Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2111 results about "Exception handling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
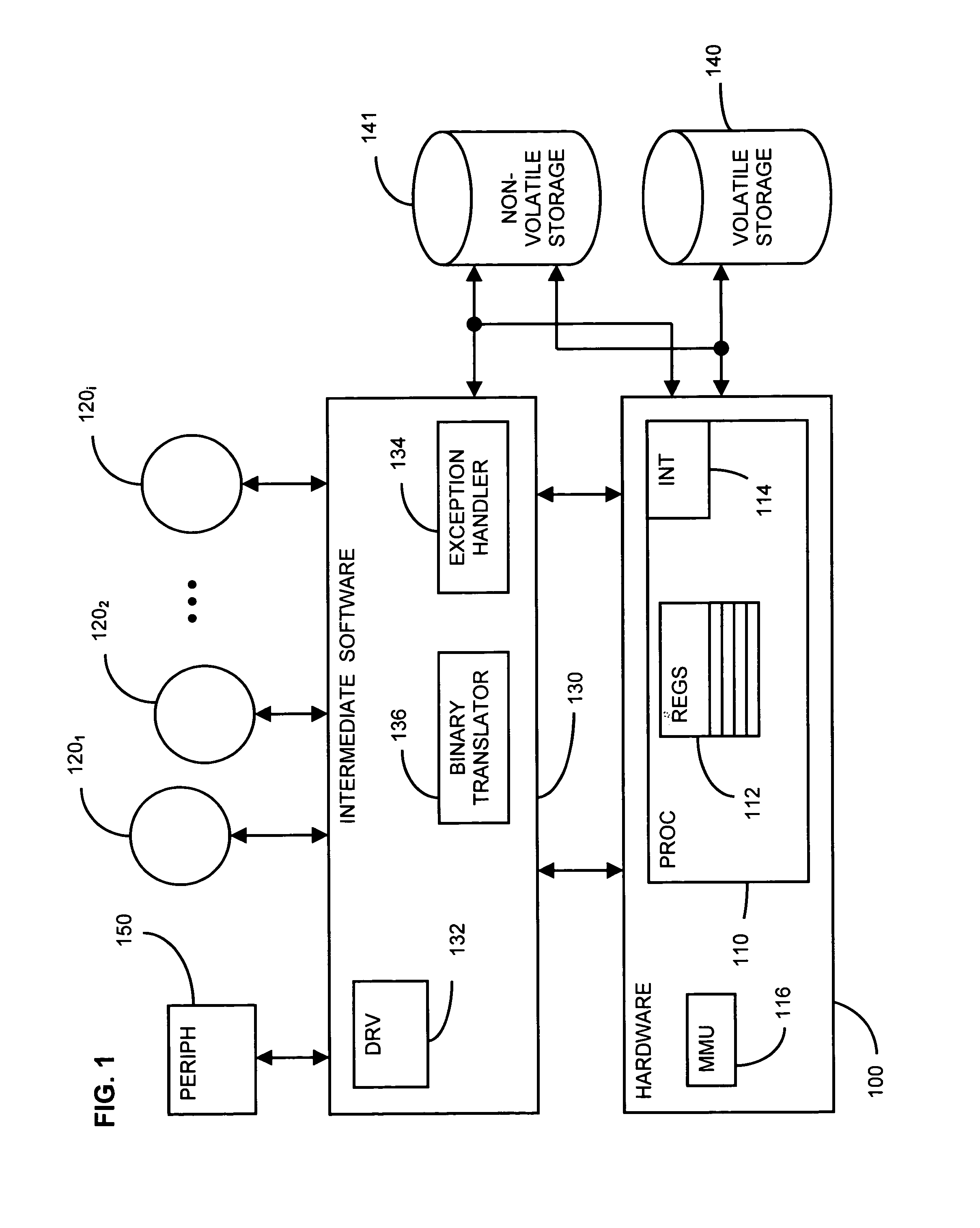
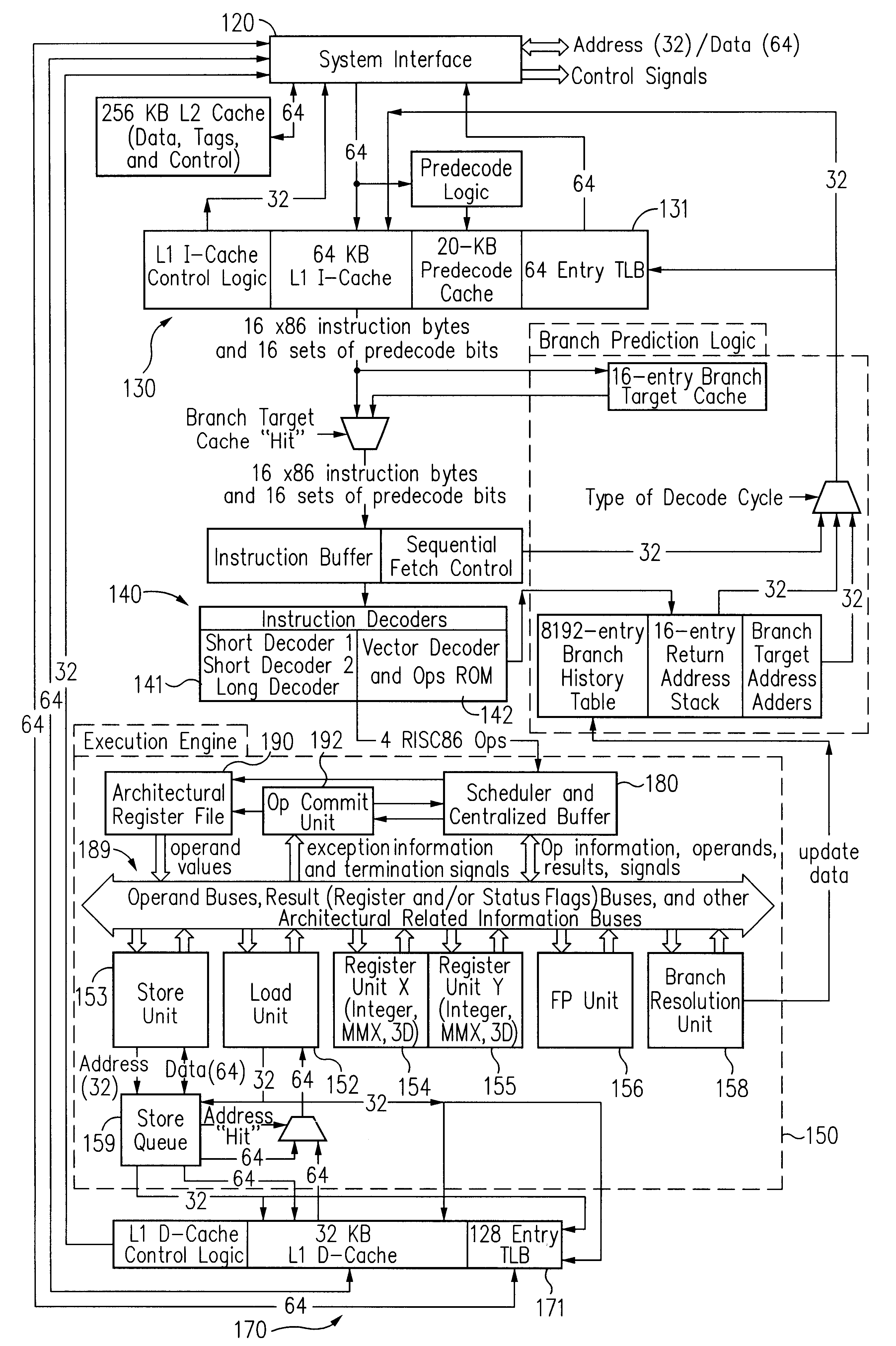
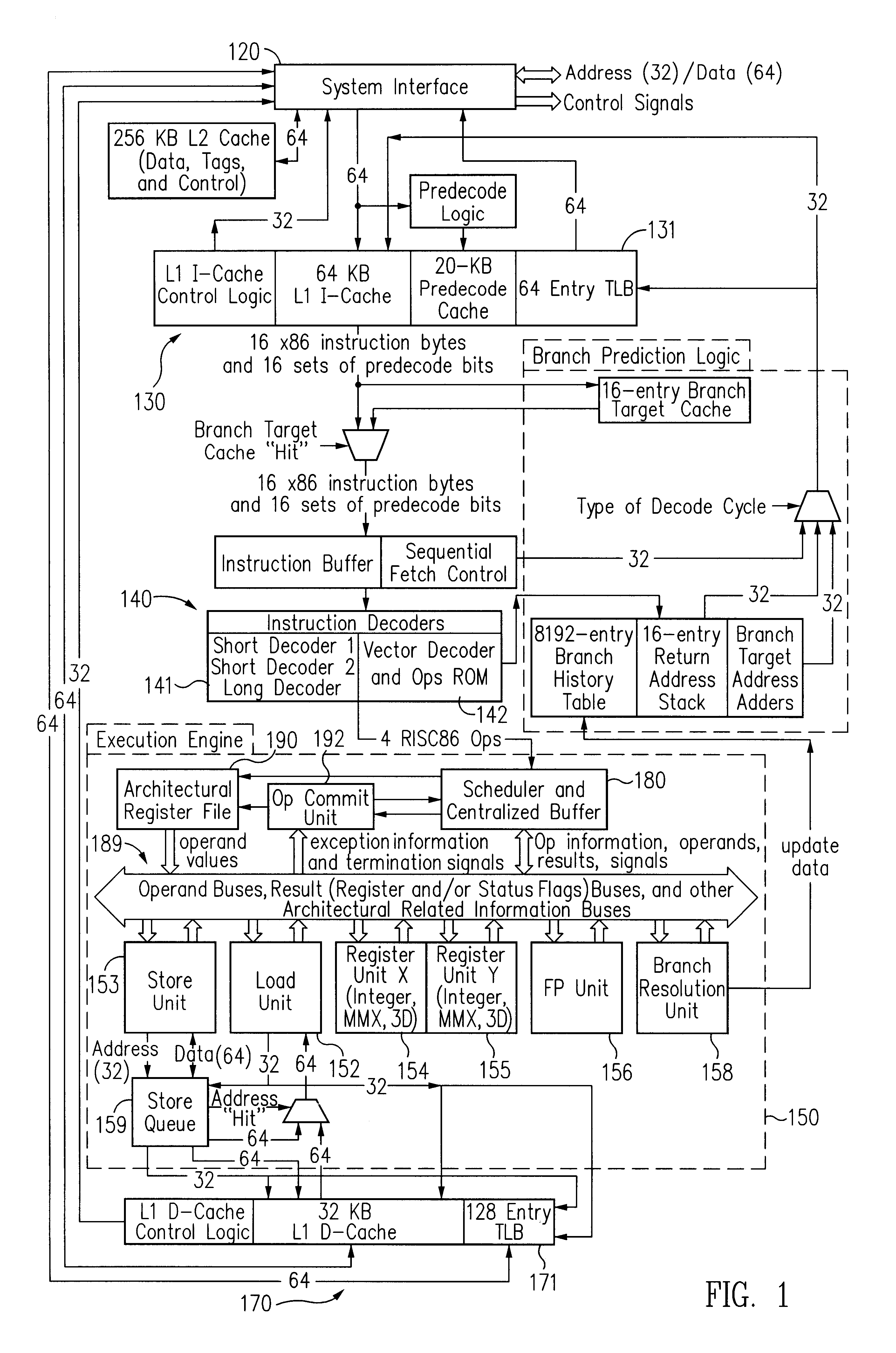
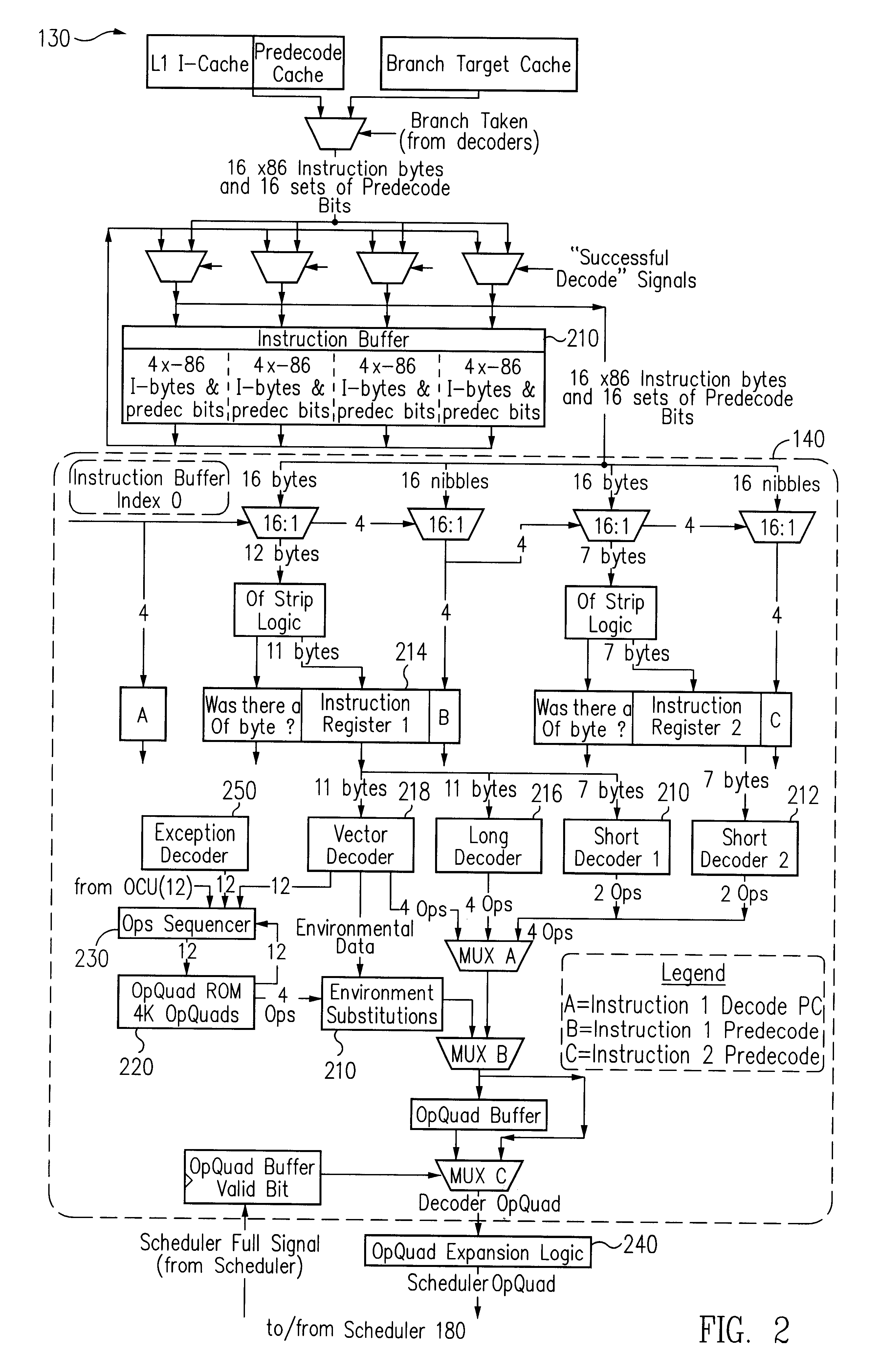
Exception handling is the process of responding to the occurrence, during computation, of exceptions – anomalous or exceptional conditions requiring special processing – often disrupting the normal flow of program execution. It is provided by specialized programming language constructs, computer hardware mechanisms like interrupts or operating system IPC facilities like signals.
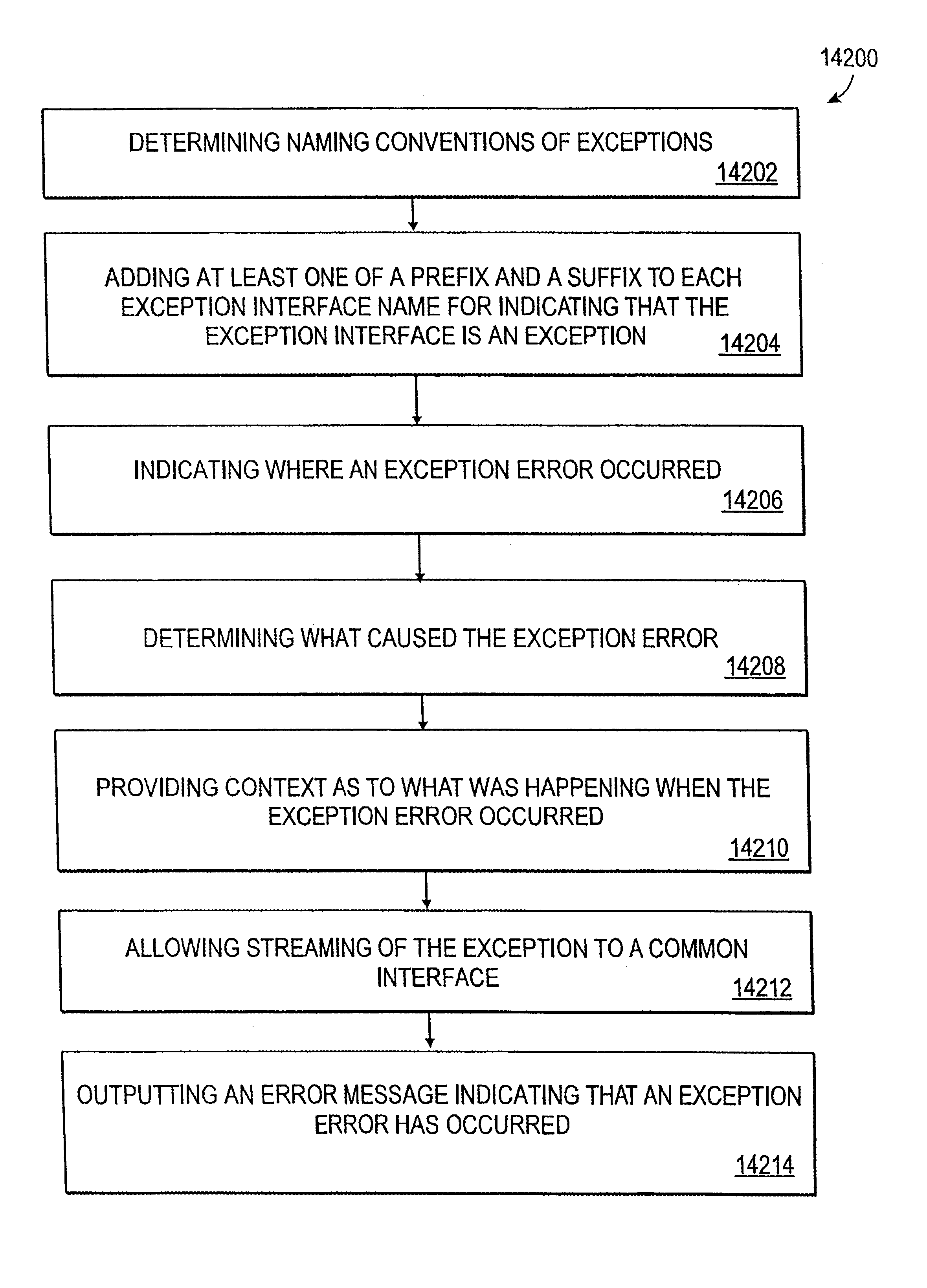
Common interface for handling exception interface name with additional prefix and suffix for handling exceptions in environment services patterns
A system, method and article of manufacture are provided for creating a common interface for exception handling. Naming conventions of exceptions are determined. A prefix and / or a suffix is added to each exception interface name for indicating that the exception interface is an exception. Where an exception error occurred is indicated and a determination is made as to what caused the exception error. Context is provided as to what was happening when the exception error occurred. Streaming of the exception is allowed to a common interface. An error message is outputted indicating that an exception error has occurred.
Owner:ACCENTURE GLOBAL SERVICES LTD
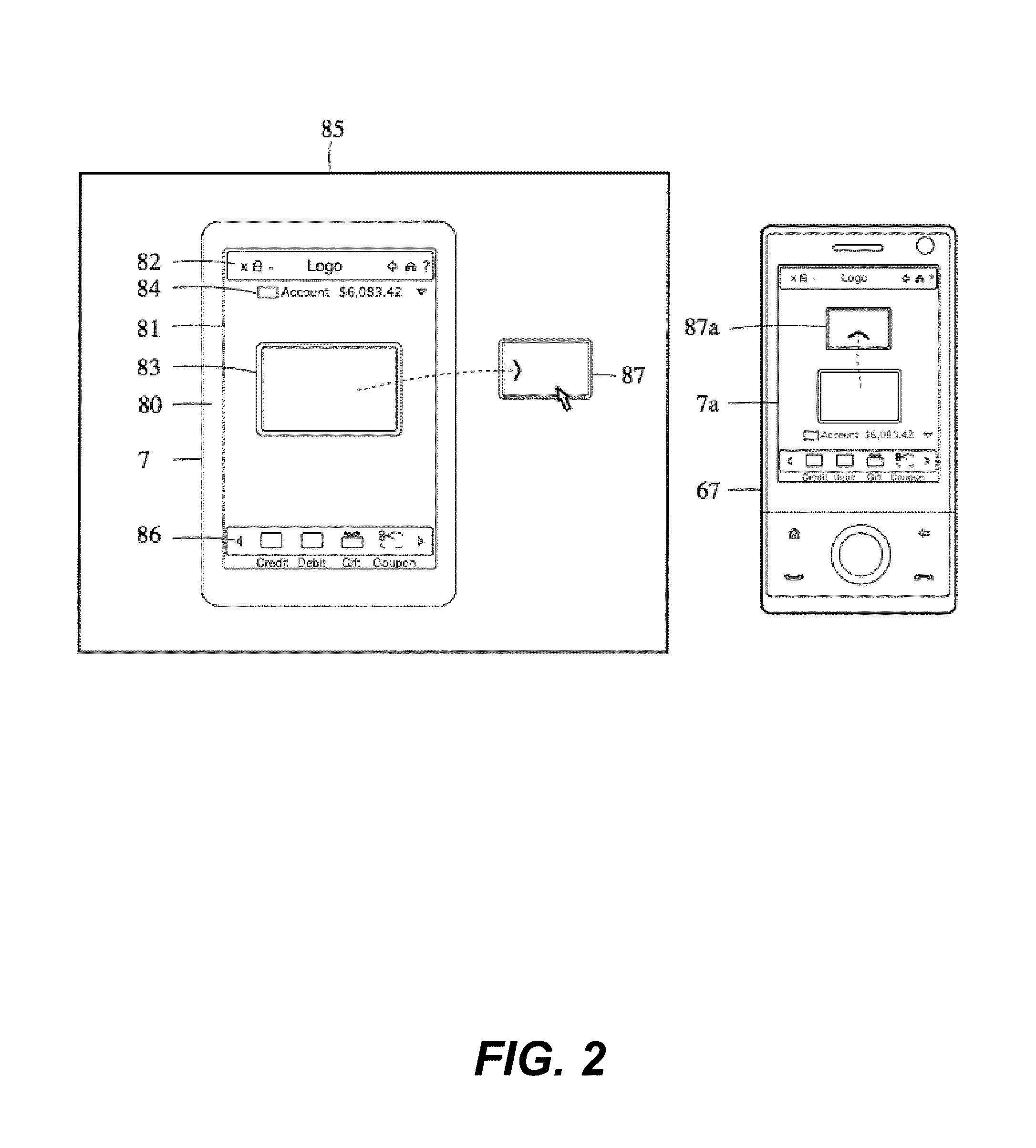
Control system for an RFID-based system for assembling and verifying outbound surgical equipment corresponding to a particular surgery
ActiveUS7492261B2Accurate and rapid processingImprove throughputLogisticsElectric signalling detailsUser inputControl system
A control system for an RFID-based system for assembling and verifying outbound surgical equipment corresponding to a particular surgery. A user enters a identification number of a surgery. The control system queries a database of surgery information and outputs a list of required surgical equipment, such as surgical instrument sets. An operator uses the list to pick instrument sets for loading into a shipping tote. Each set is tagged with an RFID inventory tag that stores identification information for that set such as a set name and ID number. The shipping tote is passed through an RFID reader and identification data read from the tags is compared against the identification data for sets required for that surgery. A status indicator is activated to alert a user as to whether the surgery is complete that is, all expected sets are present, or that exception handling is required. The control system updates a database such as an ERP system to reflect that the surgery including the required sets has shipped—and the sets are inventoried out to the intended recipient.
Owner:WARSAW ORTHOPEDIC INC
Dispensing digital objects to an electronic wallet
A configuration system and method is disclosed that includes a unified and integrated configuration that is composed of a payment system, an advertising system, and an identity management system such that the unified system has all of the benefits of the individual systems as well as several additional synergistic benefits. Also described are specific configurations including the system's access point architecture, visual wallet simulator user interface, security architecture, coupon handling as well as the system's structure and means for delivering them as targeted advertising, business card handling, membership card handling for the purposes of login management, receipt handling, and the editors and grammars provided for customizing the different types of objects in the system as well as the creation of new custom objects with custom behaviors. The configurations are operable on-line as well as through physical presence transactions.
Owner:GOOGLE LLC
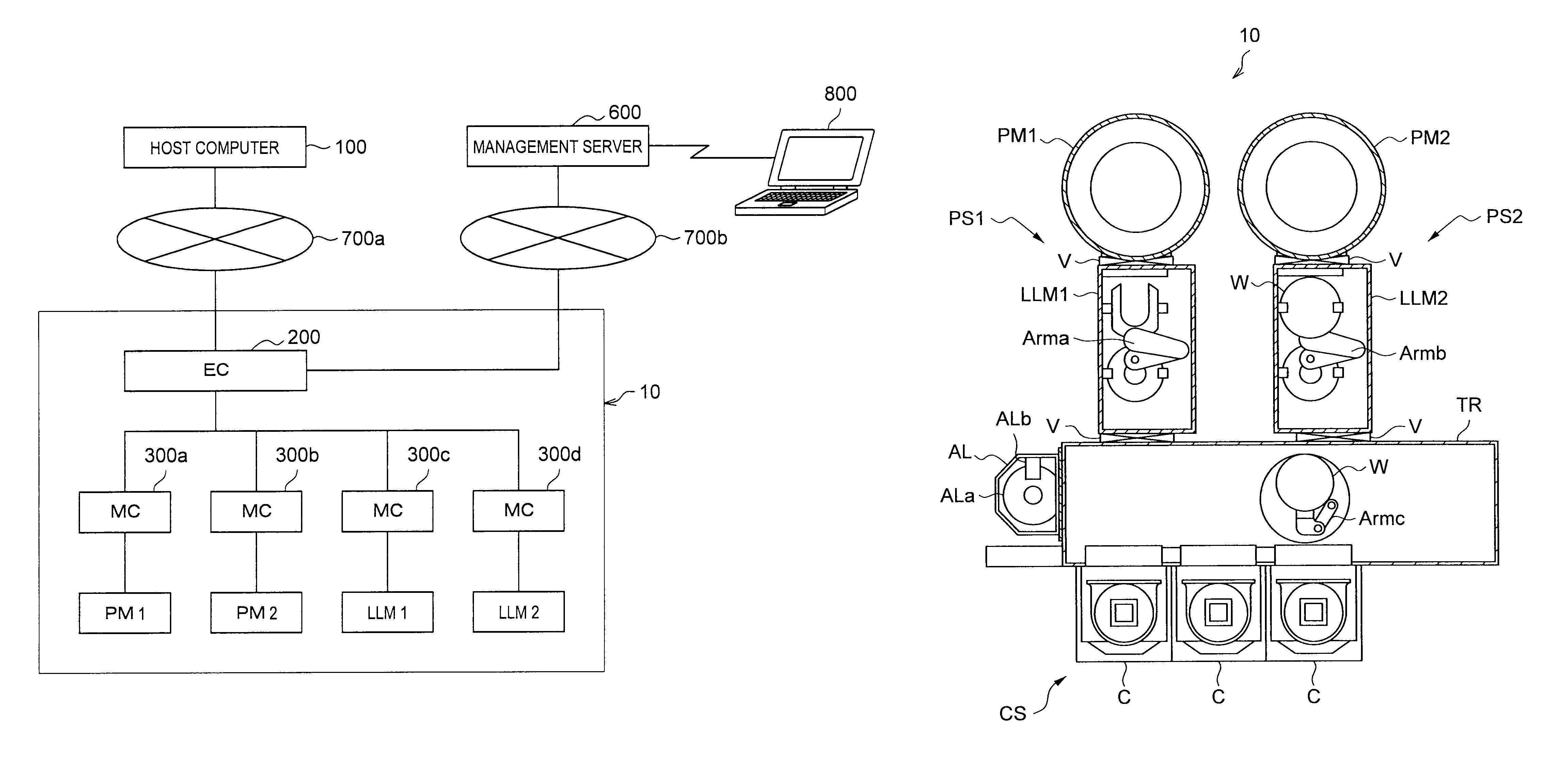
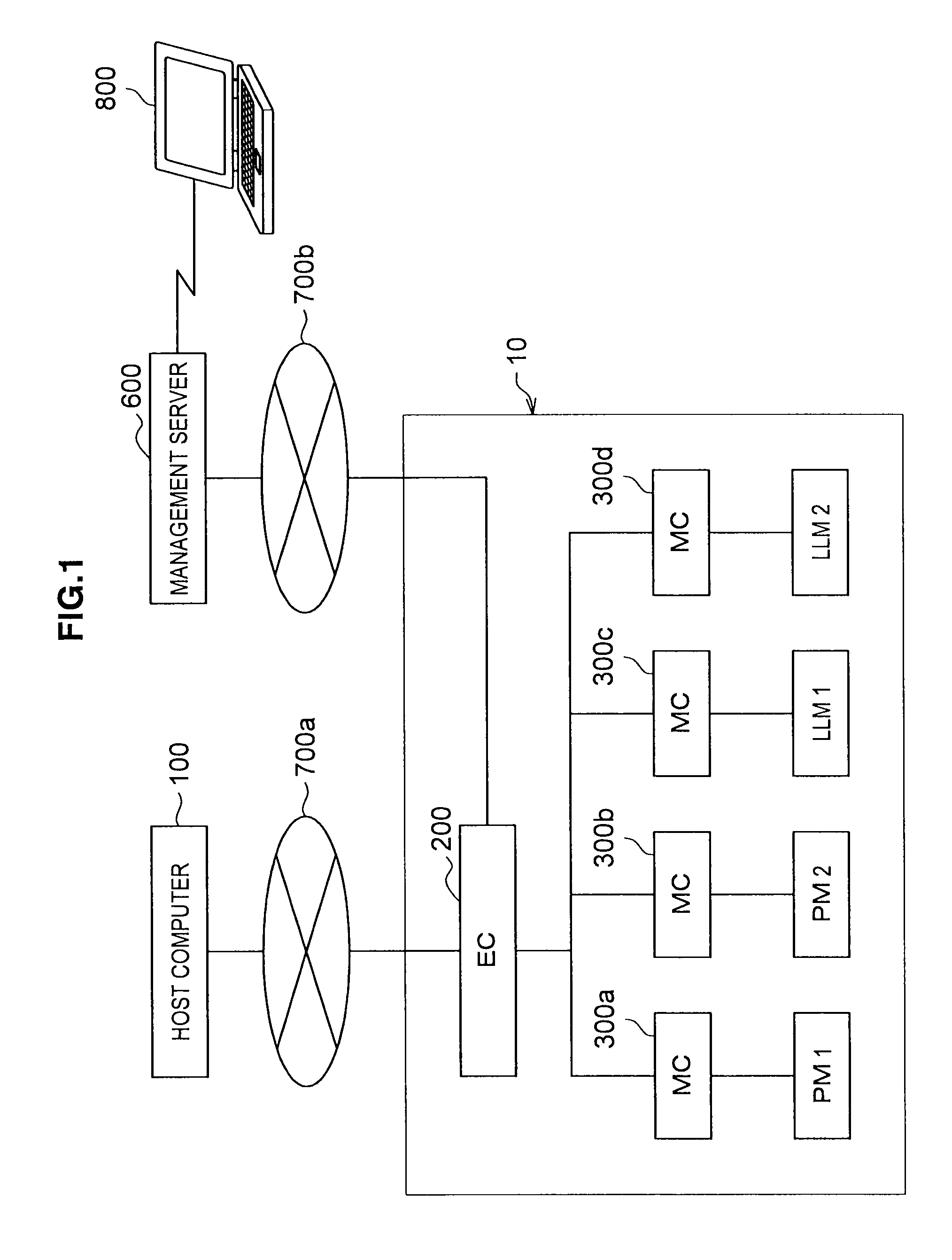
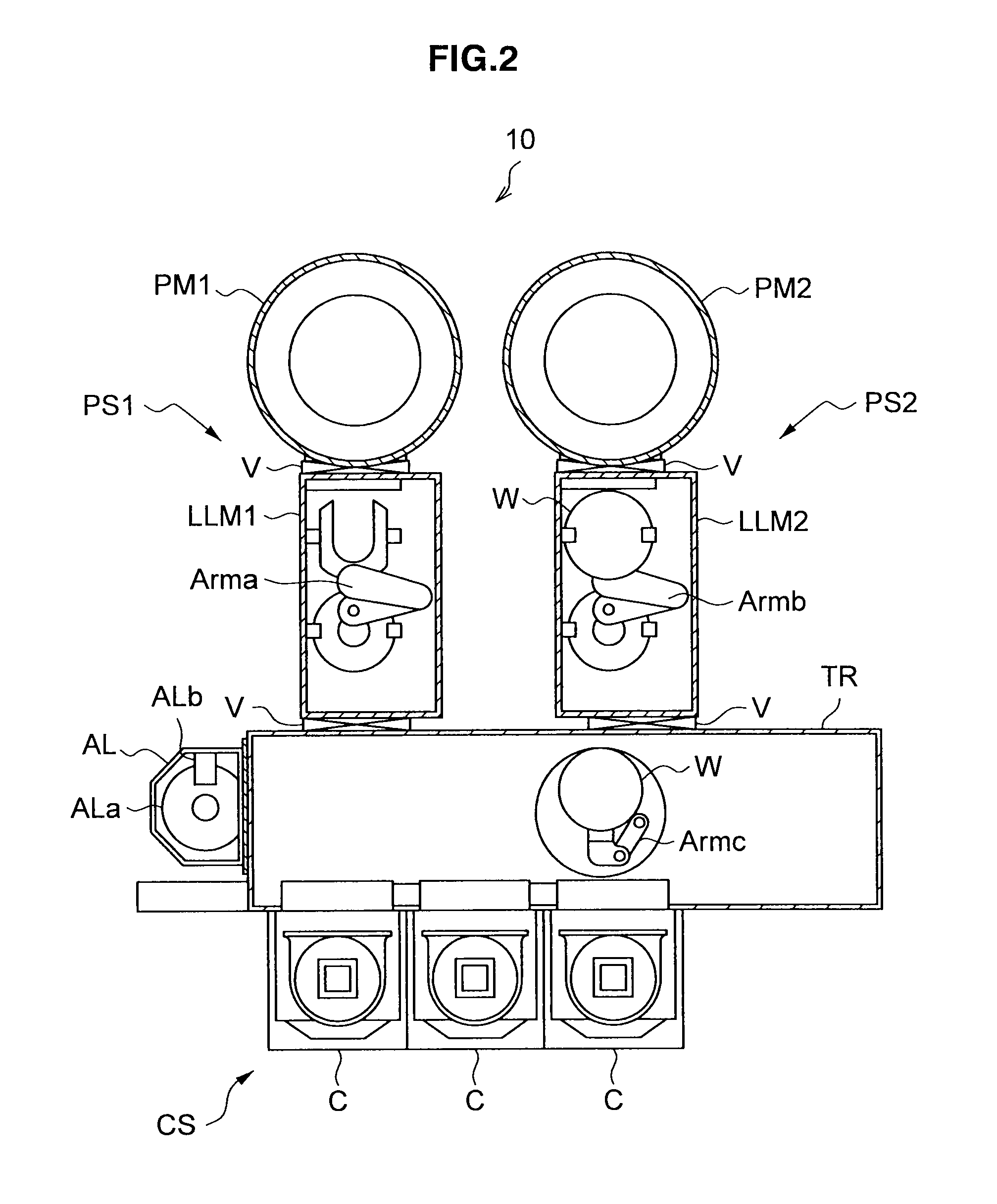
Device for controlling processing system, method for controlling processing system and computer-readable storage medium stored processing program
ActiveUS8055378B2Production of product can be suppressedIncrease productionProgramme controlDigital data processing detailsProcess moduleComputer module
A processing system includes process modules, load lock modules, an equipment controller, and a machine controller. The equipment controller controls transfer and processing of wafers in the processing system. A transfer destination determining portion determines the transfer destination of each wafer such that each wafer is sequentially transferred to a normally operating process module. When an abnormality occurs in a process module, an evacuation portion temporarily evacuates to a cassette stage the wafer determined is to be transferred to the abnormal process module and that has not yet been transferred to the abnormal process module. When a new transfer destination of the evacuated wafer is determined, if a process that is performed immediately before processing the evacuated wafer in the processing module as the new transfer destination satisfies a predetermined condition, a transfer inhibition portion inhibits the transfer of the evacuated wafer to the new transfer destination.
