Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
55 results about "Vulnerability (computing)" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer security, a vulnerability is a weakness which can be exploited by a threat actor, such as an attacker, to perform unauthorized actions within a computer system. To exploit a vulnerability, an attacker must have at least one applicable tool or technique that can connect to a system weakness. In this frame, vulnerability is also known as the attack surface.
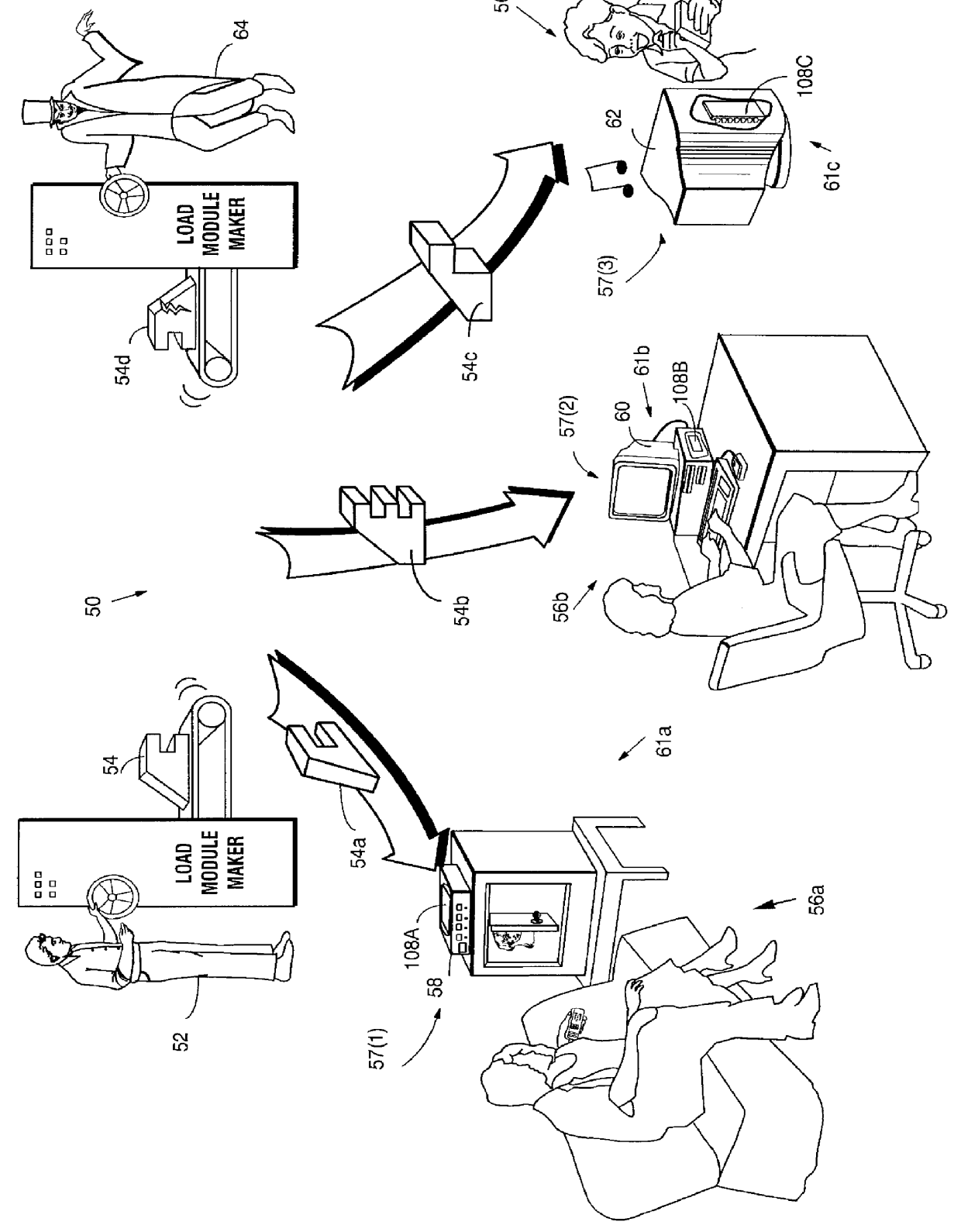
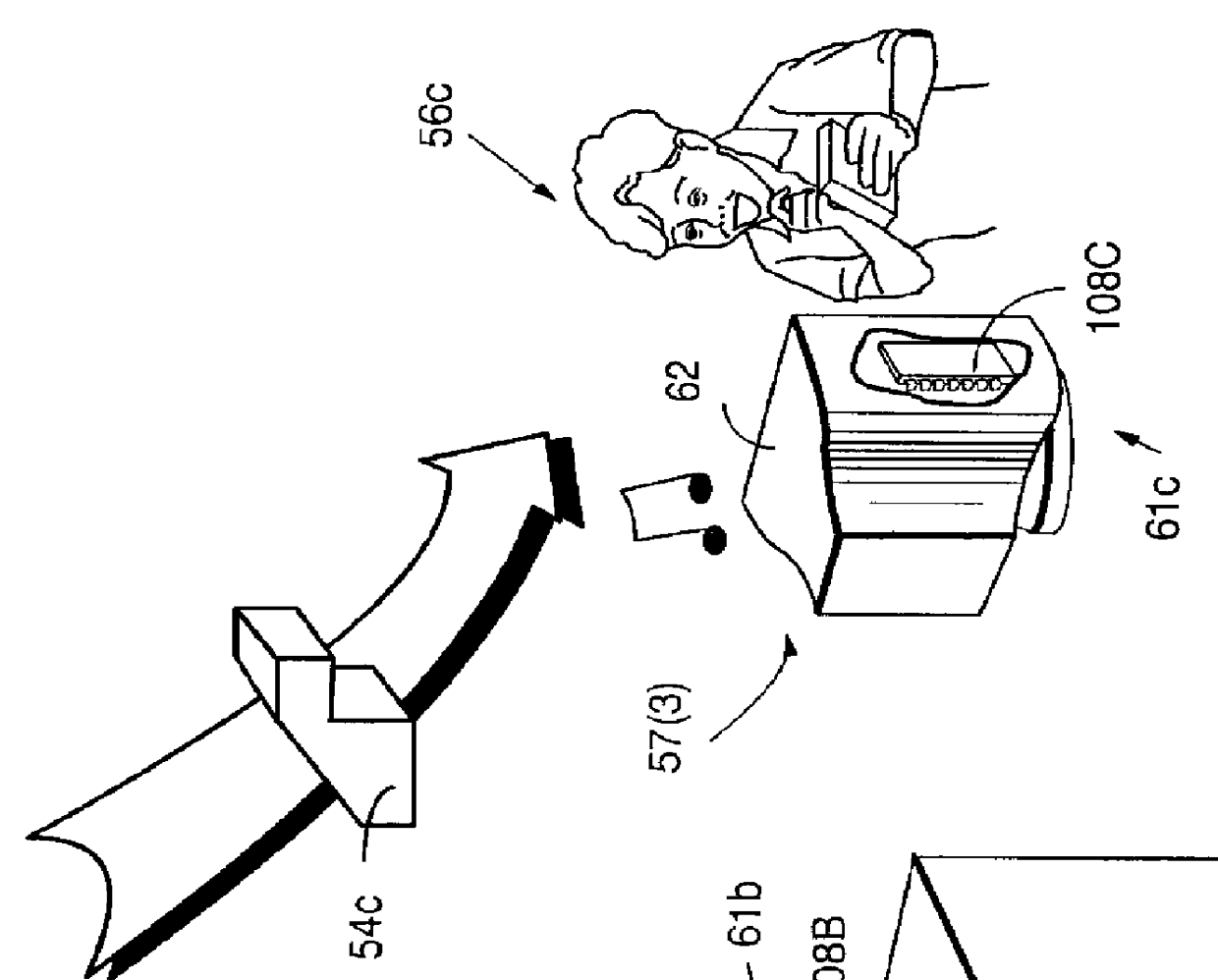
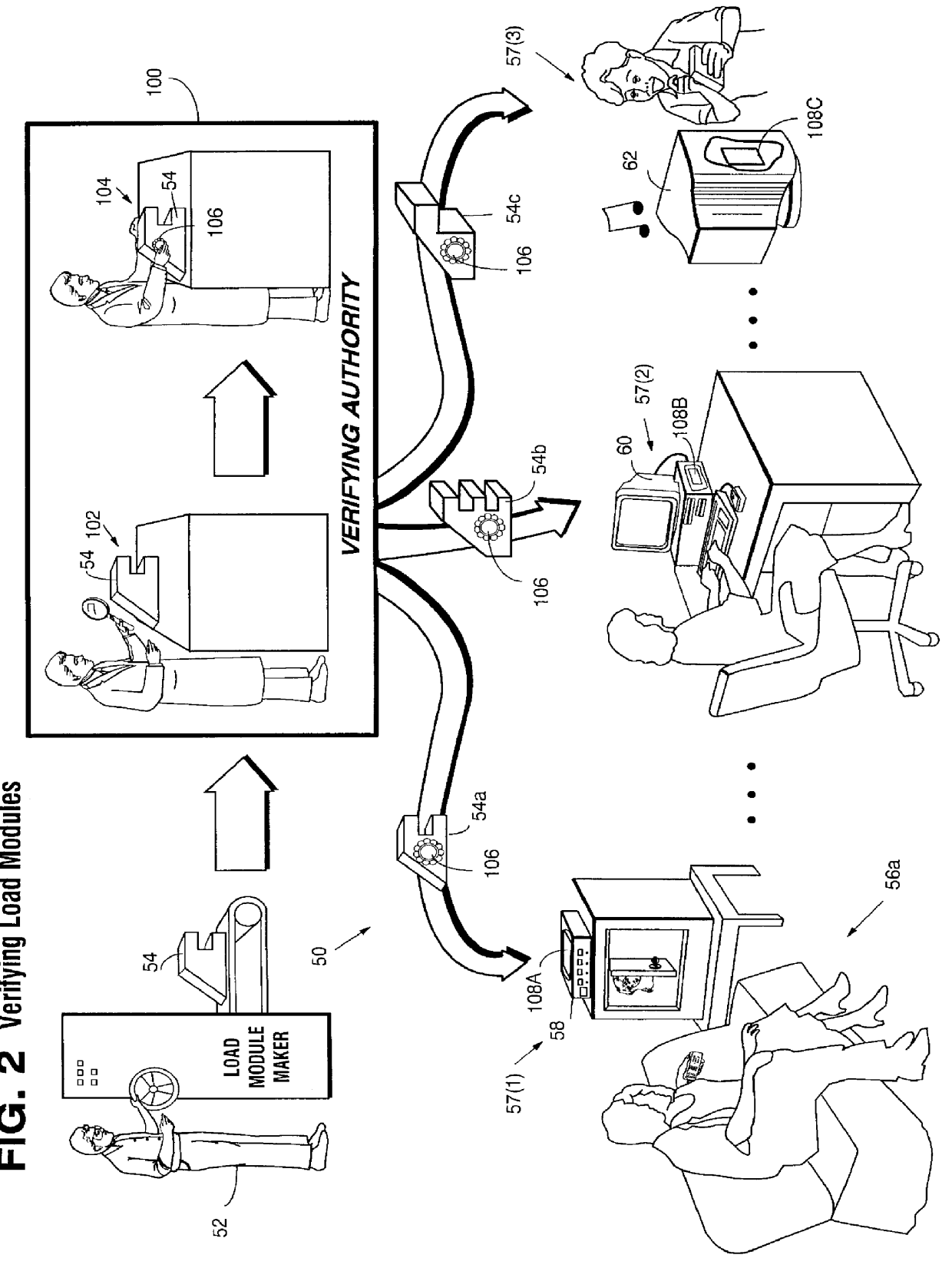
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
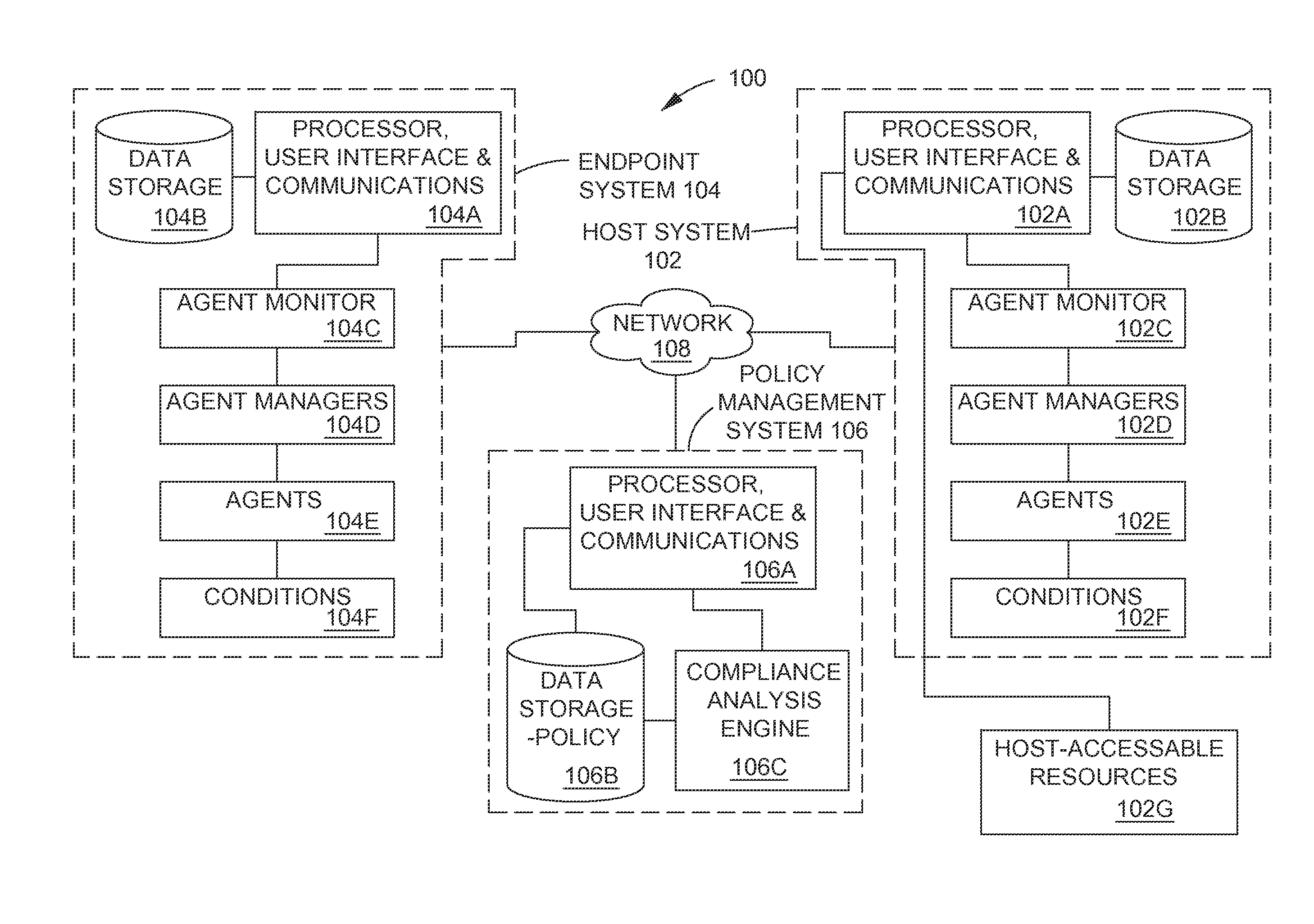
Methods and systems for controlling access to computing resources based on known security vulnerabilities
ActiveUS20130254833A1Error detection/correctionPlatform integrity maintainanceEngineeringVulnerability (computing)
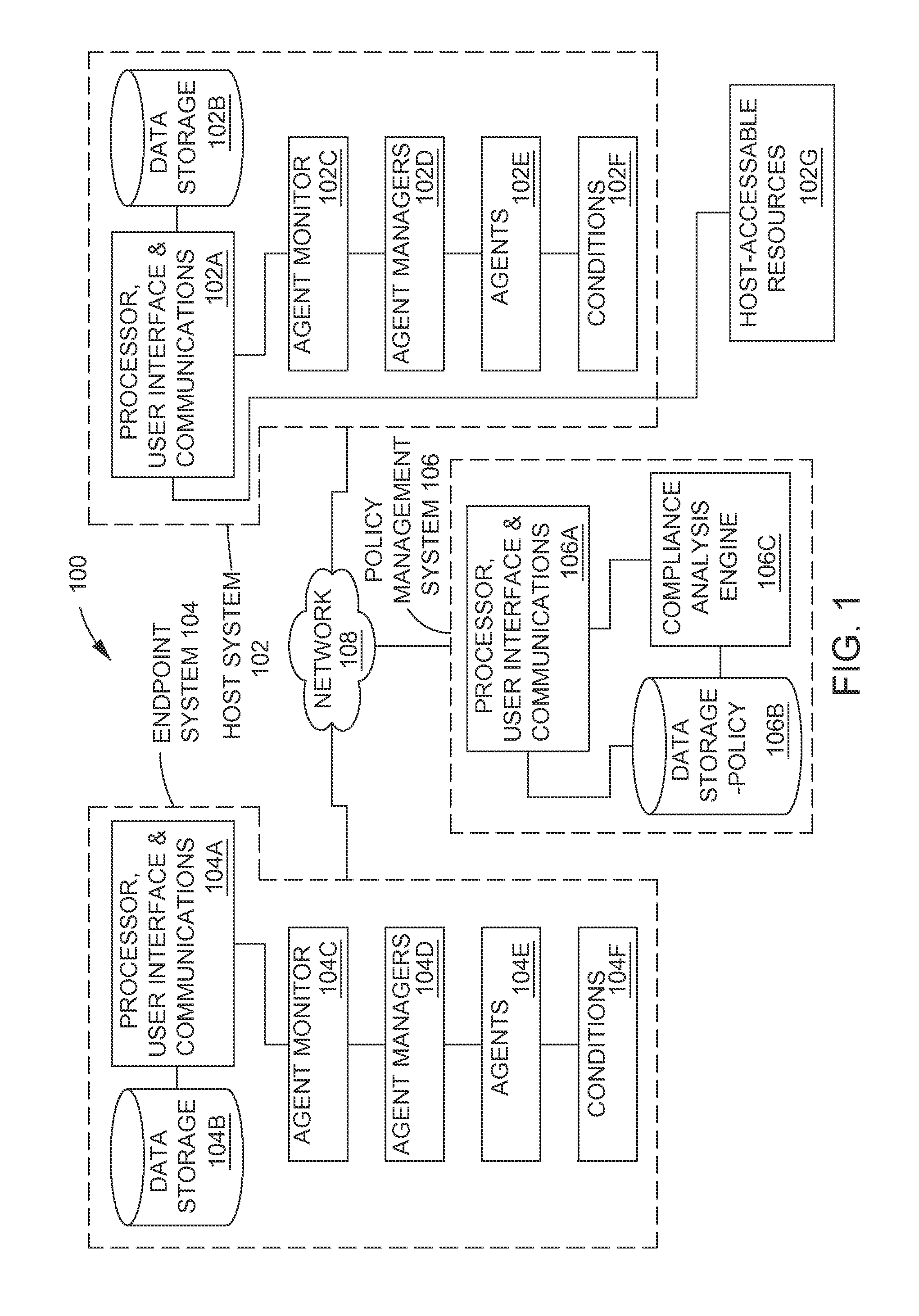
Methods and systems are provided for fine tuning access control by remote, endpoint systems to host systems. Multiple conditions / states of one or both of the endpoint and host systems are monitored, collected and fed to an analysis engine. Using one or more of many different flexible, adaptable models and algorithms, an analysis engine analyzes the status of the conditions and makes decisions in accordance with pre-established policies and rules regarding the security of the endpoint and host system. Based upon the conditions, the policies, and the analytical results, actions are initiated regarding security and access matters. In one described embodiment of the invention, the monitored conditions include software vulnerabilities.
Owner:TAASERA LICENSING LLC
Device vulnerability management
ActiveUS10992698B2Web data indexingPlatform integrity maintainanceVulnerability managementEngineering
A computer-implemented process of remediating device security vulnerabilities is carried out by determining identifications of electronic devices associated with an entity and calculating, for each device, a security cyber-vulnerability score. For instance, the cyber-vulnerability score is calculated by generating a device cyber-vulnerability score based upon known threats and vulnerabilities, generating a device level cyber-vulnerability score by augmenting the generated device cyber-vulnerability score based upon at least one device level parameter, generating an environmental cyber-vulnerability score, and computing an overall cyber-vulnerability score based upon the device level cyber-vulnerability score and the environmental cyber-vulnerability score. The computer-implemented process also comprises prioritizing the electronic devices based upon the computed overall cyber-vulnerability score, identifying whether a patch is available for at least one electronic device, and initiating a remediation / mitigation workflow to patch at least one electronic device.
