Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
140 results about "Compliance check" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic menu document creator in a virtual financial environment
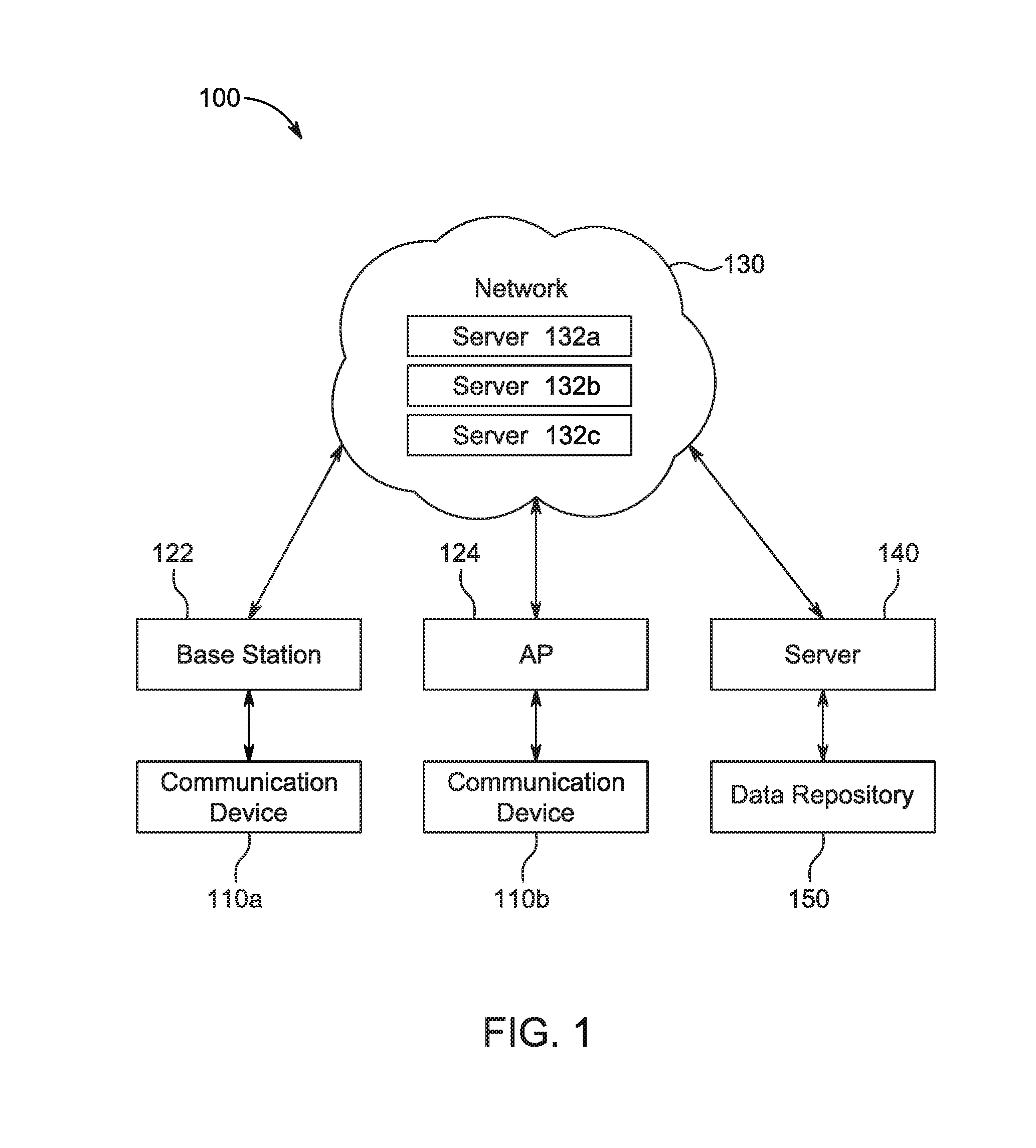
The disclosure provides for creating a finalized document relating to a transaction. A buyer selects documents associated with a proposed transaction and indicates trade terms of an agreement relating to the documents selected. The trade terms are presented to a seller on an electronic form via an electronic document platform. The electronic form includes a combined purchase order proforma invoice, a transportation document, and a shipping document. The seller can amend the trade terms on the form, and each amendment creates a new version of the form. Negotiations of the trade terms between the buyer and the seller are conducted electronically and the negotiated fonn detailing the negotiation of the trade terms is generated and displayed electronically, also. A compliance check is performed and is triggered in response to a digital signature of the form. Payment is initiated to the seller after a verification of credit of the buyer.
Owner:ACCENTURE GLOBAL SERVICES LTD
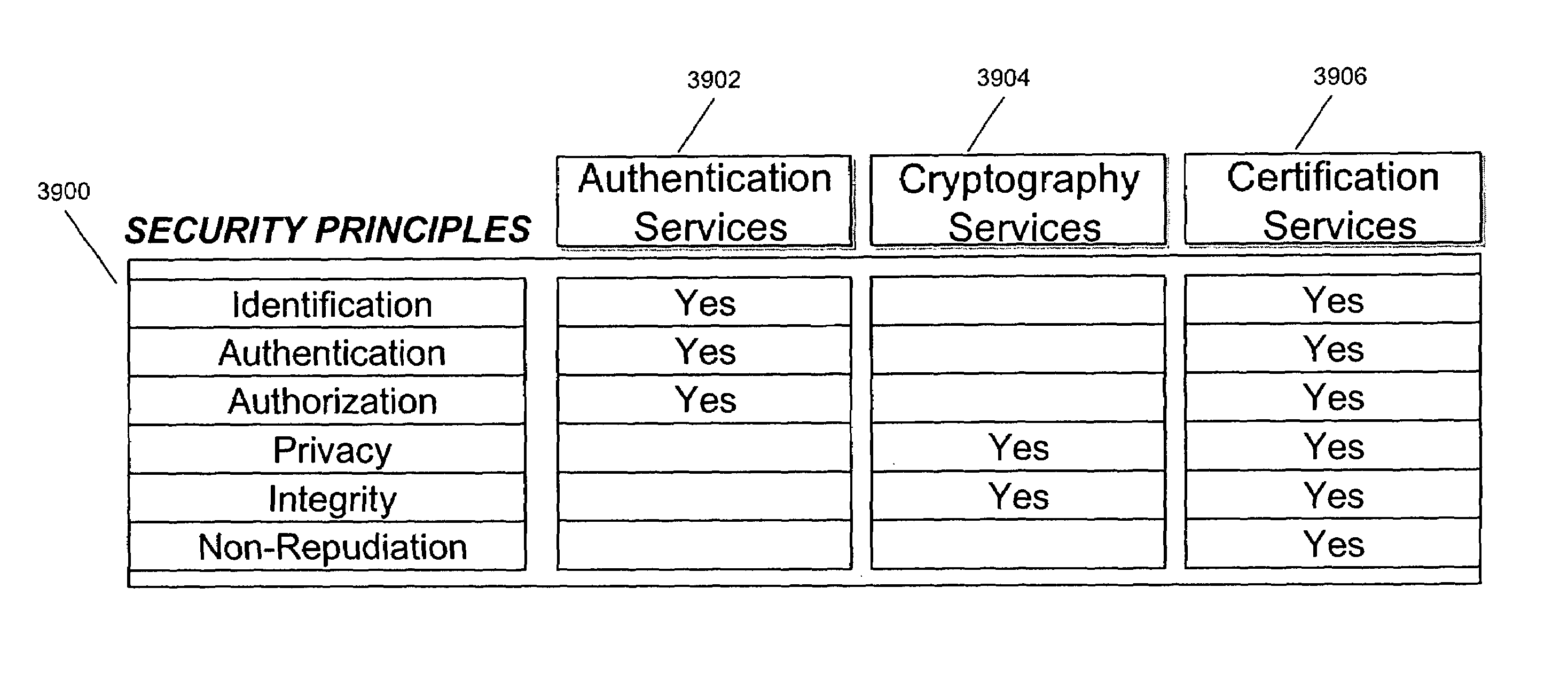
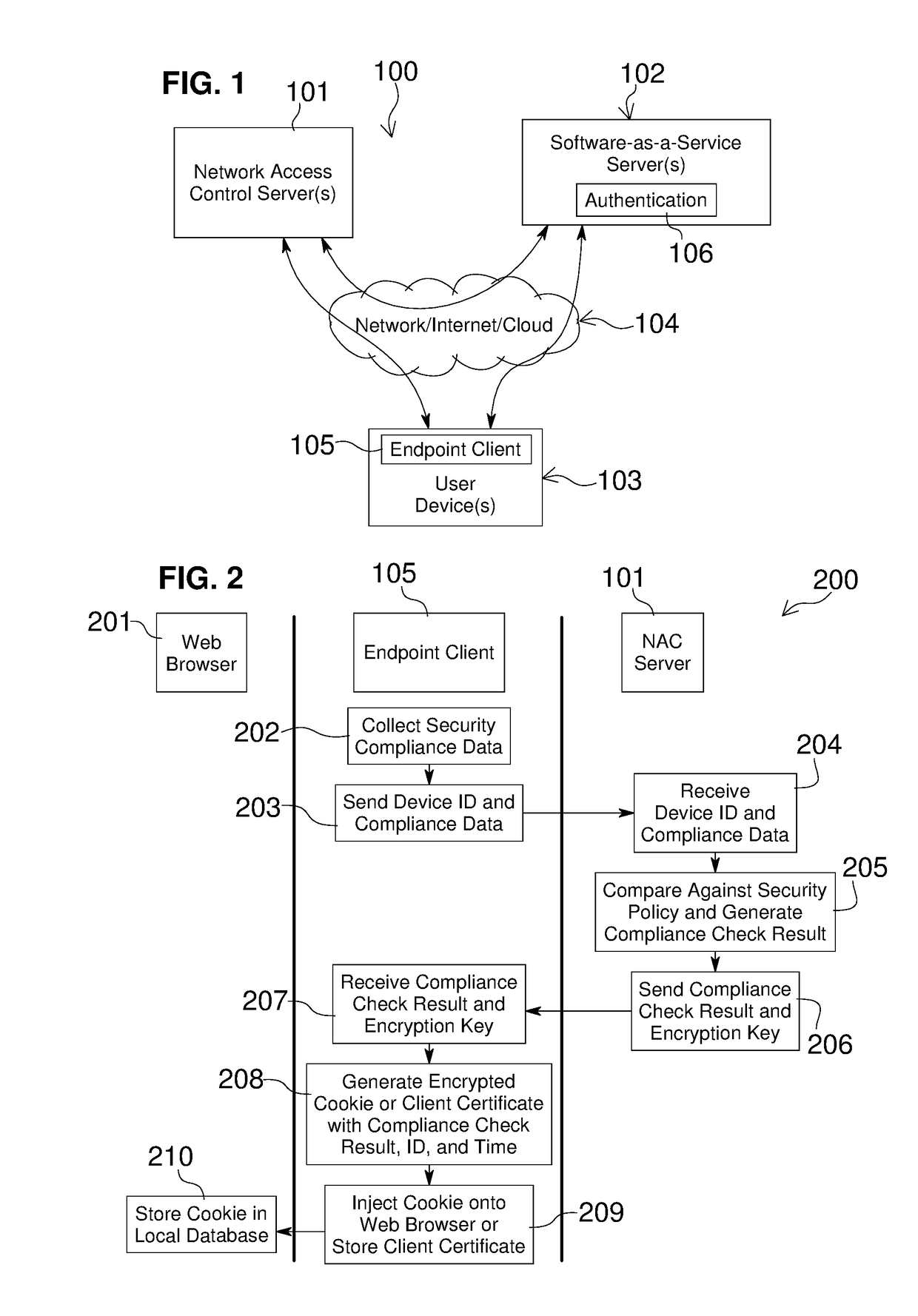
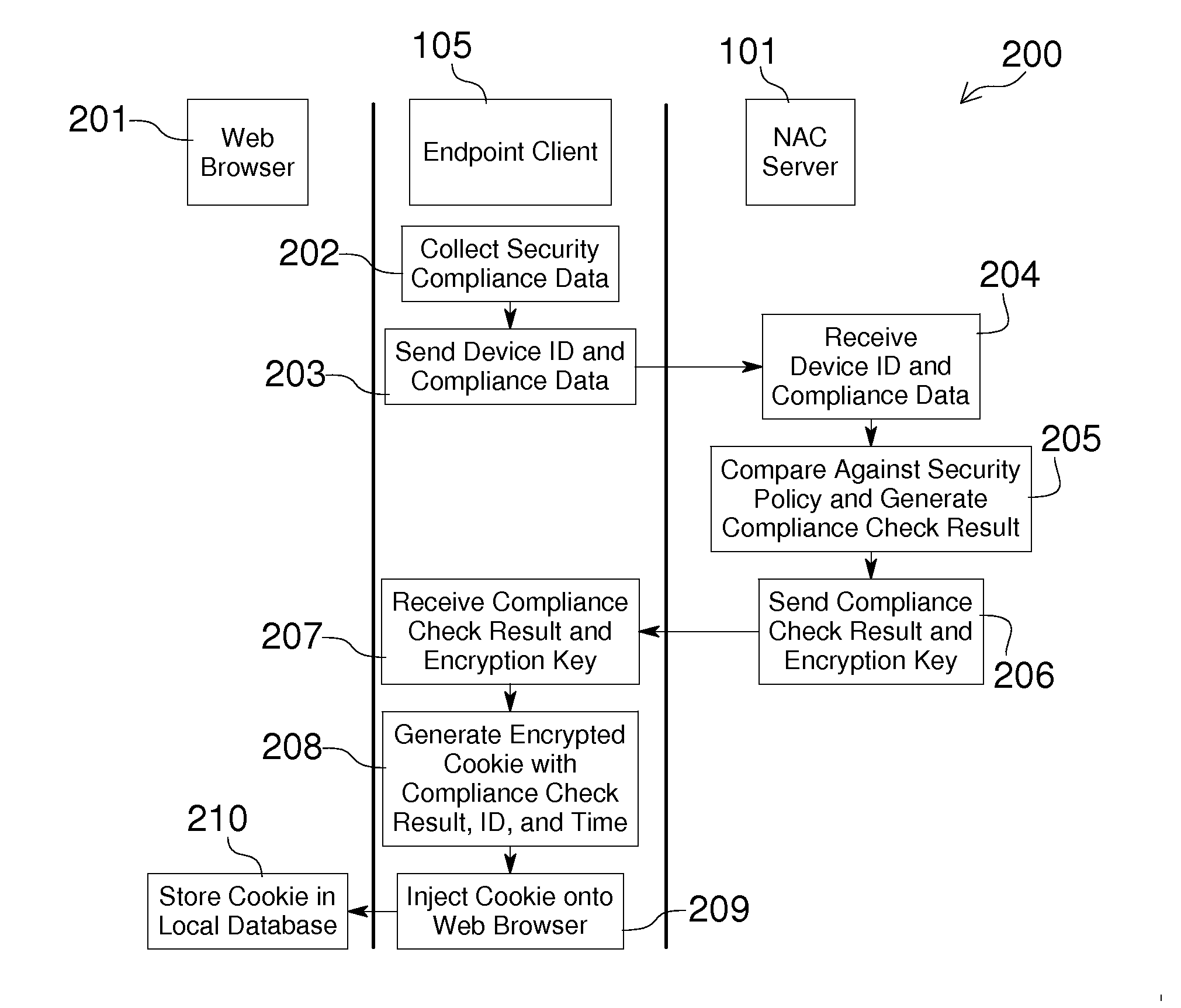
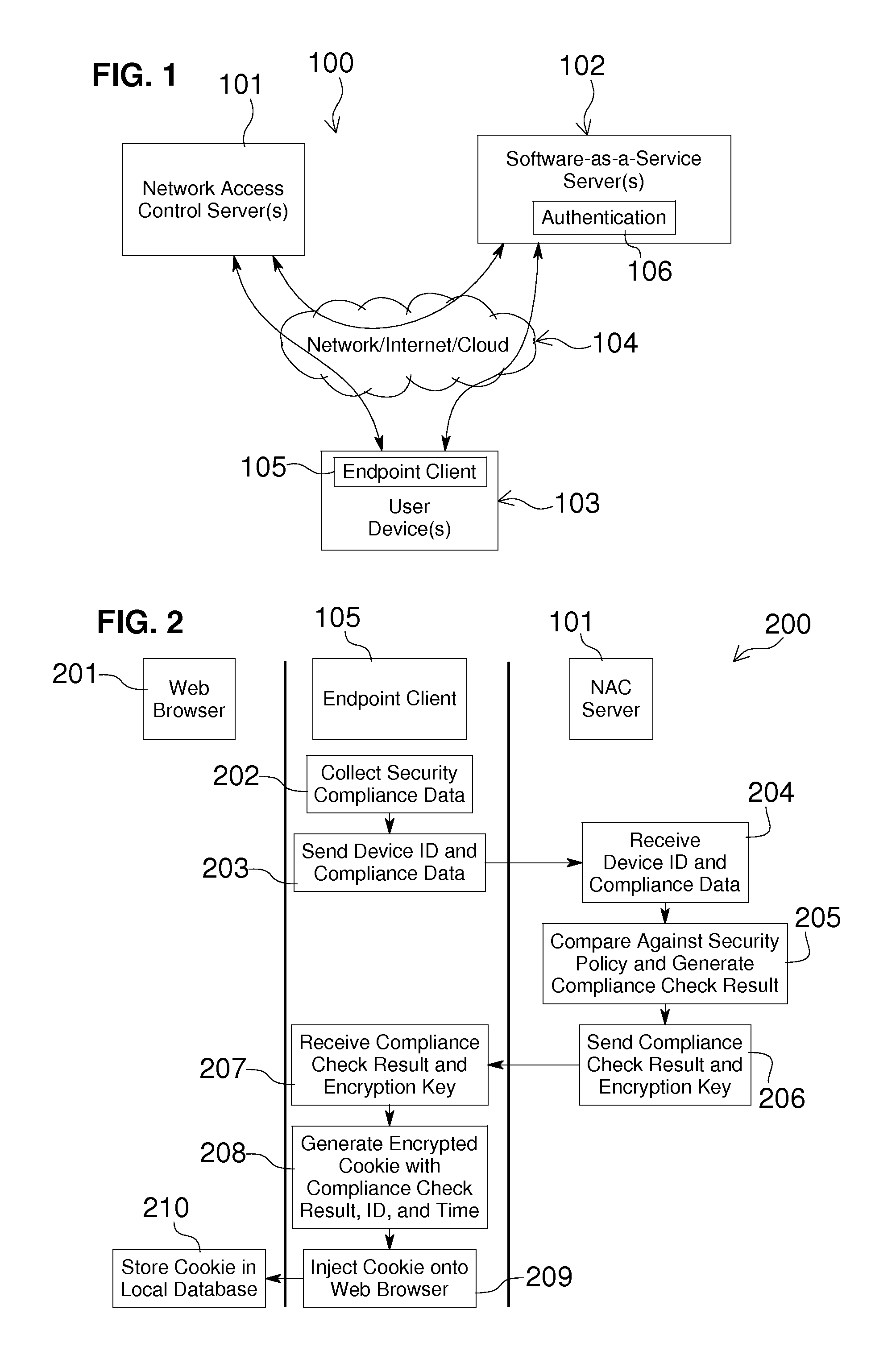
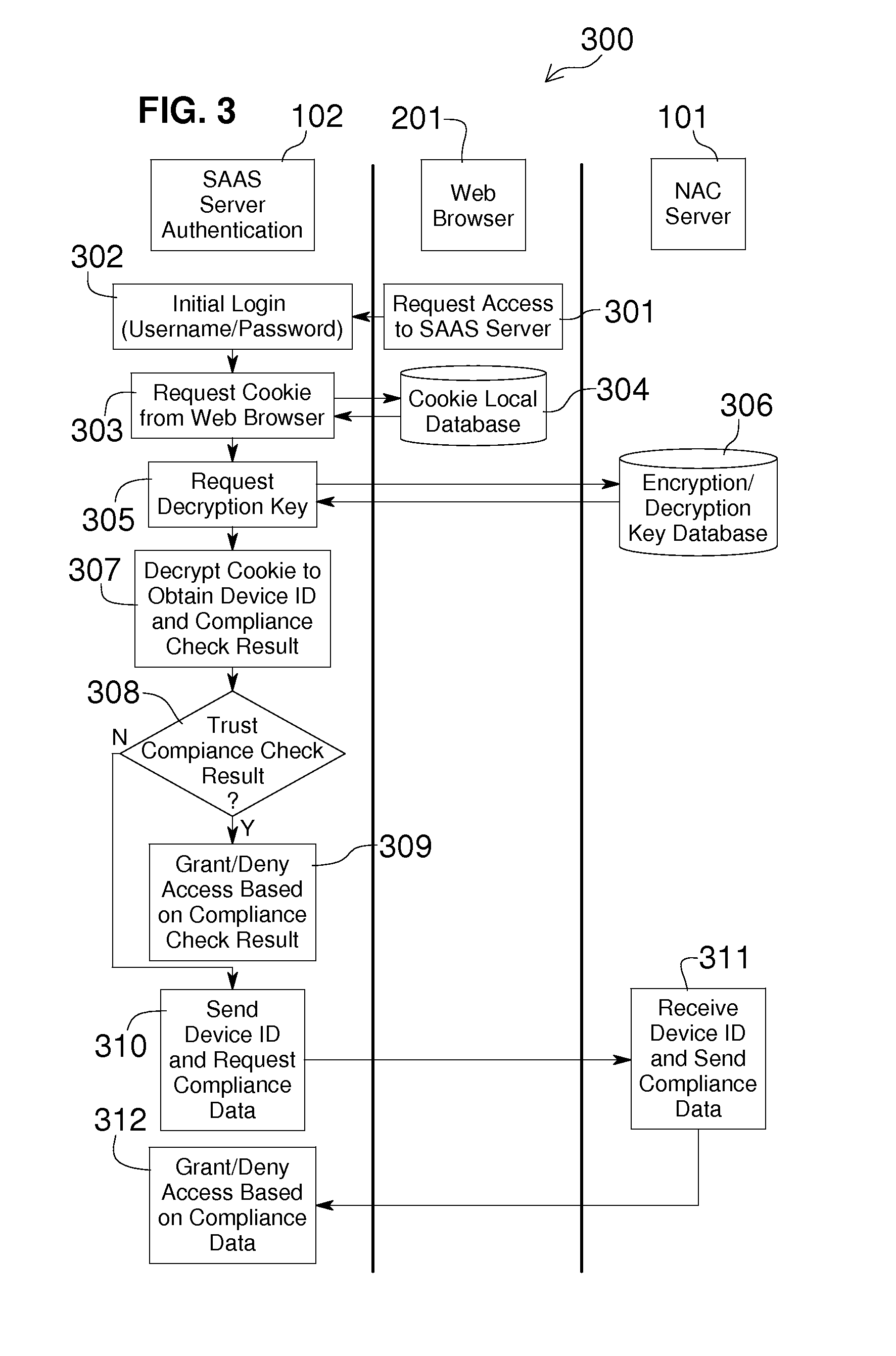
Network Access Control with Compliance Policy Check
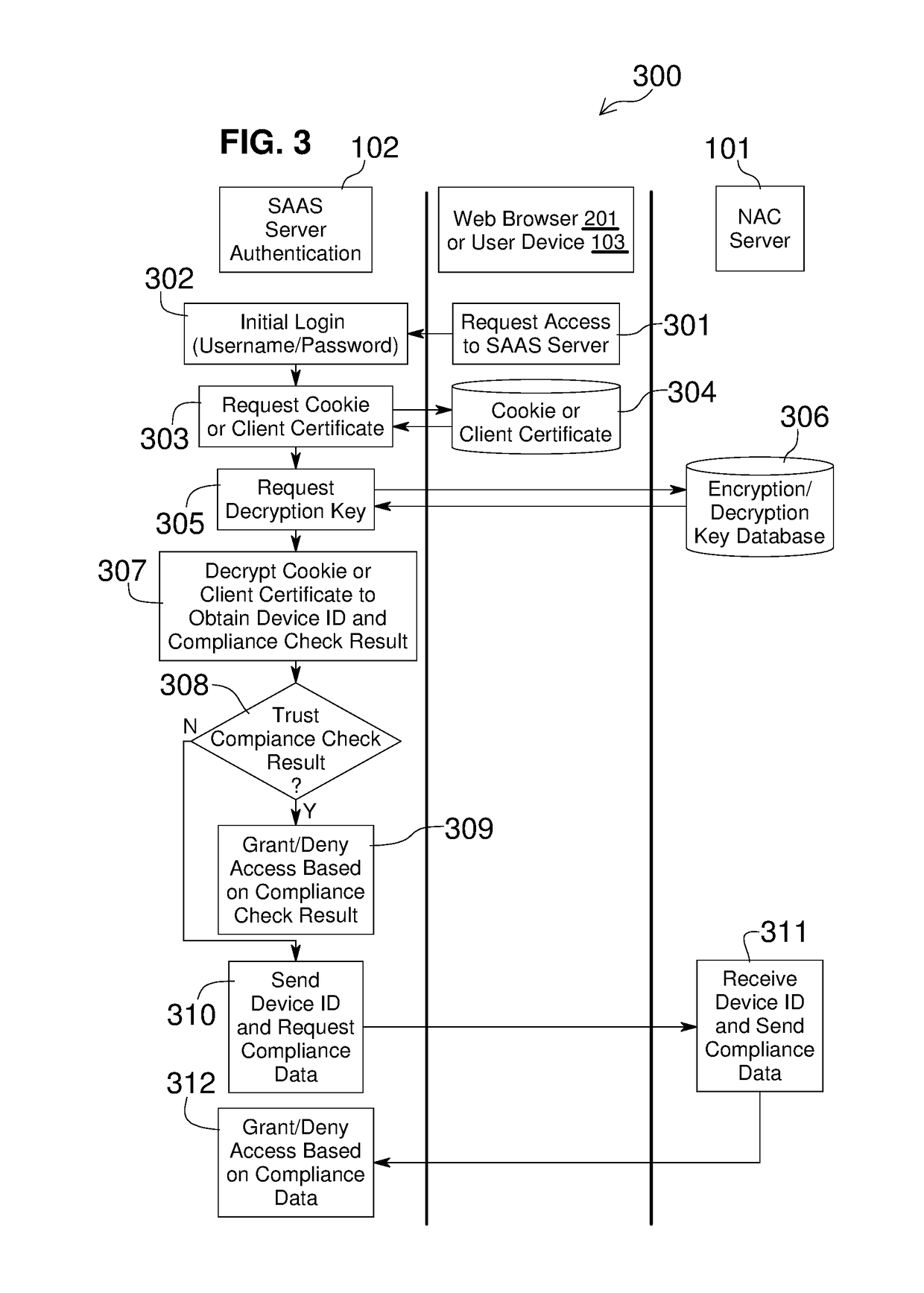
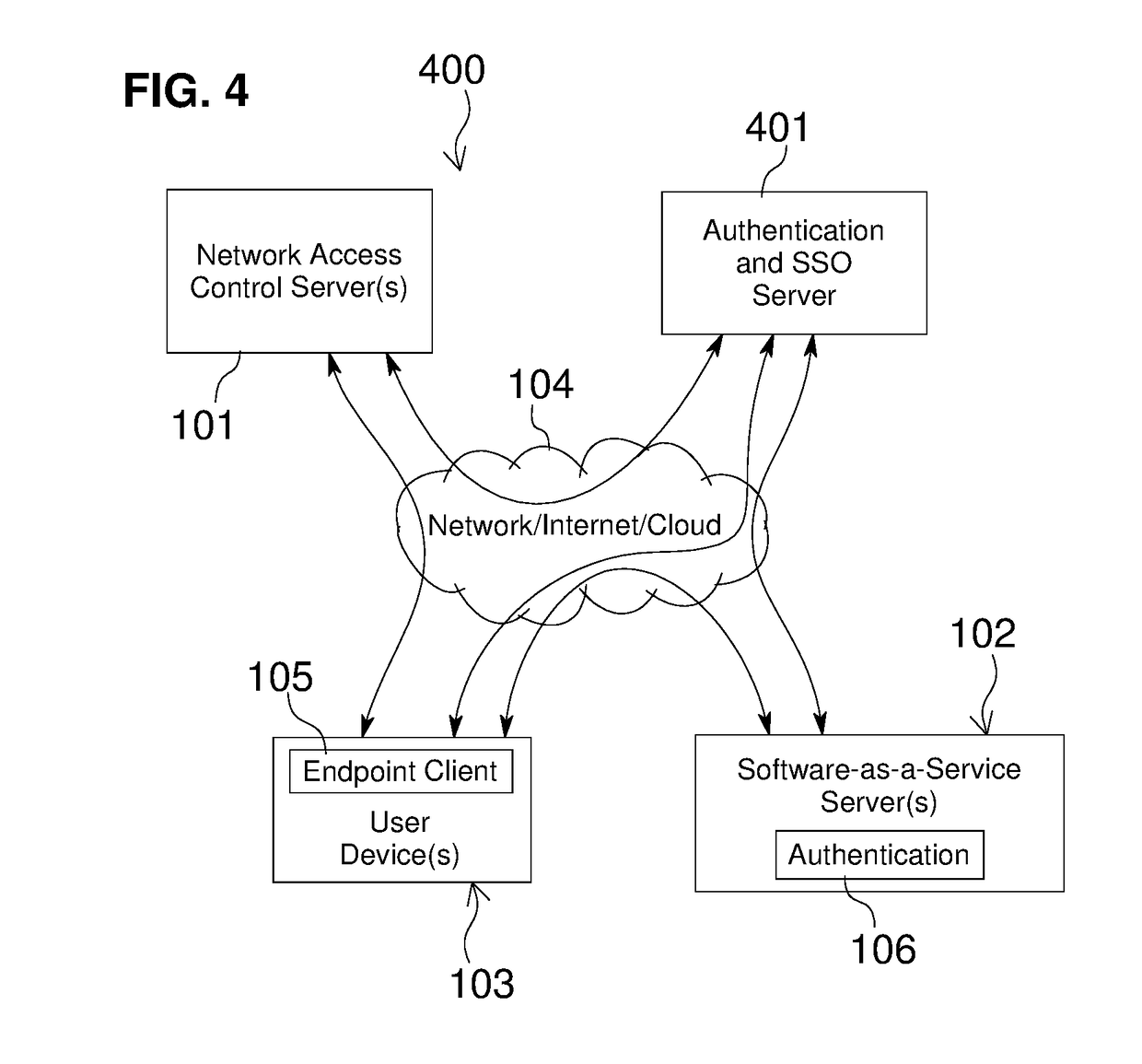
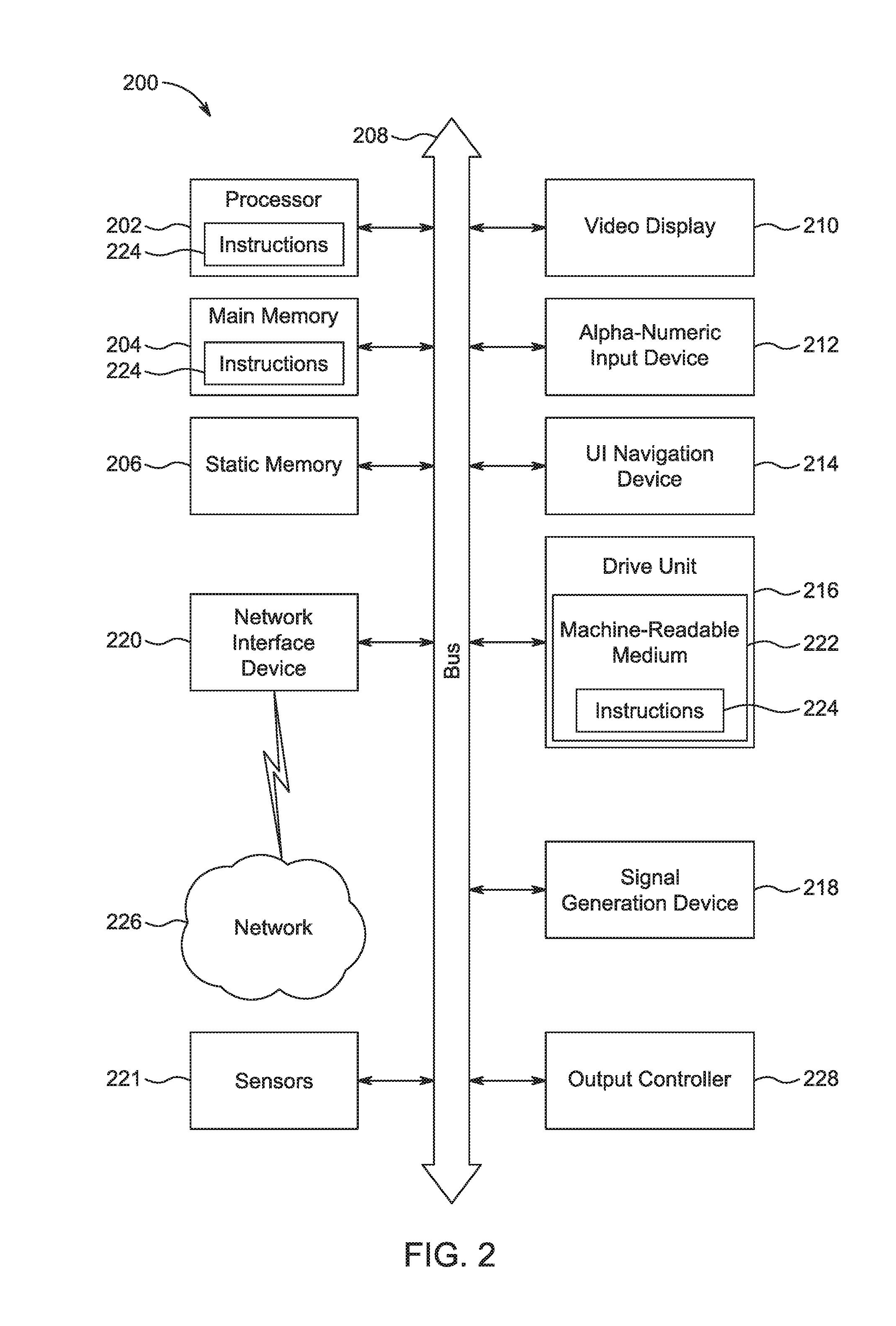
