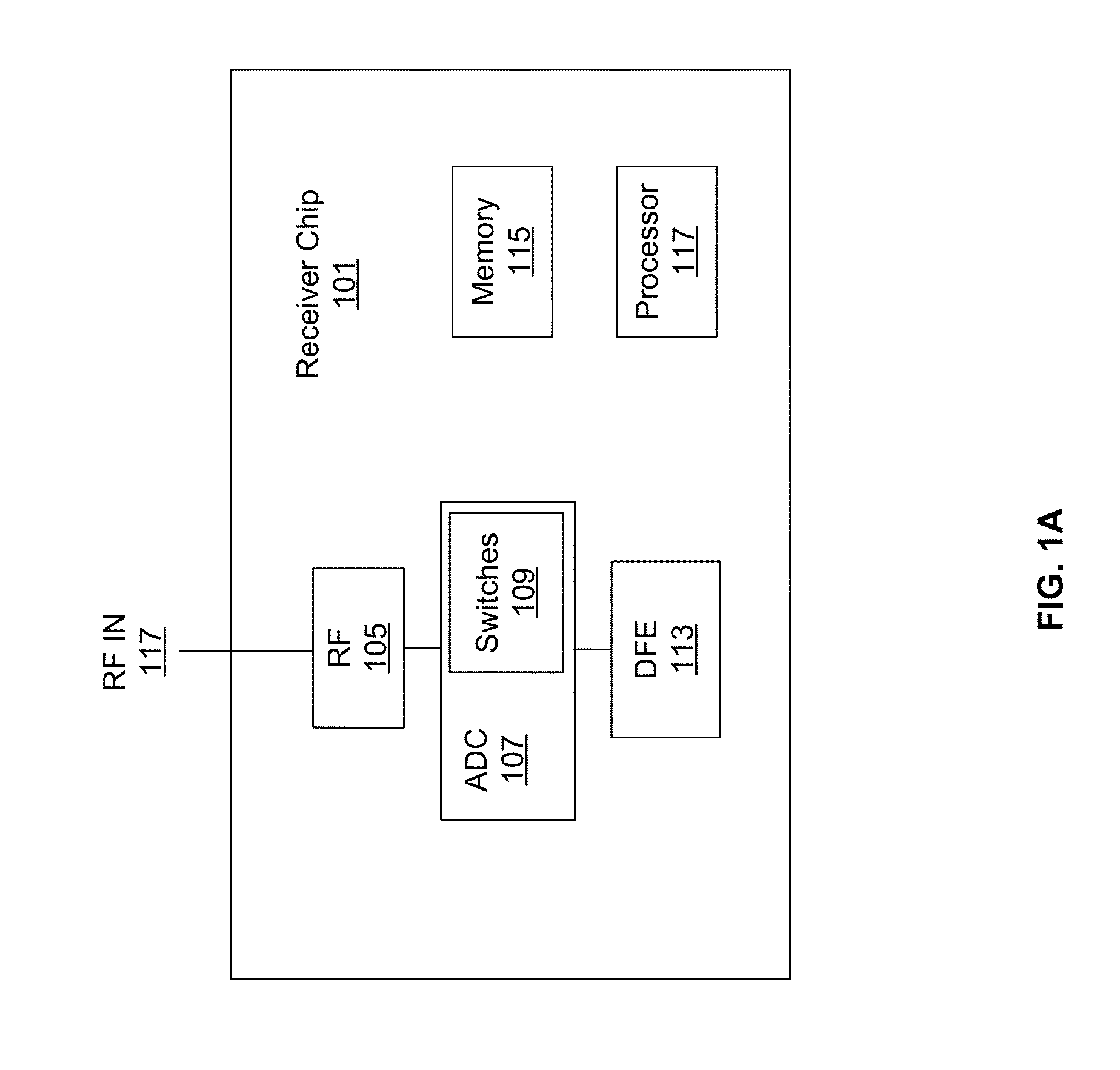
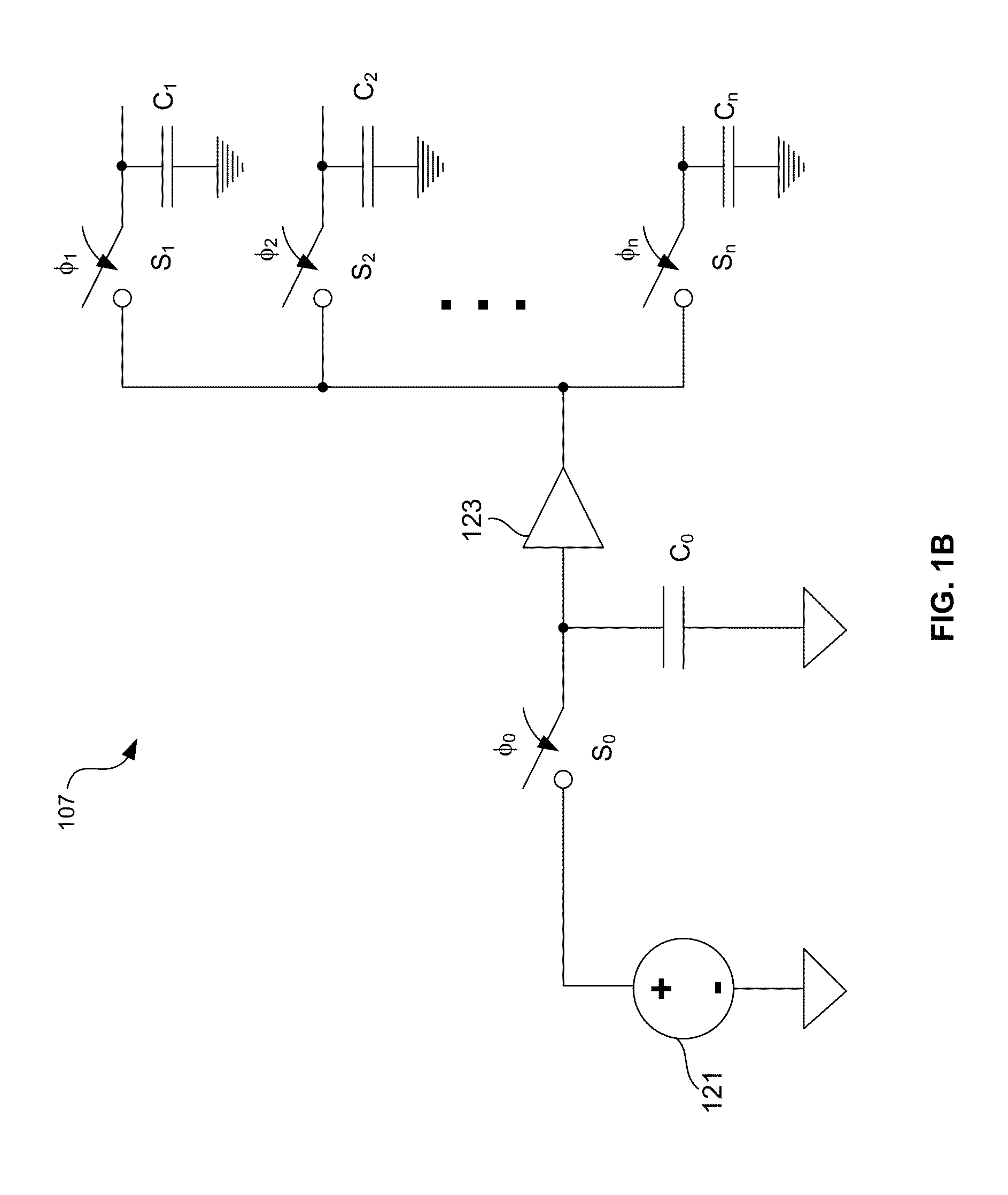
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
73 results about "Bootstrapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In general, bootstrapping usually refers to any process that is completed bilaterally from the start point to the end. In computer technology the term (usually shortened to booting) usually refers to the process of loading the basic software into the memory of a computer after power-on or general reset, especially the operating system which will then take care of loading other software as needed.
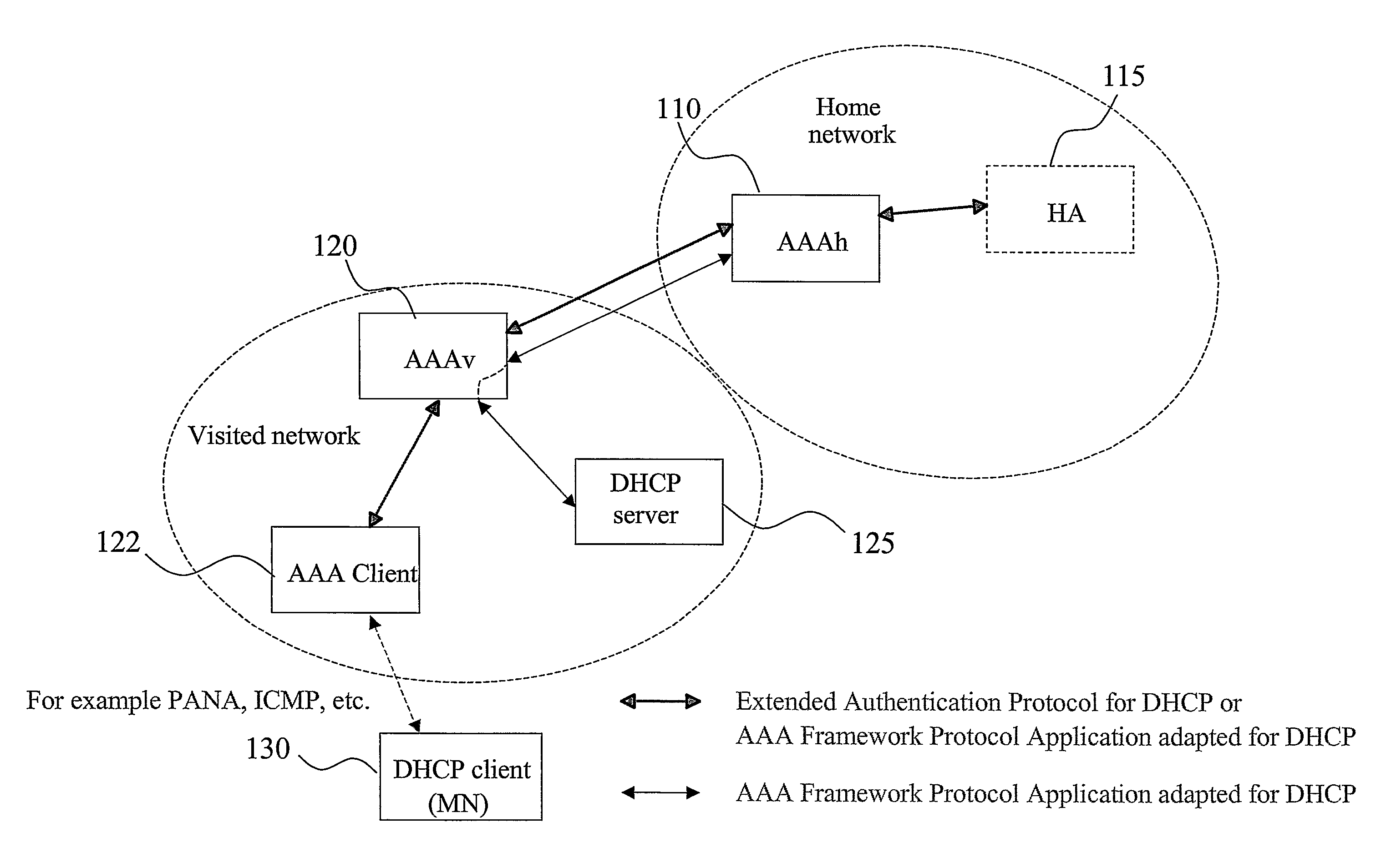
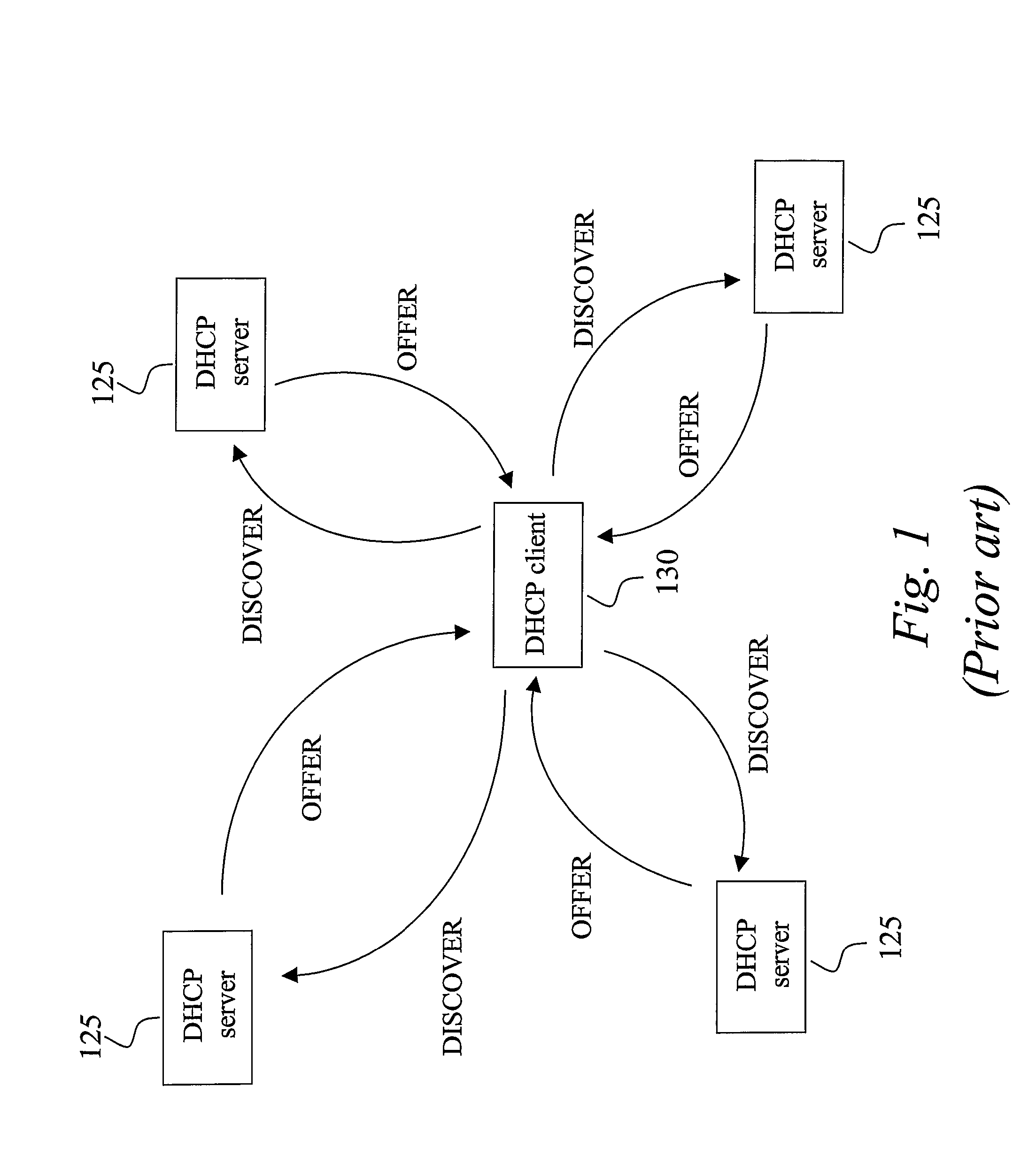
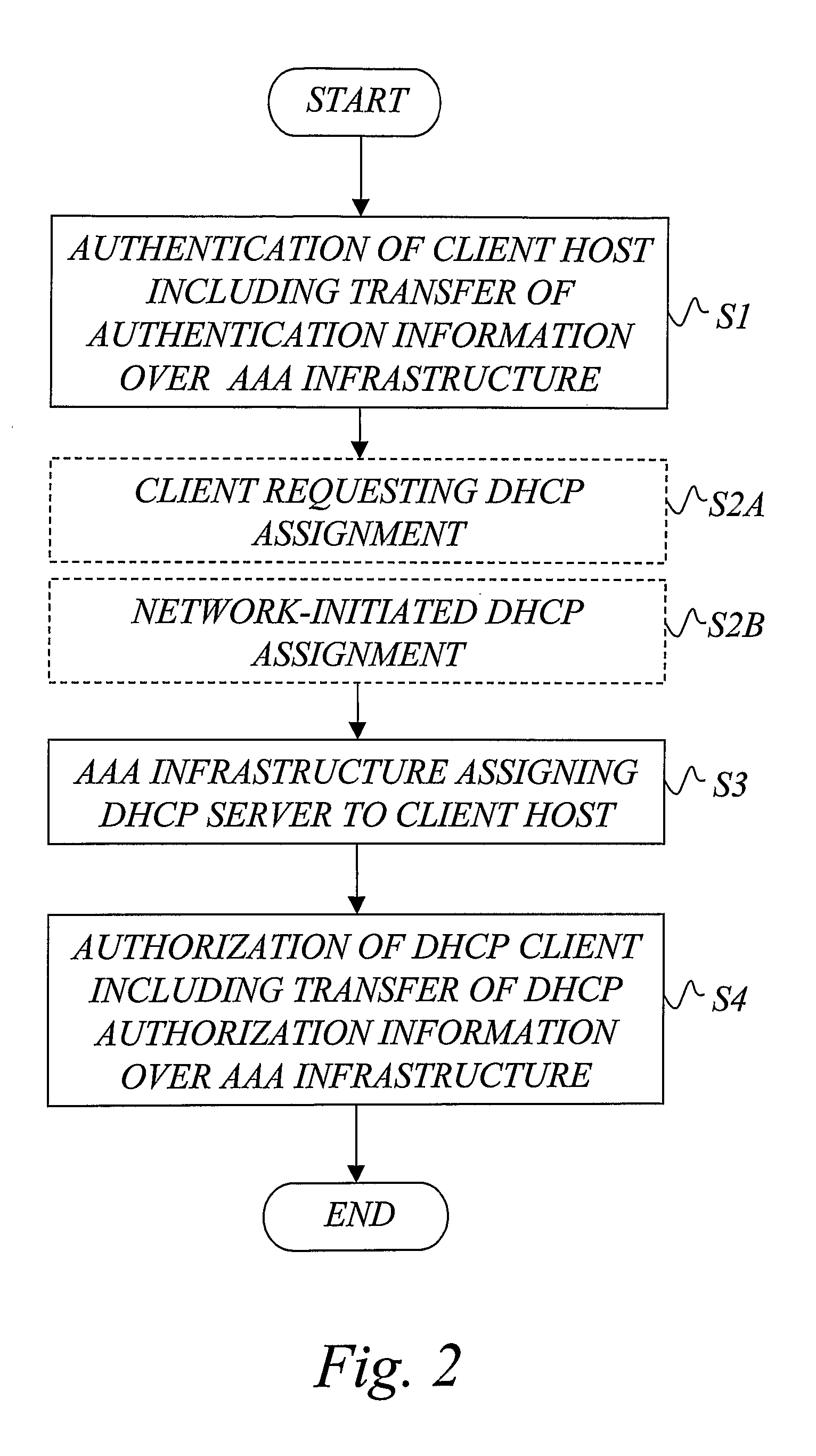
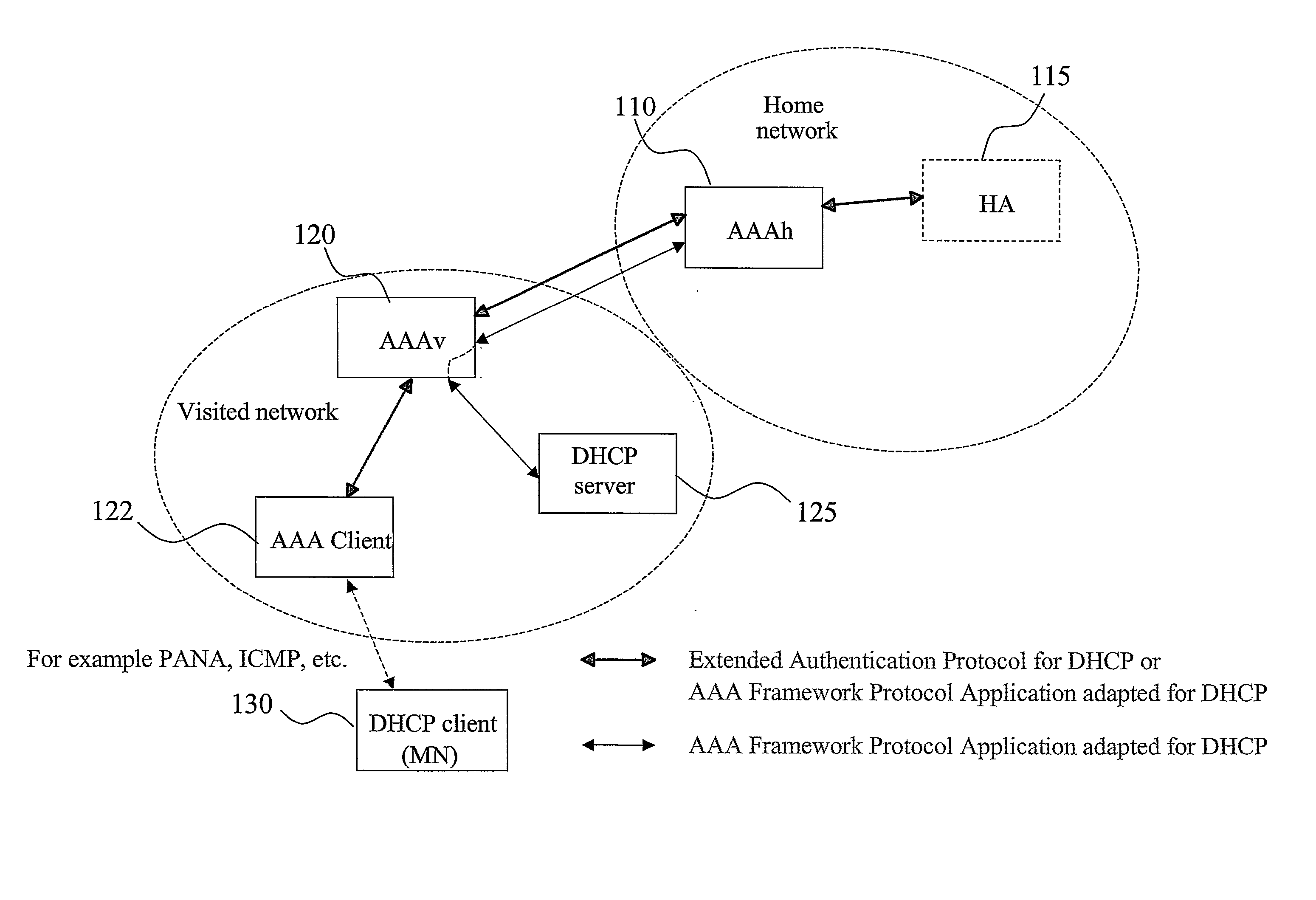
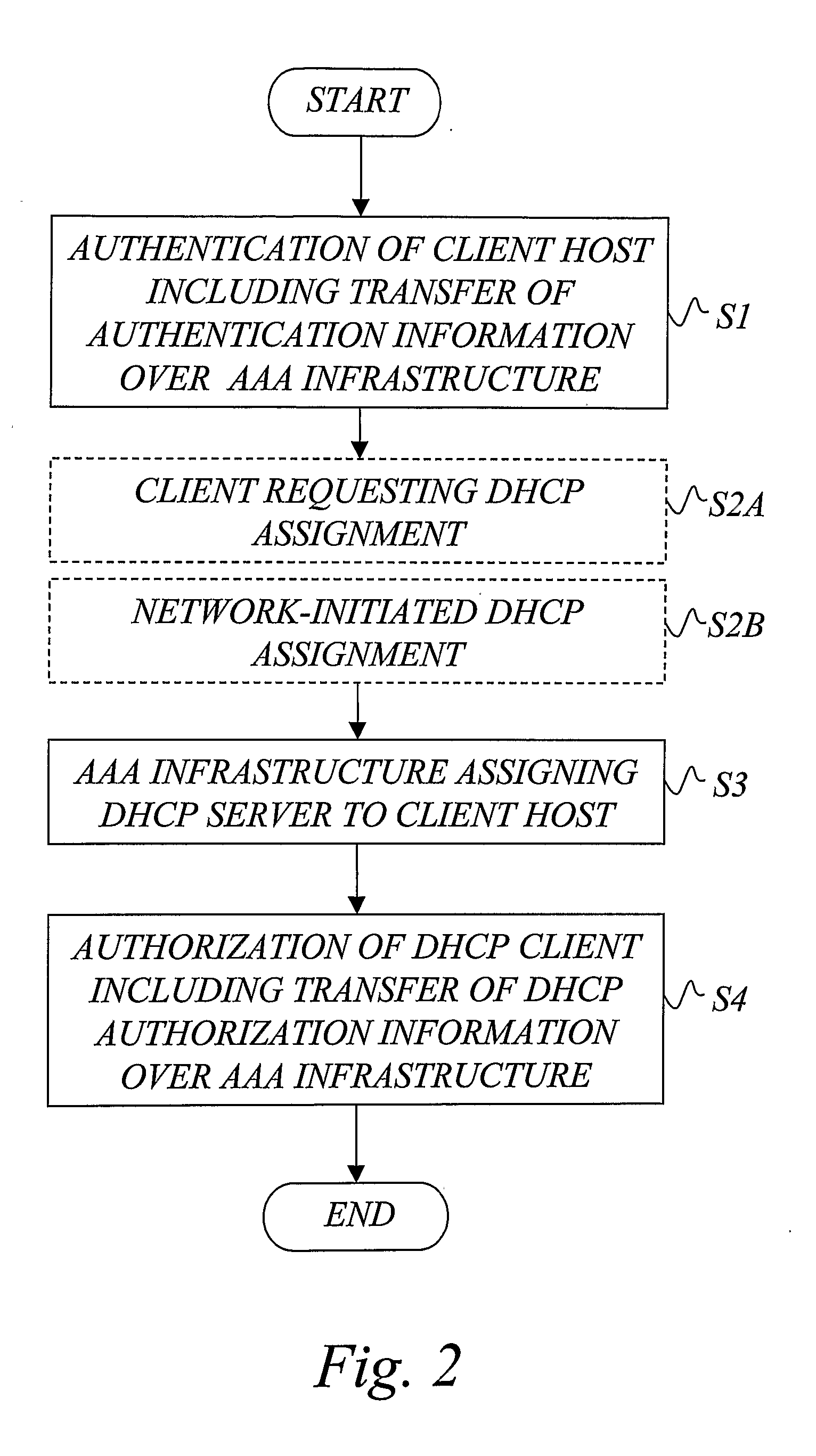
AAA support for DHCP
InactiveUS7983418B2Add supportEasy transferDigital data processing detailsMultiple digital computer combinationsKey-agreement protocolClient-side
Owner:TELEFON AB LM ERICSSON (PUBL)
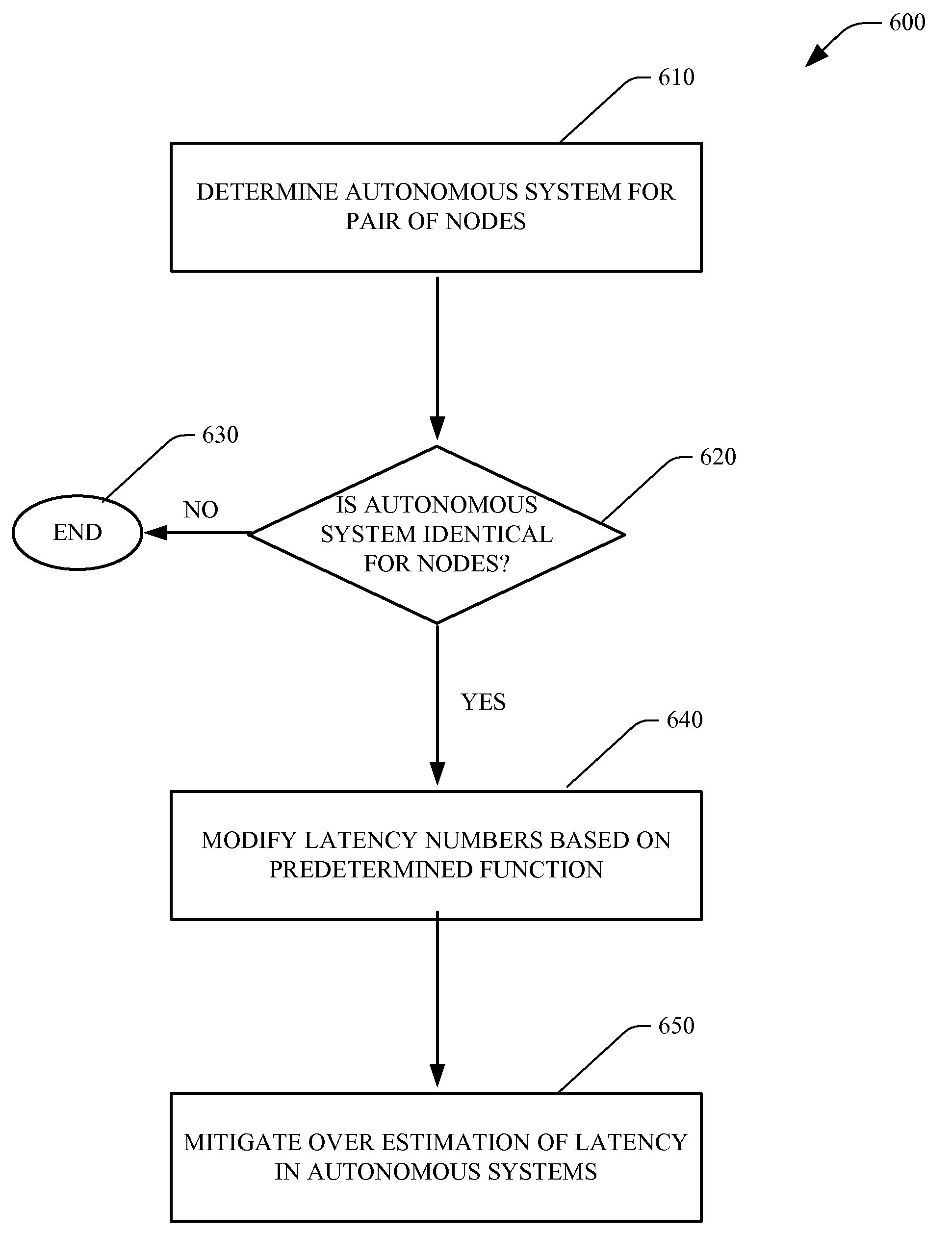
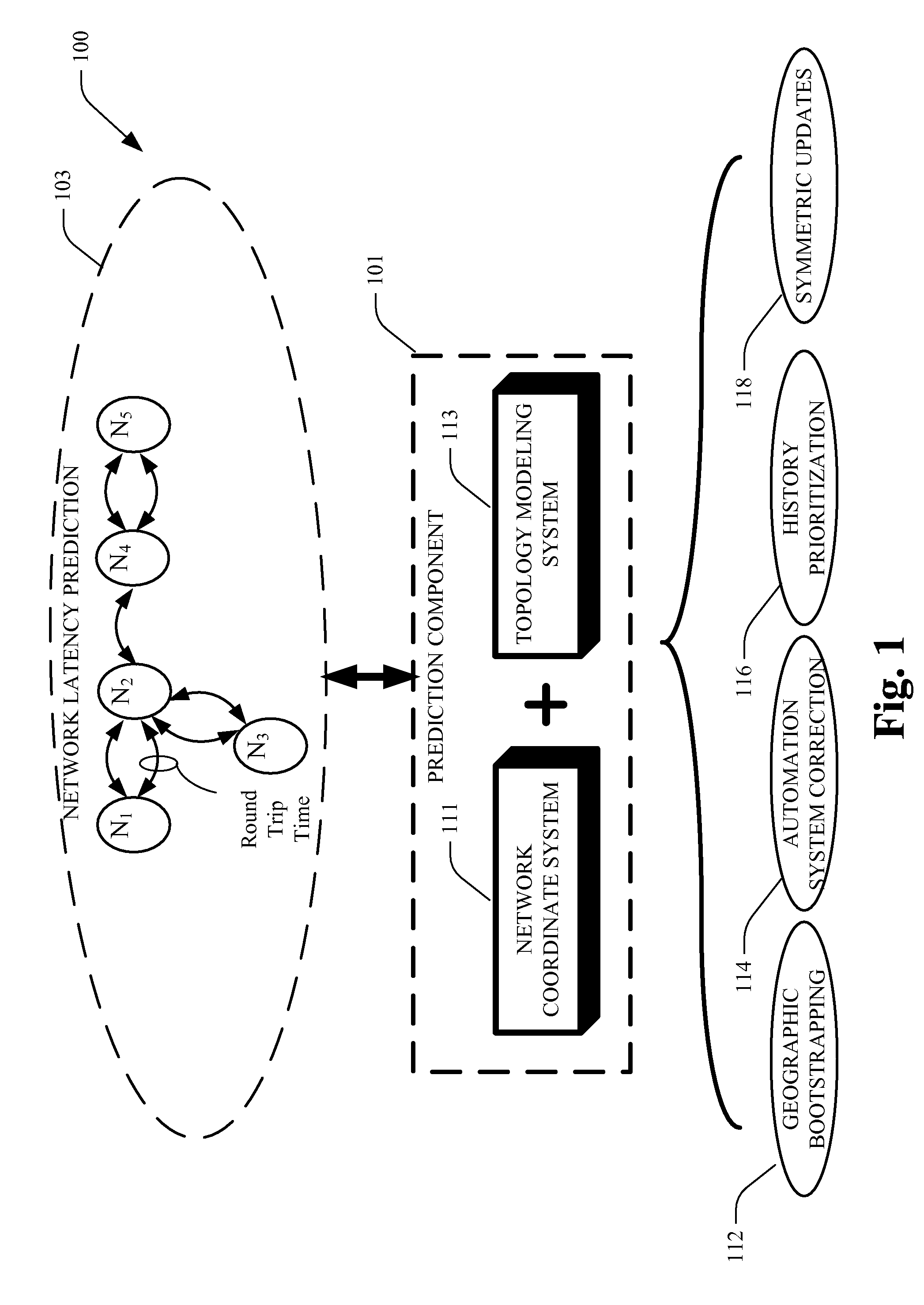
Network coordinate systems using IP information
ActiveUS8144611B2Improves prediction of network latencyIncrease heightError preventionTransmission systemsVirtual coordinate systemsTopology information
Systems and methods that improve predictions of network latency in network coordinate systems (NCS) based on combining Internet topology information therewith. Topology information can be incorporated into the NCS by system / methodologies represented by geographic bootstrapping; autonomous system (AS) correction; history prioritization; symmetric updates or a combination thereof. Such can improve latency estimation between nodes when using a virtual coordinate system based on latency measurements between nodes.
