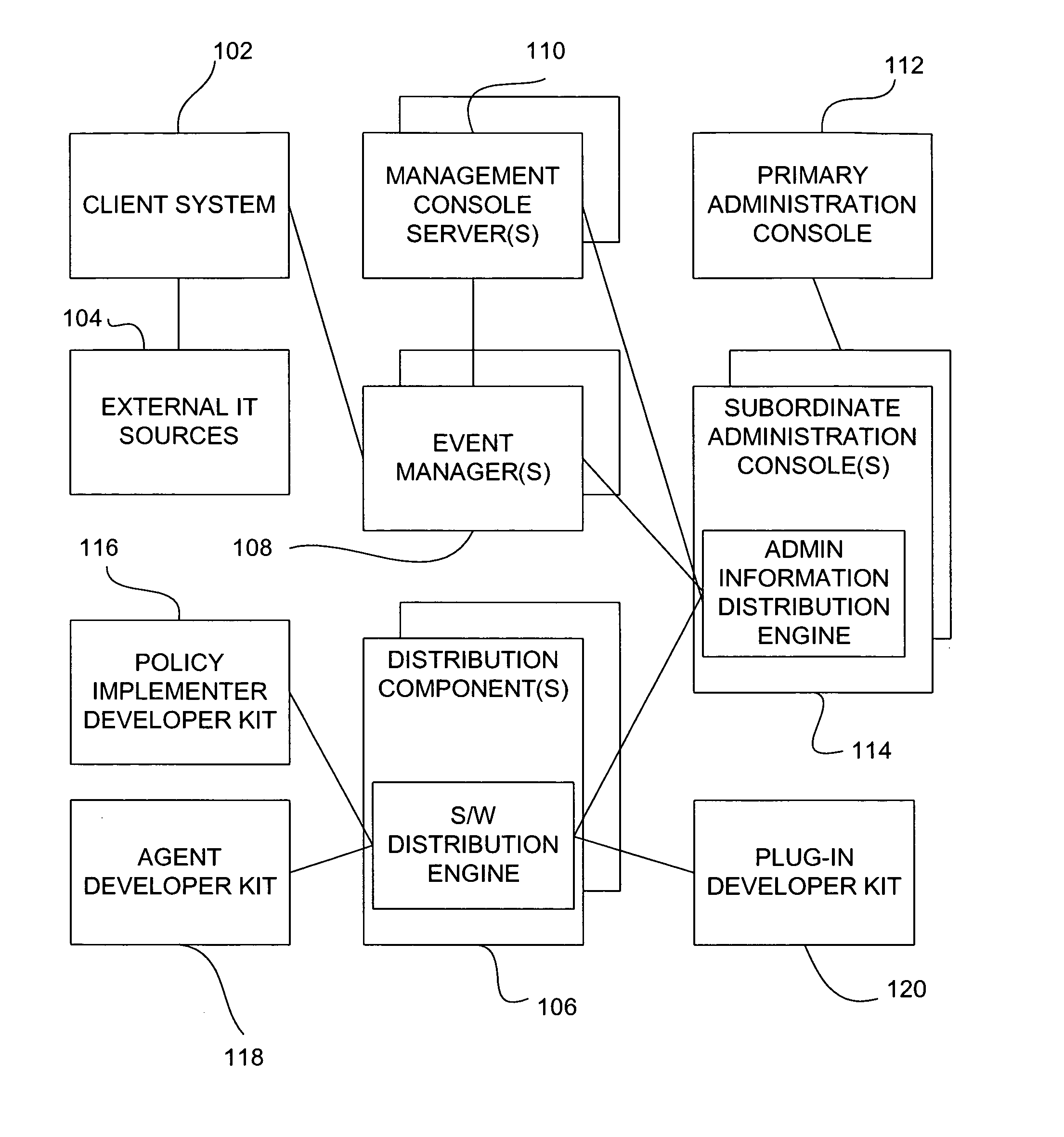
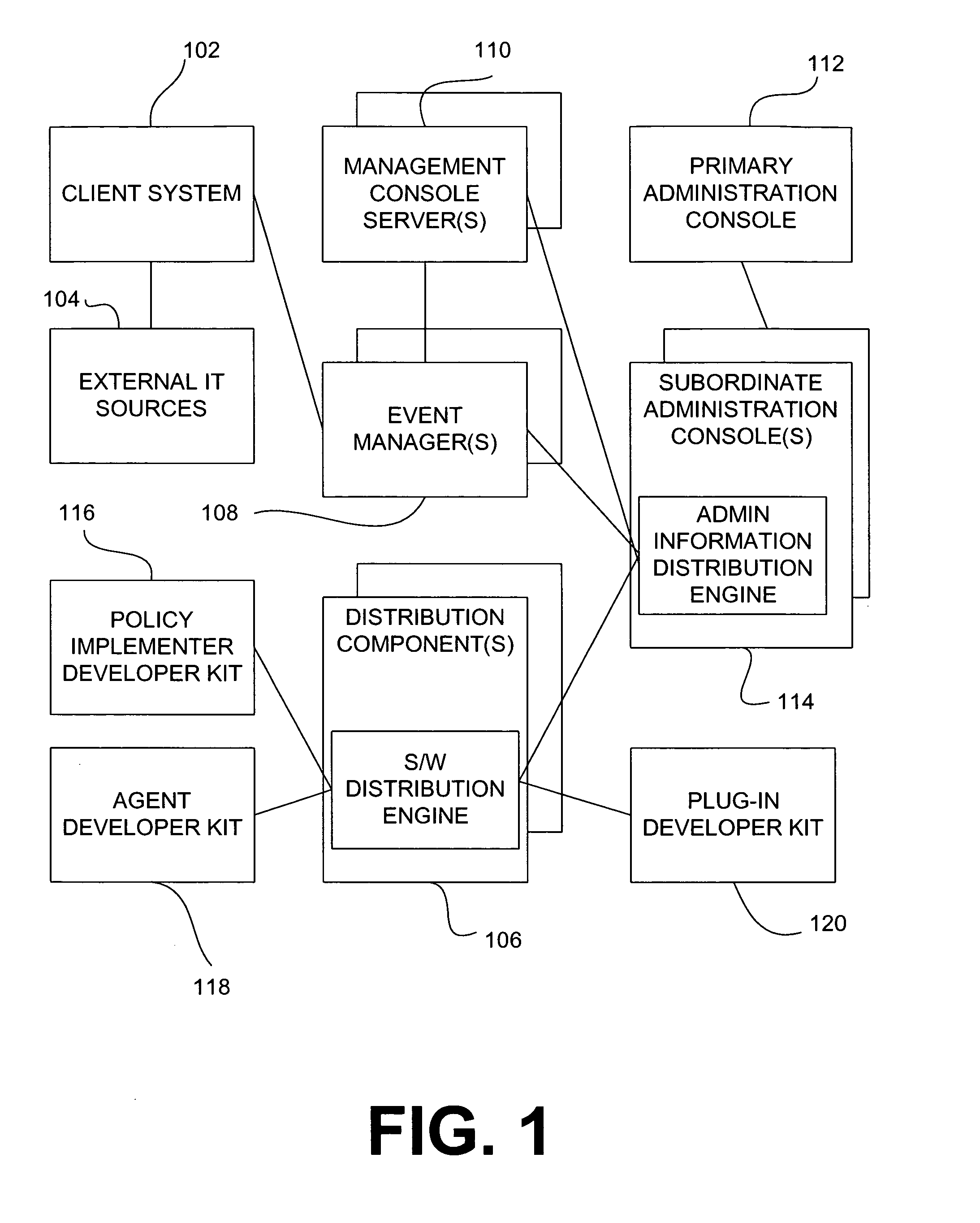
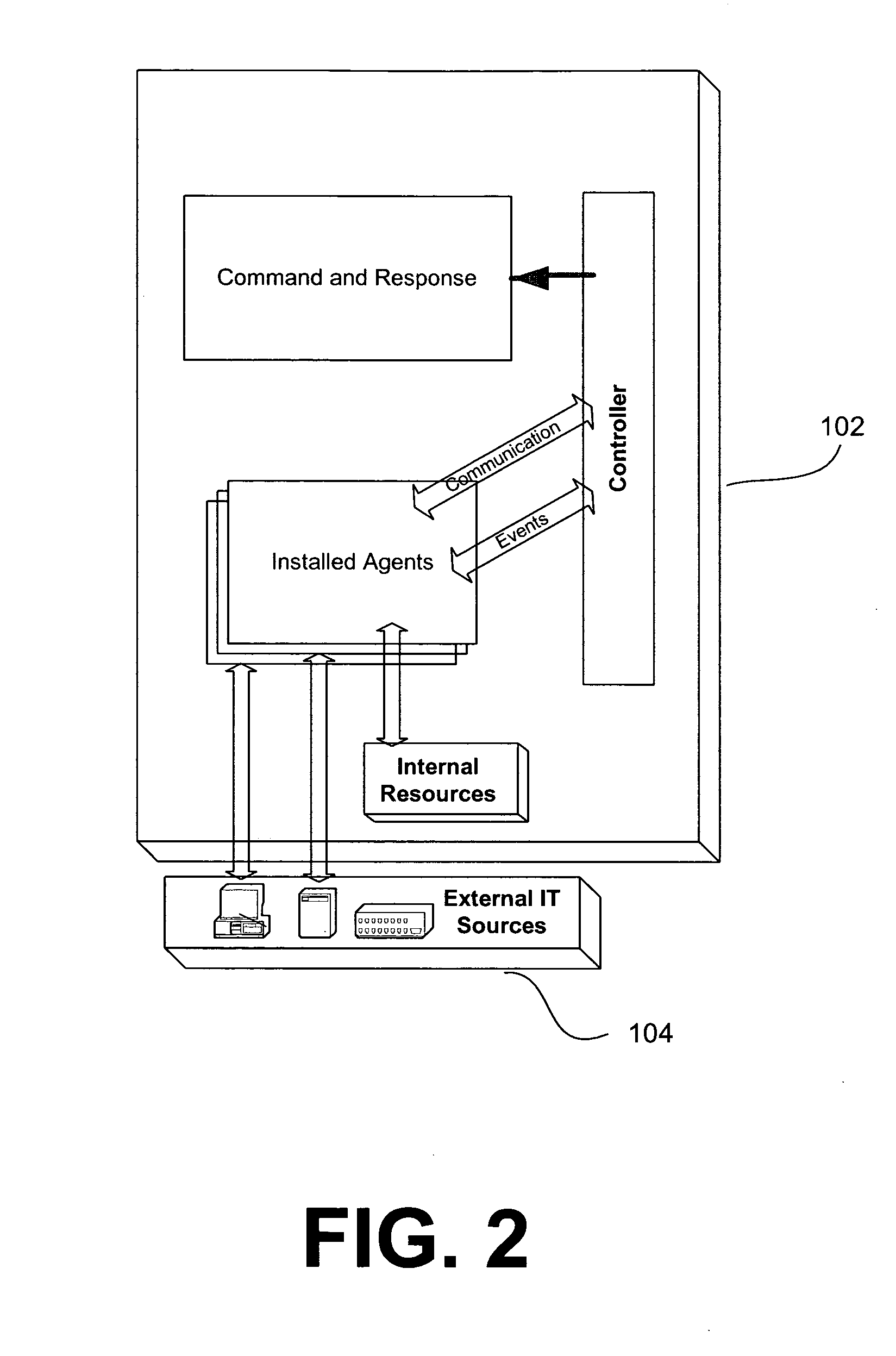
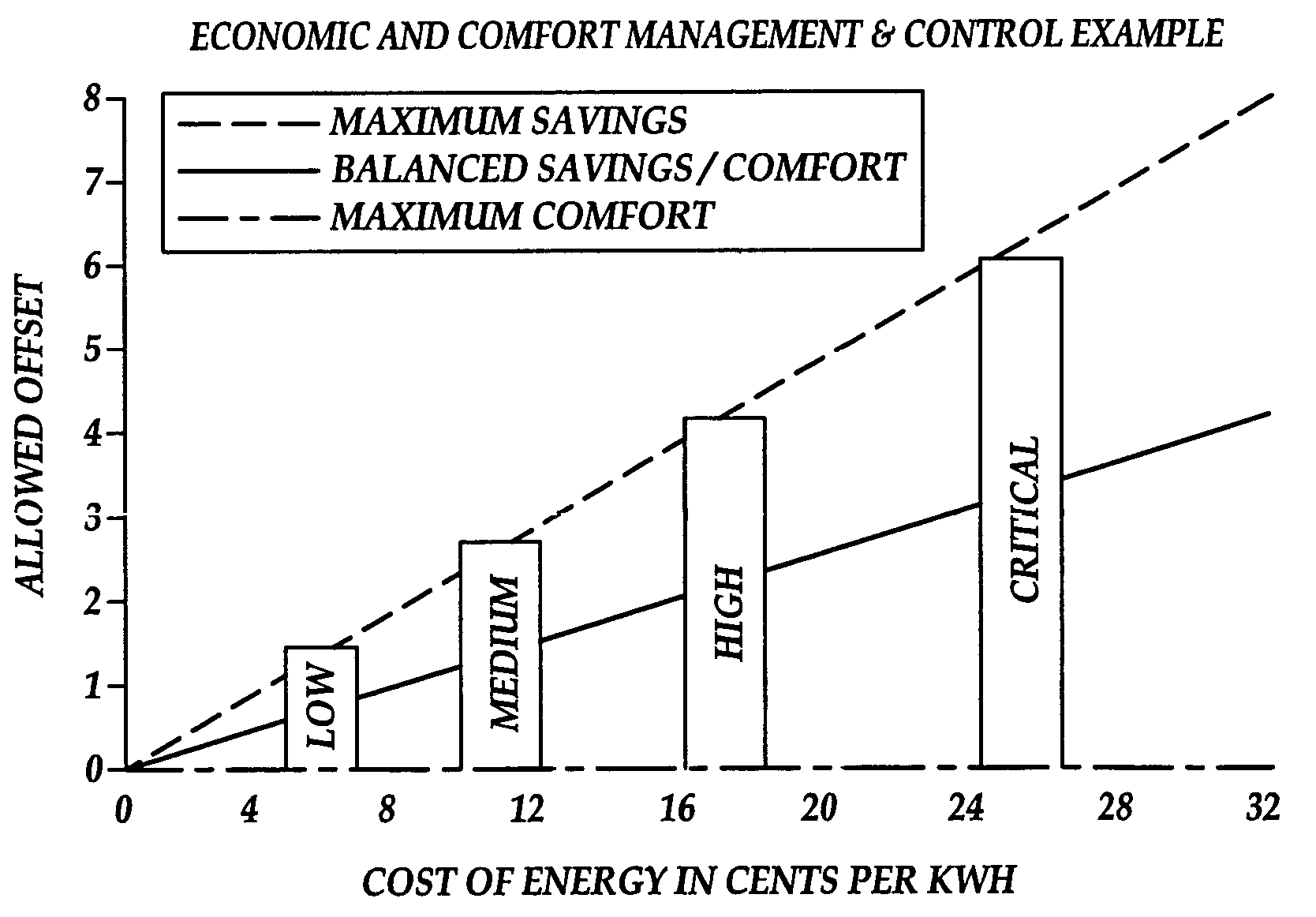
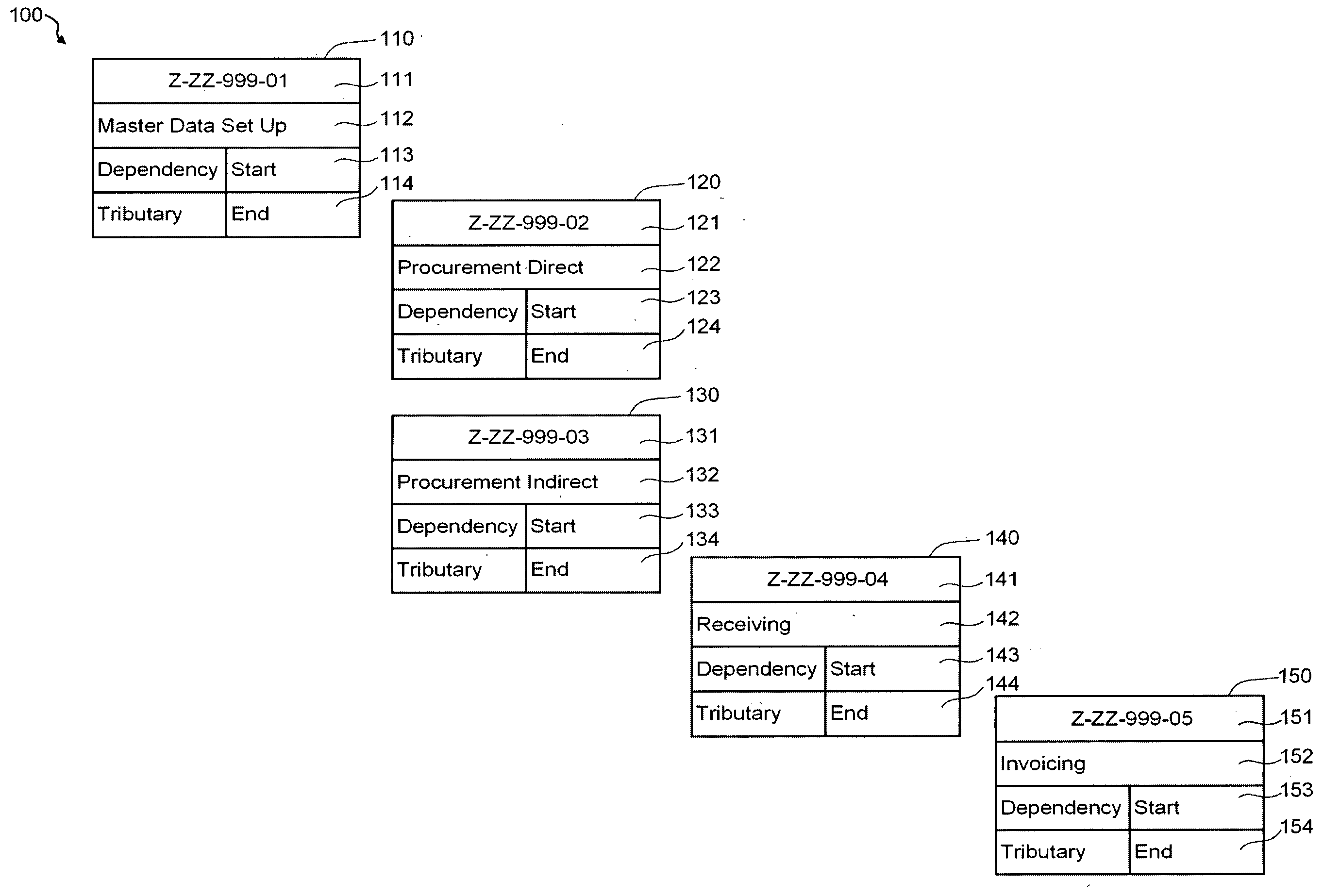
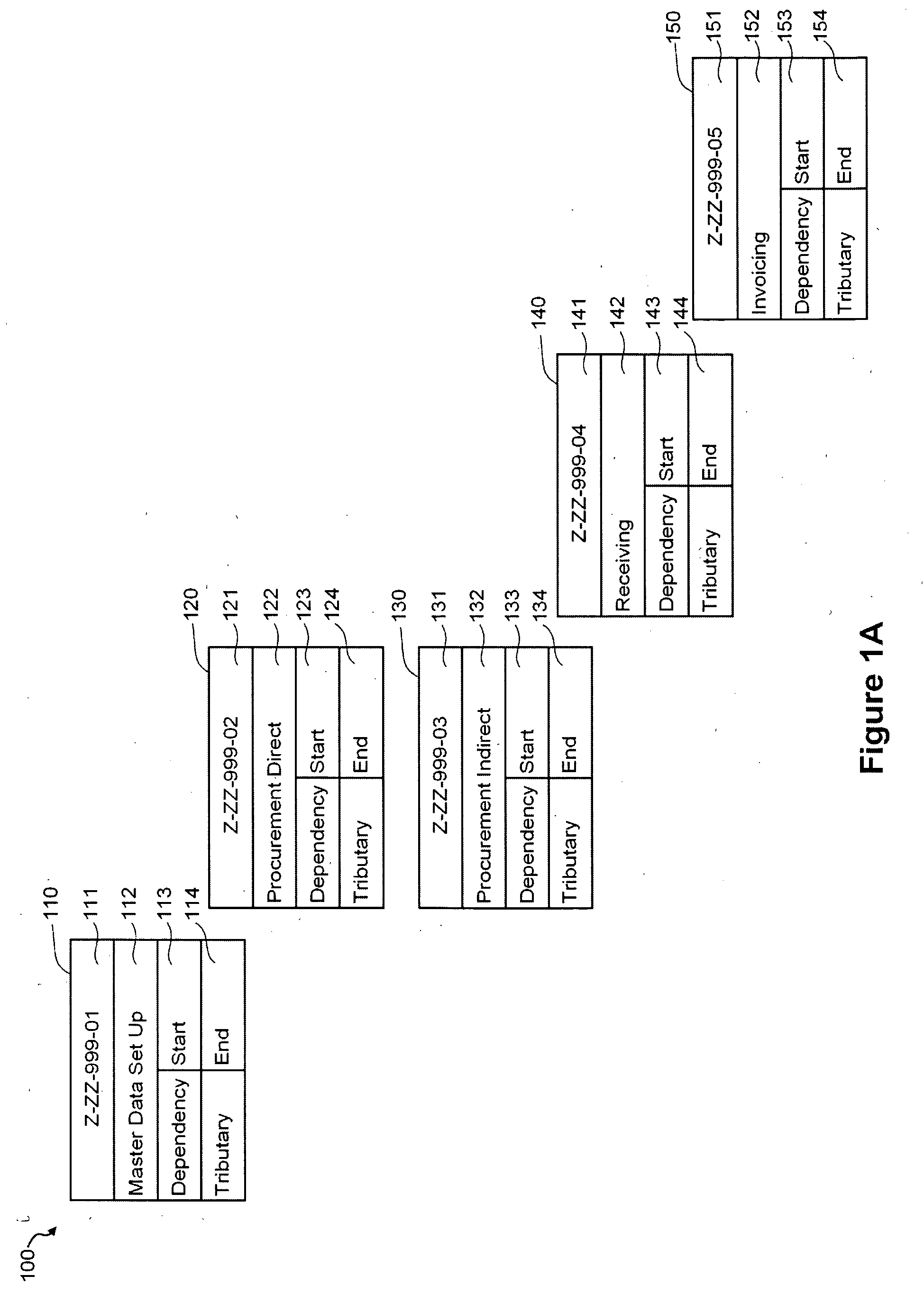
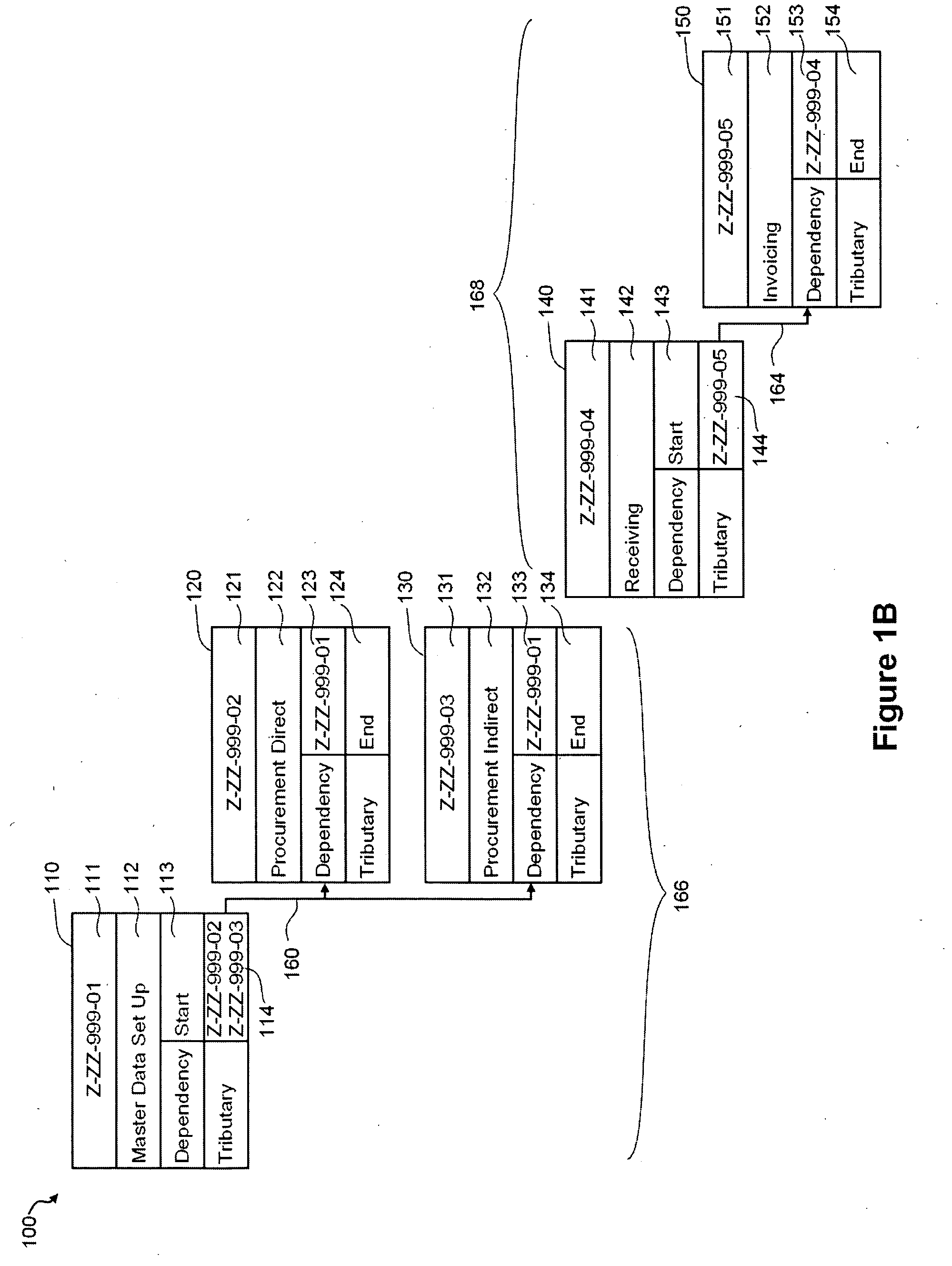
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
241546 results about "Reliability engineering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Reliability engineering is a sub-discipline of systems engineering that emphasizes dependability in the lifecycle management of a product. Reliability, describes the ability of a system or component to function under stated conditions for a specified period of time. Reliability is closely related to availability, which is typically described as the ability of a component or system to function at a specified moment or interval of time.
Method for utilizing temperature to determine a battery state
InactiveUS7348763B1Effective conditioningEfficiently determinedBatteries circuit arrangementsElectrical testingCharge and dischargeEmpirical data
A method for determining the state of a battery, or battery pack, that is independent of the type of battery technology under test. The method employs one or more charging and discharging cycles, and measures one or more parameters of battery voltage, temperature, charging time, and charging cycle counts to produce a test value that is compared to empirical data. Based on the comparison, the state is determined, for example, on a pass / fail basis. The method may be embodied as instructions stored in memory and implemented by means of a microprocessor coupled to the memory. In another embodiment, the empirical data is stored within another memory located internal to the battery pack under test.
