Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
24885 results about "Network packet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
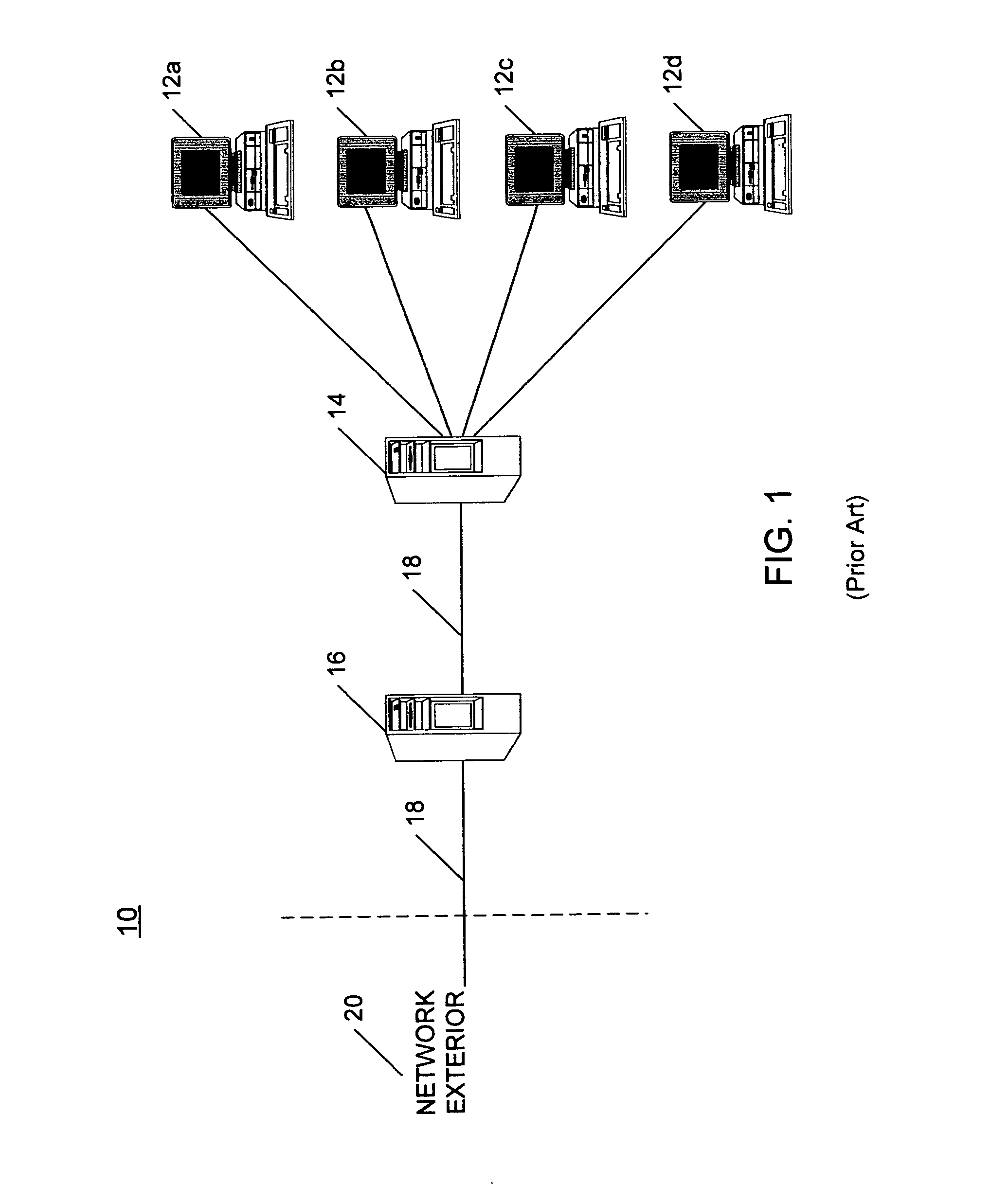
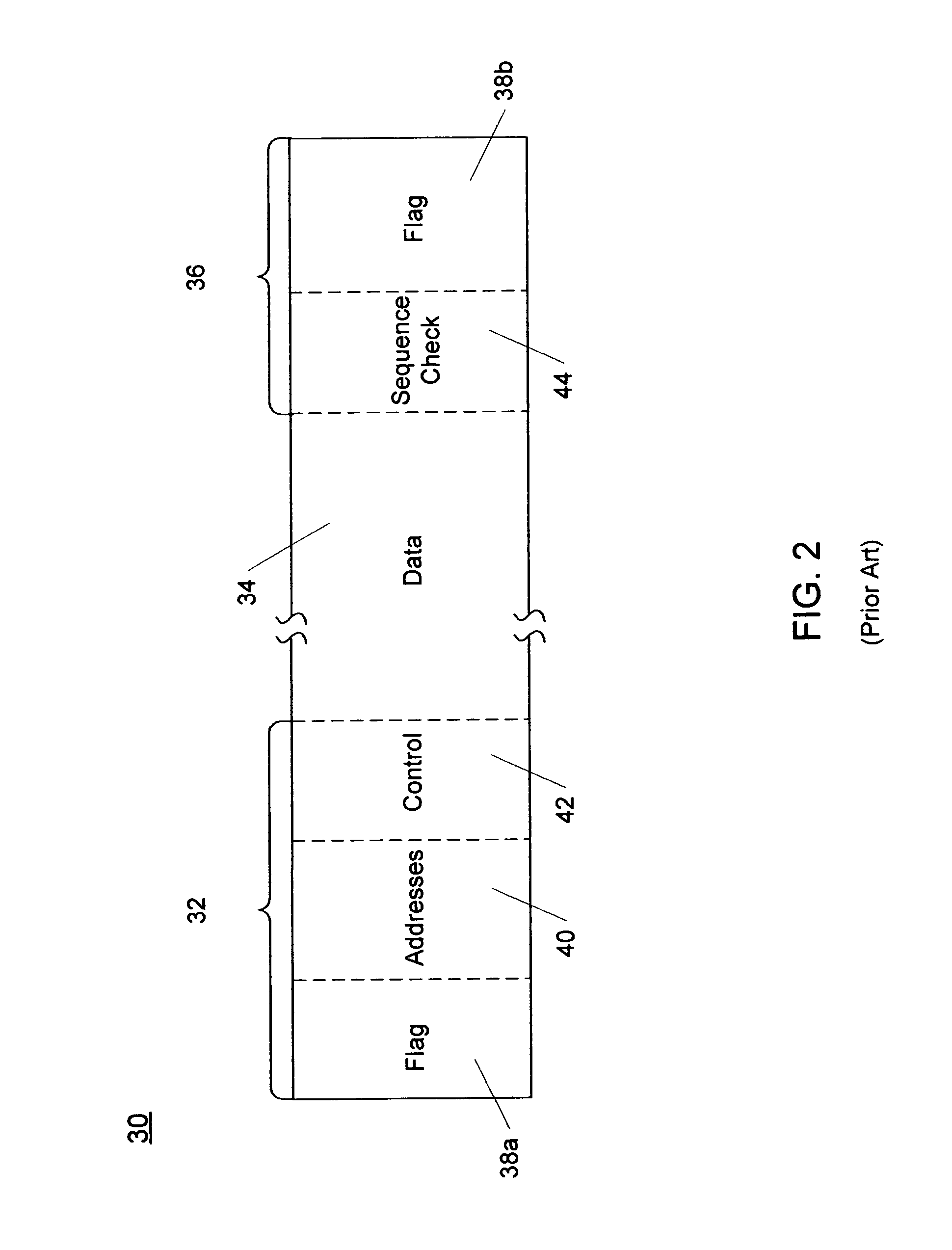
A network packet is a formatted unit of data carried by a packet-switched network. A packet consists of control information and user data, which is also known as the payload. Control information provides data for delivering the payload, for example: source and destination network addresses, error detection codes, and sequencing information. Typically, control information is found in packet headers and trailers.
Object oriented video system
InactiveUS20070005795A1Reduce colorNo extra data overhead and processing overheadTelevision system detailsPulse modulation television signal transmissionGraphicsData stream
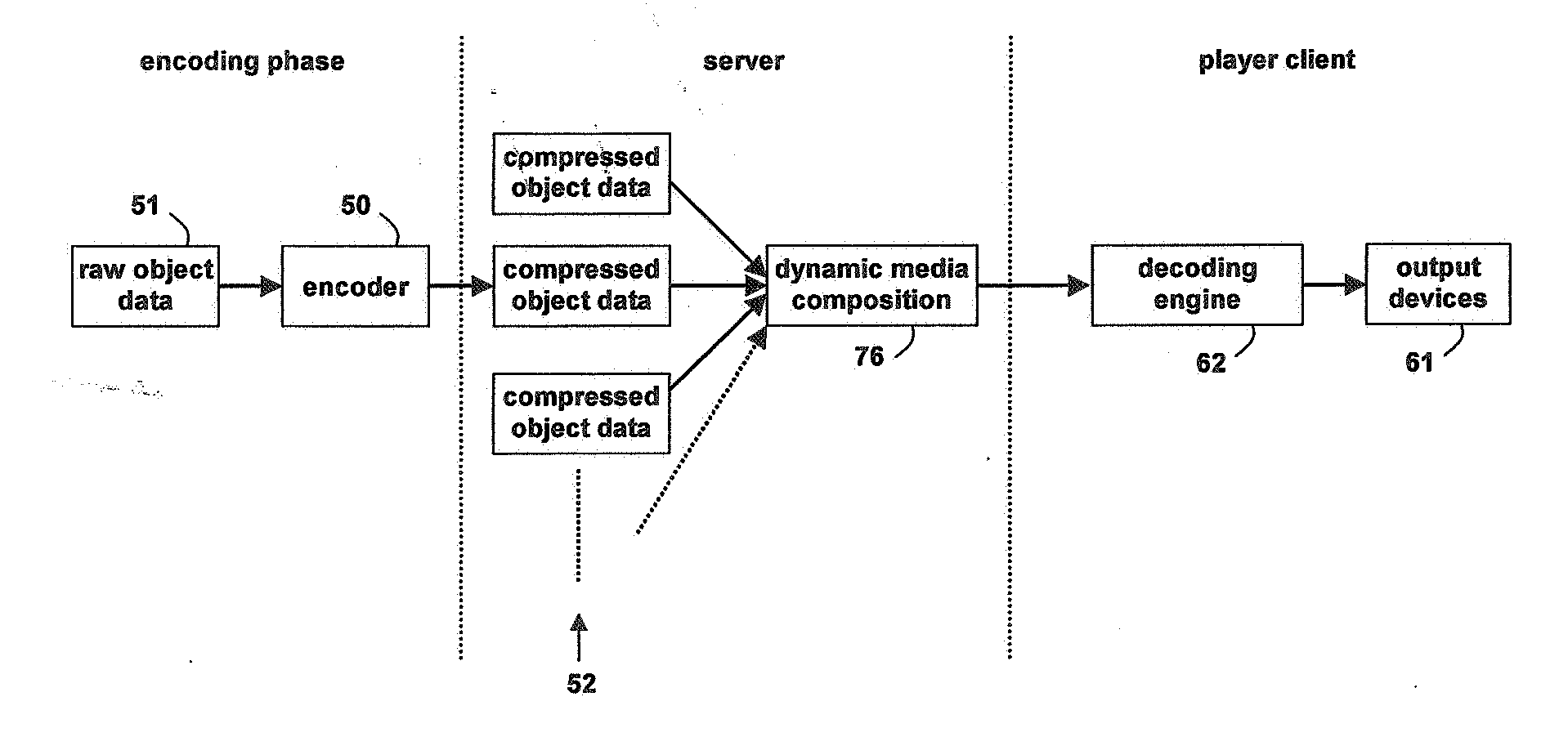
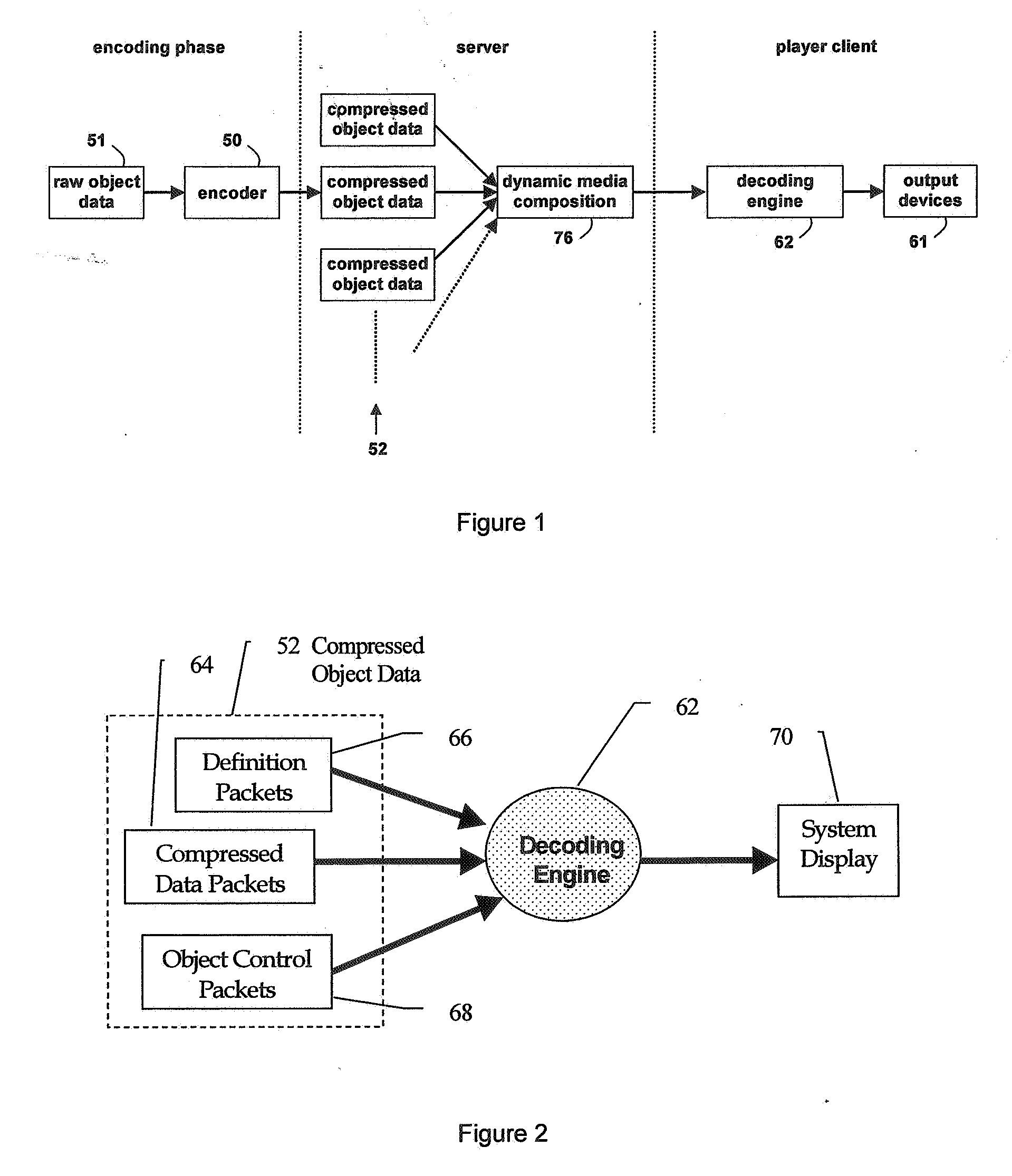
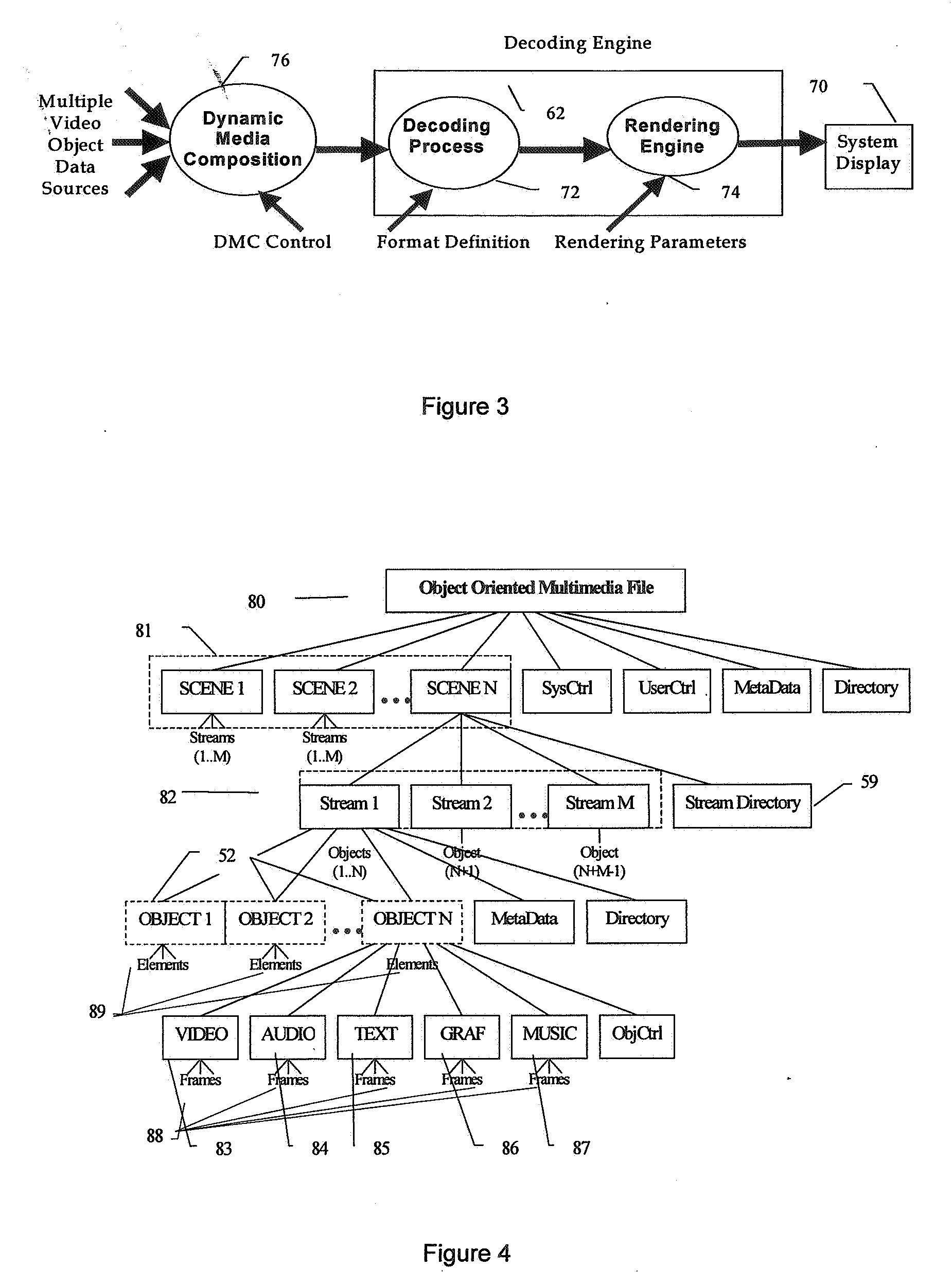
A method of generating an object oriented interactive multimedia file, including encoding data comprising at least one of video, text, audio, music and / or graphics elements as a video packet stream, text packet stream, audio packet stream, music packet stream and / or graphics packet stream respectively, combining the packet streams into a single self-contained object, said object containing its own control information, placing a plurality of the objects in a data stream, and grouping one or more of the data streams in a single contiguous self-contained scene, the scene including format definition as the initial packet in a sequence of packets. An encoder for executing the method is provided together with a player or decoder for parsing and decoding the file, which can be wirelessly streamed to a portable computer device, such as a mobile phone or a PDA. The object controls provide rendering and interactive controls for objects allowing users to control dynamic media composition, such as dictating the shape and content of interleaved video objects, and control the objects received.
Owner:ACTIVESKY
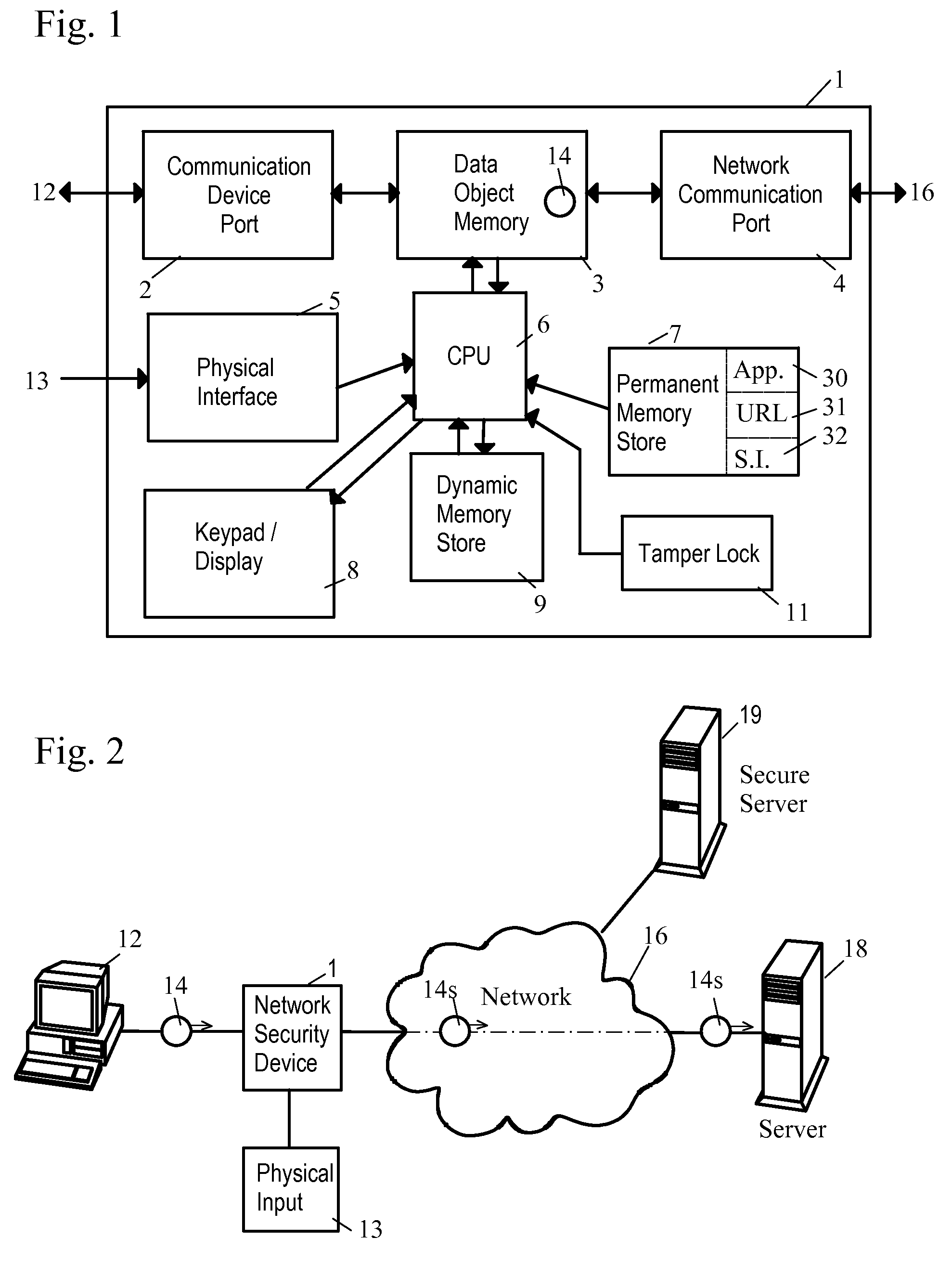
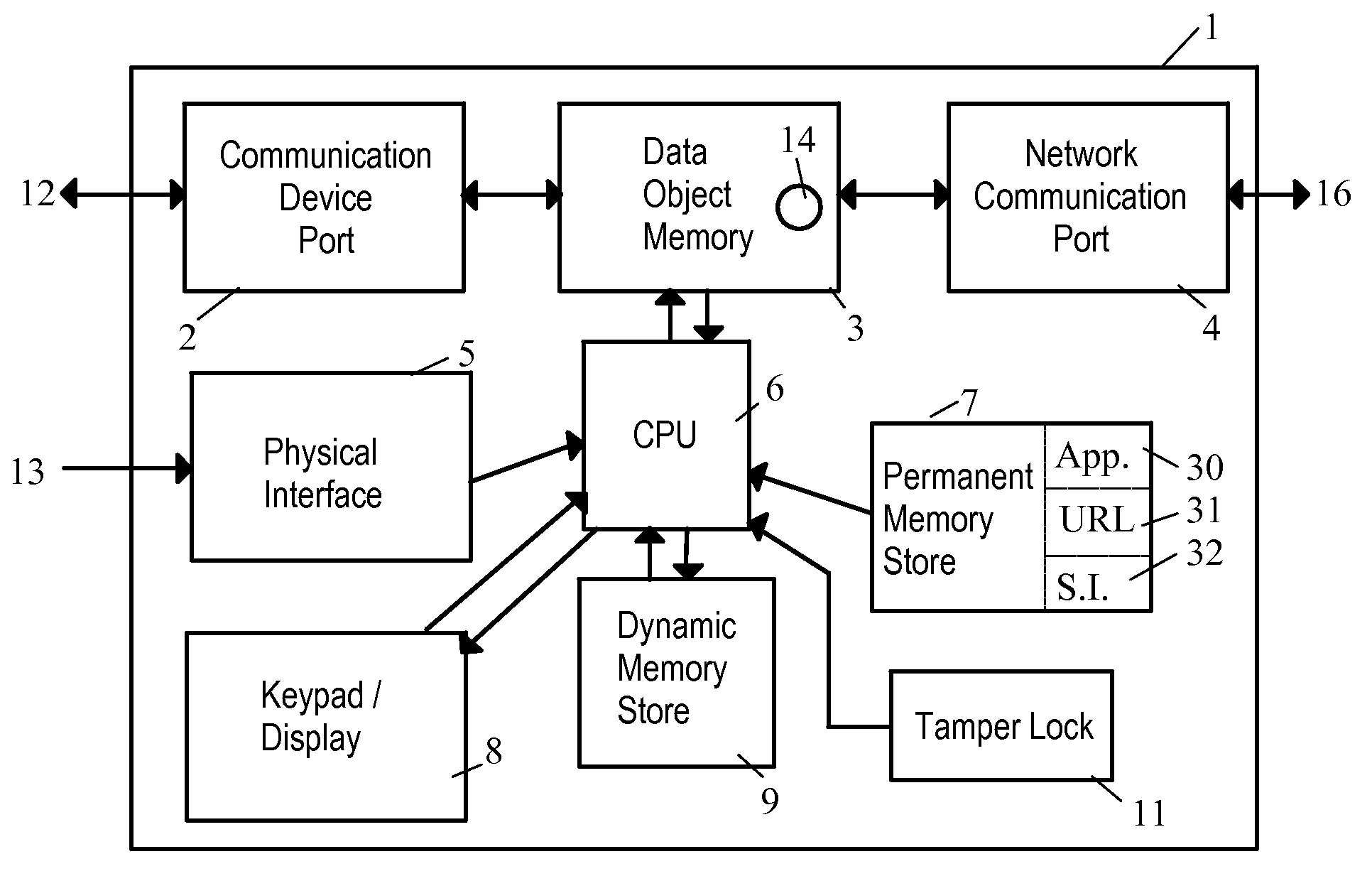
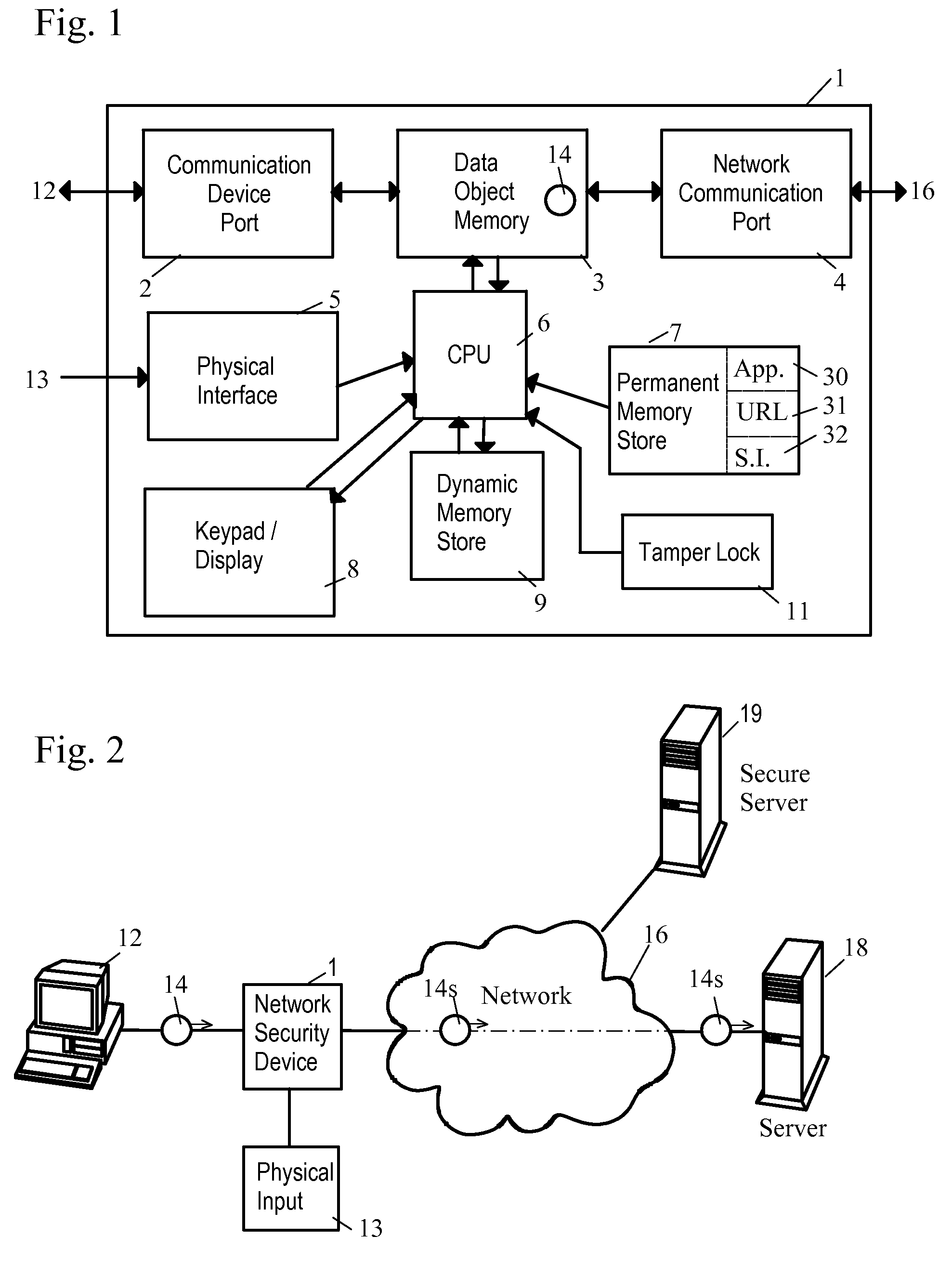
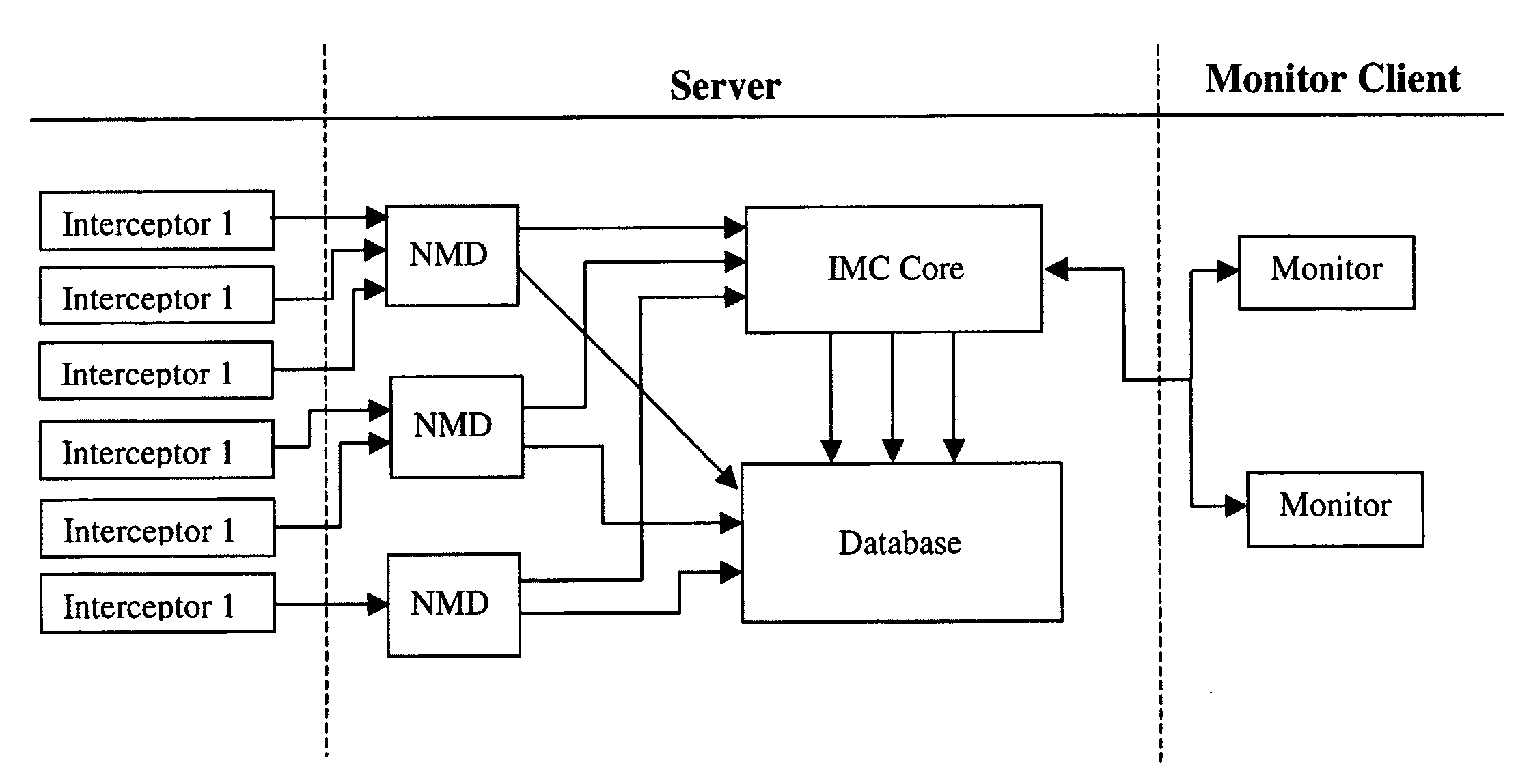
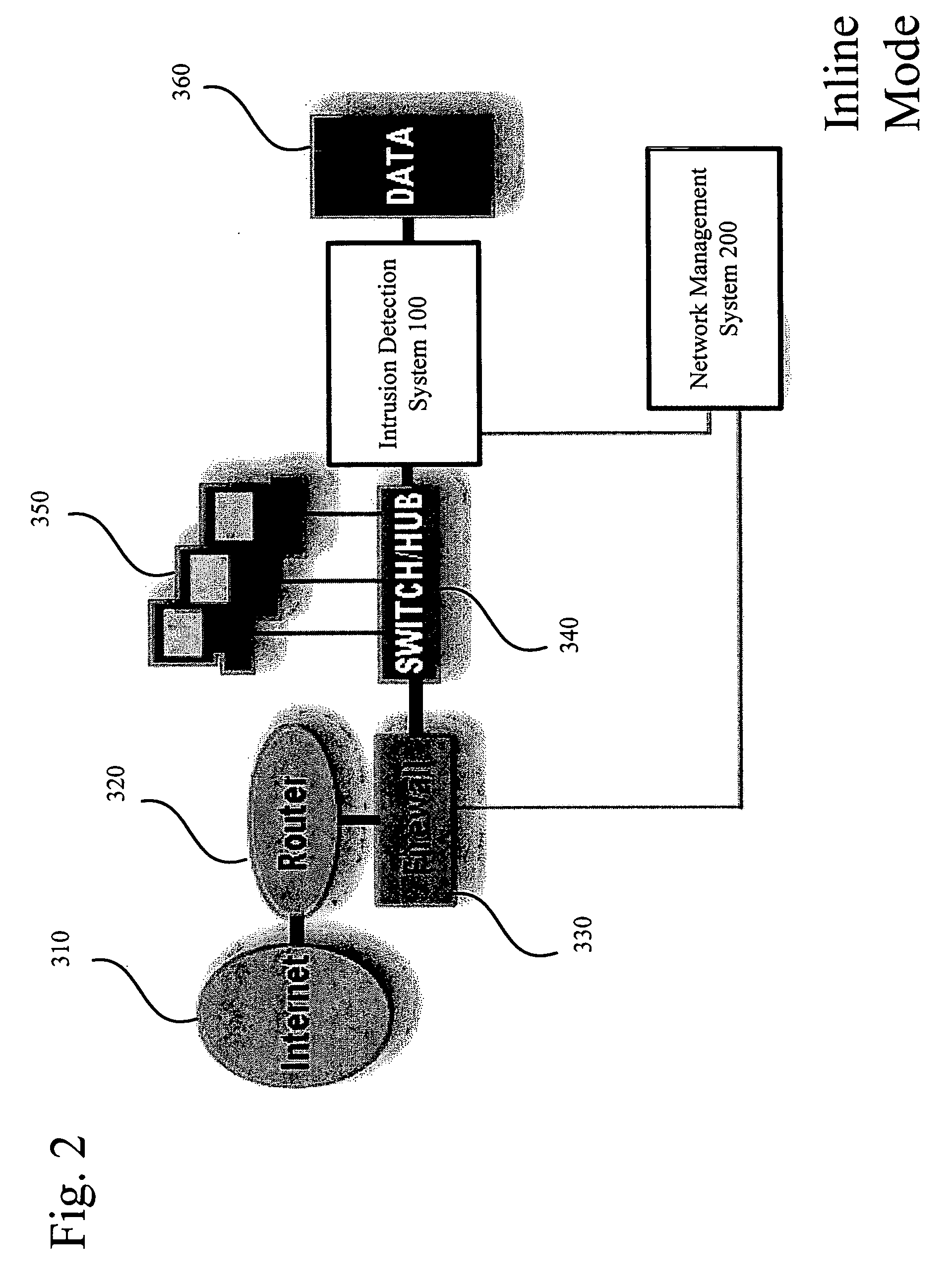
Network Security Device
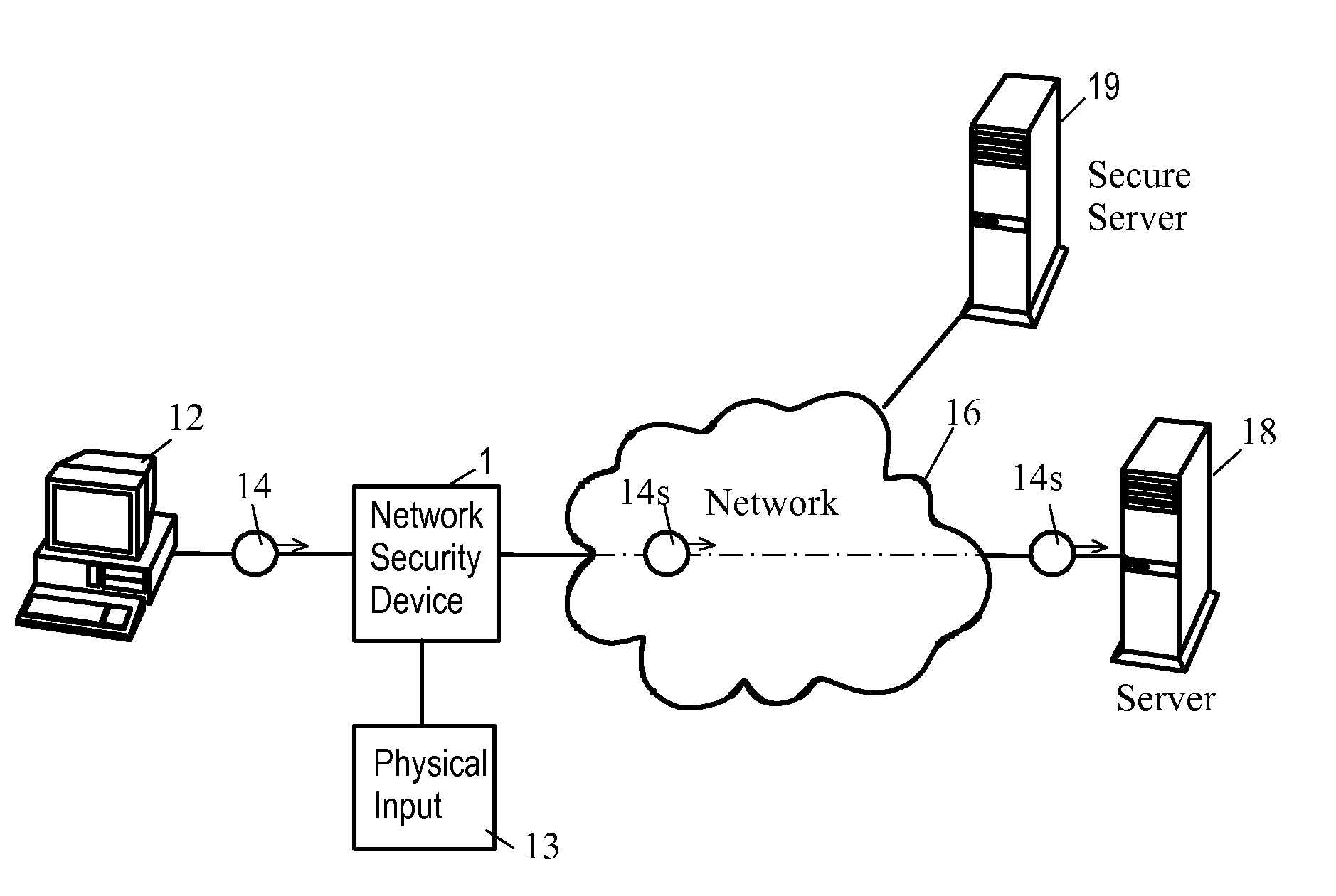
ActiveUS20070261112A1Function providedFacilitate law enforcement effortDigital data processing detailsUser identity/authority verificationNetwork packetDatapath
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
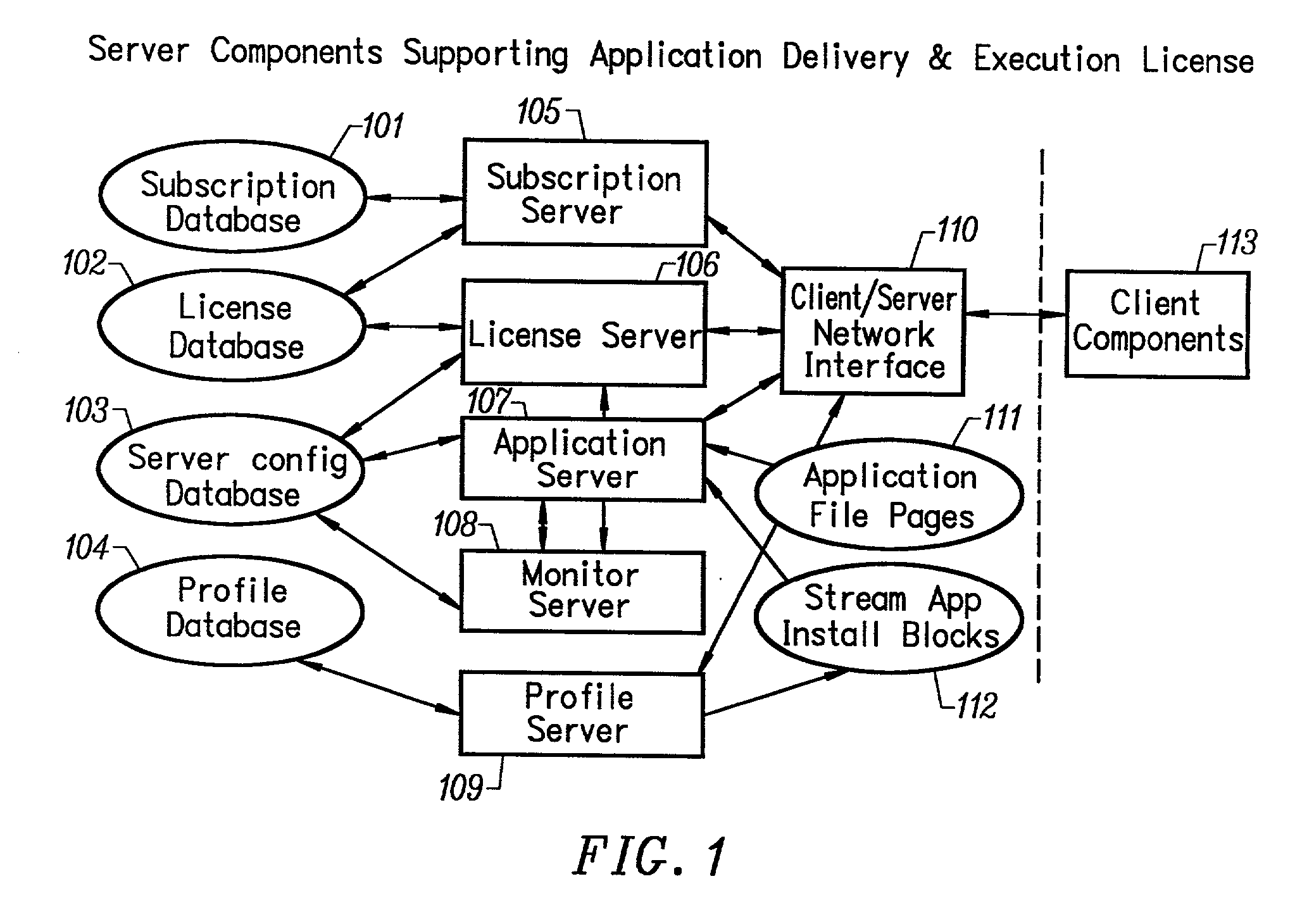
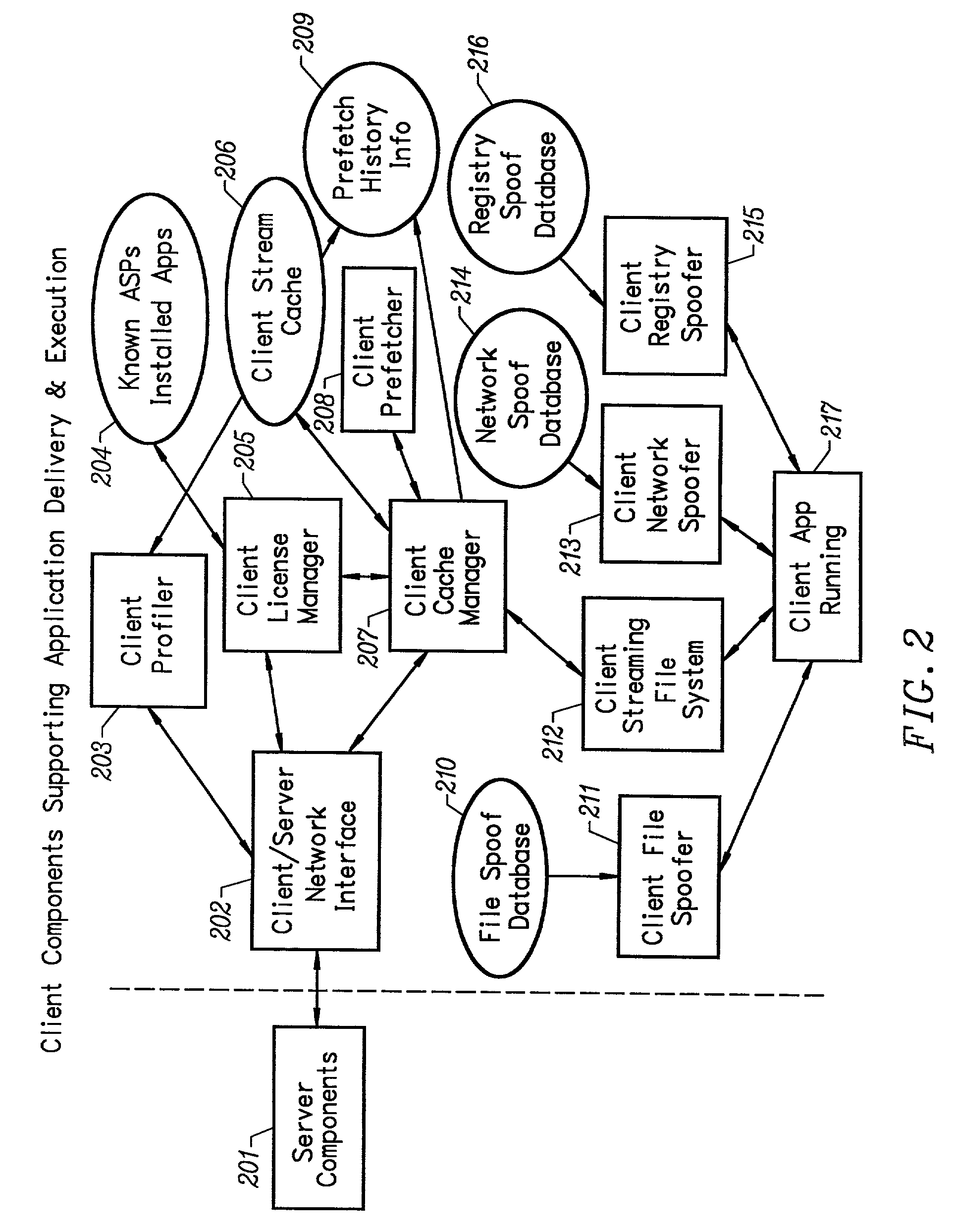
Network caching system for streamed applications
InactiveUS20030009538A1Data processing applicationsMultiple digital computer combinationsApplication serverNetwork packet
