Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
843 results about "Secure computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
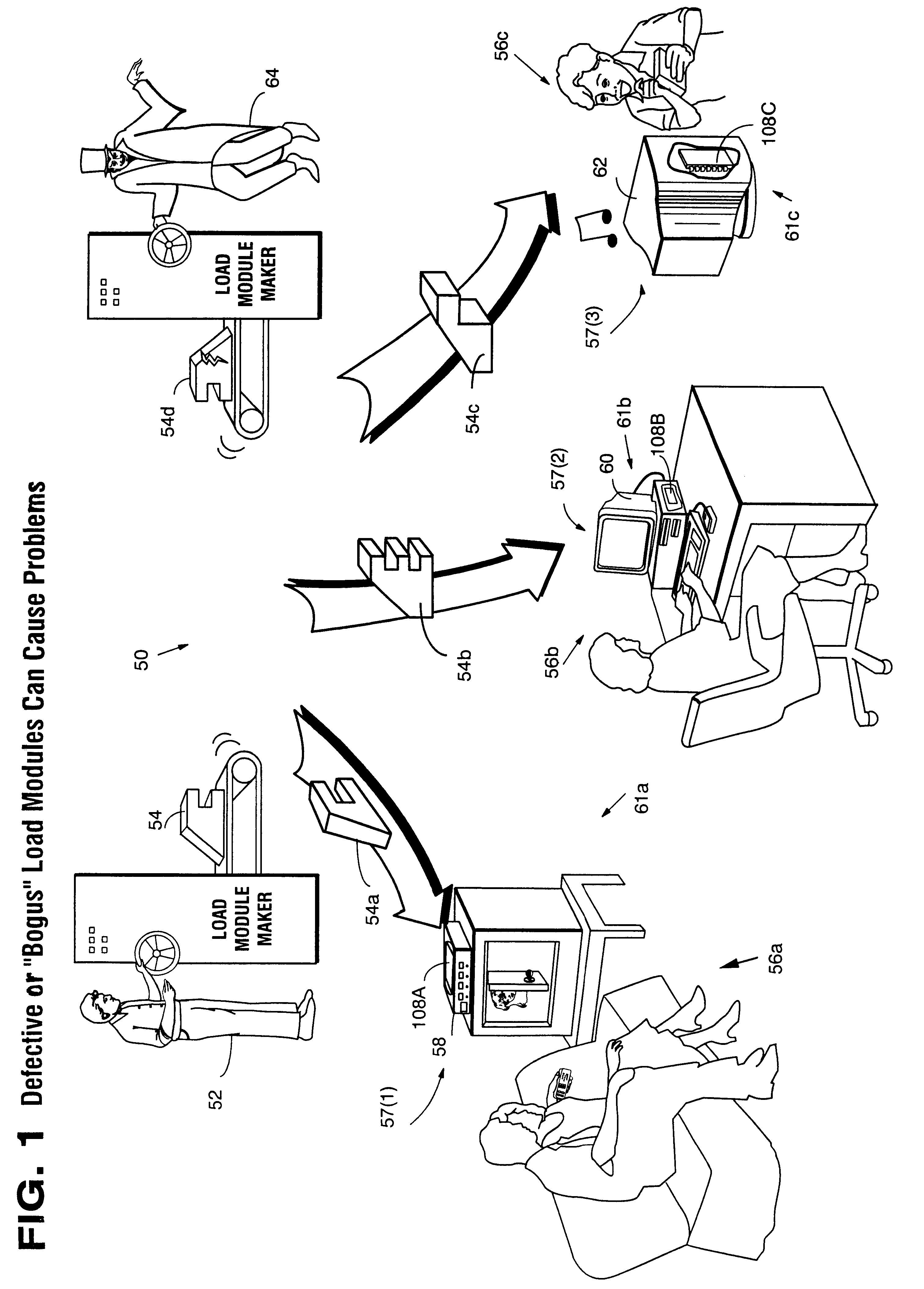
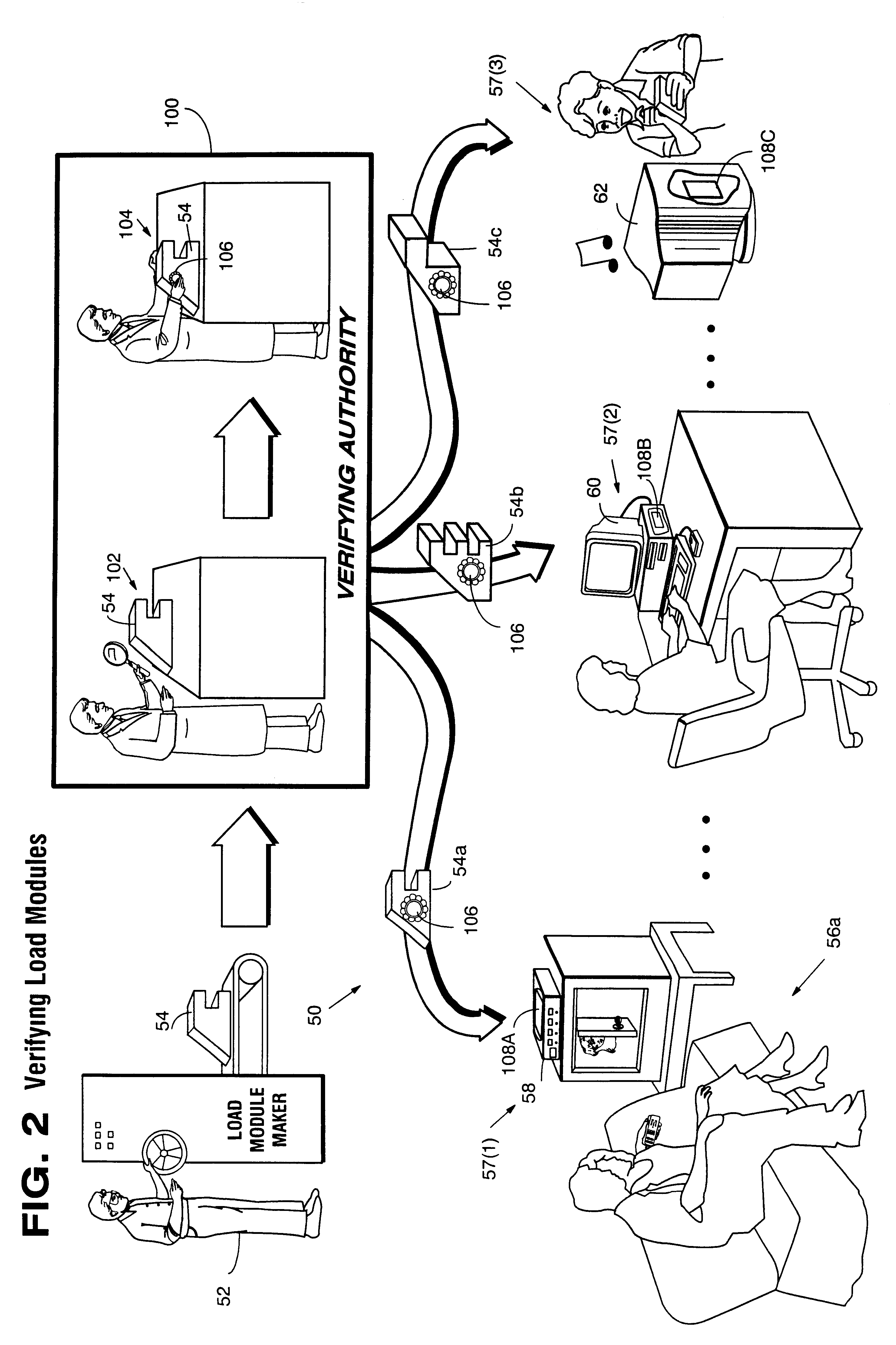
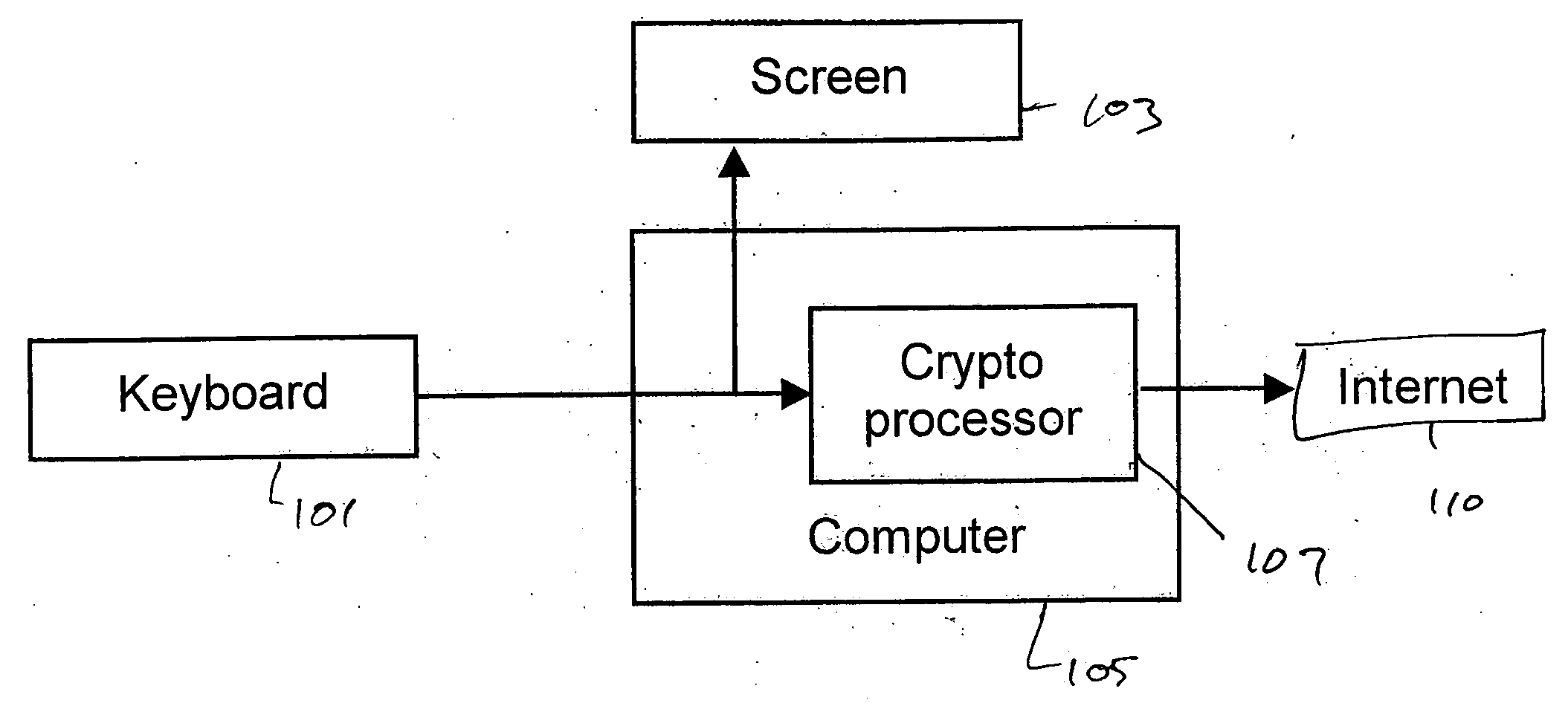
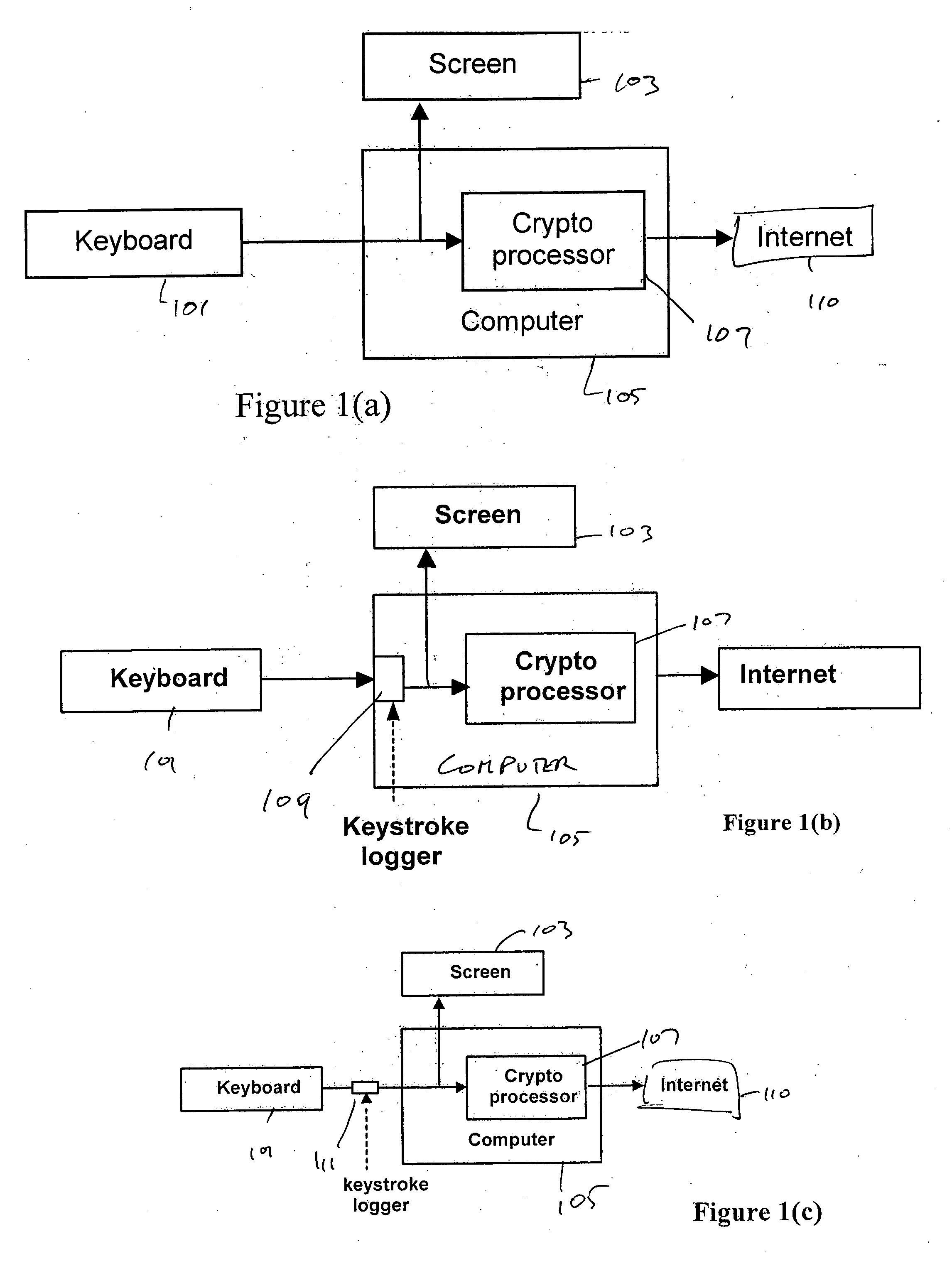
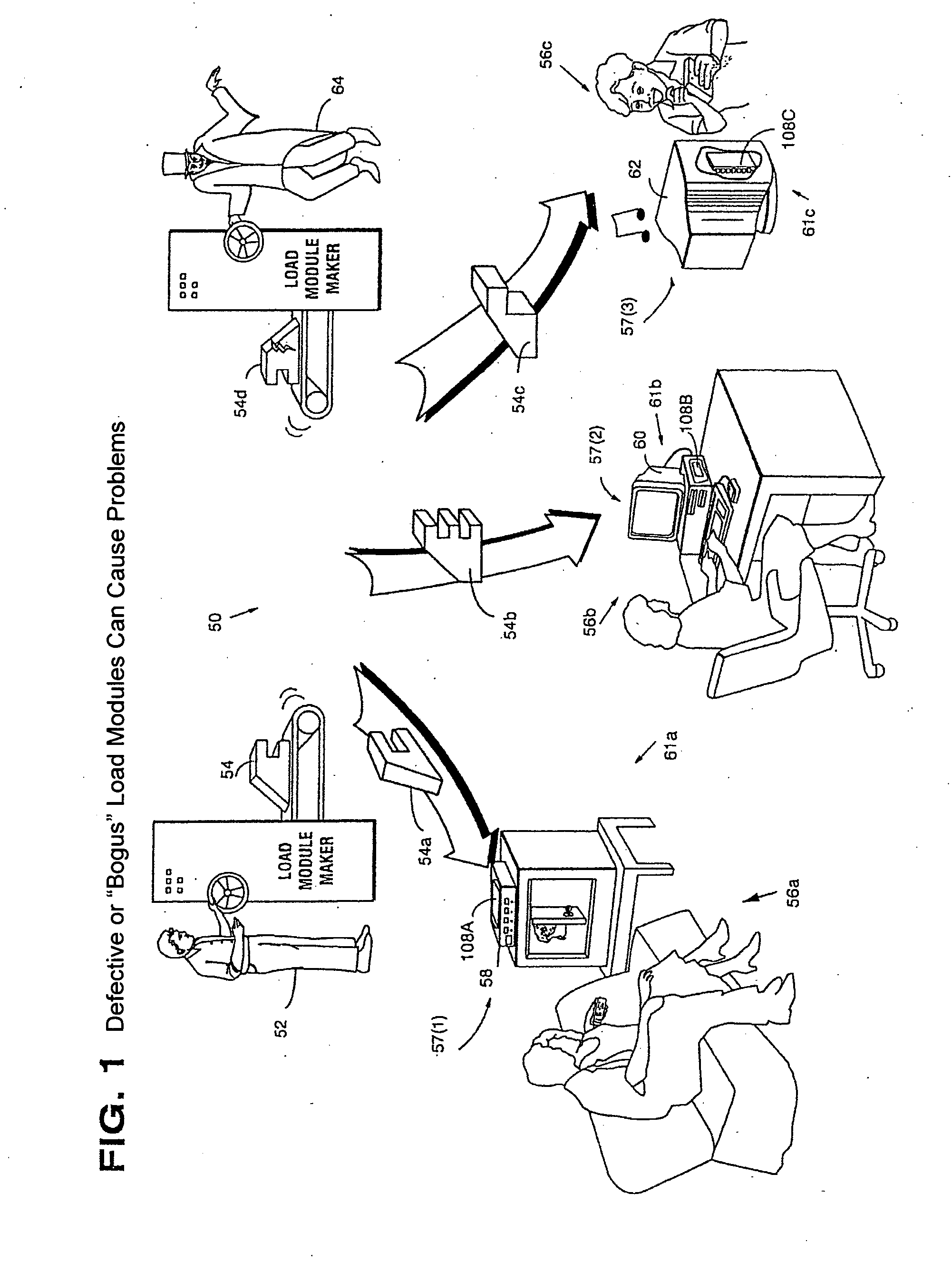
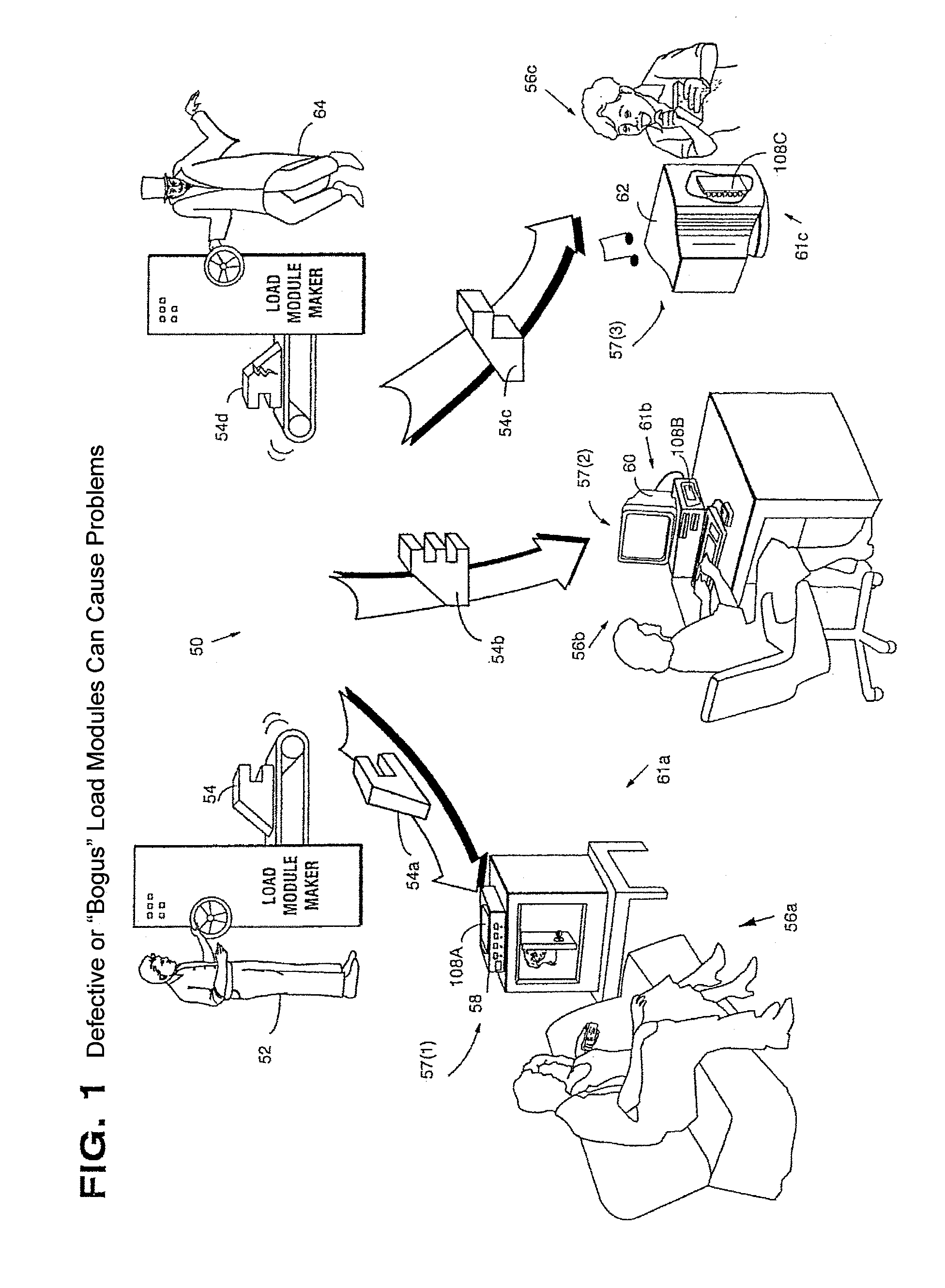
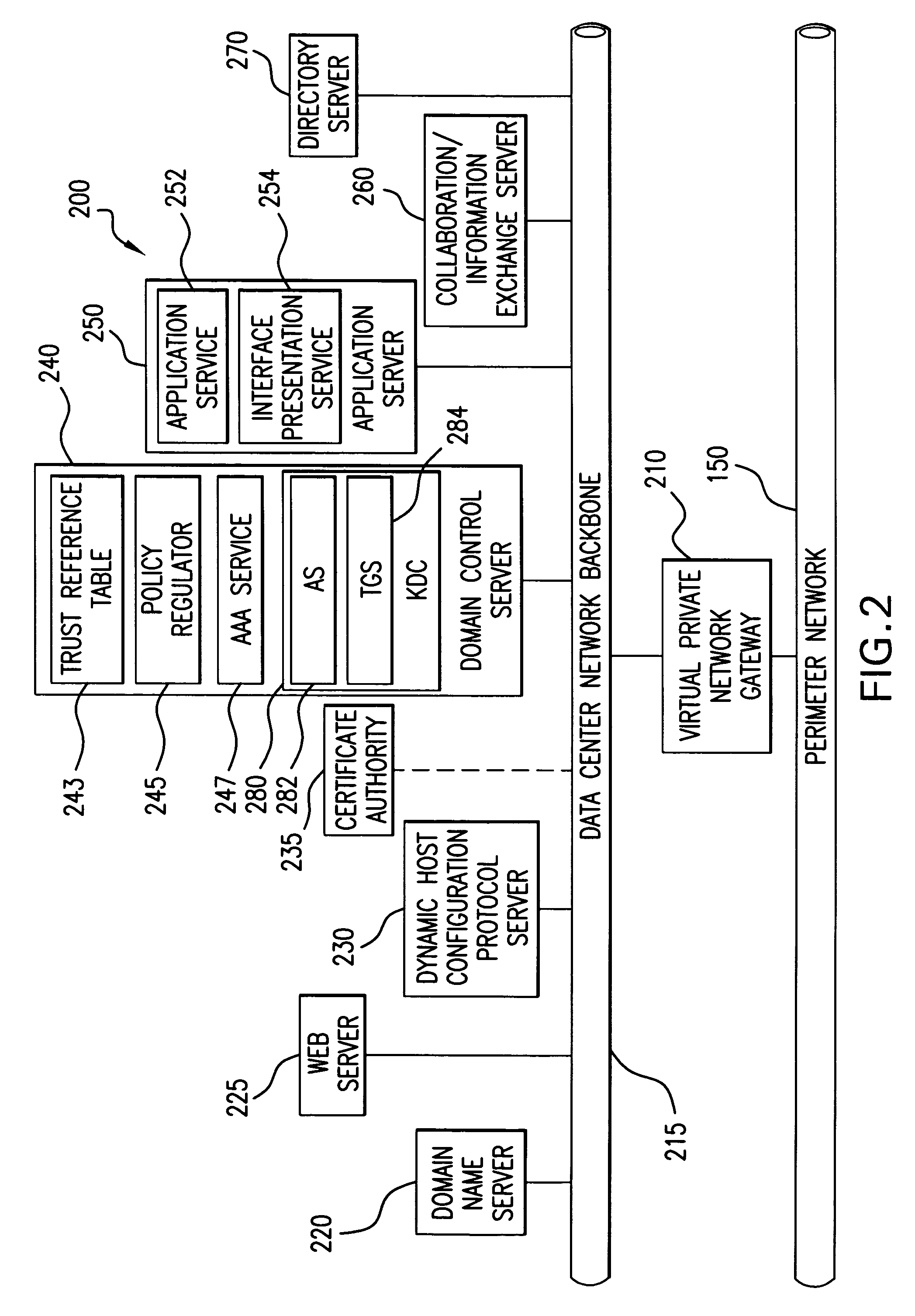
Systems and methods using cryptography to protect secure computing environments
InactiveUS6157721AProtection from disclosureSpeeding up digital signature verificationRecording carrier detailsDigital data processing detailsThird partyTamper resistance
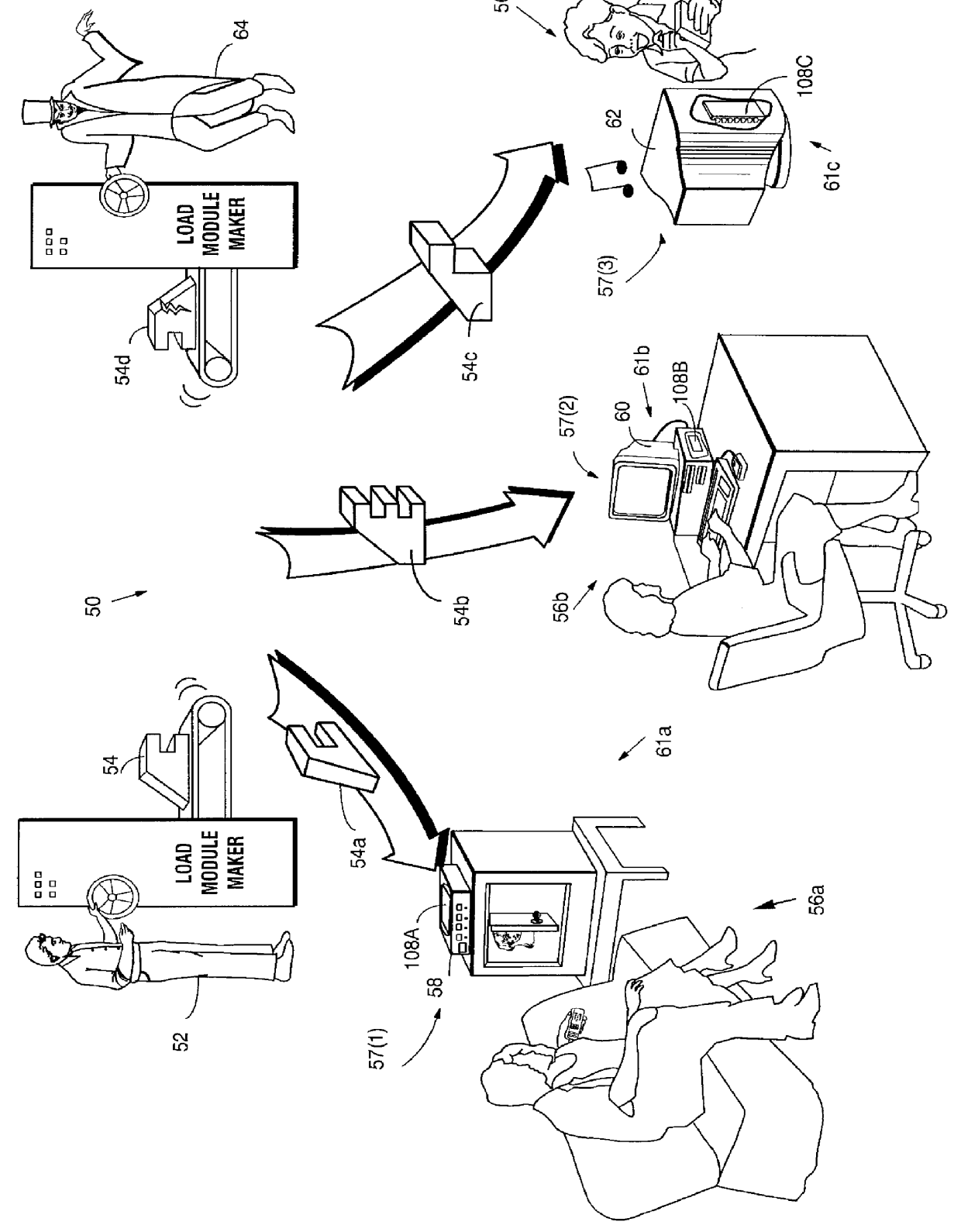
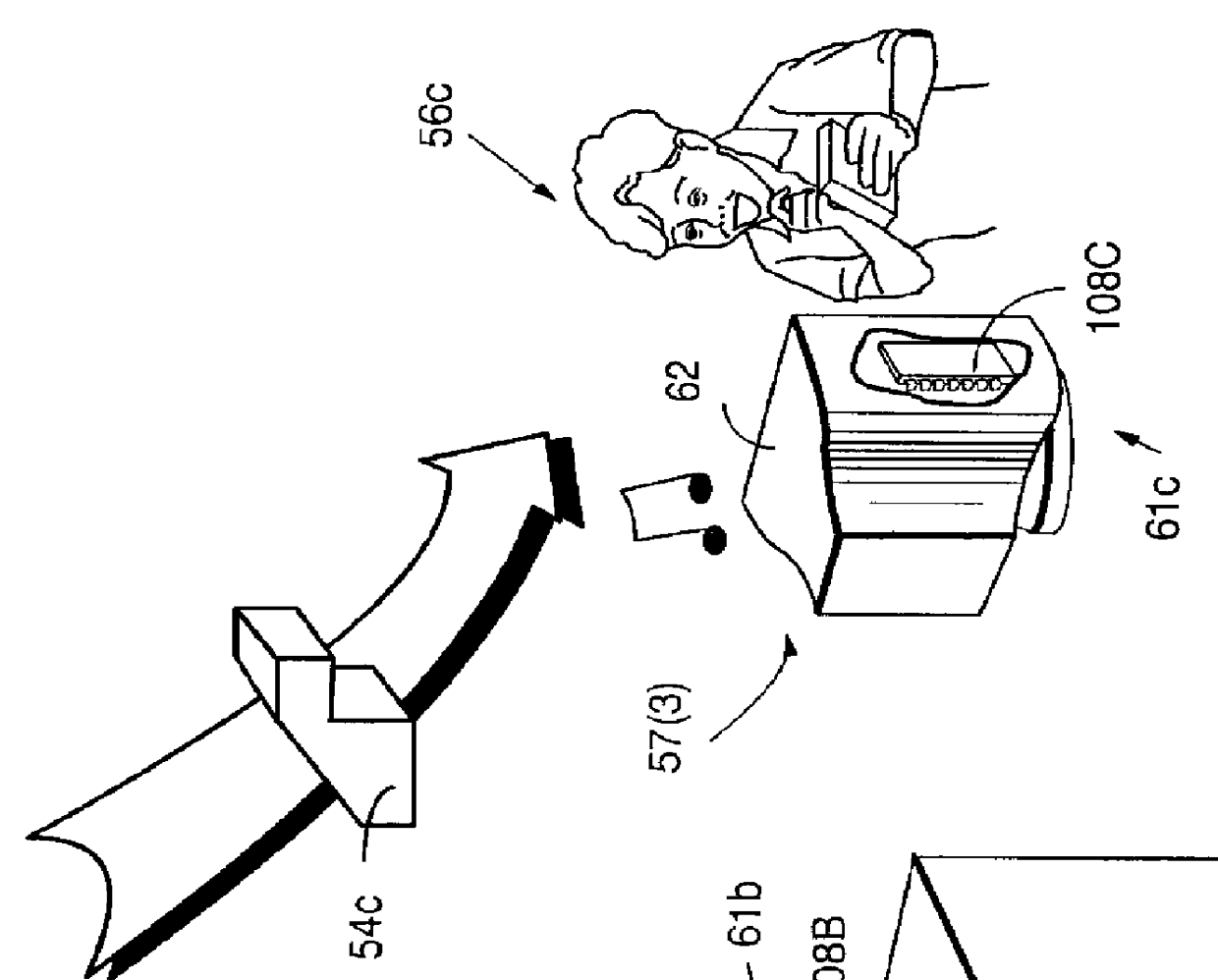
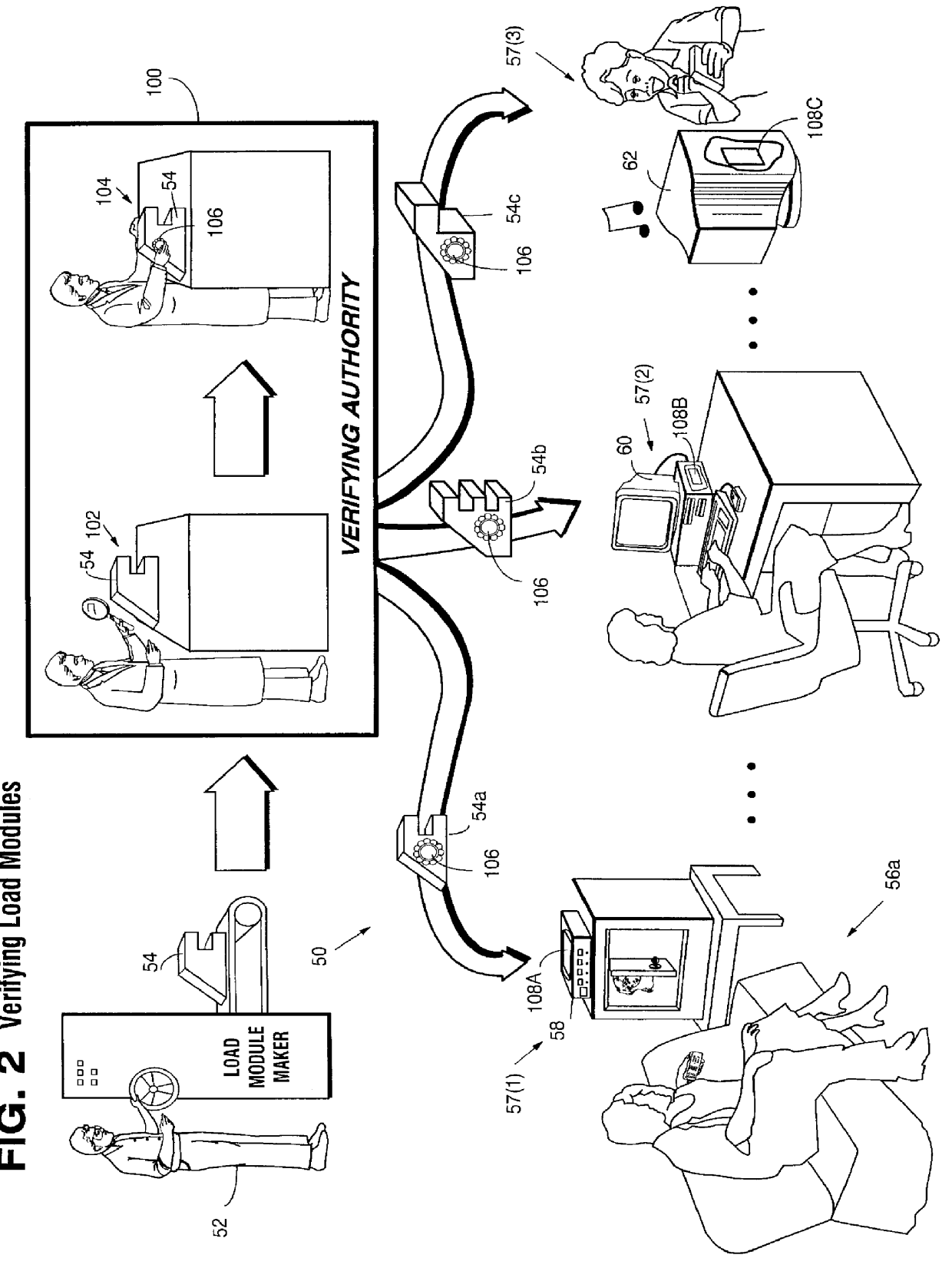
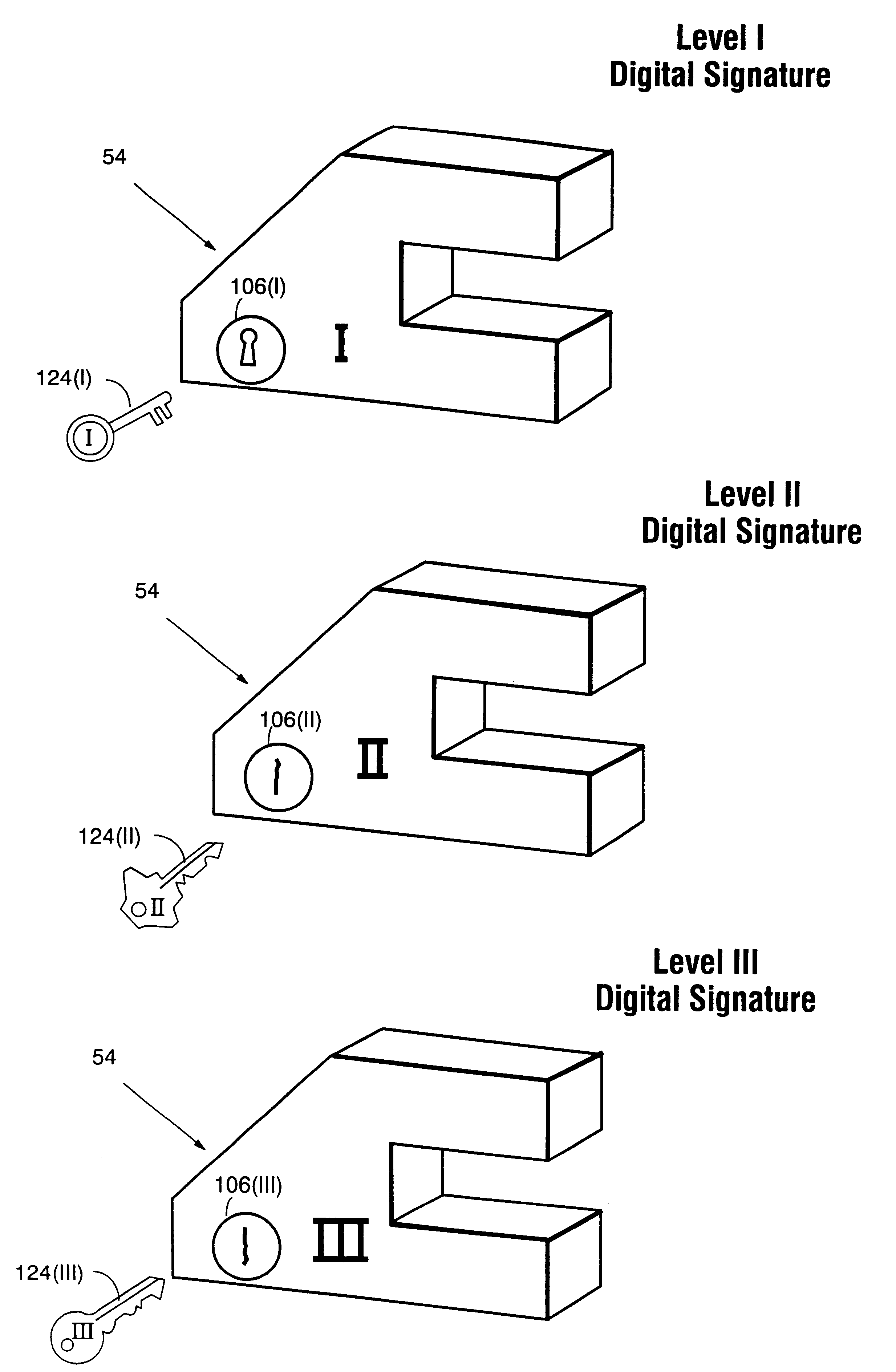
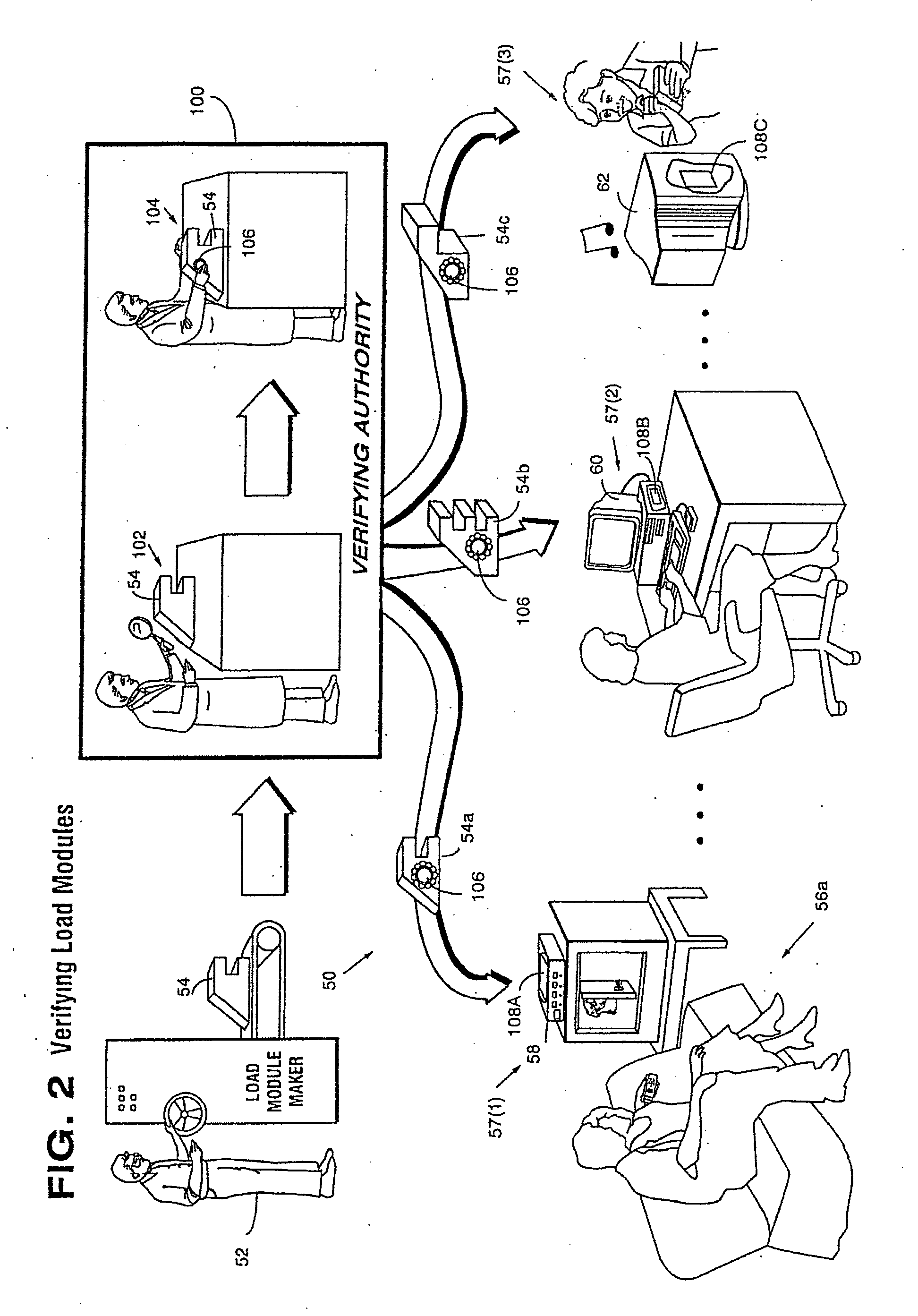
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm compromise, and subsets of multiple digital signatures may be used to reduce the scope of any specific compromise.
Owner:INTERTRUST TECH CORP
Systems and methods using cryptography to protect secure computing environments
InactiveUS6292569B1Improve connectivityComputationally orRecording carrier detailsError detection/correctionThird partyTamper resistance
Secure computation environments are protected from bogus or rogue load modules, executables and other data elements through use of digital signatures, seals and certificates issued by a verifying authority. A verifying authority-which may be a trusted independent third party-tests the load modules or other executables to verify that their corresponding specifications are accurate and complete, and then digitally signs the load module or other executable based on tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different verification digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys)-allowing one tamper resistance work factor environment to protect itself against load modules from another, different tamper resistance work factor environment. Several dissimilar digital signature algorithms may be used to reduce vulnerability from algorithm.
Owner:INTERTRUST TECH CORP
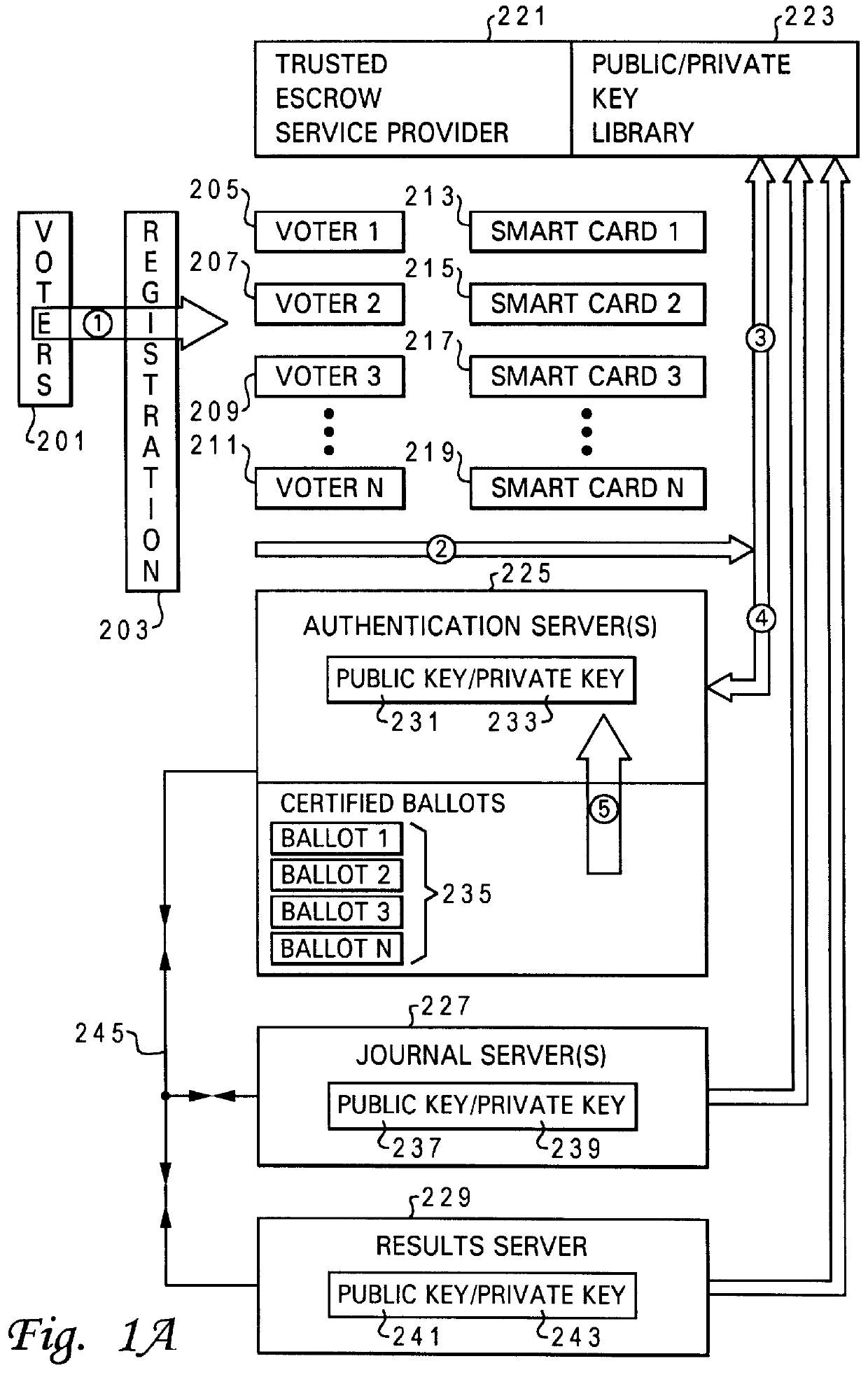
Method and system for secure computer moderated voting
InactiveUS6081793AVoting apparatusMultiple keys/algorithms usageData processing systemAuthentication server
