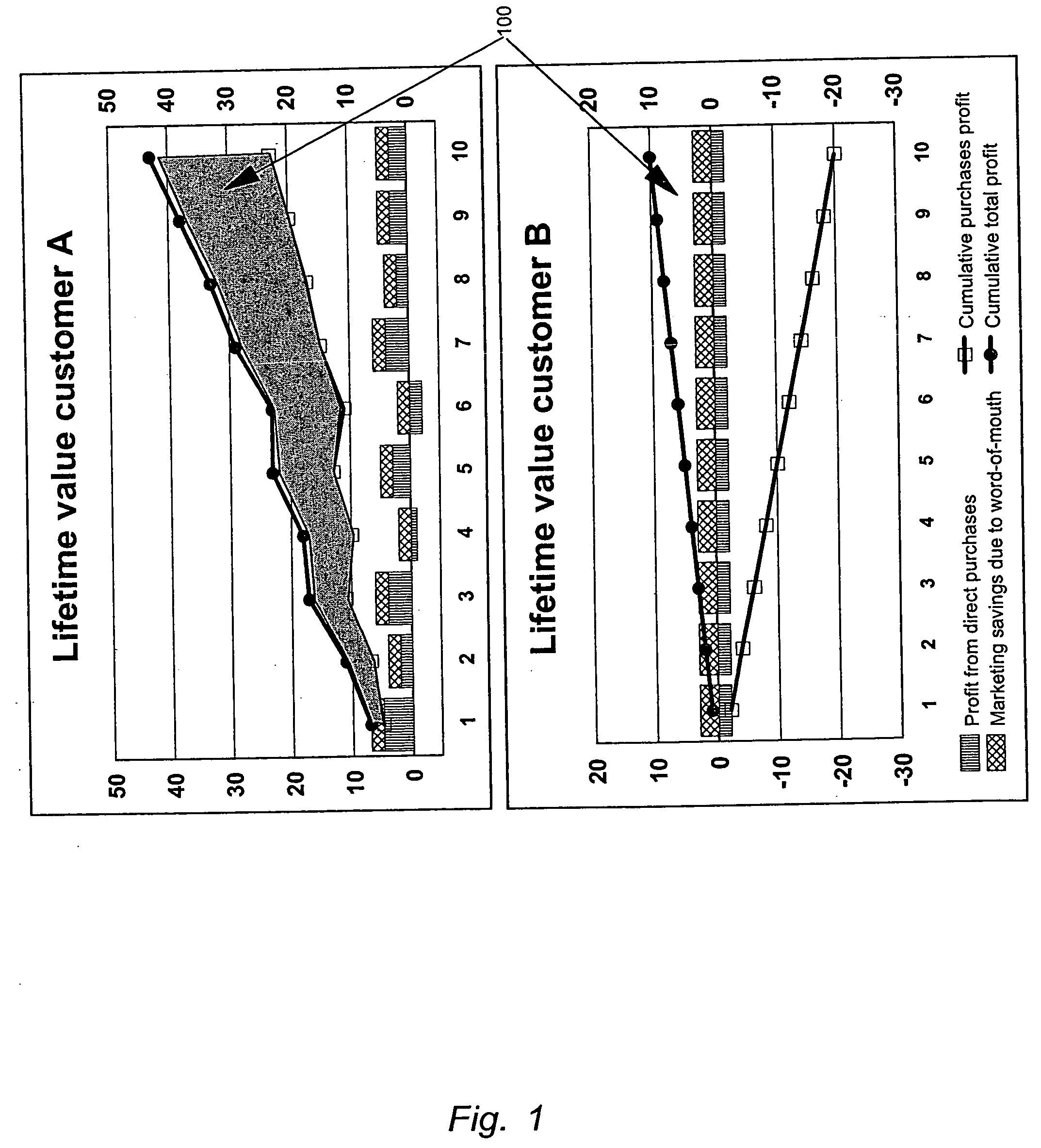
Method and system for managing customer network value
A method, system and computer program product are disclosed for evaluating a customer network value of a set of customers for a given marketing campaign, said method comprising the steps of storing for each customer static information, collecting for each customer, historical and time cumulative network behavior data, building a customer network map from network behavior data said map describing network relation between nodes, one node representing one customer, computing the social network parameters for the nodes of the network map, selecting the most relevant social network parameters according to the objectives of the given marketing campaign, and, computing for each customer a Customer Network Value Index (NVI) by combining the most relevant social network parameters and static information. When a static information profile is defined for an extended customer population, applying data mining techniques on this population allows estimating a probabilistic NVI for each customer in the extended customer population for which no NVI has been computed.
Owner:RAKUTEN GRP INC
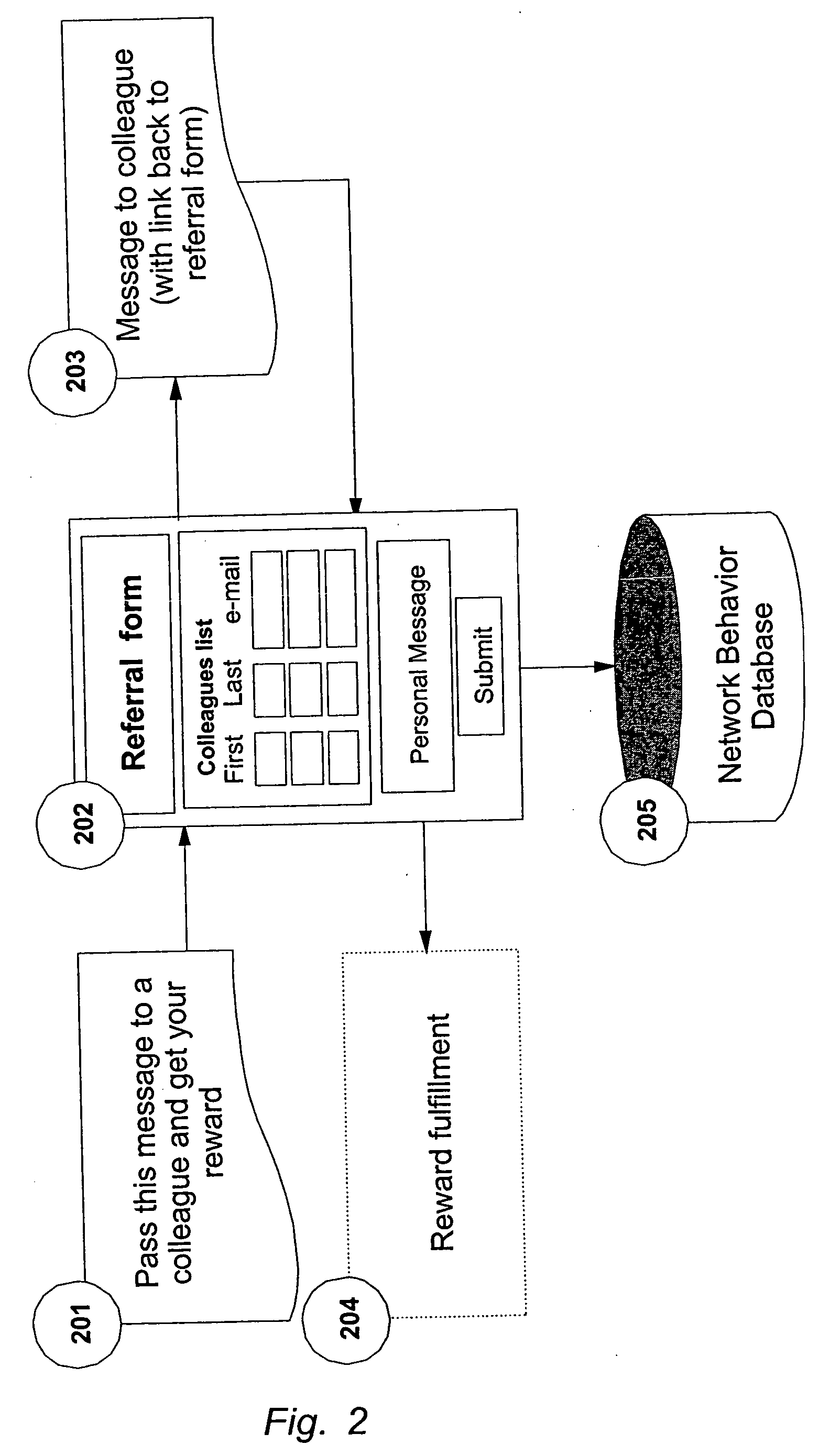
Method and system for monitoring online computer network behavior and creating online behavior profiles
InactiveUS7996912B2Digital data processing detailsAnalogue secracy/subscription systemsNetwork behaviorInternet privacy
Owner:CONNEXITY AUDIENCE INC
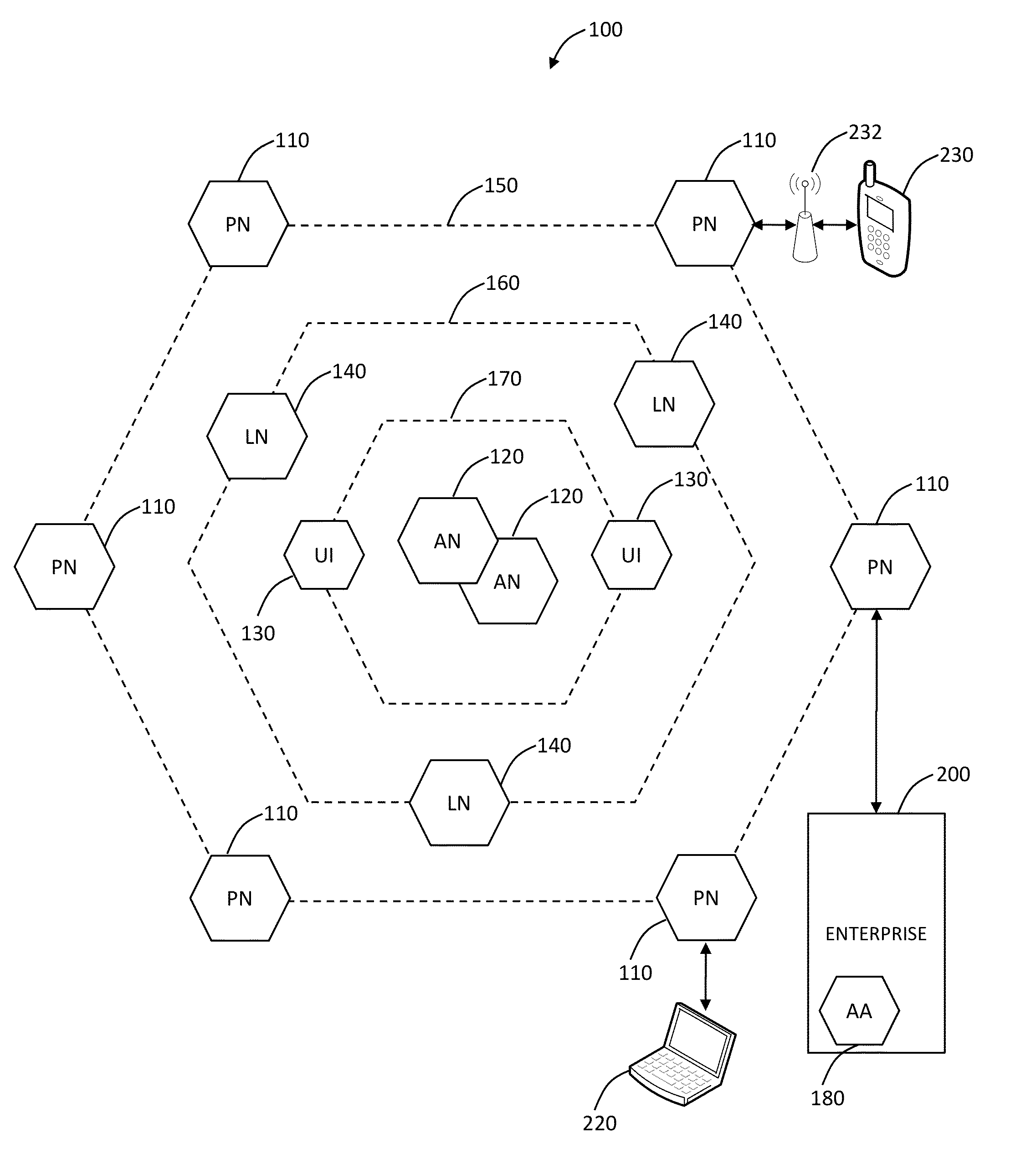
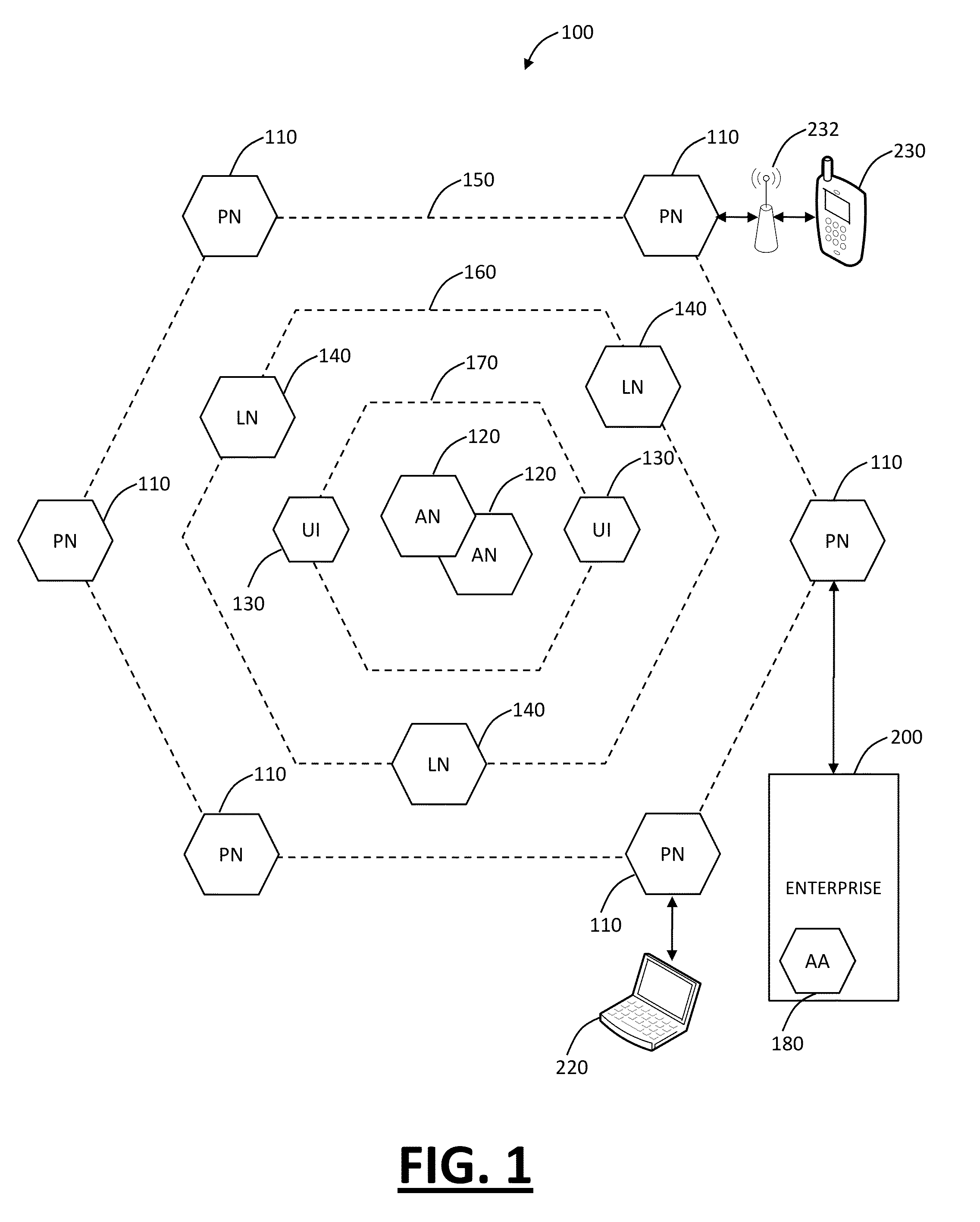
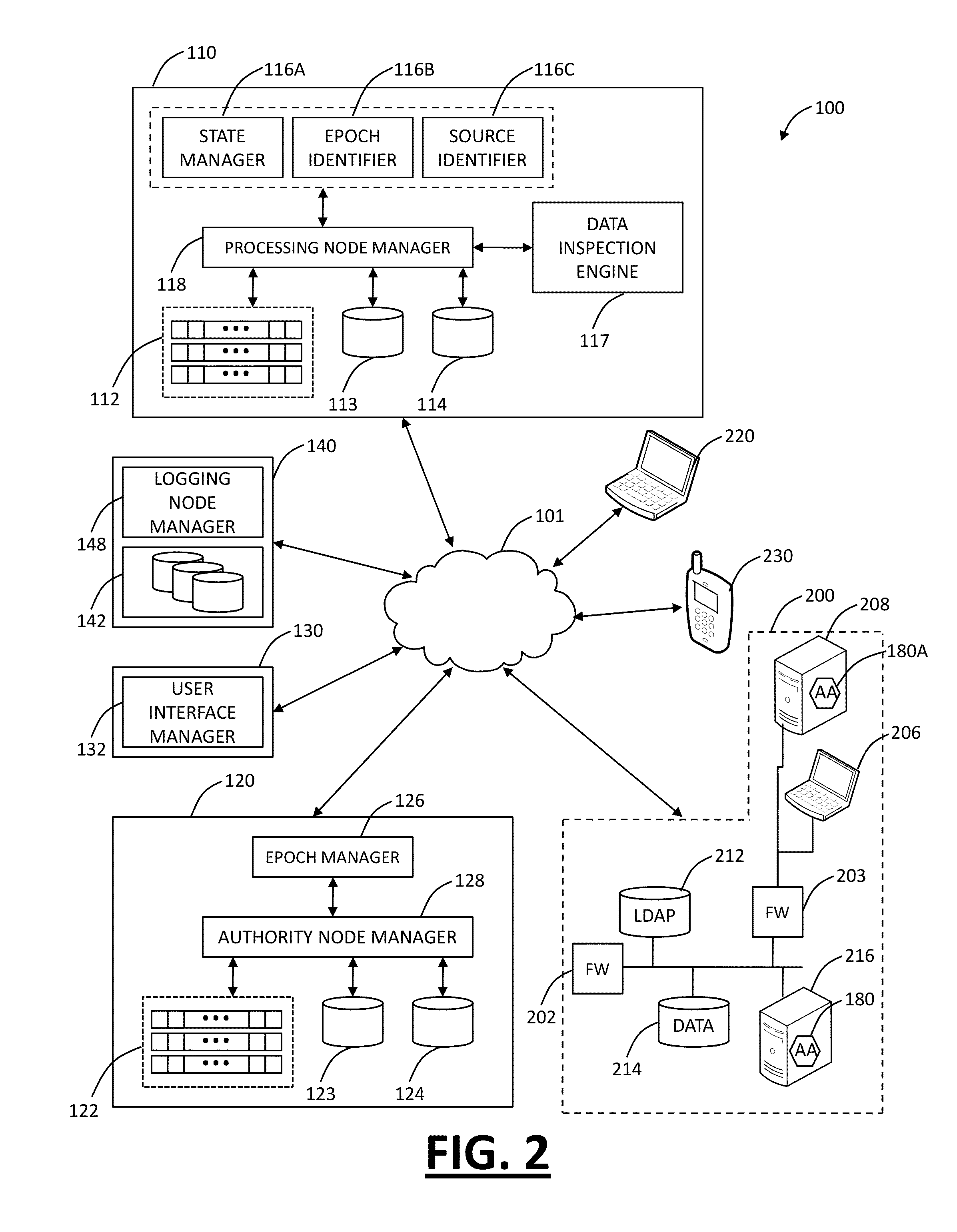
Distributed, multi-tenant virtual private network cloud systems and methods for mobile security and policy enforcement
ActiveUS8464335B1Computer security arrangementsMultiple digital computer combinationsCloud systemsPrivate network
The present disclosure provides distributed, multi-tenant Virtual Private Network (VPN) cloud systems and methods for mobile security and user based policy enforcement. In an exemplary embodiment, plural mobile devices are configured to connect to one or more enforcement or processing nodes over VPN connections. The enforcement or processing nodes are configured to perform content filtering, policy enforcement, and the like on some or all of the traffic from the mobile devices. The present invention is described as multi-tenant as it can connect to plural clients across different companies with different policies in a single distributed system. Advantageously, the present invention allows smartphone and tablet users to protect themselves from mobile malware, without requiring a security applications on the device. It allows administrators to seamless enforce policy for a user regardless of the device or network they are connecting to, as well as get granular visibility into the user's network behavior.
Owner:ZSCALER INC
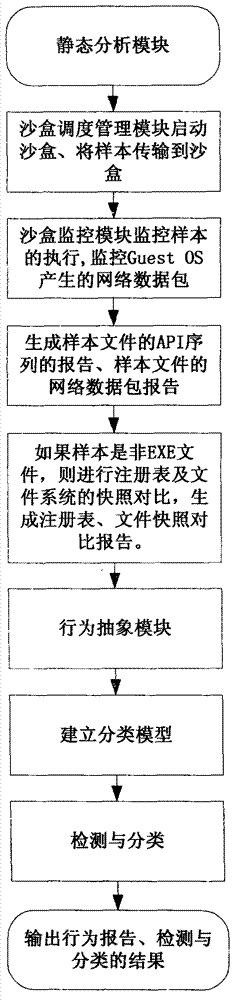
System and method for automatically analyzing, detecting and classifying malicious program behavior
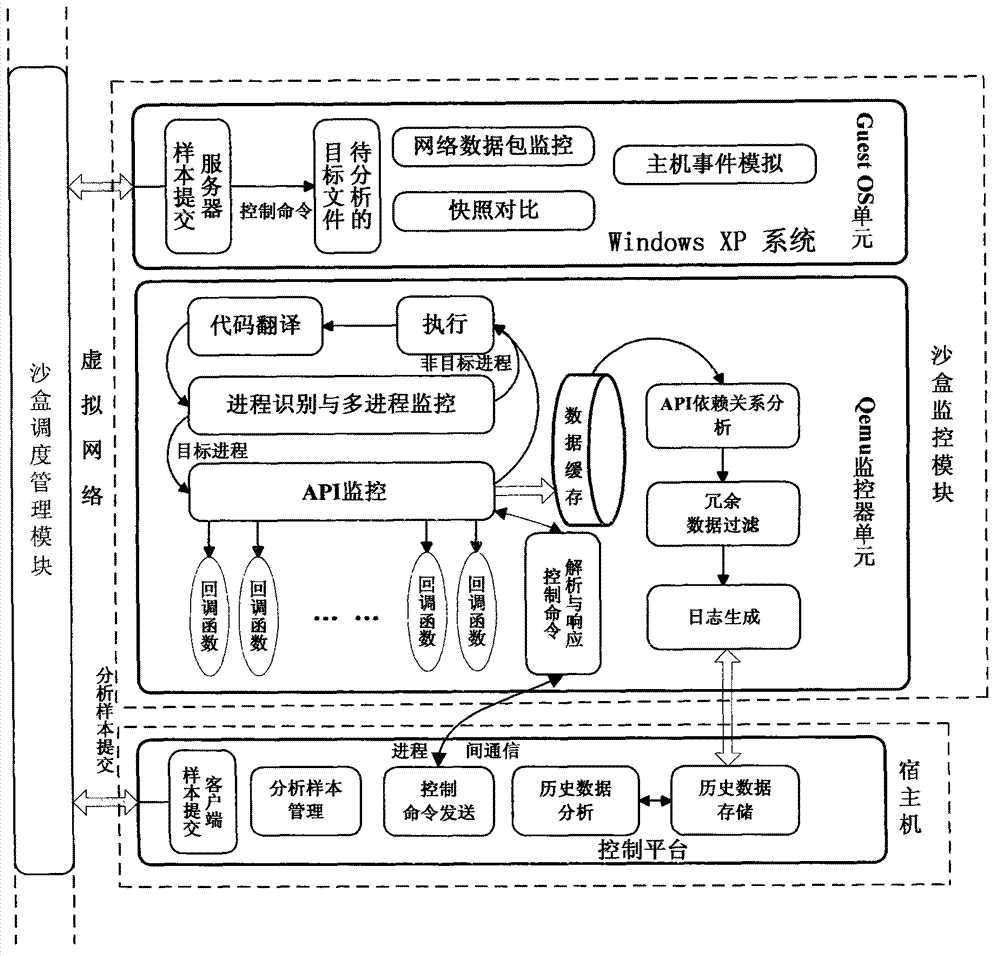
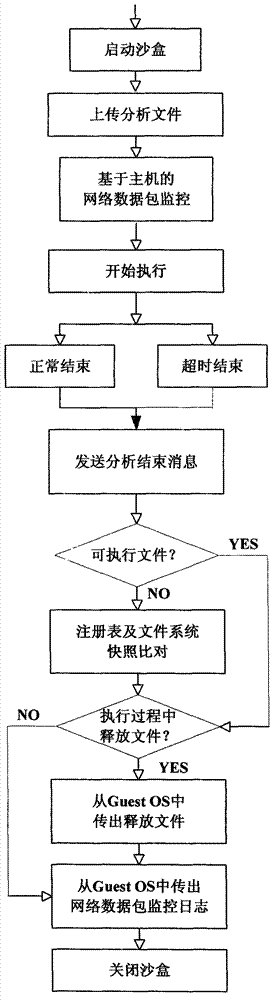
ActiveCN102930210ACause damageOvercome shortcomings such as inability to perform adequatelyPlatform integrity maintainanceSpecial data processing applicationsDomain nameNetwork behavior
The invention discloses a system and a method for automatically analyzing, detecting and classifying a malicious program behavior. The system comprises a static analysis module, a sandbox dispatching management module, a sandbox monitoring module, a behavior abstraction module and a detection and classification module. Compared with the prior art, the system has the advantages that 1, the system is based on a behavior monitoring technology in an instruction set simulation environment; and 2, a virtual Internet is established in a sandbox through means of environment configuration, server program modification and the like, and a common network service is simulated, so that operations such as domain name server (DNS) resolution, http access, file download, Email login and mailing initiated by a malicious program can be successfully executed, the malicious program is inveigled to generate a malicious network behavior, the network behaviors are prevented from damaging a host machine and a real network, and the defects that the malicious program network behavior cannot be fully expressed during dynamic behavior analysis of a malicious program and the like are overcome.
