Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
418 results about "Internet security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet security is a branch of computer security specifically related to not only Internet, often involving browser security and the World Wide Web, but also network security as it applies to other applications or operating systems as a whole. Its objective is to establish rules and measures to use against attacks over the Internet. The Internet represents an insecure channel for exchanging information, which leads to a high risk of intrusion or fraud, such as phishing, online viruses, trojans, worms and more.
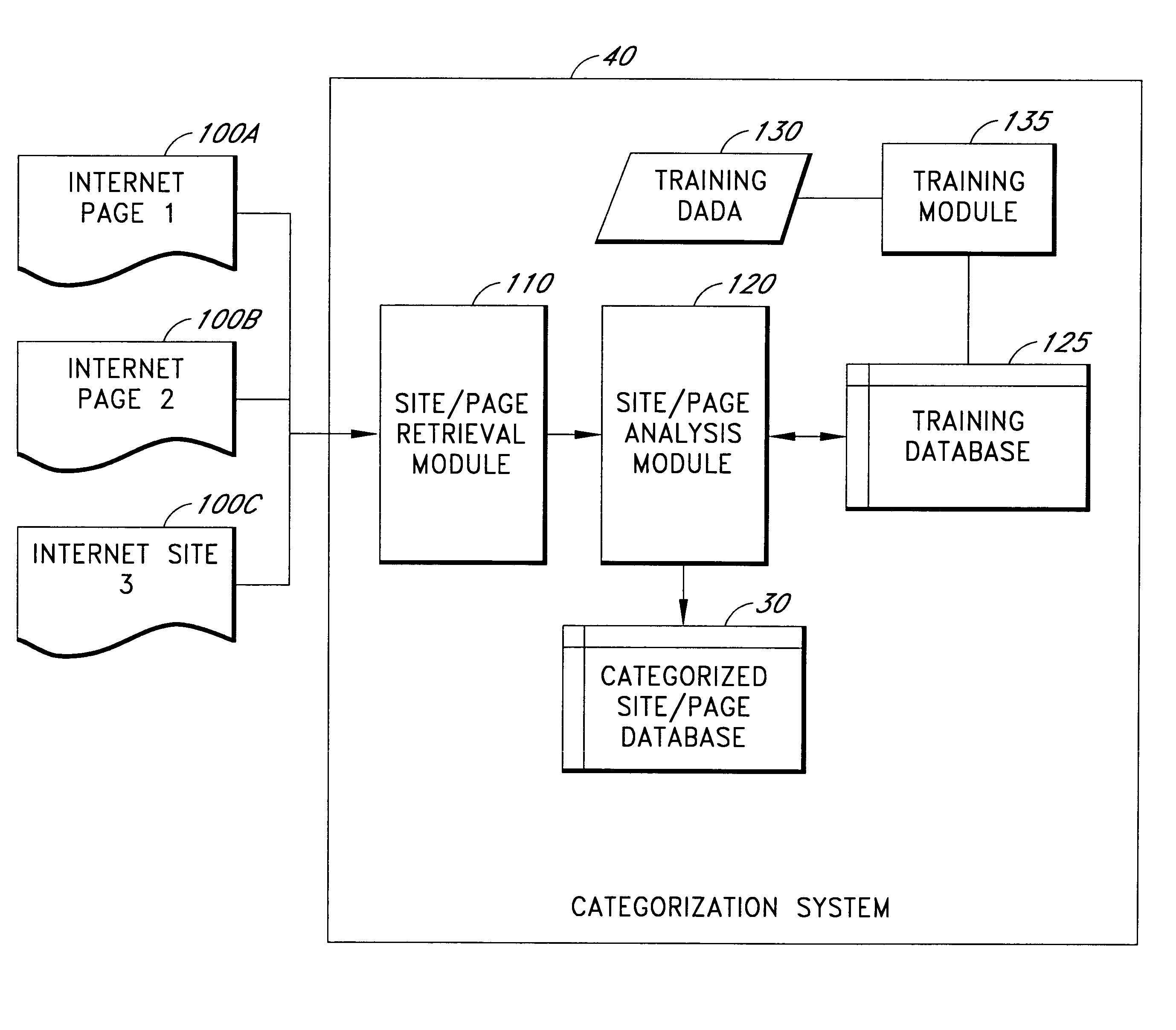
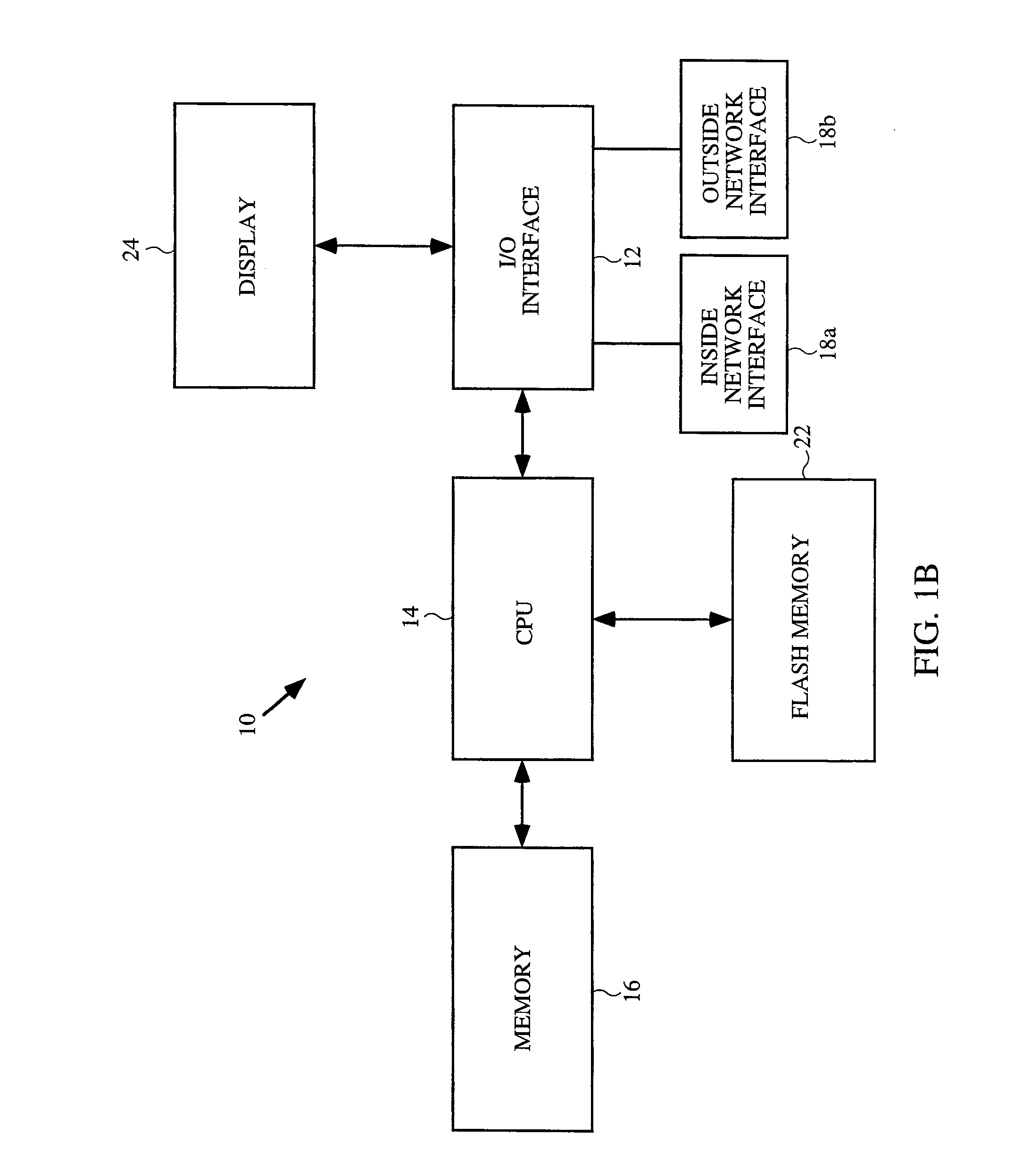
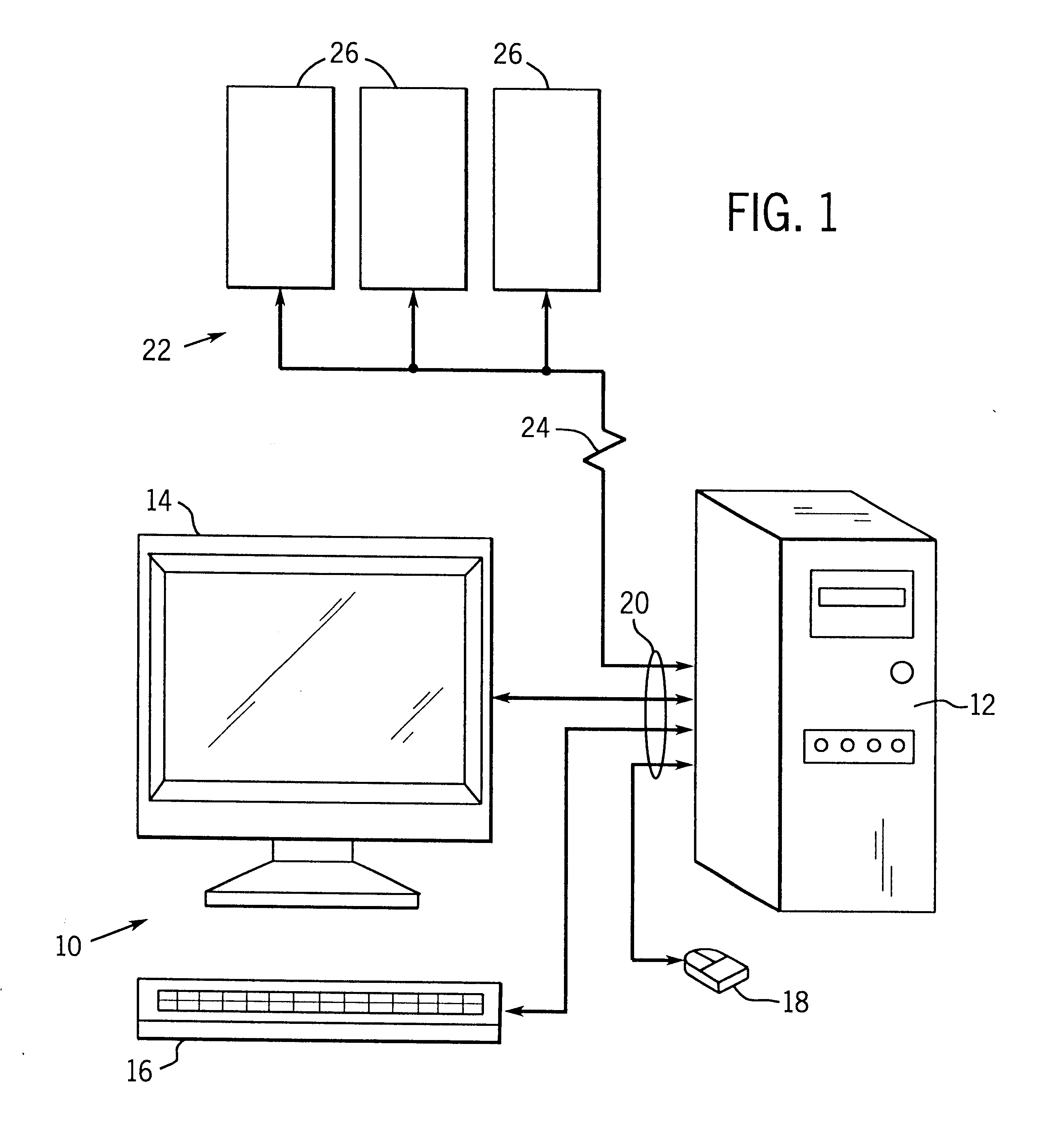
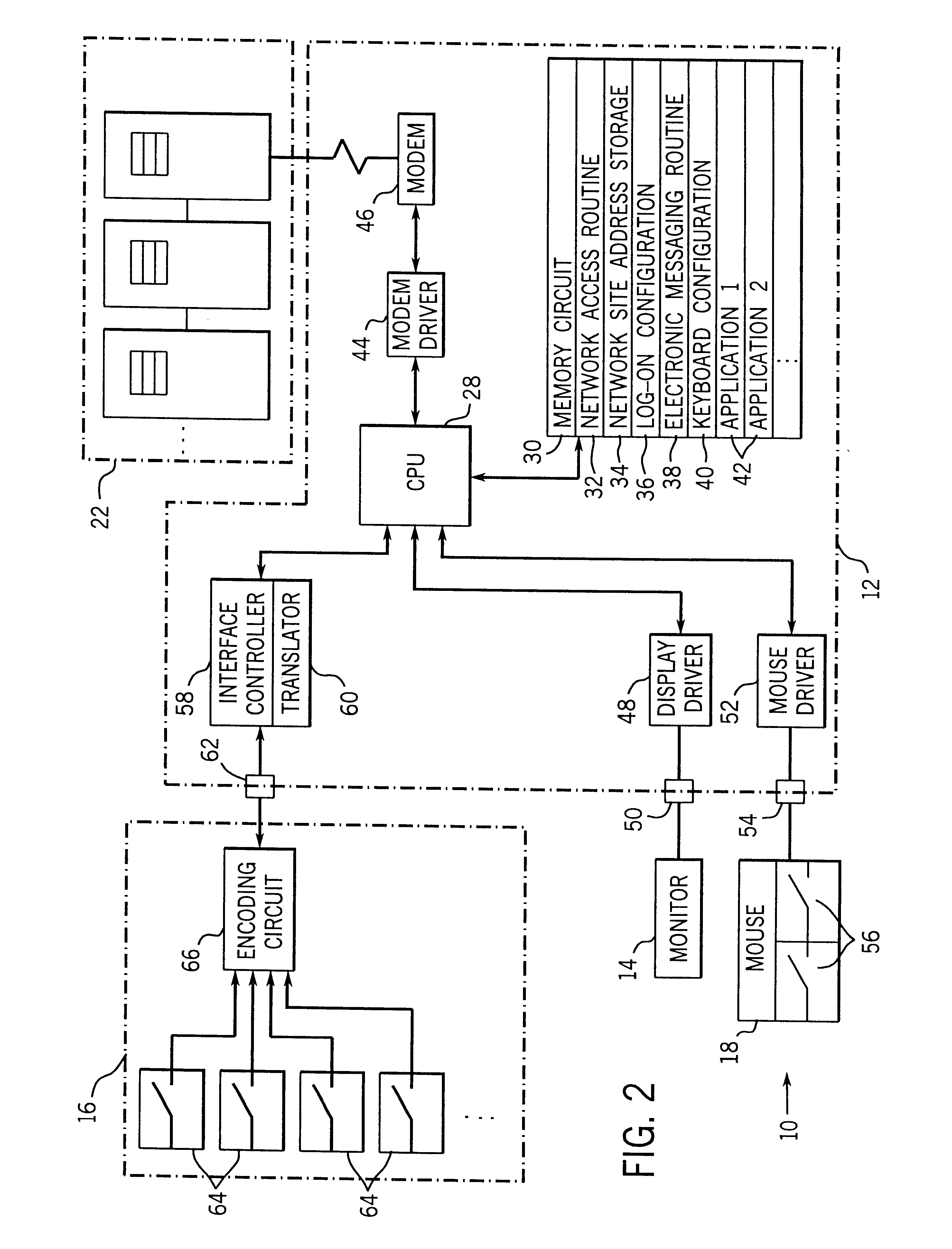
System and method for controlling access to internet sites
InactiveUS6606659B1Digital data information retrievalDigital data processing detailsThe InternetInternet security
A method and system for providing flexible access to Internet sites is described. The system includes a database of Internet sites that have been categorized so that the system determines the category of information that a user is accessing on the Internet. The system is also programmed so users are only allowed to access sites within a particular category a limited number of times. Moreover, users can requested a postponed access, wherein the site they are requesting is stored to a server, and available to the user at a later time. In addition, if a user chooses to access a site that is within certain predefined categories, they are presented with the option of retrieving the page, but notified that their access will be logged to a file.
Owner:FORCEPOINT LLC
Filtering techniques for managing access to internet sites or other software applications
A method and system for providing flexible access resources or services related to particular software applications are described. The system includes a database of Internet sites that have been categorized so that the system determines the category of information that a user is accessing on the Internet. The system is also programmed so users are only allowed to access sites a limited number of times. The system is further programmed to limit a user's access to the Internet based on the network's current bandwidth usage. Moreover, users can requested a postponed access, wherein the resource or service they are requesting is stored to a server, and available to the user at a later time. In addition, if a user chooses to access a resource or service that is within certain predefined categories, they are presented with the option of retrieving the resource or service, but notified that their access will be logged to a file.
