Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2370 results about "Network application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Computer network applications are network software applications that utilize the Internet or other network hardware infrastructure to perform useful functions for example file transfers within a network. They help us to transfer data from one point to another within the network.
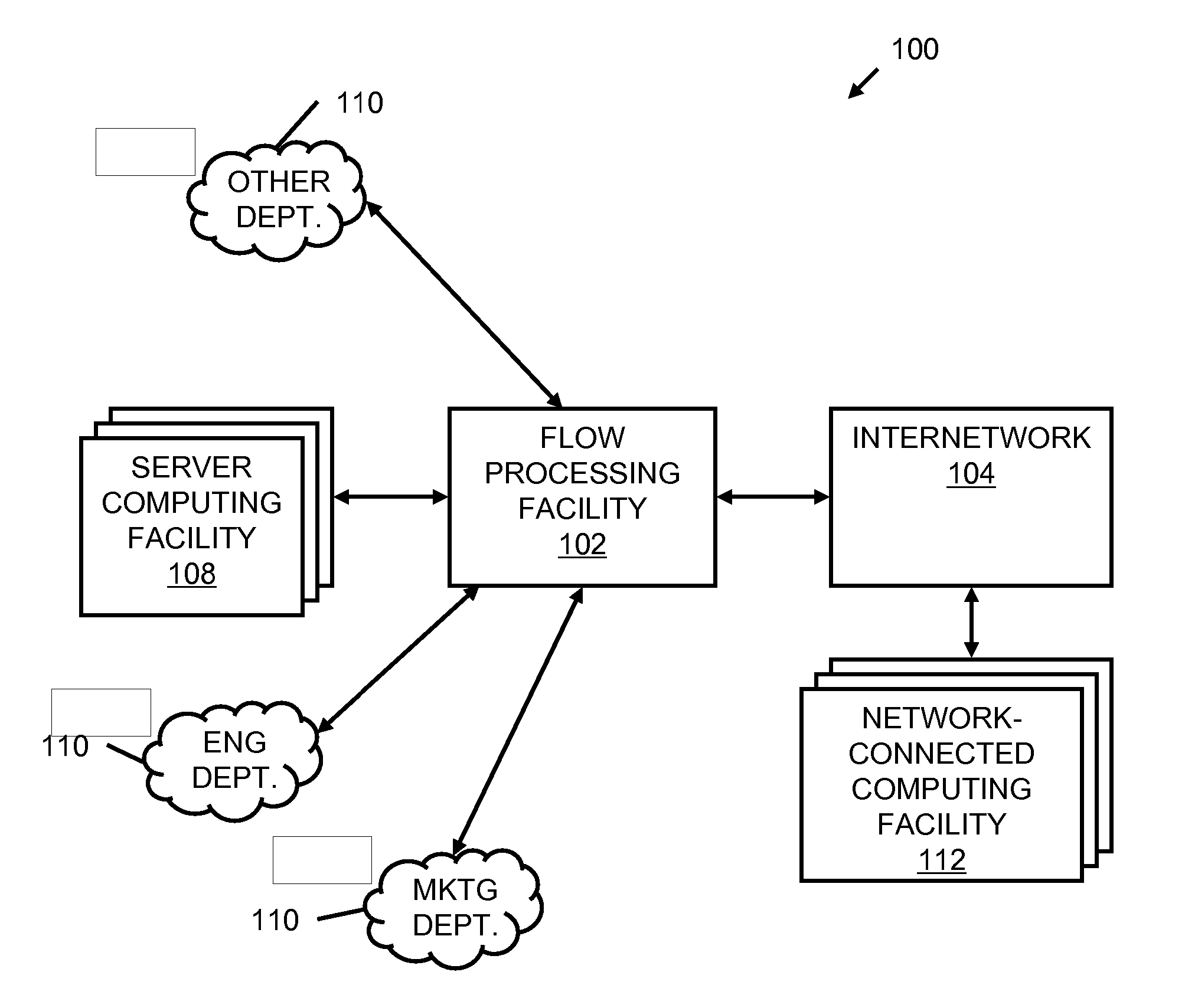
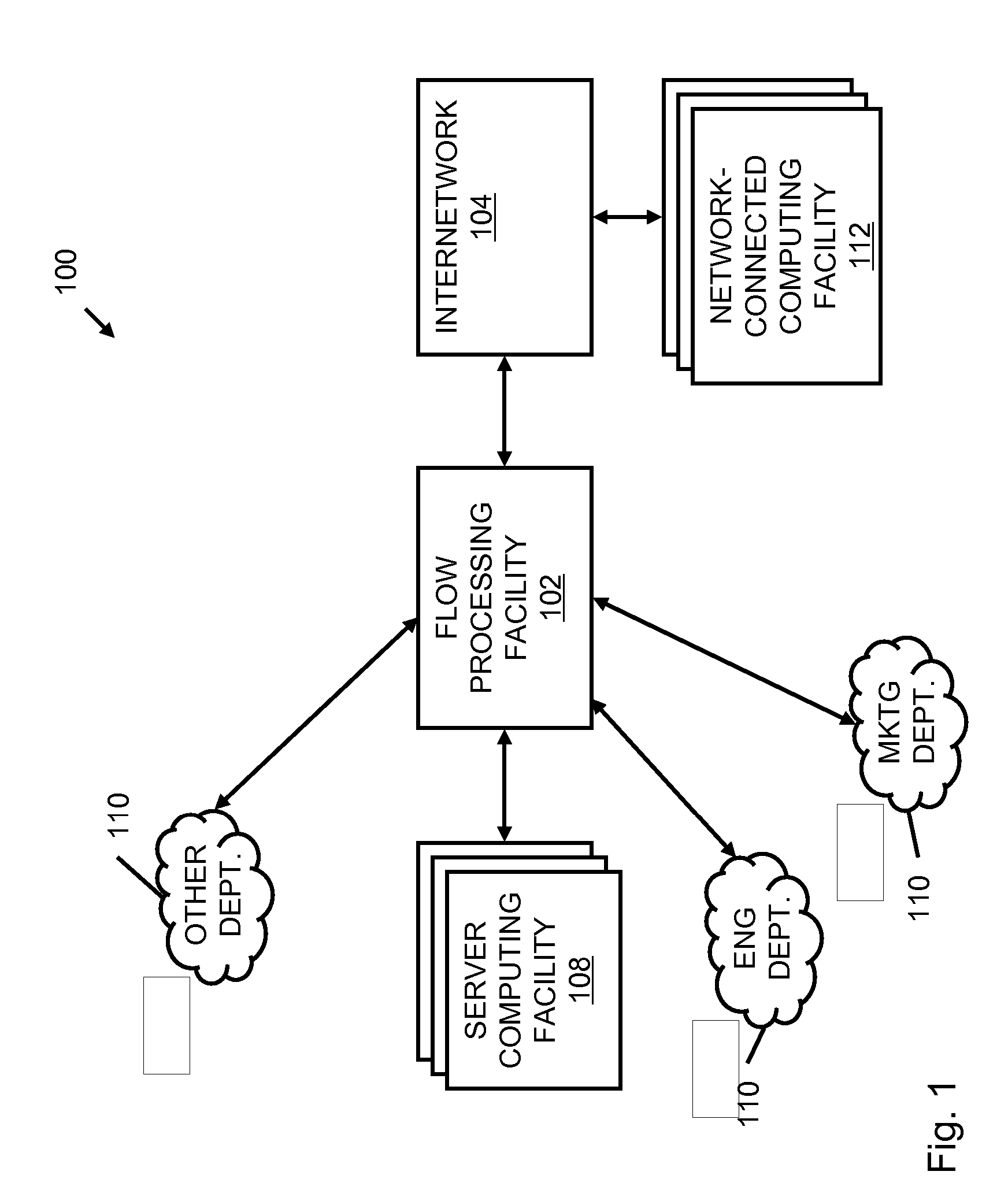
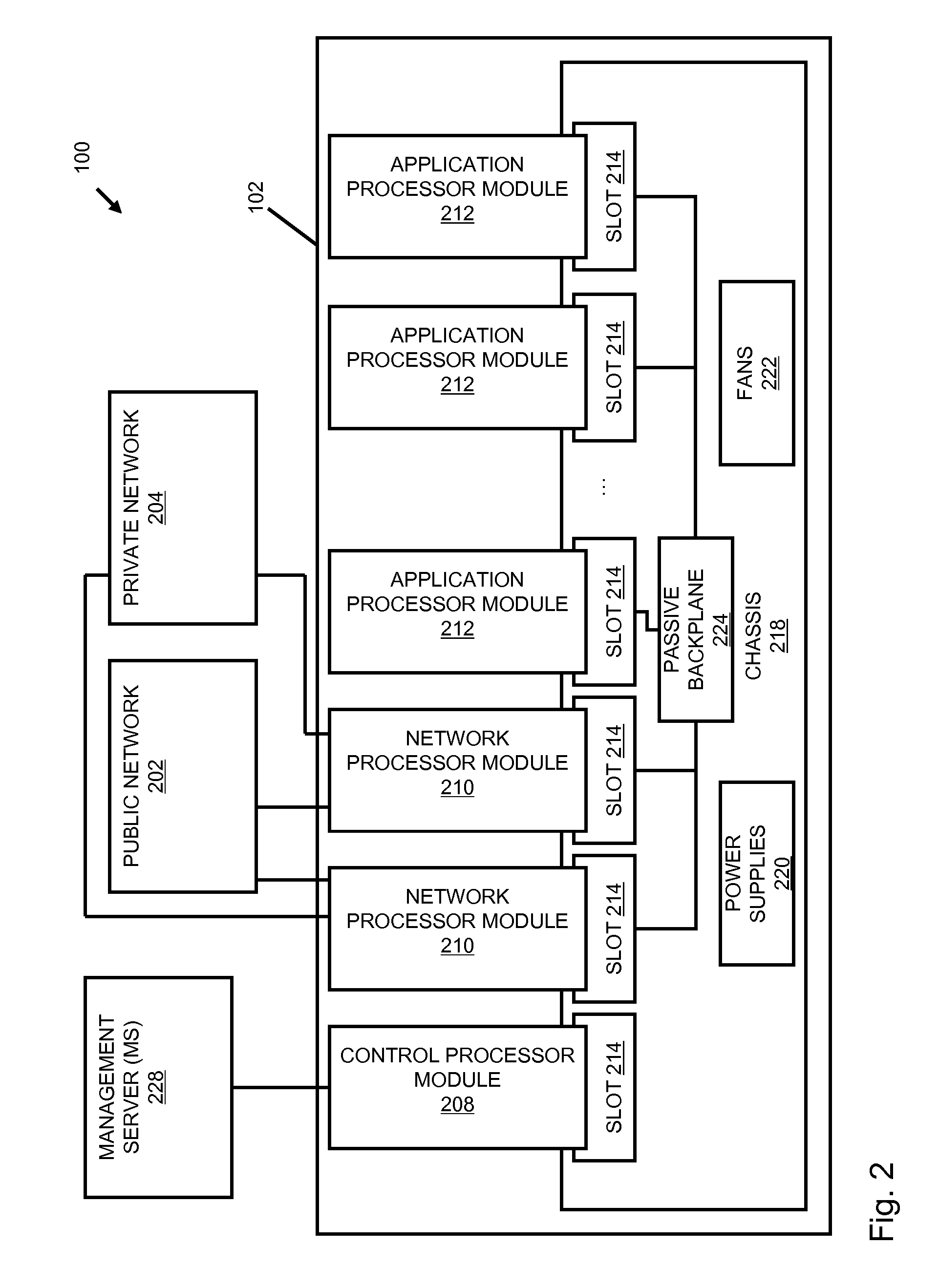
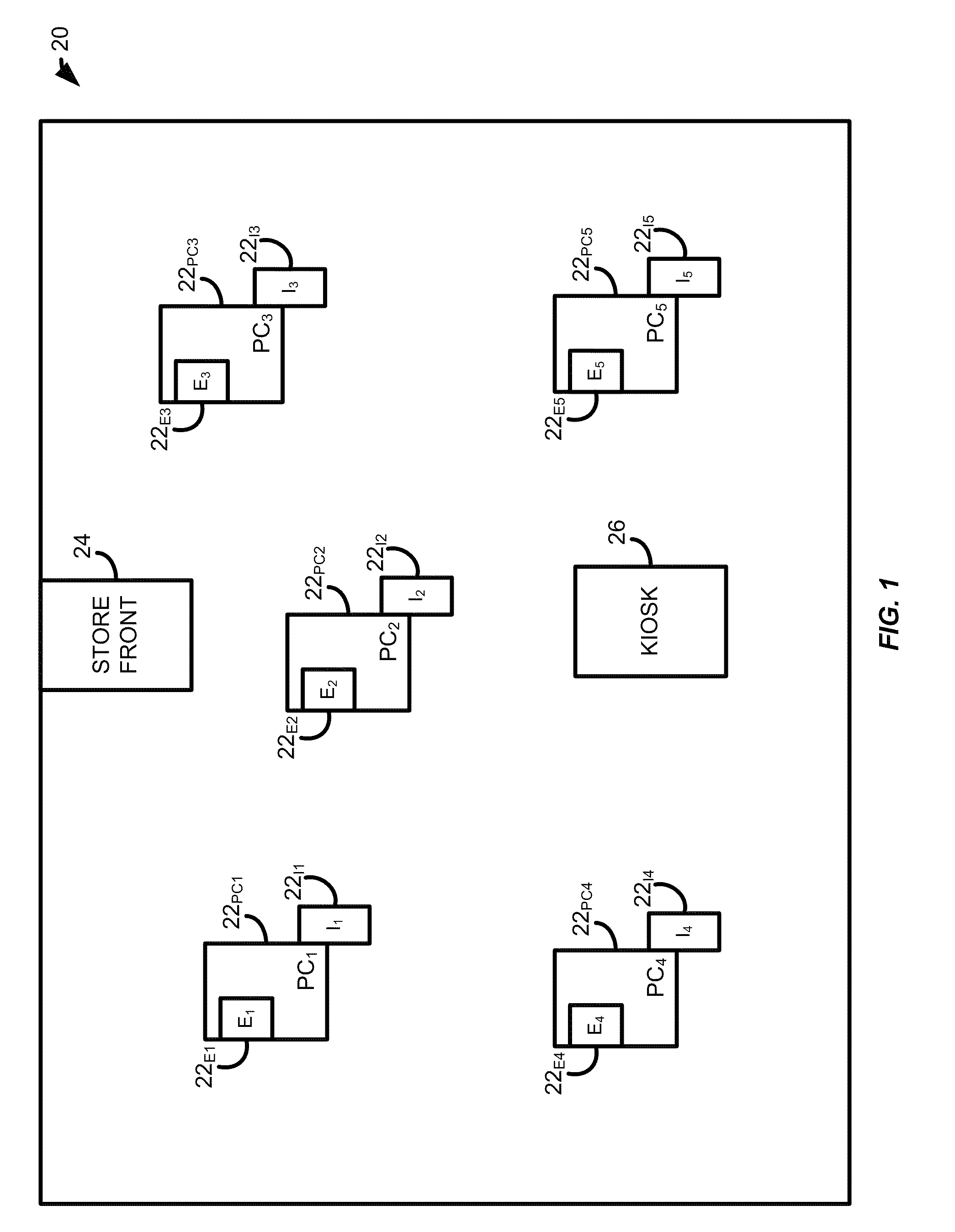
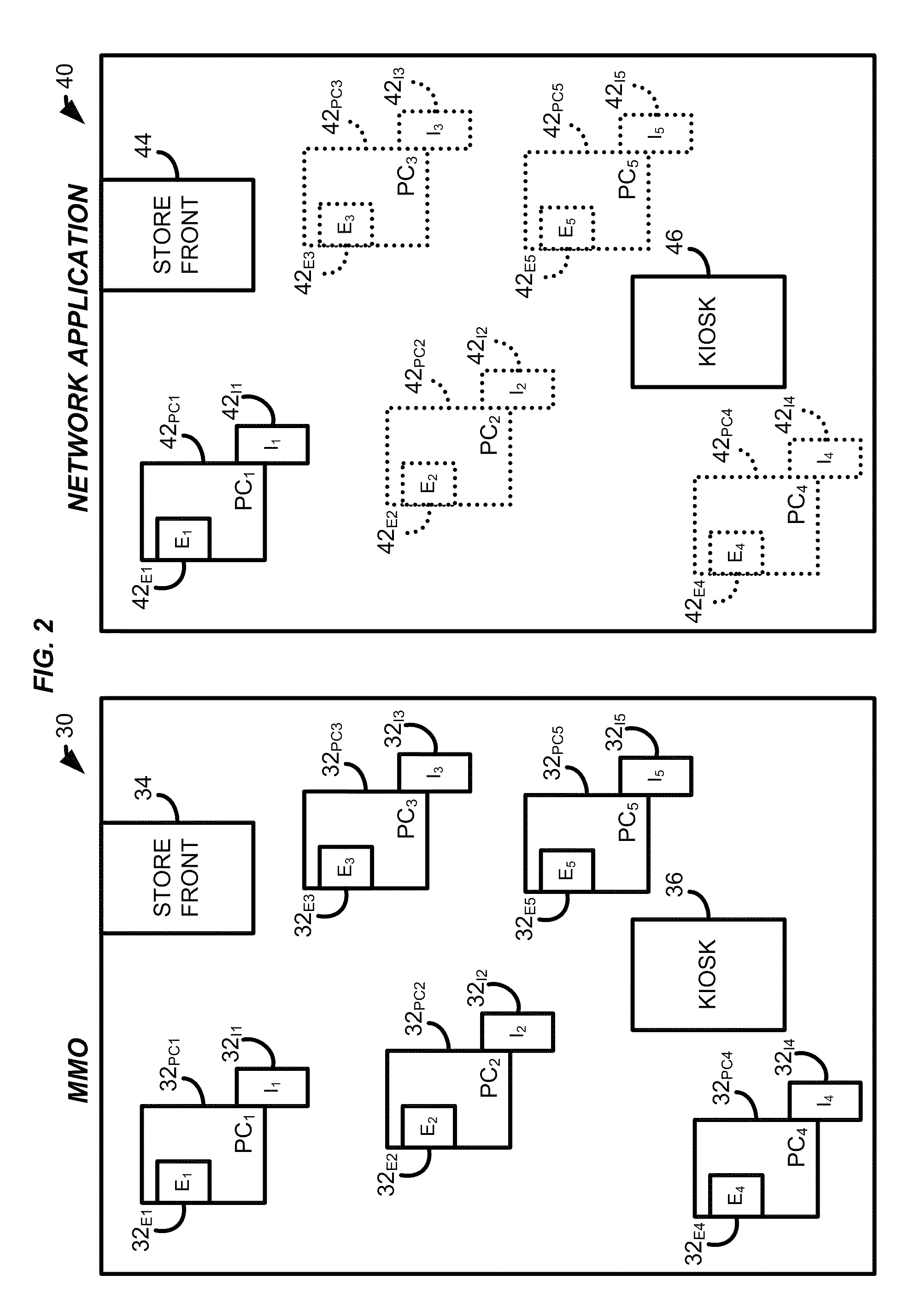
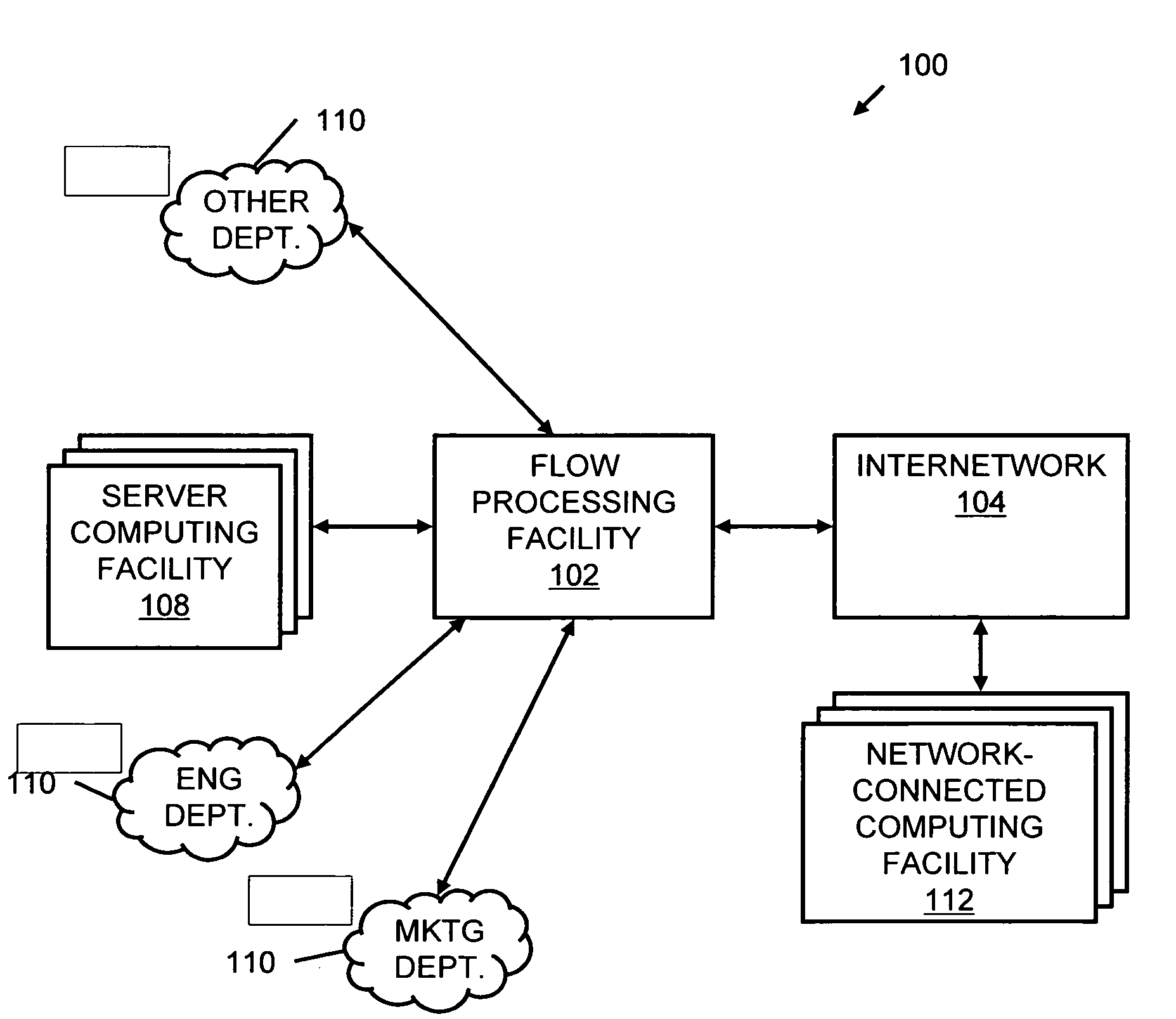
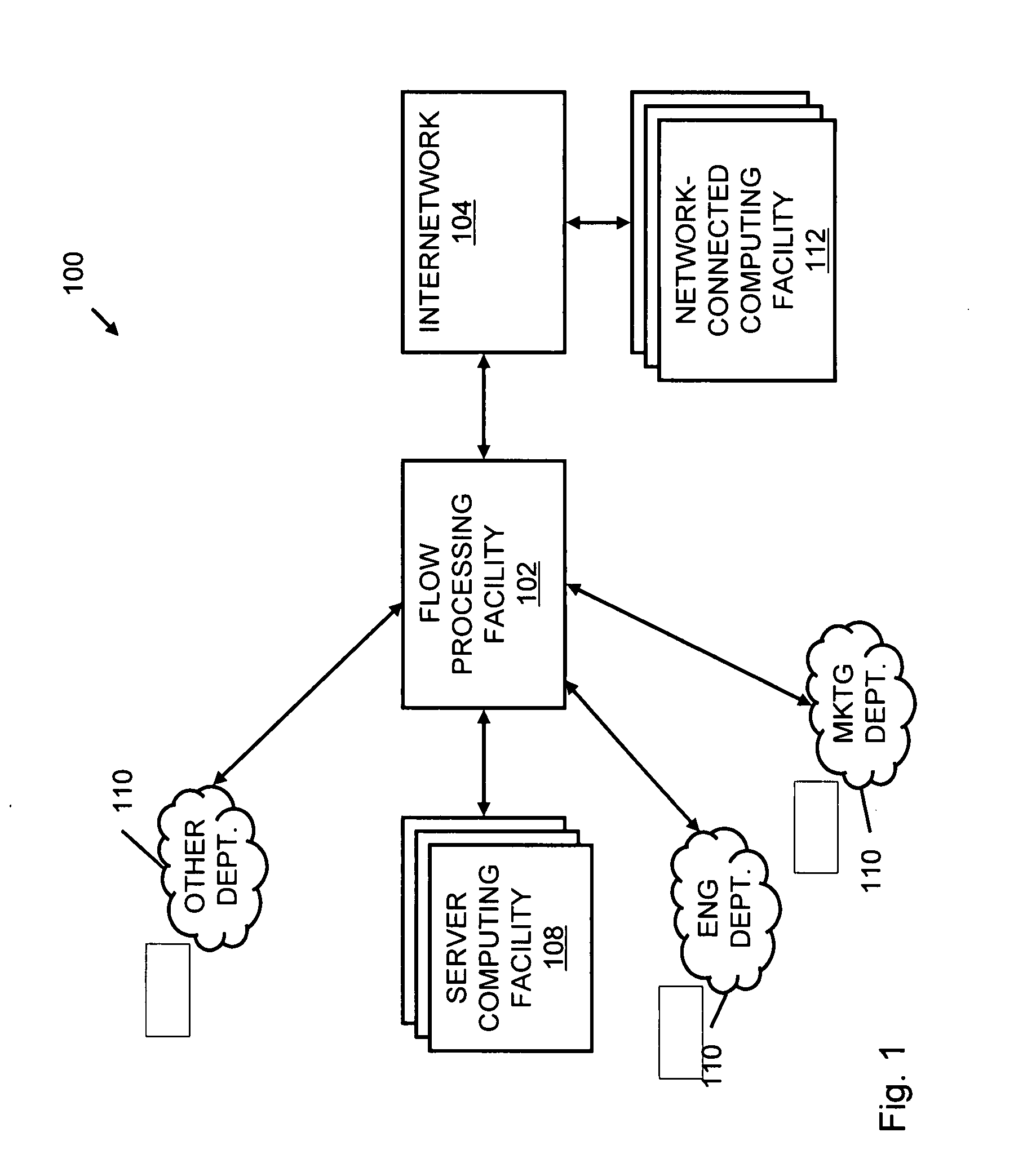
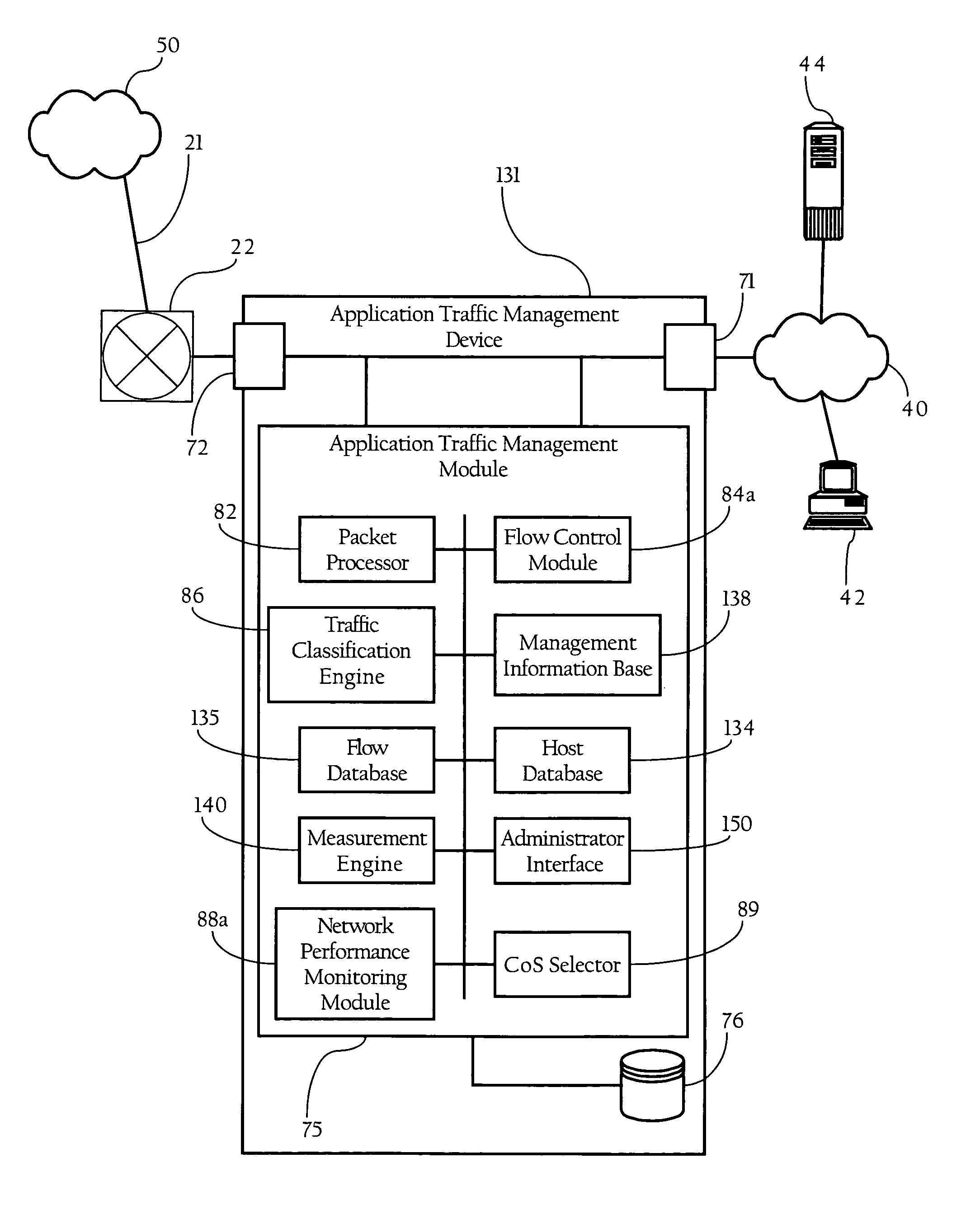
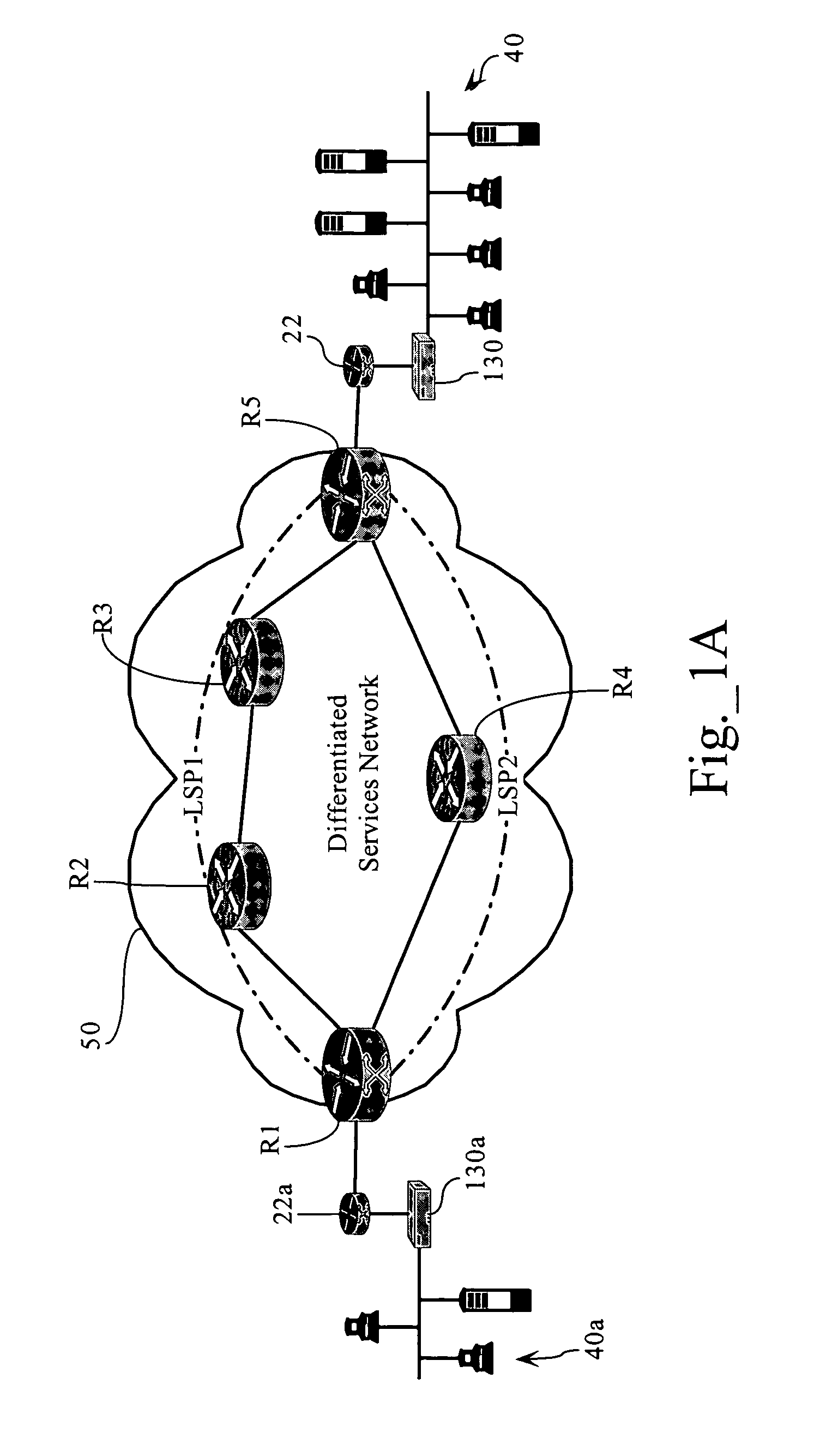
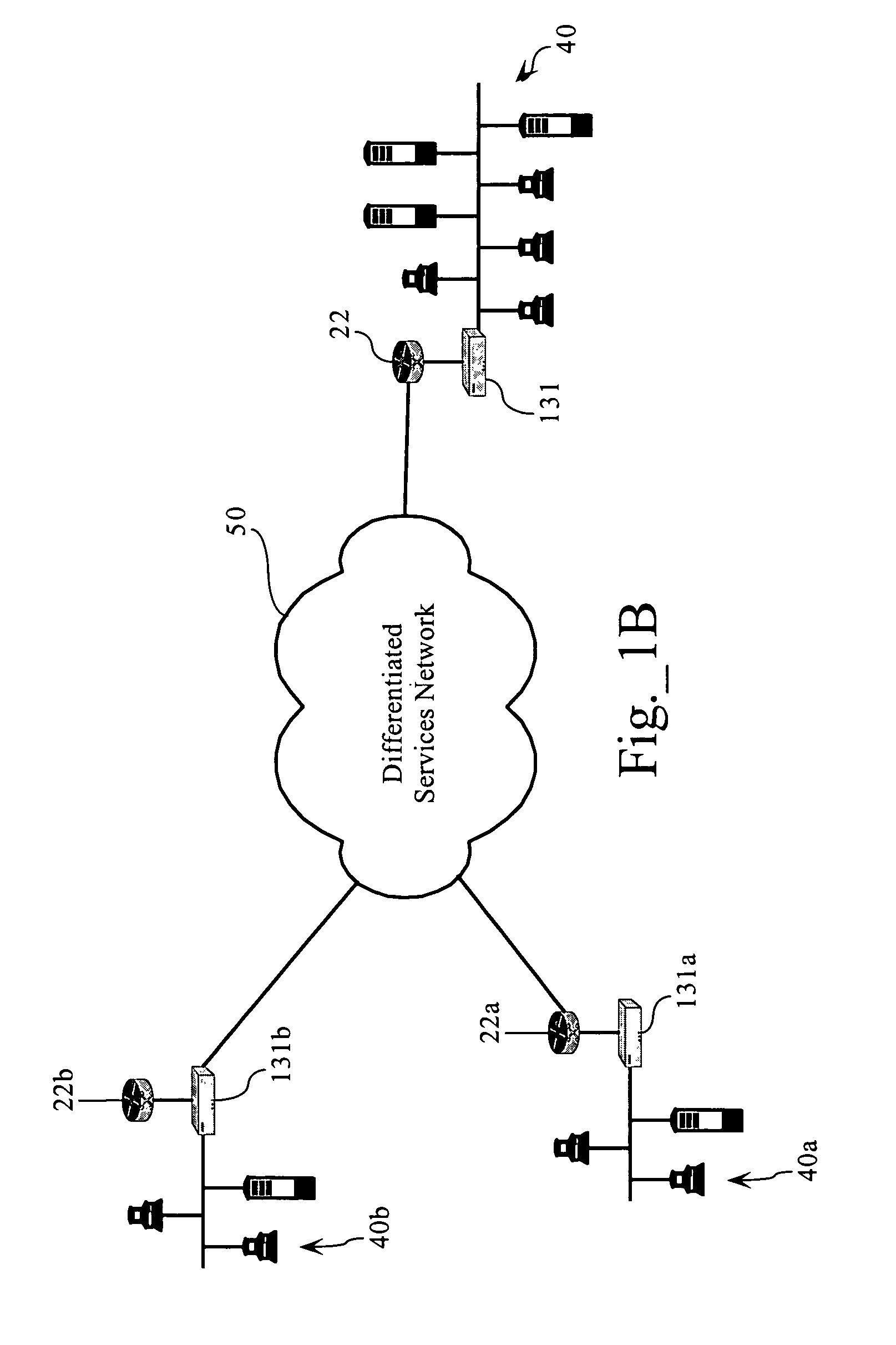
