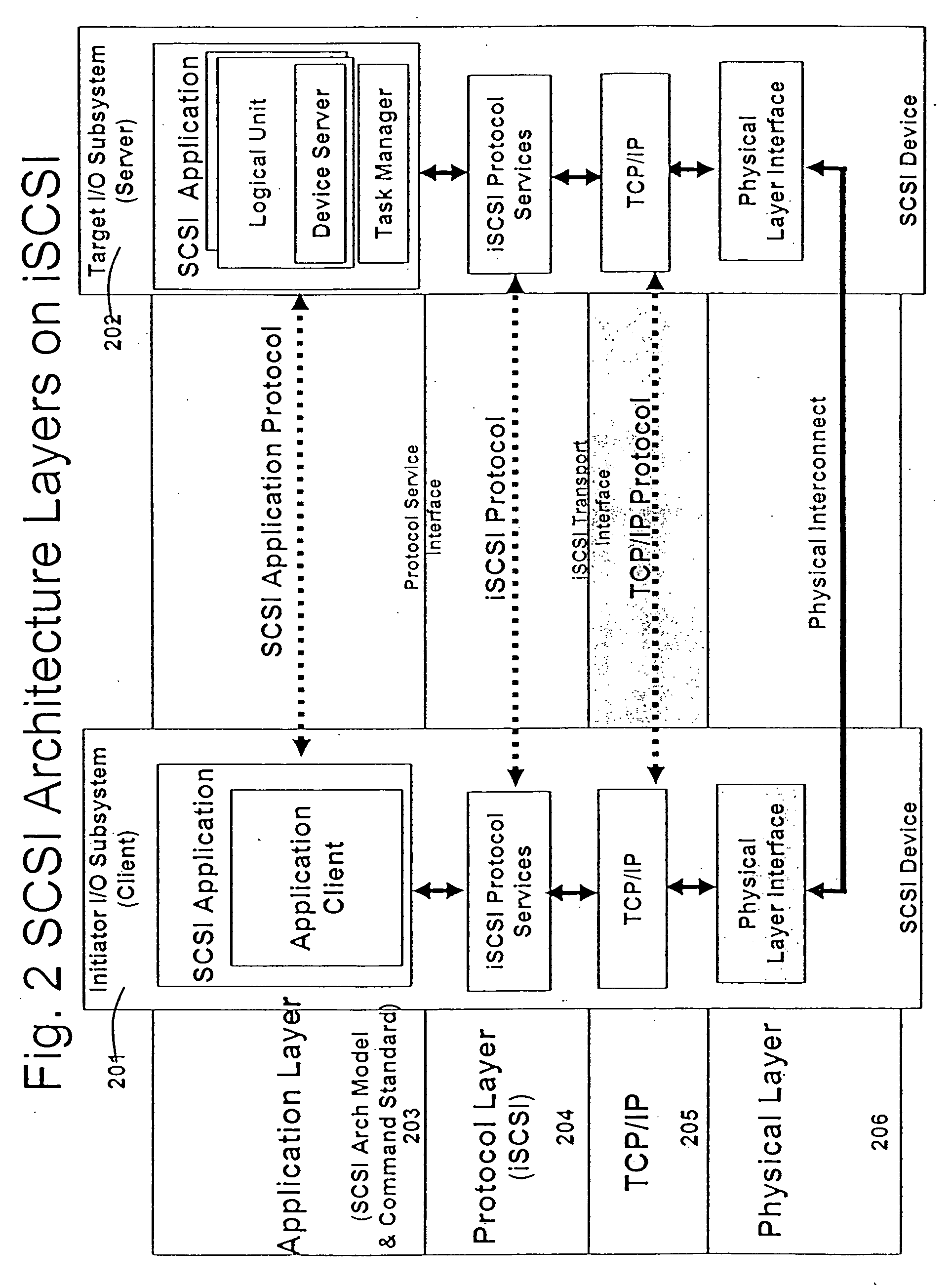
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
26755 results about "Data pack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A data pack (or fact pack) is a pre-made database that can be fed to a software, such as software agents, Internet bots or chatterbots, to teach information and facts, which it can later look up. In other words, a data pack can be used to feed minor updates into a system.
Storage system and a storage management system
InactiveUS20060047907A1Improve matchMemory loss protectionMultiple digital computer combinationsData packStorage management
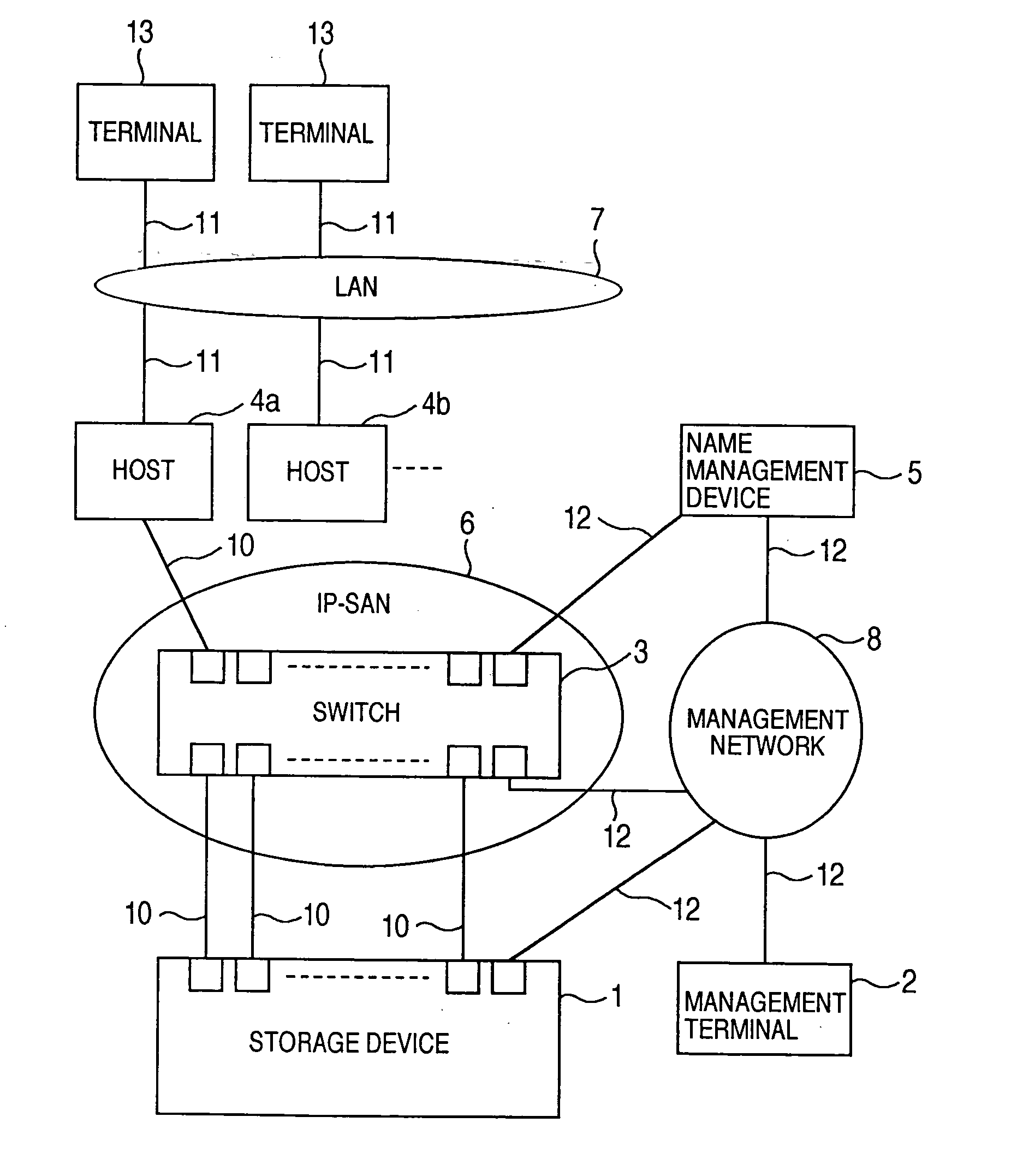
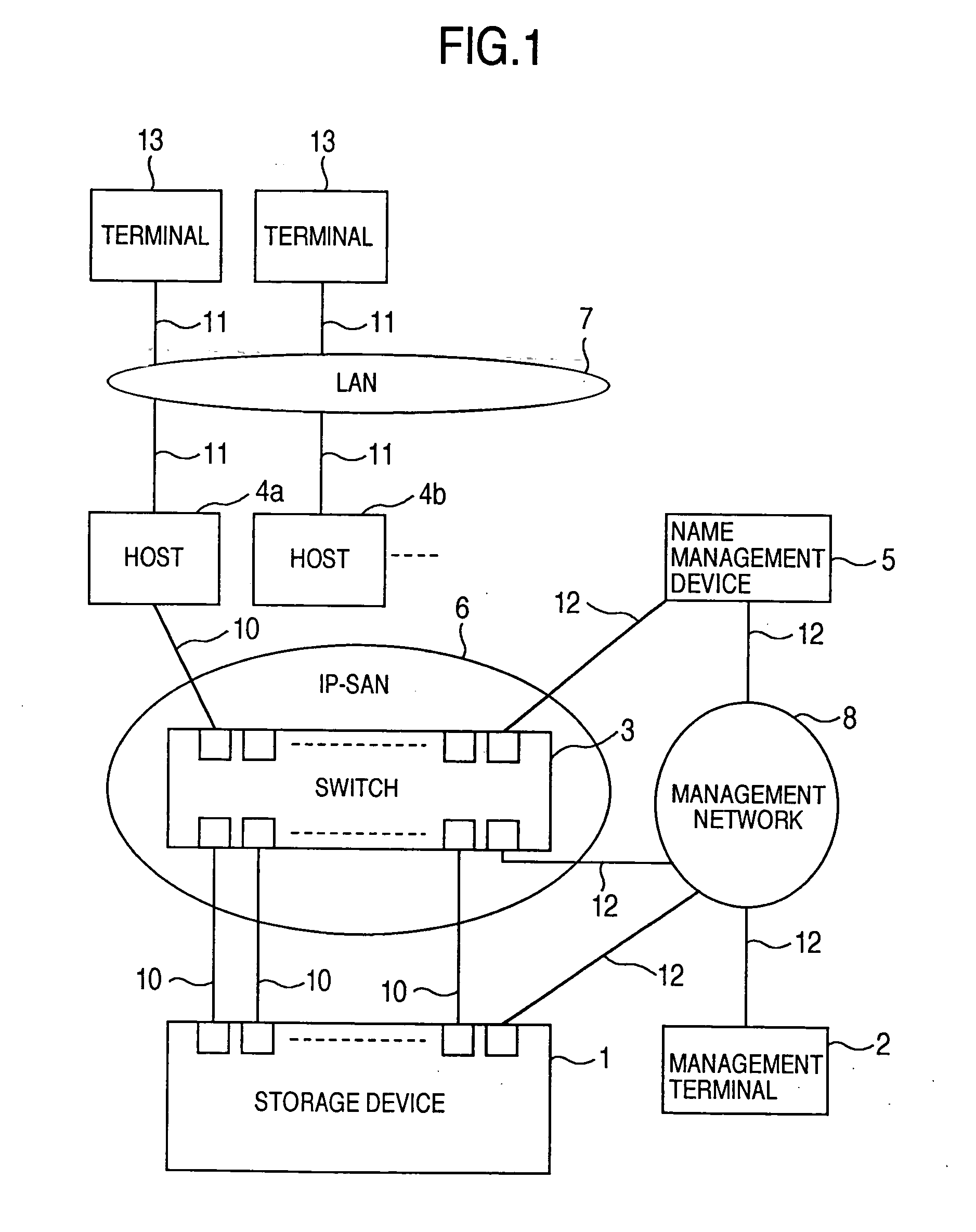
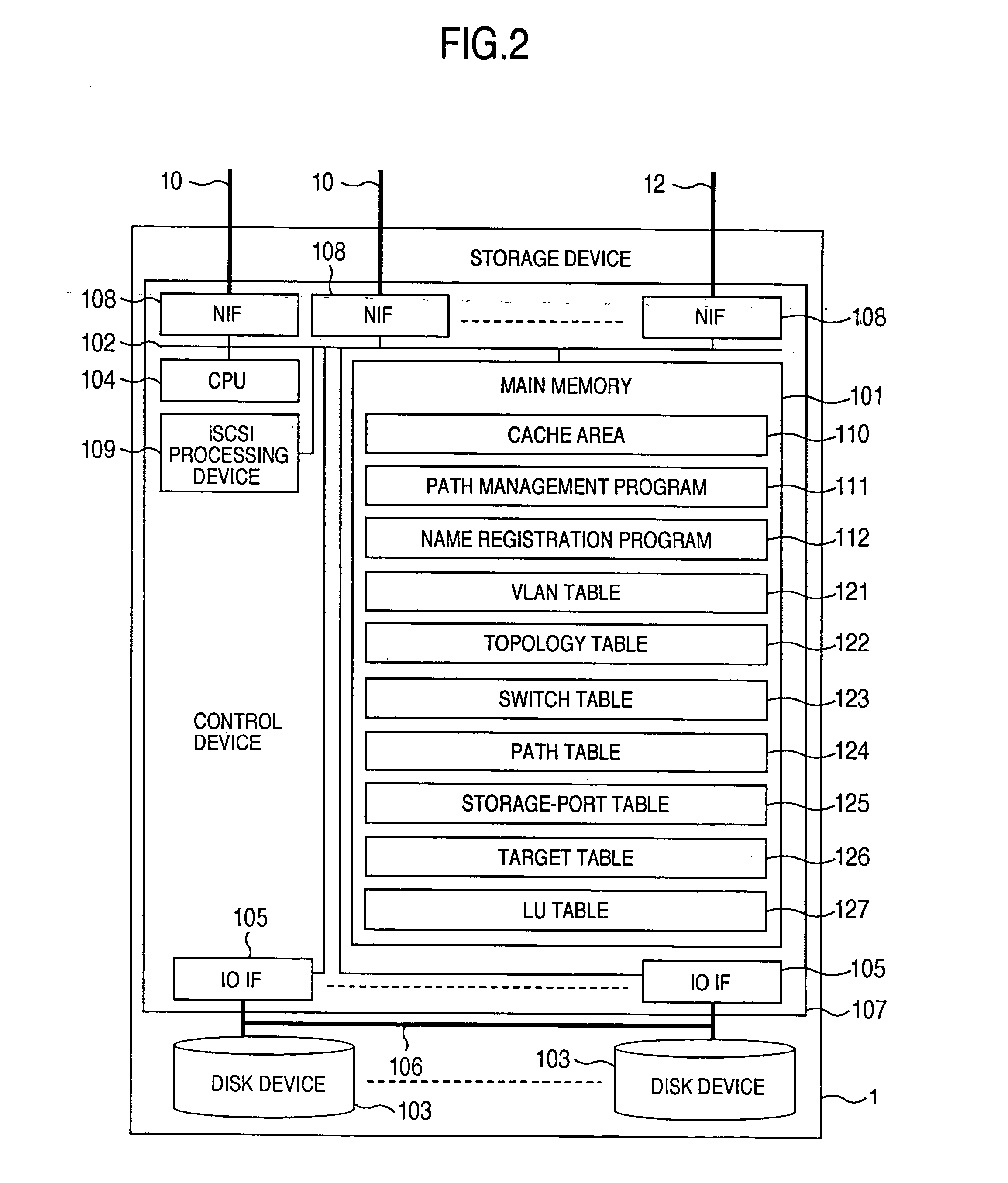
A storage device managing one or more logical volumes is connected with a name management device through an IP-SAN 6 composed of a switch. The storage device stores a topology table saving connecting relation among physical ports of host, physical ports of the storage device and physical ports of the switch, reads an identifier of the host and an identifier of the logical volume, selects a unused first physical port of the switch by referring to the topology table, selects a second physical port of the switch connected with the storage device, registers a group composed of the host and the logical volume with the name management device, and executes a configuration of allowing packets to be transferred between the first and the second physical ports with respect to the switch.
Owner:GOOGLE LLC
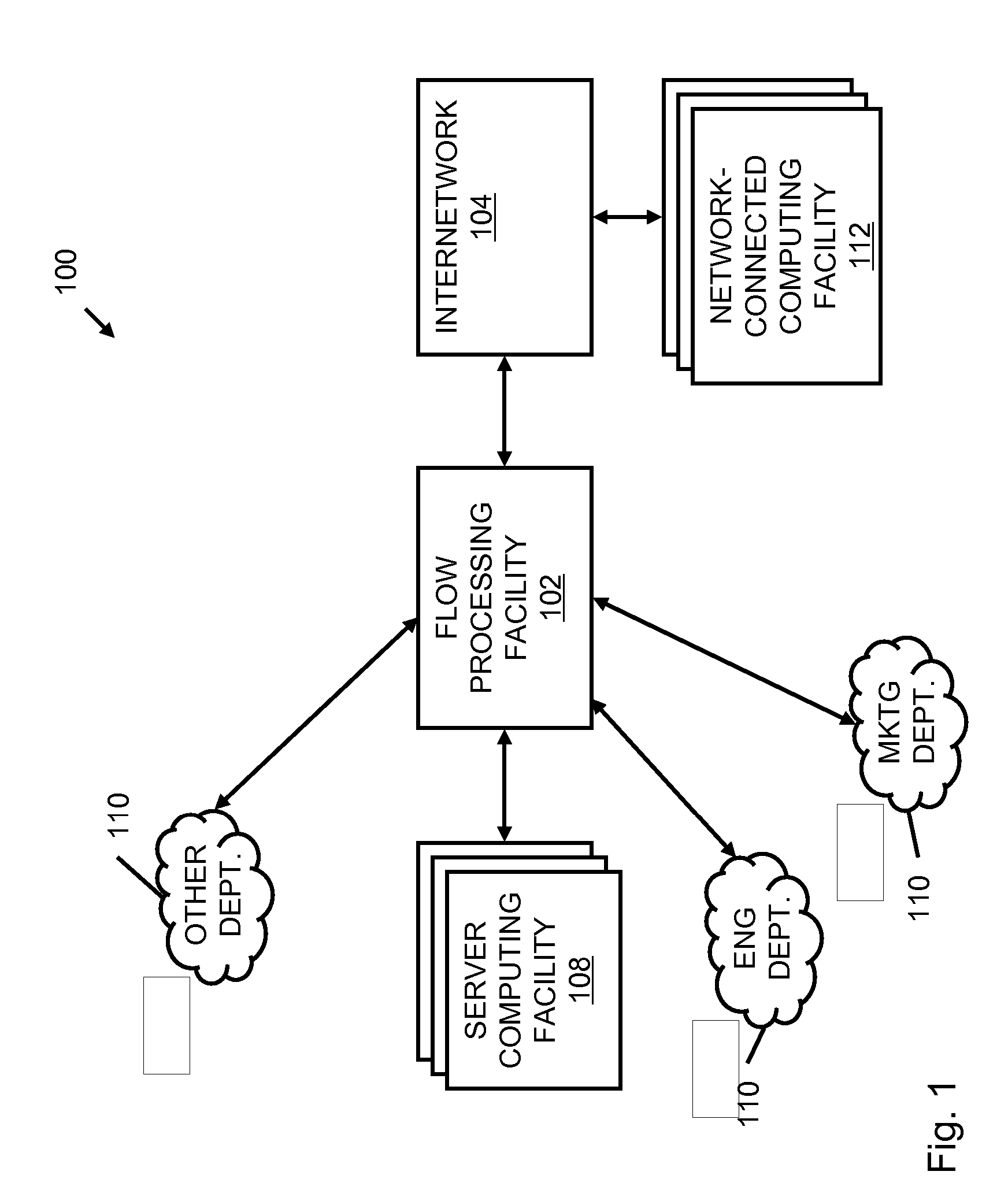
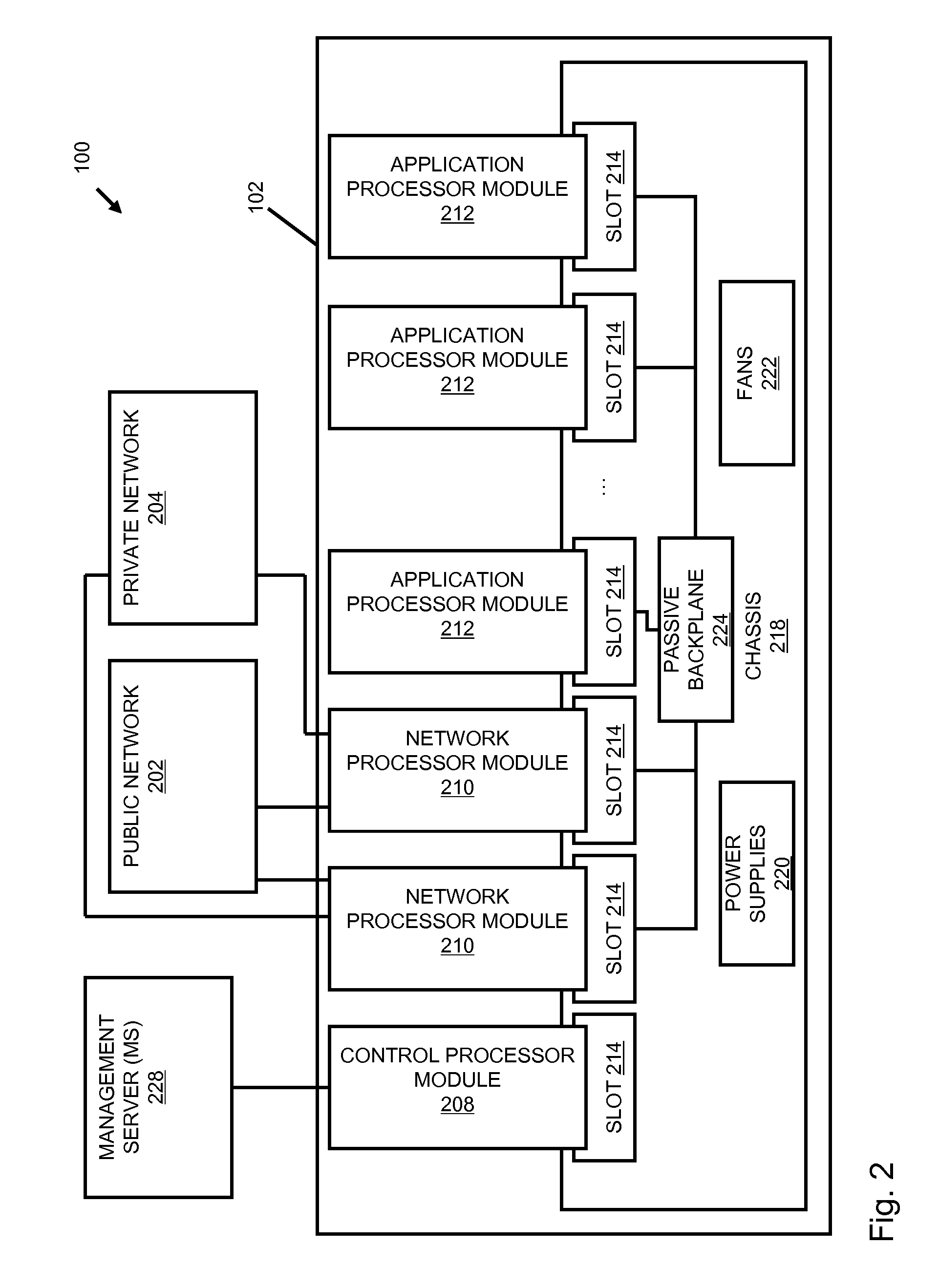
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
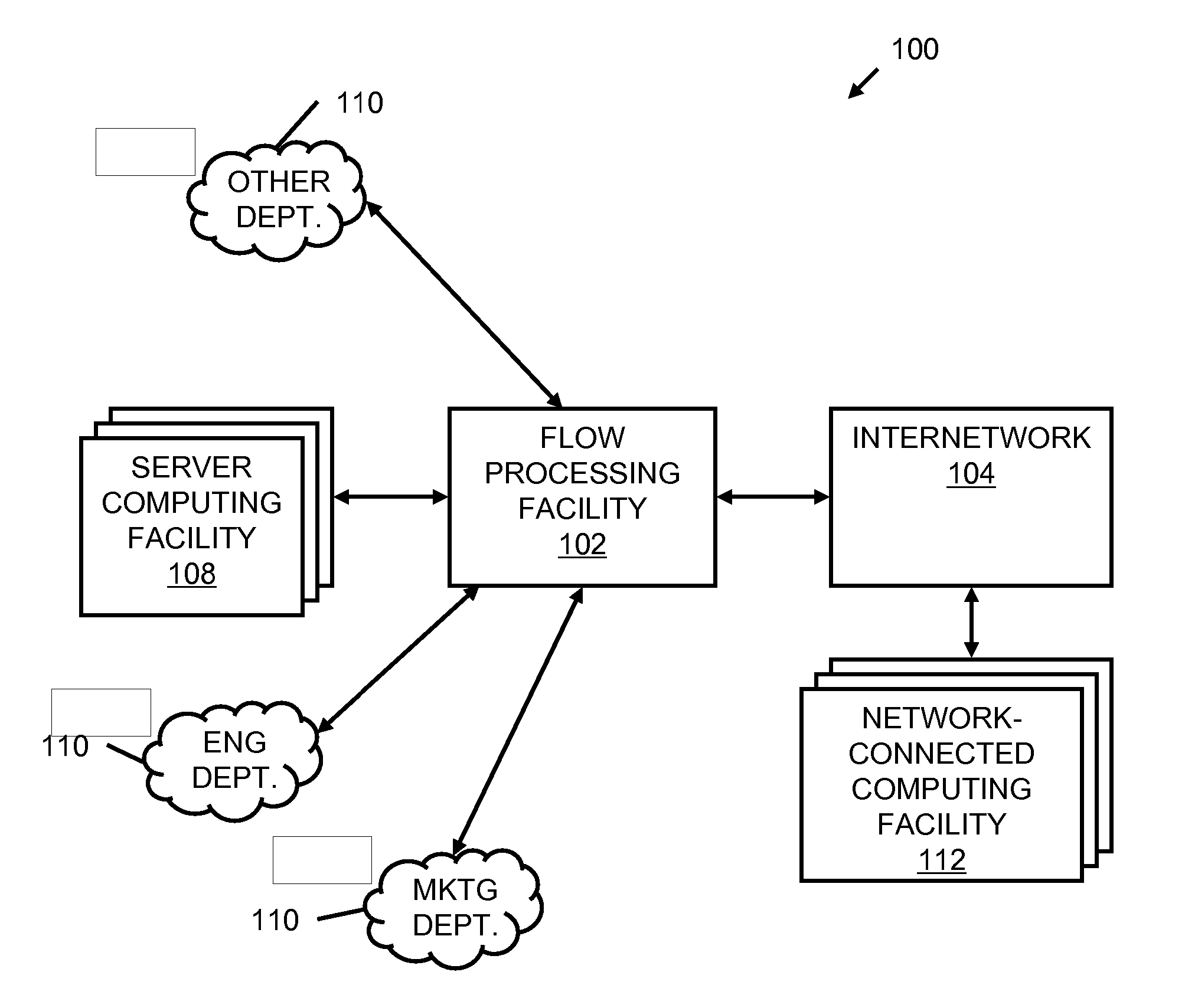
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Runtime adaptable search processor
ActiveUS20060136570A1Reduce stacking processImproving host CPU performanceWeb data indexingMultiple digital computer combinationsData packInternal memory
A runtime adaptable search processor is disclosed. The search processor provides high speed content search capability to meet the performance need of network line rates growing to 1 Gbps, 10 Gbps and higher. he search processor provides a unique combination of NFA and DFA based search engines that can process incoming data in parallel to perform the search against the specific rules programmed in the search engines. The processor architecture also provides capabilities to transport and process Internet Protocol (IP) packets from Layer 2 through transport protocol layer and may also provide packet inspection through Layer 7. Further, a runtime adaptable processor is coupled to the protocol processing hardware and may be dynamically adapted to perform hardware tasks as per the needs of the network traffic being sent or received and / or the policies programmed or services or applications being supported. A set of engines may perform pass-through packet classification, policy processing and / or security processing enabling packet streaming through the architecture at nearly the full line rate. A high performance content search and rules processing security processor is disclosed which may be used for application layer and network layer security. scheduler schedules packets to packet processors for processing. An internal memory or local session database cache stores a session information database for a certain number of active sessions. The session information that is not in the internal memory is stored and retrieved to / from an additional memory. An application running on an initiator or target can in certain instantiations register a region of memory, which is made available to its peer(s) for access directly without substantial host intervention through RDMA data transfer. A security system is also disclosed that enables a new way of implementing security capabilities inside enterprise networks in a distributed manner using a protocol processing hardware with appropriate security features.