Owner:FORCEPOINT LLC
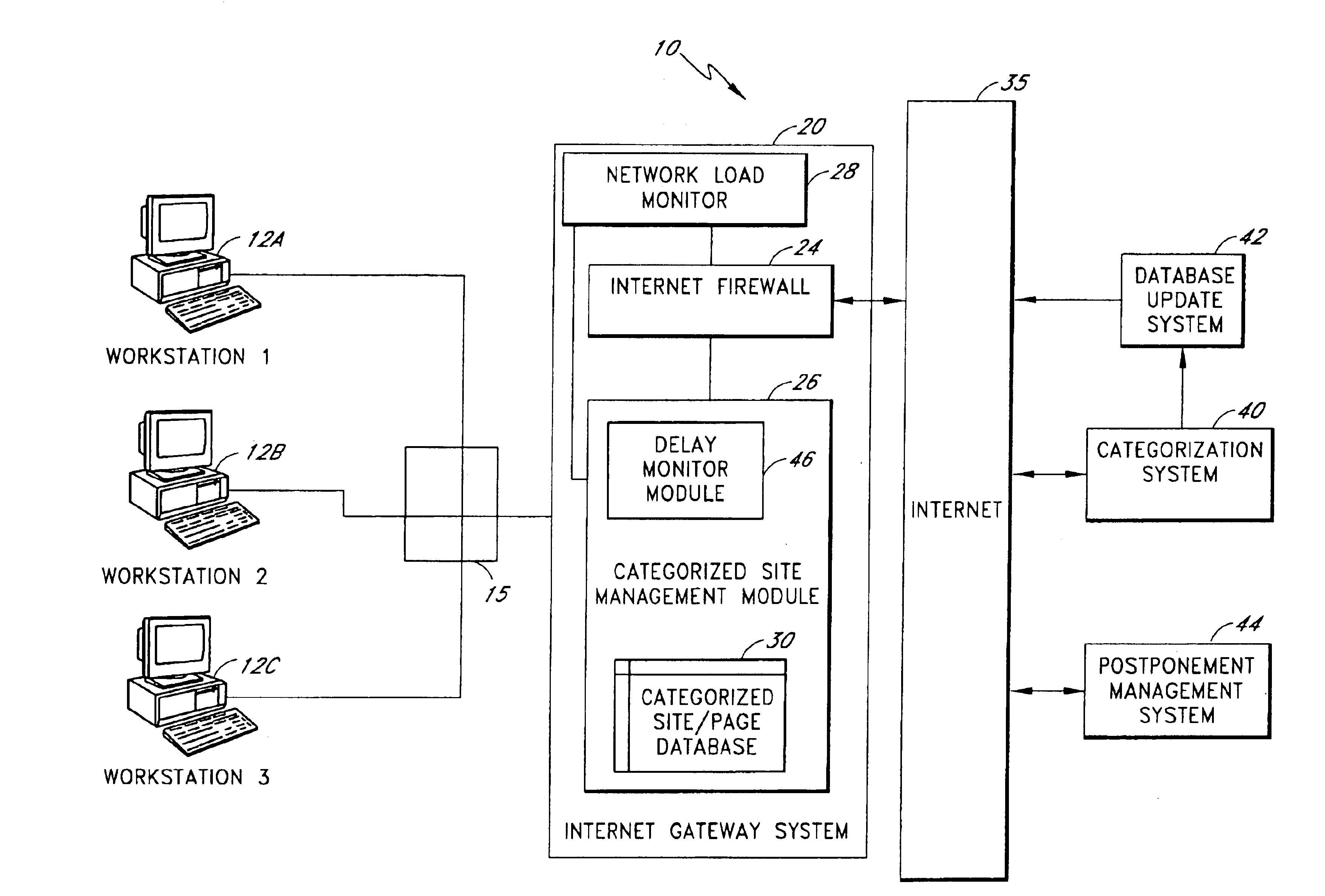
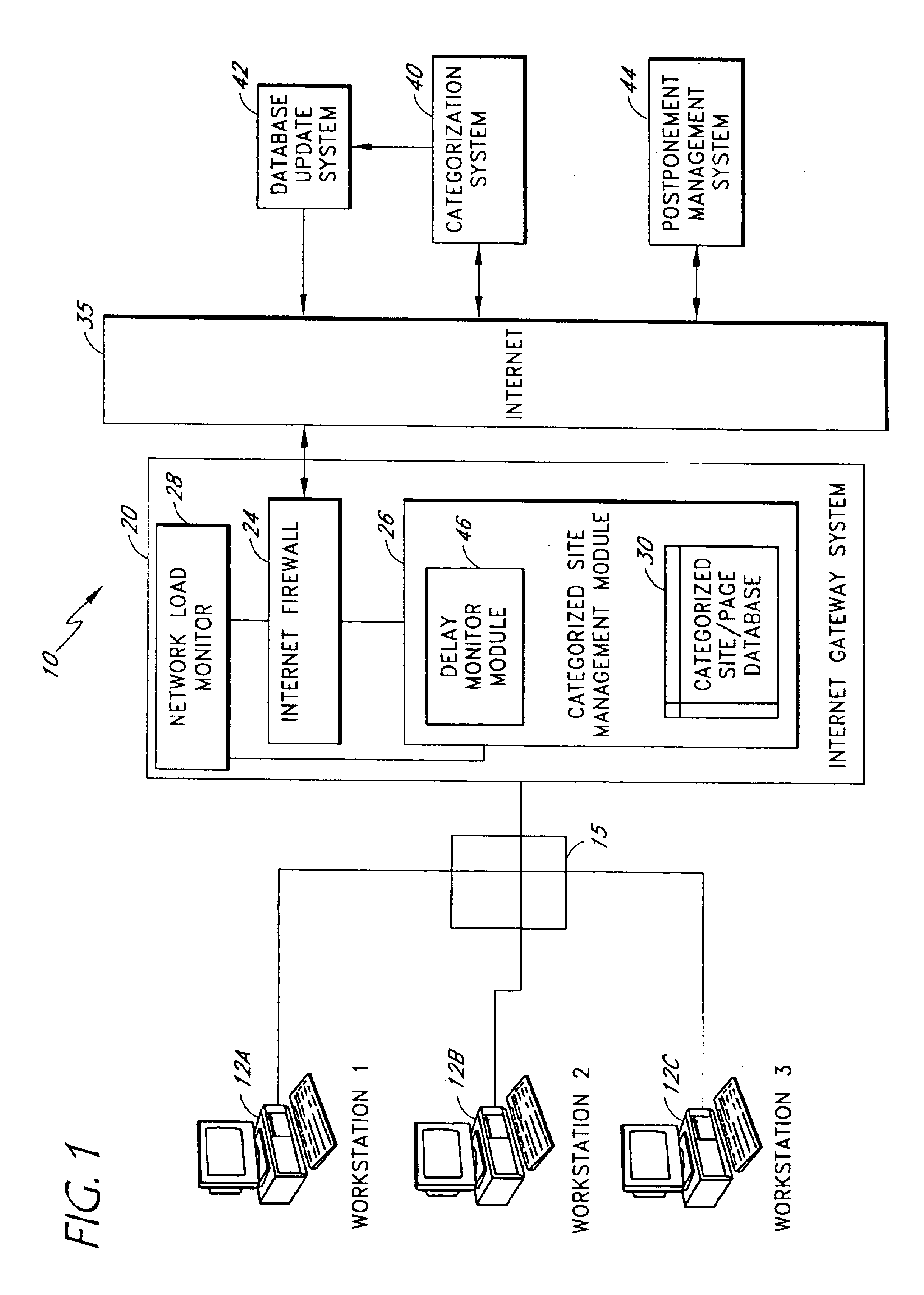
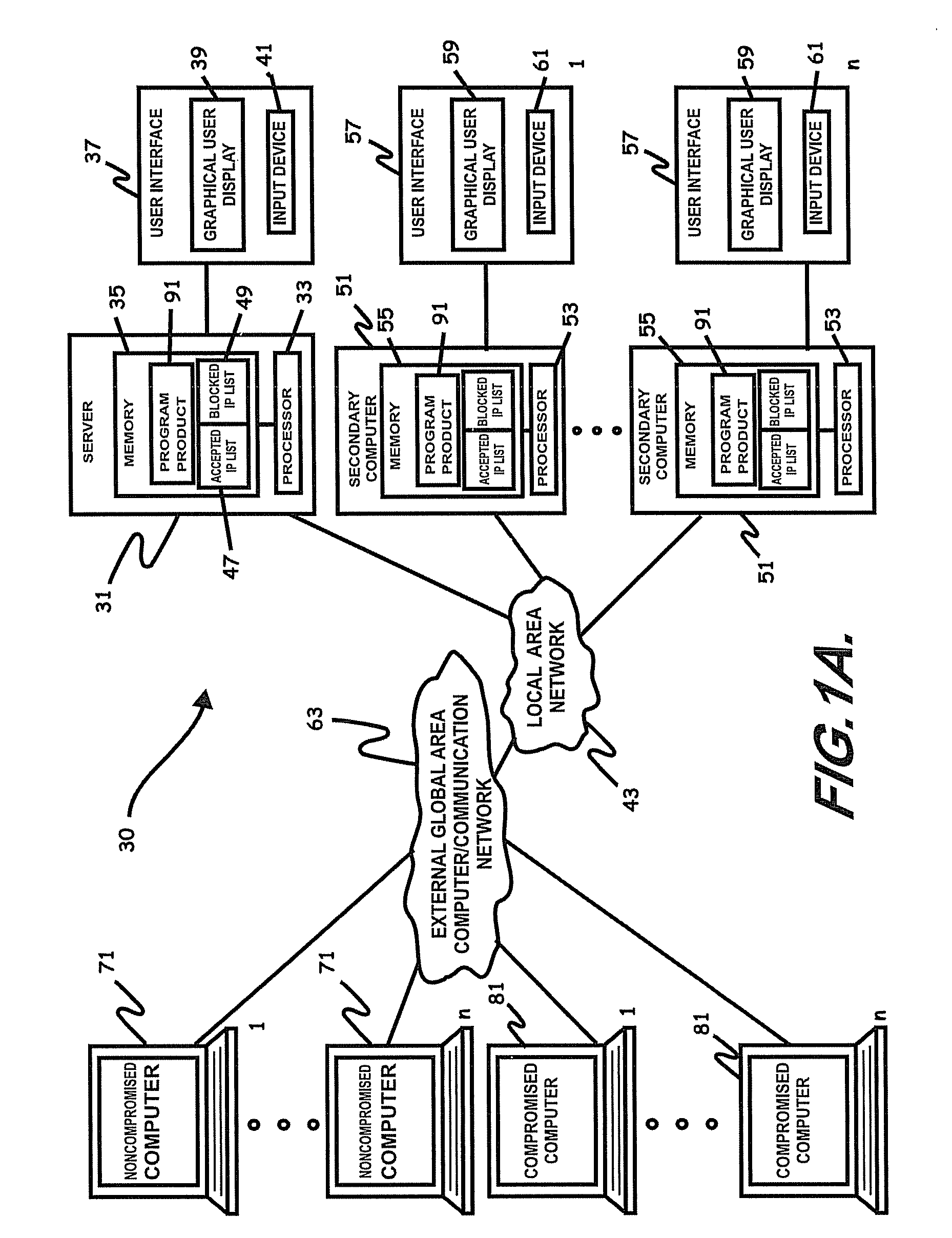
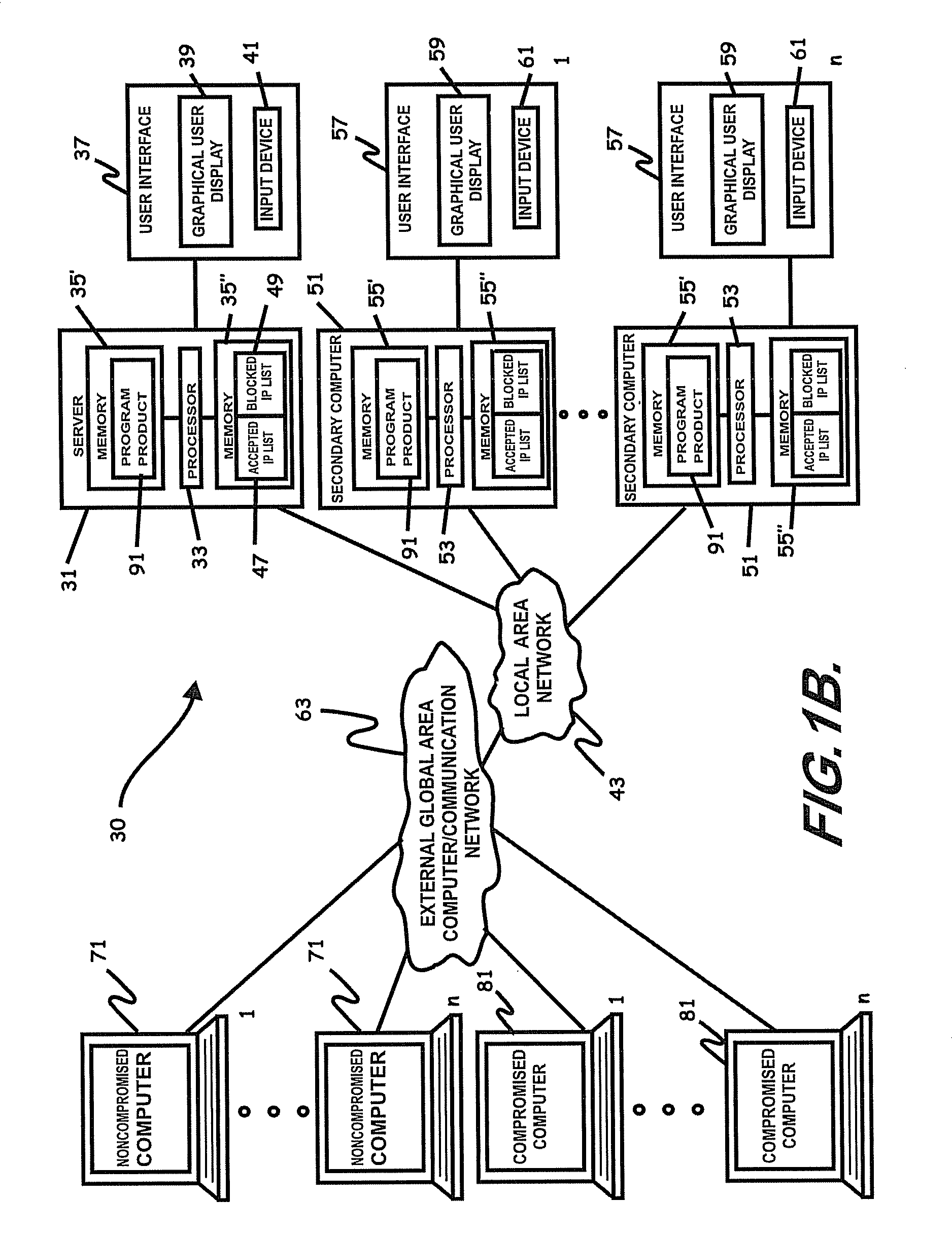
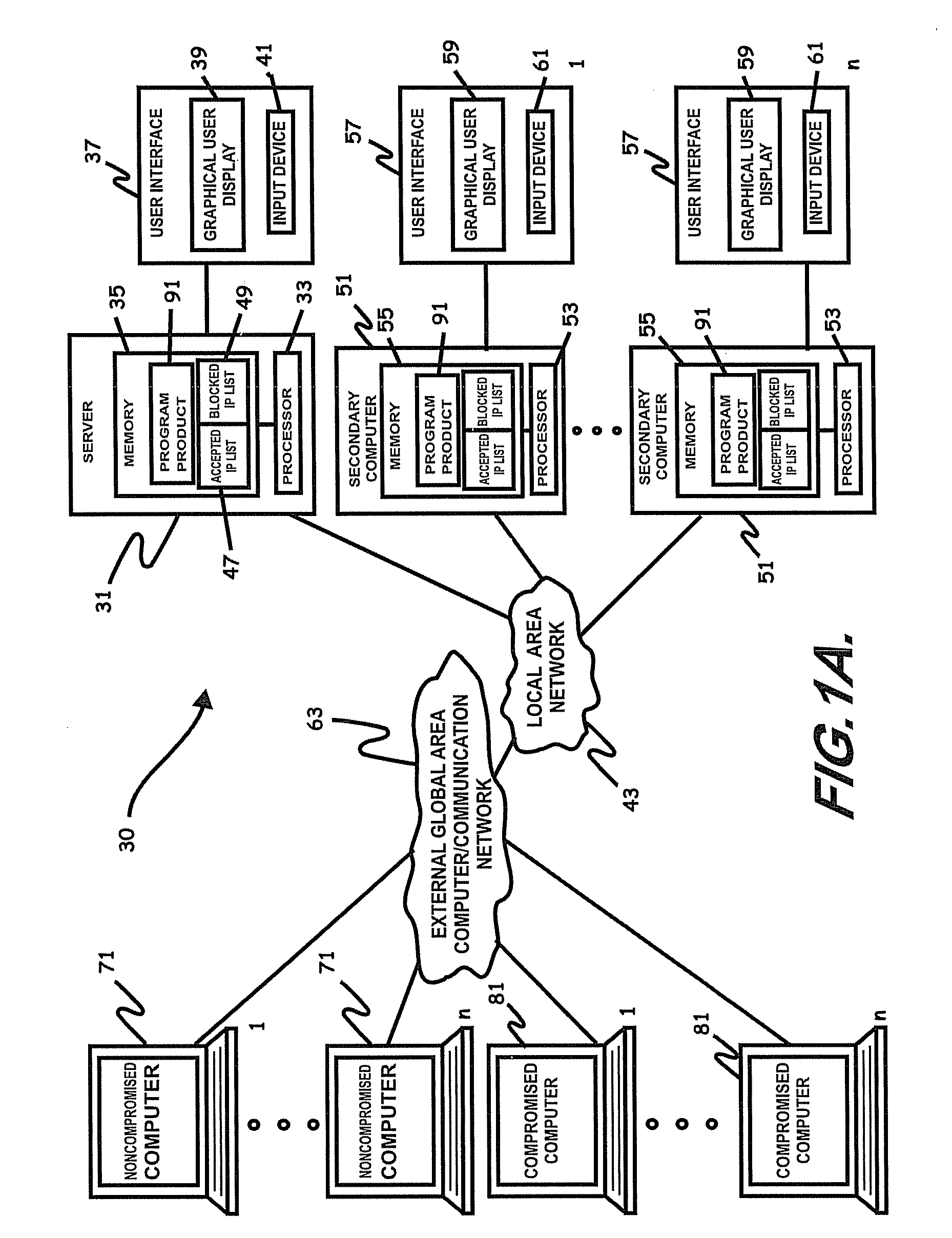
Internet security dynamics assessment system, program product, and related methods
ActiveUS8069471B2Prevent malicious attacksLimited accessMemory loss protectionDigital data processing detailsIp addressThe Internet
Owner:LOCKHEED MARTIN CORP
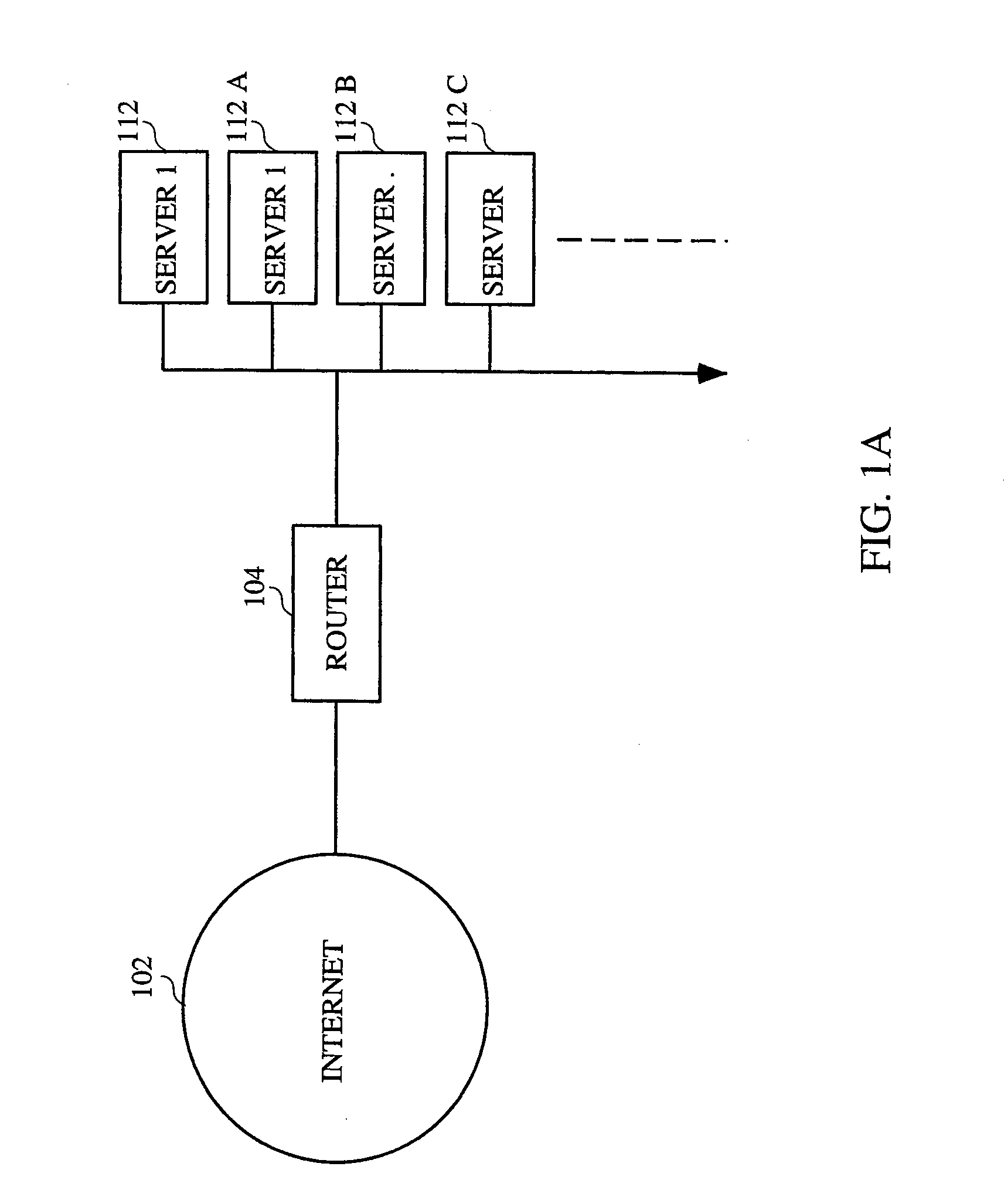
System for Distributing Load Over Multiple Servers at an Internet Site
Owner:CISCO TECH INC
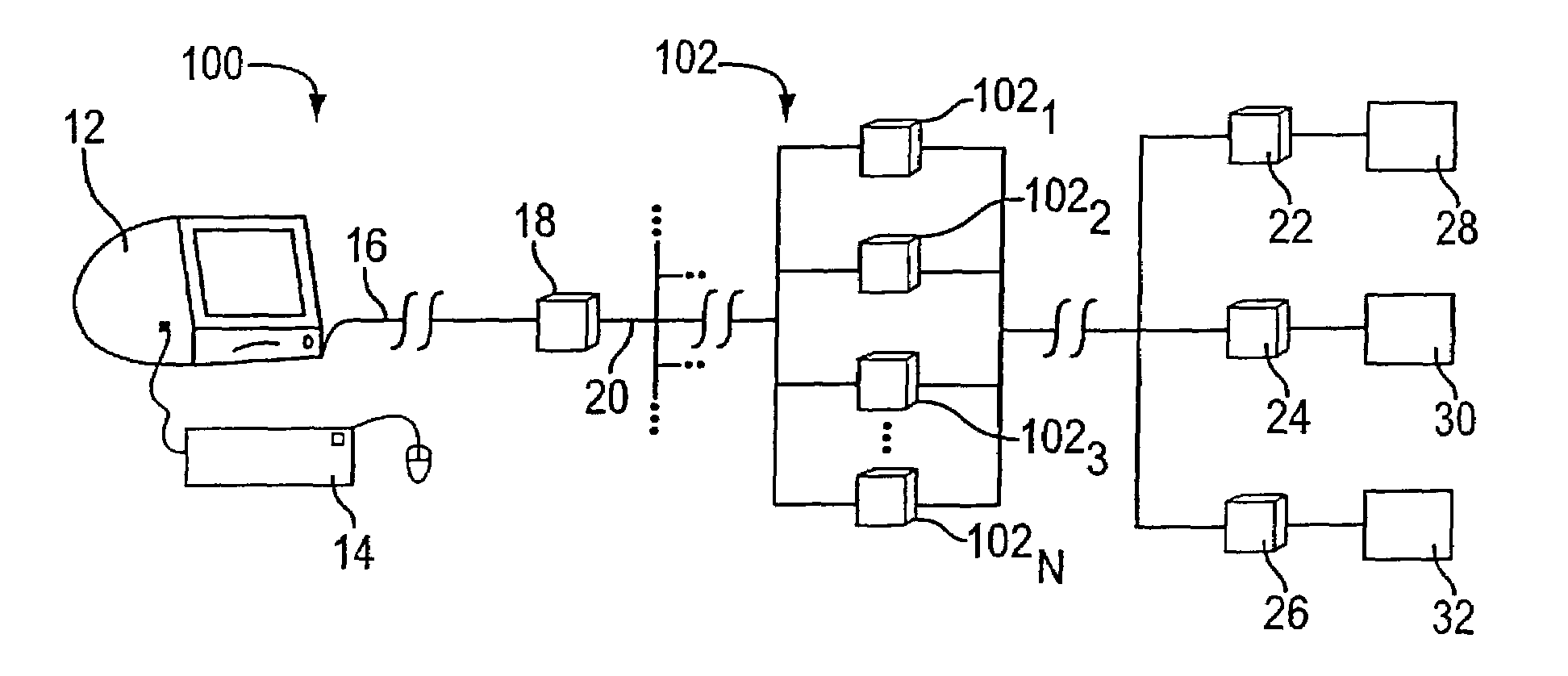
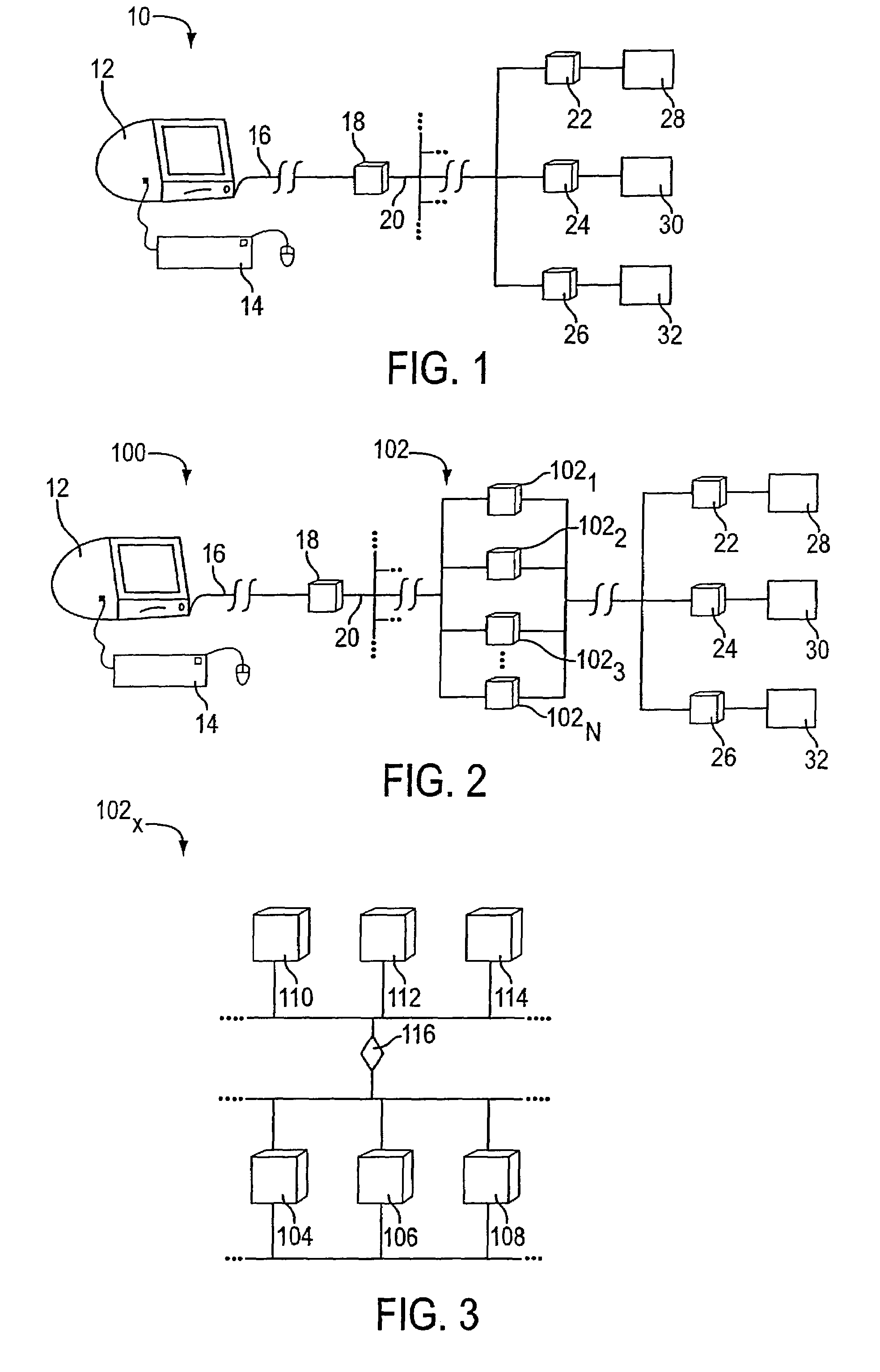
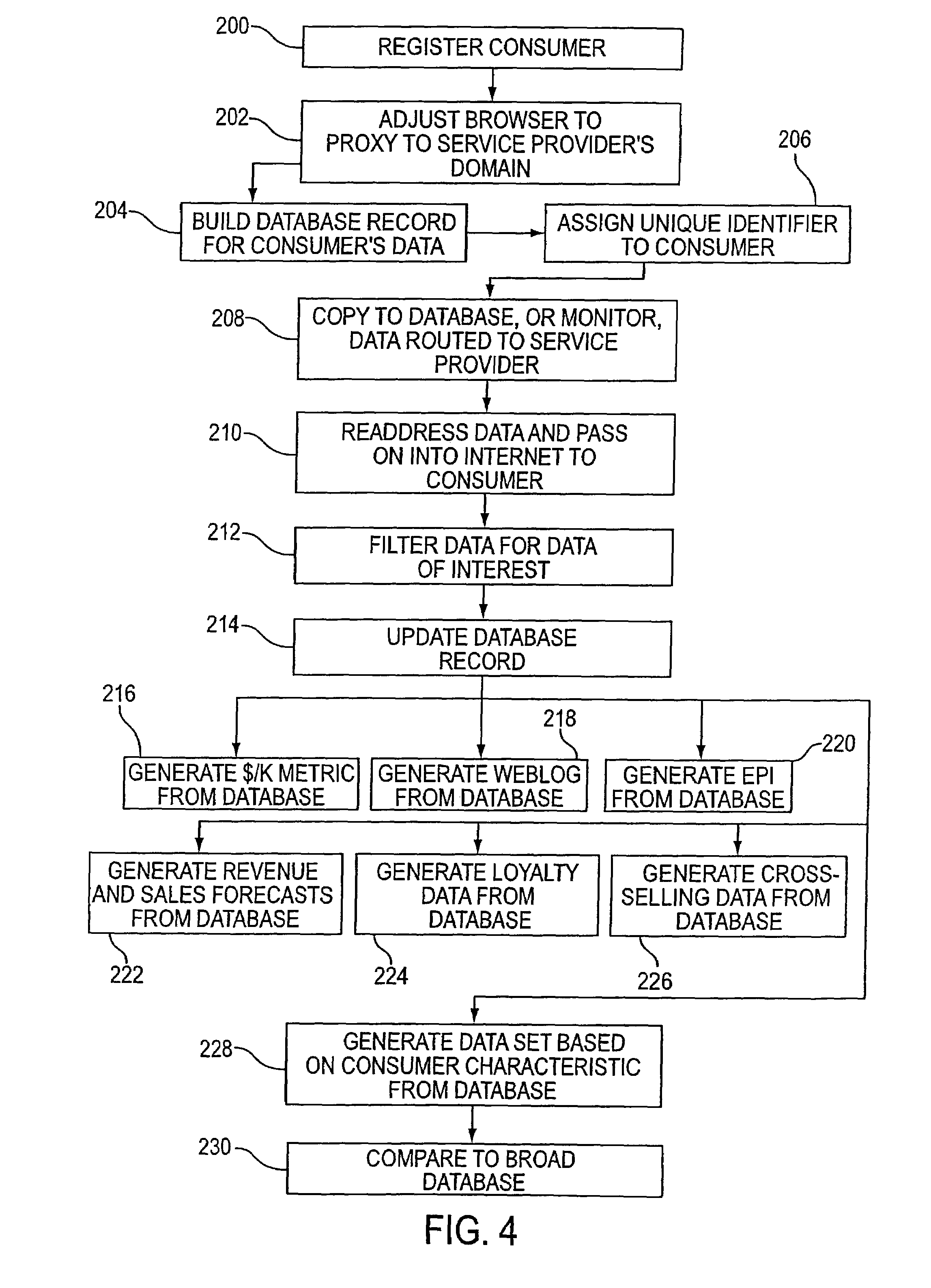
Systems for and methods of placing user identification in the header of data packets usable in user demographic reporting and collecting usage data
InactiveUS7493655B2Digital data processing detailsMultiple digital computer combinationsData setMarket place
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE
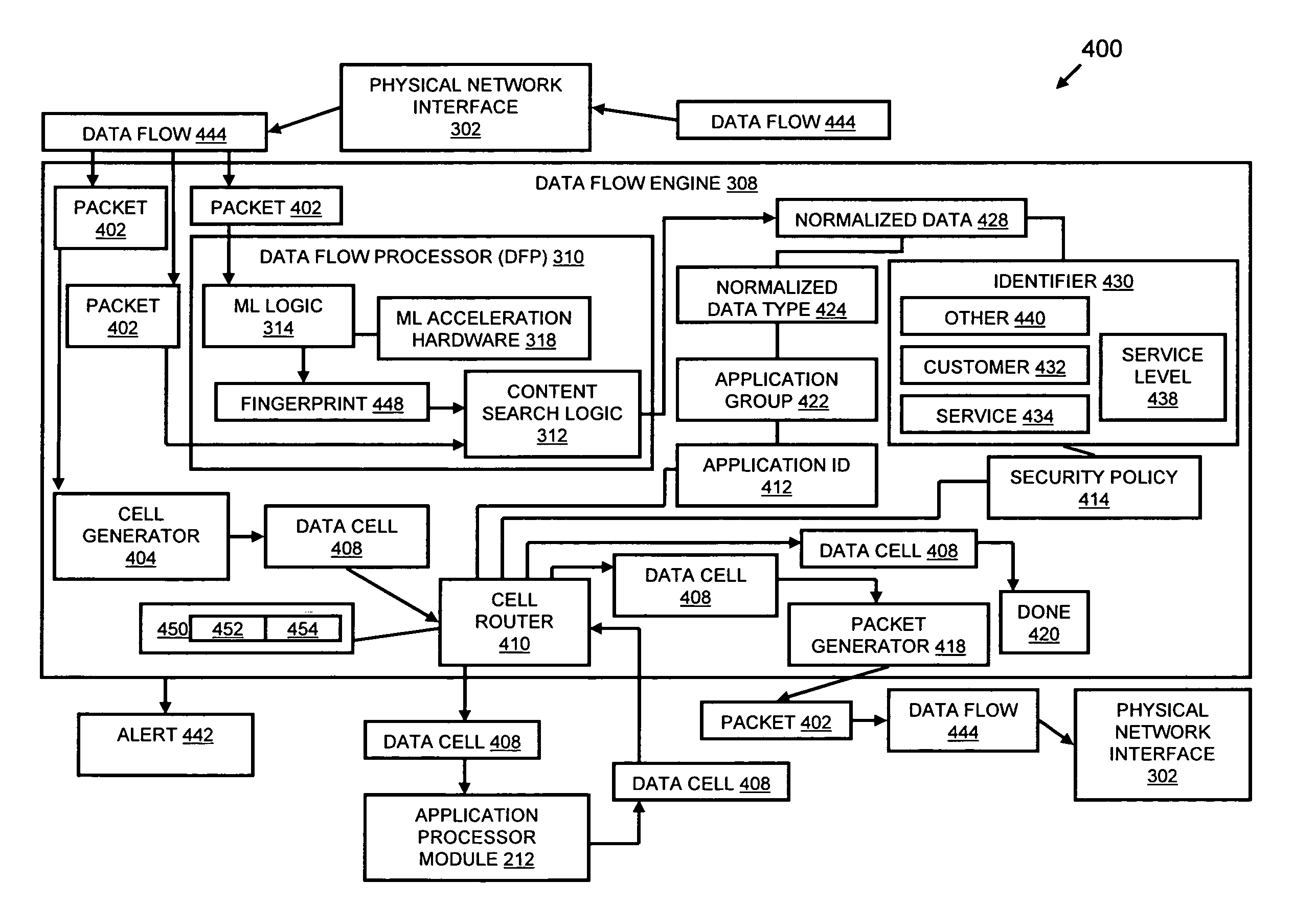
Systems and methods for processing data flows
InactiveUS8010469B2Increased complexityAvoid problemsMemory loss protectionError detection/correctionData streamSelf-organizing map
Methods and systems for flow processing and switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security are described. Such flow processing facilities may be used for inspecting network traffic packet payloads to detect security threats and intrusions across accessible layers of the network IP stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources.