Owner:TOKYO ELECTRON LTD
Apparatus for performing storage virtualization
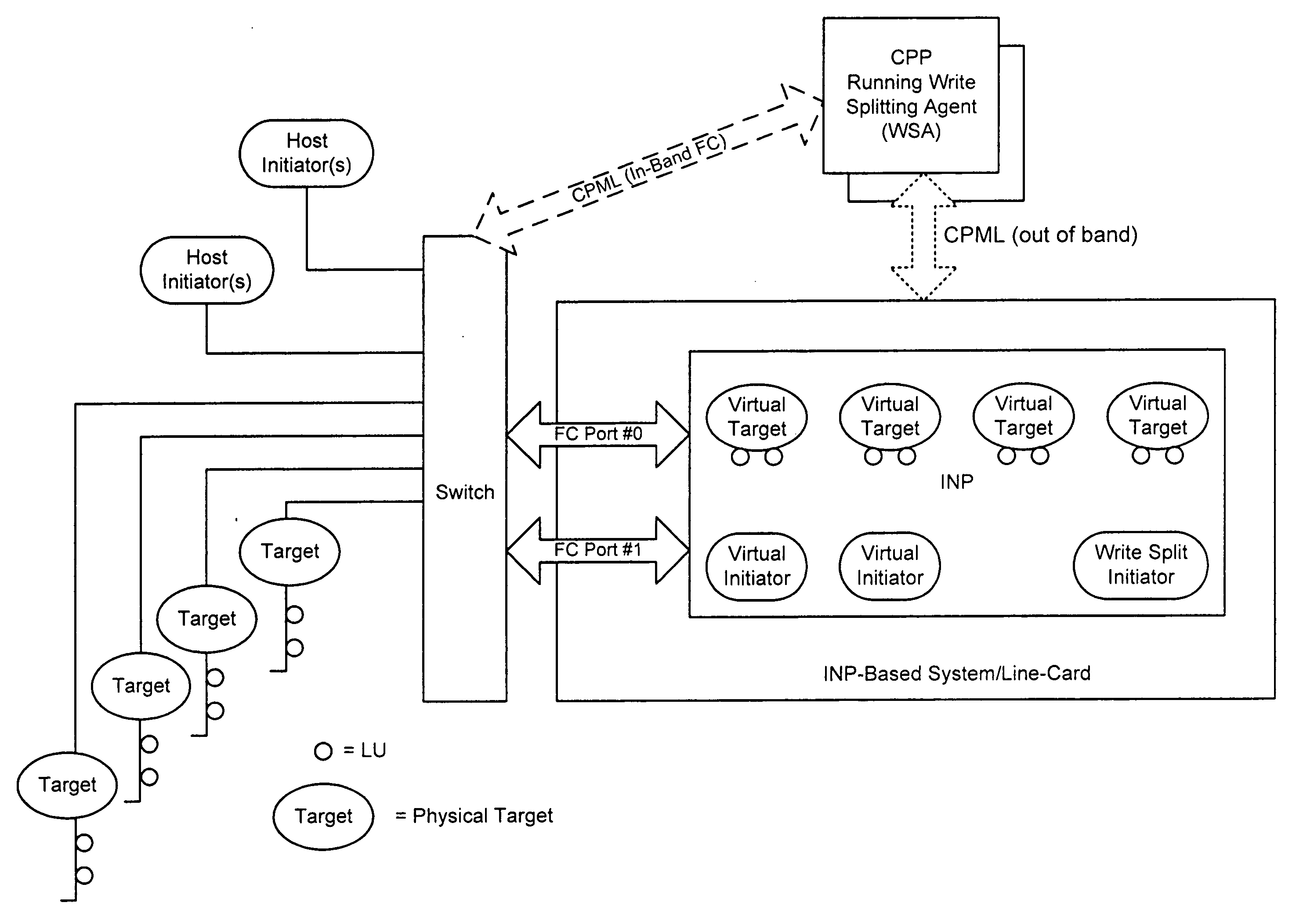
ActiveUS20070239944A1Simplify writingIncrease overheadError detection/correctionMemory adressing/allocation/relocationVirtual targetData management
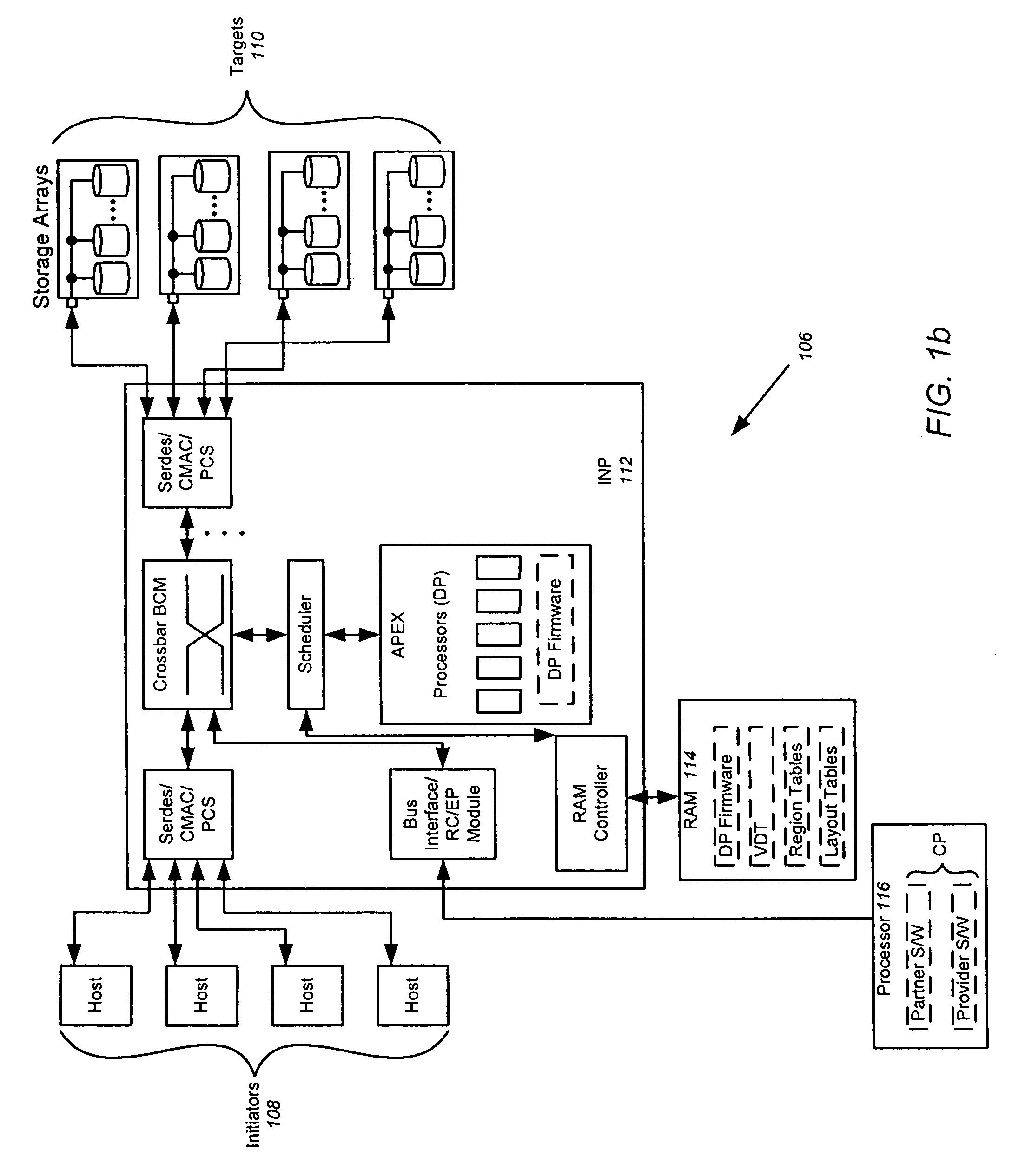
The splitting of storage applications and functions into a control path (CP) component and a data path (DP) component is disclosed. Reads and writes may be handled primarily in the DP. The CP may be responsible for discovery, configuration, and exception handling. The CP can also be enabled for orchestrating complex data management operations such as snapshots and migration. Storage virtualization maps a virtual I / O to one or more physical I / O. A virtual target (vTarget) in the virtual domain is associated with one physical port in the physical domain. Each vTarget may be associated with one or more virtual LUNs (vLUNs). Each vLUN includes one or more vExtents. Each vExtent may point to a region table, and each entry in the region table may contain a pointer to a region representing a portion of a pExtent, and attributes (e.g. read / write, read only, no access) for that region.
Owner:AVAGO TECH INT SALES PTE LTD
Taint tracking mechanism for computer security
ActiveUS8510827B1Easy to trackAvoid modificationMemory loss protectionDigital data processing detailsInformation dispersalOperation mode
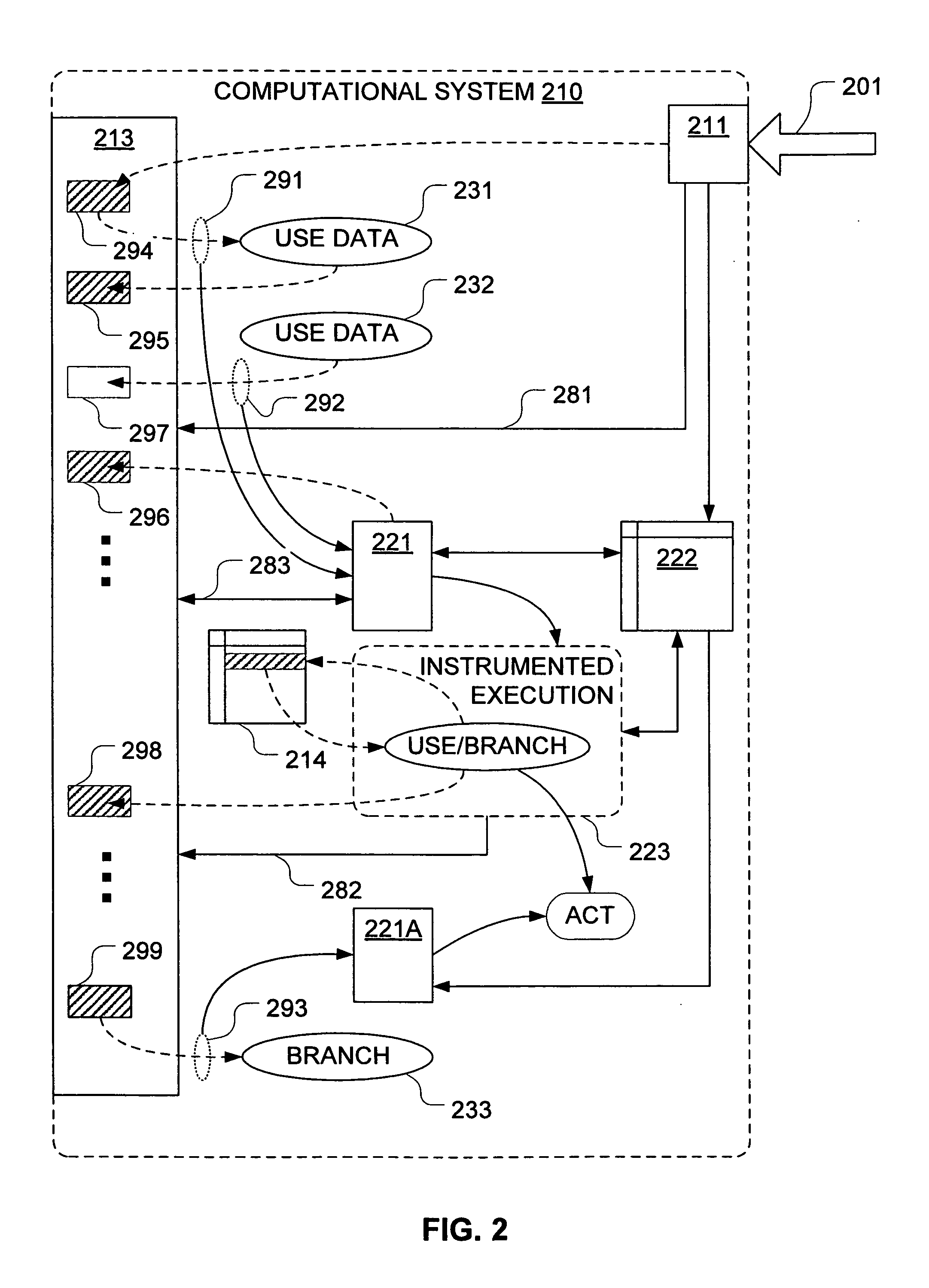
Mechanisms have been developed for securing computational systems against certain forms of attack. In particular, it has been discovered that, by maintaining and propagating taint status for memory locations in correspondence with information flows of instructions executed by a computing system, it is possible to provide a security response if and when a control transfer (or other restricted use) is attempted based on tainted data. In some embodiments, memory management facilities and related exception handlers can be exploited to facilitate taint status propagation and / or security responses. Taint tracking through registers of a processor (or through other storage for which access is not conveniently mediated using a memory management facility) may be provided using an instrumented execution mode of operation. For example, the instrumented mode may be triggered by an attempt to propagate tainted information to a register. In some embodiments, an instrumented mode of operation may be more generally employed. For example, data received from an untrusted source or via an untrusted path is often transferred into a memory buffer for processing by a particular service, routine, process, thread or other computational unit. Code that implements the computational unit may be selectively executed in an instrumented mode that facilitates taint tracking. In general, instrumented execution modes may be supported using a variety of techniques including a binary translation (or rewriting) mode, just-in-time (JIT) compilation / re-compilation, interpreted mode execution, etc. Using an instrumented execution mode and / or exception handler techniques, modifications to CPU hardware can be avoided if desirable.
Owner:VMWARE INC
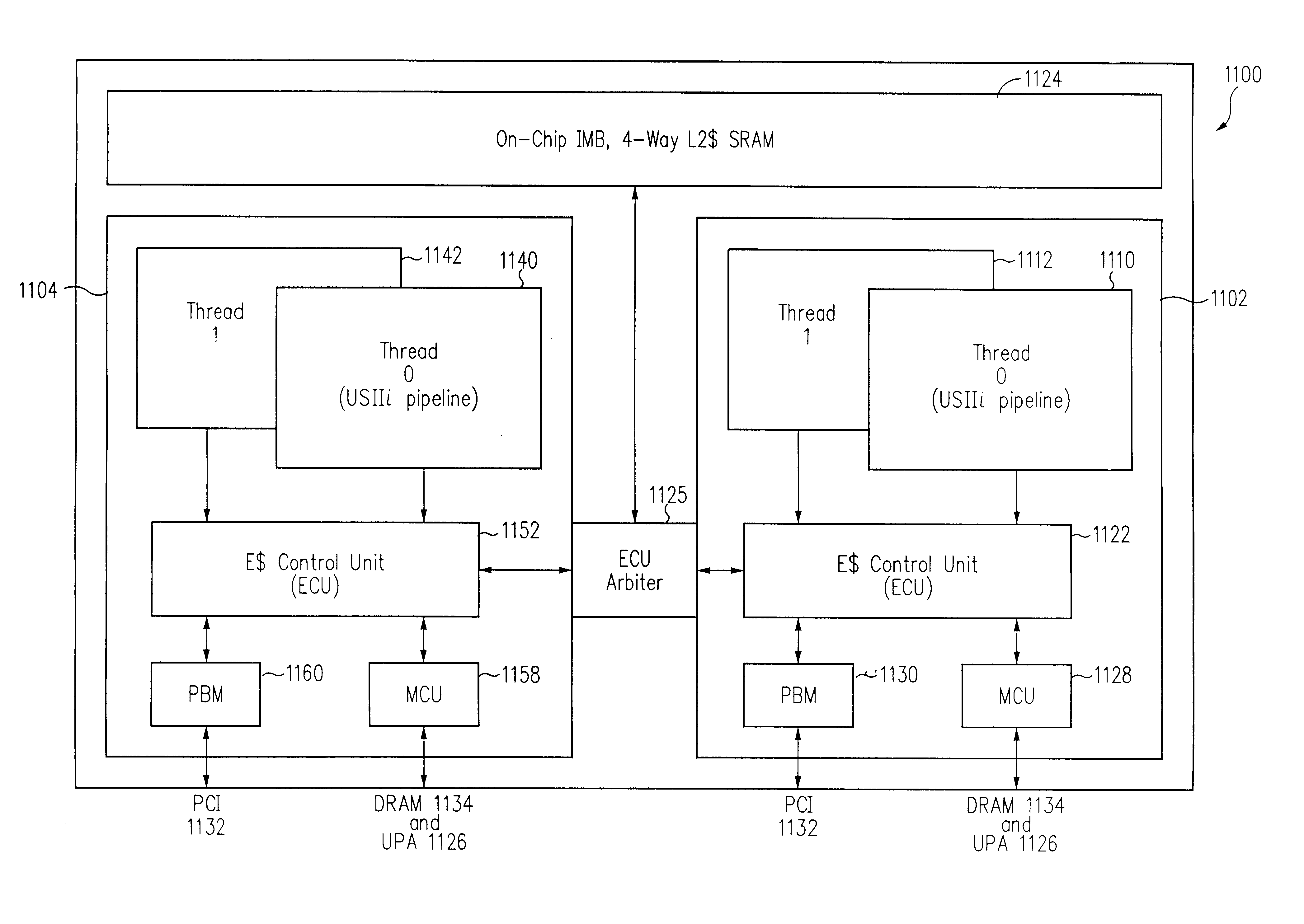
Switching method in a multi-threaded processor
InactiveUS6507862B1Program initiation/switchingDigital computer detailsOperational systemEmbedded system
A processor includes logic for attaining a very fast exception handling functionality while executing non-threaded programs by invoking a multithreaded-type functionality in response to an exception condition. The processor, while operating in multithreaded conditions or while executing non-threaded programs, progresses through multiple machine states during execution. The very fast exception handling logic includes connection of an exception signal line to thread select logic, causing an exception signal to evoke a switch in thread and machine state. The switch in thread and machine state causes the processor to enter and to exit the exception handler immediately, without waiting to drain the pipeline or queues and without the inherent timing penalty of the operating system's software saving and restoring of registers.
Owner:ORACLE INT CORP
Tcp/udp acceleration
ActiveUS20040111523A1Special service provision for substationInput/output to record carriersComputer hardwareComputer science
A method for accelerating TCP / UDP packet switching. The method involves determining whether exception processing is necessary; if not, the packet is forwarded to a special stack for expedited processing. Packets requiring exception processing are forwarded to the conventional stack.
Owner:ORACLE INT CORP
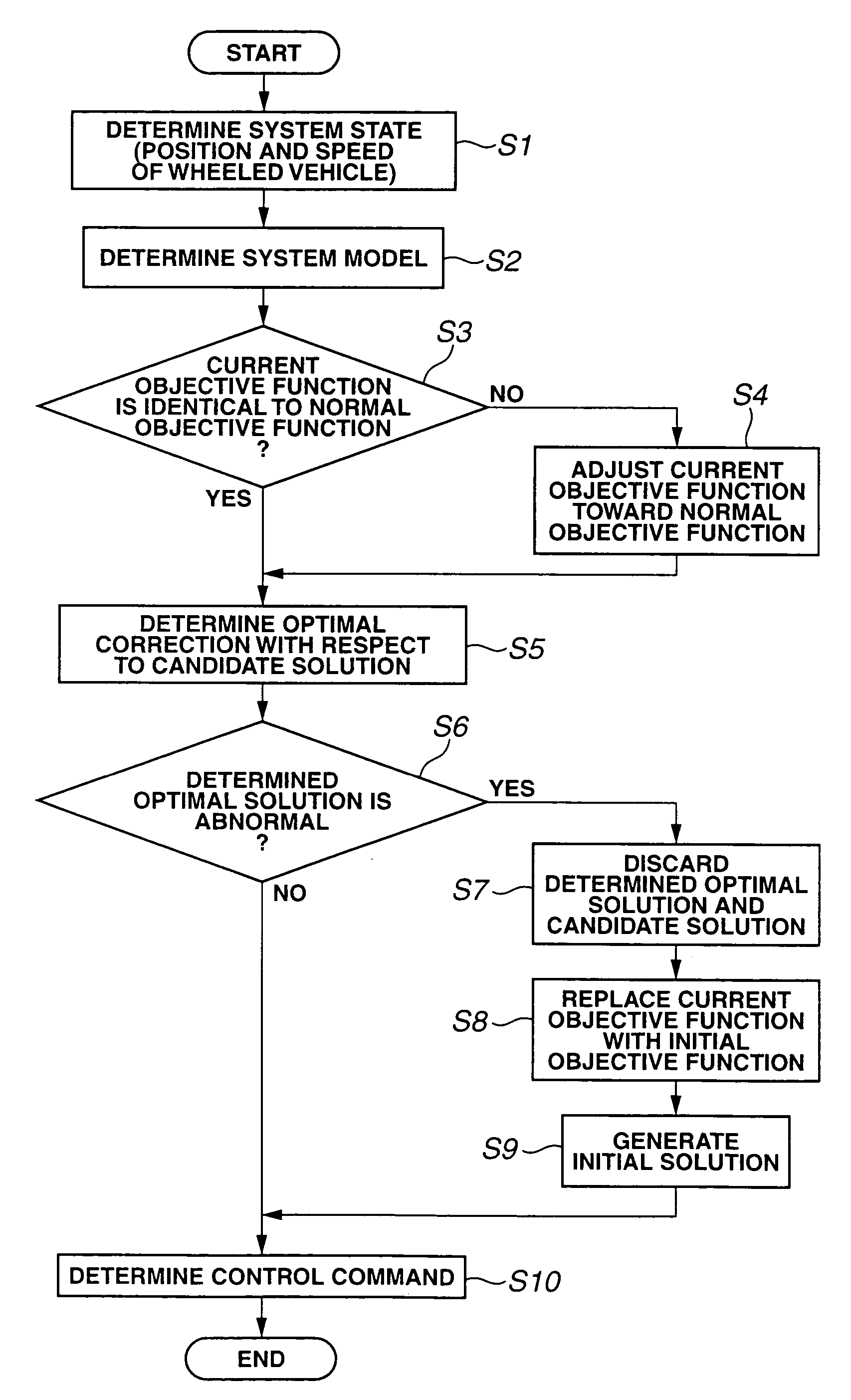
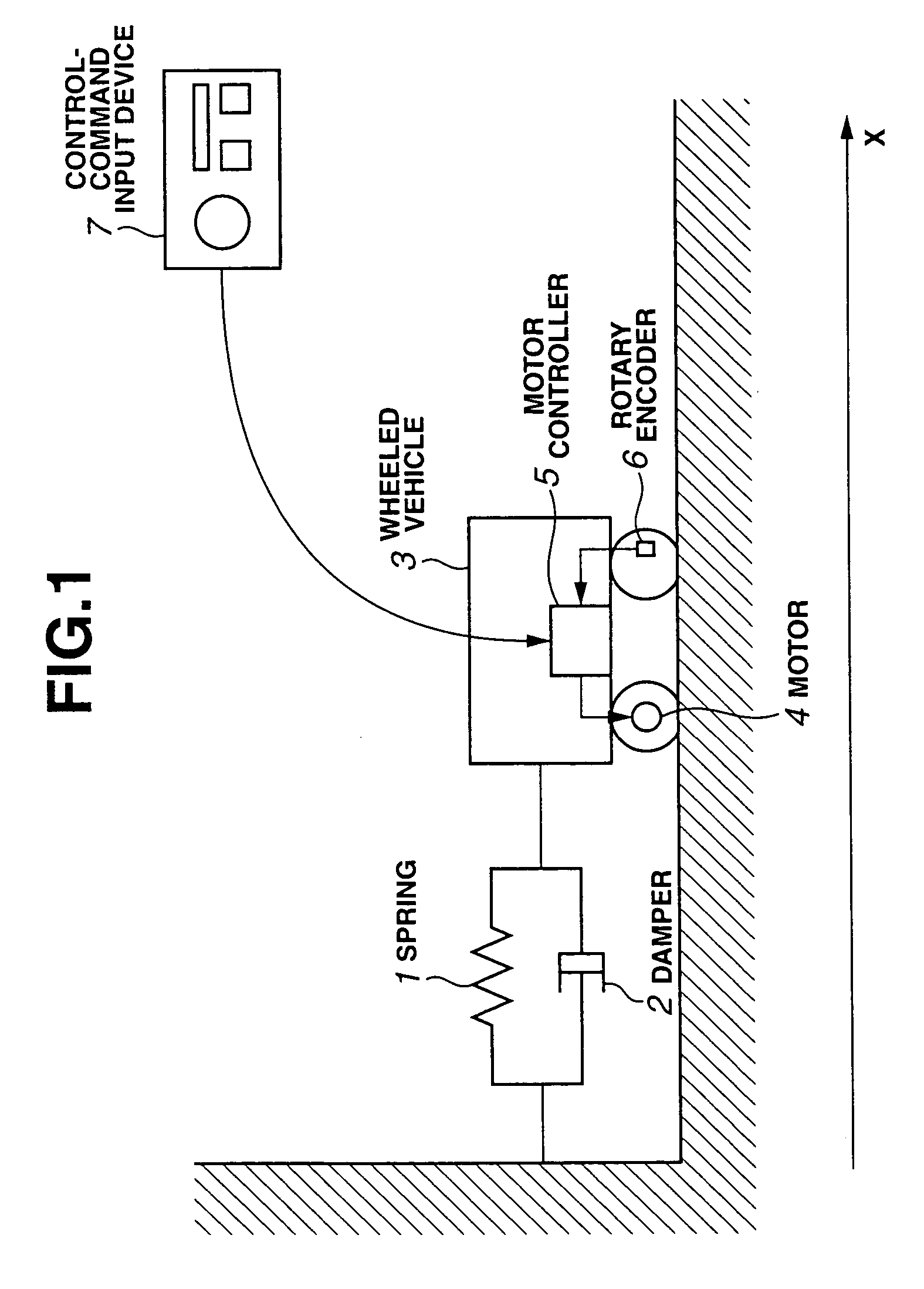
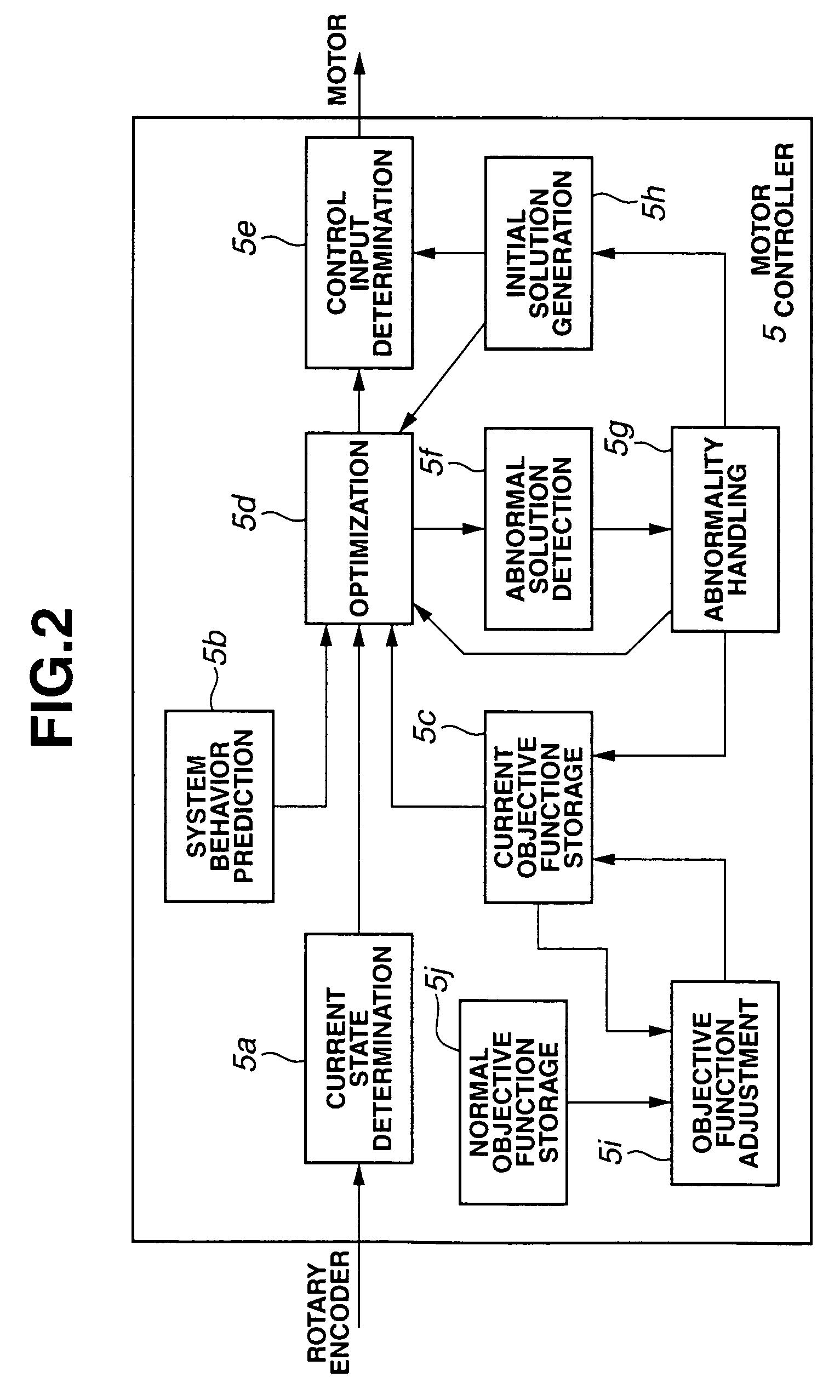
Model predictive control apparatus
InactiveUS7418372B2Quick responseAnalogue computers for vehiclesVehicle fittingsModel predictive controlEngineering
A model predictive control apparatus includes an initial solution generation section, an abnormality handling section, and an objective function adjustment section. The abnormality handling section performs initial solution generation when it is determined that performed optimization is abnormal. The initial solution generation section generates an initial optimal value of a future time series control input in accordance with an initial objective function, without reference to a candidate value of the time series control input. The objective function adjustment section adjusts the current objective function so that the current objective function varies stepwise with time toward the normal objective function when it is determined that the current objective function is different from the normal objective function.
