Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2962 results about "Identicon" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
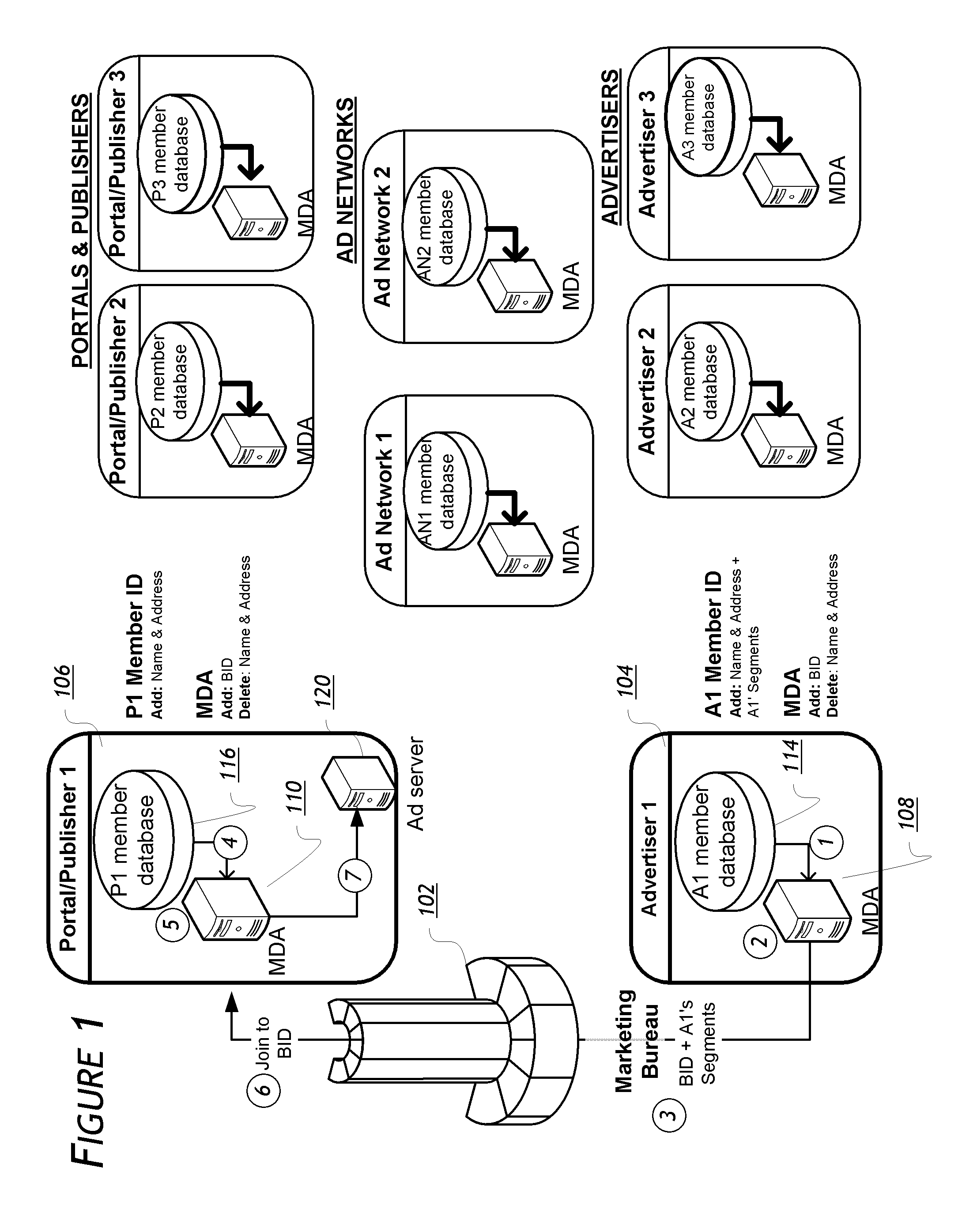
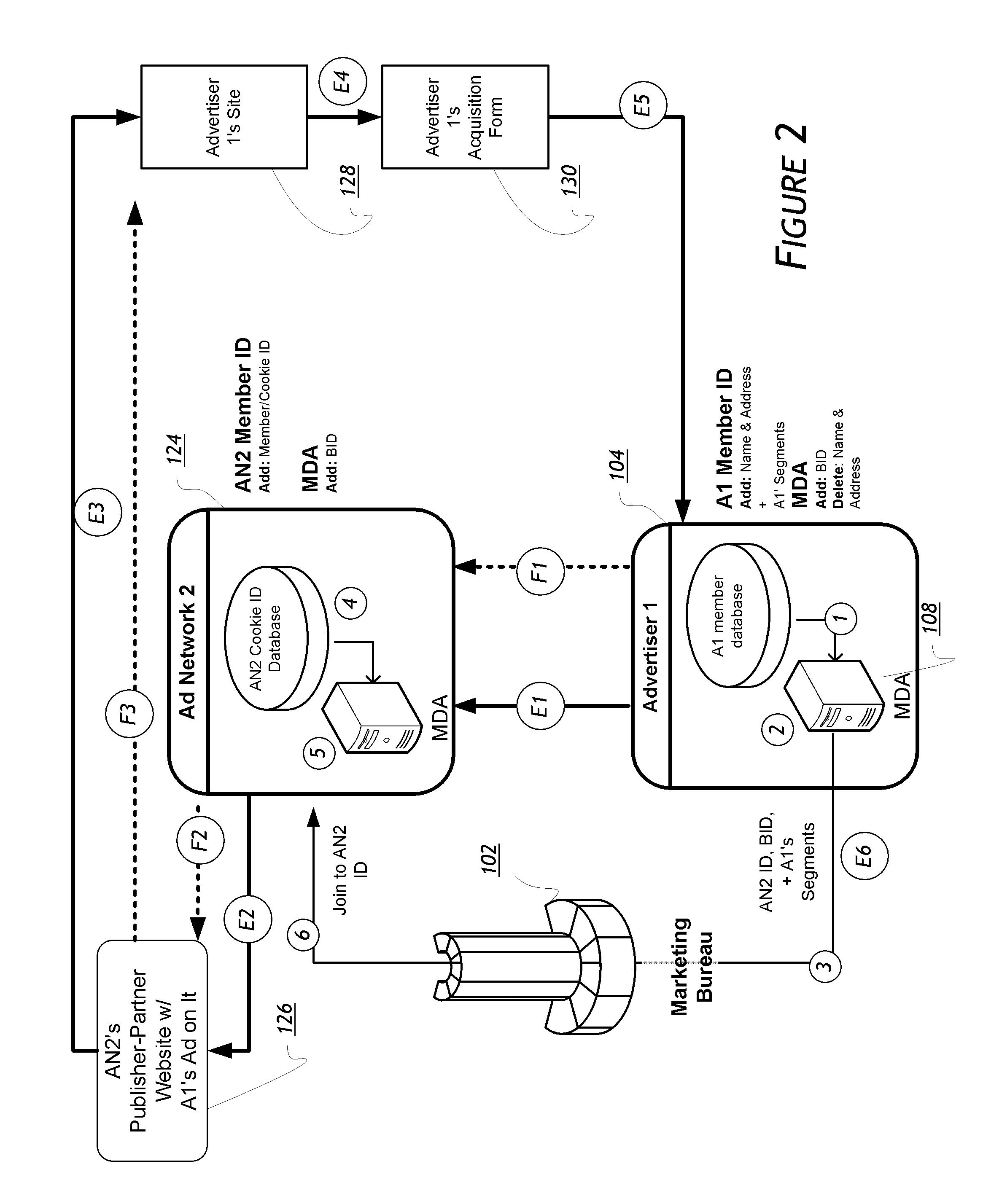
An Identicon is a visual representation of a hash value, usually of an IP address, that serves to identify a user of a computer system as a form of avatar while protecting the users' privacy. The original Identicon was a 9-block graphic, and the representation has been extended to other graphic forms by third parties.
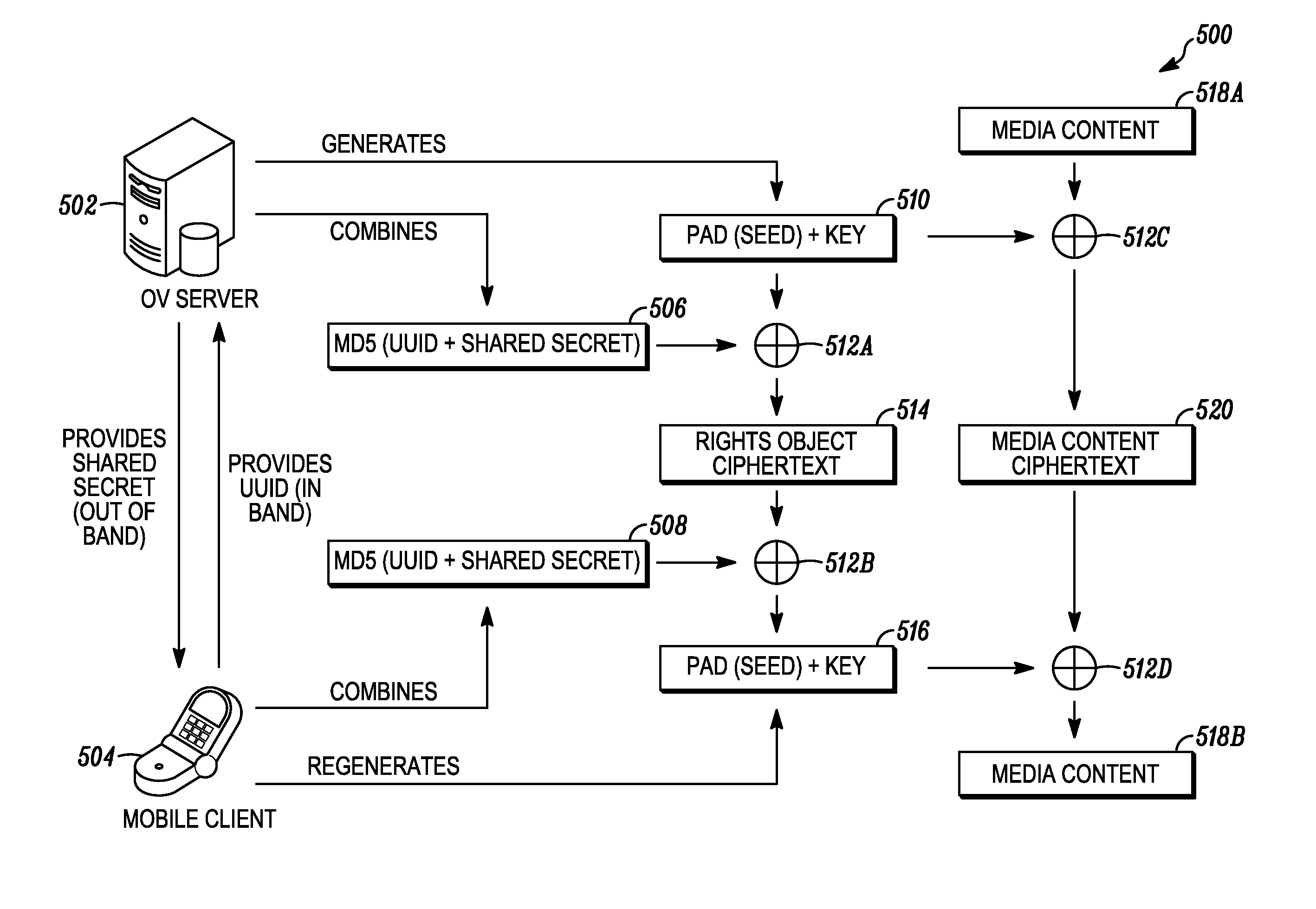
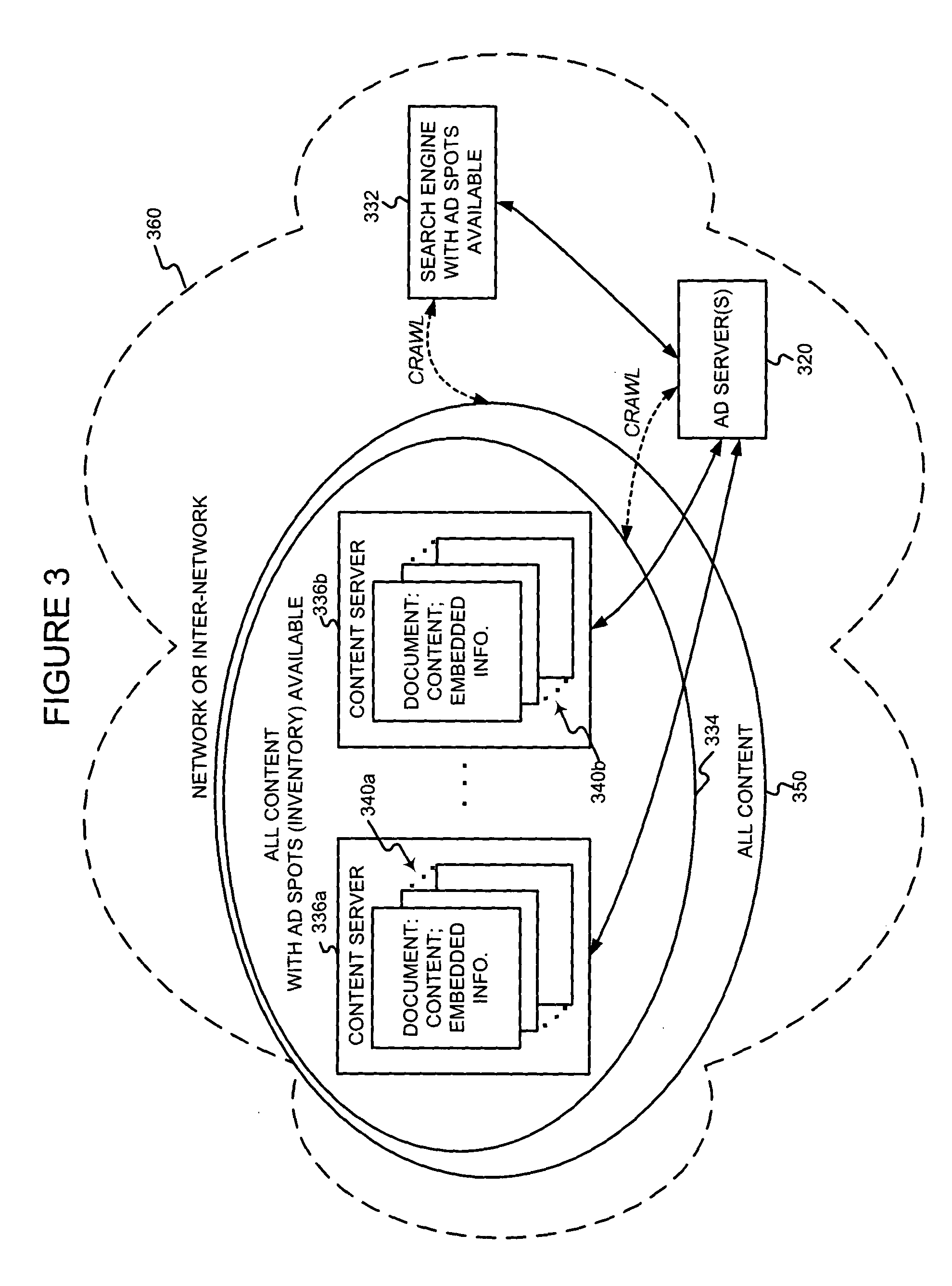
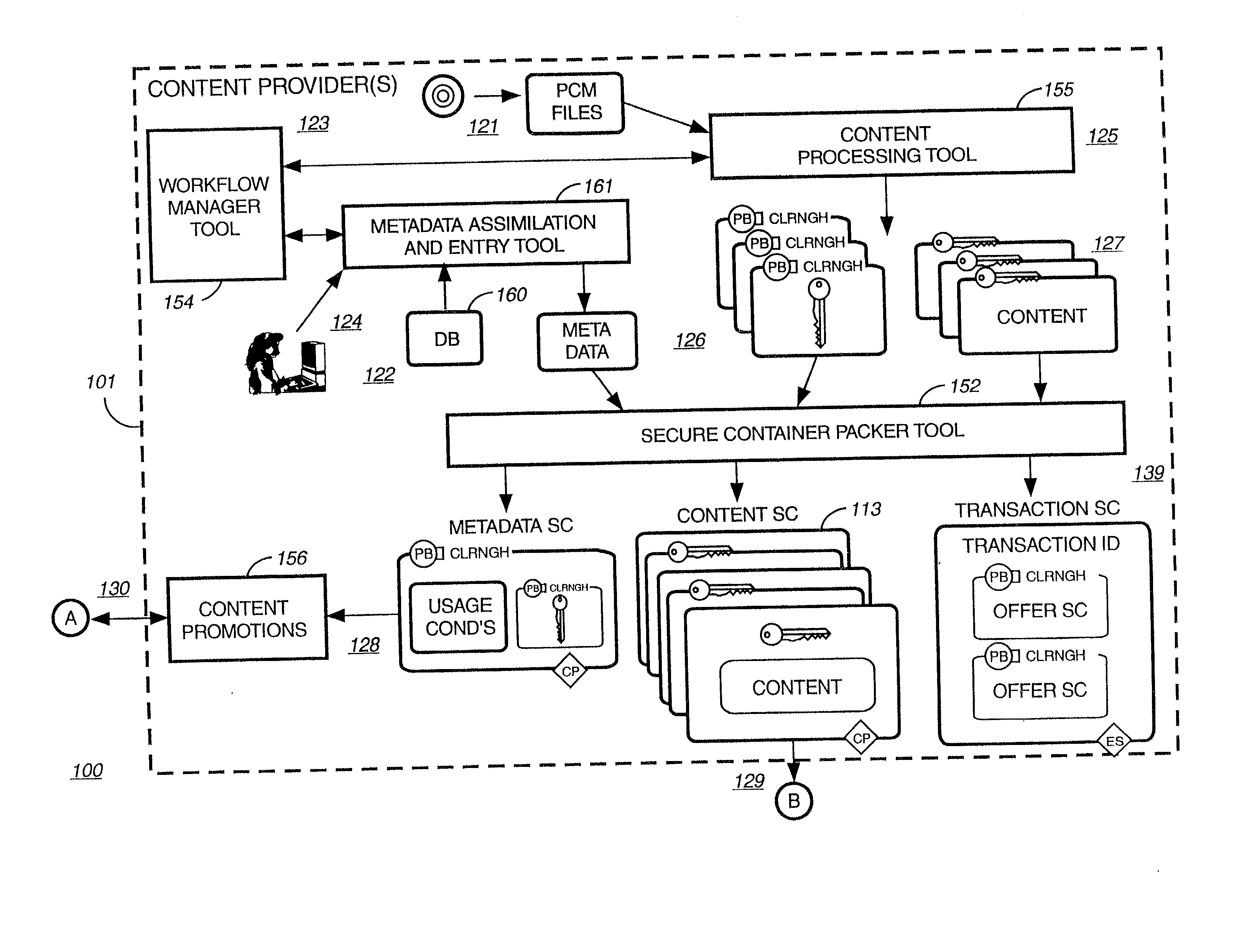
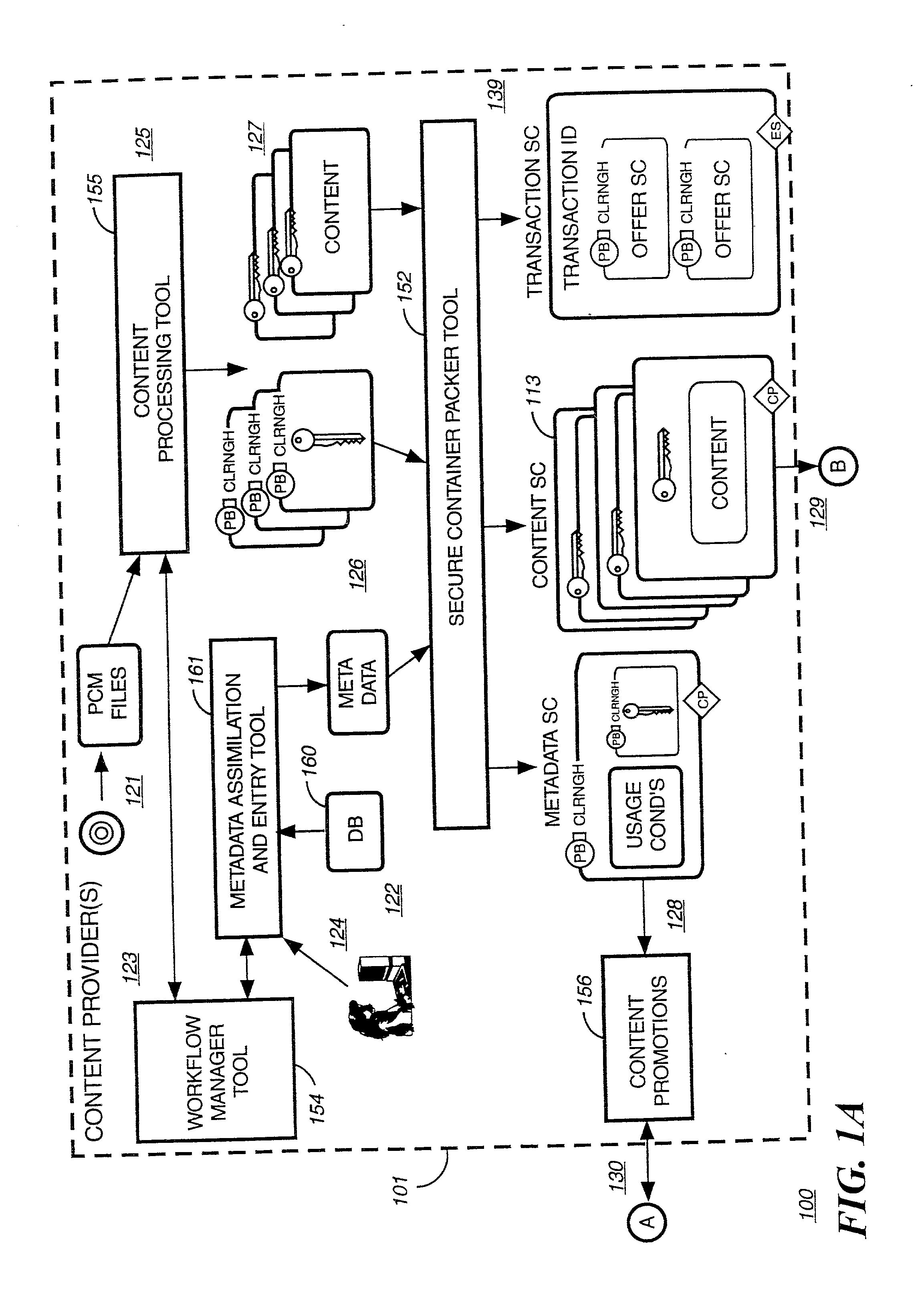
Digital rights management in a mobile environment
ActiveUS20110225417A1Facilitating access to contentOptimization of content deliveryOffice automationResourcesComputer hardwareDigital rights management
Embodiments provide a method that causes a plurality of virtual machine instructions to be interpreted for indications of a mobile device's hardware identification information, thus forming a plurality of hardware instruction interpretations. The embodiment also combines each of the plurality of hardware instruction interpretations and hashes the combination to form a quasi-hardware device identifier. An encryption process is based on the quasi-hardware encryption device identifier and the media is then encrypted using the encryption process. The encrypted media is transferred to the mobile device wherein the mobile device decrypts the media based at least in part on the mobile device's internal knowledge of the quasi-hardware device identification.