A network caching system for streamed applications provides for the caching of streamed applications within a computer network that are accessible by client systems within the network. Clients request streamed application file pages from other client systems, proxy servers, and application servers as each streamed application file is stored in a cache and used. Streamed application file page requests are broadcast to other clients using a multicast packet. Proxy servers are provided in the network that store a select set of streamed application file pages and respond to client requests by sending a response packet containing the requested streamed application file page if the streamed application file page is stored on the proxy server. Streamed application servers store all of the streamed application file pages. Clients try to send requests to streamed application servers as a last resort. Clients can concurrently send requests to other clients, to a proxy server, and to a streamed application server. Clients measure the response time to the clients requests placing a positive weighting on the more responsive request path and sending subsequent requests to the more positively weighted request path first.
Owner:NUMECENT HLDG
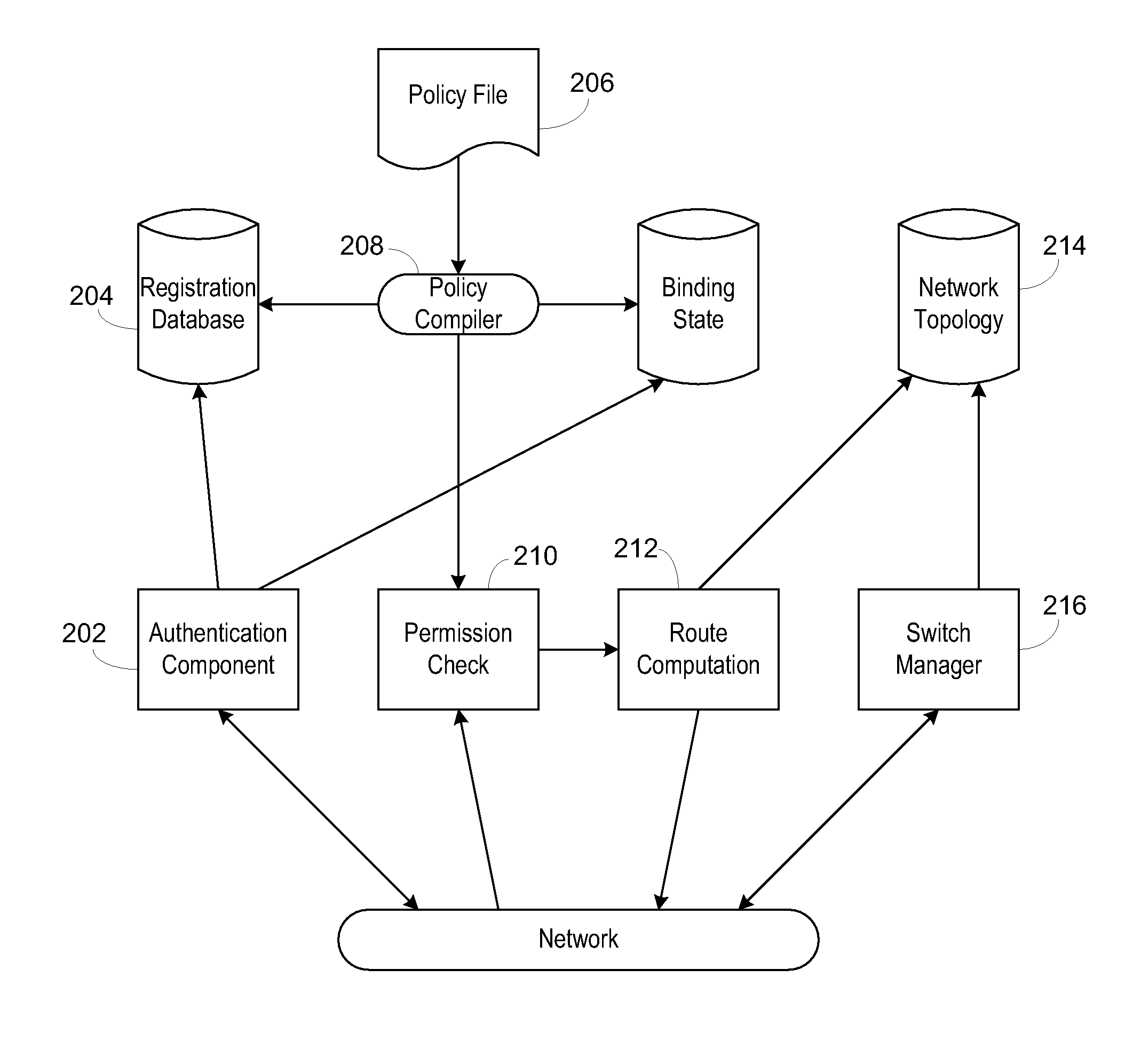
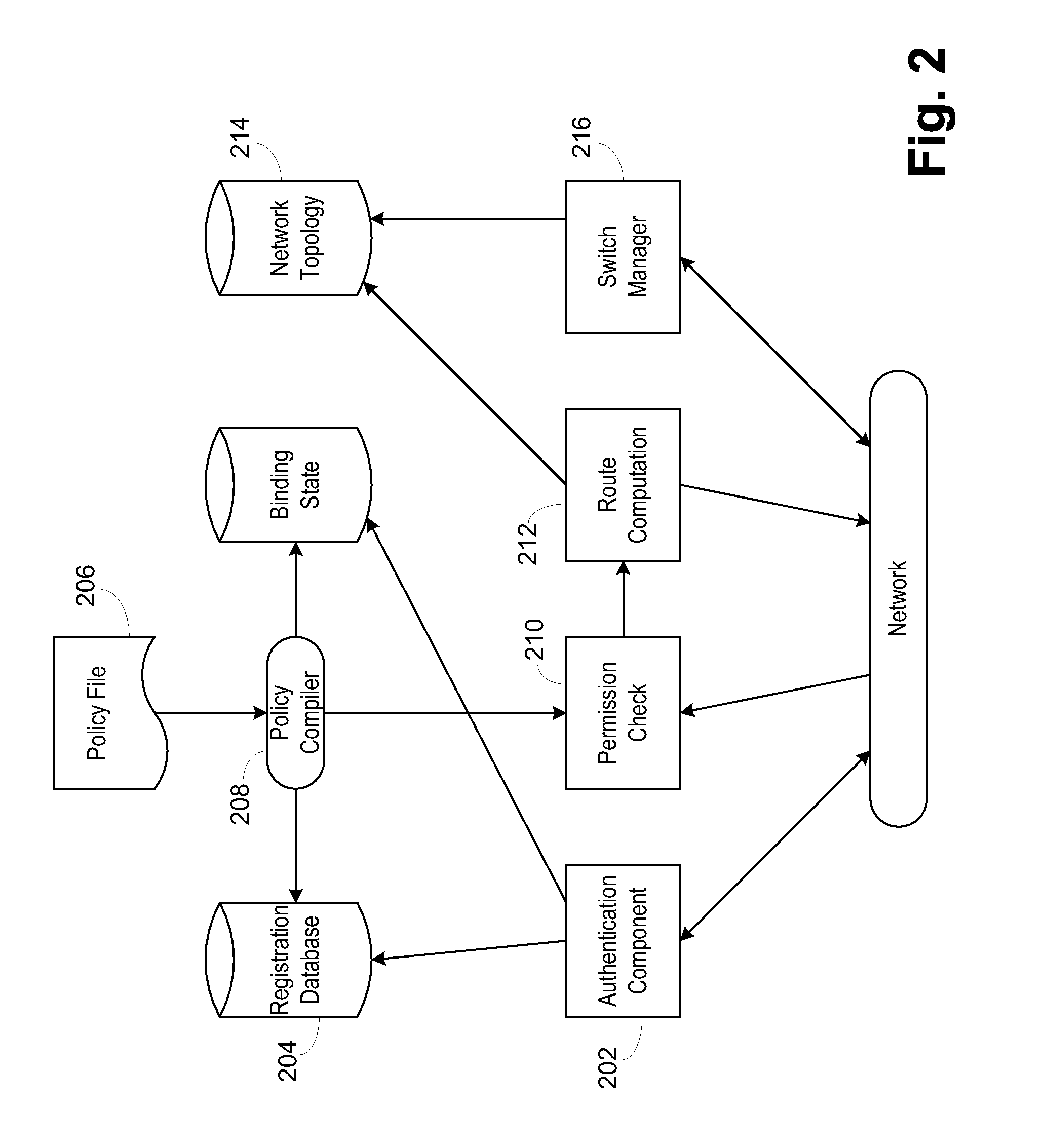
Secure network switching infrastructure
InactiveUS20080189769A1Reduces the trusted computing baseReduce overheadDigital data processing detailsUser identity/authority verificationNetwork packetNetwork control
Use of a centralized control architecture in a network. Policy declaration, routing computation, and permission checks are managed by a logically centralized controller. By default, hosts on the network can only route to the network controller. Hosts and users must first authenticate themselves with the controller before they can request access to the network resources. The controller uses the first packet of each flow for connection setup. When a packet arrives at the controller, the controller decides whether the flow represented by that packet should be allowed. The switches use a simple flow table to forward packets under the direction of the controller. When a packet arrives that is not in the flow table, it is forwarded to the controller, along with information about which port the packet arrived on. When a packet arrives that is in the flow table, it is forwarded according to the controller's directive.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Method and apparatus for regulating data flow between a communications device and a network
ActiveUS7890612B2Digital data processing detailsComputer security arrangementsTraffic capacityData stream
A network security device which acts as an “airlock” for traffic between a communications device and a network. Data is screened using rules based analysis by the security device to counter various threats, including viruses, phishing, attempts to “hijack” communications, communications with known malicious addresses or unknown addresses, and transmission of sensitive information. Data packets can be reassembled into files for screening, and decoded or expanded as necessary, but is never executed. The data path for the data being screened is kept separate from the operations of the network security device itself, so that the device is incorruptible—its programming cannot be compromised from outside sources. Updates for rules and entry of sensitive data for screening, etc., must be done through a physical interface, not via the normal data communications channel. The device is invisible—it cannot be “seen” by the network, and thus cannot be attacked.