Owner:LINVATEC
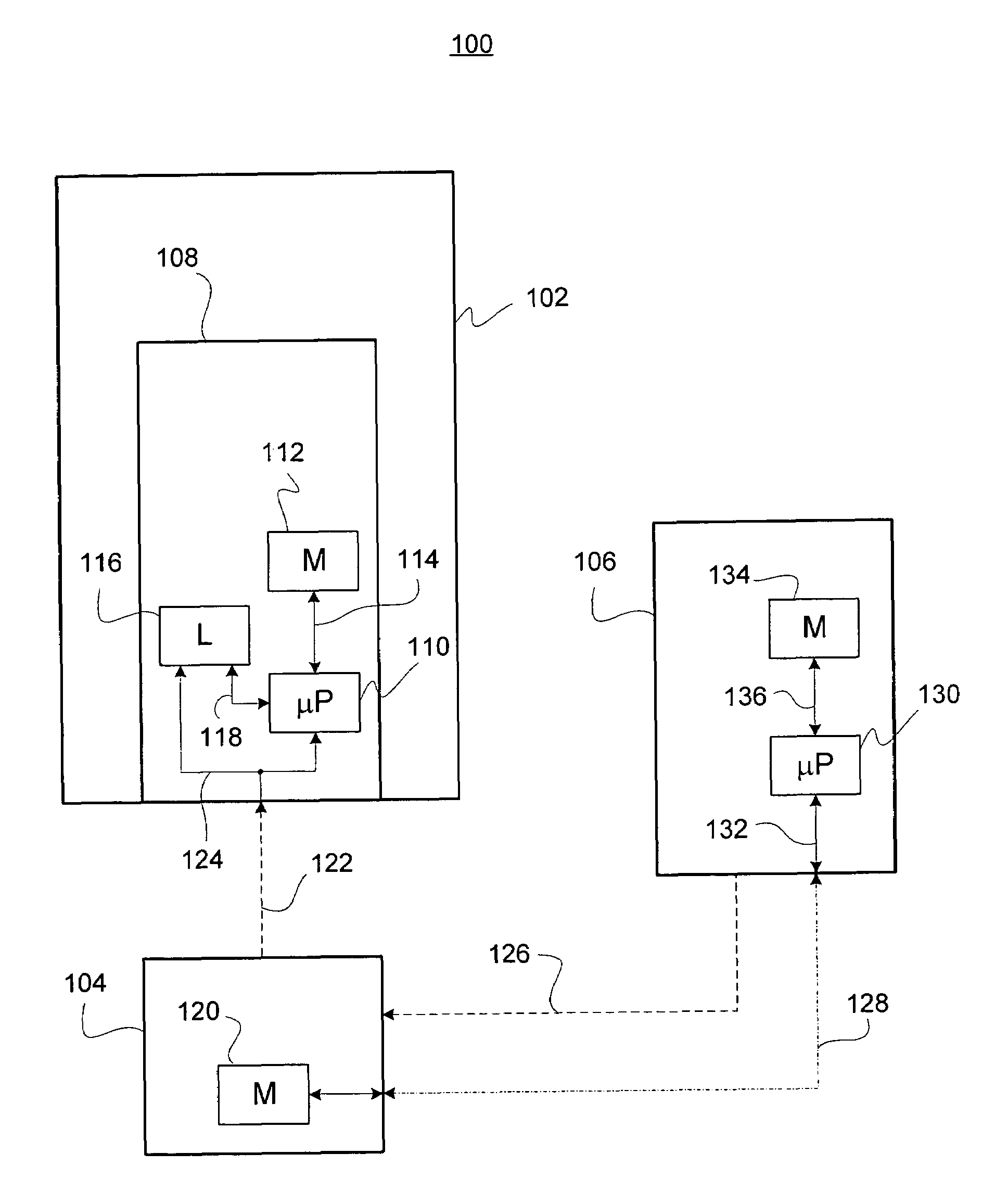
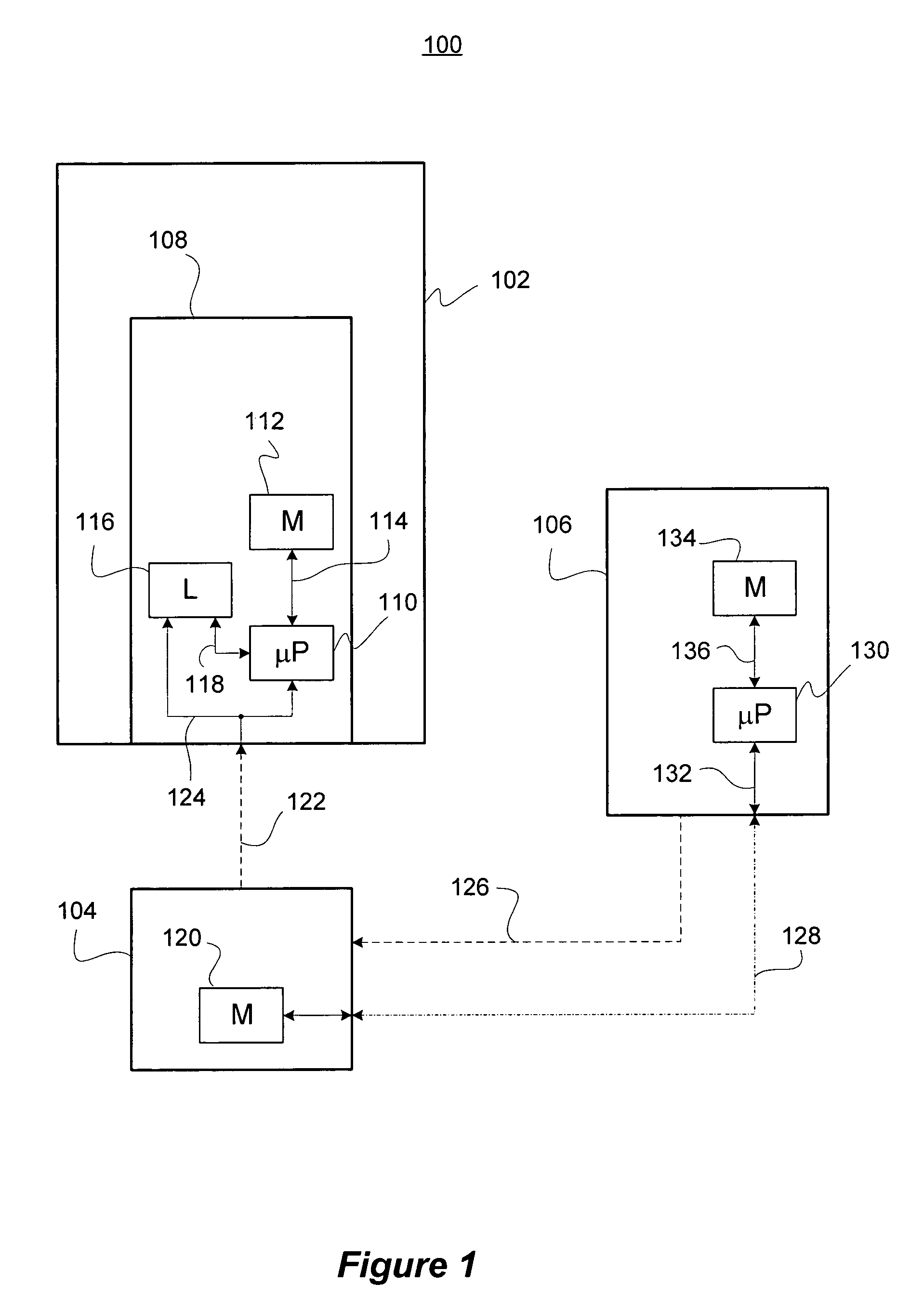
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
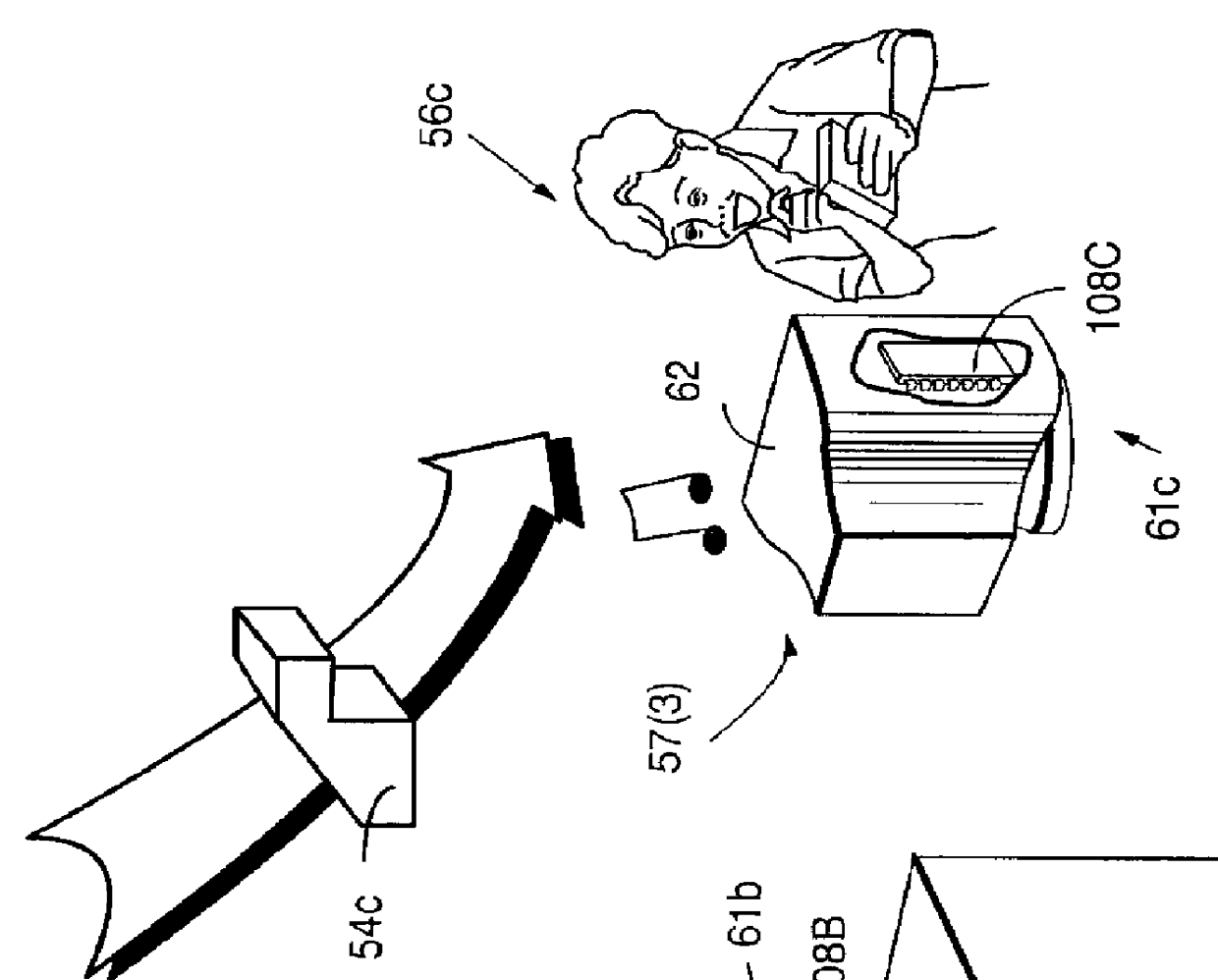
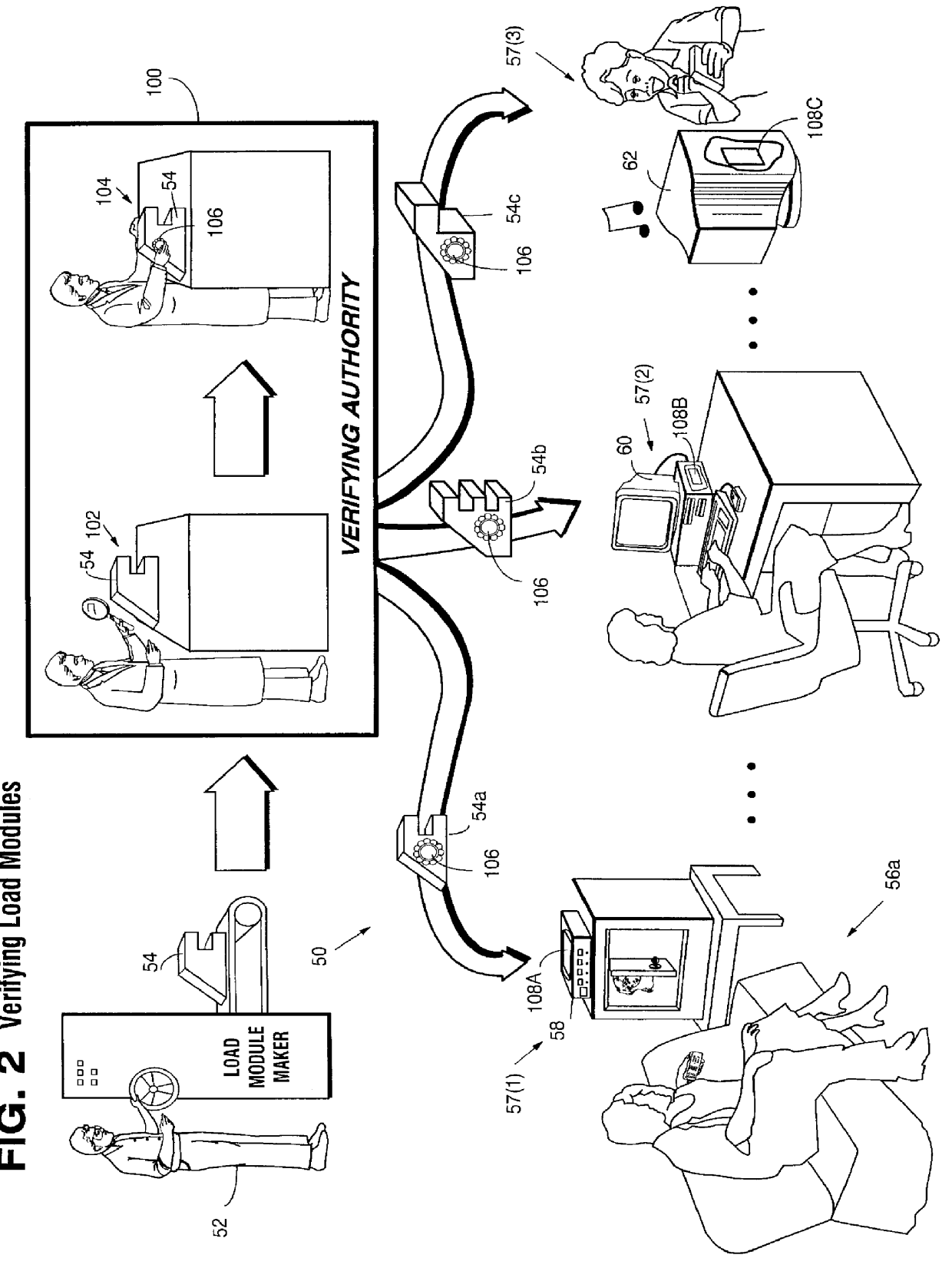
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
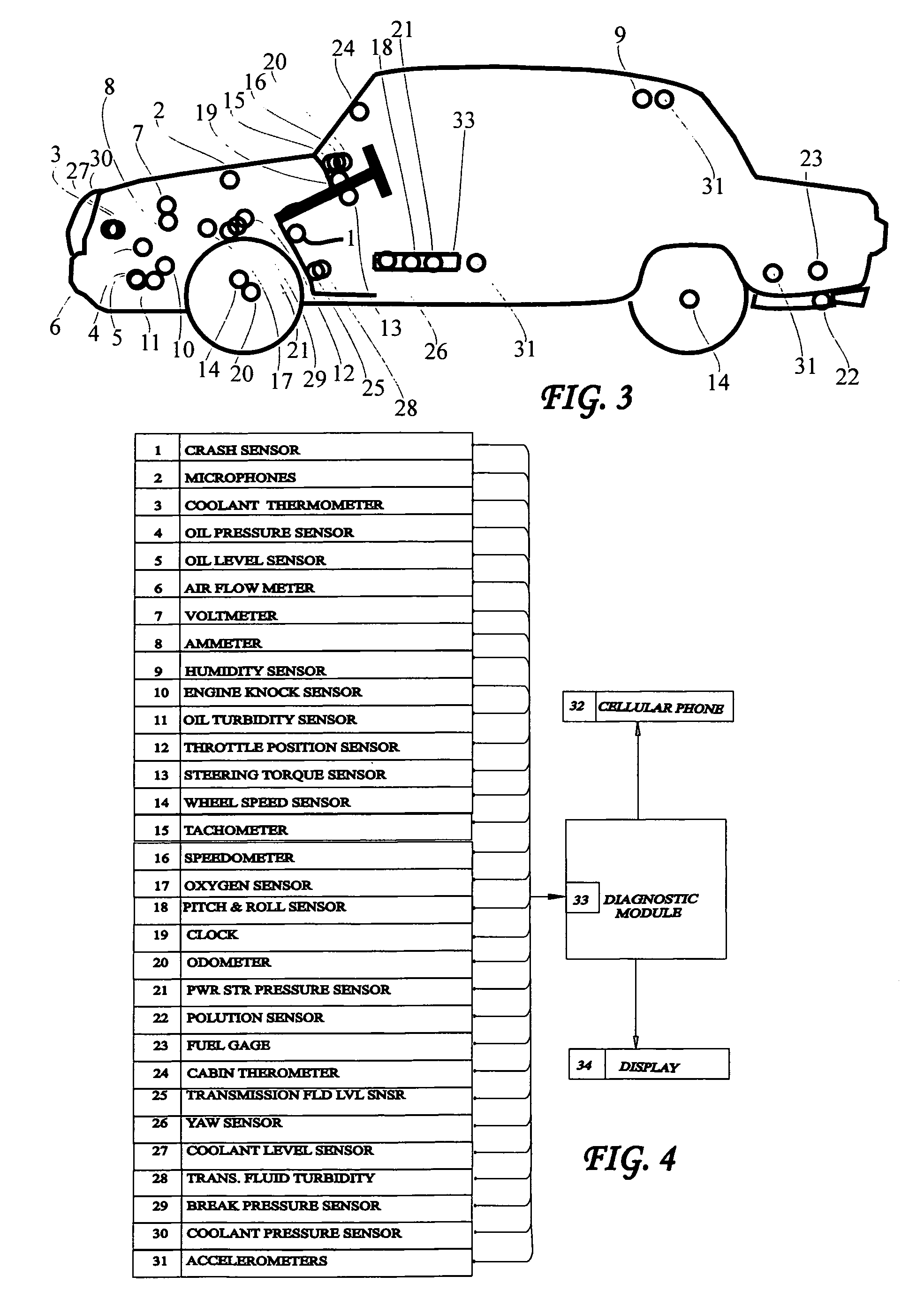
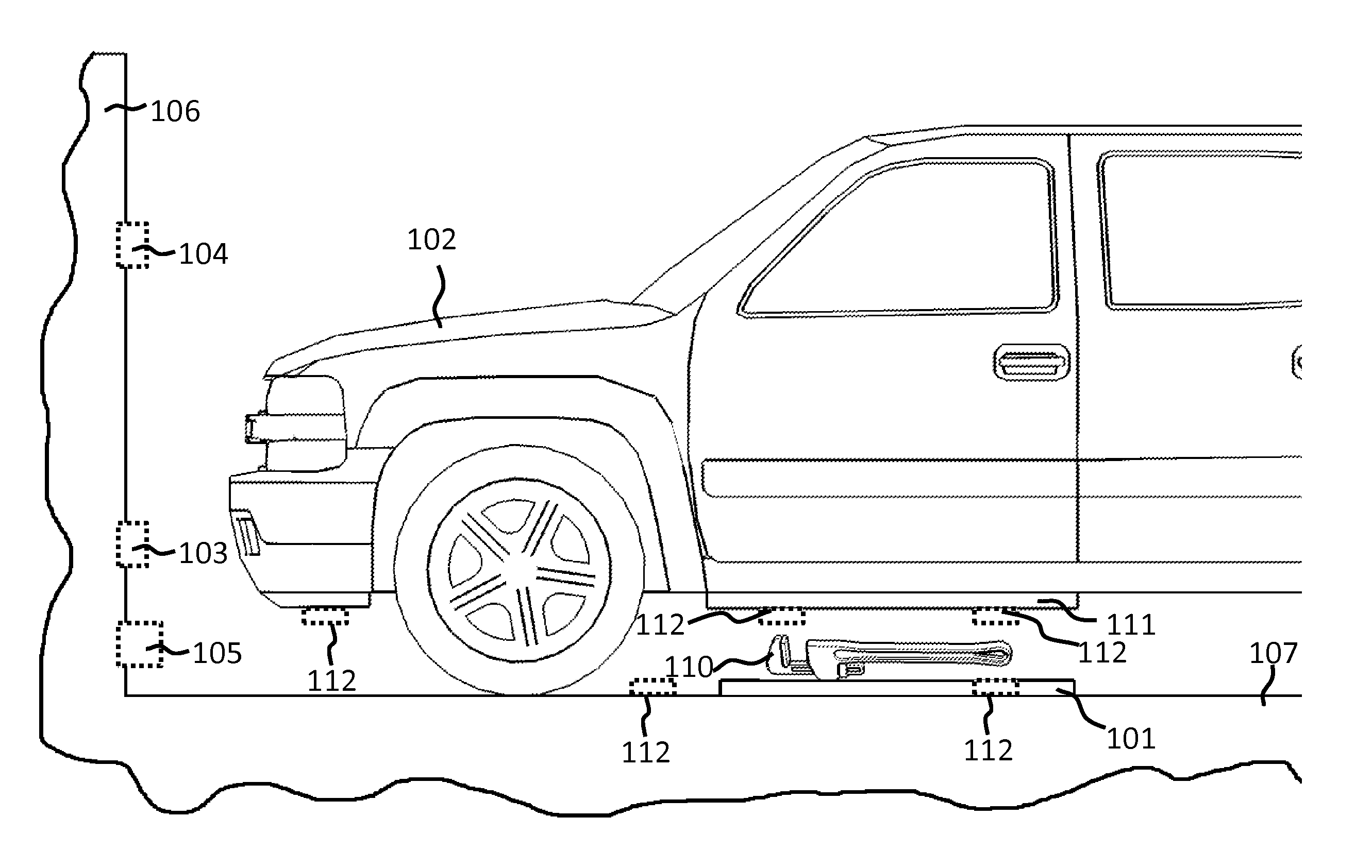
System and method for vehicle diagnostics
InactiveUS7103460B1Low costPrecise positioningVehicle testingRegistering/indicating working of vehiclesReliability engineeringDiagnostic methods
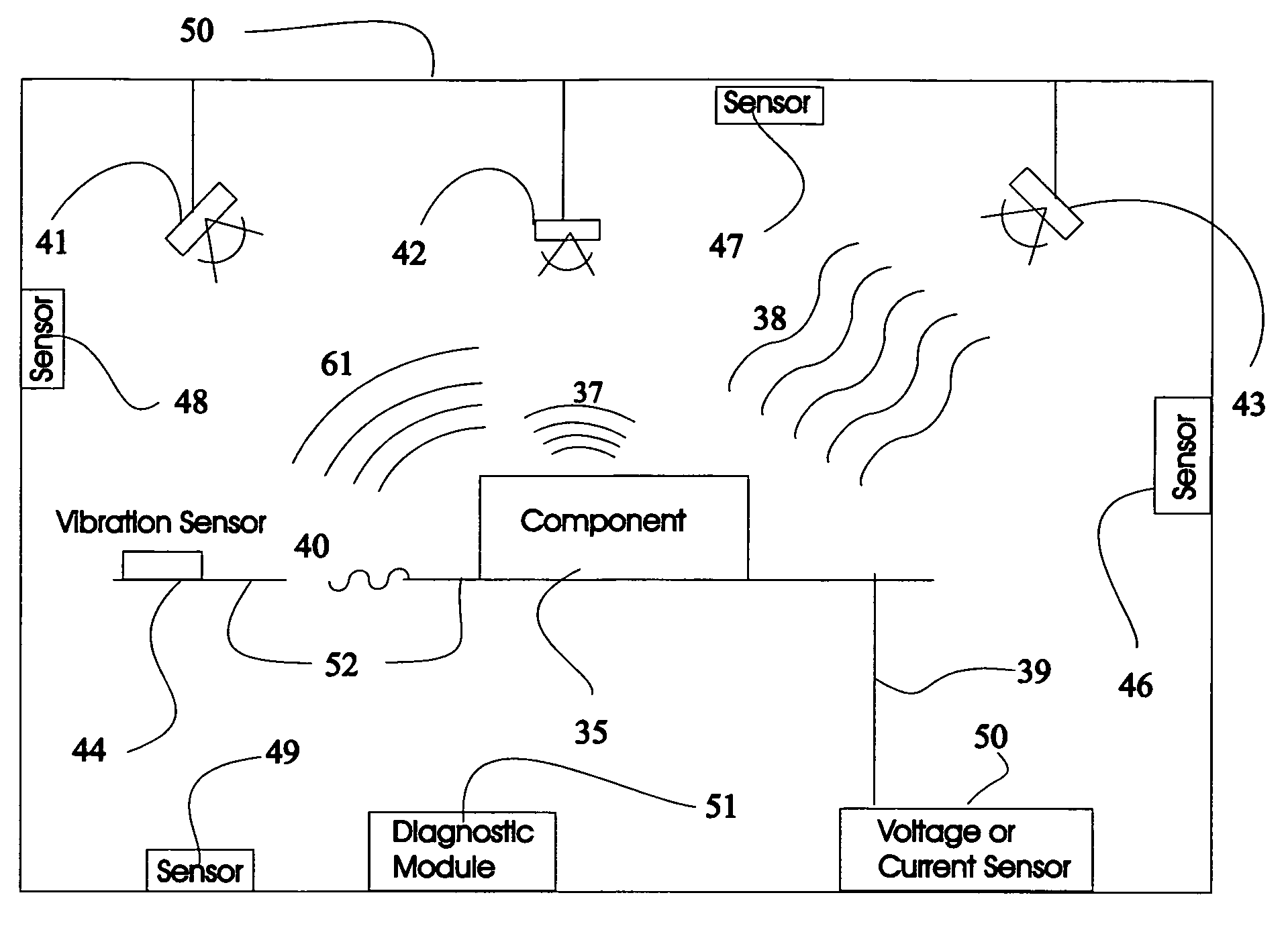
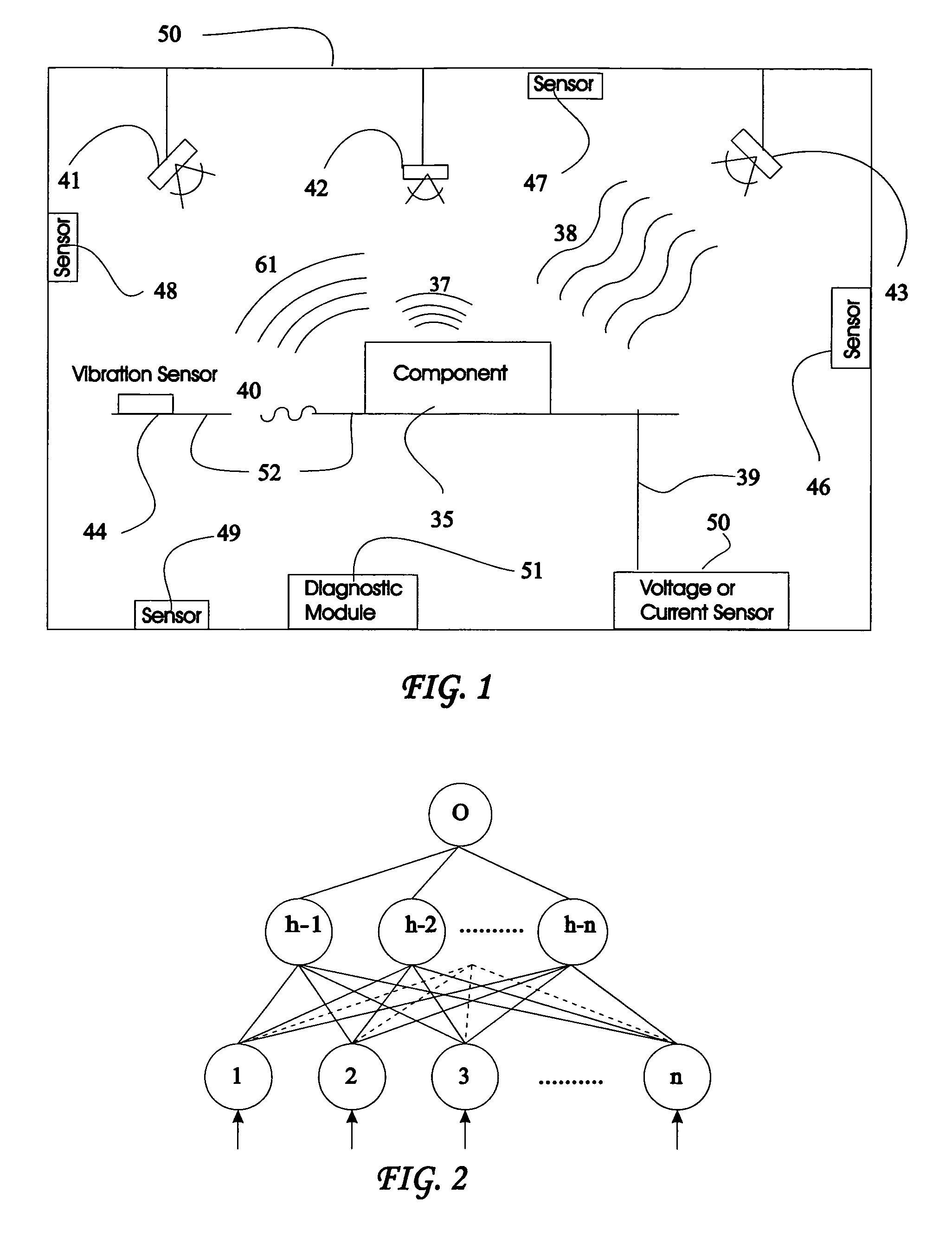
Method and system for diagnosing whether vehicular components are operating abnormally based on data obtained from sensors arranged on a vehicle. In a training stage, output from the sensors during normal operation of the components is obtained, each component is adjusted to induce abnormal operation thereof and output from the sensors is obtained during the induced abnormal operation. A determination is made as to which sensors provide data about abnormal operation of each component based on analysis of the output from the sensors during normal operation and during induced abnormal operation of the components. During operation of the vehicle, the output from the sensors is obtained and analyzed, e.g., by inputting it into a pattern recognition algorithm or neural network generated during the training stage, in order to output an indication of abnormal operation of any components being diagnosed.
Owner:AMERICAN VEHICULAR SCI
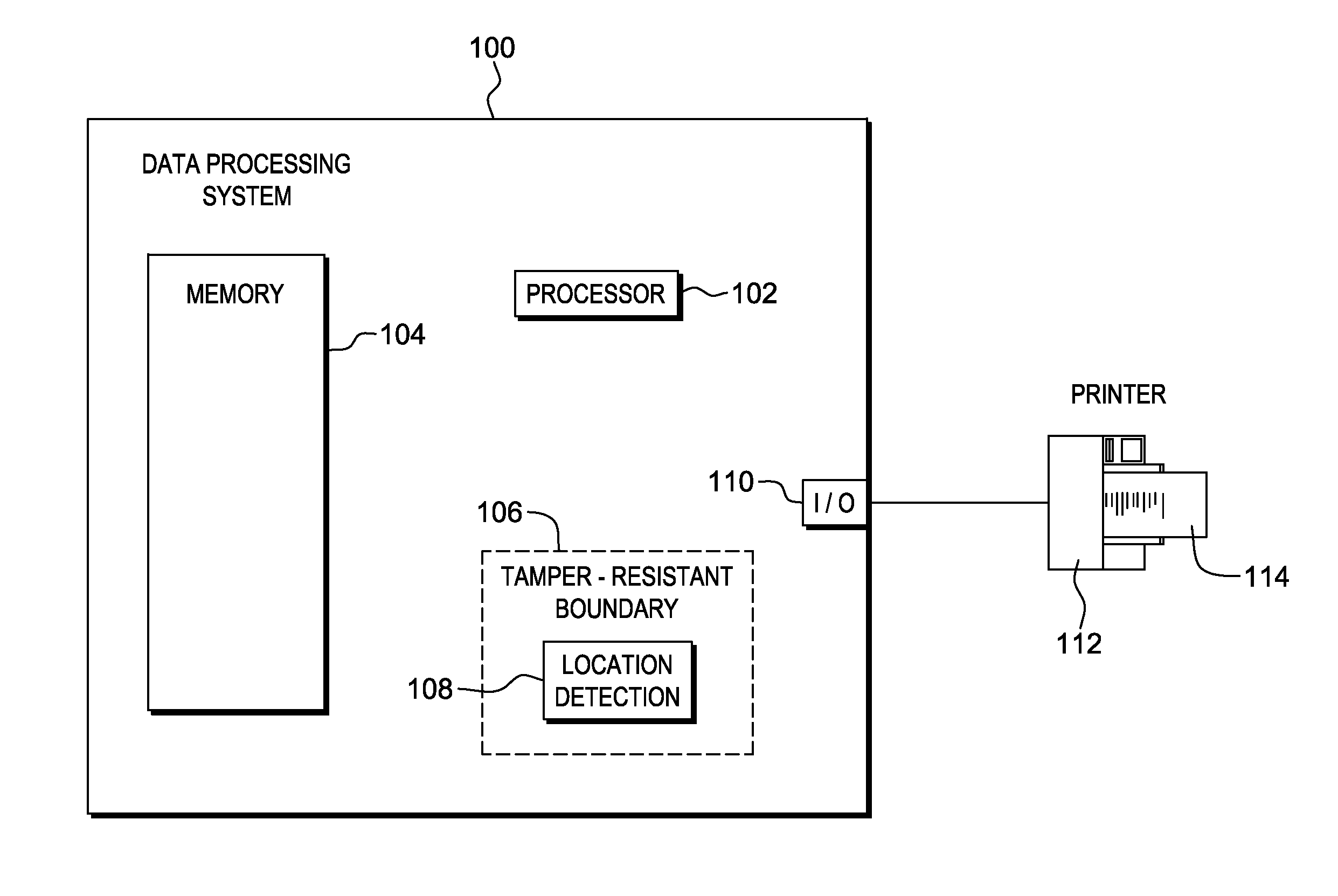
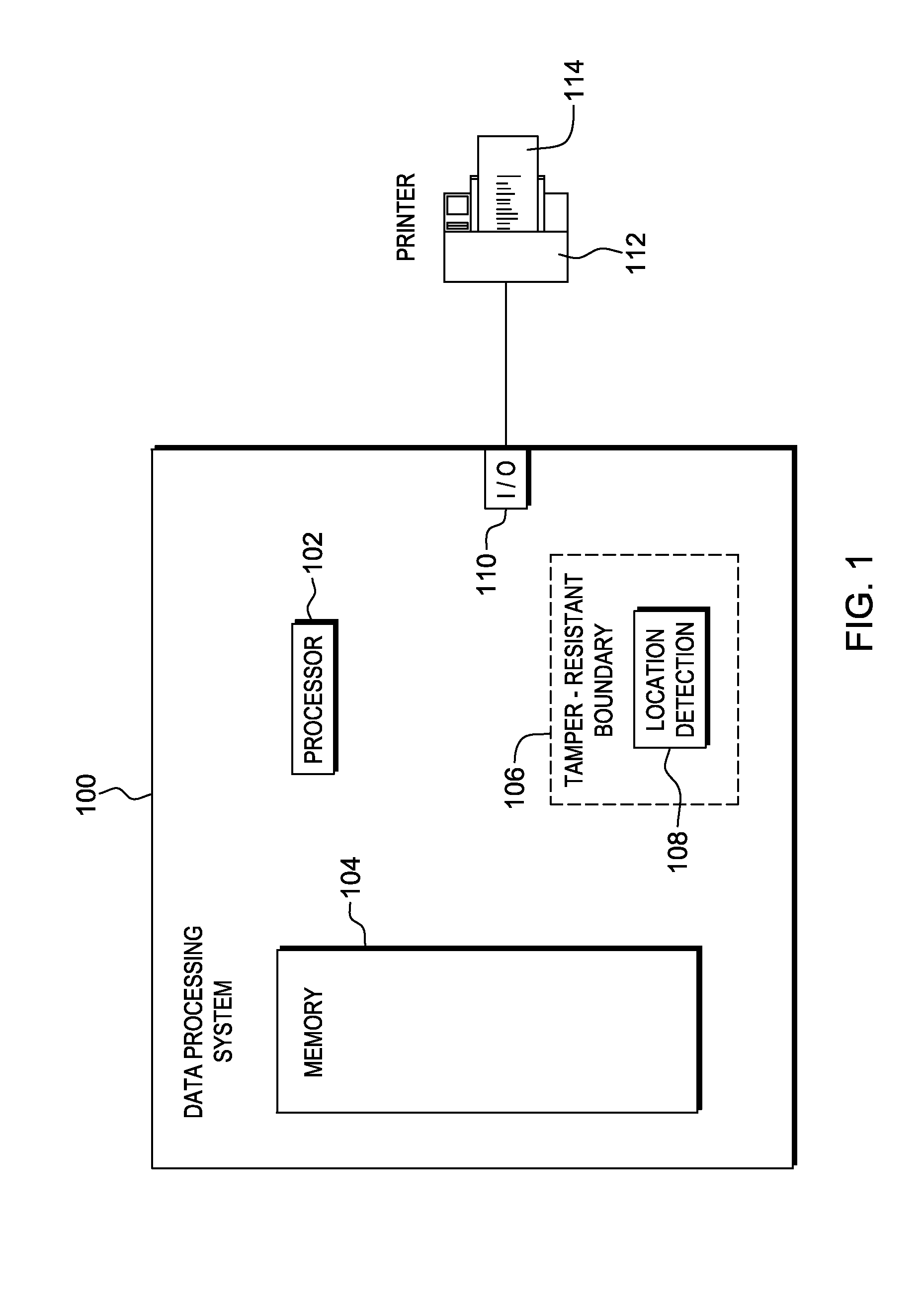
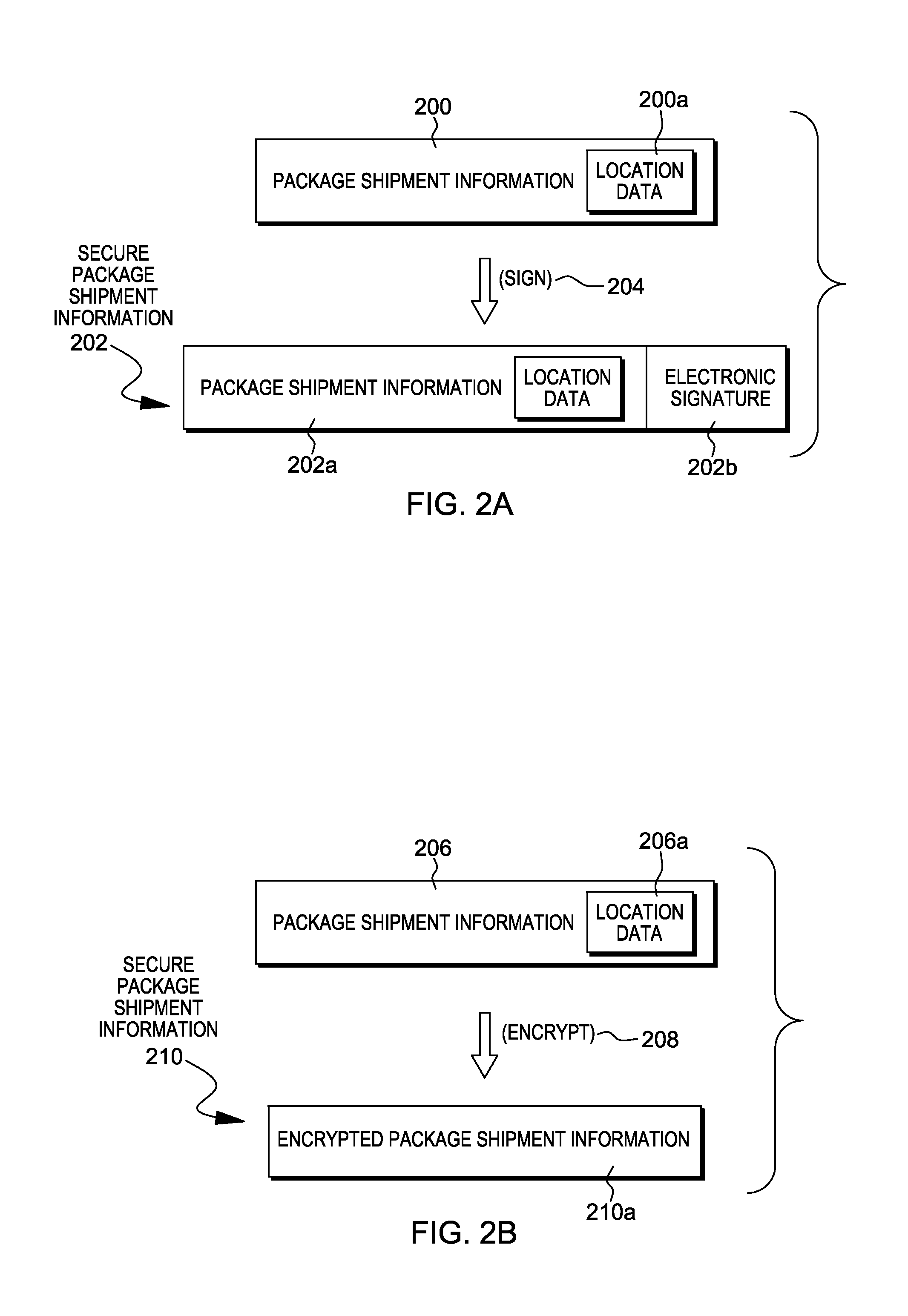
Package source verification
InactiveUS20140074746A1Convenient verificationOvercomes shortcomingCommerceLogisticsData terminalTamper resistance
Verification of a source of a package is facilitated. A data terminal certified by an authority obtains location data from a location detection component. The location data indicates a source location from which the package is to be shipped, and is detected by the location detection component at the source location. Secure package shipment information, including the location data, is provided with the package to securely convey the detected source location to facilitate verifying the source of the package. The data terminal can be a portable data terminal certified by the authority and have a tamper-proof boundary behind which resides the location detection component and one or more keys for securing the package shipment information. Upon tampering with the tamper-resistant boundary, the certification of the portable data terminal can be nullified.
Owner:HAND HELD PRODS
System and method for policy management
InactiveUS20070180490A1Computer security arrangementsSpecial data processing applicationsStrategy makingComputer security
The invention provides a system and method for providing policy-based protection services. As a new threat is understood, one or more protection techniques are considered for protecting the asset, the organization assigns responsibilities to carry out or protect the asset, and a policy is constructed. After the policy is developed a plan is put into action to protect the asset, and a policy implementer is developed and / or purchased, distributed, configured, and managed. Finally, the policy, its enforcement, and its effectiveness, are reviewed to determine any changes needed, and new requirements are discovered, closing the lifecycle.
Owner:ALLEGENT TECH GROUP
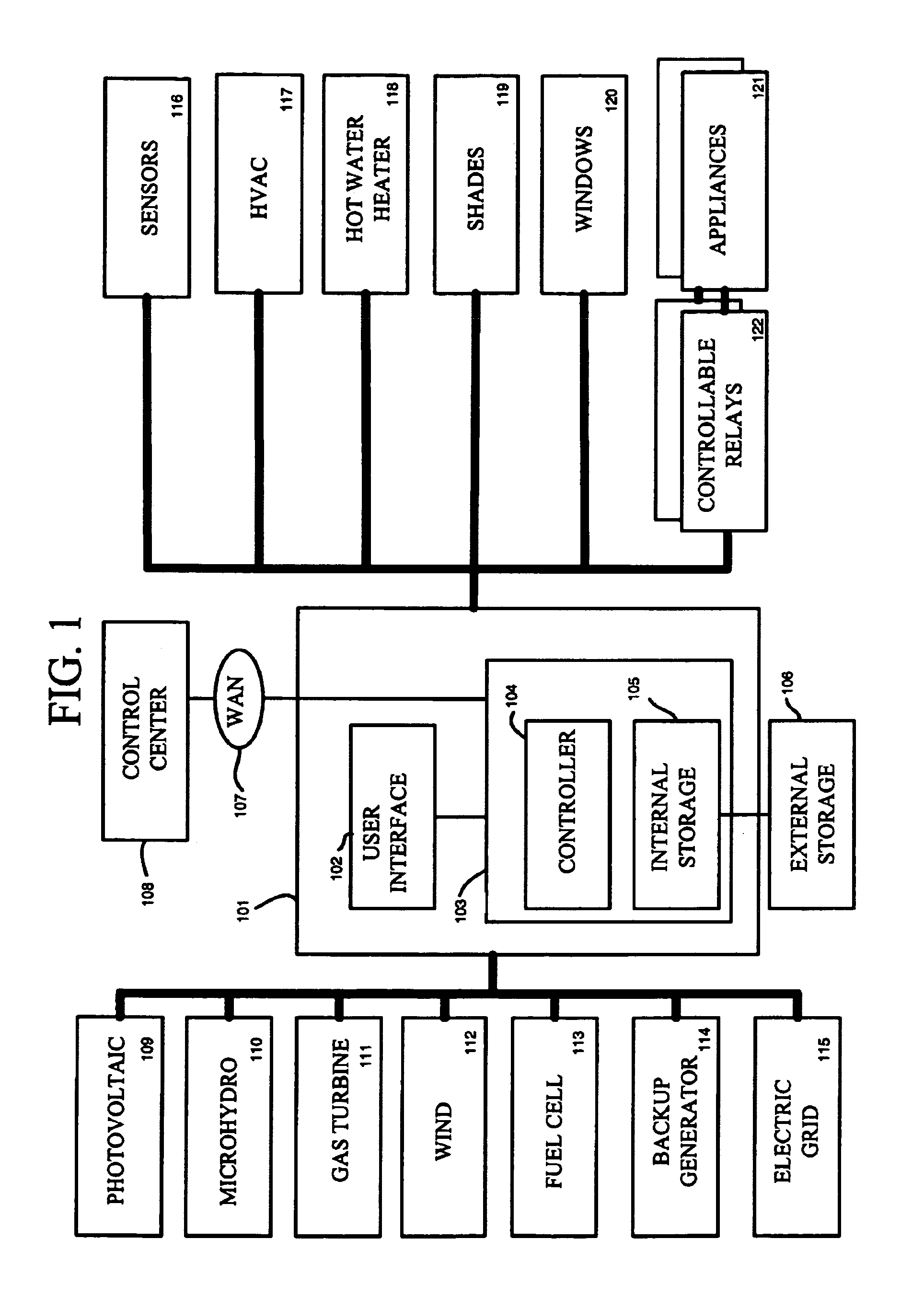
System and method of controlling an HVAC system
A system and method manage delivery of energy from a distribution network to one or more sites. Each site has at least one device coupled to the distribution network. The at least one device controllably consumes energy. The system includes a node and a control system. The node is coupled to the at least one device for sensing and controlling energy delivered to the device. A control system is coupled to the node and distribution network for delivery to the node at least one characteristic of the distribution network. The node controls the supply of energy to the device as a function of the at least one characteristic.
