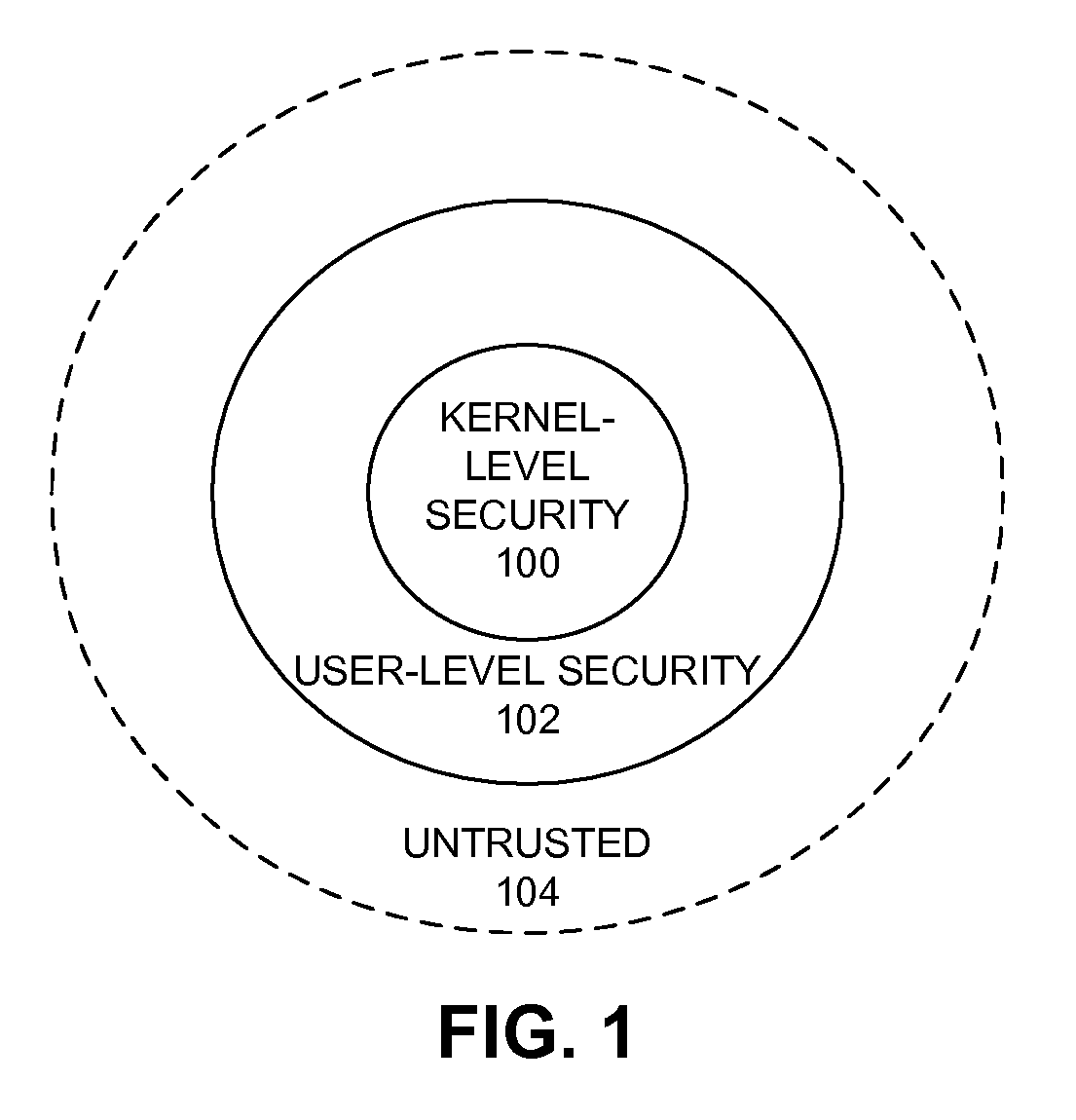
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52results about How to "Ensuring Safe Execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
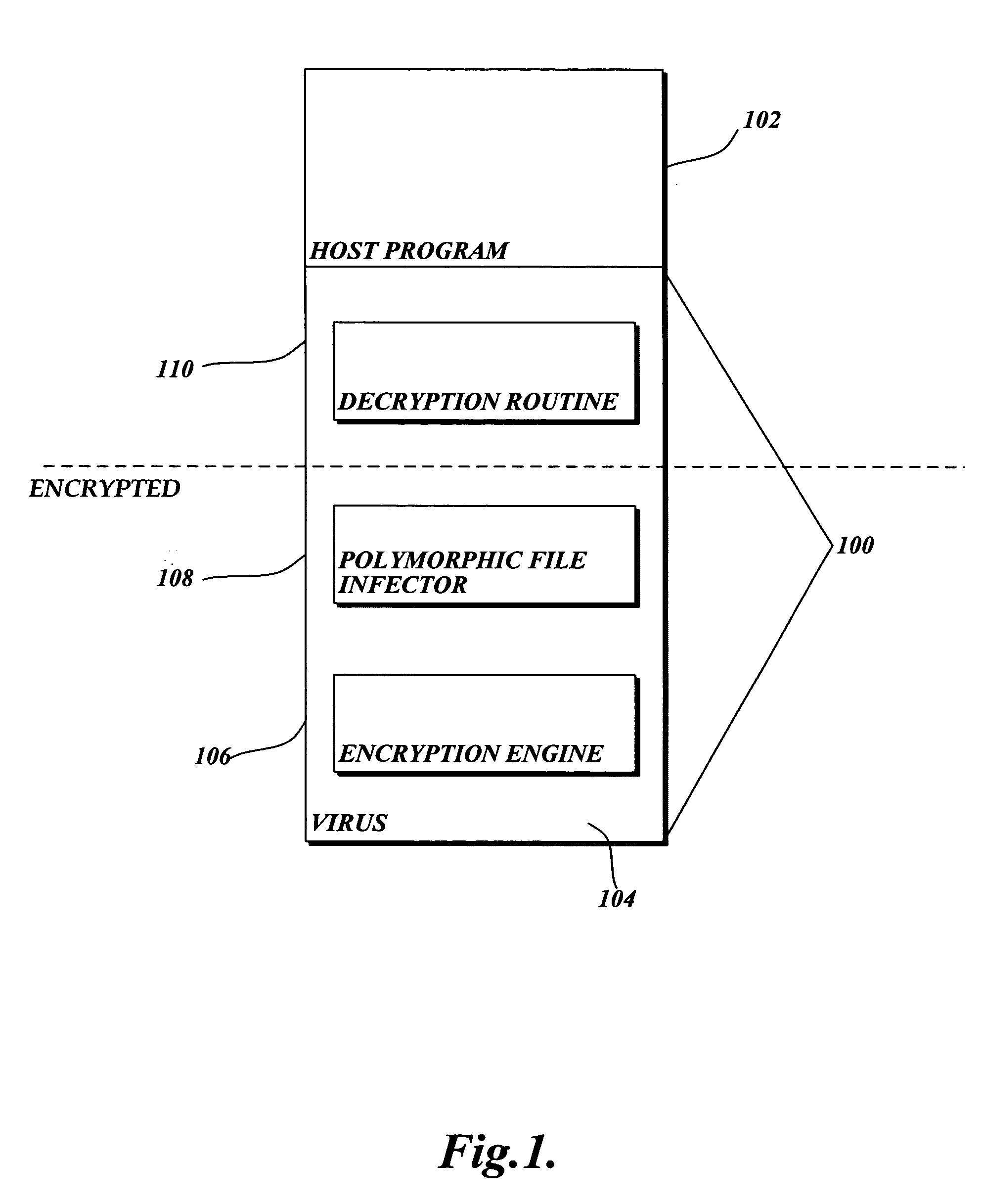
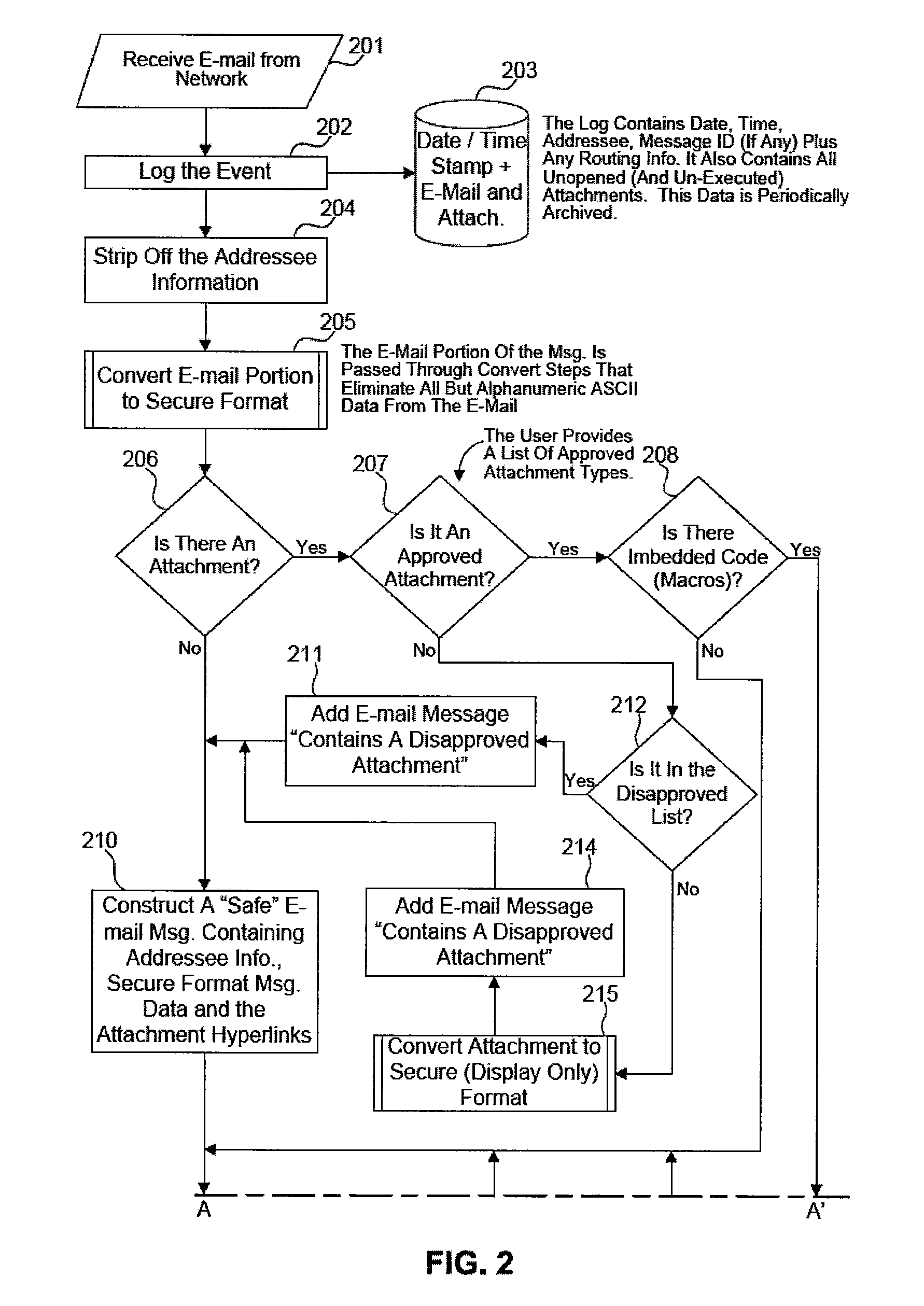
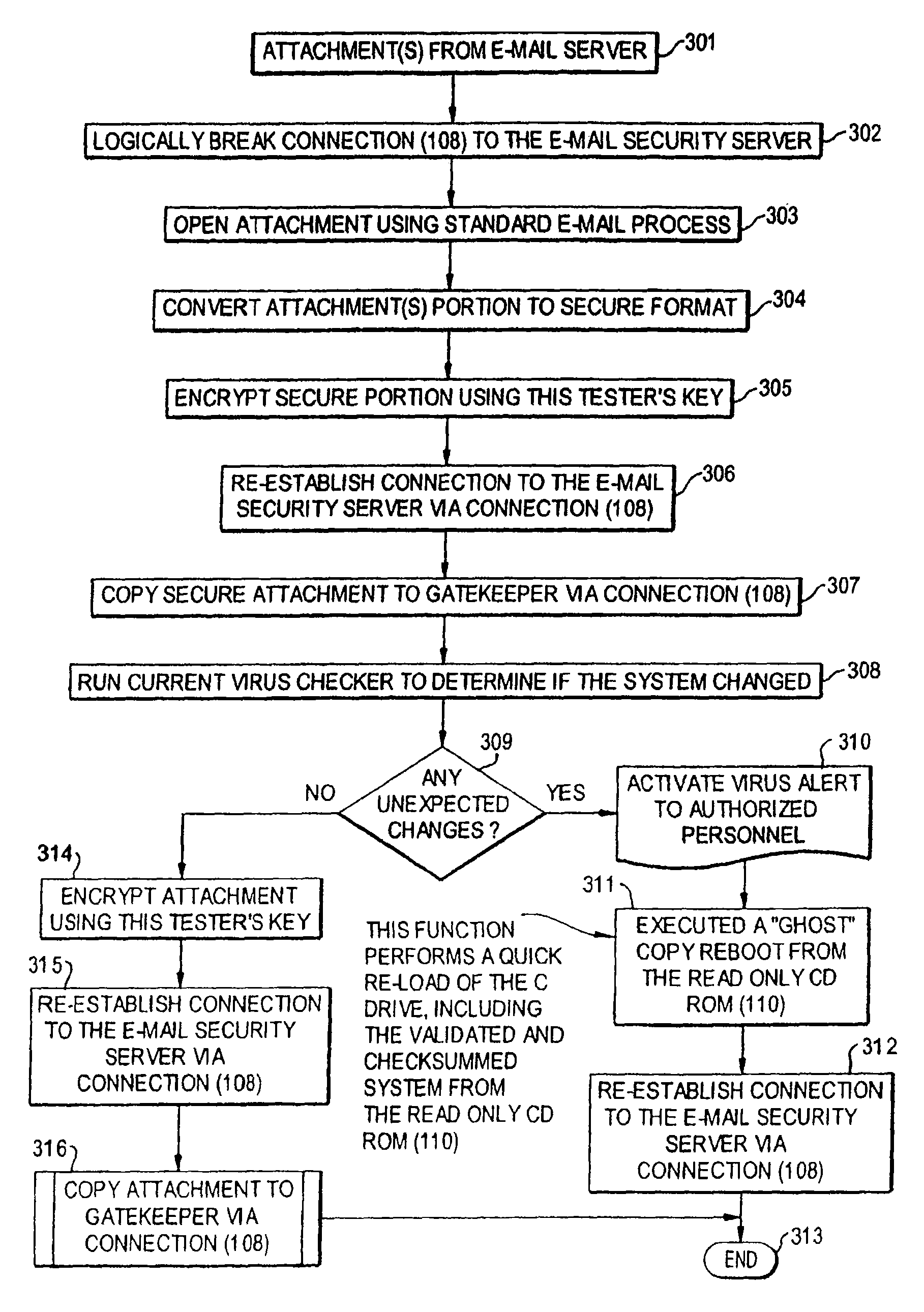
E-mail virus protection system and method
InactiveUS7506155B1Detection securityEnsuring Safe ExecutionHardware monitoringPlatform integrity maintainanceAdobeProtection system
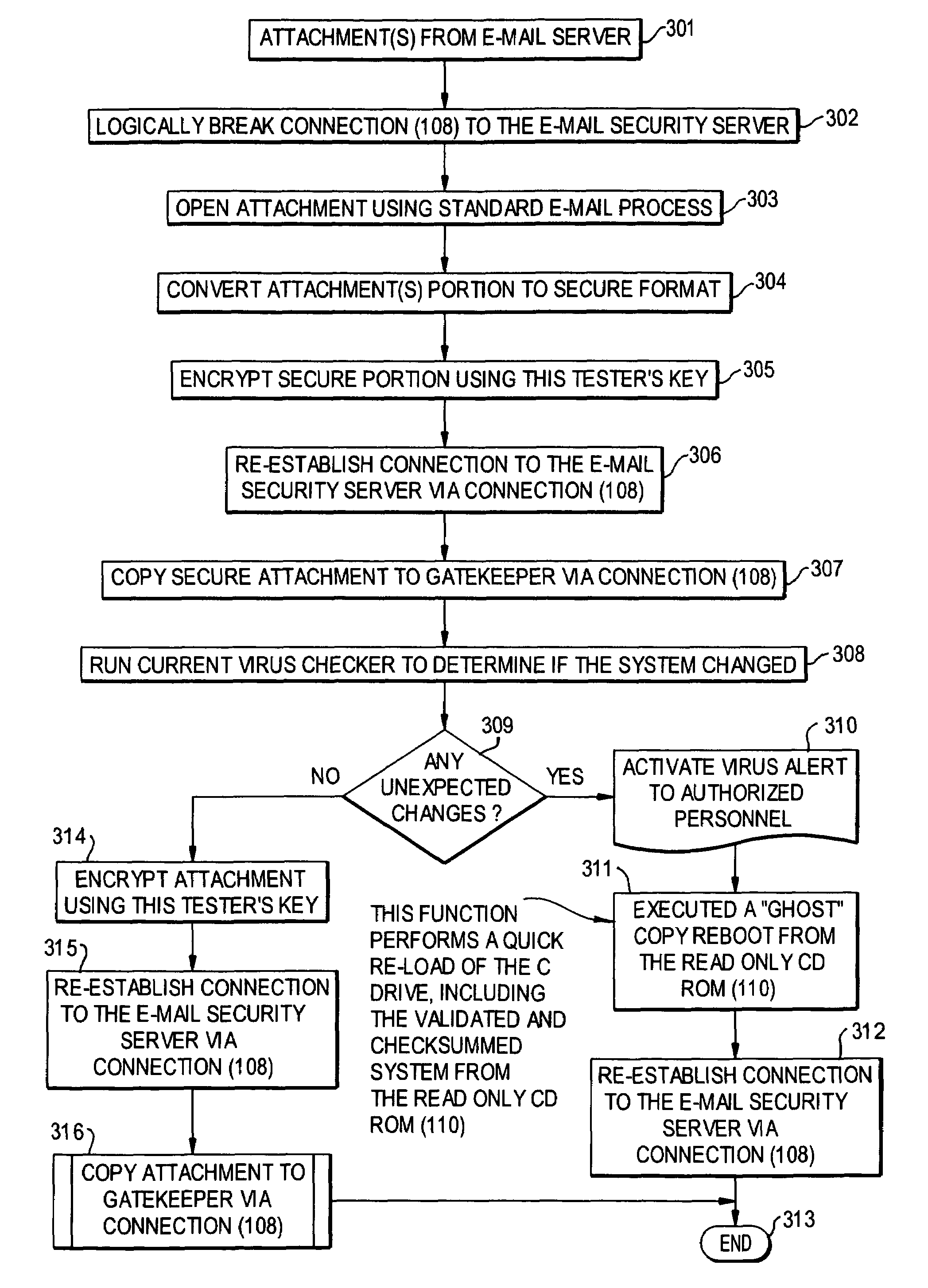
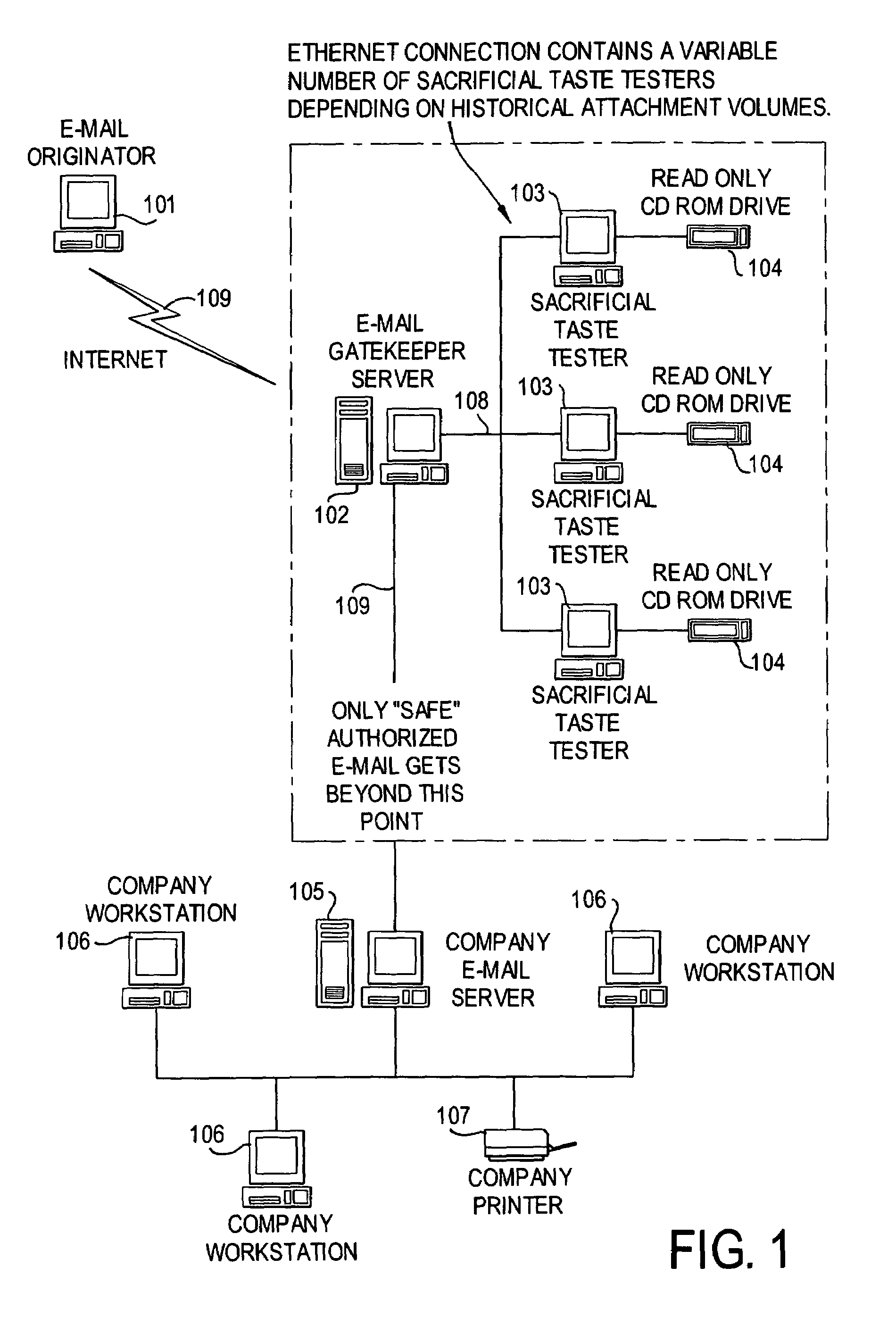
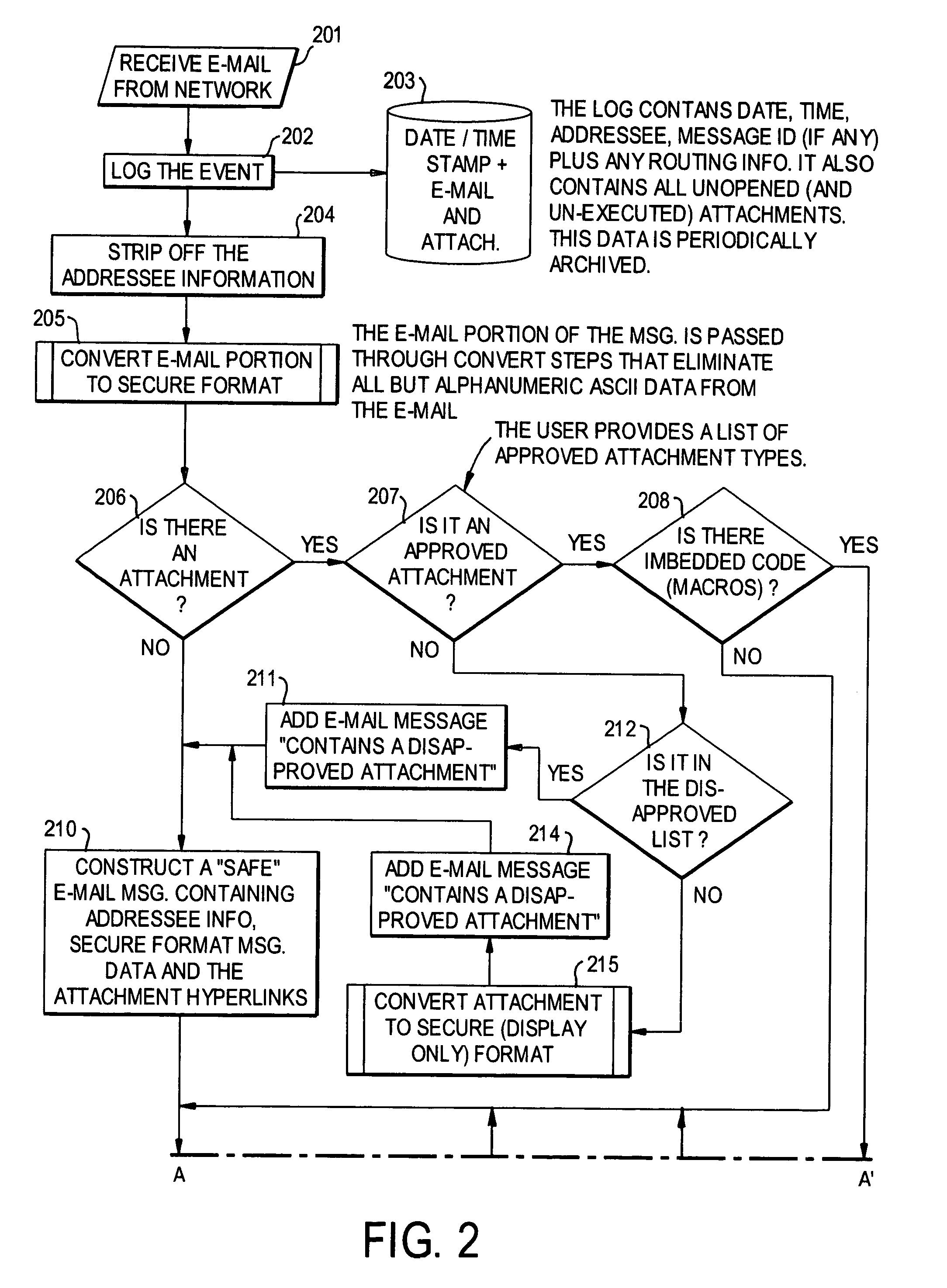
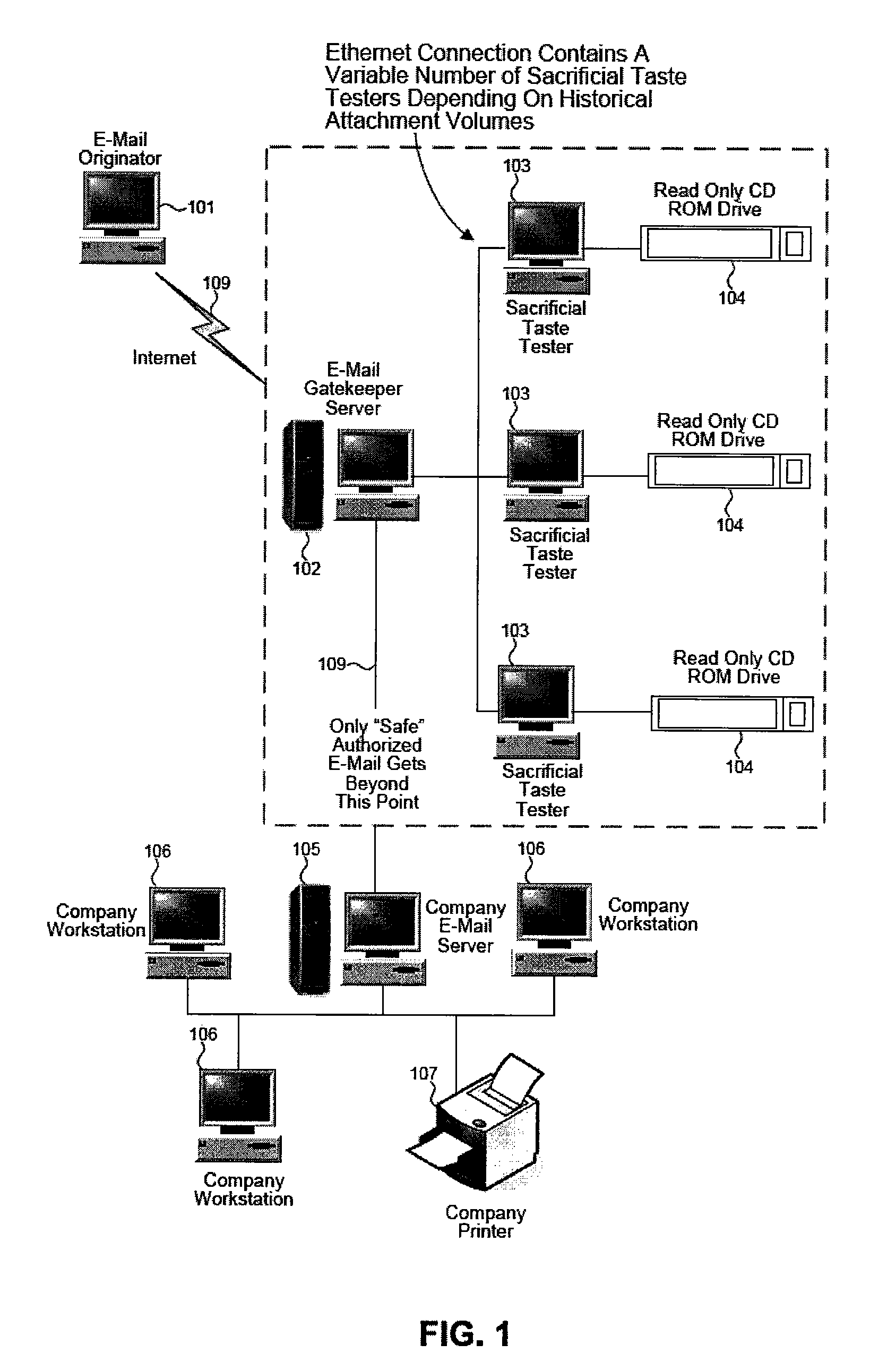
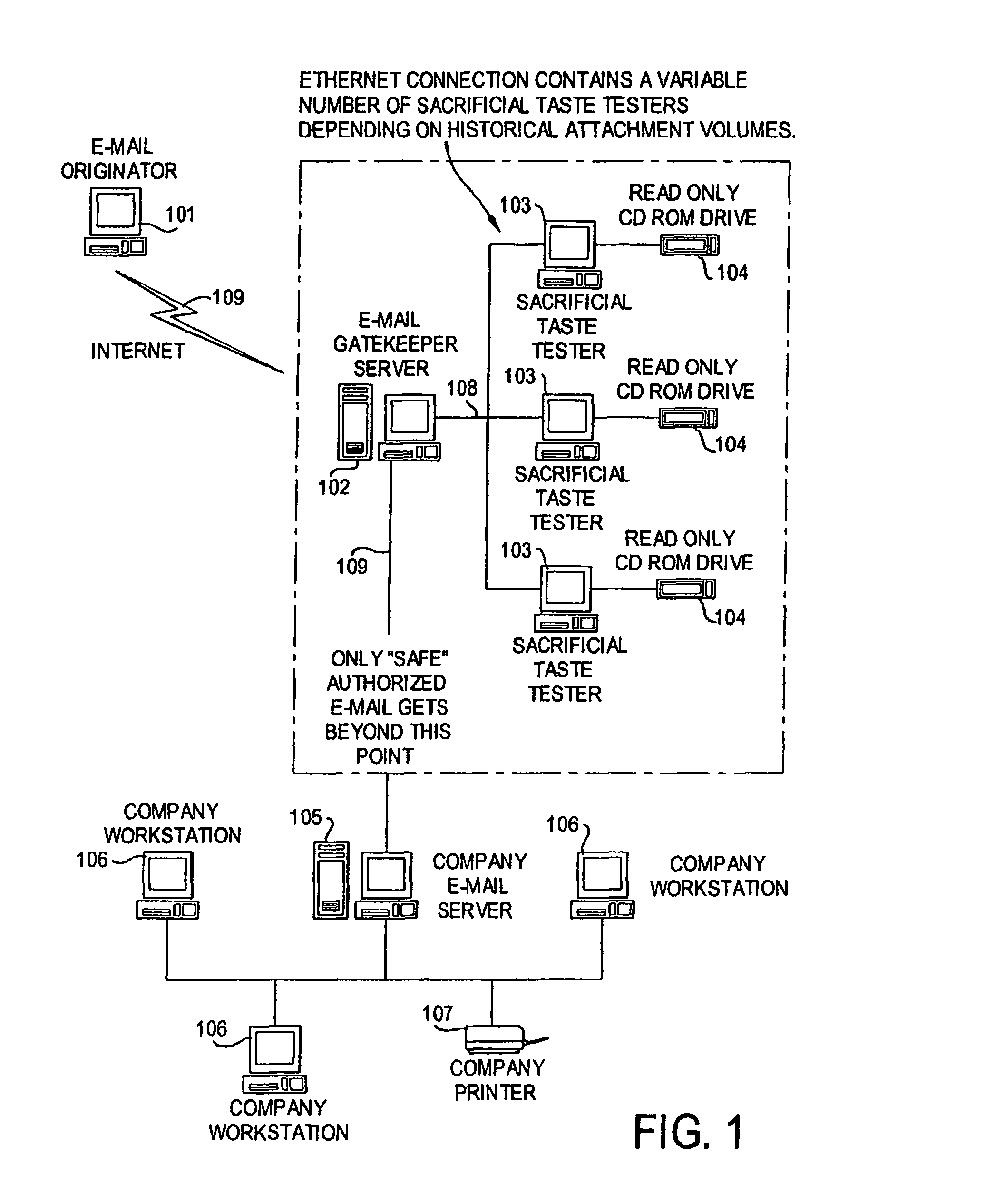
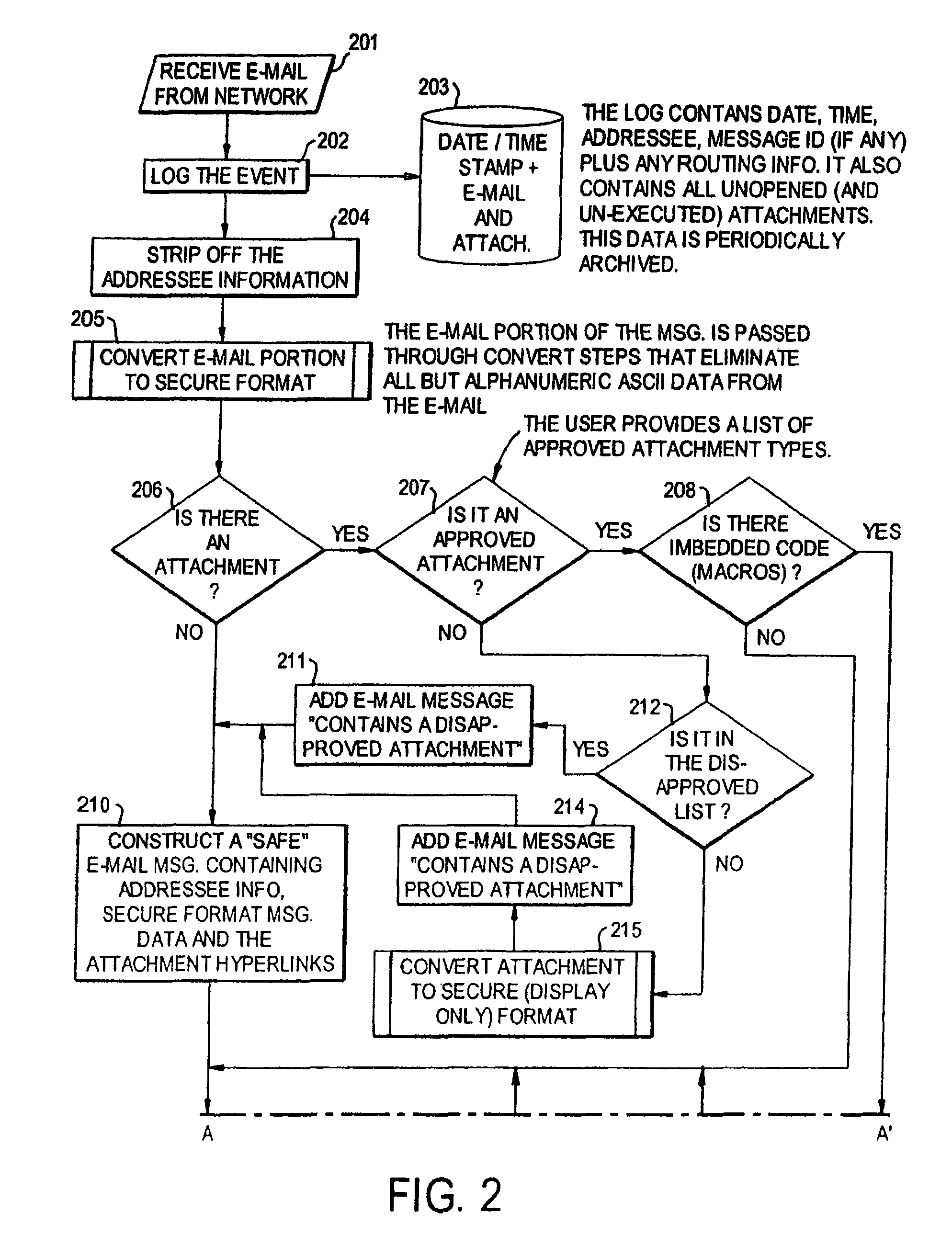
A network is protected from e-mail viruses through the use of a sacrificial server. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
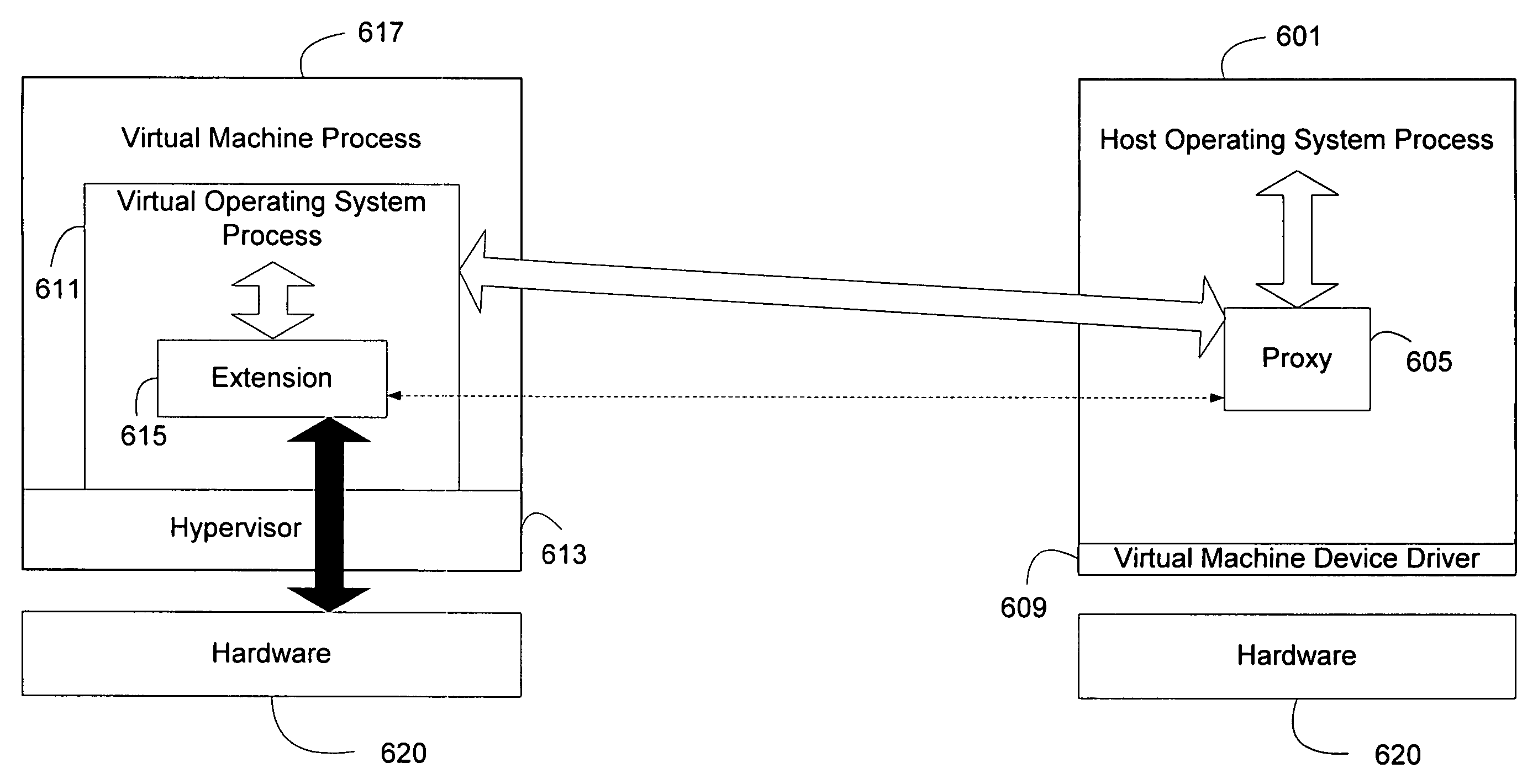
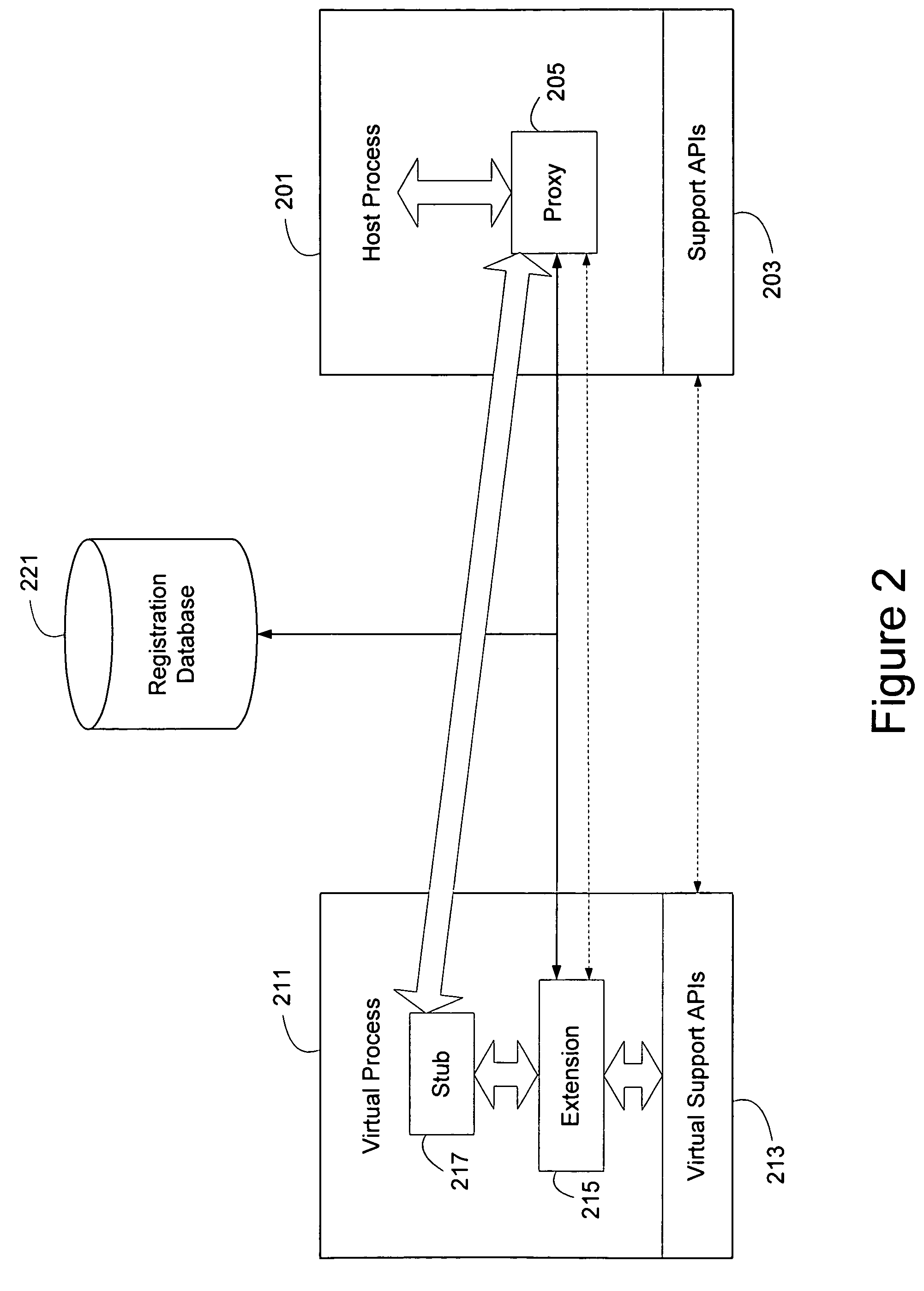
VEX-virtual extension framework
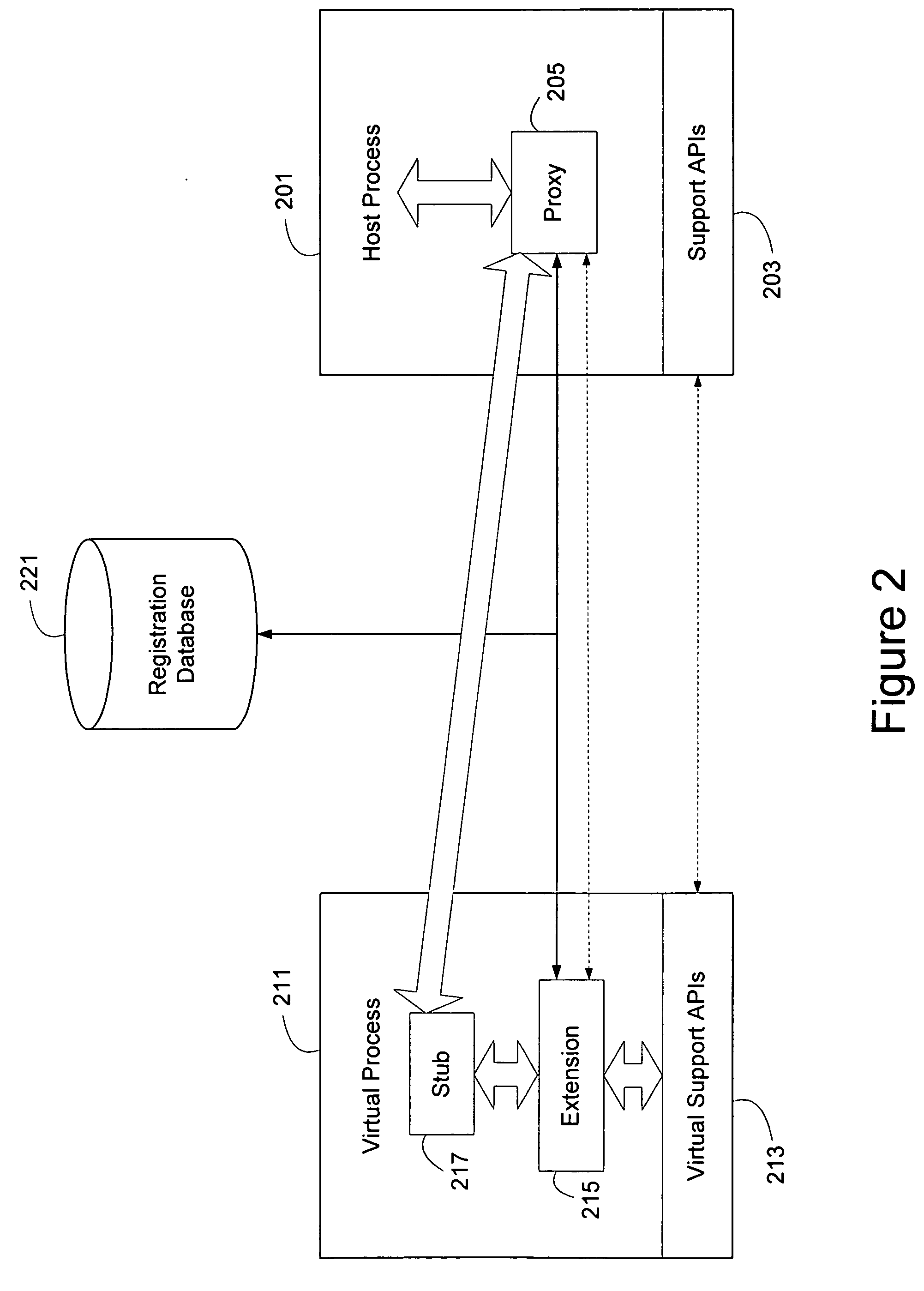
InactiveUS20050246718A1Provide benefitsImprove instabilityFault responseInterprogram communicationOperational systemApplication software
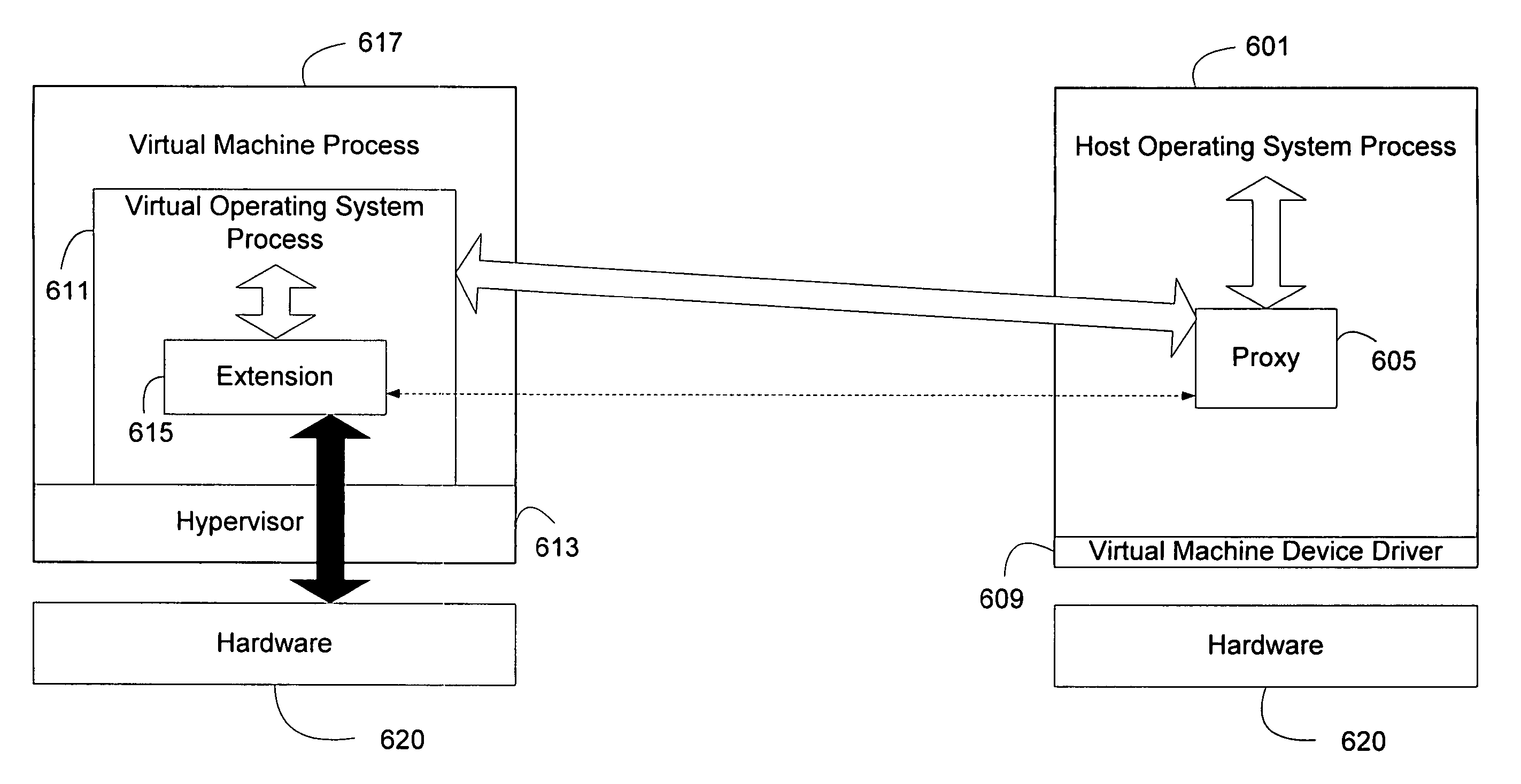
Extensions to operating systems or software applications can be hosted in virtual environments to fault isolate the extension. A generic proxy extension invoked by a host process can coordinate the invocation of an appropriate extension in a virtual process that can provide the same support APIs as the host process. Furthermore, a user mode context can be provided to the extension in the virtual process through memory copying or page table modifications. In addition, the virtual process, especially a virtual operating system process running on a virtual machine, can be efficiently started by cloning a coherent state. A coherent state can be created when a virtual machine starts up, or when the computing device starts up and the appropriate parameters are observed and saved. Alternatively, the operating system can create a coherent state by believing there is an additional CPU during the boot process.
Owner:MICROSOFT TECH LICENSING LLC
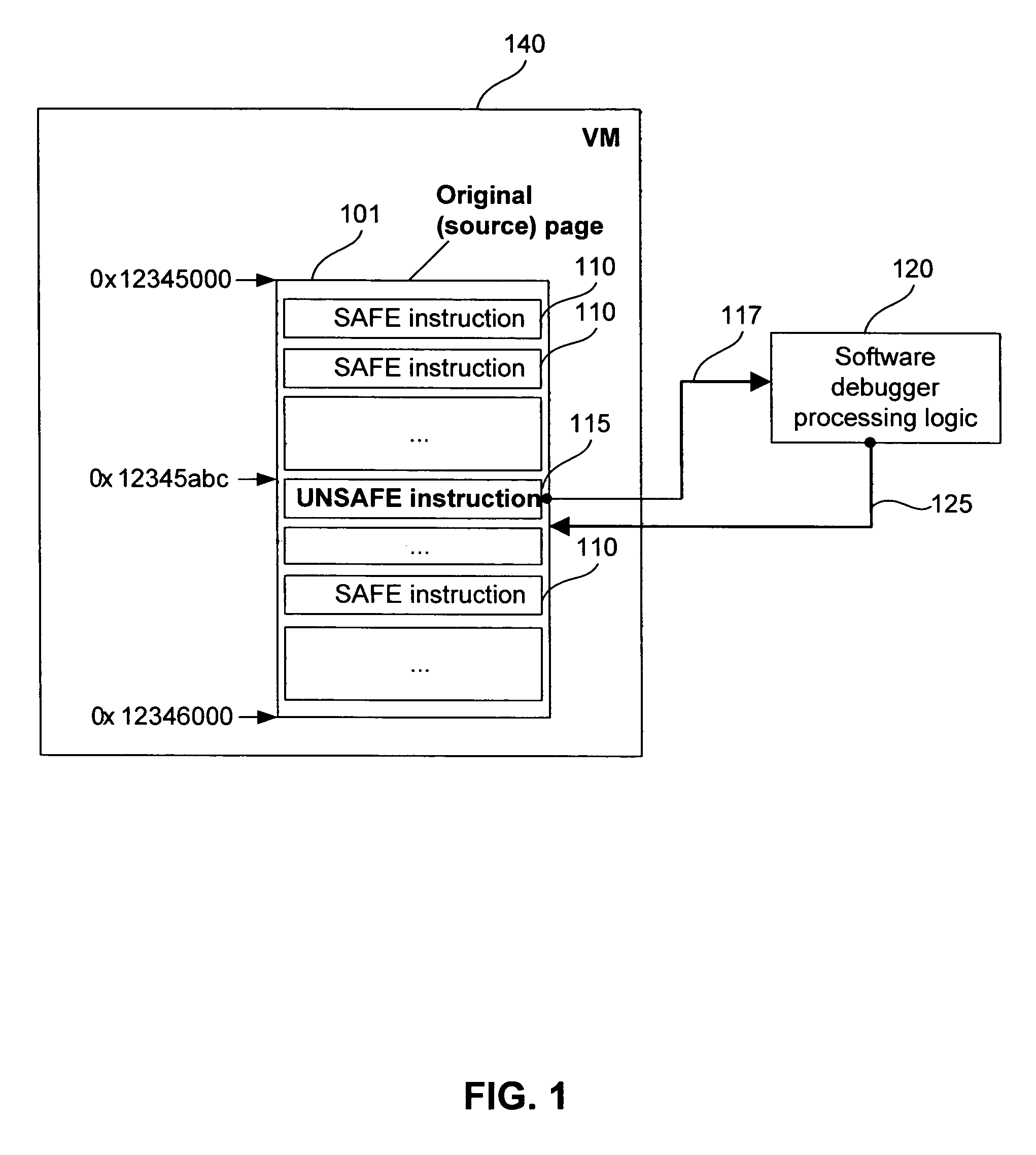
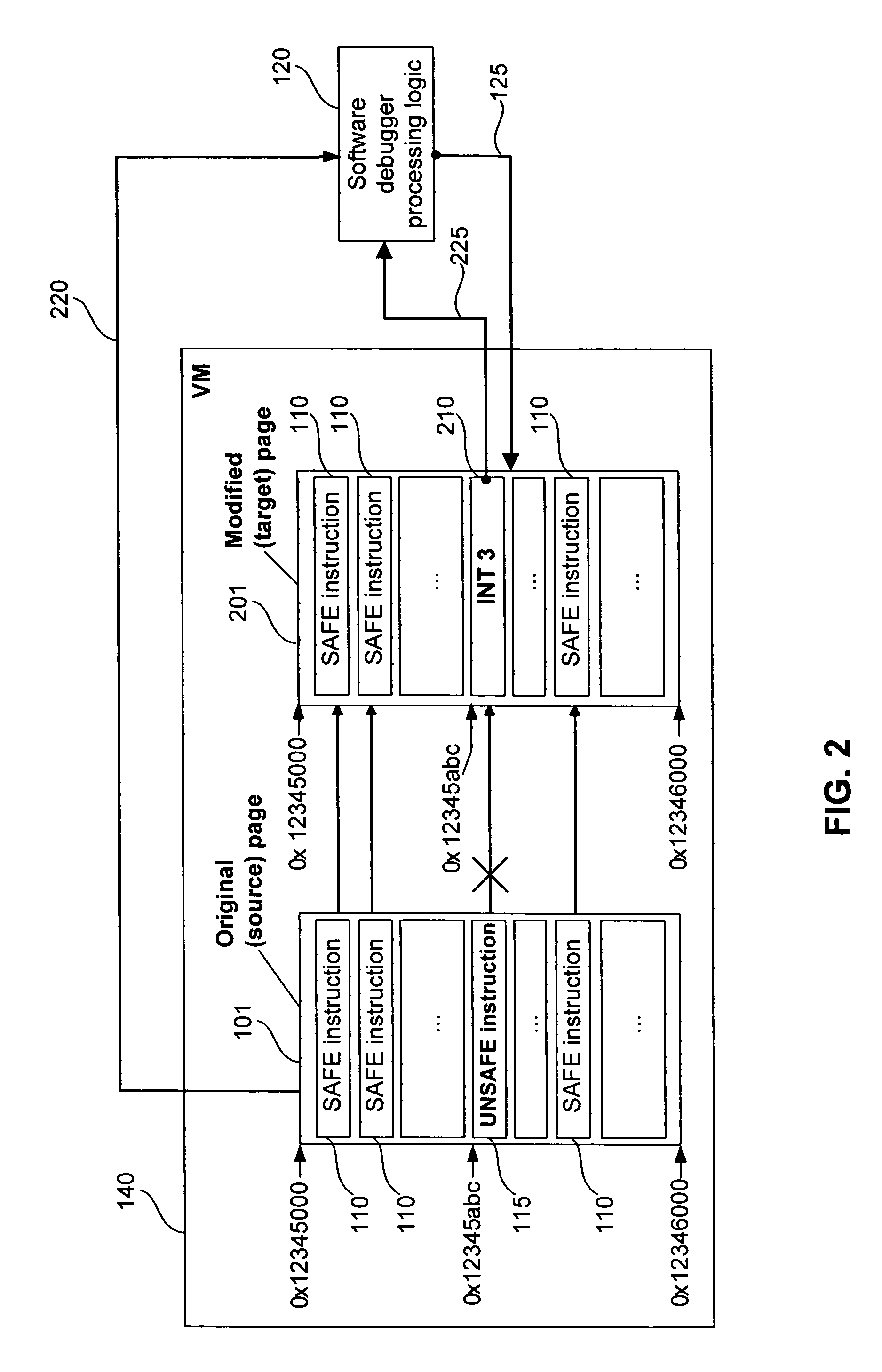
Methods and systems for safe execution of guest code in virtual machine context