Owner:ELECTRO GUARD CORP
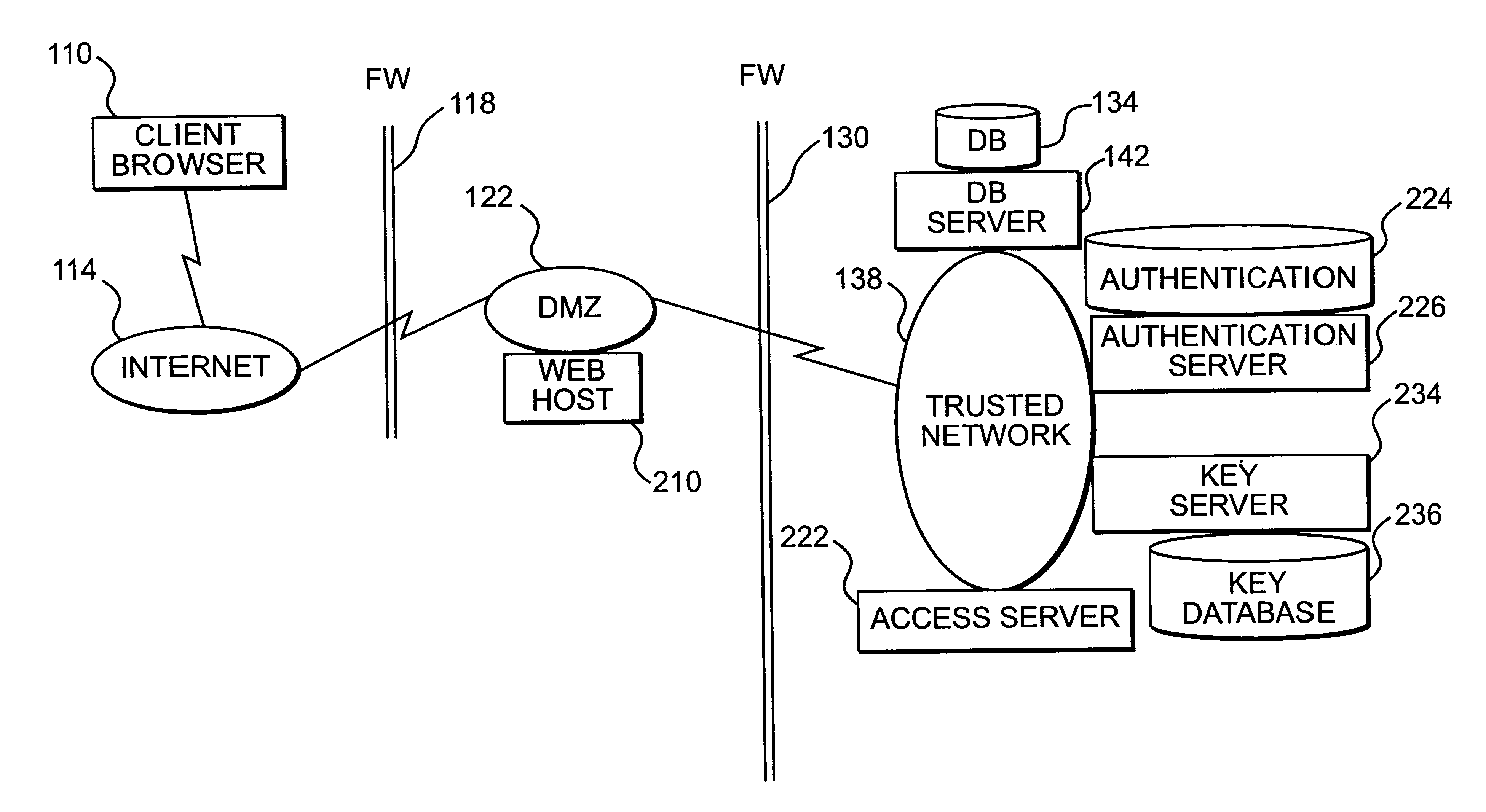
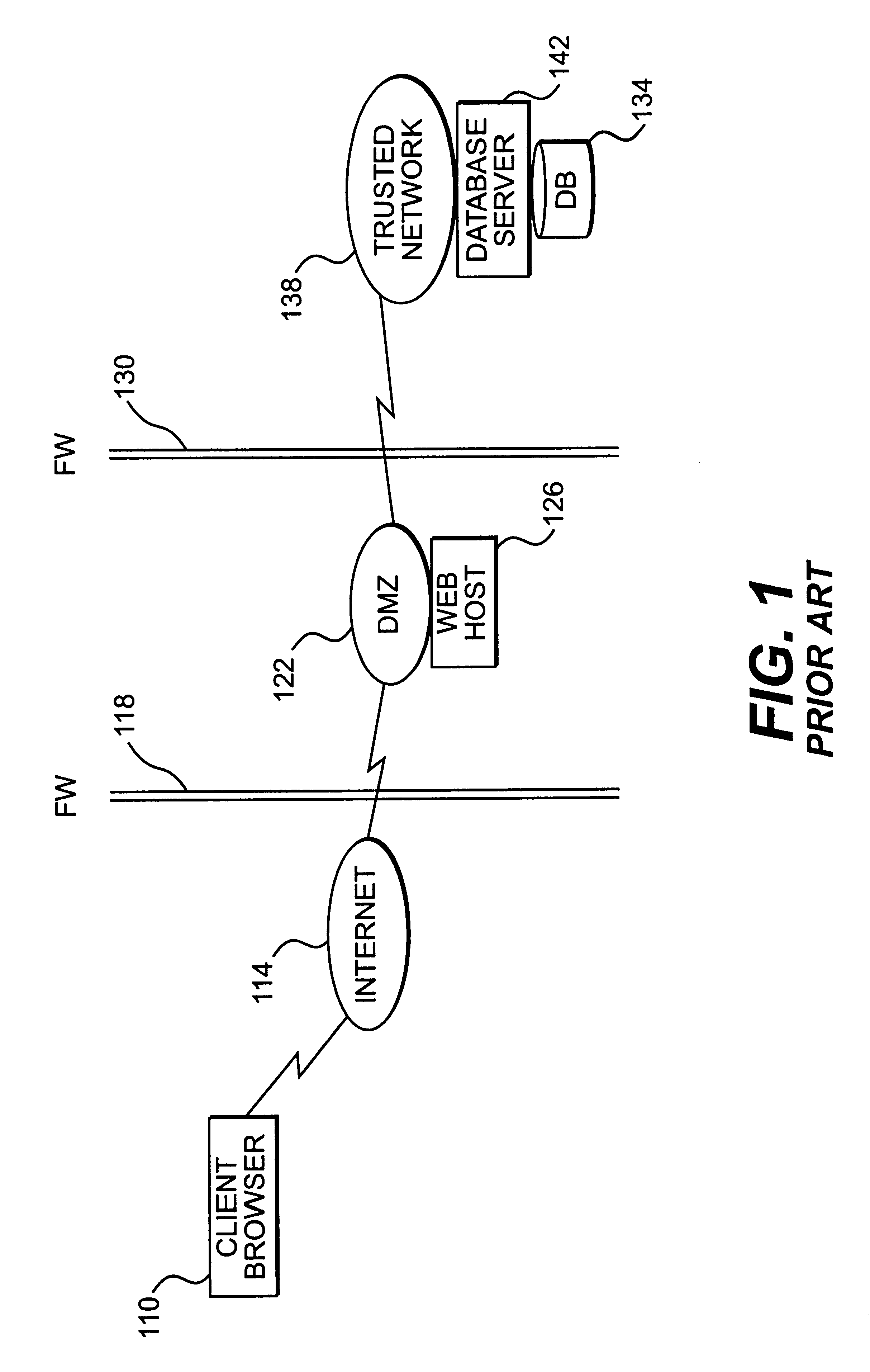
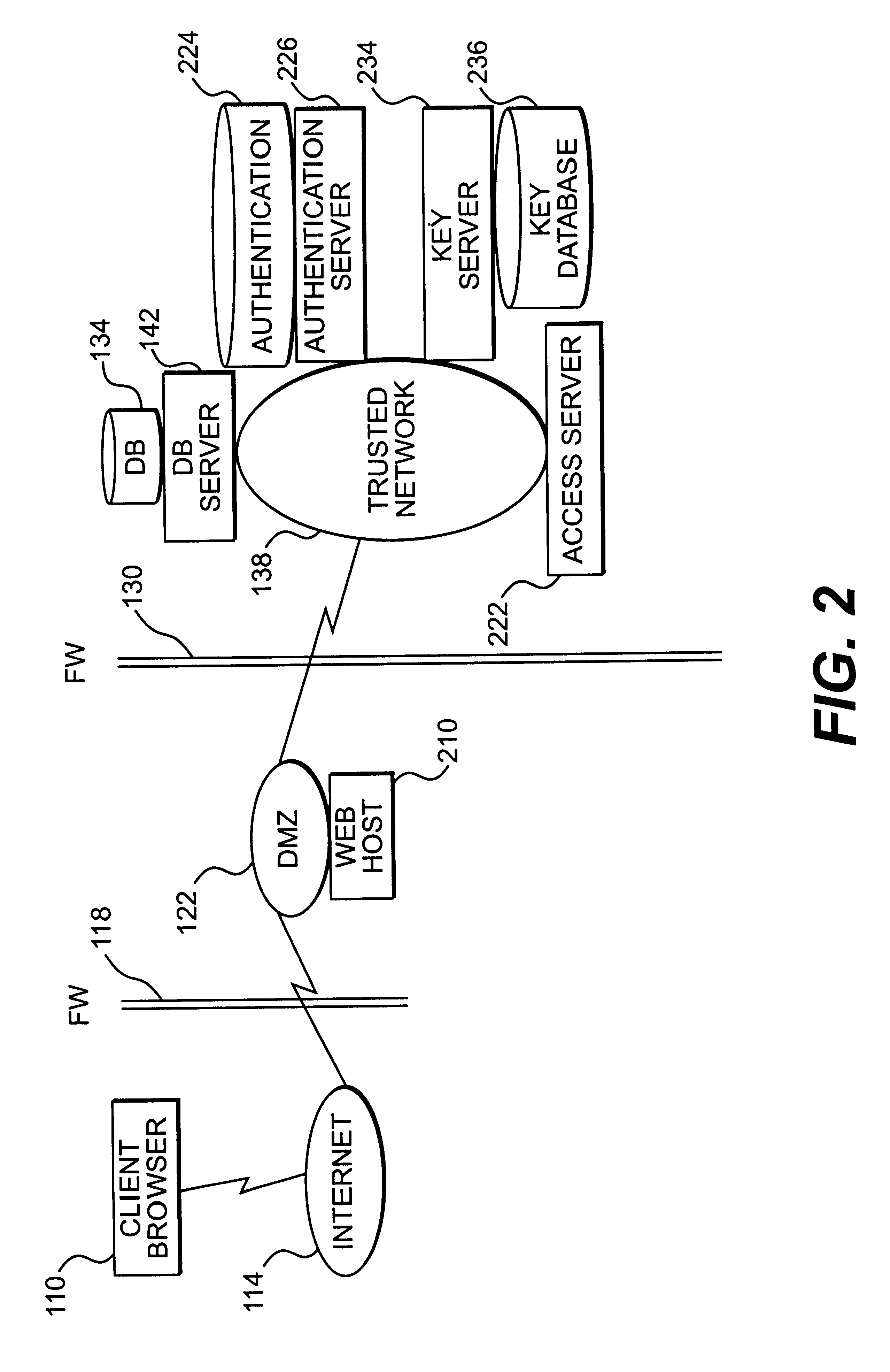
Apparatus and method for providing trusted network security
InactiveUS6199113B1Digital data processing detailsMultiple digital computer combinationsNetwork packetNetwork security policy
A session key is established for accessing a trusted network from a browser. An authentication process receives identification information from a user at the browser, and authenticates the user by checking the identification information against an authentication database. If the authentication database authenticates the user, a session key is created and stored at the browser. If the user is authenticated, a user profile defining access rights for the user is also retrieved. The user is then presented with access options based on the access rights defined in the user profile. In response to a user selection from the access page, the browser forwards an information request to the trusted network. The request includes a session key. A speaker object processes the information request and session key to form a network request packet. The network request packet is formed in a manner that allows authentication of the speaker object. The session packet is forwarded to a trusted network and processed. The packet is first authenticated to determine if it originated from the speaker object, and then the key is checked for validity at the trusted server. If the key is valid, the information request is processed and the information is returned to the user for display on the browser.
Owner:ORACLE INT CORP
Multiple network protocol encoder/decoder and data processor
InactiveUS6034963AReduce system costLow costTime-division multiplexData switching by path configurationRaw socketByte
A multiple network protocol encoder / decoder comprising a network protocol layer, data handler, O.S. State machine, and memory manager state machines implemented at a hardware gate level. Network packets are received from a physical transport level mechanism by the network protocol layer state machine which decodes network protocols such as TCP, IP, User Datagram Protocol (UDP), PPP, and Raw Socket concurrently as each byte is received. Each protocol handler parses and strips header information immediately from the packet, requiring no intermediate memory. The resulting data are passed to the data handler which consists of data state machines that decode data formats such as email, graphics, Hypertext Transfer Protocol (HTTP), Java, and Hypertext Markup Language (HTML). Each data state machine reacts accordingly to the pertinent data, and any data that are required by more than one data state machine is provided to each state machine concurrently, and any data required more than once by a specific data state machine, are placed in a specific memory location with a pointer designating such data (thereby ensuring minimal memory usage). Resulting display data are immediately passed to a display controller. Any outgoing network packets are created by the data state machines and passed through the network protocol state machine which adds header information and forwards the resulting network packet via a transport level mechanism.
Owner:NVIDIA CORP
Server load balancing using IP option field approach to identify route to selected server
InactiveUS20060233155A1Improve efficiencyData switching by path configurationRouting decisionField methods
A router for routing data from a client through load-balancing nodes to a selected load-balanced server among a plurality of servers in a network involves: receiving, at a last load balancing node associated with a selected server among the plurality of servers, a first packet of a server reply to a request from the client; storing identifiers of ingress interfaces on which the packet arrives, in a send path list for server load balancing, as the first packet of the server reply is routed from the last load balancing node to the client using hop-by-hop decisions; receiving subsequent packets of the client request; and forwarding the subsequent packets to the selected server only on a route that is defined by the send path list and without hop-by-hop routing decisions. Packet flows are routed from the same client to the same server without hop-by-hop routing decisions or repeated load-balancing decisions.
Owner:CISCO TECH INC
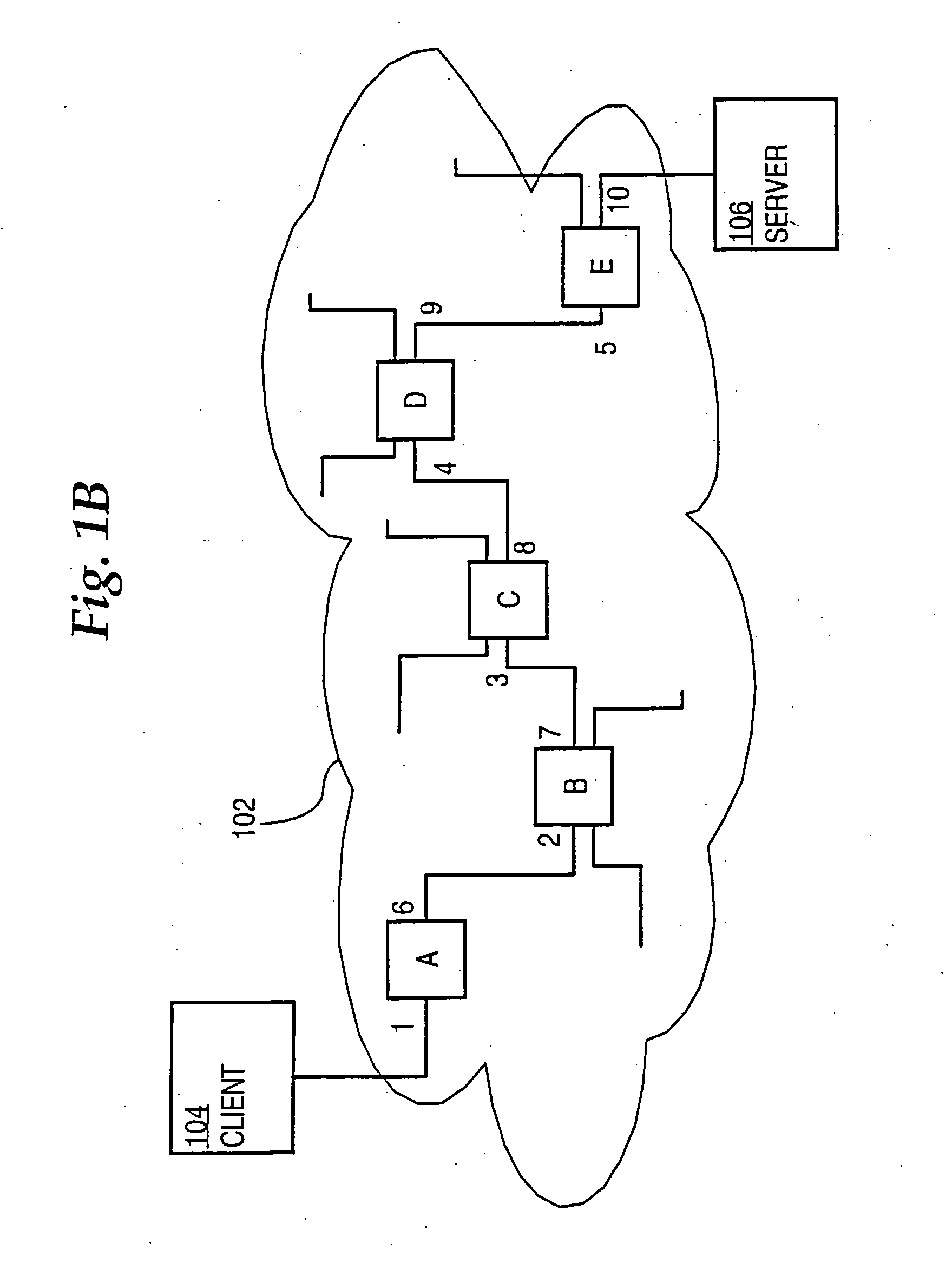
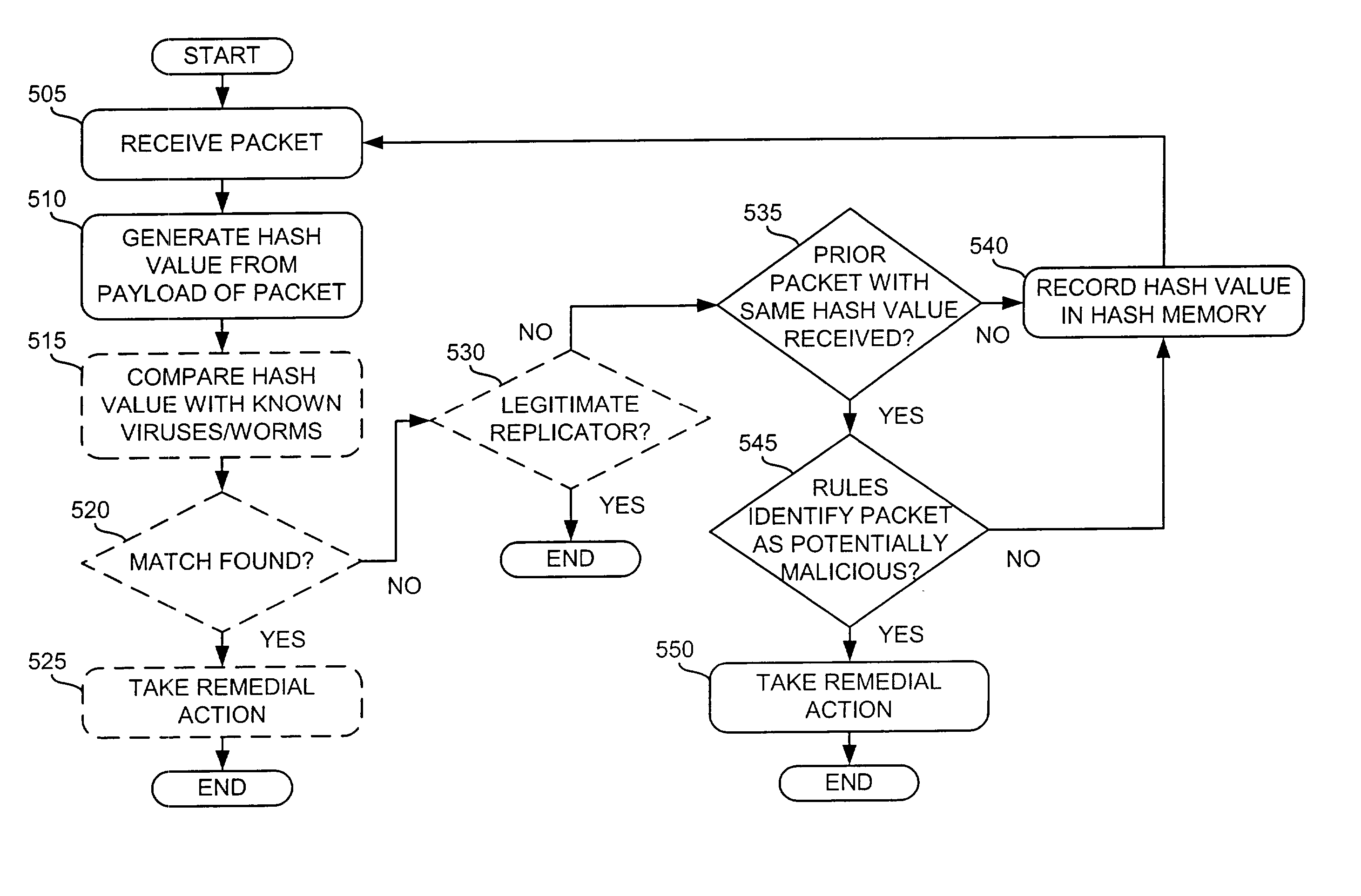
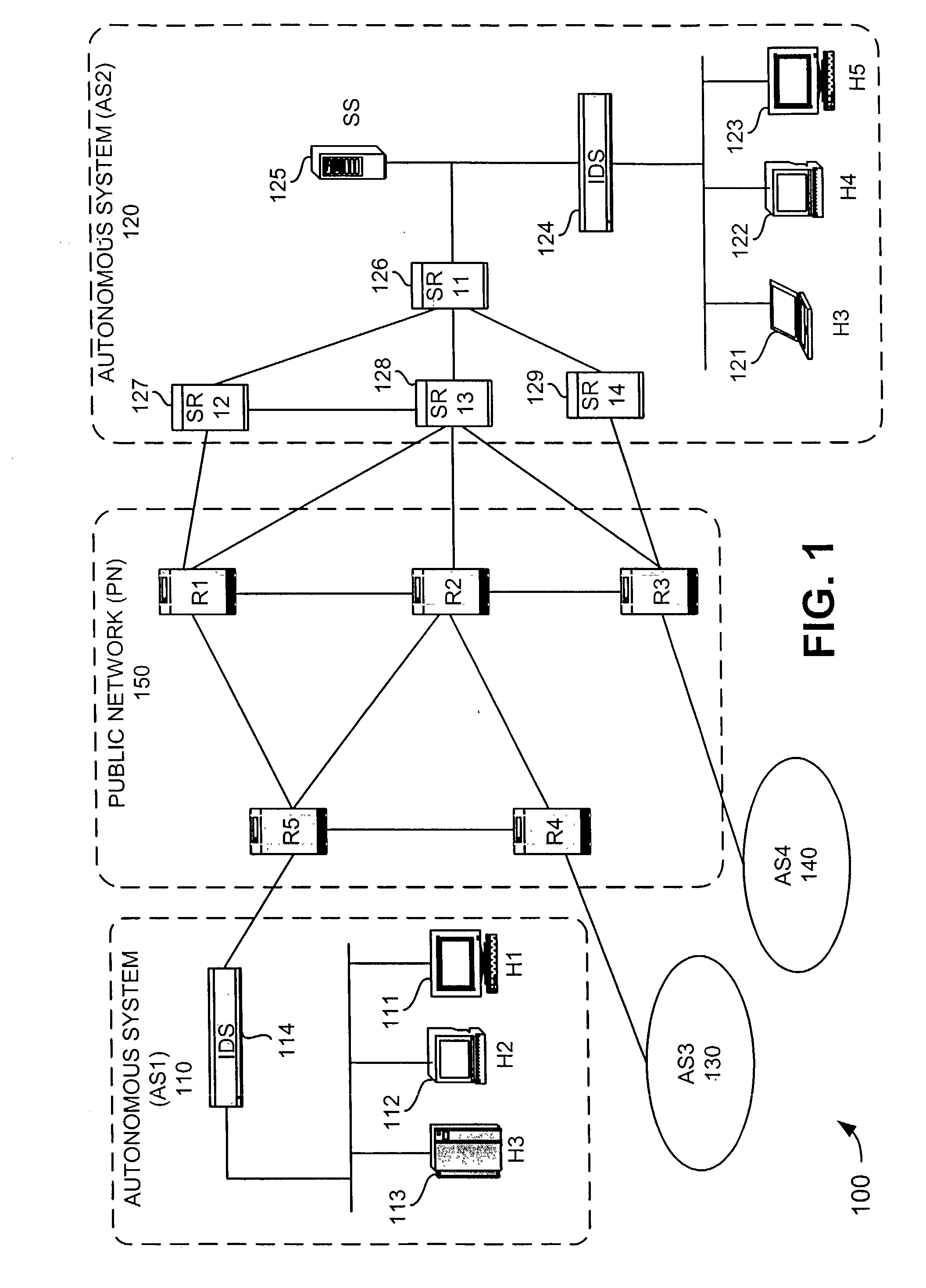
Hash-based systems and methods for detecting, preventing, and tracing network worms and viruses
A system (126-129) detects transmission of potentially malicious packets. The system (126-129) receives packets and generates hash values corresponding to each of the packets. The system (126-129) may then compare the generated hash values to hash values corresponding to prior packets. The system (126-129) determines that one of the packets is a potentially malicious packet when the generated hash value corresponding to the one packet matches one of the hash values corresponding to one of the prior packets and the one prior packet was received within a predetermined amount of time of the one packet. The system (126-129) may also facilitate the tracing of the path taken by a potentially malicious packet. In this case, the system (126-129) may receive a message that identifies a potentially malicious packet, generate hash values from the potentially malicious packet, and determine whether one or more of the generated hash values match hash values corresponding to previously-received packets. The system (126-129) may then identify the potentially malicious packet as one of the previously-received packets when one or more of the generated hash values match the hash value corresponding to the one previously-received packet.
Owner:STRAGENT
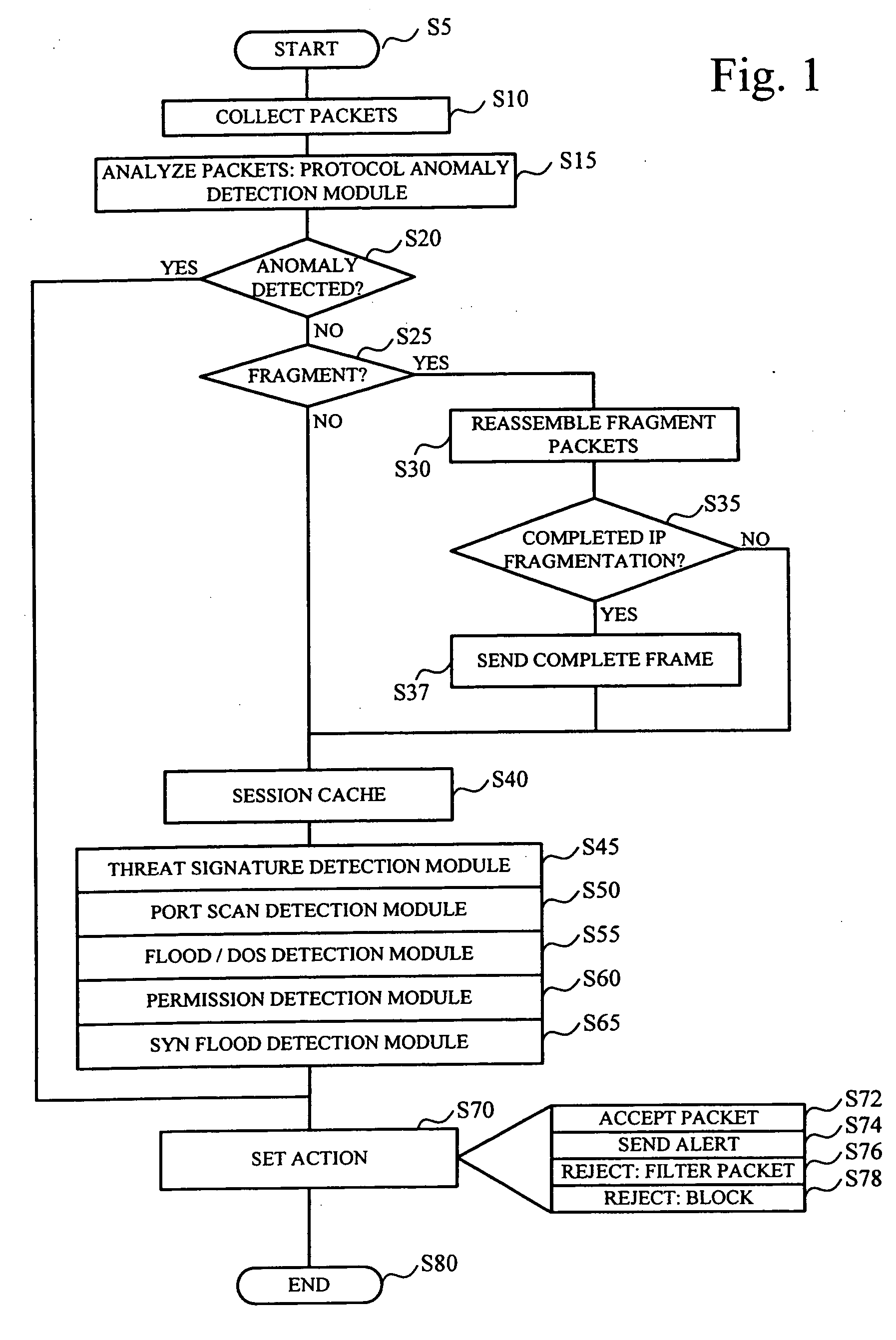
System and method for threat detection and response
InactiveUS20050018618A1Error preventionFrequency-division multiplex detailsNetwork packetDistributed computing
In accordance with varying embodiments of the invention, systems, devices and methods for analyzing a network packet received from a remote source and destined for a network resource, the network packet having associated packet data, and for identifying a plurality of network threats are disclosed.
Owner:STRATACLOUD
Data indicator for persistently allocated packets in a communications system
ActiveUS20110182245A1Error preventionWireless commuication servicesCommunications systemNetwork packet
An apparatus 310 employable in a communication system configured to determine a value for a new data indicator for semi-persistently allocated or scheduled resources. In one embodiment, the apparatus 310 includes a processor 320 configured to receive a cell radio network temporary identifier indicating a semi-persistent scheduling. The processor 320 is also configured to treat a reception of data with a new data indicator flag in accordance with the semi-persistent scheduling as one of a persistent initial transmission if a value of the new data indicator flag is equal to a first predefined value, and a retransmission of semi-persistent scheduling data if the value of the new data indicator flag is equal to a second predefined value.
Owner:NOKIA CORP
Audio and video decoder circuit and system
InactiveUS6369855B1Accelerates memory block moveAvoid confictTelevision system detailsPulse modulation television signal transmissionCoprocessorNetwork packet
An improved audio-visual circuit is provided that includes a transport packet parsing circuit for receiving a transport data packet stream, a CPU circuit for initializing said integrated circuit and for processing portions of said data packet stream, a ROM circuit for storing data, a RAM circuit for storing data, an audio decoder circuit for decoding audio portions of said data packet stream, a video decoder circuit for decoding video portions of said data packet stream, an NTSC / PAL encoding circuit for encoding video portions of said data packet stream, an OSD coprocessor circuit for processing OSD portions of said data packets, a traffic controller circuit moving portions of said data packet stream between portions of said integrated circuit, an extension bus interface circuit, a P1394 interface circuit, a communication coprocessors circuit, an address bus connected to said circuits, and a data bus connected to said circuits.
