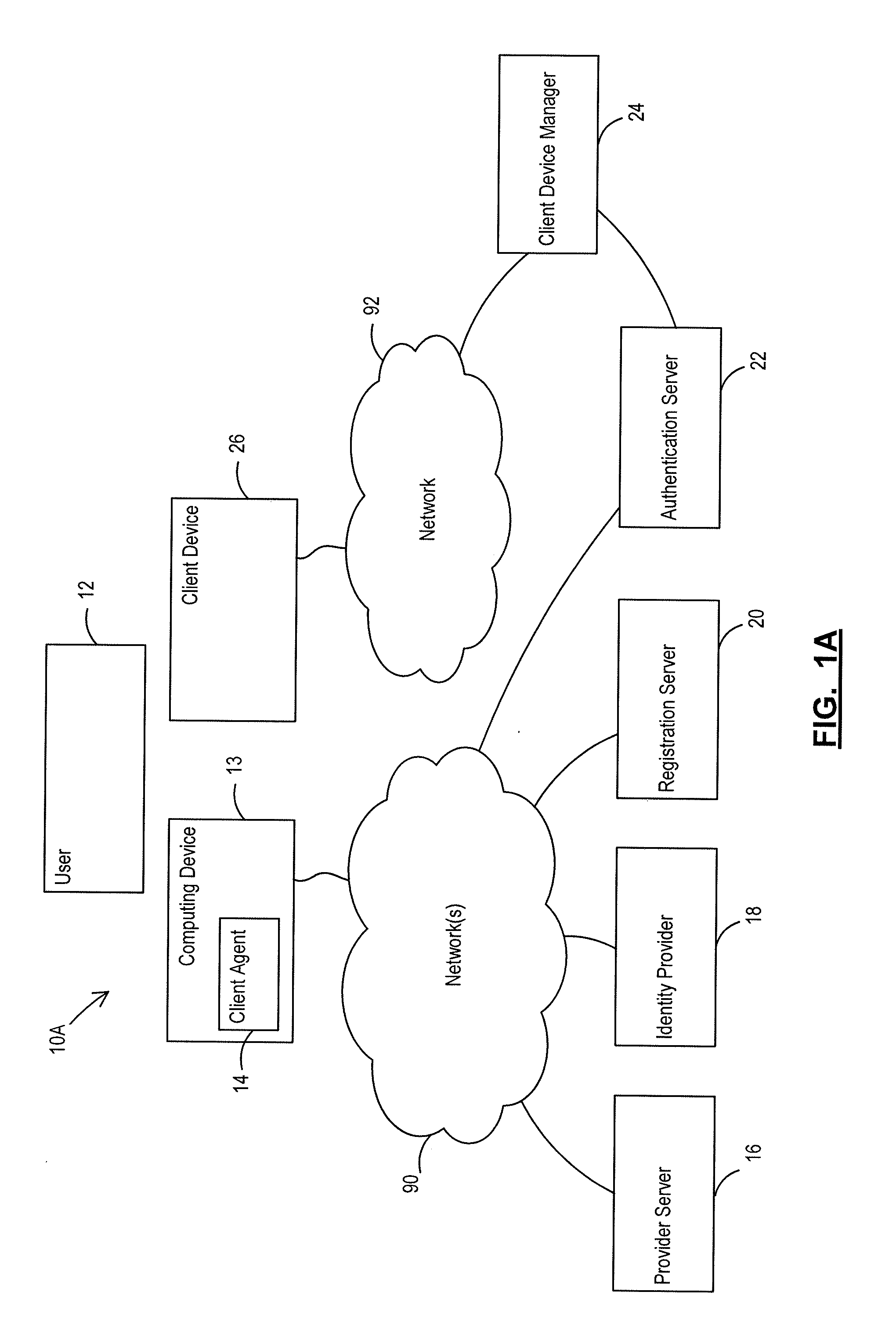
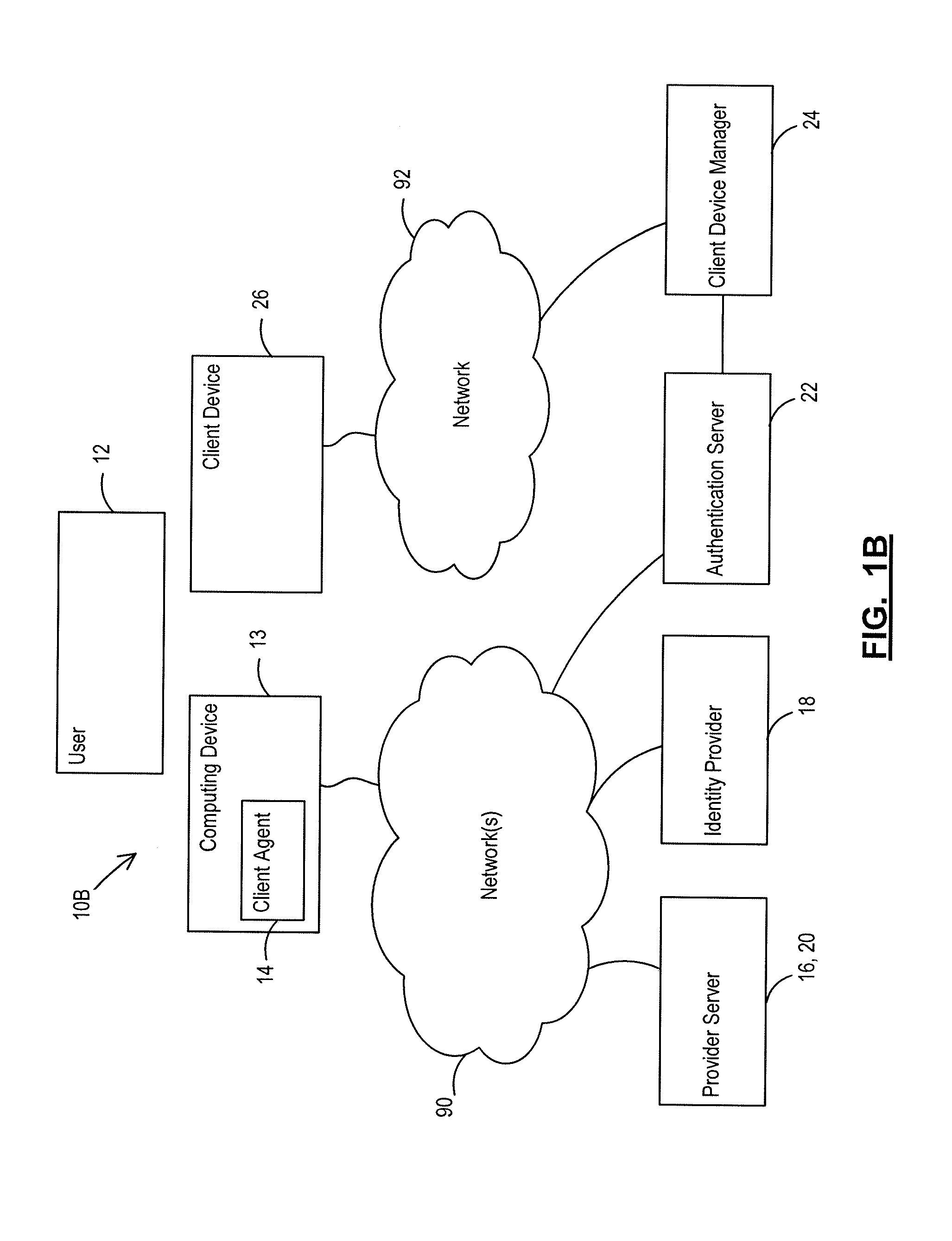
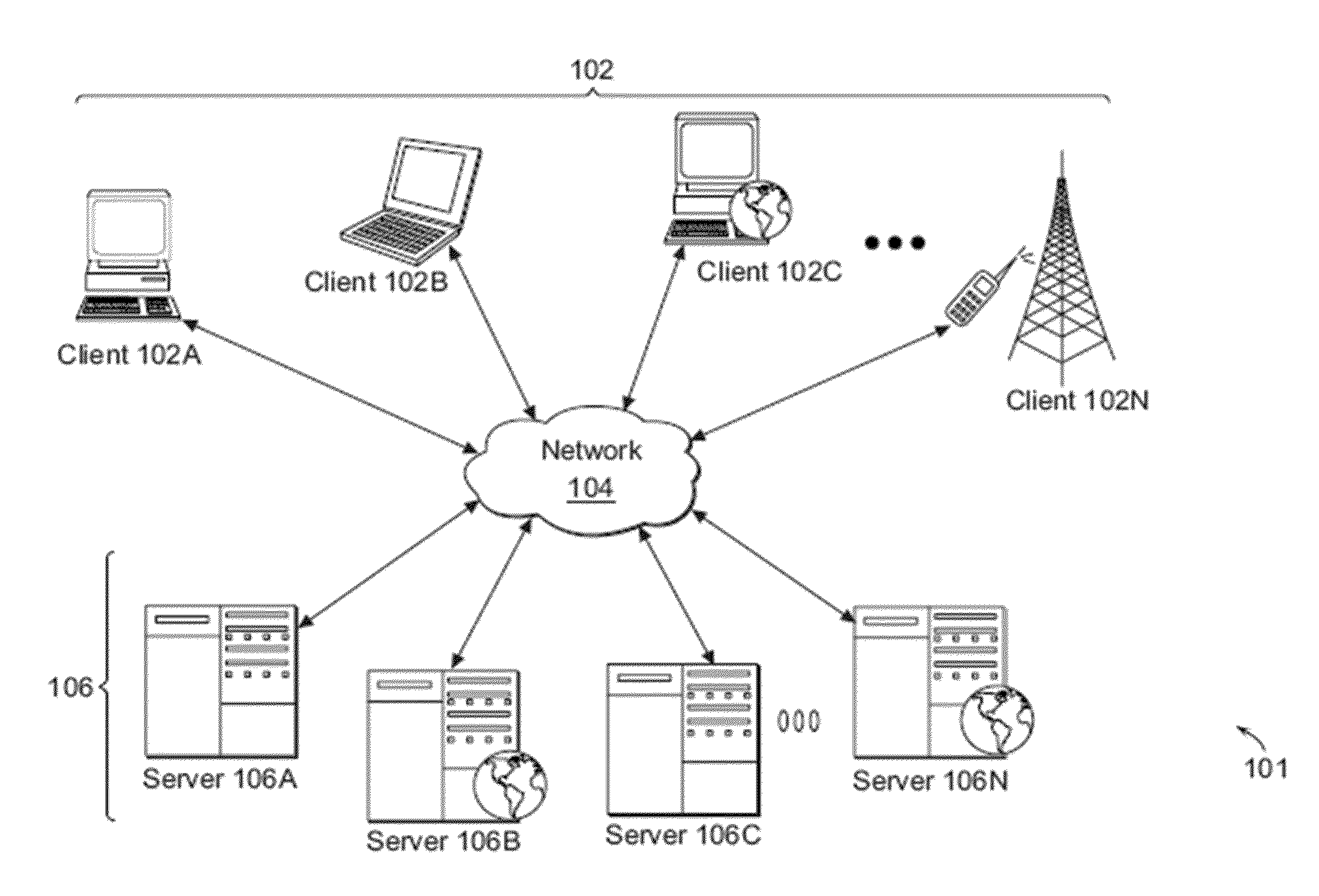
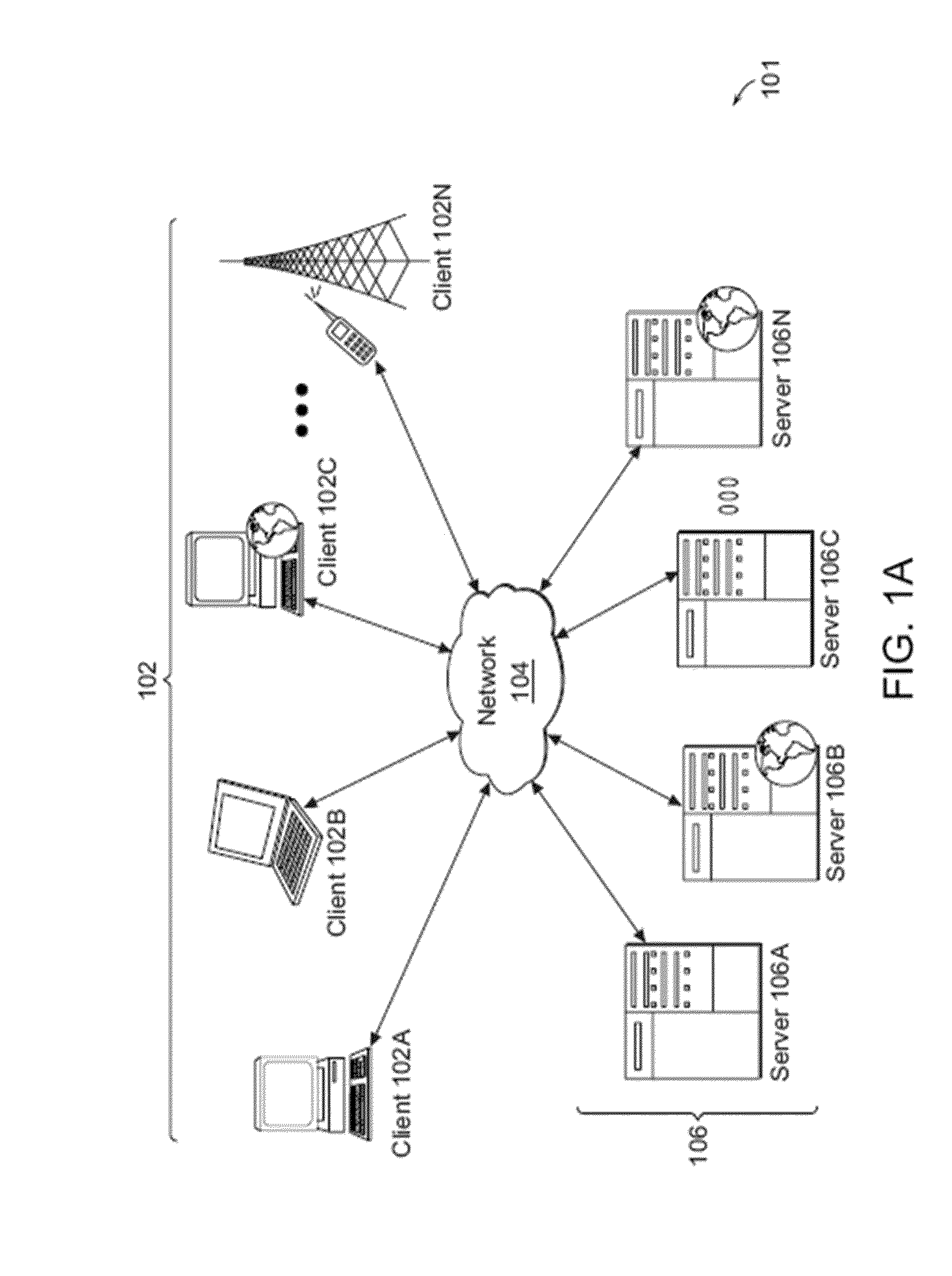
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
349 results about "Client agent" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
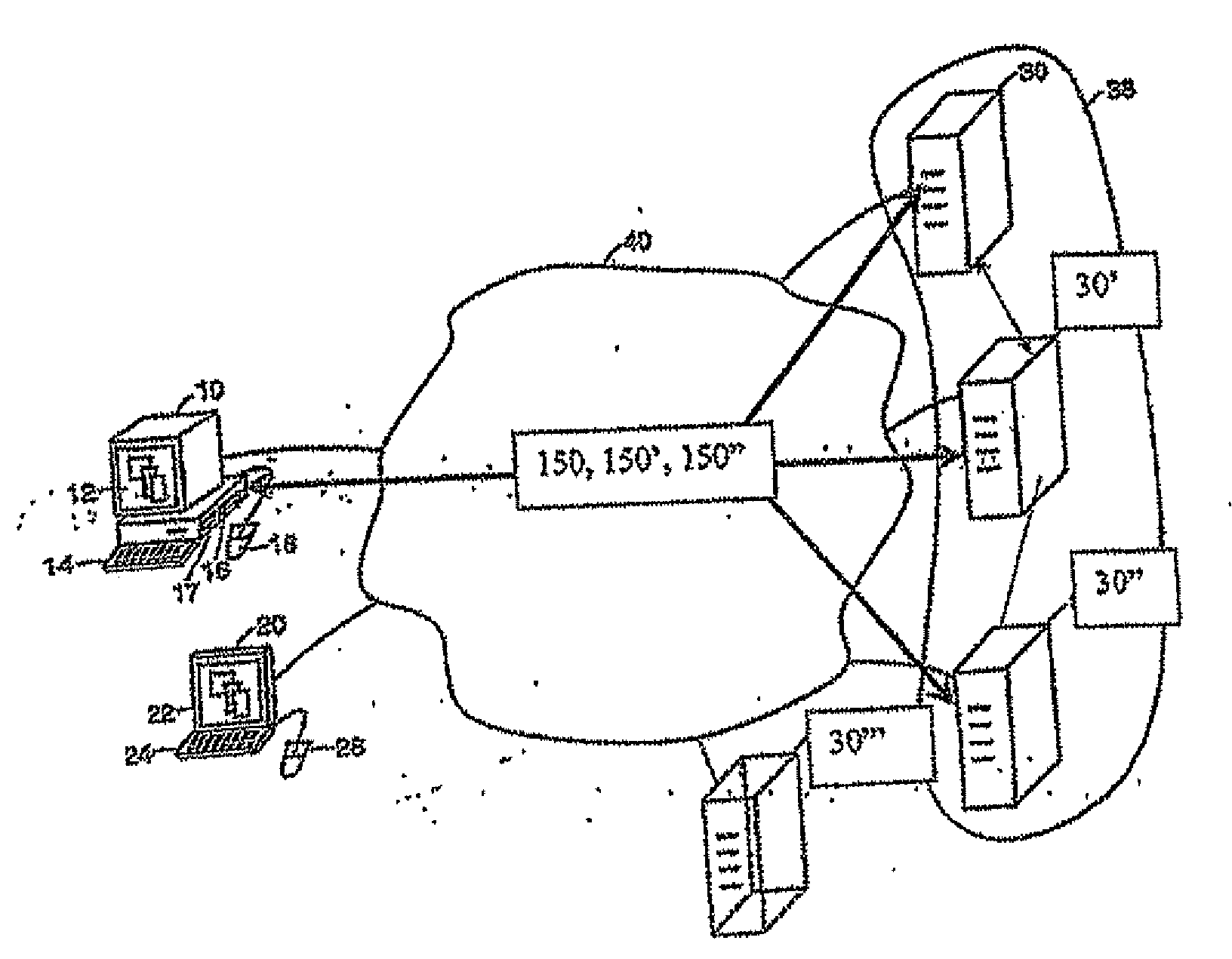
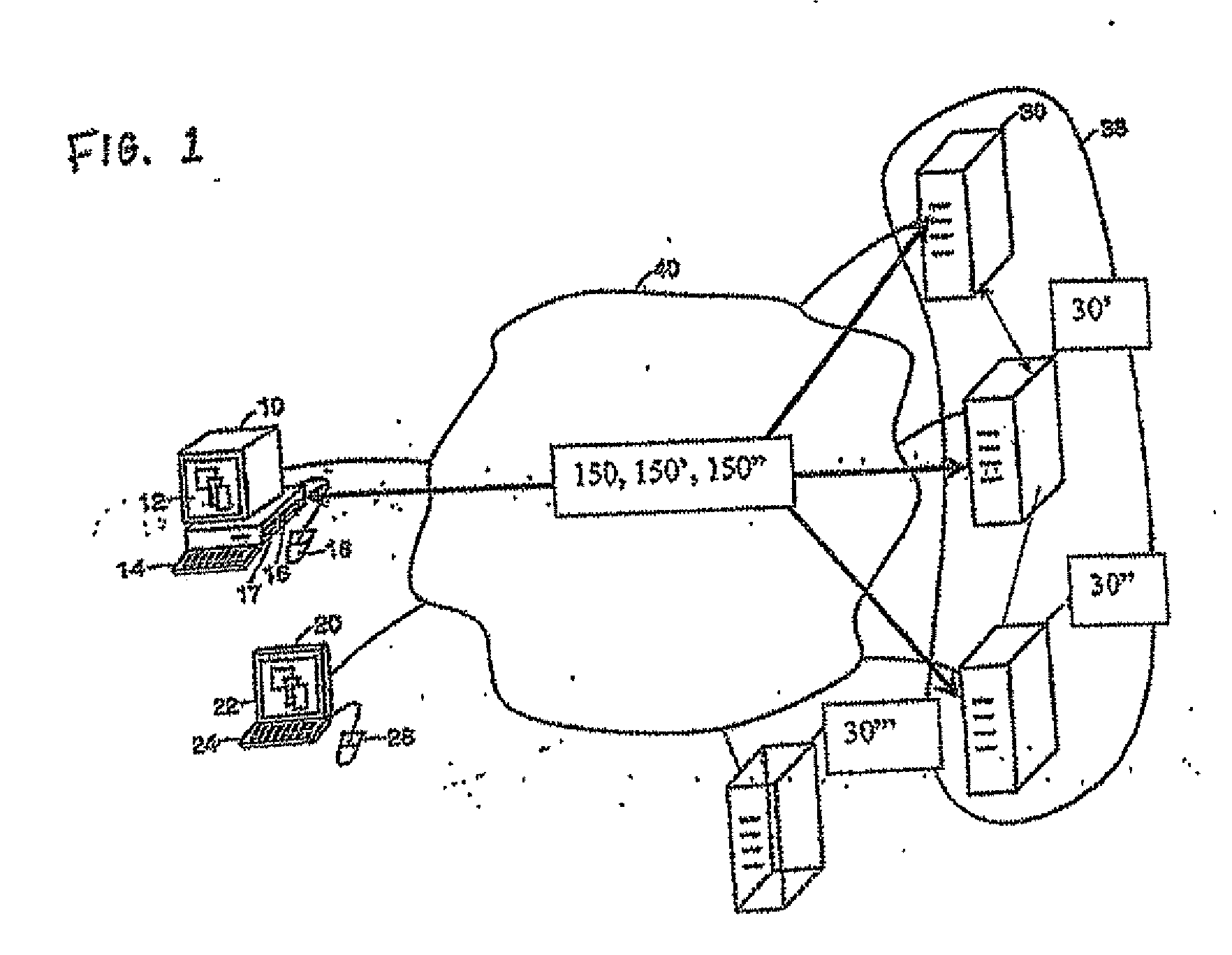
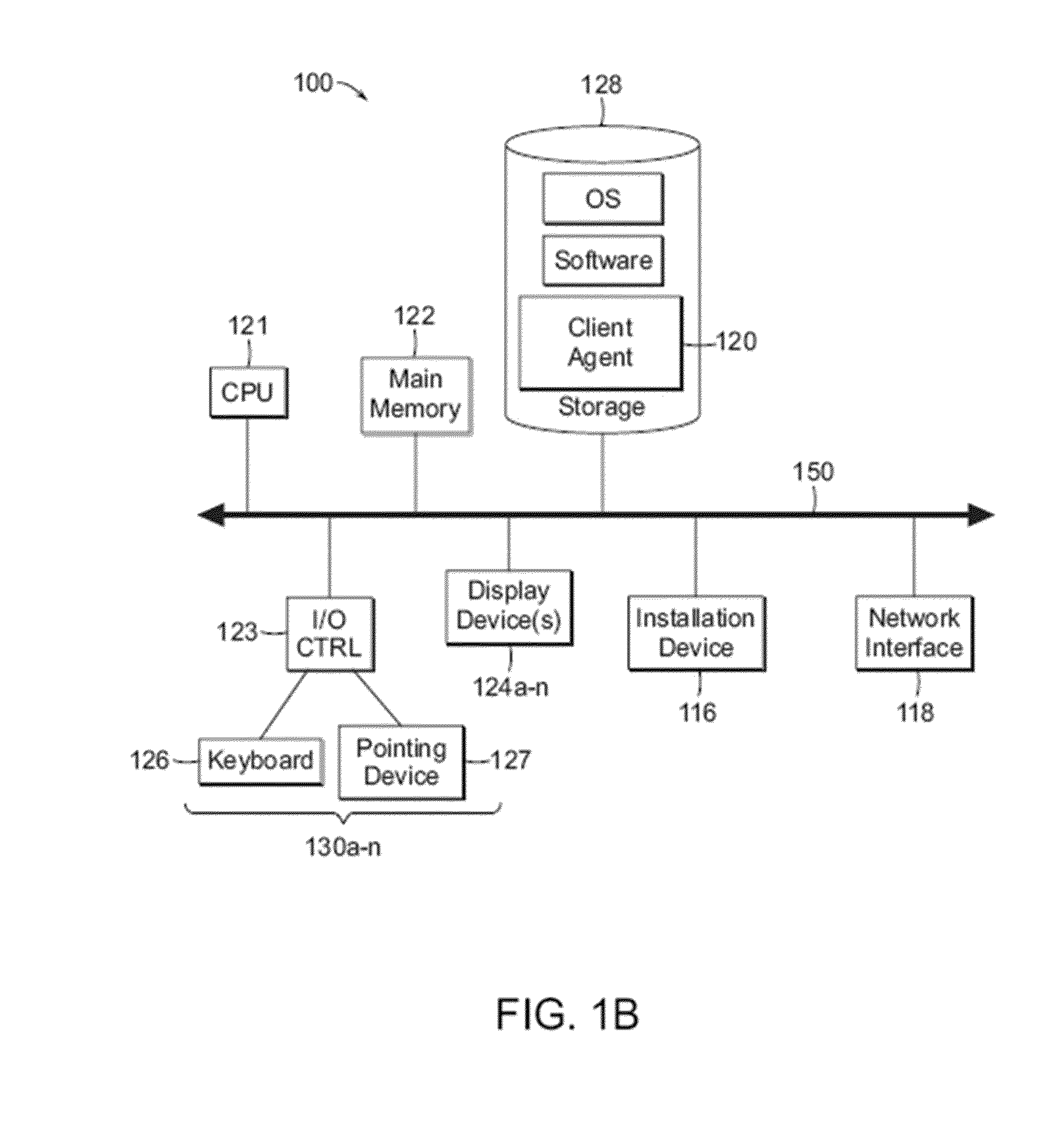
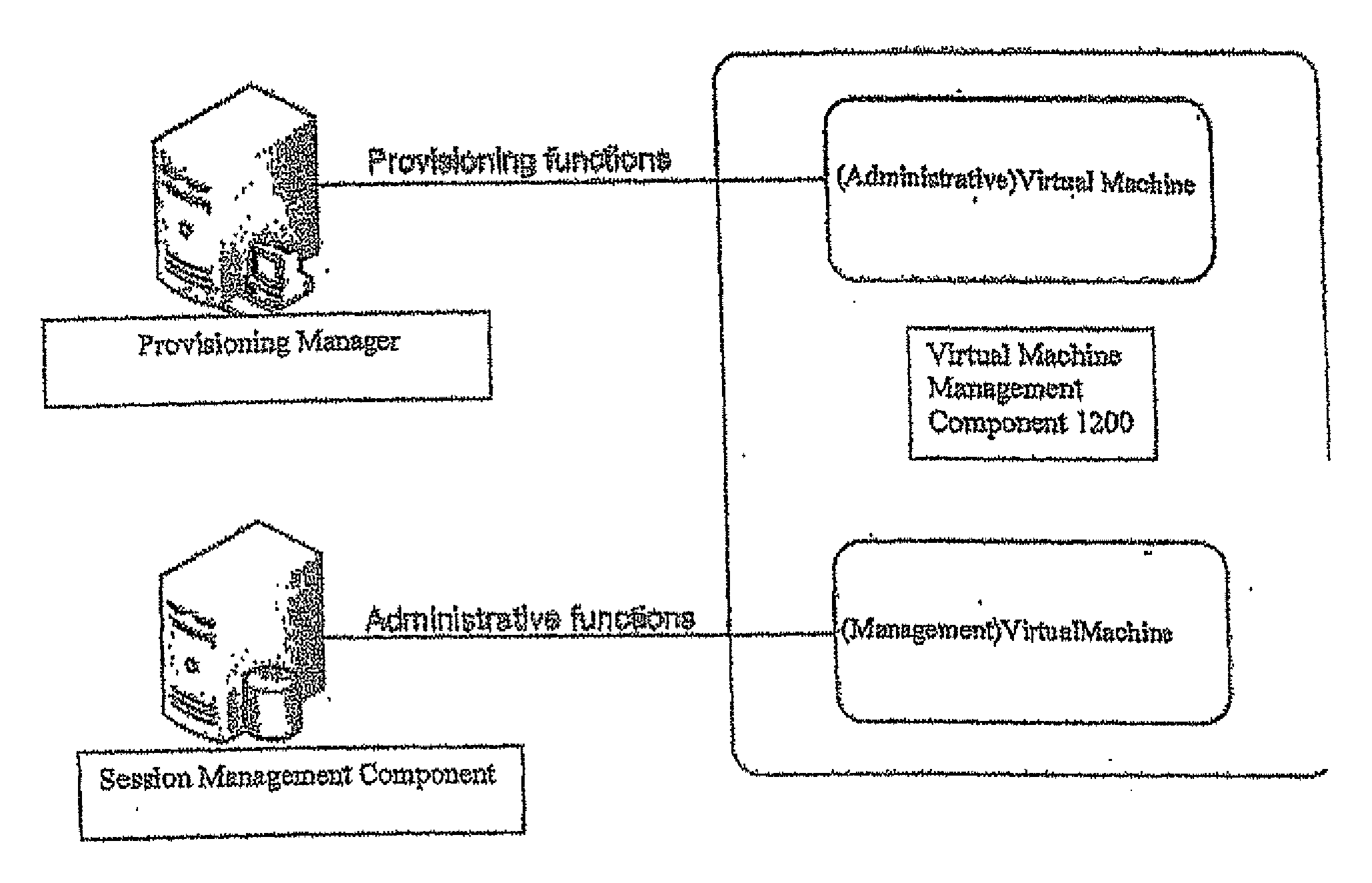
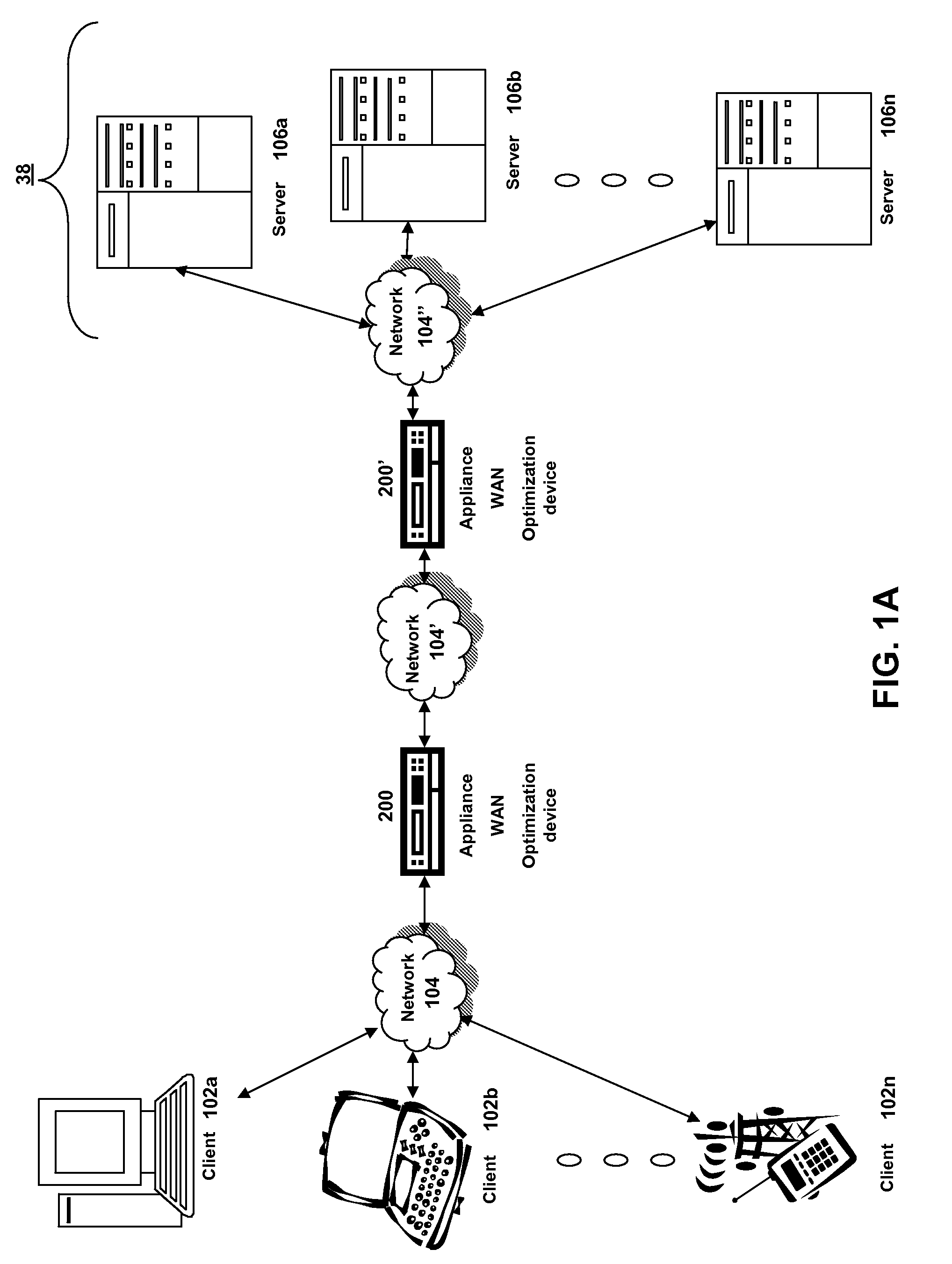
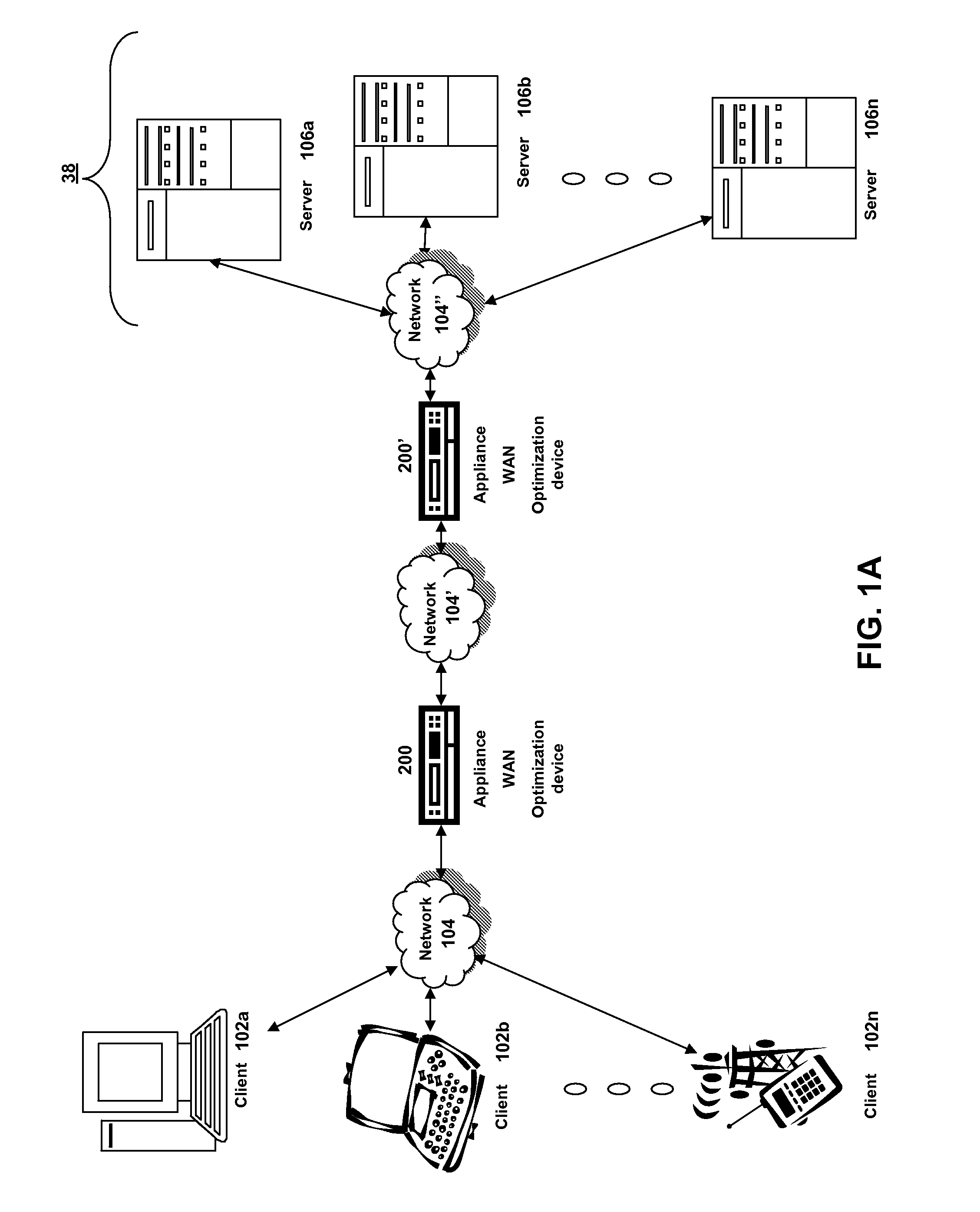
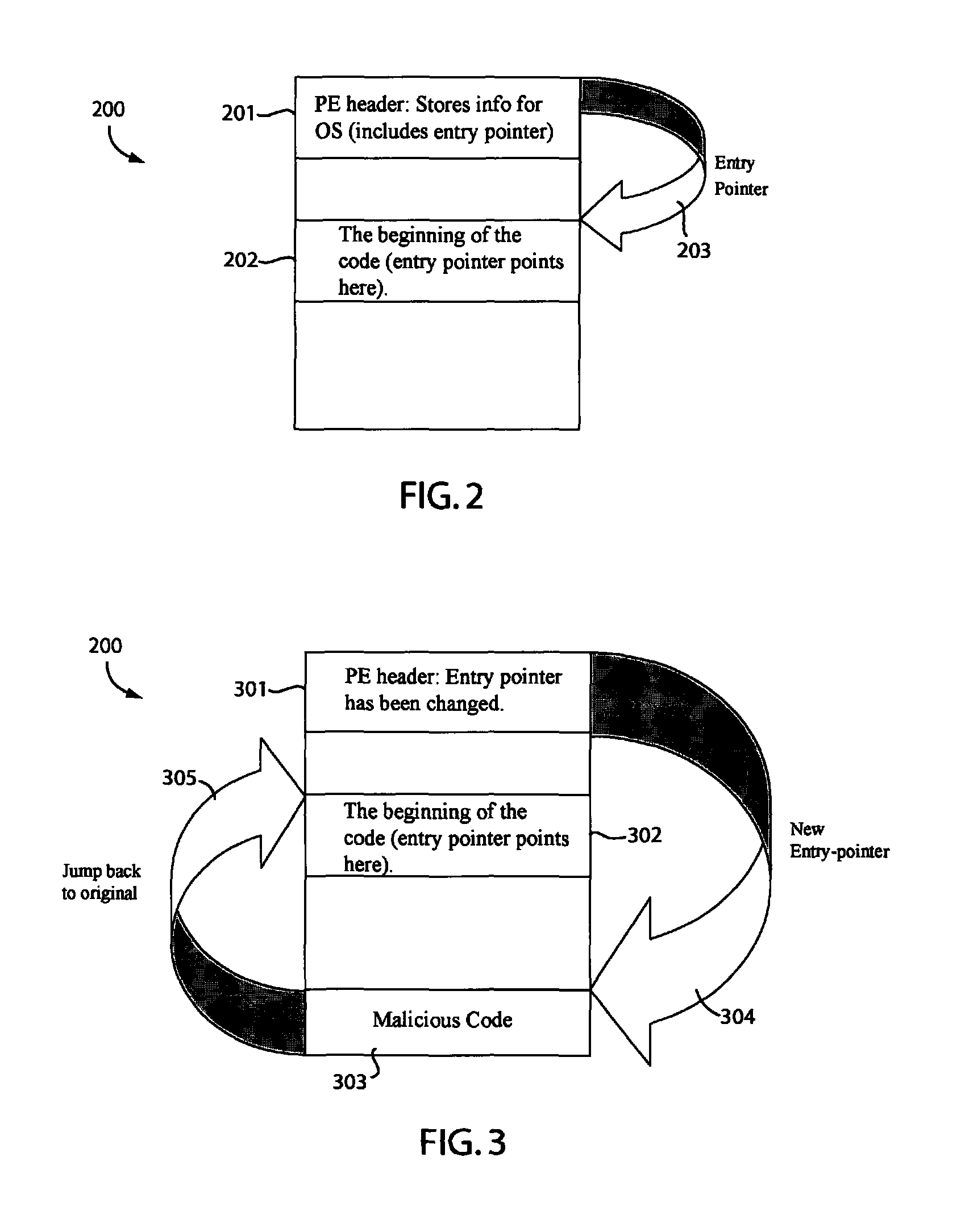
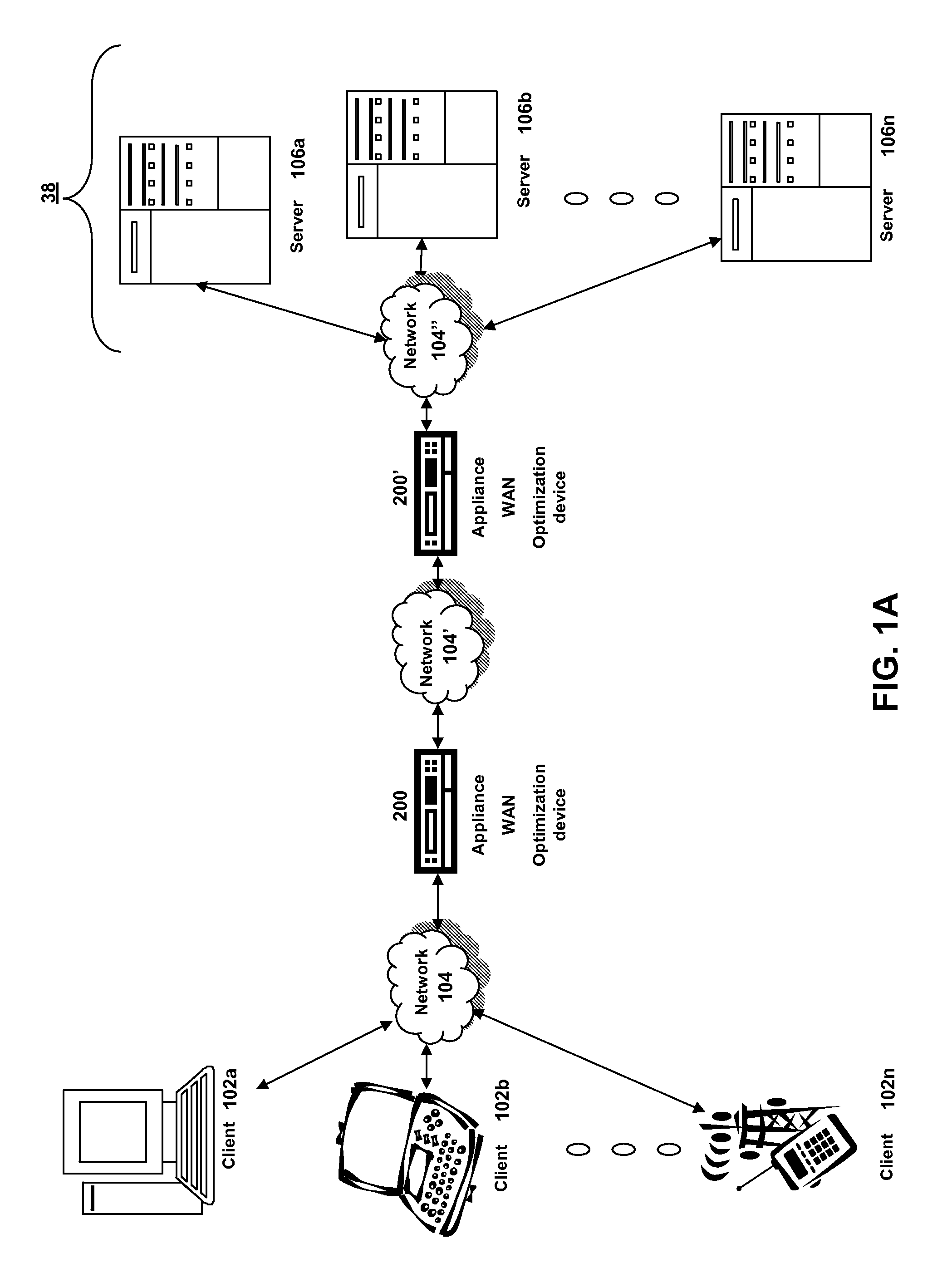
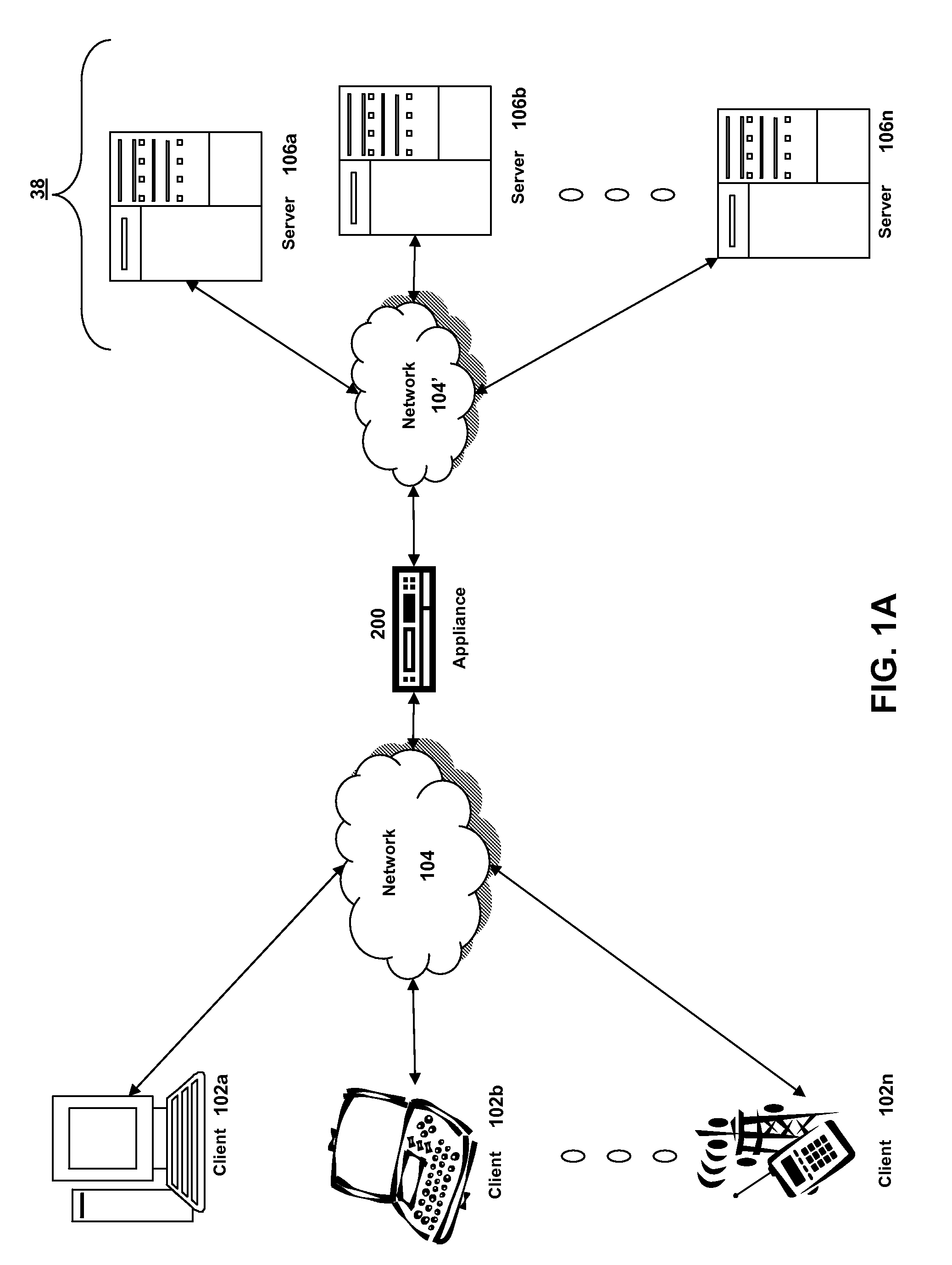
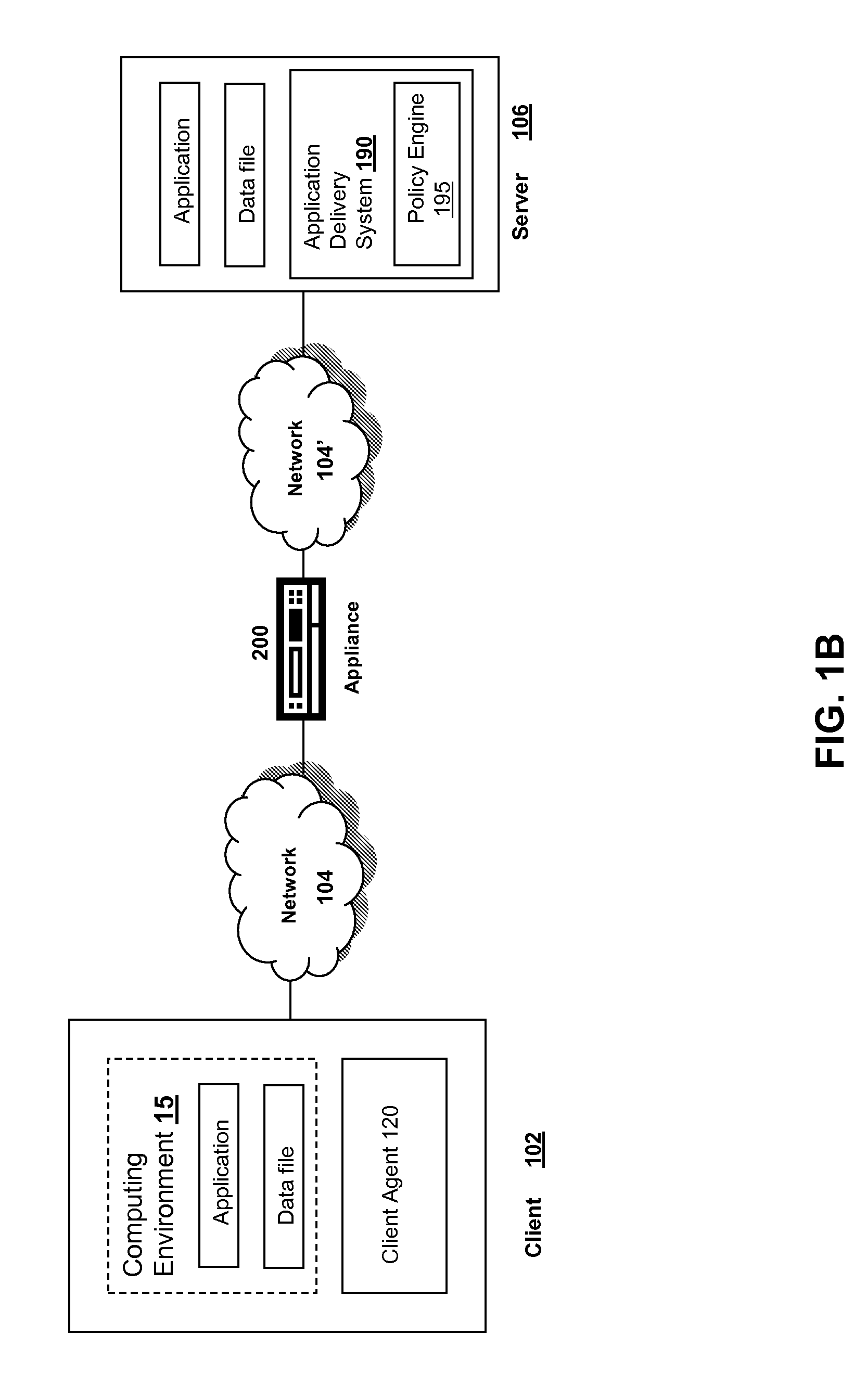
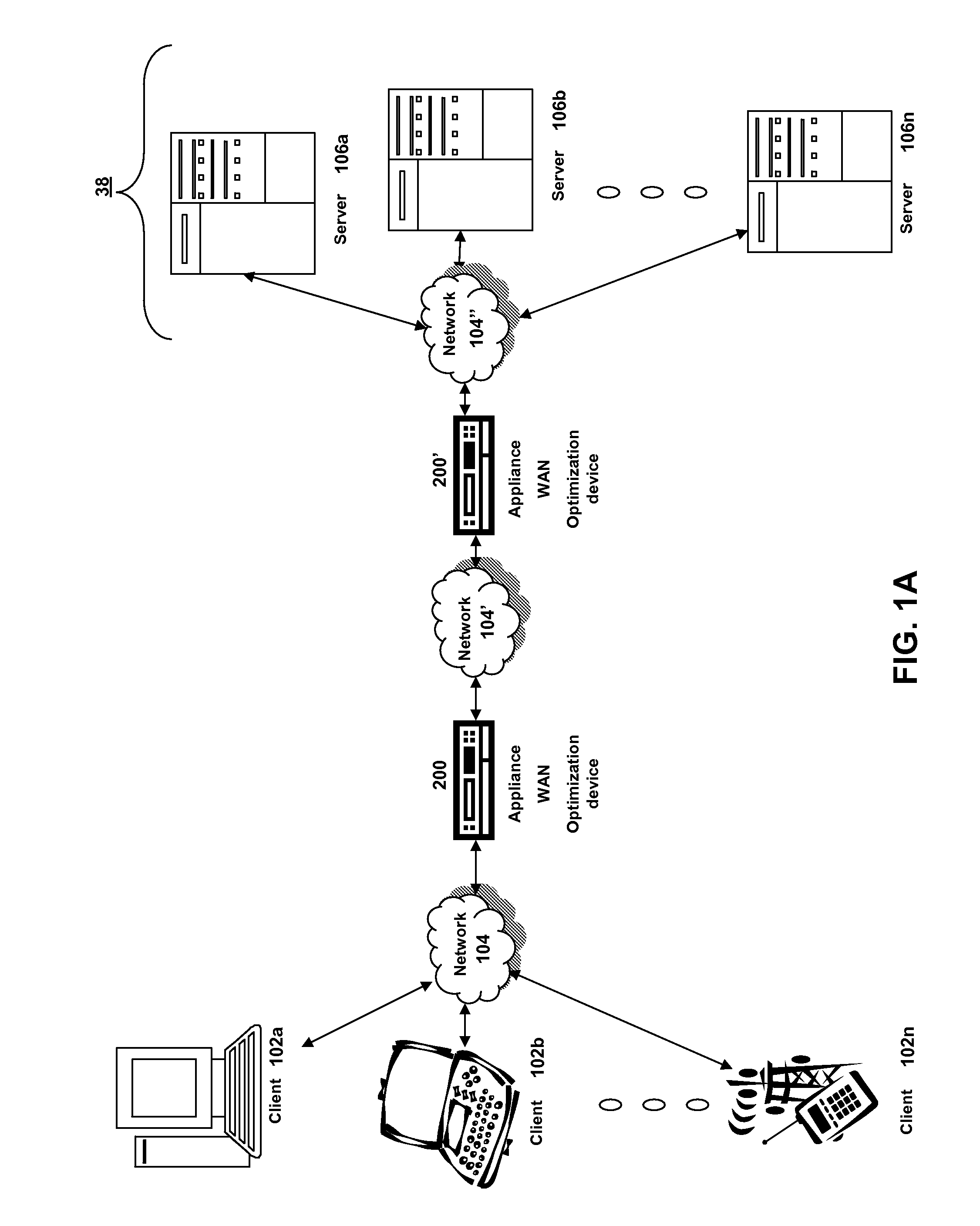
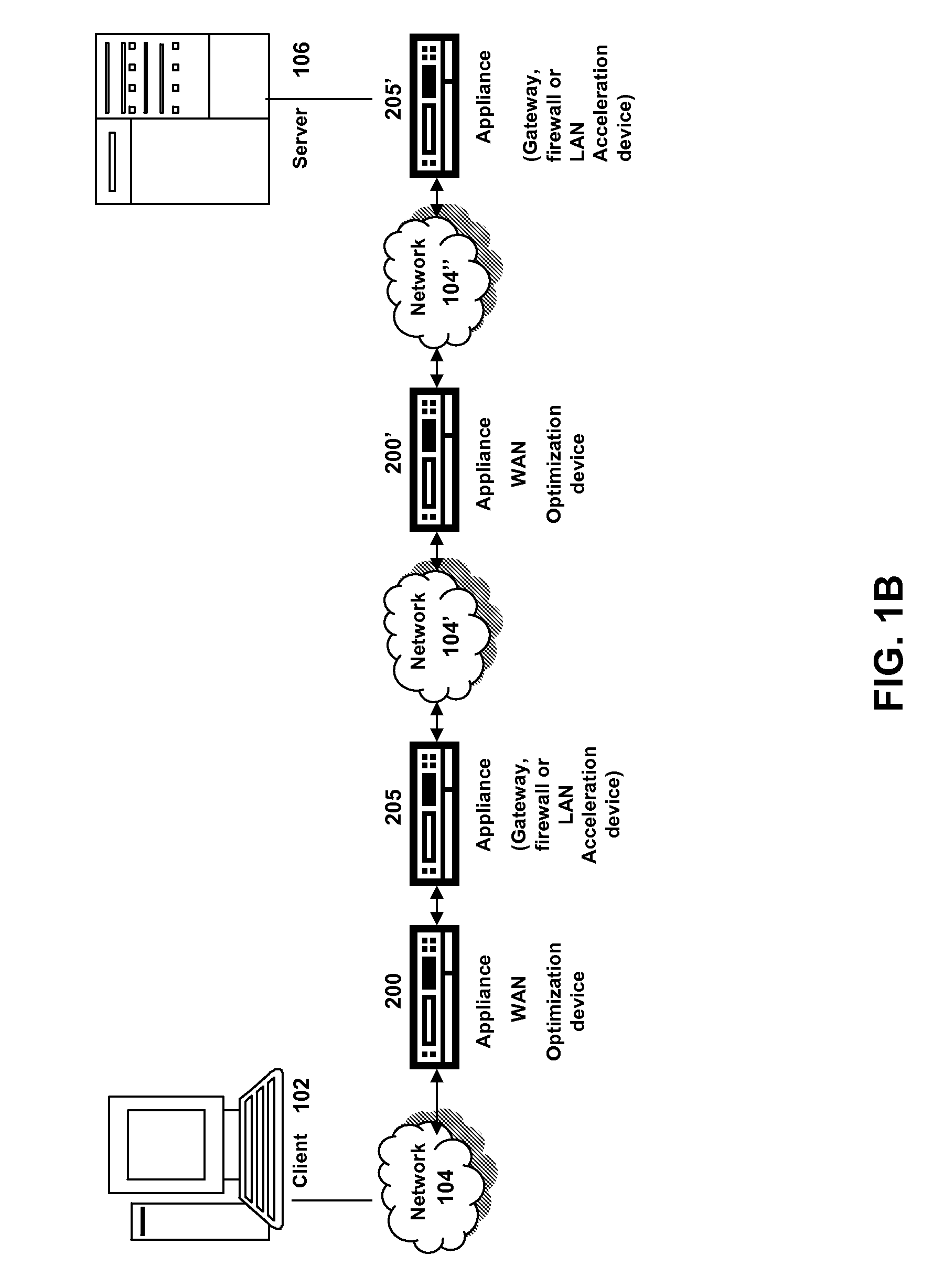
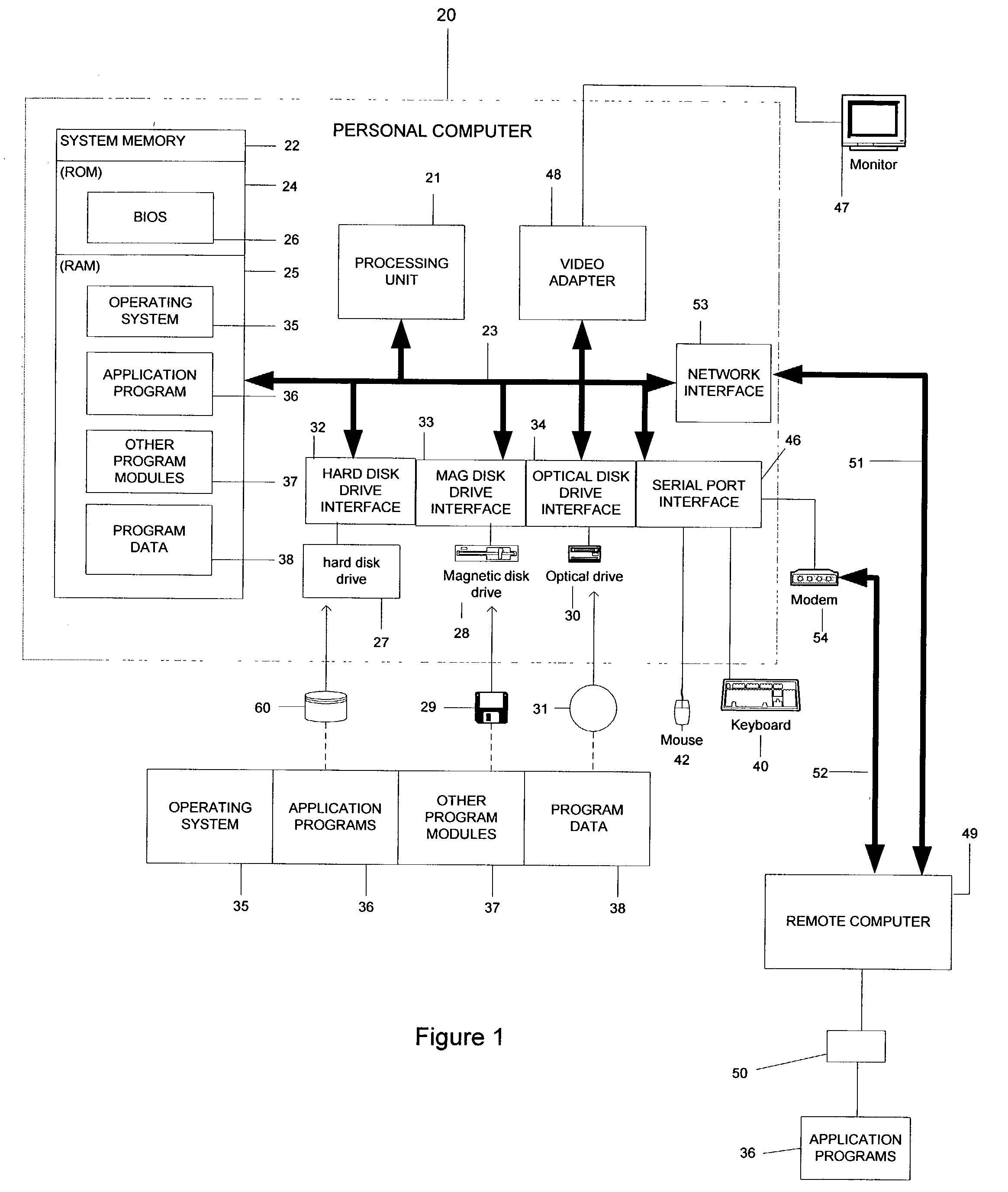
Methods and systems for interacting, via a hypermedium page, with a virtual machine executing in a terminal services session
ActiveUS20070171921A1Low costReduce difficultyDigital data information retrievalInterprogram communicationHyperlinkClient agent
A method for making a hypermedium page interactive, the hypermedium page displayed by a network browser, includes the step of selecting a hyperlink on the hypermedium page displayed on a client machine, the hyperlink identifying a desired computing resource. A hyperlink configuration file is retrieved, the hyperlink configuration file corresponding to the hyperlink and identifying a server machine. A client agent is started on the client machine. The client agent creates, via a terminal services session, a communication link to a virtual machine executing on the server identified by the hyperlink configuration file, the virtual machine executed by a hypervisor executing in the terminal services session provided by an operating system executing on the server. The client agent receives data from the virtual machine and displays, on the client machine, the received data without intervention by the network browser.
