Method for arranging key in IP multimedia service subsystem network
A technology for multimedia services and subsystems, applied in transmission systems, digital transmission systems, and key distribution, can solve the problems of application layer security problems in IMS networks that are not provided, and achieve the effect of high applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
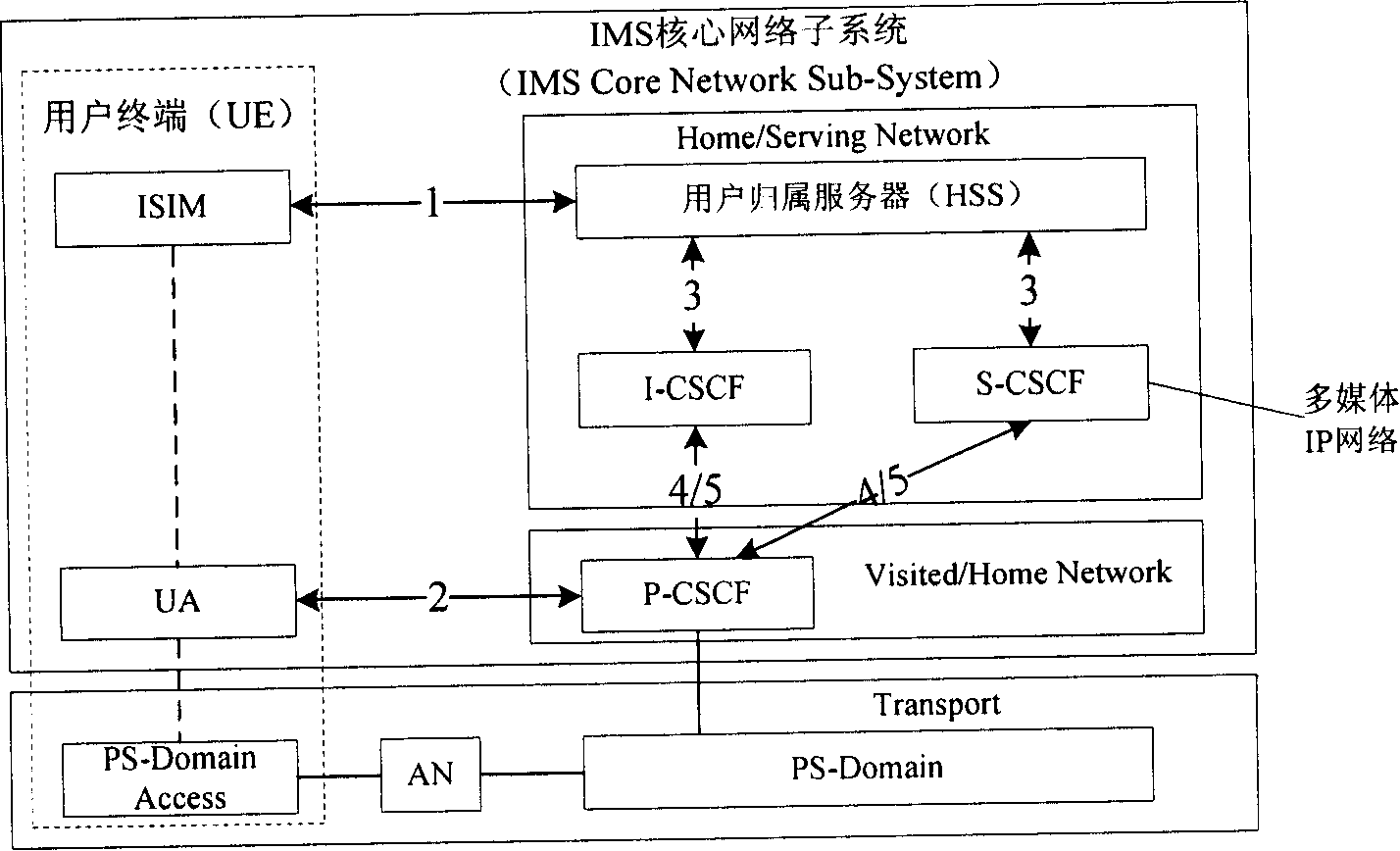
[0023] In order to illustrate the technical solution of the present invention more clearly, first, a brief description is given to the flow of the present invention defined in the third generation mobile communication system (3G).