Owner:TEXAS INSTR INC
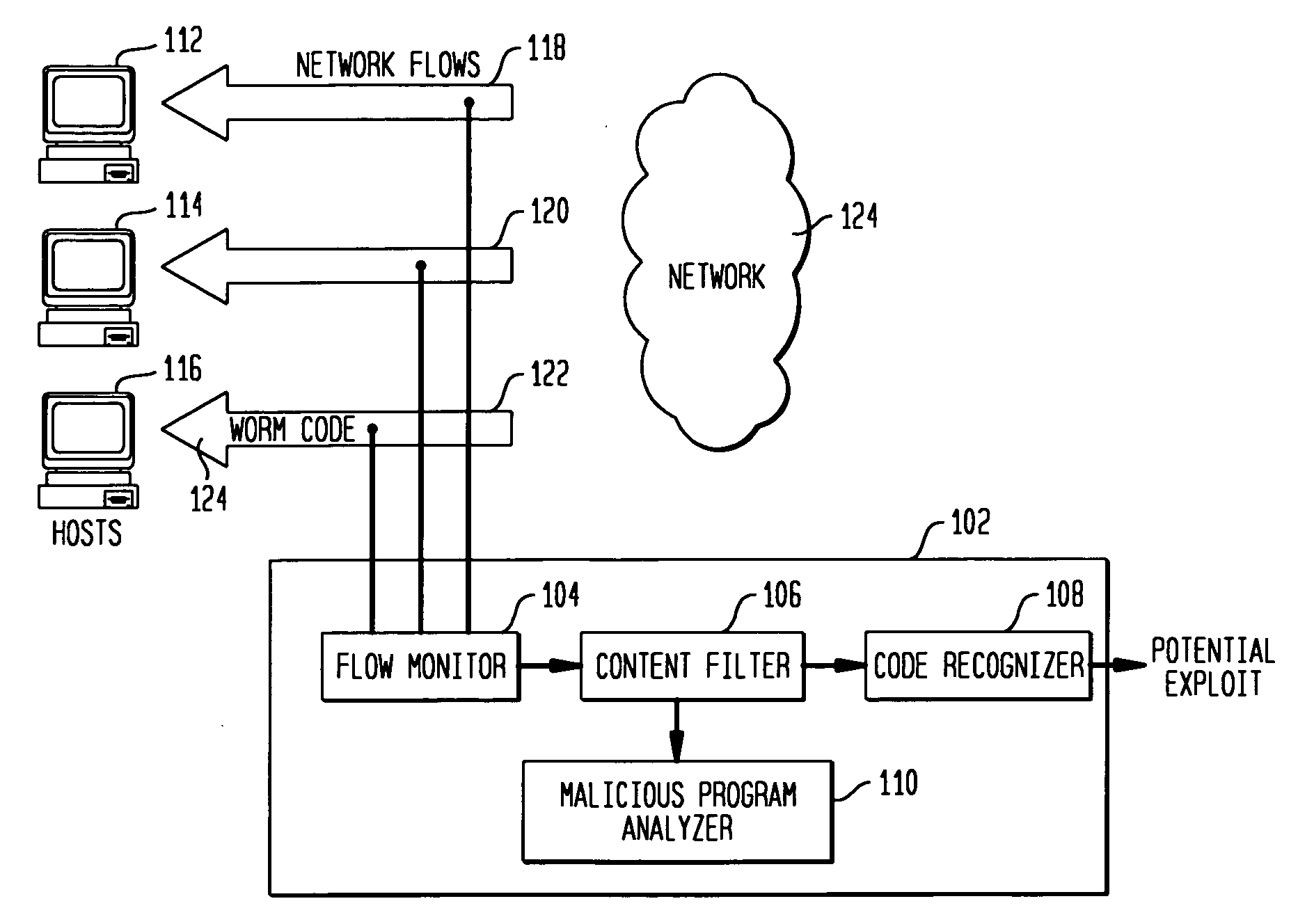
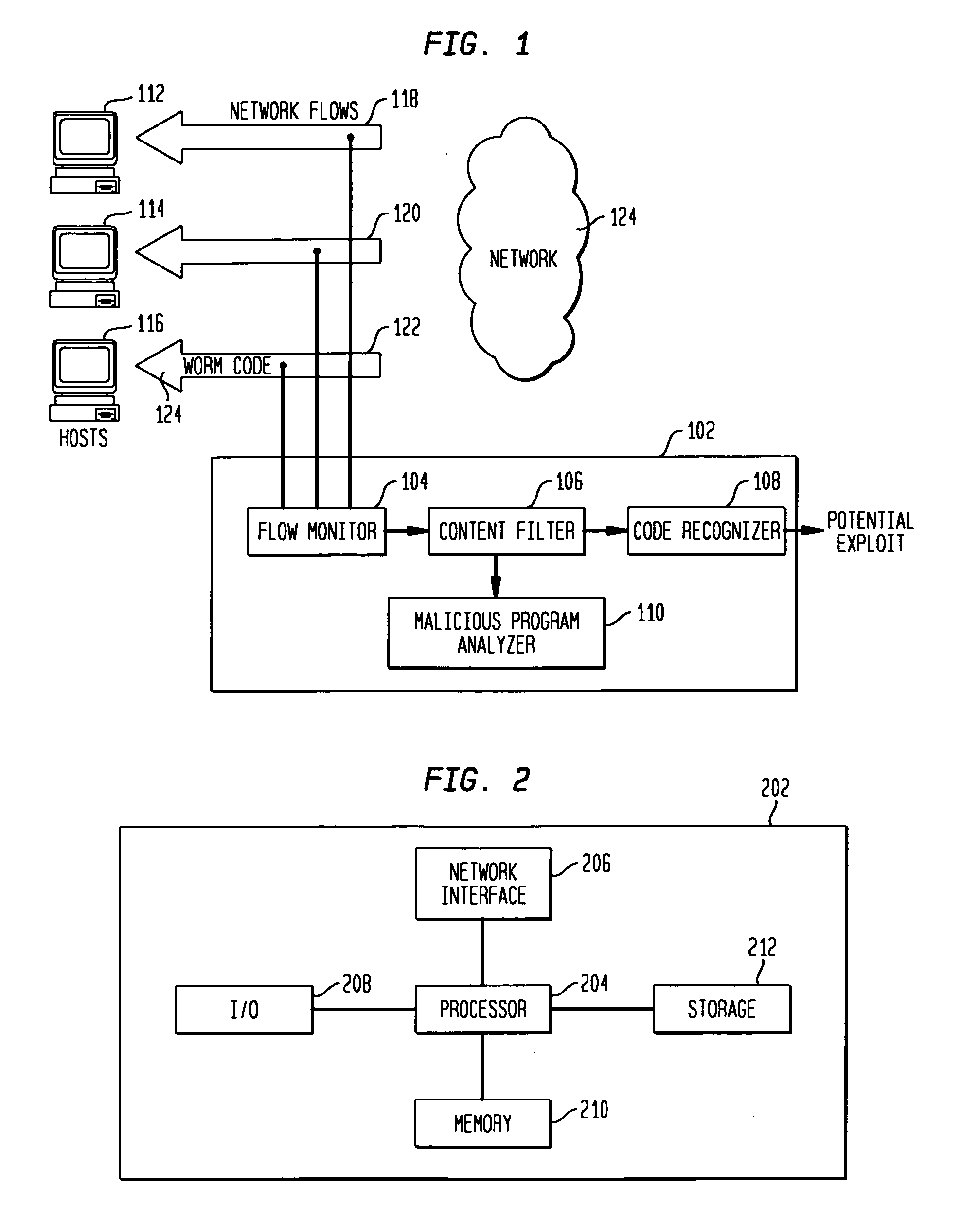
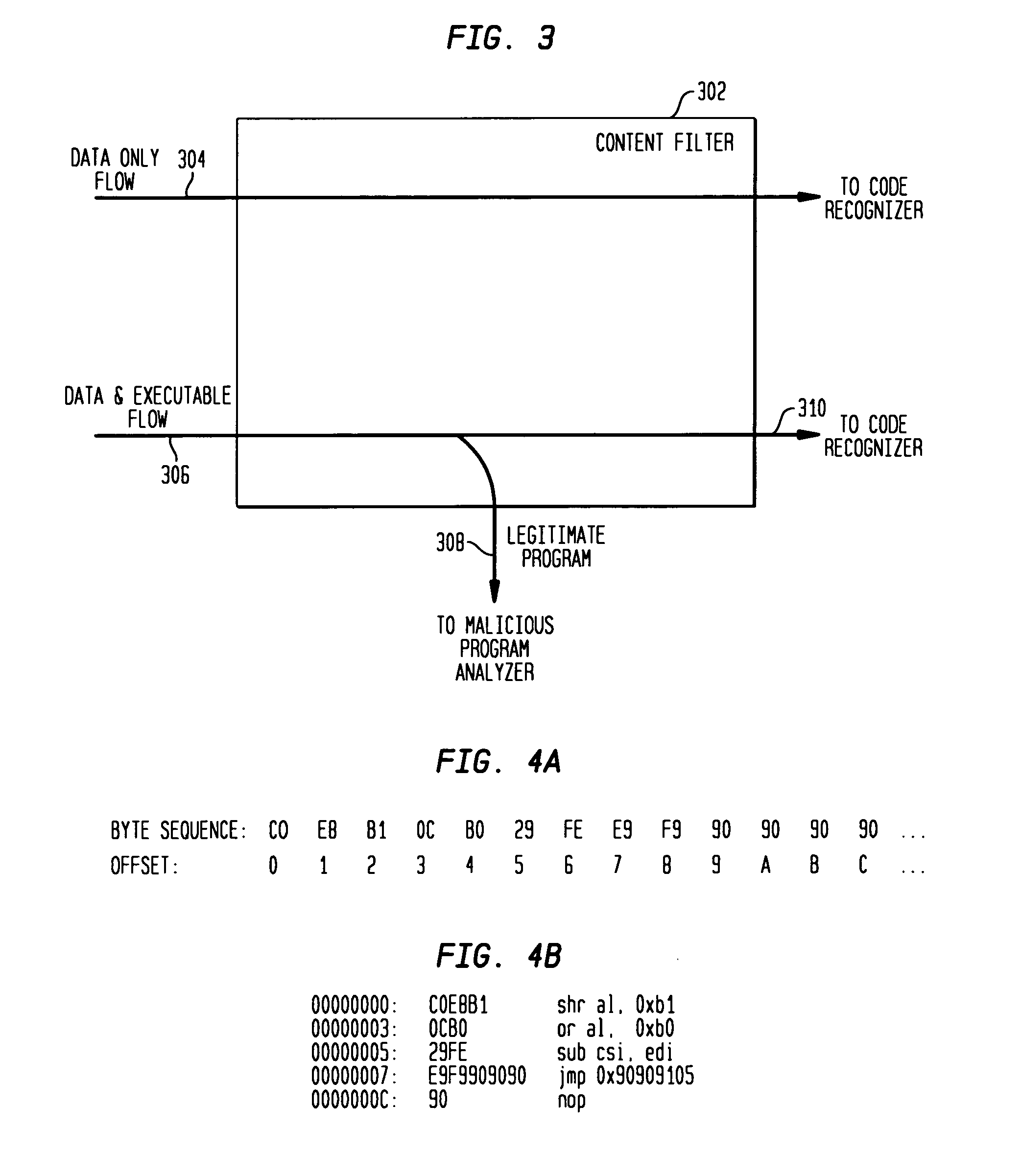
Detecting exploit code in network flows
InactiveUS20090328185A1Memory loss protectionUnauthorized memory use protectionData streamNetwork packet
Disclosed is a method and apparatus for detecting exploit code in network flows. Network data packets are intercepted by a flow monitor which generates data flows from the intercepted data packets. A content filter filters out legitimate programs from the data flows, and the unfiltered portions are provided to a code recognizer which detects executable code. Any embedded executable code in the unfiltered data flow portions is identified as a suspected exploit in the network flow. The executable code recognizer recognizes executable code by performing convergent binary disassembly on the unfiltered portions of the data flows. The executable code recognizer then constructs a control flow graph and performs control flow analysis, data flow analysis, and constraint enforcement in order to detect executable code. In addition to identifying detected executable code as a potential exploit, the detected executable code may then be used in order to generate a signature of the potential exploit, for use by other systems in detecting the exploit.
Owner:TELCORDIA TECHNOLOGIES INC
Method and system for queuing traffic in a wireless communications network
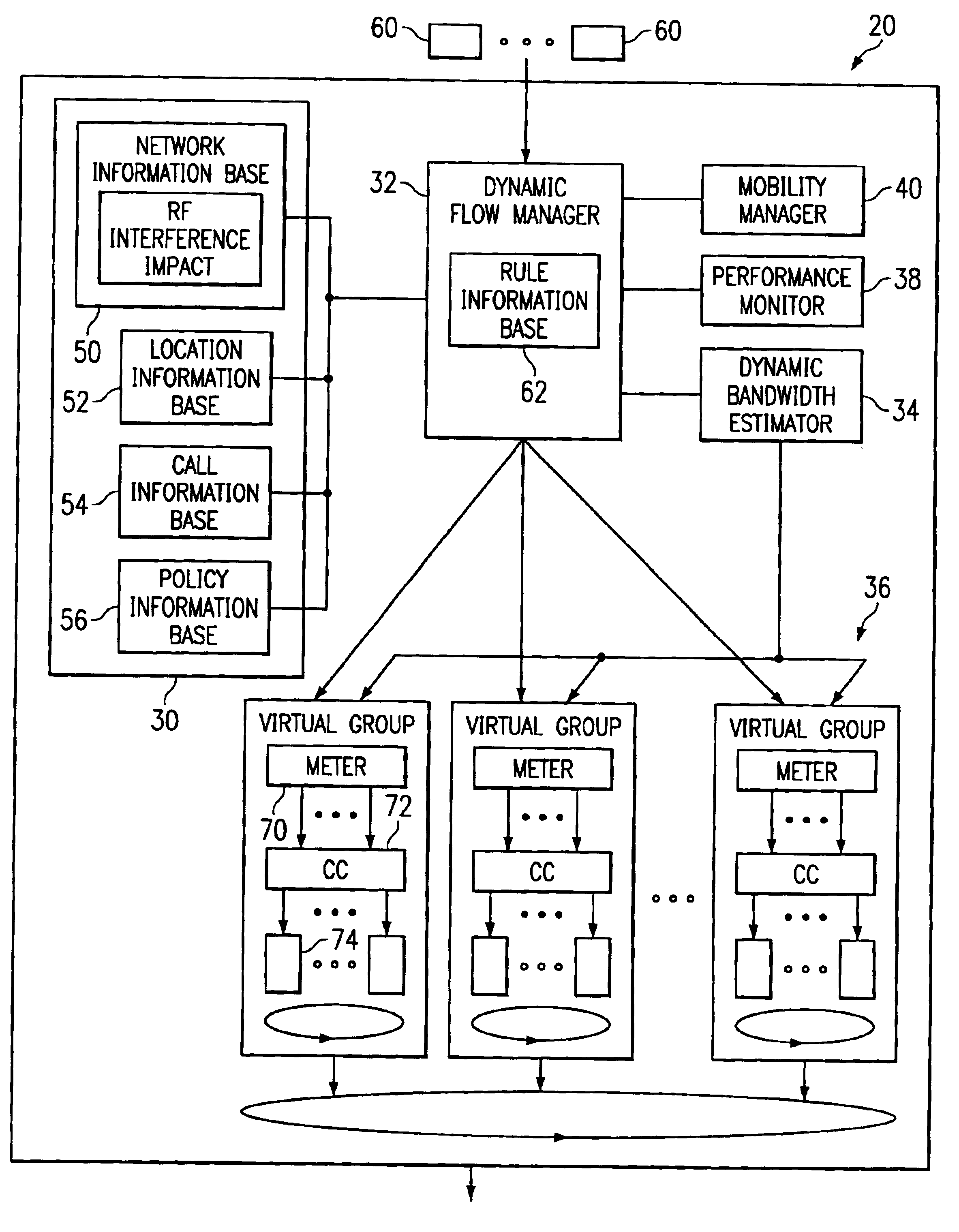
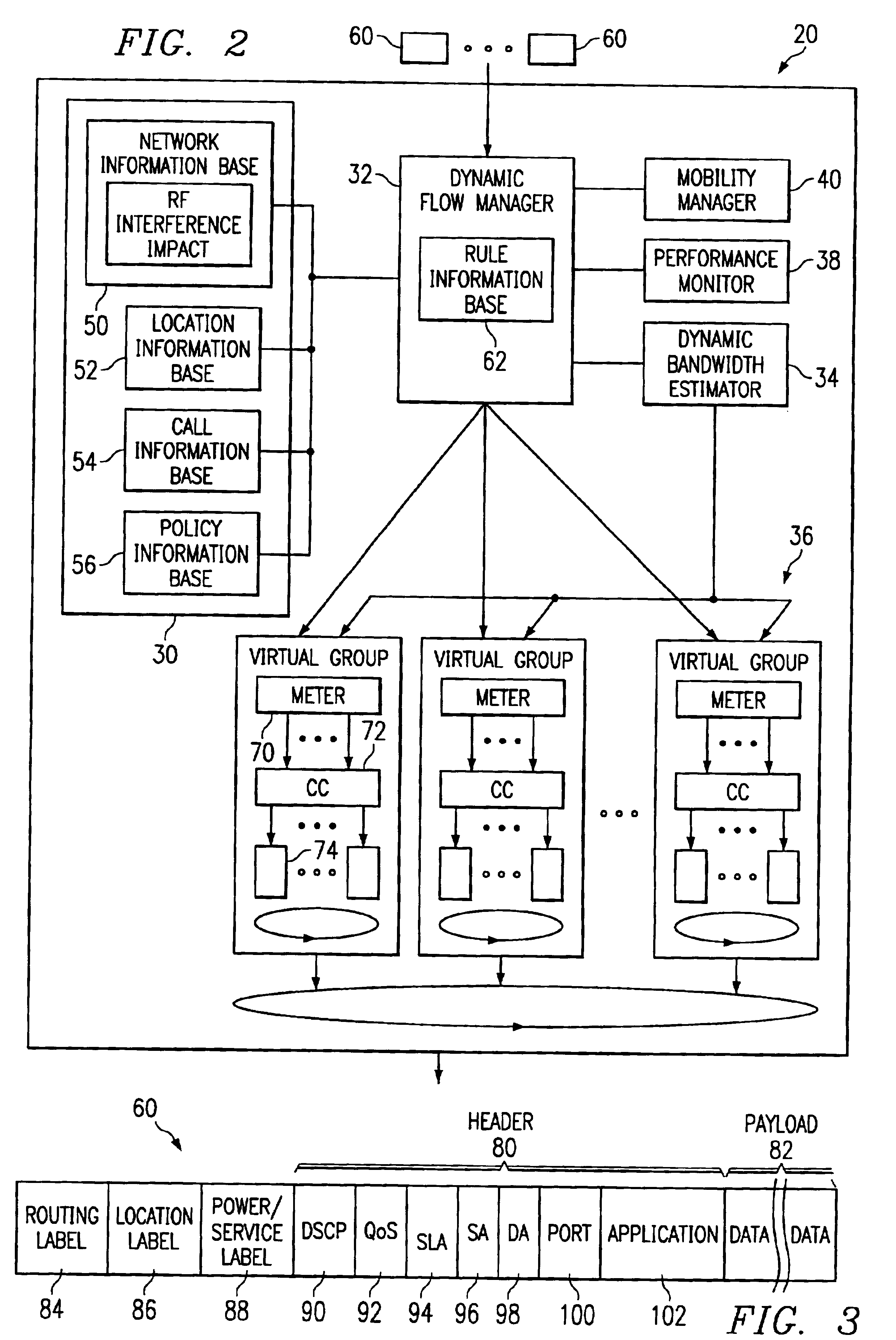
InactiveUS6865185B1Minimizing conflictPrevents indiscriminately penalizingNetwork traffic/resource managementData switching by path configurationNetwork packetWireless network
A method and system for queuing traffic in a wireless network includes receiving a stream of packets for transmission in the wireless network. Each packet includes a flow identifier and is assigned to one of the plurality of virtual groups based on the flow identifier. The virtual groups include discrete transmission resources. Each packet is queued in an assigned virtual group for transmission in the wireless network.
Owner:CISCO TECH INC
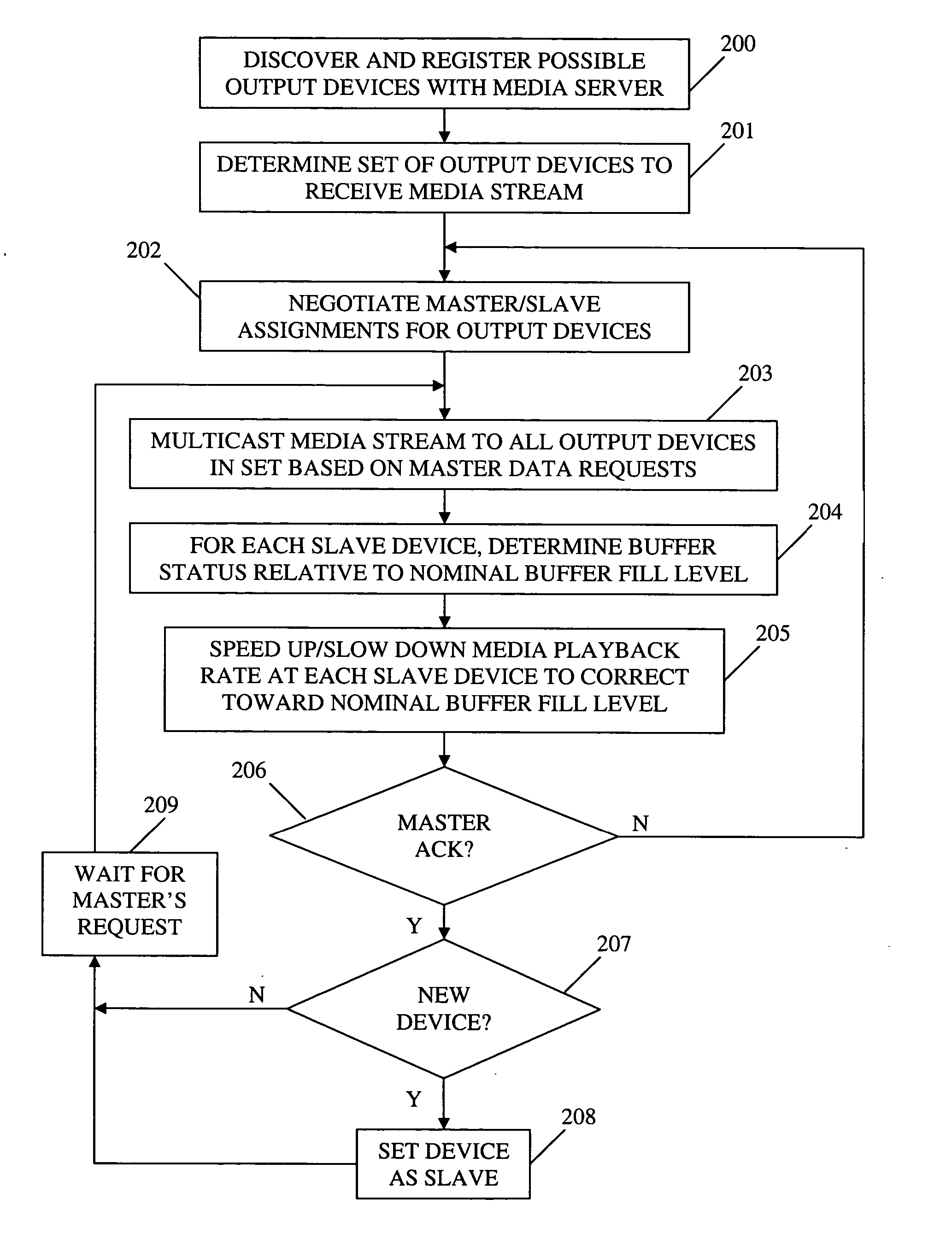
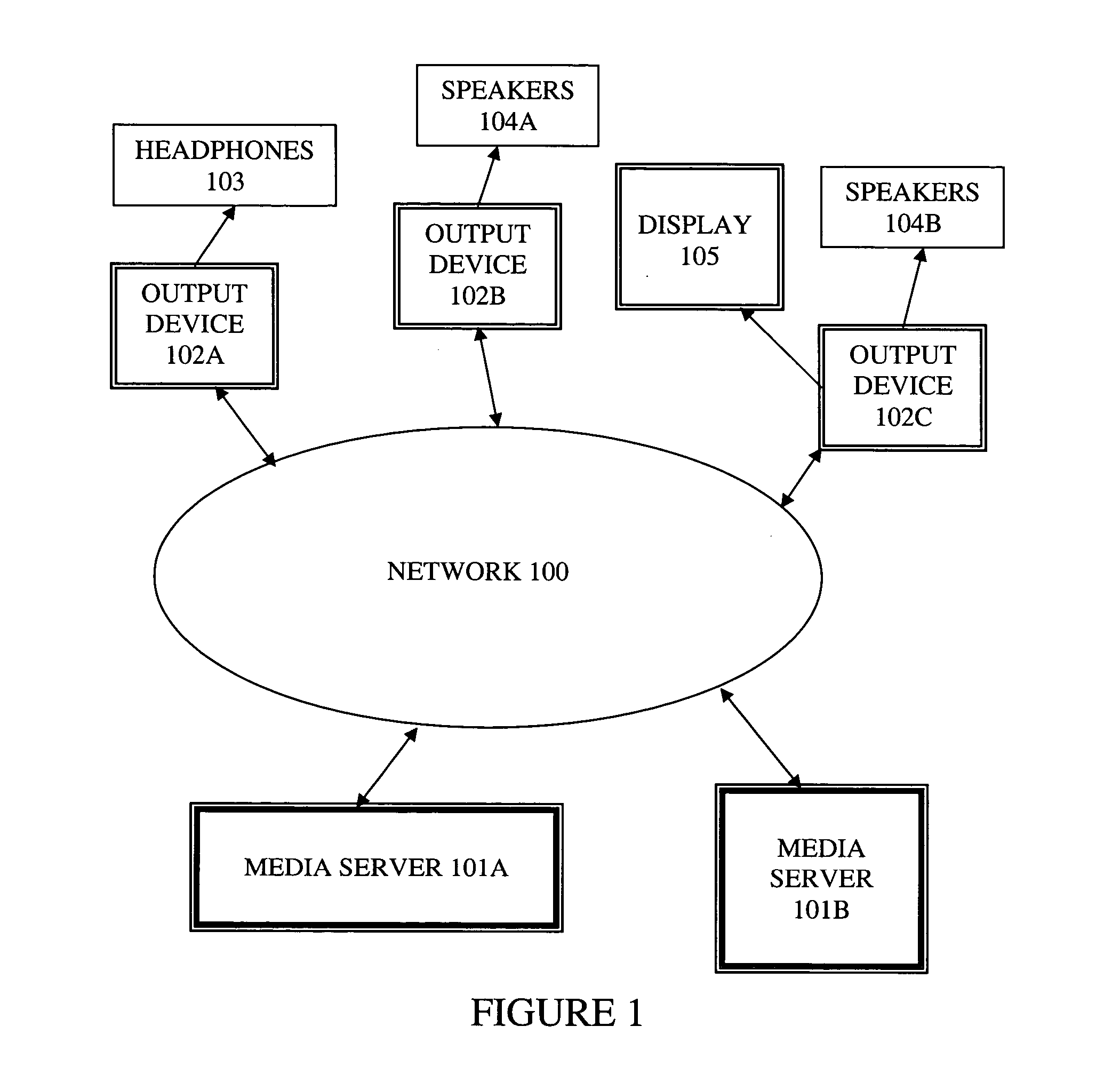
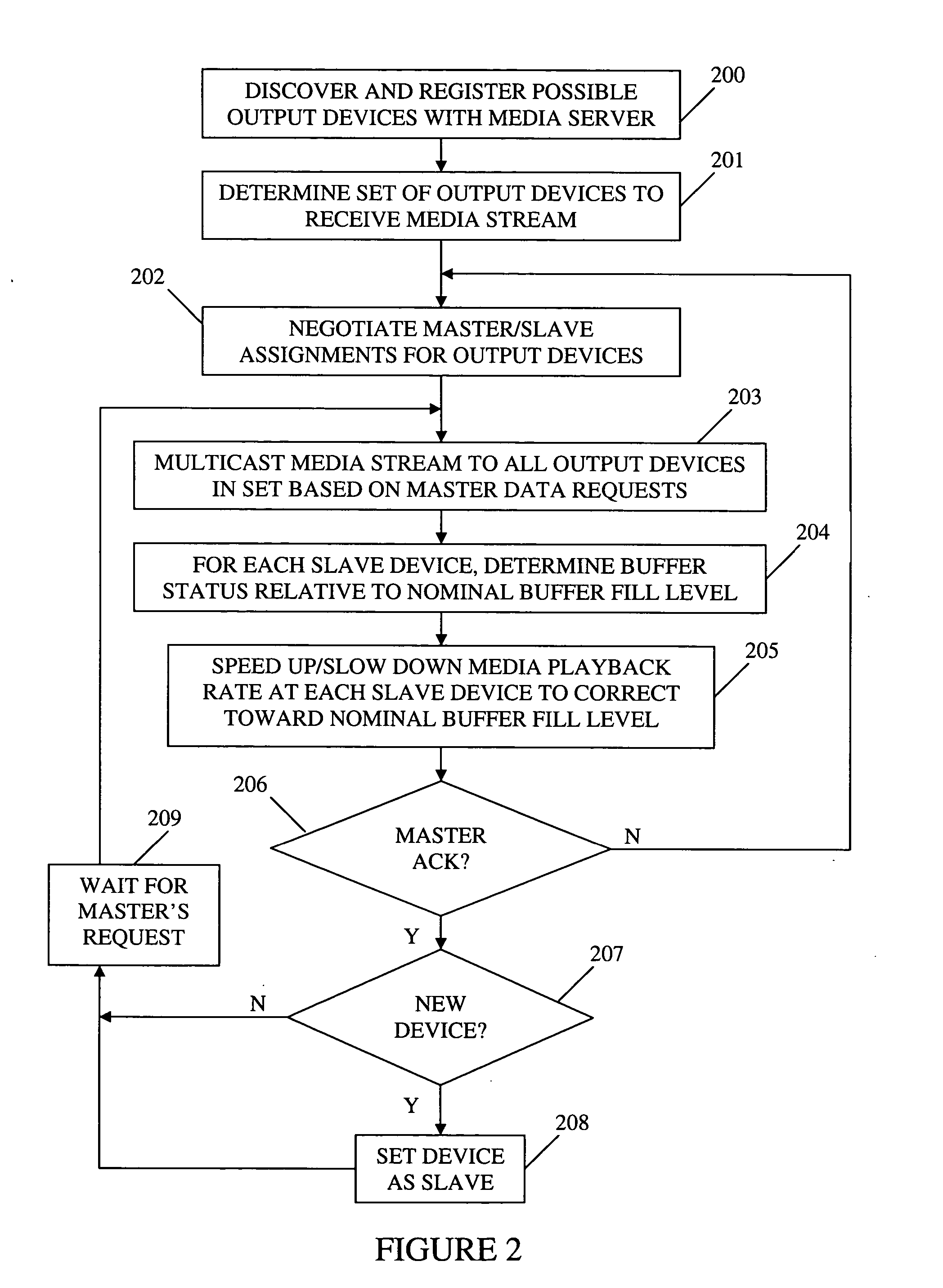
Method and apparatus for synchronizing playback of streaming media in multiple output devices
ActiveUS20060149850A1Maintaining average timing synchronizationError preventionTransmission systemsStreaming dataTimestamp
A method and apparatus for synchronizing streaming media with multiple output devices. One or more media servers serve media streams to one or more output devices (i.e., players). For playback synchronization, one output device is the “master”, whereas the remaining output devices are “slaves”. More data is requested from the media server by the “master” device to maintain a nominal buffer fill level over time. The “slave” devices receive streamed data from the media server at the rate determined by the master device's data requests, and the average rate of data flow over the streaming network is thus controlled by the frequency of the single “master” device's crystal. “Slave” devices make playback rate corrections to maintain respective buffer fill levels within upper and lower threshold levels. For slow networks, each media data packet timestamp is calculated from the time the master's buffer reaches nominal level.
Owner:SNAP ONE LLC
Method and apparatus for monitoring traffic in a network
InactiveUS20040083299A1Energy efficient ICTDigital data information retrievalTraffic capacityNetwork packet
A monitor for and a method of examining packets passing through a connection point on a computer network. Each packets conforms to one or more protocols. The method includes receiving a packet from a packet acquisition device and performing one or more parsing / extraction operations on the packet to create a parser record comprising a function of selected portions of the packet. The parsing / extraction operations depend on one or more of the protocols to which the packet conforms. The method further includes looking up a flow-entry database containing flow-entries for previously encountered conversational flows. The lookup uses the selected packet portions and determining if the packet is of an existing flow. If the packet is of an existing flow, the method classifies the packet as belonging to the found existing flow, and if the packet is of a new flow, the method stores a new flow-entry for the new flow in the flow-entry database, including identifying information for future packets to be identified with the new flow-entry. For the packet of an existing flow, the method updates the flow-entry of the existing flow. Such updating may include storing one or more statistical measures. Any stage of a flow, state is maintained, and the method performs any state processing for an identified state to further the process of identifying the flow. The method thus examines each and every packet passing through the connection point in real time until the application program associated with the conversational flow is determined.