Owner:MEDITECHSAFE INC
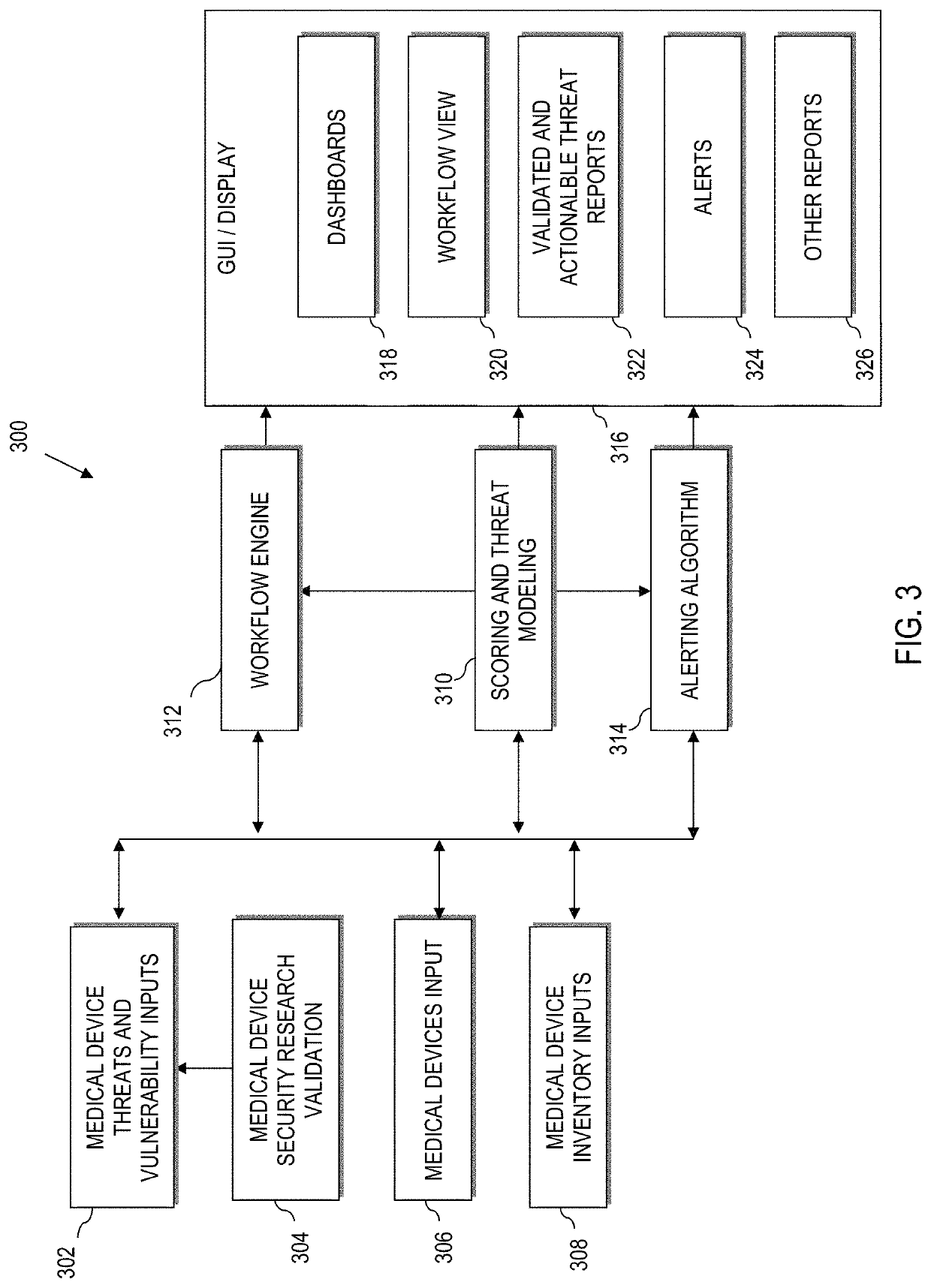
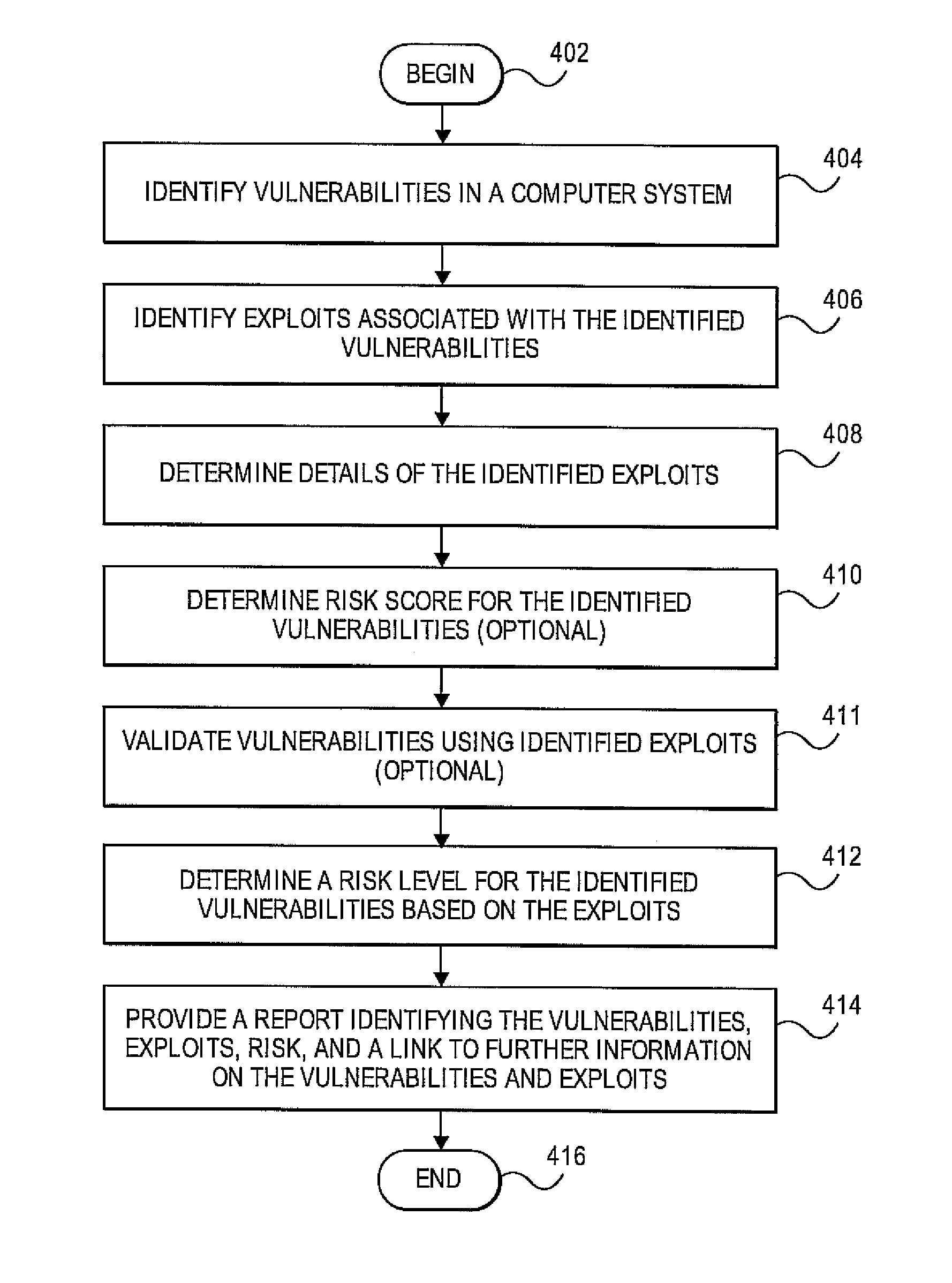
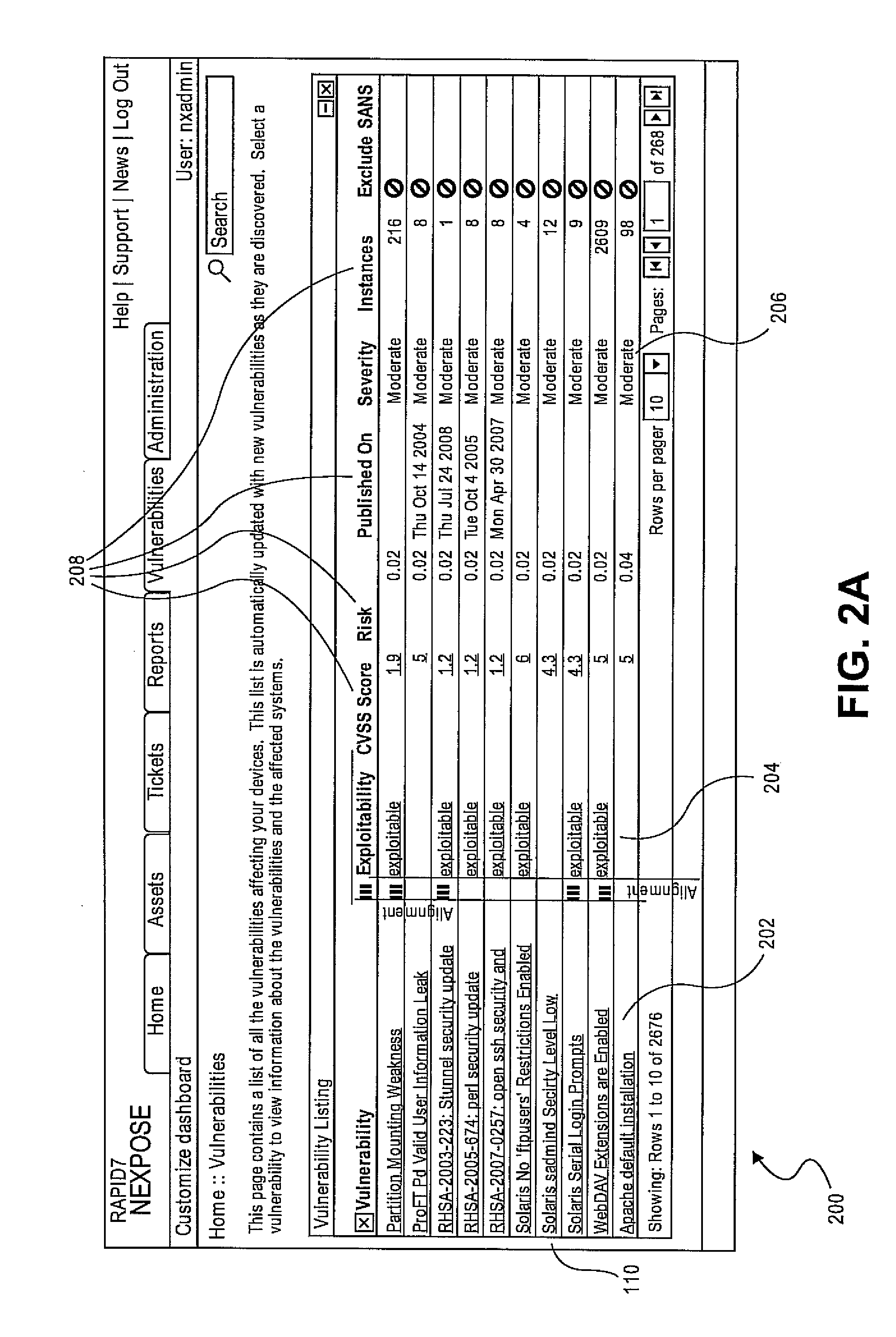
Methods and systems for testing and analyzing vulnerabilities of computing systems based on exploits of the vulnerabilities
A security tool can identify vulnerabilities in a computing system and determine a risk level of the vulnerabilities. The security tool can determine the risk level based on exploits associated with the vulnerabilities. The security tool can determine the risk level based on factors associated with the exploits such as whether an exploit exists, a rank of the exploit, a number of exploits that exist for the vulnerability, a difficulty to identify whether the exploit exists, and an effect of the exploit on the vulnerability. The security tool can a report identifying the vulnerabilities of the computing system, the exploits associated with the vulnerabilities, and the risk level of the vulnerabilities. The report can also include links to information about the exploits.
Owner:RAPID7
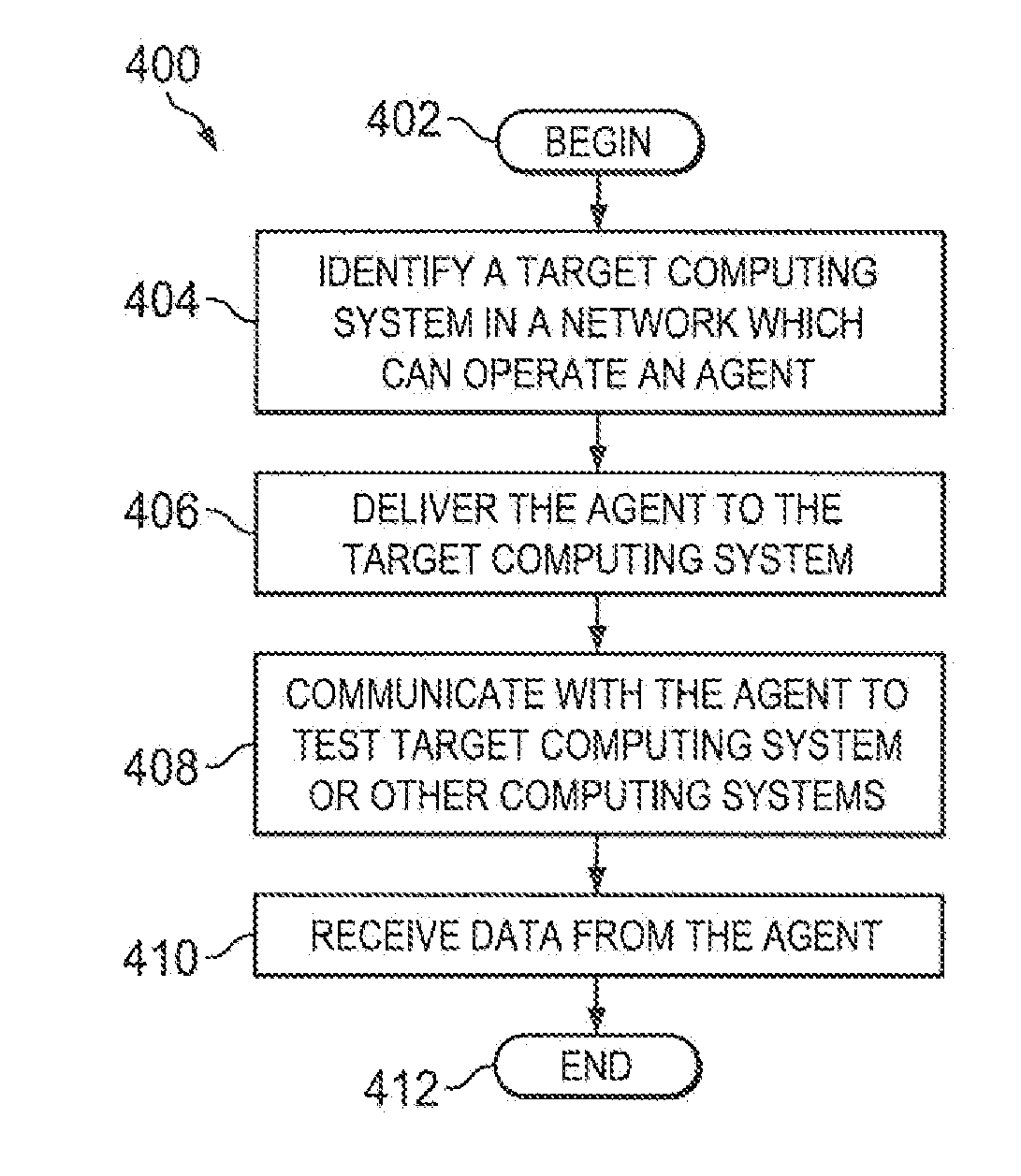
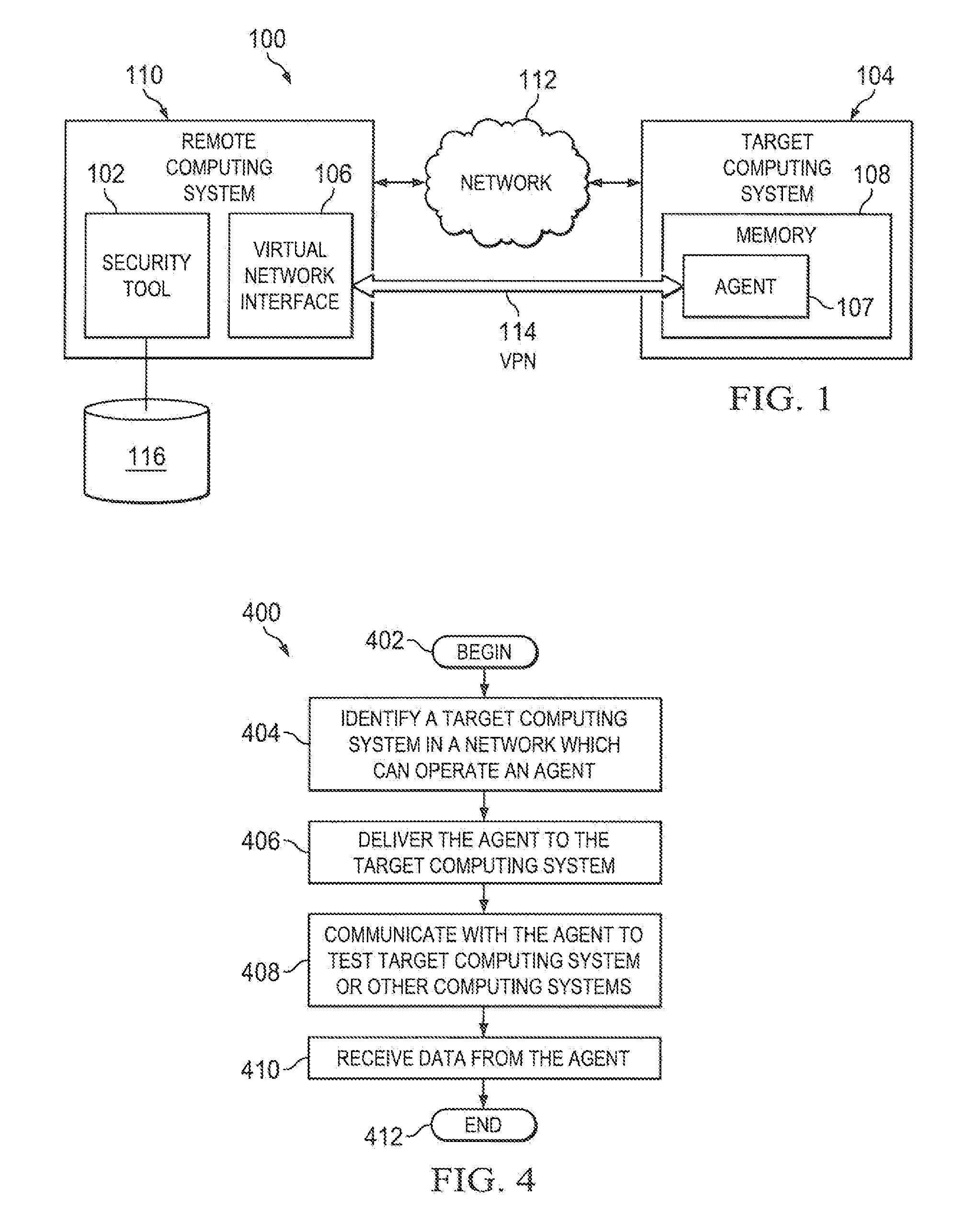
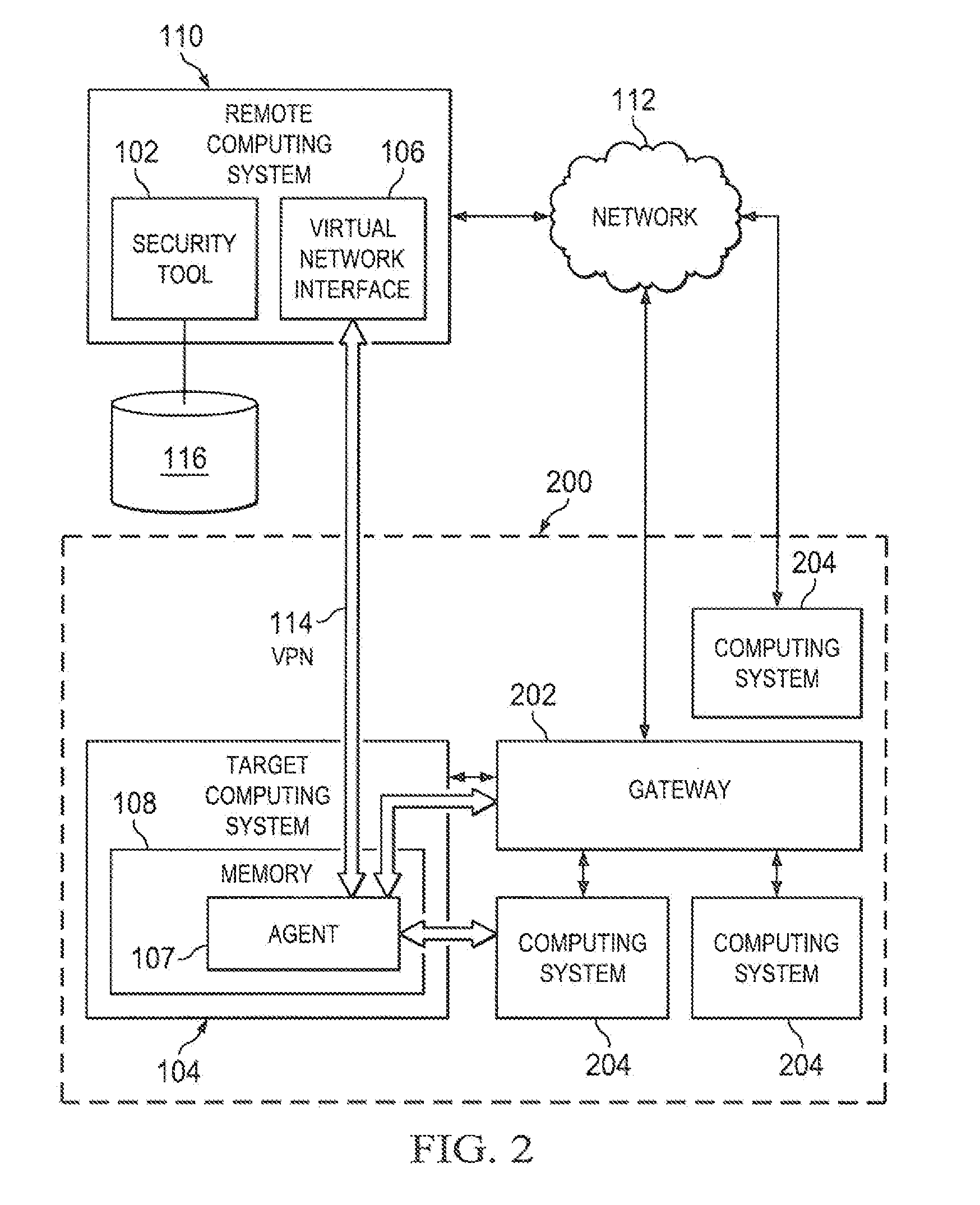
Methods and systems for providing a framework to test the security of computing system over a network
A security tool can utilize a vulnerability in a computing system or credentials for the computing system to gain access to the computing system. Once access is gained, the security tool can deliver an agent to the computing system. The agent can execute, detected or undetected, on the computing system in order to establish a network link between the computing system and the security tool. Once established, the security tool creates a virtual network interface on the computing system on which it is running and instructs the agent to relay network traffic between the virtual network interface of the computing system executing the security tool and the existing network interfaces of computing system executing the agent.
Owner:RAPID7
Methods and systems for evaluating software for known vulnerabilities
A vulnerability identification and resolution (VIR) computer device for identifying security vulnerabilities in a computer system is provided. The VIR computer device includes a memory device for storing data including data representing computing assets installed in the computer system and a processor in communication with the memory device. The VIR computer device is programmed to receive an asset identifier identifying a computing asset selected for evaluation and execute a query on at least one database storing security vulnerabilities, the query searching for security vulnerability data associated with the selected computing asset. The VIR computer device is further programmed to receive the security vulnerability data at the VIR computer device in response to the query.
Owner:MASTERCARD INT INC
Network security system and method for preemptively identifying or remediating security vulnerabilities
A system, a method, and a computer program for analyzing network security data from diverse data sources to predict and remediate a vulnerability at a node in a computer network, comprising receiving network security data from a plurality of data sources, extracting feature vectors from the received network security data, applying a machine learning model to the extracted feature vectors to generate a weighted vulnerability value, predicting a computing resource vulnerability at a node in the computer network based on the weighted vulnerability value, and transmitting the predicted computing resource vulnerability to a computing device which is configured to remediate the predicted computing resource vulnerability.
Owner:SAUDI ARABIAN OIL CO
Attestation protocol for securely booting a guest operating system
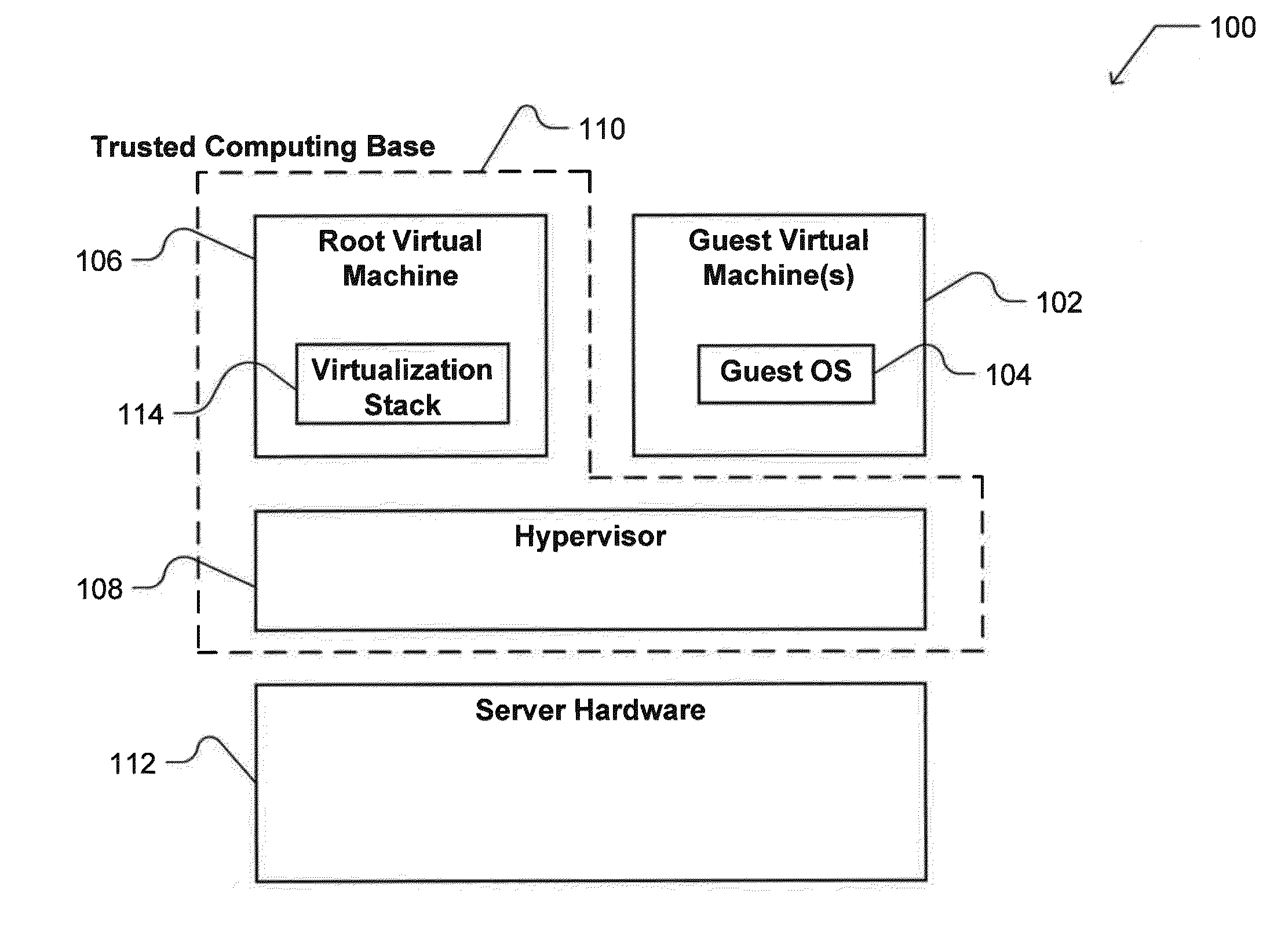
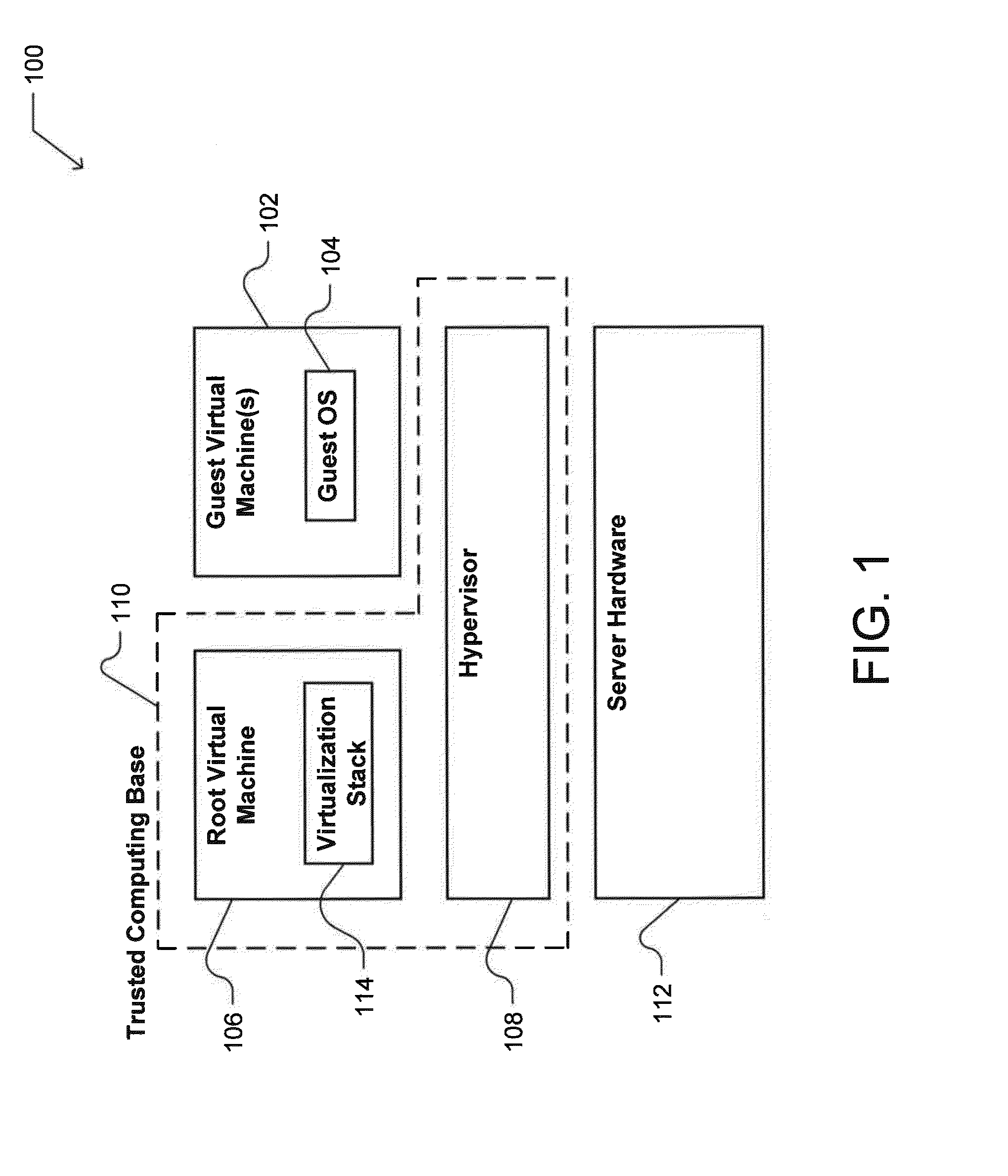
ActiveUS20140359270A1Few security vulnerabilityReduced virtualizationDigital computer detailsBootstrappingOperational systemCoprocessor
In a cloud computing environment, a production server virtualization stack is minimized to present fewer security vulnerabilities to malicious software running within a guest virtual machine. The minimal virtualization stack includes support for those virtual devices necessary for the operation of a guest operating system, with the code base of those virtual devices further reduced. Further, a dedicated, isolated boot server provides functionality to securely boot a guest operating system. The boot server is isolated through use of an attestation protocol, by which the boot server presents a secret to a network switch to attest that the boot server is operating in a clean mode. The attestation protocol may further employ a secure co-processor to seal the secret, so that it is only accessible when the boot server is operating in the clean mode.