Owner:JIANGSU JINLING TECH GRP CORP
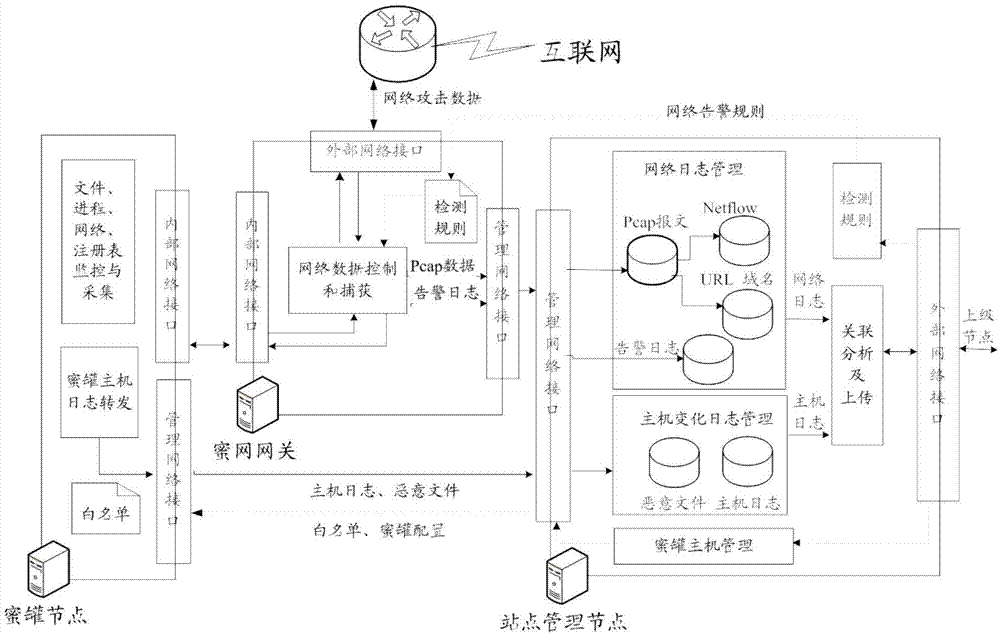
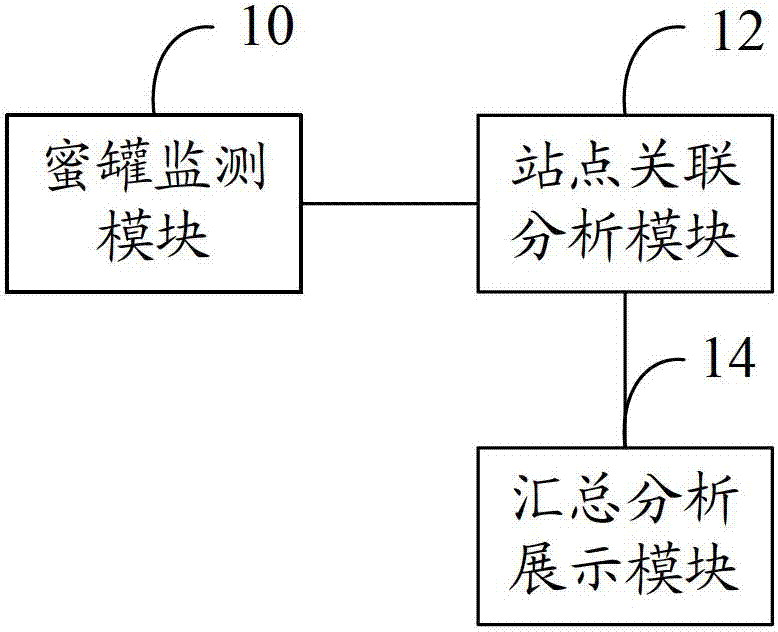
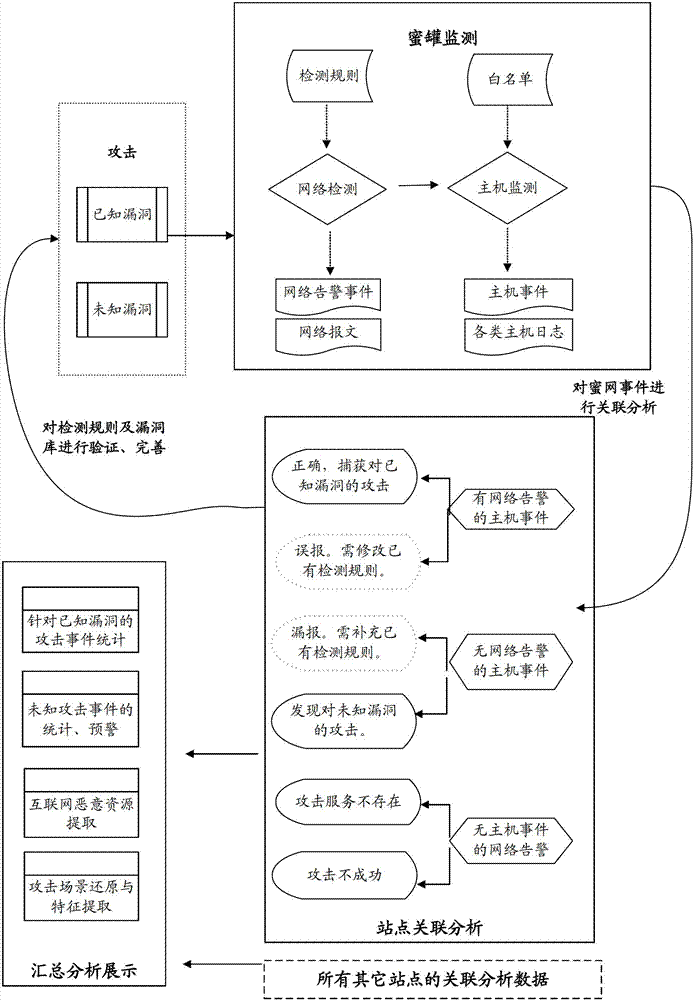
High-interaction honeypot based network security system and implementation method thereof
InactiveCN102739647AImplement auto-discoveryAchieve acquisitionData switching networksResource informationNetwork behavior
The invention discloses a high-interaction honeypot based network security system and an implementation method thereof. The system comprises a honeypot monitoring module, a website correlation analysis module, a summarizing analysis / display module, wherein the honeypot monitoring module is used for carrying out classified acquisition on the attack incidents network behavior logs and host behavior logs; the website correlation analysis module is used for carrying out summarization and automatic correlation analysis on the attack incidents network behavior logs and the host behavior logs, and filtering invalid network alarms, capturing known attack incidents, automatically finding out unknown attack incidents, and extracting concealed Internet malicious resource information according to the automatic correlation analysis results; and the summarizing analysis / display module is used for summarizing and accounting known attack incidents and / or unknown attack incidents captured on all honeypot websites, displaying and reducing selected attack incidents for users, and carrying out automatic detection on concealed Internet malicious resources according to the concealed Internet malicious resource information.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
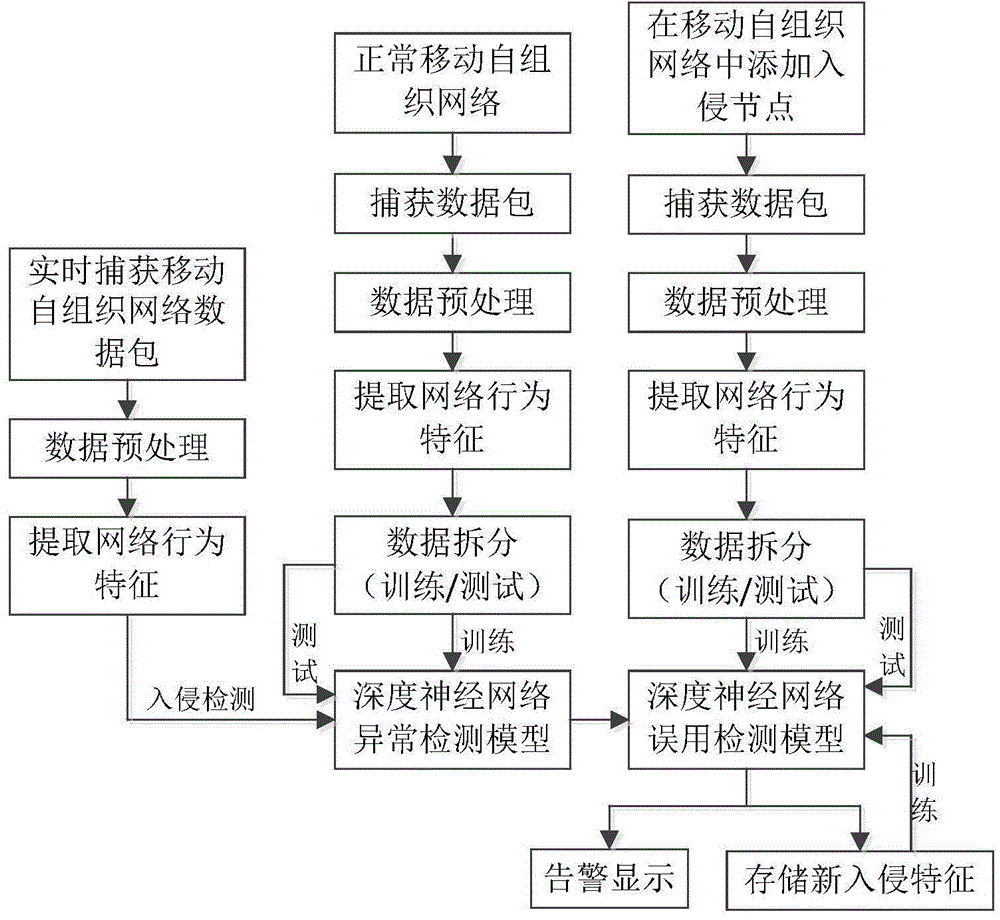
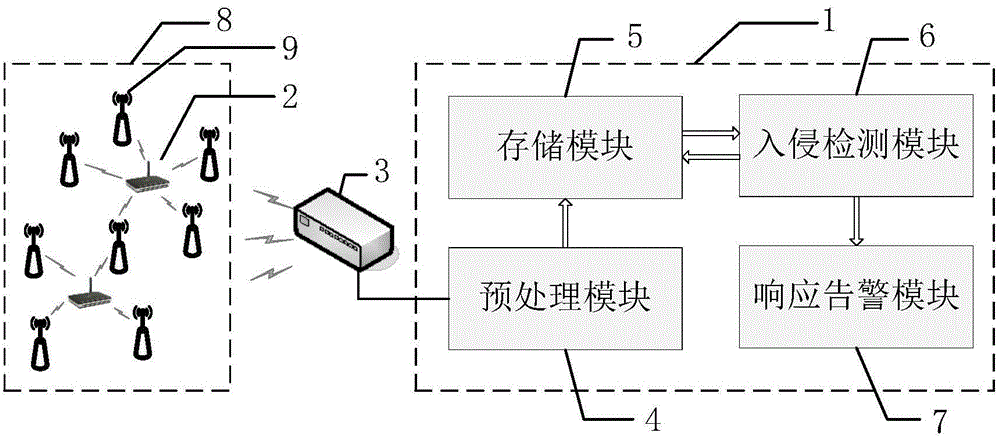
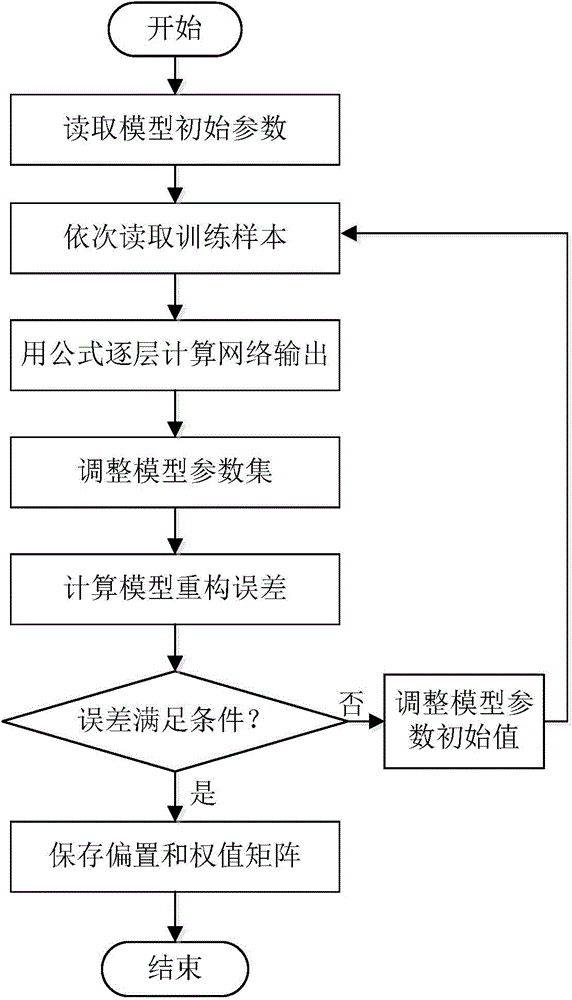
Mobile ad hoc network intrusion detection method and device based on deep learning
ActiveCN104935600AEnsure training efficiencyGuaranteed detection efficiencyTransmissionSecurity arrangementData acquisitionWireless data
The invention discloses a mobile ad hoc network intrusion detection method and device based on deep learning, relating to the field of wireless network safety. The device comprises a data acquisition module, a data fusion module, a preprocessing module, a storage module, an intrusion detection module and a response warning module. After fusion and redundancy elimination of captured wireless data packages, network behavior features are extracted and stored; after deep learning of the network behavior features, a deep neural network model expressing network behaviors is established; and to-be-detected network data is input into the deep neural network model, after intrusion is judged and recognized, response and warning are performed. According to the method, network behavior feature vectors which are detected and are considered to be abnormal are stored and are used for training the deep neutral network. When occurring again, the intrusion types can be detected and recognized. While the model training and detection efficiency are guaranteed, the detection accuracy is improved, and the safety of the mobile ad hoc network is further improved.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
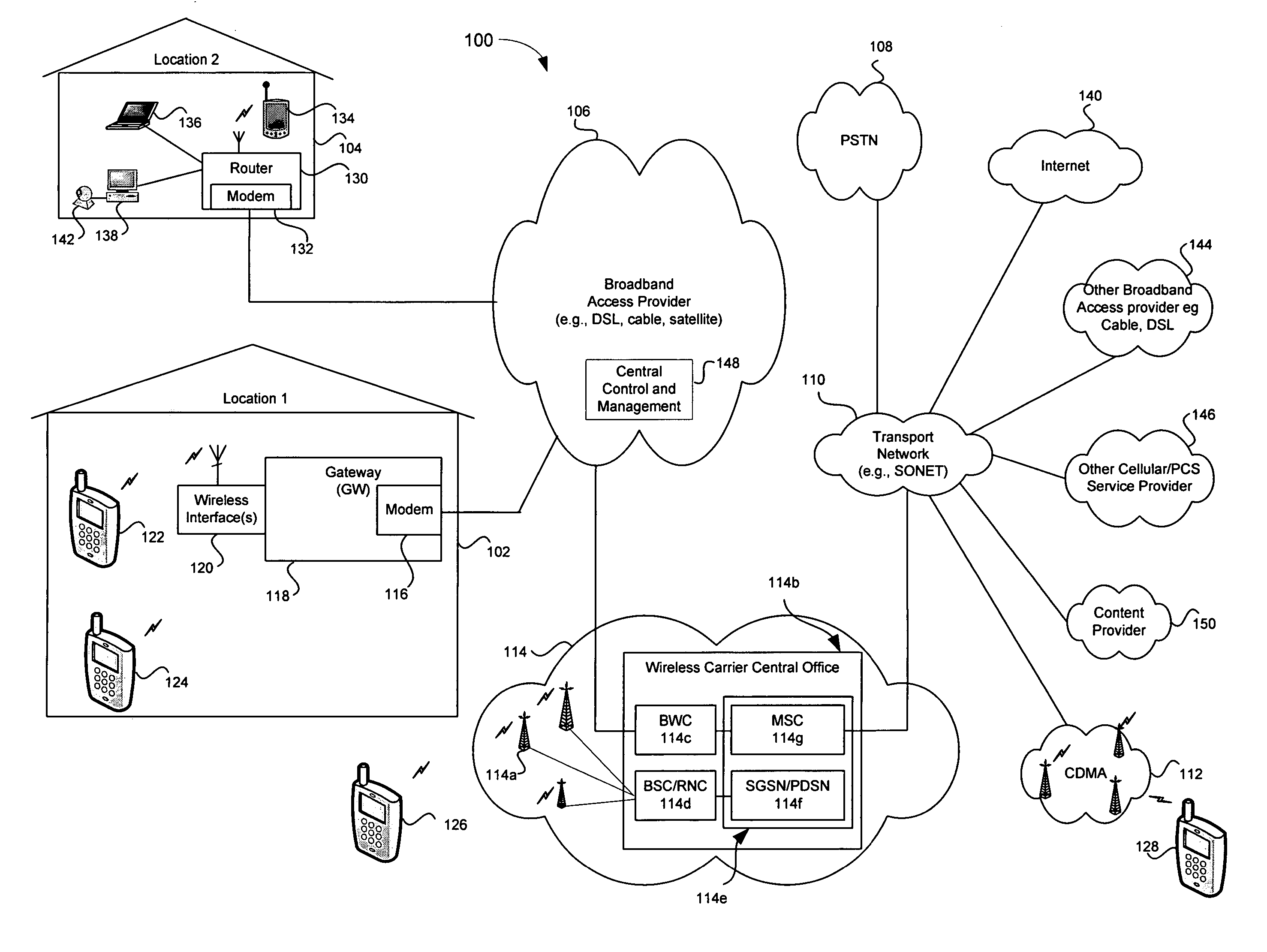
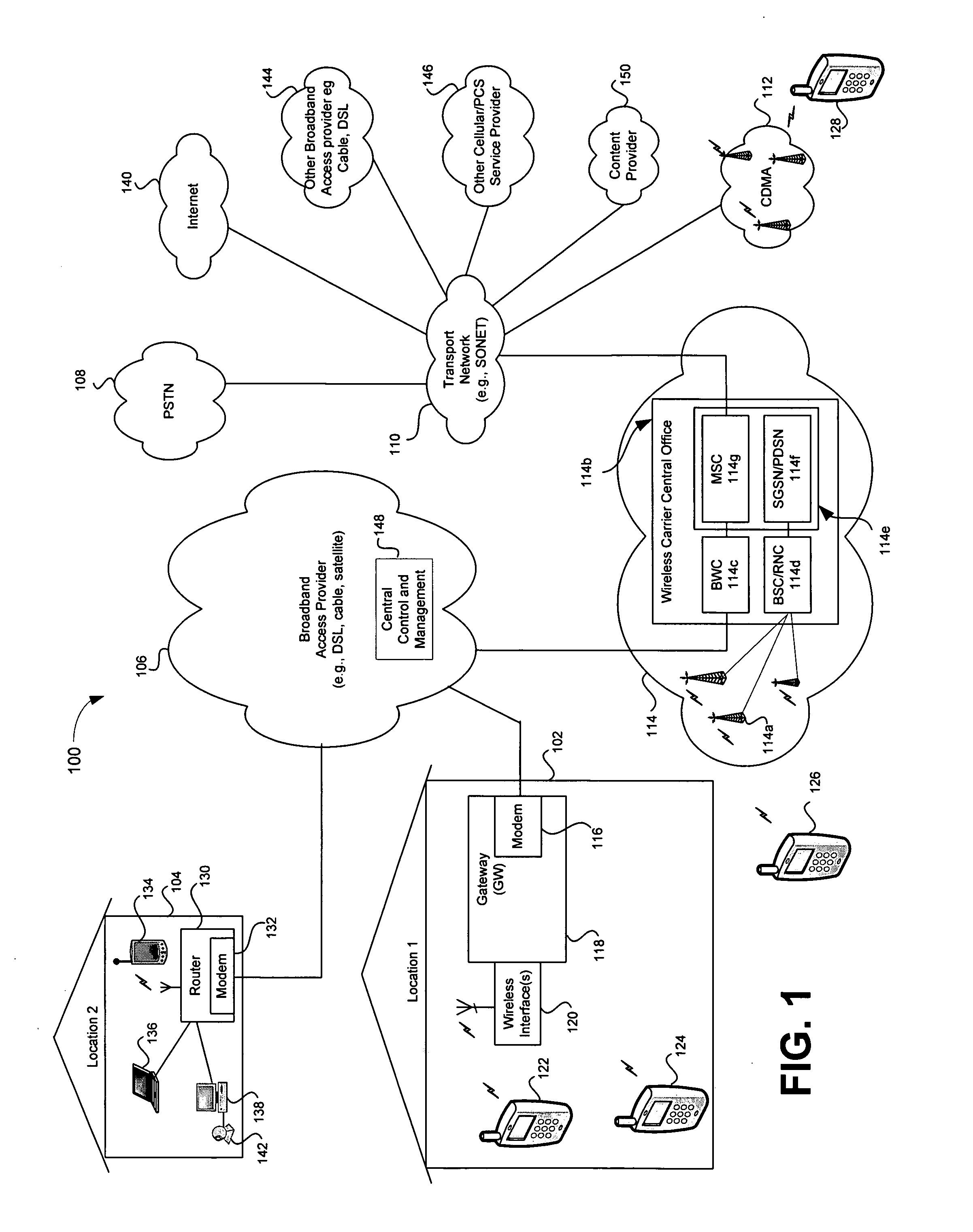
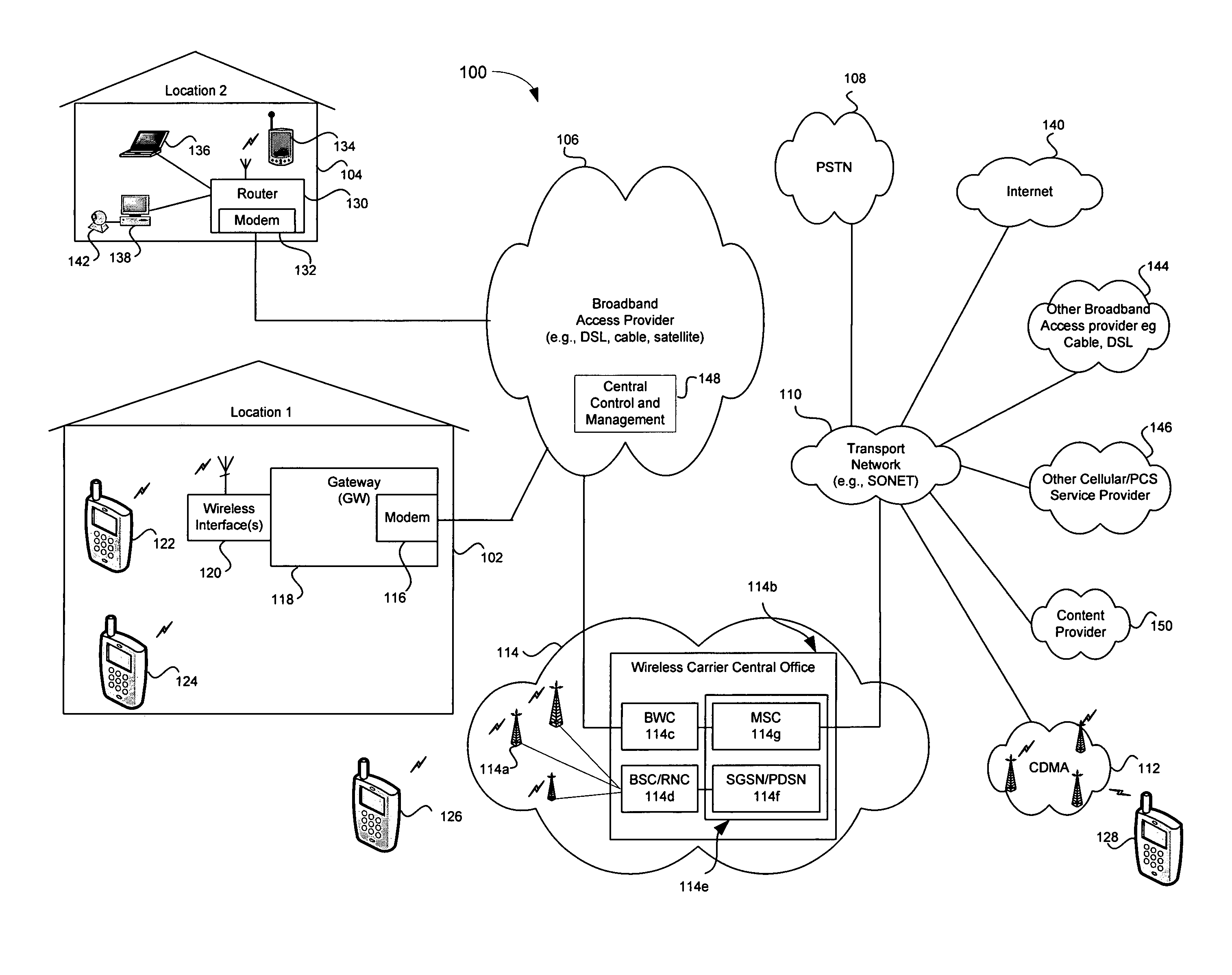
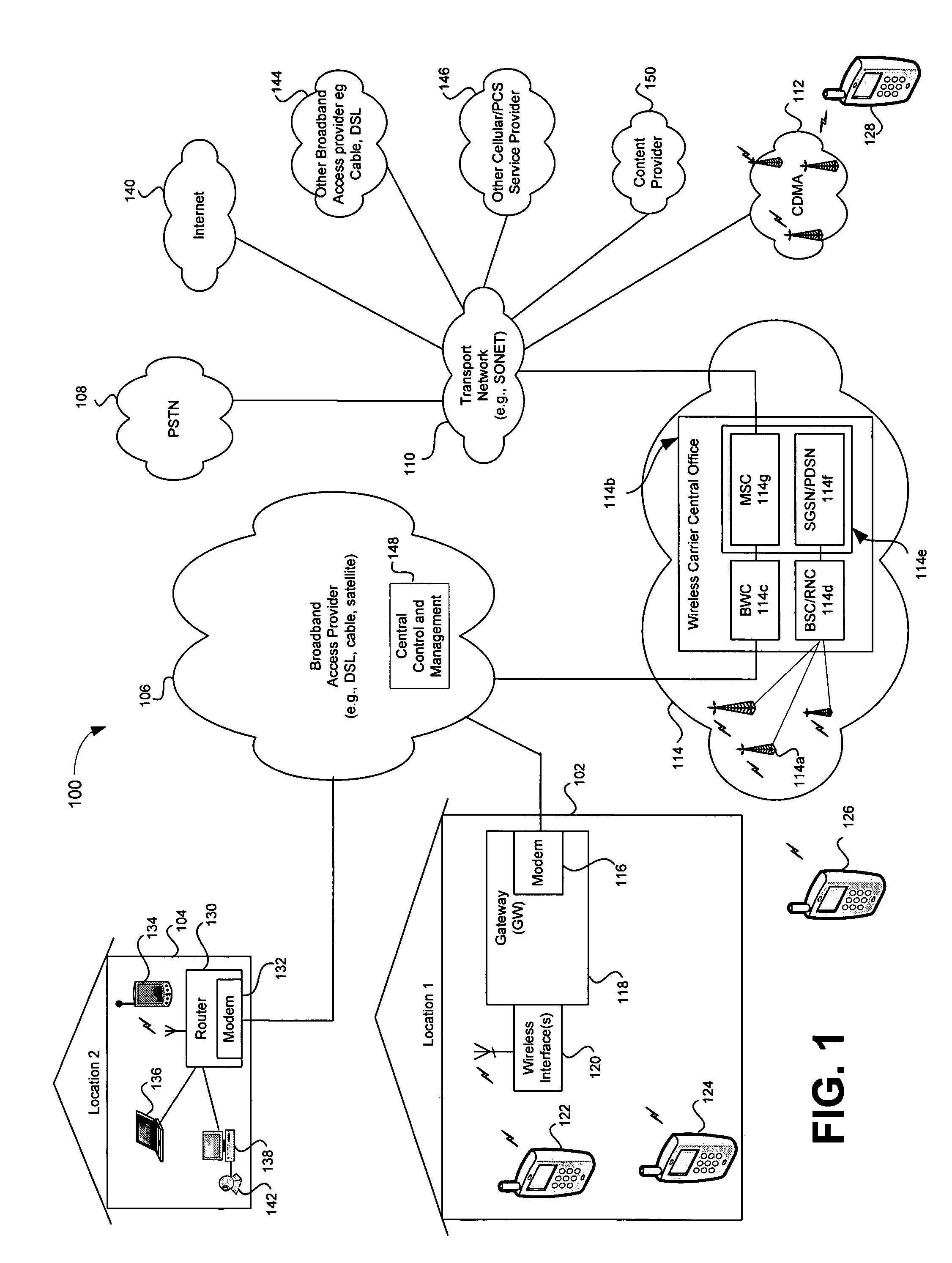
Location-aware application based quality of service (QOS) Via a broadband access gateway
ActiveUS20050233728A1Network traffic/resource managementData switching by path configurationQuality of serviceNetwork behavior
A system and method supporting access to multimedia information based upon user-defined quality of service criteria is disclosed. A broadband access gateway may coordinate network behavior during the transition of an access device among communication pathways having different available capacities. Adjustments in bit rates and levels of compression may be made based upon the user-defined quality of service criteria. The user may be notified when network conditions disallow support for the desired quality of service, and may choose to override selected criteria. The user-defined quality of service criteria may be stored within the gateway and associated with a user, or may be located in the access device and accessible to the gateway.