Owner:PACKET INTELLIGENCE
LED light communication system
InactiveUS20080310850A1Easy to transportFirmly connectedPower distribution line transmissionElectric/electromagnetic visible signallingTransceiverPhotovoltaic detectors
An LED light and communication system includes at least one optical transceiver, the optical transceiver including a light support and a processor. The light support has a plurality of light emitting diodes and at least one photodetector attached thereto, the light emitting diodes receiving power from a power source. The processor is in communication with the light emitting diodes and the at least one photodetector, the processor capable of illuminating the light emitting diodes to simultaneously create at least one first light signal, and at least one second light signal, the first light signal being observable to the unaided eyes of an individual and the second light signal not being observable to the unaided eyes of the individual. The second light signal includes at least one data packet. The at least one data packet comprises global positioning system (GPS) location information.
Owner:FEDERAL LAW ENFORCEMENT DEV SERVICES
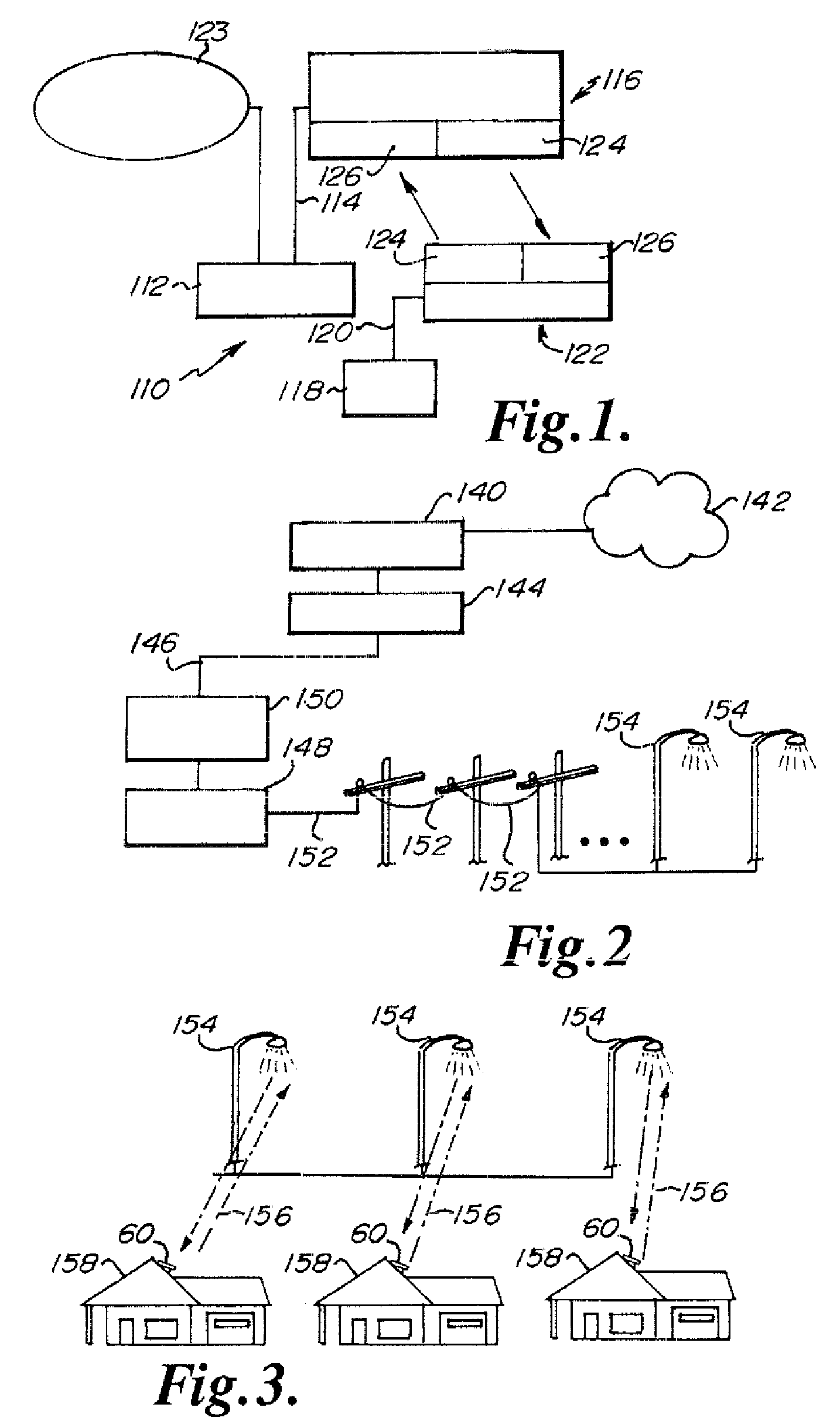
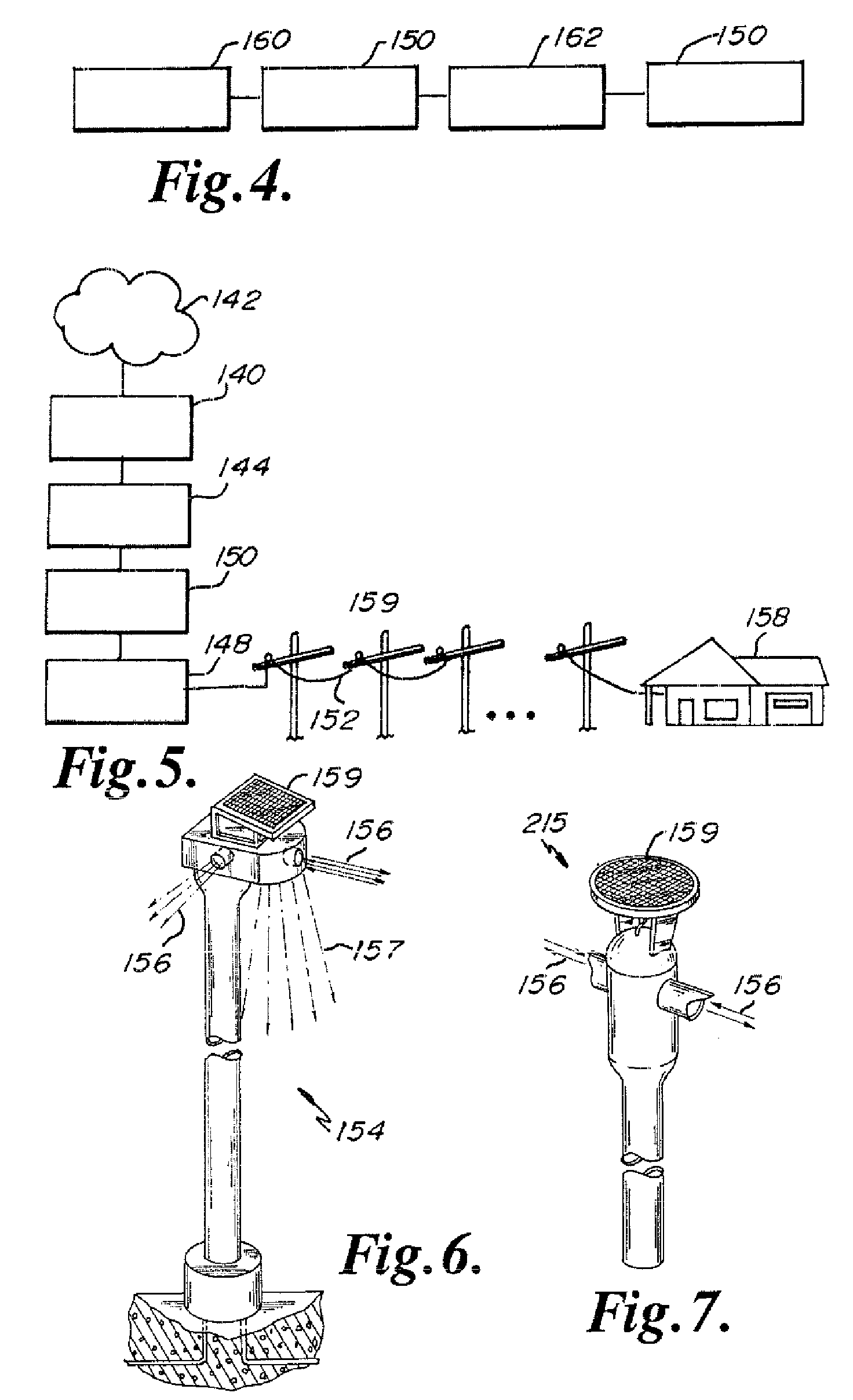
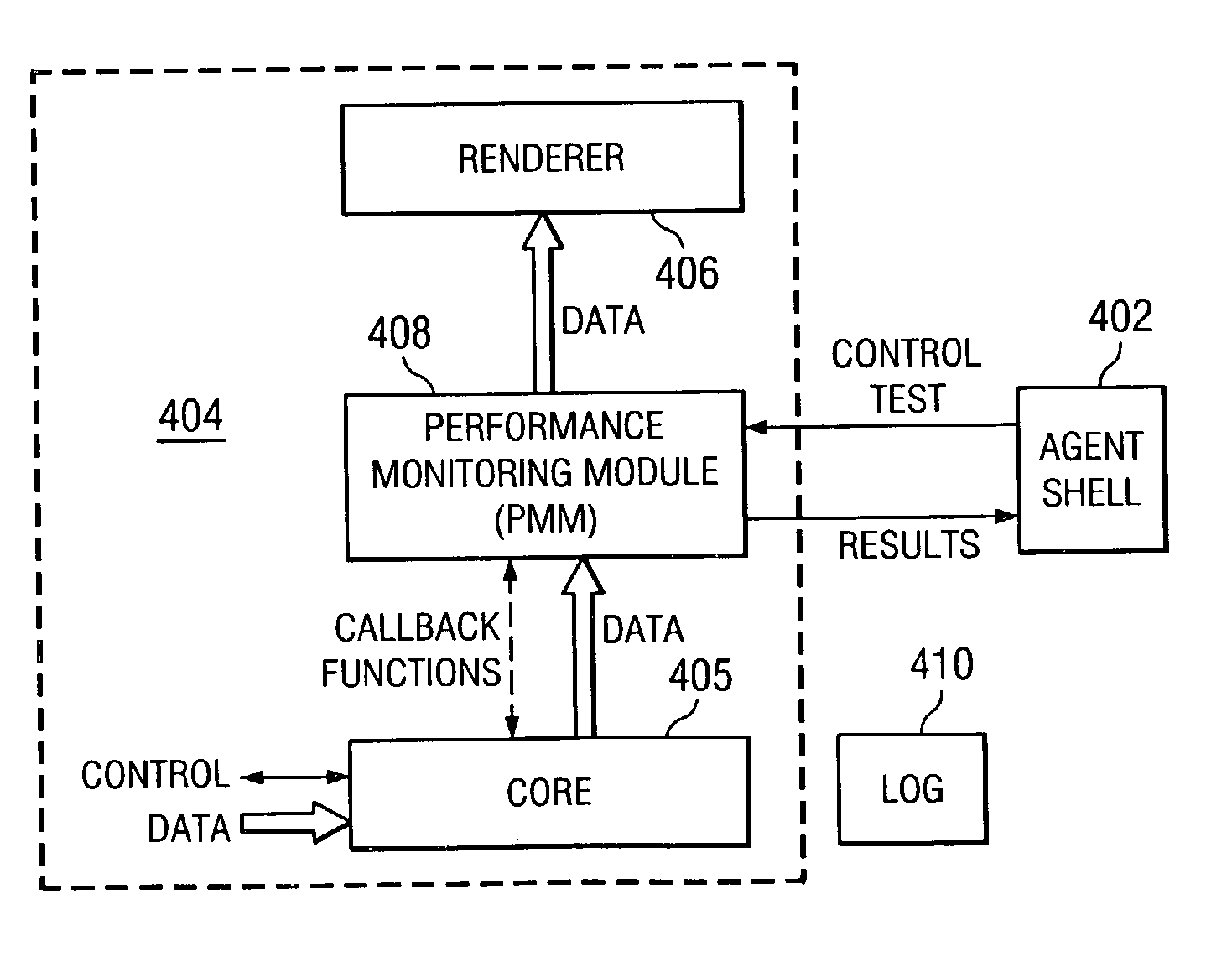
Method and apparatus for measuring stream availability, quality and performance
InactiveUS7010598B2Improve accuracyAccurate measurementError preventionFrequency-division multiplex detailsApplication programming interfaceService provision
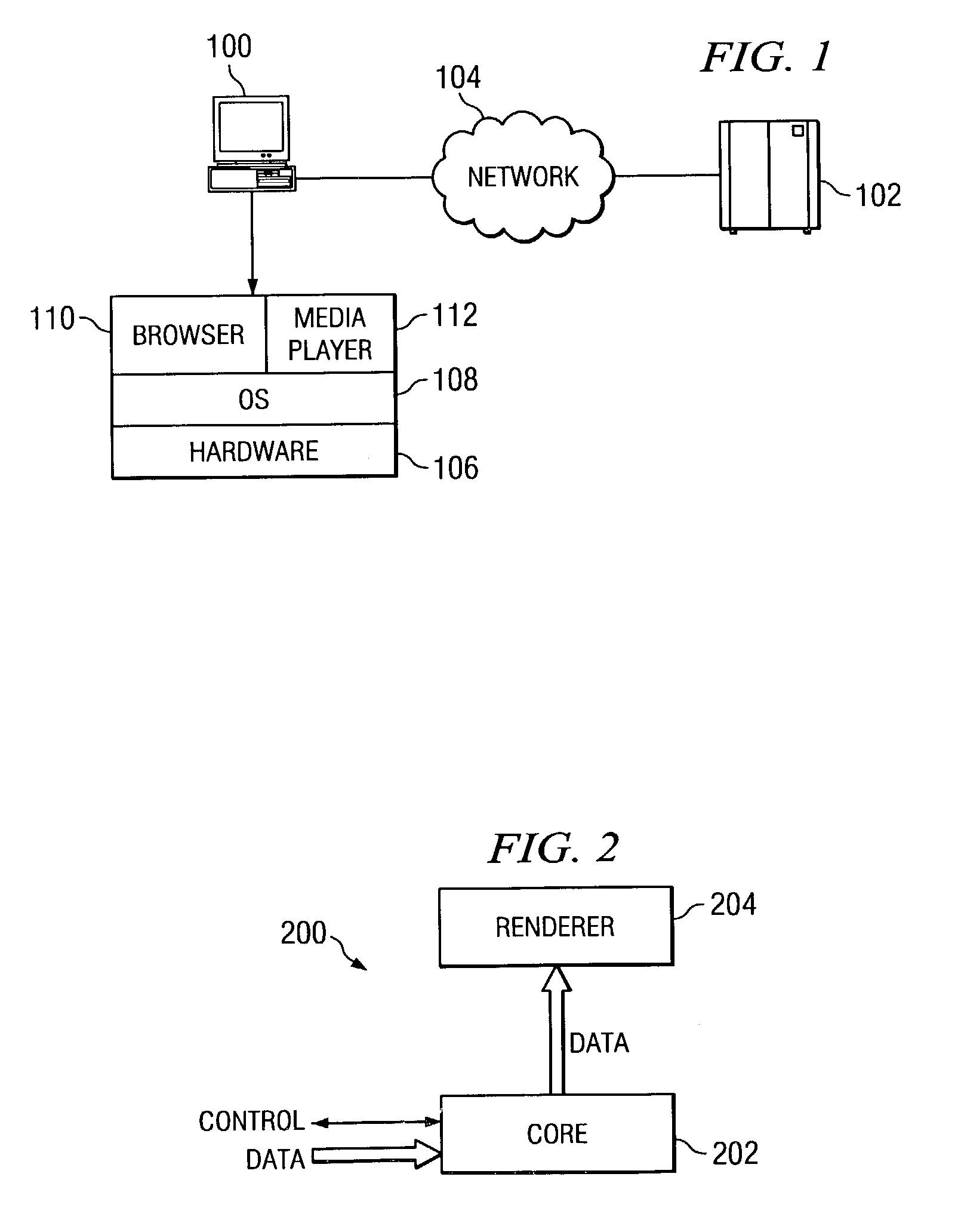
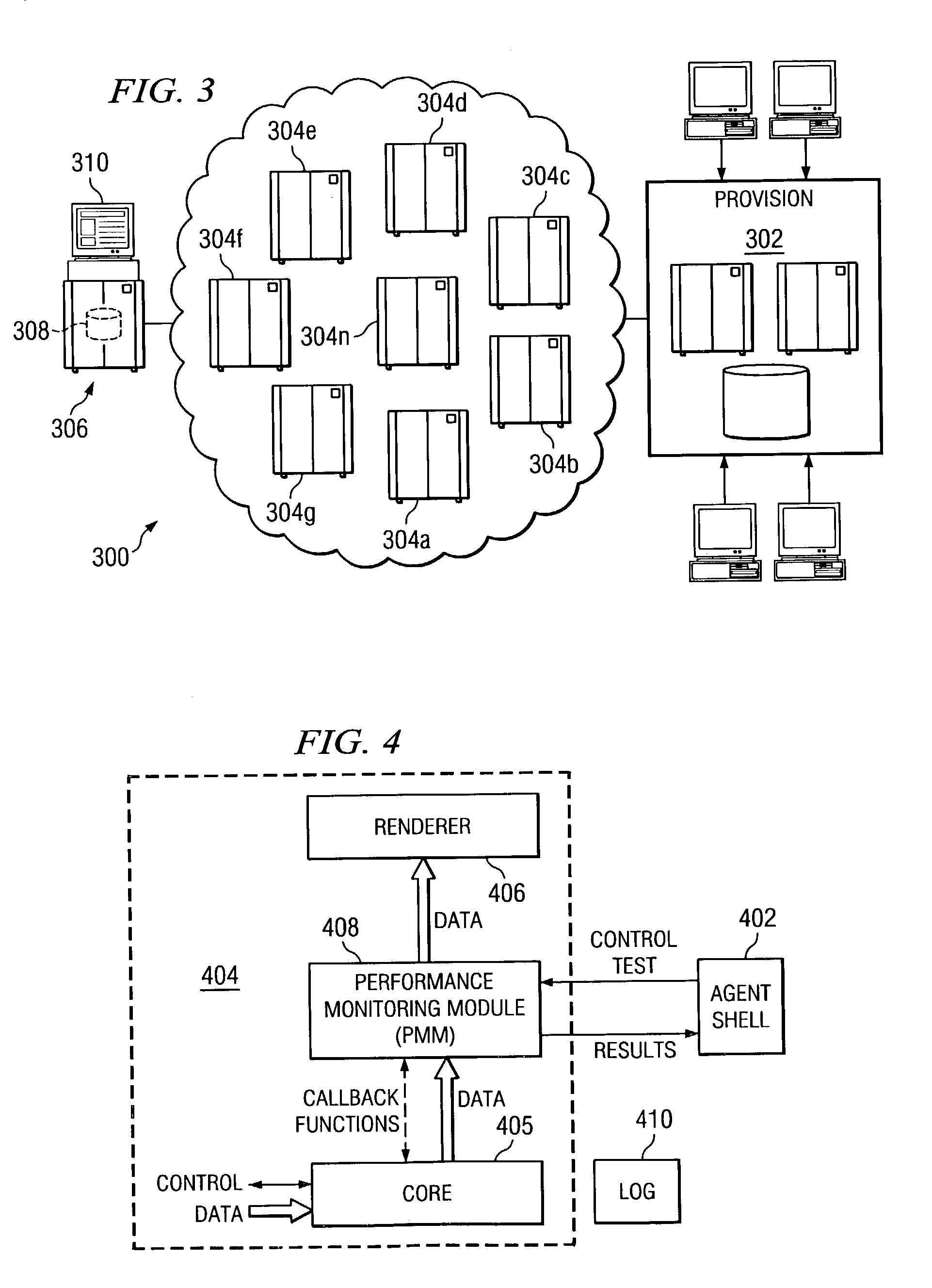
A streaming measurement agent designed to experience, measure, and report on a media stream as an actual end user would experience the stream. Preferably, agent resides transparently within a streaming media player itself so that it can monitor stream packet flows within the player as the measured streams are being played. In an illustrative embodiment, the agent comprises a performance monitoring module (PMM), which is software that resides in an interface between an existing core module and a renderer of a media player. The agent PMM intercepts each useful packet as it goes from the core to the renderer and, as a result, it is able to compute quality metrics about the playback. The agent functions “transparently” to the media player by presenting the core with an application programming interface (API) that emulates the API that the renderer normally presents to the core. Thus, when the core believes it is calling the renderer, it is actually calling the agent PMM, which can then receive all the packets from the core and process them. After computing relevant performance metrics using the packets it receives, the agent PMM calls the renderer. A set of performance agents can be managed by a service provider to enable a content provider to determine how a stream is perceived by end users.
Owner:AKAMAI TECH INC
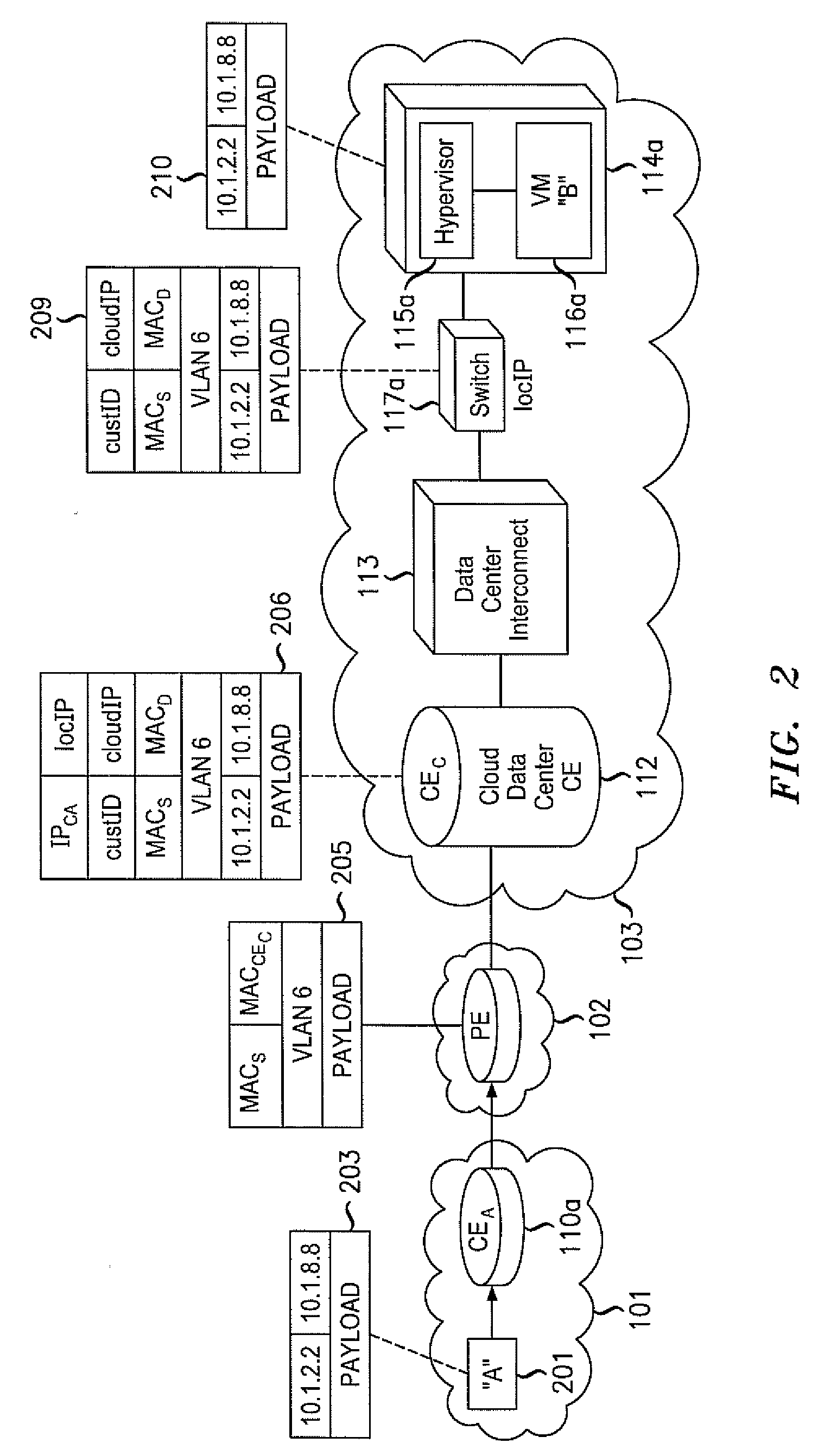
Layer 2 seamless site extension of enterprises in cloud computing
ActiveUS20110075667A1Ensure safetyHighly-dynamic scalability of cloud resourcesMultiple digital computer combinationsNetworks interconnectionNetwork packetIp address
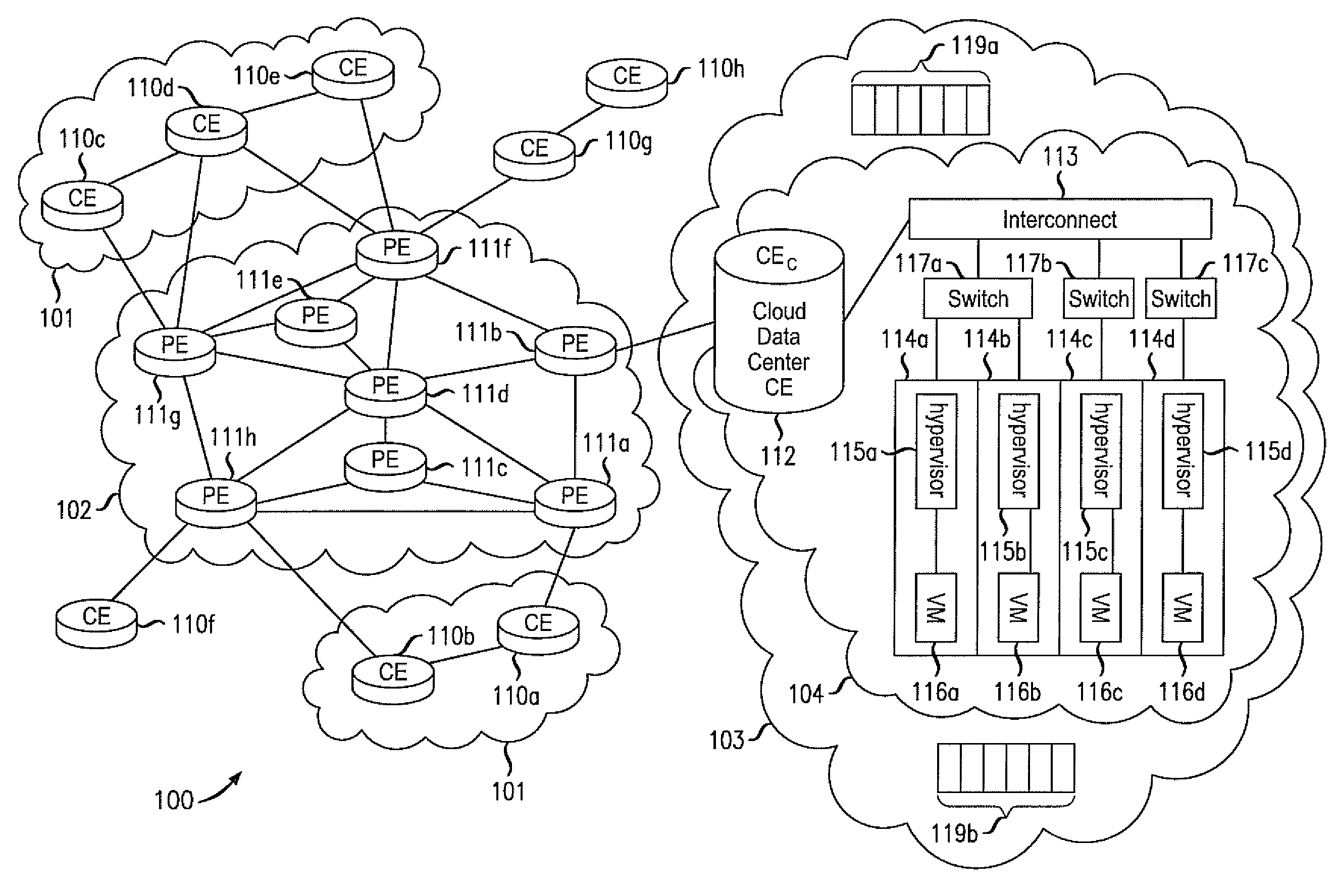
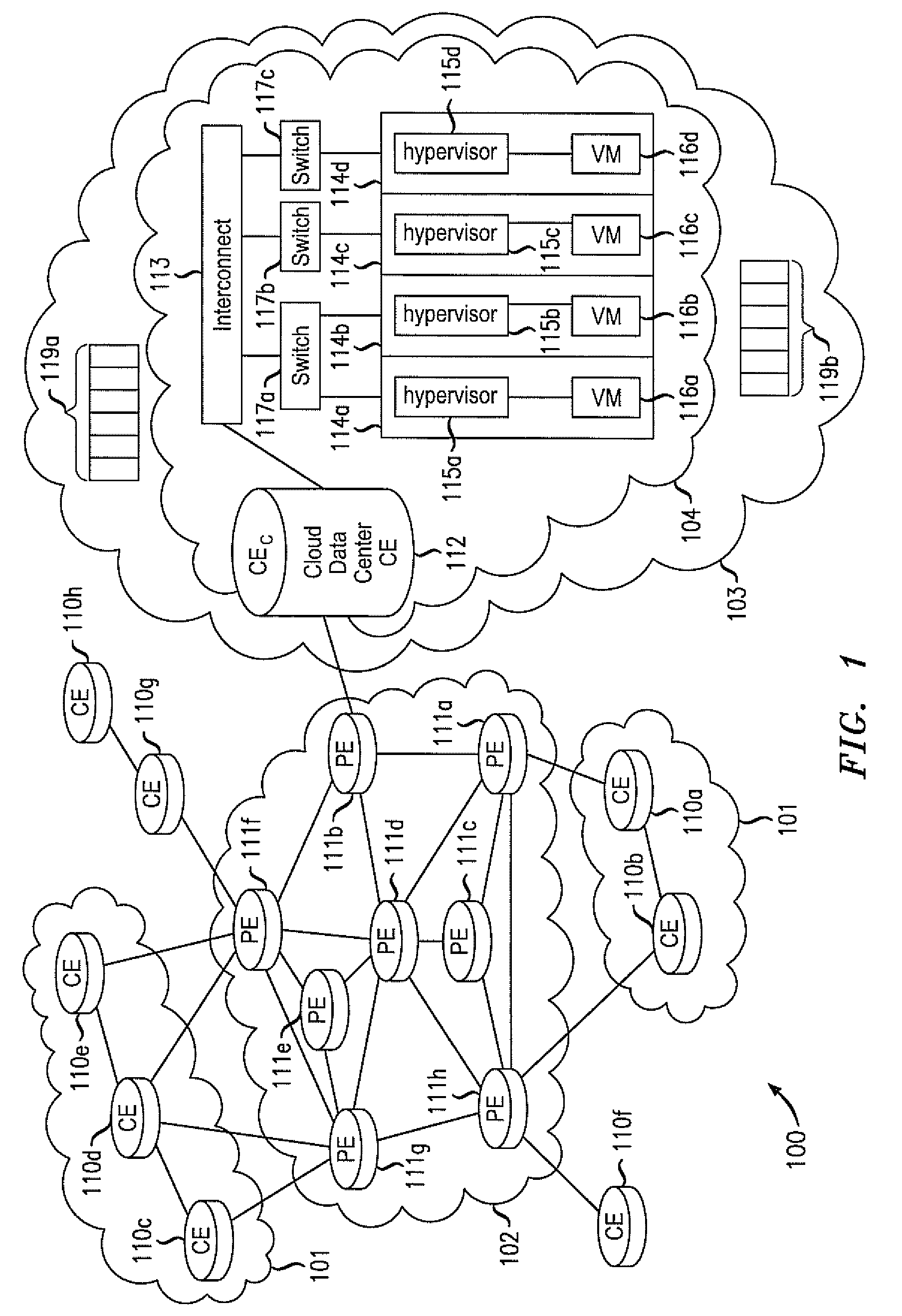
Various embodiments relate to a Cloud Data Center, a system comprising the Cloud Data Center, and a related method. The Cloud Data Center may include a logical customer edge router to send packets between addresses in a private enterprise network and addresses in a logical network within a cloud network using Layer 2 protocol and MAC addressing. The logical network may have resources, known as virtual machines, allocated to the private enterprise network and may share a common IP address space with the private enterprise network. A directory at the Cloud Data Center may correlate the enterprise IP addresses of virtual machines with a MAC address, cloud IP address, and a location IP address within the logical network. The Cloud Data Center may double encapsulate packets with MAC, cloudIP, and locIP headers, when sending a packet to a destination in the logical network.