ActiveUS7647589B1Ensuring Safe ExecutionError detection/correctionPlatform integrity maintainanceSoftware engineeringLogisim
Methods and systems for safe execution of guest code in virtual machine context are presented. A method for running a virtual machine in a computing system includes (a) launching a virtual machine monitor (VMM) that uses a software debugger; (b) launching a virtual machine (VM) that can natively run safe instructions; (c) determining, at runtime, if the instruction is safe or potentially unsafe; (d) executing safe instructions in a native mode; and (e) activating control logic to process potentially unsafe instructions in the software debugger. The software debugger can bypass at least one of the potentially unsafe instructions. The potentially unsafe instructions include instructions that cannot be safely executed in the context of the VM, and instructions that can cause unpredictable results in the context of the VM.
Owner:PARALLELS INT GMBH
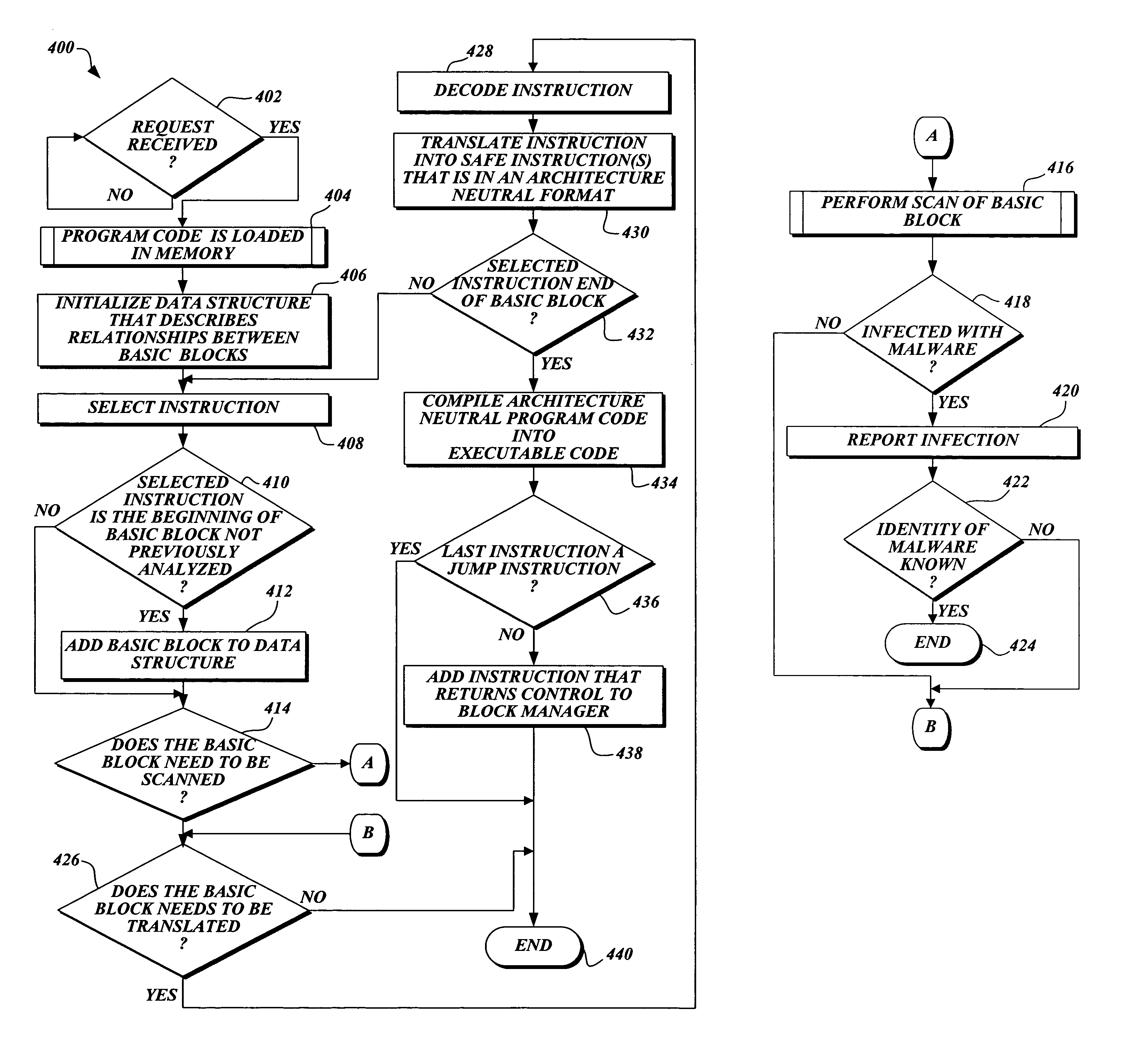
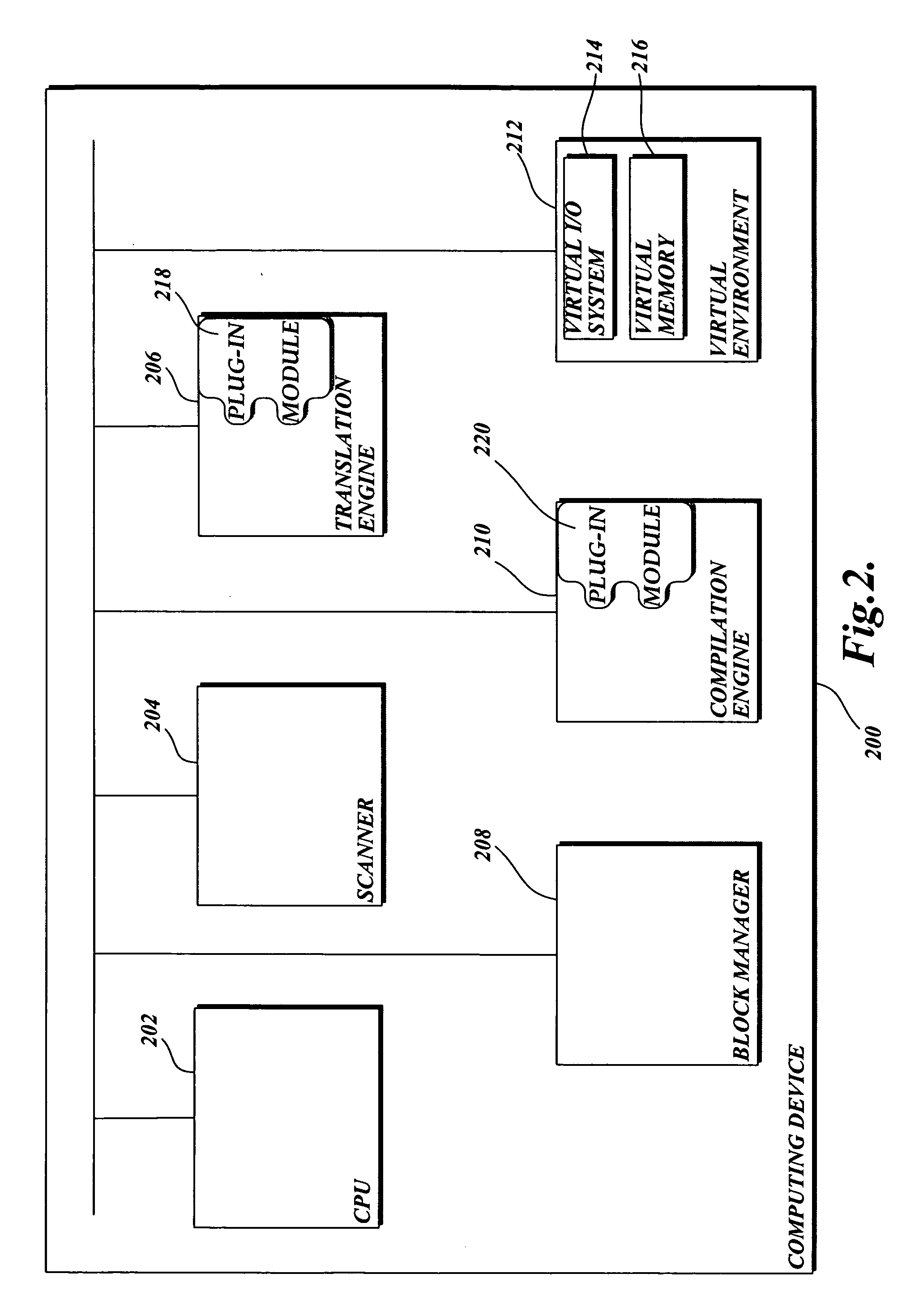
Proactive computer malware protection through dynamic translation
ActiveUS20060123244A1Ensuring Safe ExecutionSafely executedMemory loss protectionUser identity/authority verificationMalwareComputer memory
The present invention includes a system and method for translating potential malware devices into safe program code. The potential malware is translated from any one of a number of different types of source languages, including, but not limited to, native CPU program code, platform independent .NET byte code, scripting program code, and the like. Then the translated program code is compiled into program code that may be understood and executed by the native CPU. Before and / or during execution, the present invention causes a scanner to search for potential malware stored in memory. If malware is not detected, the computing device causes the CPU to execute the translated program code. However, execution and / or analysis of potential malware may be interrupted if computer memory that stores potential malware is altered during execution. In this instance, the potential malware now stored in memory is translated into safe program code before being executed.