Owner:NISSAN MOTOR CO LTD
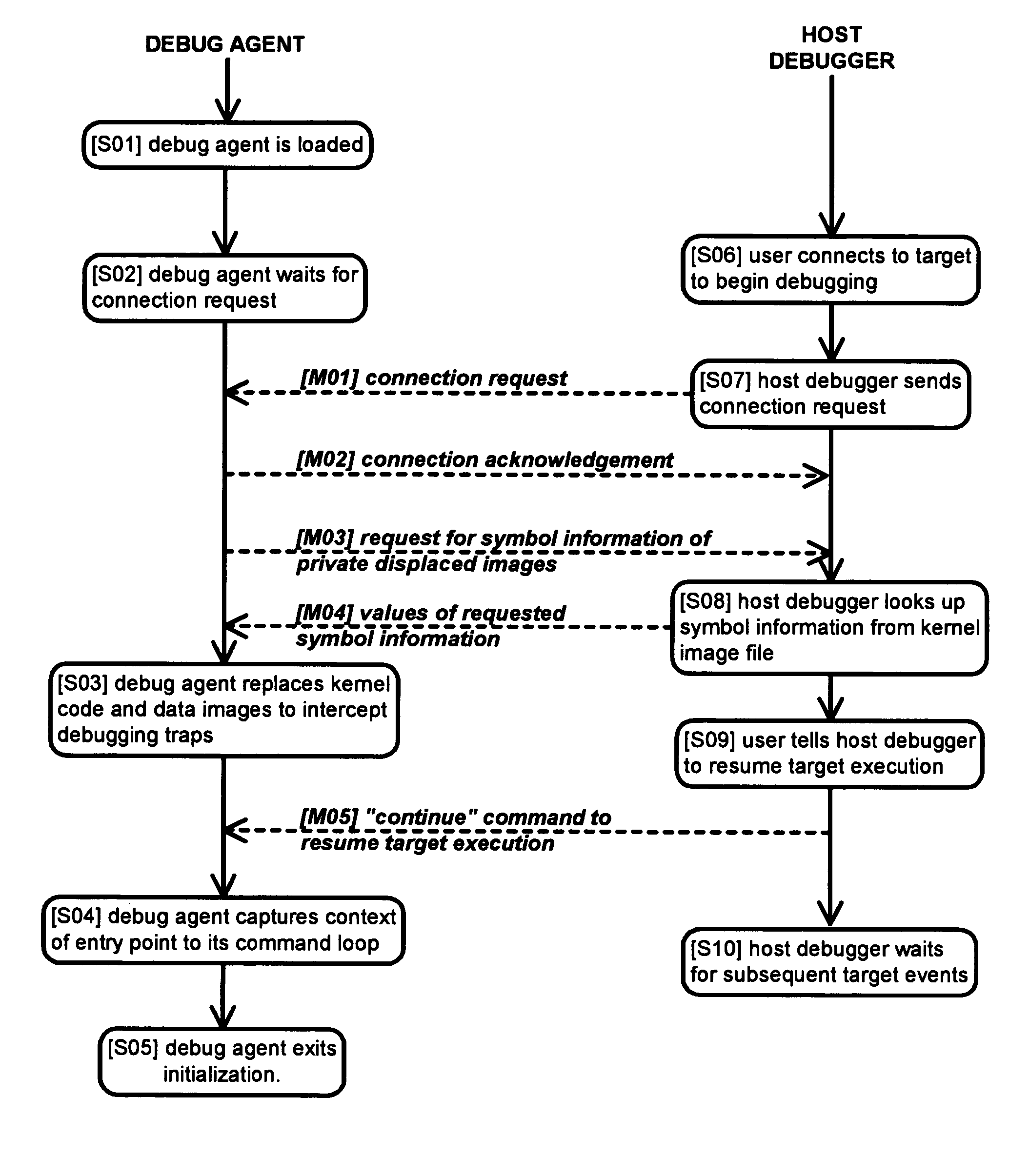
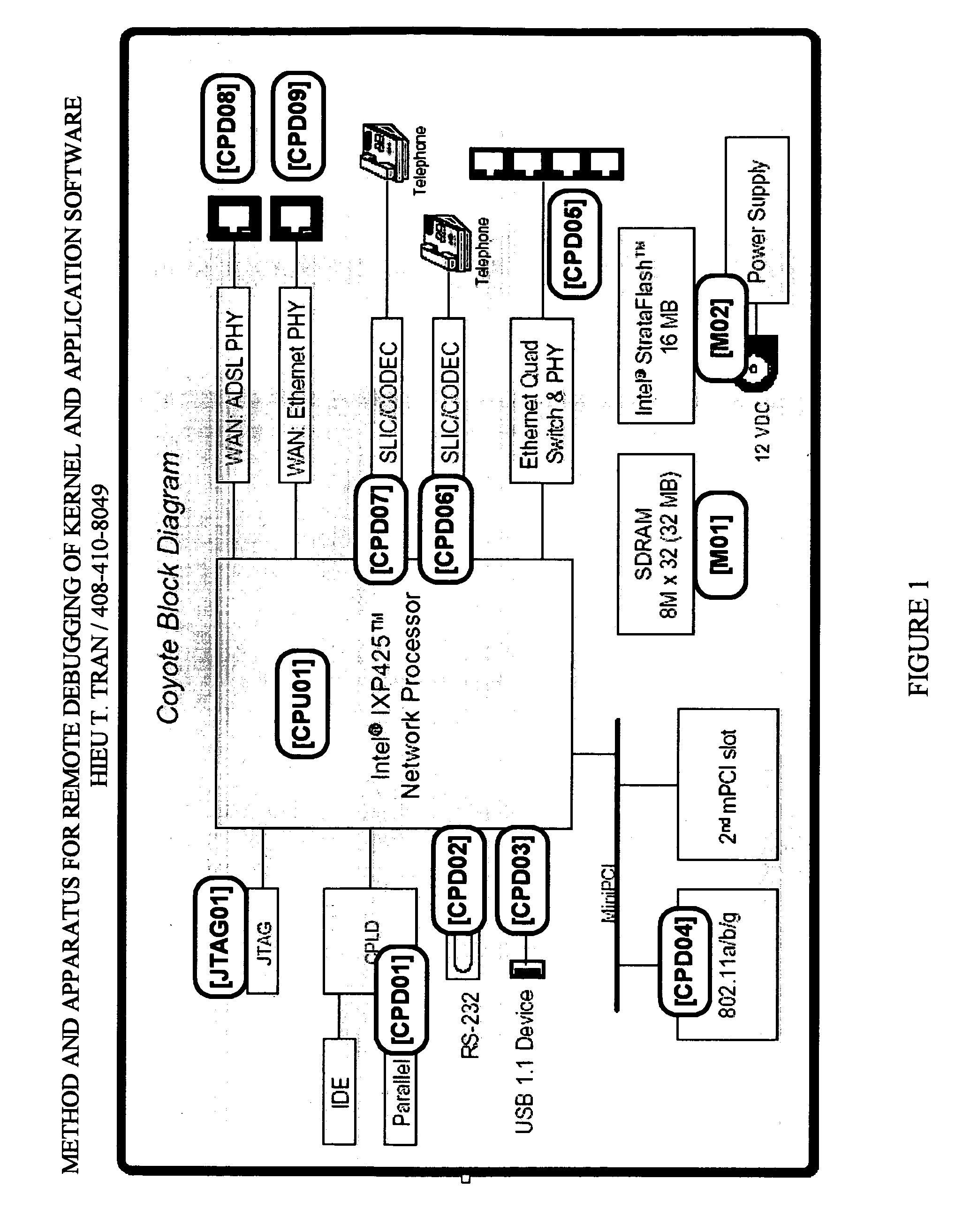
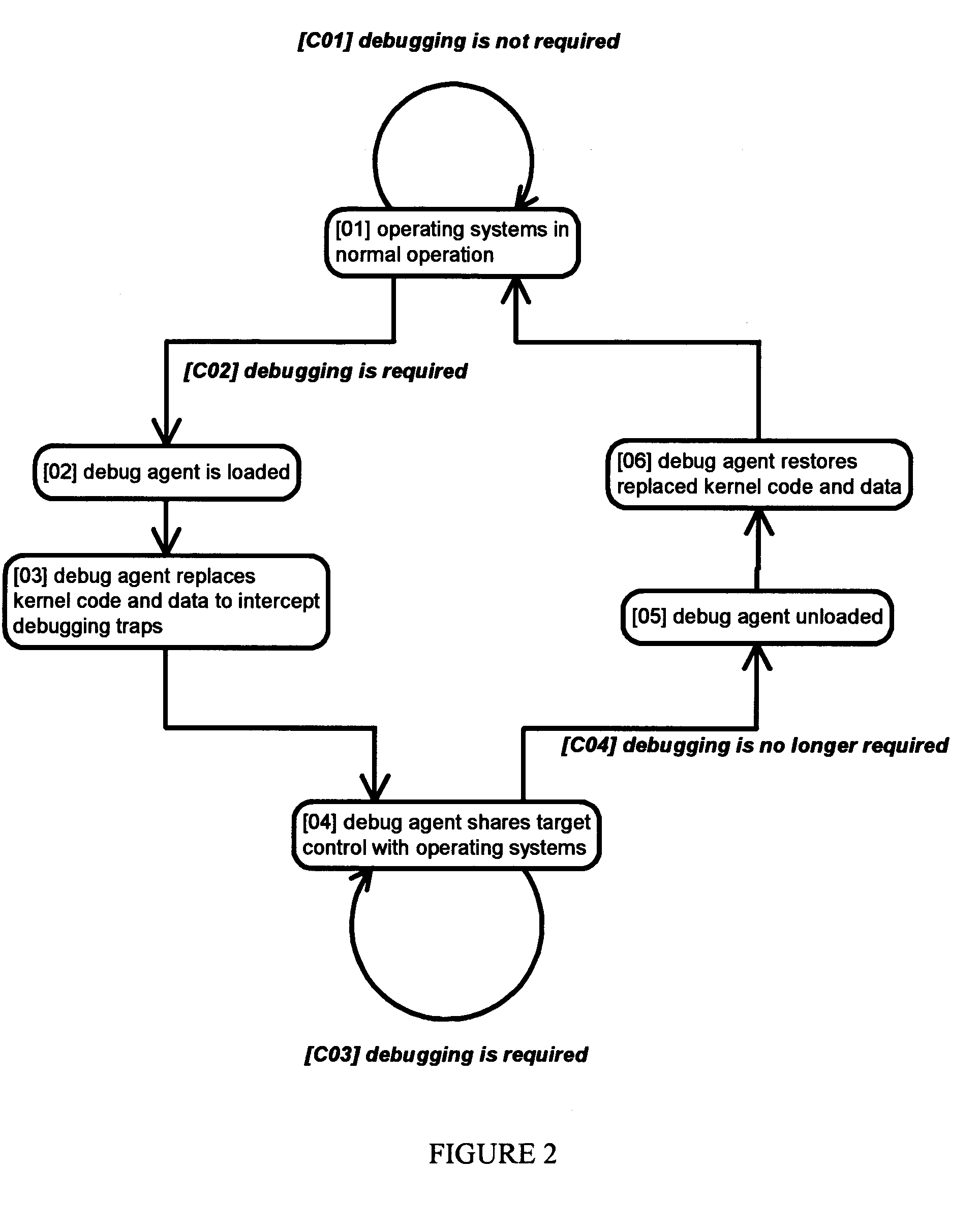
Method and apparatus for remote debugging of kernel and application software
InactiveUS20050216895A1Modified dynamicallyError detection/correctionSpecific program execution arrangementsOperational systemSystem call
A method and apparatus for debugging of OS kernel and applications software that does not require use of a hardware probe; can debug both user-mode programs and a significant body of the OS kernel code; allows the OS to continue servicing exceptions while debugging; leverages OS built-in device drivers for communicating devices to communicate with the host debugger; and can debug a production version of the OS kernel. When debugging is required, the running OS kernel dynamically loads a software-based debug agent on demand whereby such debug agent dynamically modifies the running production OS kernel code and data to intercept debugging traps and provide run-control. To provide debugging of loadable module, the debug agent implement techniques to intercept the OS module loading system call; set breakpoints in the loaded module initialization function; calculate the start address of the debugged module in memory; and asynchronously put the system under debug. By structuring command loop to execute in non-exception mode, and devising a process to transfer execution from the debug agent exception handler to the debug agent command loop and back, the debug agent can communicate with the host debugger using interrupt-driven input / output devices as well as allowing the system to service interrupts while under debug.
Owner:TRAN HIEU TRUNG
Framework to model cross-cutting behavioral concerns in the workflow domain
InactiveUS20060074704A1Extend the workflow modelSoftware designResourcesCross cutTheoretical computer science
Selecting and applying a behavioral component to a portion of a componentized workflow. The behavioral component defines error and exception handling, among other concerns, to the portion of the workflow selected by a user. During execution of the workflow, the behavioral components executes responsive to output from the selected portion of the workflow.
Owner:MICROSOFT TECH LICENSING LLC
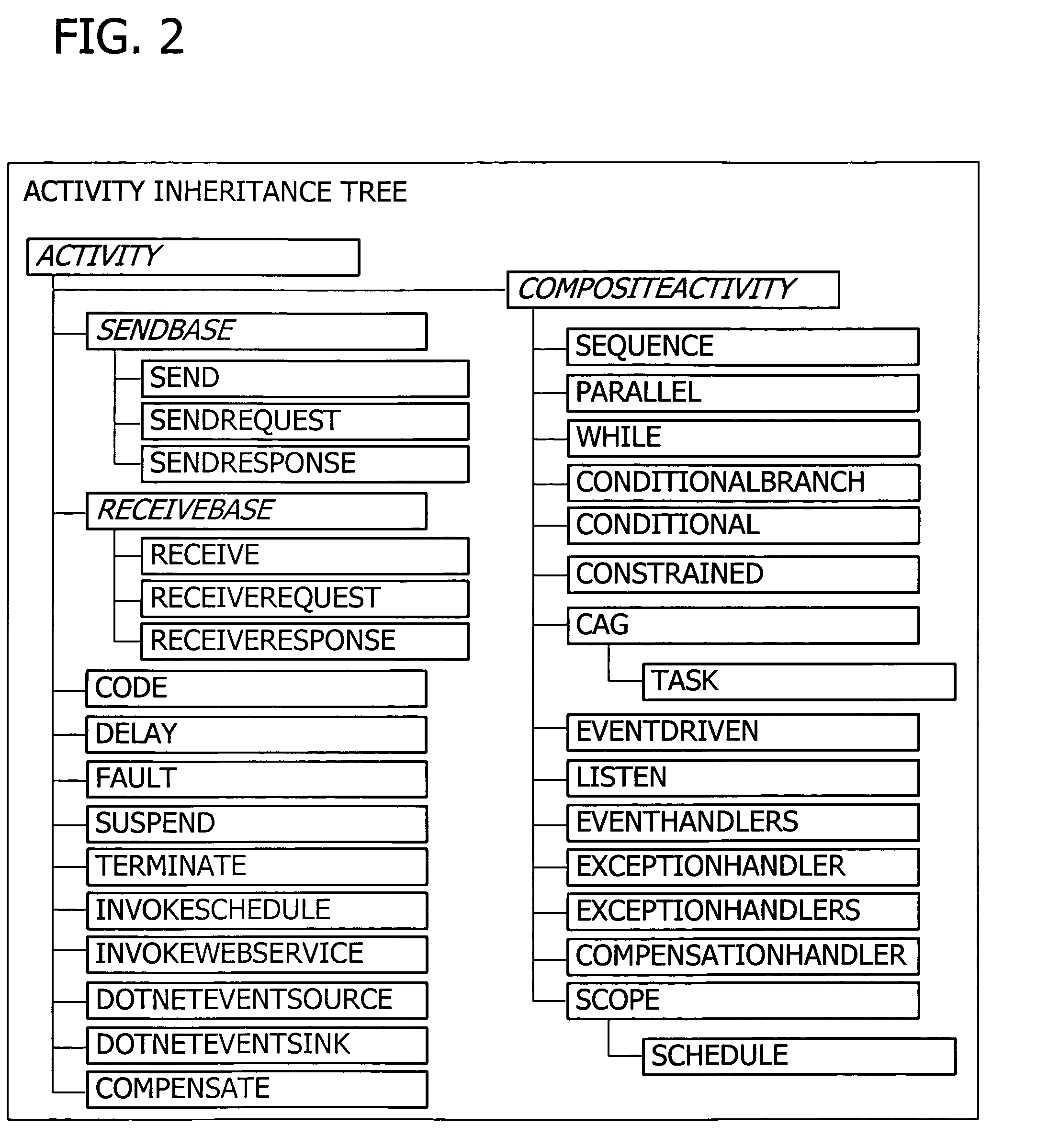
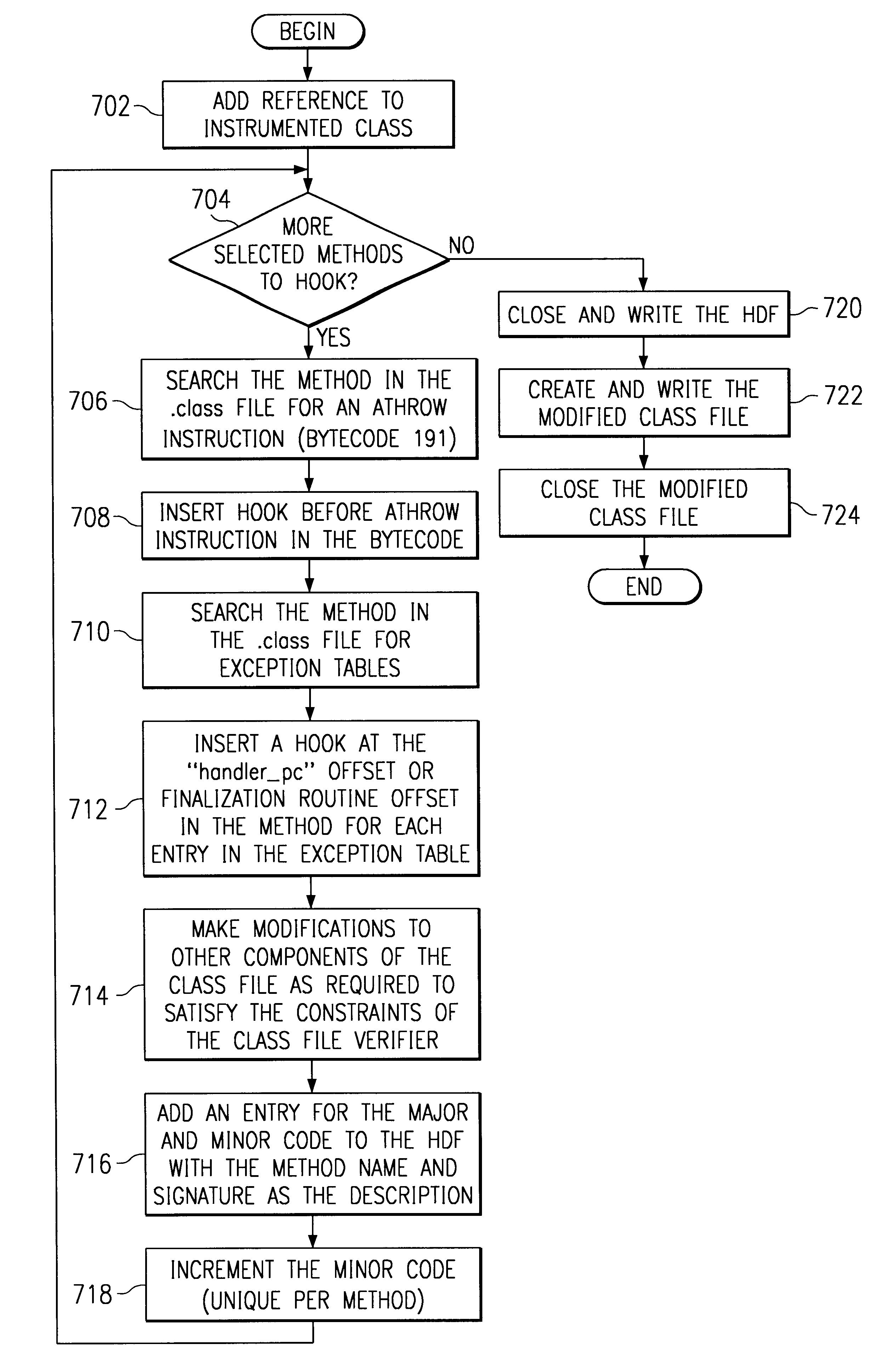
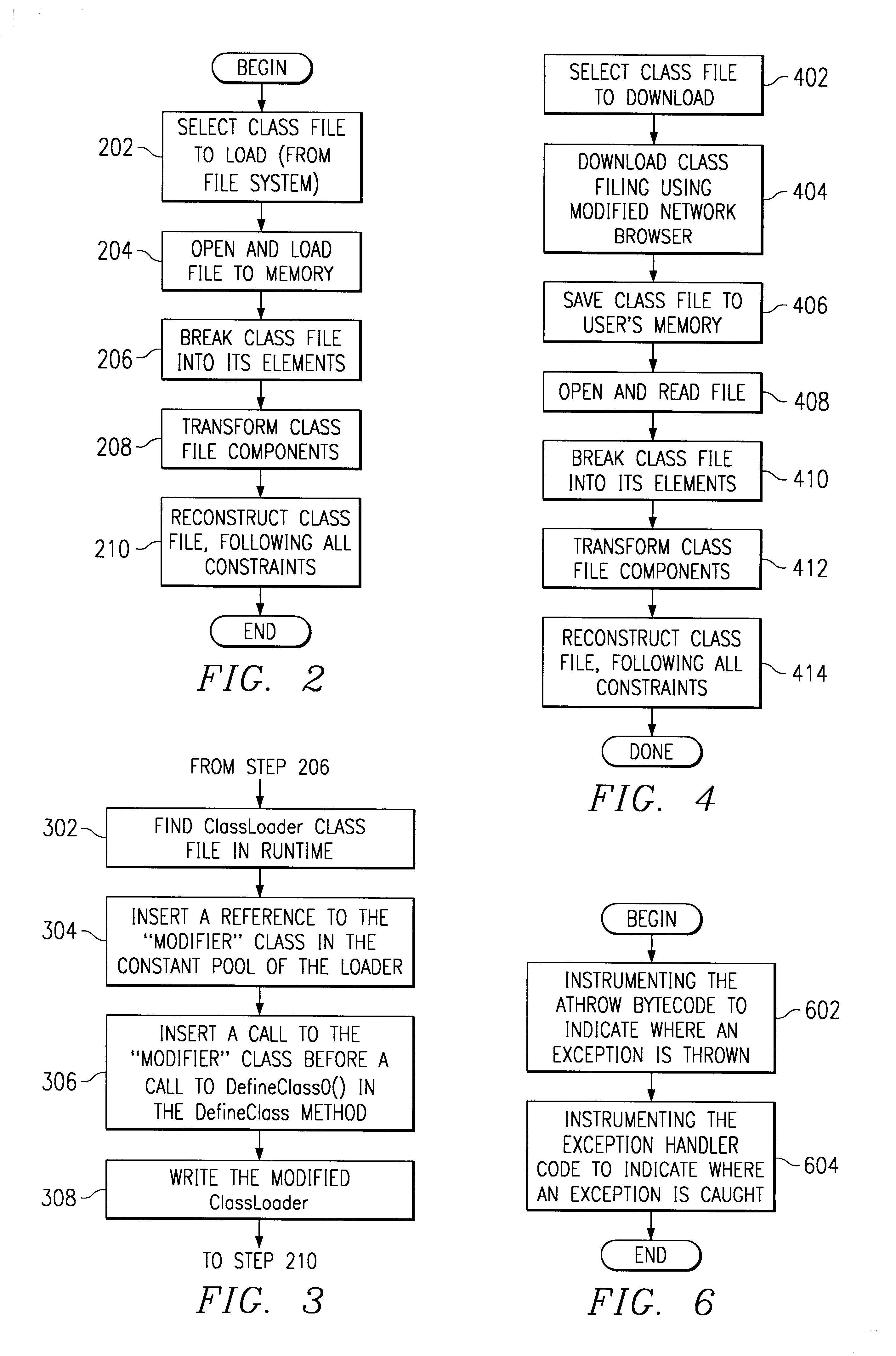
System and method for injecting hooks into Java classes to handle exception and finalization processing
InactiveUS6662359B1Software testing/debuggingSpecific program execution arrangementsEntry pointJava classes
The present invention is directed to a system, method and instructions for handling path flow exception and finalization processing in an object oriented programming language. Initially, each instrumentation method is checked for a code to indicated an exception being thrown. A hook is inserted before the exception code and identifies the method throwing the exception. Methods must also be checked for exception tables. When an exception table is found, then a hook is inserted at the entry point of each exception handler for every entry in the exception table. This hook identifies the method which catches the exception.
