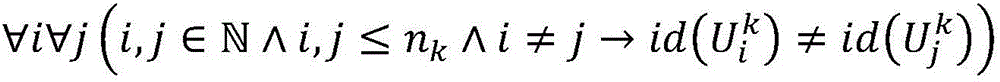Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
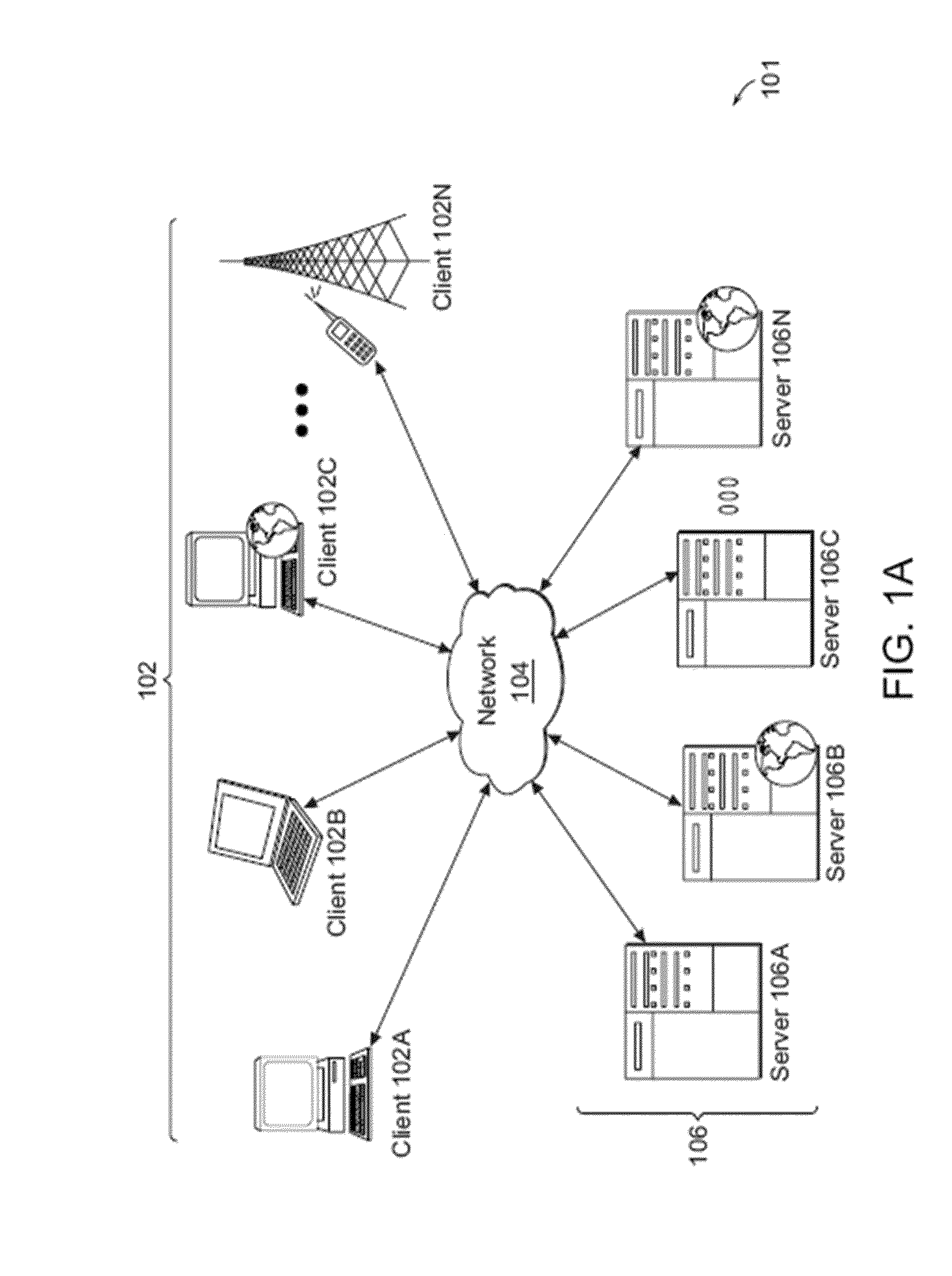
129 results about "Trusted client" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
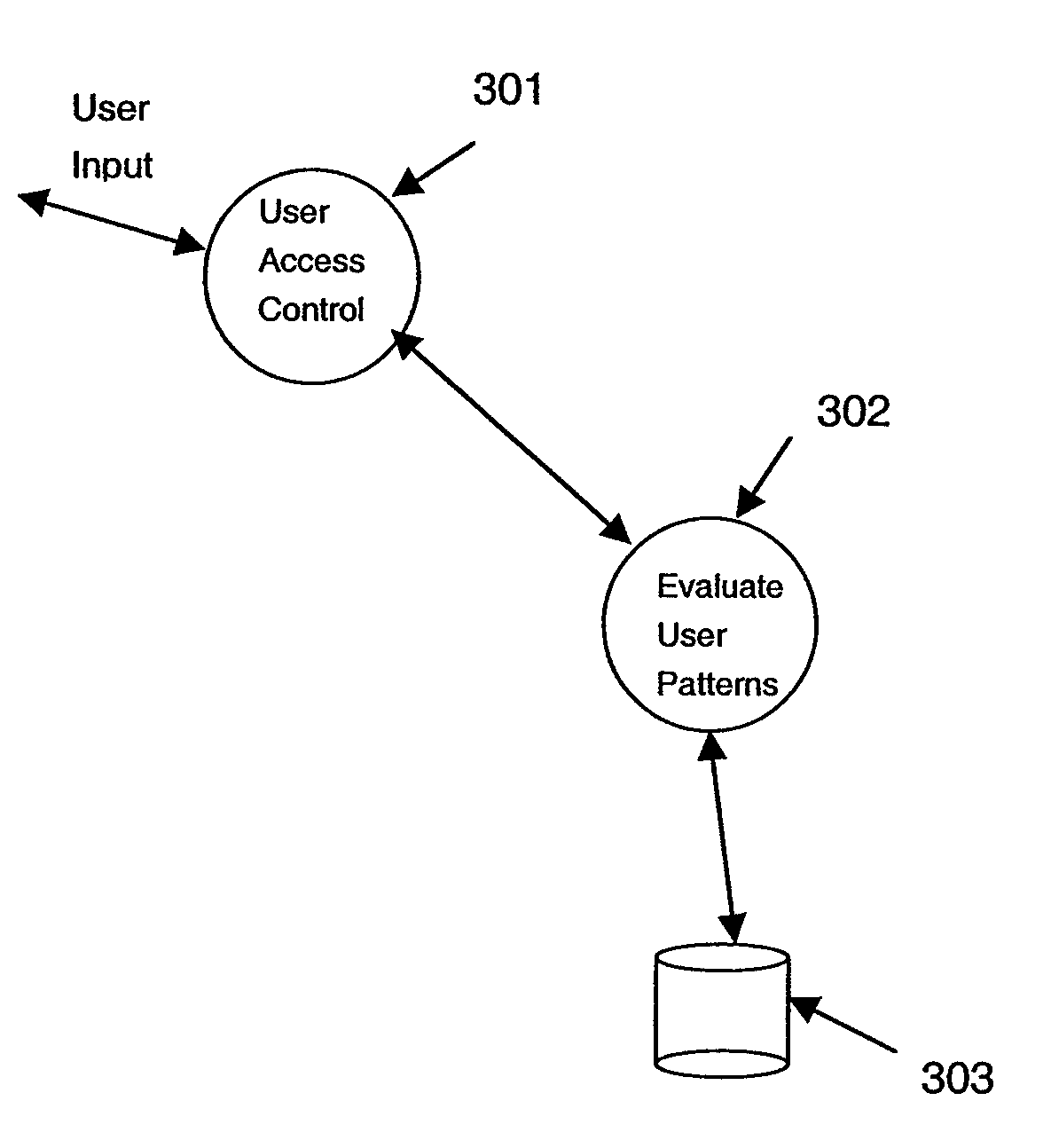
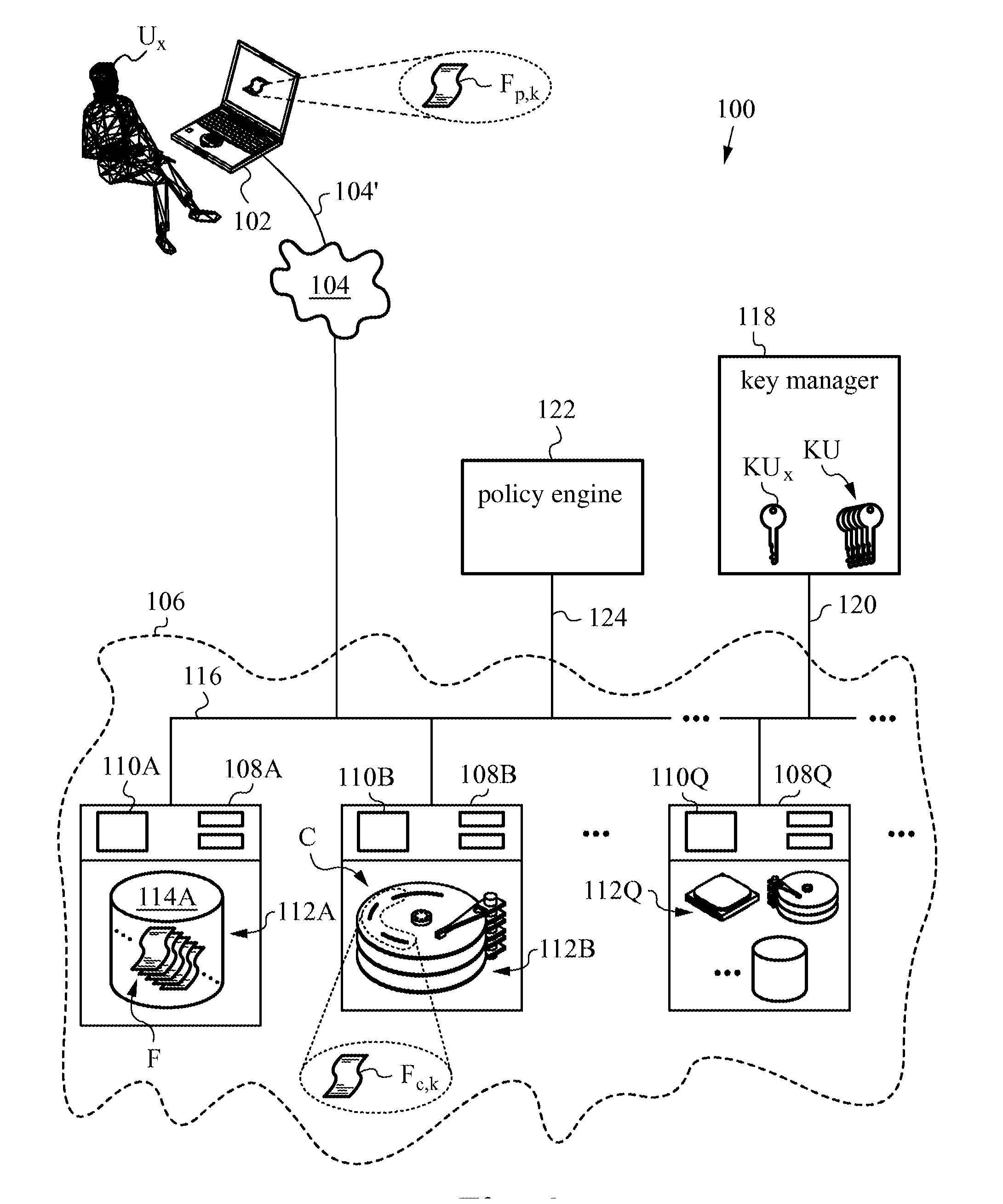
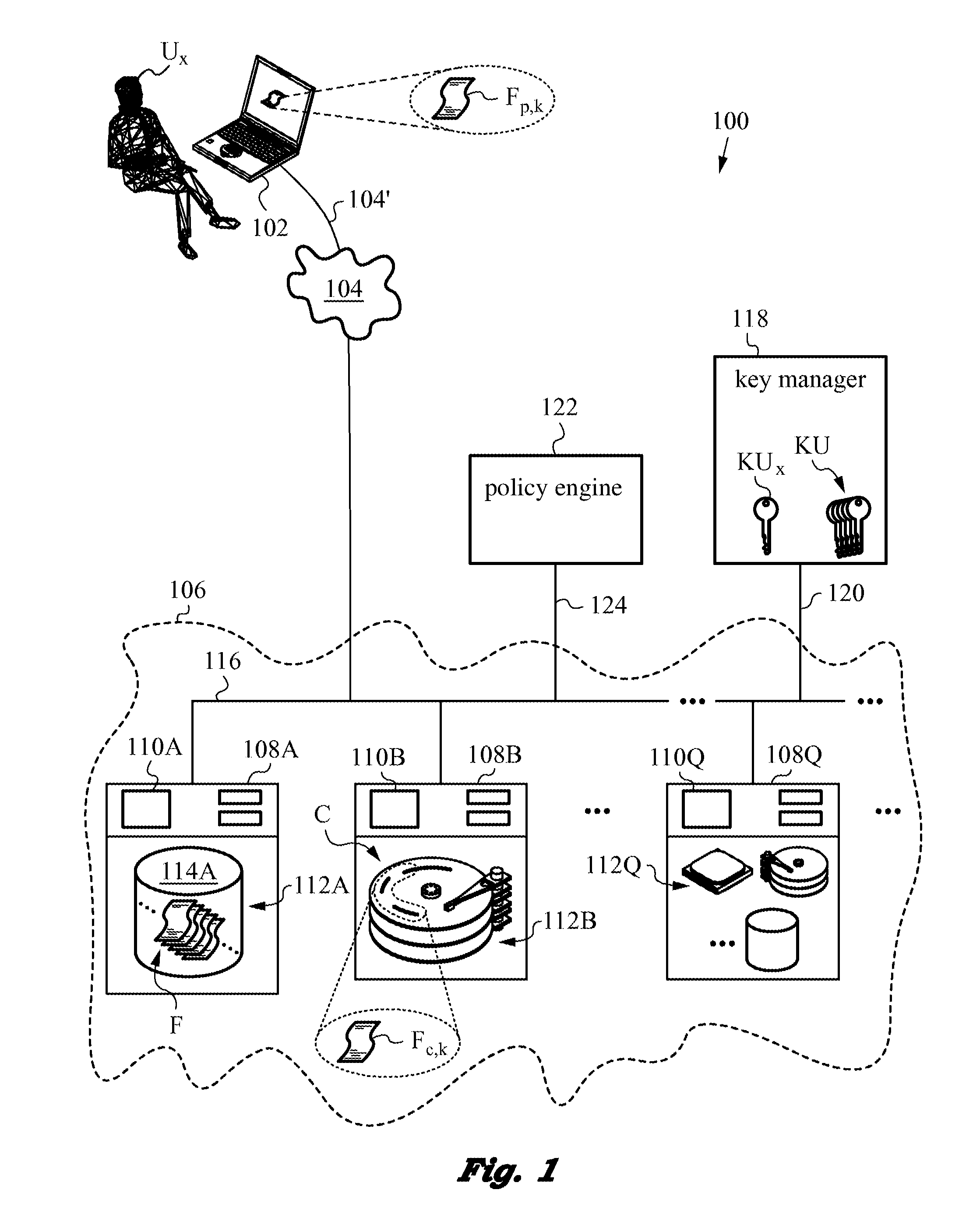
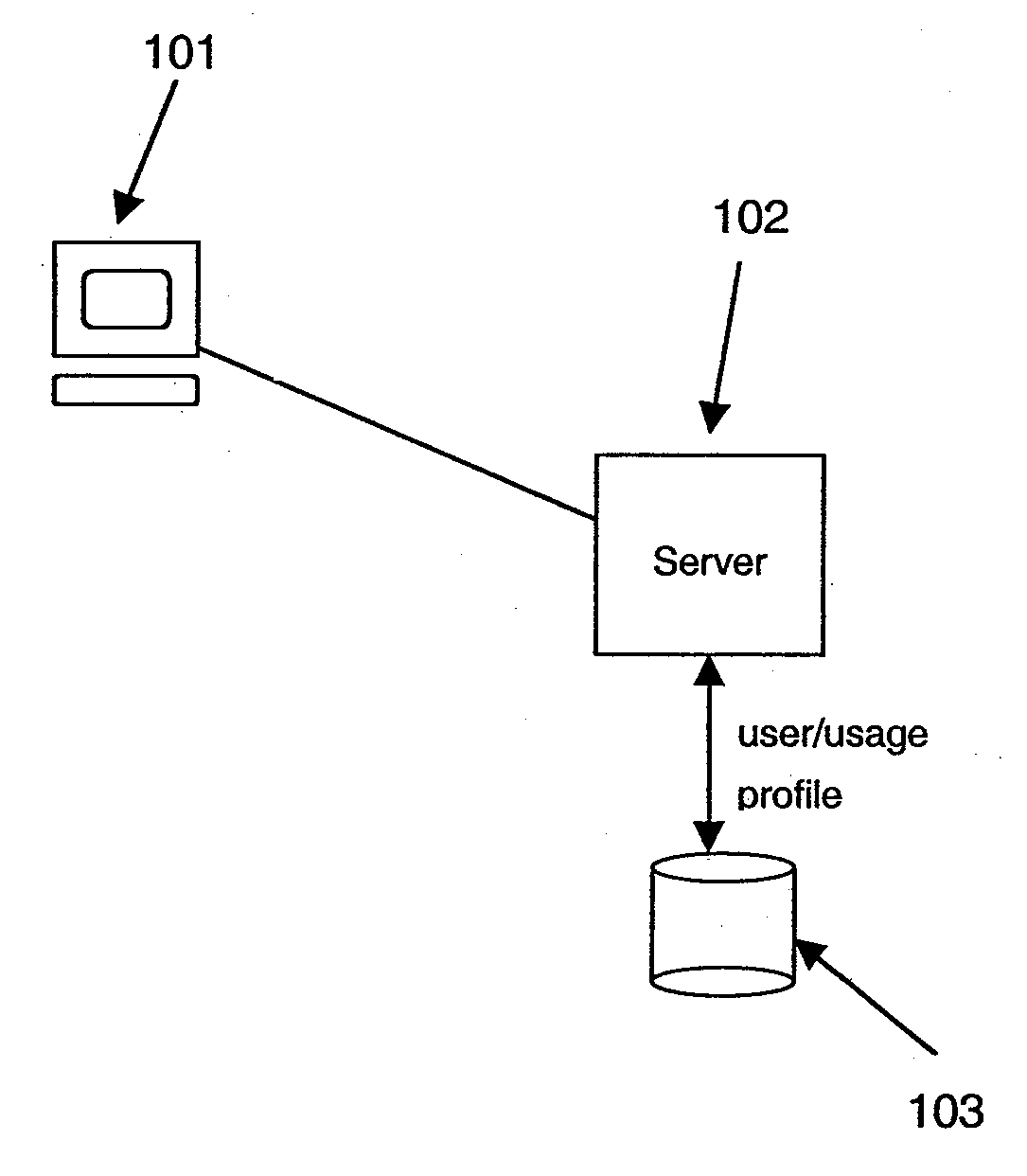
In computing, a trusted client is a device or program controlled by the user of a service, but with restrictions designed to prevent its use in ways not authorized by the provider of the service. That is, the client is a device that vendors trust and then sell to the consumers, whom they do not trust. Examples include video games played over a computer network or the Content Scramble System (CSS) in DVDs.