Owner:ALCATEL LUCENT SAS
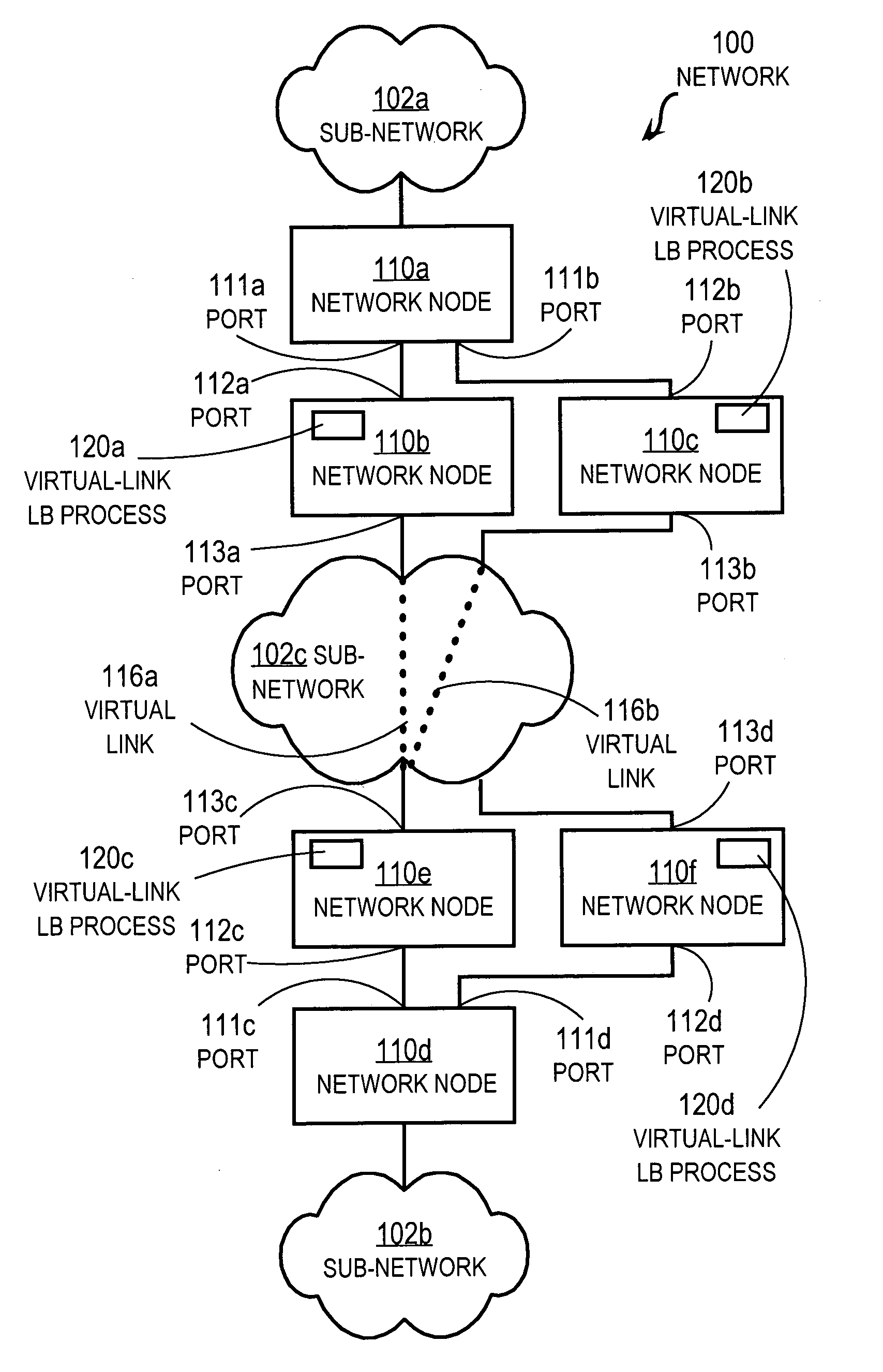
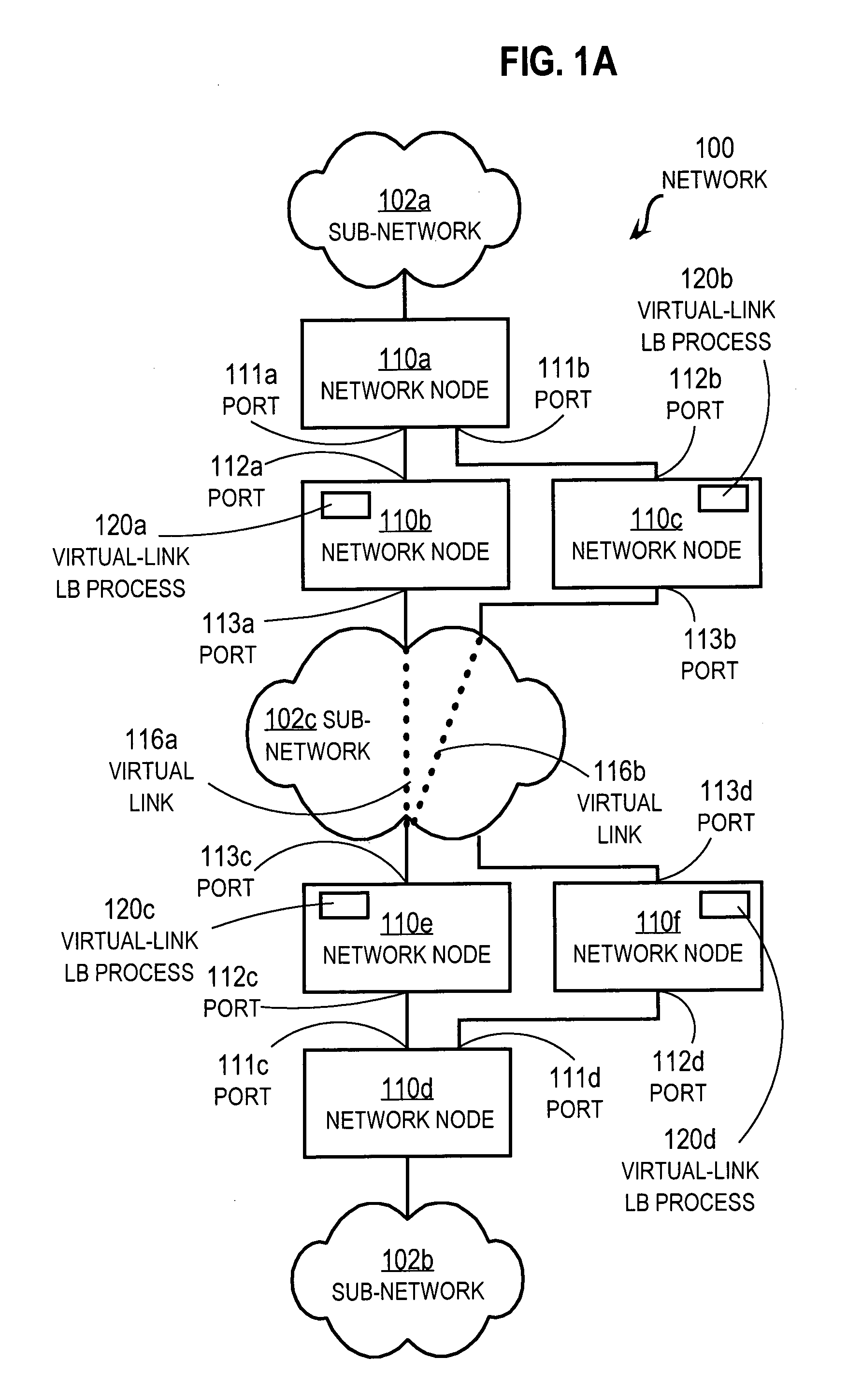
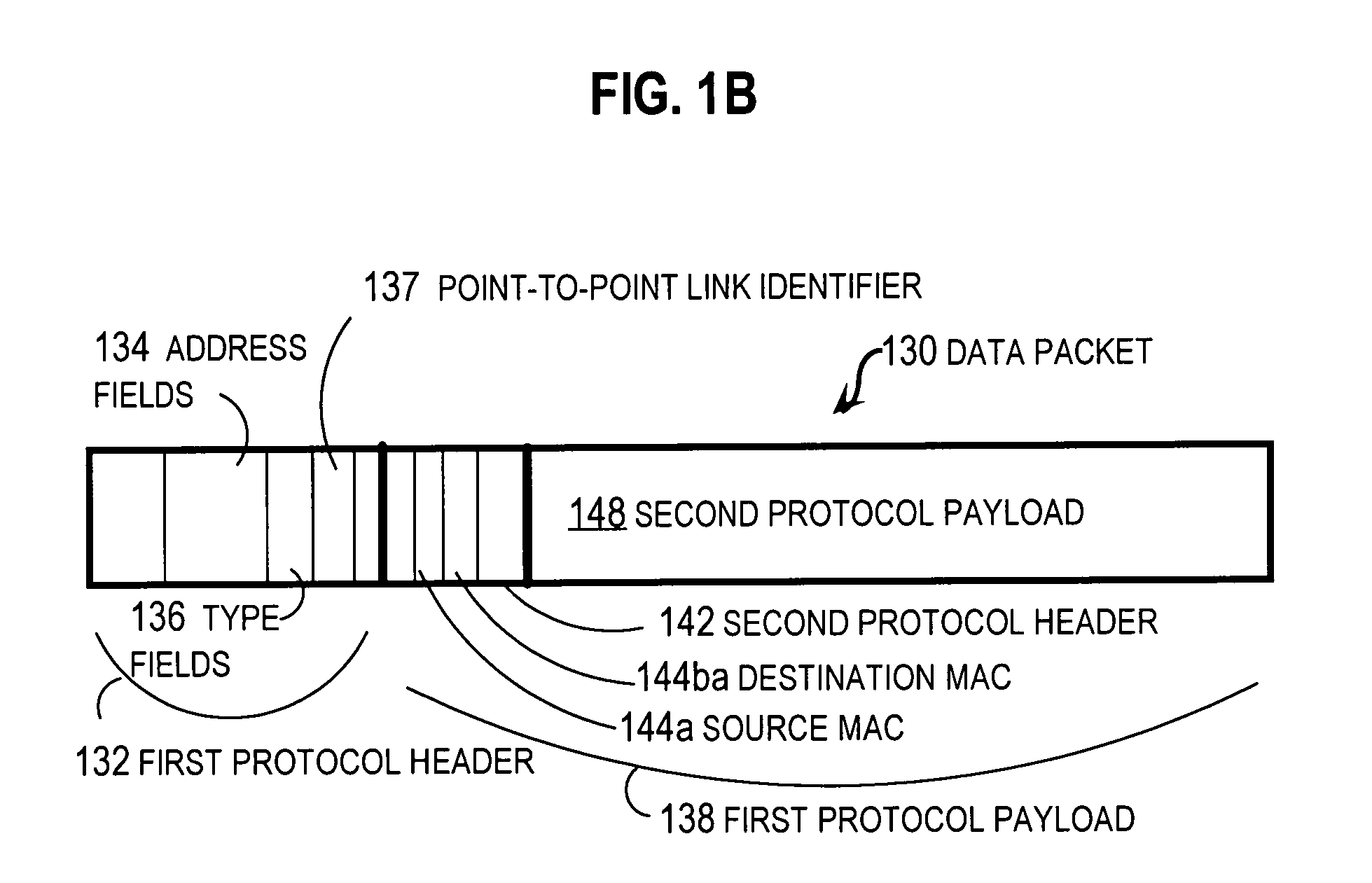
Method and apparatus for load balancing over virtual network links
Techniques for load balancing network traffic over virtual point-to-point data links at a data-link layer include determining a particular group of virtual point-to-point data links that reach a particular local area network of one or more network nodes. A particular data-link address for a particular node of the particular local area network is associated with each virtual point-to-point data link of the particular group. When a data packet is received that includes data that indicates the particular data-link address as a destination; one virtual point-to-point data link of the group is determined to balance traffic among the group. The data packet is sent only over the one virtual point-to-point data link. These techniques enable virtual point-to-point data links through two or more intermediate network nodes, such as a pair of provider edge nodes, to be bundled for load balancing purposes.
Owner:CISCO TECH INC
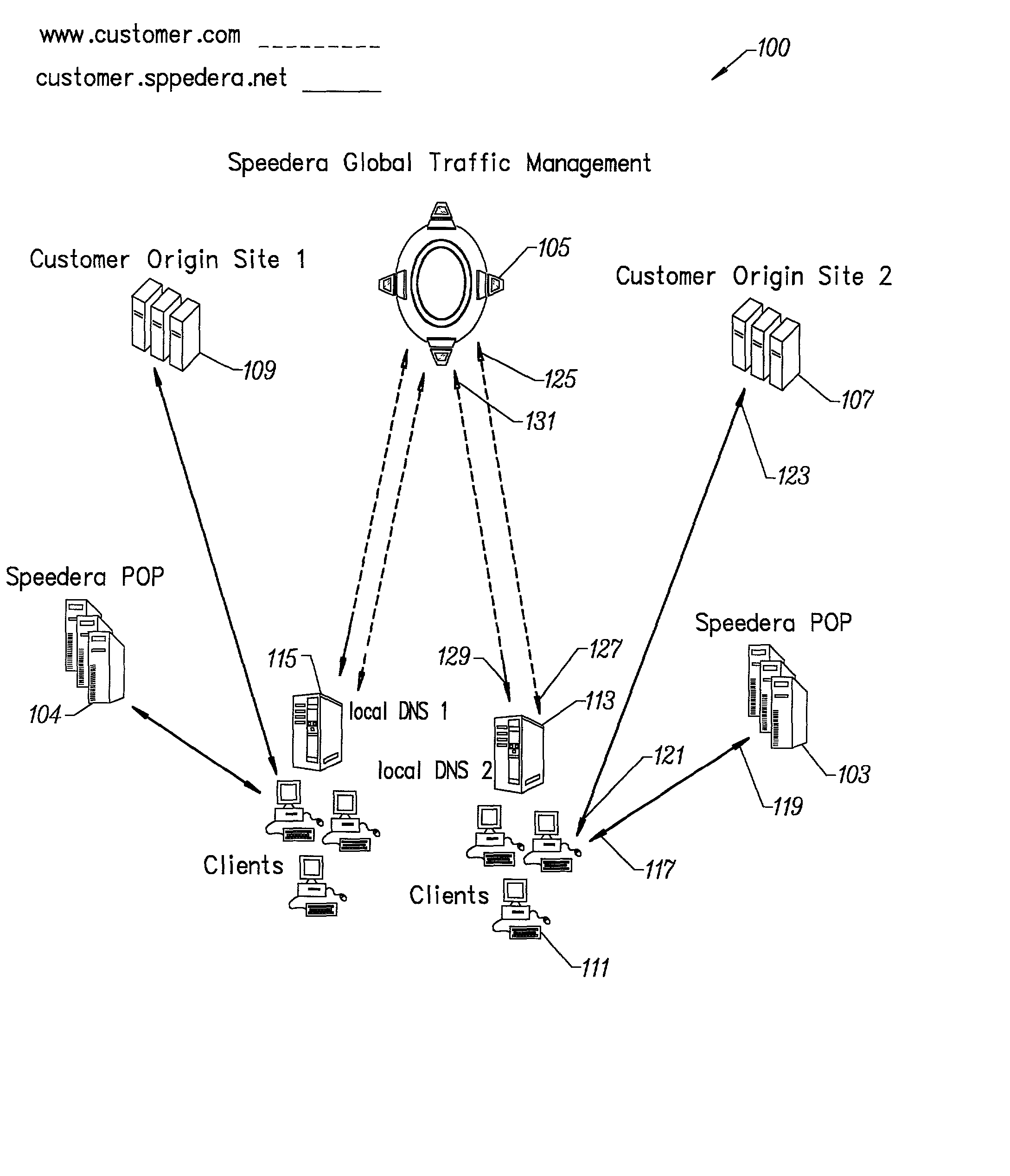
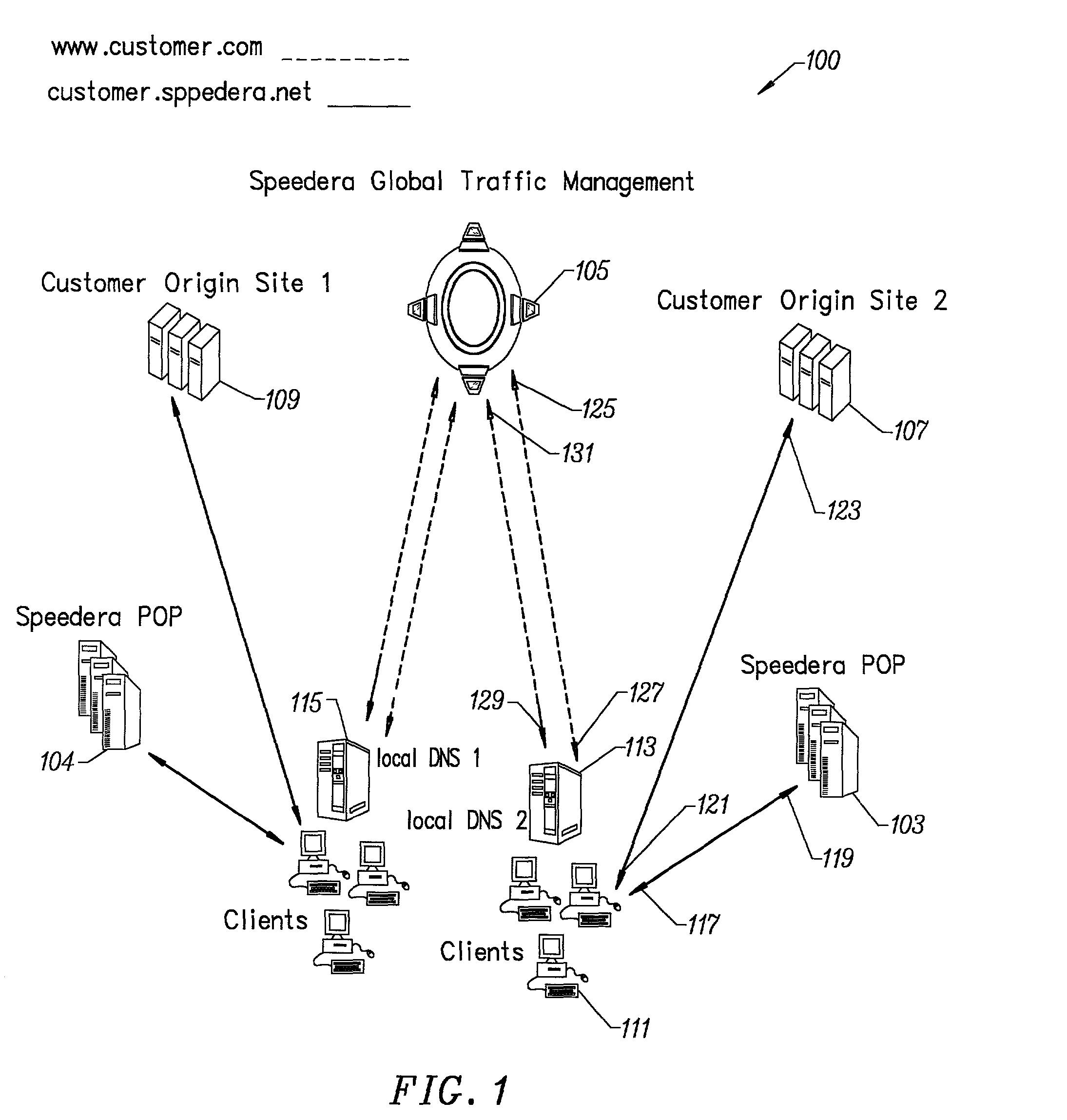
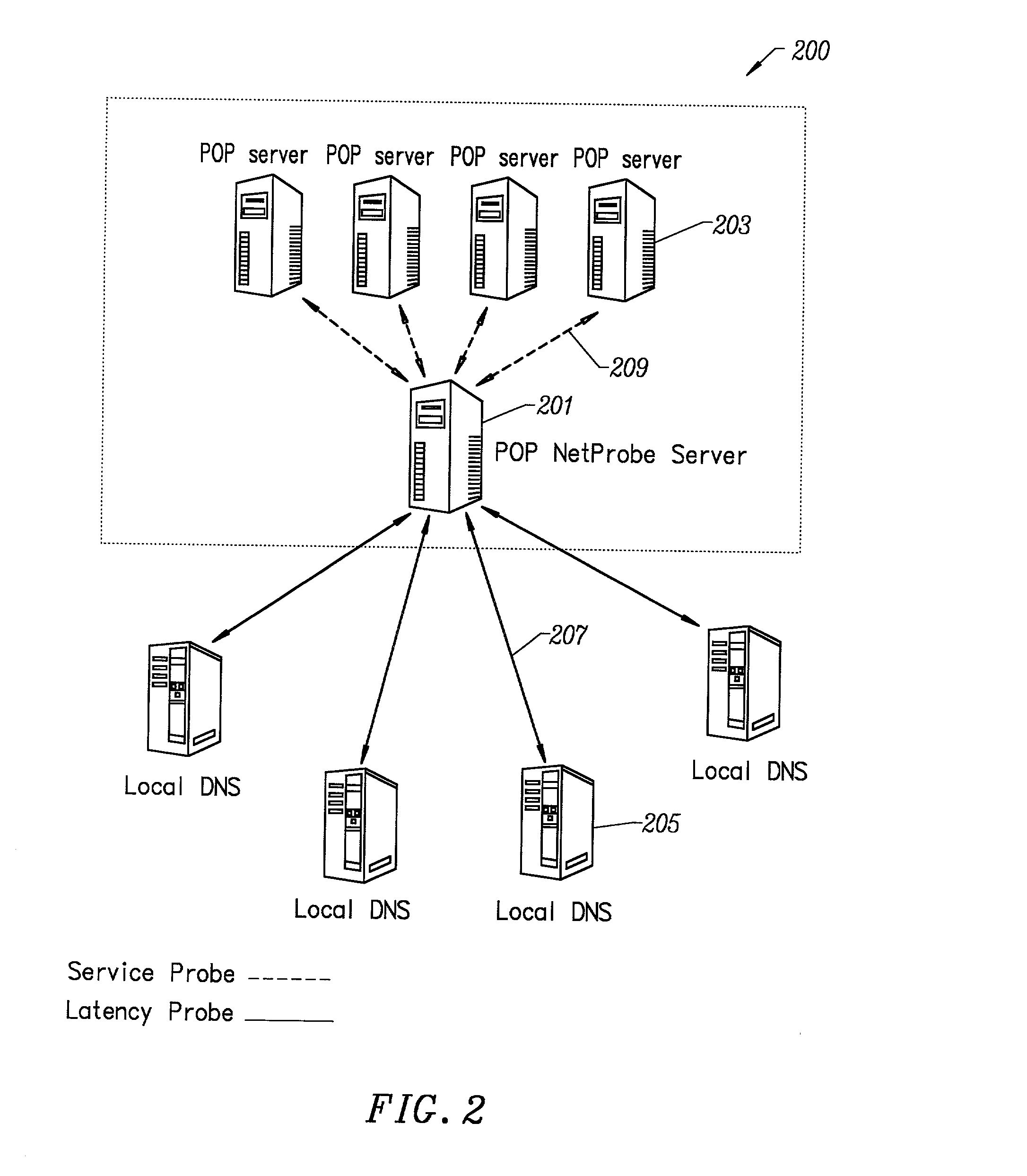
Method for determining metrics of a content delivery and global traffic management network
ActiveUS20030065763A1Metering/charging/biilling arrangementsError preventionTraffic capacityNetwork packet
Owner:AKAMAI TECH INC
Undetectable firewall
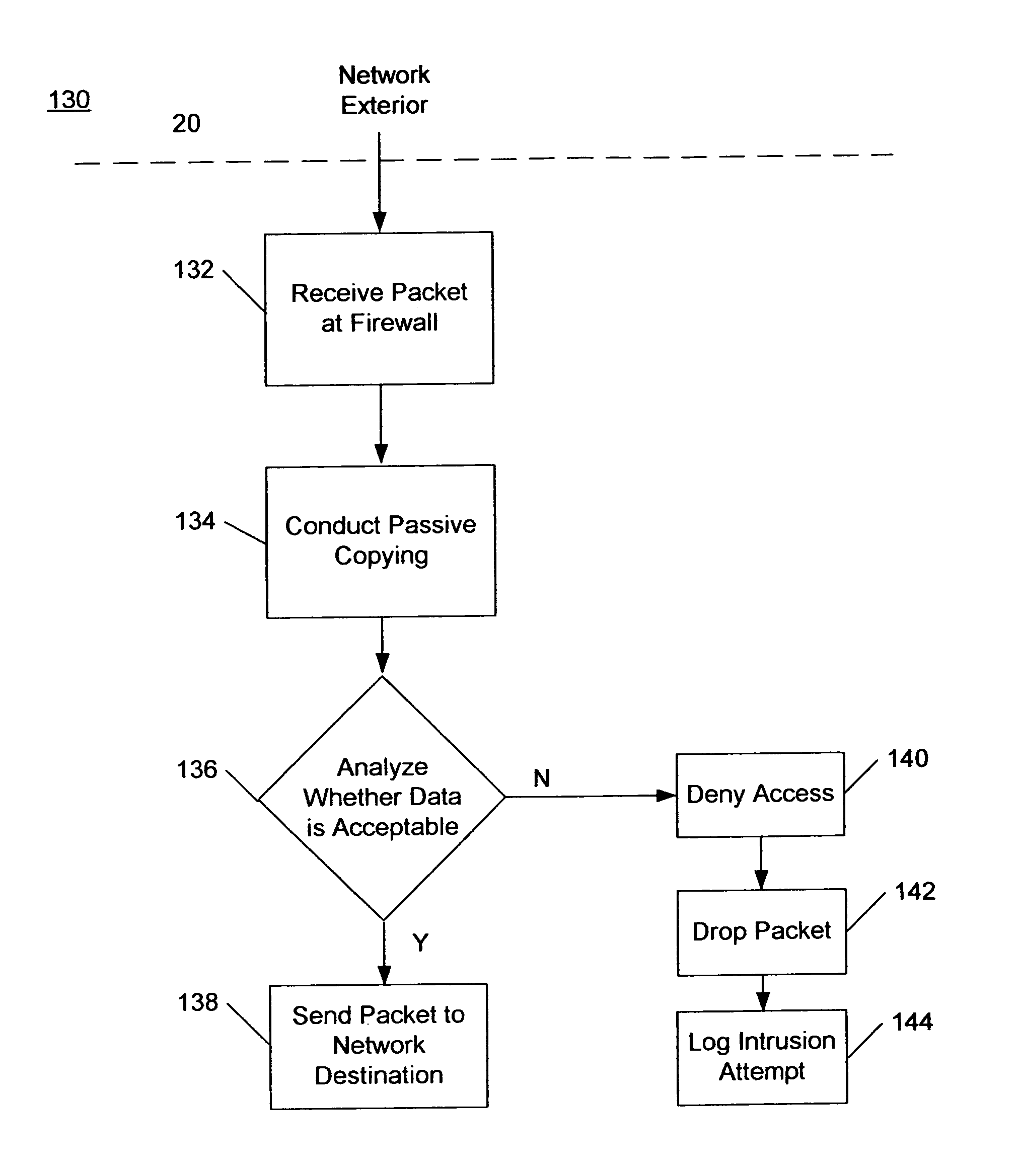
ActiveUS7100201B2Prevent unauthorized accessMemory loss protectionDigital data processing detailsAnalysis dataNetwork packet
An undetectable firewall for network protection has been developed. The invention includes a method of preventing unauthorized access to a computer system. The firewall receives a data packet and copies its contents exactly. Next, the firewall analyzes the data packet and determines if it is authorized to access the network. If the packet is authorized to access the network, it is sent on to its destination. If the packet is unauthorized to access the network, it is dropped by the firewall.