Owner:IBM CORP
Switching method in a multi-threaded processor
InactiveUS6694347B2Program initiation/switchingDigital computer detailsOperational systemComputer science
Owner:SUN MICROSYSTEMS INC
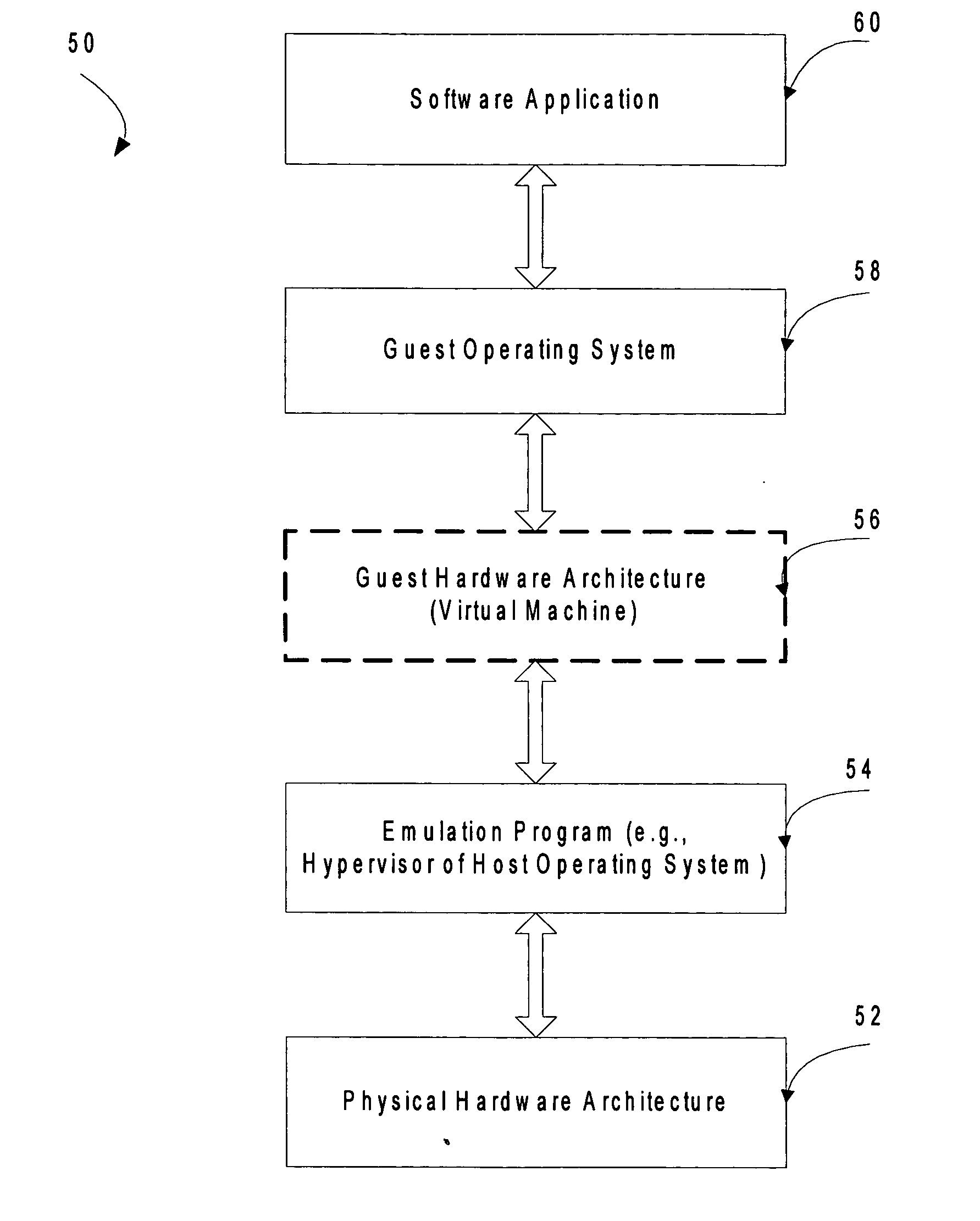
Virtual operating system device communication relying on memory access violations
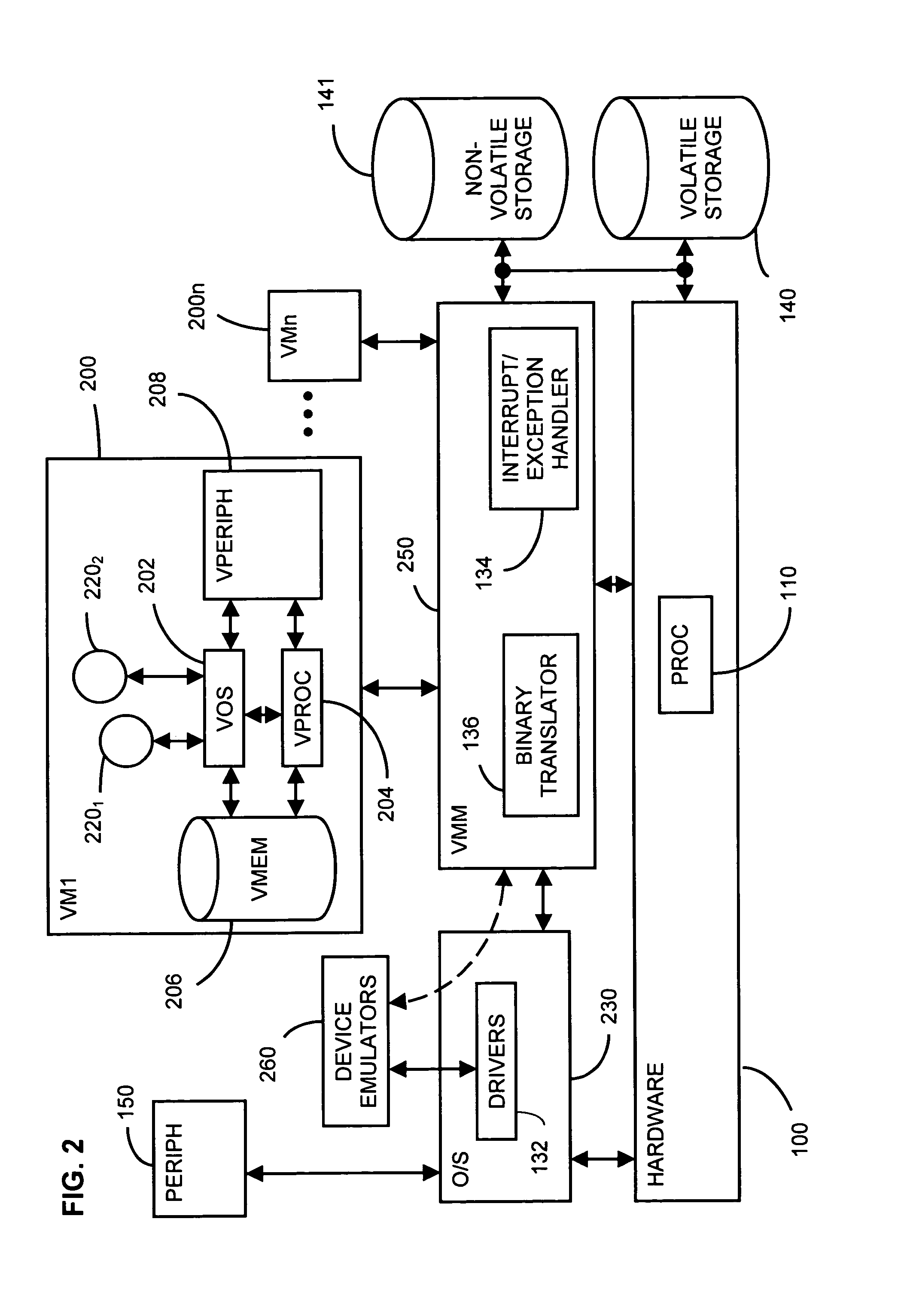
InactiveUS20060259292A1Reducing permissionInternal/peripheral component protectionSoftware simulation/interpretation/emulationVirtualizationOperational system
Attempts by drivers of a virtualized legacy computer game to communicate with nonexistent legacy game system hardware are converted into calls to actual hardware of the host computer game system. An access control list (ACL) restricting and / or reducing page permissions is used to explicitly forbid the drivers of the legacy computer game operating on the virtualized legacy computer game platform from writing to the MMIO addresses of the legacy computer game system. When the operating system of the virtualized legacy computer game platform attempts to touch its driver memory by writing to the MMIO addresses, the operating system of the host computer game system perceives a memory access violation, suspends the virtual machine implementing the virtualized computer game platform, and passes the intended write to an exception handler of the host operating system. The exception handler of the host operating system translates the attempted hardware access command into the command language of the host operating system and then returns control to the operating system of the virtualized legacy computer game platform. The legacy game is completely unaware of this address translation in that it sees only a successful hardware result and proceeds.
Owner:MICROSOFT TECH LICENSING LLC
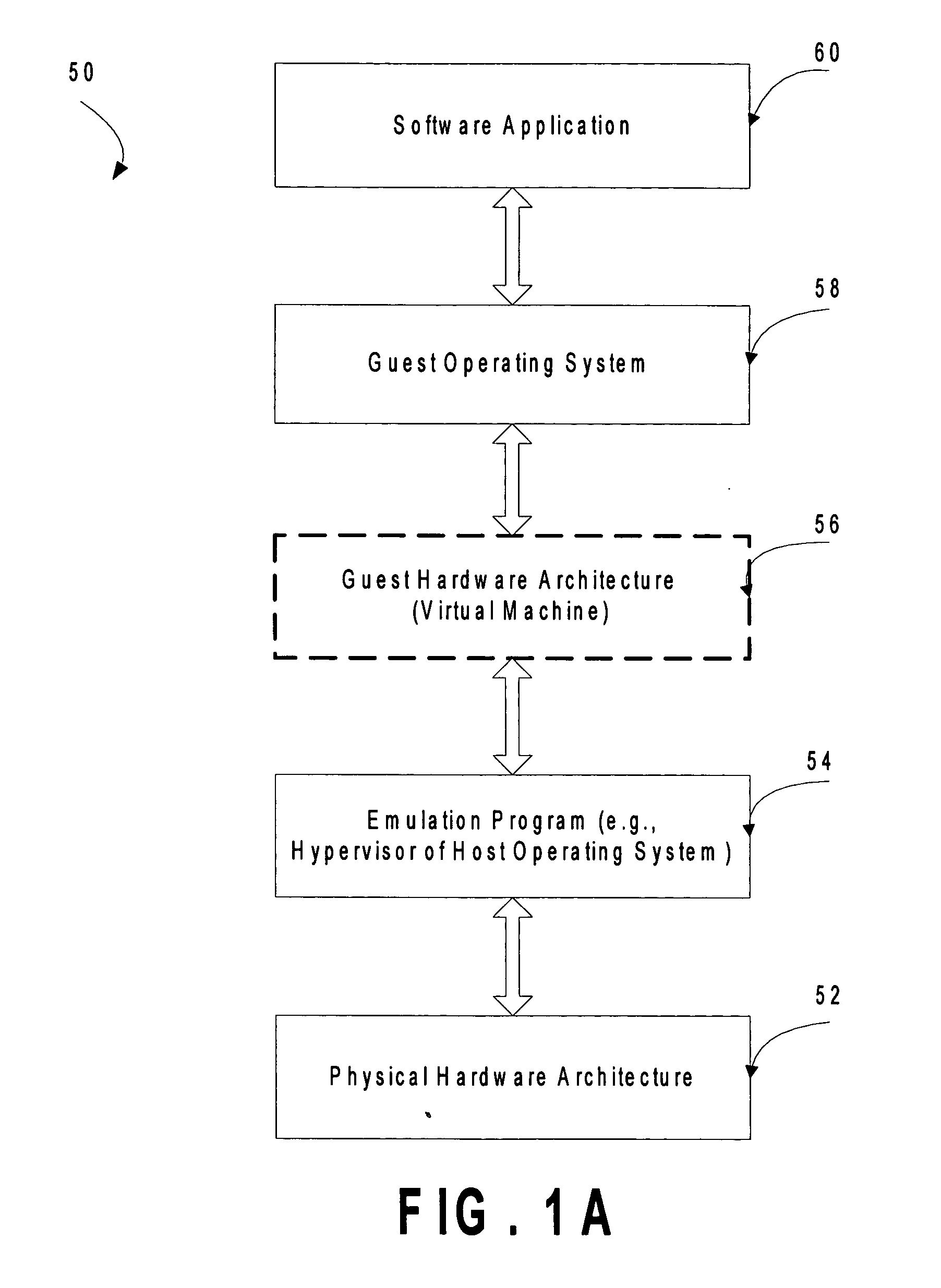
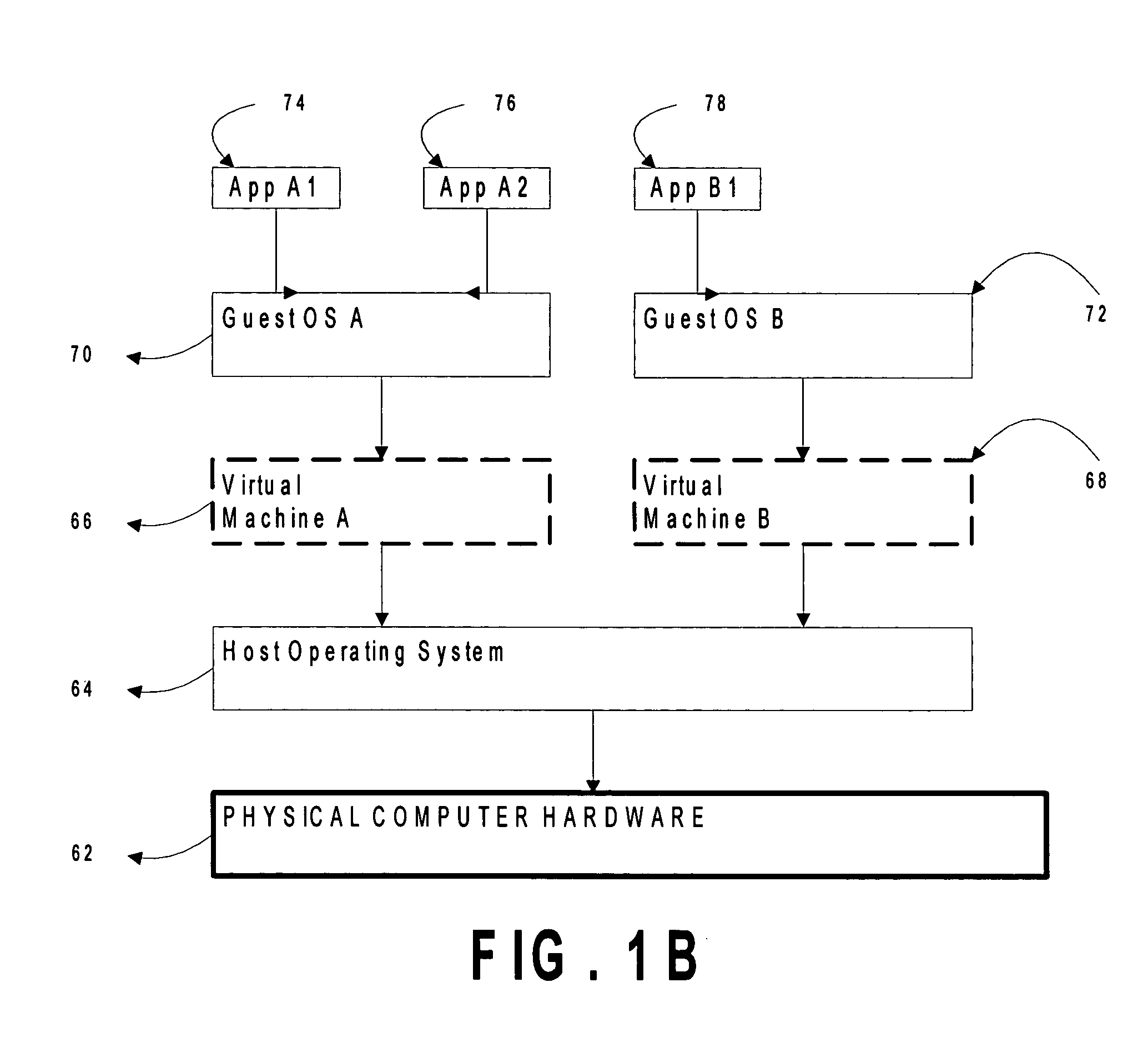
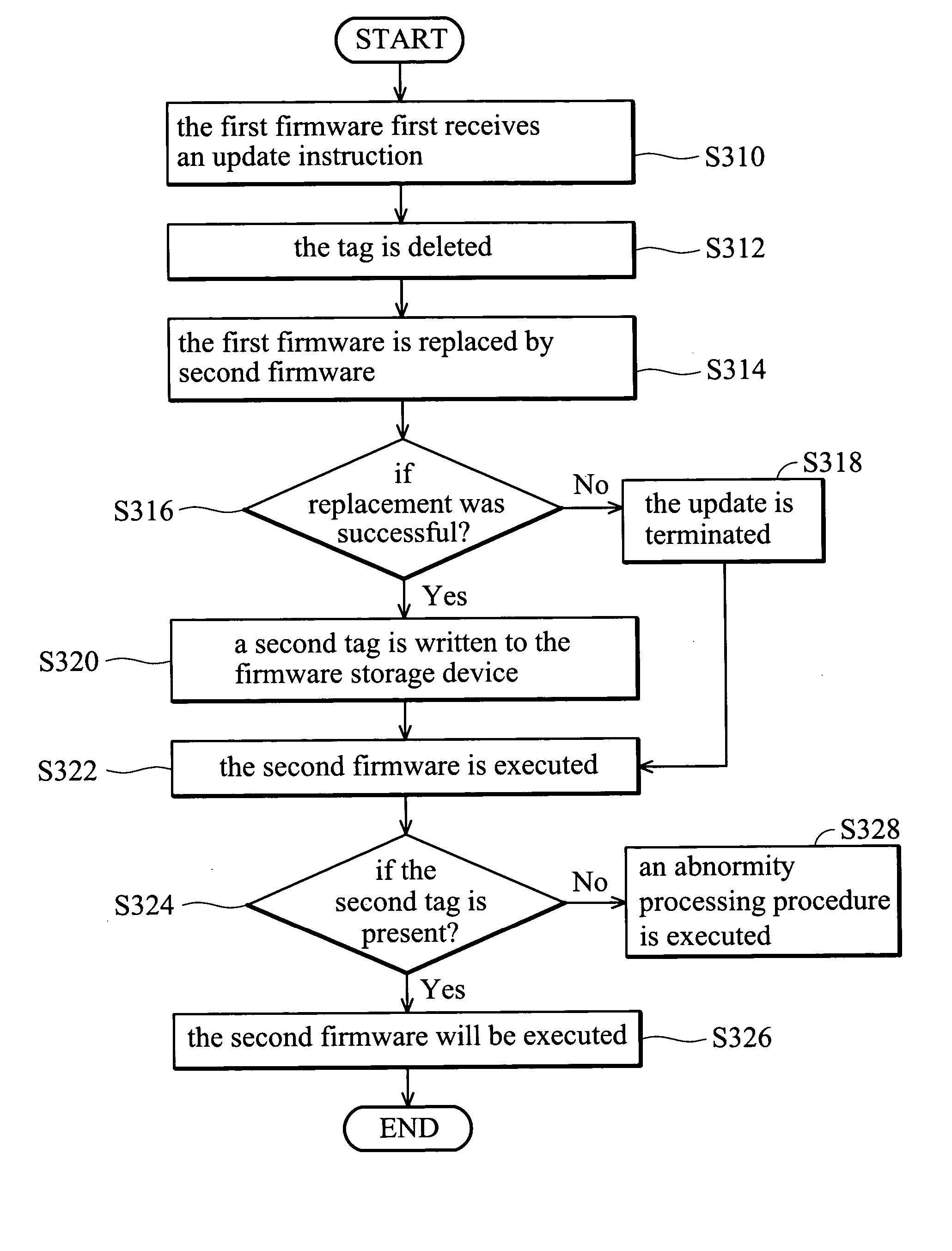
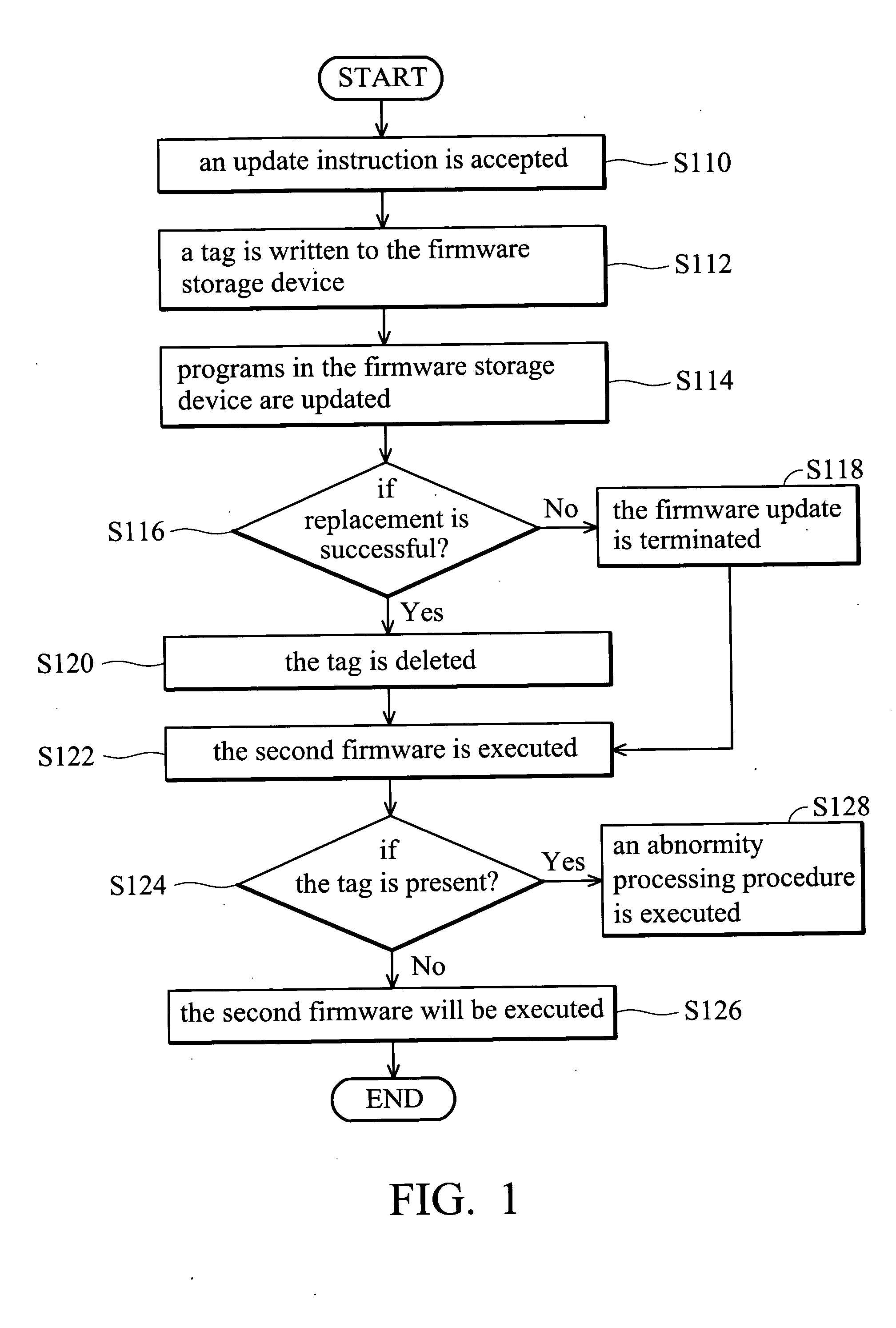
Firmware update method and system
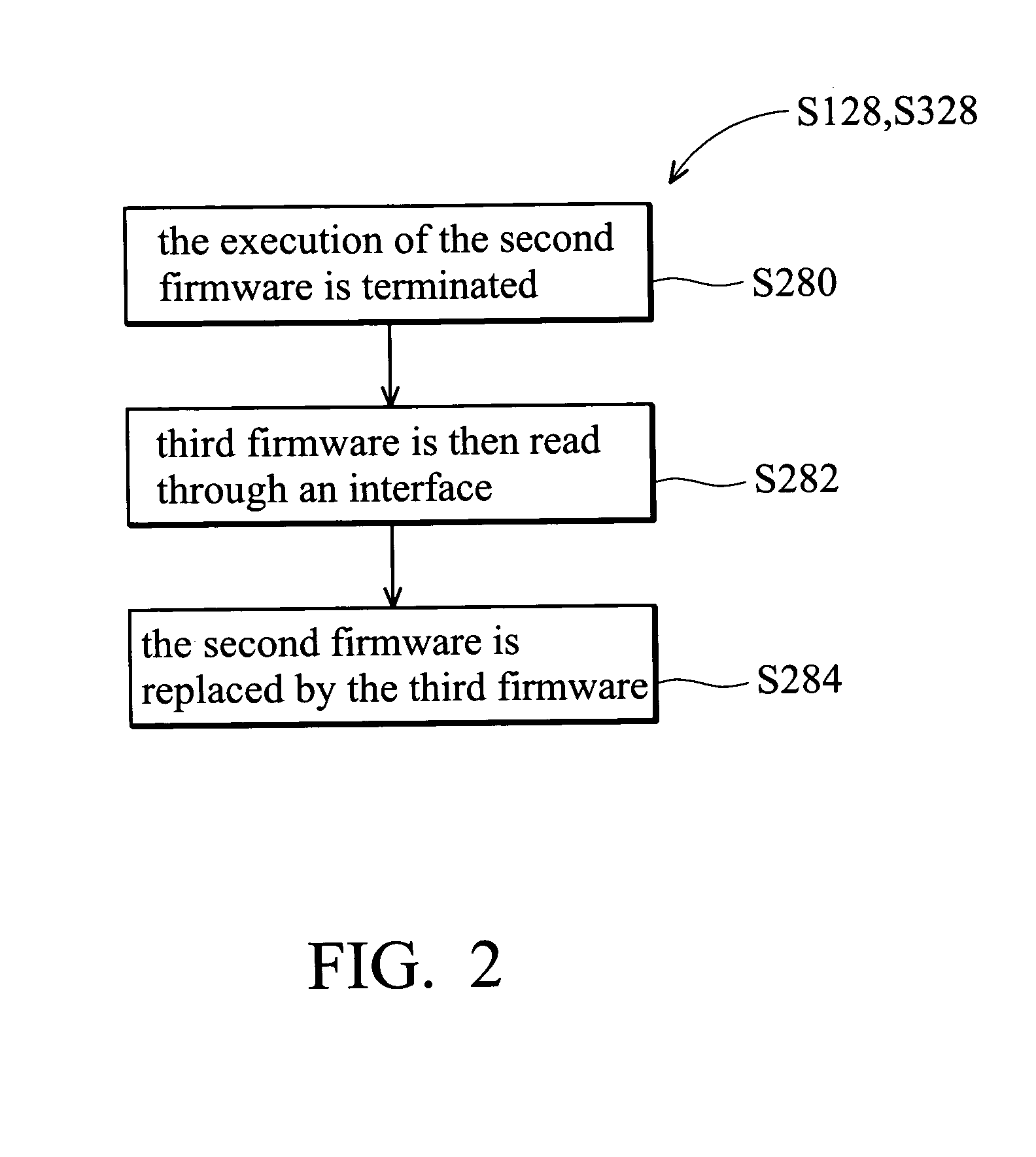
InactiveUS20050097542A1Ensuring Safe ExecutionGuaranteed uptimeProgram loading/initiatingMemory systemsException handlingFirmware
A firmware update method. First, a tag is written to a firmware storage device. Next, first firmware in the firmware storage device is replaced by second firmware. If the replacing step is successful, the tag is deleted. Before the execution of the second firmware, a verification operation is executed. If the tag is not present, the second firmware is executed. If the tag is present, an abnormity processing procedure is executed. The abnormity processing procedure terminates of execution of the second firmware, reads third firmware via an interface, and replaces the second firmware with the third firmware.
Owner:ASUSTEK COMPUTER INC
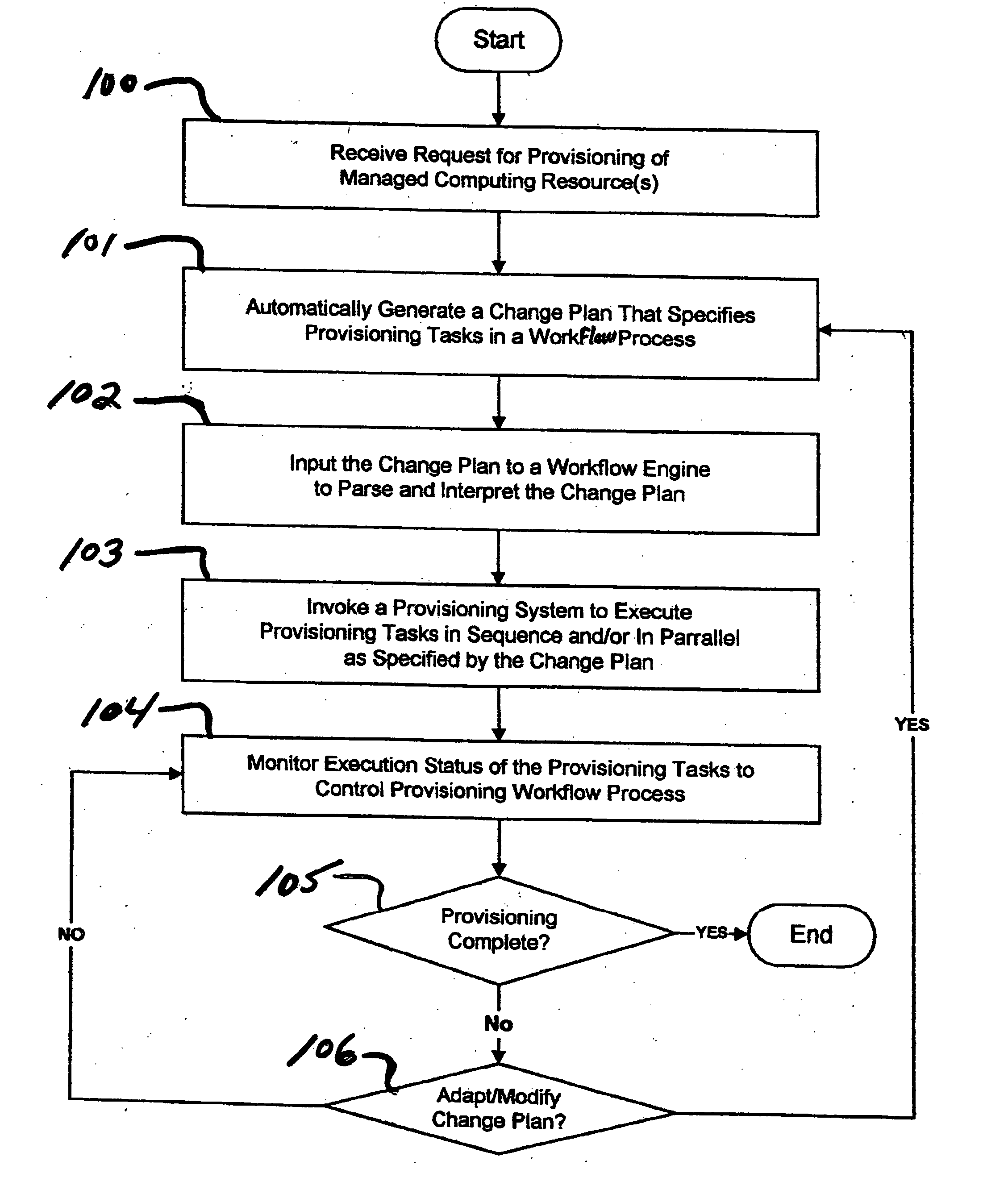
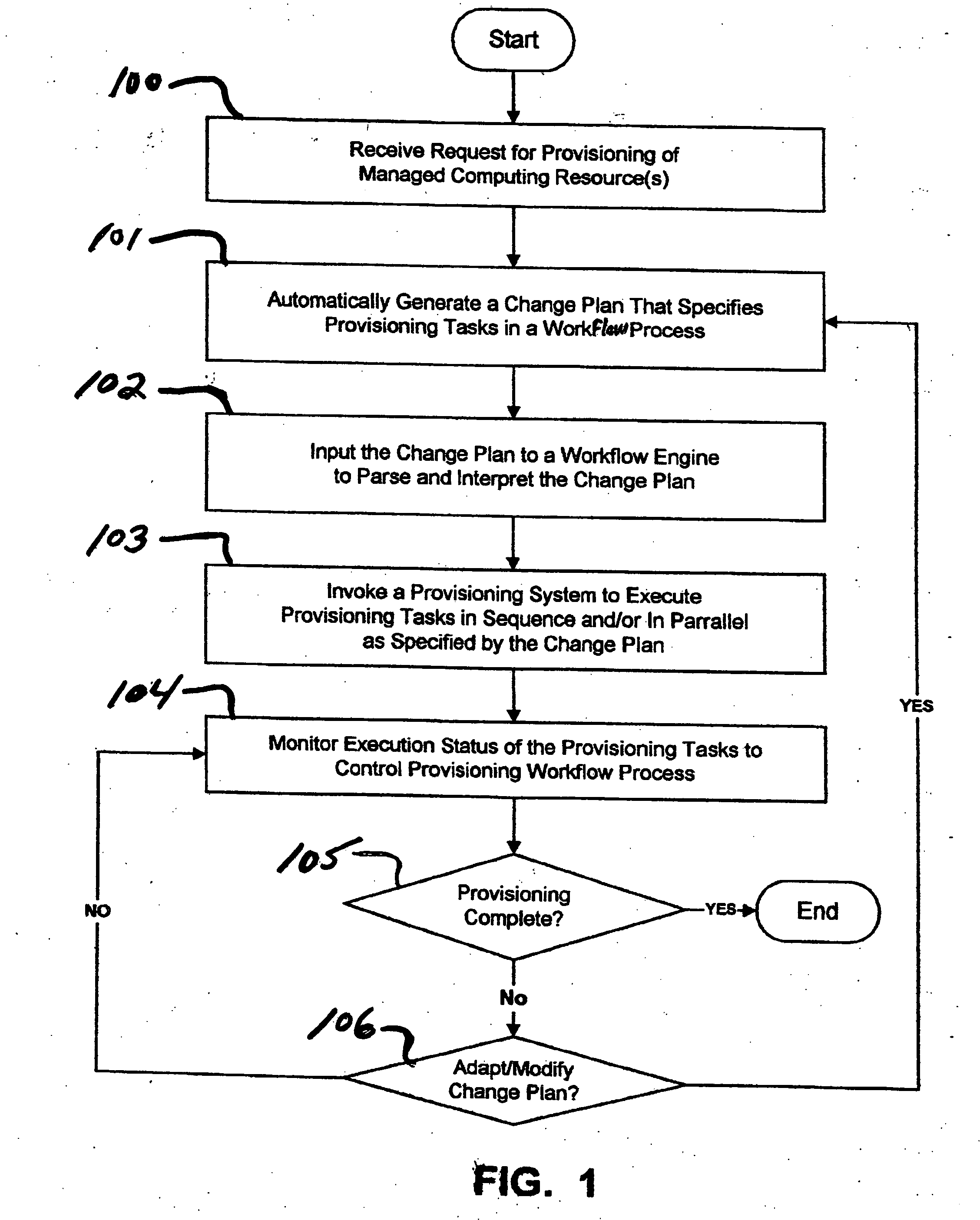
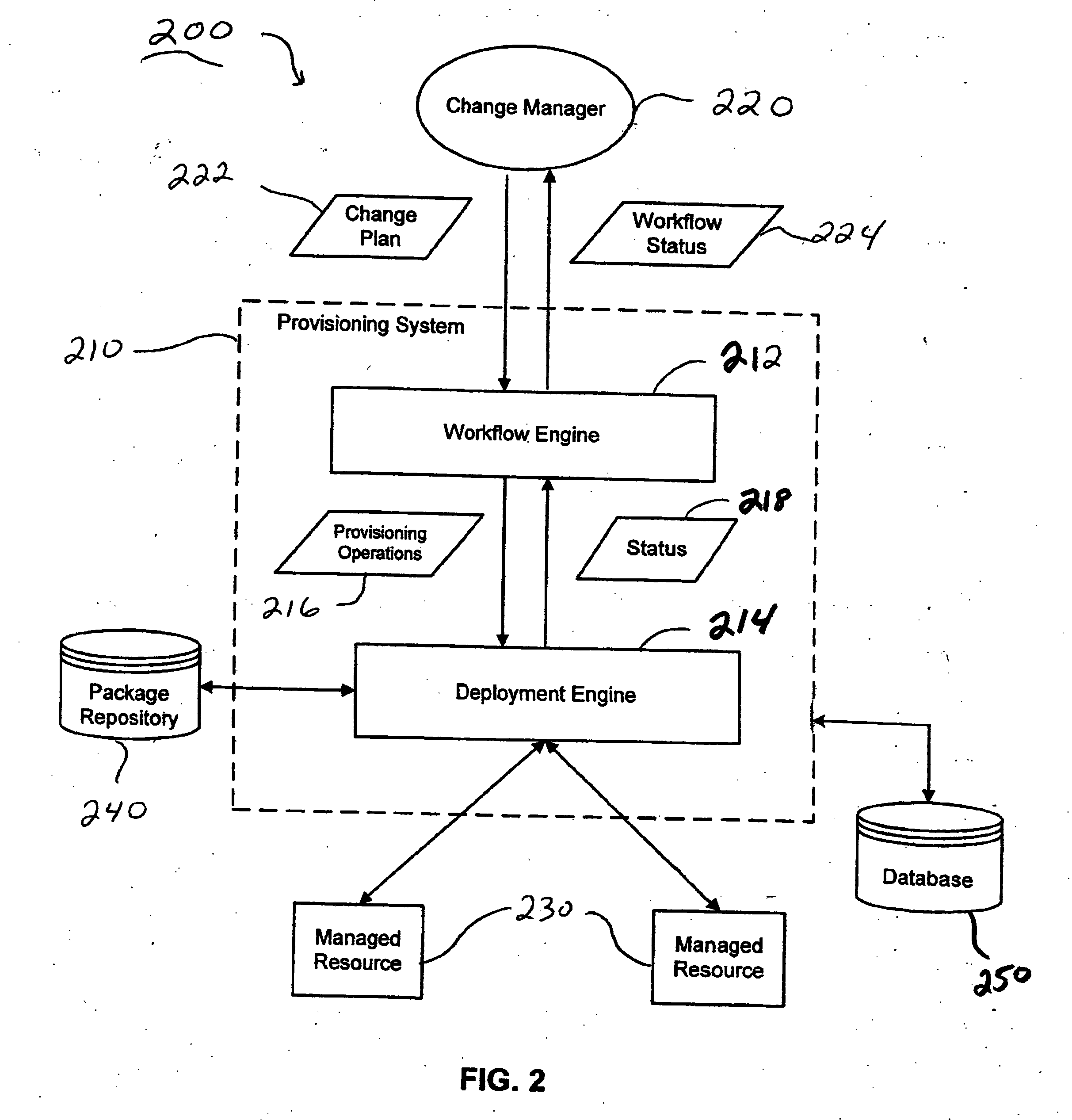
Systems and methods for automated provisioning of managed computing resources
ActiveUS20070083588A1Multiple digital computer combinationsProgram controlChange managementAuto-configuration
Systems and methods are provided for automated provisioning of managed resources in a distributed computing environment. Automated provisioning of managed resources is realized by systems and methods that support automated execution of provisioning workflows through programmatic invocation of provisioning tasks (sequentially and / or parallel invocation) supported by a provisioning system, as well as automated control and coordination of task execution and exception handling through automated message exchange. Systems and methods support automated provisioning through seamless integration of provisioning and change management systems, whereby provisioning systems can automatically interpret and execute reusable change plans that are generated (on-the-fly) by change management systems. The change plans comprise provisioning workflow processes that are described using a standard, platform-independent workflow language.