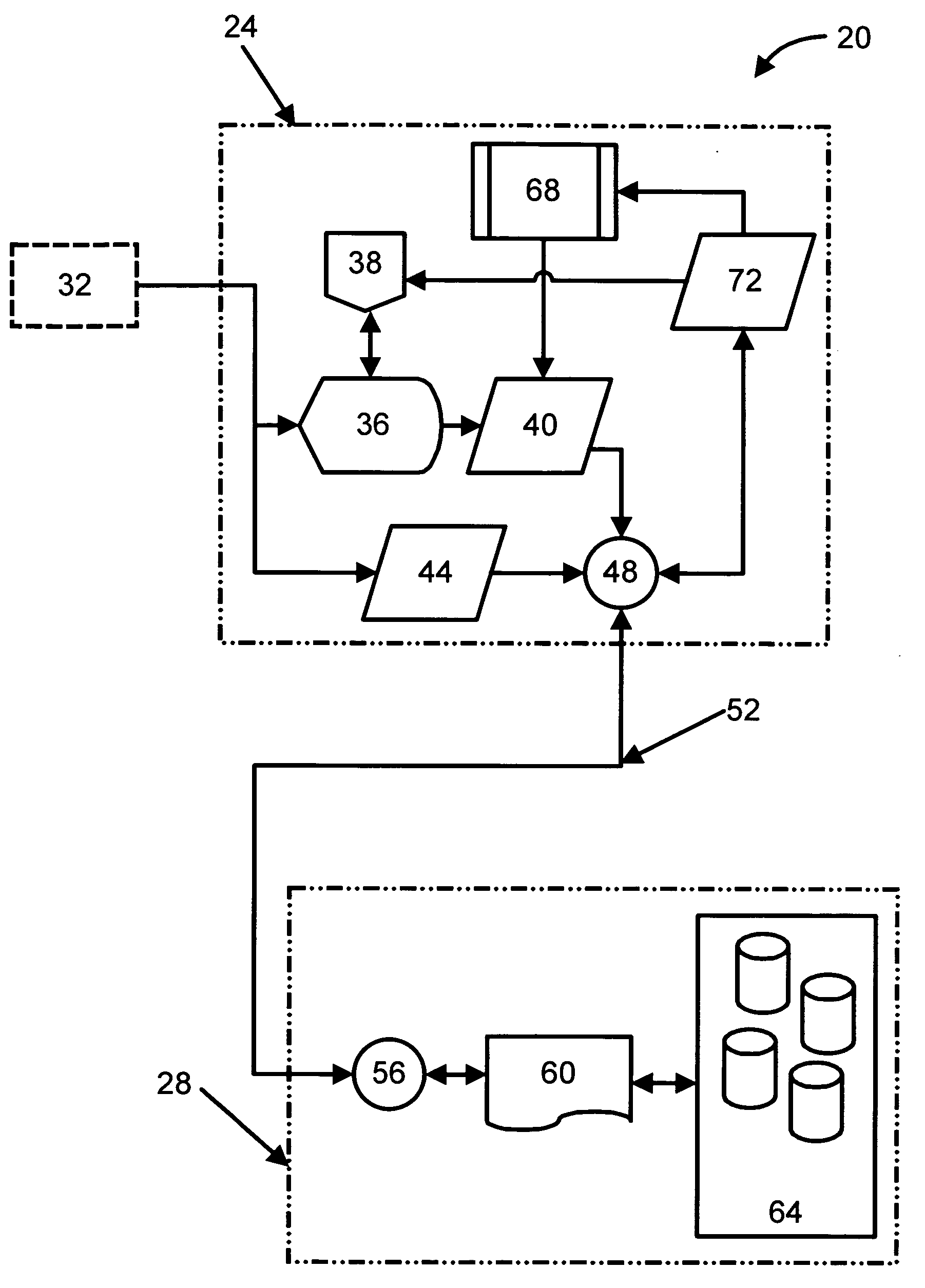
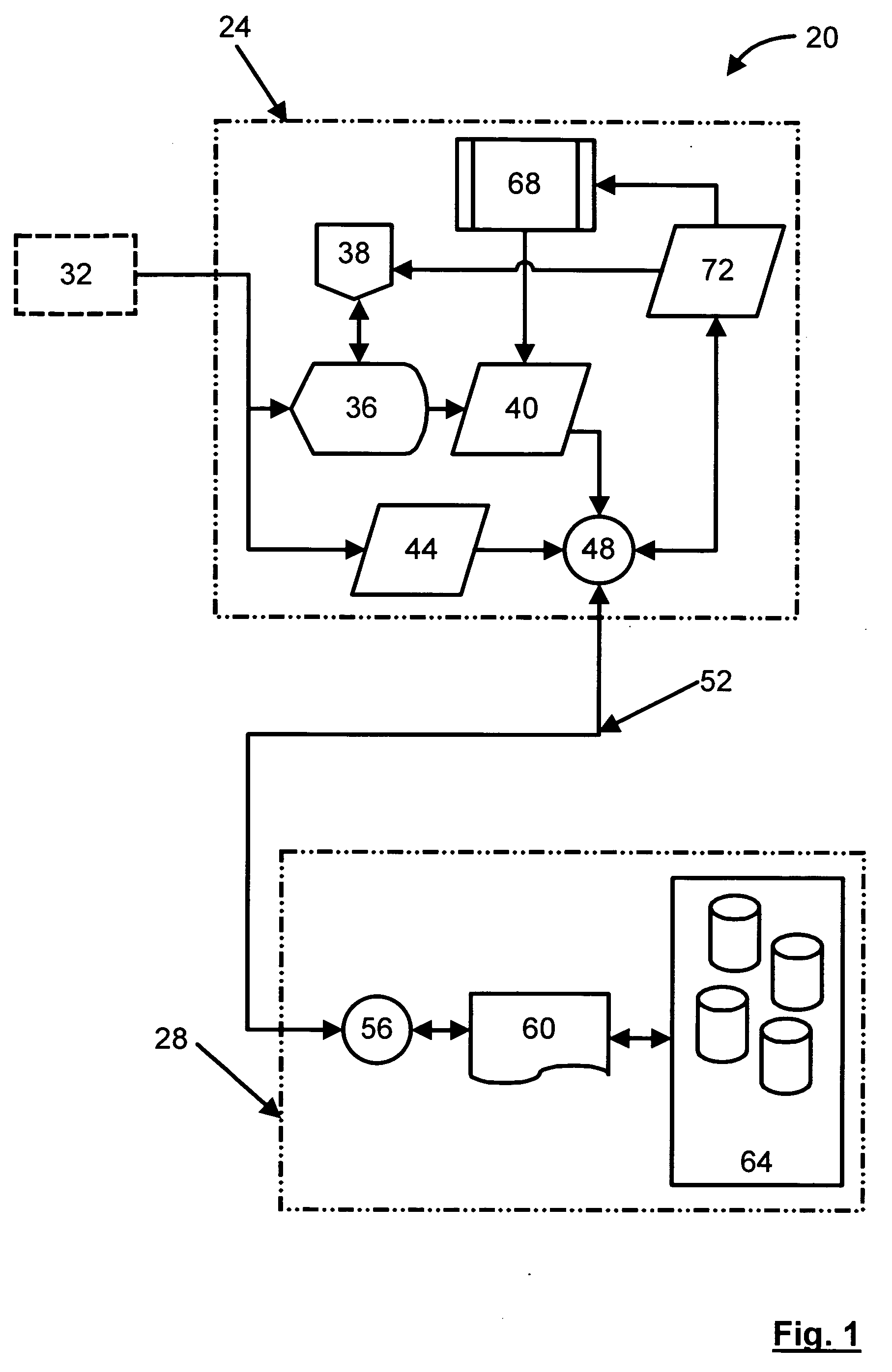
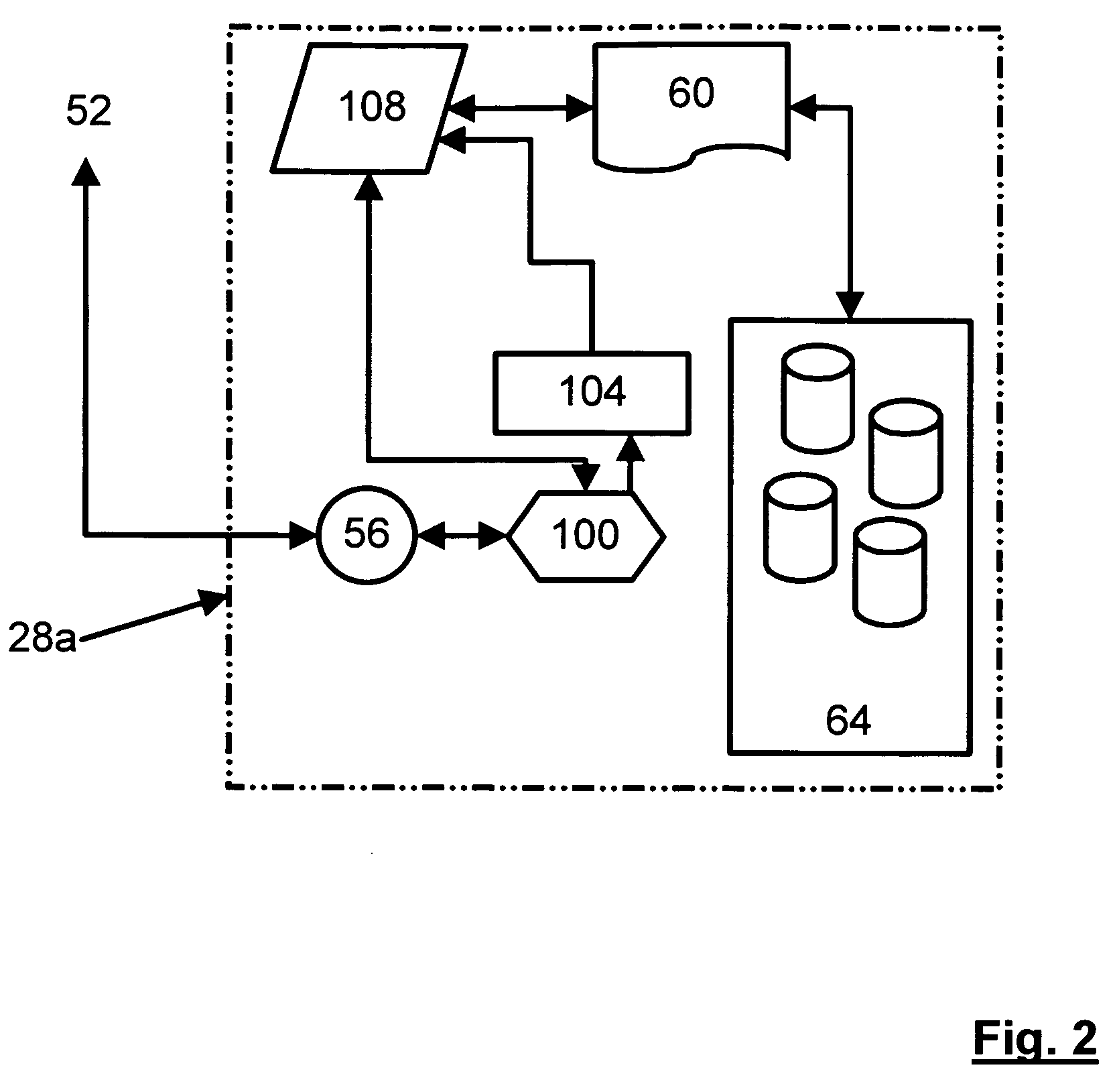
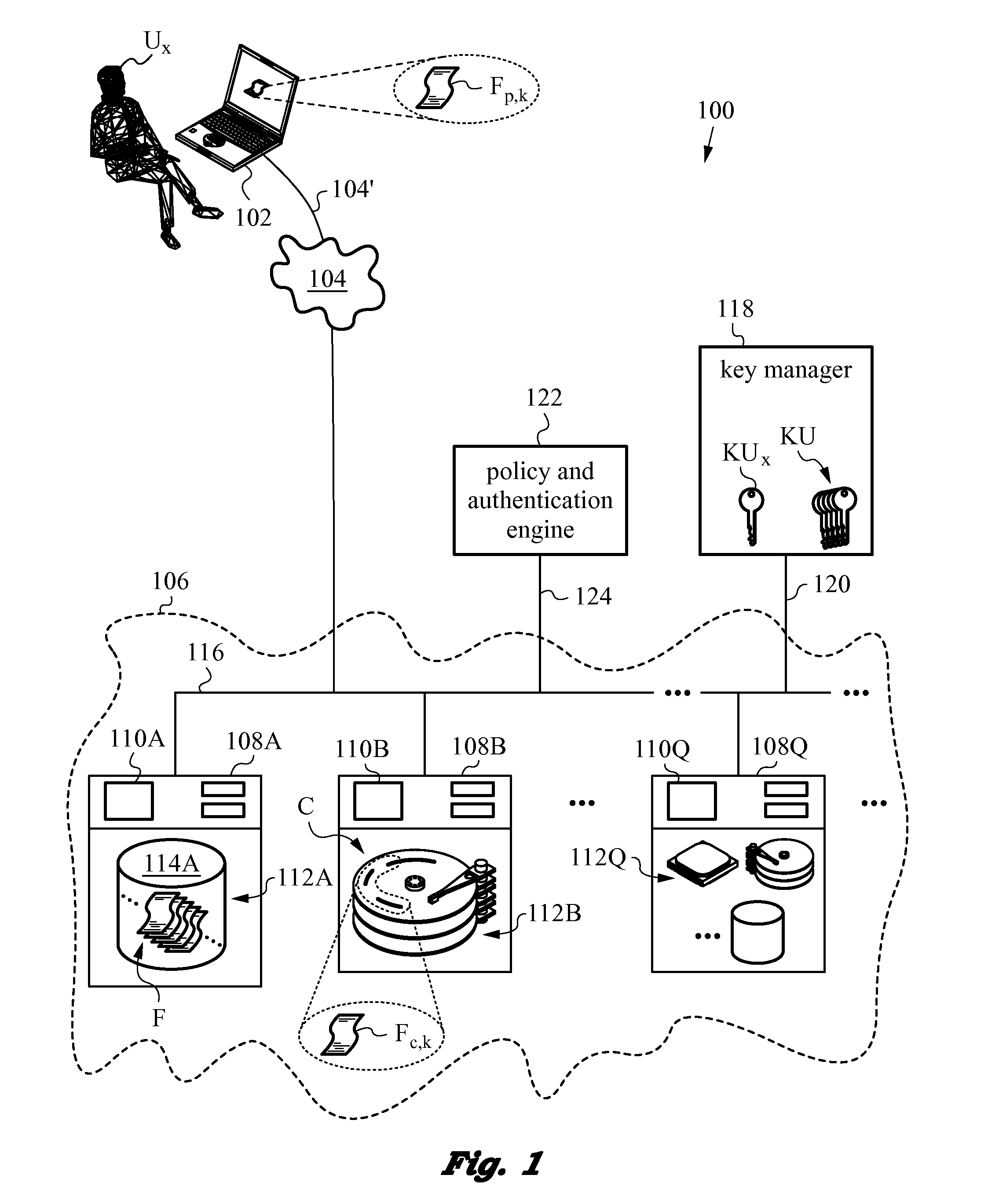
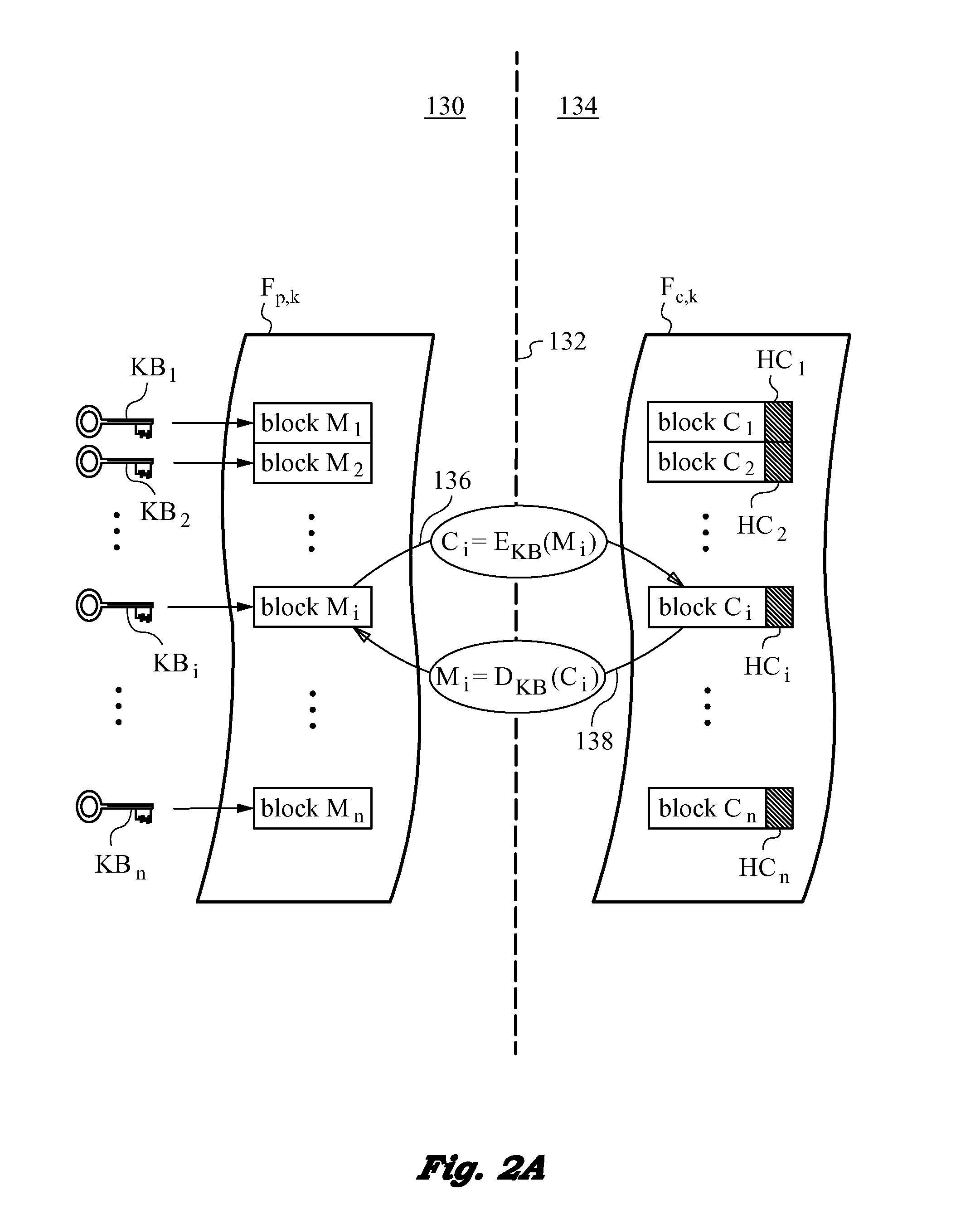
Secure and searchable storage system and method
ActiveUS20060101285A1Safe storageUnauthorized memory use protectionHardware monitoringElectronic documentTrusted client
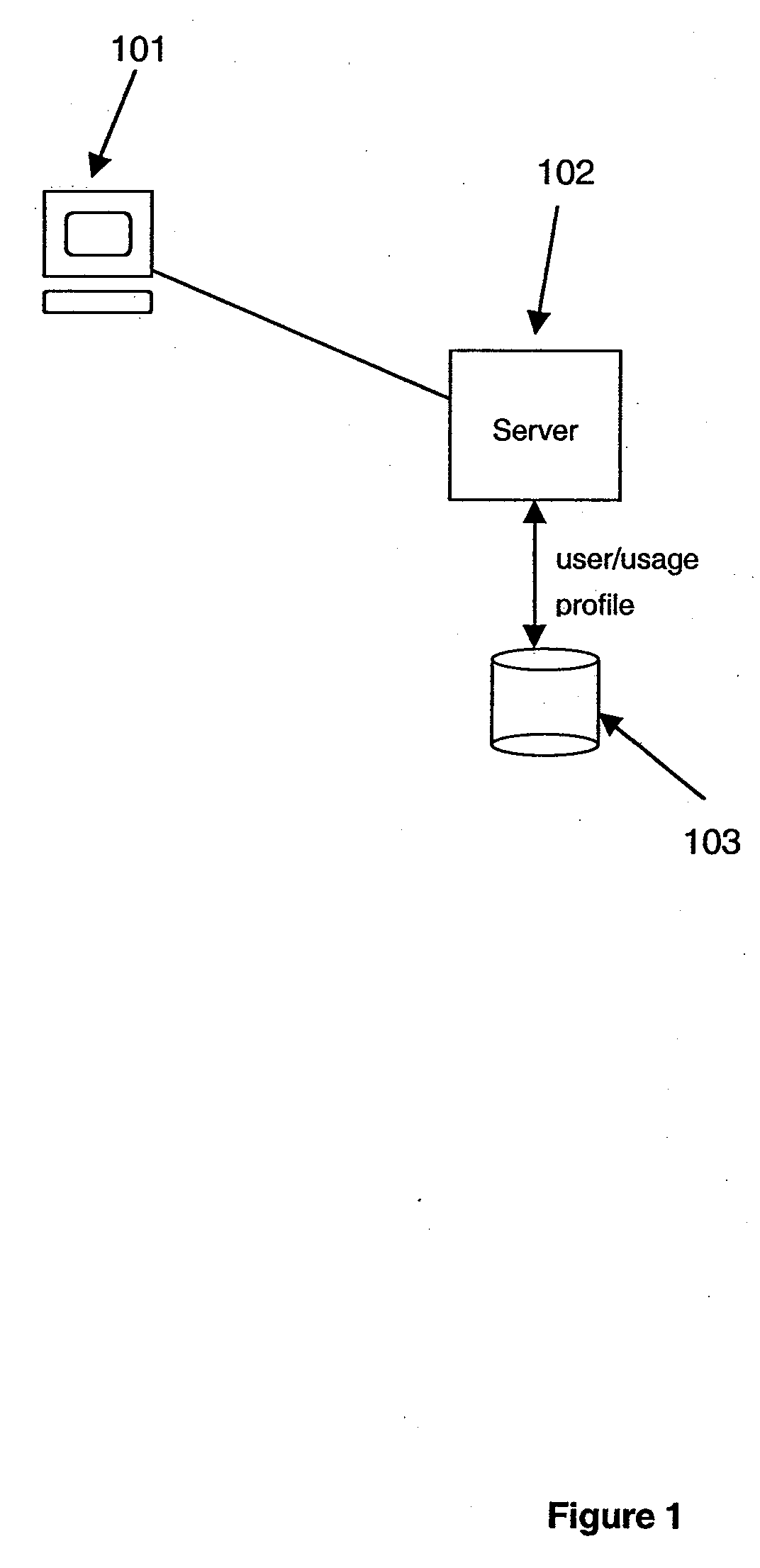
A system and method for securely storing electronic documents is provided. The system includes a client portion and a server portion and the client portion is located at a trusted location. The client portion encrypts each electronic document and produces a list of terms of interest relating to the document, which terms are also encrypted. The encrypted document and the encrypted terms are transferred to a server portion which need not be located at a trusted location. The document is stored at the server portion in a manner which allows for locating the document again via the encrypted terms and returning the encrypted document to the trusted client portion, where it can be decrypted. Attachments to documents can also be encrypted and stored at the server, as can copies of dynamic documents, such as web pages. The server portion can also have a retention manager and encryptor which is used to implement document retention and destruction policies defined by the user of the system.