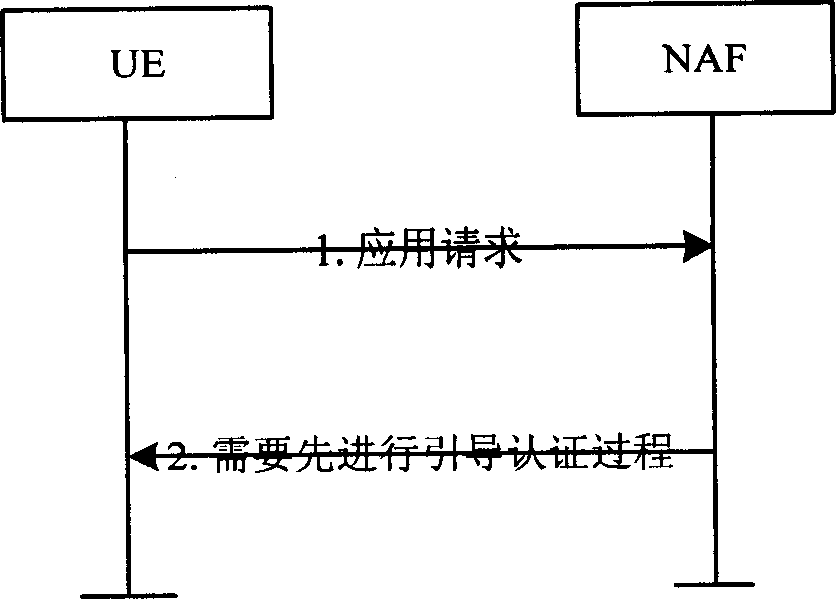
[0024] image 3 Describes how to trigger the startup of the Bootstrapping process. When the UE communicates with the Network Application Function (NAF), if the NAF considers that the UE needs to be authenticated and needs to share the security key of the application layer, the UE is required to start the Bootstrapping process.
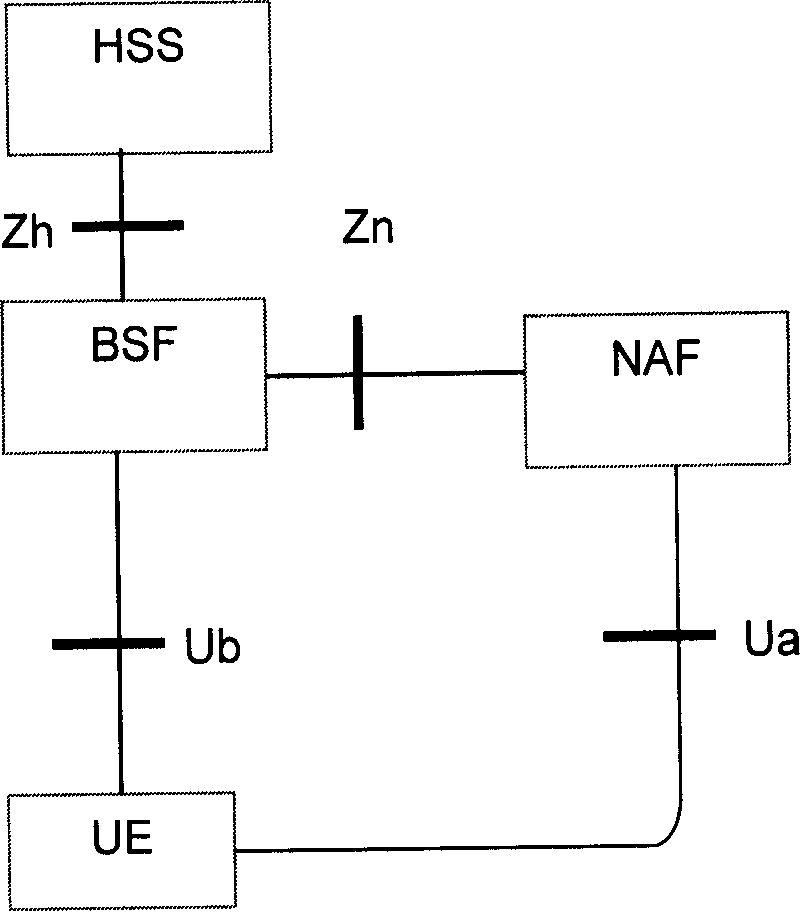
[0025] Figure 4 Describes the Bootstrapping process. Through this process, the UE completes the two-way authentication with the BSF / HSS, and at the same time completes the key distribution between the UE and the BSF (Bootstrapping Server Function). The network side key Ks is provided by the user's home server (Home Subscriber Server , HSS) allocation, stored in the BSF, and after the Bootstrapping process is successful, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com