Owner:DIRECTV LLC
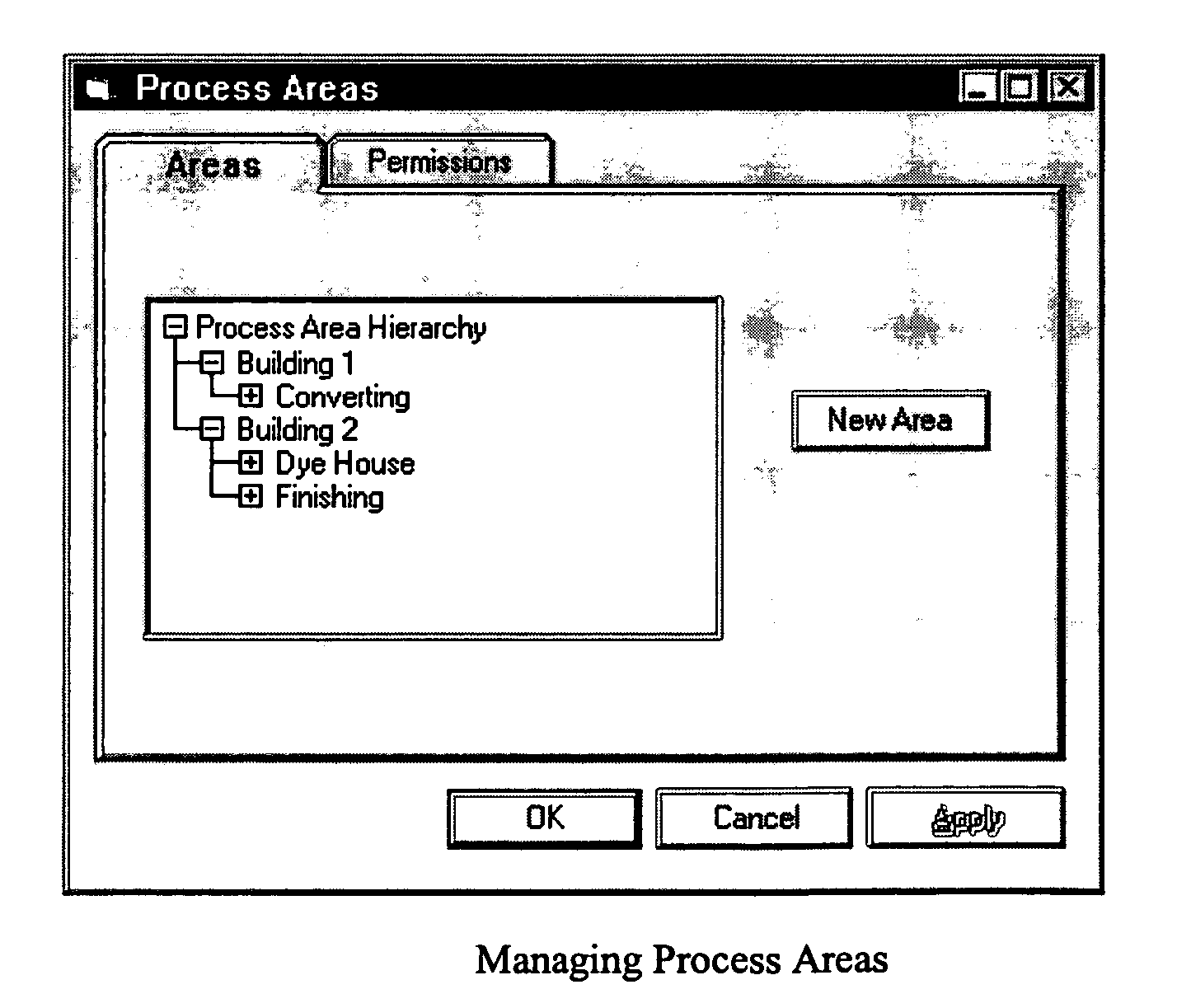
Methods and apparatus for control configuration with versioning, security, composite blocks, edit selection, object swapping, formulaic values and other aspects
InactiveUS7272815B1OptimizationOptimize system configurationData processing applicationsDigital data processing detailsGraphical user interfaceComposite object
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
Serving content-relevant advertisements with client-side device support
ActiveUS20040167928A1Special service provision for substationText processingInternet privacyDocument Identifier
A client-side application (such as a browser, a browser plug-in, a browser toolbar plug-in, etc. on an end user's computer) is used to support the serving of content-relevant ads to the client device. The client-side application may provide such support by sending document information (such as a document identifier, document content, content relevance information, etc.) to a content ad server. The client-side application may also be used to combine content of the document and the content-relevant ads. For example, the client-side application may combine content of the document and the ads in a window (e.g., in a browser window), may provide the ads in a window above, below, adjacent to a document window, may provide the ads in "chrome" of the browser, etc.
Owner:GOOGLE LLC
Method and system for securing local database file of local content stored on end-user system
InactiveUS20020002468A1Digital data processing detailsUnauthorized memory use protectionDatasheetDigital content
A method and system for forming a data table in memory on an end user system. The data table forming a library index of storage locations to electronic digital content in memory. The method consists of retrieving an encrypted file from storage. The file has a beginning, an end and a trailer section located just prior to the end. The file is read from the end a predetermined distance to verify if an identifier is present. Reading and decrypting the trailer section from the file read. Determining if there are any updates in the trailer section. In the case there are no updates in the trailer section then decrypting the reference table containing one or more data table location indicators for data items with the first decrypting key. Next, decrypting one or data items with the first decrypting key. Populating the data table with data items at locations specified in the reference table.
Owner:IBM CORP
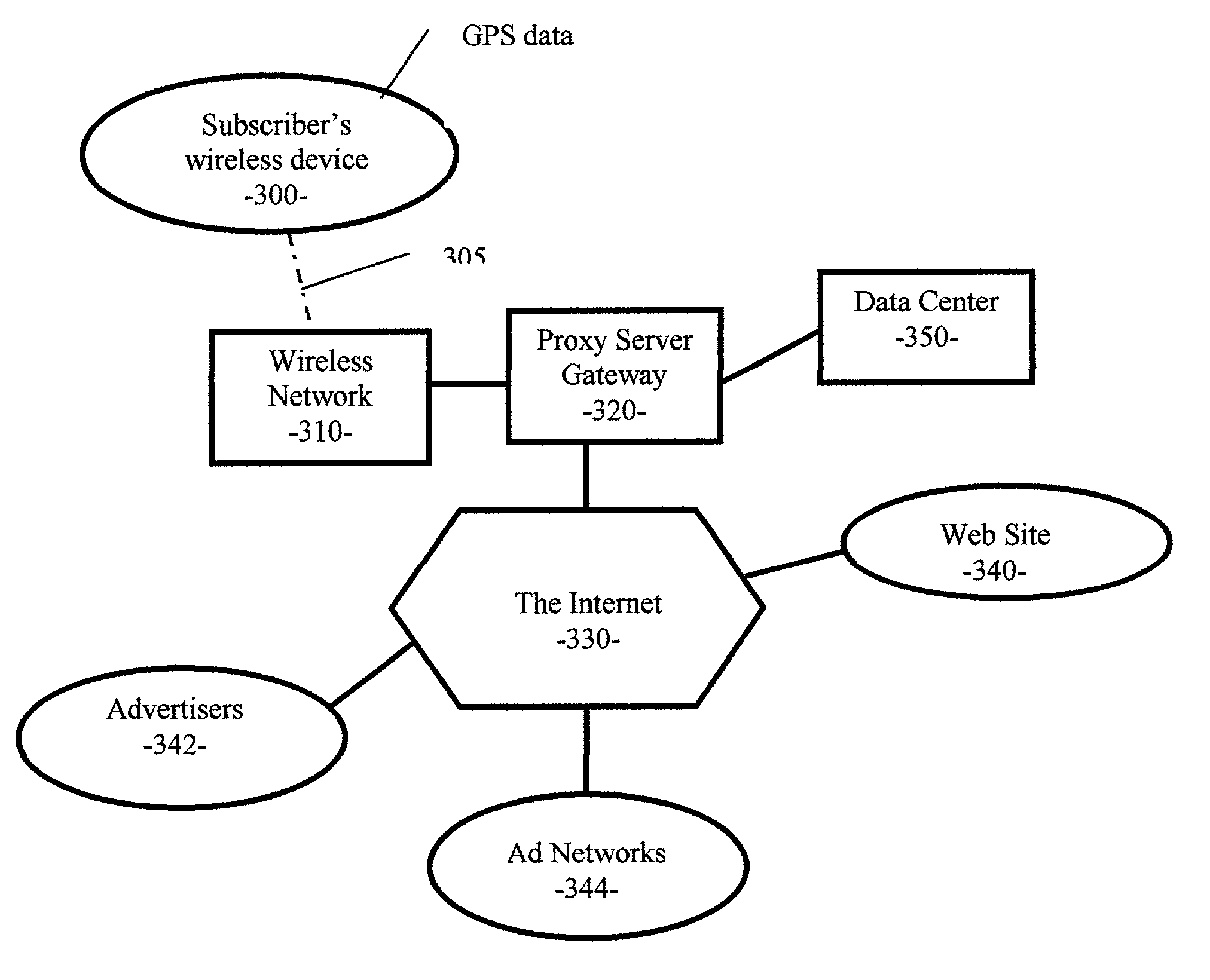
Method and apparatus for generating targeted impressions to internet clients
InactiveUS20020046104A1Saving in computing timeSave bandwidthMarketingSpecial data processing applicationsClient-sideDatabase retrieval
A method and system of using a server to facilitate a transaction between a subscriber and providers for a right to advertise to the subscriber is disclosed. The server is configured to have access to a profile database storing a set of information regarding the subscriber. The method comprises the steps of connecting the subscriber to the server, generating an identifier to specify the subscriber, retrieving from the profile database at least a set of information regarding the subscriber with the identifier, forwarding the retrieved information to the providers, receiving an offer from the providers, the offer being responsive to the information of the subscriber, accepting an offer from the providers based on given criteria, and forwarding the buyer's advertisement to the subscriber.
Owner:GEOMICRO
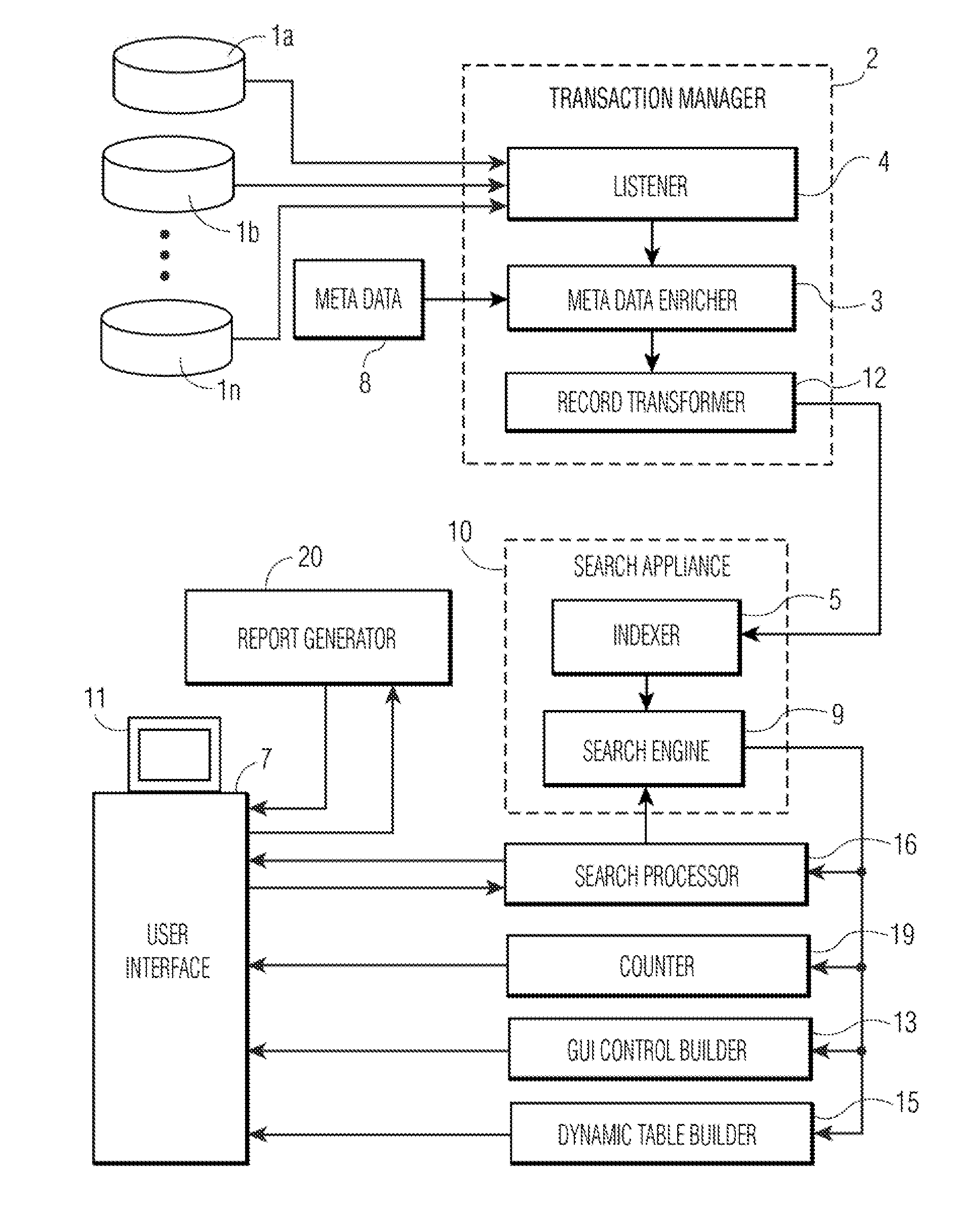
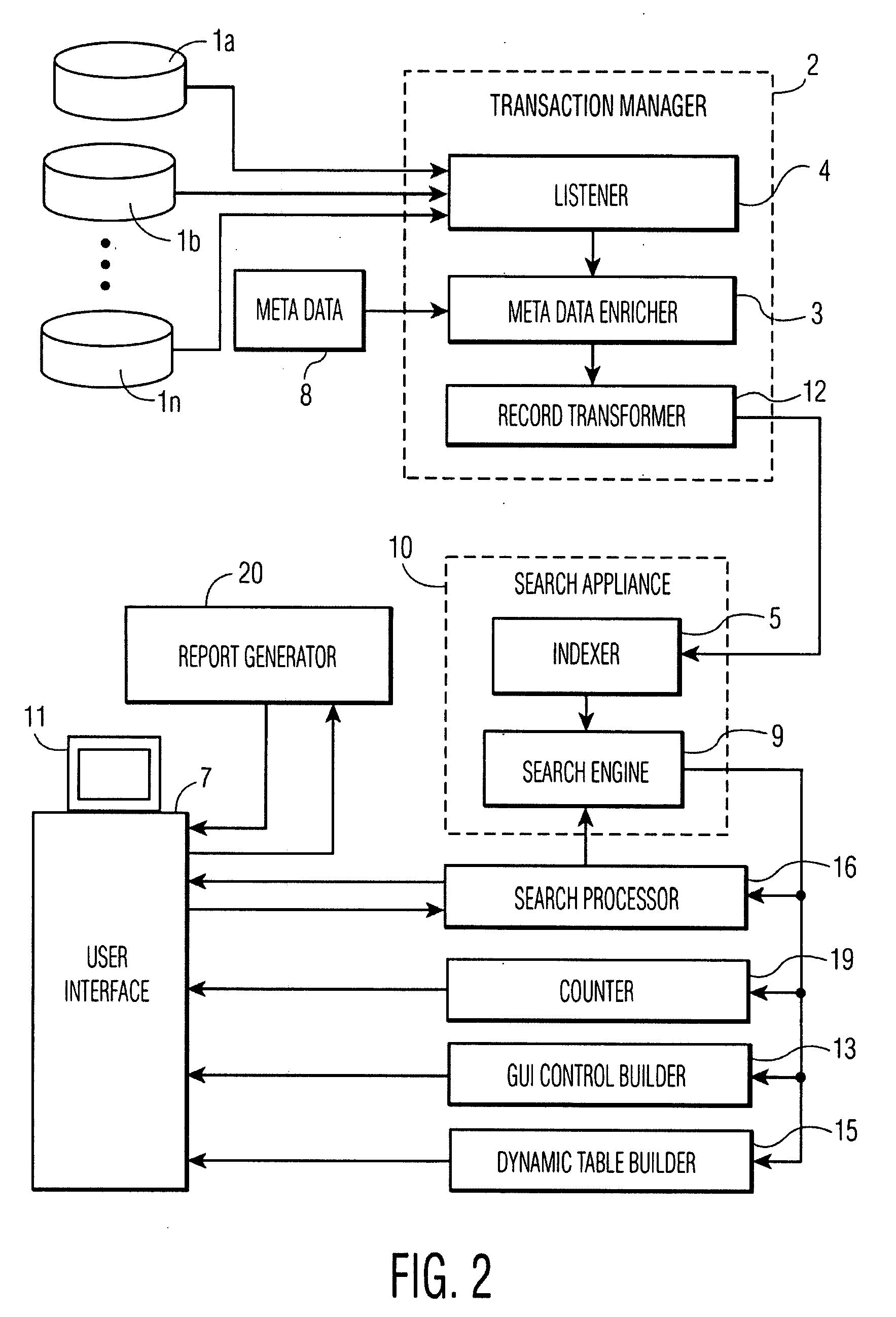
Apparatus and Method for Conducting Searches with a Search Engine for Unstructured Data to Retrieve Records Enriched with Structured Data and Generate Reports Based Thereon
InactiveUS20080104542A1Improve practicalityWeb data indexingSpecial data processing applicationsGraphicsRecordset
Records in databases or unstructured files are enriched with metadata and are indexed for retrieval by a search engine. In response to a search request, a graphical user interface (GUI) control based on the metadata associated with the search hits is constructed and displayed with the search results in a standard view. Selection of a metadata value via the GUI control filters the previously matched records down to those matching the value selected via the GUI control. The metadata in the search results is arranged in a tabular view which is embedded in the display of search results and rendered invisible until selected by the user. Reports can be constructed from an identifier each returned record set for presenting, analyzing and modifying the data, and for generating further reports.
Owner:INFORMATION BUILDERS INC
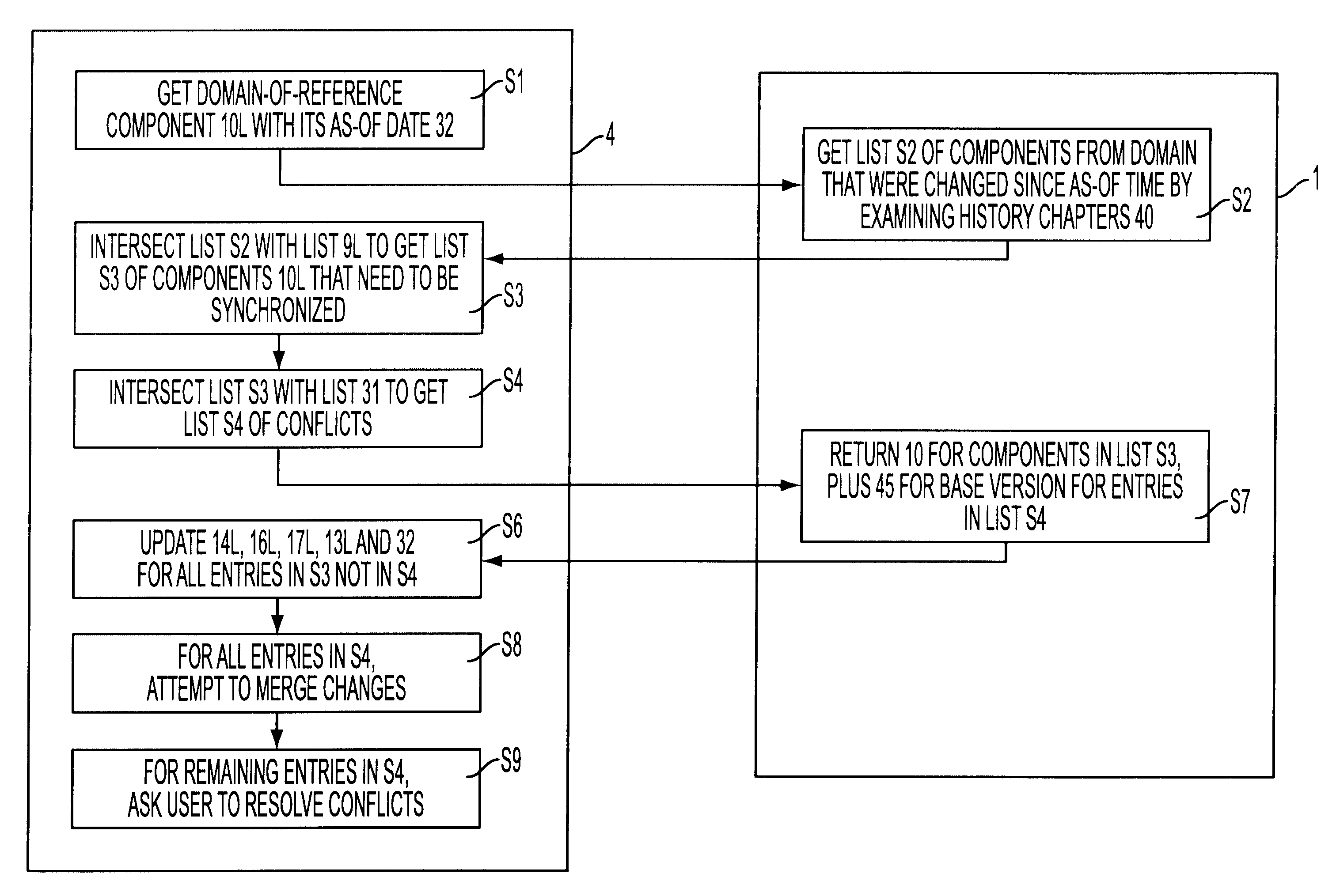
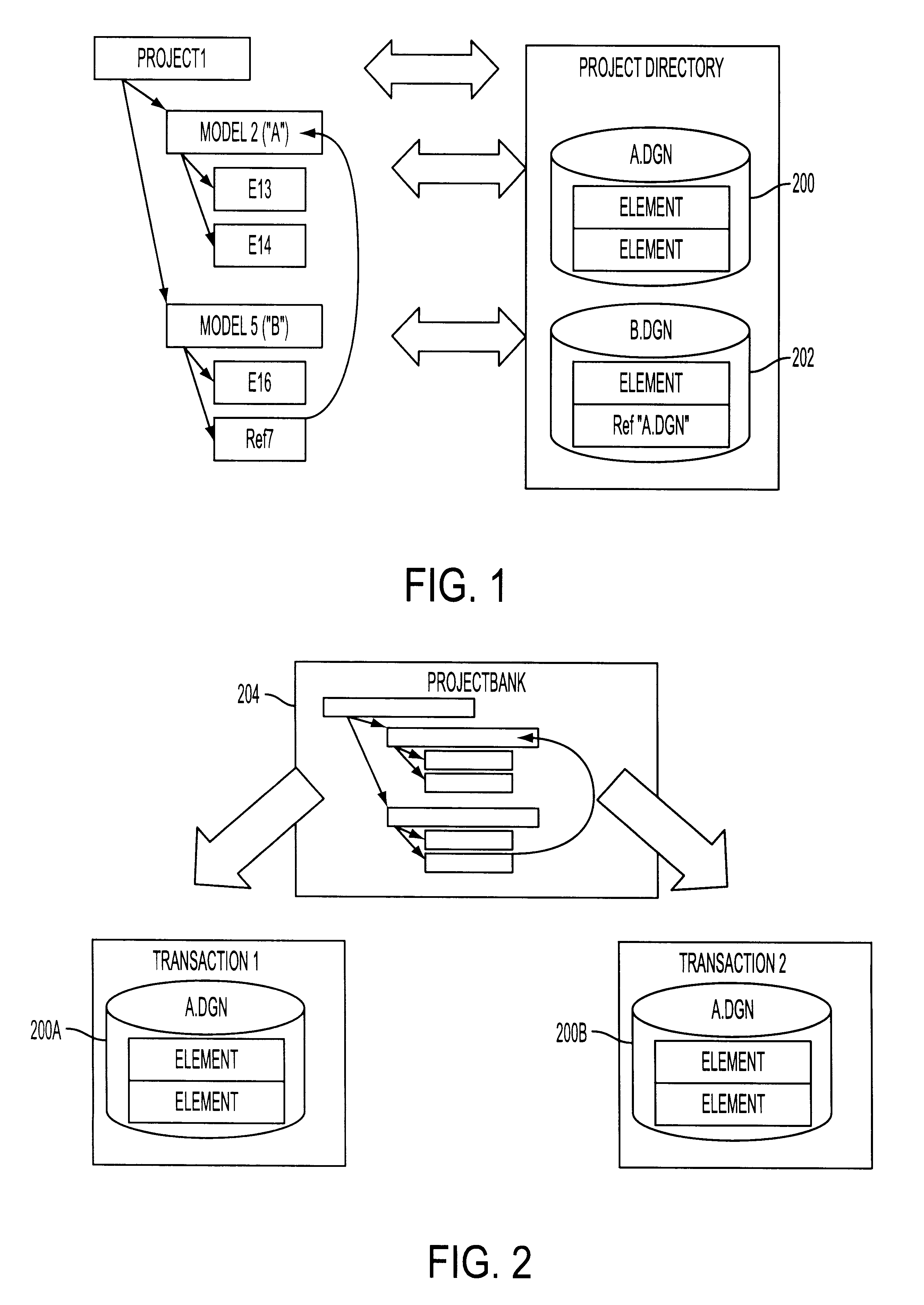
System for collaborative engineering using component and file-oriented tools
InactiveUS6341291B1Improve the level ofHigh currentData processing applicationsCAD network environmentSoftware engineeringIdenticon
Conventional file-based engineering design data for an engineering model are represented by a plurality of components. Each component has a unique identifier, a set of fields, each field having a data type and a data value, and a program which interprets and modifies the fields. The plurality of components are stored in a repository of a server. The repository also stores a history of any changes made to the components. A plurality of client computers are bidirectionally connected to the server. Each client computer may obtain the current version of the components and may send locally edited versions of the components back to the server to replace the current versions in the repository. At the client computer, the user interacts with the components using conventional file-based software. Before locally edited versions of the components are committed to the server to replace the current versions, a synchronization and merging process occurs whereby the latest version of the components are downloaded to the client computer and are compared to the locally edited version of the components to detect resolvable (compatible) and unresolvable (incompatible) conflicts therebetween. The commit process is performed only if no unresolvable conflicts exist between the two versions of the components. To facilitate translation between file-based data and components, a schema is written to "wrap" each of the engineering file formats. Each schema is a set of classes that capture all of the information in the file-based data.