Owner:WRP IP MANAGEMENT LLC
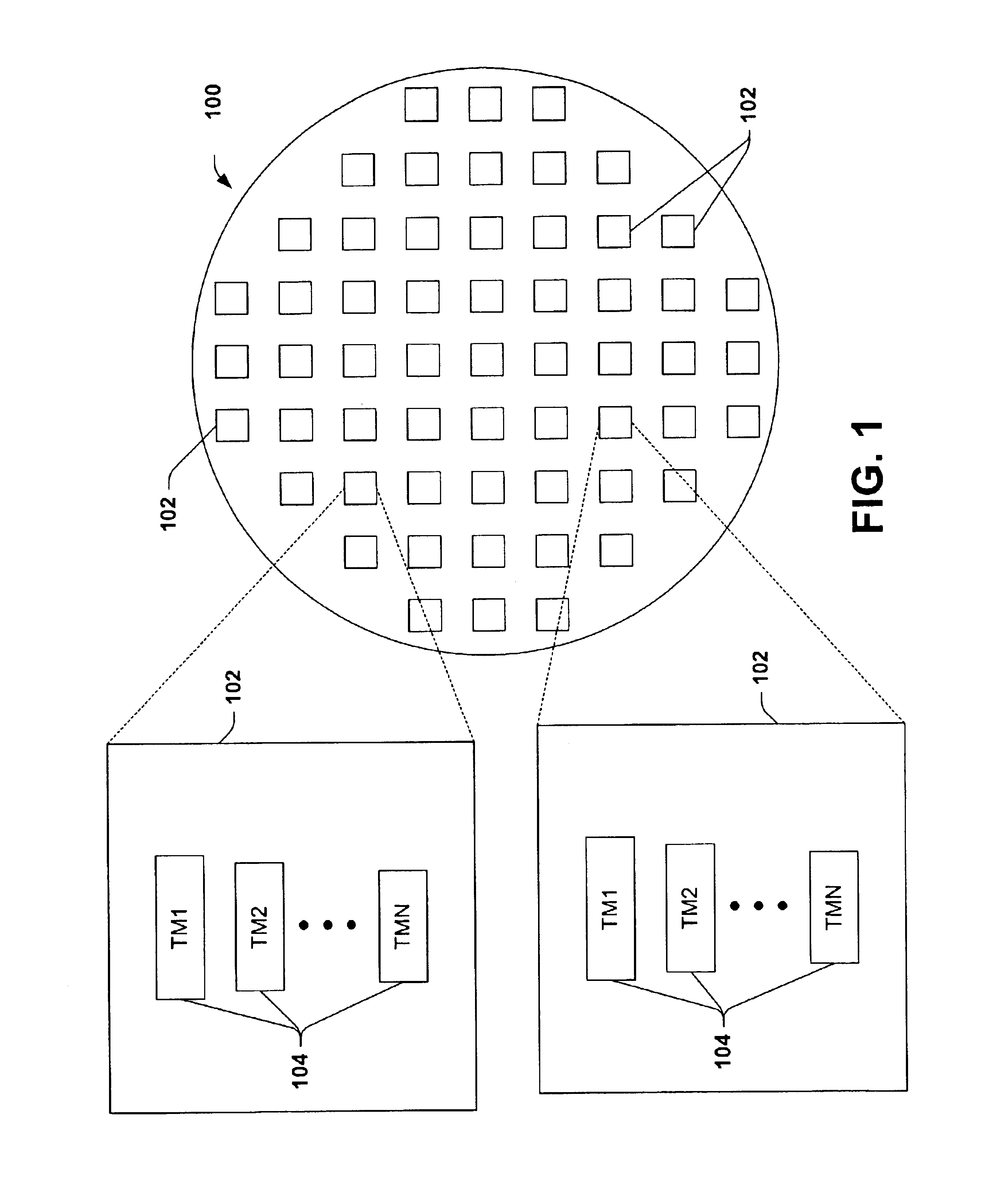
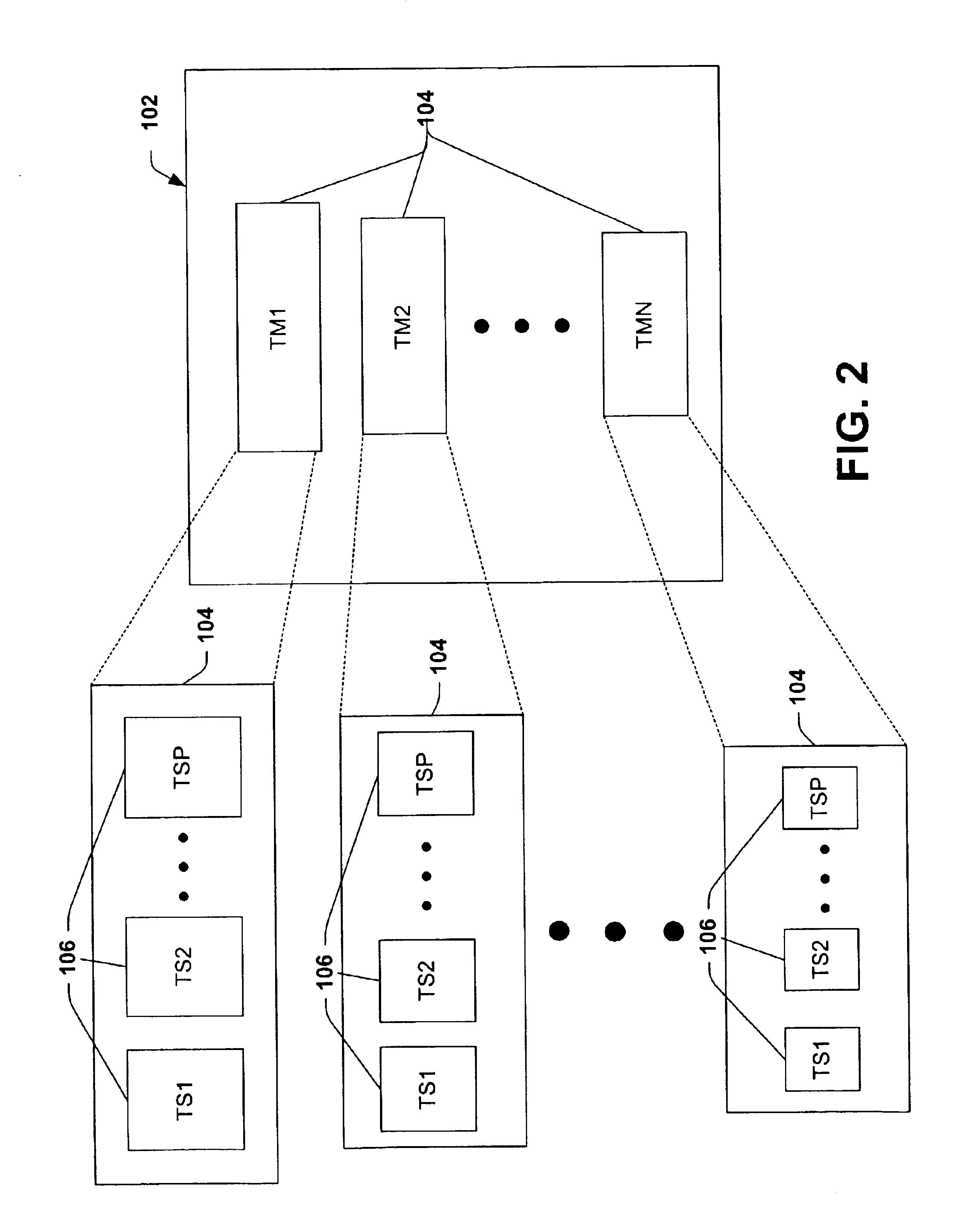
Sensitive test structure for assessing pattern anomalies
InactiveUS6967110B2Well formedEasy to identifySemiconductor/solid-state device testing/measurementSemiconductor/solid-state device detailsSemiconductorException handling
Owner:TEXAS INSTR INC
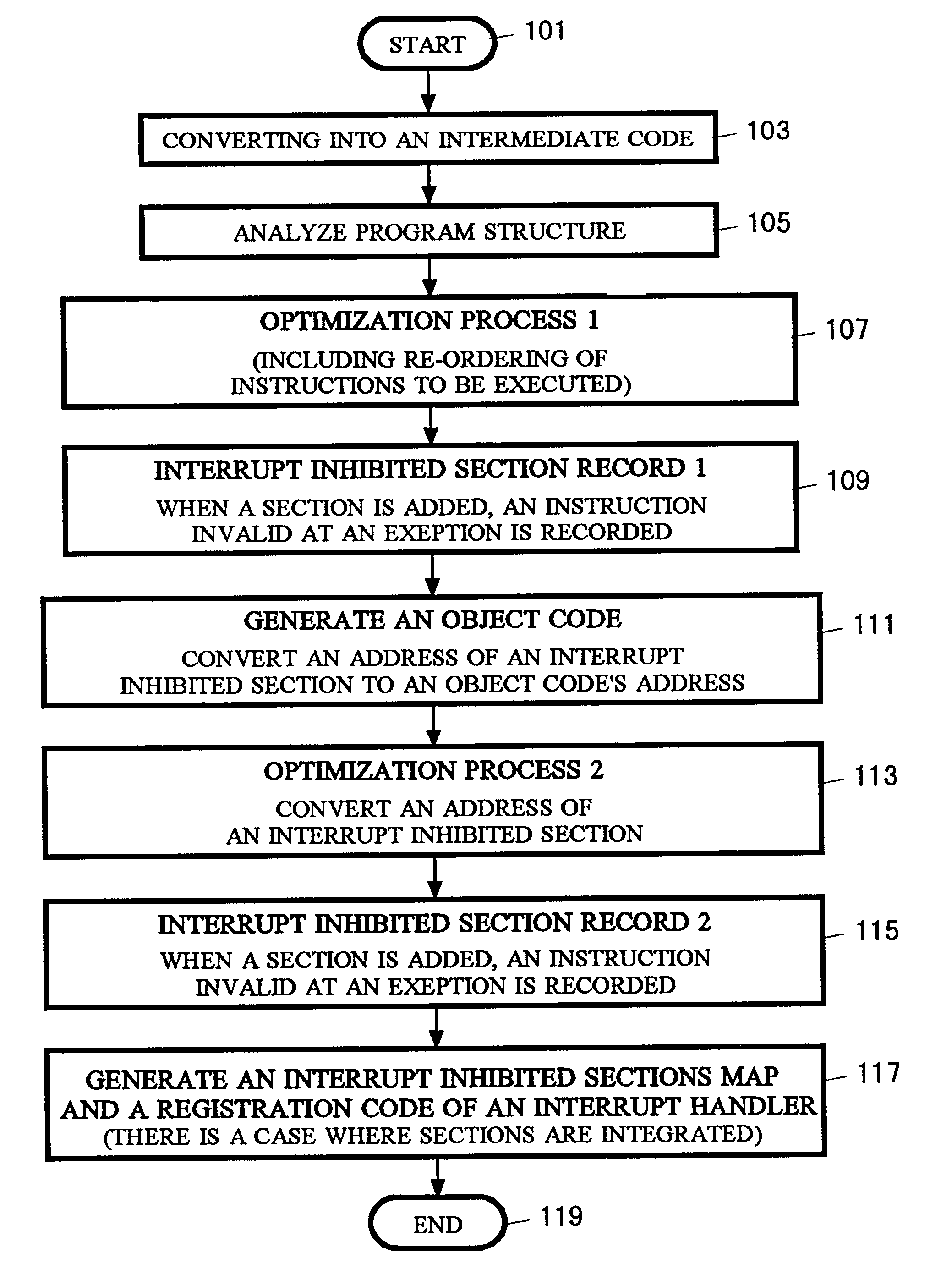
Compile method, exception handling method and computer
InactiveUS6634023B1Easy to getDecreasing can be registeredProgram initiation/switchingSoftware engineeringPDAT enzymeInterrupt handler
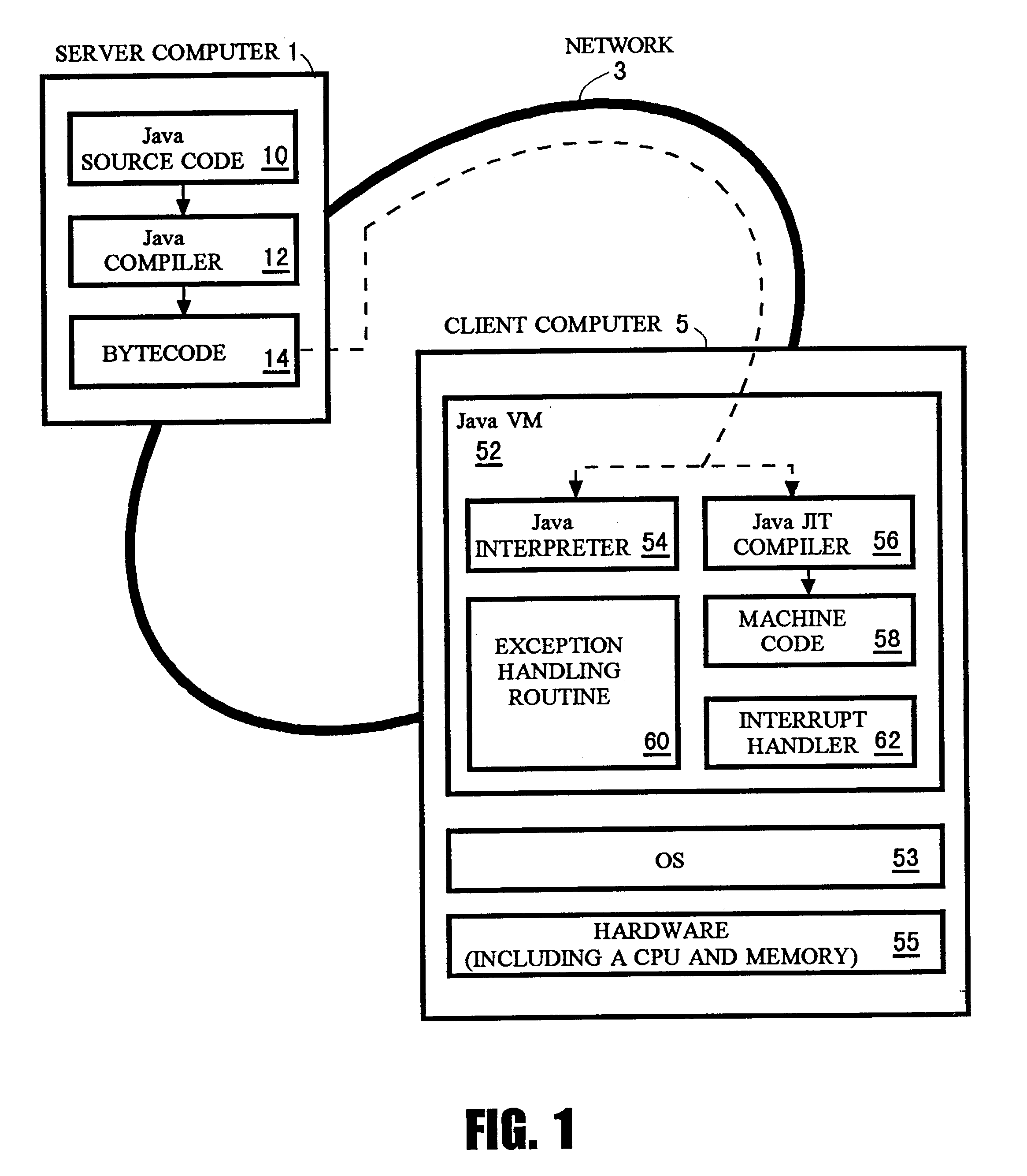
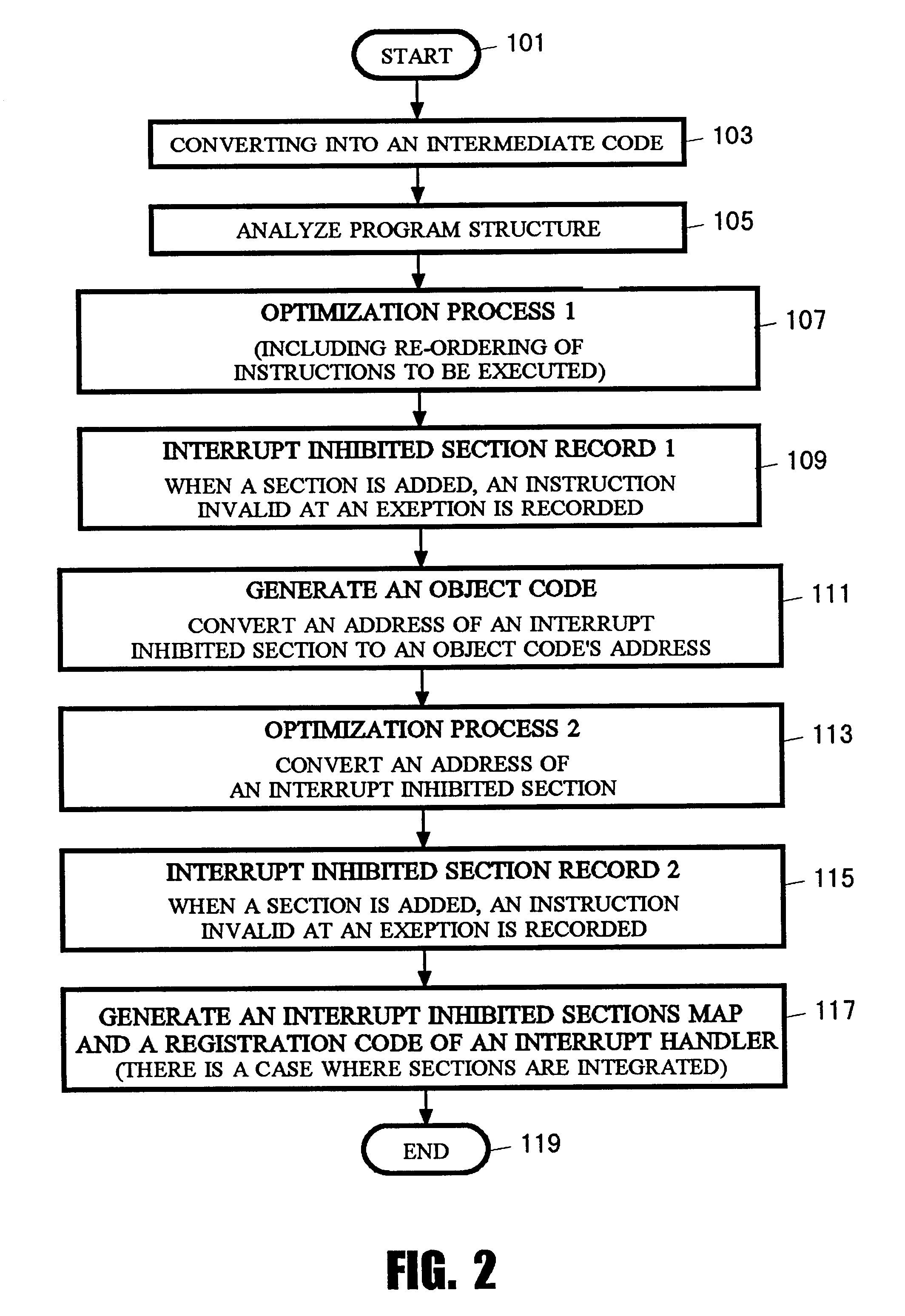
The present invention enables re-ordering of instructions to be executed while assuring a precise exception. In Java language, an optimization process of re-ordering instructions to be executed is performed by Just-In-Time compiler. For instance, the instructions lining in order from instruction E<HIL><PDAT>1 < / BOLD><PDAT>which was moved forward to instruction S<HIL><PDAT>2< / BOLD><PDAT>which had been located before E<HIL><PDAT>1 < / BOLD><PDAT>is registered as interrupt inhibited section R<HIL><PDAT>1< / BOLD><PDAT>, and from instruction S<HIL><PDAT>4 < / BOLD><PDAT>which was moved forward to instruction S<HIL><PDAT>3 < / BOLD><PDAT>which had been located before S<HIL><PDAT>4 < / BOLD><PDAT>is registered as interrupt inhibited section R<HIL><PDAT>2 < / BOLD><PDAT>(S is an instruction which has an affect observable from the outside at the execution, and E is an instruction which may cause an exception). Also, in FIG. <HIL><PDAT>7< / BOLD><PDAT>, S<HIL><PDAT>4 < / BOLD><PDAT>which was an instruction behind E<HIL><PDAT>1 < / BOLD><PDAT>in the original order is registered as R<HIL><PDAT>1< / BOLD><PDAT>'s instruction invalid at an exception. If E<HIL><PDAT>1 < / BOLD><PDAT>causes an exception, an interrupt handler is activated and the instructions of interrupt inhibited section R<HIL><PDAT>1 < / BOLD><PDAT>are copied to another area. S<HIL><PDAT>4 < / BOLD><PDAT>is not copied in that case. In addition, a branch code to an exception handling routine is attached to the end of the copy. If execution is restarted from S<HIL><PDAT>1< / BOLD><PDAT>, the instructions required to be executed for assuring the precise exception are executed, and it may move on to an exception handling routine thereafter.< / PTEXT>
Owner:GOOGLE LLC
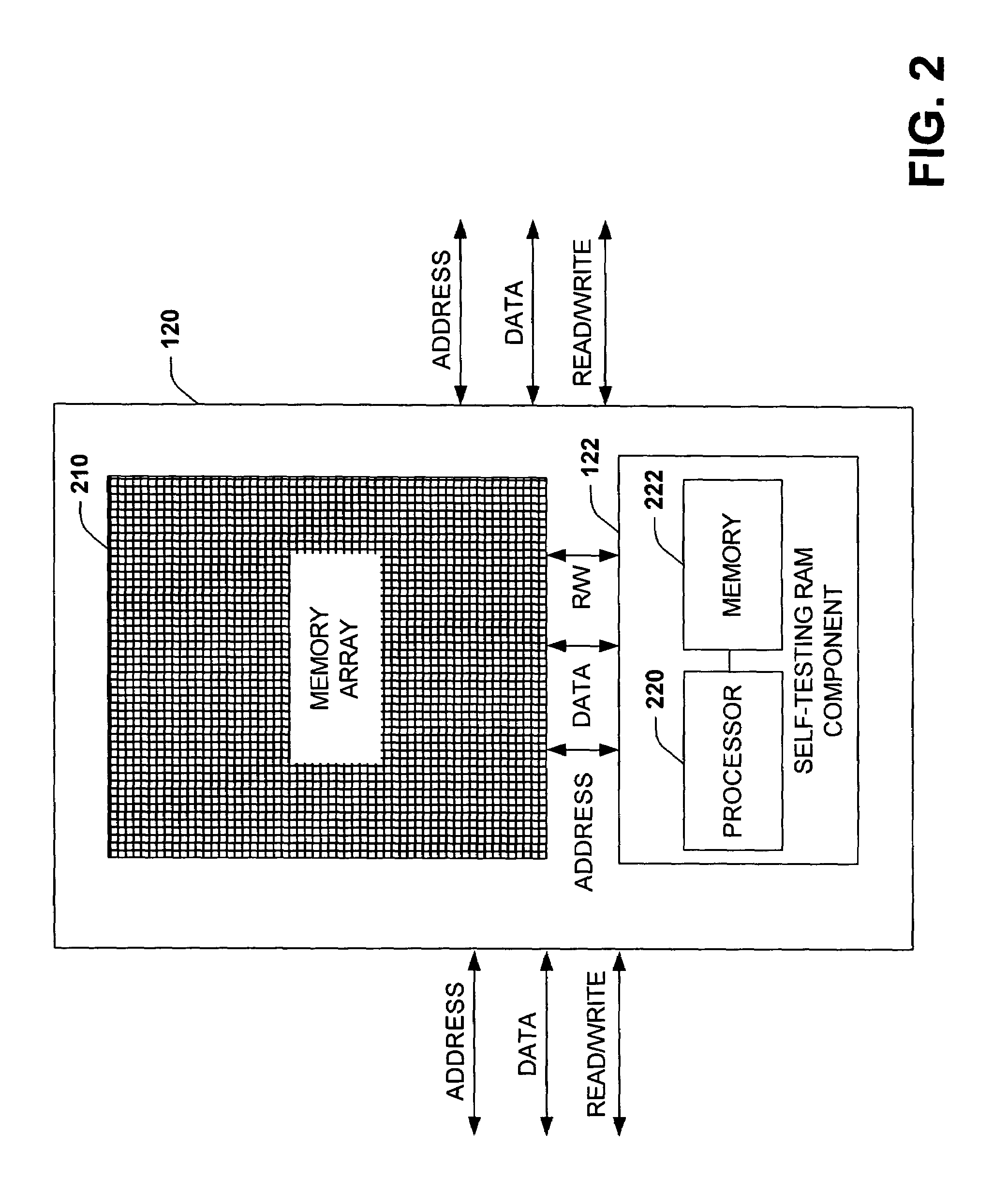
Self-testing RAM system and method
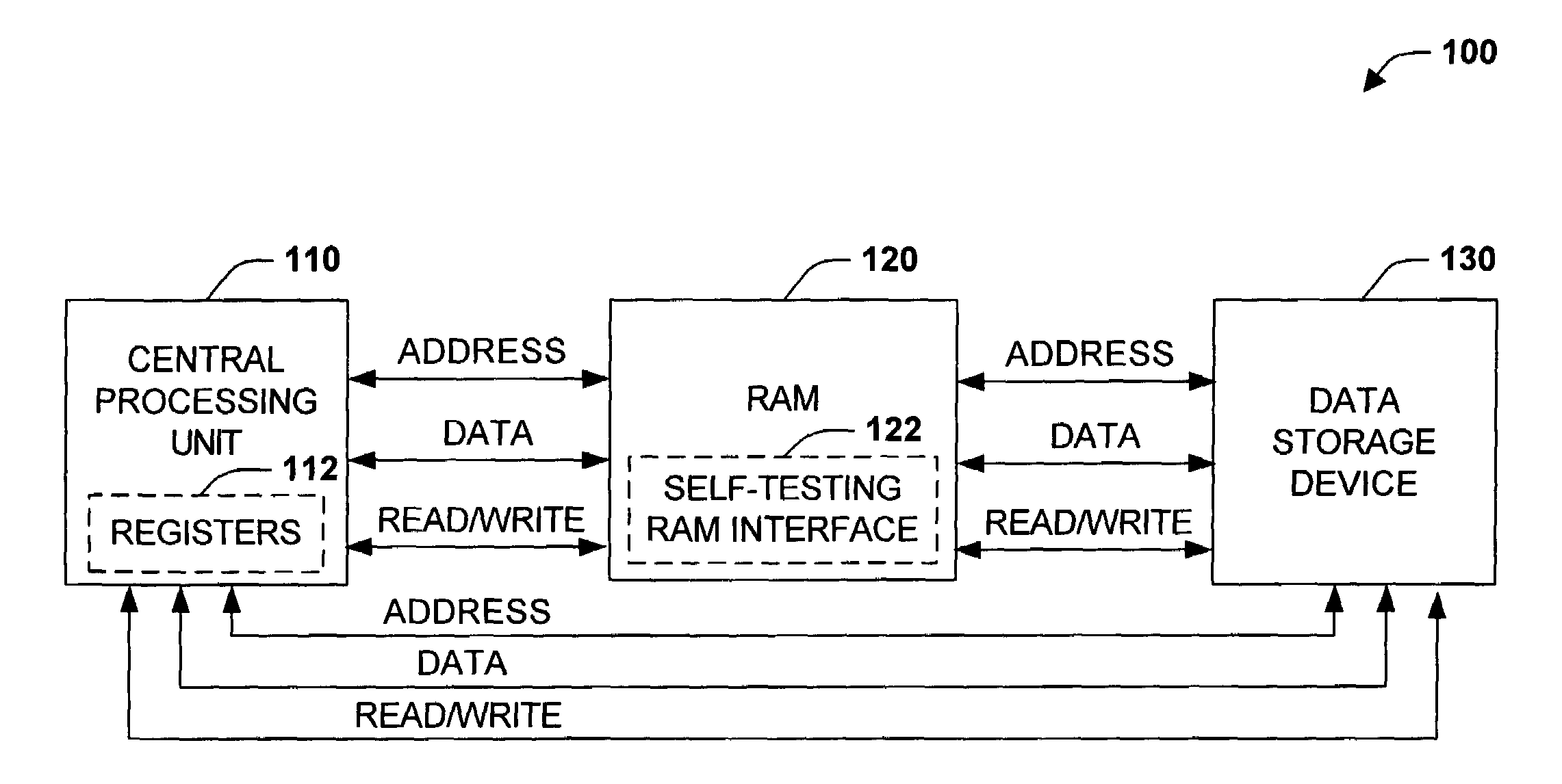
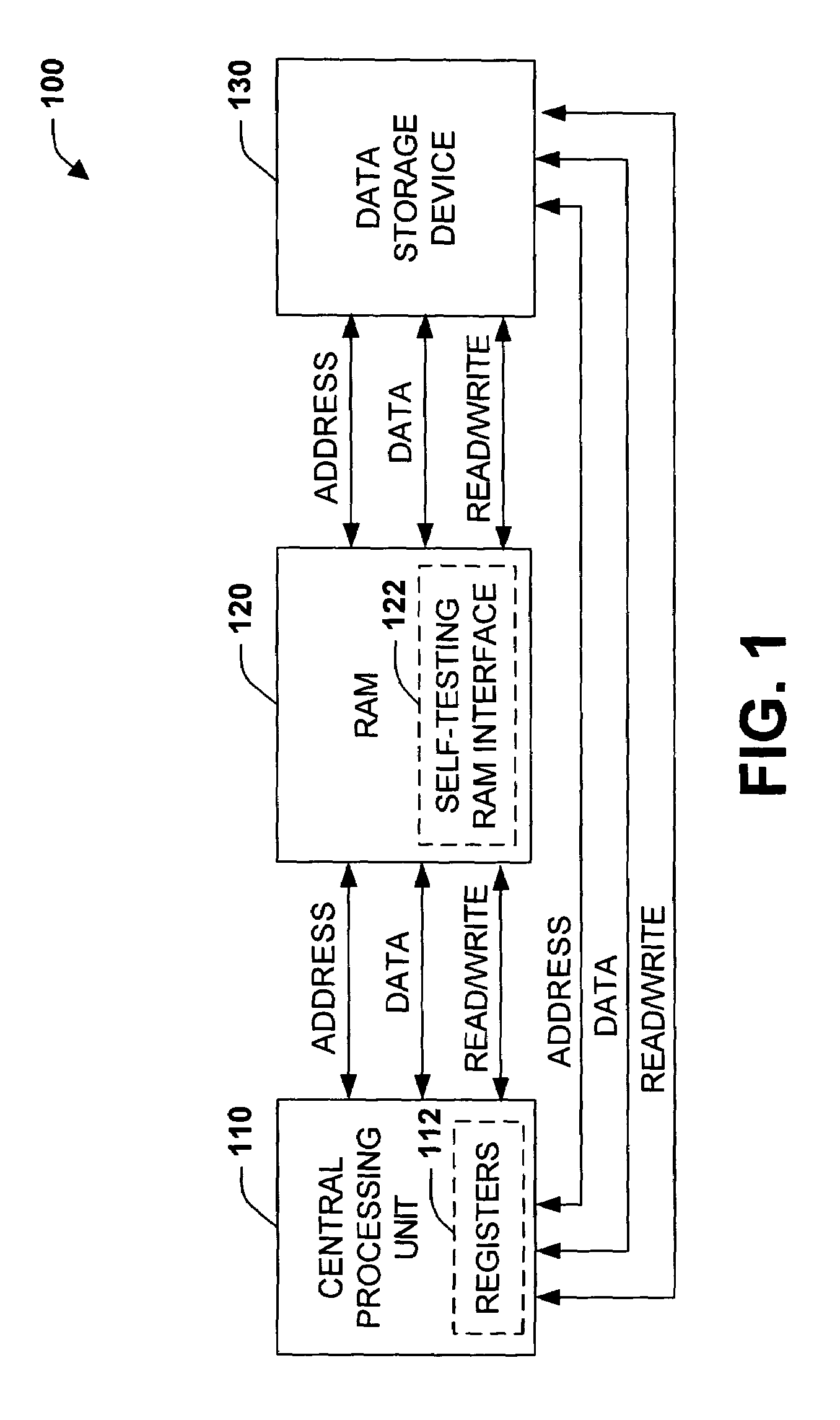
ActiveUS7334159B1Easy to testTedious to testUnauthorized memory use protectionDigital storageData integrityMemory interface
A self-testing and correcting random access memory (RAM) device and methodology is disclosed herein. The device includes at least one array of memory to enable data storage and self-testing RAM interface for evaluating, correcting, and / or compensating for memory cell errors. The RAM device, via the self-testing RAM interface, supports interaction with a central processing unit (CPU) to facilitate testing of the CPU to memory interface as well as the device memory array. Upon detection of memory errors, the self-testing RAM interface can notify the CPU, notify an exception handler, correct, and / or compensate for the errors. Error correction can be accomplished using error correction codes (ECCs) alone or in combination with retrieval and replacement of erroneous data with correct data stored in different locations. Memory cells that are physically defective and incapable of maintaining data integrity can be compensated for by mapping defective cells to a plurality of reserved replacement cells.