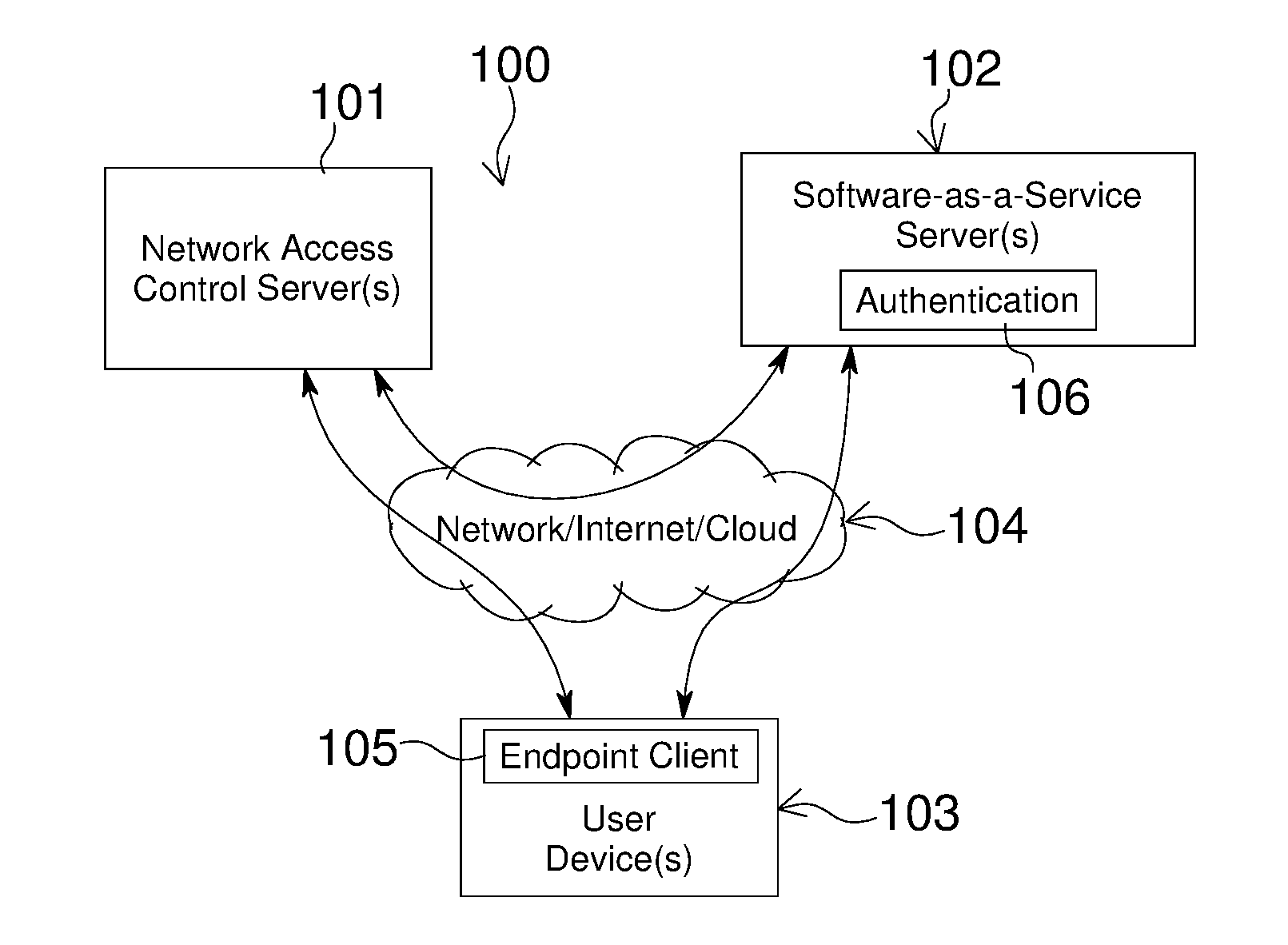
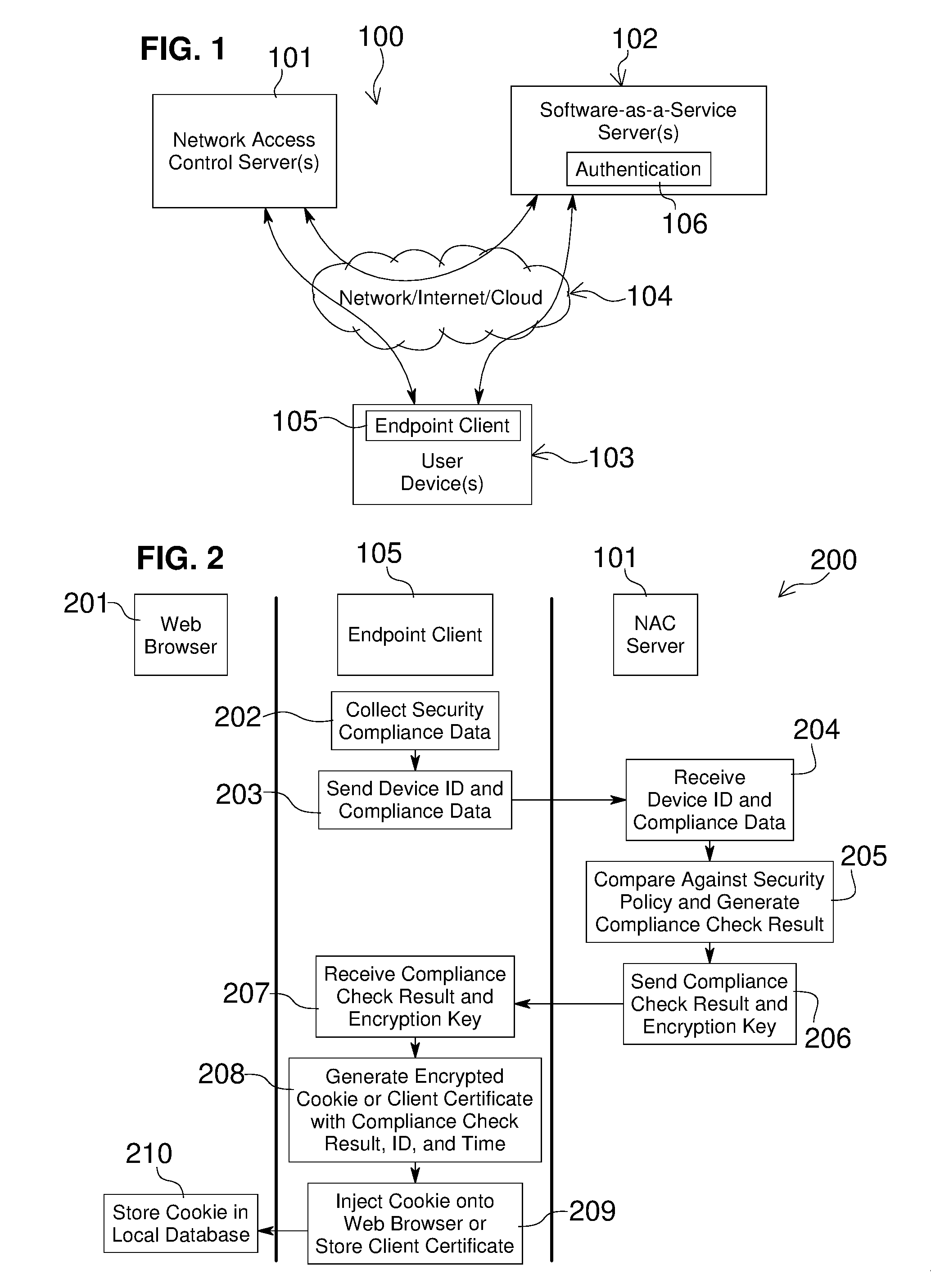
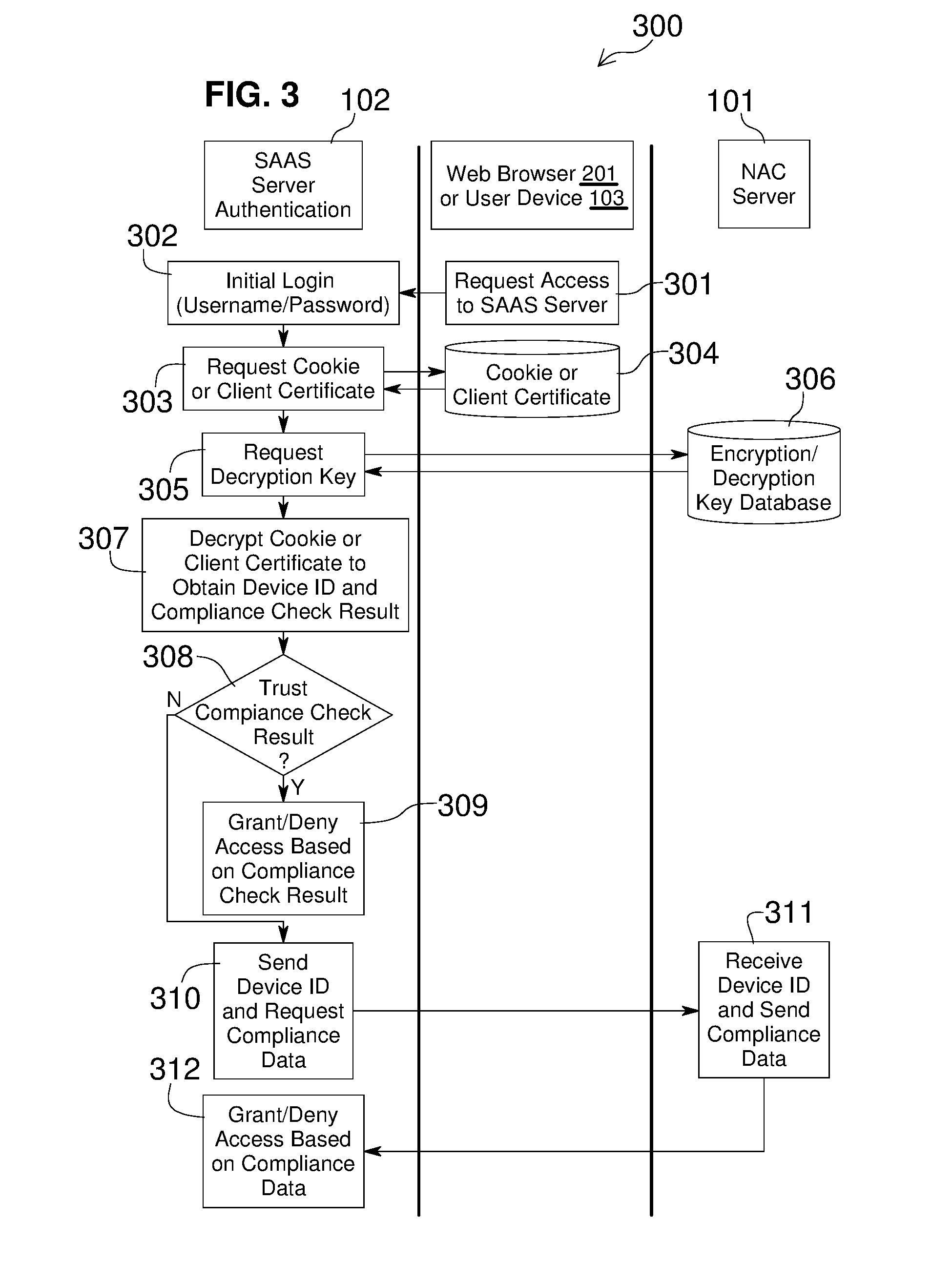
Embodiments of the present invention include methods involving an authentication application, a client application, or a combination of a network access control server with the authentication application and the client application. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result or a user device identifier is stored in a web browser cookie or a client certificate on the user device.
Owner:OPSWAT INC
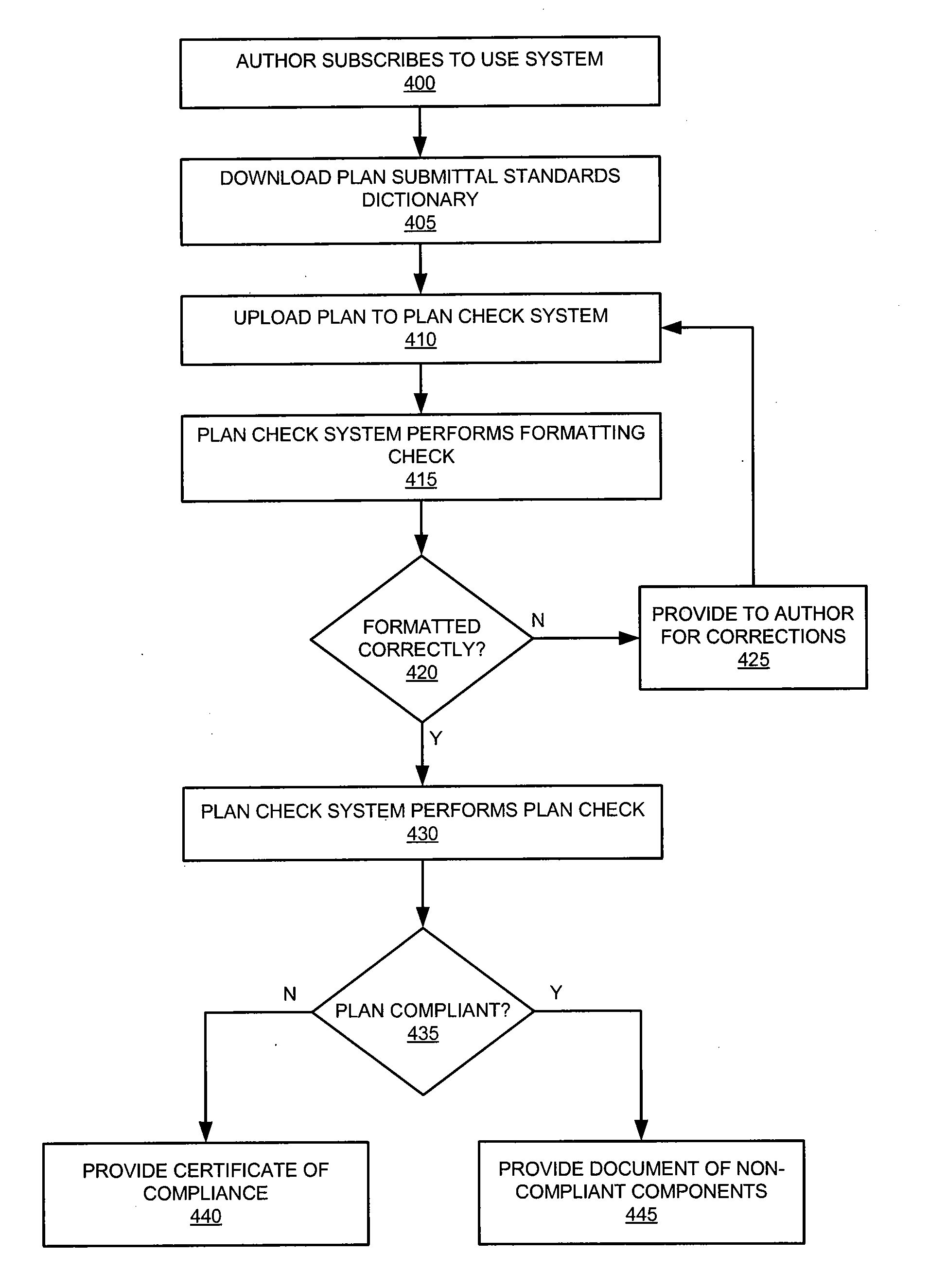
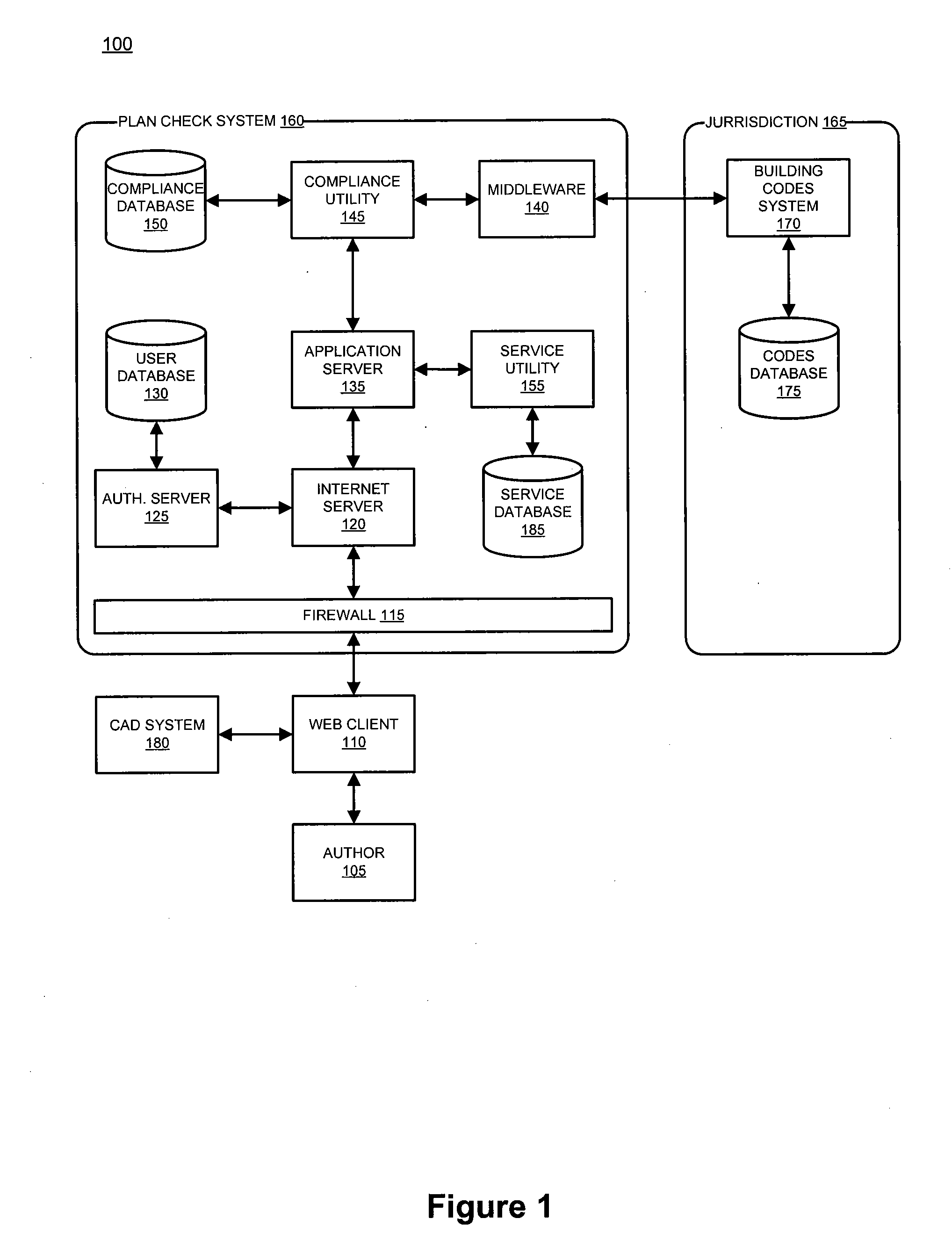
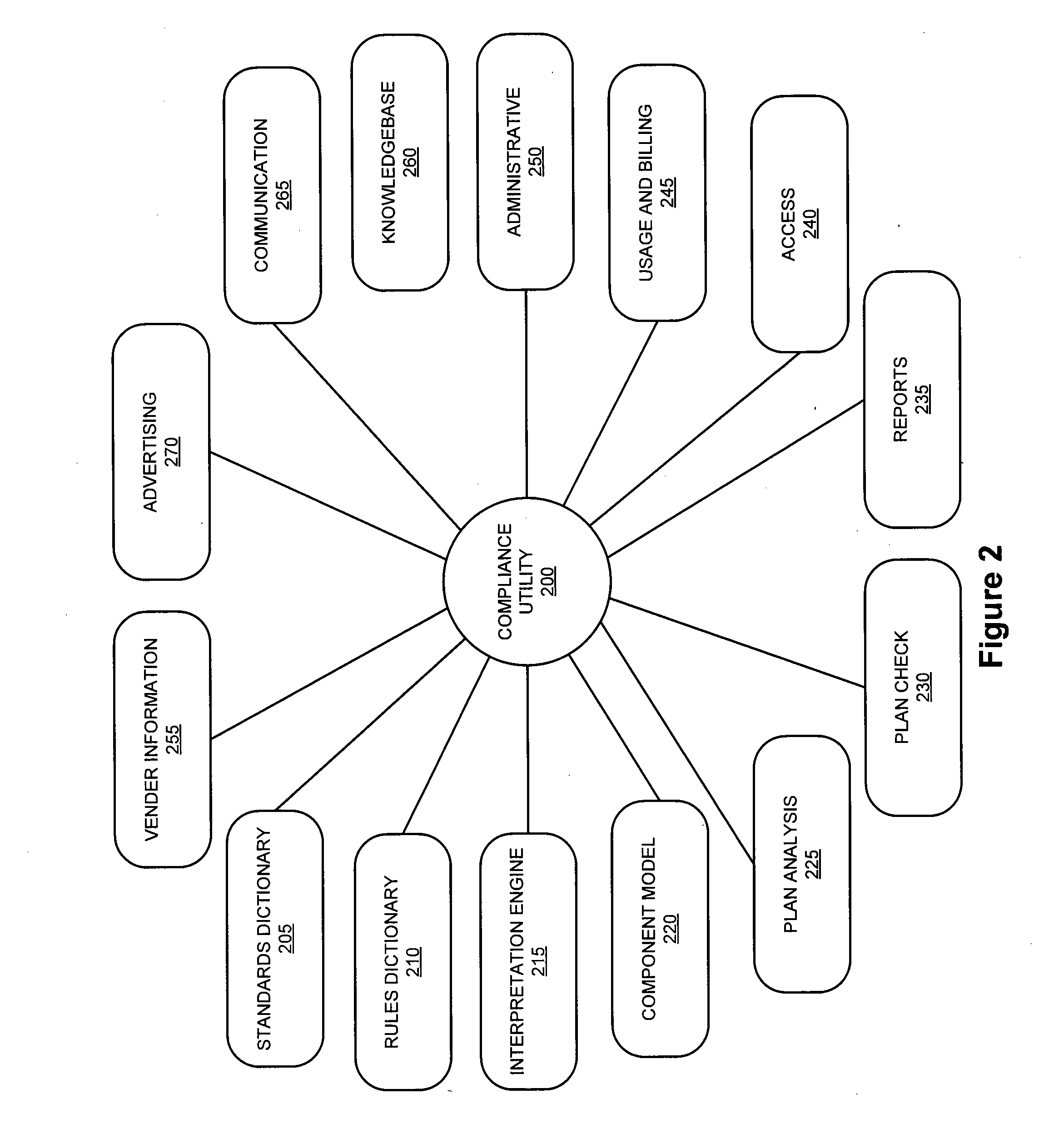
Building plan compliance system and method
A system for performing a computerized building code compliance check with an appropriate jurisdiction is disclosed. The system enables a user to connect to a compliance utility by way of the Internet in order to upload a CAD file. When a CAD file is received, the system performs an analysis to determine whether the building plan was compiled in accordance with defined naming conventions. When a plan is determined to be of the appropriate format, the system extracts building elements from the CAD file, compares each element against a corresponding jurisdictional code, and determines whether the building plan is compliant. When the system determines that a building plan is compliant, the user is provided with a certificate of compliance. The system further analyzes building plans to provide highly targeted offers and enables vendors to bid to provide goods and services based on plan details.