Owner:ARXCEO CORP
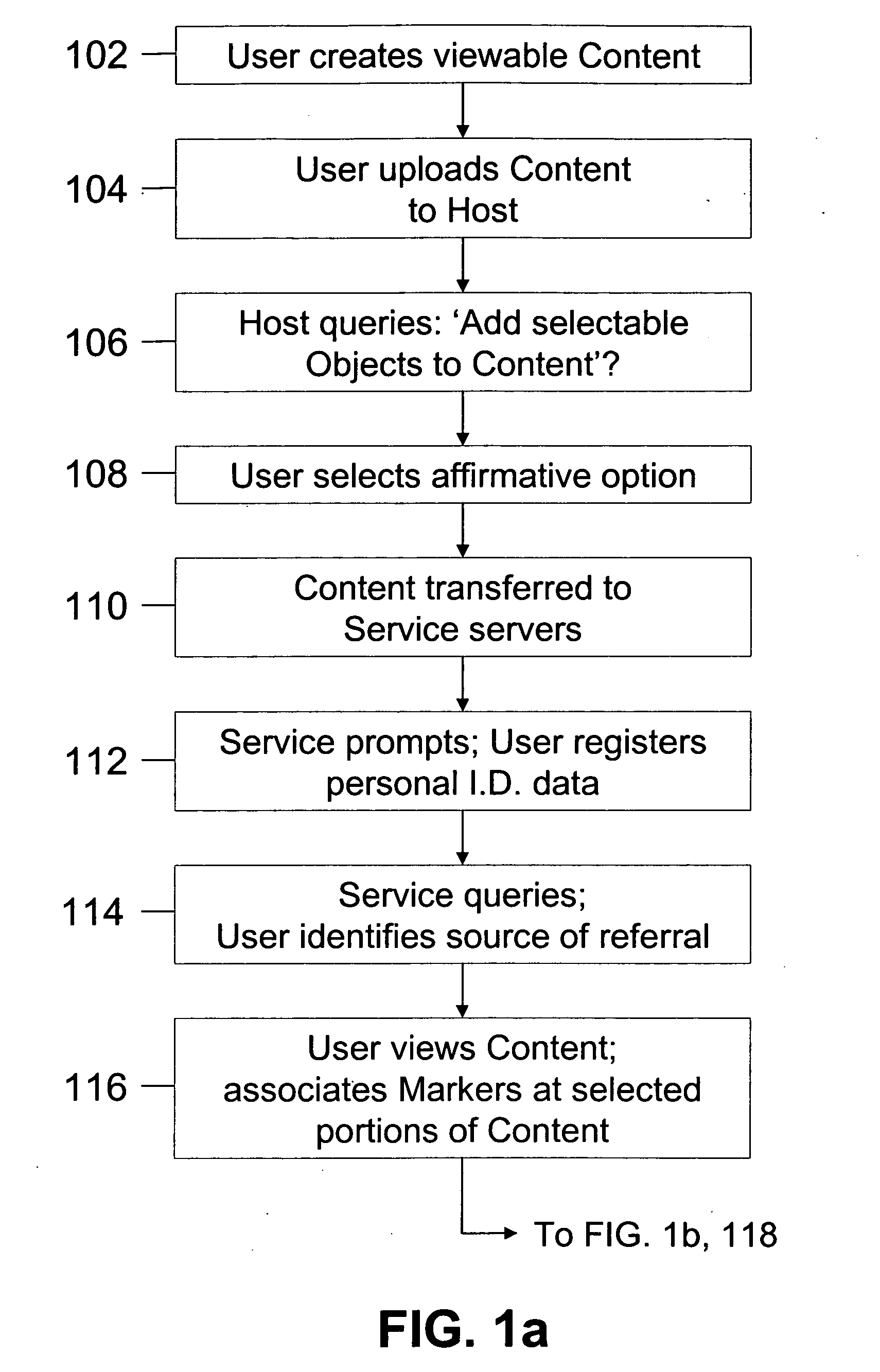
Method and apparatus for preventing network traffic analysis
InactiveUS6917974B1Not replace and duplicate and reduce needAugments the protection provided by encryptionHardware monitoringMultiple digital computer combinationsTraffic capacityNetwork packet
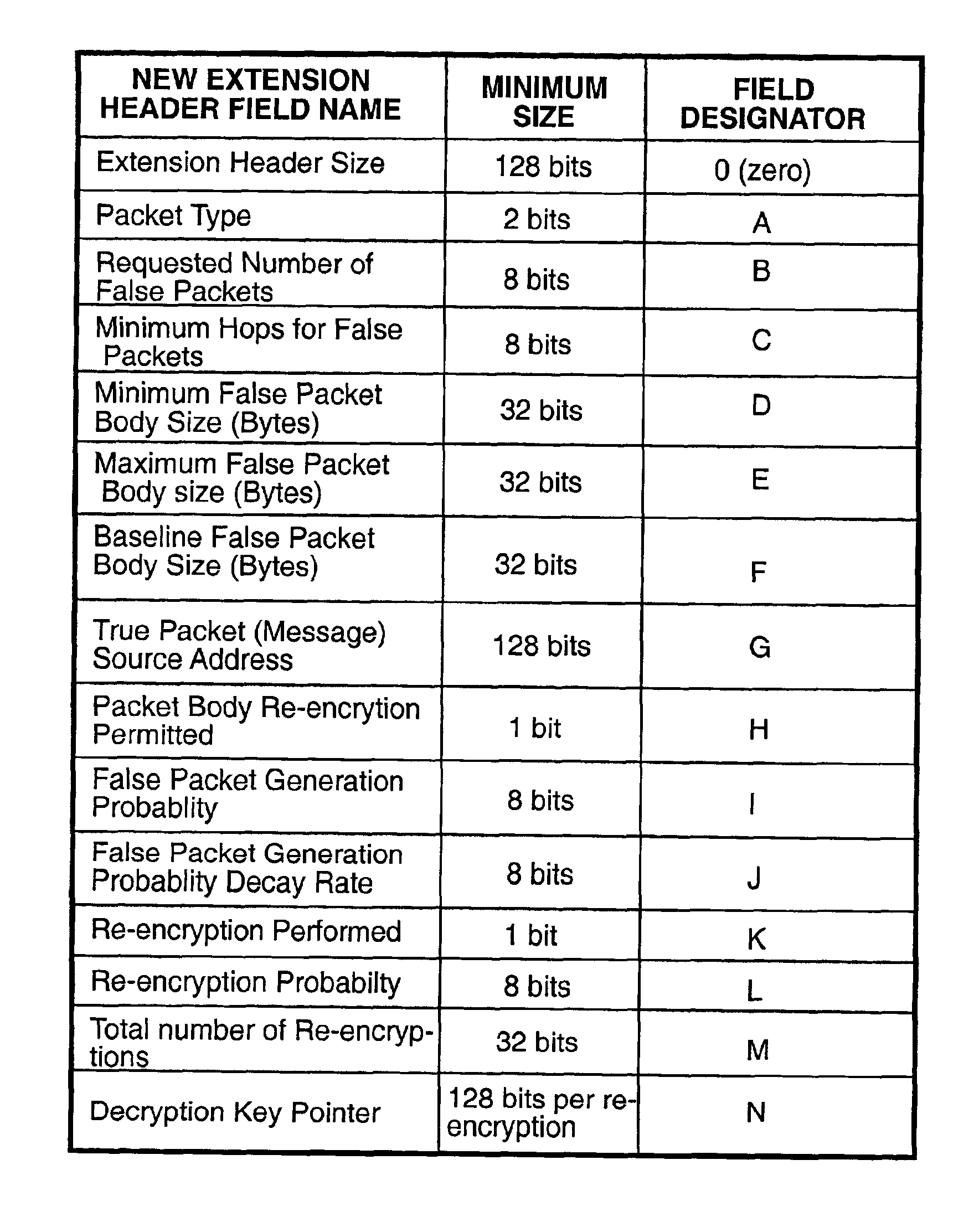
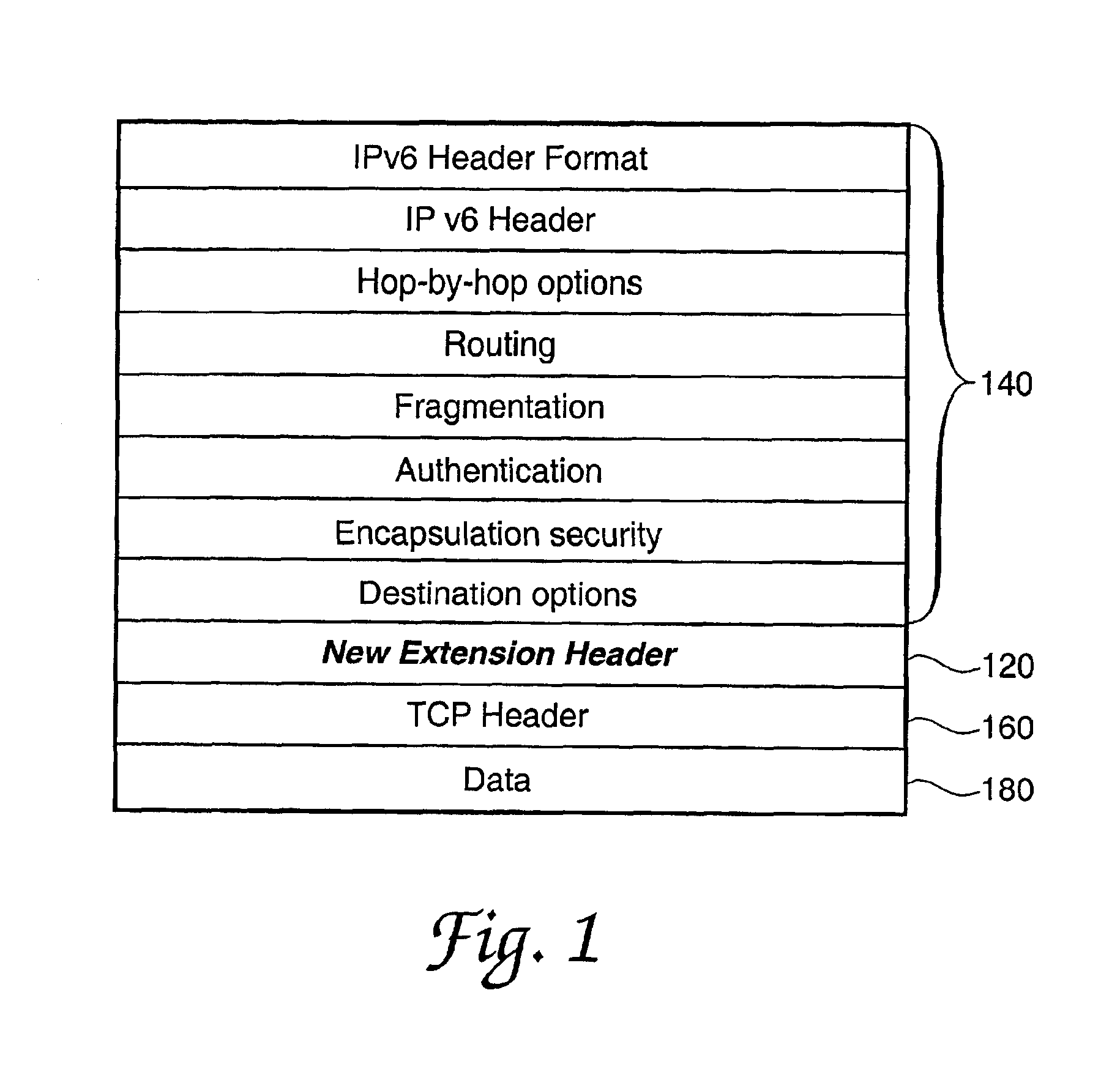
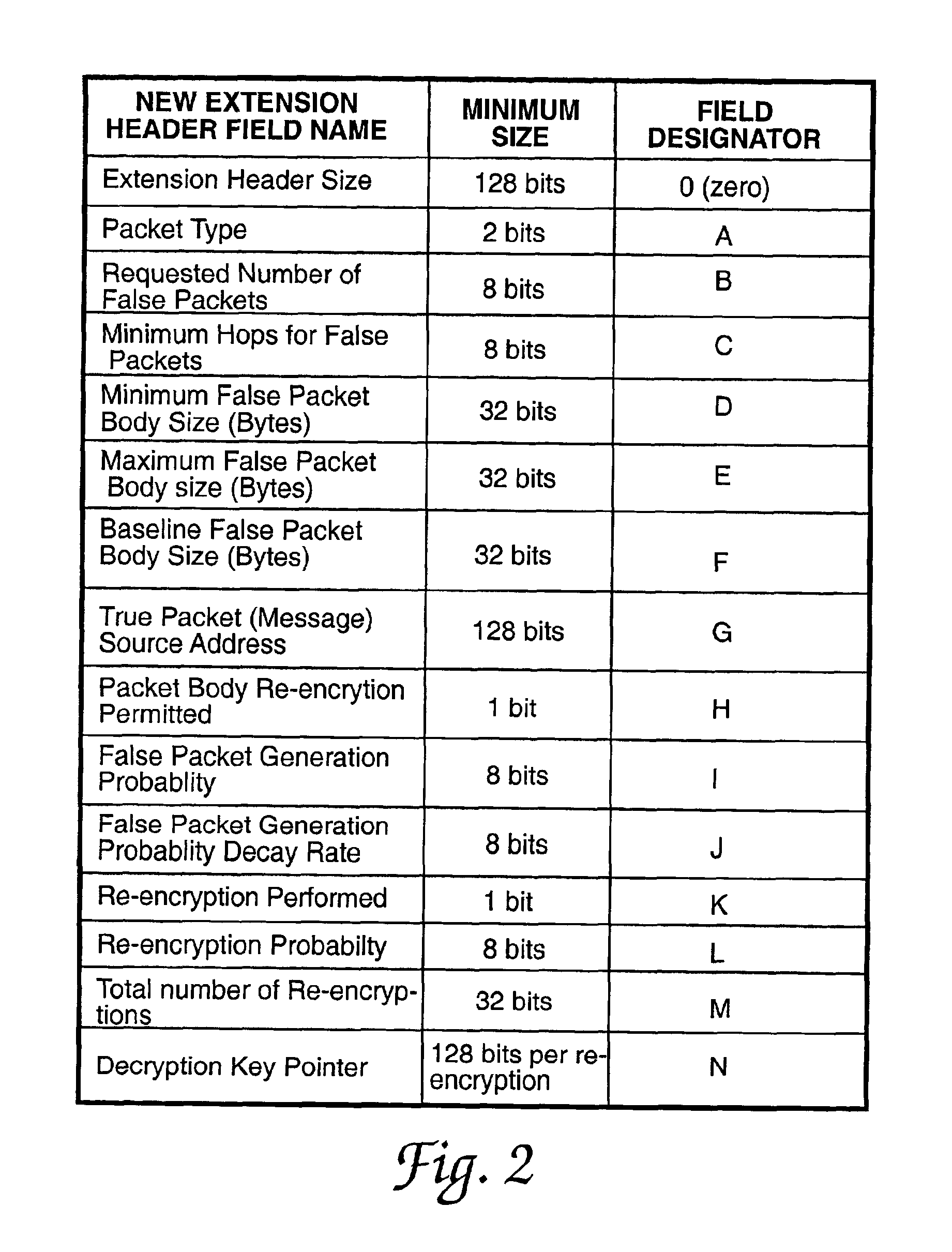
A system and method for generating and transmitting false packets along with a true packet to thereby hide or obscure the actual message traffic. A new extension header having a plurality of fields is positioned in the hierarchy of Internet protocol headers that control passage of the false packets and the true packet through the network. A sending host computer generates a plurality of false packets for each true packet and transmits the false packets and the true packet containing the Internet protocol headers and the extension header over the network. The new extension header is decrypted and re-encrypted each host that handles a message packet that uses the new extension header to control the random re-encryption of the true packet body at random hosts and the random generation of false packets at each host visited by a true packet, at the recipient of the true packet, and at any hosts that receive a false packet.
Owner:AIR FORCE GOVERNMENT OF THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SEC OF THE THE
Method and apparatus for re-ordering data packets in a network environment
InactiveUS6246684B1Lower Level RequirementsAvoid changeMultiplex system selection arrangementsData switching by path configurationTime delaysNetwork packet
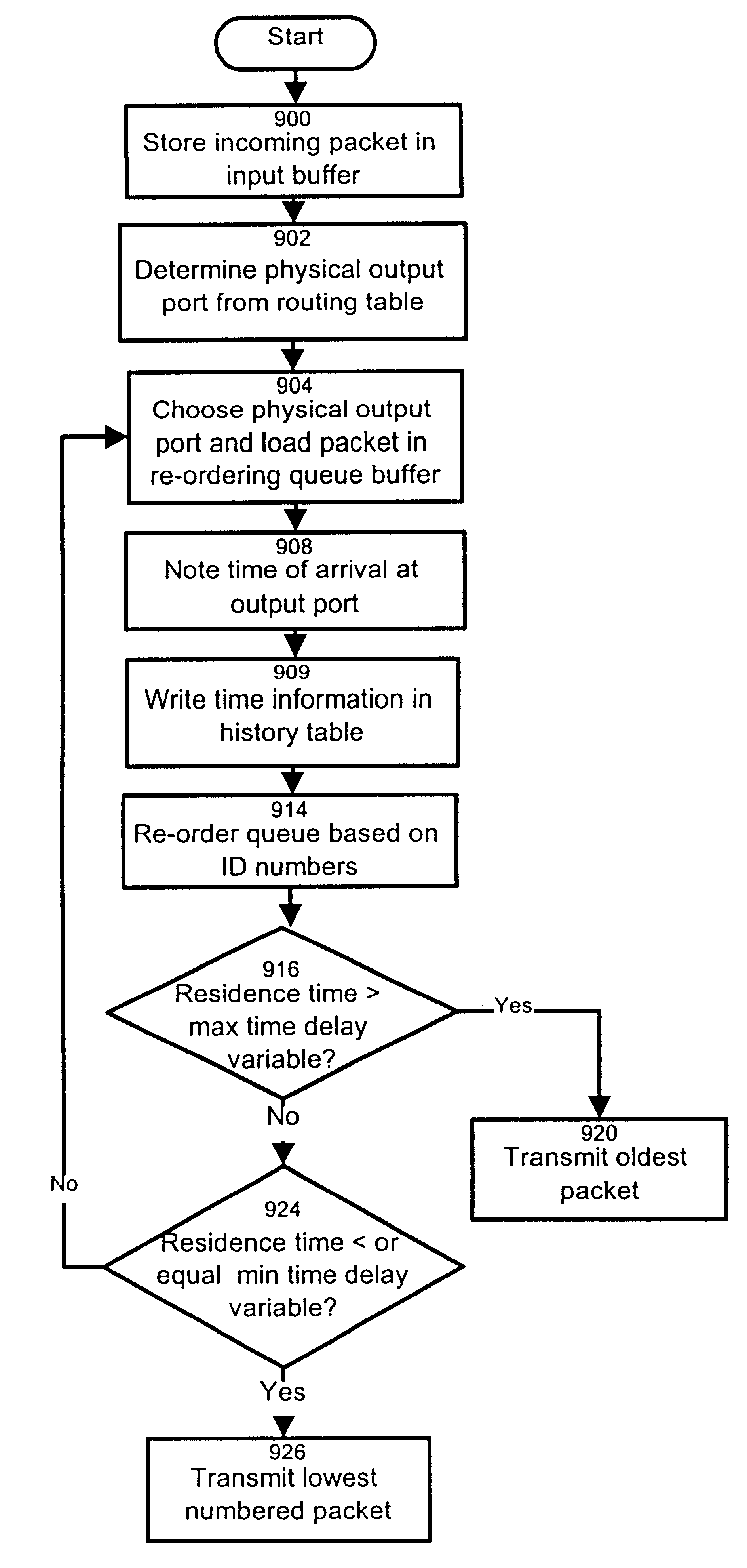
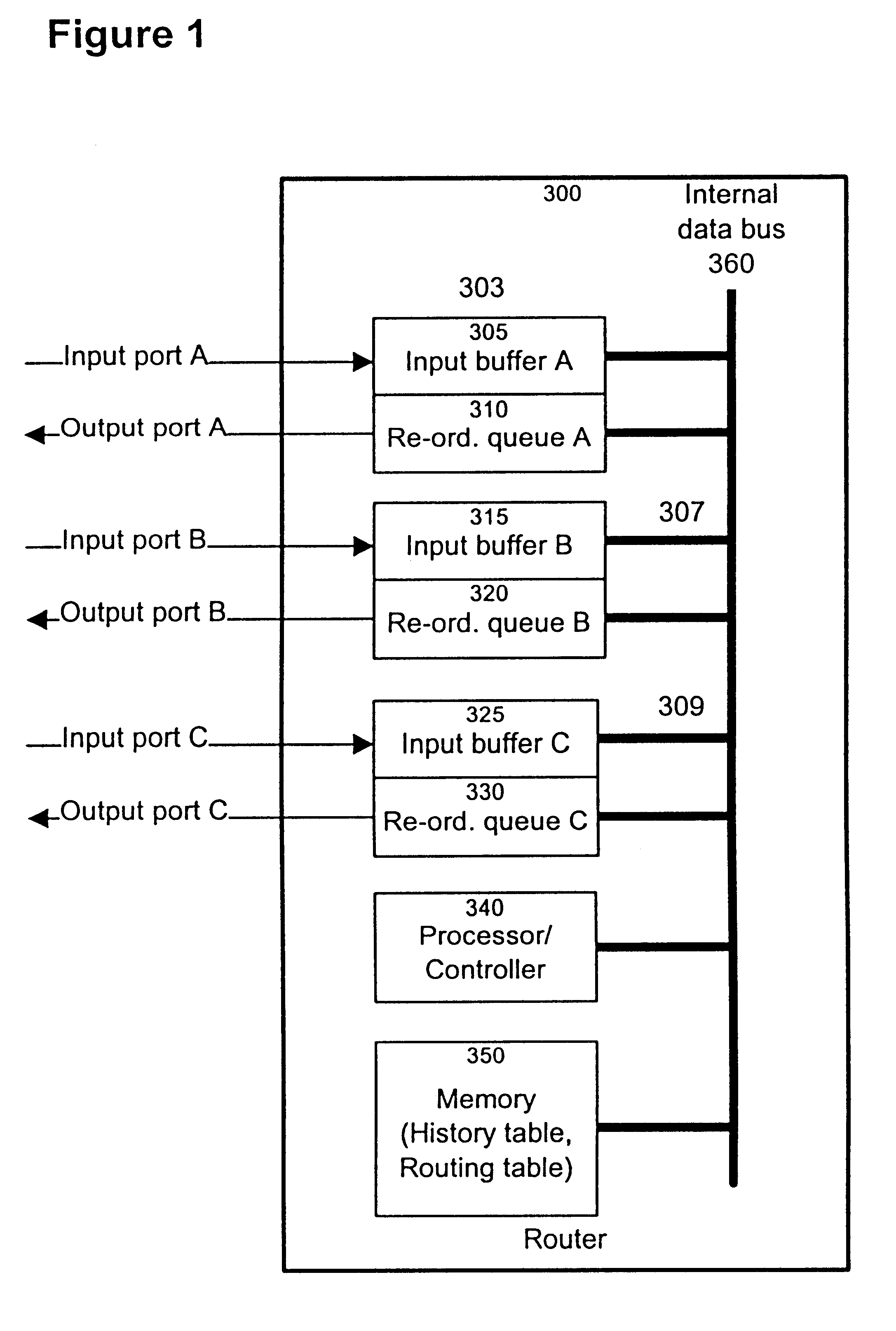
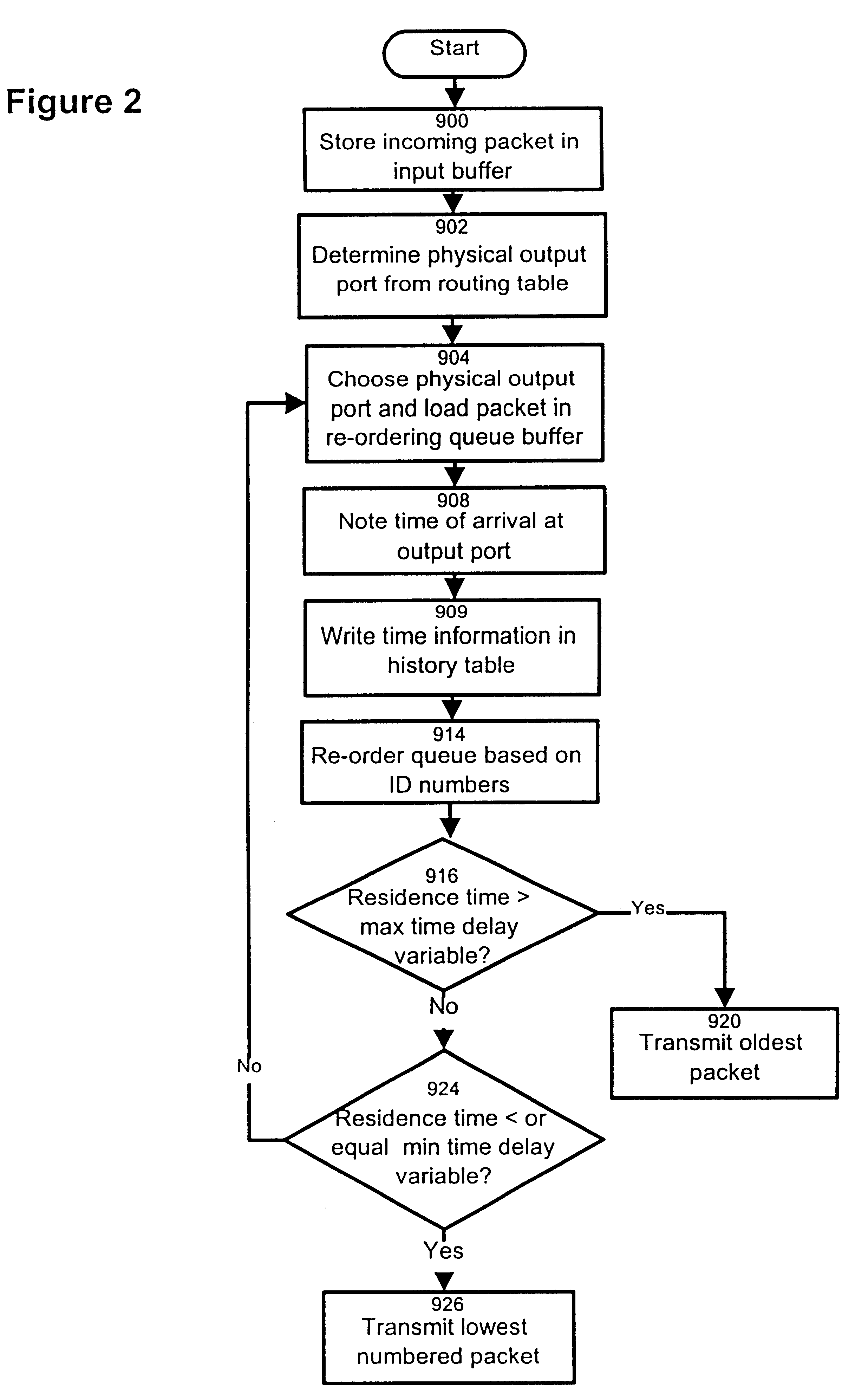
The invention provides a method and apparatus for re-ordering data traffic units, such as IP data packets, that may have been miss-ordered during a transmission over a multi-pathway link between a source node and a destination node in a network. The re-ordering apparatus includes a storage medium for intercepting the IP data packets and holding the IP data packets to allow IP data packets delayed on slower pathways to catch-up. The IP data packets in the storage medium are re-ordered based on their sequence number in an attempt to restore the original order of the IP data packets. A maximal time delay variable determines how long a certain IP data packet can be held in the storage medium. The TP data packet is released prior to the maximal time delay variable or as the maximal time delay variable is exceeded.