Owner:MICROSOFT TECH LICENSING LLC
Mimicry defense construction method and system for edge computing cloud center
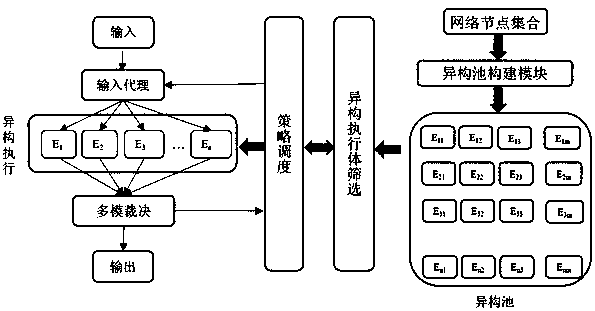
ActiveCN111478928ASimultaneous Mimic TaskImprove robustnessPlatform integrity maintainanceTransmissionAttackEdge computing
The invention discloses a mimicry defense construction method and system for an edge computing cloud center. The method is applied to the technical field of network security, and comprises the steps of obtaining edge node information, constructing a heterogeneous pool, screening out a heterogeneous execution body set from the heterogeneous pool, synchronizing a mimicry task between a cloud centerand the heterogeneous execution body set, scheduling heterogeneous execution bodies in the heterogeneous execution body set by a dynamic heterogeneous redundancy module, and re-screening out the heterogeneous execution body set. According to the invention, the heterogeneity existing in the edge computing network is utilized to construct the heterogeneous pool and form the heterogeneous execution body set; the cloud center synchronizes the mimicry task to the heterogeneous execution body, a dynamic redundancy heterogeneous defense mechanism is established, attacks of hackers on specific systemsor software vulnerabilities are blocked, the redundancy mechanism can prevent functional anomalies caused by unknown vulnerabilities to a certain extent, the robustness and safety of an edge computing network are improved, and the cost of mimicry defense is reduced.
Owner:NANJING REDMATRIX NETWORK SECURITY TECH R & D INST
Cybersecurity vulnerability classification and remediation based on installation base
ActiveUS20210037038A1Reduce the risk of cyber attacksDiagnosticsSurgical navigation systemsCyber-attackSeverity level
A system, a method, and a computer program for remediating a cyberattack risk for a computing resource located at a node in a computer network having a plurality of nodes. The solution includes receiving vulnerability score data that has a severity level for a vulnerability in the computing resource at the node, receiving a number of installations value (NCRi) that indicates a number of instances the computing resource is included in the plurality of nodes, determining a percentile of occurrence value (POCRi) for the computing resource based on the number of installations value (NCRi), applying a severity adjustment matrix to the severity level to determine a true severity level for the vulnerability in the computing resource, reprioritized the vulnerability in the computing resource based on the true severity level, and mitigating the cyberattack risk for the computing resource based on the true severity level.
Owner:SAUDI ARABIAN OIL CO
Cybersecurity vulnerability classification and remediation based on network utilization
ActiveUS20200162498A1Accurately vulnerabilityComputer security arrangementsData switching networksCyber-attackInternet traffic
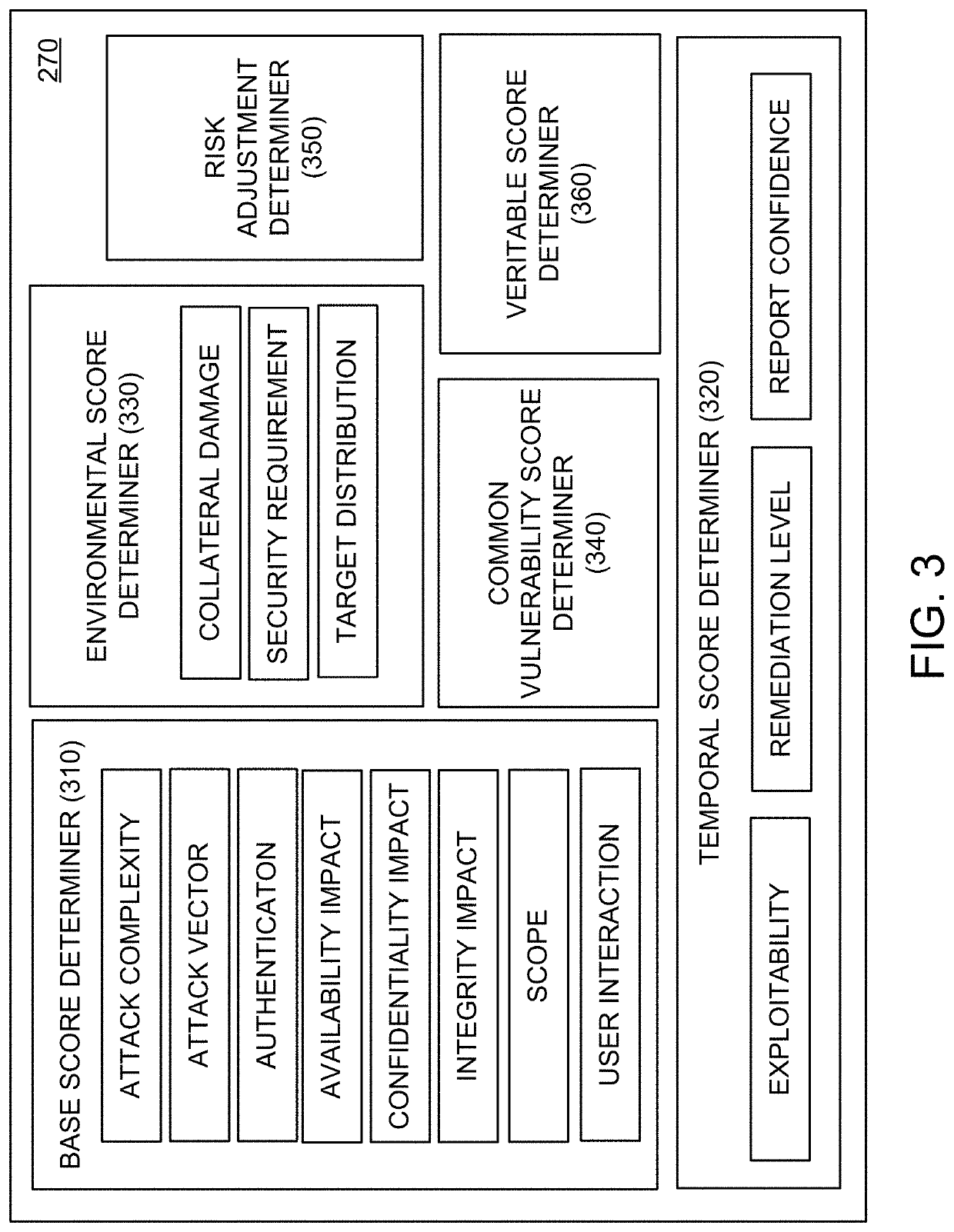
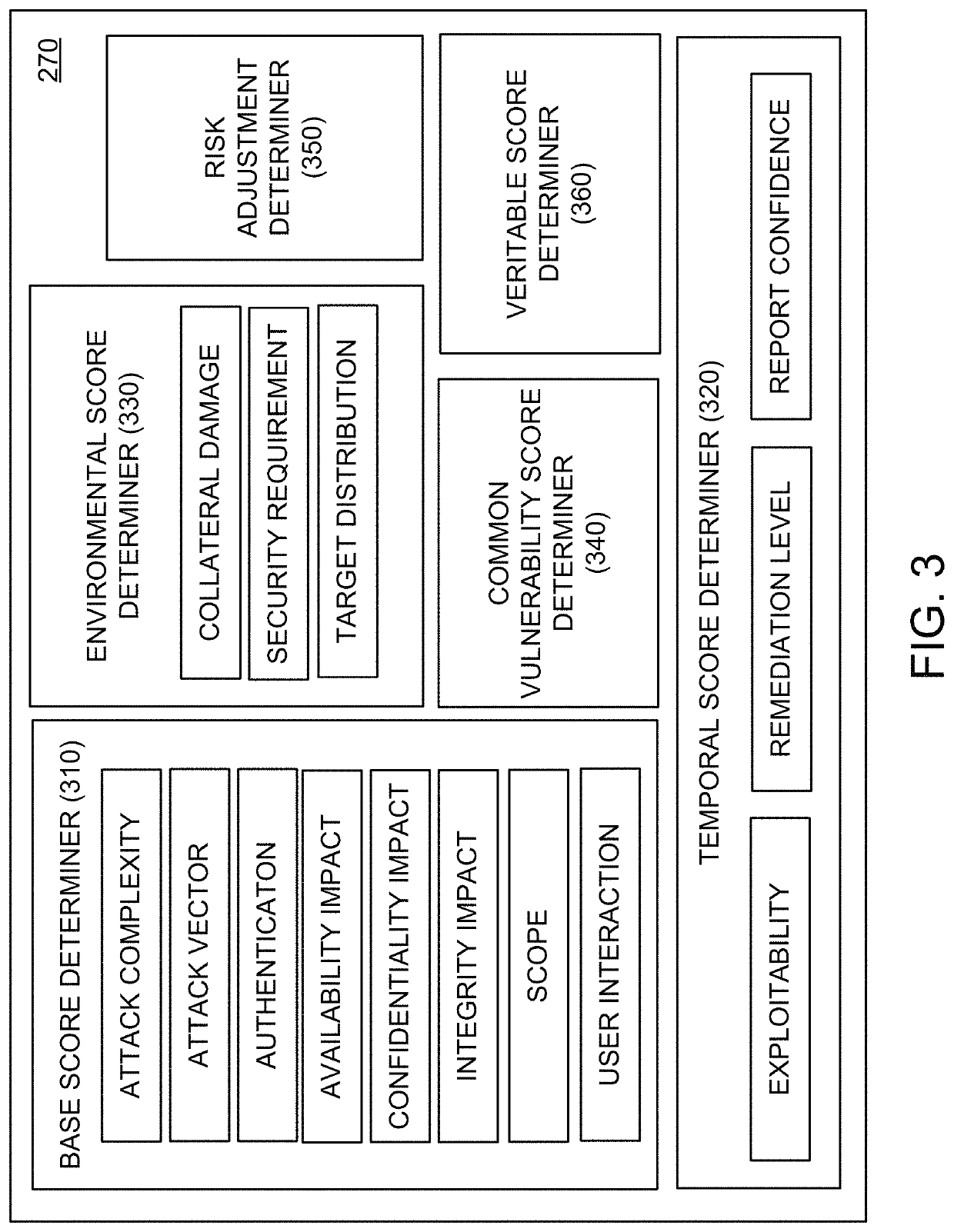
A technology solution for remediating a cyberattack risk in a computing resource asset in a network system. The technology solution includes monitoring data traffic directed to the computing resource asset in the network system along with data traffic to one or more additional computing resource assets in the network system, generating network utilization data based on the monitored data traffic to the computing resource asset and the monitored data traffic to the one or more additional computing resource assets in the network system, receiving a common vulnerability score (CVSS) for a vulnerability in the computing resource asset, determining a network traffic adjustment (NTA) value for the common vulnerability score (CVSS) based on the network utilization data, adjusting the common vulnerability score (CVSS) by the network traffic adjustment (NTA) value to generate a prioritized common vulnerability score (PCVSS) for the computing resource asset, and remediating the computing resource asset to resolve the vulnerability based on the prioritized common vulnerability (PCVSS) score.
Owner:SAUDI ARABIAN OIL CO
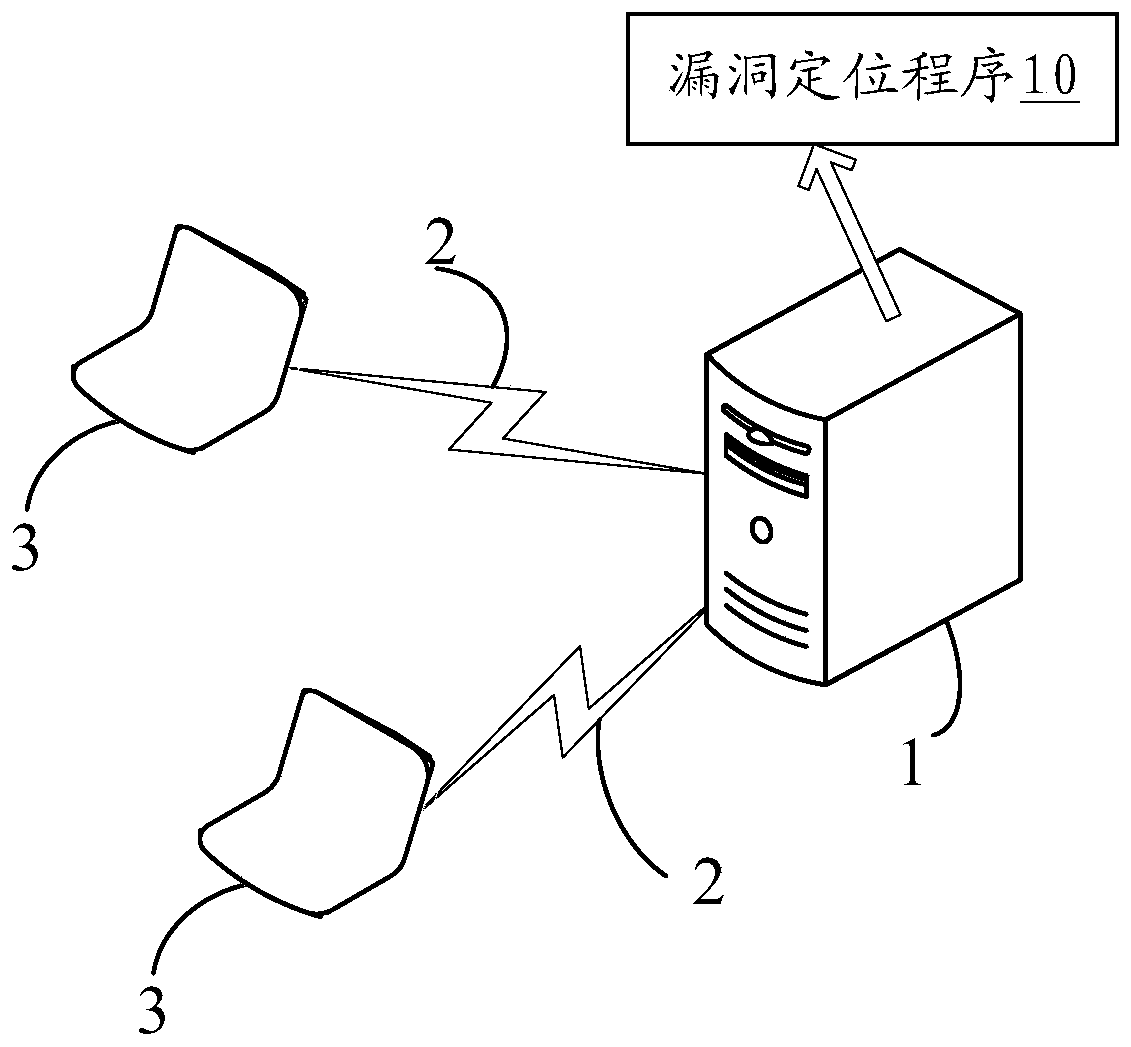
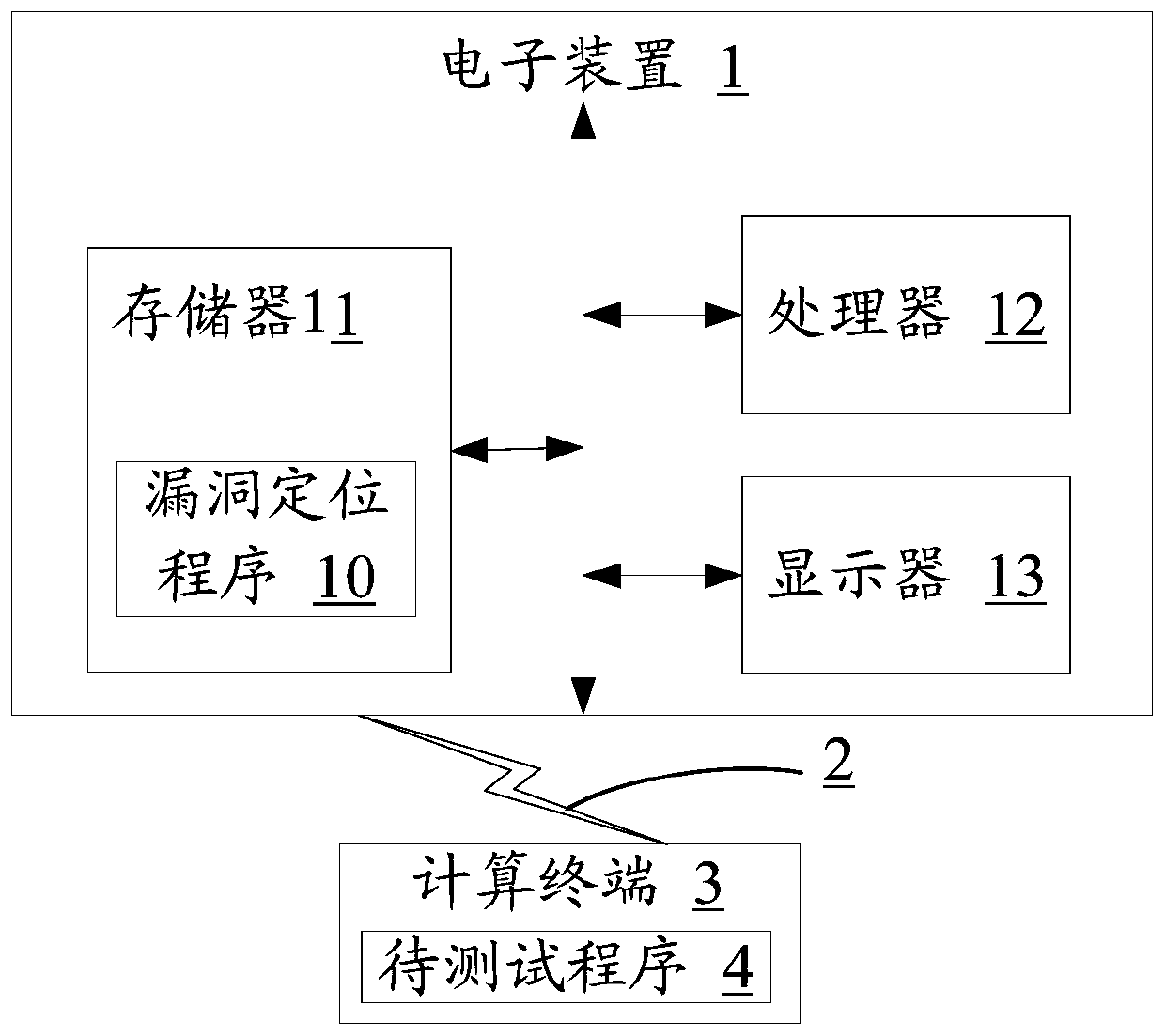
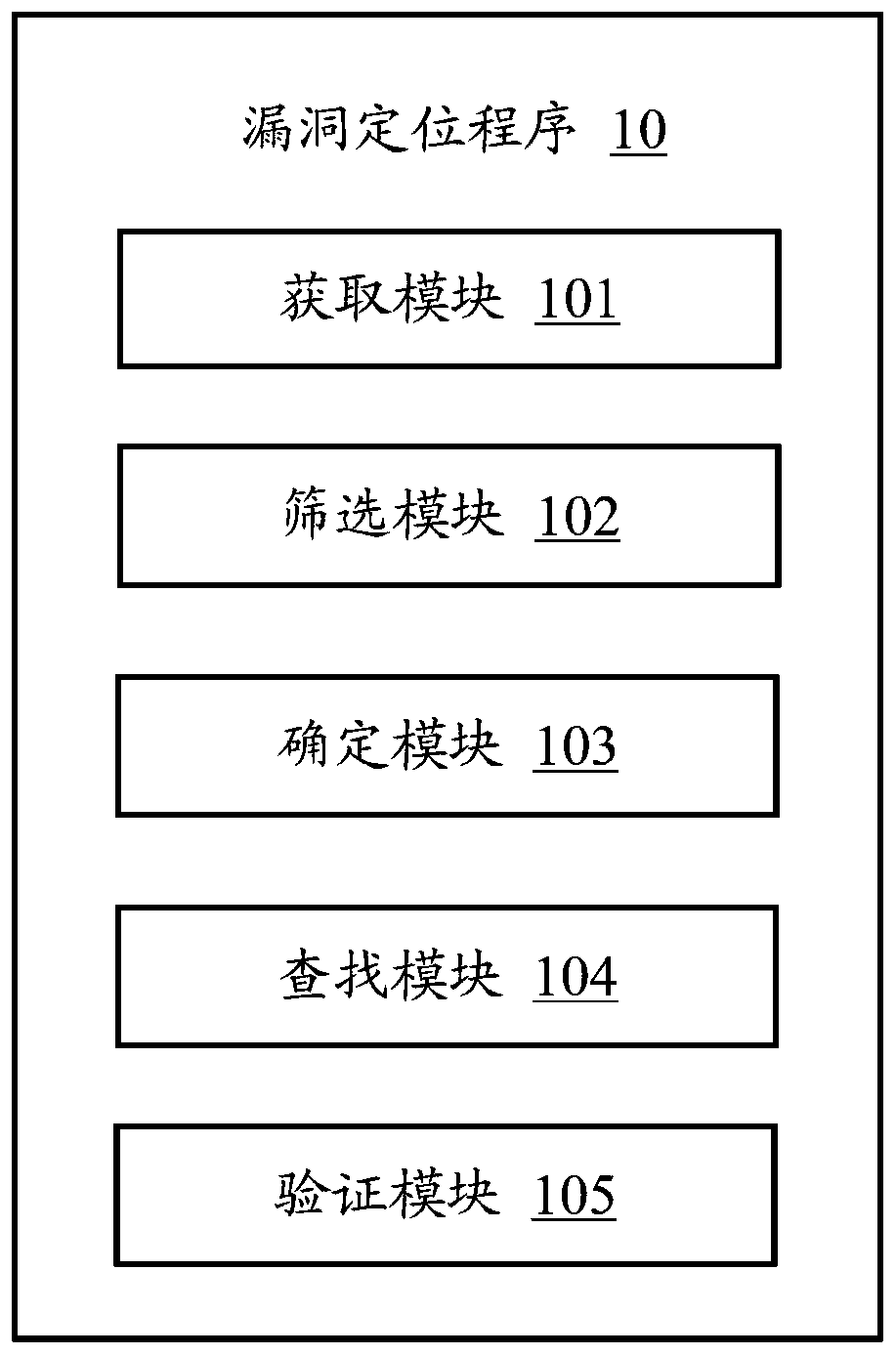
Quick vulnerability positioning method, electronic device and storage medium
PendingCN110866258ASoftware testing/debuggingPlatform integrity maintainanceCoding blockVulnerability (computing)
The invention relates to the technical field of security detection, and provides a rapid vulnerability positioning method, an electronic device and a computer storage medium. The method comprises thesteps of obtaining current abnormal information fed back when a to-be-tested program operated by a computing terminal is abnormal; screening out abnormal information with the same semanteme as the current abnormal information from the abnormal information pre-stored in the database by utilizing a word2vec tool; determining a target character string of the program bug corresponding to the current abnormal information according to a mapping relationship between preset abnormal information and the character string representing the program bug corresponding to the abnormal information, and findingout a code block containing the target character string from the to-be-tested program; and finally, when the found code block is abnormal, judging that the found code block has a bug and determiningthe position of the bug. The code block corresponding to the abnormal information appearing in the program running process is rapidly found out by establishing the abnormality searching mechanism, thecode block is verified, and the vulnerability in the program is rapidly positioned.