A method and system is provided for improved electronic voting. The system optionally allows paper type ballots to be utilized. A plurality of cryptographic routines are utilized in a distributed data processing system to maximize the privacy of both the voter's identity and the content of completed ballots. An authentication server is utilized to interact with a voter to issue electronic ballots and receive completed electronic ballots in a manner which determines the authenticity of the identification of the voter, while maintaining the content of the completed ballot confidential. The distributed data processing system further includes a results server which tabulates the content of completed ballots in a manner which maintains the identity of the voters associated with the particular ballots confidential. The distributed data processing system may further include a journal server which records completed ballots, in a manner which facilitates the challenge of ineligible votes and the correction of erroneous votes.
Owner:LENOVO PC INT
Integrated computer security management system and method
InactiveUS7331061B1Centralized controlIncrease speedMemory loss protectionError detection/correctionSafety management systemsSecurity management
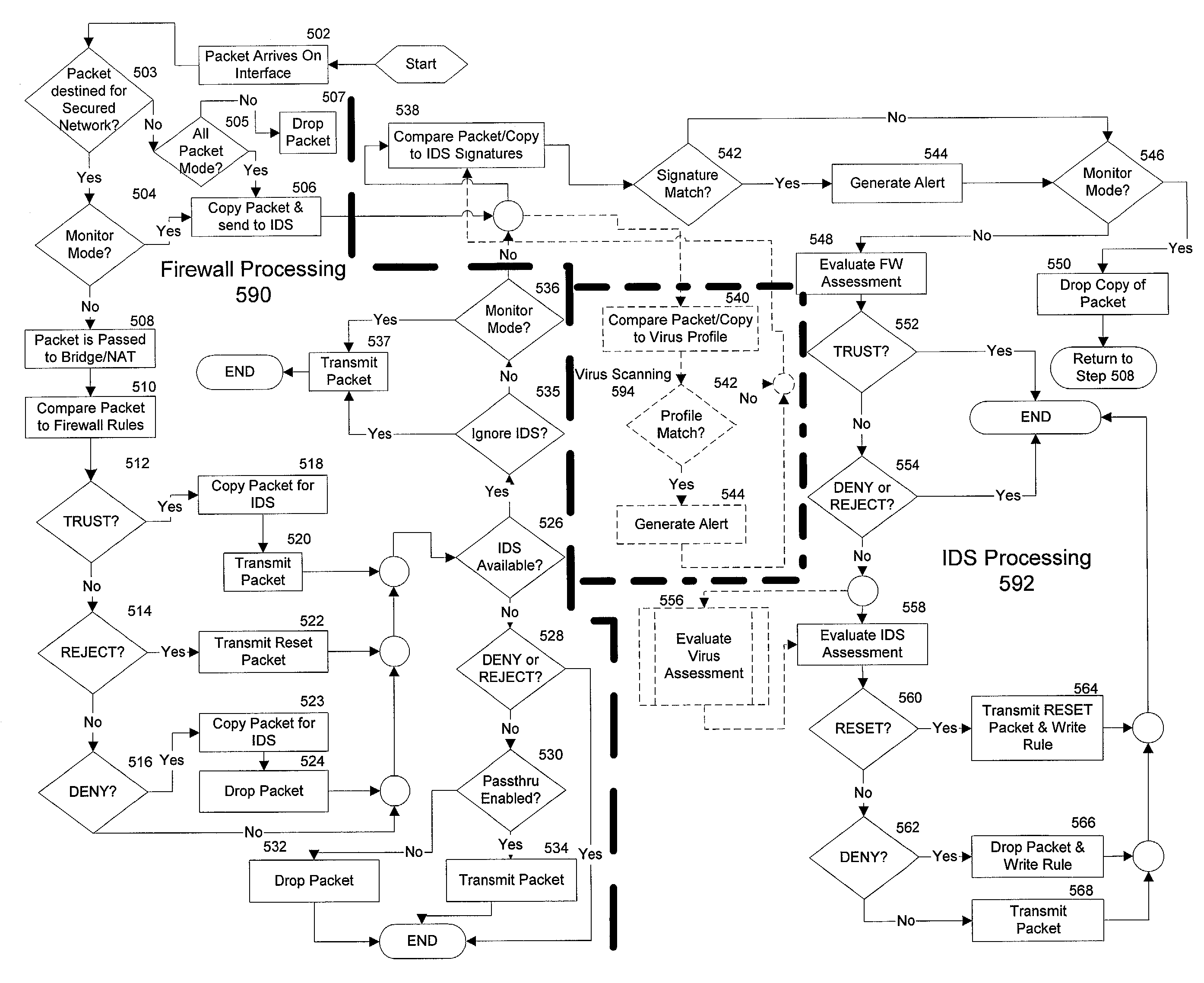
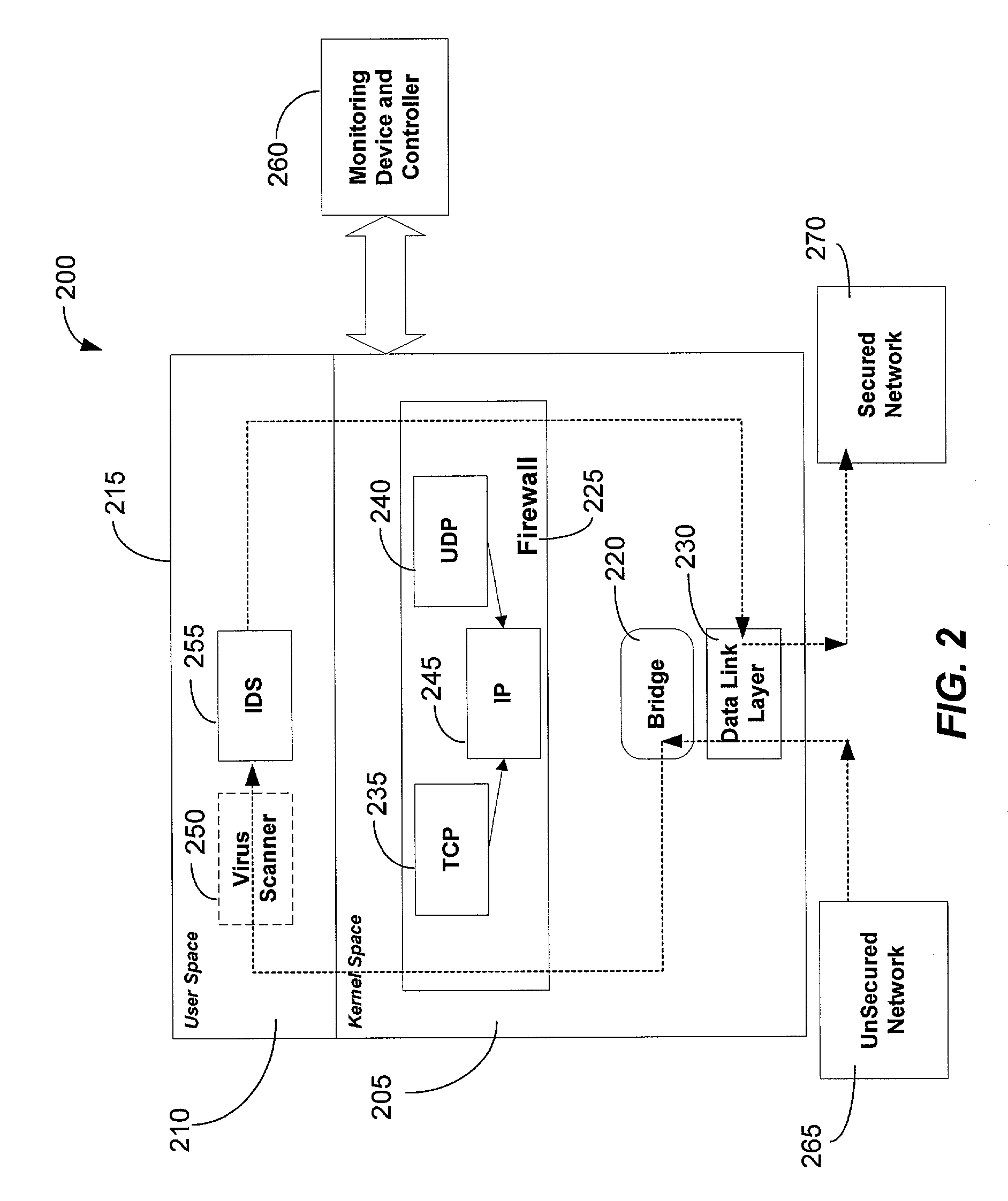
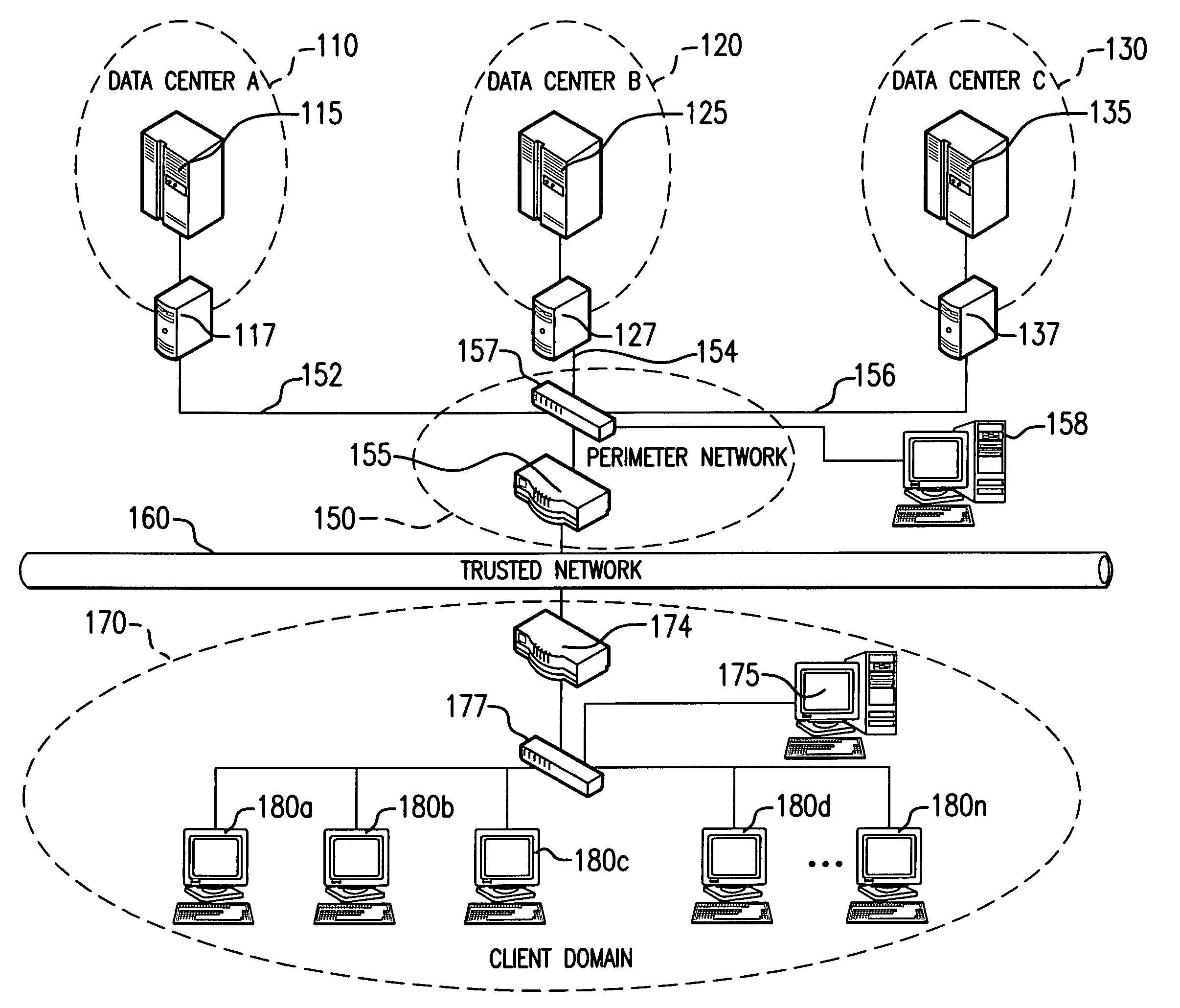
The present invention is generally directed to a computer security management system that integrates a firewall with an intrusion detection system (IDS). In other words, the firewall and IDS of the present invention can be designed to communicate process or status information and packets with one another. The present invention can facilitate centralized control of the firewall and the IDS and can increase the speed at which packets are passed between a secured computer network and an external network. Increased packet processing speed can be achieved in several ways. For example, the firewall and IDS can process packets in series, in parallel, and sometimes singularly when one of the components is not permitted to process a packet. Alternatively, singular processing can also be performed when one component is permitted to pass a packet to the secured computer network without checking with the other component.