Owner:PLANCHECK INT CORP
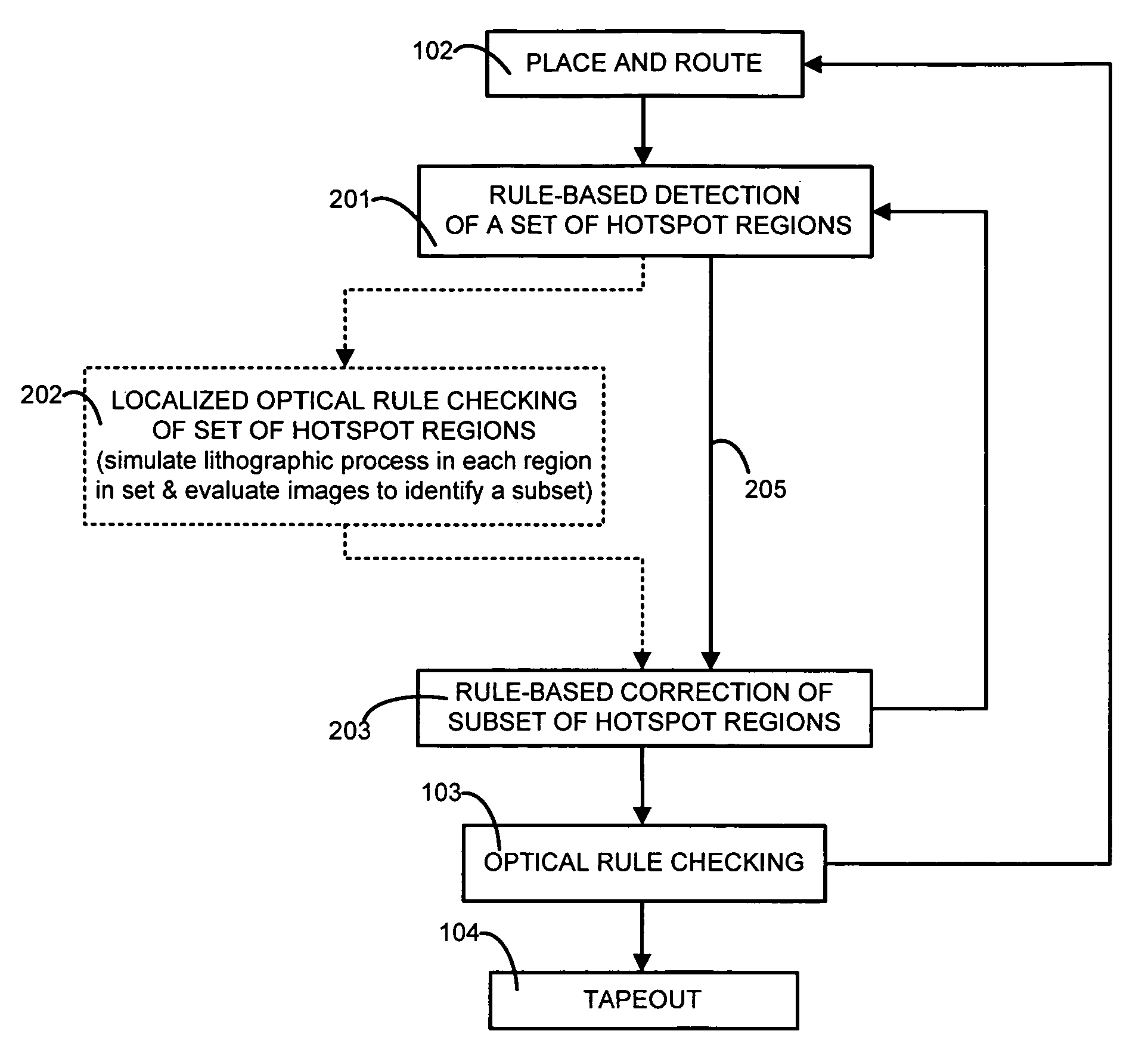
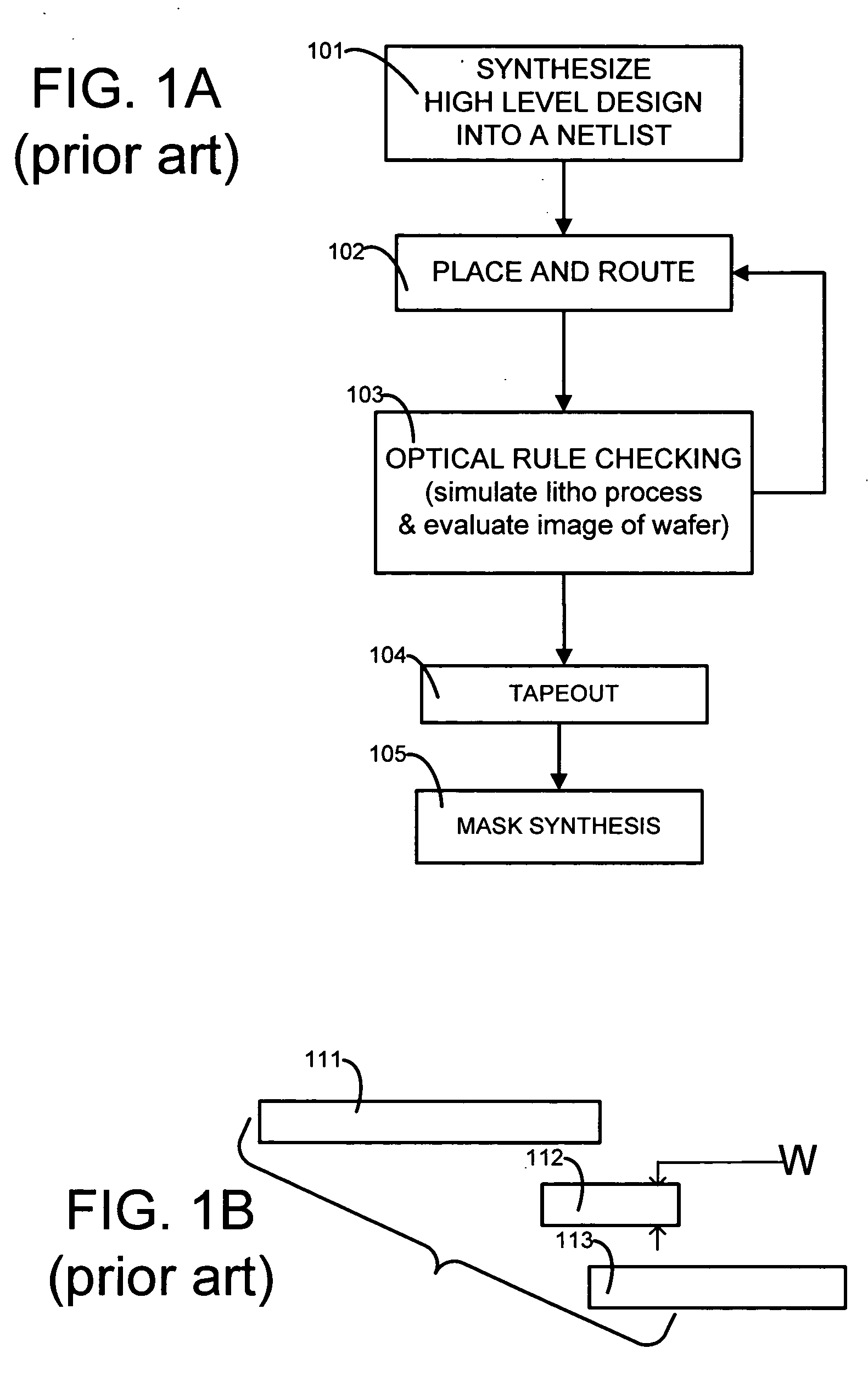
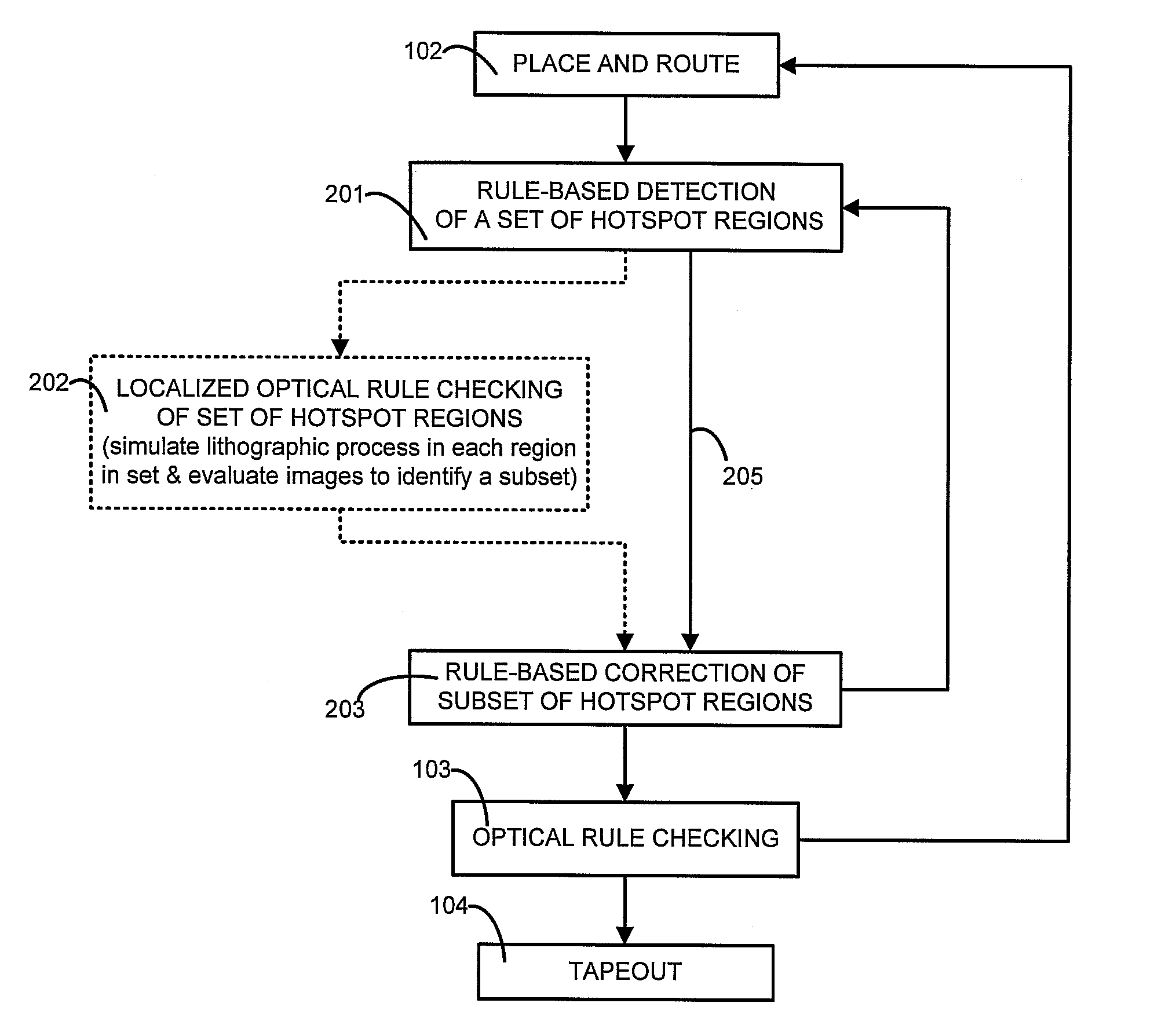
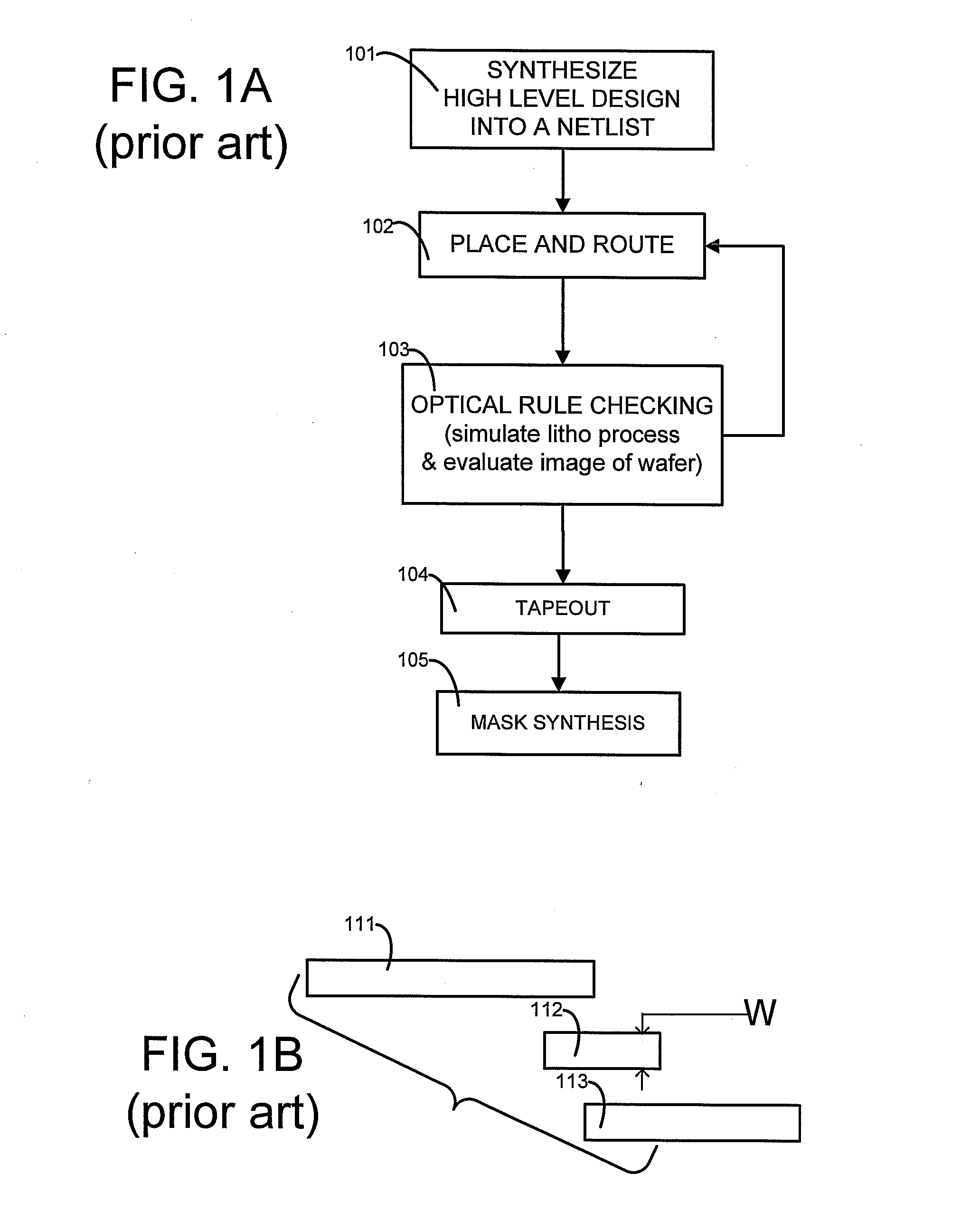
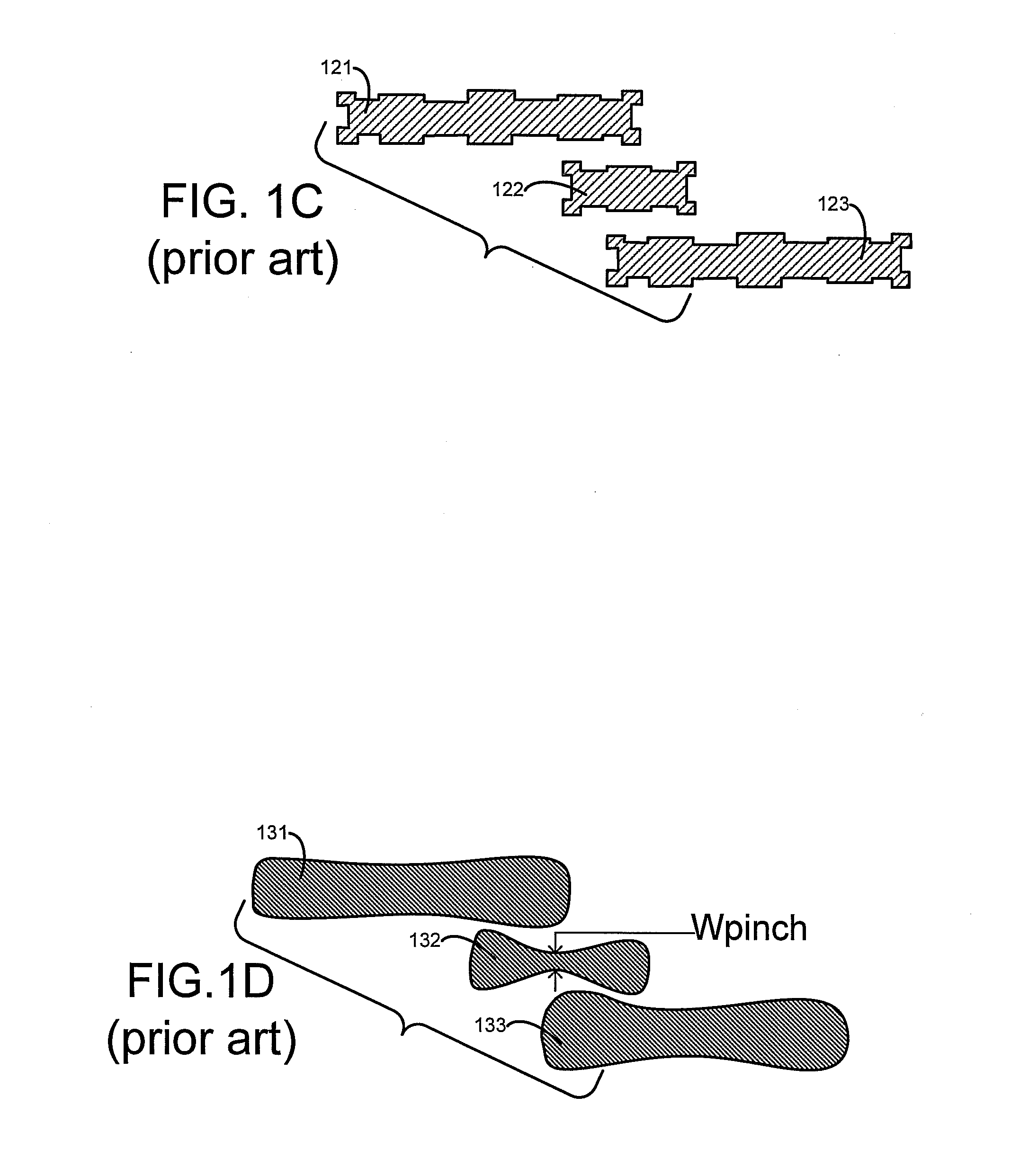
Fast lithography compliance check for place and route optimization
A computer is programmed to use at least one rule to identify from within a layout of an IC design, a set of regions likely to fail if fabricated unchanged. An example of such a rule of detection is to check for presence of two neighbors neither of which fully overlaps a short wire or an end of a long wire. The computer uses at least another rule to change at least one region in the set of regions, to obtain a second layout which is less likely to fail in the identified regions. An example of such a rule of correction is to elongate at least one of the two neighbors. The computer may perform optical rule checking (ORC) in any order relative to application of the rules, e.g. ORC can be performed between detection rules and correction rules i.e. performed individually on each identified region prior to correction.
Owner:SYNOPSYS INC
System and method of detecting design rule noncompliant subgraphs in circuit netlists
ActiveUS20130125072A1Increase flexibilityEasy to useCAD circuit designSoftware simulation/interpretation/emulationGraphicsTheoretical computer science
An automated system and method of performing electronic design rule checking on the netlist of an integrated circuit composed of a plurality of subgraphs. The electronic design rule is embodied as a two part template with a target subgraph specification and a design rule compliance check specification. The target subgraph specification often is at least partially defined by an interactive visual programming section that allows the user to construct a graphic specification of the target netlist. The method first searches the netlist for target subgraphs that match the target subgraph specification, and the user can verify proper target selection. The method then performs rule checks on these search targets, and non compliant subnets identified. Flexibility is enhanced by use of search wildcards, attribute ranges, and various short user scripts which may contain various Boolean logical operations.
Owner:INSIGHT EDA
System, method and program product for dynamically performing an audit and security compliance validation in an operating environment
ActiveUS20100071066A1Secure transmissionMemory loss protectionError detection/correctionSecurity complianceApplication software
A system, method and program product for dynamically performing an audit and security compliance validation. The method includes providing a tool for performing a compliance check of installed computer applications running on a system, the tool including a first set and a second set of plug-ins. Further, the method includes scanning the system, using plug-ins selected from the first set to obtain a current inventory of applications currently installed on the system and selecting plug-ins from the second set to be run on the system in response to the current inventory of applications obtained, and automatically running the plug-ins selected from the second set for performing the compliance check on the system in response to a scheduling criteria identified for the system, where the second set of plug-ins perform the compliance check for only the applications currently installed on the system.
Owner:FINJAN BLUE INC
Systems and Methods for Engineering and Publishing Compliant Content
InactiveUS20170270535A1Streamline task managementEfficient processingSemantic analysisMultiple digital computer combinationsInternet privacyComputerized system
Systems and methods for engineering compliant communications are disclosed. In one embodiment, a computer system is provided that comprises processors and computer-readable storage media having stored thereon computer-executable instructions executable by the processors to cause the computer system to analyze a communication for compliance before publishing the communication. The computer-executable instructions include instructions that are executable to cause the computer system to perform at least the following: receive a communication, compare the communication against a set of predefined compliance standards, execute a compliance check to determine compliance with the predefined compliance standards, compile a compliance result of the compliance check, and prompt a user to review the compliance result before publishing the communication. Additional embodiments include computer executable instructions that cause the computer system to allow the user to modify the communication and / or to prohibit publication of the communication until it passes the compliance check.