Owner:CITRIX SYST INC
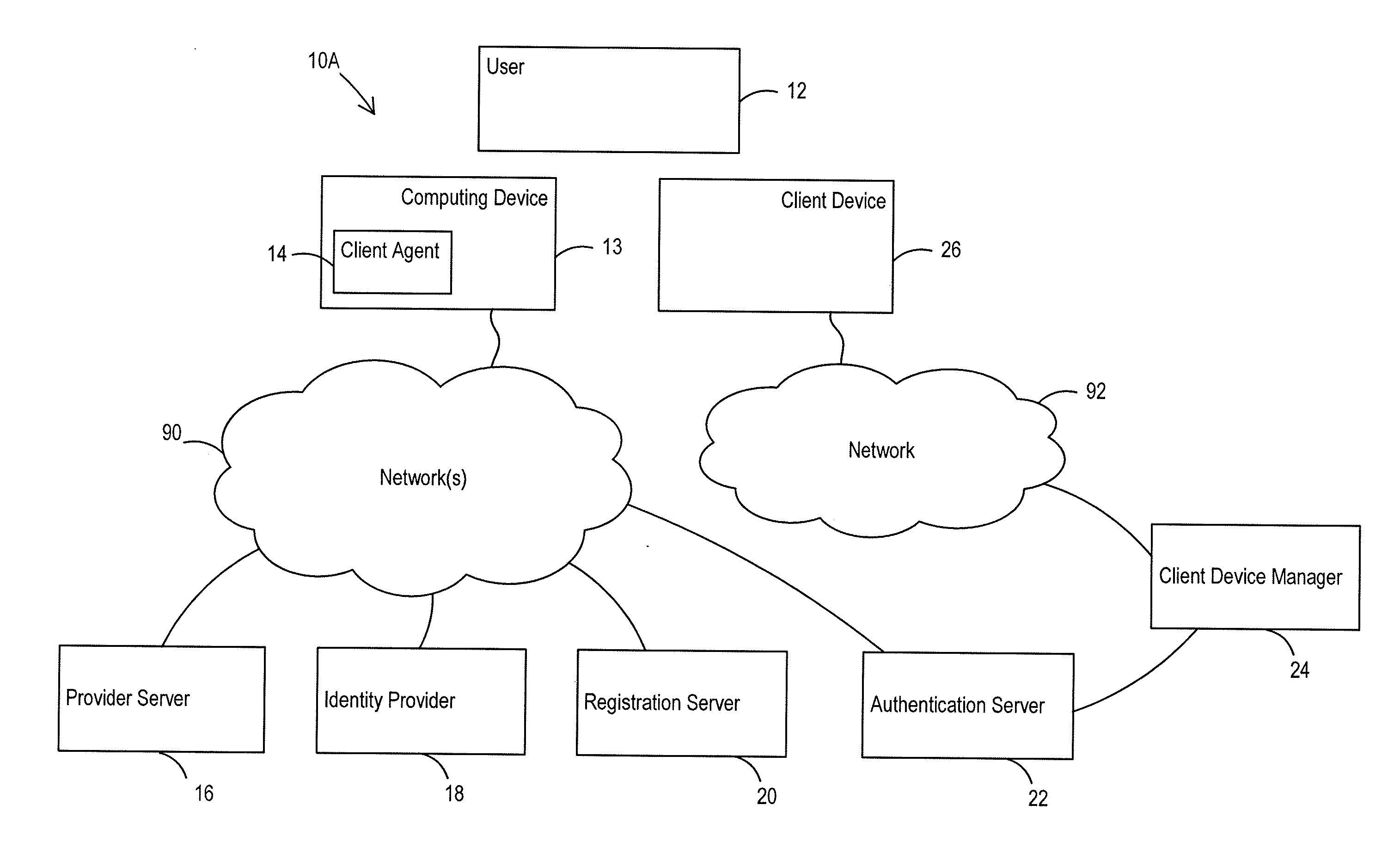
Methods and systems for using derived credentials to authenticate a device across multiple platforms
ActiveUS20140020073A1Digital data processing detailsMultiple digital computer combinationsClient agentThird party
Methods and systems for adapting existing service provider servers to support two-factor authentication by leveraging an authentication server, which may be operated by a third party. Where a user desires to access content or services offered by a service provider server, the user may employ a client agent (for example, a web browser) in order to authenticate with the service provider server. Service provider server can redirect client agent to an authentication server to process at least a second factor or derived credential.
Owner:SECUREKEY TECH
Methods and systems for securing sensitive information using a hypervisor-trusted client
ActiveUS20110141124A1Internal/peripheral component protectionDigital data authenticationClient agentGraphics
The methods and systems described herein provide for securing sensitive information using a hypervisor-trusted client, in a computing device executing a hypervisor hosting a control virtual machine and a non-trusted virtual machine. A user of a non-trusted virtual machine requests to establish a connection to a remote computing device. Responsive to the request, a control virtual machine launches a client agent. A graphics manager executed by the processor of the computing device assigns a secure section of a memory of a graphics processing unit of the computing device to the client agent. The graphics manager renders graphical data generated by the client agent to the secure section of the graphics processing unit memory.
Owner:CITRIX SYST INC
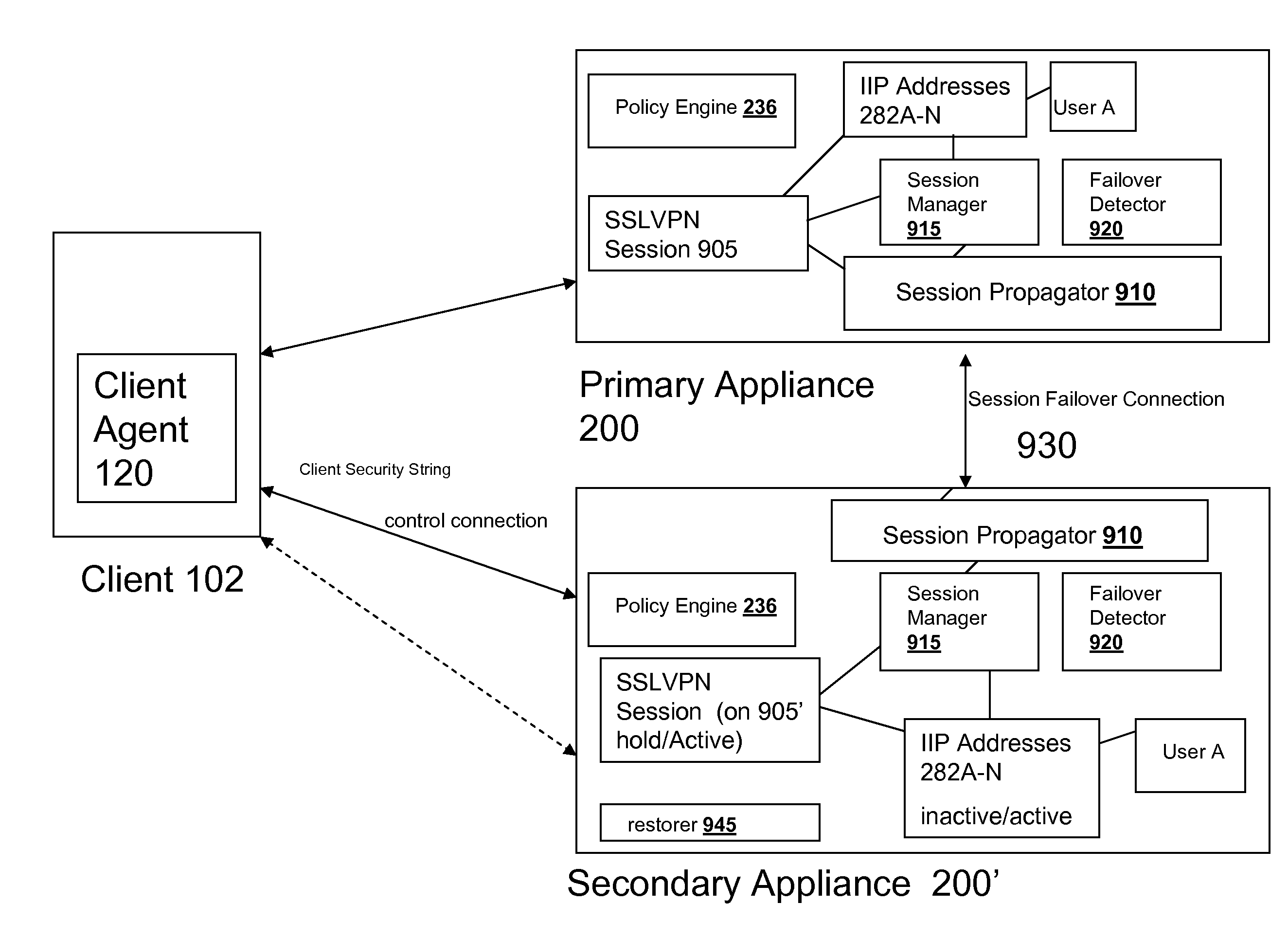
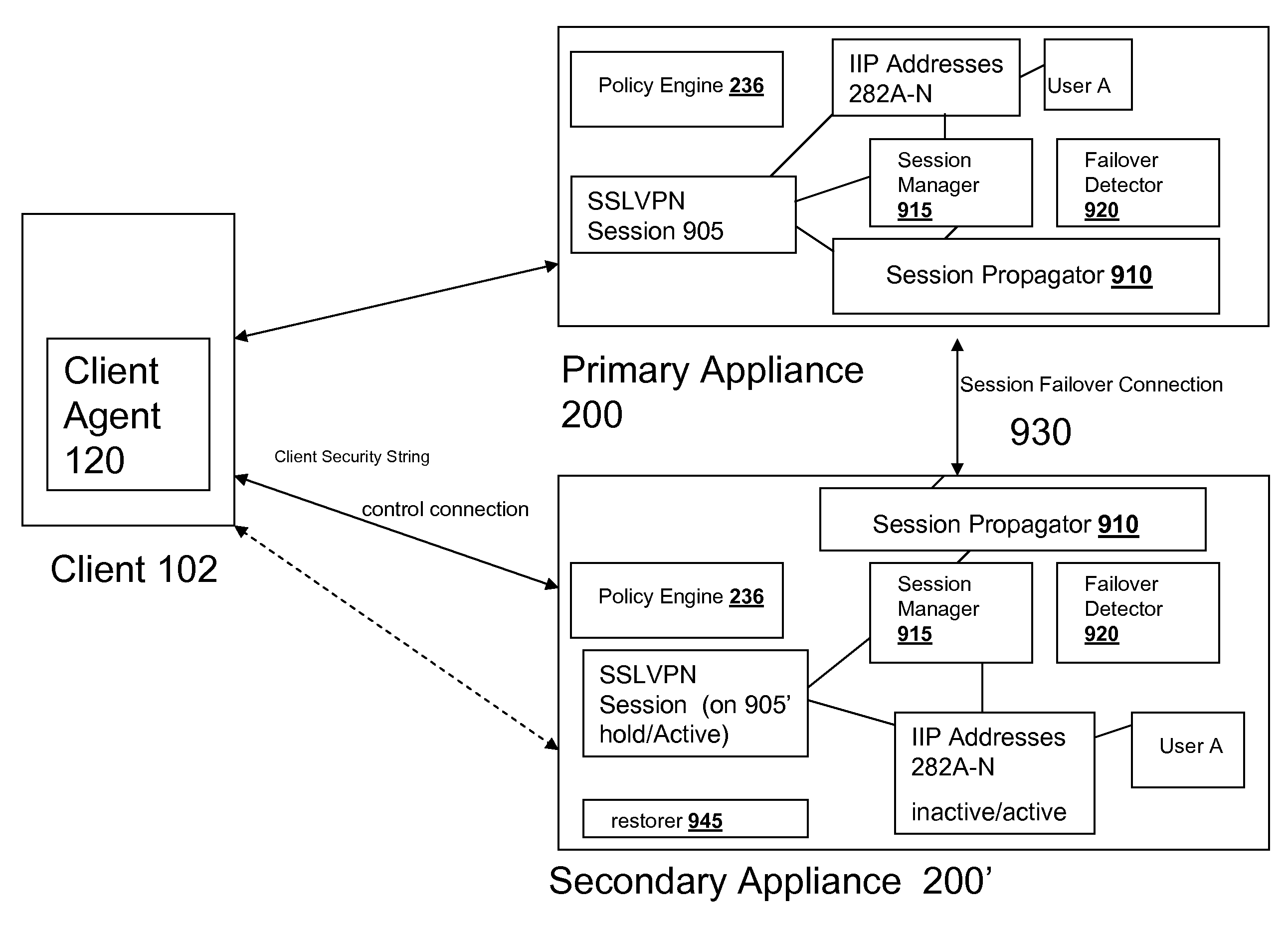
Systems and Methods for Providing IIP Address Stickiness in an SSL VPN Session Failover Environment
The SSL VPN session failover solution of the appliance and / or client agent described herein provides an environment for handling IP address assignment and end point re-authorization upon failover. The appliances may be deployed to provide a session failover environment in which a second appliance is a backup to a first appliance when a failover condition is detected, such as failure in operation of the first appliance. The backup appliance takes over responsibility for SSL VPN sessions provided by the first appliance. In the failover environment, the first appliance propagates SSL VPN session information including user IP address assignment and end point authorization information to the backup appliance. The backup appliance maintains this information. Upon detection of failover of the first appliance, the backup appliance activates the transferred SSL VPN session and maintains the user assigned IP addresses. The backup appliance may also re-authorize the client for the transferred SSL VPN session.
Owner:CITRIX SYST INC
Methods and systems for interacting, via a hypermedium page, with a virtual machine
InactiveUS20070180447A1Low costReduce difficultyDigital data information retrievalInterprogram communicationClient agentHyperlink
Owner:CITRIX SYST INC
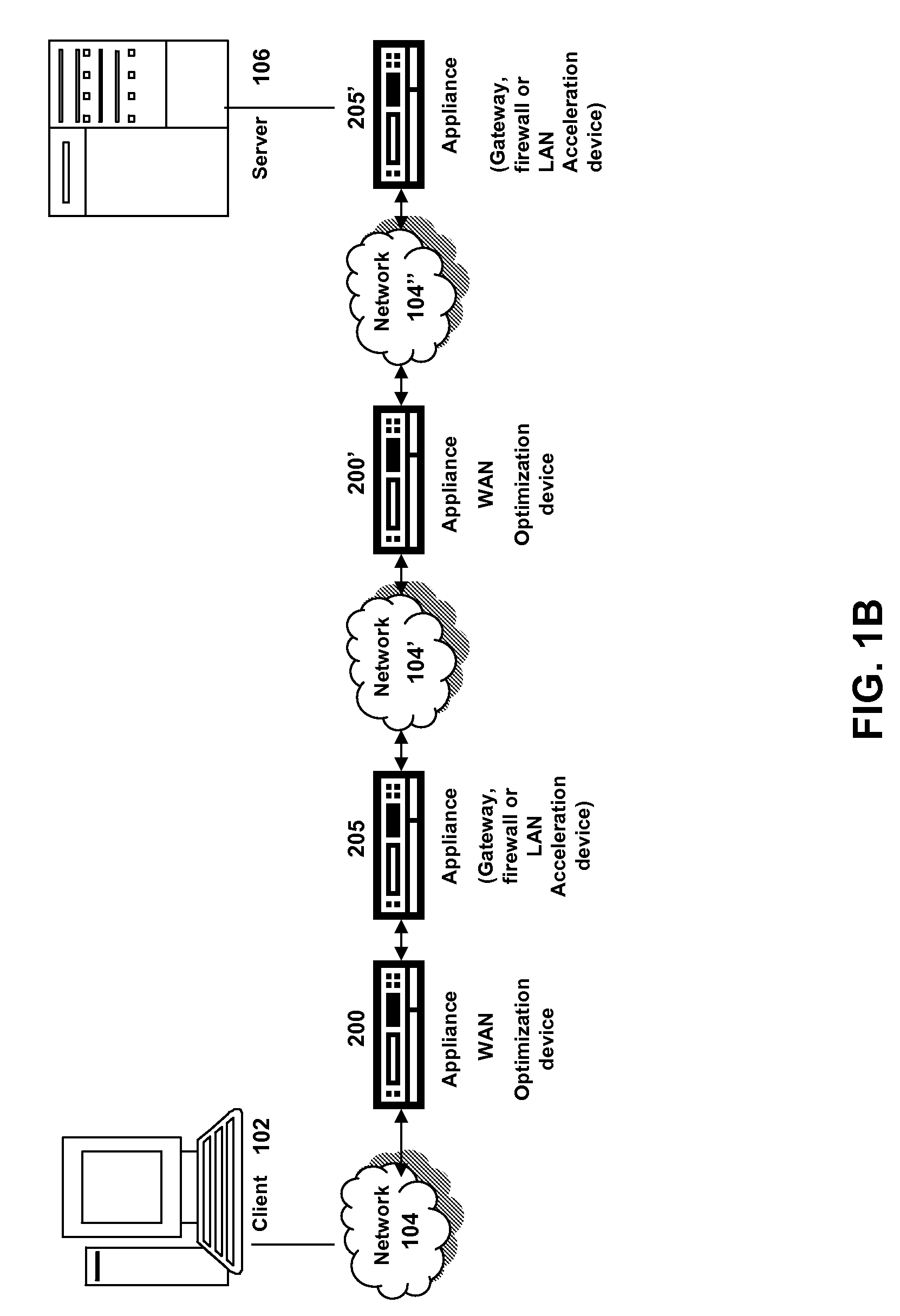
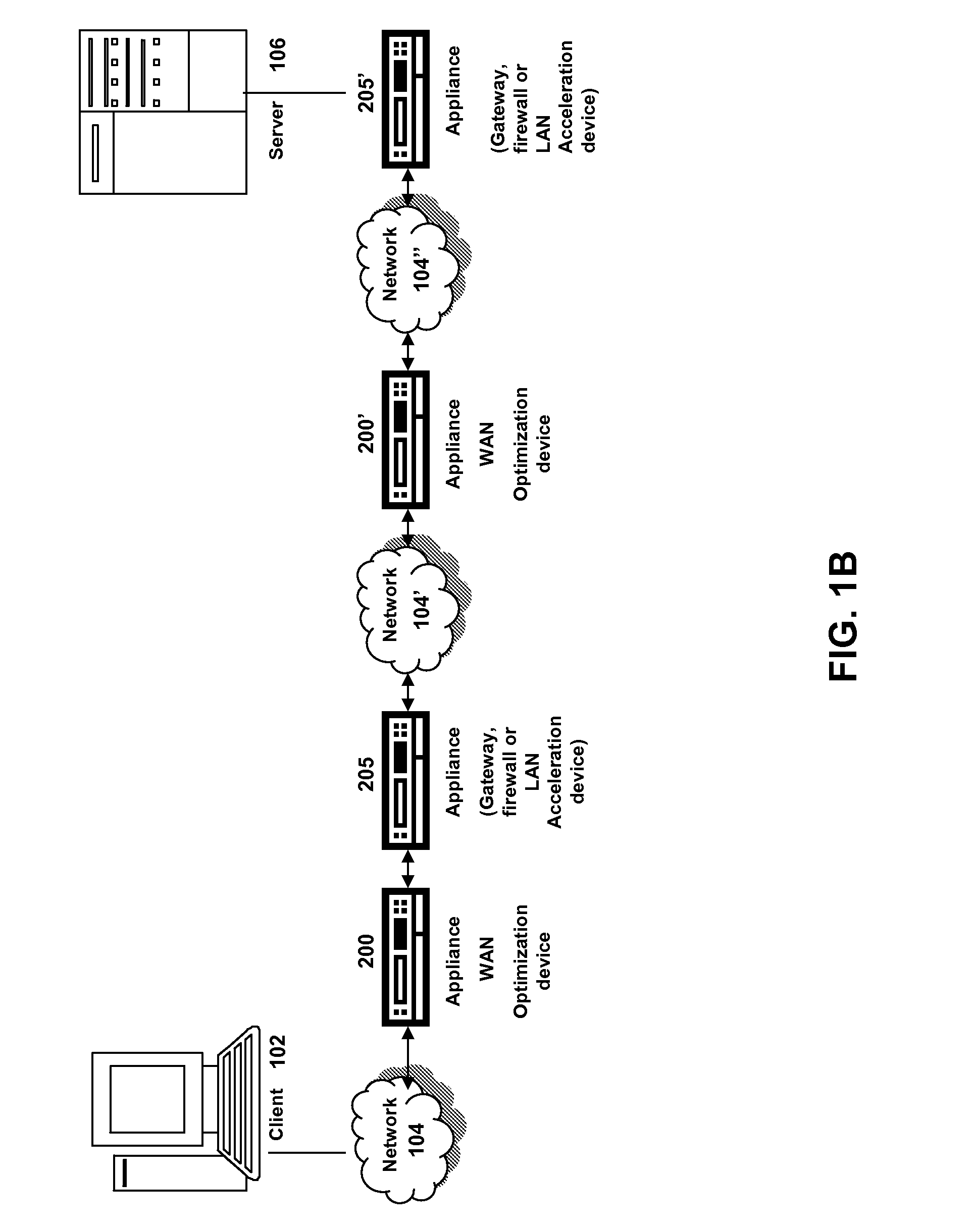
Systems and methods of using the refresh button to determine freshness policy