Owner:SECUREWORKS
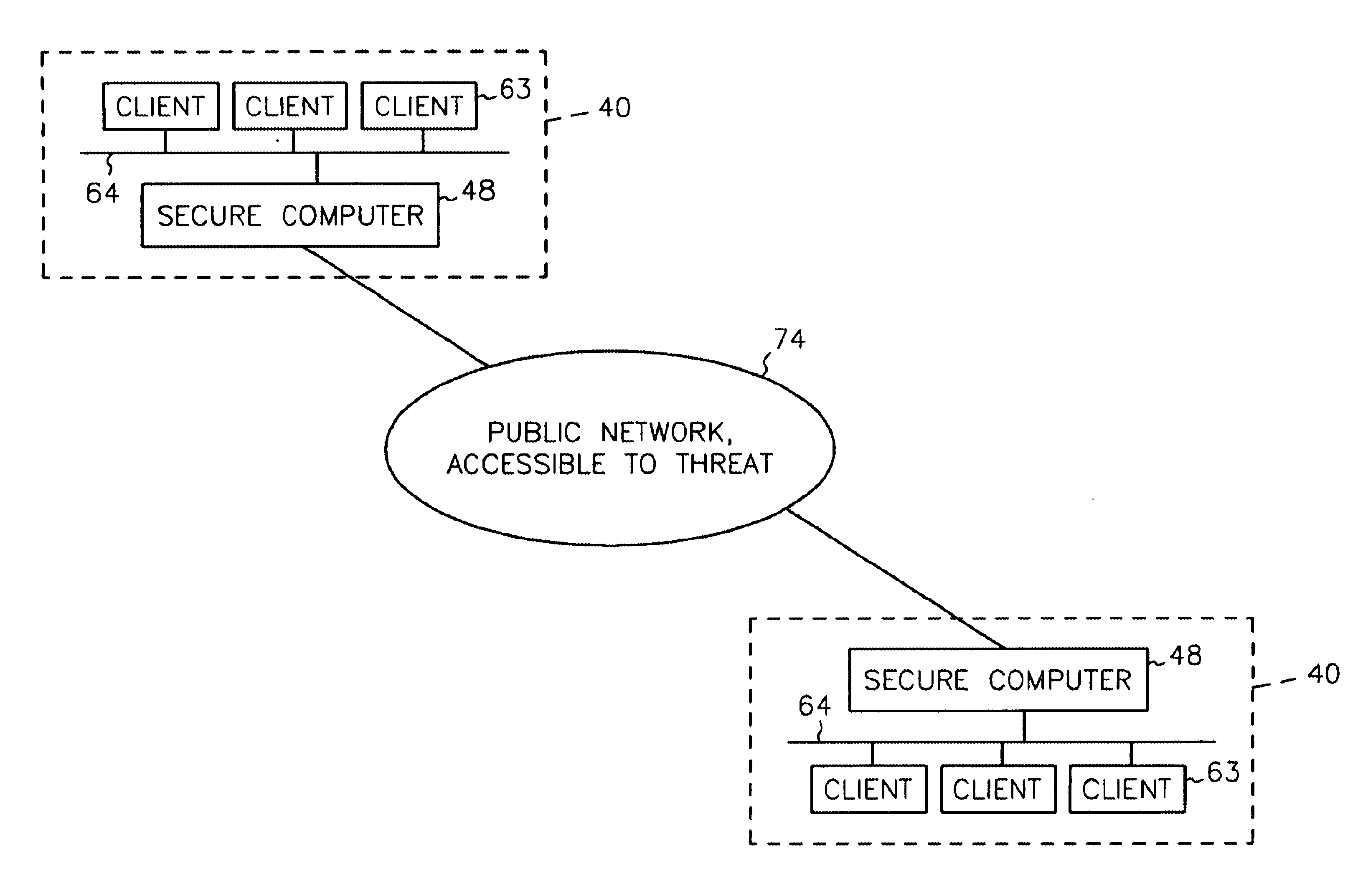
System and method for preventing identity theft using a secure computing device
ActiveUS20050071282A1Secure transmissionDigital data processing detailsMultiple digital computer combinationsSecure transmissionIdentity theft
A system and method for effecting secure transactions over a computer network in a manner designed to foil identity theft perpetrated from an untrusted computer. A connection from a client computer to the network wherein the client computer provides a user interface for a user, a connection from a server computer to the network, and a connection from a portable secure computing device to the network provides for secure transmission of private confidential user information from the user to a server. The private information is transmitted directly from the secure computing device to the server over the secure connection without possibility of capture on the computer with which the user is interacting.
Owner:GEMPLU
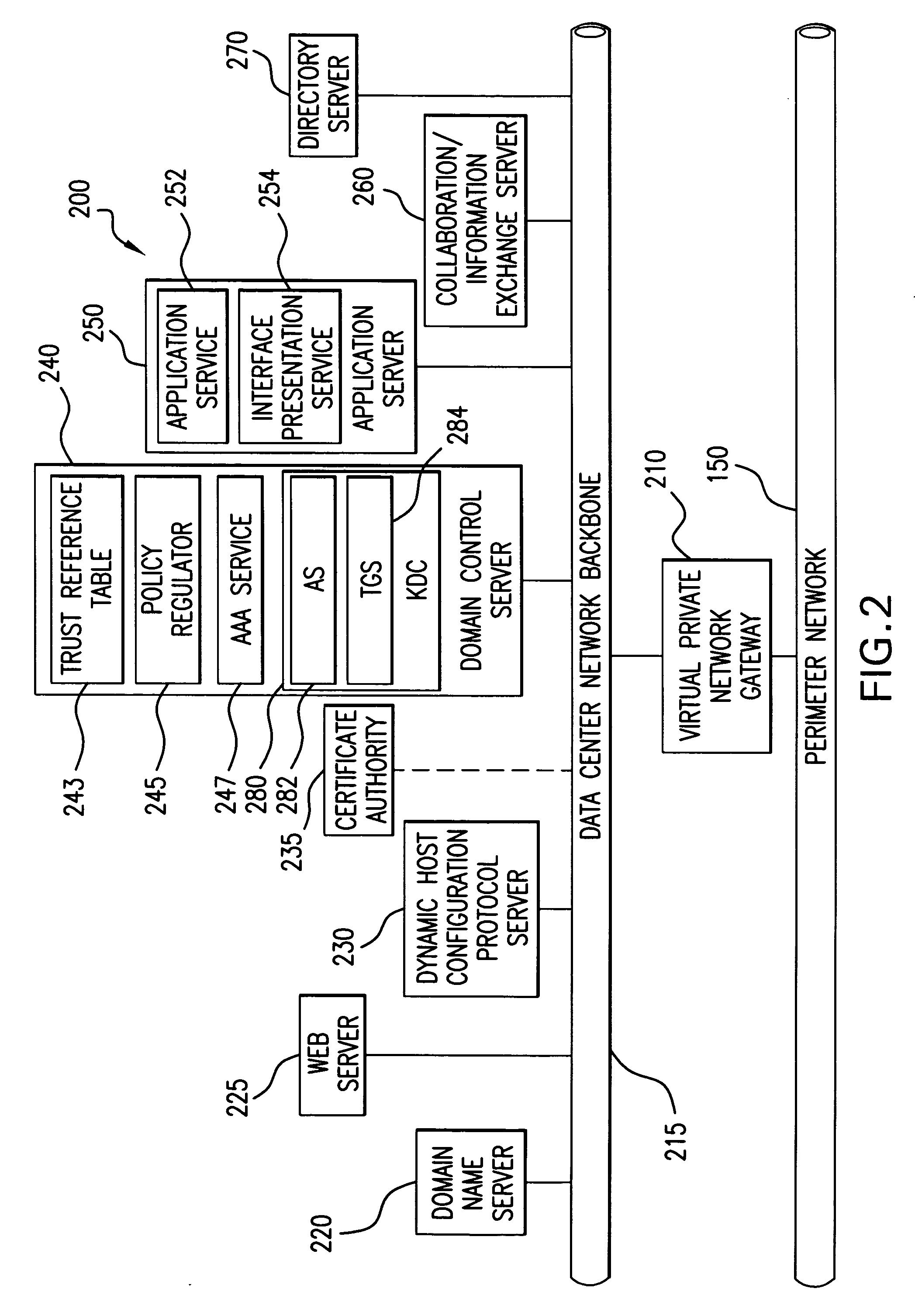
System for secure computing using defense-in-depth architecture
ActiveUS20060041761A1Key distribution for secure communicationUnauthorized memory use protectionPrivate networkCombined use
A secure computing system is provided which utilizes a unique combination of Public Key Infrastructure (PKI), Virtual Private Networking (VPN), and server-based computing on thin client devices. The combination of technology and components provide secure computing through Defense-in-Depth using commercial off-the-shelf components.
Owner:MITRE SPORTS INT LTD
System and method for providing secure internetwork services via an assured pipeline
InactiveUS6772332B1Multiple digital computer combinationsPlatform integrity maintainanceSecure transmissionPrivate network
A system and method for the secure transfer of data between a workstation connected to a private network and a remote computer connected to an unsecured network. A secure computer is inserted into the private network to serve as the gateway to the unsecured network and a client subsystem is added to the workstation in order to control the transfer of data from the workstation to the secure computer. The secure computer includes a private network interface connected to the private network, an unsecured network interface connected to the unsecured network, wherein the unsecured network interface includes means for encrypting data to be transferred from the first workstation to the remote computer and a server function for transferring data between the private network interface and the unsecured network interface.
Owner:MCAFEE LLC
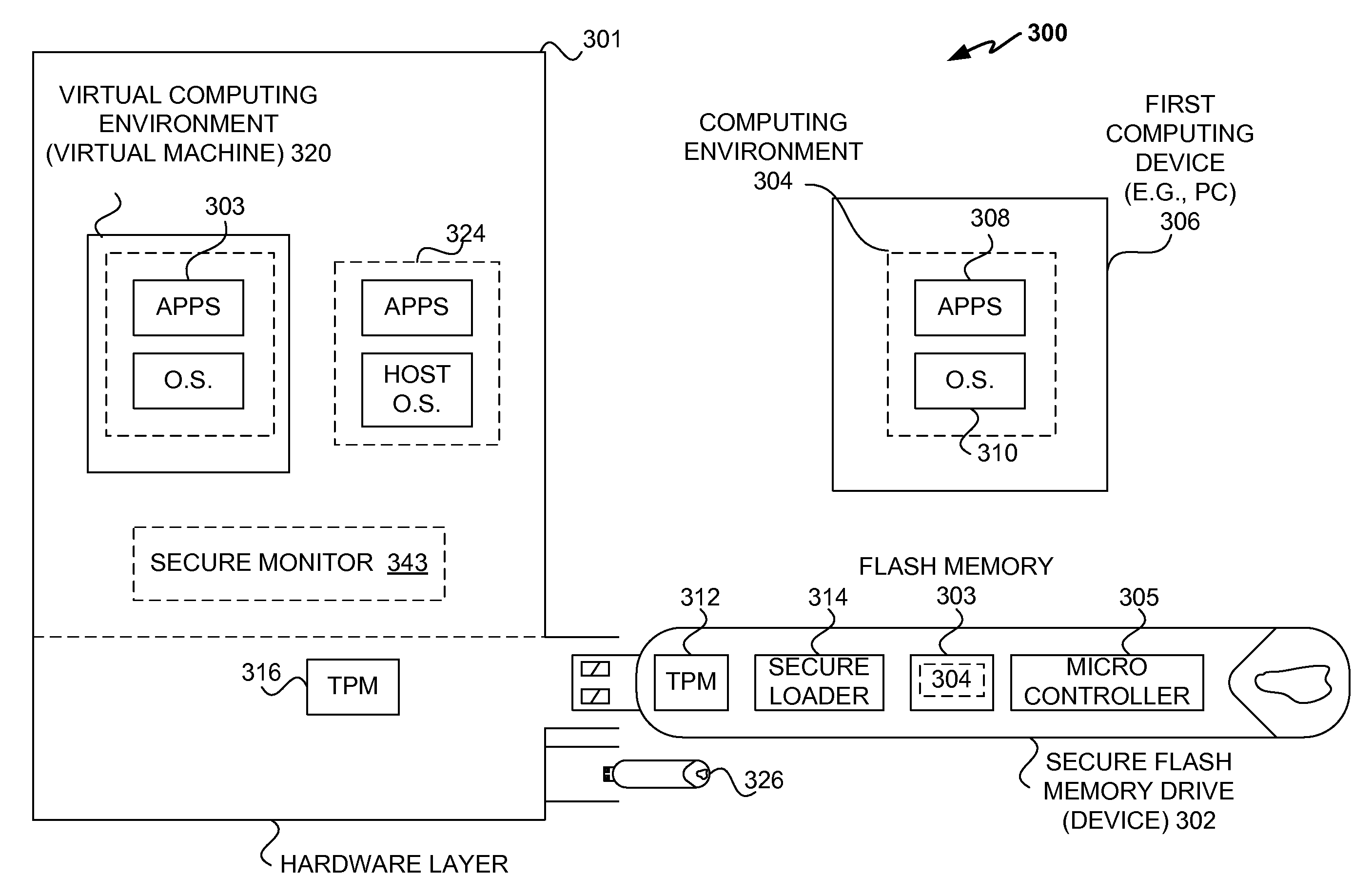
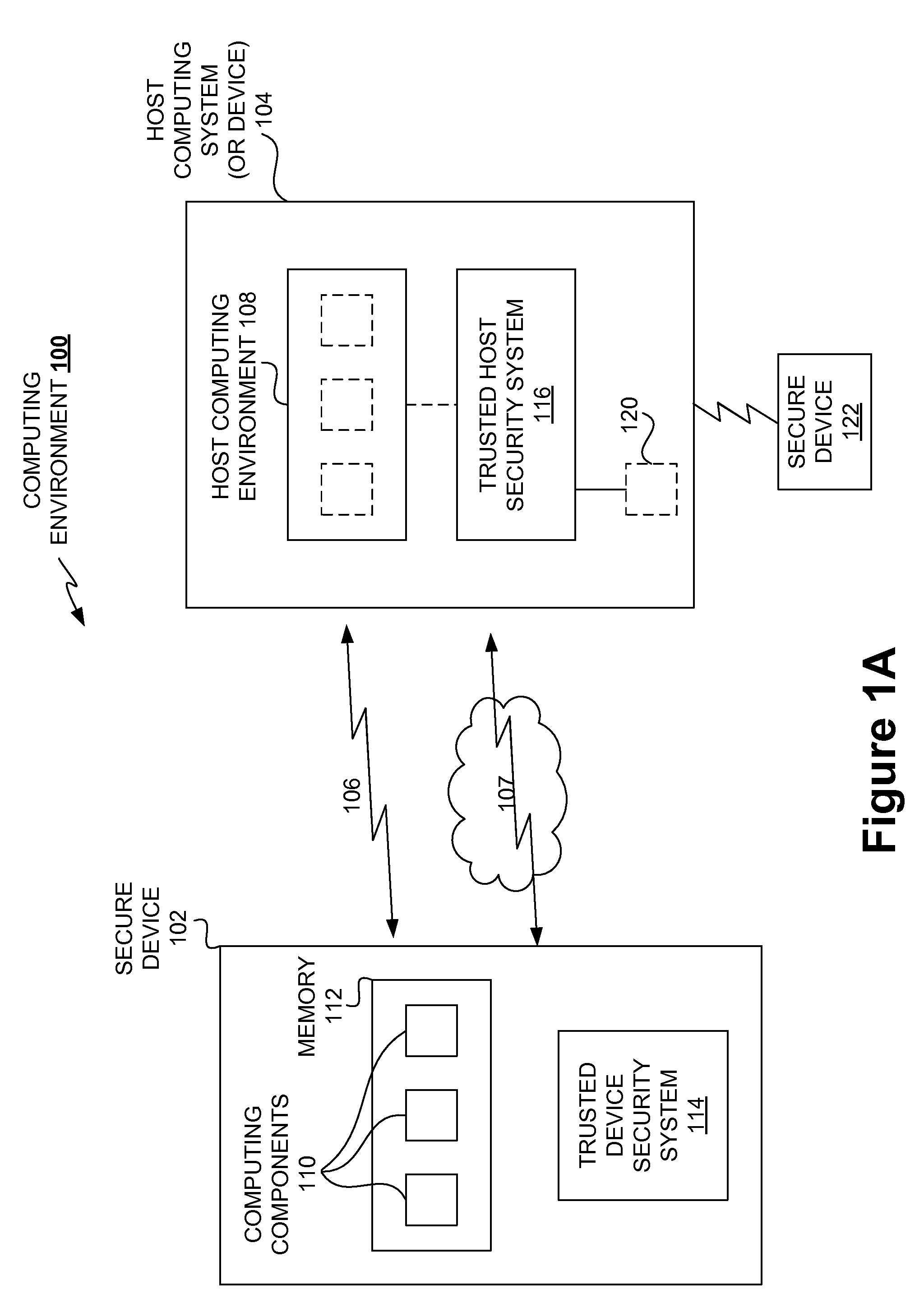
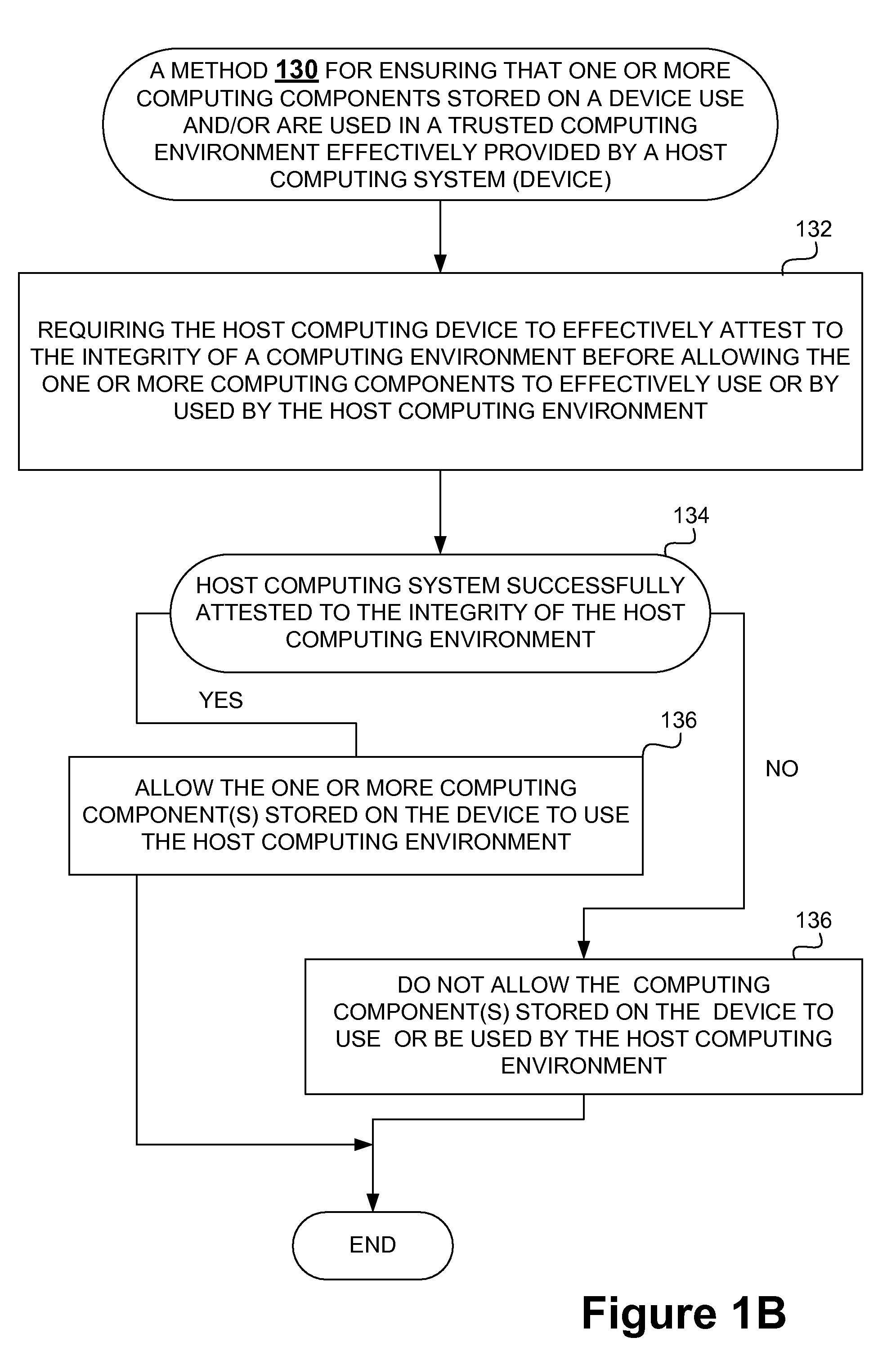
Securing stored content for trusted hosts and safe computing environments
InactiveUS20090049510A1Safe computing environmentEasy to usePublic key for secure communicationDigital data processing detailsHosting environmentComputer science
Techniques for protecting content to ensure its use in a trusted environment are disclosed. The stored content is protected against harmful and / or defective host (or hosted) environments. A trusted security component provided for a device can verify the internal integrity of the stored content and the host before it allows the content to come in contact with the host. As a counter part, a trusted security component provided for the host can verify and attest to the integrity of the host and / or specific host computing environment that can be provided for the content stored in the device. The trusted security component provided for a device effectively verify the host integrity based on the information attested to by the trusted security component provided for the host. If the trusted security component trusts the host, it allows the trusted host to provide a trusted host computing environment trusted to be safe for the content stored in the device. A trusted host can effectively provide a safe virtual environment that allows a content representing a copy (or image) of an original computing environment to operate on the host computing system to give a similar appearance as the original computing environment.
Owner:SAMSUNG ELECTRONICS CO LTD
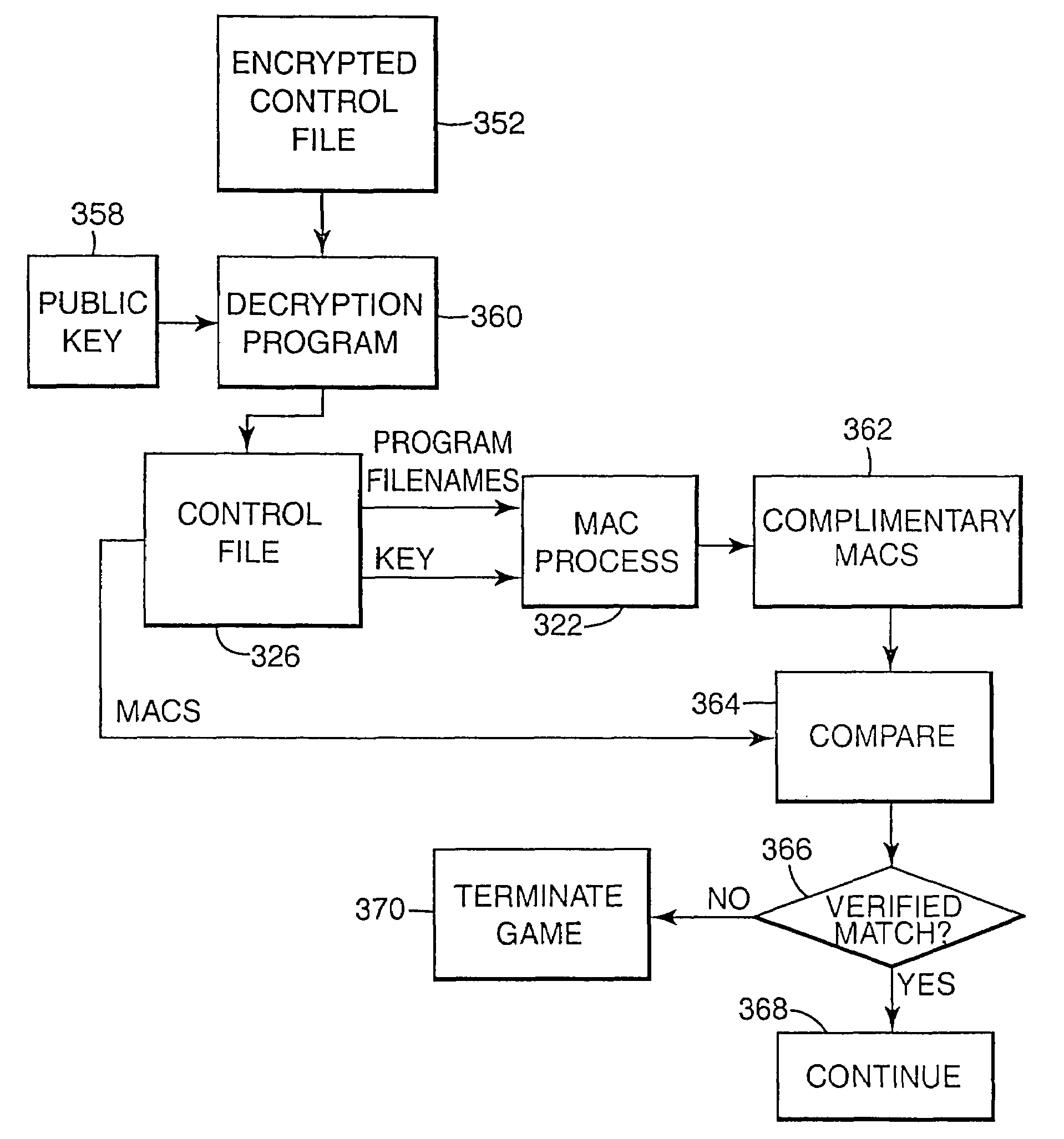
Encryption in a secure computerized gaming system
InactiveUS7116782B2Easy to managePublic key for secure communicationUser identity/authority verificationHash functionDigital signature
The present invention provides an architecture and method for a gaming-specific platform that features secure storage and verification of game code and other data, provides the ability to securely exchange data with a computerized wagering gaming system, and does so in a manner that is straightforward and easy to manage. Some embodiments of the invention provide the ability to identify game program code as certified or approved, such as by the Nevada Gaming Regulations Commission or other regulatory agency. The invention provides these and other functions by use of encryption, including digital signatures and hash functions as well as other encryption methods.