Owner:LEADTRAIN INC
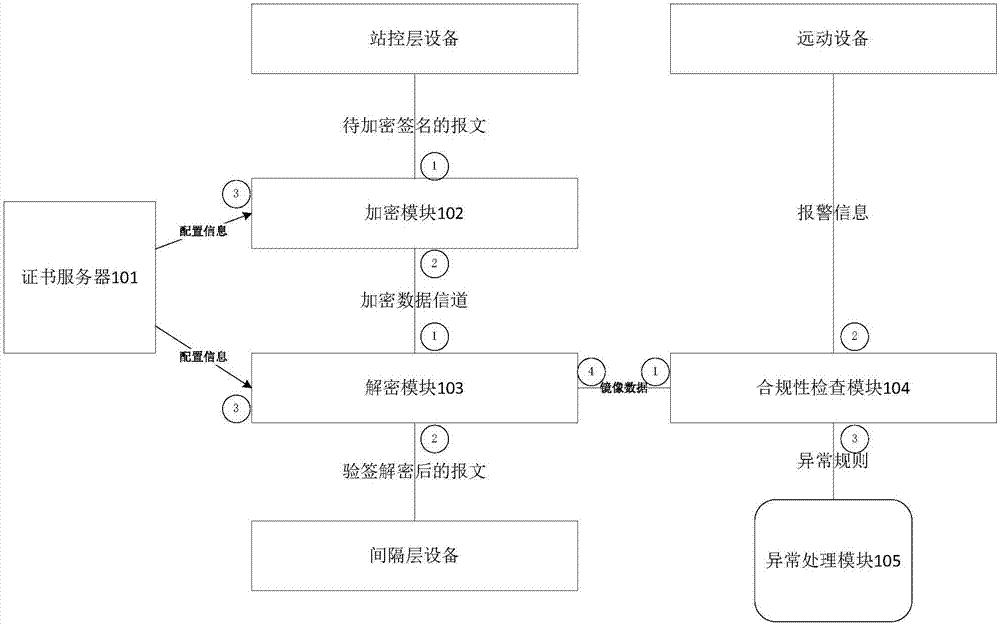
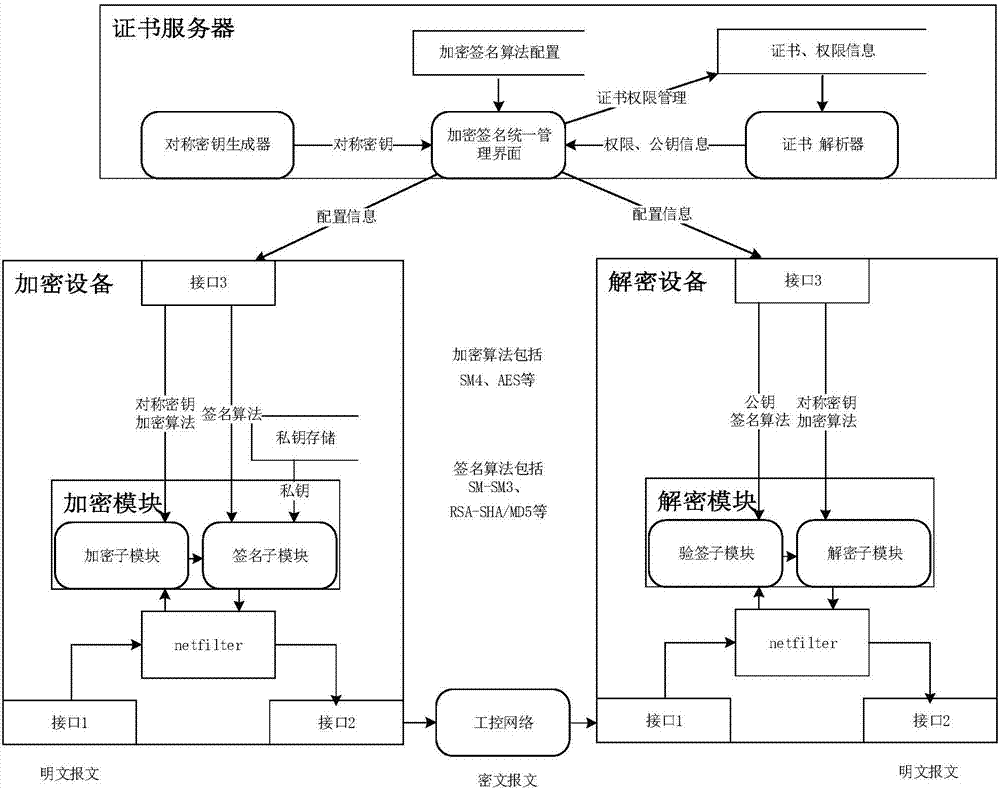
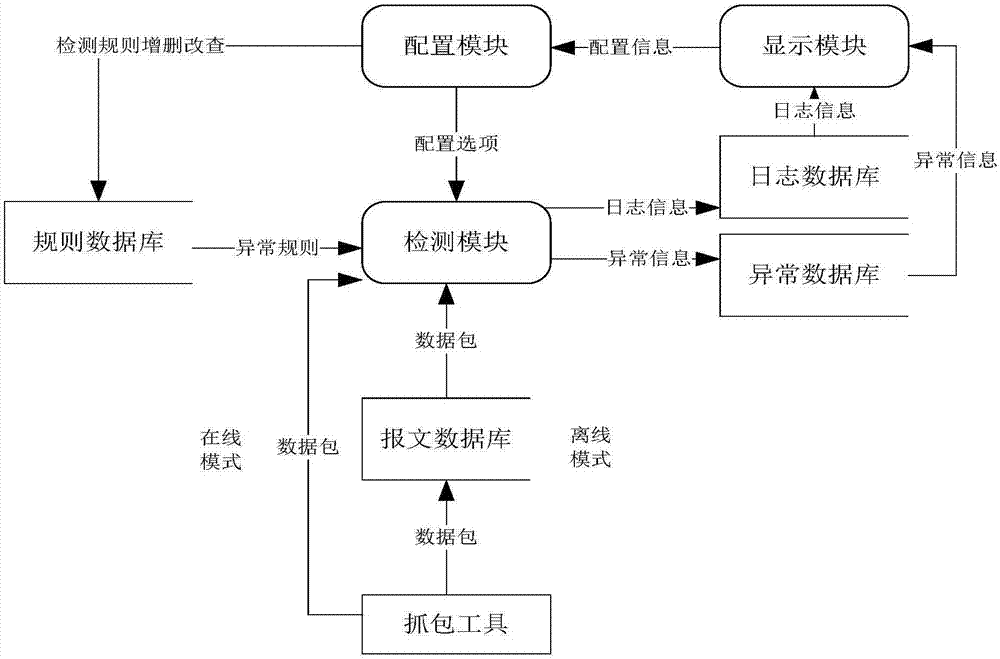
Smart grid information transmission safety protection device and safety protection method
ActiveCN107483444AEasy to deployReduce maintenance costsUser identity/authority verificationPlaintextInformation transmission
The invention discloses a smart grid information transmission safety protection device and a safety protection method, which relate to the technical field of smart grid information transmission safety. The device comprises a certificate server, an encryption and decryption module, a compliance check module and an exception handling module, wherein the encryption and decryption module is wholly serially connected between a station level and a bay level for carrying out encryption signature and signature verification decryption functions on original transparently-transmitted data; the compliance check module grabs a plaintext data packet in an offline or online mode and submits the plaintext data packet to the detection module for compliance check, and as for a compliance message, an analysis result is stored to a log database in a log format; and exception information is independently stored in an exception database through the exception handling module, and an administrator is notified. In the case of permissible delay in the smart grid, the encryption and decryption module together protects the internal information of the smart grid, behaviors that the internal data are tampered and destructed in the case of transmission are resisted, and the safety of the grid is further improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM +2
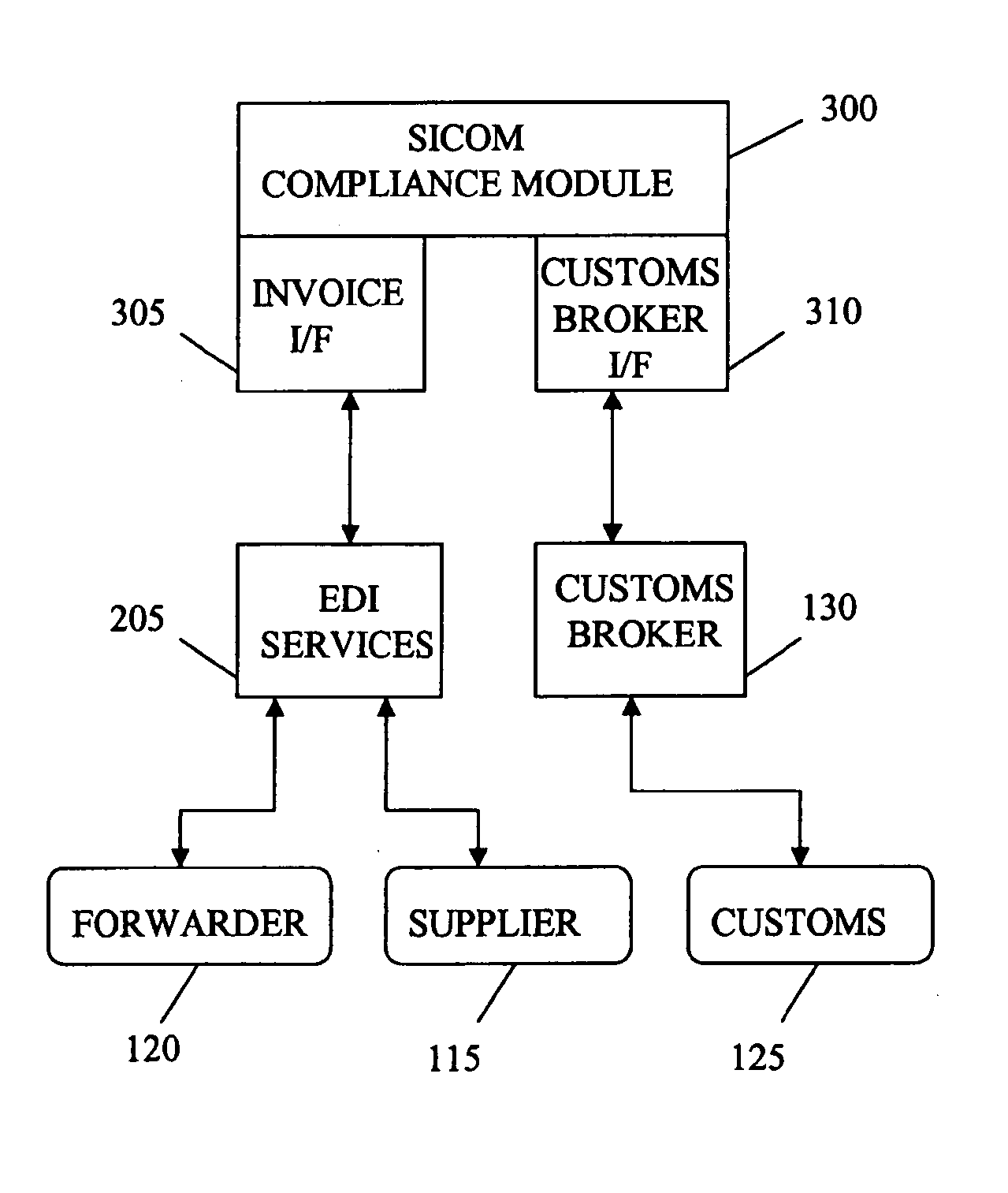
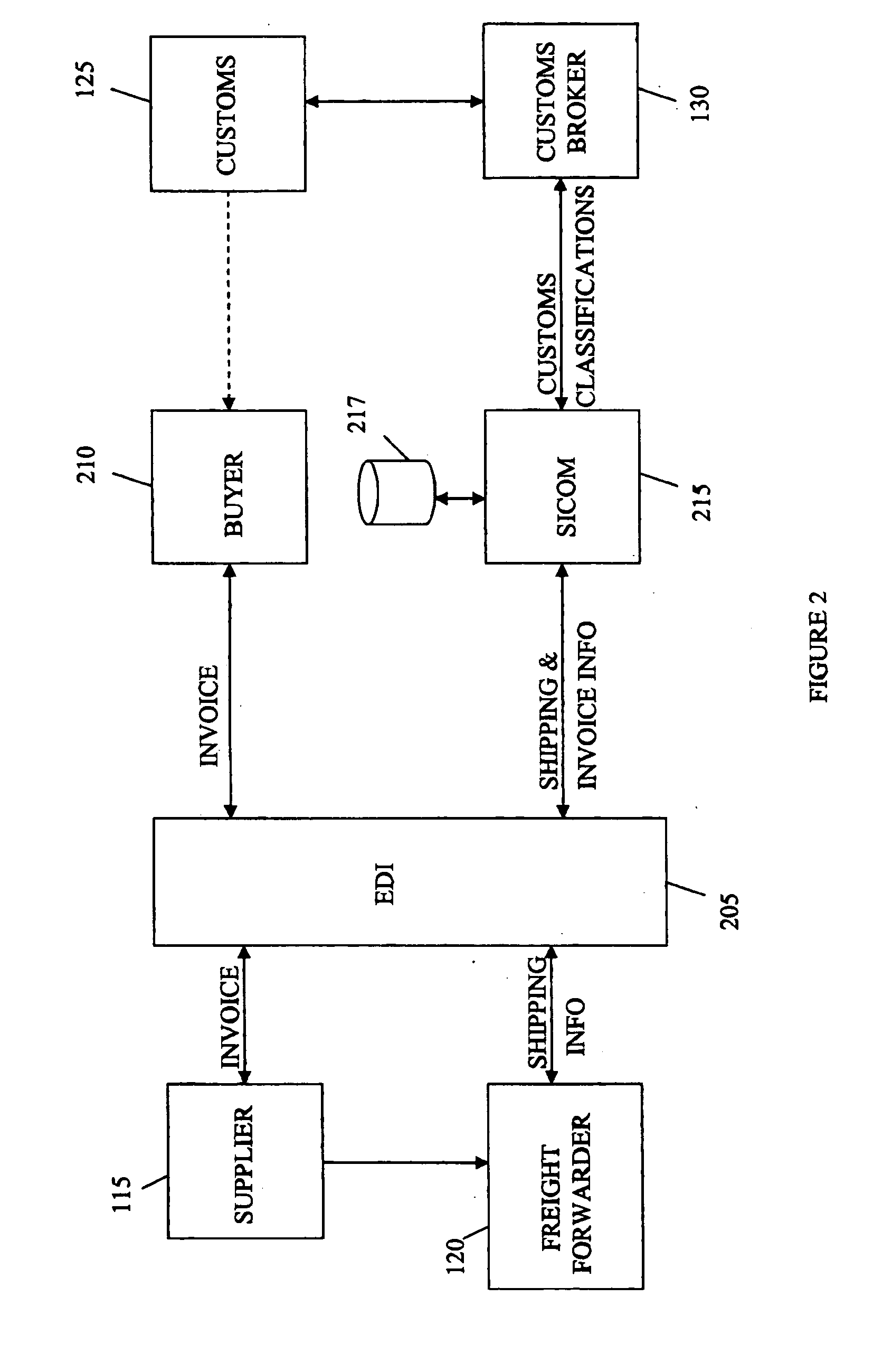
Import compliance system and method
A system and method for managing exportation and importation of goods and managing the data and interactions of various entities involved. Timely importation of goods requires a number of various activities to be coordinated and cross-checked for accuracy and compliance. Suppliers and freight forwarders may submit invoices and shipping notifications, respectively, which may be cross-checked against various conformance requirements and checked for compliance with customs and other governmental agencies prior to submission of an entry declaration. In this way, errors or improper documentation may be avoided, often while the goods are still in the exporting country, and prior to submission of entry documents to customs. Further, a reverse compliance check may be performed on the submitted entry declaration with information supplied to a customs broker for accuracy.
Owner:SIEMENS SHARED SERVICES
Automated compliance checking through analysis of cloud infrastructure templates
ActiveUS20170026416A1Digital data information retrievalData switching networksGraphicsVirtualization
Systems and methods for determining a state of an information technology (IT) environment are disclosed. A server accesses an infrastructure-as-code (IaC) template for the IT environment, where the IT environment is virtualized and cloud-based. The server deconstructs, using a parser for the IaC template, the IaC template to a graph database representation of the IT environment, wherein the graph database representation implements a predefined cloud resource ontology (CRO). The server determines, using the graph database representation, the state of the IT environment. The server provides, as a digital transmission, an output corresponding to the determined state of the IT environment.
Owner:RAYTHEON CO
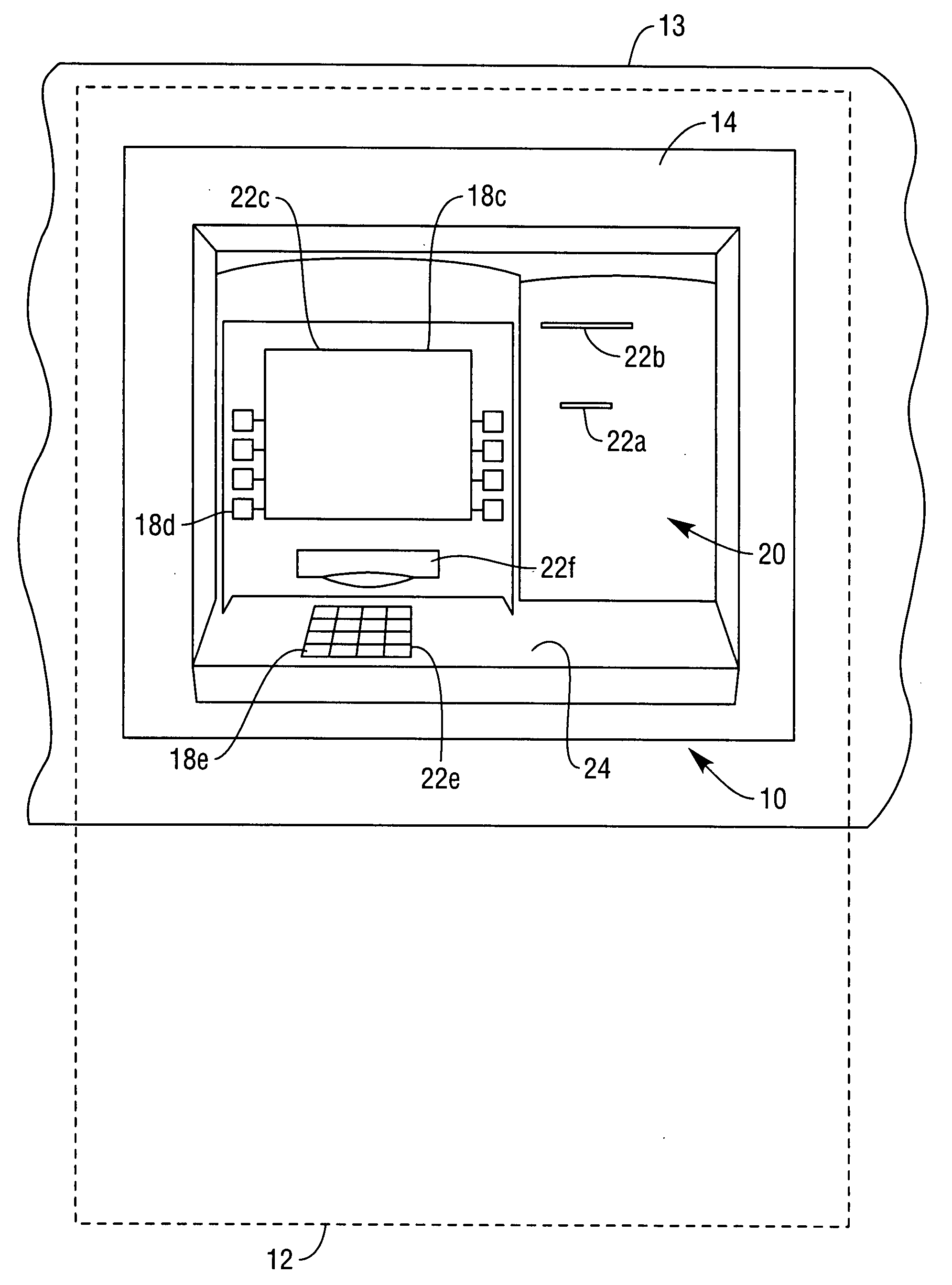
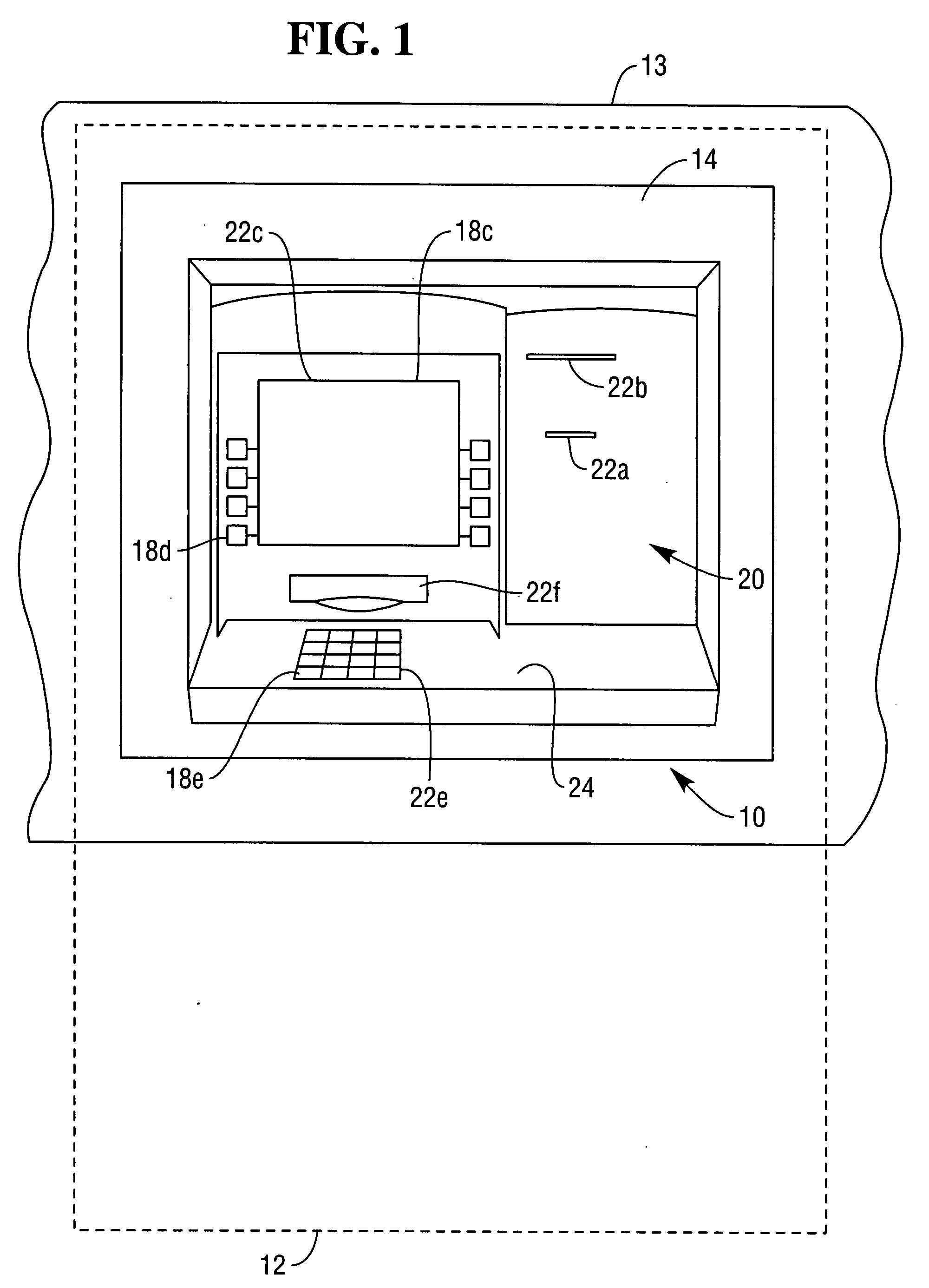
Self-service terminal
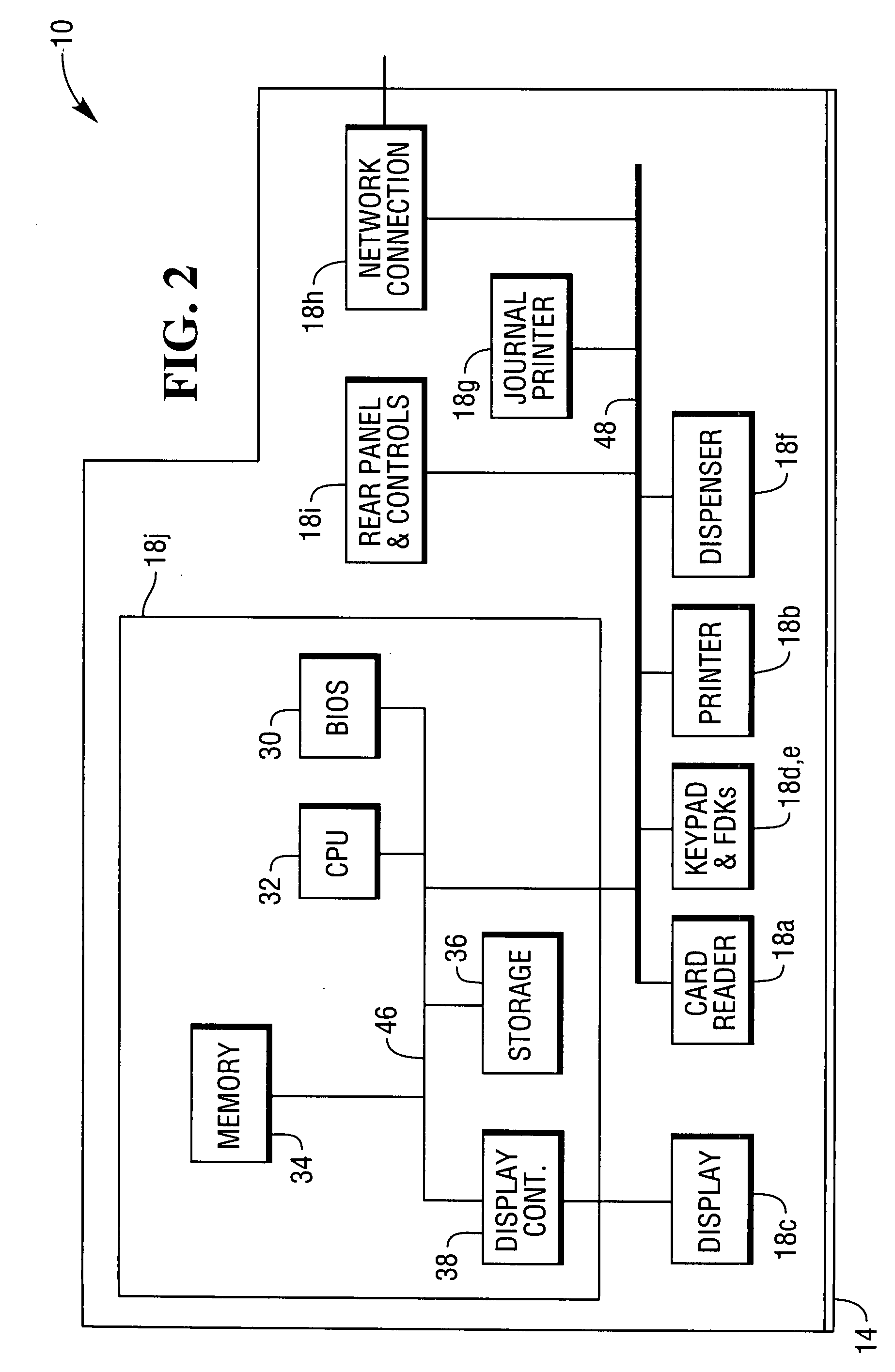
A method of operating a self-service terminal and a network of self-service terminals. The method comprises: receiving notification that a maintenance operation has been performed on the terminal; performing a compliance check on the terminal; and issuing a code in the event that the compliance check is successful. The code can be used to audit and / or validate that the maintenance operation was performed successfully and that the terminal was left in working order.
Owner:NCR CORP
Network Access Control with Compliance Policy Check
ActiveUS20160197962A1User identity/authority verificationSpecial data processing applicationsUser deviceWeb browser
Embodiments of the present invention include methods involving an authentication application, a client application, or a combination of a network access control server with the authentication application and the client application. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result or a user device identifier is stored in a web browser cookie or a client certificate on the user device.