Owner:MEMORY ACCESS TECH LLC
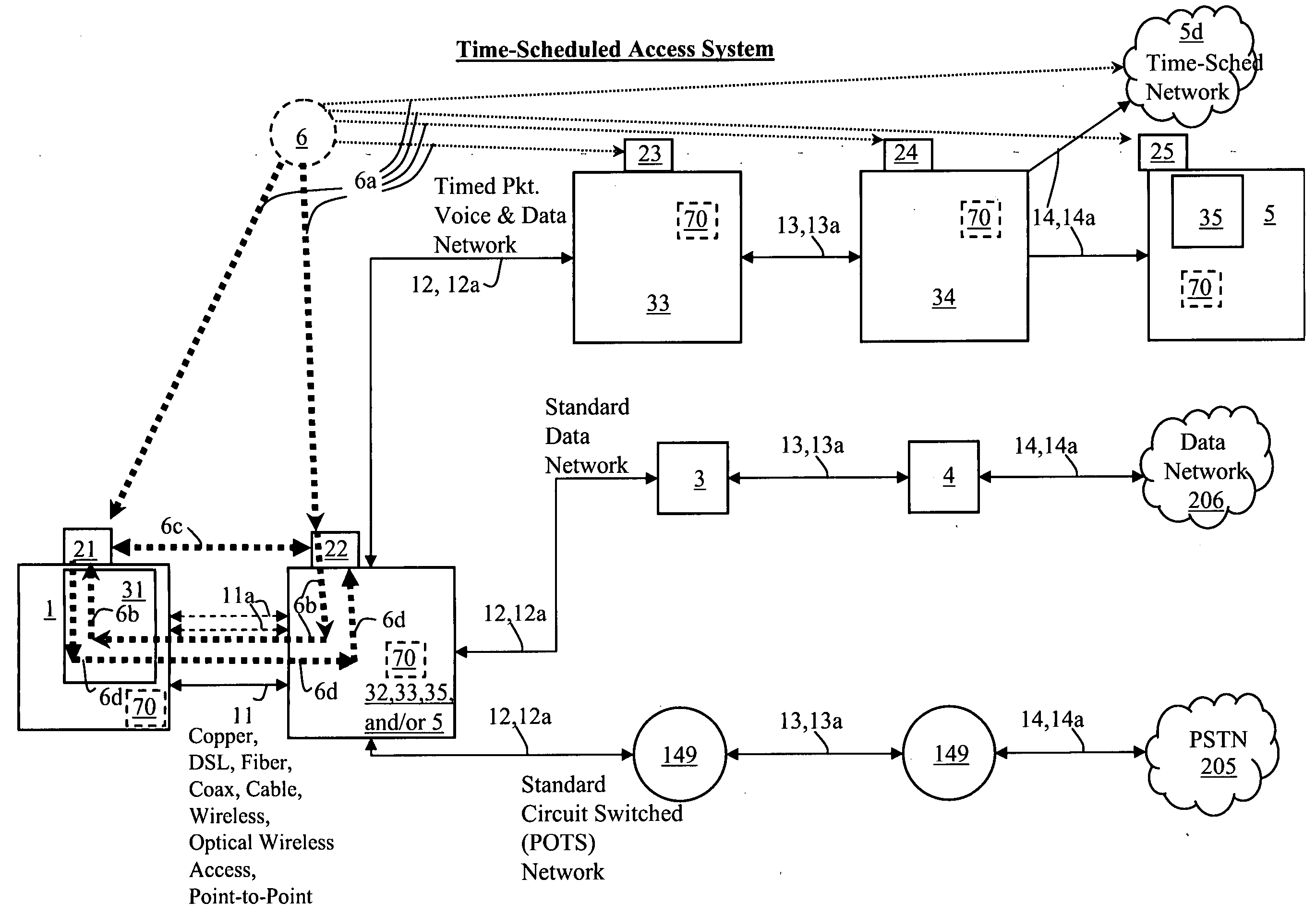
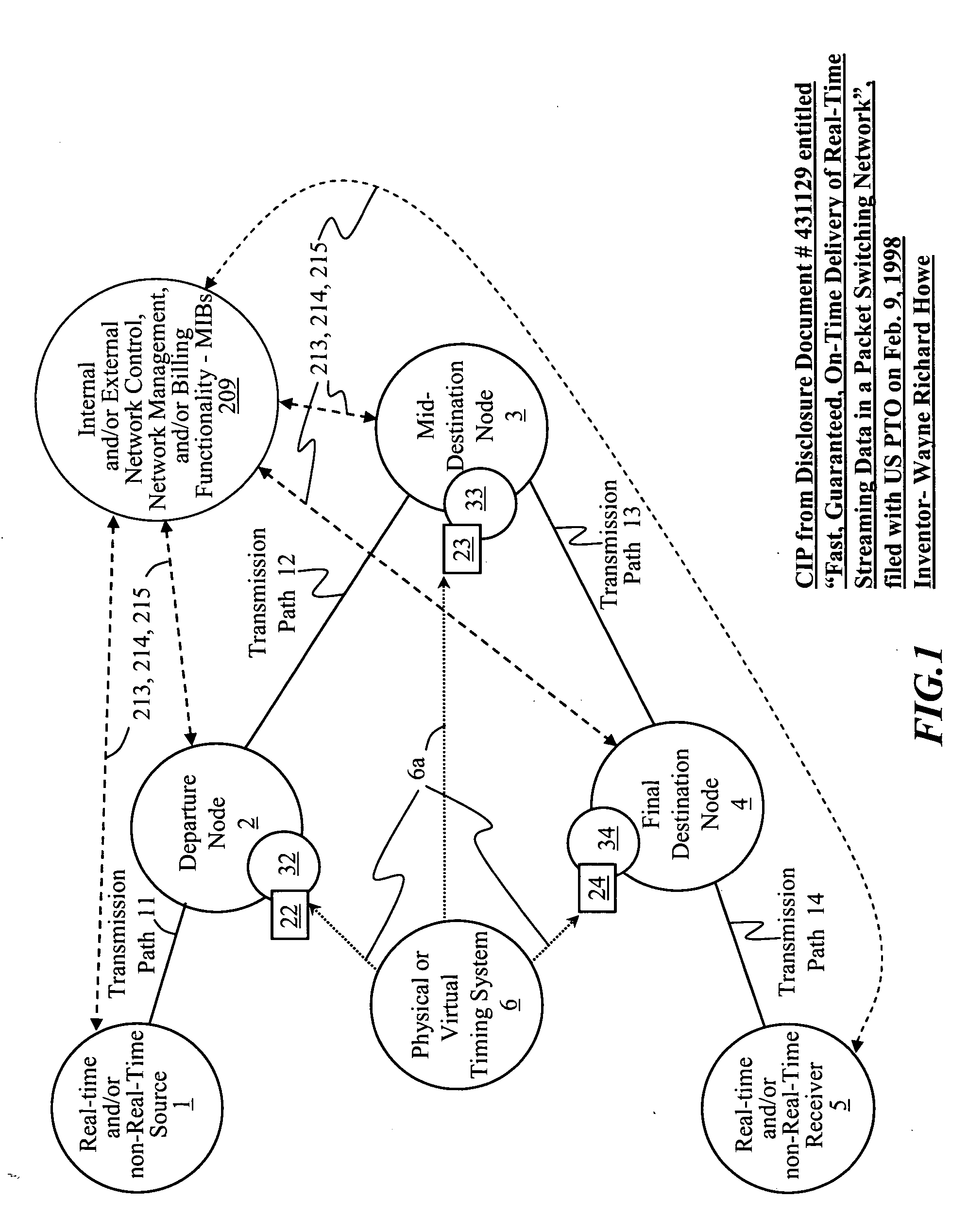
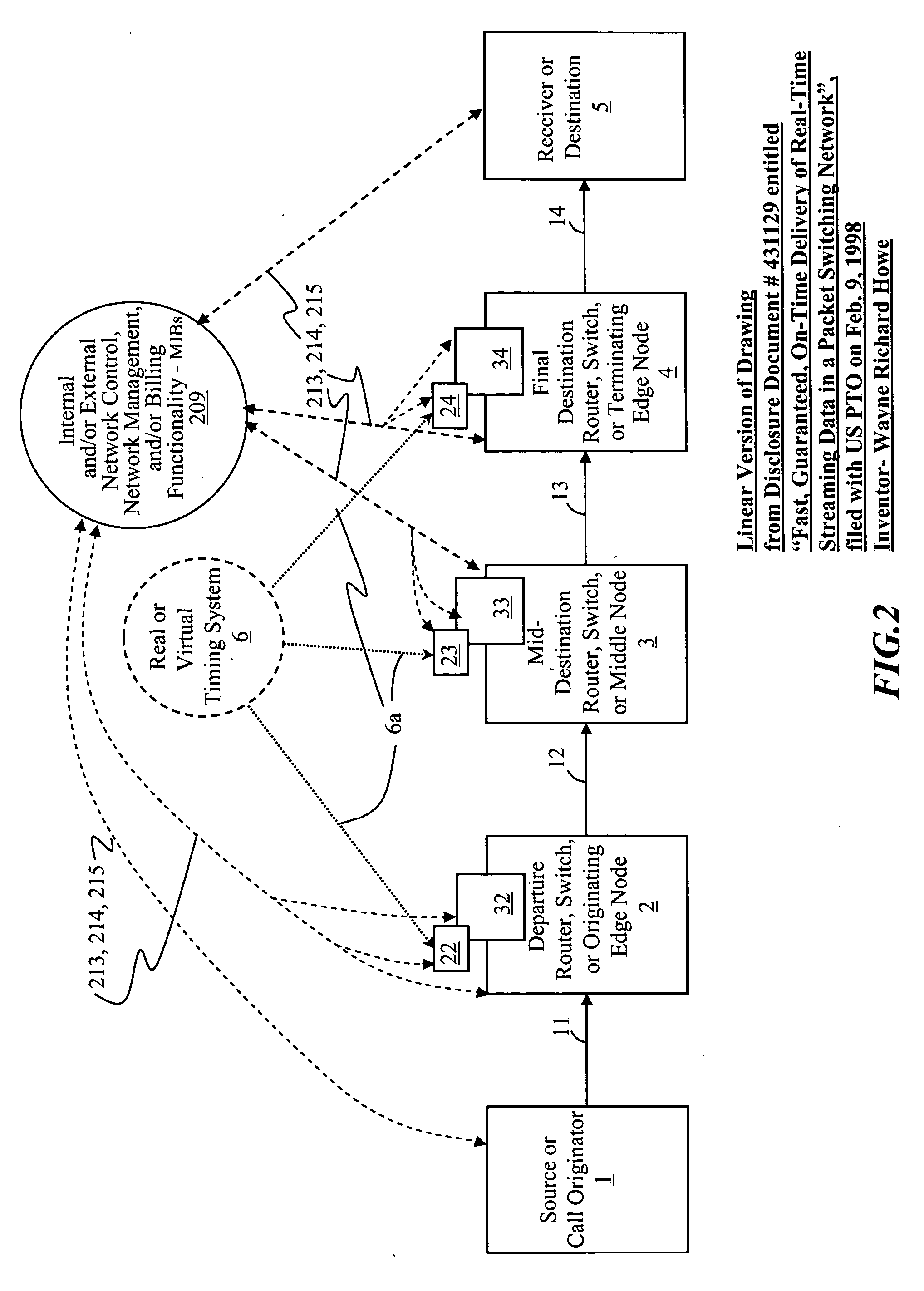
Time-scheduled and time-reservation packet switching
InactiveUS20050058149A1Optimum advantage and efficiencyImprove accuracyMultiplex system selection arrangementsTime-division multiplexData packTime schedule
Systems, methods, devices, processes, procedures, algorithms, networks, and network elements are described for time-scheduled and / or time-reserved dat networks. Invention provides capabilities for synchronizing data networks and / or data network links; for establishing time-schedules, time-reservations, time-schedule reservations, and / or reservation time-slots for packets, cells, frames, and / or datagrams; and for transferring, transmitting, switching, routing, and / or receiving time-sensitive, high-reliability, urgent, and / or other time-scheduled, time-reserved, time-allocated, and / or time-scheduled-reservation packets, cells, frames, and / or datagrams, such as real-time and high-priority messages over these networks. The invention(s) enables packet-, cell-, datagram- and / or frame-based networks to thereby efficiently, reliably, and in guaranteed real-time, to switch and / or route data such as voice, video, streaming, and other real-time, high-priority, high-reliability, and / or expedited data with guaranteed delivery and guaranteed quality of service. Networks may be fixed, point-to-point, mobile, ad-hoc, optical, electrical, and / or wireless.
Owner:HOWE WAYNE RICHARD
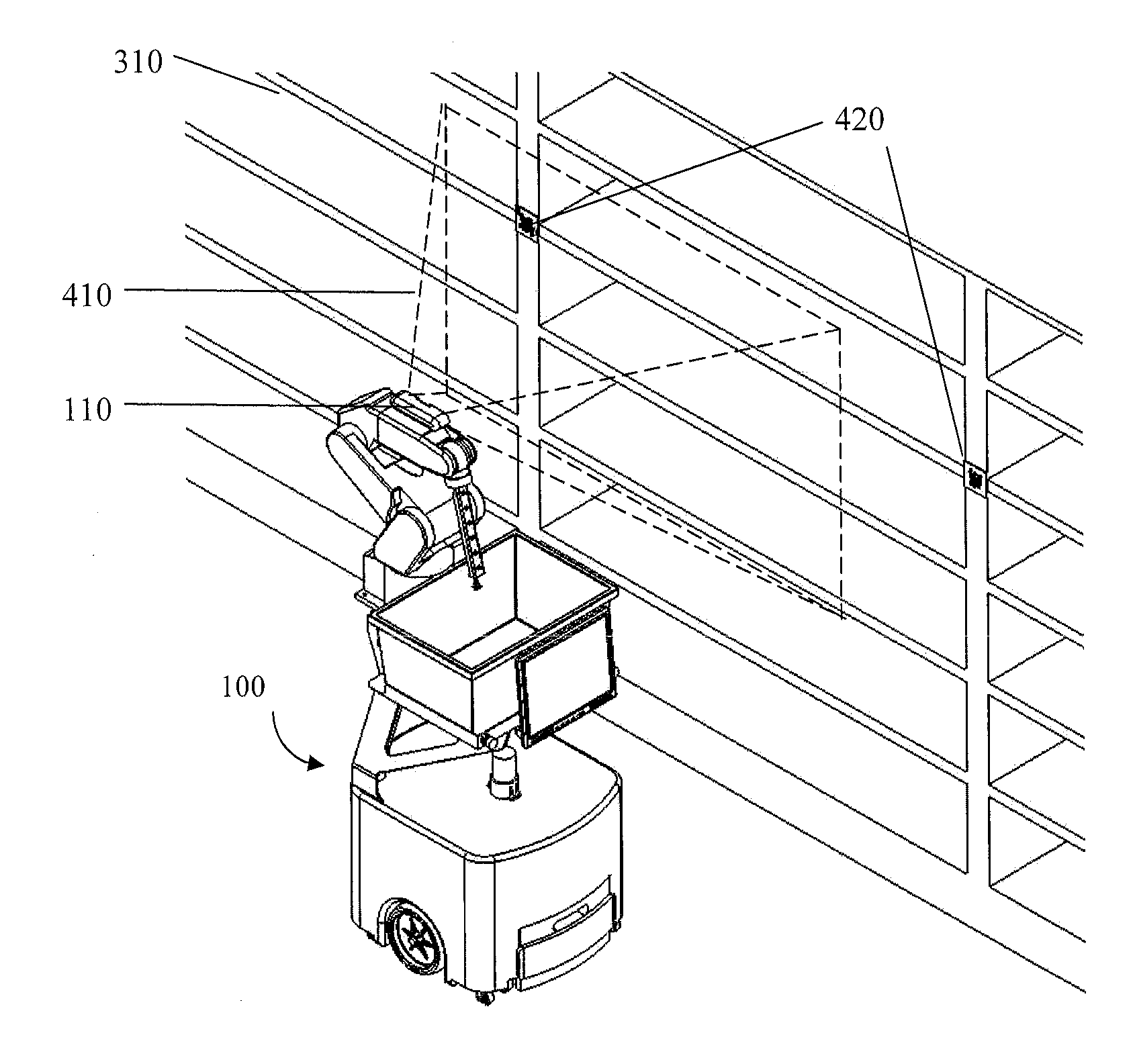
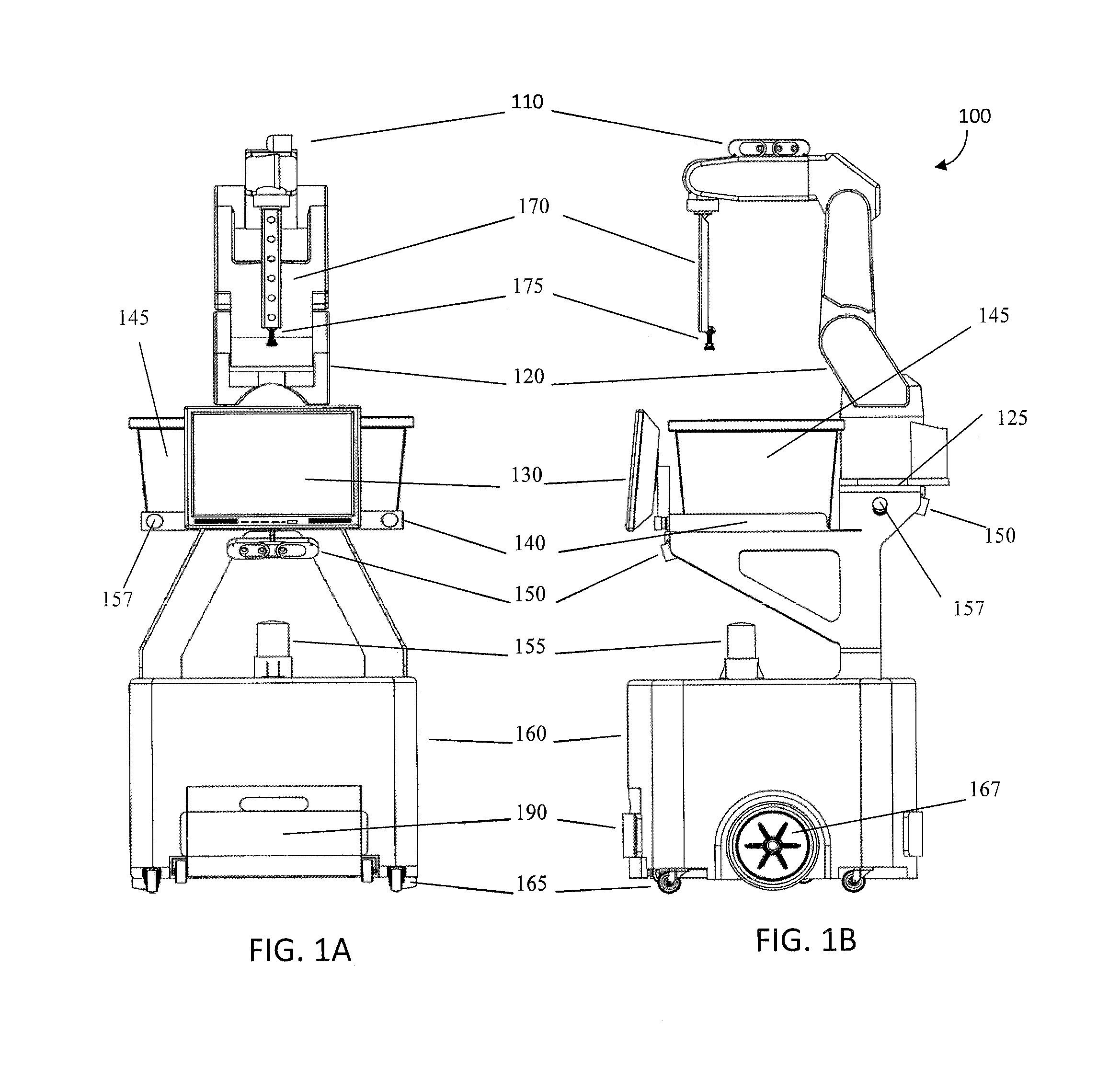
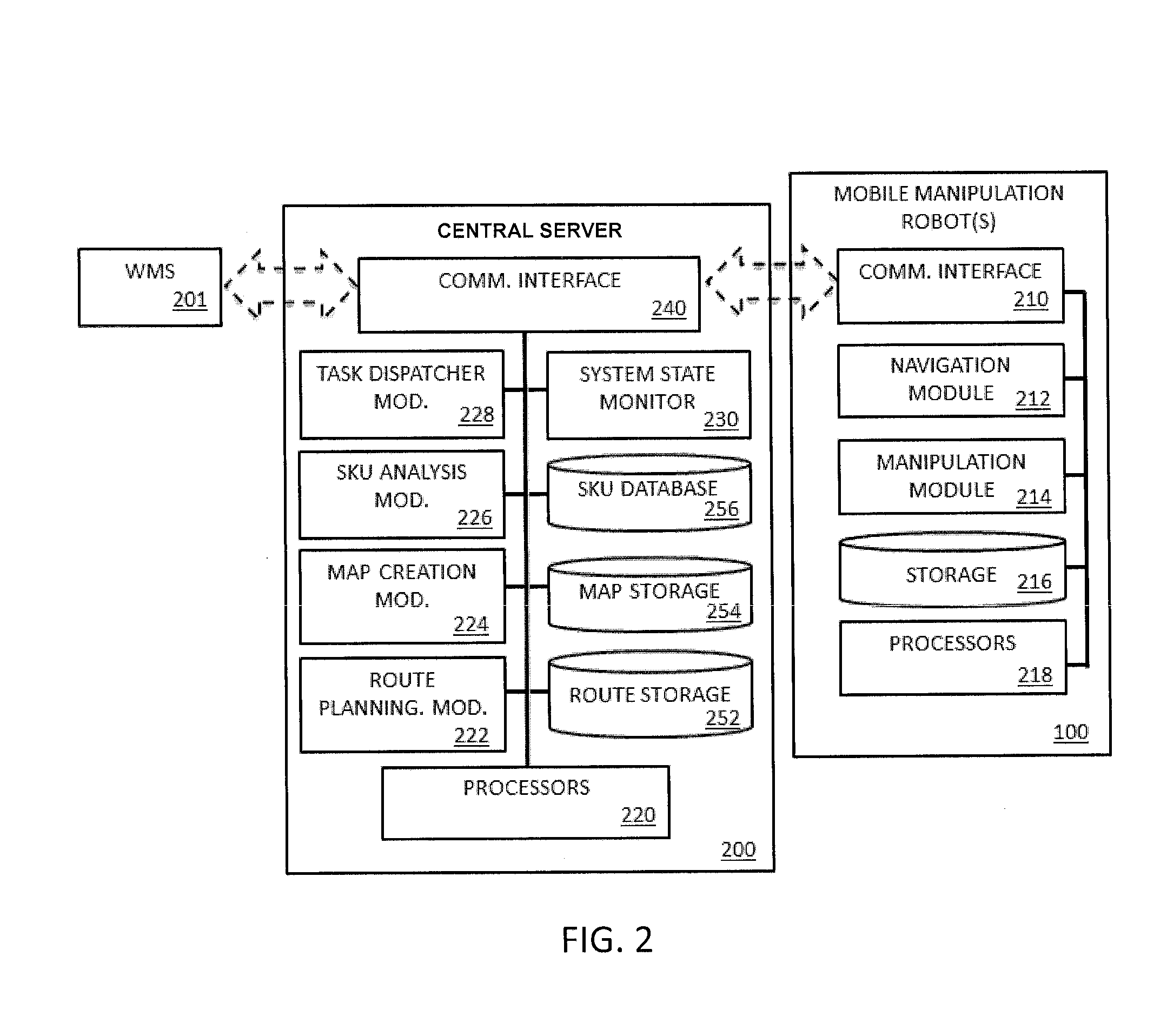
System and method for piece-picking or put-away with a mobile manipulation robot
ActiveUS20150032252A1Overcomes shortcomingReduce complexity and costProgramme-controlled manipulatorAutonomous decision making processLogistics managementPosition dependent
A method and system for piece-picking or piece put-away within a logistics facility. The system includes a central server and at least one mobile manipulation robot. The central server is configured to communicate with the robots to send and receive piece-picking data which includes a unique identification for each piece to be picked, a location within the logistics facility of the pieces to be picked, and a route for the robot to take within the logistics facility. The robots can then autonomously navigate and position themselves within the logistics facility by recognition of landmarks by at least one of a plurality of sensors. The sensors also provide signals related to detection, identification, and location of a piece to be picked or put-away, and processors on the robots analyze the sensor information to generate movements of a unique articulated arm and end effector on the robot to pick or put-away the piece.