Owner:AVAGO TECH INT SALES PTE LTD
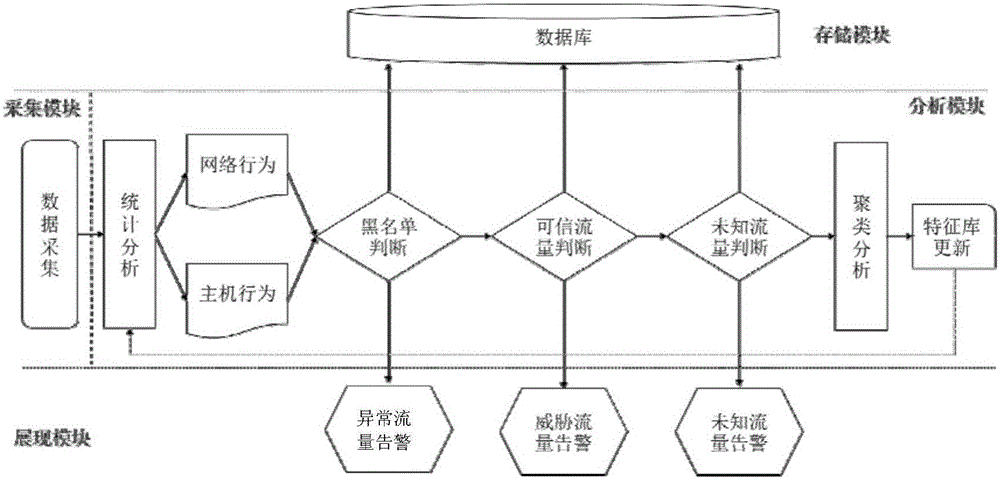
Method and system for detecting network security threat based on trusted business flow
The invention discloses a method and a system for detecting a network security threat based on trusted business flow. The method comprises the following steps of establishing a blacklist and a white list of network flow and constructing a baseline model, wherein the white list is the trusted business flow and is a feature contour library of normal network behavior and host behavior; comparing real-time monitoring flow data and the baseline model; when the real-time data is matched with the blacklist, outputting an abnormal flow alarm; when the real-time data is matched with the white list and a deviation exceeds a preset threshold, outputting a threat flow alarm; and when the real-time data is mismatched with the blacklist and the white list, treating as a gray list and outputting an unknown flow alarm. According to the method and the system, the network security threat can be comprehensively and effectively detected at a low false alarm rate and high anti-virus efficiency, and the method and the system can adapt to a more granular network attack and defense confrontation environment.
Owner:STATE GRID CORP OF CHINA +1
Location-aware application based quality of service (QOS) via a broadband access gateway
ActiveUS7283803B2Network traffic/resource managementData switching by path configurationQuality of serviceNetwork behavior
Owner:AVAGO TECH INT SALES PTE LTD
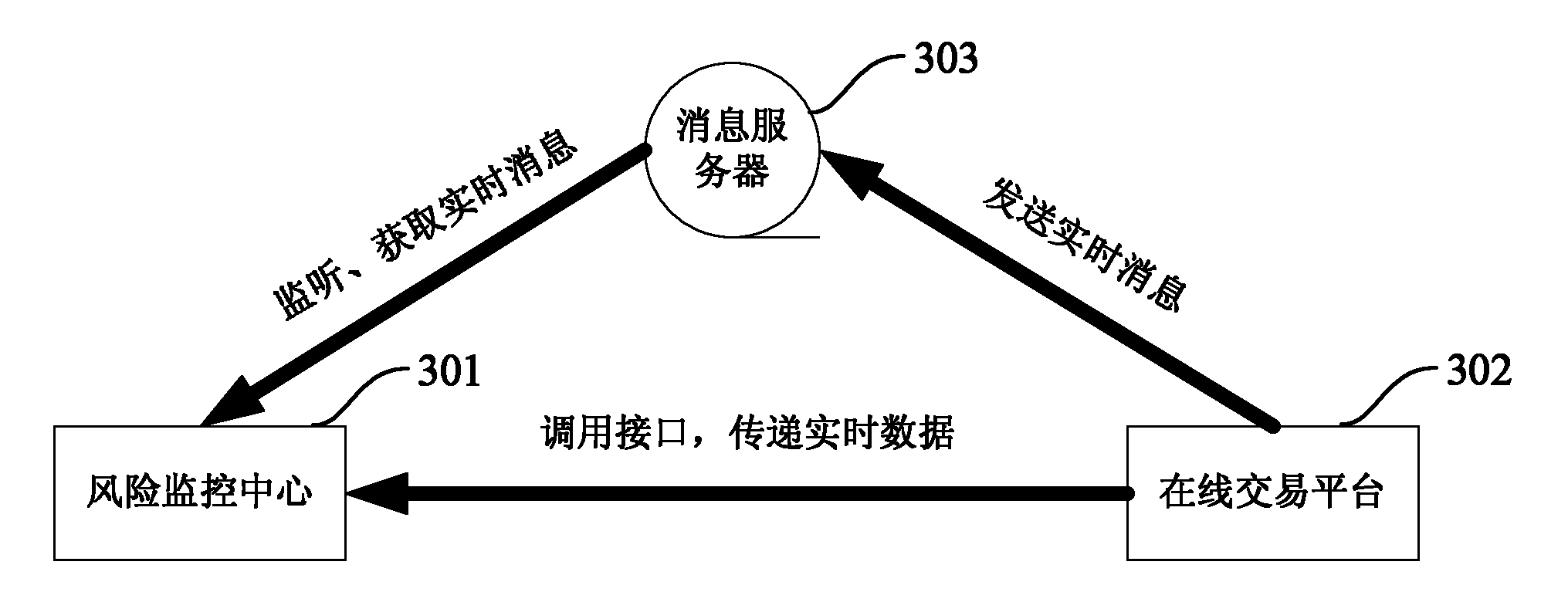
Method and system for monitoring network behavior data
The invention provides a method and system for monitoring network behavior data. The method particularly comprises the steps of: obtaining network behavior data of a user from an online application program periodically or regularly, and regarding the network behavior data as historical network behavior data for collective storage; determining a corresponding risk model based on the historical network behavior data of the user; calling the collectively stored historical network behavior data for historical risk identification based on the definition of the risk model, and regarding a corresponding historical risk identification result as a parameter of the risk model for storage; obtaining the online network behavior data of the user in real time; performing online risk identification on the online network behavior data based on the risk model so as to obtain an online risk identification result; and processing a credit object associated with the user based on the online risk identification result. The method and system for monitoring the network behavior data can improve timeliness and accuracy of credit risk monitoring.
Owner:ALIBABA GRP HLDG LTD
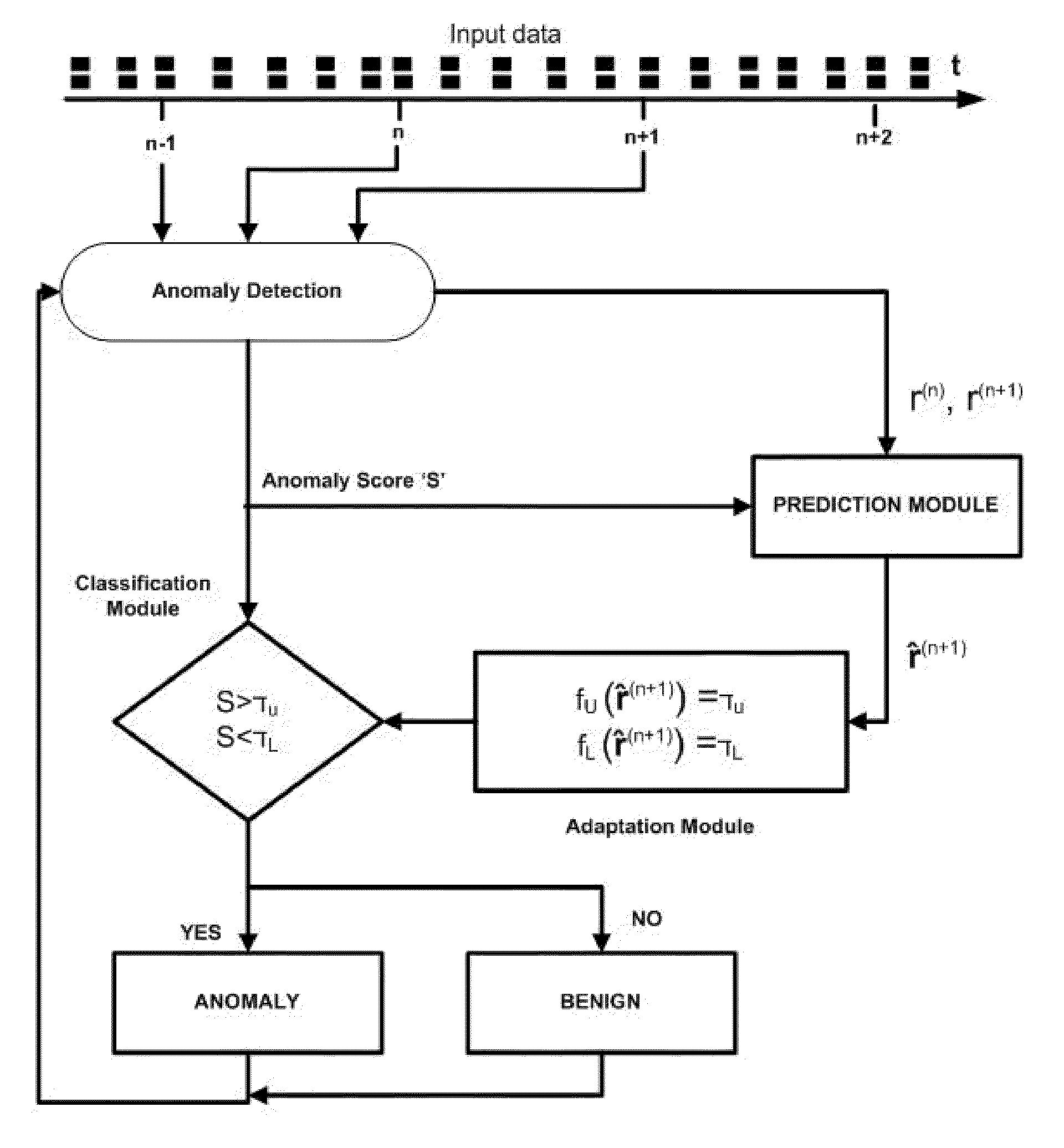
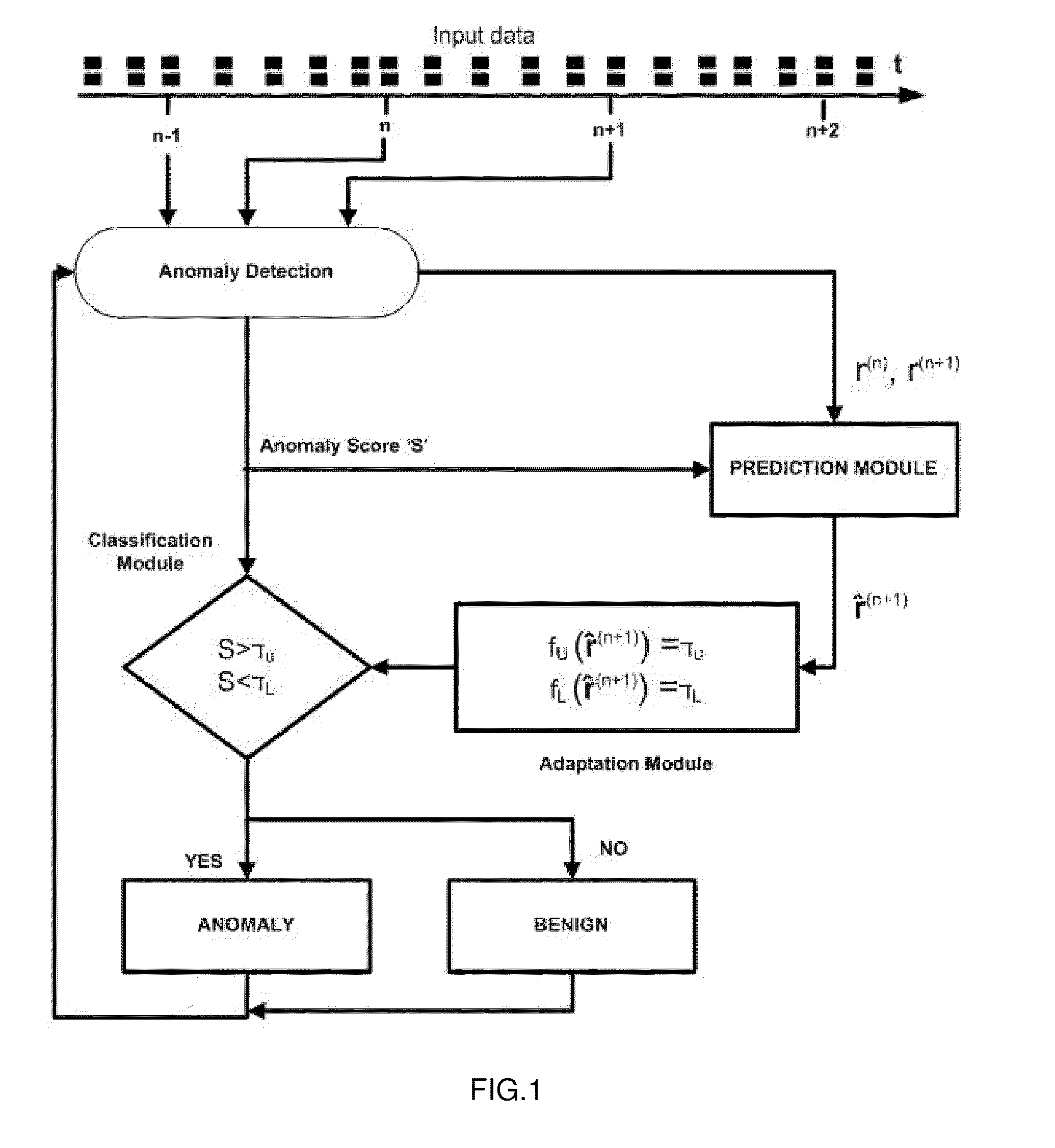
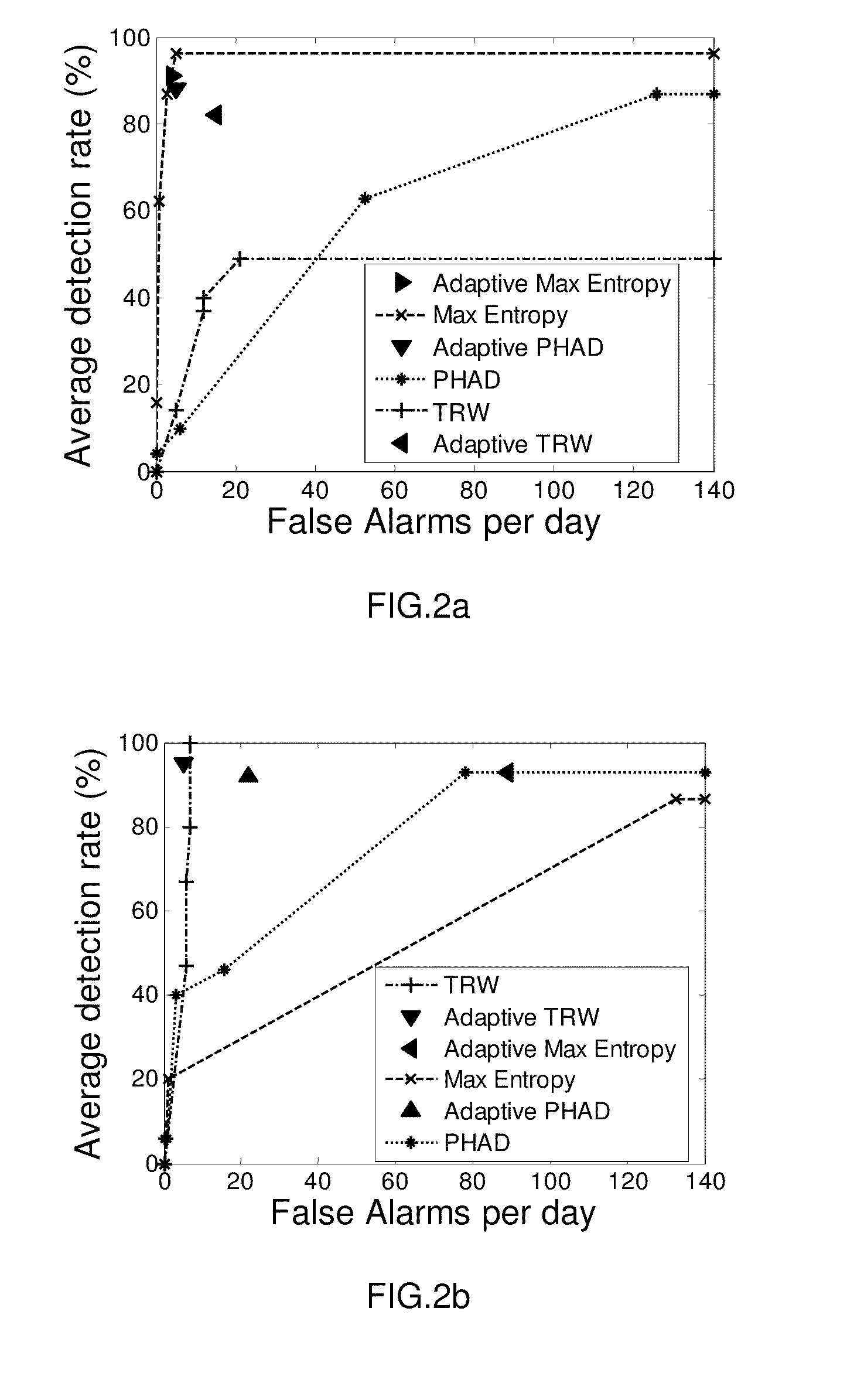
Method and system for adaptive anomaly-based intrusion detection
InactiveUS20110185422A1Convenient and accuratePoint becomes highMemory loss protectionError detection/correctionTime correlationNetwork behavior
The input characteristics of a real-time IDS change continuously with time therefore setting a rigid (time and behavior invariant) classification threshold limits the accuracy that the IDS can potentially achieve. A generic threshold tuning method and system is proposed which can adaptively tune the detection threshold of a real-time IDS in accordance with varying host and network behavior. The method and system perform statistical and information-theoretic analyses of network and host-based IDSs' anomaly based intrusions to reveal a consistent time correlation structure between benign activity periods which is used to predict future anomaly scores and to adapt an IDS' detection threshold accordingly.