Owner:IGT
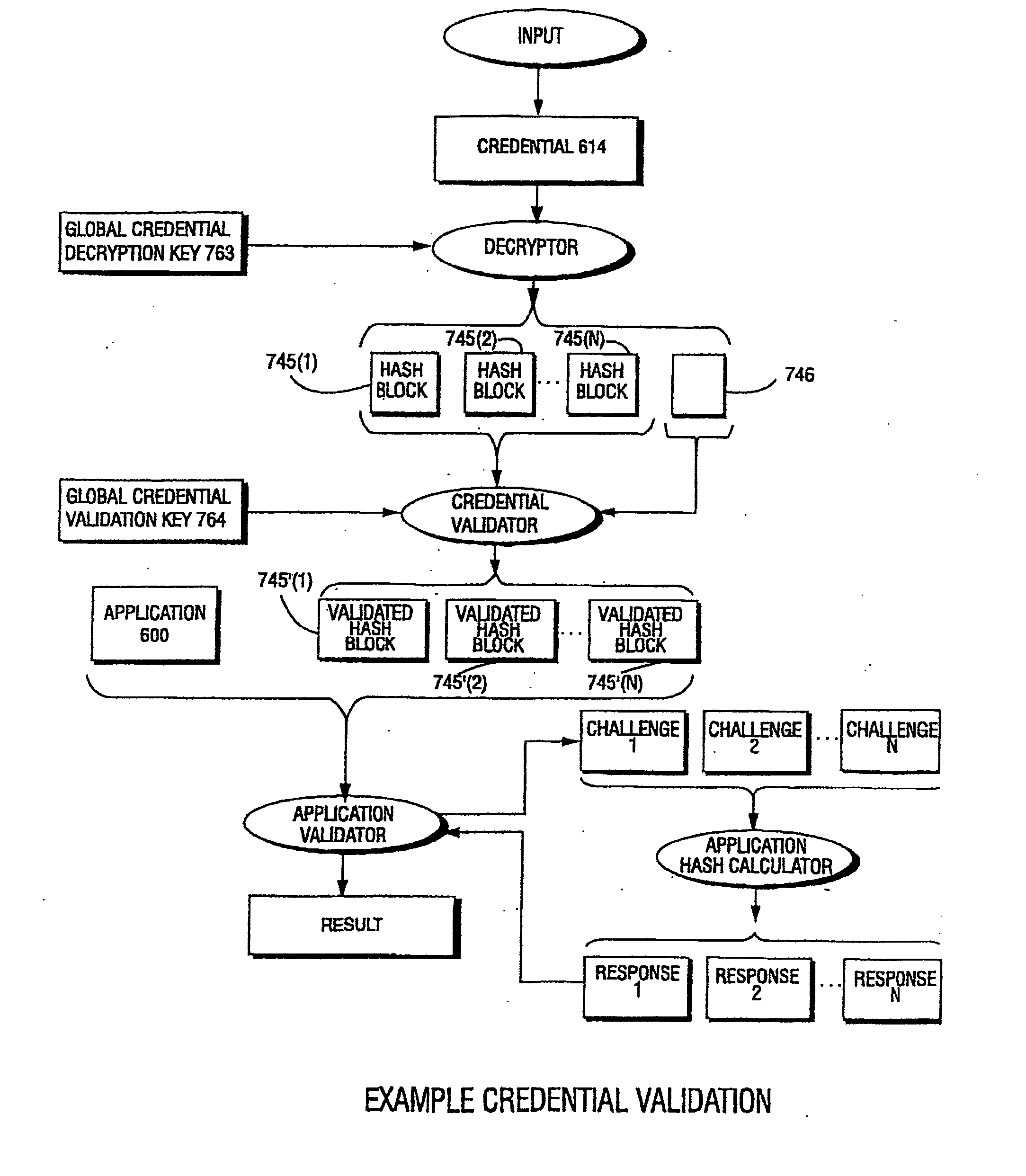
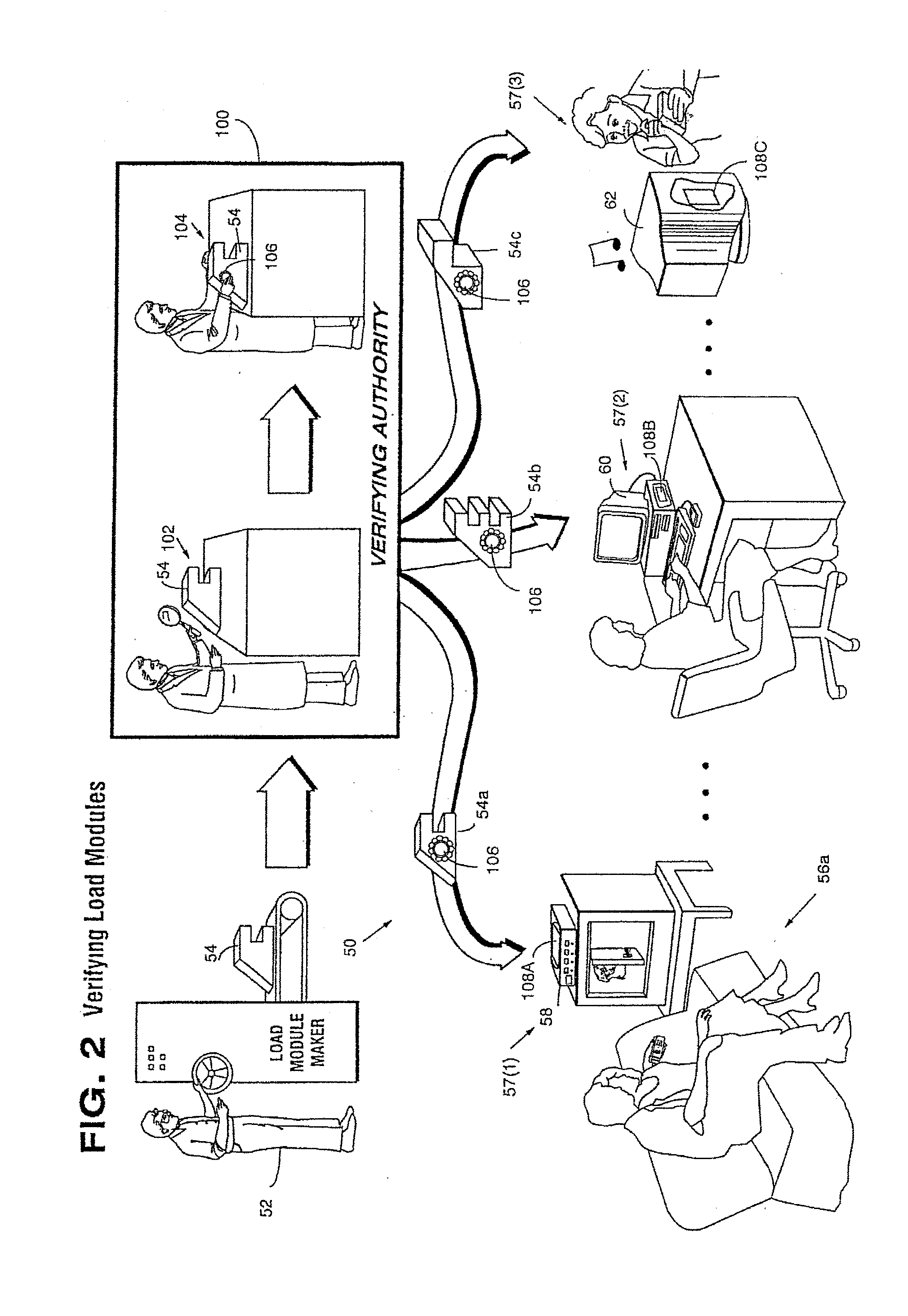
Systems and methods for using cryptography to protect secure and insecure computing environments
InactiveUS20070226798A1Memory loss protectionDigital data processing detailsThird partyTamper resistance
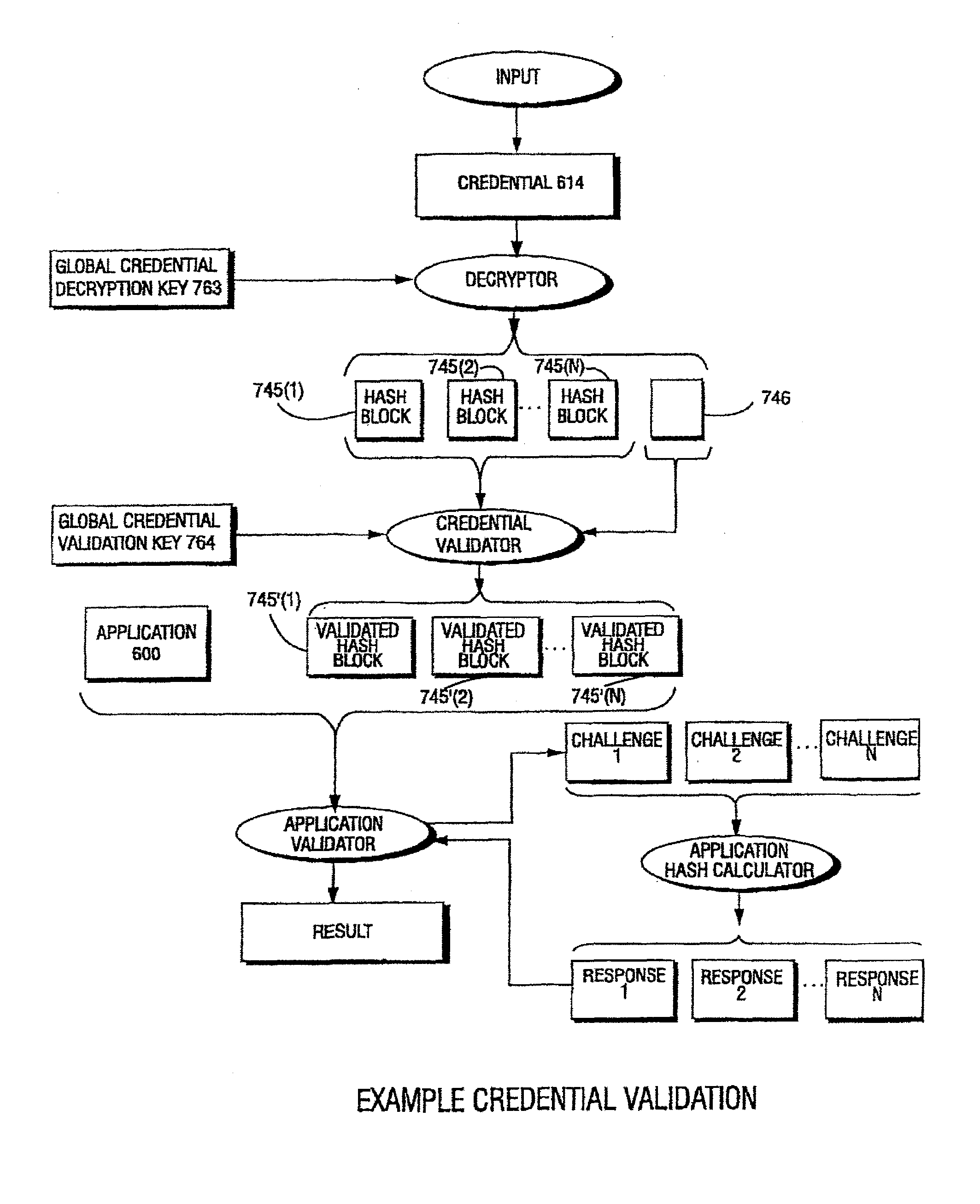
Computation environments are protected from bogus or rogue load modules, executables, and other data elements through use of digital signatures, seals, and certificates issued by a verifying authority. A verifying authority—which may be a trusted independent third party—tests the load modules and / or other items to verify that their corresponding specifications are accurate and complete, and then digitally signs them based on a tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys), allowing one tamper resistance work factor environment to protect itself against load modules from another tamper resistance work factor environment. The verifying authority can provide an application intended for insecure environments with a credential having multiple elements covering different parts of the application. To verify the application, a trusted element can issue challenges based on different parts of the authenticated credential that the trusted element selects in an unpredictable (e.g., random) way, and deny service (or take other appropriate action) if the responses do not match the authenticated credential.
Owner:INTERTRUST TECH CORP
Multichannel device utilizing a centralized out-of-band authentication system (COBAS)
InactiveUS20060041755A1Improve securityElectric signal transmission systemsImage analysisPasswordAuthentication system
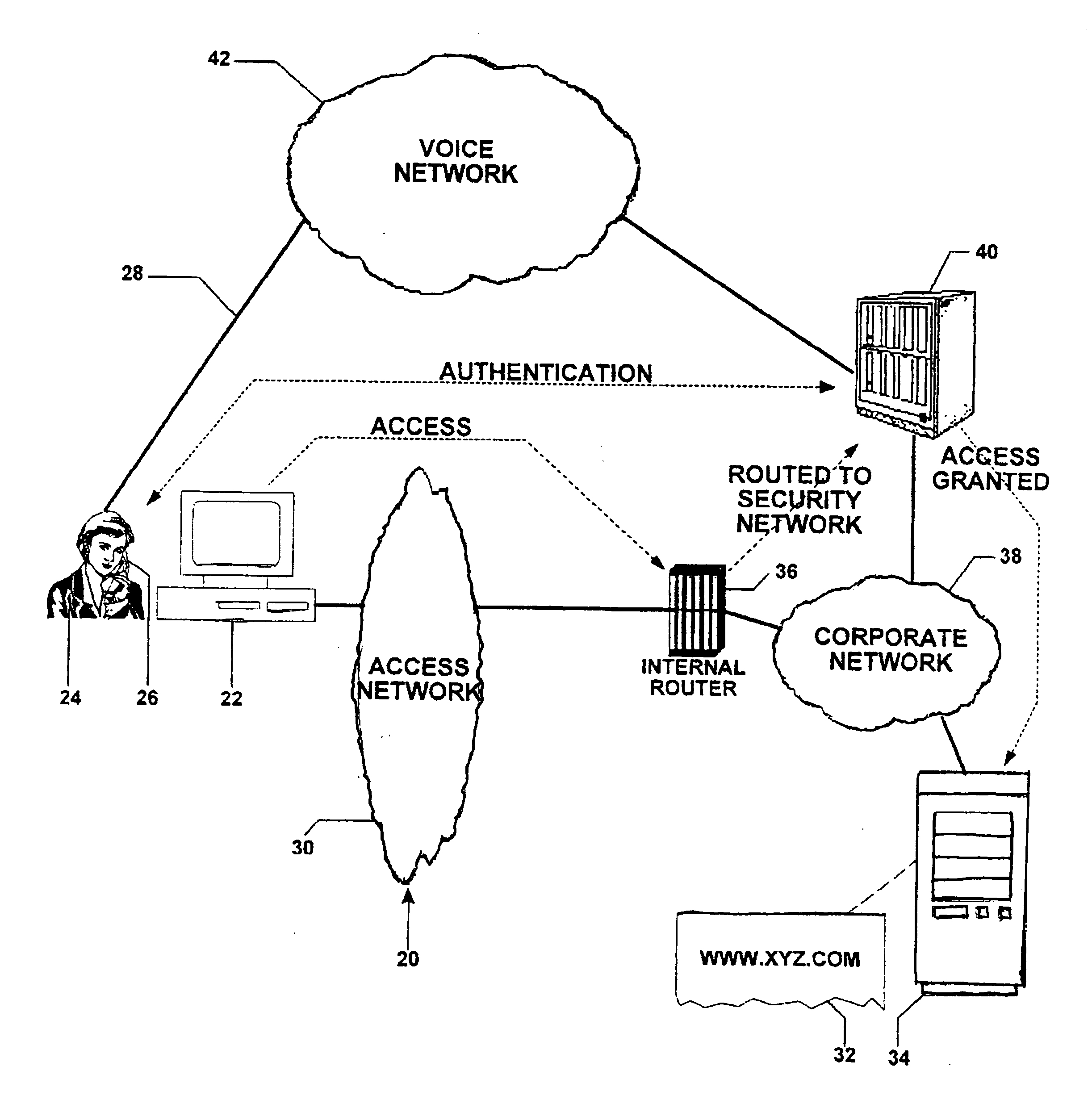
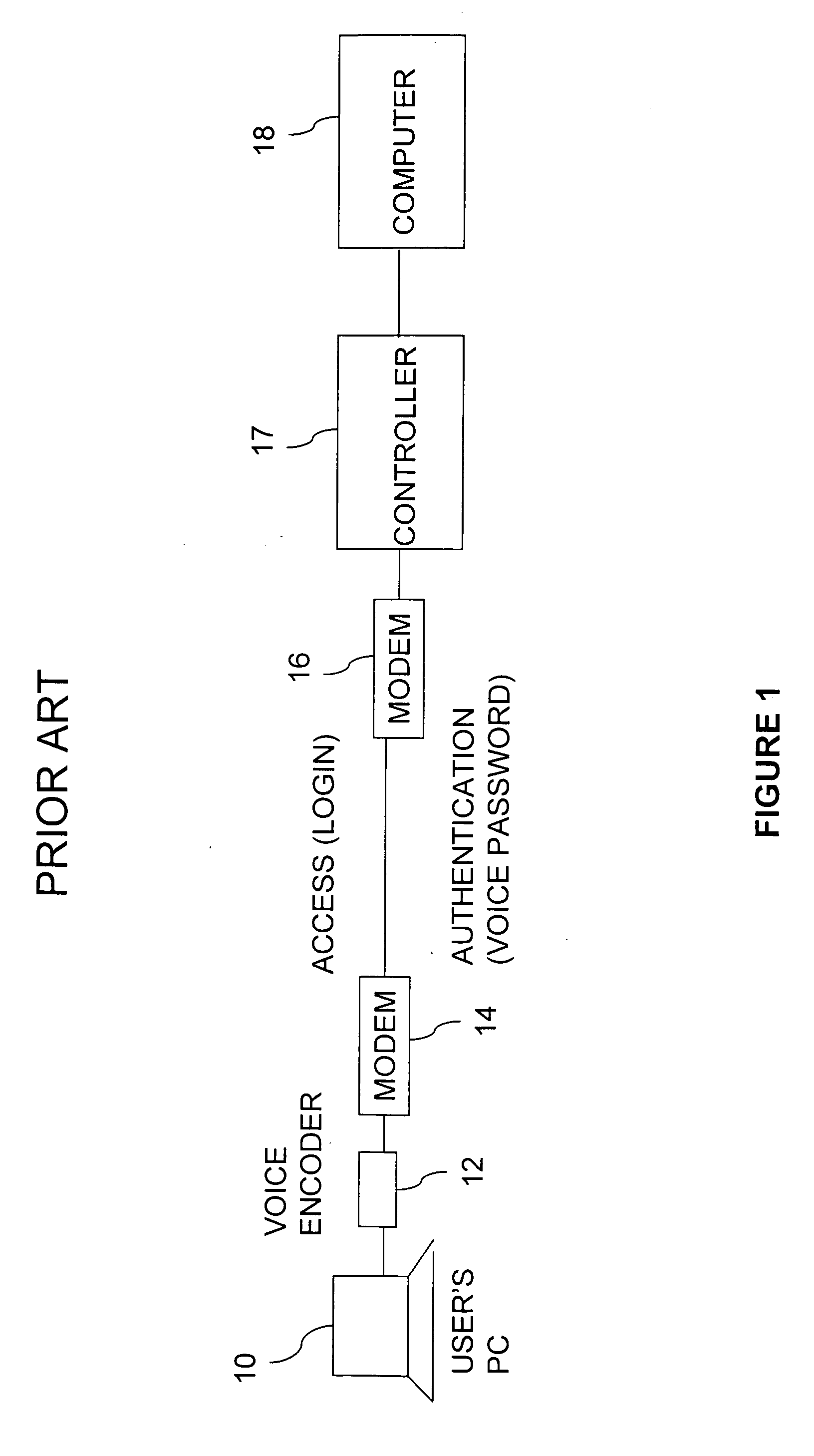
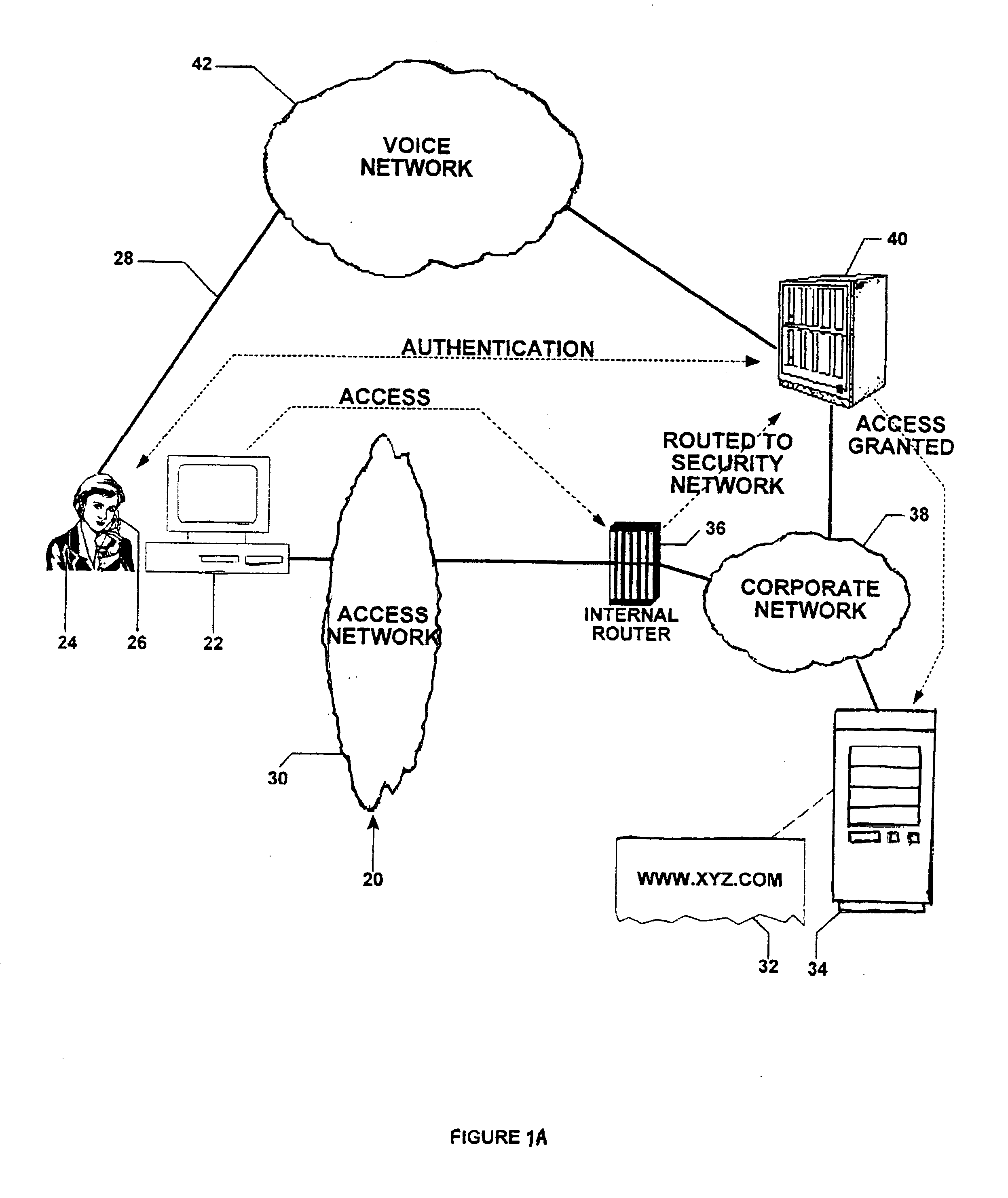
A multichannel security system is disclosed, which system is for granting and denying access to a host computer in response to a demand from an access-seeking individual and computer. The access-seeker has a peripheral device operative within an authentication channel to communicate with the security system. The access-seeker initially presents identification and password data over an access channel which is intercepted and transmitted to the security computer. The security computer then communicates with the access-seeker. A biometric analyzer—a voice or fingerprint recognition device—operates upon instructions from the authentication program to analyze the monitored parameter of the individual. In the security computer, a comparator matches the biometric sample with stored data, and, upon obtaining a match, provides authentication. The security computer instructs the host computer to grant access and communicates the same to the access-seeker, whereupon access is initiated over the access channel.
Owner:STRIKEFORCE TECH
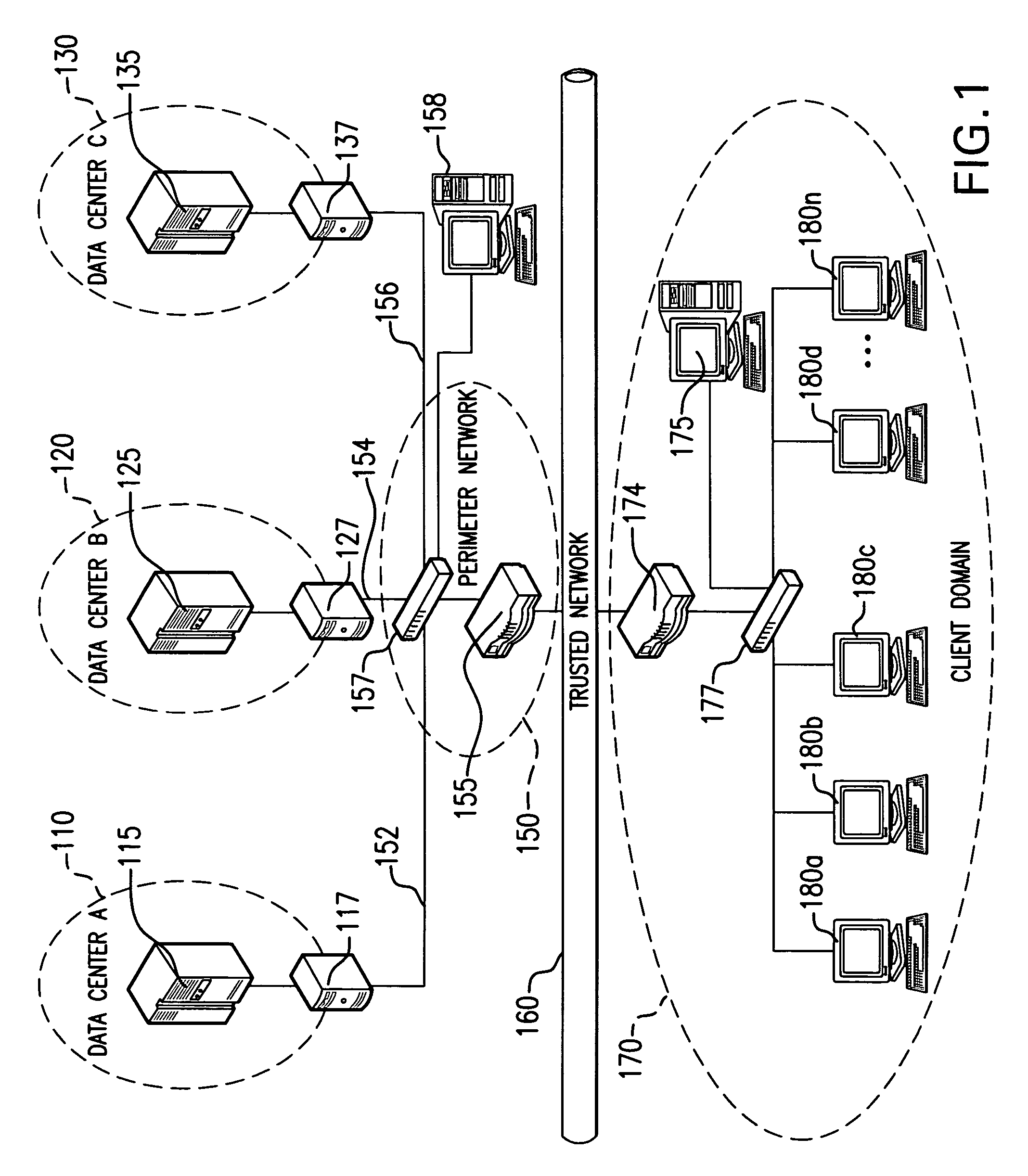
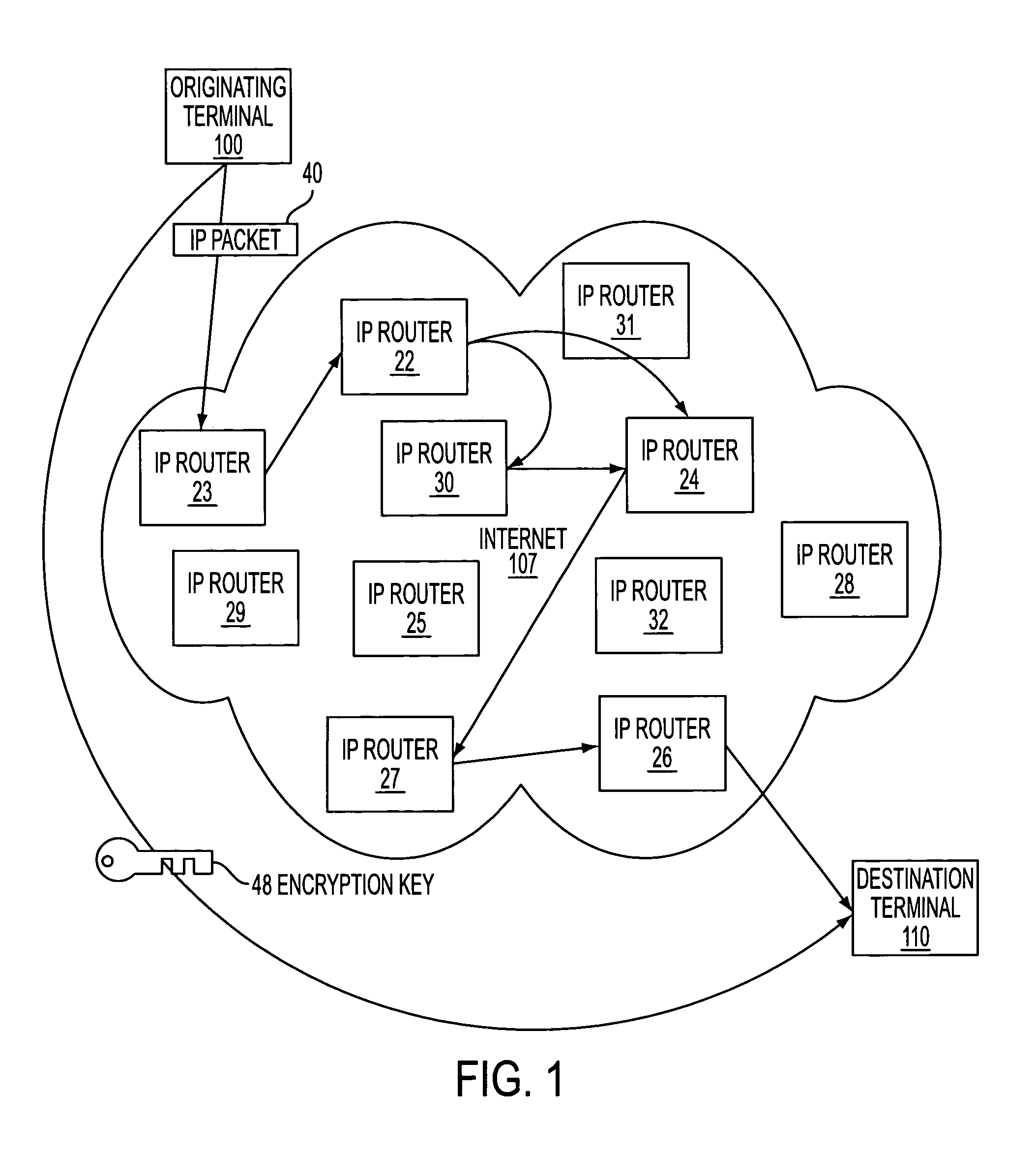
Agile network protocol for secure communications using secure domain names
InactiveUS7418504B2Conveniently establishedWeb data indexingDigital computer detailsSecure communicationNetwork addressing
A secure domain name service for a computer network is disclosed that includes a portal connected to a computer network, such as the Internet, and a domain name database connected to the computer network through the portal. The portal authenticates a query for a secure computer network address, and the domain name database stores secure computer network addresses for the computer network. Each secure computer network address is based on a non-standard top-level domain name, such as .scom, .sorg, .snet, .snet, .sedu, .smil and .sint.