Owner:XENOGENIC DEV LLC
Switching method in a multi-threaded processor
InactiveUS20020078122A1Program initiation/switchingDigital computer detailsOperational systemEmbedded system
A processor includes logic for attaining a very fast exception handling functionality while executing non-threaded programs by invoking a multithreaded-type functionality in response to an exception condition. The processor, while operating in multithreaded conditions or while executing non-threaded programs, progresses through multiple machine states during execution. The very fast exception handling logic includes connection of an exception signal line to thread select logic, causing an exception signal to evoke a switch in thread and machine state. The switch in thread and machine state causes the processor to enter and to exit the exception handler immediately, without waiting to drain the pipeline or queues and without the inherent timing penalty of the operating system's software saving and restoring of registers.
Owner:SUN MICROSYSTEMS INC
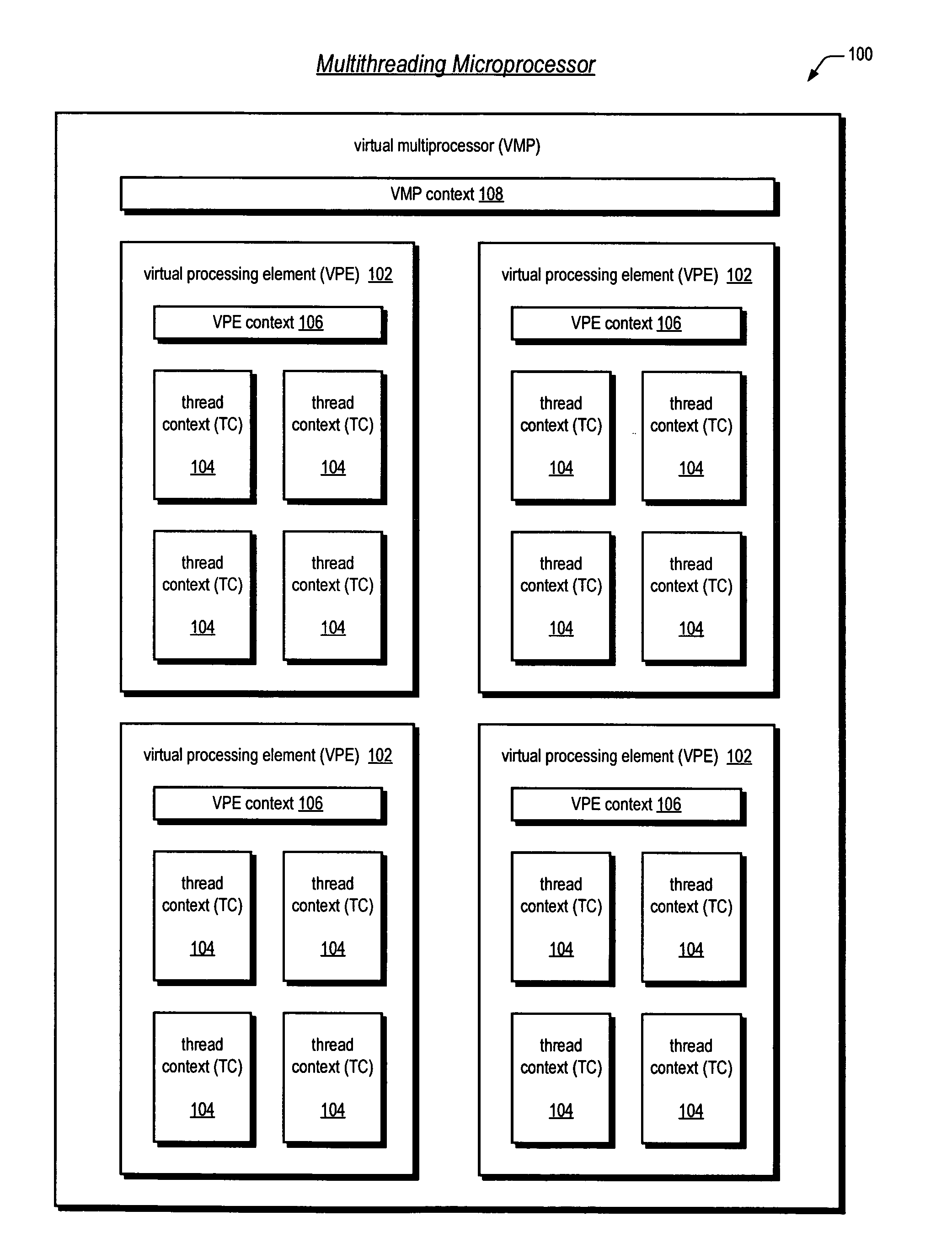
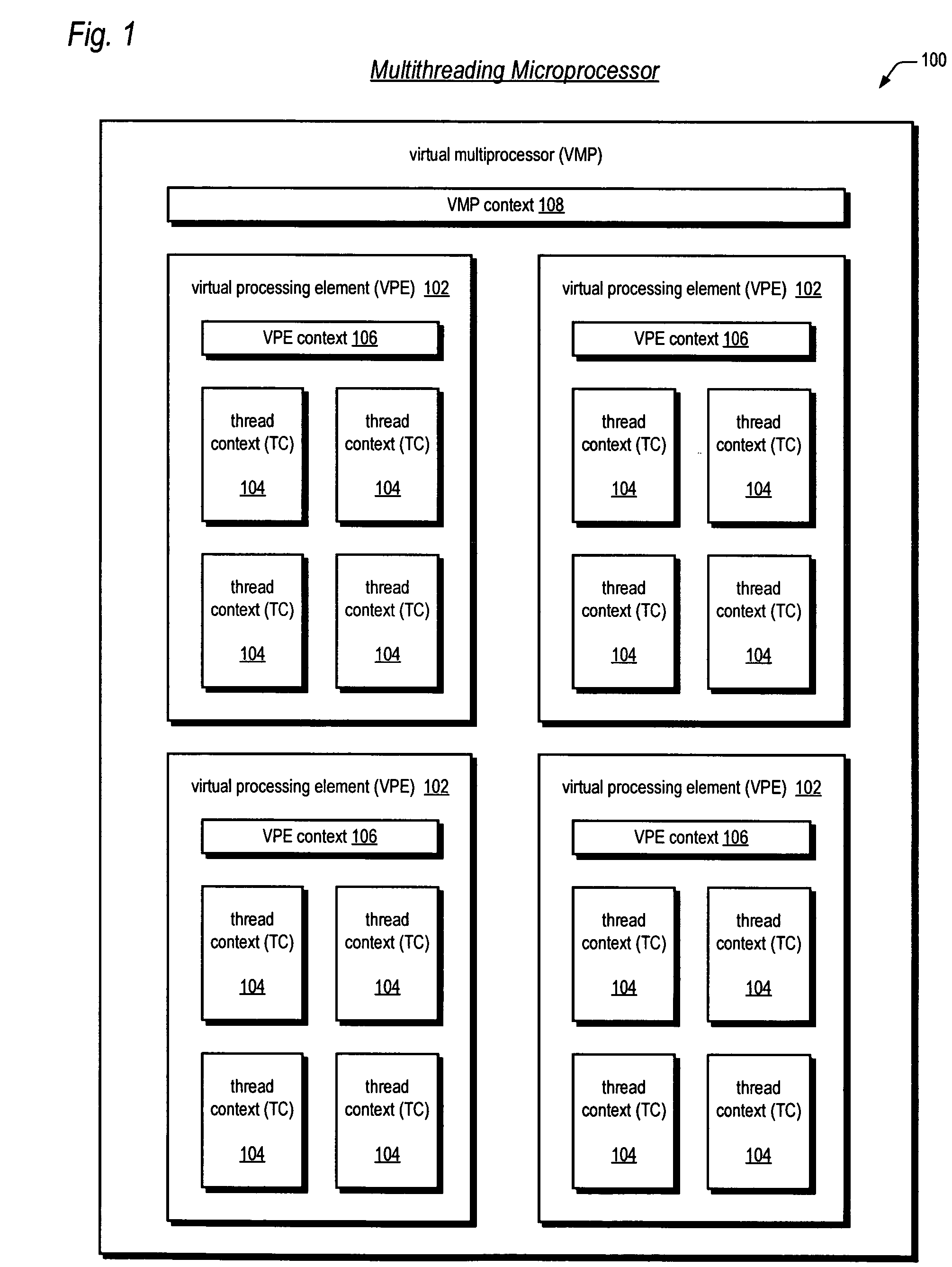
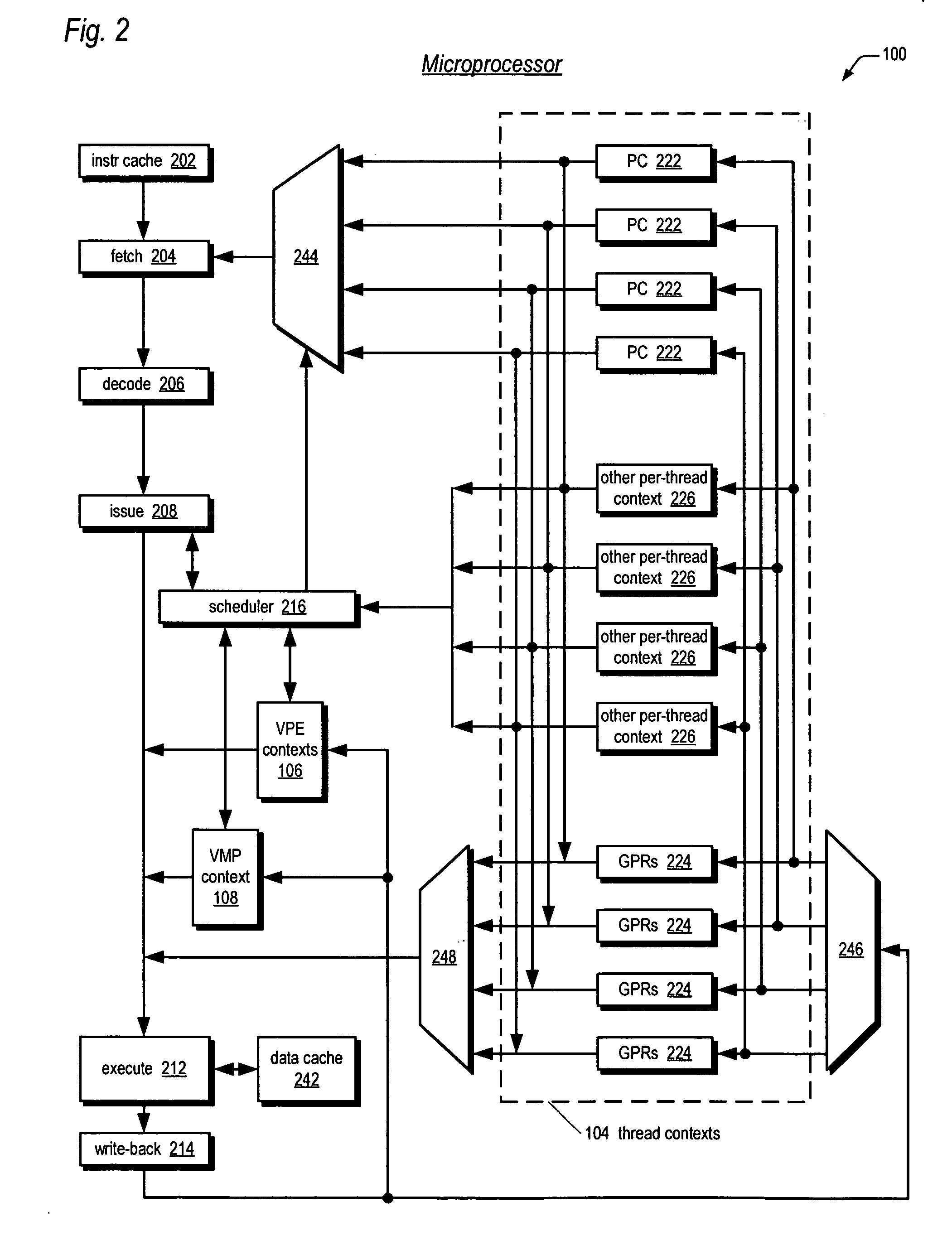
Software emulation of directed exceptions in a multithreading processor
ActiveUS20060161421A1More scalableSave areaDigital computer detailsSoftware simulation/interpretation/emulationGeneral purposeSoftware emulation
A multithreading microprocessor has a plurality of thread contexts (TCs) each including sufficient state, such as general purpose registers and program counter, to execute a separate thread of execution as one of a plurality of symmetric processors controlled by a multiprocessor operating system. However, the microprocessor hardware does not support the ability for one TC to direct an exception to another TC, i.e., to specify to which of the other TCs the exception is directed. A first thread running on a first TC of the operating system executes architected instructions to halt a second thread (either user or kernel thread) running on a second TC, save state of the second TC, write the second TC state to emulate an exception—including writing a restart register with the address of an exception handler, and unhalt the second TC to execute the exception hander.
Owner:MIPS TECH INC
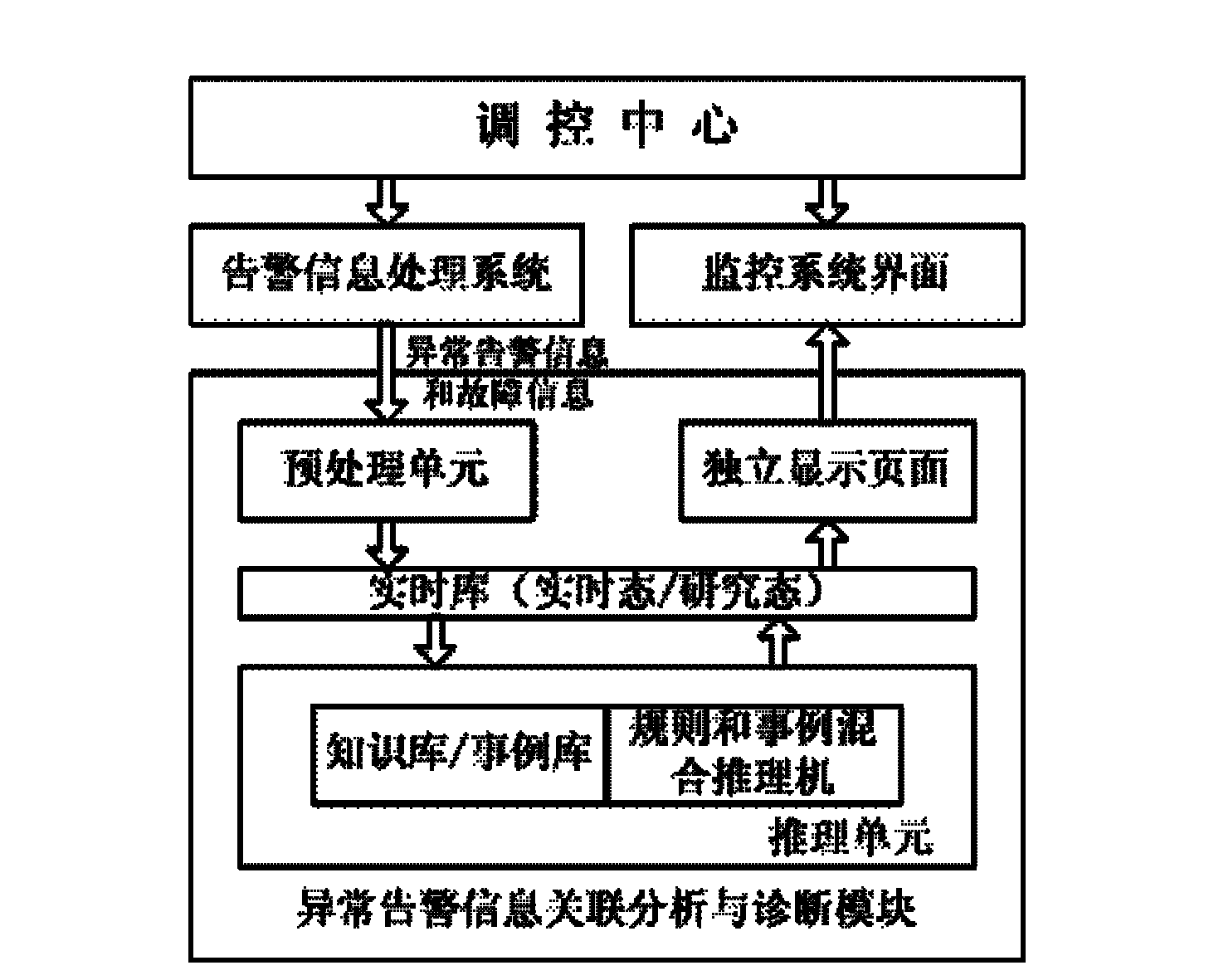
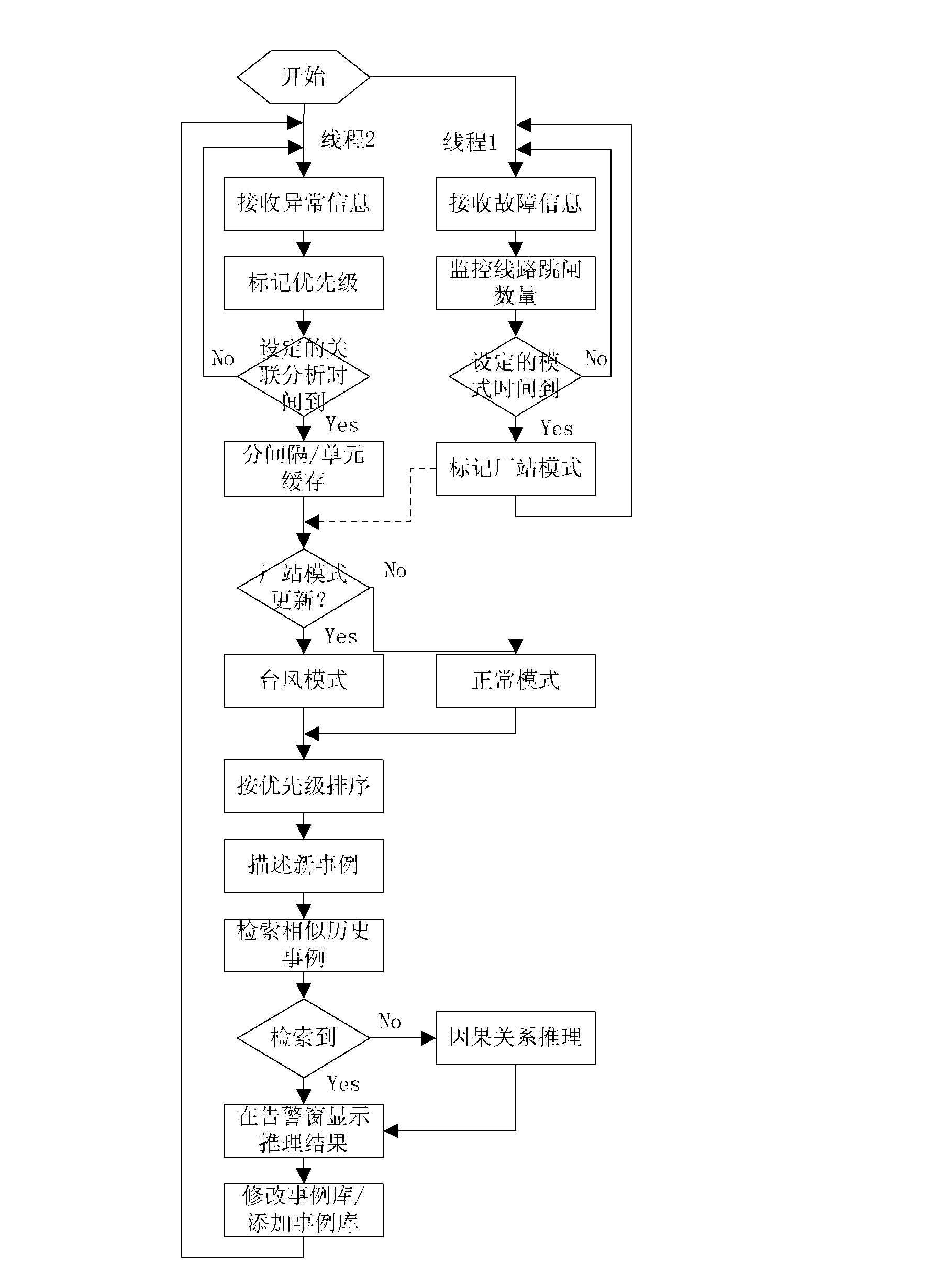
District power network equipment abnormal alarm signal association analysis and diagnosis method
InactiveCN102638100AIntegrity guaranteedGuarantee authenticityCircuit arrangementsInformation processingPower system scheduling
The invention discloses a district power network equipment abnormal alarm signal association analysis and diagnosis method in the field of automation of scheduling of electric power systems. According to the method disclosed by the invention, the weather situation of a plant station region at which abnormal alarm information is located can be automatically identified so as to determine the information processing mode. The method disclosed by the invention has the beneficial effects that by realizing intelligent association analysis and auxiliary decision making of the equipment abnormal alarm information under the real-time state, and performing playback on historical alarm information and performing real-time treatment on manual set information under the research state, the abnormal treatment time is greatly reduced, the incidence of accidents is reduced, a real-time, rich and intelligent auxiliary decision-making support is provided for regulation and control staff, and the safe, high-quality, economical and stable operation of an electric fence is further ensured.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
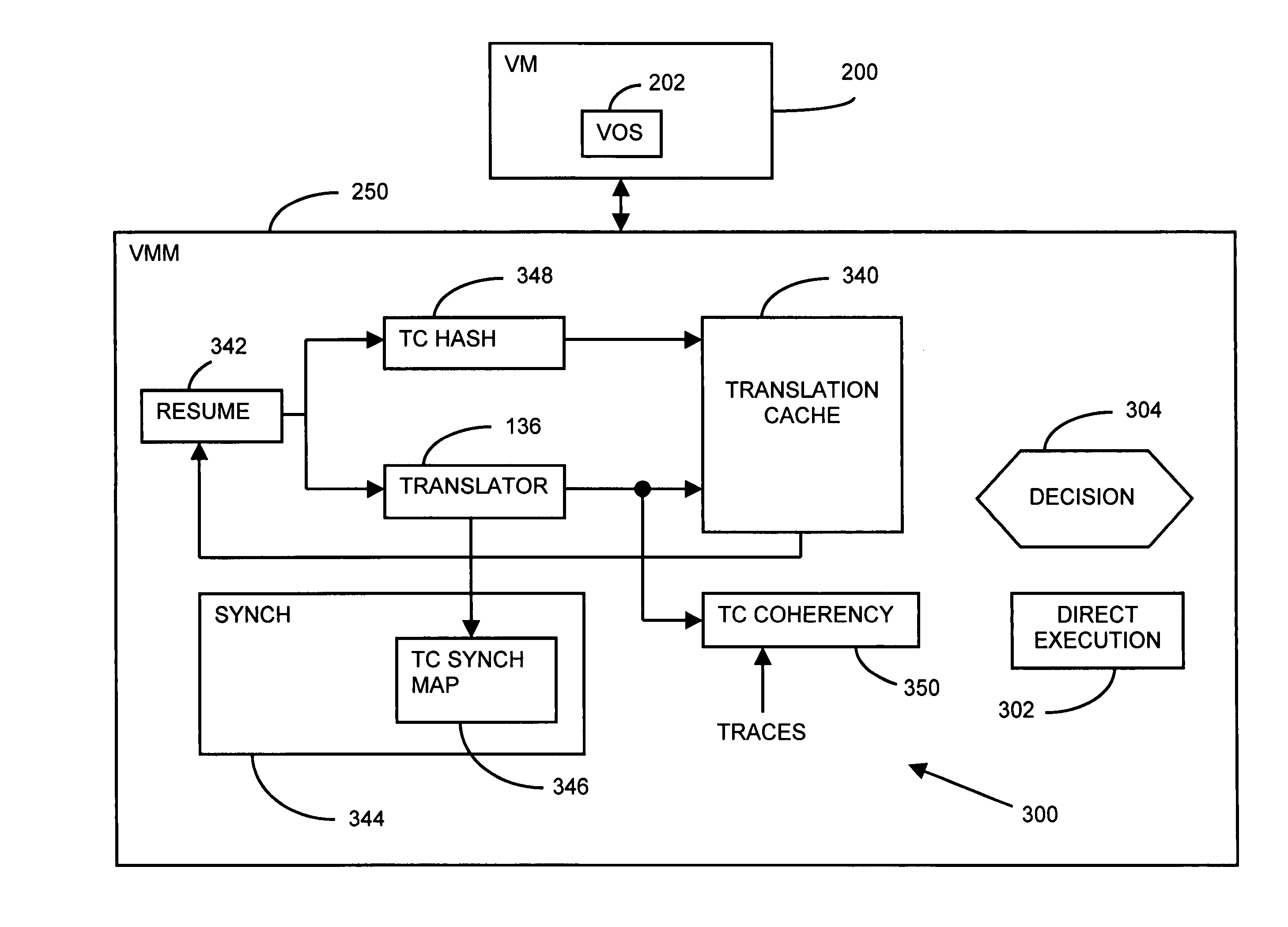
Binary translator with precise exception synchronization mechanism
InactiveUS7516453B1Digital computer detailsConcurrent instruction executionComputerized systemGoal system
A source computer system with one instruction set architecture (ISA) is configured to run on a target hardware system that has its own ISA, which may be the same as the source ISA. In cases where the source instructions cannot be executed directly on the target system, the invention provides binary translation system. During execution from binary translation, however, both synchronous and asynchronous exceptions may arise. Synchronous exceptions may be either transparent (requiring processing action wholly within the target computer system) or non-transparent (requiring processing that alters a visible state of the source system). Asynchronous exceptions may also be either transparent or non-transparent, in which case an action that alters a visible state of the computer system needs to be applied. The invention includes subsystems, and related methods of operation, for detecting the occurrence of all of these types of exceptions, to handle them, and to do so with precise reentry into the interrupted instruction stream; by “precise” is meant that the atomic execution of the source instructions is guaranteed, and that the application of actions, including those that originate from asynchronous exceptions, occurs at the latest at the completion of the current source instruction at the time of the request for the action. The binary translation and exception-handling subsystems are preferably included as components of a virtual machine monitor which is installed between the target hardware system and the source system, which is preferably a virtual machine.
