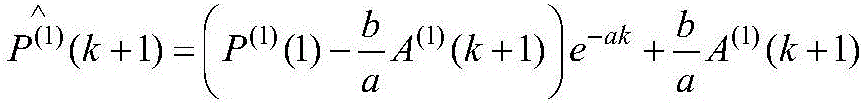Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
184 results about "Online security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Online Security. The internet offers access to a world of products and services, entertainment and information. At the same time, it creates opportunities for scammers, hackers, and identity thieves.
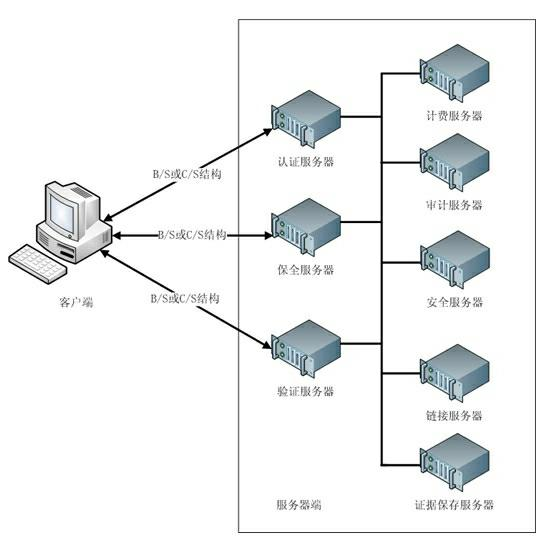
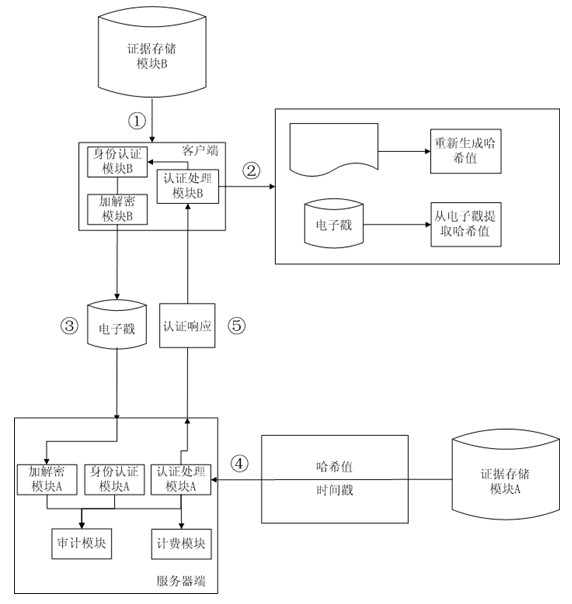
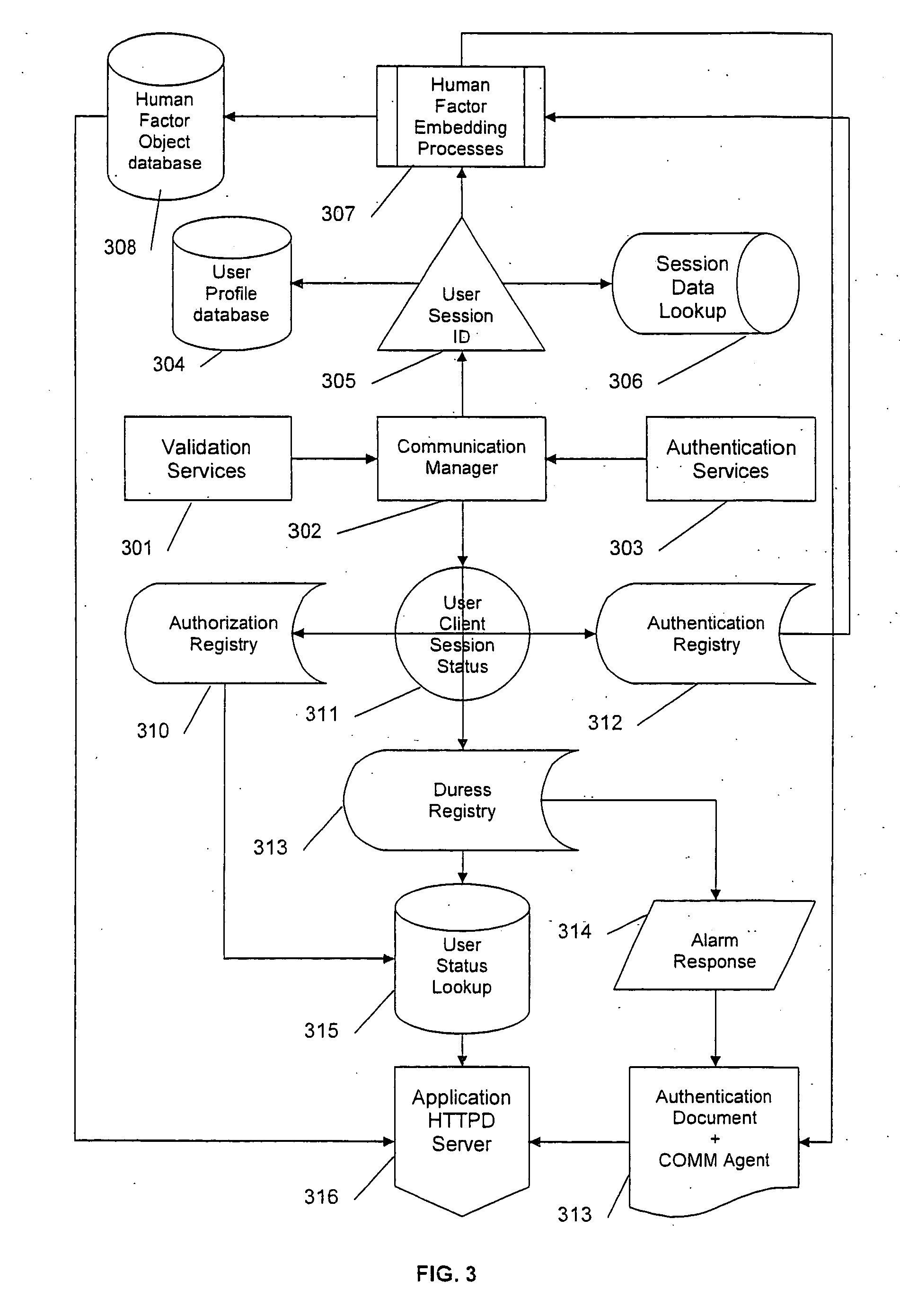
Third-party authentication security protection system and third-party authentication security protection method based on online security protection of electronic evidence
InactiveCN102223374AGuaranteed to be objective and trueGuaranteed reasonablenessUser identity/authority verificationThird partyInformation processing
The invention discloses a third-party authentication security protection system and a third-party authentication security protection method based on the online security protection of an electronic evidence and relates to an information processing technology of a computer. The method comprises the following steps that: after sending a security protection request to a server side, a client side generates a Hash value associated with electronic data which is subjected to security protection and transmits the Hash value to the server side for storage; the client side sends an authentication security protection request, and the server side compares a client side Hash value which is stored in the system with the Hash value which is transmitted by the client side to judge whether the security protection behaviors of the client side are objective and real; communication between the client side and the server side is encrypted by using a secure cryptographic algorithm; the server side carries out association processing on all Hash values in the system to ensure that the Hash value which is stored in the server side and associated with the electronic data cannot be falsified; and when the used cryptographic algorithm is decoded, the client side applies for updating of security protection, and carries out security protection processing on data to be required for security protection and result data generated by the last security protection application again so as to ensure the continuous security of the system.
Owner:重庆兴际云大数据科技有限公司
Method and system for online secure patient referral system
The present invention provides a system and method, relating to the transfer of patient files over a secure, HIPAA compliant, patient file transfer and outpatient order system and a computer site therefore. The method includes obtaining and compiling a patient record pertaining to a patient; electronically inputting the patient record obtained into a secure computer database containing other patient records, allowing physician access to the patient record wherein the access includes allowing the physician to order outpatient services and send part of the patient information, including certain defined fields for a complete record and to send and receive referrals including certain defined fields for a complete record.
Owner:SCHEDULING COM
Method and system for online security trading
ActiveCN101789934ASolve the replay attack problemPrevent replay attacksKey distribution for secure communicationFinanceProtection systemOnline security
The invention discloses a method and a system for online security trading, wherein the method for the online security trading comprises the following steps that: intelligent key equipment and a server verify the validities of each other by mutually exchanging authentication information; after both sides are verified be valid by each other, the server integrates the operational data of the user into a signature command, and transfers the signature command and signature information to the intelligent key equipment by a client; after the intelligent key equipment verifies the validity of the signature information, the intelligent key equipment executes the signature command and returns the signature result to the server; and the server processes the operational data of the user according to the signature result. By the mutual authentication of the server and the intelligent key equipment and operations such as verification on the data in a session, the system can effectively judge whether the received data are valid and further prevent the replay attach of the hackers and protect the security operation of the system.
Owner:FEITIAN TECHNOLOGIES
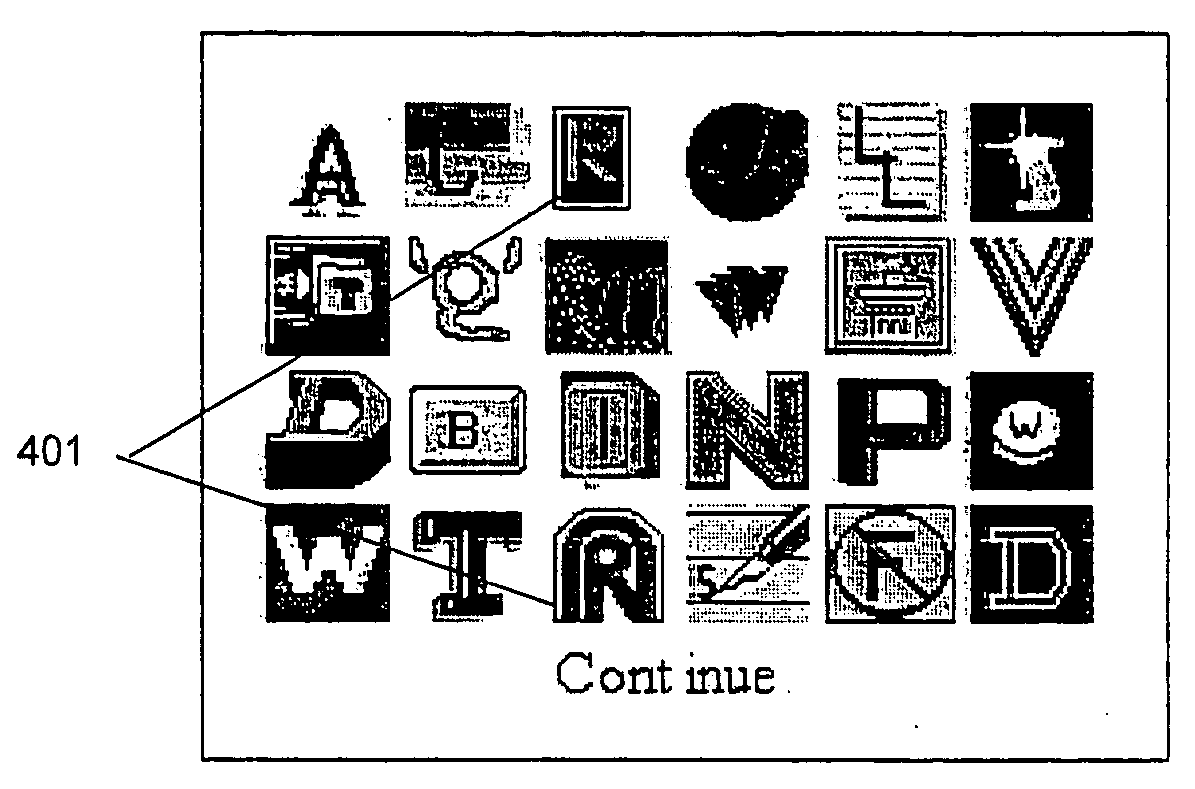
Human-factors authentication
InactiveUS20070130618A1Digital data processing detailsUser identity/authority verificationObject definitionHuman–computer interaction
A method of enhancing online security by requiring the user to choose from among multiple objects presented to the user an object which falls within an abstract object definition previously provided by the user. The presented objects are therefore unknown to the user but include at least one with a particular quality known to the user.