Owner:INVENSYS SYST INC
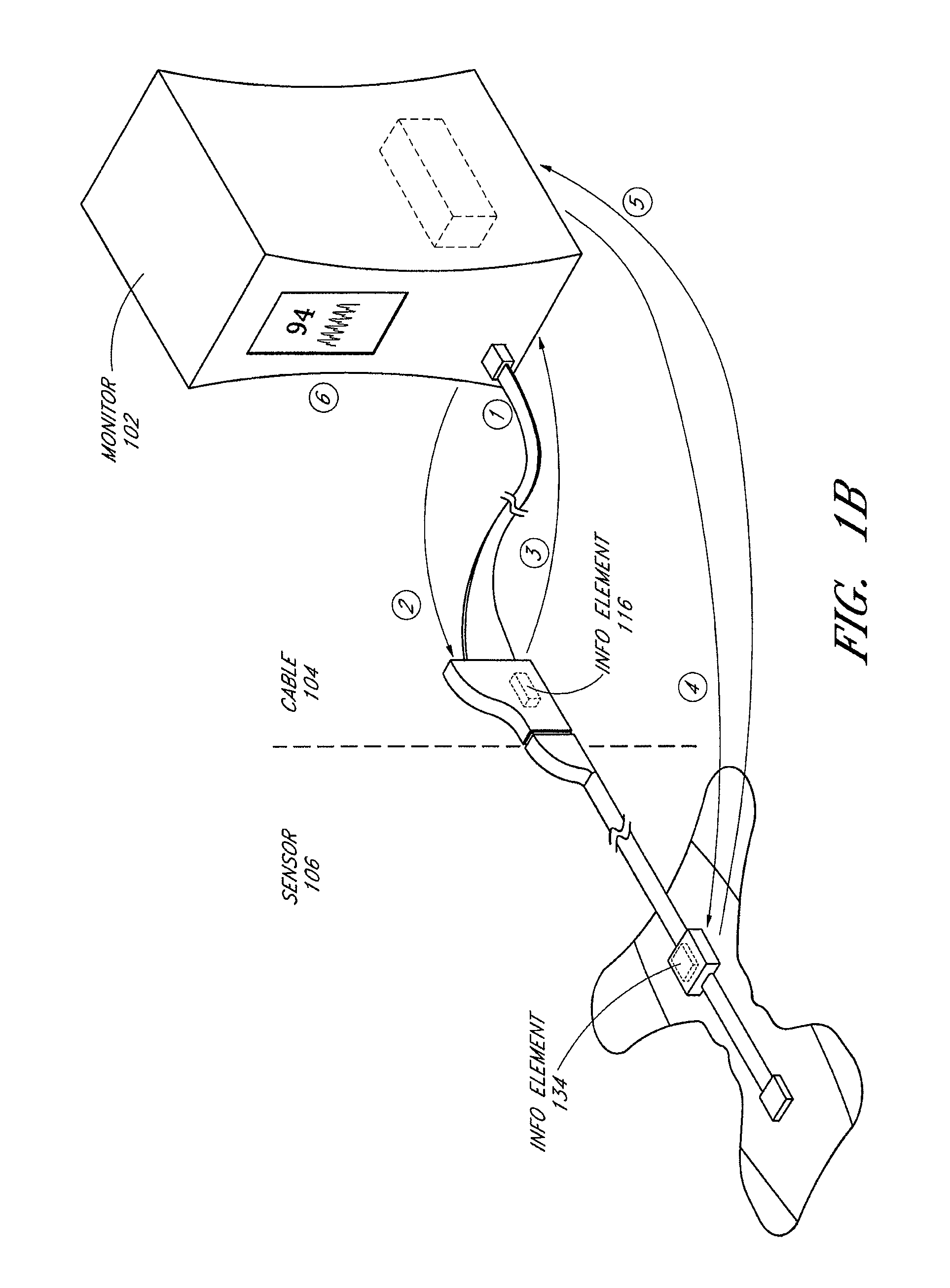
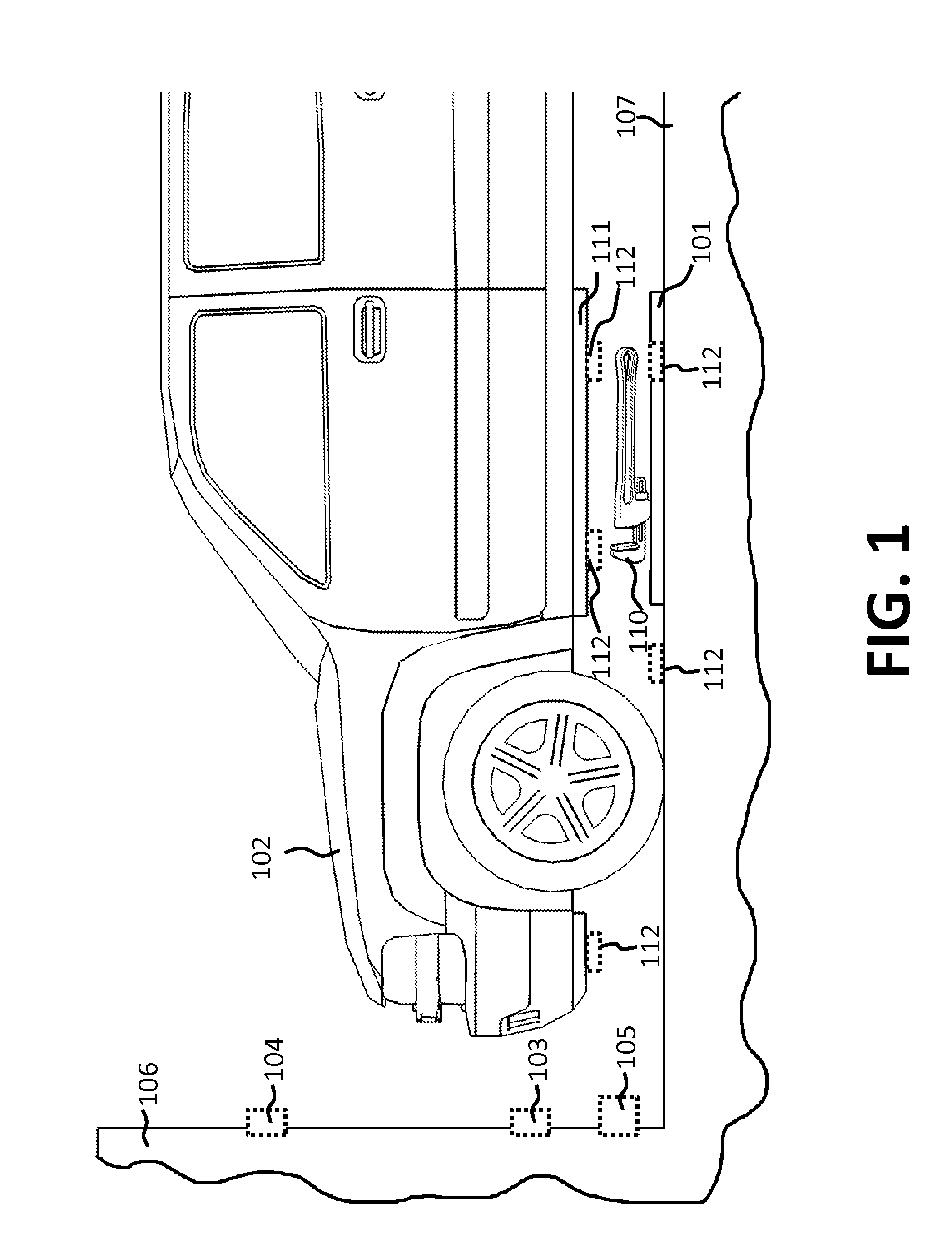
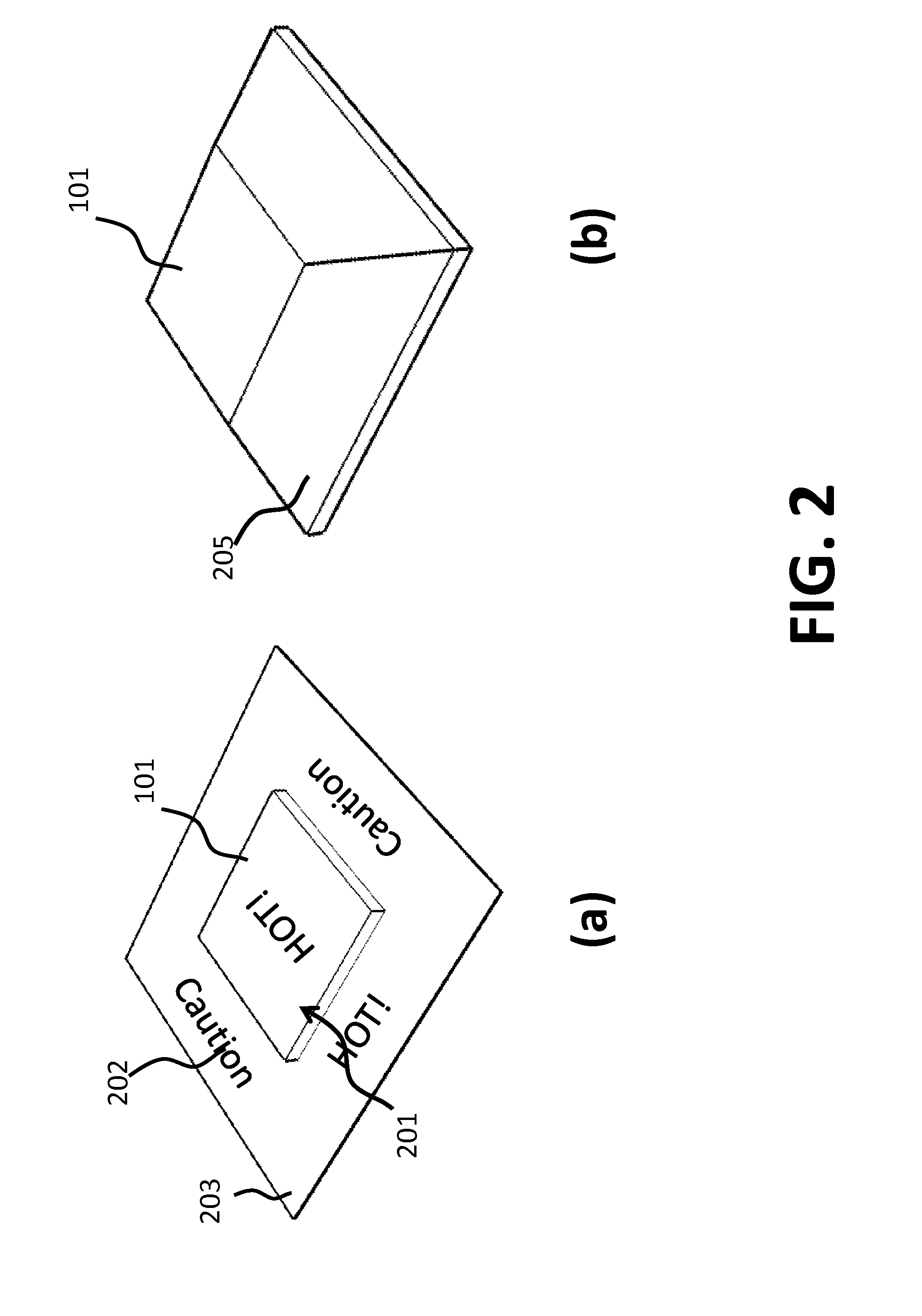
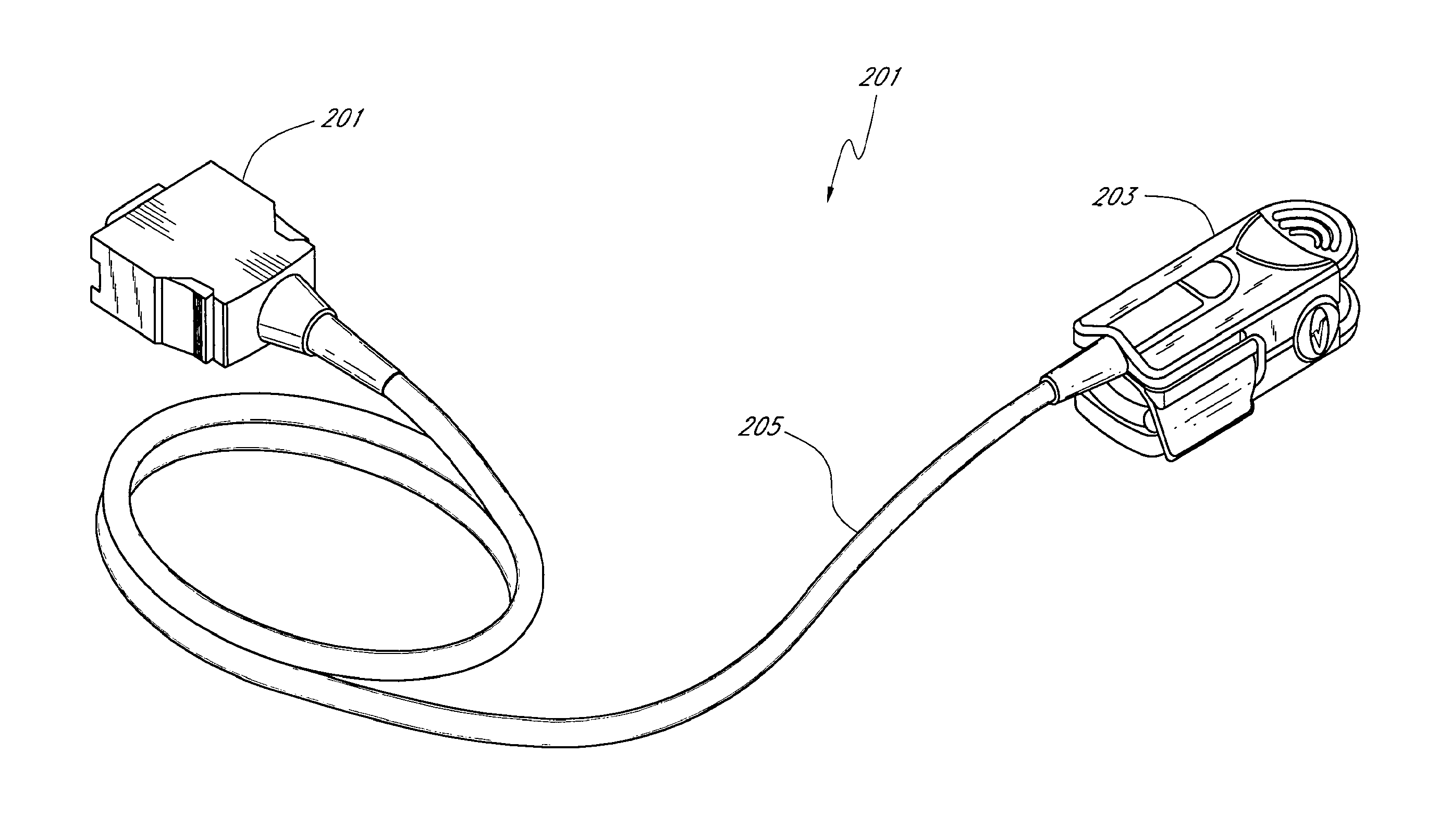
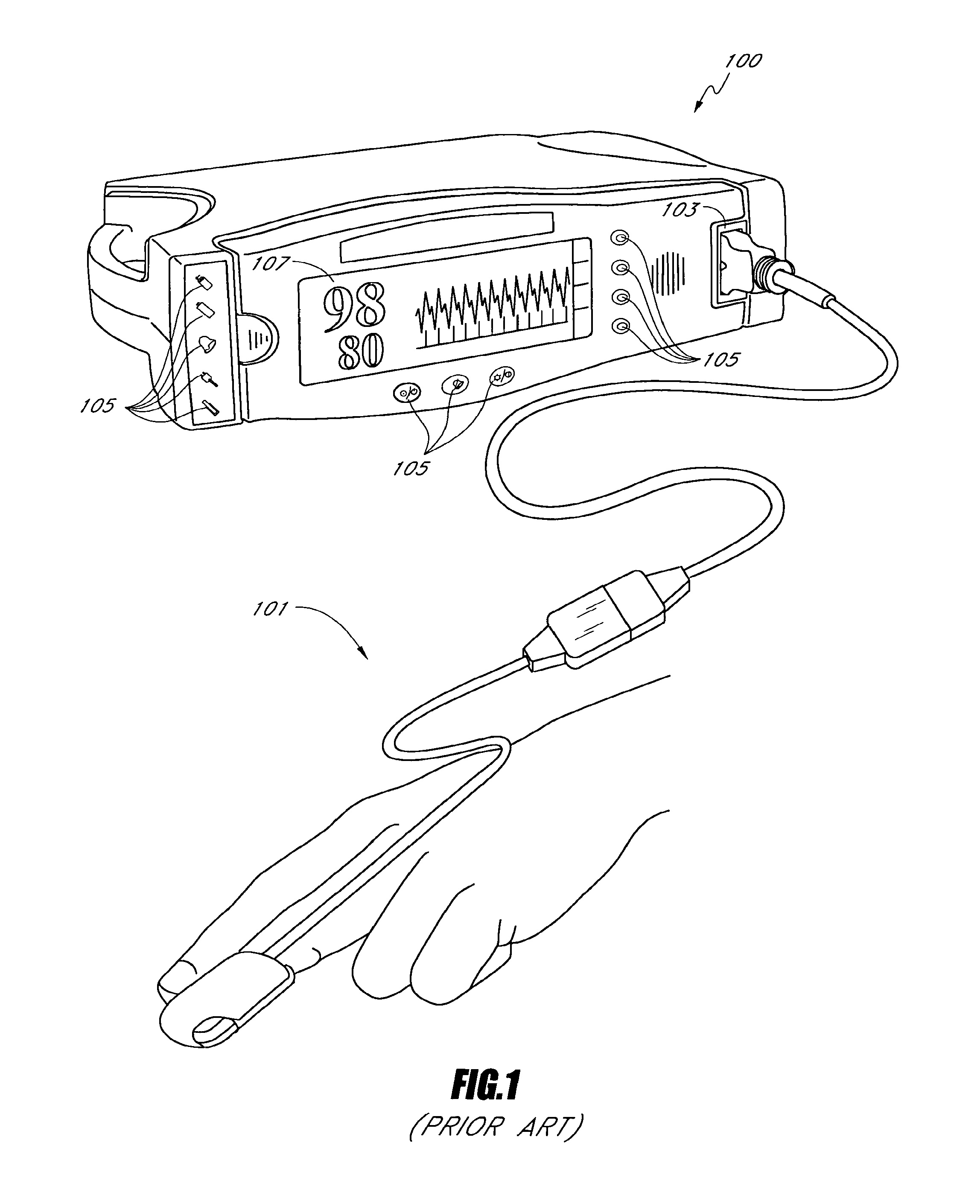
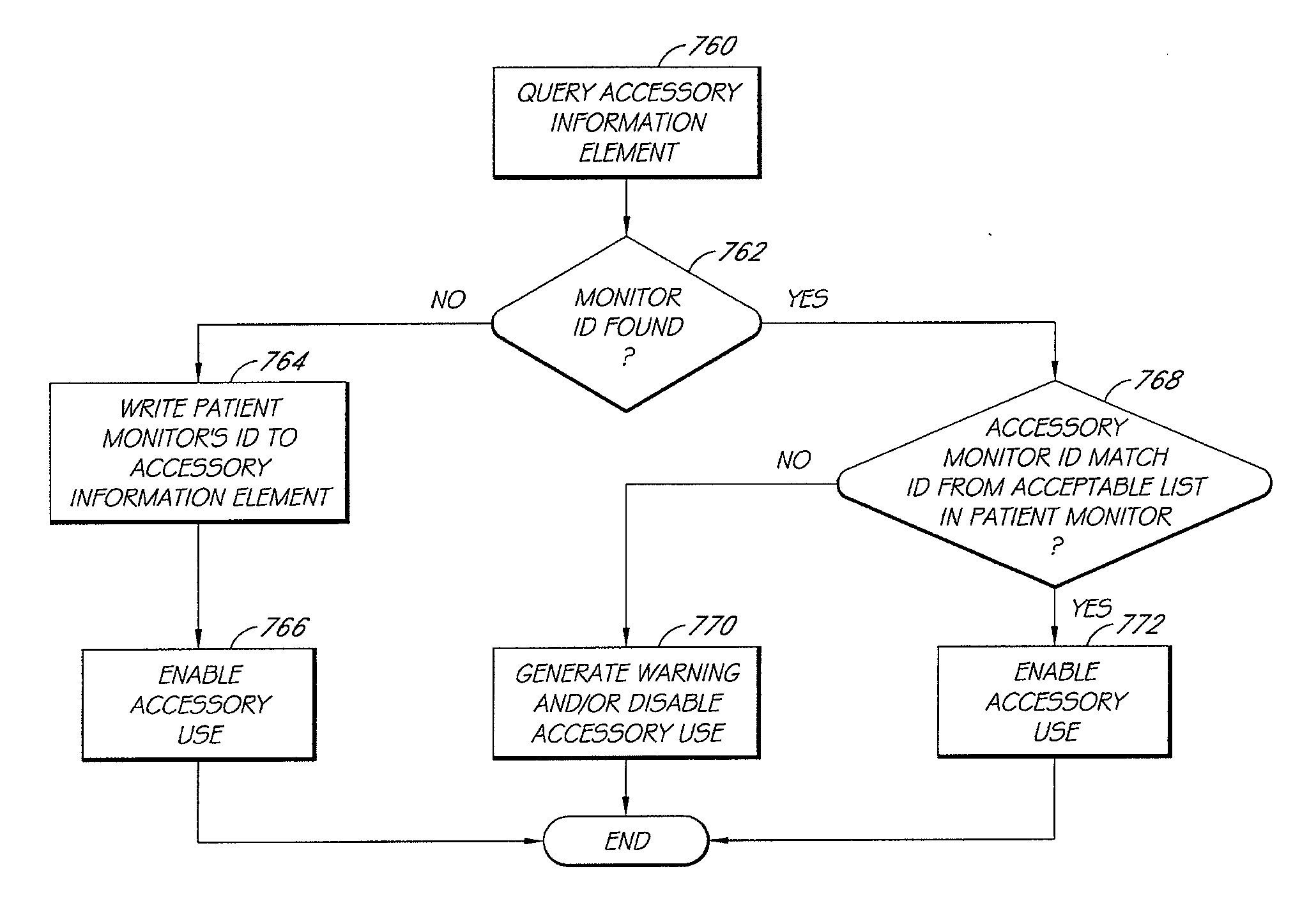
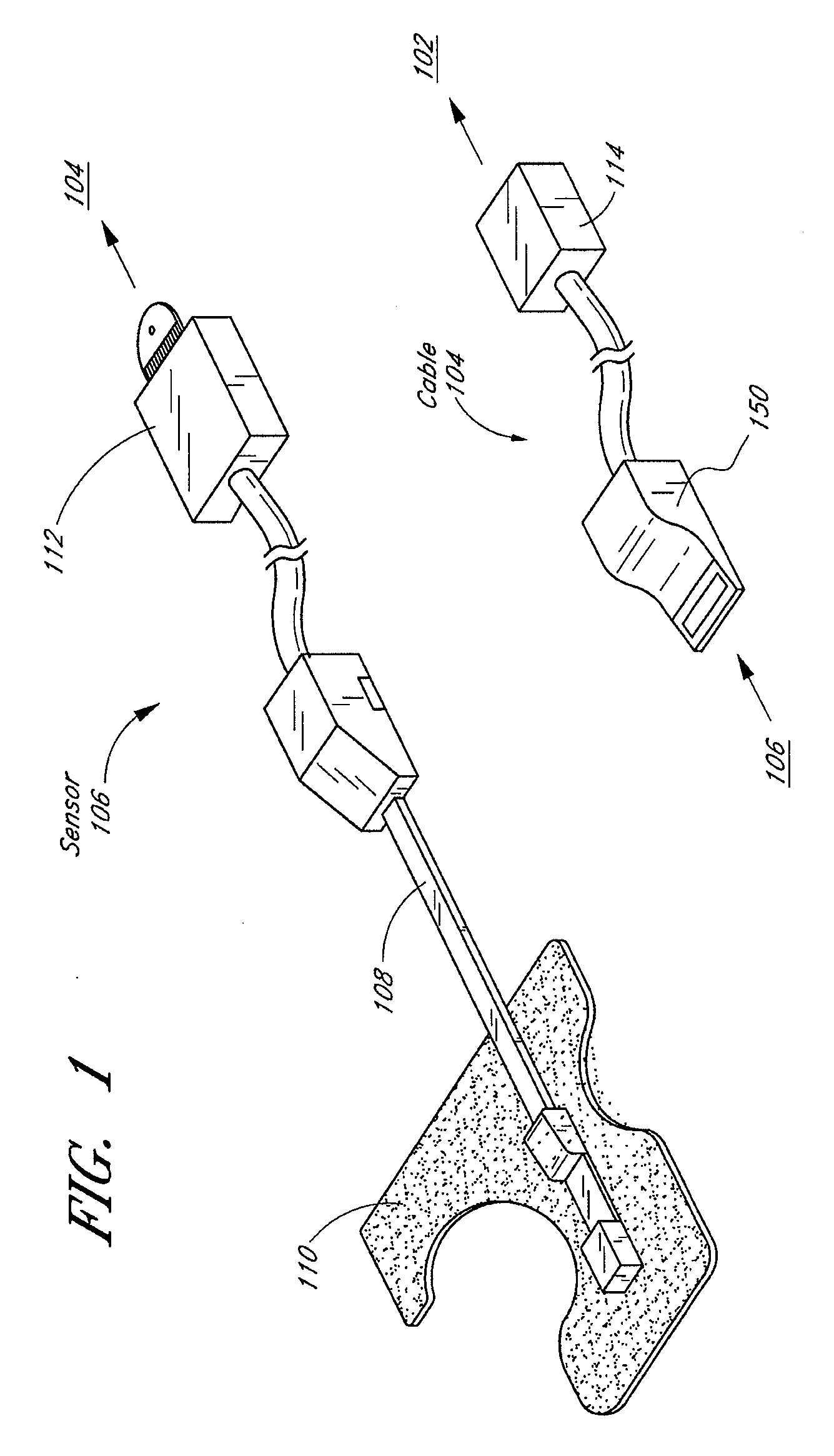
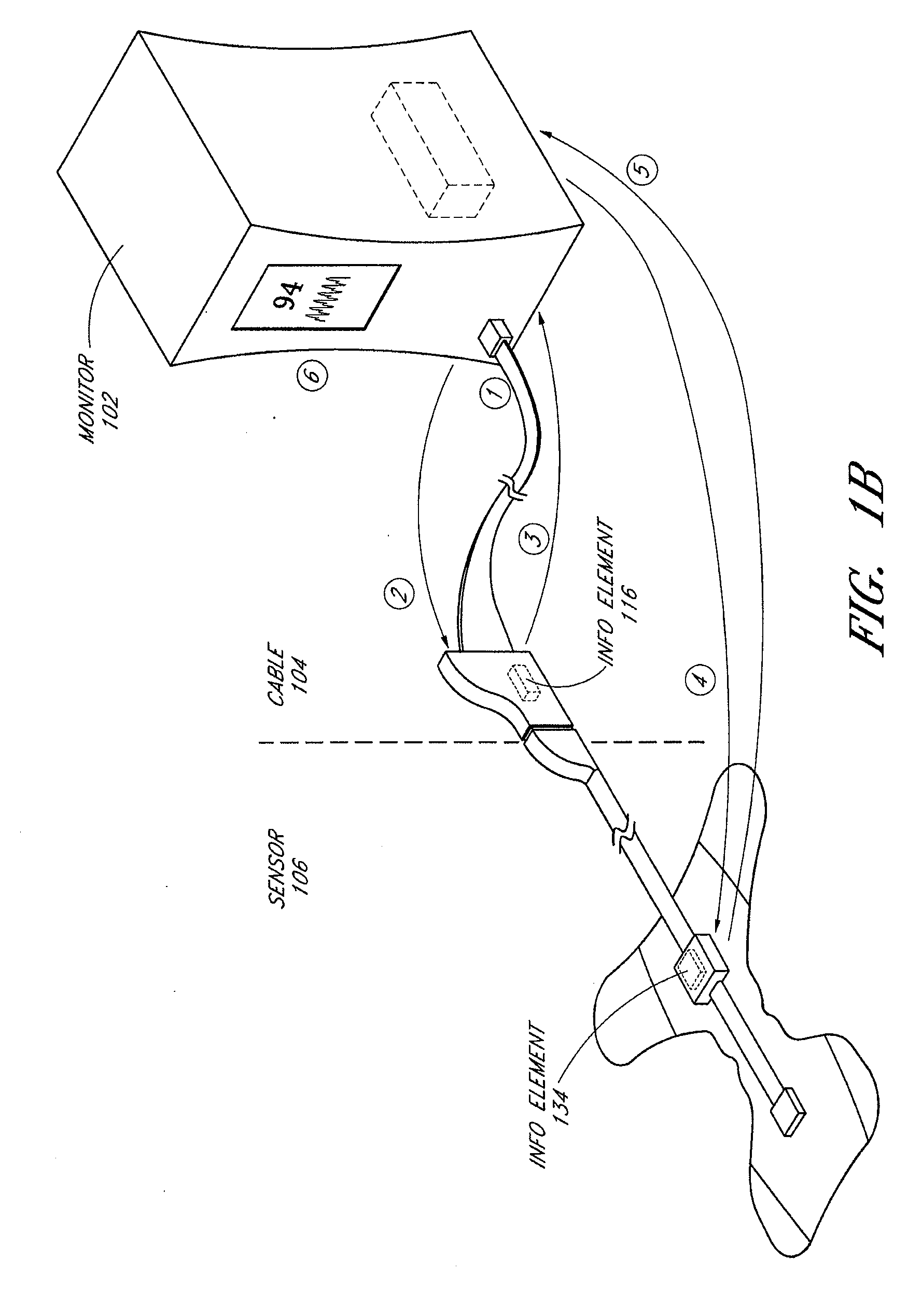
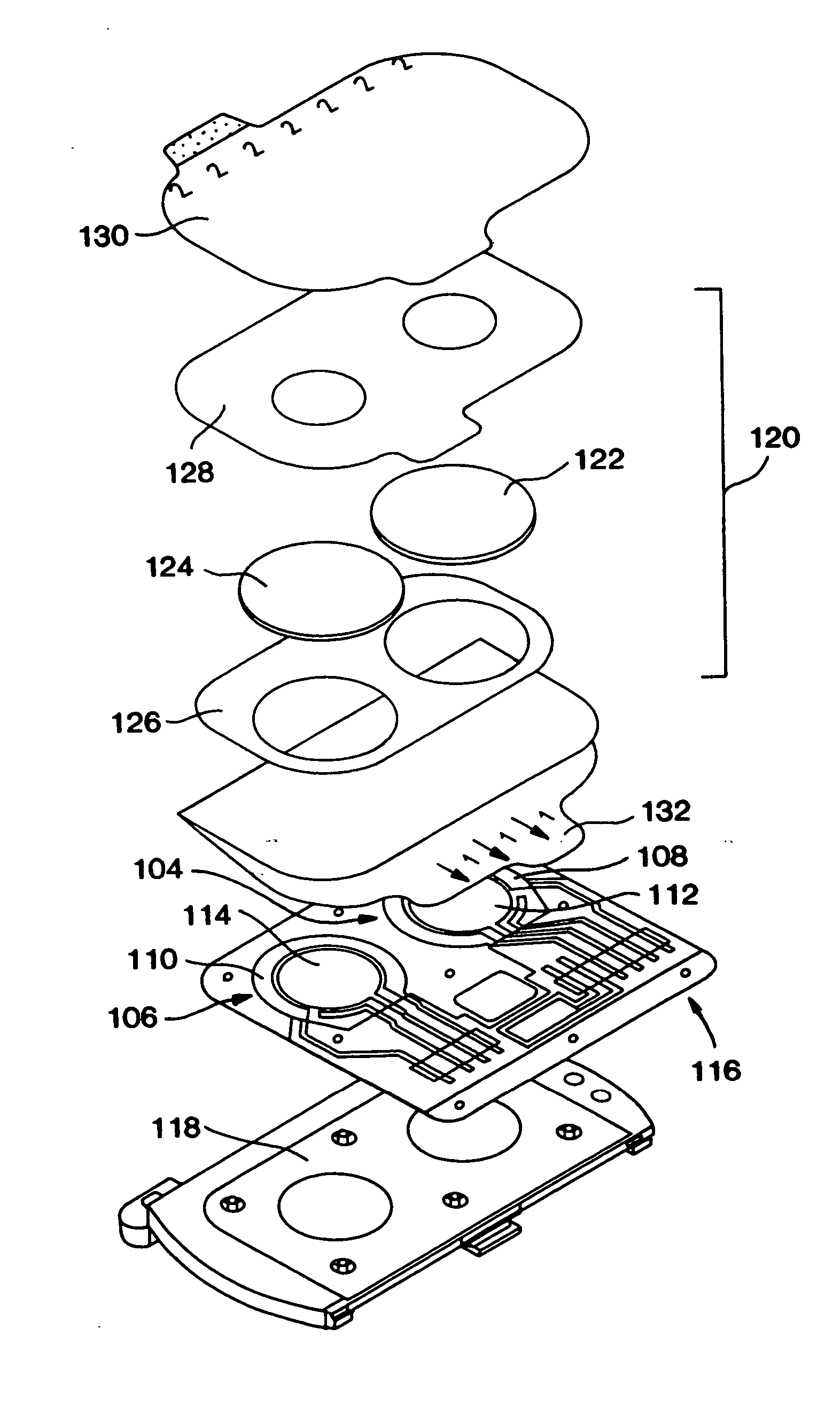
Patient monitor capable of monitoring the quality of attached probes and accessories
ActiveUS8255026B1Reduce capacityReduce the possibilityDiagnostic recording/measuringSensorsQuality controlPulse oximetry
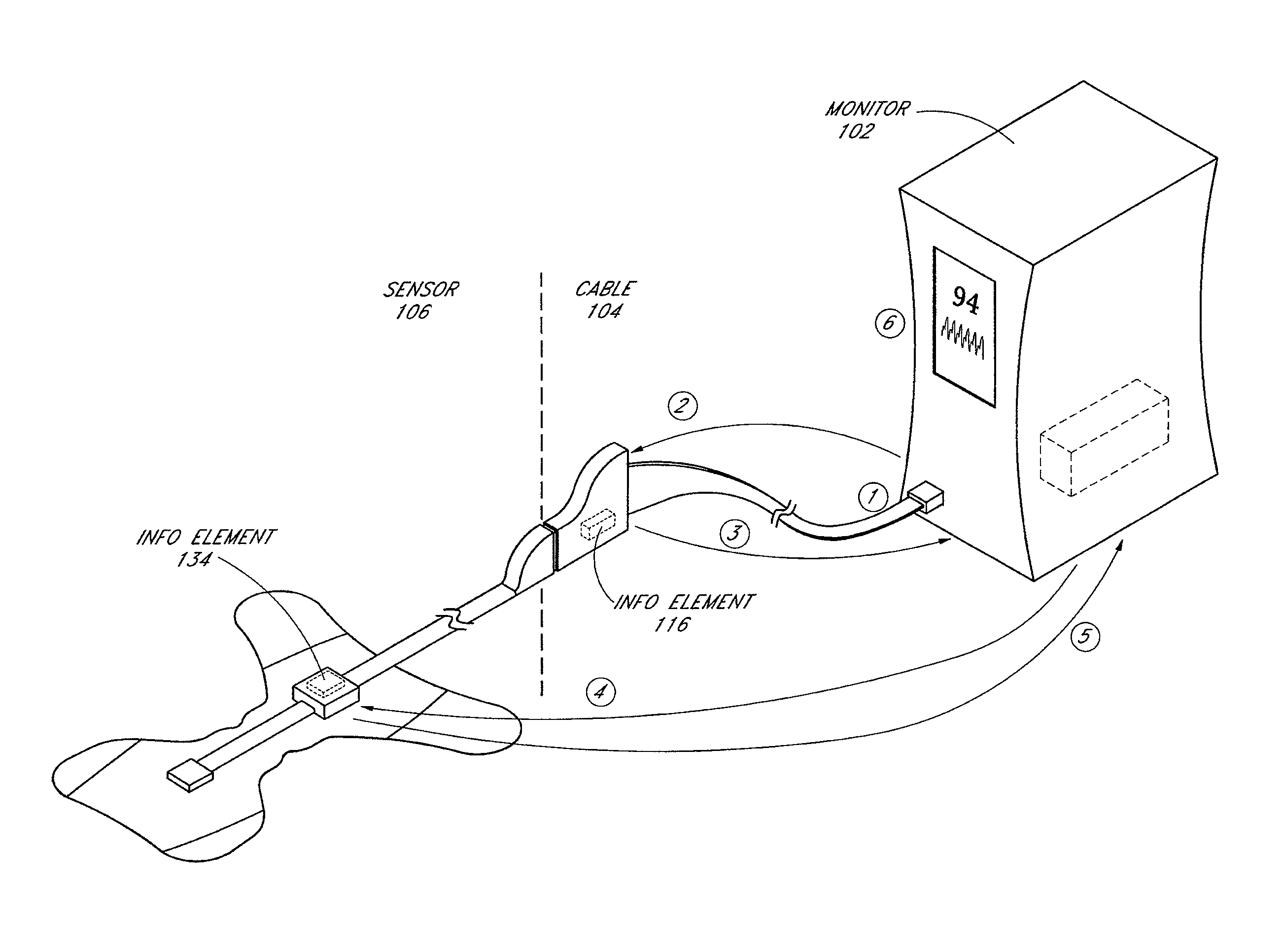
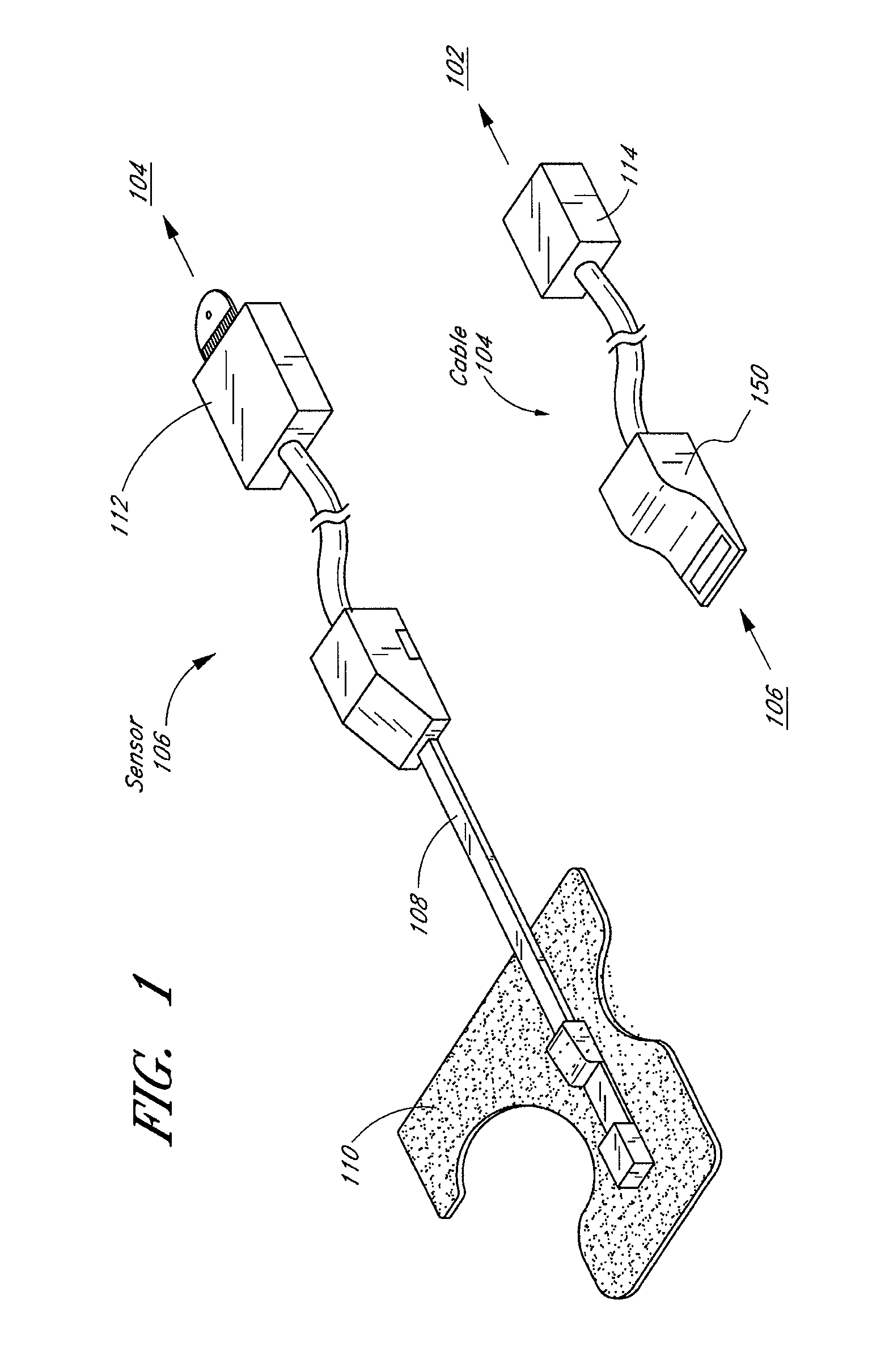
A system and method to help maintain quality control and reduce cannibalization of accessories and attached probes in a highly sensitive patient monitor, such as a pulse oximetry system. One or more attached components may have information elements designed to designate what quality control mechanisms a patient monitor should look to find on that or another component or designate other components with which the one component may properly work. In a further embodiment, such information elements may also include data indicating the appropriate life of the component.