Owner:MICROSOFT TECH LICENSING LLC
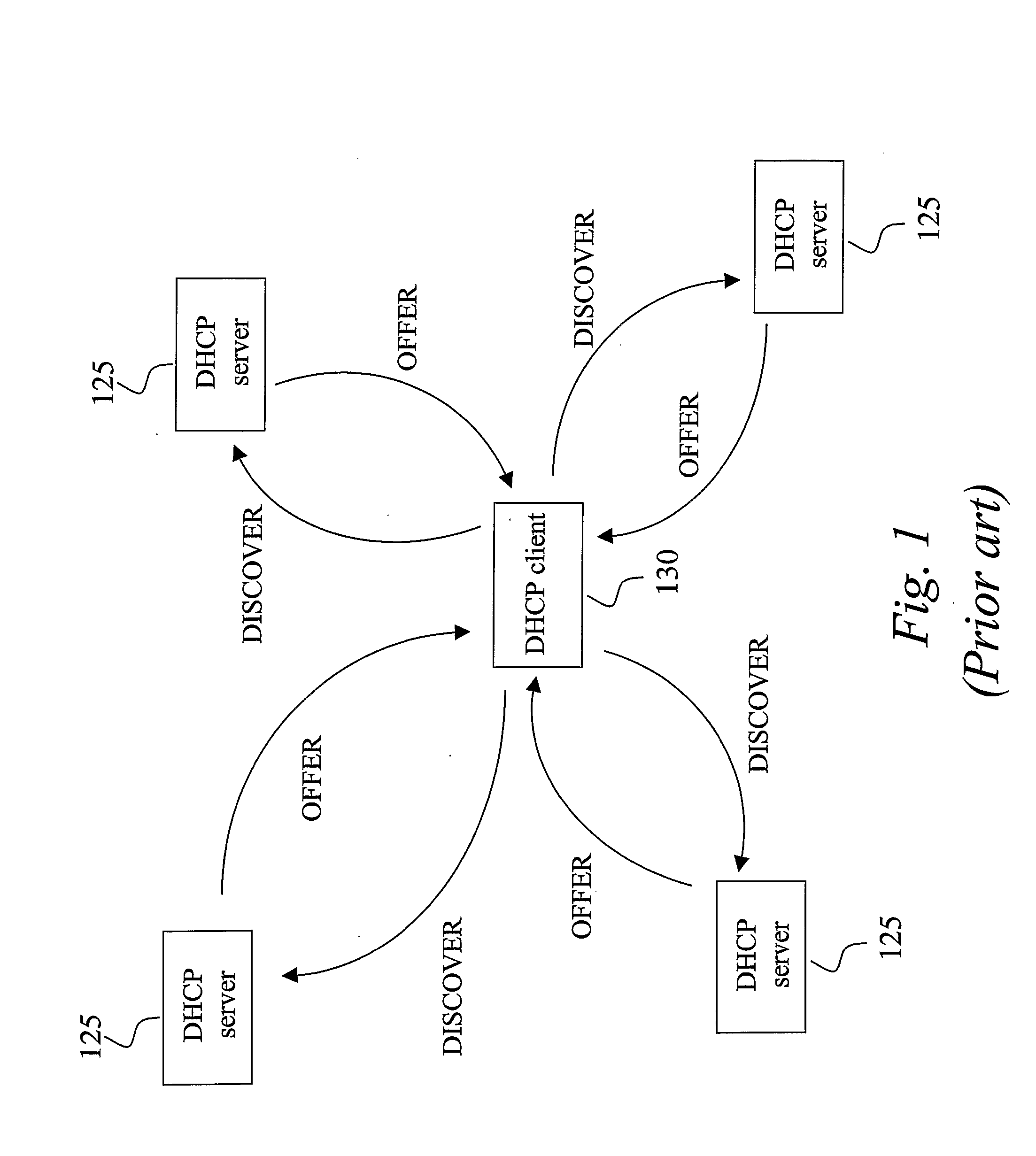
Aaa Support for Dhcp
InactiveUS20080282325A1Minimum of backward compatibility problemFlexible useDigital data processing detailsUser identity/authority verificationKey-agreement protocolClient-side
A basic idea is to use the AAA infrastructure to assign (S3) an appropriate DHCP server to DHCP client for the DHCP service, and transferring DHCP-related information over the AAA infrastructure for authenticating (S1) and authorizing (S4) the DHCP client for DHCP service with the assigned DHCP server. Instead of the more complex DHCP server discovery process known from the prior art, the AAA infrastructure, and more particularly a suitable AAA server or equivalent AAA component, is used for assigning an appropriate DHCP server to the DHCP client. Consequently, there is no longer any mandatory dependency on the DHCP discovery-related messages. The invention preferably provides AAA protocol support for facilitating assignment of appropriate DHCP servers and providing an out-of-band key agreement protocol for DHCP clients and servers by carrying DHCP related information facilitating the bootstrapping of DHCP authentication extension (RFC3118).
Owner:TELEFON AB LM ERICSSON (PUBL)
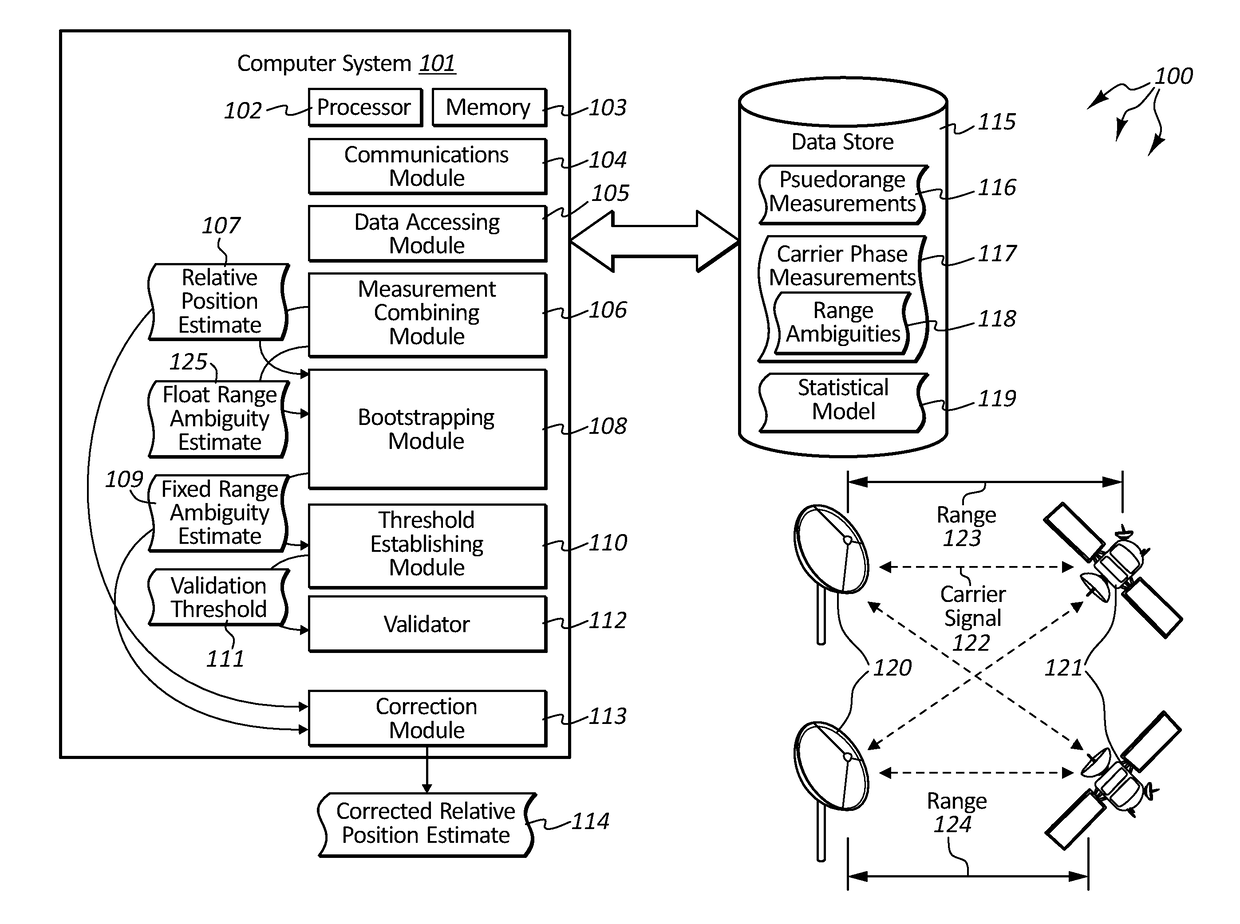
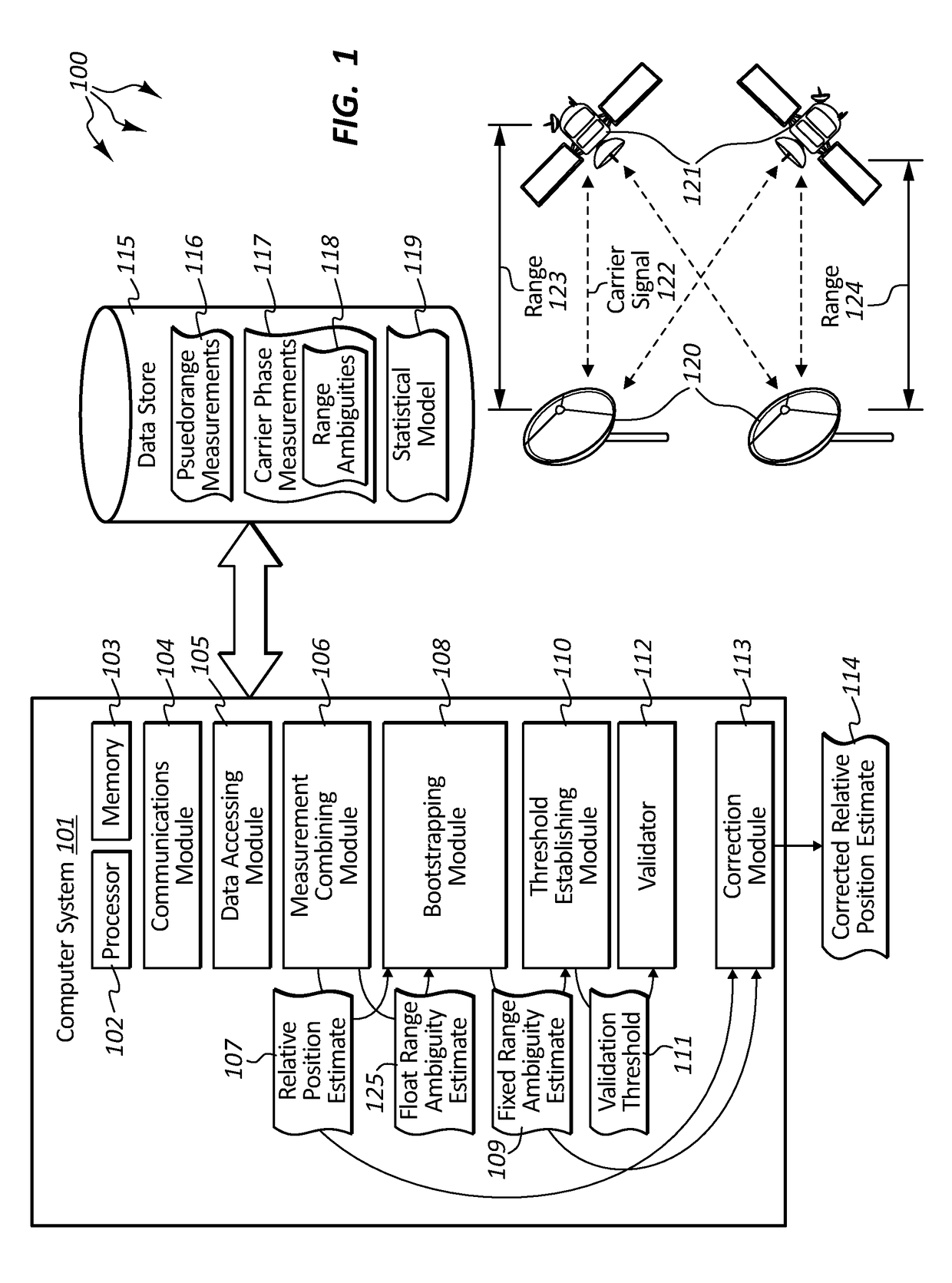
Assured validation of carrier-phase integer ambiguities for safety-of-life applications
Embodiments are directed to performing integer ambiguity validation in carrier phase differential positioning and to calculating a protection level for safety-of-life applications. In one scenario, a computer system accesses double-differenced pseudorange measurements and carrier phase measurements which are combined to produce an estimate of the relative position between receivers. Integer bootstrapping is performed to produce fixed range ambiguity estimates that are integer multiples of a carrier signal wavelength. A validation threshold is then established based on a statistical model of the pseudorange and carrier wave measurements that ensures that a specified probability of correct ambiguity resolution is met. A data-driven validation is initiated on the difference between the float range ambiguity estimates and the fixed range ambiguity estimates to validate the correctness of the fixed range ambiguity estimate. Then, upon determining that the fixed range ambiguity estimates are valid, the estimate of the relative position between the receivers is corrected.
Owner:COHERENT TECHN SERVICES
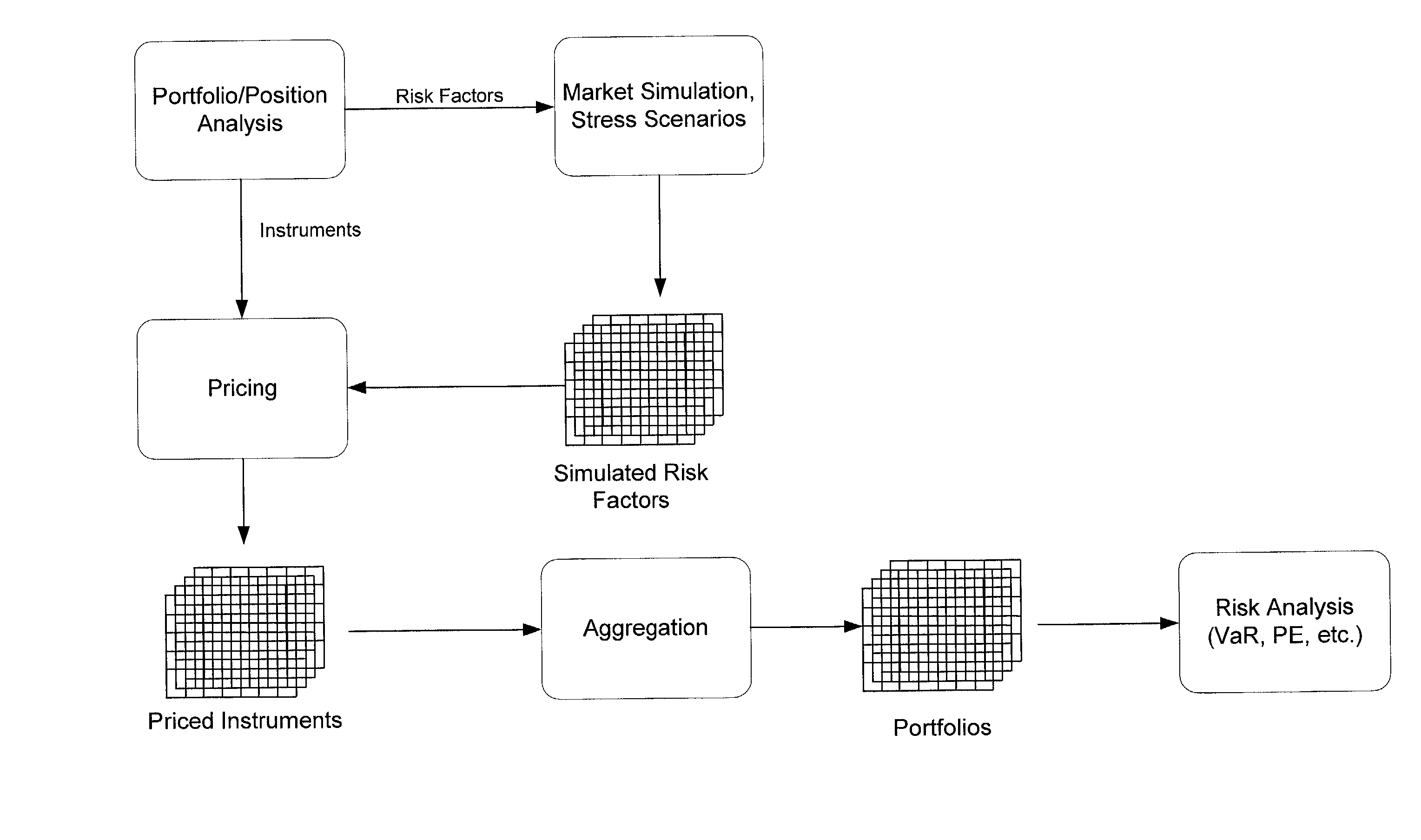
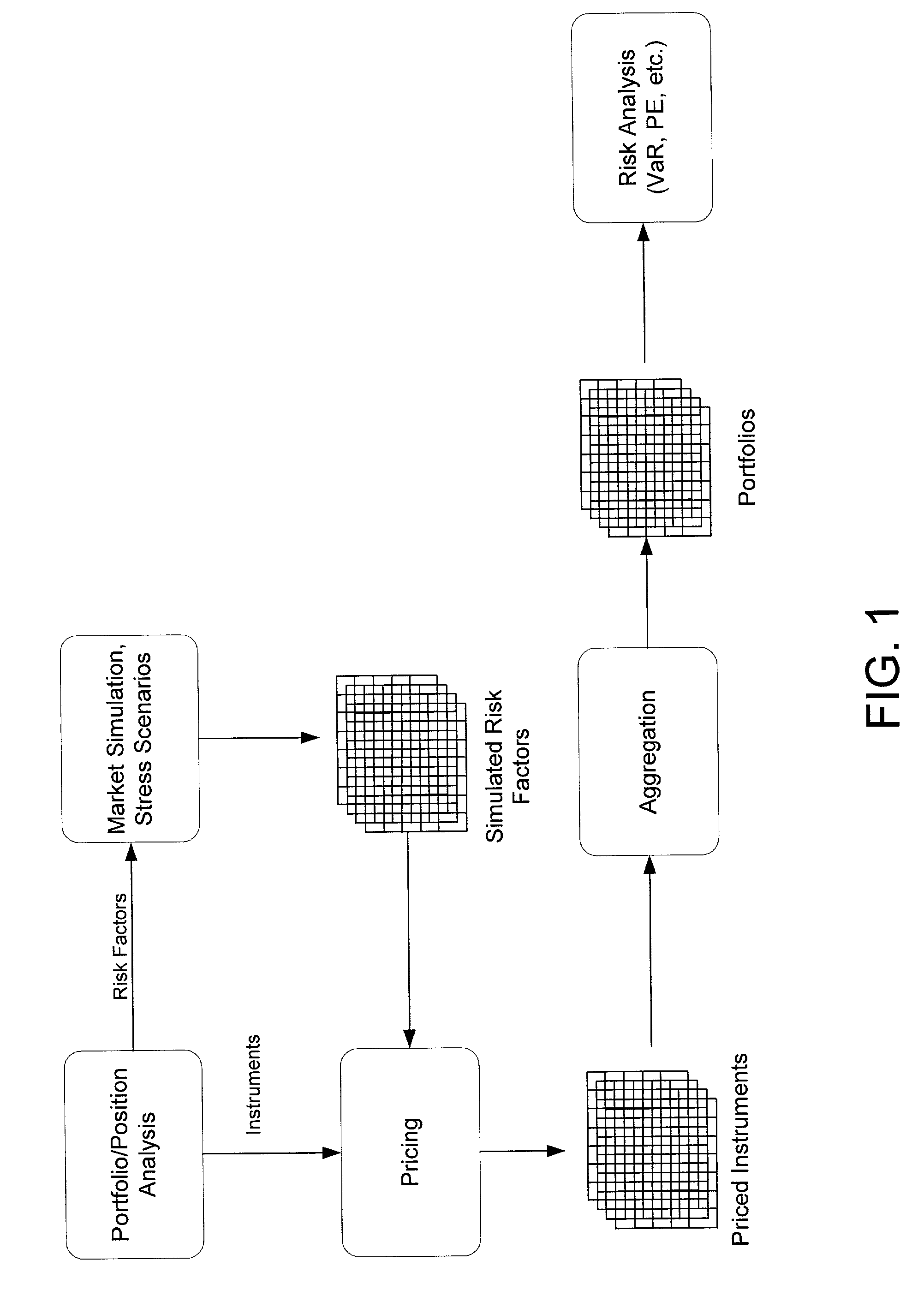
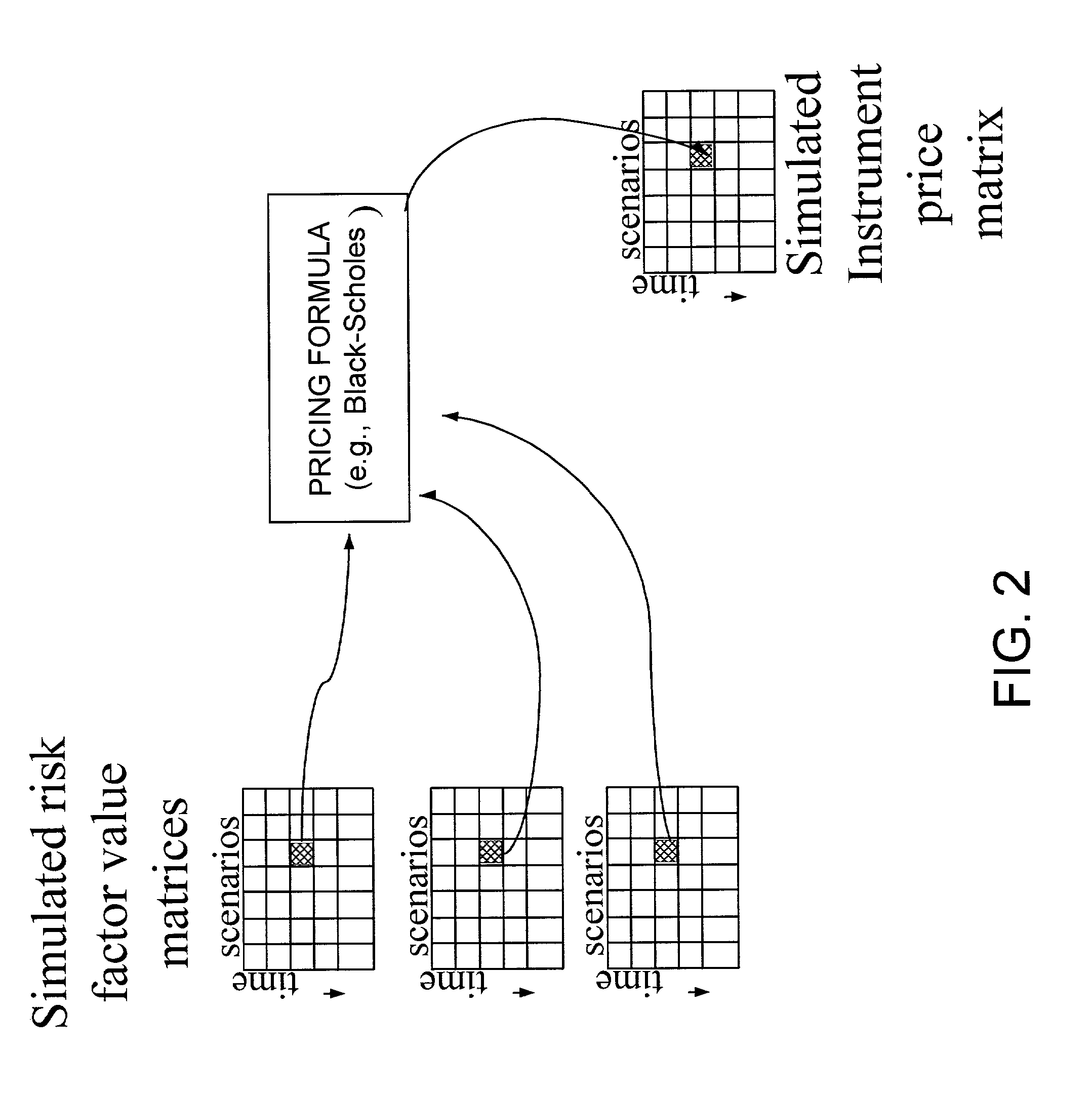
Method and system for simulating risk factors in parametric models using risk neutral historical bootstrapping
An improved method for simulating noise-varying risk factor values in a parametric simulation comprises analyzing historical data to determine the actual value of the risk factors and other attributes in the model and using this data to generate historical residual values which reproduces the historical price when used in the model with corresponding historical attribute values. The set of historical residual values is standardized and can be bootstrapped to increase the number of members in the set or vary the sets properties. Values of the historical residuals are then selected, e.g., at random, and used in place of the random noise components to produce simulated risk factor values which are used in the parametric model to simulate the evolution of the instrument price.