Owner:PROOFPOINT INC
Methods and systems for securing sensitive information using a hypervisor-trusted client
ActiveUS20110141124A1Internal/peripheral component protectionDigital data authenticationClient agentGraphics
The methods and systems described herein provide for securing sensitive information using a hypervisor-trusted client, in a computing device executing a hypervisor hosting a control virtual machine and a non-trusted virtual machine. A user of a non-trusted virtual machine requests to establish a connection to a remote computing device. Responsive to the request, a control virtual machine launches a client agent. A graphics manager executed by the processor of the computing device assigns a secure section of a memory of a graphics processing unit of the computing device to the client agent. The graphics manager renders graphical data generated by the client agent to the secure section of the graphics processing unit memory.
Owner:CITRIX SYST INC
Secure and searchable storage system and method
ActiveUS7512814B2Safe storageUnauthorized memory use protectionHardware monitoringElectronic documentTrusted client
A system and method for securely storing electronic documents is provided. The system includes a client portion and a server portion and the client portion is located at a trusted location. The client portion encrypts each electronic document and produces a list of terms of interest relating to the document, which terms are also encrypted. The encrypted document and the encrypted terms are transferred to a server portion which need not be located at a trusted location. The document is stored at the server portion in a manner which allows for locating the document again via the encrypted terms and returning the encrypted document to the trusted client portion, where it can be decrypted. Attachments to documents can also be encrypted and stored at the server, as can copies of dynamic documents, such as web pages. The server portion can also have a retention manager and encryptor which is used to implement document retention and destruction policies defined by the user of the system.
Owner:PROOFPOINT INC
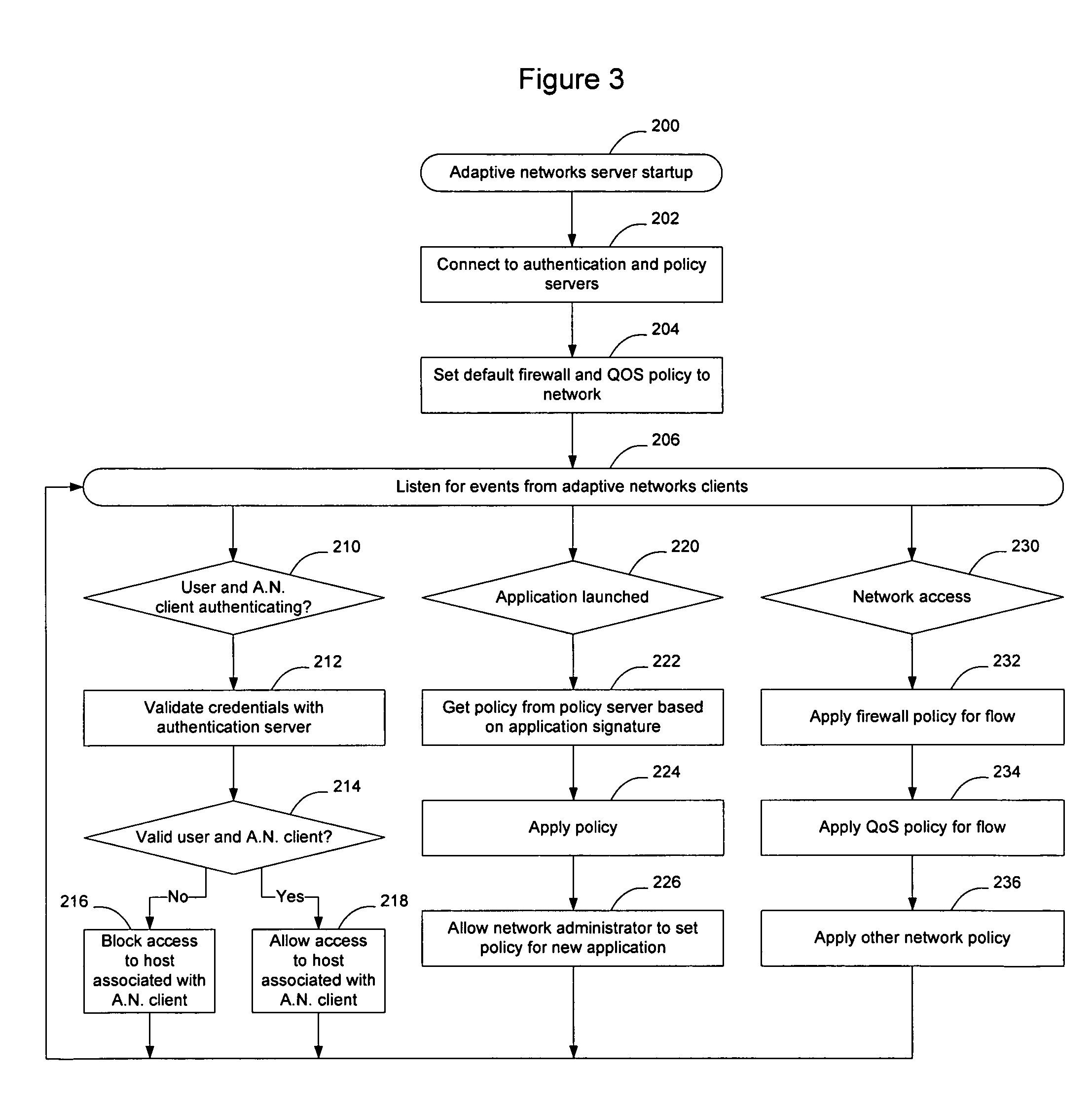
Method and apparatus for adapting a communication network according to information provided by a trusted client
InactiveUS20080282080A1Digital data processing detailsUser identity/authority verificationTraffic capacityTrusted client
Hosts connecting to the network implement an adaptive networks client that monitors other applications on the host and provides information to an adaptive networks server to provide information about traffic being generated by the host. The client may also capture information about the user, host, access type, and other information of interest. The information provided by the adaptive network client may allow the network to adapt to the user, the device, the application, and the protocol being used. Users and applications can be authenticated and trusted. From a network standpoint, having a trusted client associated with the host allows the same benefits as deep packet inspection, regardless of whether the traffic is encrypted, and without requiring the network elements to actually perform deep packet inspection. The administrator may also centrally apply policy to control which applications are allowed to run on the hosts.
Owner:AVAYA INC
System and method for establishing historical usage-based hardware trust
InactiveUS7174454B2Improve trustPromote recoveryDigital data processing detailsUser identity/authority verificationThird partyPassword
Establishing trust according to historical usage of selected hardware involves providing a usage history for a selected client device; and extending trust to a selected user based on the user's usage history of the client device. The usage history is embodied as signed statements issued by a third party or an authentication server. The issued statement is stored either on the client device, or on an authentication server. The usage history is updated every time a user is authenticated from the selected client device. By combining the usage history with conventional user authentication, an enhanced trust level is readily established. The enhanced, hardware-based trust provided by logging on from a trusted client may eliminate the necessity of requiring secondary authentication for e-commerce and financial services transactions, and may also be used to facilitate password recovery and conflict resolution in the case of stolen passwords.
Owner:MICROSOFT TECH LICENSING LLC
System and method for establishing historical usage-based hardware trust
InactiveUS7849307B2Improve trustPromote recoveryDigital data processing detailsUser identity/authority verificationThird partyPassword
Establishing trust according to historical usage of selected hardware involves providing a usage history for a selected client device; and extending trust to a selected user based on the user's usage history of the client device. The usage history is embodied as signed statements issued by a third party or an authentication server. The issued statement is stored either on the client device, or on an authentication server. The usage history is updated every time a user is authenticated from the selected client device. By combining the usage history with conventional user authentication, an enhanced trust level is readily established. The enhanced, hardware-based trust provided by logging on from a trusted client may eliminate the necessity of requiring secondary authentication for e-commerce and financial services transactions, and may also be used to facilitate password recovery and conflict resolution in the case of stolen passwords.
Owner:MICROSOFT TECH LICENSING LLC
Securing files under the semi-trusted user threat model using per-file key encryption
ActiveUS20160277373A1Improve security levelEnsure integrityInterprogram communicationComputer security arrangementsFile allocationCiphertext
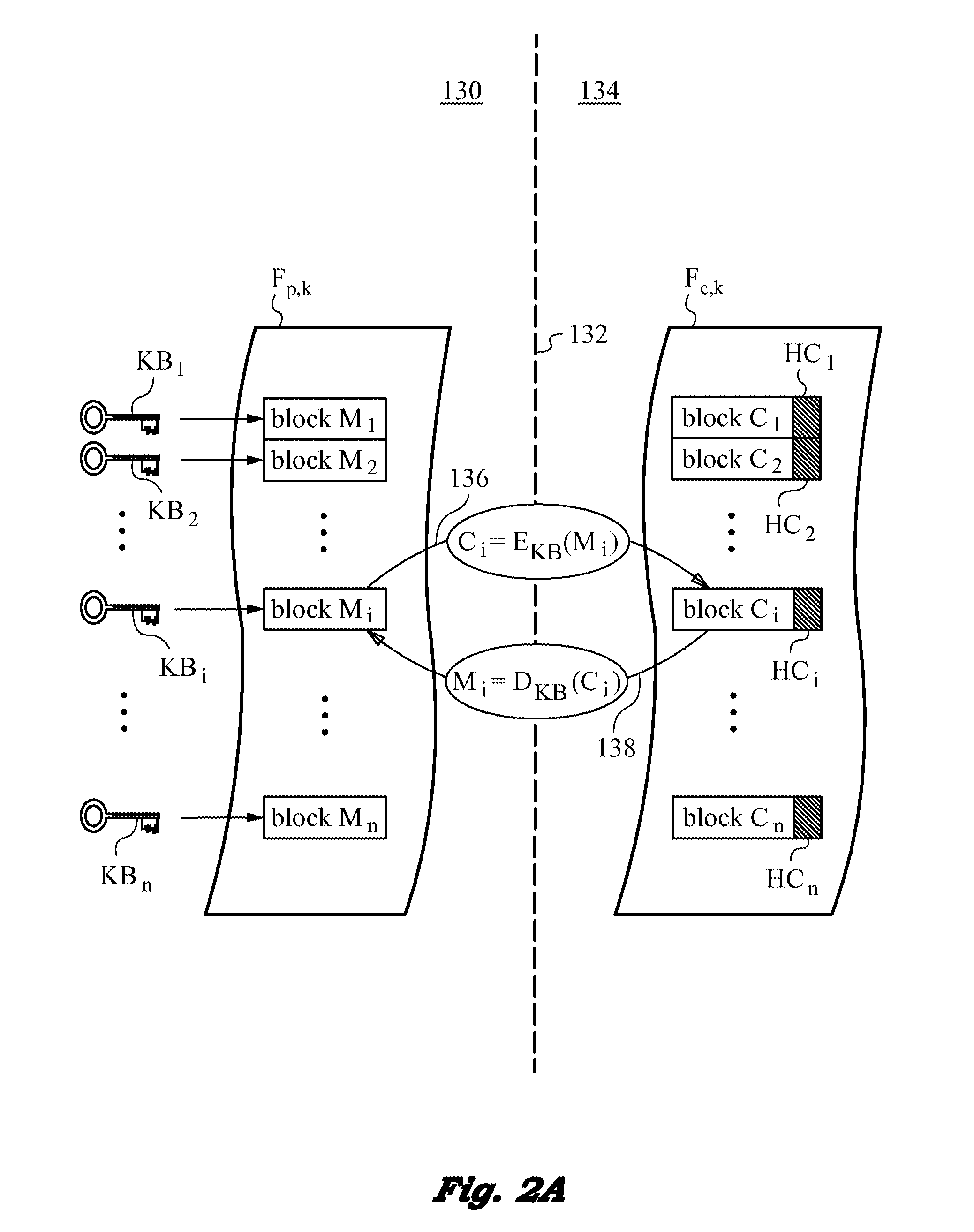
A computer system and methods for securing files in a file system with storage resources accessible to an authenticable user using an untrusted client device in a semi-trusted client threat model. Each file is secured in the file system in one or more ciphertext blocks along with the file metadata. Each file is assigned a unique file key FK to encrypt the file. A wrapping key WK assigned to the file is used for encrypting the file key FK to produce a wrapped file key WFK. The file is encrypted block by block to produce corresponding ciphertext blocks and corresponding authentication tags. The authentication tags are stored in the file metadata, along with an ID of the wrapping key WK, wrapped file key WFK, last key rotation time, an Access Control List (ACL), etc. The integrity of ciphertext blocks is ensured by authentication tags and the integrity of the metadata is ensured by a message authentication code (MAC).
Owner:ZETTASET
Secure searchable and shareable remote storage system and method
ActiveUS20190087432A1Improve data securityLimited expressivenessDigital data protectionFile access structuresPlaintextRelevant information
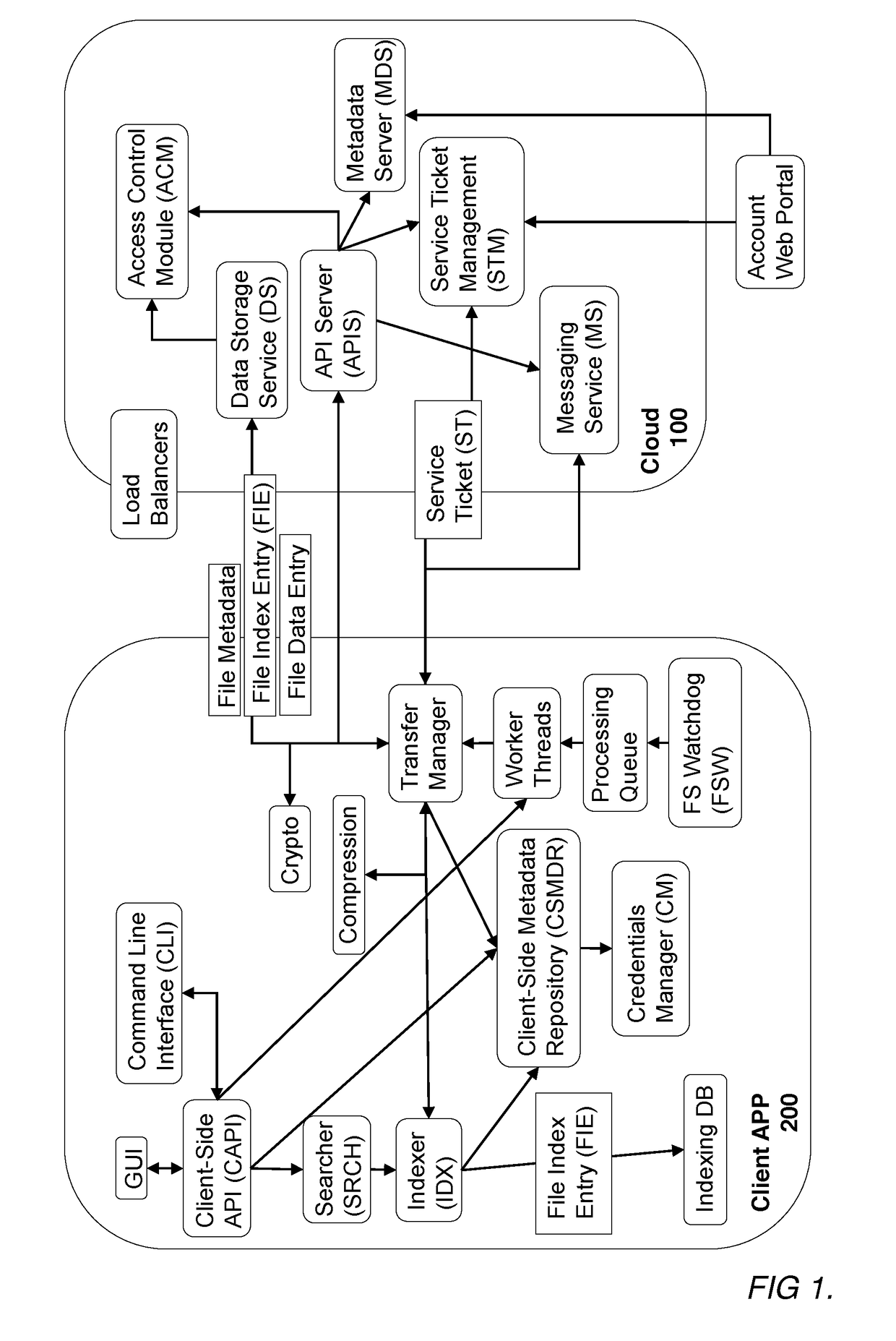
A secure searchable and shareable remote storage system and method which utilizes client side processing to enable search capability of the stored data, allow the synchronizing of stored data between multiple discrete devices, and allow sharing of stored data between multiple discrete users. Such a remote storage system and method includes a networked remote computer server which receives and stores encrypted data and manages access thereto and a client device configured to index data to be stored, upload secured data and related information, perform searches on the stored data and related information locally, and implement cryptographic protocols which allow the stored data and related information to be synchronized with other desired client devices. Advantageously, since trusted client-side search code may directly access mostly plaintext data, it may operate orders of magnitude faster than the equivalent server code which may access encrypted data only.
Owner:PRIVATE MACHINES INC
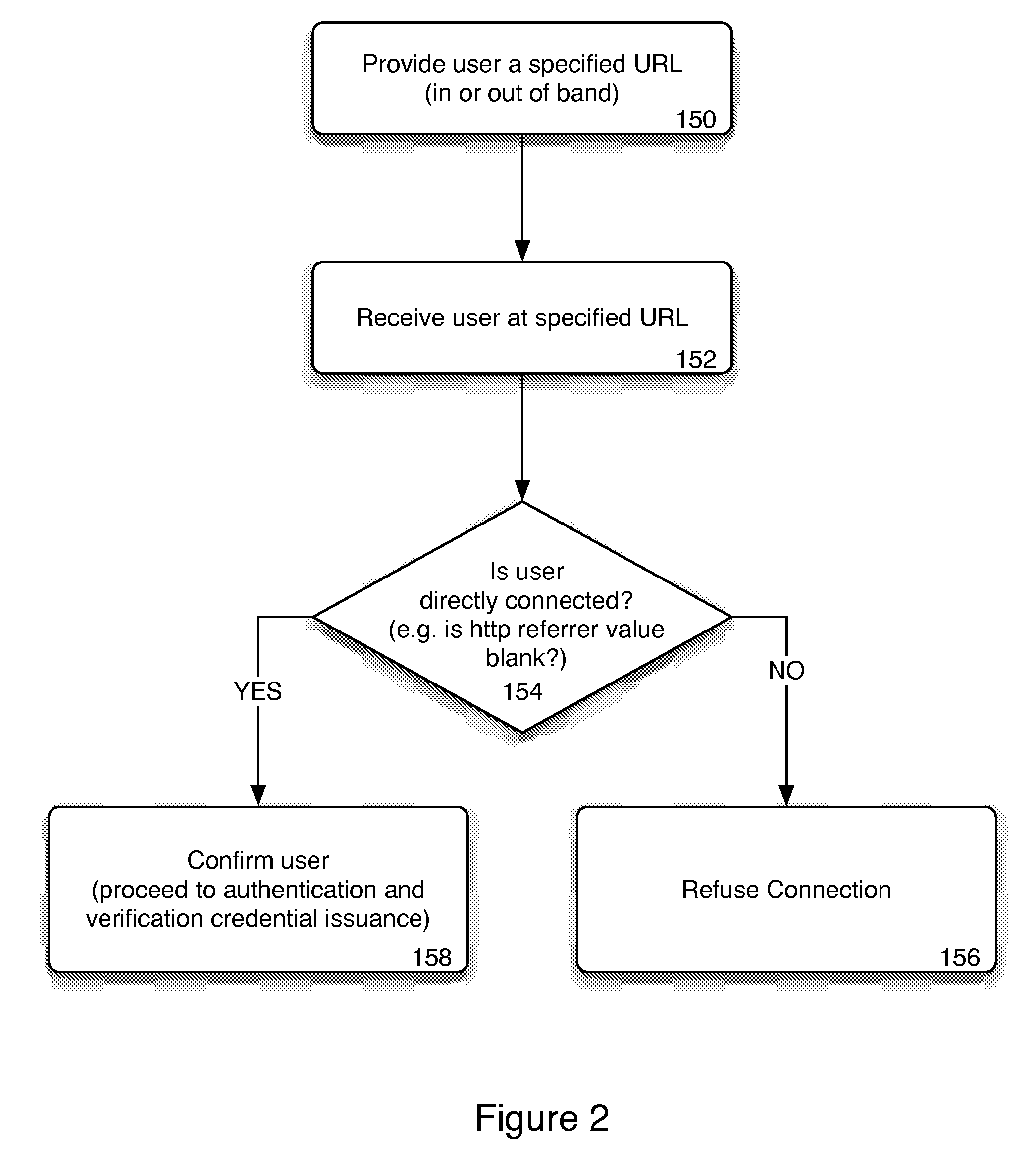
Method and system for trusted client bootstrapping
InactiveUS20100050243A1Reduce disadvantagesDigital data processing detailsUser identity/authority verificationHyperlinkWeb browser
Bootstrapping a trusted cryptographic certificate or other credentials into a client web browser application can be used to provide protection against “phishing” and “man-in-the-middle” attacks made over a computer network. Verification credentials are provided to users who connect directly to an authentication server and provide sufficient authentication information. The authentication server can rely upon the use of private URLs associated with each user as part of the verification process and can reject users who connect by clicking on a hyperlink directed to the authentication server.