Owner:JPMORGAN CHASE BANK NA
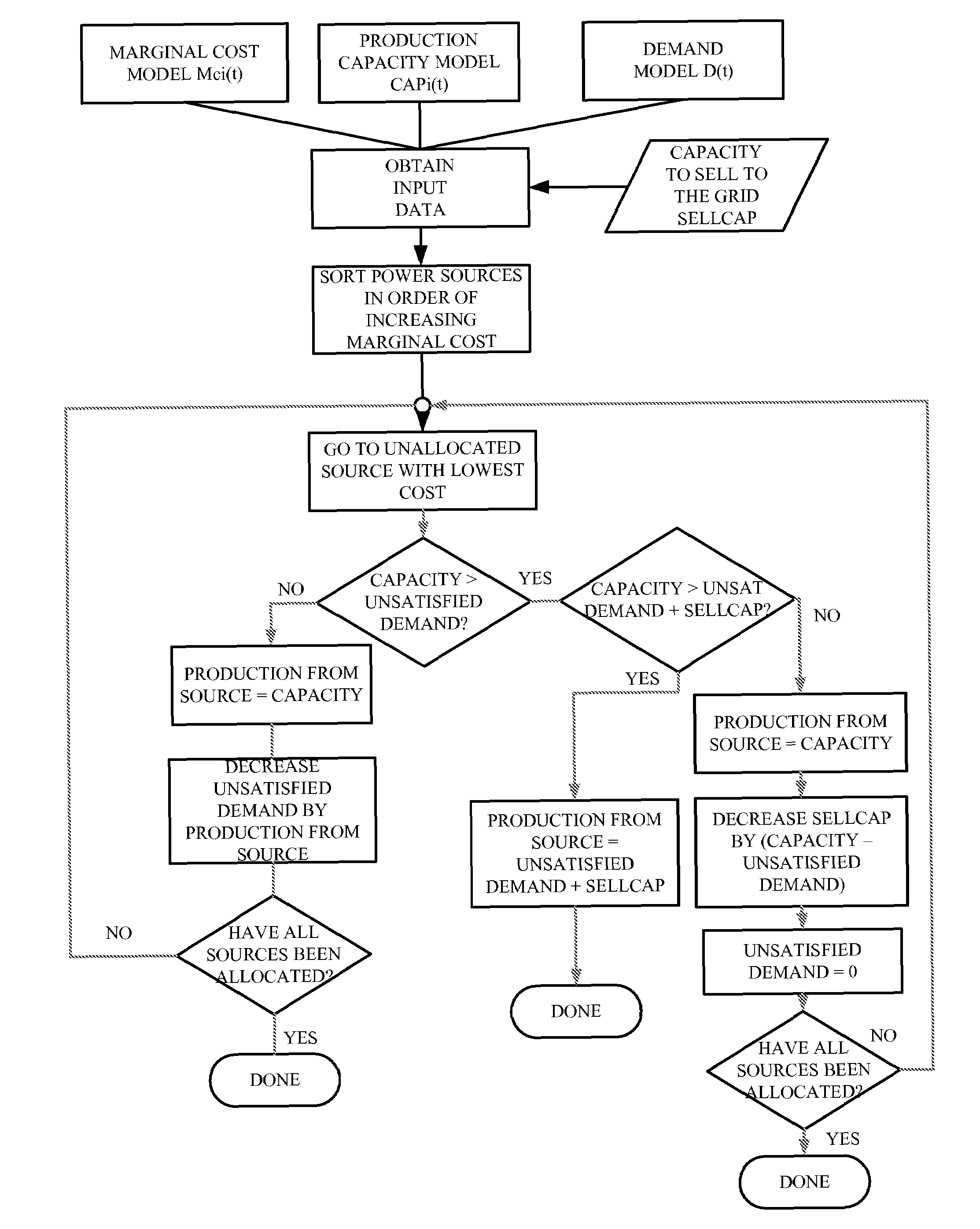
Optimized energy management system
Methods and systems are provided for optimizing the control of energy supply and demand. An energy control unit includes one or more algorithms for scheduling the control of energy consumption devices on the basis of variables relating to forecast energy supply and demand. Devices for which energy consumption can be scheduled or deferred are activated during periods of cheapest energy usage. Battery storage and alternative energy sources (e.g., photovoltaic cells) are activated to sell energy to the power grid during periods that are determined to correspond to favorable cost conditions.
Owner:GRIDPOINT
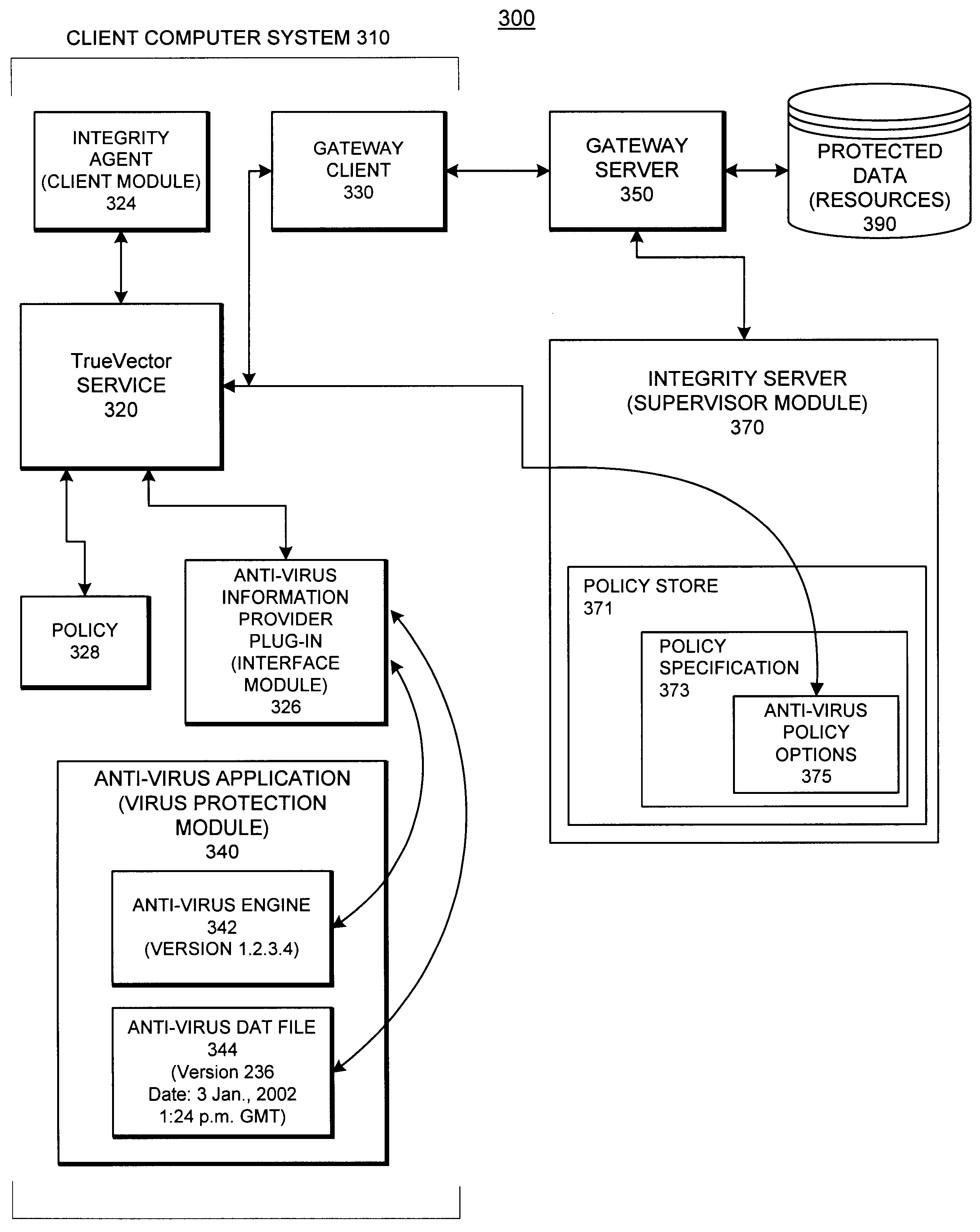
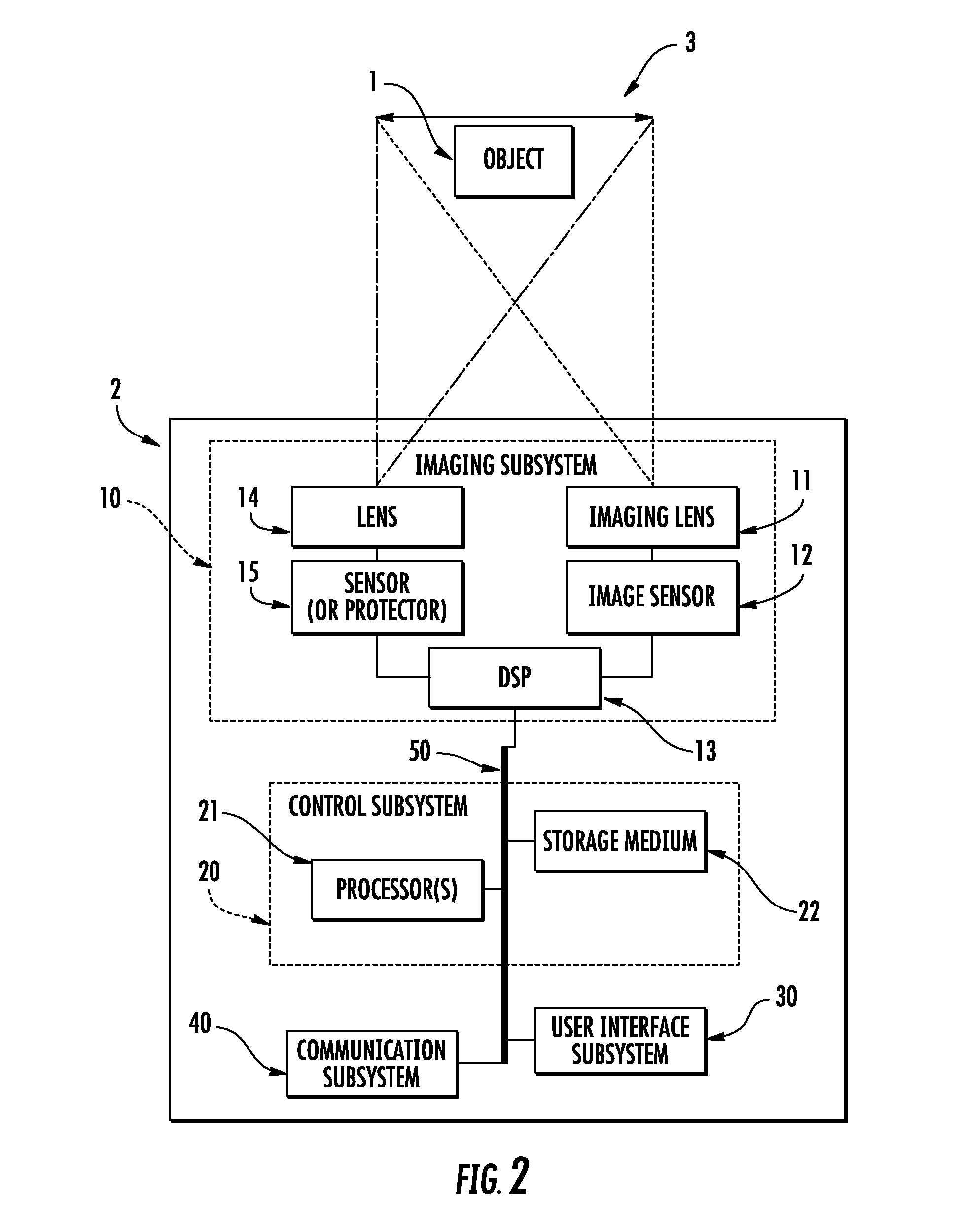
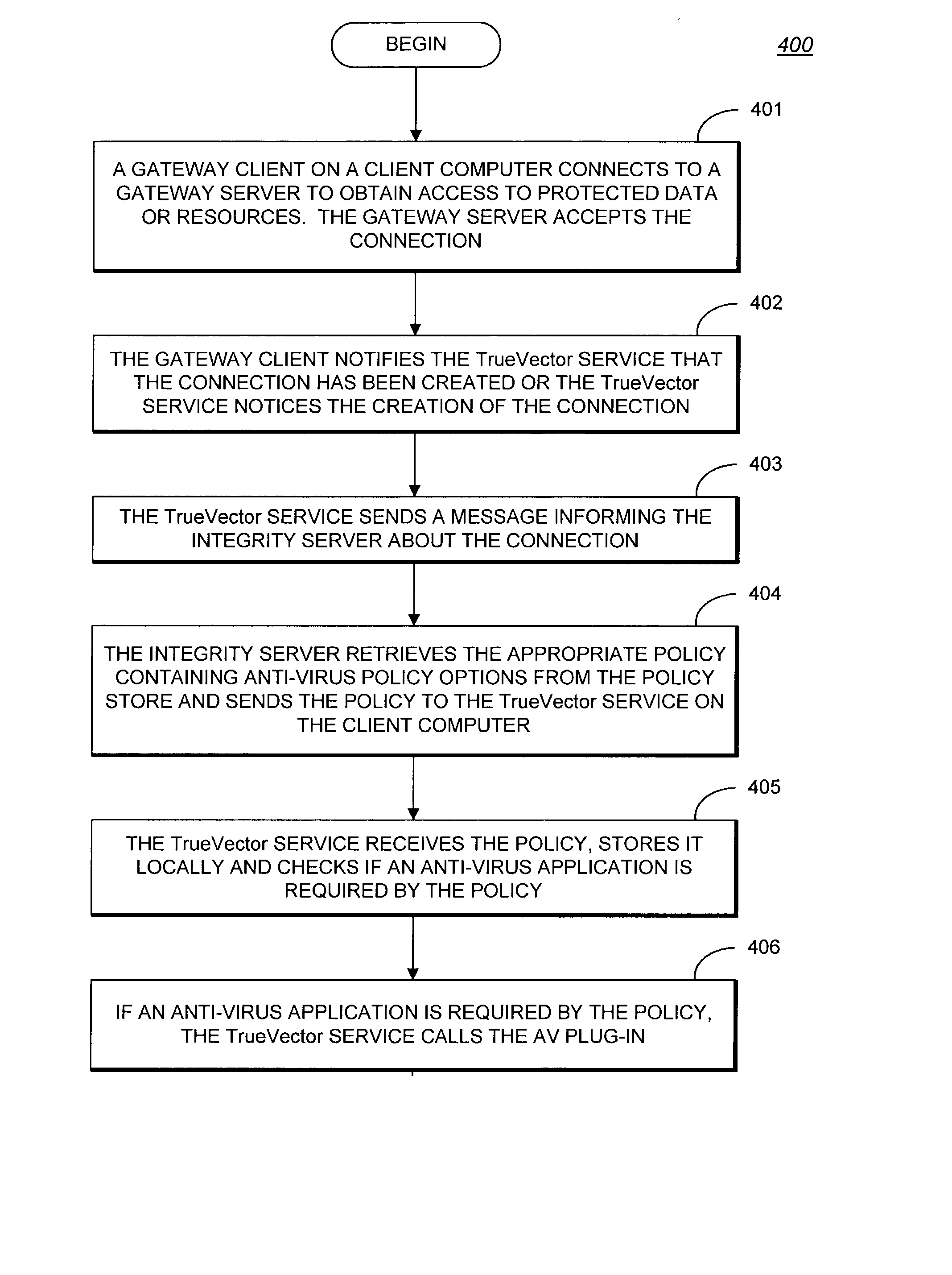
System and methods providing anti-virus cooperative enforcement
InactiveUS6873988B2Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
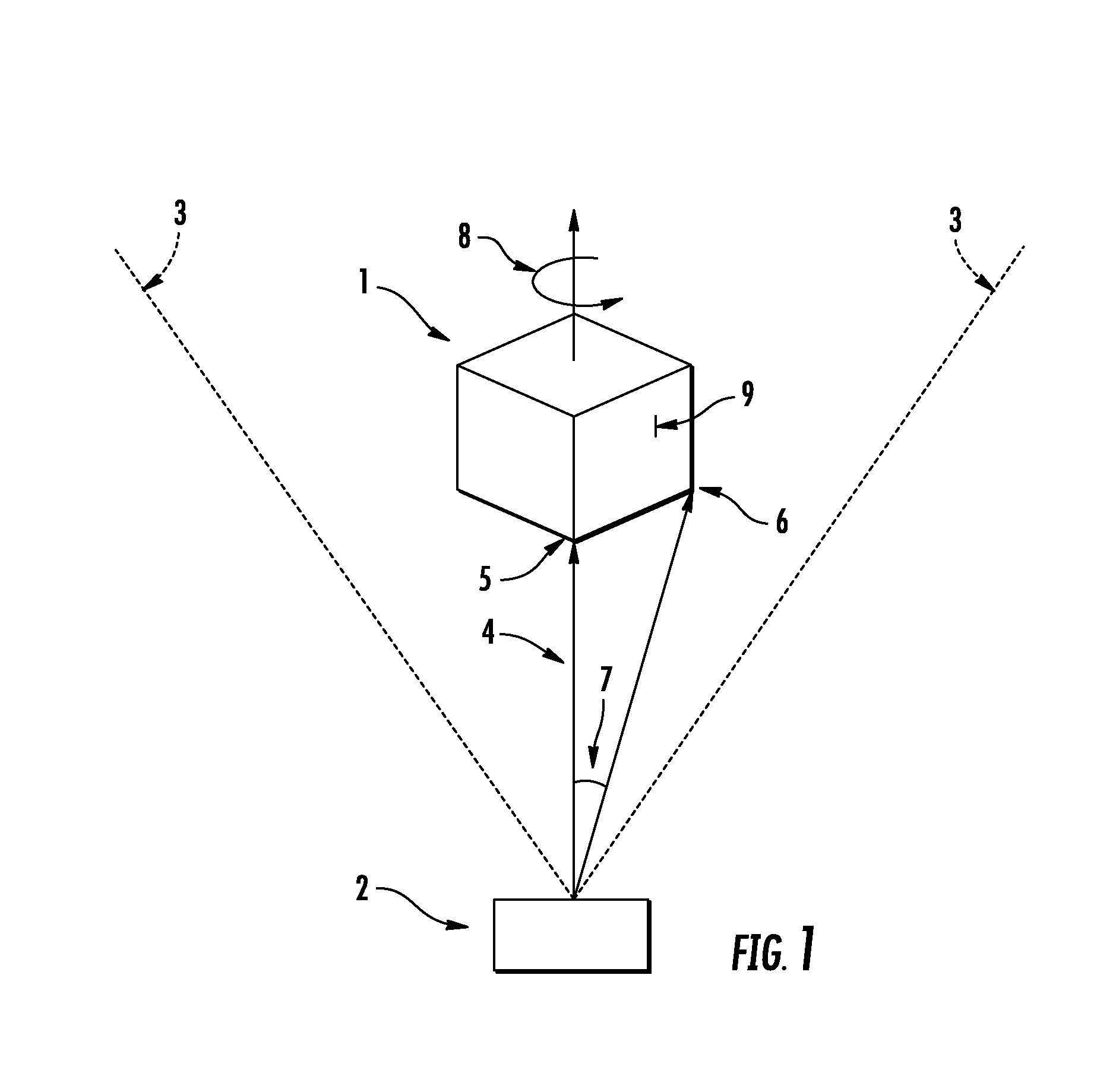
Handheld dimensioning system with measurement-conformance feedback
ActiveUS20160109219A1Color television detailsClosed circuit television systemsTechnical standardDimension measurement
A system and method for obtaining a dimension measurement that conforms to a conformance criteria is disclosed. The dimensioning system provides either (i) feedback to confirm that the measurement complies with the criteria or (ii) information on how the measurement geometry could be adjusted in order to provide a compliant measurement in a subsequent dimension measurement.
Owner:HAND HELD PRODS
System and methods providing anti-virus cooperative enforcement
InactiveUS20030055994A1Data processing applicationsMultiple digital computer combinationsAnti virusComputer network
A system providing methods for anti-virus cooperative enforcement is described. In response to a request from a device for access to protected resources, such as a network or protected data, a determination is made as to whether an anti-virus policy applies to the request for access made by the device. If an anti-virus policy is applicable, information pertaining to virus protection available on the device is collected. The virus protection information that is collected is evaluated to determine whether the device is in compliance with the anti-virus policy. If the device is determined to be in compliance with the anti-virus policy, the device is allowed to access the protected resources.
Owner:CHECK POINT SOFTWARE TECH INC
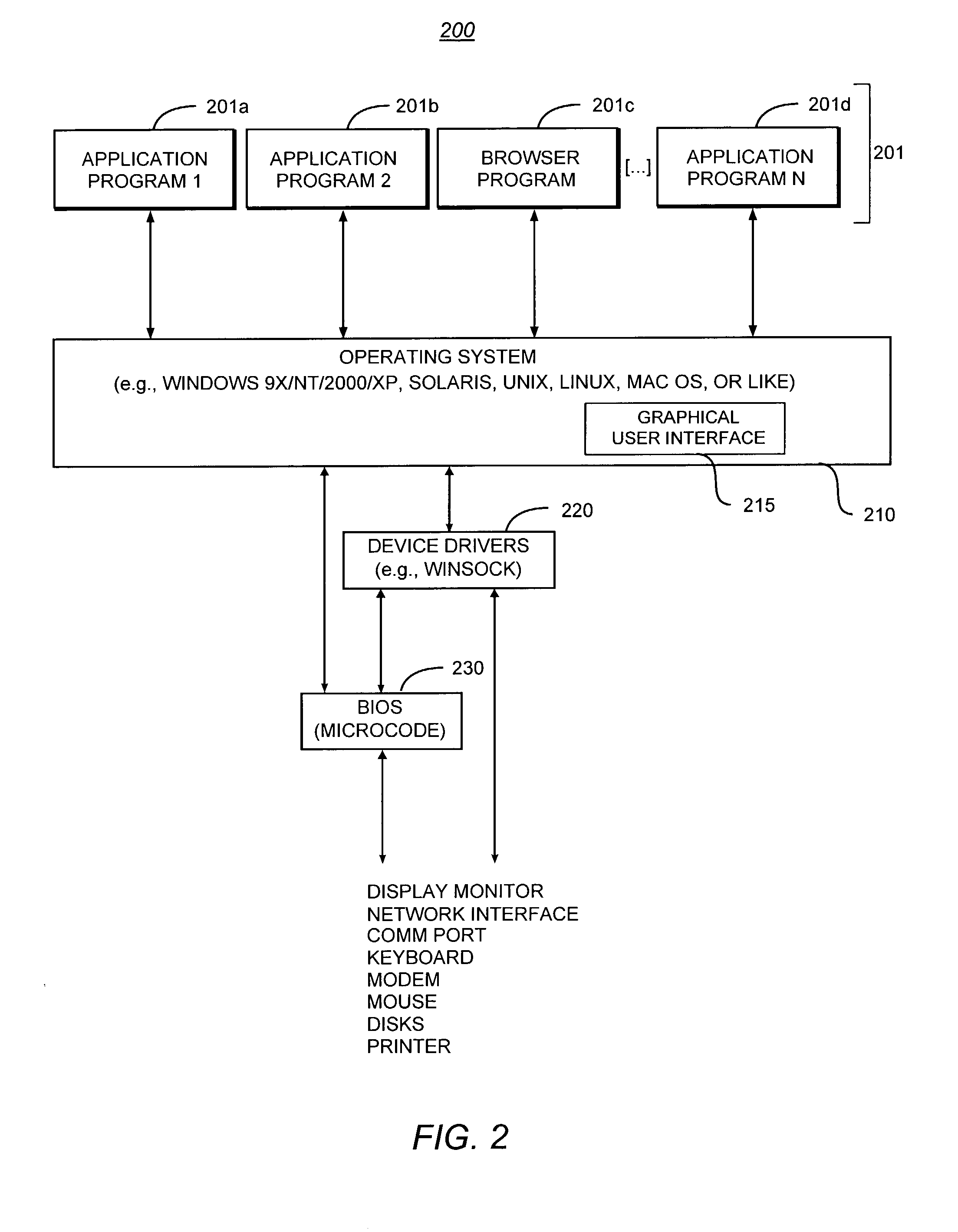
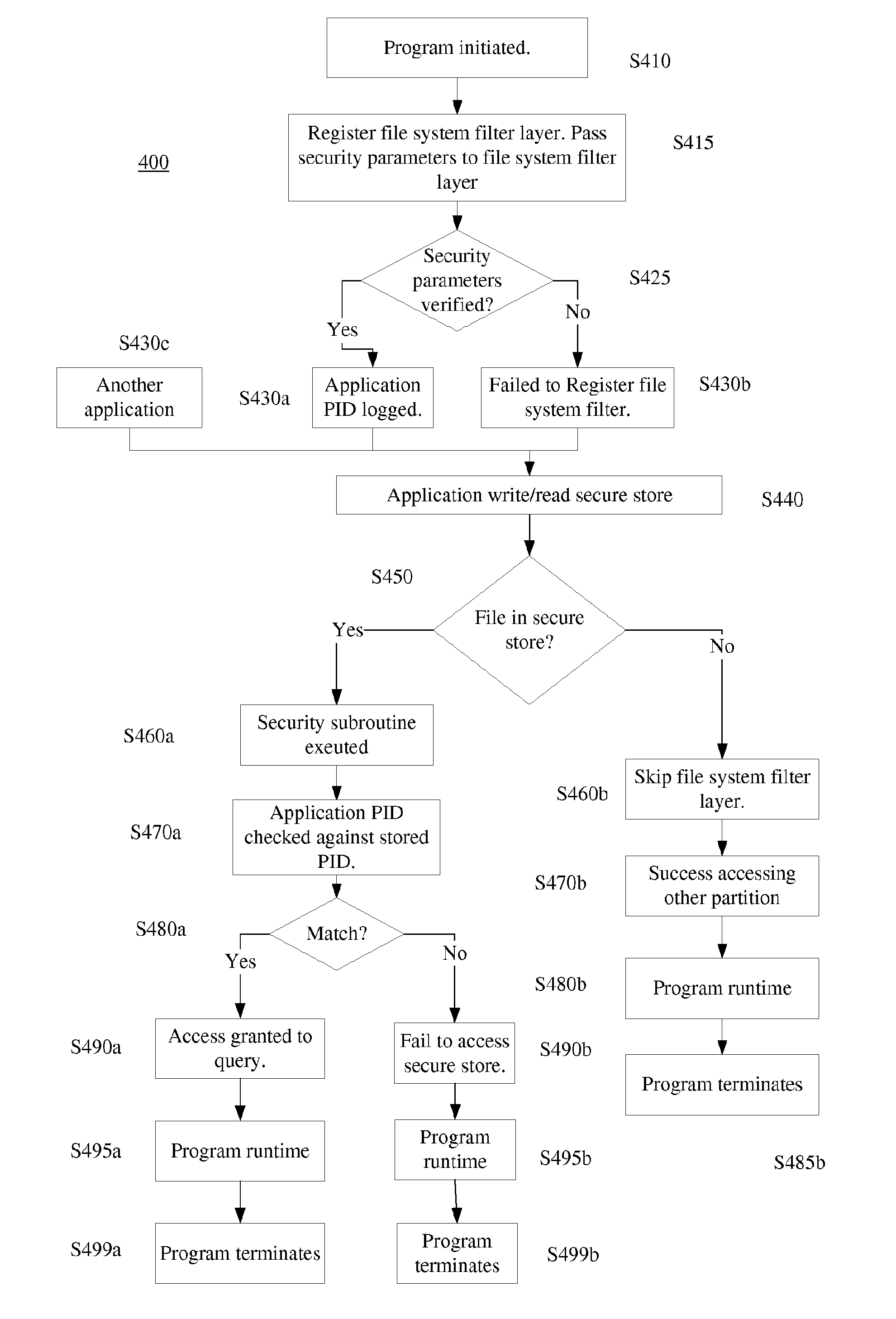
Design pattern for secure store
ActiveUS20150220753A1Improve securityDigital data processing detailsAnalogue secracy/subscription systemsPathPingFile system
A computer system, computer product, and method for accessing a secure store, which includes receiving a request to access a secure store, checking the file path of the request to make sure it exists in the secure store, verifying security parameters from the process at the file system filter layer, saving the PID of the process by the file system filter layer, comparing the saved PID to the process's PID, and allowing the process to access the path in the secure store specified in the request.