Owner:VIRNETX
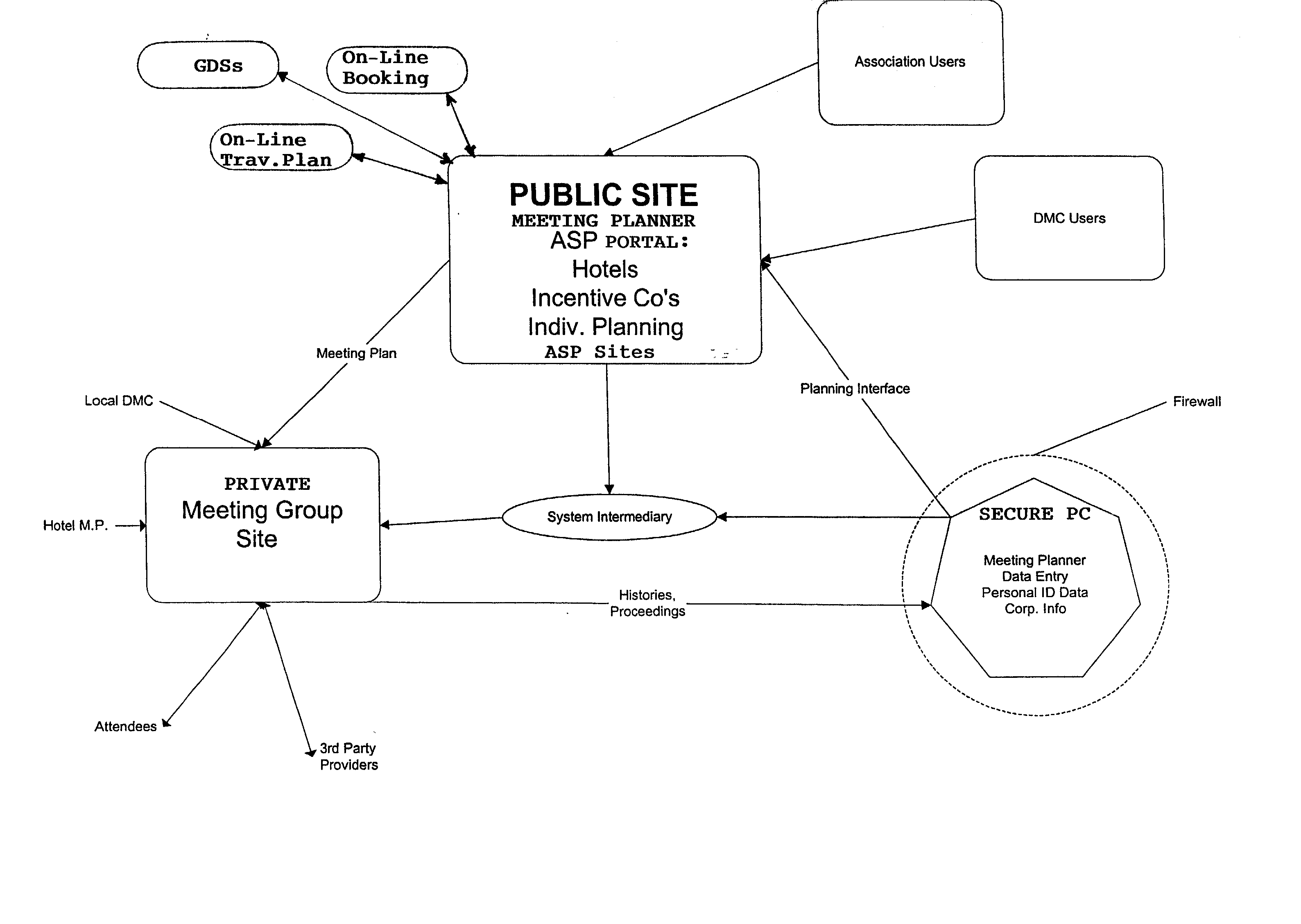
Online meeting planning system with 3-node configuration
A 3-node online meeting planning system includes a secure computer as a first node which is protected from unauthorized access running a meeting planner application program for entering meeting planning data which includes sensitive data of persons authorized as attendees at a meeting event and non-sensitive group data, a public online site as a second node which receives only the non-sensitive group data uploaded from the first node and assembles a unique meeting group program for the group using the non-sensitive group data, and a private online site as a third node which receives the assembled meeting group program from the second node and the sensitive data downloaded from the first node and combines them in an online private meeting group site accessible only to authorized attendees of the meeting event. Using this 3-node system, the meeting planner at the secure computer can retain control of the sensitive data, while using the non-sensitive group data for resource browsing and meeting planning functions on the public online site, which may be an ASP meeting planner portal which has an interface and navigation schema familiar to meeting planners and provides high-powered search tools and links to other public sites. The private meeting group site can be made the hub for a wide range of transactions, fulfillment functions, and group communications functions for the meeting event.
Owner:CHONG LEIGHTON K
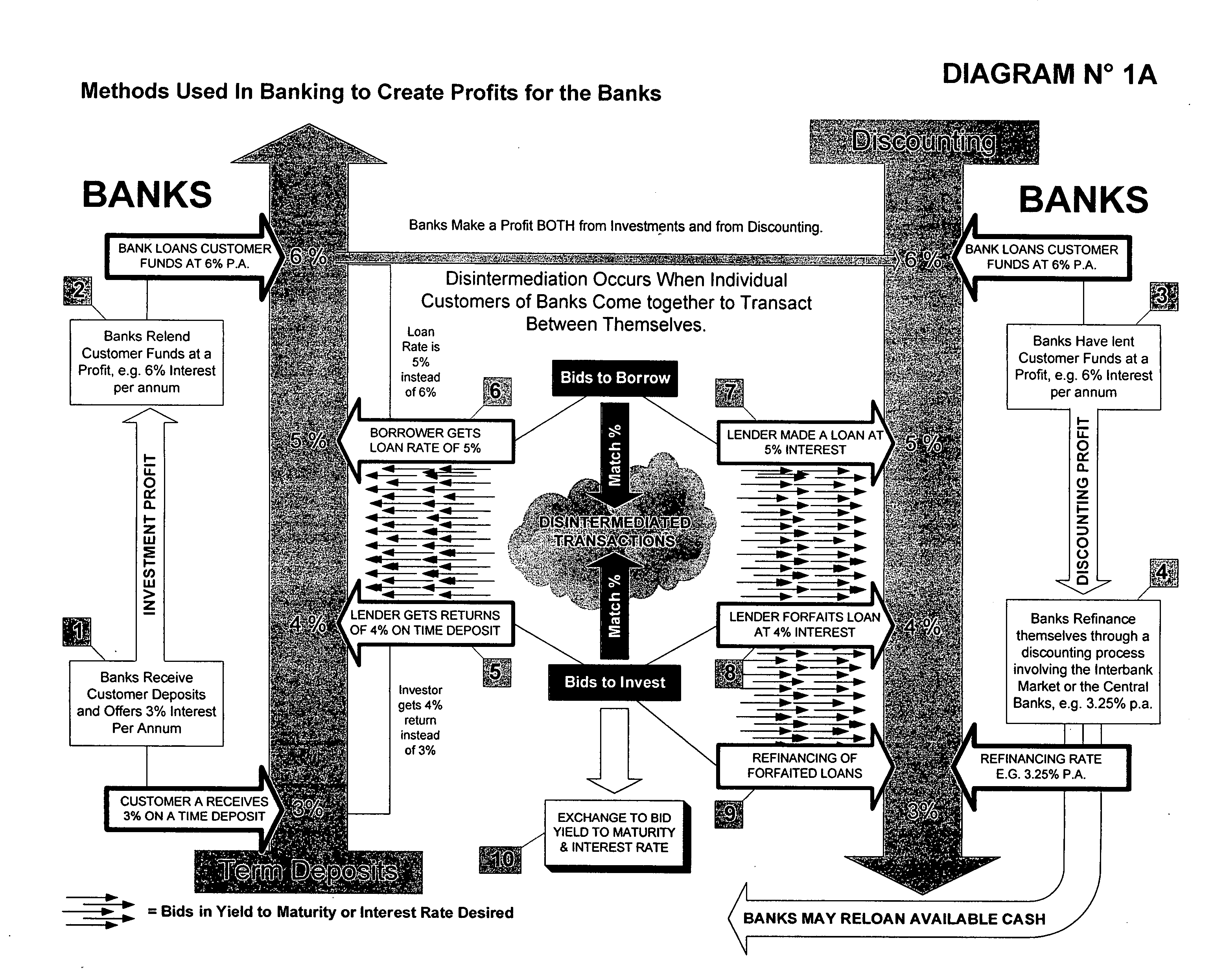
System & method for the creation of a global secure computerized electronic market-making exchange for currency yields arbitrage
InactiveUS20060155638A1Facilitates online interactionInstantly closeFinanceFinancial transactionFinancial trading
A multi-participant financial transaction with no downside risks that results in a net profit for all participants when the transaction is accomplished according to certain required steps, including the step of having simultaneously closings in escrow. A multi-step approach to issuing and selling custom-designed, specially engineered and underwritten securities or bank instruments is also described.
Owner:DE LA MOTTE ALAIN L
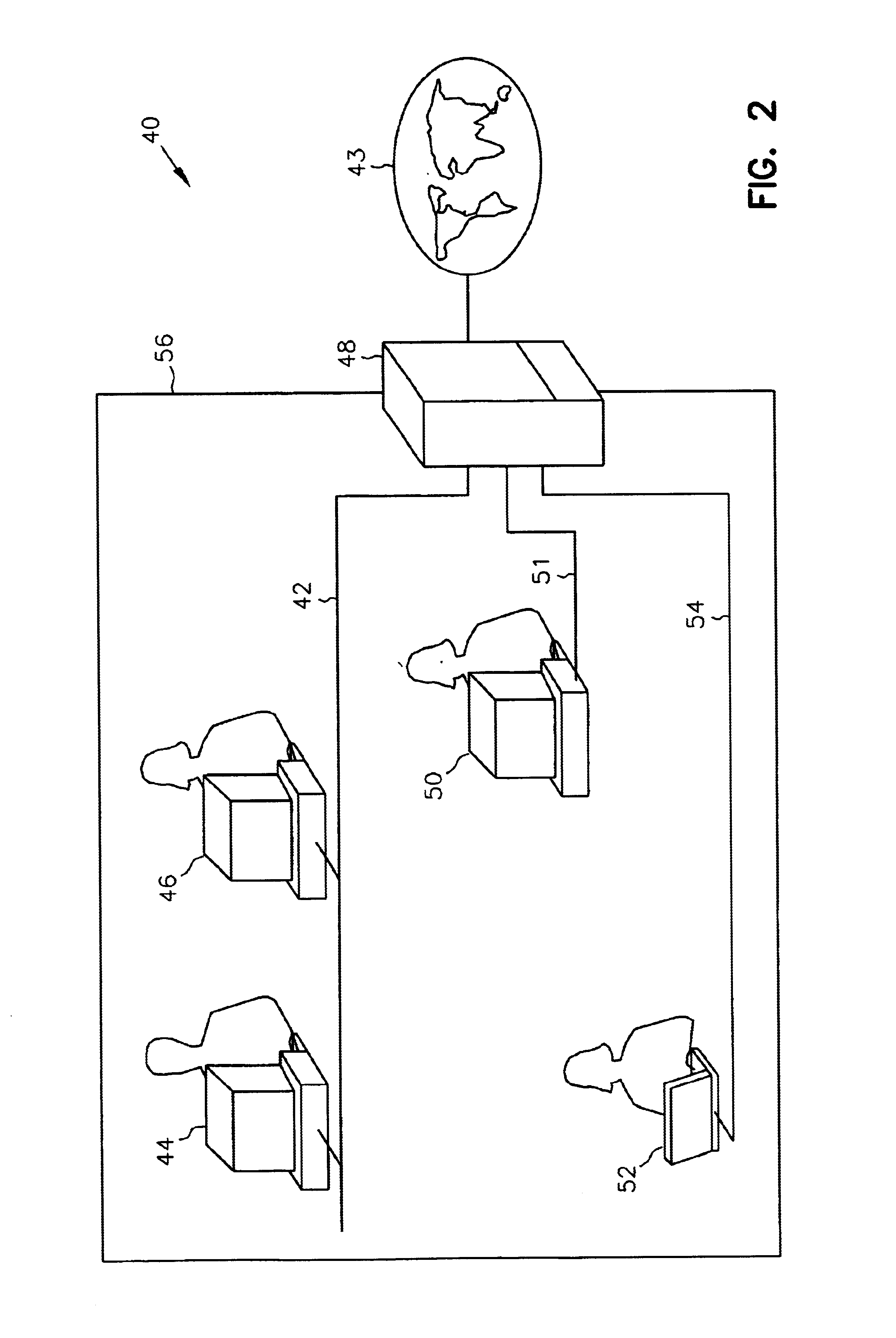
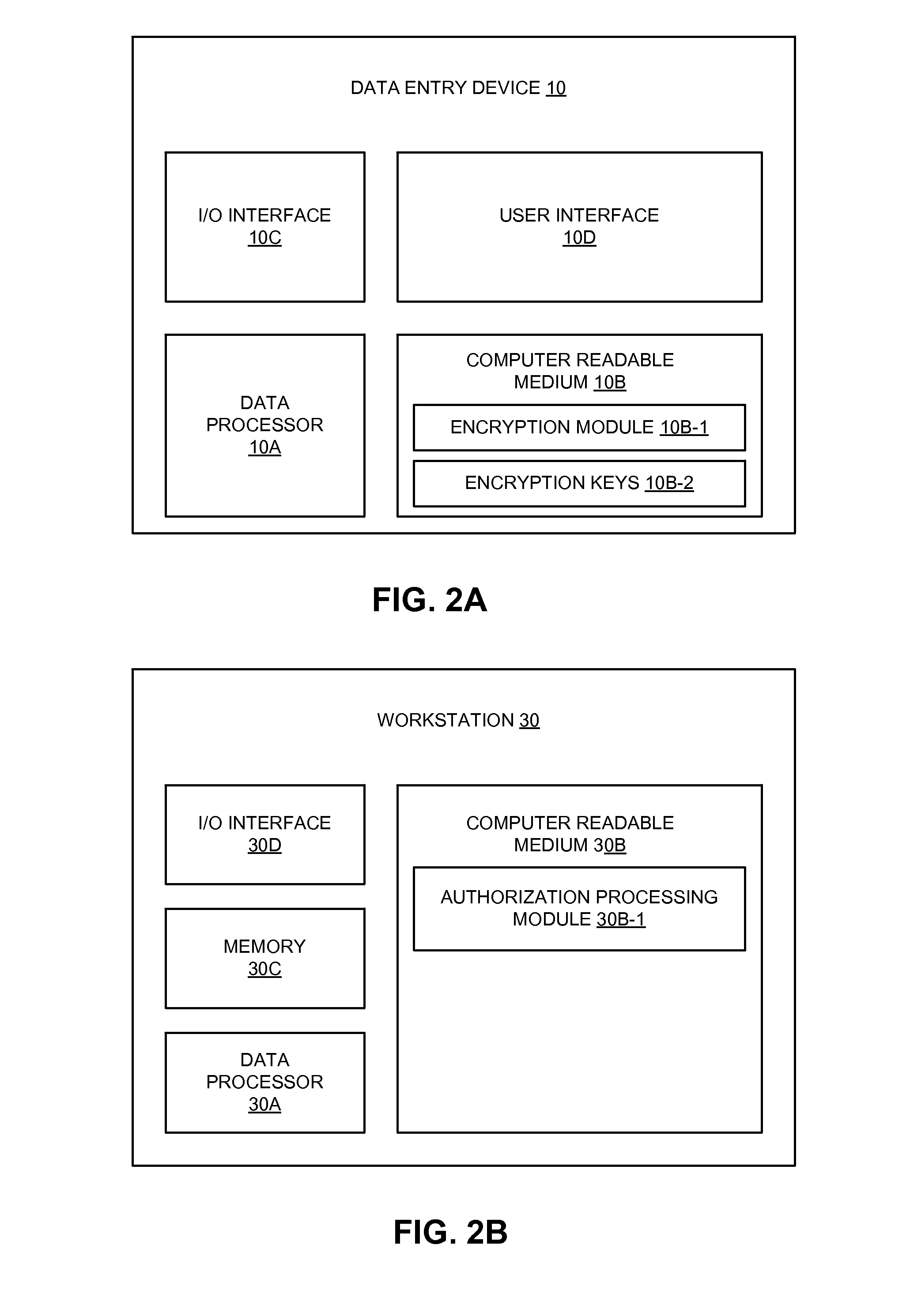
Method and apparatus for a secure computing environment
InactiveUS7260726B1Firmly connectedPortability is not issueRandom number generatorsUser identity/authority verificationUser authenticationCard reader
An apparatus to enable operation of a computer by authorized users when in a secure mode of operation is provided. One exemplary apparatus includes a hub configured to be in communication with the computer. The hub includes a card reader, a card microprocessor and an encryption engine. The apparatus also includes a card configured for insertion into the card reader. The card includes a card microprocessor. In addition, the apparatus includes a user authentication device configured to validate the user as an authorized user of the card. If the user is validated as the authorized user, then the card microprocessor passes a key to the hub microprocessor in response to the validation of the user as the authorized user of the card. The encryption engine of the hub is then activated to operate in a secure mode of operation.
Owner:RPX CORP
Projection of trustworthiness from a trusted environment to an untrusted environment
InactiveUS20050033980A1Digital data processing detailsDigital computer detailsOperational systemSafe operation
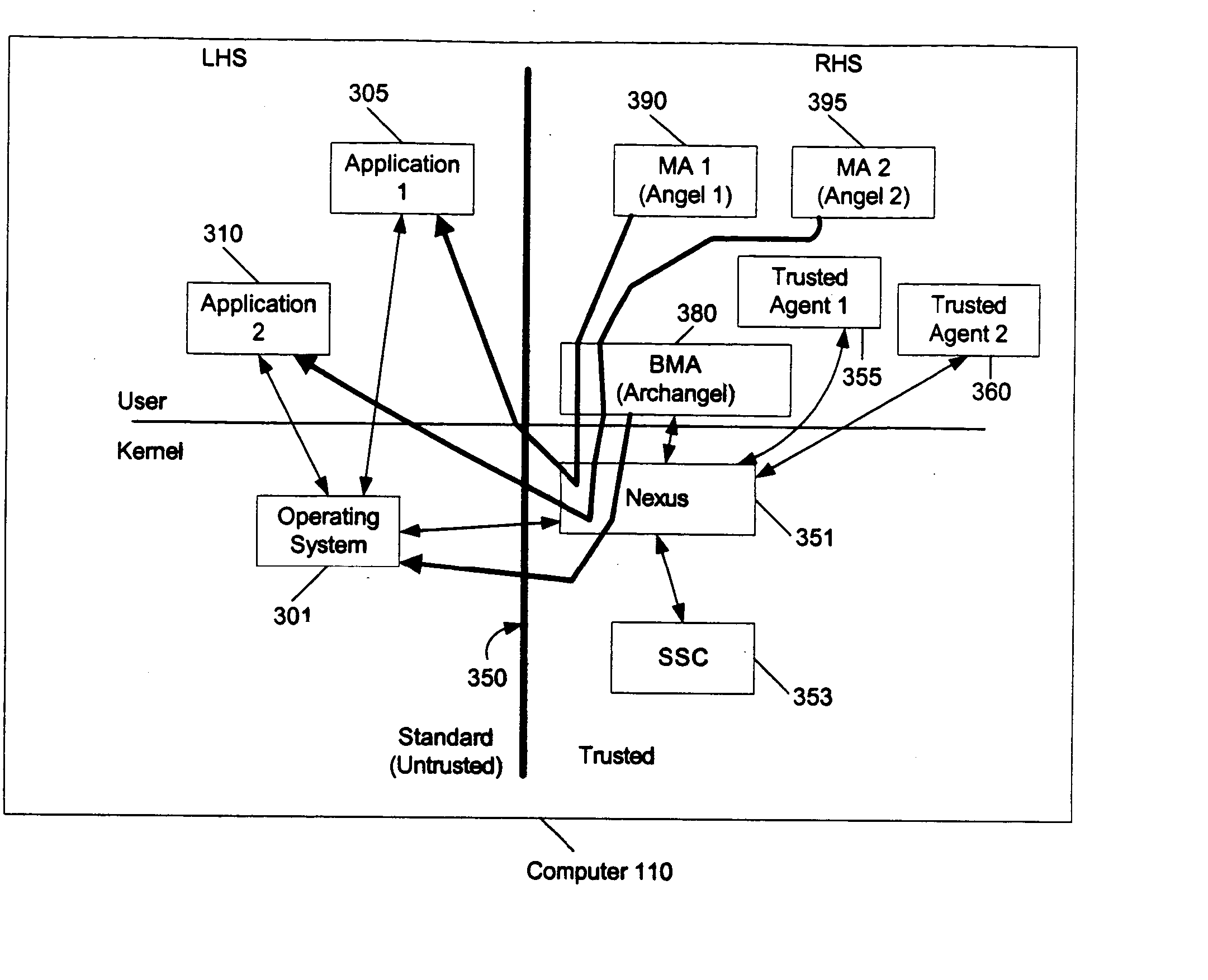
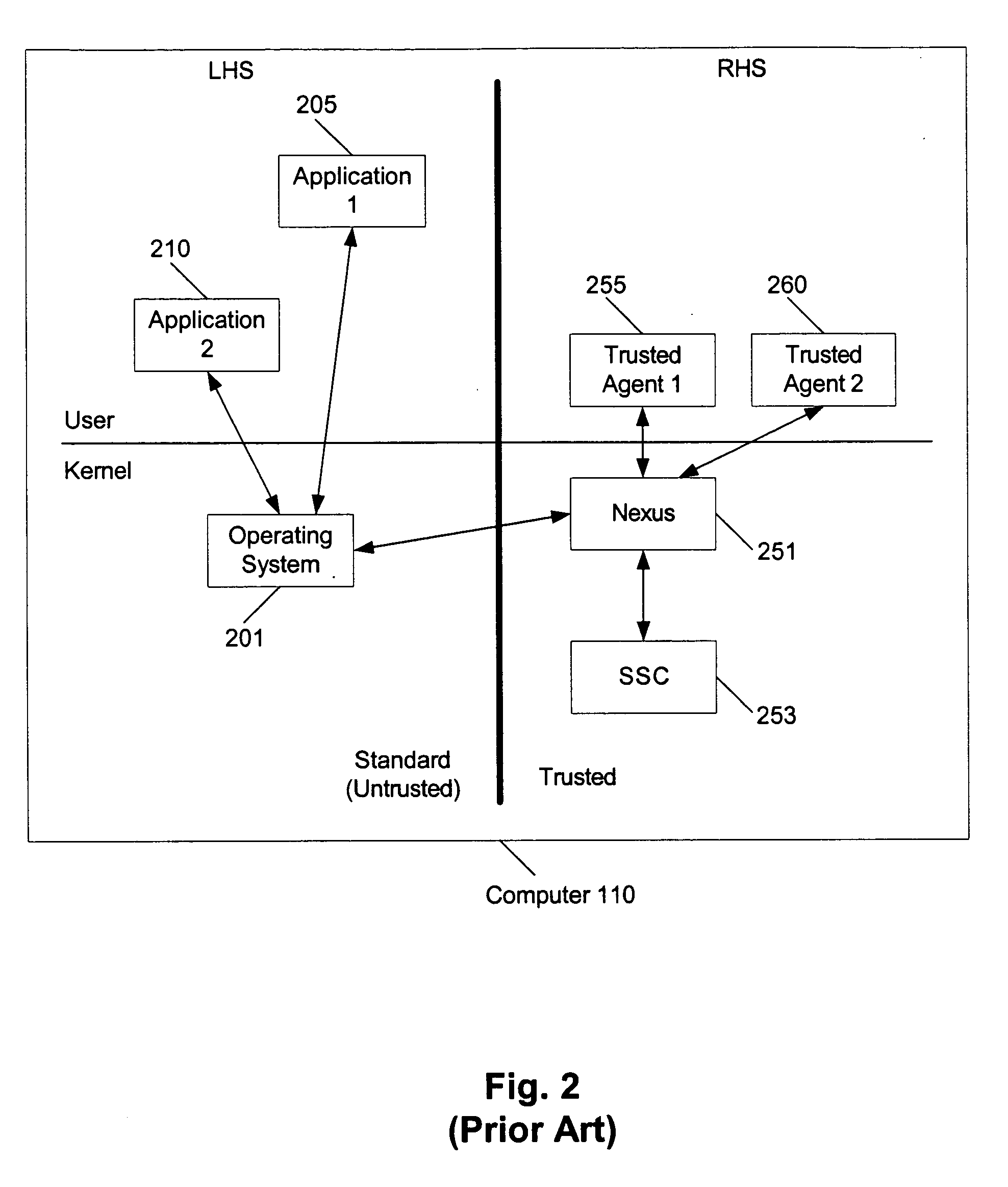
In a single machine that has entities running in an untrusted environment and entities running in a trusted environment, the trustworthiness of the entities in the trusted environment is projected to the entities in the untrusted environment. This is applicable, for example, to Microsoft®'s Next Generation Secure Computing Base (NGSCB), where a regular operating system (e.g., the Windows® operating system) hosts a secure operating system (e.g., the nexus).