Owner:CHEN CHUAN PEI
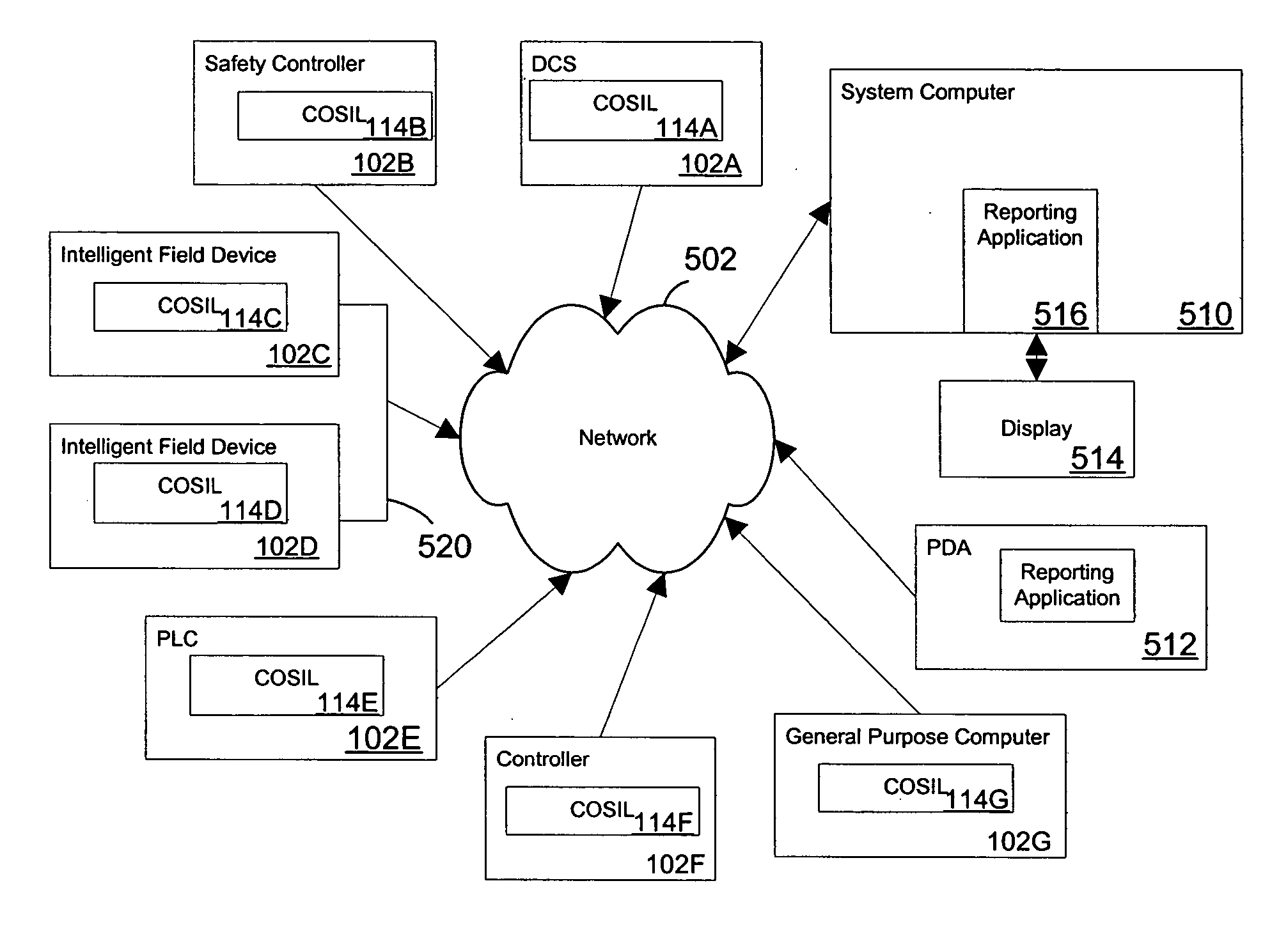
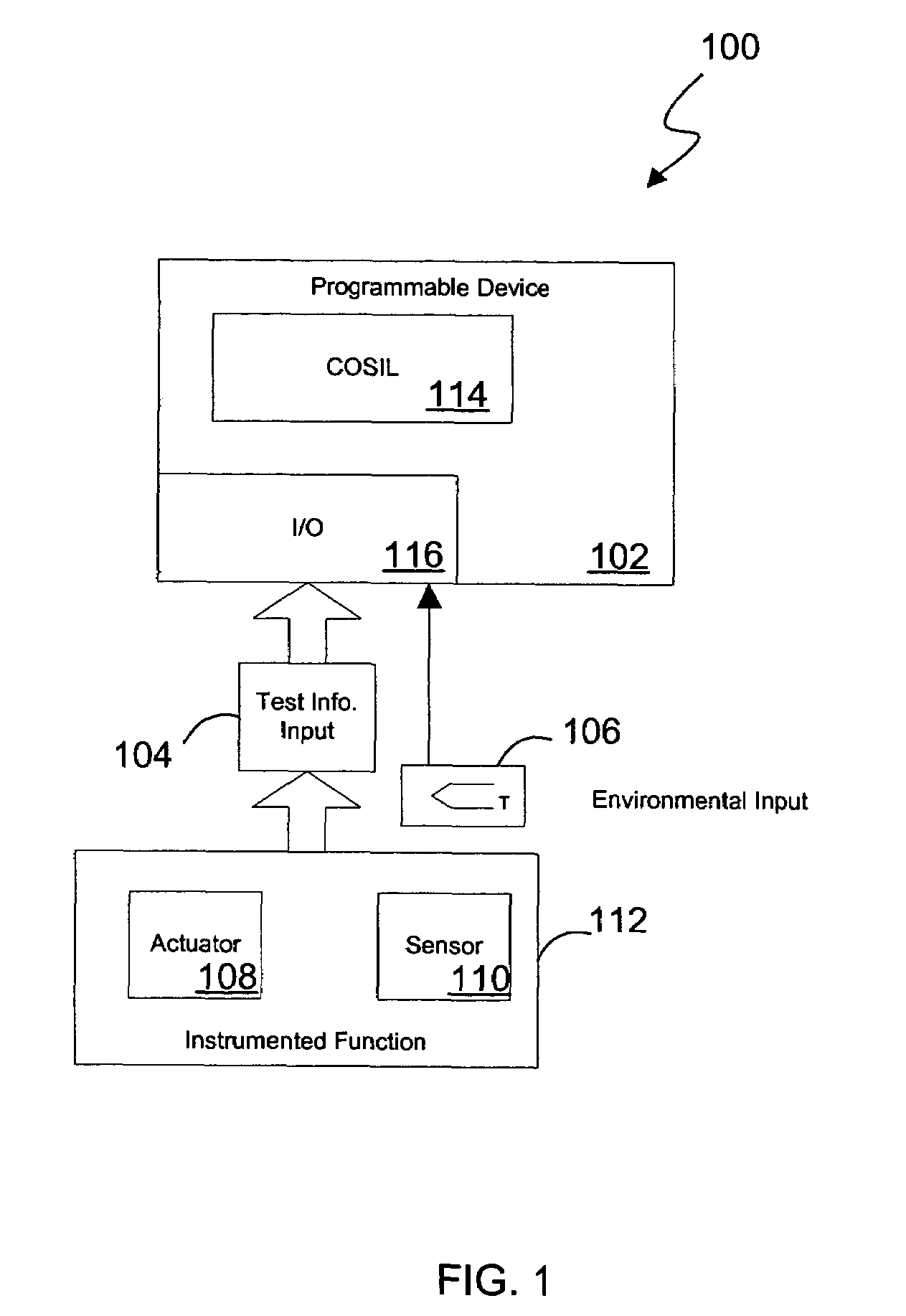
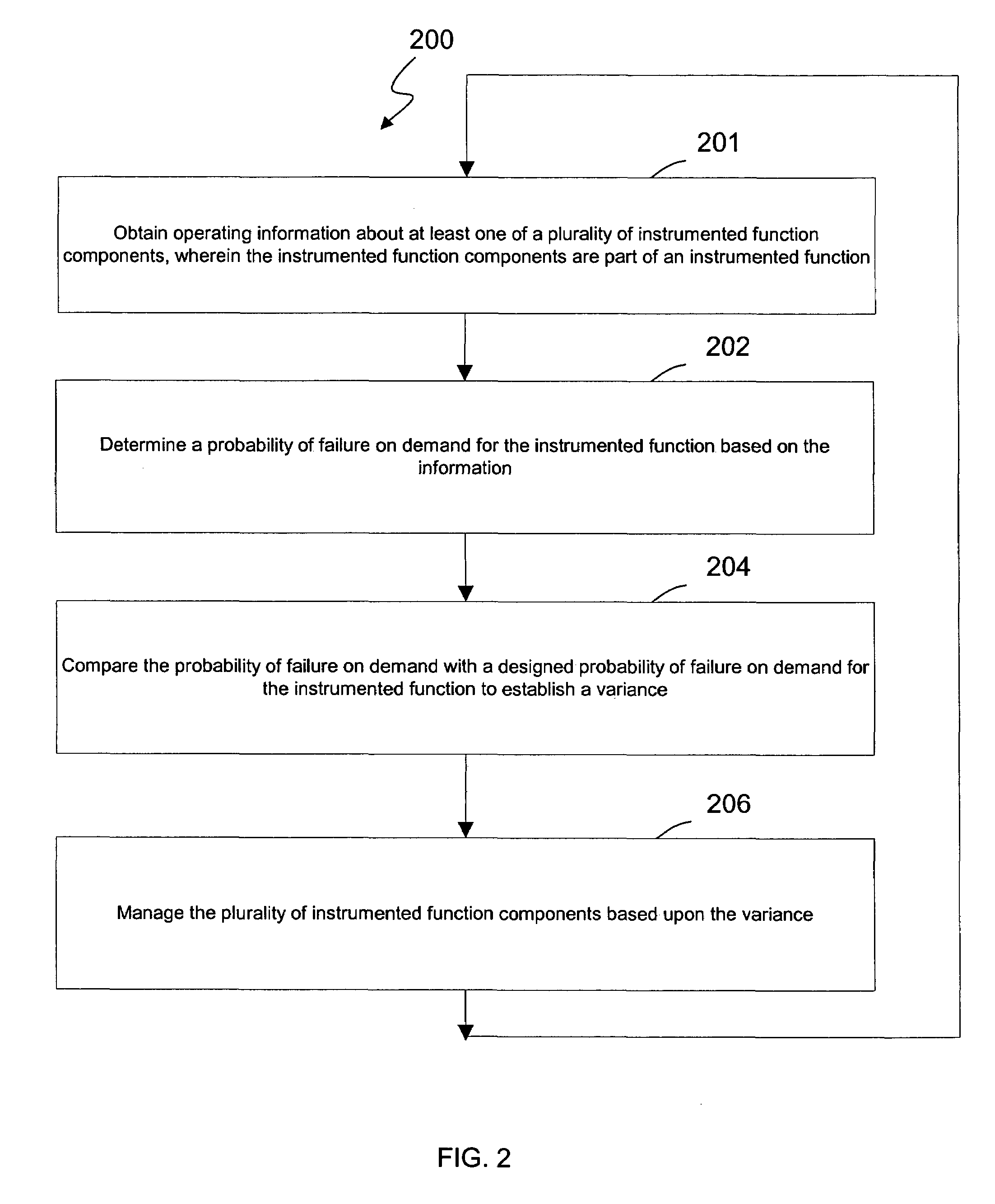
System and method for continuous online safety and reliability monitoring
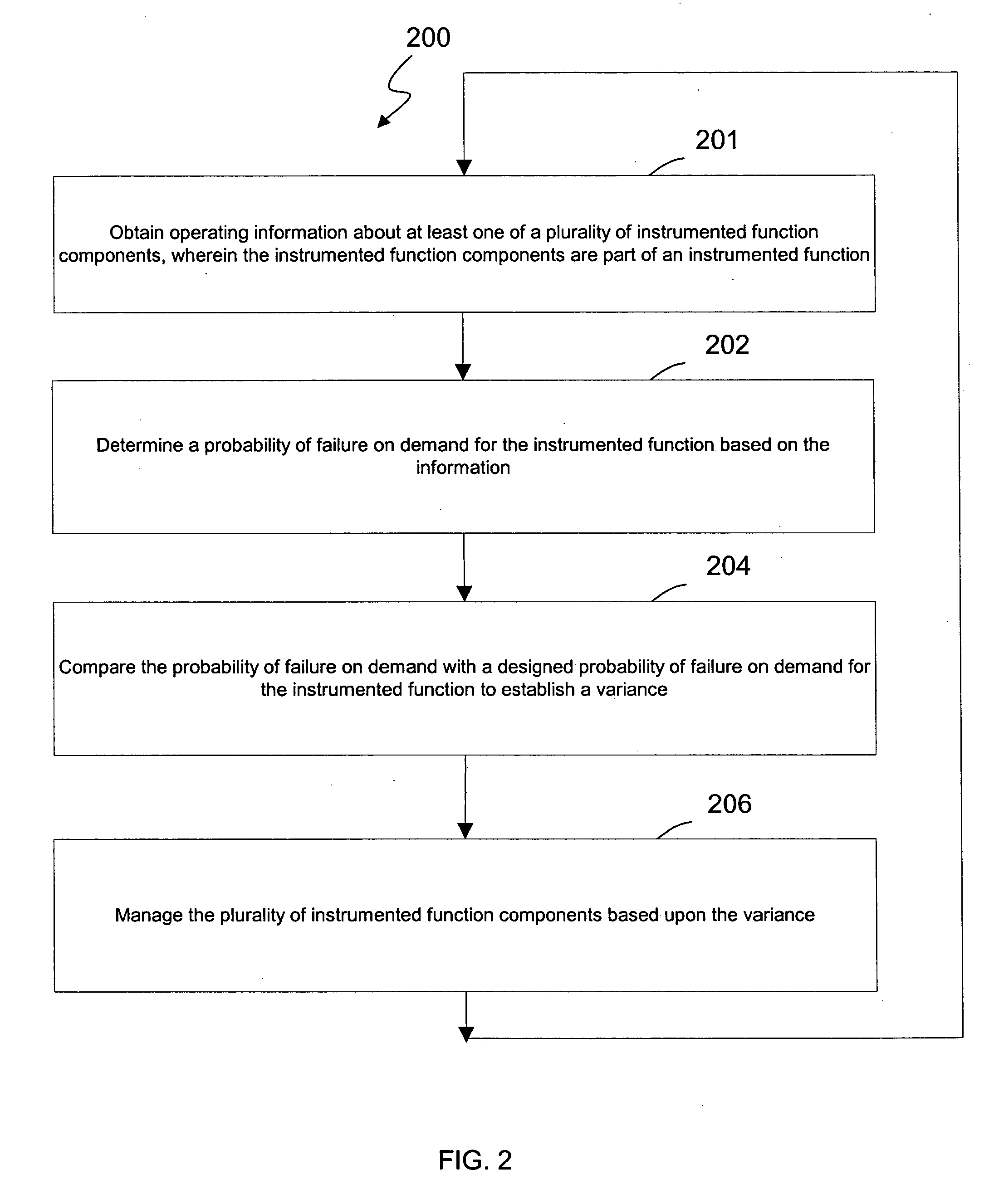
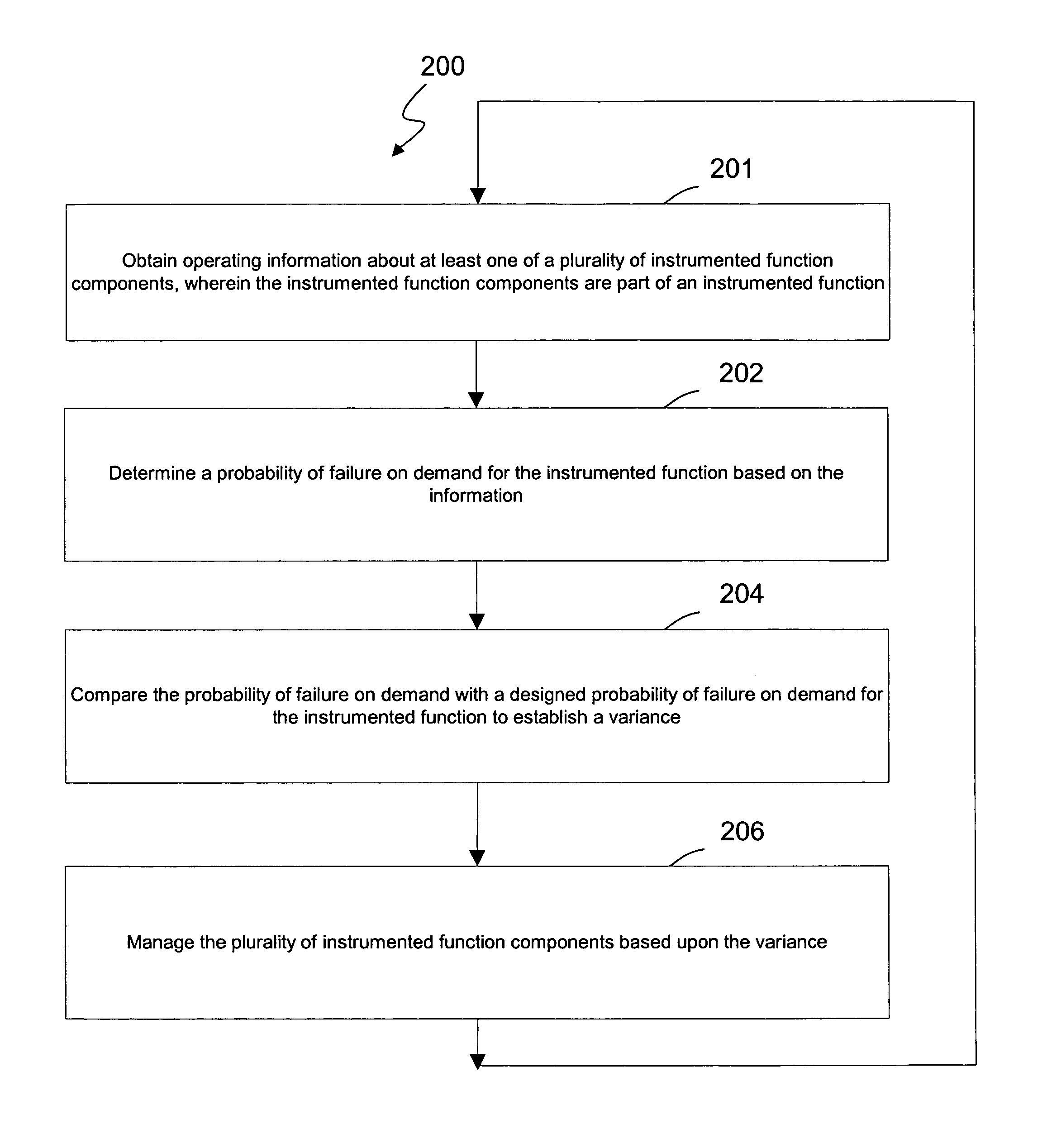
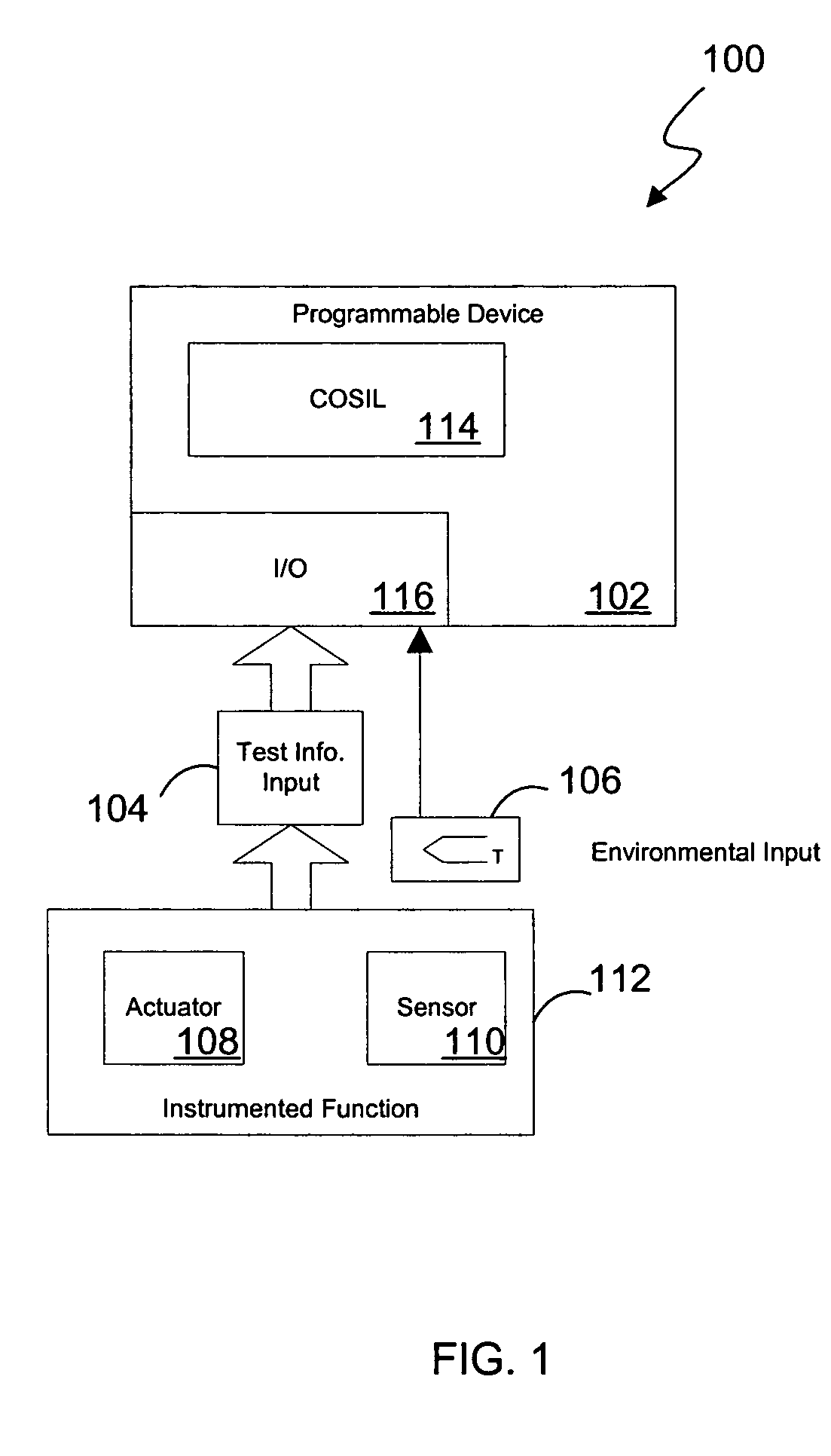
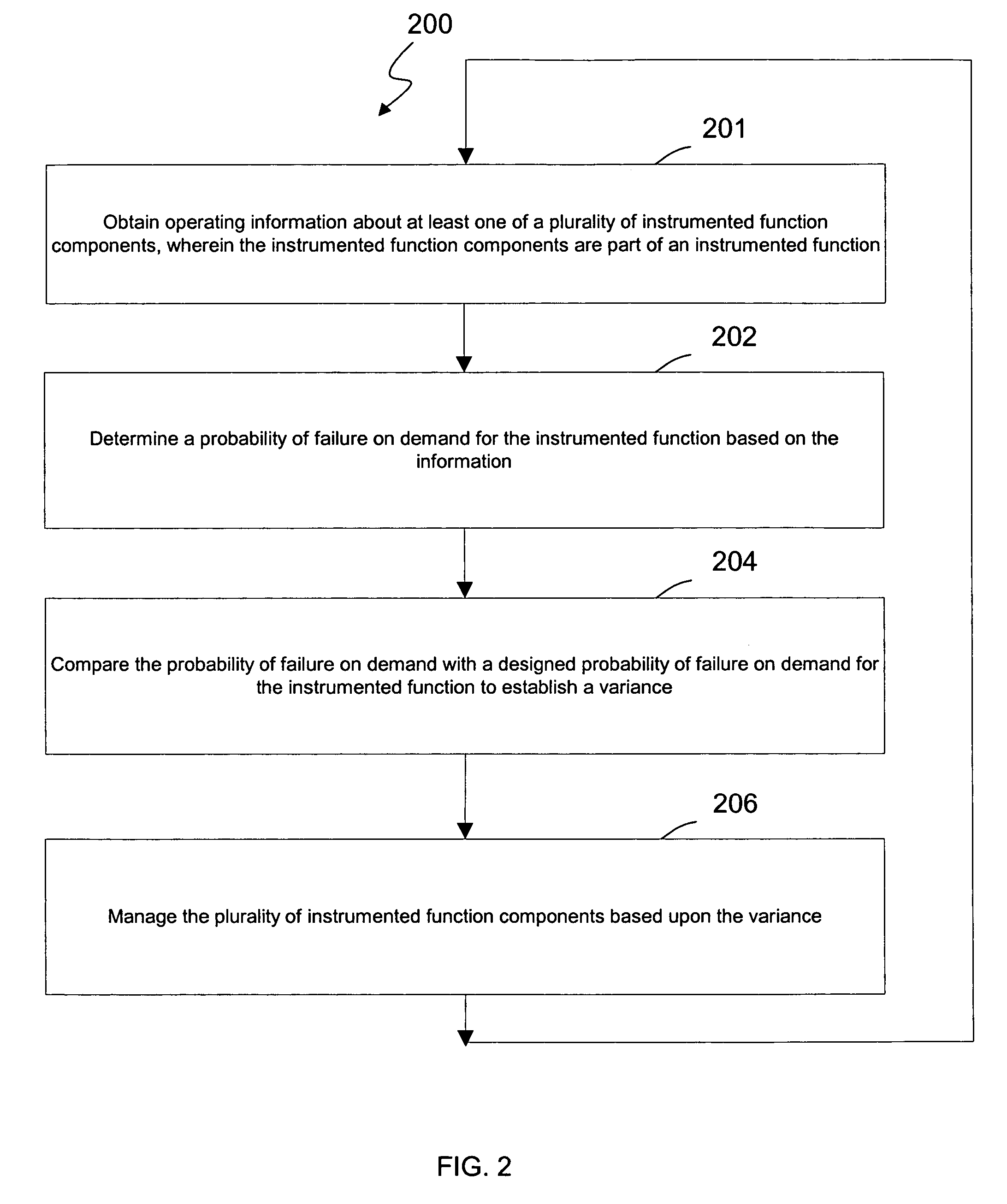
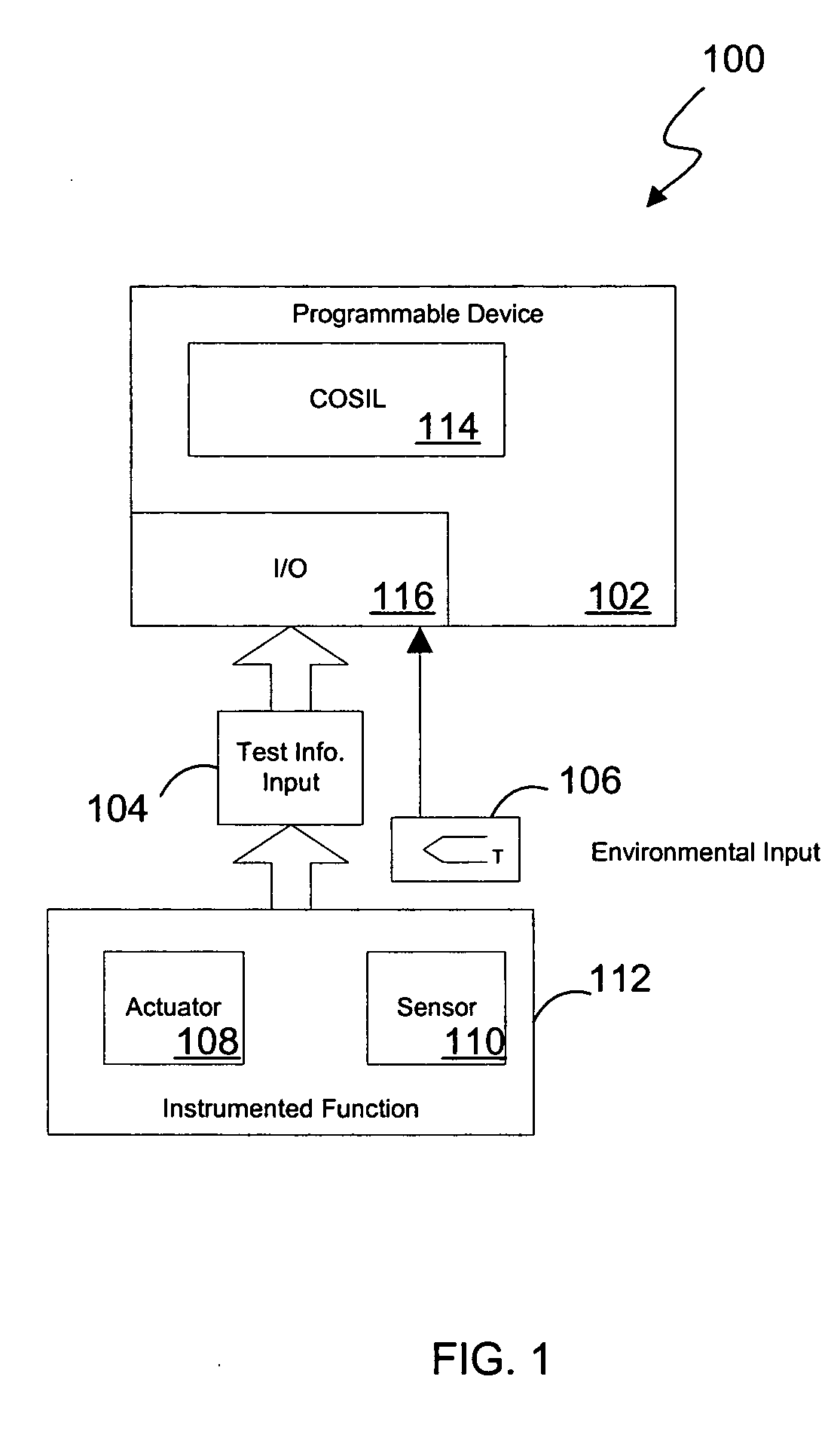
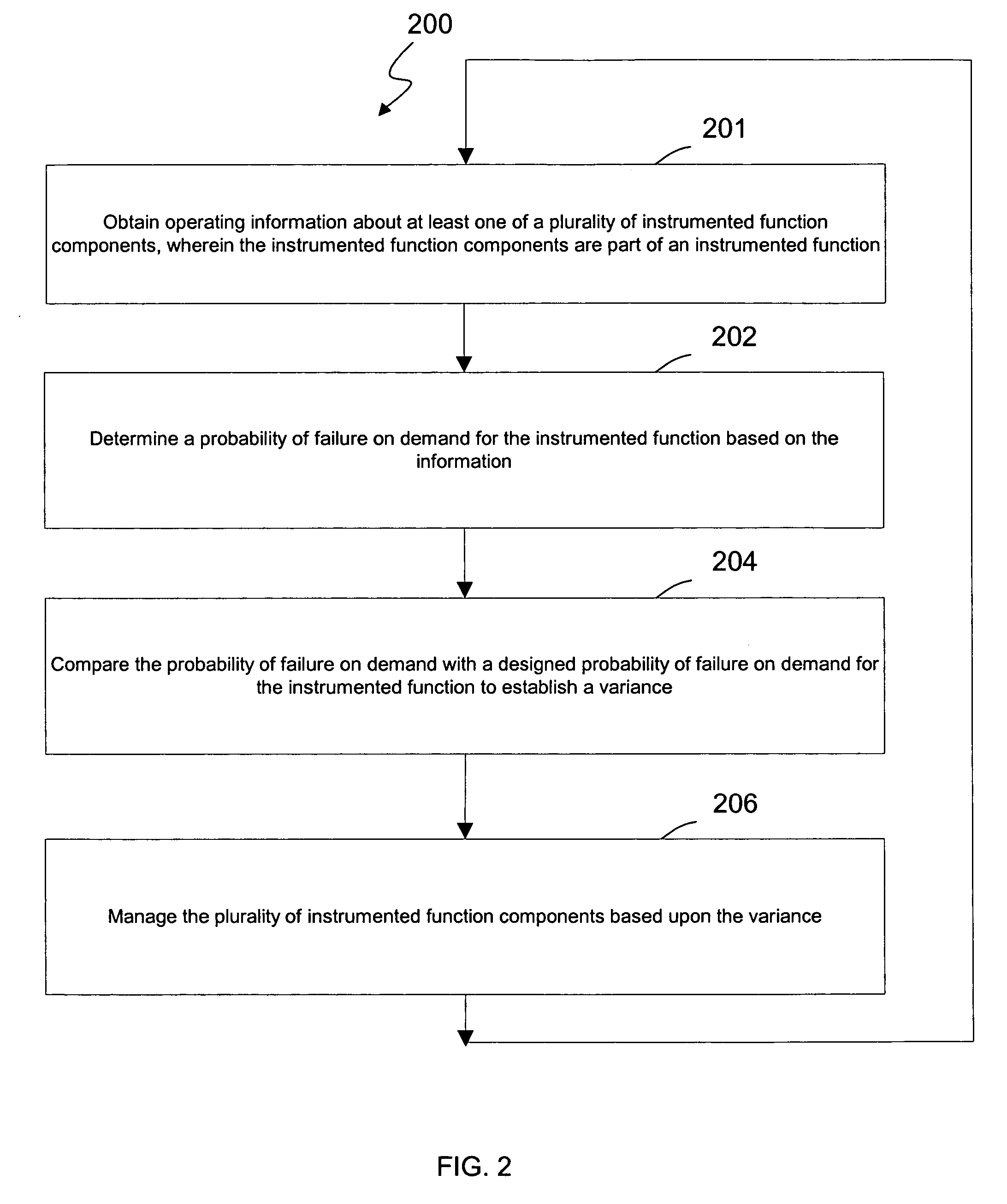
ActiveUS20050027379A1Safety arrangmentsElectric testing/monitoringInstrument functionSafety Integrity Level
A system and method for continuous online safety and reliability monitoring is disclosed. The method includes the steps of obtaining operating information about at least one of a plurality of instrumented function components, which are part of an instrumented function, and determining a probability of failure on demand for the instrumented function based on the operating information. In variations, operating information includes status information, which may be received from and / or provided to an asset management application. In some variations, instantaneous probability of failure on demand, online mean time to failure (MTTF), and online safety integrity level (SIL) are also calculated for an instrumented function. In yet further variations, the system allows a user to predict probability of failure on demand values into the future based on hypothetical and / or future planned test times.
Owner:SCHNEIDER ELECTRIC SYST USA INC
Electrical power system on-line safety and stability evaluation forecast failure collection adaptive selection method