Owner:MICROSOFT TECH LICENSING LLC
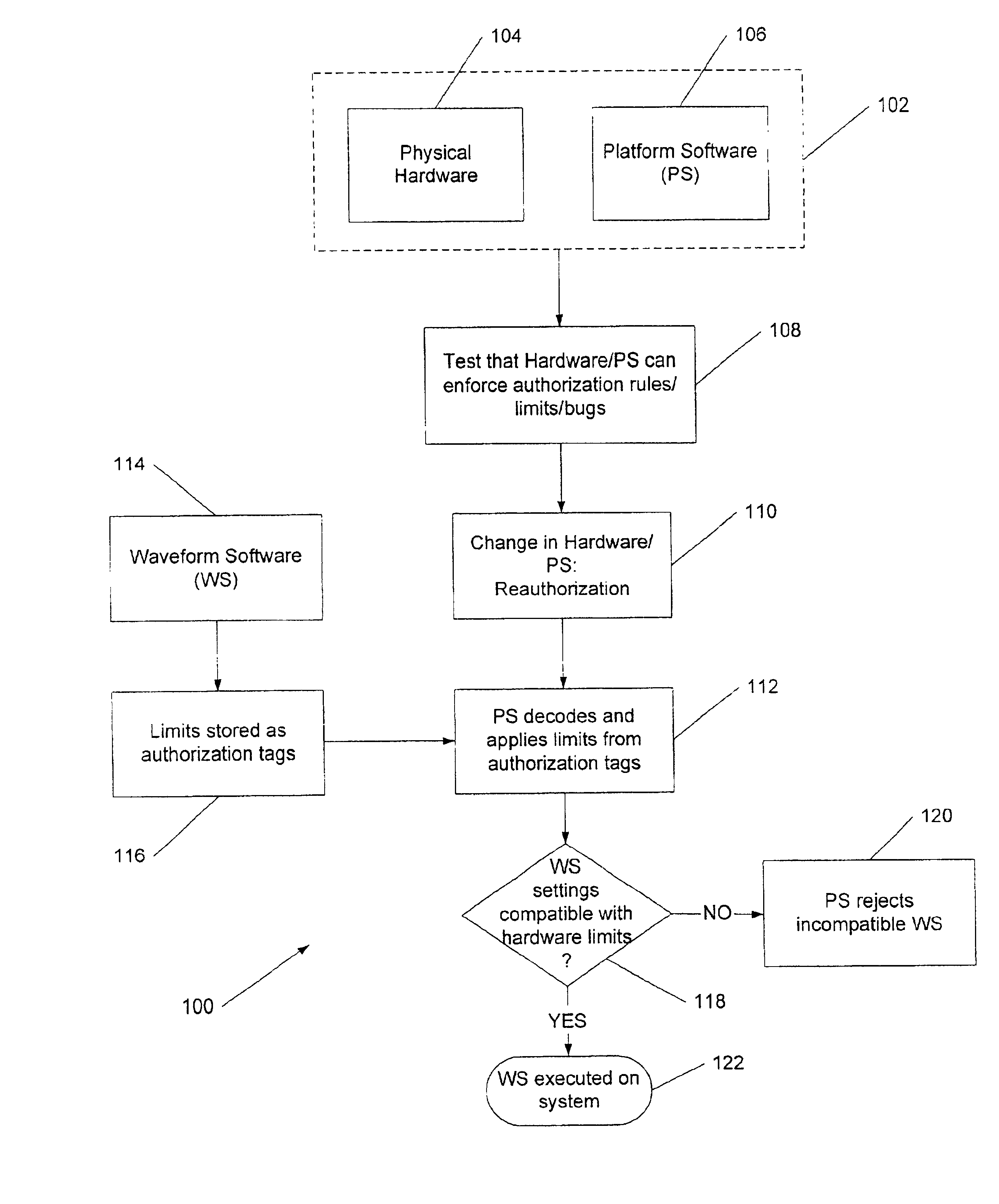
Software-defined wireless communication device
InactiveUS6876864B1Ensuring Safe ExecutionSubstation equipmentRadio transmissionComputer hardwareCommunication device
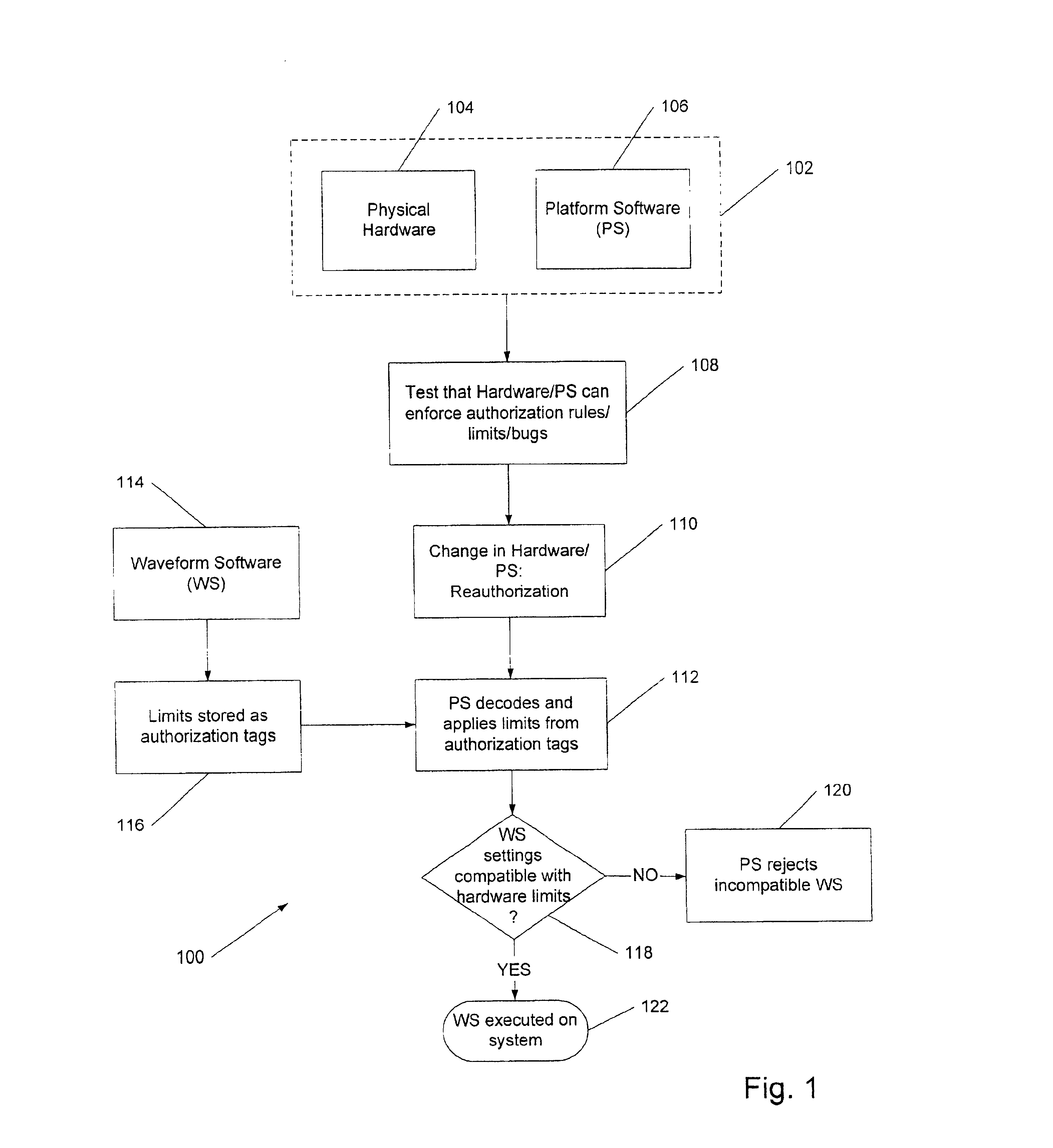
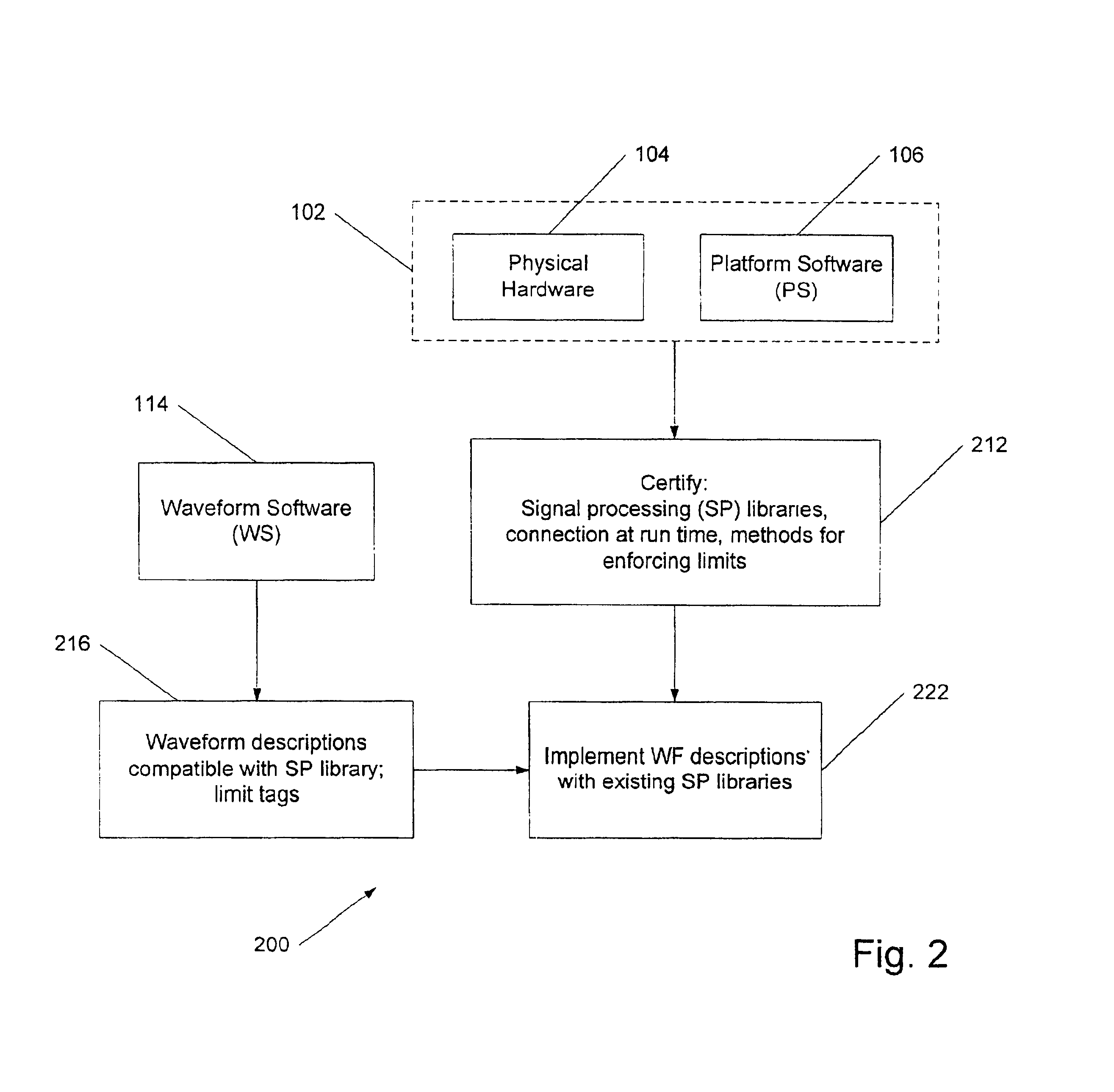
A software-defined wireless communication device is disclosed that includes a hardware platform, which can be digital or analog, as well as platform software that manages the hardware profile and waveform software that manages the signal processing functions. The software-managed hardware profiles are decoupled from the signal processing functionality of the software. In this way, waveform software can be certified, for example for compliance with FCC emissions requirement, independently from the platform software and from the hardware on which the waveform software runs.
Owner:VANU INC
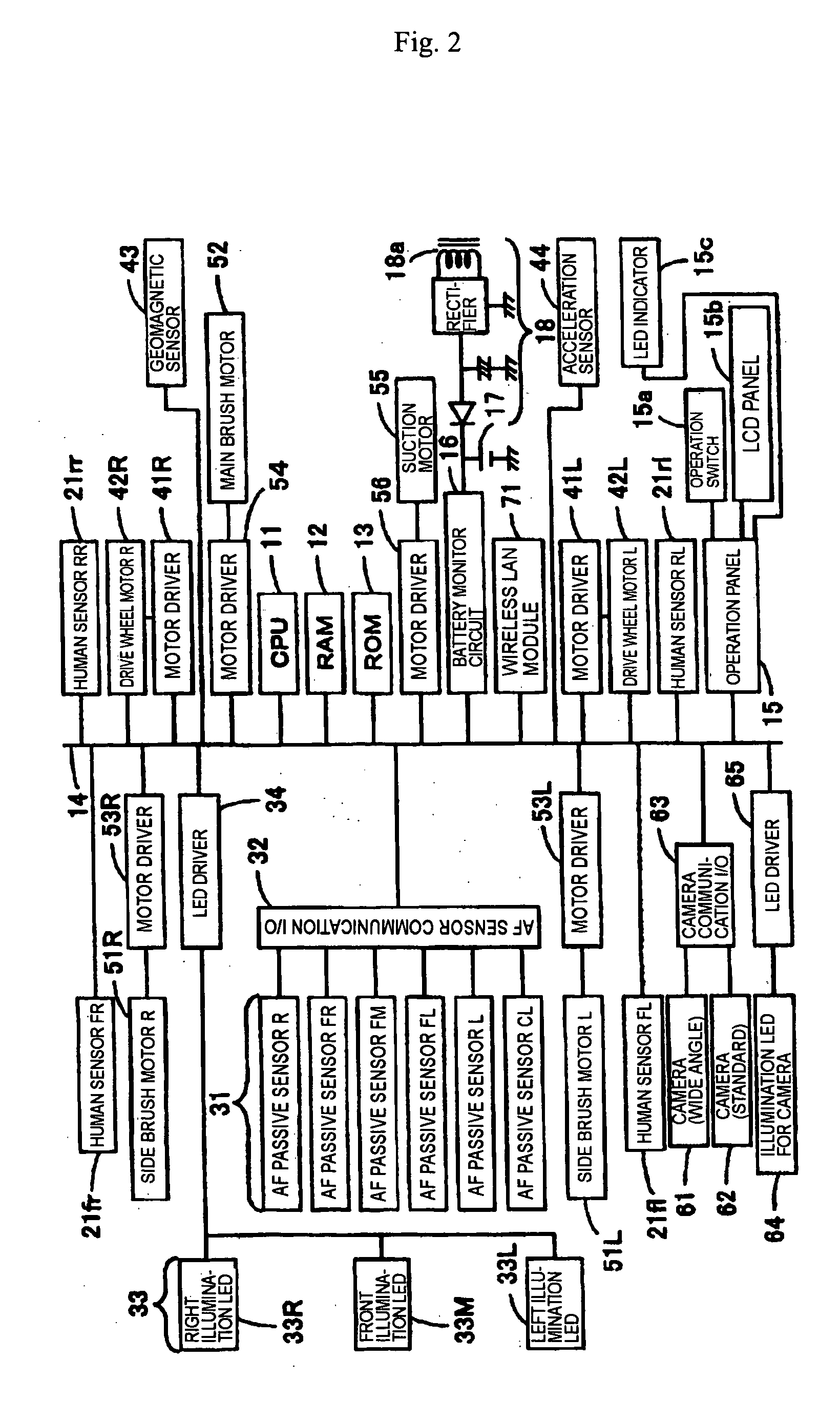
Self-propelled cleaner with monitoring camera
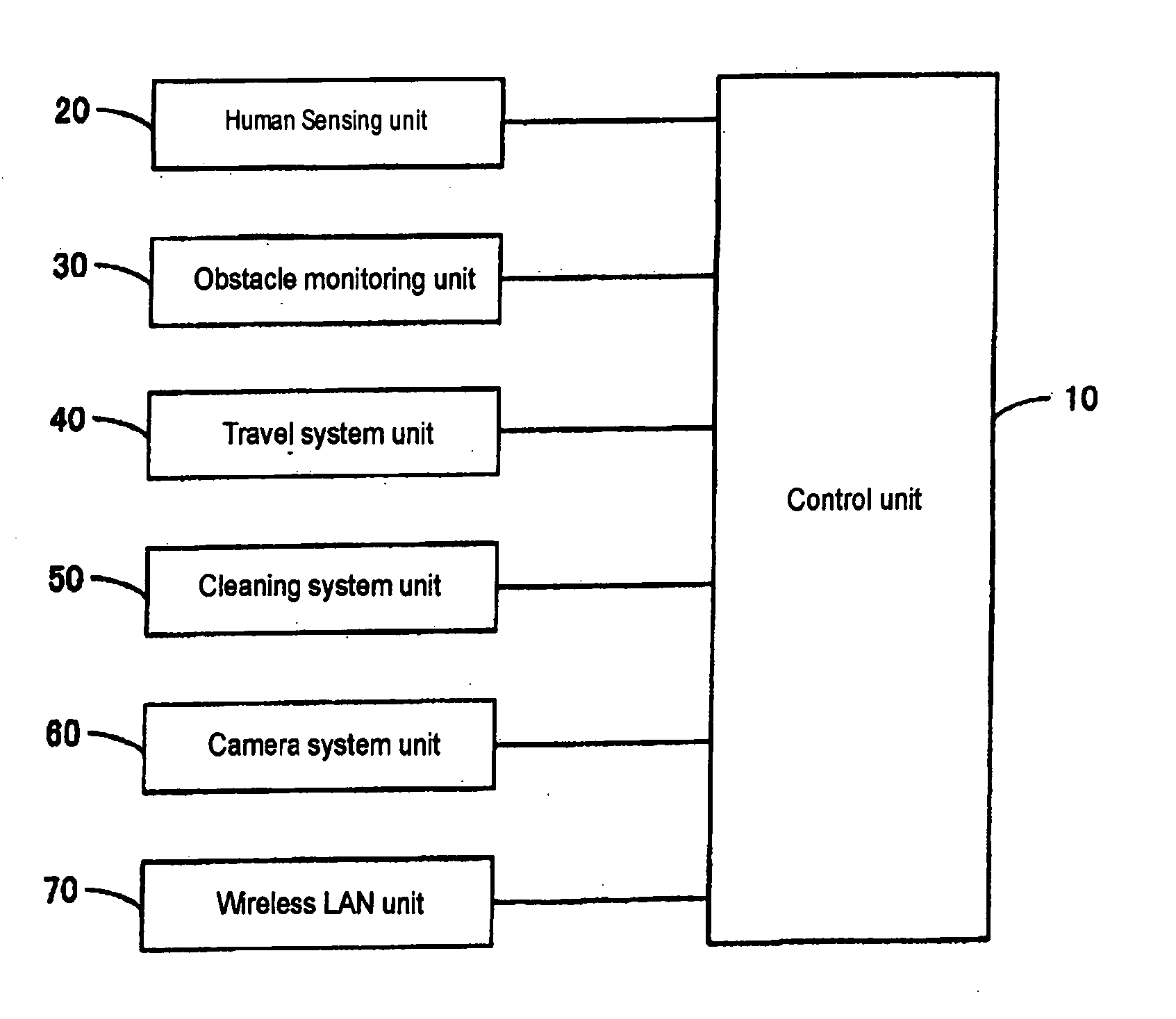
InactiveUS20050237189A1Ensuring Safe ExecutionImprove reliabilityAutomatic obstacle detectionTravelling automatic controlSurveillance cameraSound production
The prior arts have a problem that it is not precisely determined whether or not a human entering a room is an intruder, and consequently raising an alarm when there is a slightest possibility of an intruder, a malfunction may result, and raising an alarm only when there is a strong possibility of an intruder, a response to an intruder actually entered the room may be delayed. A self-propelled cleaner according to this invention is capable of executing a phased security, that is, turning on lights, flashing lights, making a loud sound, generating a go-away message, and generating a police report message upon detection of a human suspected of being an intruder, and takes an image of the room at each stage to transmit the resulting image to a family member away from the home, and determines whether or not the security level should be escalated according to an instruction from the family member
Owner:FUNAI ELECTRIC CO LTD
VEX-virtual extension framework
InactiveUS7574709B2Provide benefitsImprove instabilityFault responseInterprogram communicationOperational systemHosting environment
Extensions to operating systems or software applications can be hosted in virtual environments to fault isolate the extension. The virtual environment in which extensions designed to control hardware devices can safely execute can be efficiently created during an initial startup sequence of a host environment by indicating to the host environment that a second processing unit is present in the computing system allowing the host environment to create a coherent state. A virtual process, especially a virtual operating system process running on a virtual machine, can be efficiently started by the created coherent state. A coherent state can be created when an operating system starts up and the appropriate parameters are observed and saved. Alternatively, an operating system of the host environment can create the coherent state by receiving indication of the second processing unit during the boot process.
Owner:MICROSOFT TECH LICENSING LLC
Network configuration predictive analytics engine
InactiveUS20130290520A1Ensuring Safe ExecutionDigital computer detailsData switching networksConfiguration analysisNetwork management
A mechanism associated with a network management system (NMS) interprets and predicts the impact on a network of a network configuration change proactively. By providing pre-configuration analysis in this manner, a network administrator can determine the potential effect of the proposed configuration change in advance of actually inserting a configuration command in the network that might otherwise have unforeseen and damaging consequences. The technique is implemented using a predictive analytics engine that receives a proposed network command and, using a current network topology, executes the command against one or more NMS algorithms to verify that the command can be implemented safely.
Owner:IBM CORP
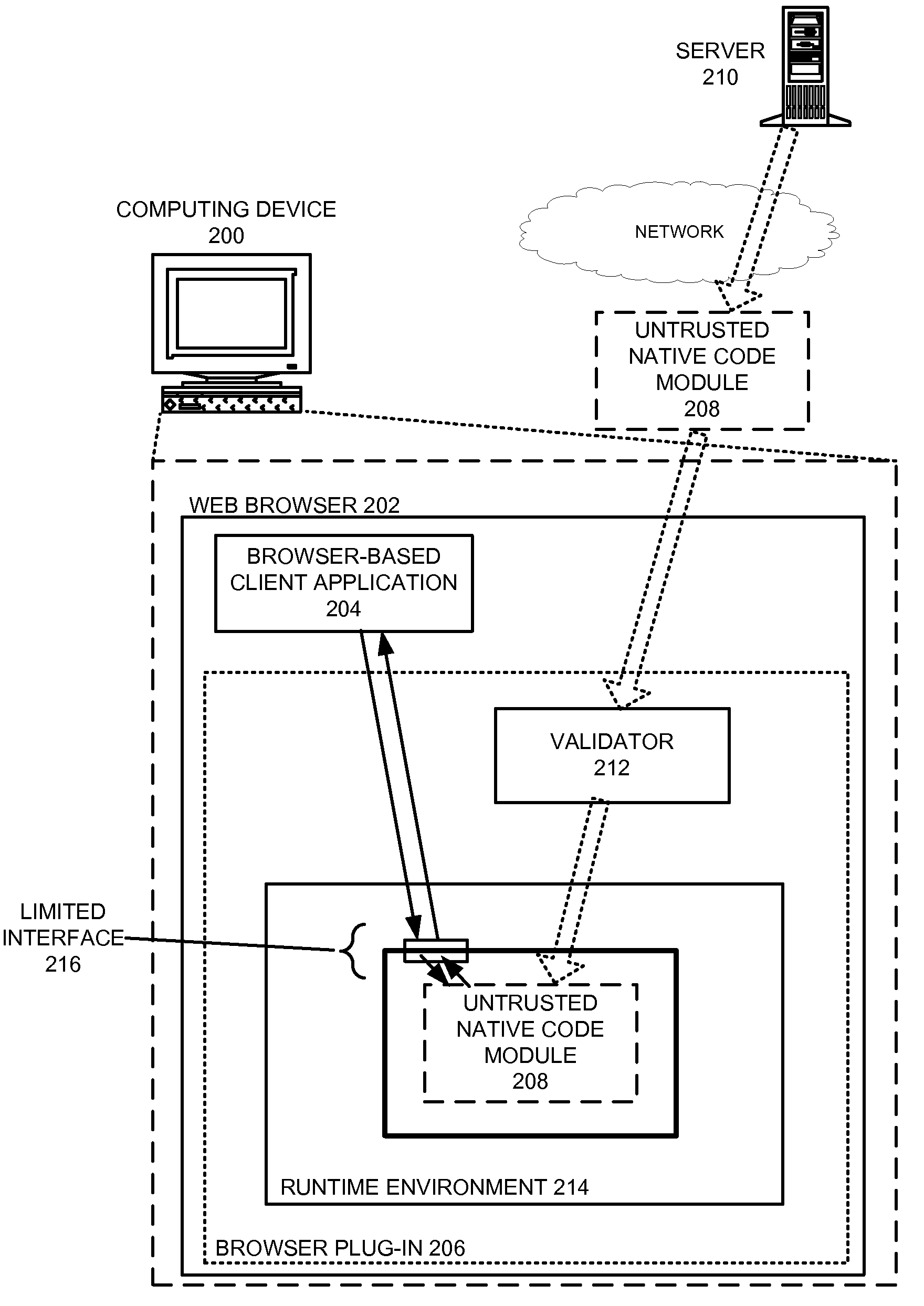
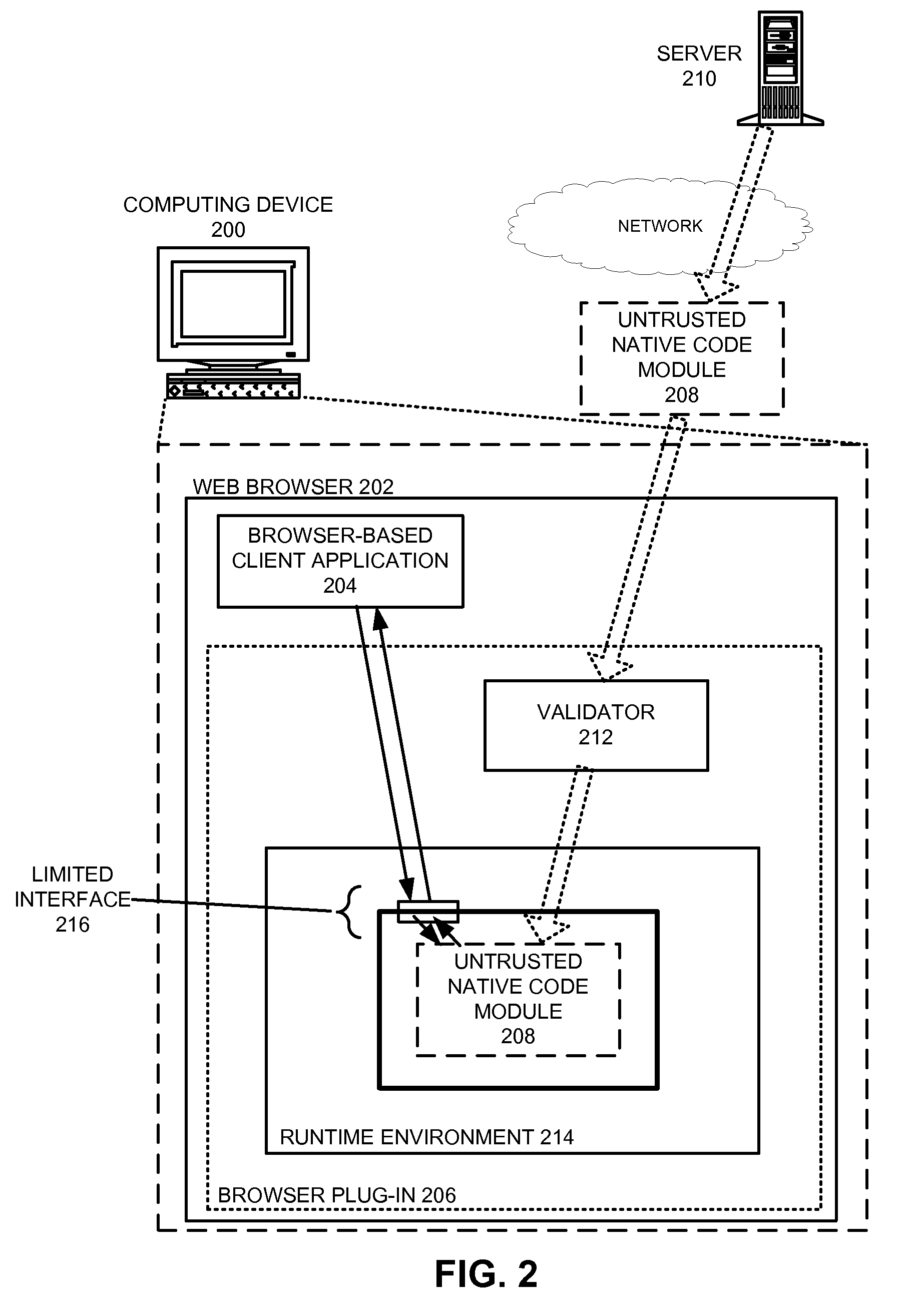
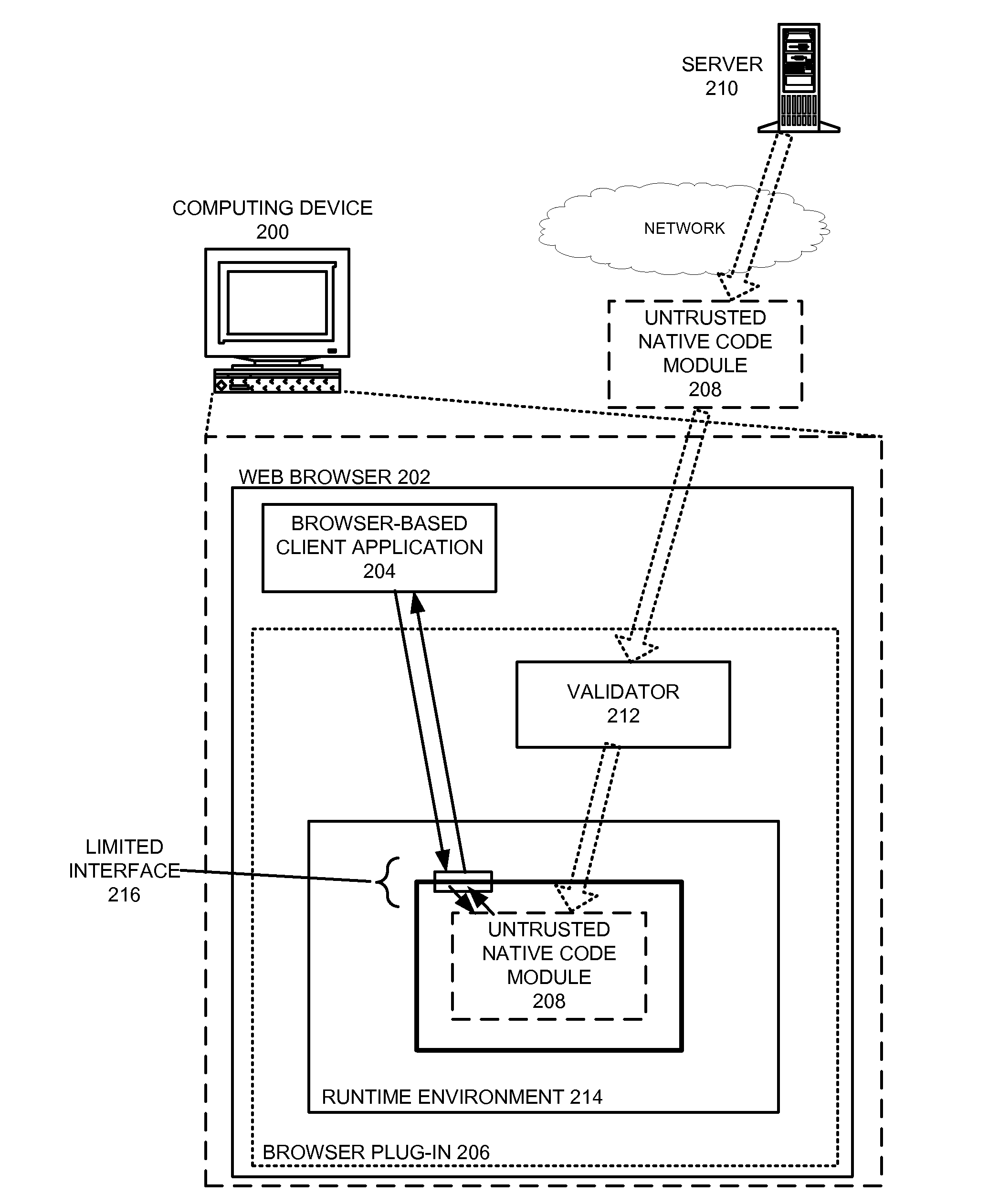
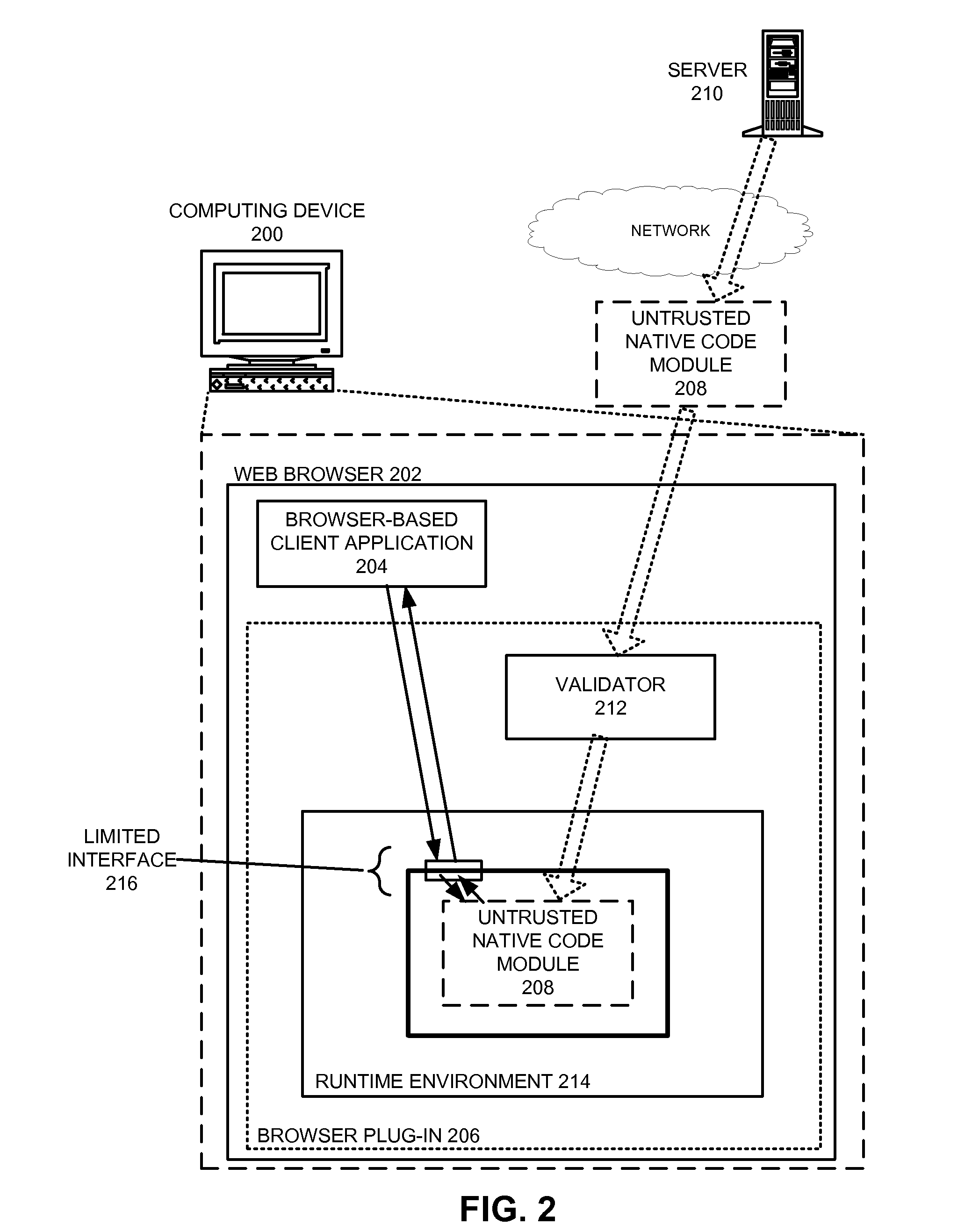
Safely executing an untrusted native code module on a computing device
ActiveUS8424082B2Ensuring Safe ExecutionEasy to implementMemory loss protectionDigital data processing detailsCode moduleControl flow
A system that safely executes a native code module on a computing device. During operation, the system receives the native code module, which is comprised of untrusted native program code expressed using native instructions in the instruction set architecture associated with the computing device. The system then loads the native code module into a secure runtime environment, and proceeds to execute a set of instructions from the native code module in the secure runtime environment. The secure runtime environment enforces code integrity, control-flow integrity, and data integrity for the native code module. Furthermore, the secure runtime environment moderates which resources can be accessed by the native code module on the computing device and / or how these resources can be accessed. By executing the native code module in the secure runtime environment, the system facilitates achieving native code performance for untrusted program code without a significant risk of unwanted side effects.