ActiveUS20080229025A1Improve efficiencyMore resolutionMemory architecture accessing/allocationMemory adressing/allocation/relocationClient agentDomain name
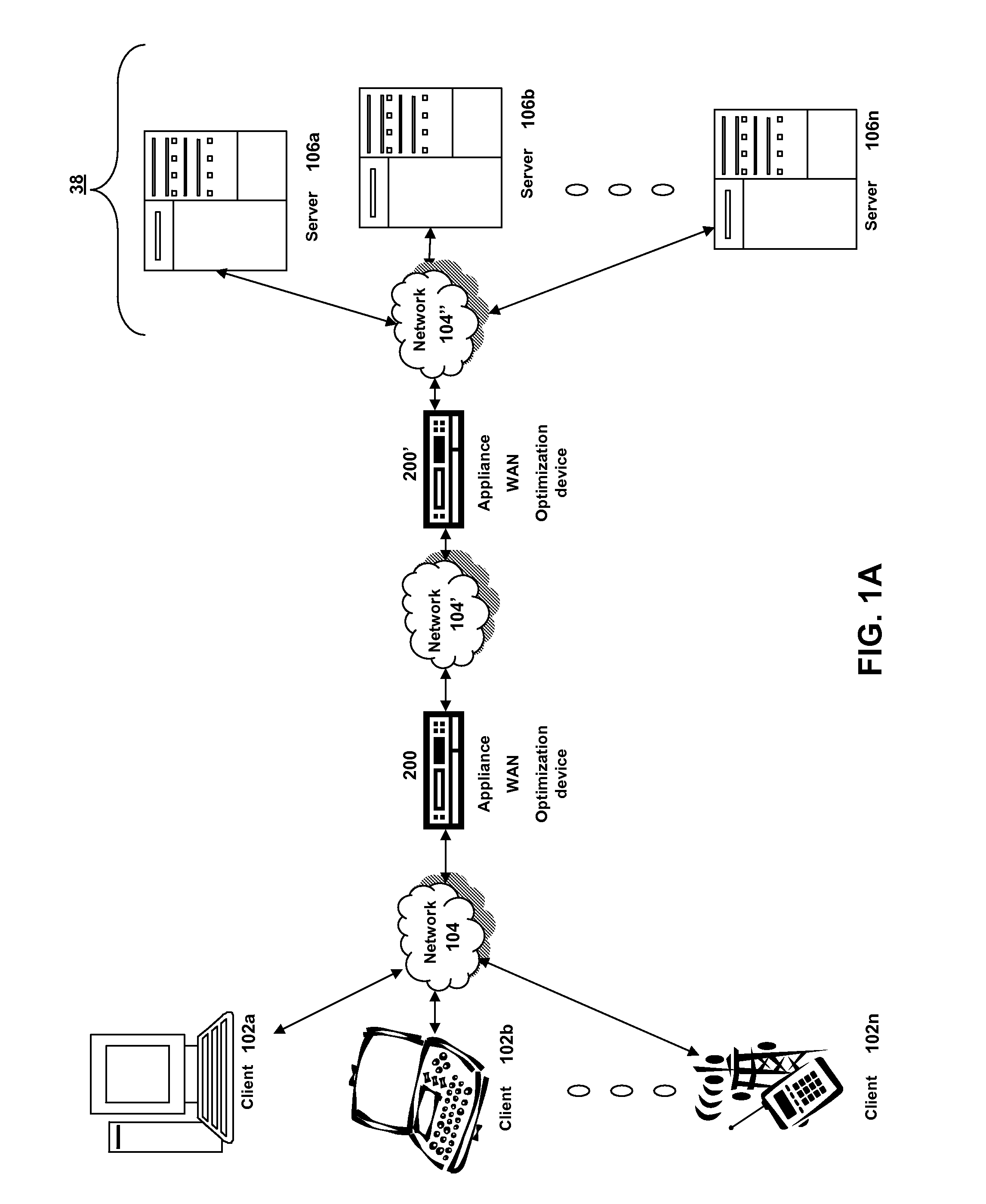
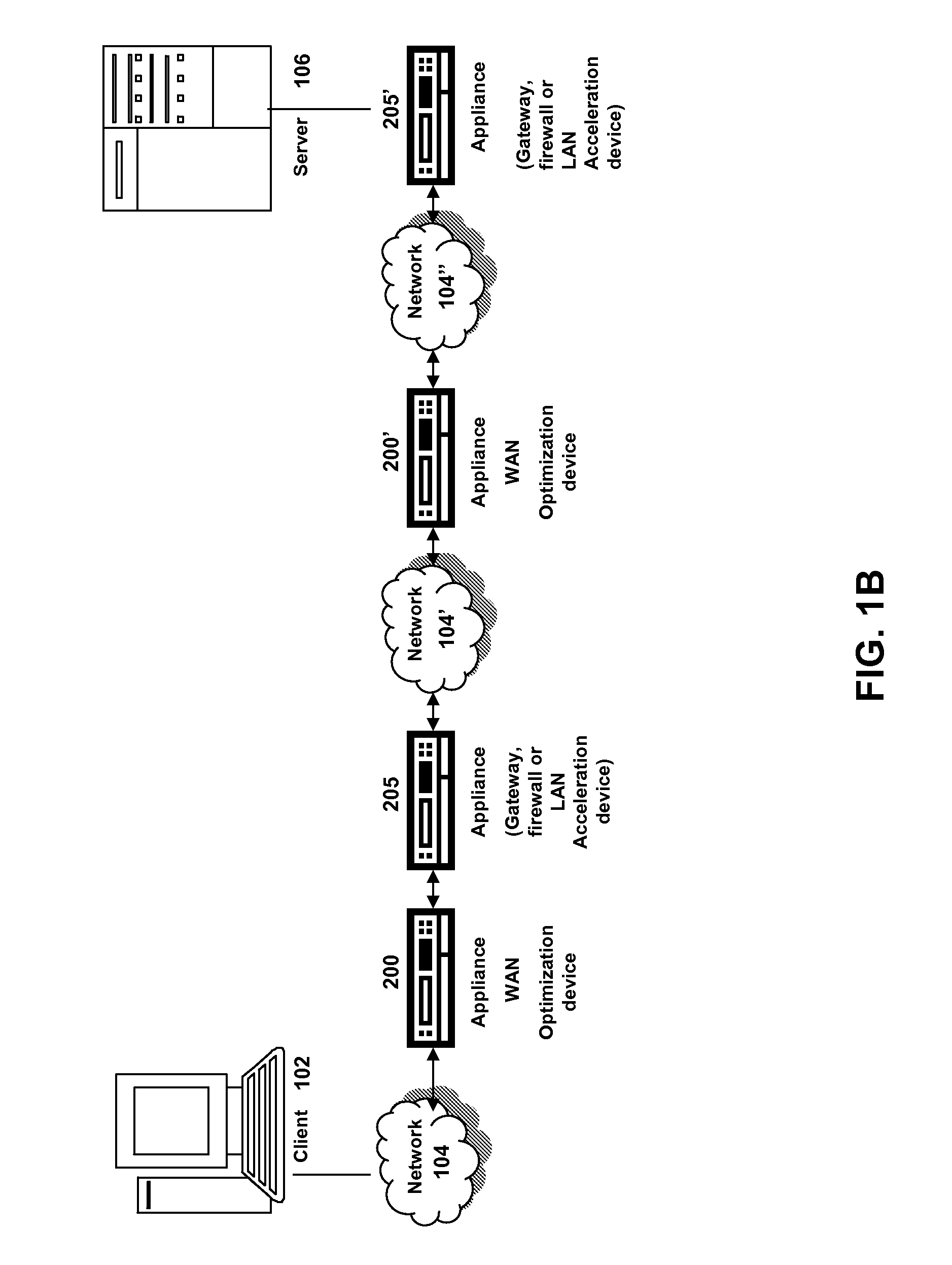
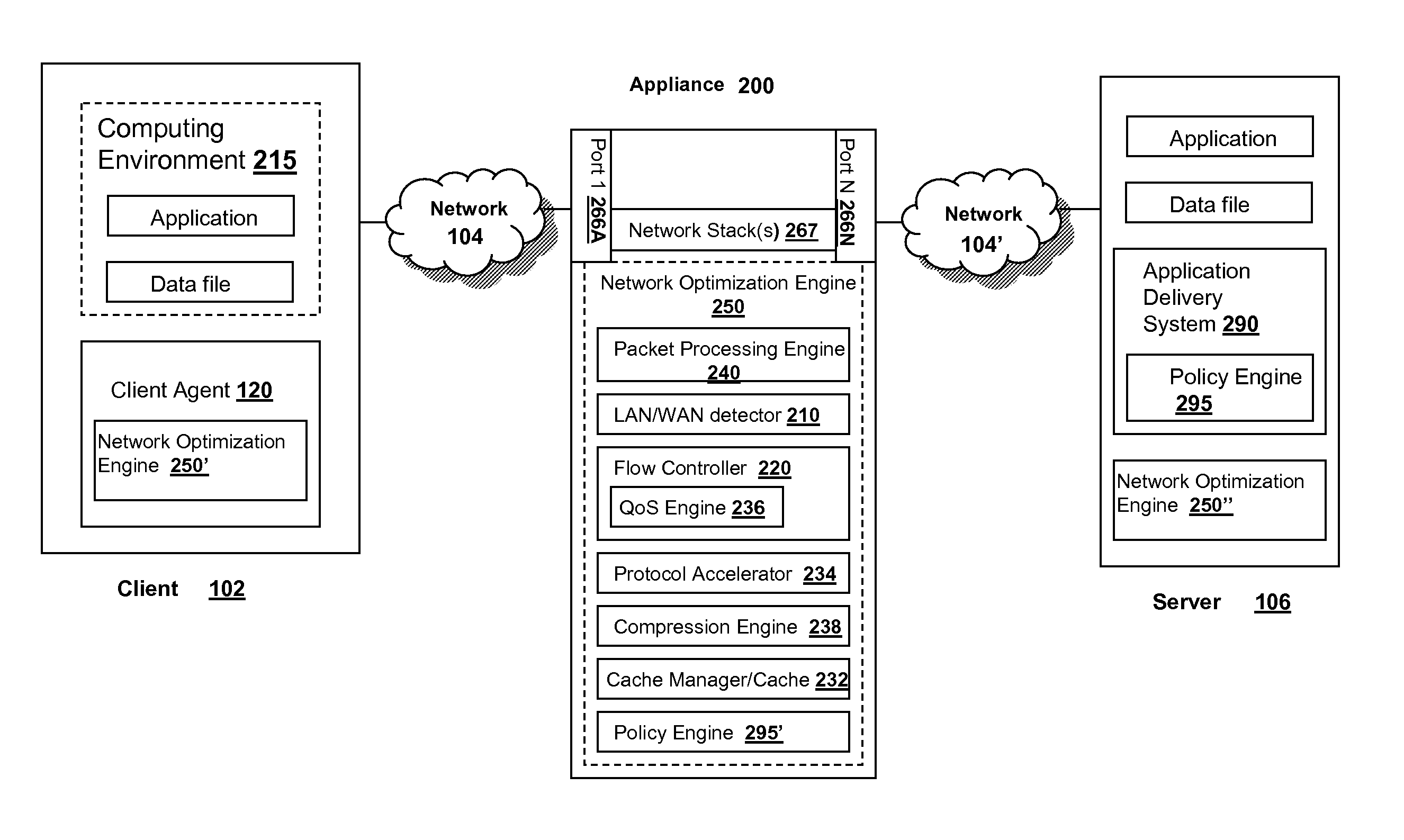
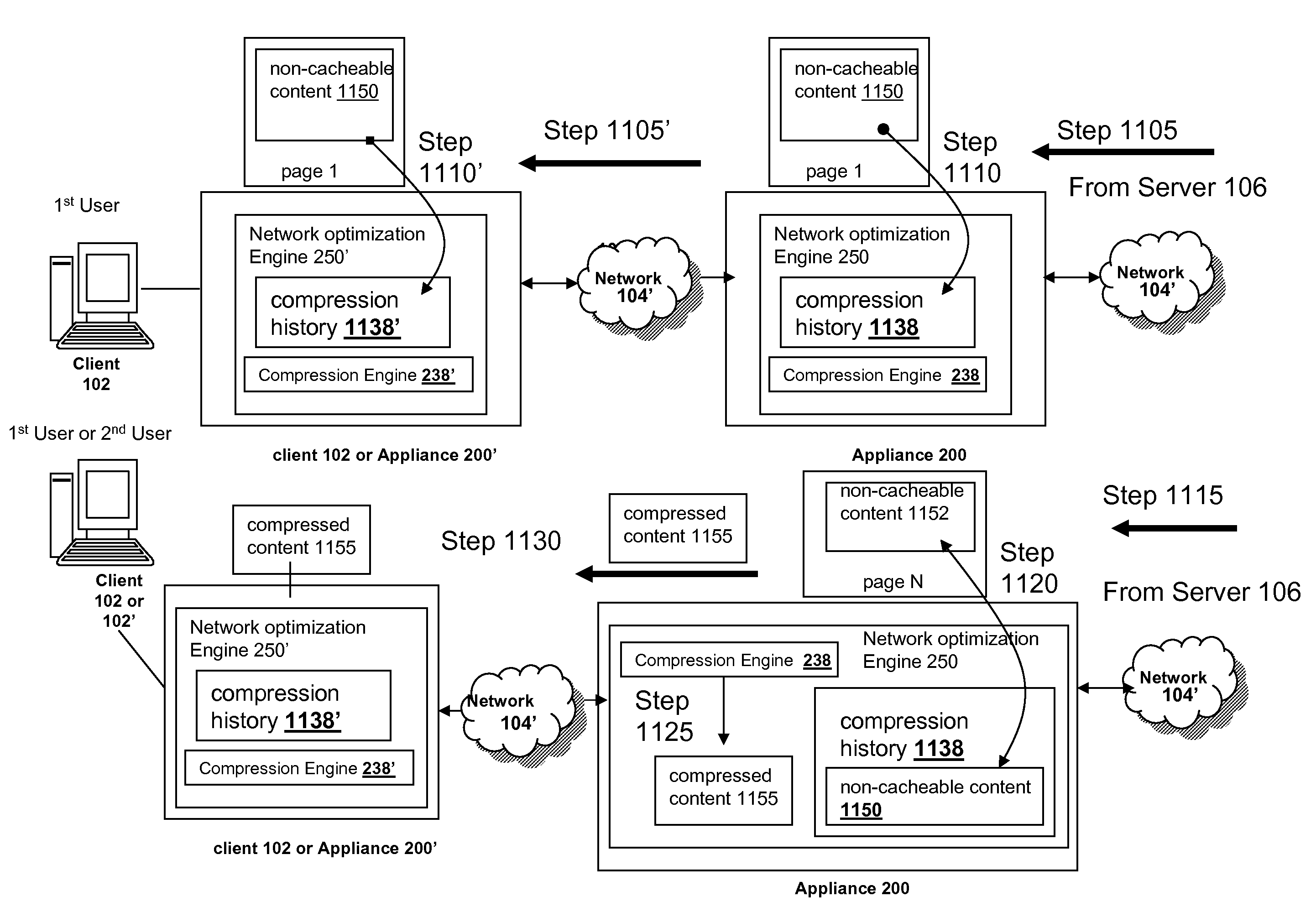
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
Method and system for extending services to cellular devices
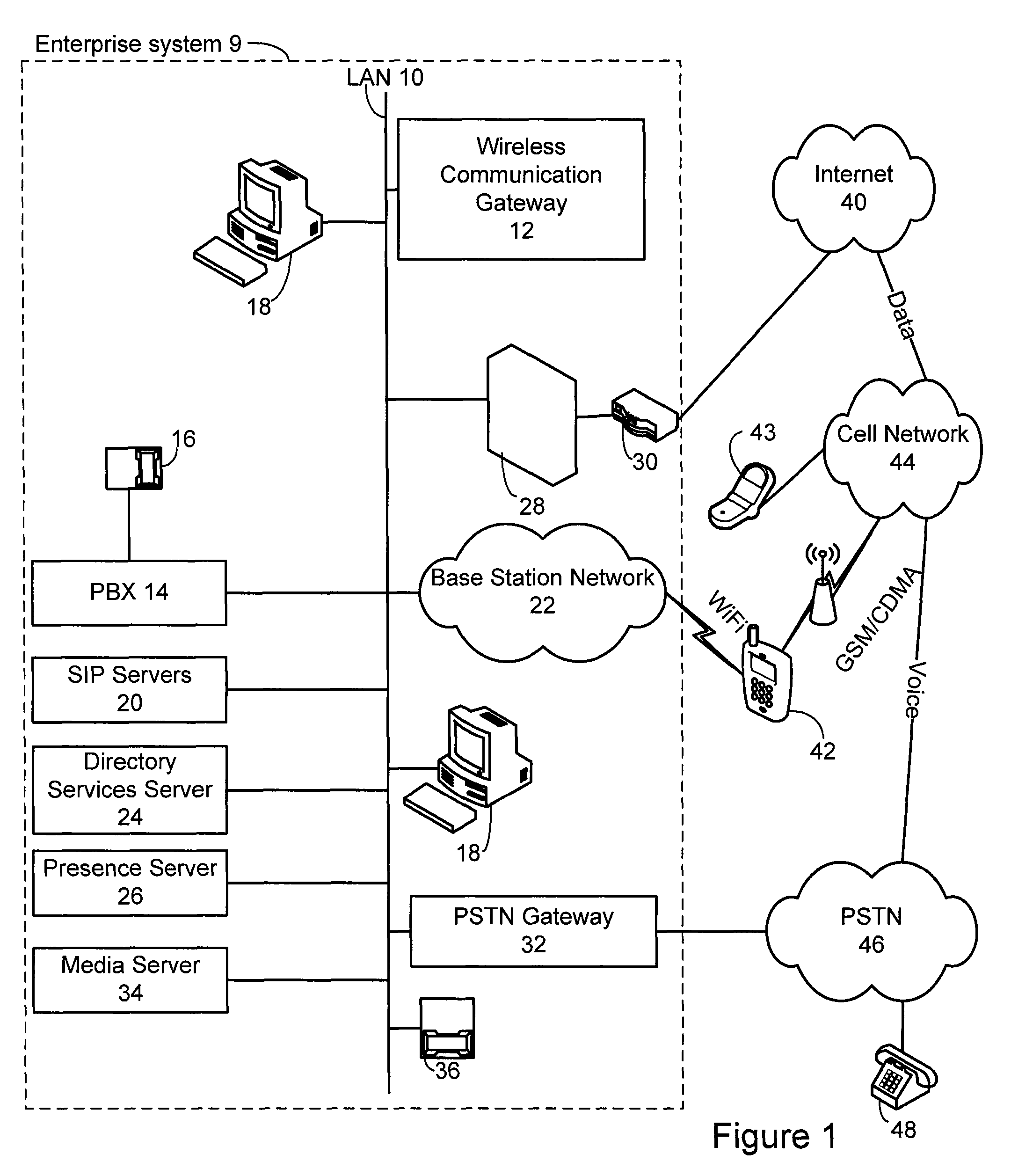
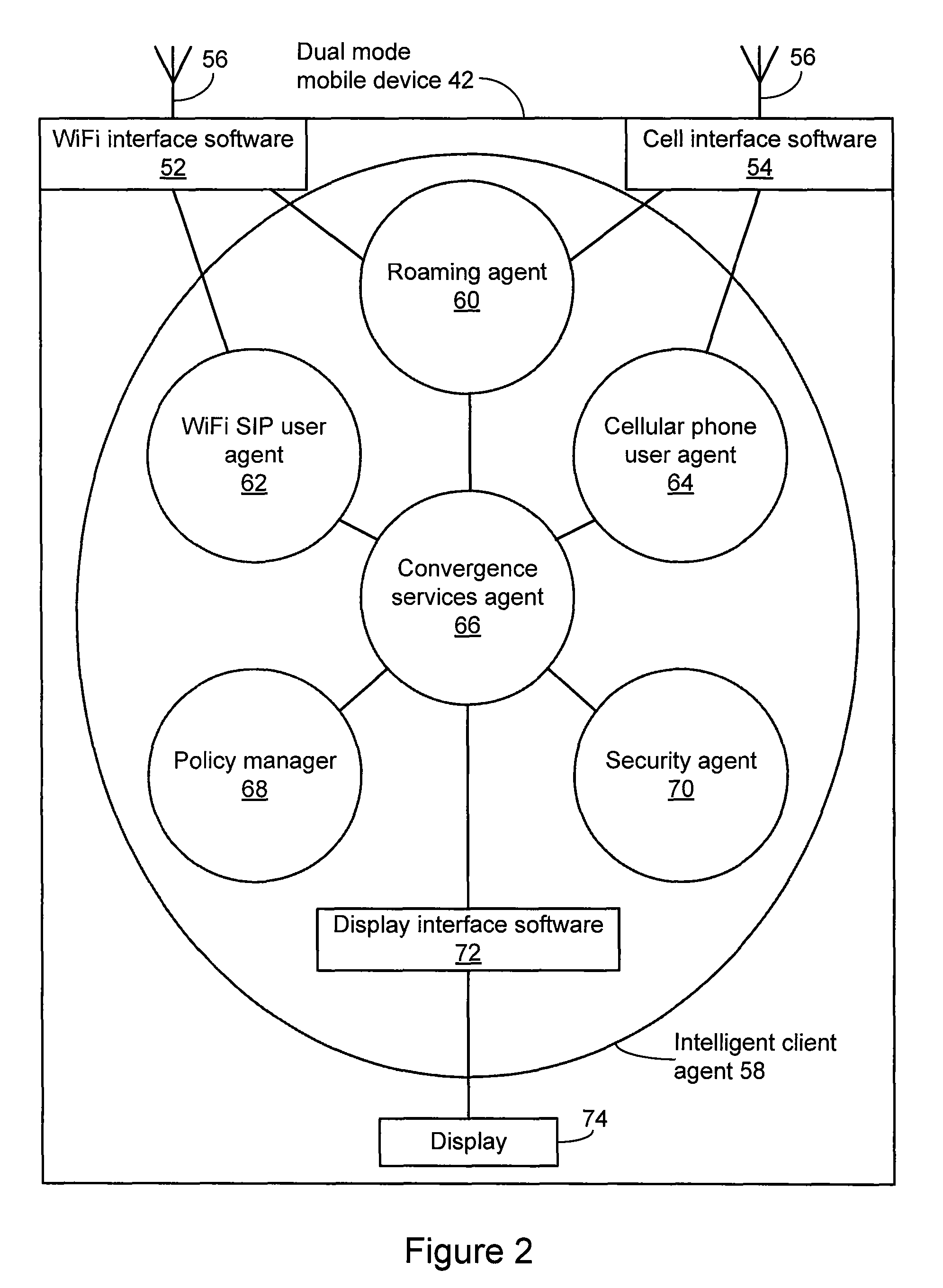
A system is provide for extending services to cellular devices. The system includes a wireless gateway having a client side with an intelligent client agent and a server side with an intelligent server agent, a wireless device having a first mode operable in a cellular system and a second mode operable in a wireless local area network and including an intelligent client agent for determining operation mode and for communicating with the intelligent client agent of the wireless gateway and a communications protocol for communication between the wireless gateway intelligent client agent and the wireless device intelligent client agent to effect services. The services include one or more of voice, directory, presence, and media services. The voice service includes at least one of call waiting, call forwarding conferencing, and caller identification. The media service includes at least one of interactive voice response (IVR), text-to-speech, speech recognition, play, record. The directory service includes a public switched telephone network (PSTN) directory, a cellular network directory, an Internet directory and a private branch exchange (PBX) directory. The communications protocol includes encapsulation for at least one of directory, mobility and security services and other protocols. The other protocols include at least one of Internet protocol (IP), session initiation protocol (SIP), and lightweight directory access protocol (LDAP).
Owner:COUNTERPATH TECH
Systems and Methods for Isolating On-Screen Textual Data
InactiveUS20080086700A1Simple processSubstation equipmentExecution for user interfacesClient agentText display
The systems and methods of the client agent describe herein provides a solution to obtaining, recognizing and taking an action on text displayed by an application that is performed in a non-intrusive and application agnostic manner. In response to detecting idle activity of a cursor on the screen, the client agent captures a portion of the screen relative to the position of the cursor. The portion of the screen may include a textual element having text, such as a telephone number or other contact information. The client agent calculates a desired or predetermined scanning area based on the default fonts and screen resolution as well as the cursor position. The client agent performs optical character recognition on the captured image to determine any recognized text. By performing pattern matching on the recognized text, the client agent determines if the text has a format or content matching a desired pattern, such as phone number. In response to determining the recognized text corresponds to a desired pattern, the client agent displays a user interface element on the screen near the recognized text. The user interface element may be displayed as an overlay or superimposed to the textual element such that it seamlessly appears integrated with the application. The user interface element is selectable to take an action associated with the recognized text.