Owner:OPSWAT
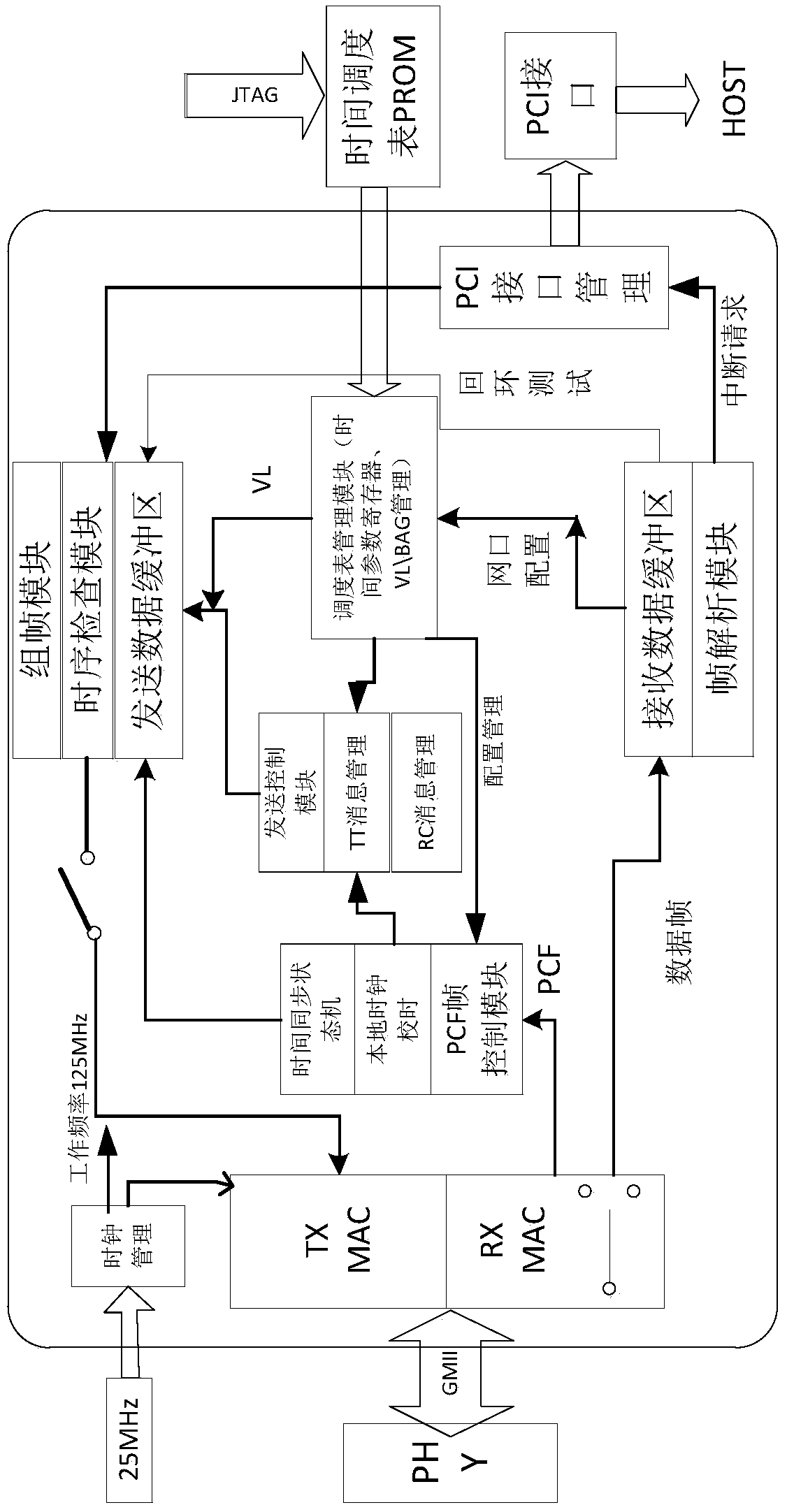
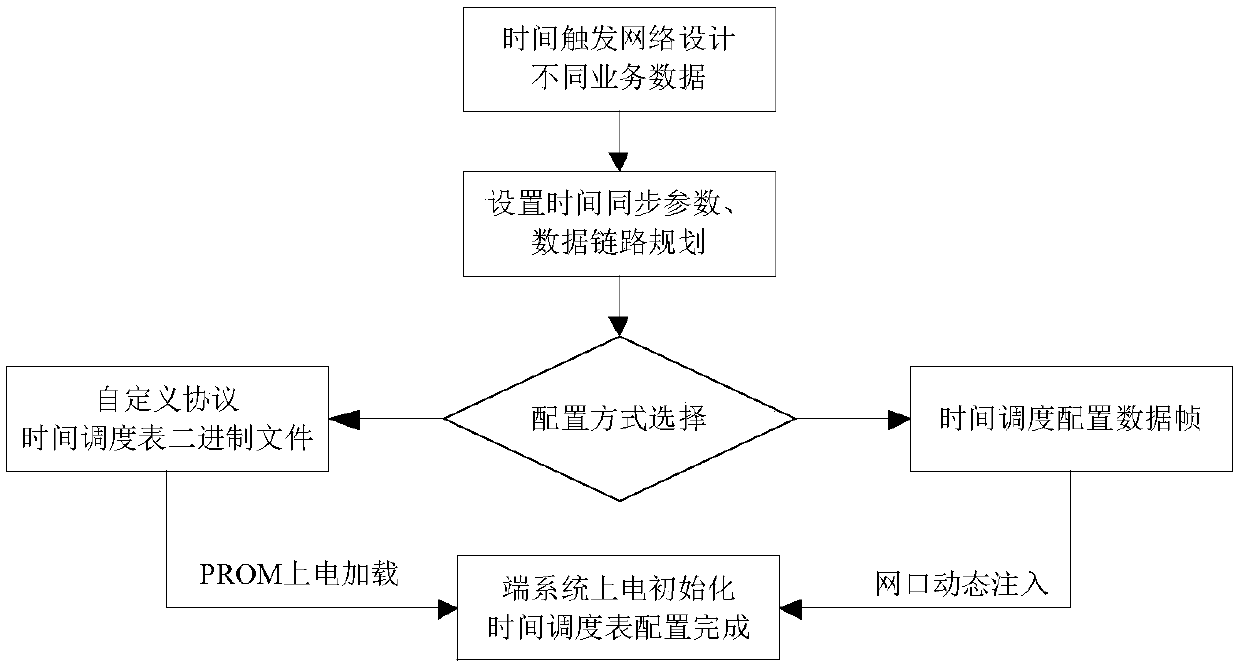
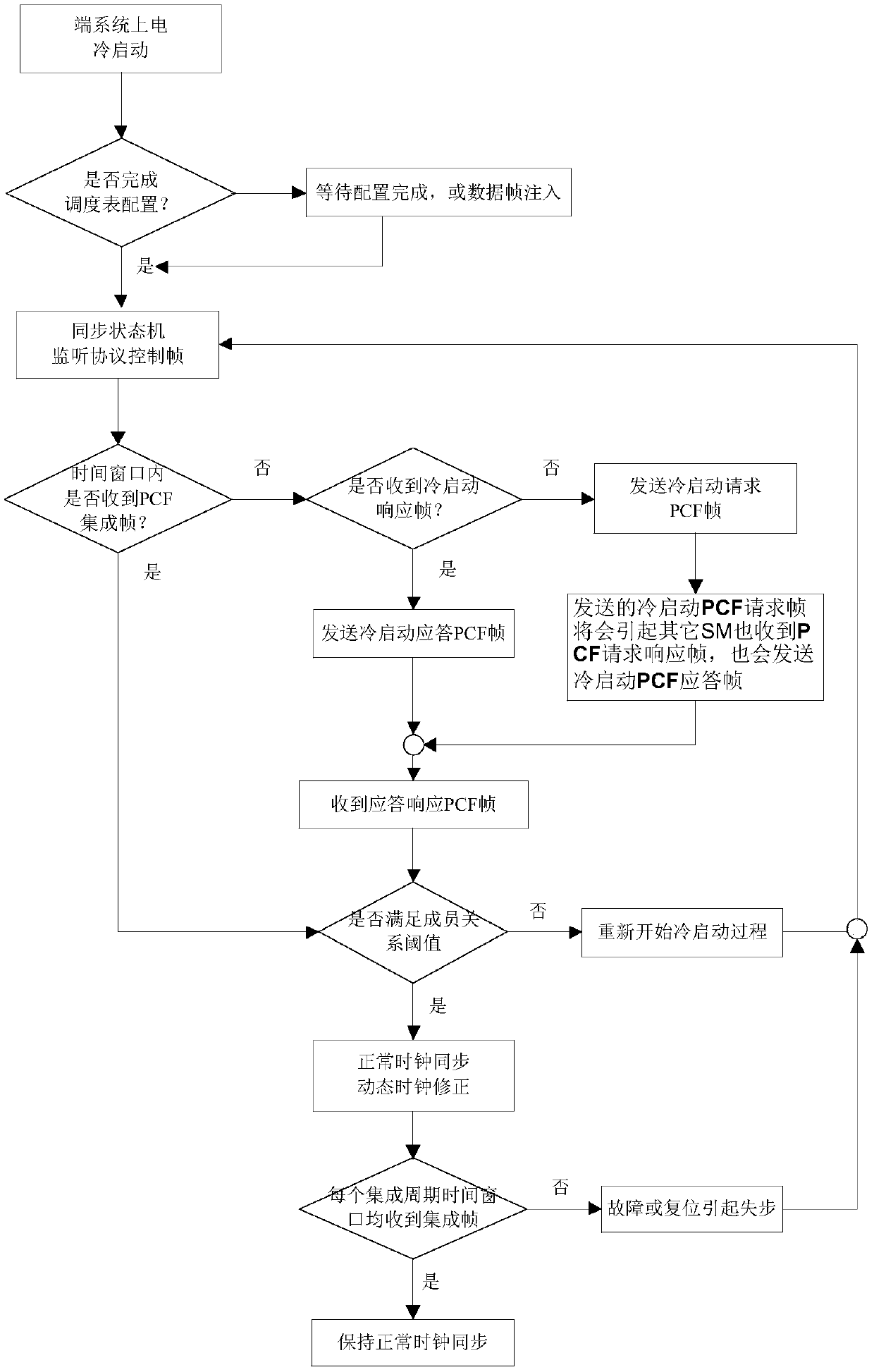
Time-triggered unified network transmission end system scheduling method and device
ActiveCN109600187AReduce overheadImprove the limited situationTime-division multiplexTransmission format adaptationEnd systemSpaceflight
The invention relates to a time-triggered unified network transmission end system scheduling method and device, which comprises the following steps of: configuring a time scheduling table which comprises static configuration and online loading configuration; carrying out clock synchronization, and completing dynamic correction of a local clock according to the time solidification point compressedby the switch; performing data scheduling: dividing data types into a time synchronization protocol control frame, a TT message data frame, an RC message data frame and a BE message data frame according to priority levels from high to low; performing data transmission reliability check, including time window conformity check of the TT message by the end system. The method has the beneficial effects that the communication service provides a time synchronization service, high reliability, time determination and strong real-time unified network transmission of different message data are ensured,the conversion expenditure of different network protocols is reduced, the reliability of the system is improved, and the method adapts to the requirement of spaceflight redundant transmission.
Owner:SHANDONG INST OF AEROSPACE ELECTRONICS TECH
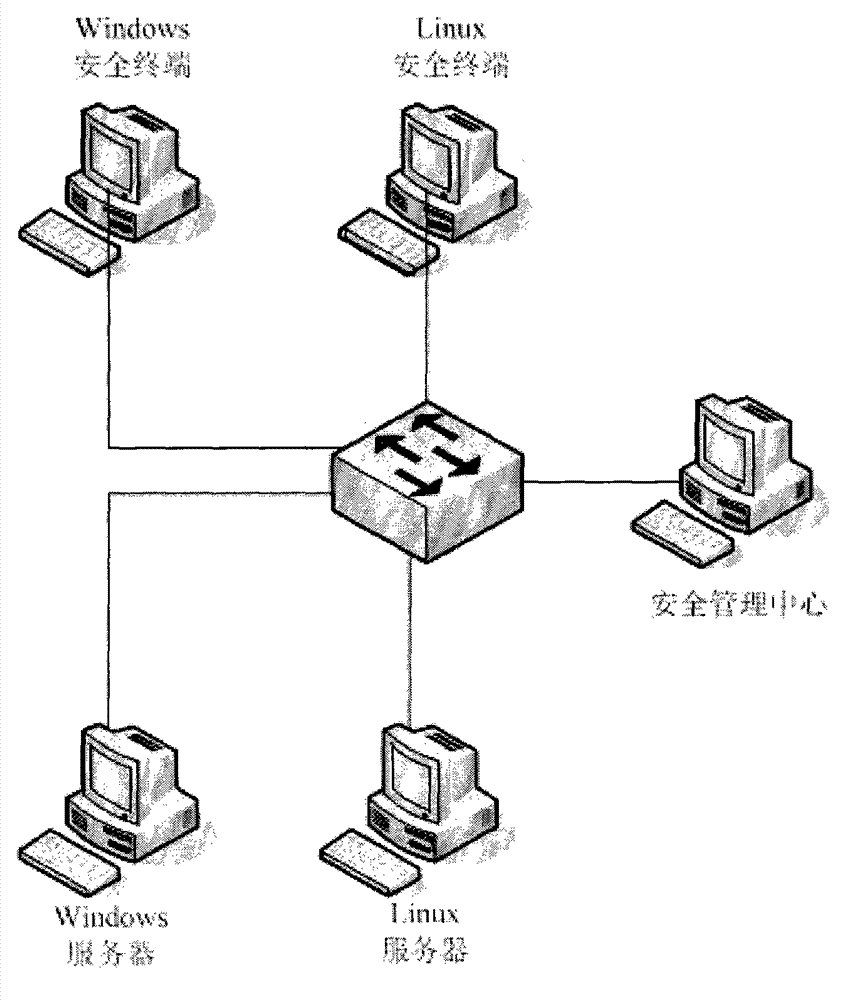
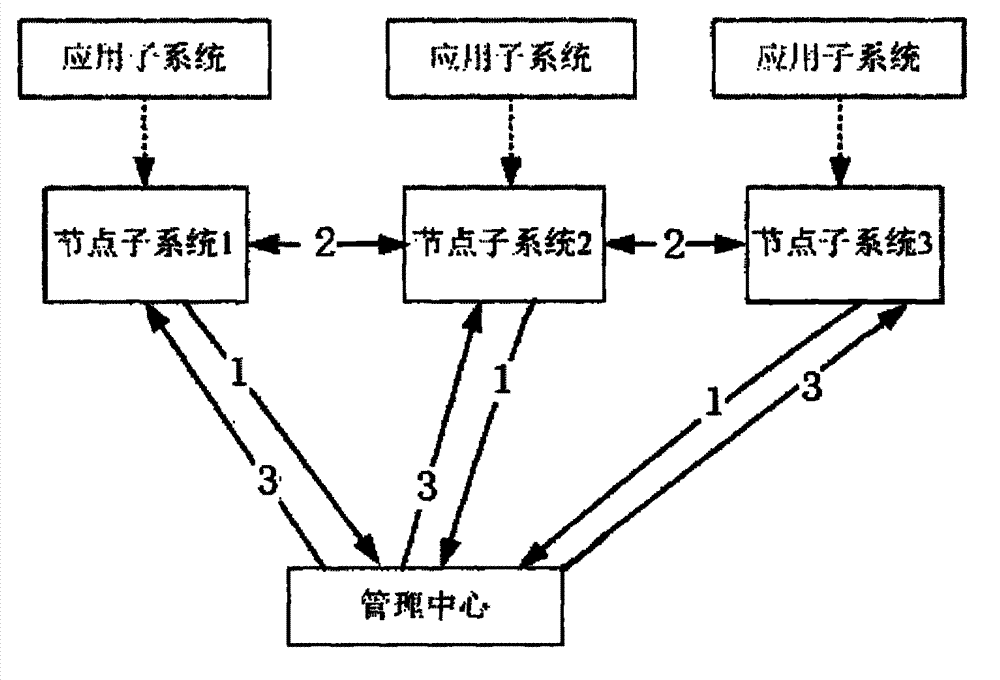
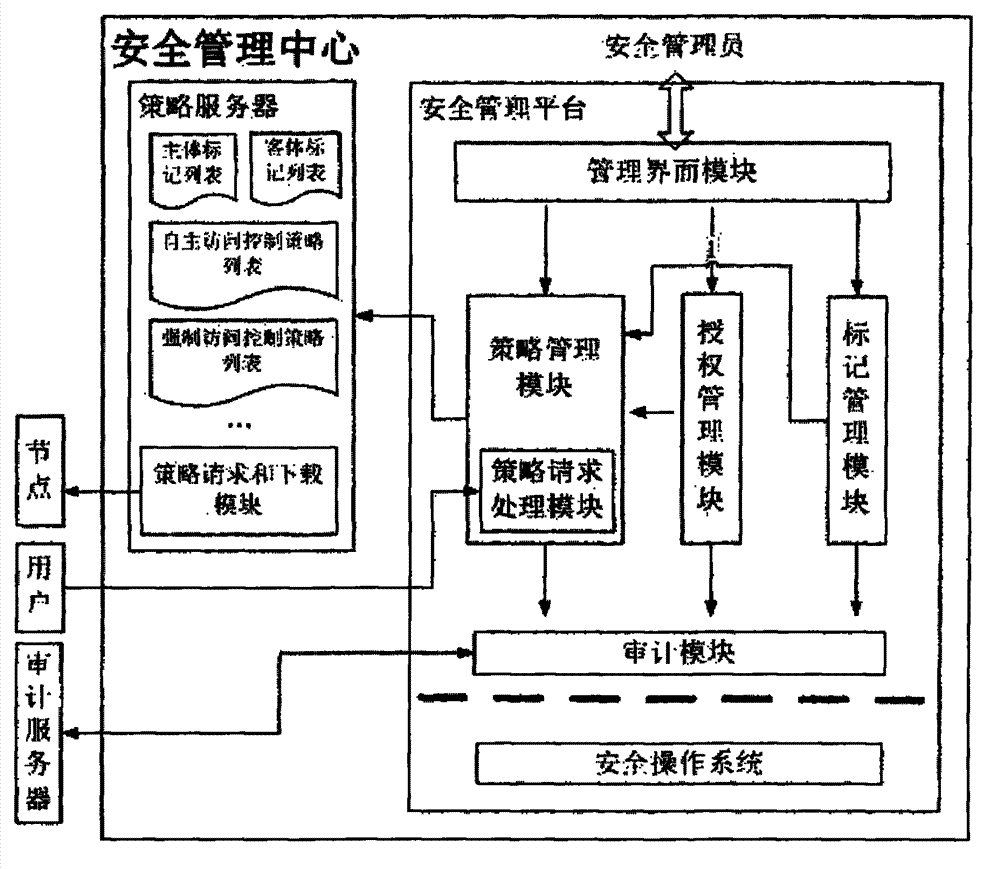
Cross-platform-unified-management-supported mandatory access controlling system and method
ActiveCN102904889AImprove reliabilityIncrease flexibilityData switching networksOperational systemConfidentiality
The invention discloses a cross-platform-unified-management-supported mandatory access controlling system. The system comprises a security management center; the security management center manages servers with different operating systems and data processing terminals which are connected with the servers, and the security management center also comprises mandatory access controlling modules, which connect the servers and the data processing terminals, in an application layer; and the mandatory access controlling modules comprise a special mandatory access controlling module, a general mandatory access controlling module, a strategy module and an audit module, wherein the general mandatory access controlling module is used for controlling mandatory access and checking strategy conformance. The invention also discloses a mandatory access controlling method based on the system, an access request is checked by the mandatory access controlling module based on a system mandatory access controlling strategy, a behavior which does not accord with the system mandatory access controlling strategy is checked, a behavior which accords with the mandatory access controlling strategy is regulated, the operation of a process on a file is controlled, the reliability of system security is improved, the confidentiality and integrity of an information system can be protected and prevented from being destroyed, and the flexibility of system security control is enhanced.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
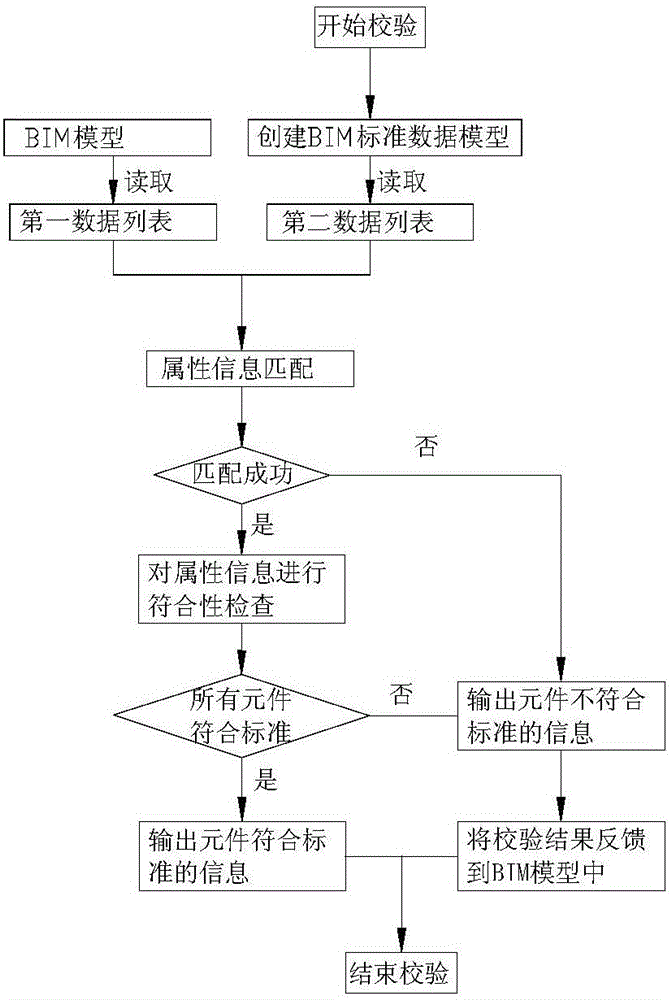
Checking method of BIM model
InactiveCN106294821AImprove verification efficiencyThe verification result is accurateSemi-structured data queryingStructured data retrievalSoftware engineeringTechnical standard
The invention provides a checking method of a BIM model. The checking method includes the steps of firstly, building a BIM standard data module; secondly, reading the attribute information of BIM model elements to form a first data list, and reading all the attribute information in the BIM standard data model to form a second data list; thirdly, matching the attribute information in the first data list and second data list, performing the fourth step is the matching succeeds, and performing the fifth step if the matching fails; fourthly, performing a conformity check, outputting information that the elements conform to standards if all the elements conform to the standards, and ending the checking; performing the fifth step if elements not conforming to the standards exist; fifthly, outputting information that elements not conforming to the standards exist, feeding a checking result back to the BIM model, displaying the elements not conforming to the BIM technical standards, and ending the checking. By the checking method, automatic checking of the BIM model can be achieved, and high checking efficiency and accurate checking result are achieved.
Owner:GUANGZHOU METRO DESIGN & RES INST
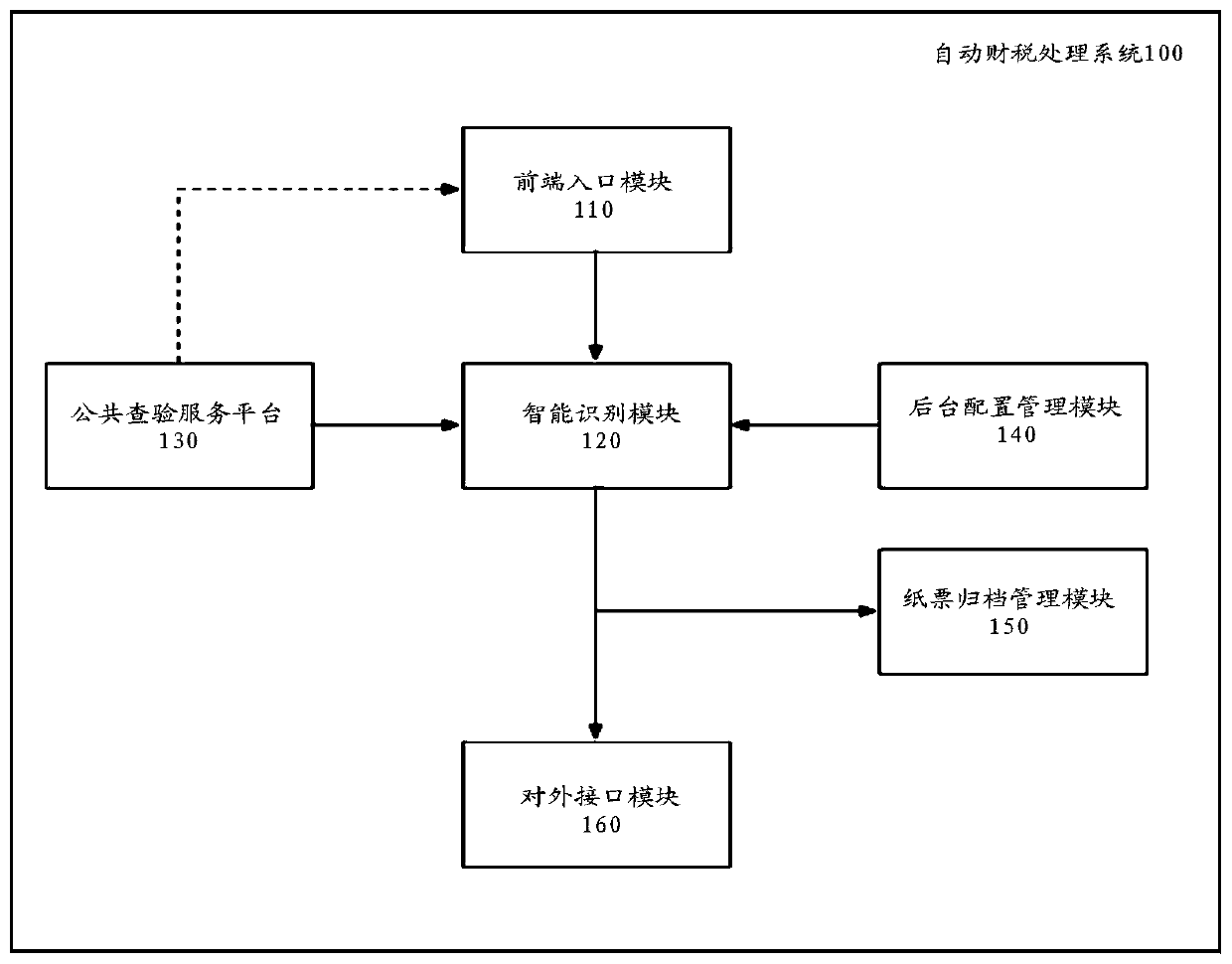
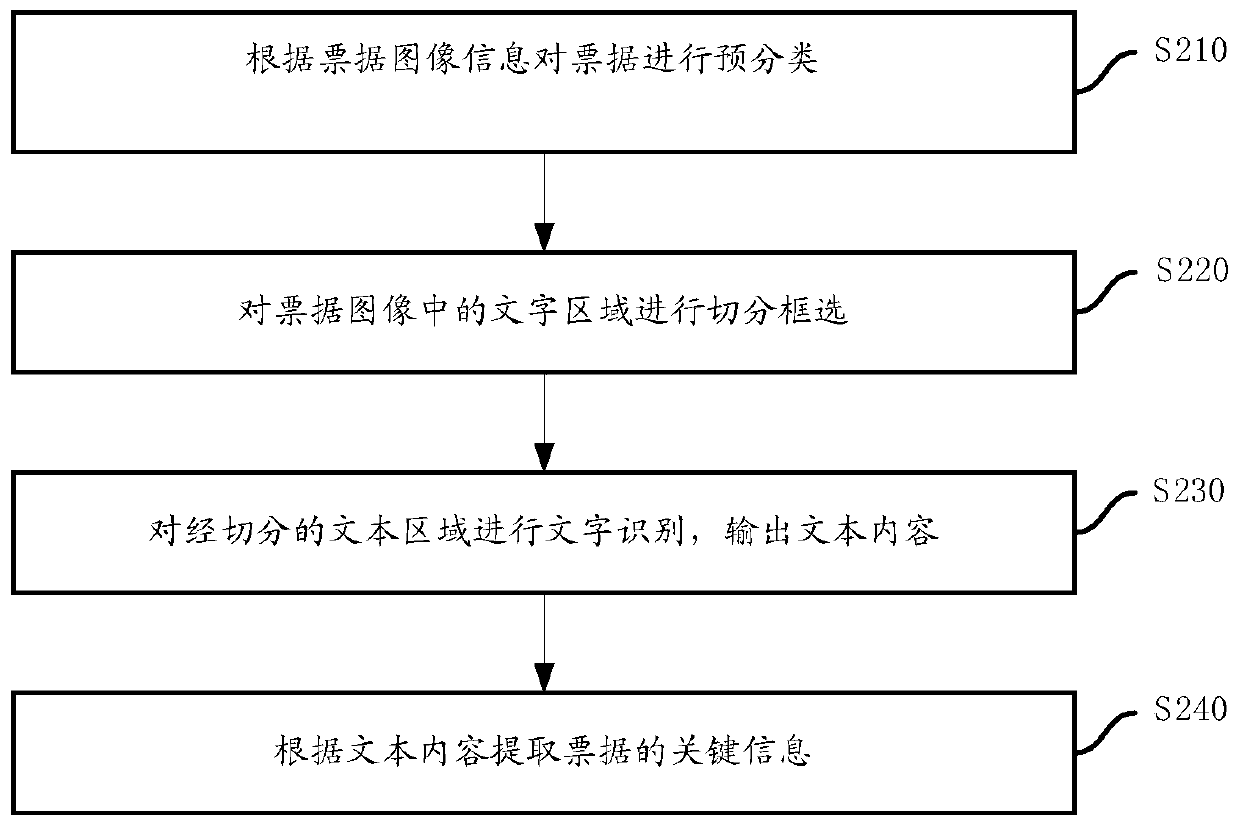
Tax processing method and system
ActiveCN109887153AReduce consumptionReduce repetitive and complex entryFinanceCharacter and pattern recognitionHandling systemDatabase
The invention provides a tax processing method and system. The method comprises the steps of: recognizing image information of received a tax bill and extracting text information of the tax bill; andmatching the extracted text information with a pre-configured check strategy so as to obtain audition information of the tax bill, wherein the check strategy represents a mapping relationship betweena compliance check item of the tax bill and an effectiveness level, and the effectiveness level of the tax bill is arranged in the audition information. The tax processing method and system can be compatible with the processing flows of paper bills and electronic flow information, so as to solve conflicts between paper bill retention and paperless reimbursement.