Owner:IAM ROBOTICS
Systems and methods for providing stuctured policy expressions to represent unstructured data in a network appliance
ActiveUS20080225748A1Efficient configurationEfficient processingData switching by path configurationTraffic capacityData stream
Owner:CITRIX SYST INC
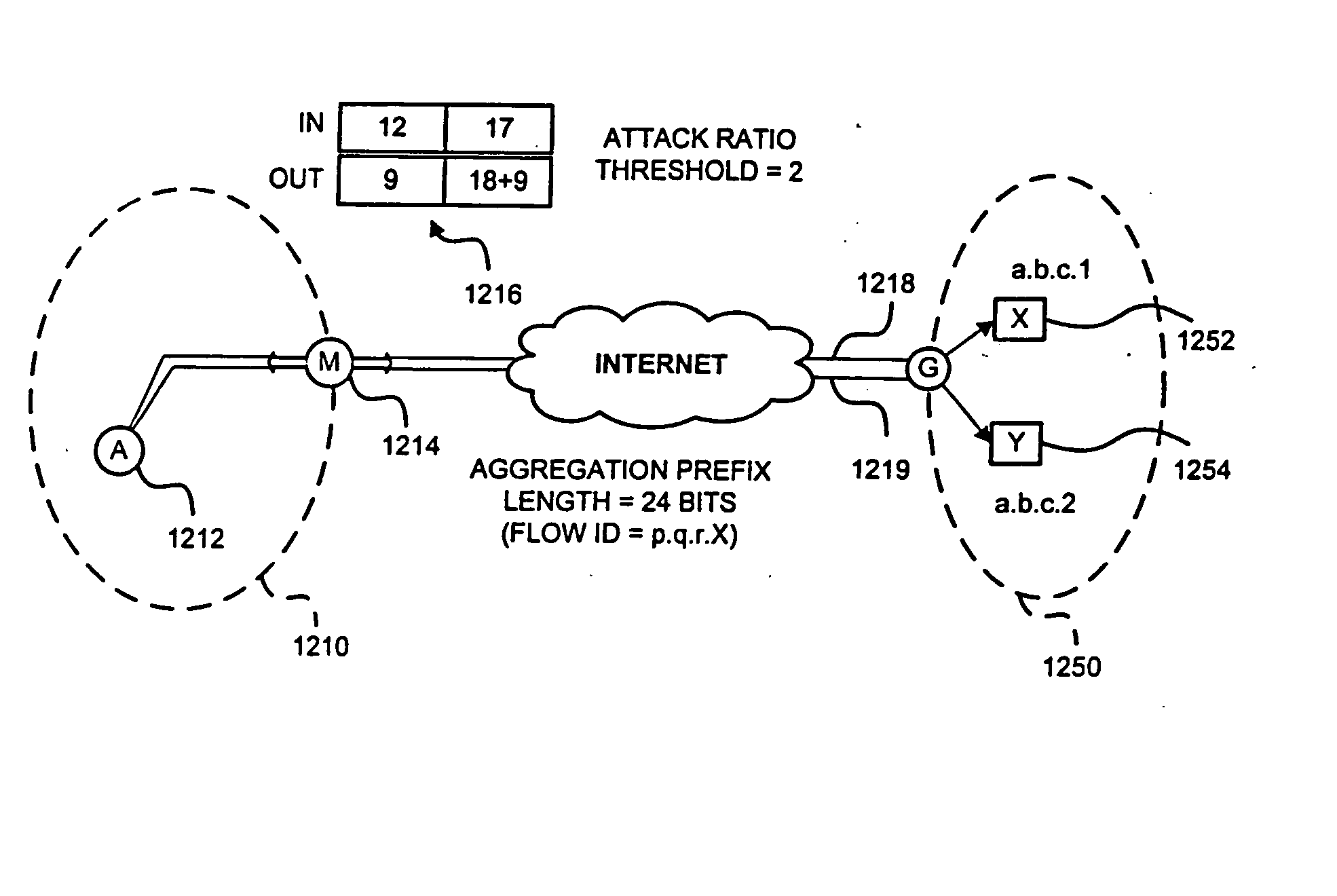
Detection of Distributed Denial of Service Attacks in Autonomous System Domains
A denial-of-service network attack detection system is deployable in single-homed and multi-homed stub networks. The detection system maintains state information of flows entering and leaving the stub domain to determine if exiting traffic exceeds traffic entering the system. Monitors perform simple processing tasks on sampled packets at individual routers in the network at line speed and perform more intensive processing at the routers periodically. The monitors at the routers form an overlay network and communicate pertinent traffic state information between nodes. The state information is collected and analyzed to determine the presence of an attack.
Owner:MARYLAND UNIV OF
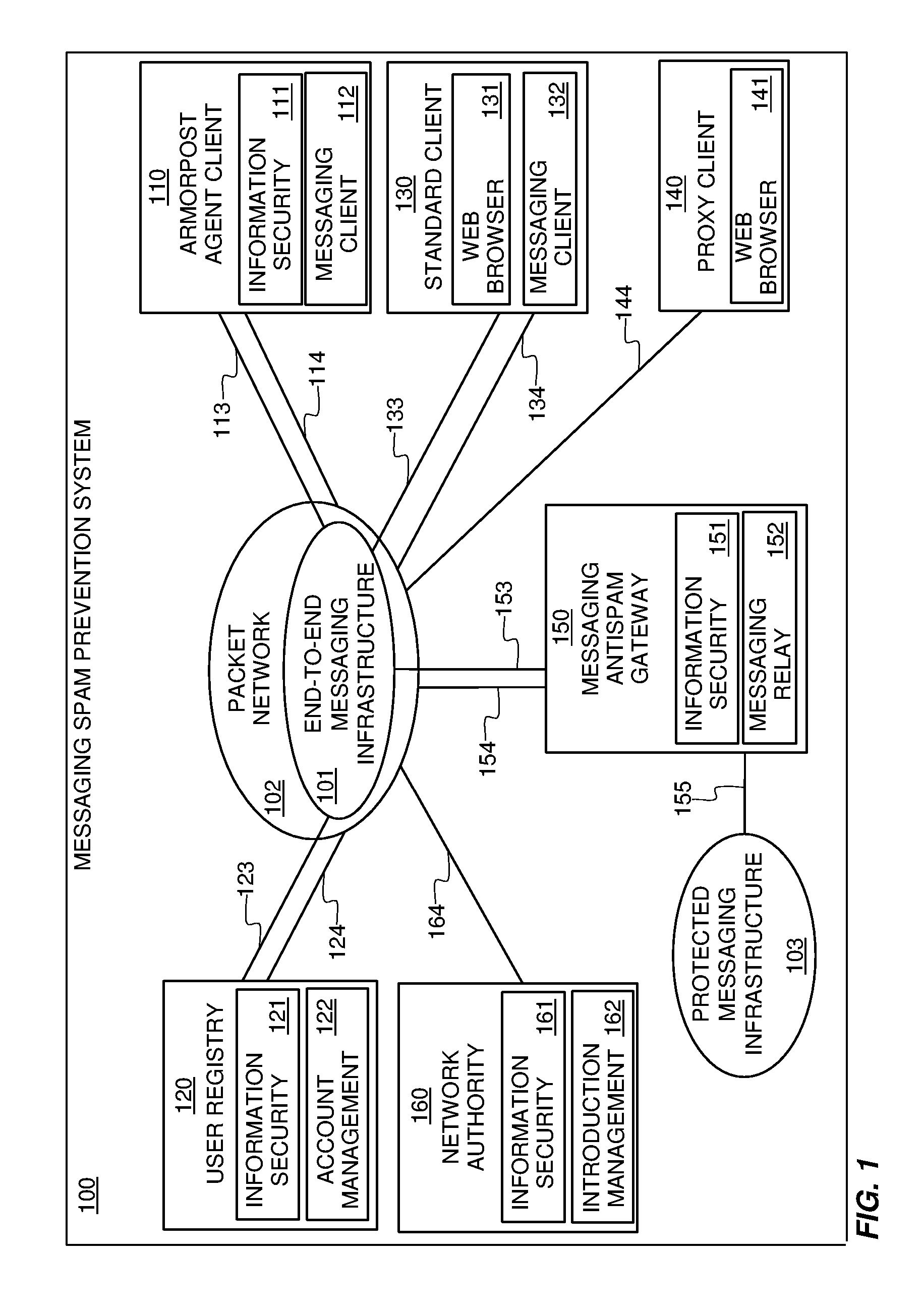
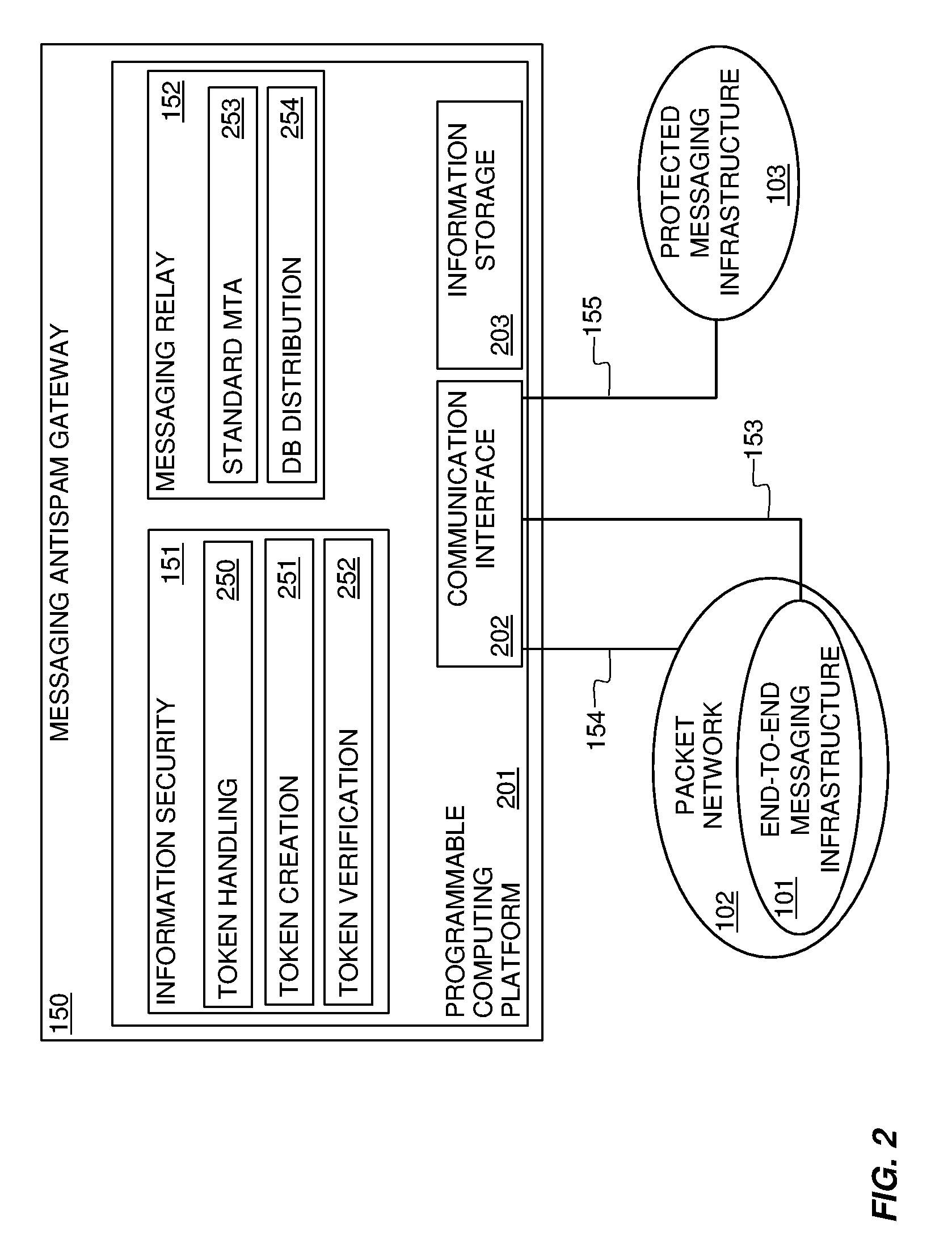
Systems and methods for preventing spam and denial of service attacks in messaging, packet multimedia, and other networks
InactiveUS20050132060A1Low costRaise priorityMultiple digital computer combinationsData switching networksData packSpamming
A system, various methods, and various apparatuses are provided for the purpose of supplying and including in an electronic message or multimedia session signalling unit a valid cryptographic authentication token, verifying said token's validity upon arrival of said message or signalling unit, and thereby providing message recipients or session parties with the assurance that said message or signalling unit is from a valid sender. A system, apparatus, and various methods are further provided for the purpose of protecting legitimate application traffic and the network elements exchanging it from intrusion by wild packets attempting to consume application resources and thereby deny service to legitimate users or network elements. A system, various methods, and various apparatuses are further provided for the purpose of enabling legitimate advertising via electronic messages, relying upon message and sender authentication to assure both advertisers and viewers of advertising messages that all participants are valid, legitimate, and accountable for any abuse that may occur.
Owner:AUTOUPTODATE LLC
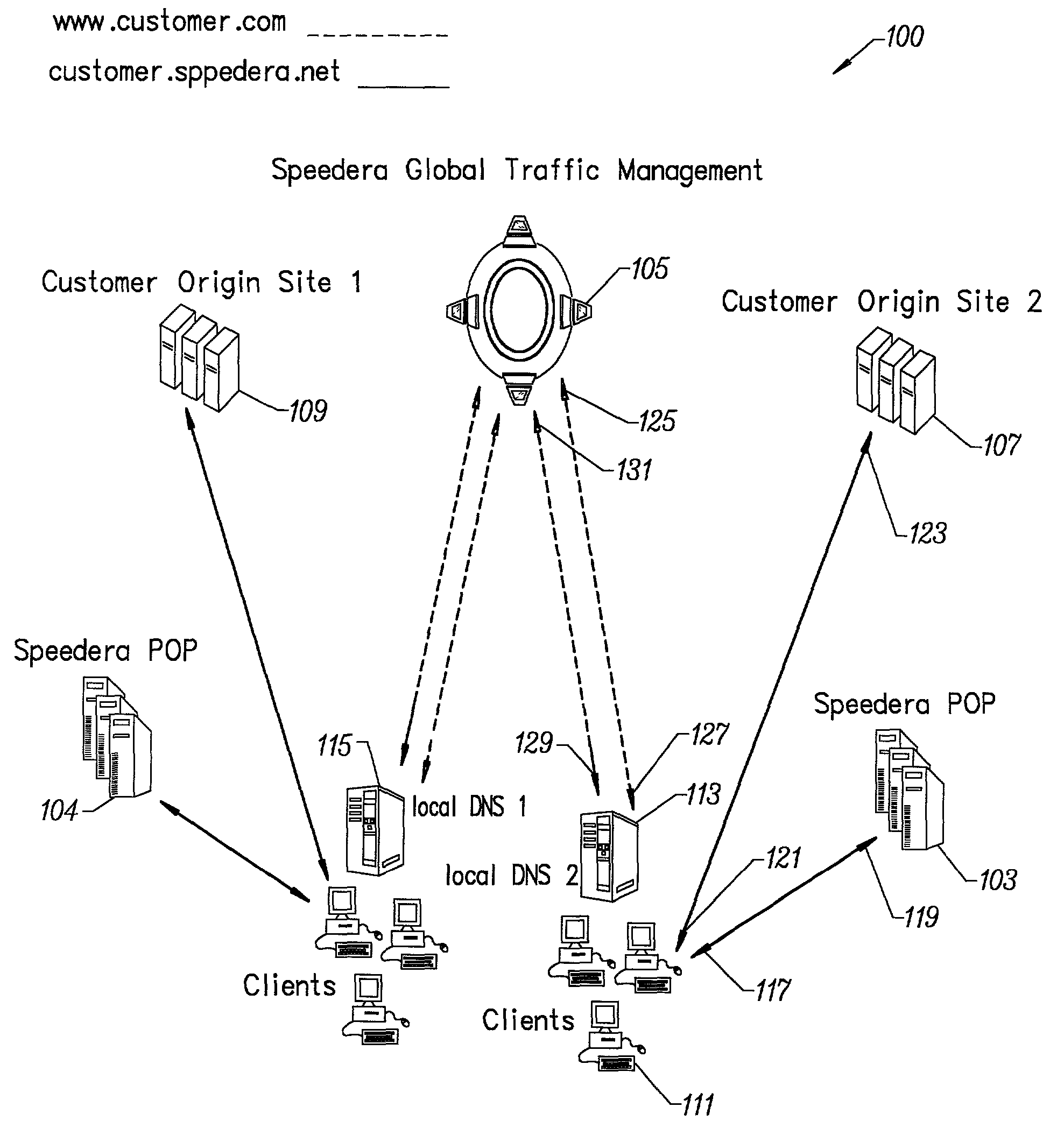
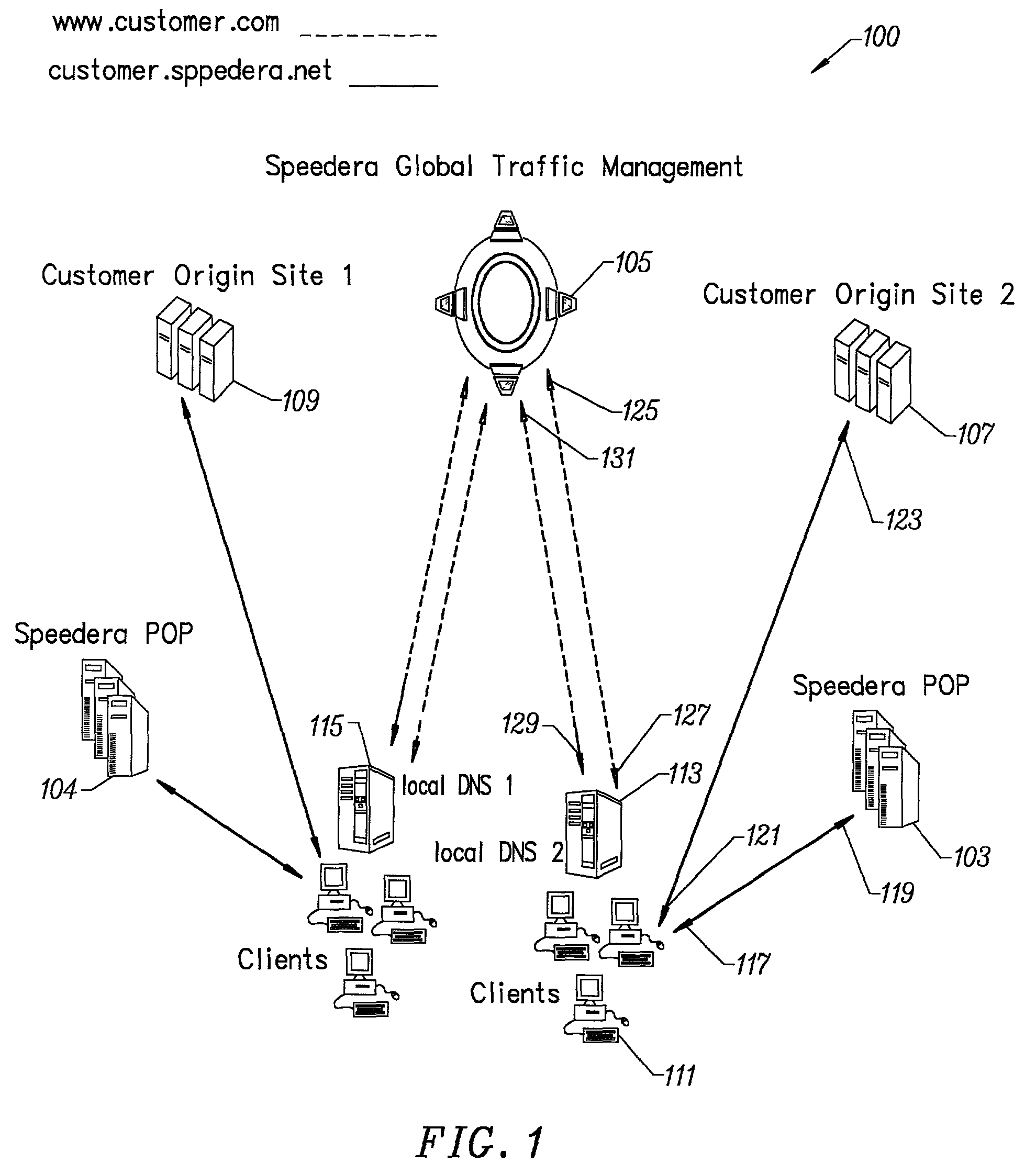
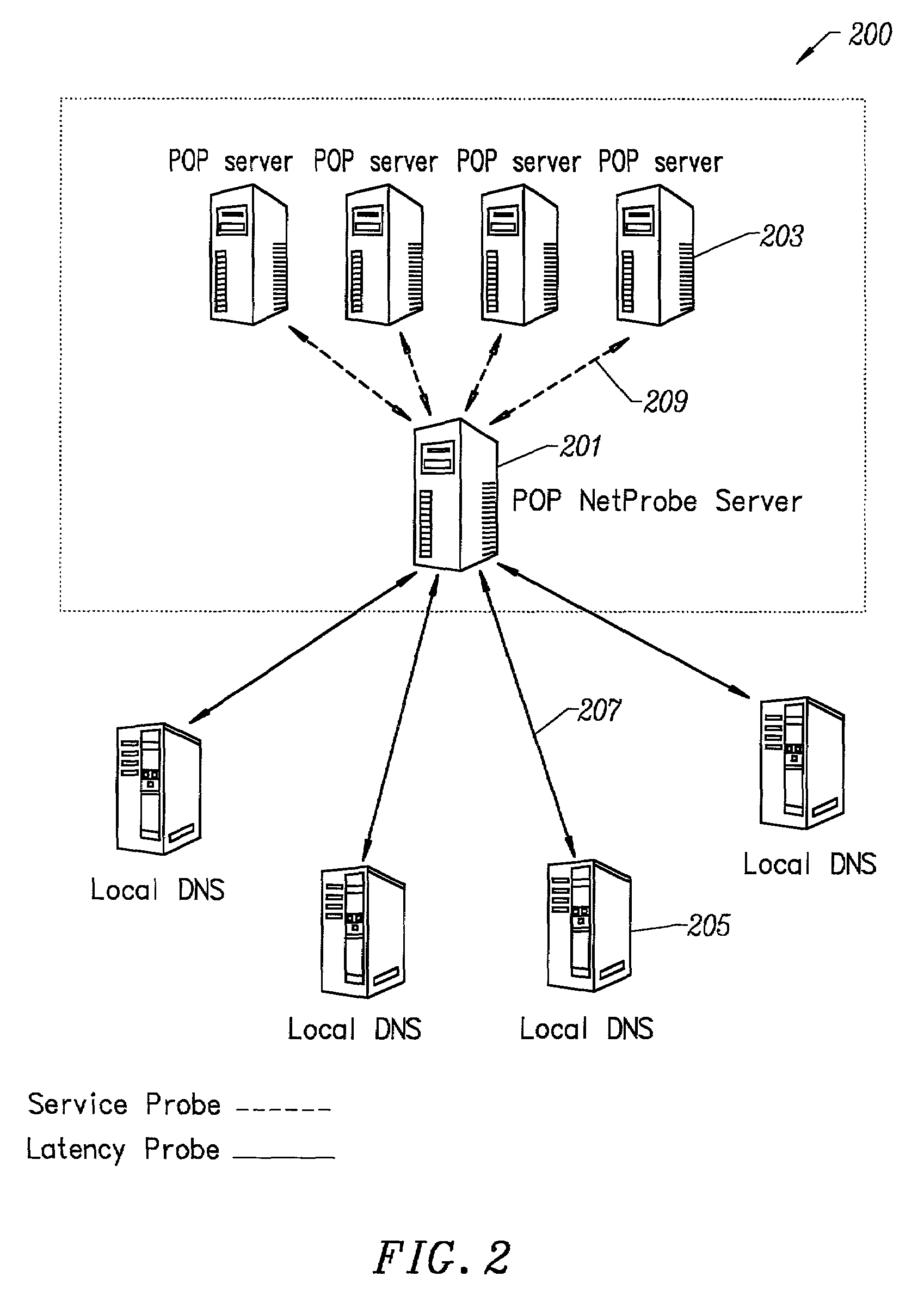
Method for determining metrics of a content delivery and global traffic management network
ActiveUS7523181B2Efficient executionMetering/charging/biilling arrangementsError preventionData packConfigfs
A method for determining metrics of a content delivery and global traffic management network provides service metric probes that determine the service availability and metric measurements of types of services provided by a content delivery machine. Latency probes are also provided for determining the latency of various servers within a network. Service metric probes consult a configuration file containing each DNS name in its area and the set of services. Each server in the network has a metric test associated with each service supported by the server which the service metric probes periodically performs metric tests on and records the metric test results which are periodically sent to all of the DNS servers in the network. DNS servers use the test result updates to determine the best server to return for a given DNS name. The latency probe calculates the latency from its location to a client's location using the round trip time for sending a packet to the client to obtain the latency value for that client. The latency probe updates the DNS servers with the clients' latency data. The DNS server uses the latency test data updates to determine the closest server to a client.