Owner:BLAME CANADA HLDG
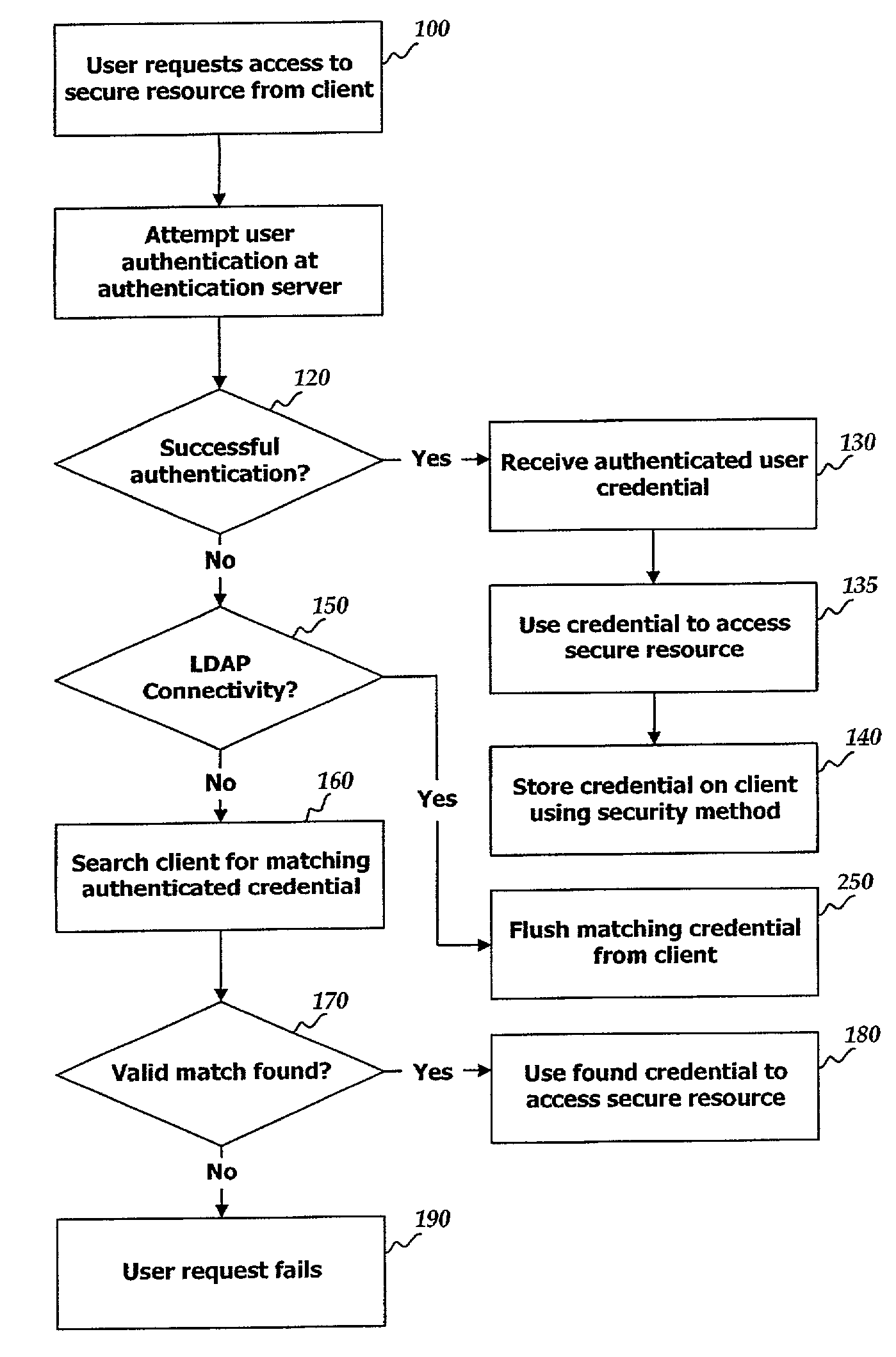
Remote authentication caching on a trusted client or gateway system
ActiveUS7234157B2Digital data processing detailsUser identity/authority verificationInternet privacyNative client
In a system providing for user access of secure resources upon user authentication by a remote authentication server, a successful user authentication is saved locally for use when the authentication server is not available. The successful user authentication returns an authenticated credential which is stored on the local client utilizing a security method such as Public Key Infrastructure which prevents tampering with the credential. If a gateway machine provides connectivity between the client and the authentication server, the credential is also stored on the gateway.
Owner:LENOVO PC INT
Mobile device throughput testing
InactiveUS20120300649A1Error preventionFrequency-division multiplex detailsComputer hardwareTime to market
The instant invention is a program applet that can be loaded onto mobile devices and directly interfaces with the operating system and automated test scripts. The program applet is capable of initiating the required transfer and will provide information regarding the progress of the transfer such that a test client can properly calculate the data throughput rates. The result is a minimization of time-to-market for test and measurement tools using software architecture that simplify and speed-up development and maintenance of test and measurement tools by removing awareness of complexity of external hardware dependencies from the actual test and measurement software code, and placing dependencies management to carefully defined components that could be reused and shared between multiple test and measurement software tools and systems at once.
Owner:W2BI
System and method for establishing historical usage-based hardware trust
InactiveUS20070118887A1Improve trustPromote recoveryDigital data processing detailsUser identity/authority verificationThird partyInternet privacy
Establishing trust according to historical usage of selected hardware involves providing a usage history for a selected client device; and extending trust to a selected user based on the user's usage history of the client device. The usage history is embodied as signed statements issued by a third party or an authentication server. The issued statement is stored either on the client device, or on an authentication server. The usage history is updated every time a user is authenticated from the selected client device. By combining the usage history with conventional user authentication, an enhanced trust level is readily established. The enhanced, hardware-based trust provided by logging on from a trusted client may eliminate the necessity of requiring secondary authentication for e-commerce and financial services transactions, and may also be used to facilitate password recovery and conflict resolution in the case of stolen passwords.
Owner:MICROSOFT TECH LICENSING LLC
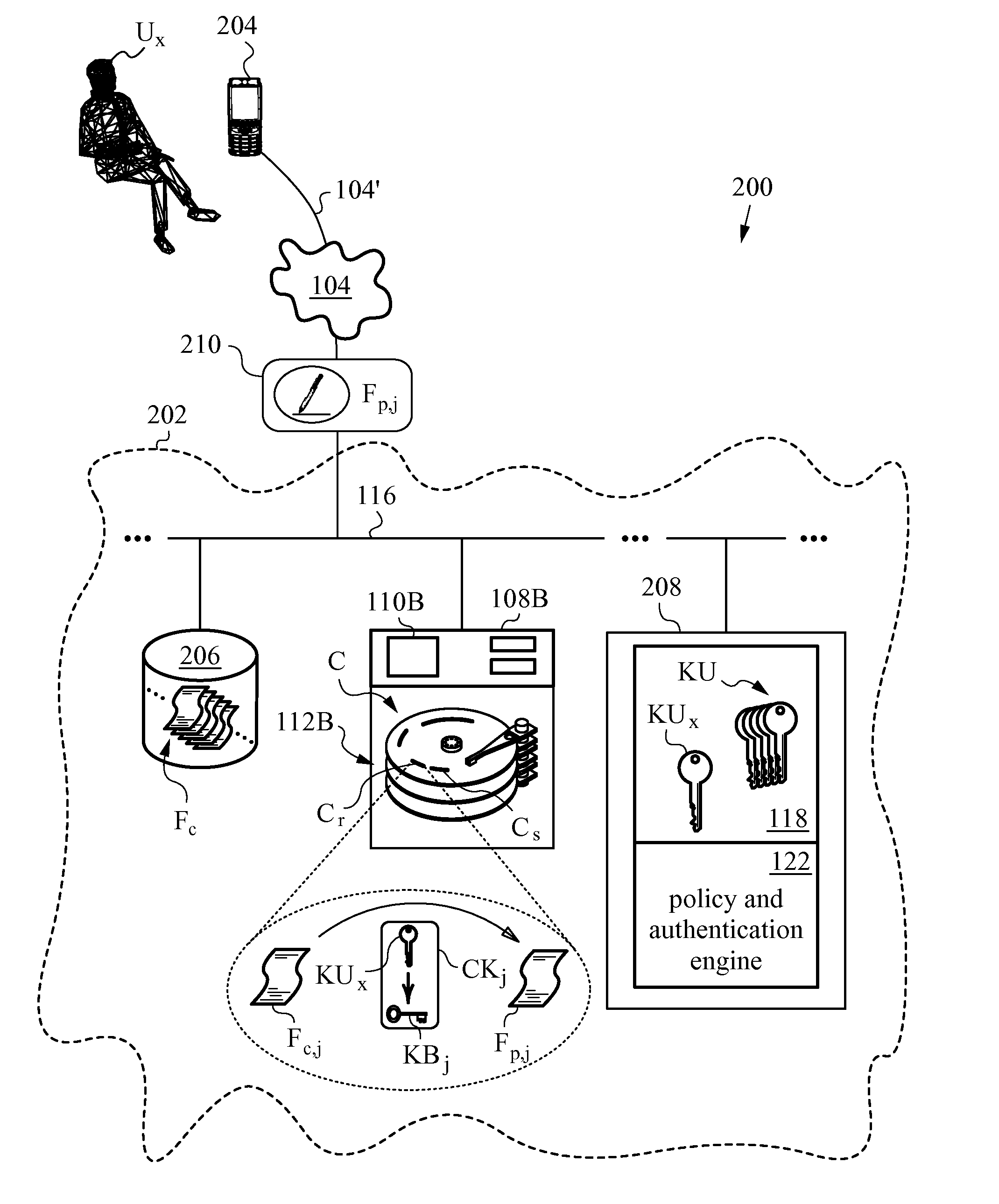
Remotable information cards
InactiveUS20090328166A1Digital data processing detailsUser identity/authority verificationInformation CardInternet privacy
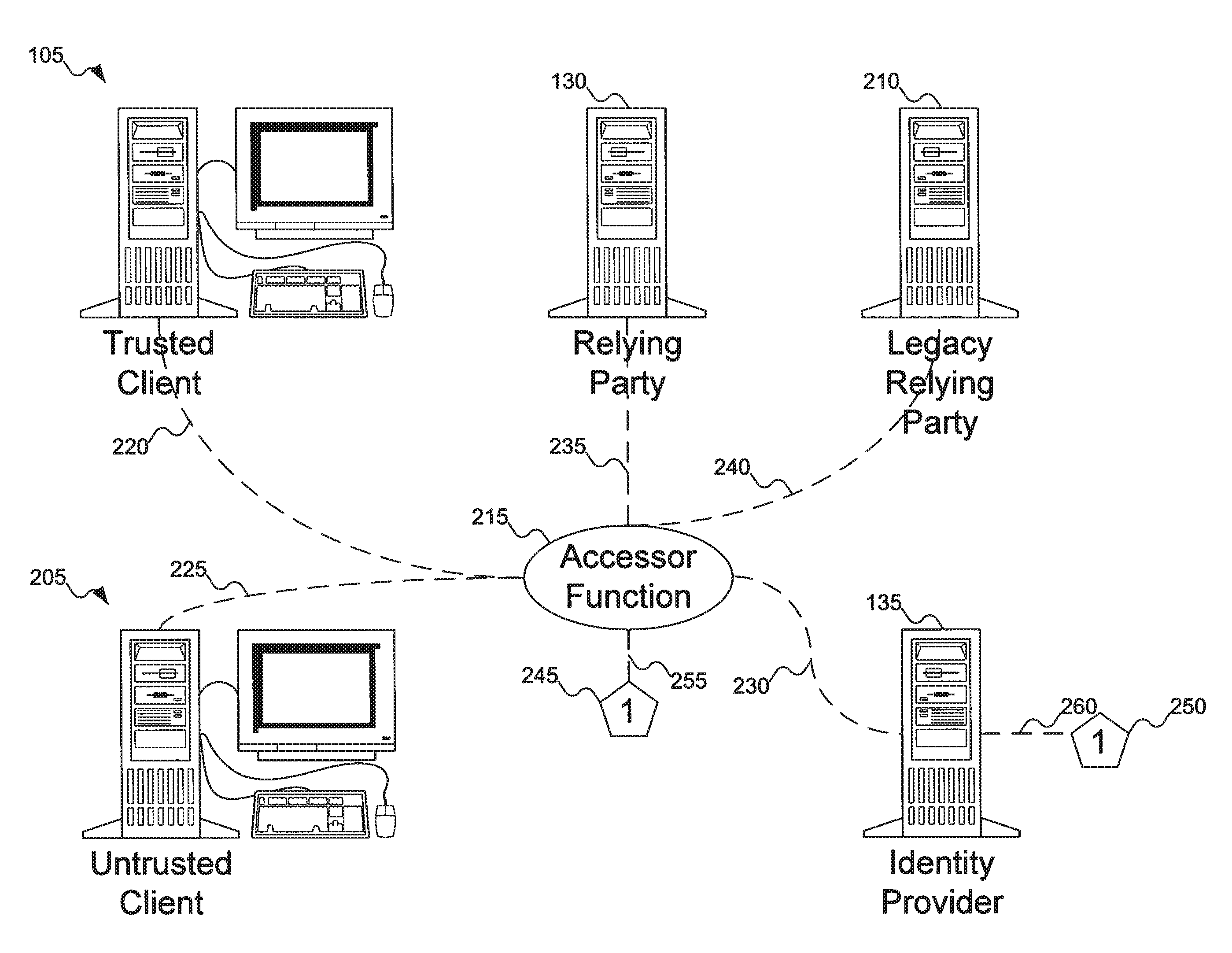
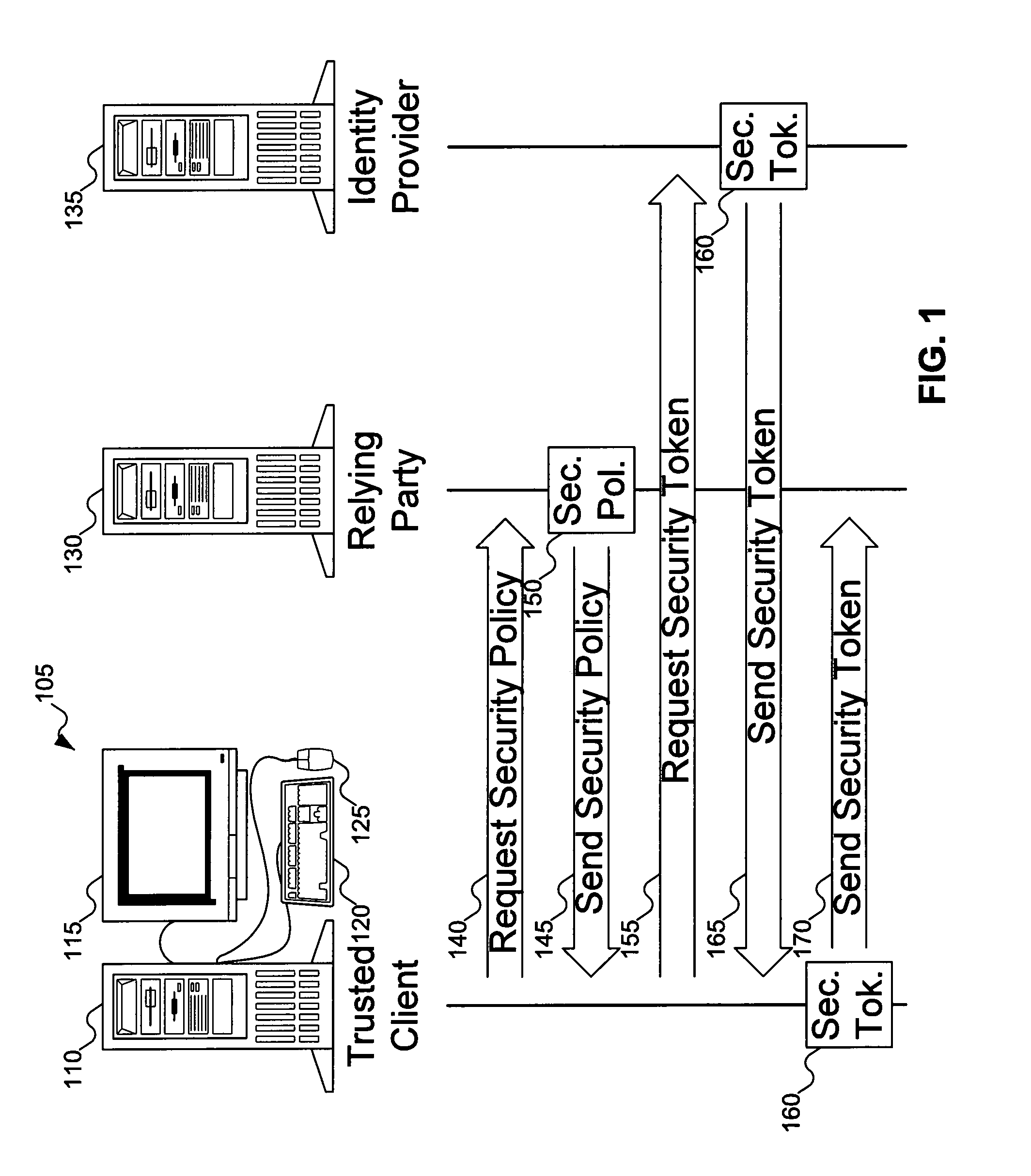
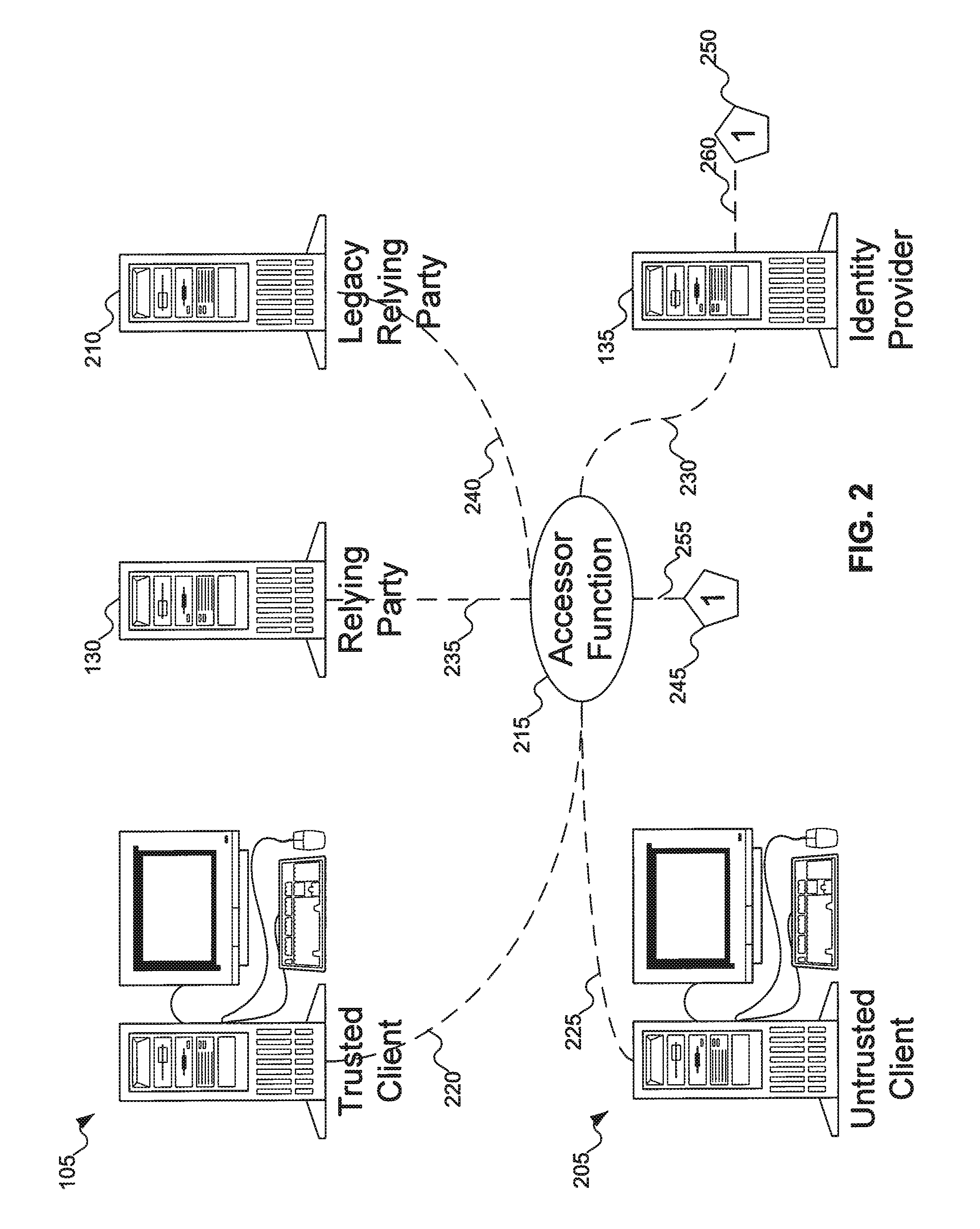
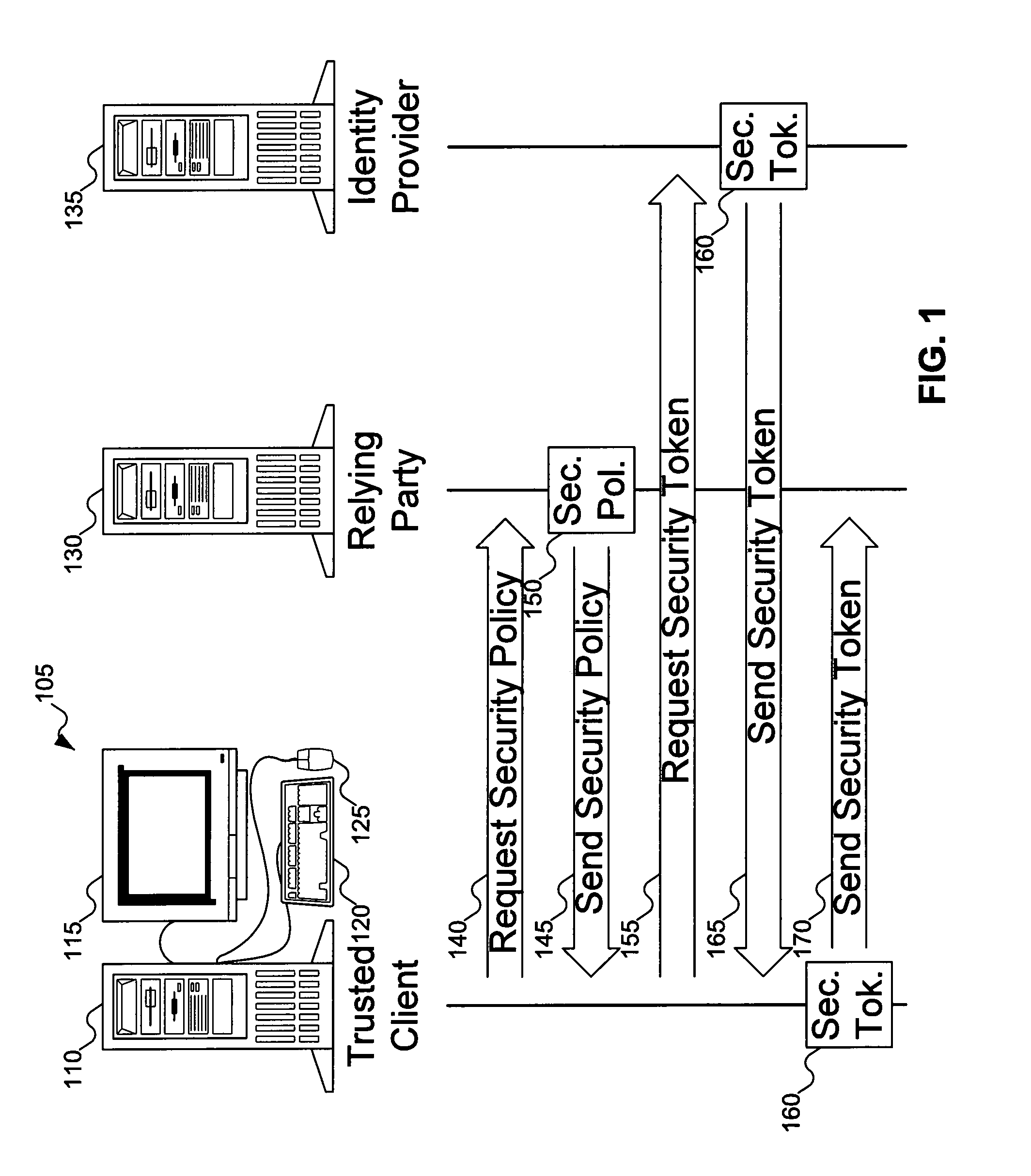
An accessor function interfaces among a client, a relying party, and an identity provider. The identity provider can “manage” personal (i.e., self-asserted) information cards on behalf of a user, making the personal information cards available on clients on which the personal information cards are not installed. The client can be an untrusted client, vulnerable to attacks such as key logging, screen capture, and memory interrogation. The accessor function can also asked as a proxy for the relying party in terms of invoking and using the information cards system, for use with legacy relying parties.