Owner:CA TECH INC
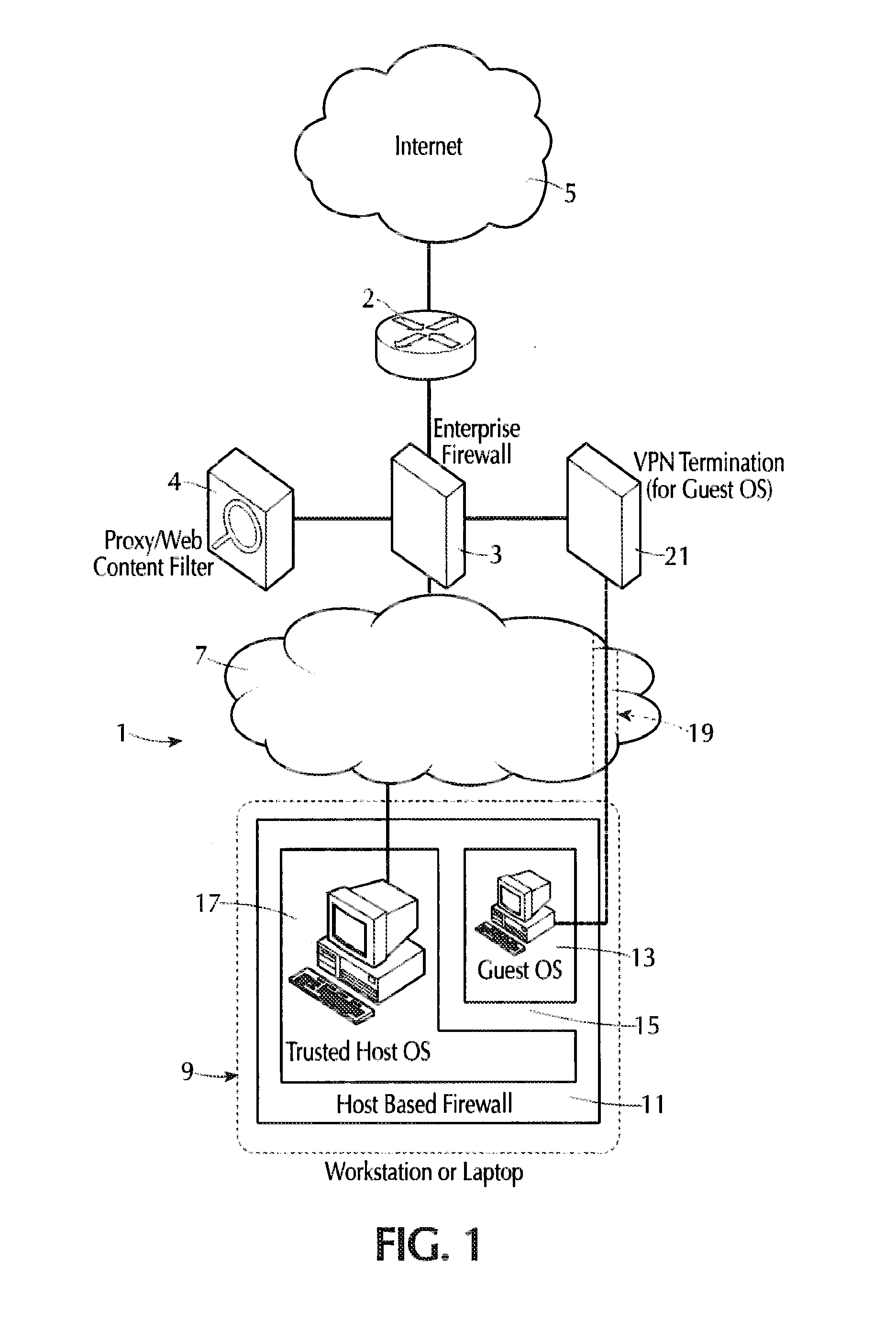
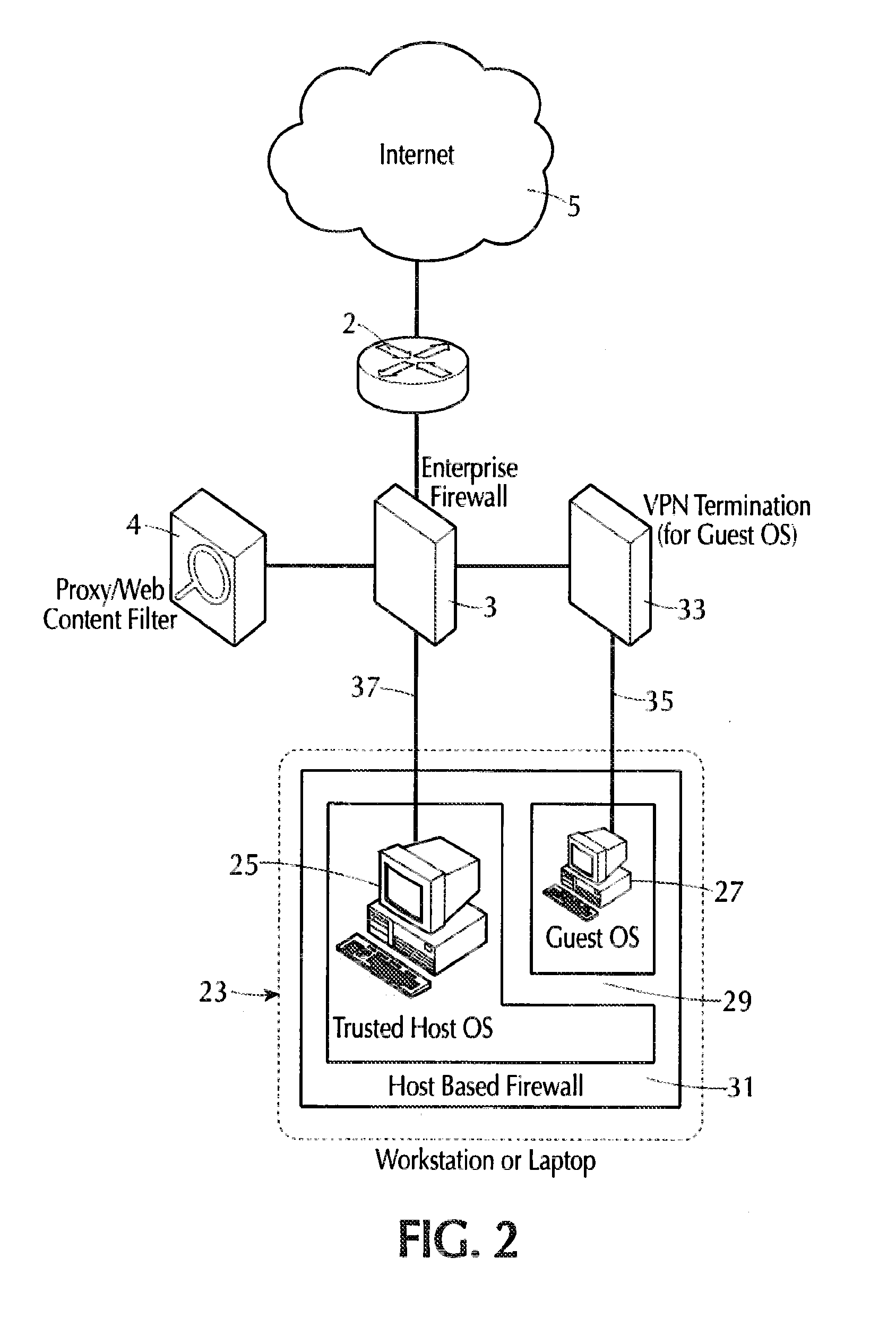
Internet isolation for avoiding internet security threats
ActiveUS20130318594A1Obviates abilityReduce the possibilityMultiple digital computer combinationsPlatform integrity maintainanceNetwork terminationPrivate network
A host computer supports a virtual guest system running thereon. The host system has a firewall that prevents it from communicating directly with the Internet, except with predetermined trusted sites. The virtual guest runs on a hypervisor, and the virtual guest comprises primarily a browser program that is allowed to contact the Internet freely via an Internet access connection that is completely separate from the host computer connection, such as a dedicated network termination point with its specific Internet IP address, or by tunneling through the host machine architecture to reach the Internet without exposing the host system. The virtual guest system is separated and completely isolated by an internal firewall from the host, and the guest cannot access any of the resources of the host computer, except that the guest can initiate cut, copy and paste operations that reach the host, and the guest can also request print of documents. The host can transfer files to and from a virtual data storage area accessible by the guest by manual operator action. No other transfer of data except these user initiated actions is permitted.