Owner:GOLDMAN SACHS & CO LLC
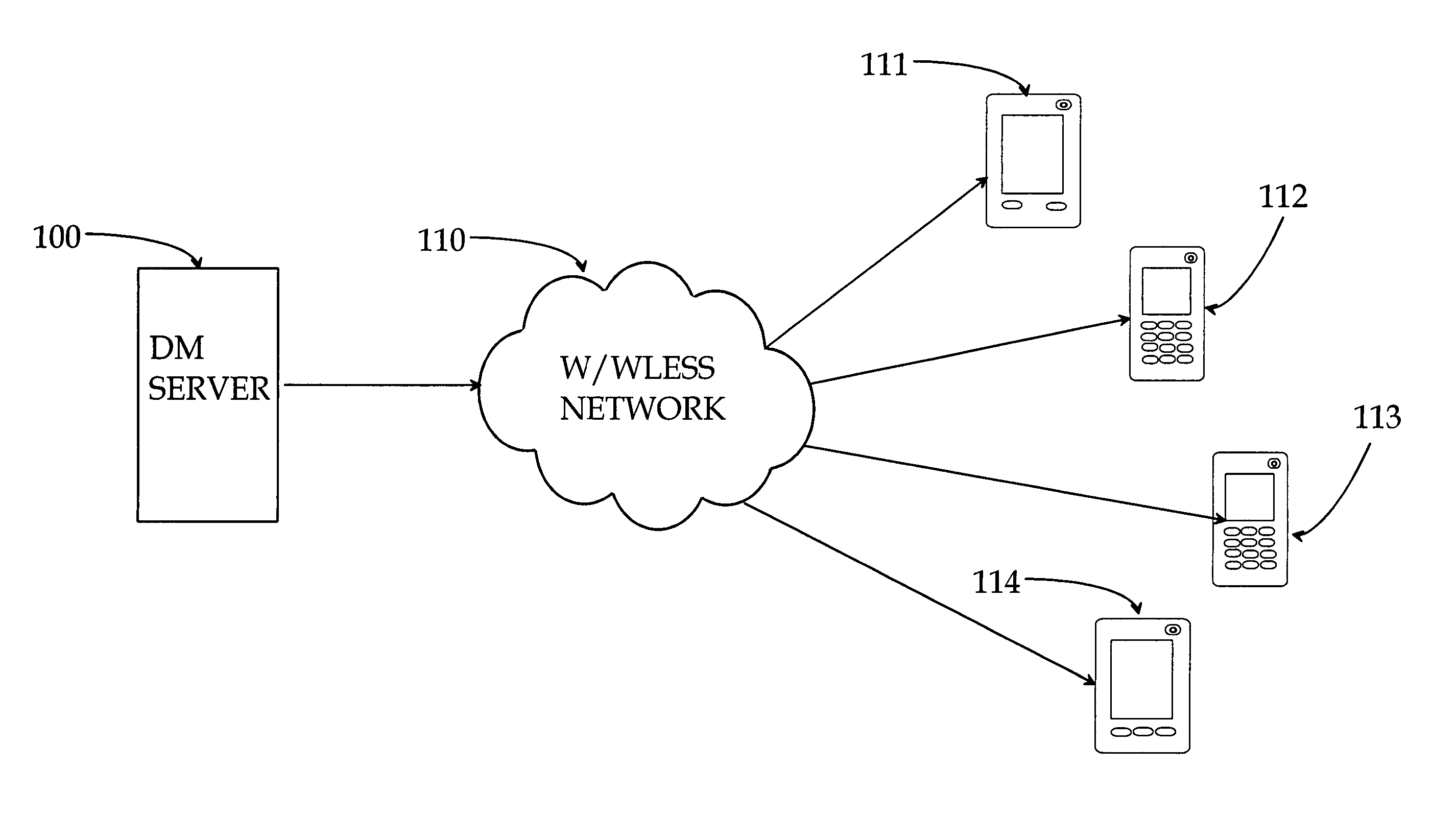
Device management with configuration information
ActiveUS20060271659A1Simplify the configuration processReduce communicationDigital computer detailsTransmissionClient-sideInformation needs
The invention relates to device management and to information needed for bootstrapping and initiation. The bootstrapping information and initiation information are sent in one message, wherein the client receives them both. According to the state of the client, one of the informations is selected and used.
Owner:NOKIA TECHNOLOGLES OY
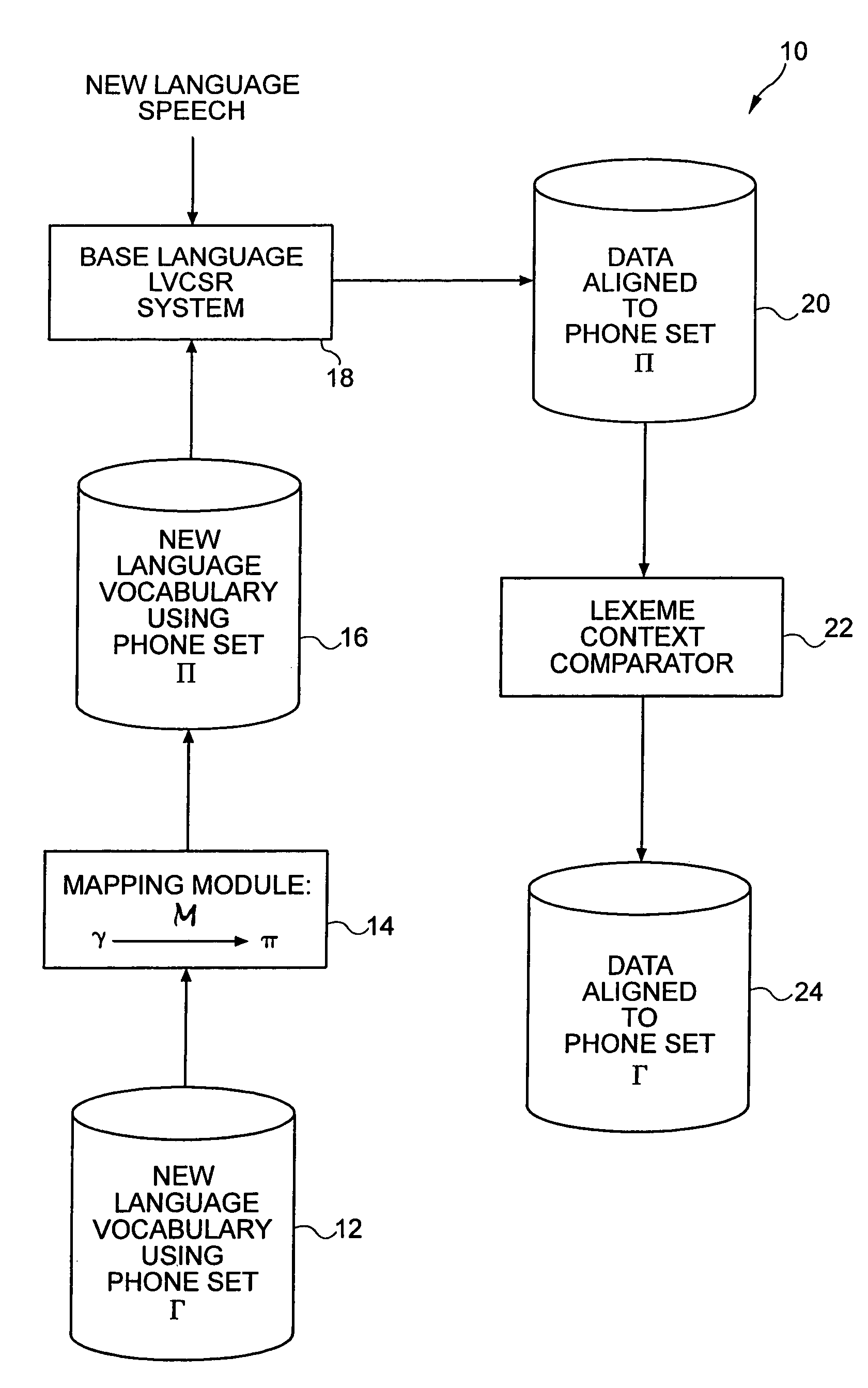
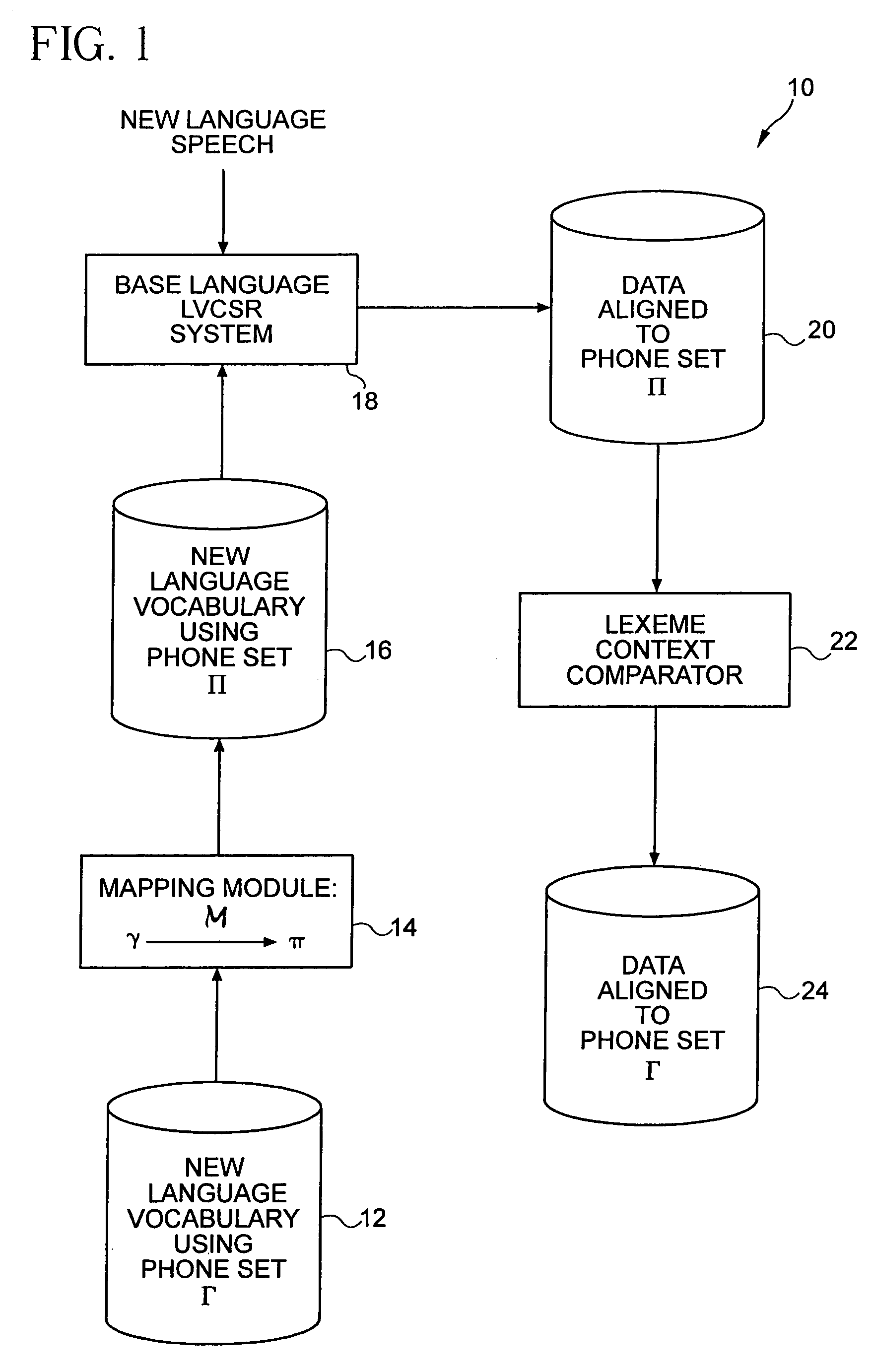
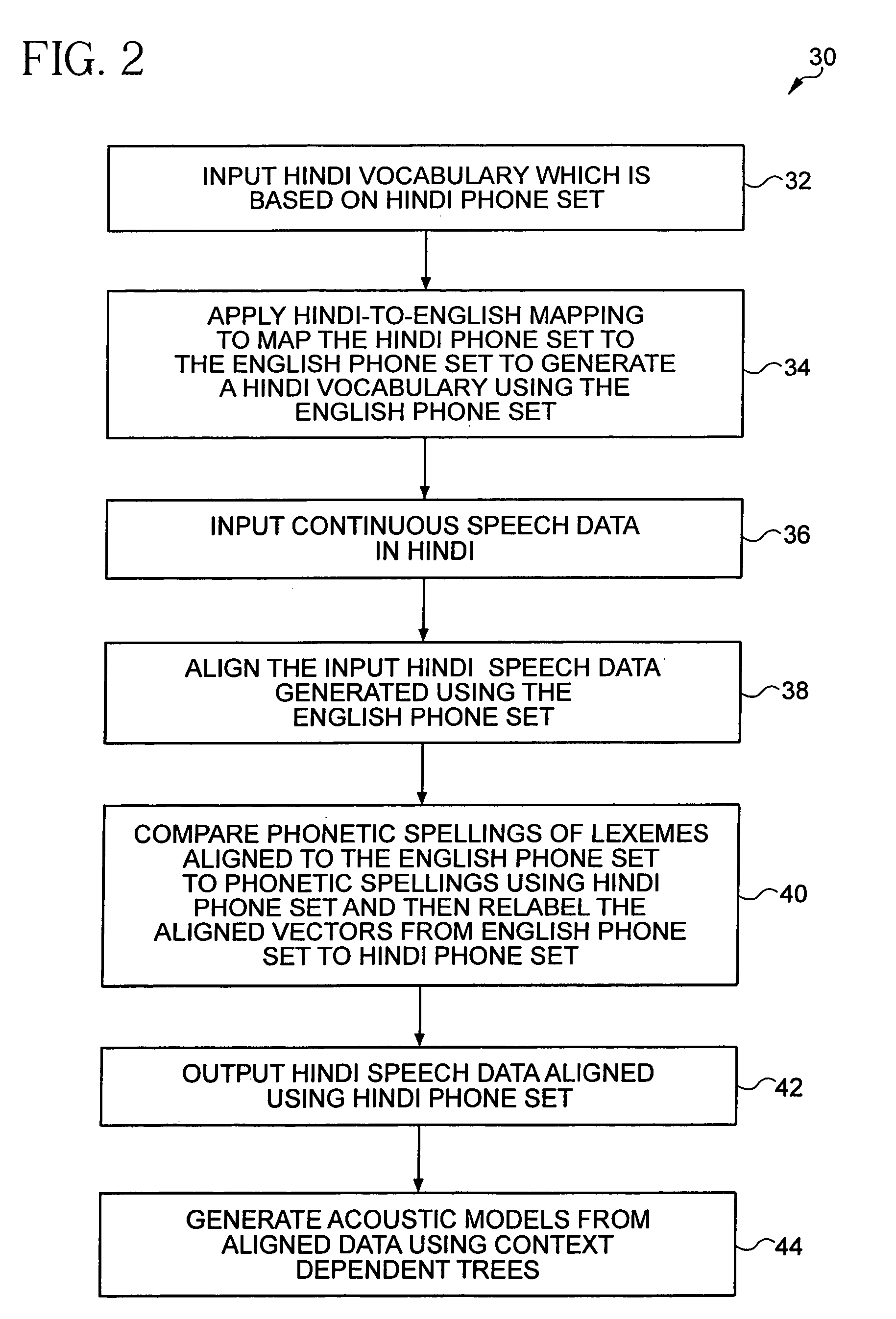
Language context dependent data labeling
Bootstrapping of a system from one language to another often works well when the two languages share the similar acoustic space. However, when the new language has sounds that do not occur in the language from which the bootstrapping is to be done, bootstrapping does not produce good initial models and the new language data is not properly aligned to these models. The present invention provides techniques to generate context dependent labeling of the new language data using the recognition system of another language. Then, this labeled data is used to generate models for the new language phones.
Owner:NUANCE COMM INC
Authentication and secure channel setup for communication handoff scenarios
Persistent communication layer credentials generated on a persistent communication layer at one network may be leveraged to perform authentication on another. For example, the persistent communication layer credentials may include application-layer credentials derived on an application layer. The application-layer credentials may be used to establish authentication credentials for authenticating a mobile device for access to services at a network server. The authentication credentials may be derived from the application-layer credentials of another network to enable a seamless handoff from one network to another. The authentication credentials may be derived from the application-layer credentials using reverse bootstrapping or other key derivation functions. The mobile device and / or network entity to which the mobile device is being authenticated may enable communication of authentication information between the communication layers to enable authentication of a device using multiple communication layers.
Owner:INTERDIGITAL PATENT HLDG INC
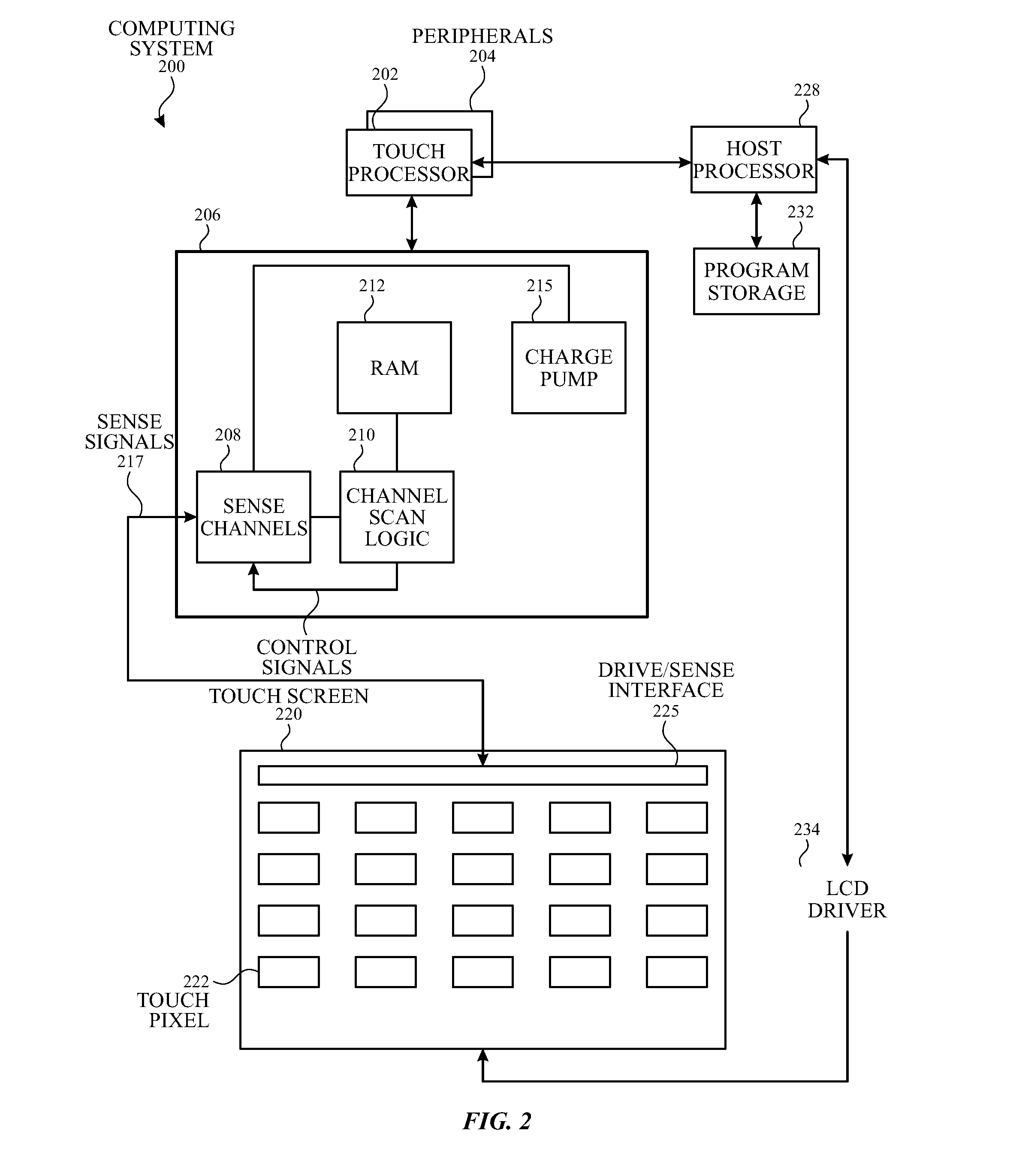
Charge pump having ac and DC outputs for touch panel bootstrapping and substrate biasing
ActiveUS20160241139A1Digital data processing detailsSemiconductor/solid-state device detailsTouch panelCapacitor
A charge pump that can be configured to operate in a first mode and a second mode is disclosed. The charge pump can comprise a charging capacitor coupled to a first node and configured to transfer a first DC voltage to the first node. The charge pump can also comprise a first output node and a second output node coupled to the first node. During the first mode, the first output node can be configured to output a second DC voltage based on the first DC voltage, and the second output node can be configured to output a third DC voltage based on the first DC voltage. During the second mode, the first output node can be configured to output the second DC voltage, and the second output node can be configured to output an AC voltage, the AC voltage being offset by the third DC voltage.
Owner:APPLE INC
Low-voltage asynchronous successive approximation analog-to-digital converter and conversion method
InactiveCN102386924AReduce design difficultySimple power consumptionAnalogue/digital conversionElectric signal transmission systemsCapacitanceLow voltage
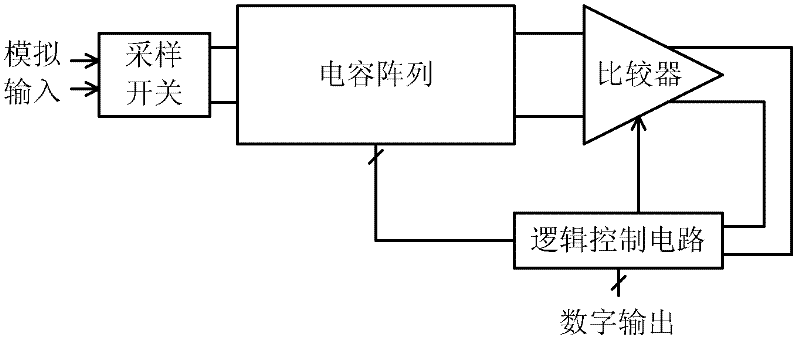
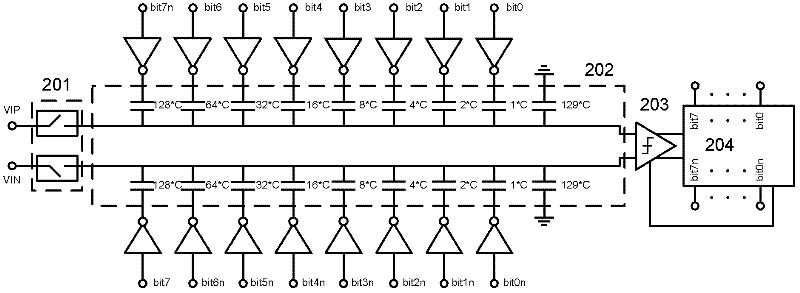
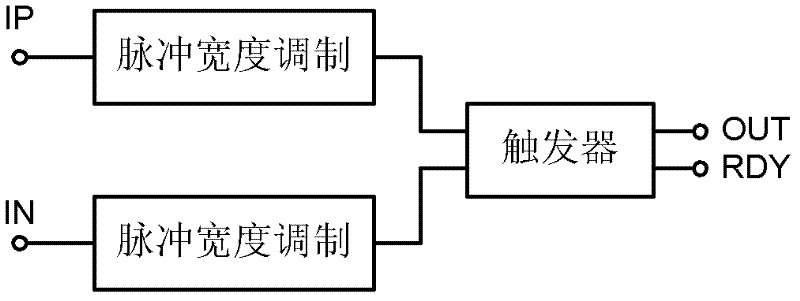
The invention discloses a low-voltage asynchronous successive approximation analog-to-digital converter and a conversion method. The analog-to-digital converter comprises: a sampling network, a capacitance array pulse width modulation time domain comparator and a logic control circuit. The sampling network of a capacitor array uses a bootstrapping switch. A size of the capacitance in the capacitance array is decreased progressively as a two times relation. All top crowns of capacitors and the bootstrapping switch are connected and output to the comparator. The time domain comparator comprises: a pulse width modulation unit and a trigger. And the time domain comparator is used to compare sizes of output voltages of the capacitor array. In the logic control circuit, the asynchronous sequence is used to make the capacitor array complete switching successively. A power consumption efficiency of the analog-to-digital converter can be effectively improved. A peripheral circuit demand can be reduced. The analog-to-digital converter and the method can be used in an advanced-technology ultra low power supply voltage design.
Owner:BEIJING UNIV OF TECH
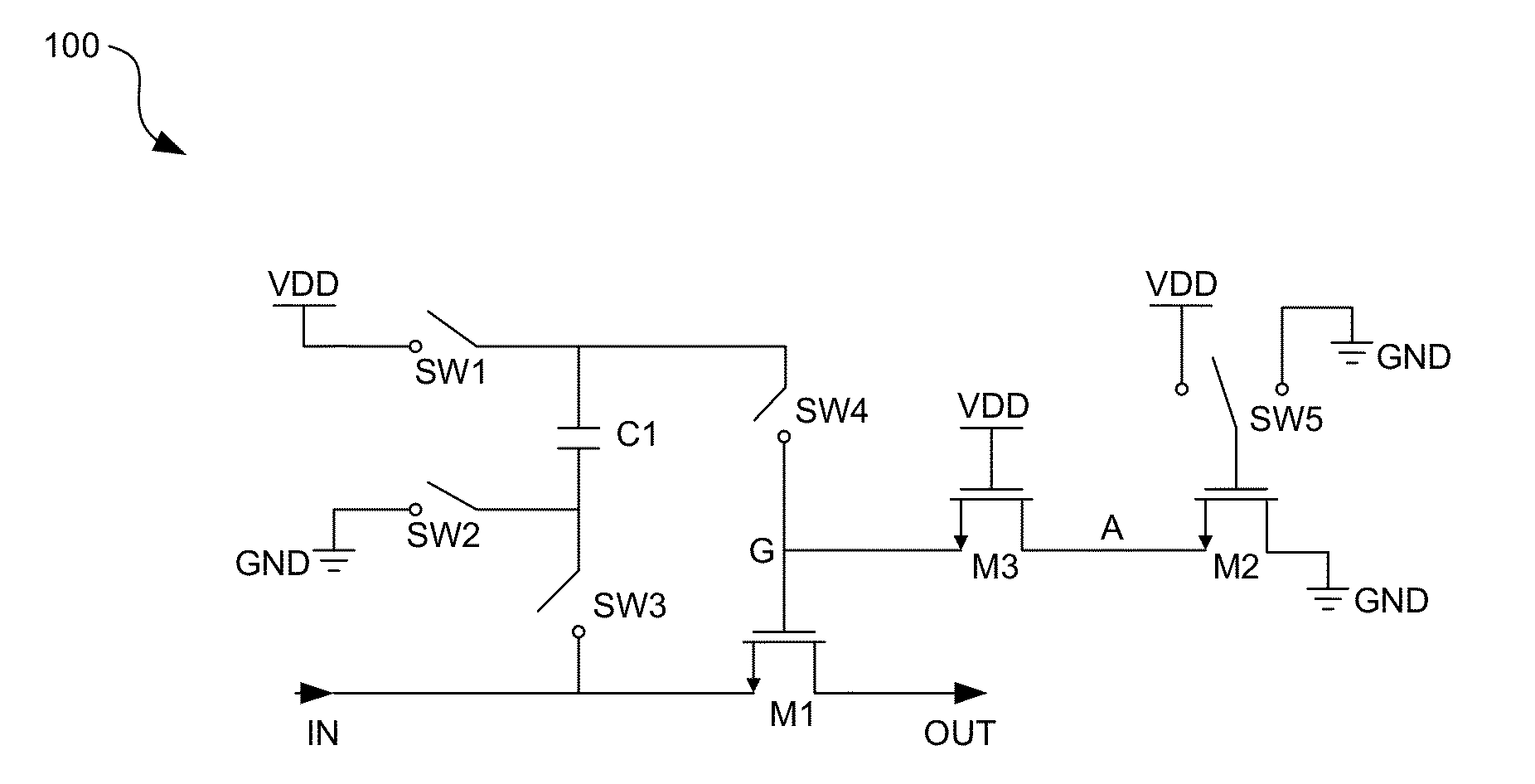
Method and system for reliable bootstrapping switches
Methods and systems for reliable bootstrapping switches may comprise sampling a received signal with a bootstrapping switch, where the bootstrapping switch comprises a switching metal-oxide semiconductor (MOS) transistor having a pull-down path coupled to a gate terminal of the switching MOS transistor. The pull-down path includes a diode-connected MOS transistor coupled in parallel with a second MOS transistor that couples the gate terminal of the switching MOS transistor to ground via third and fourth MOS transistors when the switching MOS transistor is in an OFF state. The third and fourth MOS transistors may be in series with the second MOS transistor. A gate terminal of the fourth transistor may be switched from ground to a supply voltage, VDD, to activate the pull-down path. A capacitor may be coupled between gate and source terminals of the switching MOS transistor to switch the switching MOS transistor to an ON state.
Owner:MAXLINEAR INC
Bootstrapping algorithm for extracting viewpoint evaluation objects based on dependence relationship template
ActiveCN106257455AImprove the extraction effectAvoid noiseSemantic analysisData miningPattern recognitionViewpoints
The invention relates to a Bootstrapping algorithm for extracting viewpoint evaluation objects based on a dependence relationship template. The grammar and semantic relationships between emotion words and viewpoint evaluation object words are considered, the dependence relationship template between the viewpoint evaluation object words and the emotion words is constructed, and the viewpoint evaluation objects are extracted with the Bootstrapping method. By means of the Bootstrapping algorithm, noise caused by the method that evaluation objects are extracted directly by a vocabulary context is avoided, and the extracting performance of the viewpoint evaluation objects is improved.