Owner:国信电子票据平台信息服务有限公司
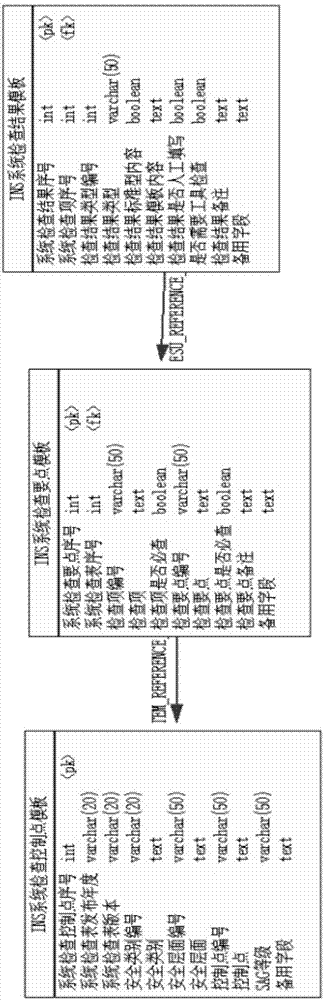
Grade-protection-oriented information system security compliance check method
ActiveCN104766166AProtect the objectivity of inspection workProtection Inspection Work SpecificationsPlatform integrity maintainanceResourcesInformation systems securityCompliance check
The invention relates to the field of information securitygrade protection, and aims at providing a grade-protection-oriented information system security compliance check method. The grade-protection-oriented information system security compliance check method comprises the steps that a check index library is built, a check task or a check plan is defined, a check object is scanned, a check result is guided in, a scanning result is decoded, a scanning result code is decoded, the scanning result is judged, a judgment result is graded, and a grade protection compliance report is generated. According to the method, information system security grade protection check work is objective, standard and fair, and the difficulty and complexity of the information security grade protection check work can be greatly reduced so that the efficiency of the information security grade protection check work can be greatly improved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
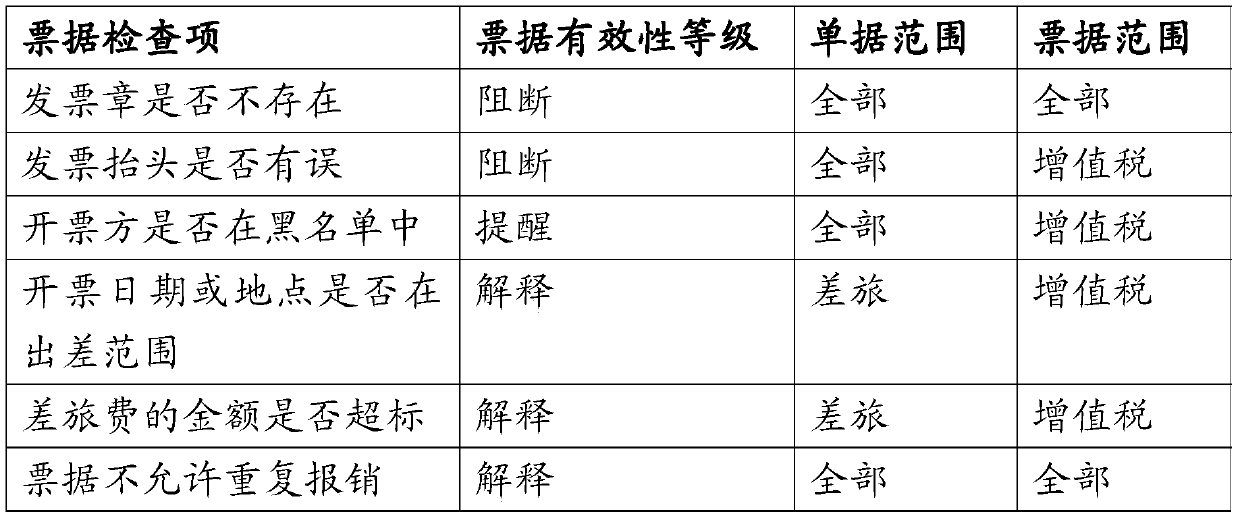
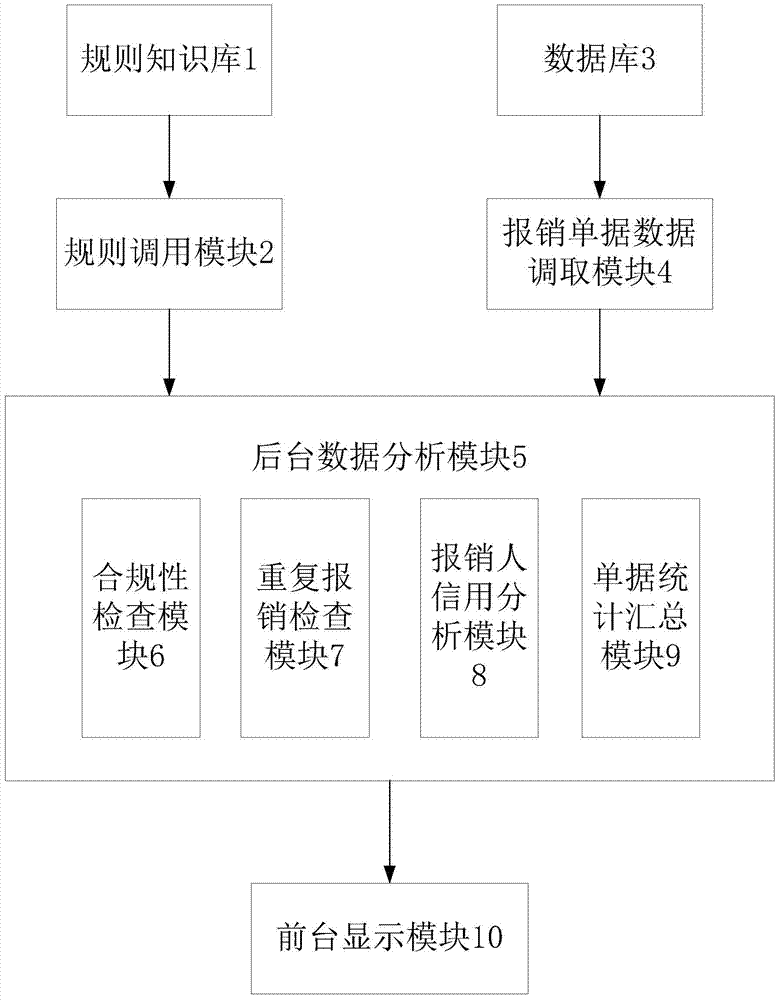
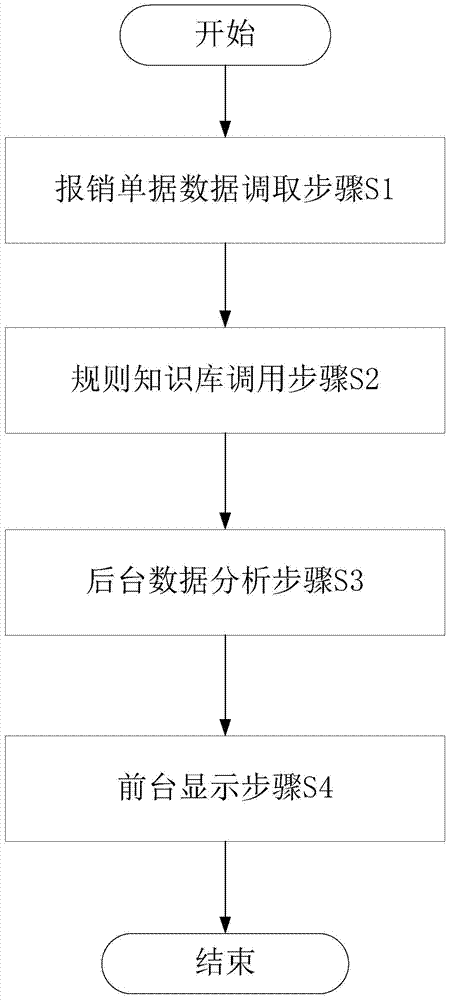
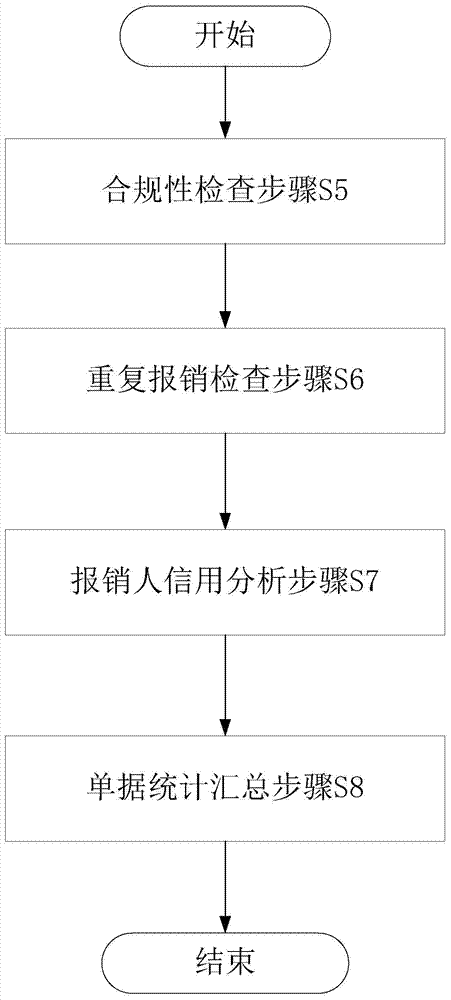
Reimbursement document auxiliary examination and approval method and apparatus
InactiveCN106934586AAccurate Approval DecisionReduce approval rateFinanceOffice automationGraphicsData retrieval
The present invention provides a reimbursement document auxiliary examination and approval method and apparatus. The method includes a reimbursement document data retrieval step, a rule knowledge base calling step, a background data analysis step and a foreground display step, wherein the background data analysis step further comprises a compliance checking step, a repeated reimbursement checking step, a reimbursement applicant credit analysis step and a document statistical summary step. When performing examination and approval, an approver can check the analysis results of a foreground display interface timely, wherein the analysis results include horizontal and vertical comparison data presented in a graph form and document abnormity point summaries presented in a table form; and the approver can make more accurate approval decisions according to these auxiliary information. The apparatus includes modules which provide implementation steps for the method. According to reimbursement document auxiliary examination and approval apparatus, documents to be examined and approved and historical reimbursement documents related to current reimbursement documents are automatically called and analyzed, and therefore, the efficiency and quality of examination and approval can be improved, the pass rate of unreasonable reimbursement documents can be decreased, and enterprises costs can be saved.
Owner:YGSOFT INC
Network access control with compliance policy check
Embodiments of the present invention involve a method and system including a network access control server, an authentication application running on a software-as-a-service server, and a client application running on a user device. The client application collects compliance data regarding the user device and communicates the compliance data to the network access control server. The network access control server generates a compliance check result based on whether the compliance data indicates that the user device is compliant with a security policy for the software-as-a-service server. The authentication application grants access by the user device when the compliance check result is positive; and the authentication application denies access by the user device when the compliance check result is negative. In some embodiments, the compliance check result is stored in a cookie of one or more web browsers installed on the user device.
Owner:OPSWAT
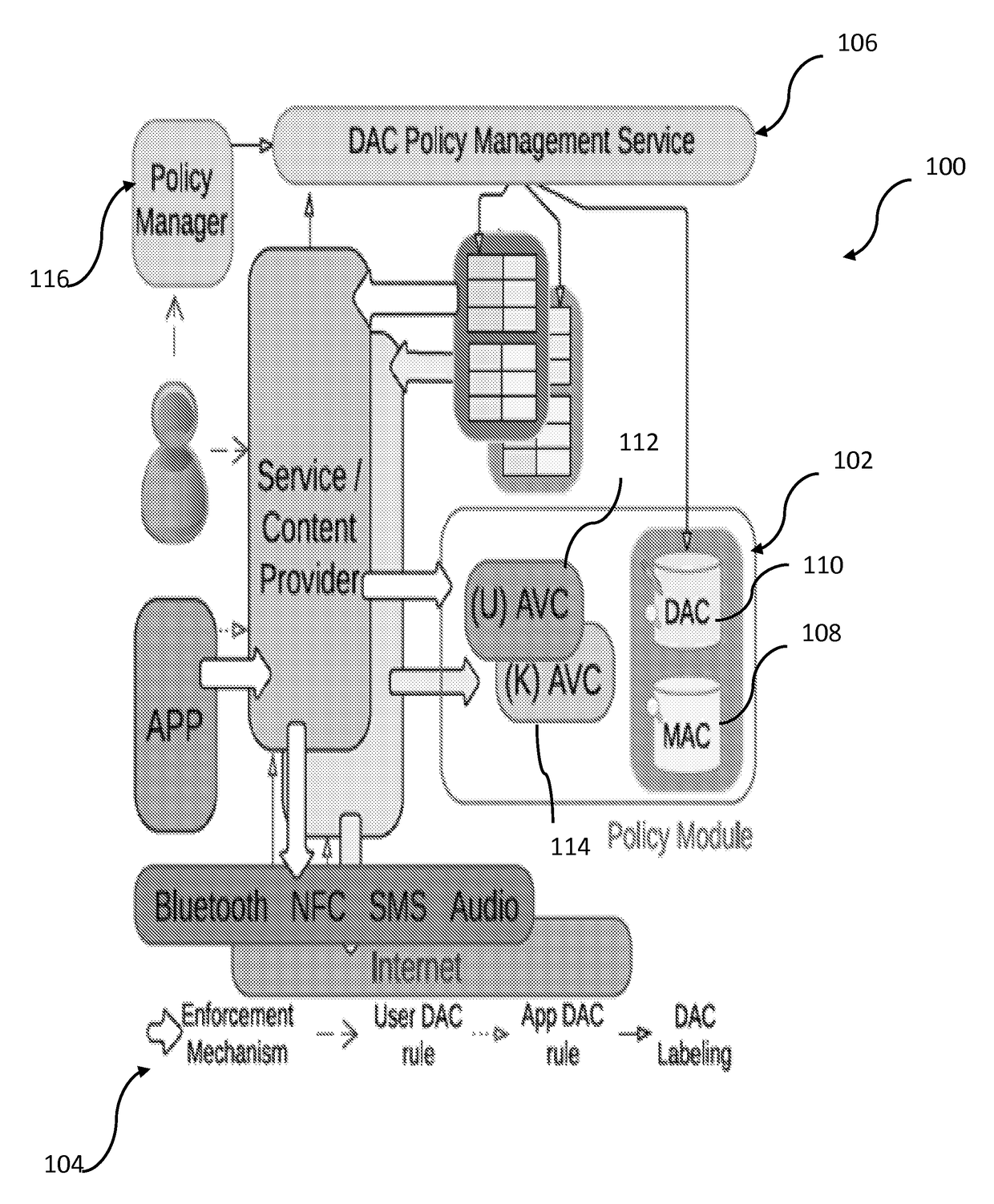
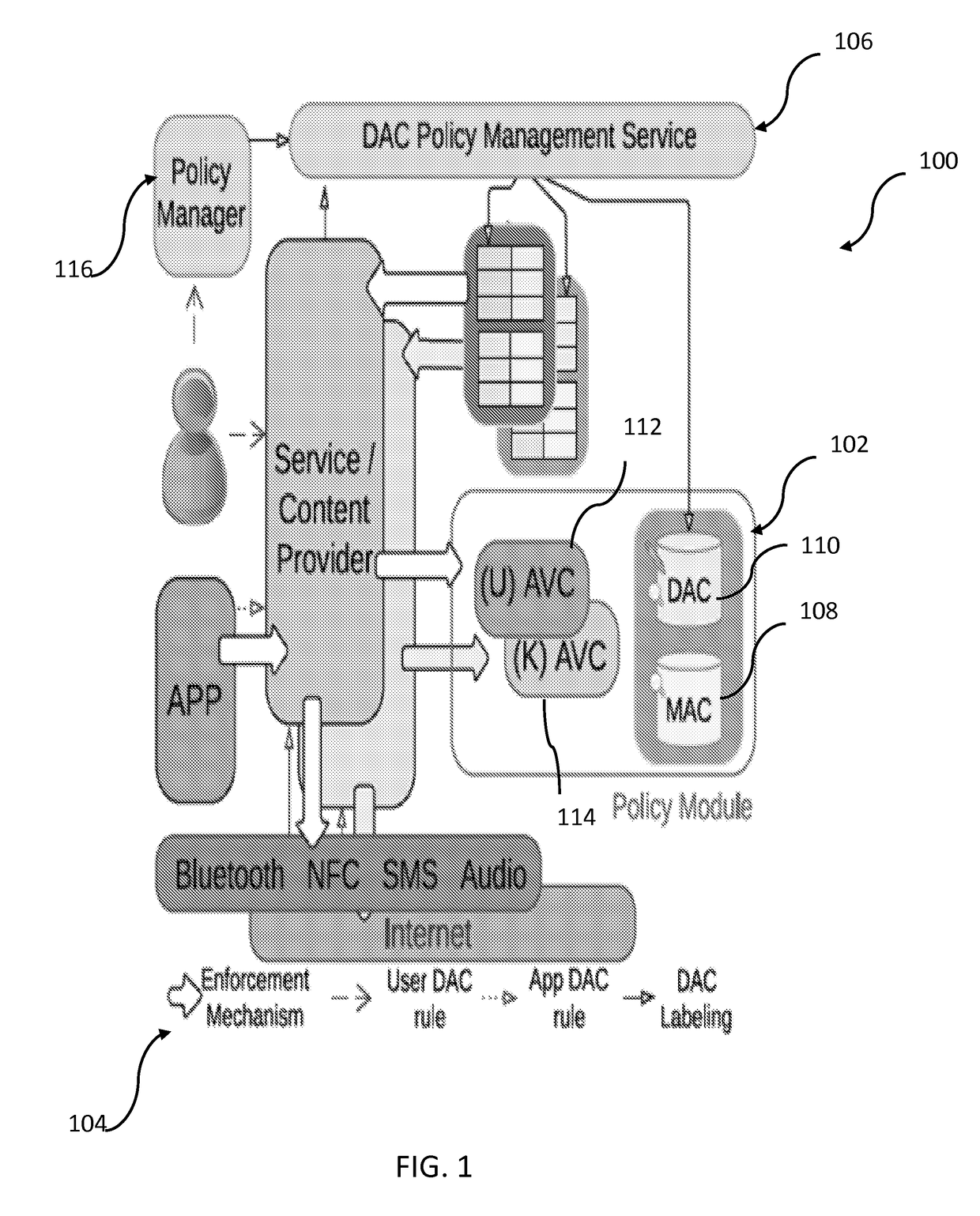
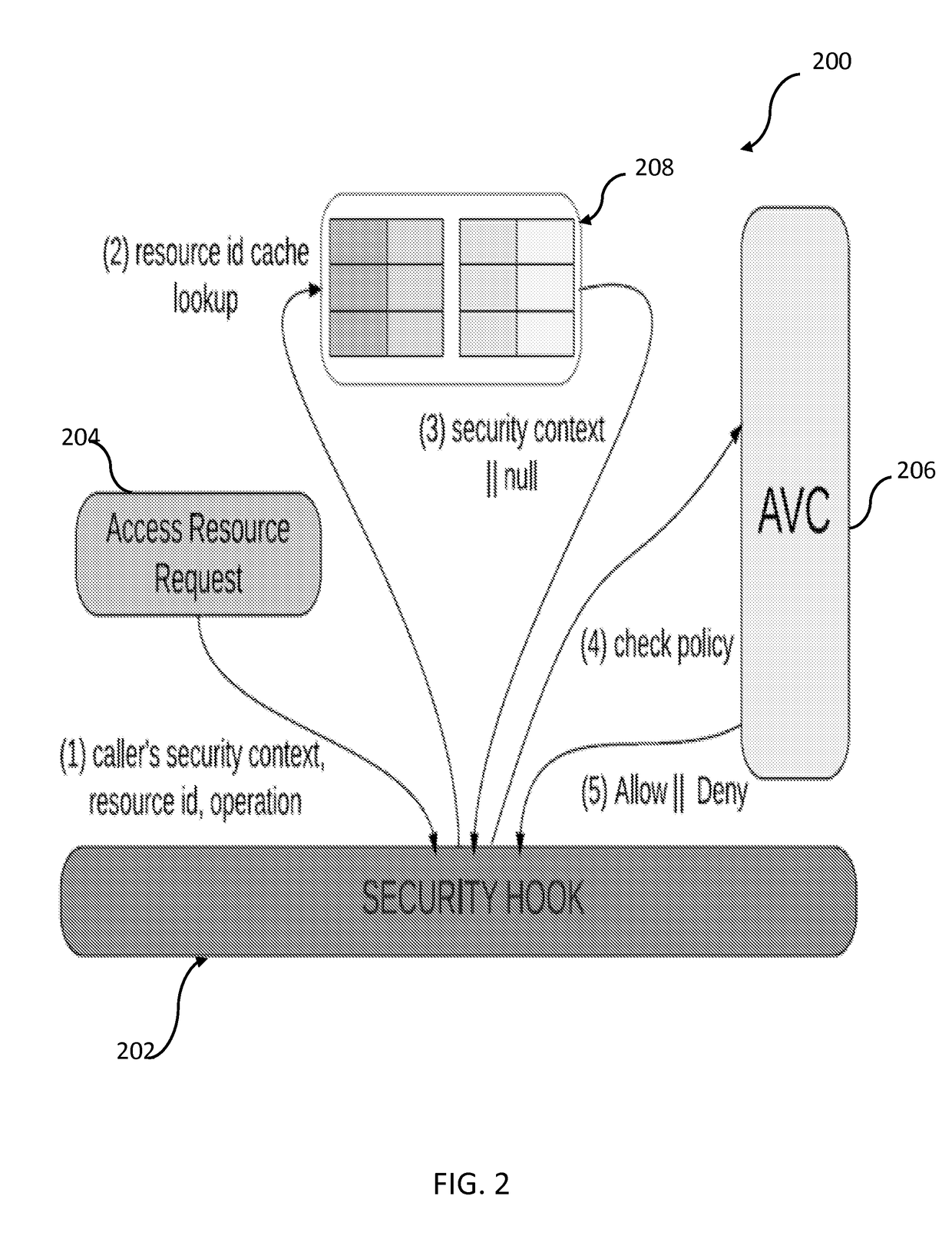
External resource control of mobile devices
The present disclosure provides a security enhanced channel control system useable on a wireless device comprising a policy module including at least one processor and memory, the policy module configured to store, in the memory, one or more security policies and apply a compliance check to a first system layer and a second system layer; and a first policy base stored in the memory of the policy module, the first policy base being associated with a mandatory access control (“MAC”) base and defining one more security polices for access to a plurality of channels associated with the first and second system layers. The policy module cooperates with the first policy base to establish one or more access control rules that are applied to at least one of the plurality of channels to preclude an unauthorized application from accessing at least one of the channels.
Owner:THE BOARD OF TRUSTEES OF THE UNIV OF ILLINOIS +1
Fast lithography compliance check for place and route optimization
ActiveUS20100131909A1Photomechanical apparatusOriginals for photomechanical treatmentAlgorithmLayout
A computer is programmed to use at least one rule to identify from within a layout of an IC design, a set of regions likely to fail if fabricated unchanged. An example of such a rule of detection is to check for presence of two neighbors neither of which fully overlaps a short wire or an end of a long wire. The computer uses at least another rule to change at least one region in the set of regions, to obtain a second layout which is less likely to fail in the identified regions. An example of such a rule of correction is to elongate at least one of the two neighbors. The computer may perform optical rule checking (ORC) in any order relative to application of the rules, e.g. ORC can be performed between detection rules and correction rules i.e. performed individually on each identified region prior to correction.
Owner:SYNOPSYS INC
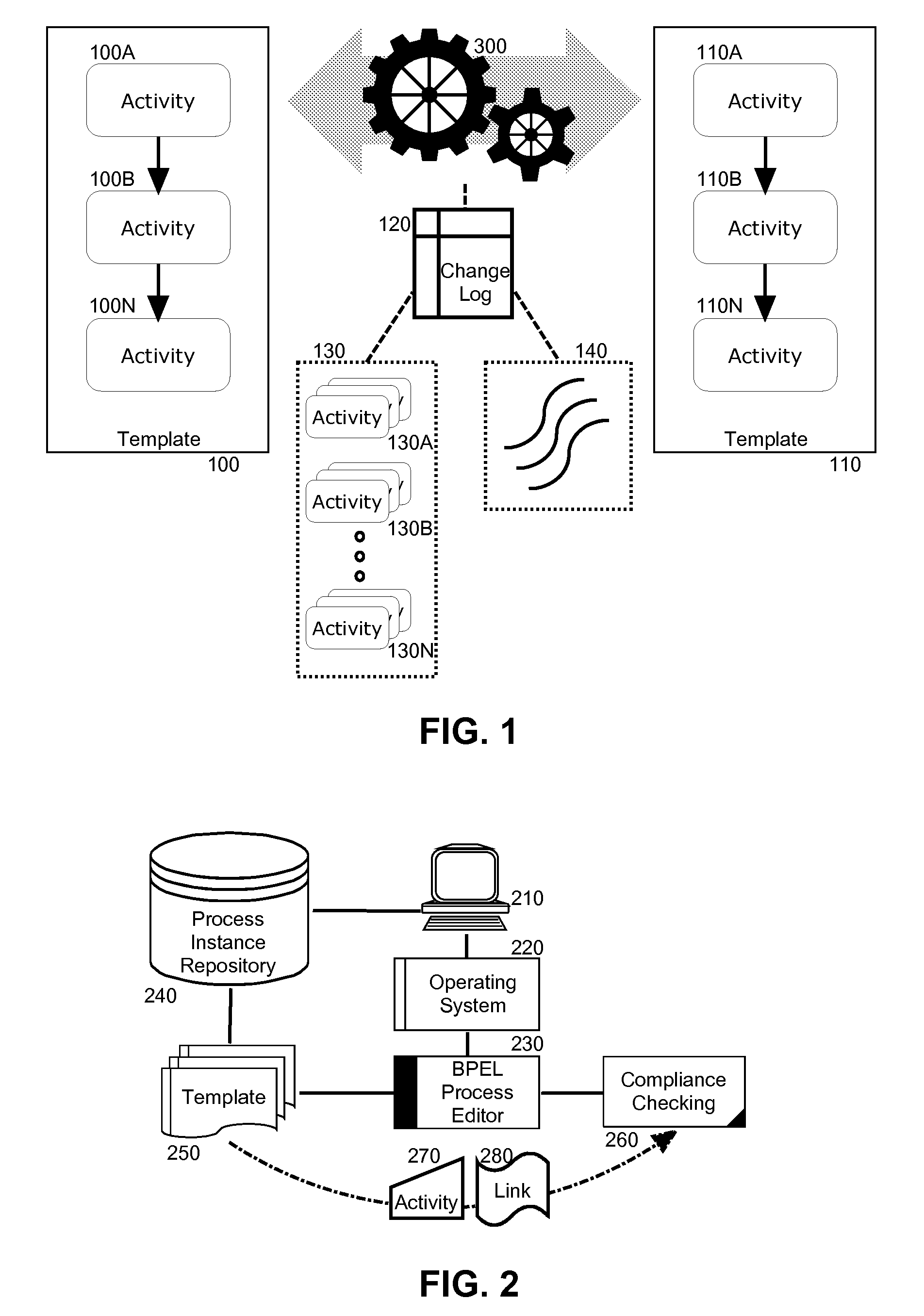
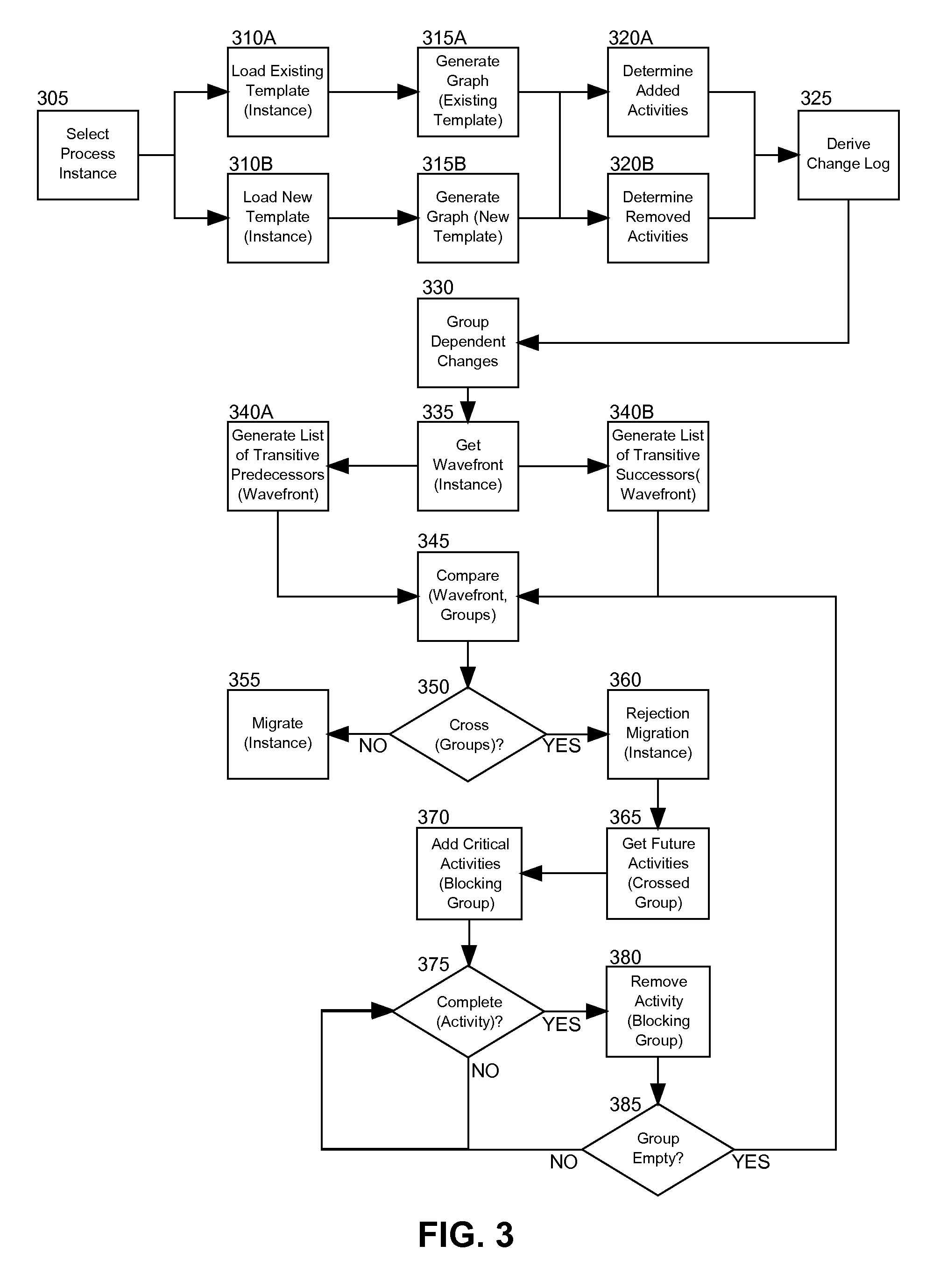
Automated compliance checking for process instance migration
A business process workflow editorial data processing system can be provided. The system can include a workflow management system such as a BPEL process editing tool, and a repository of templates each template defining a process. At least two of the templates can include a new template and an existing template for an executing instance of a business process. The system also can include compliance checking logic coupled to the workflow management system. The logic can include program code enabled to derive a log of changes between the new template and the existing template based upon added and removed activities and links between activities in the executing process instance, to group the changes in the log according to common activities, to determine a wavefront for the executing process instance, and to migrate the executing process instance to the new template only if the wavefront does not cross any of the groups of the changes, but otherwise rejecting a migration of the process instance to the new template.