Owner:L3 TECH INC
Internet security analysis system and process
InactiveUS6996845B1Memory loss protectionUnauthorized memory use protectionWeb siteSecurity analysis
An automated Web security analysis system and process identifies security vulnerabilities in a target Internet Web site by parsing through the target Web site to search for a predetermined list of common security vulnerabilities. The process is recursive, exploiting information gathered throughout the process to search for additional security vulnerabilities. A prioritized list of detected security vulnerabilities is then presented to a user, including preferably a list of recommendations to eliminate the detected security vulnerabilities.
Owner:SPI DYNAMICS HEADQUARTERS
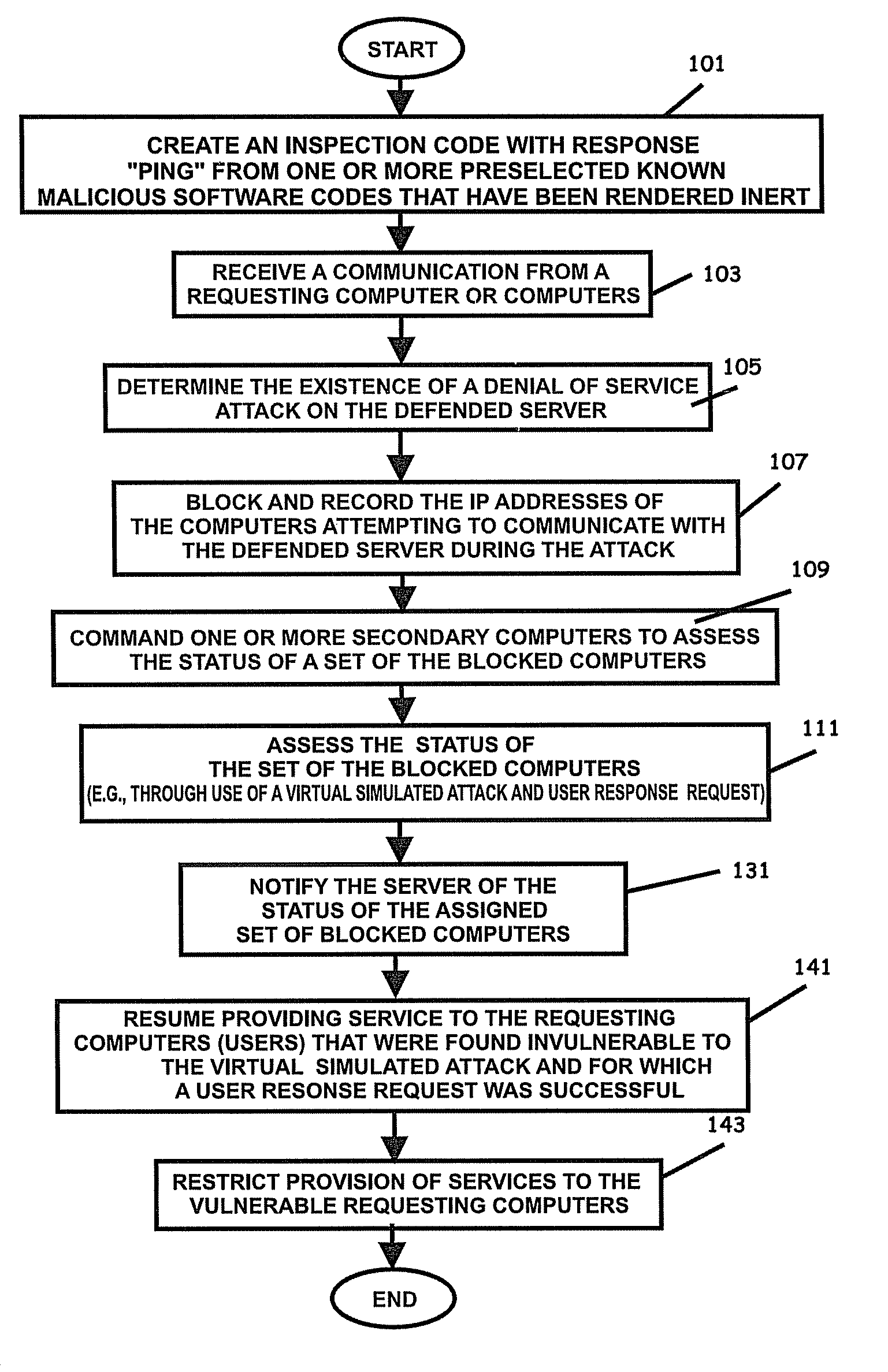
Internet security dynamics assessment system, program product, and related methods
ActiveUS20100100962A1Prevent malicious attacksLimited accessMemory loss protectionDigital data processing detailsIp addressThe Internet
Systems, program product, and methods related to dynamic Internet security and risk assessment and management, are provided. For example, a system, program product, and method of identifying and servicing actual customer requests to a defended or protected computer or server can include the steps / operations of receiving by the defended computer, a service request from each of a plurality of IP addresses associated with a separate one of a plurality of service requesting computers, sending an inspection code adapted to perform a virtual attack on each existing service requesting computers at each respective associated IP address, and restricting provision of services from the defended computer to a subset of the service requesting computers identified for restriction when a security feature of the respective service requesting computer is determined to have been defeated by the virtual attack.
Owner:LOCKHEED MARTIN CORP
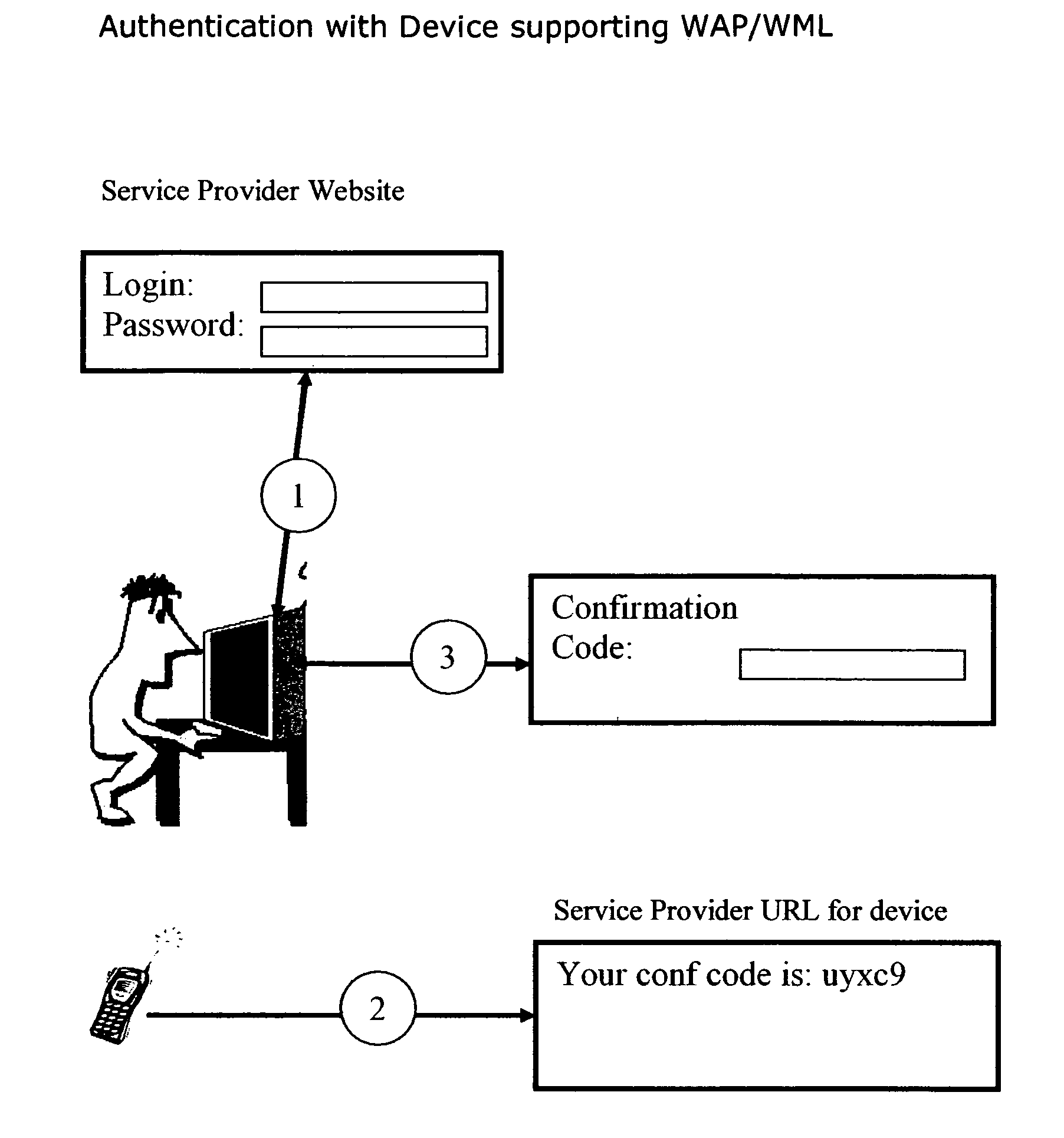
Simple two-factor authentication
InactiveUS20070107050A1Eliminate Internet fraudEasy accessRandom number generatorsUser identity/authority verificationPasswordThe Internet
Internet Security is increasingly of concern as more and more cases of identity theft of online data is reported. Simple login and password authentication for access to sensitive websites like financial, health or other personal data is no longer sufficient. Several mechanisms for additional security, called two-factor authentication have been proposed. Most of them involve the use of a physical device like a card which is read by a card reader or suggest the use of biometric authentication. Although, these are very secure, the cost of implementation of these “physical” authentications is high. This invention outlines the use of a simple two factor authentication using mobile phones, PDAs or Credit and Debit cards that most users already have, without the need for any special hardware.
Owner:JEXP
Behavioral content discovery
A system and a method for automatically collecting content, the method comprising the steps of: defining a plurality of content sites, creating a collection of virtual agents data including user characteristic data and user behavioral data, presenting the collection of virtual agents to the plurality of content sites; receiving content from the visited internet site; and storing the received content or presenting it to a user.
Owner:BI SCI 2009 LTD
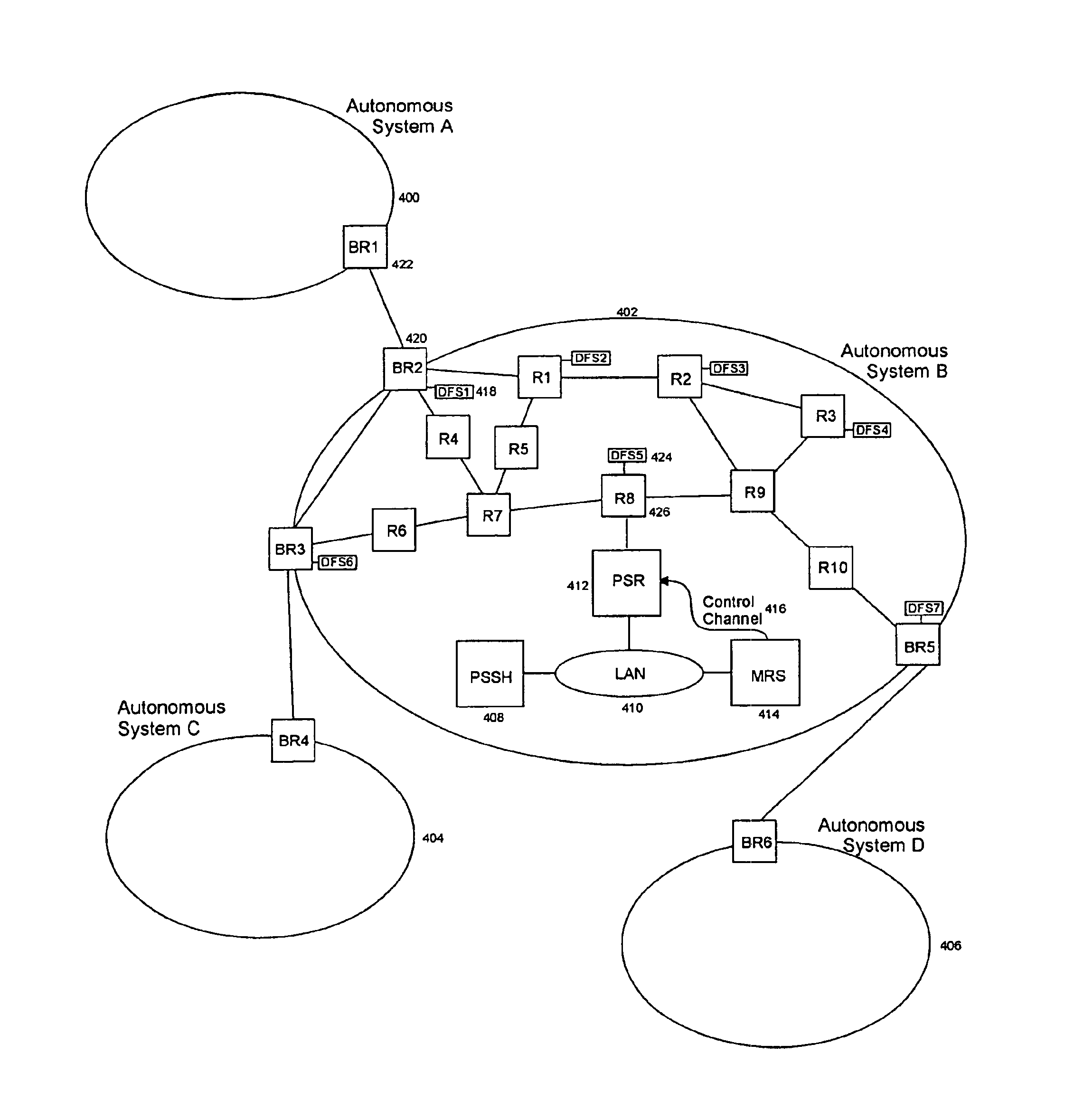
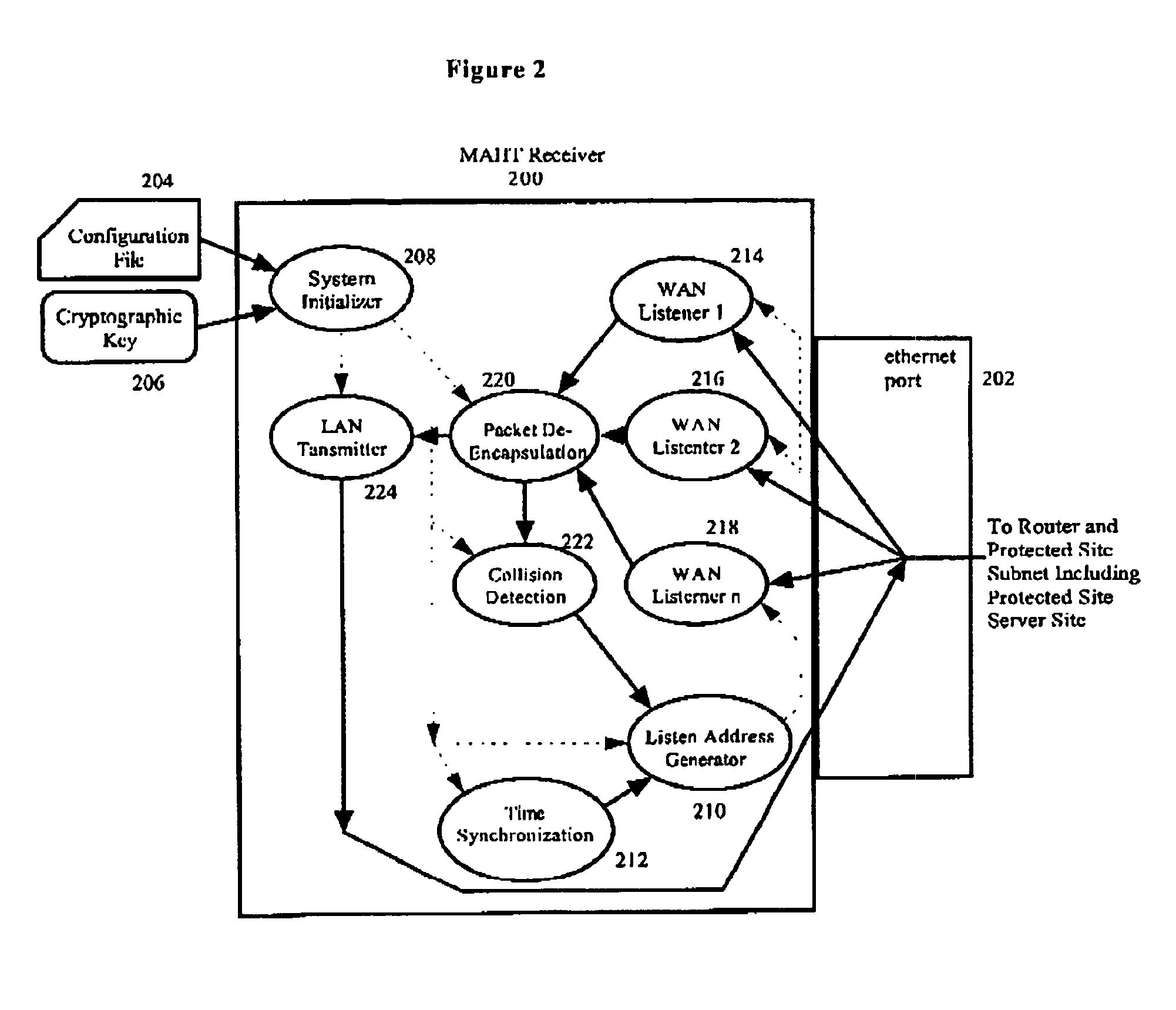
Method and system for protection of internet sites against denial of service attacks through use of an IP multicast address hopping technique
InactiveUS6880090B1Traffic analysisTimely controlSpecial service provision for substationMultiple digital computer combinationsIp addressIP multicast
The present invention relates to a method and system for Internet Protocol network communications and a use thereof for protecting Internet sites against denial of service attacks on insecure public networks such as the Internet. The method utilizes a multicast address hopping technique which selectively varies the chosen multicast IP address from a set of available multicast addresses according to a predetermined scheme known to the communicating end stations but not to unauthorized end stations. The packets associated with the multicast stream are then communicated on the chosen multicast address. The set of available multicast IP addresses may also be selectively varied according to a secret predetermined scheme known to the transmitter and subscriber end stations, particularly by adding to and dropping from the set of multicast IP addresses in a seemingly random fashion. Using the method of the present invention, potential attackers are prevented from knowing which address to disrupt or monitor for traffic between end stations.