Owner:HONEYWELL INT INC
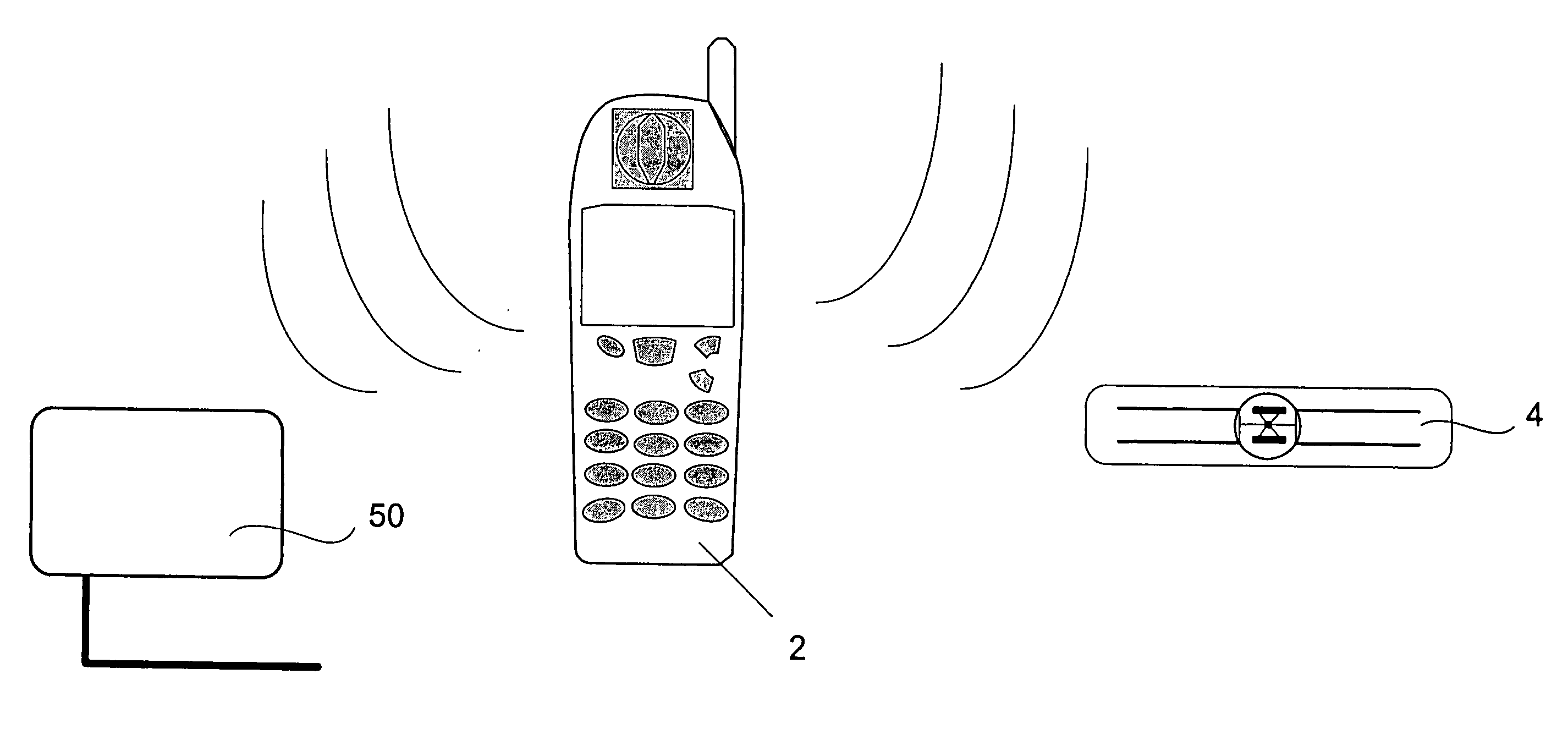
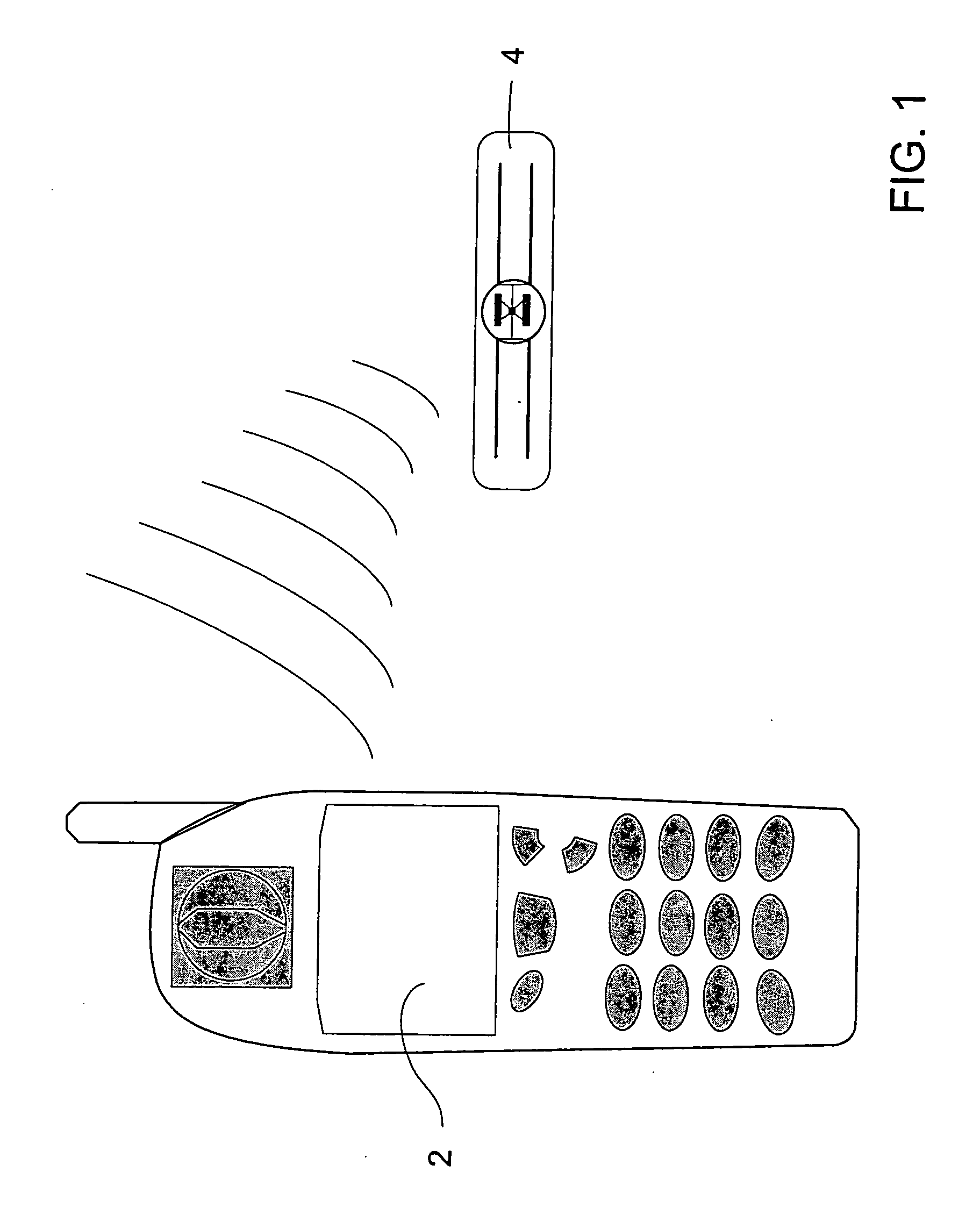
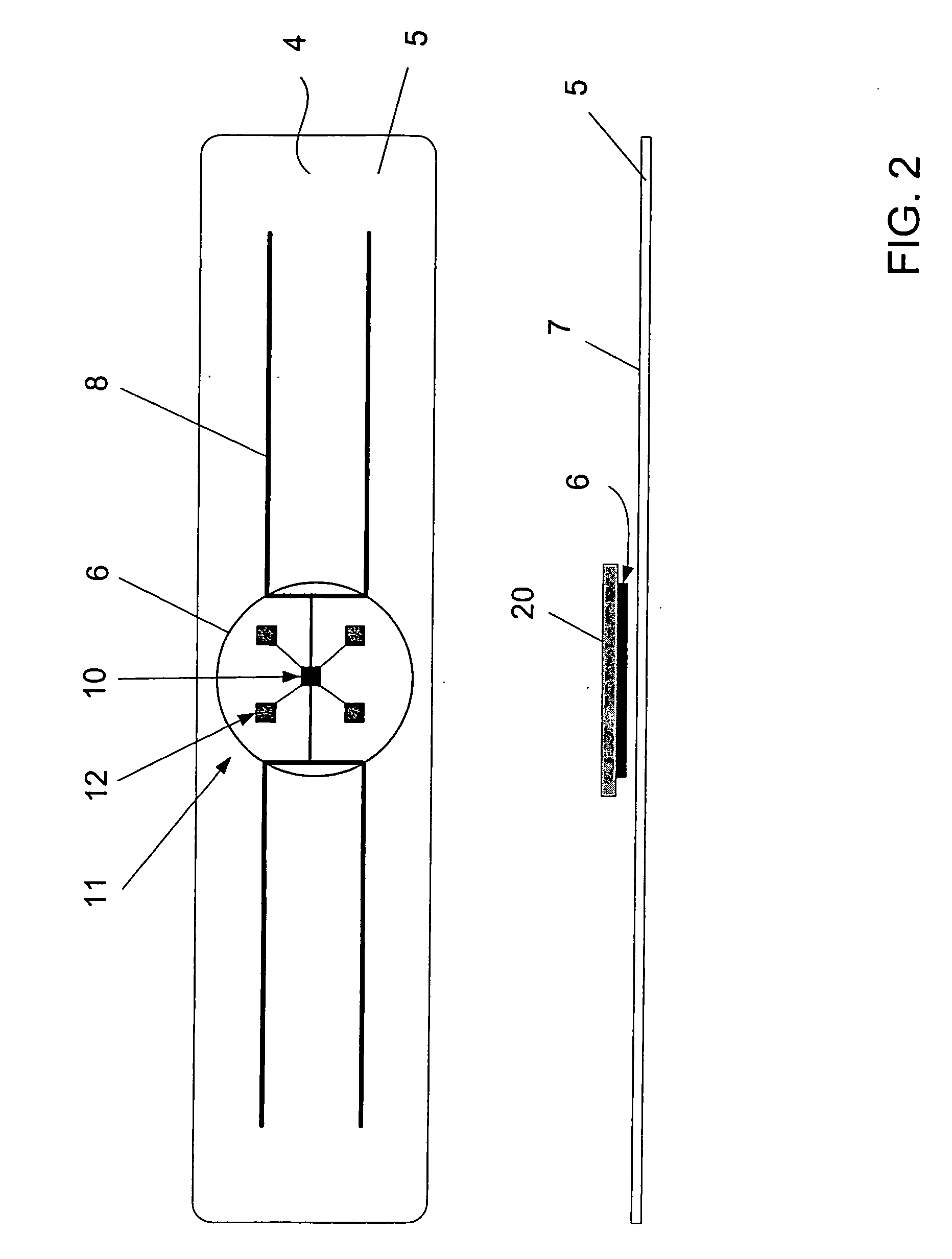
Diagnostic radio frequency identification sensors and applications thereof
ActiveUS20060290496A1Low costDevices with bluetooth interfacesBurglar alarm mechanical actuationPower sensorPoint of care
An integrated passive wireless chip diagnostic sensor system is described that can be interrogated remotely with a wireless device such as a modified cell phone incorporating multi-protocol RFID reader capabilities (such as the emerging Gen-2 standard) or Bluetooth, providing universal easy to use, low cost and immediate quantitative analyses, geolocation and sensor networking capabilities to users of the technology. The present invention can be integrated into various diagnostic platforms and is applicable for use with low power sensors such as thin films, MEMS, electrochemical, thermal, resistive, nano or microfluidic sensor technologies. Applications of the present invention include on-the-spot medical and self-diagnostics on smart skin patches, Point of Care (POC) analyses, food diagnostics, pathogen detection, disease-specific wireless biomarker detection, remote structural stresses detection and sensor networks for industrial or Homeland Security using low cost wireless devices such as modified cell phones.
Owner:ALTIVERA
Vehicle charger safety system and method
InactiveUS20110074346A1Safety concern can be addressedFix security issuesMultiple-port networksBatteries circuit arrangementsForeign objectSystem identification
Wireless vehicle charger safety systems and methods use a detection subsystem, a notification subsystem and a management subsystem. The detection subsystem identifies a safety condition. The notification subsystem provides an indication of the safety condition. The management subsystem addresses the safety condition. In particular, undesirable thermal conditions caused by foreign objects between a source resonator and a vehicle resonator are addressed by sensing high temperatures, providing a warning and powering down a vehicle charger, as appropriate for the environment in which the charger is deployed.
Owner:WITRICITY CORP
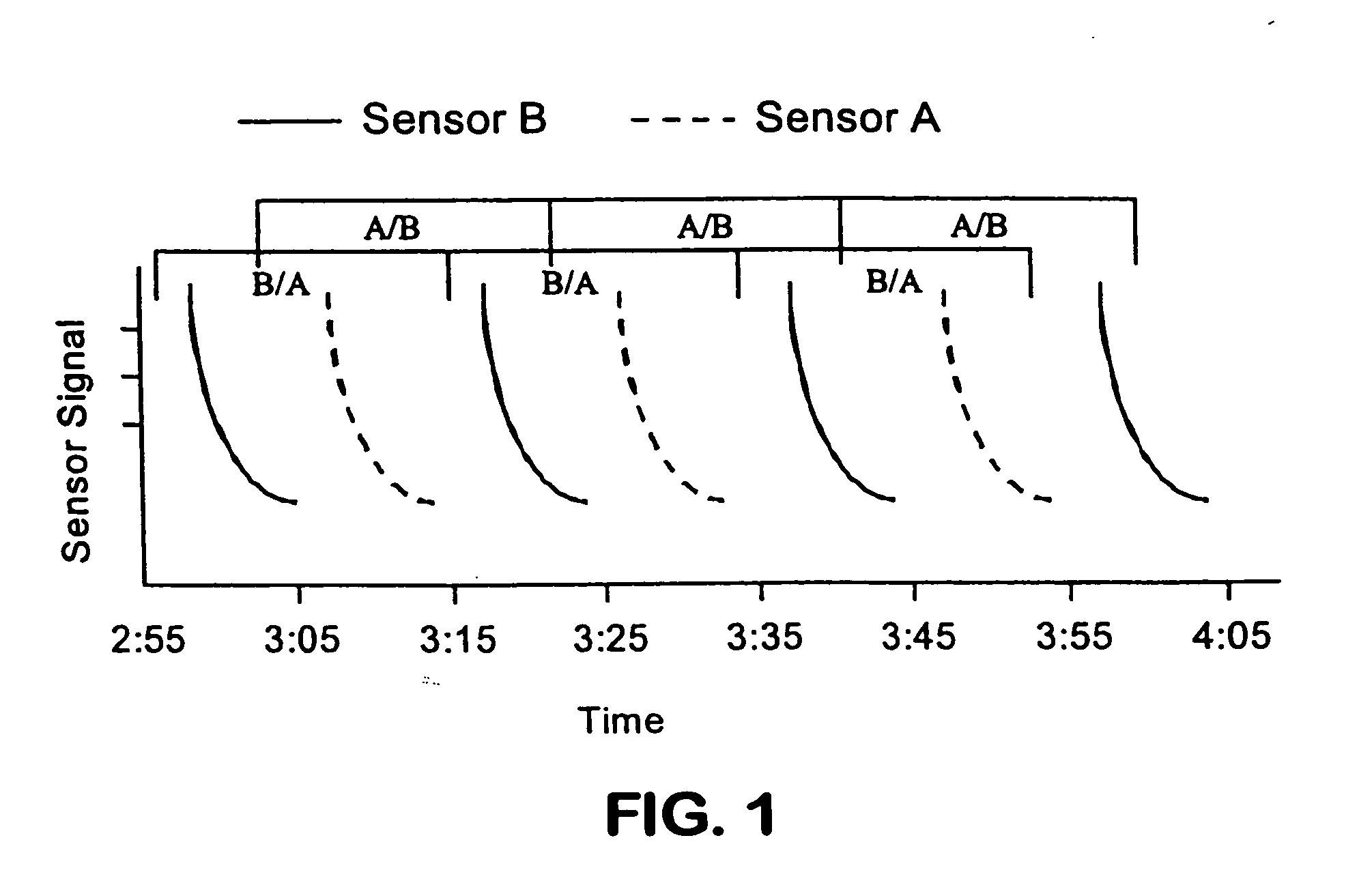
System and method for monitoring the life of a physiological sensor
Owner:JPMORGAN CHASE BANK NA
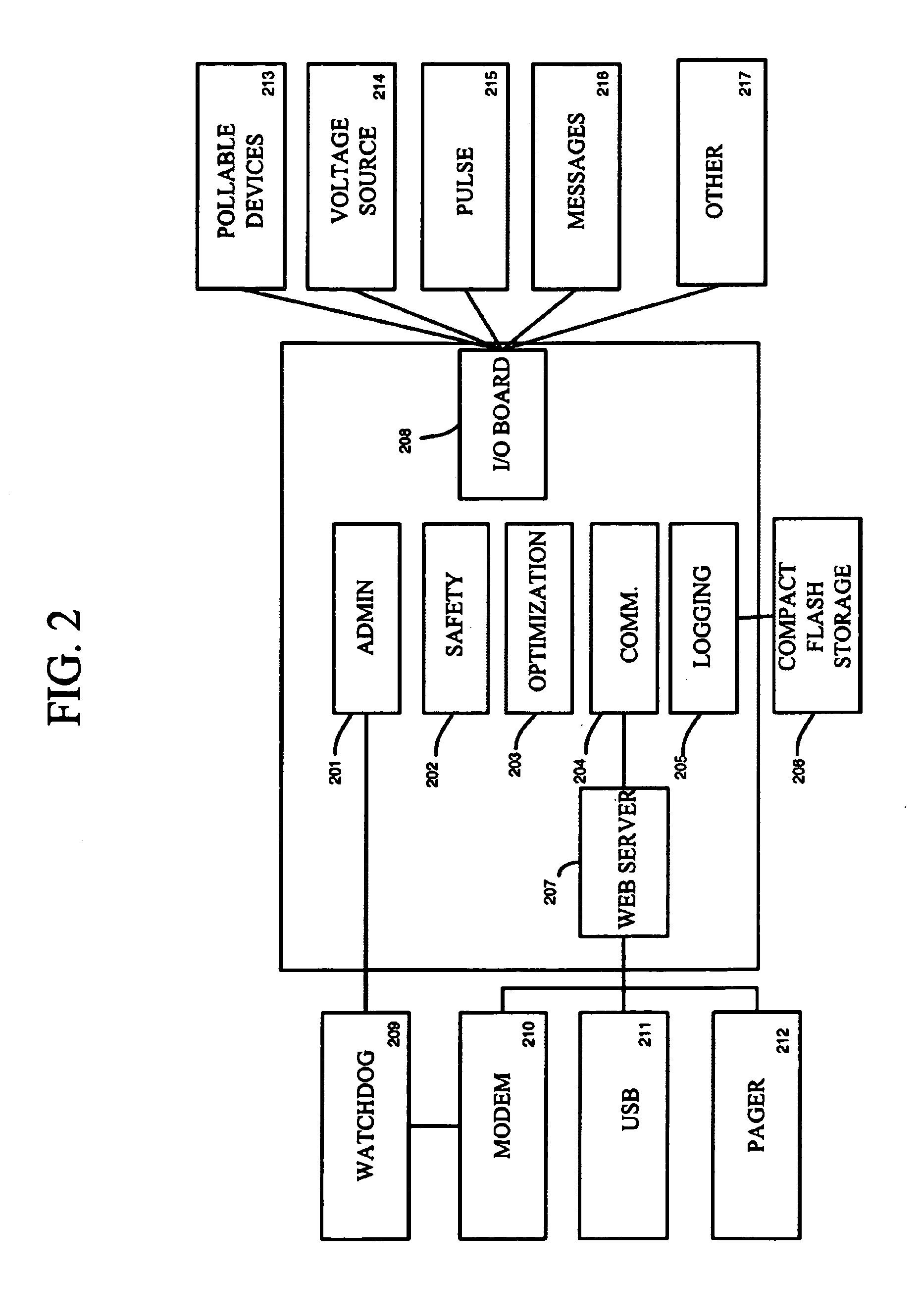
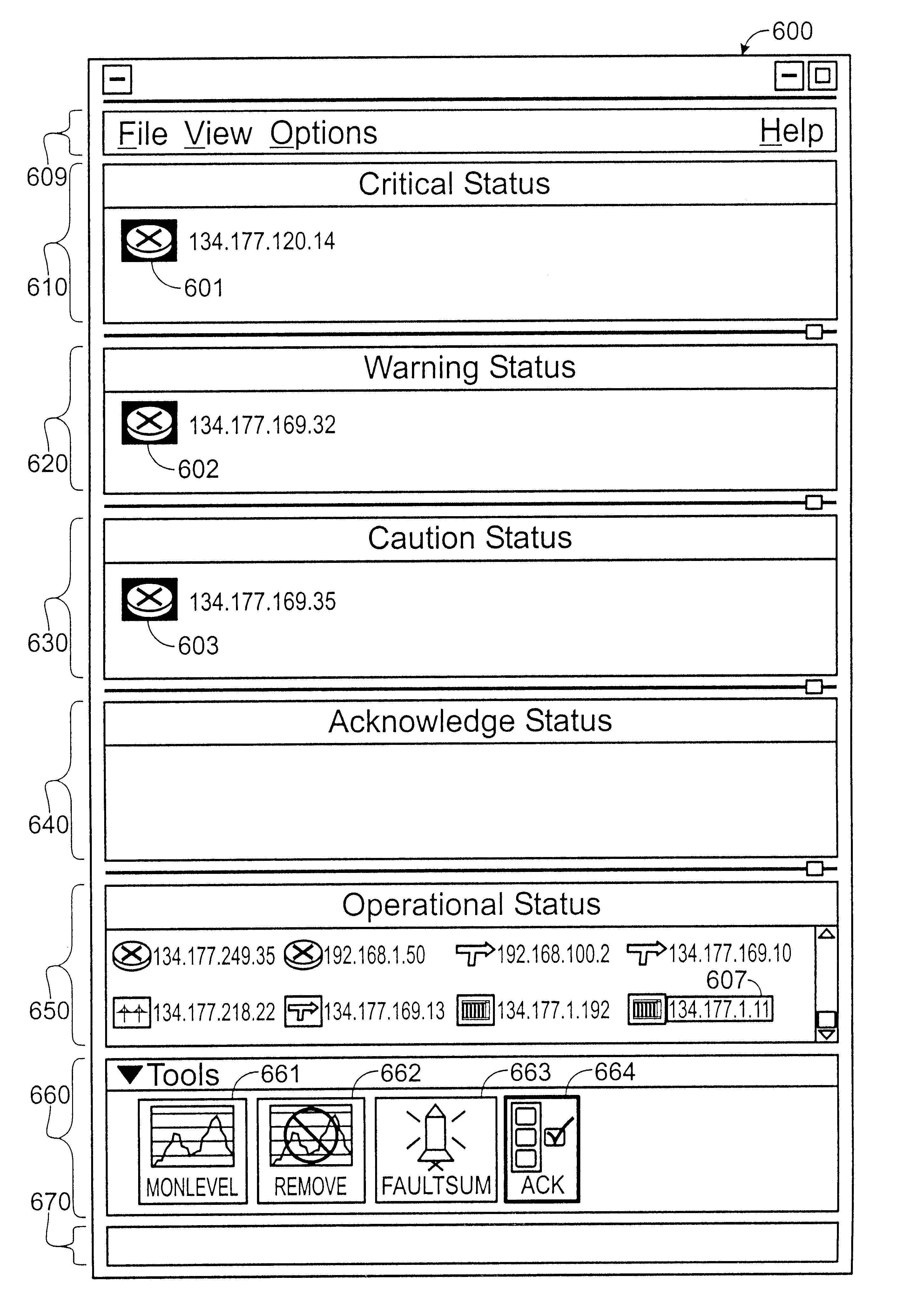
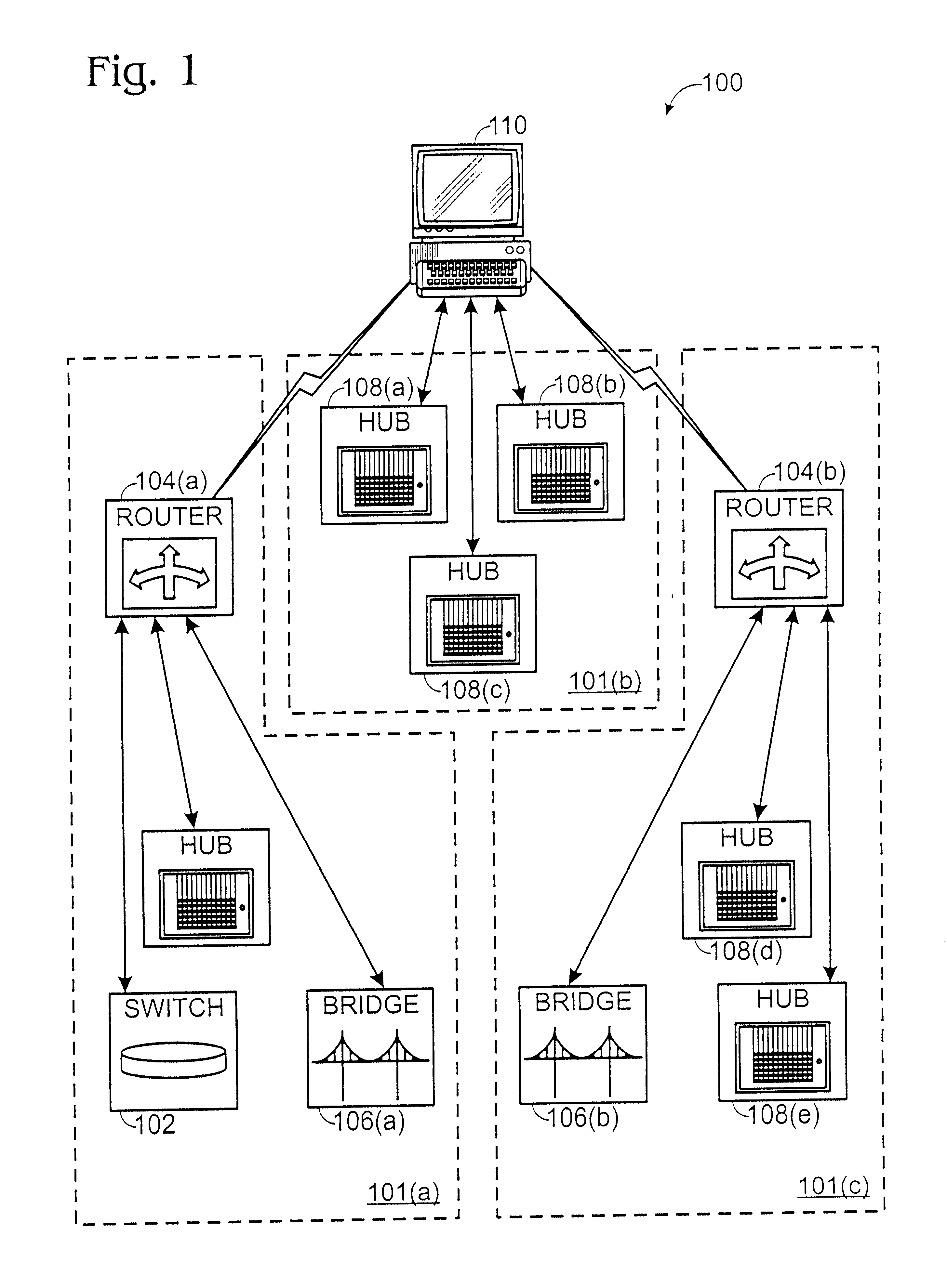
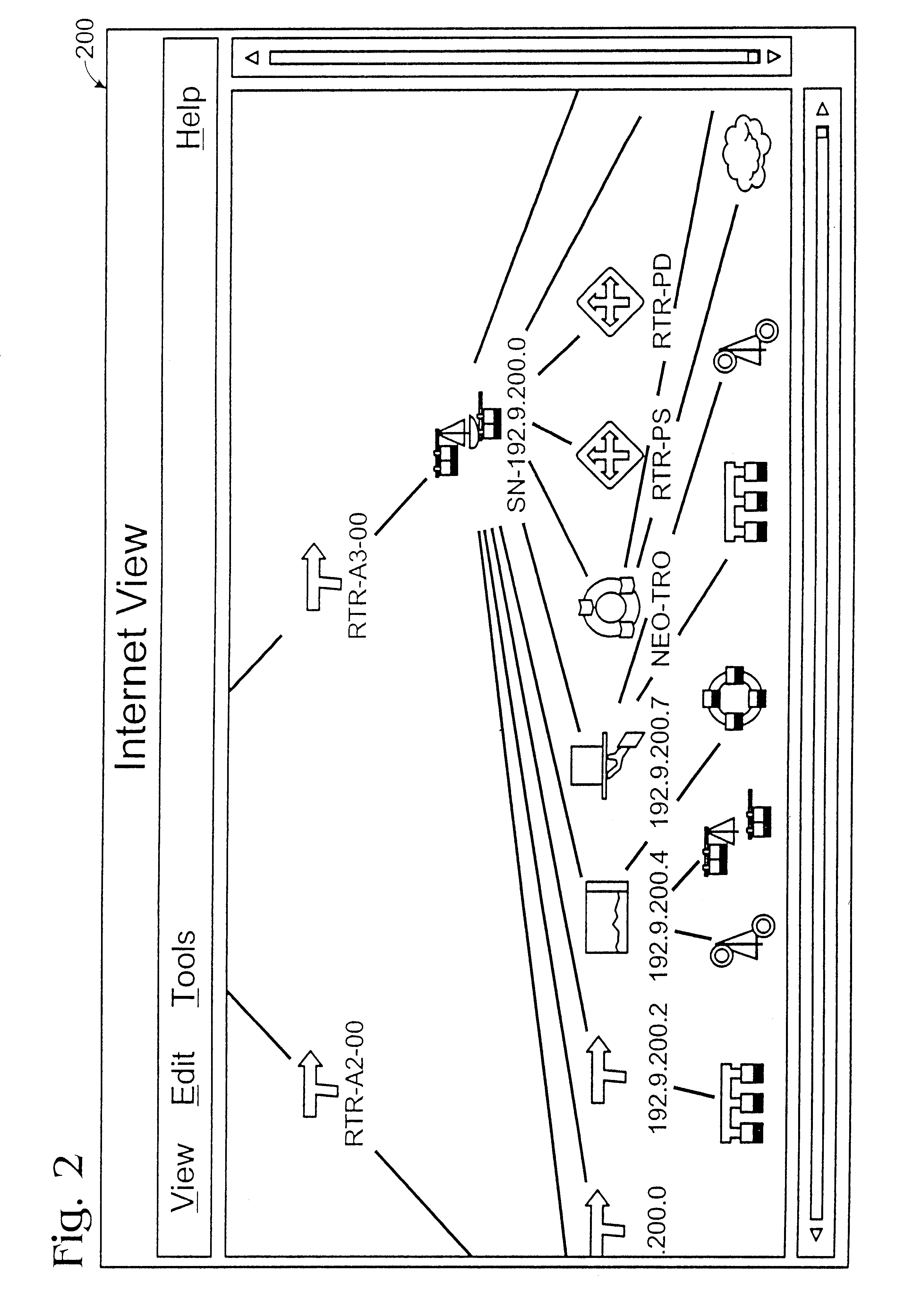
Method and apparatus for displaying health status of network devices
A method and apparatus for concurrently displaying from a single window on a network management station the health status of all network devices and objects of a computer network. The network devices may be categorized according to state or device type, as determined by the network manager. The method and apparatus provides a network manager with the ability to determine the current state of network devices and objects within an enterprise network and invoke further actions such as configuration, performance, fault, and security management tasks. The network manager can drag and drop icons from one network management system application window to another network management system application window to obtain fault information about network devices and objects, thus allowing multiple network management system applications to run concurrently on the same network management station. The network manager is further able to add new network devices and objects by dragging site, folder or device icons from one network management system application window to a second network management system application window for displaying the health status of the new devices. The dragged-in devices are added to the appropriate status panes within the second window according to the method of the present invention.
Owner:NORTEL NETWORKS LTD
Testing tool comprising an automated multidimensional traceability matrix for implementing and validating complex software systems
InactiveUS20050166094A1Easy to createSoftware testing/debuggingSpecific program execution arrangementsSoftware systemComputer science
The present invention relates to a testing tool for testing of complex software systems having a plurality of interrelated system components and a suite of test scenarios for testing the performance of the plurality of interrelated system components. The testing tool includes an Automated Multidimensional Traceability Matrix system for determining linkages between interrelated system components, a means for identifying a change in one or more of the interrelated system components, a means for applying the Automated Multidimensional Traceability Matrix, a means for executing all of or a subset of the test scenarios associated with the interrelated system components that may be affected by the change and a means for evaluating the results of the executed test scenarios.
Owner:KIMBERLY-CLARK WORLDWIDE INC
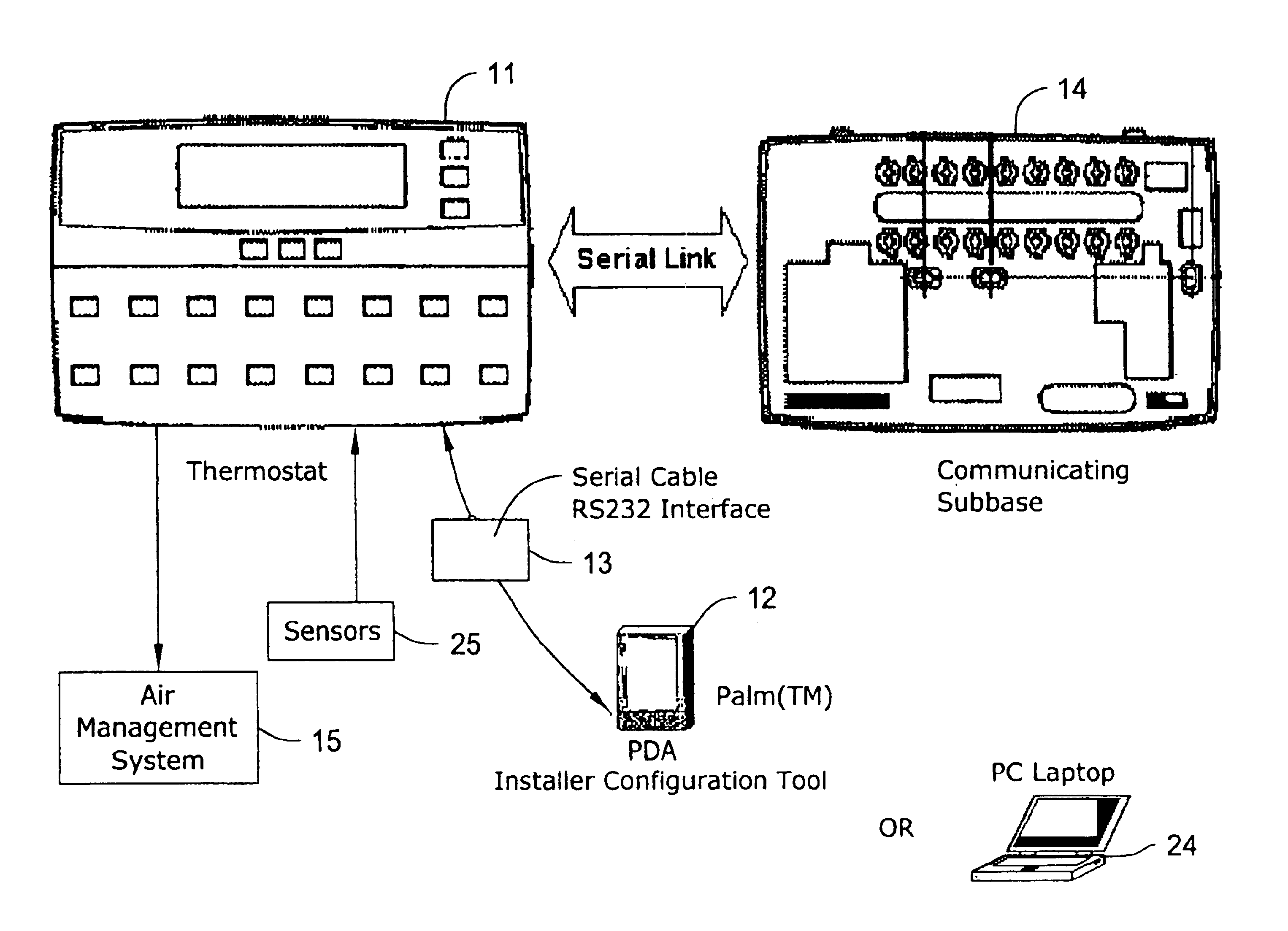
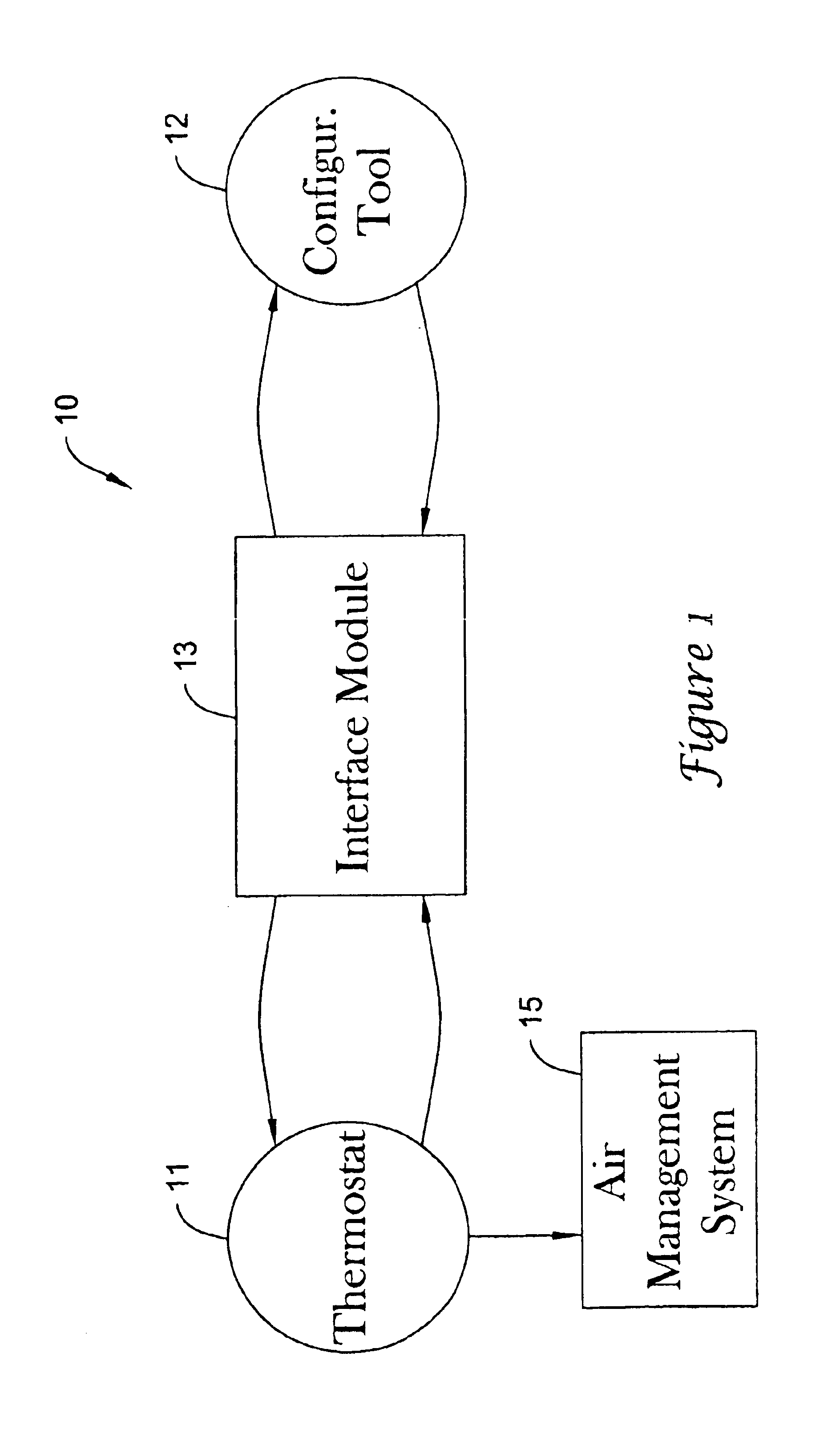
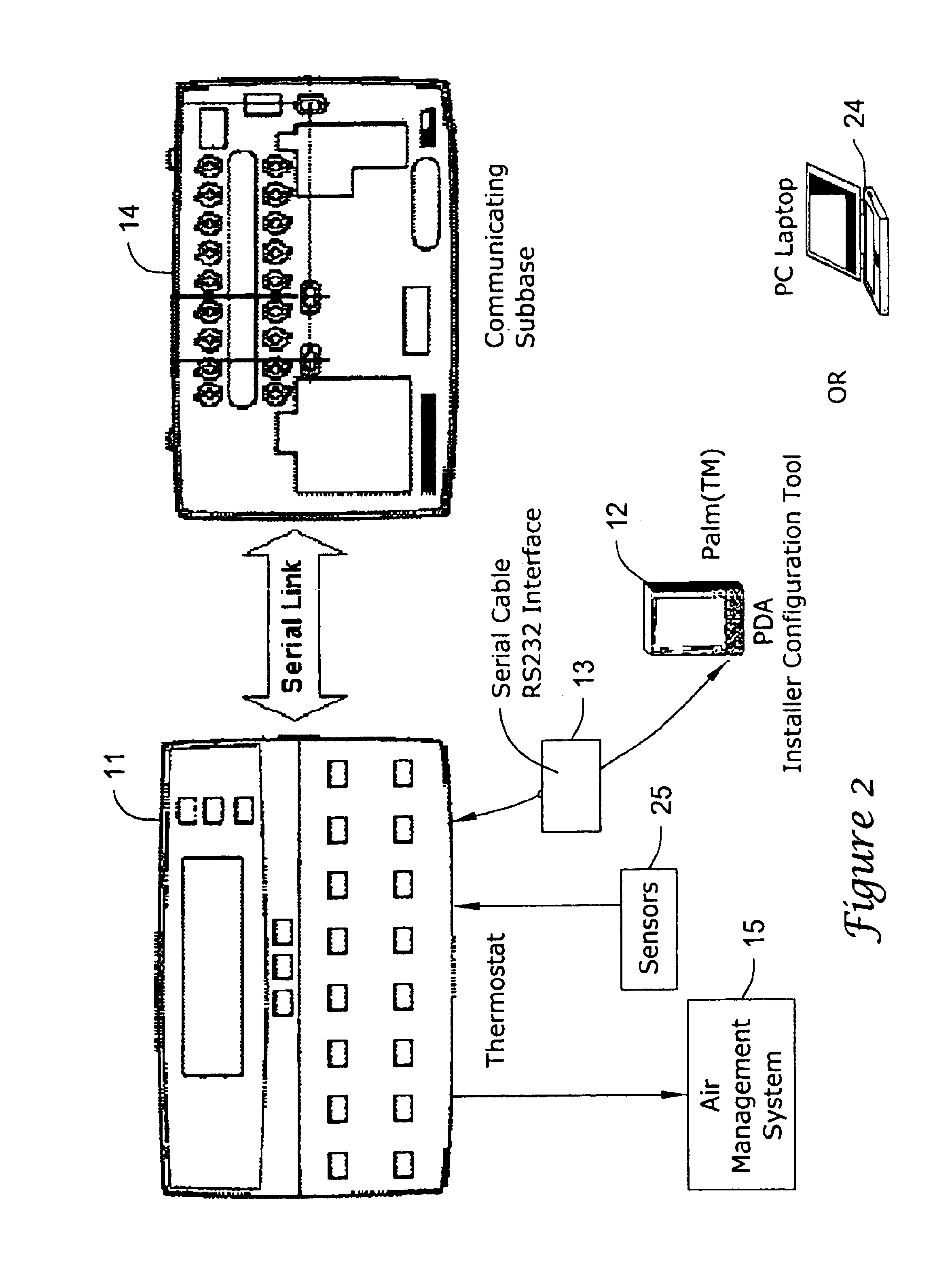
PDA diagnosis of thermostats
InactiveUS6851621B1Less expertiseActivity can be delayedMechanical apparatusStatic/dynamic balance measurementThermostatSet point
A system PDA-based on line diagnostics for automatically discovering a thermostat configuration, turning off normal controller delays, temporary overriding sensor inputs and set points, and verifying proper output action including the monitoring the discharge air temperature for the resulting temperature behavior based on the equipment stages activated. The diagnosis may include the testing of sensors, set points, the fan, cooling equipment, heating equipment and the wiring connecting the controls with the fan, and the cooling and heating equipment. Problems discovered may be reported, automatically recorded and the original operating parameters may be restored.