Owner:VMWARE INC
Multithreaded Processor with Lock Indicator
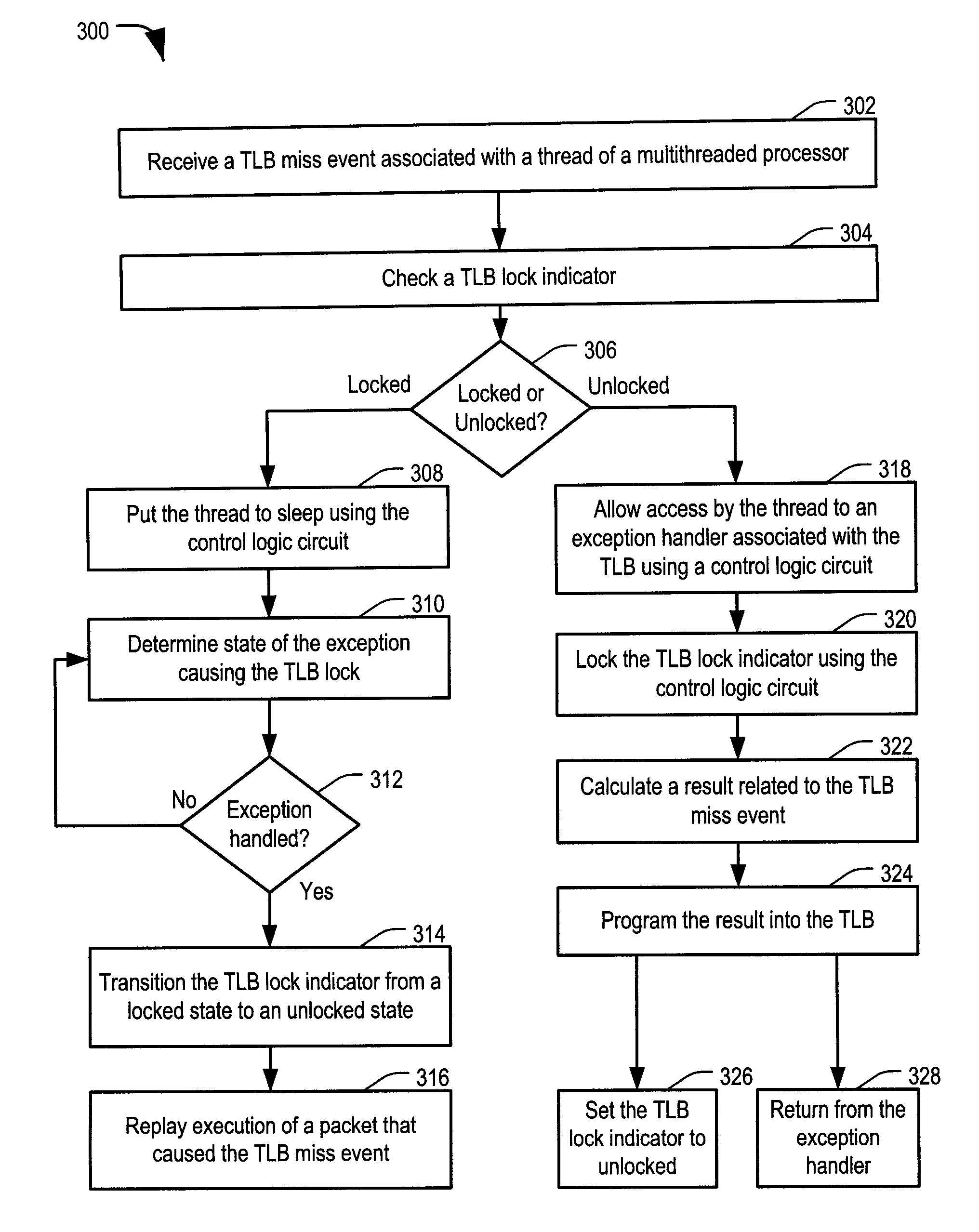
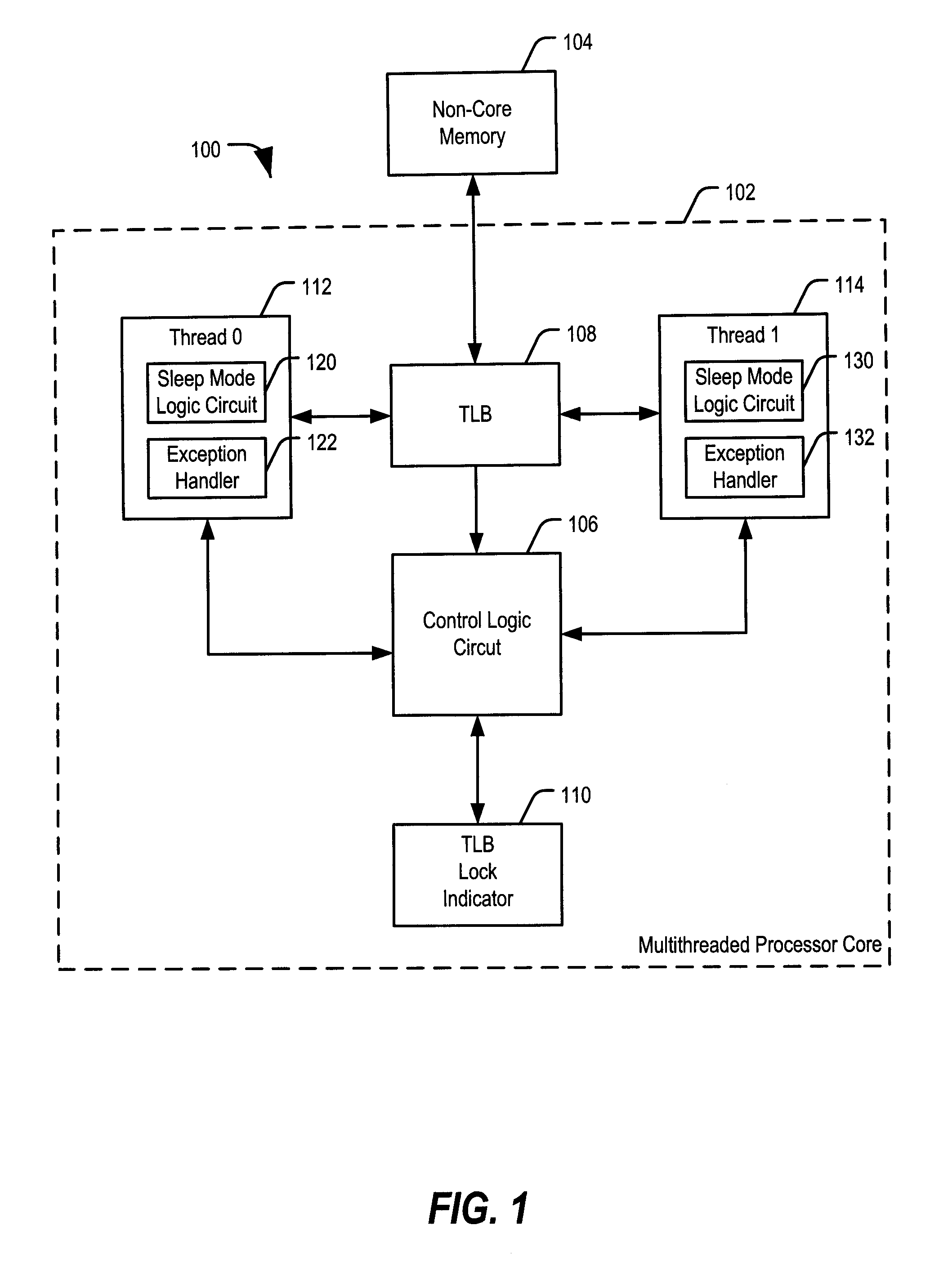
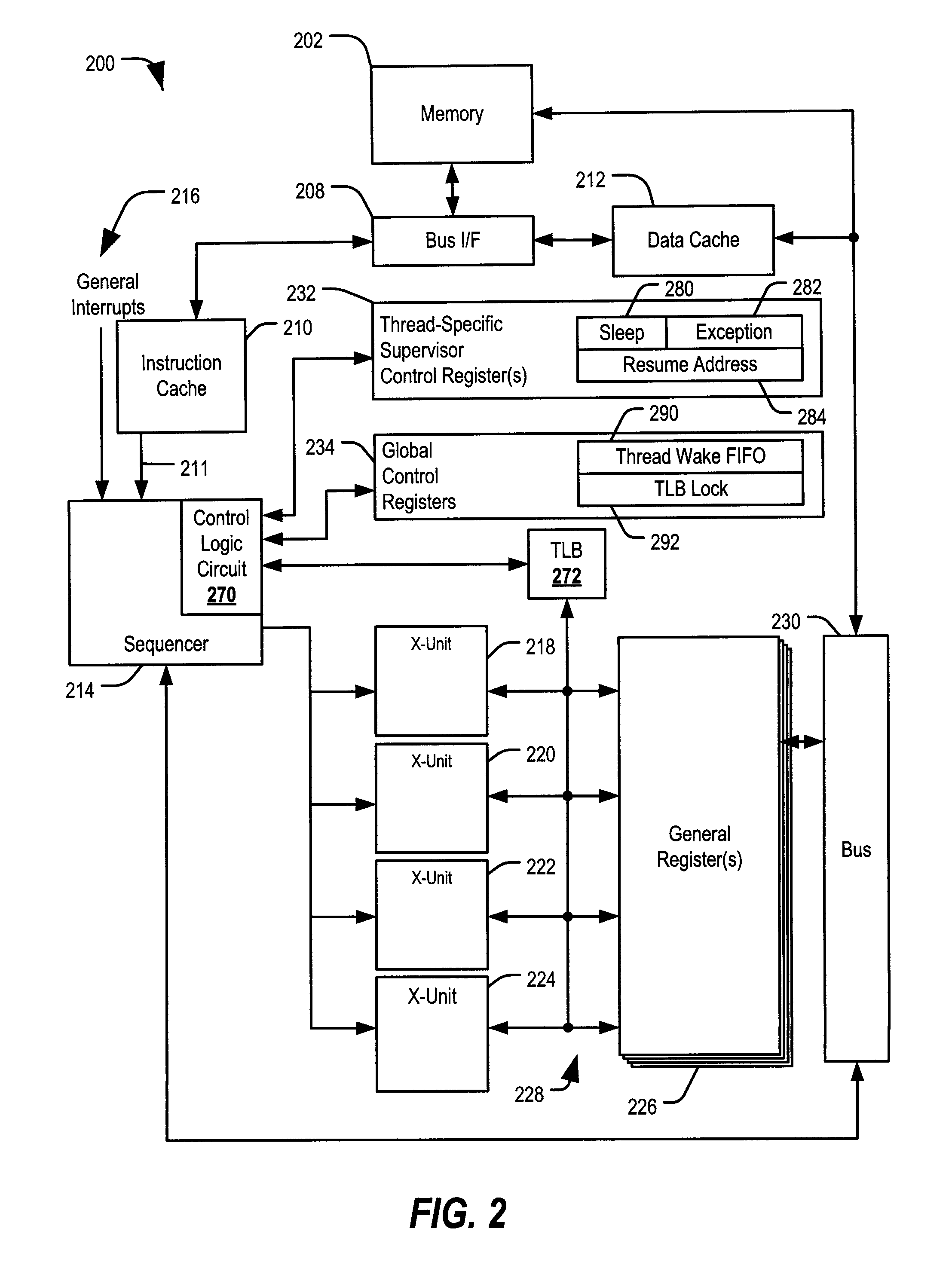
ActiveUS20090144519A1Faster unlock operationReduce dynamic power consumptionEnergy efficient ICTProgram control using stored programsShared resourceEmbedded system
Systems and methods including a multithreaded processor with a lock indicator are disclosed. In an embodiment, a system includes means for indicating a lock status of a shared resource in a multithreaded processor. The system includes means for automatically locking the shared resource before processing exception handling instructions associated with the shared resource. The system further includes means for unlocking the shared resource.
Owner:QUALCOMM INC
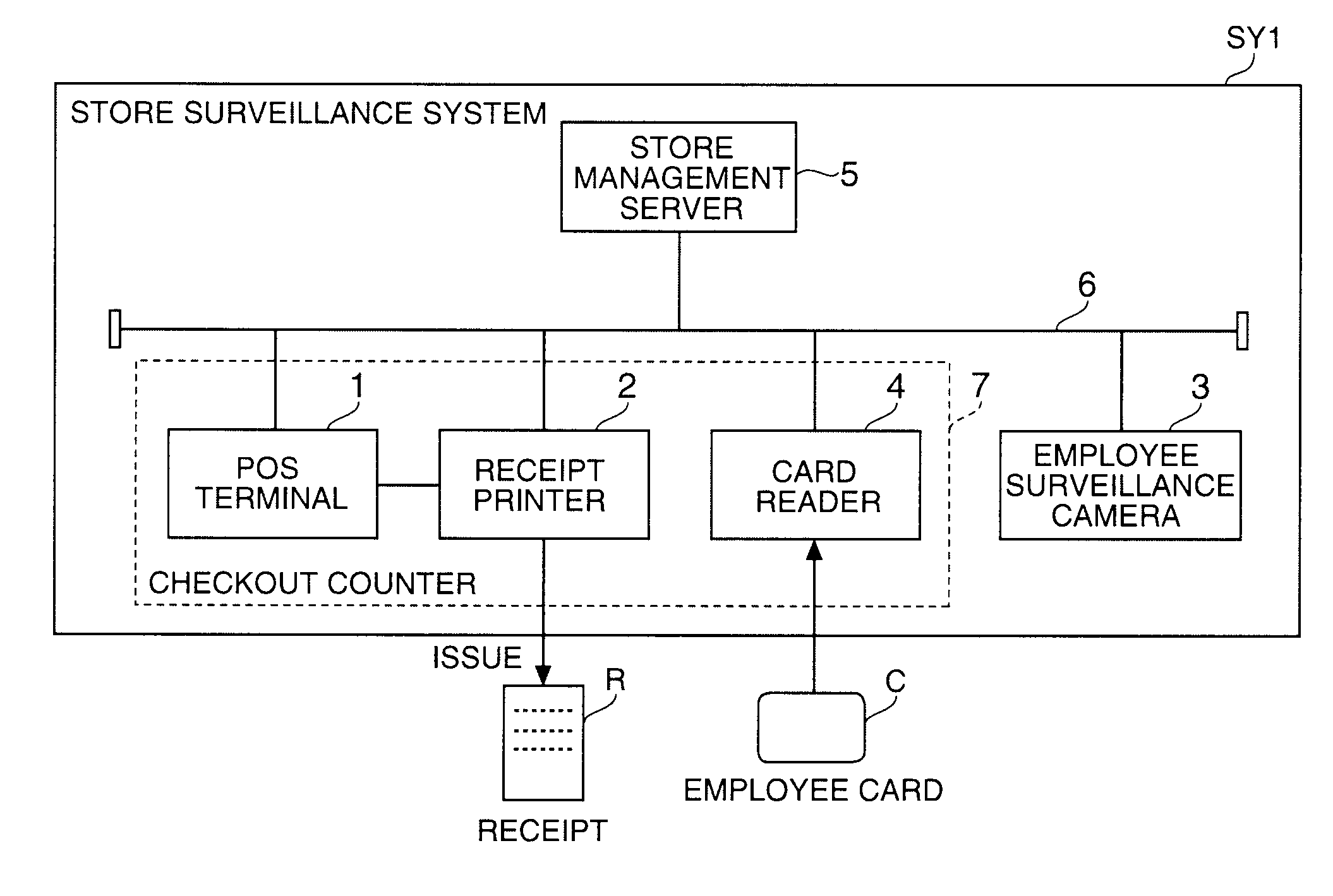
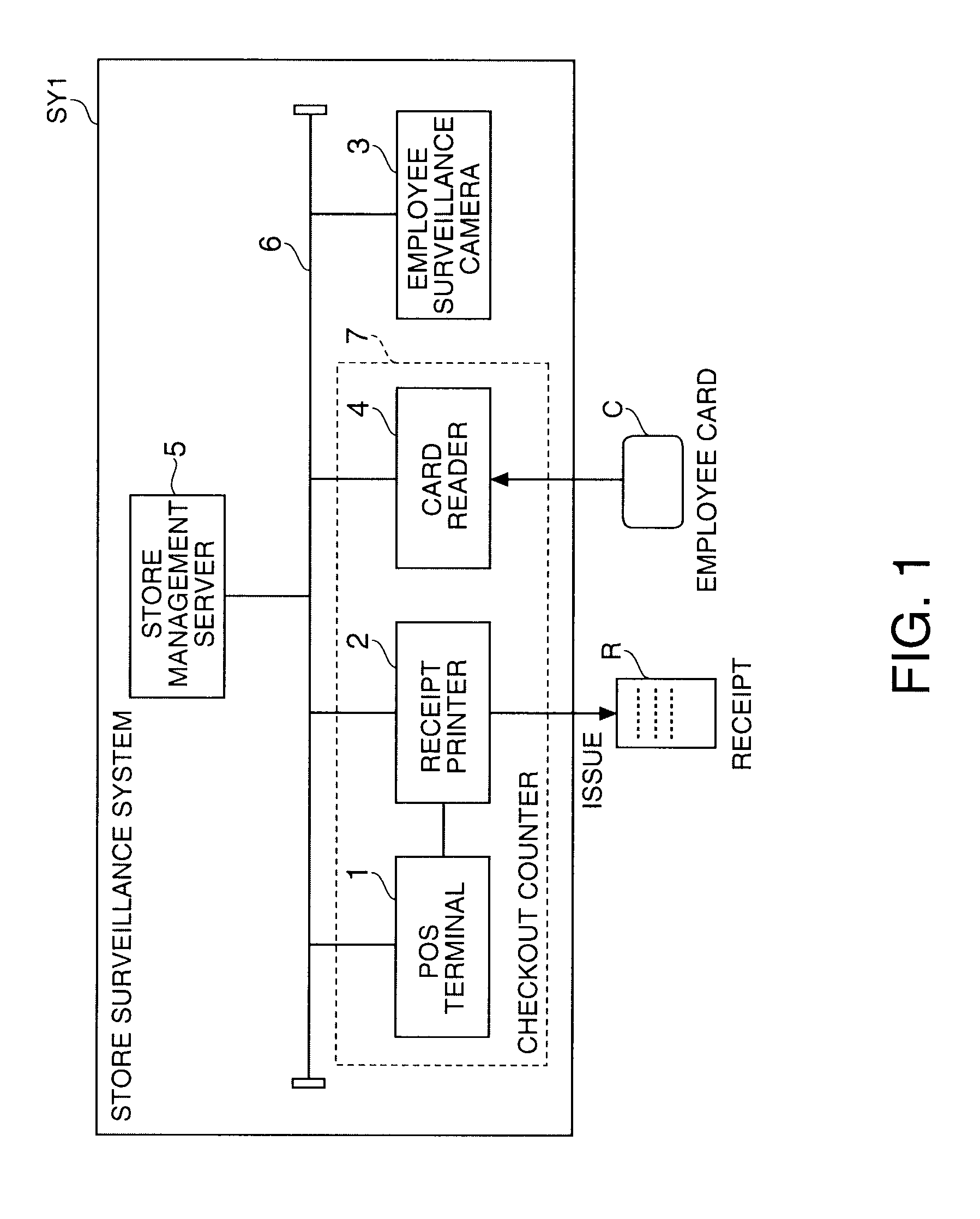
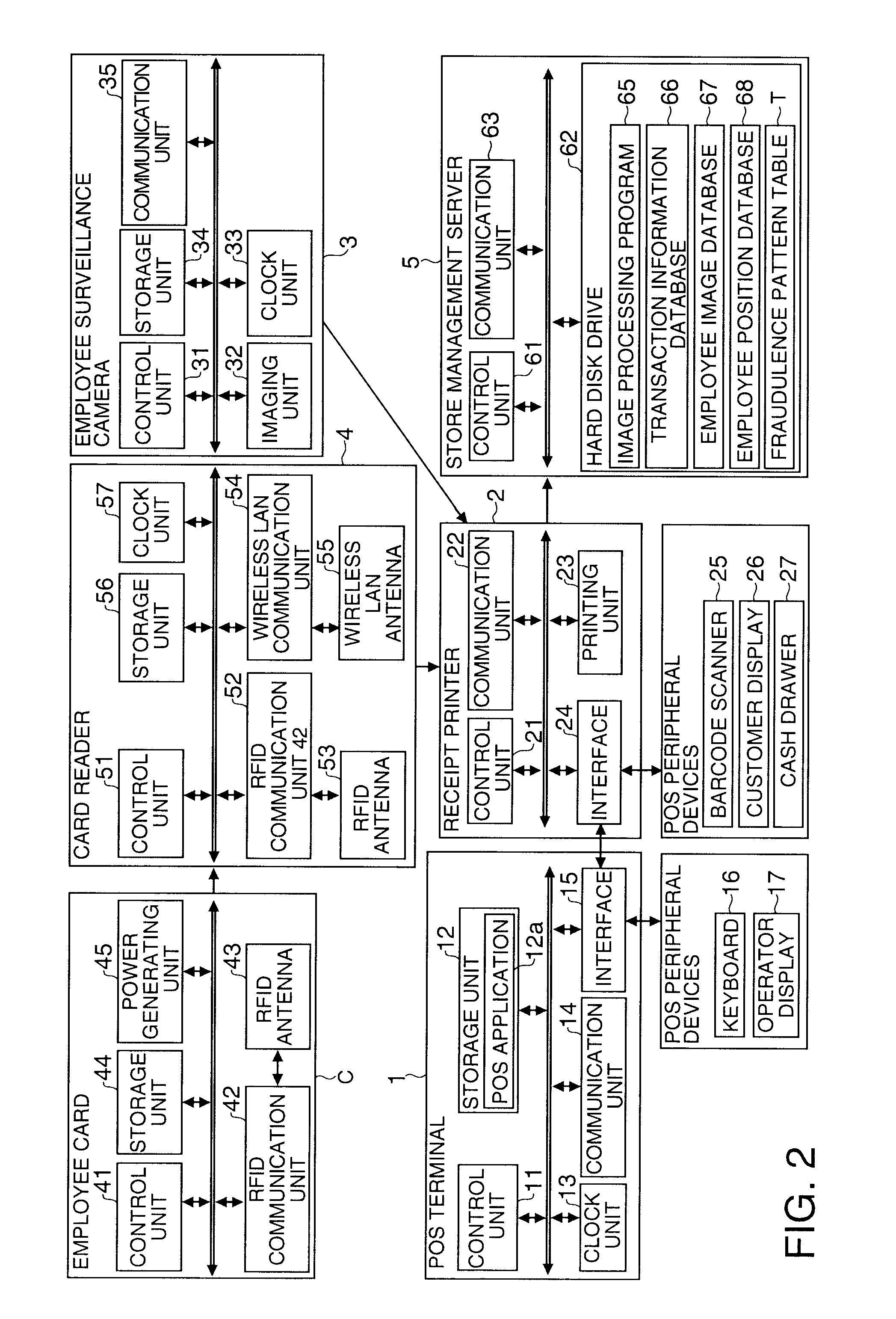
Store Surveillance System, Alarm Device, Control Method for a Store Surveillance System, and a Program
InactiveUS20110063108A1Easy to detectCash registersPayment architectureMonitoring systemComputer terminal
A store surveillance system, a warning device for use in such system, a store surveillance control method, and program-based instruction implementations of such method facilitate the detection of fraudulent activity in a retail store, supermarket, or other type of store. A store management server has a pattern storage unit that stores occurrence patterns of specific events that occur in a store; a POS terminal that executes a product transaction process; a employee surveillance camera that monitors component factors of the occurrence patterns; and a card reader. In some embodiments, when the POS terminal executes a predetermined exception process, the store management server issues a warning conditionally upon whether event occurrence conditions detected by the employee surveillance camera and card reader match a fraudulence pattern stored as an occurrence pattern, or do not match a normal pattern stored as an occurrence pattern
Owner:SEIKO EPSON CORP
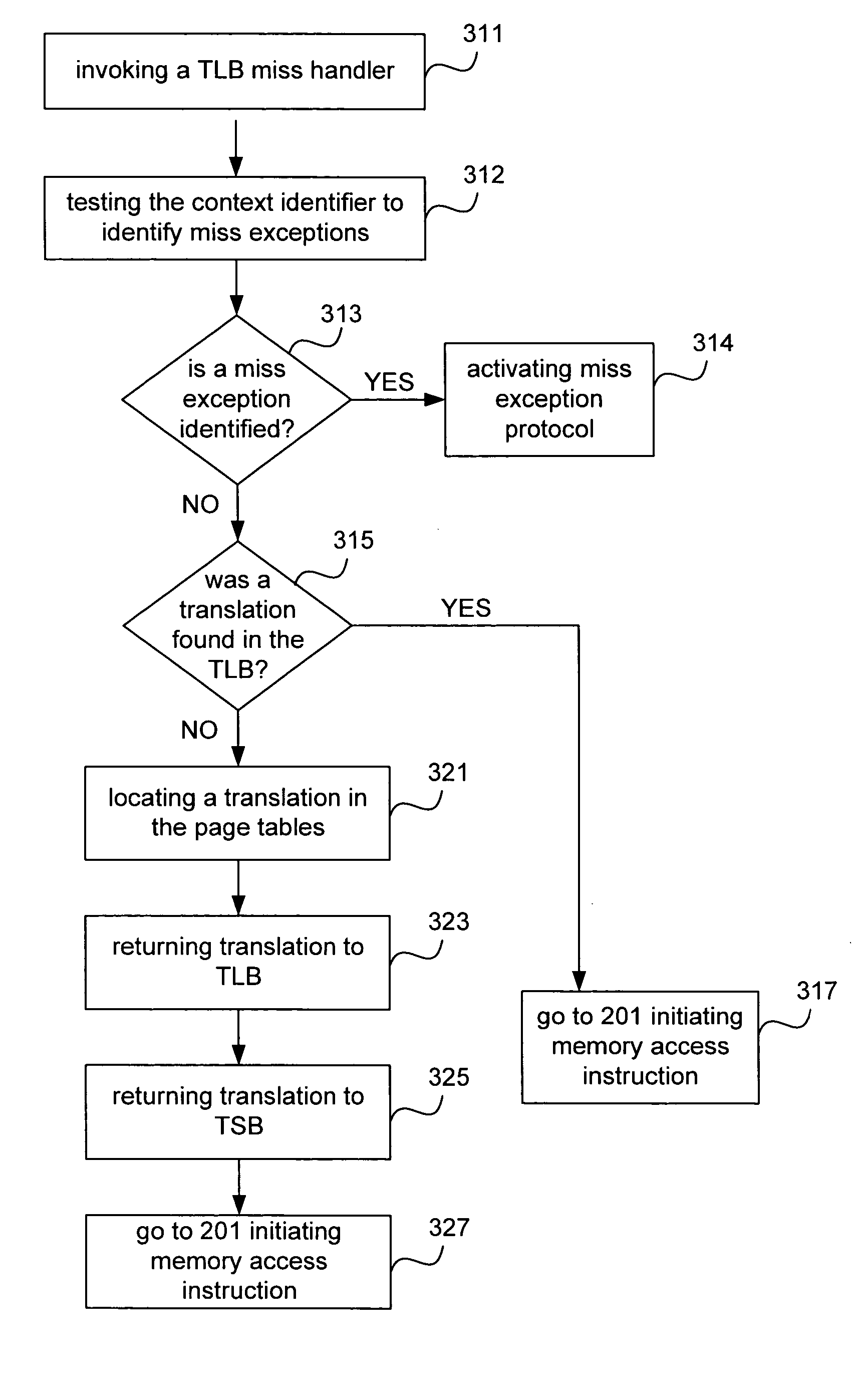
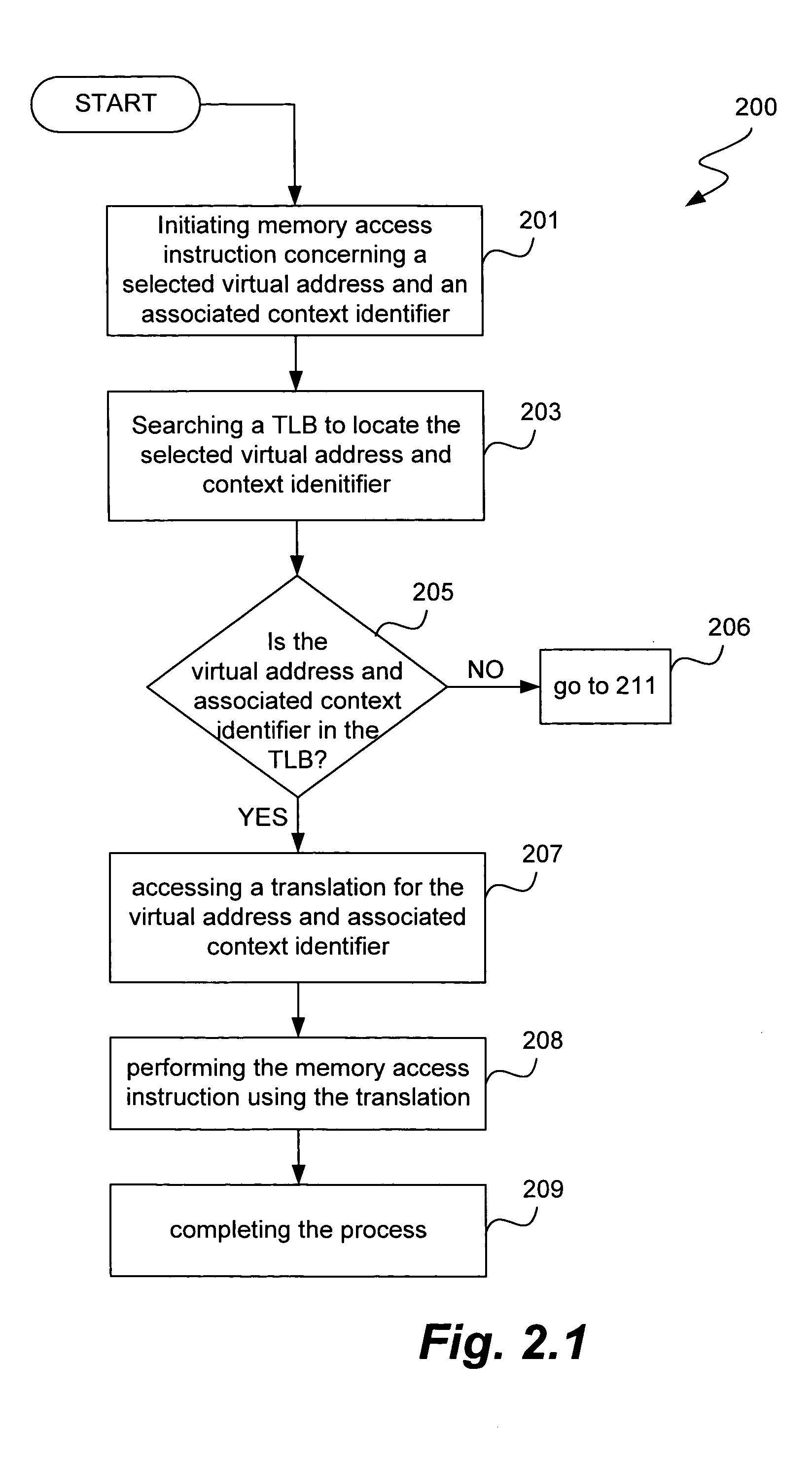
Method and apparatus for memory management in a multi-processor computer system
ActiveUS20050172099A1Avoid accessMemory architecture accessing/allocationMemory adressing/allocation/relocationManagement unitMulti processor
Improved techniques and systems for accommodating TLB shootdown events in multi-processor computer systems are disclosed. A memory management unit (MMU) having a TLB miss handler and miss exception handler is provided. The MMU receives instructions relative to a virtual address. A TLB is searched for the virtual address, if the virtual address is not found in the TLB, secondary memory assets are searched for a TTE that corresponds to the virtual address and its associated context identifier. The context identifier is tested to determine if the TTE is available. Where the TTE is available, the TLB and secondary memory assets are updated as necessary and the method initiates memory access instructions. Where the TTE is unavailable, the method either resolves the unavailability or waits until the unavailability is resolved and then initiates memory access instructions, thereby enabling the desired virtual address information to be accessed.