Owner:GOOGLE LLC
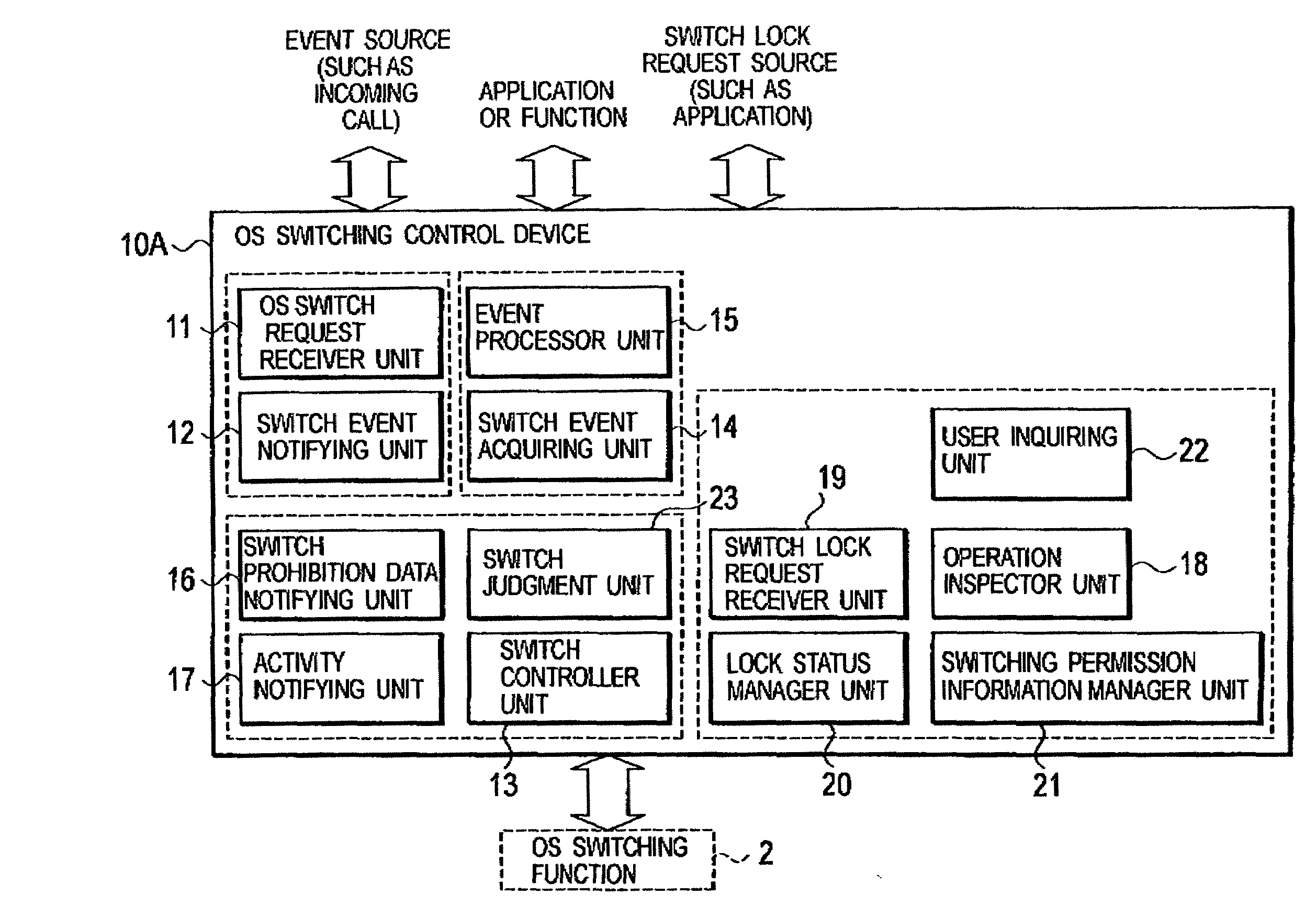
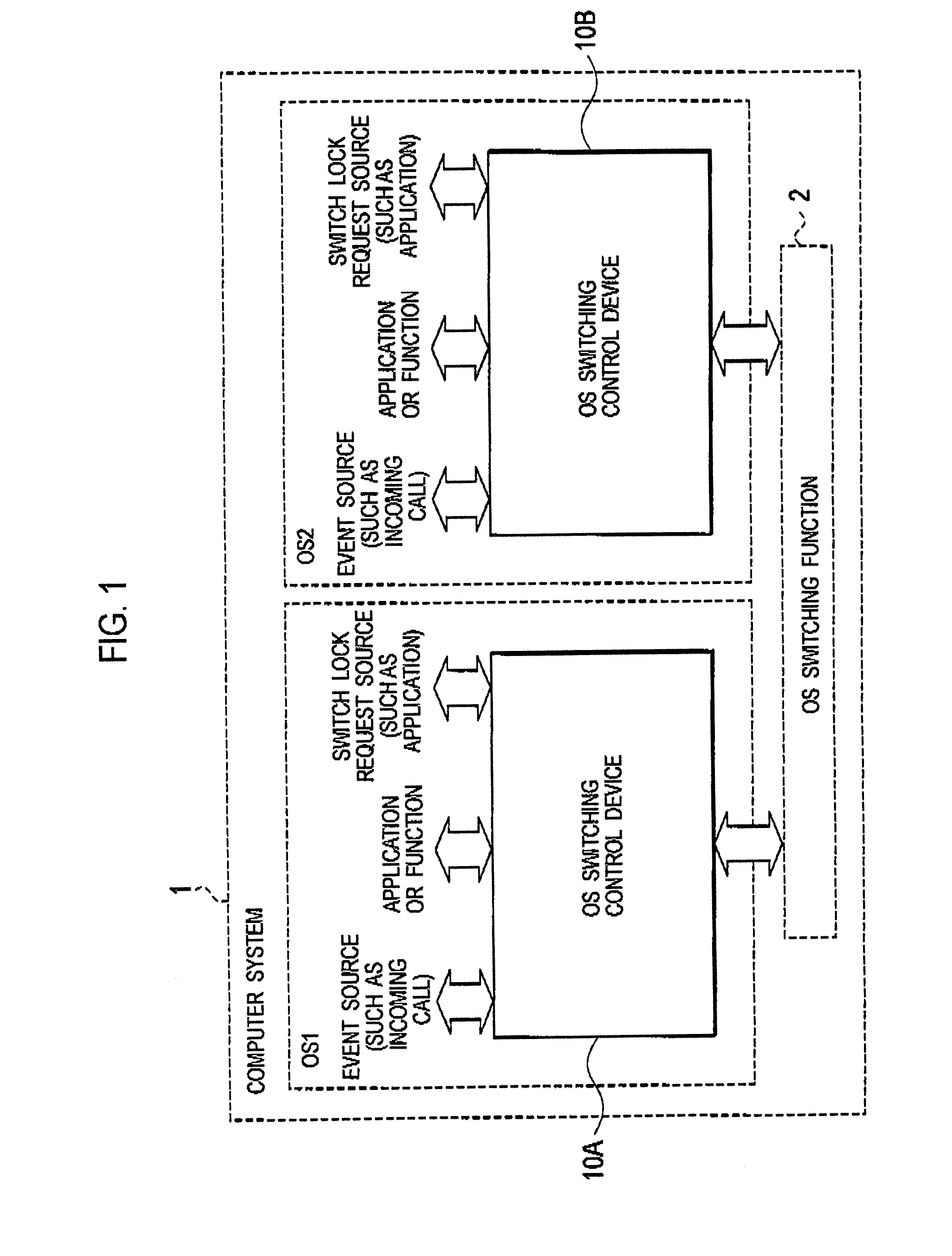
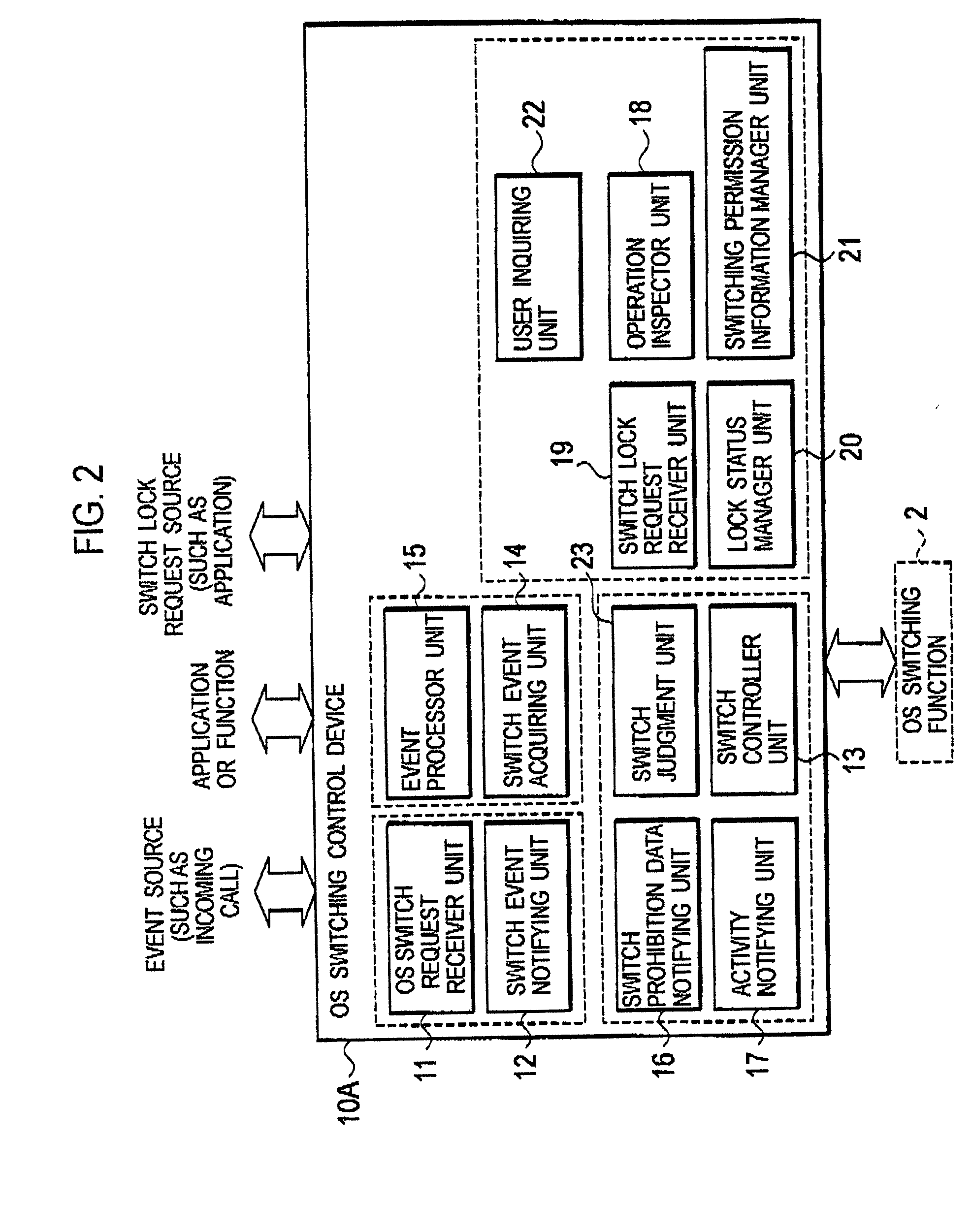
Operating system switching control device and computer system
InactiveUS20080184274A1Shorten the timeEnsuring Safe ExecutionInterprogram communicationSpecific program execution arrangementsOperational systemHandoff control
In a computer system according to the present invention, a switch-source OS controller unit includes: a OS switch request receiver unit configured to receive an OS switch request for requesting that the switch-destination OS in a suspend status becomes the OS in the active status; a switch event notifying unit configured to notify event information to the switch-destination OS or an application on the switch-destination OS, the event information being included in the received OS switch request, and requesting the switch-destination OS or the application on the switch-destination OS to perform a process; and a switch controller unit configured to call the OS switching function, by using the event information as an argument, so that the switch-destination OS becomes the OS in the active status.
Owner:NTT DOCOMO INC
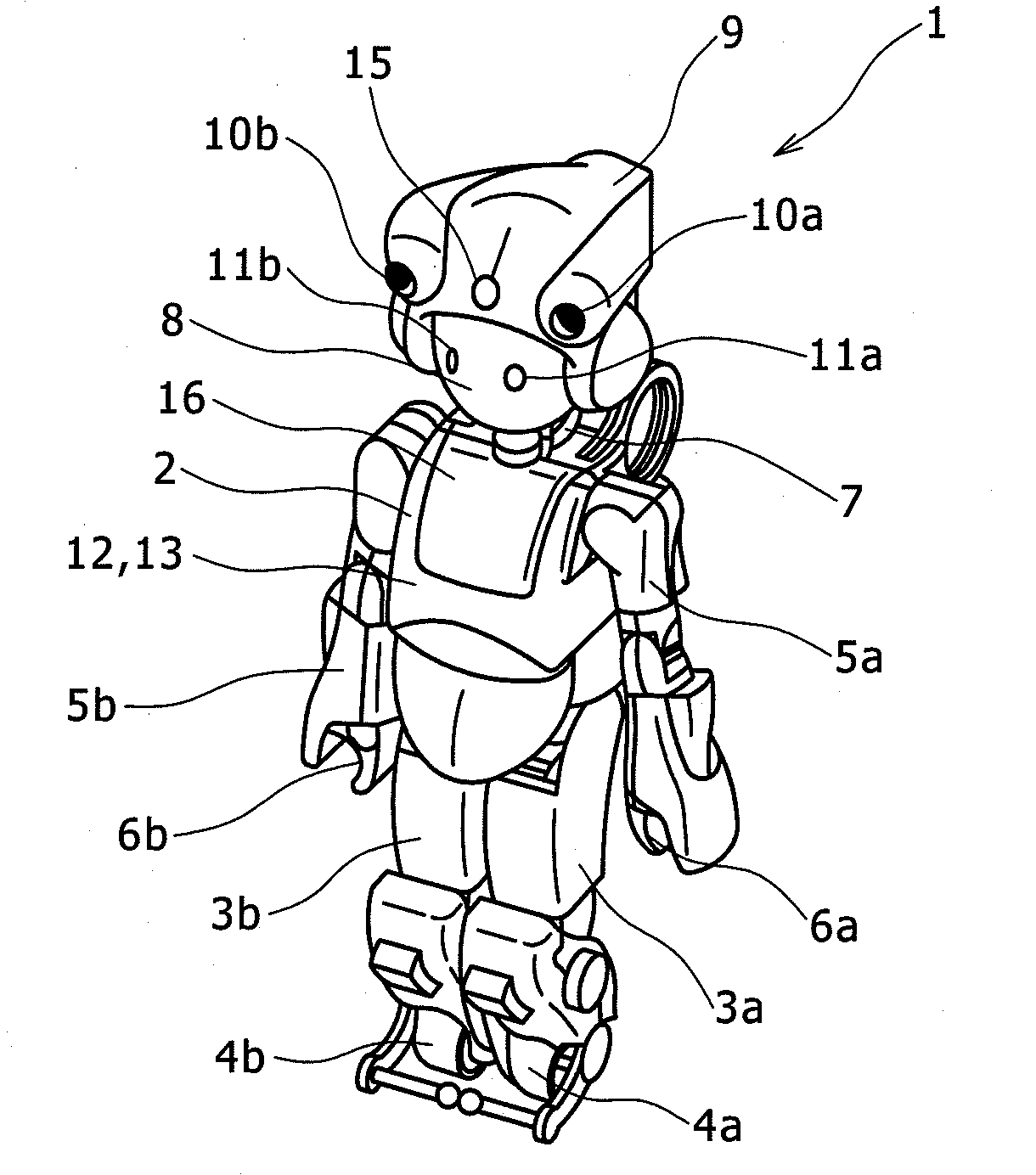
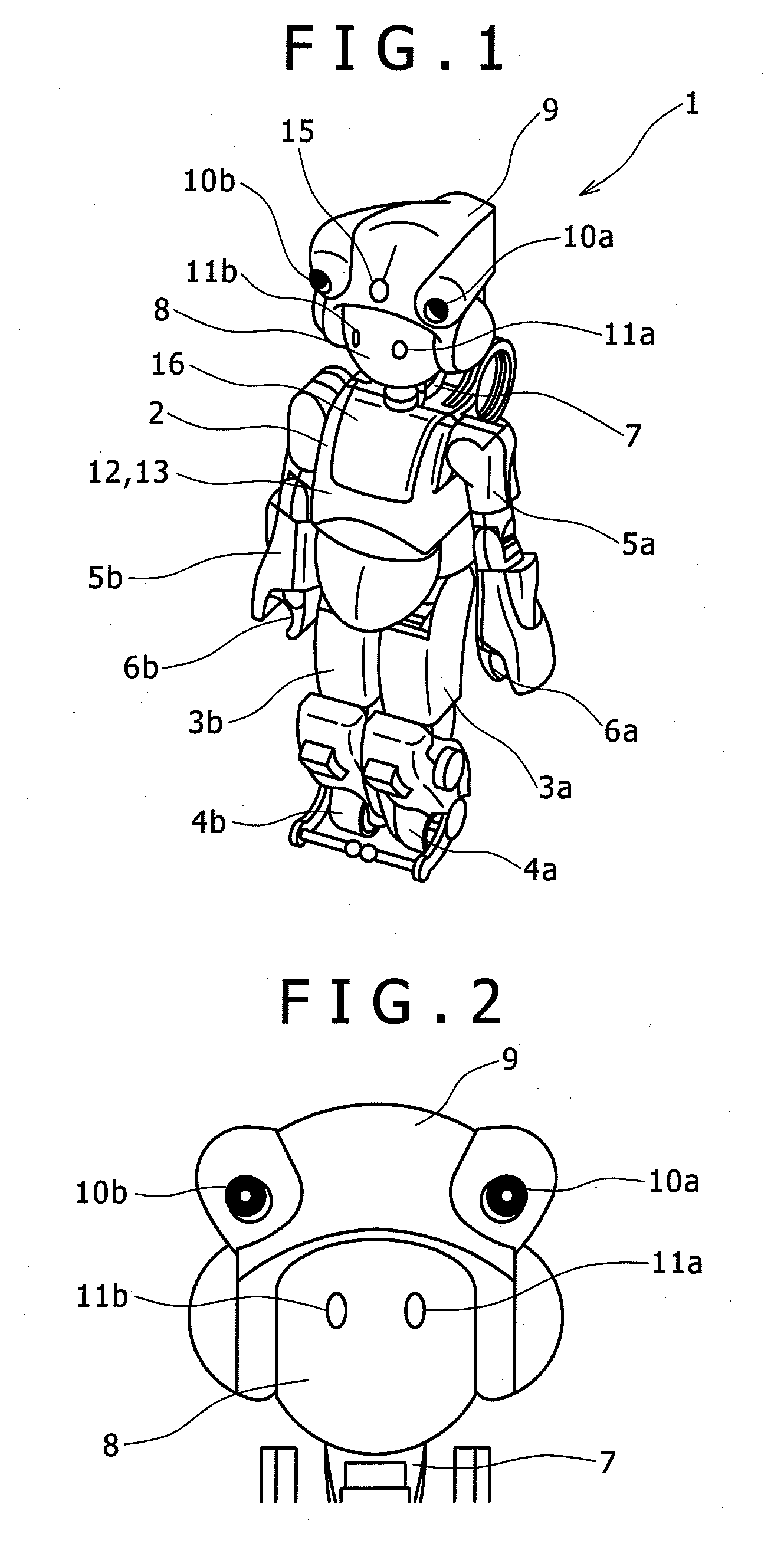
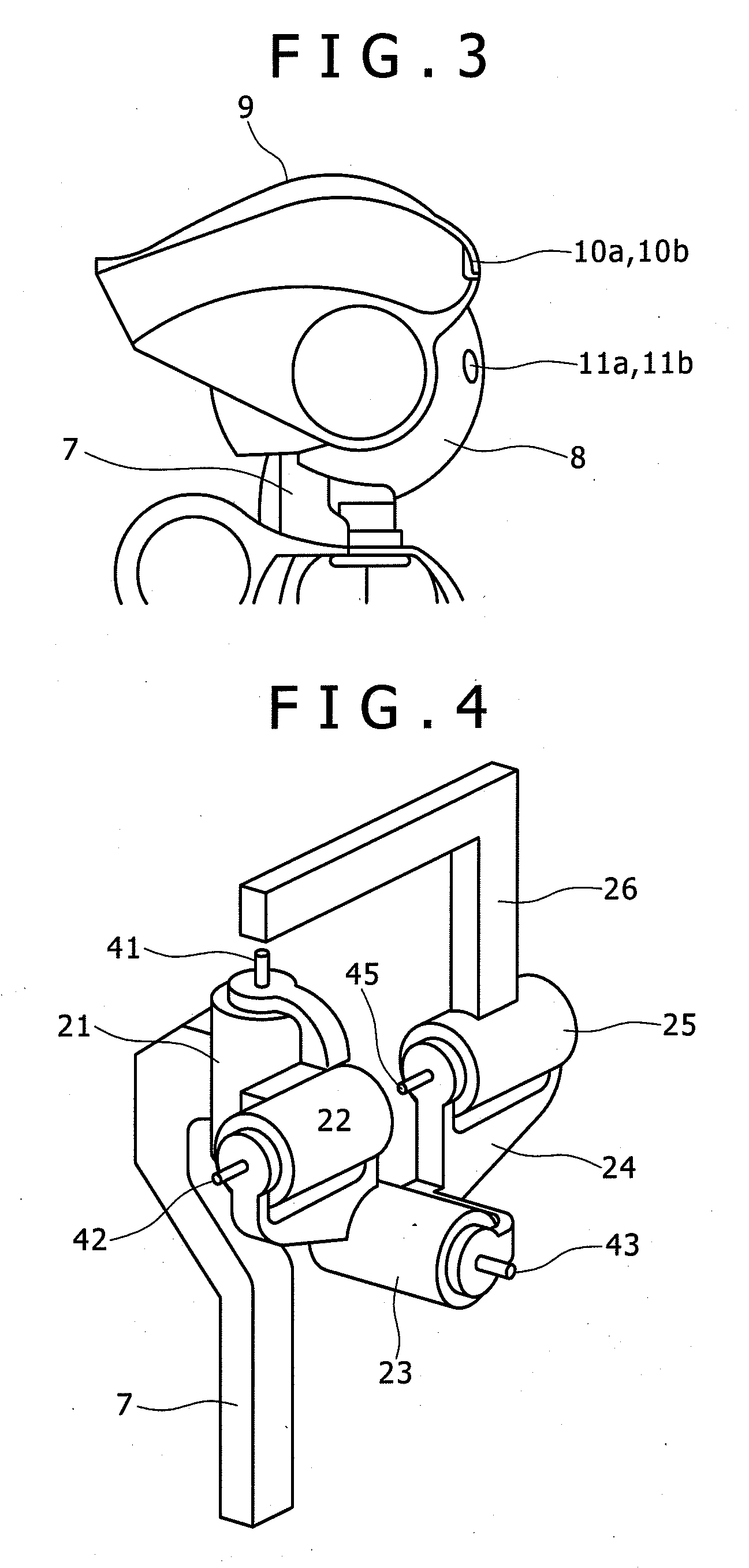
Robot
InactiveUS20090118865A1Ensuring Safe ExecutionProgramme controlProgramme-controlled manipulatorEngineeringRobot
Described herein is a robot having a camera mount that is movable along a curved surface of an upper part of the head, on a front side thereof, and two units of cameras that are mounted in the camera mount. The cameras are disposed such that the cameras are laterally separated from each other at an interval substantially equivalent to a lateral width of the head, respective extremities of the cameras are substantially flush with the front end of the head, and the cameras are positioned in close proximity of the upper end of the robot.