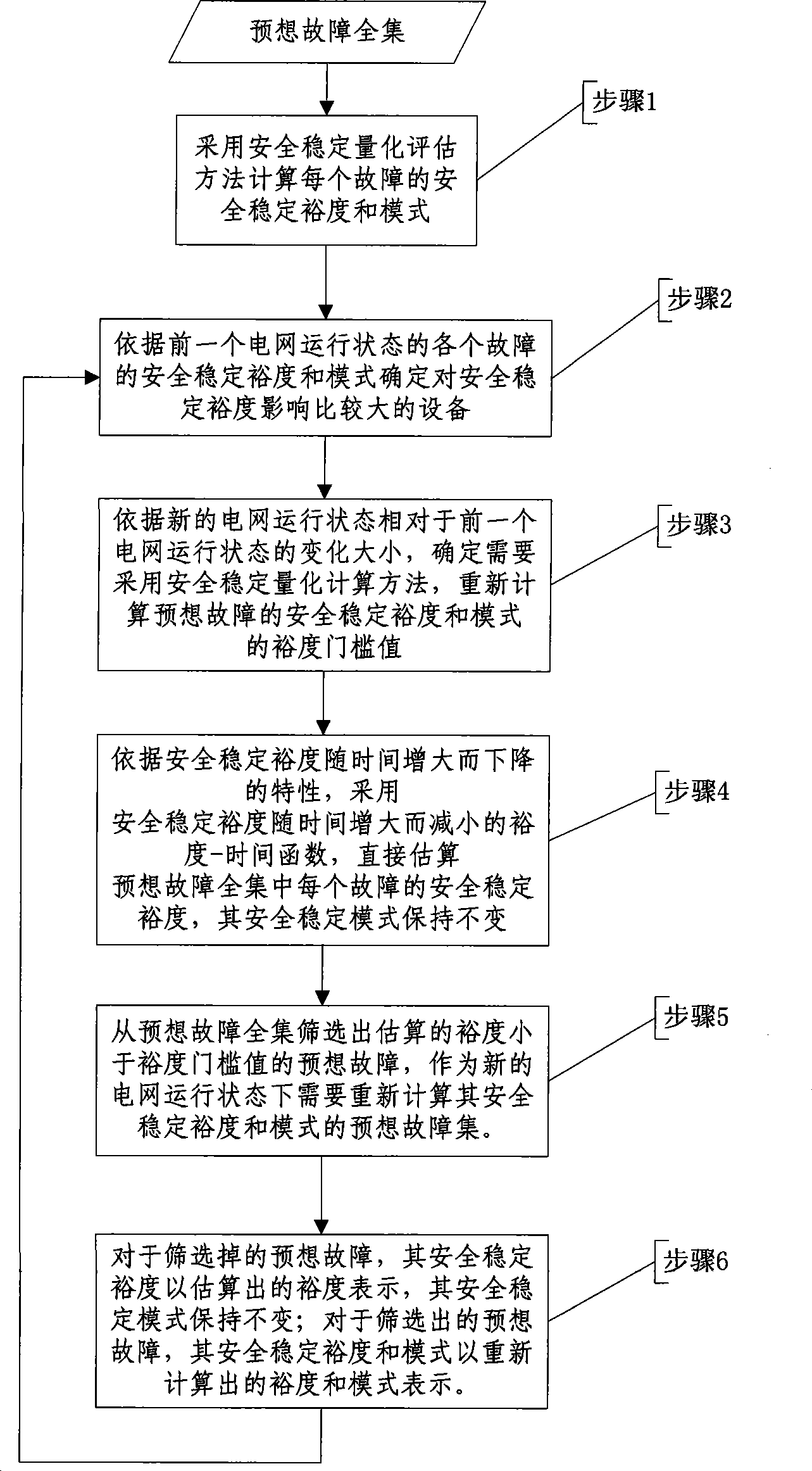
ActiveCN101425686ACalculation speedSmall scaleData processing applicationsAc network circuit arrangementsScreening methodPower grid
The invention relates to a self-adaptive screening method for an anticipated fault set in power system security and stability on-line assessment, which is suitable for determining the anticipated fault set in the static, transient and dynamic security and stability on-line assessment of the power system. The method adopts the core concept that the fault set required to be recalculated in the security and stability on-line assessment is determined according to the mode of the security and stability margin of all anticipated faults given by the security and stability on-line assessment in the previous round of the power network. The invention takes the power network security and stability margin and the security and stability mode as the quantitative index of the power network security and stability degree, takes the security and stability margin as the index, and screens the anticipated fault subset required to be recalculated from the anticipated fault universal set by combining the security and stability mode and the degree of change of the running state of the power network as the dynamic anticipated fault set which meets the practical demands of the engineering and is changed along with the running state of the power network; the scale of the anticipated fault set used for the security and stability on-line assessment under the current time section can be reduced, and the computing speed for the security and stability on-line assessment is increased.