Owner:福州果集信息科技有限公司
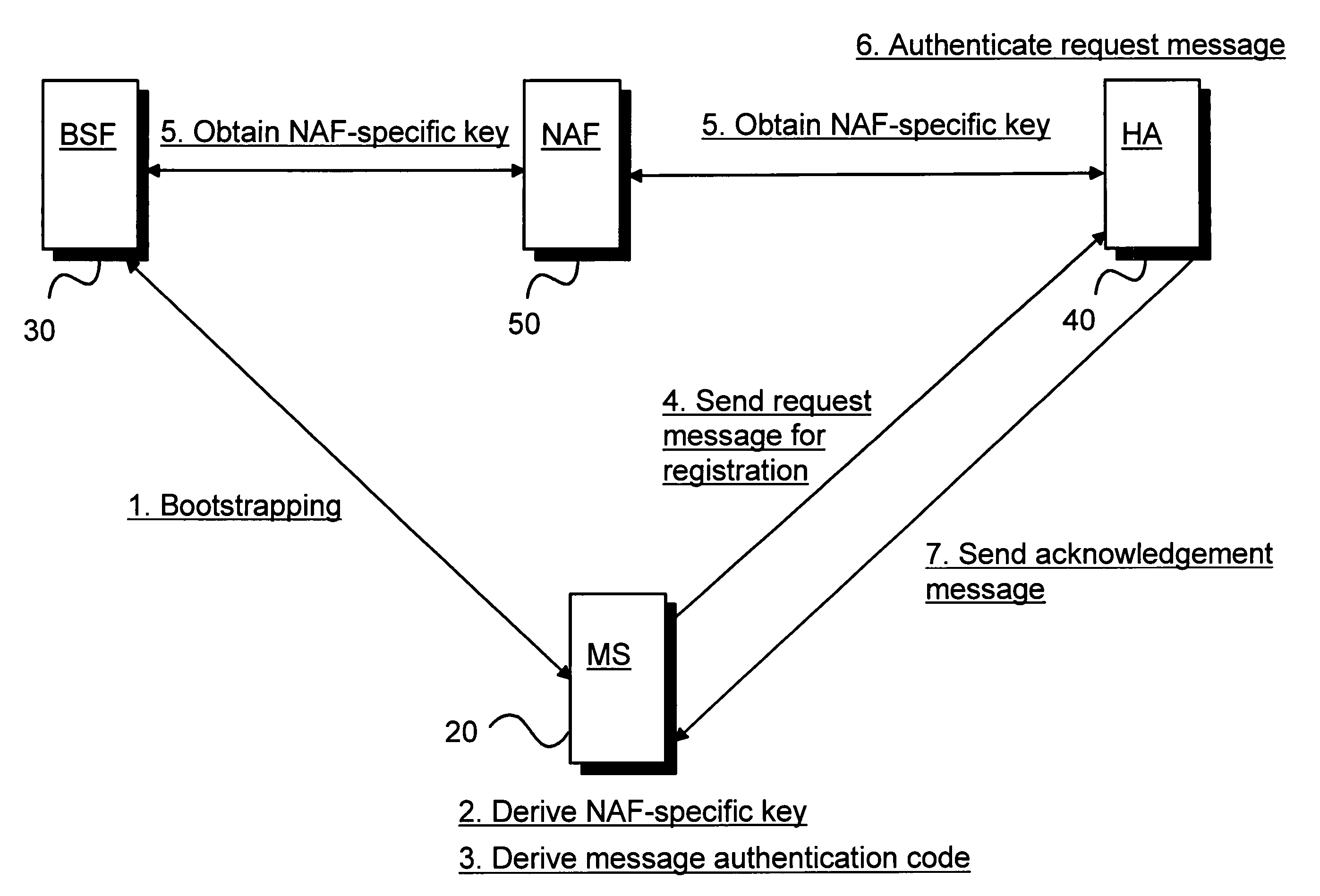
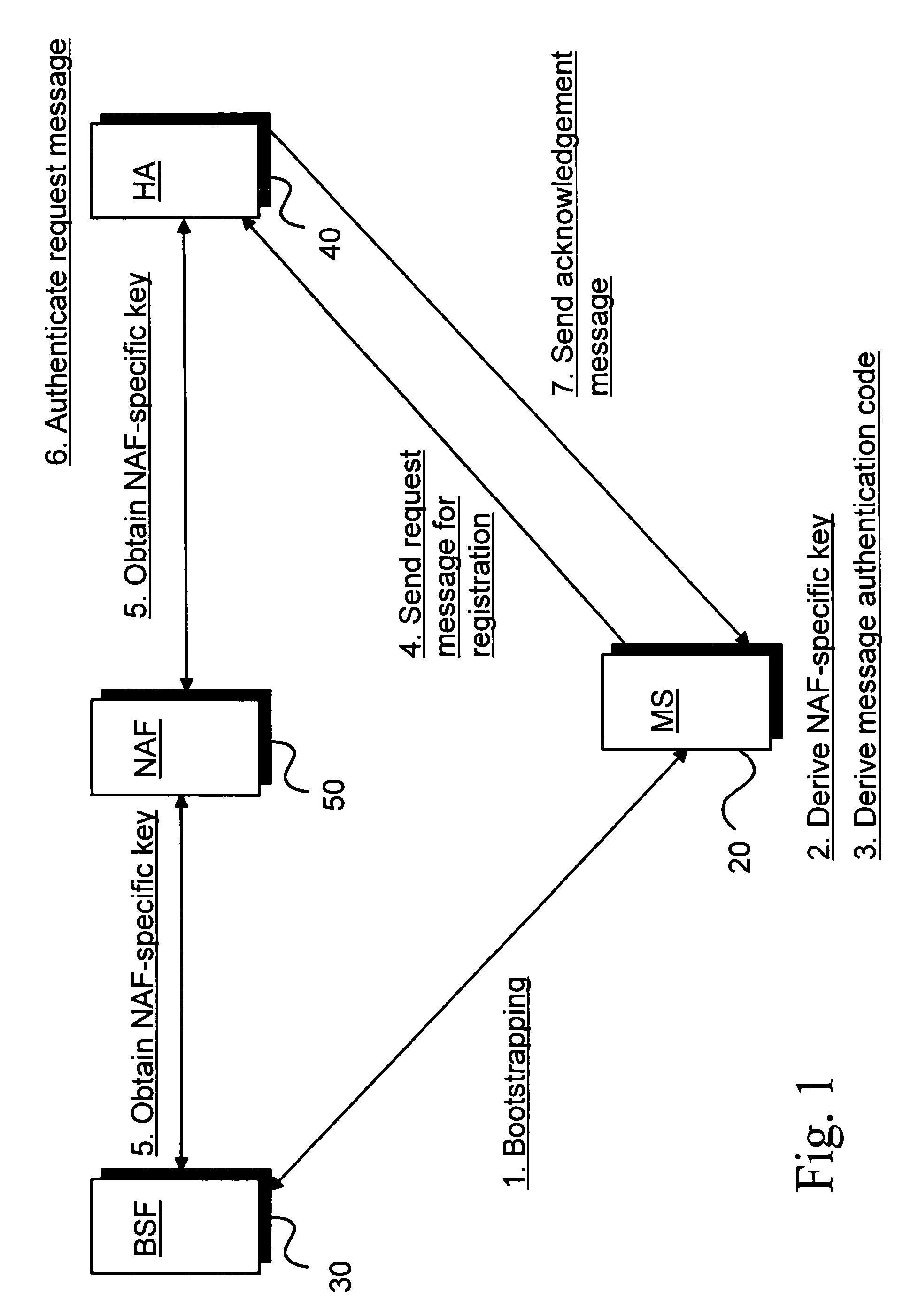
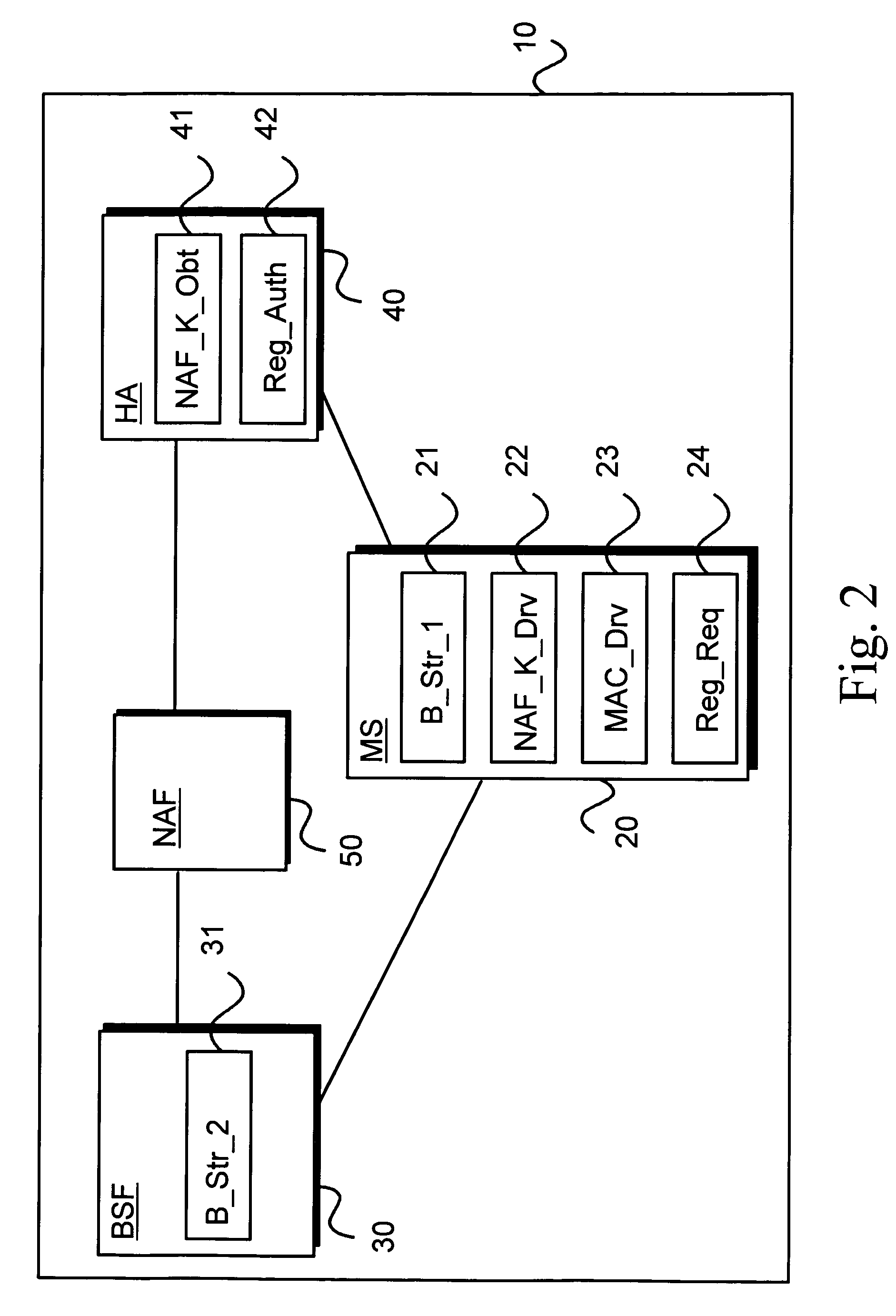
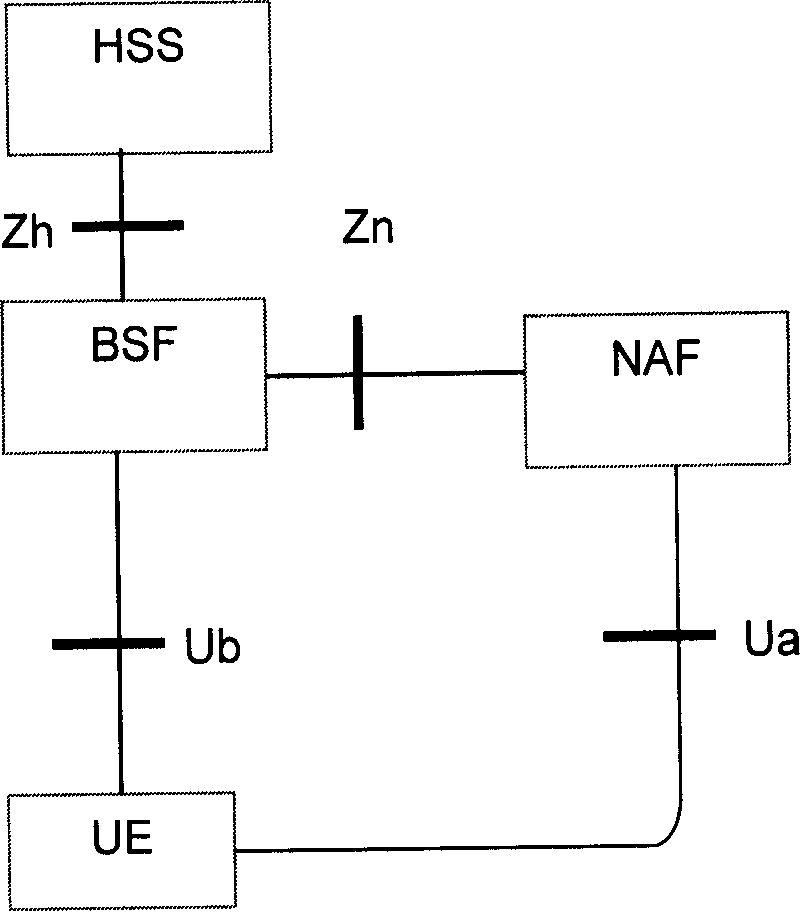
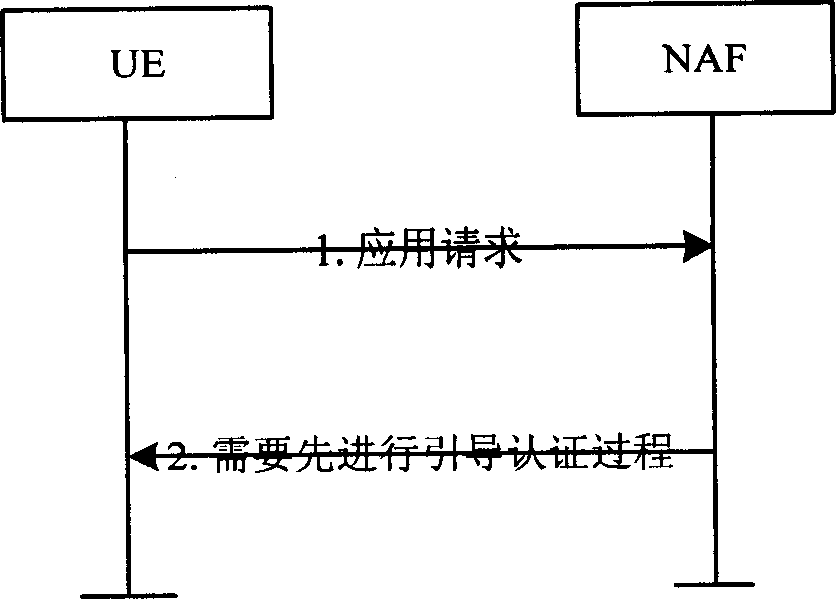
Utilizing generic authentication architecture for mobile internet protocol key distribution
The invention allows utilizing Generic Authentication Architecture for Mobile Internet Protocol key distribution. A Generic Authentication Architecture bootstrapping is performed between a mobile terminal device and a Bootstrapping Server Function. In an embodiment a resulting Bootstrapping Transaction Identifier is sent to a Home Agent which uses it to obtain a Home Agent specific key to be used in authenticating a Mobile Internet Protocol Registration Request.
Owner:WSOU INVESTMENTS LLC
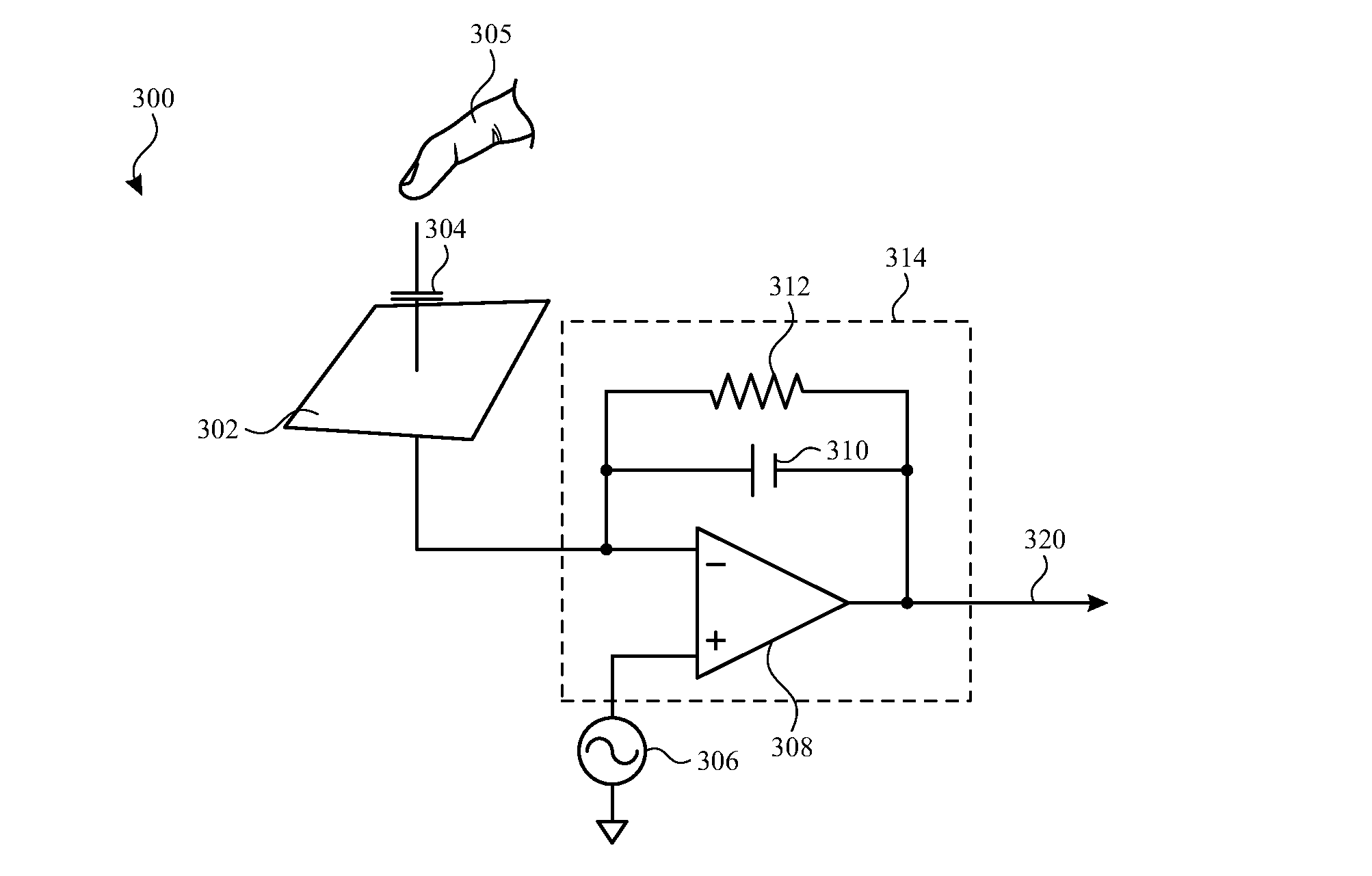
High precision follower device with zero power, zero noise slew enhancement circuit
InactiveUS20100214020A1Increase conversion rateMinimizing power outputAmplifier combinationsAmplififers with field-effect devicesAudio power amplifierTerminal equipment
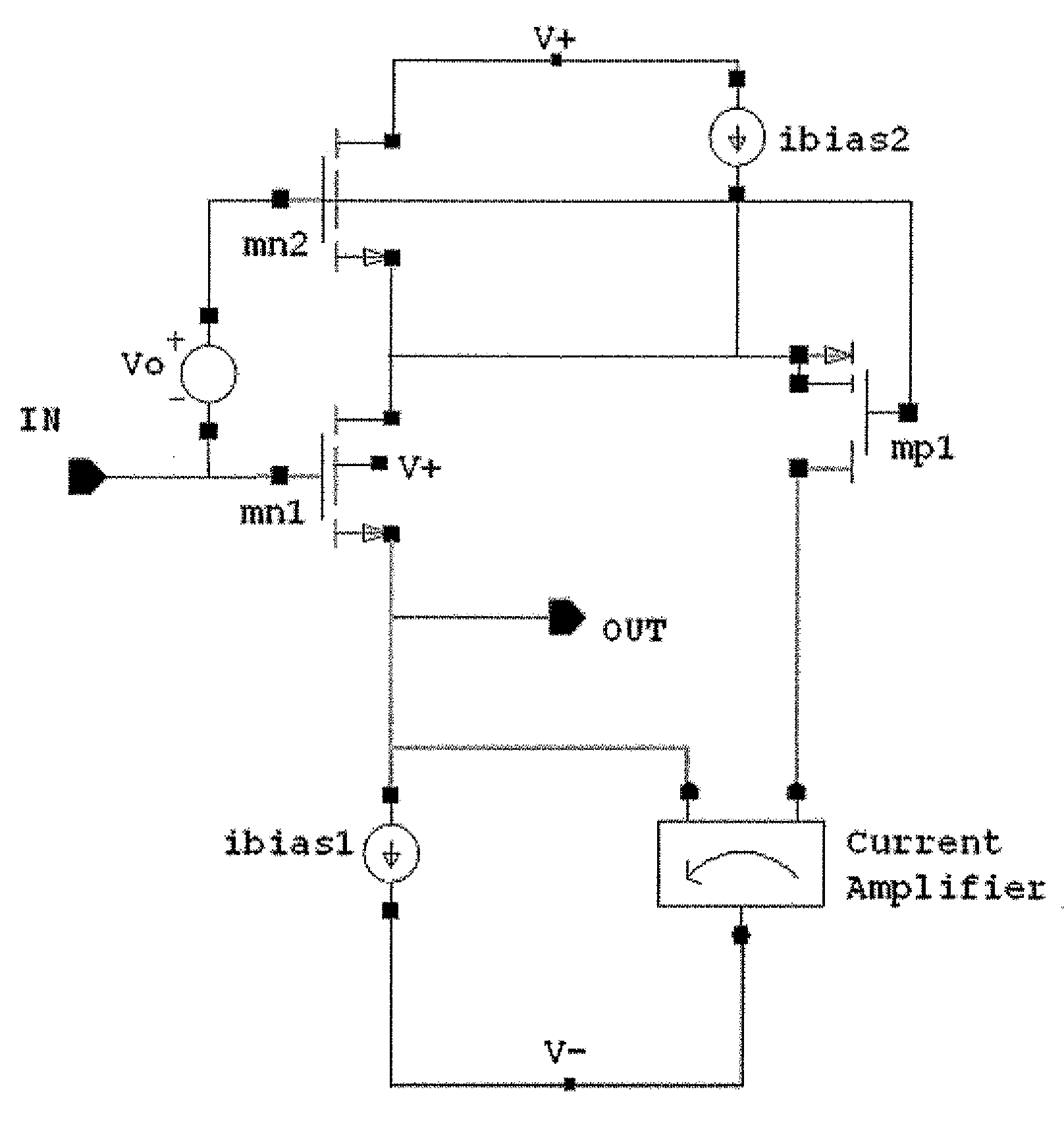
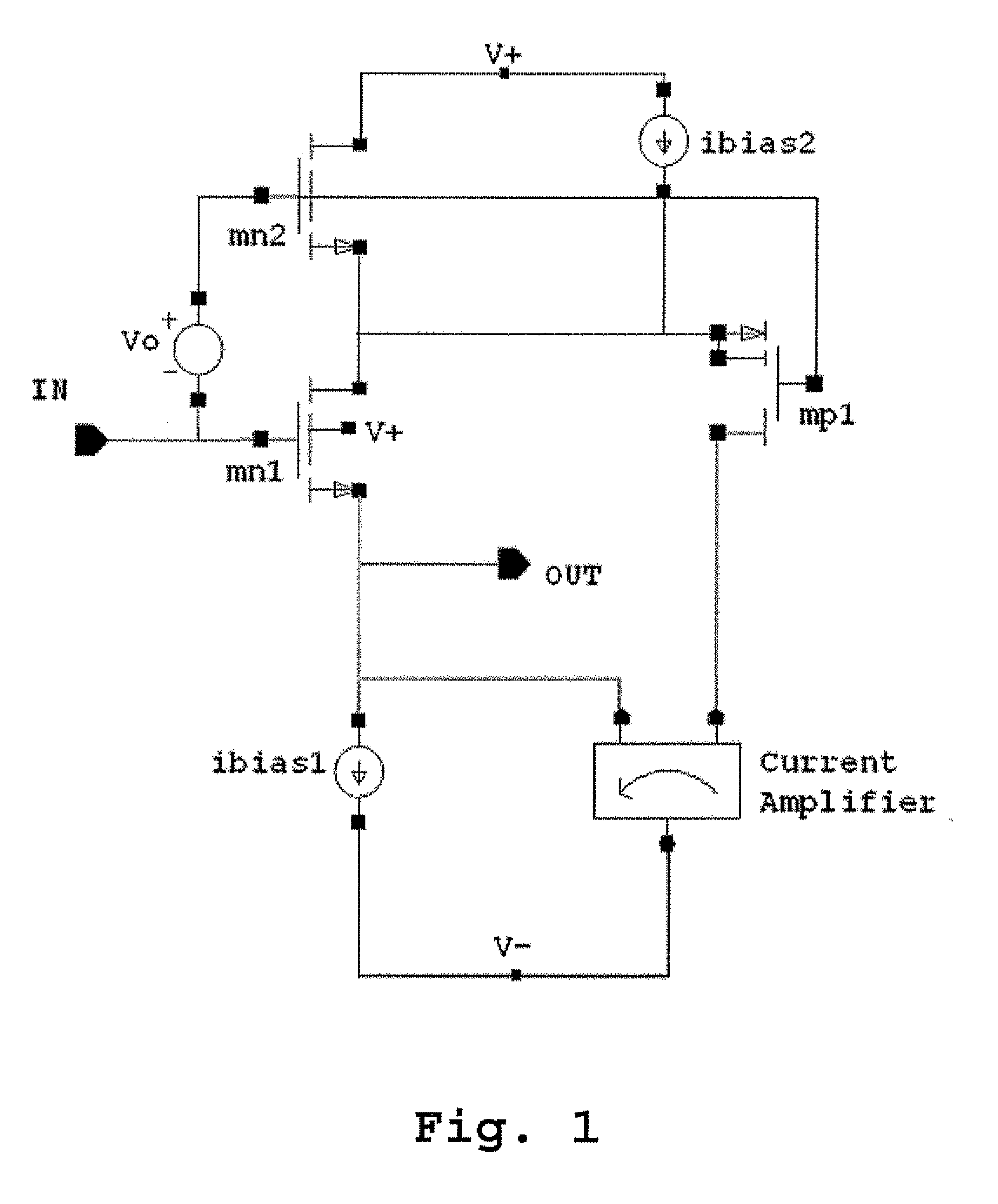
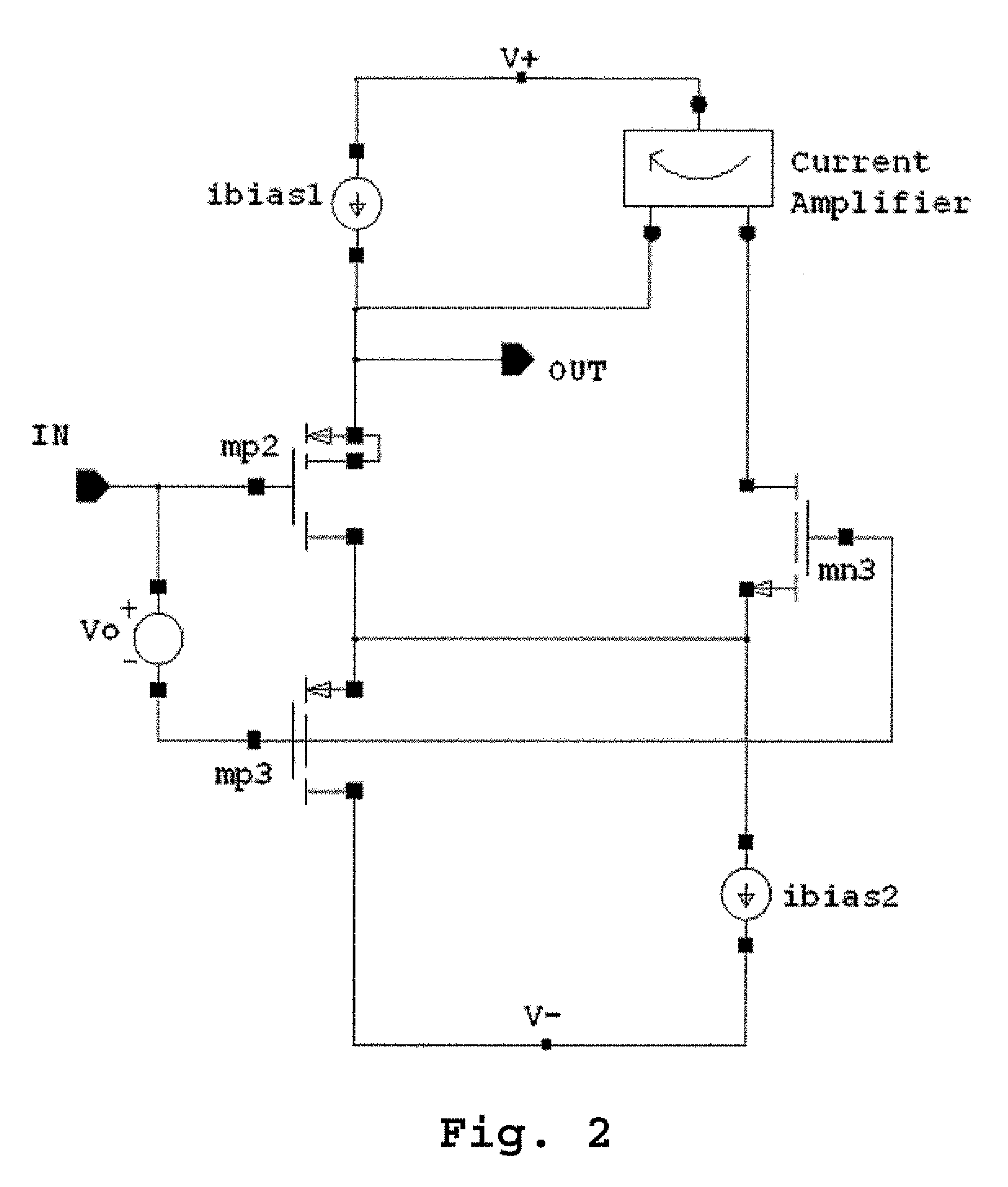
A high performance follower device coupled with a slew enhancement circuit includes an amplifier circuit containing a follower device connected to a three-terminal device, whereupon current drawn through the three-terminal device is amplified through a current amplifier and sent to the source terminal of the follower device to stabilize the output voltage when the input signal is changed rapidly or if the output voltage is disturbed by a changing output load. The presence of a cascode device also allows for the bootstrapping of the follower device.