Owner:SHAWCROSS CHARLES BYRON ALEXANDER
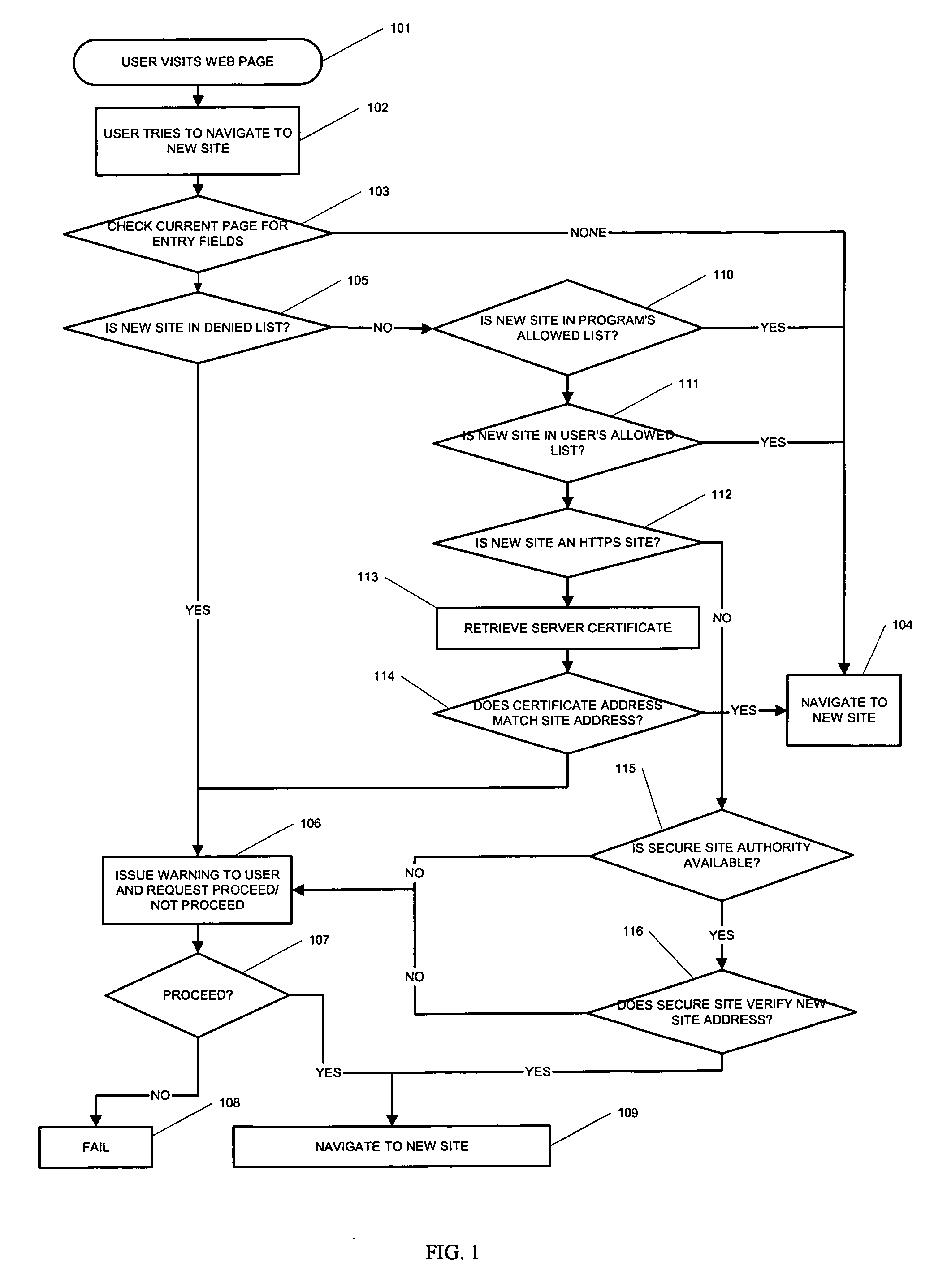
Internet security
ActiveUS20060253446A1Digital data information retrievalData processing applicationsWeb siteUser input
Redirection of user entered data to an unauthenticated website (“phishing”) is checked by, at redirection, detecting the presence of data entry fields in a user web page and, if any are present, authenticating the redirection address against lists of approved websites or the redirection web site certificate. If the new address is not authenticated, the user may still opt to be redirected.
Owner:E LOCK CORP
System and method for routing-based internet security
ActiveUS9634995B2Improve securityRandom number generatorsDigital data protectionDigital dataThe Internet
Method and system for improving the security of storing digital data in a memory or its delivery as a message over the Internet from a sender to a receiver using one or more hops is disclosed. The message is split at the sender into multiple overlapping or non-overlapping slices according to a slicing scheme, and the slices are encapsulated in packets each destined to a different relay server as an intermediate node according to a delivery scheme. The relay servers relay the received slices to another other relay server or to the receiver. Upon receiving all the packets containing all the slices, the receiver combines the slices reversing the slicing scheme, whereby reconstructing the message sent.
Owner:MAY PATENTS LTD
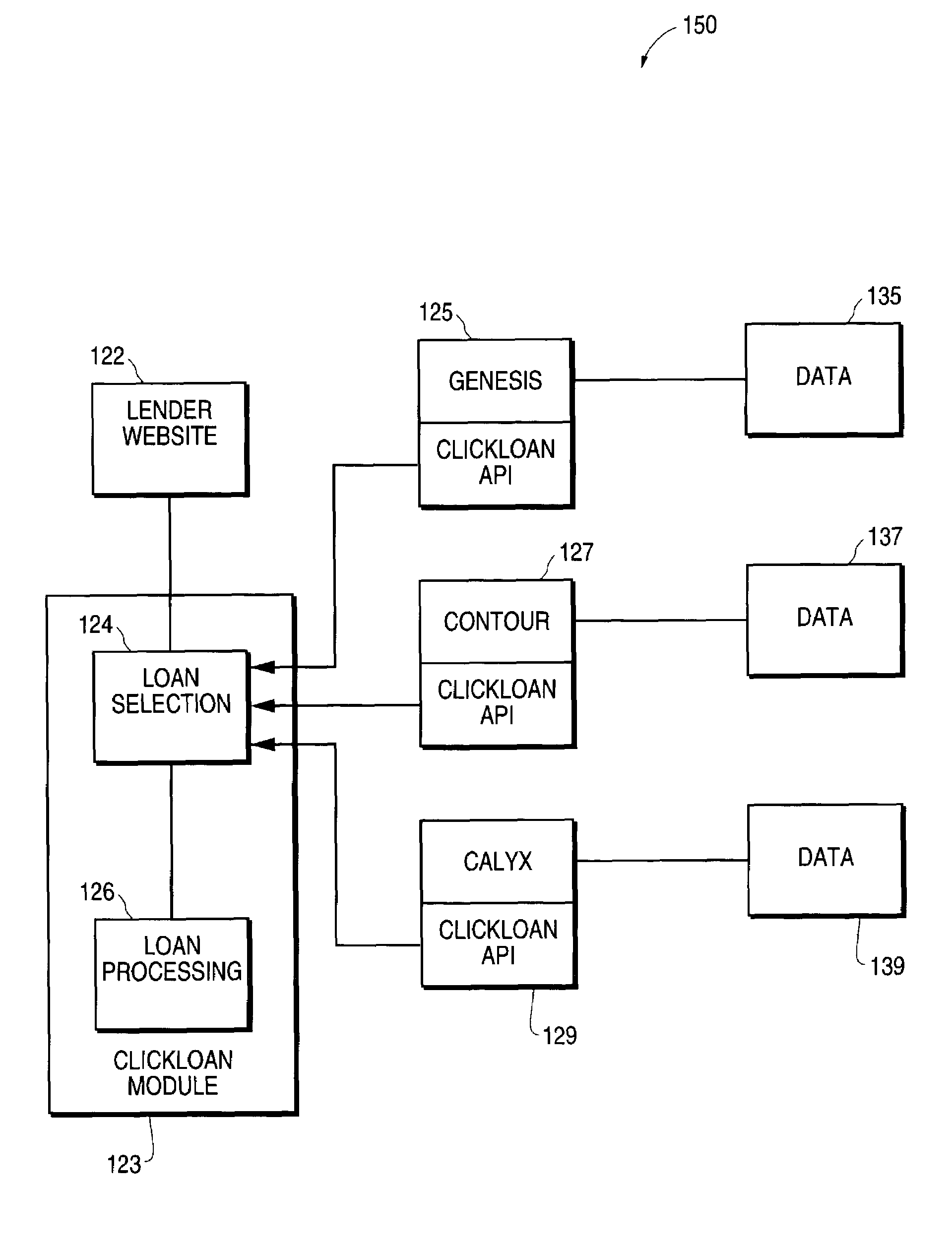
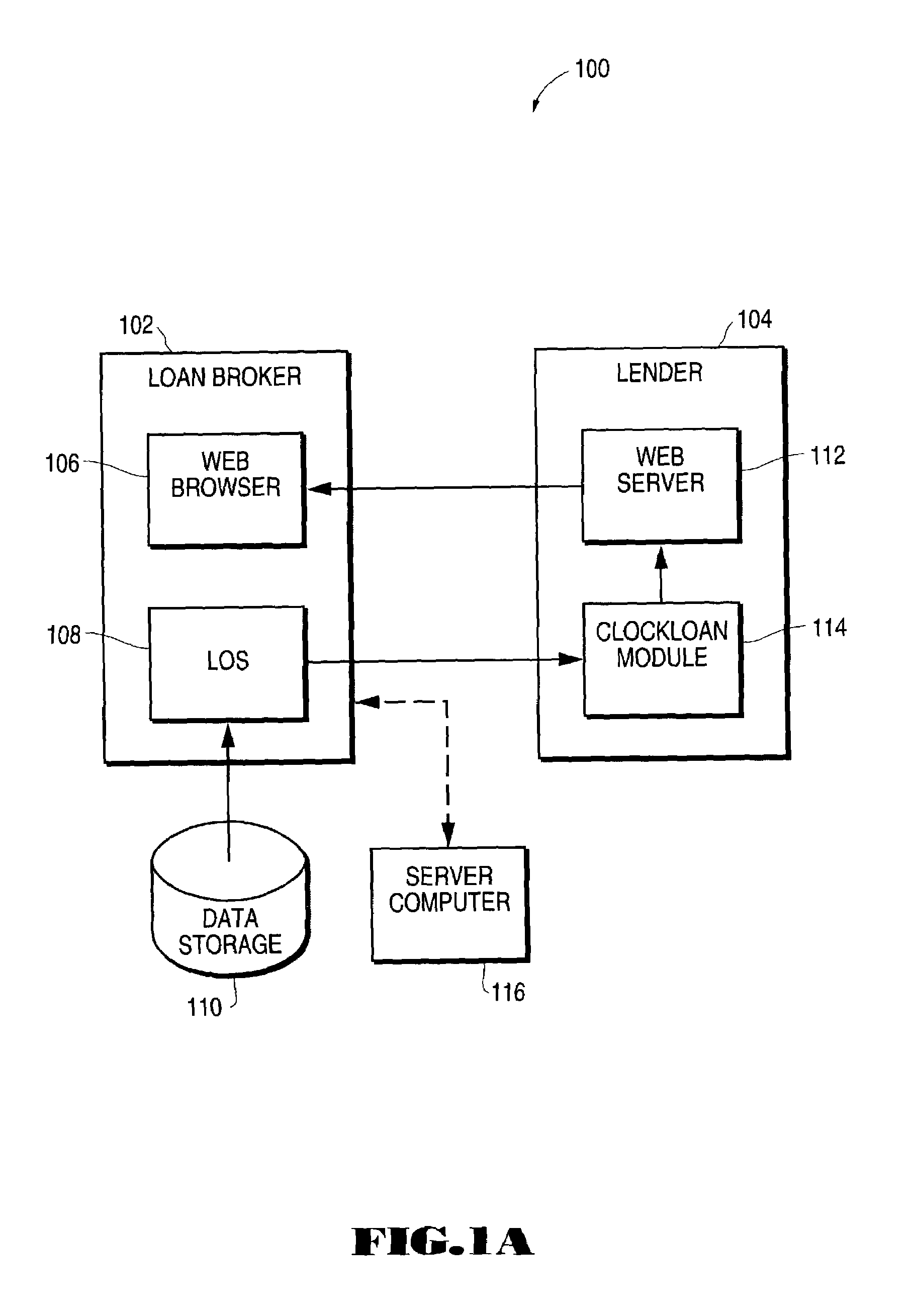
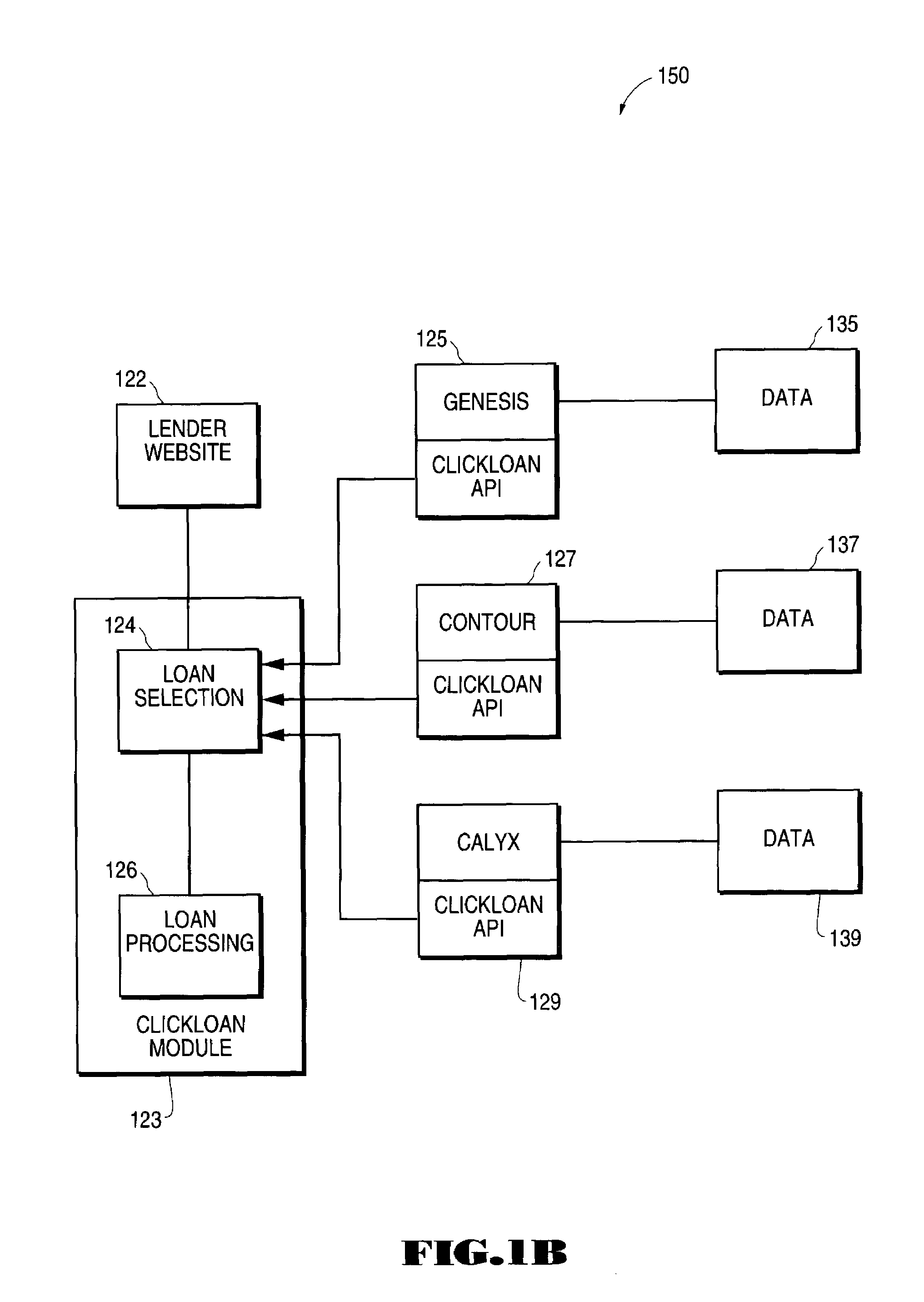
Loan origination system interface for online loan application processing
A loan origination system interface module for processing loan applications from a user through a lender web site is described. The loan originator accesses a lender web site to perform loan processing procedures. The module is included on the lender's web page through a standard object reference in HTML specification. The module contains information unique to that lender, and the lender's identification number as well as desired data format. Once the loan originator decides to transfer a loan application or supplemental data to the lender, the module examines the loan origination software pipeline and presents a selection of loan products to the user. Once the user makes a selection, the module extracts loan information stored in the loan origination software by conducting a search for each required data field, relates that data to the specific field in the vendor application format, and packages the data in a format acceptable to the lender. The module then finds the appropriate route to deliver the loan data to the lender, either directly through a standard Internet secure communication protocol, or indirectly through a separate server computer. The user can then continue the transaction on the lender's web site in an uninterrupted work flow. Loan processing occurs on the lender's web site, and the interaction of the web site and loan origination software is handled by the module.