Owner:HONEYWELL INT INC
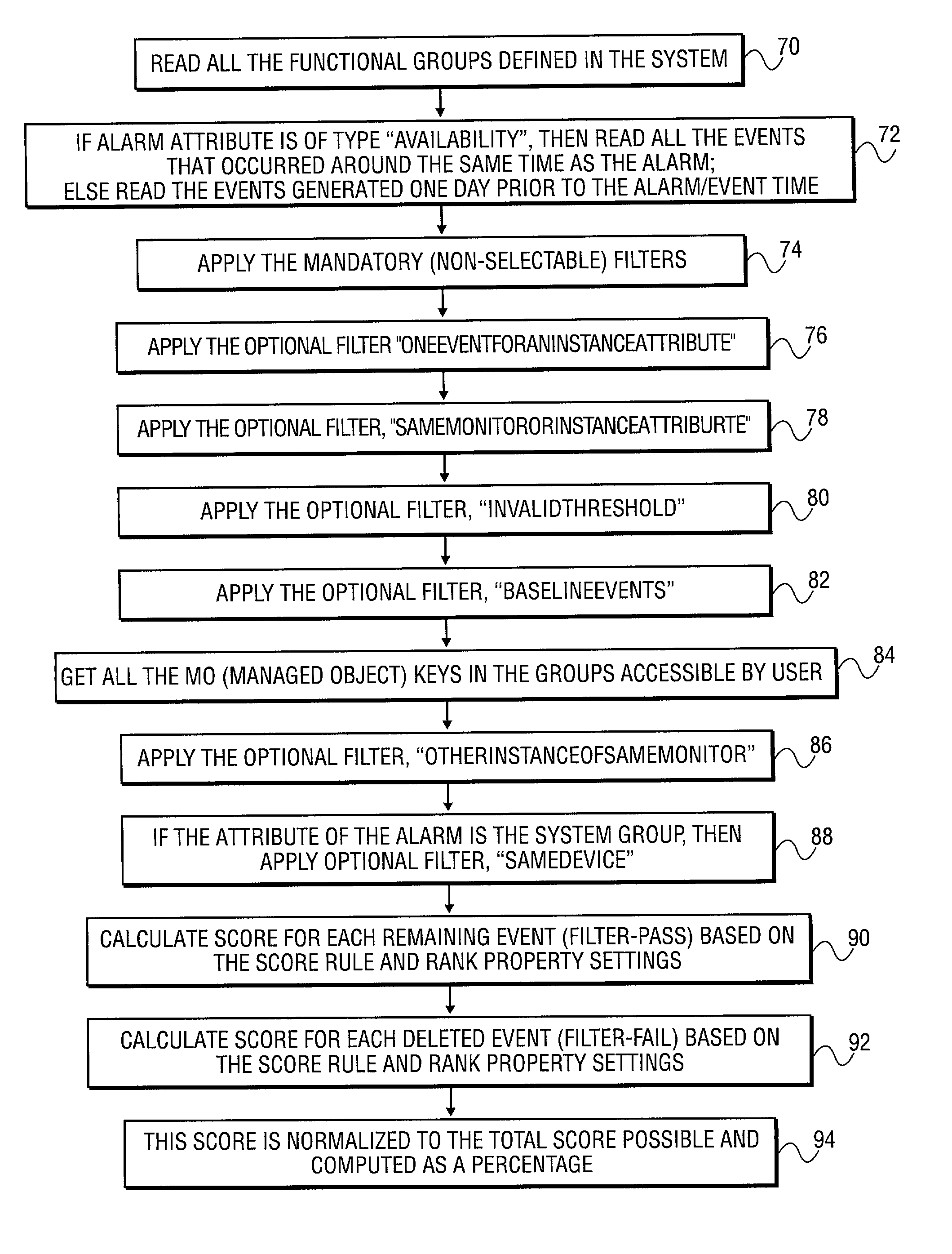
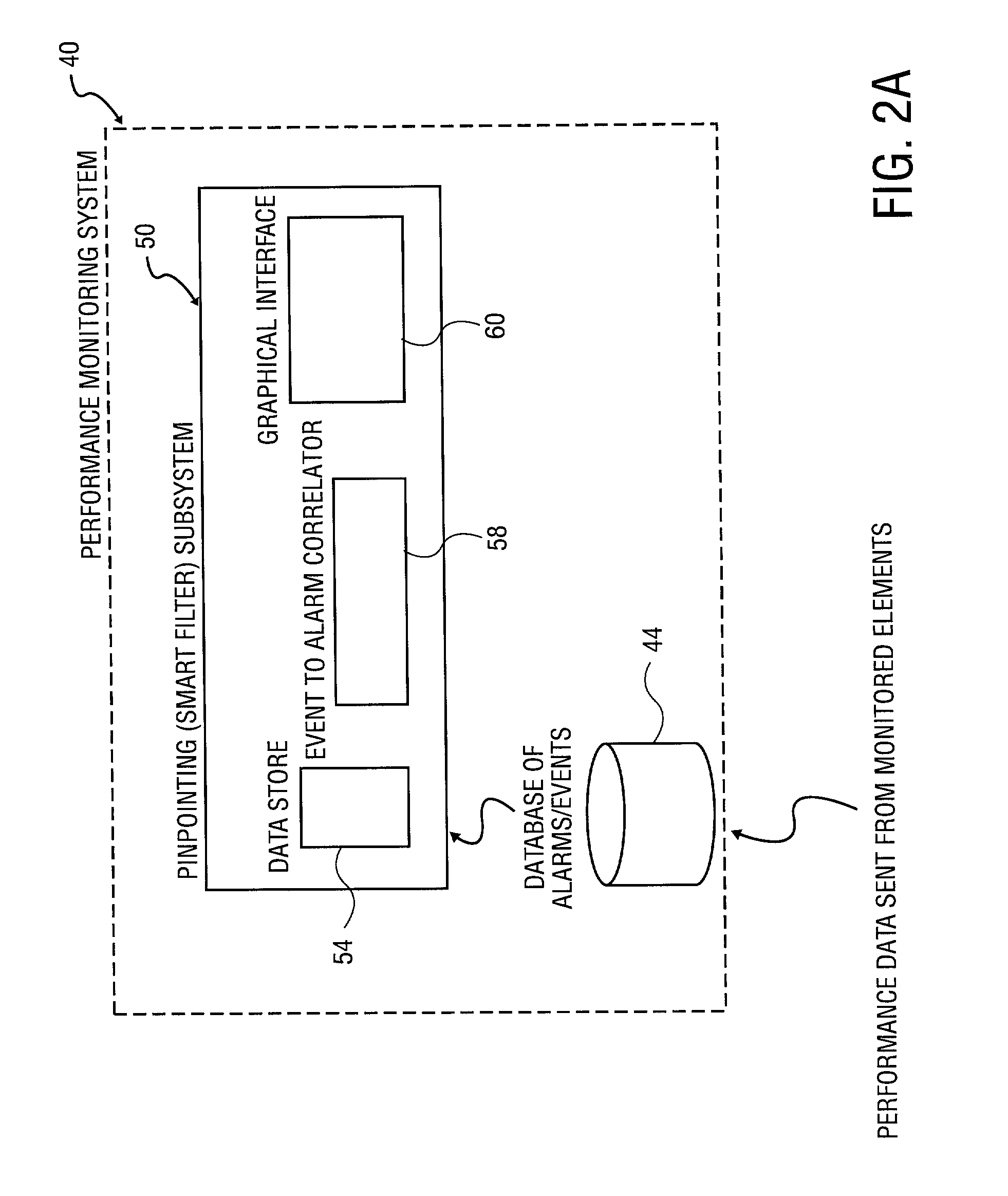
Method and system to correlate a specific alarm to one or more events to identify a possible cause of the alarm
A system is provided to monitor network performances. The system maintains a database of performance abnormalities, alarms and events from a system of monitored elements. The system automatically identifies a possible cause of a specific alarm by correlating the specific alarm with a plurality of events using the database. The system displays the cause of the specific alarm. The database includes alarms and events of network devices, network systems, and network applications. The specific alarm consists of a notification of an occurrence of the plurality of events.
Owner:BMC SOFTWARE
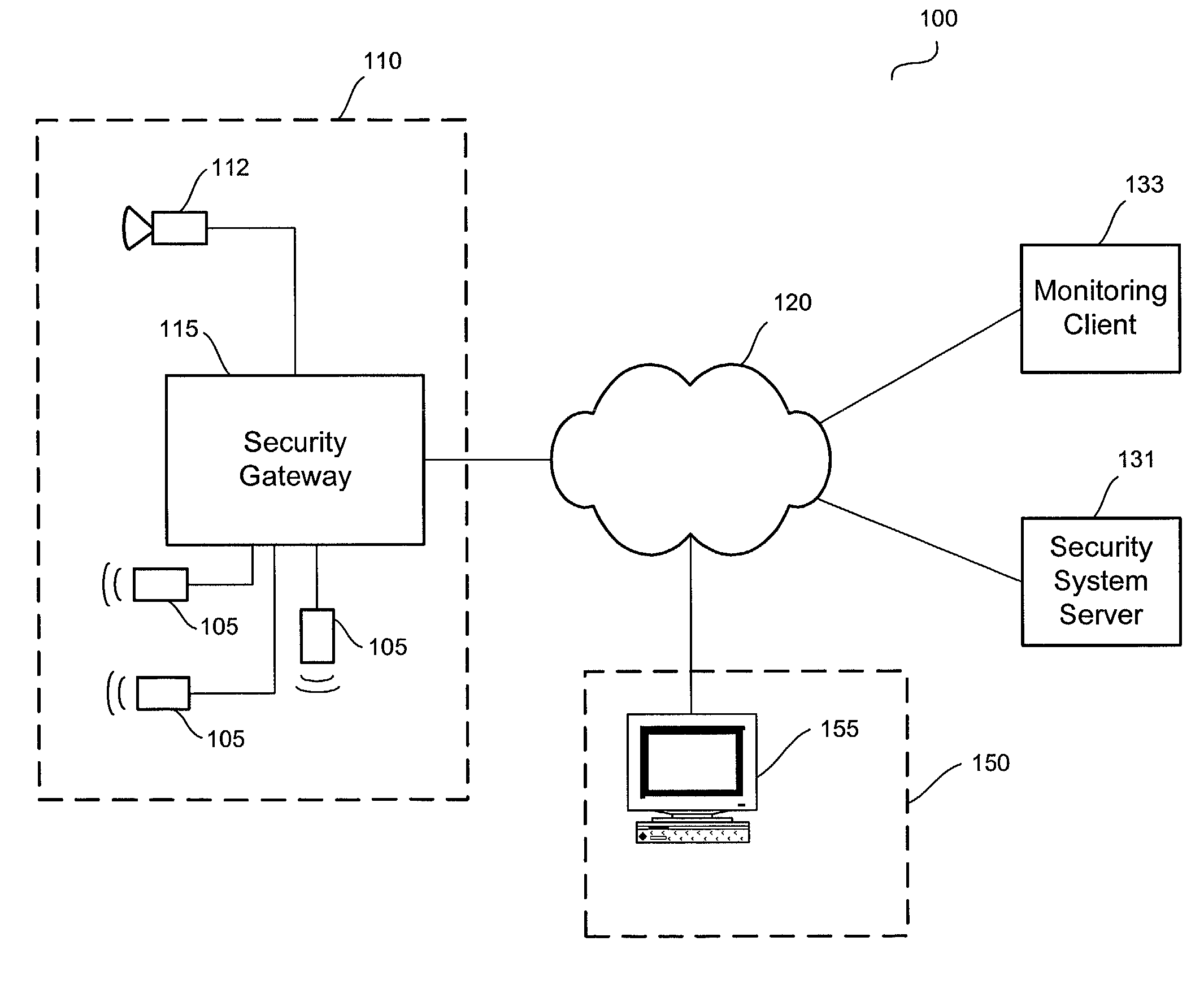
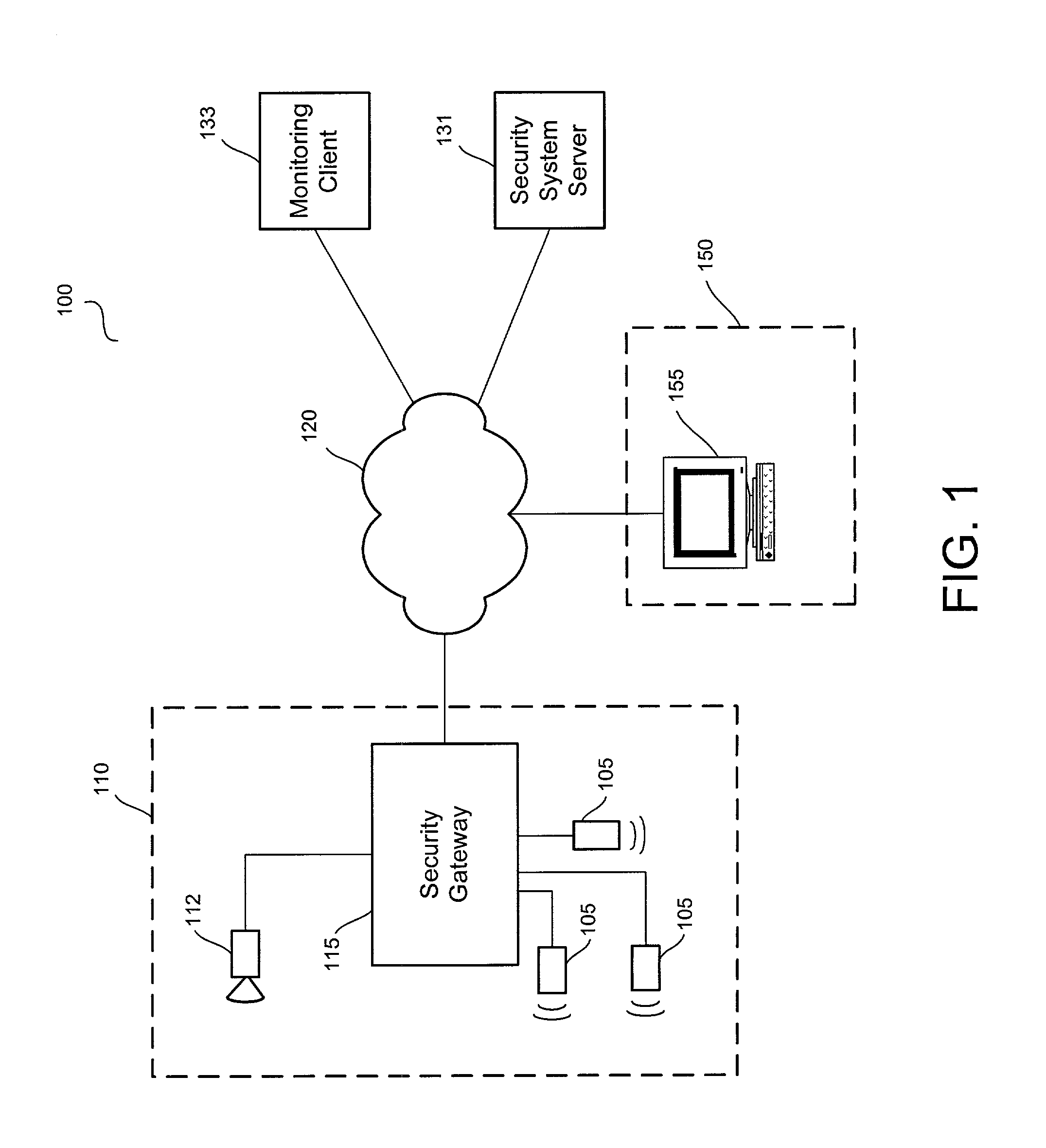
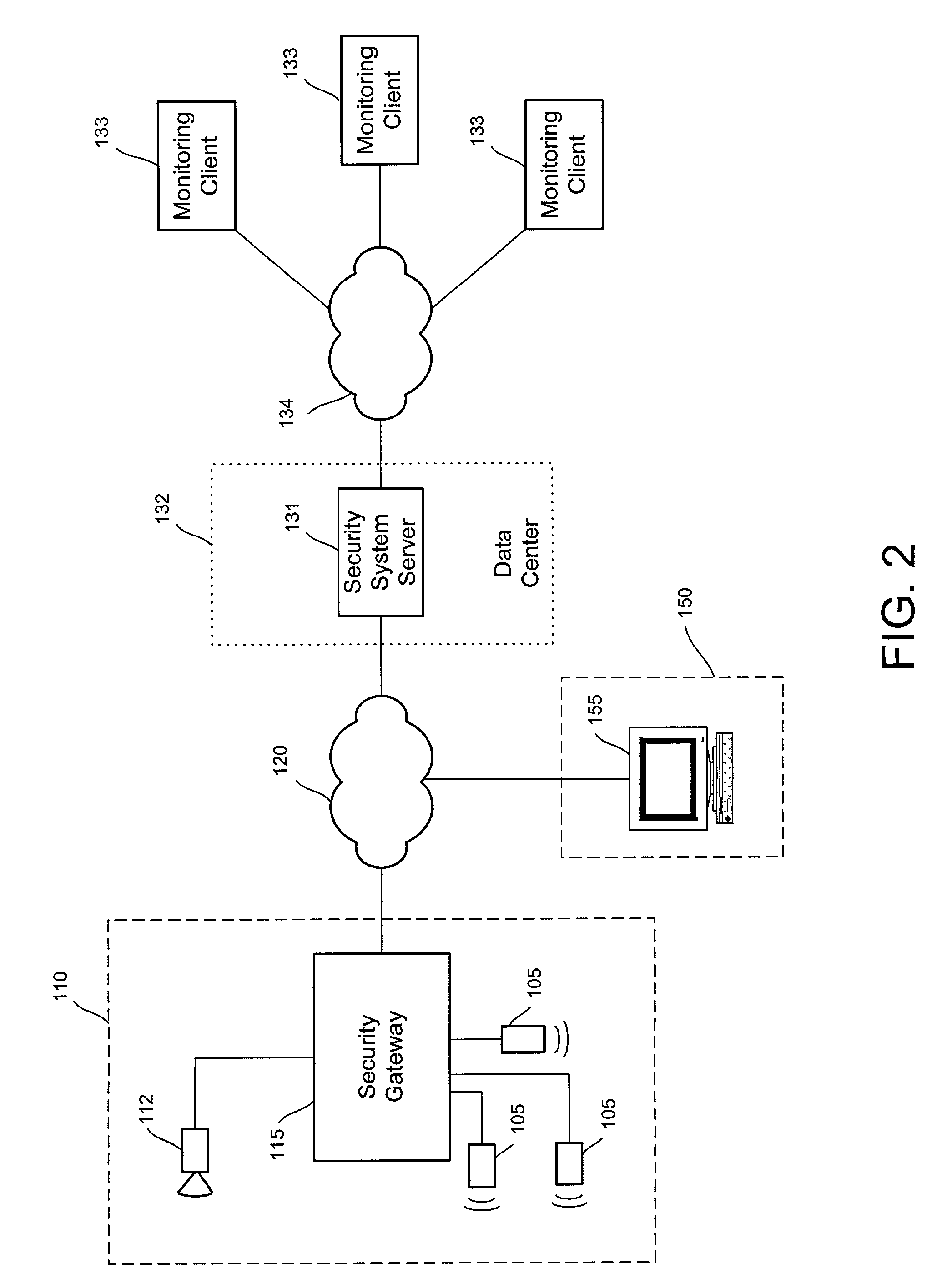
Distributed monitoring for a video security system
A system and method for distributed monitoring and remote verification of conditions surrounding an alarm condition in a security system. A security gateway detects alarm conditions at a premises and records video relating to the alarm condition. The security gateway transmits an alarm notification and the video across a network to a security system server in substantially real time. The security system server relays information to one or more distributed monitoring clients using rules-based routines for verification of the alarm condition. An operator at a monitoring client determines whether the alarm condition represents an actual alarm event and activates an appropriate response.
Owner:COMCAST CABLE COMM LLC
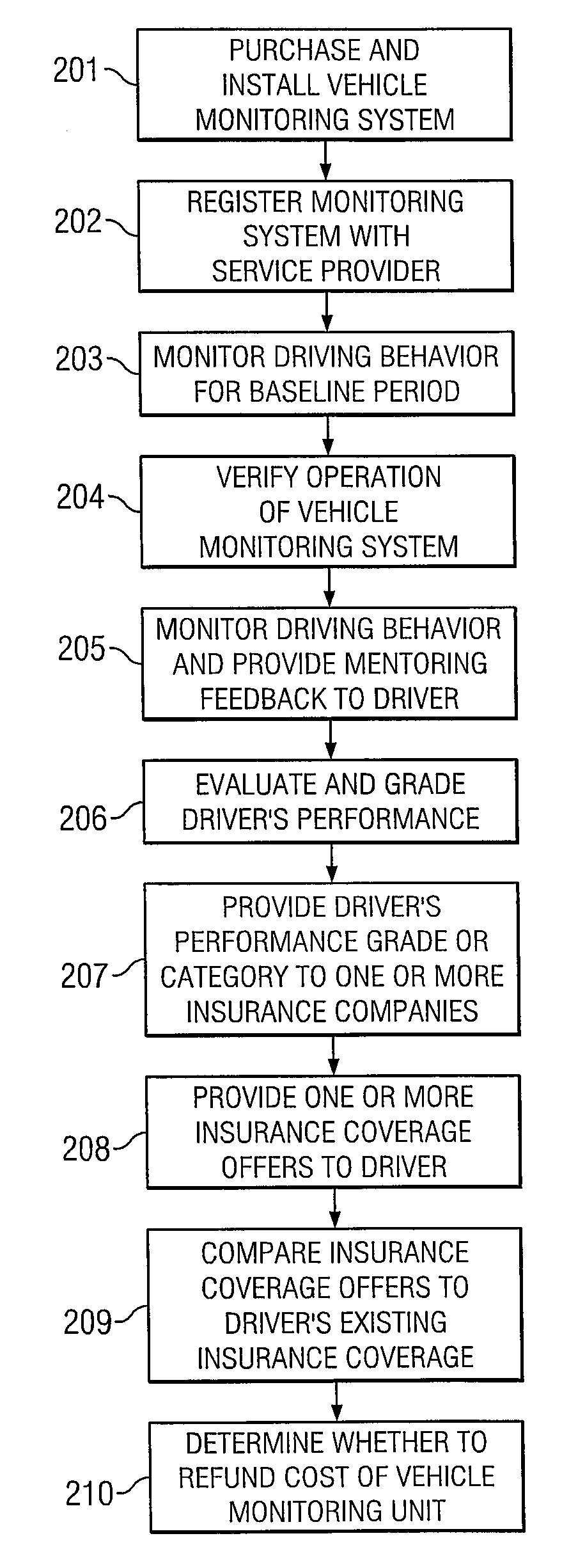
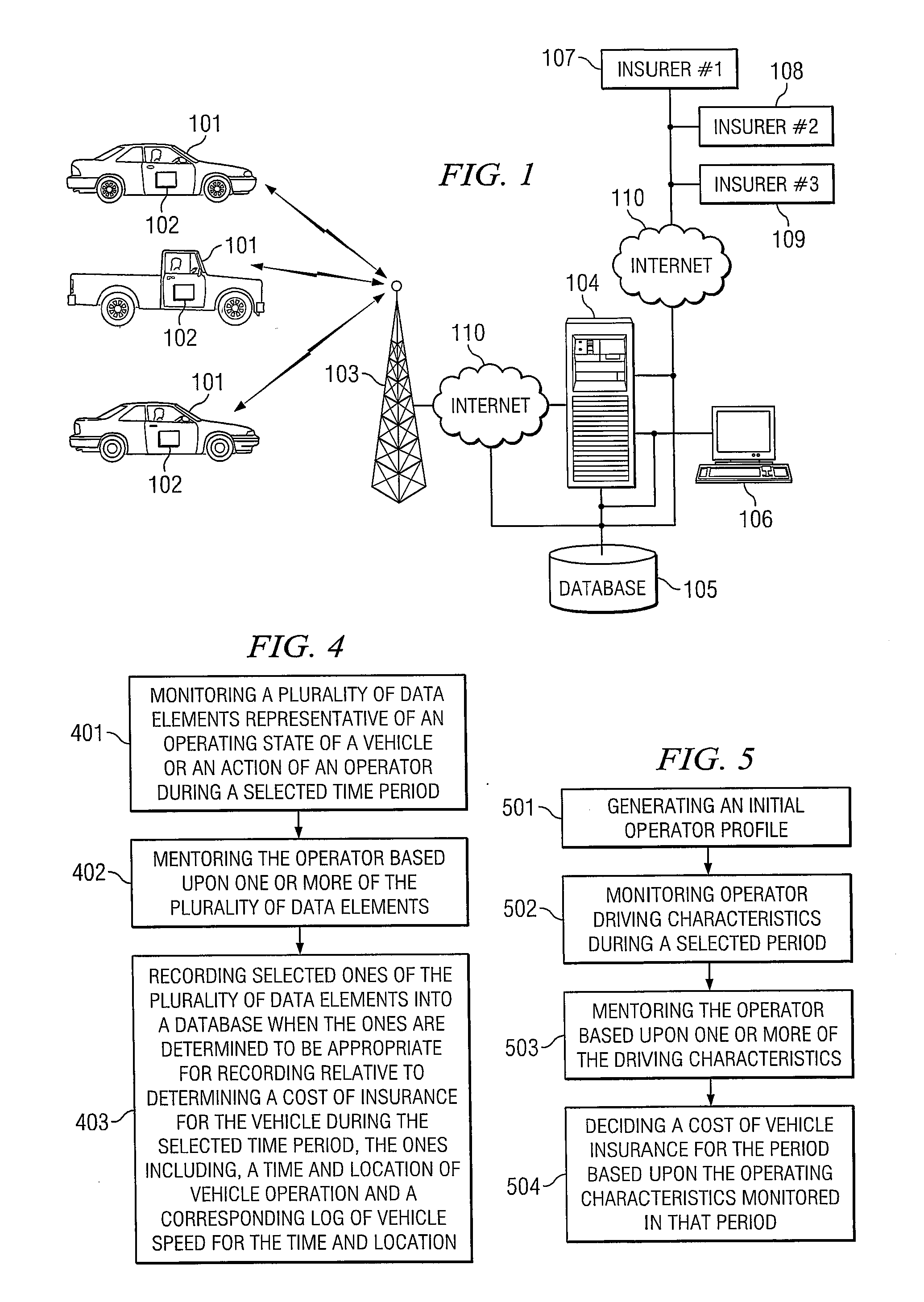
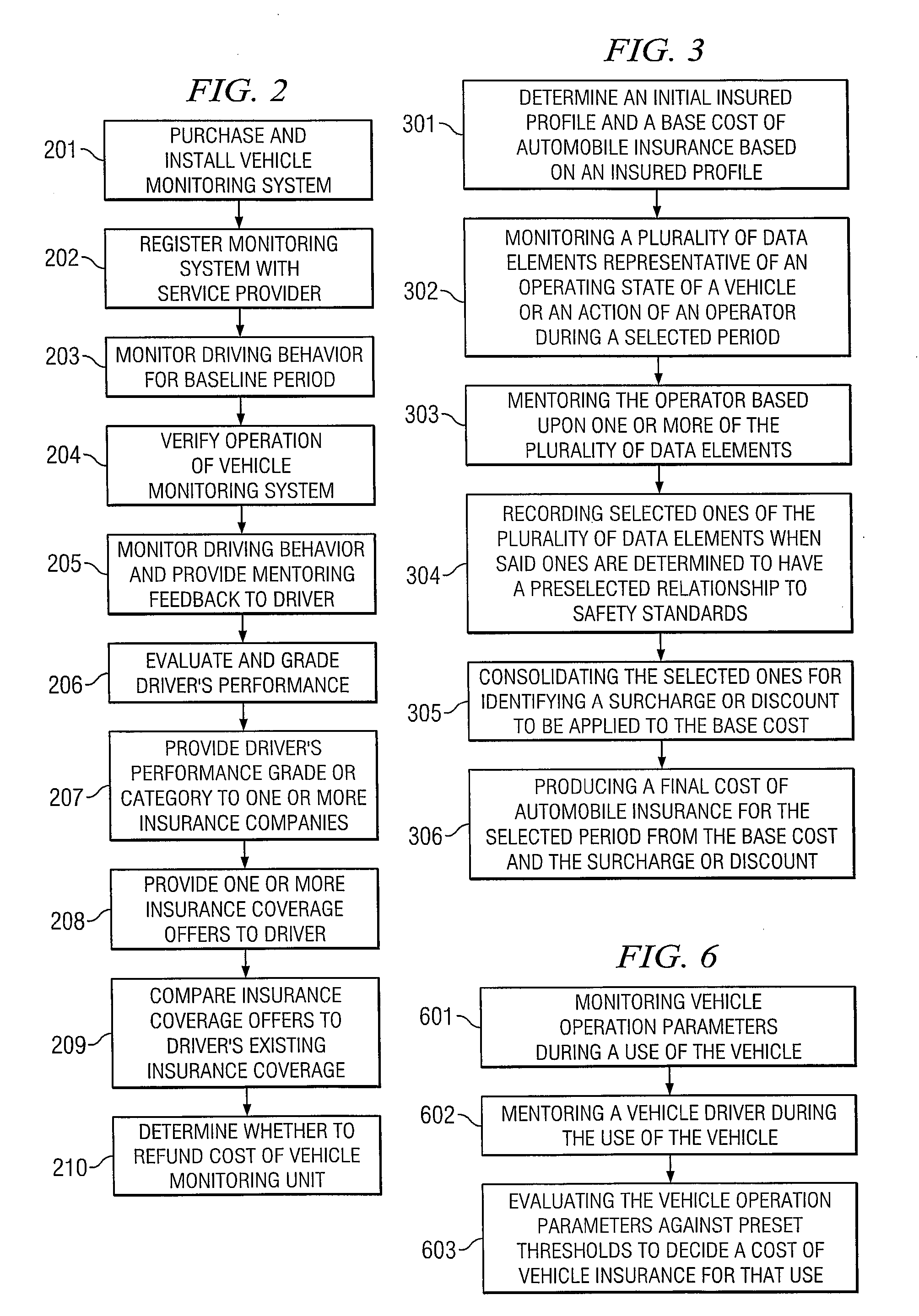
System and Method for Categorizing Driving Behavior Using Driver Mentoring and/or Monitoring Equipment to Determine an Underwriting Risk
ActiveUS20090024419A1FinanceRegistering/indicating working of vehiclesDriver/operatorMonitor equipment
System and method for monitoring and mentoring driver behavior and vehicle operation and for categorizing or grading a driver's performance. The driver's classification or grade is used to determine or adjust insurance rates, premiums or coverages for the driver. The driver may receive discounted insurance rates for using monitoring and / or mentoring equipment in the vehicle. Insurance companies may use the driver classifications or grades to bid for coverage of groups of drivers having similar classifications or grades.