Owner:THE SCHOOL OF ELECTRICAL ENG & COMP SCI SEECS NAT UNIV OF SCI & TECH NUST
Network attack abnormality detection method
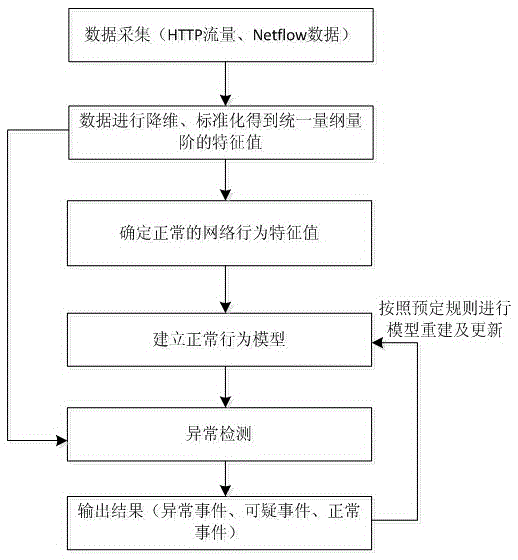
ActiveCN105553998AReduce false alarm rateAuto rebuildTransmissionNetwork behaviorDimensionality reduction
The invention discloses a network attack abnormality detection method, and relates to the technical field of information security. The technical point of the network attack abnormality detection method disclosed by the invention is as follows: a step 1, deploying a traffic data collection device at a network traffic aggregation node; a step 2, extracting a network behavior feature value from the collected traffic data; a step 3, carrying out dimensionality reduction and standardization on the network behavior feature value; a step 4, determining normal network behavior feature values, and establishing a normal behavior model based on a set of the normal network behavior feature values; and a step 5, detecting other network behavior feature values based on the normal behavior model, and judging whether abnormal network behaviors occur; and when detecting abnormal network behaviors, updating the normal behavior model according to a new normal network behavior feature value.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
System and method for network security
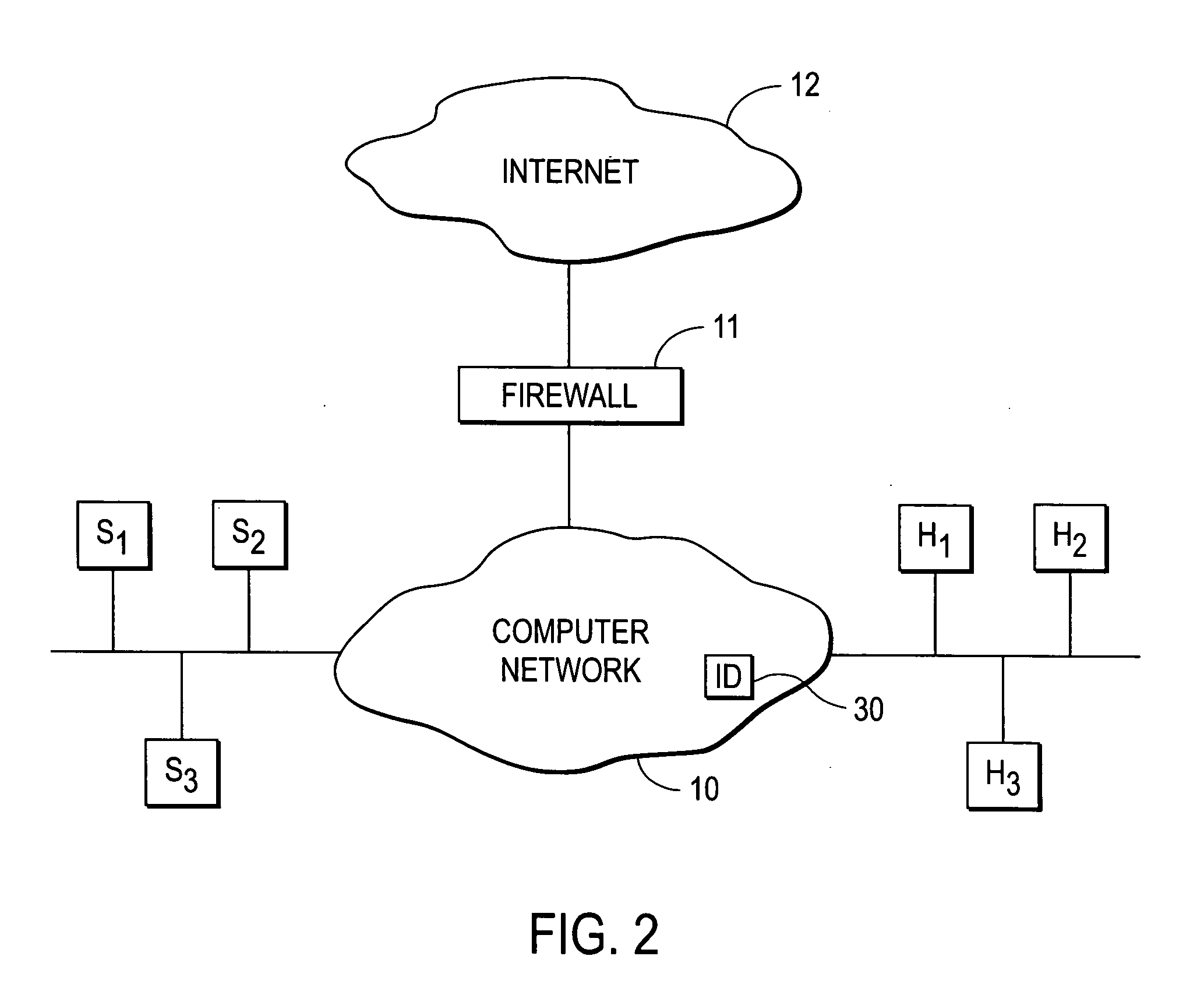
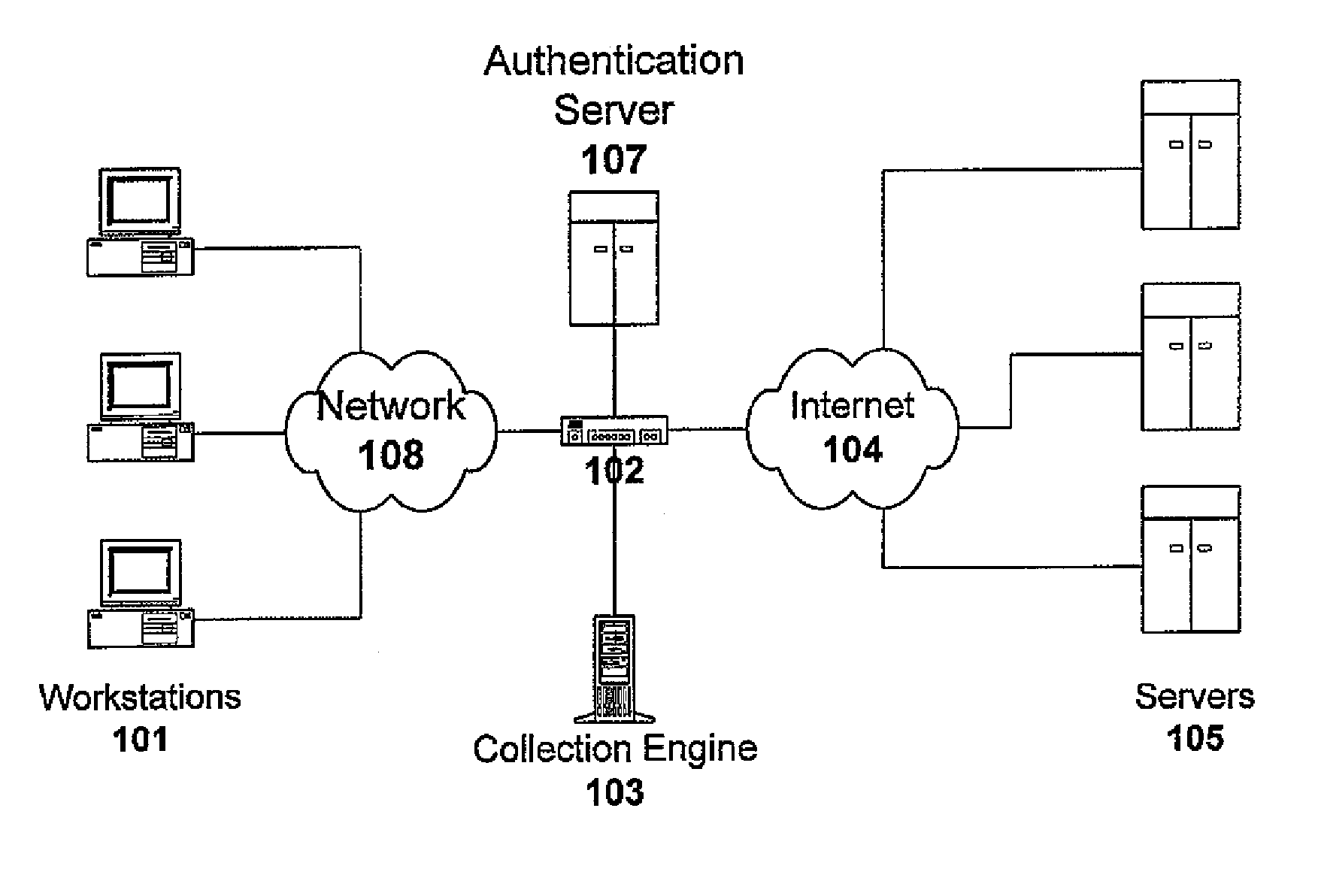
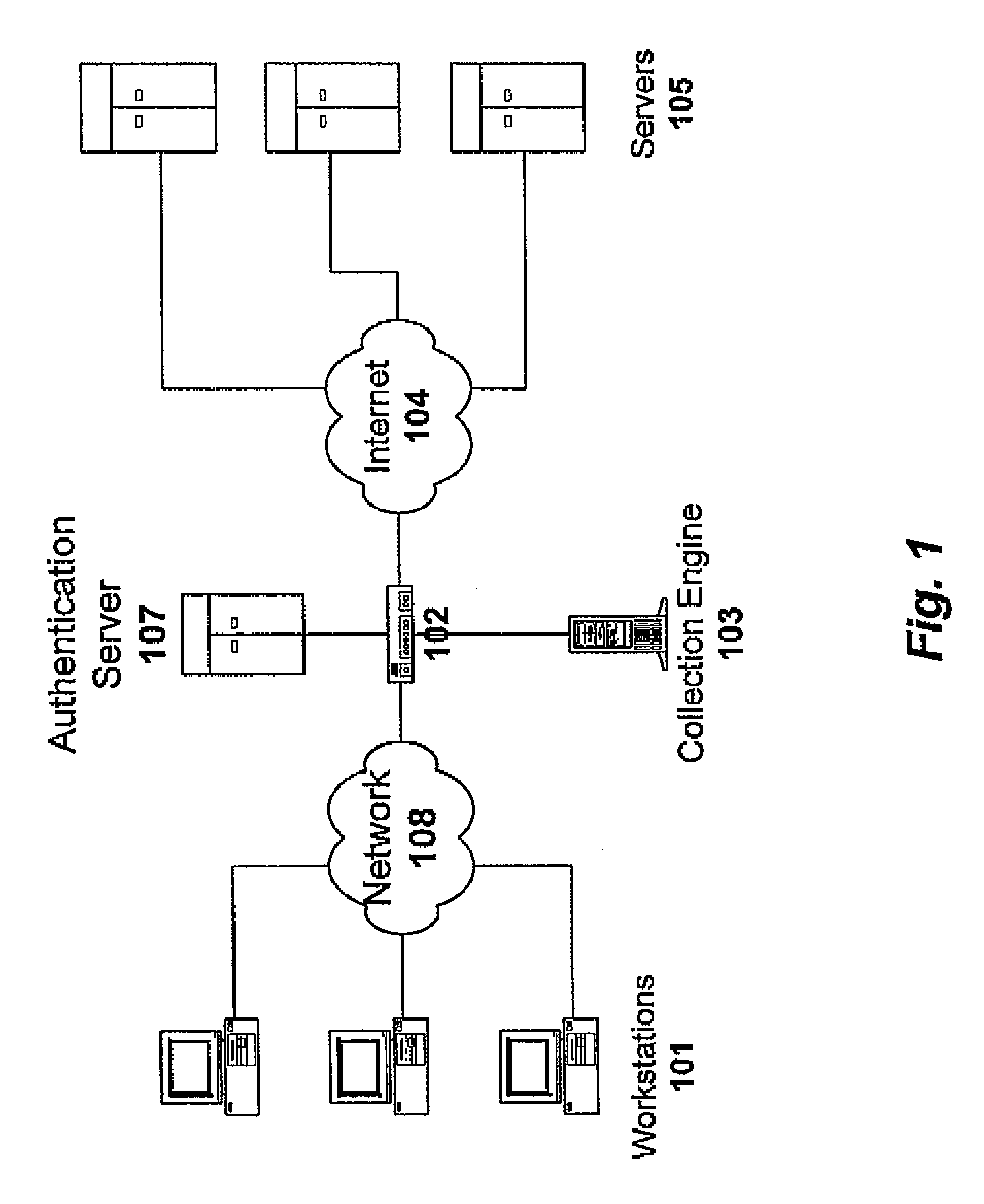
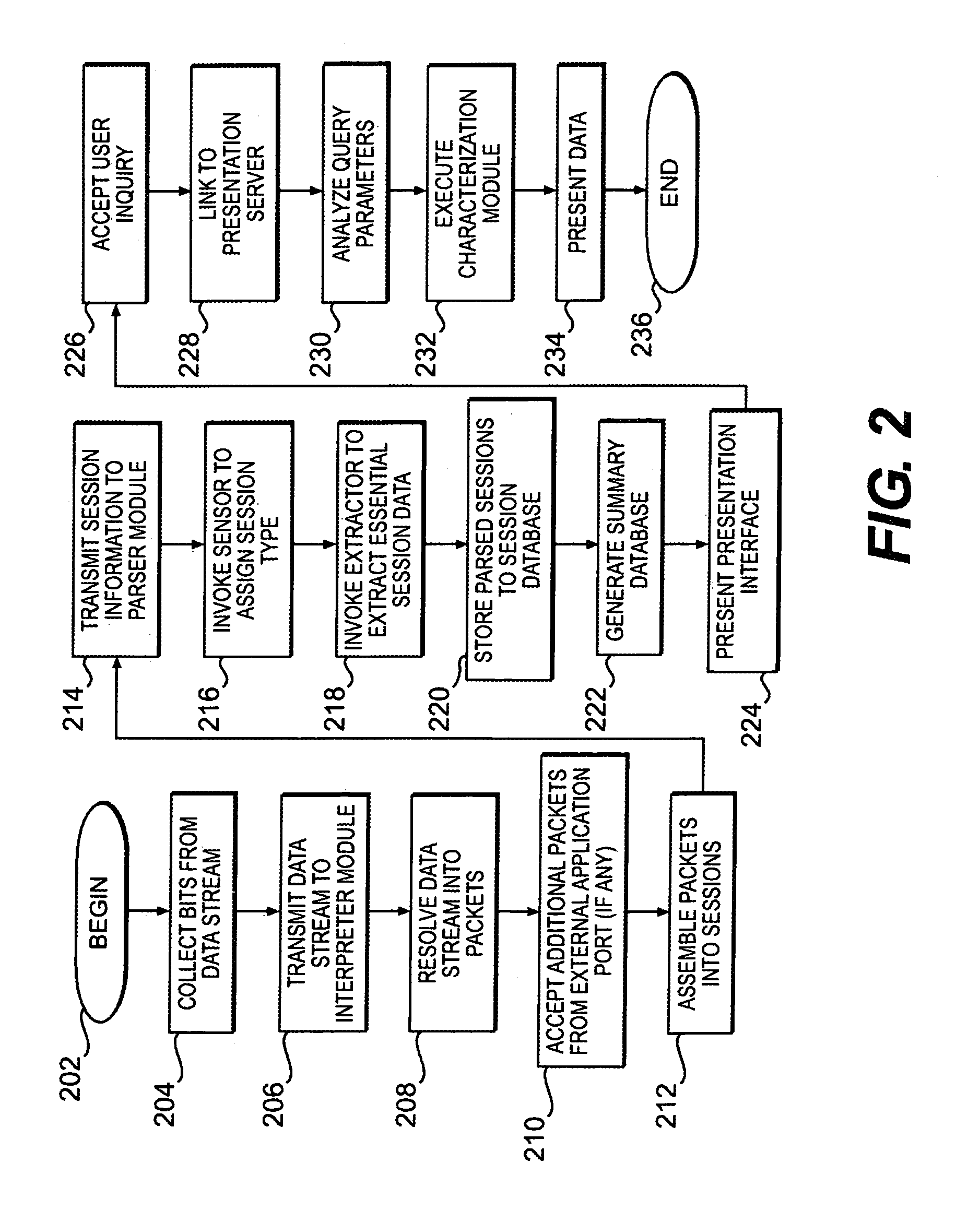
InactiveUS7016951B1Optimize networkEasy to checkMultiple digital computer combinationsTransmissionData streamThe Internet
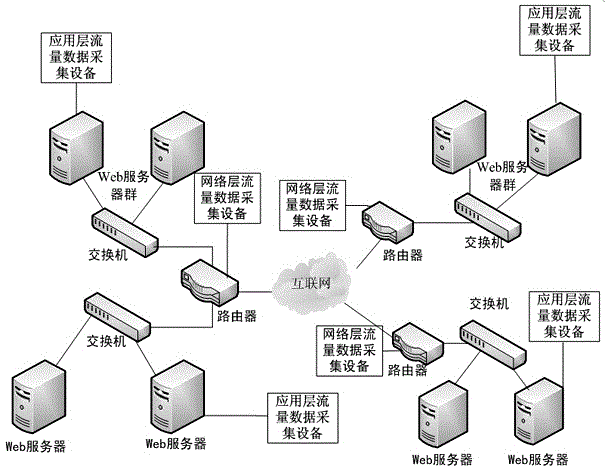
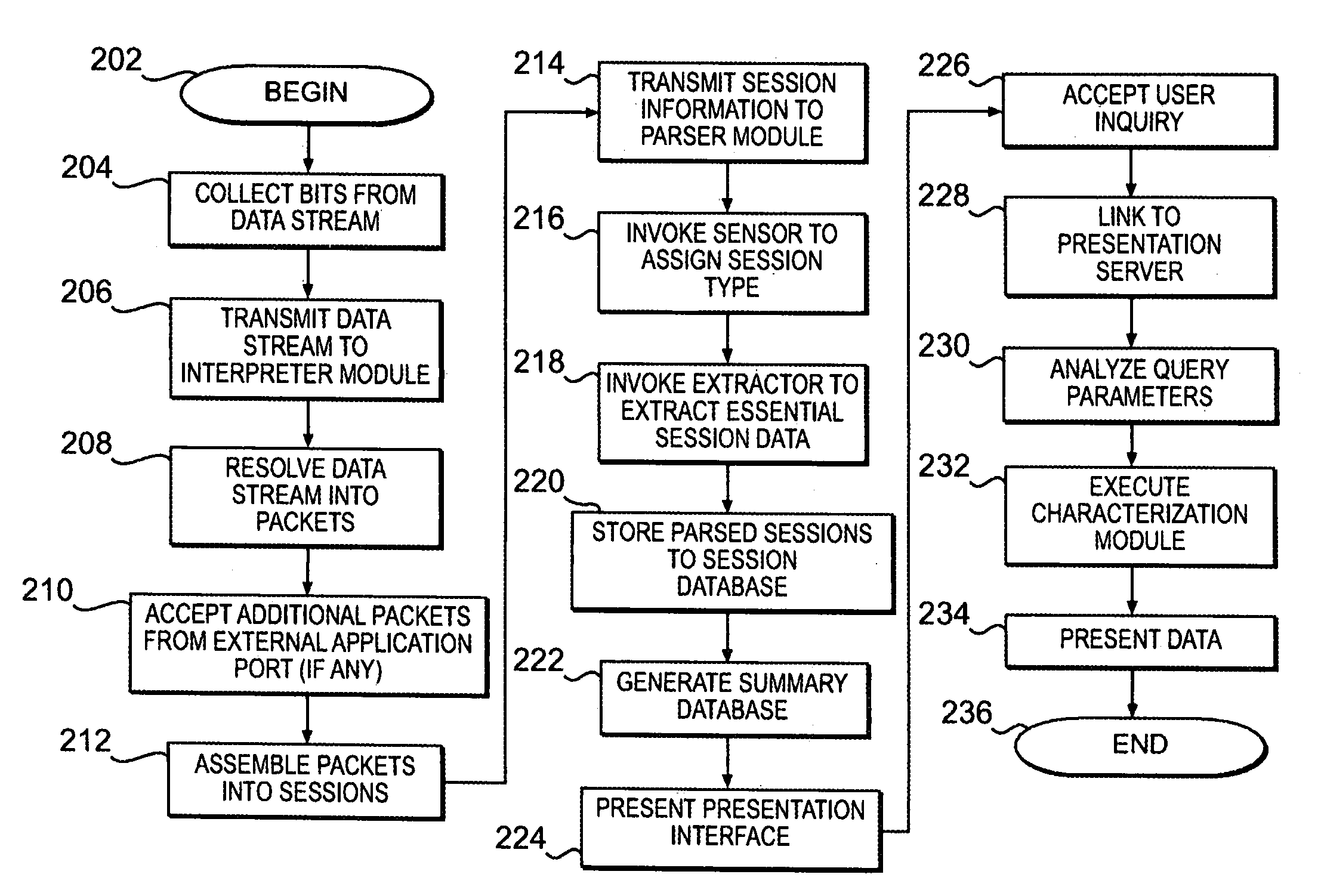
A system for network security transparently occupies an observation port on the data stream, passing the entire range of network information to a dedicated interpreter. The interpreter resolves the data stream into individual data packets, which are then assembled into reconstructed network sessions according to parameters such as protocol type, source and destination addresses, source and destination ports, sequence numbers and other variables. The different types of sessions may include the traffic of many different types of users, such as e-mail, streaming video, voice-over-Internet and others. The system detects and stores the sessions into a database. A parser module may extract only the minimum information needed to reconstruct individual sessions. A backend interface permits a systems administrator to interrogate the forensic record of the network for maintenance, security and other purposes. The invention is not constrained to detect limited types of data, but rather captures and records a comprehensive record of network behavior.