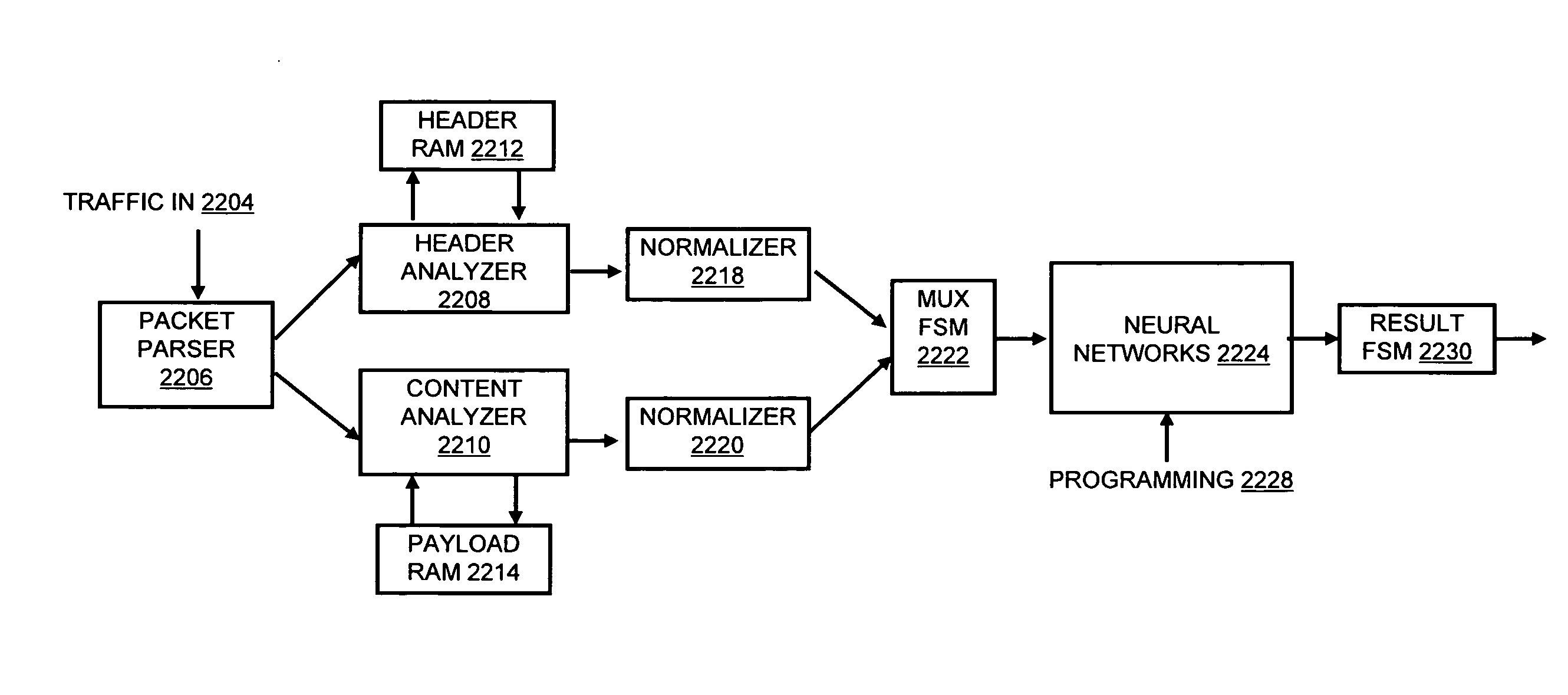
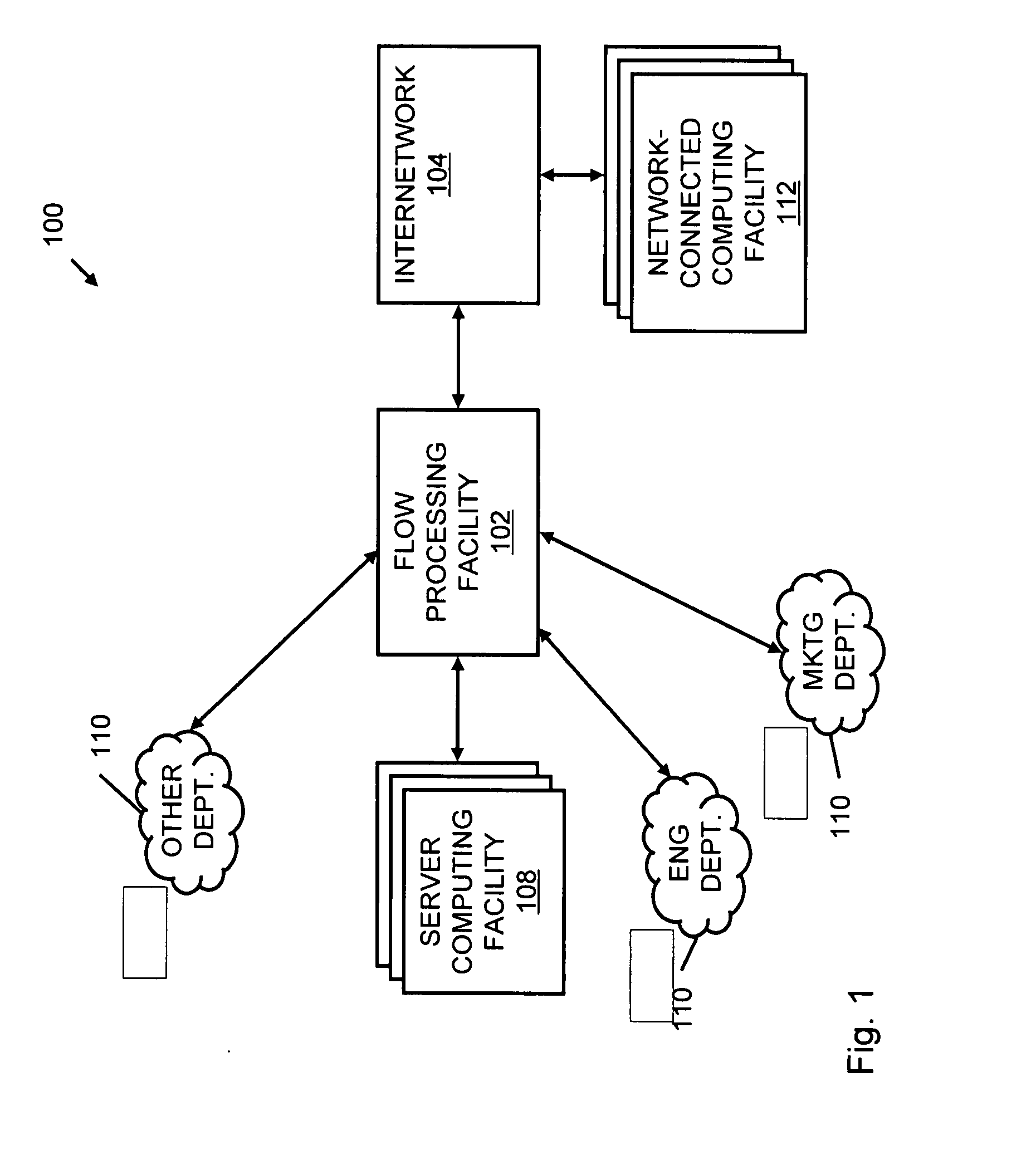
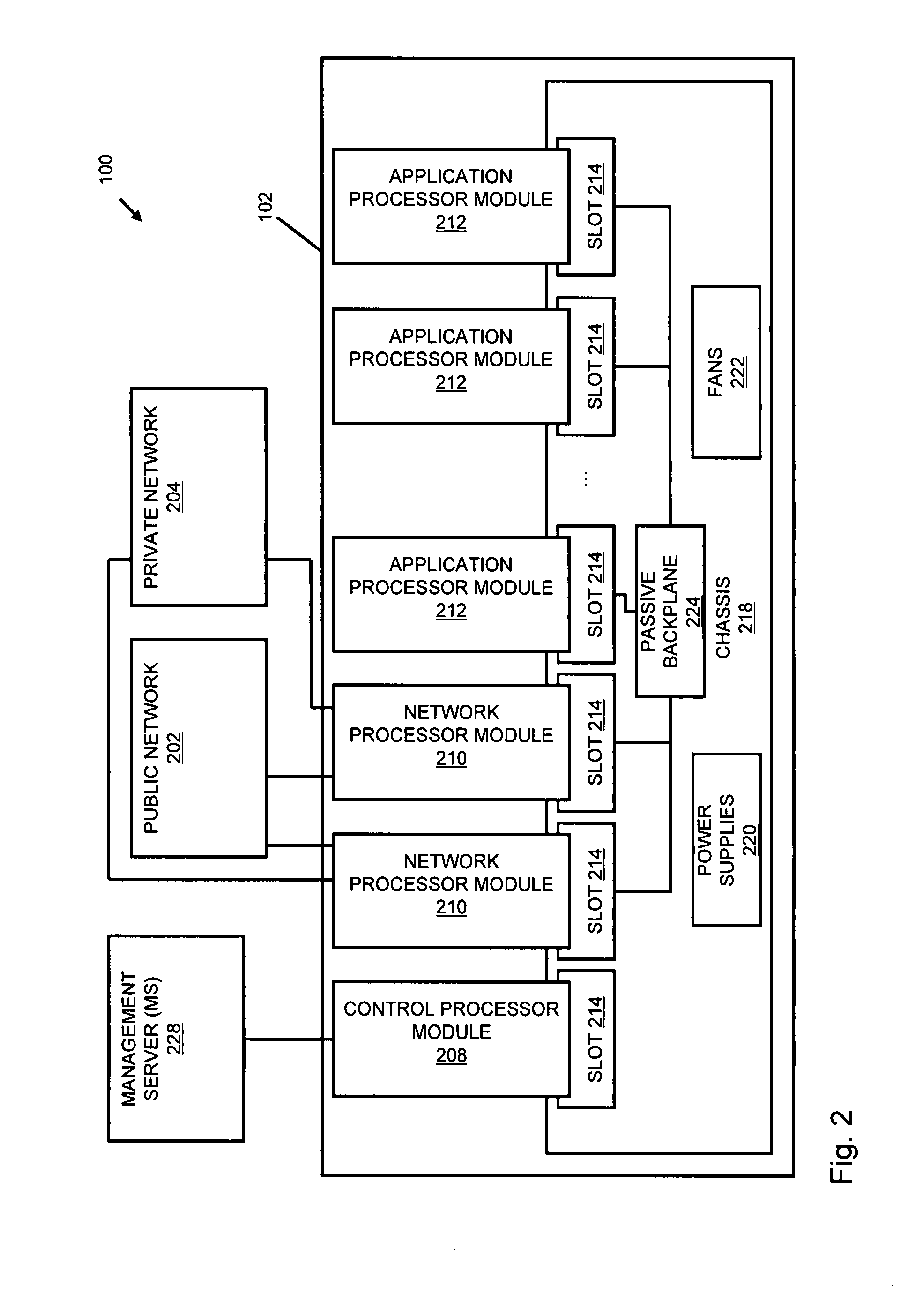
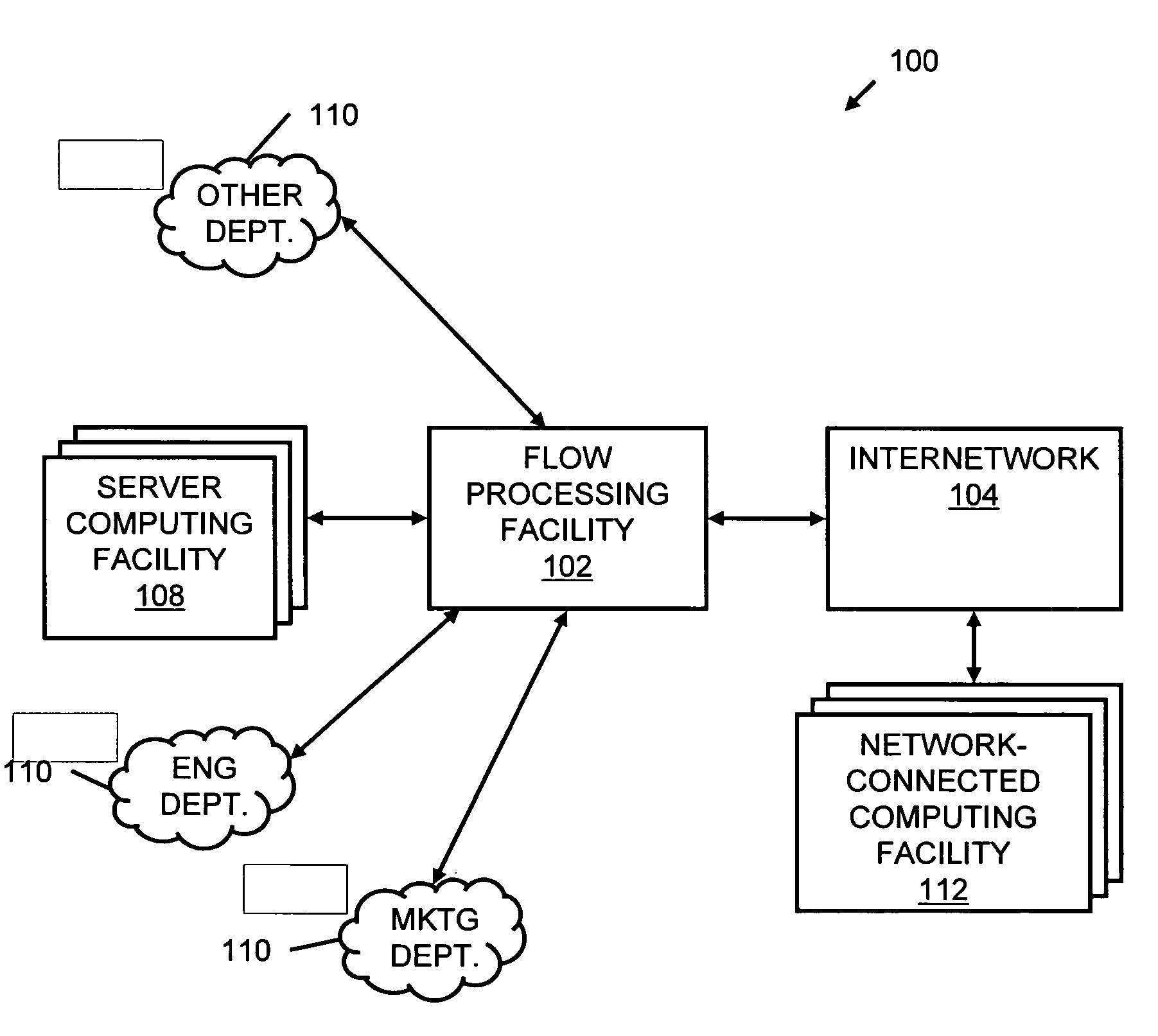
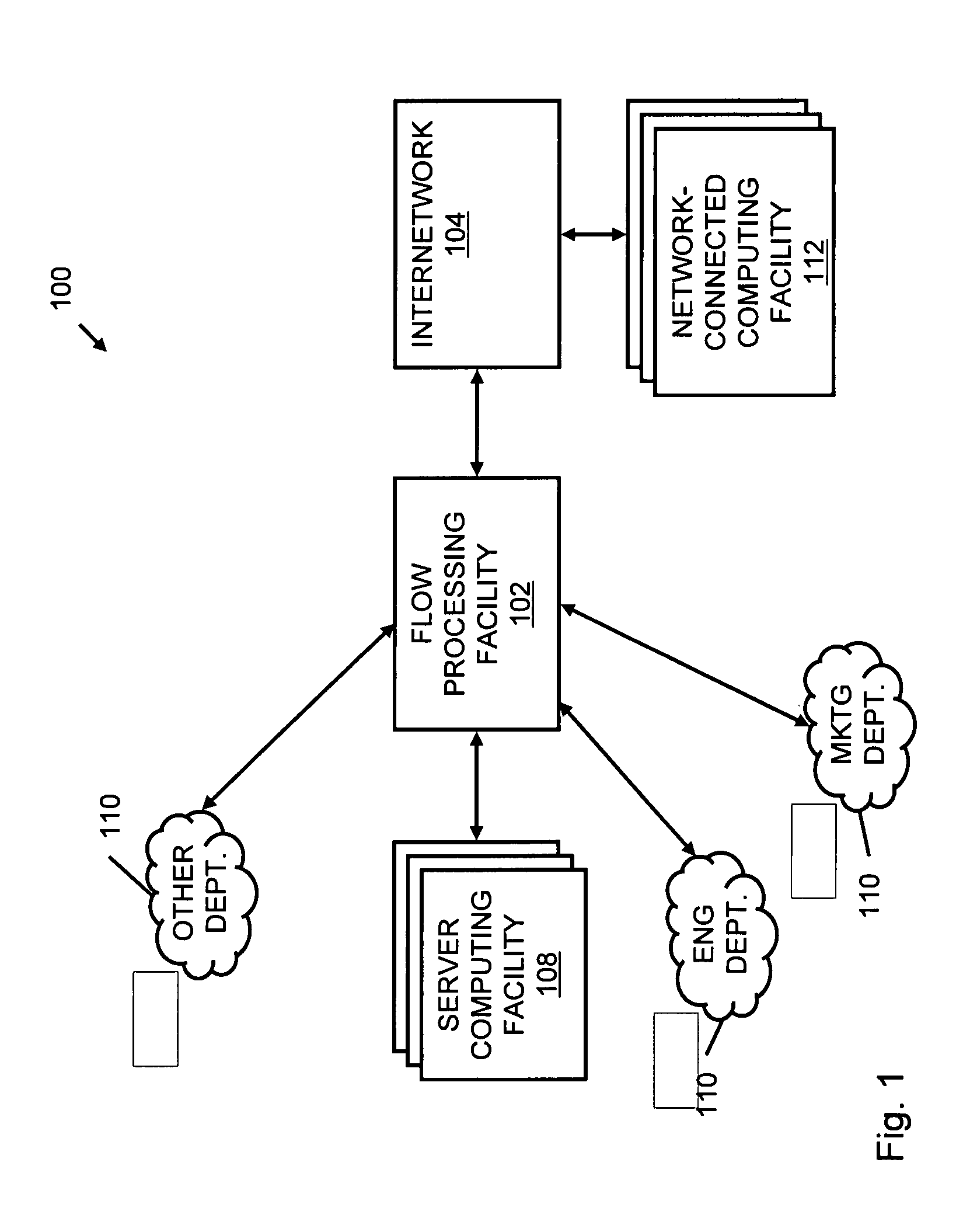
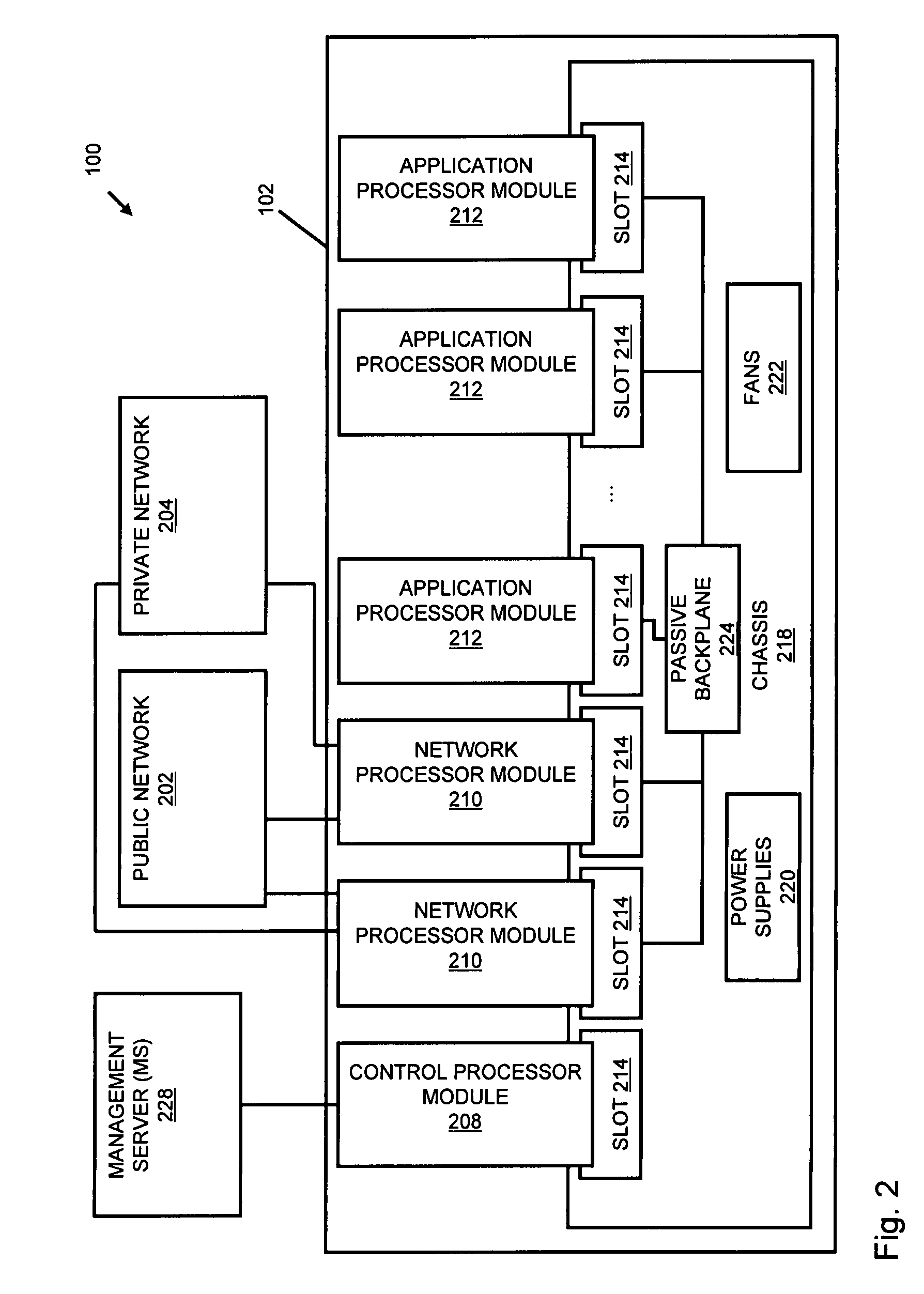
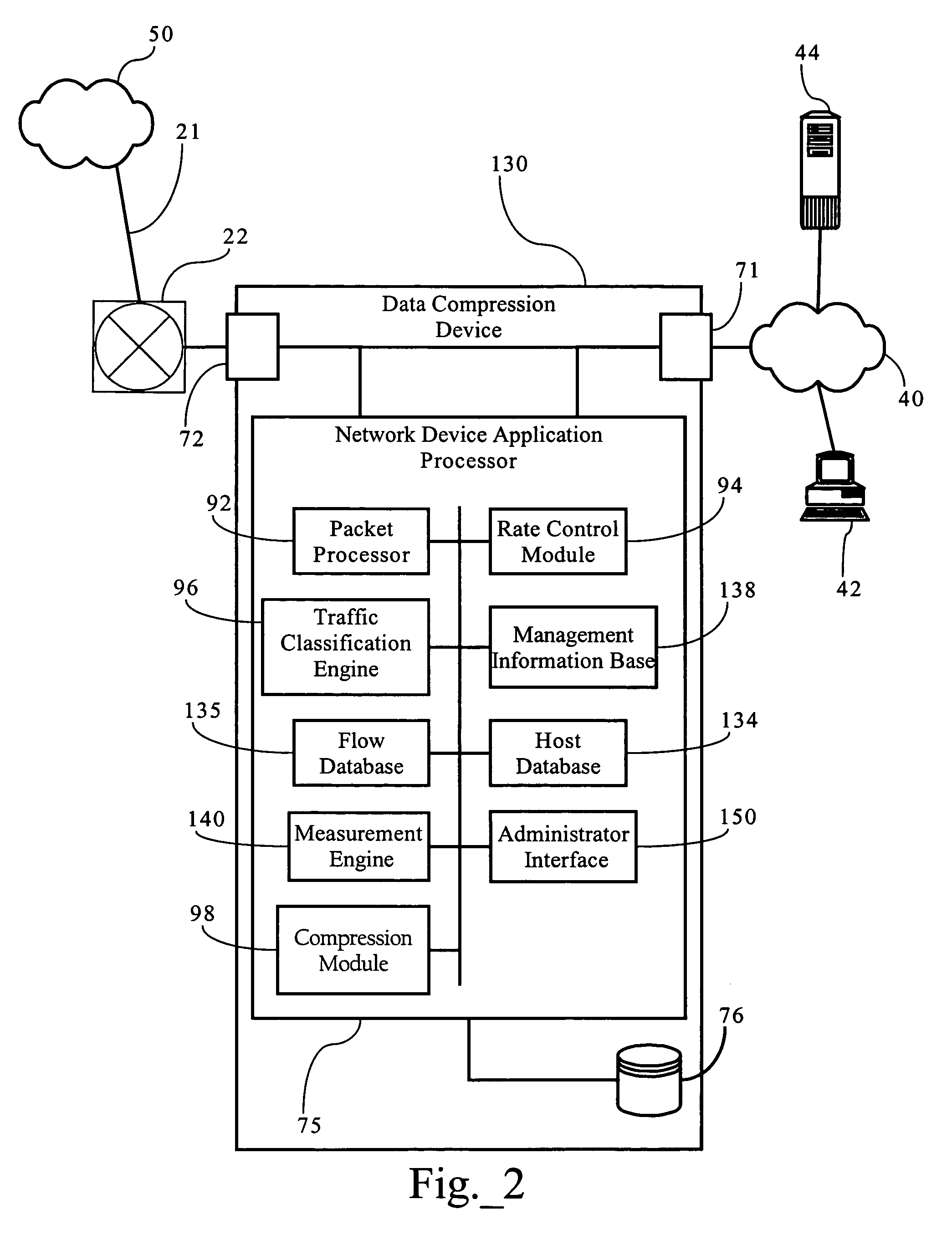
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
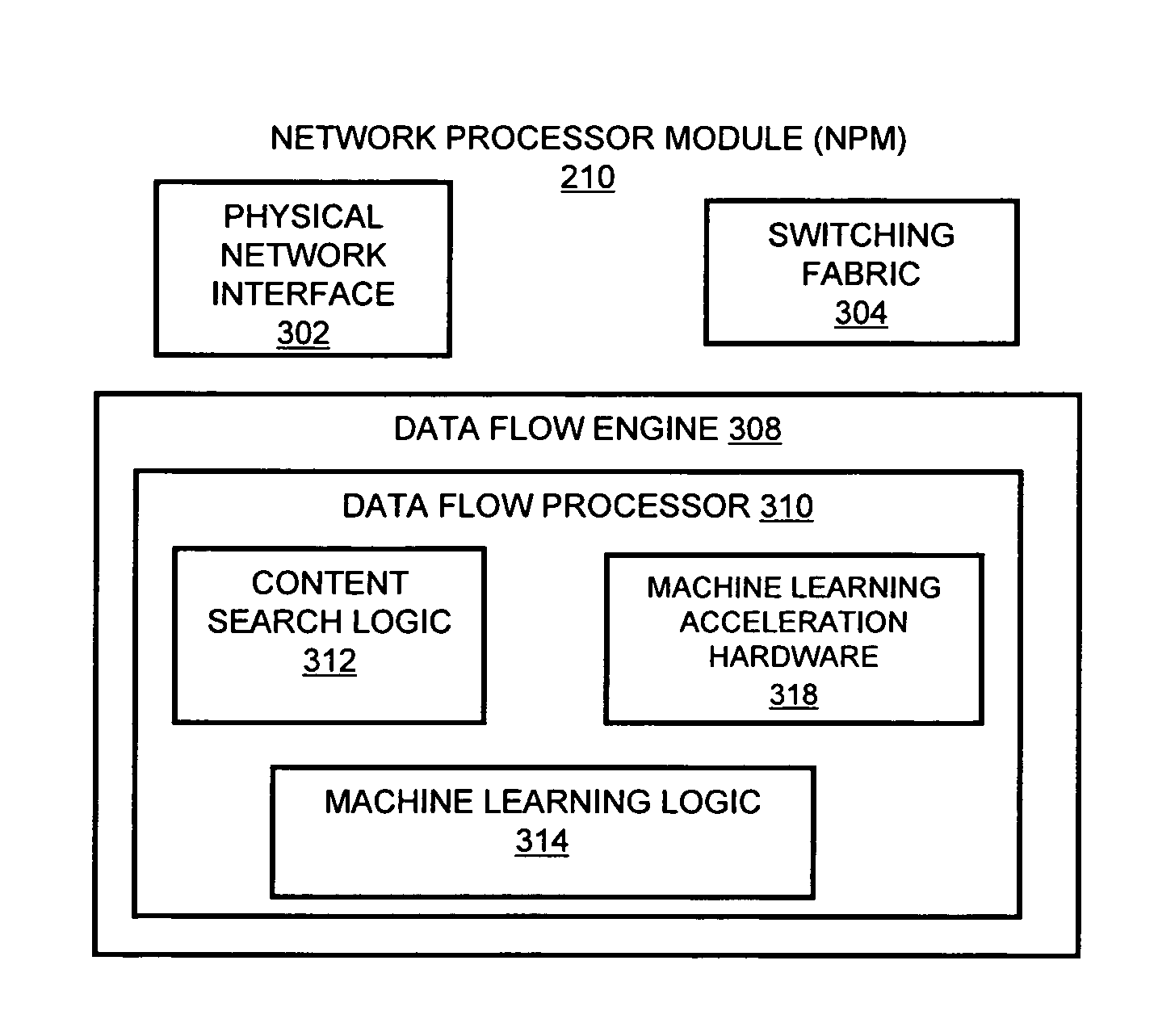
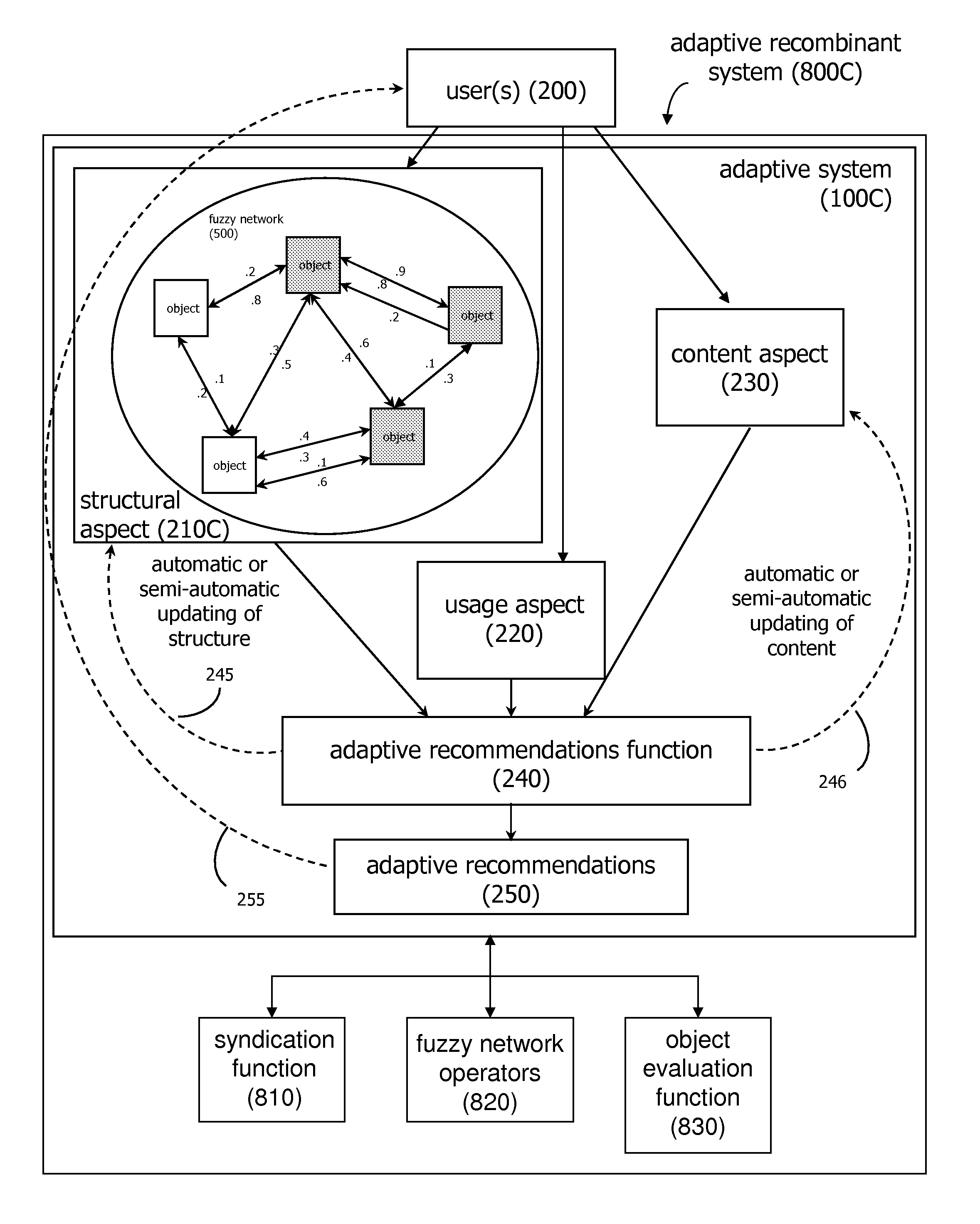
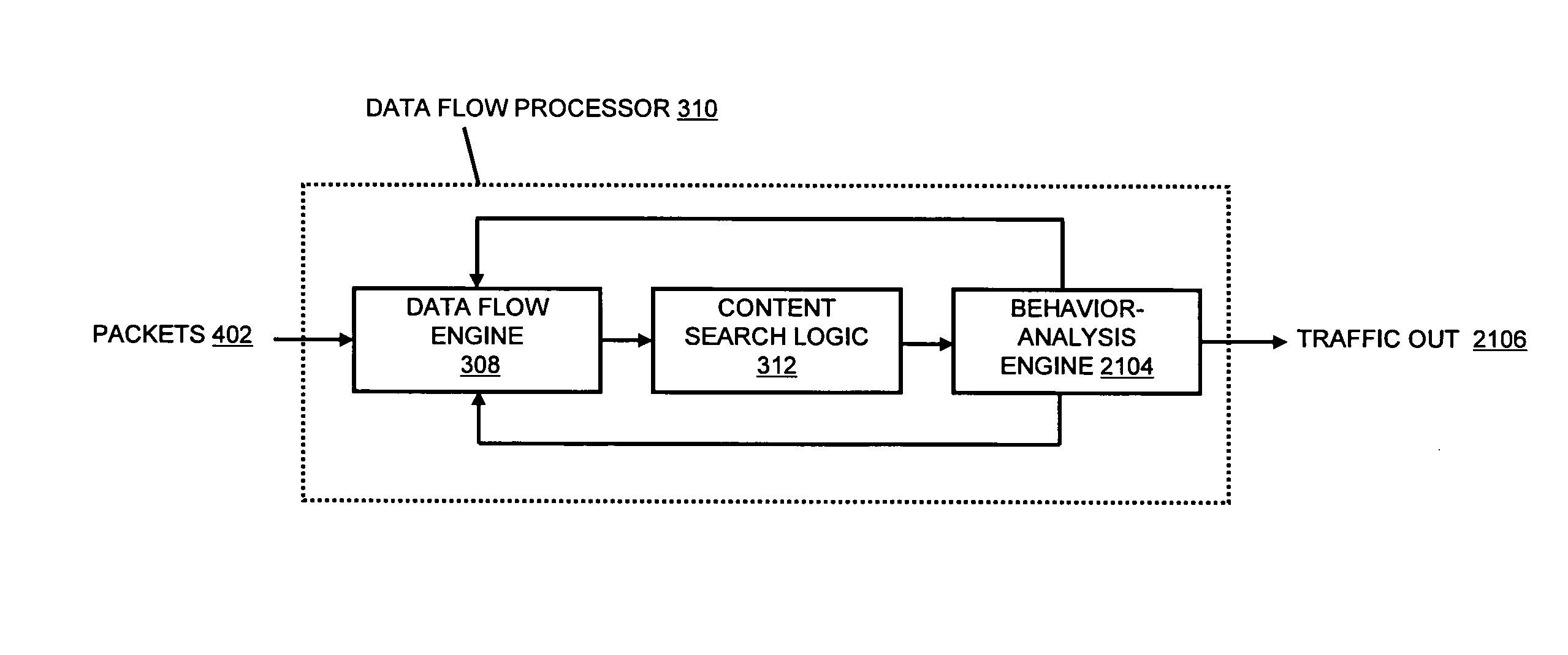
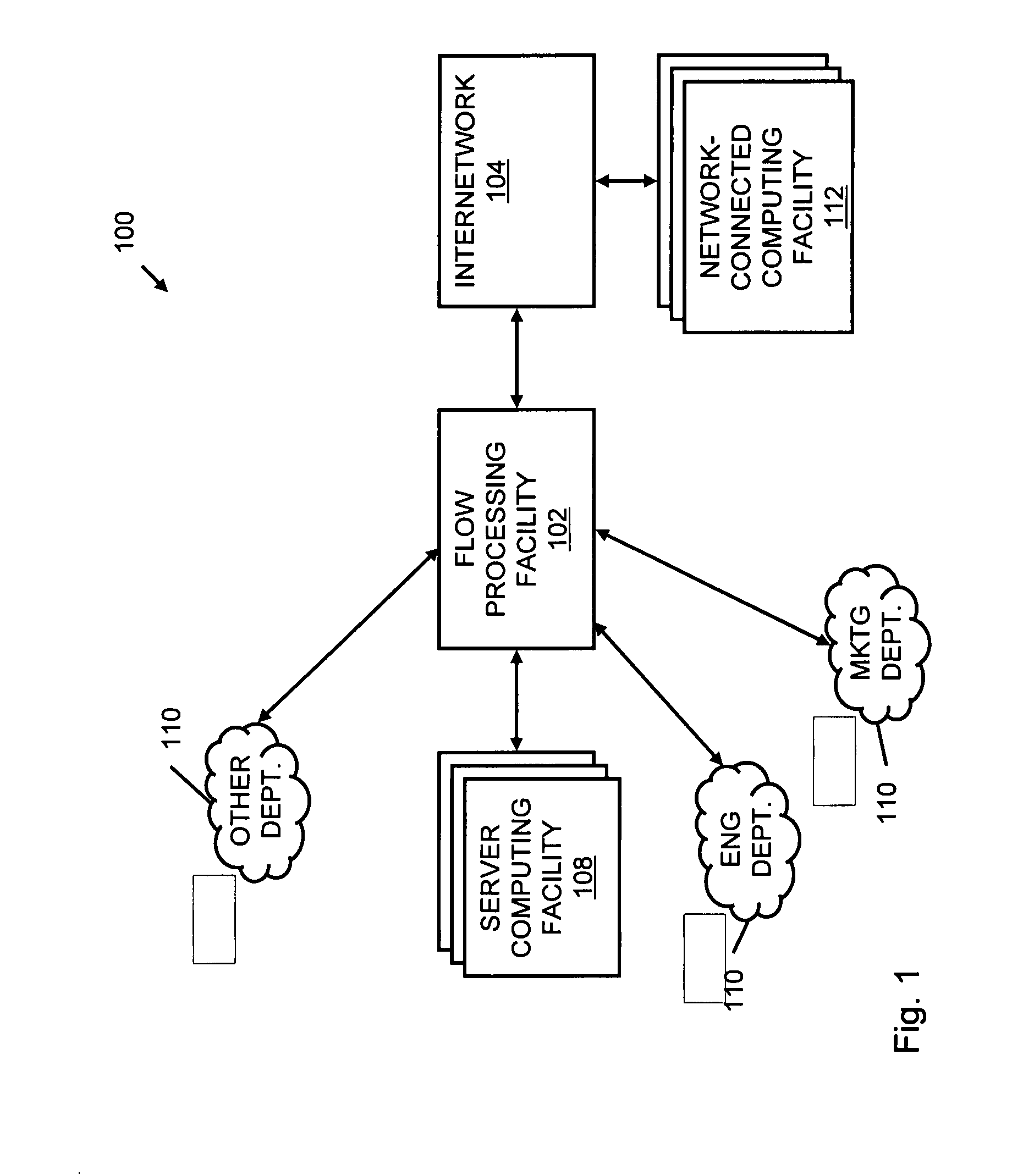
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
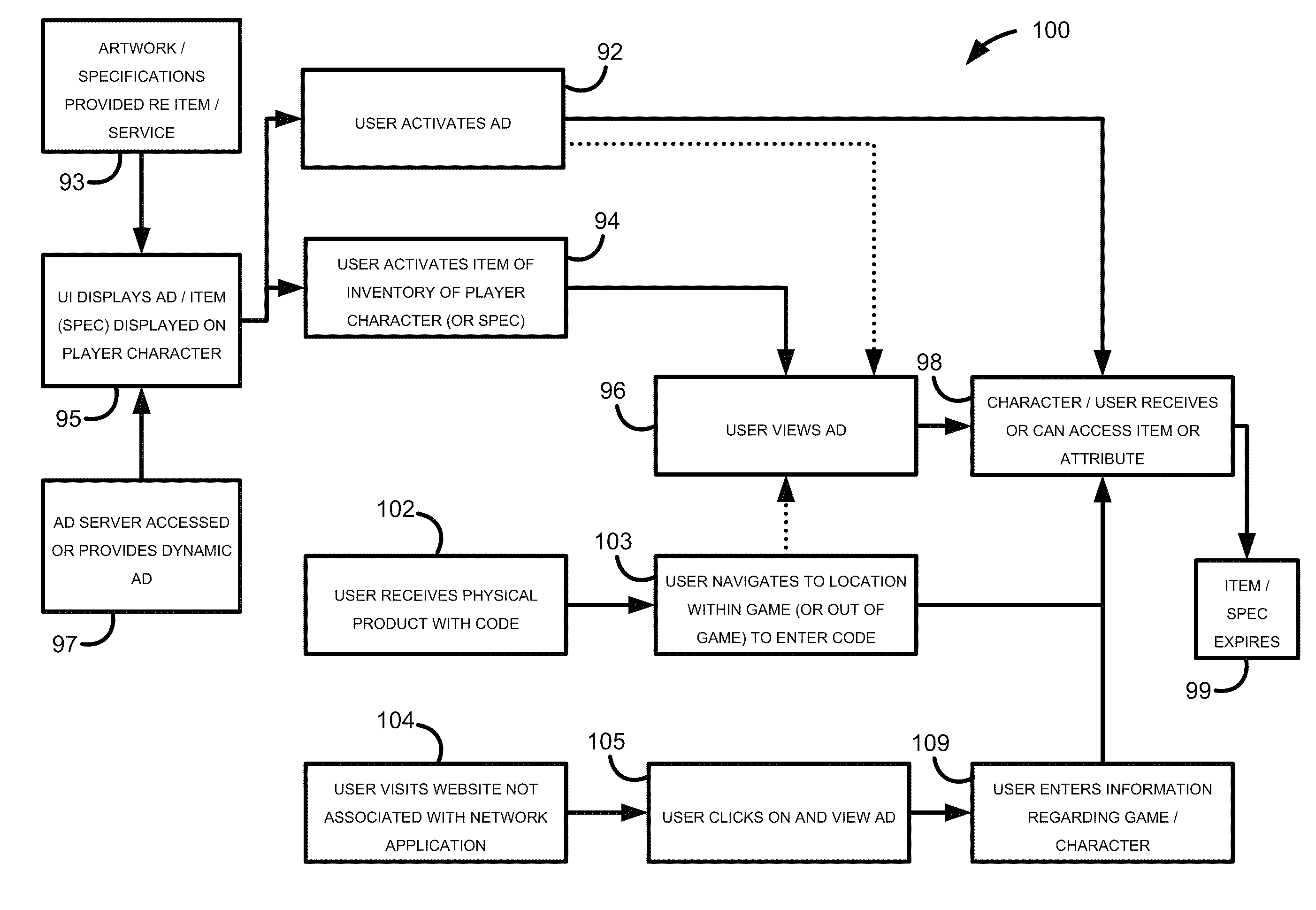
Online simulations and network applications
InactiveUS20100174593A1Enhance interestEfficient preparationDiscounts/incentivesAdvertisementsApplication softwareNetwork application
Systems and methods are provided that involve a player to a significant degree with an advertisement and its accompanying product or service. One setting of the system and method may be a network application that is adjunct to an online simulation such as an MMO game. The system and method may be implemented in either or both, or in video games that are embodied in just one of these. The system and method provide a convenient way to tie advertising to game content. By use of advertisements, the user (through the player character) can become aware of and can access in-game items, player character attribute modifications, and rewards. Such advertisements may be banner advertisements or any other type of advertising. By taking advantage of the offers presented in the advertisements, a user of the network application may obtain items for their own use or for that of a corresponding MMO character.