Owner:NARI TECH CO LTD
System and method for continuous online safety and reliability monitoring
ActiveUS7133727B2Safety arrangmentsElectric testing/monitoringInstrument functionSafety Integrity Level
A system and method for continuous online safety and reliability monitoring is disclosed. The method includes the steps of obtaining operating information about at least one of a plurality of instrumented function components, which are part of an instrumented function, and determining a probability of failure on demand for the instrumented function based on the operating information. In variations, instantaneous probability of failure on demand, online mean time to failure (MTTF), and online safety integrity level (SIL) are also calculated for an instrumented function. In other variations of the invention, alarms are reported to an operator based on the variance indicating the probability of failure on demand for the instrumented function is too high. In yet further variations, the system allows a user to predict probability of failure on demand values into the future based on hypothetical and / or future planned test times.
Owner:SCHNEIDER ELECTRIC SYST USA INC
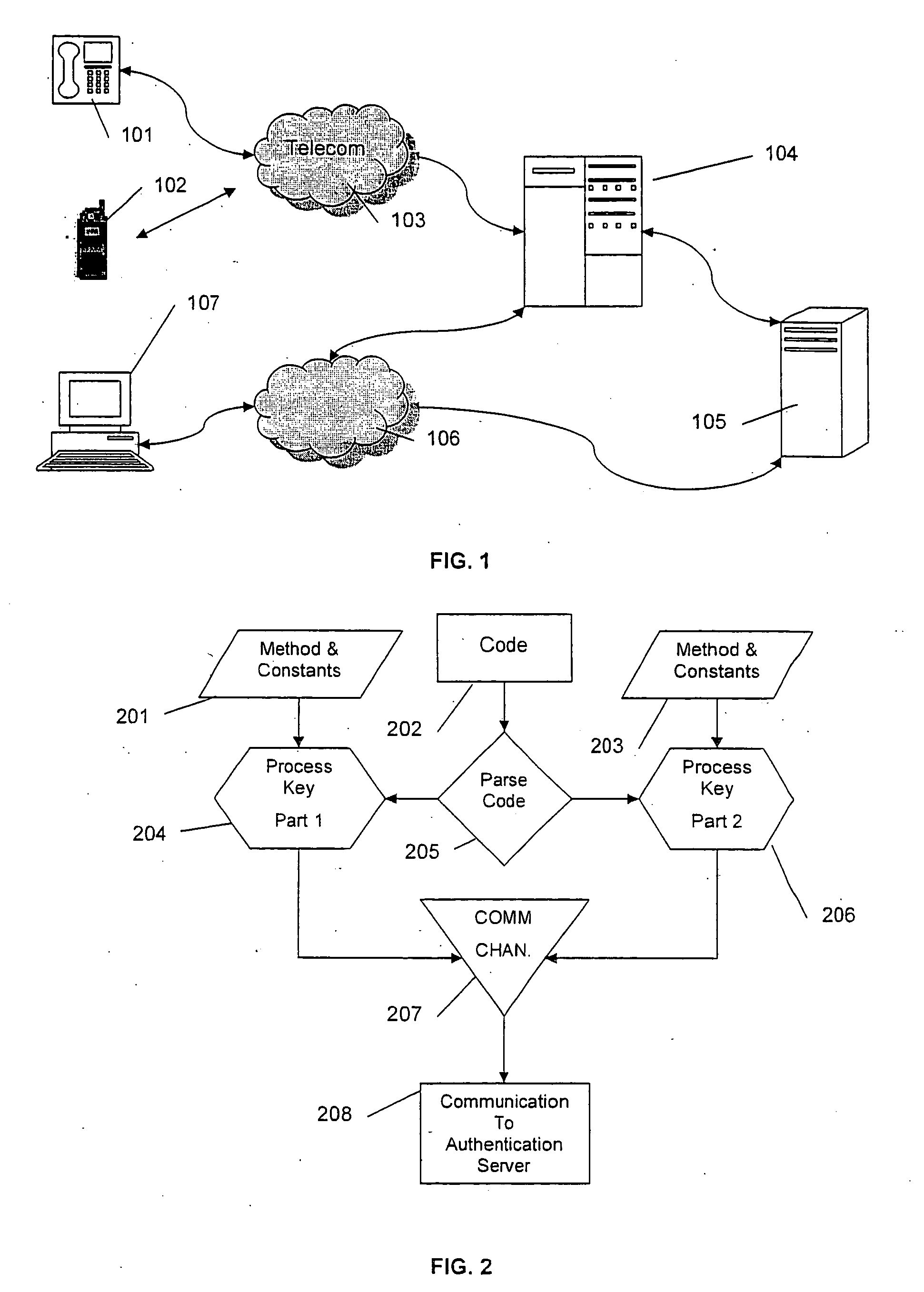
Online Security Systems and Methods
InactiveUS20120239928A1Key distribution for secure communicationPublic key for secure communicationOnline securityElectronic equipment
Described are a system and method for securing an online transaction. A request is output from an electronic device to a verification server to perform an online transaction. The verification server generates a challenge request. The challenge request is encrypted with a private key of a pair of cryptographic keys. The encrypted challenge request is decrypted with a public key of the pair of cryptographic keys. The decrypted challenge request and the challenge request generated by the verification server are compared. A verification result is generated in response to the comparison.
Owner:ID SECURITY
Receiving-end network voltage stabilization overall process situation assessment and prevention and control method based on responses
ActiveCN103279639AQuick estimateQuickly assess efficiencySpecial data processing applicationsLoad SheddingPower grid
The invention provides a receiving-end network voltage stabilization overall process situation assessment and prevention and control method based on responses. The method comprises the steps of S1, obtaining various off-line simulation data or real-time measuring data; S2, constructing equivalent power transmission models of nodes according to node practical transfer power; S3, obtaining a node quiescent voltage stability margin index Vsi of equivalent power transmission model parameters of each node; S4, constructing a node reactive compensation assessment index according to the equivalent power transmission model parameters of each node; S5, setting an early warning threshold value Ncr of the node quiescent voltage stability margin index, and calculating a load shedding estimation of a weaker node when the quiescent voltage stability margin index Vsi of each node is smaller than the Ncr. According to the receiving-end network voltage stabilization overall process situation assessment and prevention and control method based on the responses, a weak node or a weak area in a current operating mode can be found out, a rapid estimation of reactive compensation levels and load shedding of each node is achieved, and the method can be widely applied to the fields of power network planning and online security monitoring.
Owner:STATE GRID CORP OF CHINA +2
Nonlinear fuzzy detection method for operating safety of power cable tunnel
InactiveCN102621434AAchieve securityReduce abnormal power outagesElectrical testingSafety indexSocial benefits
The invention discloses a nonlinear fuzzy detection method for operating safety of a power cable tunnel. The method comprises the following steps of: determining a project layer, a subproject layer and an index layer in a model, detecting the index layer and acquiring data; establishing a comment set; establishing a deterioration grade of each evaluation index and a membership function matrix of a corresponding comment set; determining weight of each level of evaluation indexes; sequentially calculating fuzzy evaluation matrixes of the index layer and the subproject layer by using an analytic hierarchy method until a final fuzzy evaluation result vector is obtained; and determining an evaluation result of an operating safety state of the power cable tunnel by using a maximum membership degree method. Single parameter early warning of the operating state of the cable tunnels and cables is realized, comprehensive on-line safety index evaluation and early warning are realized, technical support is provided for timely and effectively processing operating hidden dangers and failures of the cables, and after the project is finished, abnormal power failure can be reduced, and major disasters can be warned in advance; and an inspection workload of a worker is reduced. After the project is finished, the method can be popularized nationwide and has high economic and social benefits.
Owner:SHANDONG UNIV
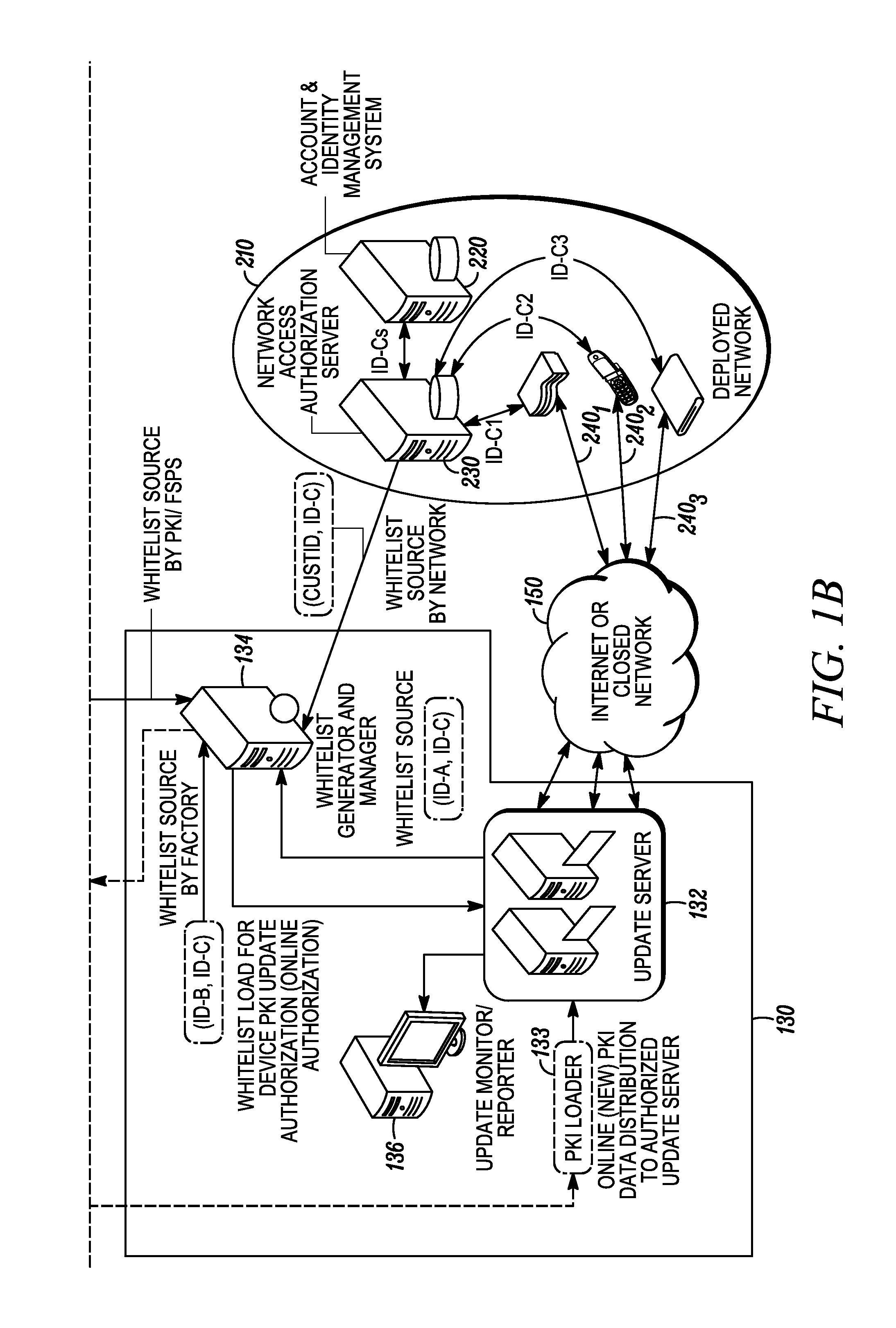
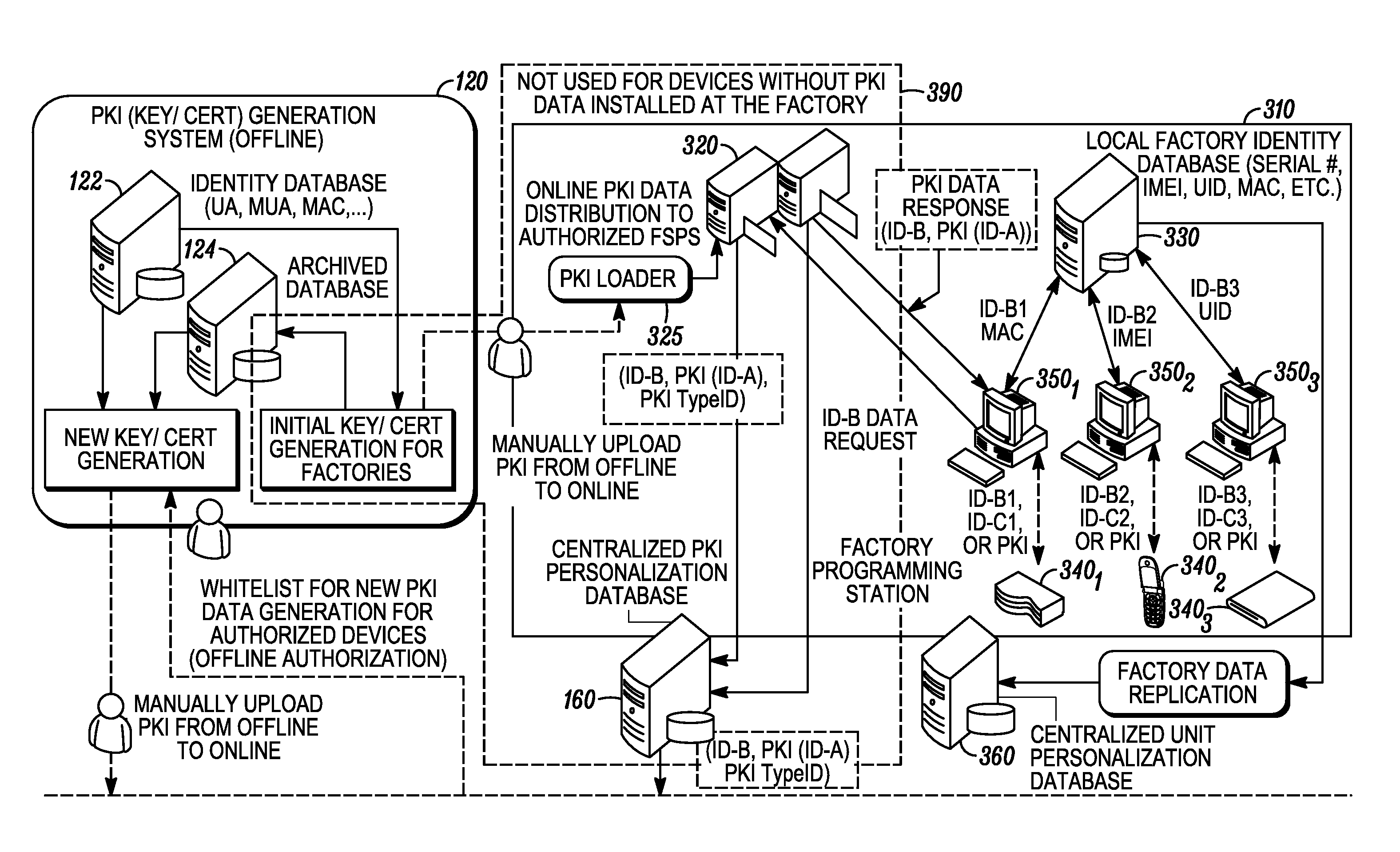
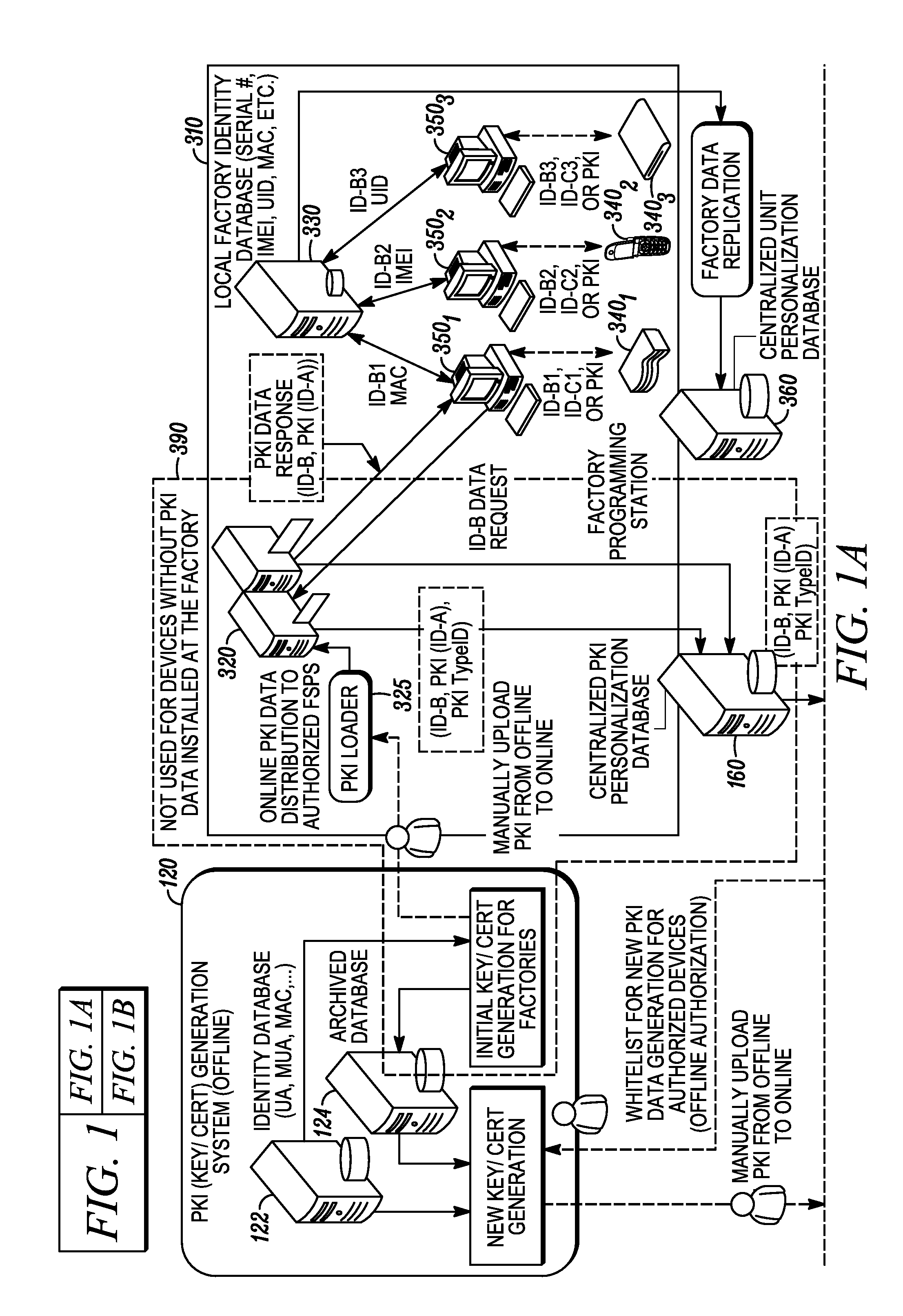
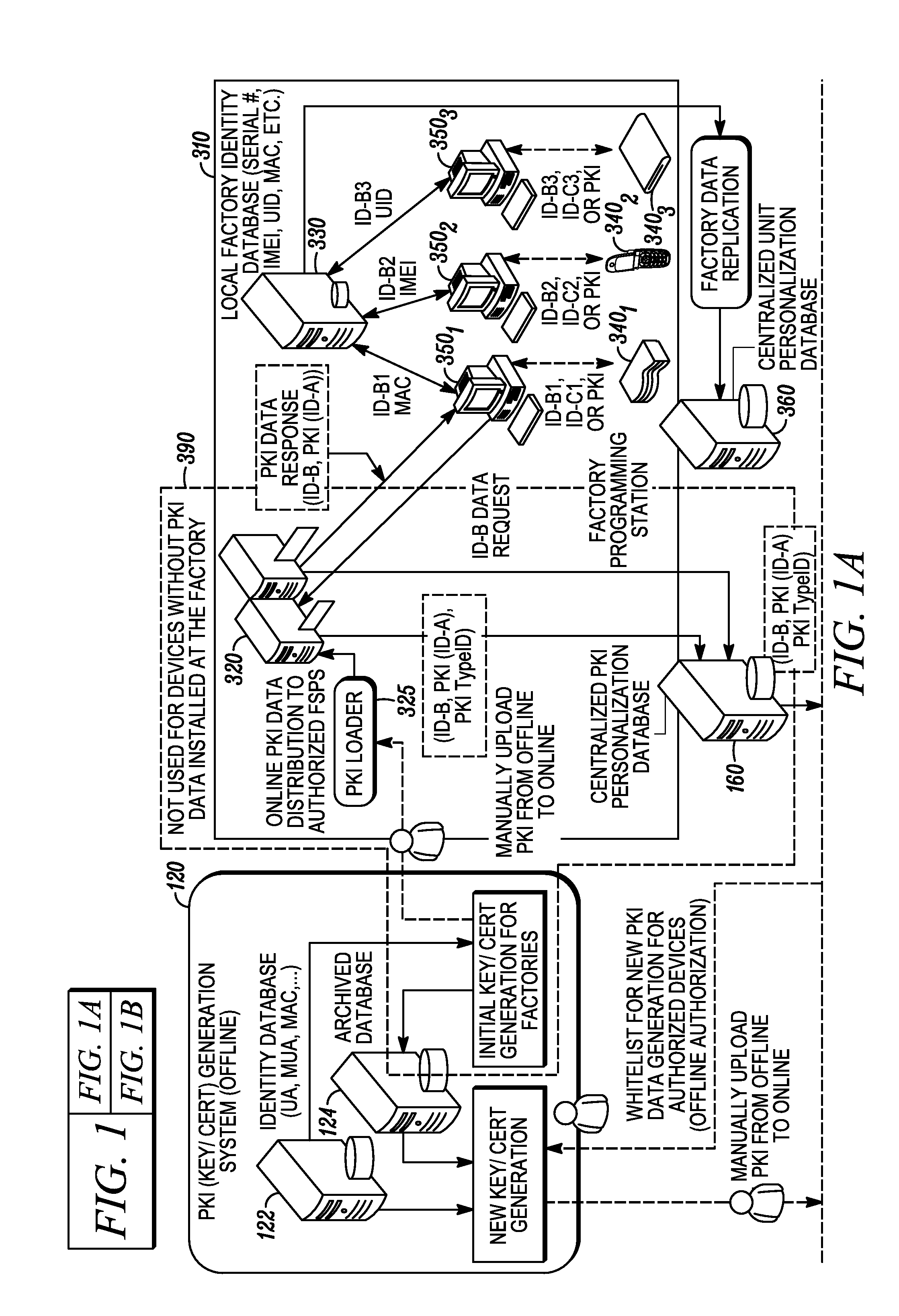
Online secure device provisioning with updated offline identity data generation and offline device binding
A system for generating new identity data for network-enabled devices includes a whitelist reader configured to extract attributes from a whitelist. The whitelist includes, for each device specified in the whitelist, a previously assigned identifier of the first type. The previously assigned identifiers of the first type are linked to identity data previously provisioned in each of the respective devices. A data retrieval module is configured to receive the identifiers of the first type from the whitelist reader and, based on each of the identifiers, retrieve each of the previously provisioned identity data records linked thereto. A new data generation module is configured to (i) obtain a cryptographic key associated with the identity data previously provisioned in the devices specified on the whitelist and the corresponding identifiers of the first type, (ii) generate new identity data records each linked to a new identifier and (iii) encrypt each of the new identity data records with one of the cryptographic keys and link each new identity data record to the identifier of the first type corresponding to each respective cryptographic key. A data output module is configured to load onto an external source the encrypted new identity data records along with their respective new identifiers and their respective previously assigned identifiers of the first type.