Owner:EMC IP HLDG CO LLC +1
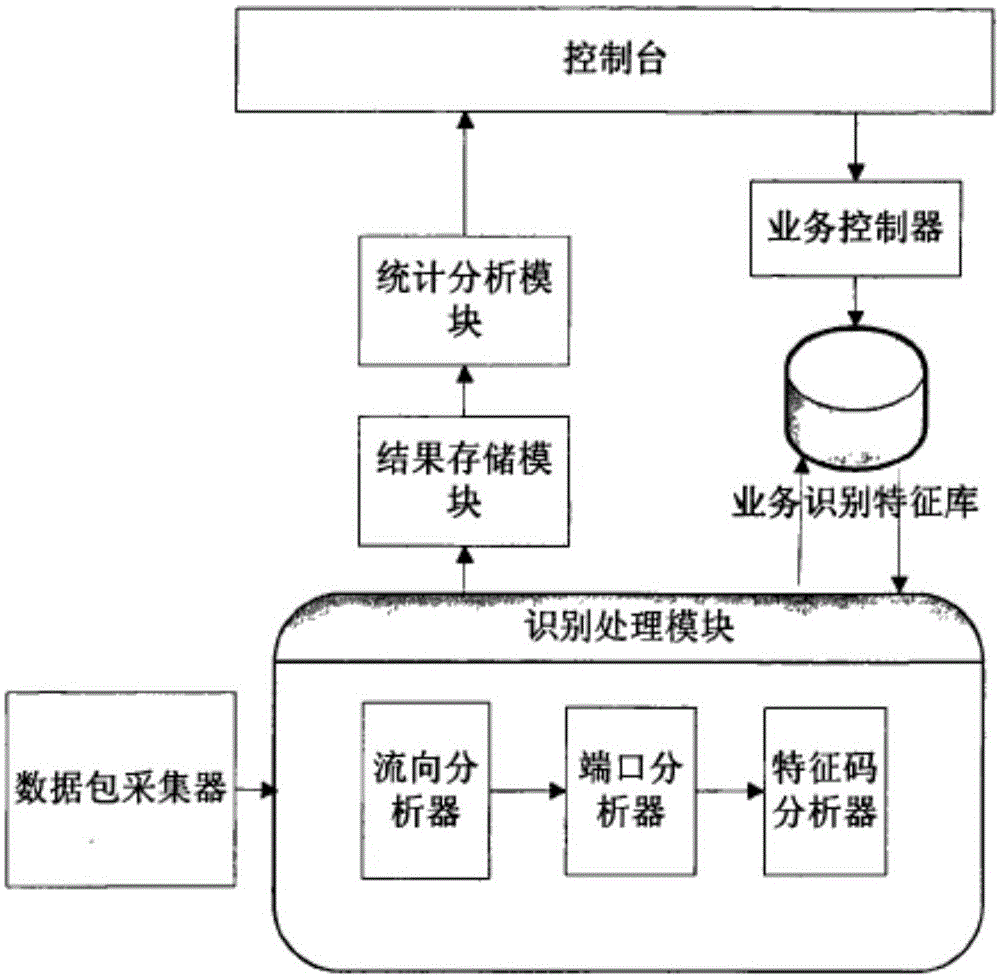
Device and method for detecting network access abnormality based on data stream behavior analysis
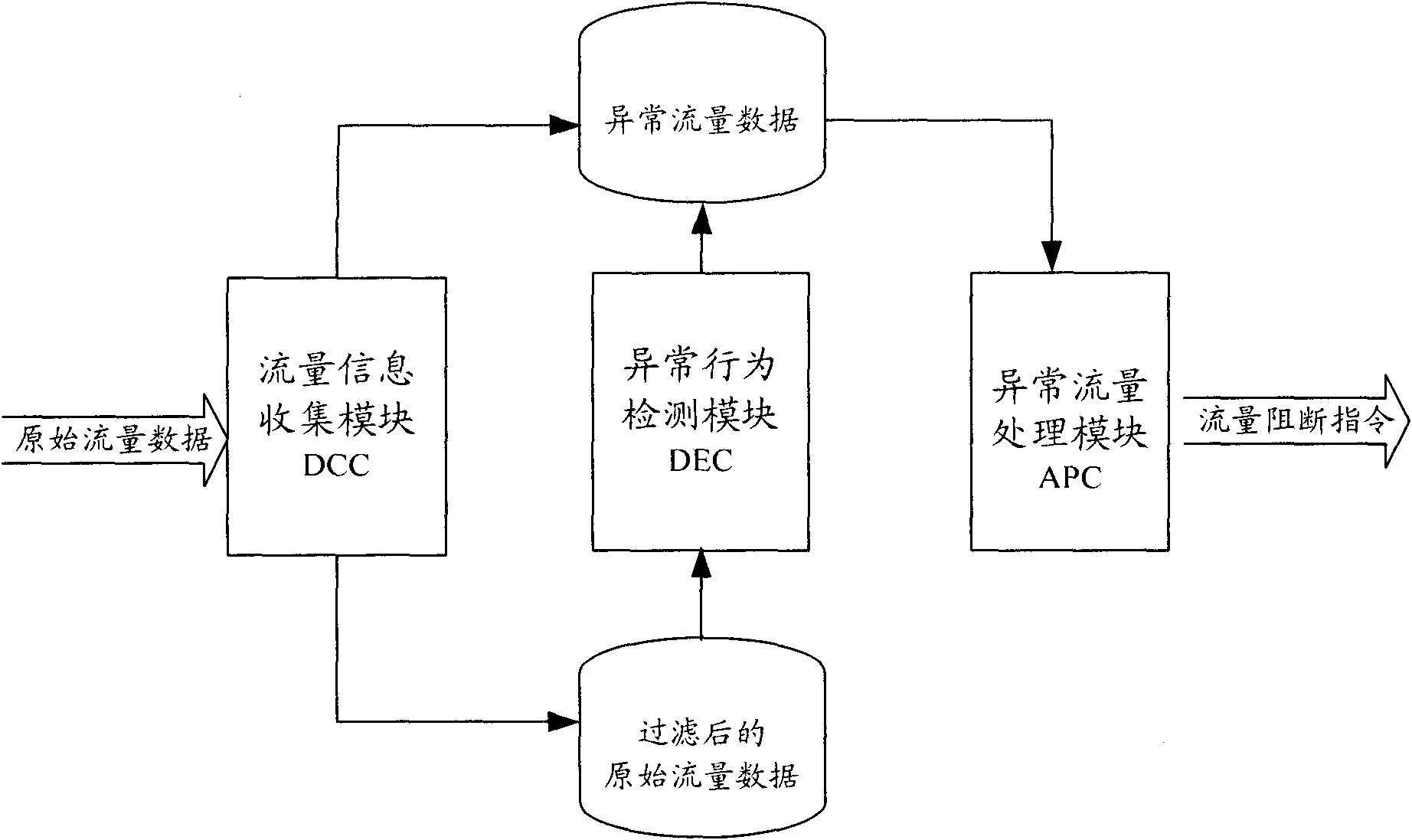
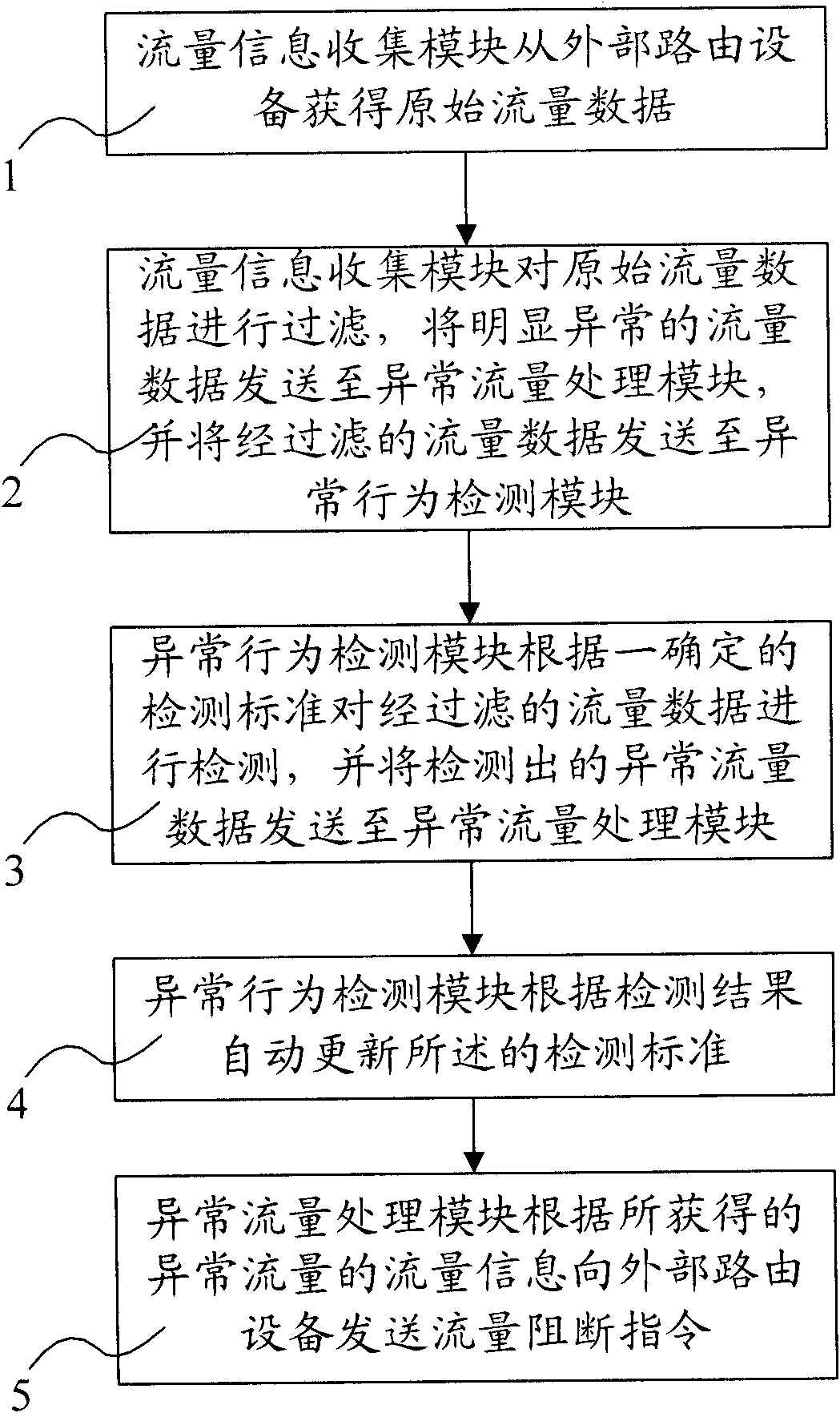
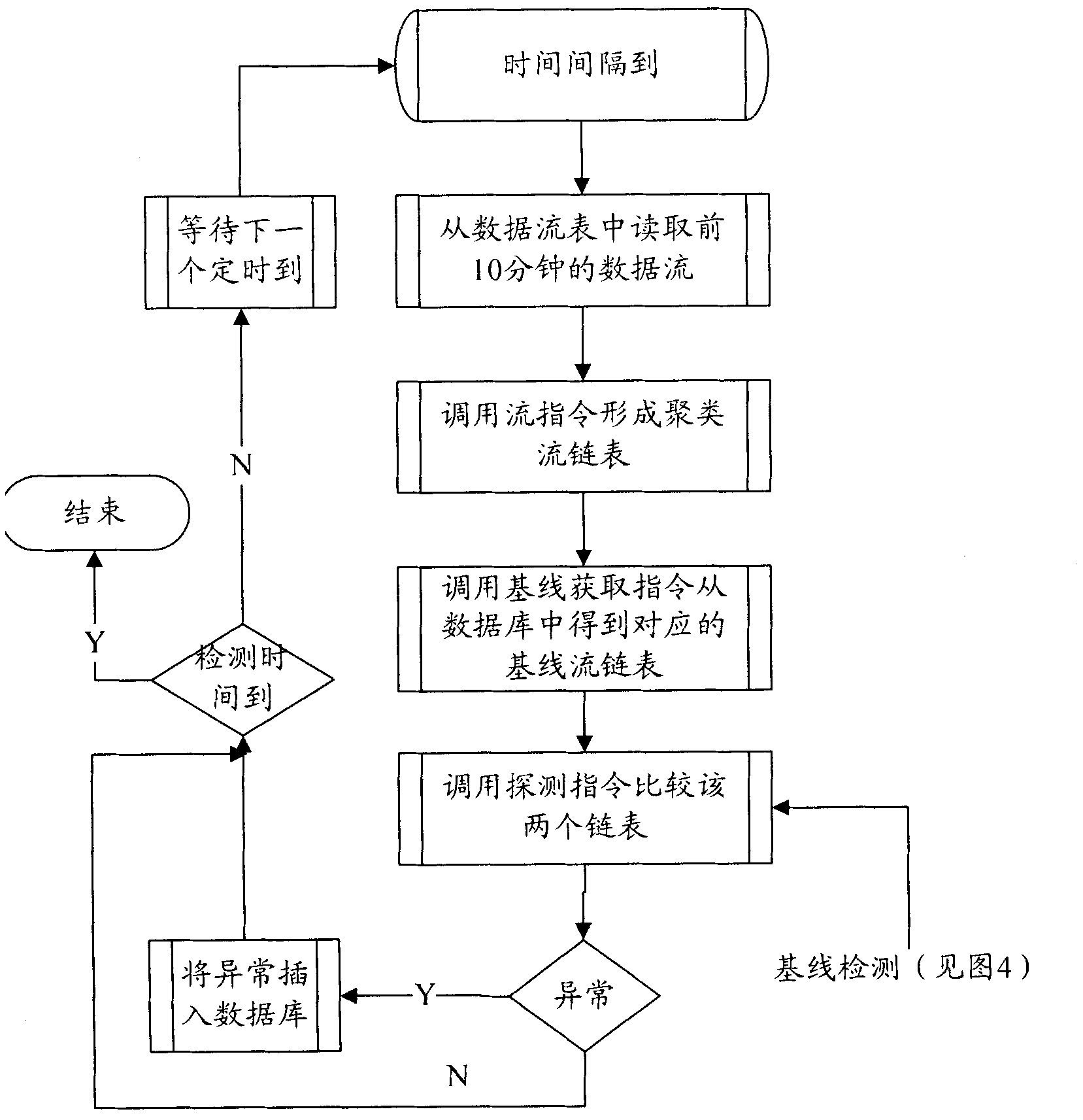
ActiveCN102130800AQuick and effective summaryEfficient identificationData switching networksReal-time dataData stream
The invention relates to a device for detecting network access abnormality based on data stream behavior analysis, comprising a flow information collection module, an abnormal behavior detection module and an abnormal flow processing module, wherein the flow information collection module is respectively connected with the abnormal behavior detection module and the abnormal flow processing module;and the abnormal behavior detection module is connected with the abnormal flow processing module. The invention also relates to a method for using the device. In the method, obvious abnormal flow data is filtered out firstly, then a network behavior model is used to detect the filtered flow data, and the network behavior model is automatically updated; and finally, the flow is blocked according to detection results. The device and method provided by the invention is utilized to establish a normal network behavior model. The model is compared with real-time data so as to detect whether real-time flow is abnormal; and the network behavior model is dynamically modified, abnormal flow sources are analyzed, and the abnormal flow is blocked, thus identifying the abnormal flow quickly and effectively and improving the accuracy of the detection.
Owner:CERTUS NETWORK TECHNANJING
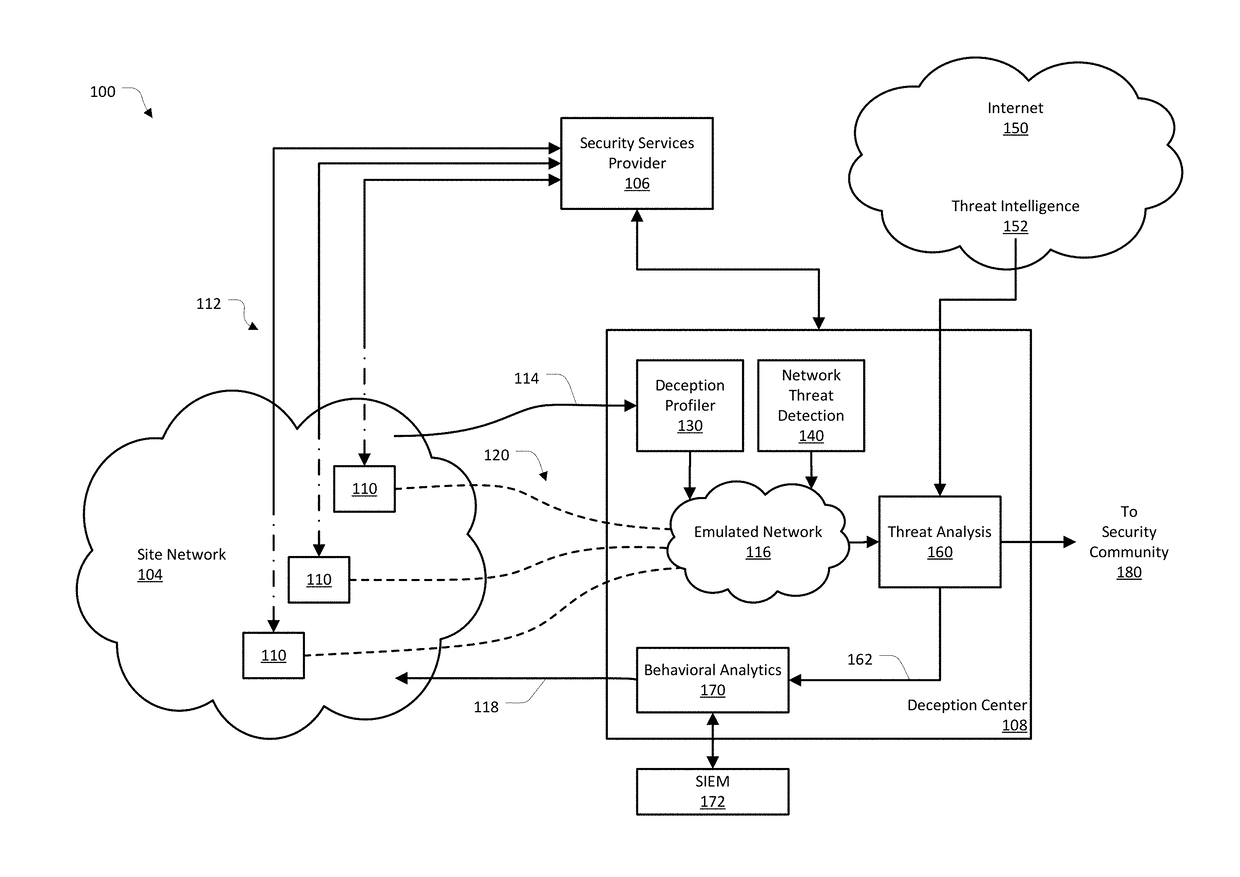
Detecting security threats by combining deception mechanisms and data science
Provided are systems, methods, and computer-program products for a network device, configured to use data science techniques to manage the deployment of deception mechanisms in a network, where the deception mechanisms can attract and detect threats to the network. In various implementations, the network device can receive network data. The network data can include data produced by an interaction with a deception mechanism. The deception mechanism can be part of the security of the network. An interaction can include a potential threat to the network. The network device can further be configured to analyze the network data using a data science engine, including identifying a pattern of network behavior. The network device can further generate an attack pattern that includes the behavior of the potential threat. The network device can further use the attack pattern to modify deception mechanisms on the network.
Owner:ACALVIO TECH
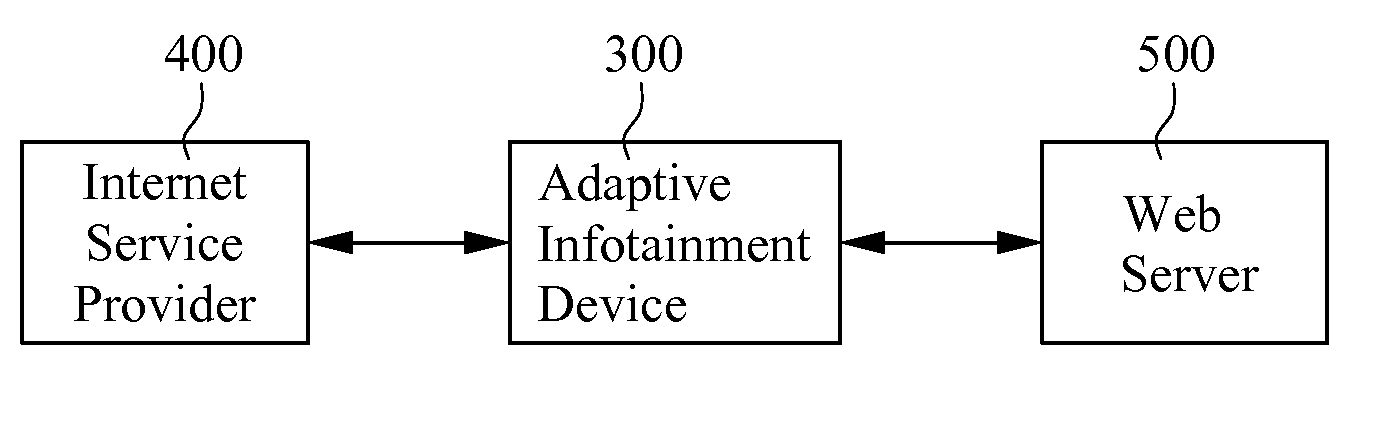
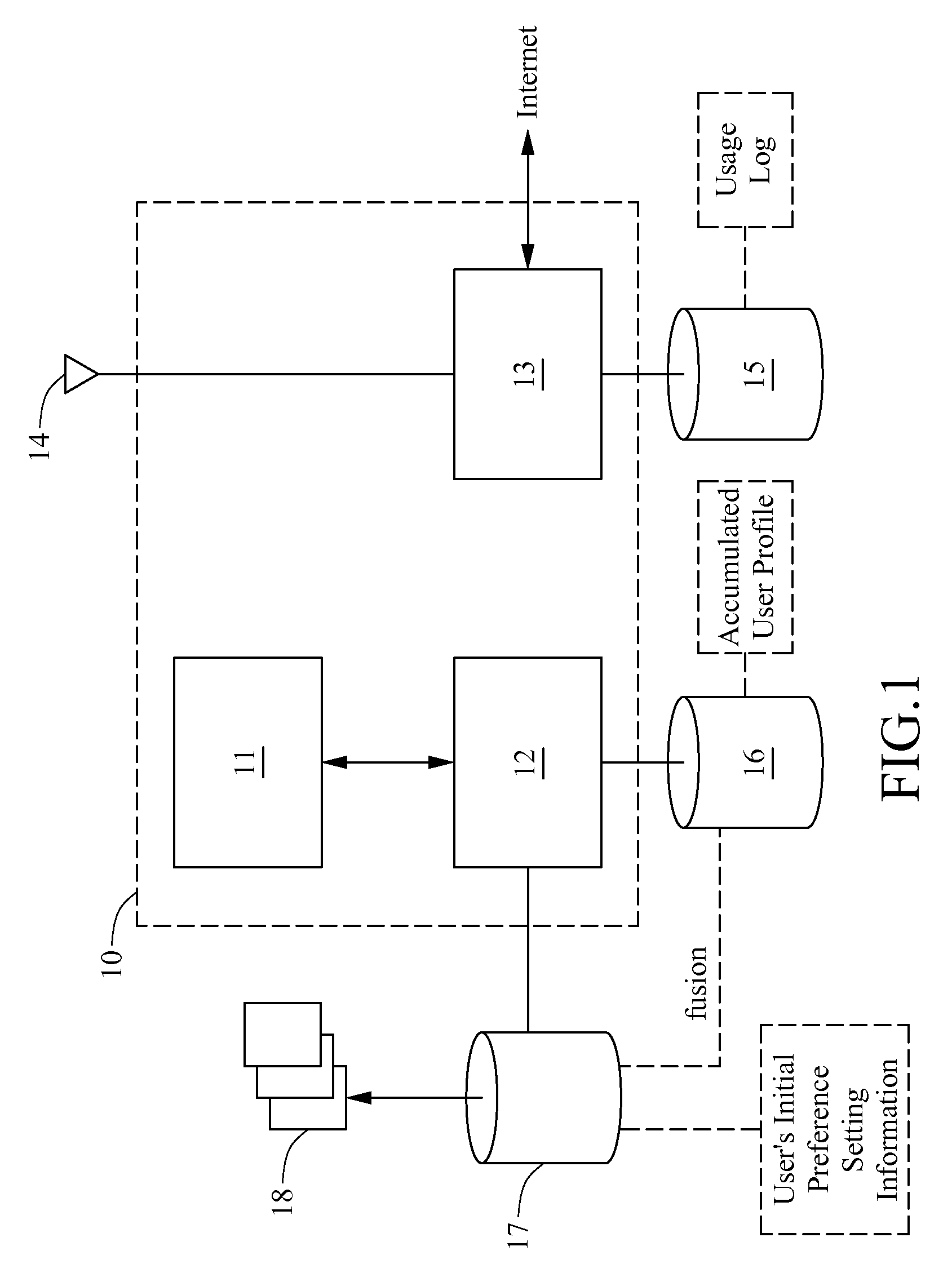
Adaptive infotainment device
InactiveUS8578279B2Easy to browseDigital data information retrievalCathode-ray tube indicatorsNetwork behaviorEngineering
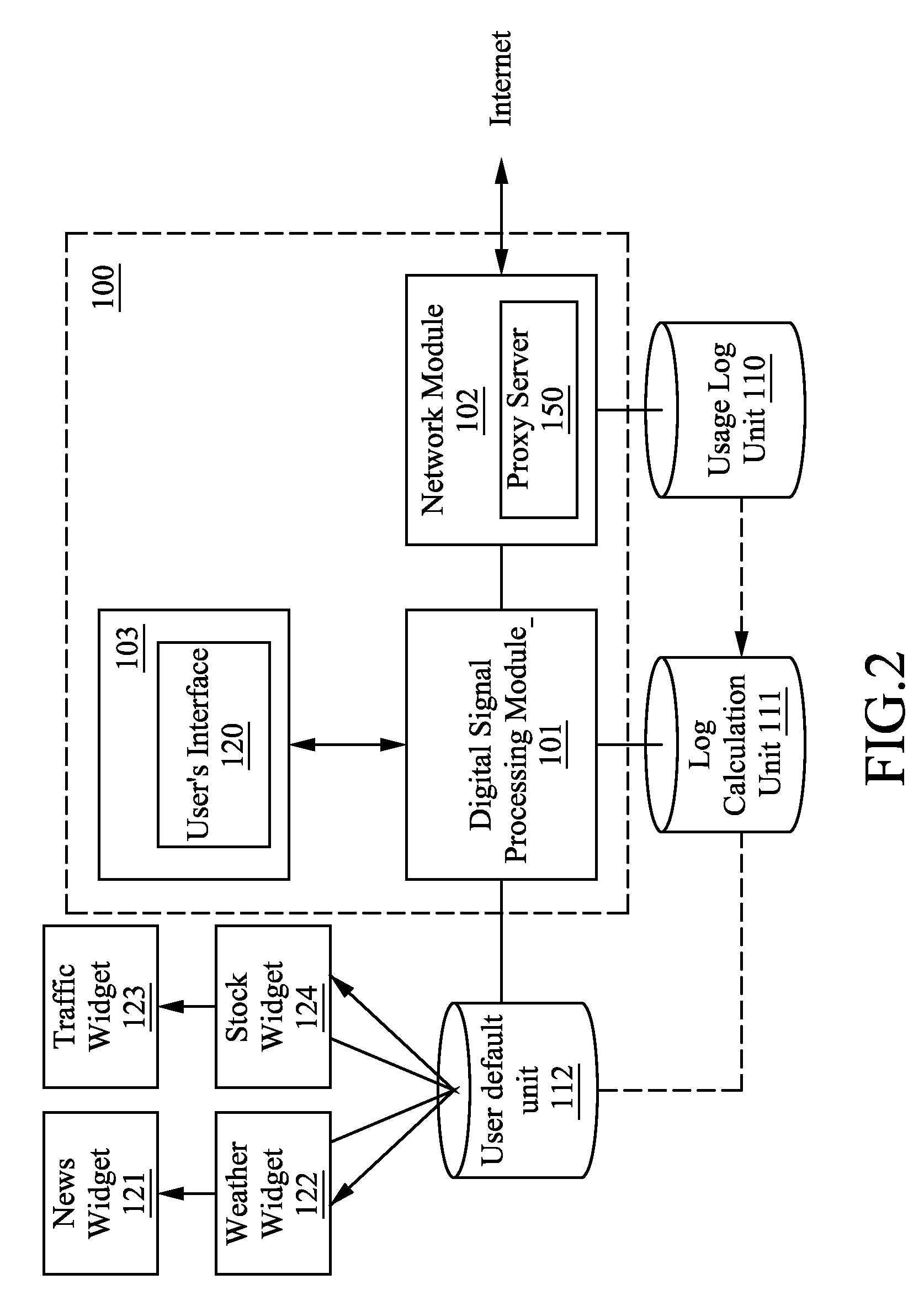
The present invention provides an adaptive infotainment device, comprising a display unit, a processing module, and a network module. The processing module is coupled to the display unit to decrypt and process the multi-media content. The network module is coupled to the processing module to receive the multi-media content and selecting paths and accessing nodes. The network module collects the usage log to be processed by the processing module to generate an accumulated user profile to be fused with user default information in a user default unit coupled to the processing module to generate at least one threshold value so that the display unit is capable of displaying the processed multi-media content according to the threshold value. Hence, the user's network behavior can be learned by combining the pre-determined preferences and the past usage preferences so as to generate the most favorable displaying means to enhance the convenience for browsing information.