Owner:DAYBREAK GAME COMPANY
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
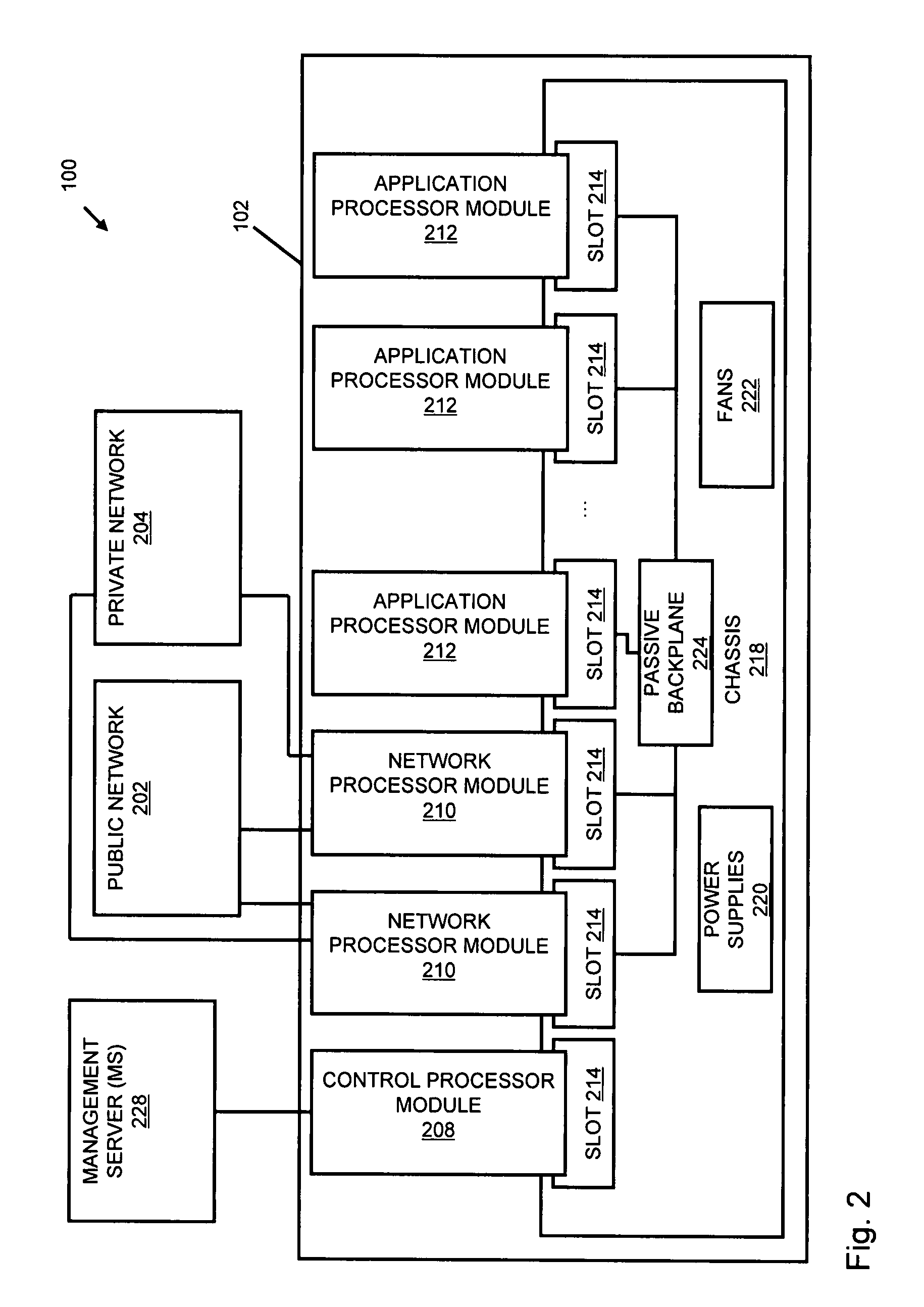
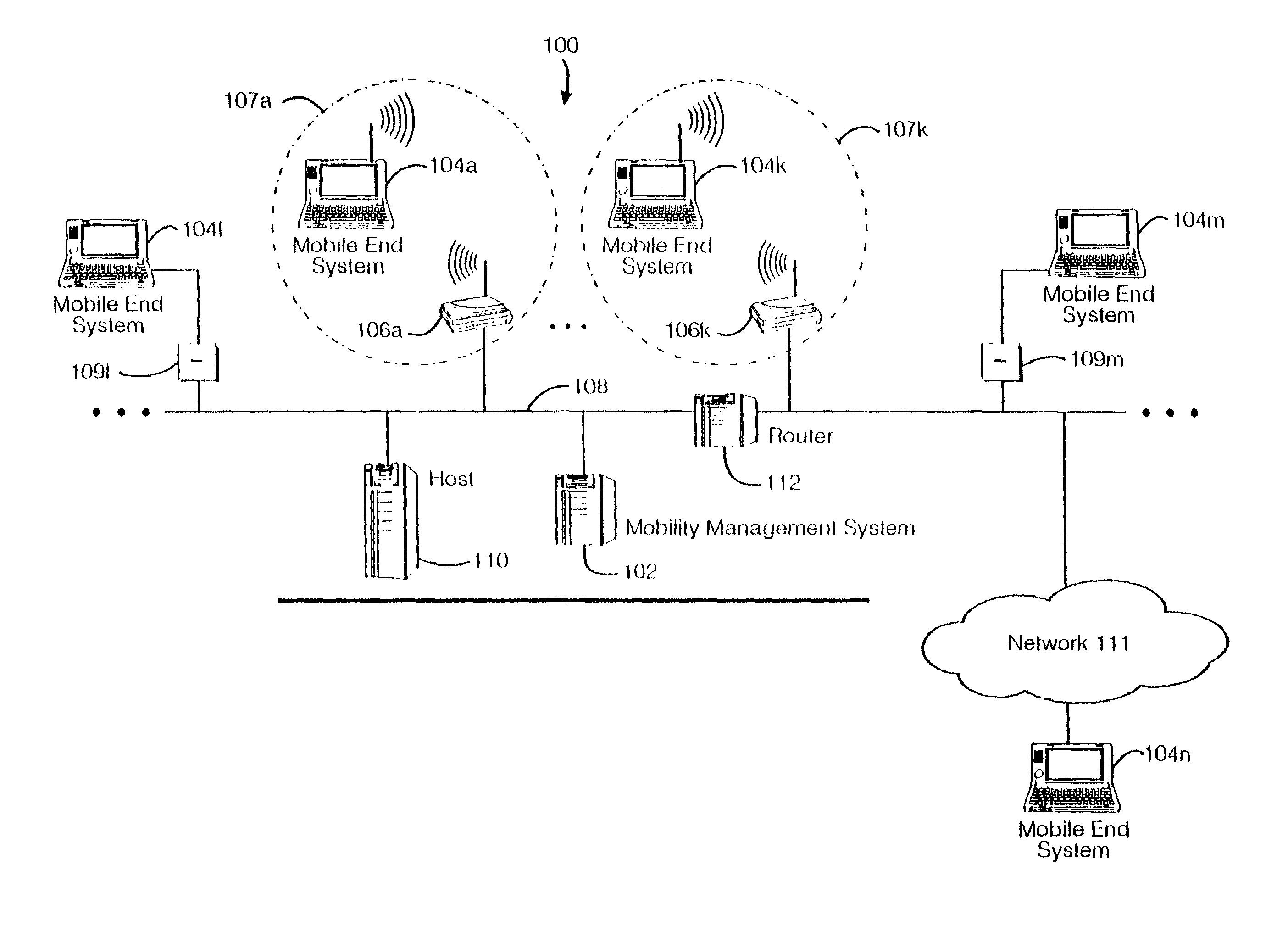
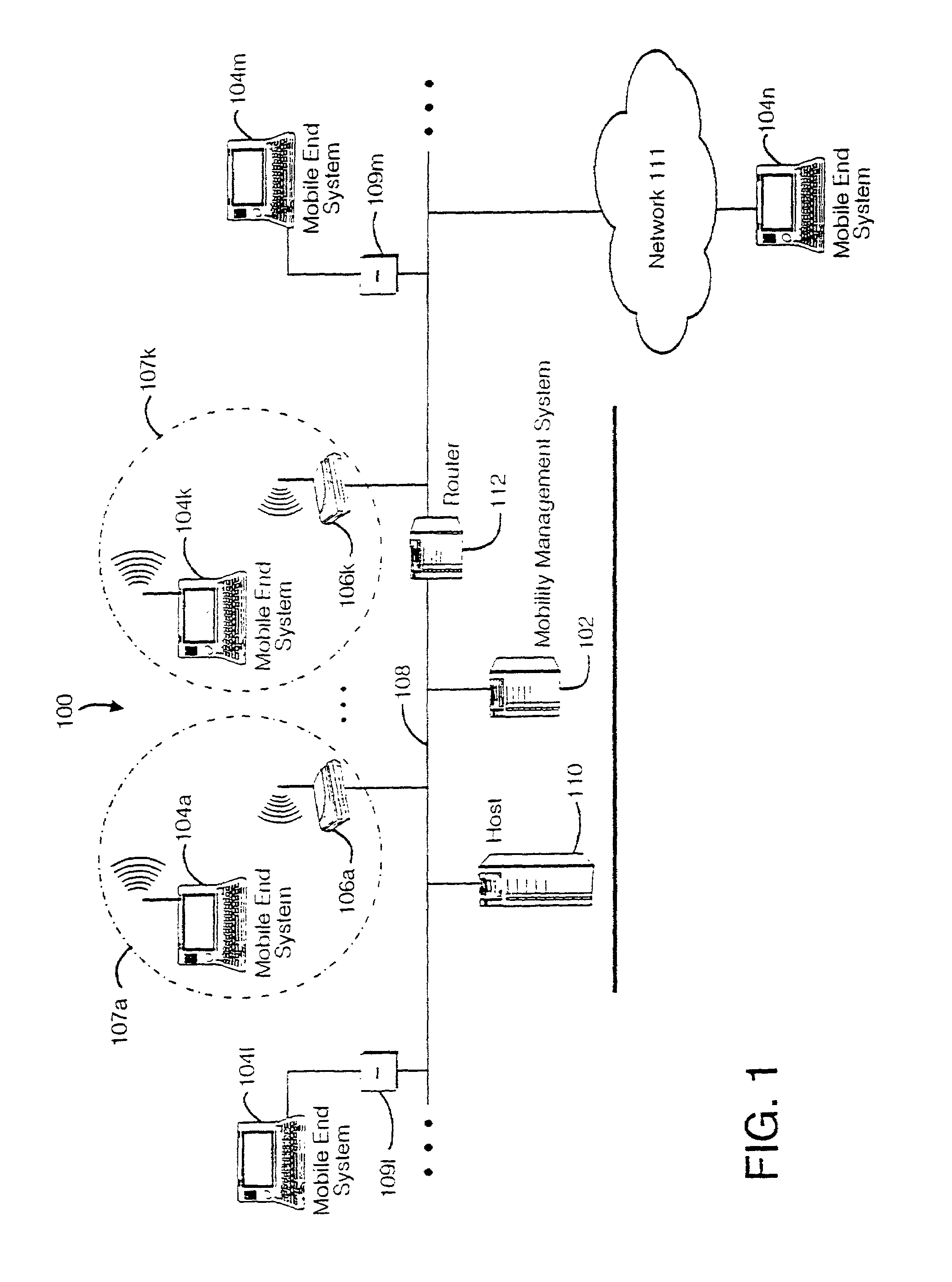
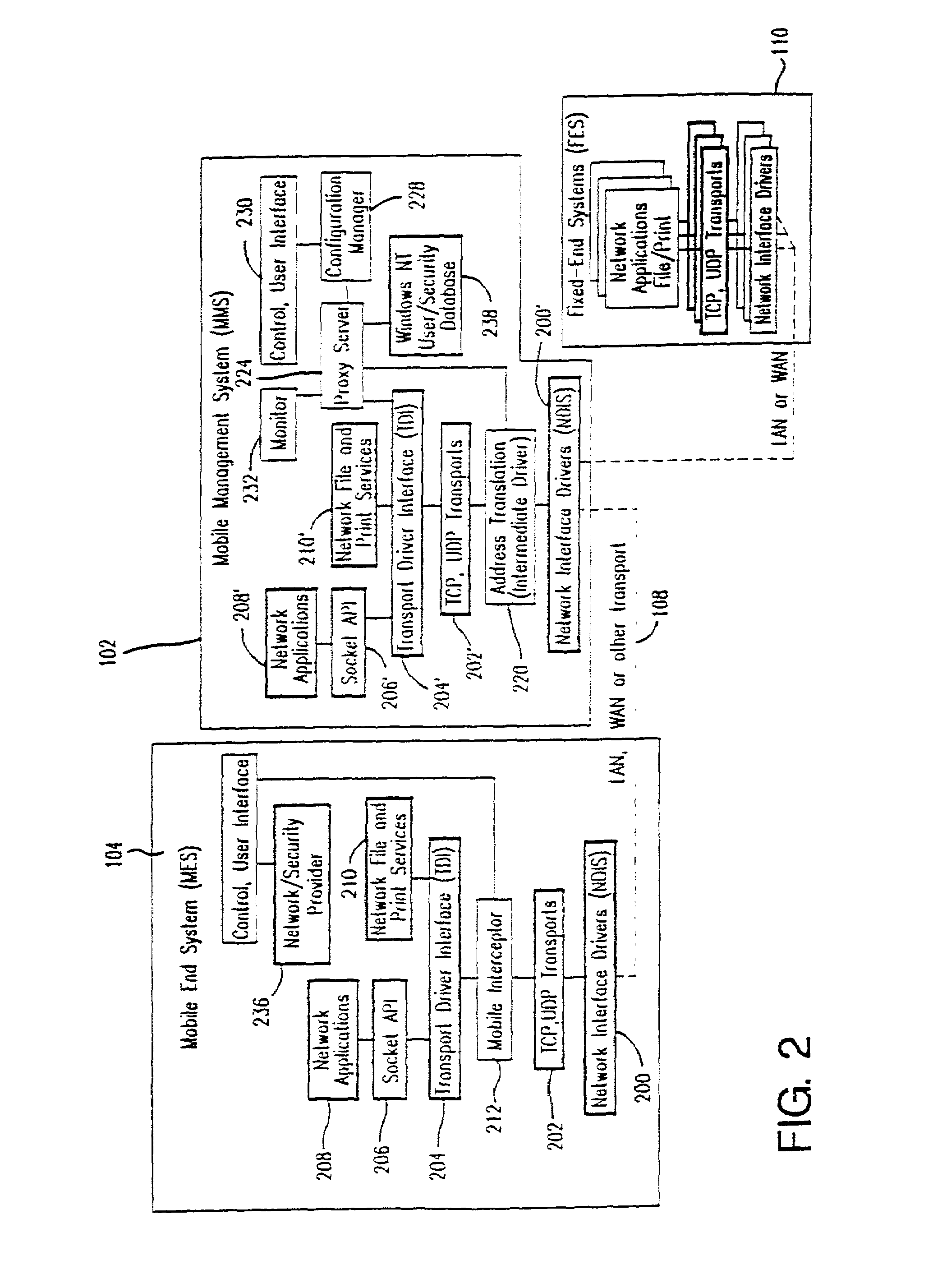
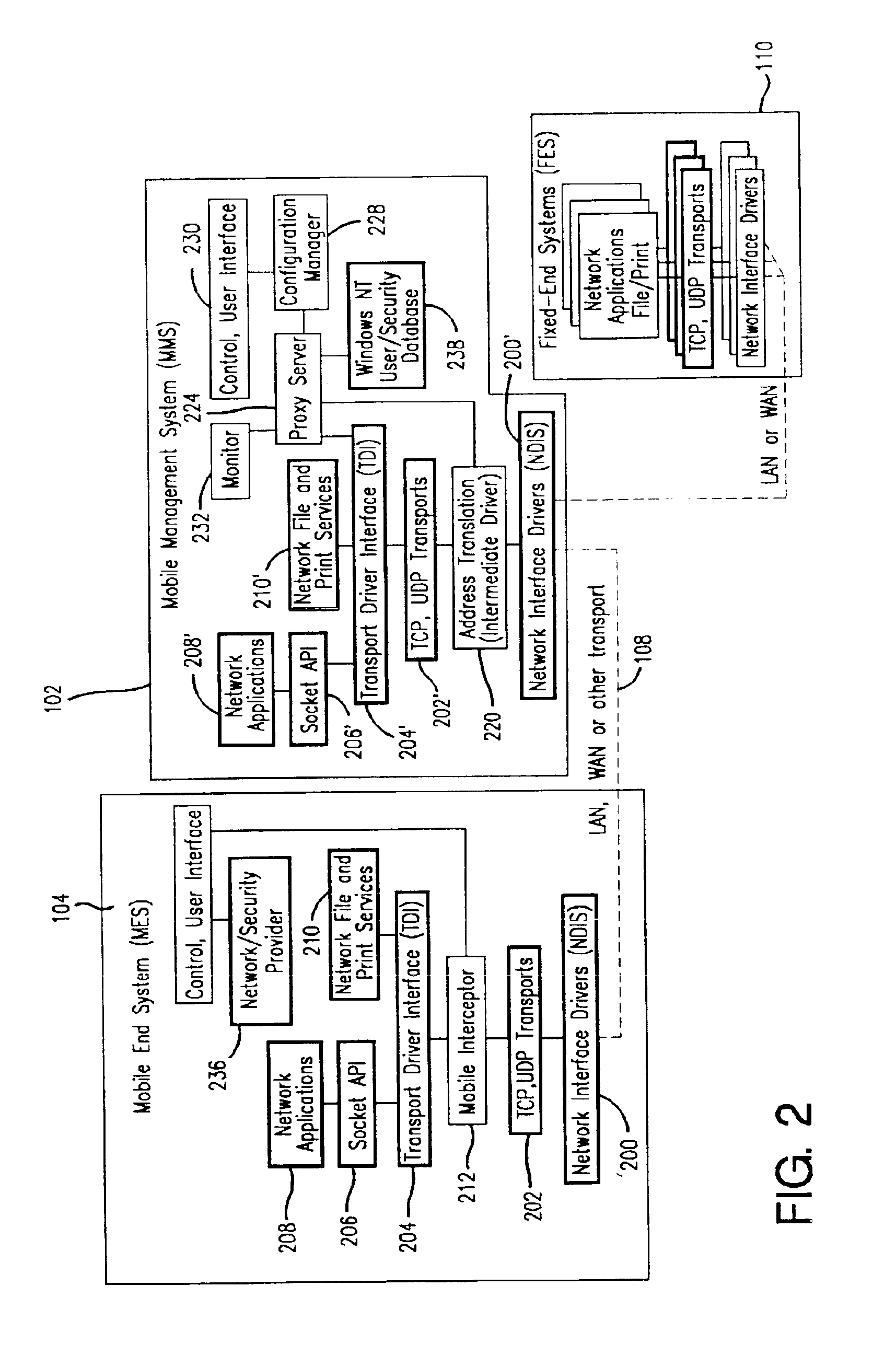
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
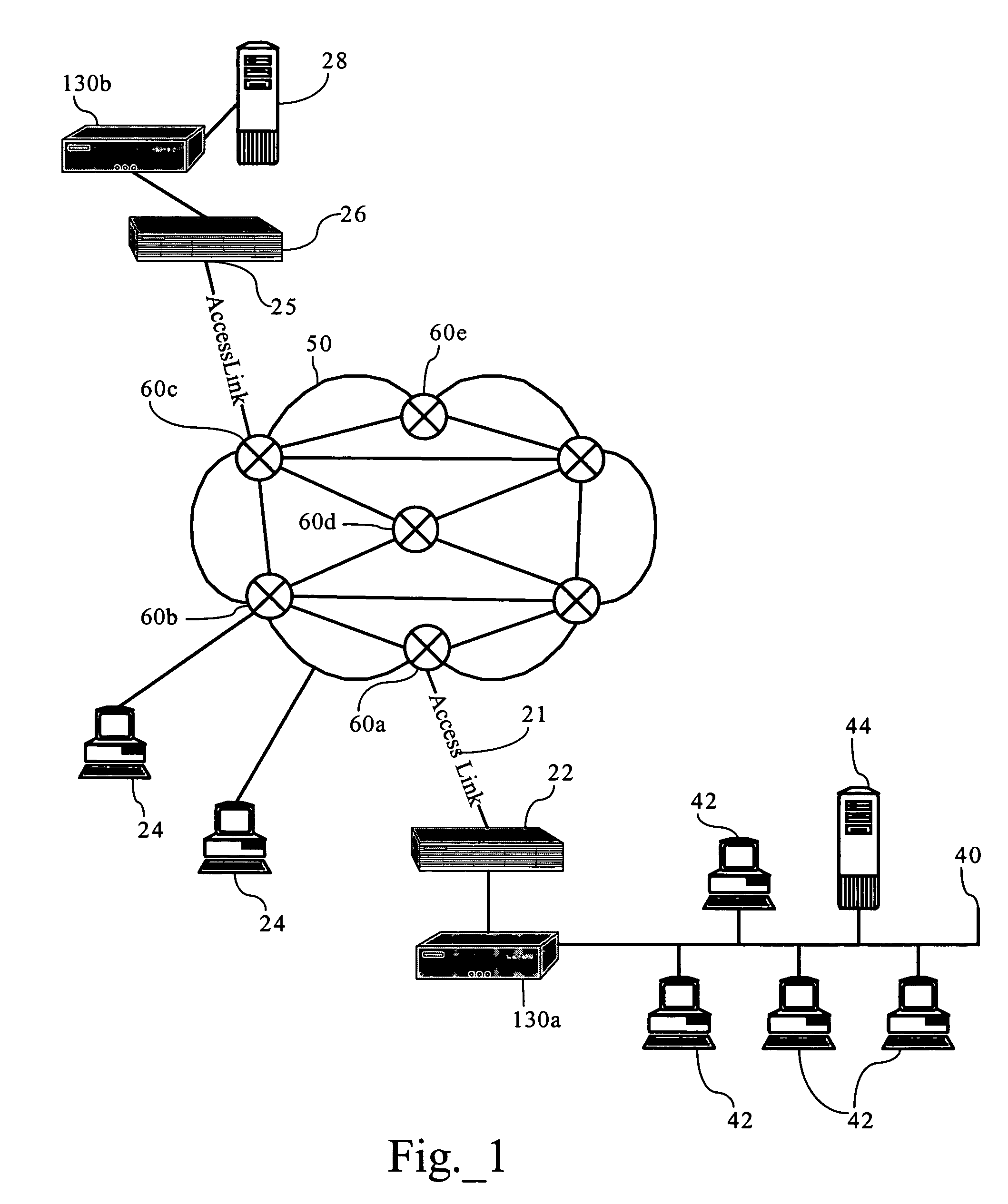
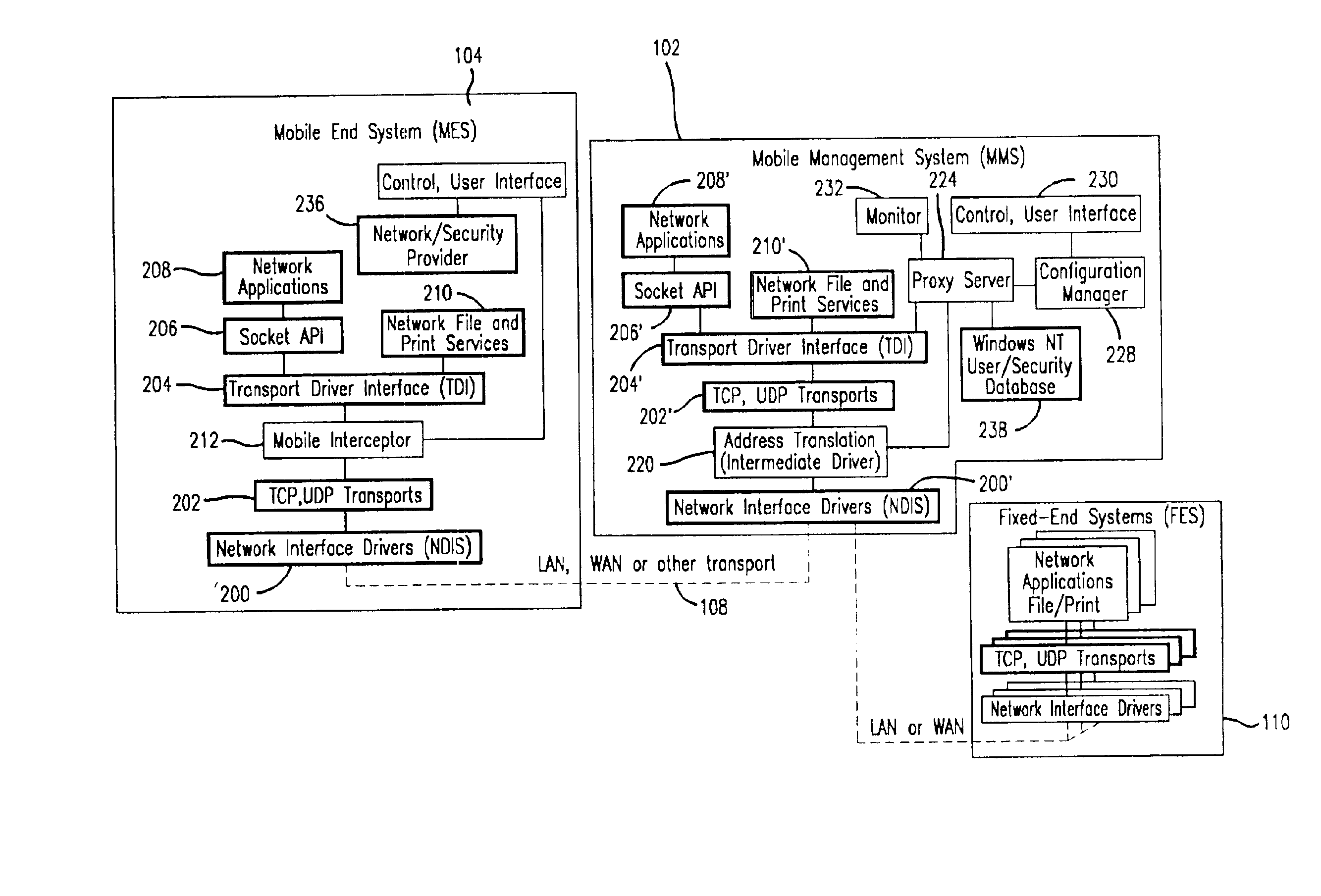
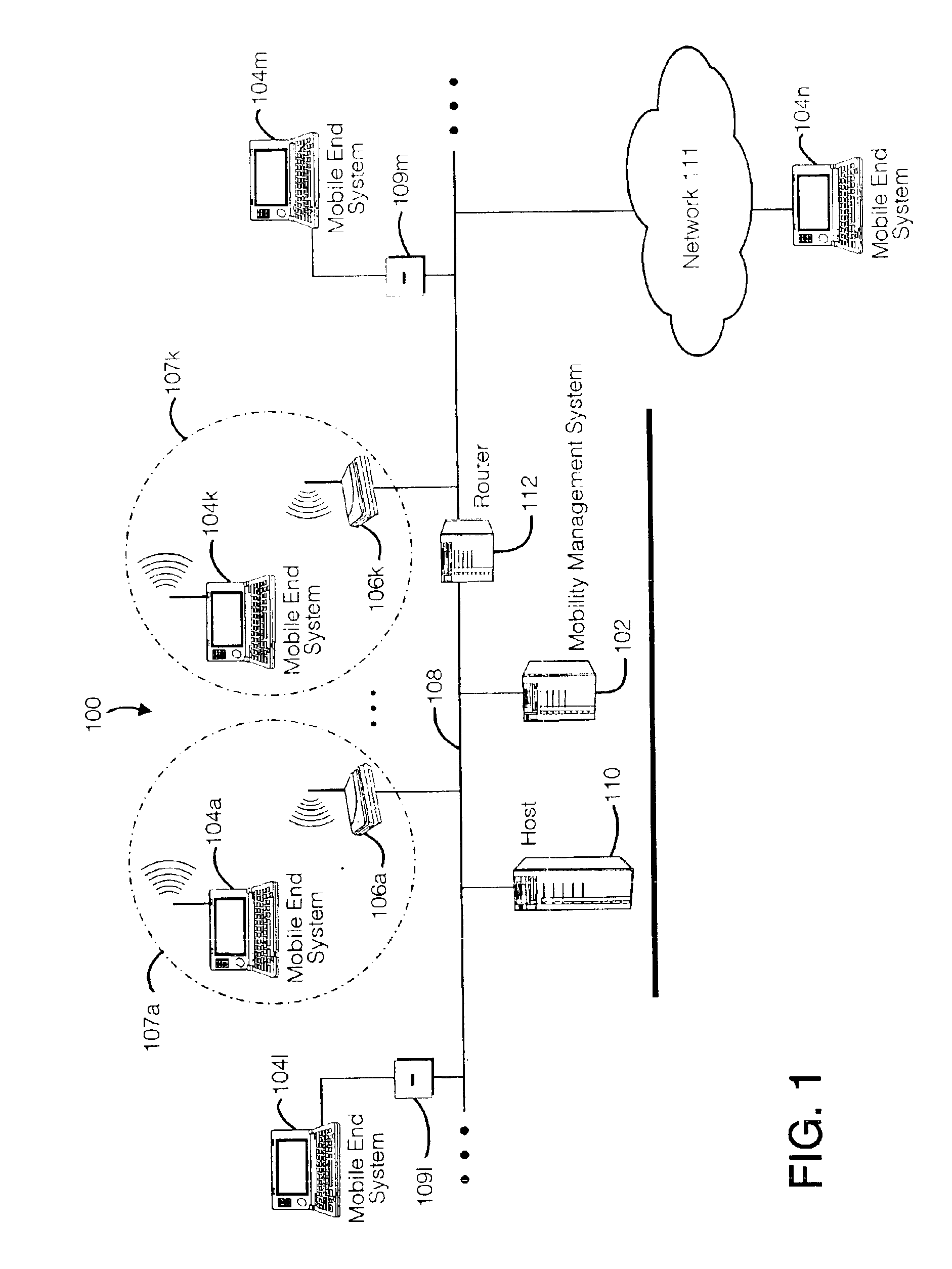
InactiveUS7136645B2Low costEasy accessError prevention/detection by using return channelNetwork traffic/resource managementNetwork connectionMobile end
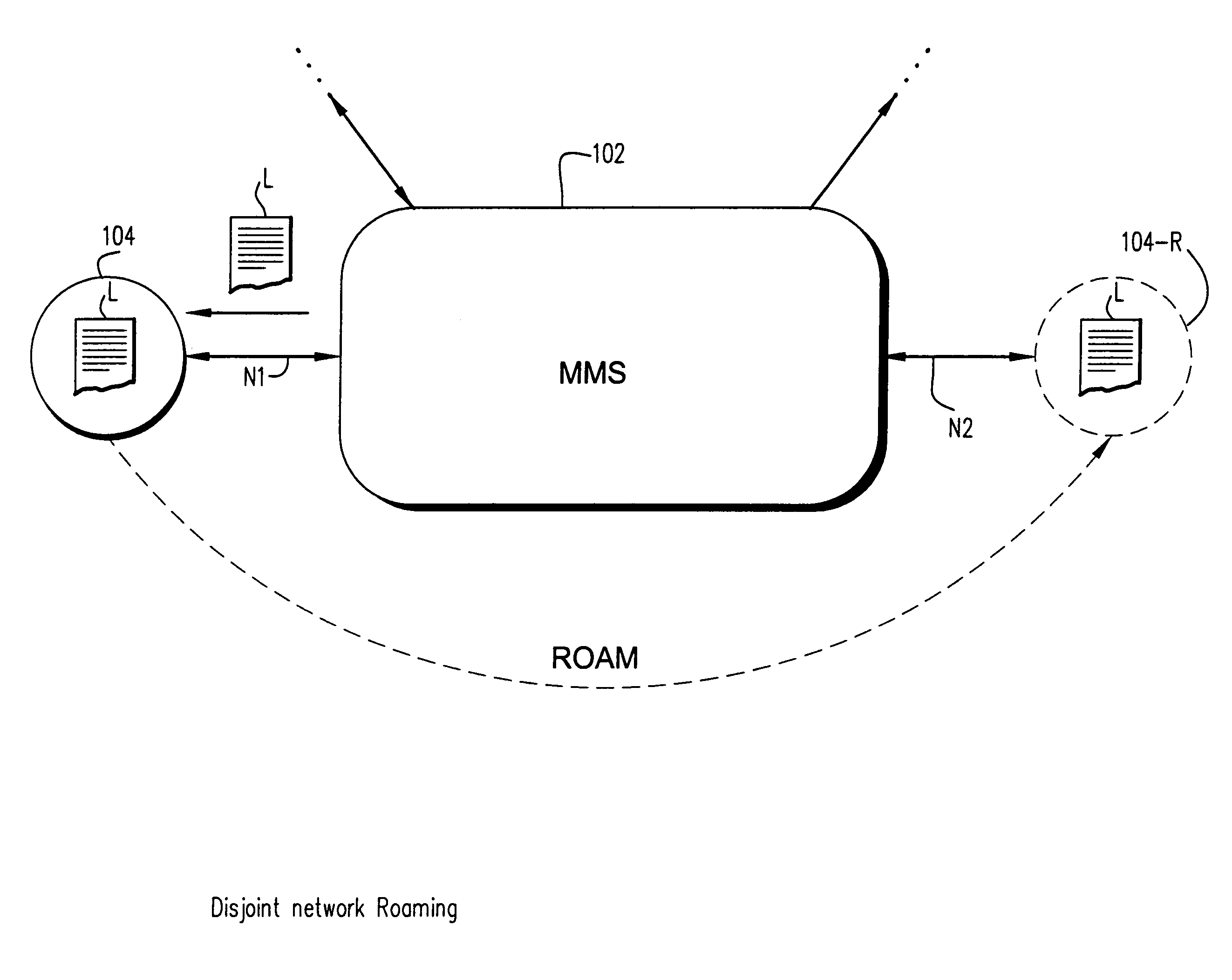
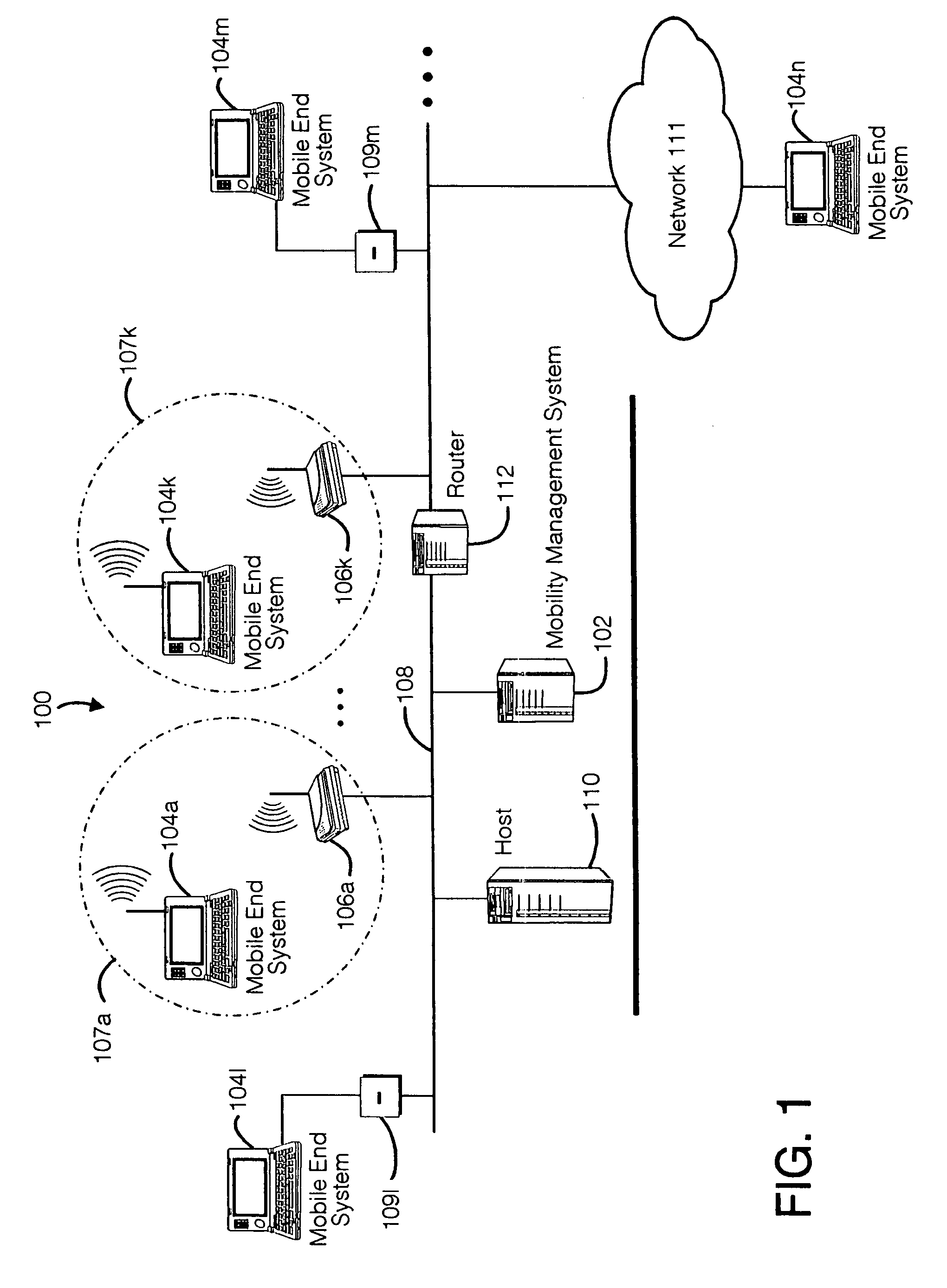
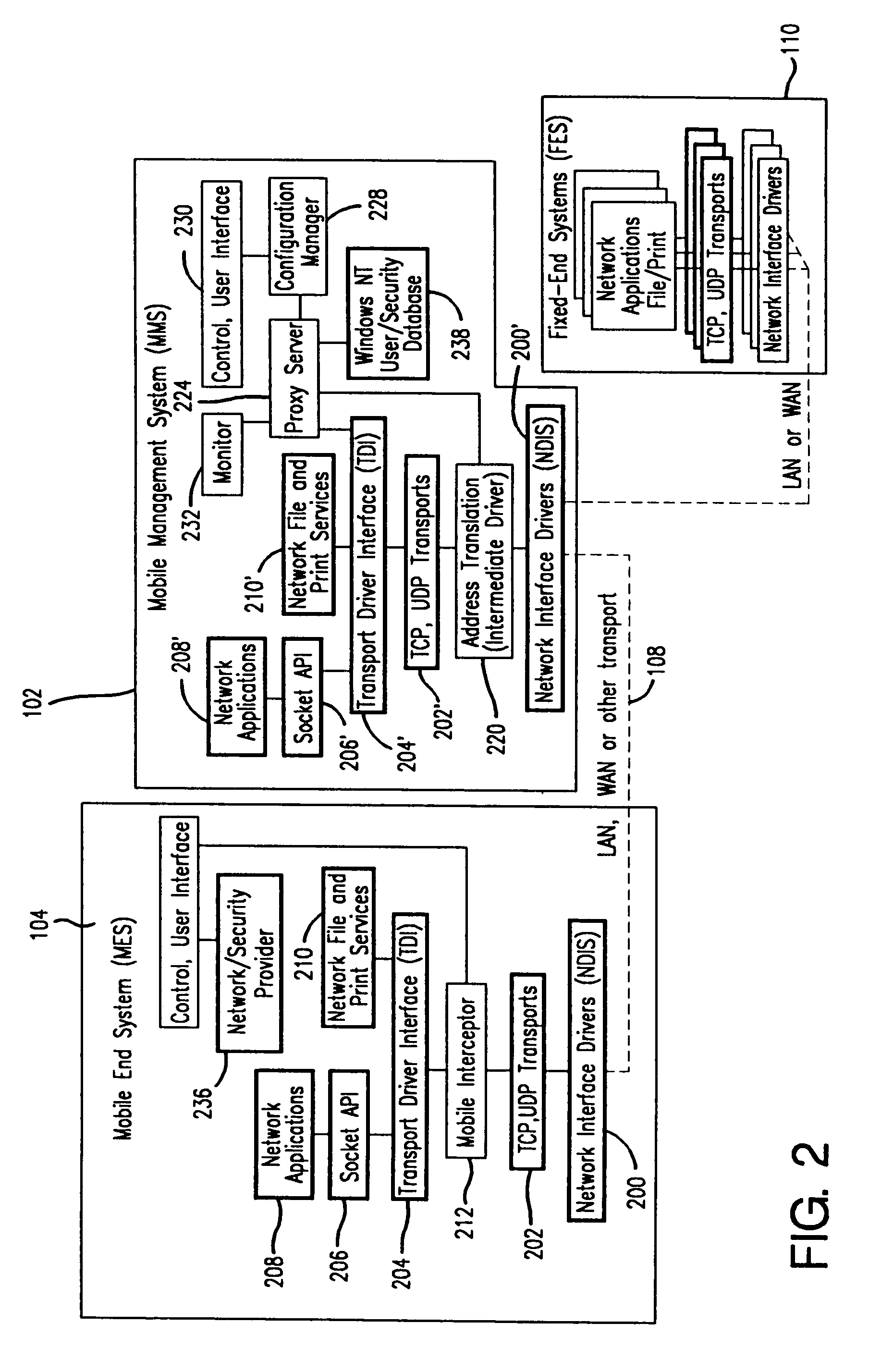
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks.