Owner:IBM CORP
Security auditing system and method for database, and server
ActiveCN108763957ASolve audit problemsImplement compliance checksDigital data protectionSpecial data processing applicationsSafe handlingCompliance check
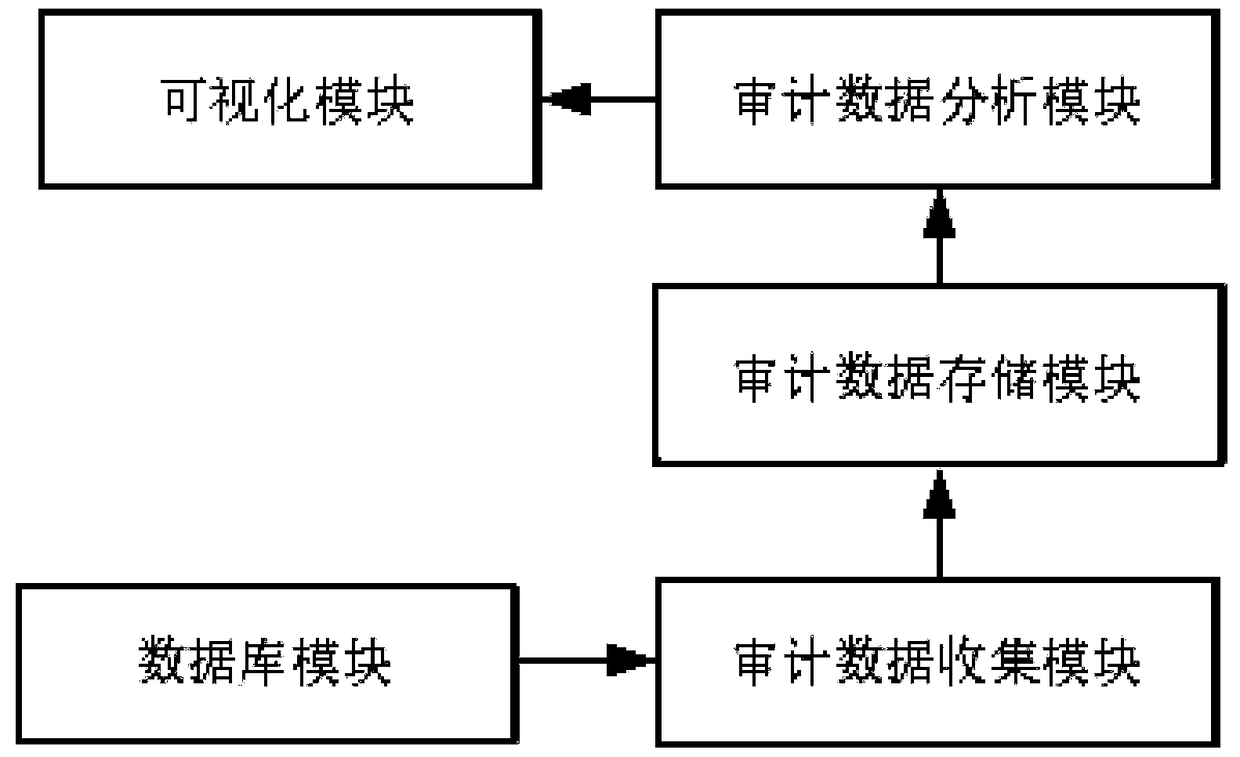
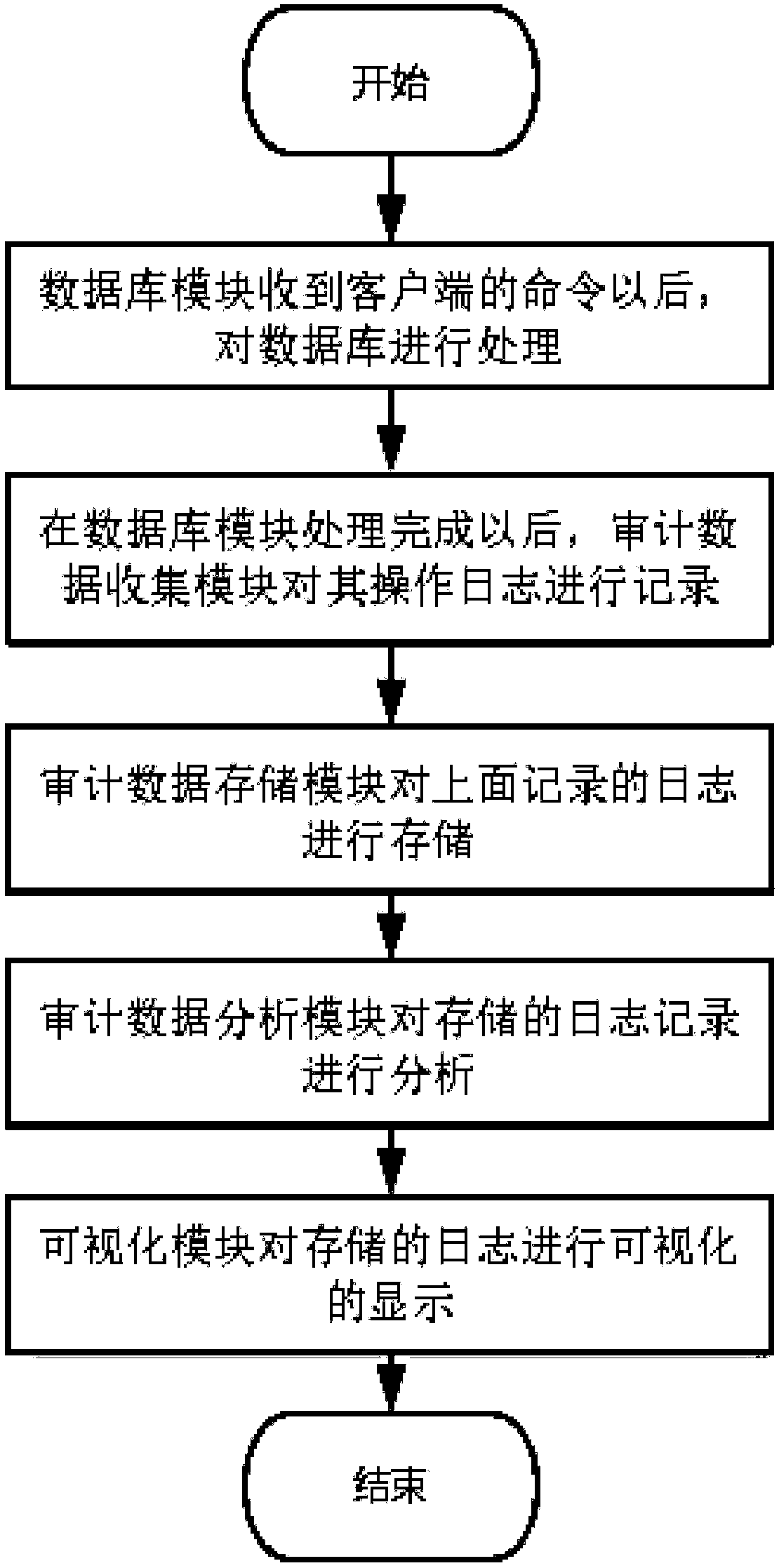
The invention relates to a security auditing system and method for a database, and a server. The security auditing system comprises a database module, an auditing data collection module, an auditing data storage module, an audit data analysis module and a visualization module; the database module processes data in the database; the auditing data collection module is used for collecting operation logs of the database module; the auditing data storage module is used for storing auditing log data, and efficient and secure processing of the auditing data is guaranteed by introducing an improved storage engine; the auditing data analysis module is used for performing analysis processing on the auditing log data; and the visualization module can visually display the auditing log data, thereby better monitoring the change situation of the database. The system can well solve the auditing problem of the database, realize the compliance check of the database, and perform early warning on the violation operation.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method and system for performing online full-automatic configuration of compliance safety audit
InactiveCN104506351ANo distractionSimple and fast operationData switching networksDevice typeOperating system
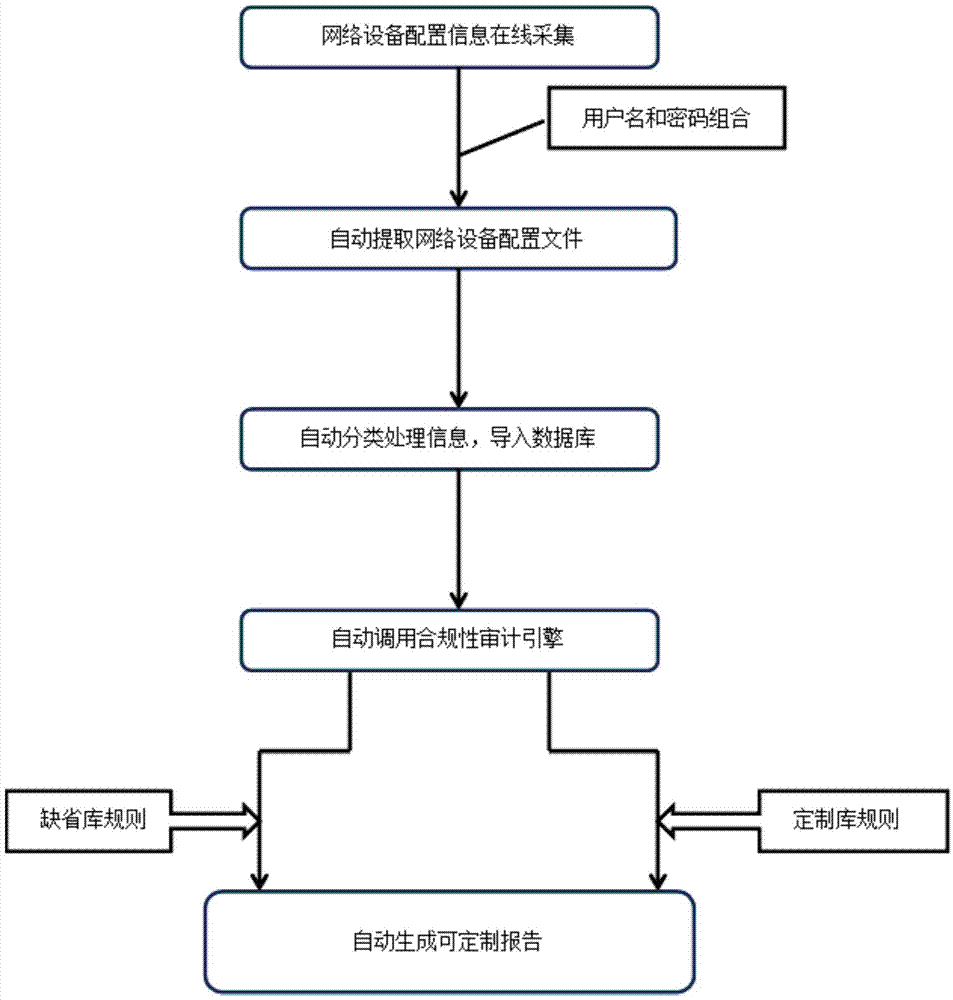
The invention discloses a method for performing online full-automatic configuration of compliance safety audit. The method comprises the following steps: according to the device type, recognized in advance, of a target device, collecting the configuration file information of the target device; performing analysis on the collected configuration file information, determining effective configuration file information of the collected configuration file information, and sorting and filing the effective configuration file information; according to pre-stored standard configuration library file information matched with the target device, auditing the effective configuration file information through a preconfigured audit strategy, wherein the audit strategy comprises the flow of performing cross-contrast and compliance checking on the effective configuration file information and the standard configuration library file information; according to an audit result, generating and outputting an audit report matched with the audit result. The method disclosed by the invention has the beneficial effects that the flow is full automatic, and is automatically executed periodically; manual intervention is not needed, and a user can receive the latest device compliance report at regular intervals.
Owner:北京随方信息技术有限公司
Collaborative generation of configuration technical data for a product to be manufactured
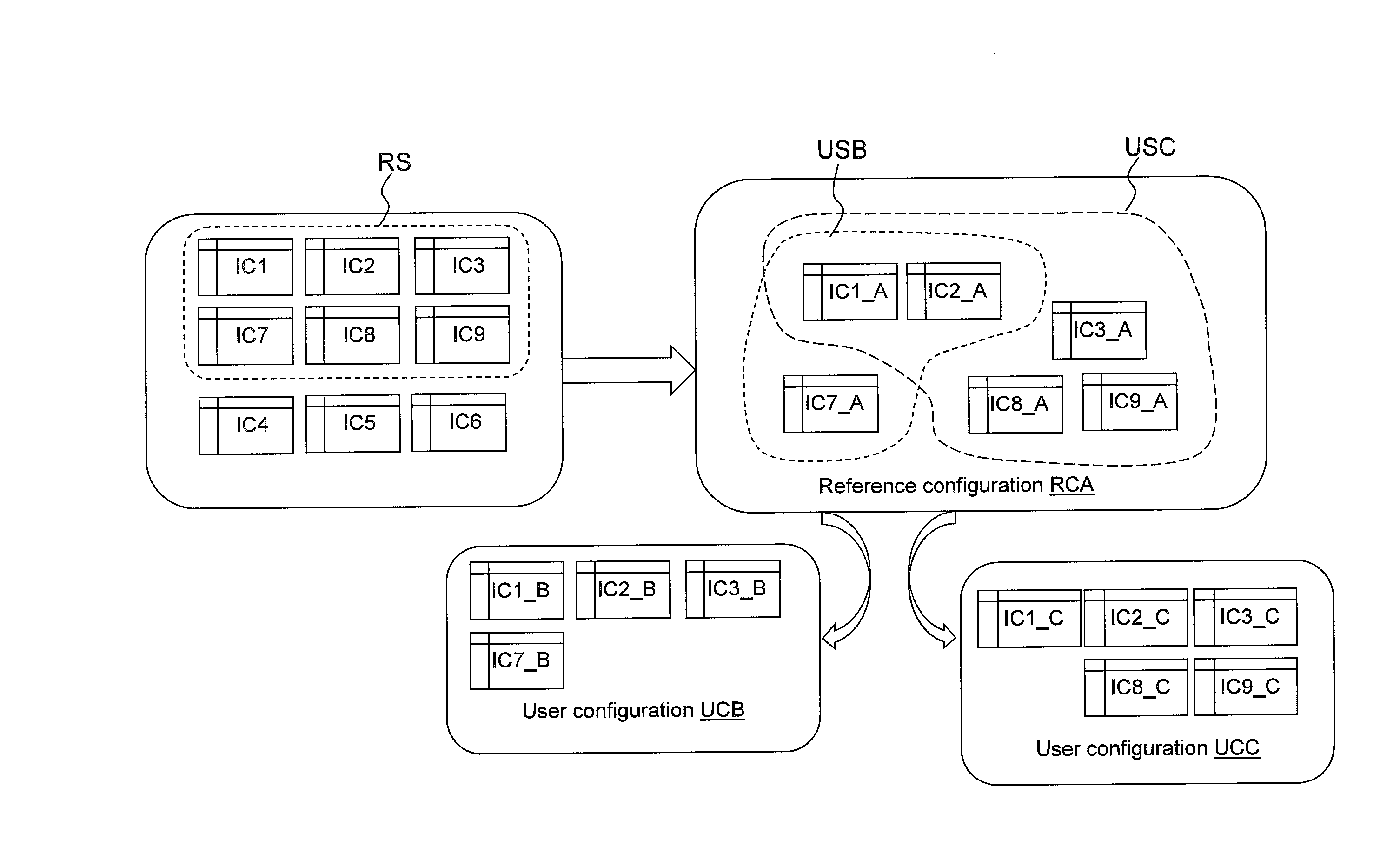
ActiveUS20160299771A1CAD network environmentConstraint-based CADReference configurationComputer science
Collaborative generation of configuration technical data for a product to be manufactured A reference configuration is defined in a main software by a set of reference data vectors, each reference data vector referring to a technical aspect of said product. A reference data vector comprises at least one configuration parameter and / or at least one constraint to be verified by a value assigned to a configuration parameter of a reference data vector. User data vectors are instantiated on the basis of a subset of reference data vectors of the reference configuration and define a user configuration.A software synchronization module 111 running on one said user terminal in the context of an auxiliary software generates at least one value for a parameter associated to a configuration parameter in the main software. The value is assigned to associated configuration parameter of at least one user data vector instantiated in the main software. A compliance check is performed relatively to constraints defined in the main software for the associated configuration parameter. An indicator representative of a result of the compliance check is sent to the software synchronization module 111. A consistency check is performed by comparing values assigned to a same configuration parameter in at least one first modified data vector of the first user configuration and in a second modified data vector of the second user configuration.
Owner:DIGITAL PROD SIMULATION
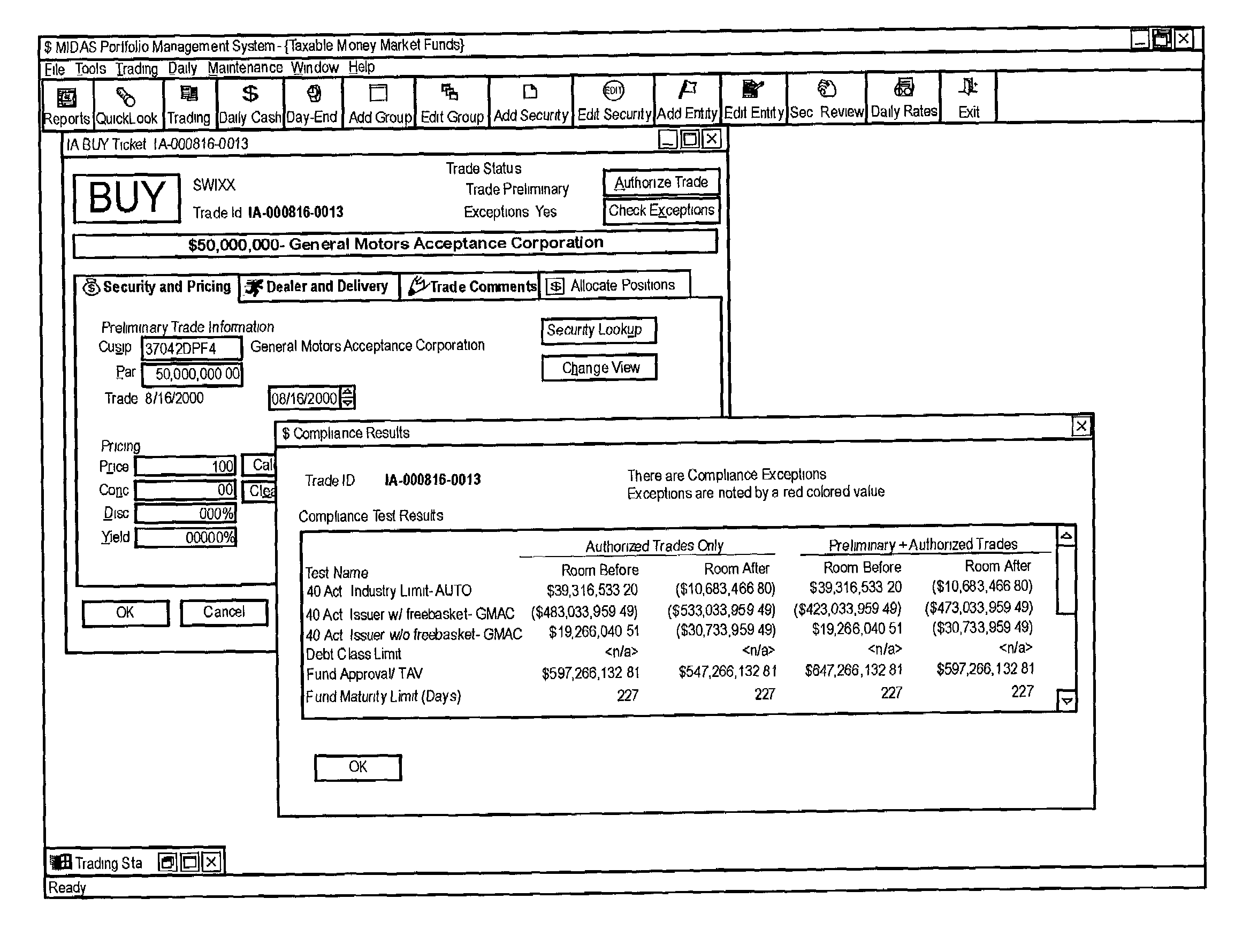
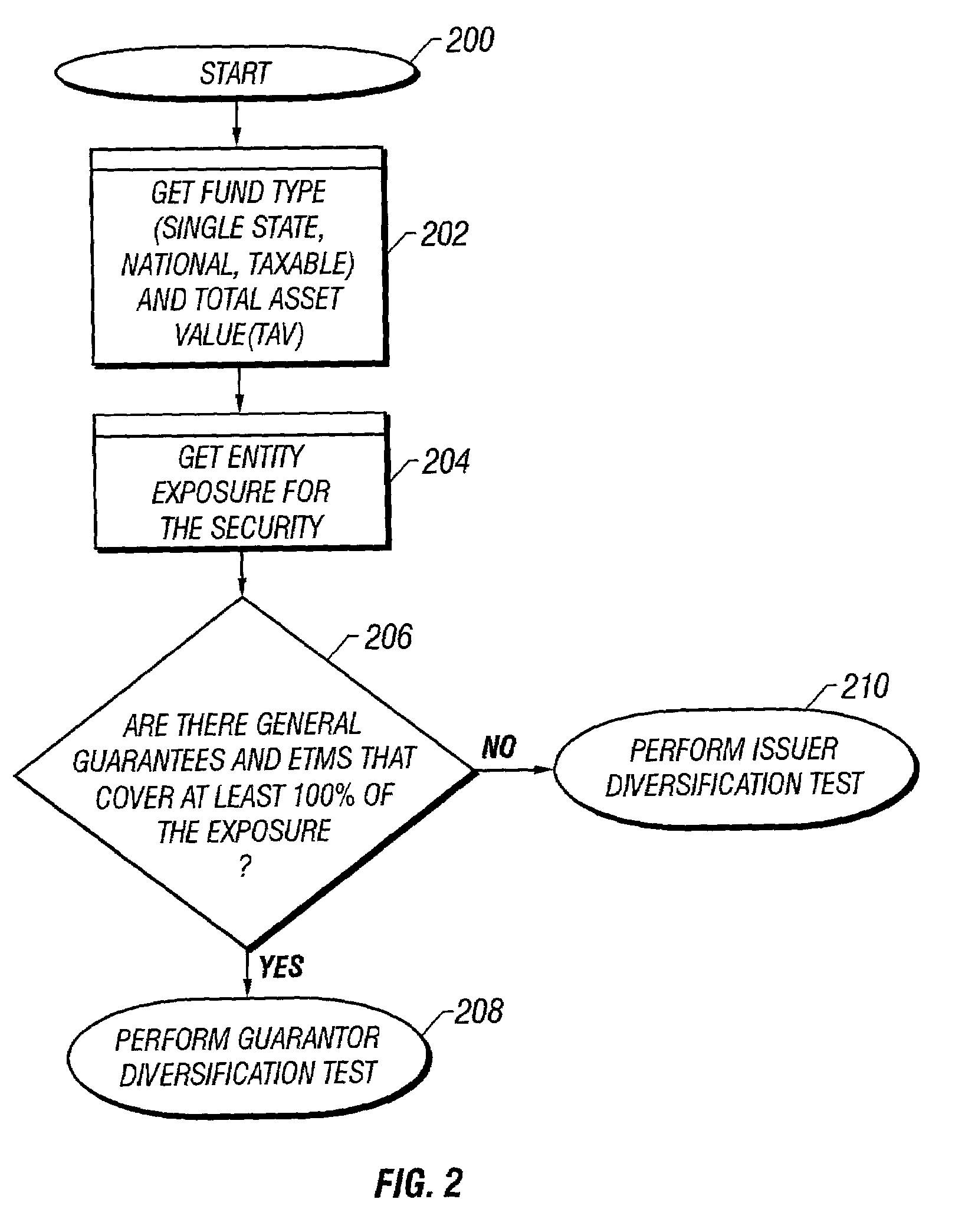
Pre-trade compliance checking in a portfolio management system
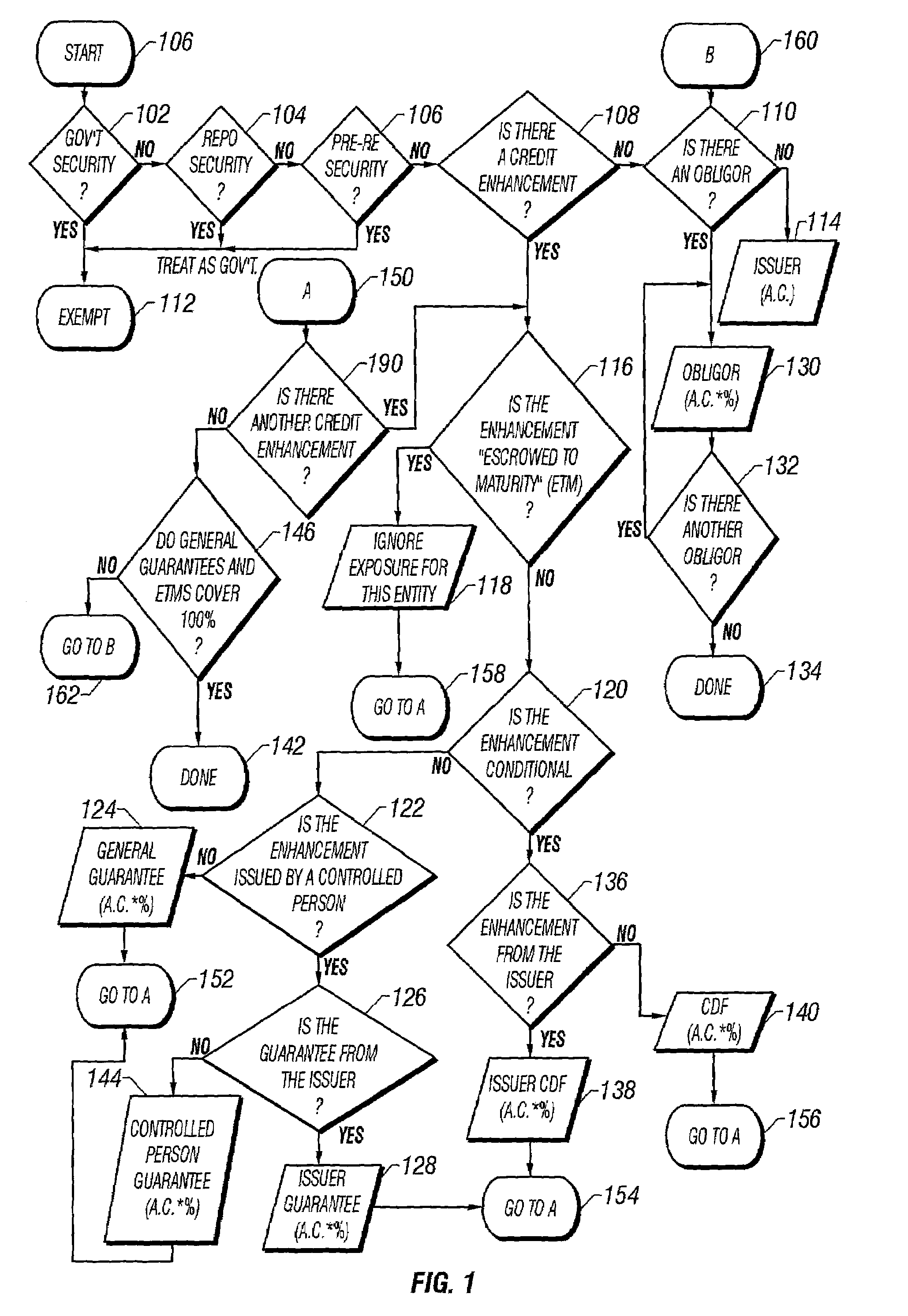
A mechanism for pre-trade compliance checking in a mutual funds portfolio management system is disclosed. The preferred embodiment of the invention records the interpretations and assumptions of each rule and limit. The preferred embodiment of the invention is specifically adapted for compliance with Rule 2a-7. The implementation of Rule 2a-7 is composed of two parts: (1) Determination of Entity Exposure; and (2) Determination of Limits. For each security traded in a money market fund in the portfolio management system, it is necessary to determine the exposure of each entity associated with the security. This exposure is composed of two parts: (1) the role the entity plays in the context of this security; and (2) the amount of exposure (in percentage). With the exposure determined, it is possible to determine where any fund is in relation to Rule 2a-7 limits.