Owner:GOOGLE TECH HLDG LLC
Cross-domain identity management for a whitelist-based online secure device provisioning framework
ActiveUS20110258454A1User identity/authority verificationDigital computer detailsData systemWhitelist
A method for managing identifiers associated with network-enabled devices and used in an identity data system provisioning the network-enabled devices with identity data includes receiving a first set data that includes a previously assigned identifier for one or more of the network-enabled devices that are authorized to be provisioned with new identity data. If identity data is currently installed on the one or more network-enabled devices, each of the previously assigned identifiers in the first set of data is associated with a corresponding identifier linked to the identity data currently installed on the one or more network-enabled devices to establish a second set of data. New identity data is bound to each of the one or more network-enabled devices by assigning a new identifier linked with the new identity data to each of the one or more network-enabled devices to establish a whitelist. The whitelist specifies, for each of the one or more network-enabled devices, its previously assigned identifier, its corresponding identifier and its new identifier that is linked with the new identity data.
Owner:GOOGLE TECH HLDG LLC
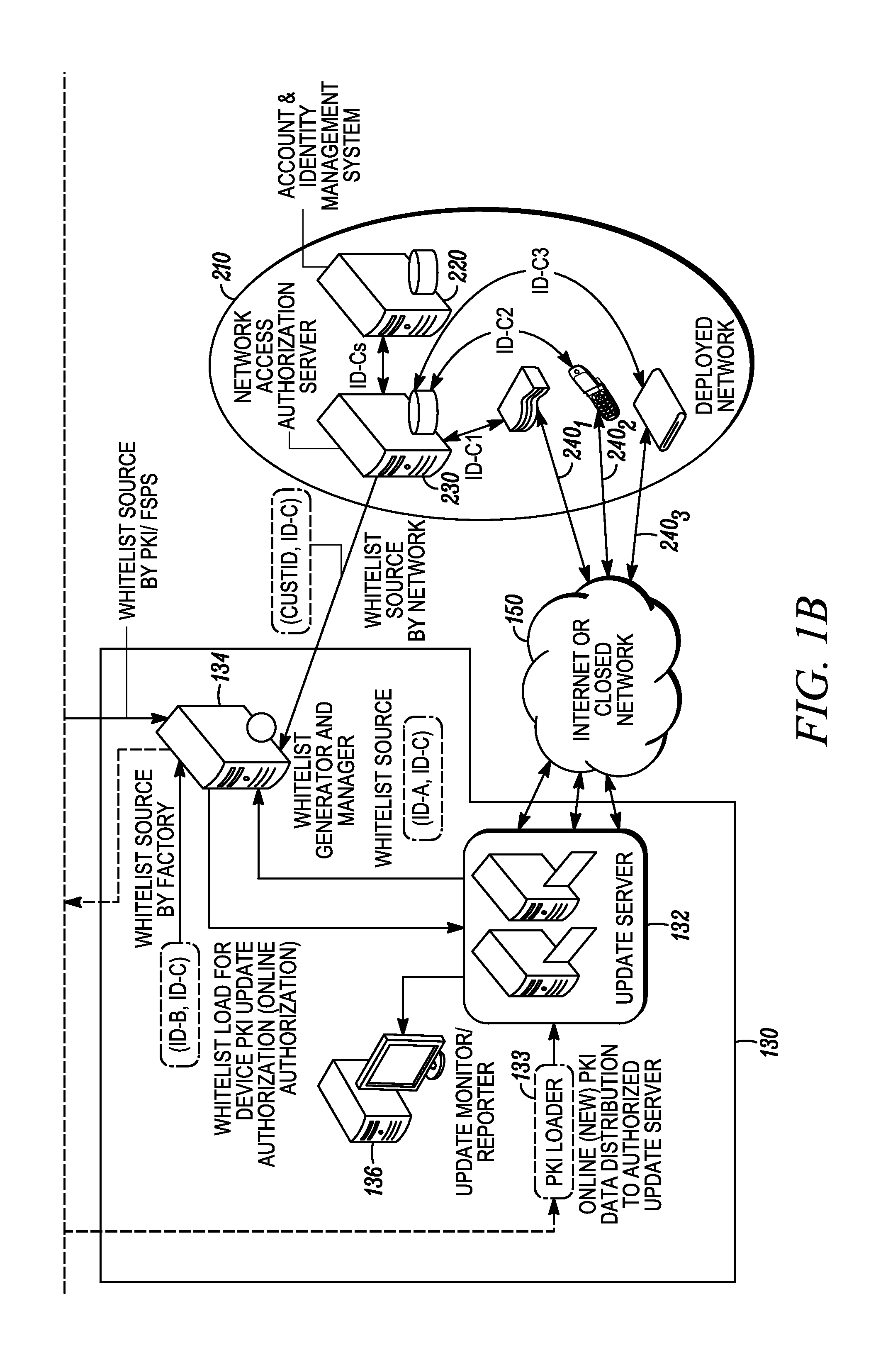
Online secure device provisioning with online device binding using whitelists
InactiveUS20120089839A1Multiple keys/algorithms usagePublic key for secure communicationSession managementProtocol processing
One or more servers are provided including a session manager, authentication module, authorization module, encryption module, database, and protocol handler. The session manager is configured to receive requests for new identity data from network-enabled devices. Each request is authenticated first by the update server via its authentication module by validating the signature of the request message as well as the certificate chain trusted by the update server. The authorization module is configured to determine if the network-enabled devices specified on a whitelist are authorized to be provisioned with new identity data. The database is configured to receive new identity records generated by an identity data generation system. Each of the new identity records includes a new identifier. The new identifier is not associated or linked to any previously assigned / used identifiers and identity data, thus all the new identity records are generated independently and then loaded to the update server.
Owner:GOOGLE TECH HLDG LLC
Analysis method for steady-state security region of electric-pneumatic interconnected integrated energy system
ActiveCN105356447AData processing applicationsSpecial data processing applicationsOperation schedulingSteady state security
The invention discloses an analysis method for a steady-state security region of an electric-pneumatic interconnected integrated energy system. The method comprises the following steps: firstly, building a steady-state energy flow model of the electric-pneumatic interconnected integrated energy system; secondly, proposing the concept of the steady-state security region of the electric-pneumatic interconnected integrated energy system by referring to a definition and a model of the steady-state security region of a power system; thirdly, obtaining a group of boundary operation points on the boundary of the security region through repeated energy flow calculation; and finally, obtaining the steady-state security region of the electric-pneumatic interconnected integrated energy system on the basis of linear hyperplane fitting. The security region model disclosed by the invention provides a theoretical basis for real-time operation scheduling and online security evaluation of the electric-pneumatic interconnected integrated energy system.
Owner:HOHAI UNIV
CPU+multi-GPU heterogeneous mode static safety analysis calculation method
InactiveCN106874113AImprove static security analysis scanning calculation efficiencyData processing applicationsResource allocationHybrid programmingMulti gpu
The invention discloses a CPU+multi-GPU heterogeneous mode static safety analysis calculation method. For the requirement for fast scanning for static safety analysis of large power grid in a practical engineering application, an OpenMp multithreading technique is adopted for allocating corresponding thread count according to a system GPU configuration condition and a calculation requirement on a CUDA unified calculation frame platform; each thread is uniquely corresponding to a single GPU; on the basis of CPU and GPU hybrid programming development, a CPU+multi-GPU heterogeneous calculation mode is constructed for collaboratively completing the preconceived fault parallel calculation; on the basis of single preconceived fault load flow calculation, the highly synchronous parallel of a plurality of cut-off load flow iterative processes is realized; the parallel processing capability of preconceived fault scanning for the static safety analysis is greatly promoted through element-grade fine grit parallel; a powerful technical support is supplied for the online safety analysis early-warning scanning of an integrated dispatching system of an interconnected large power grid.
Owner:NARI TECH CO LTD +2
Water quality on-line safe prealarm system and method based on aquatic organism avoidance behavior
The invention relates to a water quality online security early warning system and method thereof. The water quality online security early warning system comprises a biology avoidance behavior sensor which consists of two testing tubes, wherein, the two tubes are communicated through a two-way in the middle and parallel with each other; the two tubes are respectively provided with two groups of stainless steel monitoring electrodes, each group of electrodes consists of a signal transmitting electrode and a signal receiving electrode, wherein, the signal transmitting electrode forms a positive rotation low voltage alternating electric field in the testing tube, and the signal receiving electrode can induce changes of the electric field; the changes of the electric field are transmitted to a signal collecting device, and displayed through a display after being processed. The invention can display behavior change signal of a tested biology with the mode of electrical signal received from multi-point monitoring, can achieve online biology monitoring of original position, online and real time via analyzing and evaluating the electrical signal, and can warn early against unknown contaminants in water body, and has very important indicating effect for the investigations of environmental pollution, in particular for paroxysmal and severe accidental changes.