Owner:BENTLEY SYST INC
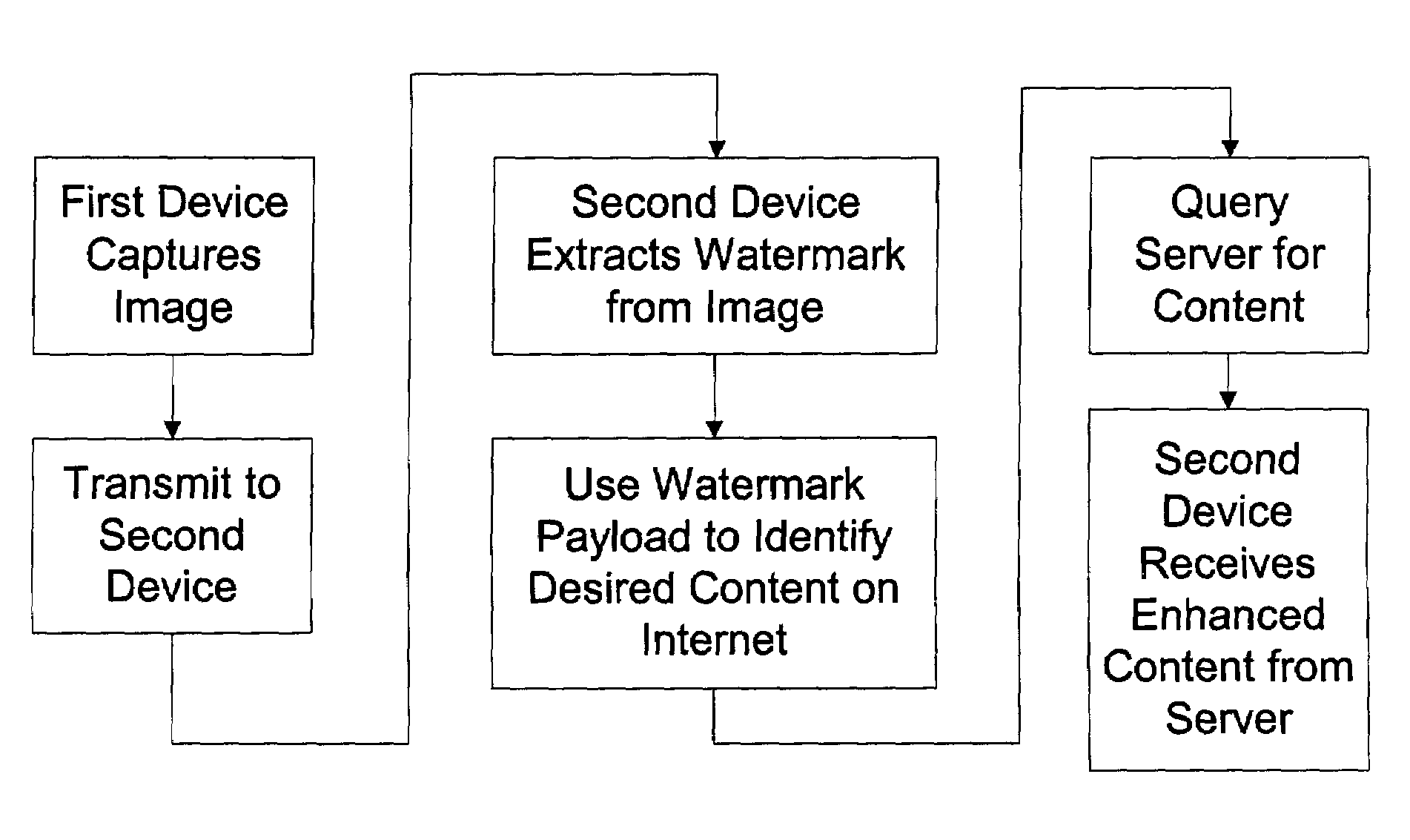
Portable devices and methods employing digital watermarking
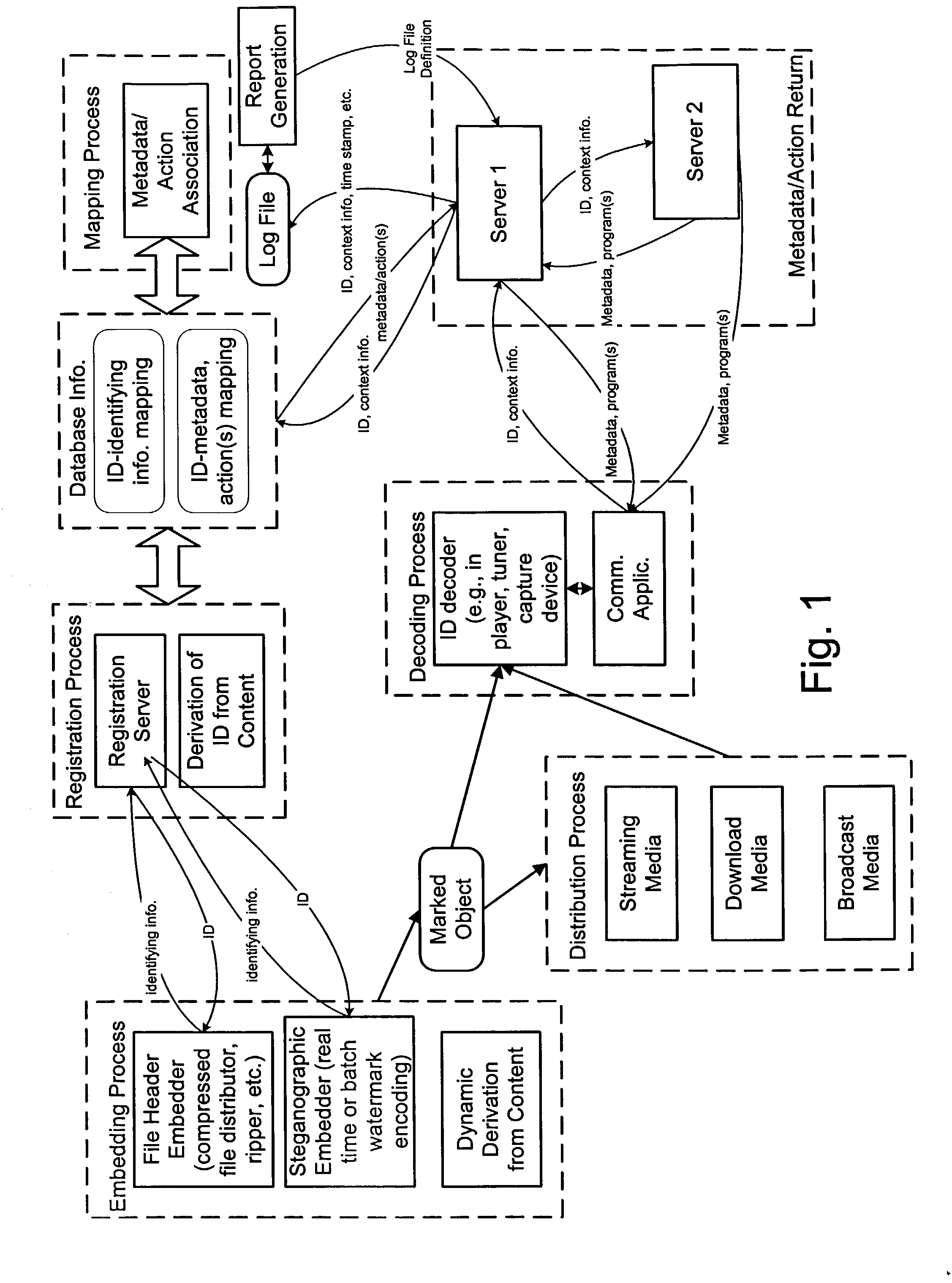
Media objects are transformed into active, connected objects via identifiers embedded into them or their containers. In the context of a user's playback experience, a decoding process extracts the identifier from a media object and possibly additional context information and forwards it to a server. The server, in turn, maps the identifier to an action, such as returning metadata, re-directing the request to one or more other servers, requesting information from another server to identify the media object, etc. The server may return a higher fidelity version of content from which the identifier was extracted. In some applications, the higher fidelity version may be substituted for the original media object and rendered to provide higher quality output. The linking process applies to broadcast objects as well as objects transmitted over networks in streaming and compressed file formats.
Owner:DIGIMARC CORP
Method, a device and computer program products for protecting privacy of users from web-trackers
InactiveUS20170142158A1Protect user privacyPrivacy protectionTransmissionSecurity arrangementWeb siteNetwork behavior
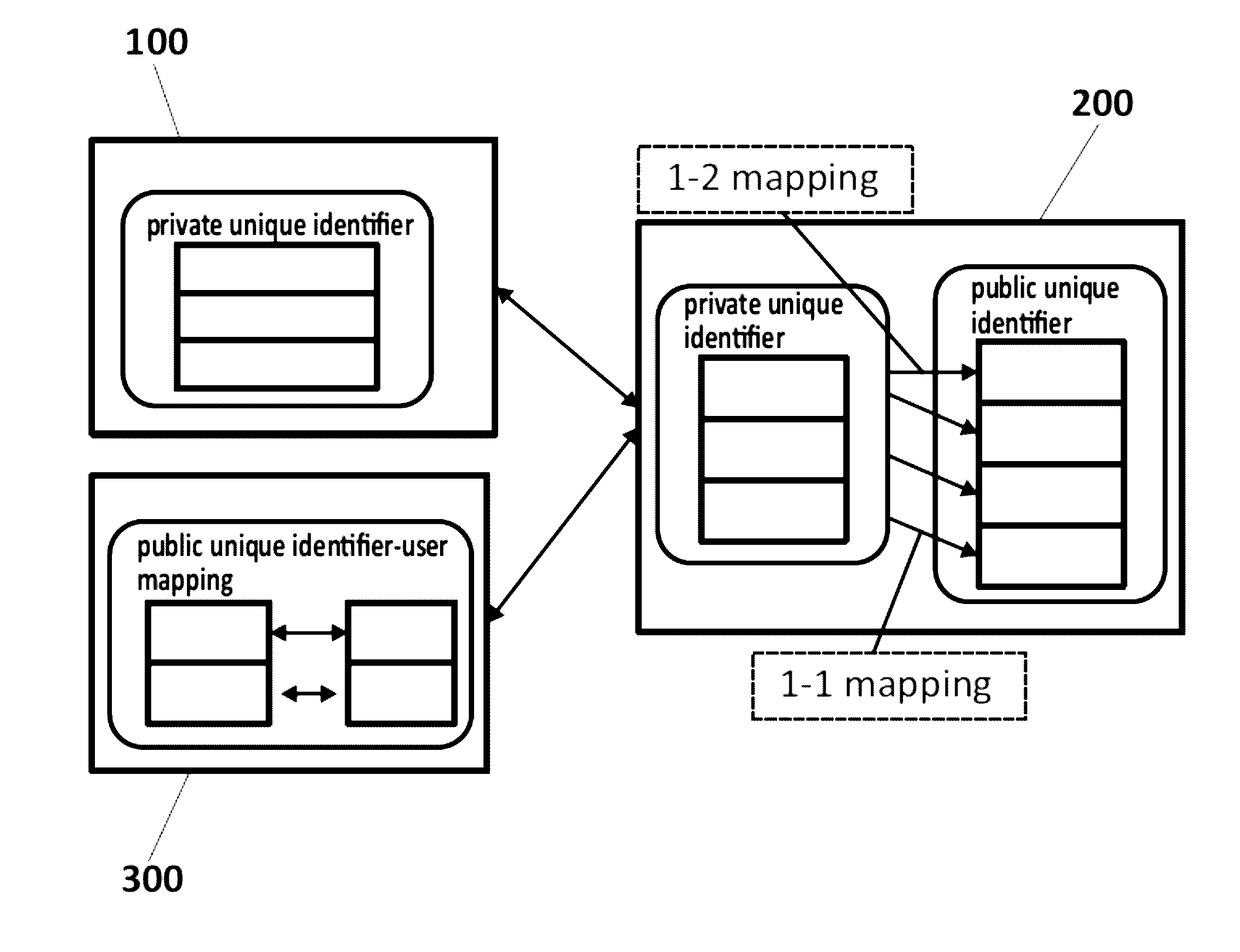
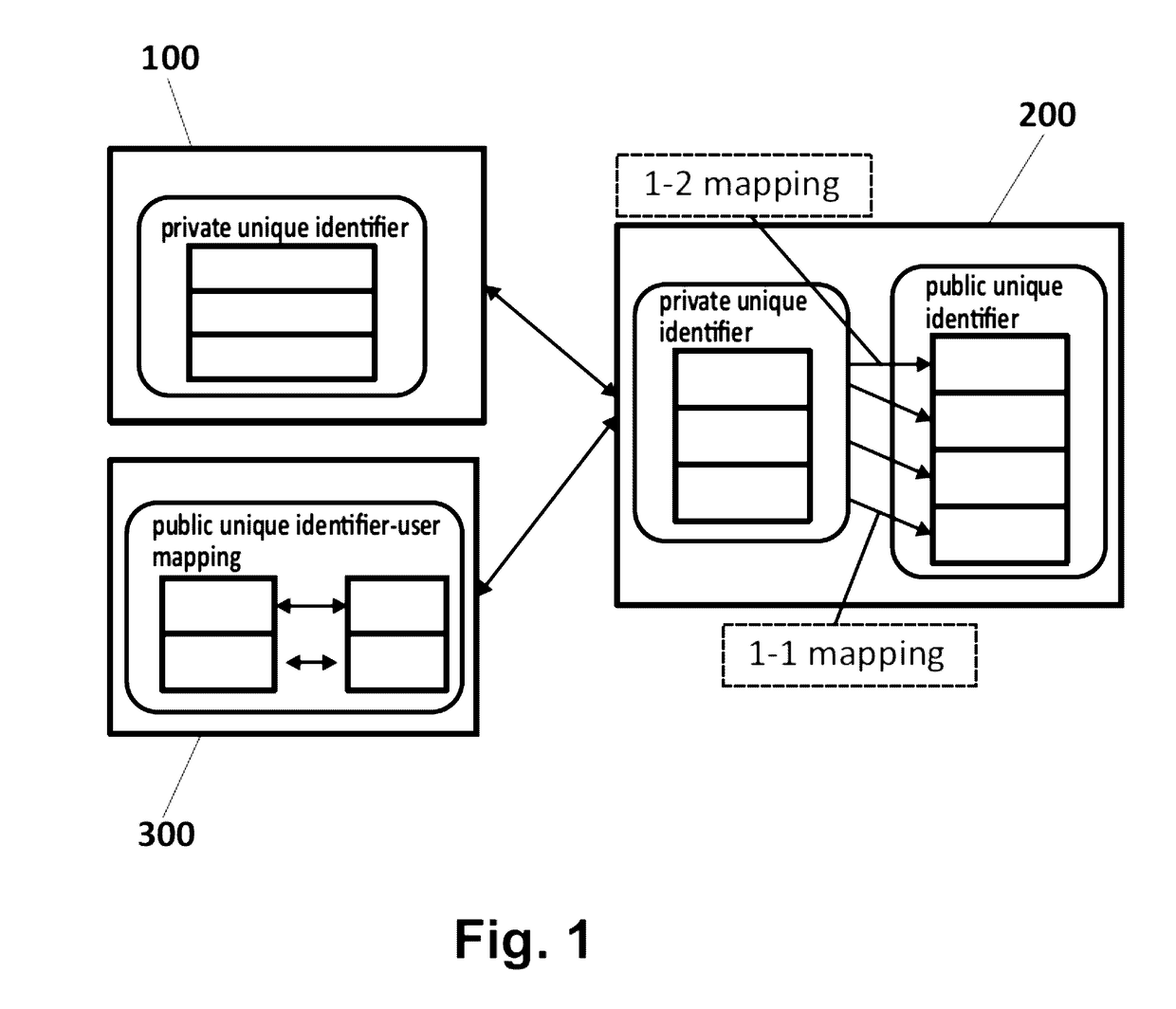
A method, a device and computer program products for protecting privacy of users from web-trackersThe method comprising:capturing and removing a public unique identifier set by a Website (300) in a computing device (100D) of a user (100);monitoring, during a first time-period, web-requests the user (100) makes to obtain a web-behavioral profile of the user (300), and storing the obtained web-behavioral profile as a first vector;tracking, during a second time-period, the web-requests to examine the effect each web-request has on assisting the de-anonymization of the user (100), obtaining a second vector;classifying, the obtained second vector taking into account a computed similarity score parameter;creating and mapping, a corresponding private unique identifier for said captured public identifier; andexecuting, based on said mapping between the private and the public unique identifiers, an intervention algorithm for said web-tracker, that considers a configured intervention policy.
Owner:TELEFONICA SA
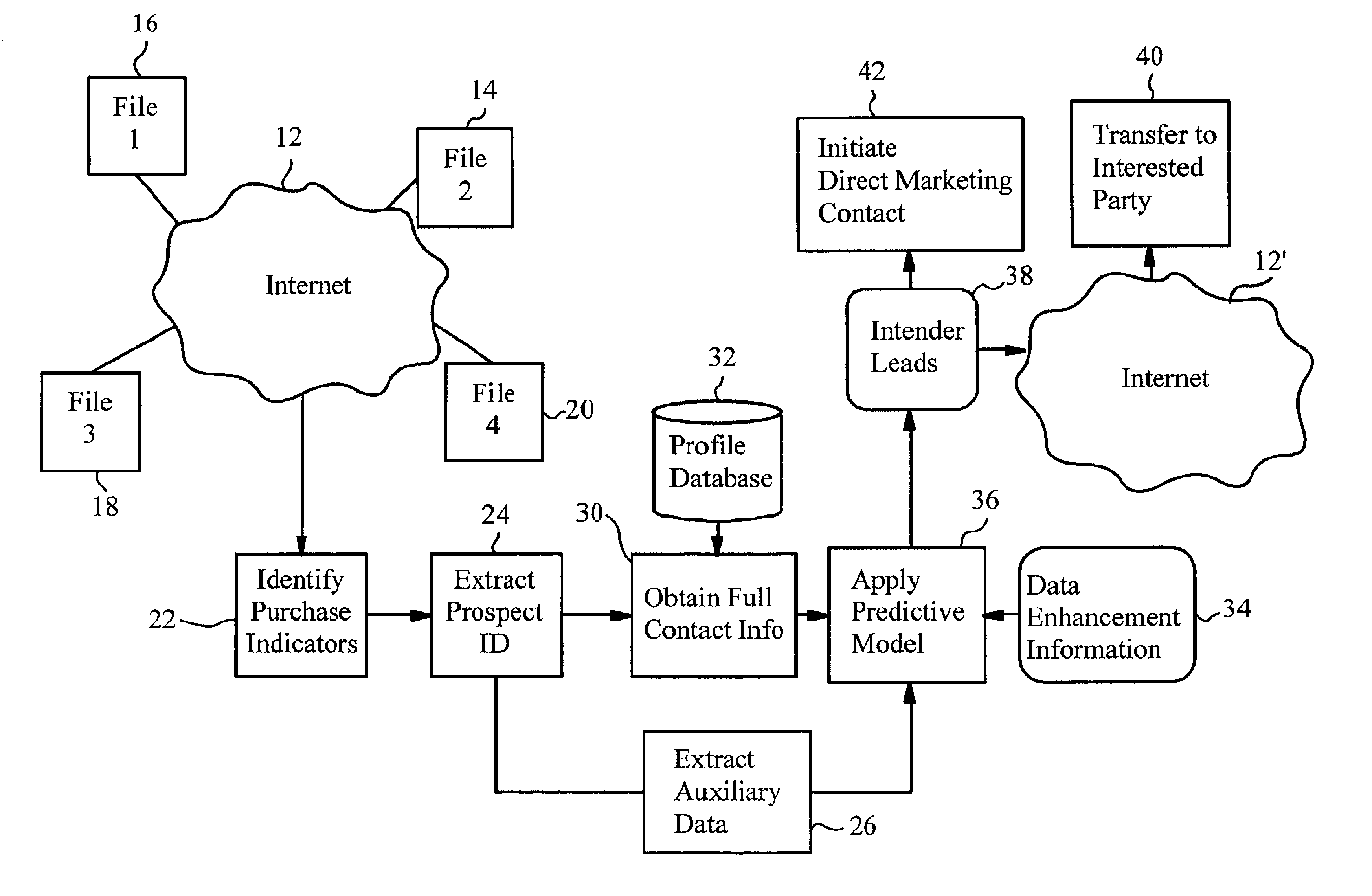
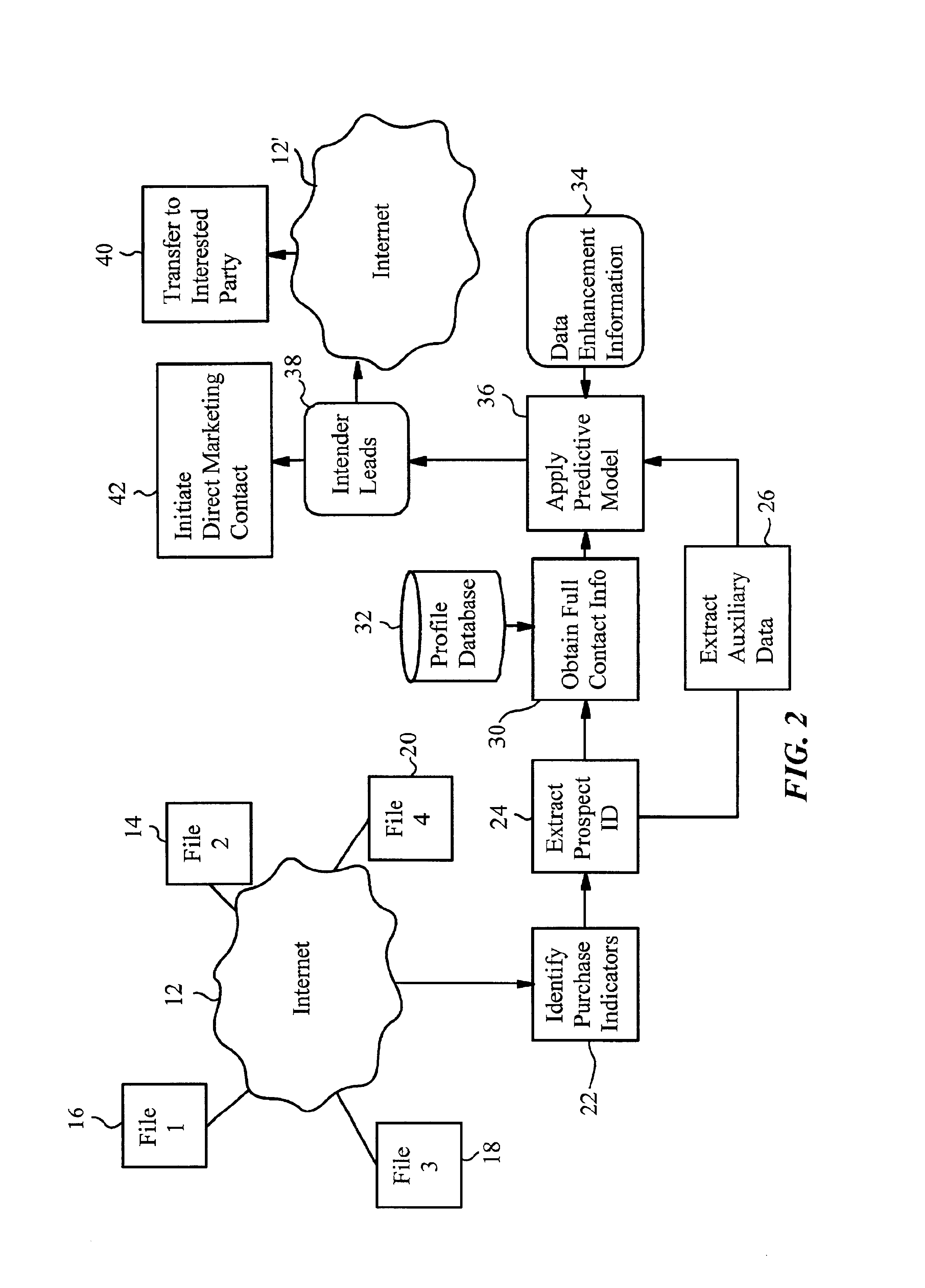
Internet-enabled lead generation
InactiveUS6868389B1Special data processing applicationsMarket data gatheringEmail addressThe Internet
A method of generating intender leads in a distributed computer system includes the steps of identifying purchase indicators and extracting prospect identifiers from the purchase indicators. Purchase indicators are pieces of data that represent a potential future purchase by a prospect. For example, an online classified advertisement selling an automobile is a purchase indicator for a potential future purchase of a new car by the old car seller. The prospect identifier, such as a telephone number or email address, uniquely identifies the prospect likely to make the future purchase. Preferably, the method also contains the steps of obtaining full contact information for the prospect from a profile database, applying a predictive model to the prospects to select intender leads, and transferring the intender leads to an interested party, such as a direct marketing service or sales force. An intender lead is a lead for a person intending to make a purchase of a particular product or service within a given time period. Only some of the prospects are actual intenders. Preferably, the method also includes the steps of extracting auxiliary data that is independent of the prospect from the purchase indicator, and obtaining data enhancement information about the prospect from data enhancement databases. The predictive model is preferably also applied to the data enhancement information and auxiliary data. The method is particularly well-suited for the Internet, which is a large source of publicly-available purchase indicators that is constantly updated. The intender leads are preferably transferred over the Internet, e.g. by email, so that they arrive at the sales force when they are still “hot.”