Owner:HITACHI LTD
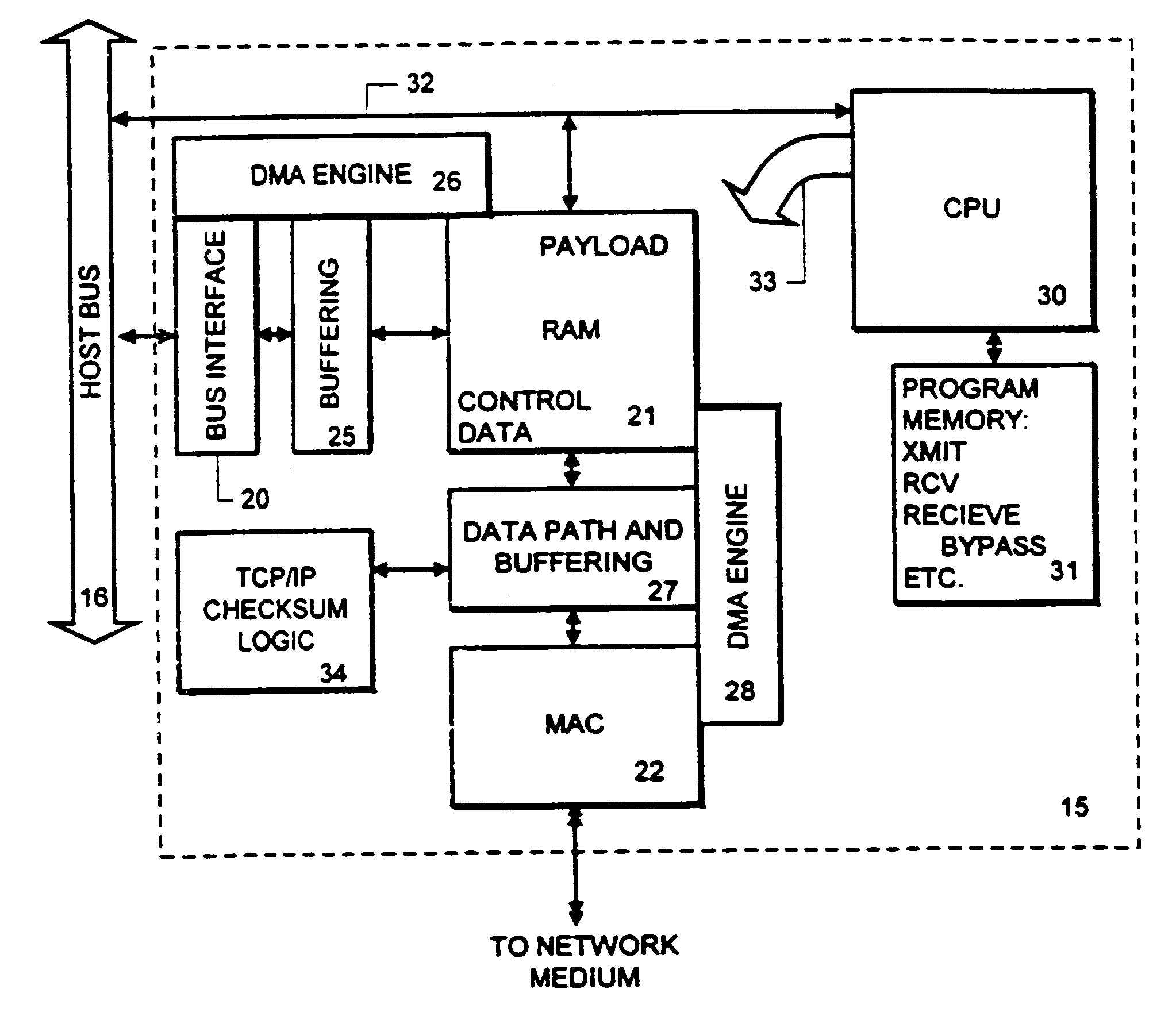
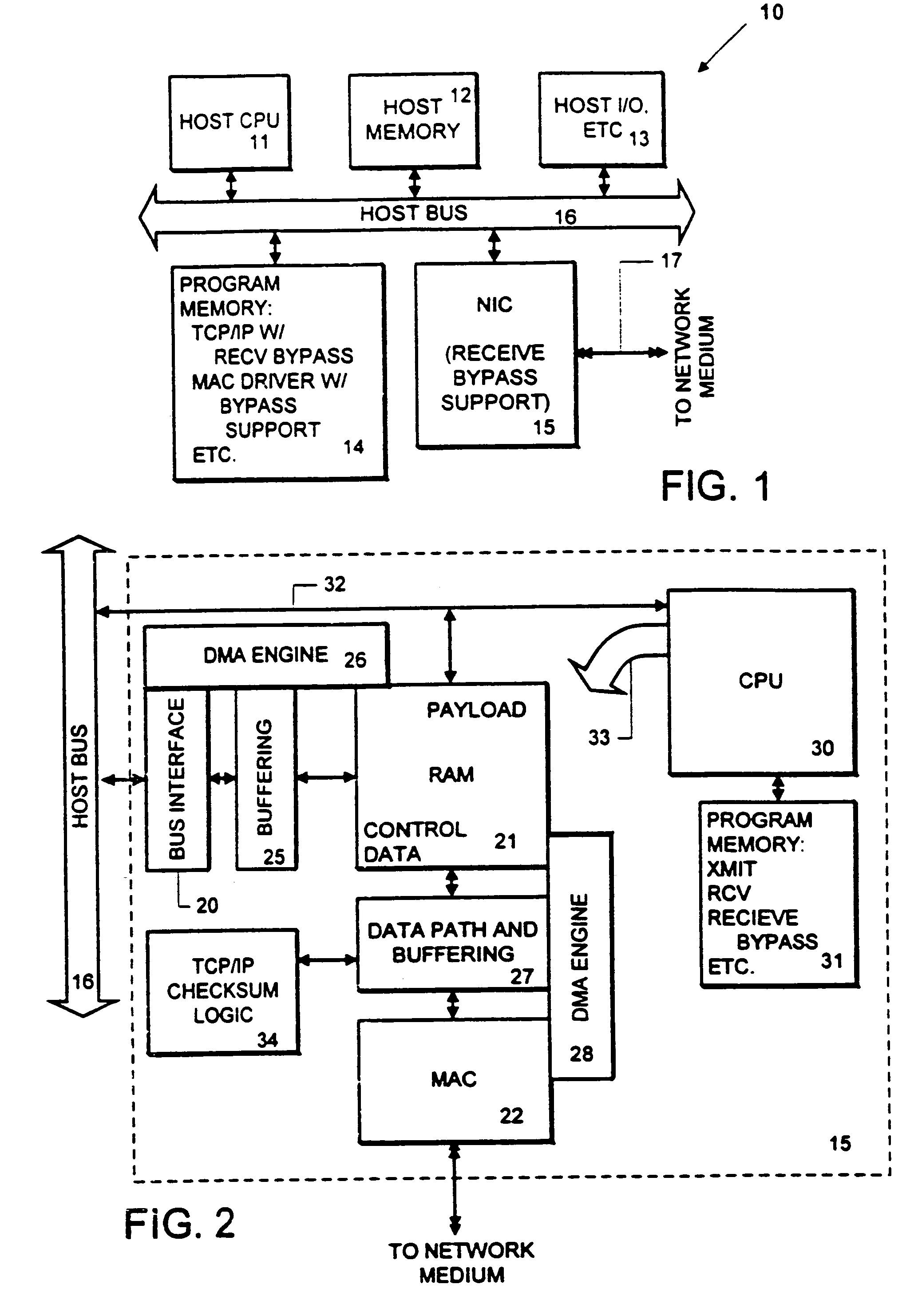
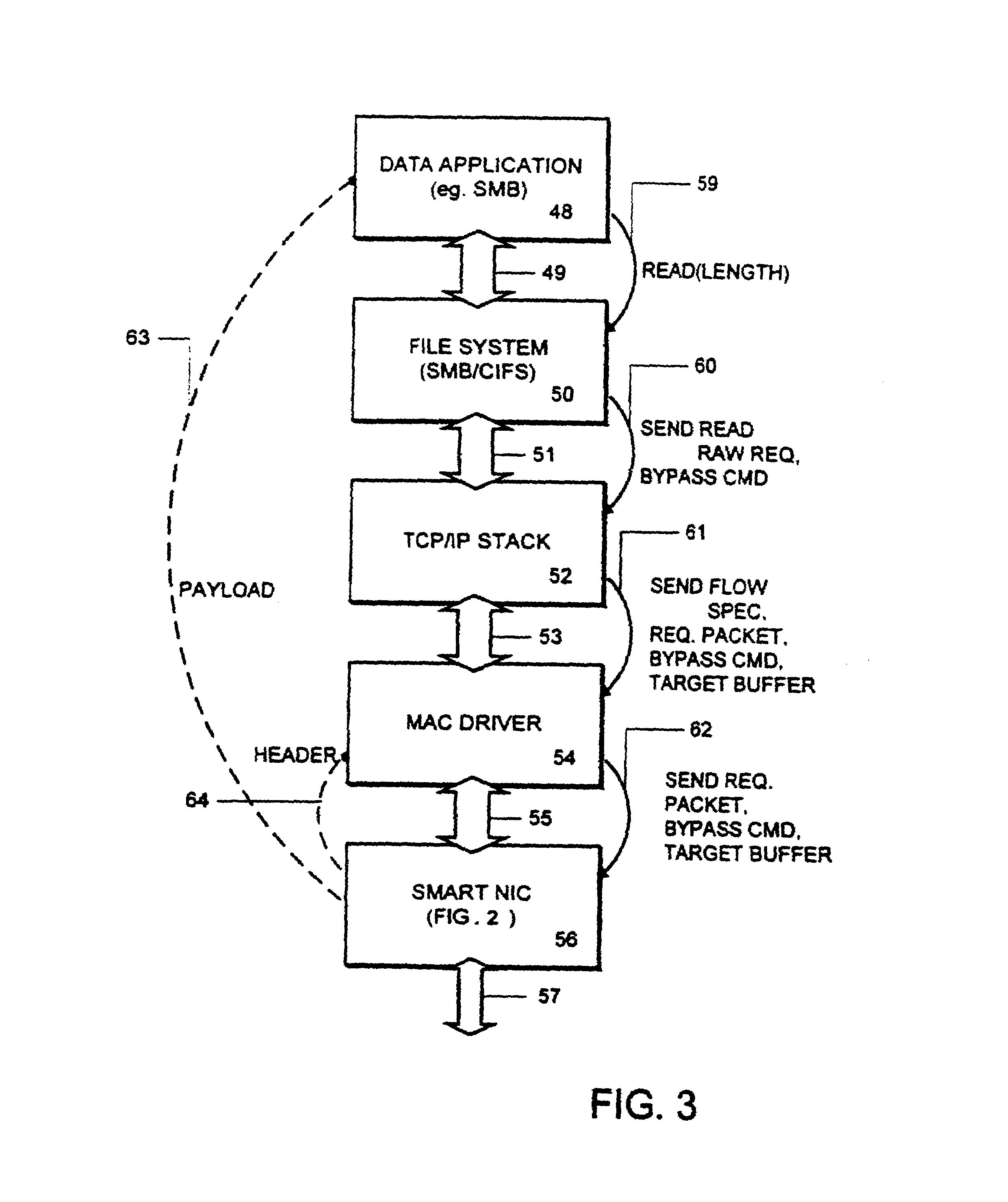
Receive processing with network protocol bypass
InactiveUS6956853B1Reducing number of time payloadPerformanceDigital computer detailsData switching by path configurationNetwork interface deviceNetworking protocol
An adapter is provided with intelligence that allows it to separate the header parts of a packet being received from the payload it carries, and in most cases move the payload directly into a destination buffer at the application layer or file system layer. Copies by the intermediate layers of the protocol stack are bypassed, reducing the number of times that the payload of a communication must be copied by the host system. At the network interface, a plurality of packets is received, and the payload of each is bypassed directly into the target destination buffer. The network interface device identifies the packets which are in the sequence of packets carrying payload to be stored in the target buffer by the flow specification carried with such packets. Also, the packets carrying data payload for the file include a sequence number or other identifier by which the network interface is able to determine the offset within the target buffer to which the packet is to be stored.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
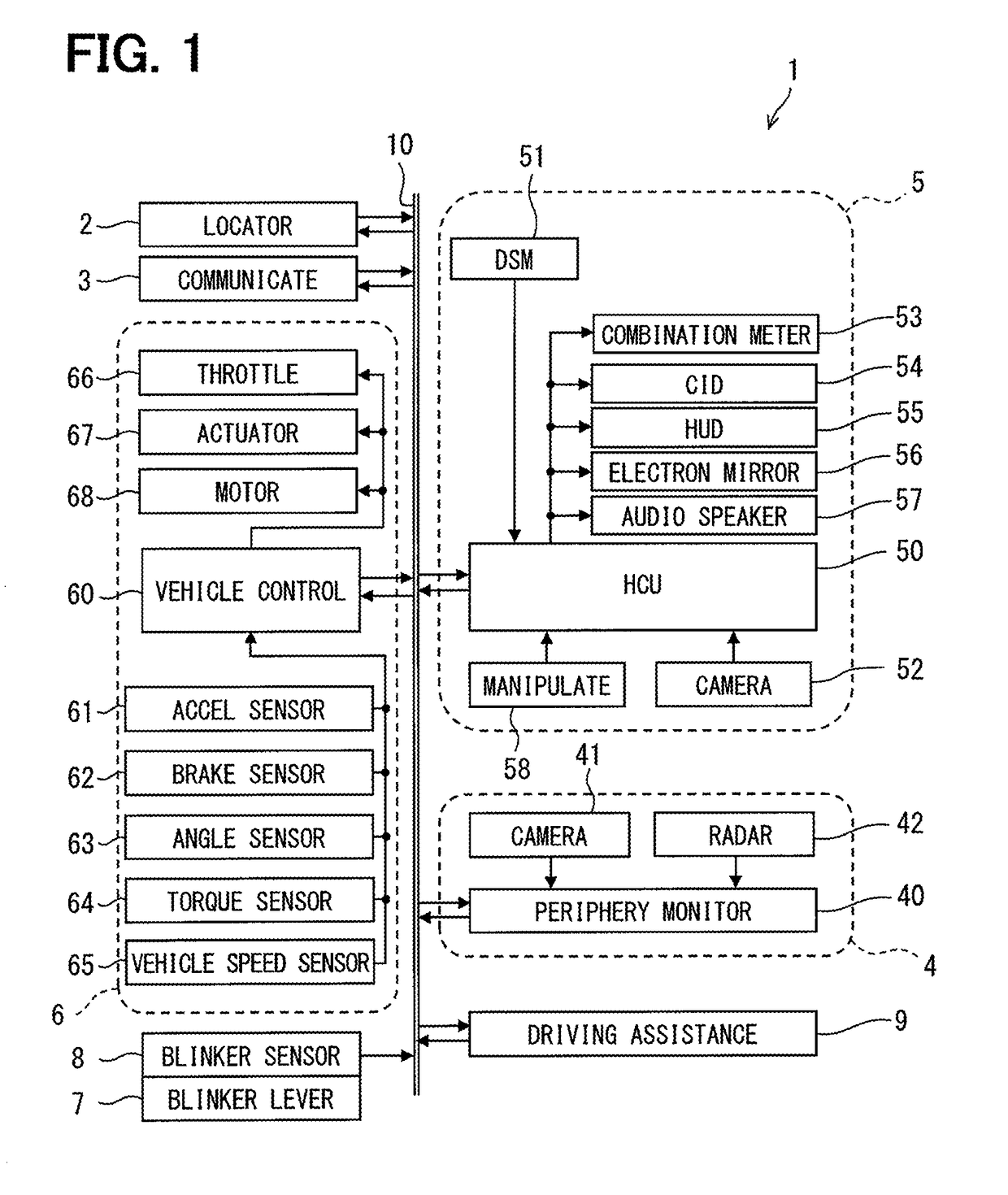
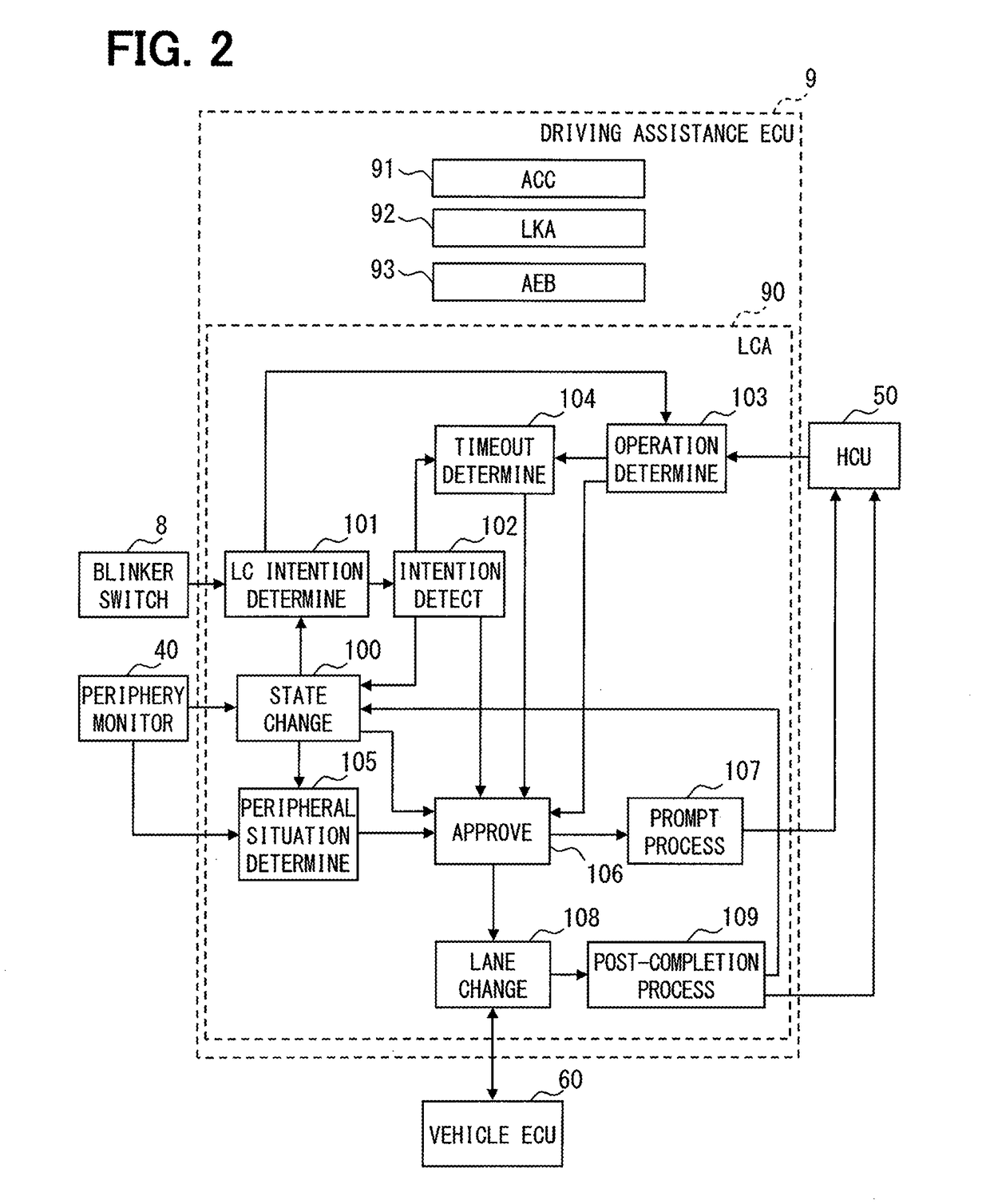
Driving assistance apparatus
InactiveUS20180354517A1Prevent lane changeEnsuring Safe ExecutionRoad vehicles traffic controlPedestrian/occupant safety arrangementDriver/operatorReliability engineering
Owner:DENSO CORP
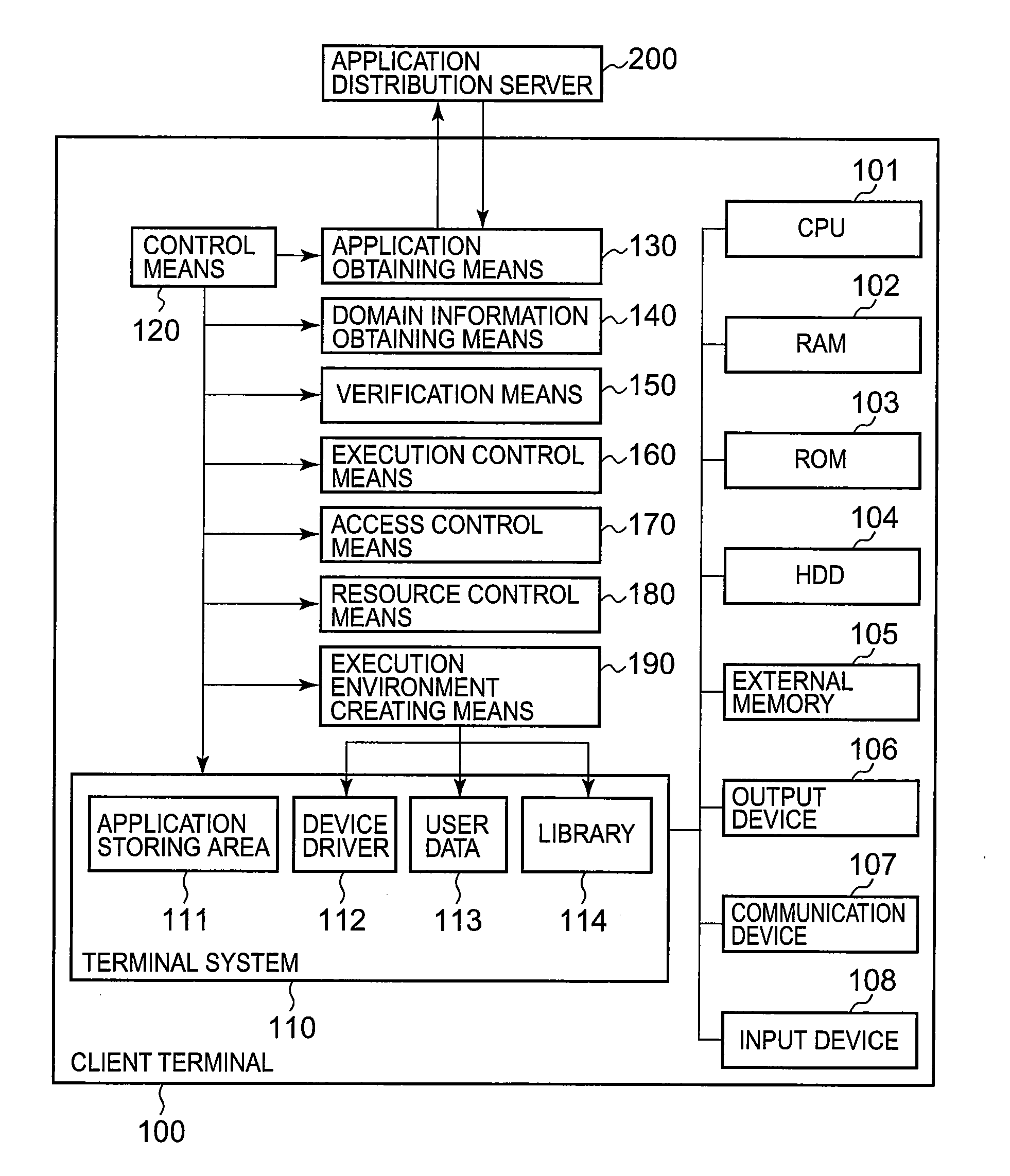
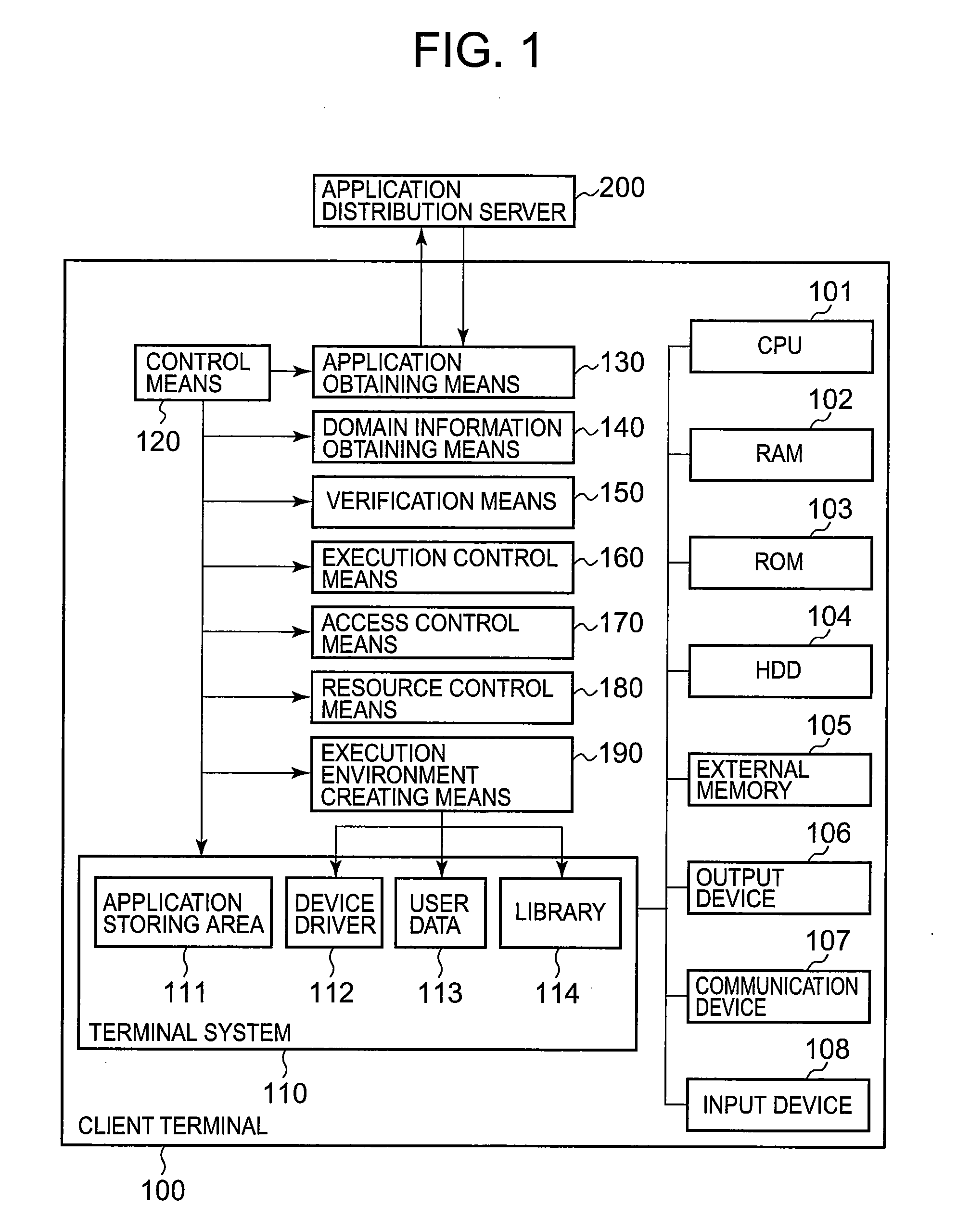
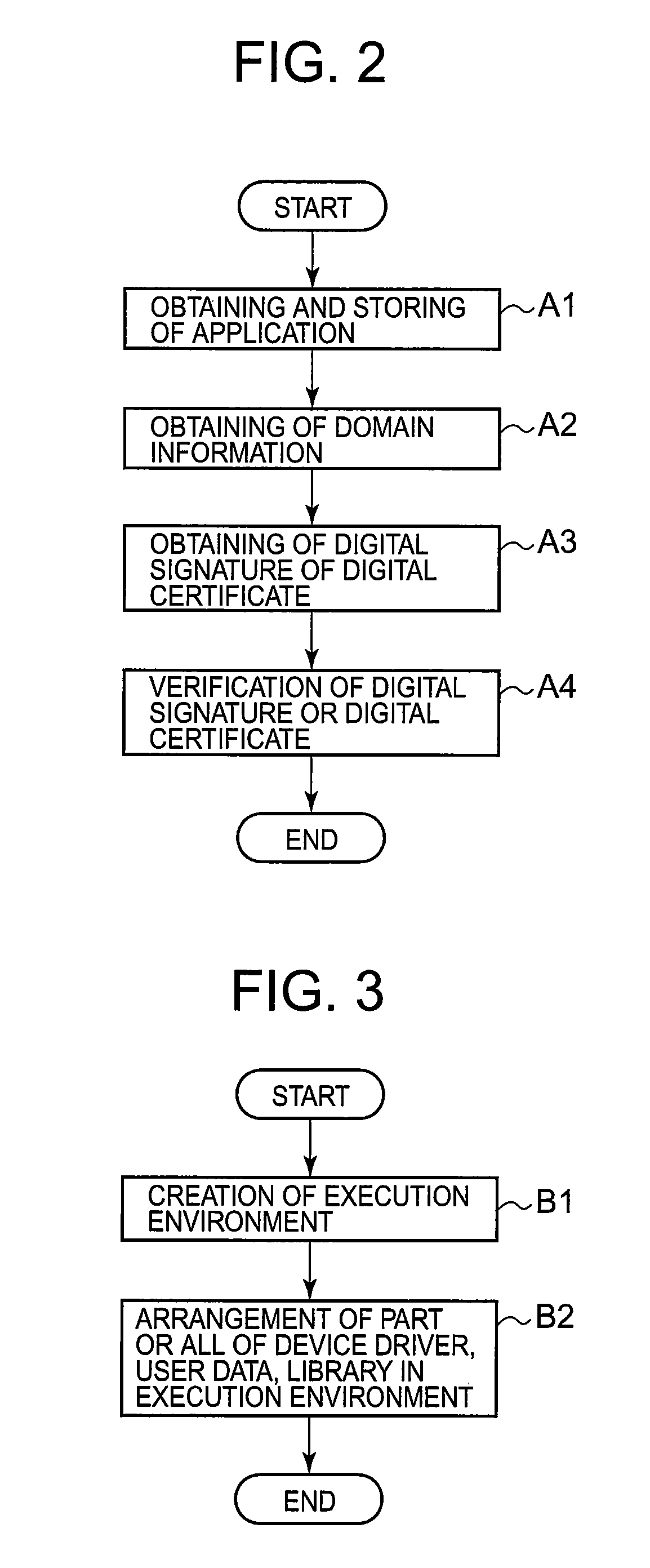
Program execution control method, its device, and execution control program for same
InactiveUS20090307781A1Reduce overhead incurredLimited accessDigital data processing detailsUnauthorized memory use protectionExecution controlComputer engineering
Provided are a program execution control method, its device, and an execution control program safely executing an application program containing an untrusted code while reducing overhead. Execution environment creating means (190) creates an execution environment in which access to the outside of the execution environment is limited and arranges at least part of a device driver (112), a library (114), and user data (113) provided in the computer in such a way that the part can be referenced from a program running in the execution environment. Execution control means (160) executes the application program introduced and obtained from an application distribution server (200).
Owner:NEC CORP
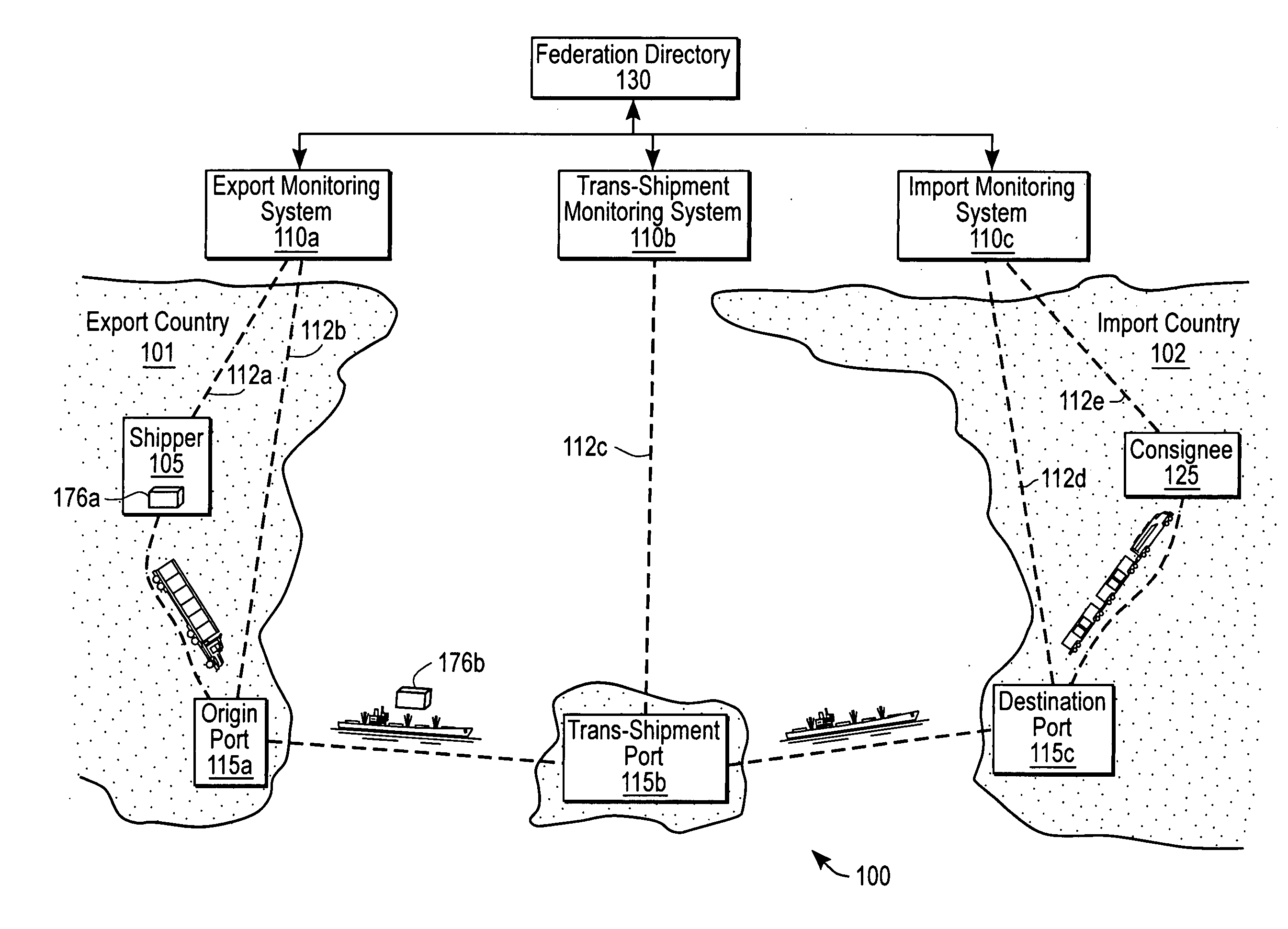
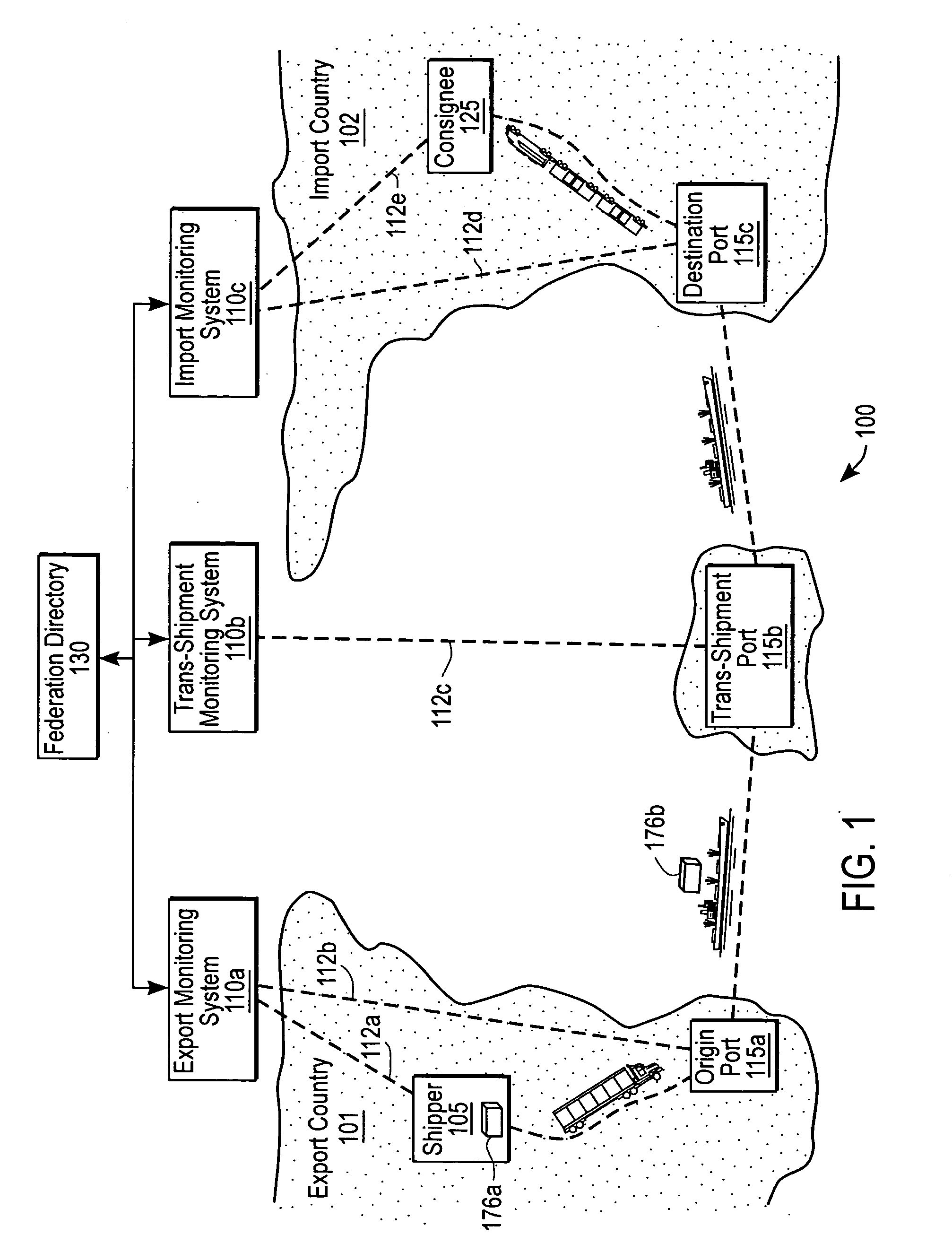
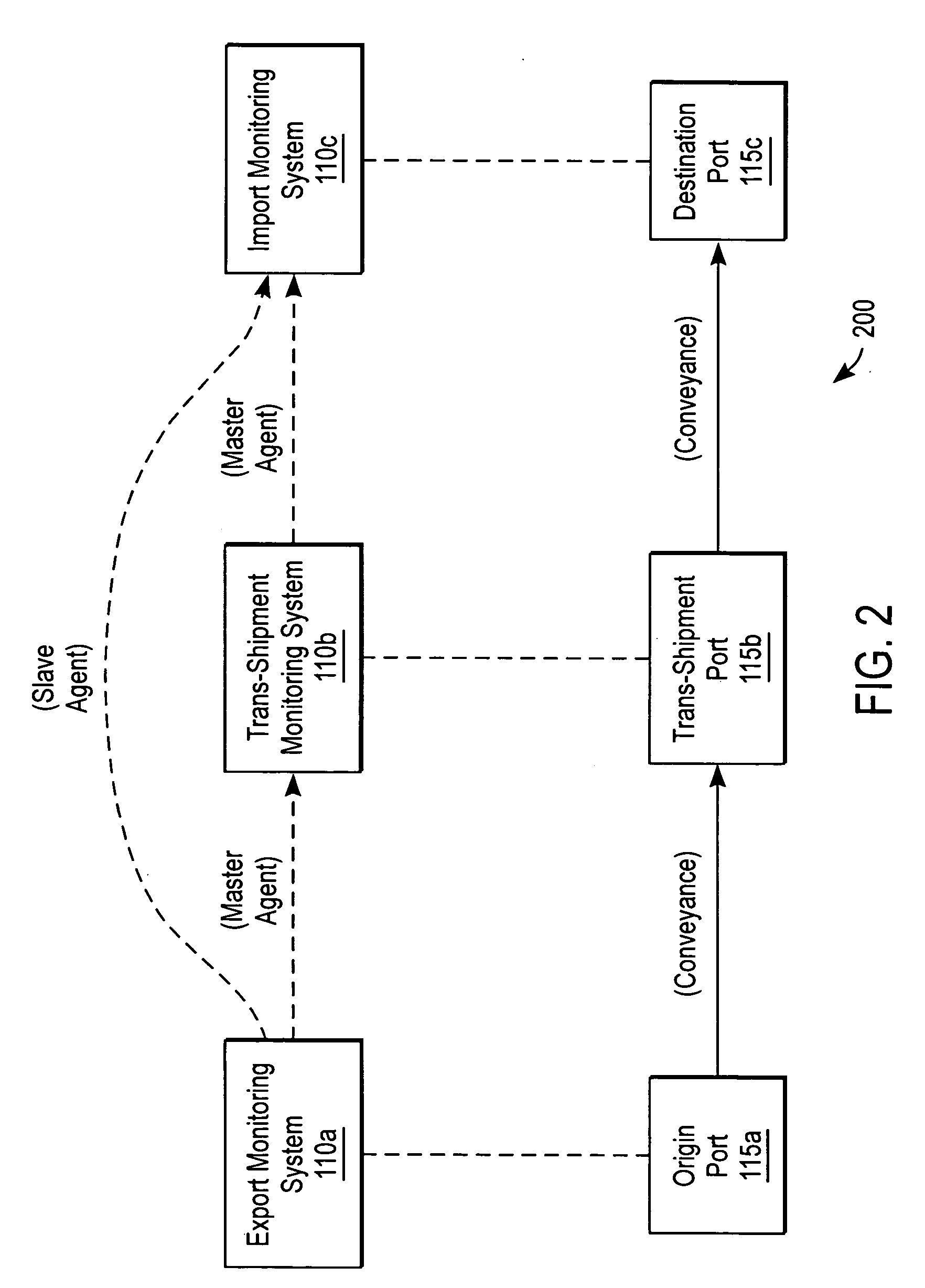
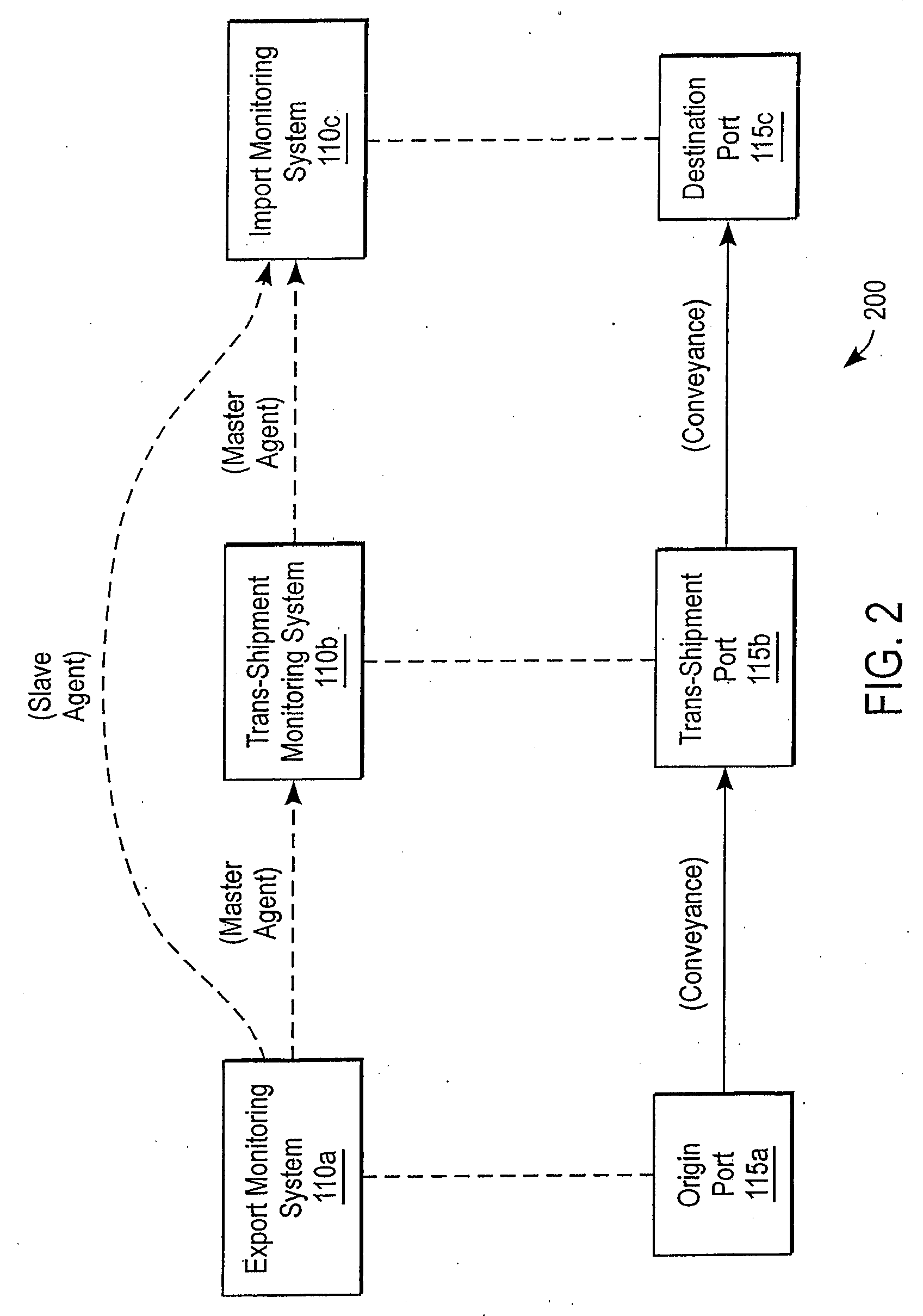
Federated system for monitoring physical assets
ActiveUS20050156736A1Ensuring Safe ExecutionLimit processor cycles available to agent threadsElectric signal transmission systemsDigital data processing detailsVisibilityMonitoring system
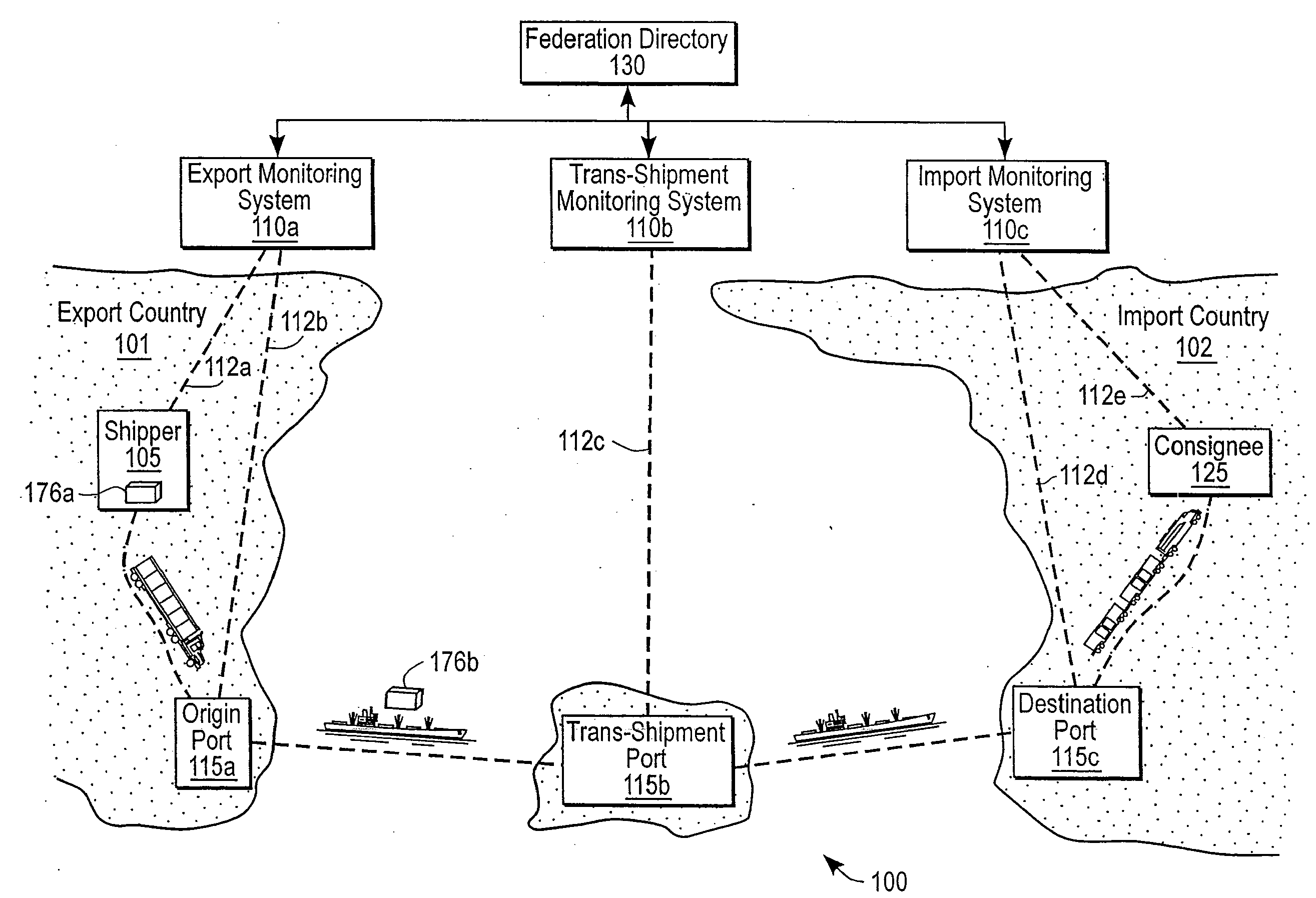
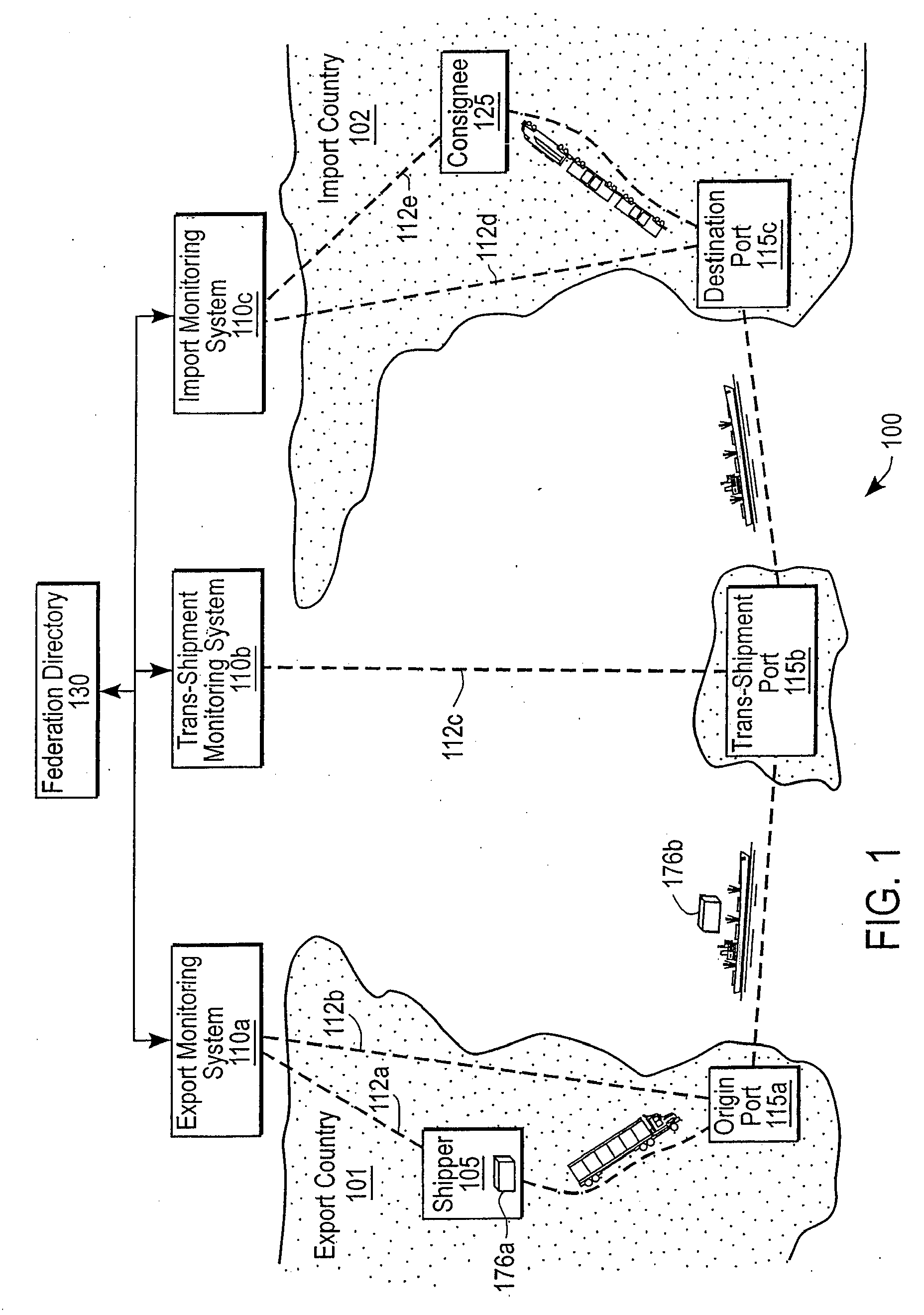
A system federates heterogeneous monitoring systems to provide end-to-end monitoring information for conveyances with item-layer visibility. A first node of the federated system comprises a first monitoring system and a first port and a second node comprises a second monitoring system and a second port. In parallel with a conveyance being transported between the first node and the second node, the first monitoring system sends an agent to the second monitoring system. The agent comprises logic and / or data necessary to implement processes on the second monitoring agent while the conveyance is at the second port. When the conveyance arrives at the second port, the second monitoring system executes the agent to determine conditions of the conveyance and / or its contents.