Owner:RES CENT FOR ECO ENVIRONMENTAL SCI THE CHINESE ACAD OF SCI
Method, apparatus and cloud server for detecting website security
InactiveCN105323210AStay safe onlineHidden dangersTransmissionSpecial data processing applicationsWeb siteIp address
The present invention is suitable for the technical field of Internet security, and provides a method, an apparatus and a cloud server for detecting website security. The method comprises the steps of: acquiring a request message of a website accessed at present, which is intercepted by a client, wherein the request message comprises an IP address; acquiring a trust degree value corresponding to the IP address; comparing the trust degree value corresponding to the IP address with a preset threshold value; and if the trust degree value corresponding to the IP address is lower than the preset threshold value, prompting the client that access risk exists in the website accessed at present. According to the method of the present invention, the security degrees of IP addresses in the Internet are graded through the cloud server, when a user accesses the IP address with a low grade, an effective prompt can be timely provided, thereby effectively attacking DNS tampering, and protecting online security of the user.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Interconnected power system oriented hierachical decomposition space-time cooperative modeling method
InactiveCN101877500ASolve conflictsSolve the integrationCircuit arrangementsInformation processingElectric power system
The invention discloses an interconnected power system oriented hierachical decomposition space-time cooperative modeling method. The method is based on IEC61970 standard, E-format standard, version management service, model combination / separation, external network equivalence, SVG graph transformation, E-format data import / export and other technologies, a standard information exchange mechanism is established between different levels of scheduling systems, a standard public information processing mechanism is established on a scheduling system platform, and the space-time cooperative modeling system of interconnected power systems is realized. The invention can solve the contradiction between the modeling modes of the interconnected large power grid and the traditional power grid, solve information integration and sharing among various application systems and among various scheduling systems in the scheduling center and provide data basis and technical support for the real-time monitoring, control and online security analysis of the interconnected large power system.
Owner:BEIJING KEDONG ELECTRIC POWER CONTROL SYST
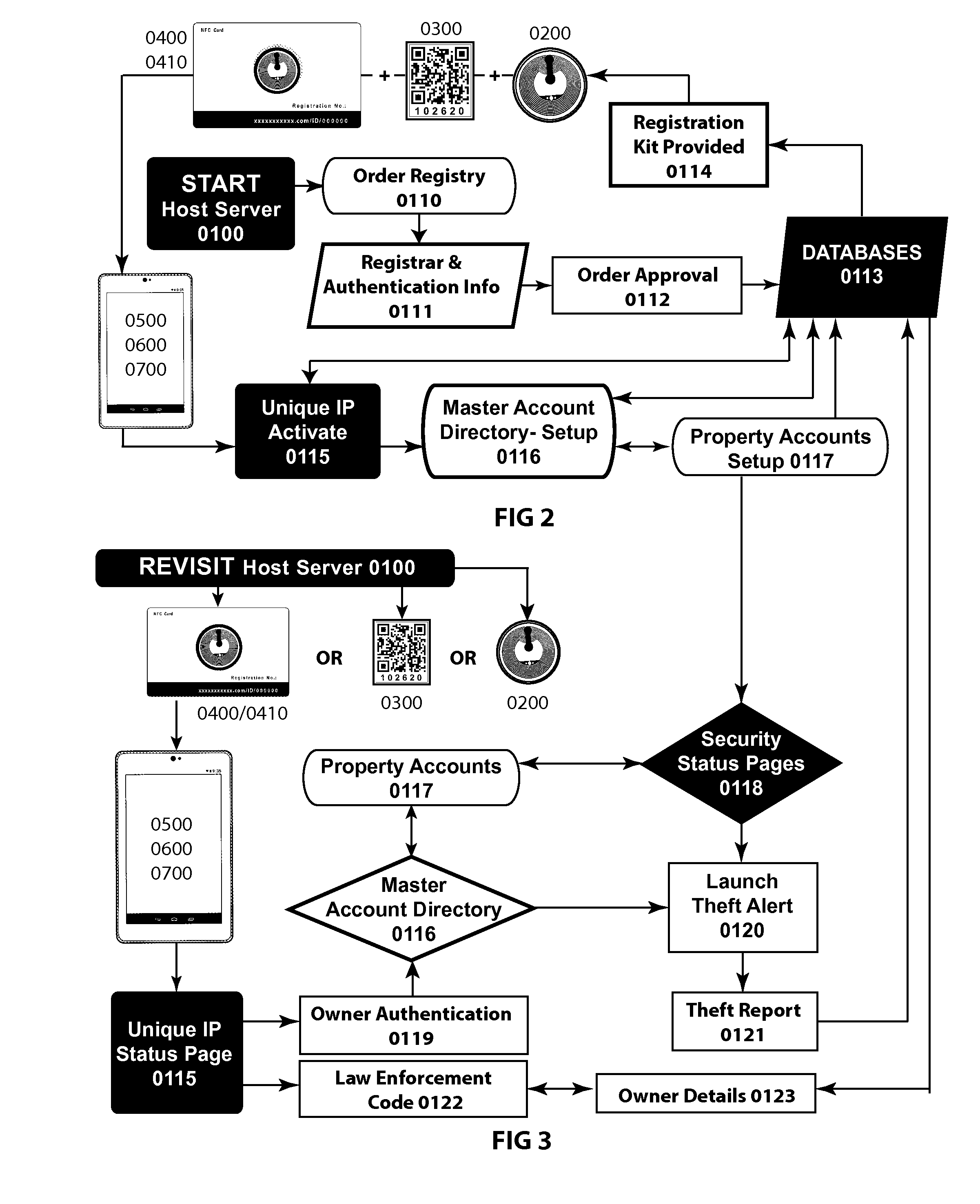
System and Method Employing Near Field Communication and QR Code Technology to Access and Manage Server-Side Personal and Business Property Security Status Accounts
InactiveUS20150035650A1Activation is simpleConvenient registrationNear-field for read/write/interrrogation/identification systemsSubscribers indirect connectionTransceiverIp address
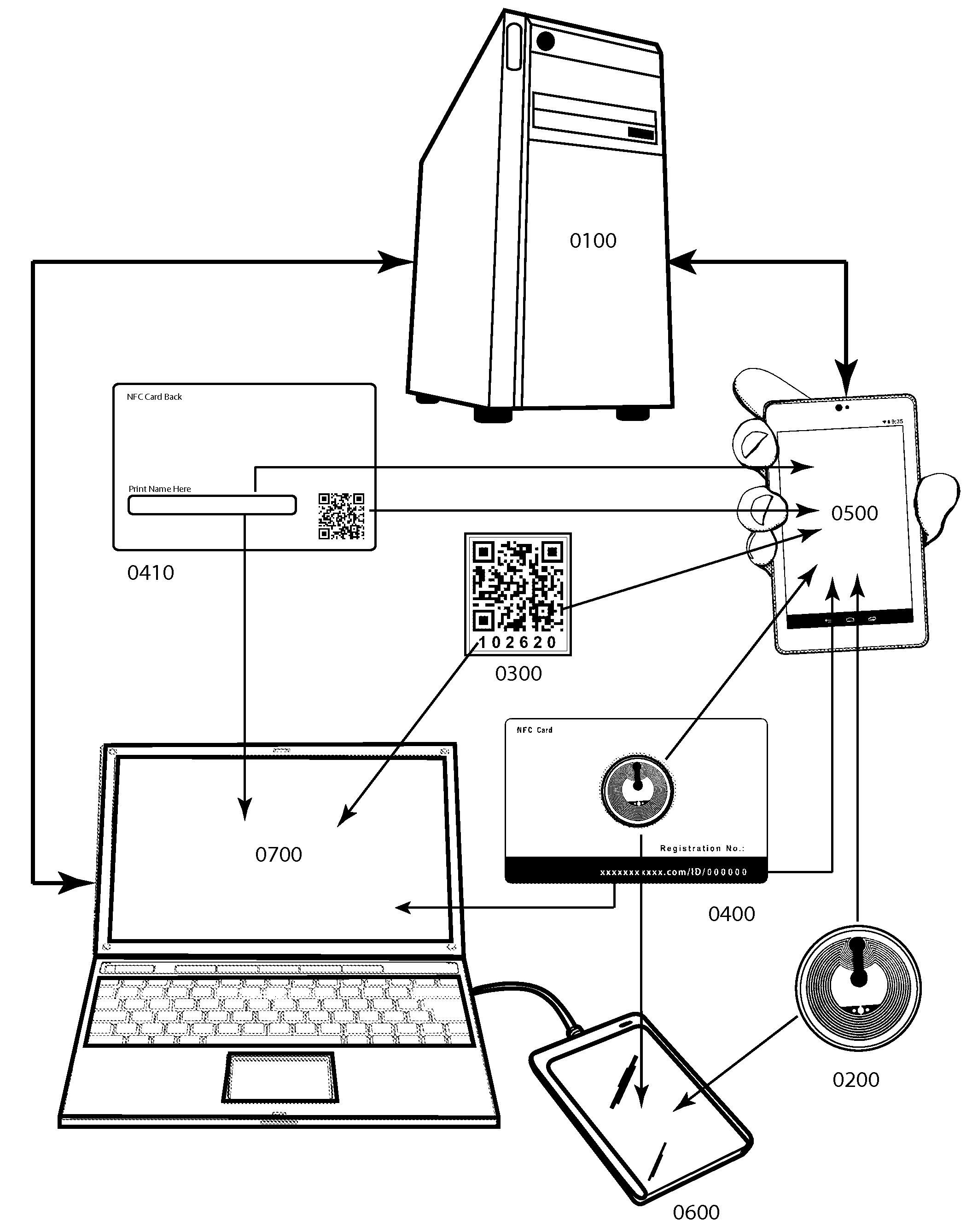
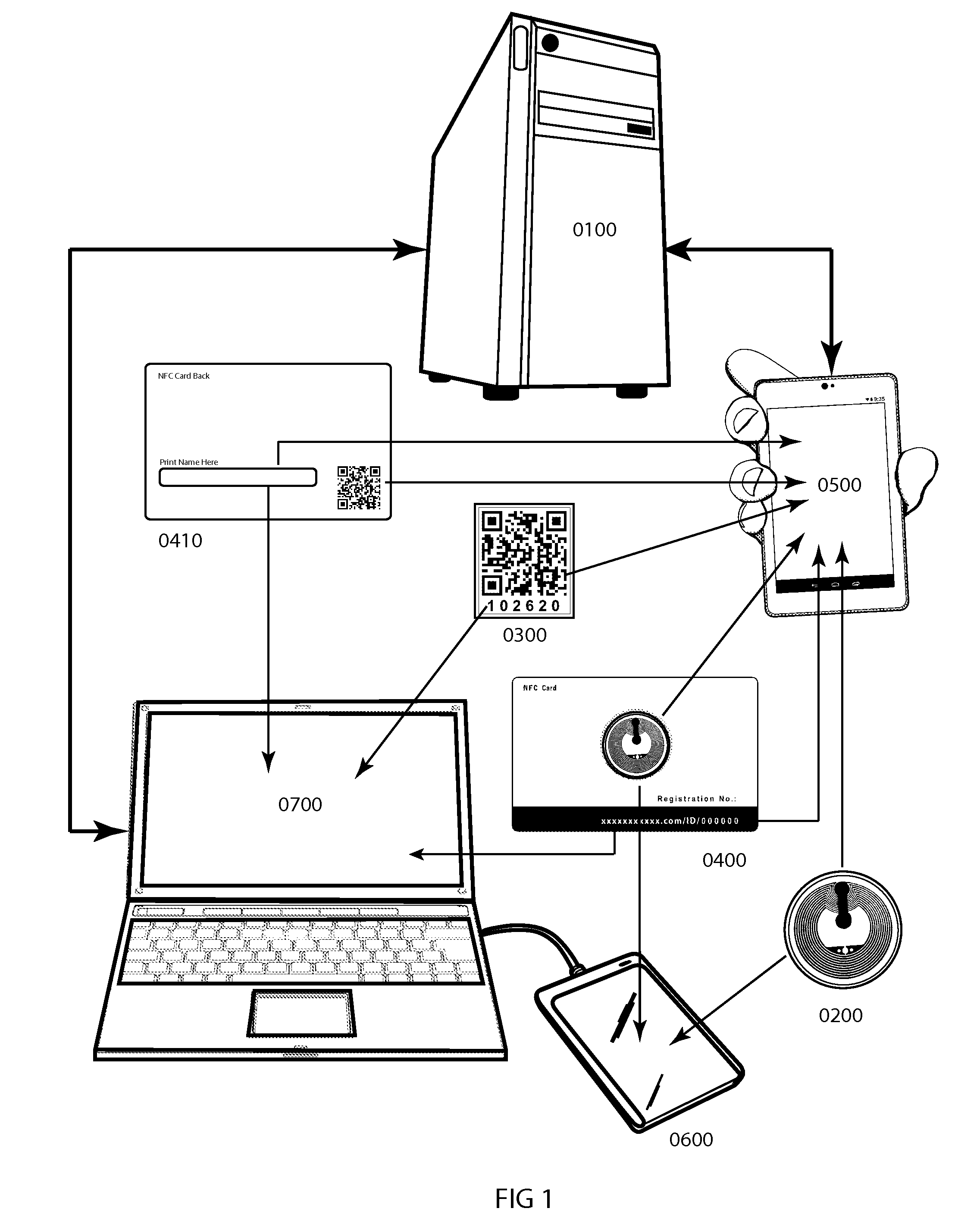
System and method for remotely viewing, managing and / or verifying online security status and ownership records of registered personal and business properties on a host server. The system is engaged using wireless or wired Internet-connected transceiver devices capable of interfacing with the host server by hyperlinking to a property's unique Internet Protocol (IP) address upon interrogation of encoded Near Field Communication (NFC) tag(s) or quick read (QR) code(s) target objects. These account-matching items are affixed to said property and also featured on the owner / registrar's smartcard ID along with the printed IP address registration number for manual Internet browser access. The system encourages public device interrogation for online viewing of property security status information, while a secure method of authentication restricts all other property account access to owner / registrar and law enforcement.
Owner:LIND MARSHALL G
Mobile terminal for backup and recovery of software and data and method thereof
InactiveCN101111017ARecover in timeRadio/inductive link selection arrangementsProgram loading/initiatingSoftware systemComputer module
The present invention discloses a mobile terminal and method to perform the backup and recovery of the software and data. On the base of the existing nonvolatile flash memory for the storing of the software and the data, the mobile terminal is increased with a backup storage module and a recovery controlling module, and when the user operation instruction can't be accepted or the mobile communication network can be accessed after the mobile terminal is started, and when the machine can't be recovered, the user can recover the mobile terminal into the security mode which can realize the basic functions through the recovery controlling module by utilizing the basic sub-ensemble in the backup storage module. The network can be further accessed, detection, restoration or online virus inspection and killing by utilizing the online security service. Even if the mobile terminal software system is damaged by the malicious code such as virus, the application of the present invention can timely restore the software system into the basic working state, for the convenience of the user to perform the further processing (such as the online virus inspection and killing, etc.).
Owner:ZTE CORP
System and method for continuous online safety and reliability monitoring
ActiveUS7117119B2Safety arrangmentsElectric testing/monitoringInstrument functionSafety Integrity Level
A system and method for continuous online safety and reliability monitoring is disclosed. The method includes the steps of obtaining operating information about at least one of a plurality of instrumented function components, which are part of an instrumented function, and determining a probability of failure on demand for the instrumented function based on the operating information. In variations, operating information includes status information, which may be received from and / or provided to an asset management application. In some variations, instantaneous probability of failure on demand, online mean time to failure (MTTF), and online safety integrity level (SIL) are also calculated for an instrumented function. In yet further variations, the system allows a user to predict probability of failure on demand values into the future based on hypothetical and / or future planned test times.
Owner:SCHNEIDER ELECTRIC SYST USA INC
System and method for continuous online safety and reliability monitoring
ActiveUS20050027374A1Safety arrangmentsDigital computer detailsInstrument functionSafety Integrity Level
A system and method for continuous online safety and reliability monitoring is disclosed. The method includes the steps of obtaining operating information about at least one of a plurality of instrumented function components, which are part of an instrumented function, and determining a probability of failure on demand for the instrumented function based on the operating information. In variations, instantaneous probability of failure on demand, online mean time to failure (MTTF), and online safety integrity level (SIL) are also calculated for an instrumented function. In other variations of the invention, alarms are reported to an operator based on the variance indicating the probability of failure on demand for the instrumented function is too high. In yet further variations, the system allows a user to predict probability of failure on demand values into the future based on hypothetical and / or future planned test times.