Owner:MOBILE SONIC INC
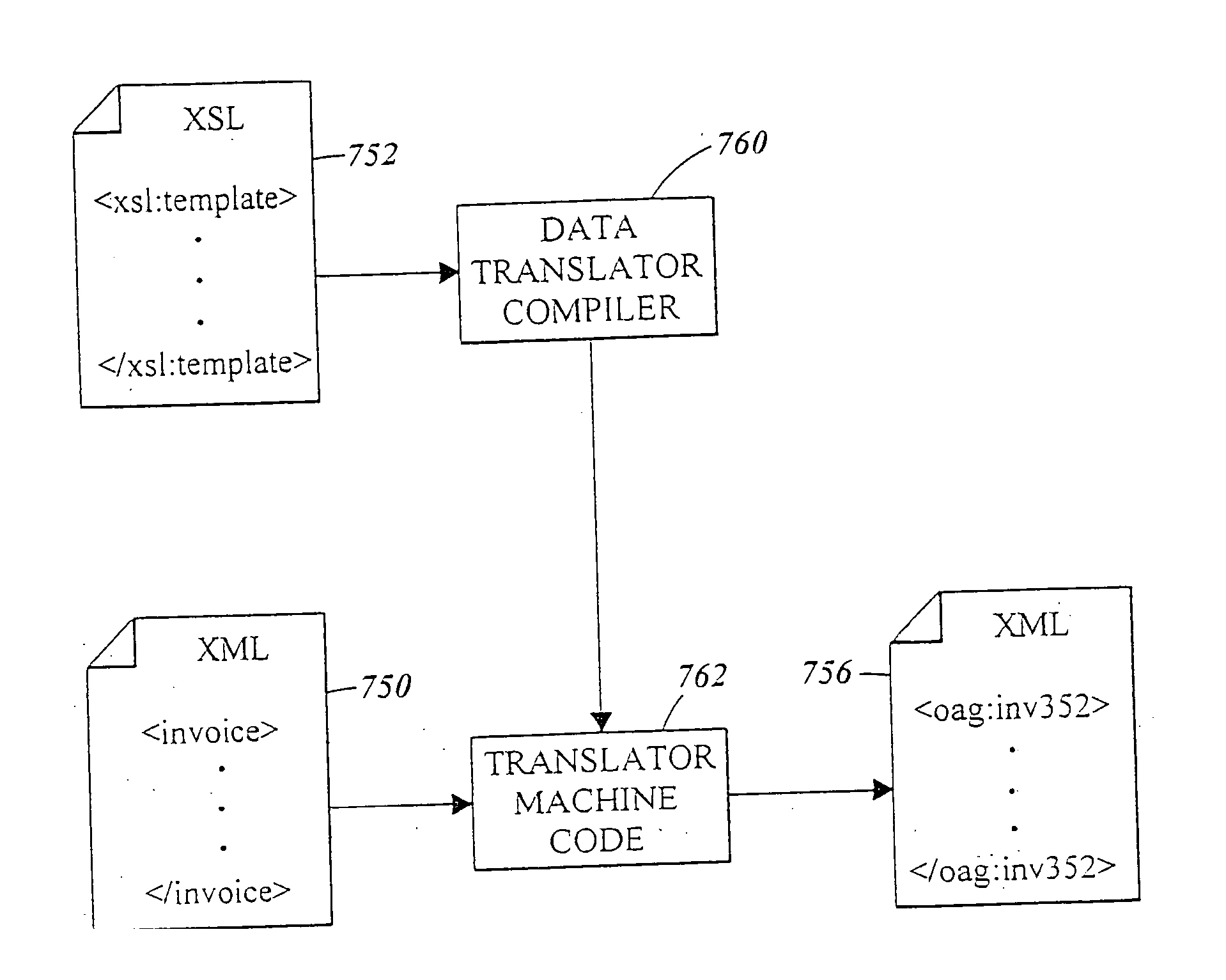
Method and apparatus of streaming data transformation using code generator and translator
InactiveUS20050273772A1Promote generationStay flexibleNatural language data processingMultiple digital computer combinationsStreaming dataObject code
A high level transformation method and apparatus for converting data formats in the context of network applications, among other places. A flexible transformation mechanism is provided that facilitates generation of translation machine code. A translator is dynamically generated by a translator compiler engine. When fed an input stream, the translator generates an output stream by executing the native object code generated on the fly by the translator compiler engine. In addition, the translator may be configured to perform a bi-directional translation between the two streams as well as translation between two distinct protocol sequences. Further a translator may working in streaming mode, to facilitate streaming processing of documents.
Owner:IBM CORP
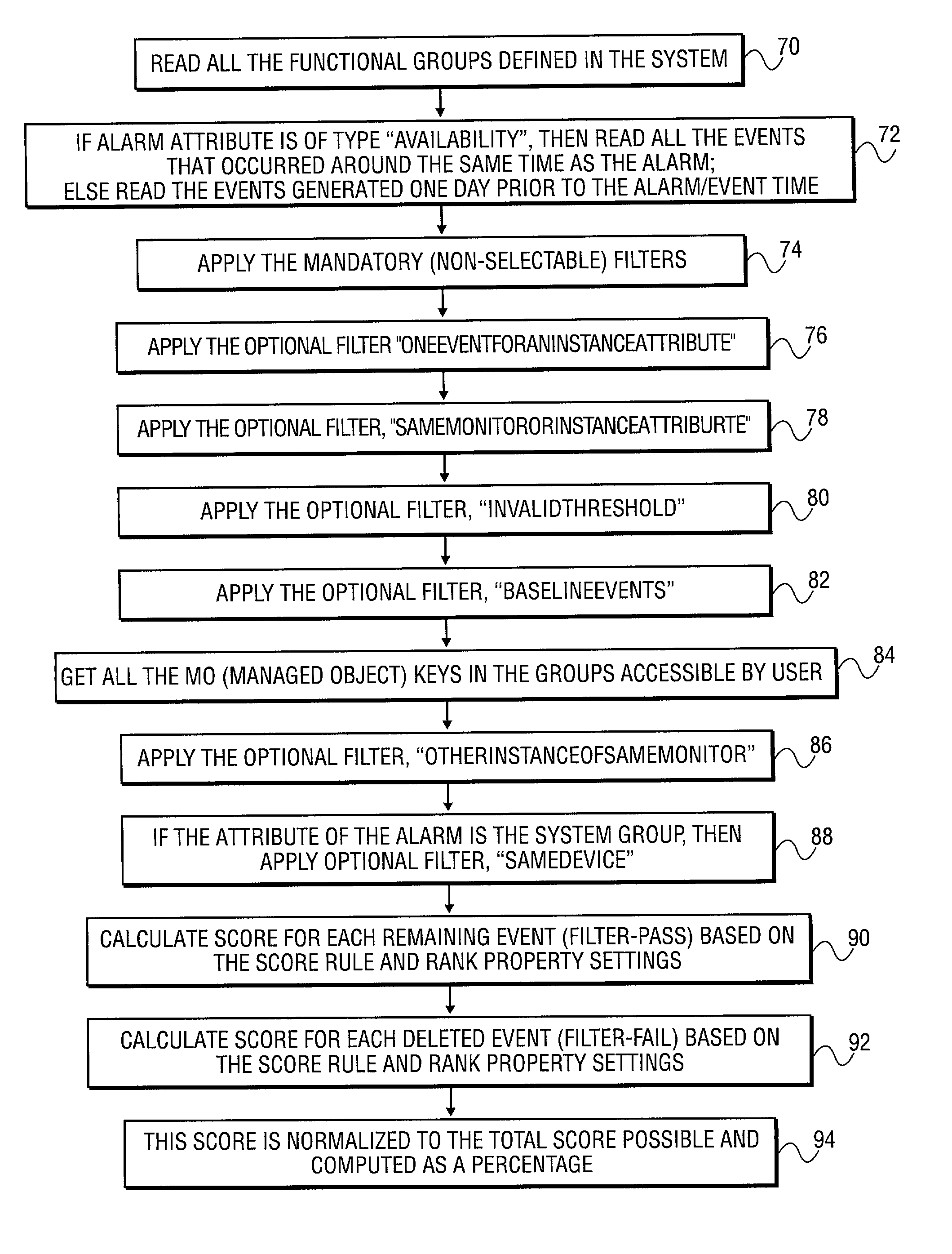
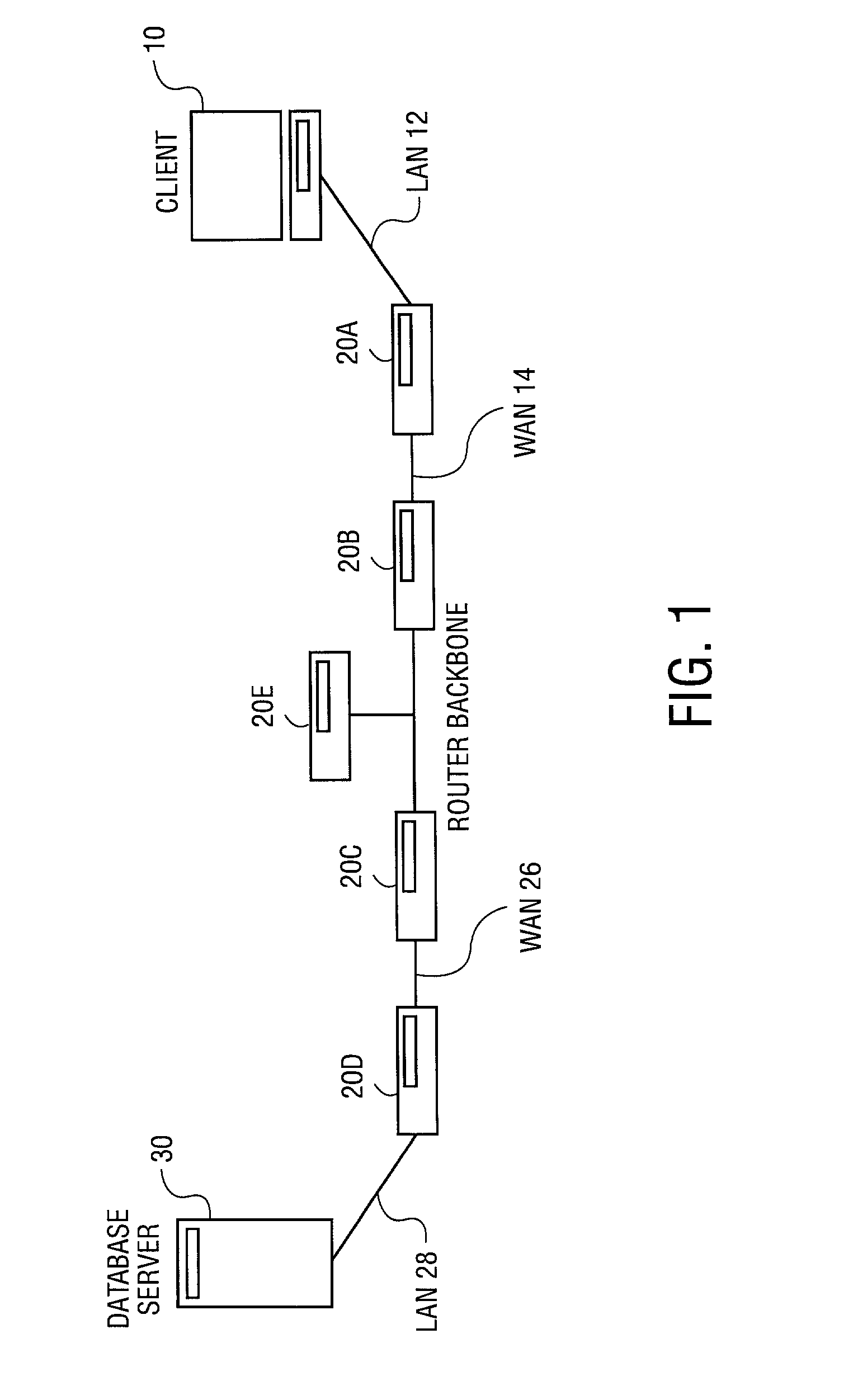
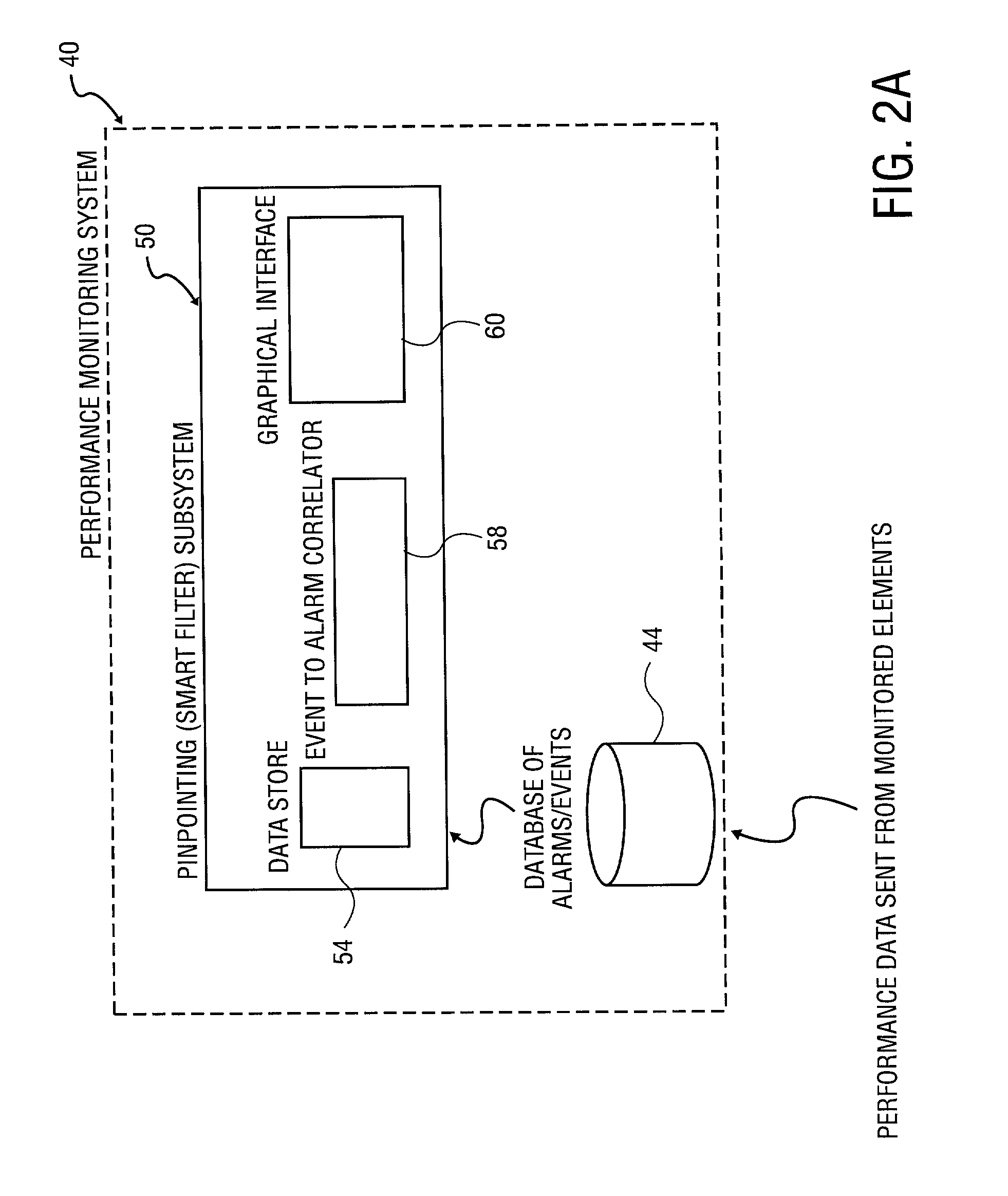
Method and system to correlate a specific alarm to one or more events to identify a possible cause of the alarm
A system is provided to monitor network performances. The system maintains a database of performance abnormalities, alarms and events from a system of monitored elements. The system automatically identifies a possible cause of a specific alarm by correlating the specific alarm with a plurality of events using the database. The system displays the cause of the specific alarm. The database includes alarms and events of network devices, network systems, and network applications. The specific alarm consists of a notification of an occurrence of the plurality of events.
Owner:BMC SOFTWARE
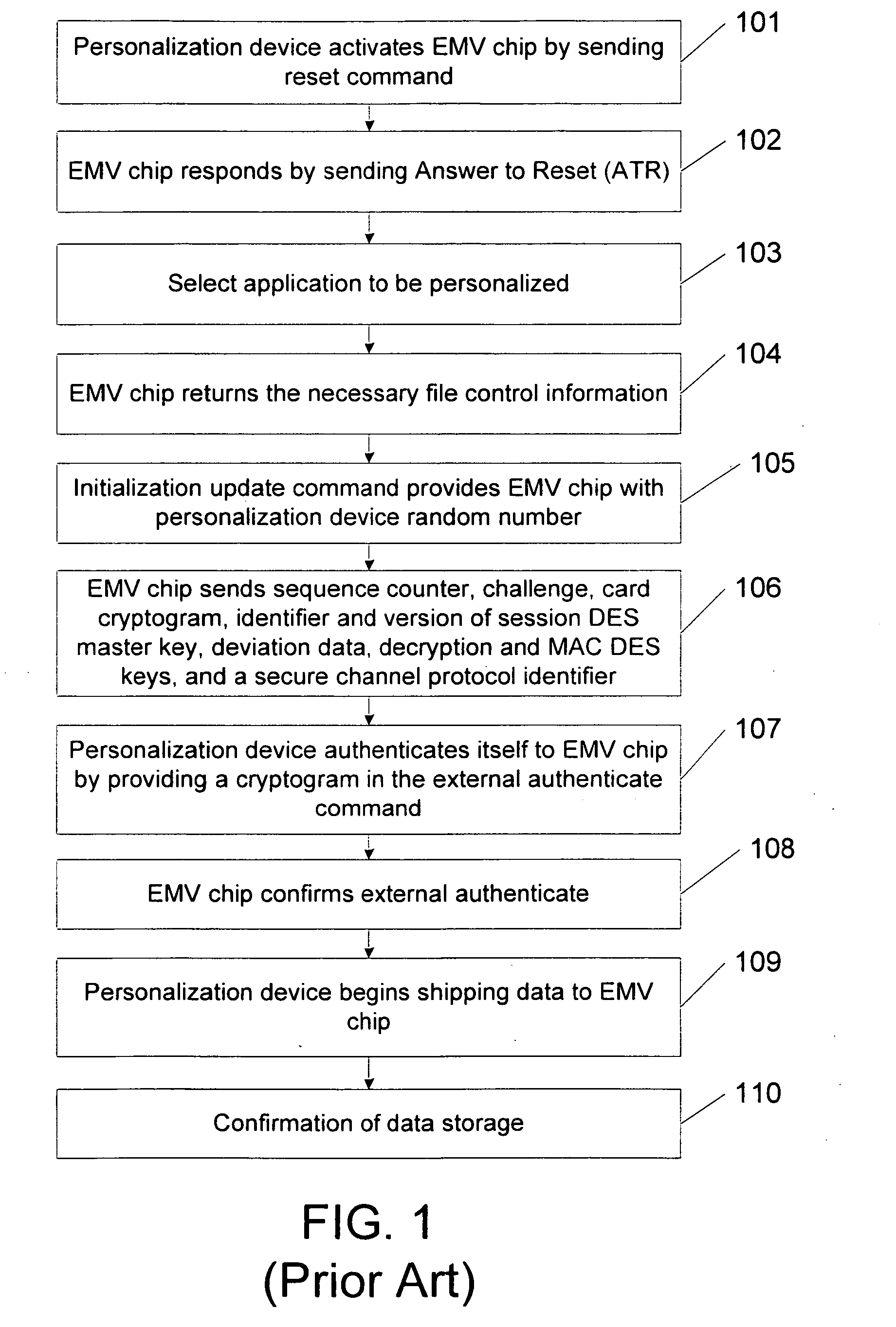
Methods, system and mobile device capable of enabling credit card personalization using a wireless network
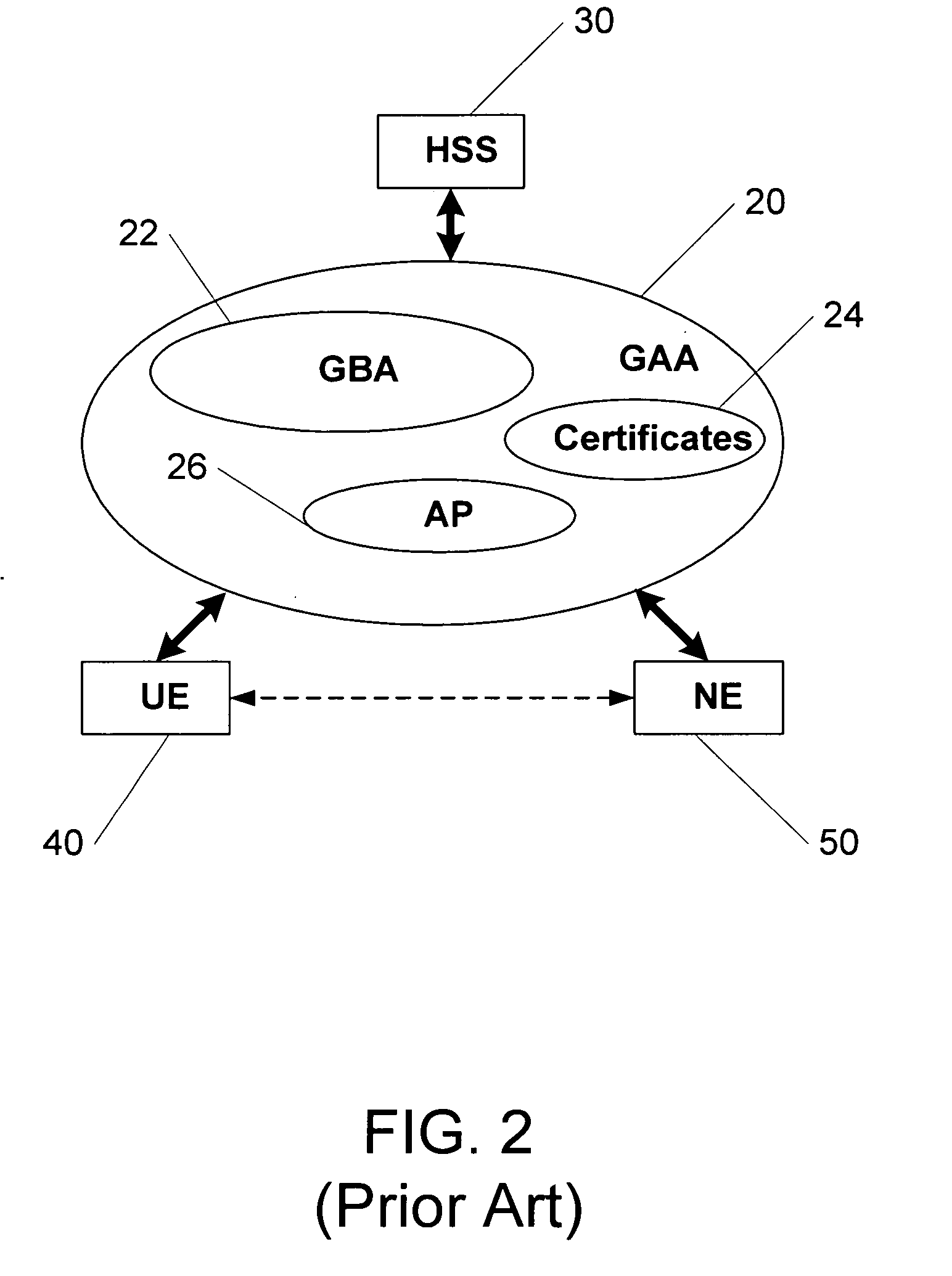
Methods of creating a secure channel over which credit card personalization data can be transmitted over the air (OTA) are provided. In particular, Generic Authentication Architecture (GAA) may be used to establish a secure communication channel between the user equipment (UE) and a personalization application server or bureau acting as a network application function (NAF) server. An user equipment, personalization application service (e.g., a NAF server), a system embodying a personalization application server and an user equipment, and a computer program product are also provided for creating a secure channel, such as via GAA, over which credit card personalization data can be transmitted OTA.