Owner:APPLE INC
Trusted database authentication through an untrusted intermediary
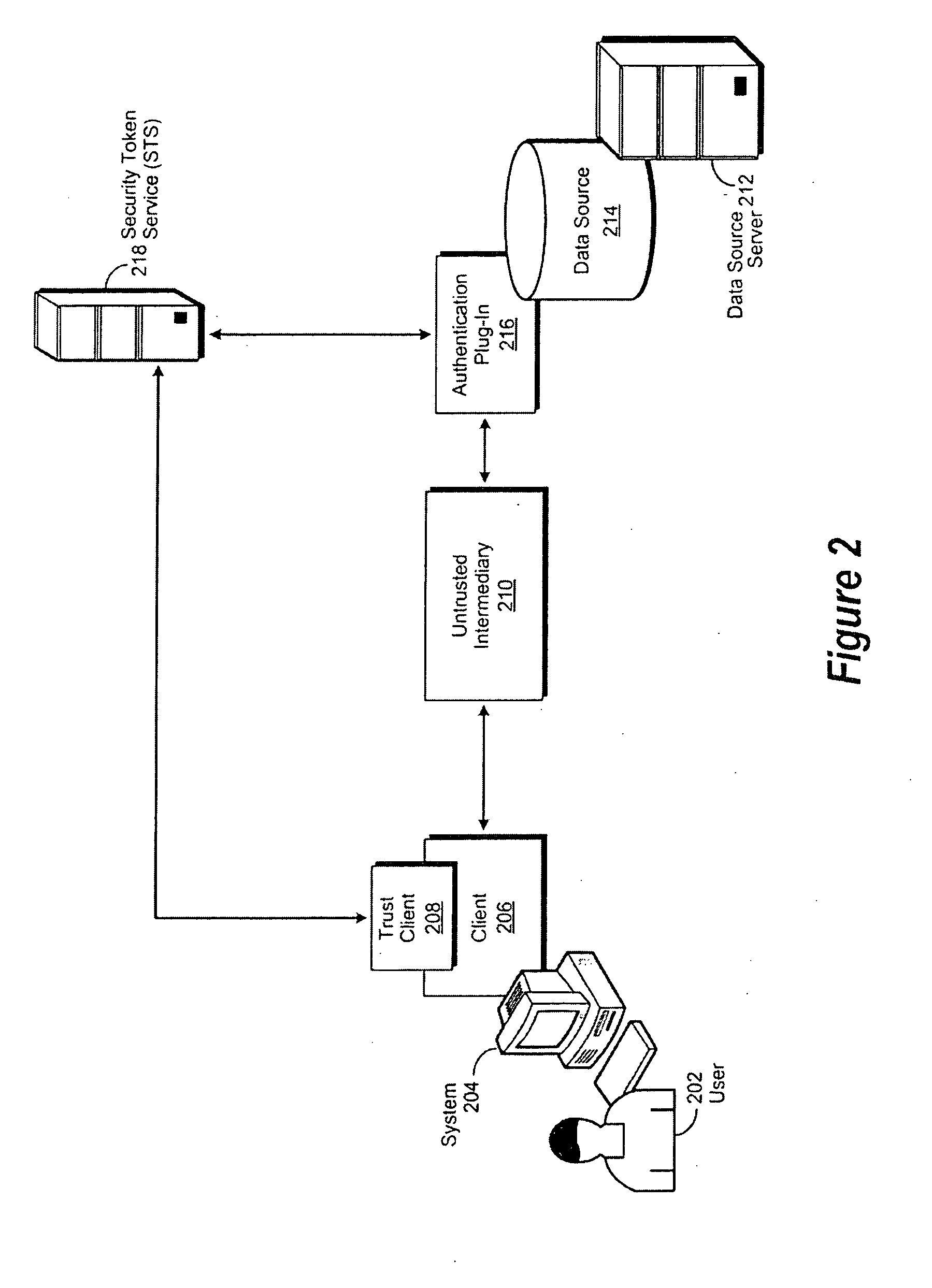
ActiveUS20100083359A1Digital data processing detailsUser identity/authority verificationTrusted clientData source
A method, system and computer-usable medium are disclosed for validating user credentials submitted to a data source by an untrusted intermediary. An untrusted intermediary attempts to access a data source on behalf of a user. The untrusted intermediary challenges the user to provide credentials of the type and format required to access the data provided by the data source. The user's trust client connects to an authentication service and identification credentials of the required type and format are generated. The identification credentials are conveyed to the user's trust client, which then provides them to the user's client, which in turn conveys them to the untrusted intermediary. The untrusted intermediary then presents the identification credentials to an authentication plug-in of the data source. The authentication plug-in validates the authenticity of the provided credentials with their associated authentication service. Once the credentials are successfully validated, the requested data is provided to the user's client by the untrusted intermediary.
Owner:IBM CORP +1
Method and system for securing a disk key
ActiveUS20090031143A1Digital data processing detailsUnauthorized memory use protectionTrusted clientMaster key
In accordance with an embodiment of the present invention, a trusted client includes a non-volatile memory programmed with an encrypted disk key. The encrypted disk key in the non-volatile memory is encrypted with a master key of a security processor. Accordingly, encrypted data received by the central processor from a disk's security logic is forwarded to a security processor along with the encrypted disk key. The security processor decrypts the encrypted disk key and then decrypts the encrypted data, utilizing the disk key. The disk key is never available to the central processing unit in the clear.
Owner:NBCUNIVERSAL
Data processing method and system
InactiveCN103533002ARelieve pressureProtection stabilityTransmissionSpecial data processing applicationsGeneration processTrusted client
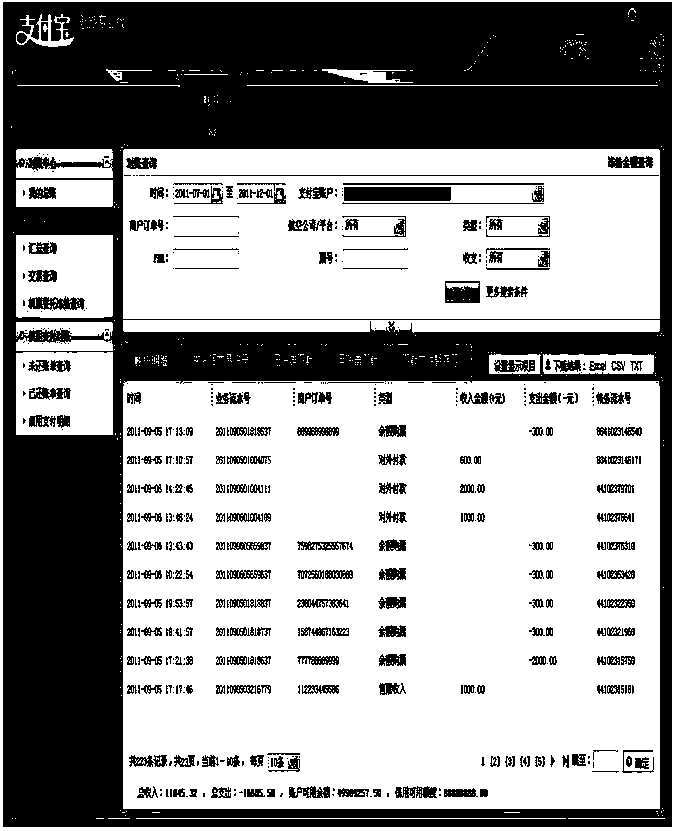
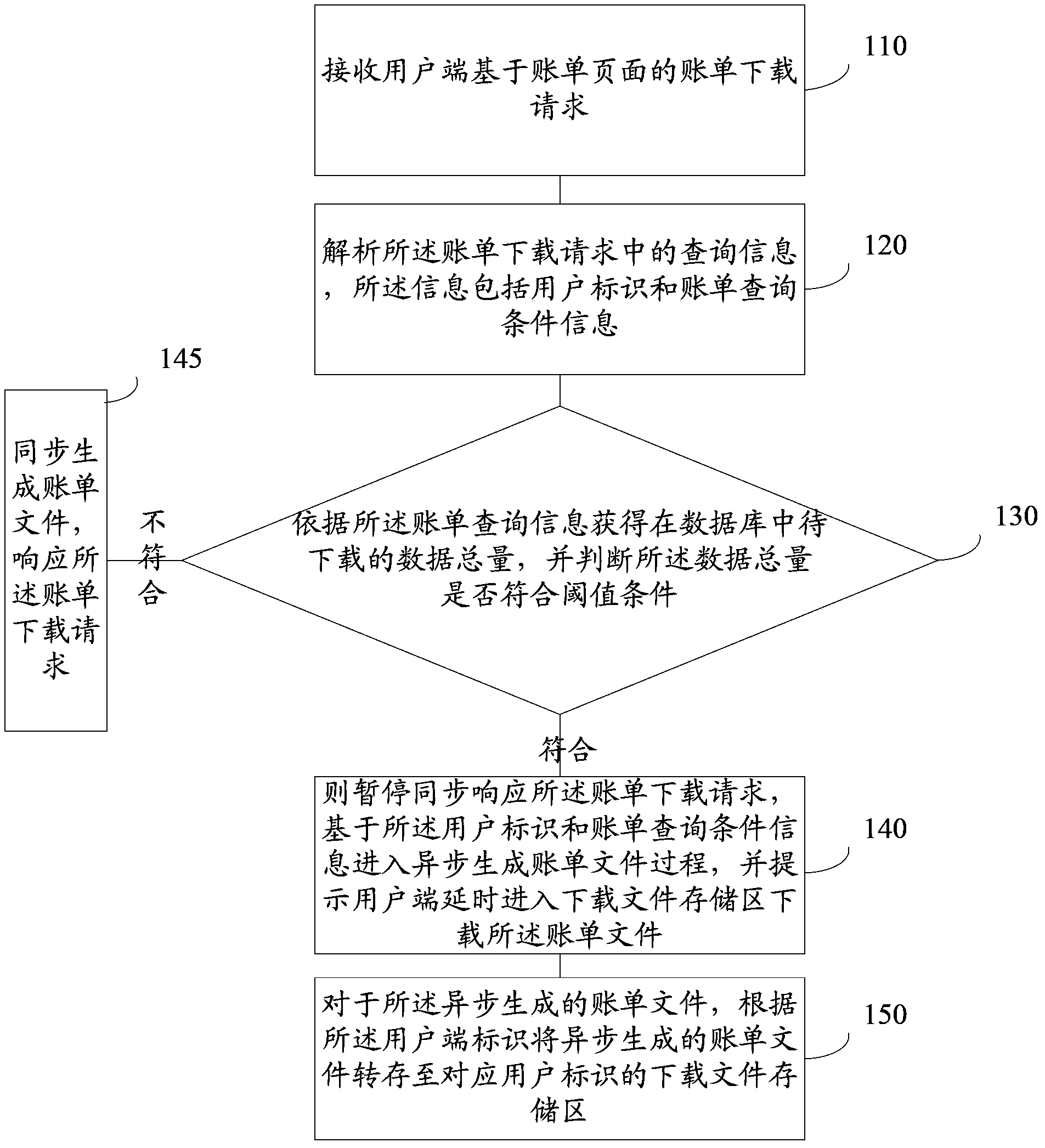
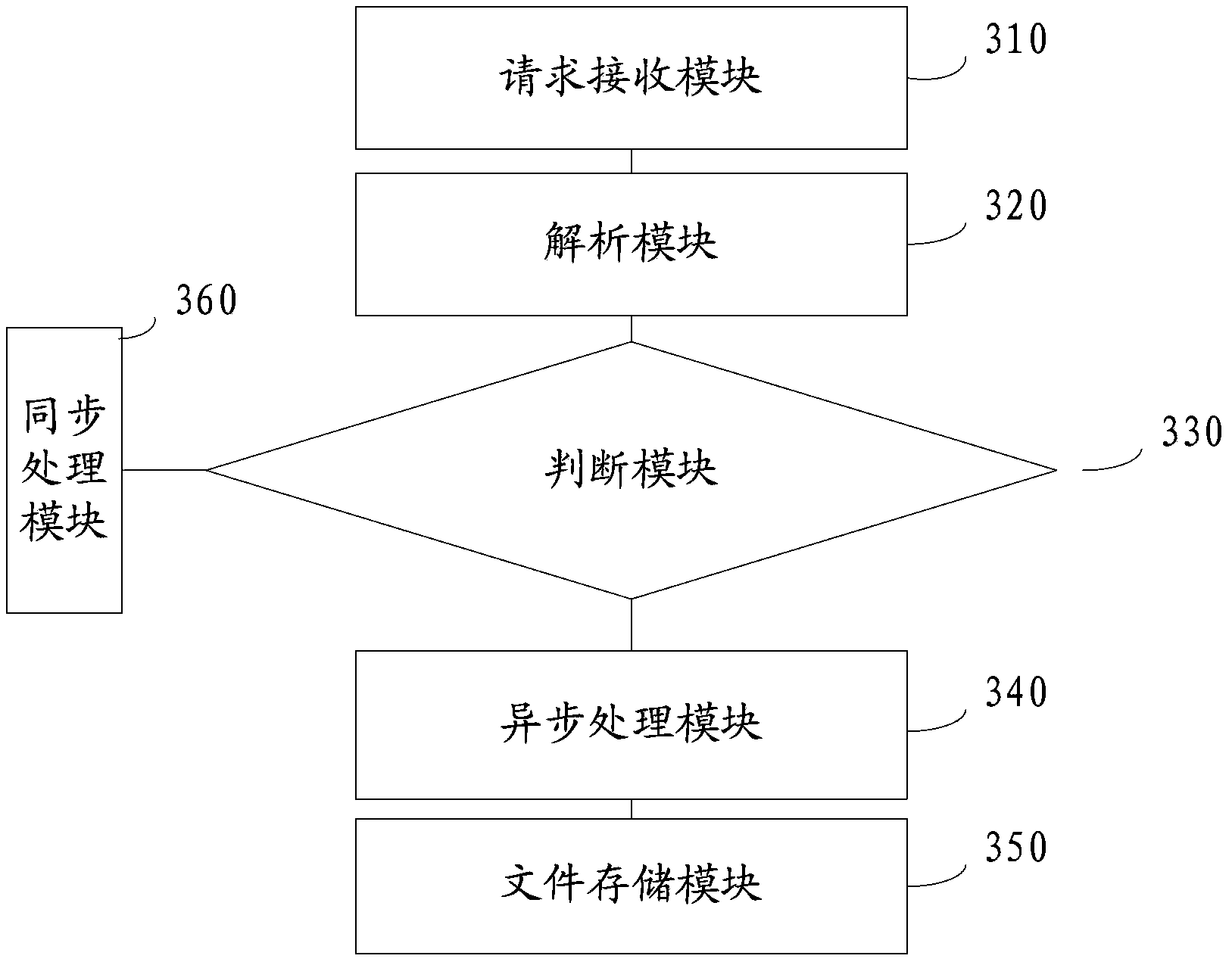
The application provides a data processing method and system and relates to the technical field of networks. The method includes: receiving a bill downloading request of a user client, based on a bill page; parsing query information in the bill downloading request, wherein the information includes a user identification and bill query condition information; acquiring the total quantity of data to be downloaded in a database according to the bill query information and judging whether the total quantity of the data satisfies a threshold condition; if yes, stopping a synchronization response to the bill downloading request and entering an asynchronous bill file generation process based on the user identification and the bill query condition and prompting the user client to enter a downloaded-file storage area in a delayed manner to download bill files; and with respect to the asynchronously generated bill files, transferring the asynchronously generated bill files to a downloaded-file storage area corresponding to the user identification according to a client identification. The data processing method and system reduce the pressure of the system through an asynchronous method so that stability of the system can be protected.
Owner:ALIBABA GRP HLDG LTD
Method of securing files under the semi-trusted user threat model using symmetric keys and per-block key encryption
ActiveUS20150288664A1Rapid and efficientImprove security levelKey distribution for secure communicationMultiple keys/algorithms usageFile systemTrusted client
A computer system and method for securing files in a file system equipped with storage resources that are accessible to an authenticable user operating with an untrusted client device under the semi-trusted client threat model. The file to be secured is stored in one or more blocks belonging to the storage resources along with symmetric per-block key(s) KBi assigned to each of the blocks in the file. The blocks are encrypted with the symmetric per-block keys to obtain encrypted blocks. The user is assigned user key(s) and each per-block key that was used for encryption is in turn encrypted with one of the user's keys to derive wrapped key(s) for each encrypted block. Wrapped key(s) are placed in encrypted block headers and introduce a level of indirection to encrypted file(s) that is appropriate for the semi-trusted client threat model.