Owner:ICE MORTGAGE TECH INC
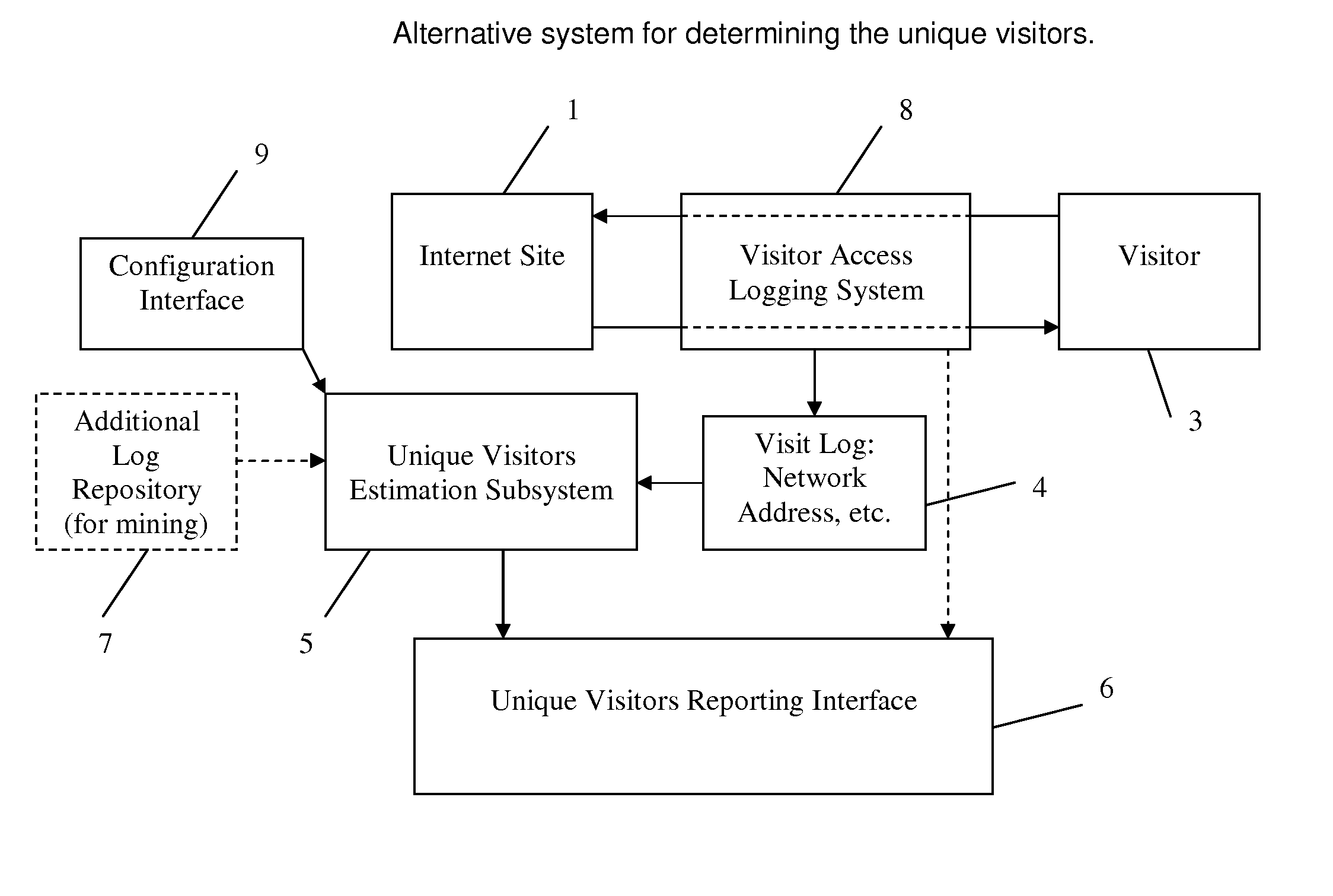
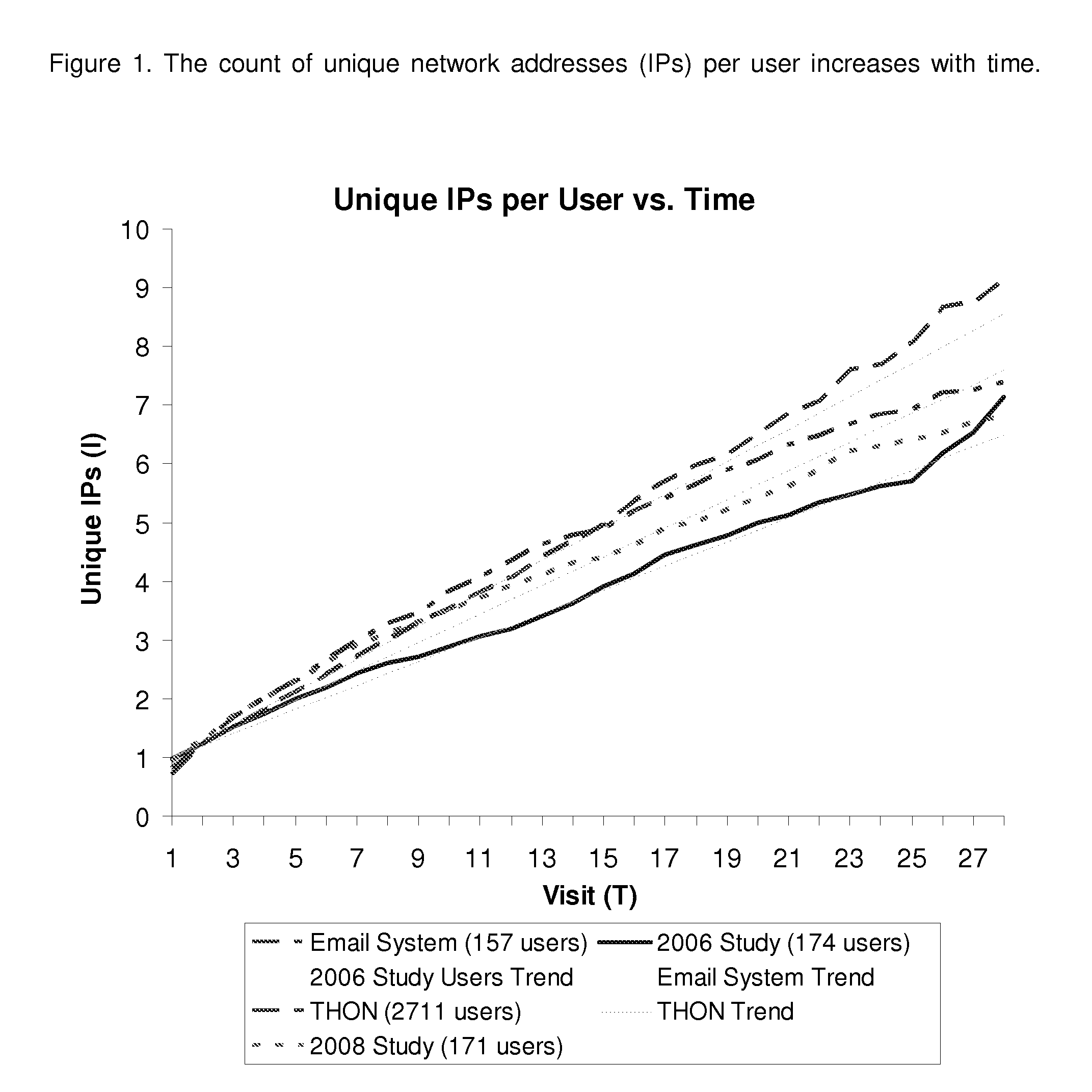
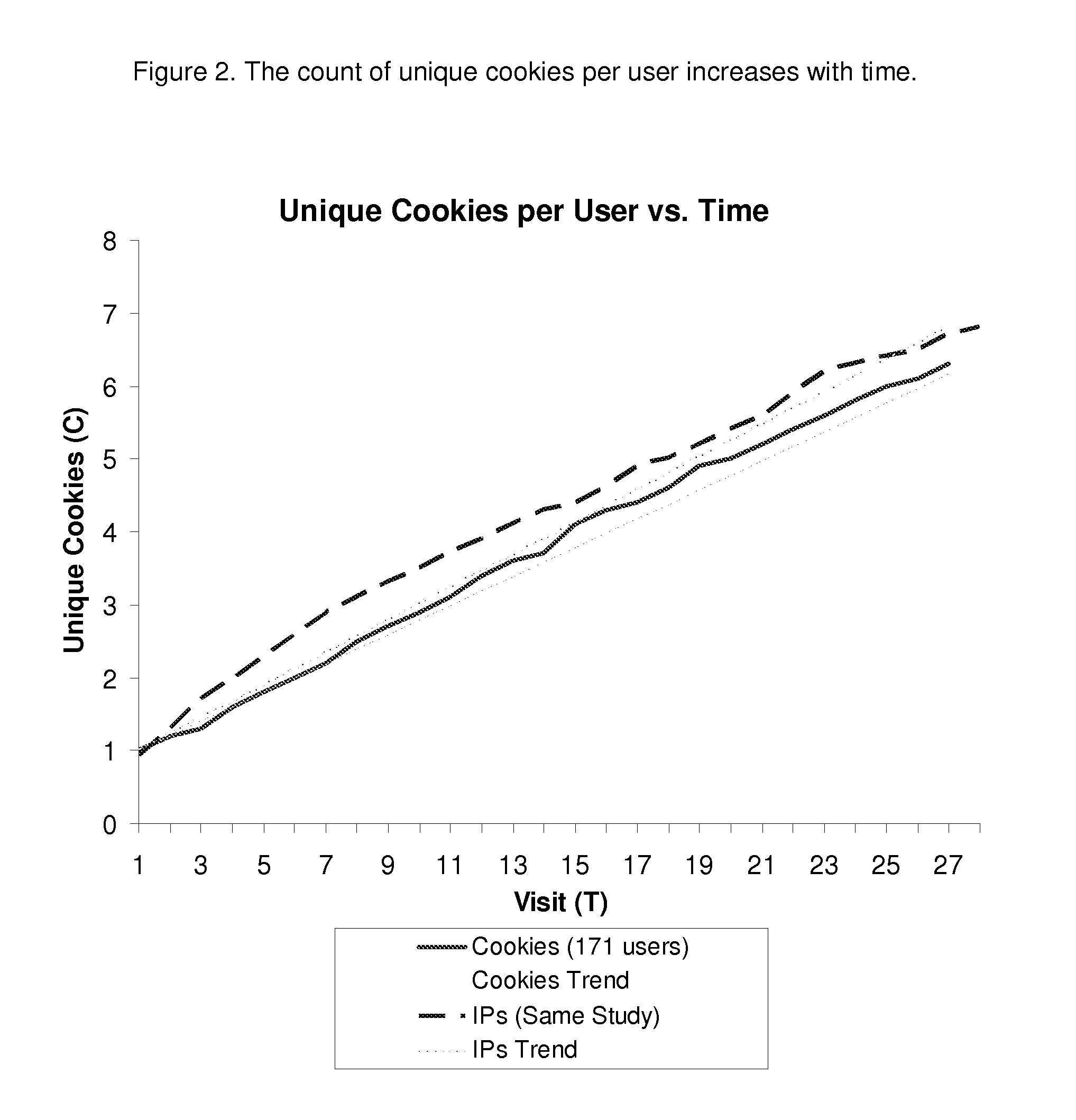
Method and System for Estimating Unique Visitors for Internet Sites
InactiveUS20100228850A1Ensure effective implementationSimplicity easeDigital computer detailsElectric testing/monitoringThird partyNetwork addressing
This invention comprises a method and system for estimating unique visitors for Internet sites that is more accurate than the existing unique cookie / unique address counting methods. The invented method relies on the count of unique user identifiers (such as network addresses or preferably cookies)—I—that can be obtained from an existing cookie tracking / user access logging system. The number of unique visitors U is calculated substantially as a ratio of the count of unique cookies (or unique network addresses) to the number of visits N times the inflation factor X plus constant on that is approximately one (exactly one in the case of cookies). The number of visits is calculated by multiplying the sampling period t to the visitation frequency T1 minus one. The resulting estimate of the unique visitors is stable and does not diverge with sampling time unlike estimates directly obtained from the unique network address or unique cookie counts. The method is also applicable when there are multiple dominant visitation frequencies by accounting to the sum by all significant visitation frequencies. All key parameters of the method can be established before hand by mining a multitude of the site's historical visit logs and / or third party site access logs; the parameters can be corrected / calculated dynamically by mining the site's current access log (or current third party logs) while focusing on unambiguously identified visitors (such as return visitors identified by their login ID or unchanged cookie value).
Owner:FOMITCHEV MAX
Systems and methods for secure biometric authentication
InactiveUS7117356B2Digitally marking record carriersElectric signal transmission systemsClient-sideAuthorization
A biometric security system is disclosed. The system includes a client security system configured to make a request for access to an application module. The application module is configured to receive the request and respond by sending an instruction to the authentication module to initiate an authentication session. The authentication module is configured to receive the instruction and respond by generating a session packet that is transferred to the client security system. The client security system is further configured to generate an authorization packet that is returned to the authentication module after being encrypted utilizing information contained in the session packet.
Owner:BIO KEY INT
Cluster-based visualization of user traffic on an internet site
InactiveUS7454705B2Significant to useData processing applicationsDigital data processing detailsTraffic capacityWeb traffic
Visualizing Internet web traffic is disclosed. In one embodiment, a number of windows are displayed, corresponding to a number of clusters into which users have been partitioned based on similar web browsing behavior. The windows are ordered from the cluster having the greatest number of users to the cluster having the least number of users. Each window has one or more rows, where each row corresponds to a user within the cluster. Each row has an ordered number of visible units, such as blocks, where each block corresponds to a web page visited by the user. The blocks can be color coded by the type of web page they represent. In one embodiment, the corresponding cluster models for the clusters are alternatively displayed in the windows.
Owner:MICROSOFT TECH LICENSING LLC
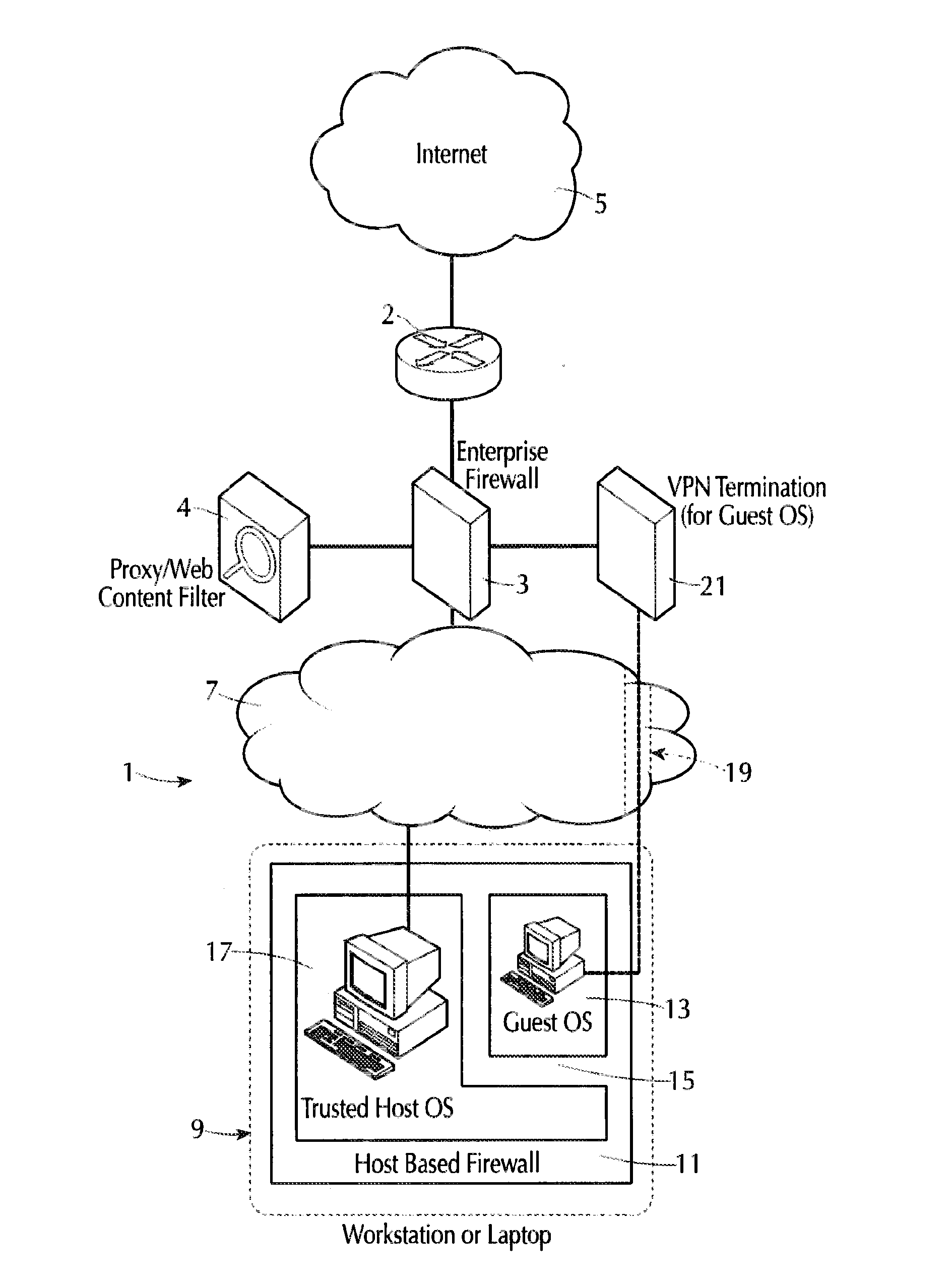
Personal computer internet security system
InactiveUS7146640B2Eradicates threat potentialMemory loss protectionDigital data processing detailsOperational systemExternal data
An intrusion secure personal computer system includes a central processing unit, a data storage means, a memory means, a primary operating system, a virtual machine operating system providing an isolated secondary operating environment functioning separate from the primary operating system and controlling operations of the personal computer system within the isolated secondary operating environment and at least one input / output (I / O) connection in operative communication with an external data source, where the personal computer system is secured from malicious code contained in a file downloaded from the external data source.
Owner:BURNT HICKORY COMPANY
Rapid network access computer system
InactiveUS6625649B1Easy accessInput/output for user-computer interactionDigital computer detailsSignal processing circuitsComputerized system
Owner:HEWLETT PACKARD DEV CO LP
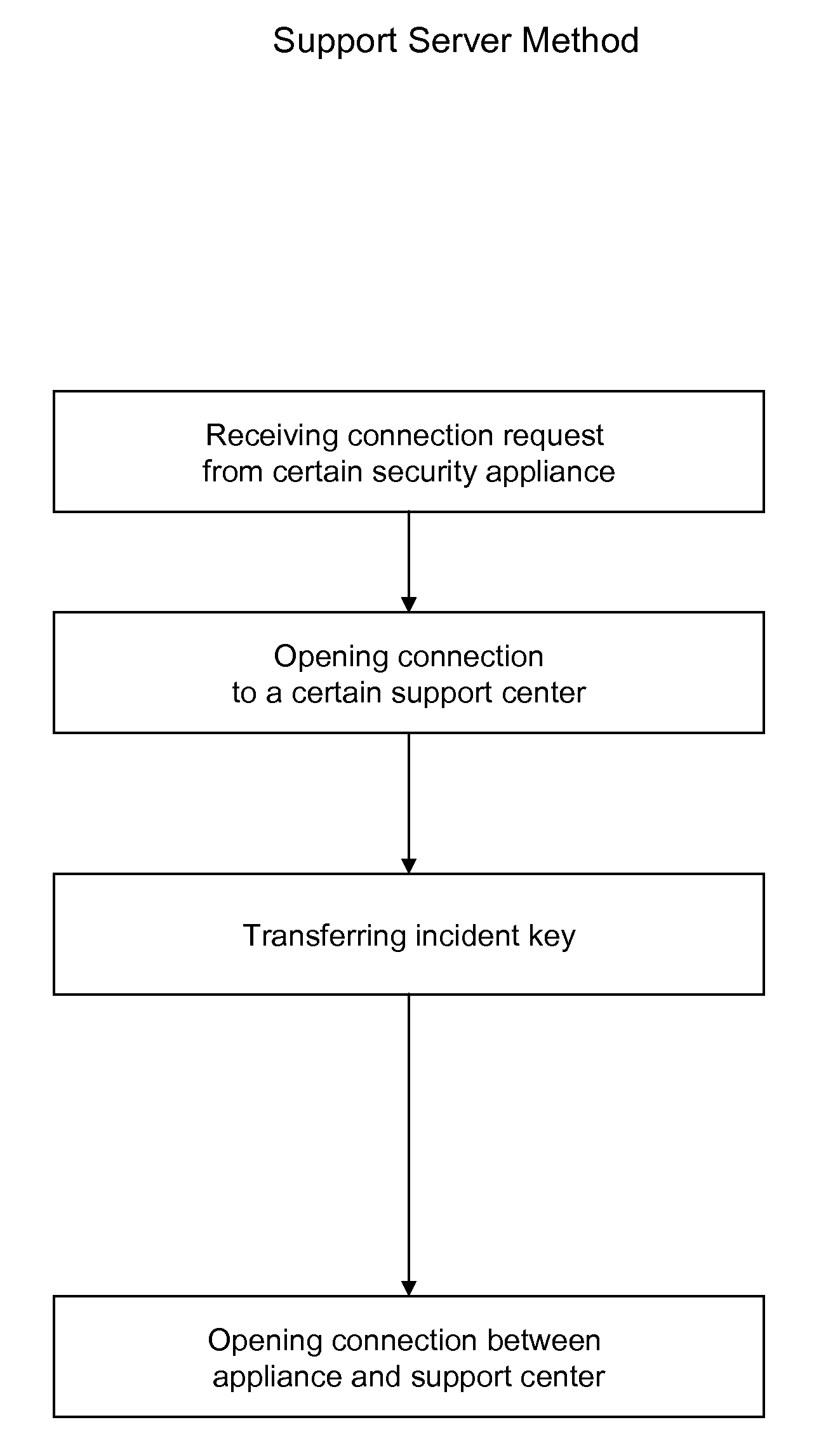
Secure remote support automation process
ActiveUS20090052675A1Connection securityKey distribution for secure communicationDigital data processing detailsNetwork address translationSupport services
Secure Remote Support Automation Process wherein a remote support server receives a support task request and schedules a predefined task to a predefined actor who also has a predefined escalation policy and notifies the support actor of the scheduled task along with a key, a key seed, or a credential to use in authentication. The method enabling privileged access to an Internet security appliance using public / private key pairs through a firewall and network address translation by a support server and an assigned support task actor.