Owner:SAVI TECH INC
Illegal analysis / falsification preventing system
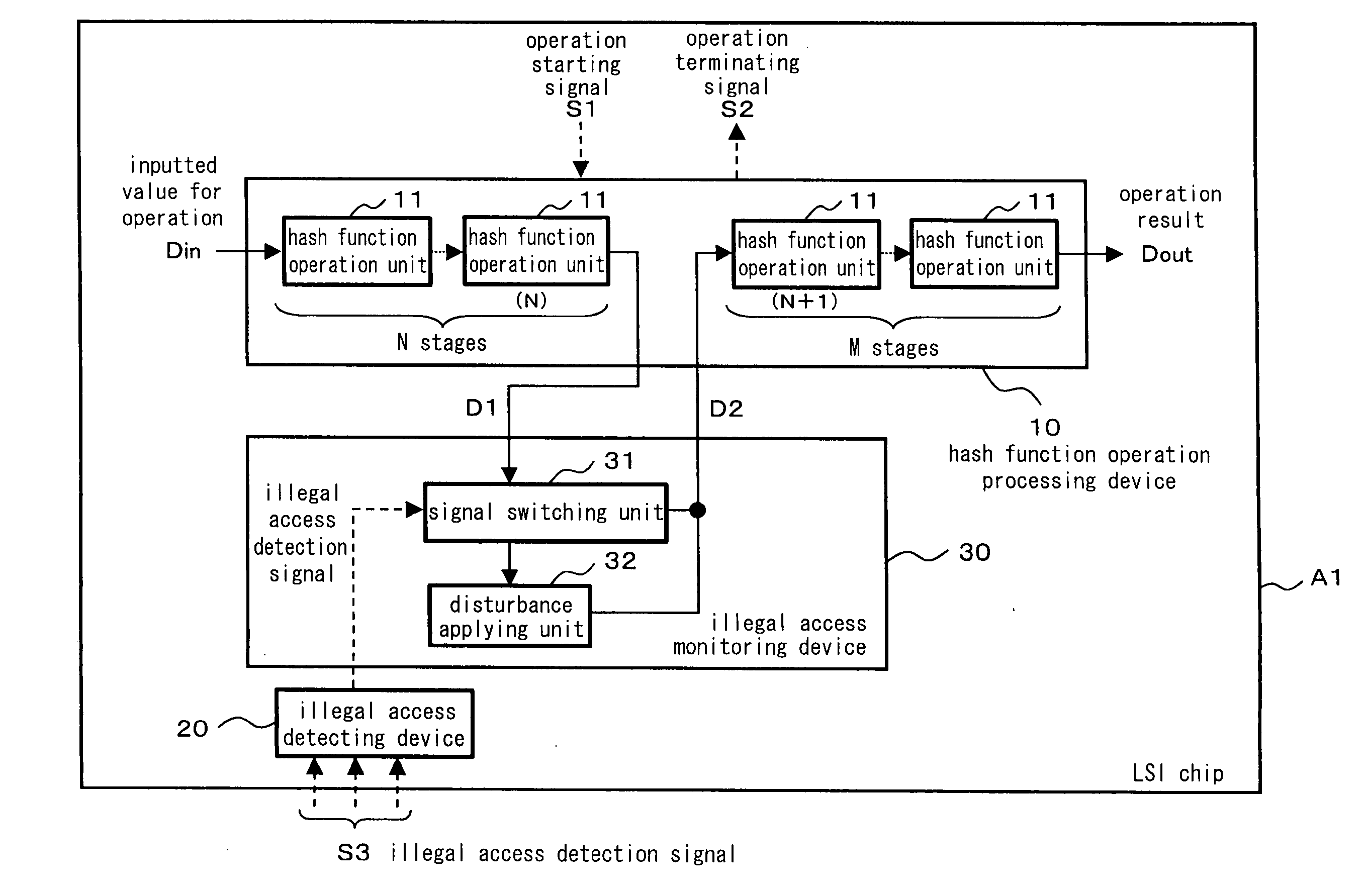
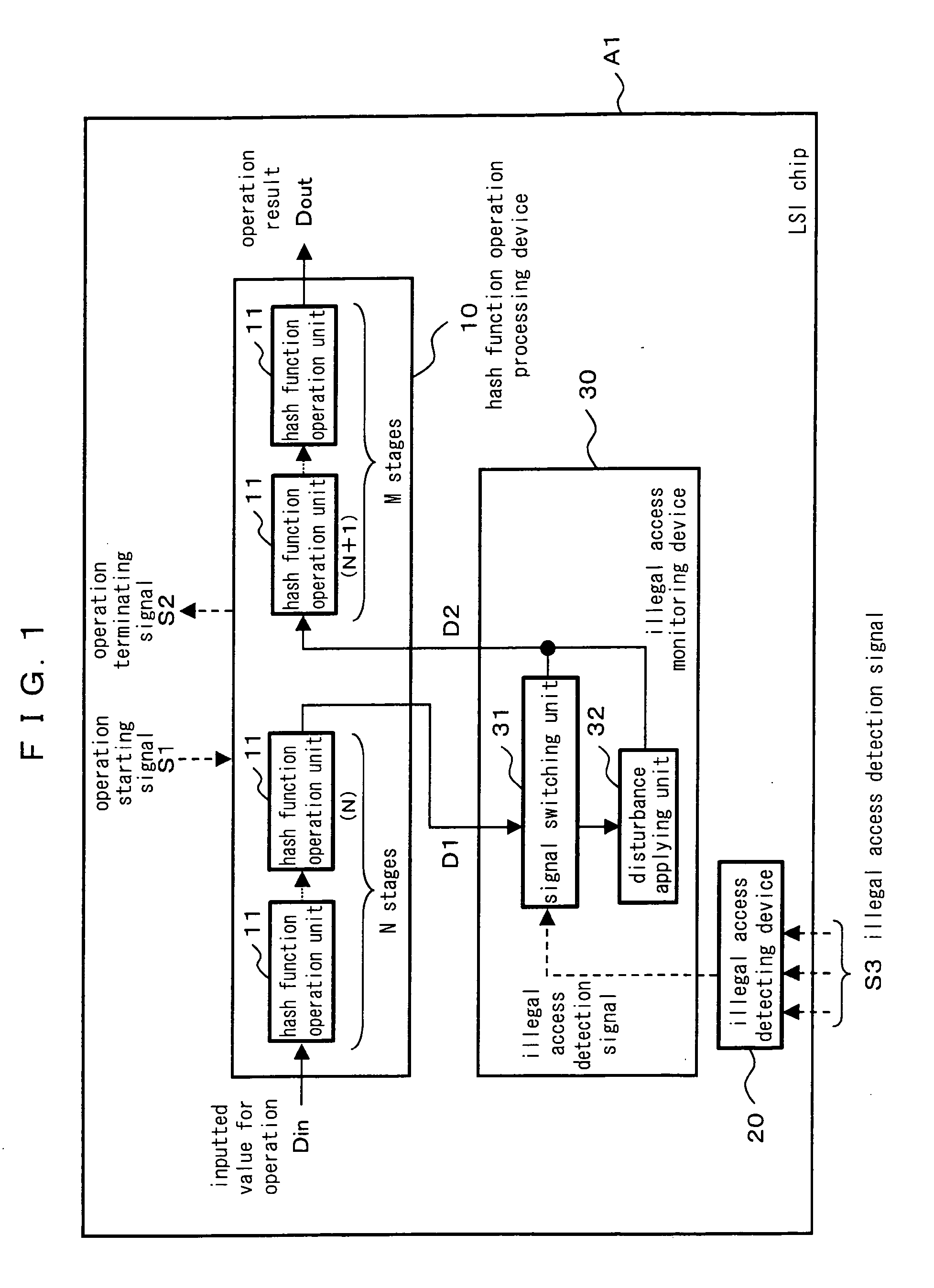
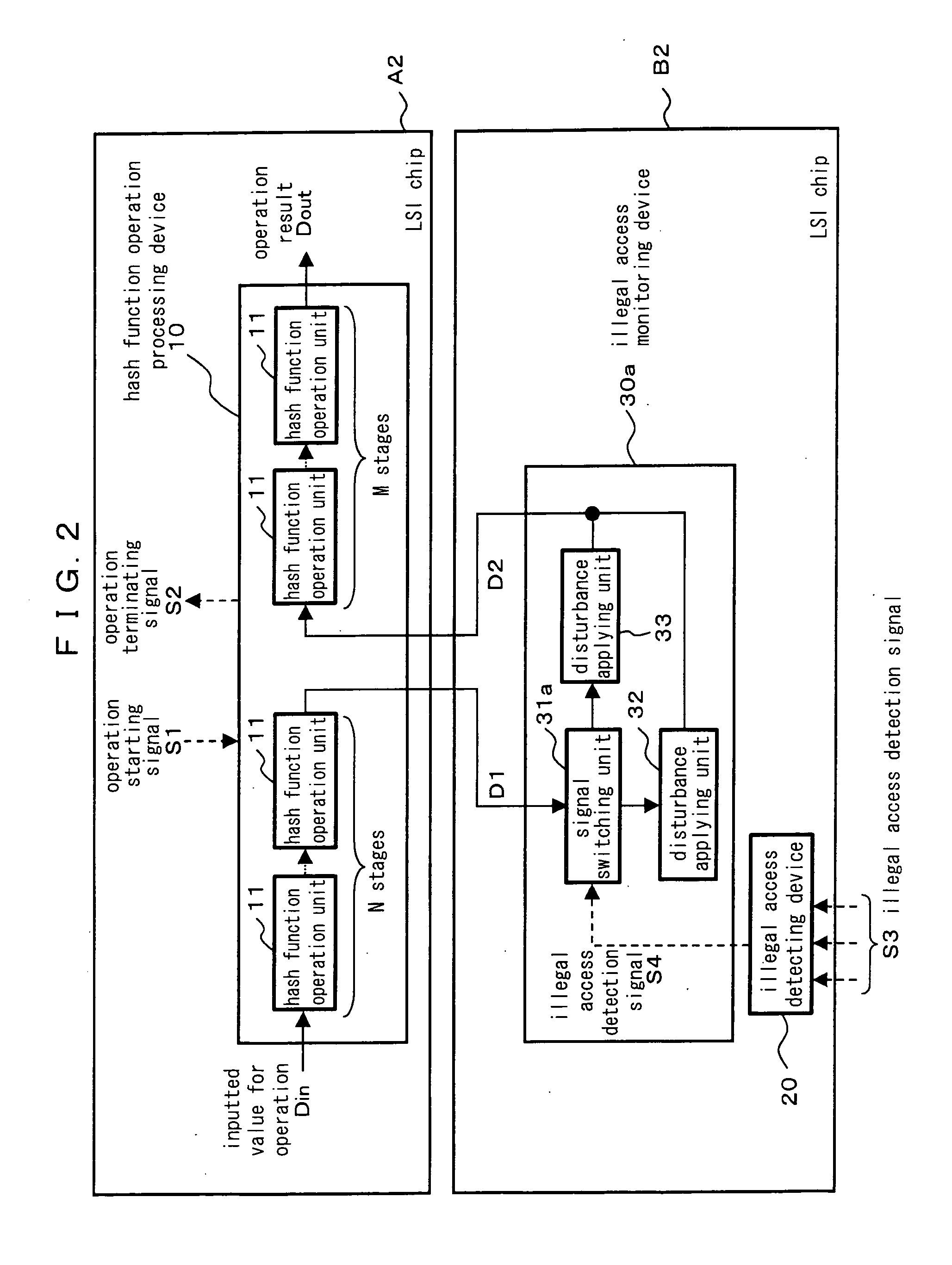
InactiveUS20060080537A1Prevent forgerySafely encryptedUser identity/authority verificationDigital data protectionHash functionOperational system
A hash function operation system comprises a hash function operation processing device comprising a plurality of hash function operation units connected in multiple stages and incapable of predicting an output from an input, an illegal access detecting device for detecting an illegal access, and an illegal access monitoring device for retrieving an output of an optional stage in a sequence of processings executed by the hash function operation units and inputting the retrieved output to the hash function operation unit in the next stage when the illegal access detecting device shows a state where the illegal access is not detected, the illegal access monitoring device further applying a disturbance to the retrieved output when the illegal access detecting device shows a state where the illegal access is detected and inputting the resulting output to the hash function operation unit in the next stage, wherein falsification is prevented and an encryption key is safely generated by executing the different hash function operations depending on the state of the illegal access.
Owner:PANASONIC CORP
Image forming apparatus having fixing device
InactiveUS20080199197A1Without deteriorationEnsuring Safe ExecutionElectrographic process apparatusLeading edgeControlled release
An image forming apparatus which forms an image on a sheet, includes a controller which executes a cleaning mode in which the controller conveys the sheet from a sheet feed tray to a fixing device without forming a toner image on the sheet, removes toner that has been adhered to a fixing member to clean. In case the cleaning mode is executed, the controller controls a releasing section to release pressure contact of a pressing member before a leading edge of the sheet in a sheet conveyance direction reaches a nip portion between the fixing member and the pressing member, and to bring the pressing member into pressure contact with the fixing member after the leading edge of the sheet has passed through the nip portion.
Owner:KONICA MINOLTA BUSINESS TECH INC
Computer Network Virus Protection System and Method
InactiveUS20080229416A1Detection securityEnsuring Safe ExecutionMemory loss protectionError detection/correctionProtection systemVirus
A network is protected from viruses through the use of a sacrificial server, which may be physical or virtual. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:G K WEBB SERVICES
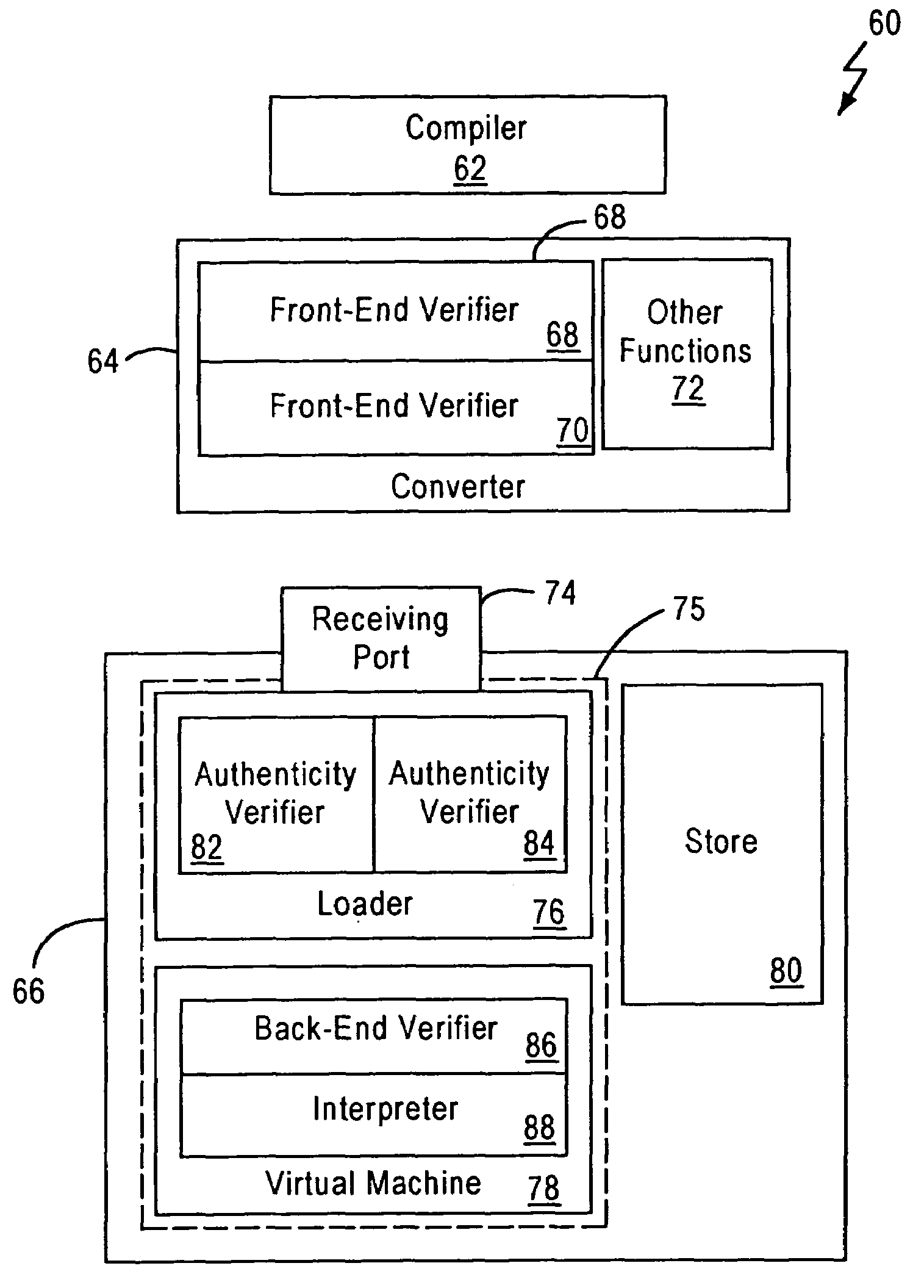
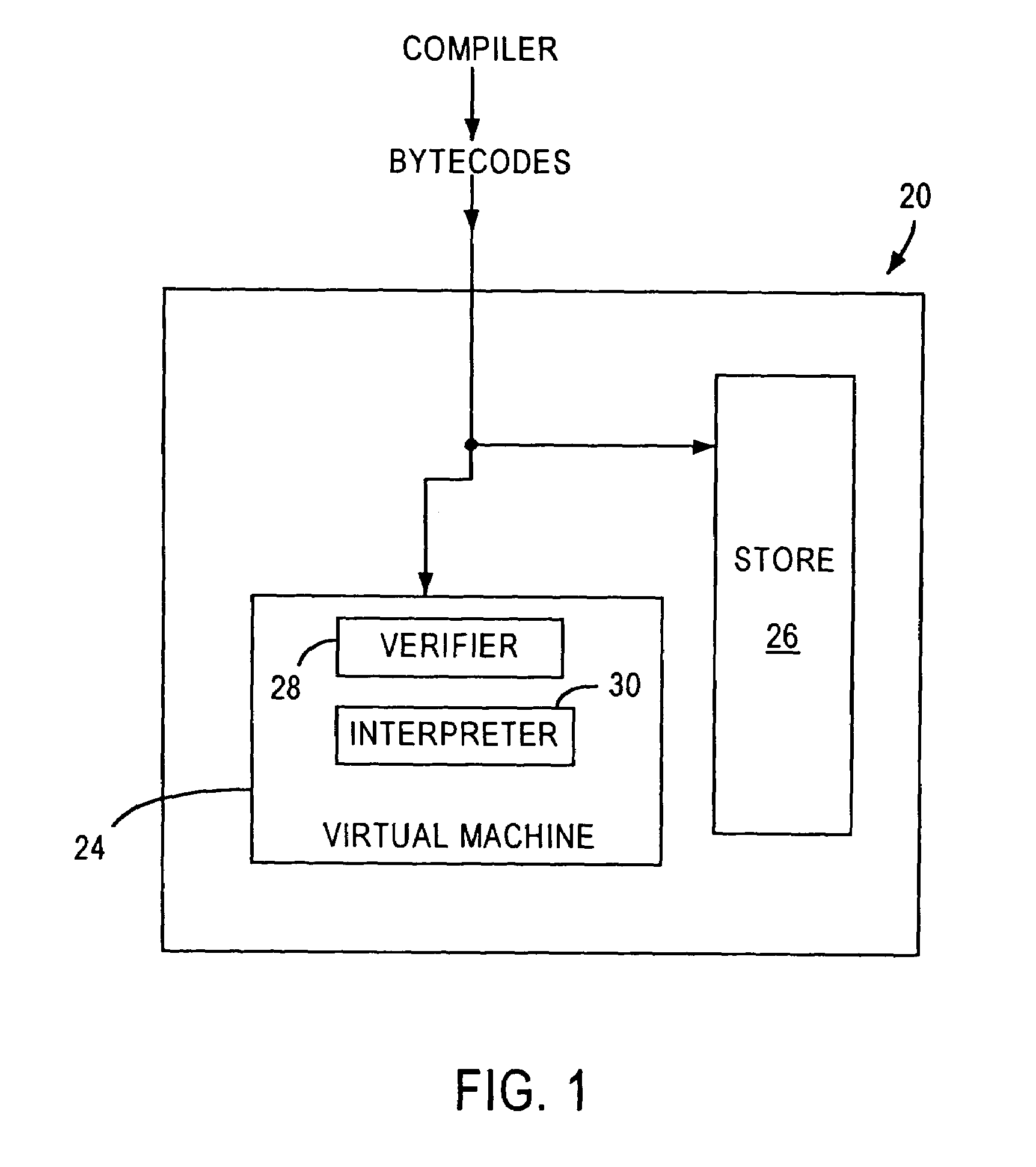
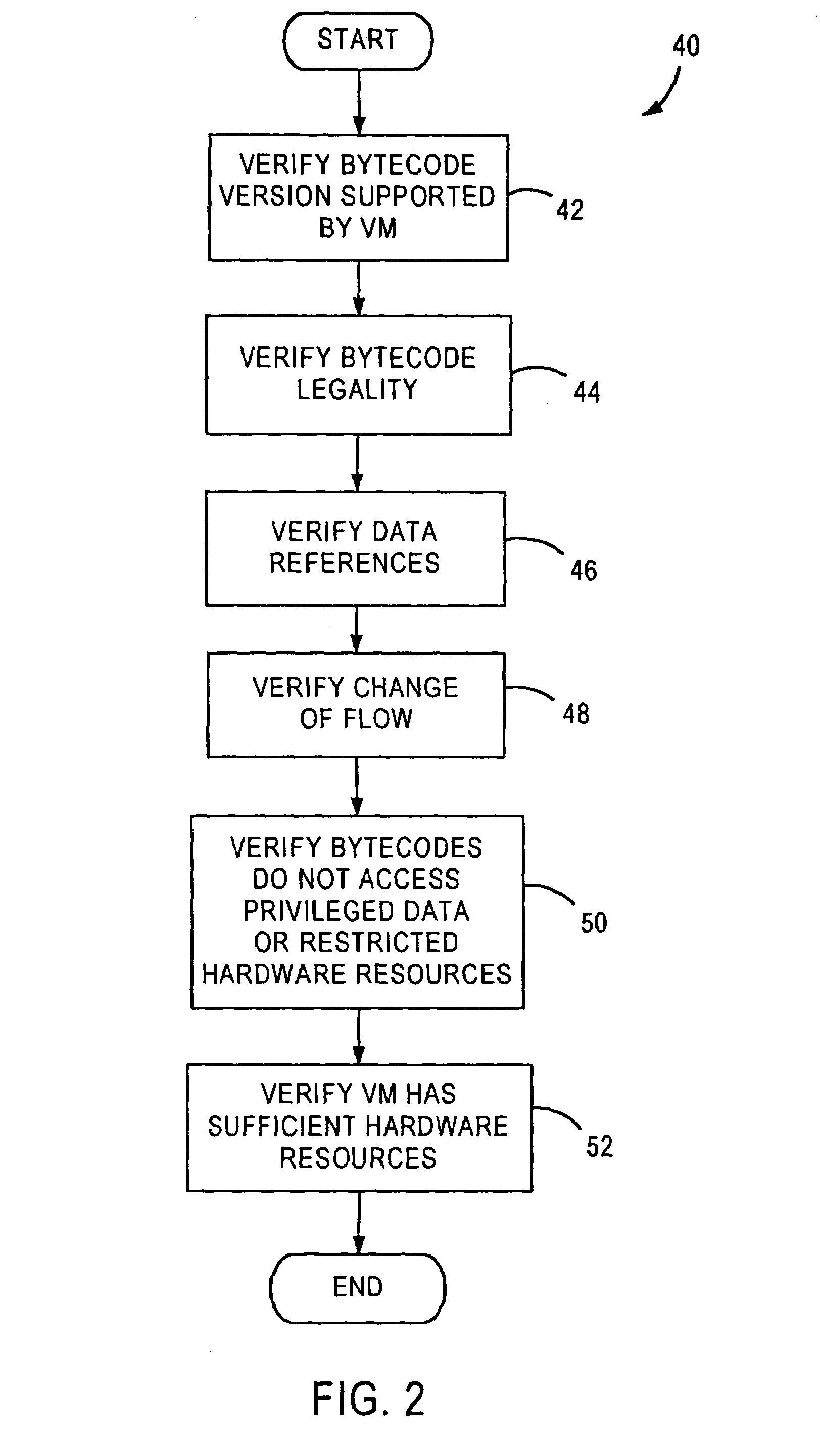
Virtual machine with securely distributed bytecode verification
InactiveUS7334136B2Reduce memory sizeImprove processing speedDigital data processing detailsUnauthorized memory use protectionApplication softwareComputing systems
A system for executing a software application comprising a plurality of hardware independent bytecodes is provided comprising a computing system that generates bytecodes, a virtual machine, remote to the computing system, that receives a plurality of bytecodes from said computing system, and executes said plurality of bytecodes, a system for testing said bytecodes against a set of predetermined criteria in which the testing is securely distributed between said virtual machine and said computing system so that the bytecode verification completed by the computing system is authenticated by the virtual machine prior to the execution of the bytecodes by said virtual machine. A method for distributed bytecode verification is also provided.