Owner:ZETTASET
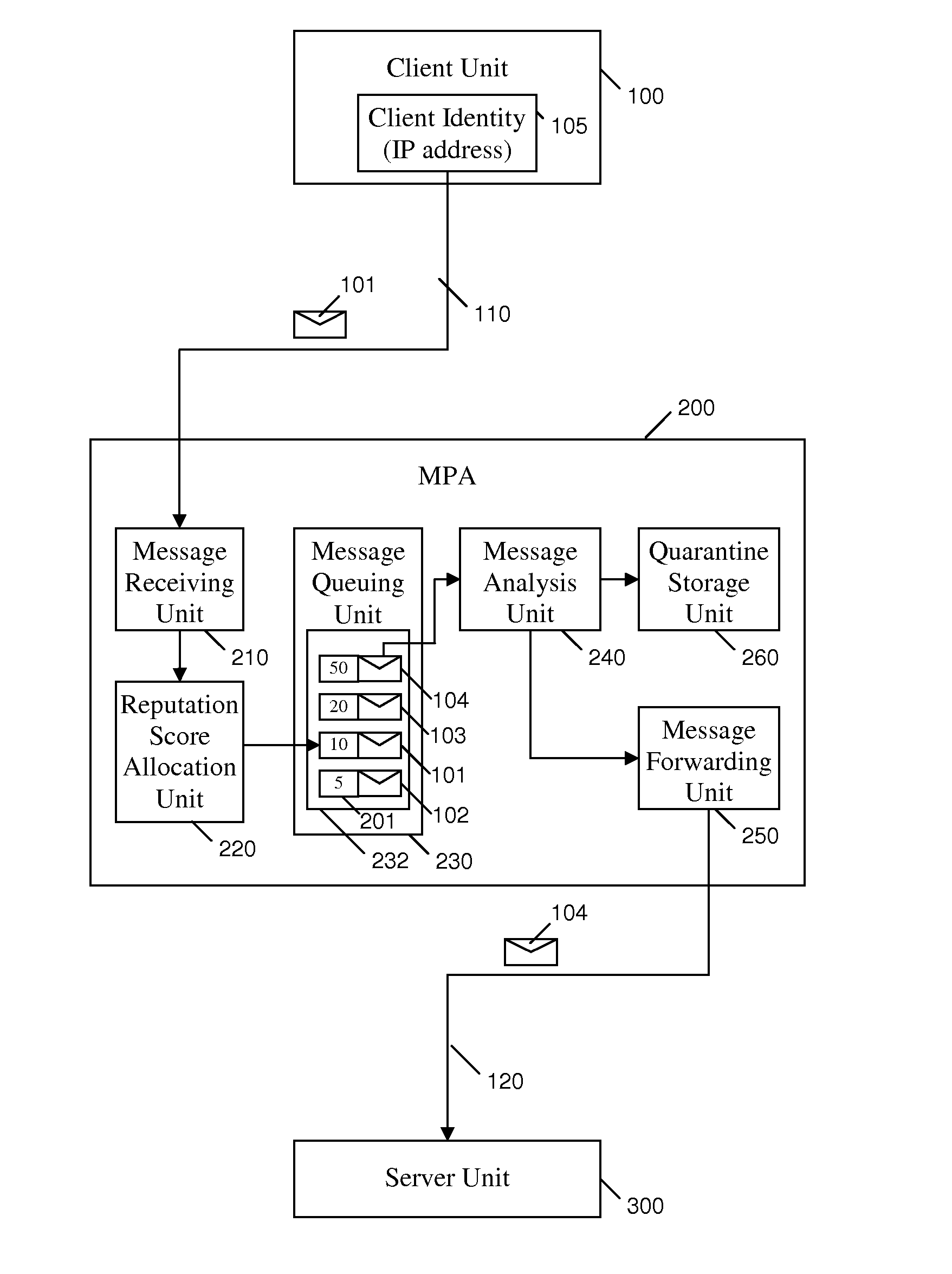
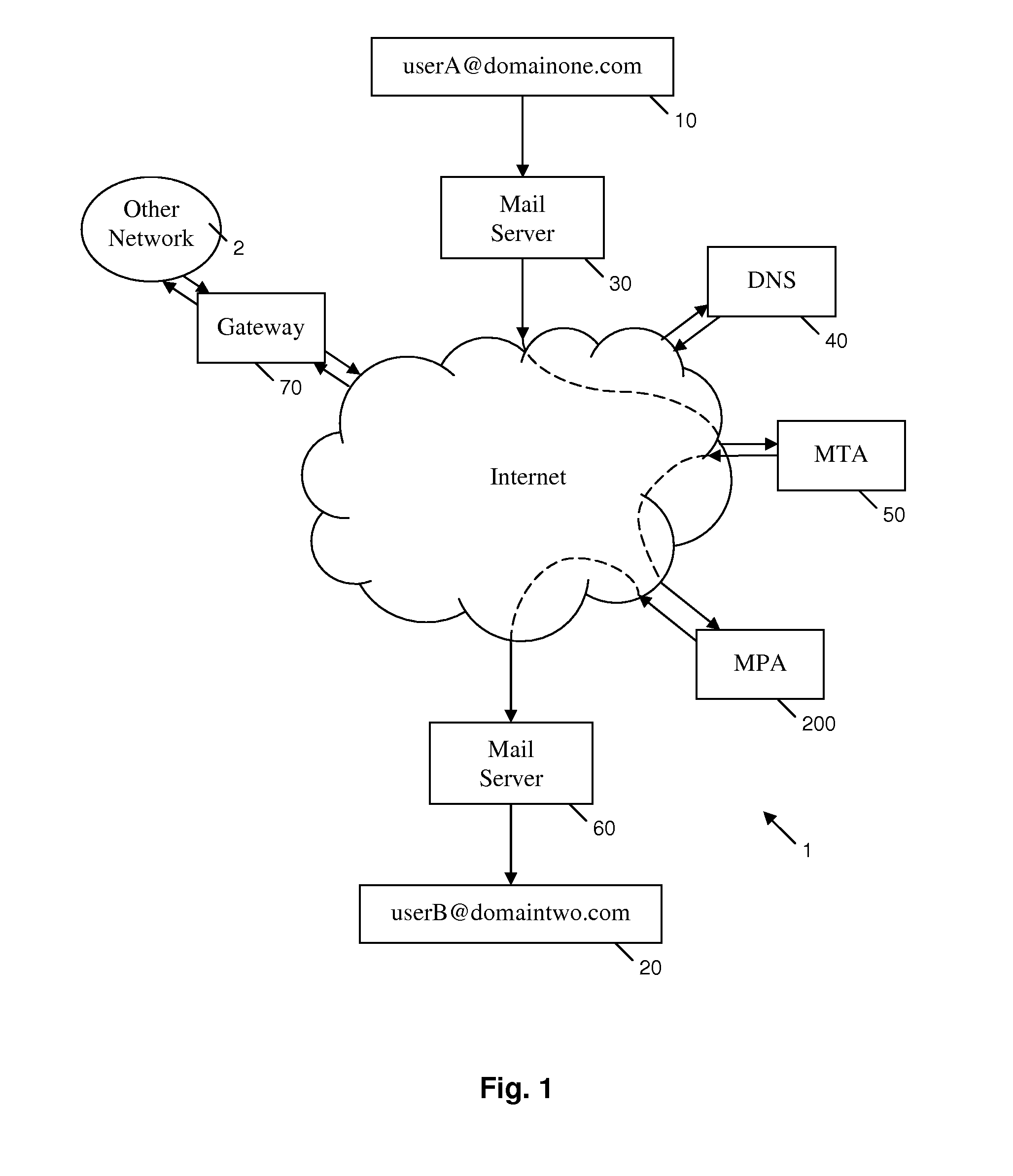
Method and apparatus for electronic mail filtering
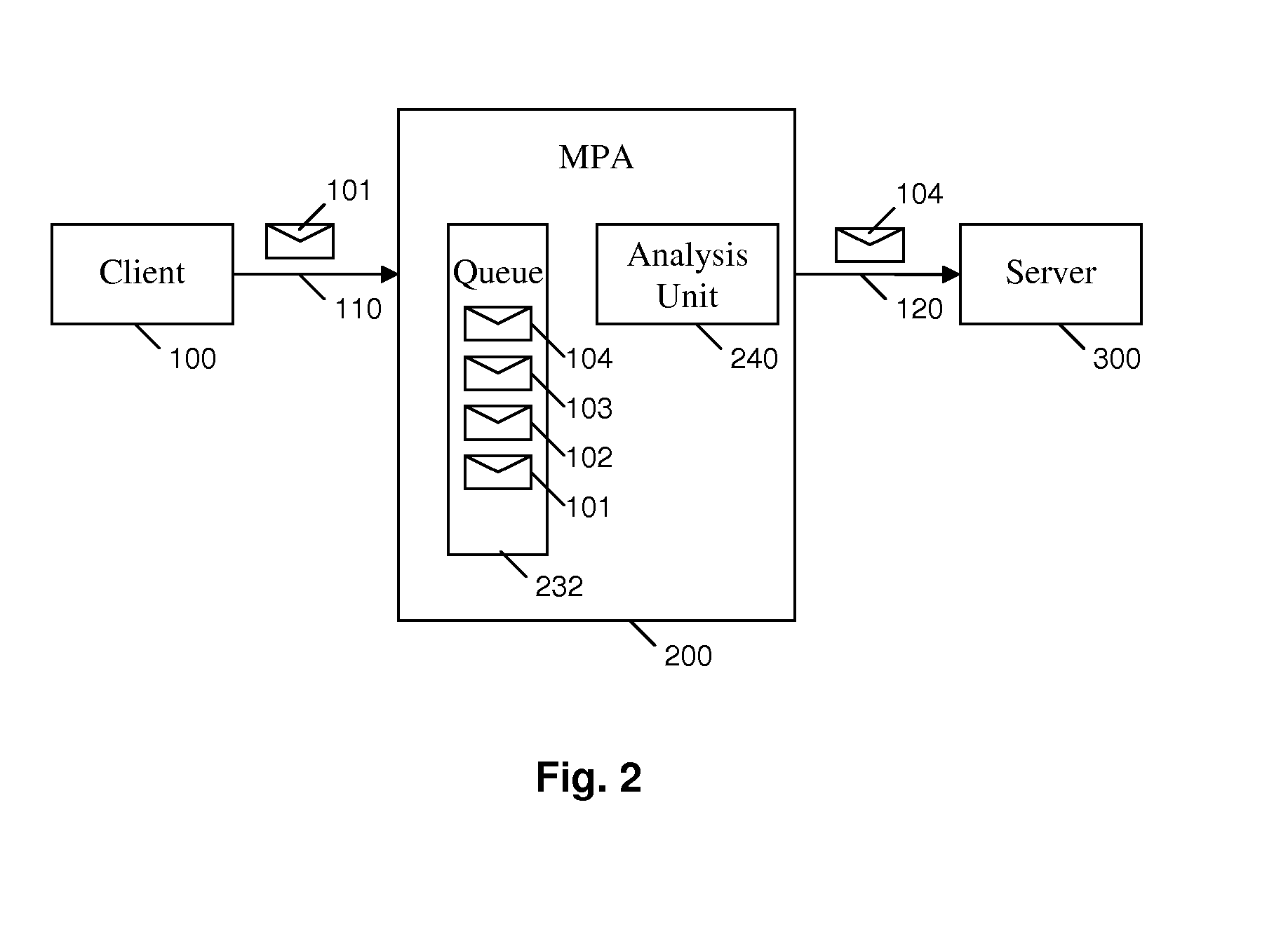
ActiveUS20100217811A1Increasing reputation scoreHigh precisionMemory loss protectionError detection/correctionTrusted clientMessage processing
A message processing apparatus (200) is provided in an electronic messaging system. The message processing apparatus (200) holds an ordered queue (232) of the electronic messages (101) and adds a new incoming message (101) to the queue (232) according to a reputation score (201) allocated to each incoming message. Messages having a highest reputation score (201) are extracted from a top of the queue (232) for detailed analysis according to one or more filtering mechanisms. A message forwarding unit (250) forwards wanted messages to a server unit (300) for onward transmission to a recipient terminal (20). Messages from a trusted client identity (105) who is most likely to send wanted messages are allocated a high reputation score (201) and take priority through the queue (232). Messages from a non-trusted client identity (105) are allocated a lower reputation score (201) and remain in the queue (232) until all messages with a higher reputation score (201) have been extracted.
Owner:FORCEPOINT LLC
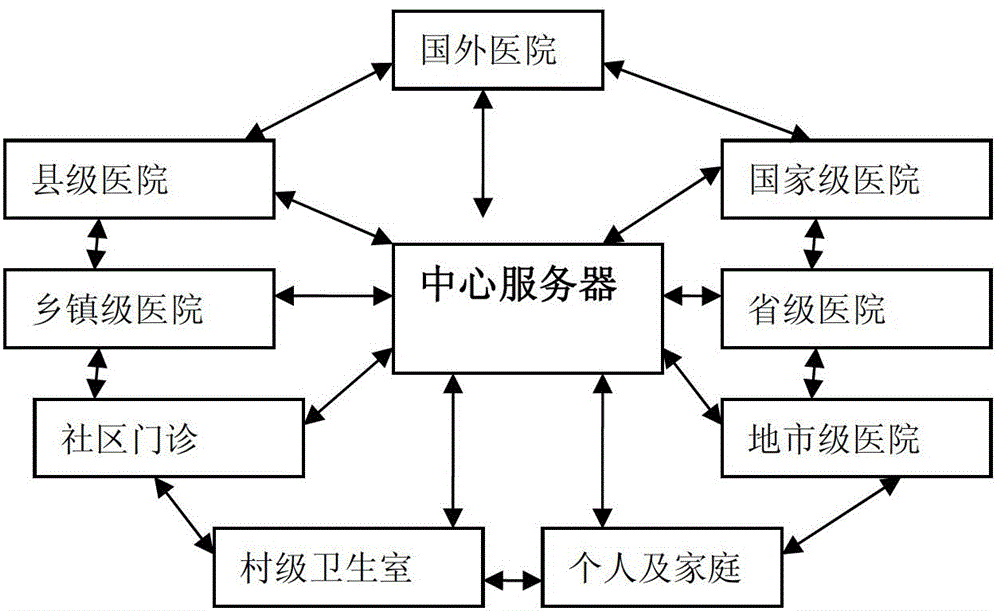
Network medical service system
InactiveCN102722659AEasy to buyReduce bandwidth requirementsTransmissionSpecial data processing applicationsTrusted clientClient-side
The invention provides a network medical service system which is used for solving the problem that the existing medical service system requires specially-designed hardware products, requires installation and maintenance of professional staff, and is troublesome in later upgrading and using and high in cost. The network medical service system comprises a user client side, a doctor client side and a central server which are communicated with each other through networks. The user client side and the doctor client side of the network medical service system can operate smoothly on computers based on mainstream configuration of windows xp, windows 7 and the like, hardware devices required by the network medical service system can be purchased and upgraded easily and are low in cost, and the network medical service system is easy to maintain, low in maintenance cost and facilitates comprehensive achievement of digital illness diagnosis.
Owner:李希海
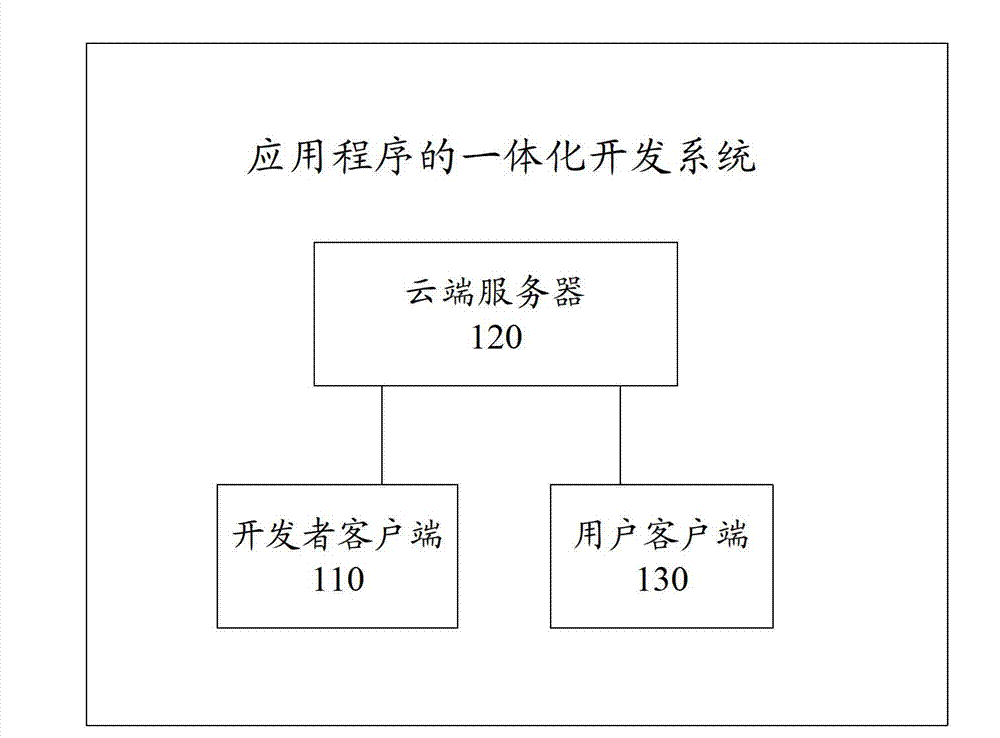
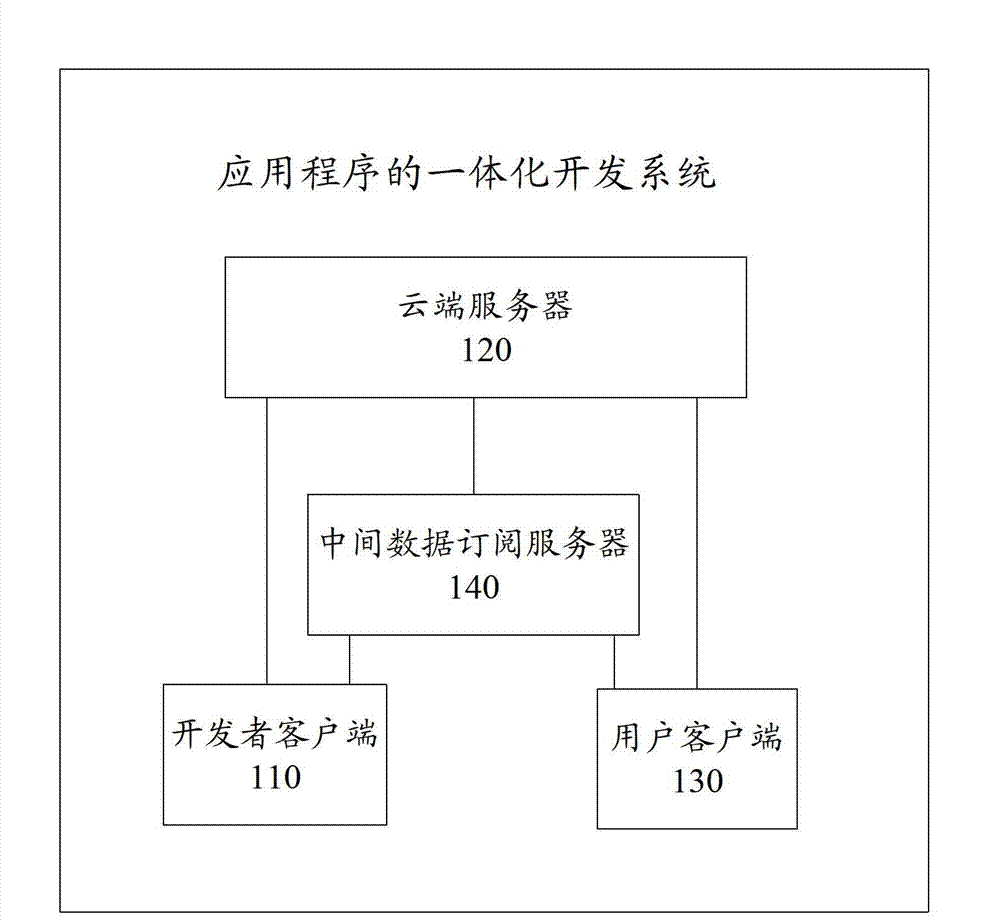
Integration development system, integration development method and integration development device for application programs
ActiveCN103593173ABreak the strict distinctionReduce complexityTransmissionSpecific program execution arrangementsWeb applicationTrusted client
The invention provides an integration development system for application programs. The integration development system comprises a developer client, a cloud server and a user client. The developer client is used for sending a developer document to the user client and the cloud server; the cloud server is used for recognizing a service logic code according to an execution environment to obtain a cloud logic code, processing a digital code and synchronizing the same with the user client; the user client is used for recognizing the service logic code according to the execution environment to obtain a user logic code and receiving the synchronized digital code sent by the cloud server. The invention further provides an integration development method for the application programs, the cloud server and the user client. The codes can be automatically determined to be executed in the cloud client or the user client according to running logic of the codes, so that the cloud server code or the user client code needs not to be distinguished during development by developers, and developer groups with random backgrounds are allowed to independently develop the complete Web application programs.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
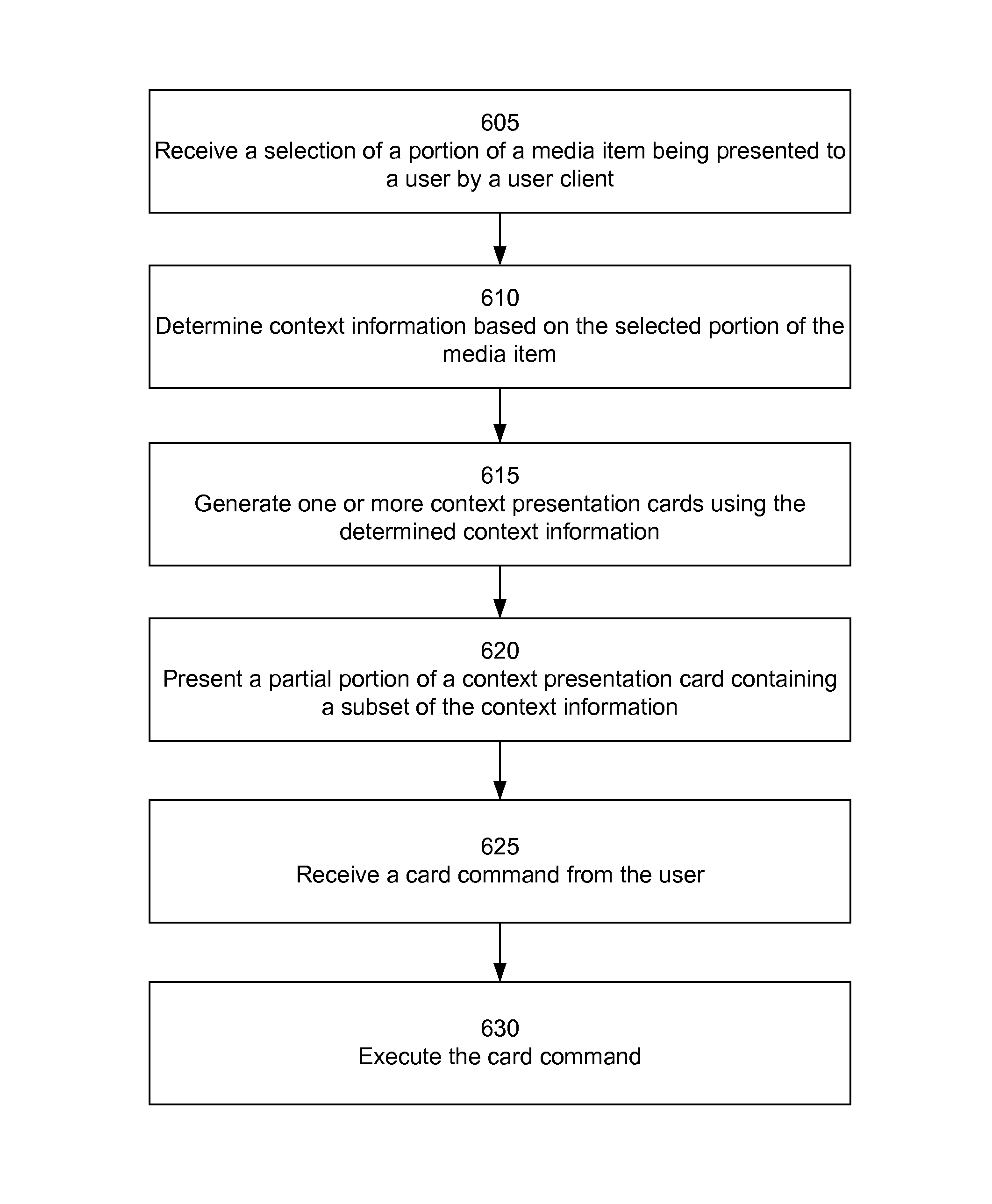
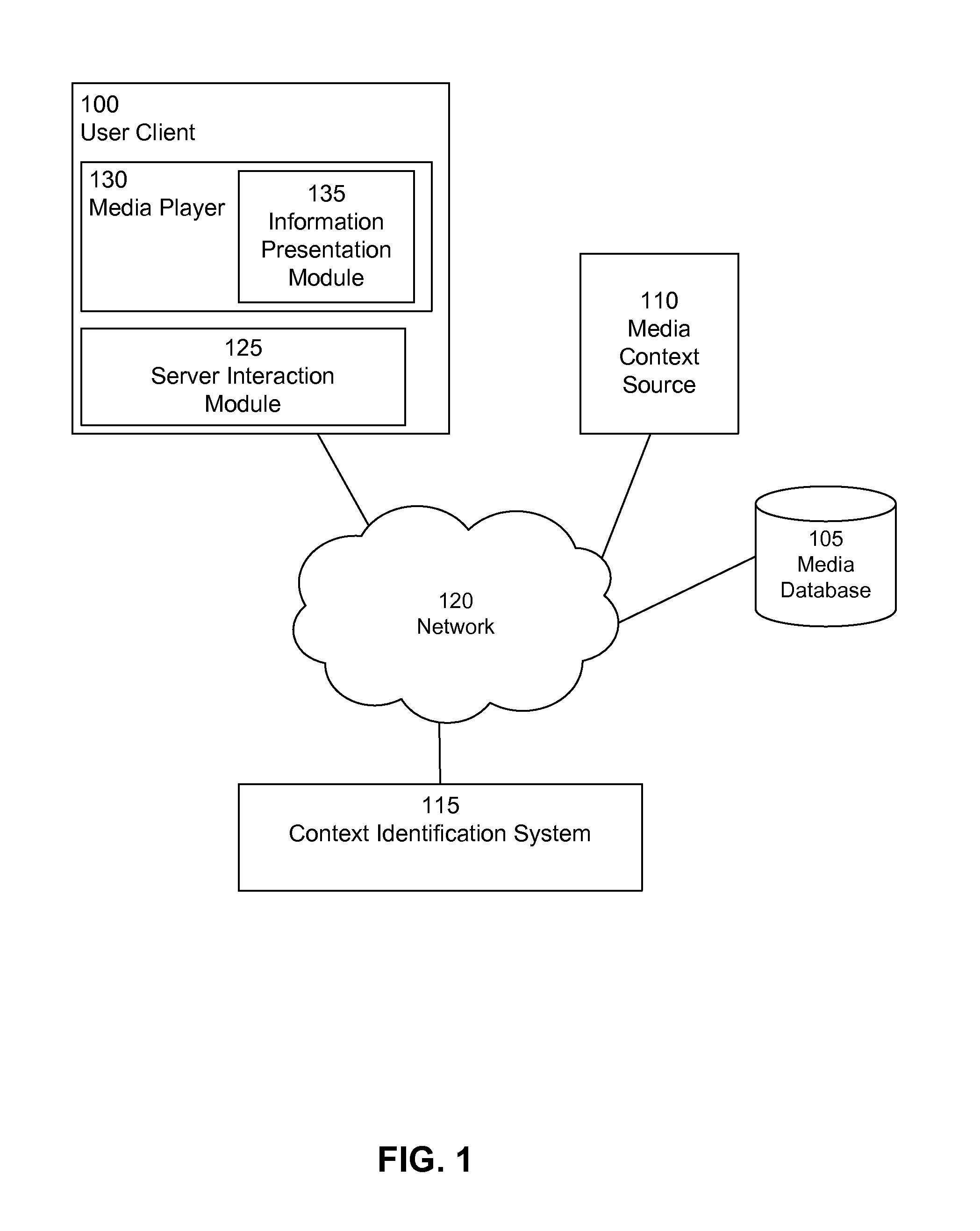
User interface for presenting contextual information
InactiveUS20140337730A1Multimedia data browsing/visualisationSpecial data processing applicationsTrusted clientWorld Wide Web
Context information associated with a selected portion of a media item is presented to a user via a user client. The user client receives a selection of a portion of the media item being presented to the user by the user client. The user client determines context information based on the selected portion of the media item, and generates a context presentation card using the determined context information. The user client presents a partial portion of the context presentation card containing a subset of the context information to the user.
Owner:GOOGLE LLC