Owner:CITRIX SYST INC
Systems and methods for prefetching objects for caching using QOS
ActiveUS7584294B2Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsData switching networksClient agentTraffic capacity
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
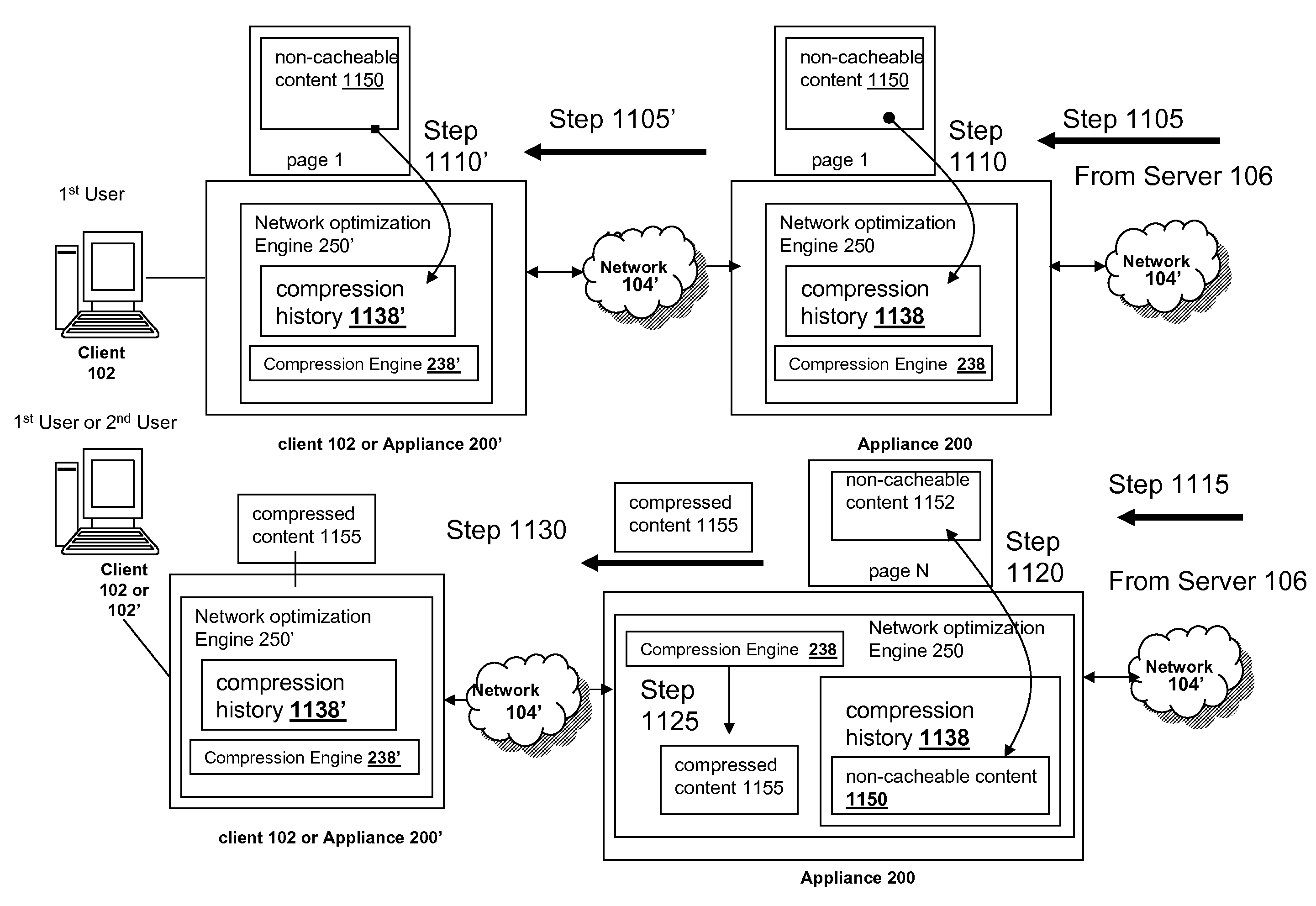
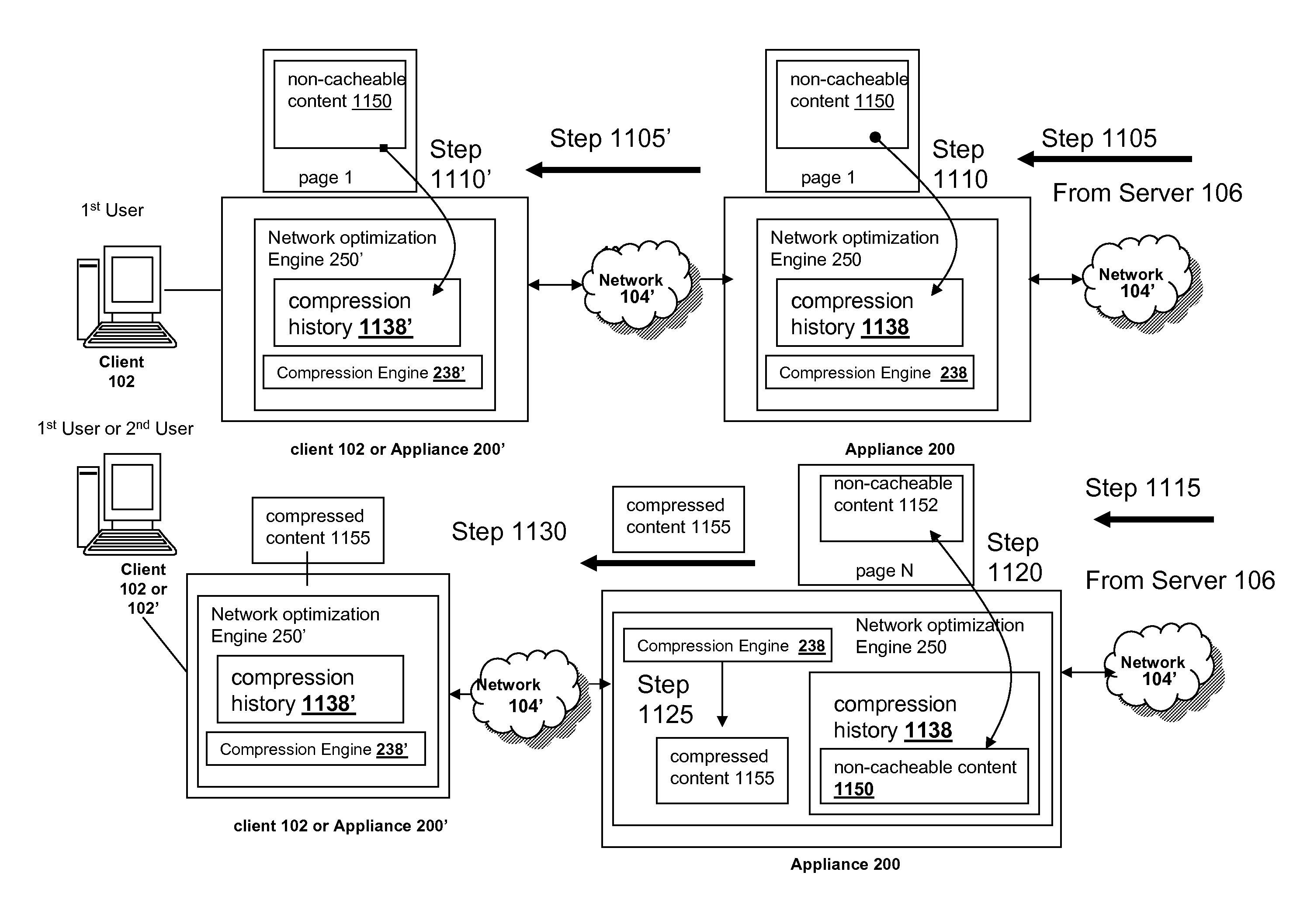
Systems and methods for prefetching non-cacheable content for compression history
InactiveUS20080228864A1Improve efficiencyMore resolutionDigital data information retrievalMultiple digital computer combinationsDomain nameClient agent
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
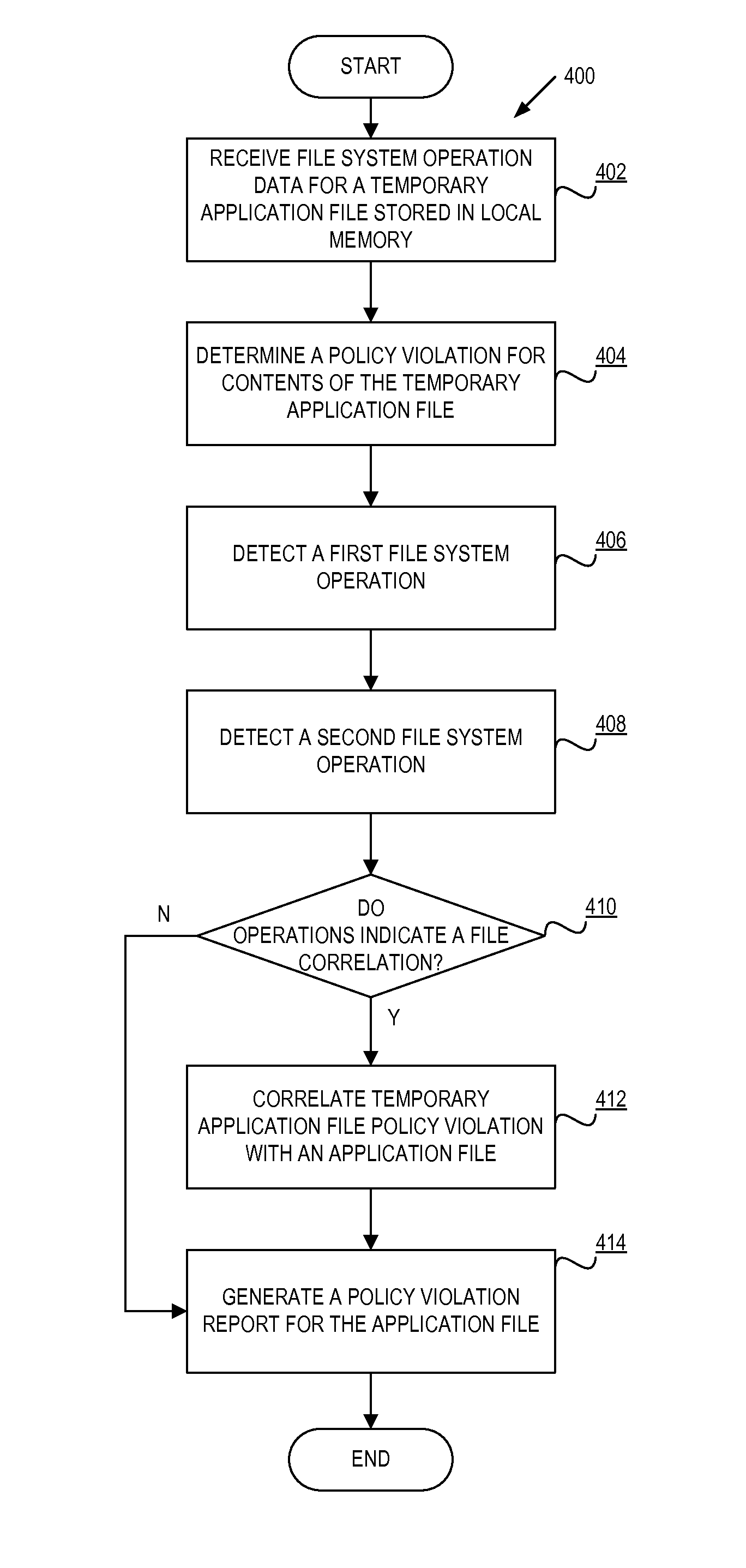
System and method for managing data loss due to policy violations in temporary files
InactiveUS7991747B1Memory loss protectionDigital data processing detailsClient agentApplication software
A method and apparatus for managing data loss due to policy violations in temporary files is described. In one embodiment, the method includes monitoring, by a client agent, information content on a client for violations of a policy. The method further includes determining, by the client agent, that a violation of the policy has occurred for content of a temporary file of an application. In one embodiment, the policy violation of the temporary file is correlated, by the client agent, with an original file of the application.
Owner:CA TECH INC
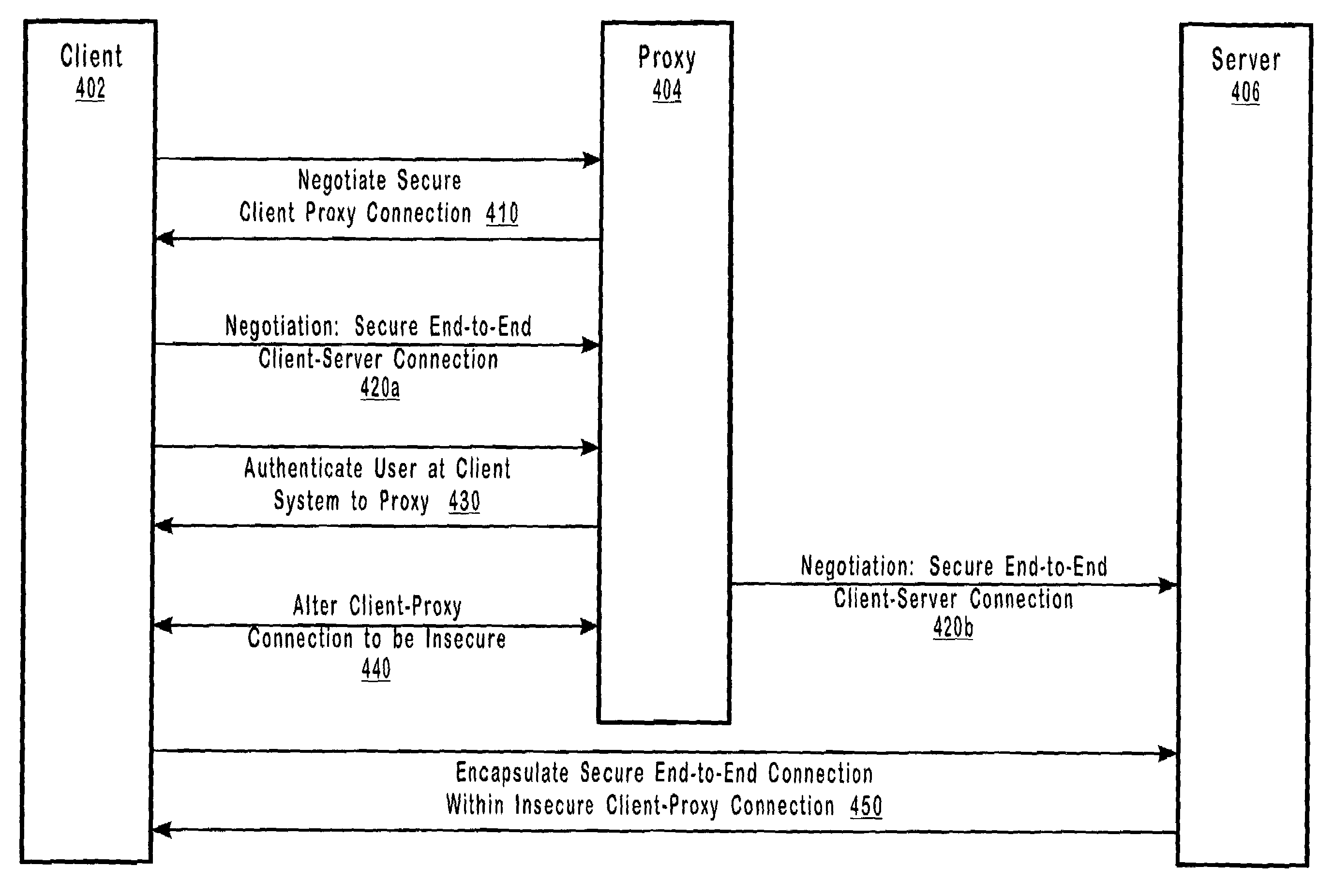
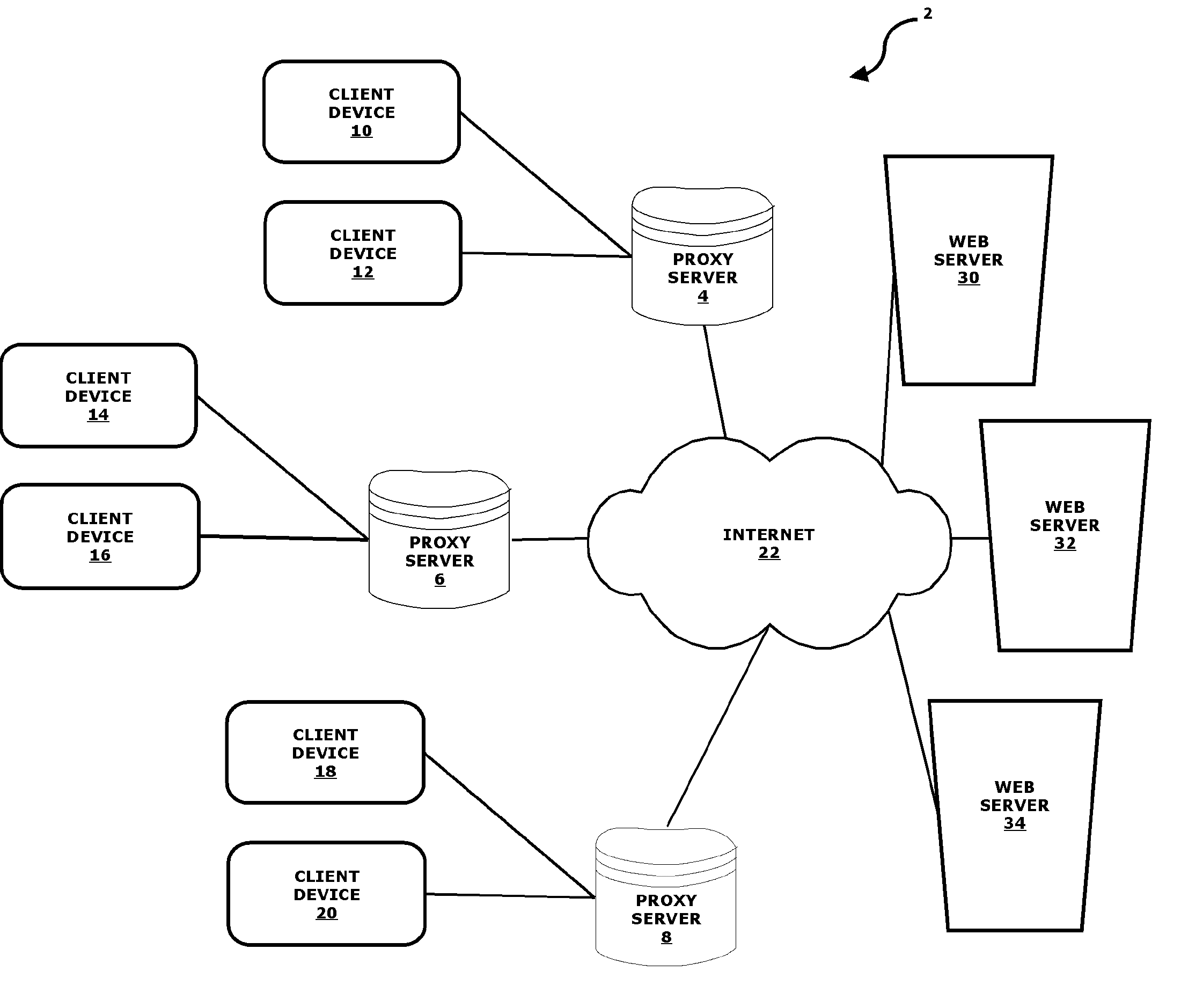
Negotiating secure connections through a proxy server
InactiveUS6996841B2Enhance layeringAdequate levelDigital data processing detailsMultiple digital computer combinationsClient-sideProxy server
Methods, systems, and computer program products for negotiating a secure end-to-end connection using a proxy server as an intermediary. The client first negotiates a secure connection between the client and the proxy so that any credentials exchanged will be encrypted. After the exchange of authentication credentials, the secure client-proxy connection is altered so that no further encryption takes place. The client and server then negotiate a secure end-to-end connection through the proxy, with the secure end-to-end connection being encapsulated within the insecure client-proxy connection. In this way, the overhead of creating a separate client-proxy connection for the secure end-to-end connection may be avoided, but the insecure client-proxy connection introduces only minimal overhead because it no longer encrypts any data that it carries.
Owner:MICROSOFT TECH LICENSING LLC
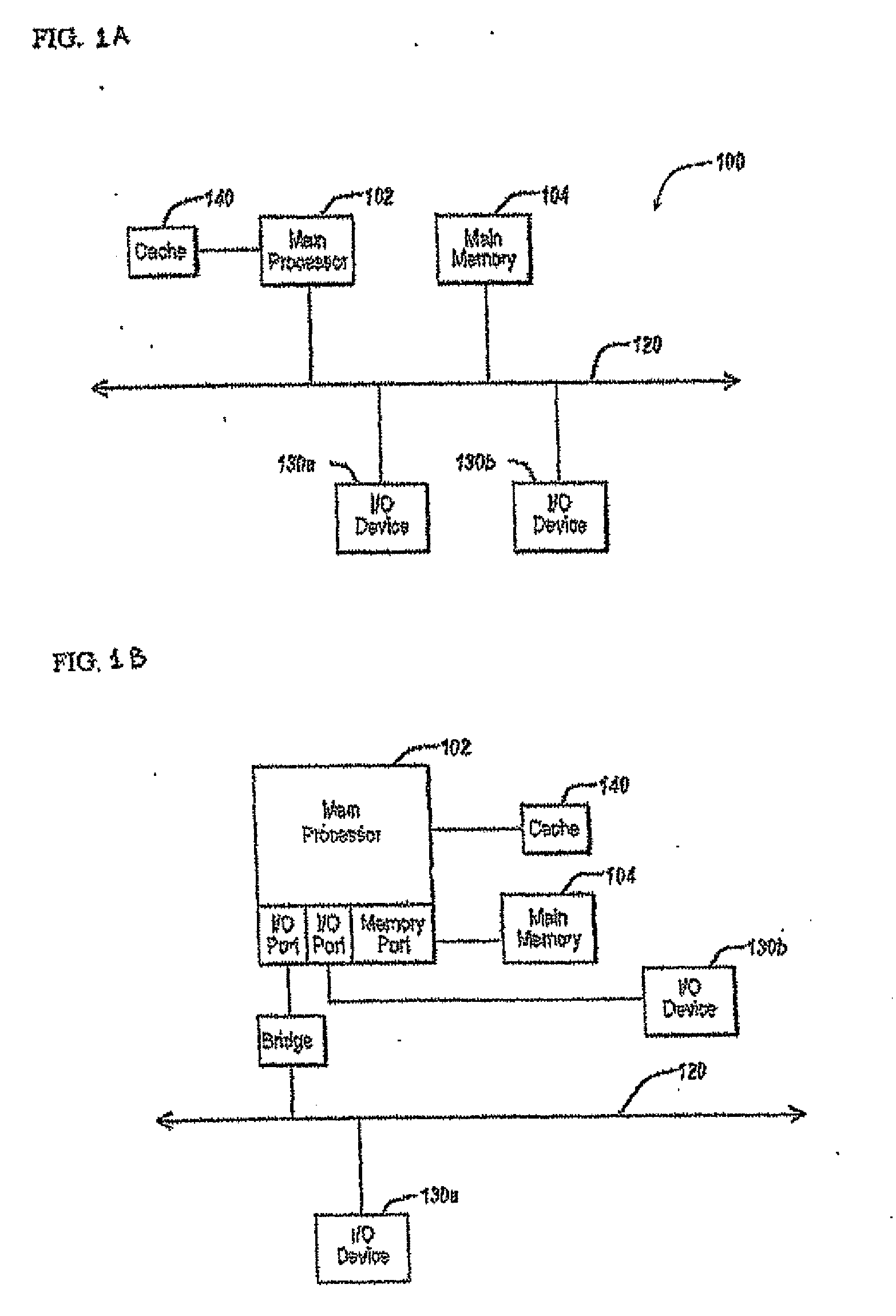
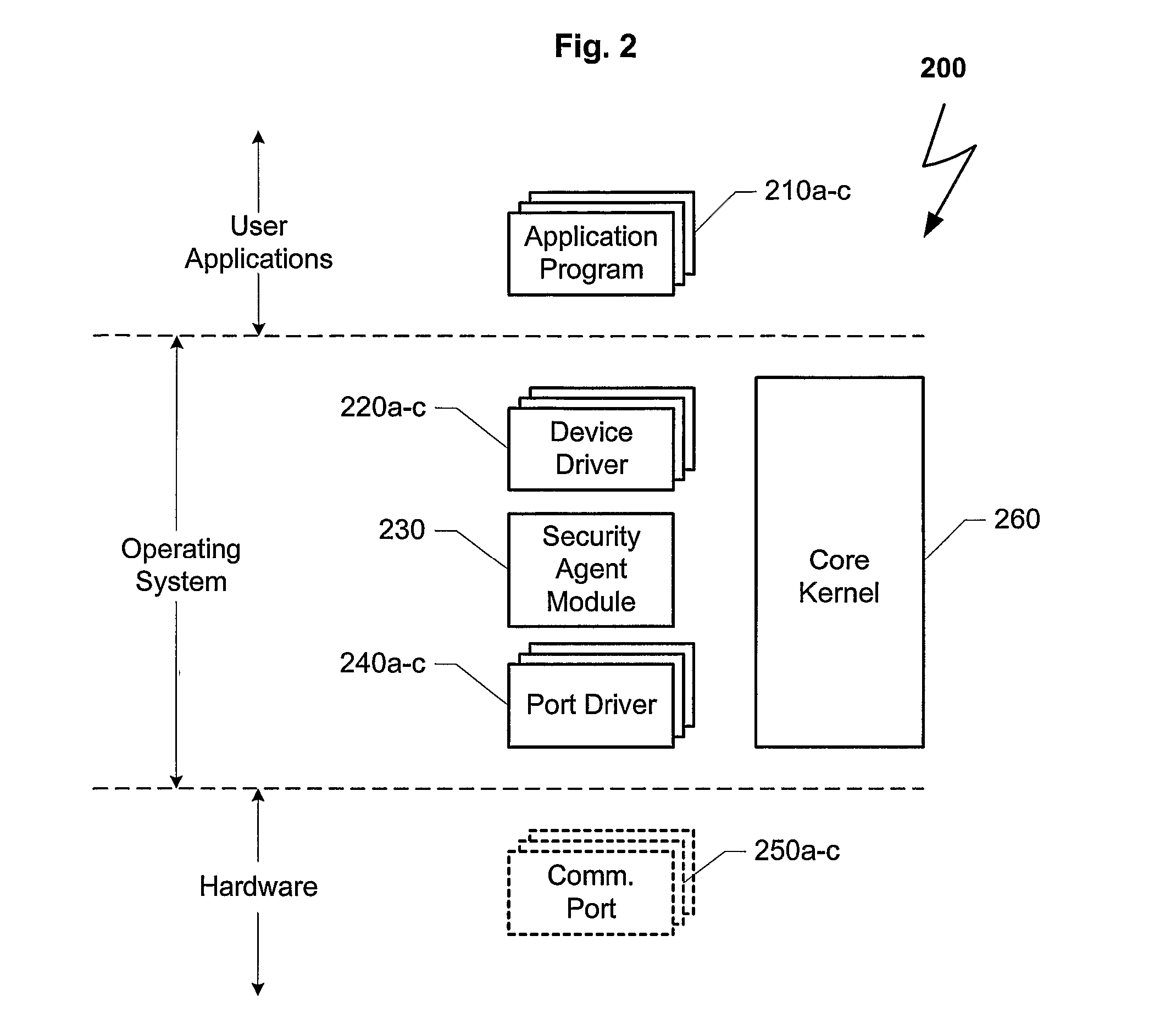
Thin client for computer security applications
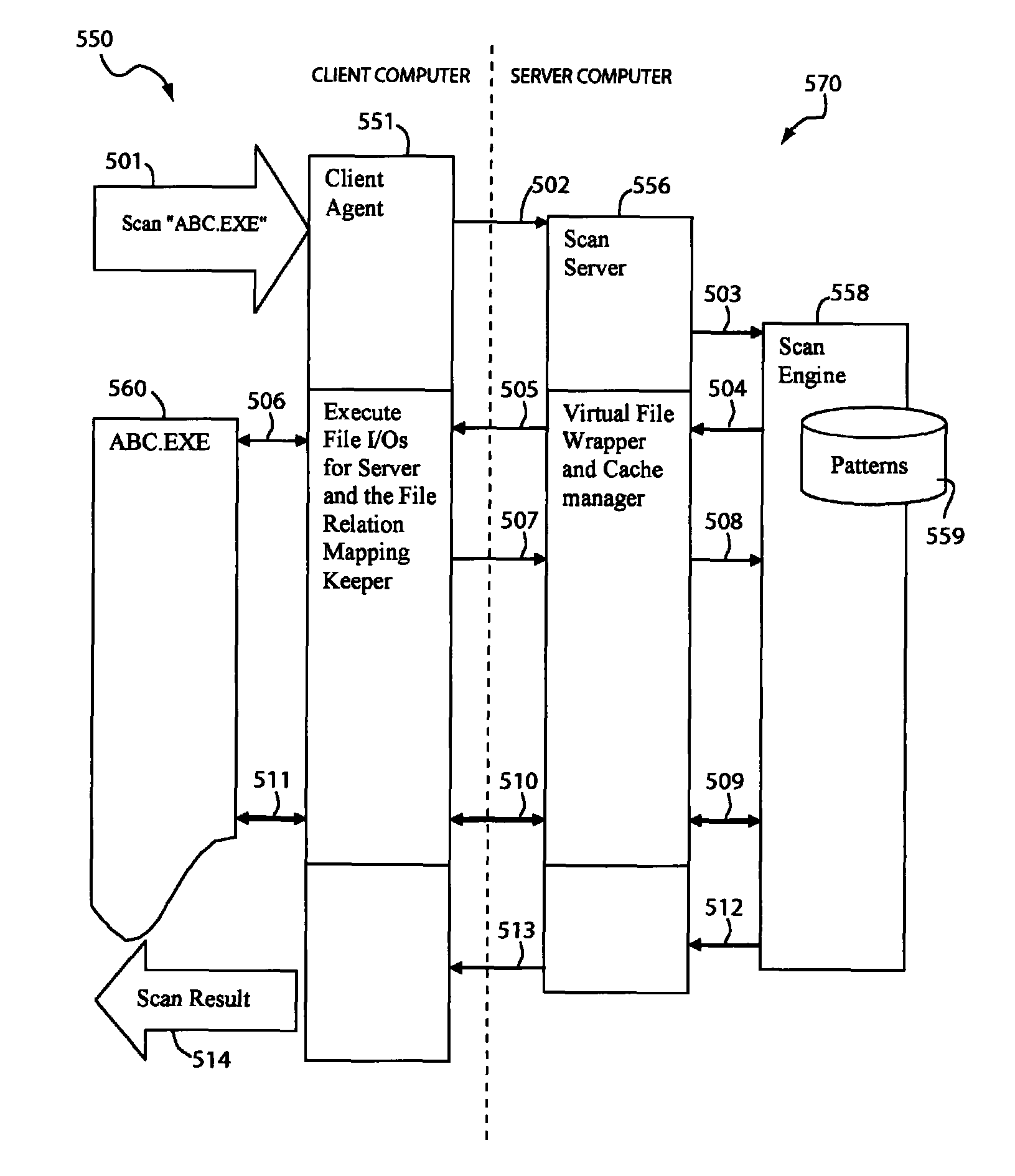
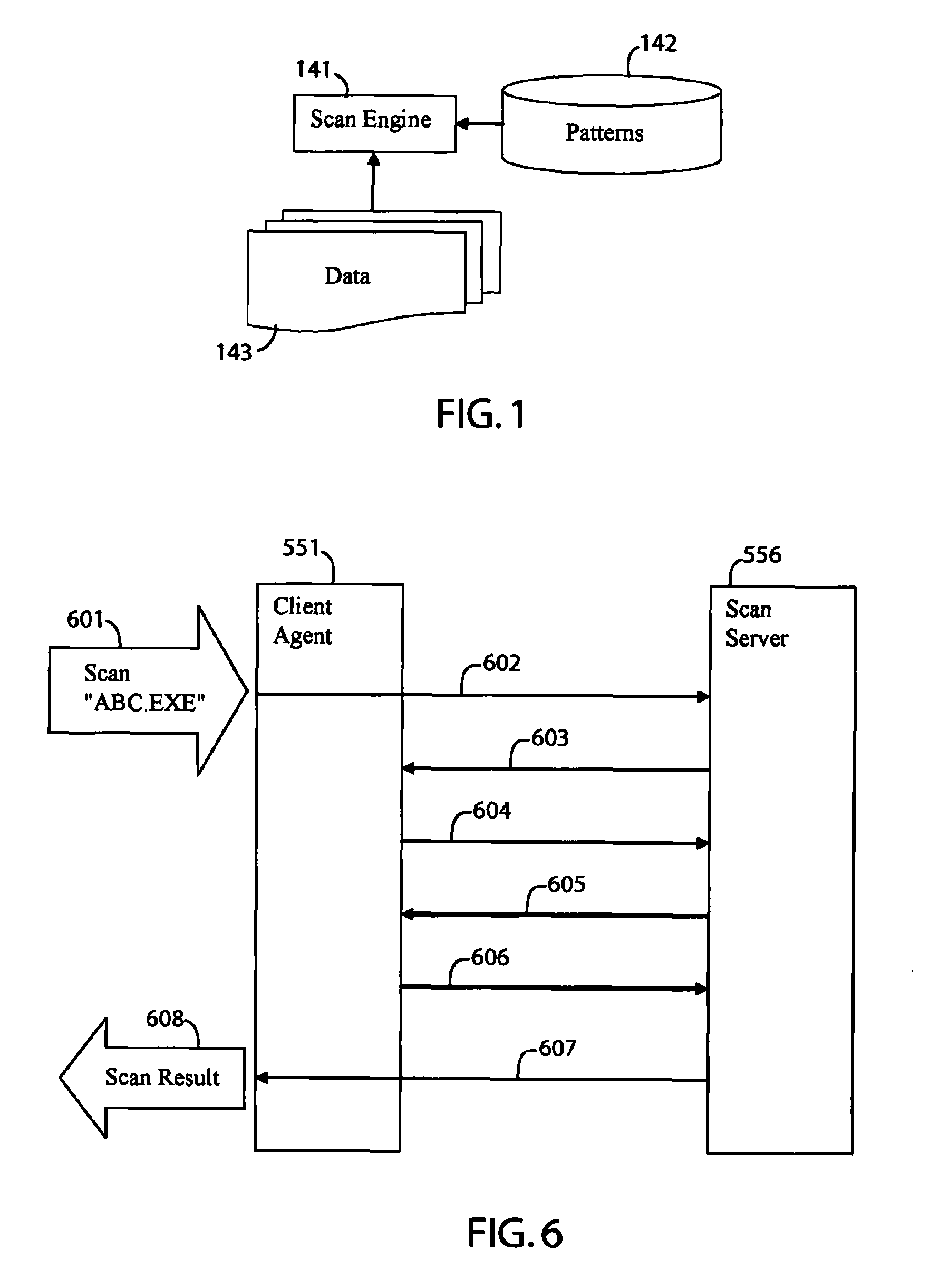
ActiveUS8127358B1Minimize network trafficTraffic minimizationMemory loss protectionError detection/correctionComputer hardwareClient agent
A system for scanning a file for malicious codes may include a client agent running in a client computer and a scan server running in a server computer, the client computer and the server computer communicating over a computer network. The client agent may be configured to locally receive a scan request to scan a target file for malicious codes and to communicate with the scan server to scan the target file using a scan engine running in the server computer. The scan server in communication with the client agent allows the scan engine to scan the target file by issuing file I / O requests to access the target file located in the client computer. The client agent may be configured to check for digital signatures and to maintain a file cache of previously scanned files to minimize network traffic.