Owner:IWI
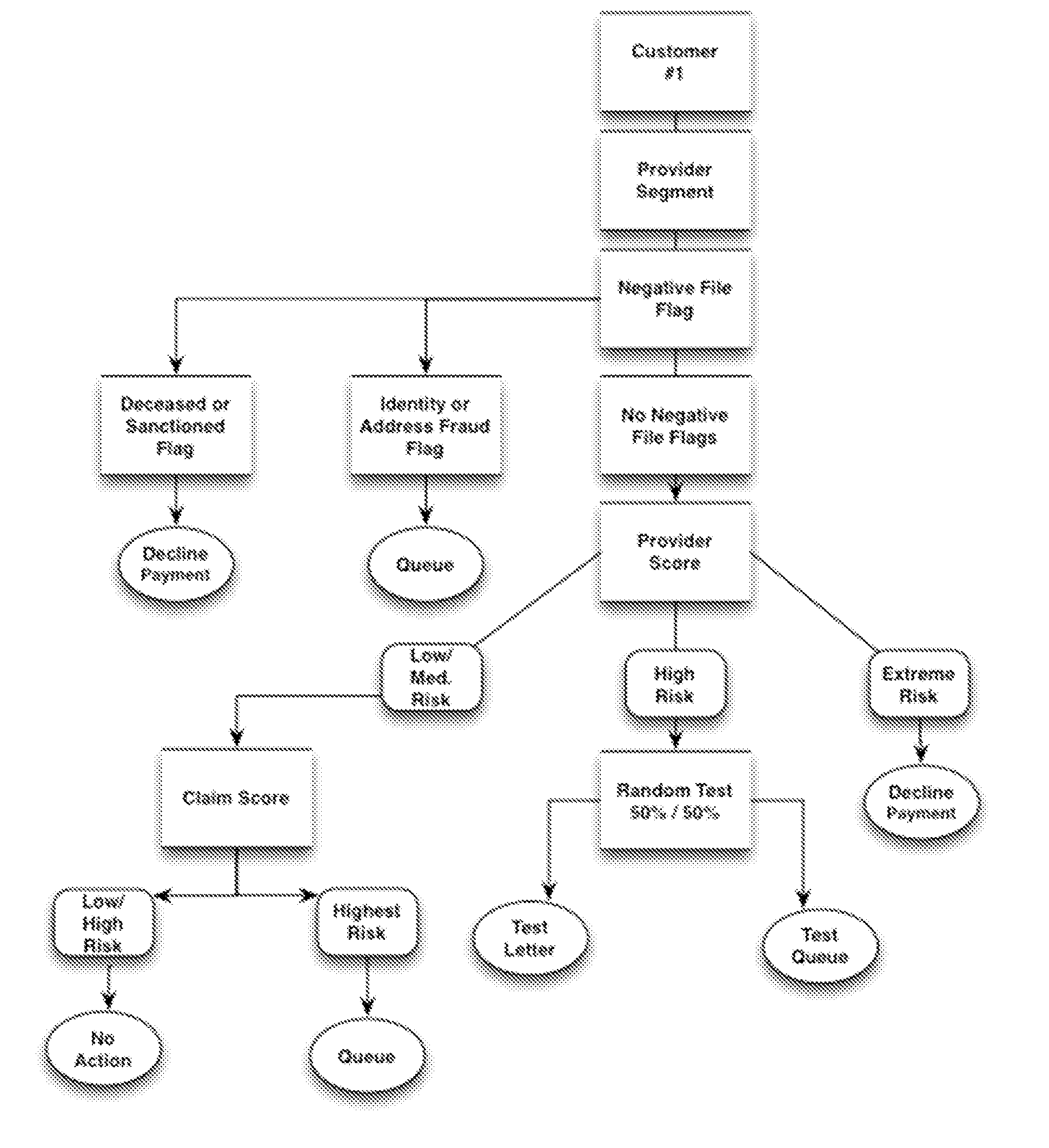
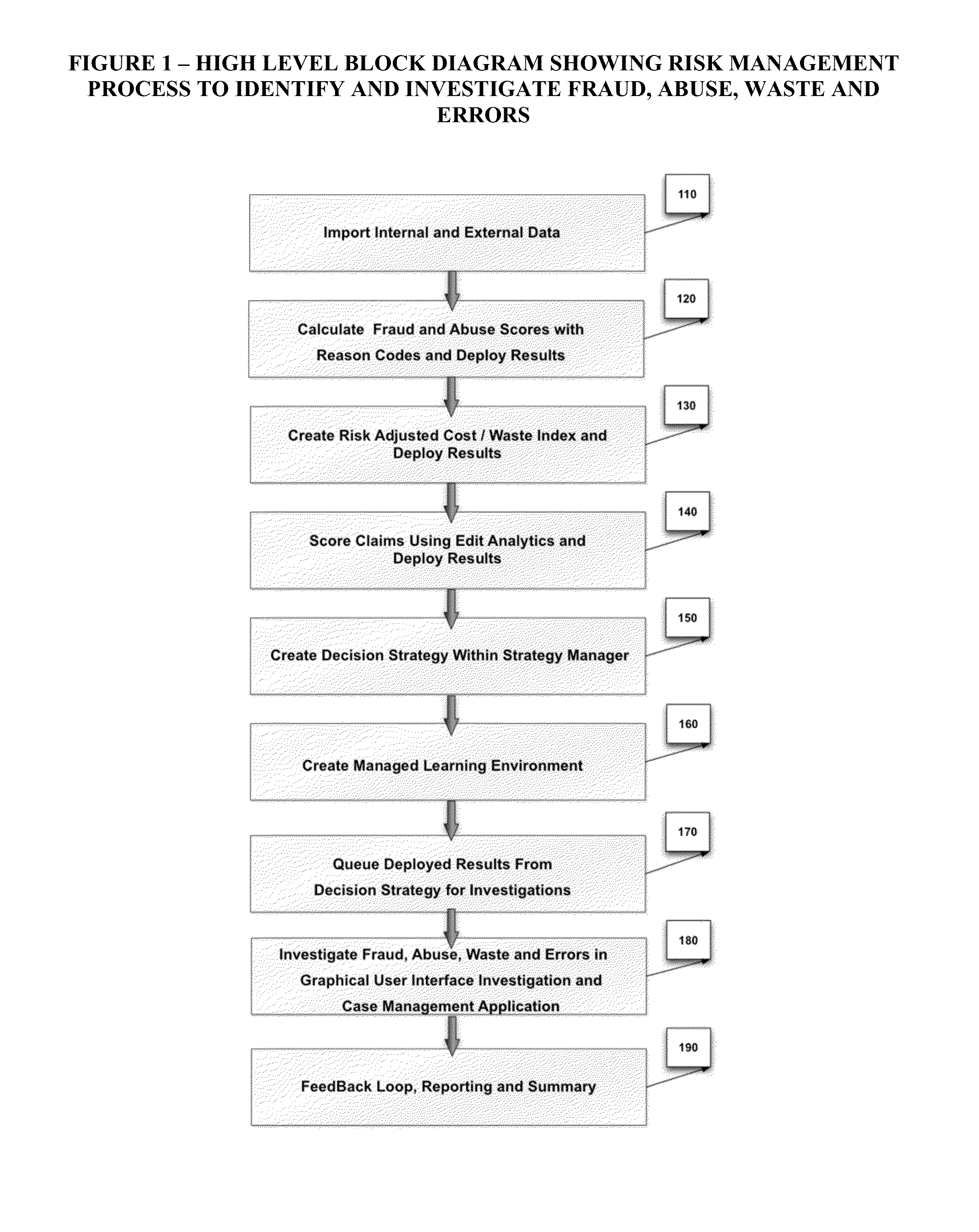
Automated Healthcare Risk Management System Utilizing Real-time Predictive Models, Risk Adjusted Provider Cost Index, Edit Analytics, Strategy Management, Managed Learning Environment, Contact Management, Forensic GUI, Case Management And Reporting System For Preventing And Detecting Healthcare Fraud, Abuse, Waste And Errors
InactiveUS20140081652A1Facilitate and enhance and implement multiple investigator decisionResource optimizationFinancePayment architectureLower riskMedical education
The Automated Healthcare Risk Management System is a real-time Software as a Service application which interfaces and assists investigators, law enforcement and risk management analysts by focusing their efforts on the highest risk and highest value healthcare payments. The system's Risk Management design utilizes real-time Predictive Models, a Provider Cost Index, Edit Analytics, Strategy Management, a Managed Learning Environment, Contact Management, Forensic GUI, Case Management and Reporting System for individually targeting, identifying and preventing fraud, abuse, waste and errors prior to payment. The Automated Healthcare Risk Management System analyzes hundreds of millions of transactions and automatically takes actions such as declining or queuing a suspect payment. Claim payment risk is optimally prioritized through a Managed Learning environment, from high risk to low risk for efficient resolution by investigators.
Owner:RISK MANAGEMENT SOLUTIONS
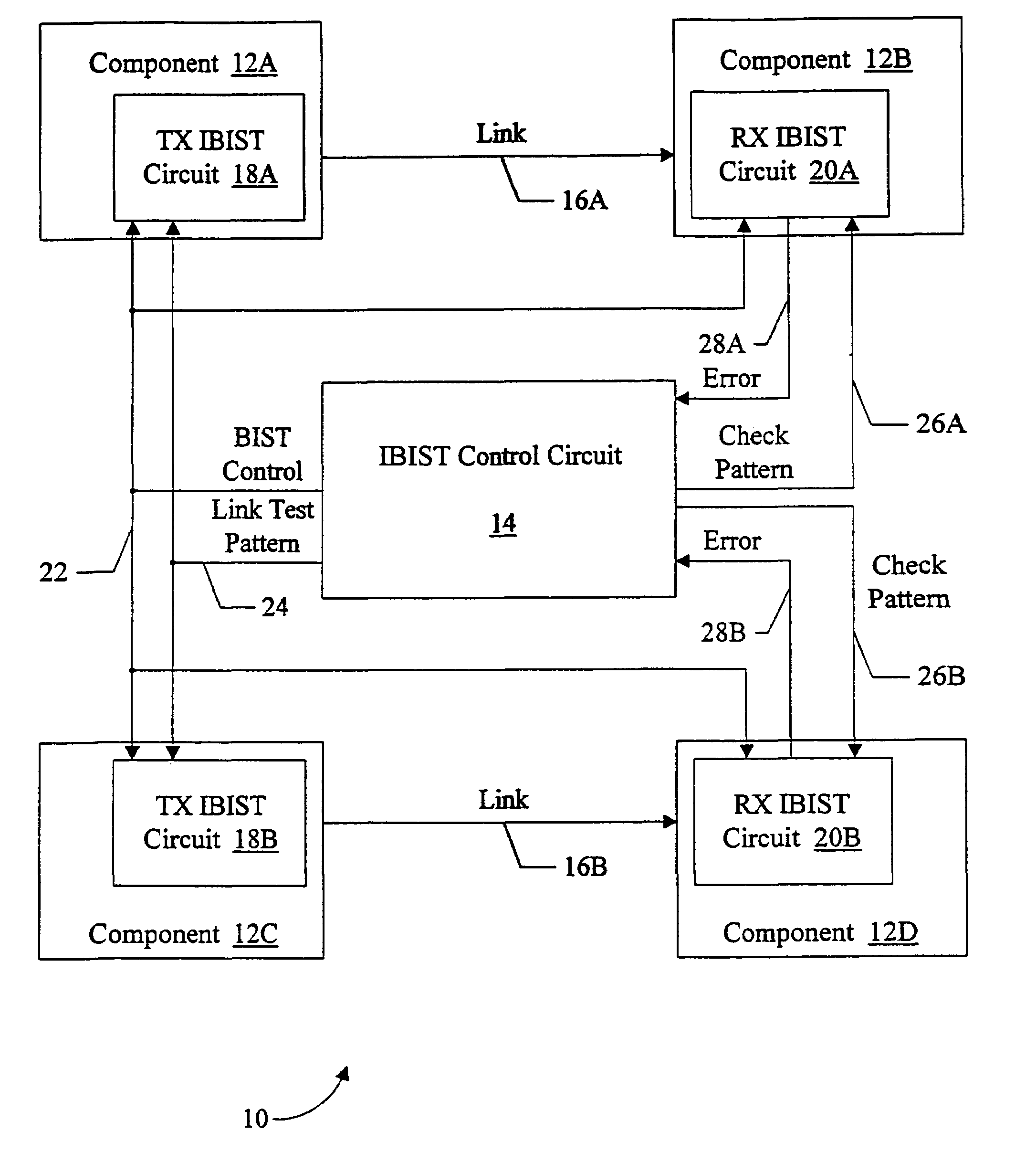
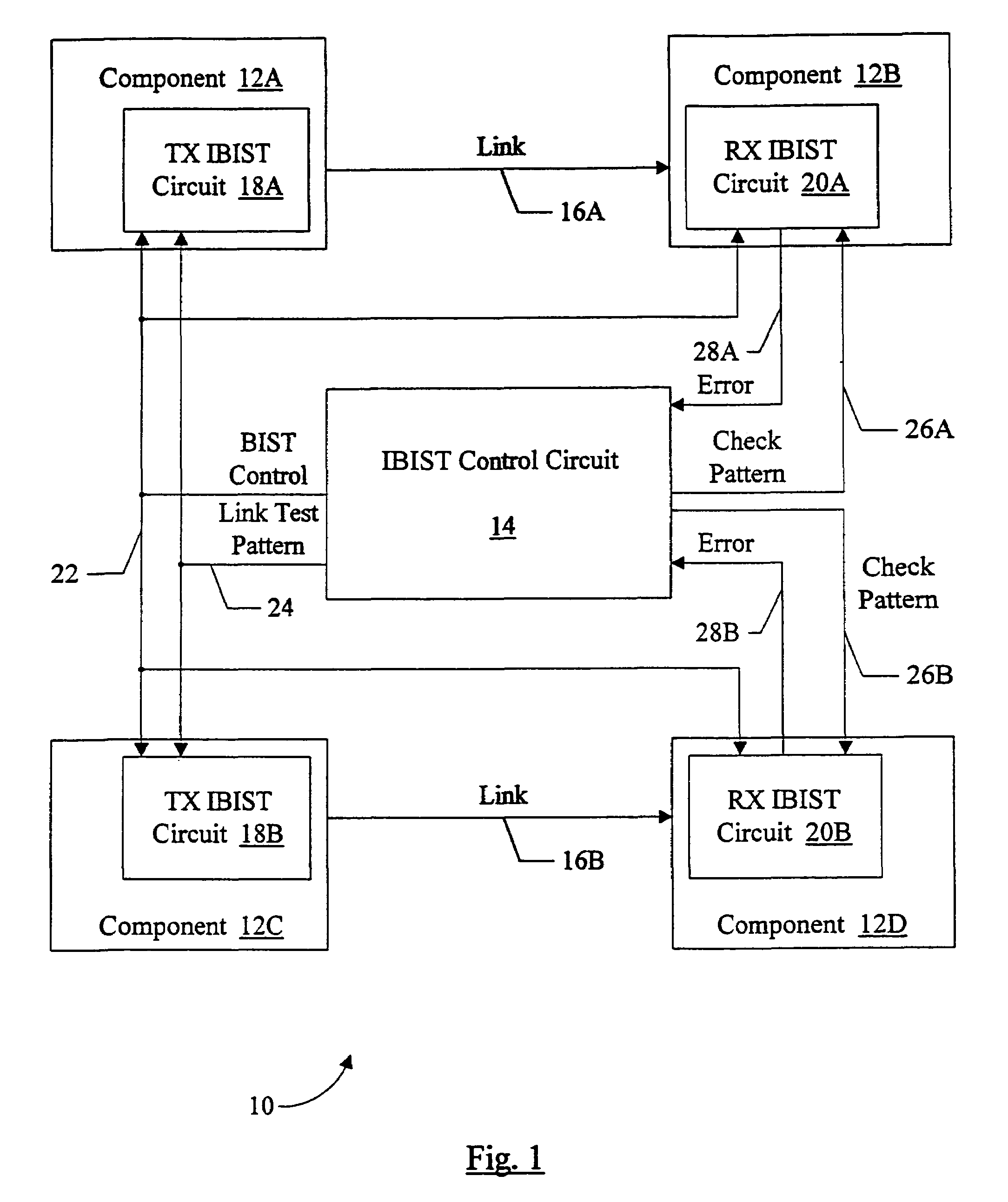
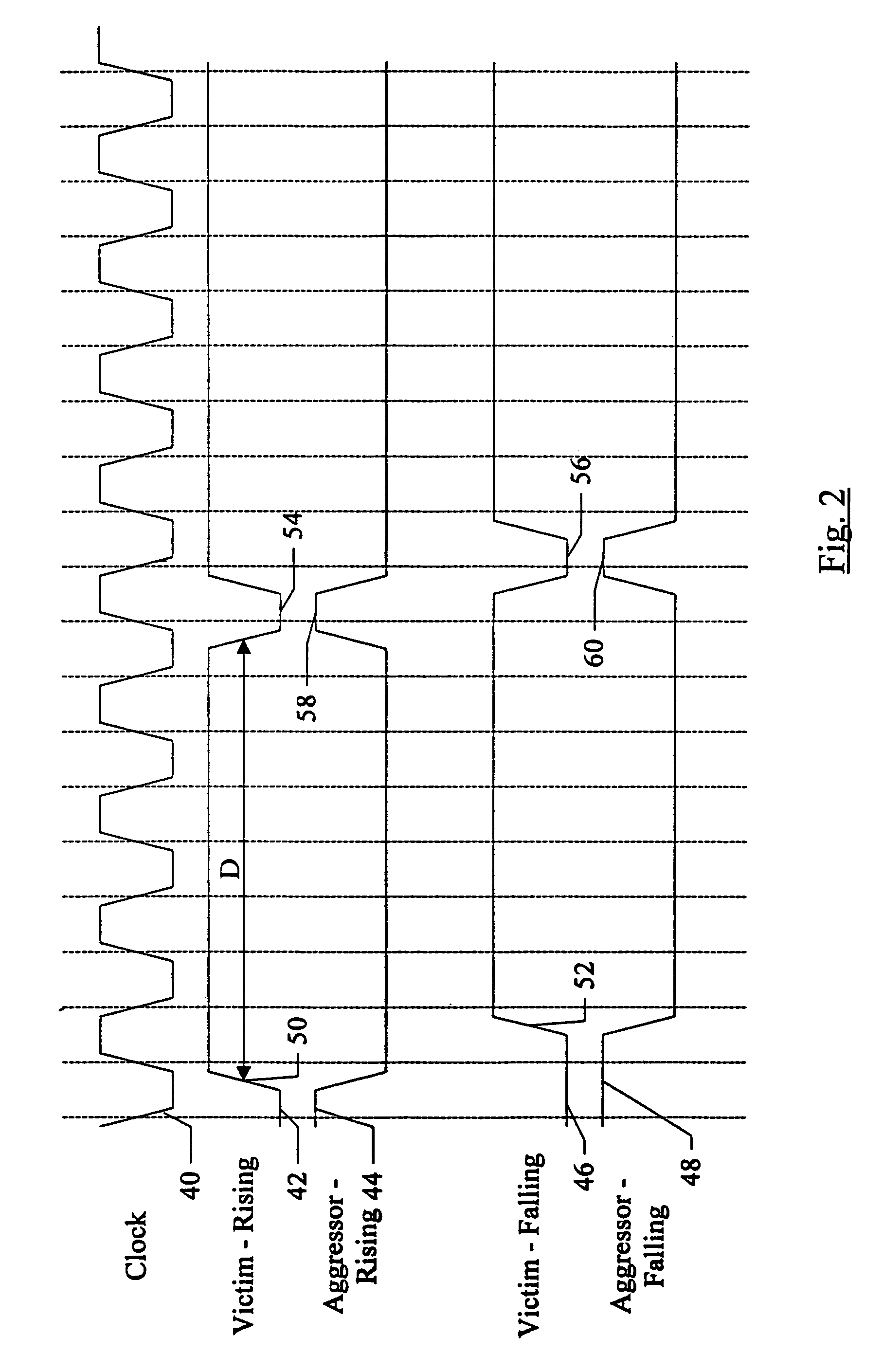
Source synchronous link integrity validation
InactiveUS6965648B1Flexible implementationCorrect operation testingElectronic circuit testingElectrical polaritySource-synchronous
A system may perform interconnect BIST (IBIST) testing on source synchronous links. The system may perform, at normal operating frequency, a source synchronous link test that tests a victim line on the source synchronous link using a transition weave pattern. The transition weave pattern causes interaction between a data transition on the victim line, previous transitions on the victim line, and transitions on the other lines of the link (the “aggressor” lines). The interaction caused may be: (i) a first crossing pulse on the victim line; (ii) a second crossing pulse of the opposite polarity on each aggressor line concurrent with the first crossing pulse on the victim line; and (iii) a reflection in the opposite direction of the first transition of the first crossing pulse, wherein the reflection results from a previous transition on the victim line.
Owner:ORACLE INT CORP
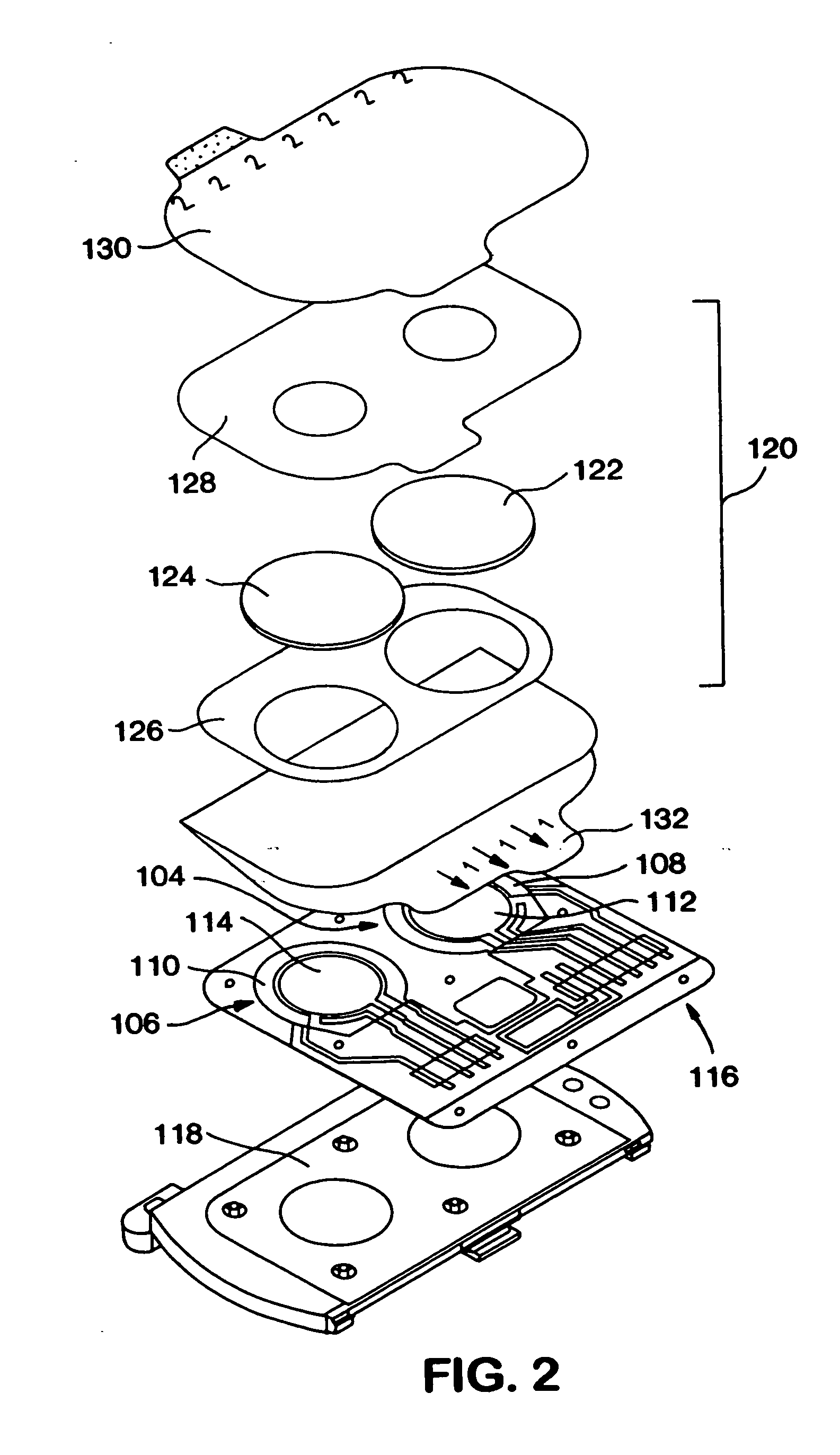
Patient monitor capable of monitoring the quality of attached probes and accessories
ActiveUS20120319816A1Reduce capacityReduce the possibilityProgramme controlElectric signal transmission systemsQuality controlPulse oximetry
A system and method to help maintain quality control and reduce cannibalization of accessories and attached probes in a highly sensitive patient monitor, such as a pulse oximetry system. One or more attached components may have information elements designed to designate what quality control mechanisms a patient monitor should look to find on that or another component or designate other components with which the one component may properly work. In a further embodiment, such information elements may also include data indicating the appropriate life of the component.
Owner:JPMORGAN CHASE BANK NA
Methods for estimating analyte-related signals, microprocessors comprising programming to control performance of the methods, and analyte monitoring devices employing the methods
ActiveUS20050049473A1Reduce morbidityReduce the probability of failureElectrotherapyDiagnostic recording/measuringAnalyteMicroprocessor
The present invention relates to methods to increase the number of analyte-related signals used to provide analyte measurement values, e.g., when two or more analyte-related signals are used to obtain a single analyte measurement value a “rolling” value based on the two or more signals can be employed. In another aspect, interpolation and / or extrapolation methods are used to estimate unusable, missing or error-associated analyte-related signals. Further, interpolation and extrapolation of values are employed in another aspect of the invention that reduces the incident of failed calibrations. Further, the invention relates to methods, which employ gradients and / or predictive algorithms, to provide an alert related to analyte values exceeding predetermined thresholds. The invention includes the above-described methods, one or more microprocessors programmed to execute the methods, one or more microprocessors programmed to execute the methods and control at least one sensing and / or sampling device, and monitoring systems employing the methods described herein.
Owner:LIFESCAN IP HLDG LLC +1
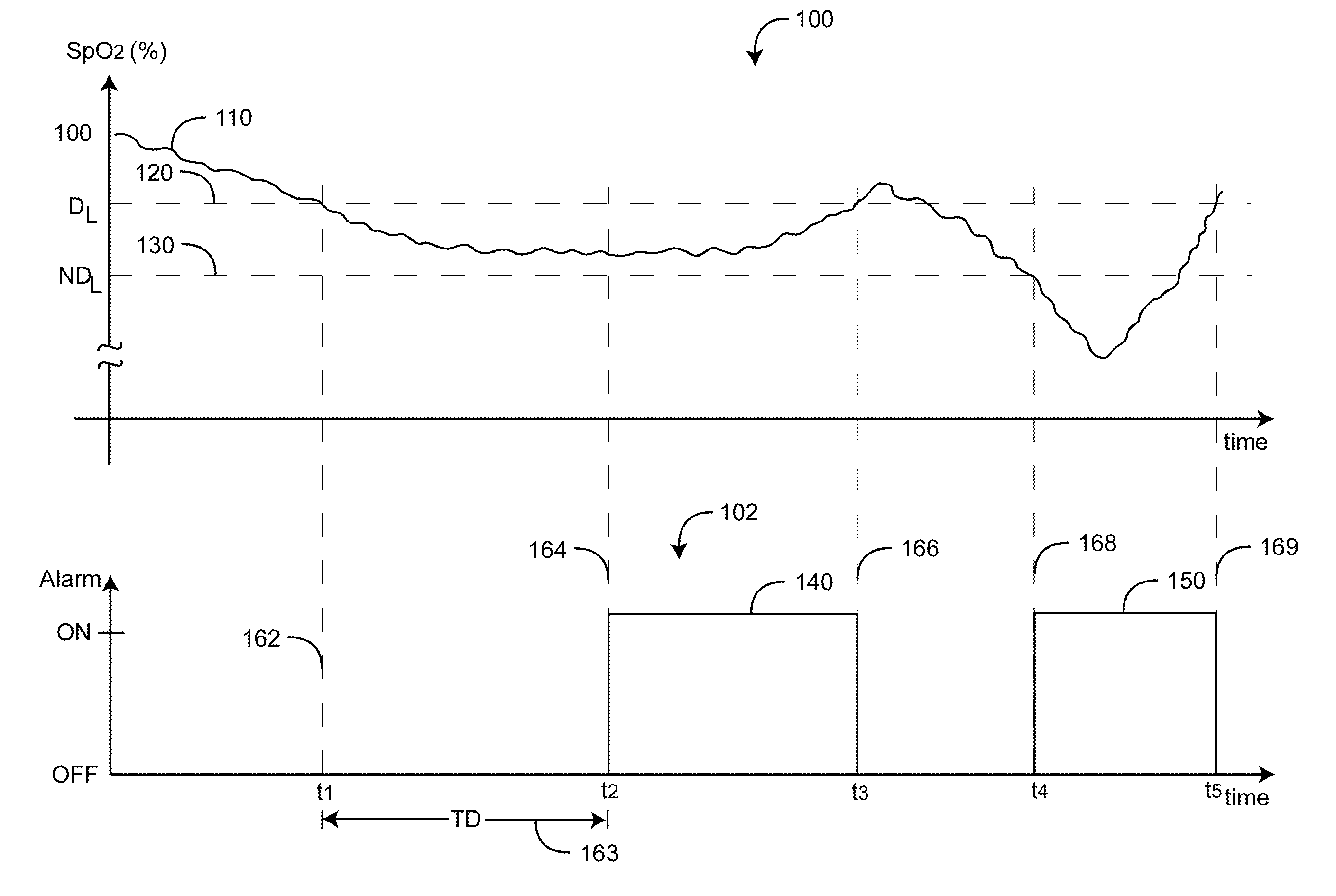
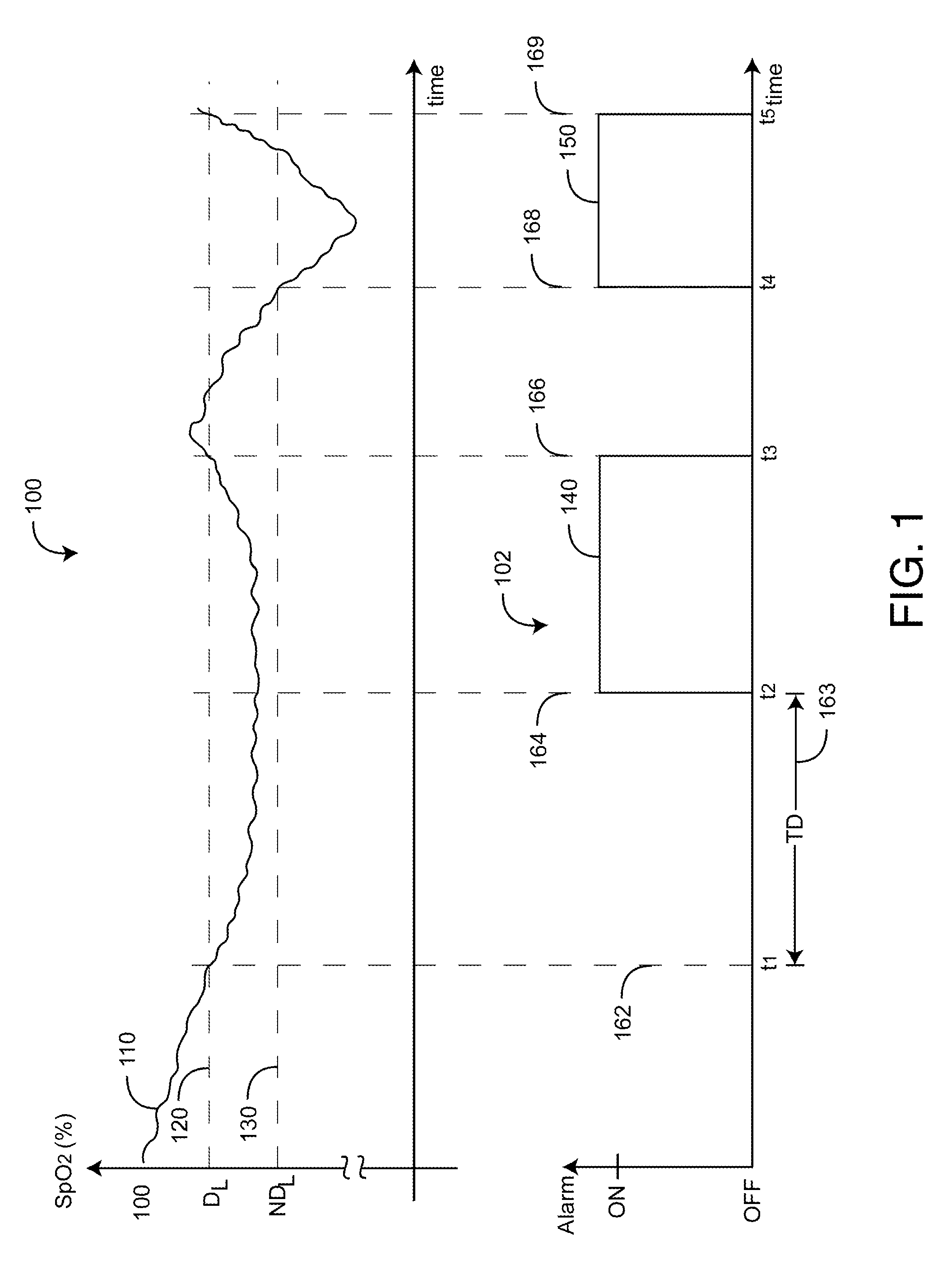
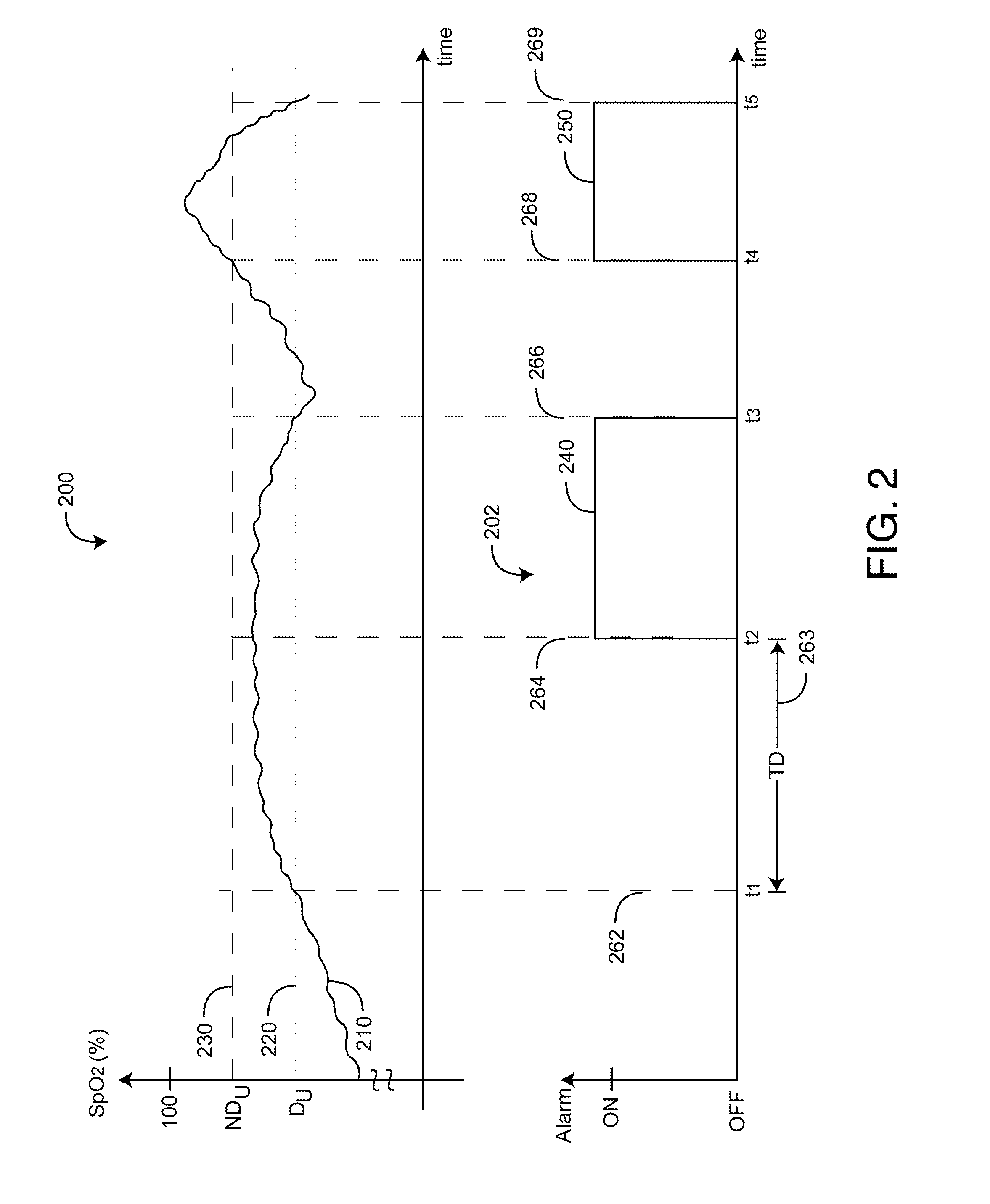
Adaptive alarm system
ActiveUS20110213212A1Small sizeReduces baseline movementUser/patient communication for diagnosticsSensorsEngineeringSelf adaptive
An adaptive alarm system is responsive to a physiological parameter so as to generate an alarm threshold that adapts to baseline drift in the parameter and reduce false alarms without a corresponding increase in missed true alarms. The adaptive alarm system has a parameter derived from a physiological measurement system using a sensor in communication with a living being. A baseline processor calculates a parameter baseline from a parameter trend. Parameter limits specify an allowable range of the parameter. An adaptive threshold processor calculates an adaptive threshold from the parameter baseline and the parameter limits. An alarm generator is responsive to the parameter and the adaptive threshold so as to trigger an alarm indicative of the parameter crossing the adaptive threshold. The adaptive threshold is responsive to the parameter baseline so as to increase in value as the parameter baseline drifts to a higher parameter value and to decrease in value as the parameter baseline drifts to a lower parameter value.