Owner:ACCTON TECHNOLOGY CORPORATION
Method and apparatus for confirming user behavior
ActiveCN101355504AEffective React Network BehaviorData switching networksNetwork behaviorData mining
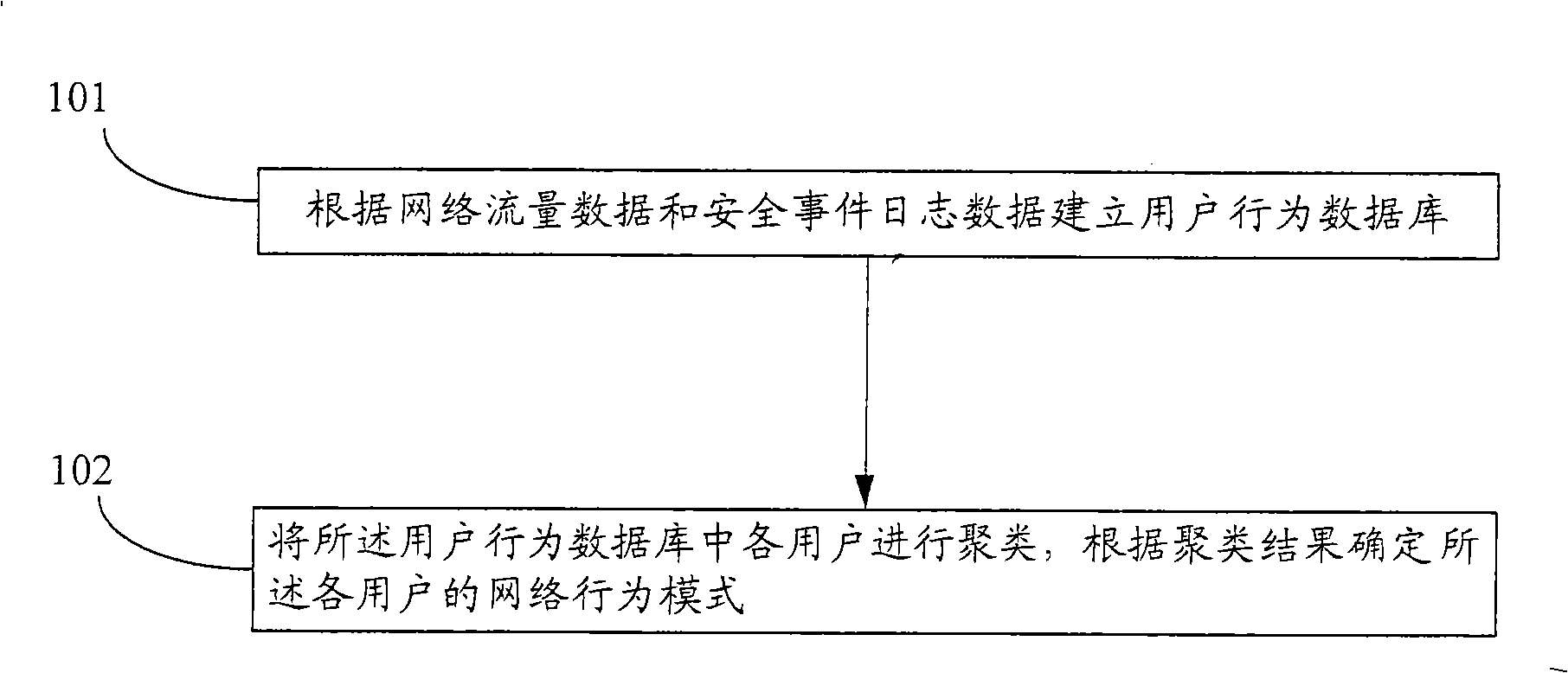
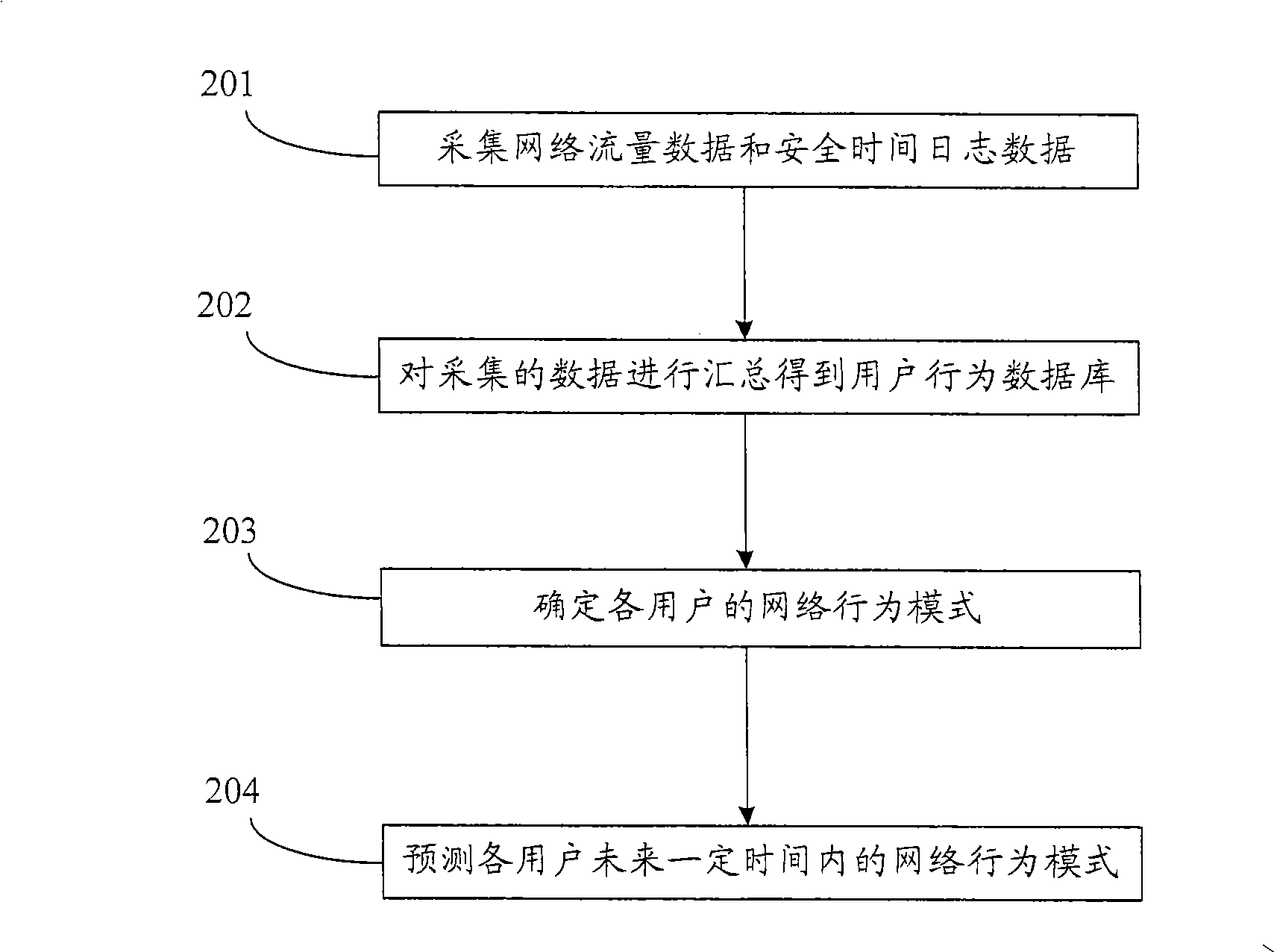
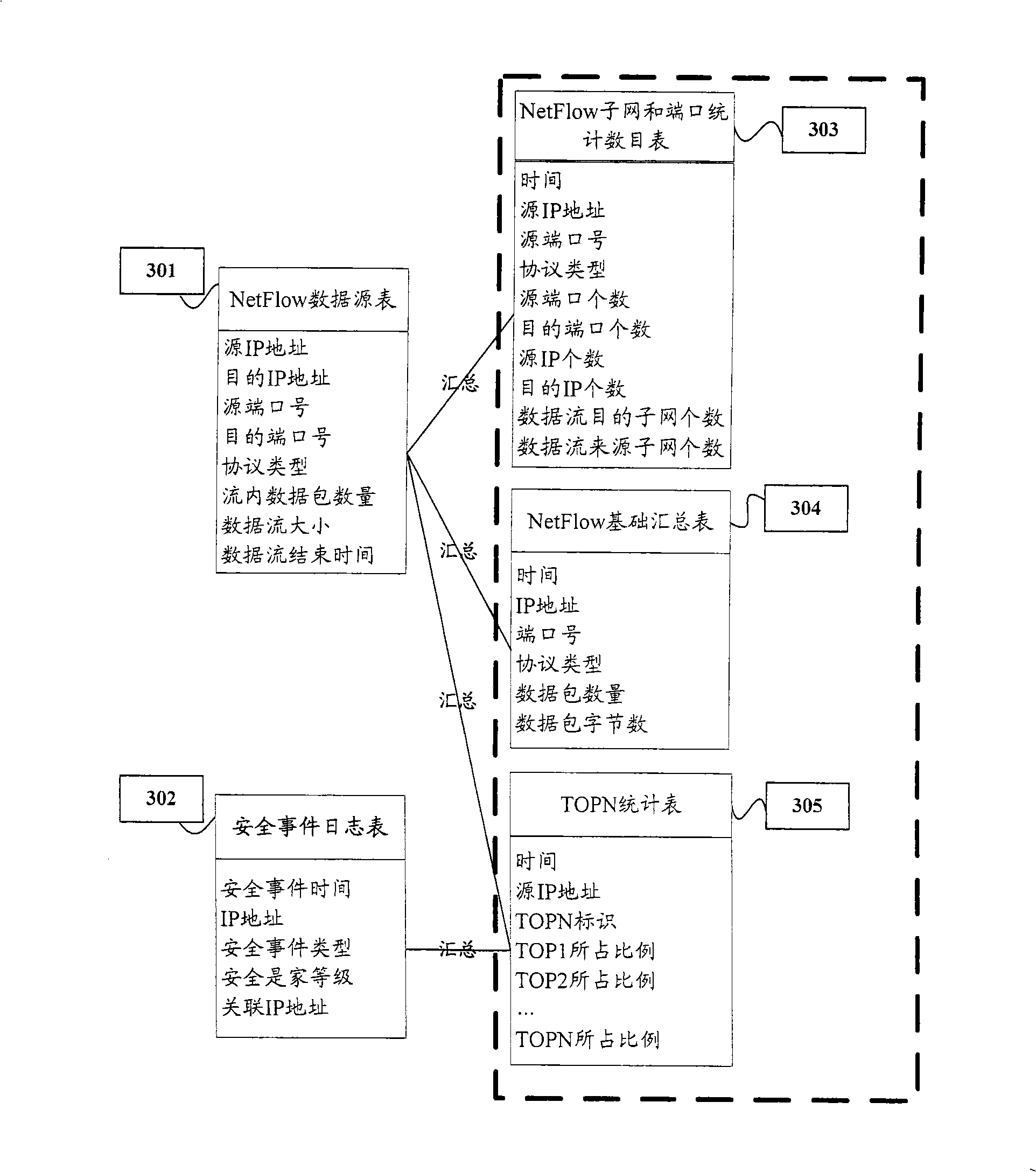
The embodiment of the invention discloses a method for determining user behaviors, comprising the following steps that a user behavior database is established according to the network flow data and the security event journal data; and various users in the user behavior database are clustered and the network behavioral pattern of the various users is determined according to the clustering result. In the embodiment of the invention, the various users in the user behavior database are clustered through establishment of the user behavior database; the network behavioral pattern of the various users is determined; and the network behaviors of the users are effectively reflected macroscopically.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
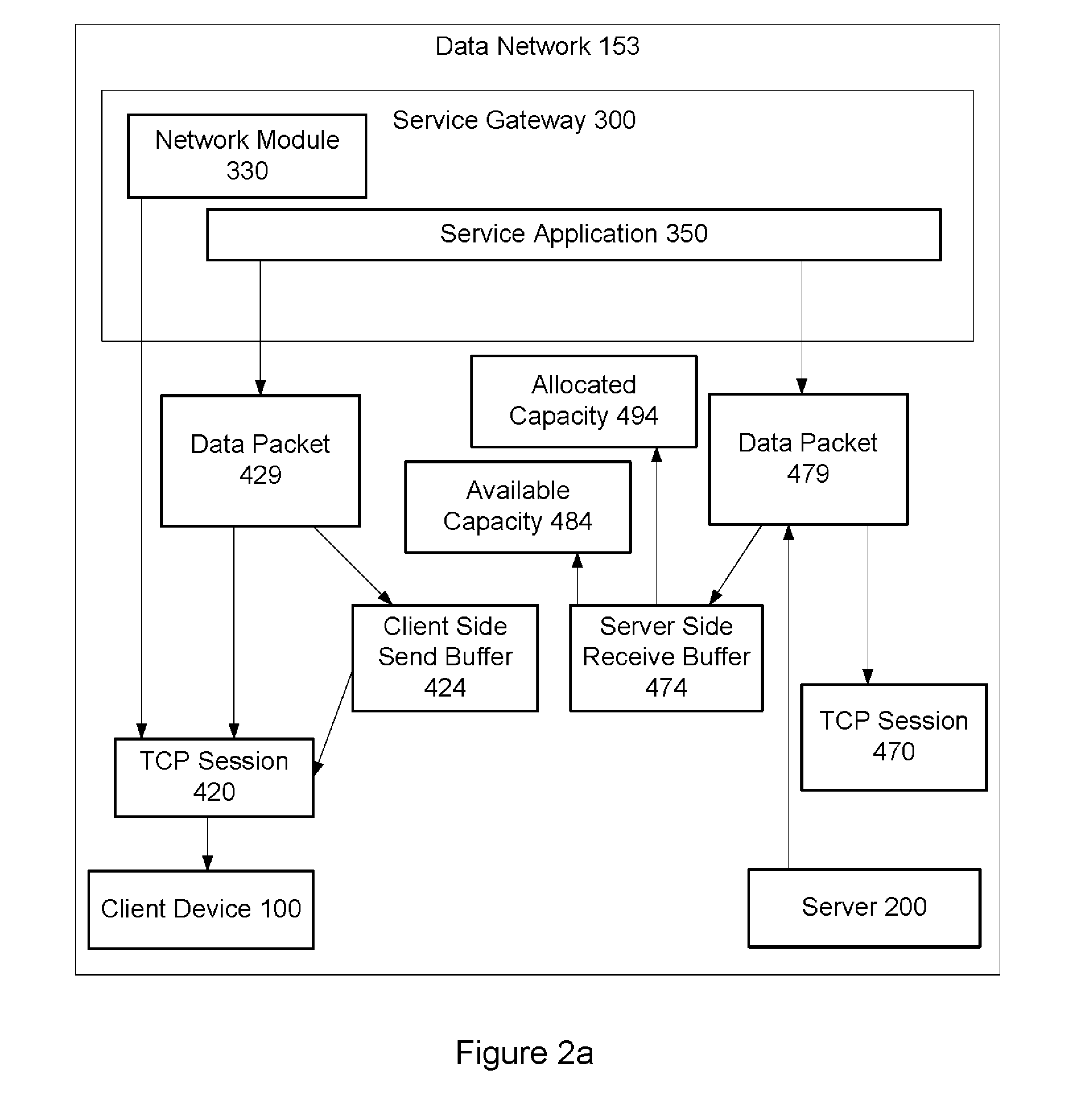
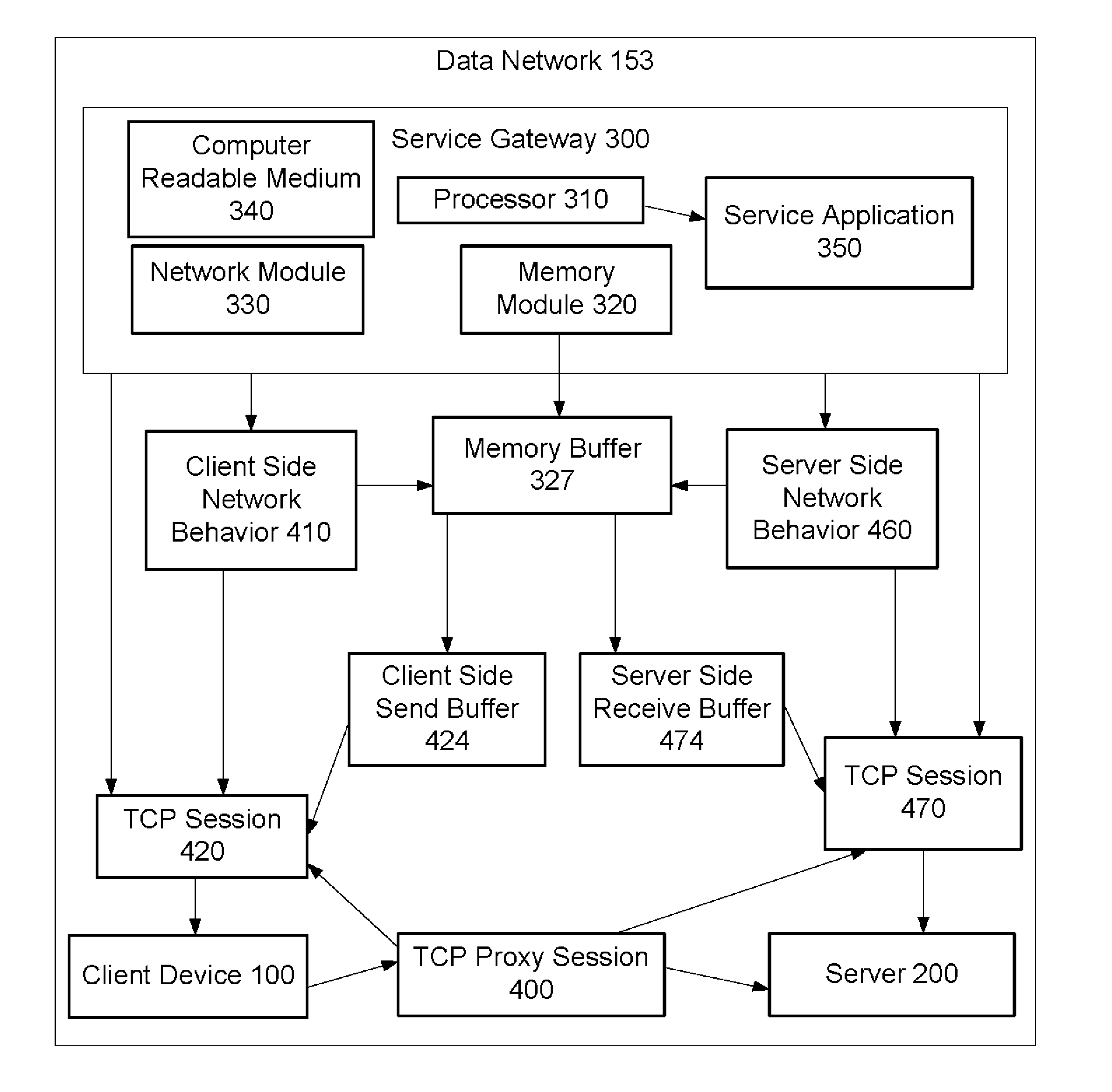
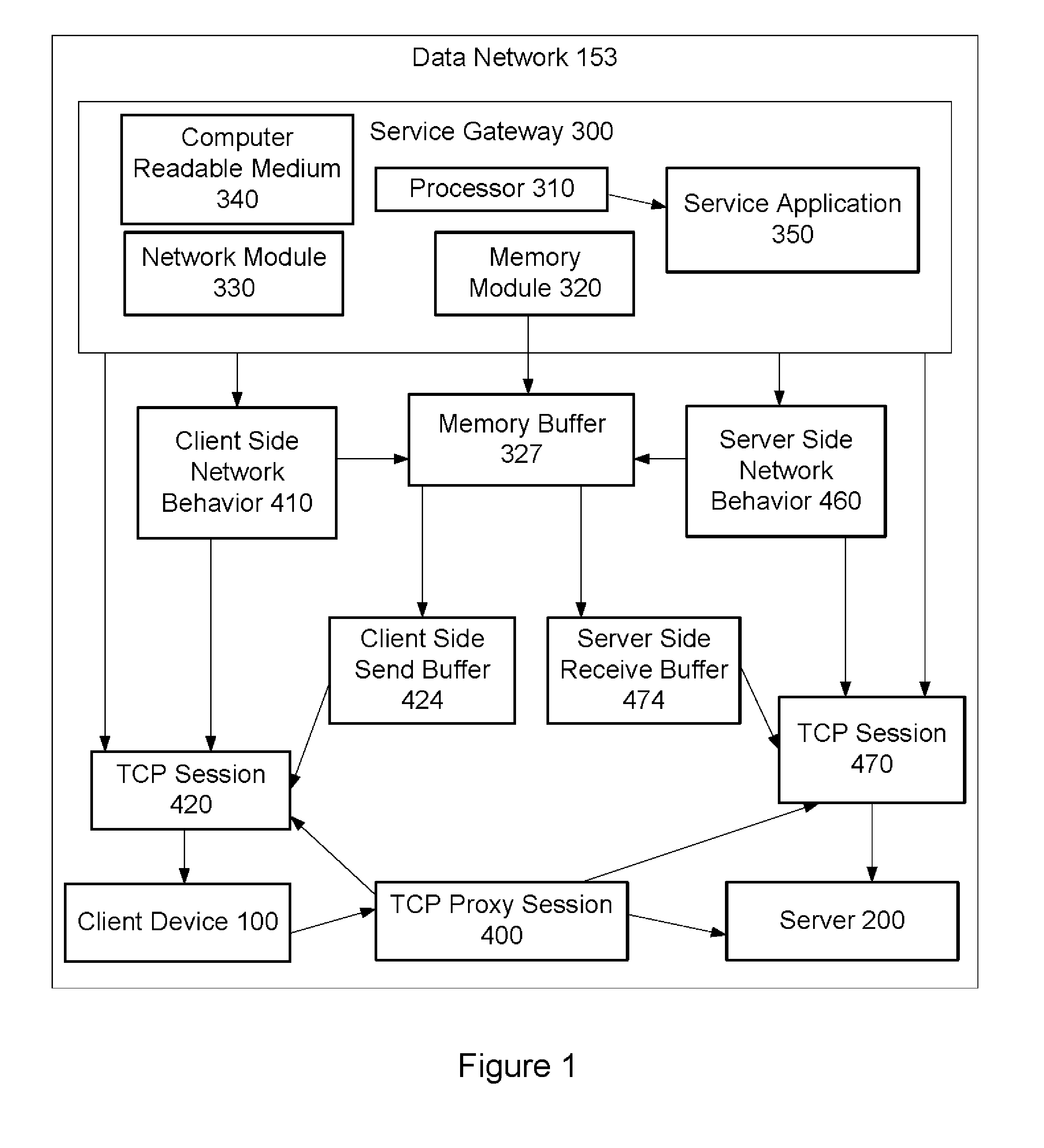
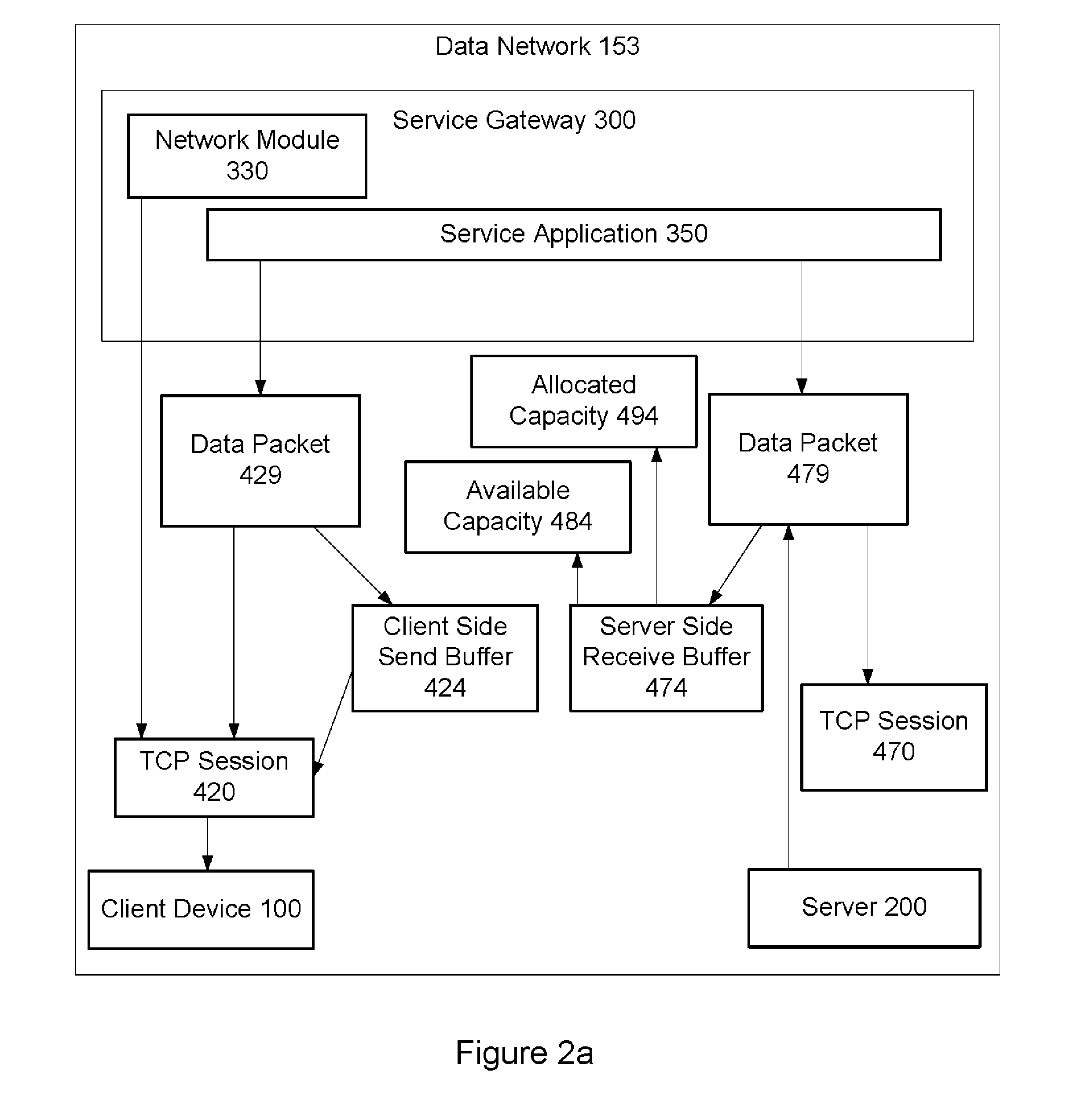
Method to allocate buffer for TCP proxy session based on dynamic network conditions
Allocation of buffers for a TCP proxy session between a client and a server by a service gateway includes: monitoring dynamic network behaviors for server and client side sessions of the TCP proxy session; and allocating capacity for a server side buffer and capacity for a client side buffer in a memory buffer based on the dynamic server side network behaviors, the dynamic client side network behaviors, and a weighted average of a capacity of the memory buffer. In one approach to the allocation, the gateway determines whether an available capacity of the server or client side buffer is sufficient to store a data packet. If not sufficient, the allocated capacity of the server or client side buffer is increased based on measurements of the dynamic network behaviors and the weighted average, and the available capacity of the server or client side buffer is adjusted accordingly.