Owner:PING AN TECH (SHENZHEN) CO LTD
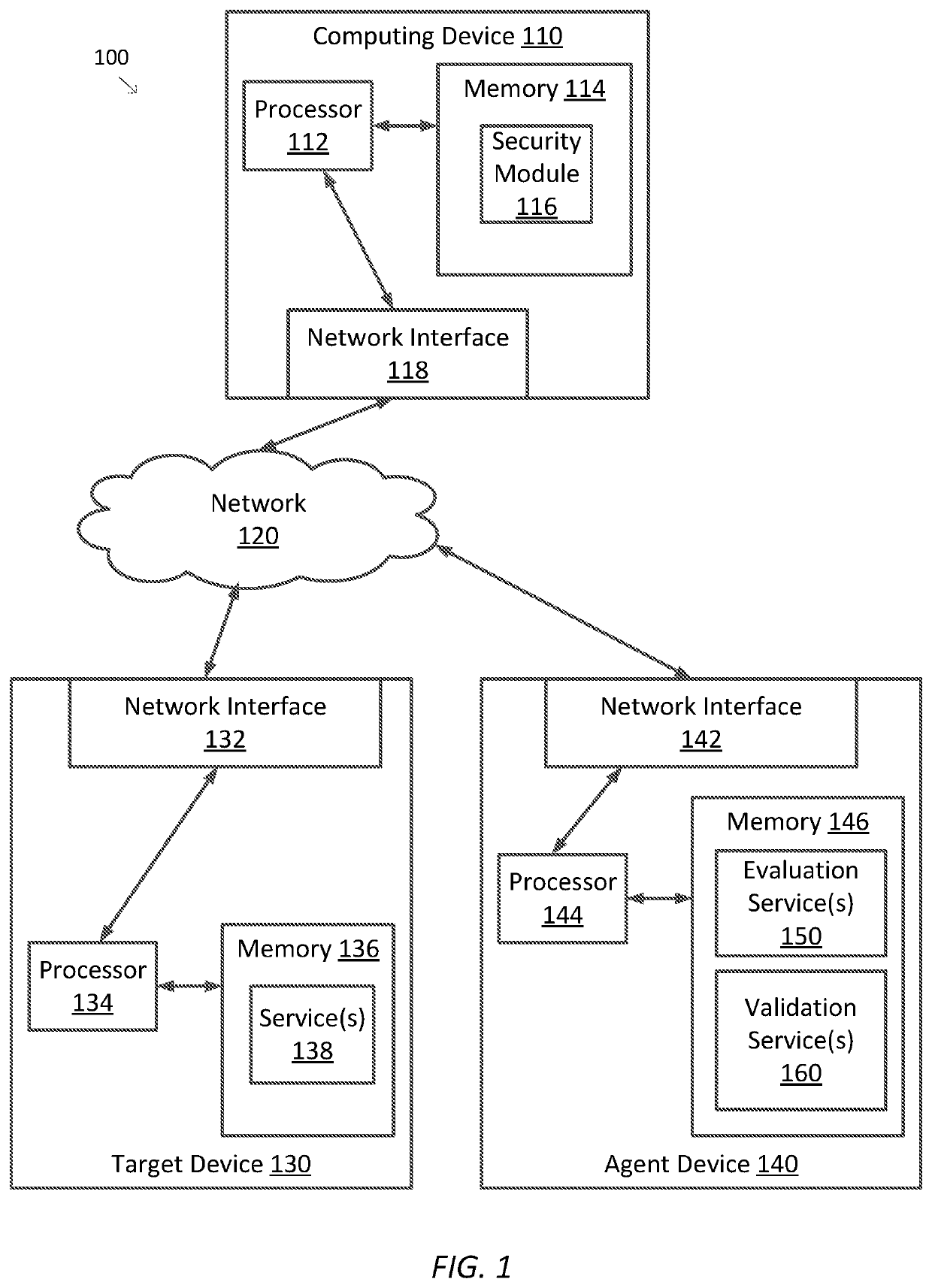
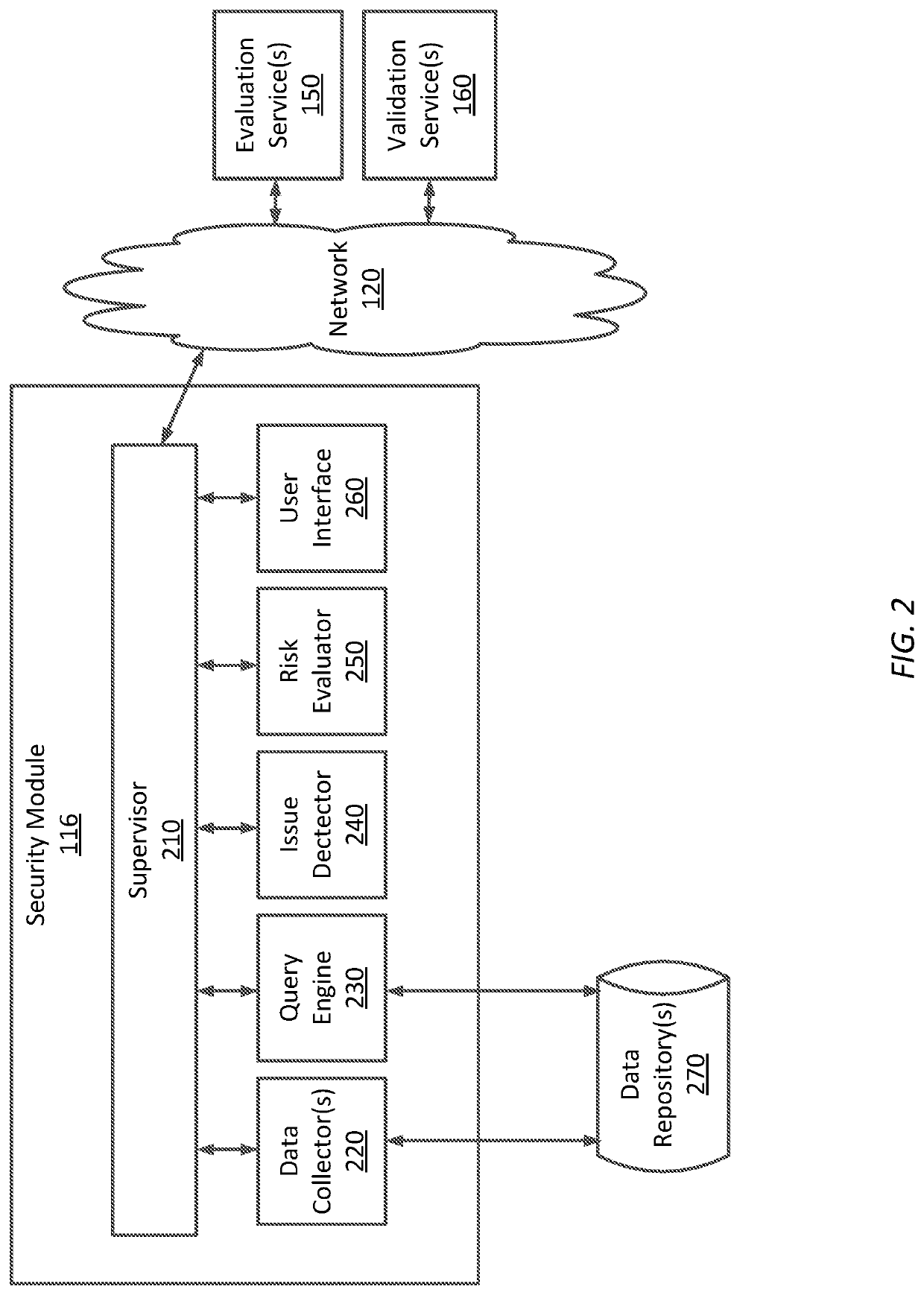
Techniques for monitoring computing infrastructure
PendingUS20210365564A1Reduce and eliminate costlyReduce and eliminate and time-consume maintenanceHardware monitoringPlatform integrity maintainanceEvaluation resultData transformation
A technique for monitoring a computing infrastructure having one or more target devices includes receiving, from a plurality of evaluation services, evaluation results of one or more target devices. The technique further includes extracting, using a different data collector for each of the plurality of evaluation services, data from each of the evaluation results. The technique further includes converting the extracted data to a common format, determining whether an issue or a vulnerability is present in the one or more target devices based on the extracted and converted data, and reporting the issue or the vulnerability.
Owner:DISNEY ENTERPRISES INC
Software vulnerability detection in managed networks
ActiveUS20210064758A1Facilitates featureImprove functionalityPlatform integrity maintainanceComputer networkConfiguration item
A system may include persistent storage containing representations of configuration items discovered in a managed network, where the configuration items include computing devices and software applications installed on the computing devices. One or more processors may be configured to: (i) obtain results of a vulnerability analysis performed on a software application, where the results indicate that the software application exhibits a vulnerability, (i) determine a count of computing devices on which the software application is installed, (iii) calculate a security threat score for the vulnerability, where the security threat score is based on a severity factor of the vulnerability and the count of computing devices, (iv) provide, to a first entity, a first indication of the software application and the vulnerability, and (v) provide, to a second entity, a second indication of the software application, the vulnerability, and the security threat score.
Owner:SERVICENOW INC
Quantumproof blockchain
PendingCN111448579AQuantum computersKey distribution for secure communicationEffective solutionComputer network
Bitcoins and the underlying blockchain technology are one of the main innovations in building decentralized applications. The effects of quantum computing on this technology are analyzed in general. Provided herein are effective solutions to address security vulnerabilities in a blockchain-based system that can be exploited by a quantum attacker.
Owner:丁津泰
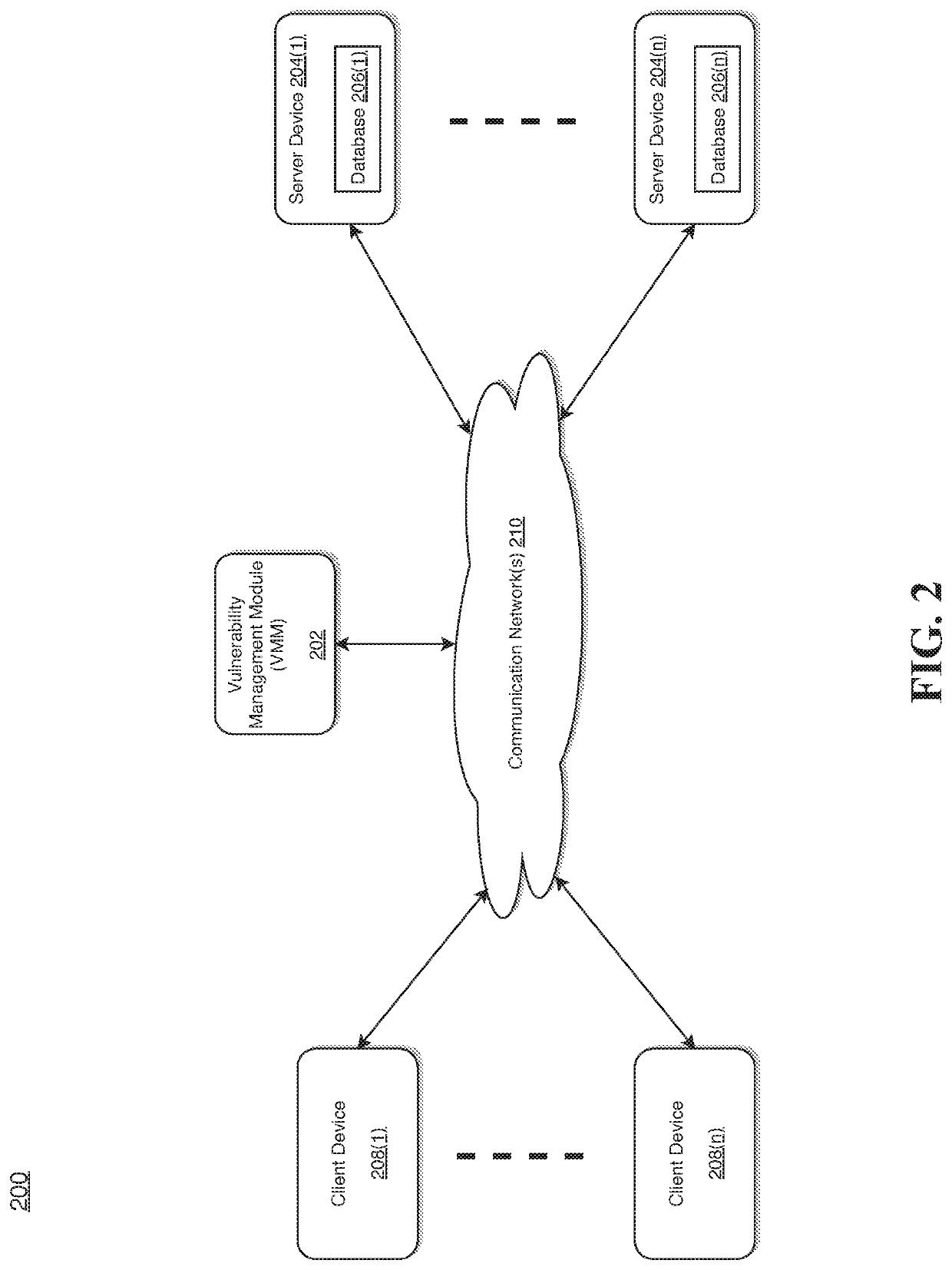
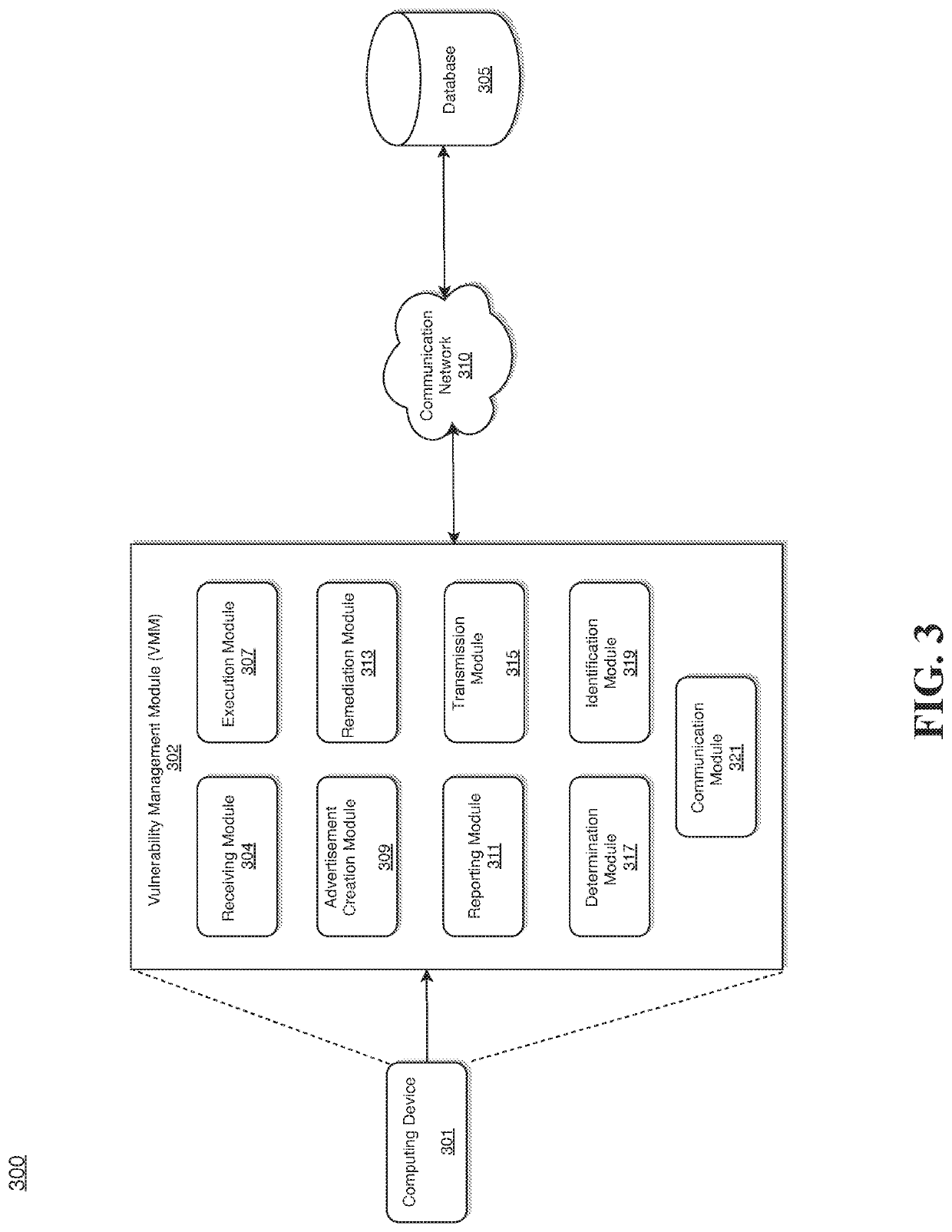
System and method for implementing a vulnerability management module
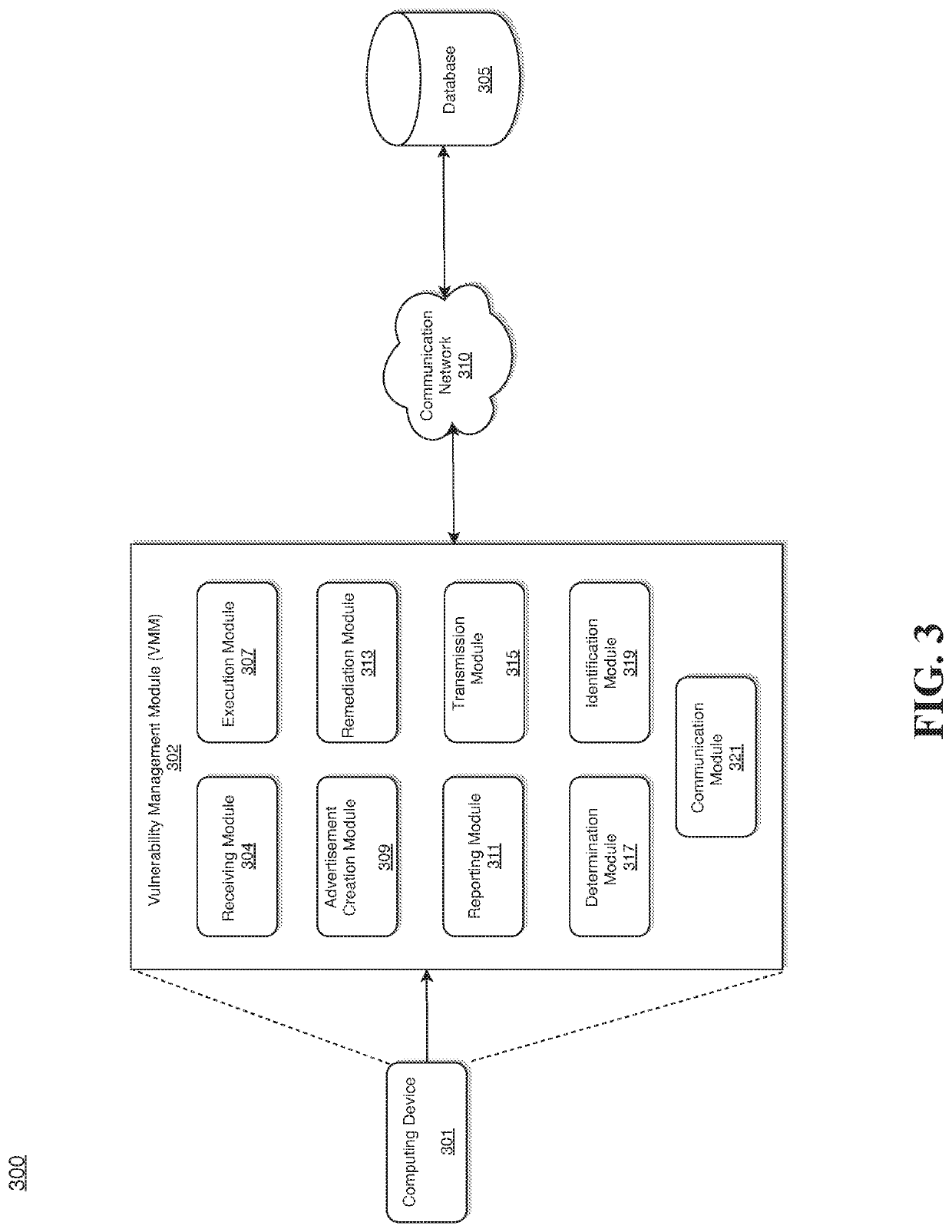
ActiveUS20210021630A1Reduce utilizationEliminate needTransmissionVulnerability managementVulnerability (computing)
Various methods, apparatuses / systems, and media for implementing a vulnerability management module are provided. A receiver receives a request for dynamically scanning vulnerability of a target computing device based on testable vulnerability criteria extracted from a database. A processor dynamically executes the testable vulnerability criteria from the SCCM based on the received request; creates a static SCCM advertisement with a dynamic pre / post validation check capability based on a result of the dynamically executing the testable vulnerability criteria; reports a success or a failure of the static SCCM advertisement related to the testable vulnerability criteria to indicate whether a vulnerability exists within the target computing device; and automatically remediates the vulnerability when it is determined that the vulnerability exists within the target computing device.