Owner:NOKIA TECHNOLOGLES OY
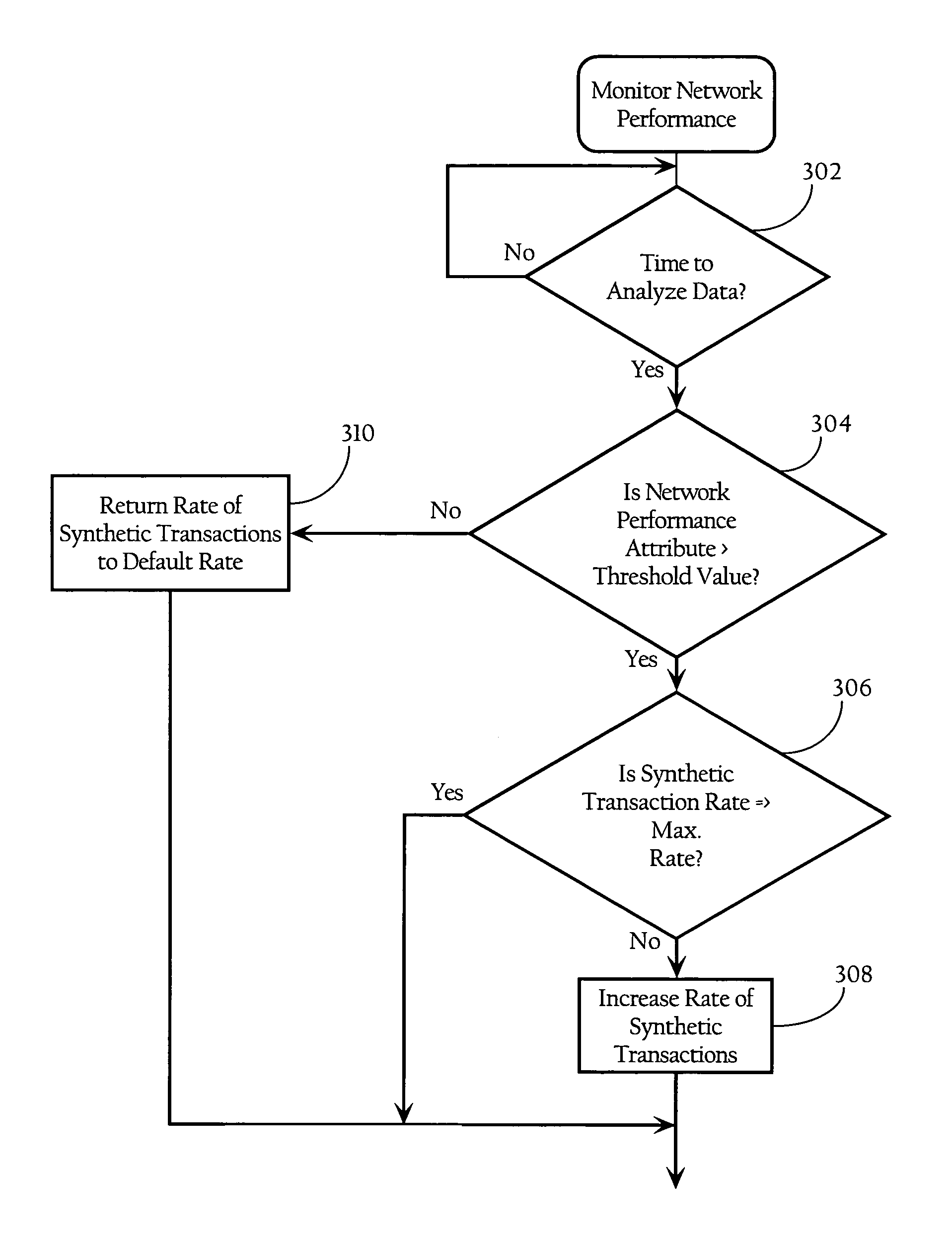
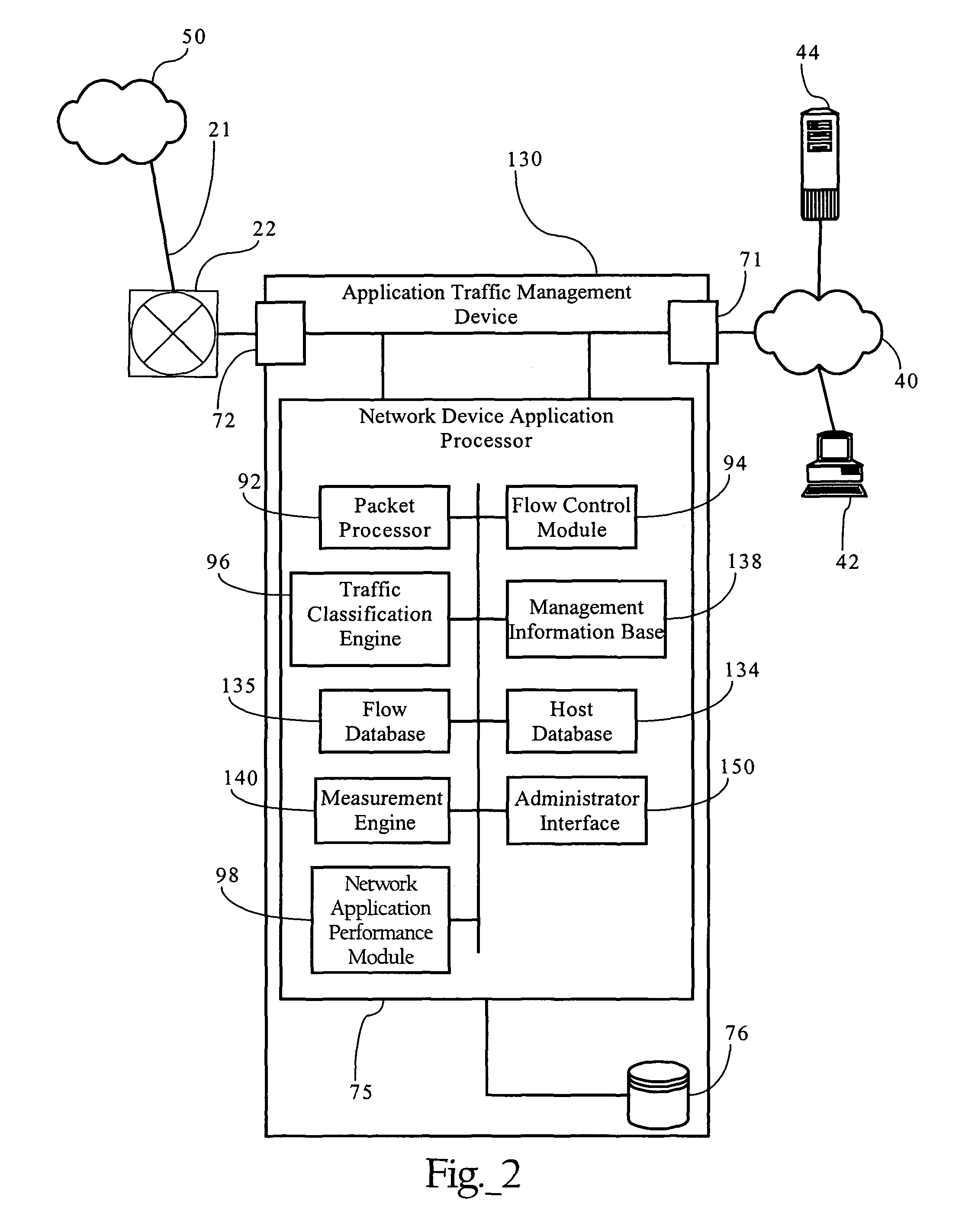
Adaptive correlation of service level agreement and network application performance
InactiveUS7822837B1Easy to useReduce network loadDigital computer detailsData switching networksService-level agreementWeb tracking
Methods, apparatuses and systems directed to adaptive monitoring of network application performance. In one implementation, the present invention improves processes used by enterprises to track, manage, and troubleshoot performance of network applications across distributed networks. In one implementation, the present invention allows for a network application performance monitoring scheme that tracks end-to-end performance of selected network applications on a passive basis, while selectively engaging more invasive (synthetic) approaches to tracking performance and troubleshooting issues when needed.
Owner:CA TECH INC
Adaptive, application-aware selection of differntiated network services
ActiveUS7843843B1Sacrificing application performanceReduce bandwidth costsError preventionFrequency-division multiplex detailsNetwork conditionsNetwork service
Methods, apparatuses and systems that dynamically adjust the selection of differentiated network services for selected classes of traffic or network applications in response to changing network conditions or application performance levels.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
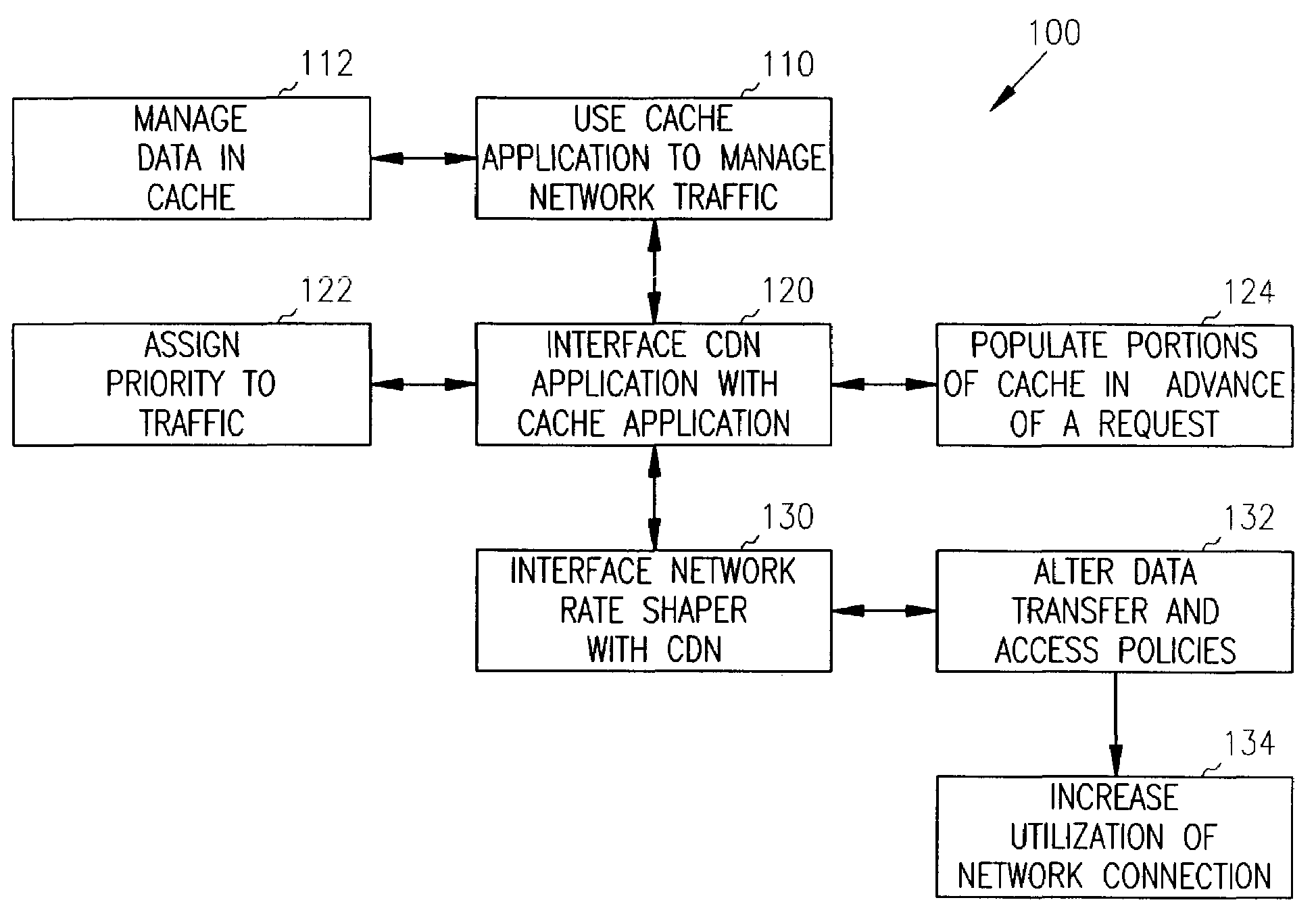
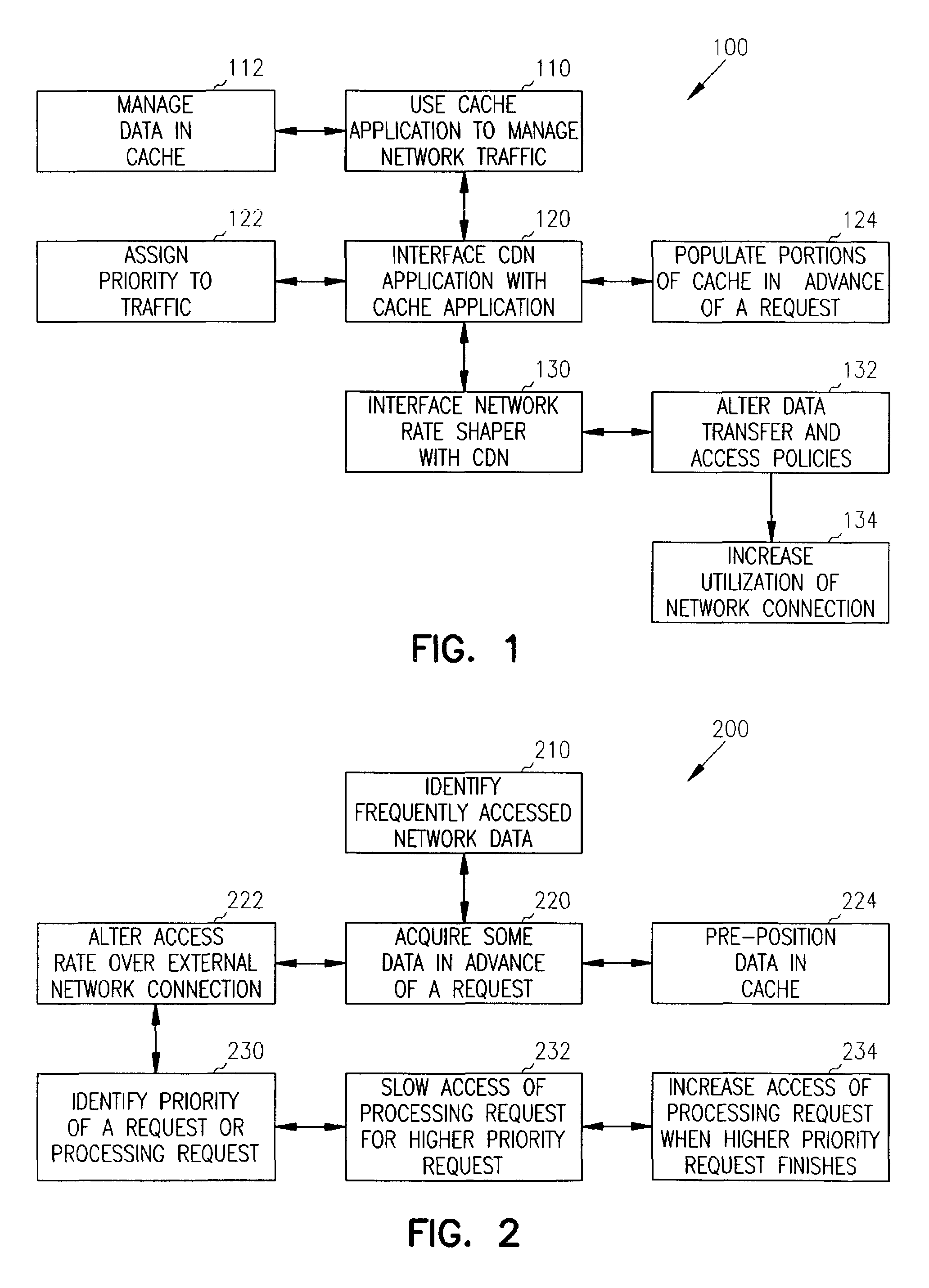
Methods and systems for managing network traffic
InactiveUS7680897B1Improve utilizationImprove in instanceMultiple digital computer combinationsData switching networksContent distributionTraffic capacity
Methods and systems for network traffic management are provided. A content distribution network application manages data in a cache. A network rate shaper application controls and manages requests for access to an external network connection. The content distribution network application determines priorities associated with requests and communicates these priorities to the rate shaper application. The rate shaper application adjusts access levels or data transfer rates for the requests based on the received priorities.
Owner:RPX CORP
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
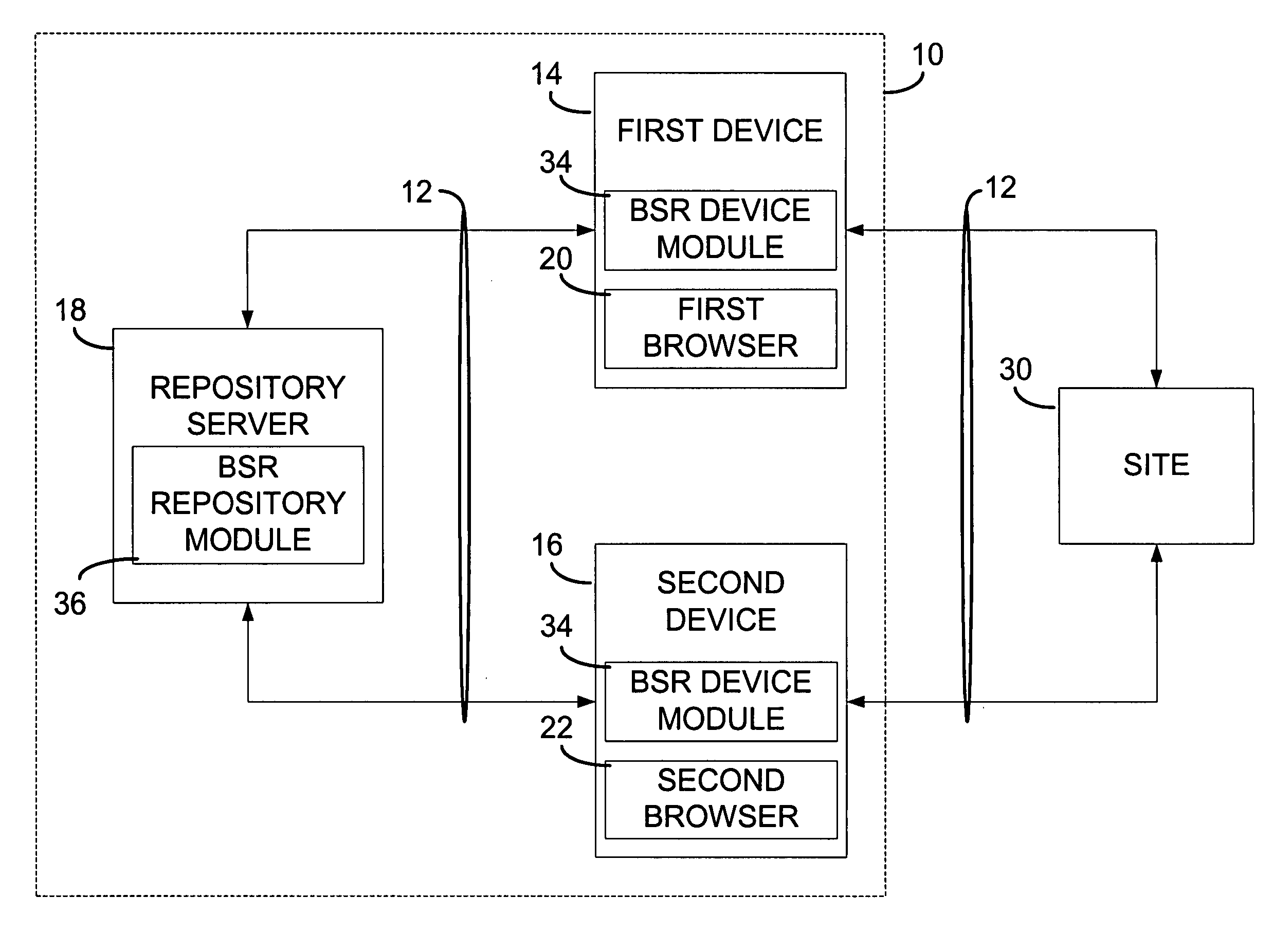
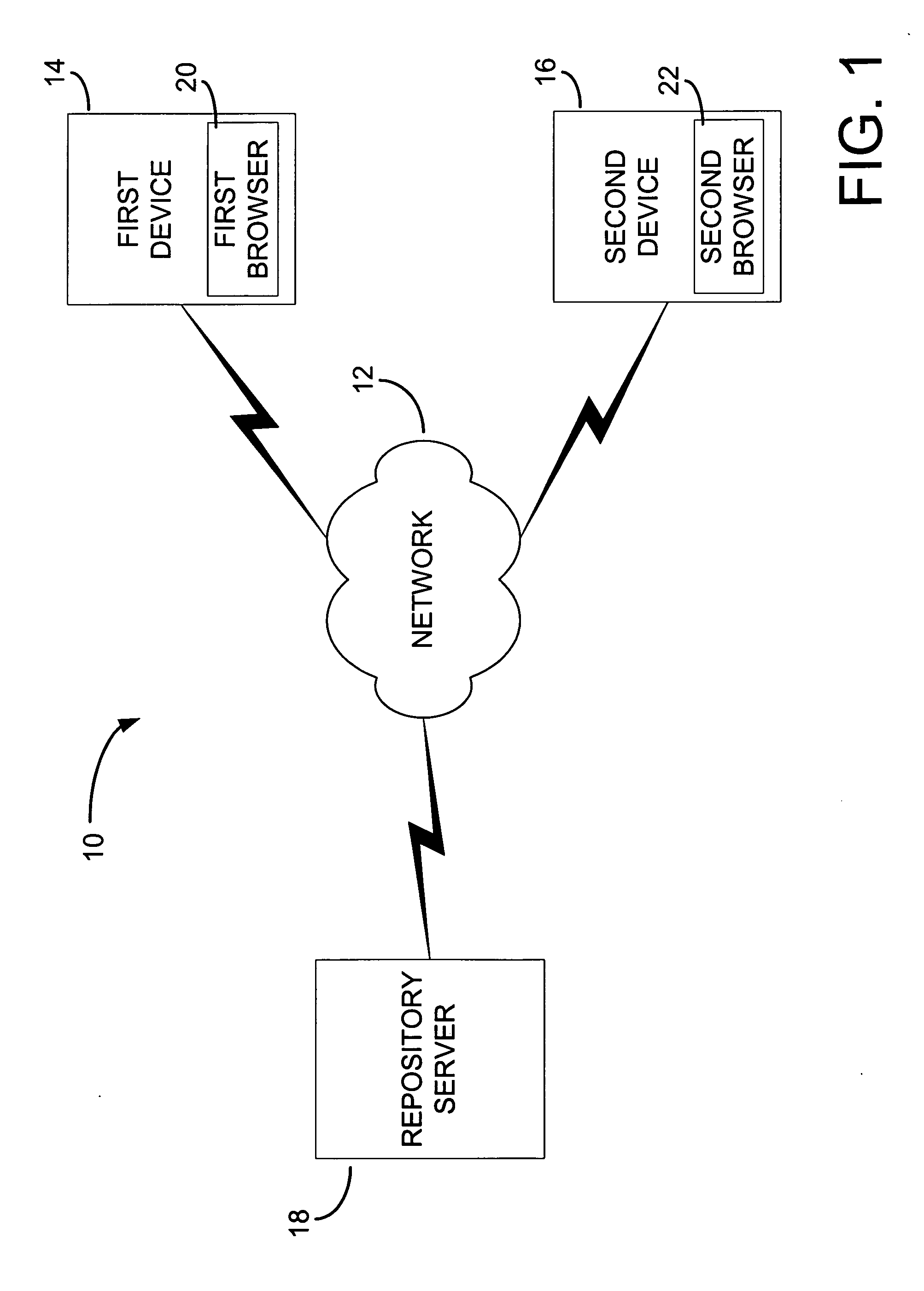
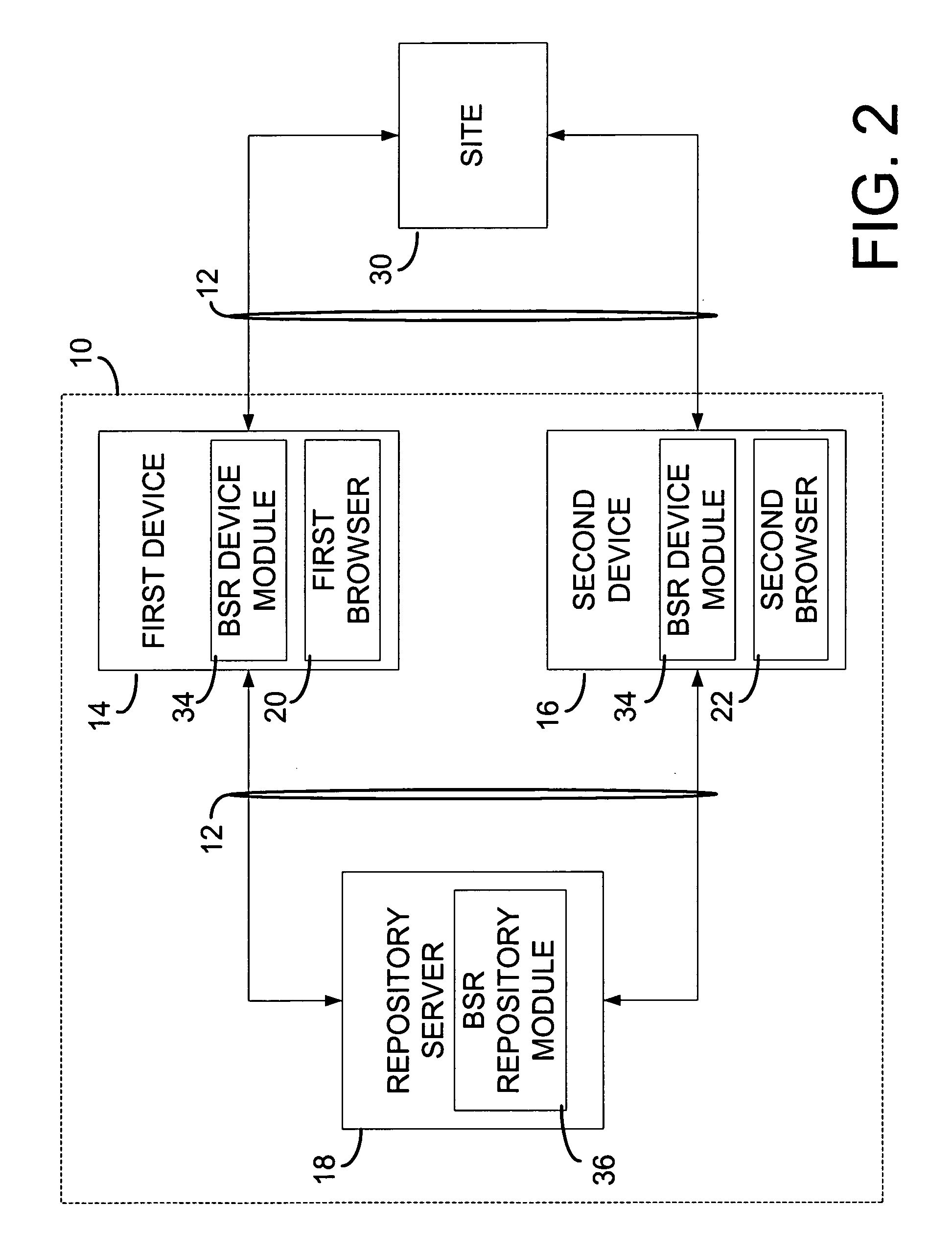
Browser session mobility system for multi-platform applications
InactiveUS20050066037A1Web data retrievalMultiple digital computer combinationsMulti platformMobility system
A browser session mobility (BSM) system allows a user to save and restore the runtime state of active sessions of multi-platform network applications established with a browser. A platform specific runtime state of an active session with a browser that includes a current browser state and a current server state may be captured from a platform specific version of a multi-platform network application. The platform specific runtime state may be transformed to a platform independent runtime state and stored. The stored platform independent runtime state may be retrieved and transformed to another platform specific version of the multi-platform network application and instantiated as the same active session.
Owner:NTT DOCOMO INC
Multi-dimensional computation distribution in a packet processing device having multiple processing architecture
InactiveUS7610330B1High bandwidthHighly-scalableMultiple digital computer combinationsTransmissionQuality of serviceTraffic capacity
Flow-aware task distribution in network devices having multiple processor architectures. In one embodiment, the present invention can be used for high bandwidth network processing in an application and flow aware Quality of Service (QoS) network device. In some implementations, the present invention provides a task distribution architecture capable of flow state awareness and link level QoS control. In some implementations, the present invention can incorporate one or more processes, such as flow distributors and device distributors, that route packets for processing among different processing units on the basis flow correspondence and / or link or network path attributes. The flow and device distributors, in one implementation, allow for the separation and paralletization of packet processing functionality into flow-specific and link-specific processing units, allowing for a highly-scalable, flow-aware task distribution in a network device that processes network application traffic.
Owner:CA TECH INC
Systems and methods for packet distribution
InactiveUS20020038339A1Multiple digital computer combinationsProgram controlNetwork applicationPayload
Embodiments of the present invention relate to methods and systems of managing delivery of data to network applications. In an embodiment, a delivery packet including a service address and a payload is received. A plurality of network applications associated with the service address of the data packet are identified. The plurality of network applications associated with the service address include a first network application and a second network application, where the first network application is different from the second network application. At least the payload of the data packet is sent to the first network application and the second network application.
Owner:SPONTANEOUS NETWORKS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Adaptive network traffic compression mechanism including dynamic selection of compression algorithms
ActiveUS7420992B1Reduce impactImprove performanceTime-division multiplexMultiple digital computer combinationsAdaptive compressionSelf adaptive
An adaptive compression mechanism that dynamically selects compression algorithms applied to network application traffic to improve performance. One implementation includes an arbitration scheme that reduces the impact on computing resources required to analyze different compression algorithms for different network applications. The adaptive compression functionality of the present invention can be integrated into network application traffic management or acceleration systems.
Owner:CA TECH INC
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS6981047B2Error prevention/detection by using return channelData switching by path configurationMobile endNetwork address
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. The solution extends the enterprise network, letting network managers provide mobile users with easy access to the same applications as stationary users without sacrificing reliability or centralized management. The solution combines advantages of existing wire-line network standards with emerging mobile standards to create a solution that works with existing network applications. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. In one example, Mobility Management Server communicates with Mobile End Systems using Remote Procedure Call and Internet Mobility Protocols.