Owner:ANALOG DEVICES INC
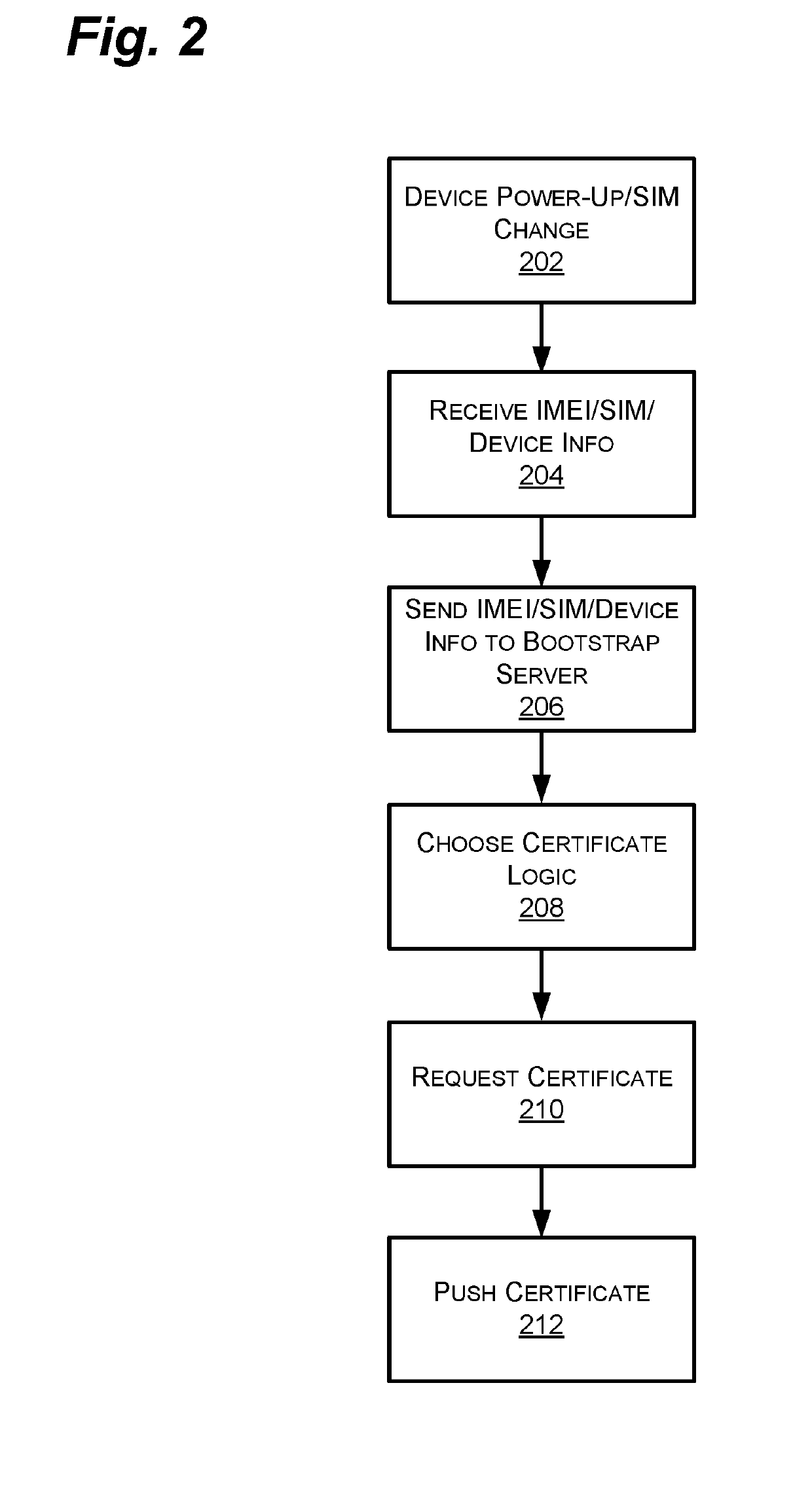
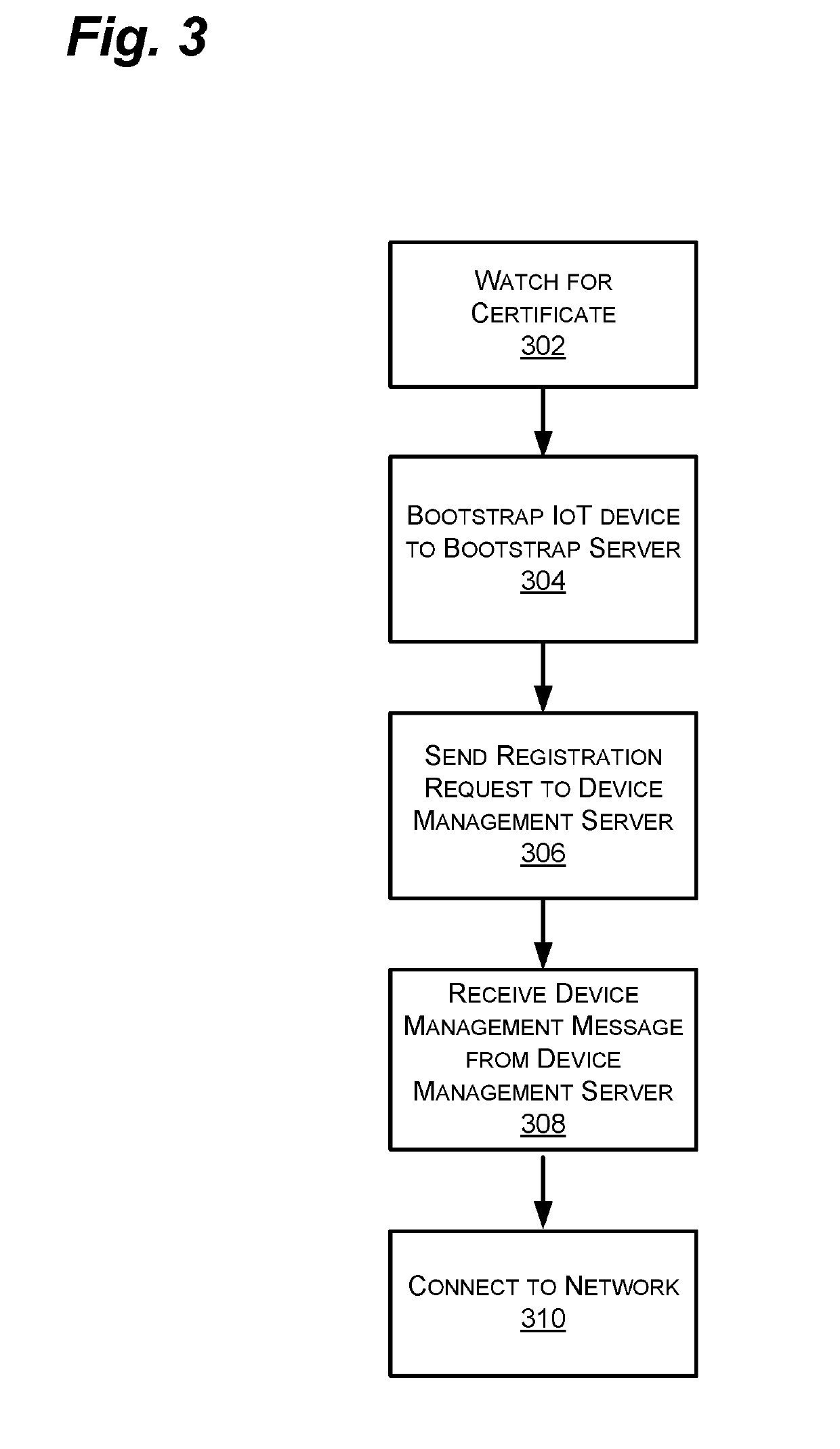
TOUCHLESS SECURE BOOTSTRAPPING OF IoT DEVICES
Systems and methods for automatically and securely connecting internet of things (IoT) devices to one or more networks. The system can include a bootstrap server and a configuration database to enable configuration settings for a plurality of IoT devices to be stored and accessed. The bootstrap server can configure an appropriate digital security certificate for an IoT device requesting access to the network. The bootstrap server can then provide a bootstrapping message to the IoT device including the digital certificate and other data. A device management server can then provide a device management message to the IoT device to provide one or more of a final configuration, applications, and software or firmware updates. The system replaces the current system, which is substantially manual, with an essentially “touchless” system that requires little or no input from the user or service provider technicians.
Owner:T MOBILE USA
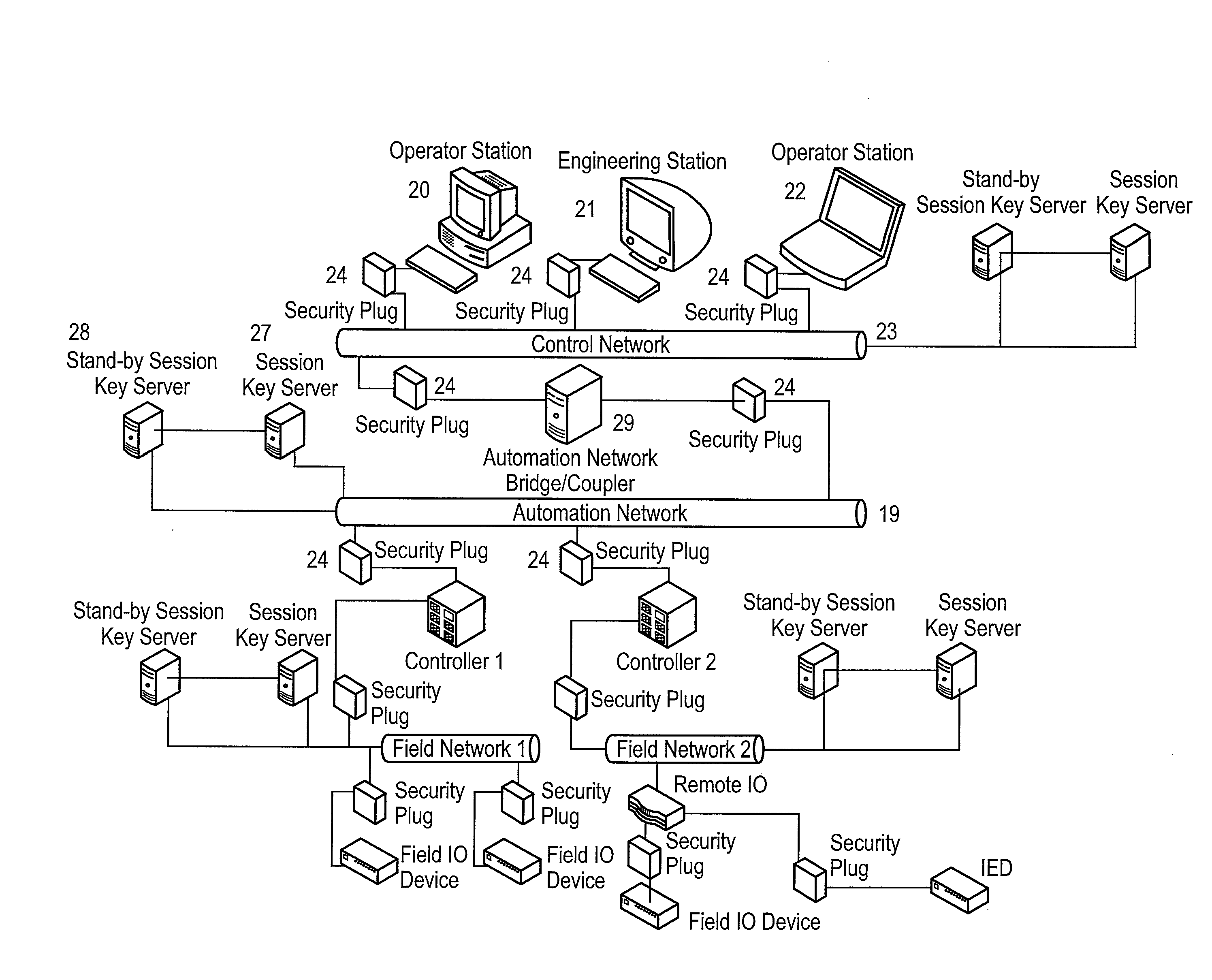
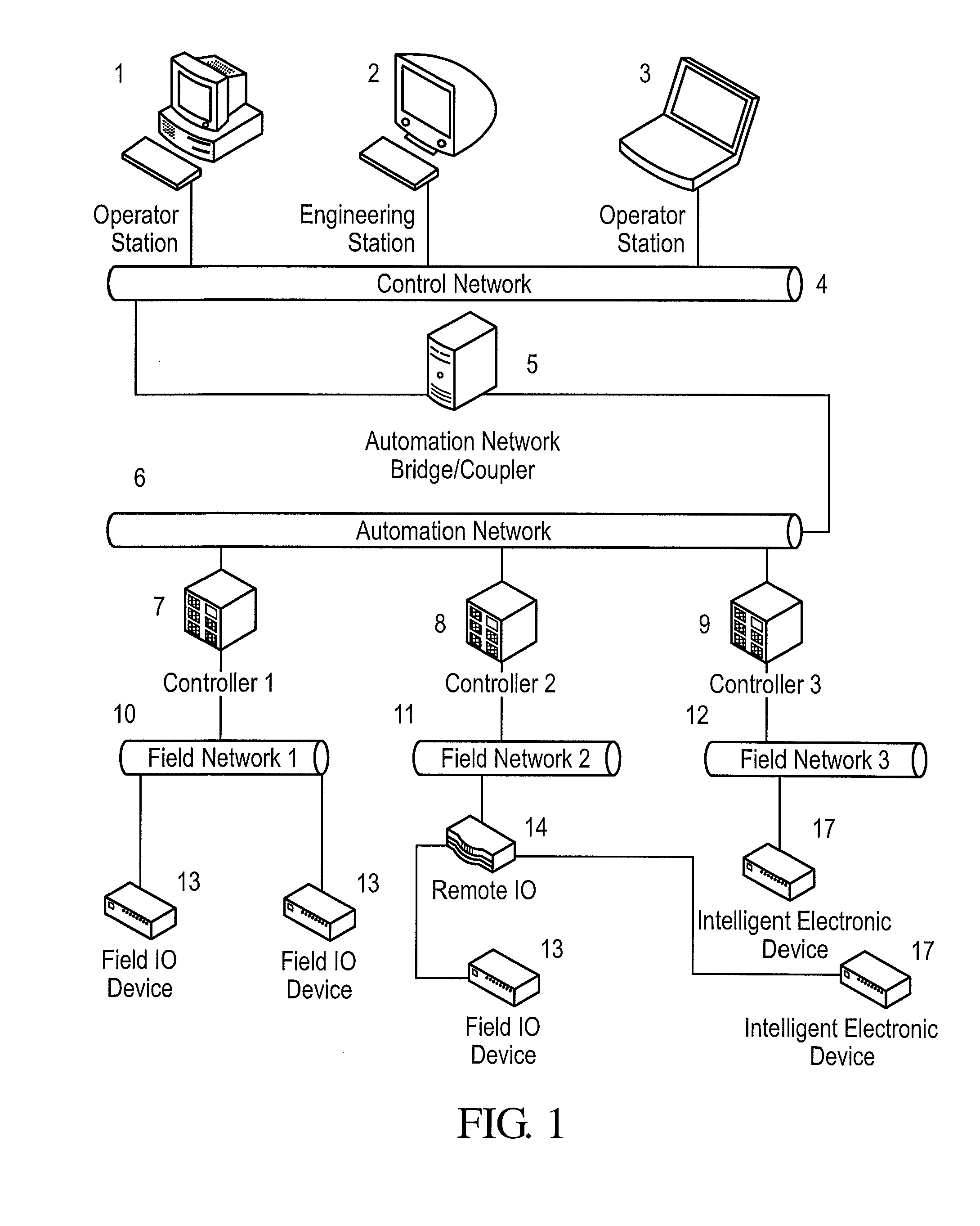
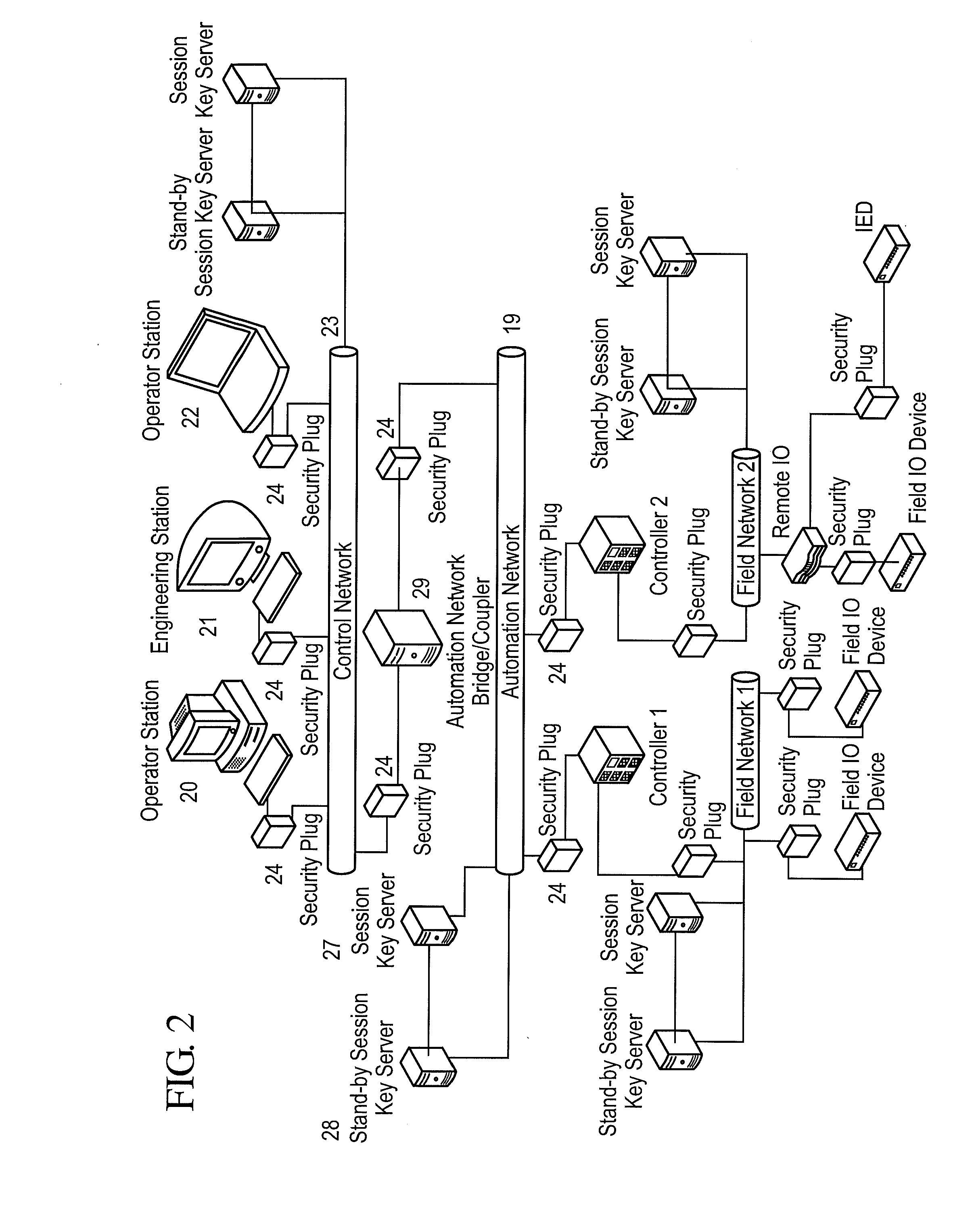
Real-time communication security for automation networks
ActiveUS20100217967A1Provide securitySpecial service provision for substationKey distribution for secure communicationCommunications securitySecure communication
A framework, device and method are disclosed for providing broadcast communication security over Ethernet within an automation system, wherein a security plug provides secure working of the automation system. The security plug can be implemented using ASIC / FPGA technology to provide compatibility with existing systems and an intuitive plug-and-play model. An exemplary system can address jitter-sensitivity by providing a real-time architecture, with minimal transmission latencies. The security plug can have separate security and communication modules that make provisions for protocol independent working of the security plug, within these networks. The method can include bootstrapping, secret key establishment and secure communication, for providing real-time guarantees.
Owner:HITACHI ENERGY SWITZERLAND AG
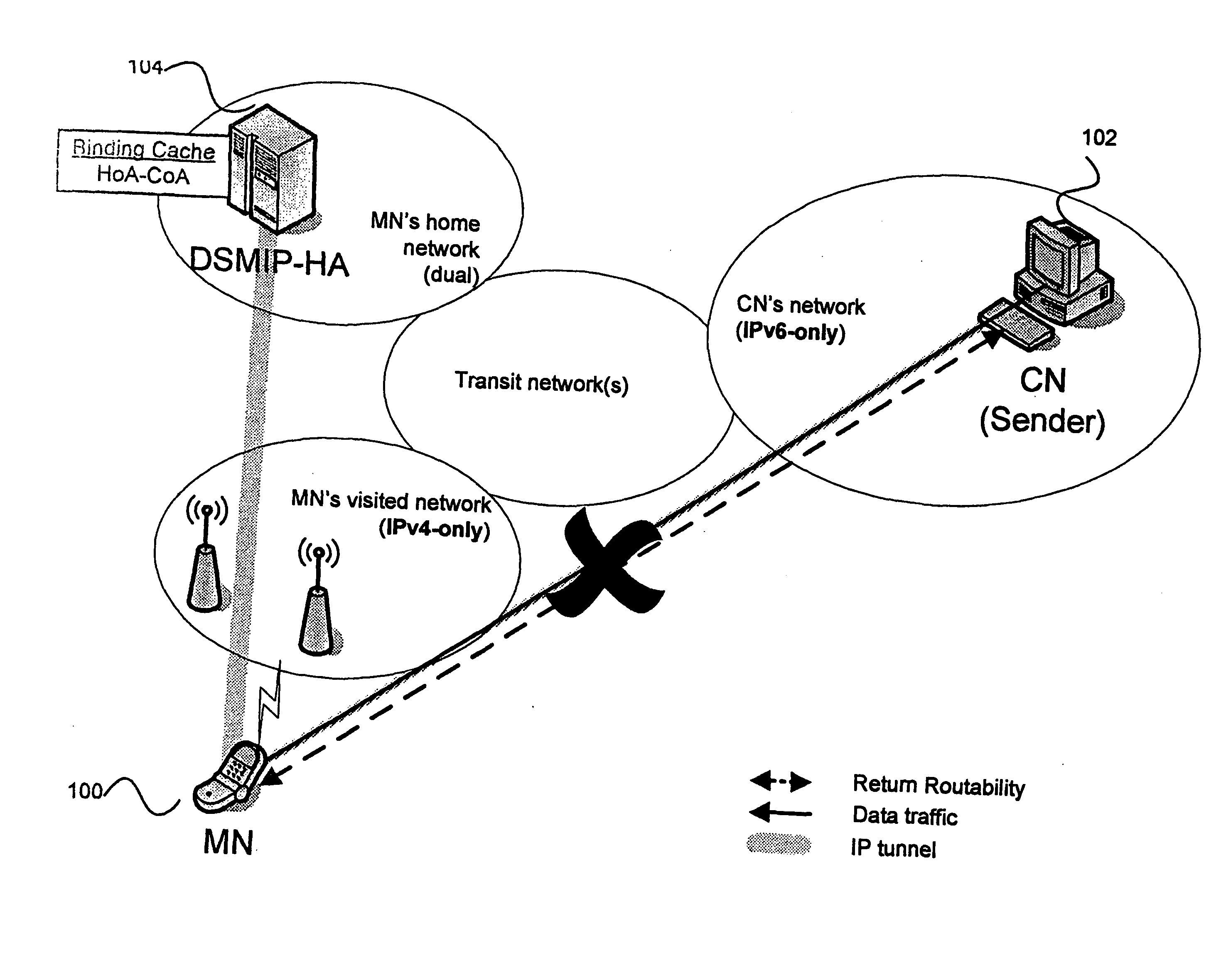
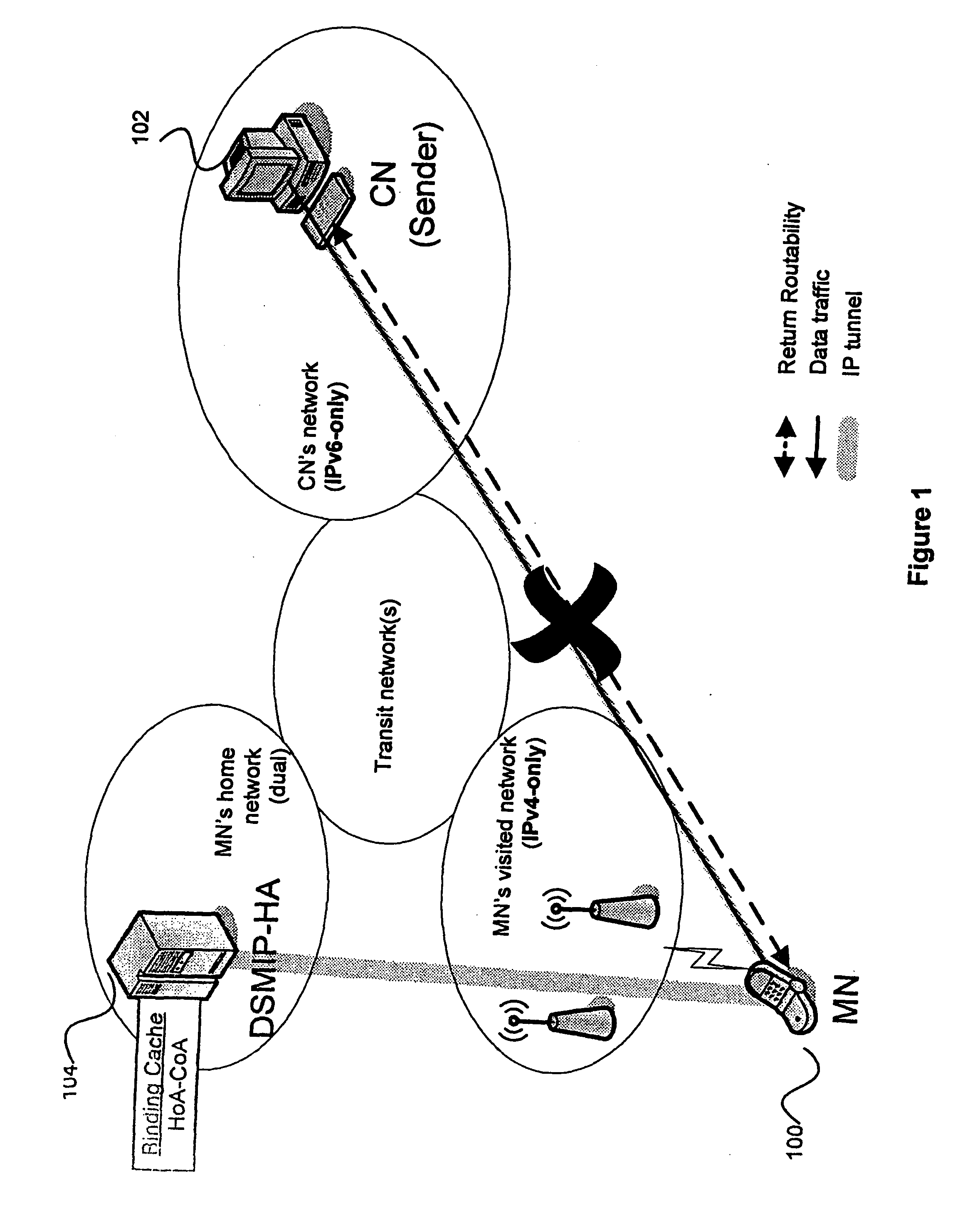
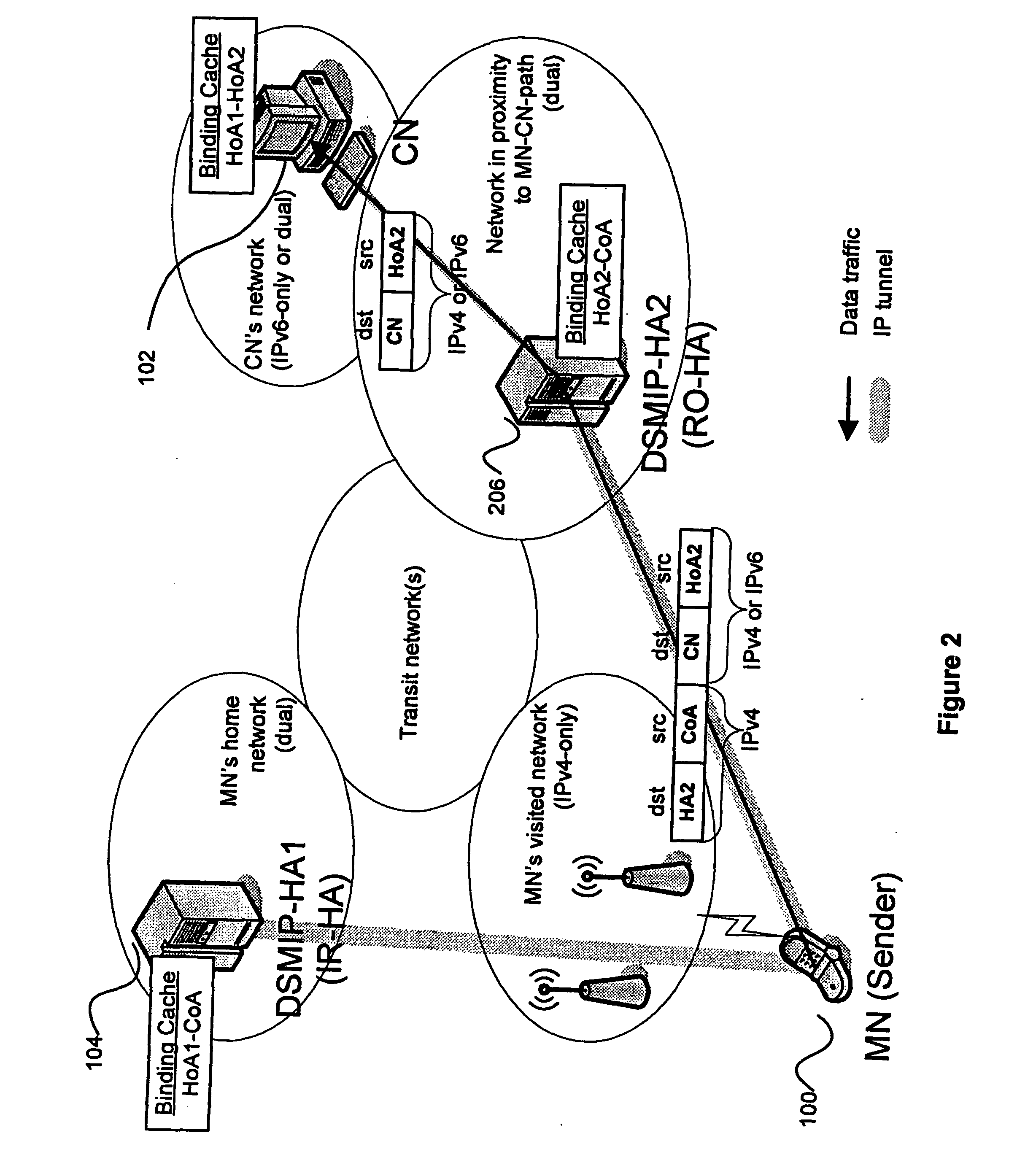
Mobile IP route optimization in IP version transition scenarios
InactiveUS20100284331A1Data switching by path configurationWireless network protocolsInternet protocol suiteTTEthernet
The invention relates to a method for routing packets in a system of packet-switched networks using different internet protocol versions. The system comprises a plurality of home agents, at least one mobile node and at least one correspondent node. A first mobile node is configured with at least one topologically correct internet protocol address of a first internet protocol version and is located in a network supporting at least routing of packets having a header of the first internet protocol version. The method comprises the following steps. Communication is requested with a first correspondent node being configured with at least an internet protocol address of a second internet protocol version and being located in a network supporting at least the routing of packets having a header of the second internet protocol version, by an application on the first mobile node. A first of the plurality of home agents is located in proximity to a direct path between the first mobile node and the first correspondent node, the first home agent being located in a network supporting at least the routing of packets to the first mobile node with the packets having a header of the first internet protocol version and the routing of packets to the first correspondent node with the packets having a header of the second internet protocol version. Bootstrapping is carried out with the first home agent to obtain a first home address of the second internet protocol version and other communication parameters. The first mobile node's location is registered with the first home agent by sending a first binding update message comprising a first mobile node's topologically correct address of the first internet protocol version as care-of address and the first home address as home address; and the first home agent is used in bi-directional tunnelling mode, the outer header of the tunnelled packets using the first internet protocol version and the inner header of the tunnelled packets using the second internet protocol version, for communication with the first correspondent node, with the communication parameters set up in the bootstrapping step and the first home address as home address.