Owner:AKAMAI TECH INC
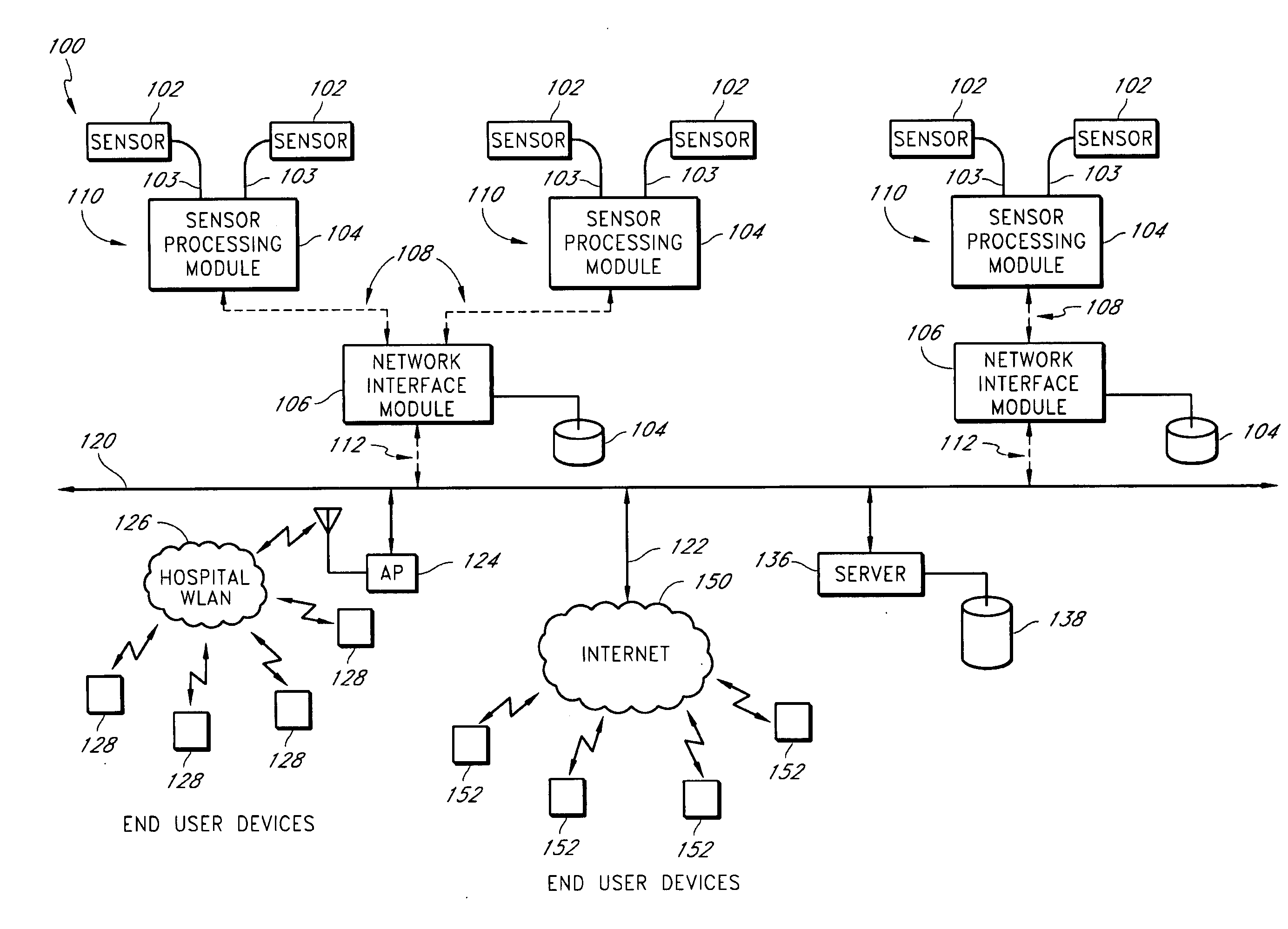
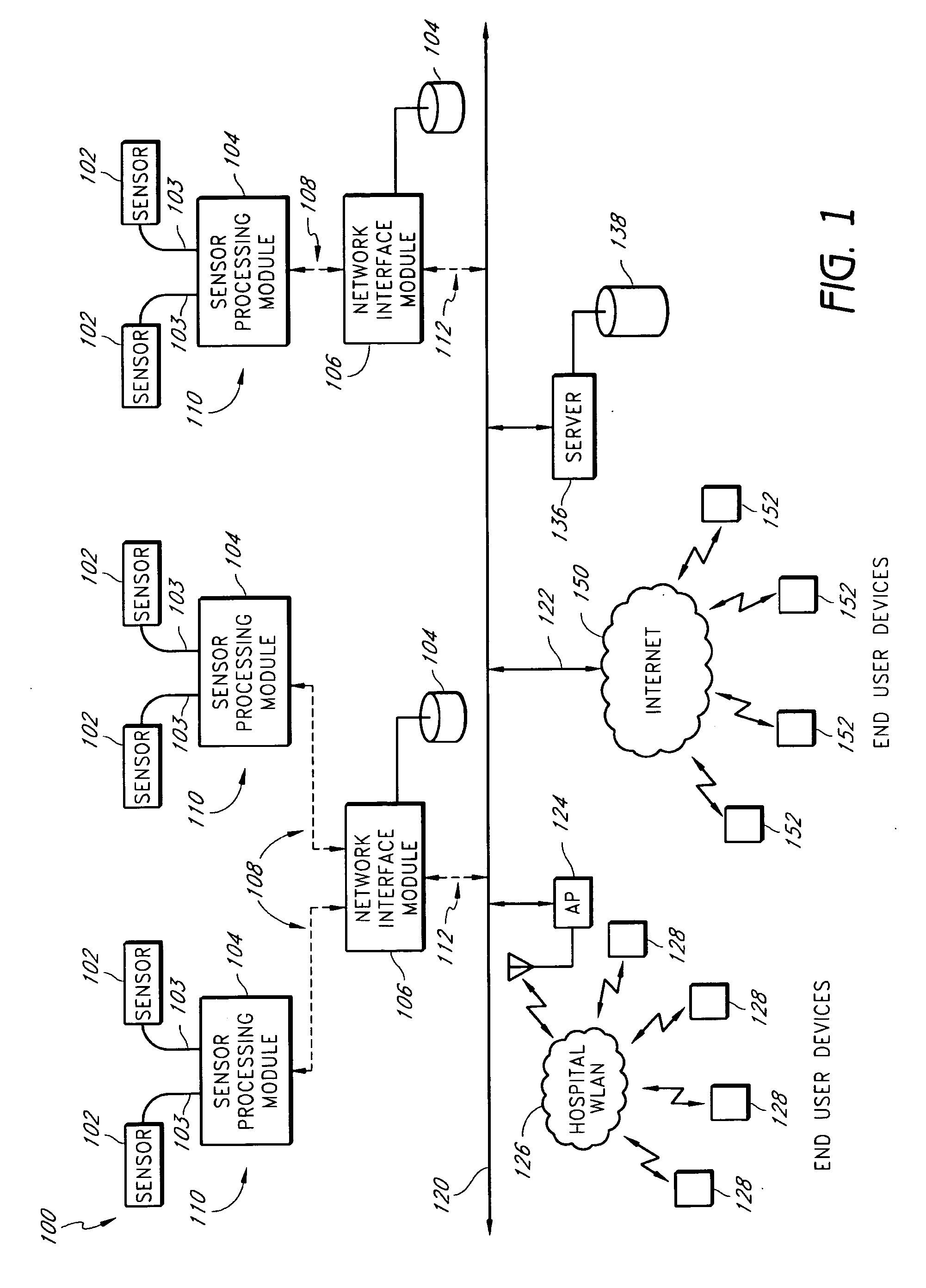
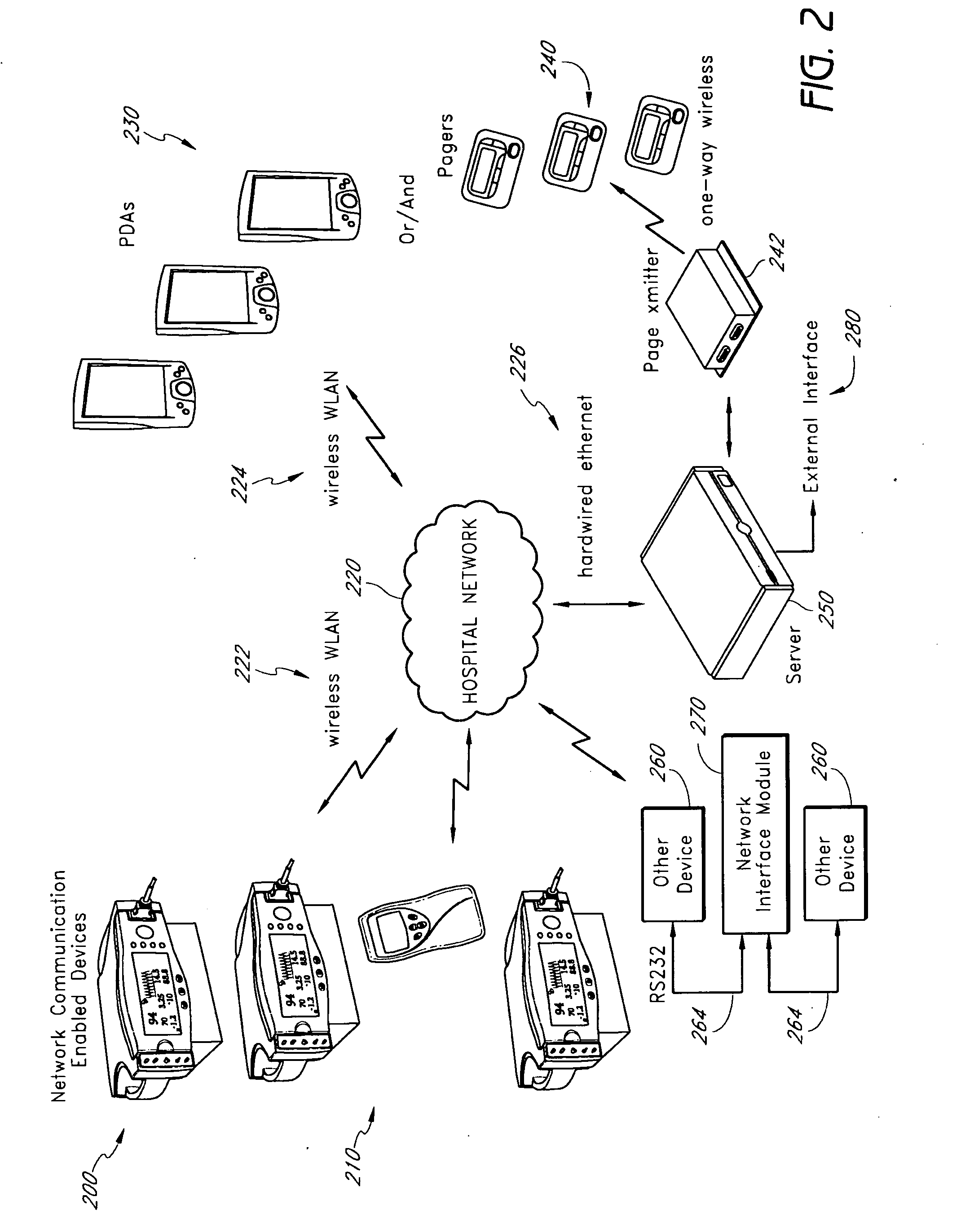
Physiological alarm notification system
A method of context-based communication of physiological information over a network includes receiving physiological information, preparing a contextual data package, establishing a network connection, and communicating the contextual data package. The physiological information is received with a portable network interface module from at least one physiological monitor coupled to a single medical patient. The physiological information is related to a physiological condition of the medical patient, and the portable network interface module is exclusively assigned to the medical patient. The contextual data package is prepared with the portable network interface module. The contextual data package includes context information related to the medical patient and the physiological information. The network connection is established with a user over a network with the portable network interface module, and the portable network interface module manages the network connection with the user. The contextual data package is communicated to the user over the network with the network connection.
Owner:JPMORGAN CHASE BANK NA
Method and Apparatus for Defending Against Zero-Day Worm-Based Attacks
InactiveUS20080098476A1Curb workloadEliminate usual spam and other simple attackMemory loss protectionError detection/correctionData packOperational system
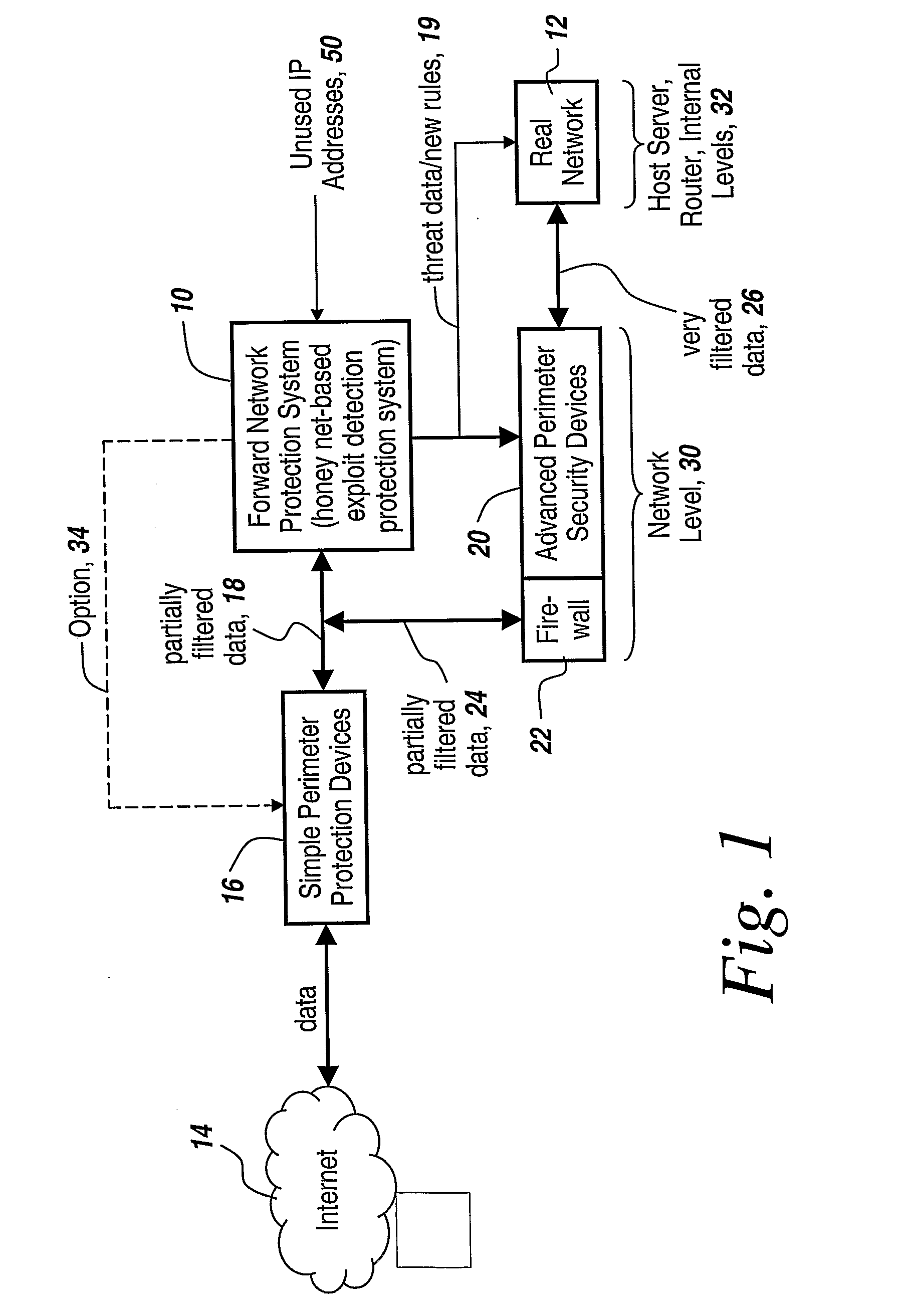
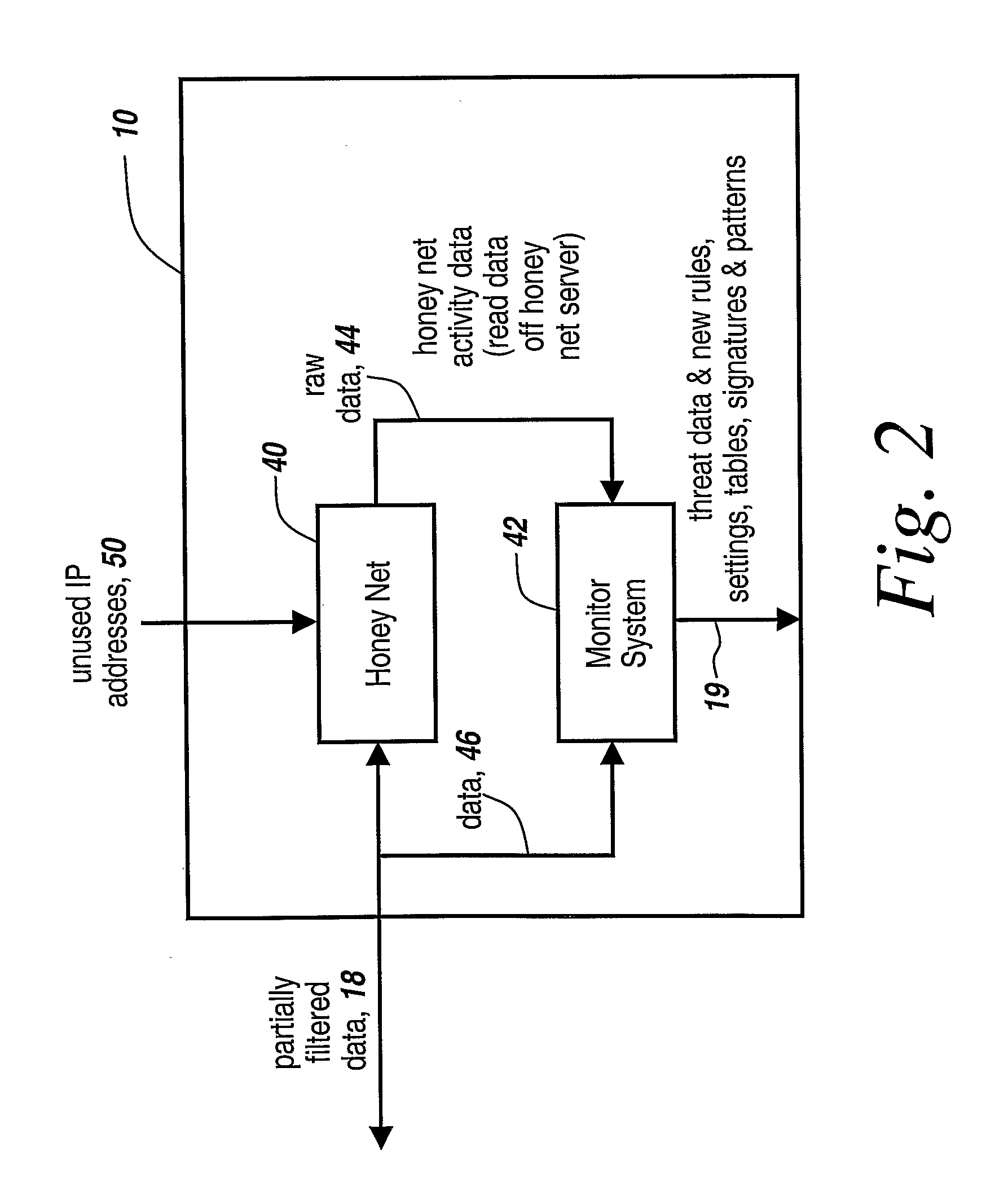
Honey pots are used to attract computer attacks to a virtual operating system that is a virtual instantiation of a typical deployed operational system. Honey nets are a collection of these virtual systems assembled to create a virtual network. The subject system uses a forward deployed honey net combined with a parallel monitoring system collecting data into and from the honey net, leveraging the controlled environment to identify malicious behavior and new attacks. This honey net / monitoring pair is placed ahead of the real deployed operational network and the data it uncovers is used to reconfigure network protective devices in real time to prevent zero-day based attacks from entering the real network. The forward network protection system analyzes the data gathered by the honey pots and generates signatures and new rules for protection that are coupled to both advanced perimeter network security devices and to the real network itself so that these devices can be reconfigured with threat data and new rules to prevent infected packets from entering the real network and from propagating to other machines. Note the subject system applies to both zero-day exploit-based worms and also manual attacks conducted by an individual who is leveraging novel attack methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC
Methods and apparatus for implementing virtualization of storage within a storage area network
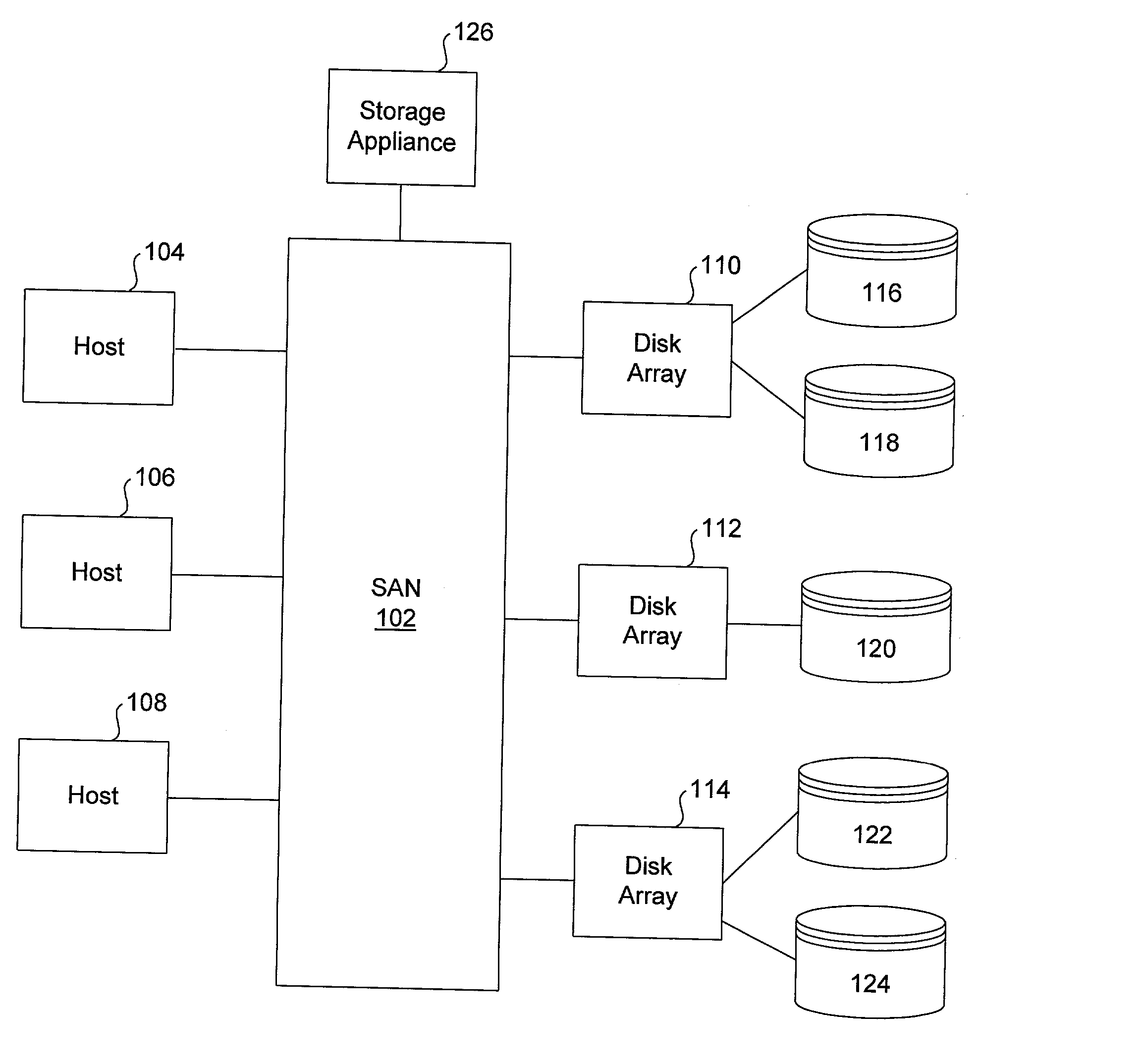
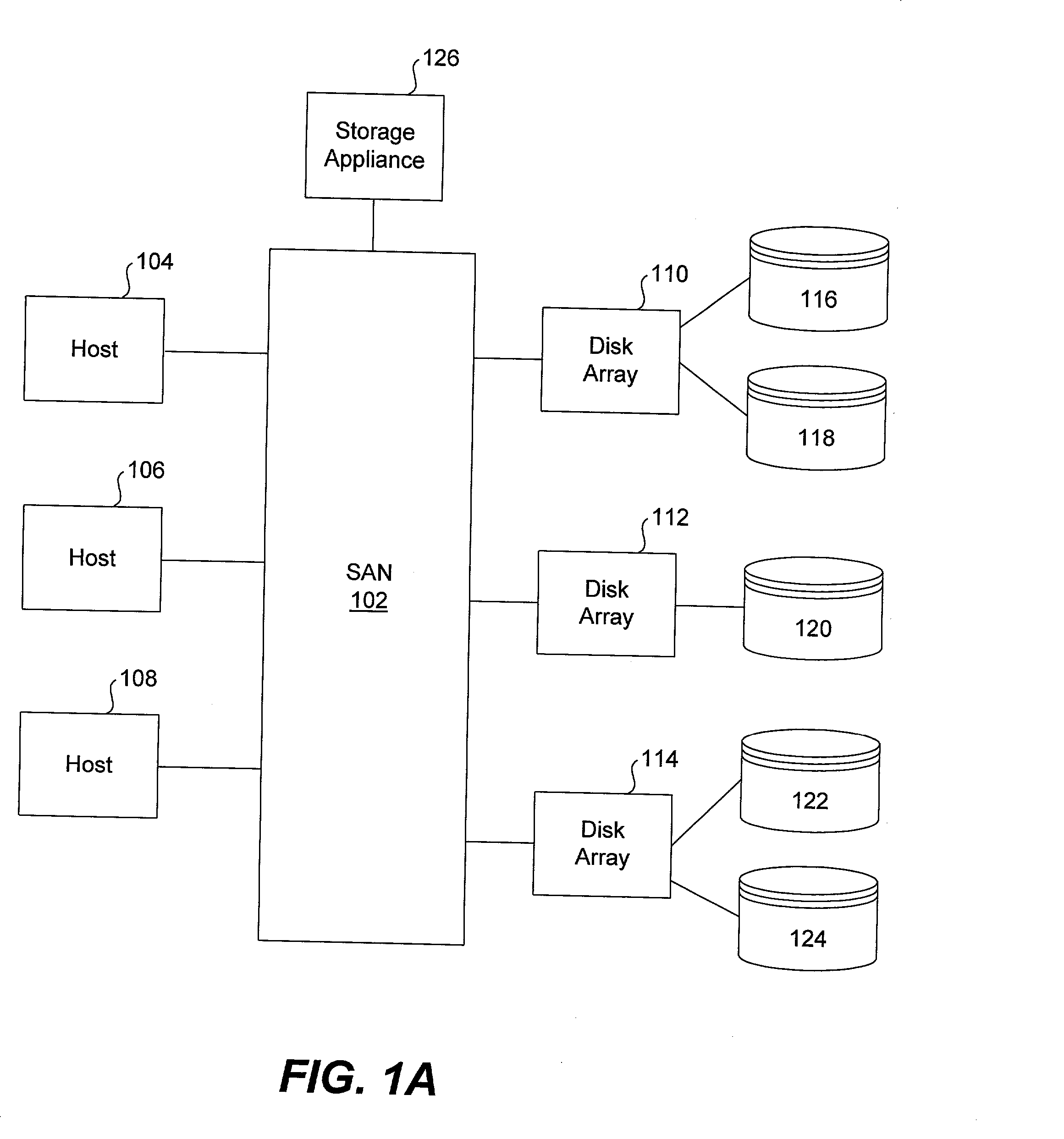
ActiveUS20030172149A1Ensure integrityInput/output to record carriersMultiple digital computer combinationsStorage area networkVirtual storage
Methods and apparatus for implementing storage virtualization on a network device of a storage area network are disclosed. A frame or packet is received at a port of the network device. It is then determined that the frame or packet pertains to access of a virtual storage location of a virtual storage unit representing one or more physical storage locations on one or more physical storage units of the storage area network. A virtual-physical mapping between the one or more physical storage locations and the virtual storage location is then obtained. A new or modified frame or packet is then sent to an initiator or a target specified by the virtual-physical mapping.
Owner:CISCO TECH INC
System and method for threat detection and response
InactiveUS20050018618A1Error preventionFrequency-division multiplex detailsNetwork packetDistributed computing
In accordance with varying embodiments of the invention, systems, devices and methods for analyzing a network packet received from a remote source and destined for a network resource, the network packet having associated packet data, and for identifying a plurality of network threats are disclosed.