Owner:BARRACUDA NETWORKS
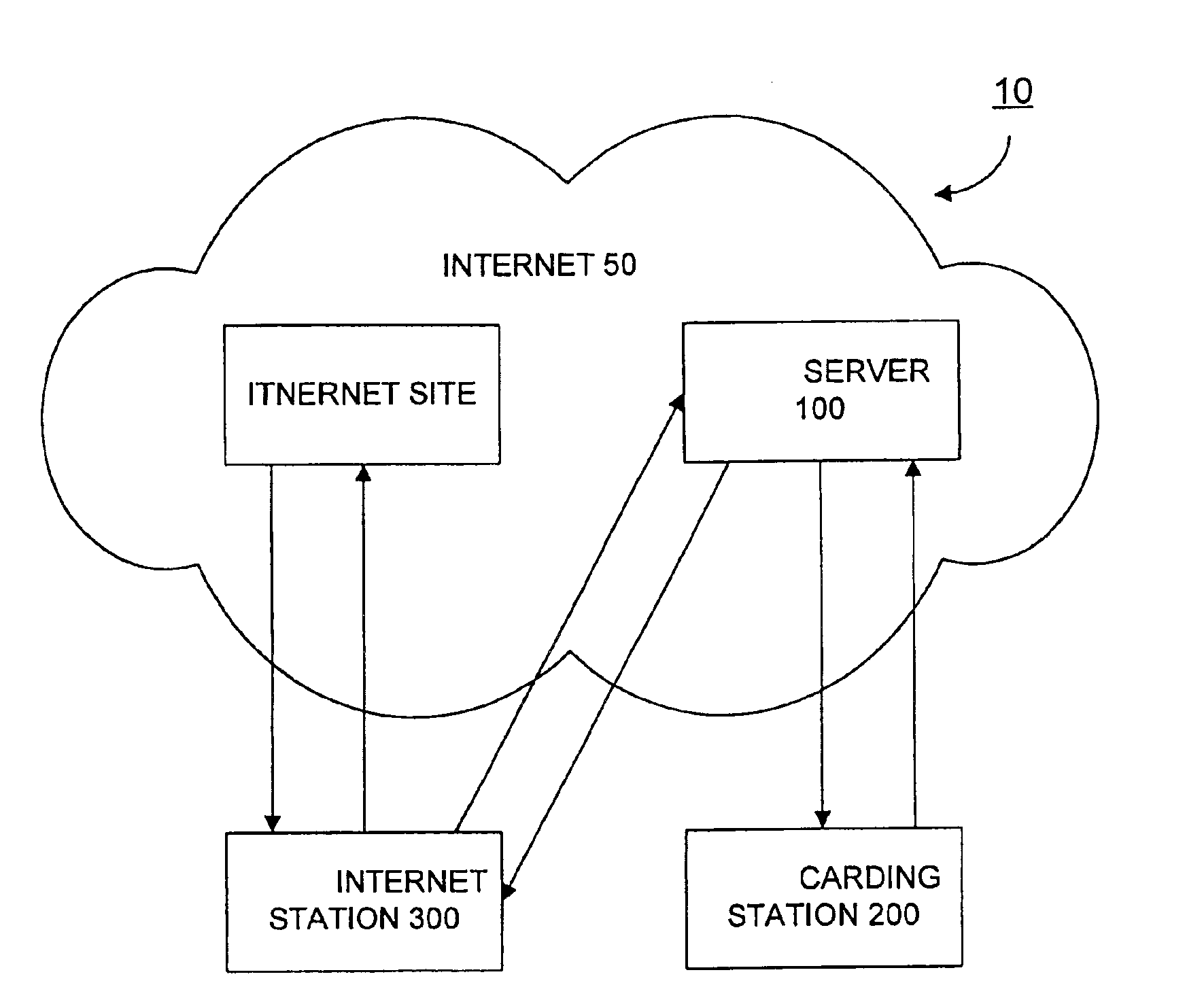
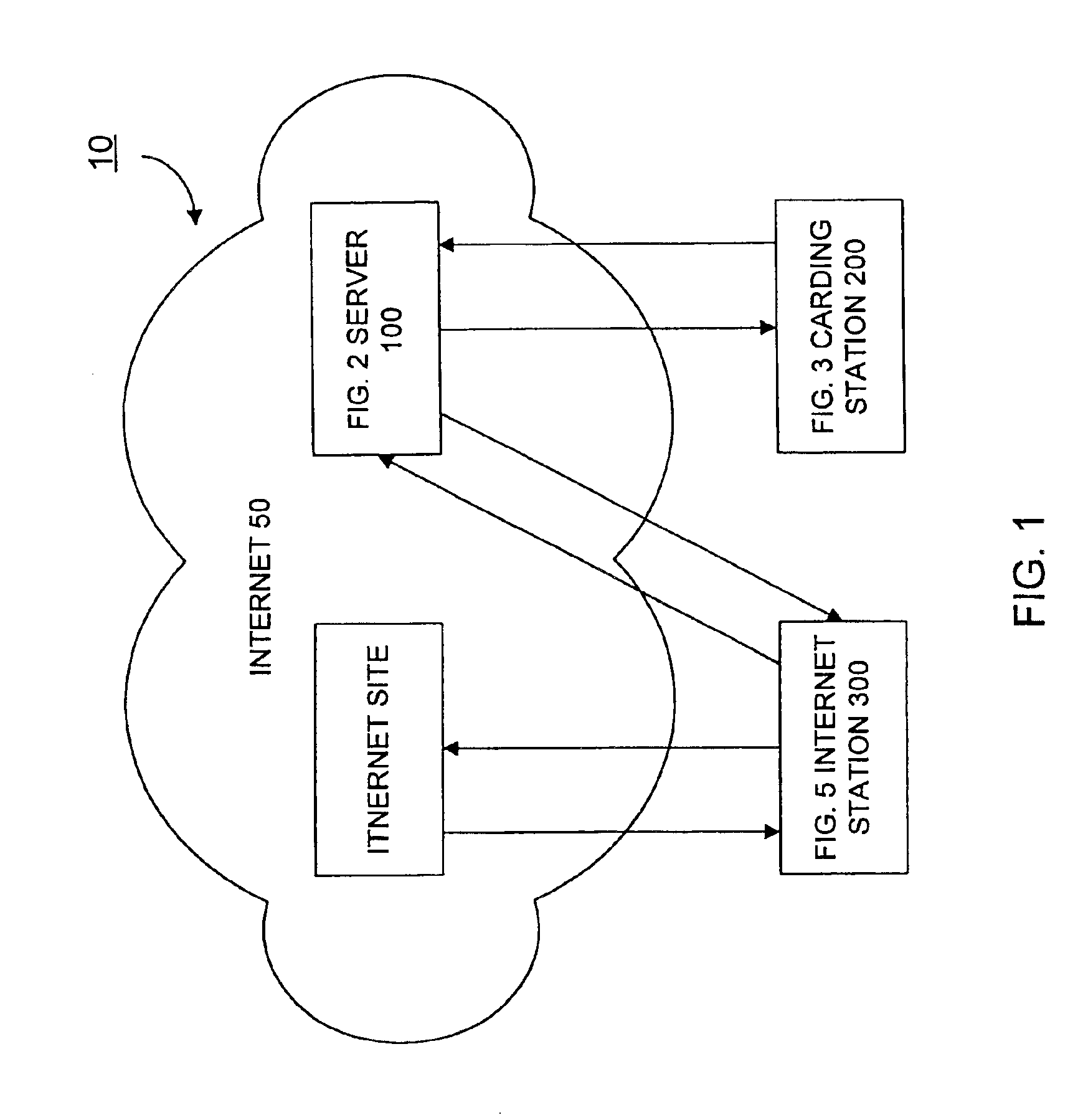
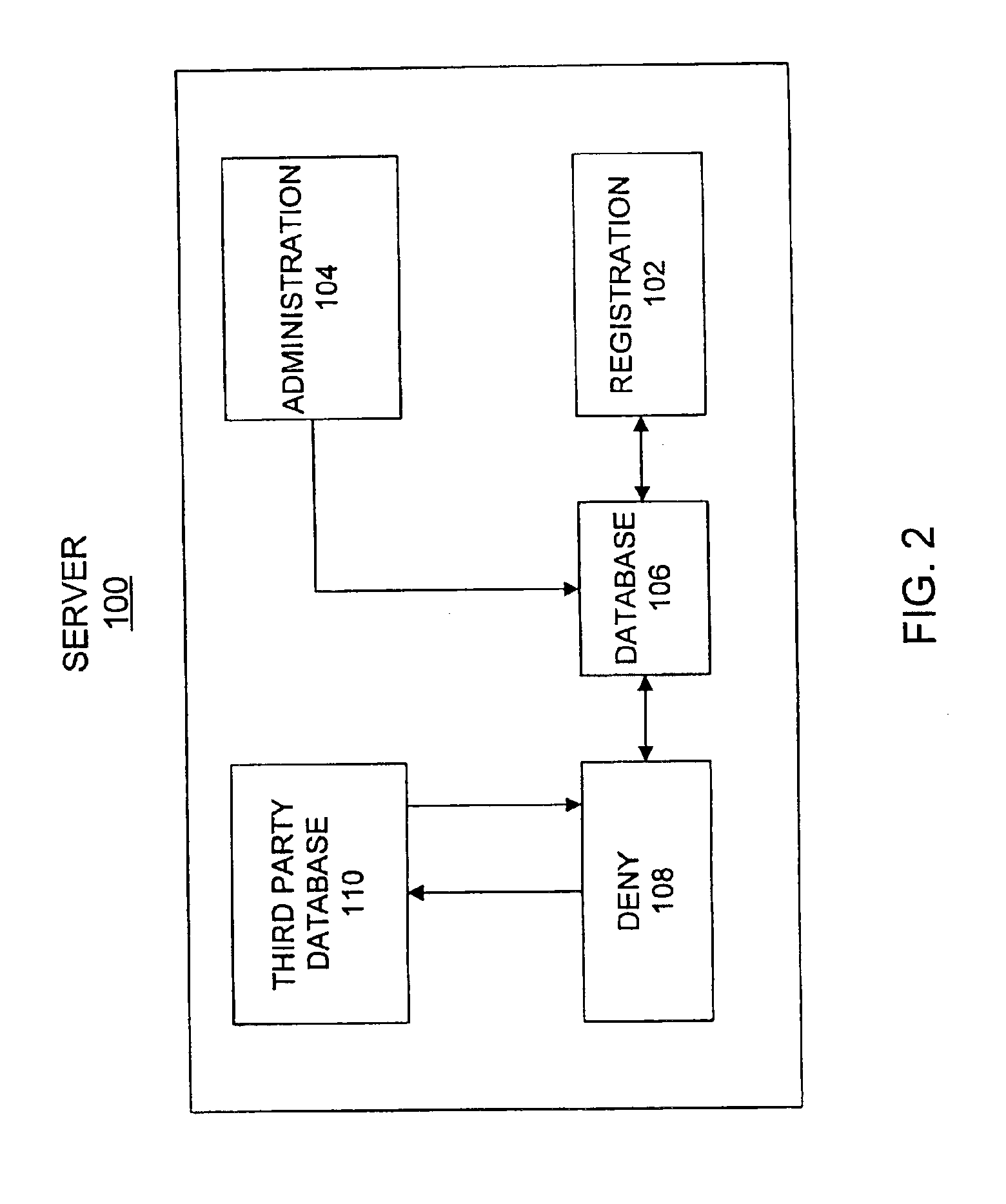
Smart card controlled internet access
InactiveUS6934841B2Provide securityDigital data processing detailsUser identity/authority verificationWeb siteCable Internet access
A system for customizing individual internet access includes a server that registers a user with the system, stores information pertaining to internet sites the user is authorized to access, and controls the user's access to internet sites. A carding station is provided to enter personal identification information about the user and information regarding internet sites the user is authorized to access into the system. The carding station also generates a personal smart card for the user that includes a read only memory storing a serial number that correlates with data about the user stored in the server. An internet station is provided to allow the user to view the internet only with his or her personal smart card. While accessing the internet, the server controls the user's access to internet sites based on whether the information stored in the server indicates that the user is authorized to access the specific internet sites that are requested to be displayed. A secure sockets layer protocol provides security for the data transferred across the internet connection.
Owner:3M INNOVATIVE PROPERTIES CO
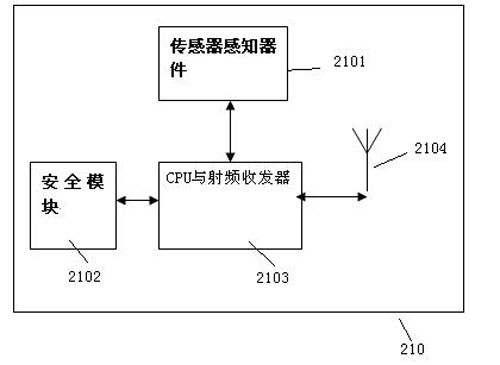
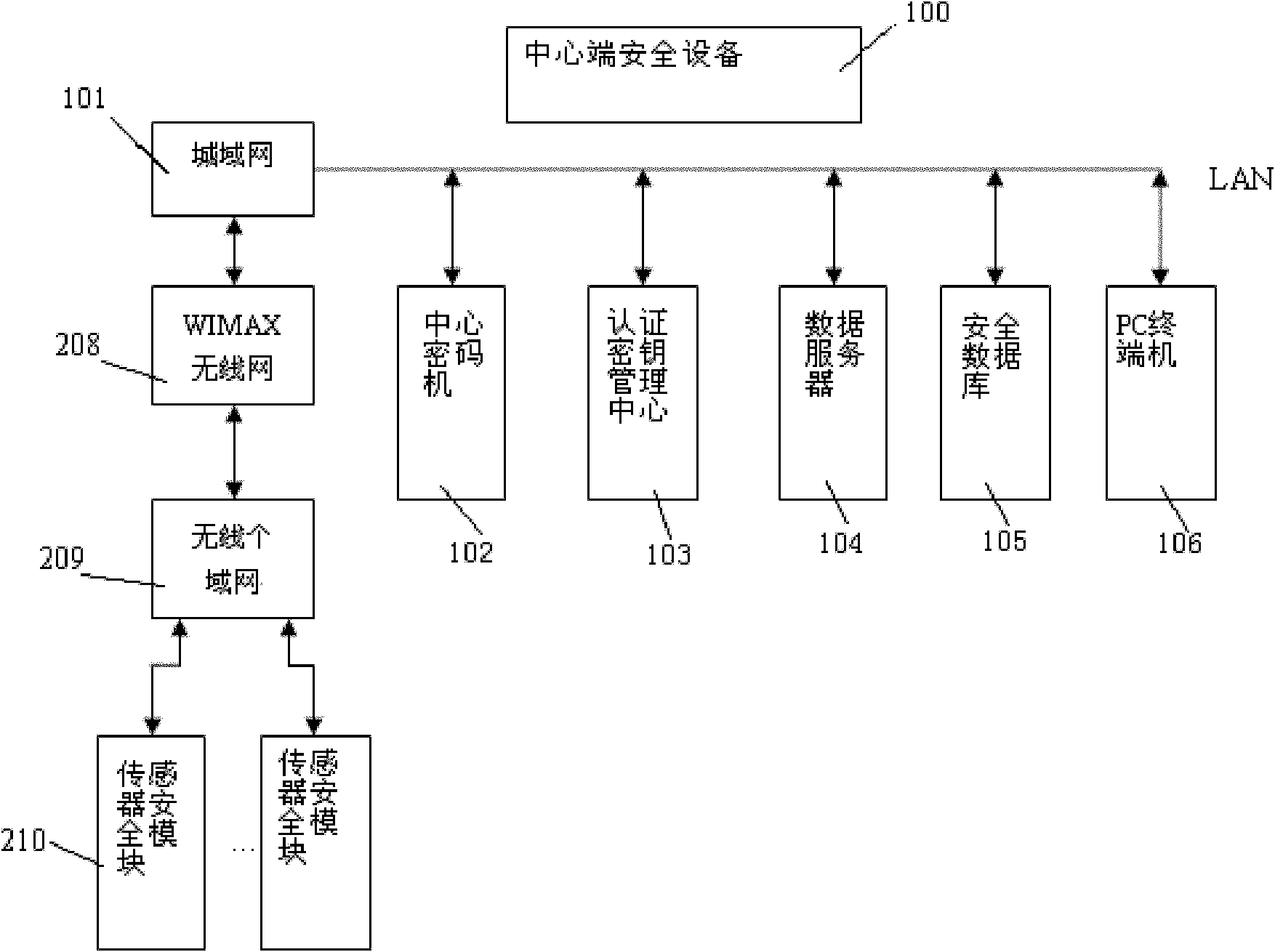
Network architecture security system for Internet of Things and security method thereof
InactiveCN102036231ARealize detection controlRealize secure transmissionNetwork topologiesTransmissionCommunications securityConfidentiality
The invention aims at providing a network architecture security system for Internet of Things and a security method thereof, comprising security protective measures sequentially established in the system from inside to outside, which are mainly reflected in that a security device at a central terminal of the Internet of Things comprises a central cipher machine, a central authentication secret key management center, a data server, a security database and the like, and then the security of each sensor terminal in a Personal Area Network and the like. Compared with the prior art, the invention has the advantages that: 1. according to the characteristics of the Internet of Things, Internet security technology of the Internet of Things is realized; 2. the security protective measures sequentially established in the system from inside to outside are mainly reflected in the security device at the central terminal and security modules at each sensor terminal, thus ensuring the security of sensing information, equipment, communication and application, as well as security management; and 3. multi-level security systems are deployed in the aspects of security mechanism and management, such as the confidentiality, integrity, authenticity and non-repudiation of data, and equipment legitimacy.
Owner:BEIJING BINGGANG TECH DEV CO LTD
Secure routable file upload/download across the internet
InactiveUS7003799B2Computer security arrangementsMultiple digital computer combinationsClient agentThe Internet
A system and method are provided for performing file transfers using an HTTP- or HTTPS-based Supplier Transport Gateway to connect Customer and Supplier Repositories located behind their respective firewalls. In some embodiments, the Transport Gateway is placed outside the Supplier firewall, and a Supplier Transport Proxy inside the firewall connects the Transport Gateway to the internal Supplier Repositories. In other embodiments, the Transport Gateway and Transport Proxy are reversed, the Proxy residing outside the Supplier firewall and relaying Customer HTTP / HTTPS traffic to the Transport Gateway inside the firewall, which then connects to the internal Supplier Repositories. In either case, the HTTP- or HTTPS-based Customer Repository connects through a Customer Proxy to the Supplier's Transport Gateway to request file upload / download operations. In turn, the Transport Gateway implements the Supplier's request validation policy, and Supplier Repository routing rules that abstract the Supplier Repository topology to the Customer. The Transport Gateway then performs a corresponding upload / download operation against the selected Supplier Repository using HTTP, HTTPS, FTP, or a similar protocol.
Owner:VALTRUS INNOVATIONS LTD
System for distributing load over multiple servers at an internet site
Disclosed is a system and method for distributing connections among a plurality of servers at an Internet site. All connections are made to a single IP address and a local director selects the server from among the plurality of servers which is to receive the connection. Thus, the DNS server is not relied upon to distribute connections, and the connection distribution scheme is not avoided when DNS is bypassed. In one embodiment, a session distribution scheme is implemented such that connections are distributed to the server in the group of servers which has the fewest connections of the group. In other embodiments, other session distribution schemes which route connections based on the predicted response times of the servers or according to a round robin scheme are used.
Owner:CISCO TECH INC
Method and system for detecting and locating network anomaly
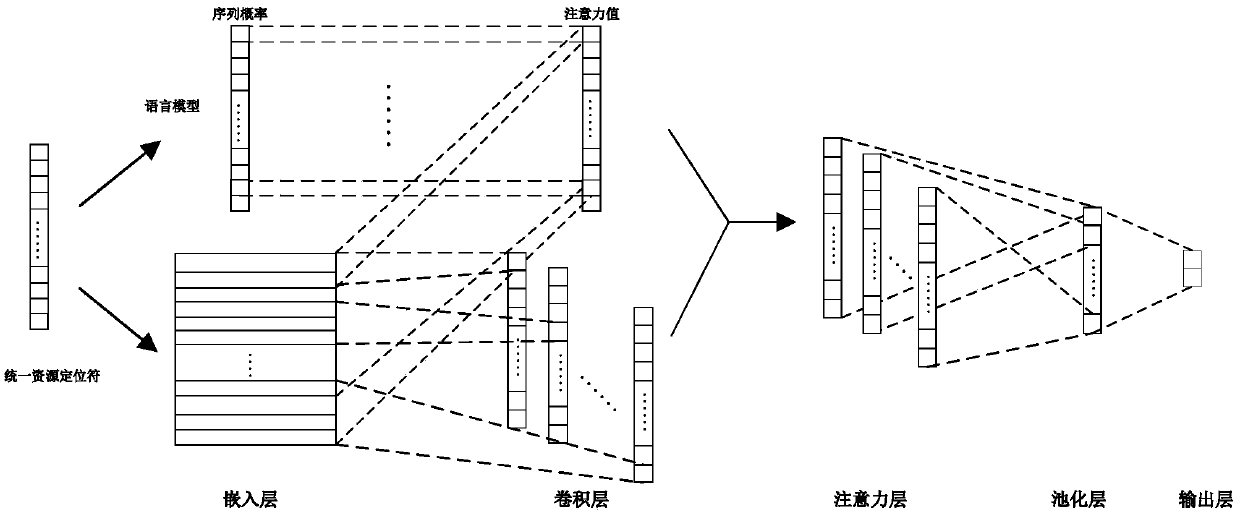
ActiveCN108667816AGuaranteed continuityConvenient expression calculationPlatform integrity maintainanceNeural architecturesNerve networkAlgorithm
The invention discloses a method and system for detecting and locating network anomaly, which relates to the fields of Internet security, deep learning and neural network. The method comprises the following steps: firstly, dividing the URL according to special characters; secondly, performing word vector encoding on the divided URL with word2vec; putting word vectors into a convolution layer for automatic feature processing; combining a convolution layer result with an attention layer which possesses a sequential attention mechanism; and finally, performing maximum pooling and full-connectionon an attention layer result to obtain a final anomaly detection result, and at the same time, using the output of the attention layer to locate the malicious code in the URL. The invention has an excellent detection effect, not only is the detection rate high, but also the malicious code fragment in the URL can be located and visualized, thus effectively avoiding the drawbacks of the artificial feature engineering and the expert knowledge method.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Integrative security system and method
ActiveUS20160232777A1Facilitate quick understandingEasy to understand quicklyClosed circuit television systemsBurglar alarm mechanical actuationSecurity systemSurveillance data
A method for monitoring and securing a facility without employing a manned control center, according to which a server acquires surveillance data from each of a plurality of distributed surveillance devices deployed within or adjacent to a given security sensitive facility. Then the server receives an intrusion alert from a guard, or from one or more of the plurality of surveillance devices to initiate a triggering event, if the acquired surveillance data is indicative of activity that has been detected at an indicated location. A first guard is alerted and presented with a full situational awareness image to assess the severity of the detected activity and the triggering event is terminated if found by the first guard to be of a low severity, or an interception operation initiated by self-dispatching or dispatching one or more additional guards to a close by location that holds tactical advantage relative to the indicated location if the triggering event was found by the first guard to be of a high severity.