Owner:PANASONIC CORP
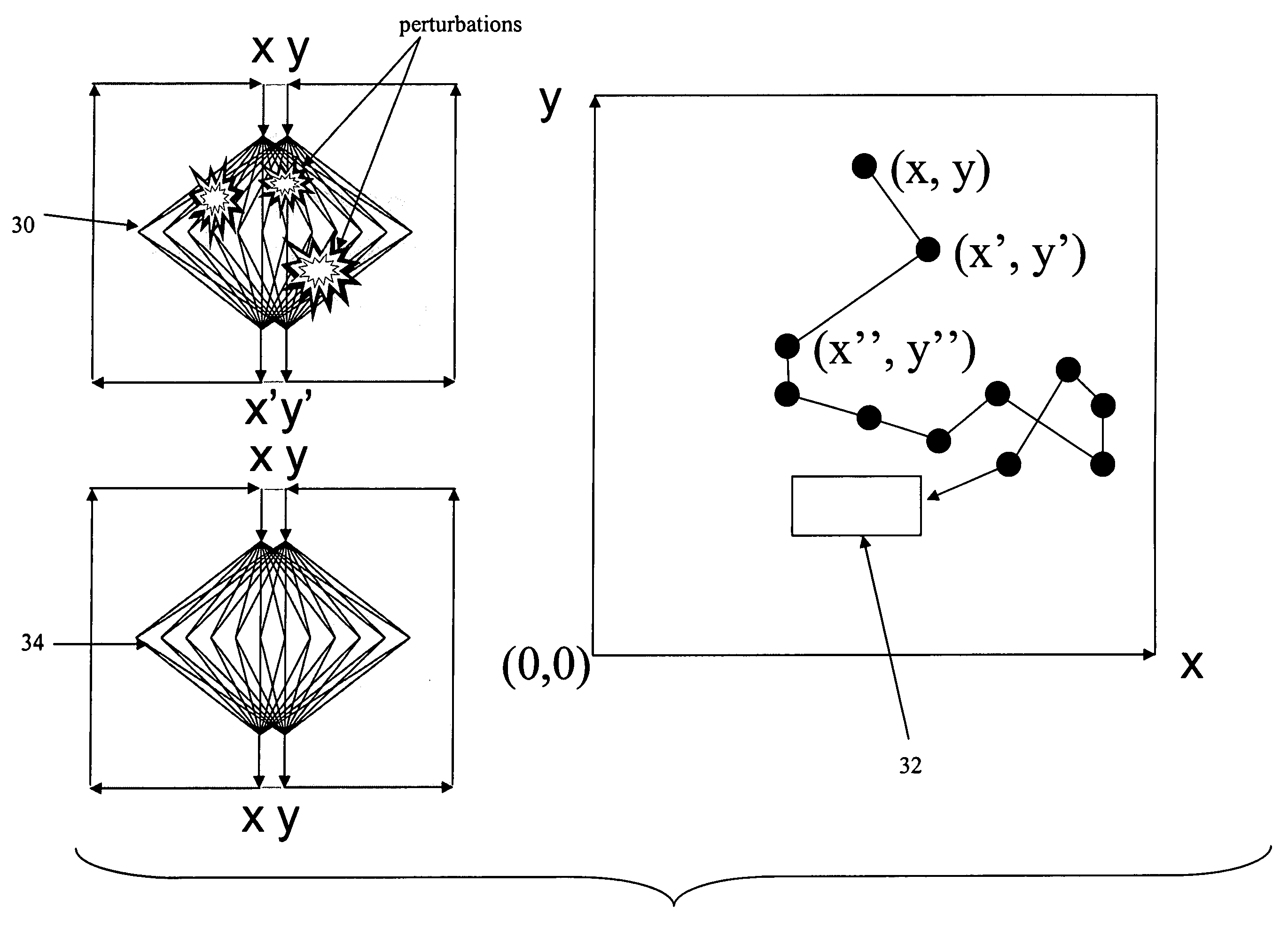
Device for the autonomous bootstrapping of useful information
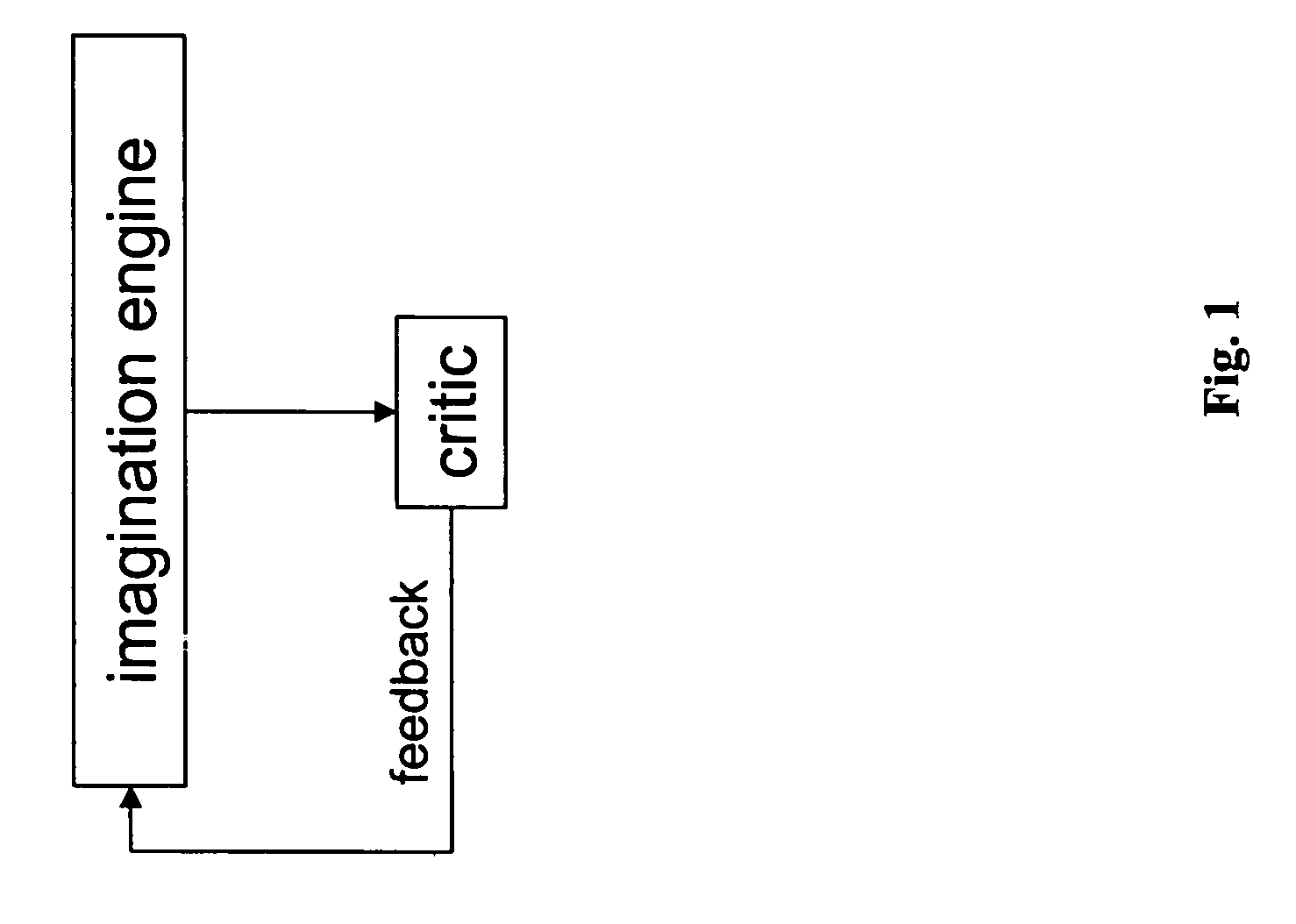
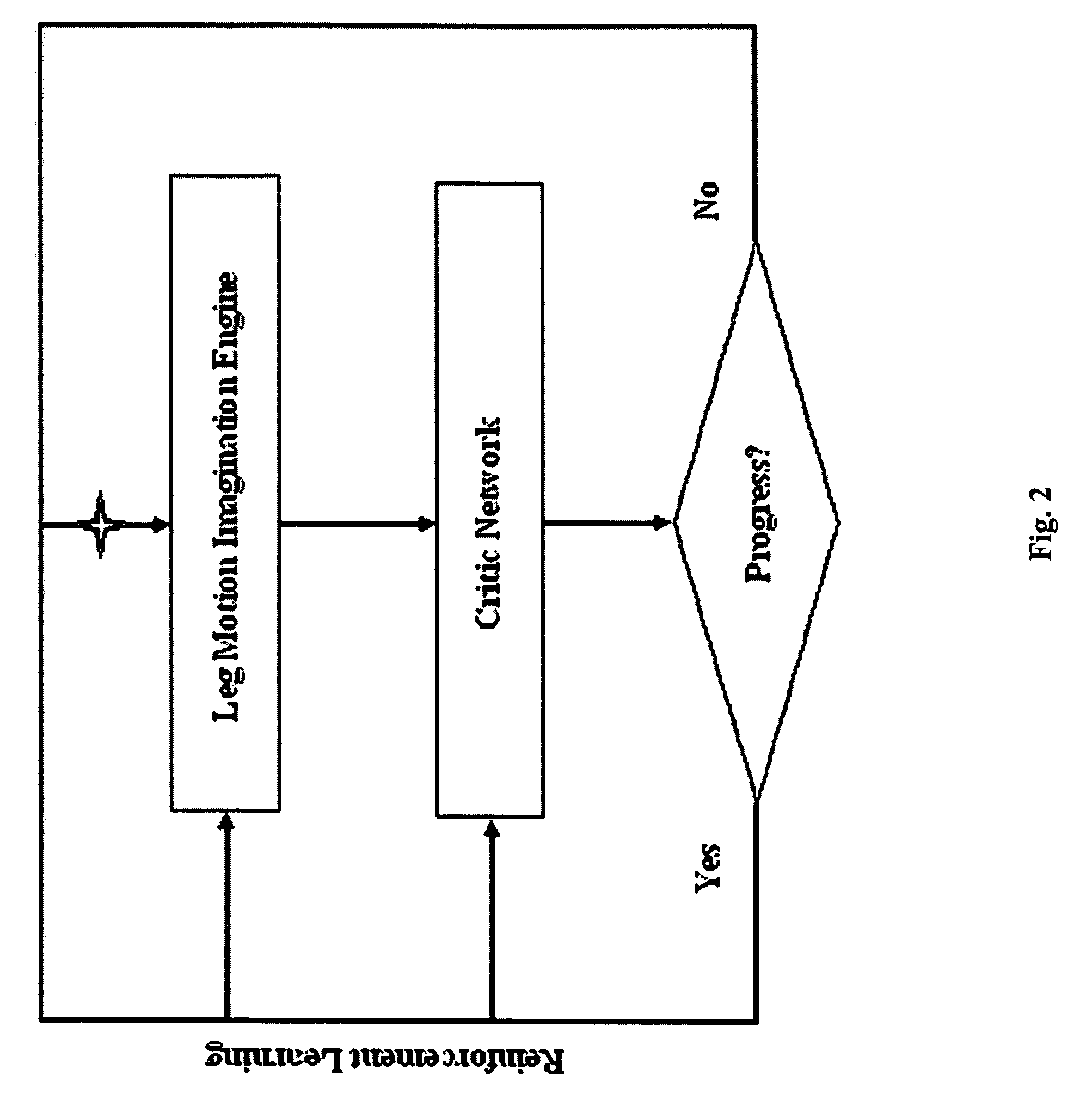
A discovery system employing a neural network, training within this system, that is stimulated to generate novel output patterns through various forms of perturbation applied to it, a critic neural network likewise capable of training in situ within this system, that learns to associate such novel patterns with their utility or value while triggering reinforcement learning of the more useful or valuable of these patterns within the former net. The device is capable of bootstrapping itself to progressively higher levels of adaptive or creative competence, starting from no learning whatsoever, through cumulative cycles of experimentation and learning. Optional feedback mechanisms between the latter and former self-learning artificial neural networks are used to accelerate the convergence of this system toward useful concepts or plans of action.
Owner:THALER STEPHEN L
Method and arrangement for integration of different authentication infrastructures
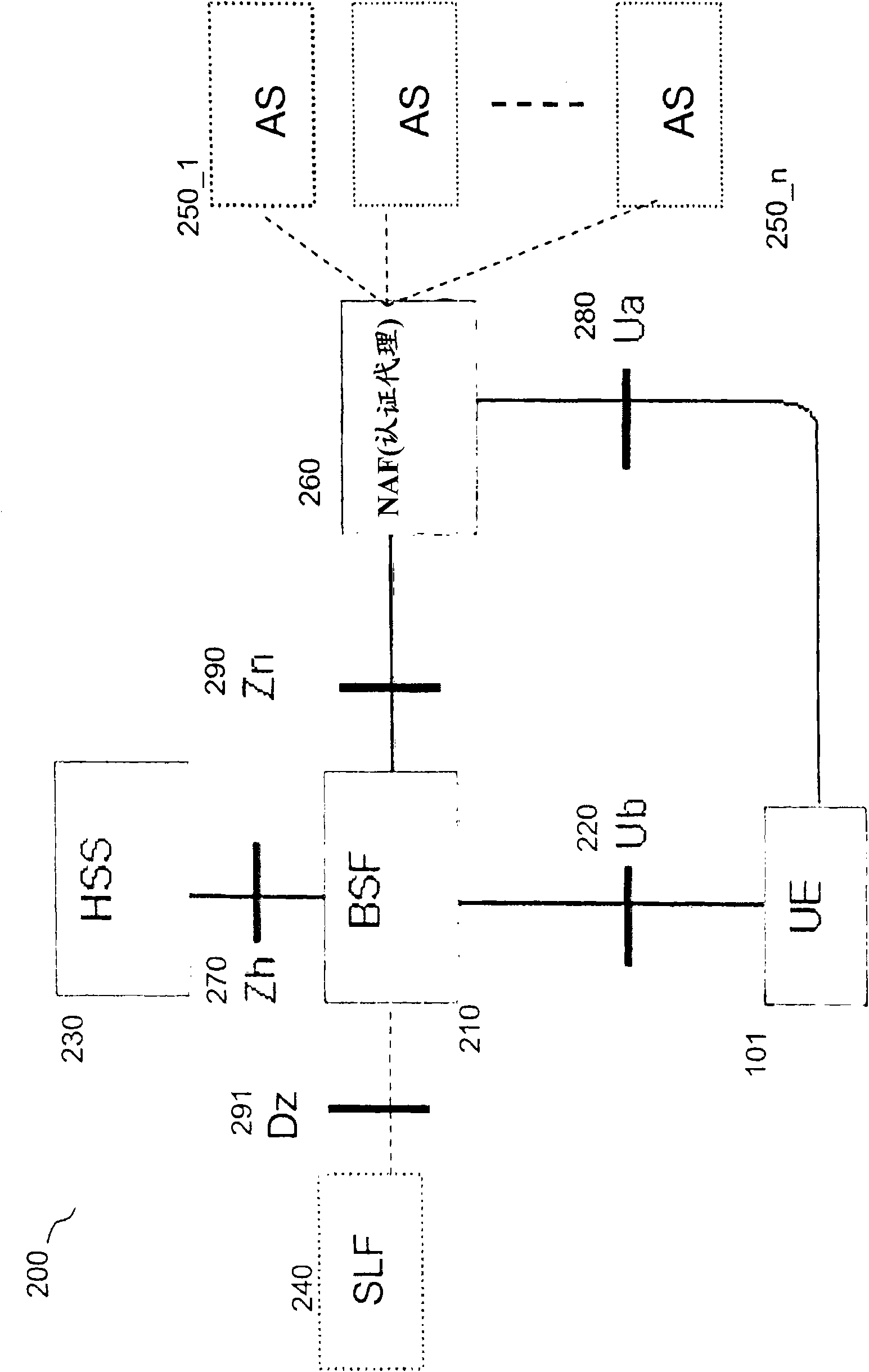
ActiveCN101569217AWireless network protocolsSecurity arrangementSession managementGeneric Bootstrapping Architecture
A method is disclosed that provides efficient integration of infrastructure for federated single sign on, e.g. Liberty ID-FF framework, and generic bootstrapping architecture, e.g. 3GPP GAA / GBA architecture. An integrated proxy server (IAP) is inserted in the path between a user and a service provider (SP). The proxy server differentiates type of access and determines corresponding operative state to act as a liberty enabled server or as a GAA / GBA network application function. A Bootstrapping, Identity, Authentication and Session Management arrangement (BIAS) leverages on 3GPP GAA / GBA infrastructure to provide an integrated system for handling Liberty Federated SSO and 3GPP GAA / GBA bootstrapping procedures at the same time. The method and arrangement provides improved use of infrastructure elements and performance for authenticated service access.
Owner:TELEFON AB LM ERICSSON (PUBL)
Device and method for the autonomous bootstrapping of unified sentience
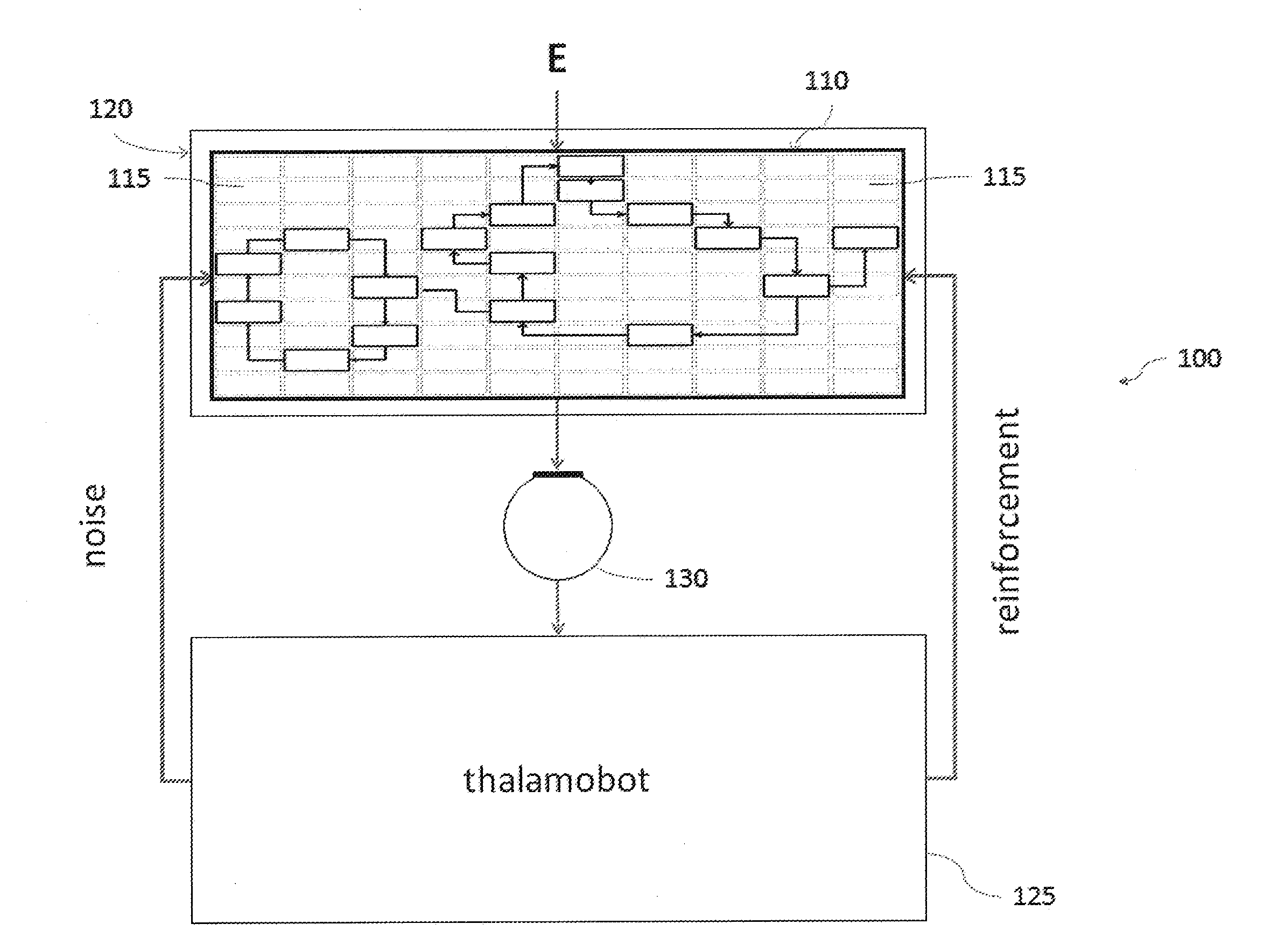
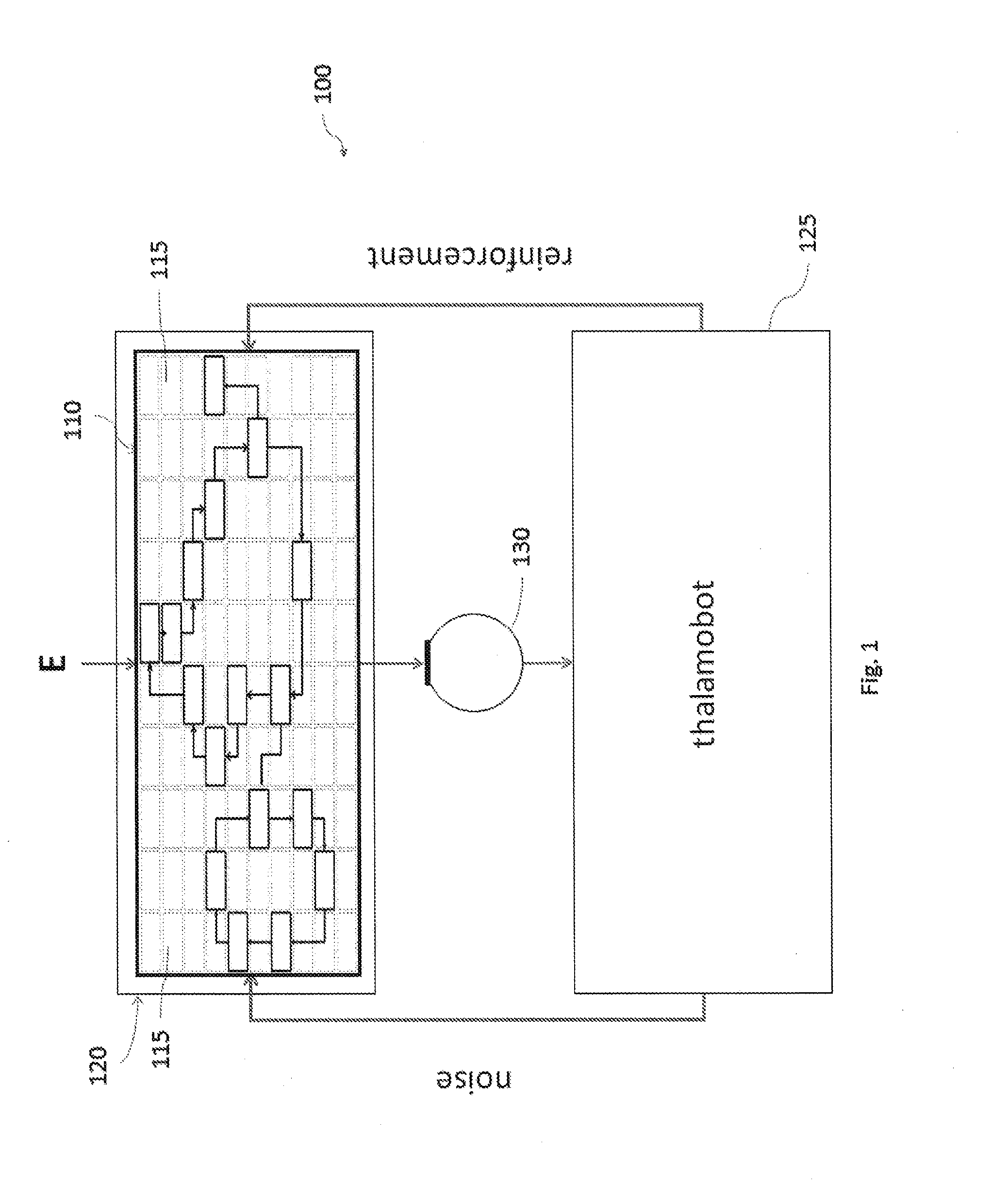
ActiveUS20150379394A1Improve connectivityImprove the level ofDigital computer detailsDigital dataData miningRecognition system
A system for monitoring an environment may include an input device for monitoring and capturing pattern-based states of a model of the environment. The system may also include a 5 thalamobot embodied in at least a first processor, in which the first processor is in communication with the input device. The thalamobot may include at least one filter for monitoring captured data from the input device and for identifying at least one state change within the captured data. The system may also include at least one critic and / or at least one recognition system.
Owner:THALER STEPHEN L
Method for arranging key in IP multimedia service subsystem network
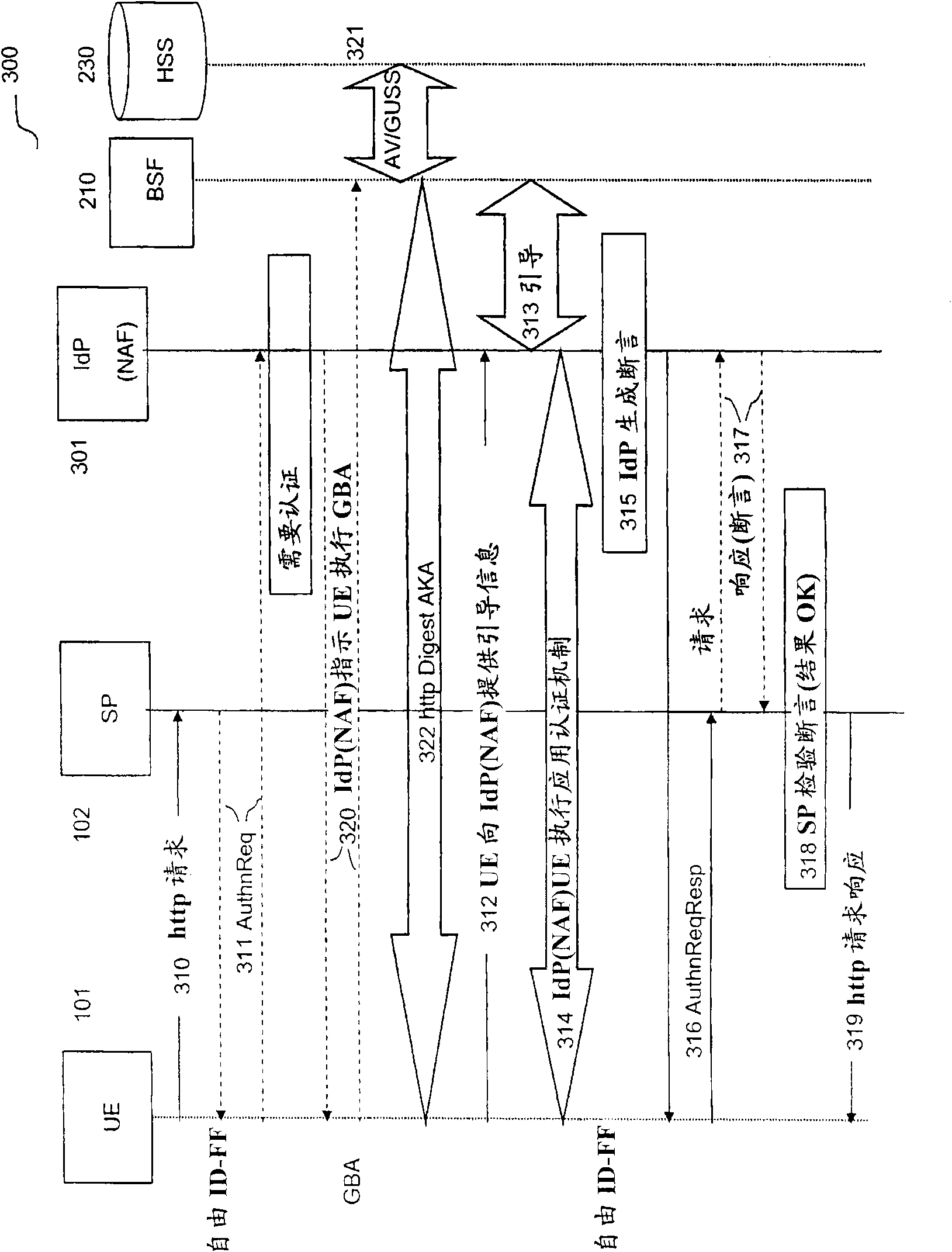
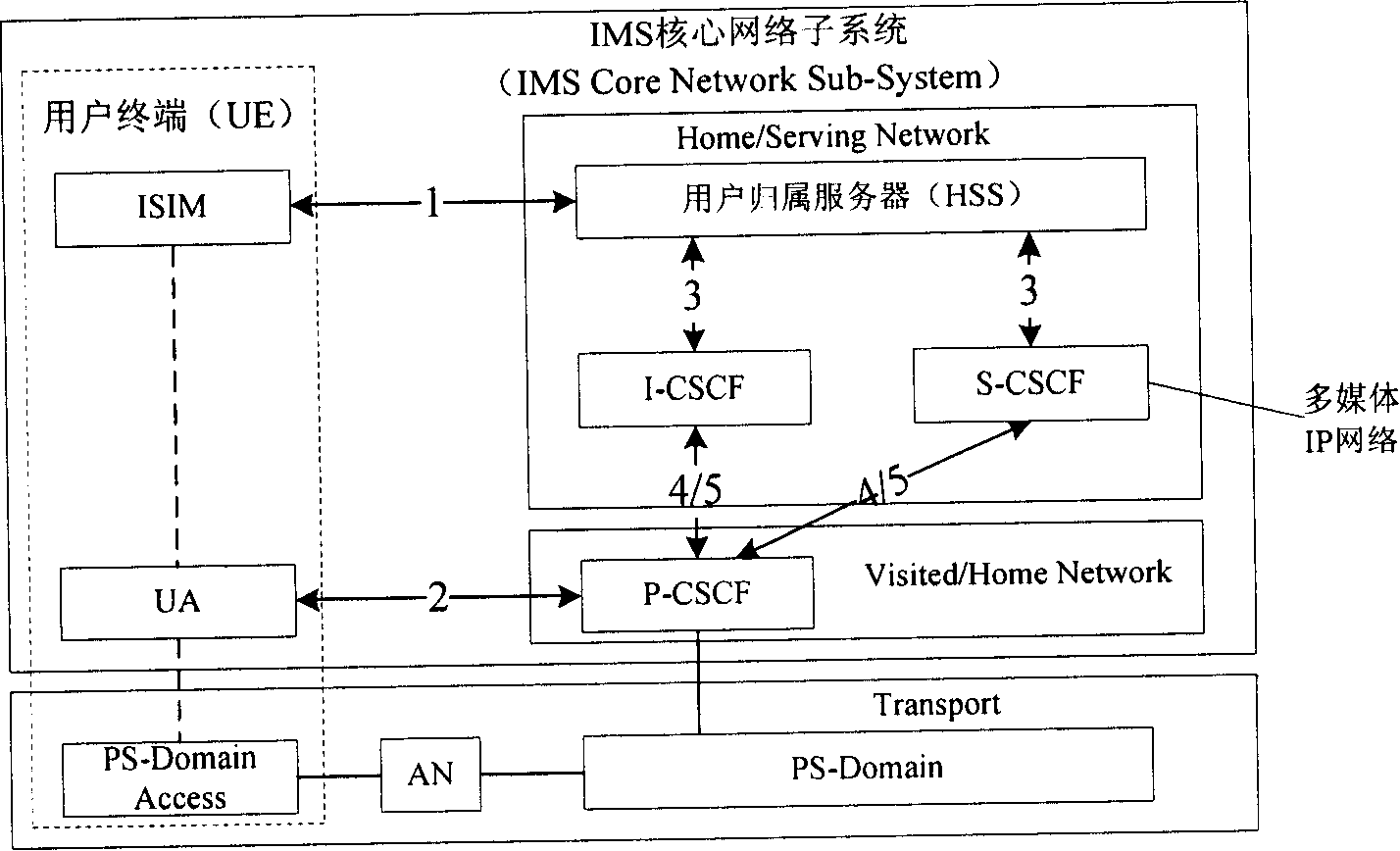
InactiveCN1801697ASolve protection problemsImprove applicabilityKey distribution for secure communicationSynchronising transmission/receiving encryption devicesProtocol ApplicationAuthentication
The invention discloses a method for cipher negotiation in IP multimedia service subsystem. Wherein, during the AKA or Digest Authentication (DA) process, generating application layer cipher and B-TID (Bootstrapping procedure Transaction identifier) label, and sending the B-TID to terminal to merge the Bootstrapping and AKA or DA processes; the terminal initiates to build dialogue, and use directly said key for protection during interactive process with NAF (such as AS).