Owner:ORACLE INT CORP
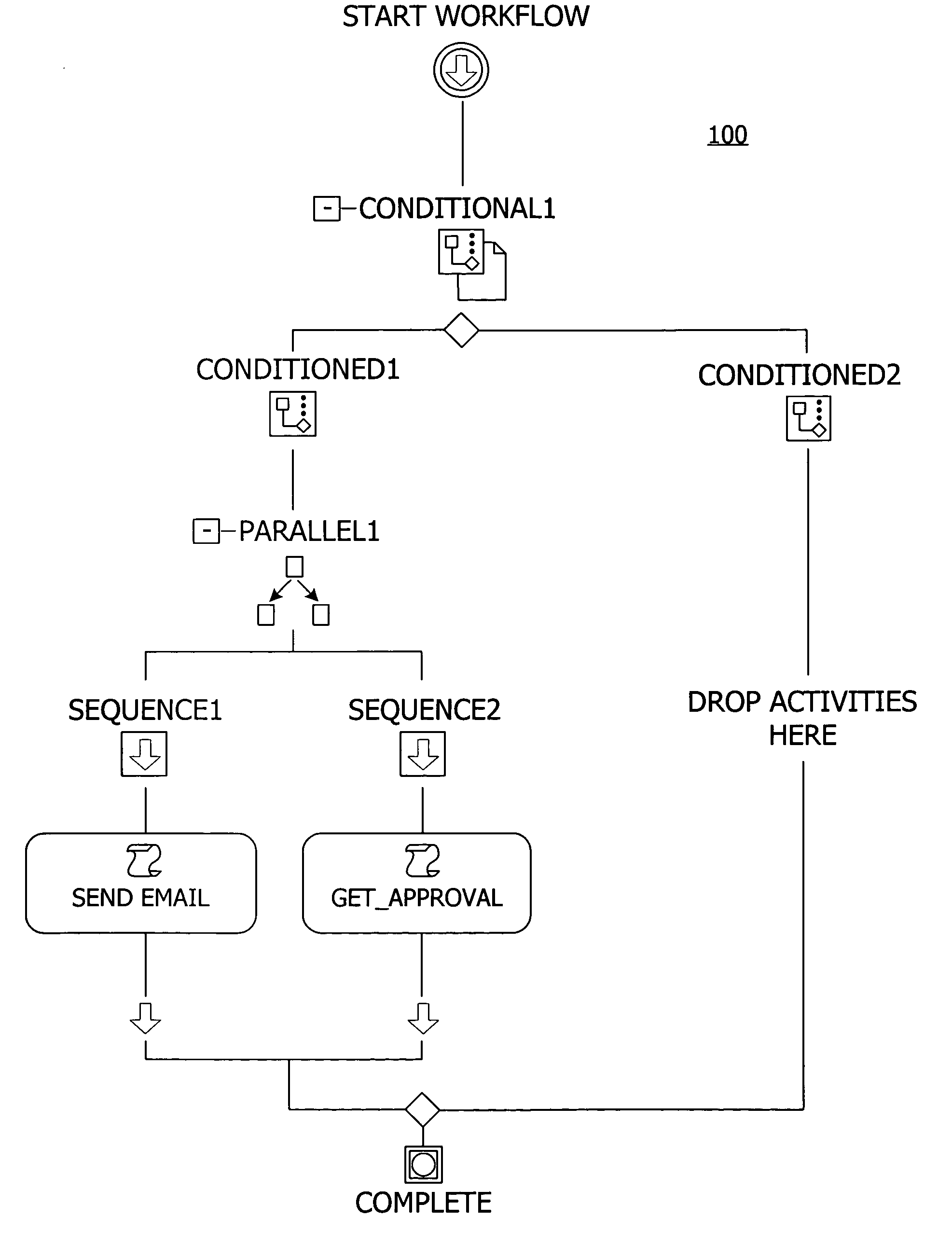
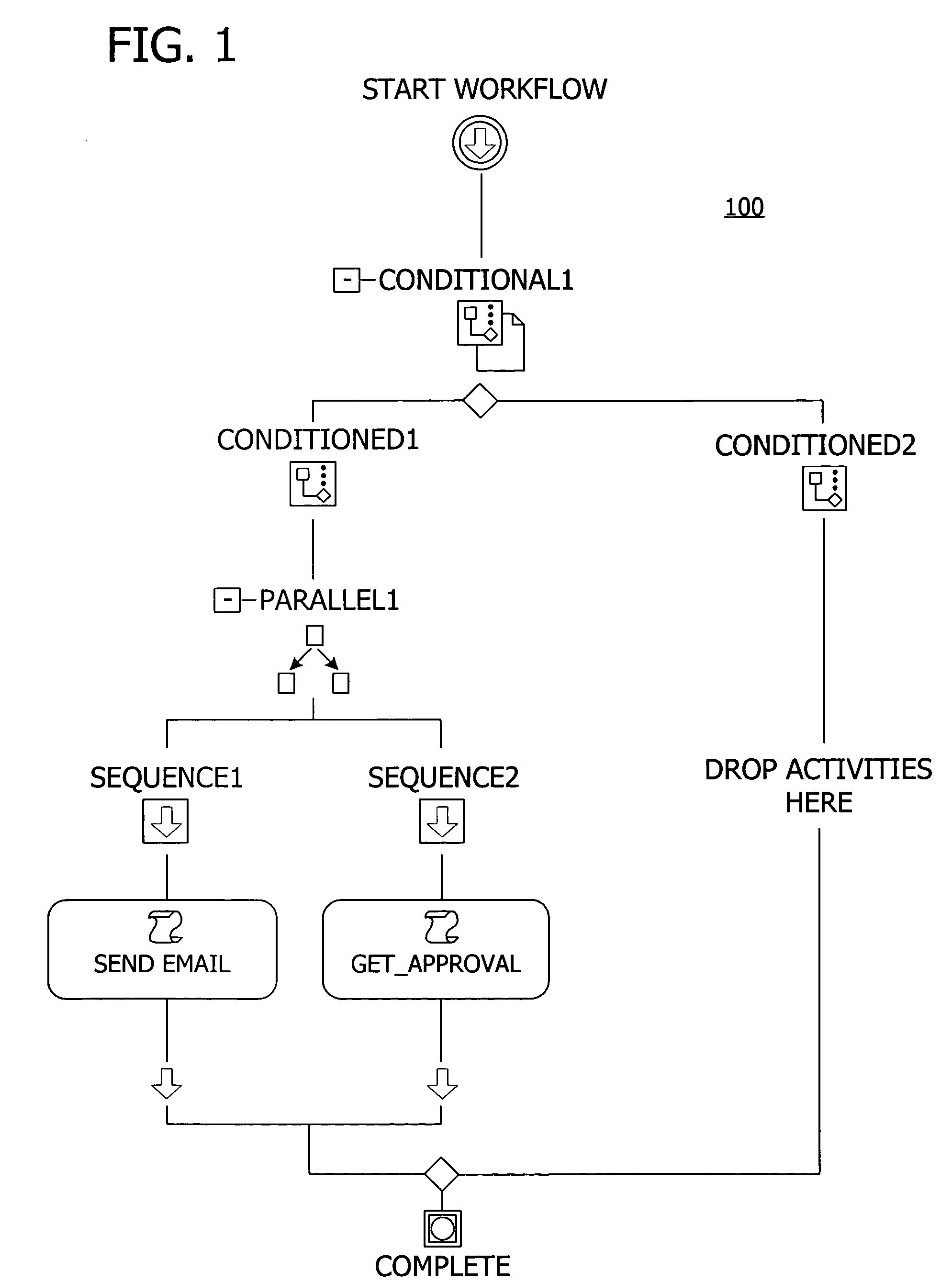
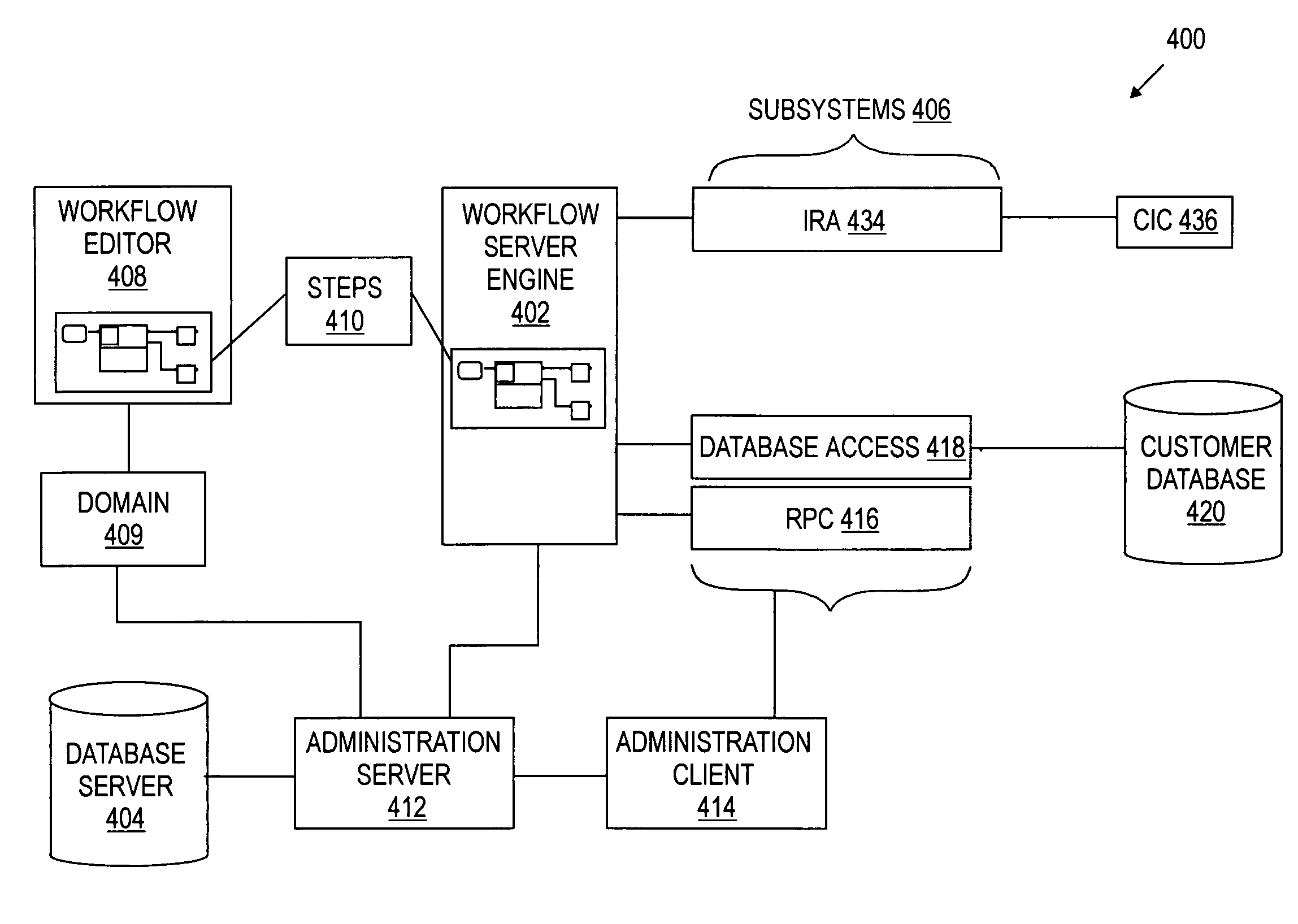
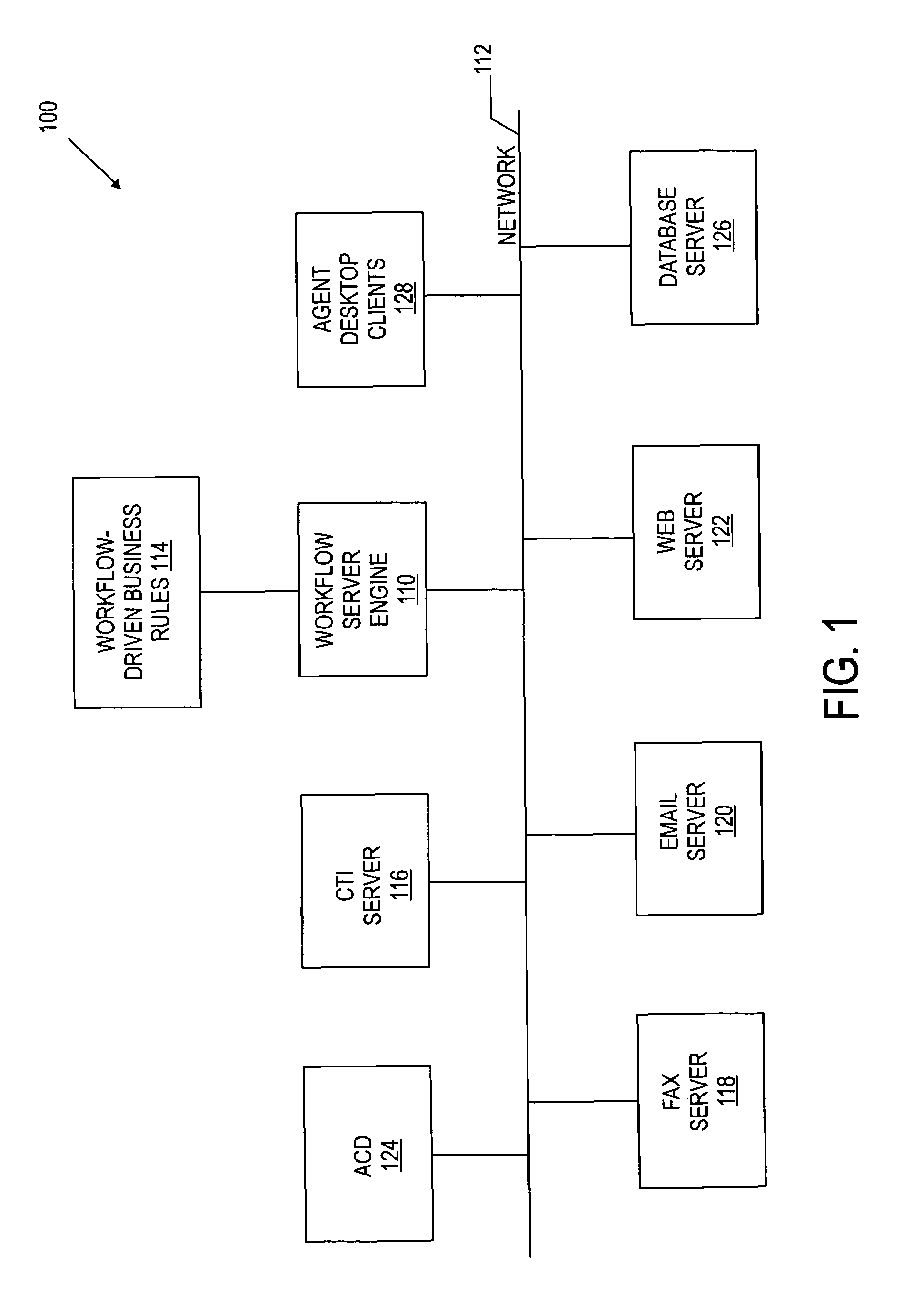
Apparatus and method for collecting and displaying information in a workflow system
InactiveUS20050093881A1Cathode-ray tube indicatorsResourcesCustomer relationship managementHandling system
A method and apparatus for extensible real-time workflows are described. The present invention allows a user of a transaction processing system, such as a customer relationship management (CRM) tool or an automatic call distribution (ACD), for example, to easily add new event sources without recompiling the core workflow server engine of the transaction processing system. The invention also supports features such as the adding of new services, the exchange of events and parameters with other systems, real-time collection and display of workflow statistical information, the use of a centralized configuration database, incremental loading and unloading of workflows and rules, and exception handling.
Owner:WILMINGTON TRUST NAT ASSOC AS ADMINISTATIVE AGENT
Prefetch instruction mechanism for processor
InactiveUS6253306B1General purpose stored program computerConcurrent instruction executionProcessor registerParallel computing
Accordingly, a prefetch instruction mechanism is desired for implementing a prefetch instruction which is non-faulting, non-blocking, and non-modifying of architectural register state. Advantageously, a prefetch mechanism described herein is provided largely without the addition of substantial complexity to a load execution unit. In one embodiment, the non-faulting attribute of the prefetch mechanism is provided though use of the vector decode supplied Op sequence that activates an alternate exception handler. The non-modifying of architectural register state attribute is provided (in an exemplary embodiment) by first decoding a PREFETCH instruction to an Op sequence targeting a scratch register wherein the scratch register has scope limited to the Op sequence corresponding to the PREFETCH instruction. Although described in the context of a vector decode embodiment, the prefetch mechanism can be implemented with hardware decoders and suitable modifications to decode paths will be appreciated by those of skill in the art based on the description herein. Similarly, although in one particular embodiment such a scratch register is architecturally defined to read as a NULL (or zero) value, any target for the Op sequence that is not part of the architectural state of the processor would also be suitable. Finally, in one embodiment the non-blocking attribute is provided by the Op sequence completing (without waiting for return of fill data) upon posting of a cache fill request to load logic of a data cache. In this way, LdOps which follow in a load pipe are not stalled by a prefetch-related miss and can instead execute concurrently with the prefetch-related line fill.
Owner:GLOBALFOUNDRIES INC
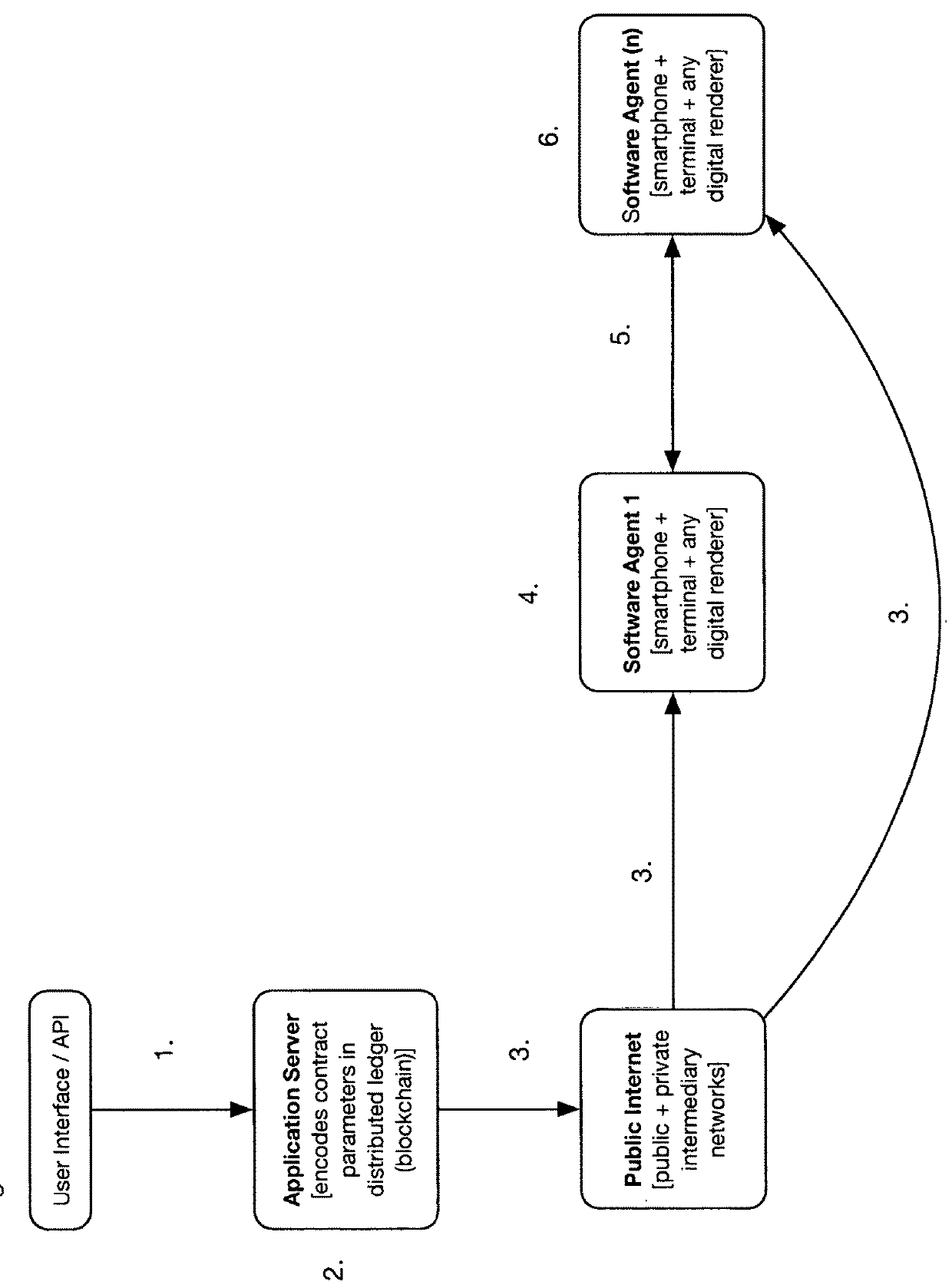
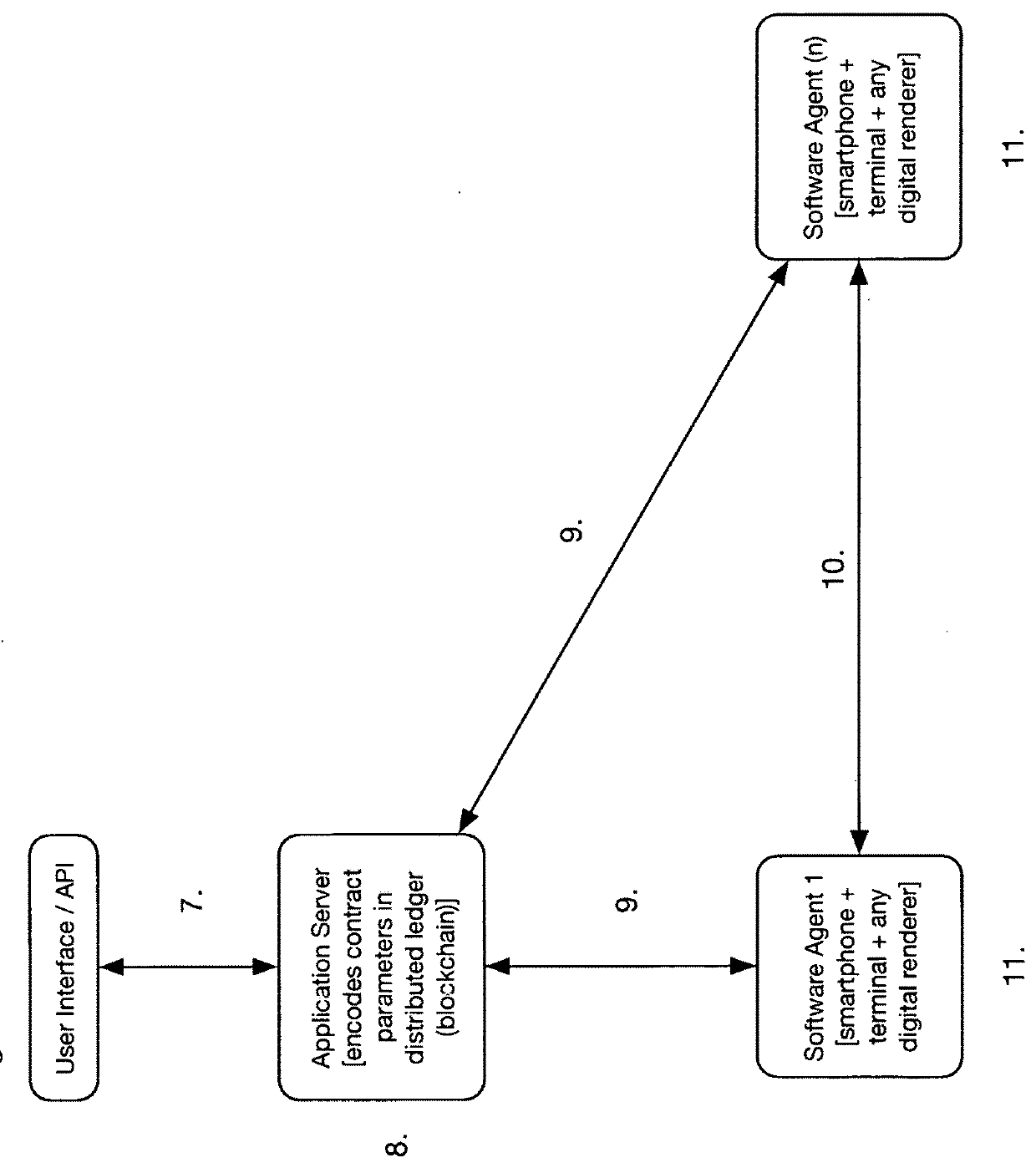
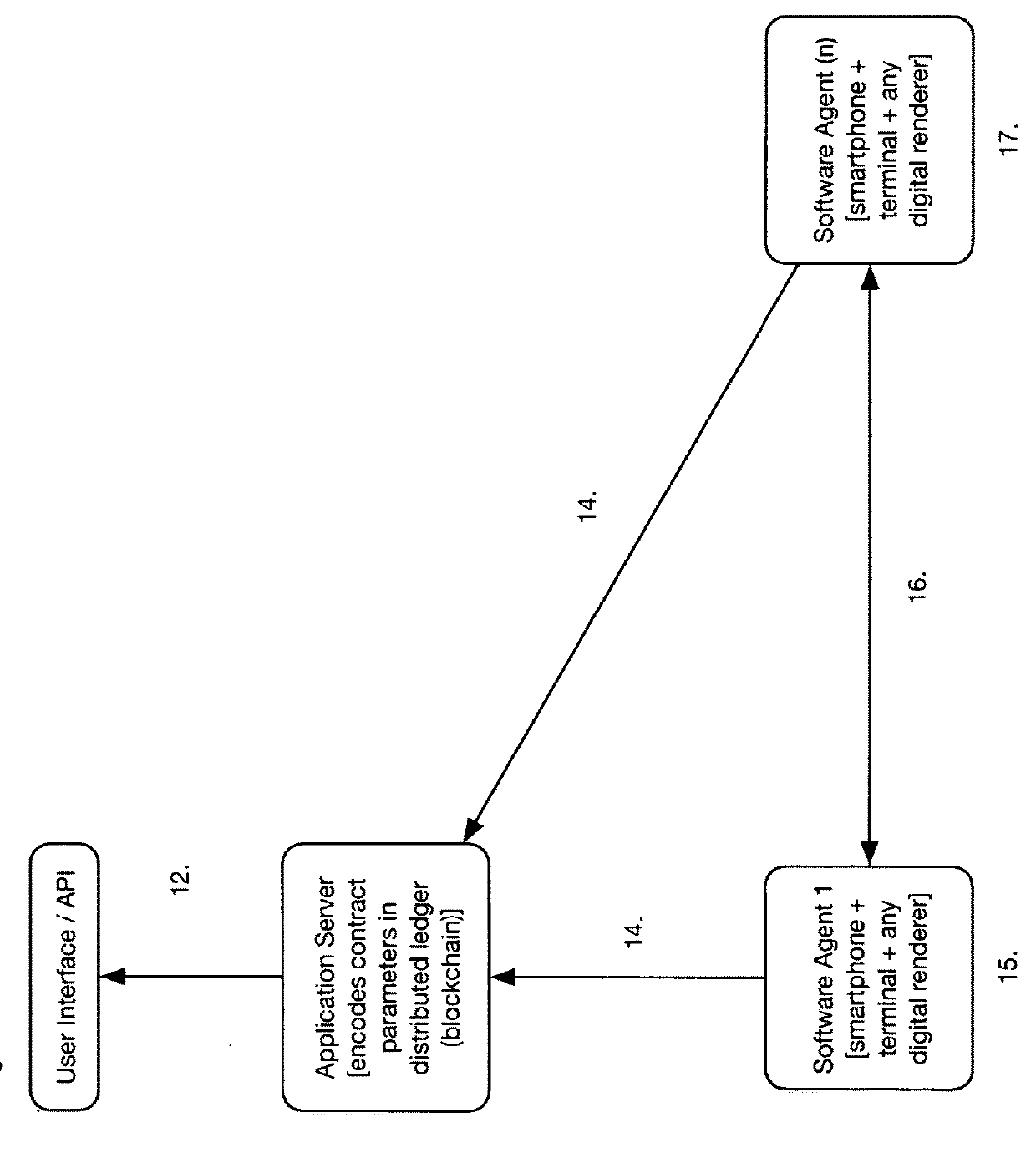
Contract ratification by automated agents through distributed ledger technology
InactiveUS20180276625A1Low costStable deliveryCryptography processingPayment protocolsE-commerceTrust relationship
The present invention relates to a method and a computerized process for automated agents (software-only through e-commerce channels, software-controlled transport such as drones and autonomous vehicles, software-based through handheld devices such as smartphones and remote terminals), which ratify contracts on behalf of principals for transfer of goods and services. This method and computerized process is embodied by software that can be used to access brokered contract parameter data, as available in distributed ledger protocols, to establish trusted relationships and workflow steps between software-based agents (artificial intelligence or otherwise algorithmically-derived). It should be further noted that software agents will send and receive workflow instructions and status to a server entity for reconciliation and exception handling.
Owner:SAYE JUSTIN +1
Apparatus and method for collecting and displaying information in a workflow system
InactiveUS7221377B1Cathode-ray tube indicatorsResourcesCustomer relationship managementHandling system
A method and apparatus for extensible real-time workflows are described. The present invention allows a user of a transaction processing system, such as a customer relationship management (CRM) tool or an automatic call distribution (ACD), for example, to easily add new event sources without recompiling the core workflow server engine of the transaction processing system. The invention also supports features such as the adding of new services, the exchange of events and parameters with other systems, real-time collection and display of workflow statistical information, the use of a centralized configuration database, incremental loading and unloading of workflows and rules, and exception handling.
Owner:ASPECT COMM +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com