Owner:JPMORGAN CHASE BANK NA
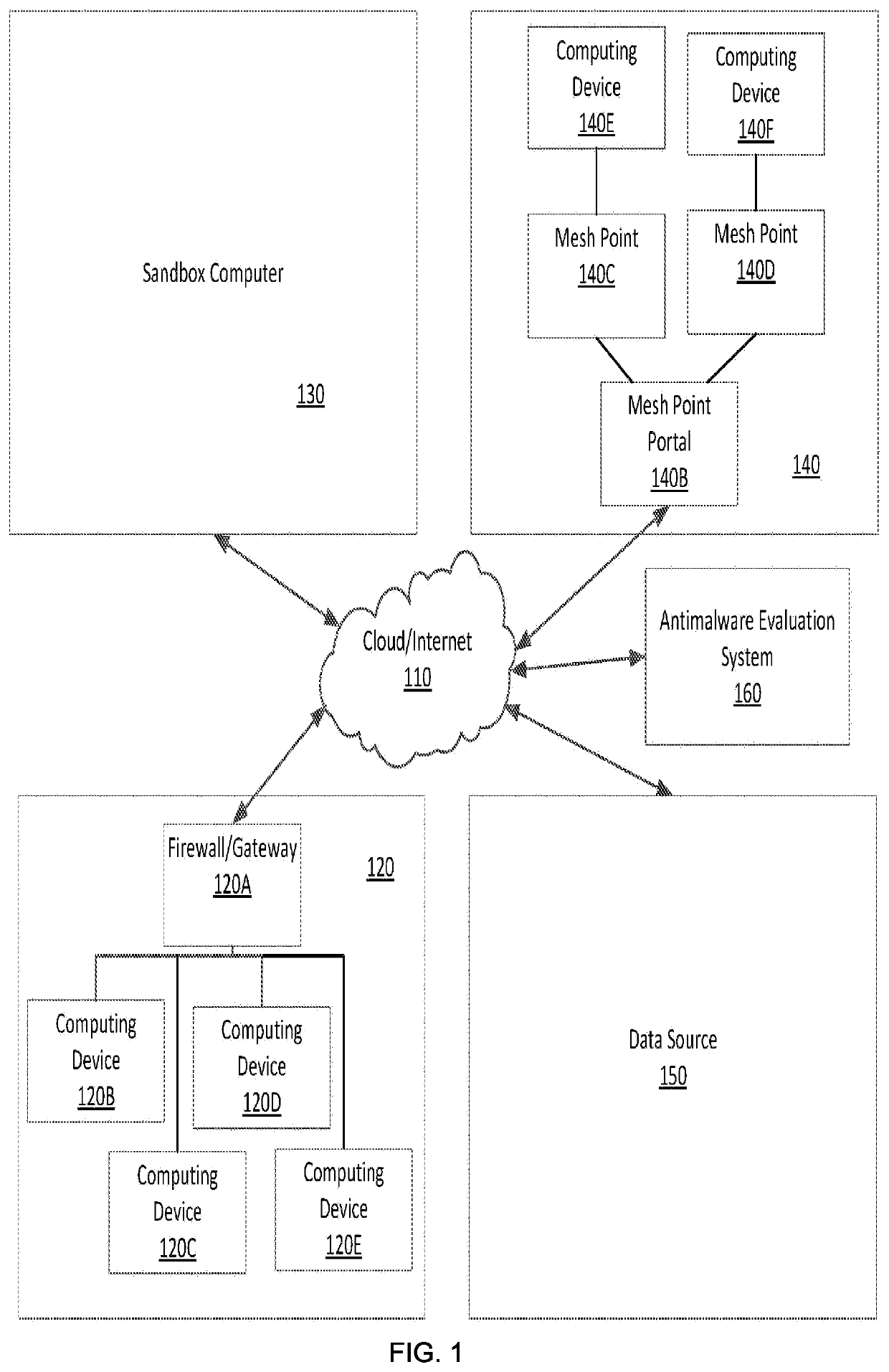
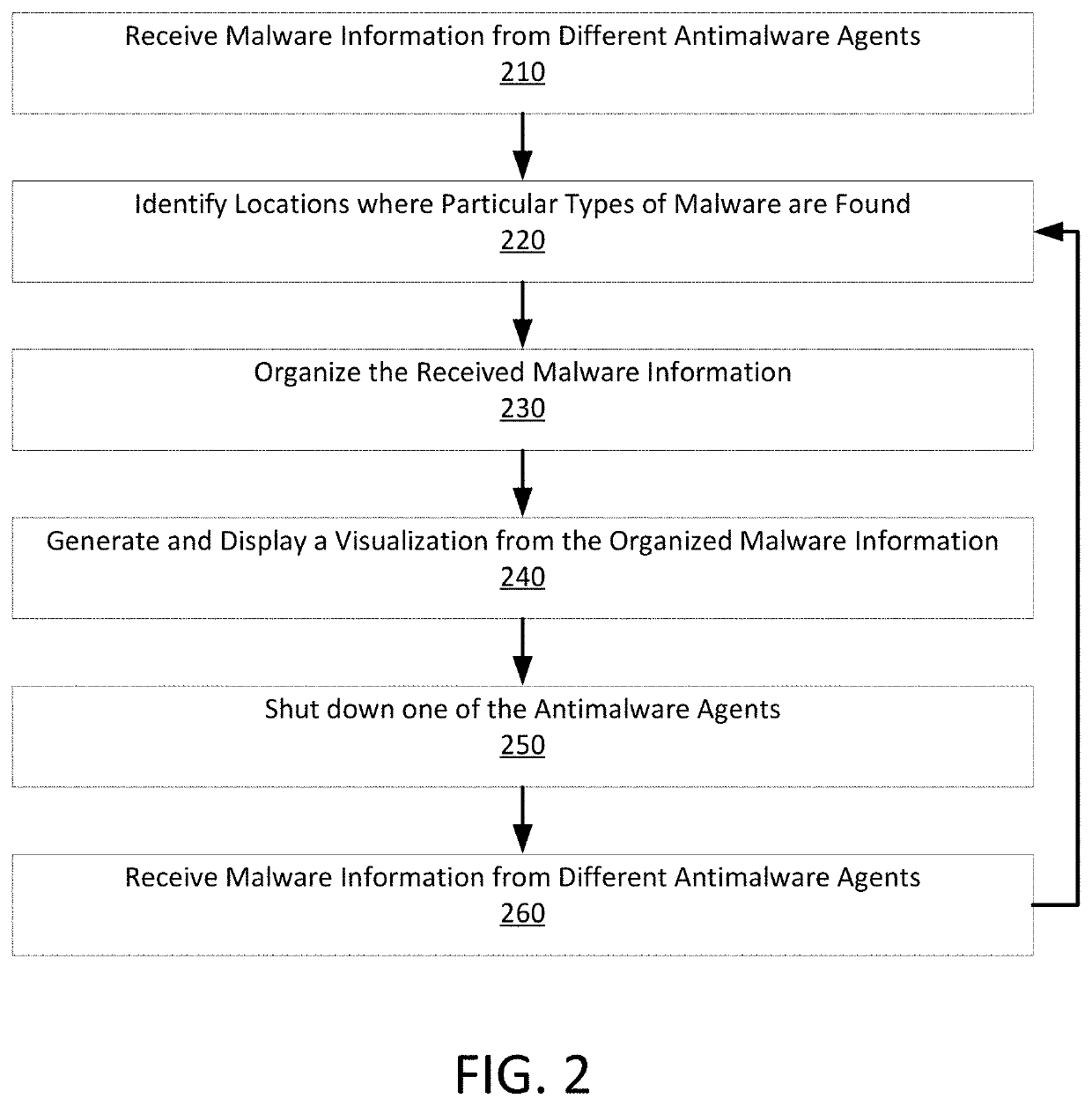
Identification of potential network vulnerability and security responses in light of real-time network risk assessment
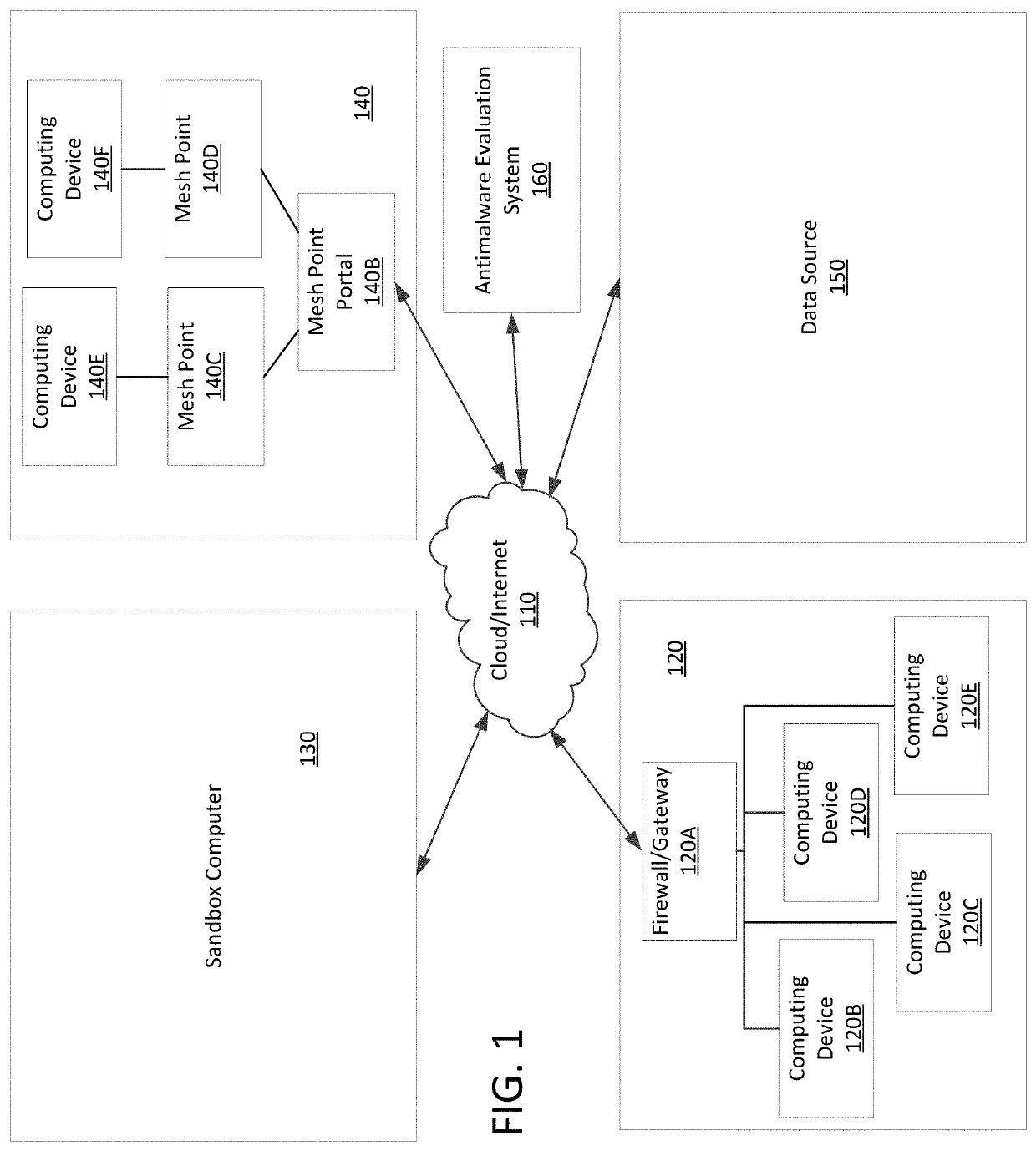
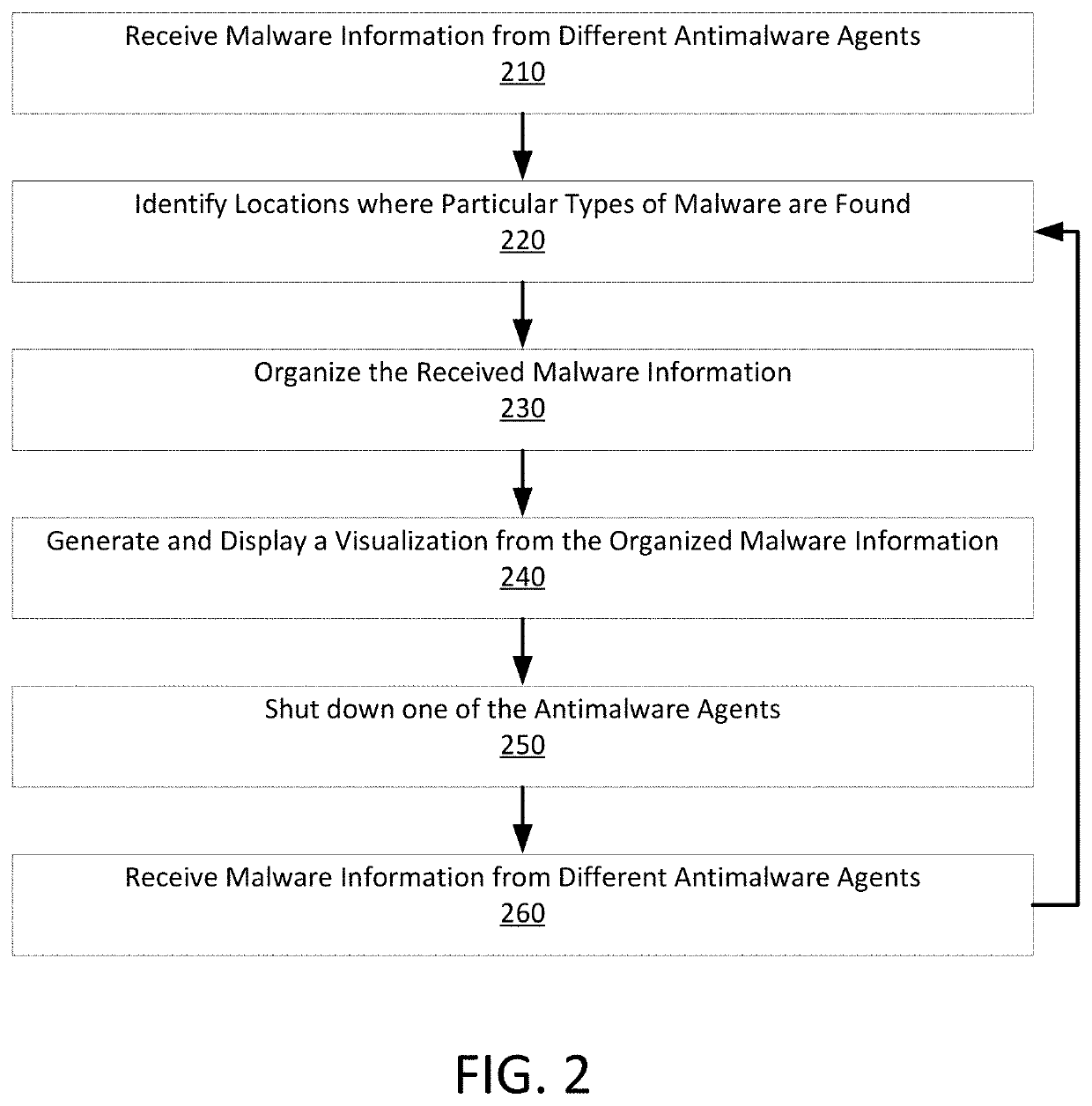
The present disclosure relates to methods and apparatus that collect data regarding malware threats, that organizes this collected malware threat data, and that provides this data to computers or people such that damage associated with these software threats can be quantified and reduced. The present disclosure is also directed to preventing the spread of malware before that malware can damage computers or steal computer data. Methods consistent with the present disclosure may optimize tests performed at different levels of a multi-level threat detection and prevention system. As such, methods consistent with the present disclosure may collect data from various sources that may include endpoint computing devices, firewalls / gateways, or isolated (e.g. “sandbox”) computers. Once this information is collected, it may then be organized, displayed, and analyzed in ways that were not previously possible.
Owner:SONICWALL
Method, system, and/or software for finding and addressing an information/data or related system's security risk, threat, vulnerability, or similar event, in a computing device or system
InactiveUS20200053117A1Facilitates and improves complianceLow costTransmissionVulnerability (computing)Security level
Owner:TELESIS CORP
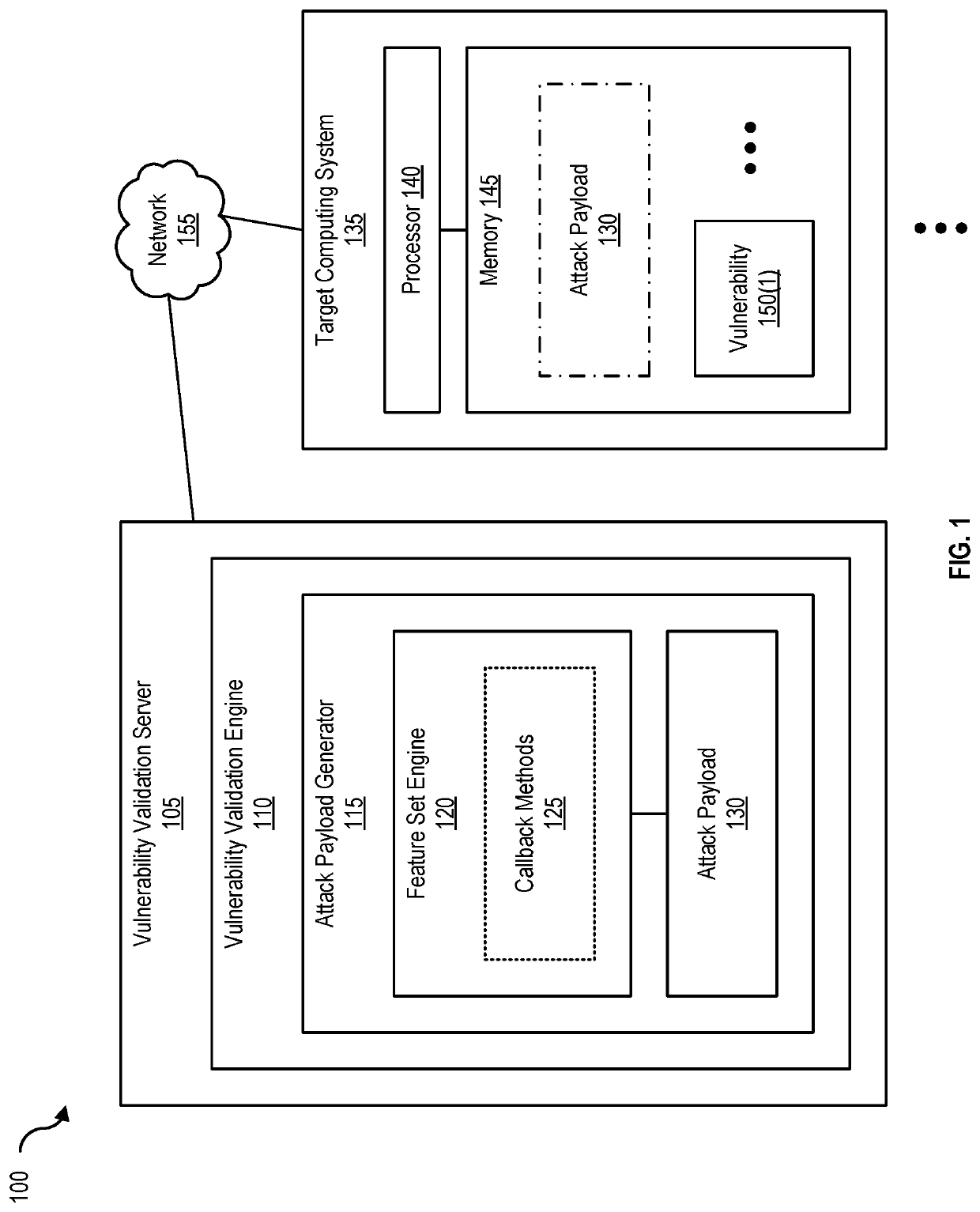
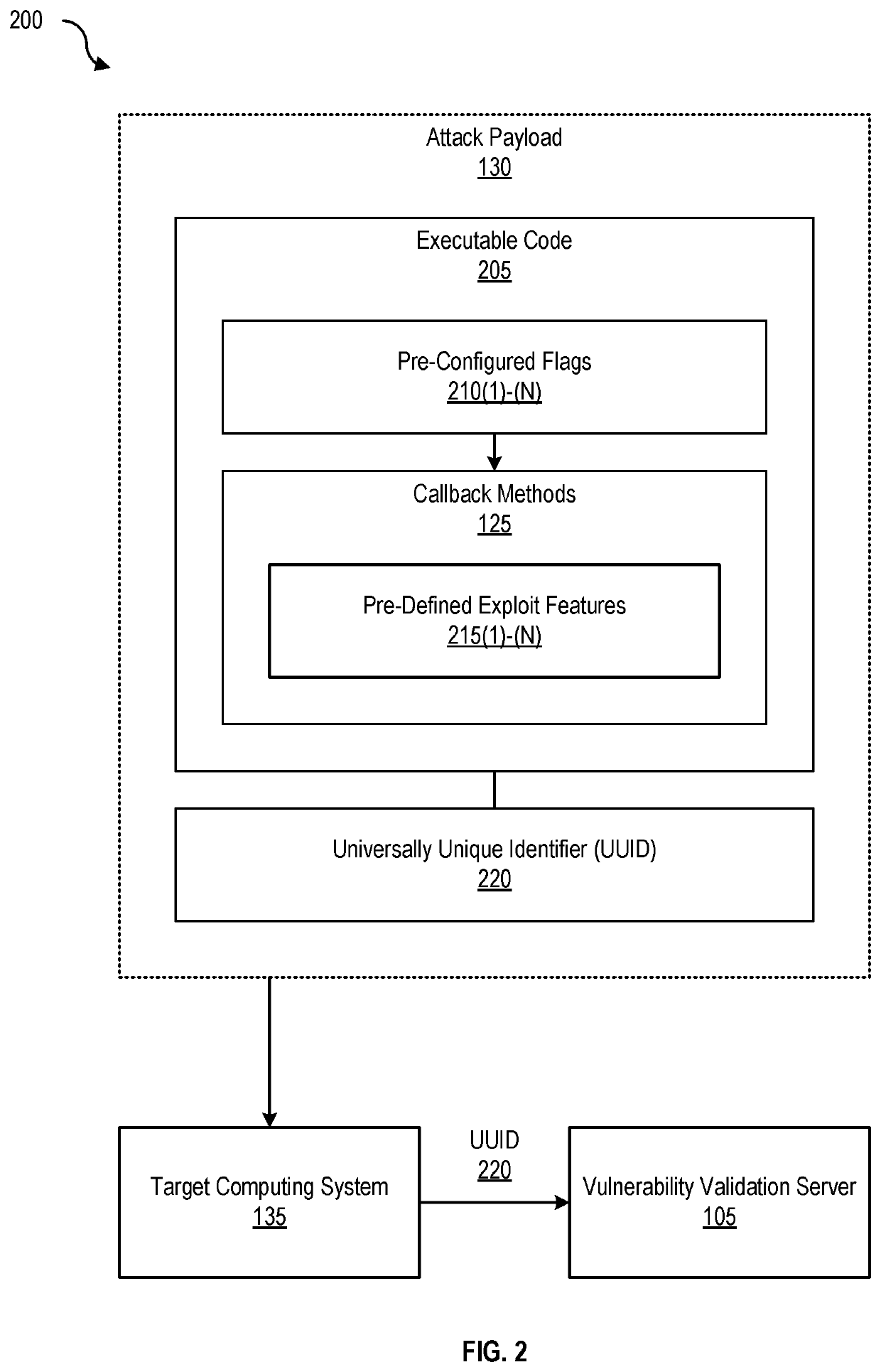
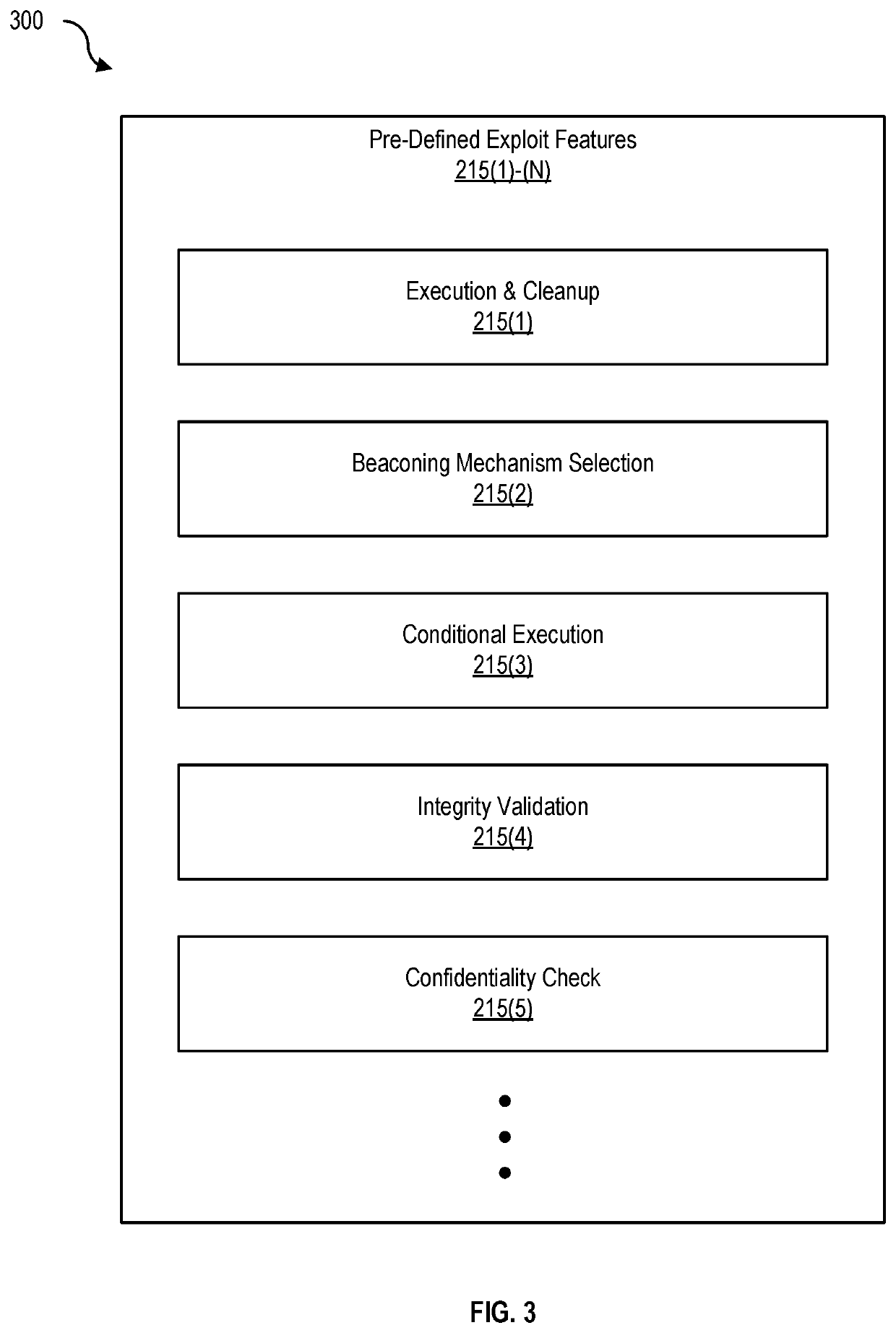
Vulnerability validation using lightweight offensive payloads
Disclosed herein are methods, systems, and processes for validating vulnerabilities using lightweight offensive payloads. An attack payload limited by an execution scope that includes pre-defined exploit features for validating code execution associated with a vulnerability is generated. The attack payload is transmitted to a target computing system and a confirmation of the code execution based on at least one pre-defined exploit feature is received, permitting a determination that the vulnerability has been validated.