Owner:HUAWEI TECH CO LTD
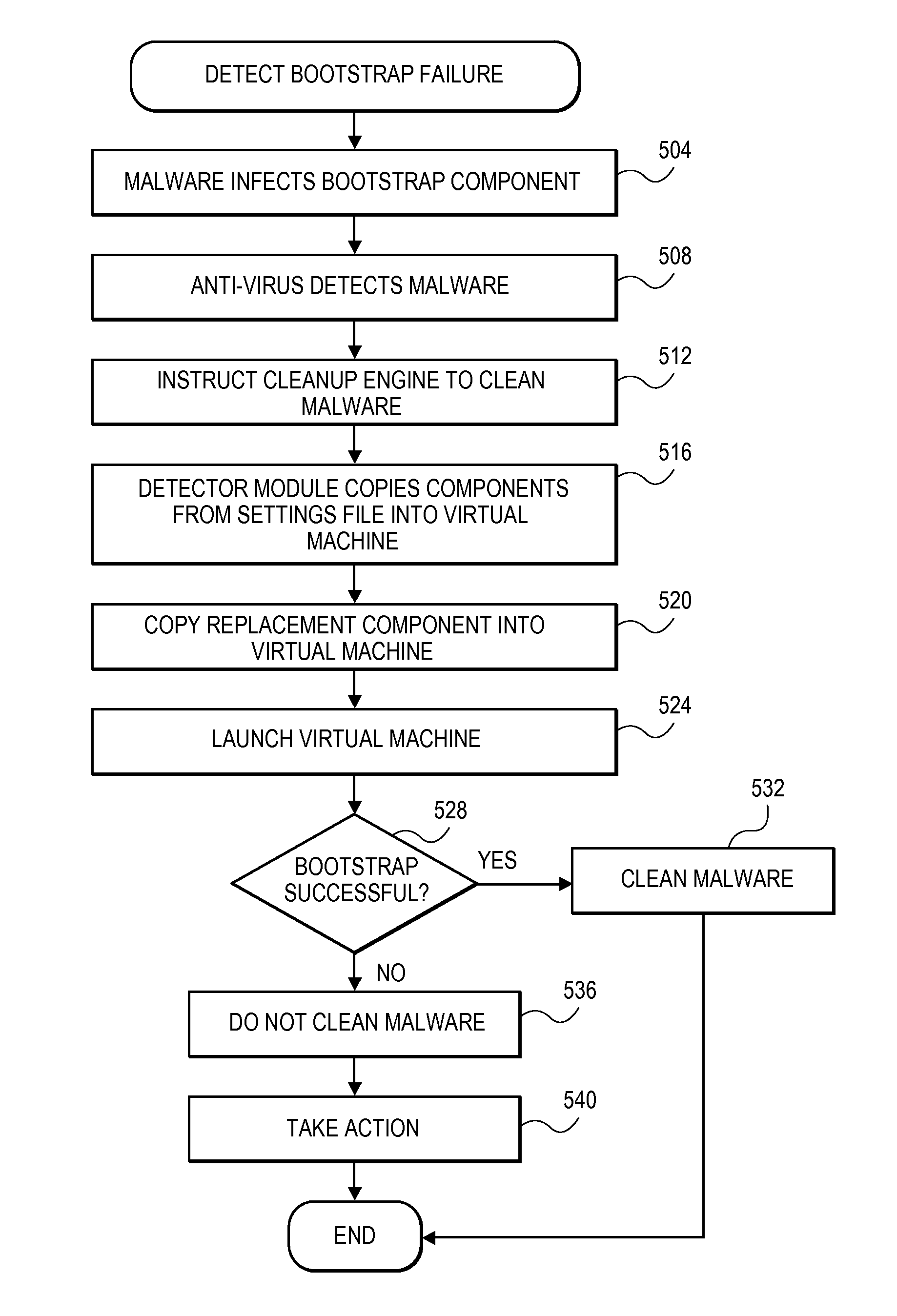
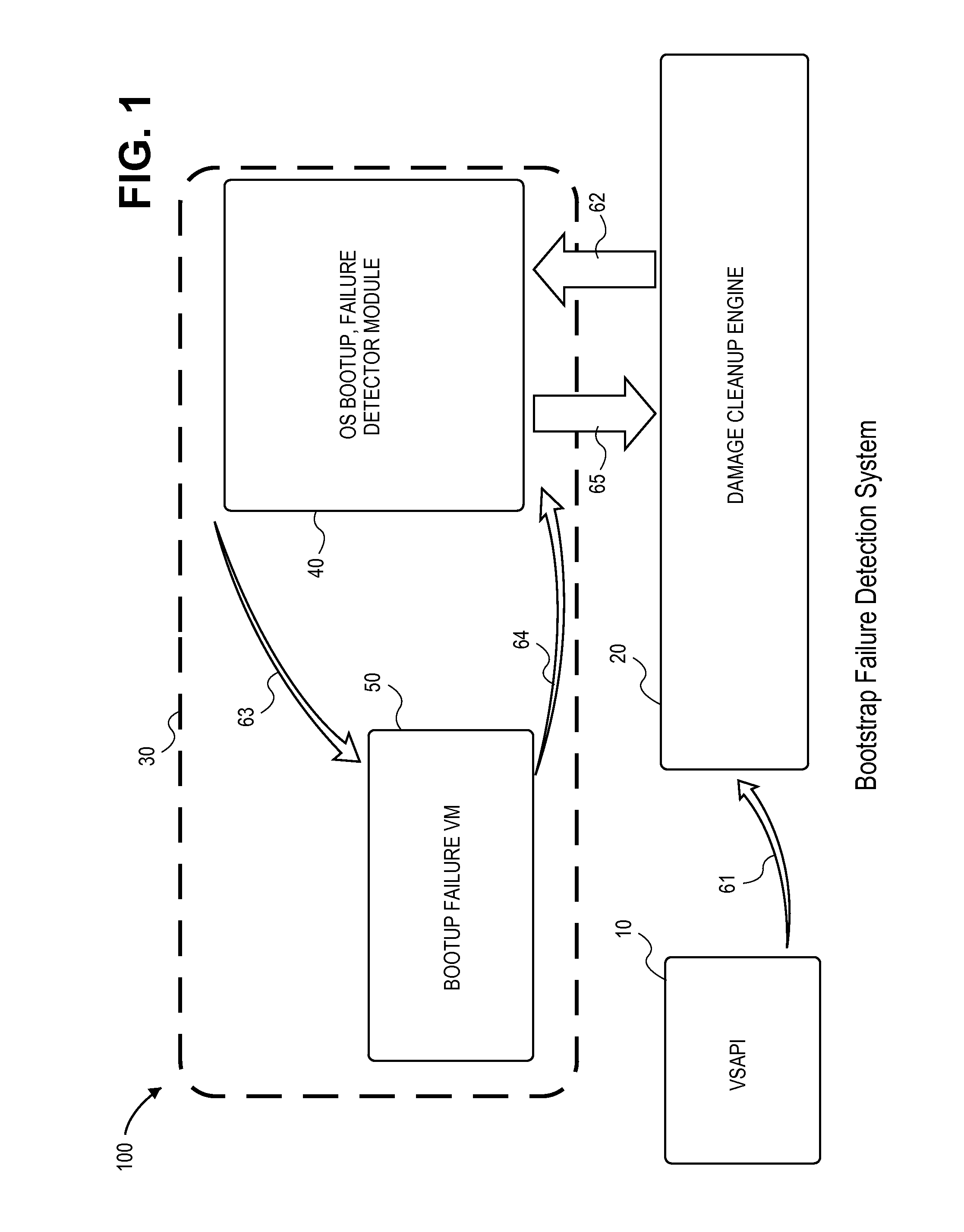
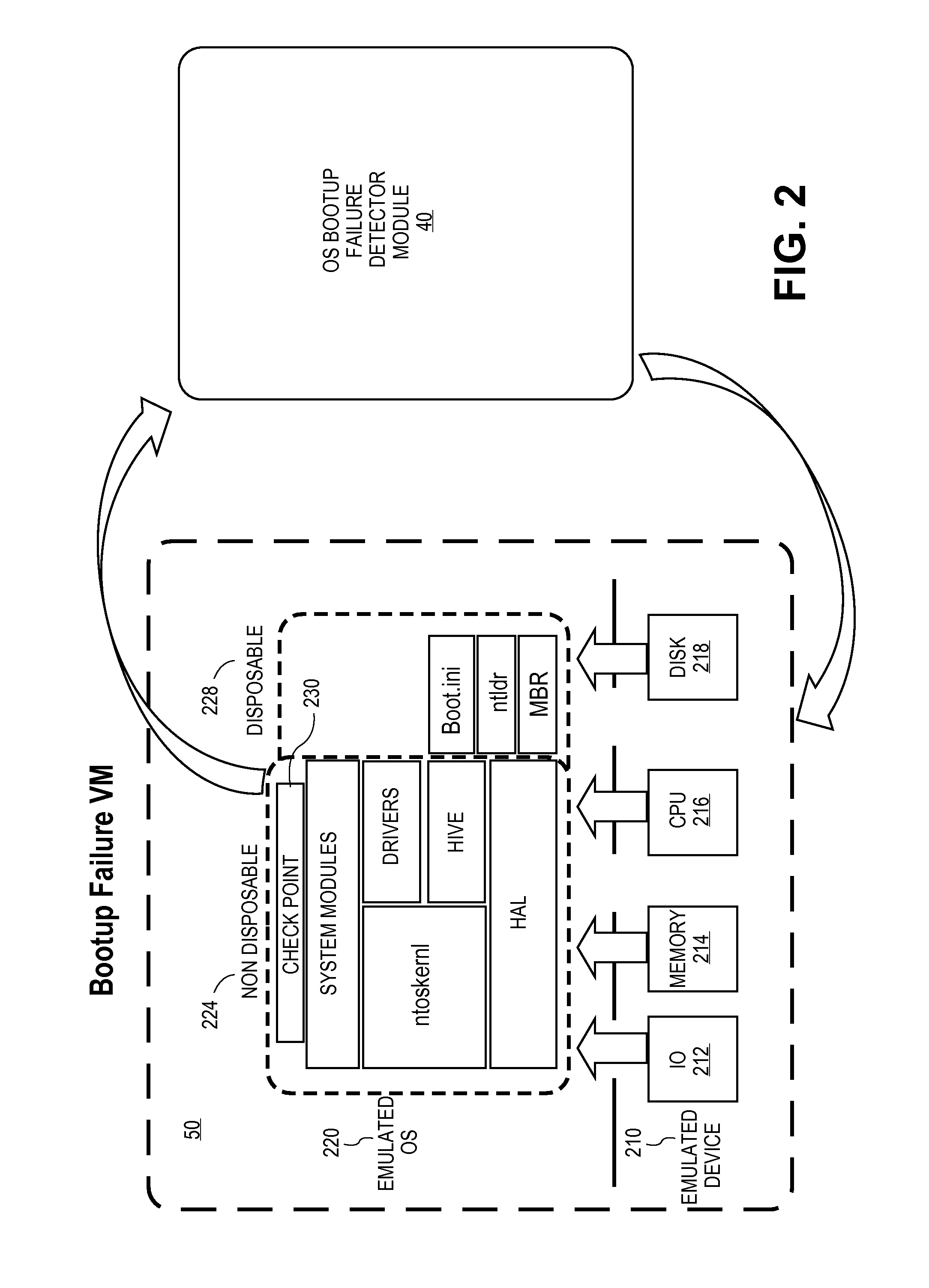
Operating system bootstrap failure detection
ActiveUS8918879B1False alarmAvoid failureMemory loss protectionError detection/correctionOperational systemMalware
During a bootstrapping process, path names of necessary bootstrap modules are collected and stored into a file. When an infected bootstrap component is detected, the method initiates emulation of the bootstrapping process within a virtual machine rather than directly cleaning malware from the infected bootstrap component. A settings file is copied into the virtual machine indicating the necessary bootstrap components in the host computer (including the infected component). Alternatively, the actual components are copied into the virtual machine. A clean version of the infected bootstrap component is made available to the virtual machine. The virtual machine is launched using the bootstrap components (including the clean version of the infected bootstrap component) and it emulates the bootstrapping process of the operating system. A successful bootstrap indicates the infected bootstrap component may be cleaned on the host computer. An unsuccessful bootstrap indicates the infected bootstrap component should not be cleaned of malware.
Owner:TREND MICRO INC
Using a connected wireless computer as a conduit for a disconnected wireless computer
InactiveUS7760654B2Facilitate communicationError preventionFrequency-division multiplex detailsClient-sideWireless computing
Systems and methods are described for using client conduits to enable bootstrapping and fault diagnosis of disconnected wireless clients. Client conduits are used to enable disconnected clients to diagnose their problems with the help of nearby clients. This technique may take advantage of the beaconing and probing mechanisms of IEEE 802.11 to ensure that connected clients do not pay unnecessary overheads for detecting disconnected clients. Methods are also described for detecting rogue devices disguising as disconnected clients.
Owner:MICROSOFT TECH LICENSING LLC
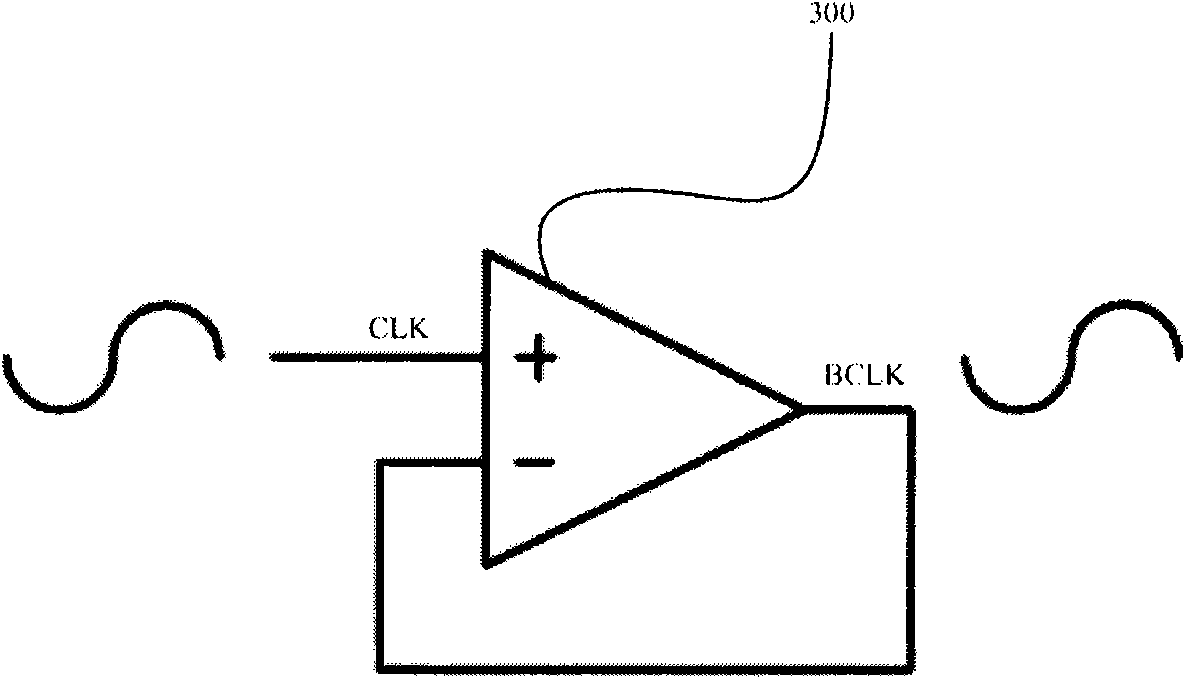
Efficacy push-pull buffer circuit, system and method for high frequency signals
InactiveCN101540603APower reduction in field effect transistorsLogic circuits coupling/interface using field-effect transistorsCapacitancePush pull
The invention relates to an efficacy push-pull buffer circuit, a system and a method for high frequency signals. The buffer circuit comprises a biasing circuit which can be operated to generate a first bias signal and a second bias signal. A capacitance network comprises an input end suitable for receiving input signals and can be operated to respond to the input signal so as to generate a first bootstrapping signal and a second bootstrapping signal. A push-pull stage comprises a first control input end, a first control output end, a second control input end and a second control output end. The push-pull stage is coupled to the biasing circuit to receive the first and the second bias signals at the first and the second control input ends respectively, and is also coupled the capacitance network to receive the first and the second bootstrapping signals at the first and the second control output ends respectively. The push-pull stage can be operated to respond to the first and the second bootstrapping signals so as to generate buffer output signals at the output ends.
Owner:STMICROELECTRONICS SHANGHAI R&D
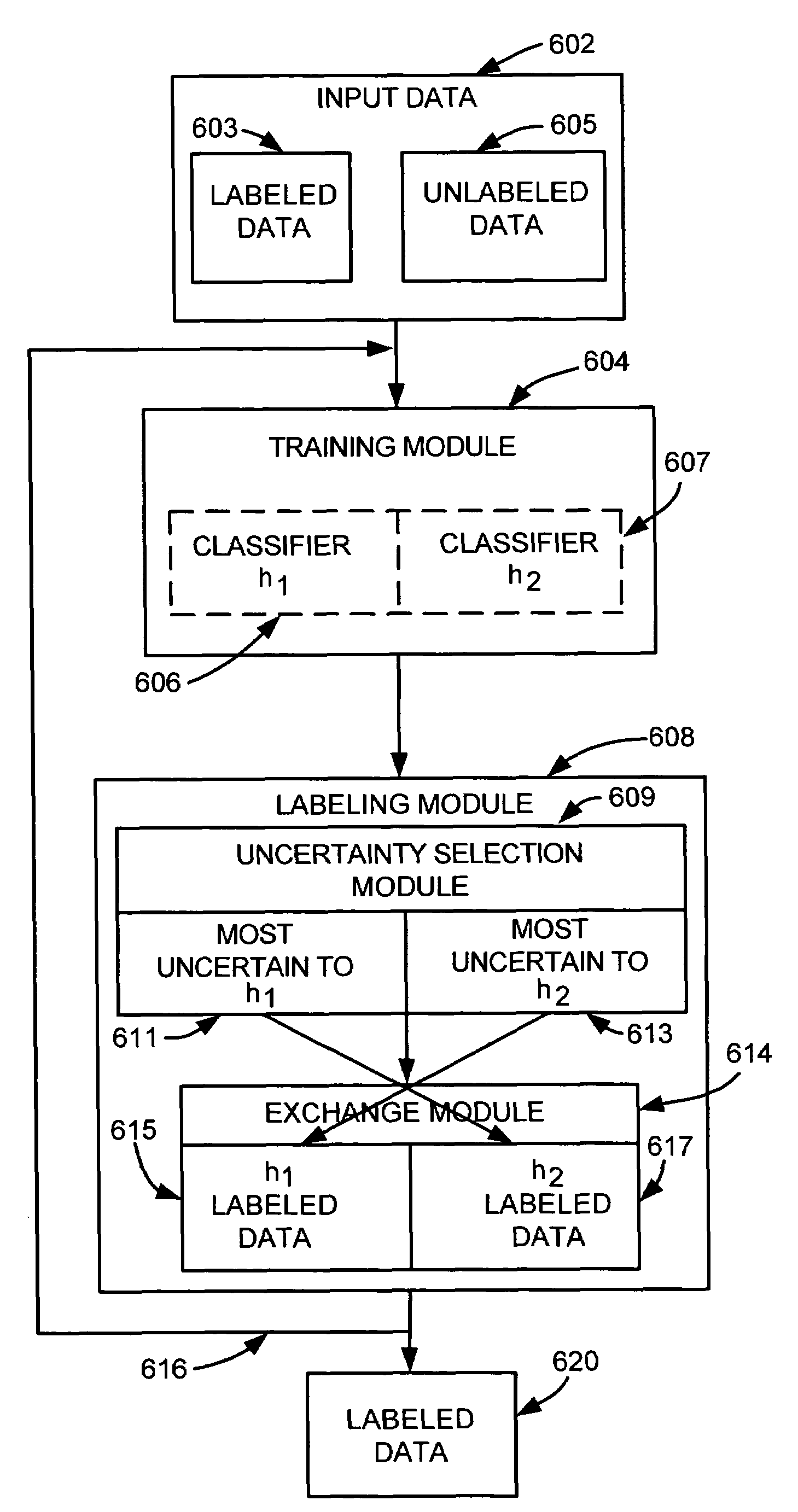
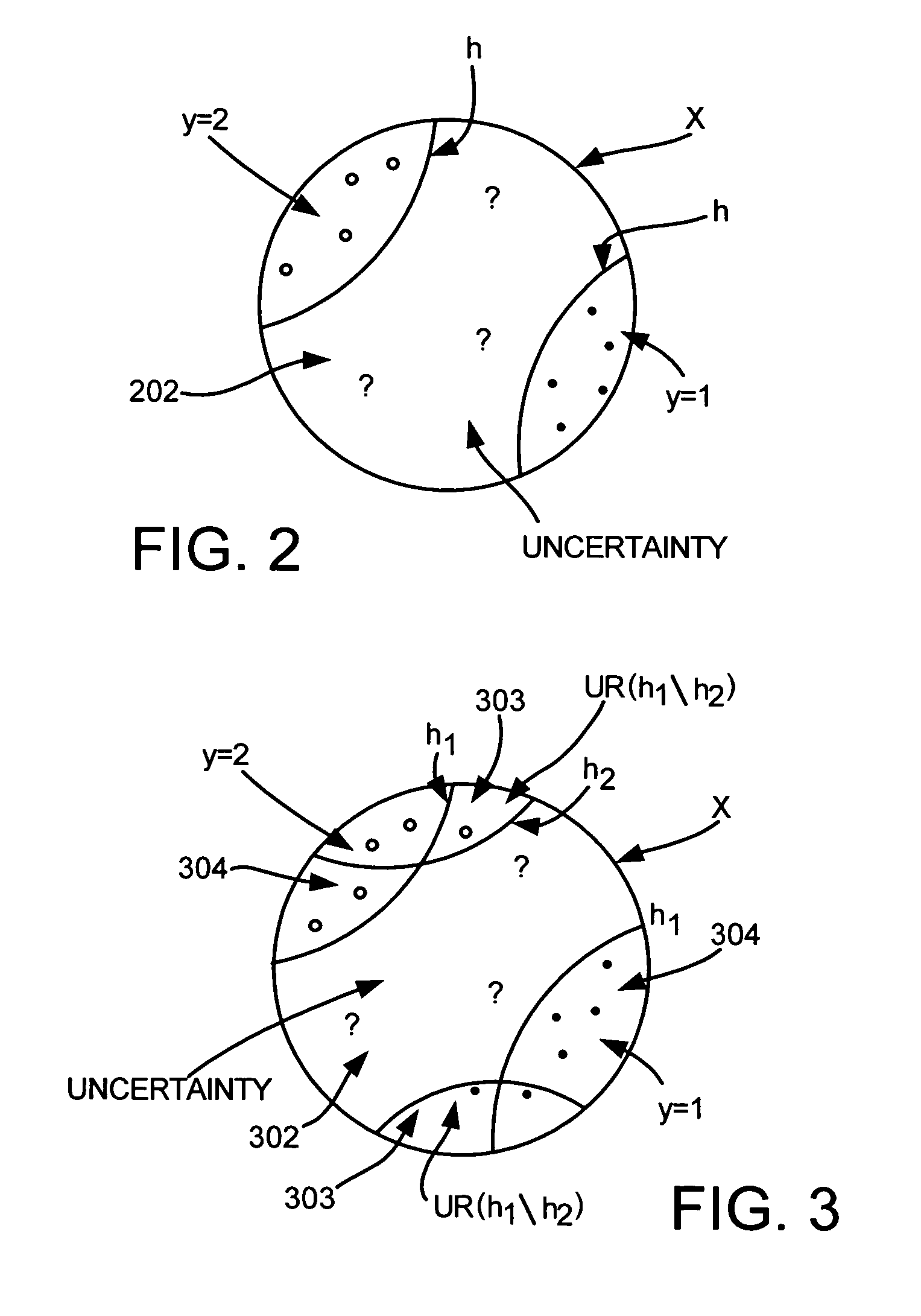
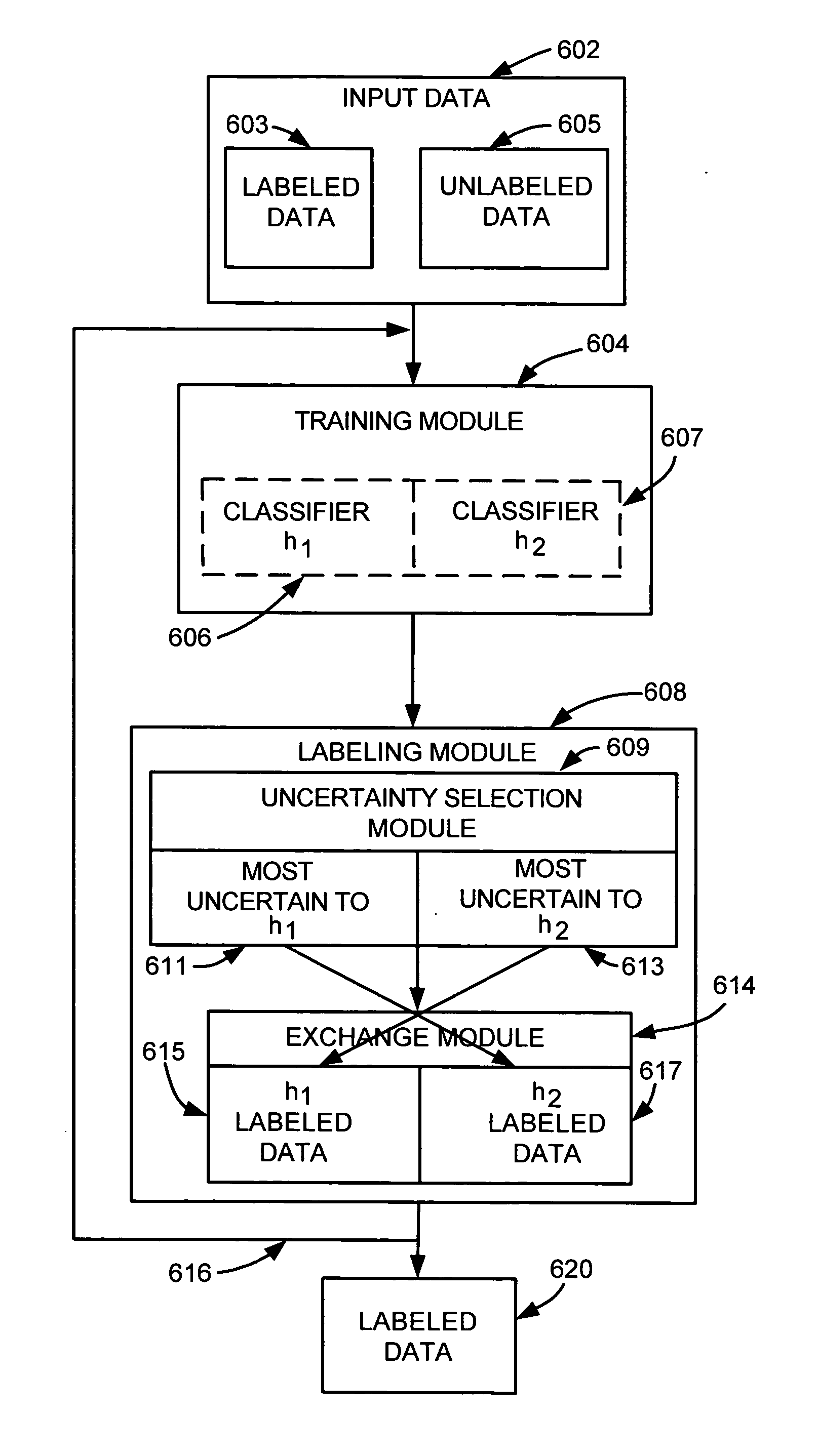
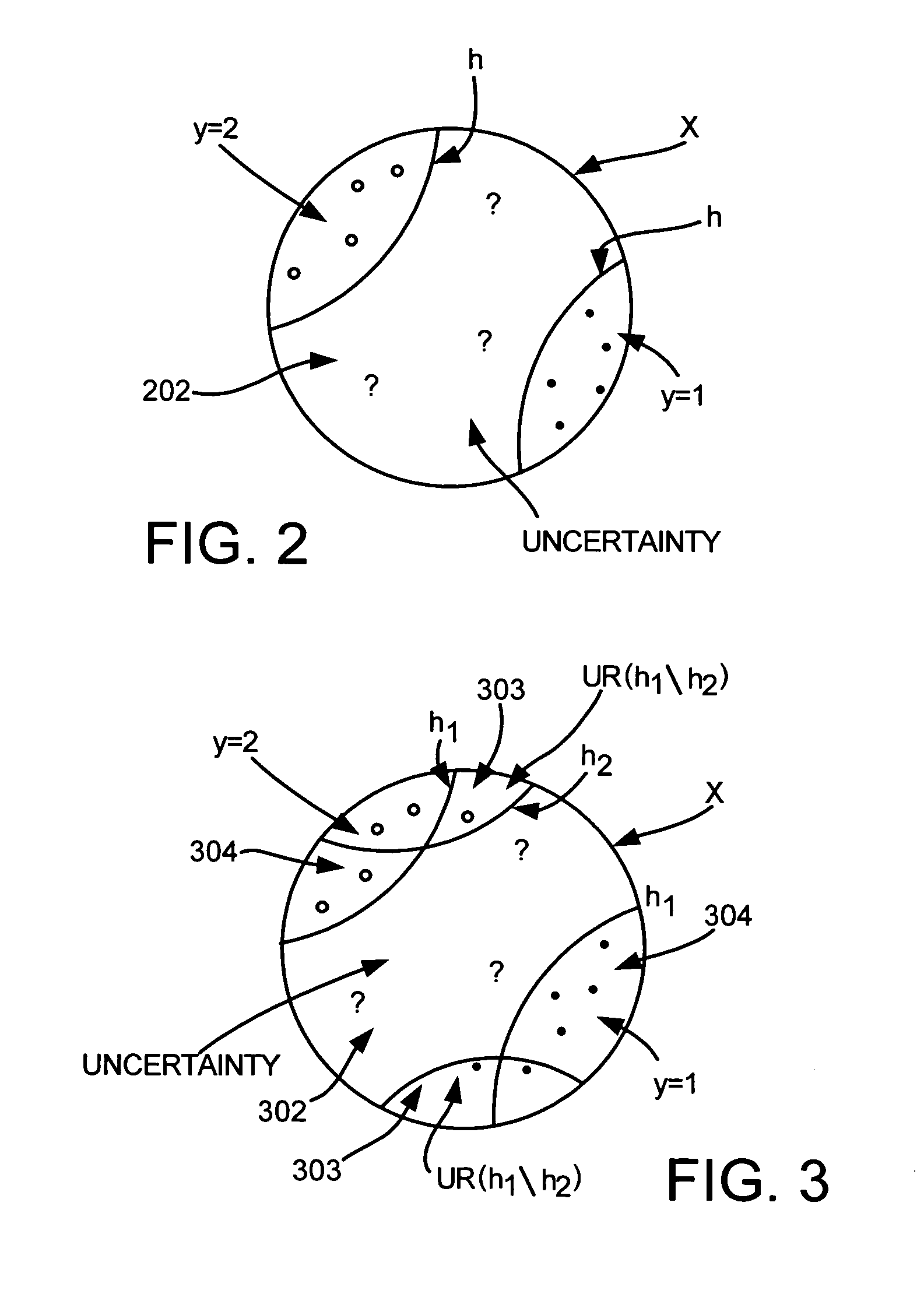
Uncertainty reduction in collaborative bootstrapping
InactiveUS7512582B2Improve classification performanceReduce uncertaintyChaos modelsNon-linear system modelsPattern recognitionParallel processing
Collaborative bootstrapping with uncertainty reduction for increased classifier performance. One classifier selects a portion of data that is uncertain with respect to the classifier and a second classifier labels the portion. Uncertainty reduction includes parallel processing where the second classifier also selects an uncertain portion for the first classifier to label. Uncertainty reduction can be incorporated into existing or new co-training or bootstrapping, including bilingual bootstrapping.