Owner:MOBILE SONIC INC
Capture and resumption of network application sessions
ActiveUS7979555B2Inhibition can be terminatedMultiple digital computer combinationsSecuring communicationUser inputClient-side
Owner:EXTRAHOP NETWORKS
Modular entertainment and gaming system configured for network boot, network application load and selective network computation farming
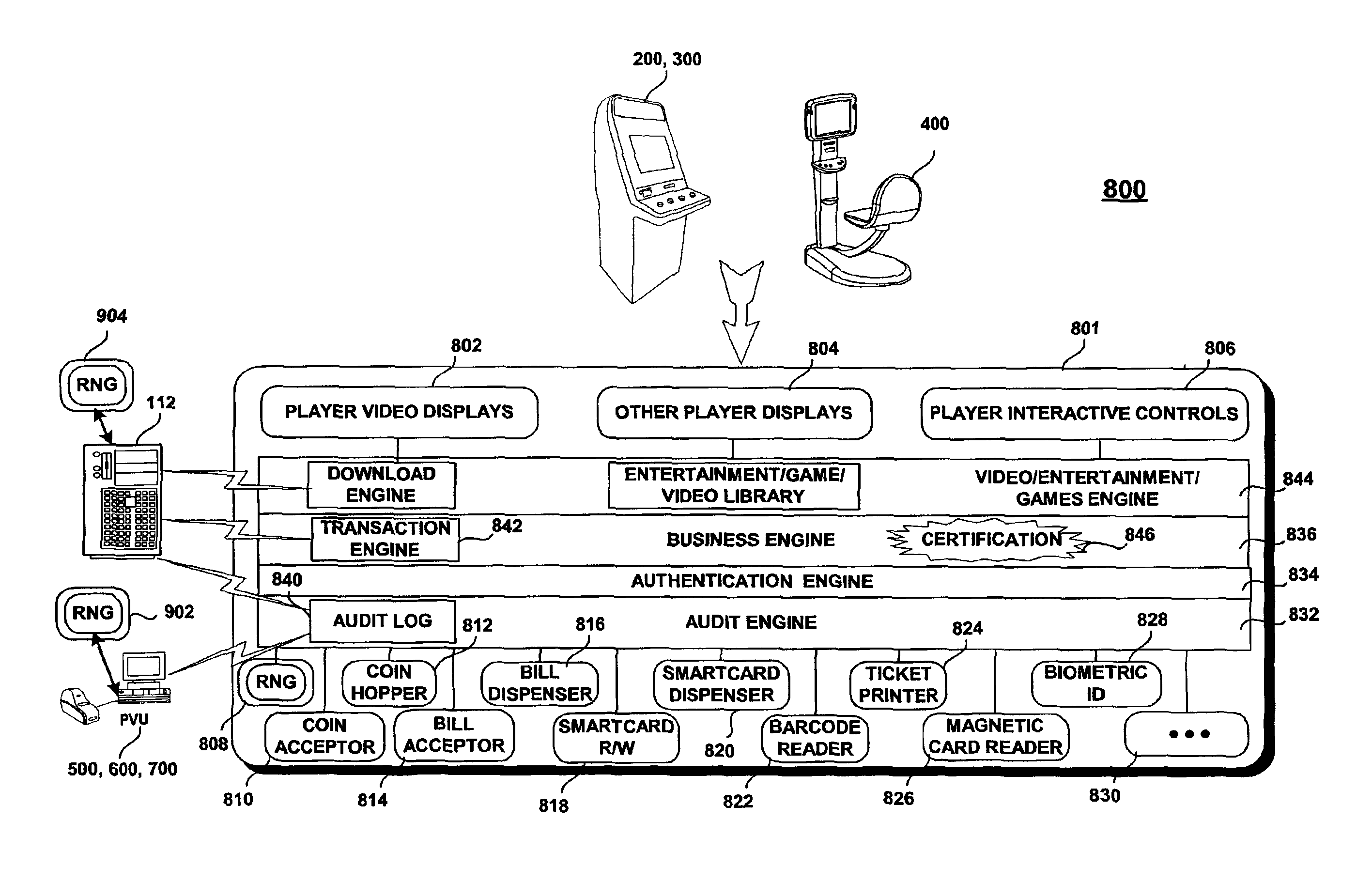
InactiveUS6908391B2Overcomes technical lagOvercomes security limitationApparatus for meter-controlled dispensingVideo gamesModularityThe Internet
A secure and modular architecture for monitoring and controlling clusters of pay entertainment and gaming devices. The architecture allows flexible and secure use of state-of-the-art multimedia and Internet technologies to attract the younger player generation used to flashy and networked games. Cash or cash-less entertainment and gaming devices are supported.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
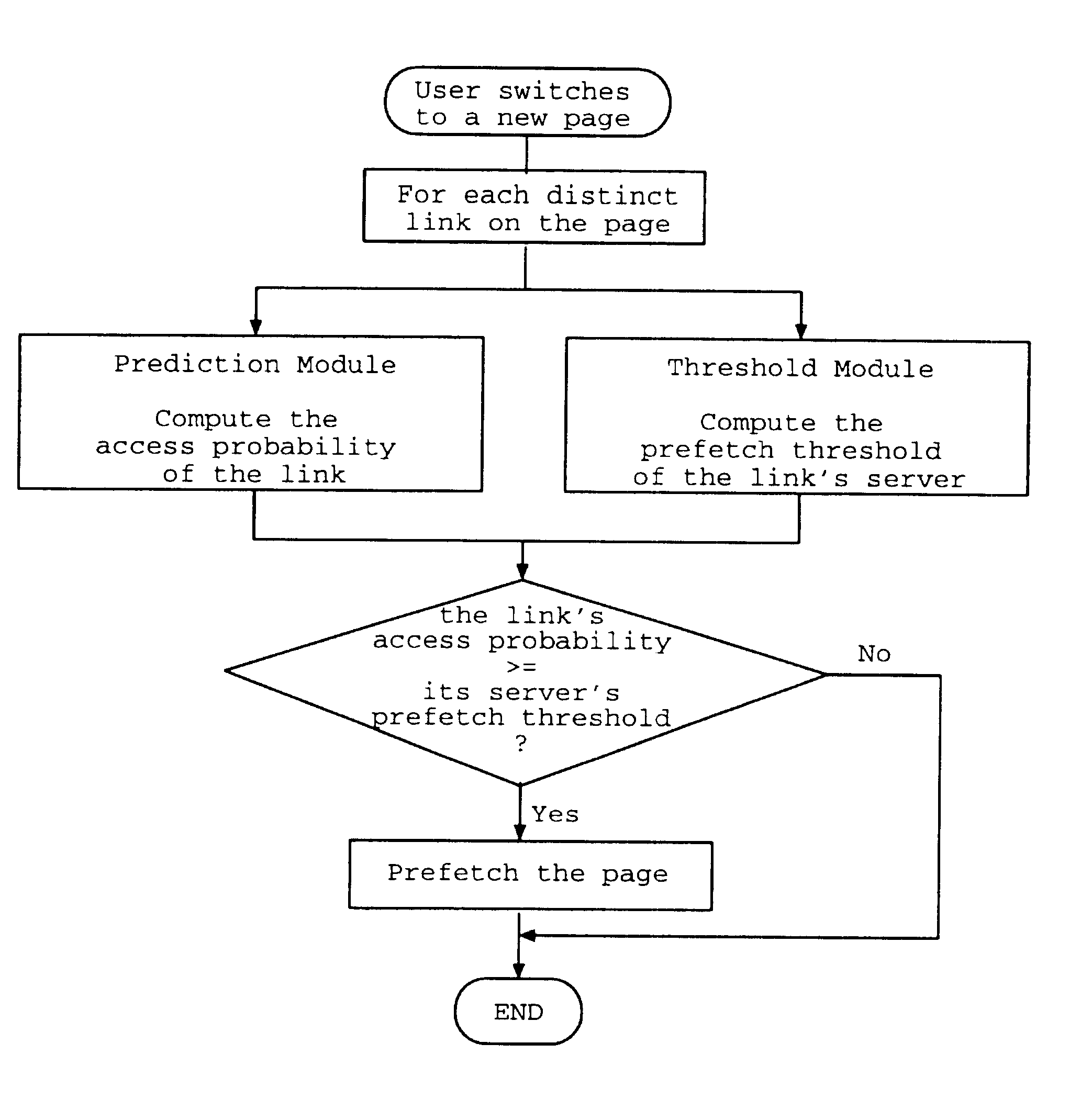
Adaptive prefetching for computer network and web browsing with a graphic user interface
InactiveUS6385641B1Multiple digital computer combinationsElectric digital data processingGraphicsGraphical user interface
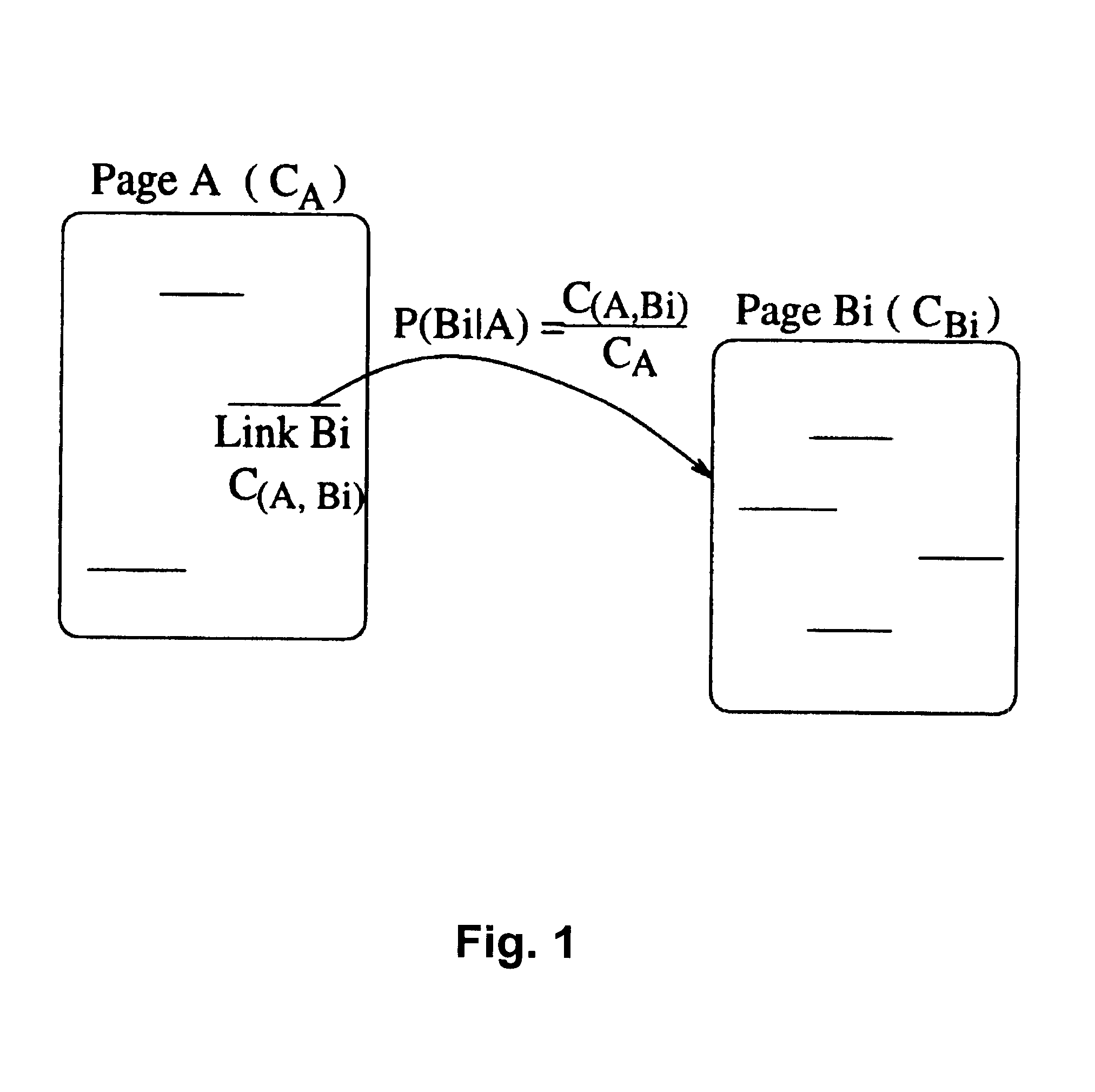
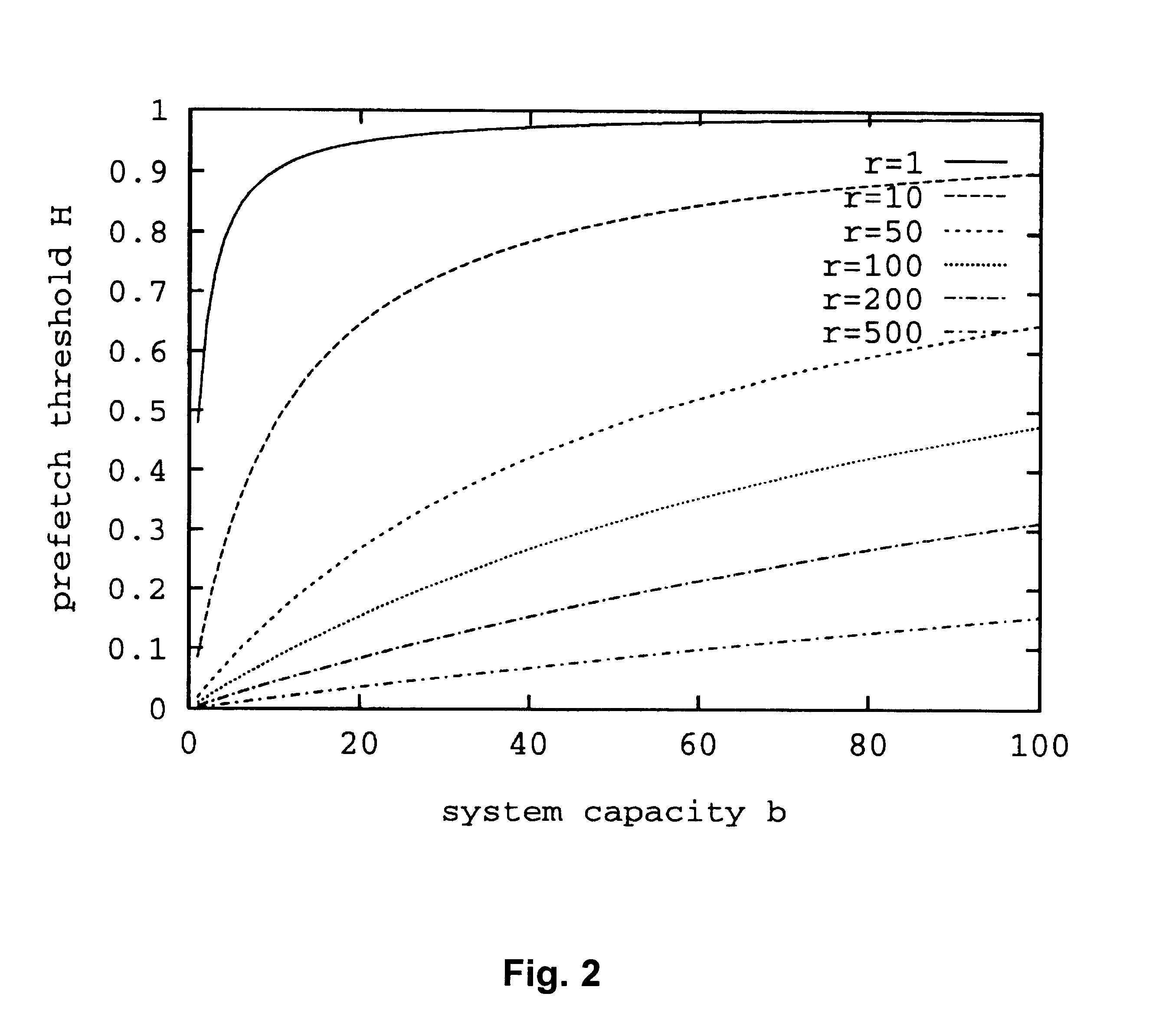
The present invention is based on a prefetching scheme consisting of two modules: a prediction module and a threshold module. After a use's request for a new file is satisfied, the prediction module immediately updates a database of history information if needed, and computes the access probability for each candidate file, where the access probability of a file is an estimate of the probability with which that file will be requested by the user in the near future. Next the threshold module determines the prefetch threshold for each related server, which contains at least one candidate file with nonzero access probability. The threshold is determined in real time based on then current network conditions. Finally, each file whose access probability exceeds or equals its server's prefetch threshold is prefetched. When prefetching a file, the file is actually downloaded if and only if no up-to-date version of the file is available on the local computer; otherwise no action is taken. Although web browsing is an important application for prefetching, the prefetch scheme of the present invention may be advantageously applied to any network application in which prefetching is possible.
Owner:RGT UNIV OF CALIFORNIA
Text messaging system and method
InactiveUS20010005859A1Network traffic/resource managementSpecial service for subscribersState managementDocumentation
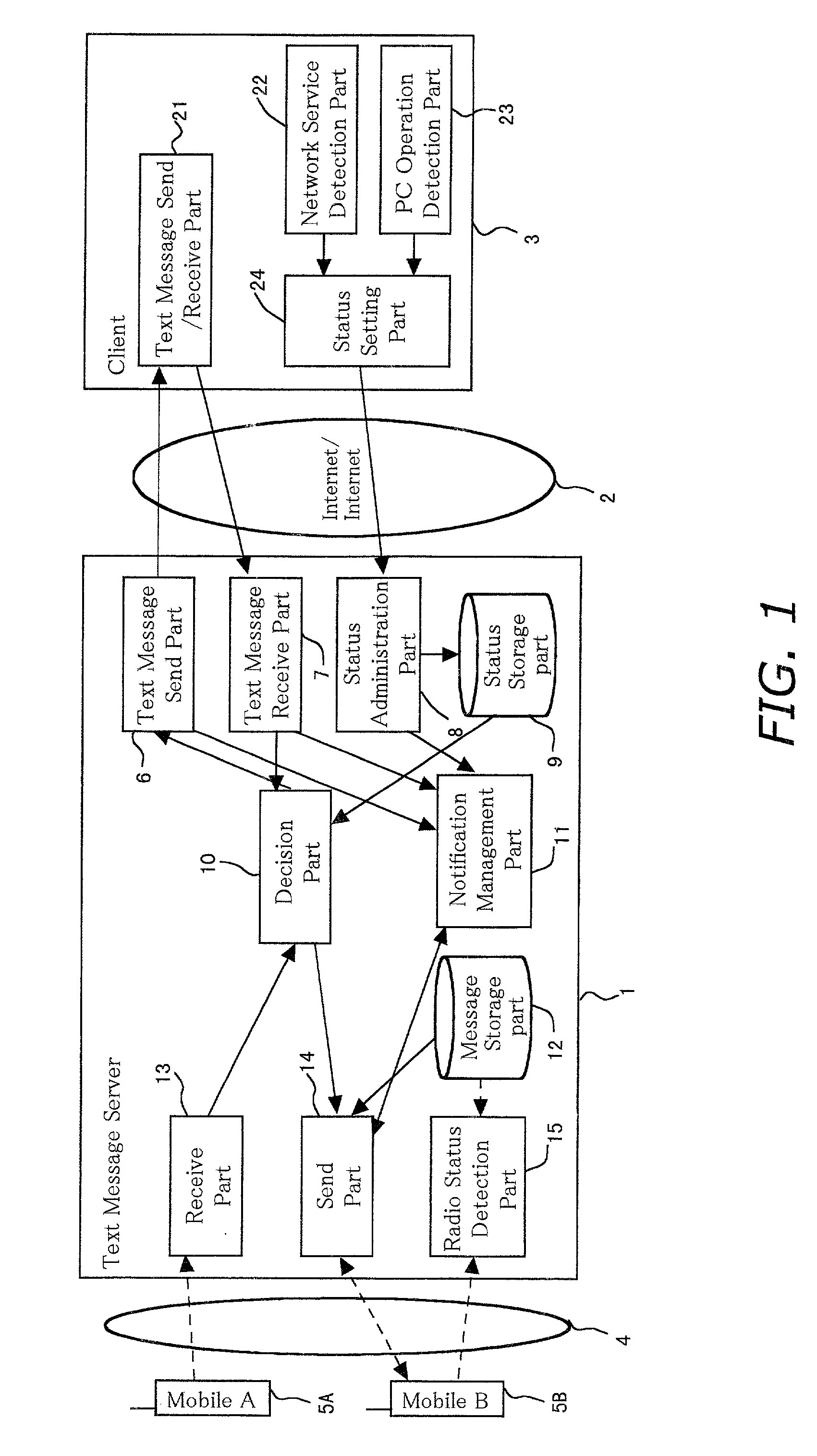
The text messaging system consists of mobile terminal (5) connected to mobile communication network (4), information terminal (3) connected to computer network (2), and server (1) connected to the mobile communication network and the computer network. The information terminal (3) has status detection means (22), (23), and (24), and detects an operational status including at least the connection status of the computer network and notifies the server (1) of it. The server (1) has status administration means (8) and (9) and decision means (10). The status administration means (8) and (9) retain the operational status of the information terminal (3) notified from status detection means (24) for each user. The decision means (10) determines a send mode according to the operational status of the information terminal such as whether to send a text message to an information terminal or to send a text message with a network application.
Owner:FUJITSU LTD
Cost-aware, bandwidth management systems adaptive to network conditions
ActiveUS8489720B1Improve load conditionsLow costMultiple digital computer combinationsData switching networksNetwork conditionsApplication software
Methods, apparatuses, and systems directed to cost-aware bandwidth management schemes that are adaptive to monitored network or application performance attributes. In one embodiment, the present invention supports bandwidth management systems that adapt to network conditions, while managing tradeoffs between bandwidth costs and application performance. One implementation of the present invention tracks bandwidth usage over an applicable billing period and applies a statistical model to allow for bursting to address increased network loading conditions that degrade network or application performance. One implementation allows for bursting at selected time periods based on computations minimizing cost relative to an applicable billing model. One implementation of the present invention is also application-aware, monitoring network application performance and increasing bandwidth allocations in response to degradations in the performance of selected applications.
Owner:CA TECH INC
Method and apparatus for providing mobile and other intermittent connectivity in a computing environment
InactiveUS7293107B1Easy accessSacrificing reliability or centralized managementNetwork traffic/resource managementMultiple digital computer combinationsNetwork connectionMobile end
A seamless solution transparently addresses the characteristics of nomadic systems, and enables existing network applications to run reliably in mobile environments. A Mobility Management Server coupled to the mobile network maintains the state of each of any number of Mobile End Systems and handles the complex session management required to maintain persistent connections to the network and to other peer processes. If a Mobile End System becomes unreachable, suspends, or changes network address (e.g., due to roaming from one network interconnect to another), the Mobility Management Server maintains the connection to the associated peer task—allowing the Mobile End System to maintain a continuous connection even though it may temporarily lose contact with its network medium. An interface-based listener uses network point of attachment information supplied by a network interface to determine roaming conditions and to efficiently reestablish connection upon roaming. The Mobility Management Server can distribute lists to Mobile End Systems specifying how to contact it over disjoint networks.
Owner:MOBILE SONIC INC
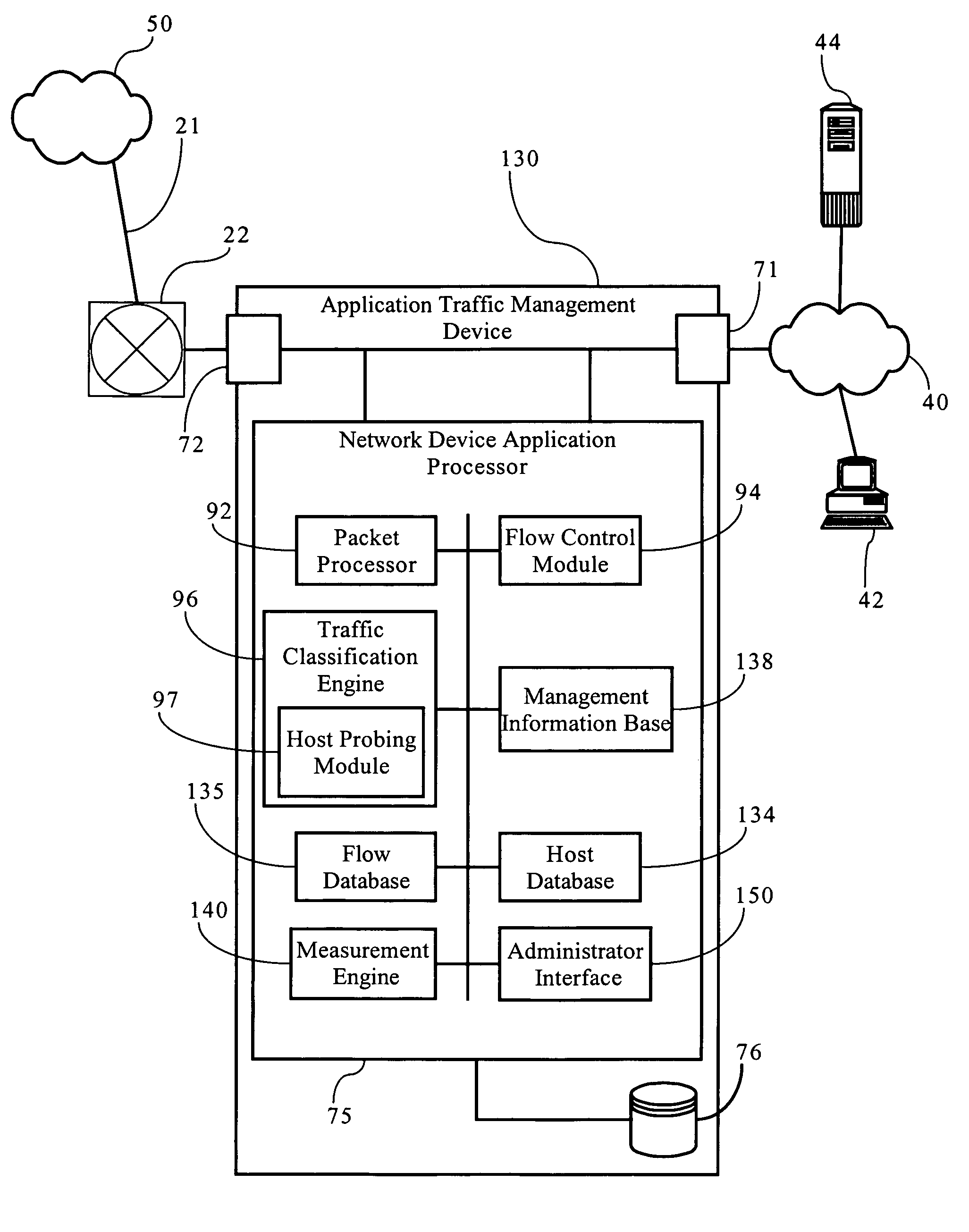
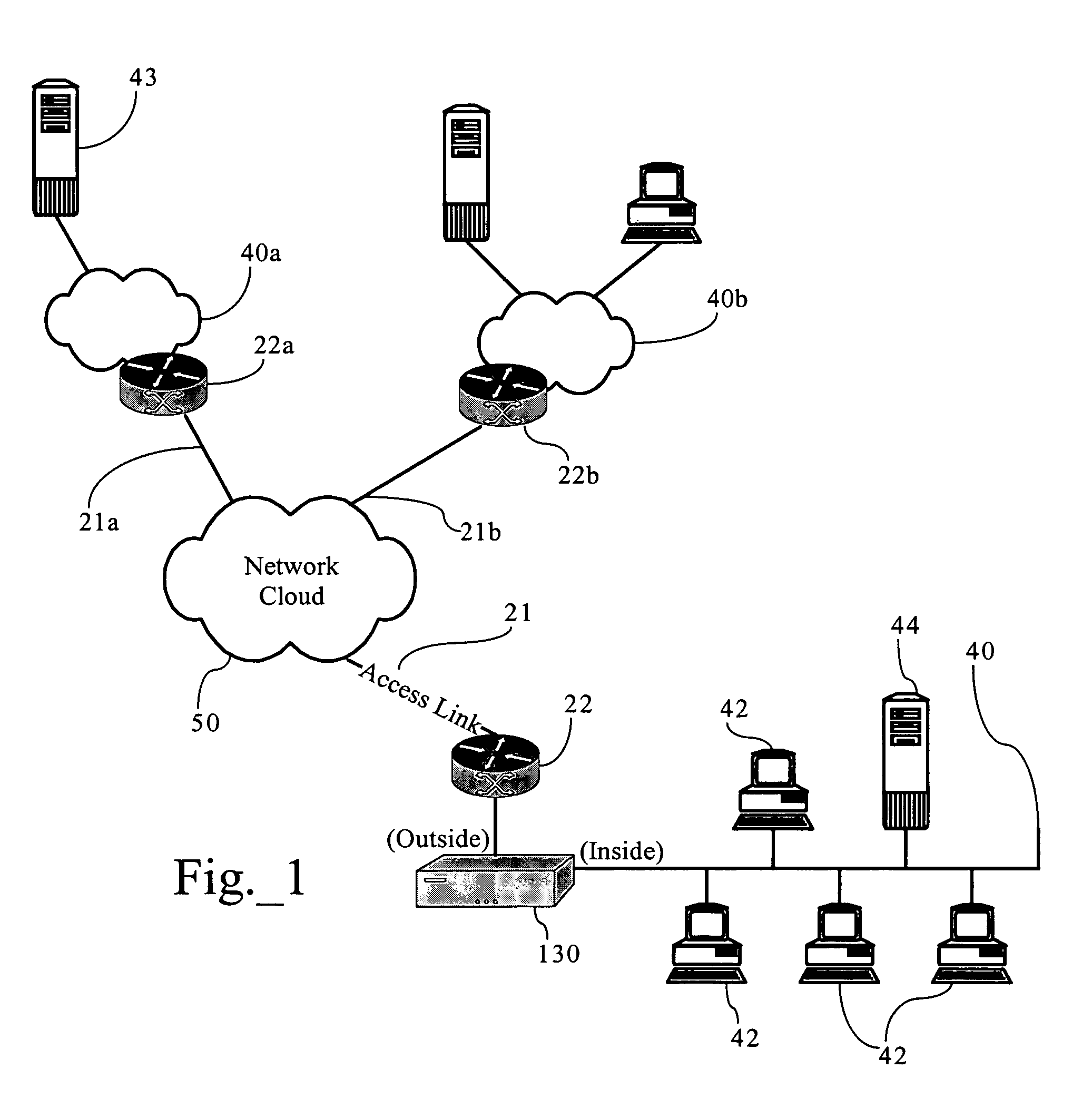
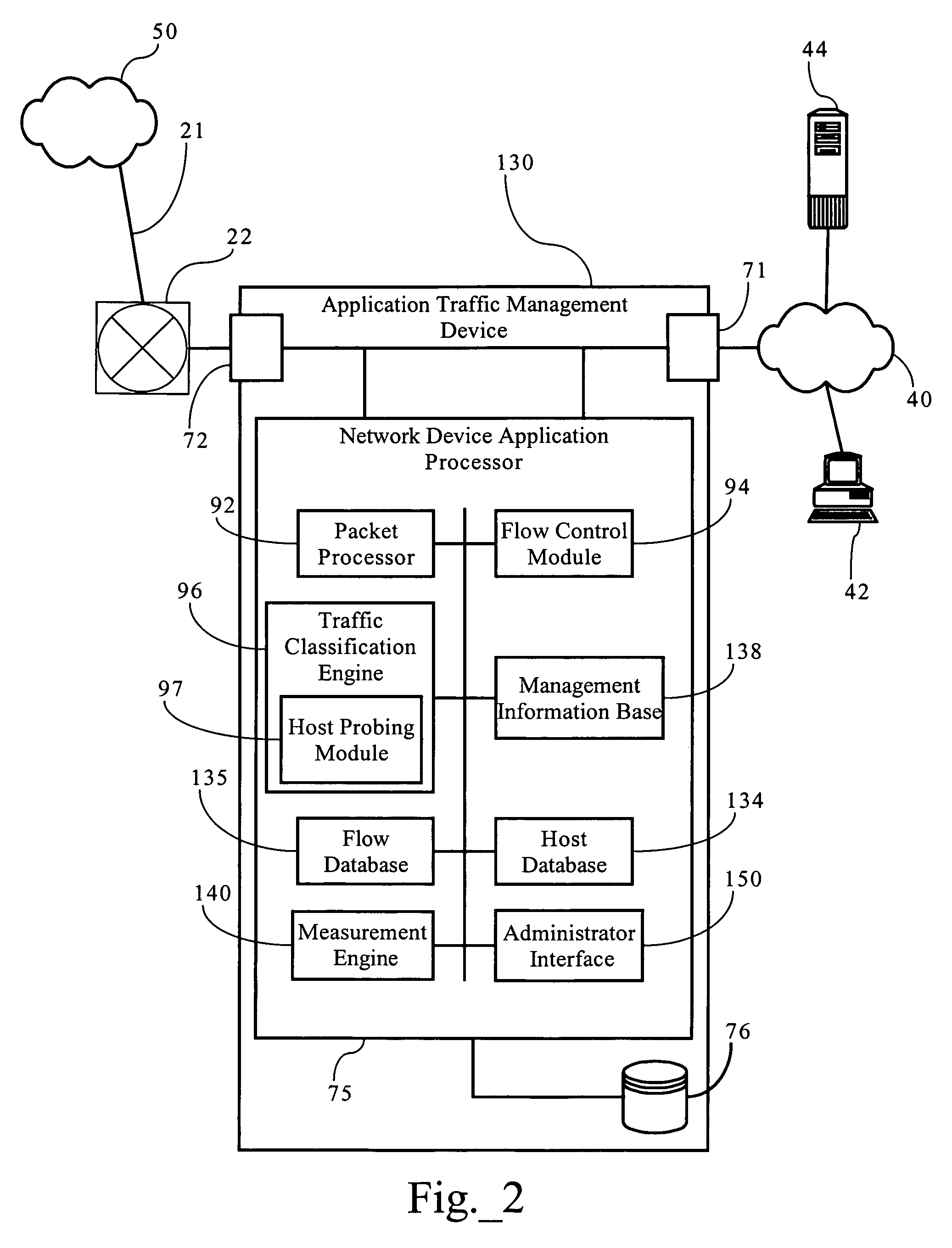
Probing hosts against network application profiles to facilitate classification of network traffic
Methods, apparatuses and systems directed to a network traffic classification mechanism that probes hosts against one or more network application profiles to facilitate identification of network applications corresponding to data flows traversing a network.