Owner:RAPID7
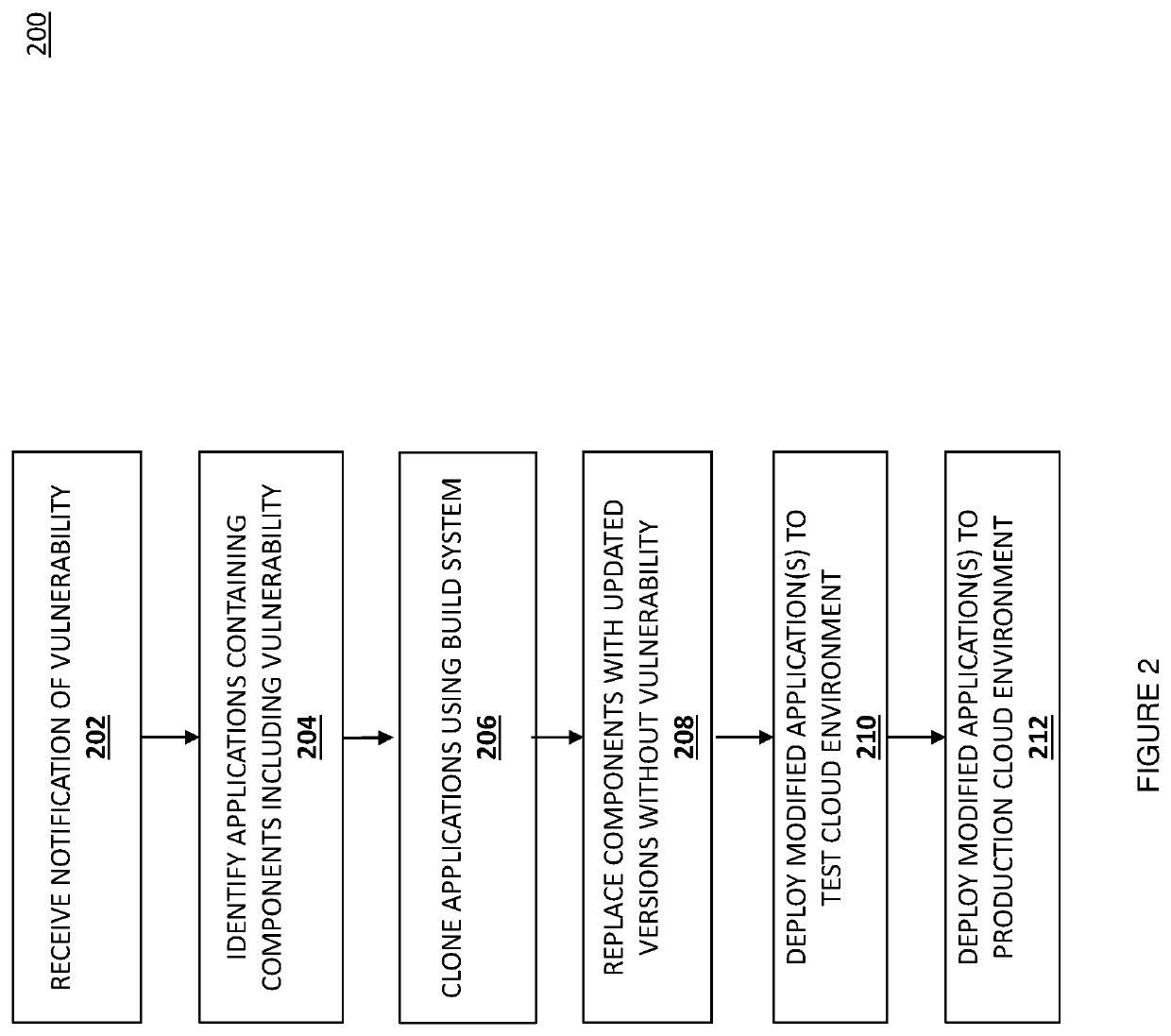
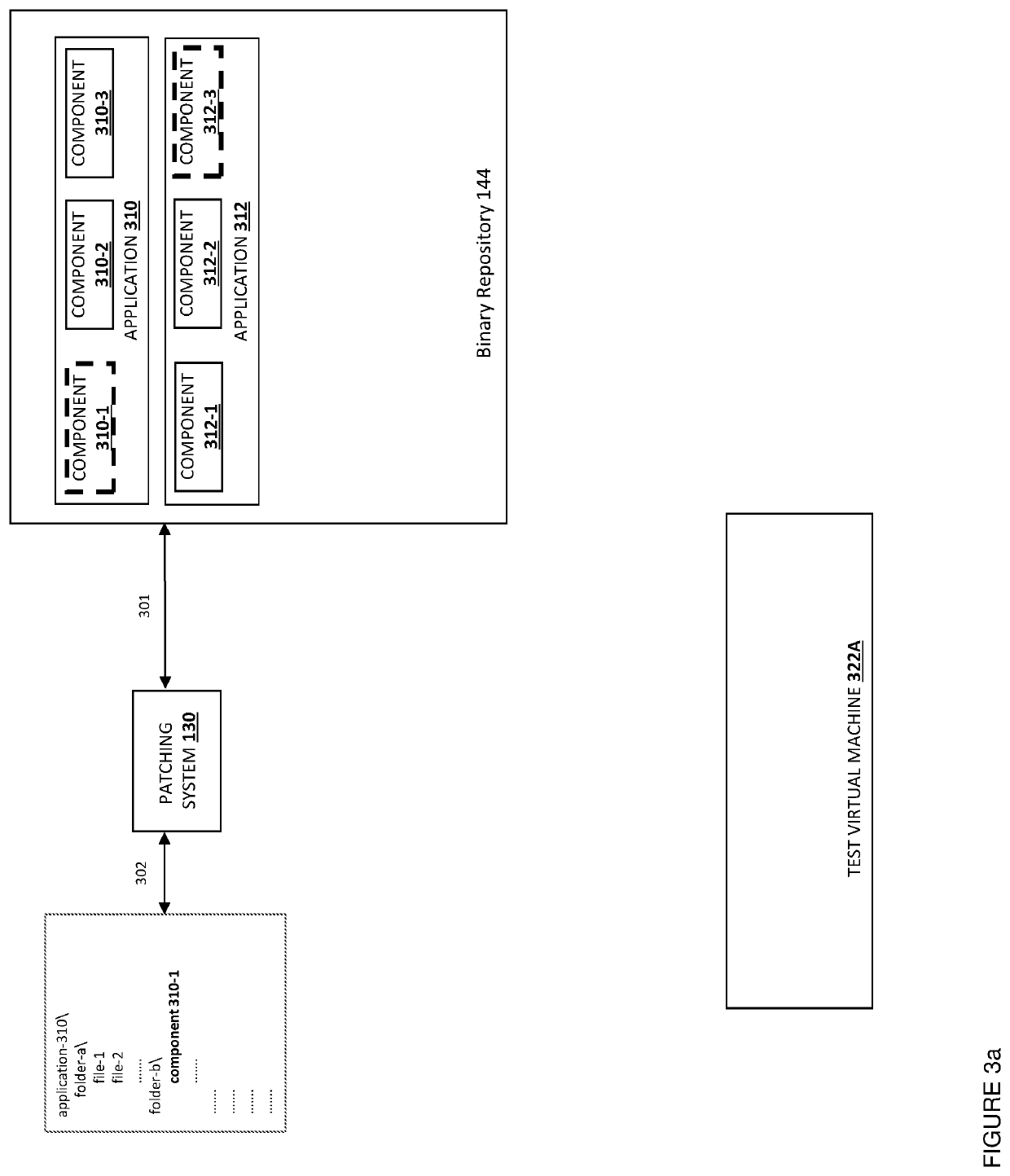
Systems and methods for patching vulnerabilities
ActiveUS10592677B2Version controlSoftware testing/debuggingSoftware engineeringVulnerability (computing)
Owner:PAYPAL INC
Cybersecurity vulnerability classification and remediation based on network utilization
ActiveUS11277429B2Accurately vulnerabilityComputer security arrangementsTransmissionCyber-attackInternet traffic
A technology solution for remediating a cyberattack risk in a computing resource asset in a network system. The technology solution includes monitoring data traffic directed to the computing resource asset in the network system along with data traffic to one or more additional computing resource assets in the network system, generating network utilization data based on the monitored data traffic to the computing resource asset and the monitored data traffic to the one or more additional computing resource assets in the network system, receiving a common vulnerability score (CVSS) for a vulnerability in the computing resource asset, determining a network traffic adjustment (NTA) value for the common vulnerability score (CVSS) based on the network utilization data, adjusting the common vulnerability score (CVSS) by the network traffic adjustment (NTA) value to generate a prioritized common vulnerability score (PCVSS) for the computing resource asset, and remediating the computing resource asset to resolve the vulnerability based on the prioritized common vulnerability (PCVSS) score.
Owner:SAUDI ARABIAN OIL CO
System and method for implementing a vulnerability management module
ActiveUS11218503B2Reduce utilizationEliminate needTransmissionVulnerability managementVulnerability (computing)
Various methods, apparatuses / systems, and media for implementing a vulnerability management module are provided. A receiver receives a request for dynamically scanning vulnerability of a target computing device based on testable vulnerability criteria extracted from a database. A processor dynamically executes the testable vulnerability criteria from the SCCM based on the received request; creates a static SCCM advertisement with a dynamic pre / post validation check capability based on a result of the dynamically executing the testable vulnerability criteria; reports a success or a failure of the static SCCM advertisement related to the testable vulnerability criteria to indicate whether a vulnerability exists within the target computing device; and automatically remediates the vulnerability when it is determined that the vulnerability exists within the target computing device.
Owner:JPMORGAN CHASE BANK NA
Analysis of historical network traffic to identify network vulnerabilities
ActiveUS20210165879A1Platform integrity maintainanceTransmissionInternet trafficTheoretical computer science
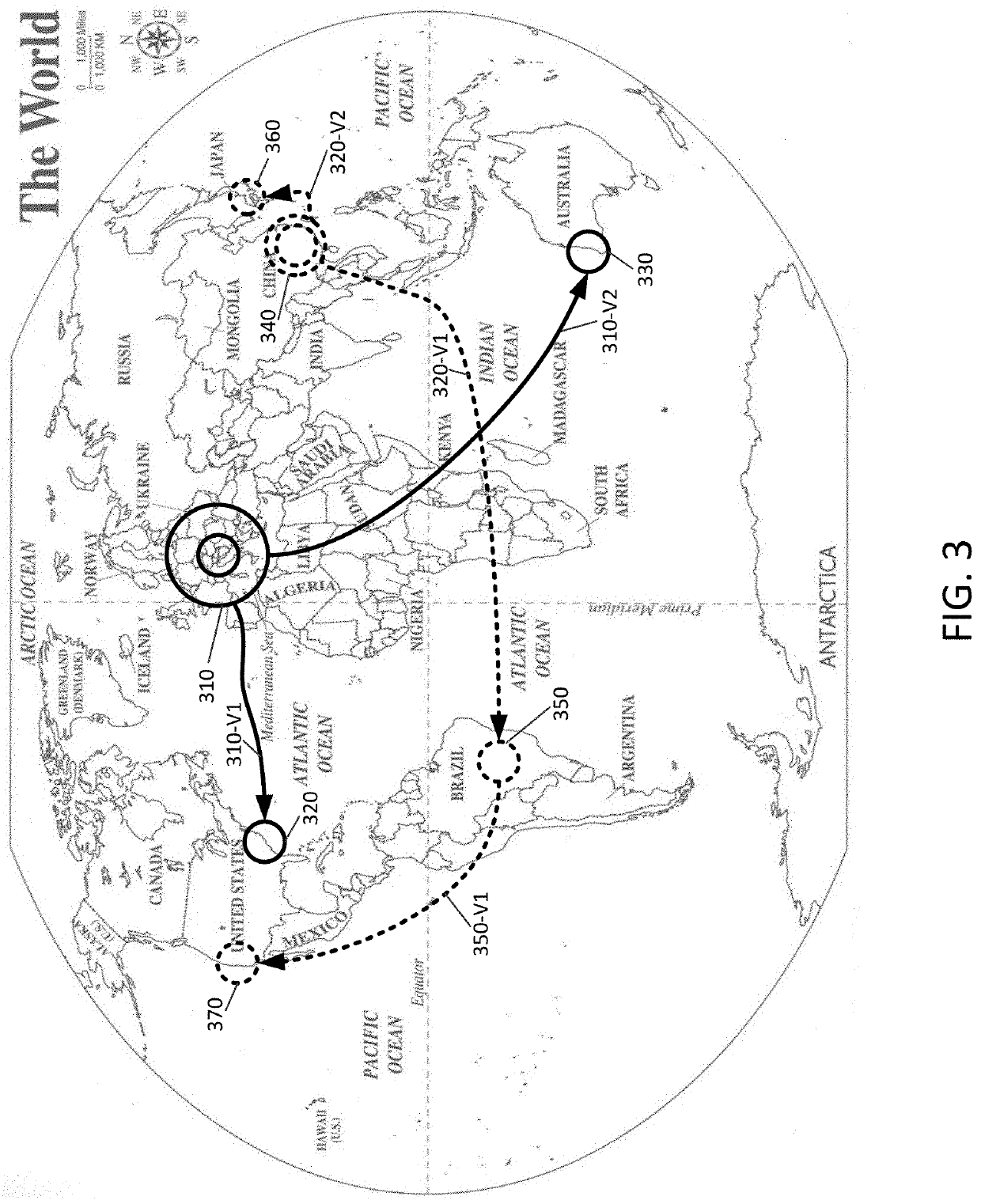
Methods and apparatus consistent with the present disclosure may be used after a computer network has been successfully attacked by new malicious program code. Such methods may include collecting data from computers that have been affected by the new malicious program code and this data may be used to identify a type of damage performed by the new malicious code. The collected data may also include a copy of the new malicious program code. Methods consistent with the present disclosure may also include allowing the new malicious program code to execute at an isolated computer while actions and instructions that cause the damage are identified. Signatures may be generated from the identified instructions after which the signatures or data that describes the damaging actions are provided to computing resources such that those resources can detect the new malware program code.
Owner:SONICWALL
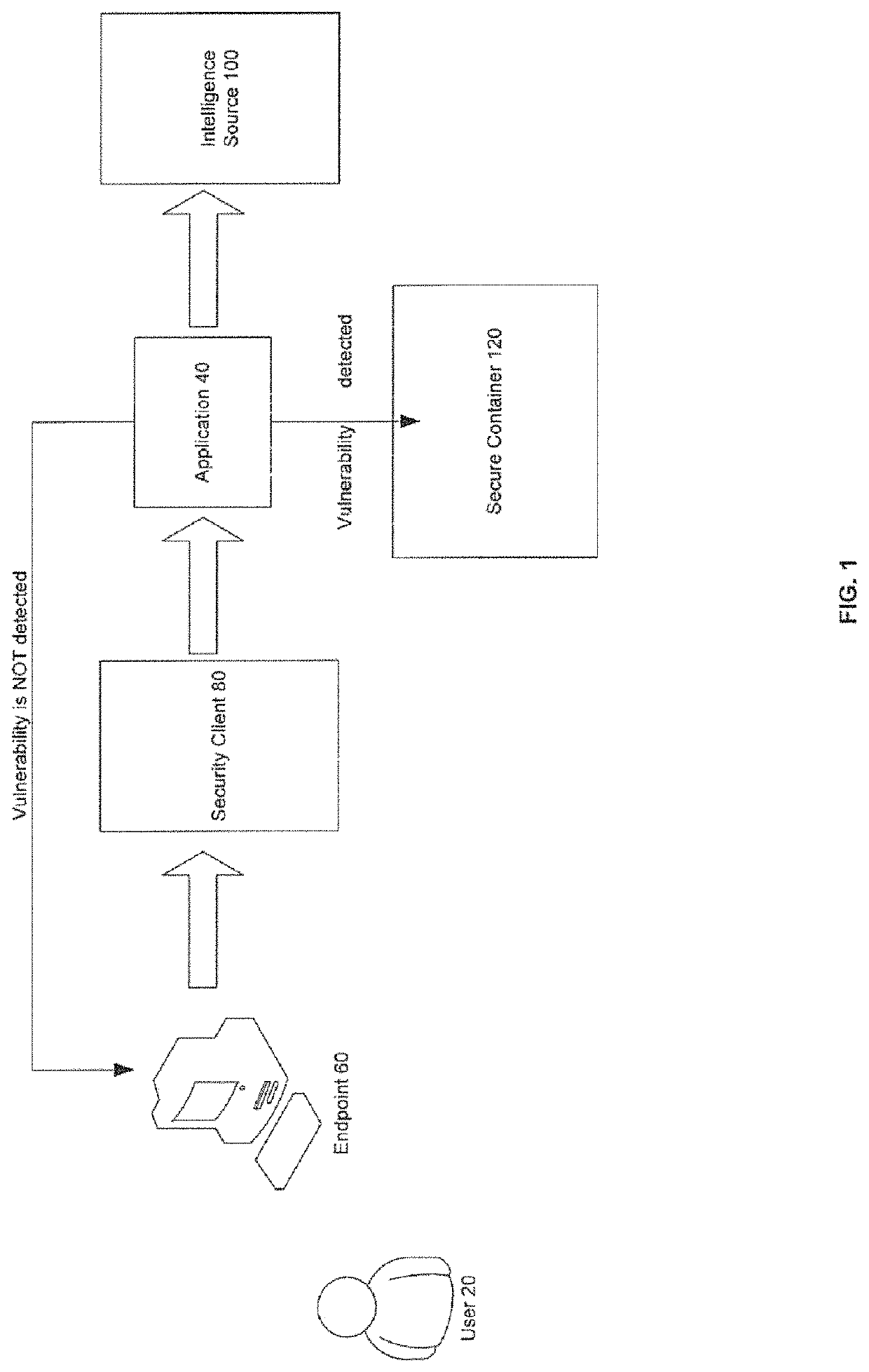
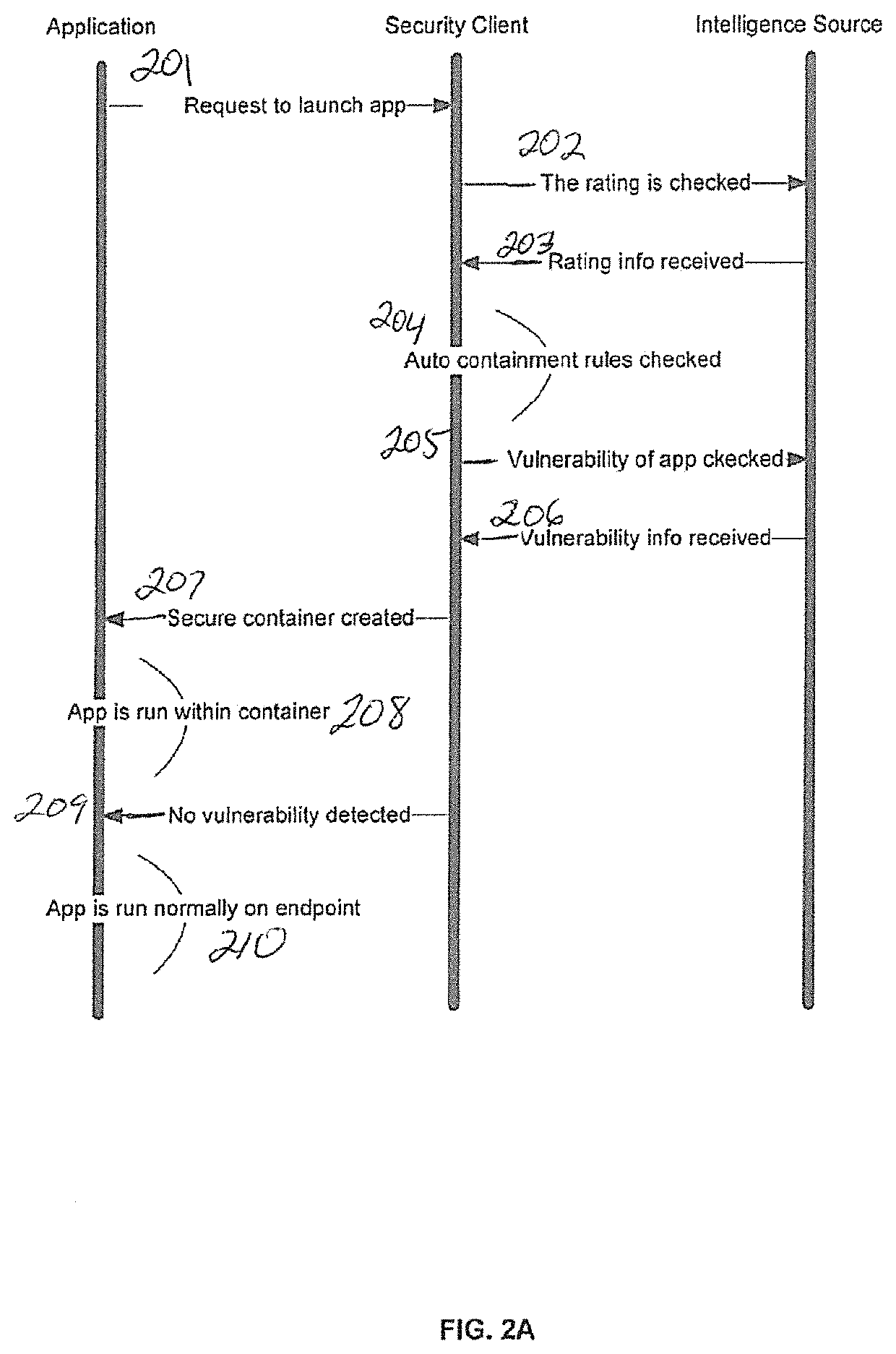
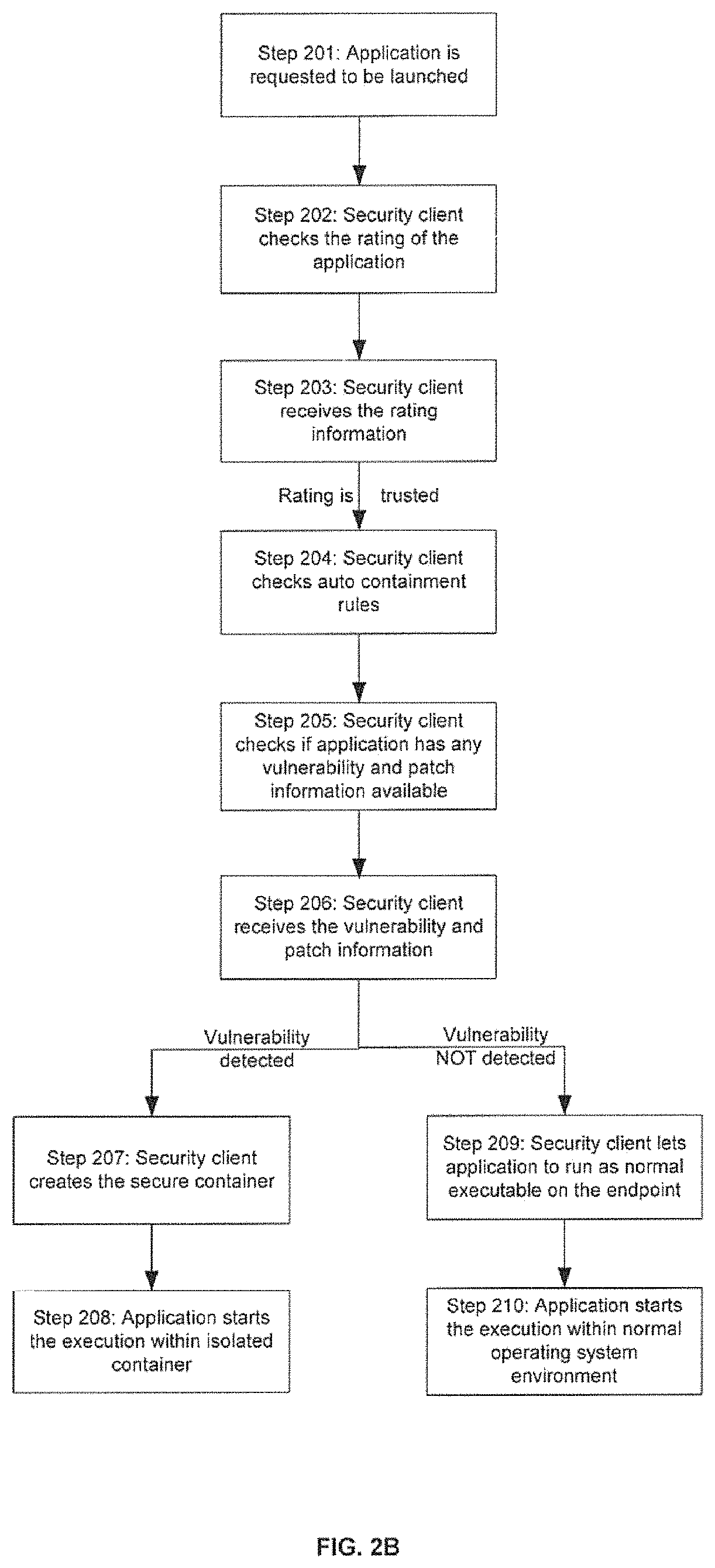
Auto-containment of potentially vulnerable applications
ActiveUS11314870B1Platform integrity maintainanceSoftware simulation/interpretation/emulationVulnerability (computing)System usage
There is provided a method and system for an advanced endpoint protection. With this methodology, when a file is requested to be executed on any endpoint, all intelligence sources would be checked to decide if that file has any known or potential vulnerability associated with it. If there is any information about any known or potential vulnerability, it would be launched inside the secure container to isolate the all resource usage of that application from the rest of the known good and secure applications in order to achieve the secure computing environment on an endpoint.