Owner:JPMORGAN CHASE BANK NA
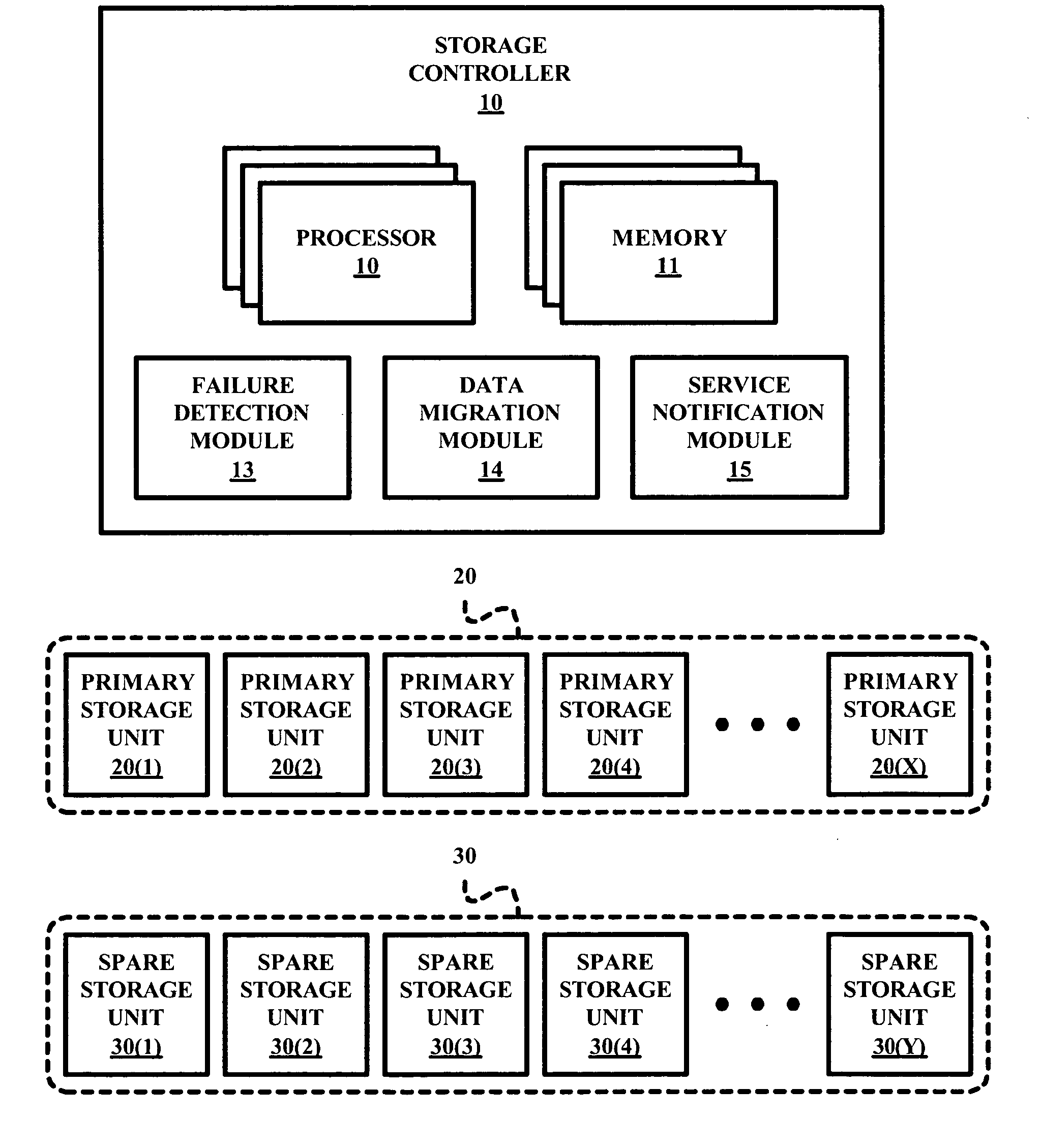
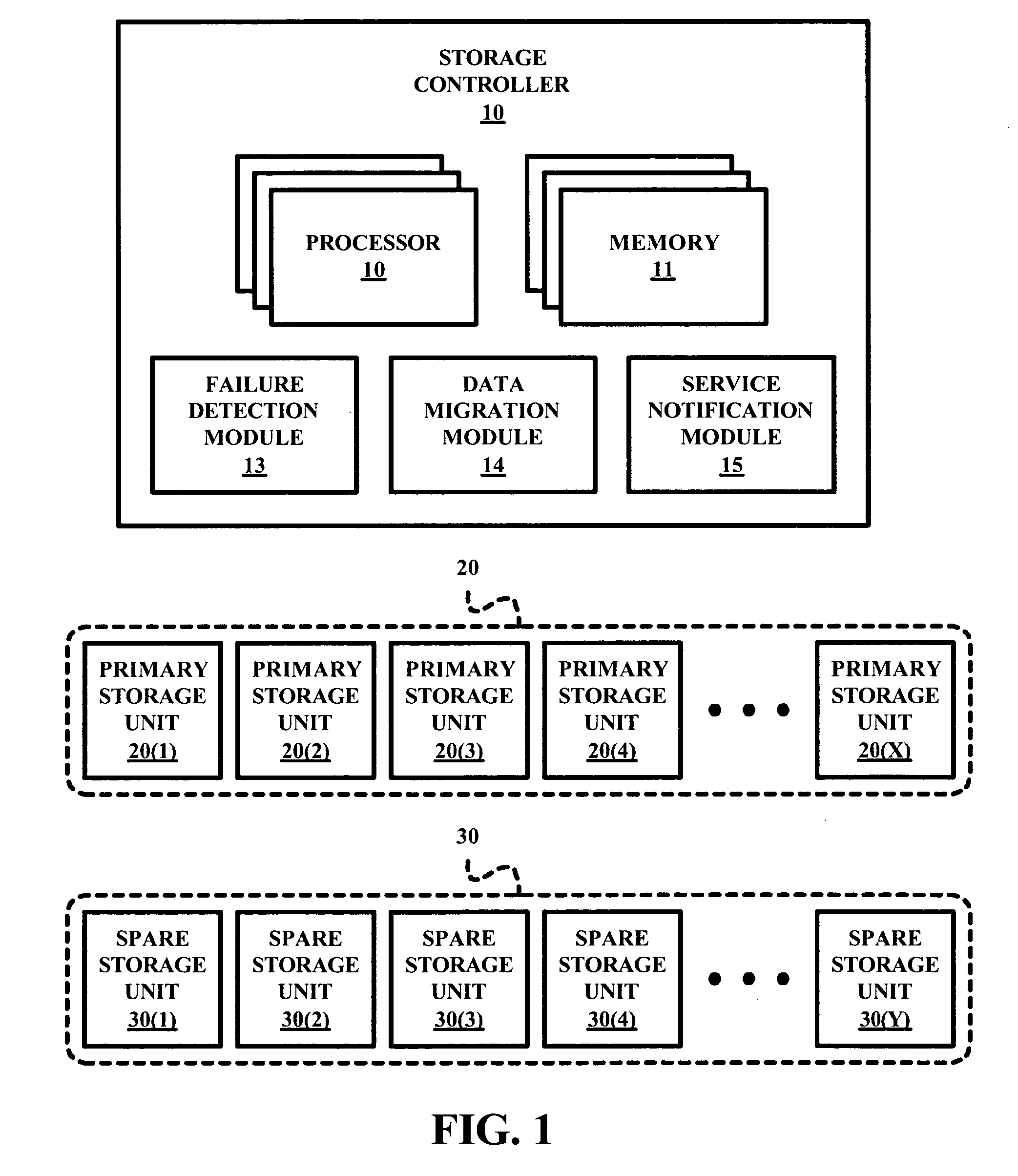
Management method for spare disk drives a RAID system
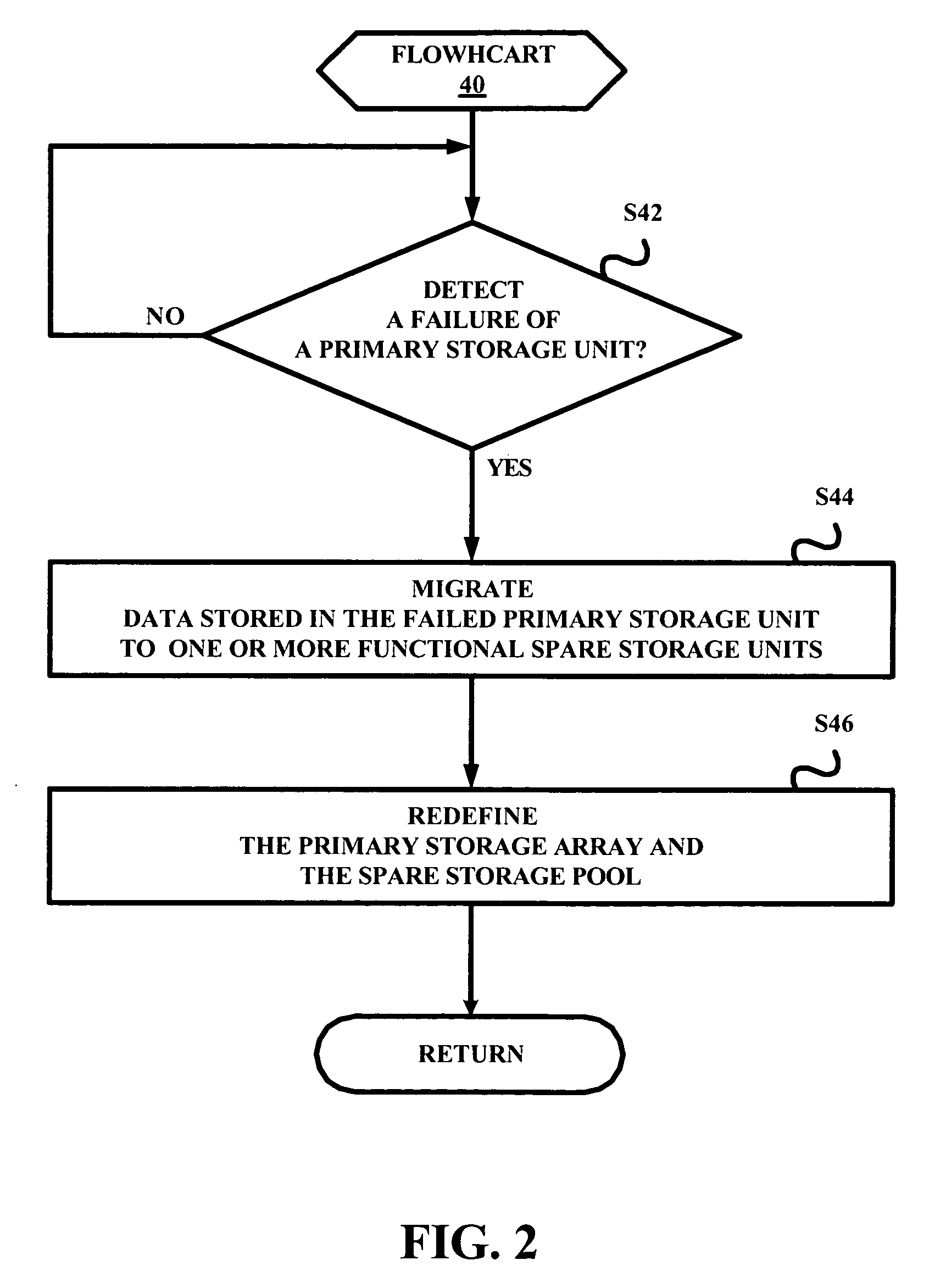
A RAID system employs a storage controller, a primary storage array having a plurality of primary storage units, and a spare storage pool having one or more spare storage units. A method of operating the storage controller in managing the primary storage array and the spare storage pool involves a testing by the storage controller of at least one repair service threshold representative of one or more operational conditions indicative of a necessity to repair at least one of the primary storage array and the spare storage unit, and a selective initiation by the storage controller of a repair service action for repairing one of the primary storage array and the spare storage unit based on the testing of the at least one repair service threshold.
Owner:IBM CORP
Inclusion of Quality of Service Indication in Header Compression Channel
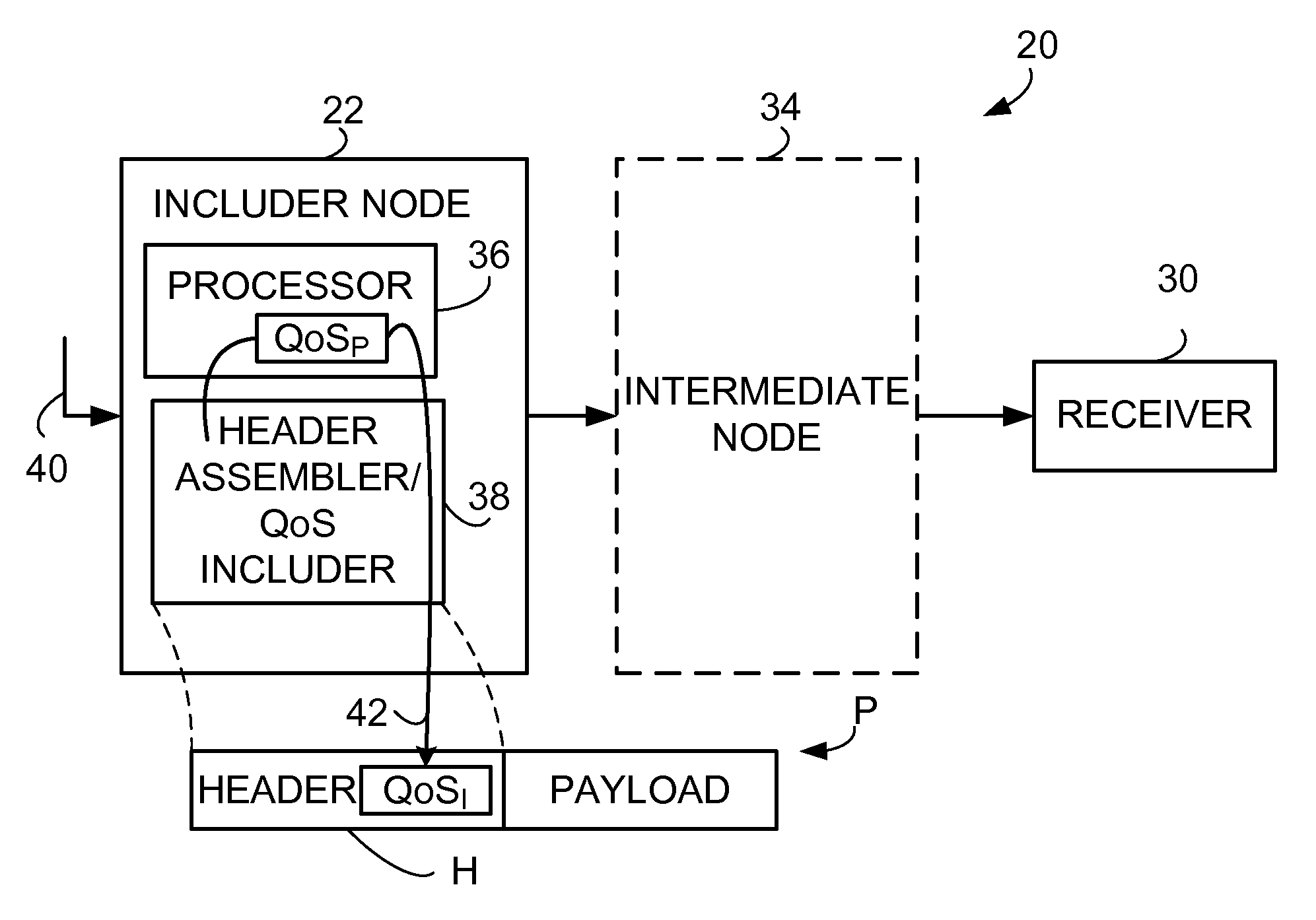
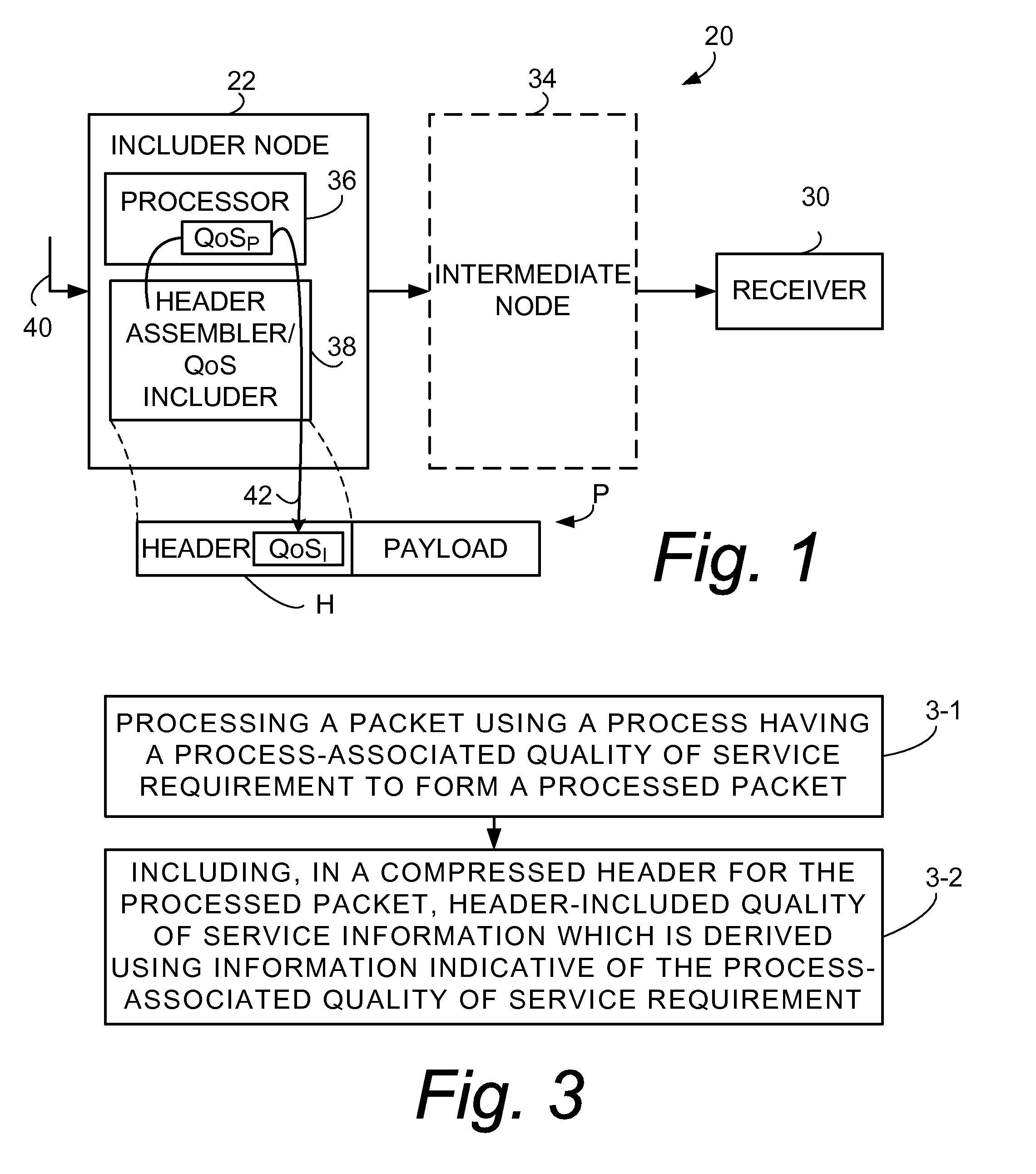
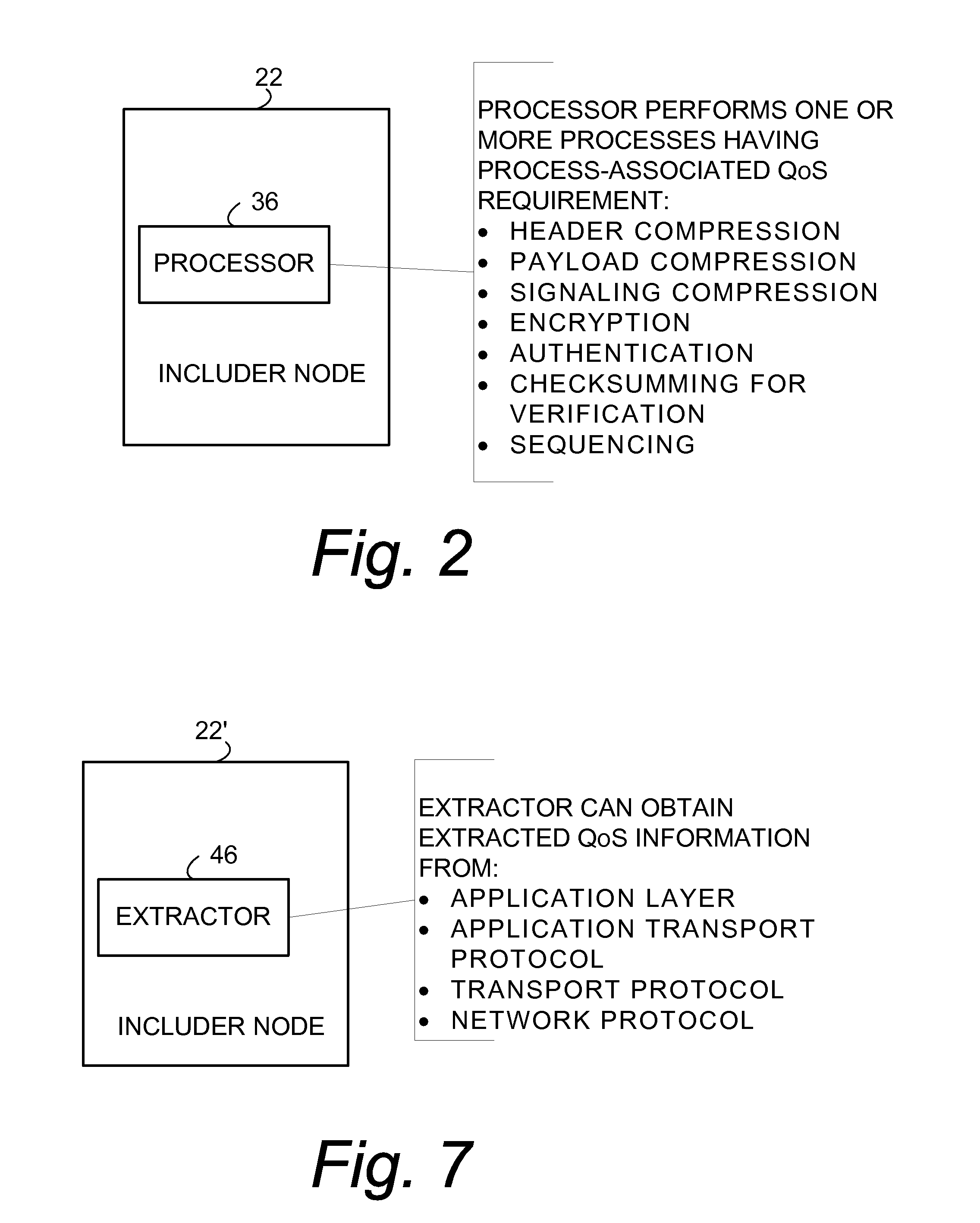
Quality of service information (QoSI) is included with a compressed header of a data packet and can be utilized by nodes supporting the header compression channel to perform QoS enforcements at a sub-flow granularity level. A basic mode of a method comprises (1) processing a packet using a process having a process-associated quality of service requirement to form a processed packet, and (2) including, with a compressed header for the processed packet, the header-included quality of service information which is derived using information indicative of the process-associated quality of service requirement. In another mode the header-included quality of service information is derived both from the process-associated quality of service requirement and quality of service information extracted from the received packet.
Owner:TELEFON AB LM ERICSSON (PUBL)
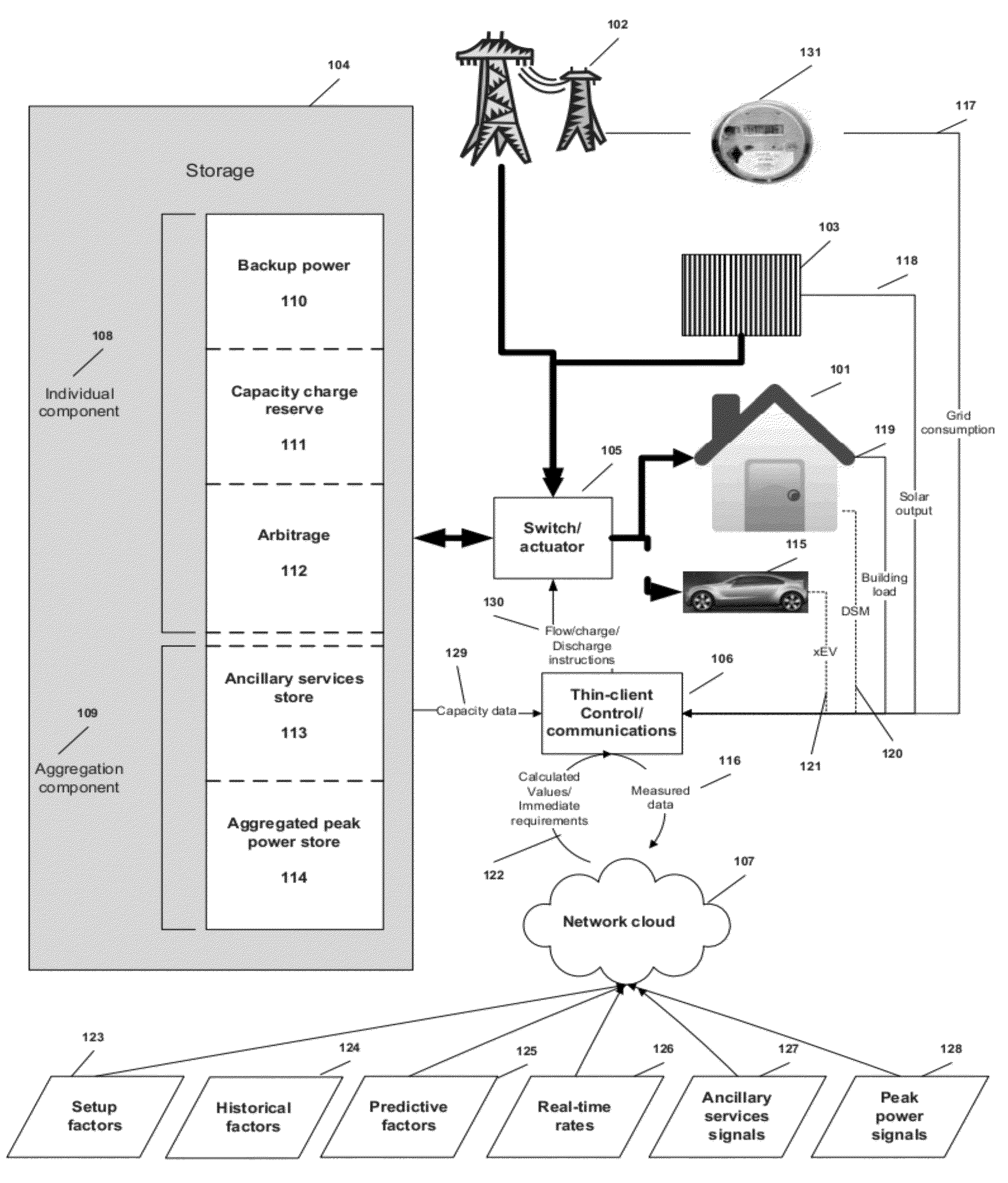
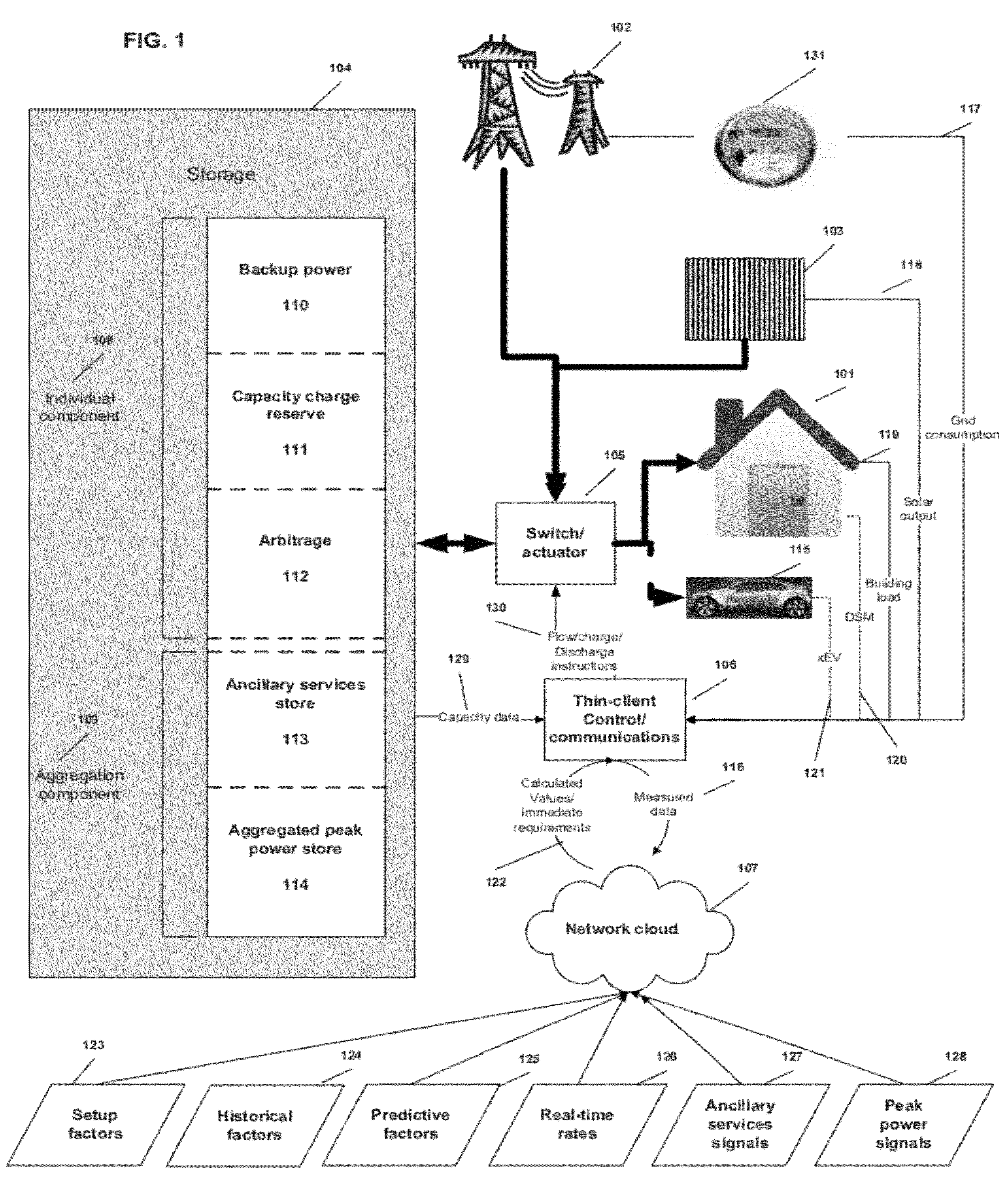
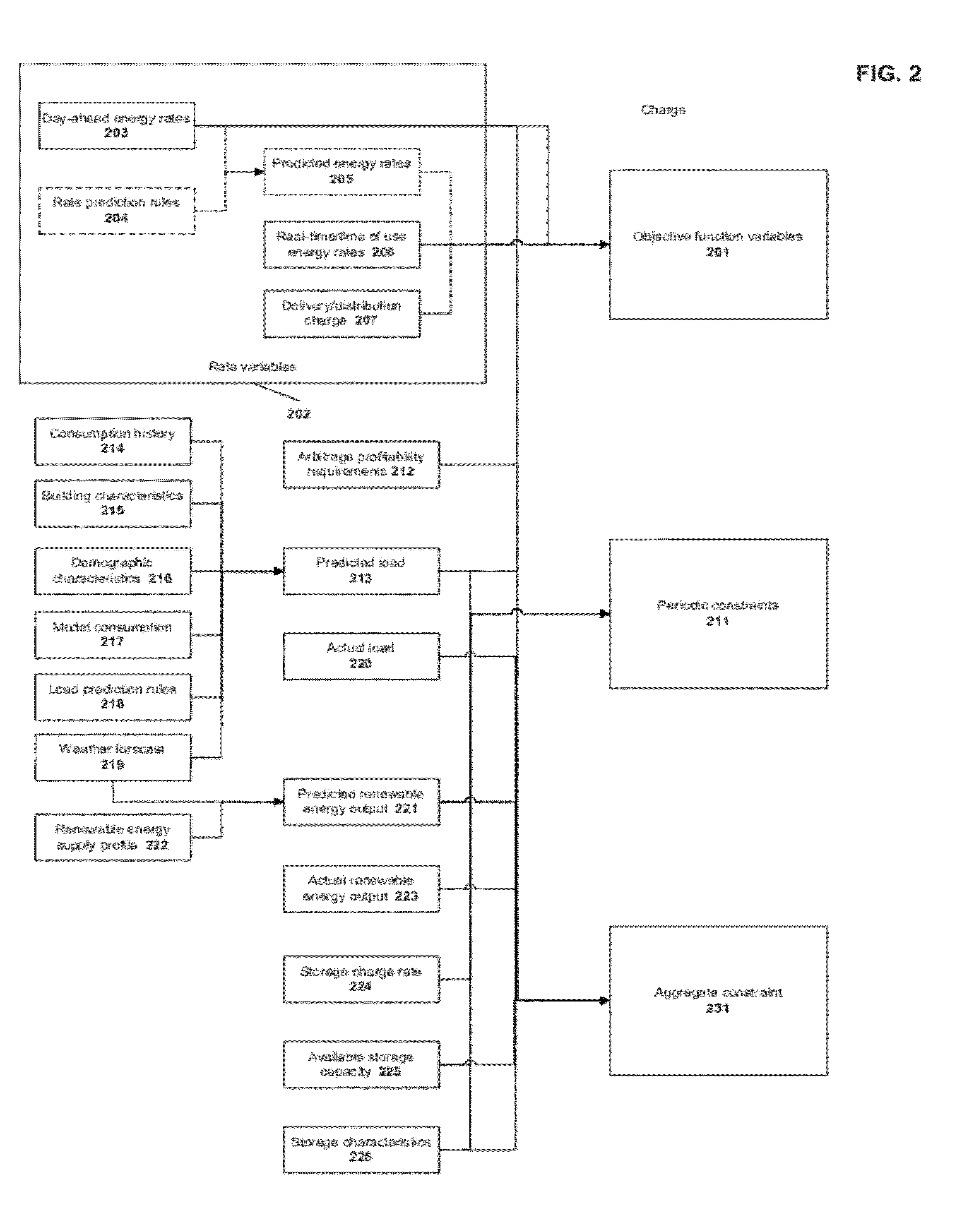
Virtual power plant system and method incorporating renewal energy, storage and scalable value-based optimization
ActiveUS20120130556A1Effective distributionLow costLevel controlWind energy generationCapital investmentPredictive factor
Methods and systems provided for creating a scalable building block for a virtual power plant, where individual buildings can incorporate on-site renewable energy assets and energy storage and optimize the acquisition, storage and consumption of energy in accordance with a value hierarchy. Each building block can be aggregated into a virtual power plant, in which centralized control of load shifting in selected buildings, based on predictive factors or price signals, can provide bulk power for ancillary services or peak demand situations. Aggregation can occur at multiple levels, including developments consisting of both individual and common renewable energy and storage assets. The methods used to optimize the system can also be applied to “right size” the amount of renewable energy and storage capacity at each site to maximize return on the capital investment.
Owner:INTELLIGENT GENERATION
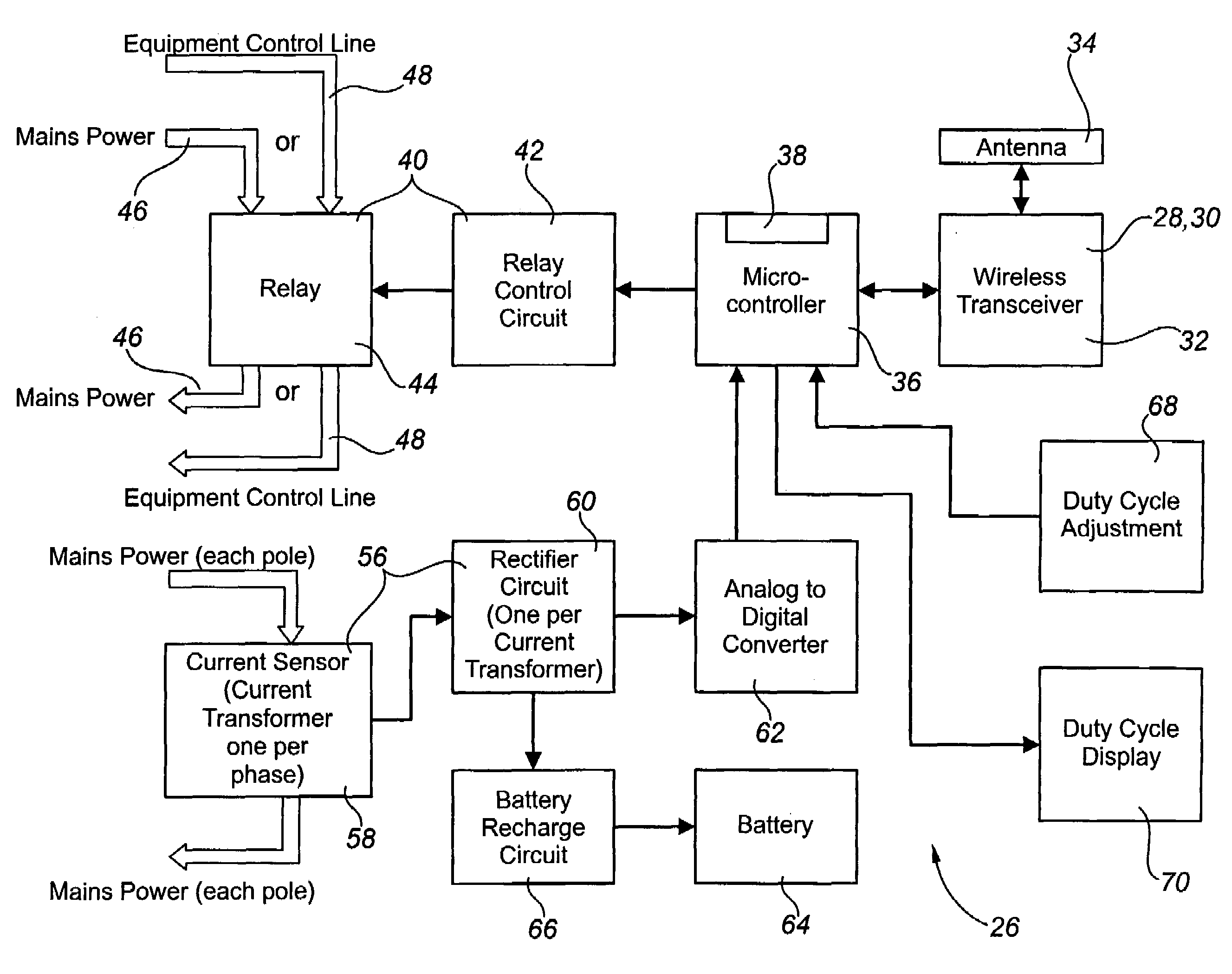
Method and apparatus for managing an energy consuming load
ActiveUS20080015742A1Reduce energy consumptionGuaranteed growthMechanical power/torque controlDc network circuit arrangementsLoad generationEngineering
A method for managing an energy consuming load in a group of energy consuming loads and a method for managing the group of energy consuming loads. The method includes generating sets of load state data from the loads, making enablement state decisions for one or more loads independently of the other loads using the sets of load state data, and implementing the enablement state decisions. An apparatus for managing an energy consuming load in a group of energy consuming loads, including a transmitter for transmitting a set of load state data generated from the load, a receiver for. receiving sets of load state data from other loads, a processor for processing the sets of load state data to make an enablement state decision for the load, and a controller for implementing the enablement state decision.
Owner:ENCYCLE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com