Owner:MICROSOFT TECH LICENSING LLC
Device management with configuration information
ActiveUS7734737B2Simplify the configuration processReduce communicationData resettingMultiple digital computer combinationsClient-sideInformation needs
The invention relates to device management and to information needed for bootstrapping and initiation. The bootstrapping information and initiation information are sent in one message, wherein the client receives them both. According to the state of the client, one of the informations is selected and used.
Owner:NOKIA TECH OY
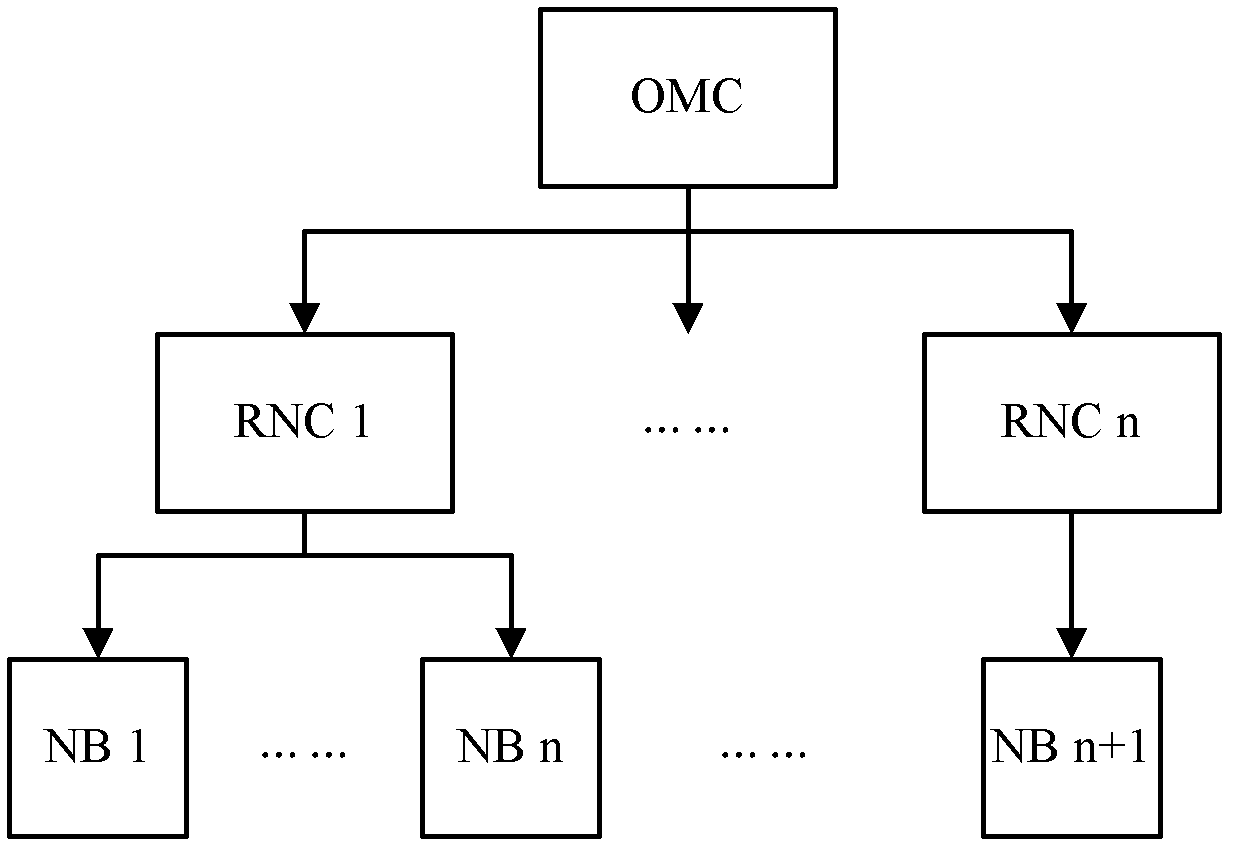
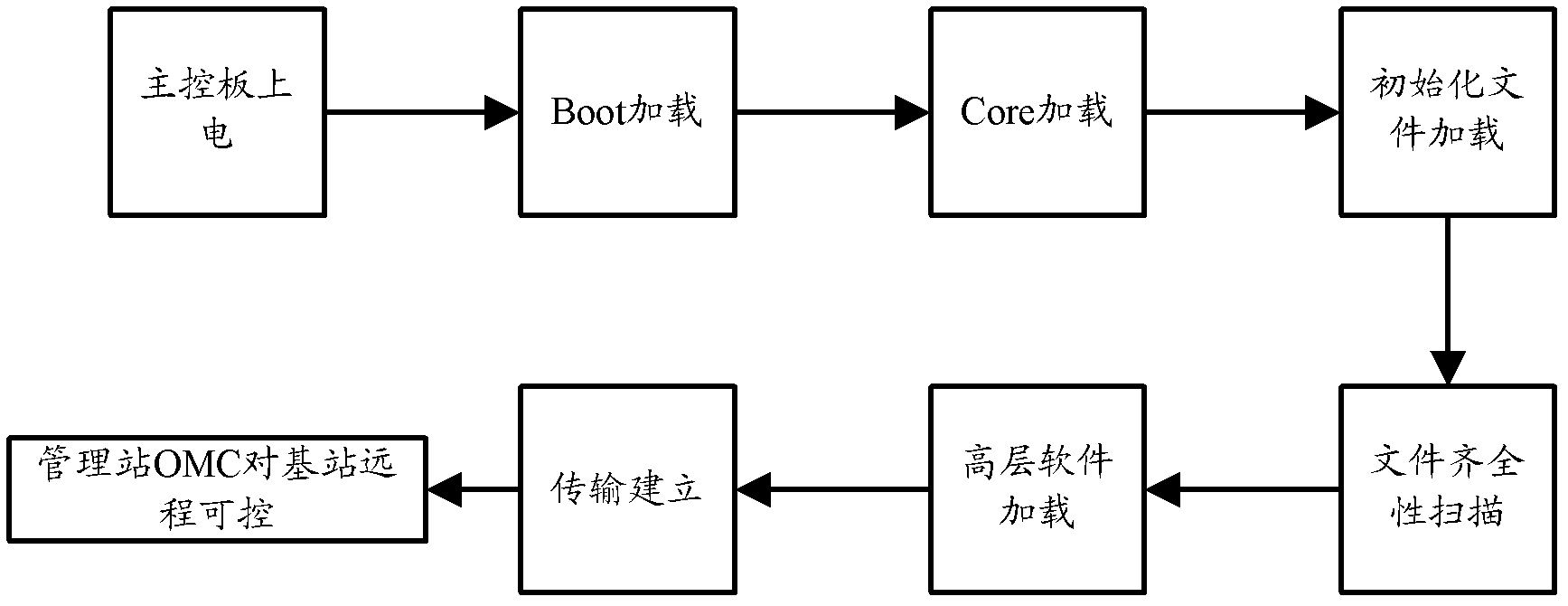
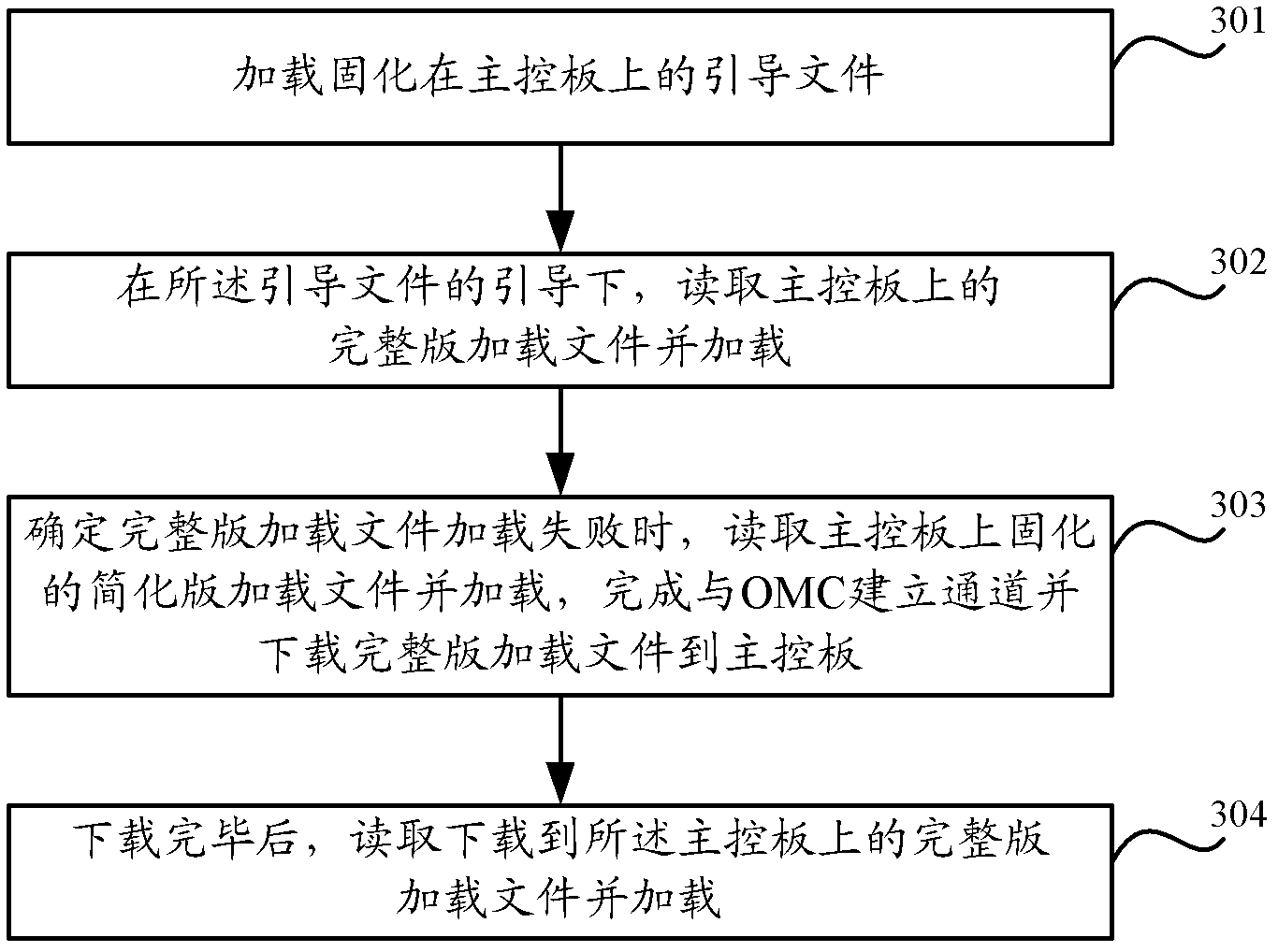
A base station and its self-starting method
ActiveCN102300239AImprove automatic exception handling capabilitiesReduce down timeWireless communicationComputer hardwareOperational maintenance
The invention discloses a base station and a self-starting method thereof. The method comprises the following steps of: loading a bootstrap file fixed on a master control board; reading a full loading file from the master control board and loading the full loading file under the bootstrapping of the bootstrap file; when the full loading file is determined to be failed to load, reading a fixed simplified loading file from the master control board, and loading the simplified loading file, wherein the simplified loading file is loaded to establish a channel with an operation and maintenance center (OMC) and download the full loading file to the master control board; and after the downloading is finished, reading the full loading file downloaded to the master control board, and loading the downloaded full loading file. The base station can be automatically recovered into an available state after a failure, the automatic abnormal failure processing capability of equipment is improved, and the competitiveness of the equipment is improved.
Owner:DATANG MOBILE COMM EQUIP CO LTD
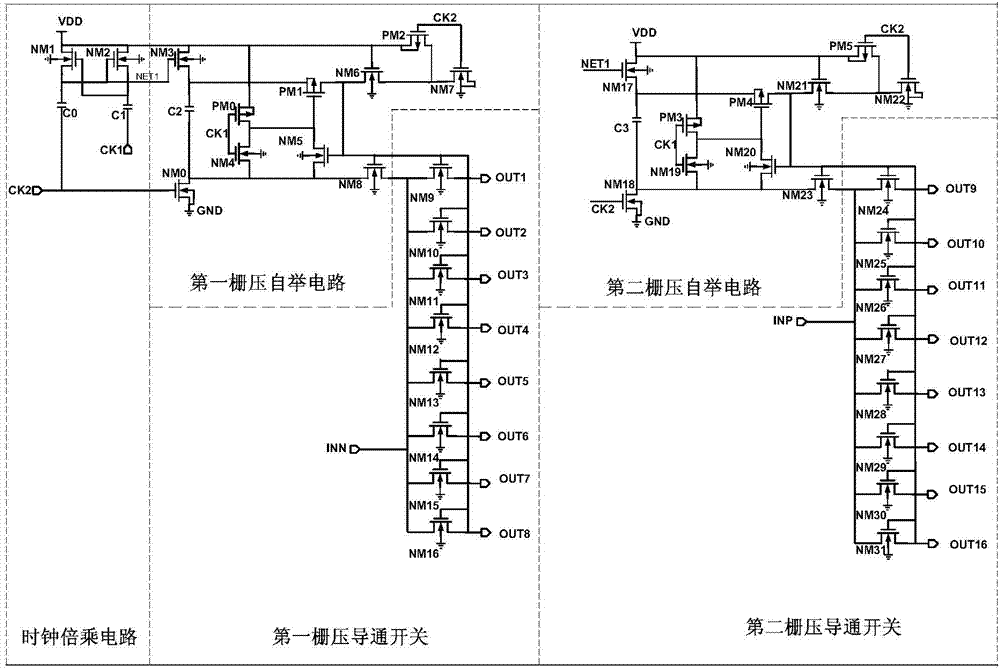
Multi-channel sampling grid voltage bootstrapping switch suitable for streamline type analog-digital converter
InactiveCN104270153AGuaranteed simultaneityReduce areaAnalogue/digital conversionElectric signal transmission systemsDifferential signalingEngineering
The invention discloses a multi-channel sampling grid voltage bootstrapping switch suitable for a streamline type analog-digital converter. Compared with a traditional grid voltage bootstrapping switch, on the basis of an original clock multiplying circuit and a grid voltage bootstrapping circuit, another grid voltage bootstrapping circuit is added, a sampling switch is arranged correspondingly, meanwhile, the added grid voltage bootstrapping circuit and the original grid voltage bootstrapping circuit share the clock multiplying circuit, accordingly, compared with a plurality of original separated grid voltage bootstrapping switches, a certain area is saved, meanwhile, the synchroneity of various clocks is guaranteed, and simultaneous sampling of multi-channel differential signals can be achieved.
Owner:SOUTHEAST UNIV
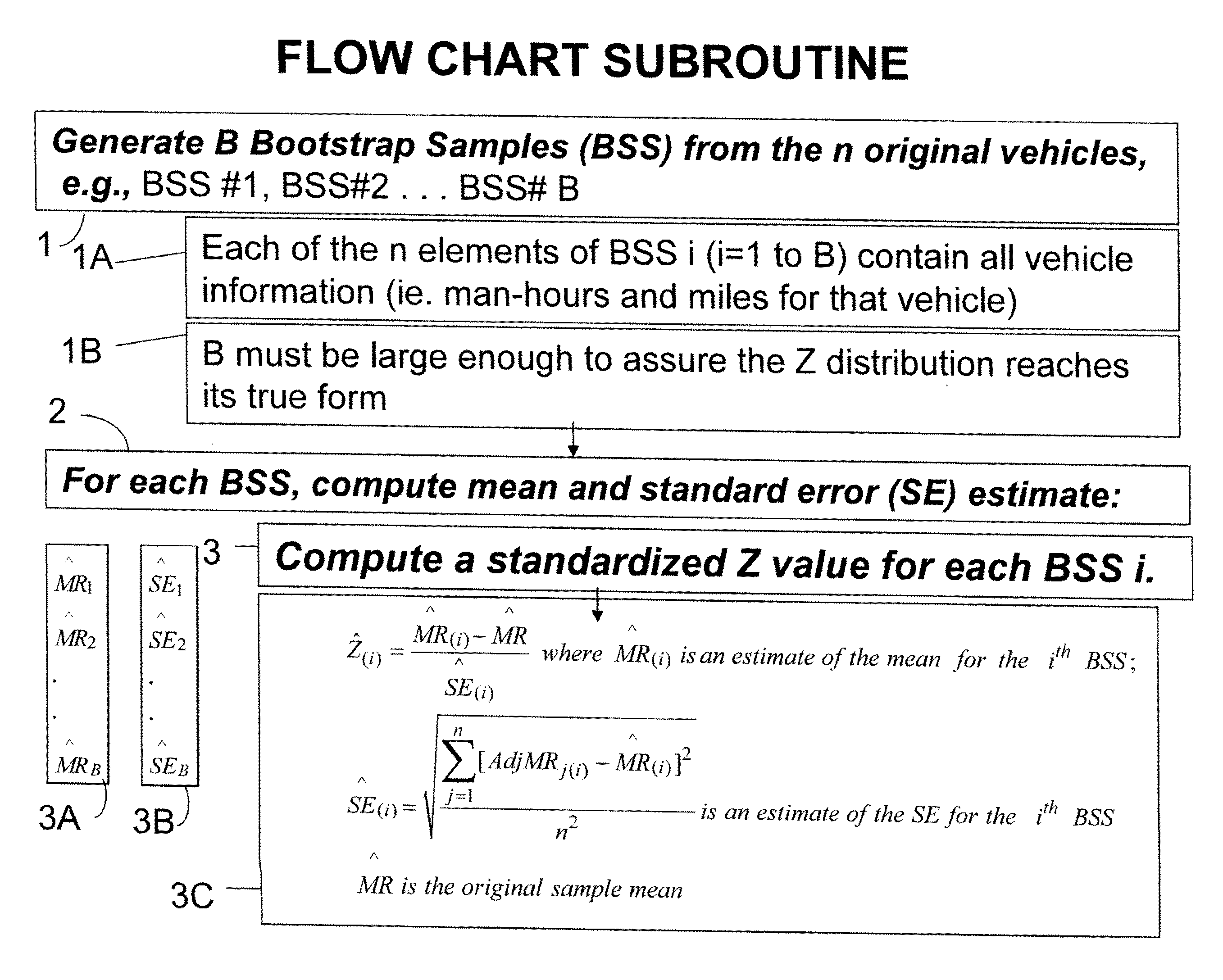
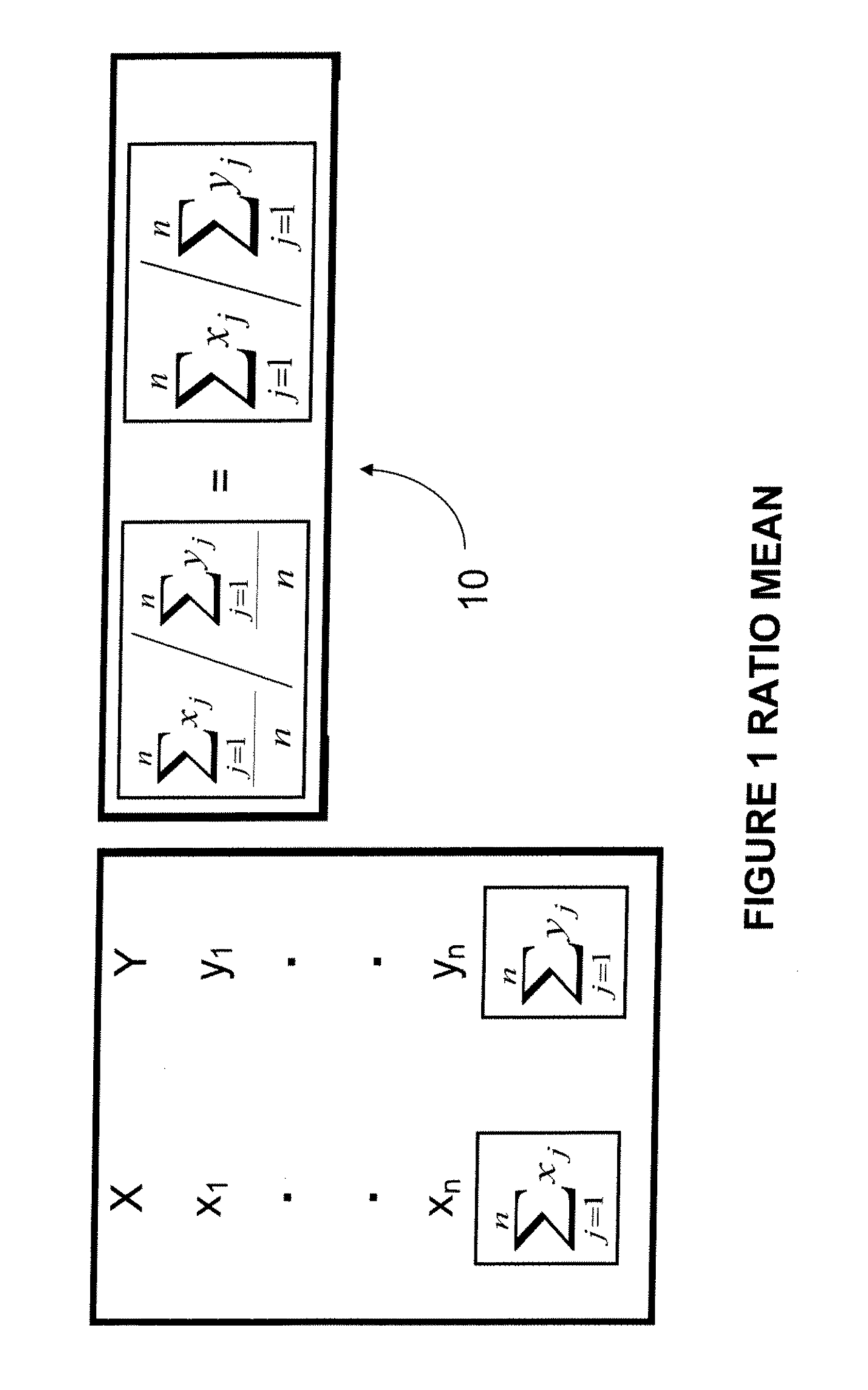
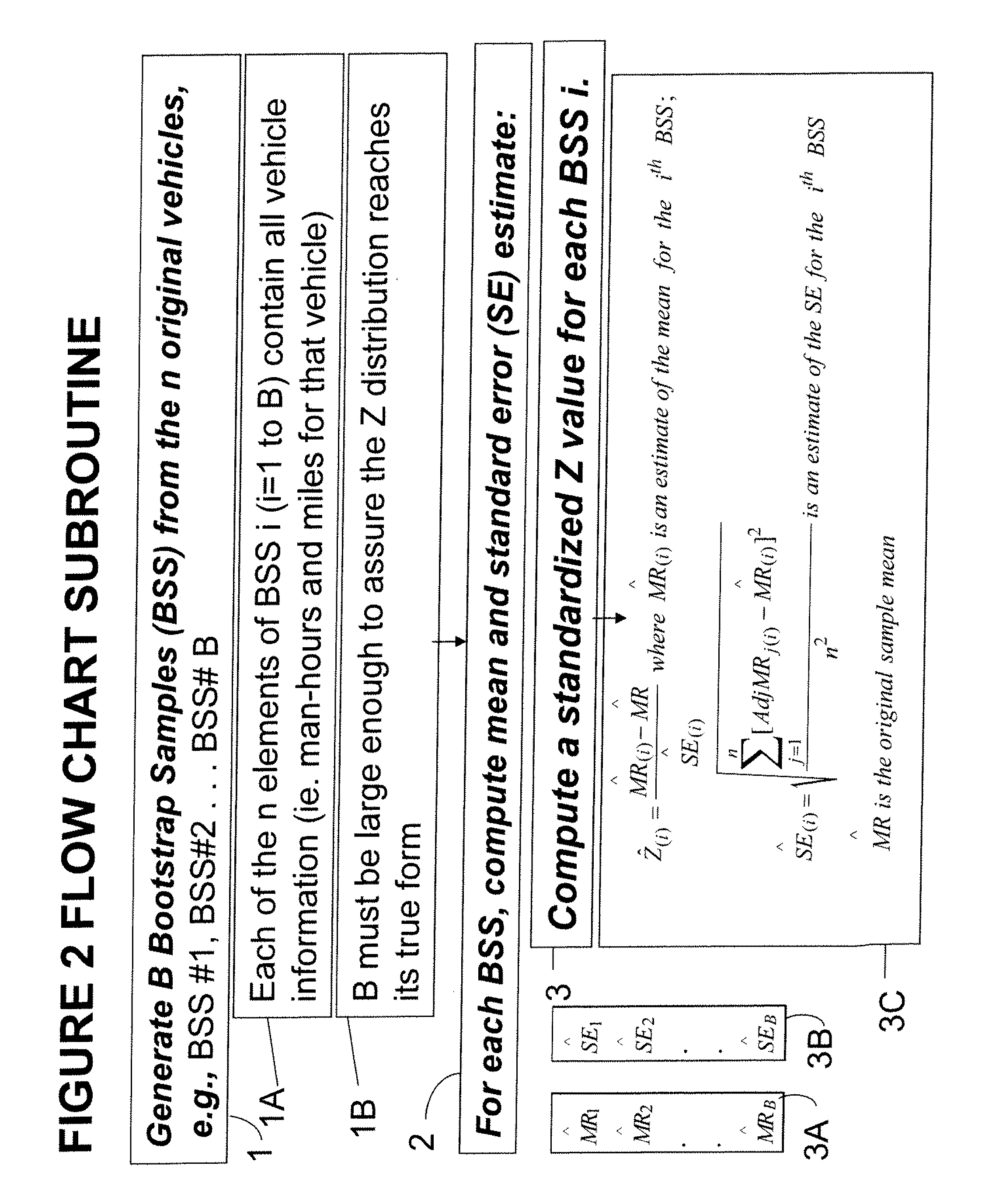
Method and system of confidence interval methodology for ratio means
InactiveUS20110054839A1Digital computer detailsComplex mathematical operationsAlgorithmErrors and residuals
A method and system for determining whether the number of samples taken from a population of units where the distribution of X and Y variables are unknown by evaluating ratio mean measurements on a computer to determine a confidence interval. The method comprising: inputting samples from the total population with each unit sample having at least two variables X and Y; redefining the multivariate data that comprises the two variables X and Y; estimating the mean; computing the standard error; using a bootstrapping method, generating boot strap samples, computing a Z distribution based upon the bootstrap samples; and computing the confidence interval. The system comprises a processor for performing the steps of the method
Owner:ARMY US SEC THE
Uncertainty reduction in collaborative bootstrapping
InactiveUS20050131850A1Improve classification performanceReduce uncertaintyChaos modelsNon-linear system modelsAlgorithmParallel processing
Collaborative bootstrapping with uncertainty reduction for increased classifier performance. One classifier selects a portion of data that is uncertain with respect to the classifier and a second classifier labels the portion. Uncertainty reduction includes parallel processing where the second classifier also selects an uncertain portion for the first classifier to label. Uncertainty reduction can be incorporated into existing or new co-training or bootstrapping, including bilingual bootstrapping.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com