Owner:STRATACLOUD
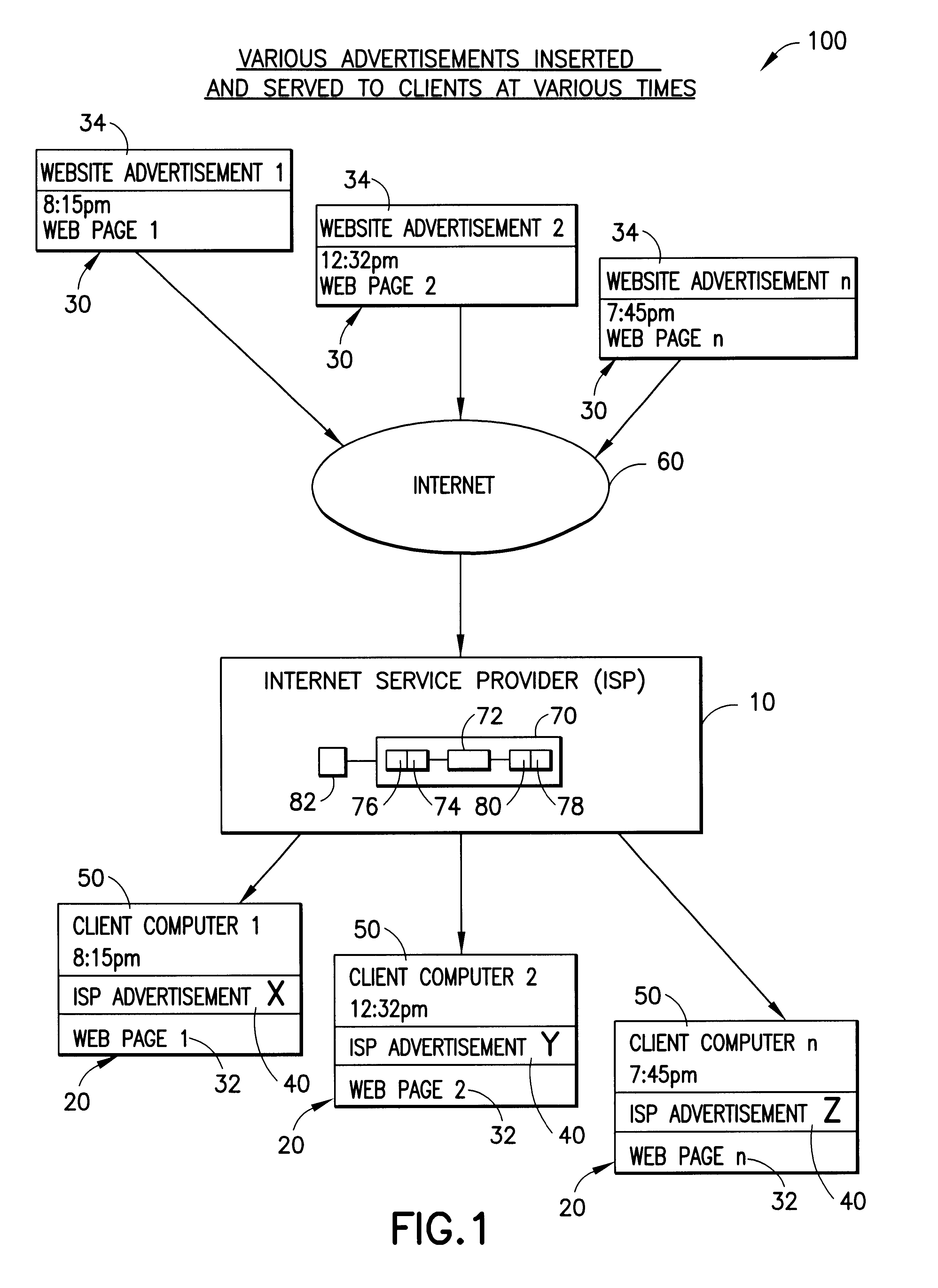
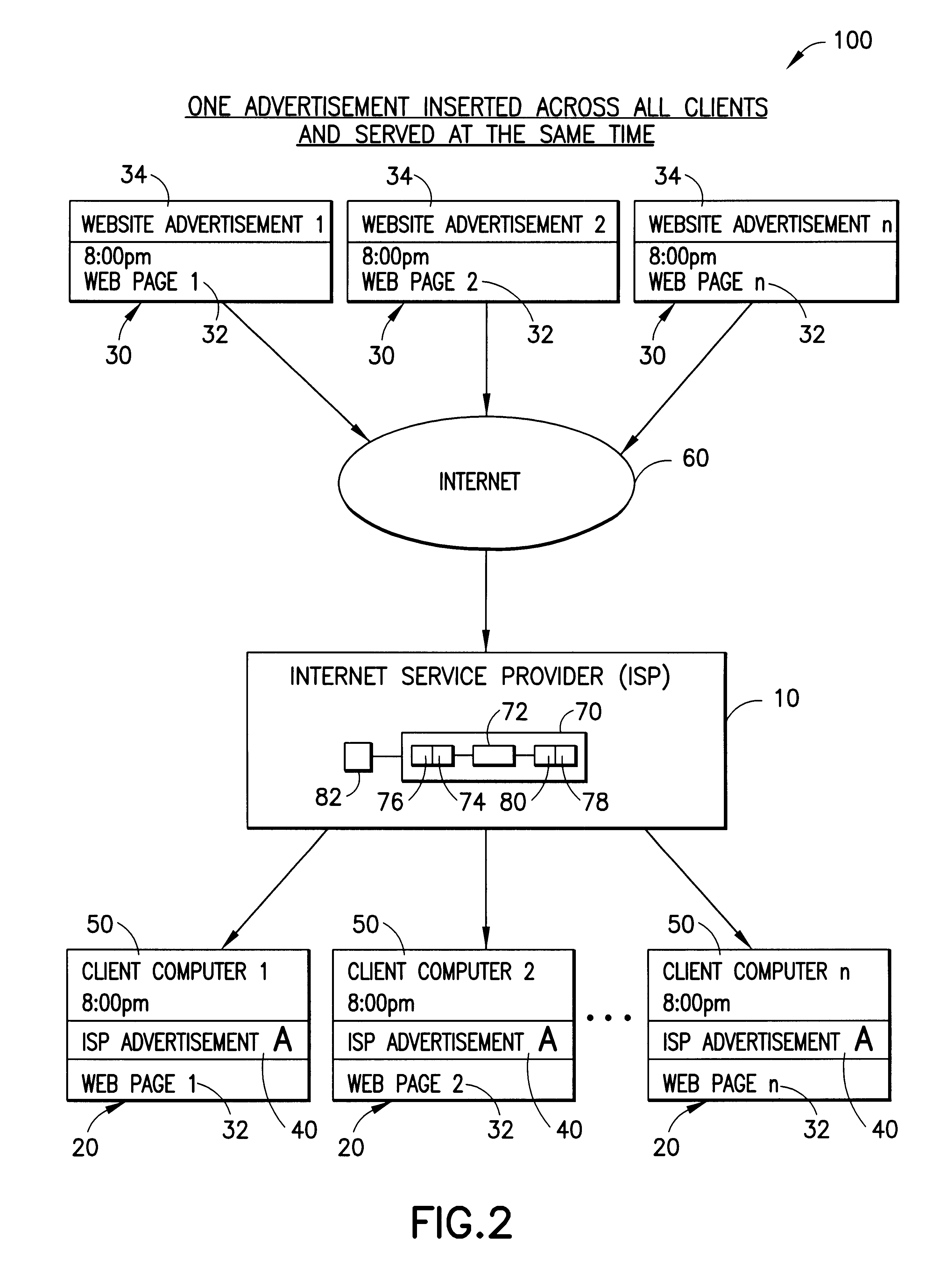
Internet service provider advertising system
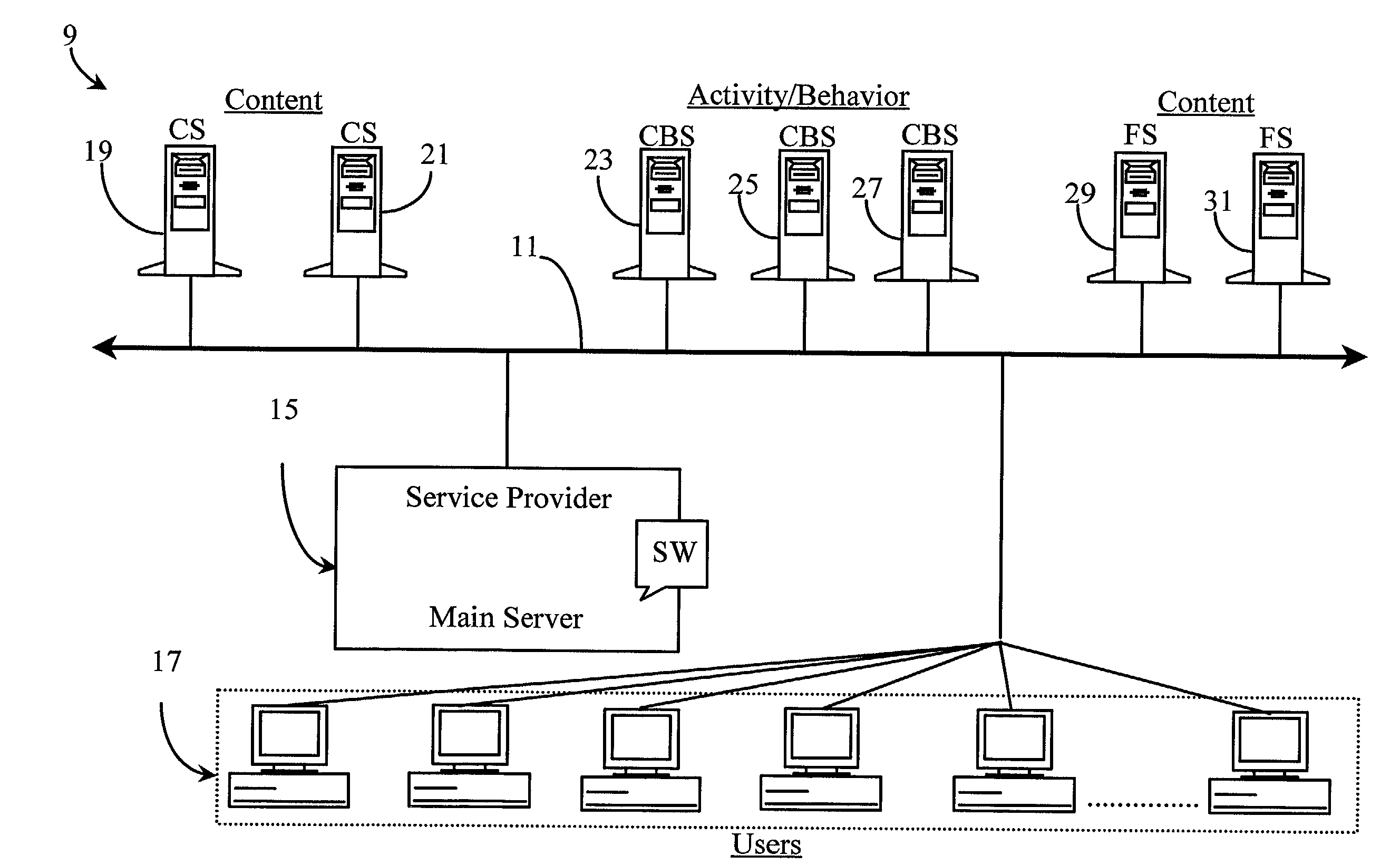
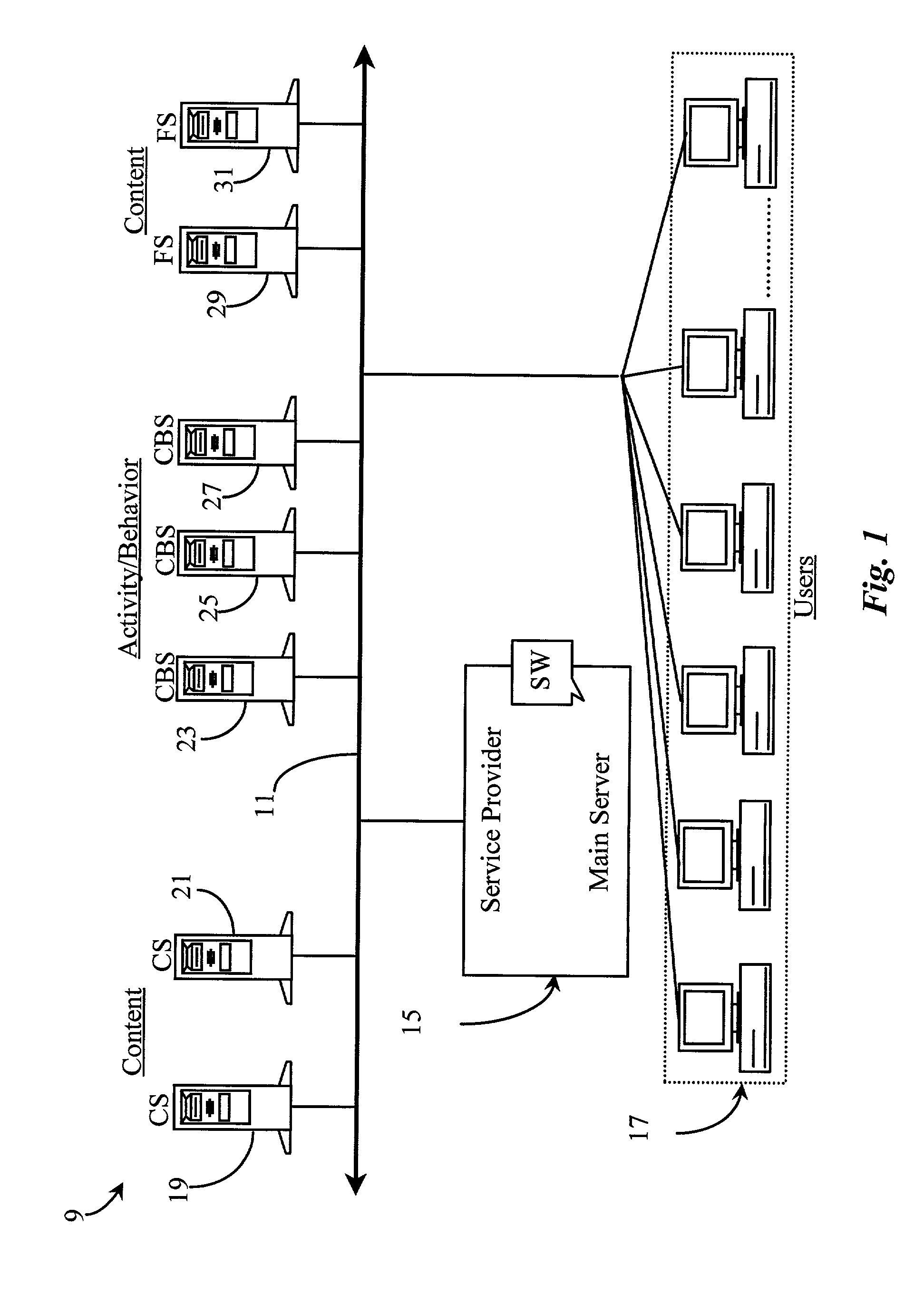
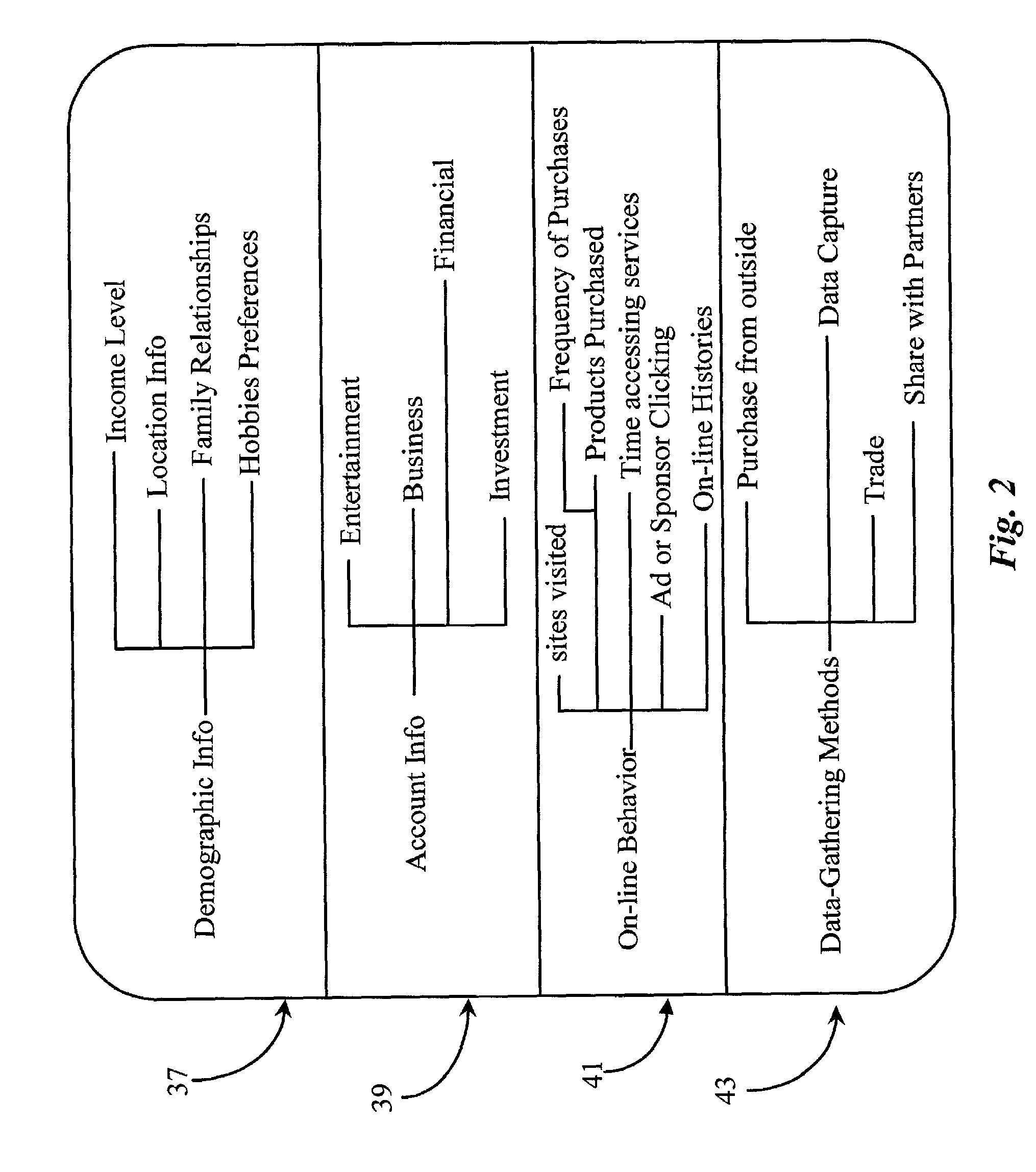
InactiveUS6339761B1Advertising dollars are well-spentAdvertisementsSpecial data processing applicationsService provisionDemographic data
The present invention advantageously provides to Internet Service Providers (ISP) precise control over who receives an advertisement. Thus, in accordance with the present invention, an ISP provider may now offer advertisers precision advertising. An ISP provider has access to precise demographic data on each of the ISP's customers. The ISP provider also has access to data on the periods of usage, including the type of customers accessing the Internet during such periods of usage. With this information, which is available only to the ISP provider, a profile may be compiled by the ISP provider that provides precise information on the ISP customers (e.g., demographic data) and the periods of heaviest Internet access by the various different ISP customer groups (e.g., 20-35 year old males, retired persons, children, etc.).
Owner:SLINGSHOT TECH LLC
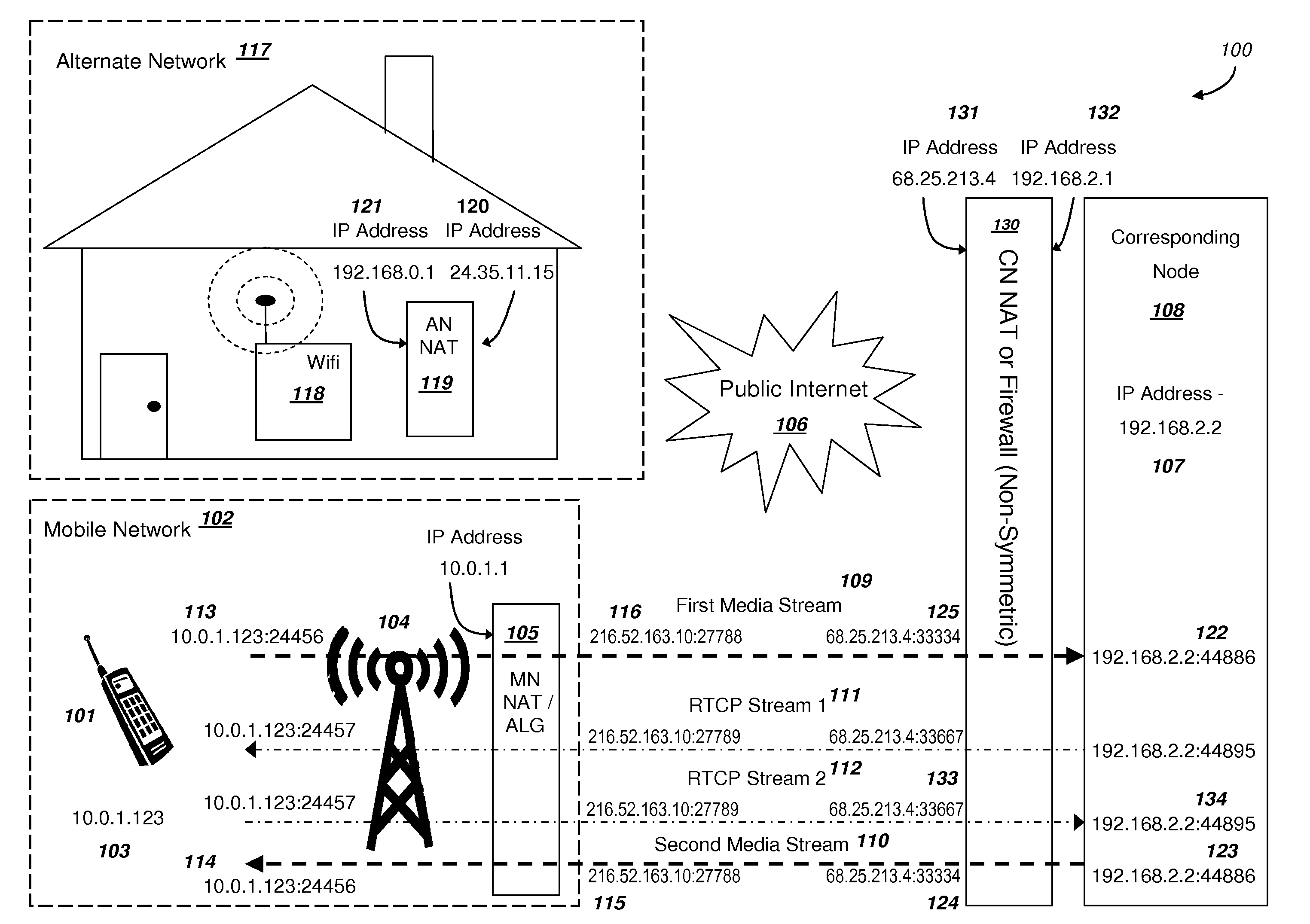
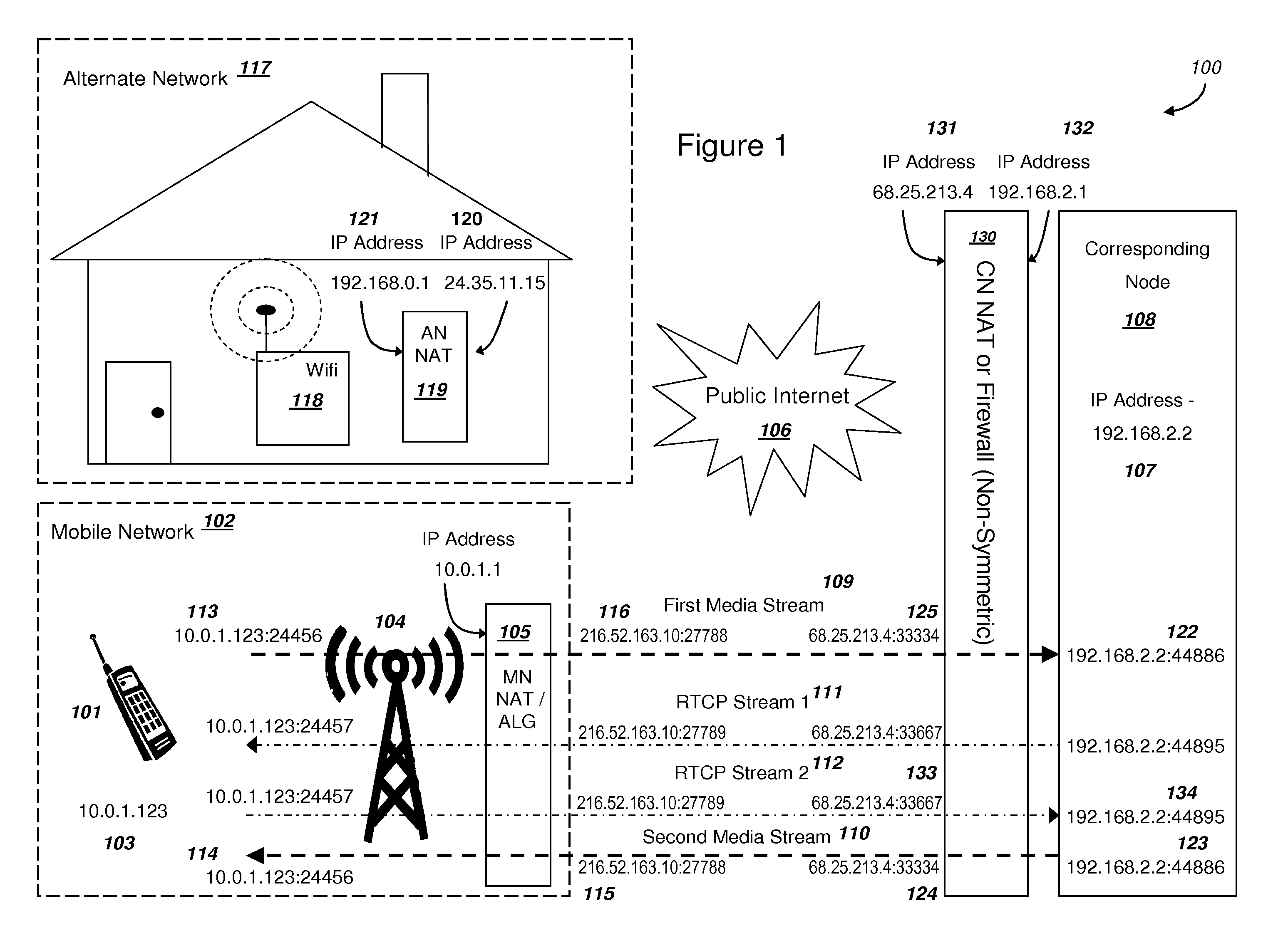
Efficient Handover of Media Communications in Heterogeneous IP Networks using LAN Profiles and Network Handover Rules
ActiveUS20090323632A1Reduce complexityImprove efficiencyWireless network protocolsRadio/inductive link selection arrangementsMedia controlsData pack
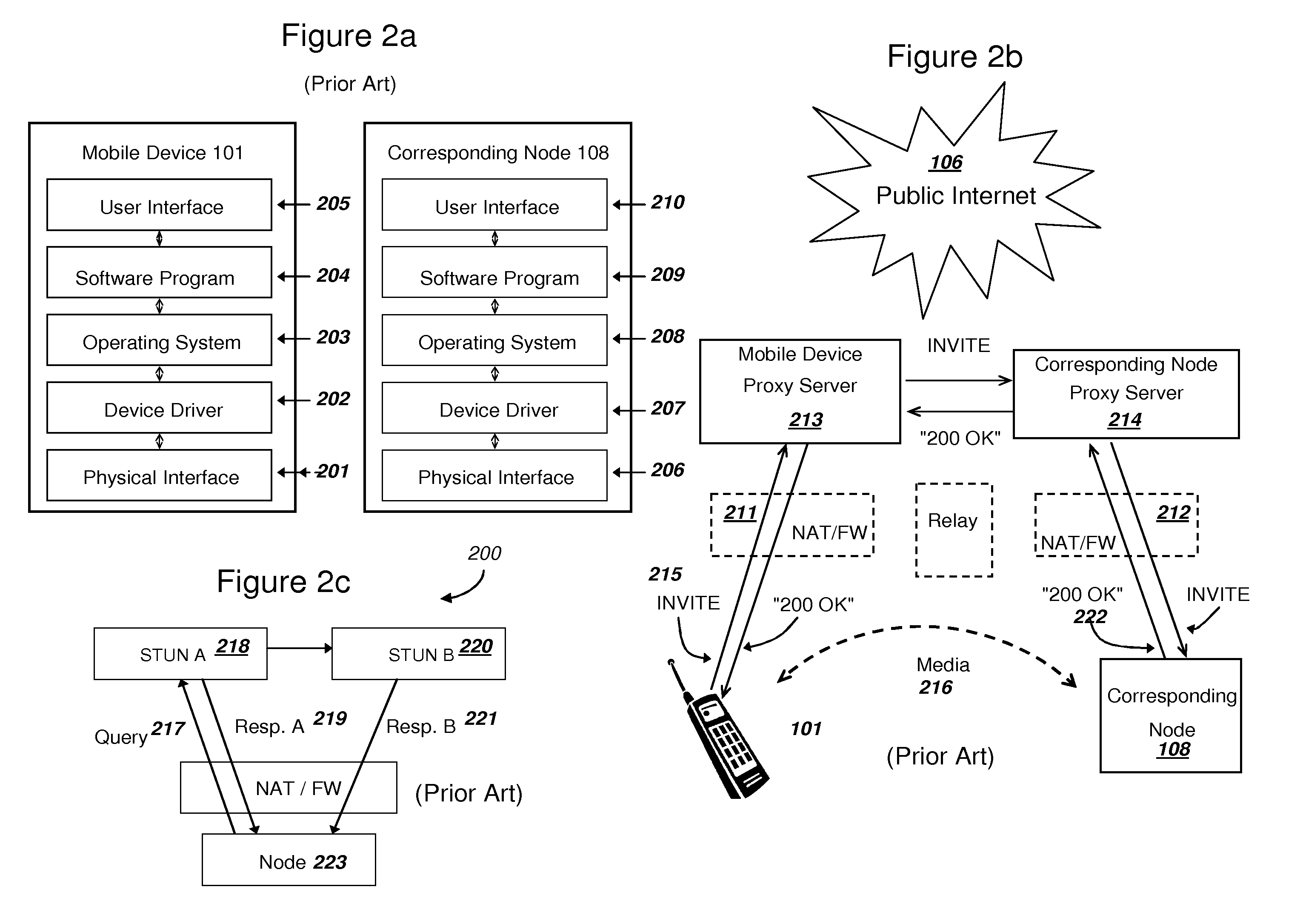
Methods and systems are provided for efficient handover of a media session between heterogeneous IP networks. A mobile device with Internet access can operate a software program to communicate with a corresponding node. The corresponding node may access the Internet through either a NAT router or a firewall. The mobile device establishes a media session with a corresponding node via the transmission of a first media stream and receipt of a second media stream, and a media control channel can optionally be implemented. The mobile device can acquire Internet access through a second IP address, and packets routed between the second IP address and the Internet may traverse a NAT router. The mobile device can evaluate the type of NAT at the second IP address from a stored LAN profile. A software routine can determine that handover of the media session from the first IP address to the second IP address is preferred. A software routine can determine efficient handover procedures according to Network handover rules. The mobile device may begin transmitting a third media stream to the corresponding node and the corresponding node can transmit a fourth media stream to the second IP address. A media control channel is optionally supported.