Owner:ORACLE INT CORP
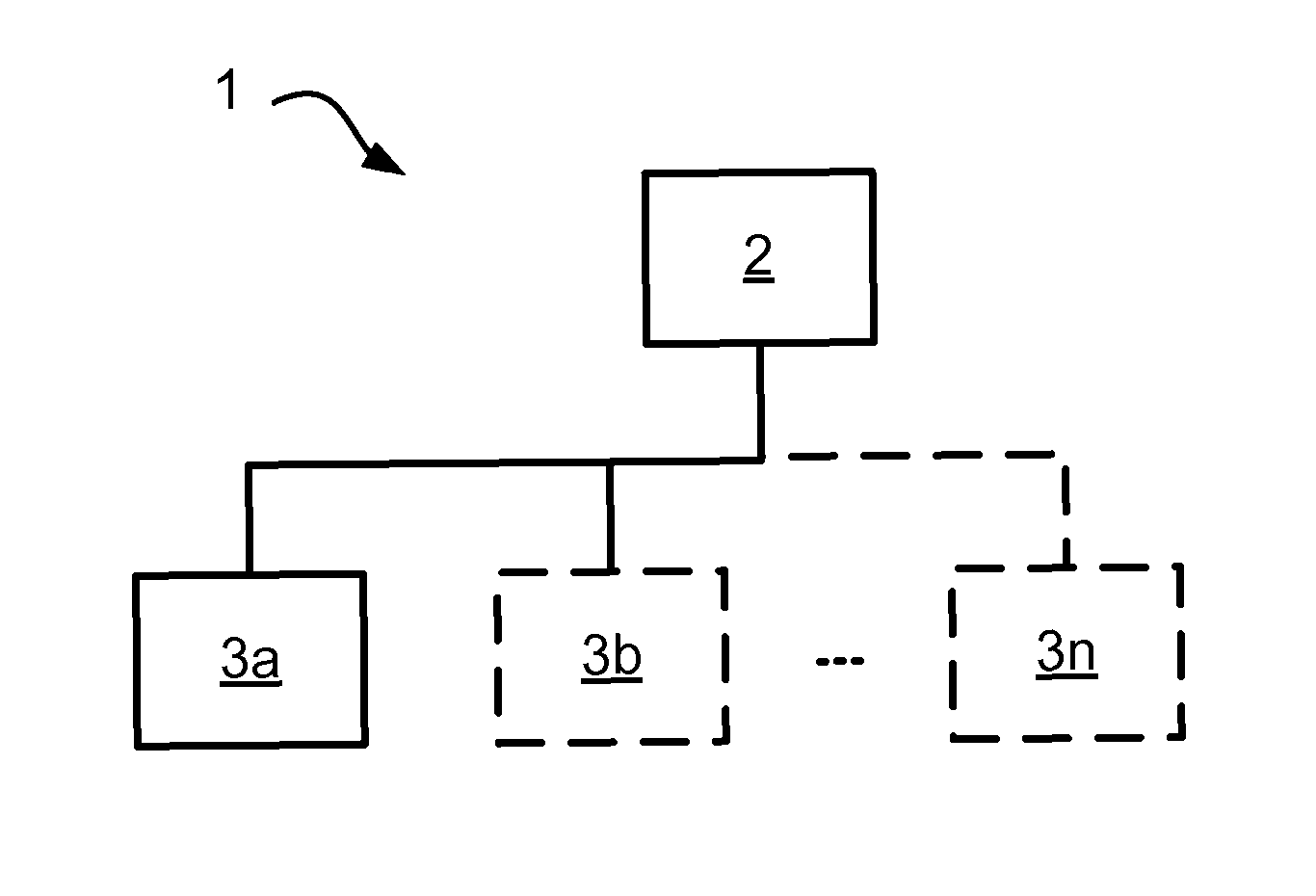
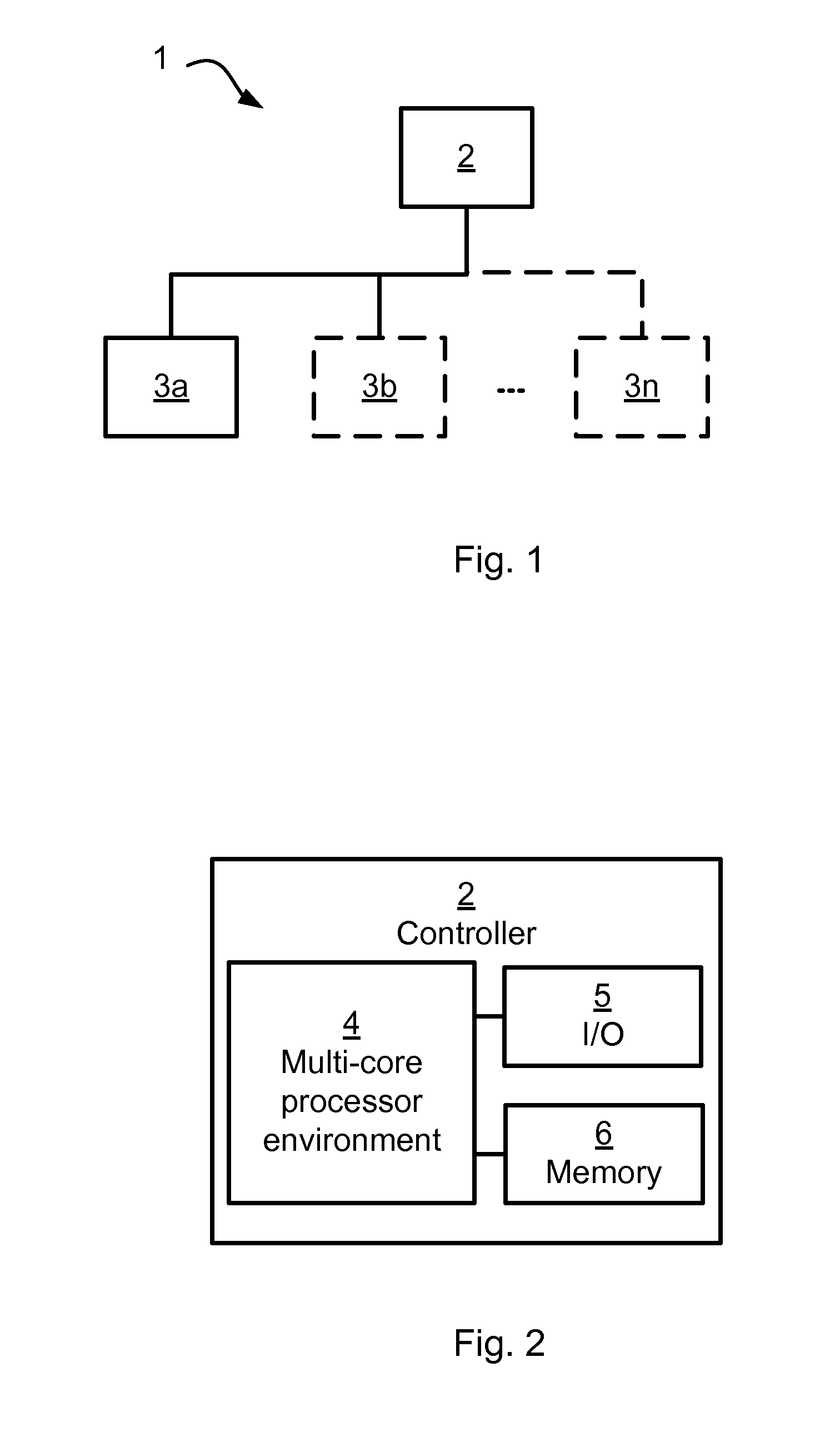
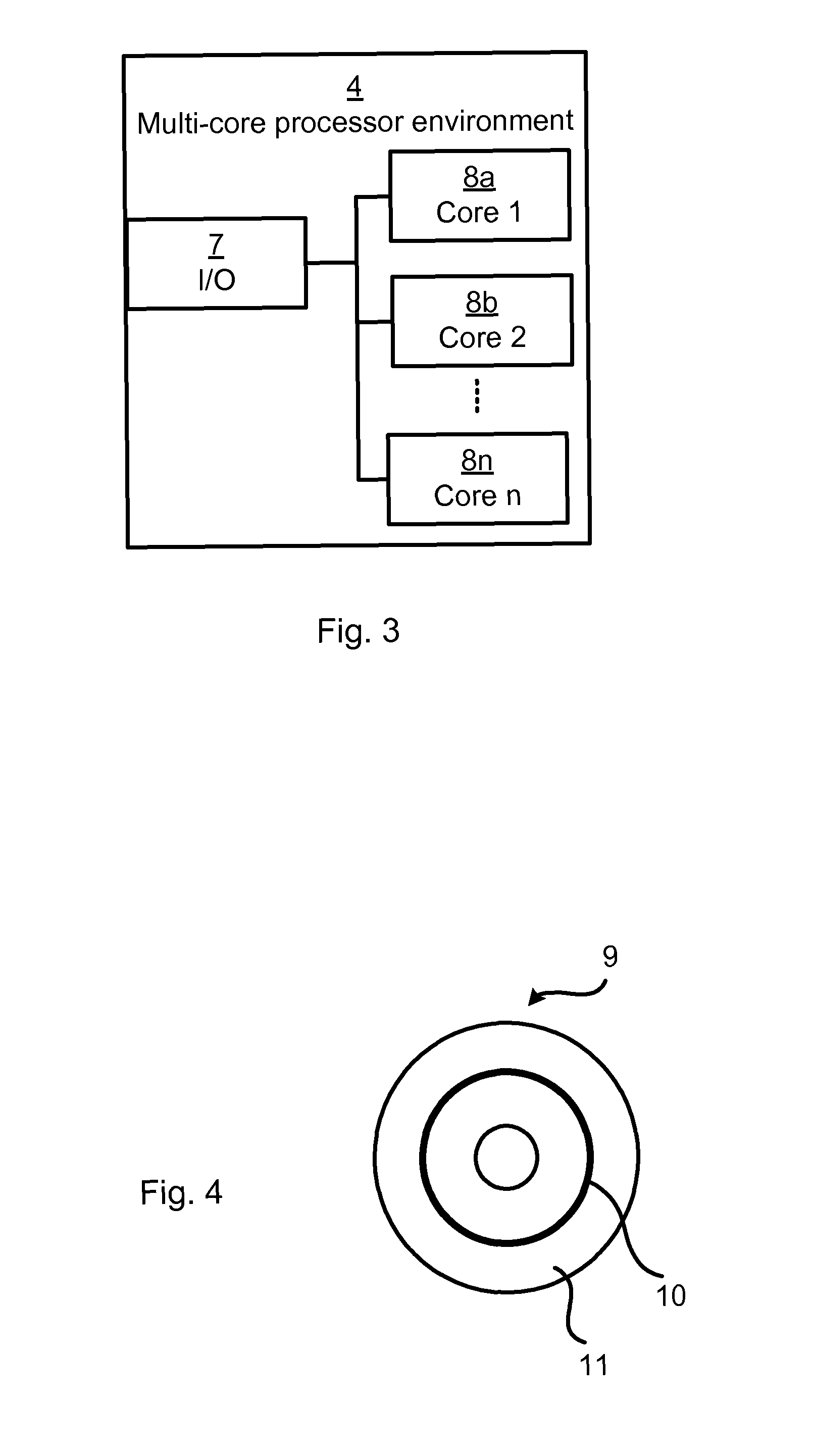
Multicore Processor Fault Detection For Safety Critical Software Applications
ActiveUS20160117210A1Increase considerationReduce impactFault responseControl systemMulti-core processor
A method for multicore processor fault detection during execution of safety critical software applications in a multicore processor environment involves dedicating the complete resources of at least a part of at least one processor core to execution of diagnostics software application whilst dedicating remaining resources to execution of a safety-critical software application, thereby enabling parallel execution of the diagnostics software application and the safety-critical software application. There is also provided a controller for multicore processor fault detection during execution of safety critical software applications in a multicore processor environment. The controller includes a multicore processor environment. The controller may be part of a control system. The method may be provided as a computer program.
Owner:ABB (SCHWEIZ) AG
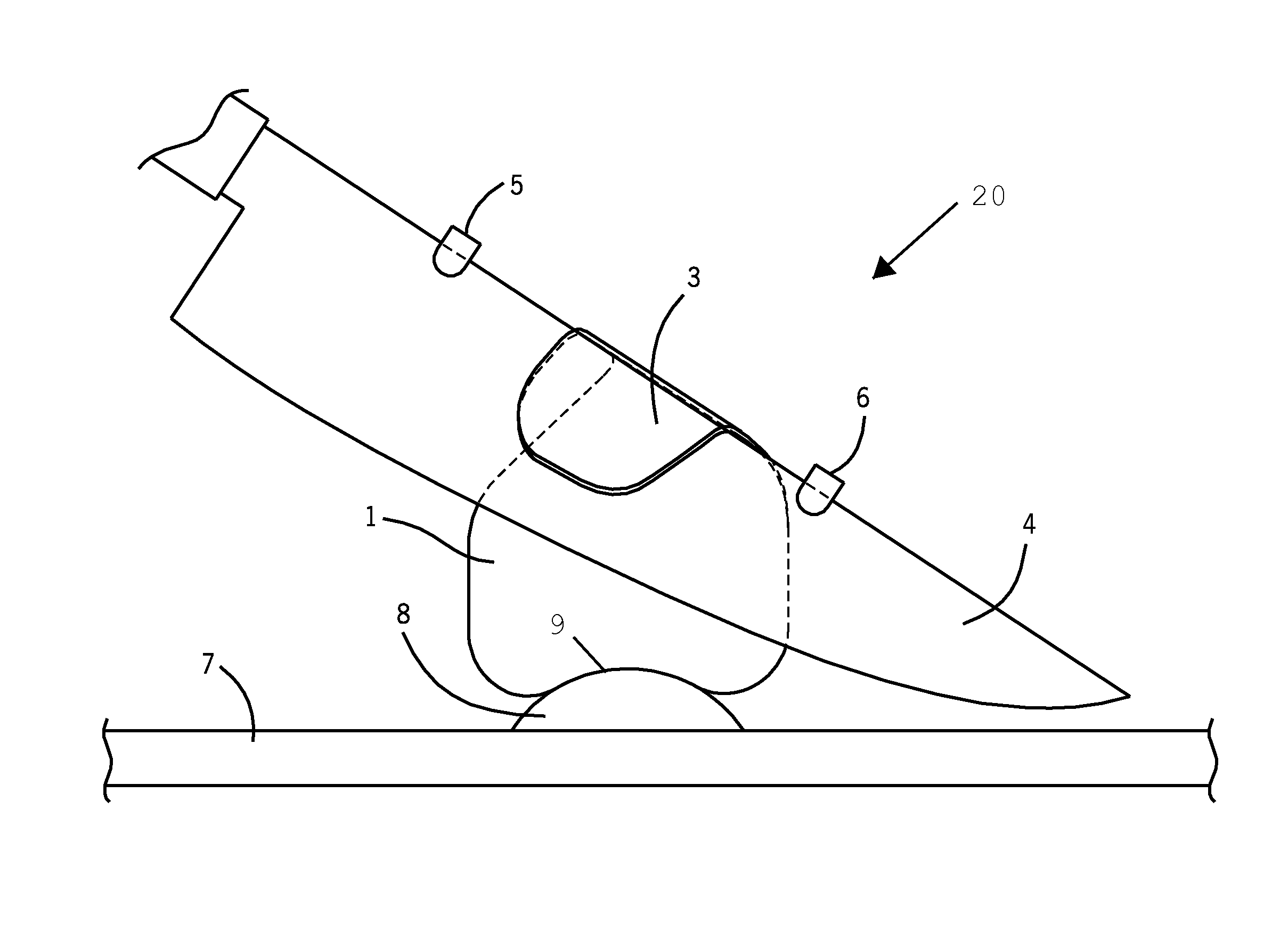
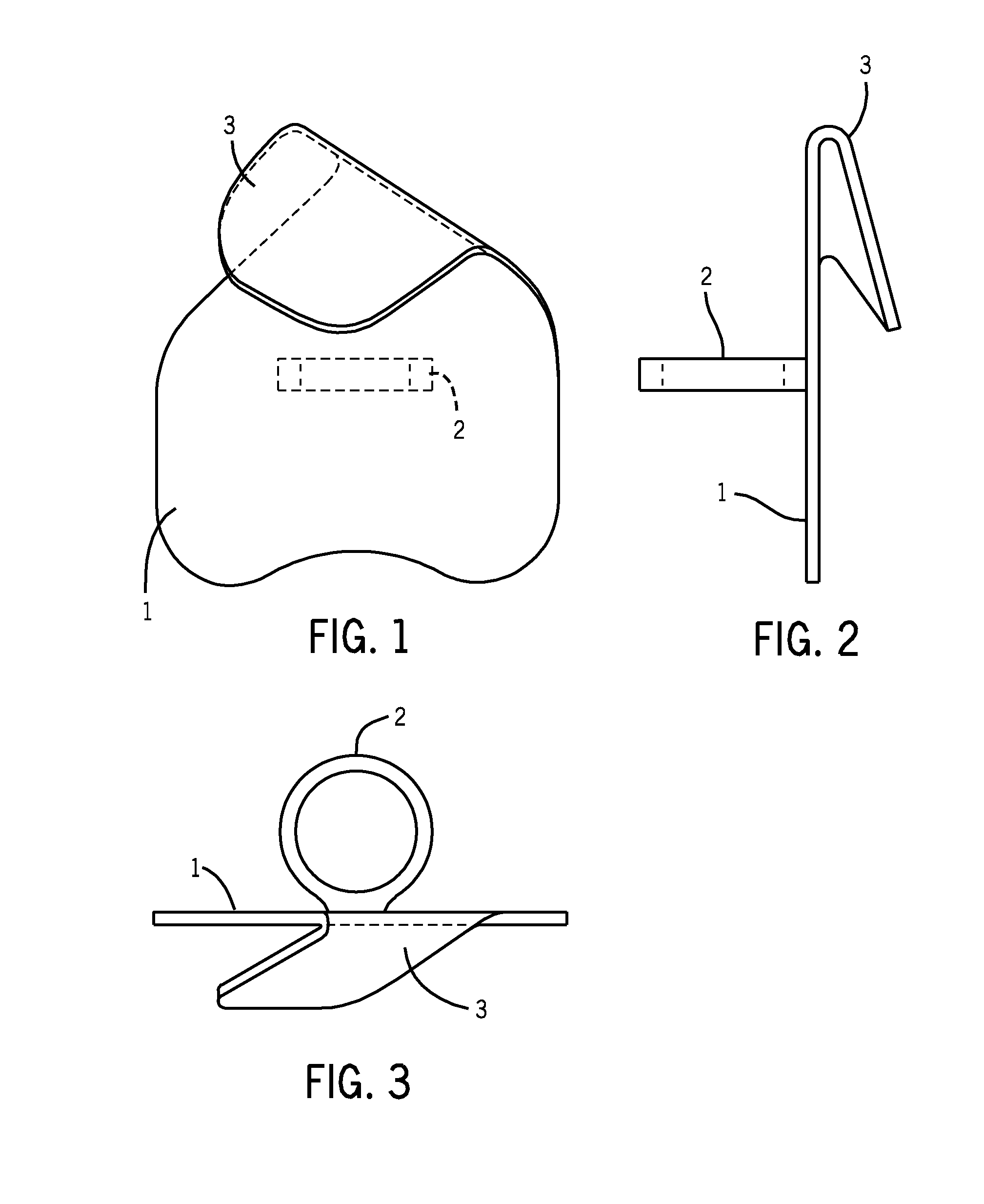
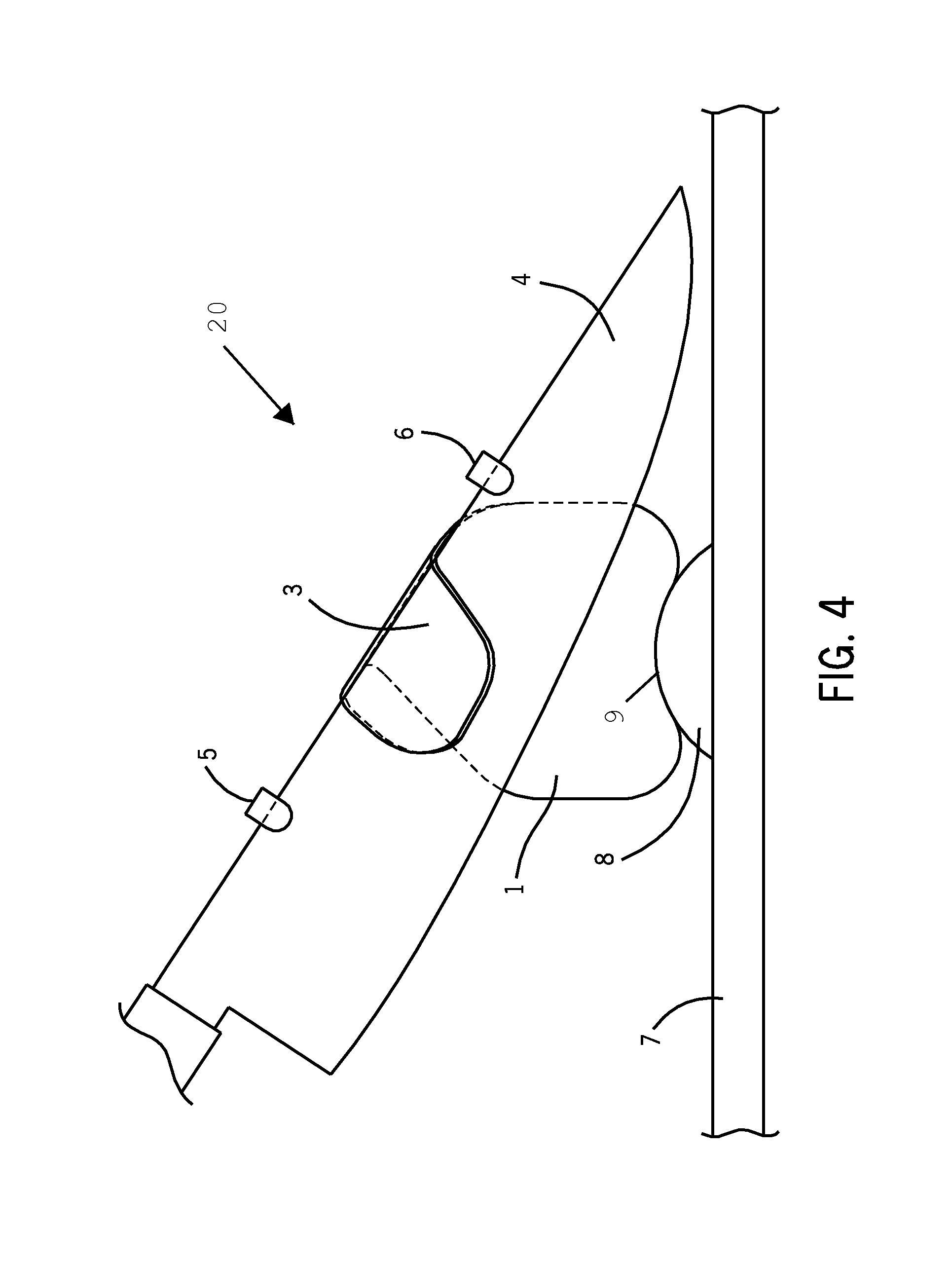
Method and system for training a user to correctly use a knife
ActiveUS8931381B2The process is simple and effectiveEnsure correct executionMetal working apparatusMetal-working hand toolsEngineering
A method of slicing food comprises providing a cutting board, knife, food product, and a food slicing system comprising a finger guard comprising a substantially flat surface having a bottom contoured edge, a finger ring connected to a first side of the finger guard, and a knife guide attached to the finger guard at a substantially straight edge, the knife guide having an area smaller than an area of the finger guard and angled relative to the finger guard by an angle between approximately 0 and 15 degrees, the substantially straight edge having a length of at least approximately one inch and angled relative to the cutting board by an angle between approximately 15 and 60 degrees when the bottom contoured edge rests against the cutting board.
Owner:PORAN DAVID ALAN
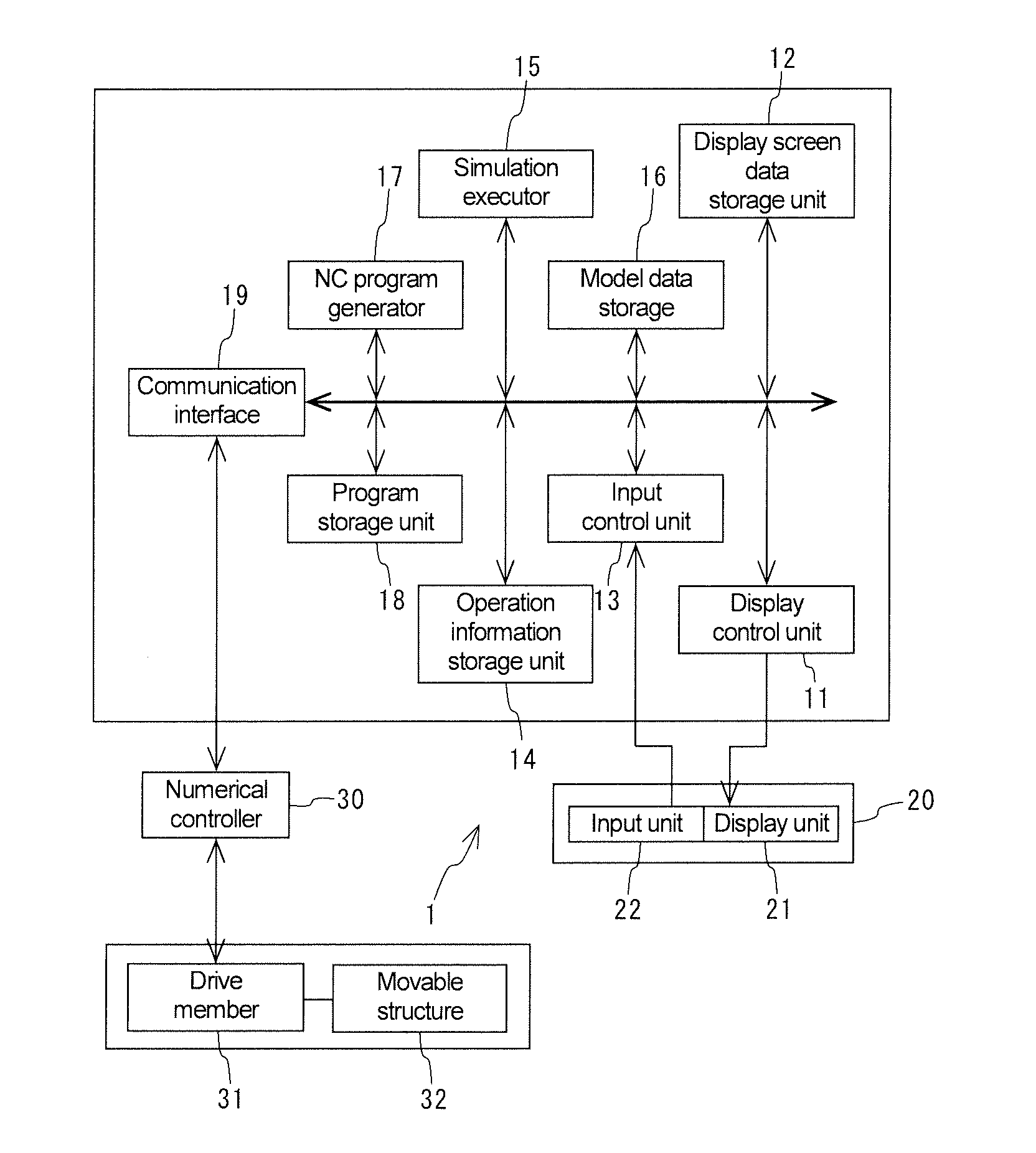
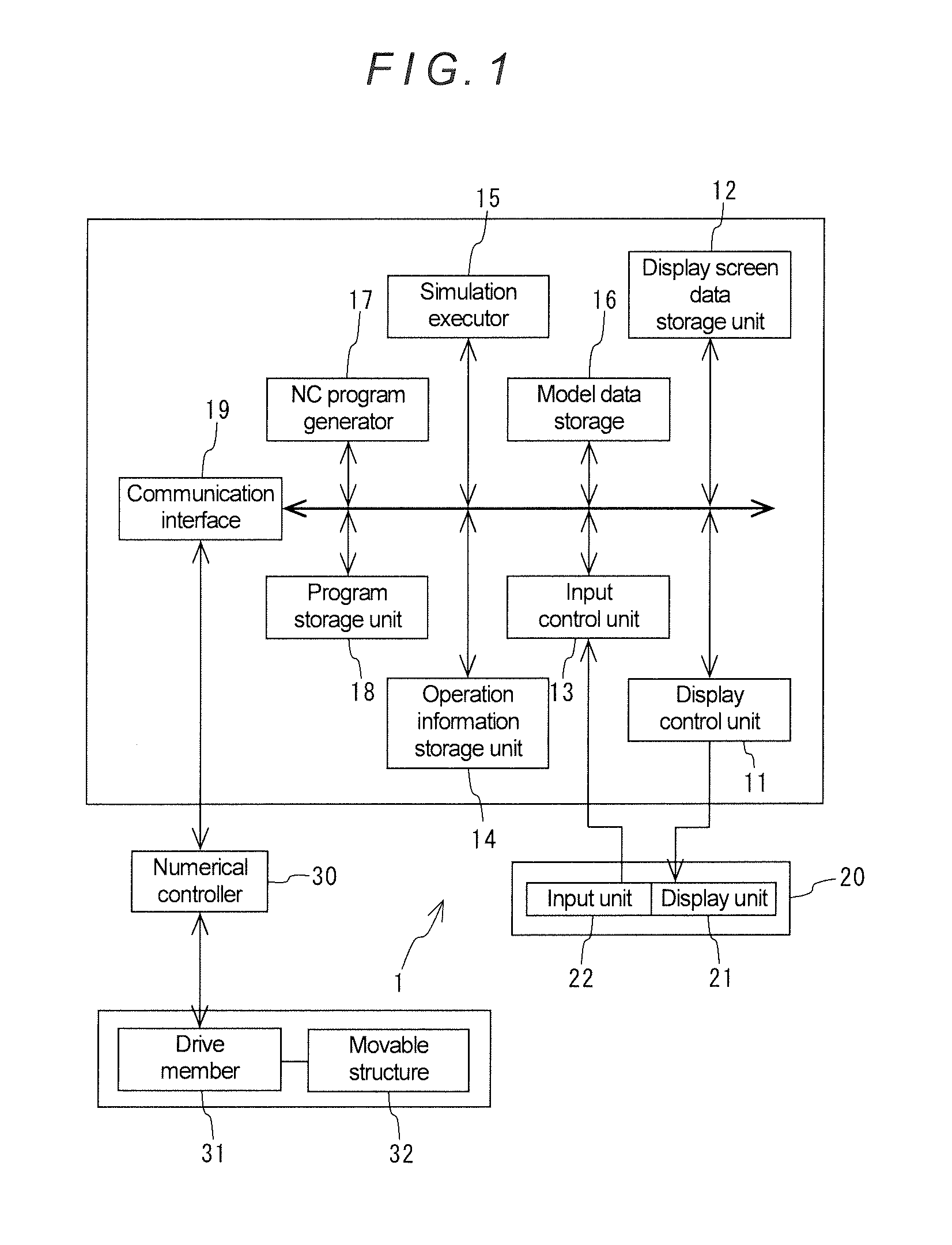
Simulation Apparatus for Manual Operation of Machine Tool
ActiveUS20150268661A1Easy to identifyEnsuring Safe ExecutionComputer controlSimulator controlInput controlMachine tool
A simulation apparatus 1 includes a touch panel 20, a display controller 11, a display screen data storage unit 12, an input control unit 13, an operation information storage unit 14, a model data storage 16, a simulation executor 15 and an NC program generator 17. The simulation executor 15 displays an image of a movable structure 12 to be operated on the touch panel 20, moves the image in accordance with a manual operation and checks occurrence of interference, and, in the case where interference occurs, stops the movement of the image and displays the occurrence of interference on the touch panel 20. Further, in the case where it is confirmed that no interference occurs, the NC program generator 17 generates an NC program based on manual operation information.