Owner:COMODO SECURITY SOLUTIONS
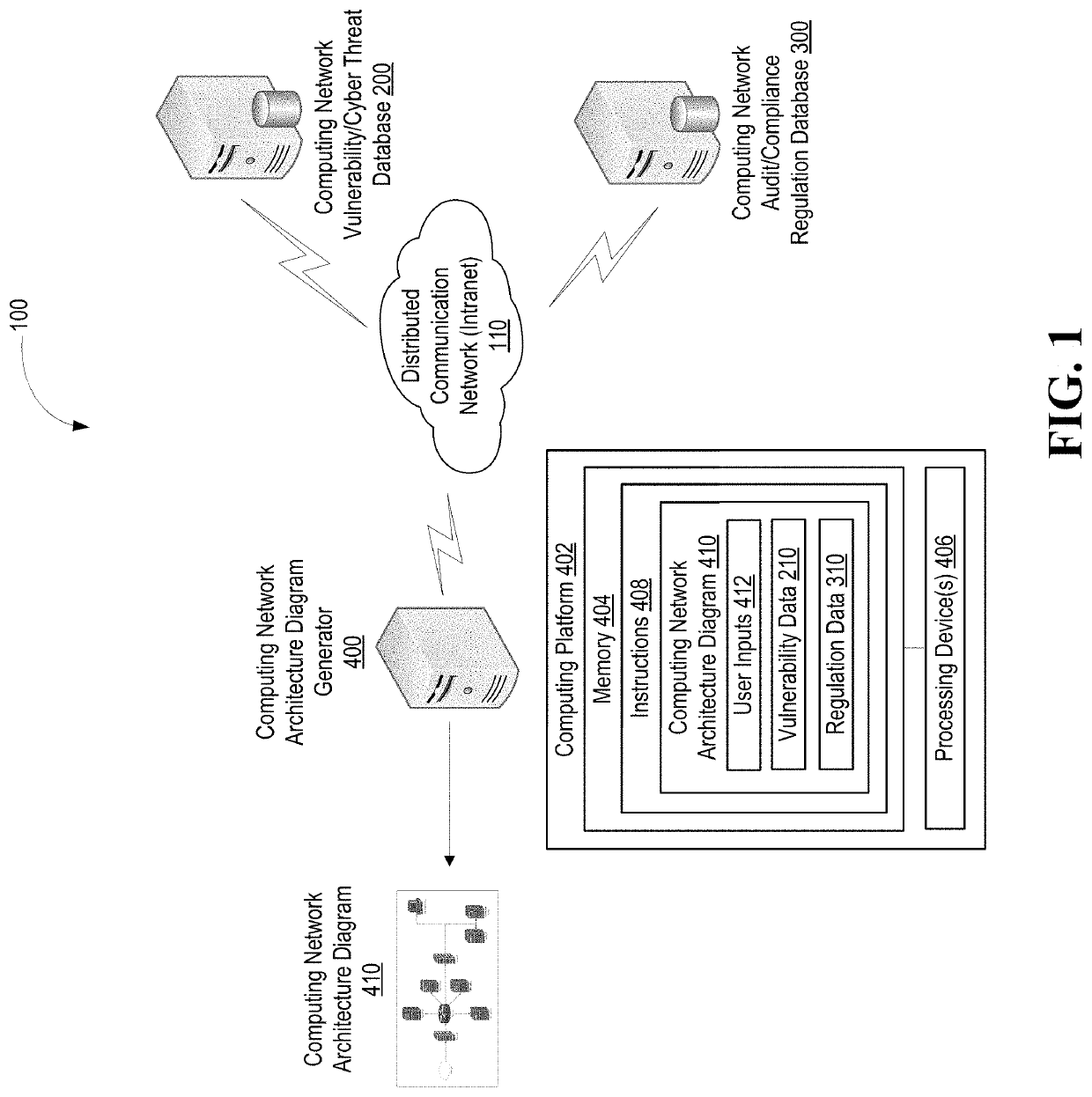
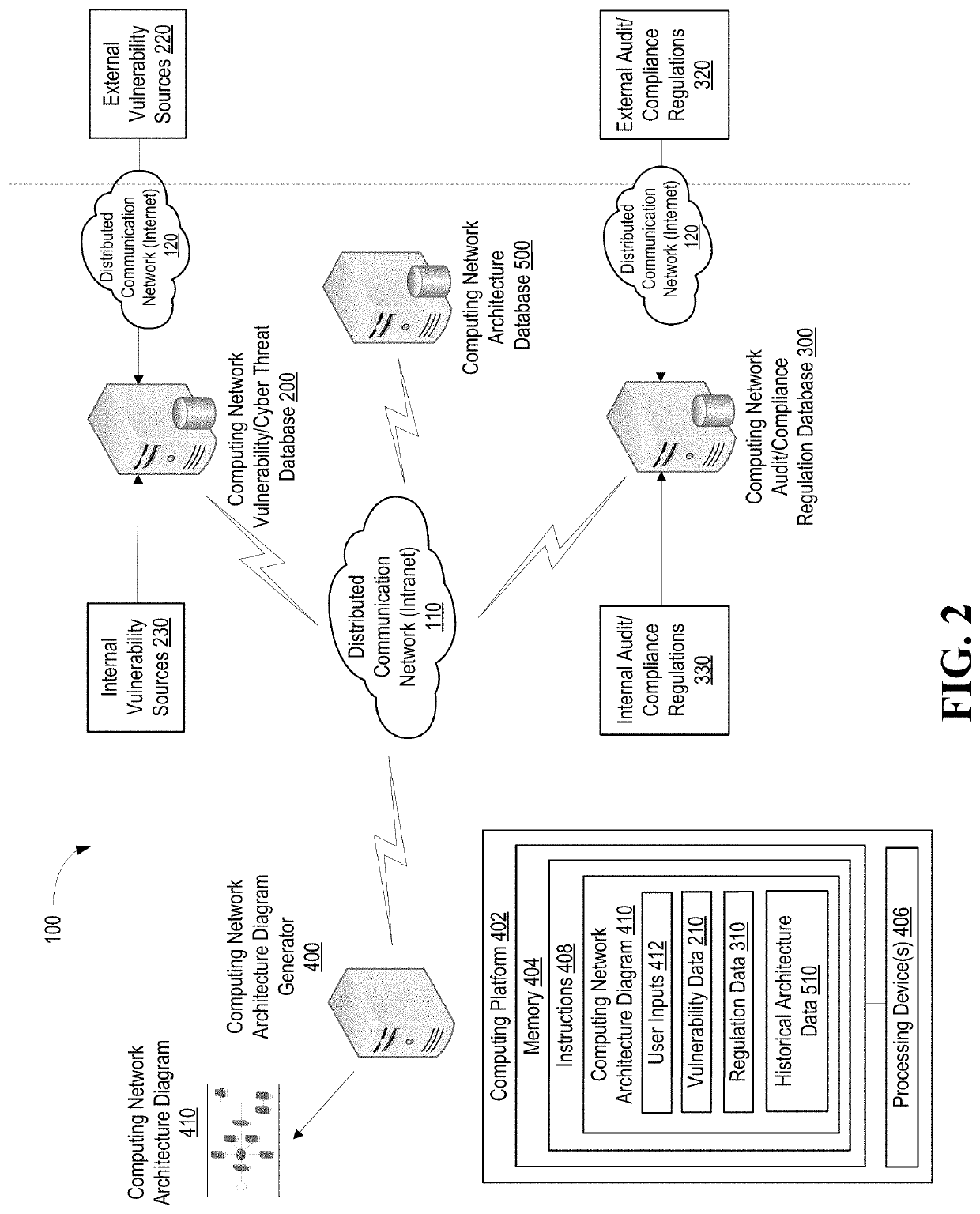
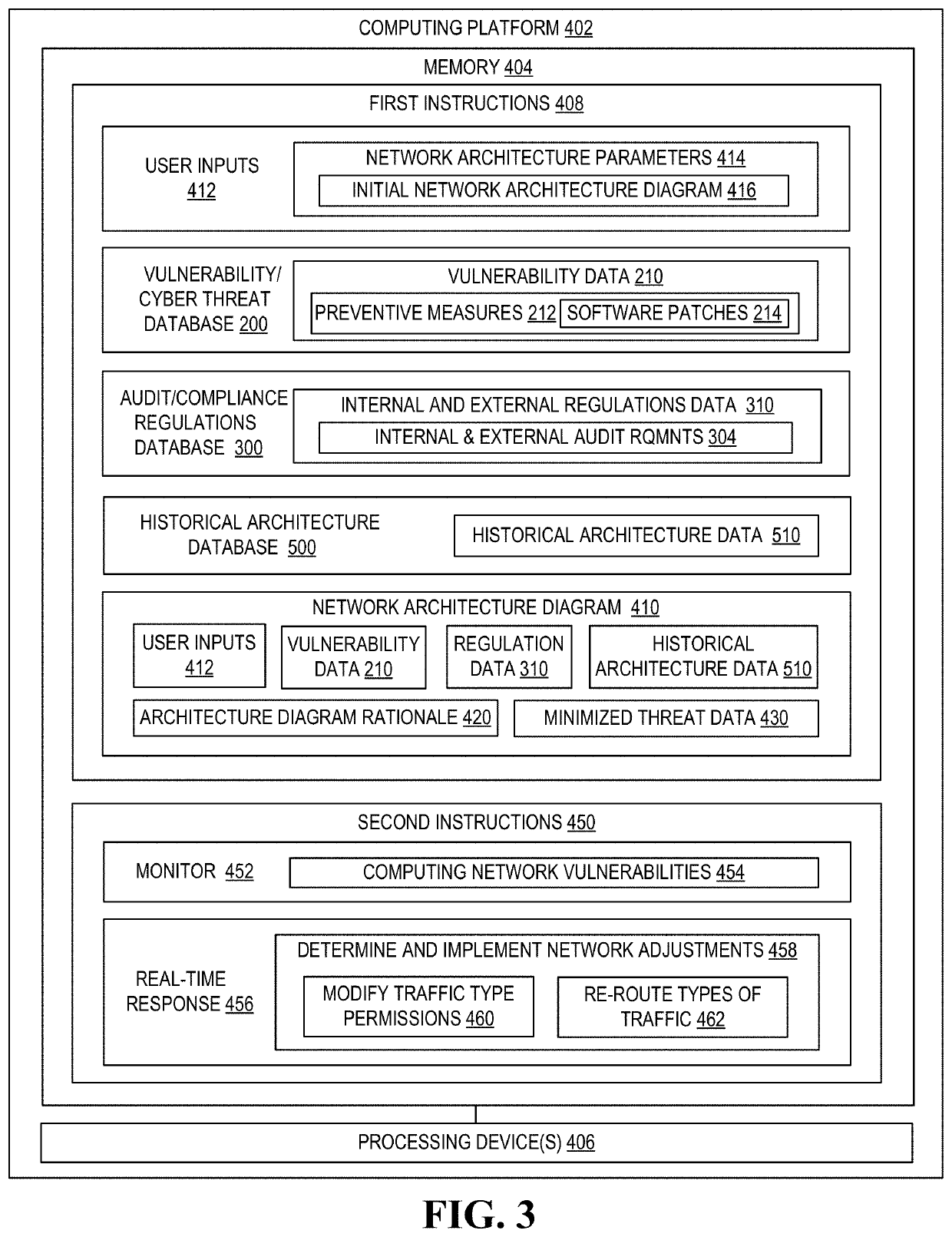
Cybersecurity architectural network based on artificial intelligence
A system for using artificial intelligence to generate a computing network architecture diagram based on user inputs, applicable vulnerability / cyber threat data and internal / external compliance / audit regulation data. In addition, machine-learning techniques may be used that leverage previously implemented computing network architectures. The computing network architecture diagram may be generated absent a baseline diagram or the user inputs may define at least a portion of an initial / baseline network architecture diagram that is modified based on the vulnerability / cyber threat data, the internal / external compliance / audit regulation data and / or the previously implemented computing network architectures. In additional embodiments of the invention, new / emerging vulnerabilities and cyber threats are detected, and in real-time response, adjustments to the computing network infrastructure and determined and implemented.
Owner:BANK OF AMERICA CORP
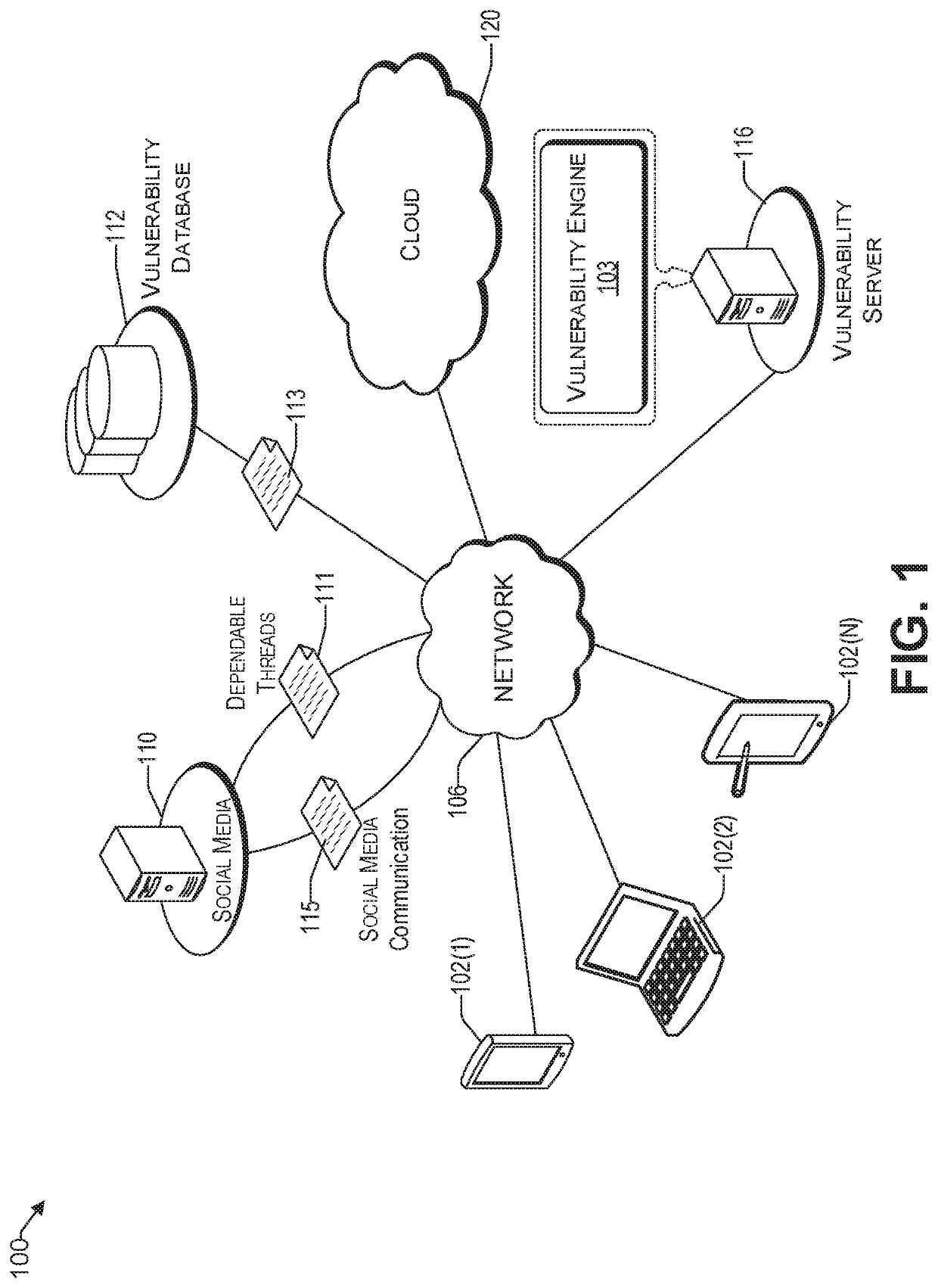
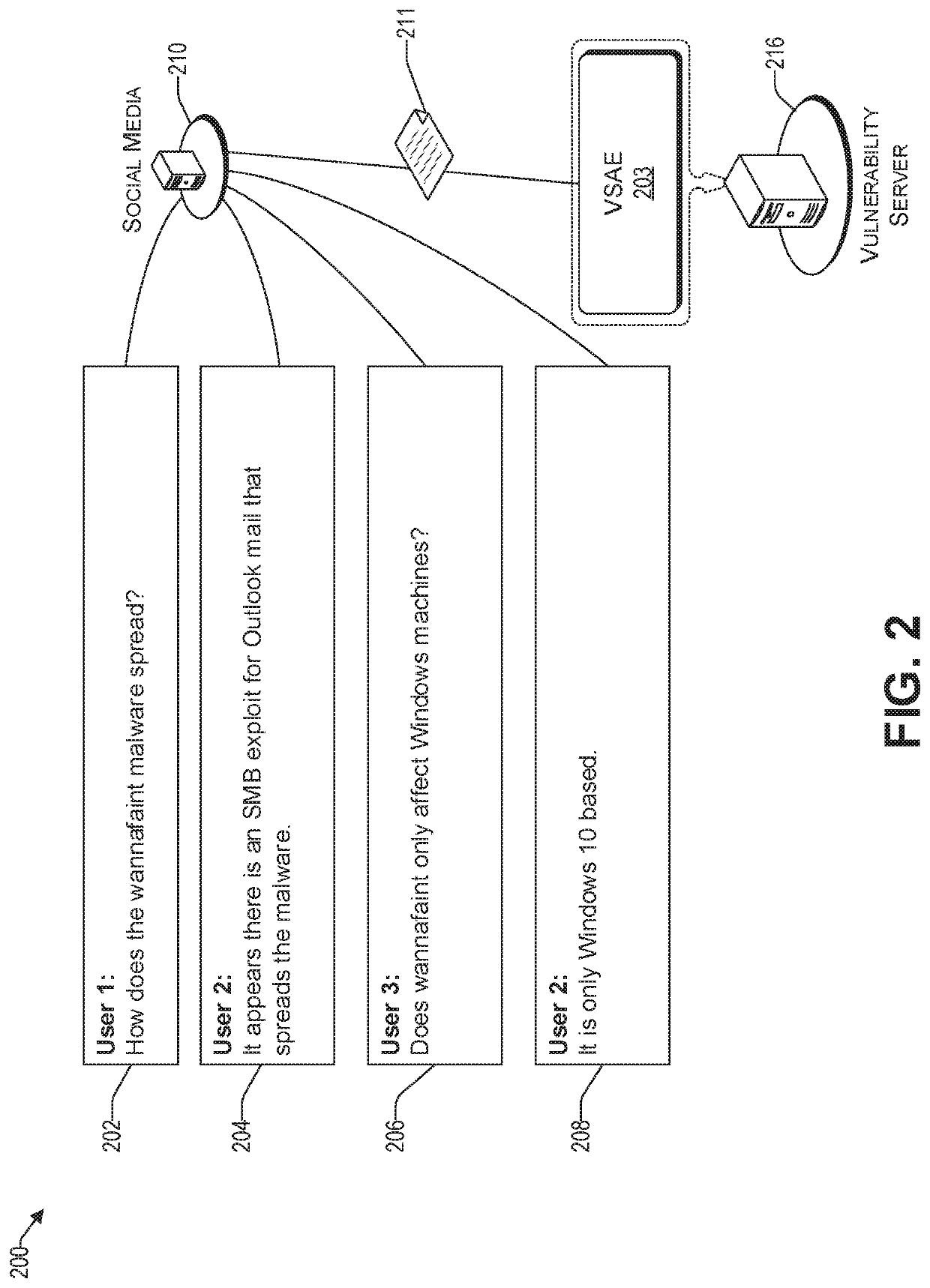
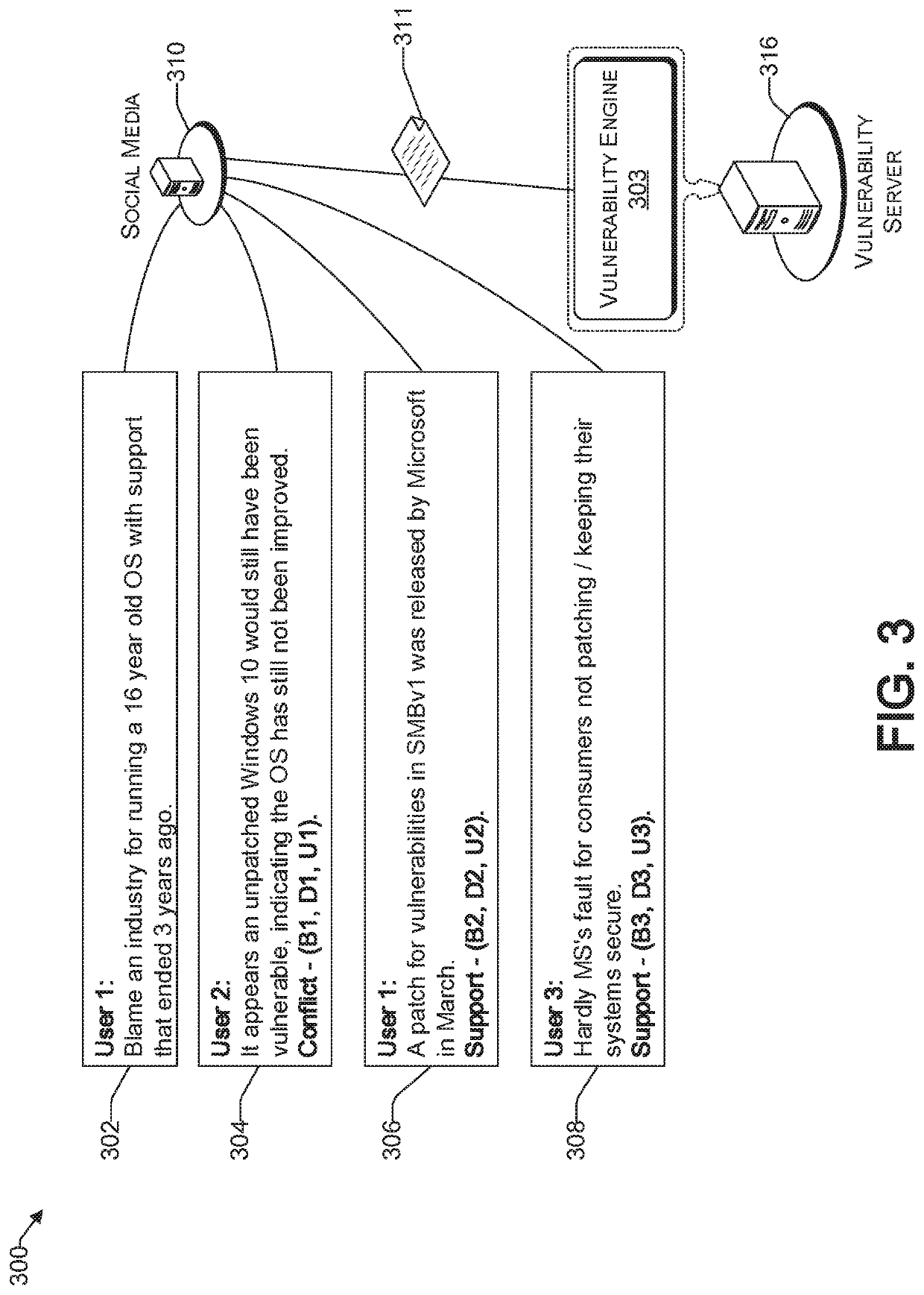
Detecting a root cause for a vulnerability using subjective logic in social media
A method and system of identifying a computing device vulnerability is provided. Social media communication is monitored. Social media threads that are related to a vulnerability, based on the monitored social media communication, are identified, filtered, and categorized into one or more predetermined categories of computing device vulnerabilities. Upon determining that a number of social media posts related to the vulnerability is above a first predetermined threshold, one or more dependable social media threads in a same one or more categories as the vulnerability are searched. One or more possible root causes of the vulnerability are determined from the searched dependable social media threads. A validity score for each of the one or more possible root causes is assigned. A possible root cause from that has a highest validity score that is above a second predetermined threshold is selected to be the root cause of the vulnerability.