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for using cryptography to protect secure and insecure computing environments
InactiveUS7243236B1Digital data processing detailsUser identity/authority verificationTamper resistanceThird party
Computation environments are protected from bogus or rogue load modules, executables, and other data elements through use of digital signatures, seals, and certificates issued by a verifying authority. A verifying authority—which may be a trusted independent third party—tests the load modules and / or other items to verify that their corresponding specifications are accurate and complete, and then digitally signs them based on a tamper resistance work factor classification. Secure computation environments with different tamper resistance work factors use different digital signature authentication techniques (e.g., different signature algorithms and / or signature verification keys), allowing one tamper resistance work factor environment to protect itself against load modules from another tamper resistance work factor environment. The verifying authority can provide an application intended for insecure environments with a credential having multiple elements covering different parts of the application. To verify the application, a trusted element can issue challenges based on different parts of the authenticated credential that the trusted element selects in an unpredictable (e.g., random) way, and deny service (or take other appropriate action) if the responses do not match the authenticated credential.
Owner:INTERTRUST TECH CORP
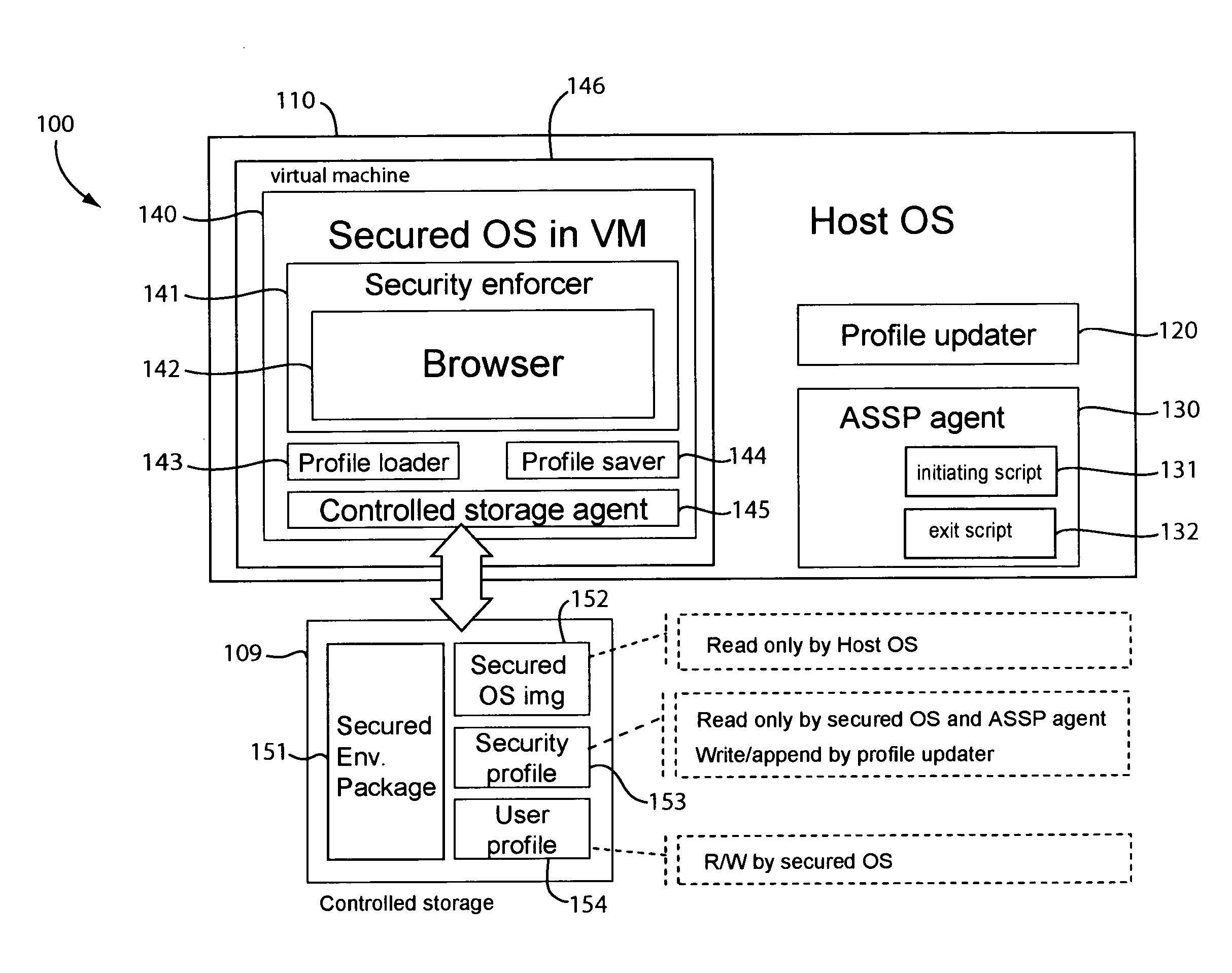
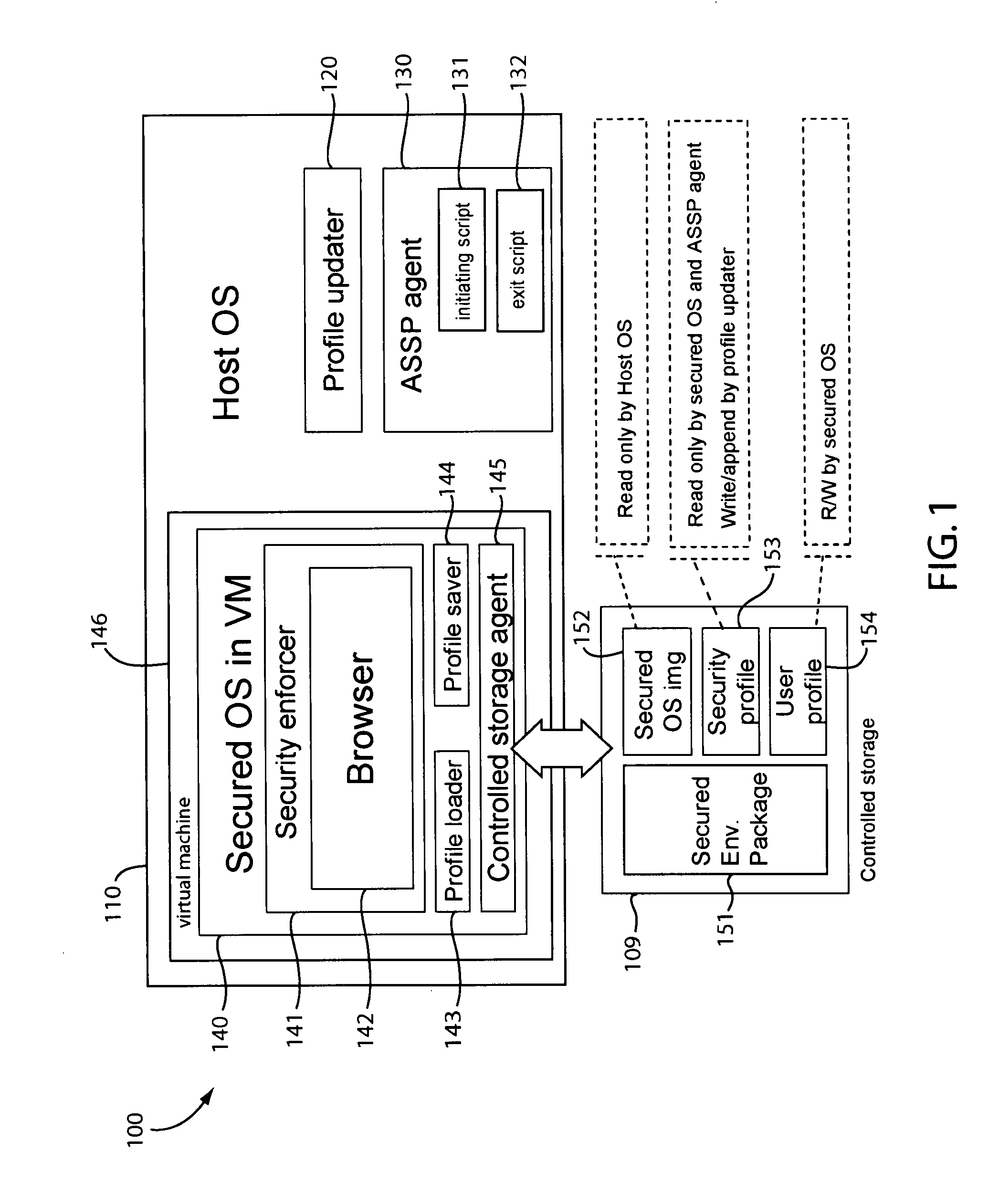
Portable secured computing environment for performing online confidential transactions in untrusted computers
ActiveUS20080256536A1Readily apparentMemory loss protectionDigital data processing detailsAccess networkOperational system
A portable secured computing environment for performing online confidential transactions in an untrusted host computer. The secured computing environment may be loaded from a portable storage device, such as a USB stick, plugged into a peripheral port of the host computer. The secured computing environment may include a virtual machine running under a host operating system of the host computer. A secured operating system may be running in the virtual machine. An online application, such as a web browser in communication with an online service, may be run under the secured operating system. Operation of the online application may be restricted by a security profile. For example, the online application may only access network addresses specifically indicated in a whitelist of the security profile.
Owner:TREND MICRO INC
Method and system for online secure patient referral system
The present invention provides a system and method, relating to the transfer of patient files over a secure, HIPAA compliant, patient file transfer and outpatient order system and a computer site therefore. The method includes obtaining and compiling a patient record pertaining to a patient; electronically inputting the patient record obtained into a secure computer database containing other patient records, allowing physician access to the patient record wherein the access includes allowing the physician to order outpatient services and send part of the patient information, including certain defined fields for a complete record and to send and receive referrals including certain defined fields for a complete record.
Owner:SCHEDULING COM
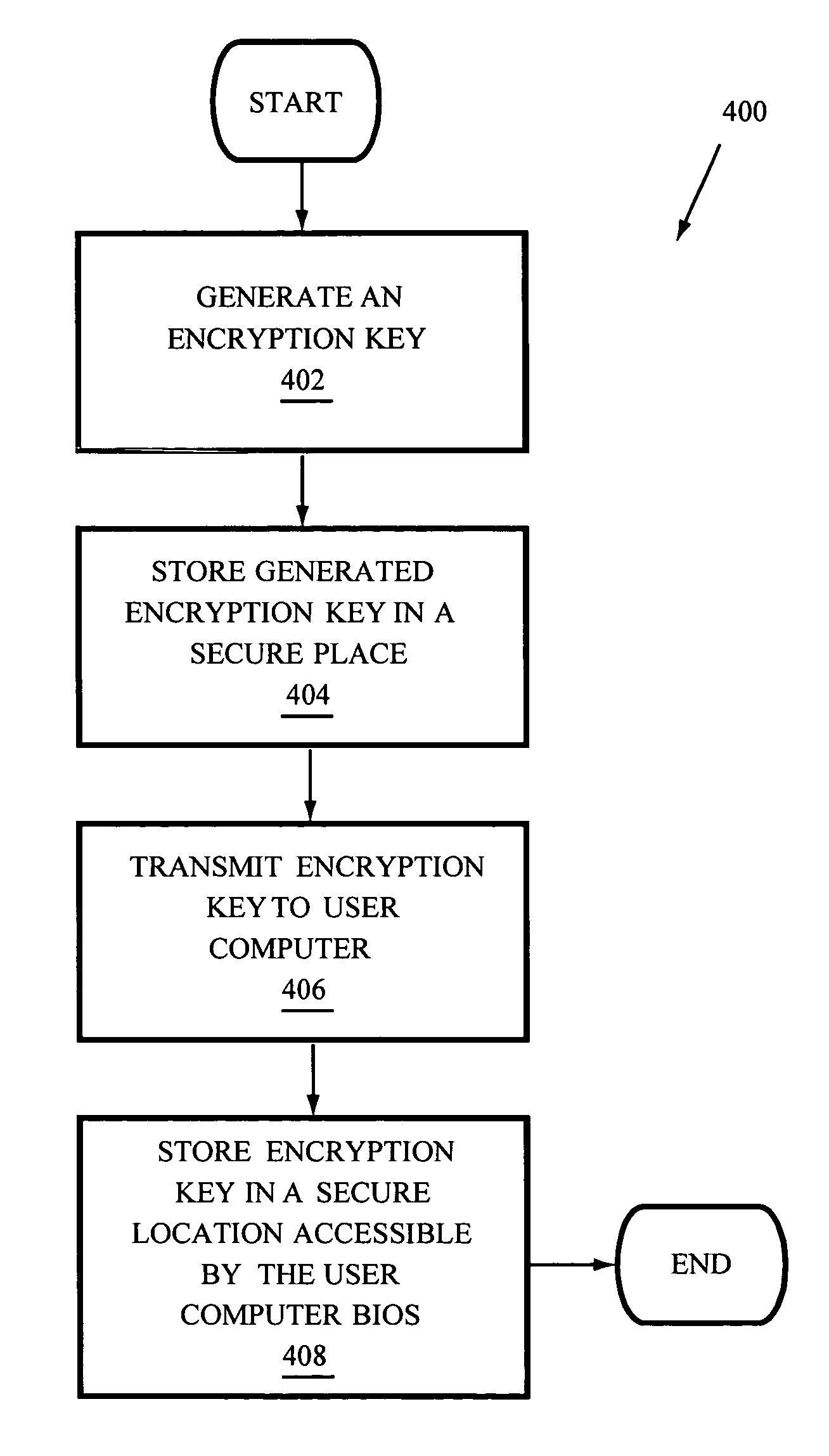
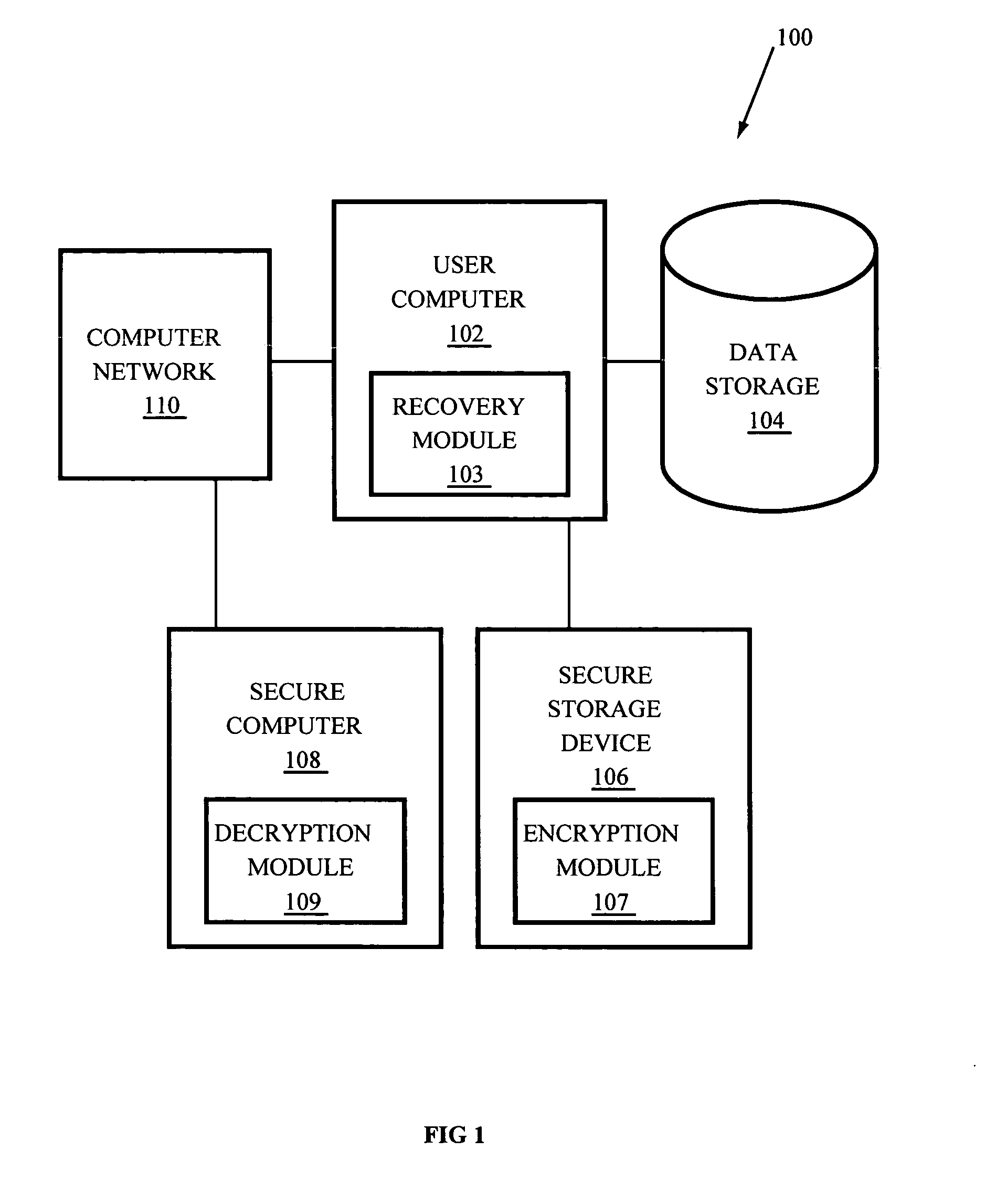
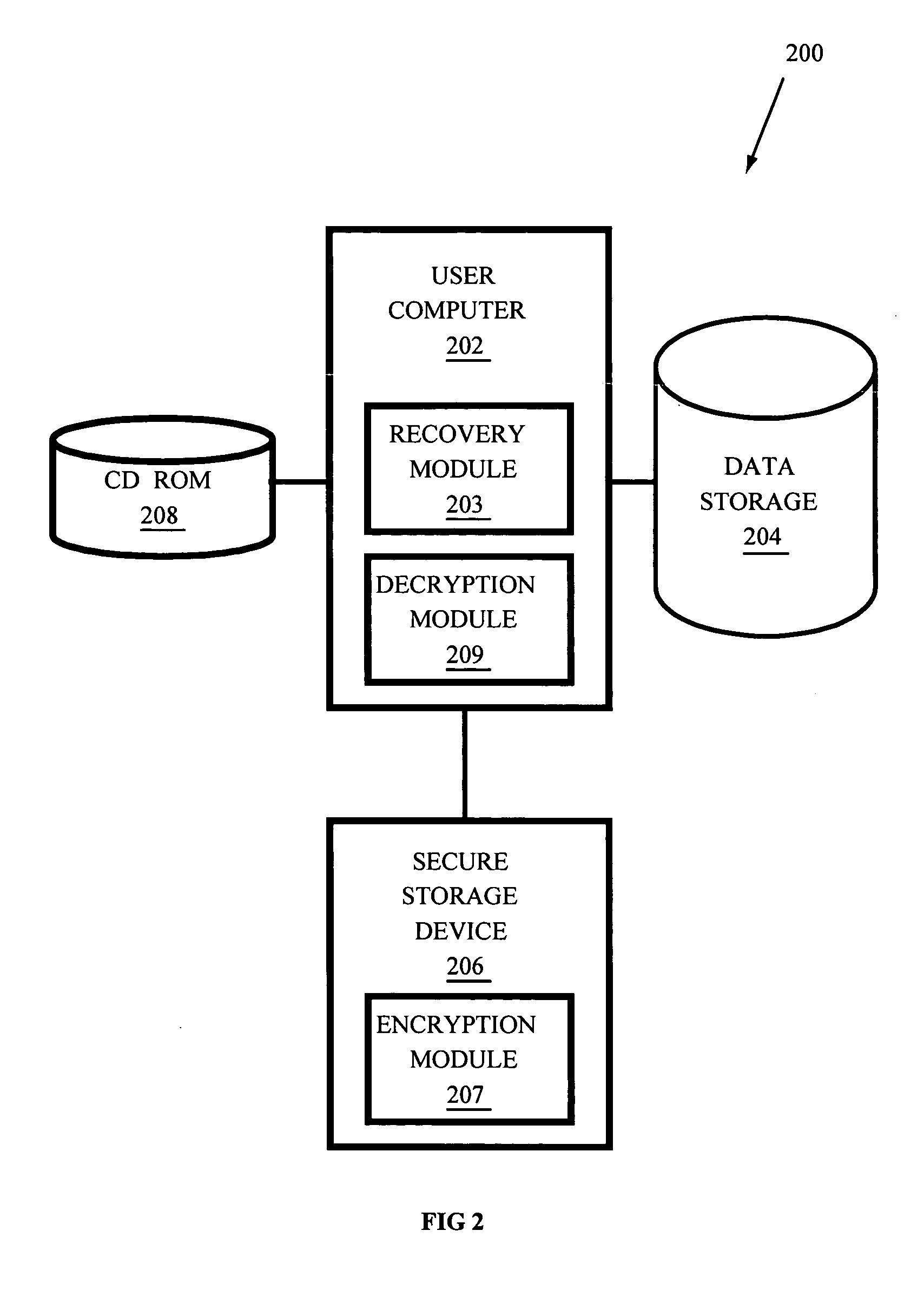
Systems and methods for recovering passwords and password-protected data
InactiveUS20060041932A1Digital data processing detailsUser identity/authority verificationHard disc drivePassword
Systems and methods to access password-protected stored data when a corresponding data password has been lost, forgotten, or is otherwise unavailable, and to recover the data password to facilitate access to the password-protected data from a digital memory device such as a hard disk drive associated with a user computer. In some embodiments the computer is communicatively coupled with a network and receives at least one encryption key from a secure computer via the network. In other embodiments the computer is a stand alone computer and receives at least one encryption key from a removable, non-volatile memory such as a CD ROM. The encryption key is used to encrypt the data password and both are stored on the hard disk drive. If the data password becomes lost, forgotten, or otherwise unavailable, the encrypted password is recovered from the hard disk drive and decrypted to recover the data password.
Owner:LENOVO (SINGAPORE) PTE LTD
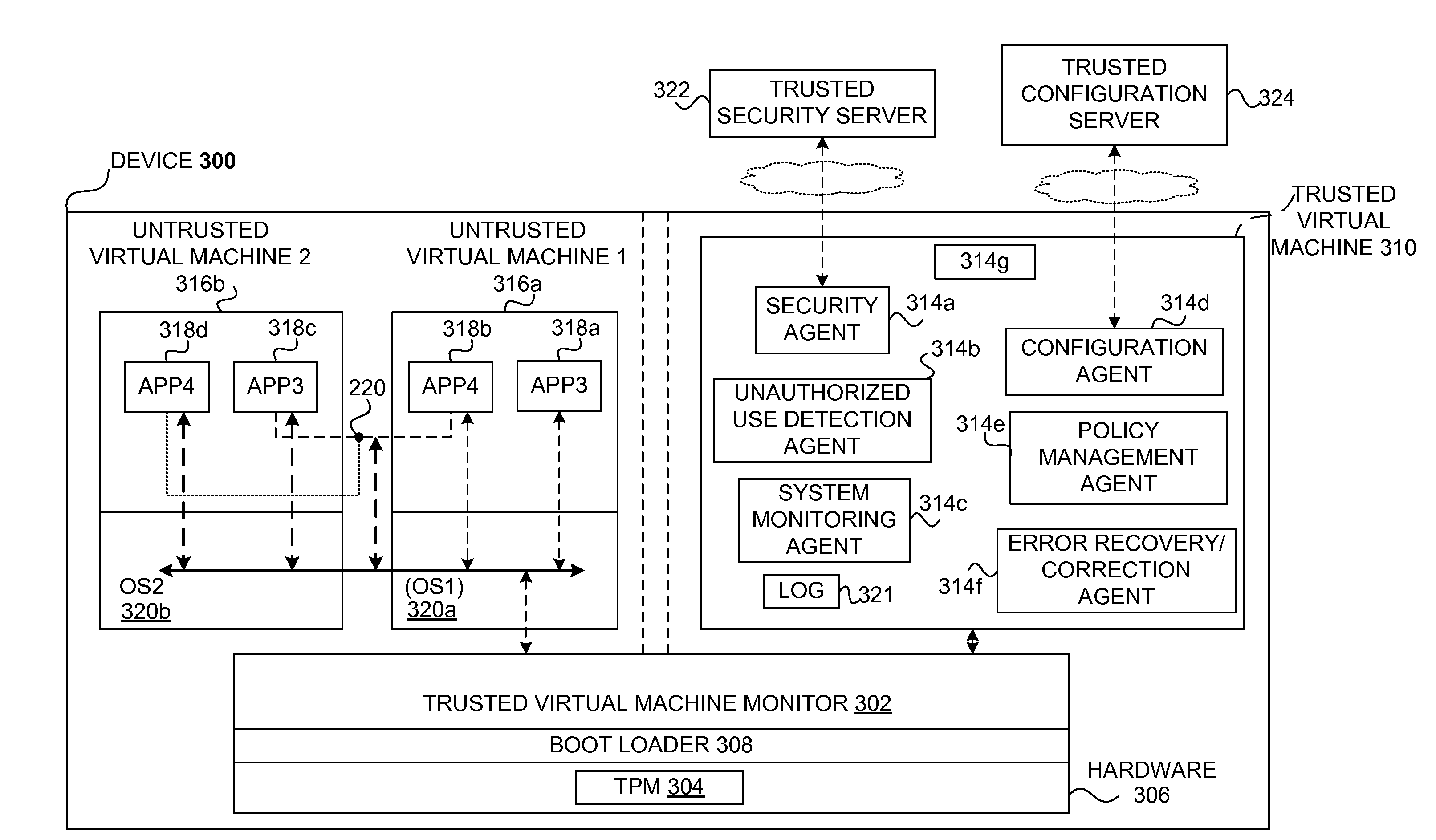
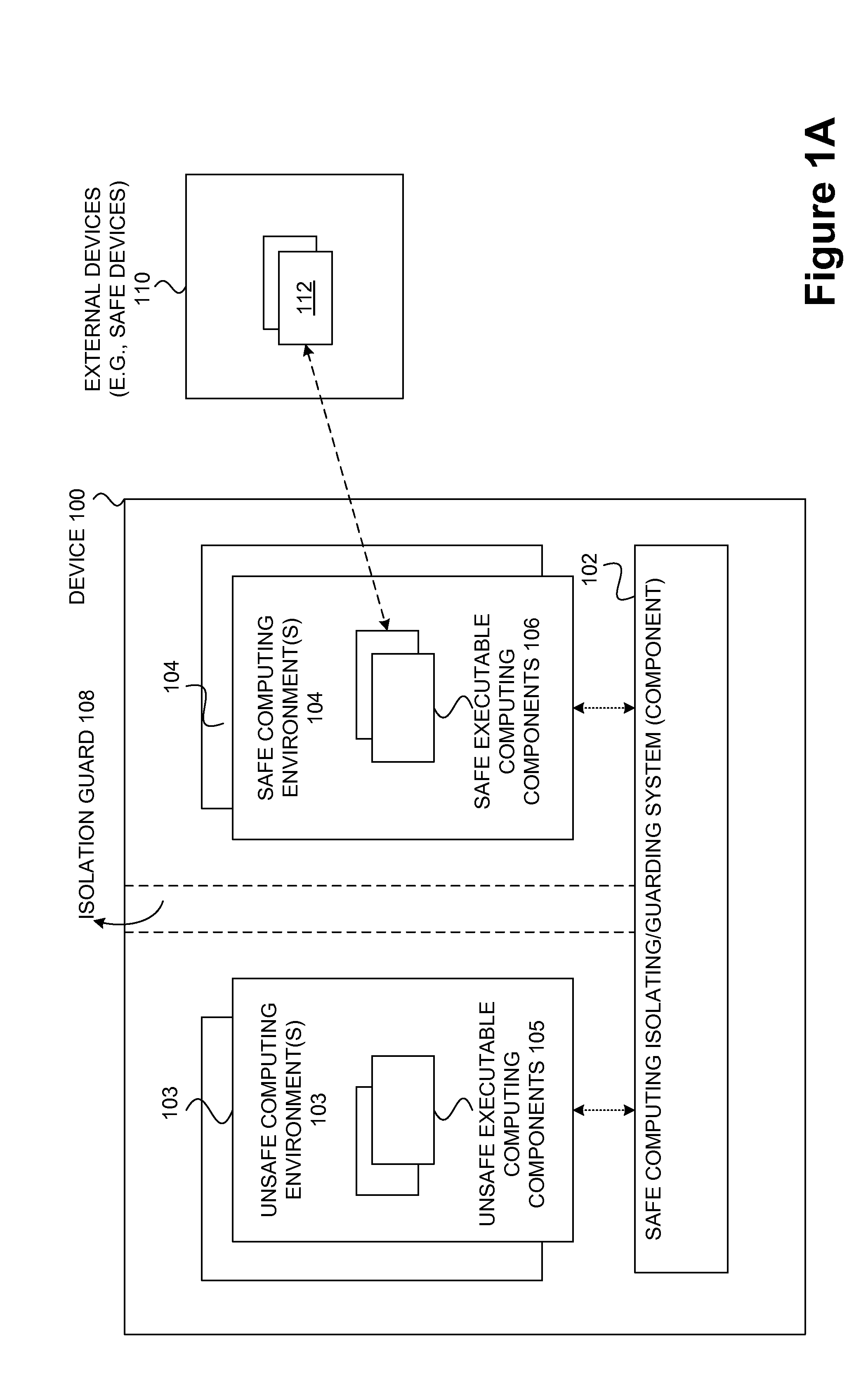
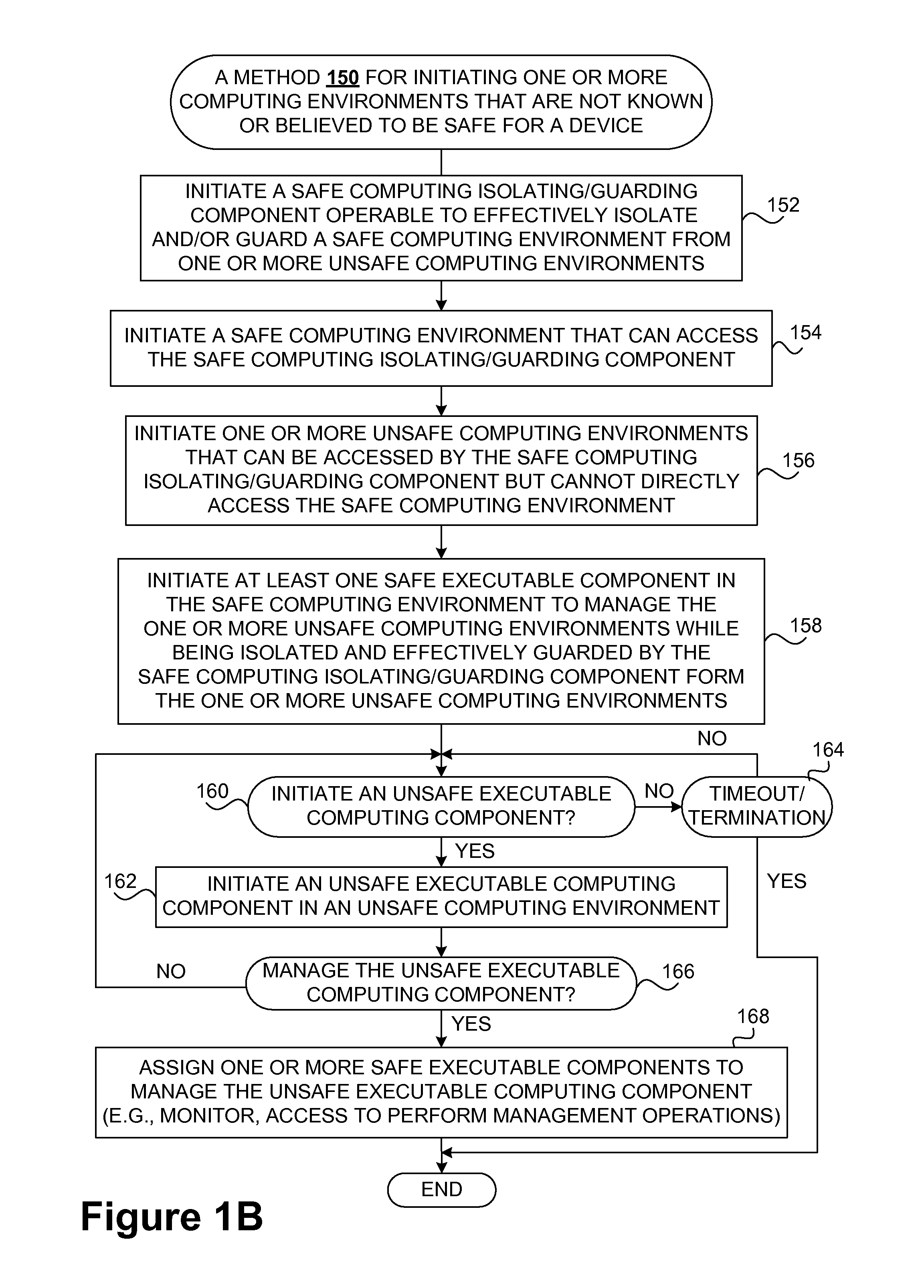
Safety and management of computing environments that may support unsafe components
InactiveUS20090265756A1Effectively guardEffective isolationMemory loss protectionError detection/correctionTrusted componentsTrusted Computing
Techniques for managing and protecting computing environments are disclosed. A safe computing environment can be provided for ensuring the safety and / or management of a device. The safe computing environment can be secured by a safe component that isolates and protects it from unsafe computing environments which may also be operating. As a result, various security and management activities can be securely performed from a safe computing environment. A safe computing environment can, for example, be provided on a device as a safe virtual computing environment (e.g., a safe virtual machine) protected by a safe virtual computing monitor (e.g., a safe virtual machine monitor) from one or more other virtual computing environments that are not known or not believed to be safe for the device. It will also be appreciated that the safe components can, for example, be provided as trusted components for a device. As such, various trusted components (or agent) can operate in a trusted computing environment secured from interference by components that many not be trusted and perform various security and / or management tasks alone or in connection, for example, with other trusted components (e.g., trusted serves).