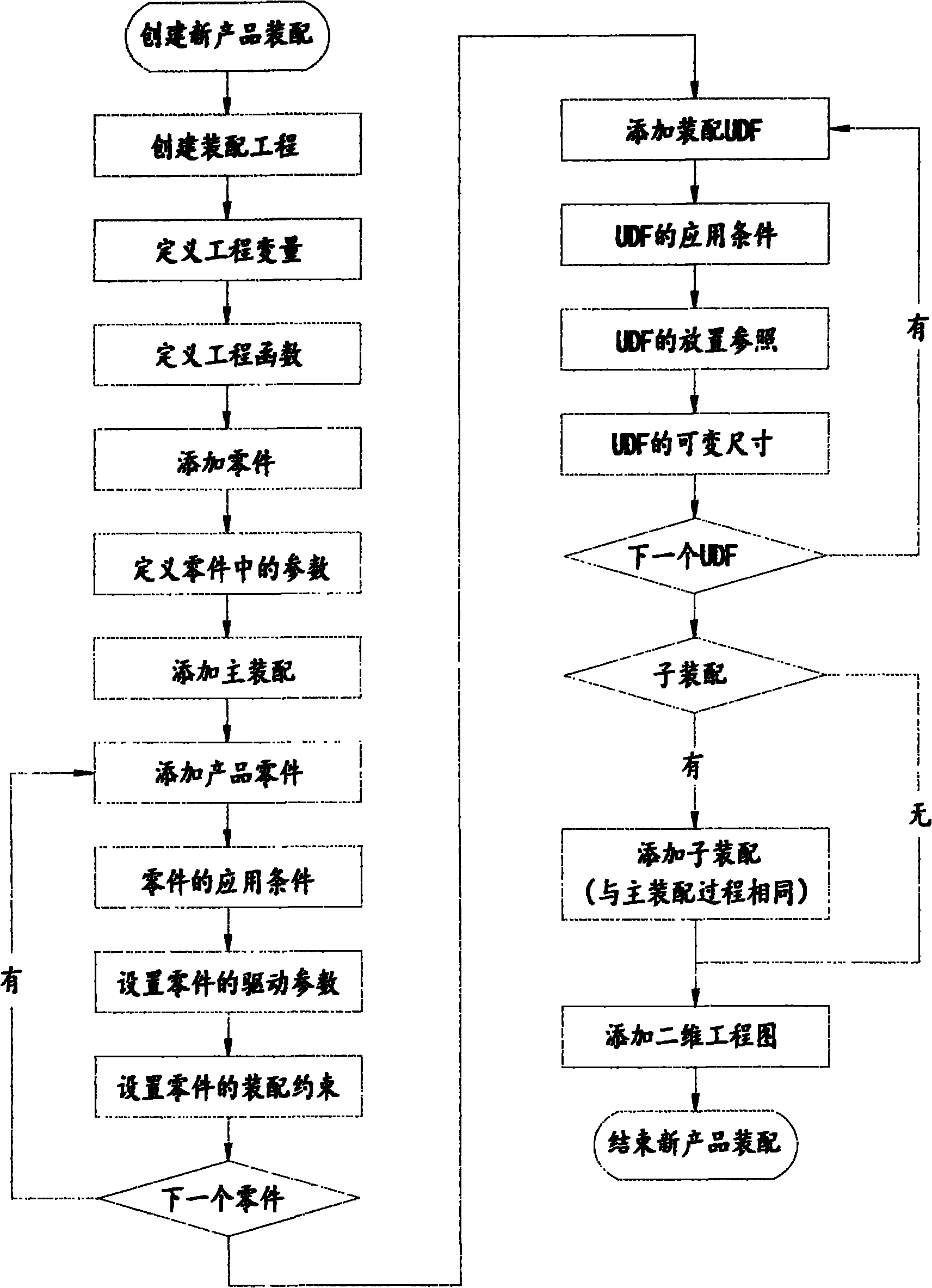
Long-distance design system and method for section product
InactiveCN102012952AQuick buildFast order productionSpecial data processing applicationsBill of materialsTrusted client
The invention discloses a long-distance design system and method which are used to rapidly design section products aiming at different demands of different clients. The system comprises a server, a design client and a user client, wherein the user client is connected with the server through an internet, and is capable of selecting an original module and inputting size data required practically from the server, and automatically generating a three-dimensional assembly module, a two-dimensional engineering drawing, a bill of material (BOM) table, a project quotation and the like of products for the user to check; after the user orders, the design client analyzes a configuration table in the order to regenerate a three-dimensional model with an actual size and a two-dimensional engineering drawing, so as to realize rapid design and production. The invention is suitable for the rapid and large-scale design, production and manufacturing of the section products.
Owner:ZHUHAI CHUNSHENG ELECTRIC CO LTD
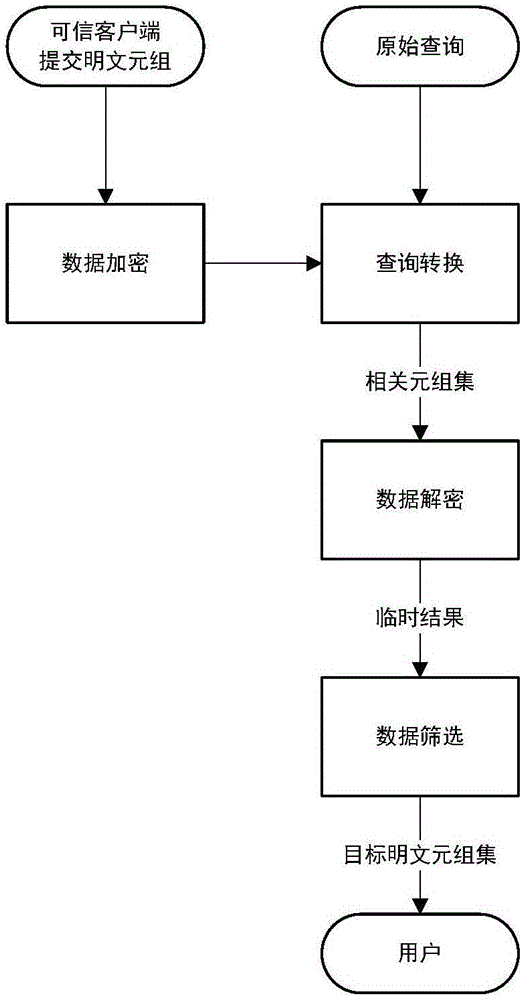
Privacy character information encryption inquiry method and system
ActiveCN106850187AImprove query efficiencyCoordinated securityKey distribution for secure communicationData stream serial/continuous modificationPlaintextInternet privacy
The invention discloses a privacy character information encryption inquiry method and system. The privacy character information encryption inquiry method comprises the following steps: (1) data encryption: converting the plaintext tuples submitted by a trusted client to ciphertext tuples; wherein the plaintext tuple comprises privacy fields; and the ciphertext tuple comprises the ciphertext data and the index data; (2) query conversion: converting the raw query condition to an index query condition, and taking the tuple set composed of the ciphertext tuples whose index data satisfies the index query condition as the relevant ciphertext tuple set; (3) data decryption: decrypting the relevant ciphertext tuple set to obtain temporary results in plaintext form; (4) data screening: executing the raw query condition to obtain the target plaintext tuple set. The privacy character information encryption inquiry system comprises a data encryption component, a query conversion component, a data decryption component and a data screening component. Compared with the prior method, the privacy character information encryption inquiry method disclosed by the invention is more flexible and safer.
Owner:上海静客网络科技有限公司
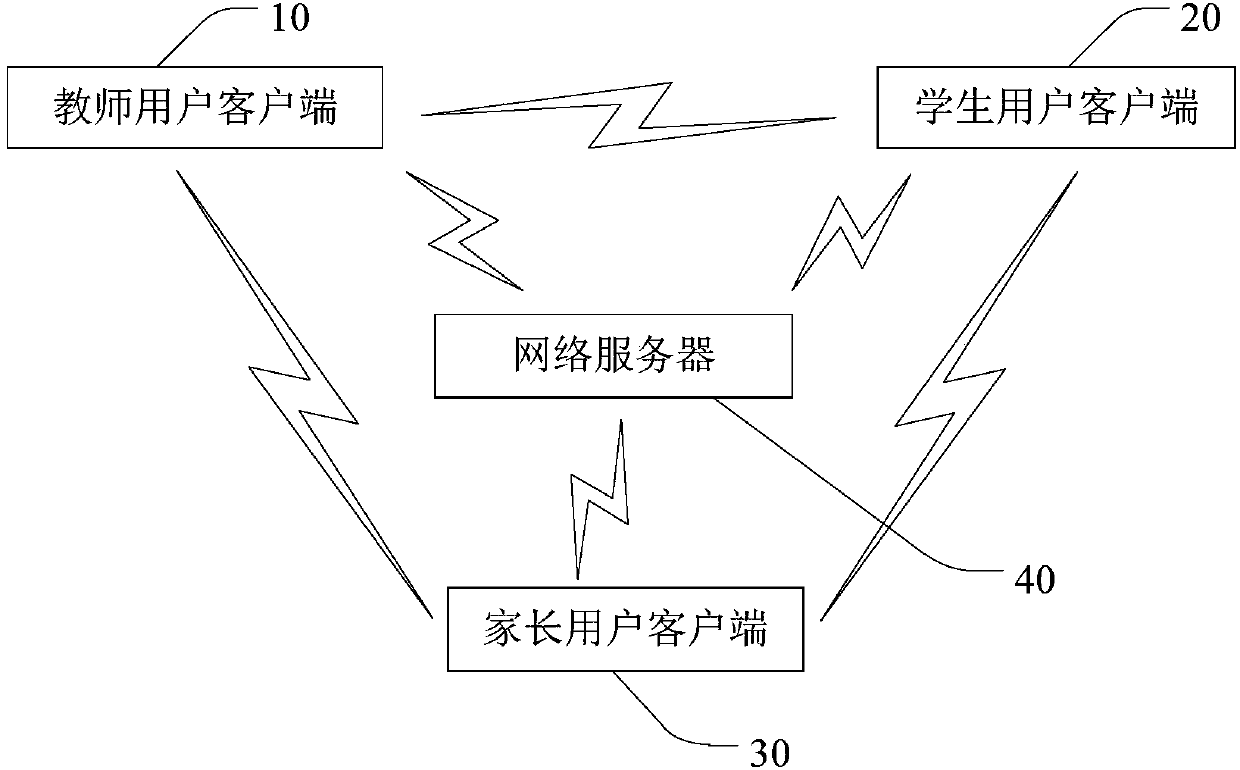
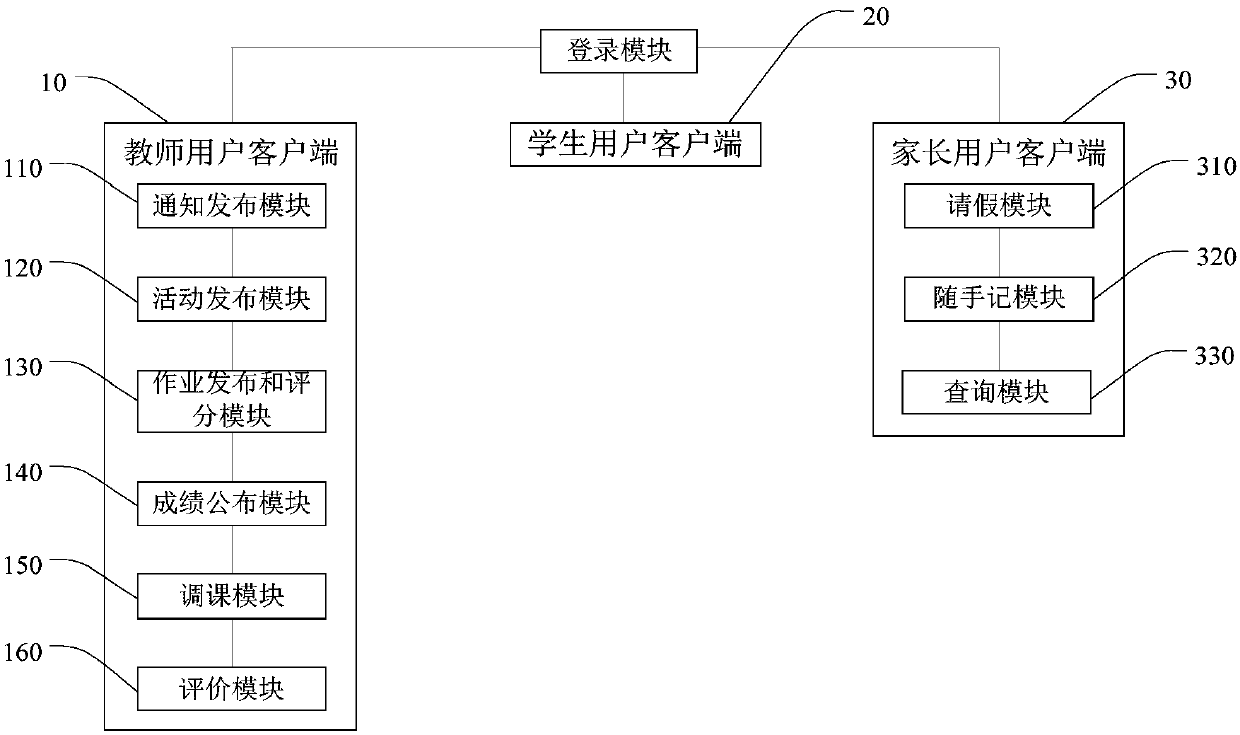
Home and school interconnection method and system and user client
InactiveCN107682332AEasy to viewData processing applicationsTransmissionTrusted clientInterconnection
The invention discloses a home and school interconnection method and system and a user client. The home and school interconnection system comprises a teacher user client, a student user client, a parent user client and a network server. The teacher user client sends information messages to the student user client and the parent user client and uploads the information messages to the network server. The information messages comprise one or more of notices, activities, homework, homework grades, scores, courses and evaluation. The parent user client receives the information messages sent by theteacher user client and checks the information messages of a corresponding student through the network server. The communication can be carried out among the teacher user client, the student user client and the parent user client and the parent user client can check the information messages of the corresponding student, so the method, the system and the user client are very convenient.
Owner:安诺(深圳)创新技术有限公司
Delegation of content filtering services between a gateway and trusted clients in a computer network
ActiveUS8082583B1Improve performanceMemory loss protectionUnauthorized memory use protectionComputer performanceTrusted client
Method and system for performing content filtering services in a computer network. A gateway computer may be configured to be in the data path of network communications between client computers in a private computer network and computers in a public computer network. A master entity in the gateway computer may be configured to determine content filtering services available in the client computers. The master entity may delegate to the client computers performance of content filtering services that may be reliably performed in the client computers. Each of the client computers may include a trusted agent in communication with the master entity to coordinate content filtering in the private computer network.