Owner:GOOGLE LLC
File server system using connection-oriented protocol and sharing data sets among data movers
InactiveUS6453354B1Digital data information retrievalMultiple digital computer combinationsMultiplexingData set
A first data mover computer services data access requests from a network client, and a second data mover computer is coupled to the first data mover computer for servicing data access requests from the first data mover computer. The first data mover computer uses a connection-oriented protocol to obtain client context information and to respond to a session setup request from the client by authenticating the client. Then the first data mover computer responds to a file system connection request from the client by forwarding the client context information and the file system connection request to the second data mover computer. Then the first data mover computer maintains a connection between the first data mover computer and the second data mover computer when the client accesses the file system and the first data mover computer passes file access requests from the client to the second data mover computer and returns responses to the file access requests from the second data mover computer to the client. In a preferred embodiment, the connection-oriented protocol is the Common Internet File System (CIFS) Protocol, and multiple clients share a Transmission Control Protocol (TCP) connection between the first data mover computer and the second data mover computer by allocation of virtual channels within the shared TCP connection and multiplexing of data packets of the virtual channels over the shared TCP connection.
Owner:EMC IP HLDG CO LLC
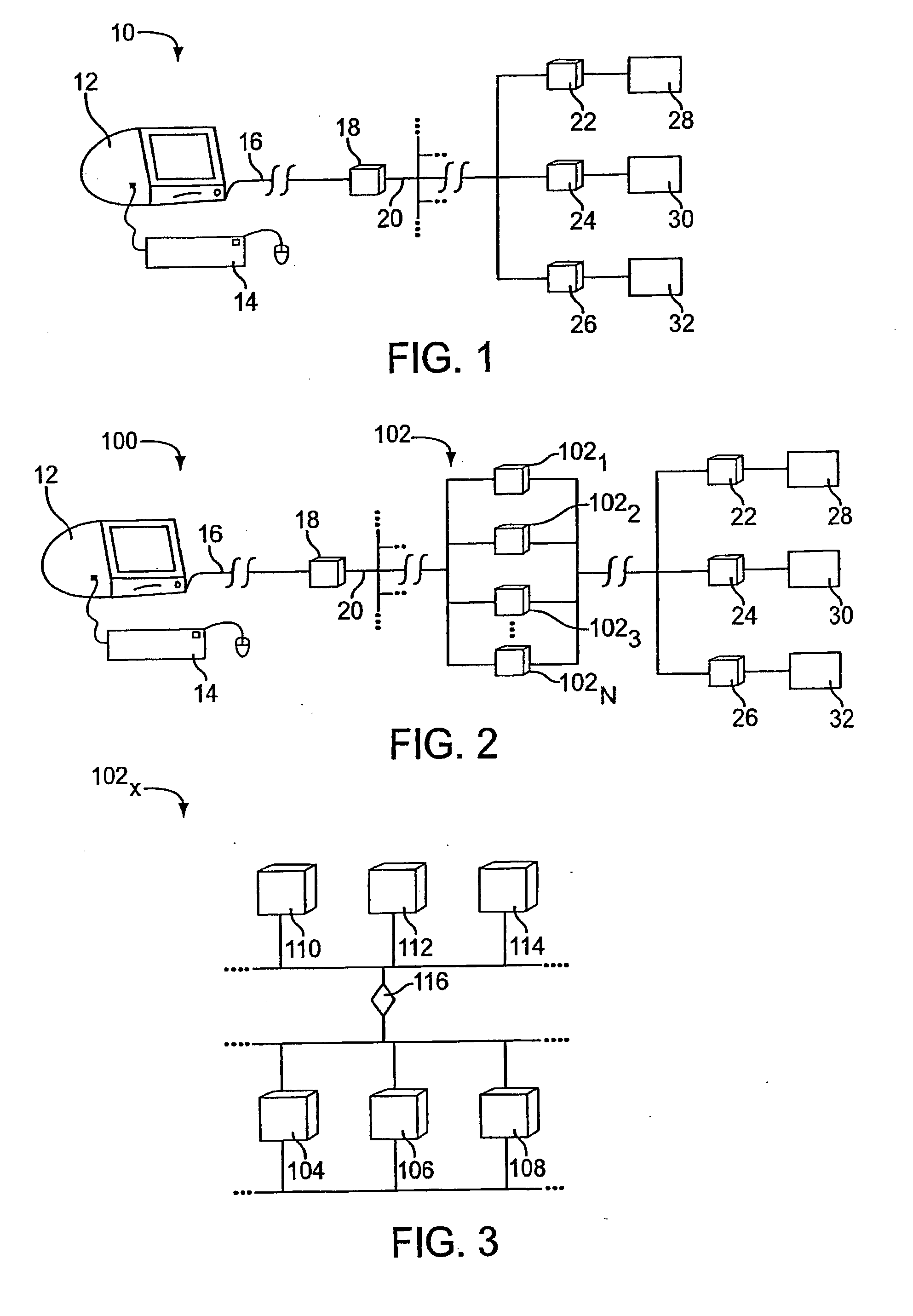
User identification in the header of data packets
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE NETWORKS
Method, systems, and computer program products for implementing function-parallel network firewall
ActiveUS20060195896A1Reduce impactMinimum delayMemory loss protectionError detection/correctionData packRule sets
Methods, systems, and computer program products for providing function-parallel firewalls are disclosed. According to one aspect, a function-parallel firewall includes a first firewall node for filtering received packets using a first portion of a rule set including a plurality of rules. The first portion includes less than all of the rules in the rule set. At least one second firewall node filters packets using a second portion of the rule set. The second portion includes at least one rule in the rule set that is not present in the first portion. The first and second portions together include all of the rules in the rule set.
Owner:WAKE FOREST UNIV
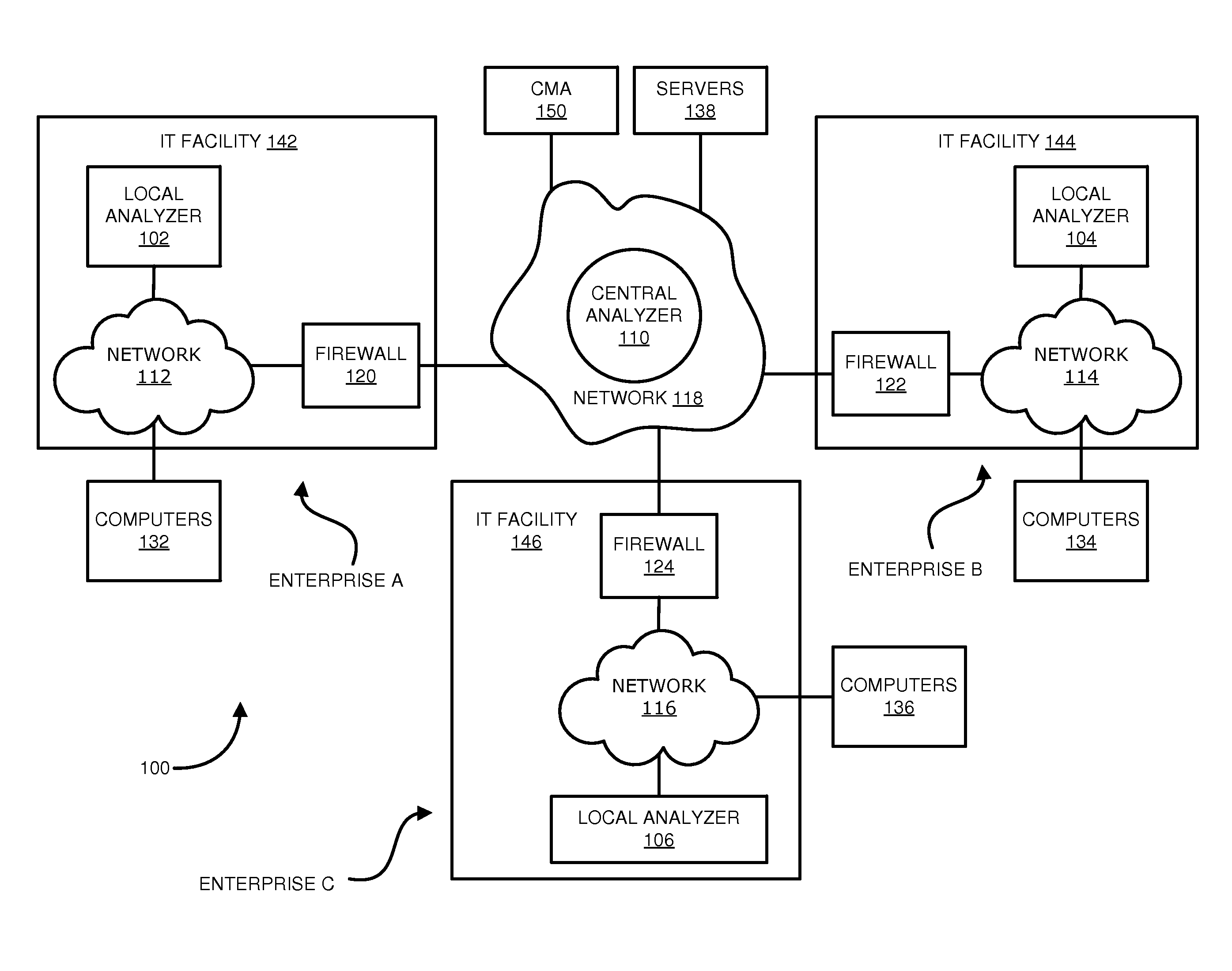
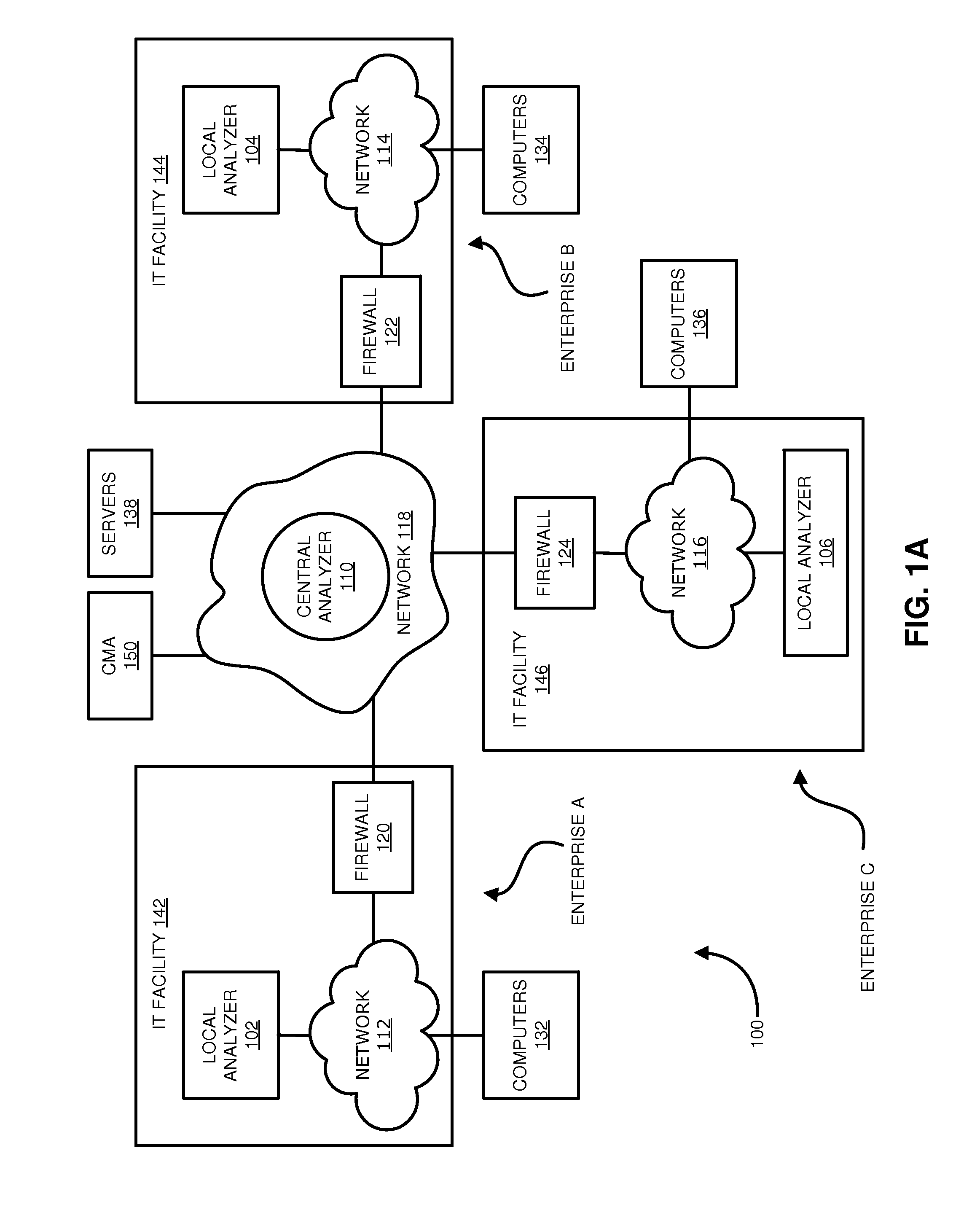
Distributed systems and methods for automatically detecting unknown bots and botnets
ActiveUS9430646B1Error detection/correctionPlatform integrity maintainanceOutbound communicationCommand and control
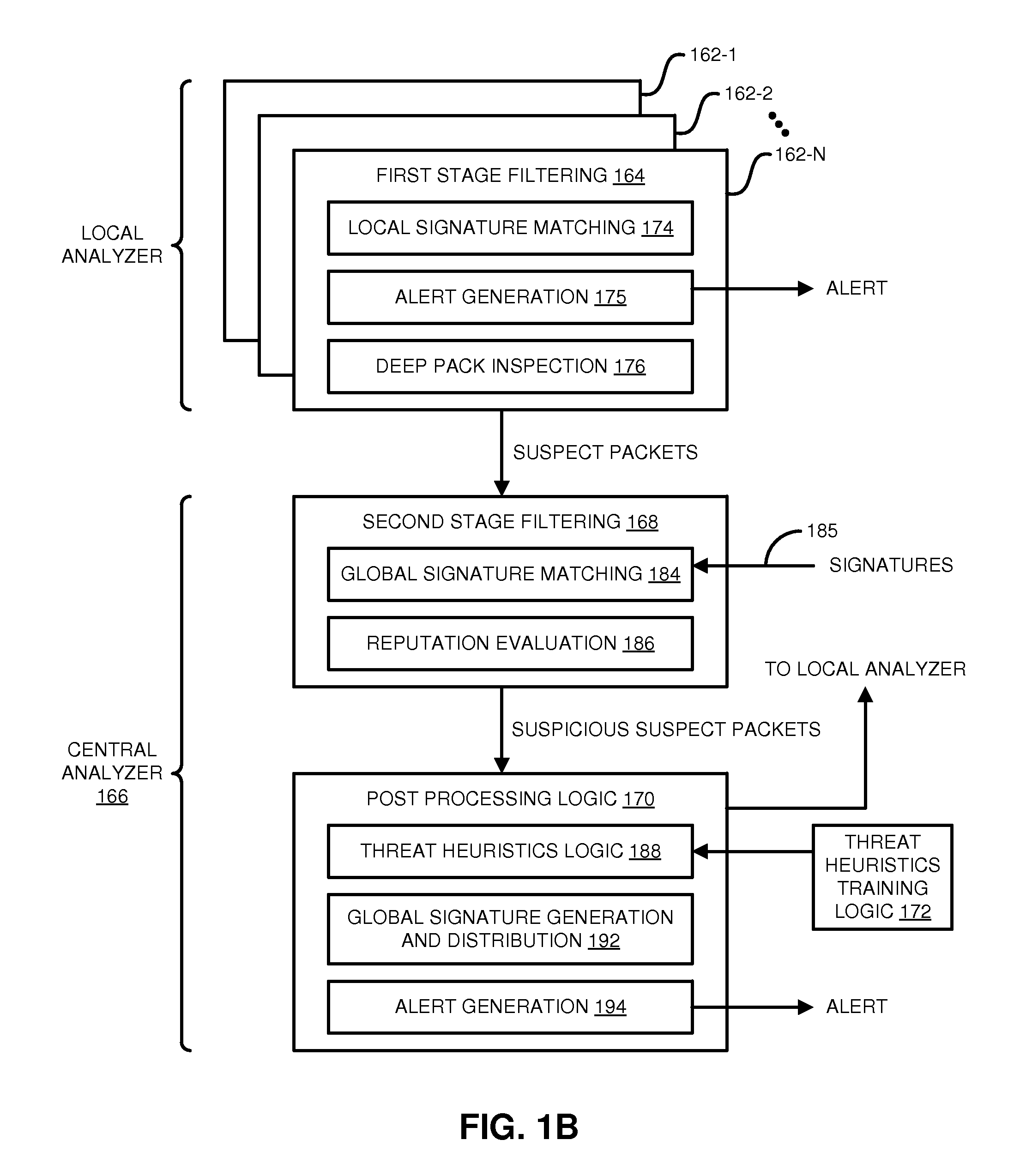
Techniques may automatically detect bots or botnets running in a computer or other digital device by detecting command and control communications, called “call-backs,” from malicious code that has previously gained entry into the digital device. Callbacks are detected using a distributed approach employing one or more local analyzers and a central analyzer. The local analyzers capture packets of outbound communications, generate header signatures, and analyze the captured packets using various techniques. The techniques may include packet header signature matching against verified callback signatures, deep packet inspection. The central analyzer receives the header signatures and related header information from the local analyzers, may perform further analysis (for example, on-line host reputation analysis); determines using a heuristics analysis whether the signatures correspond to callbacks; and generally coordinates among the local analyzers.
Owner:FIREEYE SECURITY HLDG US LLC
Target information generation and ad server
InactiveUS7155508B2Increase ratingsGreater profit margin for ad companiesDigital computer detailsTransmissionMass storageApplication software
An advertisement selection and delivery system for selecting advertisements based on profile information and rendering the advertisements as accessible to a user operating a network-capable appliance connected to a data-packet-network is provided. The system comprises, a first server node connected to the network, the first server node functioning as a user access point on the network, a mass storage repository accessible to the first server node, the repository for storing and serving user profile data, a second server node connected to the network, the second server node for generating user preference data, at least one advertisement server connected to the network, the advertisement server for serving advertisement data, a software application for generating user preference lists and performing advertisement selection and at least one network-capable appliance connected to the network the network-capable appliance for receiving the advertisement data. A user operating the network-capable appliance accesses the first server node and receives the advertisement data, the advertisement data selected for service by matching the user preference data to stored advertisements and rendered accessible to the user during the time of user access to the system from the network-capable appliance.
Owner:YODLEE COM INC
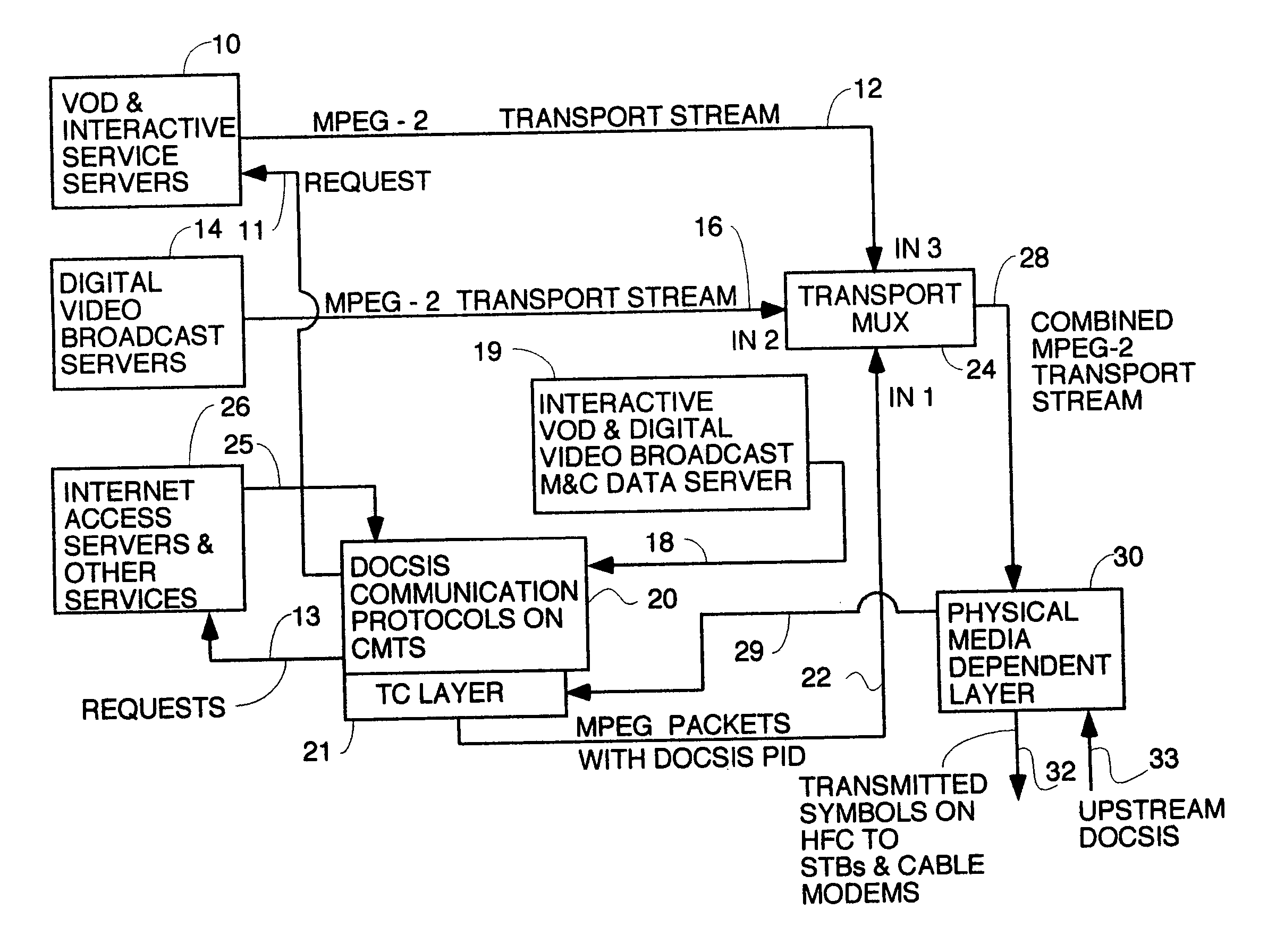
Thin DOCSIS in-band management for interactive HFC service delivery
InactiveUS20040181811A1Simplifies STBsLess-expensive to buildAnalogue secracy/subscription systemsBroadcast information monitoringDOCSISMPEG transport stream
Circuitry and processed carried out thereby are disclosed for transmitting video-on-demand and interactive service data and other service data on an MPEG multiplex and sending management and control data including conditional access EMM key data in-band in said MPEG multiplex in MPEG packets having the DOCSIS PID. Processes to send conditional access data by sending ECM messages containing control words encrypted with session keys in said MPEG multiplex and sending EMM messages containing session keys encrypted with private set top box users keys are disclosed. The EMM messages are sent in-band in MPEG packets having the DOCSIS PID to only the set top boxes that request them and which have ordered an encrypted service. A head end with routing / switching capability to route MPEG transport streams encapsulated in IP packets is also disclosed.
Owner:TERAYON COMM SYST
Systems and methods for packet distribution
InactiveUS20020038339A1Multiple digital computer combinationsProgram controlNetwork applicationPayload
Embodiments of the present invention relate to methods and systems of managing delivery of data to network applications. In an embodiment, a delivery packet including a service address and a payload is received. A plurality of network applications associated with the service address of the data packet are identified. The plurality of network applications associated with the service address include a first network application and a second network application, where the first network application is different from the second network application. At least the payload of the data packet is sent to the first network application and the second network application.
Owner:SPONTANEOUS NETWORKS
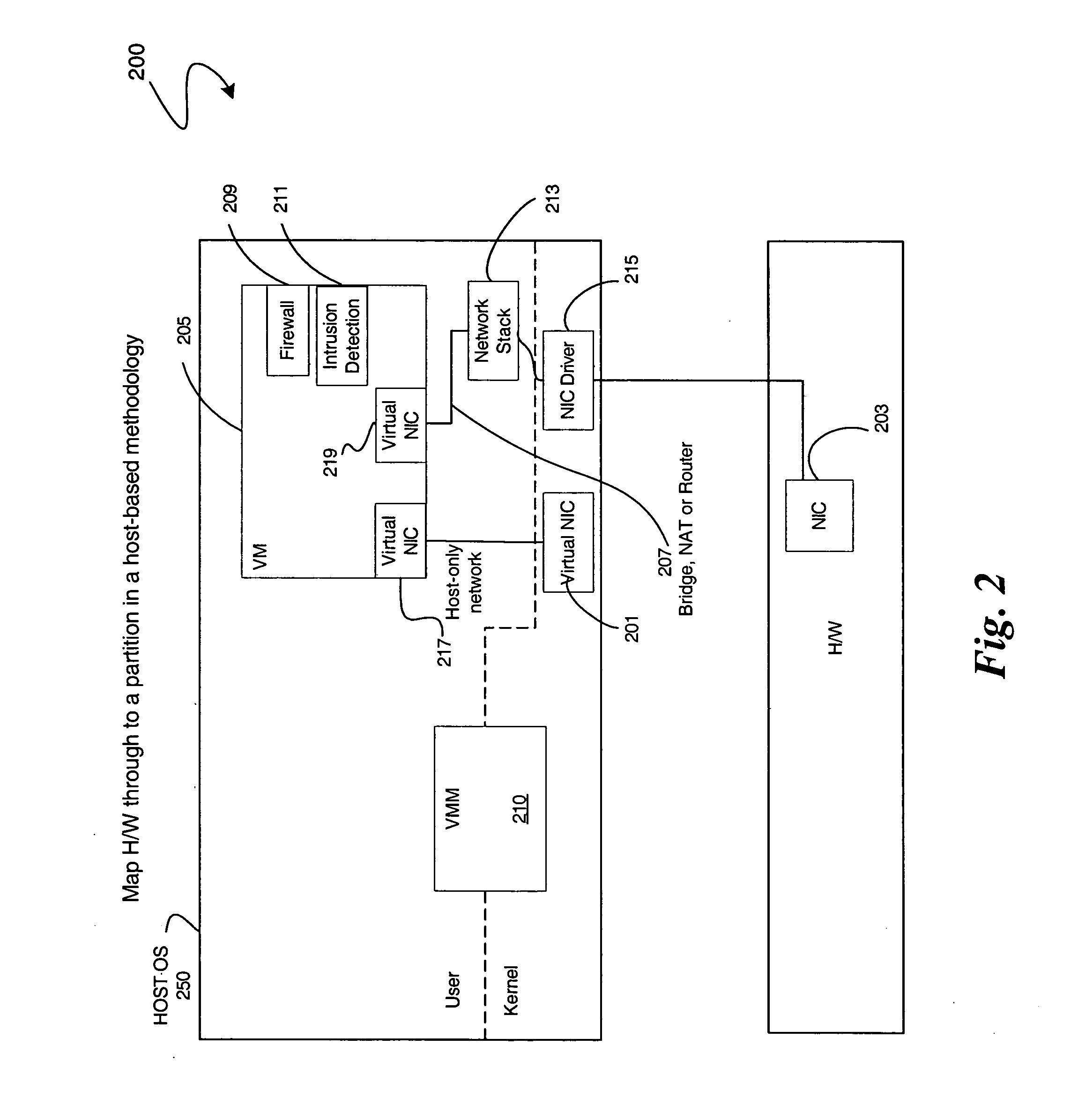
Enabling platform network stack control in a virtualization platform
InactiveUS20060070066A1TransmissionSoftware simulation/interpretation/emulationVirtualizationData pack
In some embodiments, the invention involves protecting network communications in a virtualized platform. An embodiment of the present invention is a system and method relating to protecting network communication flow using packet encoding / certification and the network stack. One embodiment uses a specialized engine or driver in the network stack to encode packets before being sent to physical network controller. The network controller may use a specialized driver to decode the packets, or have a hardware implementation of a decoder. If the decoded packet is certified, the packet is transmitted. Otherwise, the packet is dropped. An embodiment of the present invention utilizes virtualization architecture to implement the network communication paths. Other embodiments are described and claimed.