Owner:TREND MICRO INC
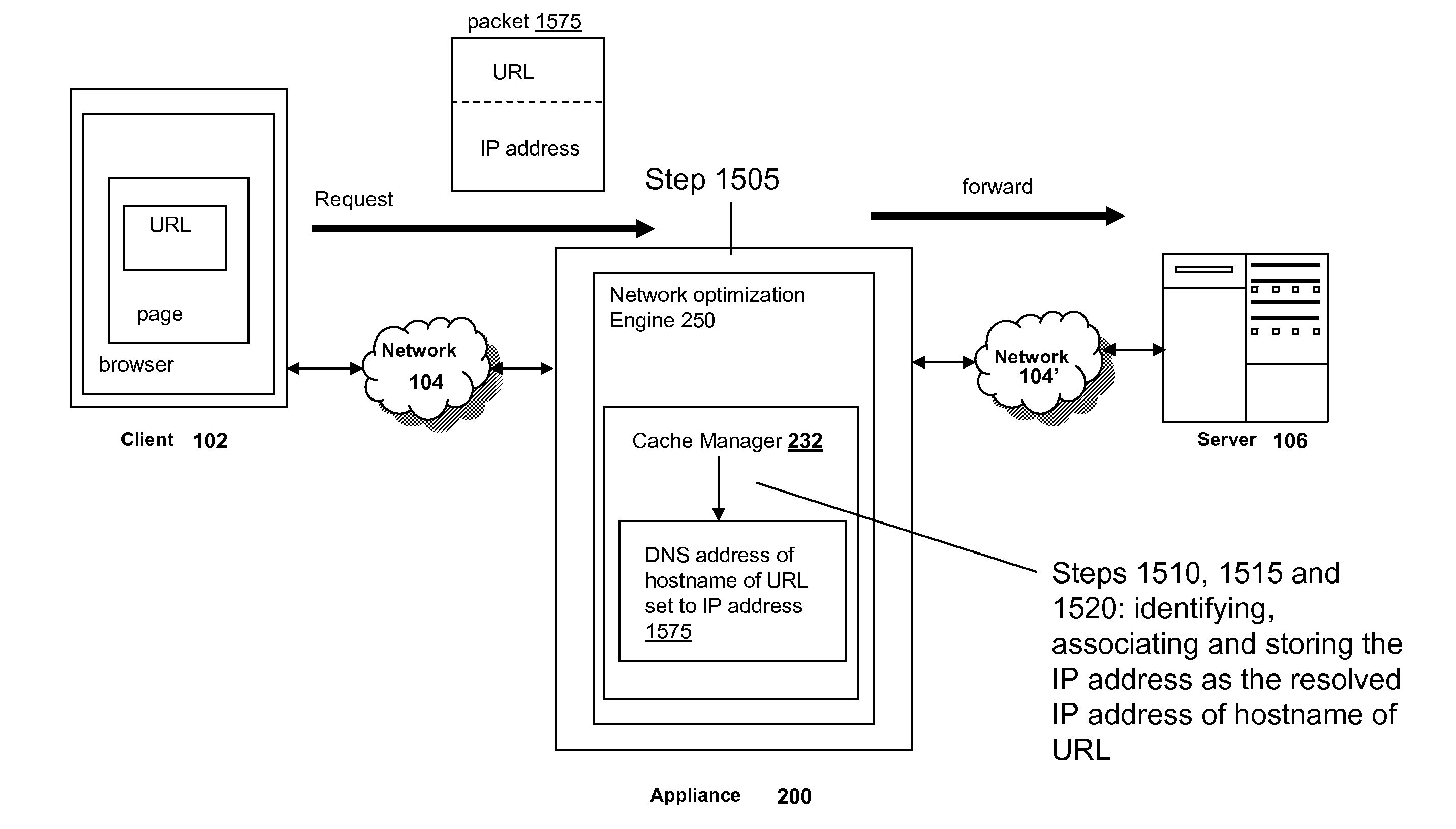
Systems and methods for domain name resolution interception caching
ActiveUS20100088398A1Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsTransmissionTraffic capacityDomain name
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
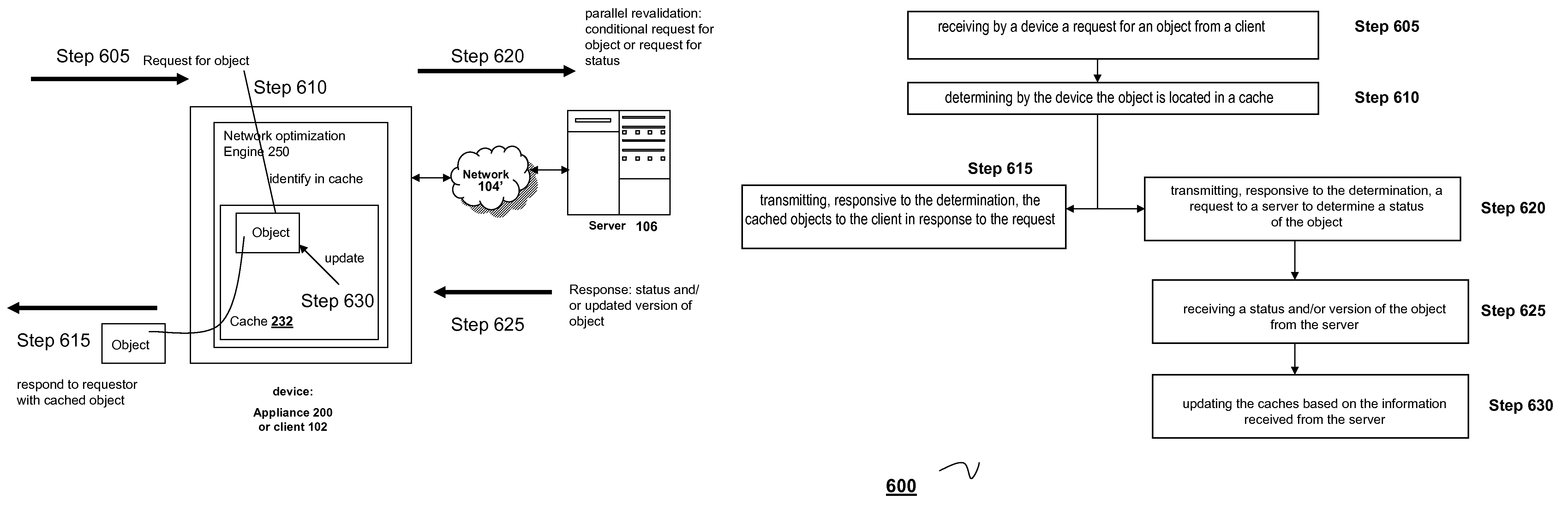
Systems and methods of revalidating cached objects in parallel with request for object
ActiveUS7783757B2Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsTransmissionDomain nameClient agent
Owner:CITRIX SYST INC
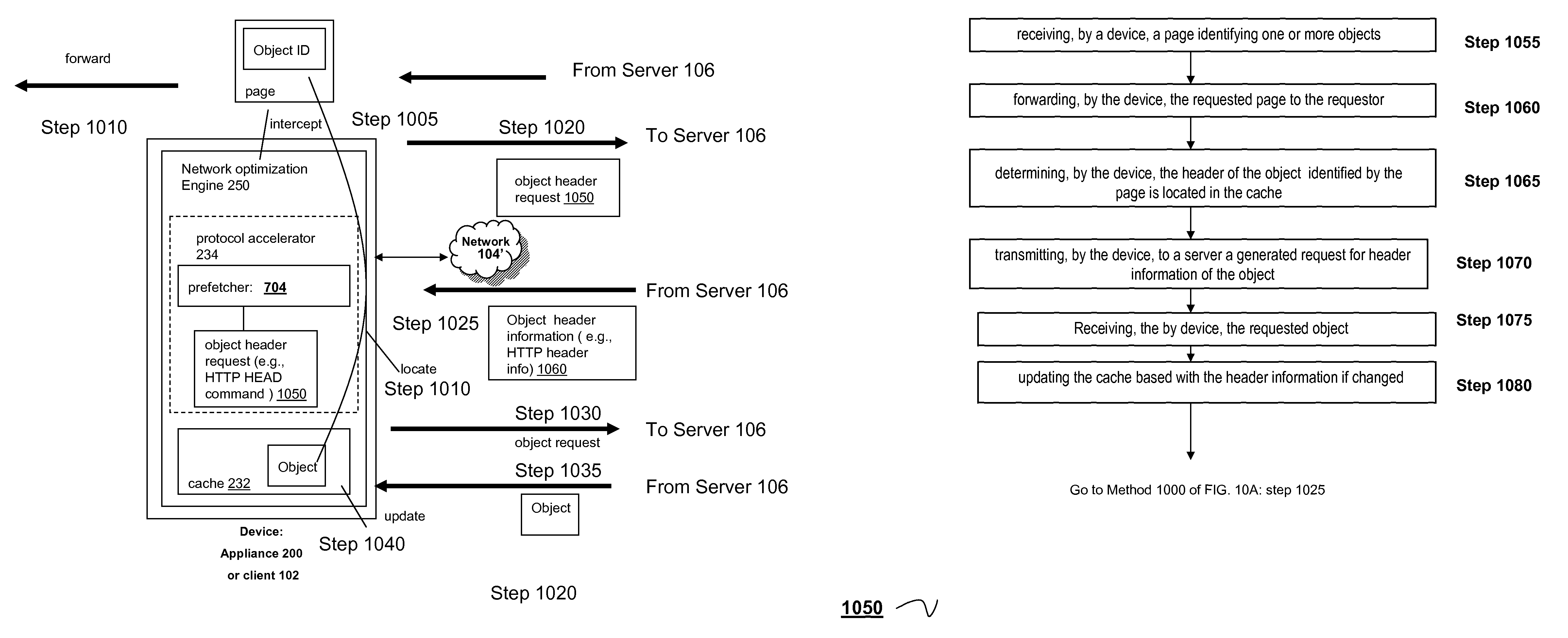
Systems and method of using HTTP head command for prefetching
ActiveUS7809818B2Improve efficiencyImprove intermediary or proxy cachingMultiple digital computer combinationsTransmissionClient agentDomain name
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
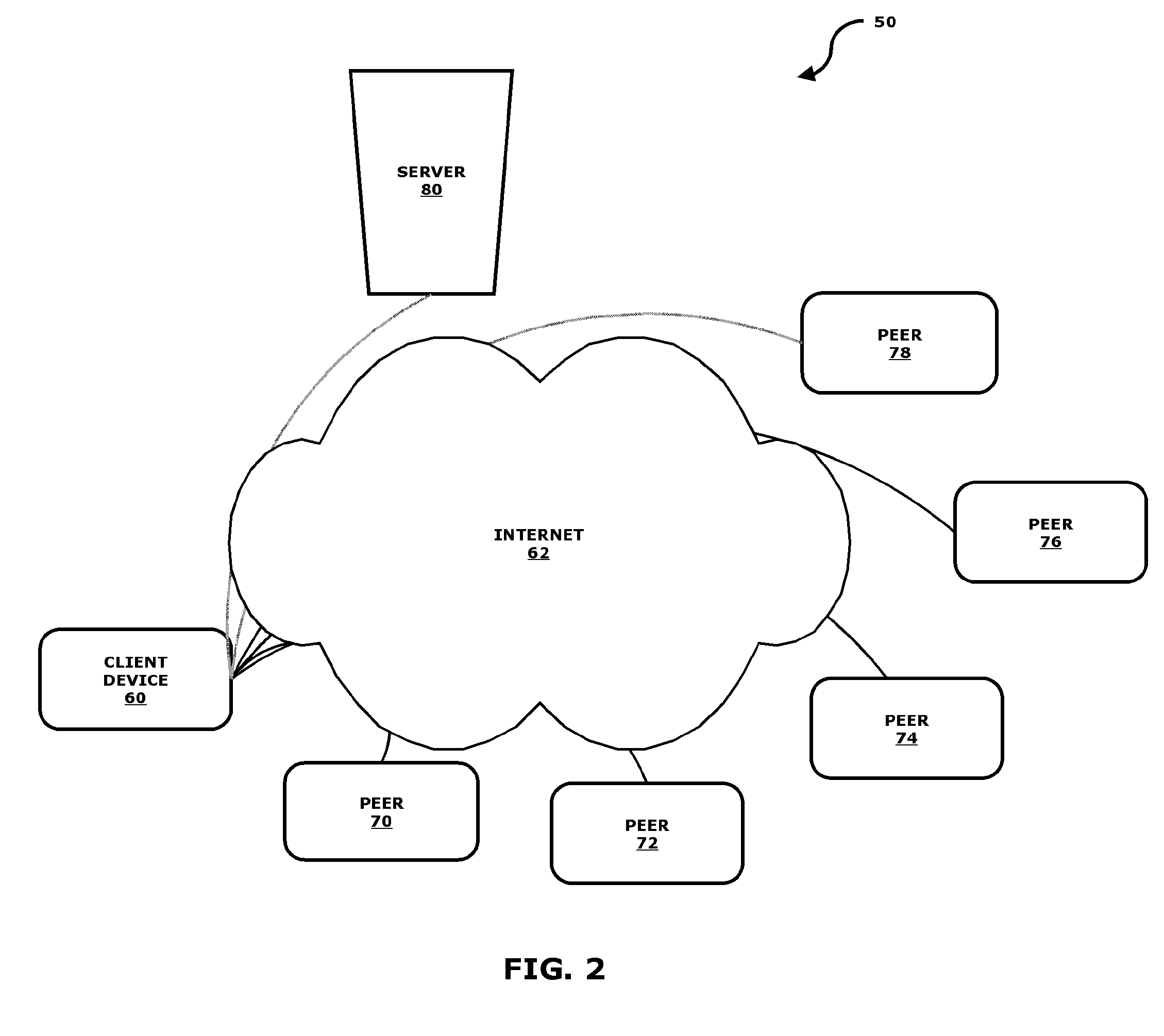
System and method for providing faster and more efficient data communication
ActiveUS20110087733A1Faster and efficient data communicationMultiple digital computer combinationsTransmissionClient agentIp address
A system designed for increasing network communication speed for users, while lowering network congestion for content owners and ISPs. The system employs network elements including an acceleration server, clients, agents, and peers, where communication requests generated by applications are intercepted by the client on the same machine. The IP address of the server in the communication request is transmitted to the acceleration server, which provides a list of agents to use for this IP address. The communication request is sent to the agents. One or more of the agents respond with a list of peers that have previously seen some or all of the content which is the response to this request (after checking whether this data is still valid). The client then downloads the data from these peers in parts and in parallel, thereby speeding up the Web transfer, releasing congestion from the Web by fetching the information from multiple sources, and relieving traffic from Web servers by offloading the data transfers from them to nearby peers.
Owner:BRIGHT DATA LTD
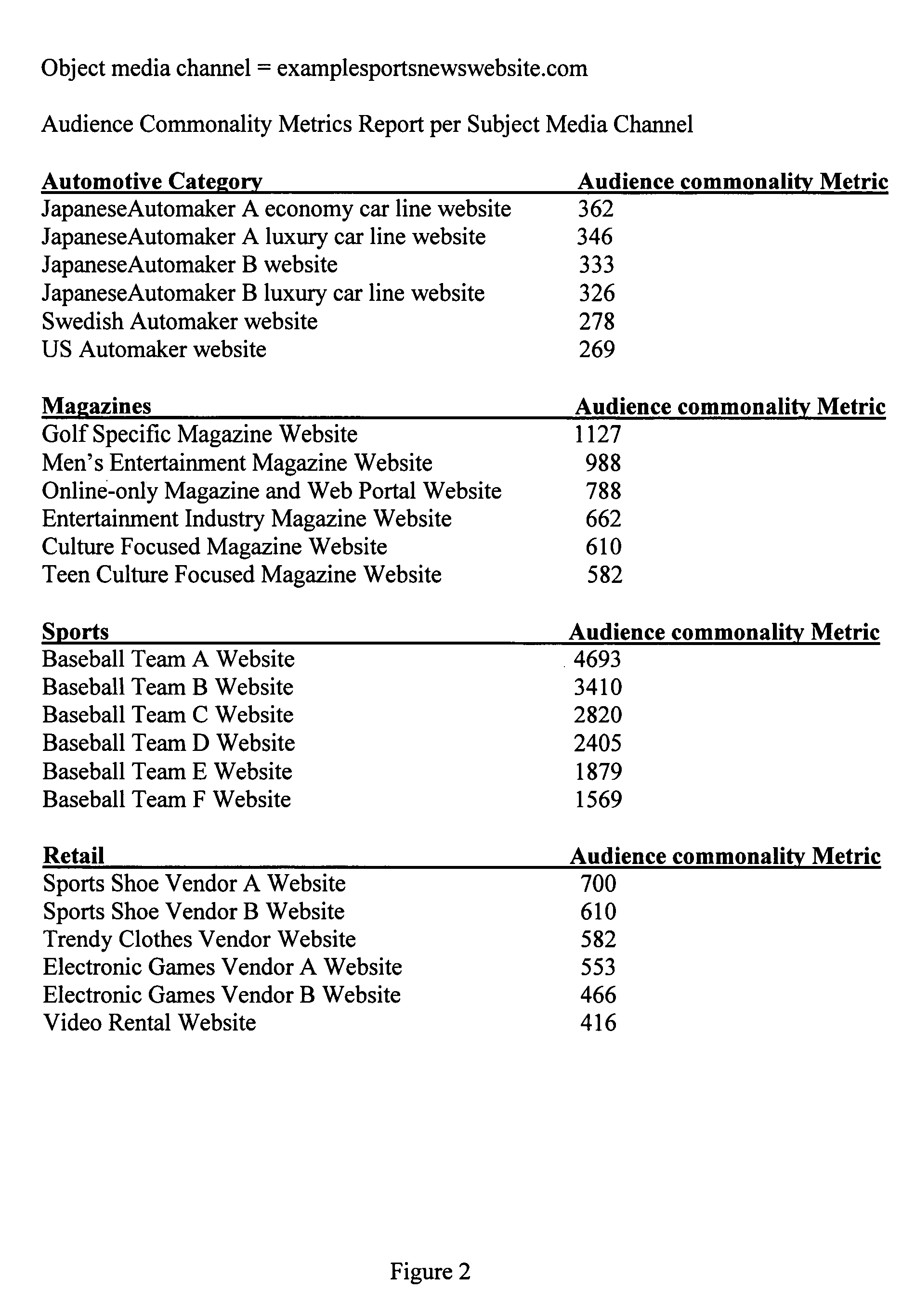
Audience commonality and measurement
InactiveUS20080086741A1Analogue secracy/subscription systemsBroadcast information monitoringNetwork activityClient agent
Audience commonality metrics for characterizing the relationship between networked media channels based on audience overlap of identified visitor entities and their related media consumption histories. Audience commonality metrics may be scalars or multi-dimensional metrics and may take into account and / or be used in conjunction with data related to on- or off-network media channels, on- or off-network activities, sociographics and / or demographics. The current invention may be used in the design of networked advertising campaigns, identification of new or unusual market segments and / or valuation of media buys. A system according to the current invention comprises access to a configuration, an input for receiving audience commonality data, an audience commonality metrics engine and an output for providing calculated audience commonality metrics. Data related to identified visitor entities may be received, determined and / or inferred from resources such as a cookie, log file, sniffer, firewall, proxy server, client agent, tracking pixel and / or tool
Owner:QUANTCAST CORP
Systems and Methods for Authorizing a Client in an SSL VPN Session Failover Environment
The SSL VPN session failover solution of the appliance and / or client agent described herein provides an environment for handling IP address assignment and end point re-authorization upon failover. The appliances may be deployed to provide a session failover environment in which a second appliance is a backup to a first appliance when a failover condition is detected, such as failure in operation of the first appliance. The backup appliance takes over responsibility for SSL VPN sessions provided by the first appliance. In the failover environment, the first appliance propagates SSL VPN session information including user IP address assignment and end point authorization information to the backup appliance. The backup appliance maintains this information. Upon detection of failover of the first appliance, the backup appliance activates the transferred SSL VPN session and maintains the user assigned IP addresses. The backup appliance may also re-authorize the client for the transferred SSL VPN session.
Owner:CITRIX SYST INC
Systems and methods of prefreshening cached objects based on user's current web page
ActiveUS8504775B2Improve efficiencyImprove intermediary or proxy cachingDigital data information retrievalSpecial data processing applicationsTraffic capacityClient agent
The present solution provides techniques that may accelerate and optimize network traffic in the areas of proxy caching, protocol acceleration, domain name resolution acceleration, and compression improvements using prefetching and / or prefreshening techniques to improve intermediary caching. Techniques described herein may improve the efficiency of obtaining and servicing data from originating servers to requesting clients and accelerates domain name resolution. The present solution may further help accelerate resolution of URLs into IP addresses. The present solution may improve compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
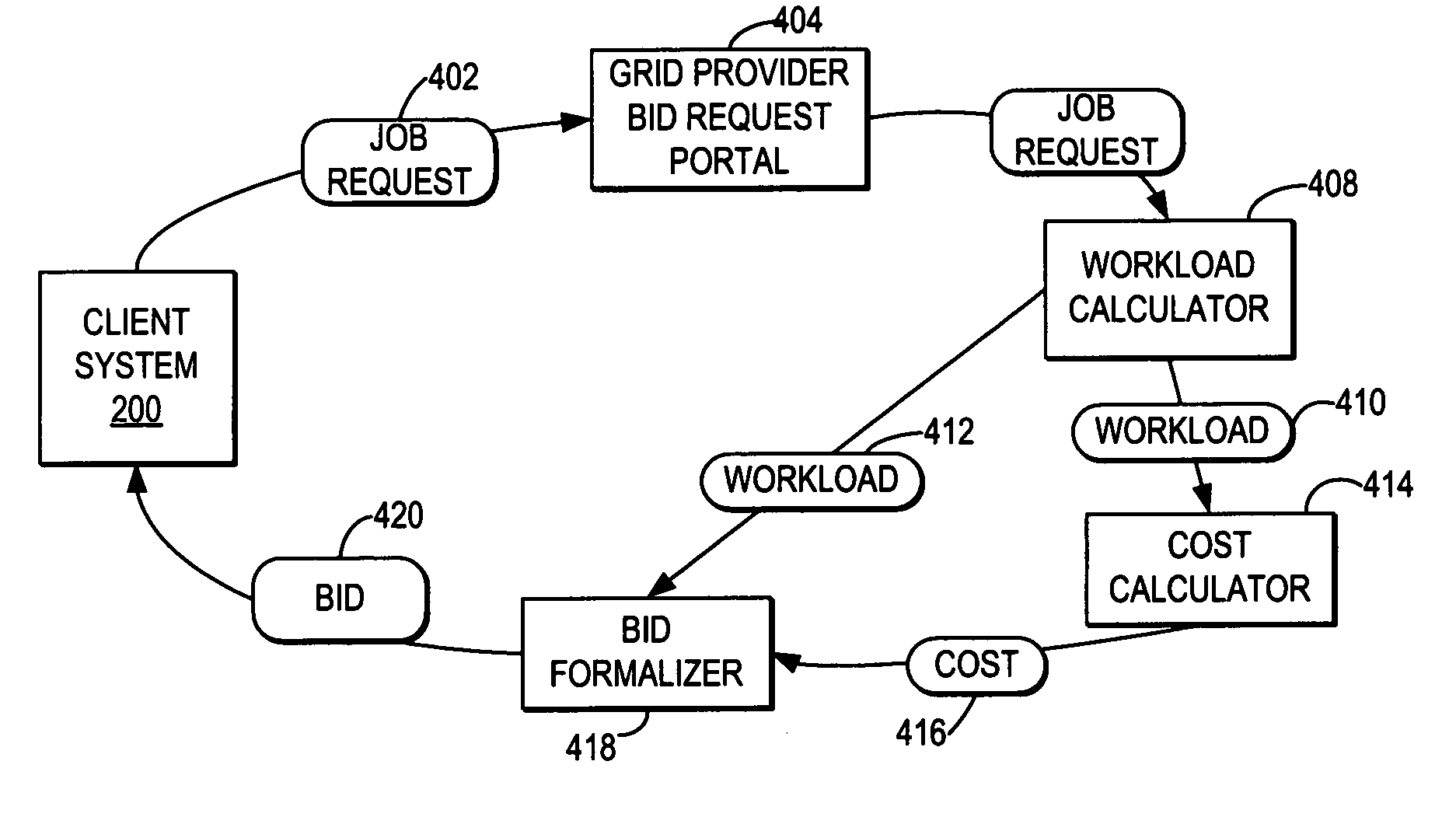
Estimating future grid job costs by classifying grid jobs and storing results of processing grid job microcosms
A method, system, and program for estimating future grid job costs by classifying grid jobs and storing results of processing grid job microcosms are provided. In general, a client side agent estimates future grid job costs by comparing a current grid job of a particular classification with a history of stored costs for other grid jobs of that customer of that particular classification. In particular, the grid client agent for a client system enabled to submit grid jobs to a grid provider that facilitates a grid environment, calculates a ratio of an application based metric to a grid provider metric for processing a particular grid job. Then, the grid client agent creates a table with an entry comparing the application based metric to a cost per grid provider metric for the grid provider based on the calculated ratio. Next, the grid client agent stores the table with the entry. Then, responsive to detecting a next grid job, the grid client agent estimates a cost for the grid provider to process the next grid job based on a particular number of application based metric operations required for the next grid job, translated by the ratio into the grid provider metric and multiplied by the cost per grid provider metric.