Owner:TREND MICRO INC
Method and system for securing a disk key
ActiveUS7900060B2Digital data processing detailsUnauthorized memory use protectionTrusted clientMaster key
In accordance with an embodiment of the present invention, a trusted client includes a non-volatile memory programmed with an encrypted disk key. The encrypted disk key in the non-volatile memory is encrypted with a master key of a security processor. Accordingly, encrypted data received by the central processor from a disk's security logic is forwarded to a security processor along with the encrypted disk key. The security processor decrypts the encrypted disk key and then decrypts the encrypted data, utilizing the disk key. The disk key is never available to the central processing unit in the clear.
Owner:NBCUNIVERSAL
Remotable information cards
InactiveUS8151324B2Digital data processing detailsUser identity/authority verificationInformation CardInternet privacy
An accessor function interfaces among a client, a relying party, and an identity provider. The identity provider can “manage” personal (i.e., self-asserted) information cards on behalf of a user, making the personal information cards available on clients on which the personal information cards are not installed. The client can be an untrusted client, vulnerable to attacks such as key logging, screen capture, and memory interrogation. The accessor function can also asked as a proxy for the relying party in terms of invoking and using the information cards system, for use with legacy relying parties.
Owner:APPLE INC
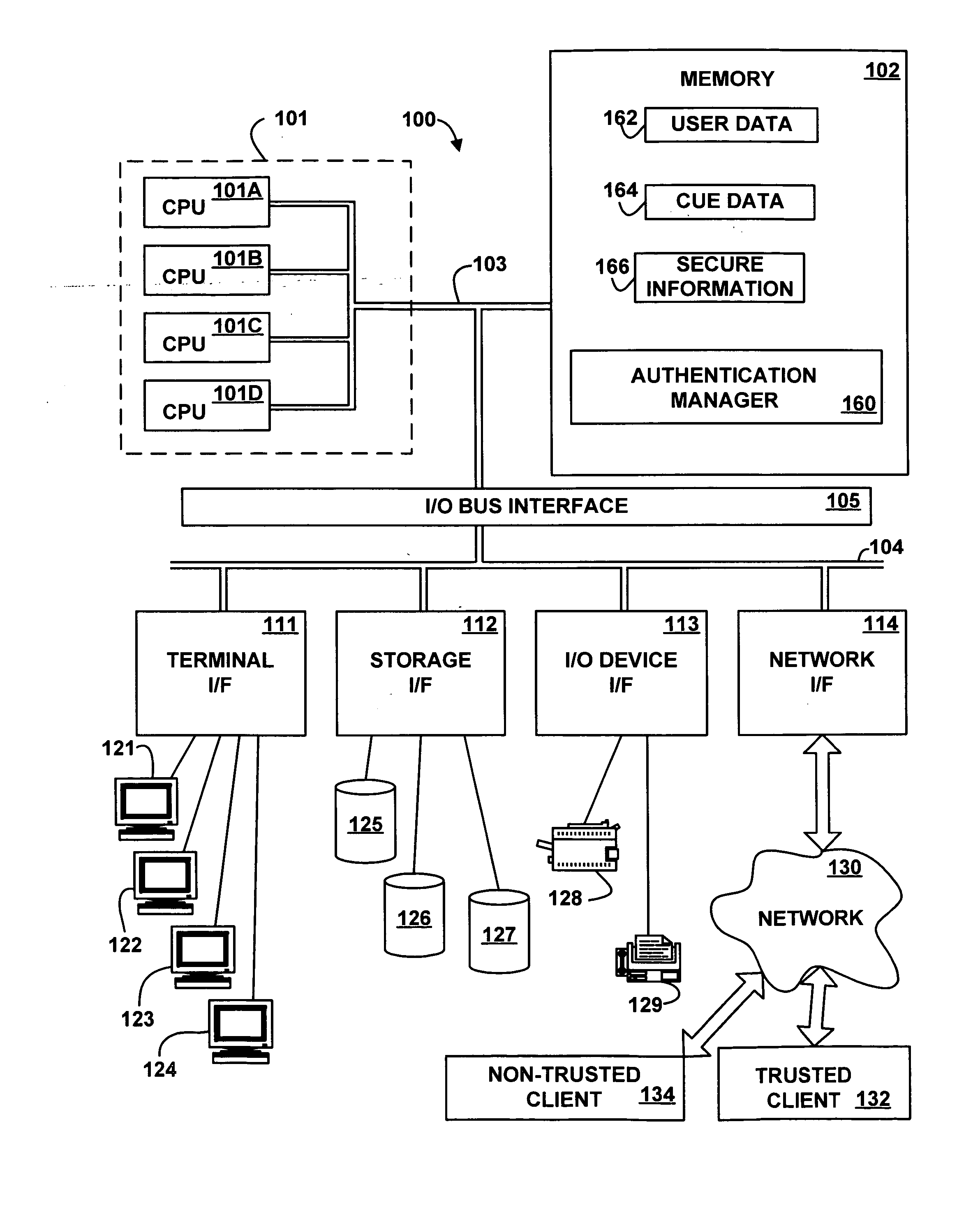
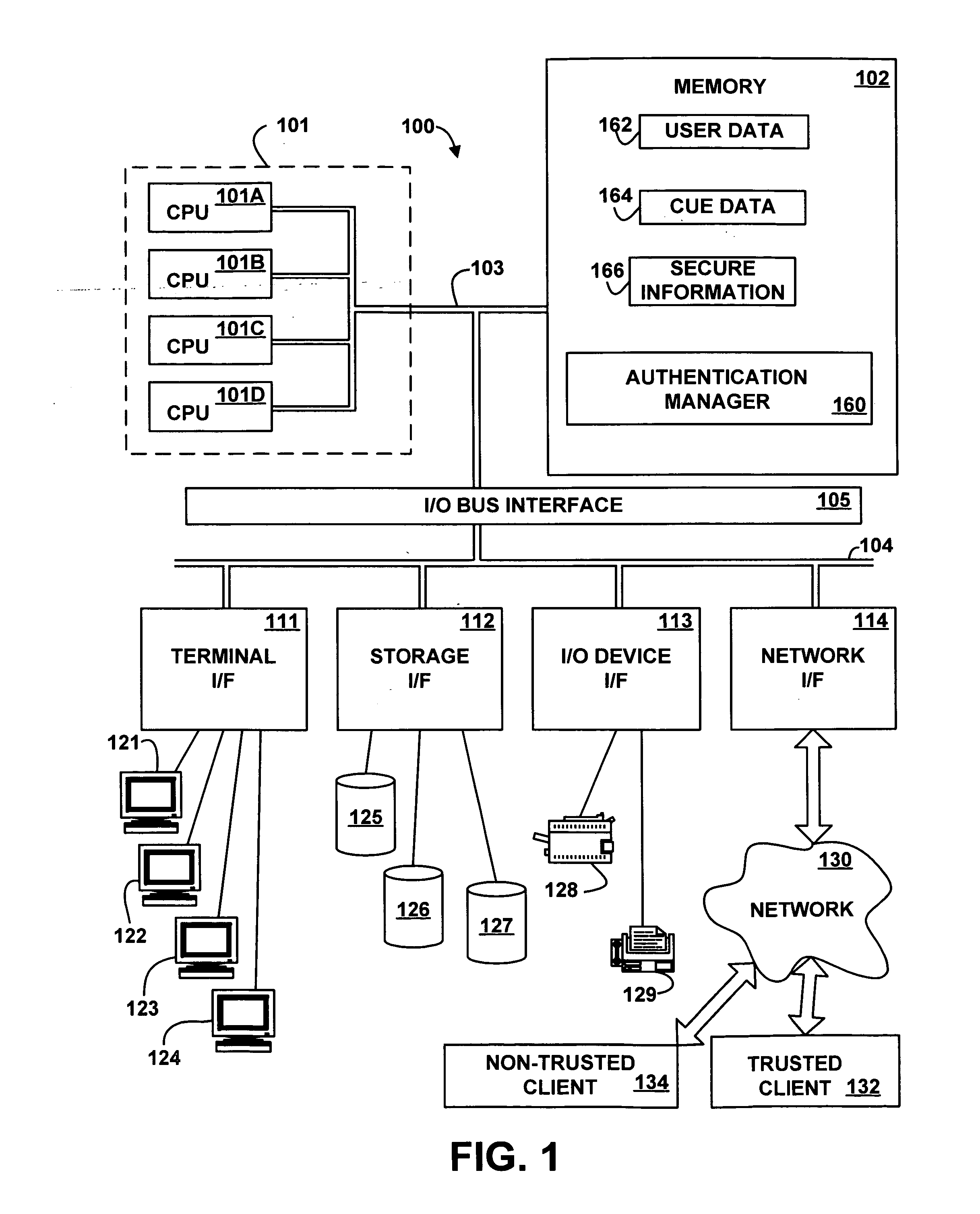
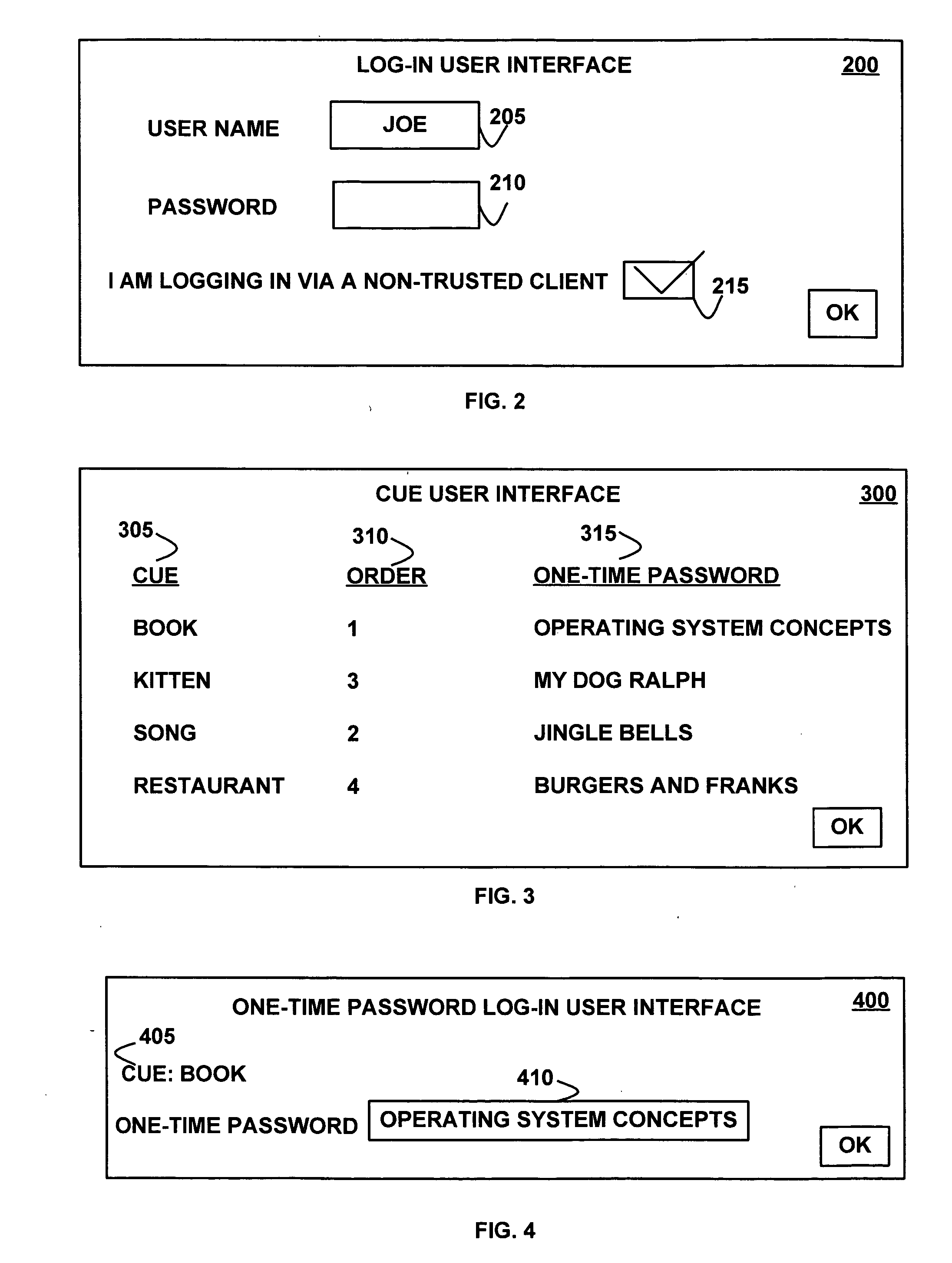
Cued one-time passwords
InactiveUS20070061865A1Improve securityAccess is deniedDigital data processing detailsUnauthorized memory use protectionTrusted clientOne-time password
A method, apparatus, system, and signal-bearing medium that, in an embodiment, receive cues, one-time passwords, and a presentation order. The cues and one-time passwords are associated with a user name. In response to a cue request, the cues are presented in the presentation order and input data is received. If the input data matches the associated one-time password, then access to secure information is granted and the one-time password is invalidated. If the input data does not match the associated one-time password, then access to secure information is denied. In various embodiments, the cues may be text, images, audio, or video. In this way, in an embodiment, one-time passwords may be used in response to cues, which may increase security when accessing information from a non-trusted client because if the one-time password is misappropriated via the non-trusted client, the one-time password is no longer valid for future use.
Owner:IBM CORP
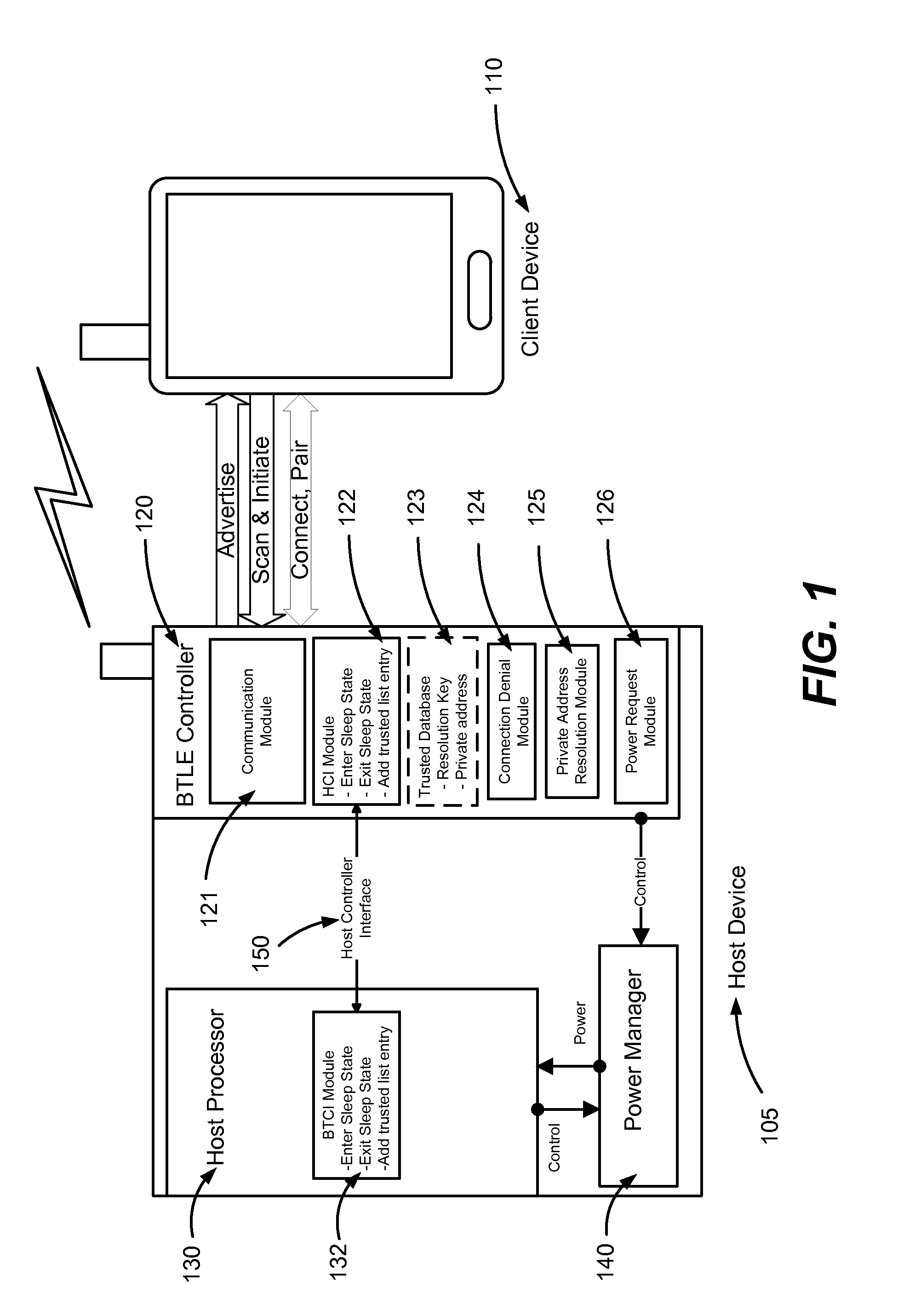
Bluetooth low energy hostless private address resolution
Conventional Bluetooth low energy (or like personal wireless network) controllers cannot resolve private addresses without some calculation from a host processor but leaving the host processor on or awaking it from a sleep each time a non-trusted device attempts to connect wastes power. Hostless private address resolution allows a host controller to enter a sleep state off while the Bluetooth controller advertises its device name, primary services, rejects connection requests from non-trusted devices with public and private addresses, and awakens the host controller upon a connection request from a trusted client device with a public or private address. Not only does this approach reduce power consumption by allowing the host processor to remain in the sleep state it simultaneously ensures security by allowing the private address resolution to remain active on the Bluetooth controller.
Owner:GOPRO
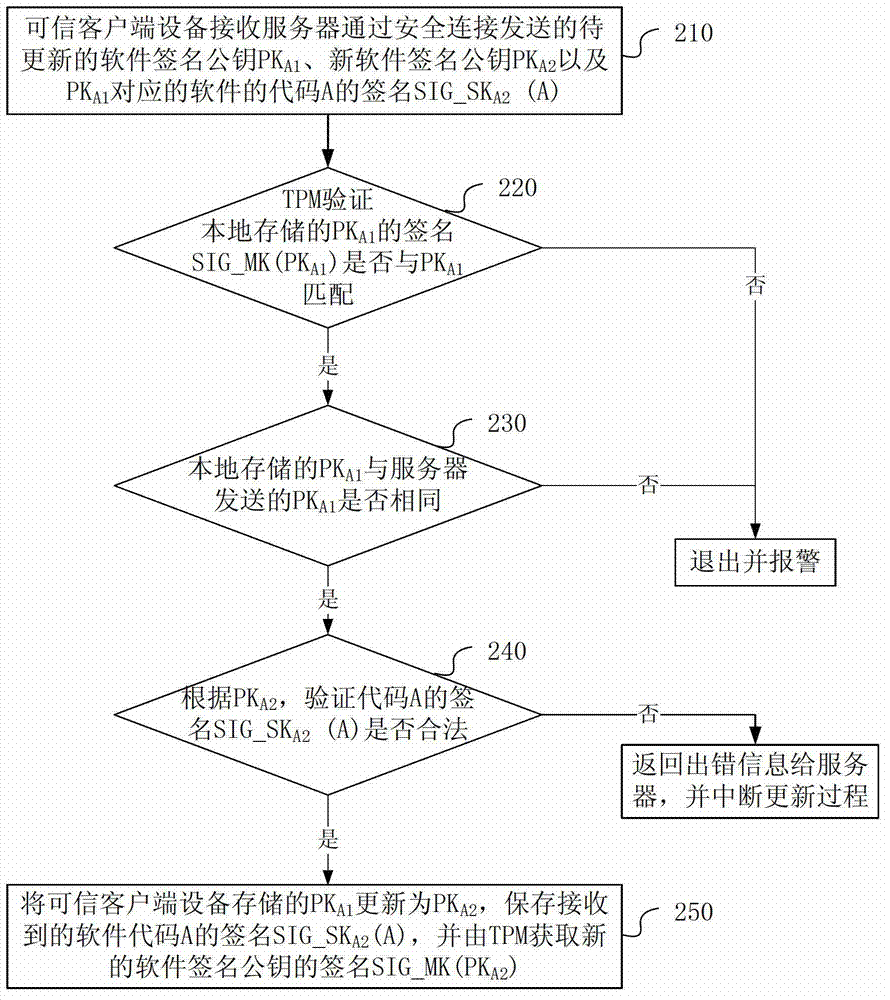
Software secret key updating method and device
ActiveCN103595530APrevent unable to update issuesKey distribution for secure communicationUser identity/authority verificationComputer hardwareTrusted client
Provided in an embodiment of the present invention are a software key updating method and device. A trusted client device receives key information and verification information corresponding to the software and transmitted by a server, the key information containing a to-be-updated first software public key signature and a new second software public key signature, and the verification information containing software verification information; if a valid first software public key signature corresponding to the software and stored in the trusted client device is consistent with the received first software public key signature, then checking whether the software verification information is valid; and if the software verification information is valid, then updating the valid first software public key signature corresponding to the software and stored in the trusted client device as a second software public key signature. With the above solution, the present invention can remotely update a software key signature on a trusted client device, thus preventing the problem of being unable to update an invalid key.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com