Owner:INTEL CORP
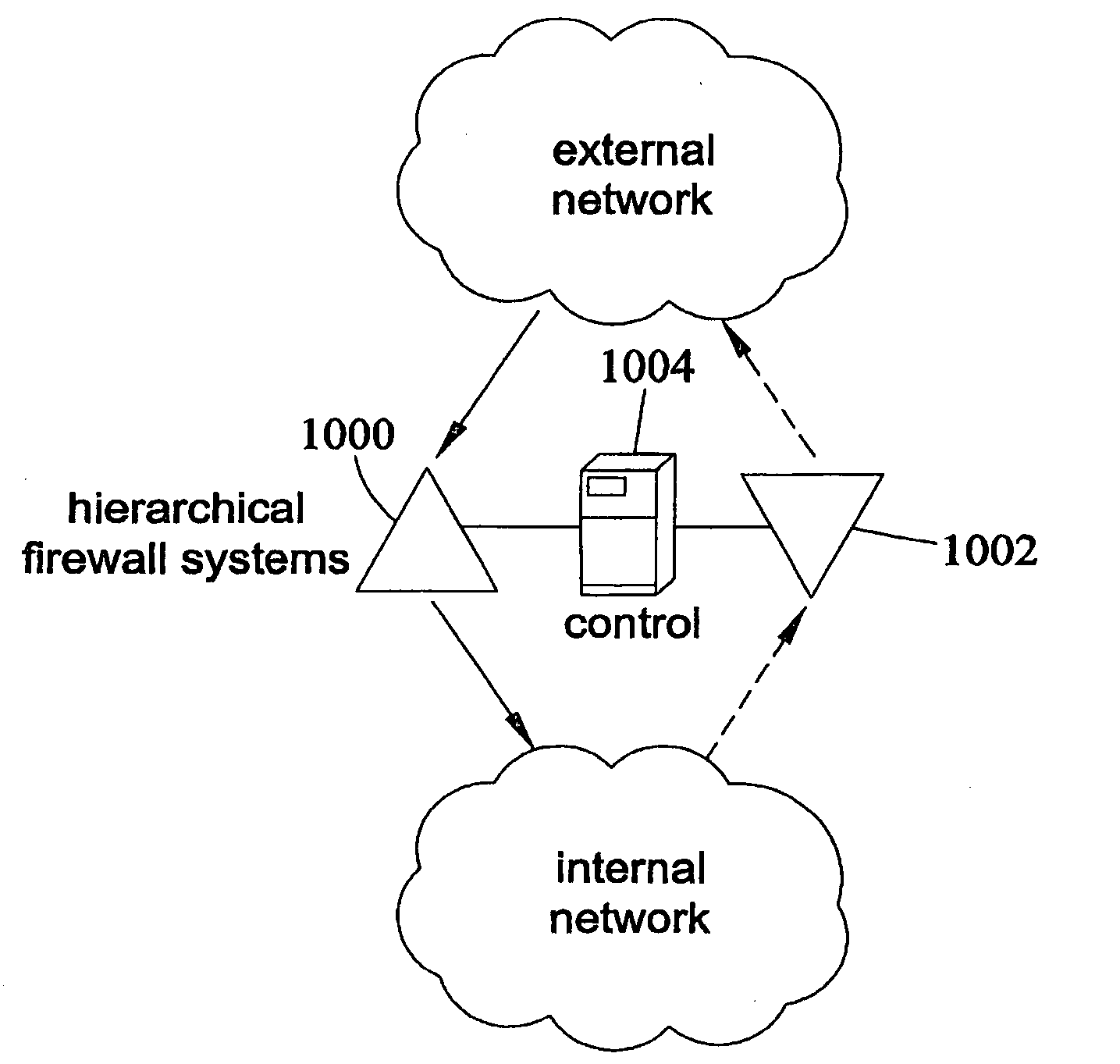
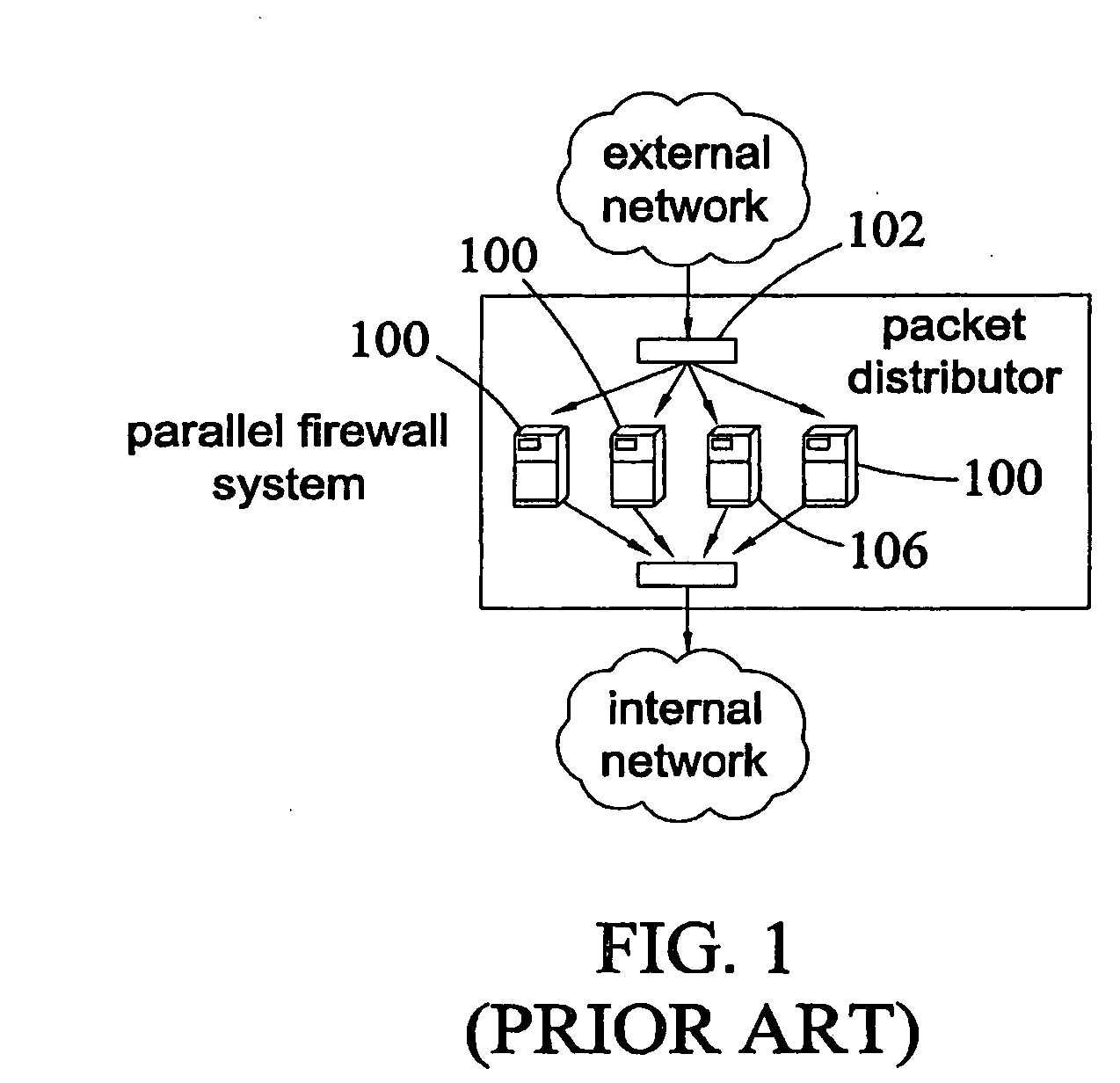
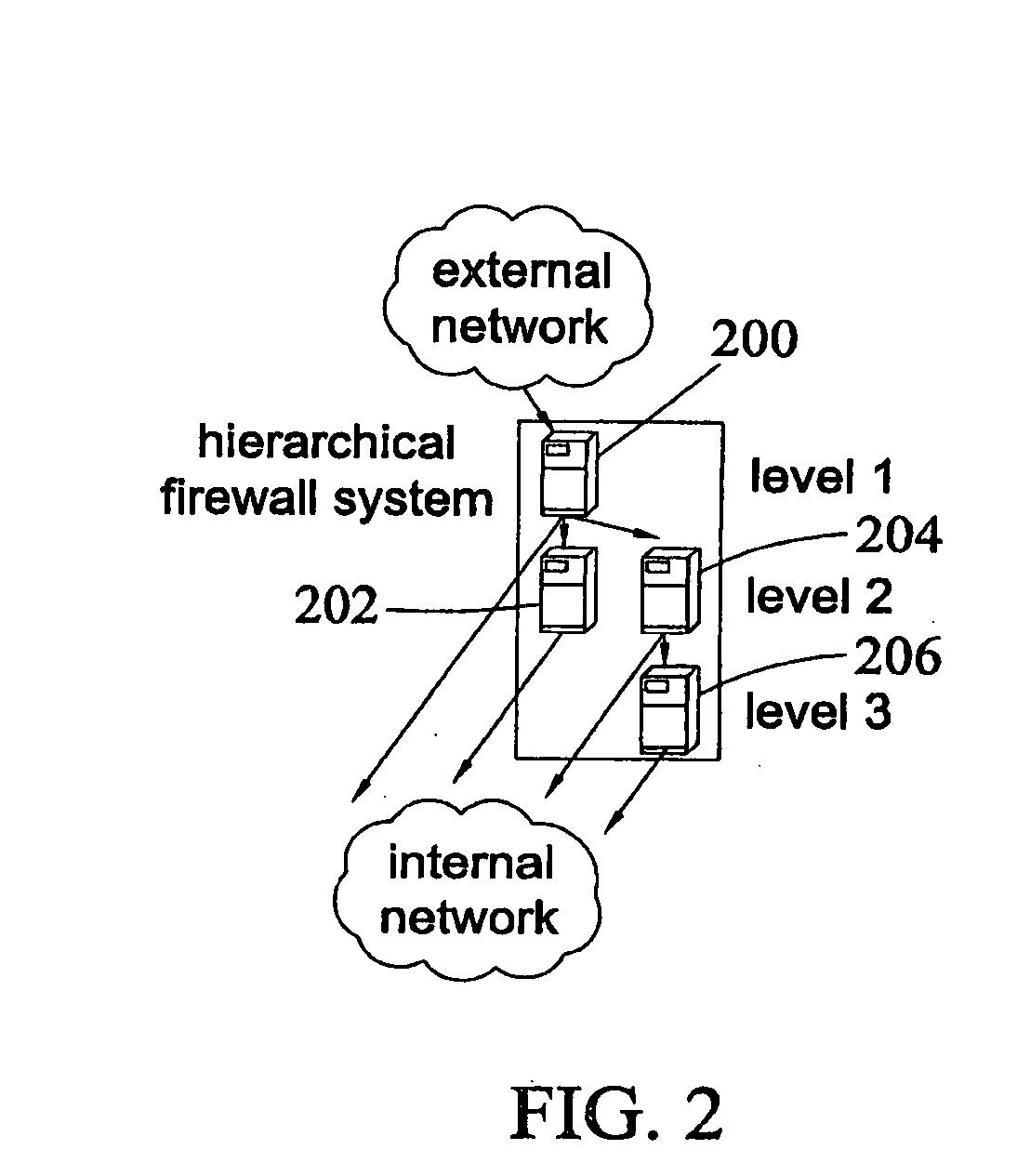
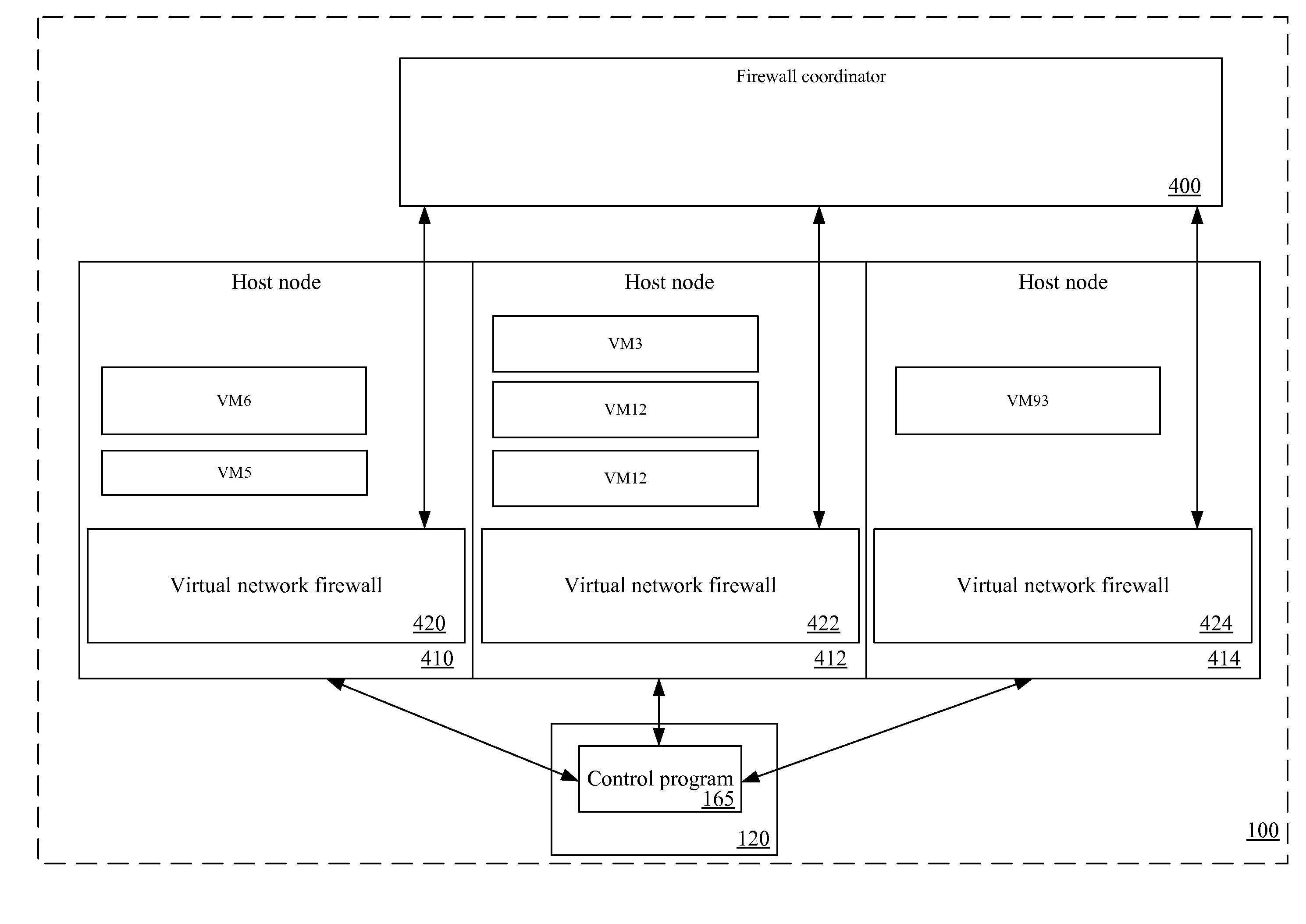
Hierarchical firewalls
InactiveUS20090249472A1Provide securityError preventionFrequency-division multiplex detailsData packEngineering
A method of implementing a firewall that receives a layer of policies from each of multiple entities with different levels of authority. The method evaluates received packets based on the received layers of policies. A layer of policies of a higher level of authority can accept a received packet, block the received packet, or delegate a decision of whether to accept or block the received packet to a layer of policies of a lower level of authority.
Owner:JUMIPER NETWORKS INC
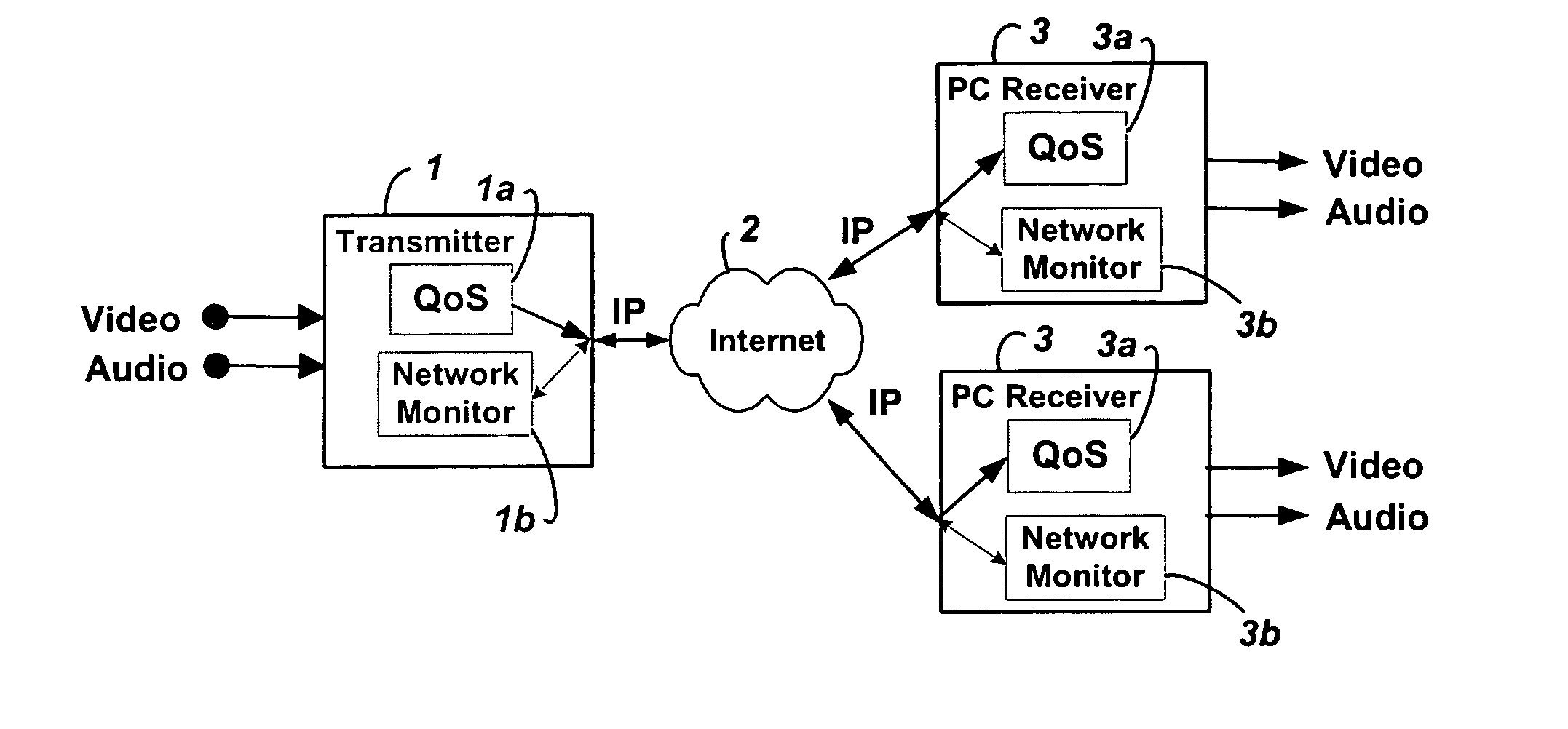
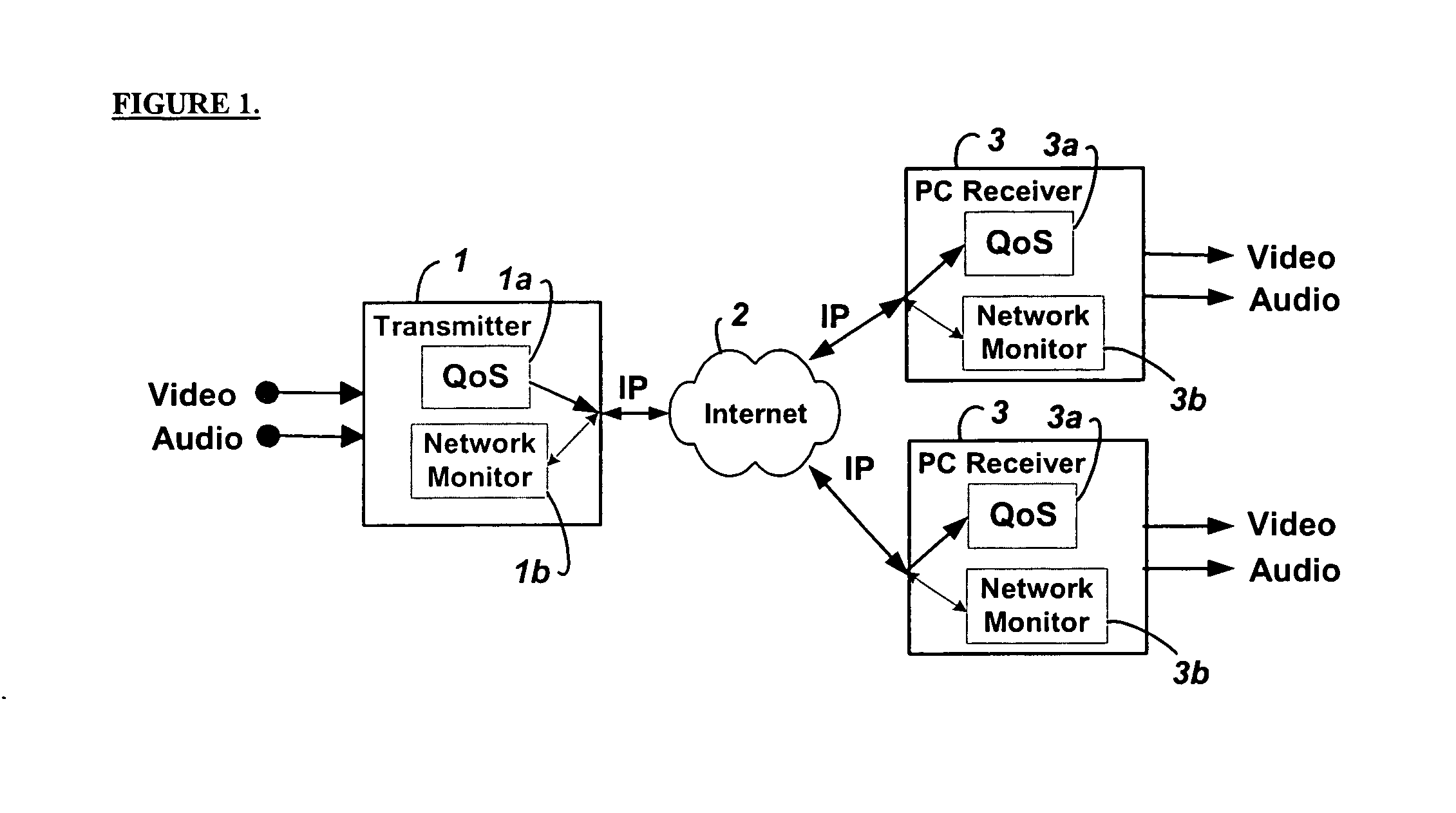
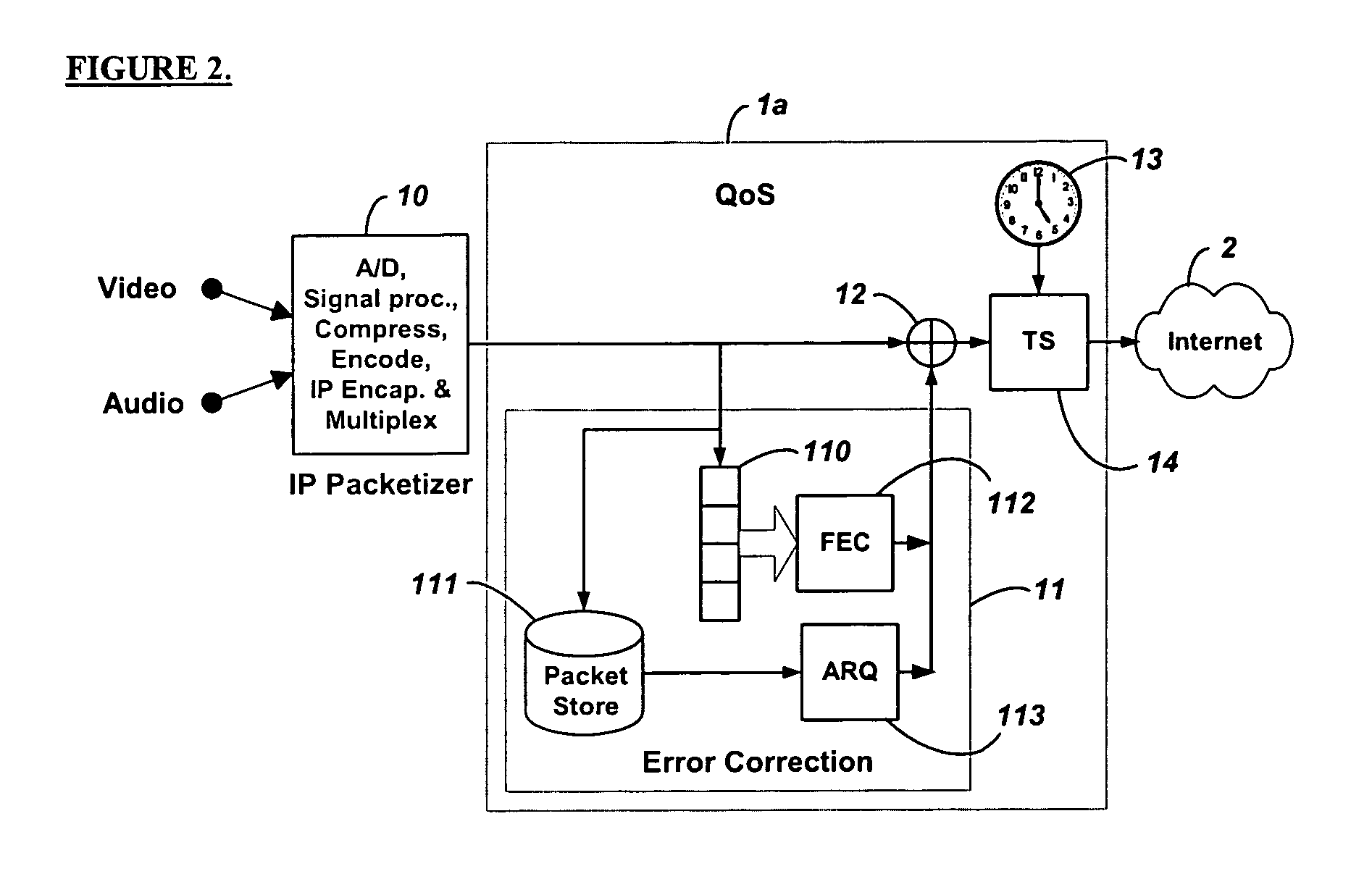
Method and system for providing site independent real-time multimedia transport over packet-switched networks
InactiveUS20060007943A1Minimal latency site-independenceAchieve independenceTime-division multiplexData switching by path configurationData packTimestamp
Embodiments of the invention enable minimum latency site independent real-time video transport over packet switched networks. Some examples of real-time video transport are video conferencing and real-time or live video streaming. In one embodiment of the invention, a network node transmits live or real-tine audio and video signals, encapsulated as Internet Protocol (IP) data packets, to one or more nodes on the Internet or other IP network. One embodiment of the invention enables a user to move to different nodes or move nodes to different locations thereby providing site independence. Site independence is achieved by measuring and accounting for the jitter and delay between a transmitter and receiver based on the particular path between the transmitter and receiver independent of site location. The transmitter inserts timestamps and sequence numbers into packets and then transmits them. A receiver uses these timestamps to recover the transmitter's clock. The receiver stores the packets in a buffer that orders them by sequence number. The packets stay in the buffer for a fixed latency to compensate for possible network jitter and / or packet reordering. The combination of timestamp packet-processing, remote clock recovery and synchronization, fixed-latency receiver buffering, and error correction mechanisms help to preserve the quality of the received video, despite the significant network impairments generally encountered throughout the Internet and wireless networks.