Owner:MEDIA DIRECT
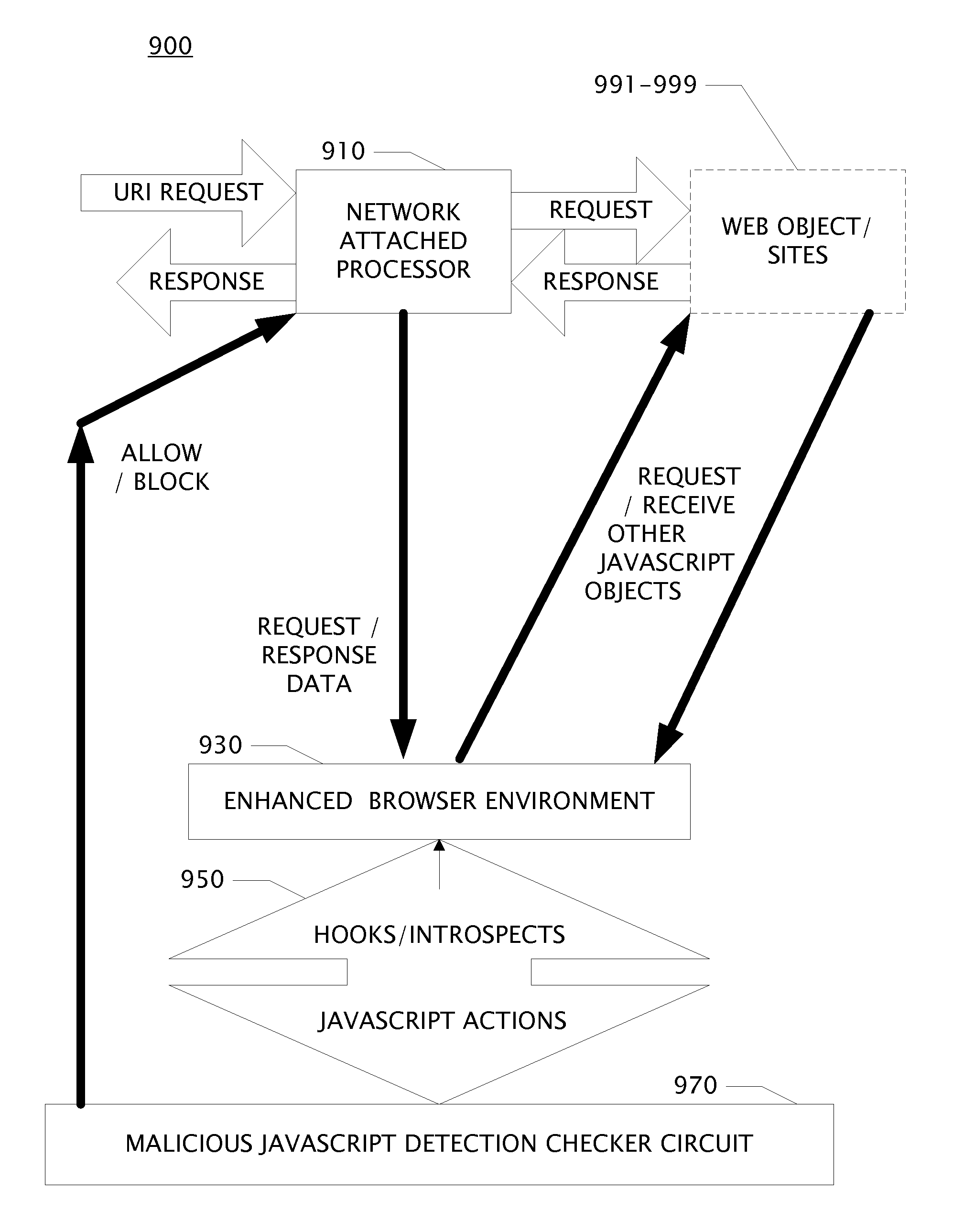
Method for detecting malicious javascript
ActiveUS20110289582A1Memory loss protectionError detection/correctionWeb siteUniform resource identifier
An apparatus and system for scoring and grading websites and method of operation. An apparatus receives one or more Uniform Resource Identifiers (URI), requests and receives a resource such as a webpage, and observes the behaviors of an enhanced browser emulator as controlled by javascript provided by the webpage. The enhanced browser emulator tracks behaviors which when aggregated imply malicious intent.
Owner:BARRACUDA NETWORKS
Remote Network Access Via Virtual Machine
ActiveUS20070300220A1User identity/authority verificationMultiple digital computer combinationsPrivate networkSoftware engineering
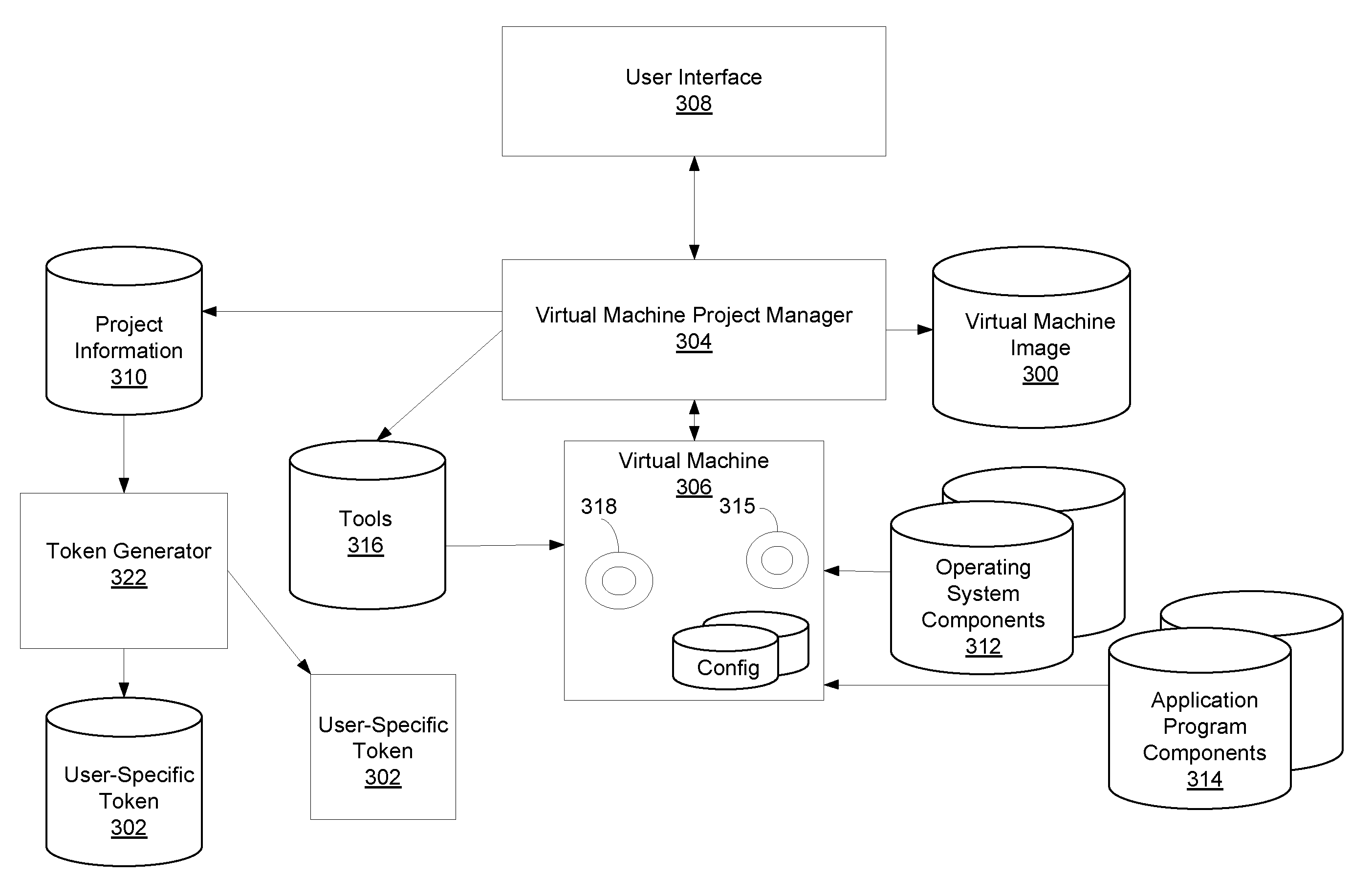
A virtual machine project manager creates a generic, i.e., not user-specific, virtual machine image file. Copies of this image file may be distributed to one or more users, each of whom may then use an automated procedure to generate a user-specific virtual machine image file and, thus, a user-specific virtual machine on his / her remote host computer. The generic virtual machine image file may be distributed on computer-readable media, such as a DVD disks, or the file may be stored on a server and downloaded (such as via the Internet) by the users. Each user also receives or downloads a token, which contains a small amount of user-specific information that is used by the automated procedure to provision the generic virtual machine image file for the particular user. A virtual machine accesses a security token connected to a host computer to automatically authenticate or re-authenticate a user, such as when a virtual private network connection is restarted. Substantially identical session identifiers are used by a host computer and a virtual machine, or by two or more virtual machines and, when communicating with an integrated access server. A file server stores virtual machine images that are accessed by a plurality of host computers.
Owner:MICROSOFT TECH LICENSING LLC
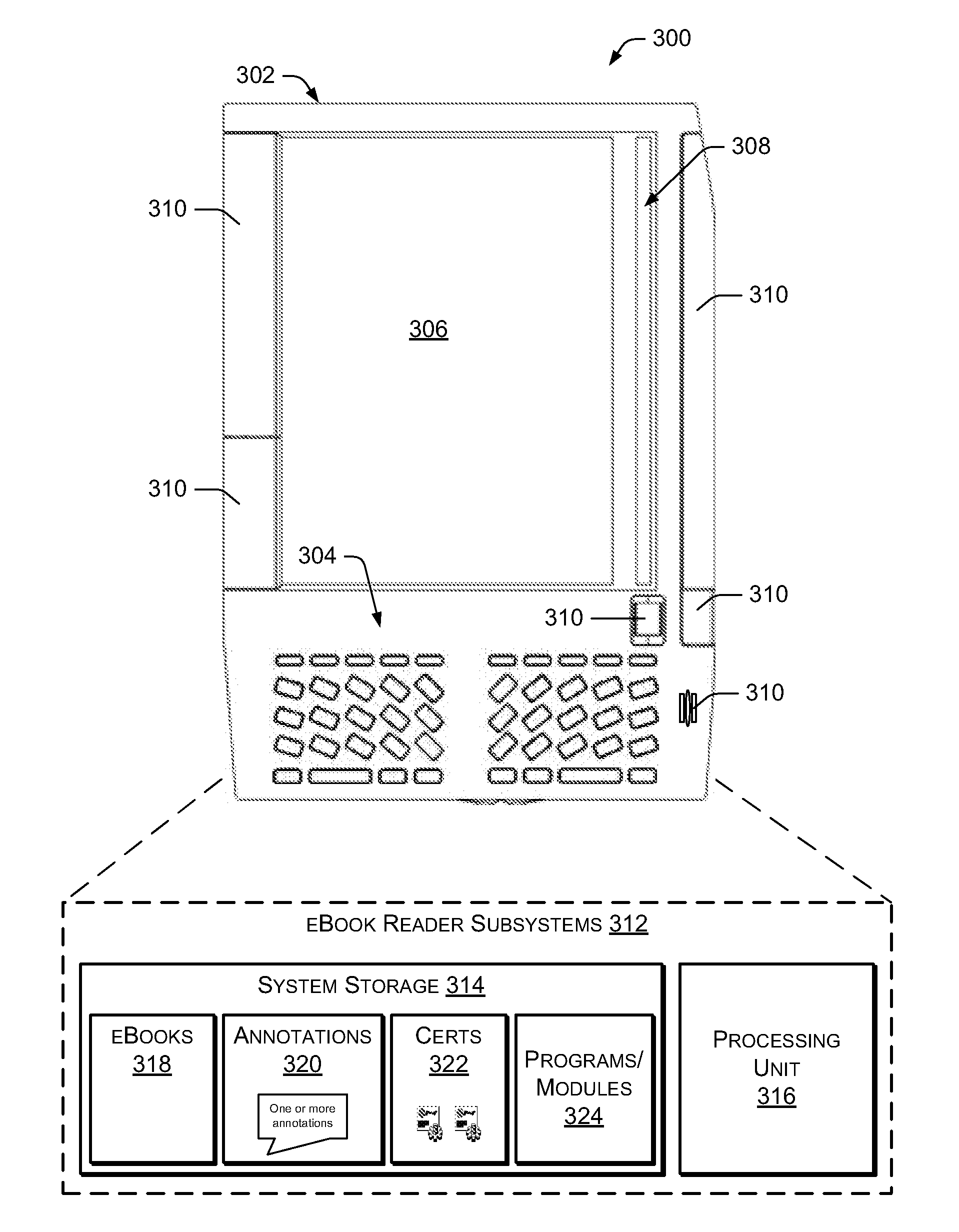
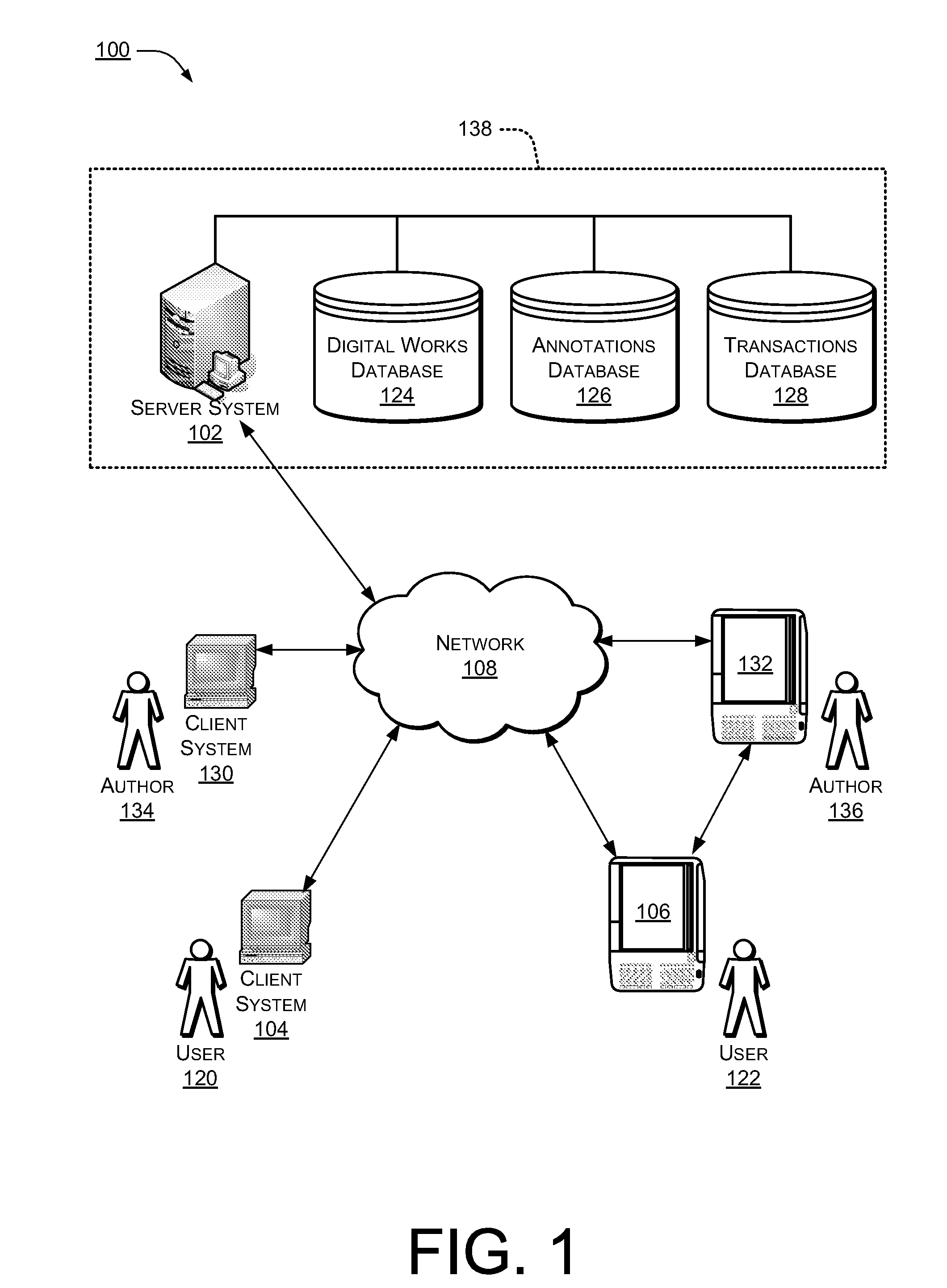
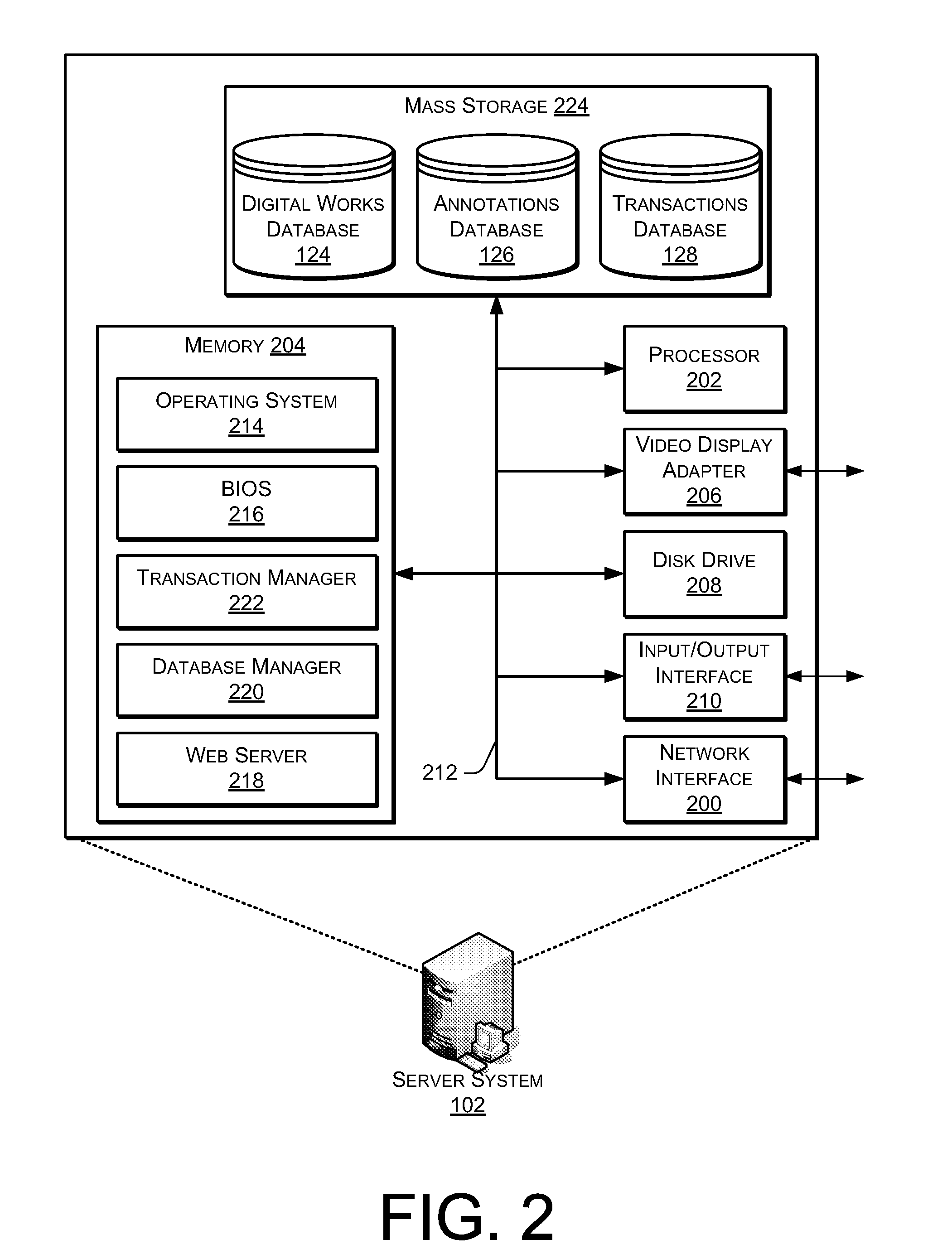
Providing Annotations of a Digital Work
ActiveUS20080168073A1Wide applicabilityReduce fatMultimedia data indexingNatural language data processingAuthorization certificateAuthorization
A digital work may be annotated using an eBook reader device. Upon receiving an annotation relating to a specific portion of the digital work, an invariant location reference identifier corresponding to the specified portion of the digital work may be appended to the annotation. The annotation may then be stored in association with the digital work for later reference. In some instances, an annotation may be presented on an eBook reader device upon receipt of a valid authorization credential granting access to the annotation.
Owner:AMAZON TECH INC
Task window navigation method and system
InactiveUS6215490B1Data processing applicationsDigital output to display deviceGraphical user interfaceControl equipment
A method of managing a plurality of windows organized and displayed on the graphical user interface of a computer. At any given time, one of the plurality of windows has a focus on the graphical user interface and a remainder of the windows are at least partly obscured behind the window having the focus. The method begins by displaying a graphical control device on the GUI, The graphical control device preferably has a plurality of identifiers each of which is associated with a given one of the plurality of windows. Thus, the graphical control device may be a slider, with each of the identifiers being a "notch". As the graphical pointer is moved in a predetermined manner relative to the notches, respective windows are selectively positioned at the focus position on the GUI. Thus, the user may easily locate any desired window by traversing the graphical pointer across the slider notches. As each notch is traversed, the window associated therewith is brought into the focus position. This is a fast and simple technique for locating a hidden or partially obscured window on the interface.