Owner:IBM CORP
Method for distributing and geographically load balancing location aware communication device client-proxy applications
InactiveUS20050246711A1Resource allocationMultiple digital computer combinationsClient agentThe Internet
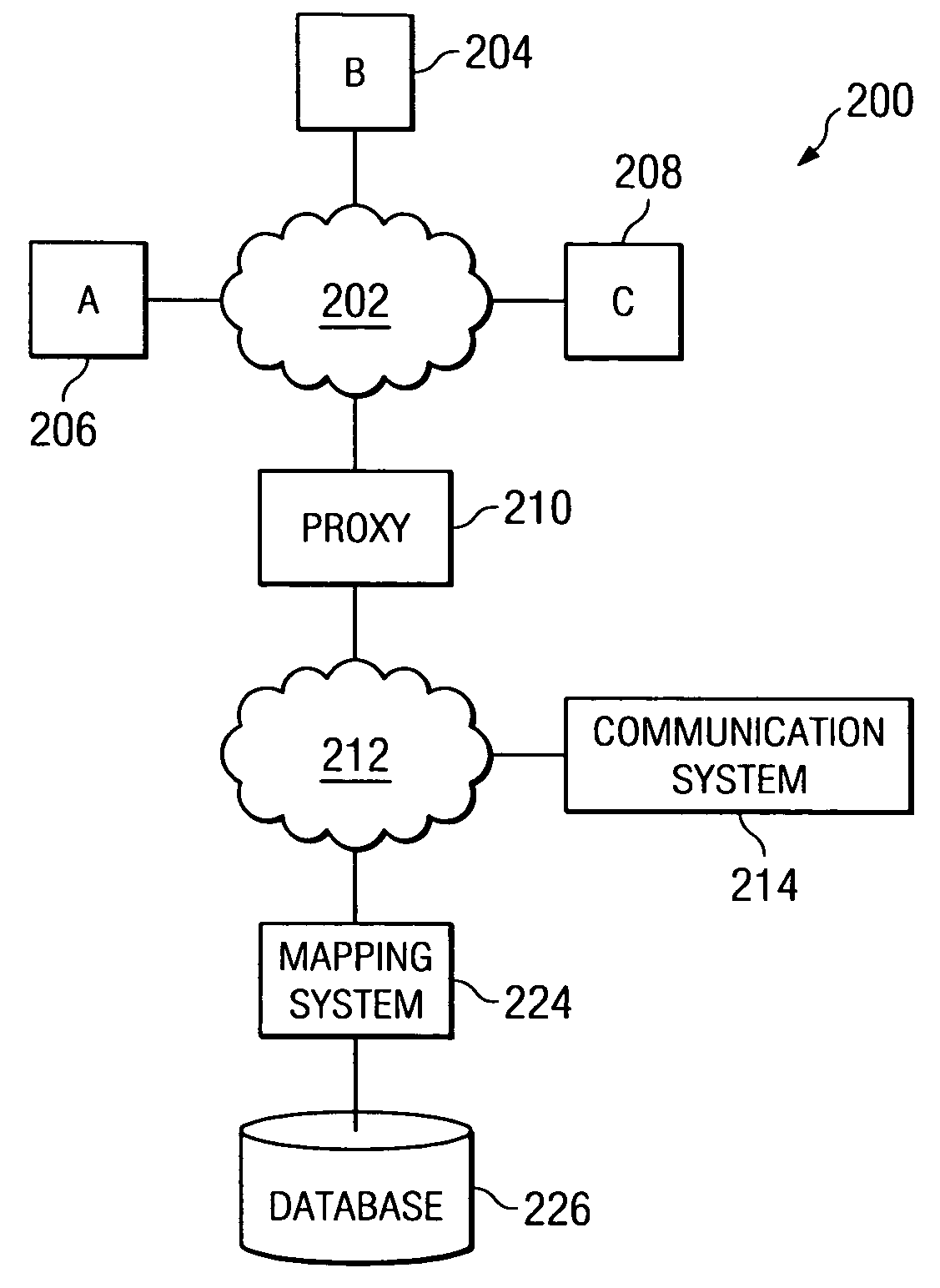
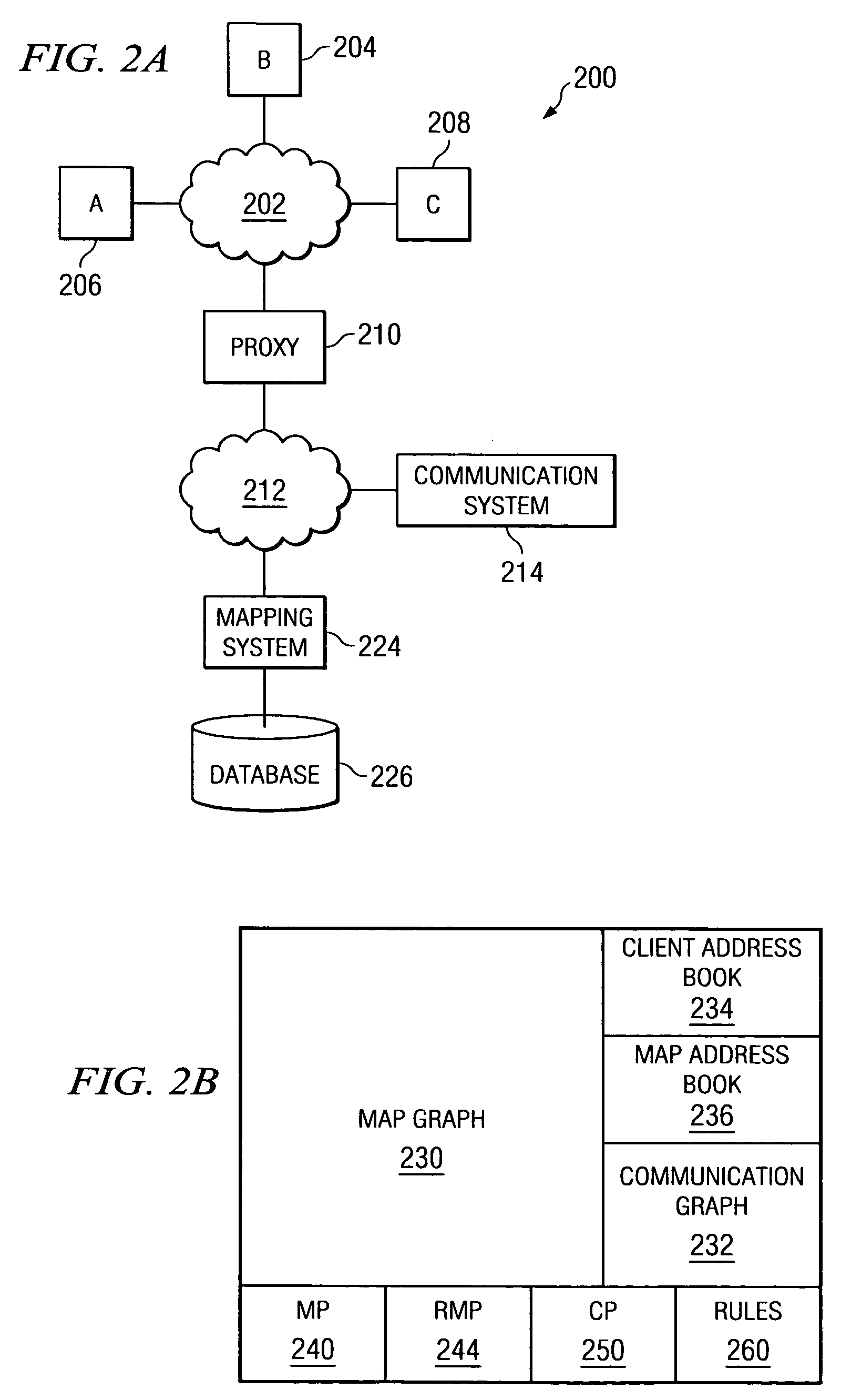
A method and system for balancing server work load for cellular phone client-proxy applications in an environment where the clients change position within a given geographic area is disclosed. The method comprises the steps of mapping, monitoring, automatically re-mapping the system when required, updating a map address book, and updating a client address book. The system has a mapping system and a communication system connected to a plurality of servers, proxy servers and applications by an internal network. The proxy servers are connected to a plurality of clients by the Internet. If a threshold is exceeded, the monitoring program sends a message to a mapping program. Upon receipt of the message, the mapping program uses a rules engine to calculate a new map graph to remove load from an overloaded server (or servers) and to adjust communication requirements for data by reconfiguring partitions.
Owner:ACTIVISION PUBLISHING
Method and system for updating/reloading the content of pages browsed over a network
InactiveUS20050108418A1Digital data information retrievalMultiple digital computer combinationsClient agentReal-time web
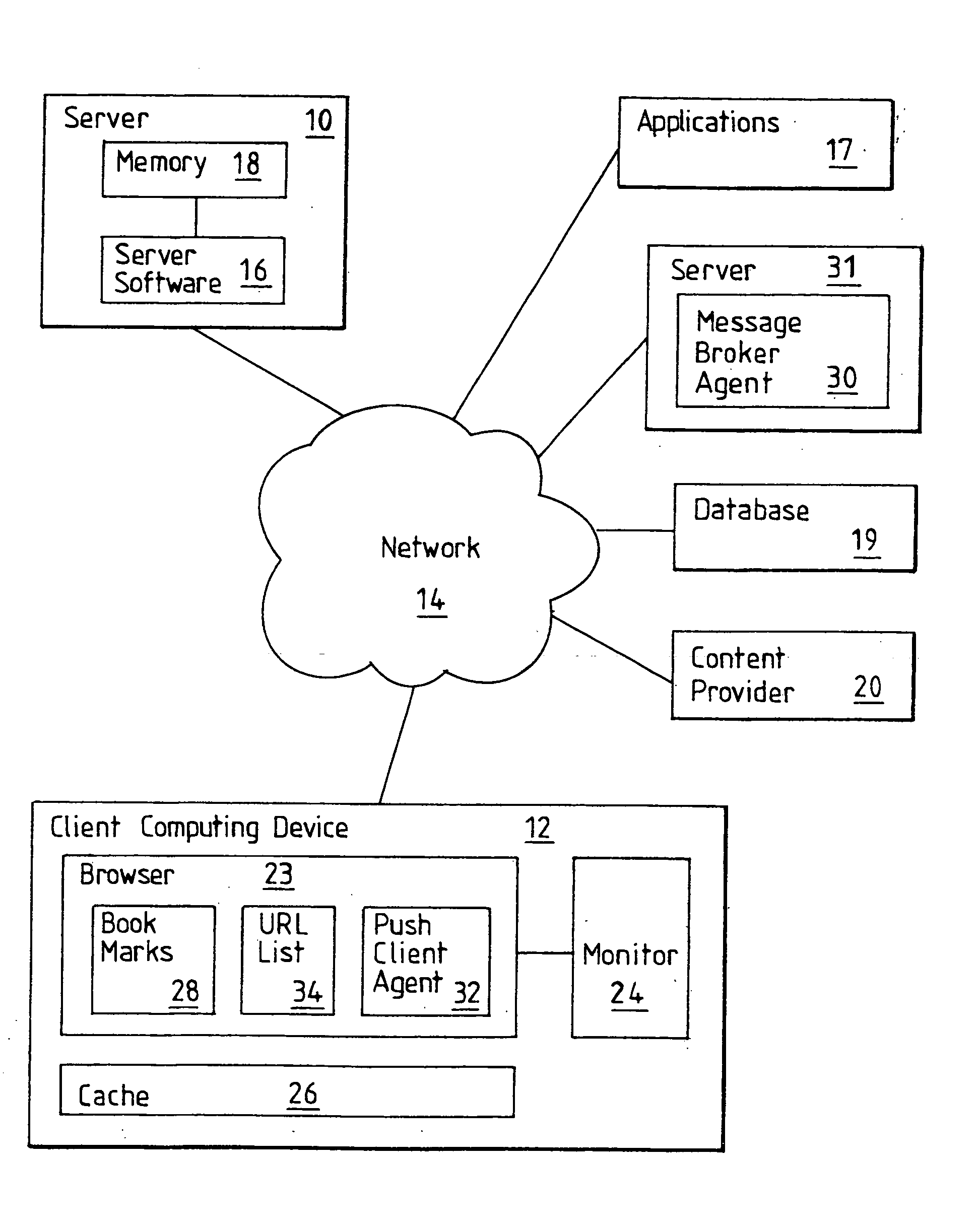
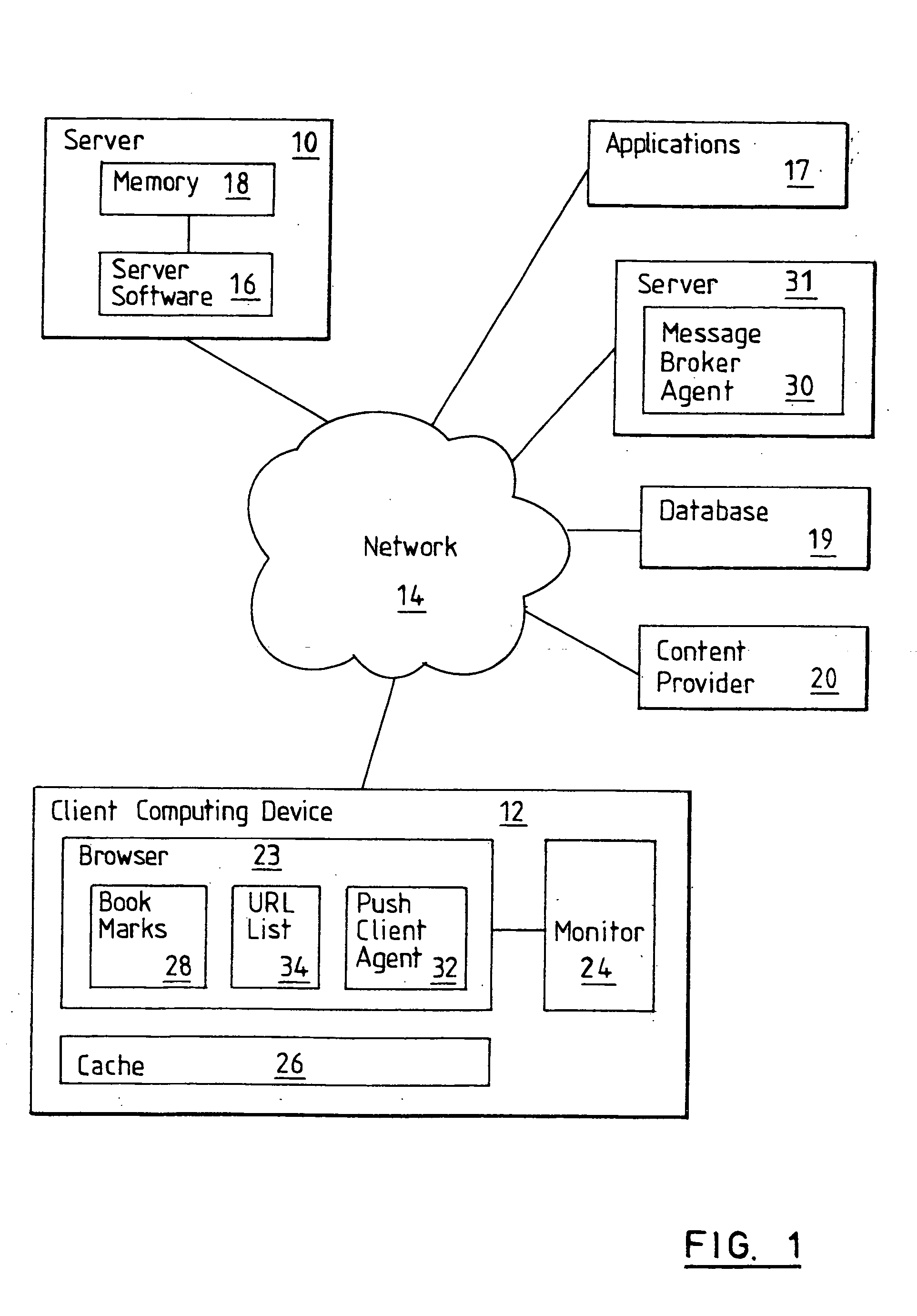
The present invention provides a real-time means of automatically updating the content of a user pre-selected set of web pages without any activity required on the part of the user to initiate each web page updating procedure. This is achieved by incorporating into a browser of a user's computing device software code that is responsive to real-time web page content change notification messages to cause the browser to reload a URL identified in the change notification message. Alternatively, the software code may comprise a Java applet or the like embedded in a downloaded web page that is responsive to change notification messages to cause the browser to reload a web page whose URL is identified in the message or to reload a currently displayed web page. The change notification messages are generated by applications whose web page content has changed and the messages are relayed in real-time to push client agents comprising said software code by a message broker agent. The invention offers many advantages including reducing unnecessary web page reload operations and thus reducing network traffic.
Owner:IBM CORP
Methods, systems, and computer program products for providing automated customer service via an intelligent virtual agent that is trained using customer-agent conversations
ActiveUS7305345B2Automatic call-answering/message-recording/conversation-recordingSpeech recognitionData processing systemClient agent
A customer communication is responded to by receiving an utterance from the customer at an agent that executes on a data processing system. The agent uses a knowledge base that includes information extracted from one or more exemplary conversations to generate a response to the received utterance. The agent then sends the generated response to the customer.
Owner:ASTUTE
Remote Access to Home Communication Services
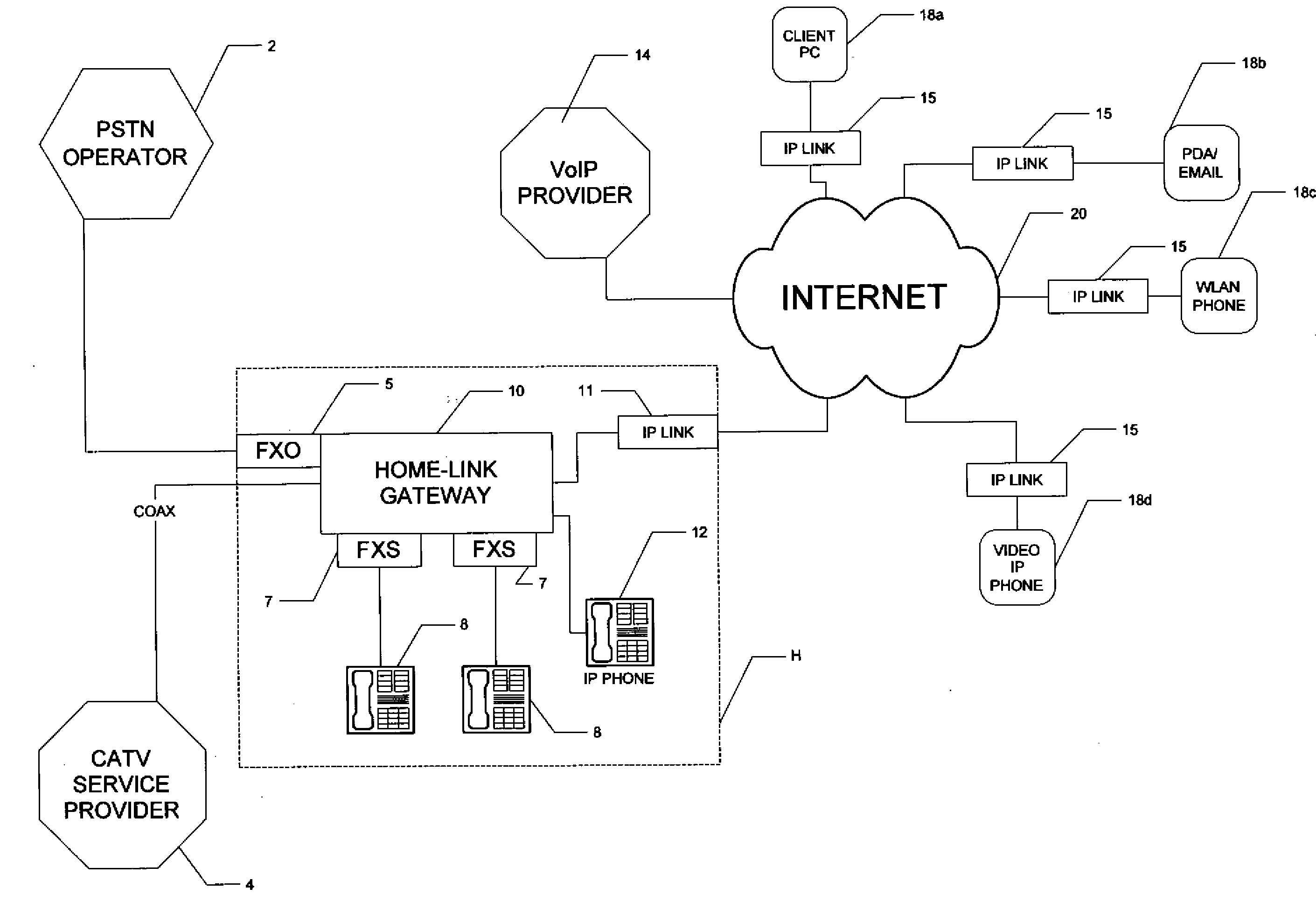
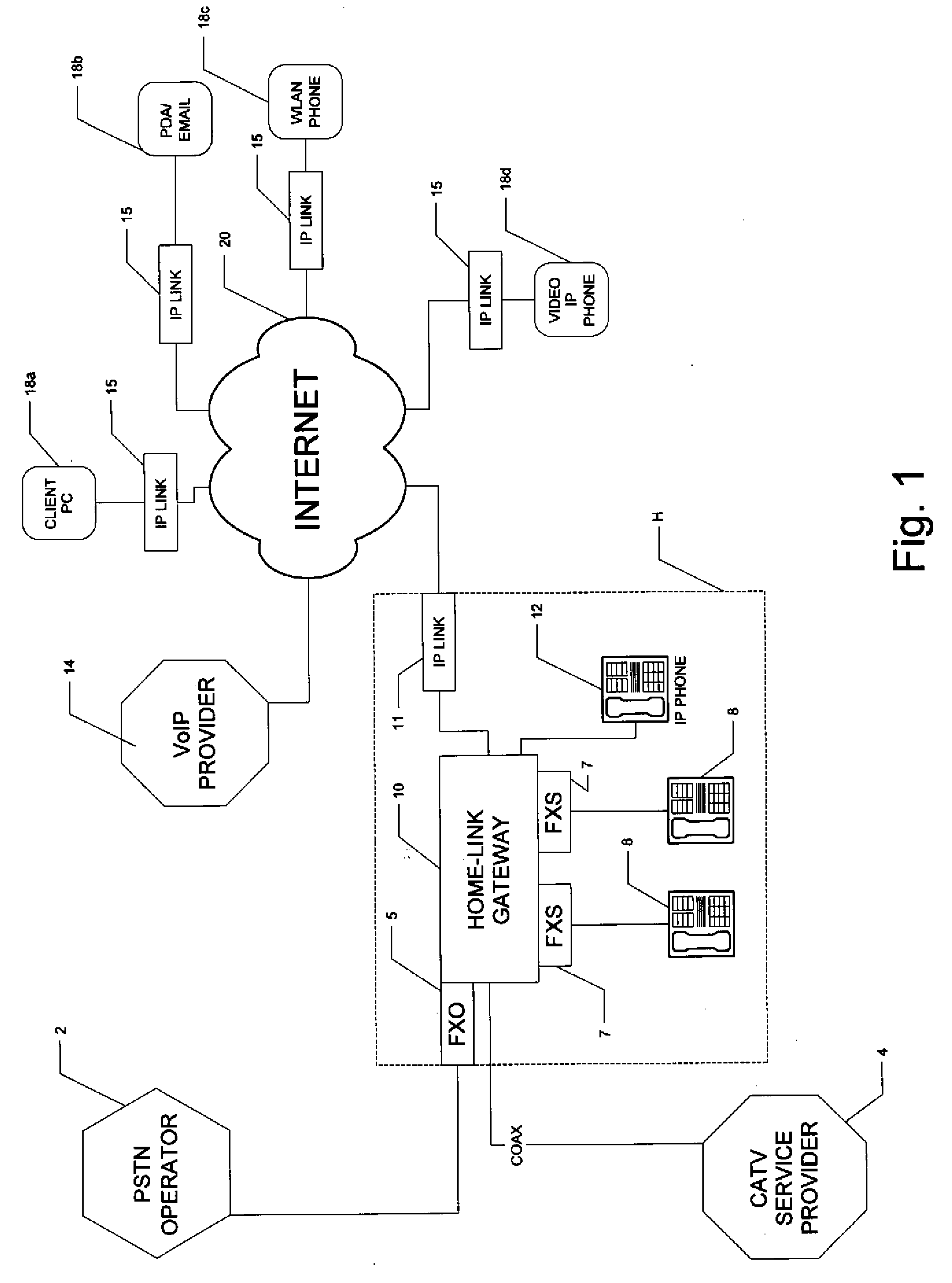
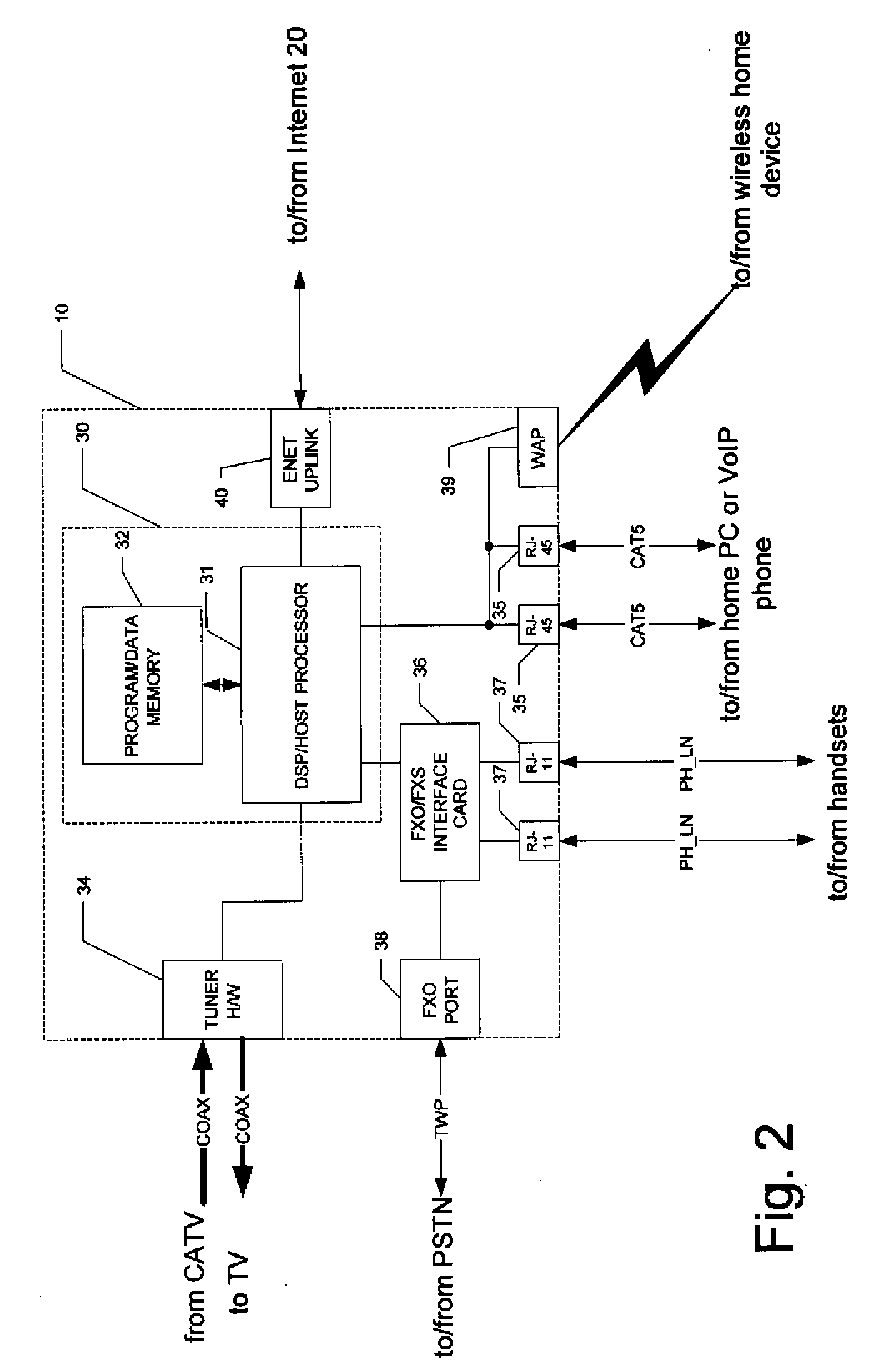
InactiveUS20080247401A1Interconnection arrangementsData switching by path configurationClient agentThe Internet
A home-link gateway system for providing remote access to contracted telephone services at a home or other physical location is disclosed. The home-link gateway manages communications at the home location, for example between a PSTN or VoIP telephone network and local telephone handsets. A remote client agent requests access to telephone services, via the Internet. Following authorization and registration, the home-link gateway couples the remote client agent to the telephone network, or to local handsets, as though the remote client agent were deployed at the home location.