Owner:A10 NETWORKS
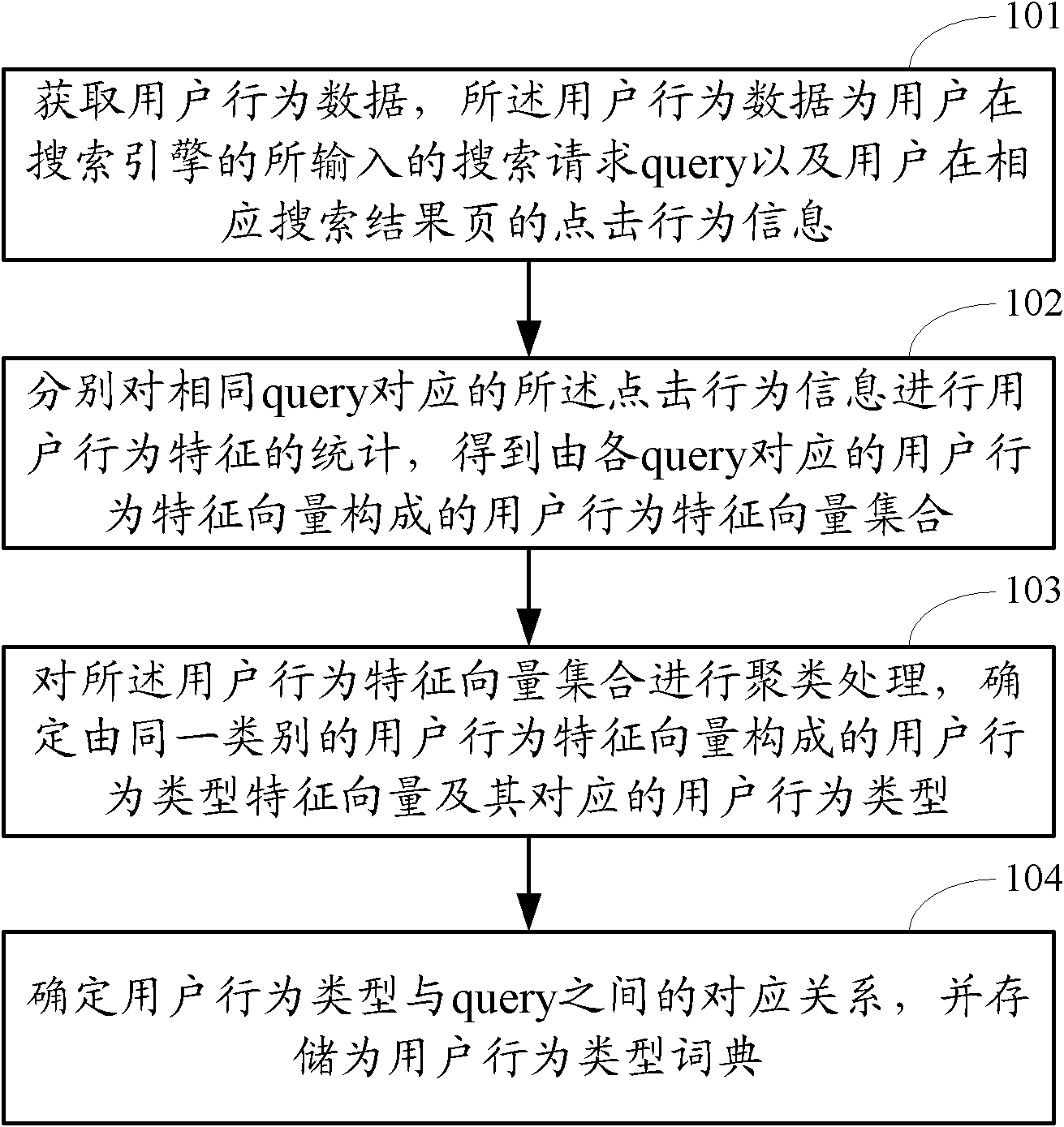
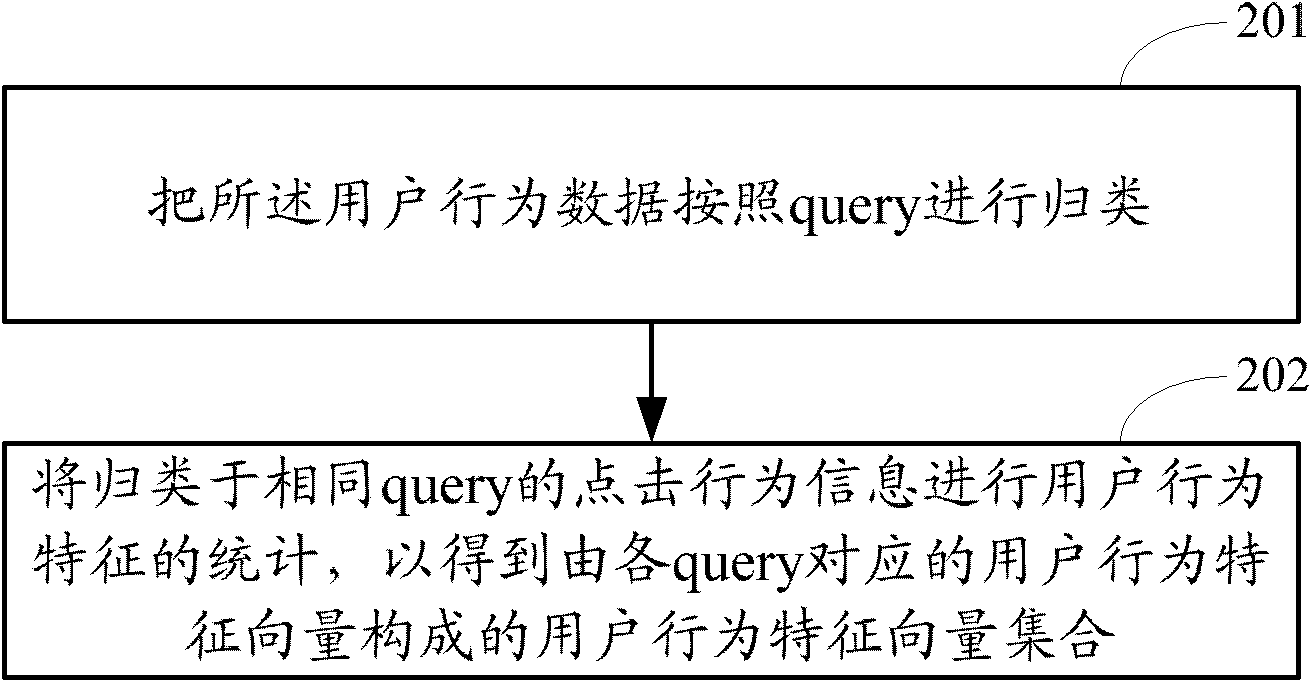
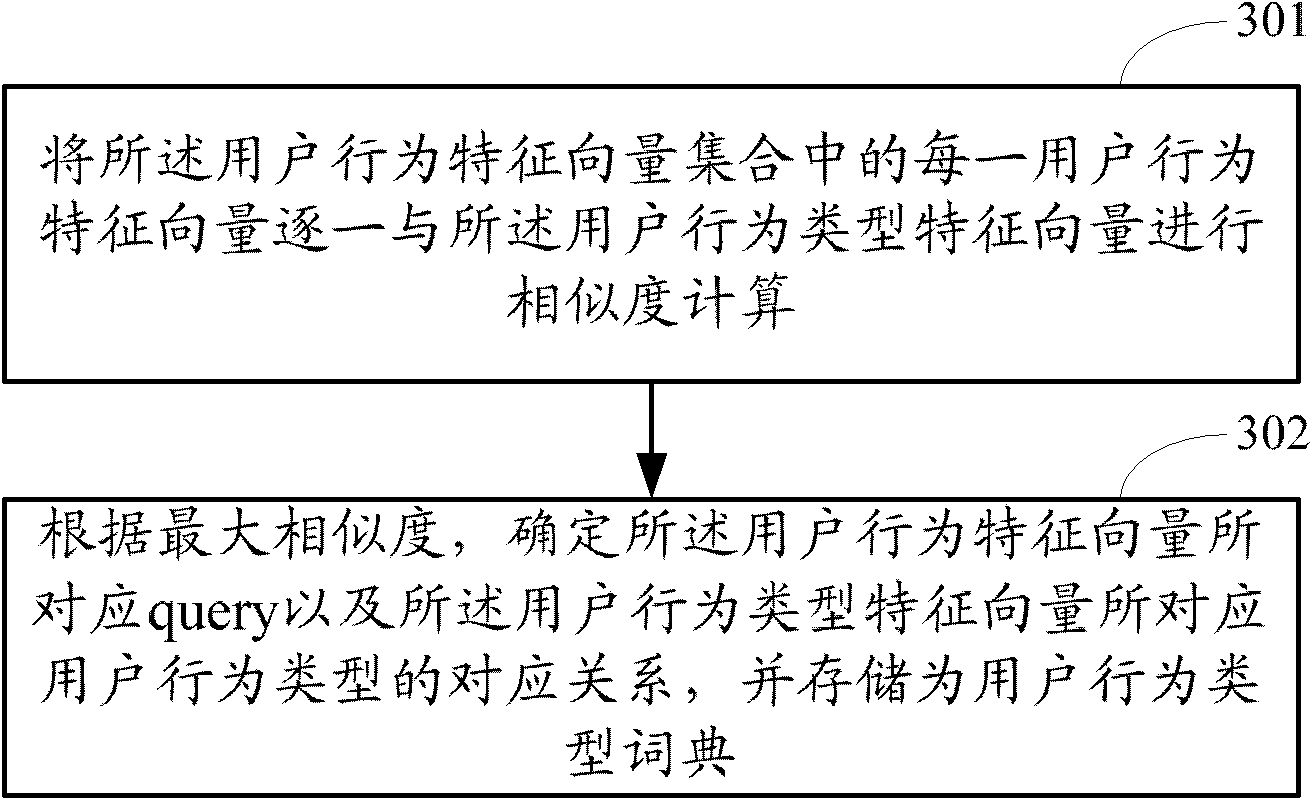
Classification method and device for user network behaviors and search method and device for user network behaviors
ActiveCN102760138AImprove accuracySpecial data processing applicationsFeature vectorNetwork behavior
The invention discloses classification method and device for users' network behaviors and search method and device for users' network behaviors. The classification method includes: data of user behaviors is acquired, the data of the user behaviors include queries input in an search engine by users and information of clicks performed on corresponding search engine results pages by the users; information of the clicks corresponding to the same query are counted in terms of user behavior features, and a user behavior feature vector set consisting of user behavior feature vectors corresponding to the queries is obtained; the user behavior feature vector set is clustered to determine a user behavior pattern feature vector consisting of same patterns of the user behavior feature vectors and a user behavior pattern corresponding to the user behavior pattern feature vector; correspondence between the user behavior patterns and the queries is determined and is stored as a user behavior pattern dictionary. Post-search clicks performed by the users are classified, and accordingly accuracy in services or applications based on user behavior data is improved effectively.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
System and method for separating addresses from the delivery scheme in a virtual private network
InactiveUS6970941B1Overcomes shortcomingCommunication securityMultiple digital computer combinationsNetworks interconnectionSecure communicationNetwork behavior
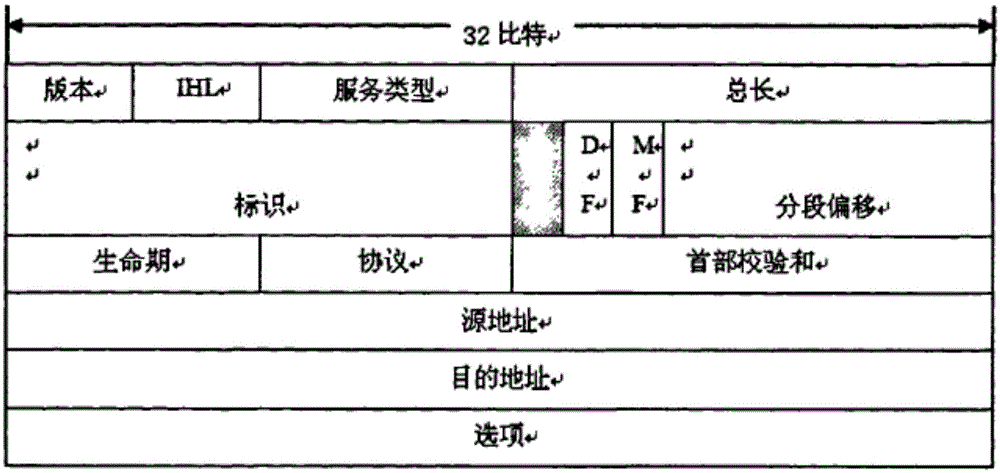
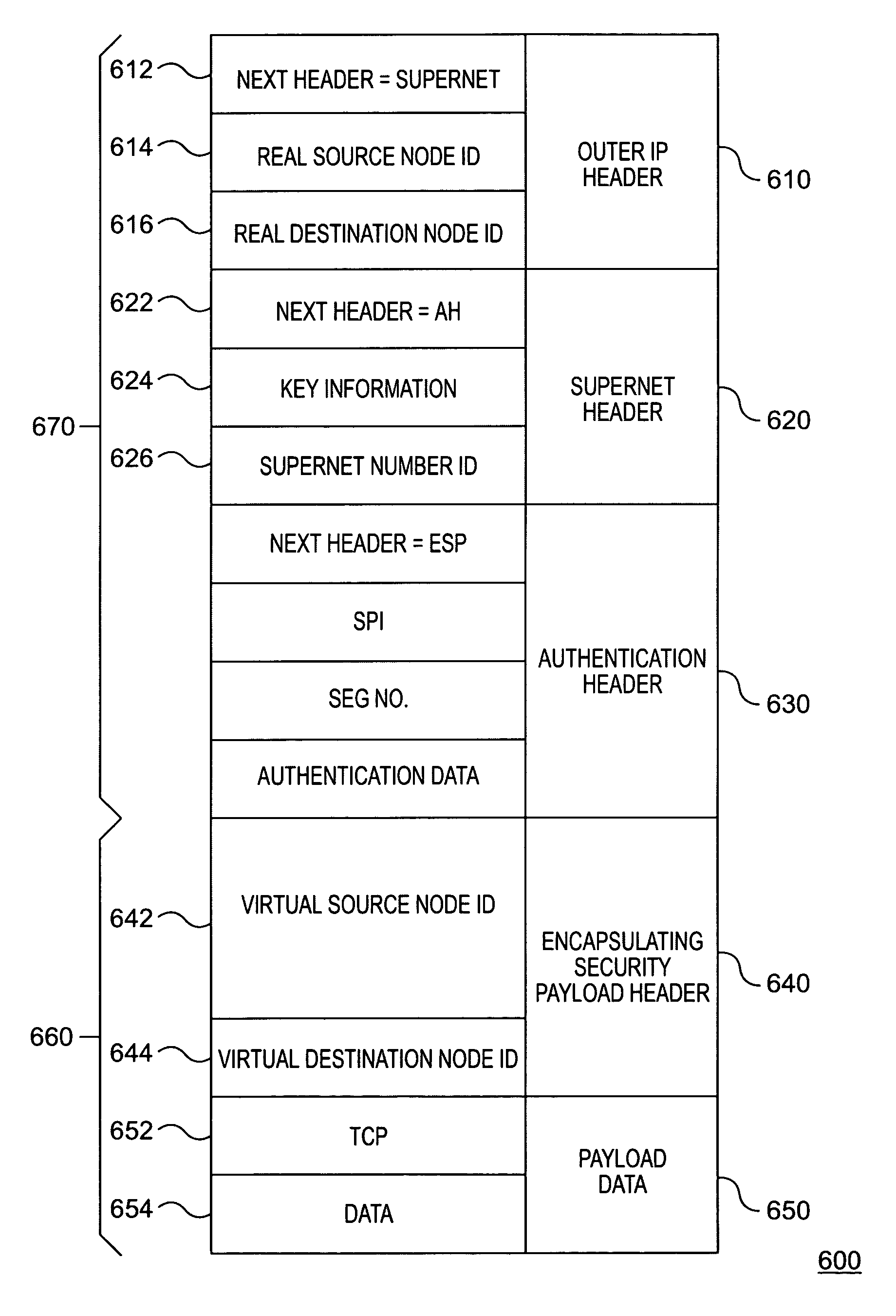
Methods and systems consistent with the present invention establish a virtual network on top of current IP network naming schemes. The virtual network uses a separate layer to create a modification to the IP packet format that is used to separate network behavior from addressing. As a result of the modification to the packet format, any type of delivery method may be assigned to any address or group of addresses. The virtual network also maintains secure communications between nodes, while providing the flexibility of assigning delivery methods independent of the delivery addresses.