Owner:IBM CORP
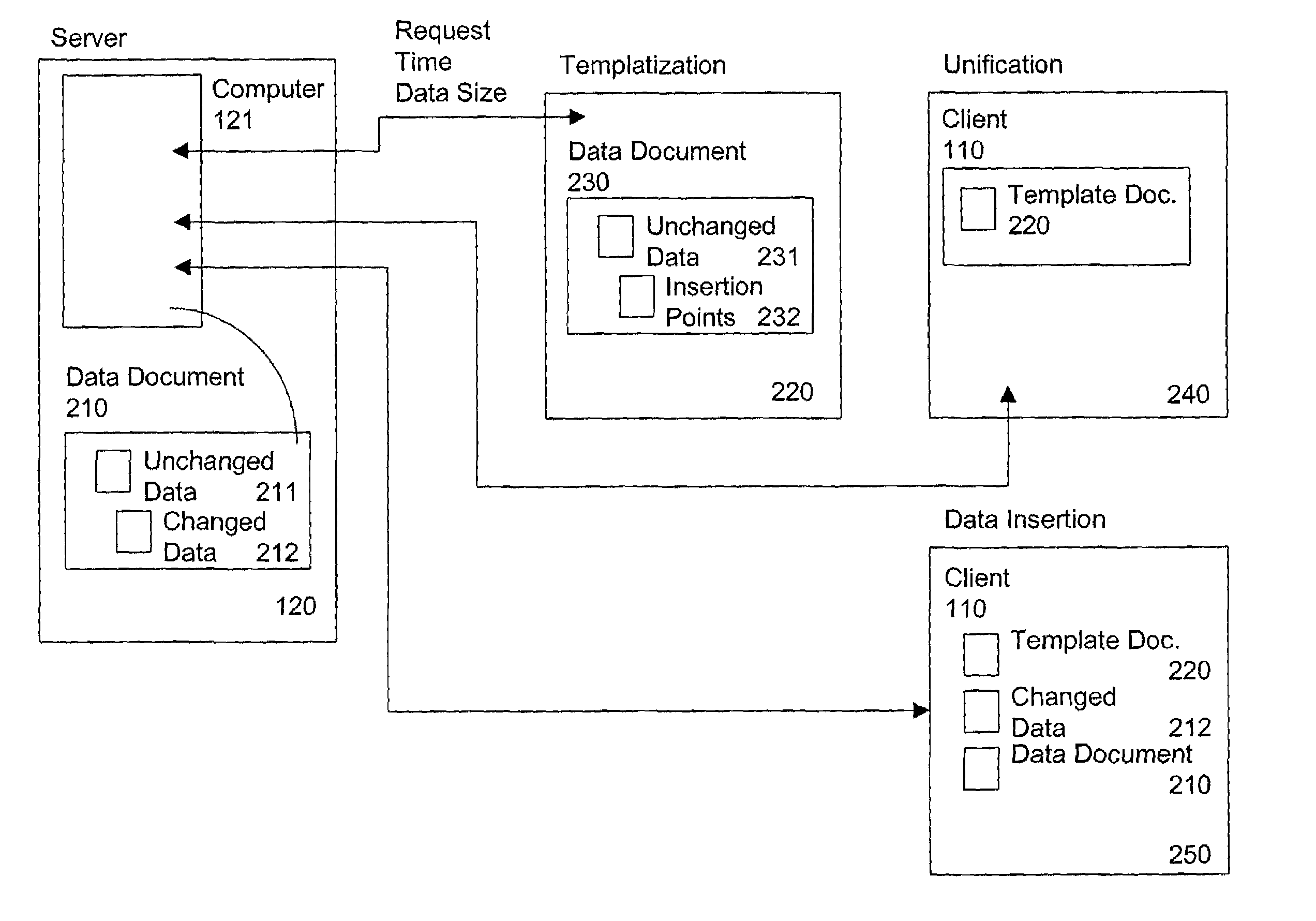
Server-originated differential caching
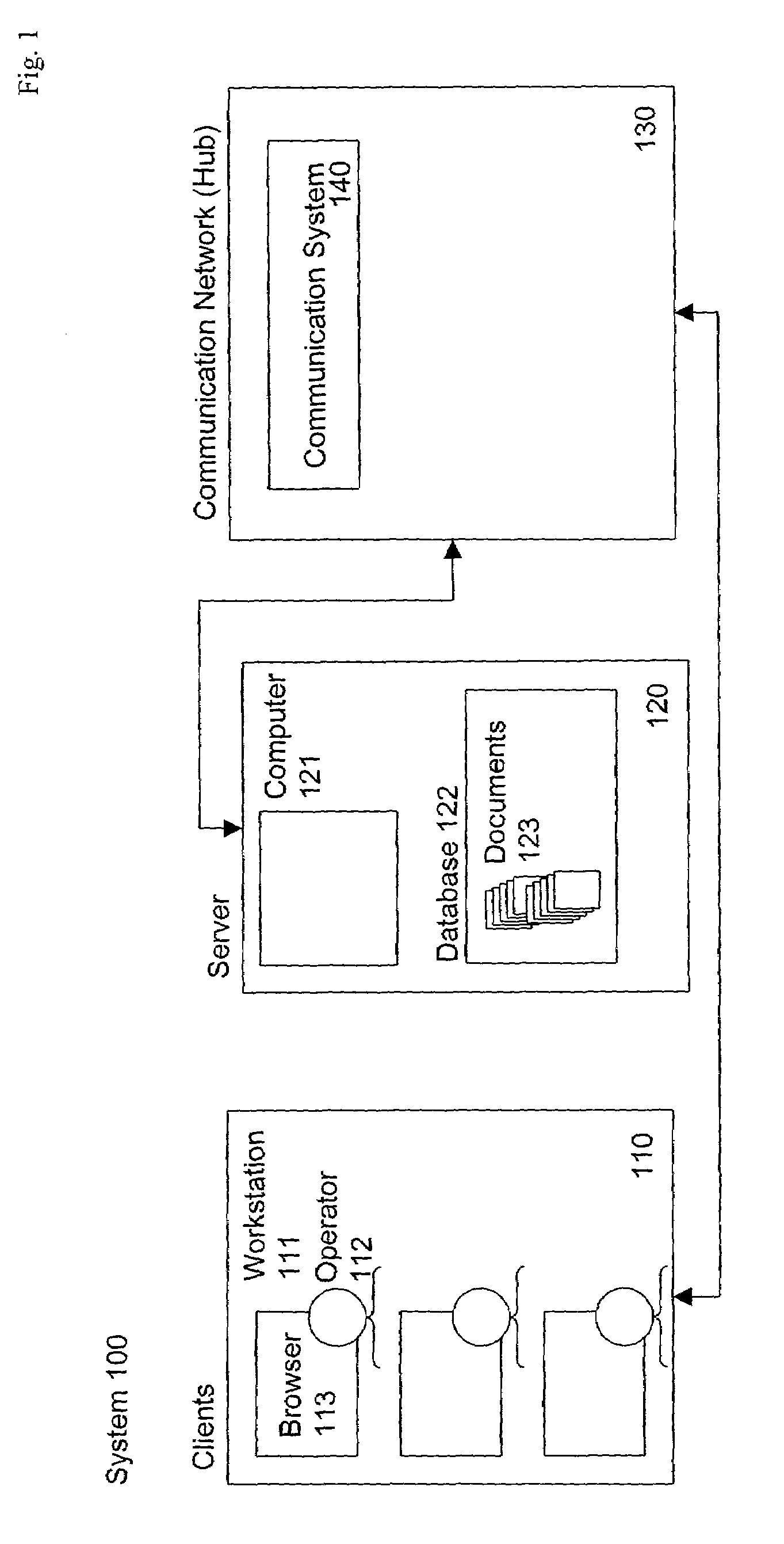
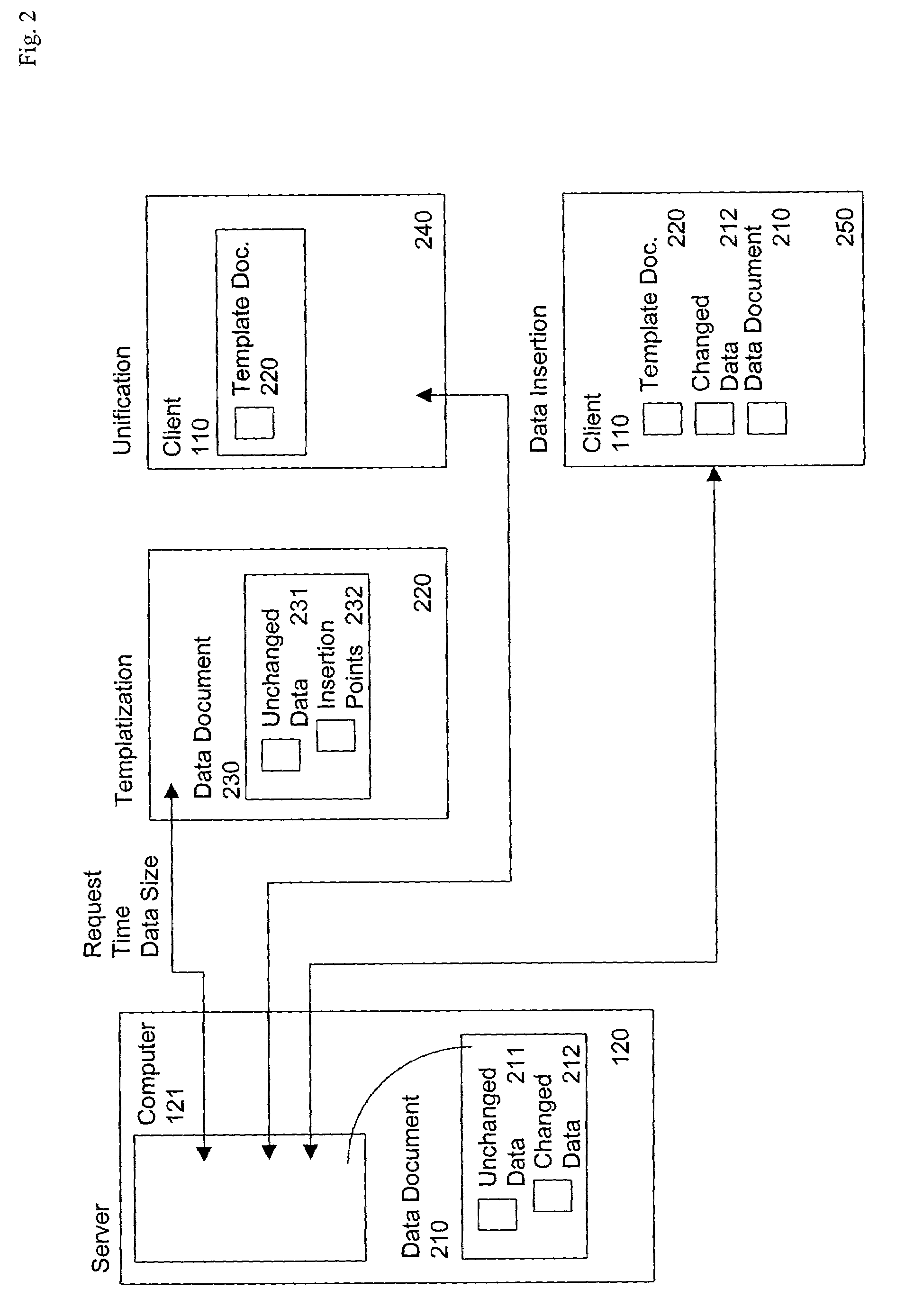
InactiveUS7269784B1Minimize timeReduce the amount requiredDigital data information retrievalBiological modelsUnique identifierClient-side
The invention provides a method and system for sending relatively identical web pages, when requested by subsequent users, with substantial reduction of bandwidth. The server determines a “template web page” corresponding to the actual information on the web page, and having a set of insertion points, at which changed data can be inserted by the client. The server sends a JavaScript program corresponding to the template web page, which makes reference to the template web page and the changed data, along with sending the actual changed data itself. A first user requesting the web page receives the entire web page, while a second user requesting the web page (or the first user re-requesting the web page at a later time) receives the template information plus only the changed data. The server re-determines the template web page from time to time, such as when a ratio of changed data to template web page data exceeds a selected threshold. The server identifies the particular template web page to the client using a unique identifier (an “E-tag”) for the particular data sent in response to the request. Since the E-tag refers to the template, not the underlying web page, when the standard client makes its conditional request for the web page “if not changed”, the server responds that the web page is “not changed” even if it really is, but embeds the changed data in a cookie it sends to the client with the server response to the client request.
Owner:DIGITAL RIVER INC
Rendering content-targeted ads with e-mail
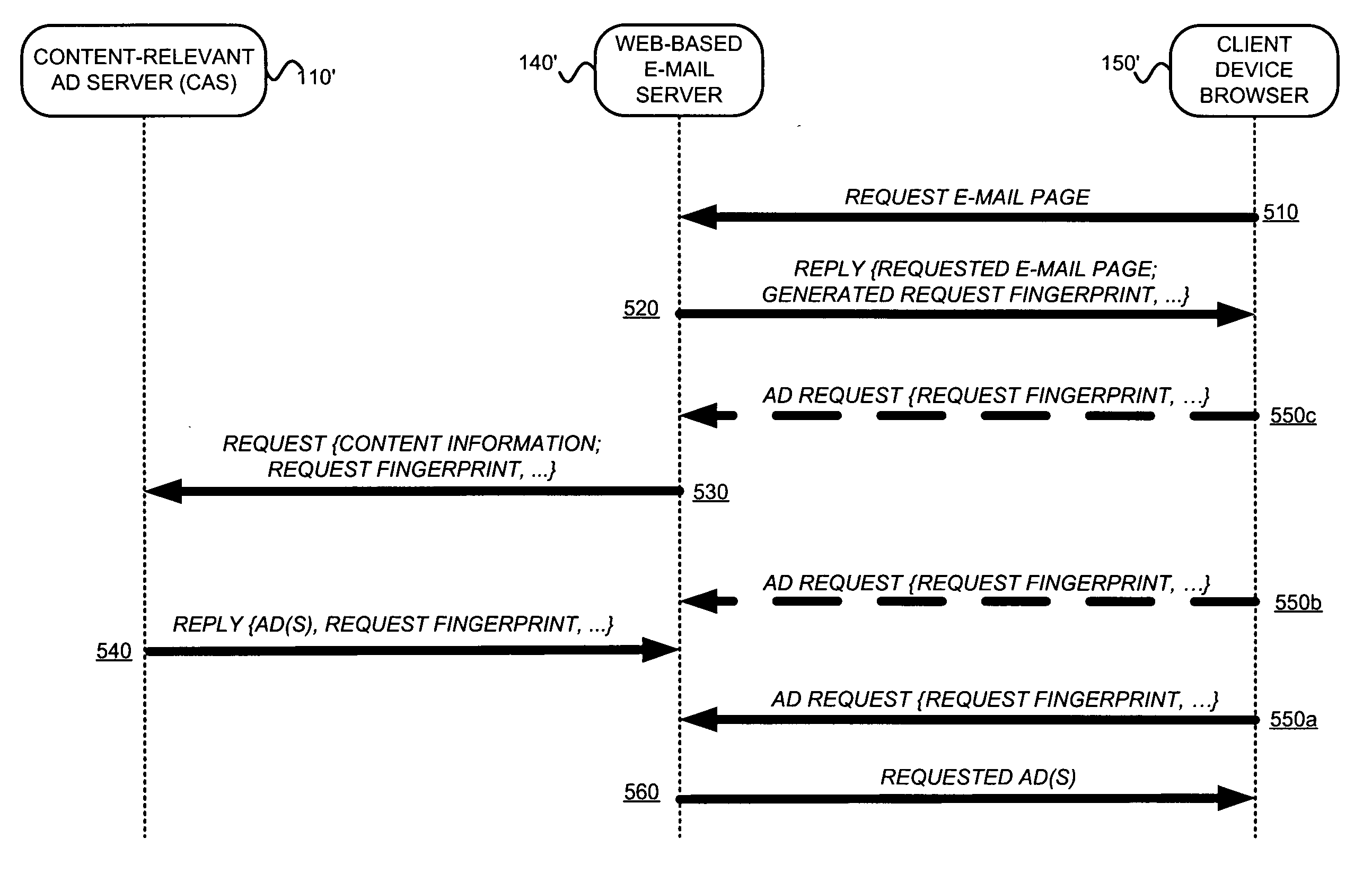
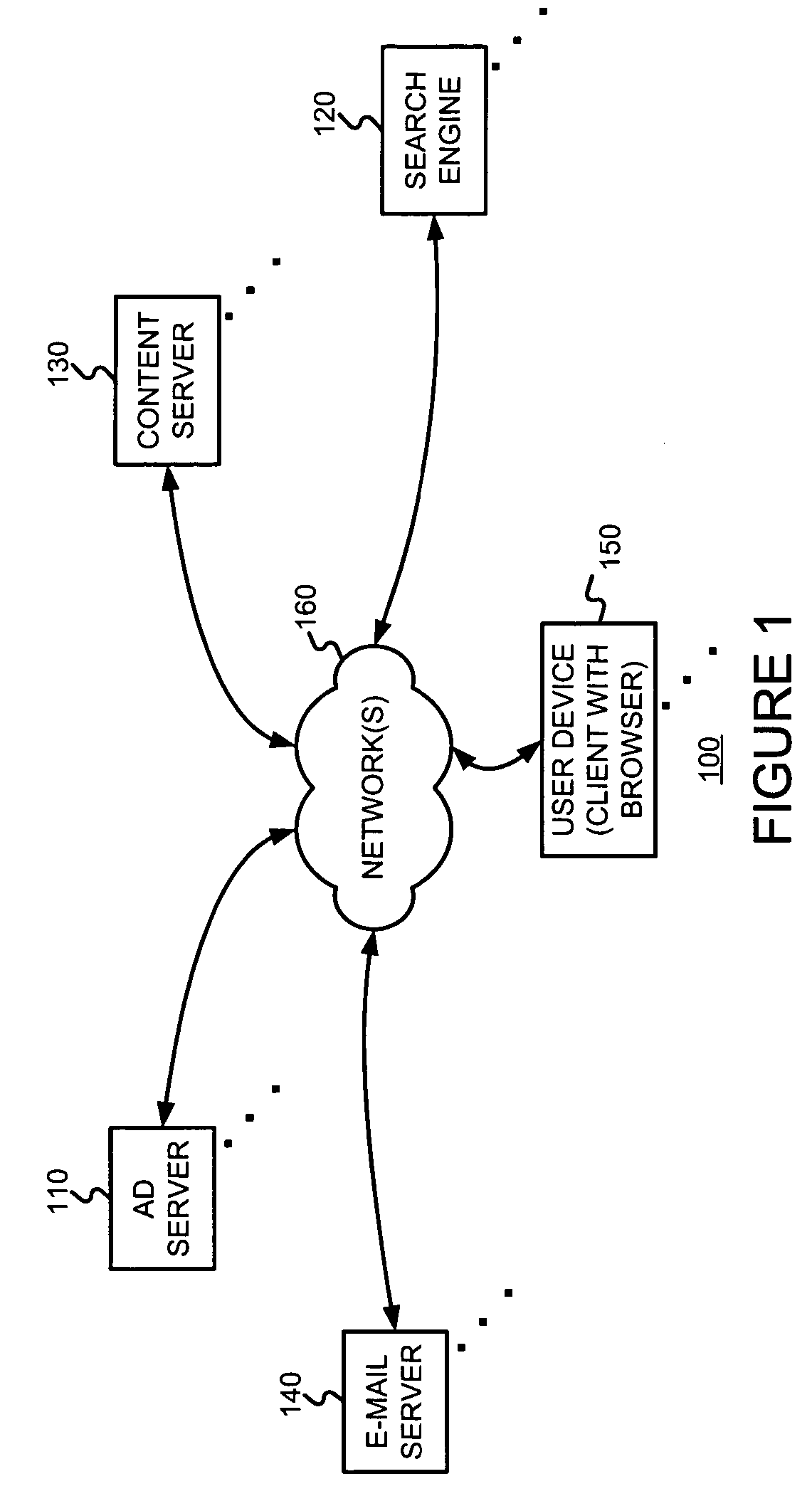
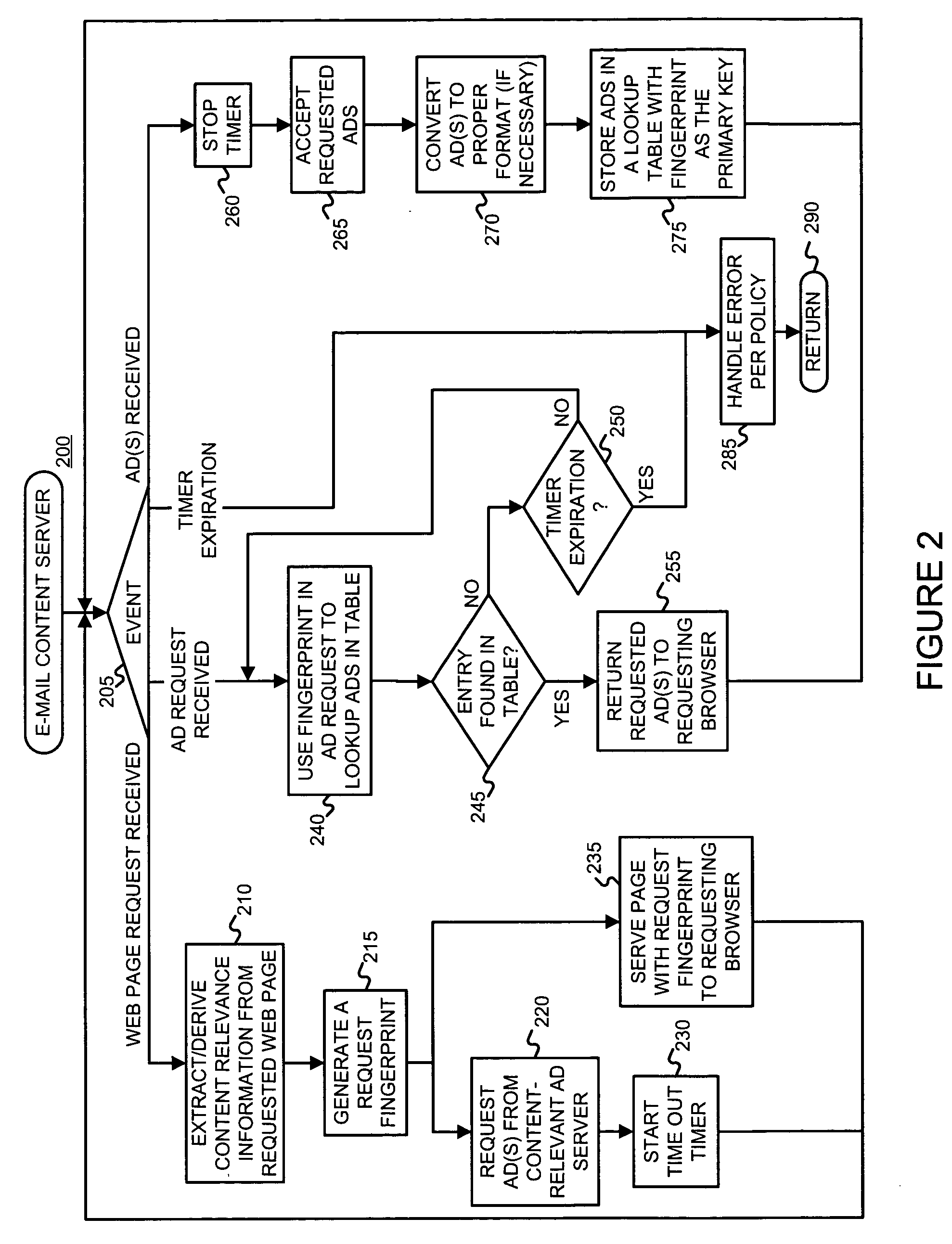
InactiveUS20050222903A1Good serviceMarketingSpecial data processing applicationsPaper documentDocument preparation
An asynchronous and opportunistically available scheme under which a user's e-mail (or a document including e-mail content) is rendered immediately, and later updated with appropriate advertisements if and when they became available, is described. This scheme ensures that the availability of advertisements will not adversely affect the rendering of the e-mail content. For example, a Web-based e-mail server may facilitate the serving of advertisements with e-mail by (a) accepting a request for a document including e-mail, (b) generating a request identifier, (c) serving the requested document in association with the request identifier, and (d) obtaining at least one ad relevant to content of the e-mail. The Web-based e-mail server may further (e) store the obtained ad(s), (f) accept an ad request, (g) read the stored ad(s) using information from the ad request, and (h) serve the ad(s).
Owner:GOOGLE LLC
System-Level Correction Service
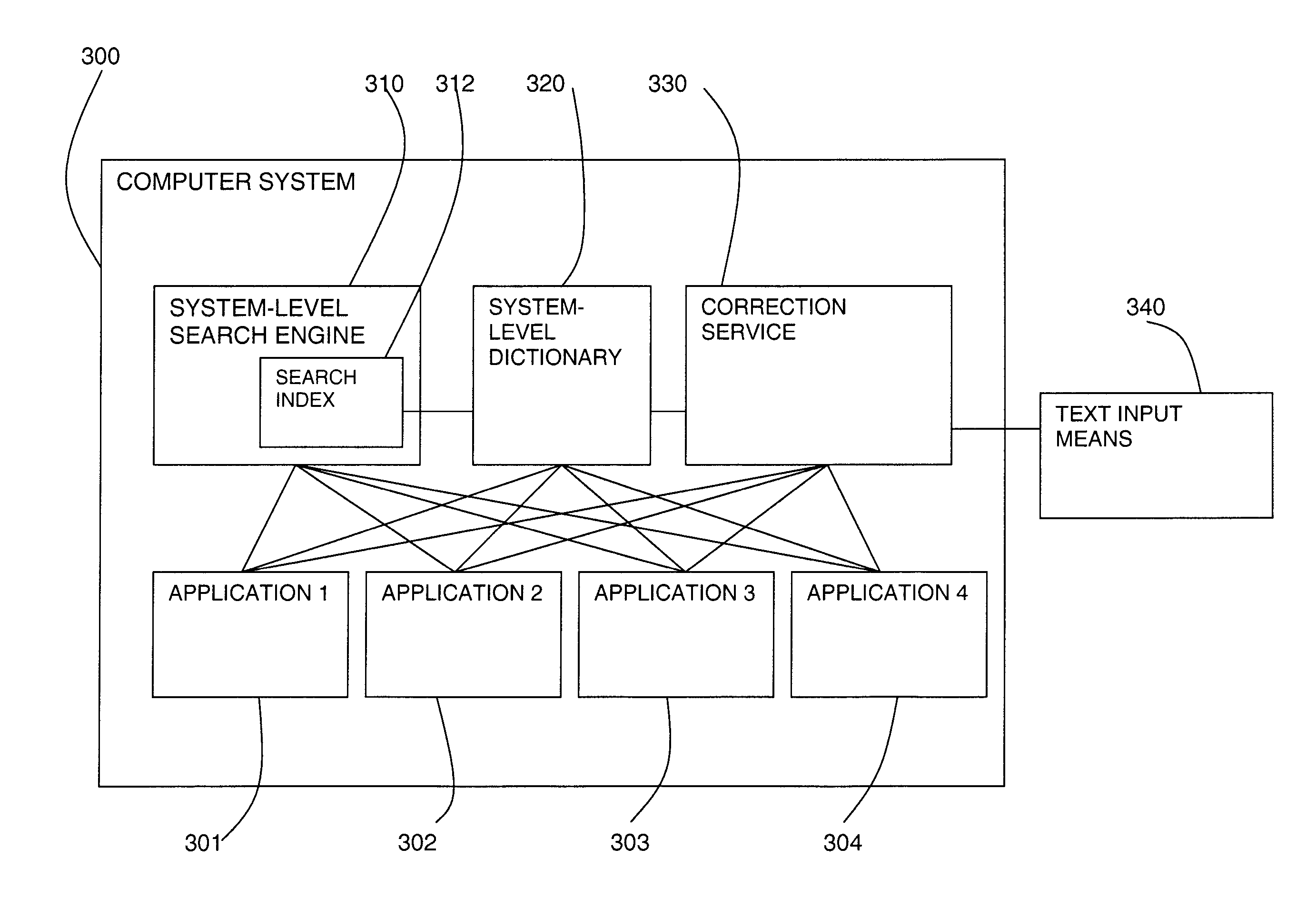
InactiveUS20070265831A1Natural language data processingSpecial data processing applicationsComputerized systemSystem level
A system-level text correction service (330) is provided. The service (330) includes monitoring (410) the input of text (340) on a computer system, identifying an incorrect input word in a first application. Correction proposal words are retrieved from a system-level dictionary (320), wherein the system-level dictionary (320) stores a reference word with an identifier of at least one application type in which the reference word is used. The correction proposal words are ranked according to the similarity of the proposal word to the input word and by comparing the first application to the application types of the reference word.