Owner:RPX CLEARINGHOUSE +1
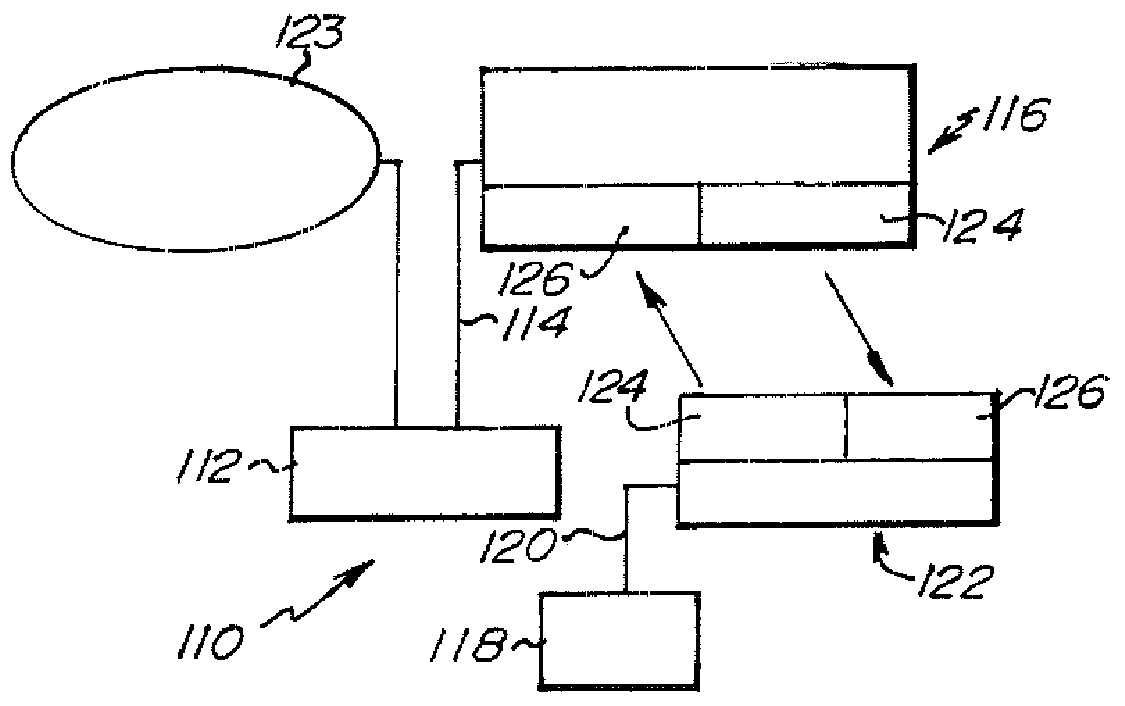
Method and apparatus for remotely monitoring a site
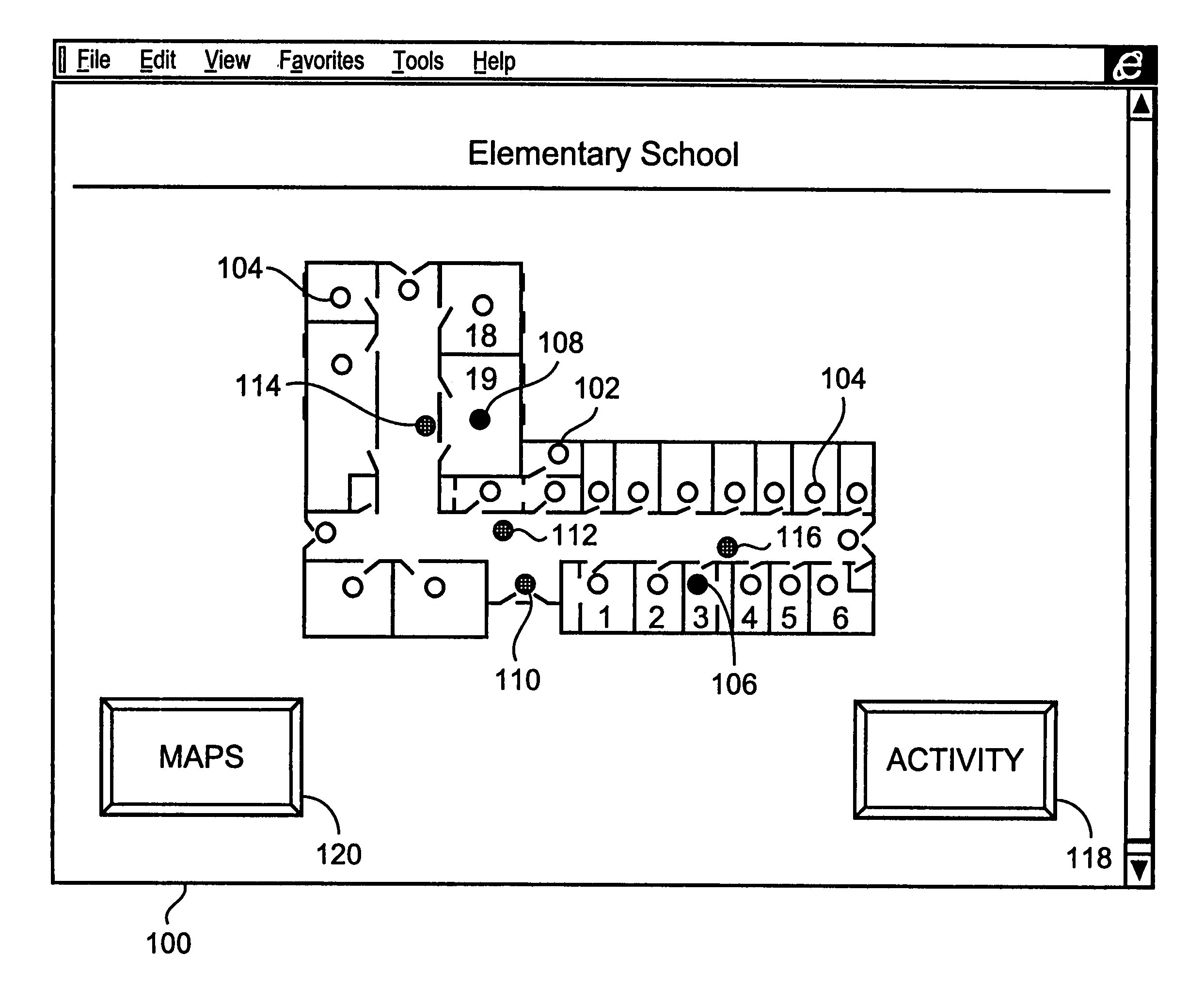
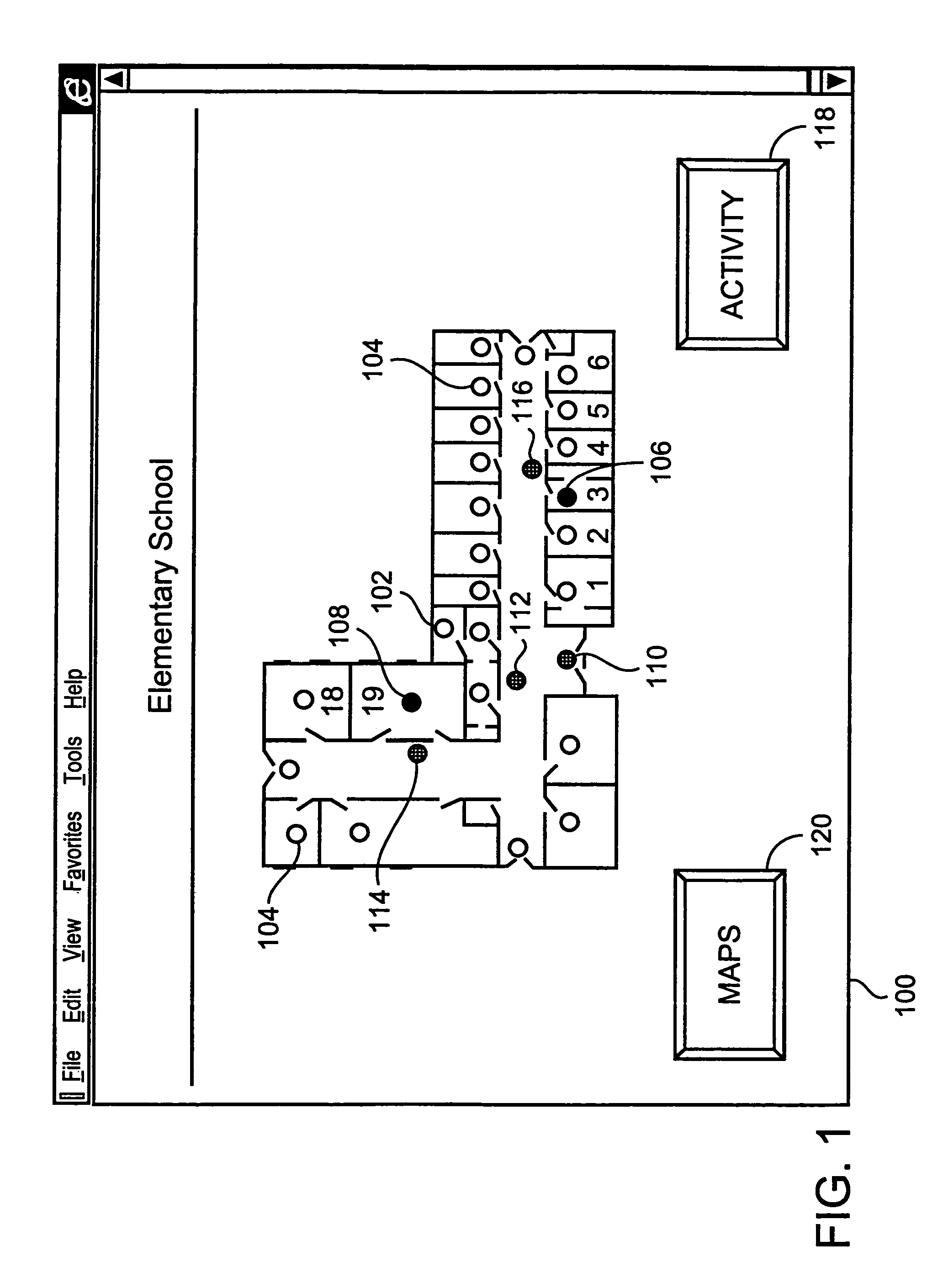
InactiveUS6972676B1Easy to distinguishAccurate locationElectric testing/monitoringElectric/electromagnetic visible signallingTime informationOperating energy
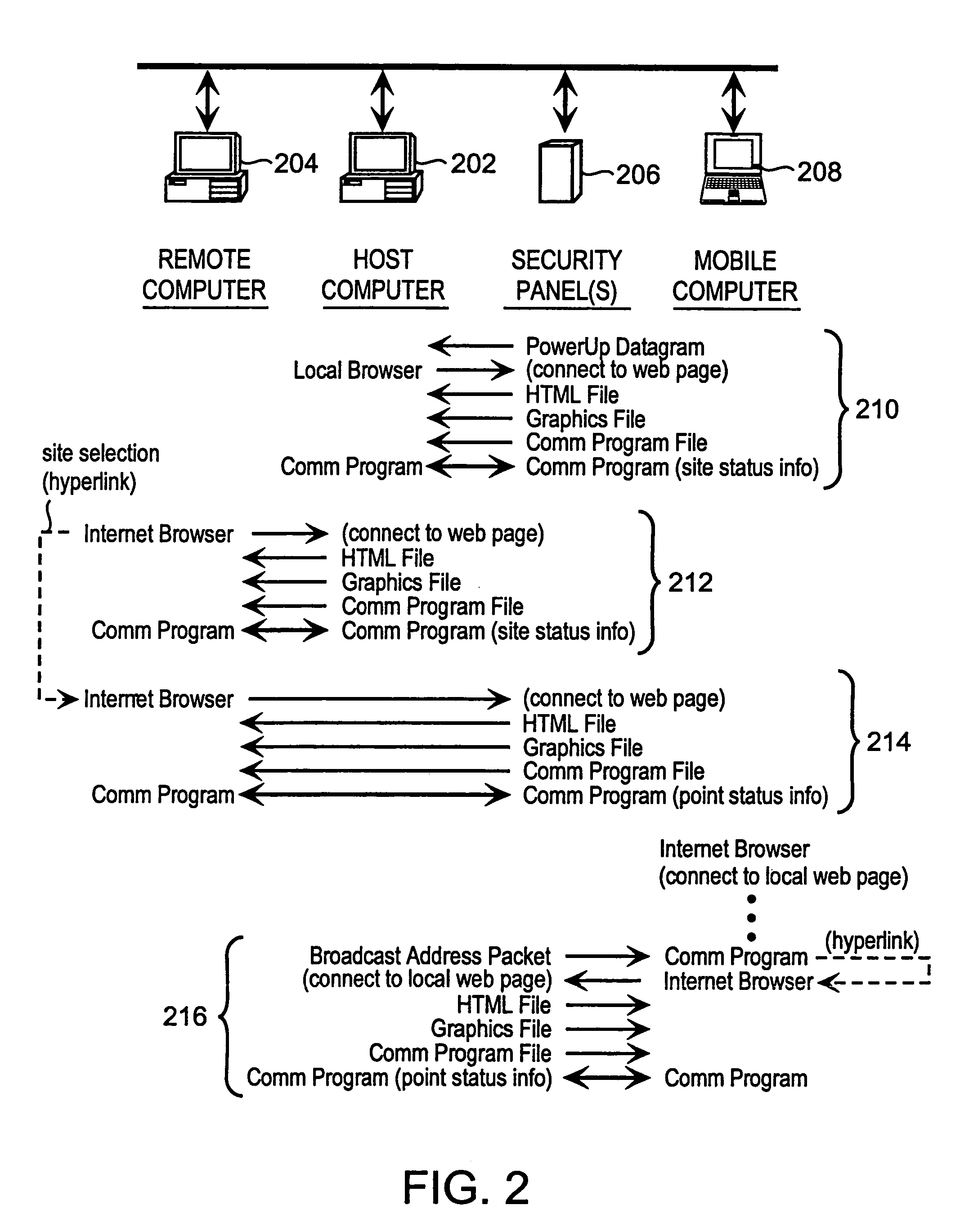
The present invention is directed to providing systems and methods for remotely monitoring sites to provide real time information which can readily permit false alarms to be distinguished, and which can identify and track the precise location of an alarm. In exemplary embodiments, monitoring capabilities such as intrusion / fire detection and tracking capabilities, can be implemented through the use of multistate indicators in a novel interface which permits information to be transmitted using standard network protocols from a remote site to a monitoring station in real-time over preexisting communication networks, such as the Internet. A wireless network can also be established using browser encapsulated communication programs (for example, active X control, Java applets, and so forth) to transmit data packets which comply with any standard wireless local area network protocol. Communications can thereby be established between a web server embedded in a centrally located host monitoring station and a separate security panel deployed in each of the buildings to be remotely monitored. In exemplary embodiments, communications can be handed off from the centrally located host monitoring station to a mobile monitoring station (for example, to a laptop computer in a responding vehicle, such as a police or fire vehicle). The handoff can be such that direct communications are established between a security panel site being monitored and the laptop, or over, for example, a cellular network or indirect communications can be established via the host monitoring station.
Owner:NETTALON SECURITY SYST
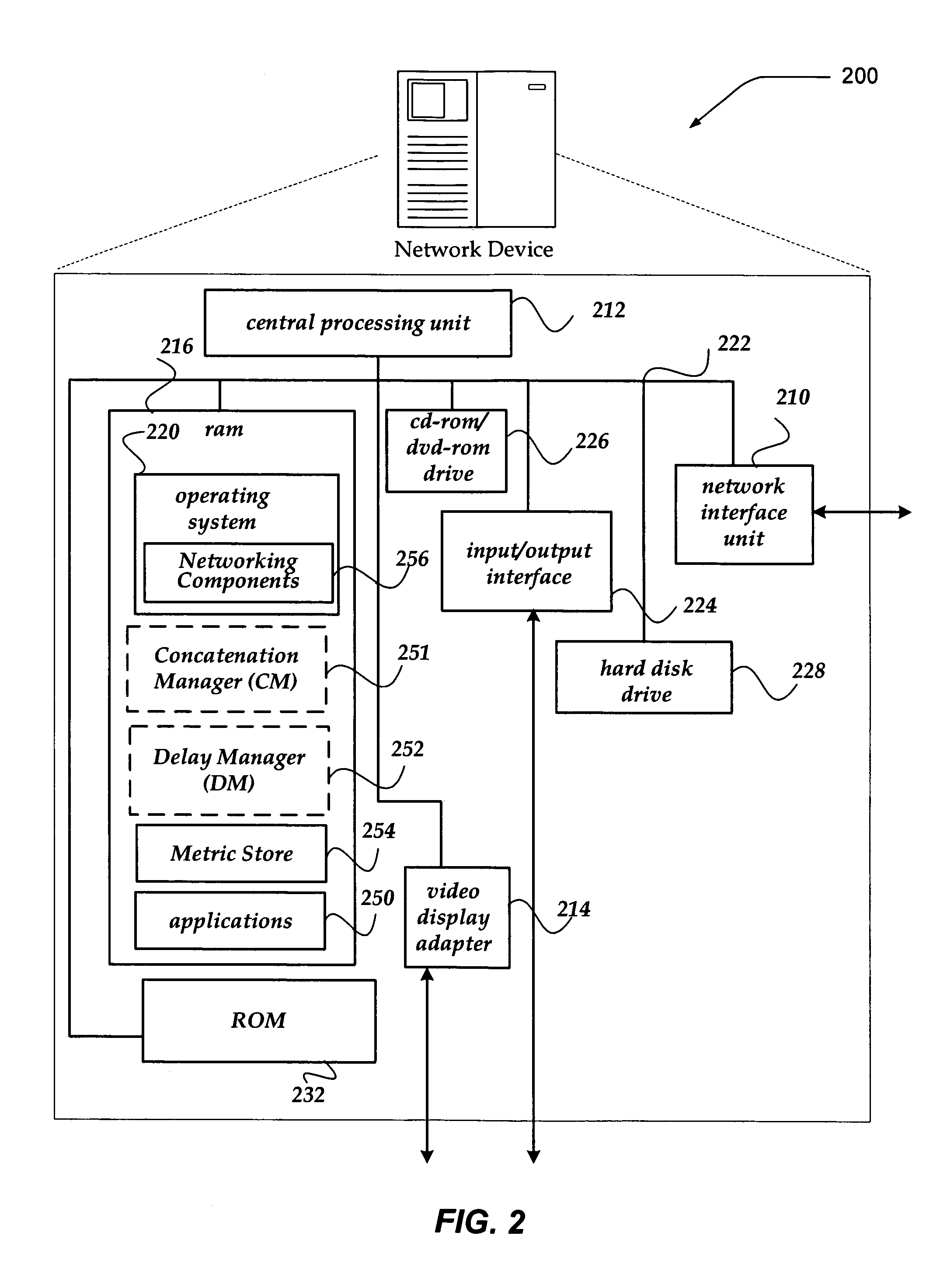
Selectively enabling network packet concatenation based on metrics
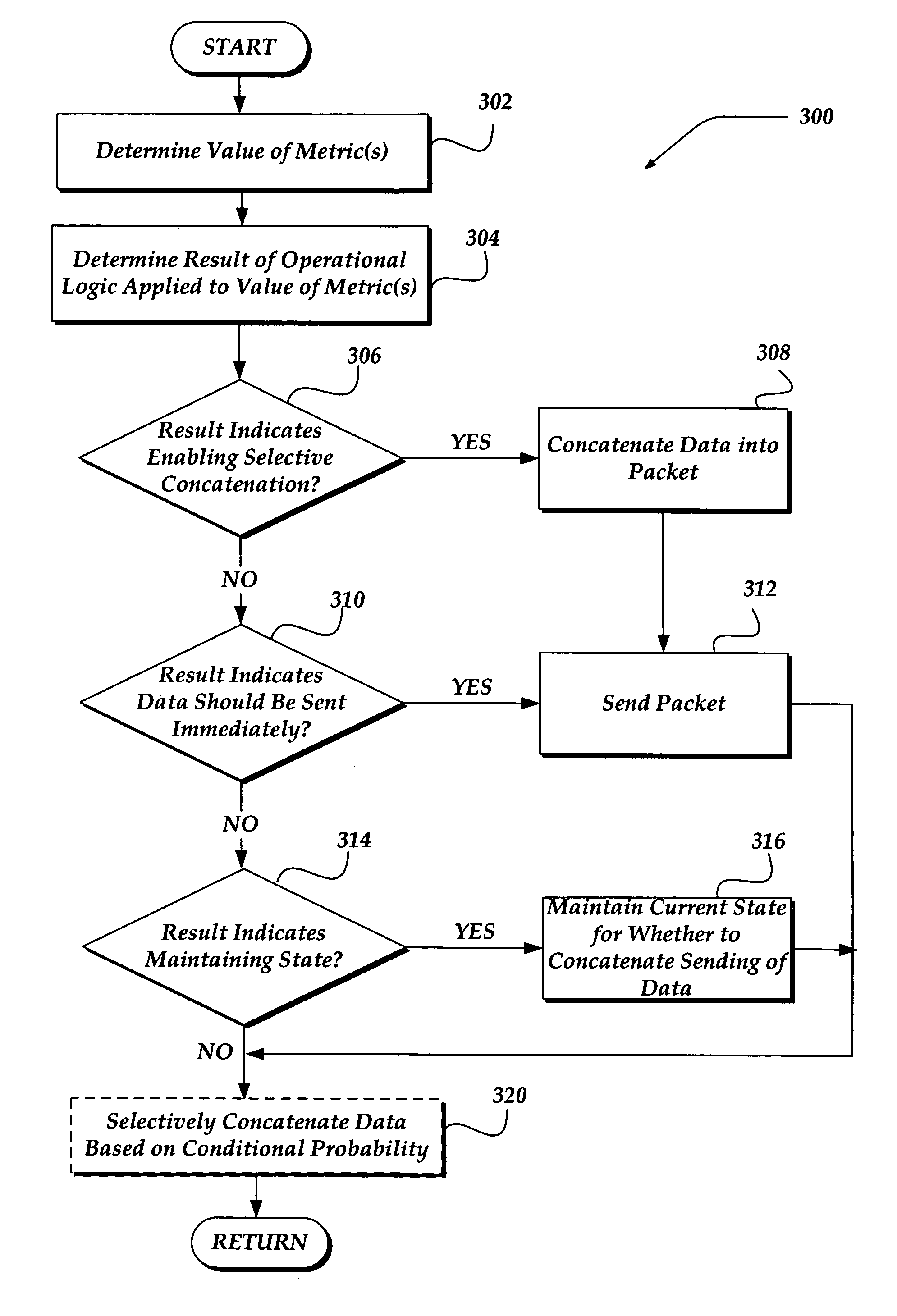
InactiveUS7873065B1Data switching by path configurationStore-and-forward switching systemsData connectionNetwork packet
A method, system, and apparatus are directed towards selectively concatenating data into a packet to modify a number of packets transmitted over a network based on a combination of network and / or send-queue metrics. In one embodiment, Nagle's algorithm is used for concatenating data into a packet. The concatenation may be selectively enabled based on heuristics applied to the combination of metrics. In one embodiment, the result may indicate that there should be a concatenation, or that data should be sent immediately, or that a current state for whether to concatenate or not should be maintained. The heuristics may include an expert system, decision tree, truth table, function, or the like. The heuristics may be provided by a user, or another computing device. In another embodiment, the concatenation may be enabled based on a conditional probability determined from the combination of metrics.
Owner:F5 NETWORKS INC
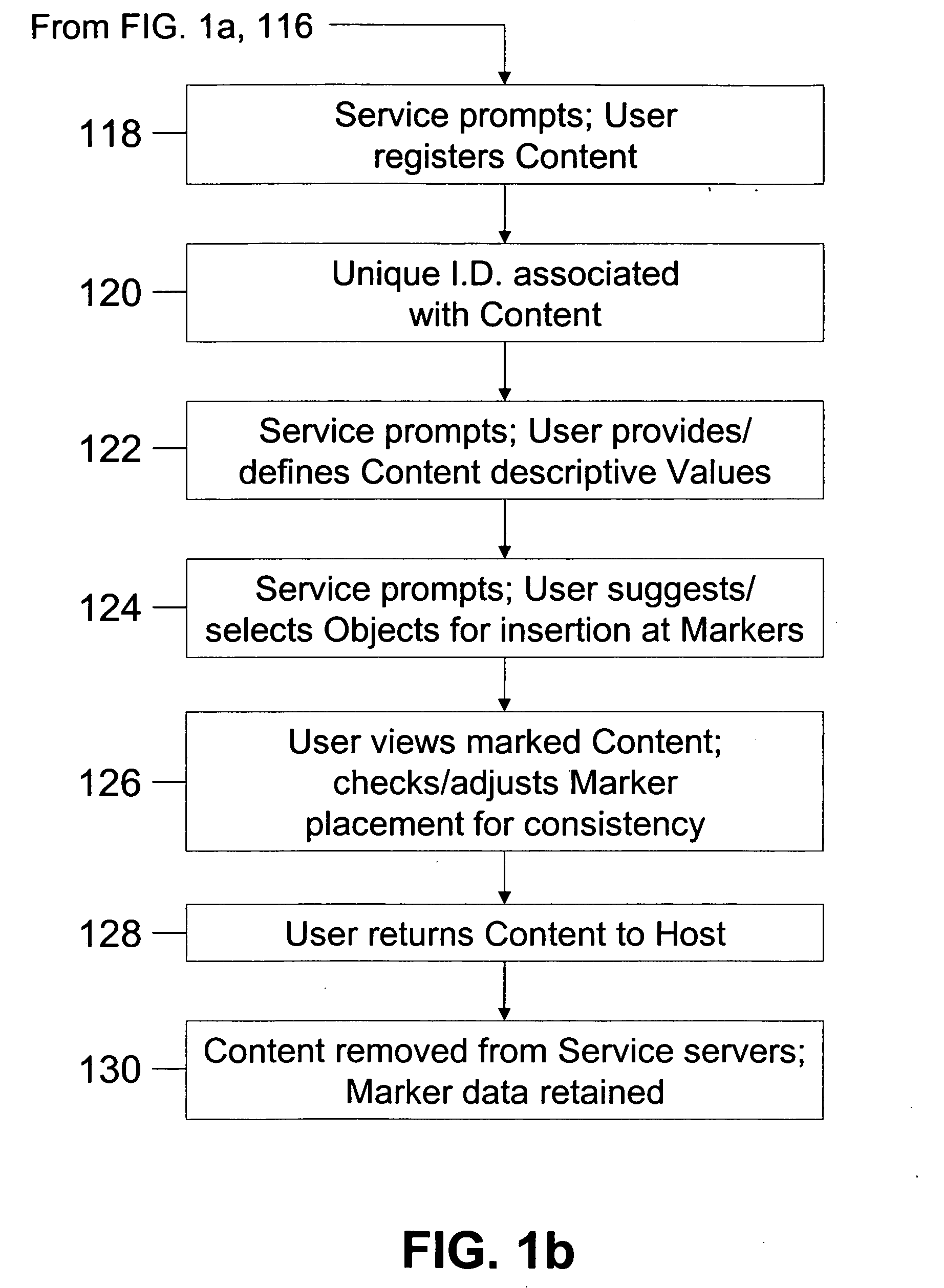
System and method for implementing logical switches in a network system
InactiveUS7197572B2Multiple digital computer combinationsData switching networksComputer hardwareNetwork packet
Owner:TAHOE RES LTD
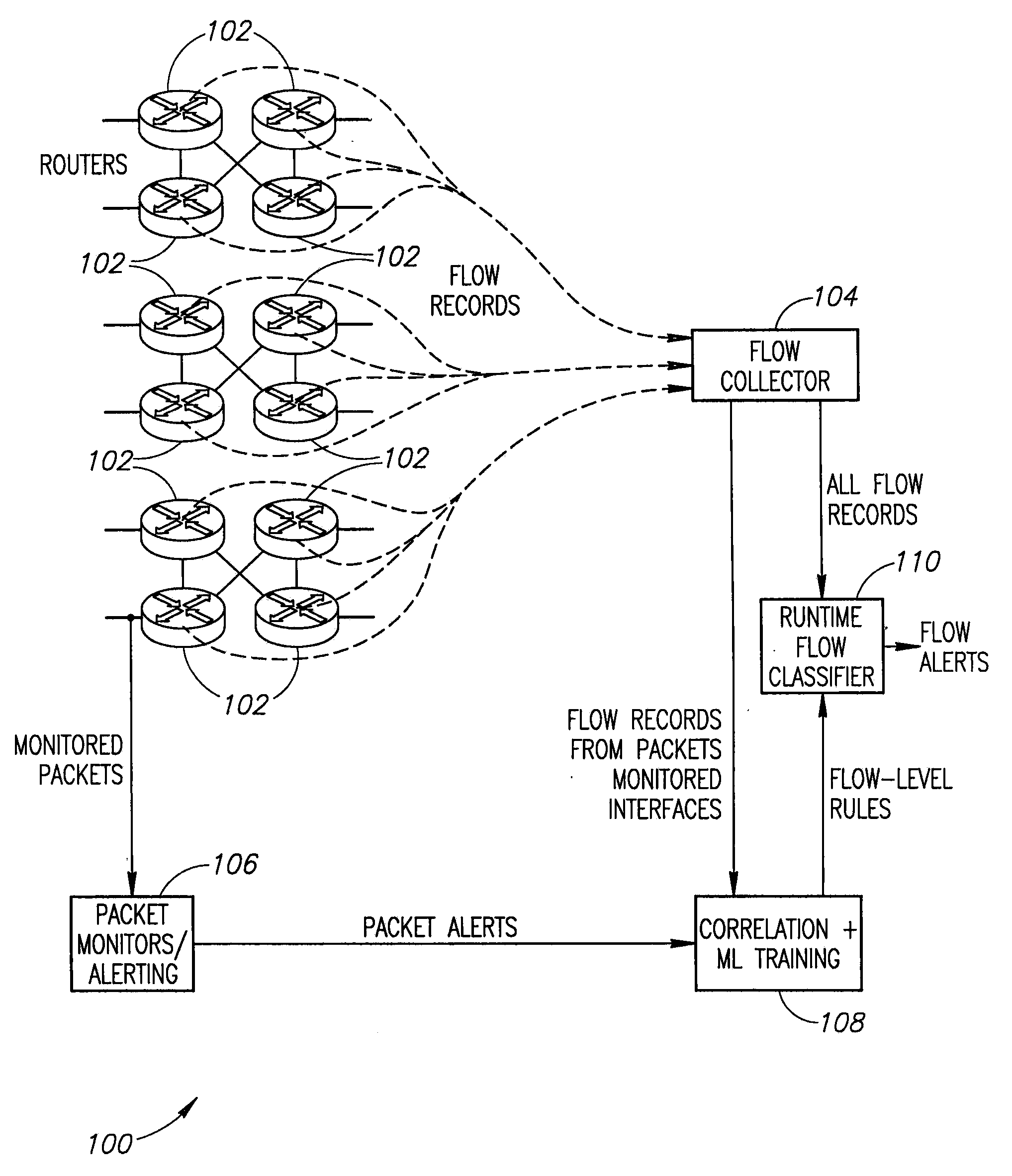
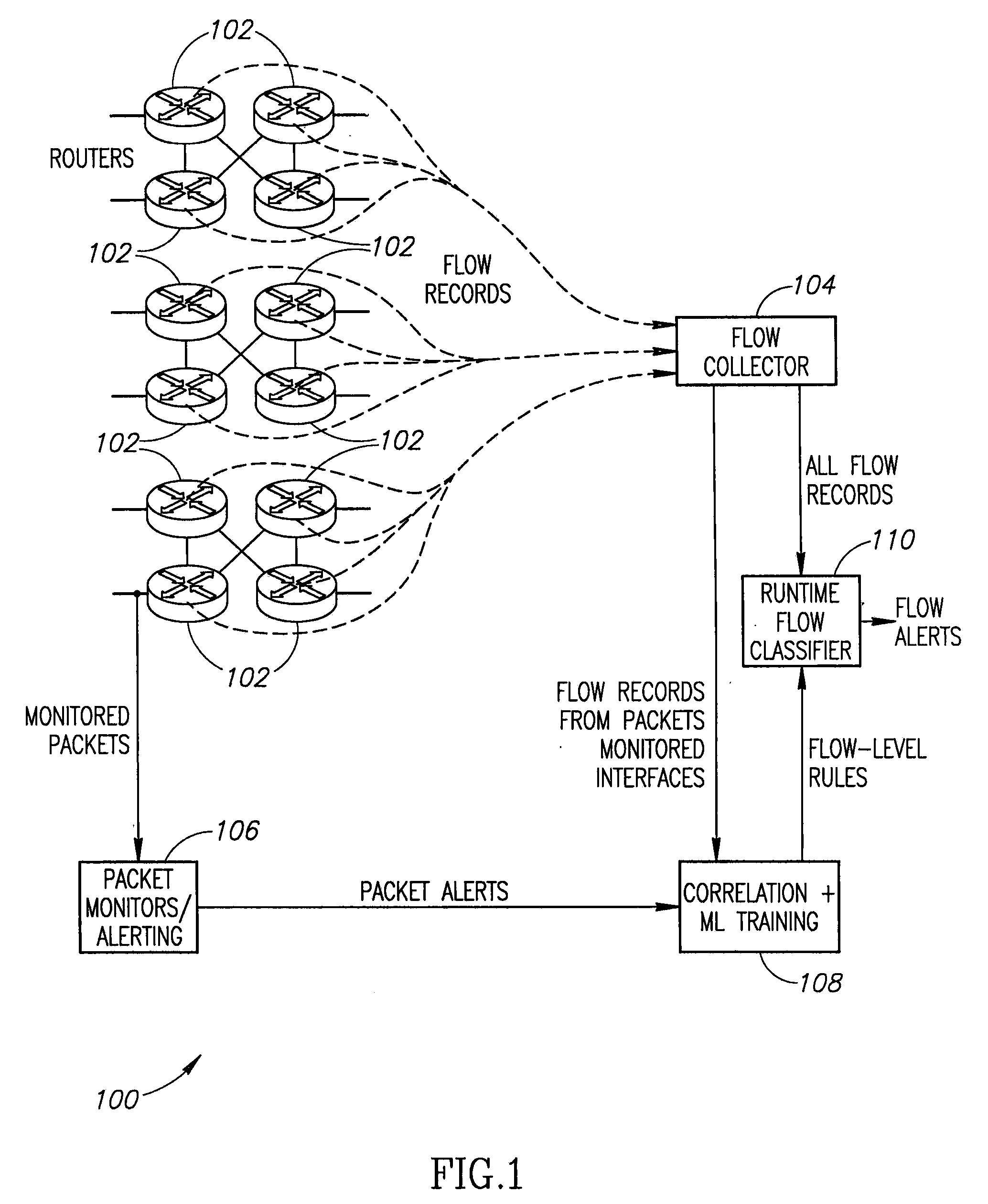
Systems and methods for rule-based anomaly detection on IP network flow
A system to detect anomalies in internet protocol (IP) flows uses a set of machine-learning (ML) rules that can be applied in real time at the IP flow level. A communication network has a large number of routers that can be equipped with flow monitoring capability. A flow collector collects flow data from the routers throughout the communication network and provides them to a flow classifier. At the same time, a limited number of locations in the network monitor data packets and generate alerts based on packet data properties. The packet alerts and the flow data are provided to a machine learning system that detects correlations between the packet-based alerts and the flow data to thereby generate a series of flow-level alerts. These rules are provided to the flow time classifier. Over time, the new packet alerts and flow data are used to provide updated rules generated by the machine learning system.
Owner:AT&T INTPROP I L P
Method of inserting/overlaying markers, data packets and objects relative to viewable content and enabling live social networking, N-dimensional virtual environments and/or other value derivable from the content
ActiveUS20080163379A1Low costReduced flexibilityDigital data processing detailsAnalogue secracy/subscription systemsNetwork packetSocial web
A method by which a User can associate selectable Markers, Data Packets and / or Objects with Content. The Content may generally be distributed electronically, and the Markers allow for insertion and / or overlay of Objects when the Content is selected for viewing by a Viewer. Objects and Data Packets are generally provided by a User, Promoter, Host, Service, or other entity to convey information to a Viewer. A Service provides tools and capabilities to both the User and the Promoter to facilitate their respective actions according to embodiments of the invention, including enabling the creation of live social networks (such as those linked to a specific Service provider, a specific User group, activities by a specific Promoter, and / or to specific Data Packets) and the creation of n-dimensional Virtual Environments.
Owner:NEONEKT LLC
Internal bus system for DFPS and units with two- or multi-dimensional programmable cell architectures, for managing large volumes of data with a high interconnection complexity
InactiveUS7010667B2Multiple digital computer combinationsArchitecture with single central processing unitNetwork packetInterconnection
An internal bus system for DFPs and units with two- or multi-dimensional programmable cell architectures, for managing large volumes of data with a high interconnection complexity. The bus system can transmit data between a plurality of function blocks, where multiple data packets can be on the bus at the same time. The bus system automatically recognizes the correct connection for various types of data or data transmitters and sets it up.
Owner:PACT XPP TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com