Owner:QVIDIUM TECH
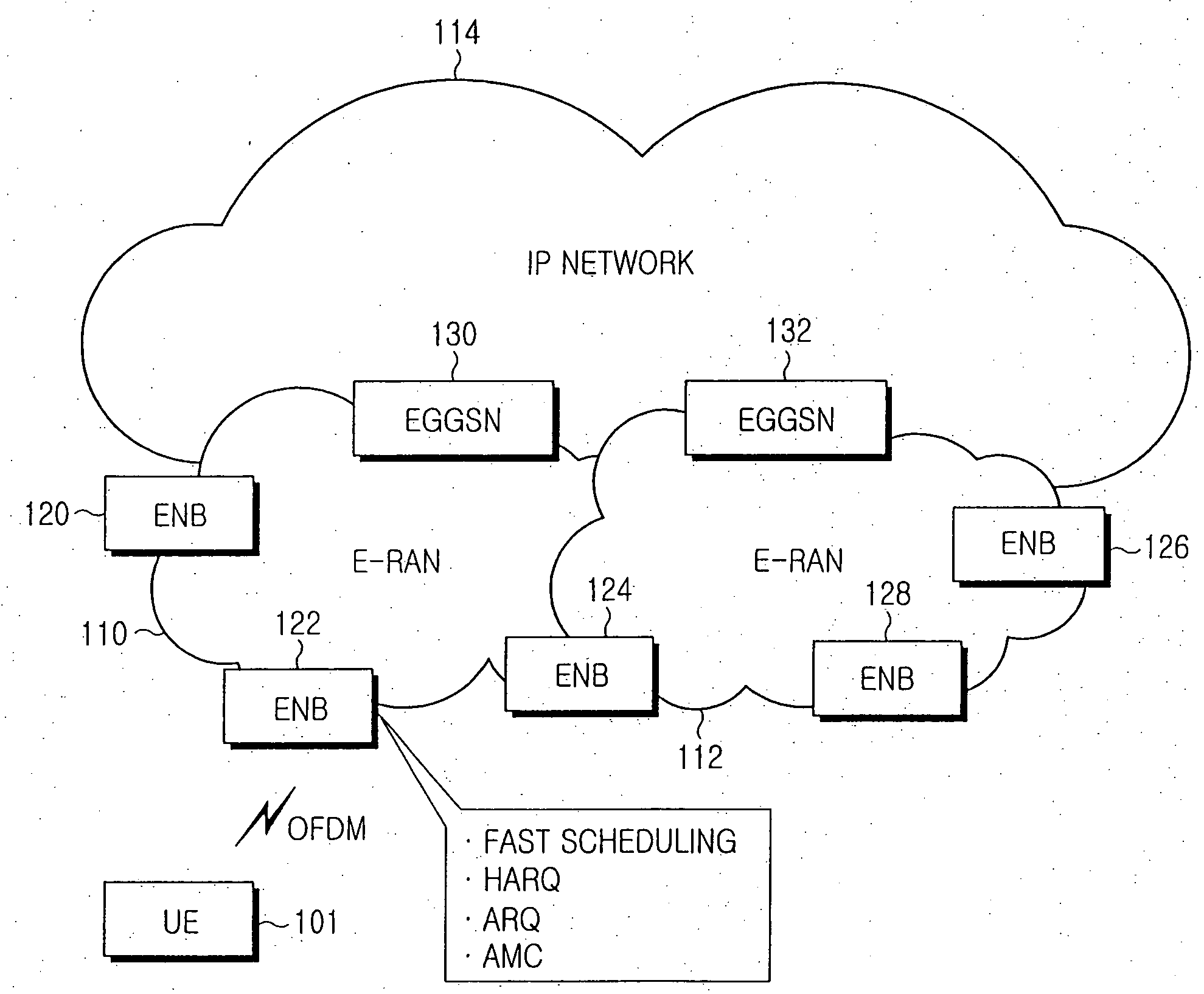
Method and apparatus for transmitting and receiving status report comprising received status of packet data in a mobile communication system
A method and terminal apparatus for transmitting a status report comprising a received status of packet data in a mobile communication system are provided, in which whether transmission of an implicit Negative Acknowledge (NACK) signal is required for requesting retransmission of at least one non-received data packet whose sequence number is unidentified is determined, if transmission of the implicit NACK signal is required, the implicit NACK signal including a sequence number of the last packet is generated among successfully received data packets, and a status report including the implicit NACK signal is transmitted to the transmitter, and if transmission of the implicit NACK signal is not required, a status report is transmitted to the transmitter including at least one of an ACK signal comprising a sequence number of a successfully received data packet and an explicit NACK signal comprising a sequence number of a non-received data packet whose sequence number is identified.
Owner:SAMSUNG ELECTRONICS CO LTD
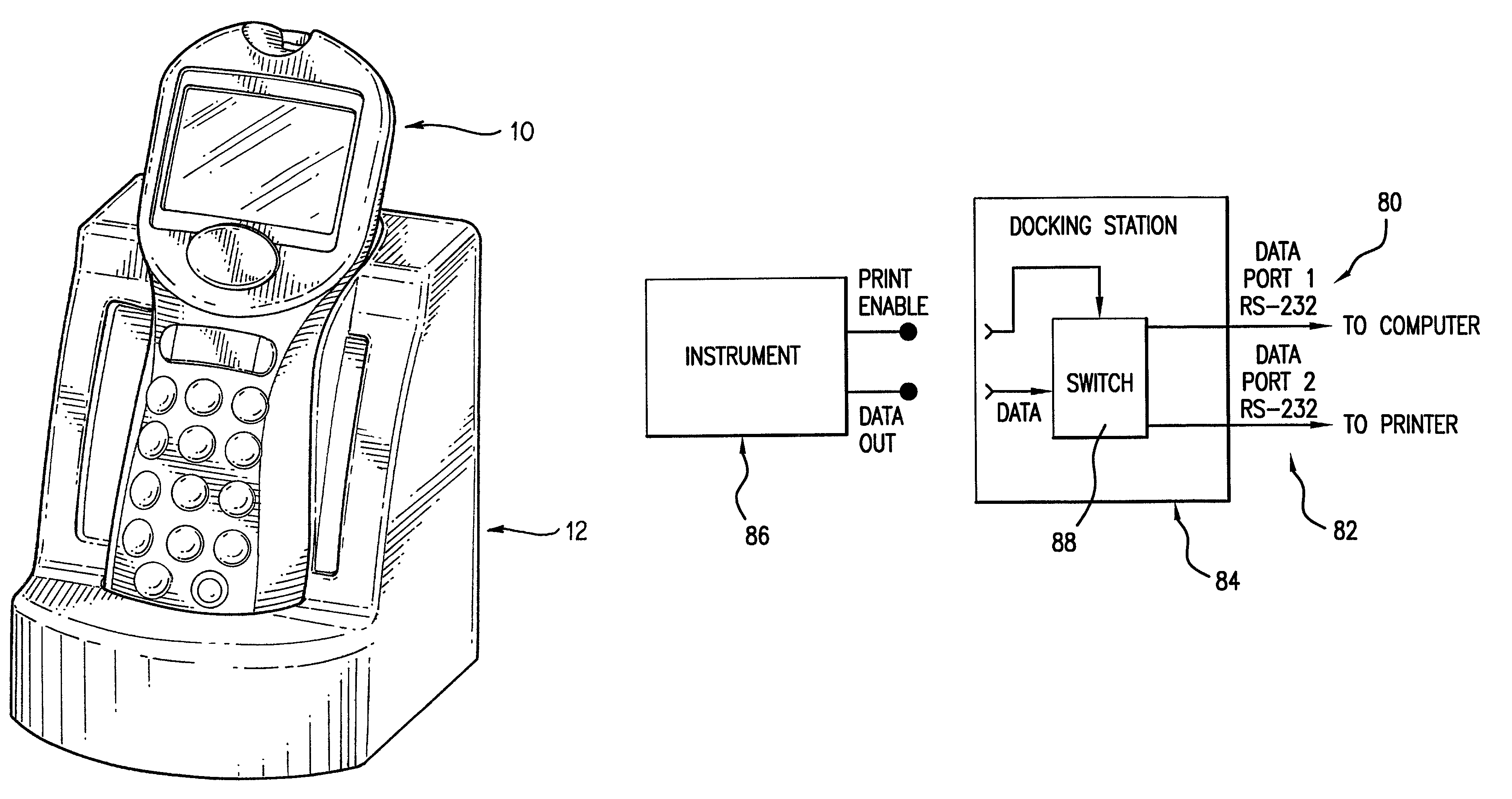
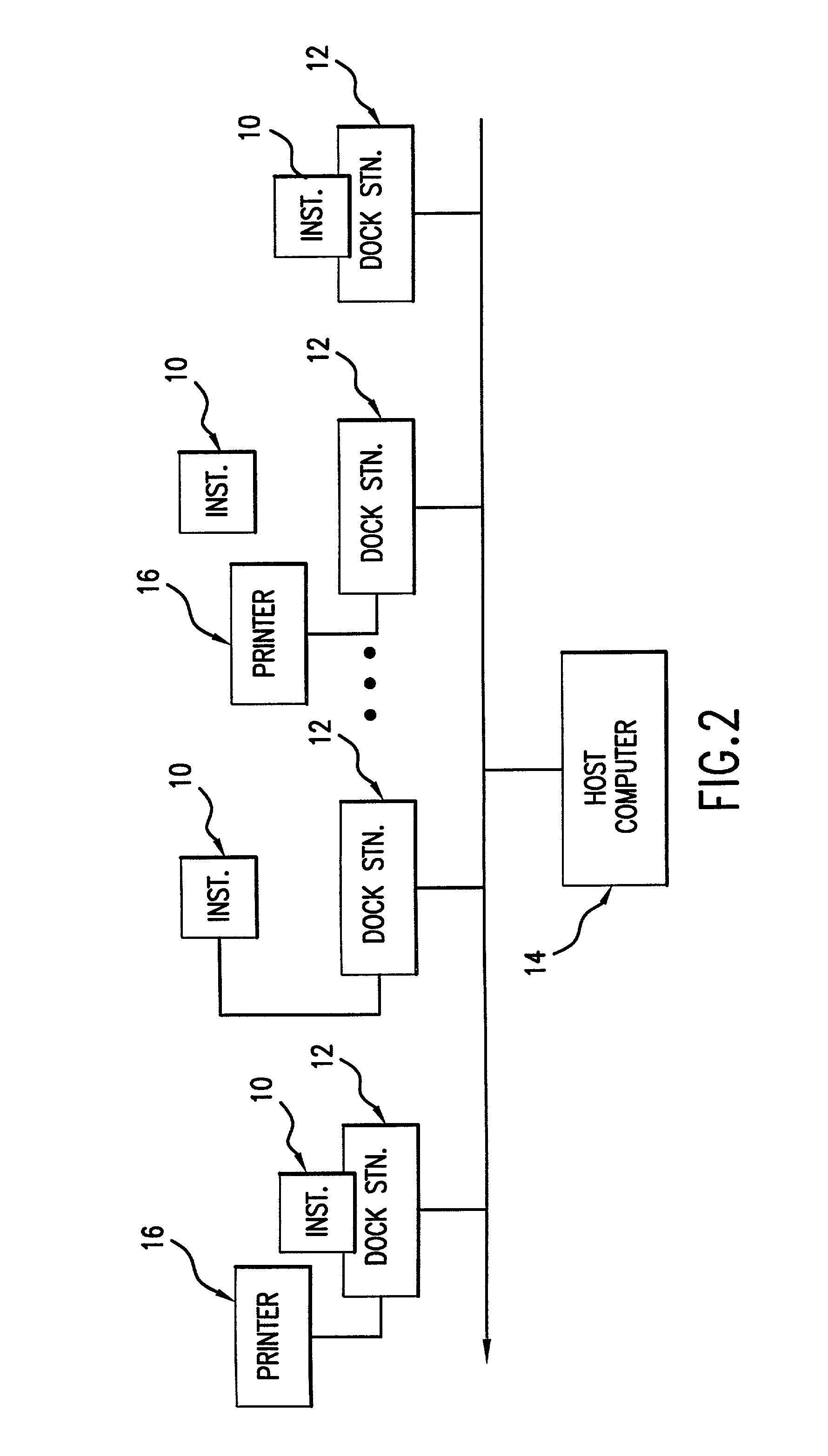
Analyte test instrument system including data management system
InactiveUS7077328B2Computer-assisted medical data acquisitionCharacter and pattern recognitionSwitched communication networkInstrumentation
A method of managing data for a plurality of analyte test instruments connected to a data communication network. The method comprises the steps of: detecting via a host computer the connection of each instrument to the data communication network; uploading data received from each instrument to the host computer; processing the uploaded data on the host computer for operator review; and downloading configuration data from the host computer to each test instrument, the downloaded data comprising instrument-specific setup and control data. The invention further involves a hand-held analyte test instrument and a docking station for the test instrument.
Owner:ABBOTT DIABETES CARE INC
Methods and apparatus and data structures for providing access to an edge router of a network
Aggregating physical connections from customers for presentation to an access router and de-aggregating traffic from a shared link(s) from the access router. Ports of an aggregation unit may be configured such that each has a unique identifier in the place of information (e.g., the layer 2 address) originally in the layer 2 header. The layer 2 (e.g., MAC) address of the customer device connected with the port can be associated with, and therefore determined from, the IP address of the attached device. When a packet is received from a customer, information in the layer 2 header is changed to a unique identifier assigned to a logical port or interface associated with the physical port. When a packet is received from the access router, it is placed on the port assigned to the logical port associated with the destination layer 2 address (or associated with other bits of the unique bit string and at least some of those bits are replaced with the destination layer 2 address of the device associated with the port.
Owner:VERIZON PATENT & LICENSING INC
Method and arrangement for implementing IPSEC policy management using filter code
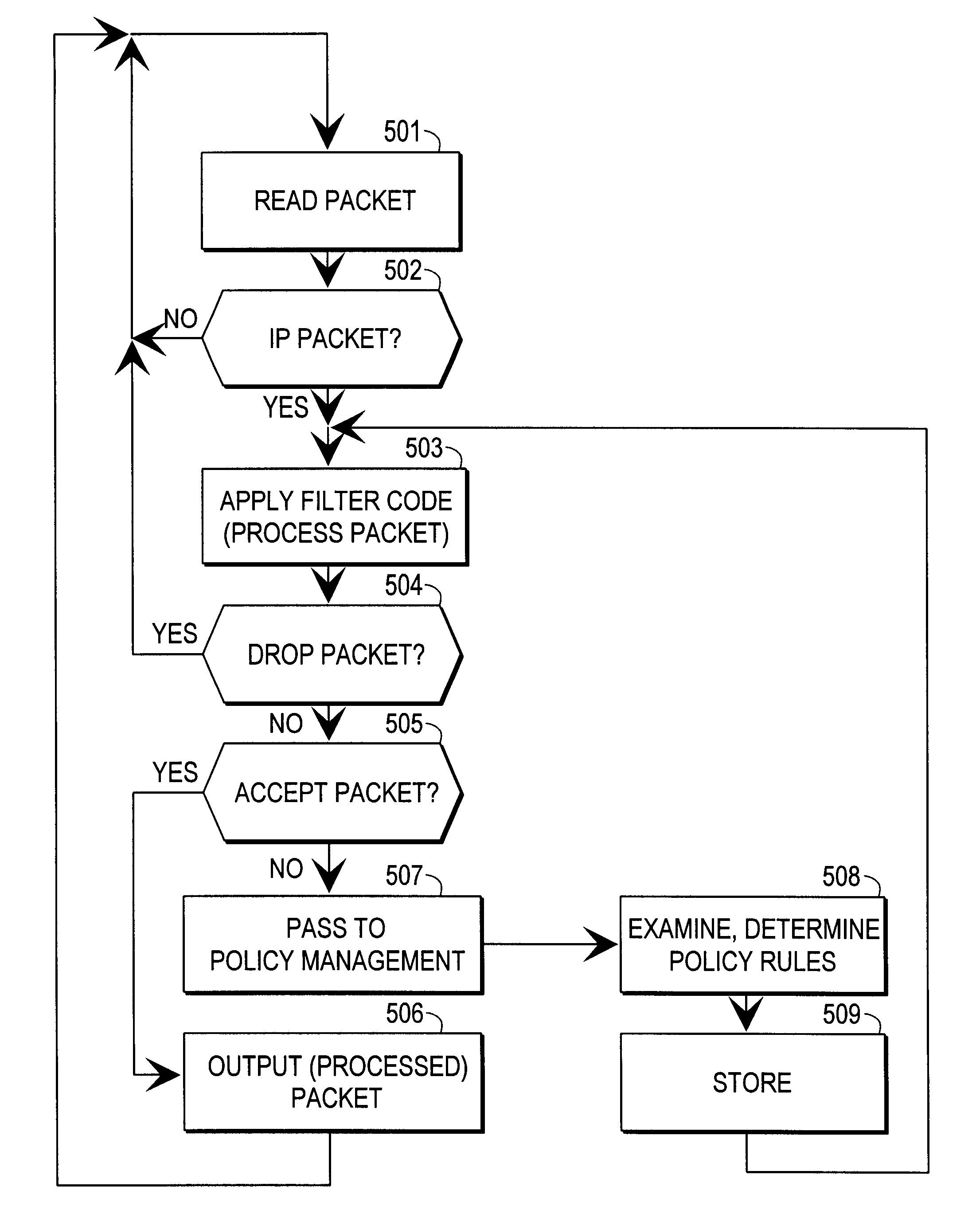
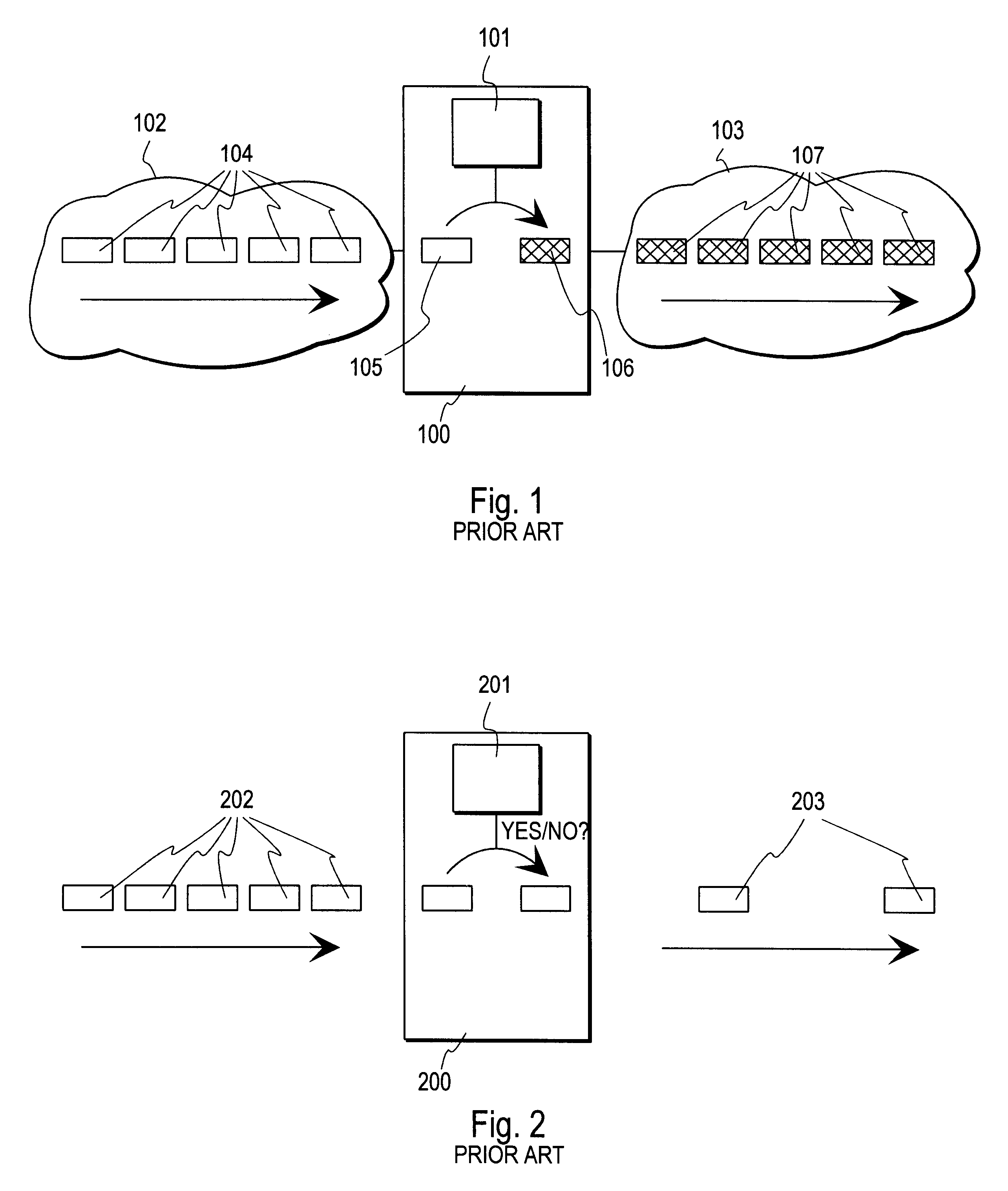
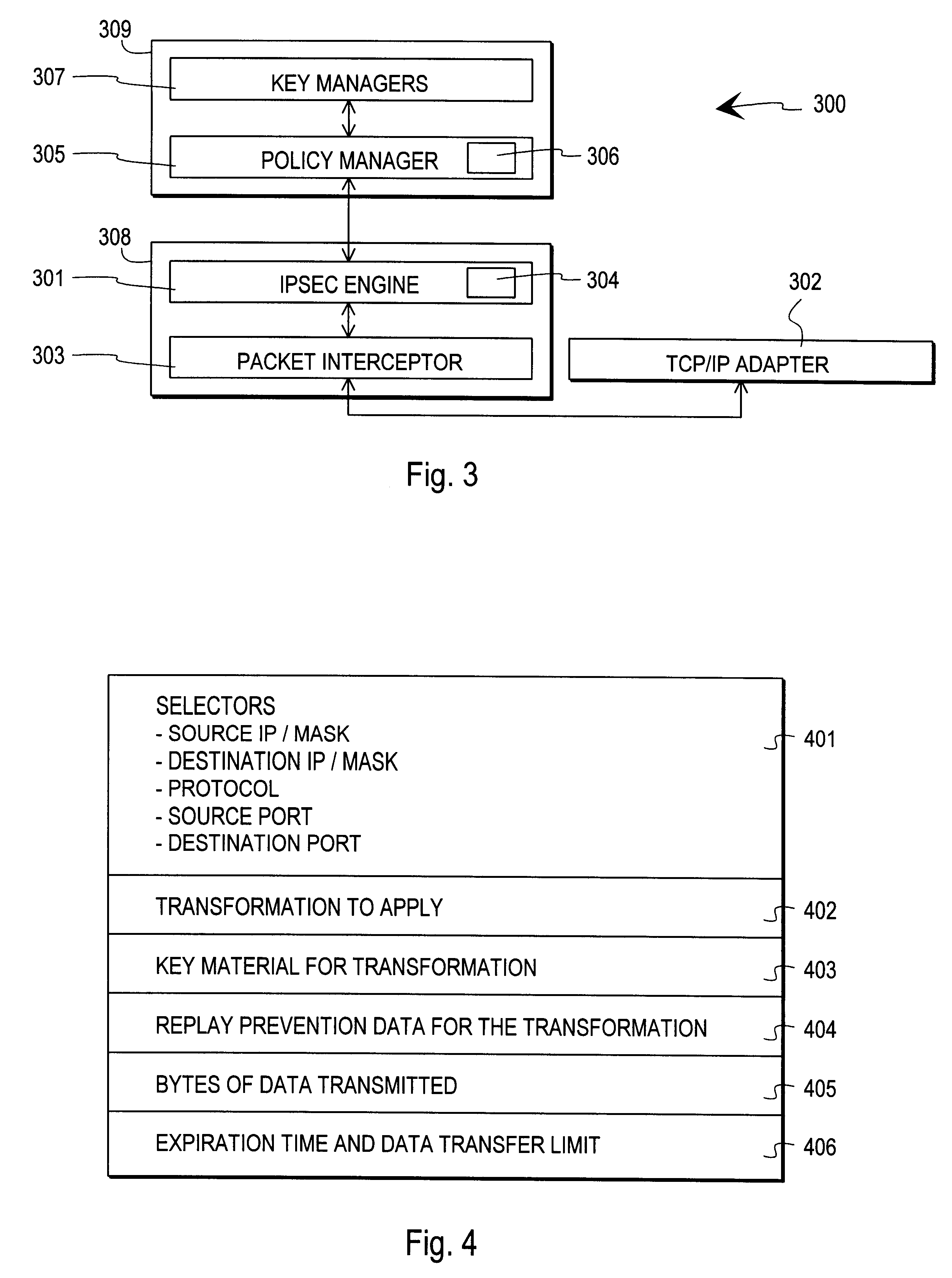
InactiveUS6253321B1User identity/authority verificationData resettingData processing systemComputer network
A data processing system implements a security protocol based on processing data in packets. The data processing system comprises processing packets for storing filter code and processing data packets according to stored filter code, and a policy managing function for generating filter code and communicating generated filter code for packet processing. The packet processing function is arranged to examine, whether the stored filter code is applicable for processing a certain packet. If the stored filter code is not applicable for the processing of a packet, the packet is communicated to the policy managing function, which generates filter code applicable for the processing of the packet and communicates the generated filter code for packet processing.
Owner:TECTIA
Method and apparatus for DNS pre-fetching for multiple clients
InactiveUS20050262248A1Quick responseQuick connectionMultiple digital computer combinationsTransmissionDomain nameData pack
In one embodiment, the present invention is a method and apparatus for DNS pre-fetching for multiple clients. In one embodiment, all packets coming into or going out of a local network are scanned for application protocol, domain names, and / or other information. If pre-defined criteria indicate that the network is interested in a particular domain name, a DNS lookup is performed and the corresponding IP address is cached by the local DNS server. The local DNS server is thereby able to quickly respond to future requests for the cached domain name. Moreover, because the IP address is cached at the local DNS server, any client connected to the local DNS server on the local network can request the cached domain name from the local DNS server and be quickly connected to the indicated domain name.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com