Owner:IBM CORP
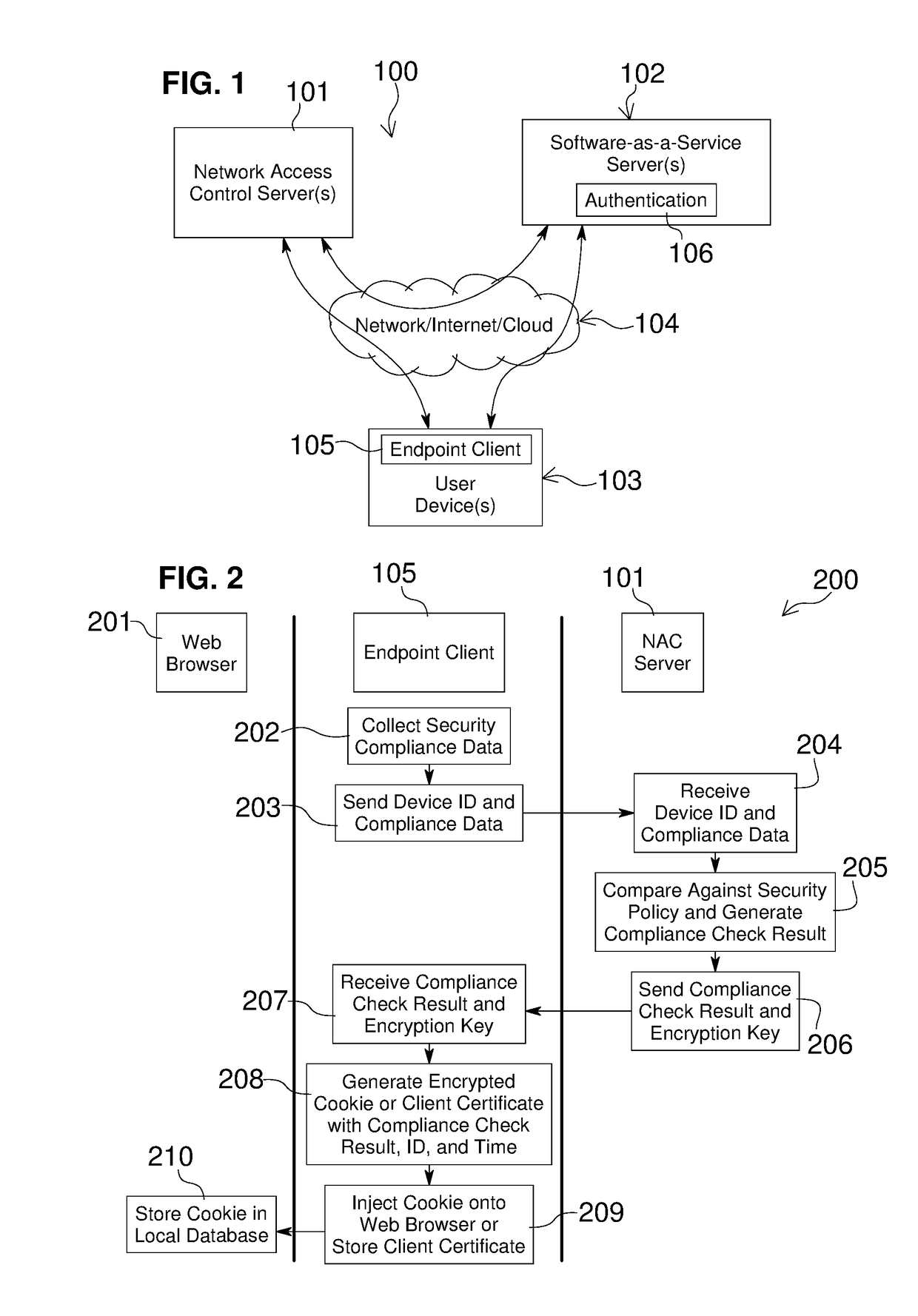
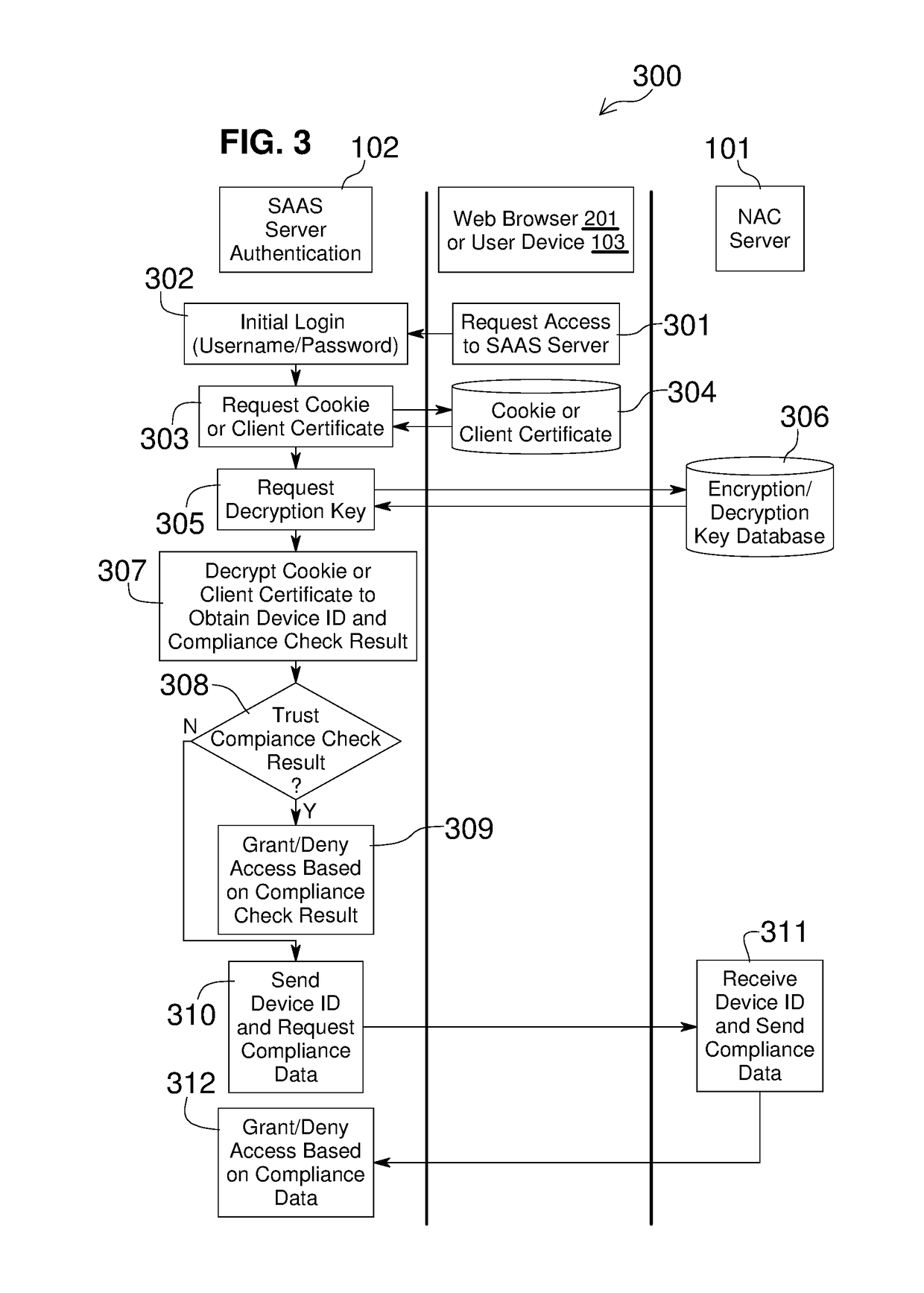
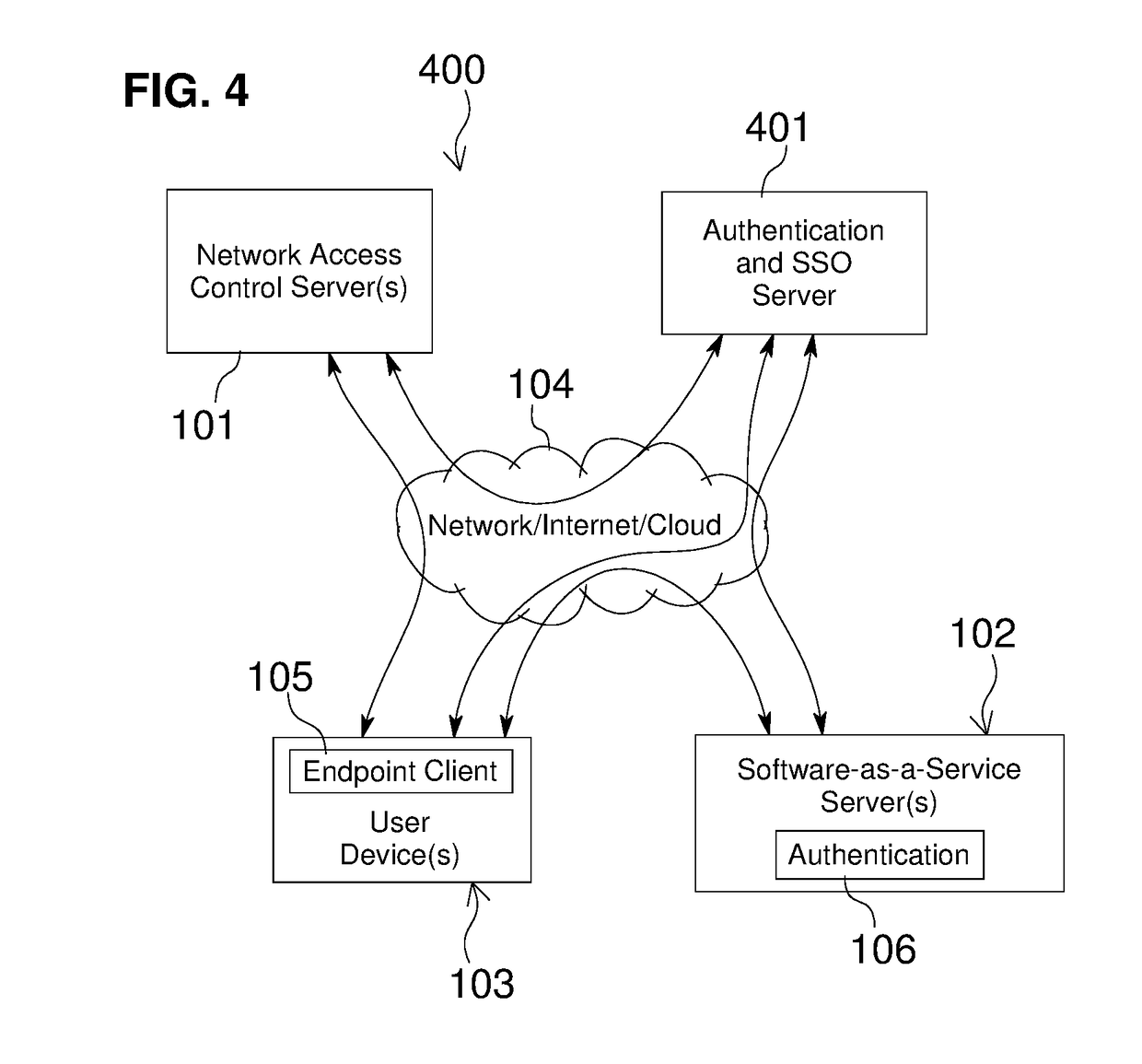
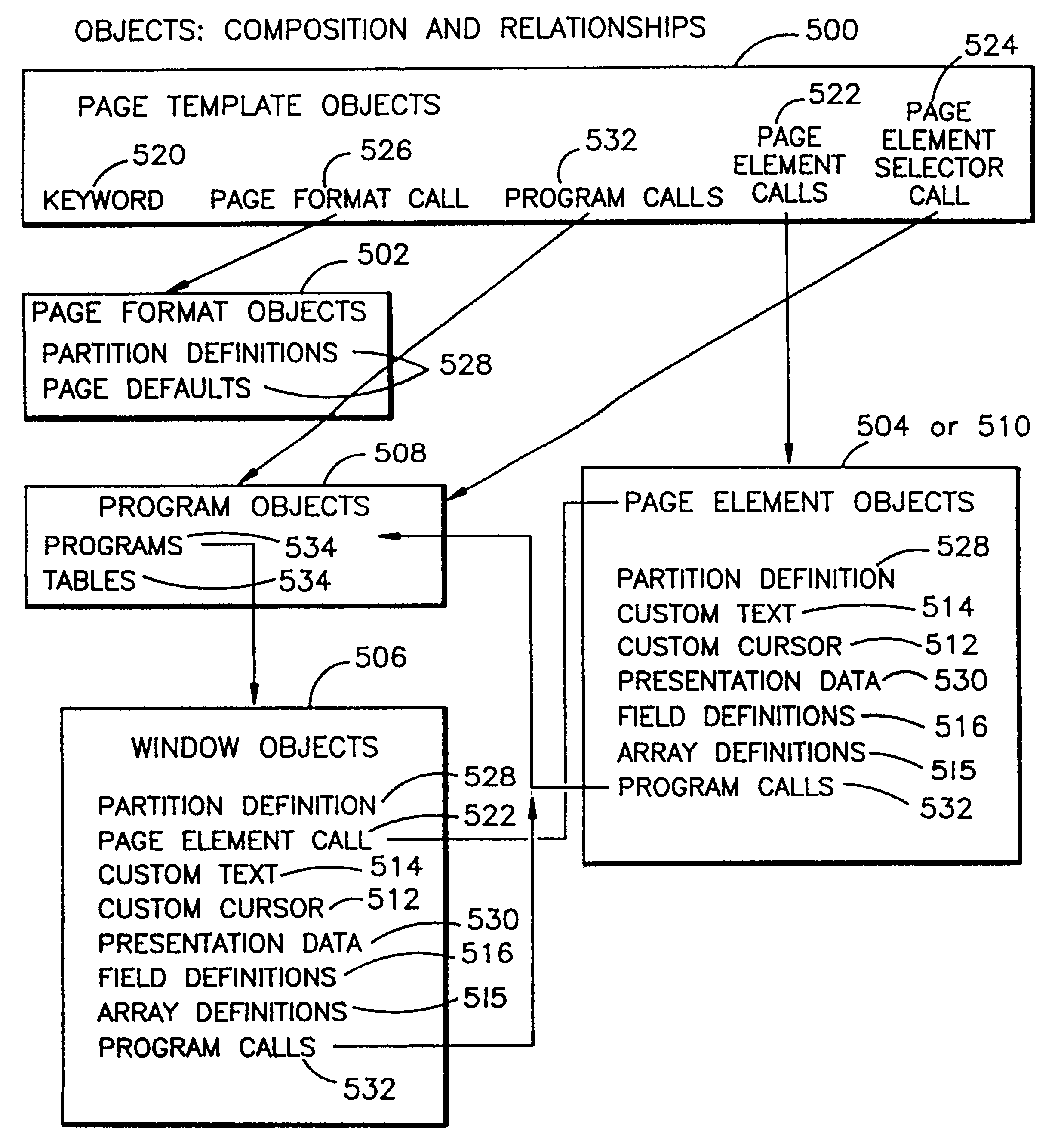
Network Access Control with Compliance Policy Check
Embodiments of the present invention include methods involving an authentication application, a client application, or a combination of a network access control server with the authentication application and the client application. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result or a user device identifier is stored in a web browser cookie or a client certificate on the user device.
Owner:OPSWAT INC
Method for locating application records in an interactive-services database
InactiveUS6195661B1Involvement is limitedExecuted quickly and easilyImpression capsDental impression compositionsPersonalizationSubject matter
A method for locating application records in an interactive-service database is described. The method features steps for creating multiple search tables which represent subsets of the database to be interrogated; for example the applications of an interactive service. In accord with the method, steps are provided for arranging the tables with keyword, record locators, indexed to record identifiers. Additionally, the method includes steps for providing each table with a unique coding and steps for generating table codes at the user reception system in response to a query for a database record entered with a variety of search strategies; as for example, character string searching approximating the record sought, alphabetized record searching, subject matter category searching and personalized record searching, among others. Further, the method includes steps for comparing the table code generated with available table codes for the database to select a table suited for the query. Thereafter, the appropriate table is presented at the reception system so the table keywords can be reviewed and a desired record selected and presented.
Owner:INT BUSINESS MASCH CORP
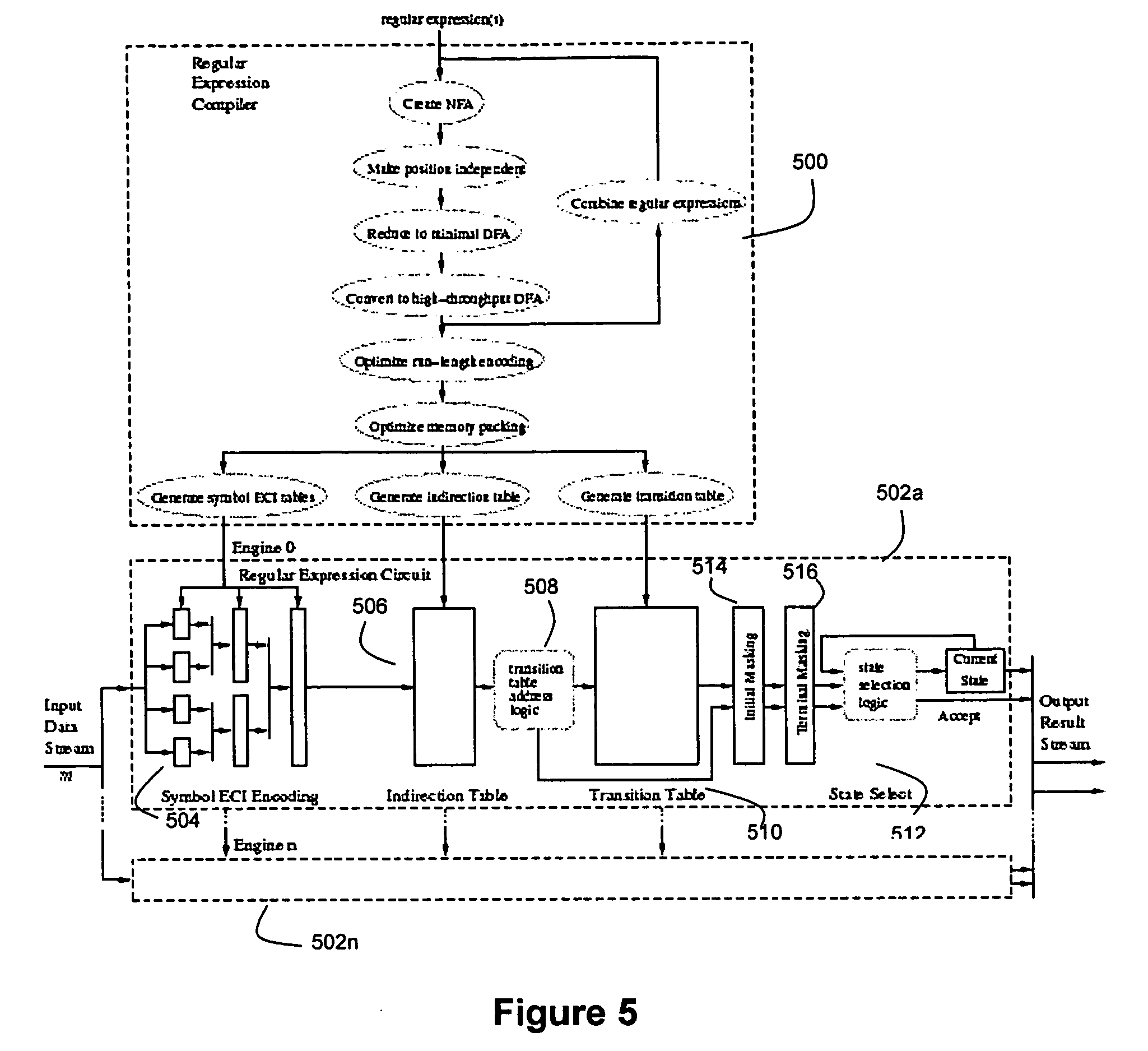
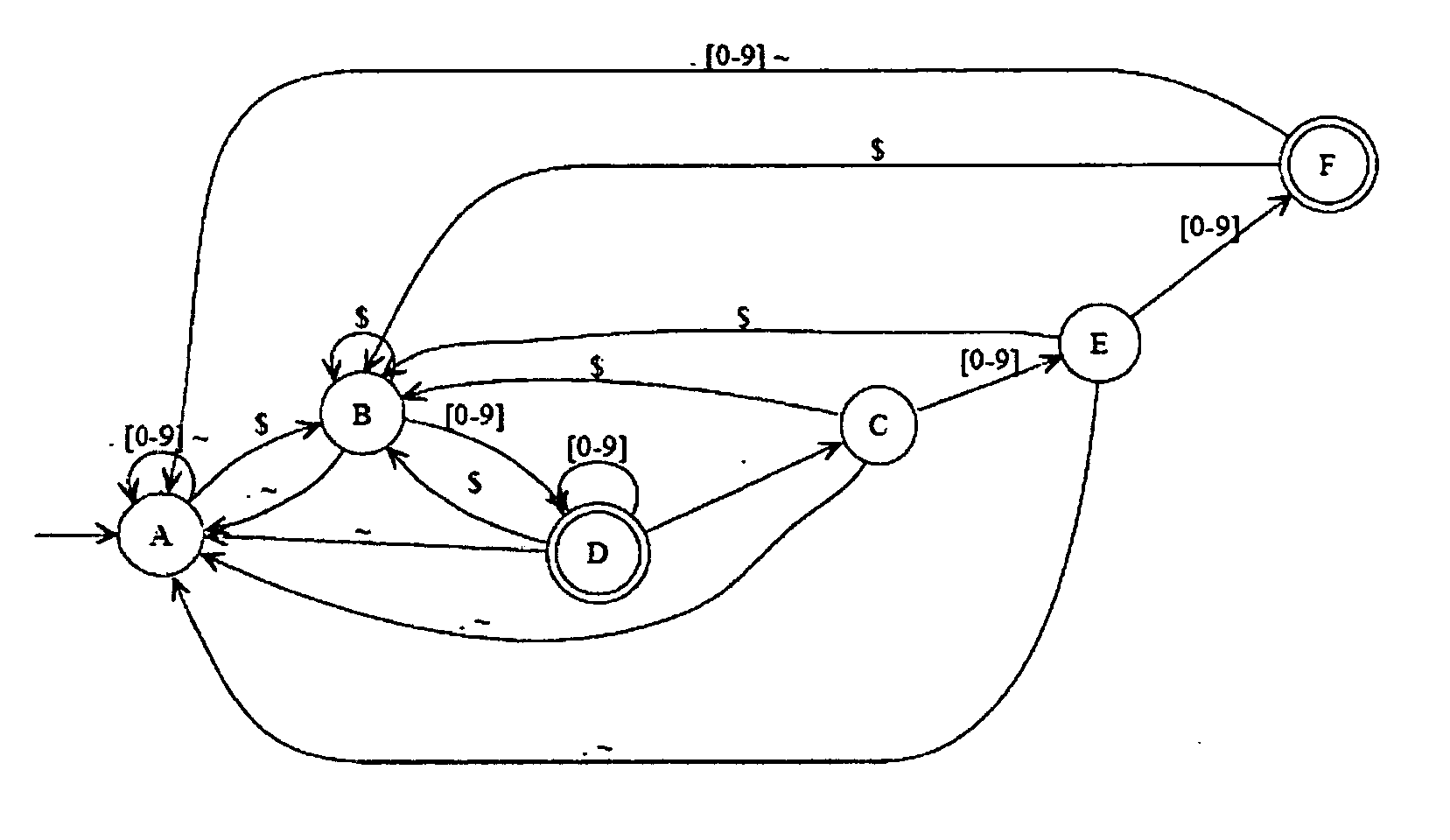
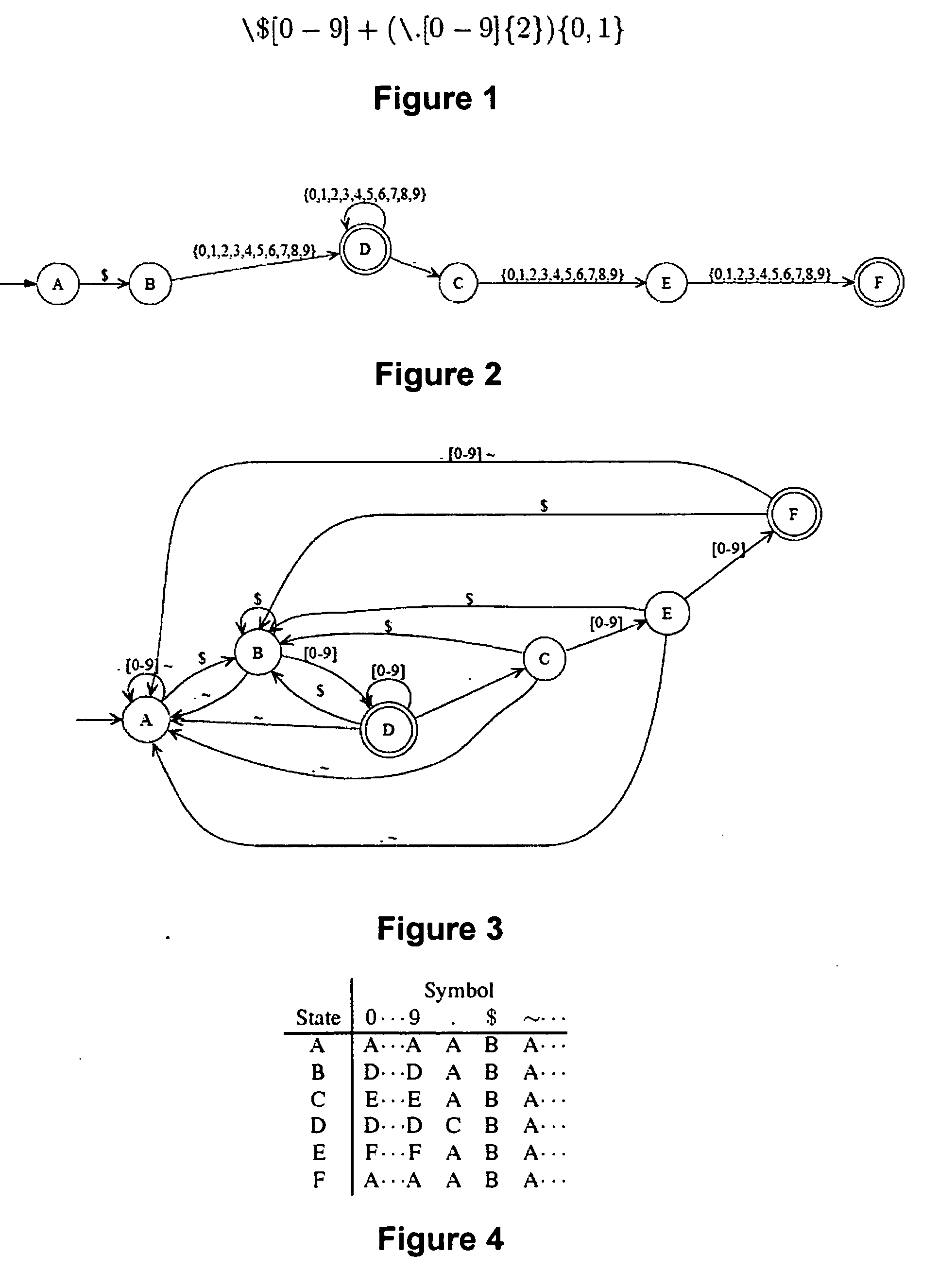
Method and device for high performance regular expression pattern matching
ActiveUS7702629B2Minimize the numberData processing applicationsDigital data information retrievalState dependentPattern matching
Disclosed herein is an improved architecture for regular expression pattern matching. Improvements to pattern matching deterministic finite automatons (DFAs) that are described by the inventors include a pipelining strategy that pushes state-dependent feedback to a final pipeline stage to thereby enhance parallelism and throughput, augmented state transitions that track whether a transition is indicative of a pattern match occurring thereby reducing the number of necessary states for the DFA, augmented state transition that track whether a transition is indicative of a restart to the matching process, compression of the DFA's transition table, alphabet encoding for input symbols to equivalence class identifiers, the use of an indirection table to allow for optimized transition table memory, and enhanced scalability to facilitate the ability of the improved DFA to process multiple input symbols per cycle.