Owner:SCHNEIDER ELECTRIC SYST USA INC
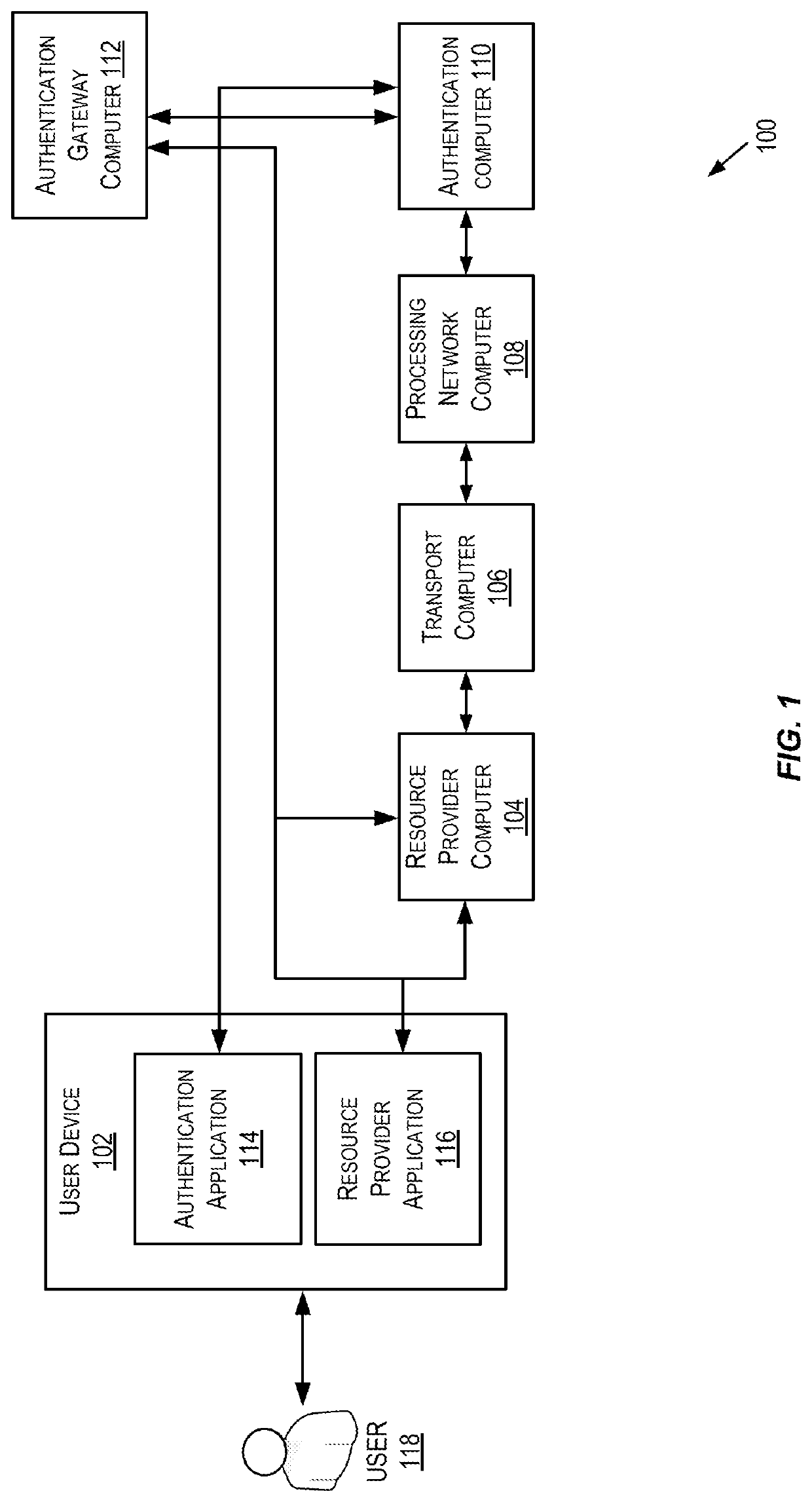
Online secure transaction verification system proxy server and method
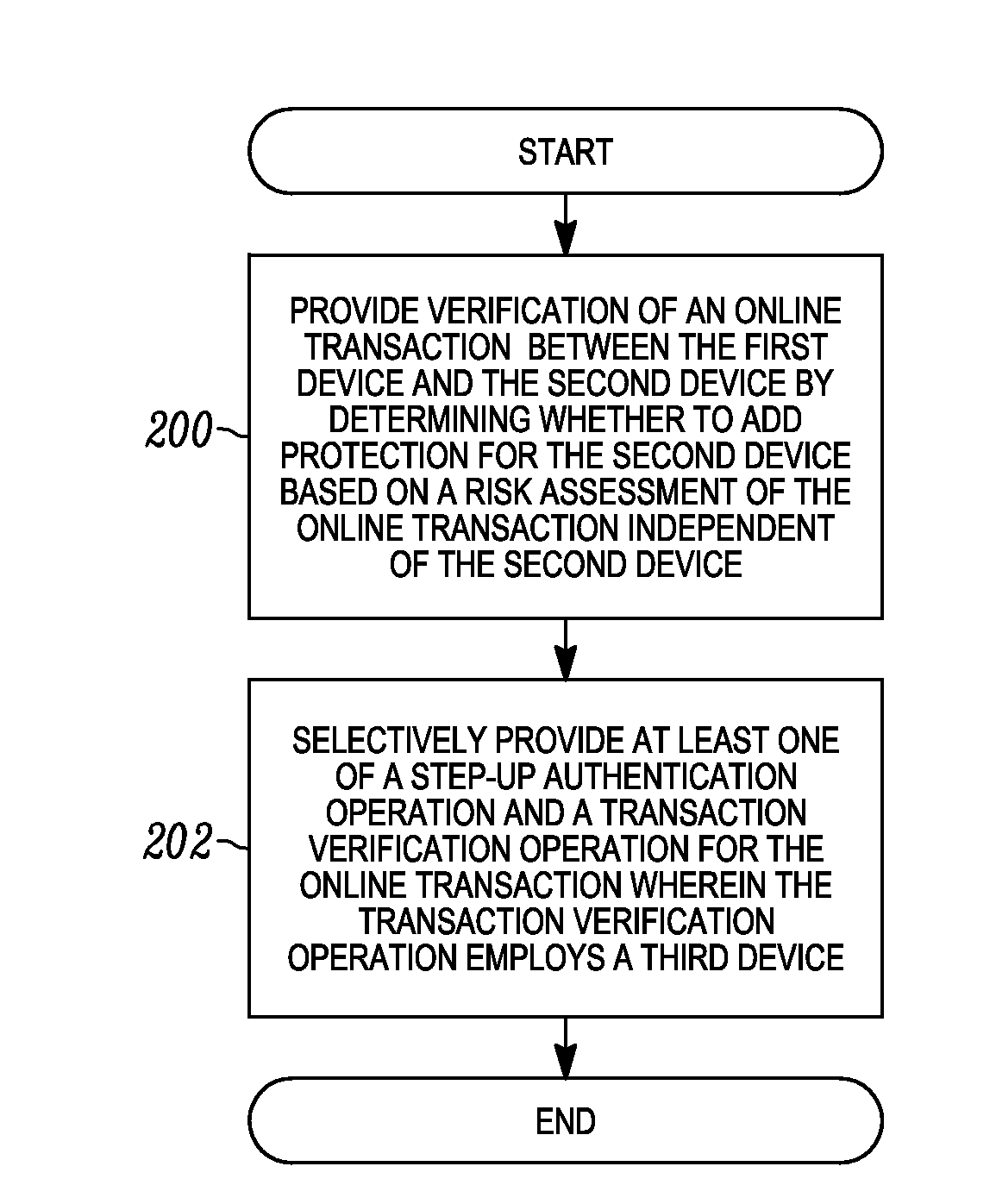
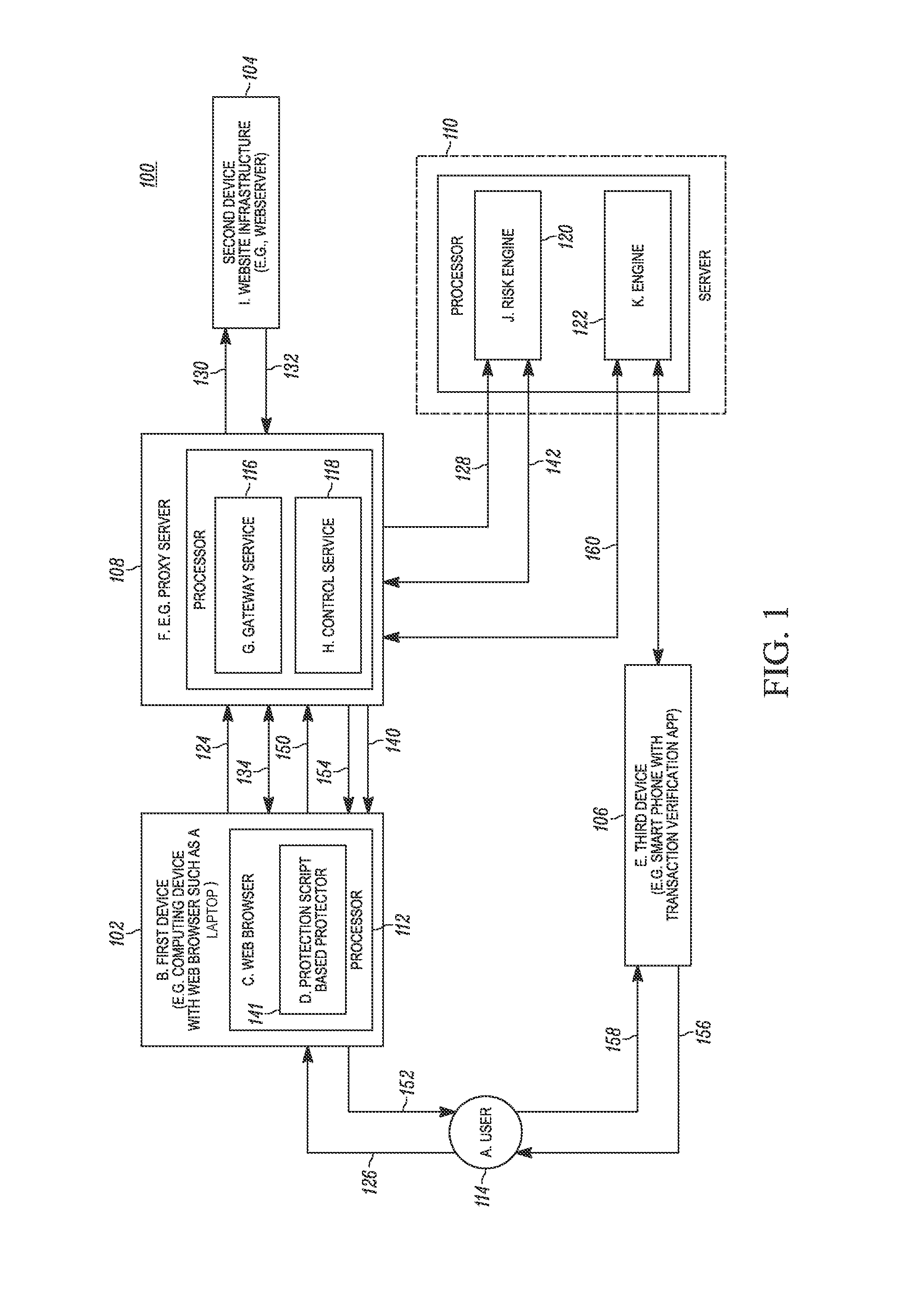
ActiveUS20140373093A1Digital data processing detailsMultiple digital computer combinationsUser deviceWeb browser
In one example, a proxy server acts as a gateway to a website and modifies the traffic between a web browser on a user device and the website server, as necessary to request protection by providing step-up authentication and / or transaction verification. The proxy server blocks transactions when protection is required but has not occurred (either because the authentication was not proper or due to the detection of another problem). Associated methods and systems are also provided.
Owner:ENTRUST
Online, safe service technique for automated libraries
ActiveUS7255525B2Record information storageAutomatic cassette changing arrangementsNormal modeOperating system
A safety system for online servicing of a media library is provided, wherein the library comprises a plurality of media storage cells and at least one media picker robot that moves along the media storage cells, and wherein the library is contained within an enclosure having at least one access means. The safety system detects whether the access means in the enclosure is open or closed and operates the robot in the media library in one of two corresponding modes. If the access means is closed, the robot operates in a normal mode at a first specified speed. If the access means is open, the robot operates in a safe mode at a second specified speed that is slower than the first speed of the normal mode. In another embodiment, while in safe mode, the picker robot is excluded from moving within a restricted zone in the library.
Owner:ORACLE INT CORP
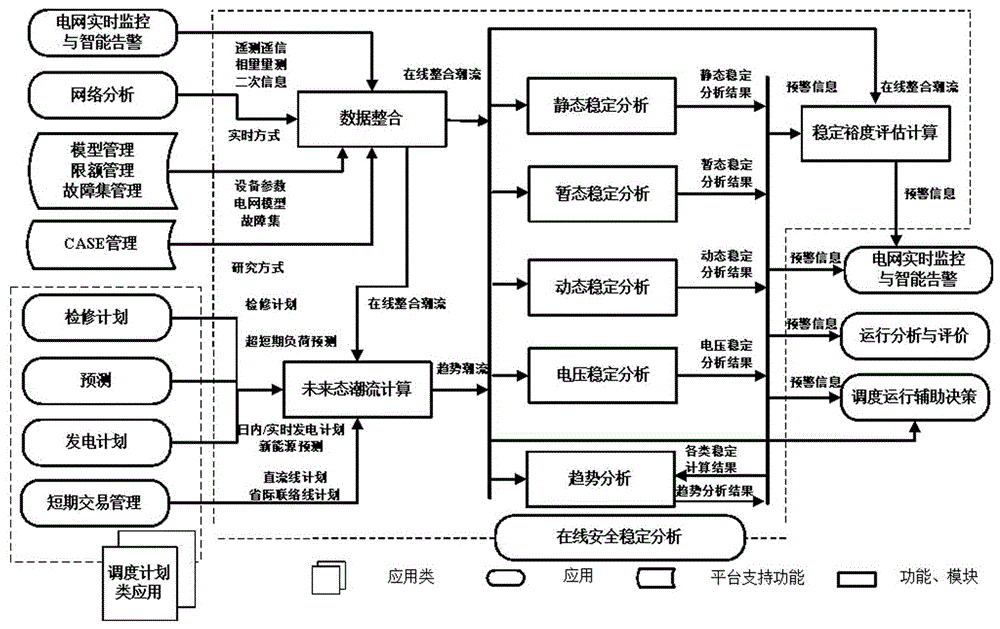
On-line platform-based power grid accident pre-arranged plan automatic realization method
The invention discloses an on-line platform-based power grid accident pre-arranged plan automatic realization method which comprises the following steps: a forecast trend of a power grid is obtained; an anticipated accident set is established; emergency control aid decisions and control objects and post-accident power grid preventive control aid decisions and control objects for the anticipated accident set are generated; an accident pre-arranged plan is generated and is chosen as a matching pre-arranged plan, and therefore a power grid accident pre-arranged plan is realized. According to the on-line platform-based power grid accident pre-arranged plan automatic realization method provided in the invention, based on an on-line safety and stability analyzing system, complete power grid accident pre-arranged plan automatic realization processes are designed via strict trend prediction, scientific accident anticipation and fault surface search, and mature operation analysis check and control aid decisions; a function mechanism via which power grid accident pre-arranged plans can be automatically edited, the pre-arranged plans can be instantly popped out when accidents occur and safety monitoring of whole processes can be realized is established; improvement and high-efficiency application of pre-arranged plan quality are facilitated, and labor intensity and accident processing risk of dispatchers are lowered.