Owner:ORACLE INT CORP
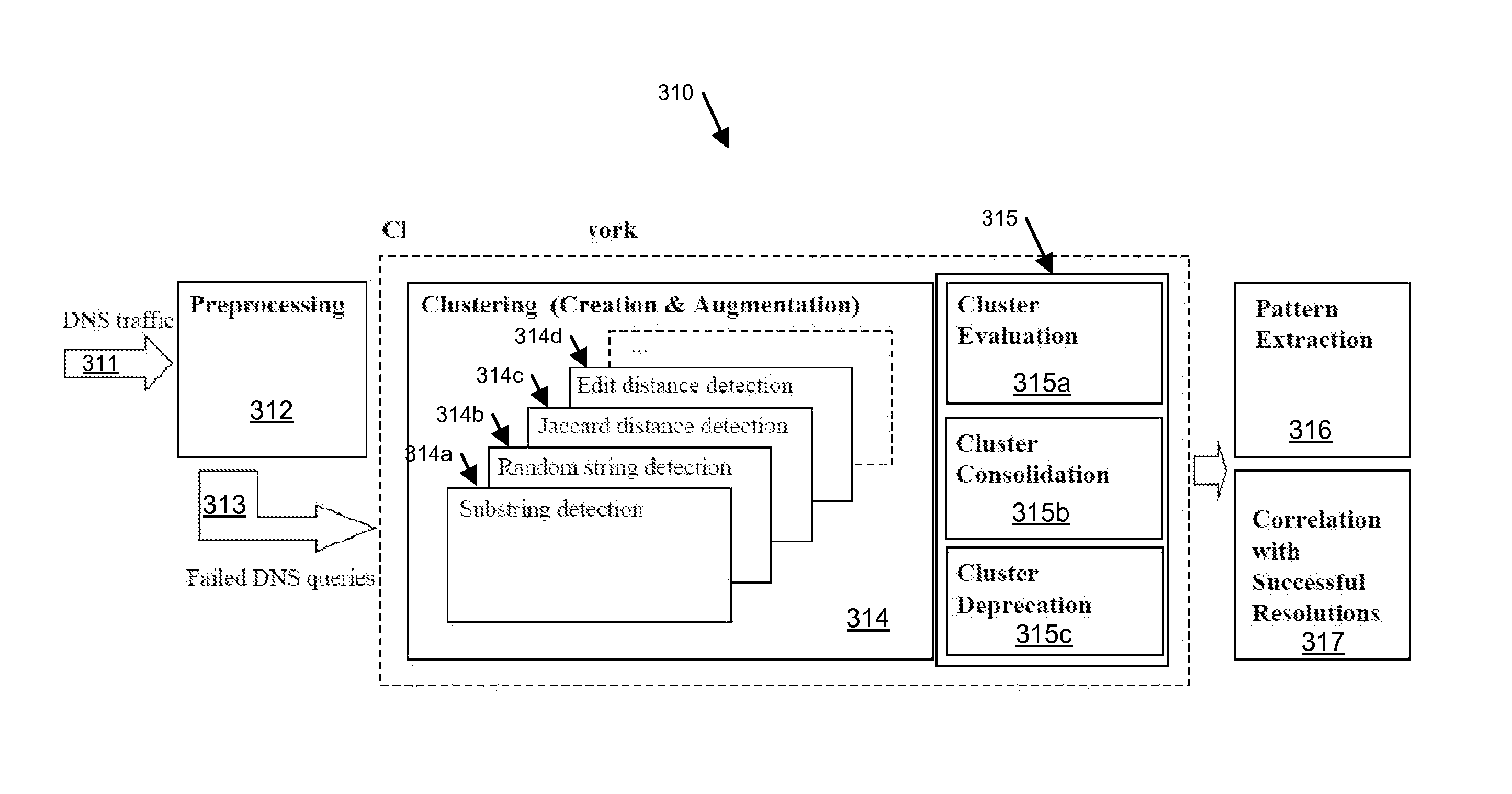
Detecting suspicious network behaviors based on domain name service failures
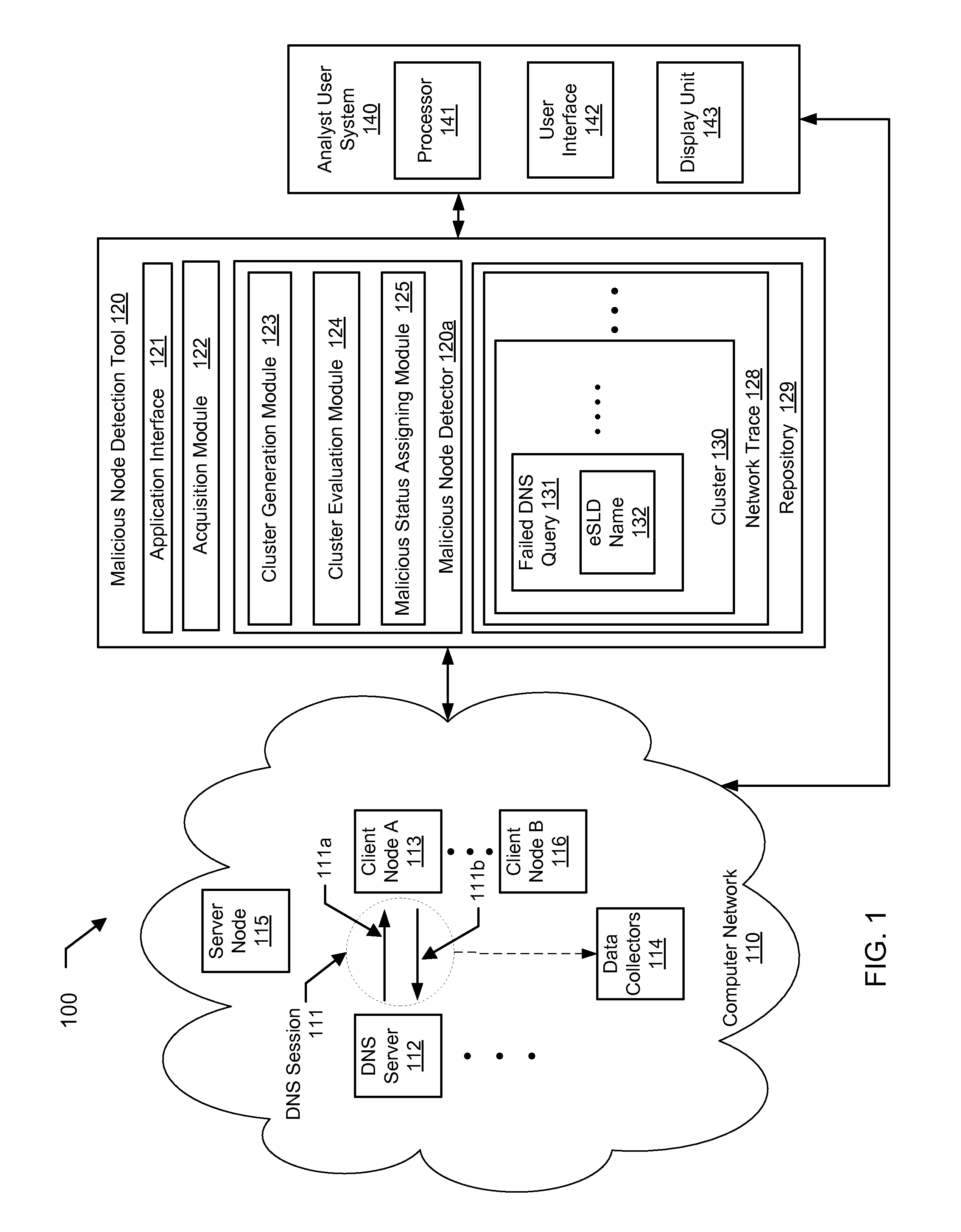
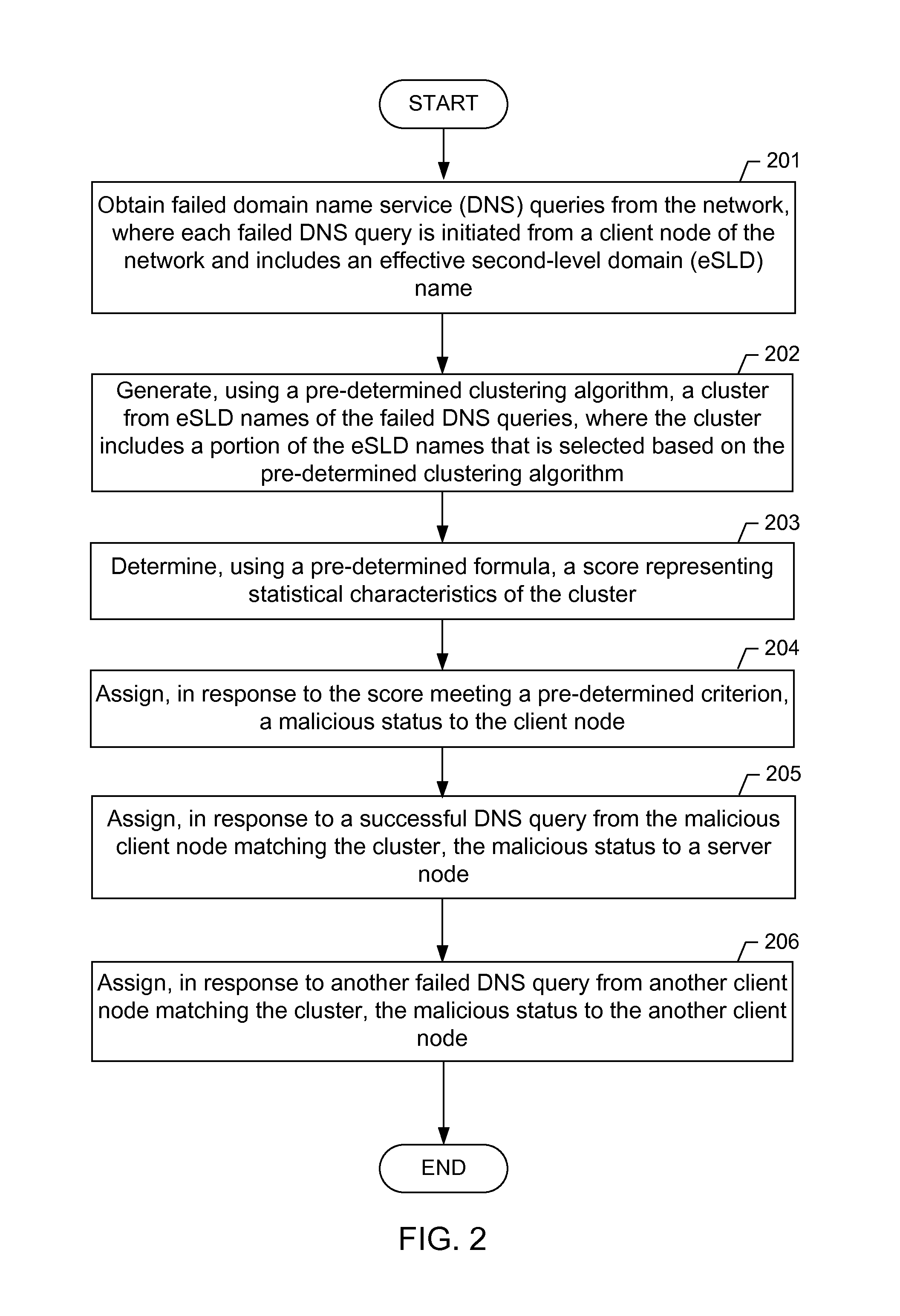
A method for detecting a malicious node in a network. The method includes obtaining a plurality of failed domain name service (DNS) queries from the network, wherein each of the plurality of failed DNS queries is initiated from a client node of the network and comprises an effective second-level domain (eSLD) name, generating, by a computer processor and using a pre-determined clustering algorithm, a cluster from a plurality of eSLD names comprising the eSLD name of each of the plurality of failed DNS queries, wherein the cluster comprises a portion of the plurality of eSLD names that is selected based on the pre-determined clustering algorithm, determining, by the computer processor and using a pre-determined formula, a score representing statistical characteristics of the cluster, and assigning, in response to the score meeting a pre-determined criterion, a malicious status to the client node.
Owner:THE BOEING CO
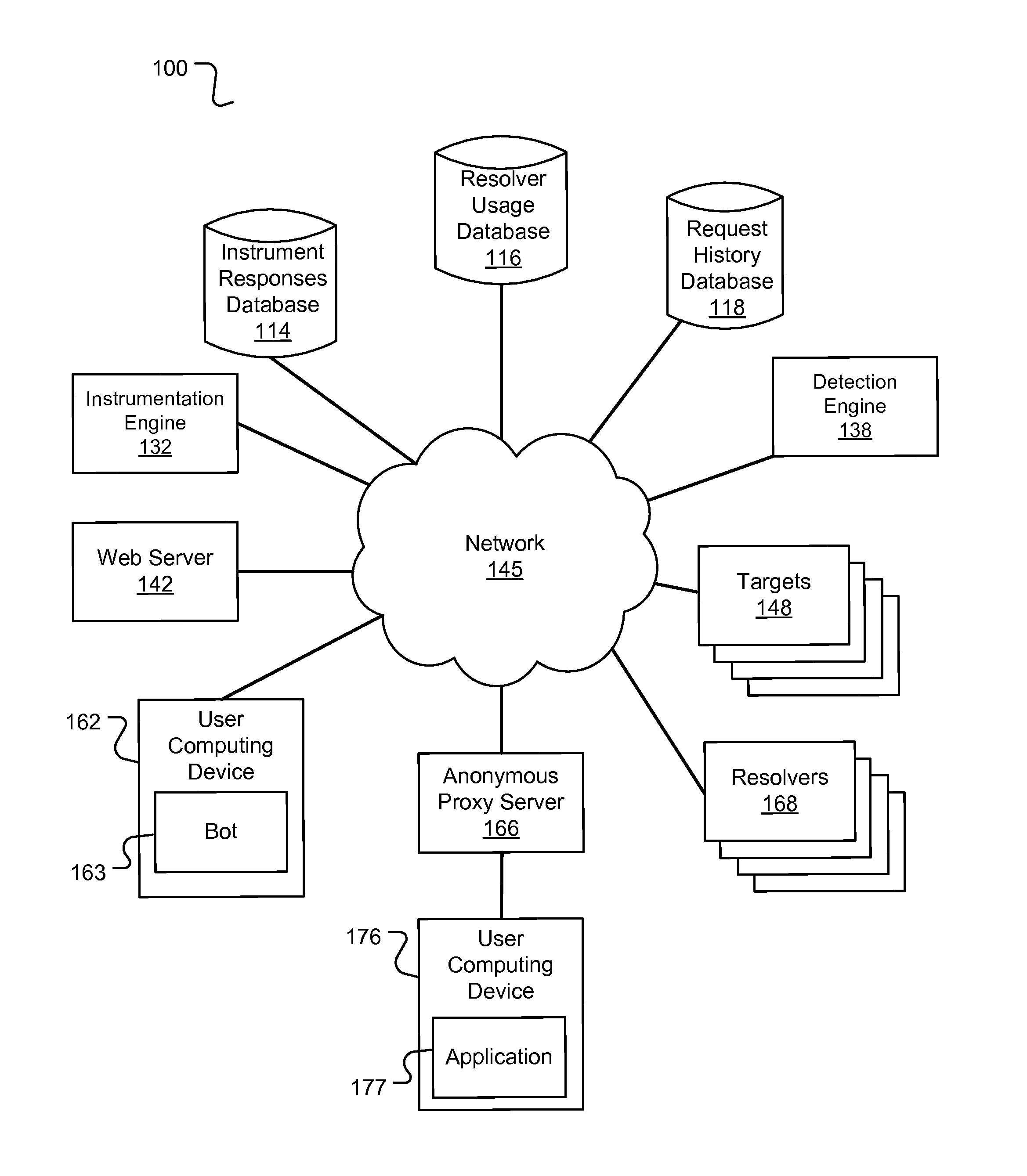
Confidence scoring of device reputation based on characteristic network behavior
The technology disclosed relates to detection of anonymous proxies and bots making requests to a cloud based resource on the Internet, such as a web server or an App server. The technology can leverage one or more of: instrumentation of web pages that samples response times and other characteristics of communications by a requestor device over multiple network segments; lack of prior appearance of the requestor device across multiple, independently operated commercial web sites; and resolver usage by the requestor. These signals can be analyzed to score a requesting device's reputation. A location reported by a user device can be compared to a network characteristic determined location.
Owner:CITRIX SYST INC
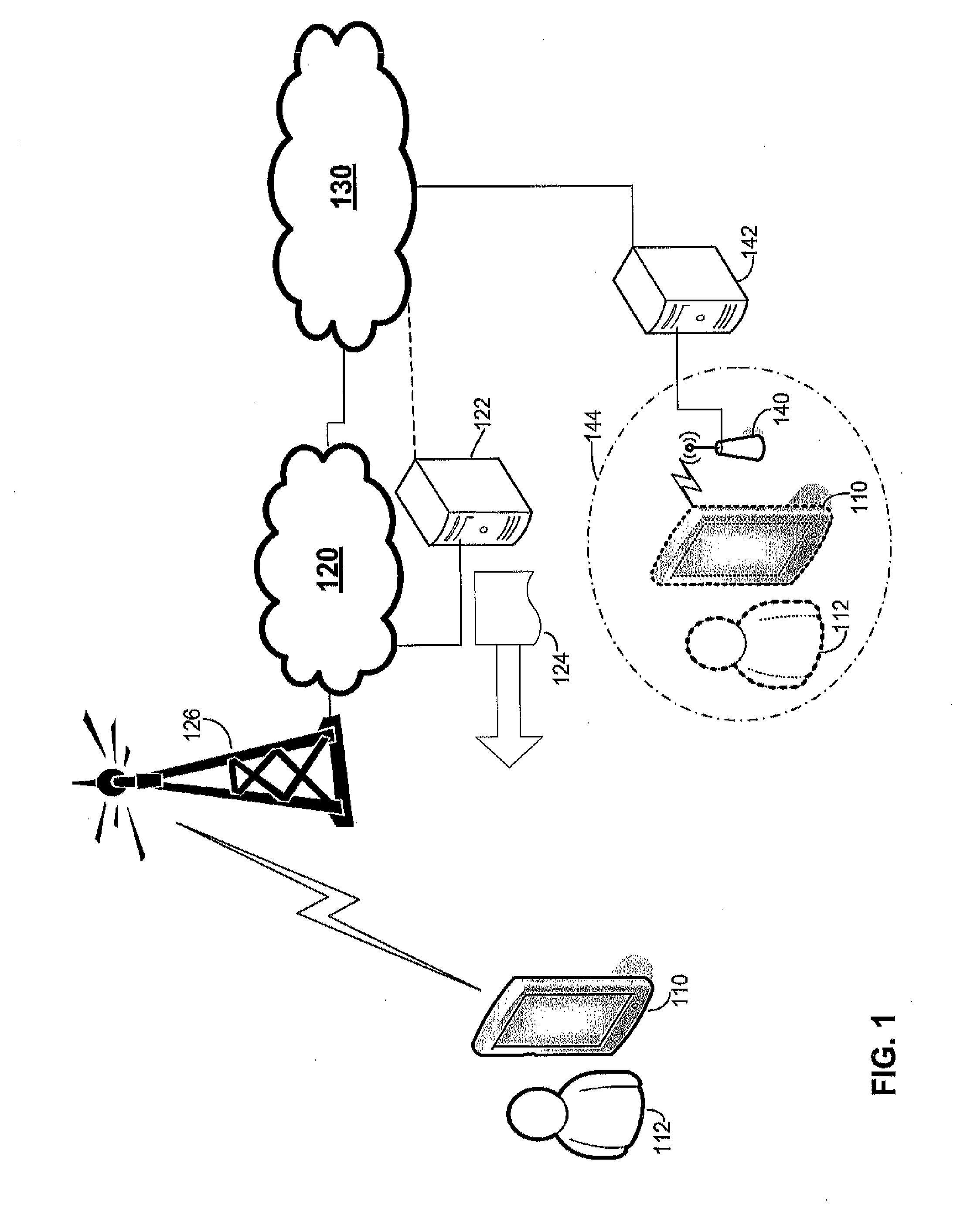
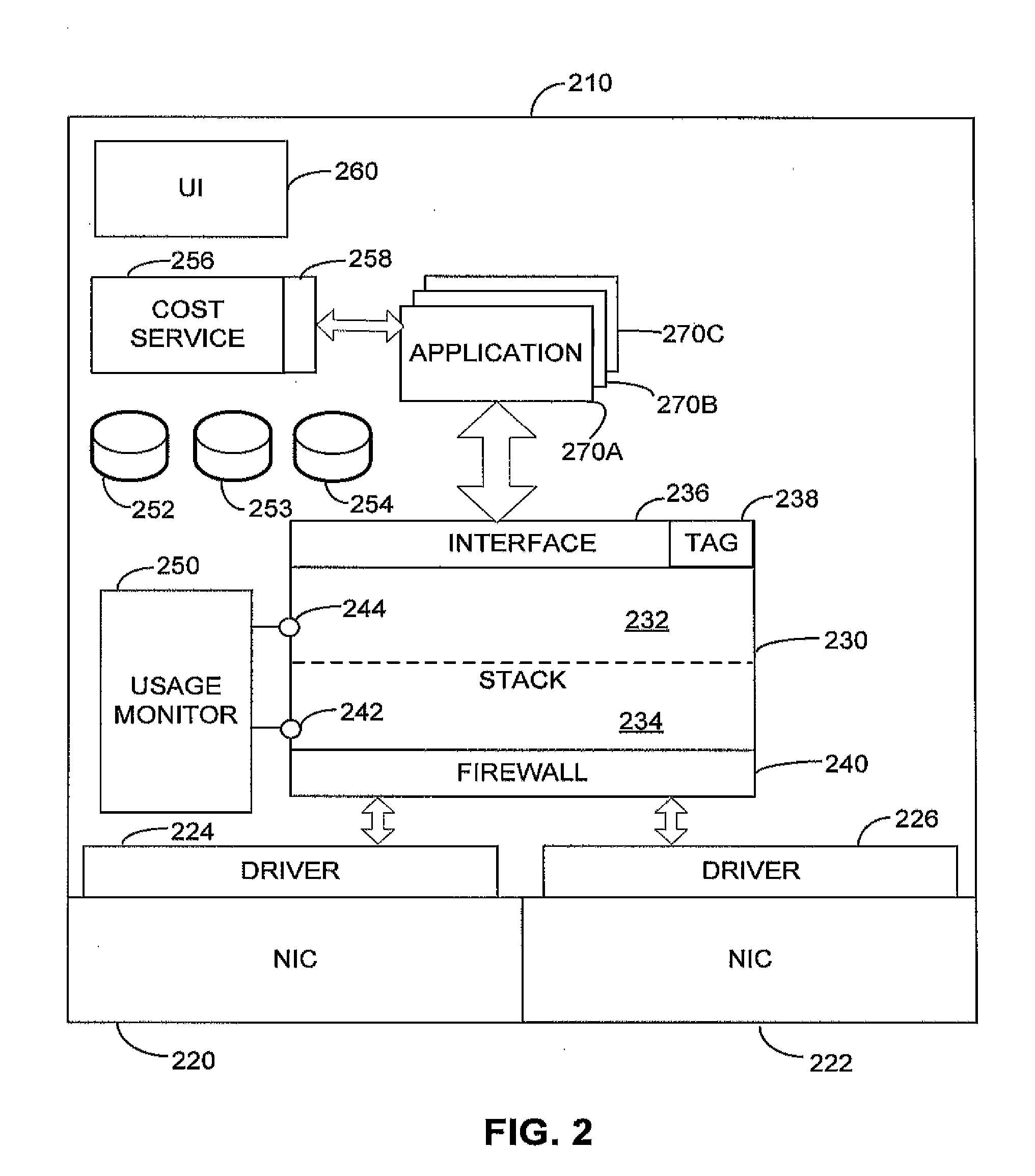
Operating system supporting cost aware applications
InactiveUS20120158947A1Improve experienceAccounting/billing servicesDigital computer detailsOperational systemNetwork behavior
A mobile computing device that supports cost aware network behavior. An operating system of the mobile computing device may associate data for transmission with a entity and, based on a policy applicable to that entity and information on data usage, determine appropriate processing for the data. The processing may include transmitting the data, with or without throttling, or blocking transmission of the data. The policy, for example, may be supplied by a user or may be encoded in a tag supplied with the data for transmission. The policies may be specified for entities such as an application, an operating system service, a user account or a category of applications. Enforcement of the determined processing may be based on action within the stack or a separate enforcement mechanism, such as a firewall.
Owner:MICROSOFT TECH LICENSING LLC
Method to Allocate Buffer for TCP Proxy Session Based on Dynamic Network Conditions
ActiveUS20140012972A1Optimize capacity allocationDigital computer detailsTransmissionNetwork behaviorNetwork conditions
Allocation of buffers for a TCP proxy session between a client and a server by a service gateway includes: monitoring dynamic network behaviors for server and client side sessions of the TCP proxy session; and allocating capacity for a server side buffer and capacity for a client side buffer in a memory buffer based on the dynamic server side network behaviors, the dynamic client side network behaviors, and a weighted average of a capacity of the memory buffer. In one approach to the allocation, the gateway determines whether an available capacity of the server or client side buffer is sufficient to store a data packet. If not sufficient, the allocated capacity of the server or client side buffer is increased based on measurements of the dynamic network behaviors and the weighted average, and the available capacity of the server or client side buffer is adjusted accordingly.
Owner:A10 NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com