Owner:IP RESERVOIR
Project workspace prioritization
Prioritization of project workspaces is provided herein. Data items are grouped into project workspaces based on workspace identifiers with which the data items have been tagged. Grouped data items included in a project workspace are tagged with a common workspace identifier that indicates association with a project corresponding to the project workspace, the project including tasks for a user. Priority of the project workspace is determined relative to priority of other project workspaces and based on ascertaining priorities of the tasks of the project by analyzing the grouped data items included in the project workspace. An indication of the priority of the project workspace relative to priority of the other project workspaces is provided for graphical presentation to the user, in order to facilitate focusing the user to a highest priority project workspace of the project workspaces.
Owner:KYNDRYL INC
Method and system for model-based heterogeneous server configuration management
ActiveUS20030233431A1Error detection/correctionInterprogram communicationReference modelingReal time services
A method and system for configuring heterogeneous servers across a network through modules that can browse, snapshot, track changes, track compliance, correct server objects on each of the servers, and provision new servers is provided. In one embodiment, server objects on multiple servers can be browsed in real time. While browsing, a collection of server object identifiers can be selected and collected in a template. The values of the server objects identified in the template can be recorded for a "gold server" through a "snapshot" process, which collects the values and saves them in a reference model. By comparing other live servers to the reference model, discrepancies in configuration of the other live servers can be identified and corrected. The reference models can also be used to provision a new server. Alternative to the reference model, an arbitrary snapshot or scheduled snapshots of a server can be used to track change and compliance in that server.
Owner:BLADELOGIC
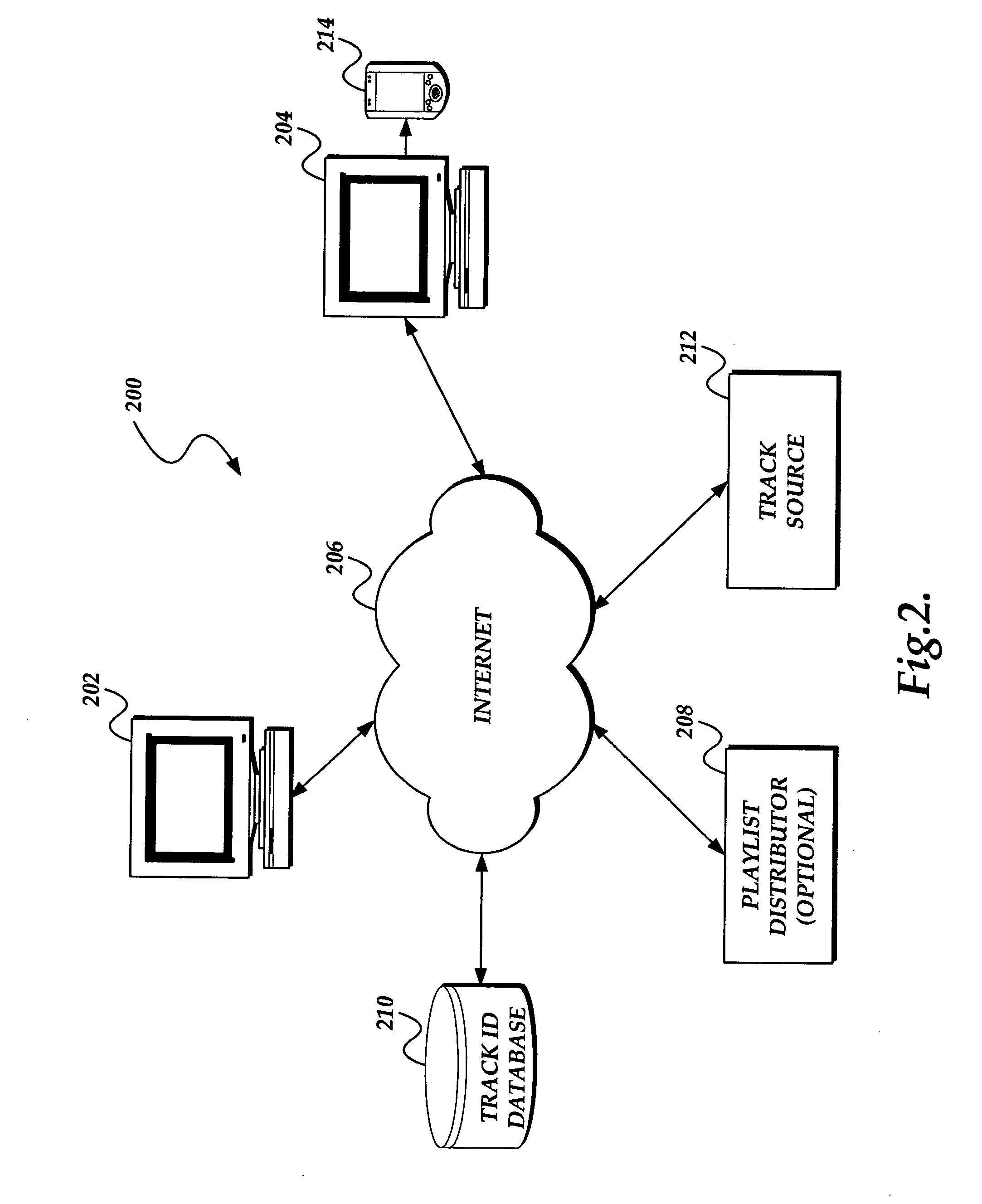
System and method for creating and playing globally relevant playlists
InactiveUS20050060264A1Using non-detectable carrier informationRecord information storageComputer visionEngineering
Owner:MICROSOFT TECH LICENSING LLC
Method and device for high performance regular expression pattern matching
ActiveUS20070130140A1Minimize the numberData processing applicationsDigital data information retrievalAlgorithmPattern matching
Disclosed herein is an improved architecture for regular expression pattern matching. Improvements to pattern matching deterministic finite automatons (DFAs) that are described by the inventors include a pipelining strategy that pushes state-dependent feedback to a final pipeline stage to thereby enhance parallelism and throughput, augmented state transitions that track whether a transition is indicative of a pattern match occurring thereby reducing the number of necessary states for the DFA, augmented state transition that track whether a transition is indicative of a restart to the matching process, compression of the DFA's transition table, alphabet encoding for input symbols to equivalence class identifiers, the use of an indirection table to allow for optimized transition table memory, and enhanced scalability to facilitate the ability of the improved DFA to process multiple input symbols per cycle.
Owner:IP RESERVOIR
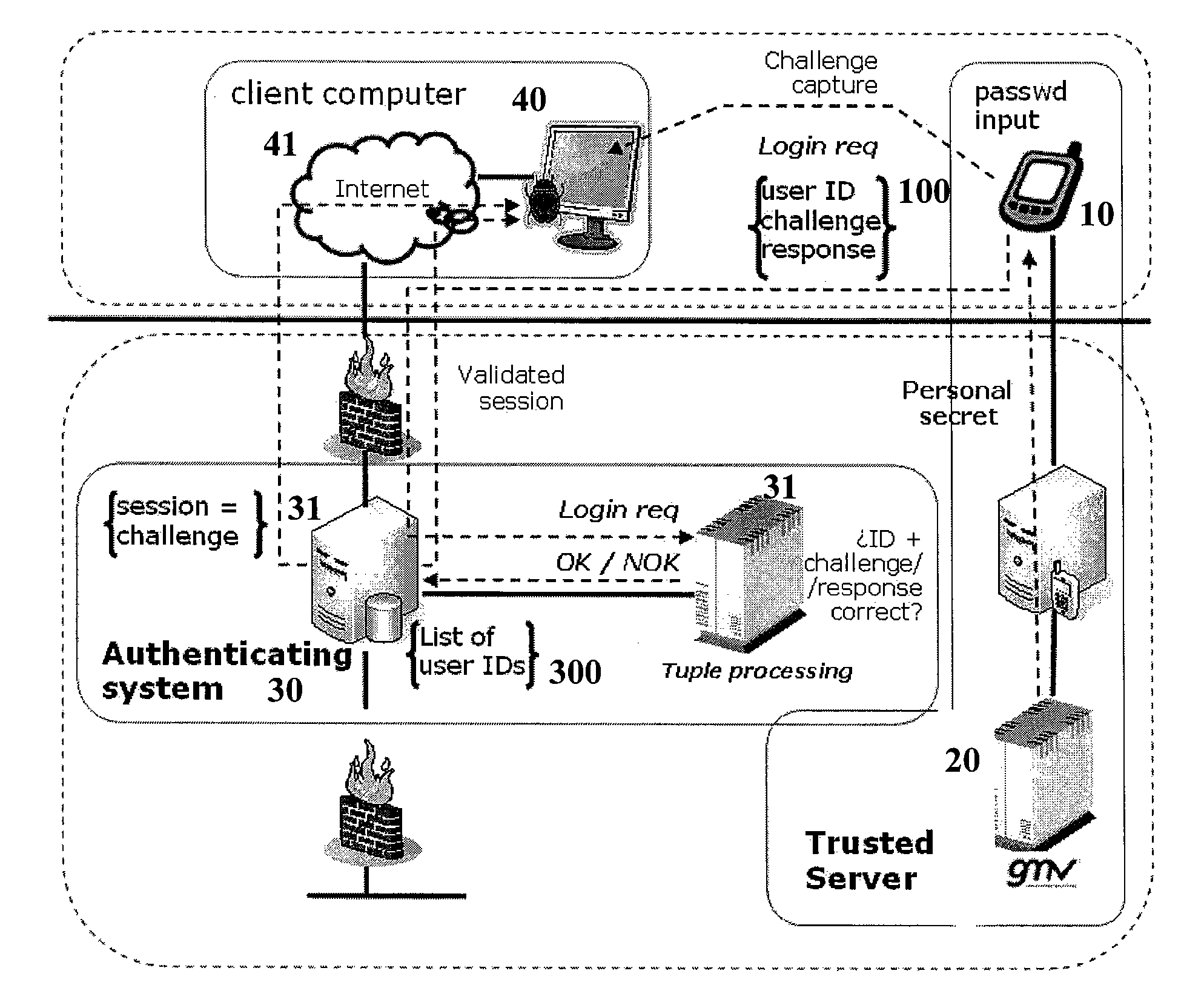
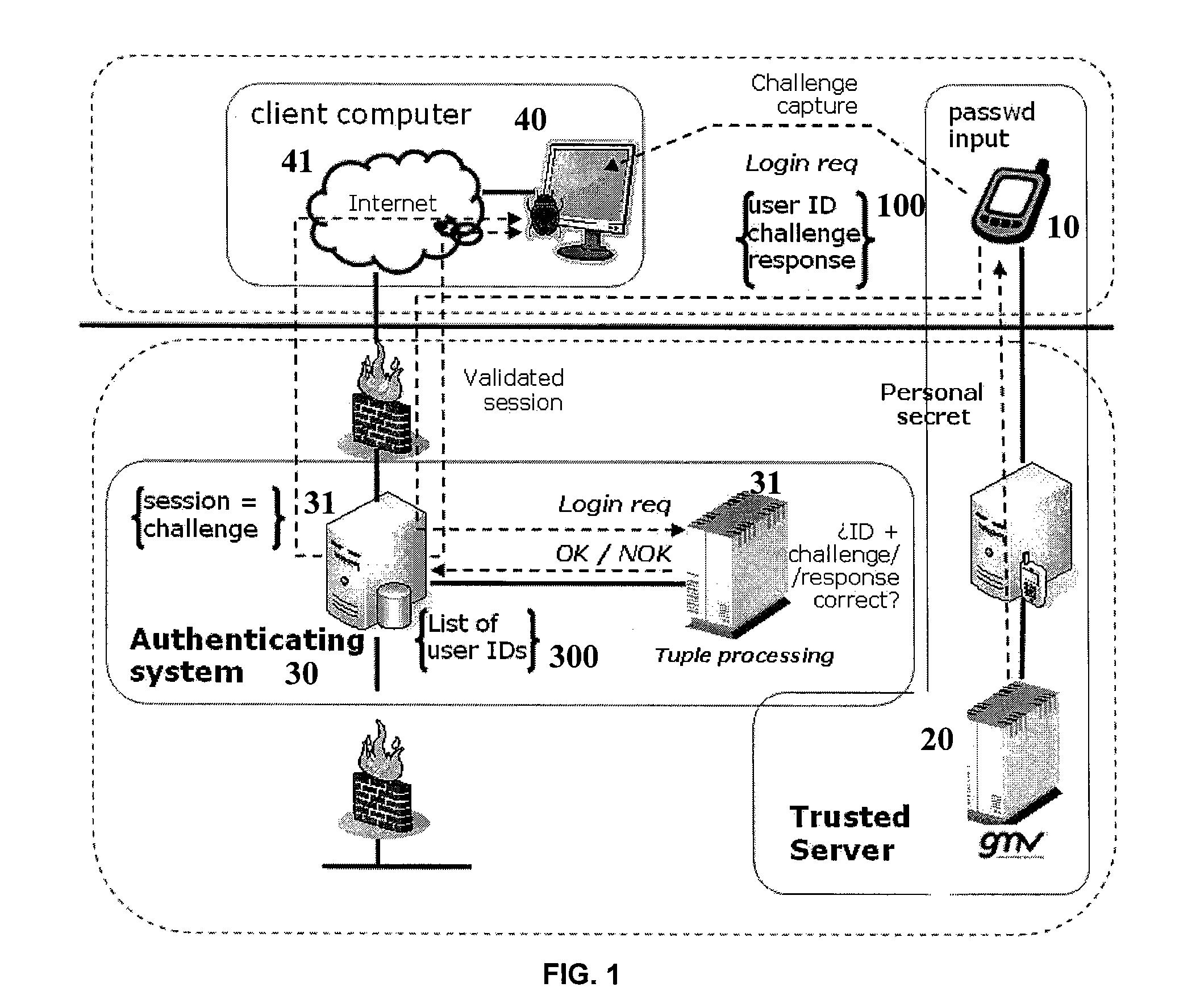
Method and system for authenticating a user by means of a mobile device
ActiveUS20100070759A1Reduce riskDigital data processing detailsUser identity/authority verificationClient-sideUser identifier
The invention relates to a method for authenticating a user of a mobile device (10) against a remote authenticating system (30) which is connected to a client computer accessible to said user, which comprises:i—reading a 2D-code displayed to the client computer (40) by means of a 2D-code reader provided in said mobile device, a URL address of the authenticating system and a codified challenge generated by authenticating system being embedded in said 2D-code;ii—processing said codified challenge and computing a response to it using a personal secret, which is a string of characters univocally related to a user identifier (user ID) of said user of the mobile device and to a time stamp;iii—sending a message to the authenticating system which includes a tuple (100) whose elements are said user ID, the challenge and its response;iv—analyzing the tuple elements and determining the tuple is valid if the response to the challenge has been generated using the personal secret of the user whose user identifier is in the tuple for a given period of time, and in case said tuple is valid:v—checking in a users list (300) in the authenticating system if the user identifier in the tuple is in said users list, and if the user identifier is in the users list, it is verified if the challenge in the tuple is in a session list in the authenticating system, and if the challenge is in the session list, the authenticating system pushes a welcome screen to the client computer that corresponds to a session identification number in the session list where the challenge is.The invention also to a system for authenticating a user of a mobile device.
Owner:GMV SOLUCIONES GLOBALES INTERNET
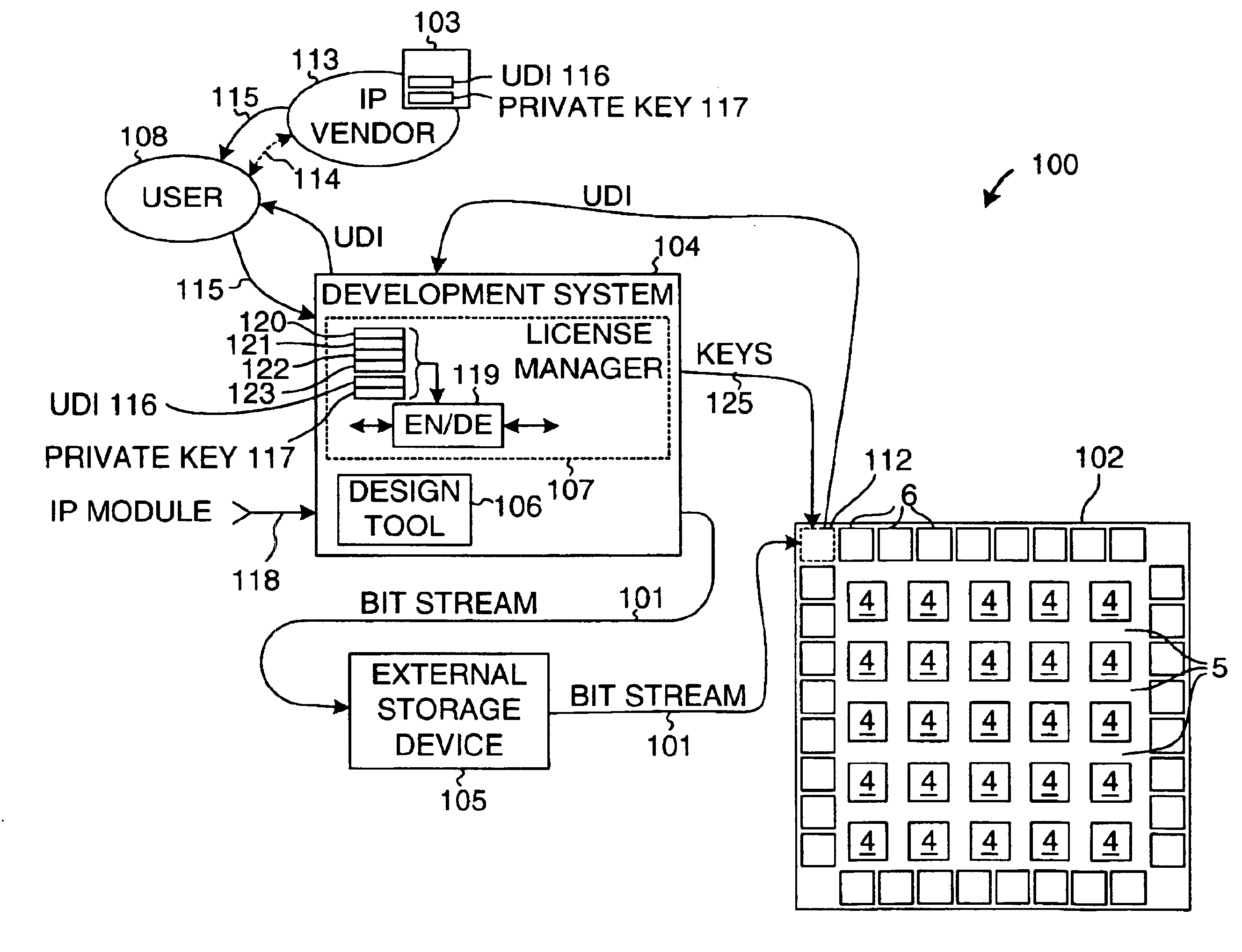
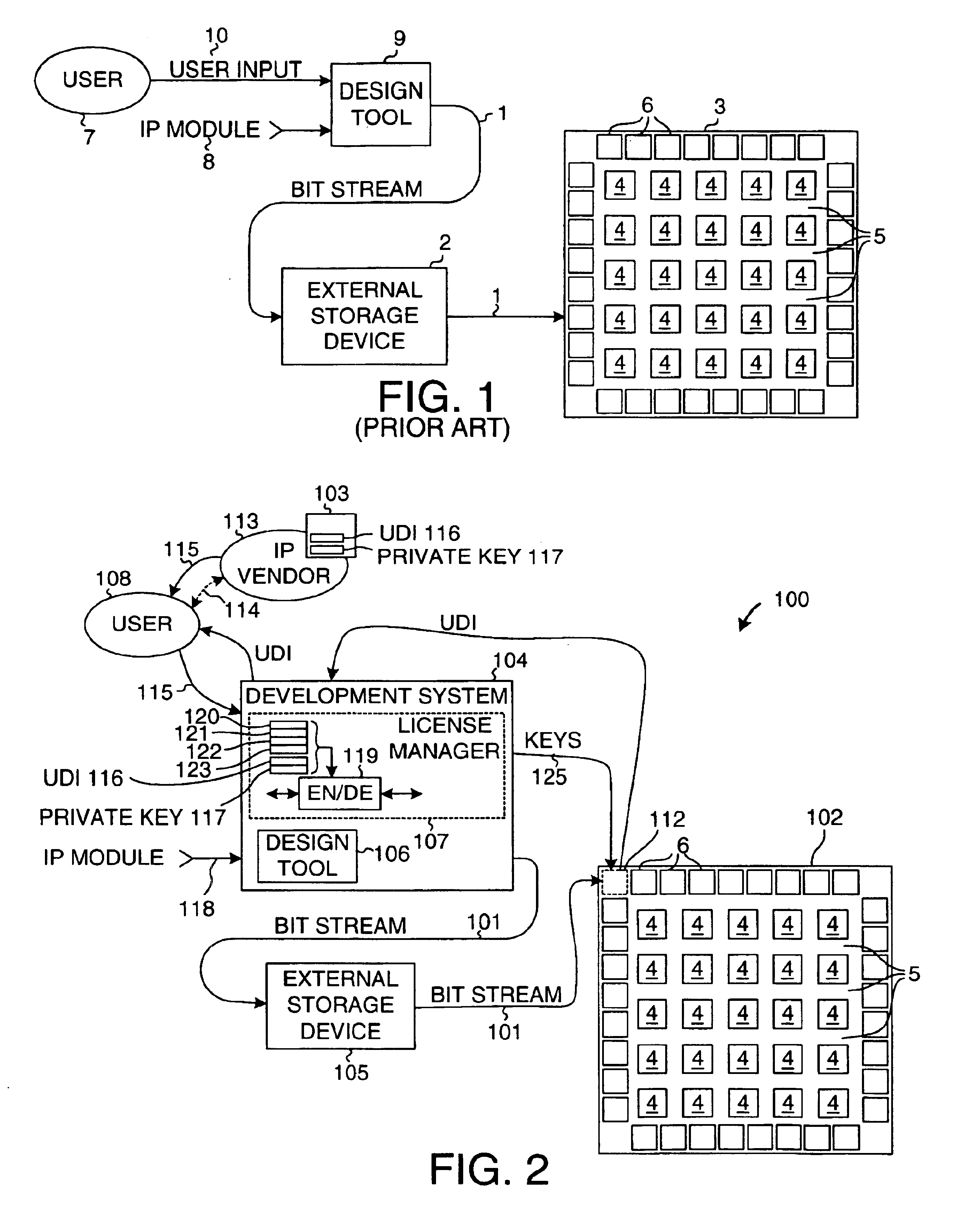
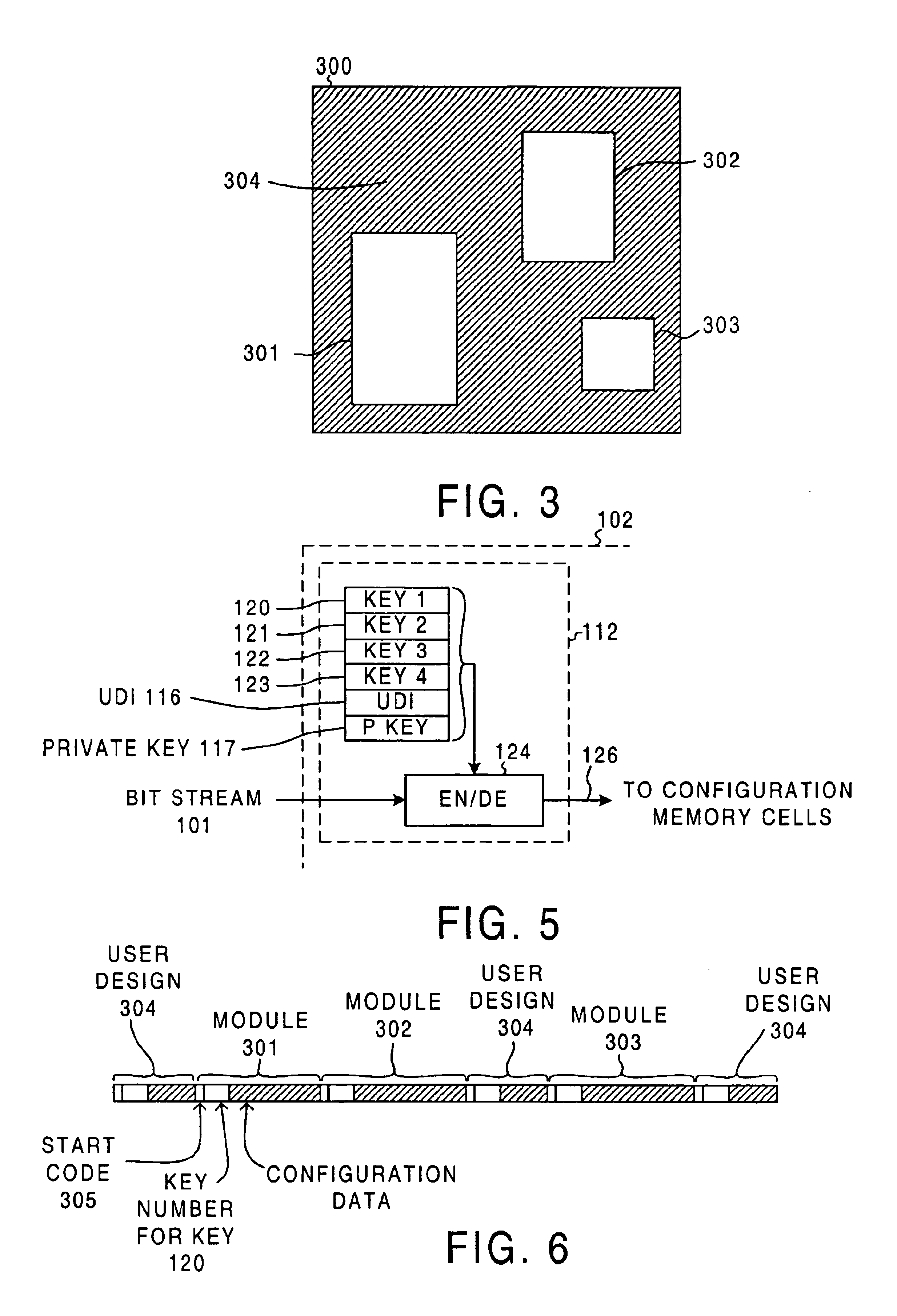
Intellectual property protection in a programmable logic device
InactiveUS6904527B1Copy protectionUser identity/authority verificationUnauthorized memory use protectionProgrammable logic deviceUnique device identifier
Individual IP vendors can directly license their IP modules to PLD users. Each PLD has a unique device identifier (UDI). If a user obtains a license to use an IP module on a particular PLD, then the IP vendor issues the user an authorization code (AC). The user supplies the AC to a license manager. The license manager decrypts the AC and checks that the UDI of the supplied AC matches the UDI of the PLD. If the two match, then the license manager encrypts a key, and sends the encrypted key to the PLD. The PLD uses a private key to decrypt the key. When the configuration bitstream for the design is later sent to the PLD, the license manager encrypts the IP module portion of the bitstream with the key. The PLD receives the bitstream and uses the decrypted key to decrypt the IP module portion.