Owner:DMG MORI CO LTD
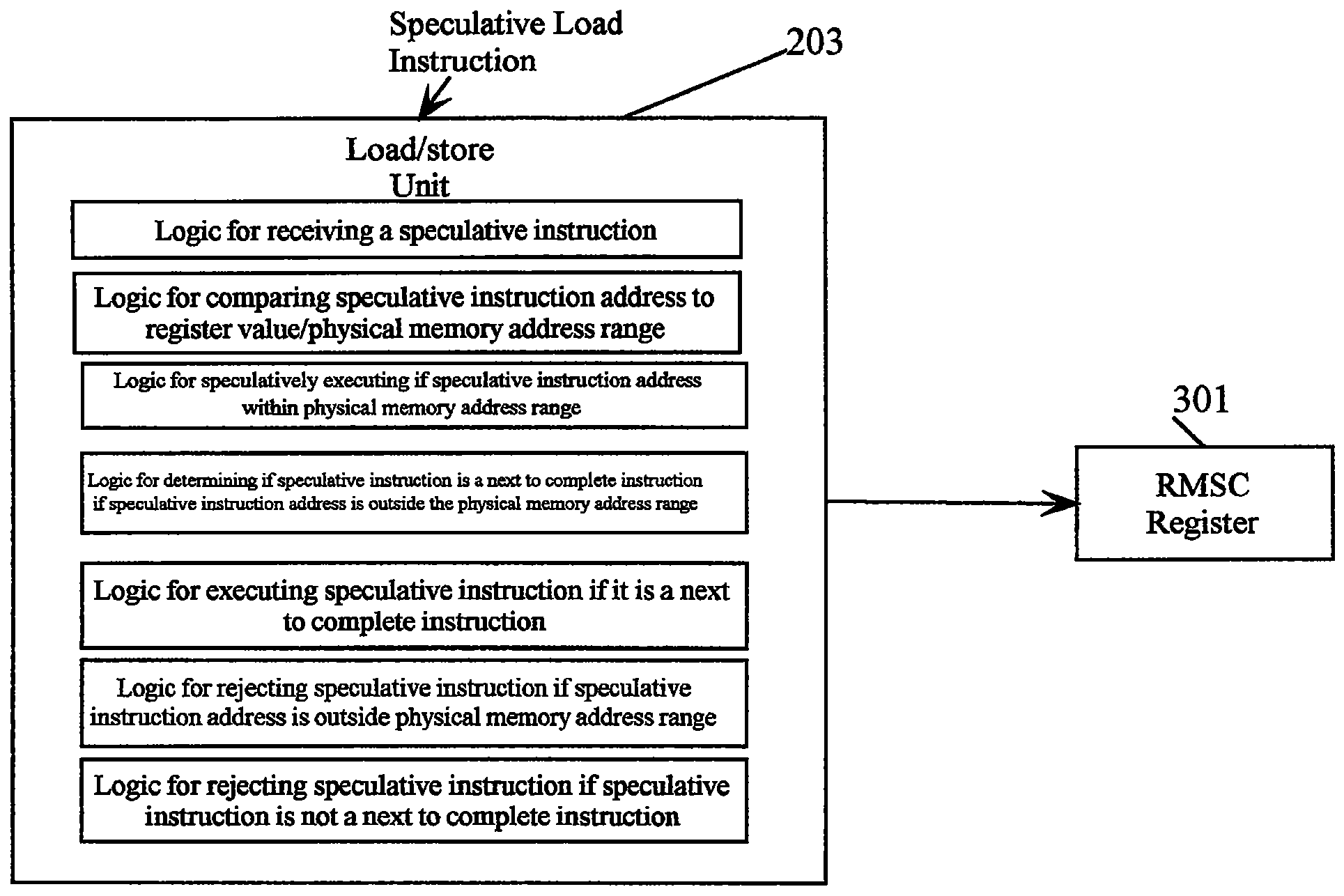
Mechanism for avoiding check stops in speculative accesses while operating in real mode
InactiveUS7370177B2Ensuring Safe ExecutionError detection/correctionDigital computer detailsLoad instructionProcessor register
A method and processor for avoiding check stops in speculative accesses. An execution unit, e.g., load / store unit, may be coupled to a queue configured to store instructions. A register, coupled to the execution unit, may be configured to store a value corresponding to an address in physical memory. When the processor is operating in real mode, the execution unit may retrieve the value stored in the register. Upon the execution unit receiving a speculative instruction, e.g., speculative load instruction, from the queue, a determination may be made as to whether the address of the speculative instruction is at or below the retrieved value. If the address of the speculative instruction is at or below this value, then the execution unit may safely speculatively execute this instruction while avoiding a check stop since all the addresses at or below this value are known to exist in physical memory.
Owner:IBM CORP
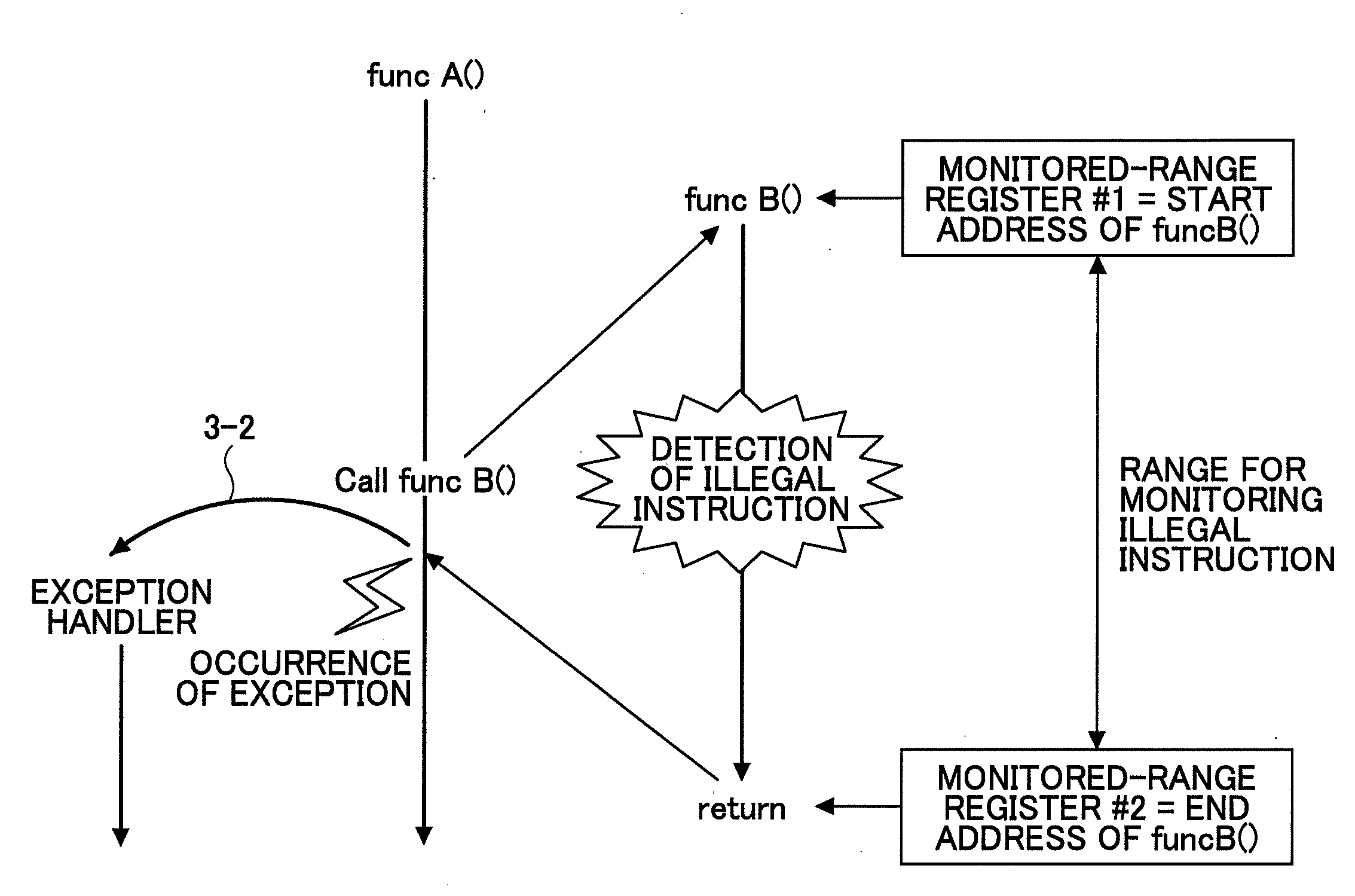
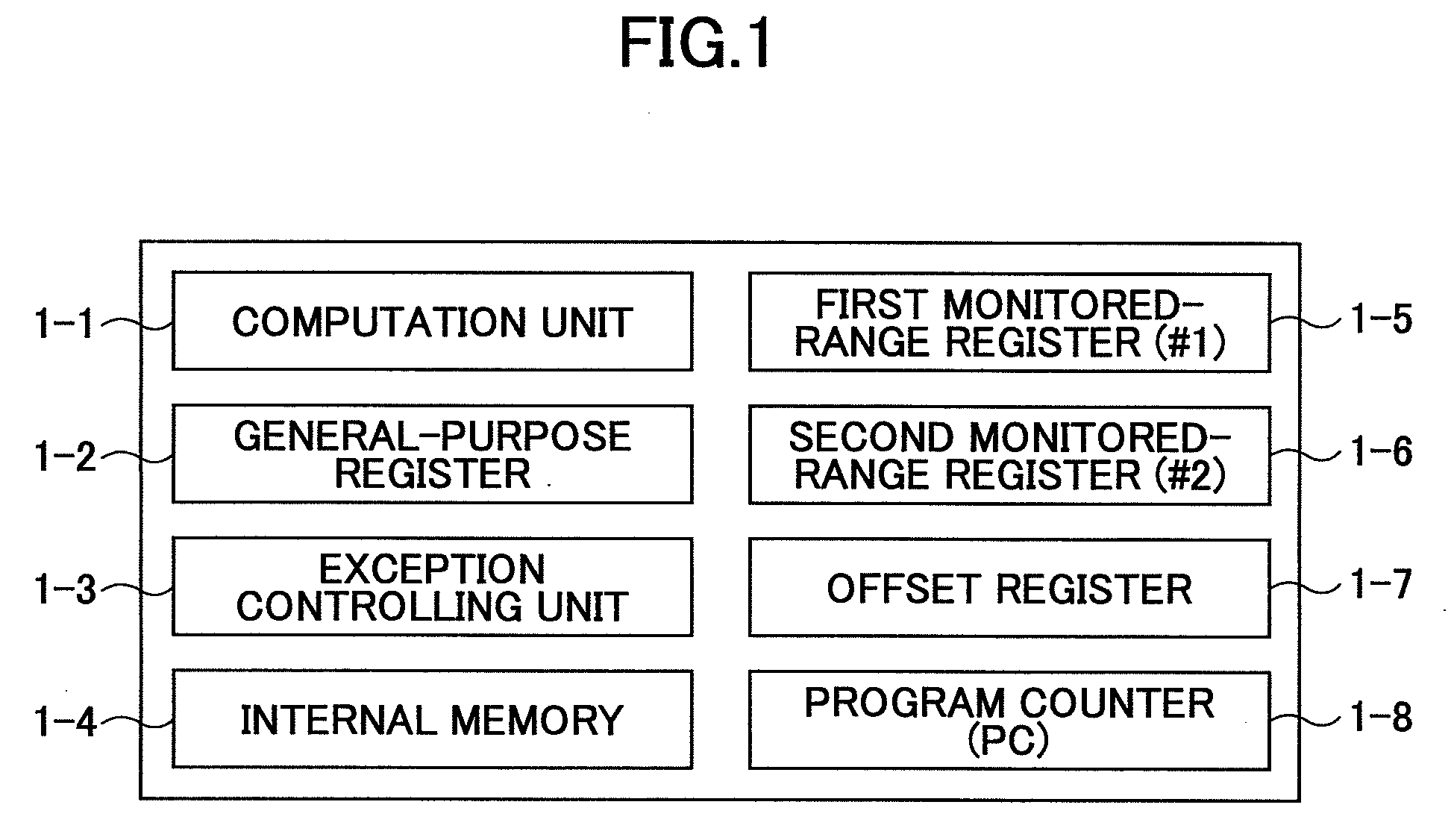
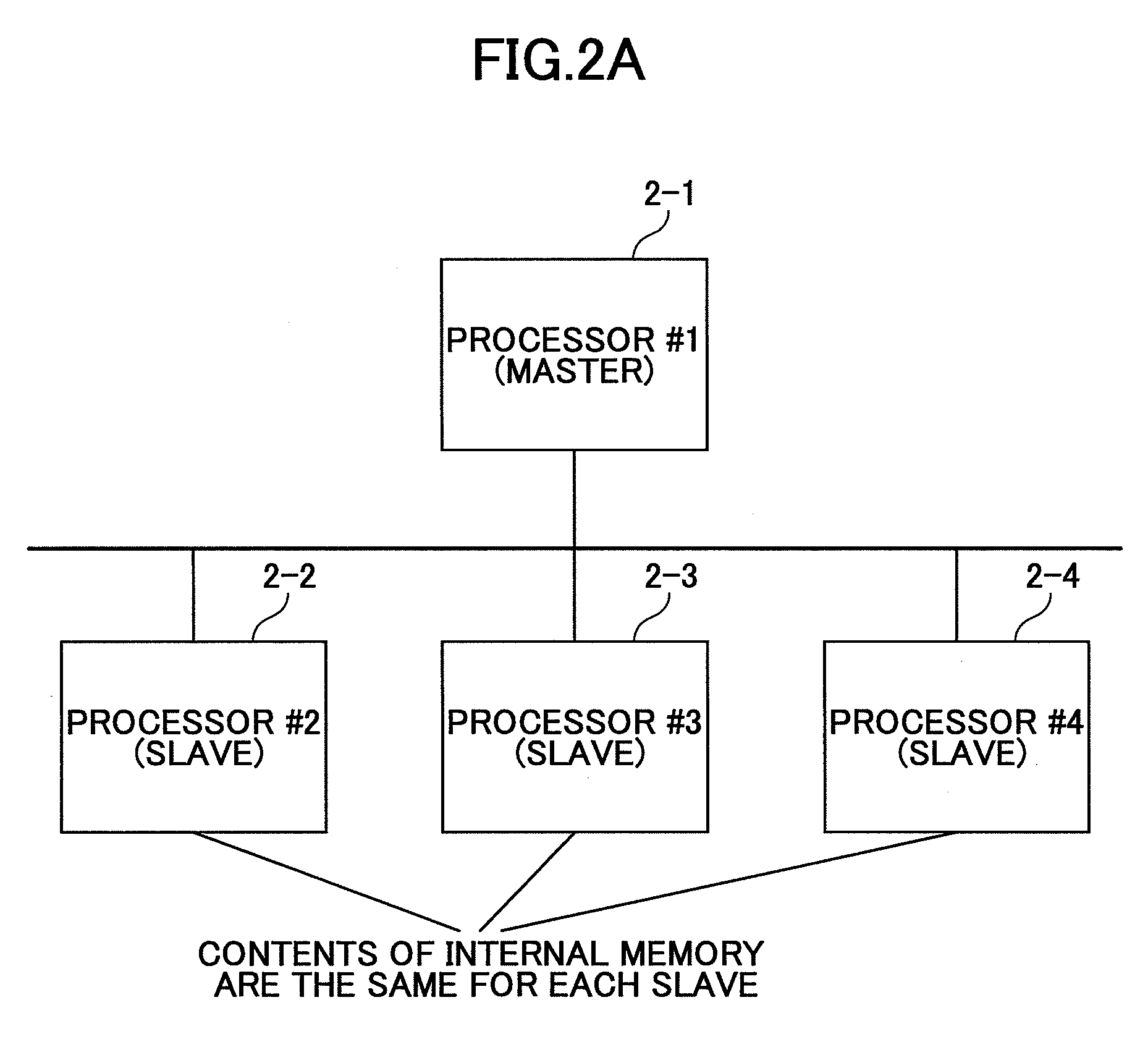
Multiprocessor system for continuing program execution upon detection of abnormality
InactiveUS20080148016A1Ensuring Safe ExecutionEnsure correct executionInstruction analysisDigital computer detailsInternal memoryProgram instruction
A multiprocessor system includes a plurality of processors, wherein instruction codes of a program executed by the processors are stored in an internal memory of each of the processors, wherein one of the processors includes a program counter configured to indicate an address of a program instruction being executed in the internal memory and an offset register configured to store a predetermined offset value, and wherein upon detecting abnormality due to execution of an illegal instruction code fetched from the internal memory of the one of the processor, the one of the processor fetches an instruction code for execution from the internal memory of another one of the processors based on an address that is obtained by adding the offset value stored in the offset register to the address of a program instruction being executed stored in the program counter.
Owner:FUJITSU LTD
Computer network virus protection system and method
InactiveUS7913078B1Detection securityEnsuring Safe ExecutionMemory loss protectionError detection/correctionProtection systemElectronic mail
A network is protected from viruses through the use of a sacrificial server, which may be physical or virtual. Any executable programs or other suspicious parts of incoming e-mail messages are forwarded to a sacrificial server, where they are converted to non-executable format such as Adobe Acrobat PDF and sent to the recipient. The sacrificial server is then checked for virus activity. After the execution is completed, the sacrificial server is rebooted.
Owner:INTELLECTUAL VENTURES I LLC
Federated System for Monitoring Physical Assets
ActiveUS20070120673A1Limit processor cycles available to agent threadsPrevent malicious code from harming native dataLogisticsCommerceVisibilityReal-time computing
A system federates heterogeneous monitoring systems to provide end-to-end monitoring information for conveyances with item-layer visibility. A first node of the federated system comprises a first monitoring system and a first port and a second node comprises a second monitoring system and a second port. In parallel with a conveyance being transported between the first node and the second node, the first monitoring system sends an agent to the second monitoring system. The agent comprises logic and / or data necessary to implement processes on the second monitoring agent while the conveyance is at the second port. When the conveyance arrives at the second port, the second monitoring system executes the agent to determine conditions of the conveyance and / or its contents.
Owner:SAVI TECH INC
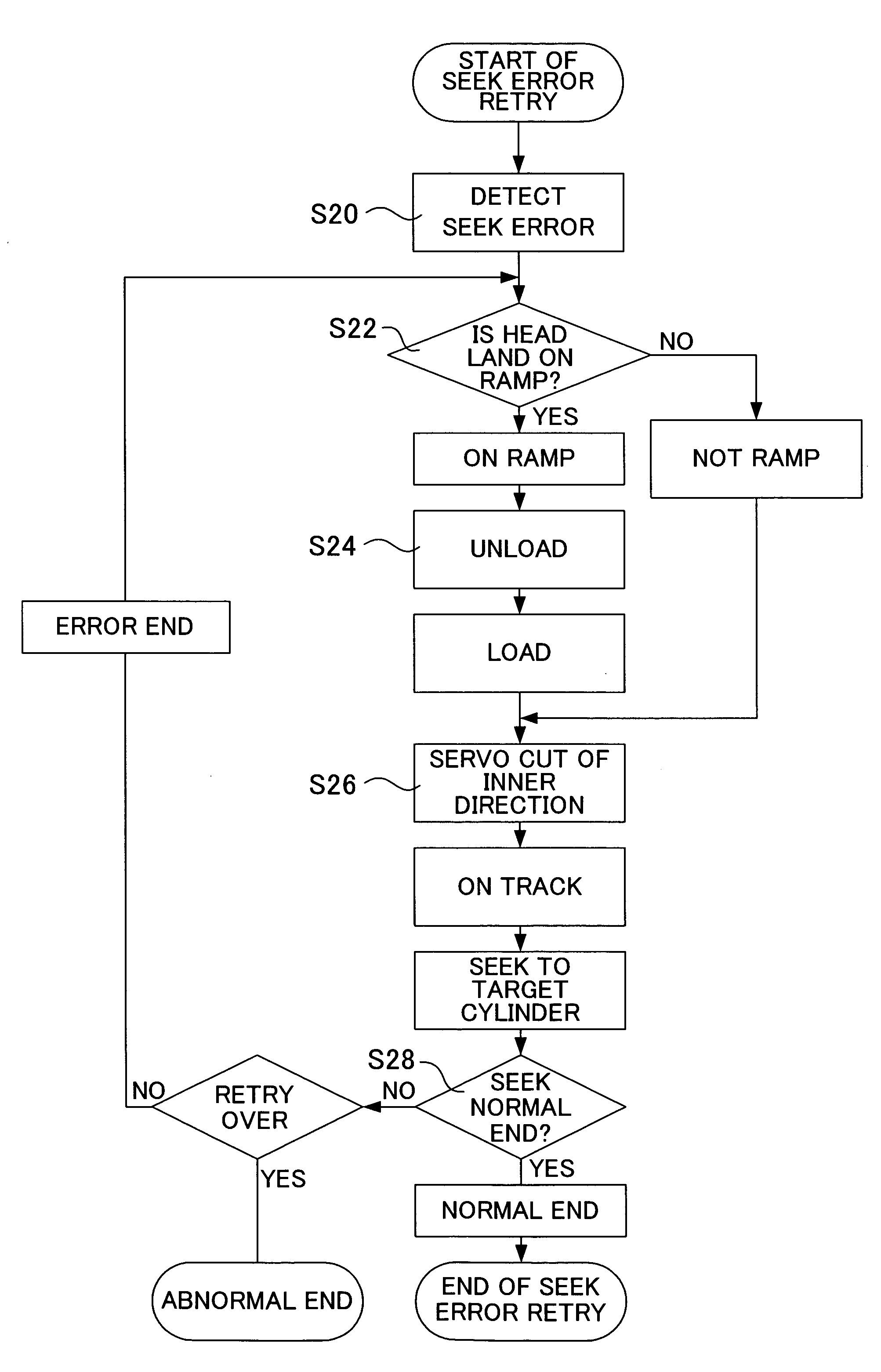
Seek error retry method of a disk device and disk device
ActiveUS7113363B2Safely executedPrevent crashTrack finding/aligningRecord information storageComputer hardware
Owner:KK TOSHIBA
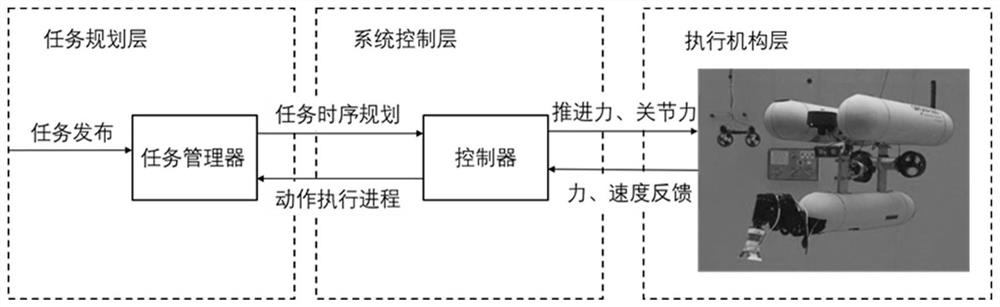
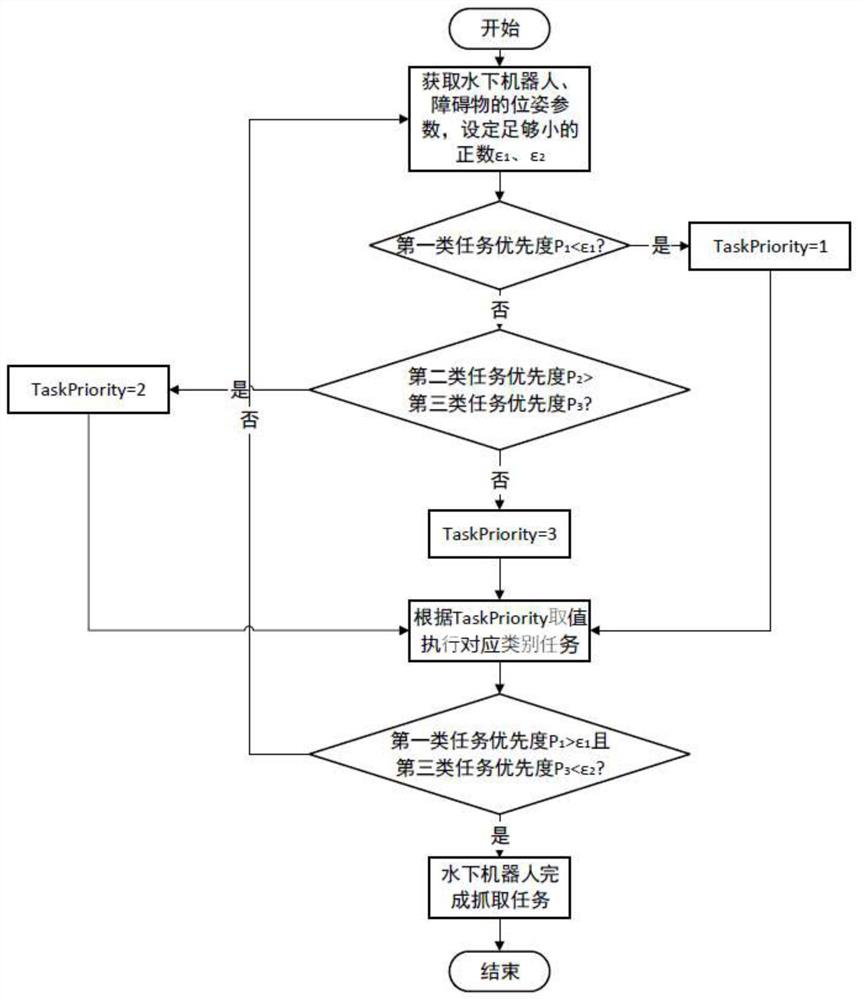
Underwater unmanned ship-double mechanical arm cooperative control method based on task grading time sequence optimization
ActiveCN112068576AReduce the difficulty of underwater operation controlImprove coordinationAltitude or depth controlControl engineeringManipulator
The invention discloses an underwater operation-oriented underwater unmanned ship-double mechanical arm cooperative motion planning method and an application thereof. According to the invention, underwater double-mechanical-arm control is combined with a planning method based on task grading time sequence optimization, actions needing to be executed by the underwater robot are subdivided into a plurality of tasks, and the execution sequence is reasonably optimized and divided so that dynamic disturbance caused by mechanical arm movement to the underwater unmanned ship is reduced, and the underwater unmanned ship can run more stably. According to the control method, tasks of keeping a hovering height of the unmanned ship and avoiding obstacles are set to be high in priority, and the safetyof equipment is guaranteed as much as possible. A problem that an underwater unmanned ship-double arm manipulator is difficult to control is solved, purposes that the underwater double-arm manipulatoroperates autonomously and safely and an overall operation platform composed of the underwater unmanned ship-double arm manipulator operates stably in pose are achieved, and safe and stable platform technical support is created for improving a underwater operation capacity.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for Validating an Untrusted Native Code Module
ActiveUS20140359765A1Facilitates safely executingWithout significant risk of unwanted side effectMemory loss protectionError detection/correctionCode moduleControl flow
A system that validates a native code module. During operation, the system receives a native code module comprised of untrusted native program code. The system validates the native code module by: (1) determining that code in the native code module does not include any restricted instructions and / or does not access restricted features of a computing device; and (2) determining that the instructions in the native code module are aligned along byte boundaries such that a specified set of byte boundaries always contain a valid instruction and control flow instructions have valid targets. The system allows successfully-validated native code modules to execute, and rejects native code modules that fail validation. By validating the native code module, the system facilitates safely executing the native code module in the secure runtime environment on the computing device, thereby achieving native code performance for untrusted program binaries without significant risk of unwanted side effects.
Owner:GOOGLE LLC
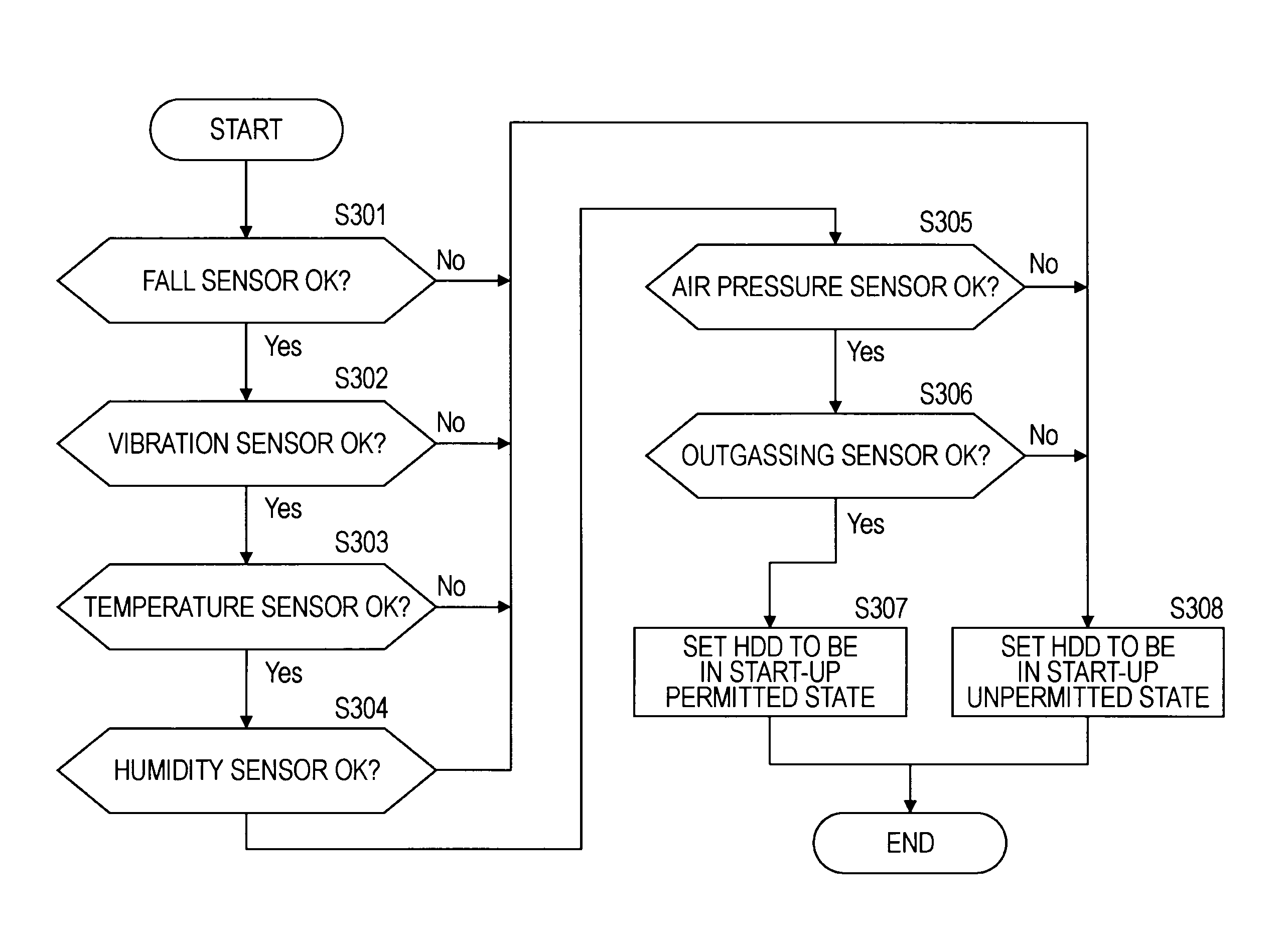
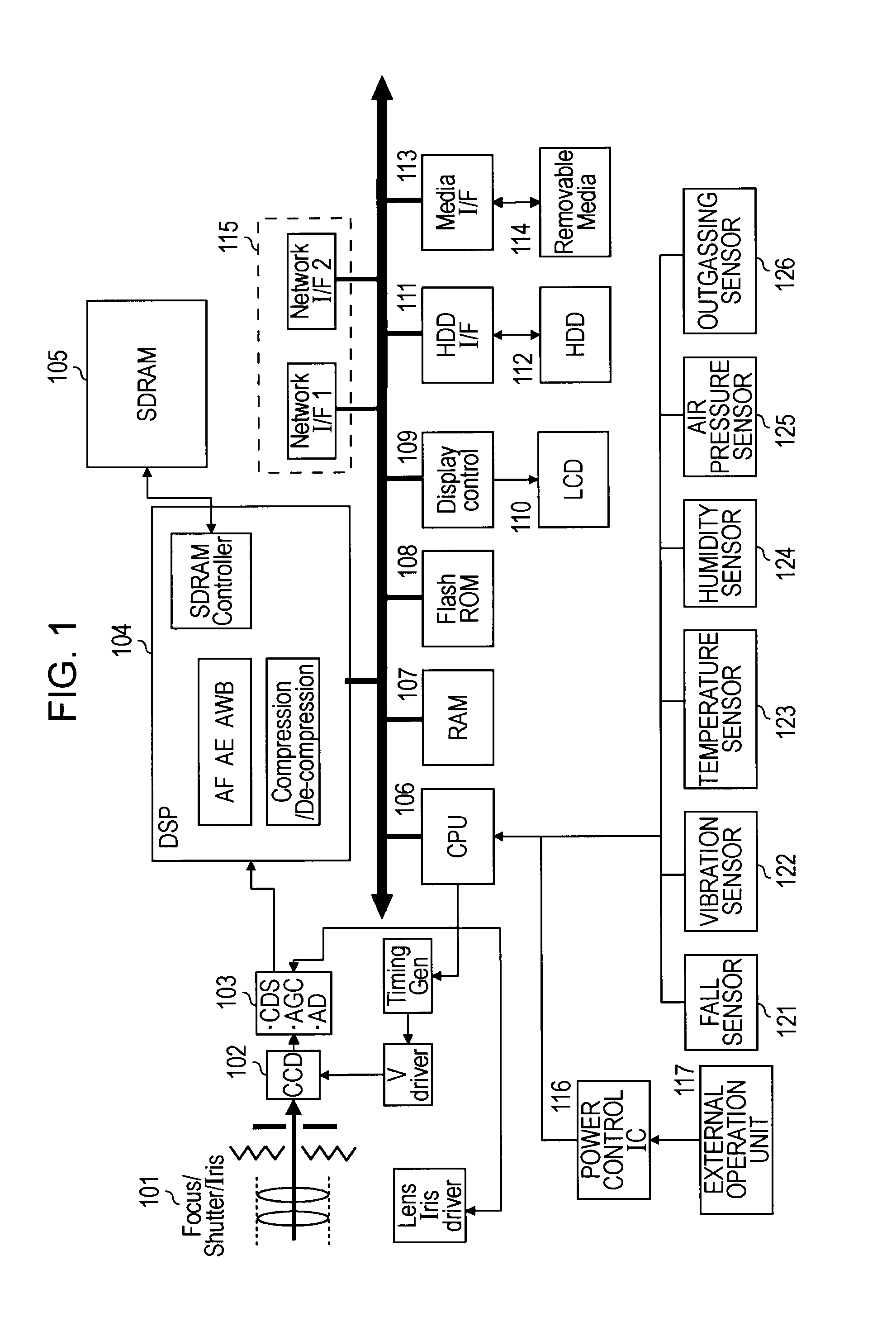
Information processing apparatus, image pick-up device, information processing method and computer program
InactiveUS20100165146A1Ensuring Safe ExecutionAvoid lostTelevision system detailsRecord information storageInformation processingHigh humidity
A structure is provided that prevents damage to an HDD and loss of recorded data by prohibiting the hard disk from being shifted to the active state in a state in which there is a problem with an environment. On the basis of detection information of each of sensors such as a fall sensor and a temperature sensor, it is determined whether or not data recording or a playback process utilizing the hard disk can be executed safely. The hard disk is caused to be shifted from being in a suspended state to being in an active state on condition that it is determined that safe data recording or playback is possible, and a data recording and playback process utilizing the hard disk is executed. By using this structure, the hard disk is prevented from being shifted to being in the active state in a state in which there is a problem with the environment, for example, in the case of falling, the case of high temperature or high humidity, or the like, and damage to the HDD and loss of recorded data can be prevented.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com