Owner:LIQUID 360 LTD
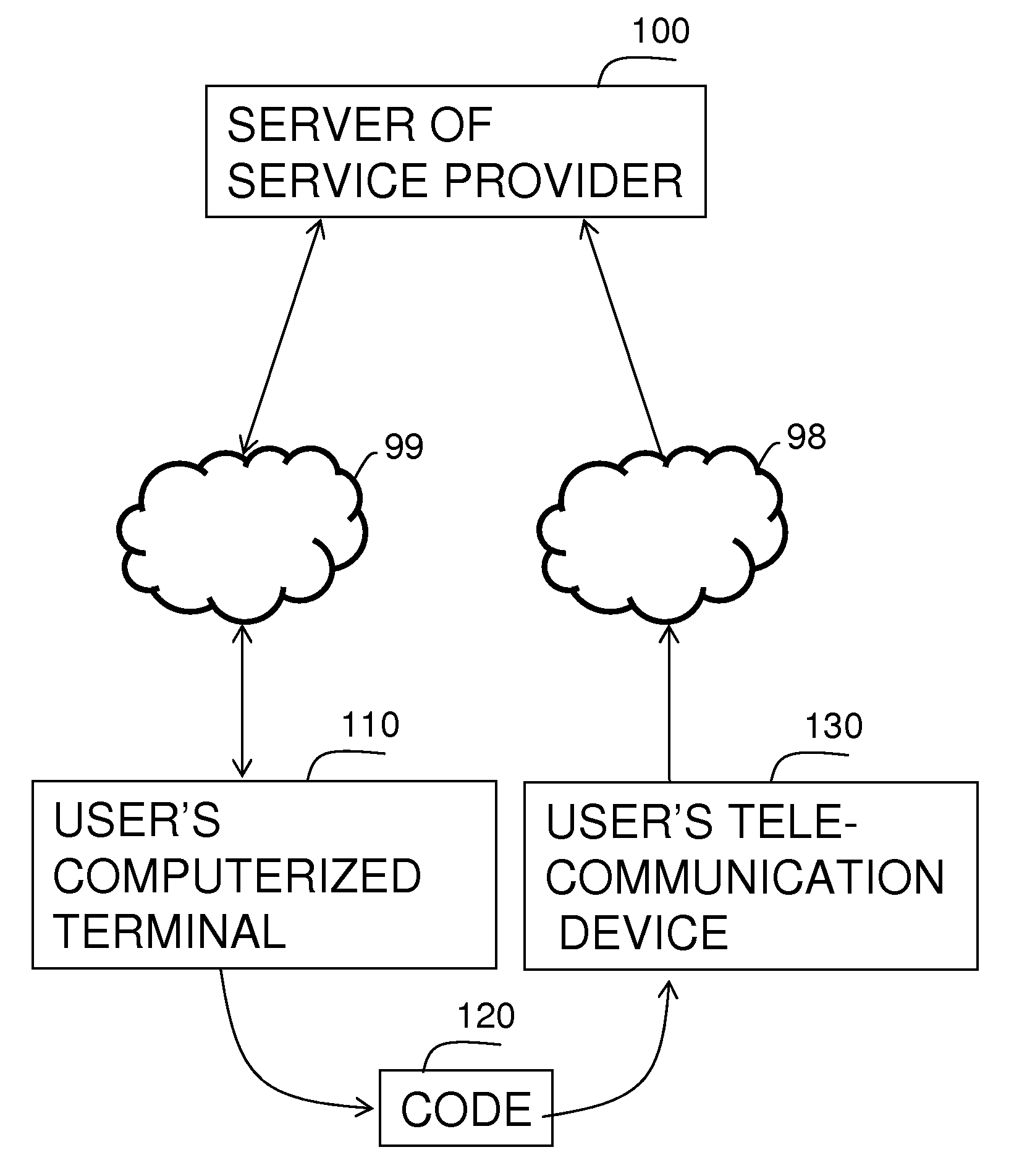
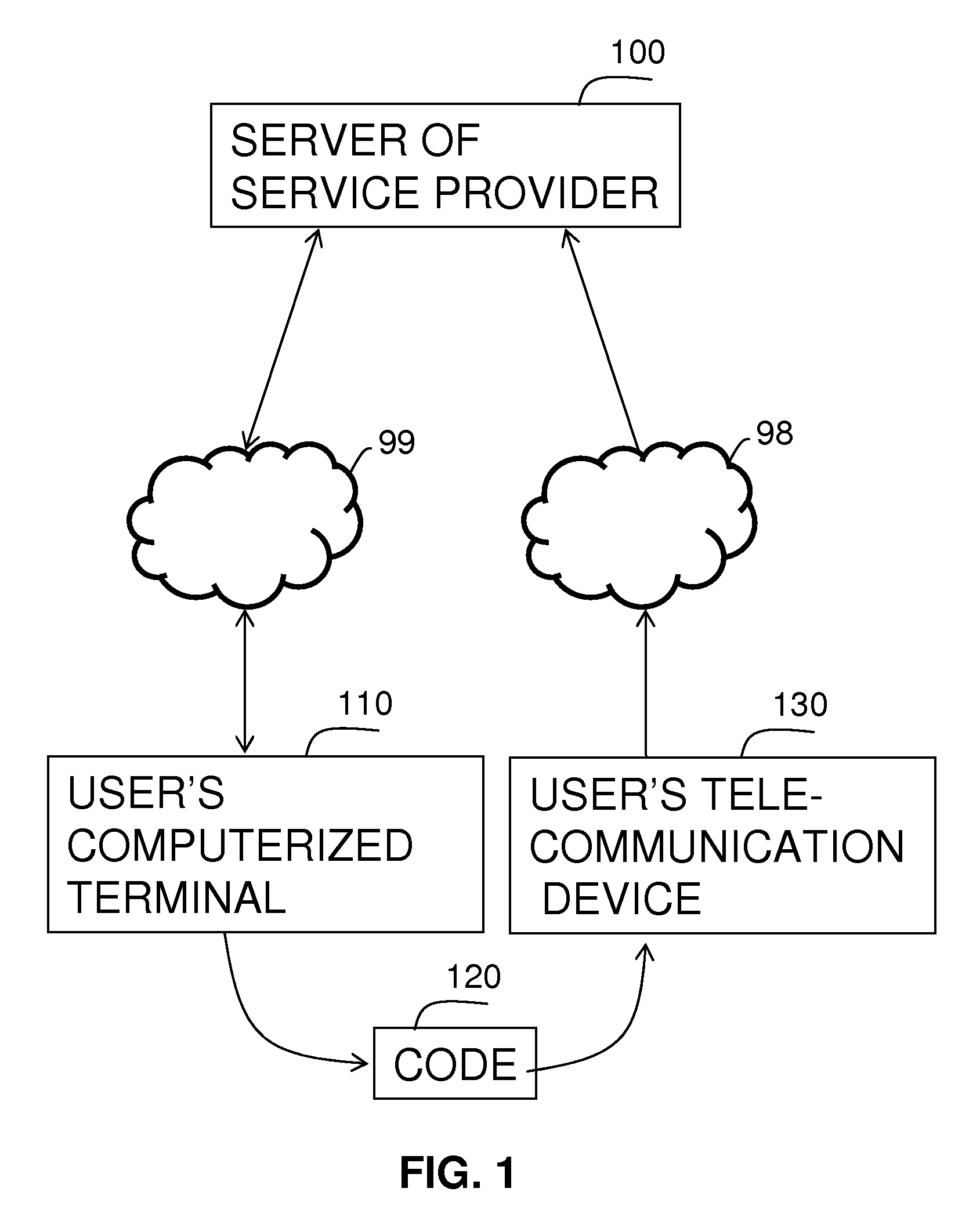
Method and system for monetary billing for the use of content services in internet sites, by sending SMS messages from cellular phones
InactiveUS20080254765A1Telephonic communicationApparatus for meter-controlled dispensingTelecommunications linkWeb service
A system and method for billing web services provided by a service provider to a user. A server of the service provider is connected to a computerized terminal of the user, and to a telecommunication device of the user via a communication link. The system and method generate codes related to each user, web service and price for using the web service. The server sends the code and receives the code from the telecommunication device. Upon reception the server provides the web service to the user, and bill the price from the account of the telecommunication device.
Owner:ELIAZ ARI
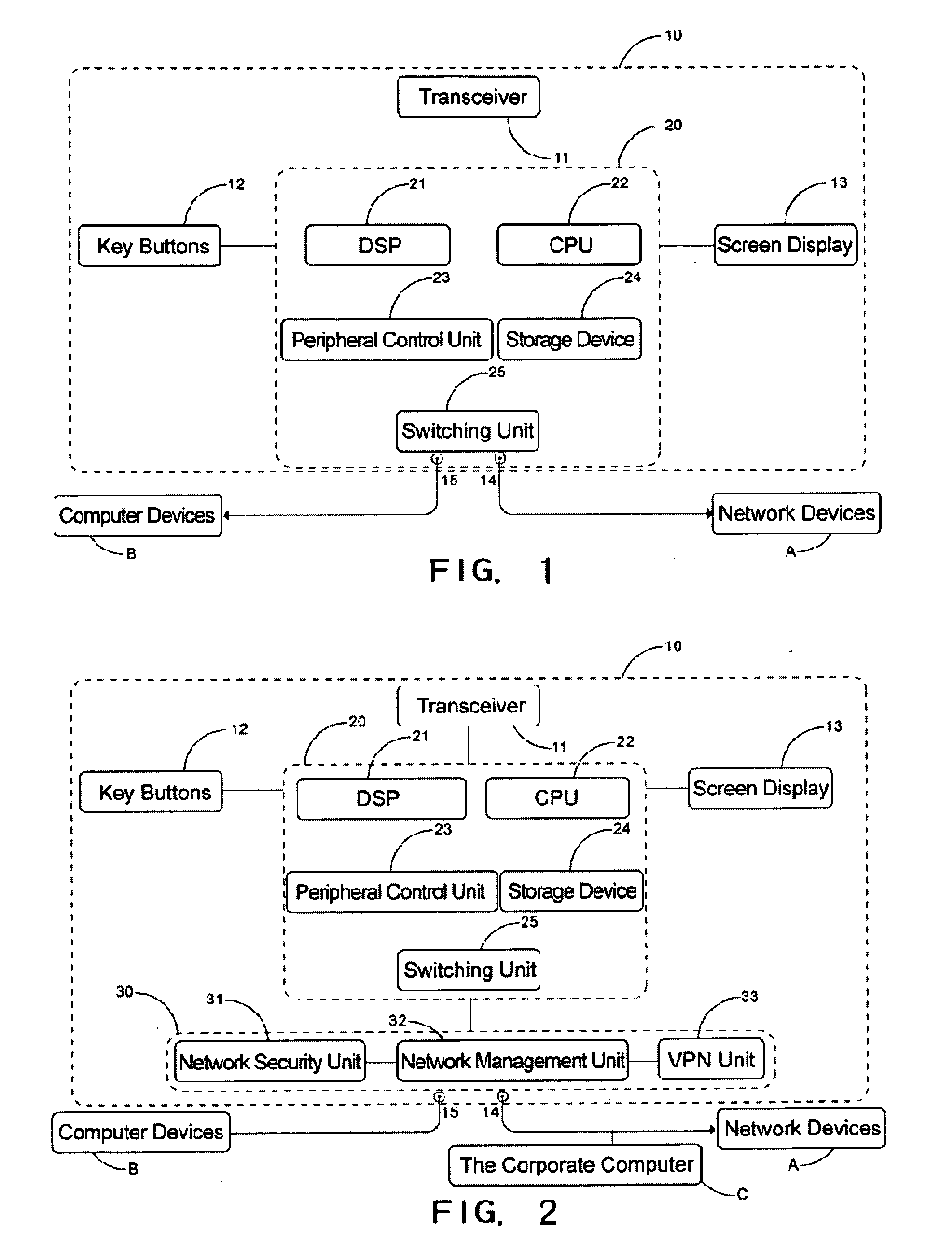
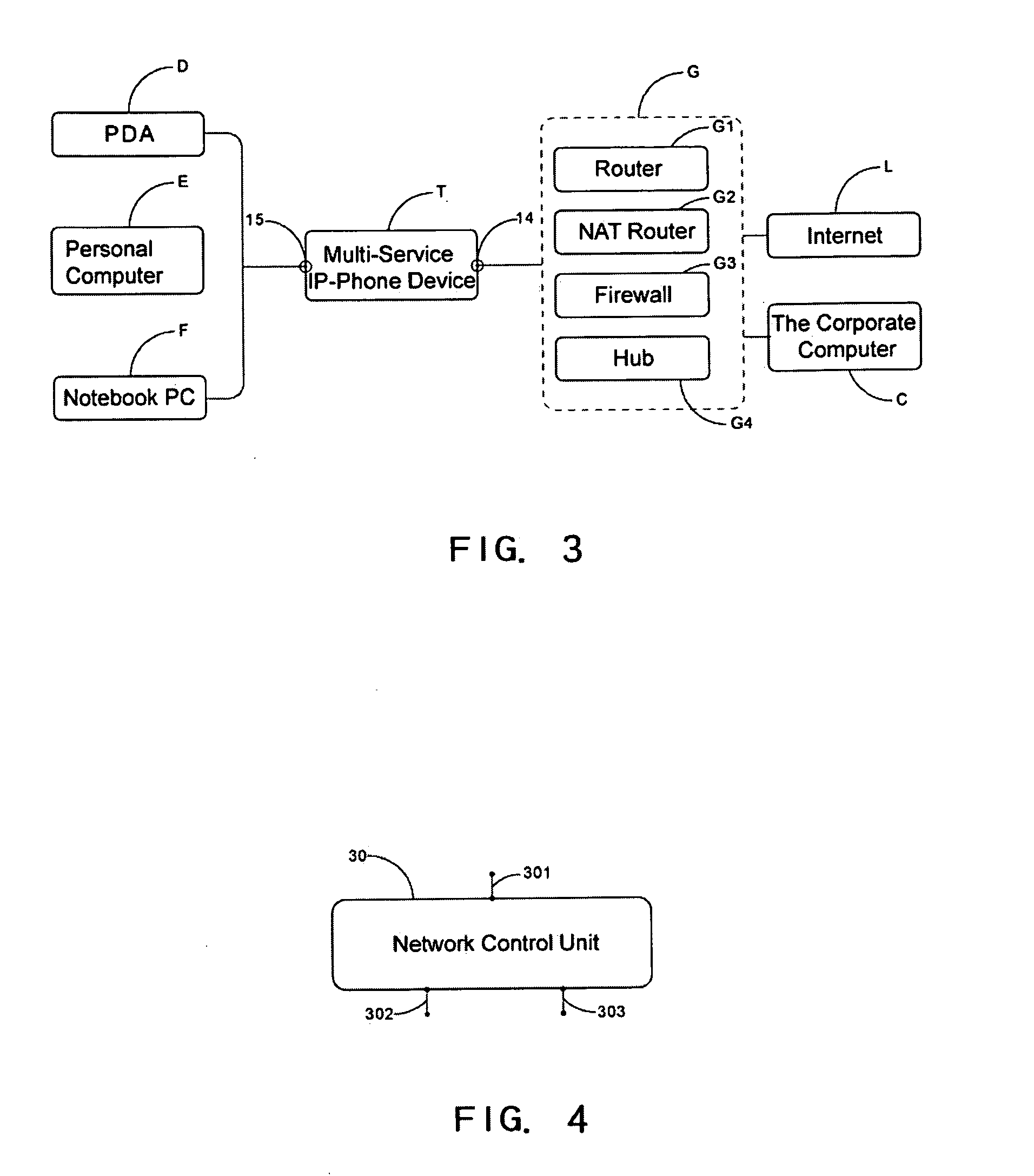
Device and method of multi-service IP-phone
InactiveUS20070248098A1Reduce business costsSave valuable office spaceData switching by path configurationSubstation equipmentPrivate networkThe Internet
The present invention relates to a device, as well as a method, of a multi-service IP-phone. The device and method comprise an IP-phone, to be used for making intercom and inbound / outbound phone calls through a LAN or the Internet, and a network control unit, to be used to control the data transmitting through the network. By connecting the IP-phone with network devices and computer devices, one can not only use the IP-phone to receive and make phone calls, but also use the computer devices to access the LAN or the internet via the IP-phone, which at the same time, with its built-in network control unit, provides such functions as LAN / internet security, data security, packet filtering, bandwidth management, traffic shaping (load balance), and virtual private network (VPN).
Owner:ESSENCE TECH SOLUTION
Method for intelligently intercepting threat IP based on cloud protection
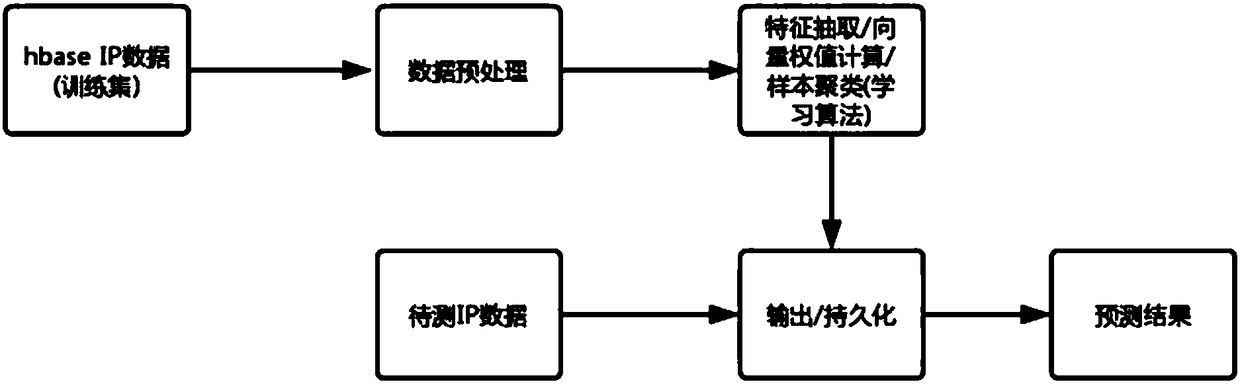
The invention relates to the field of Internet security, and aims to provide a method for intelligently intercepting a threat IP based on cloud protection. The method for intelligently intercepting athreat IP based on cloud protection comprises the steps that: after receiving a cloud protection log, a big data log analysis server performs analysis according to a preset analysis rule, and stores the analyzed field information to an hbase cluster; a machine learning cluster establishes an analytic statistics model, the analytic statistics model can identify the behavior characteristics of an IPafter training, the machine learning cluster pushes the threat IP and corresponding domain name information to a cloud protection platform engine in real time, and the cloud protection platform engine dynamically adds the threat IP and the corresponding domain name information to a blacklist after receiving and implements corresponding interruption based on the attack threat level. The IP blacklist has high real-time property, and the configuration can be dynamically added and changed according to the log analysis result to effectively reduce the problem that the rule is bypassed and falselyreported.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com