Owner:XILINX INC
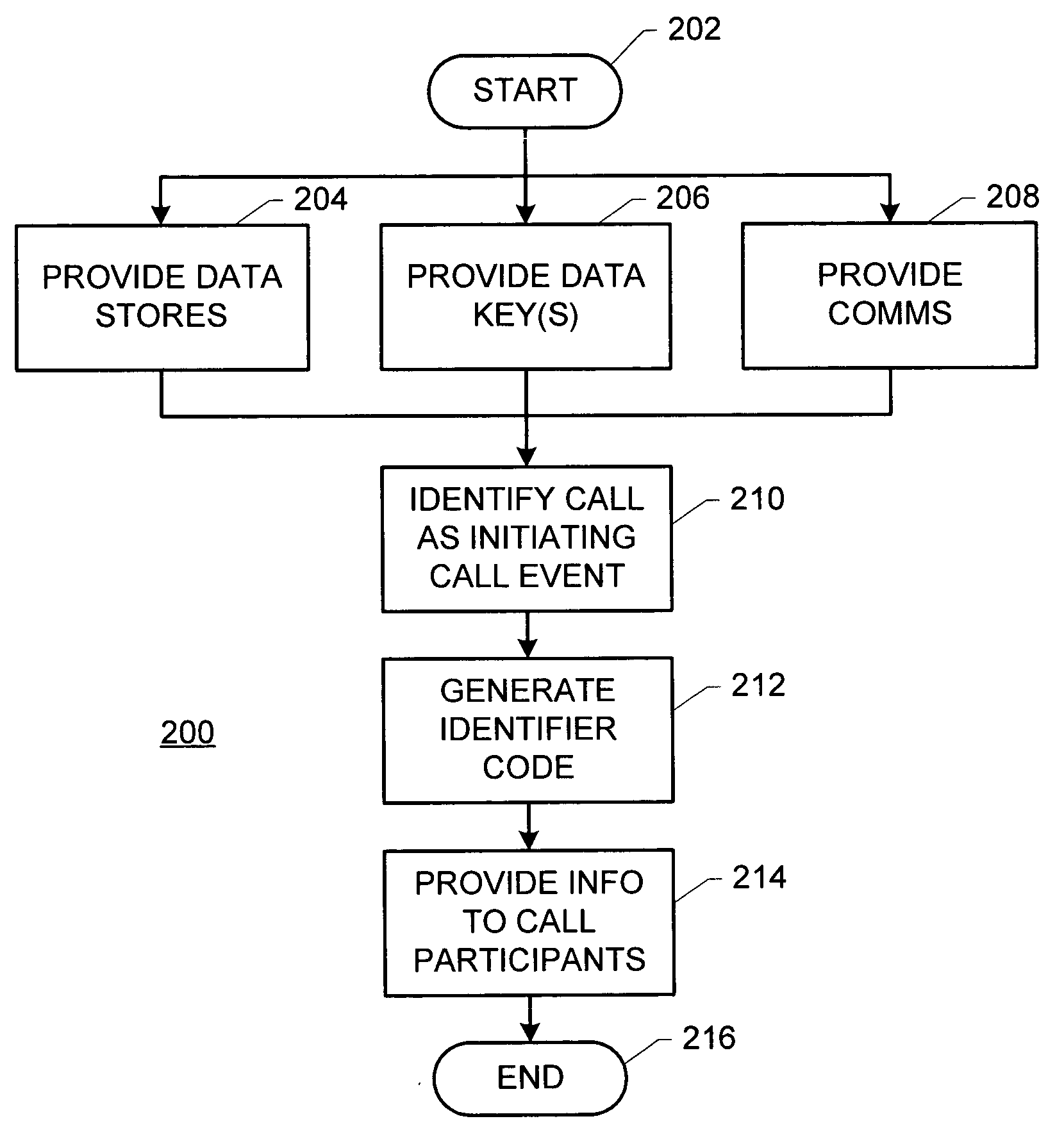
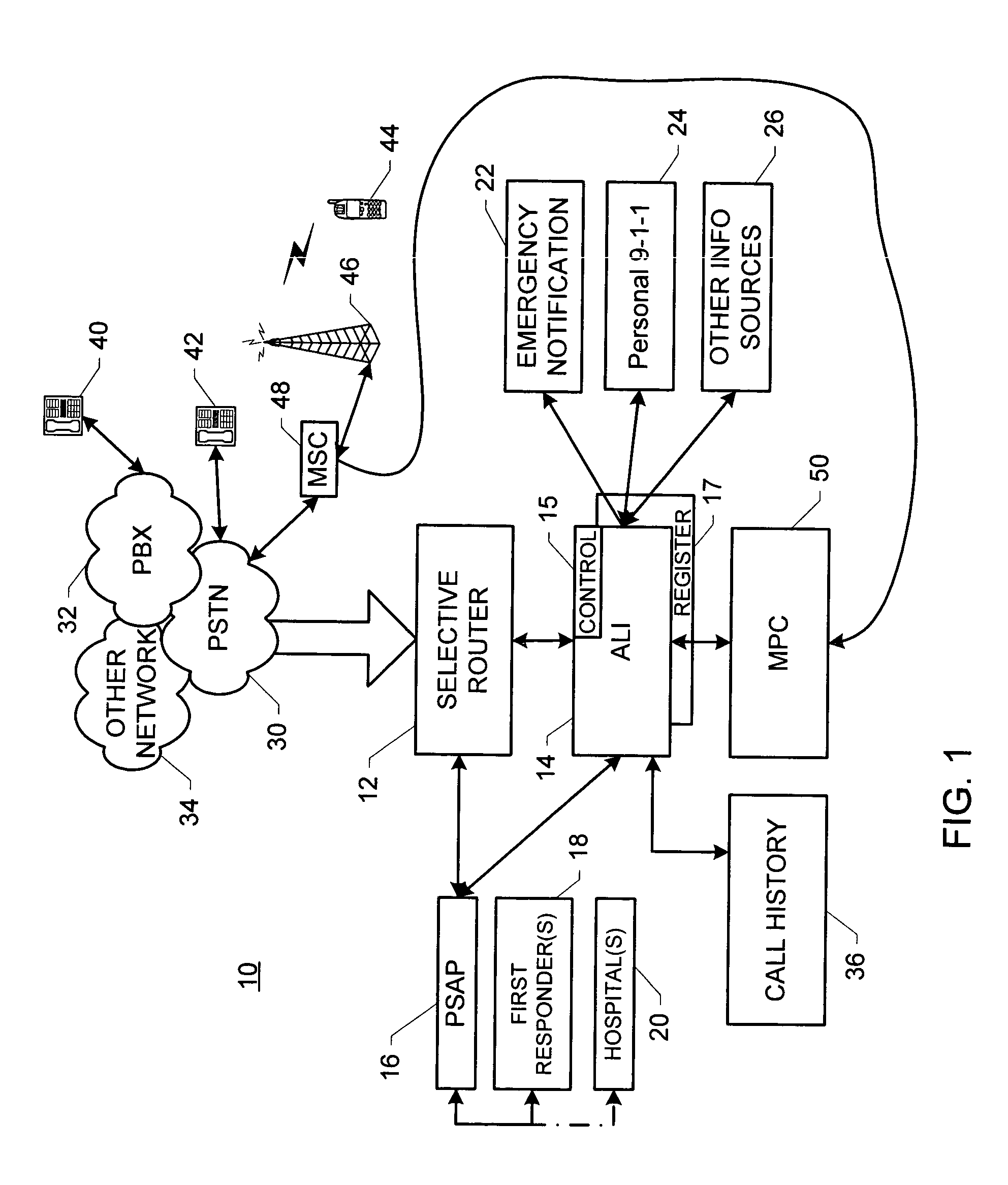
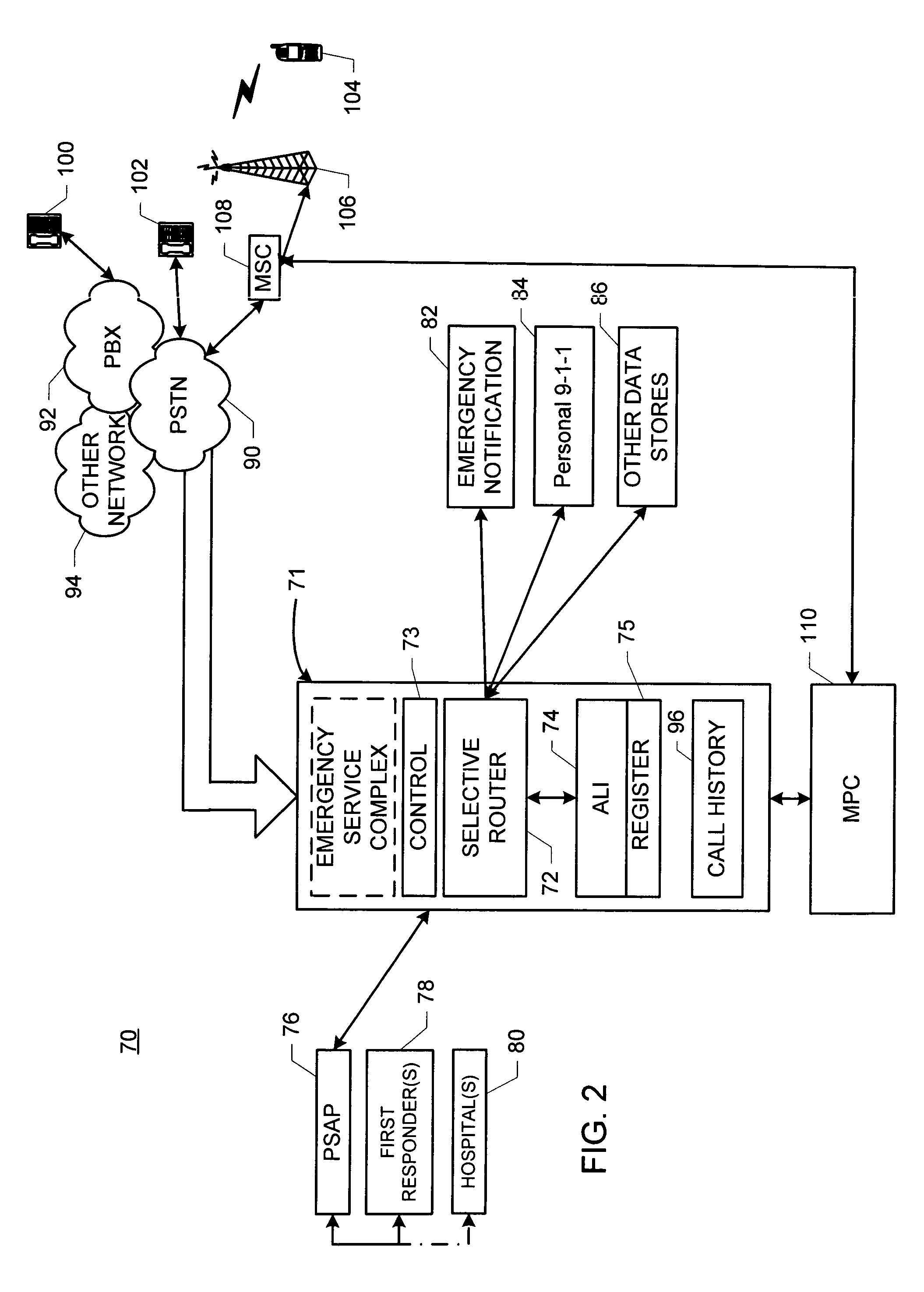
Method and system for availing participants in a special number call event and others of information contained in a plurality of data stores
ActiveUS20050053209A1Emergency connection handlingSpecial service for subscribersData memoryData storing
A method for availing participants and others in a special number call event of information contained in a plurality of data stores includes the steps of: (a) in no particular order: (1) providing the plurality of data stores; (2) providing at least one respective data key for accessing the information contained in each respective data store of the plurality of data stores; and (3) providing communications among the participants and the plurality of data stores; (b) identifying a respective call as initiating a special number call event; (c) generating an identifier code for uniquely identifying the special number call event; the identifier code including relational data; the relational data being mappable on the at least one the respective data key to effect accessing the information; and (d) employing the communications to effect cooperation by the identifier code with each respective data store for providing the information to the participants.
Owner:INTRADO LIFE & SAFETY INC
Systems and methods for providing anonymized user profile data
ActiveUS20110060905A1Reduce deliveryIncrease contentCryptography processingOffice automationData transformationInternet privacy
Embodiments facilitate confidential and secure sharing of anonymous user profile data to improve the delivery of customized content. Embodiments of the invention provide a data appliance to an entity such as a business to convert profile data about the business's customers into anonymous identifiers. A similar data appliance is provided to a content provider in one embodiment to generate identifiers for its user profile data. Because the anonymous identifiers are generated with the same anonymization method, identical identifiers are likely generated from profile data of the same users. Therefore, the identifiers can be used to anonymously match the customers of the business to the users of the content provider. Therefore, data can be shared to improve customized content such as advertisements that the business wishes to place with the content provider without requiring the business to disclose customer data in an unencrypted form, and any non-matched data can remain confidential.
Owner:FRITZ SCHAFER +1
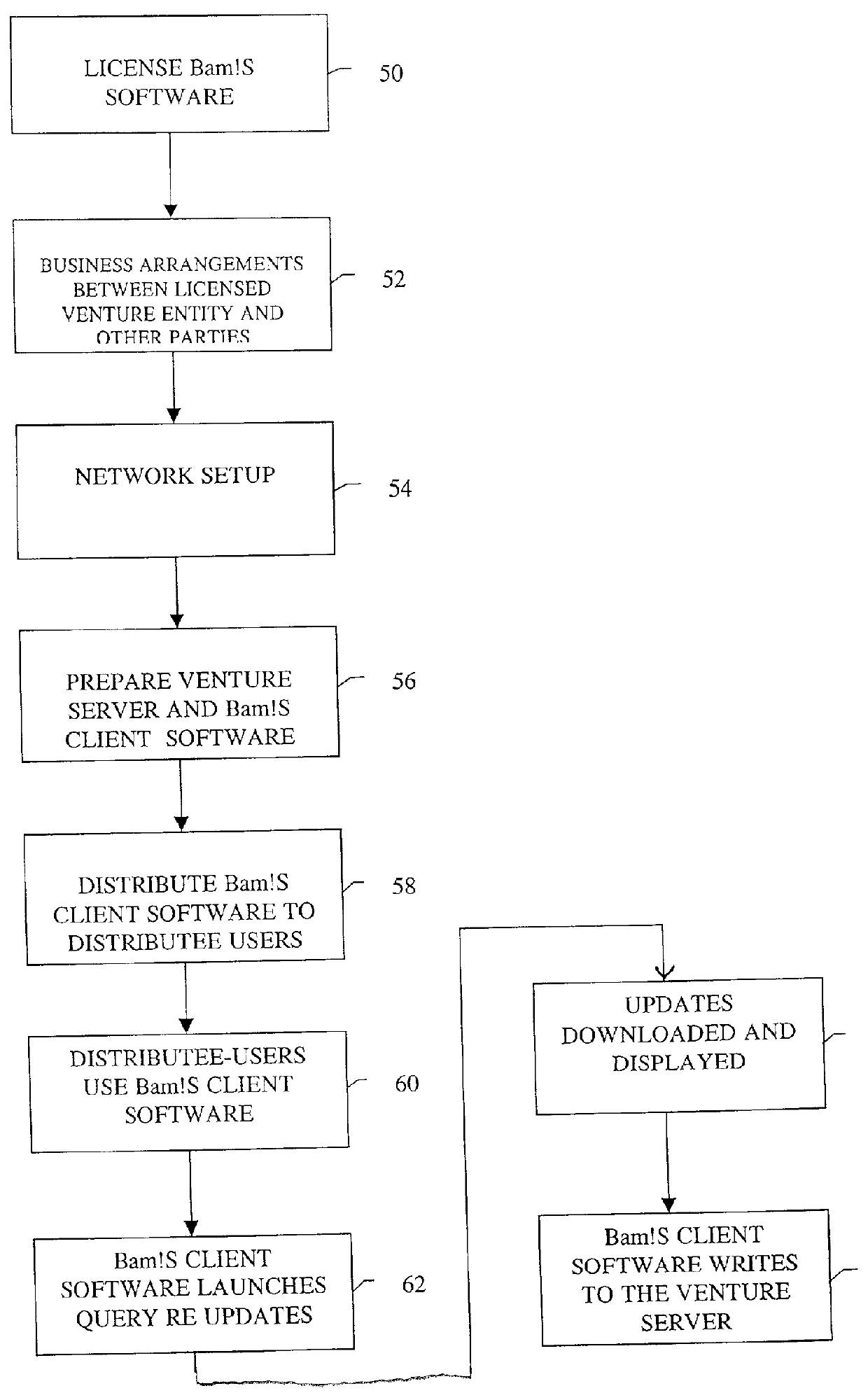
Method of direct communication between a business and its customers
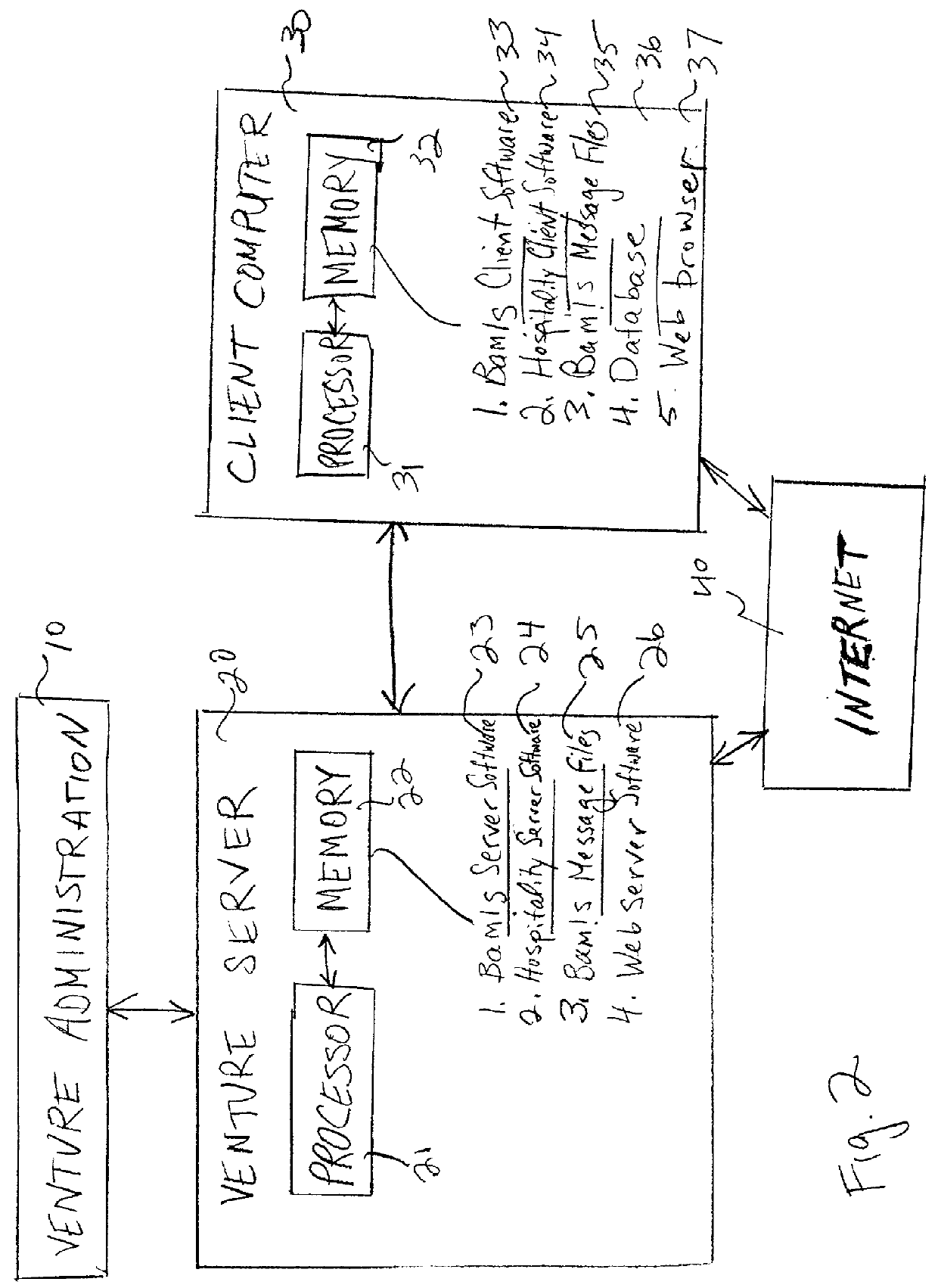
A business model, system, and method for a business entity to distribute branding, advertising, marketing, and service (BAMS) data to consumer-users is described. The business entity establishes and maintains a venture server that transmits BAMS data to client applications installed on the electronic devices of consumer-users and controls usage and display of the BAMS data at the electronic devices. The client application, which is prepared and assigned a unique identifier by the business entity, performs a useful function that requires a graphical user interface (GUI) to be displayed in the display of the user's electronic device. After receiving the BAMS data, the client application stores it, and displays it in the GUI. The client application can be written so that no user information is transmitted from the electronic device to the venture server.
Owner:INTEL CORP
Systems and methods for automatic identification and hyperlinking of words or other data items and for information retrieval using hyperlinked words or data items
InactiveUS20050060162A1Overcome problemsSatisfies needDigital data information retrievalSpecial data processing applicationsHyperlinkElectronic document
A method of annotating an electronic document on a computer system comprising on a first computer system, receiving an electronic document, such as a web page, with at least one key element, consisting, for example of one or more words, recognizing the key element in the document, determining the position of the key element in the document, determining an identifier for the key element from a key list, annotating the document with data corresponding to the identifier, presenting the annotated document to a user so that the user may select the annotated key element, and retrieve data or information related to the key element.
Owner:CONNEXITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com