Owner:TEXAS INSTR INC
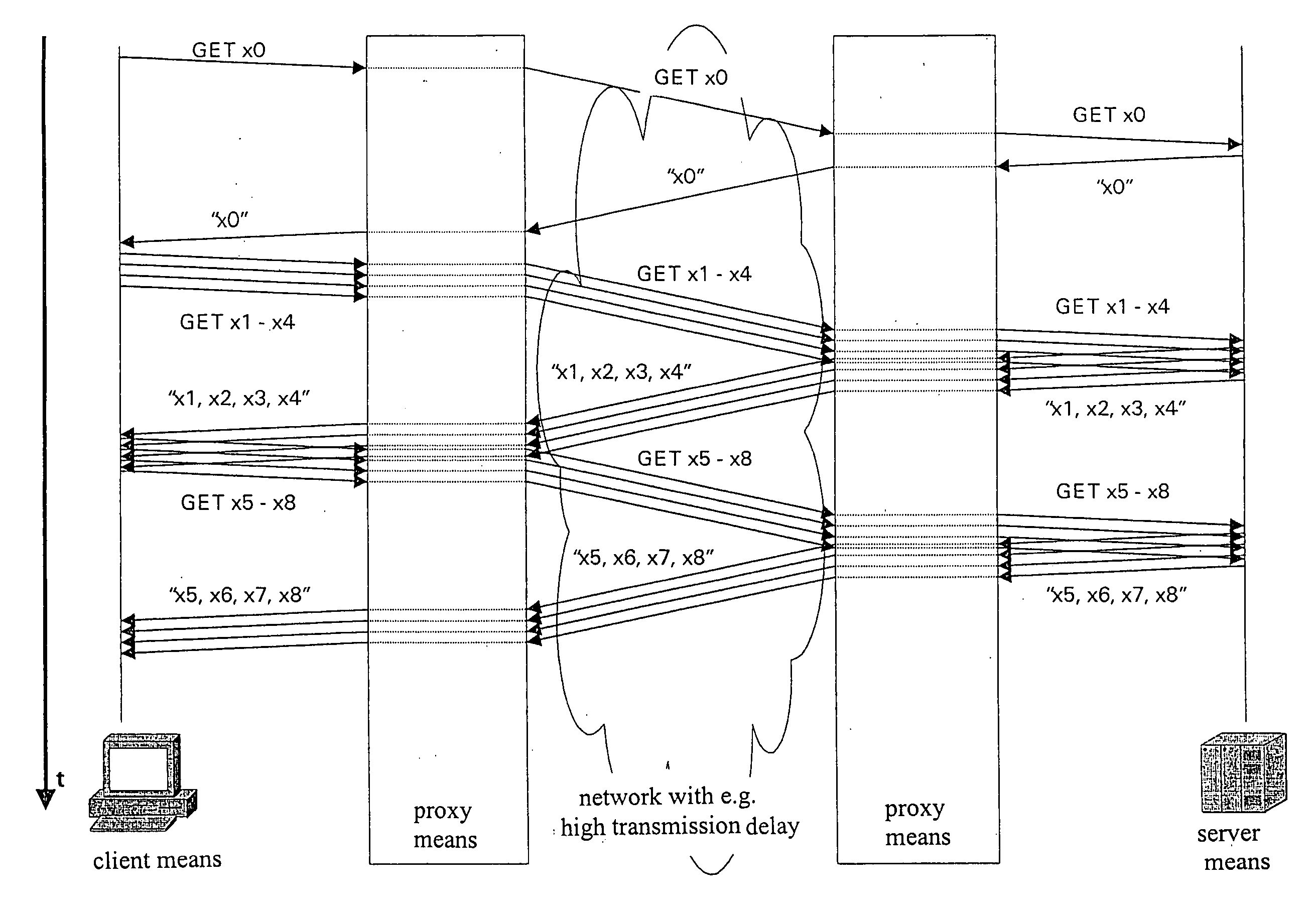
Method for prefetching of structured data between a client device and a server device
InactiveUS20040215717A1Effective transmission speedSpeed efficientMultiple digital computer combinationsTransmissionClient agentServer agent
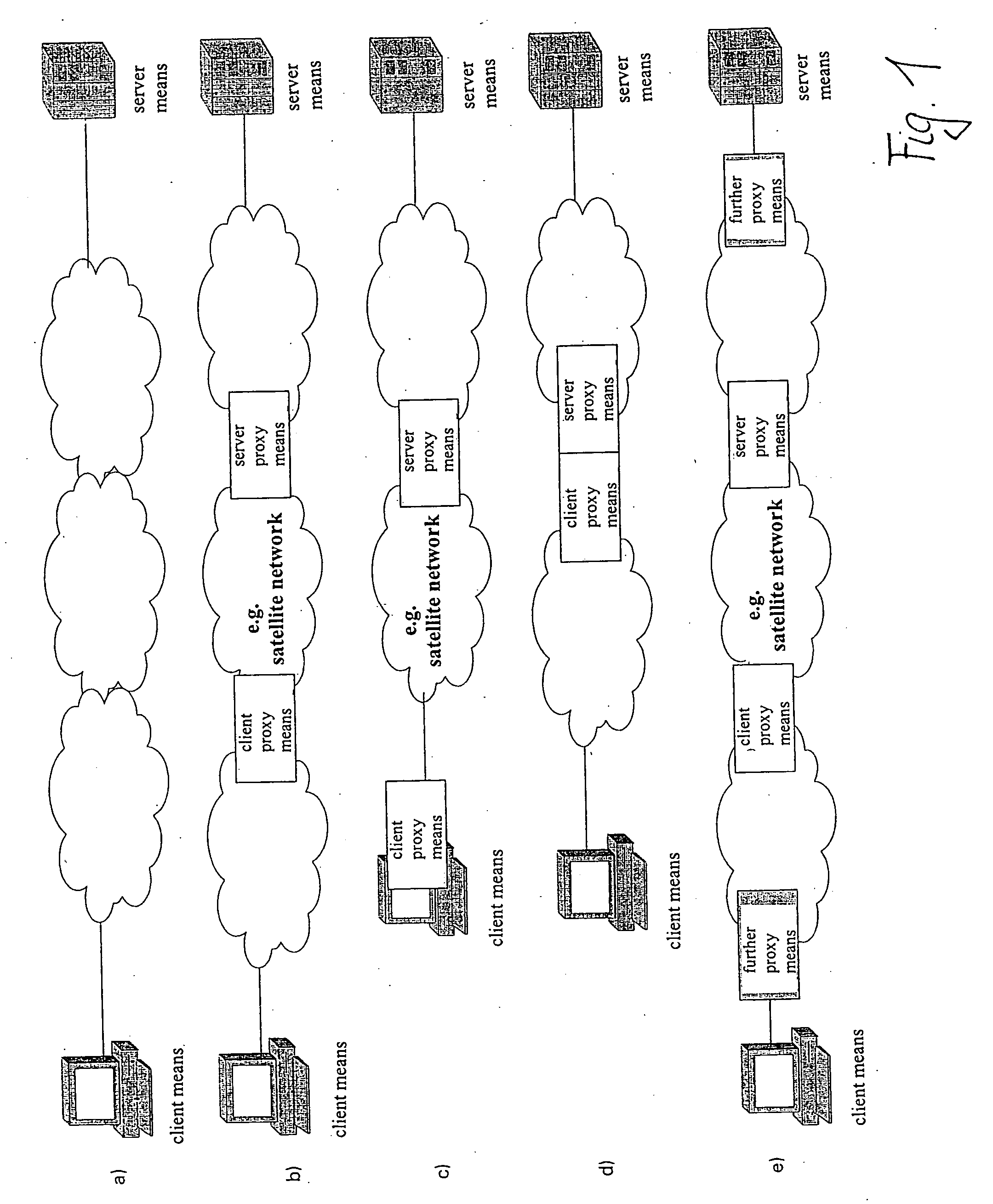
The invention relates to a method of more efficient data transmission, in particular transmission of structured data, such as web pages, in a system comprising a server means and a client means which are interconnected via a plurality of proxy means, including a server proxy means and a client proxy means.
Owner:TELLIQUE KOMMUNIKATIONSTECHN
Concurrent server and method of operation having client-server affinity using exchanged client and server keys
InactiveUS6195682B1Eliminate needMultiple digital computer combinationsPayment architectureS/KEYInformation networks
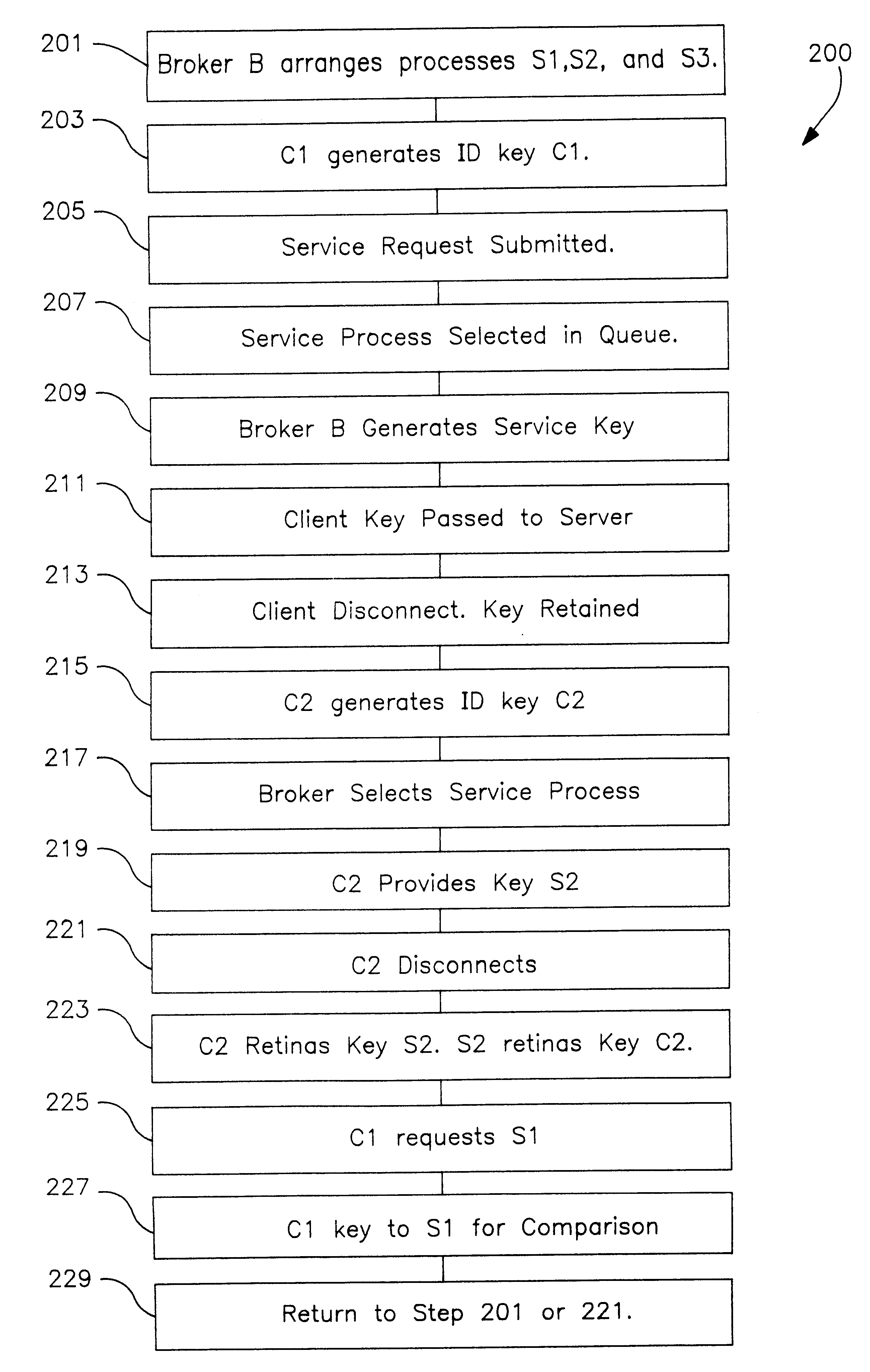
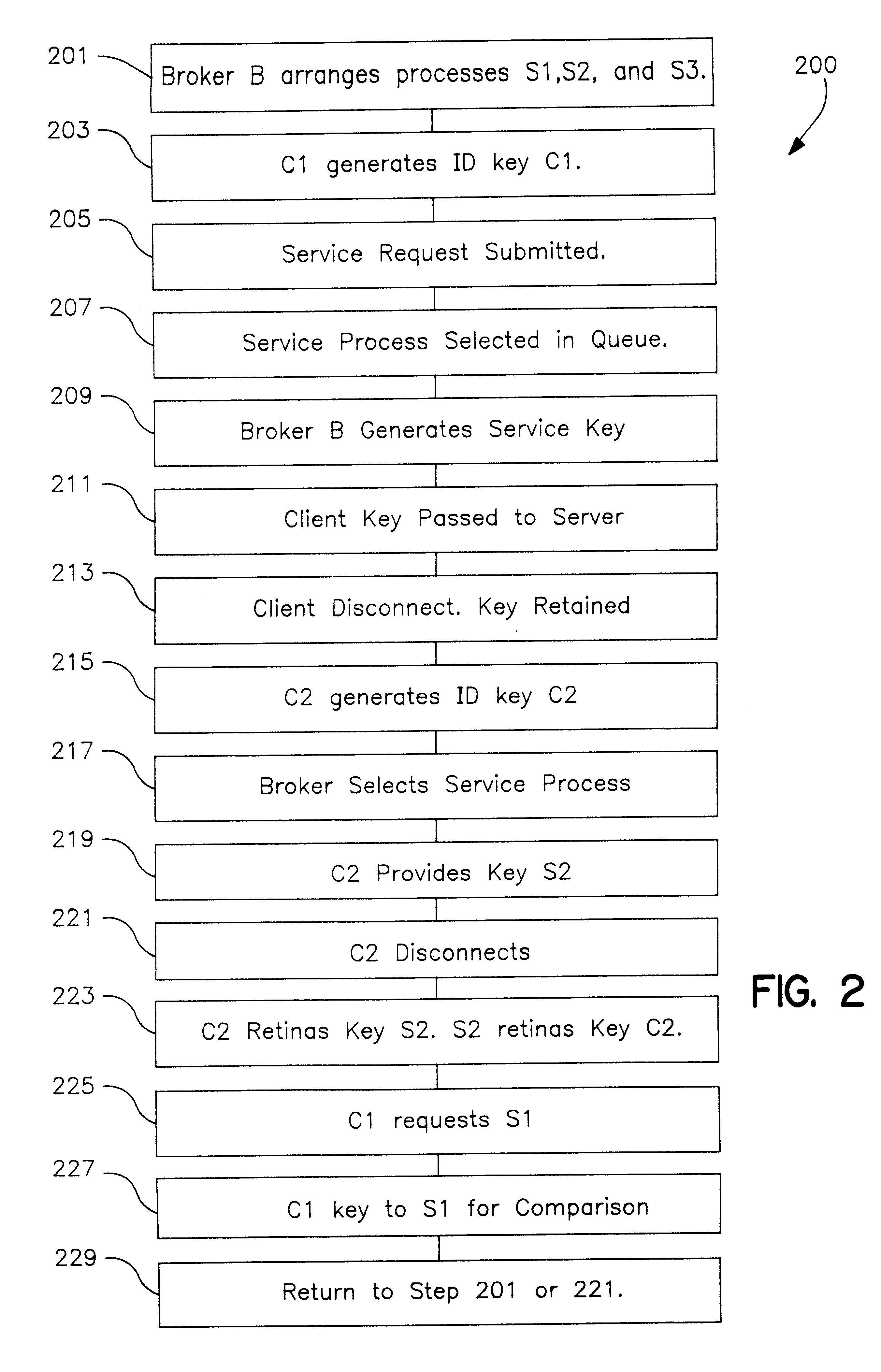
In a distributed information network, a broker server is coupled to a plurality of child servers and to a plurality of clients in the network. The broker server connects clients to a child server in a queue on a FIFO basis and provides the client with a key identifying the child server. The client provides the server with a copy of its key at the time of the initial service request. Both the child server and the client retain a copy of the other's key upon disconnect. The child server returns to the bottom of the queue after disconnect. On a subsequent client service request, the client includes the child server key in the service request and the broker automatically re-connects the client to the child server wherever S1 may be in the queue, provided the child server is not busy serving other clients. When reconnected, the client send its key to the child server which compares the key to the retained copy of the client key. If the keys match, the child server does not refresh and reload the client state data which improves server performance. If the child server is not available, the broker assigns the client to the child server at the top of the queue. The client may also be an intermediate server for other or first tier clients, in which case the intermediate server forwards the server keys to the first tier clients for service requests to the child server.
Owner:IBM CORP
Systems and methods of dynamically checking freshness of cached objects based on link status
ActiveUS20080229024A1Improve efficiencyMore resolutionMemory adressing/allocation/relocationMultiple digital computer combinationsDomain nameClient agent
The present solution provides a variety of techniques for accelerating and optimizing network traffic, such as HTTP based network traffic. The solution described herein provides techniques in the areas of proxy caching, protocol acceleration, domain name resolution acceleration as well as compression improvements. In some cases, the present solution provides various prefetching and / or prefreshening techniques to improve intermediary or proxy caching, such as HTTP proxy caching. In other cases, the present solution provides techniques for accelerating a protocol by improving the efficiency of obtaining and servicing data from an originating server to server to clients. In another cases, the present solution accelerates domain name resolution more quickly. As every HTTP access starts with a URL that includes a hostname that must be resolved via domain name resolution into an IP address, the present solution helps accelerate HTTP access. In some cases, the present solution improves compression techniques by prefetching non-cacheable and cacheable content to use for compressing network traffic, such as HTTP. The acceleration and optimization techniques described herein may be deployed on the client as a client agent or as part of a browser, as well as on any type and form of intermediary device, such as an appliance, proxying device or any type of interception caching and / or proxying device.
Owner:CITRIX SYST INC
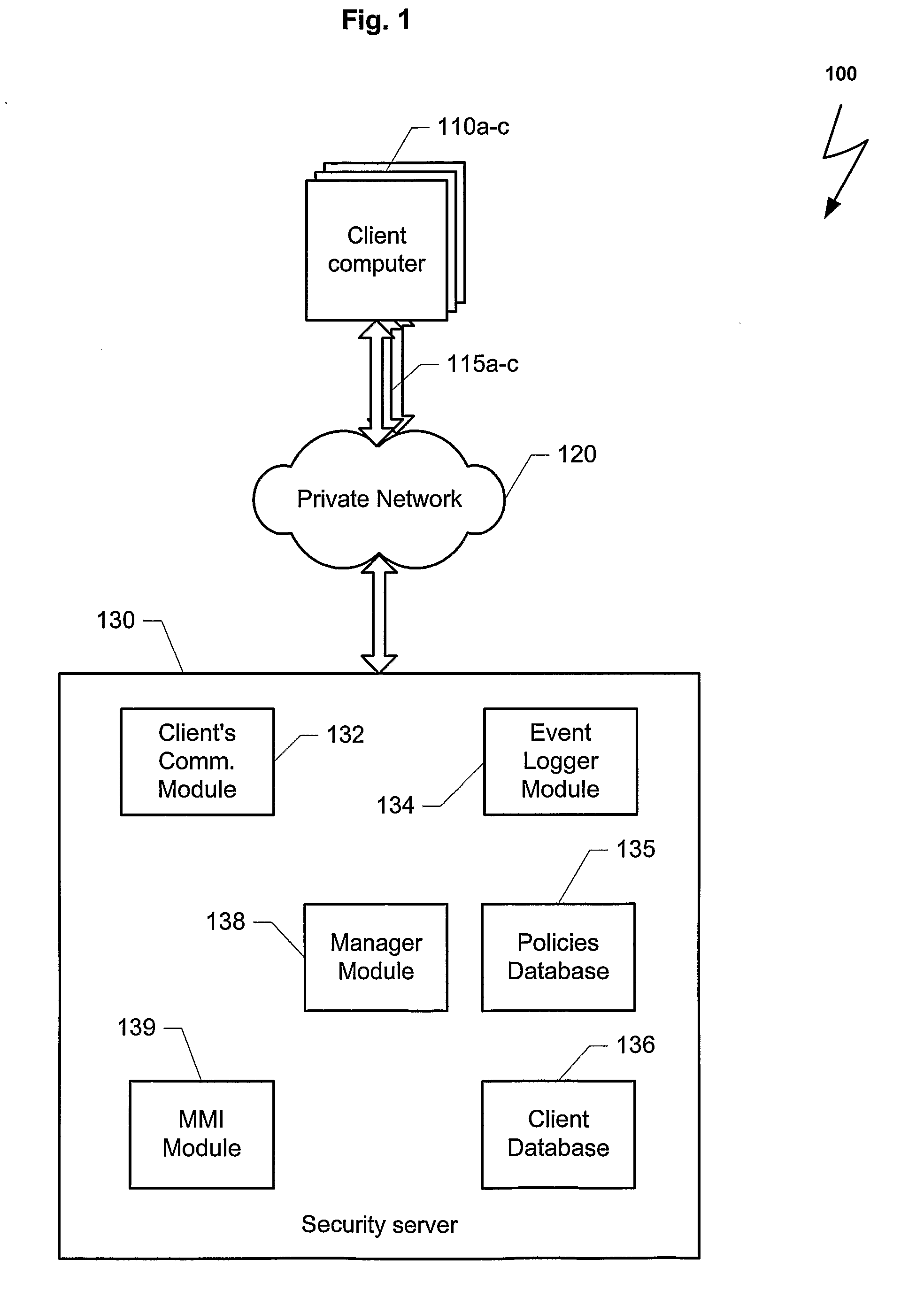
Method and system for improving computer network security
Computers connected to a private network are monitored and controlled through the use of a client agent that operates in association with the computer and a server client that establishing security parameters, privileges and authorizations for the computer. The invention can prevent access to certain devices according to an active security policy. Any activity of the computer, such as a request to transfer data to an external device, access a particular file, etc. is monitored and controlled by the client agent. No operations or procedures are allowed by the computer inconsistent with the active security policy. The security policy may be set by the administrator of the private network according to the user rights and position in the organization
Owner:SUPERCOM IP LLC
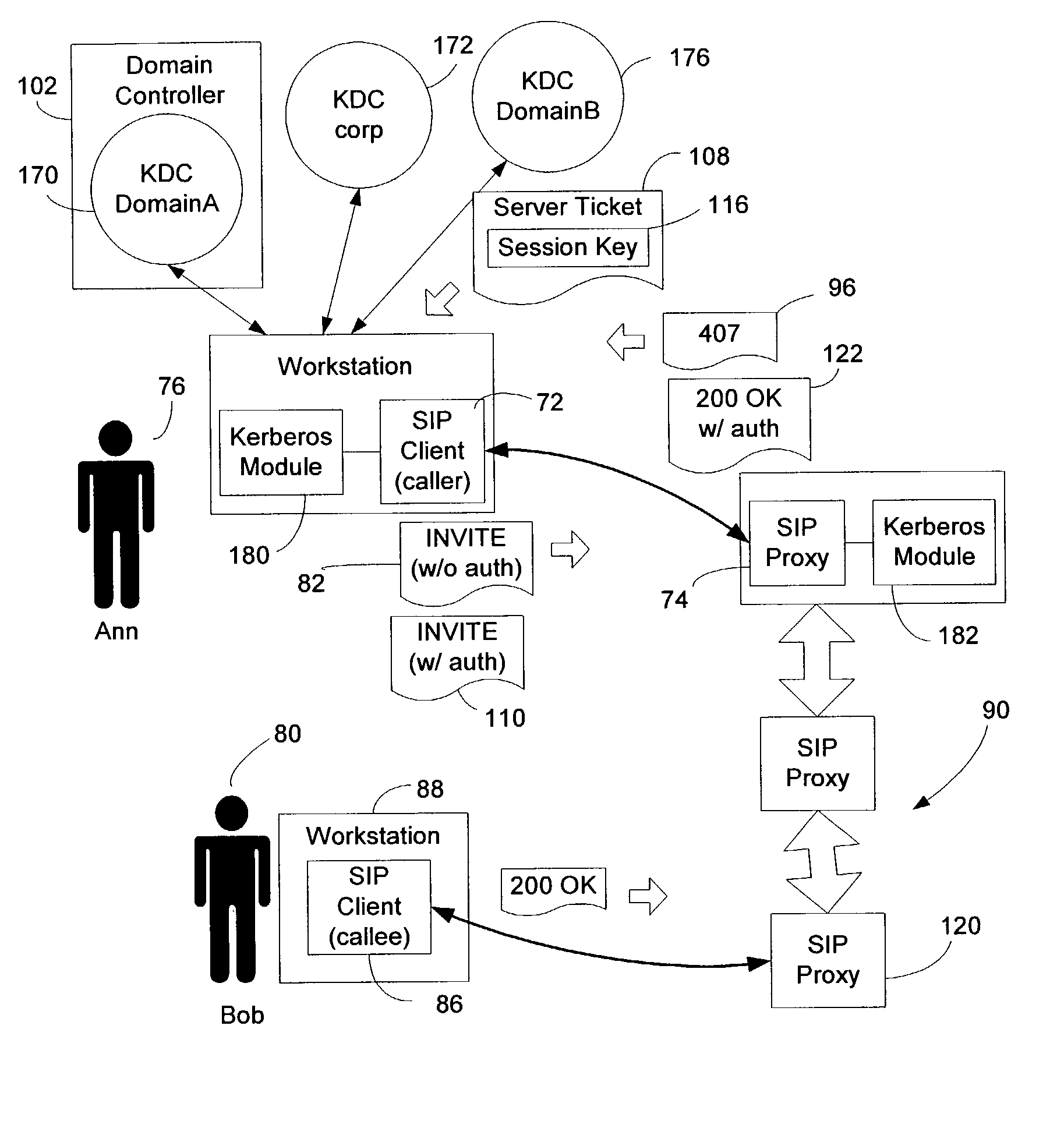
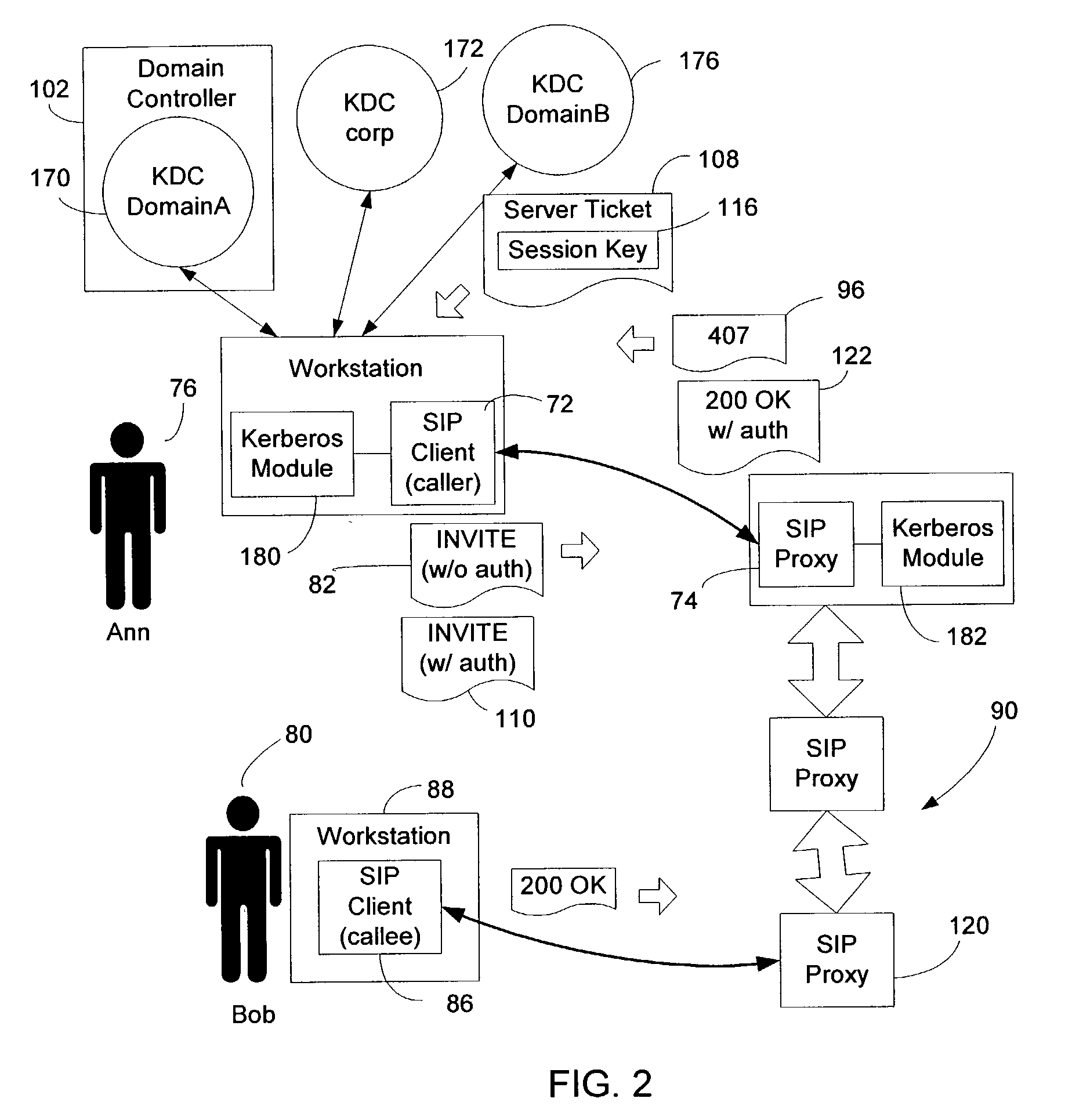
Method and system for integrating security mechanisms into session initiation protocol request messages for client-proxy authentication
InactiveUS7243370B2Random number generatorsUnauthorized memory use protectionClient agentSession Initiation Protocol
A method and system is provided to integrate the Kerberos security mechanism into the message flow of the signaling operation under the Session Initiation Protocol to allow a SIP client and a SIP proxy to authenticate each other. When the SIP proxy receives an request message, such an INVITE request, from the SIP client, it responds with a challenge message indicating that authentication based on Kerberos is required. In response, the SIP client sends a second request message with a proxy authorization header containing authentication data, including a Kerberos server ticket for the Proxy, to allow the proxy to authenticate the client's user.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com