Owner:STATE GRID CORP OF CHINA +1
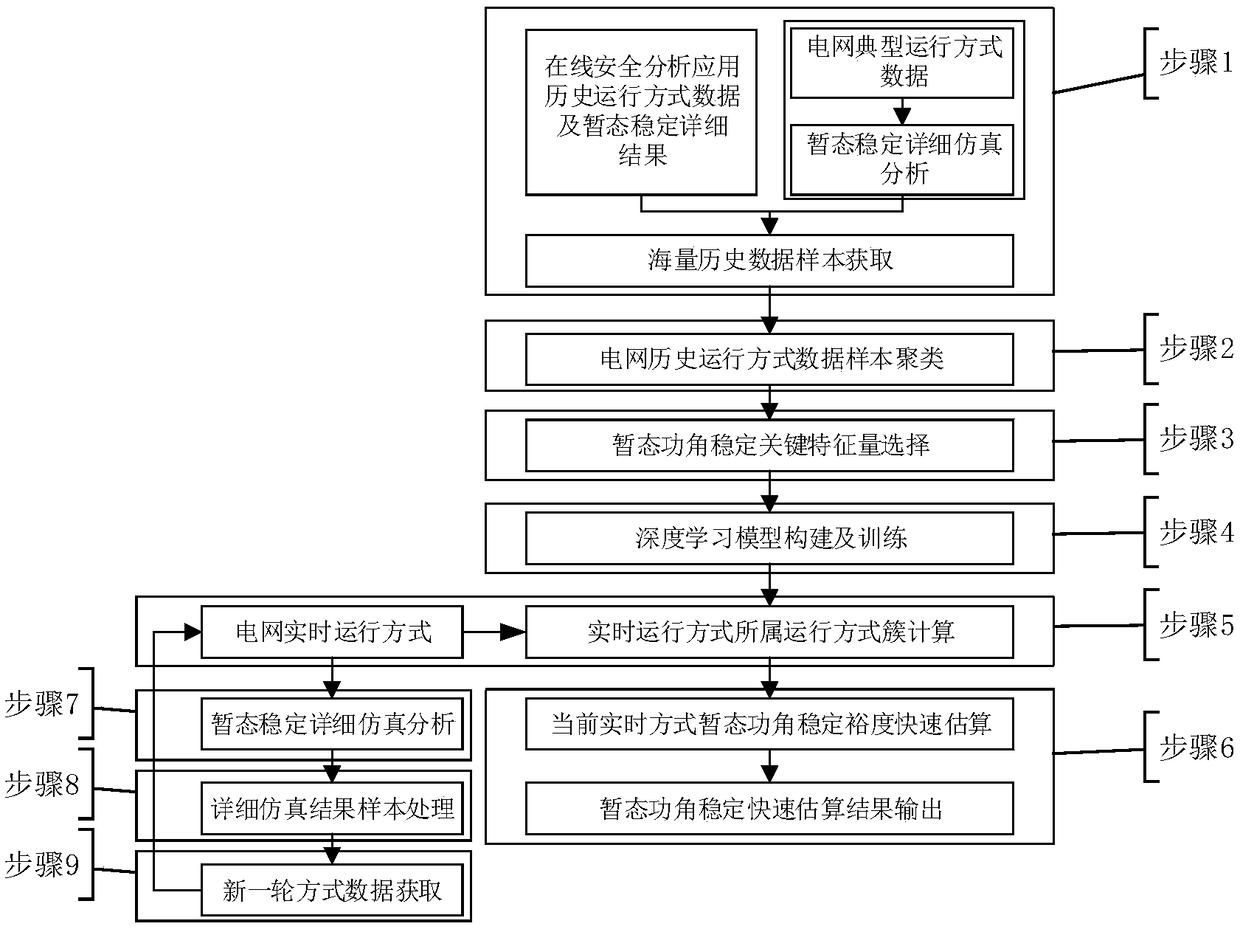
Rapid evaluation method for transient angle stability based on comprehensive causal analysis and machine learning
The invention discloses a rapid evaluation method for transient angle stability based on a comprehensive causal analysis and machine learning, which comprises dividing a historical operation mode sample into several operation mode clusters based on historical data stored by a transient stability evaluation function of online security analysis applications, describing the transient angle stabilitymargin by linearization formula according to the difference between the modes, and extracting a key feature quantity of a power grid; constructing a deep learning model and using a historical data sample to train by taking the key feature quantity as an input quantity and taking a historical operation mode cluster classification as an output quantity, establishing a relationship between a currentreal-time operation mode and the historical operation mode, and estimating the transient angle stability of the current real-time operation mode. According to the rapid evaluation method for transientangle stability based on the comprehensive causal analysis and machine learning, the calculation time consumption can be effectively reduced, and the quantitative analysis results of the power grid transient angle stability can be quickly obtained while ensuring the accuracy of the transient angle stability analysis. This helps to detect the transient operation risks existing in the power grid and improve the safe operation level of the power grid.
Owner:NARI TECH CO LTD +2
Power dispatching online trend early warning system based on ultra short term load prediction
The invention relates to the technical field of applying an online safety analysis result to load prediction, and particularly relates to a power dispatching online trend early warning system based on ultra short term load prediction. Particularly, through statistics, analysis and prediction on load data, a power grid future trend is calculated, and a power grid short term trend early warning and accident post-treatment plan is formed. The system of the invention comprises the following operation steps of short term load prediction based on electricity consumption large data analysis, trend tendency analysis through ultra short term load obtained based on an ARIMA algorithm, power grid risk assessment and warning, equipment maintenance schedule management, data access panoramic surveillance, treatment in the accident and power supply restoration after the accident. Linkage between the online trend early warning and dispatching plan change information can be realized, and a trend analysis early warning and assistant decision-making system with integration of a province and regions can be formed.
Owner:STATE GRID LIAONING ELECTRIC POWER RES INST +1
Online secure device provisioning framework
ActiveUS20110258685A1Digital data processing detailsUser identity/authority verificationUser identifierDatabase
A method for updating network-enabled devices with new identity data includes generating a plurality of new identity data records and loading the new identity data records onto an update server. A request is received at the update server for new identity data from at least one network-enabled device having a previously assigned identity linked to an identifier. The previously assigned identifier is linked to a new identifier that is linked to one of the new identity data records. One or more new identity data records are securely delivered to the network-enabled device.
Owner:GOOGLE TECH HLDG LLC
Use of biometrics and privacy preserving methods to authenticate account holders online
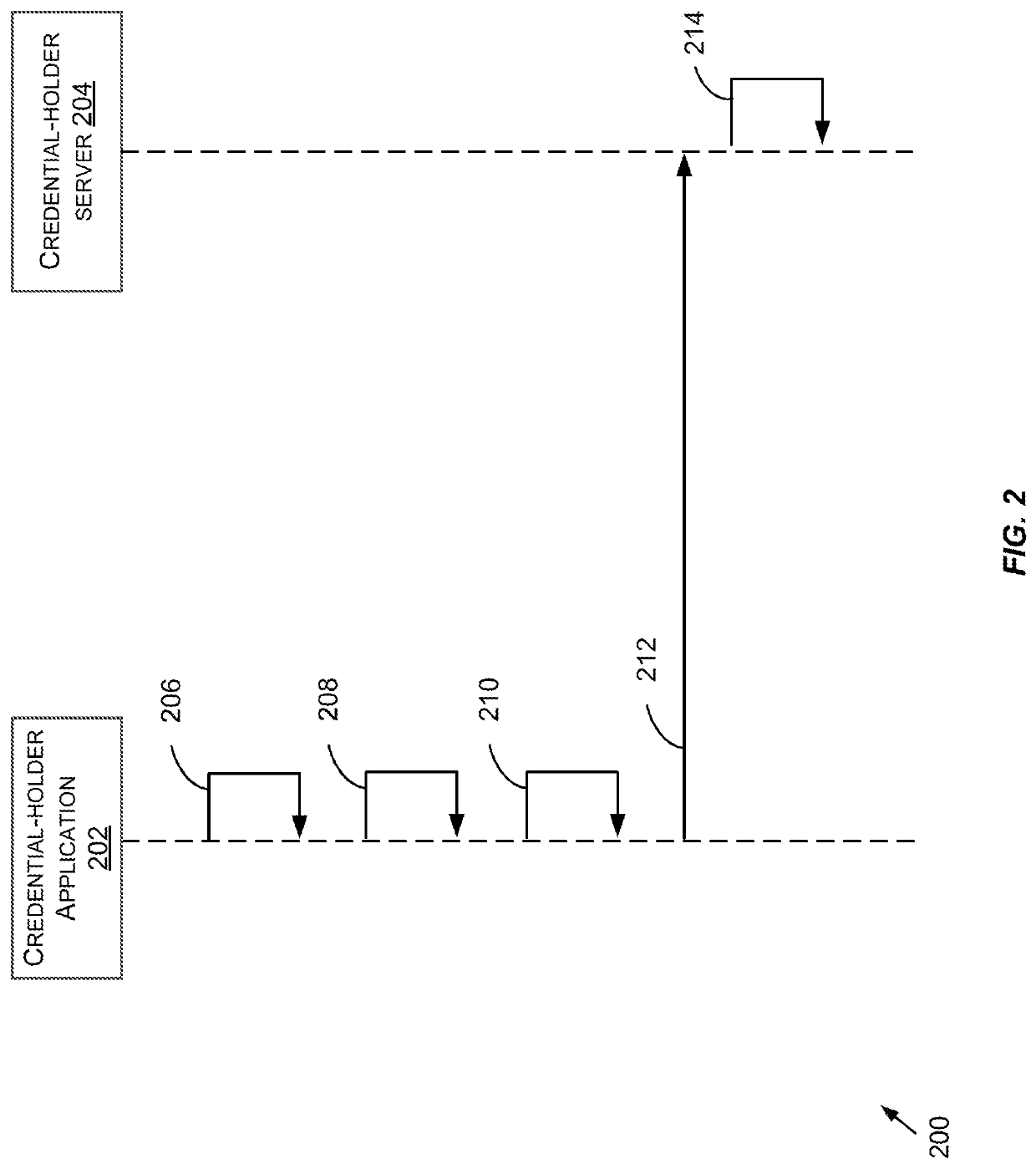
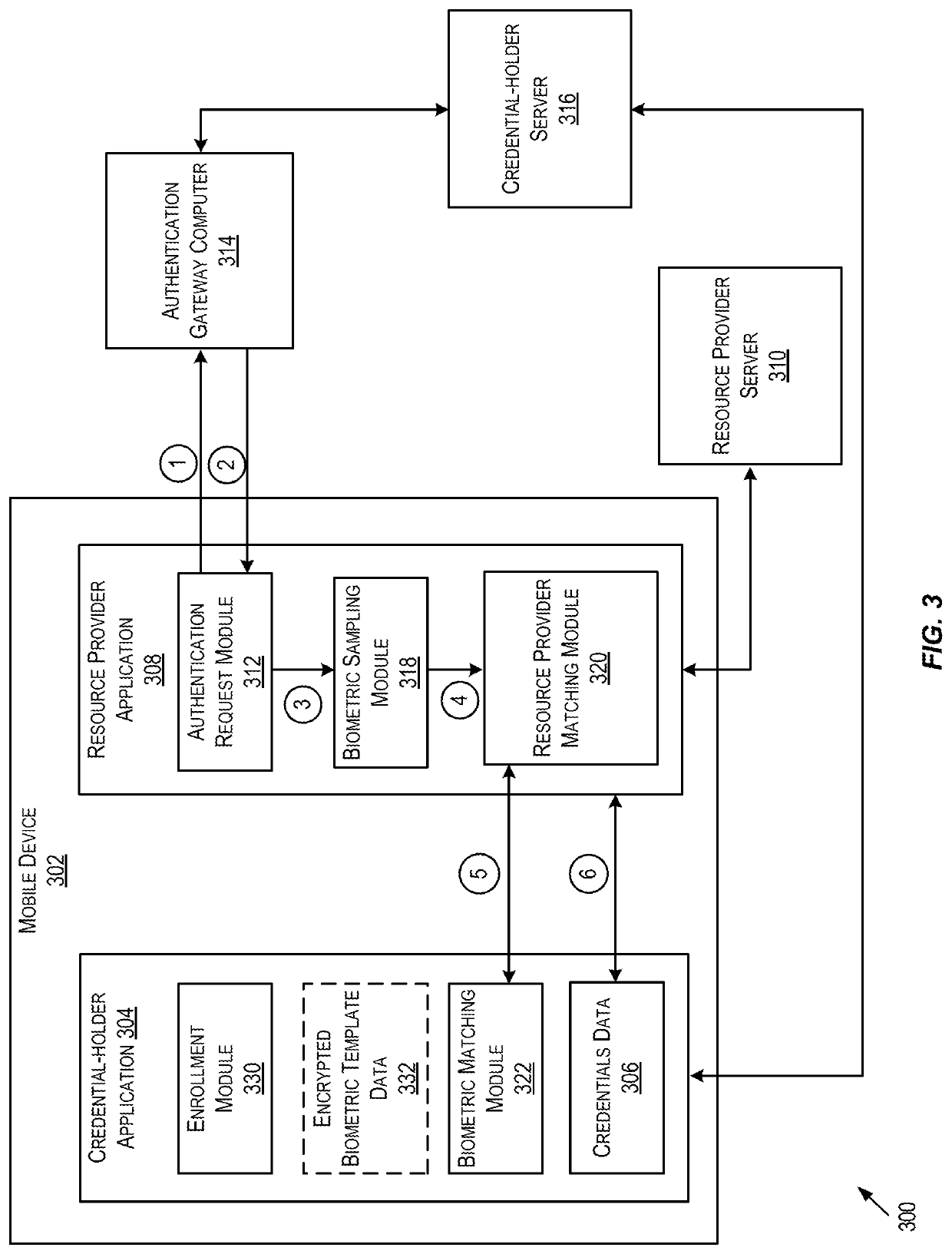
PendingUS20200228340A1Secure performanceKey distribution for secure communicationUser identity/authority verificationBiometric dataEngineering
Embodiments are directed to a method for securely performing biometric authentication online. The method described can be used to securely perform biometric authentication on a mobile device. For protecting the privacy of the users biometric data, a cryptographic comparison protocol can be used to perform matching of encrypted templates. For example, the cryptographic comparison protocol may involve Fuzzy Extractors (FE), Homomorphic Encryption (HE), and / or Secure Multi-Party Computation (SMPC).
Owner:VISA INT SERVICE ASSOC
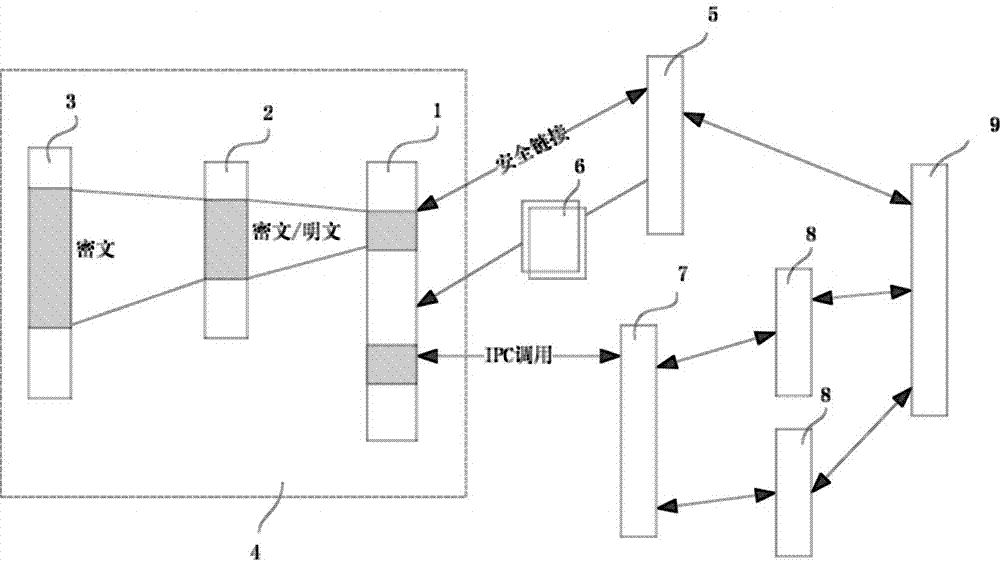
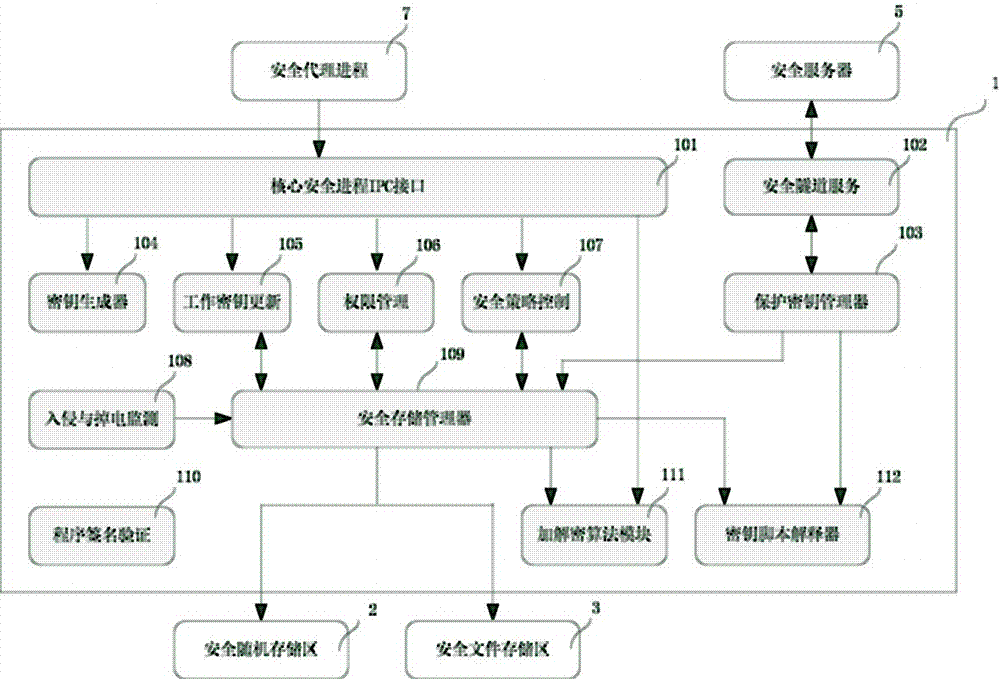
Online security key protection method and system
The present invention proposes a method and system for online security key protection. The method includes: running the core security process when the terminal is started, initializing or binding the secure random storage area and the secure file storage area; starting and running the encryption and decryption algorithm module, according to The security policy configuration provides the encryption and decryption algorithm interface for the security agent process; maintains a key life cycle parameter in the security file storage area, and automatically interacts with the security server when the life cycle expires to update the key script file; references terminal feature parameter analysis Run the key script file to dynamically generate a protection key, use the protection key to encrypt the working key, and store the ciphertext of the working key in a secure file storage area. The invention realizes a low-cost, high-security security key protection scheme that fully utilizes software technology without modifying the hardware scheme, and is applicable to information security fields such as mobile payment and data security storage.
Owner:周念东
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com