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for user identification and authentication
InactiveUS20070192601A1Improve security levelGuaranteed growthUser identity/authority verificationDigital data authenticationSecurity validationAuthorization
A user identification and authentication device provides a secure computing platform and a secure computing path for communication with a secure remote host. The device is coupled to an unsecure PC but provides for secure verification of a user's identity and authorization in participating in a transaction.
Owner:SPAIN JOHN D R +4
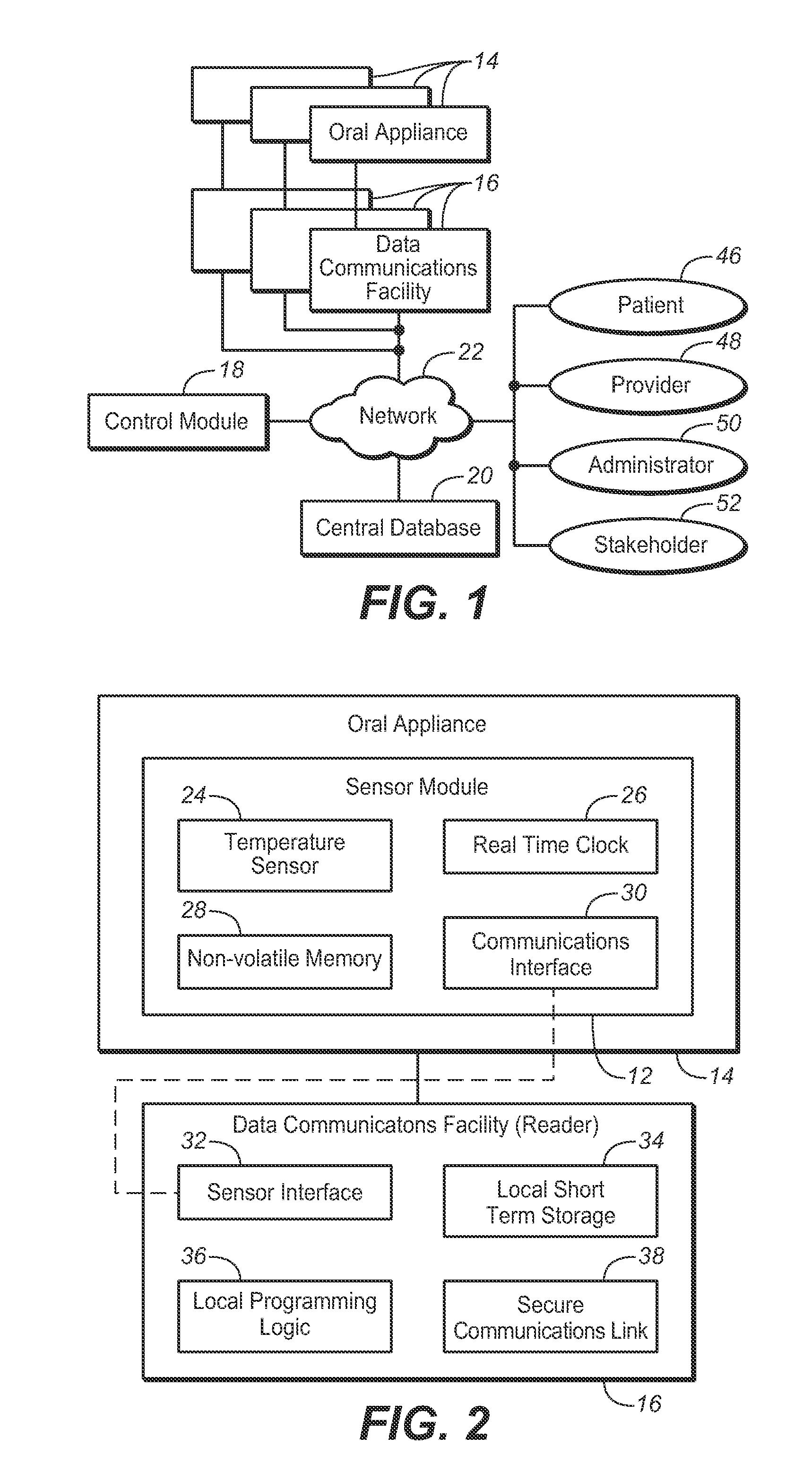
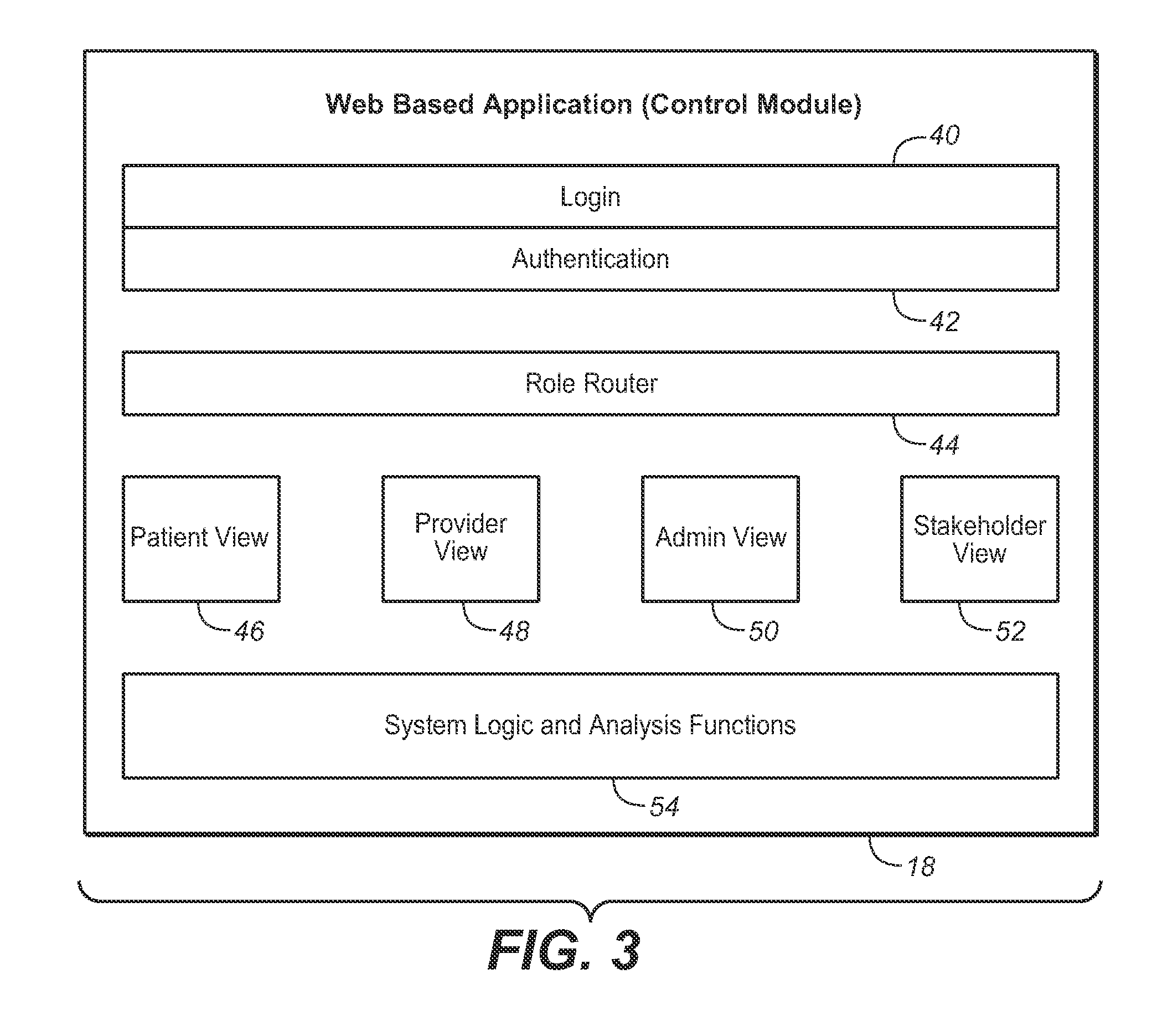
System for monitoring of and managing compliance with treatment for obstructive sleep apnea using oral appliance therapy and method therfor
InactiveUS20100312484A1Respiratory organ evaluationSensorsNetwork connectionRole-based access control
A system and method for monitoring of and managing compliance with treatment for obstructive sleep apnea using oral appliance therapy comprises a sensor module installed in an oral appliance, a data communications facility for communicating with the oral appliance, a control module, and a central database for storing data. Data stored on the sensor module is transferred to the data communications facility for local storage. The control module validates the locally stored temperature data and uploads the validated data into the central database. Temperature data stored in the central database may be viewed remotely via a secure computer network connection in graphical form by authorized users using role-based access controls. Authorized users may include the patient, the patient's provider, system administrators, and stake holders including insurance carriers providing medical coverage for OAT.
Owner:DUHAMEL JAMES B +1
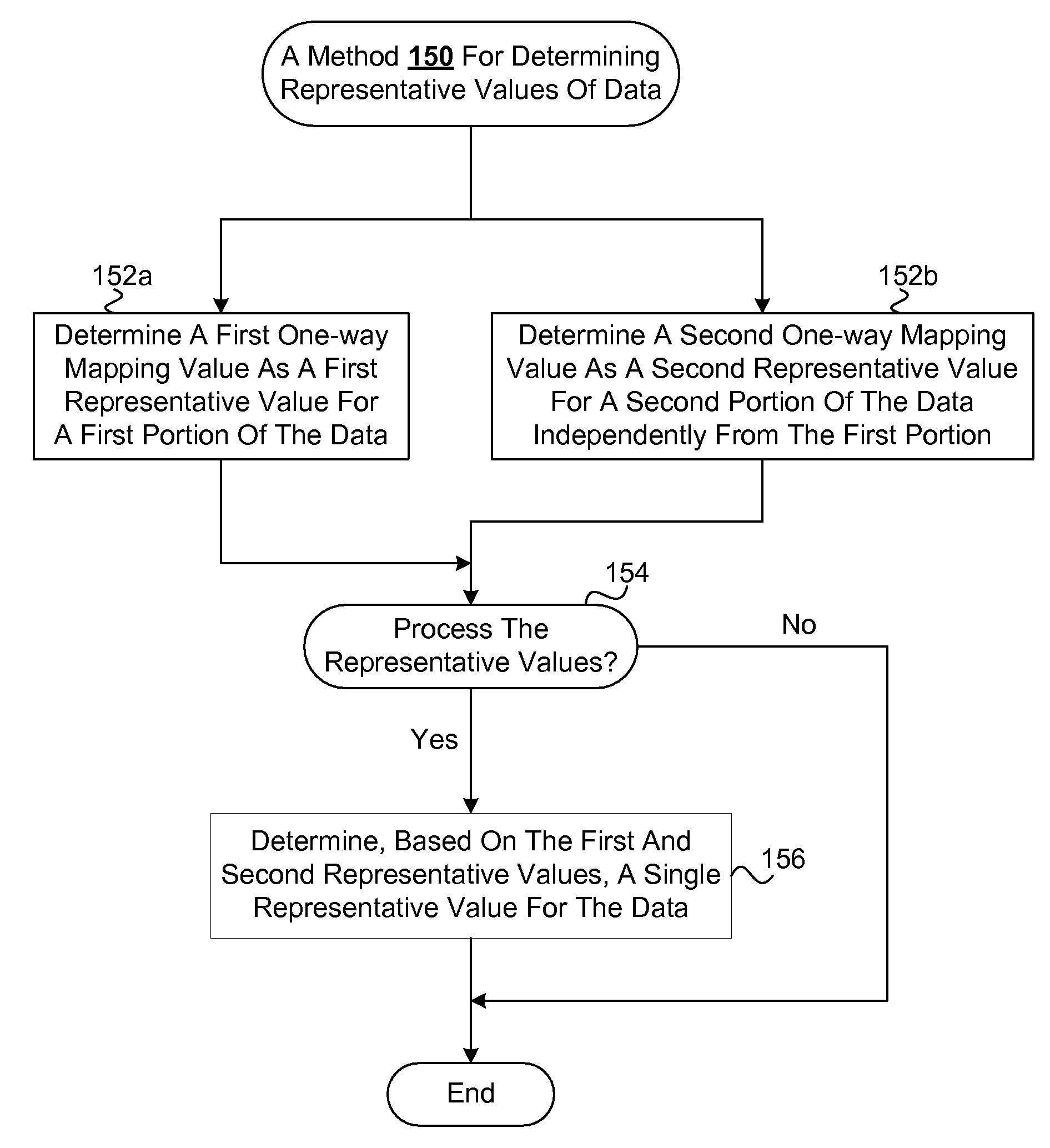
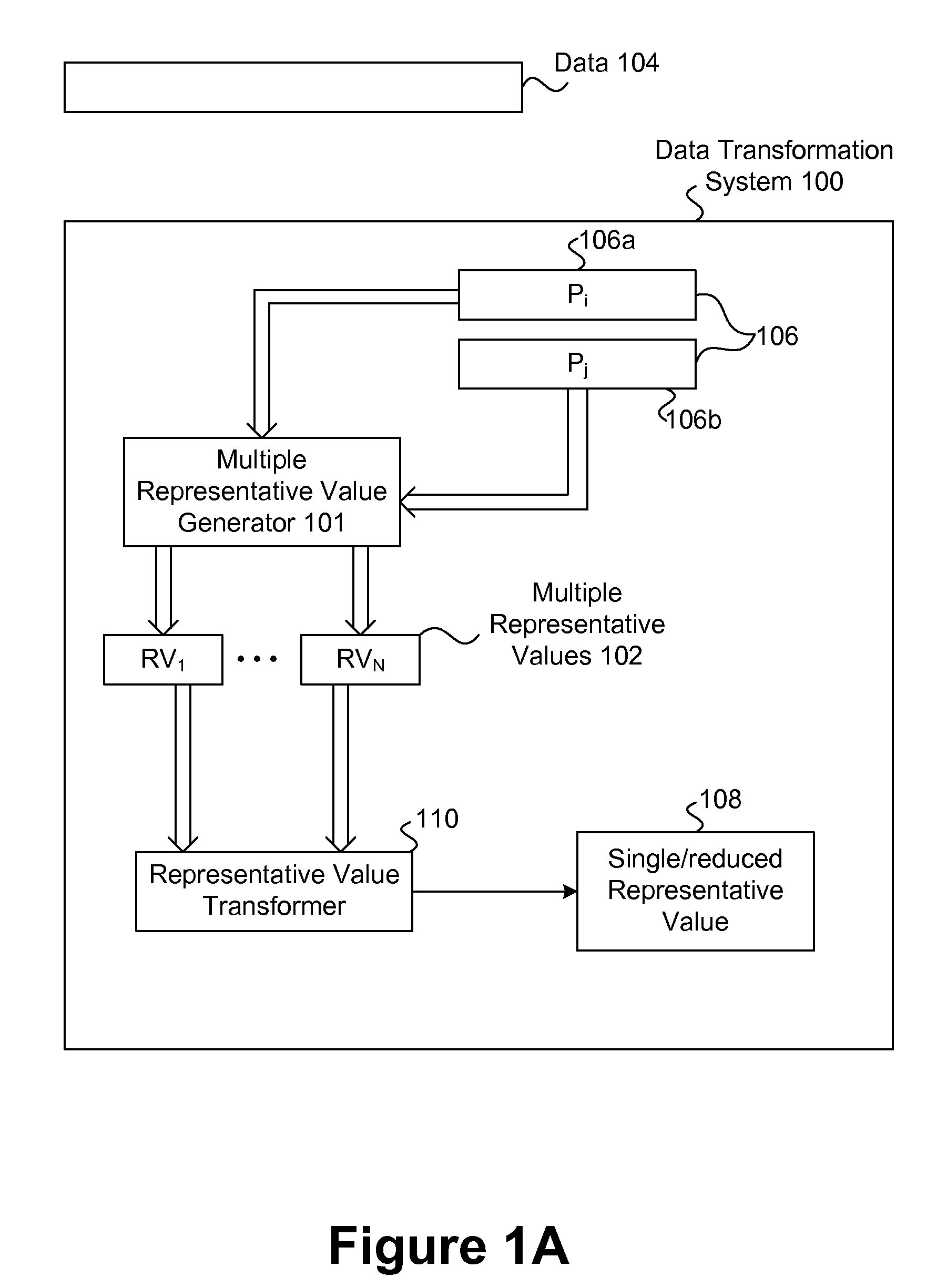
Representation and verification of data for safe computing environments and systems
InactiveUS20100106976A1Efficient verificationLess timeDigital data information retrievalUnauthorized memory use protectionDatasheetData integrity
Techniques for representation and verification of data are disclosed. The techniques are especially useful for representation and verification of the integrity of data (integrity verification) in safe computing environments and / or systems (e.g., Trusted Computing (TC) systems and / or environments). Multiple independent representative values can be determined independently and possibly in parallel for respective portions of the data. The independent representative values can, for example, be hash values determined at the same time for respective distinct portions of the data. The integrity of the data can be determined based on the multiple hash values by, for example, processing them to determine a single hash value that can serve as an integrity value. By effectively dividing the data into multiple portions in multiple processing streams and processing them in parallel to determine multiple hash values simultaneously, the time required for hashing the data can be reduced in comparison to conventional techniques that operate to determine a hash value for the data as a whole and in a single processing stream. As a result, the time required for integrity verification can be reduced, thereby allowing safe features to be extended to devices that may operate with relatively limited resources (e.g., mobile and / or embedded devices) as well as improving the general efficiency of device that are or will be using safety features (e.g., Trusted Computing (TC) device).
Owner:SAMSUNG ELECTRONICS CO LTD
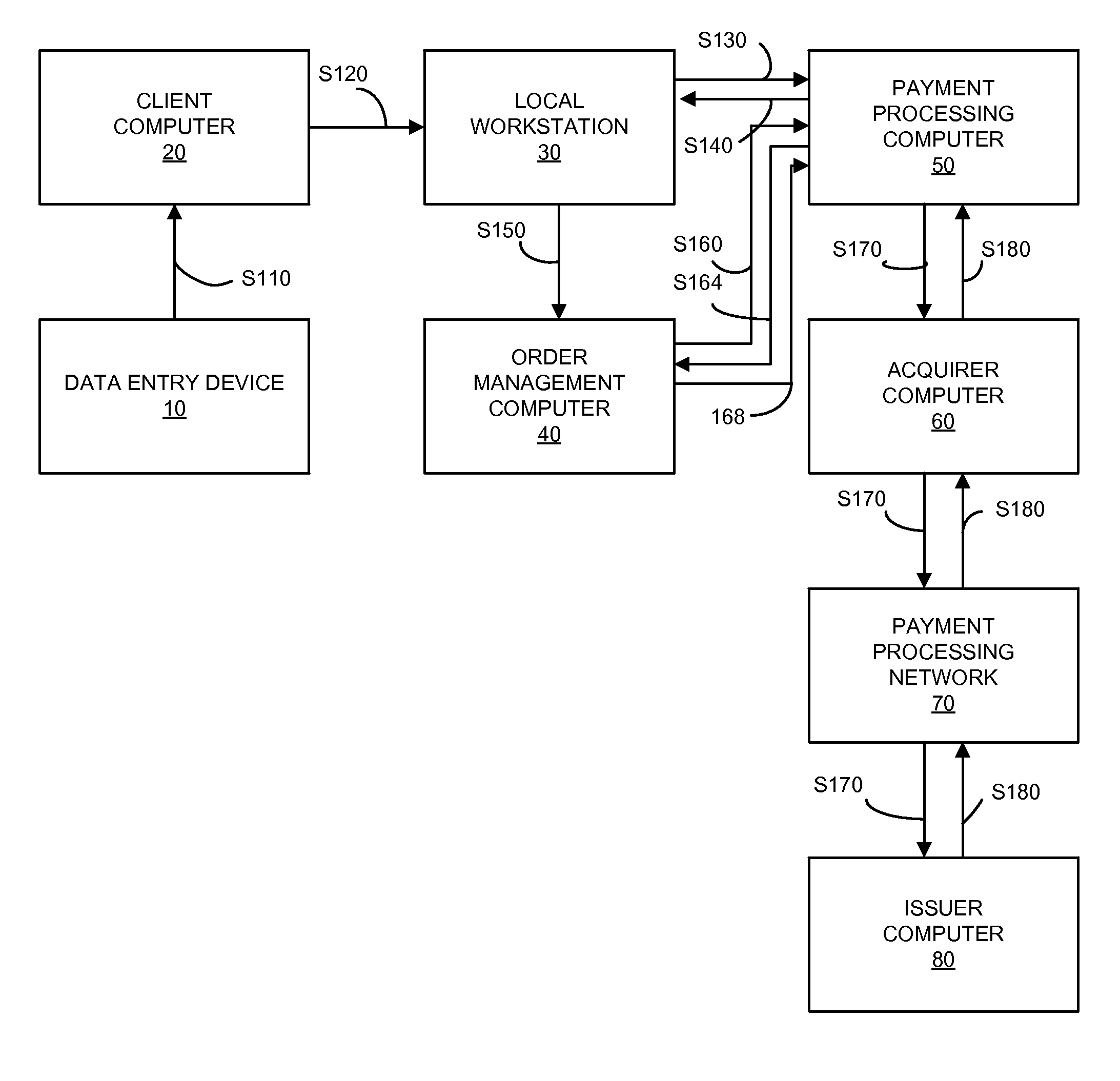
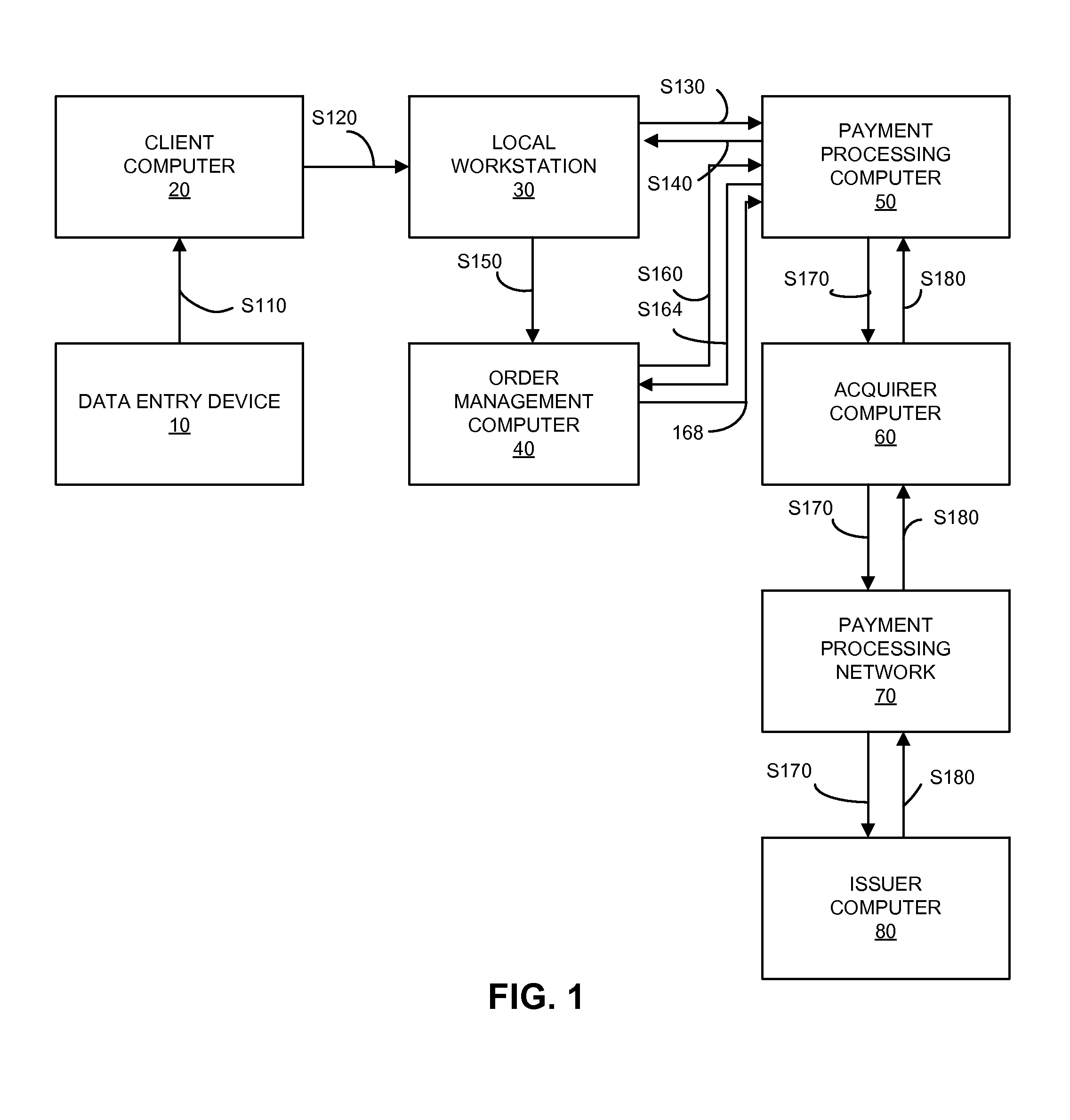
Secure payment processing using authorization request
A payment system that uses replacement account identifiers is disclosed. An encrypted primary account number (PAN) may be received by a secure computer from a data entry device. The encrypted PAN may be decrypted by the secure computer and the secure computer may transmit a zero, nominal or no dollar authorization request to an issuer. Using the zero, nominal or no dollar authorization request, the issuer may verify the account. If the account is verified, then a replacement account identifier can be issued at a later time. The replacement account identifier may be used instead of the actual PAN to conduct payment transactions.