Owner:KYNDRYL INC
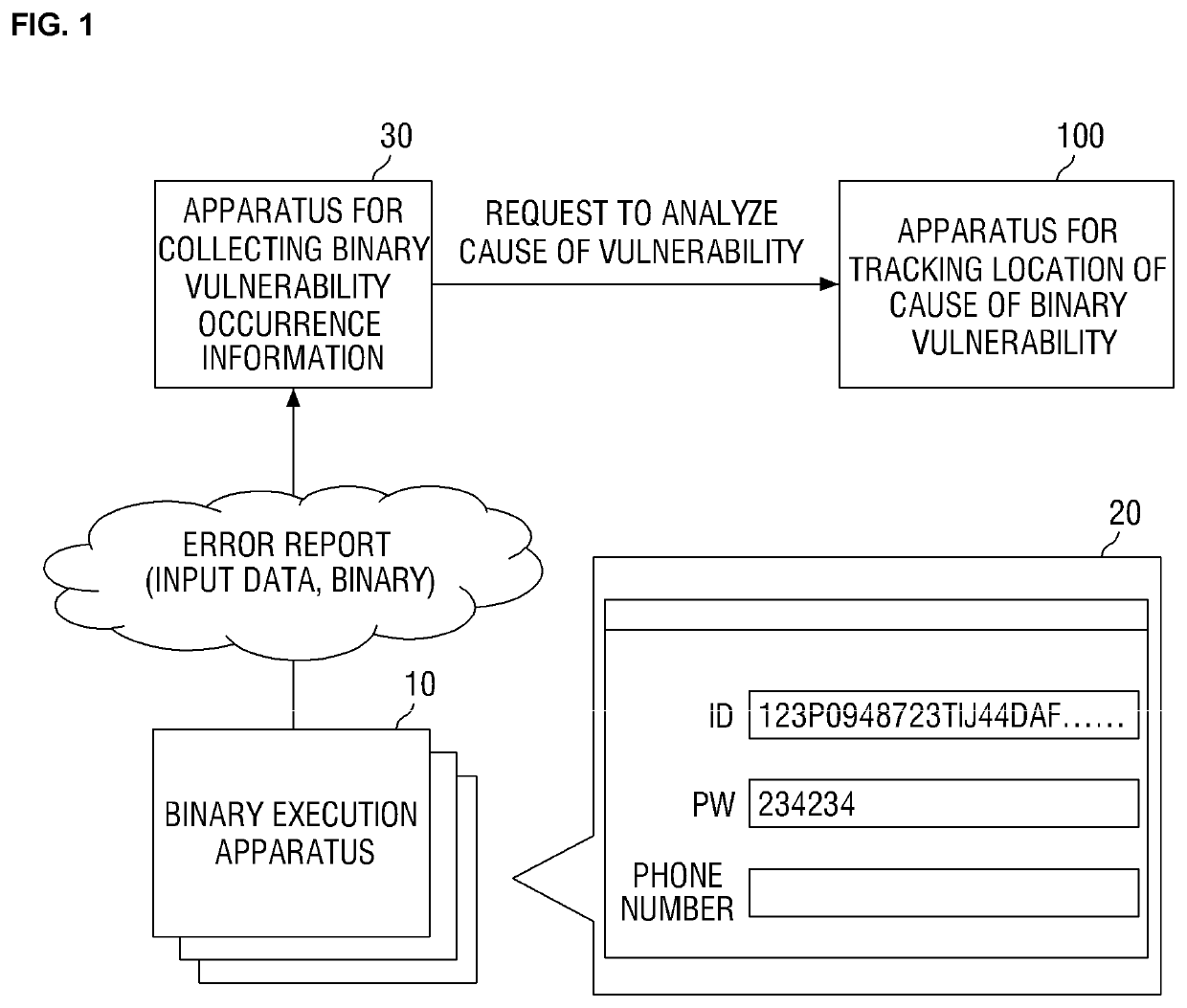
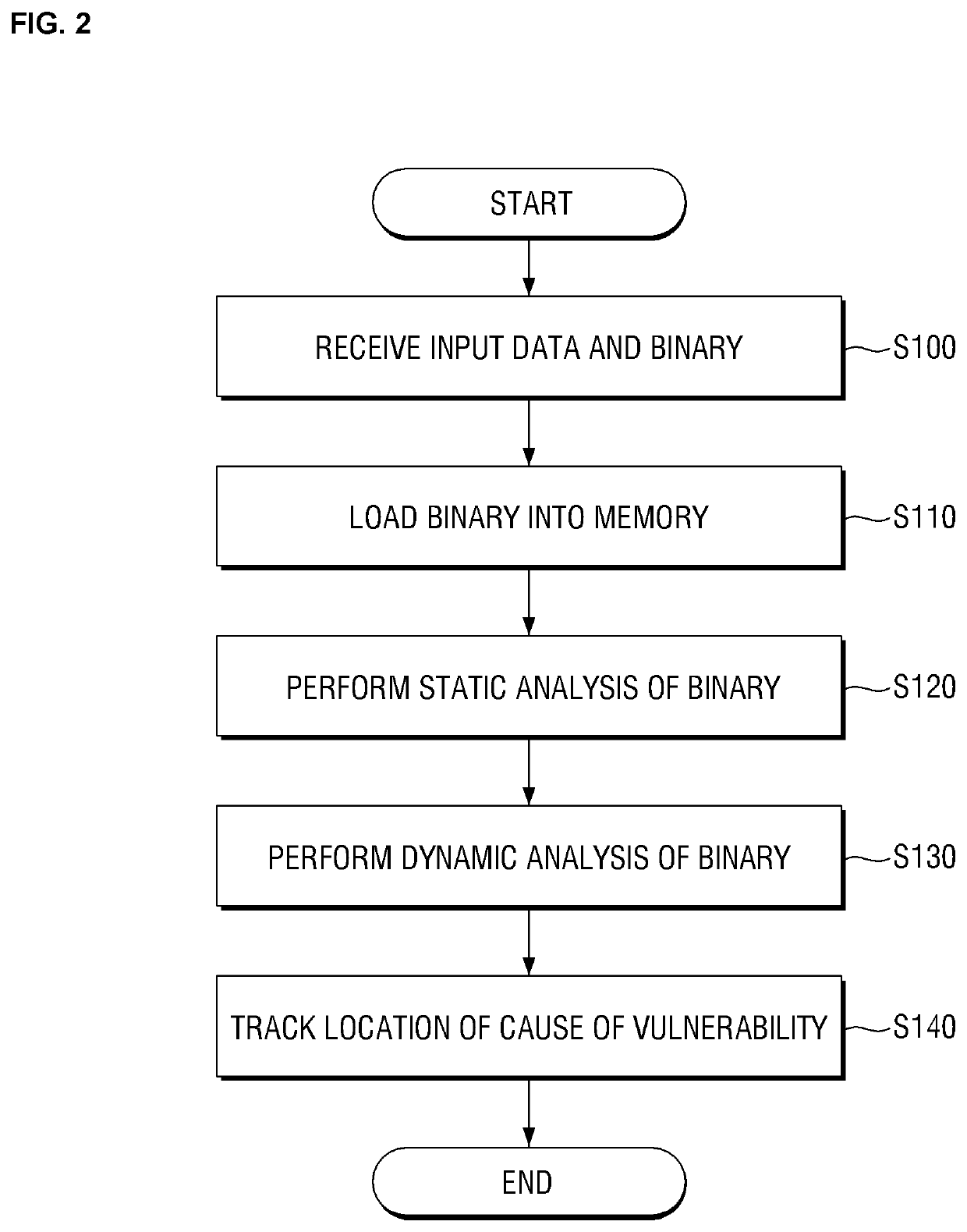
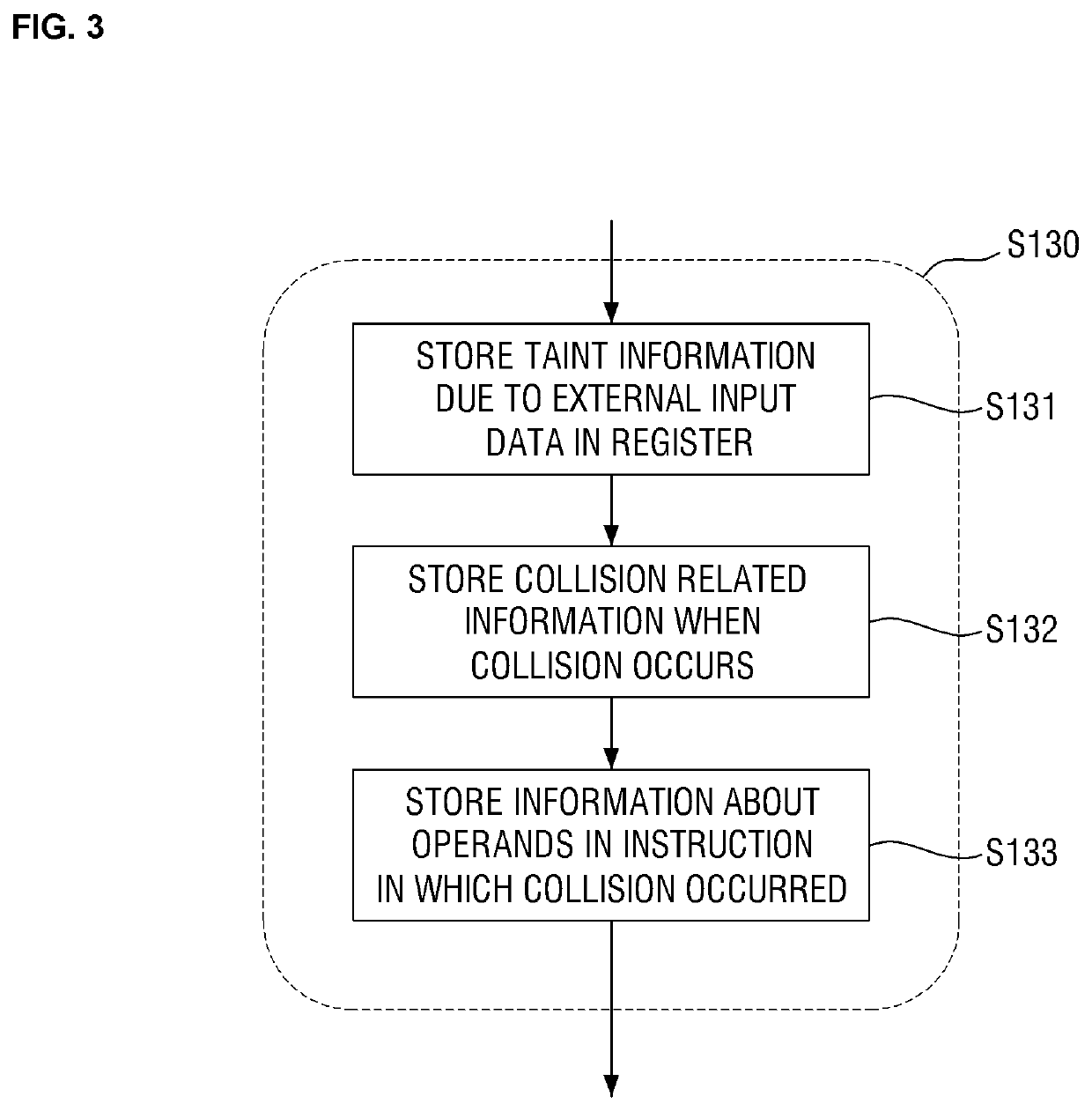
Method and apparatus for tracking location of input data that causes binary vulnerability
InactiveUS20200143061A1Register arrangementsSoftware testing/debuggingAlgorithmVulnerability (computing)
There is provided a method of tracking the location of the cause of a binary vulnerability, the method being performed by a computing apparatus and comprising: adding first taint information for a first operand register tainted by input data of an error-causing case, generating second taint information for a second operand register tainted by data of the first operand register by using the first taint information; and tracking input data that caused an error among the input data of the error-causing case by tracing back taint information of a register of each operand from a point where the error occurred.
Owner:KOREA INTERNET & SECURITY AGENCY
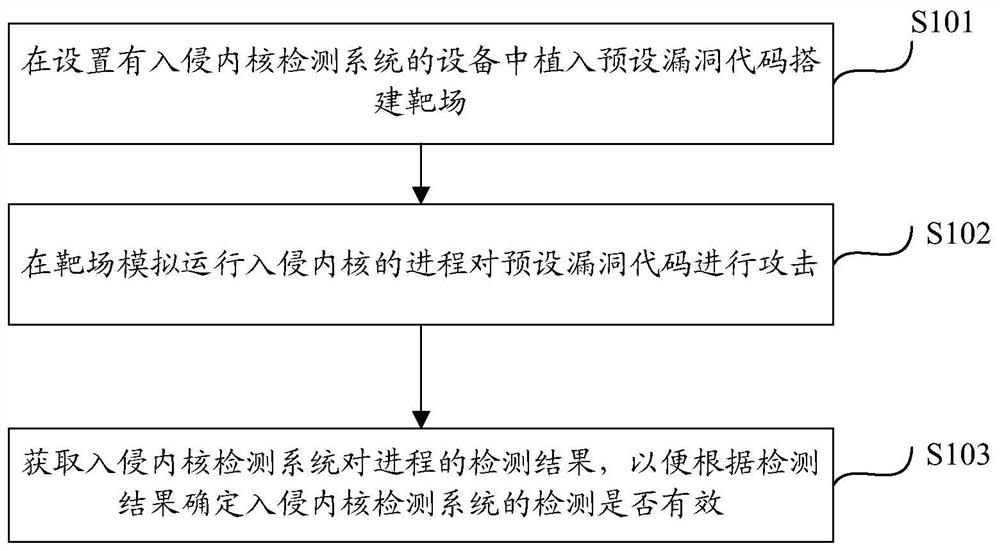
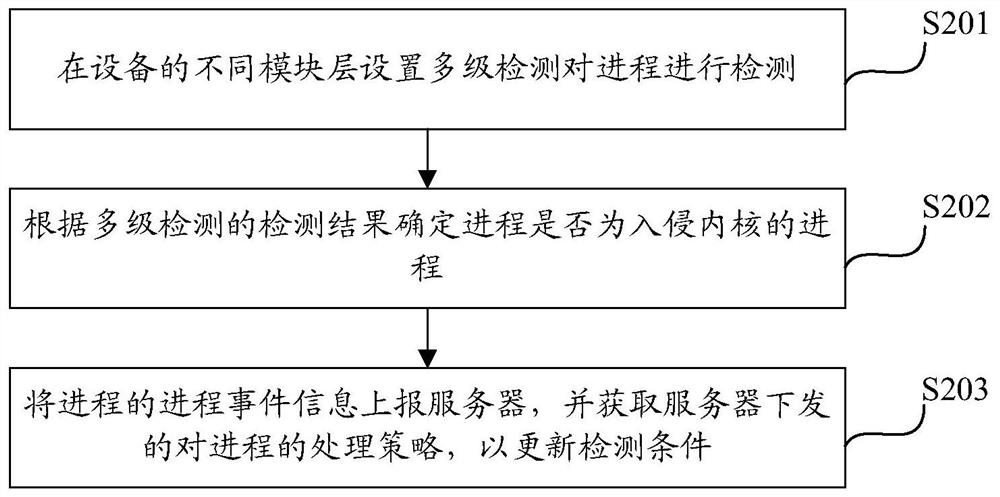
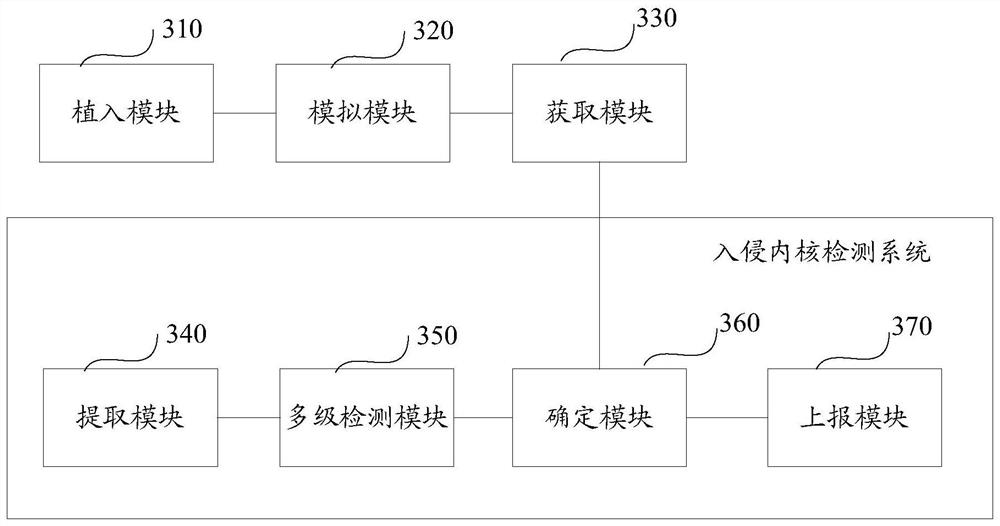
Intrusion kernel detection method and device based on target range and computing equipment
The invention discloses an intrusion kernel detection method and device based on a target range, computing equipment and a computer storage medium. The method comprises the steps of: implanting a preset vulnerability code into equipment provided with an intrusion kernel detection system to build the target range; running a process invading the kernel in a shooting range in a simulated manner to attack the preset vulnerability code; and obtaining a detection result of the intrusion kernel detection system to the process so as to determine whether the detection of the intrusion kernel detectionsystem is valid according to the detection result. The target range is built on the real equipment, the process of invading the kernel is simulated and operated, whether the invading kernel detectionsystem is effective or not can be detected, and the detection effect of the invading kernel detection system is evaluated.
Owner:BEIJING QIHOO TECH CO LTD
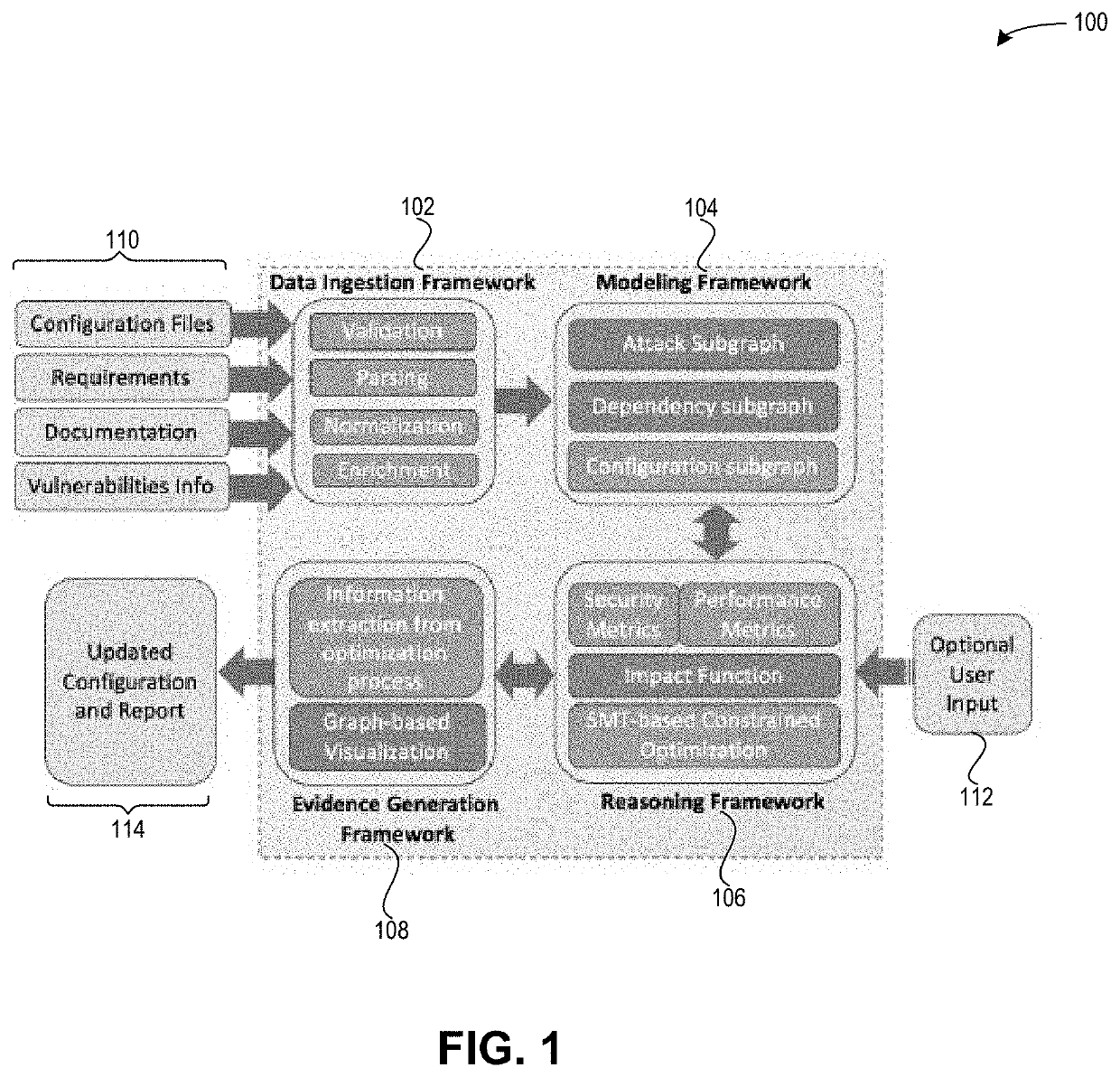
System and method for extracting configuration-related information for reasoning about the security and functionality of a composed internet of things system
ActiveUS20210014263A1Database management systemsPlatform integrity maintainanceUser deviceStandard operating procedure
Embodiments provide a system and method for extracting configuration-related information for reasoning about the security and functionality of a composed system. During operation, the system determines, by a computing device, information sources associated with hardware and software components of a system, wherein the information sources include at least specification sheets, standard operating procedures, user manuals, and vulnerability databases. The system selects a set of categories of vulnerabilities in a vulnerability database, and ingests the information sources to obtain data in a normalized format. The system extracts, from the ingested information sources, configuration information, vulnerability information, dependency information, and functionality requirements to create a model for the system. The system displays, on a screen of a user device, one or more interactive elements which allow the user to view or select the information sources and the categories of vulnerabilities, initiate ingesting the information sources, and view the extracted configuration information.
Owner:XEROX CORP
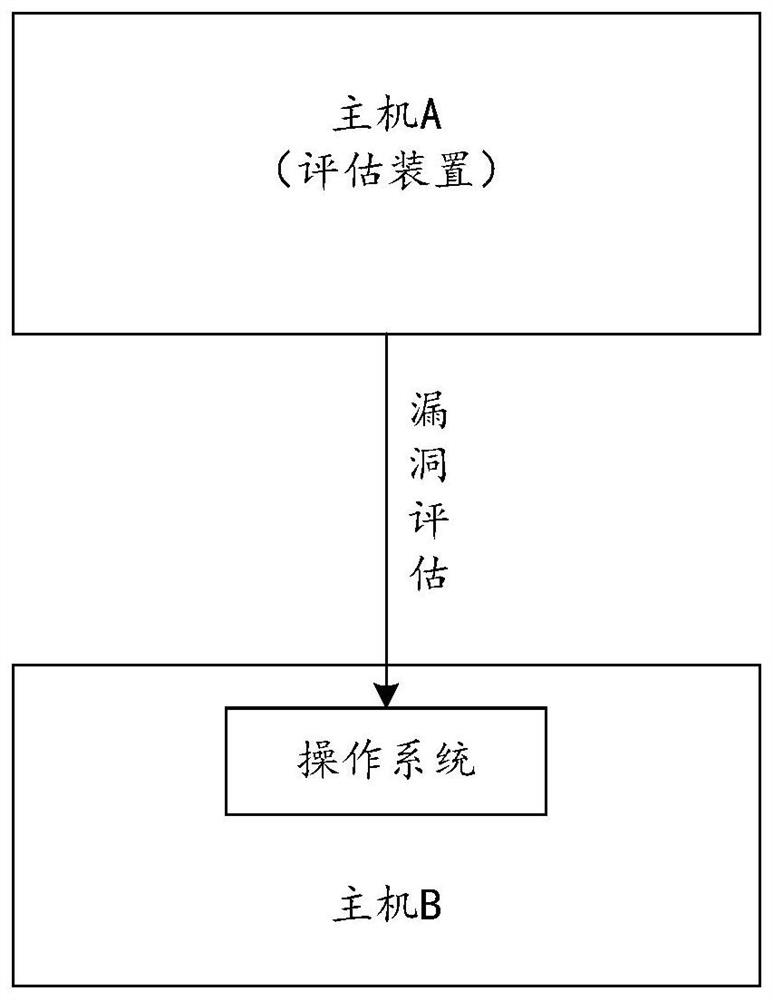
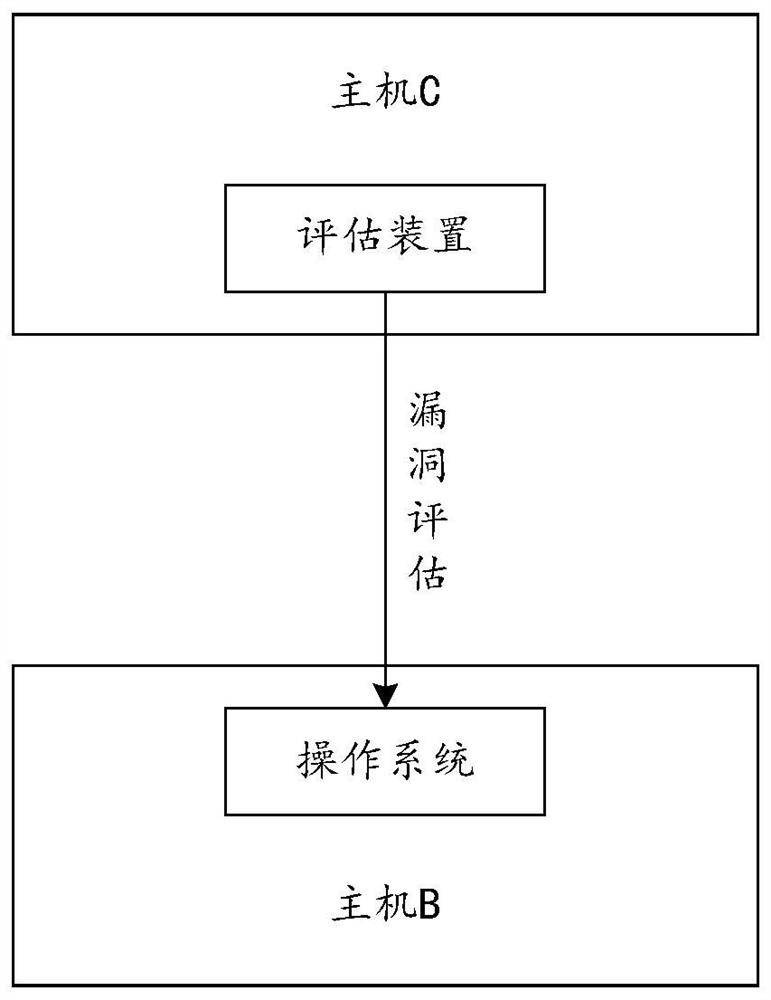
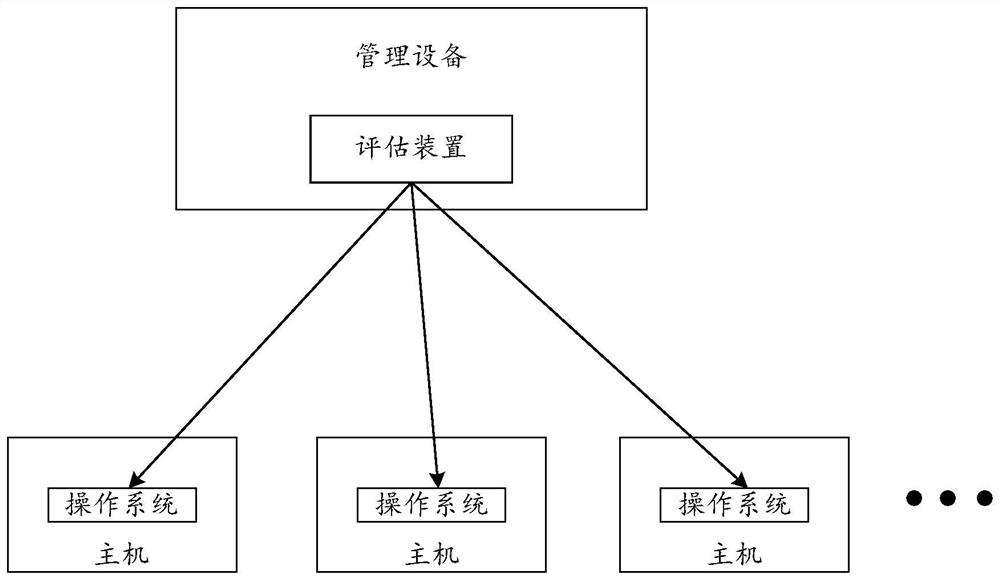
Vulnerability assessment method and device, computing equipment and storage medium
PendingCN114254322AAccurately determineImprove accuracyPlatform integrity maintainanceProgram/content distribution protectionOperational systemSoftware engineering
The embodiment of the invention provides a vulnerability assessment method and device, computing equipment and a storage medium, and belongs to the technical field of vulnerability assessment. The method comprises the steps that identification and source information of at least one piece of software installed on an evaluated operating system are obtained, target software is determined to be from a target software source according to the source information of the target software in the at least one piece of software, and the target software source is different from a provider of the operating system. And then, according to the identifier of the target software and the security announcement rule of the target software source, judging whether the target software is influenced by vulnerabilities in the security announcement rule or not. By adopting the method and the device, vulnerability assessment can be comprehensively carried out.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com