Owner:CA TECH INC
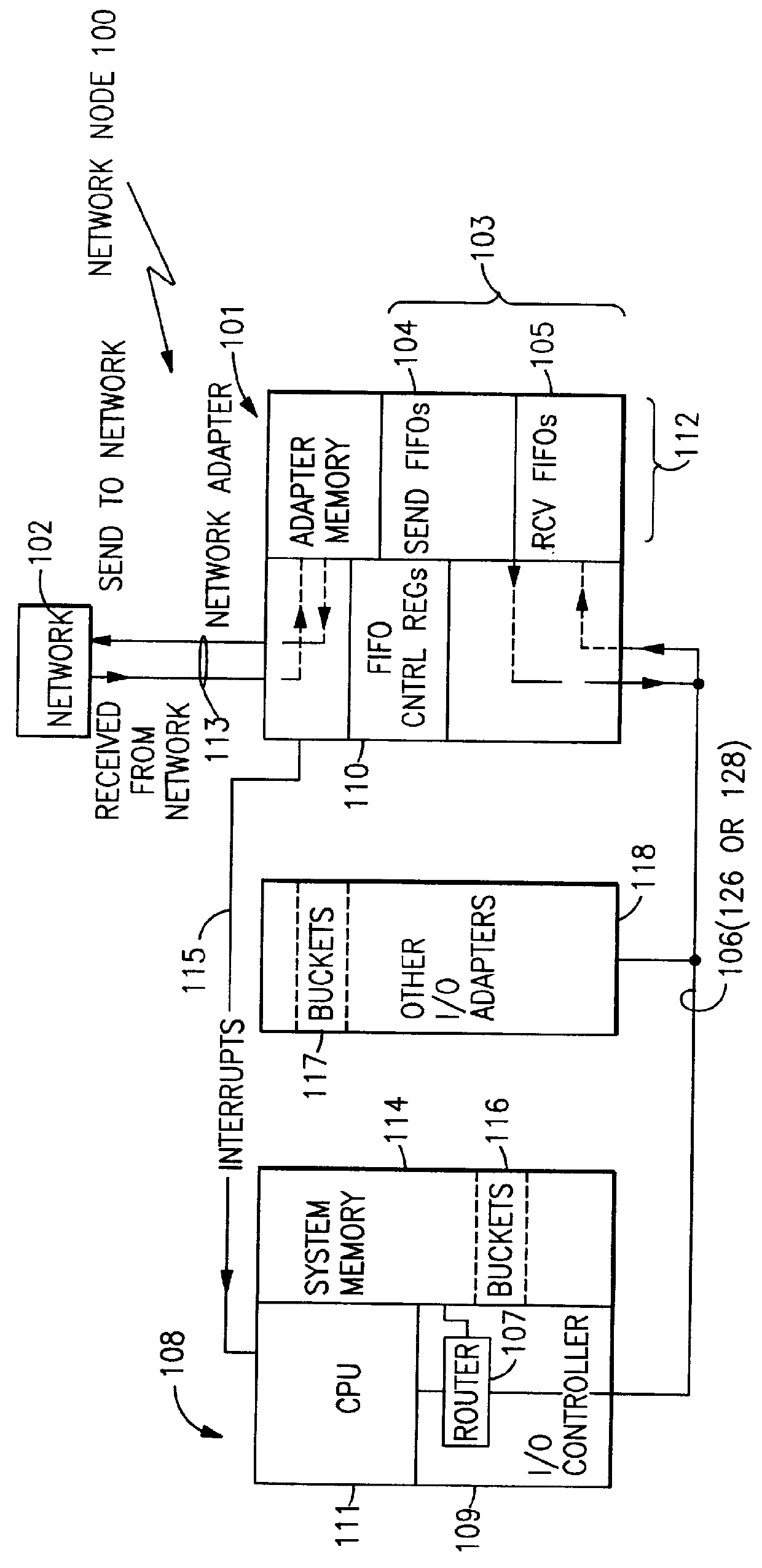
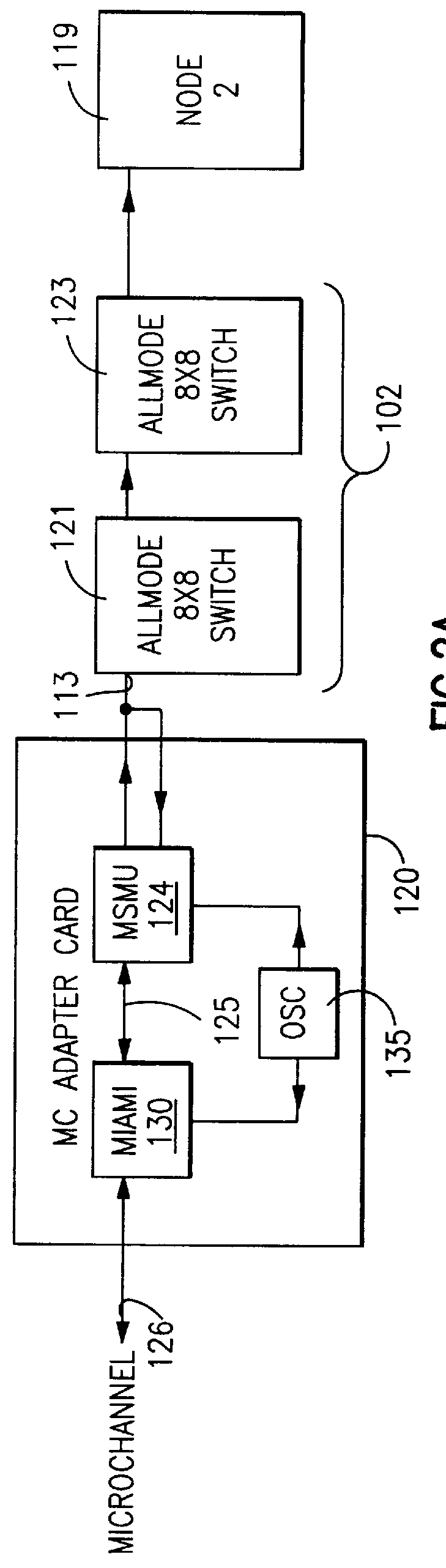
Multi-tasking adapter for parallel network applications
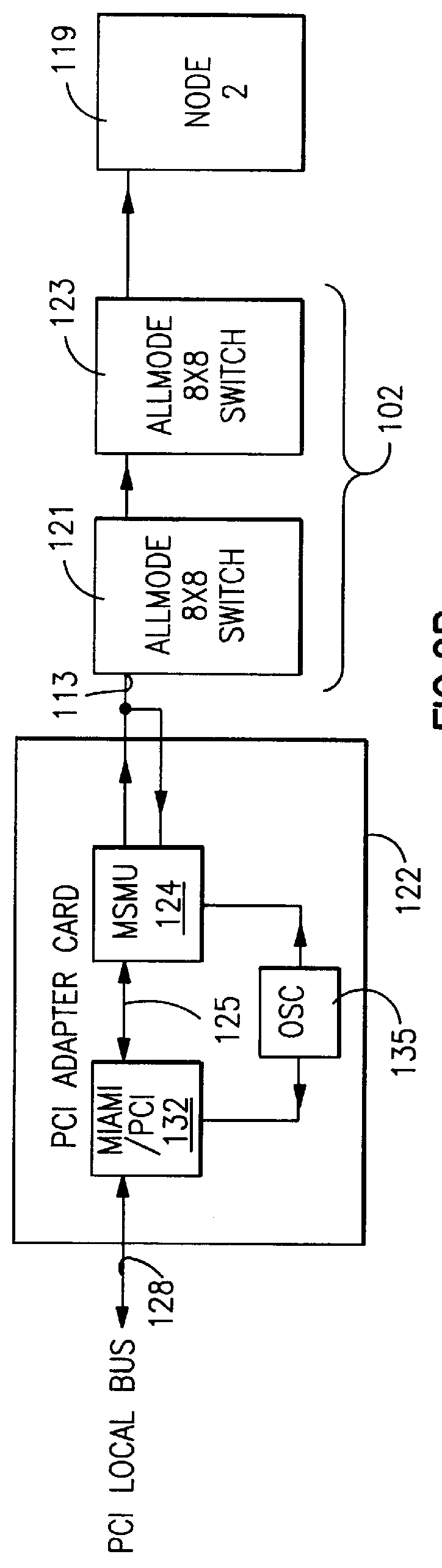
A communications apparatus is provided comprising a plurality of FIFO buffers, each with independent control and priority logic under software control for supporting different types of message traffic, both send and receive, such as comprise a multimedia server system. Processor software directs messages to specific, optimized FIFO buffers. Further, a system is provided including a plurality of nodes wherein a sending node specifies the communications path through the system, selecting specific FIFO buffers in each node for buffering its messages.
Owner:IBM CORP
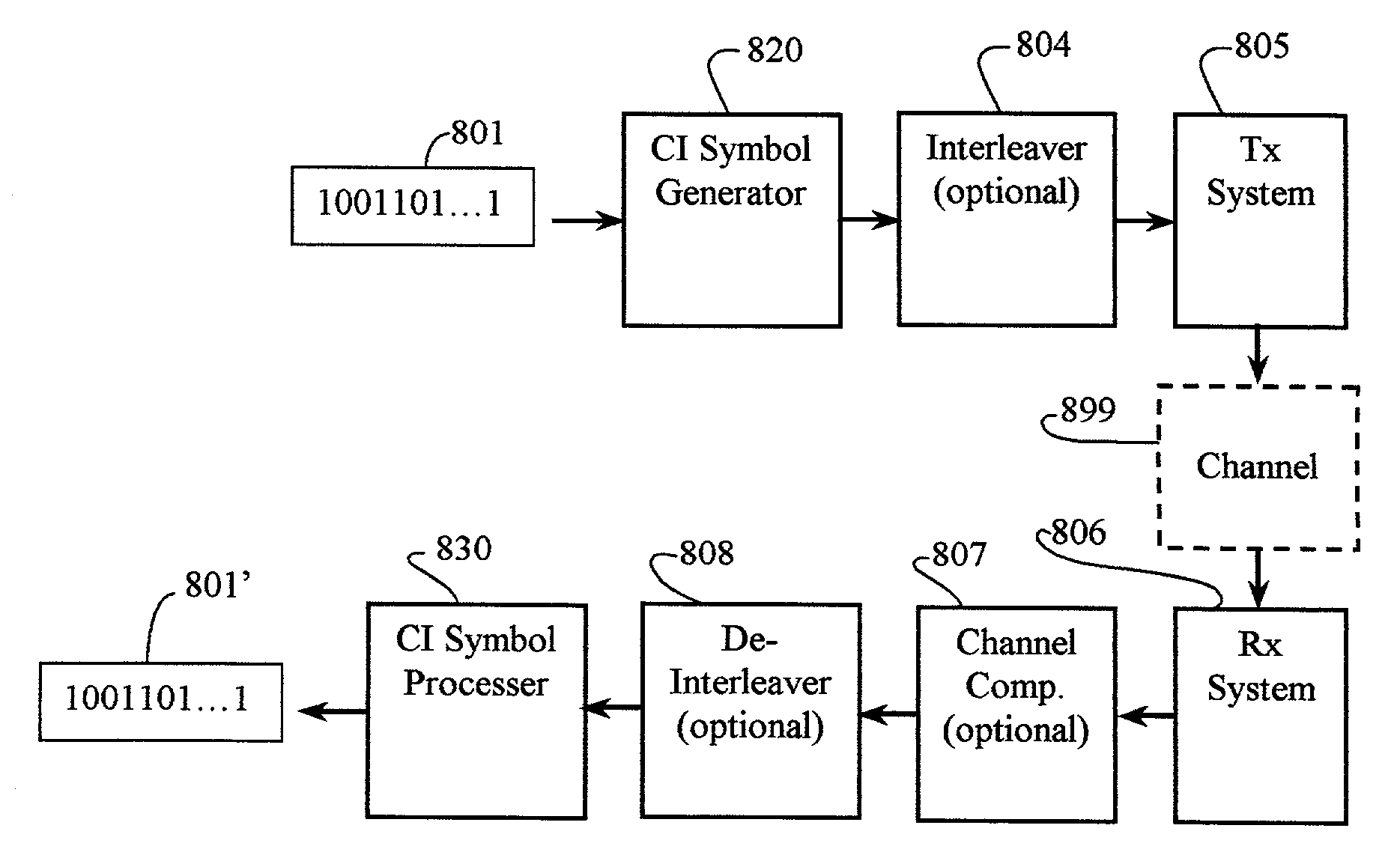
Carrier interferometry networks
ActiveUS20080095121A1Improve throughputImprove bit error rateEnergy efficient ICTModulated-carrier systemsWireless mesh networkTelecommunications link
Applications of CI processing to ad-hoc and peer-to-peer networking significantly improve throughput, network capacity, range, power efficiency, and spectral efficiency. CI-based subscriber units perform network-control functions to optimize network performance relative to channel conditions, network loads, and subscriber services. CI codes are used to identify and address network transmissions. Channel characteristics of communication links are employed to encode, address, and authenticate network transmissions. CI transceivers used as relays and routers employ unique characteristics of transmission paths to code and decode network transmissions. A central processor is adapted to perform array processing with signals received from, and transmitted by, a plurality of subscriber units in a wireless network.
Owner:GENGHISCOMM HLDG
Adaptive Social and Process Network Systems
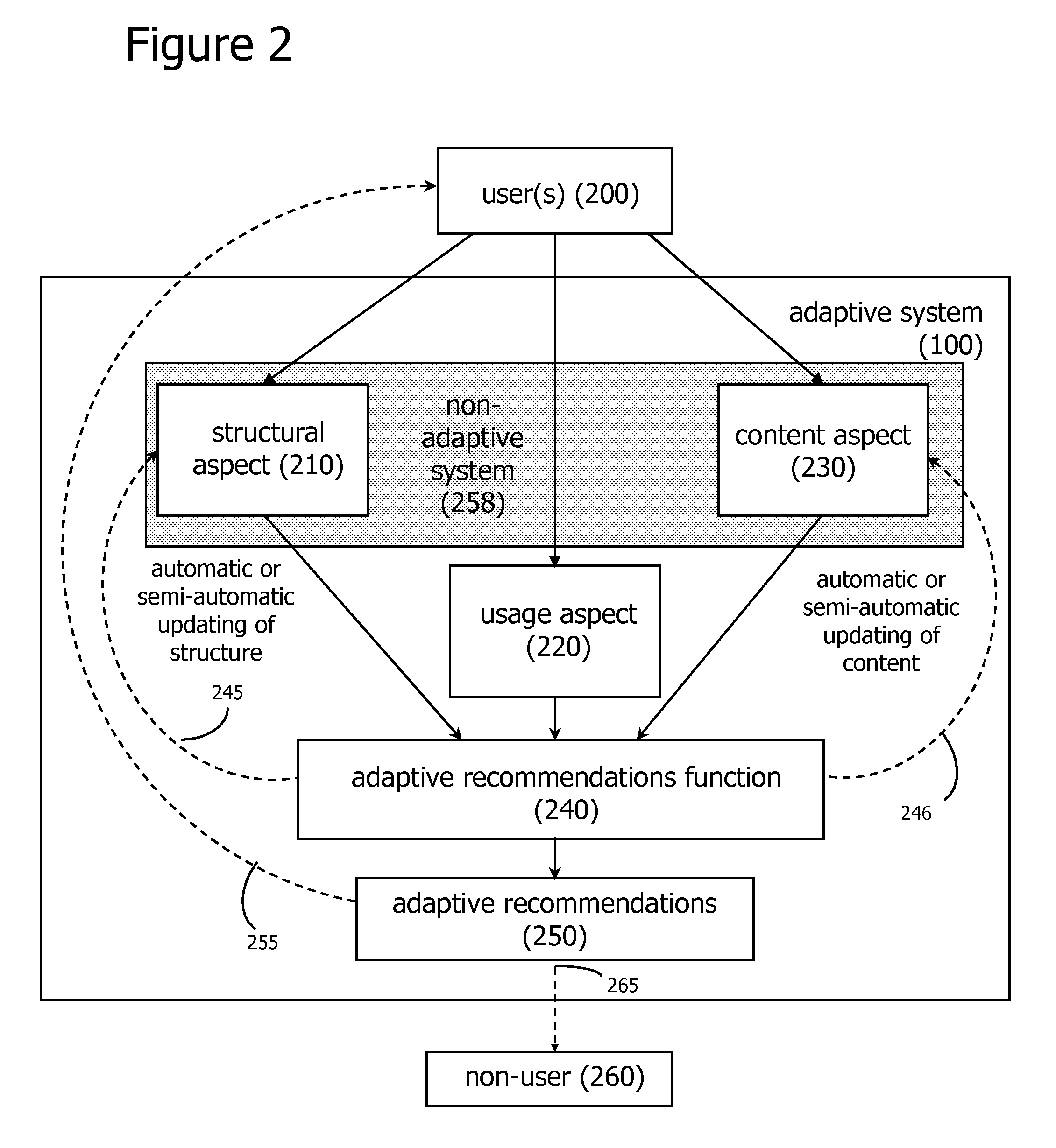
ActiveUS20060200434A1Easy to adaptEfficiently navigateAdvertisementsDigital computer detailsSelf adaptiveNetwork application
An adaptive system applied to social network and process network applications is disclosed. These adaptive social networking and tagging systems, and adaptive process network systems, apply algorithms for monitoring user usage behaviors across a plurality of usage behavior categories associated with a computer-based system, and generating recommendations based on inferences on user preferences and interests based, at least in part, on usage behaviors. Additional functions for effectively and efficiently managing social and process networks, such as social network measurement and analysis features, community tagging functions, and process network recombination functions are also described.
Owner:WORLD ASSETS CONSULTING AG
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
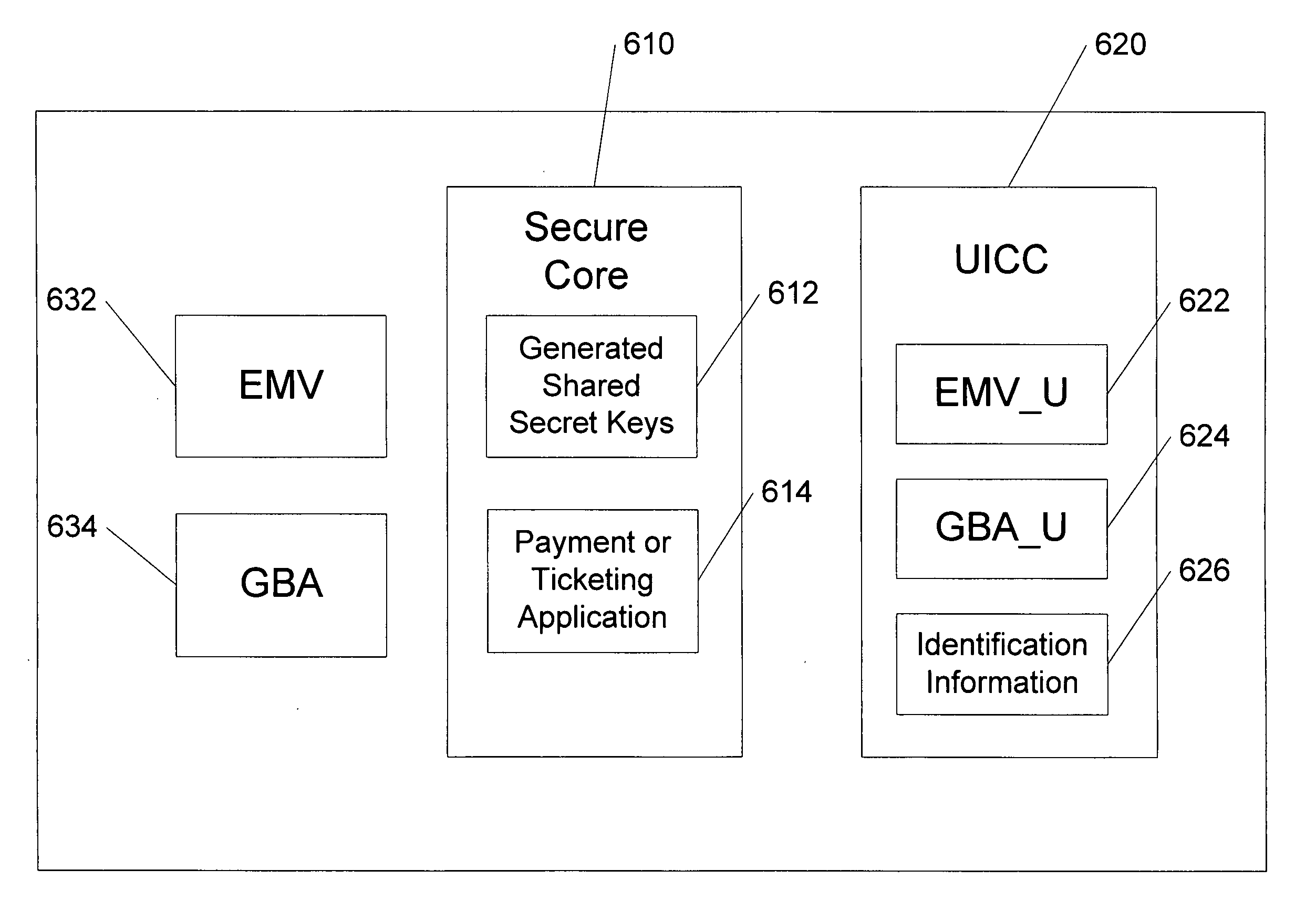
Techniques for secure channelization between uicc and a terminal
InactiveUS20090209232A1Improve integrityReduce needUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemThird generation
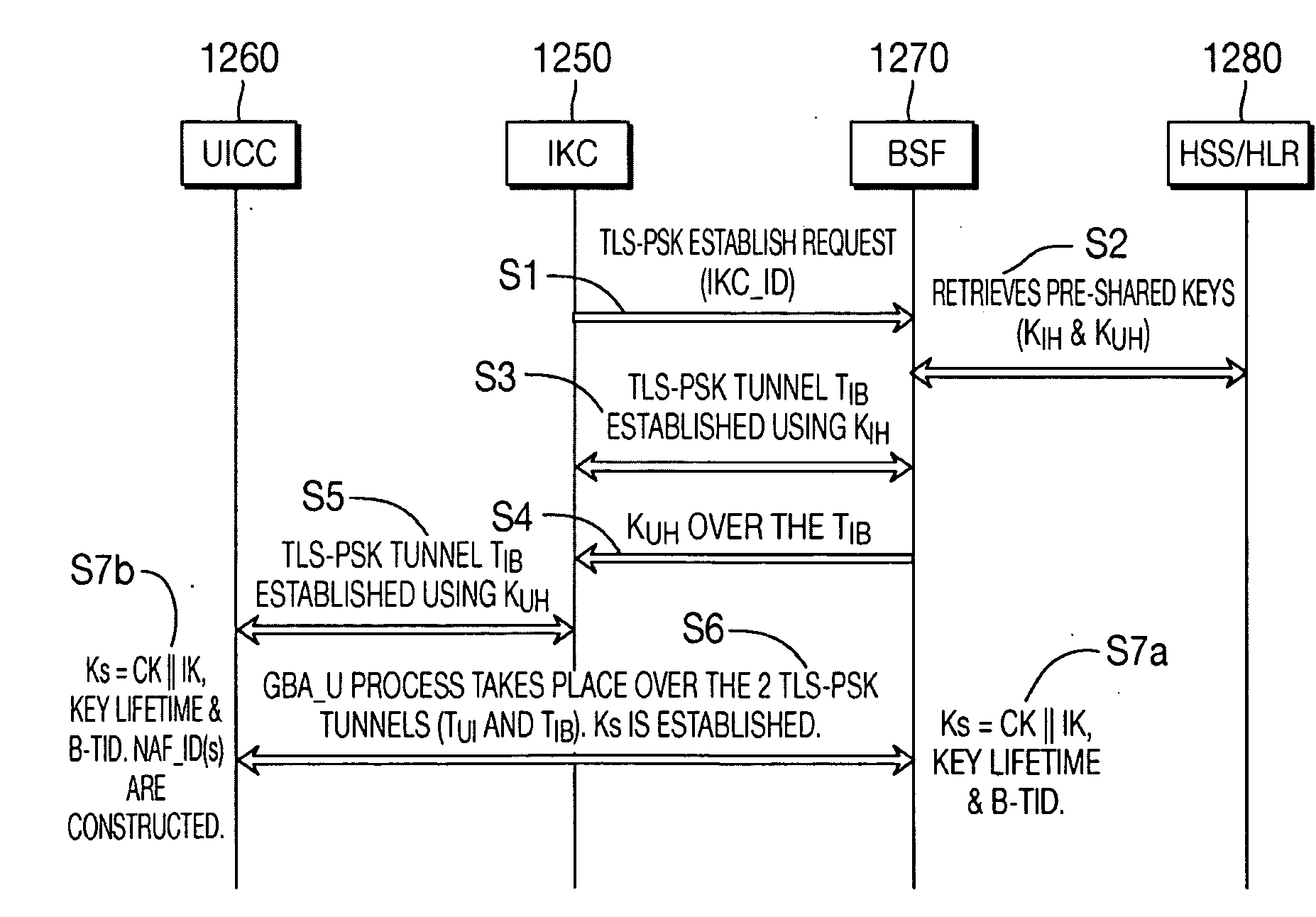
The present invention is related to a wireless communication system. 3G UMTS mobile phone systems rely on a protected smart card called the UMTS integrated circuit card (UICC) that provides UMTS subscriber identity module (USIM) applications as a basis or root of various security measures protecting the communication path between the 3G mobile terminal and the UMTS wireless network (or UTRAN). Disclosed is a method by which the UICC exchanges information with a terminal, such as an Internal Key Center (IKC 1250) and a Bootstrapping Server Function (BSF 1270) enables a procedure where multiple local keys specific to applications and Network Application Functions (NAFs) (Ks_local) are used for authentication and to encrypt and decrypt messages.
Owner:INTERDIGITAL TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com