Owner:VISA INT SERVICE ASSOC
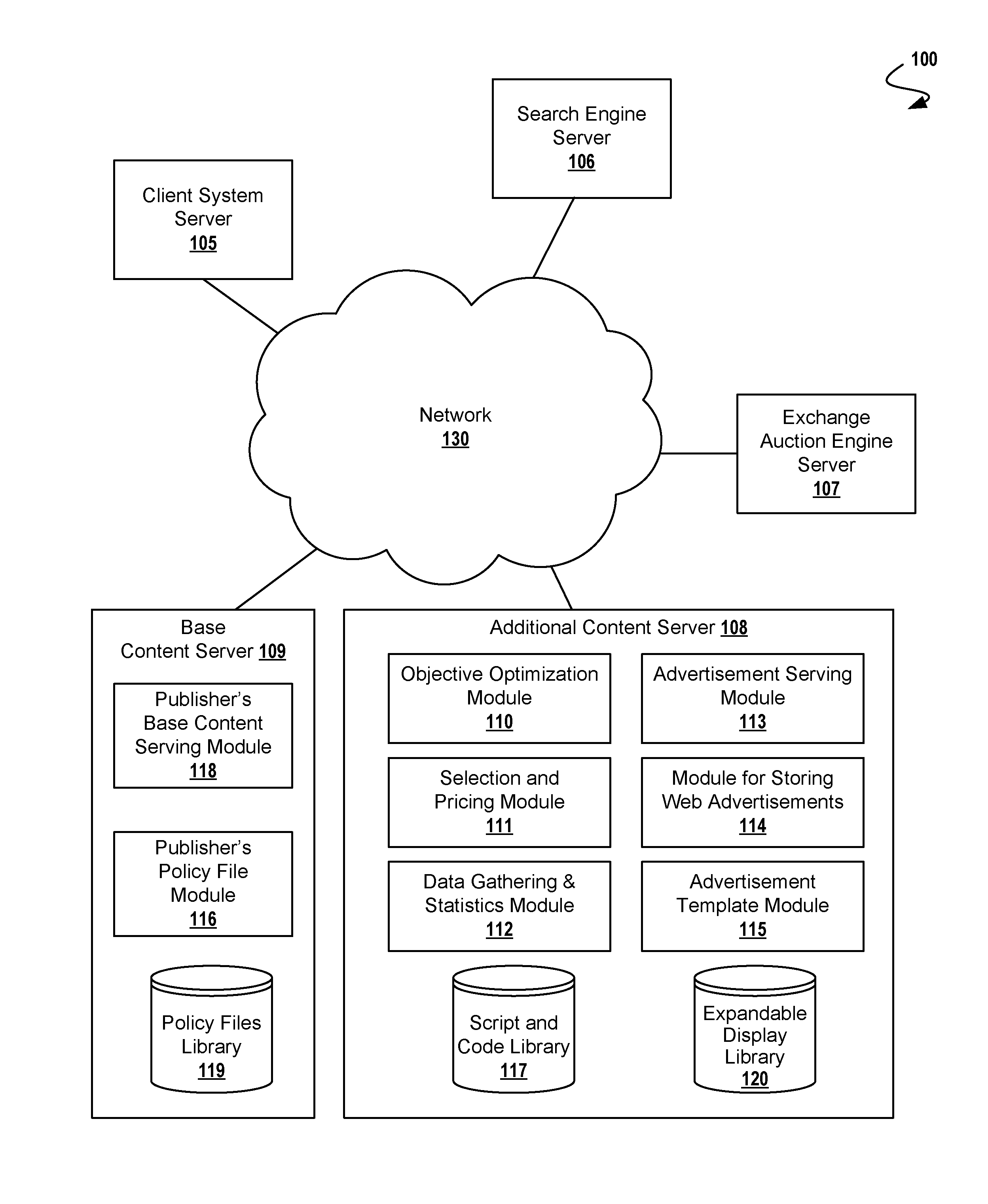
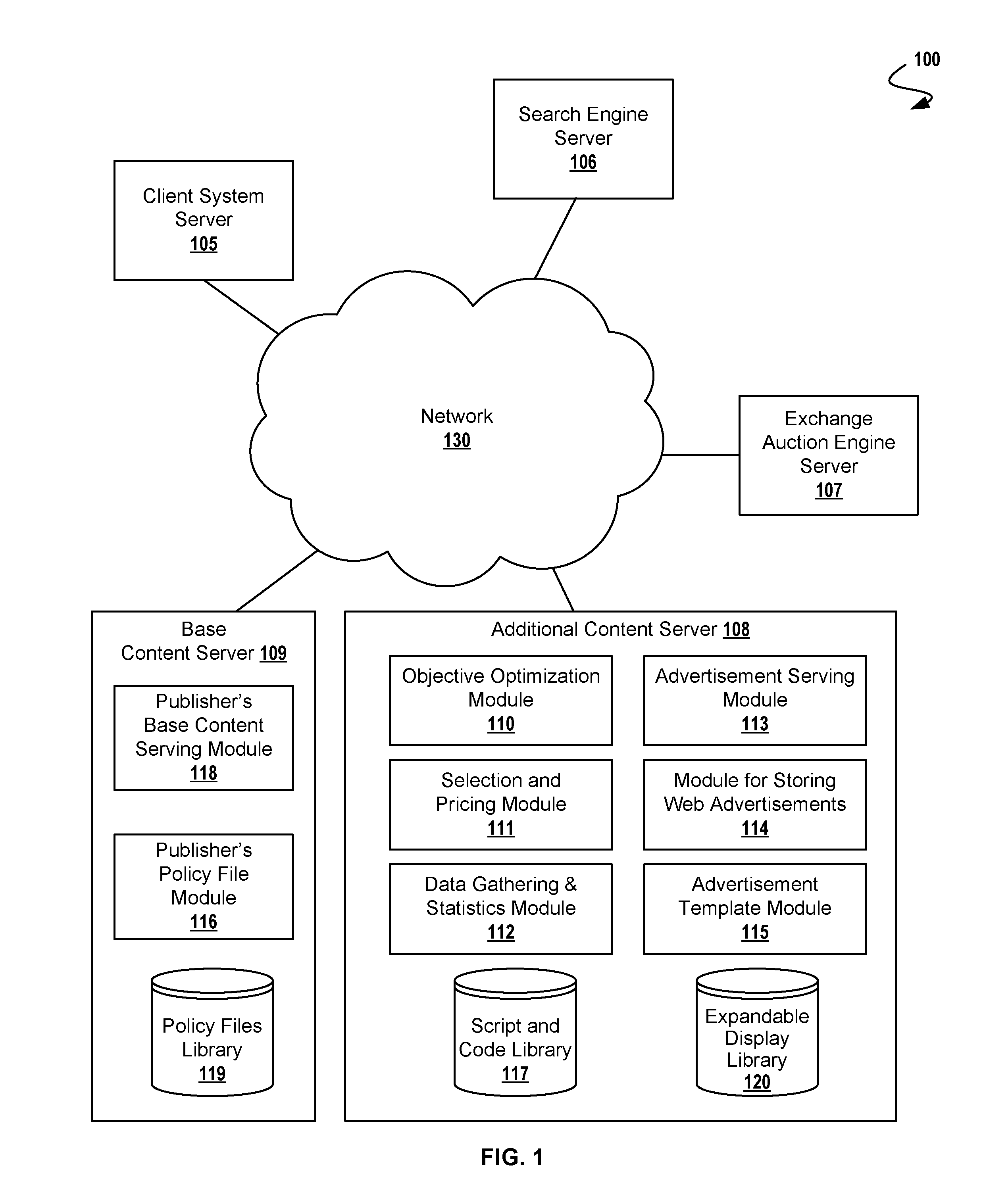
Securing Expandable Display Advertisements in a Display Advertising Environment
A method for securely presenting an HTML expandable display advertisement on a computer display, comprising: storing at a serving computer, an HTML object having an identifier associated with at least one securing computer, registering at the securing computer, the expandable display advertisement, and signaling, from a displaying computer, an expansion event for the expandable display advertisement wherein the expandable display advertisement is for display on the displaying computer. Additional operations for securely presenting an expandable display advertisement on a computer display include expanding, at the displaying computer, the expandable display advertisement; and signaling, from a displaying computer, a restoring event. Using this technique, the serving computer may be within a first domain, and the securing computer within a second domain, the second domain being different from the first domain. In some cases, a registration message received by a securing computer comprises width and height dimensions of the expandable display advertisement.
Owner:R2 SOLUTIONS
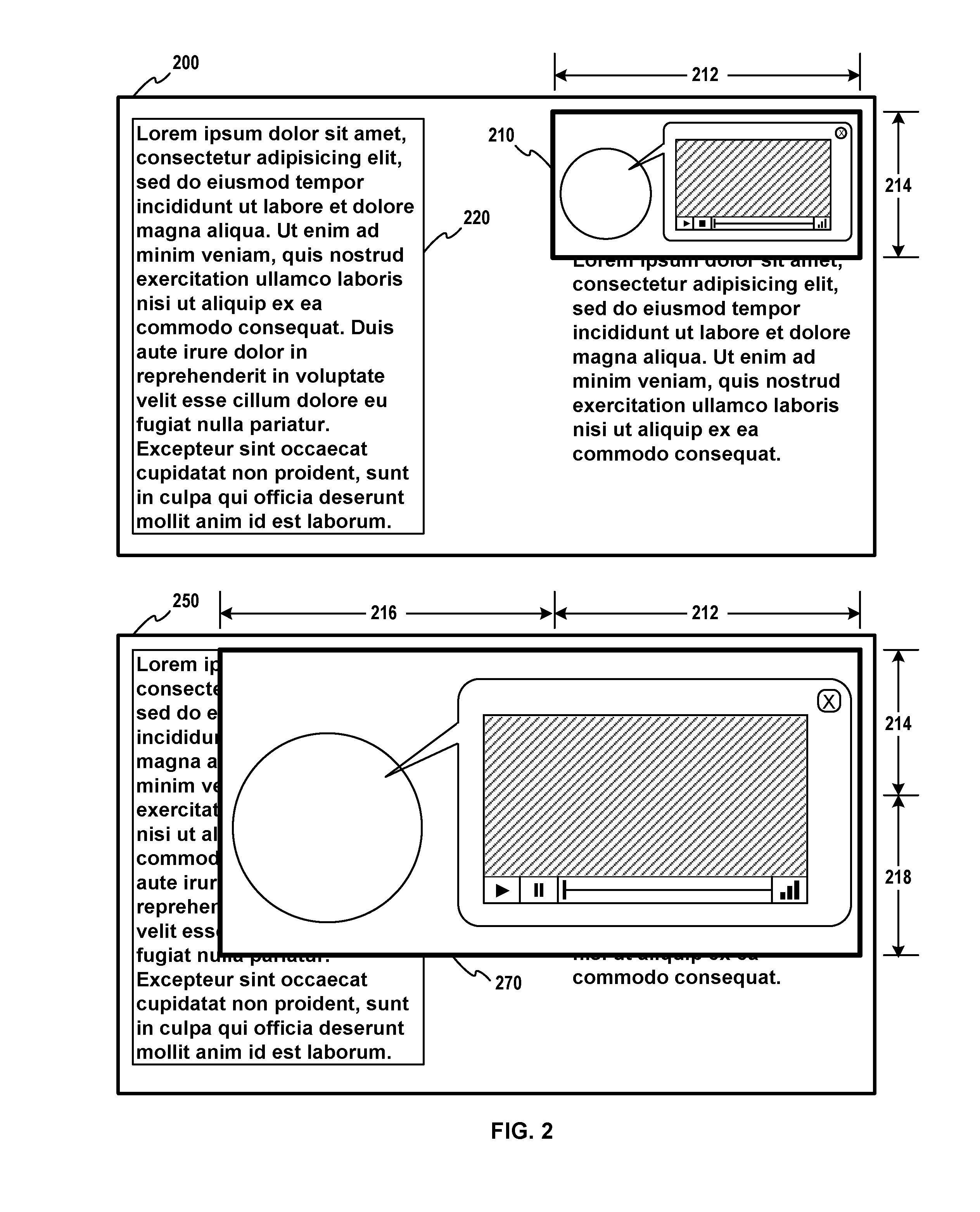
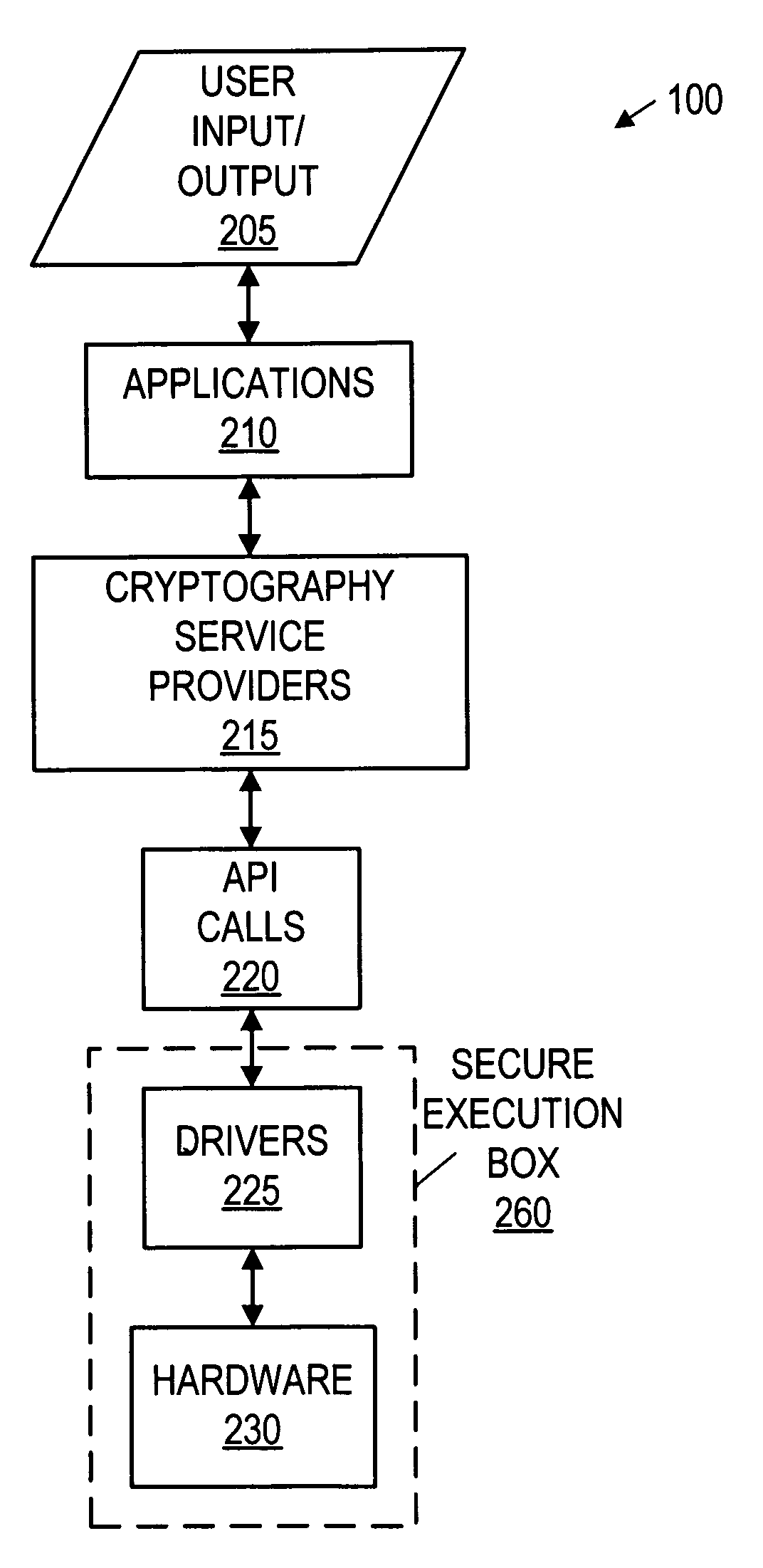
Secure execution box
A system and method for secure computing. The system includes a processor, one or more secured assets coupled to the processor, and security hardware. The processor is configured to operate in various operating modes, including a secure operating mode. The security hardware is configured to control access to the secured assets dependant upon the operating mode of the processor. The security hardware is configured to allow access to the secure assets in the secure operating mode, preferably only in the secure operating mode. The method includes switching the computer system between operating modes, while allowing or restricting access to the secured assets based on the operating modes. The second operating mode comprises a secure operating mode. The method restricts access to the secured assets in the first operating mode and permits access to the secured assets in the secure operating mode.
Owner:MEDIATEK INC
Systems and methods for performing wireless financial transactions
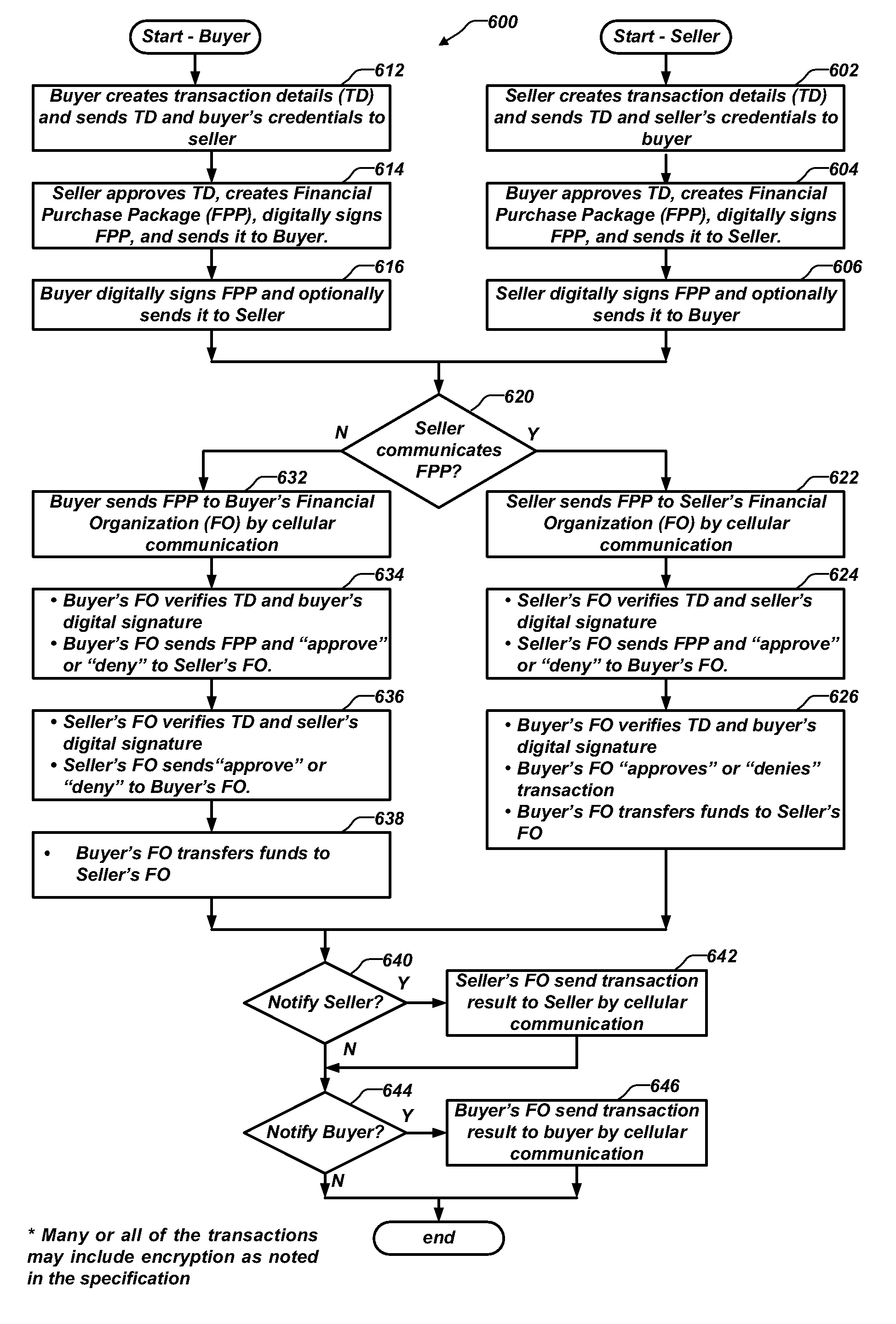
A secure computing module (SCM) is configured for connection with a host device. The SCM includes a processor for performing secure processing operations, a host interface for coupling the processor to the host device, and a memory connected to the processor wherein the processor logically isolates at least some of the memory from access by the host device. The SCM also includes a proximate-field wireless communicator connected to the processor to communicate with another SCM associated with another host device. The SCM generates a secure digital signature for a financial transaction package and communicates the package and the signature to the other SCM using the proximate-field wireless communicator. Financial transactions are performed from person to person using the secure digital signature of each person's SCM and possibly message encryption. The digital signatures and transaction details are communicated to appropriate financial organizations to authenticate the transaction parties and complete the transaction.
Owner:BATTELLE ENERGY ALLIANCE LLC
System for secure computing using defense-in-depth architecture
ActiveUS7428754B2Key distribution for secure communicationUnauthorized memory use protectionPrivate networkCombined use
Owner:MITRE SPORTS INT LTD
Multifunction data port providing an interface between a digital network and electronics in residential or commercial structures
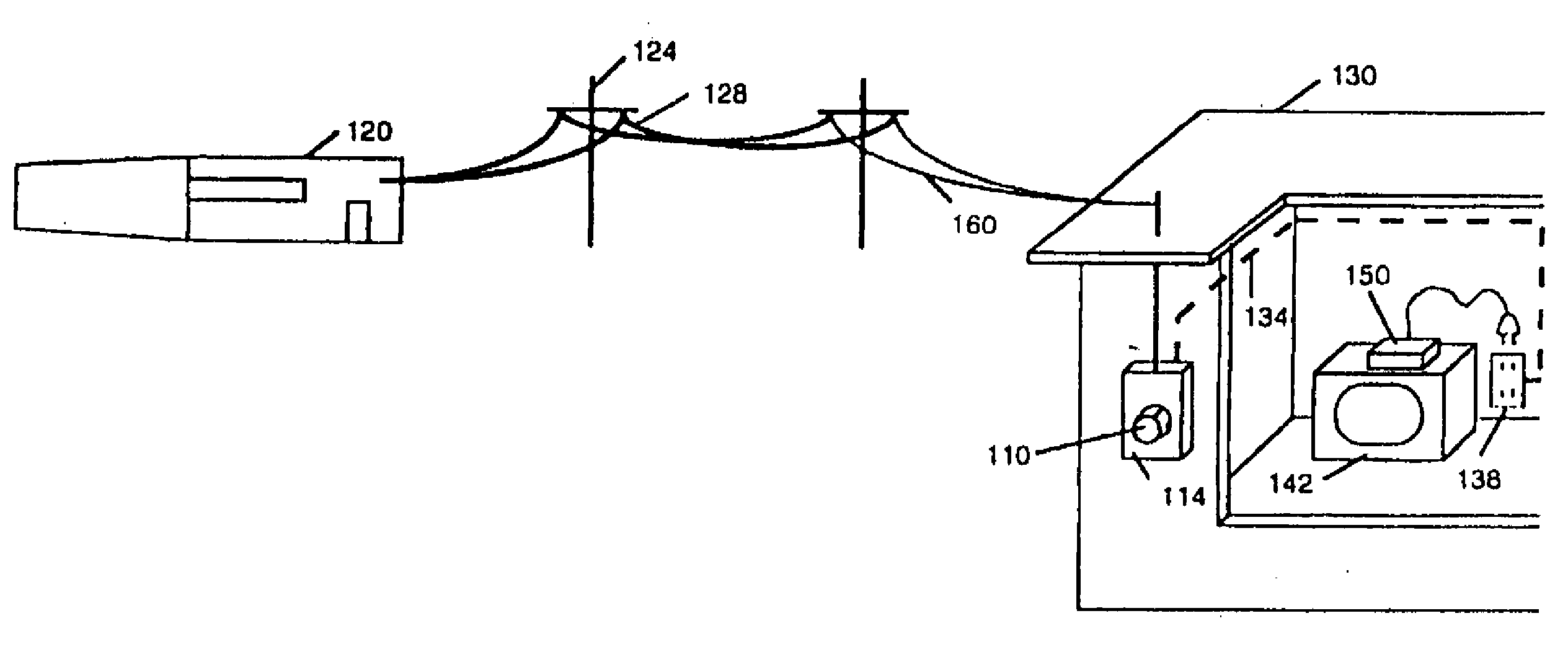
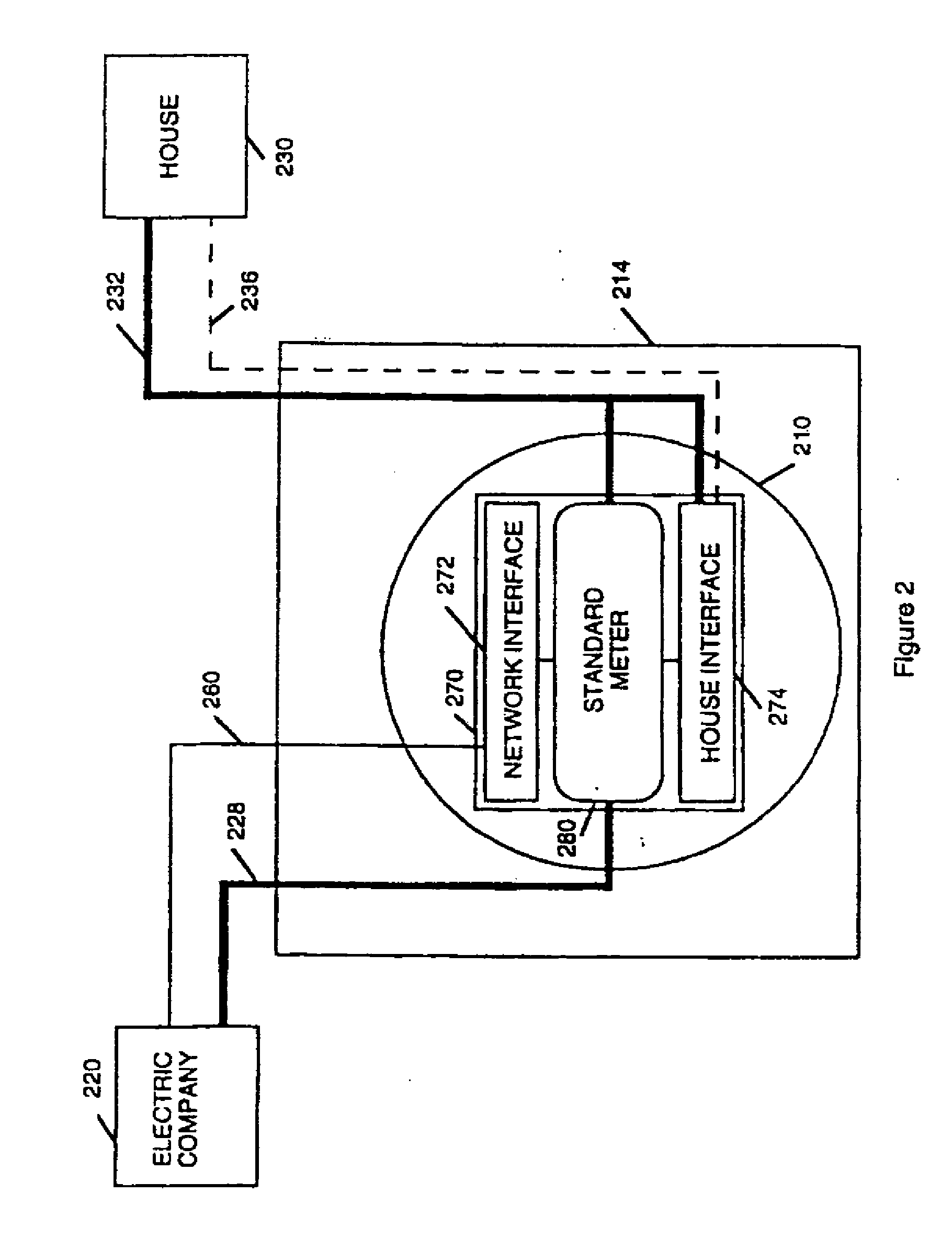
InactiveUS20090102680A1Electric signal transmission systemsTariff metering apparatusData portThe Internet
A multifunction data port is located in or attached to the utility meter or the meter box. The installation or removal of the data port requires opening the meter seal. The data port interface can provide broad band access to a digital network and the Internet. It can provide the utility customer with a secure computer terminal for commerce and telecommunications. It can provide the electric utility load management and time of use metering of electrical power.
Owner:BOH TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com