Owner:CHARLES SCHWAB & CO INC
Method and system for computer self-determination of security protocol compliance
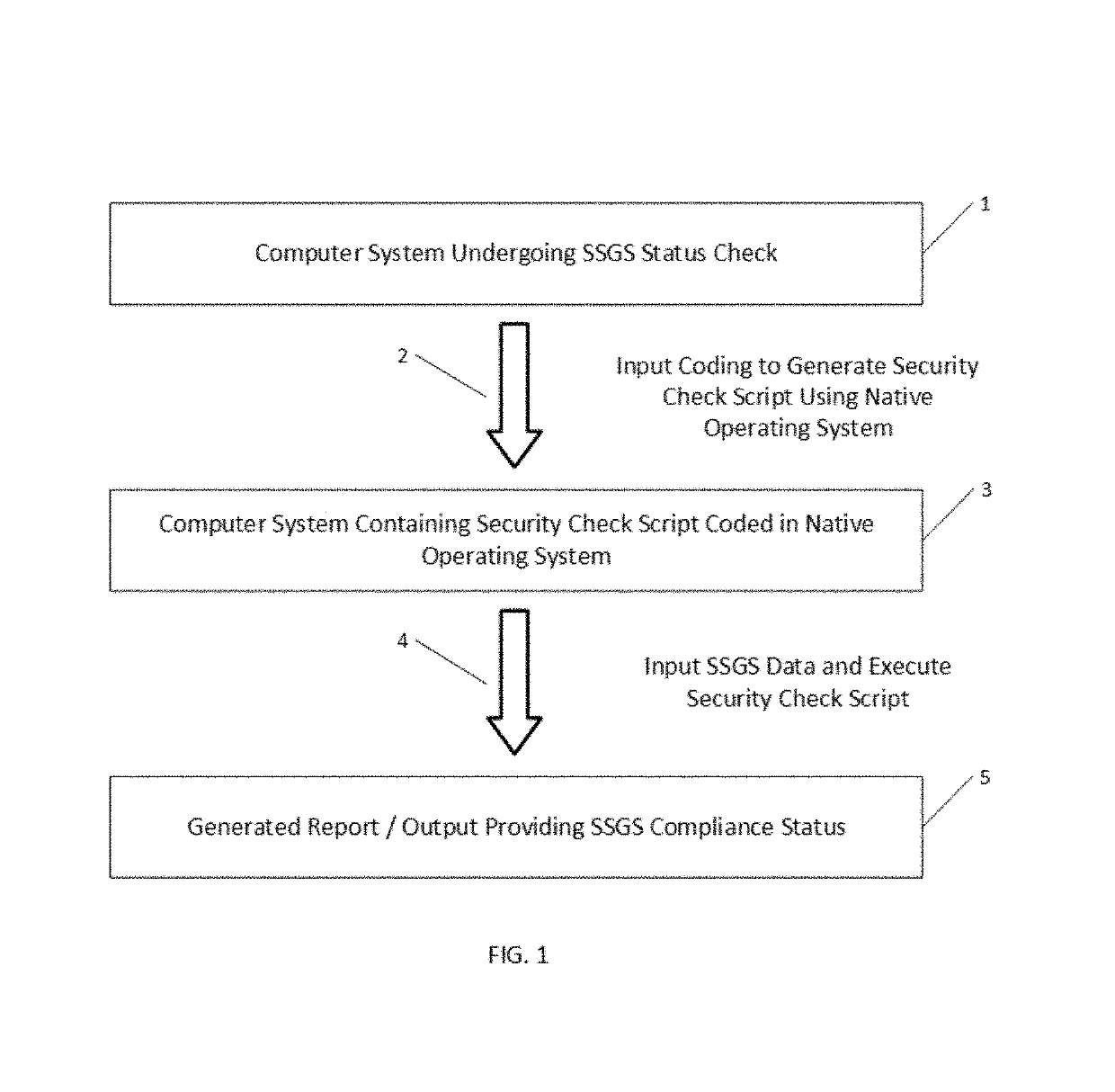
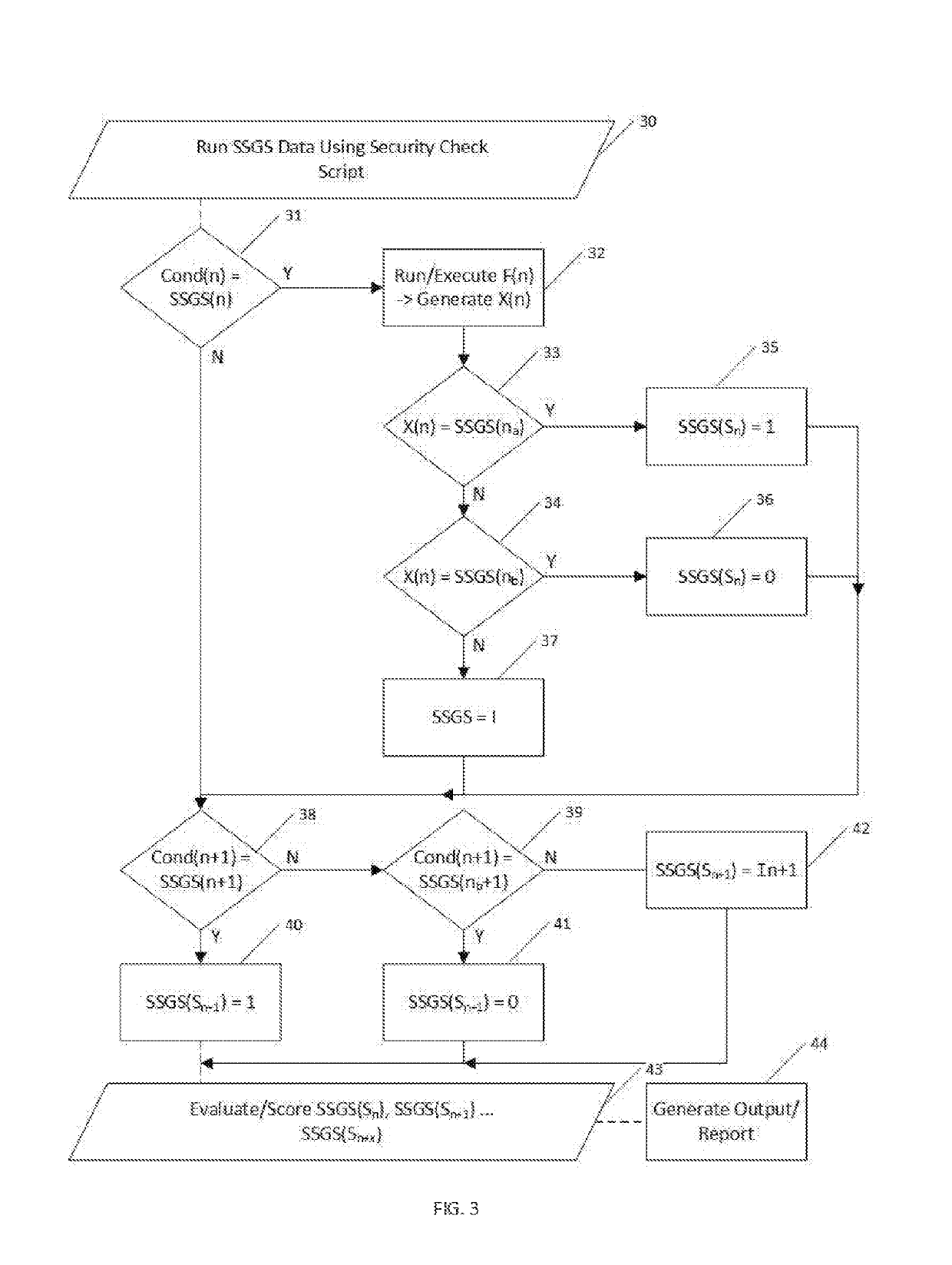
ActiveUS10360408B1Shorten the timeIncrease heightDigital data protectionPlatform integrity maintainanceGuidelineOperational system
A method and system for automating the evaluation of a computer system under a Software Security Guideline Set (SSGS) using the internal scripts and the script generating capability of the computer system under evaluation to perform much of the evaluation of the SSGS. The method and systems arranged in accordance therewith generate a security check script that adds automation to the otherwise laborious process of checking for compliance with an SSGS. By using the systems own software and script generating capabilities the computer system under review is in one sense using its own capability to check itself for compliance with an SSGS. The use of the software and data from the operating system of the computer system under review greatly simplifies the complexity of the programming necessary for such automation of SSGS compliance check, dramatically reducing the lines of code to perform such compliance evaluations. The information provided by this invention enables the owners of such systems to put them in a better state of operation.
Owner:SECURESTRUX LLC
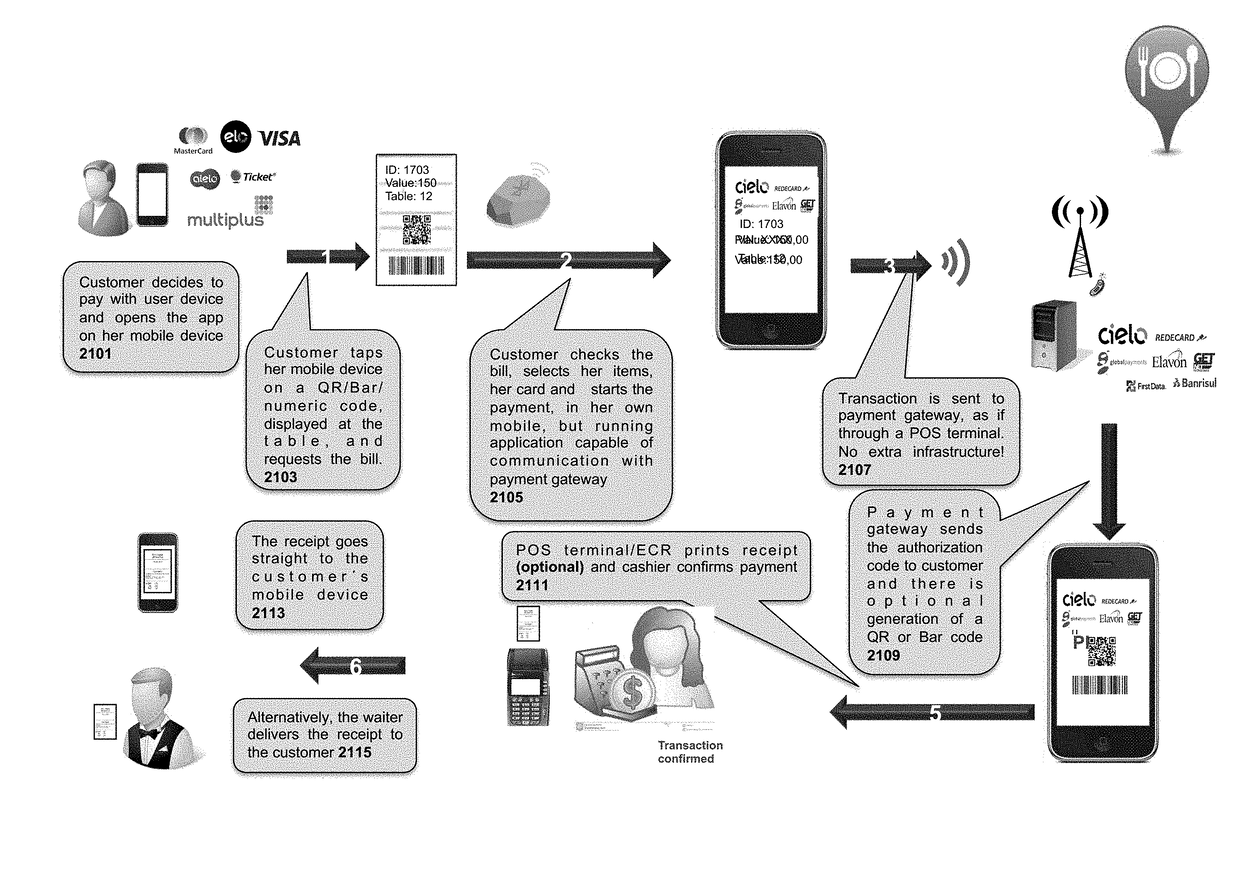
Point of Sale Apparatuses, Methods and Systems
Transformation of inputs including beacon inputs, Global Positioning System (GPS) inputs, captured panorama inputs, user-penned descriptive inputs, and payment-amount-specifying inputs, via components, into outputs including user device POS configuration setting outputs and / or payment-gateway-directed authorization request outputs. Further, transformation of inputs including POS scanner inputs, POS keyboard inputs, and / or POS printer-directed inputs, via components, into outputs including compliance check outputs, tagged omnibus record outputs, SKU-UPC mapping outputs, and / or convergence / correlation outputs. Additionally, transformation of inputs including older limited-capability POS software image inputs and / or newer limited-capability POS software image inputs, via components, into outputs including update directive outputs. Functionality set forth includes allowing user devices to directly communicate with payment gateways, capturing and making use of scanner-obtained data and printer-destined data in a way that does not require code alternation of already-installed POS software, and allowing software of limited-capability POS devices to be updated without sending large, full-overwrite software images.
Owner:IDID TECNOLOGIA LTDA
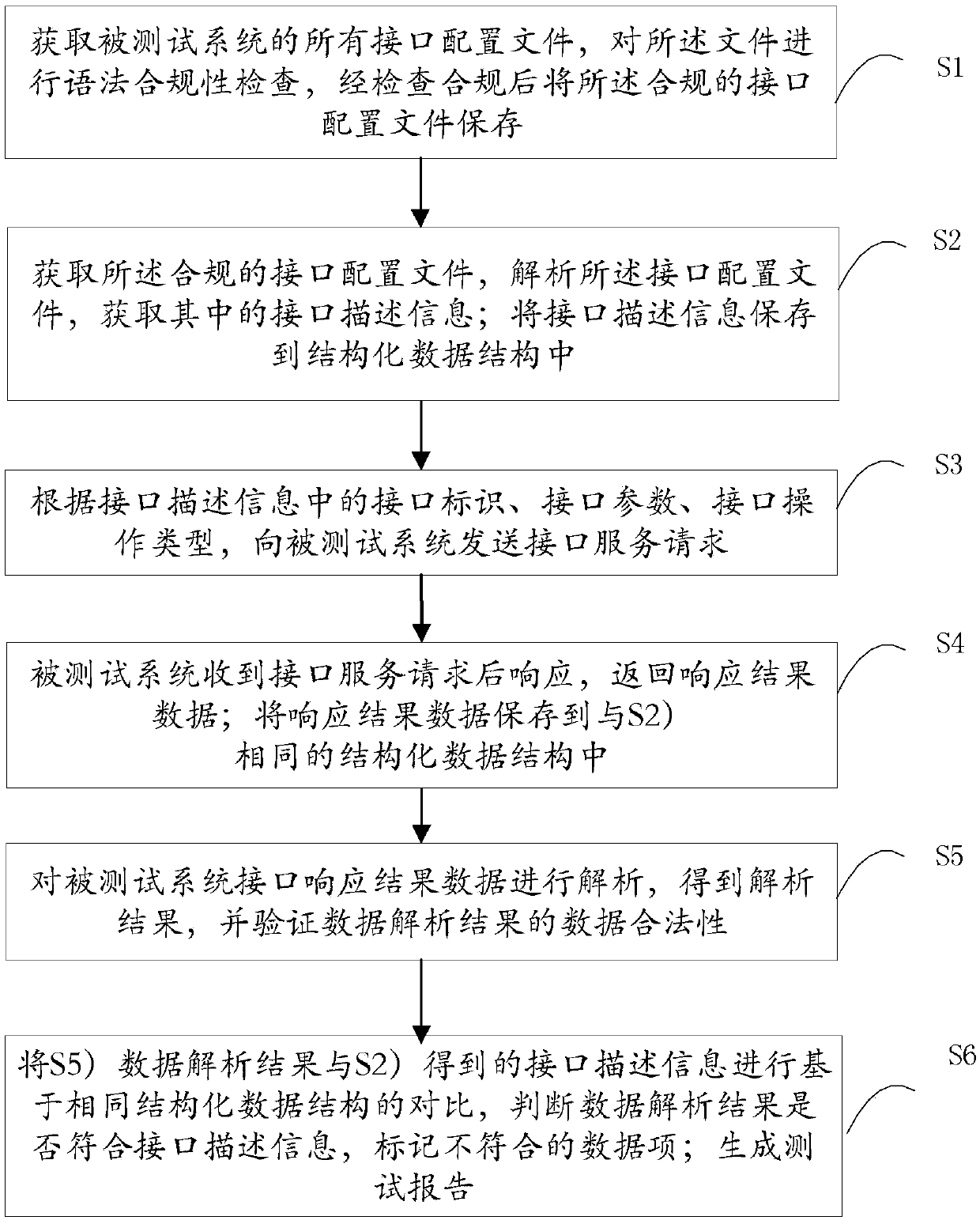
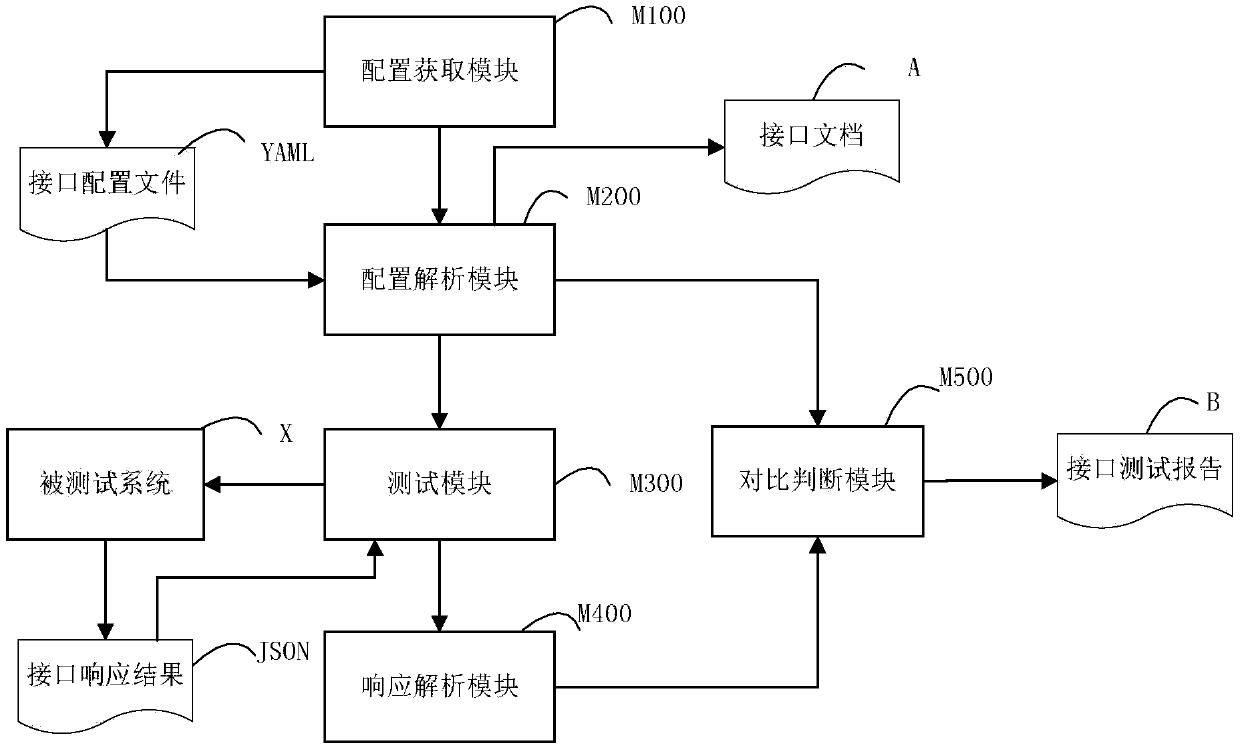
Automatic interface testing method and device
PendingCN110908890AAchieve separationShorten the timeSoftware testing/debuggingSoftware engineeringDocumentation
The invention provides an automatic interface testing method which comprises the following steps: acquiring all interface configuration files of a tested system, and performing grammar compliance check; acquiring the compliant interface configuration file and interface description information in the compliant interface configuration file; generating an interface document; sending an interface service request to the tested system according to the interface identifier, the interface parameter and the interface operation type in the interface description information; enabling the tested system torespond after receiving the interface service request and return an interface response result; analyzing the interface response result data of the tested system, and verifying the data legality of the data analysis result; judging whether the interface response result data conforms to the type of return response result data in the interface description information or not, and marking inconformitydata items; generating interface test reports. In addition, the invention further provides an automatic interface testing device. Efficient butt joint of interface joint debugging is achieved, time is saved, and an interface document is automatically generated.
Owner:BOCO INTER TELECOM
Compliance checking method and device for service recorded sound
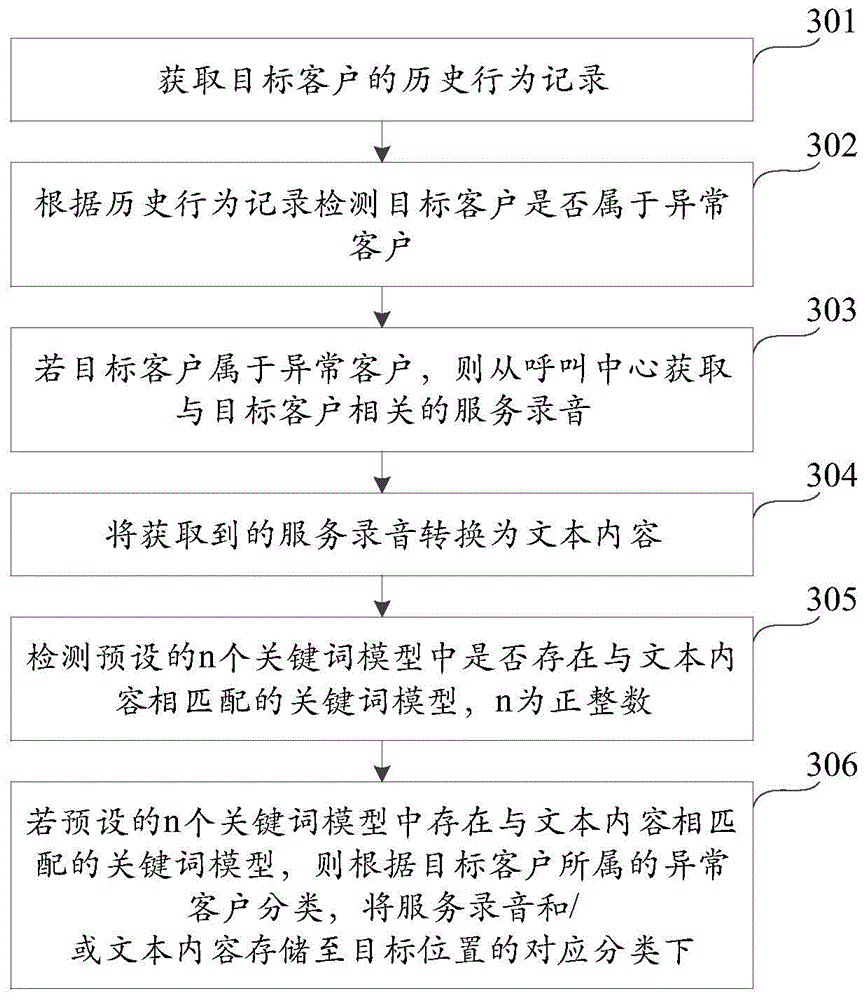
ActiveCN105187674AReduce processingSolve the situationSpecial service for subscribersSupervisory/monitoring/testing arrangementsQuality controlComputer science
The invention discloses a compliance checking method and device for service recorded sound, and belongs to the technical field of communication. The method comprises the following steps: detecting whether a target customer belongs to an unusual customer or not according to a history behavior record of the target customer; if the target customer belongs to the unusual customer, acquiring service recorded sound relevant to the target customer from a call center; converting the service recorded sound into text content; detecting whether the service recorded sound conforms to a service specification or not according to the text content; and if the service recorded sound does not conform to the service specification, storing the service recorded sound and / or the text content to a target location. Through adoption of the compliance checking method and device, the problems of the presence of a large number of missed detection situations and low efficiency due to adoption of a random drawing way in the prior art are solved. On one aspect, the missed detection situations are fully reduced. On the other aspect, the service recorded sound which is detected to be non-conforming service recorded sound is supplied to quality control personnel, and the quality control personnel only needs to perform re-checking, so that the quality control personnel can perform checking in a targeted way, and the checking efficiency is increased.
Owner:上海金大师网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com