Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3400 results about "Control flow" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, control flow (or flow of control) is the order in which individual statements, instructions or function calls of an imperative program are executed or evaluated. The emphasis on explicit control flow distinguishes an imperative programming language from a declarative programming language.
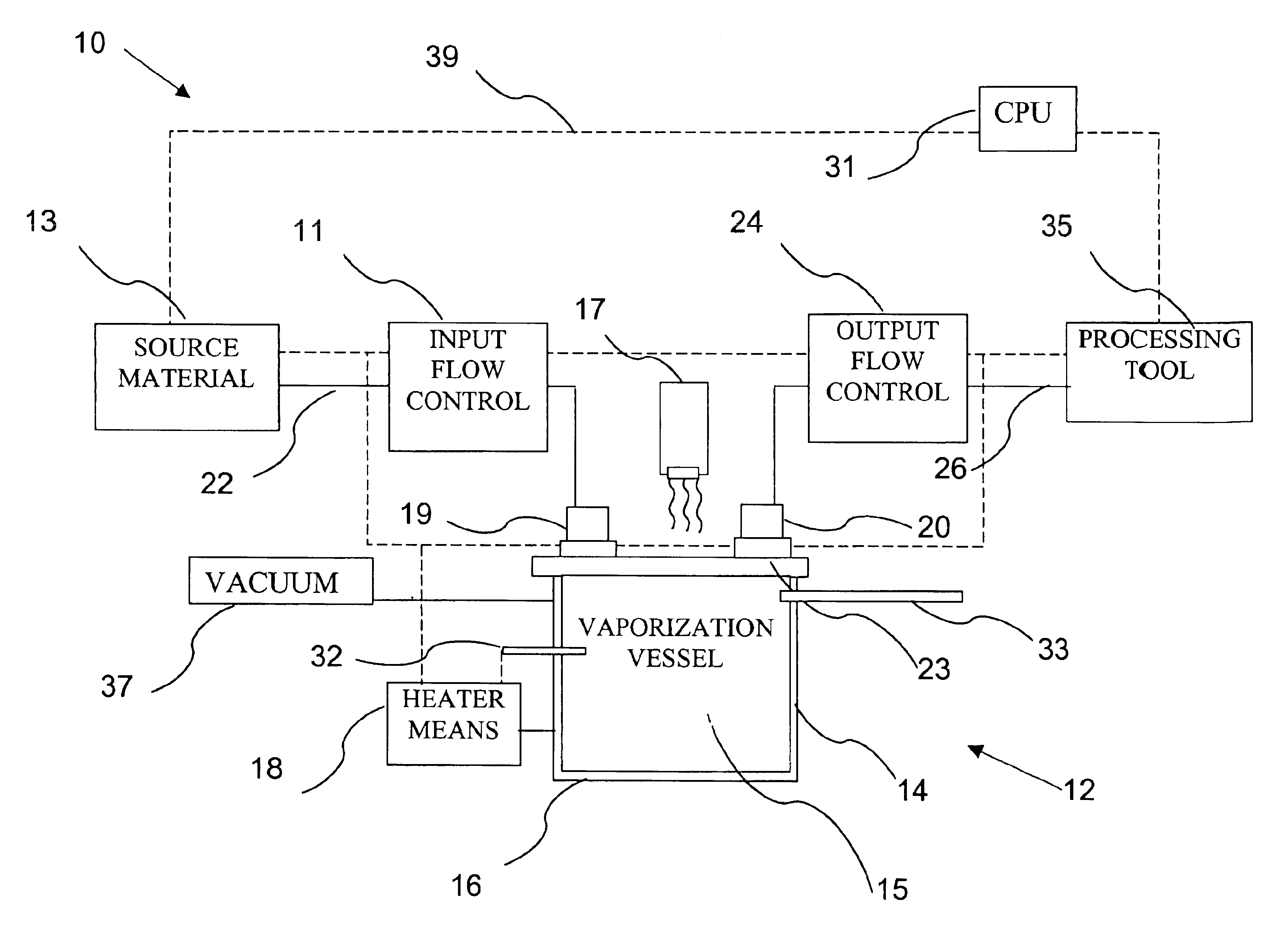
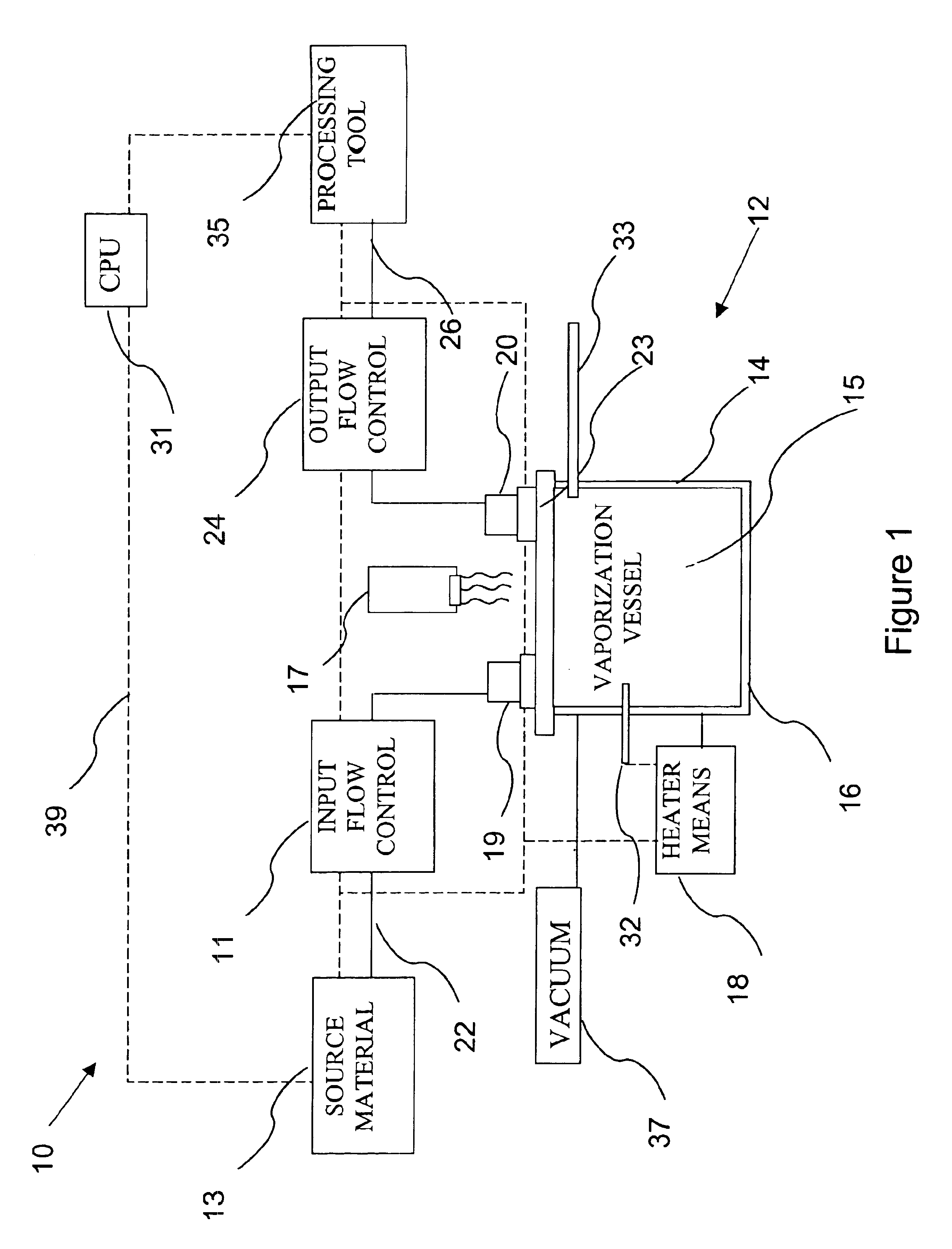
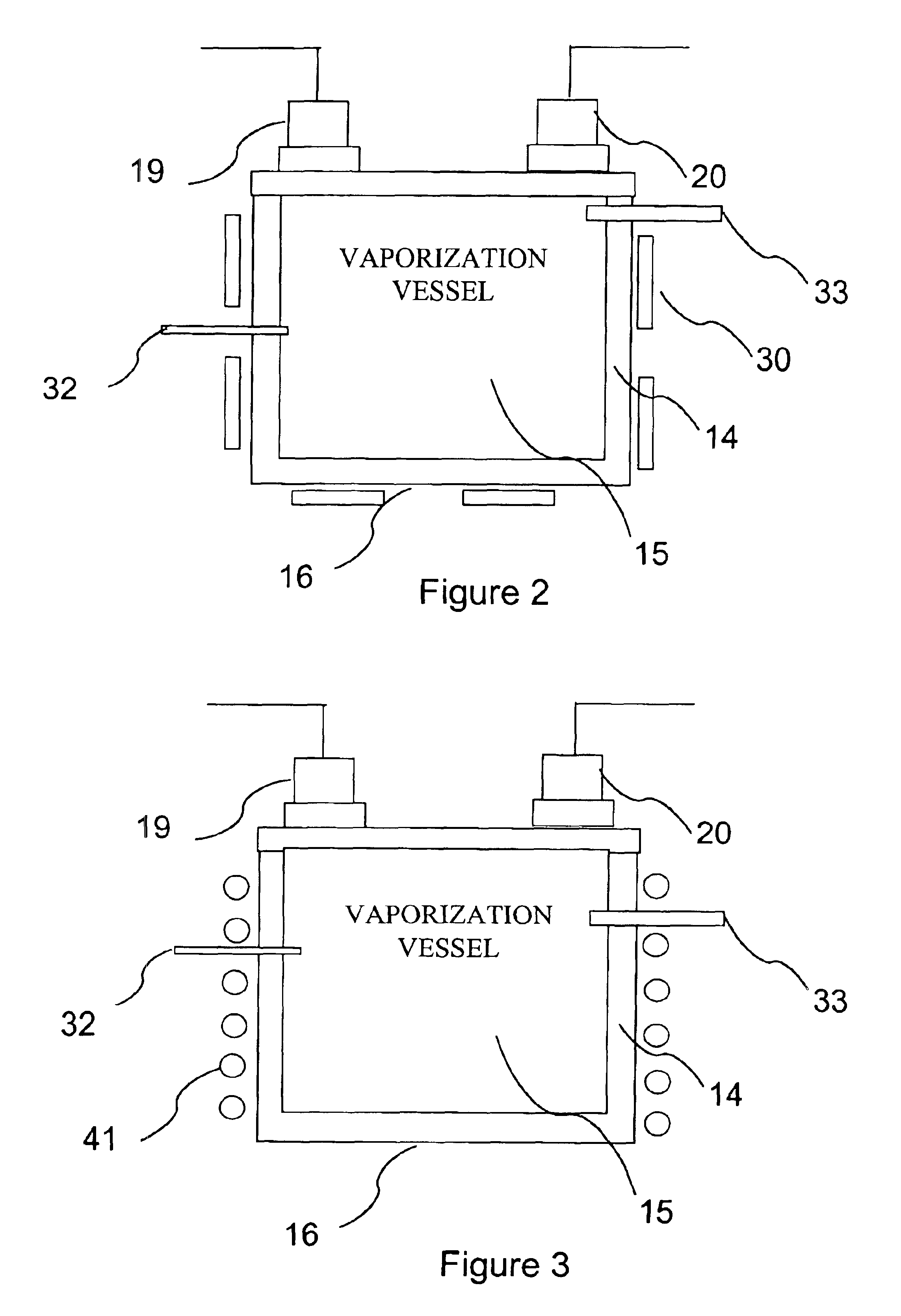
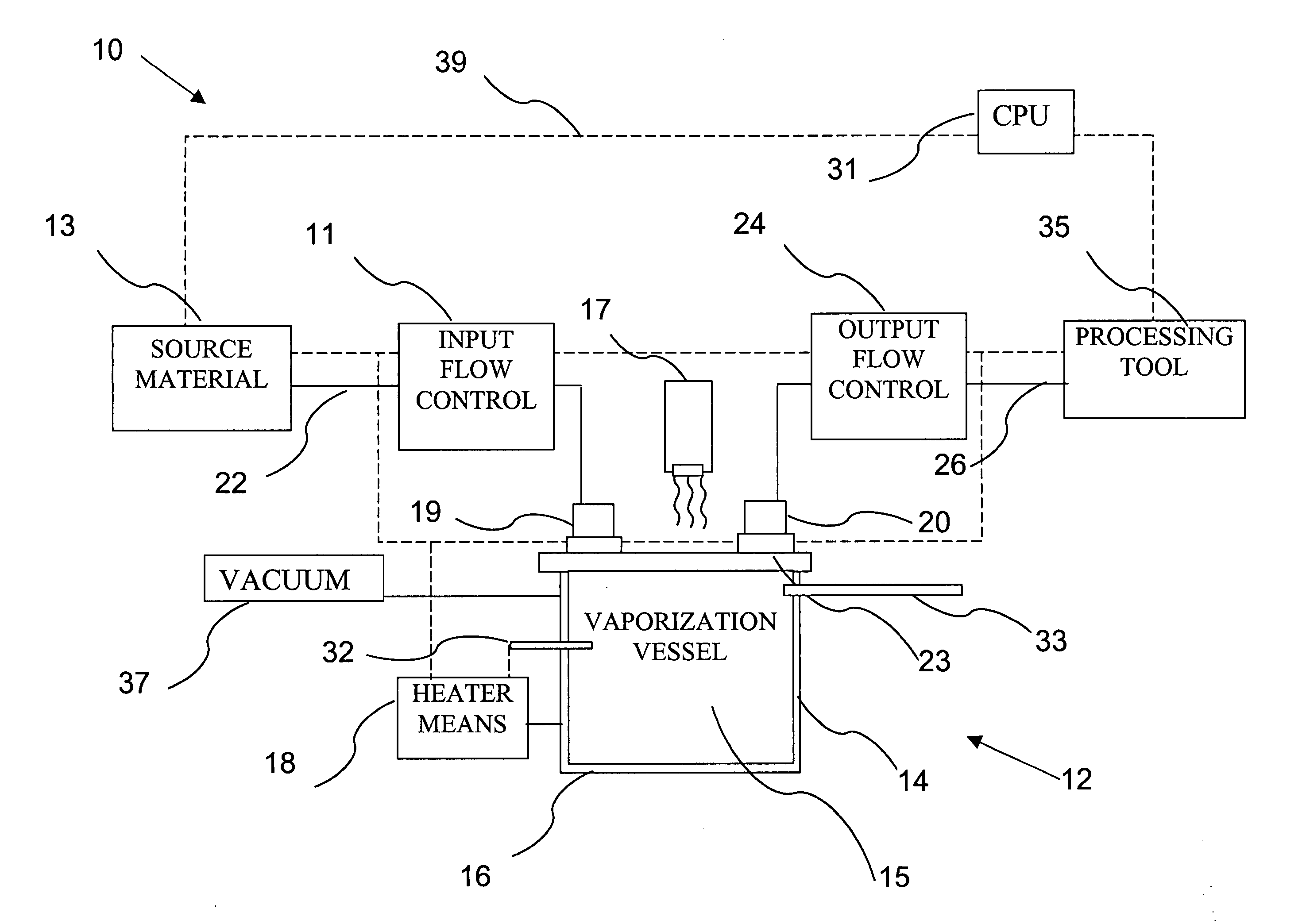
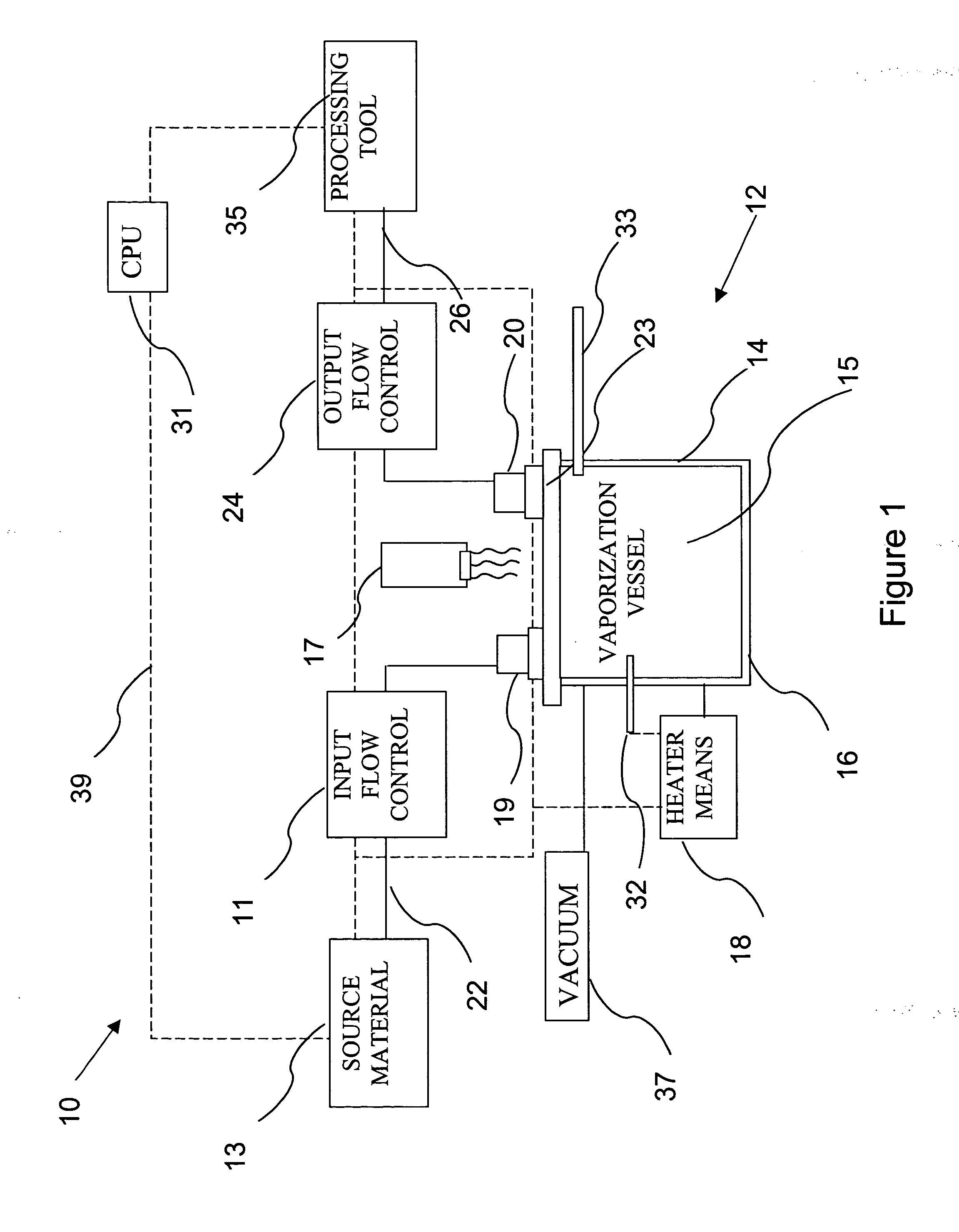
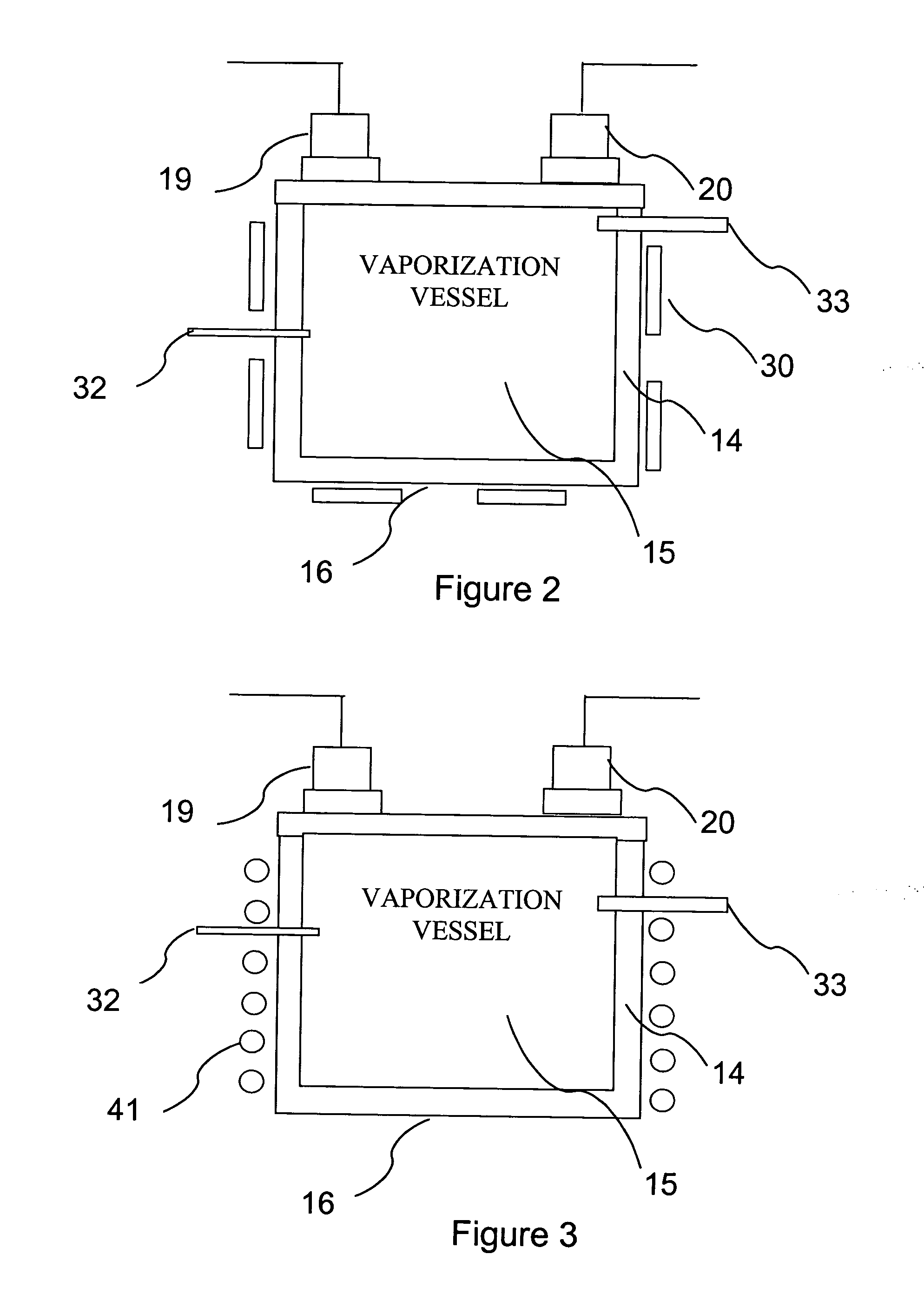
Delivery systems for efficient vaporization of precursor source material
InactiveUS6909839B2Precise deliveryVacuum evaporation coatingSputtering coatingControl flowSource material
The present invention relates to a delivery system for vaporizing and delivering vaporized solid and liquid precursor materials at a controlled rate having particular utility for semiconductor manufacturing applications. The system includes a vaporization vessel, a processing tool and a connecting vapor line therebetween, where the system further includes an input flow controller and / or an output flow controller to provide a controlled delivery of a vaporizable source material to the vaporization vessel and a controlled flow rate of vaporized source material to the processing tool.
Owner:ENTEGRIS INC
Delivery systems for efficient vaporization of precursor source material
InactiveUS20050019026A1Precise deliveryVacuum evaporation coatingSemiconductor/solid-state device manufacturingControl flowSource material
The present invention relates to a delivery system for vaporizing and delivering vaporized solid and liquid precursor materials at a controlled rate having particular utility for semiconductor manufacturing applications. The system includes a vaporization vessel, a processing tool and a connecting vapor line therebetween, where the system further includes an input flow controller and / or an output flow controller to provide a controlled delivery of a vaporizable source material to the vaporization vessel and a controlled flow rate of vaporized source material to the processing tool.
Owner:ENTEGRIS INC
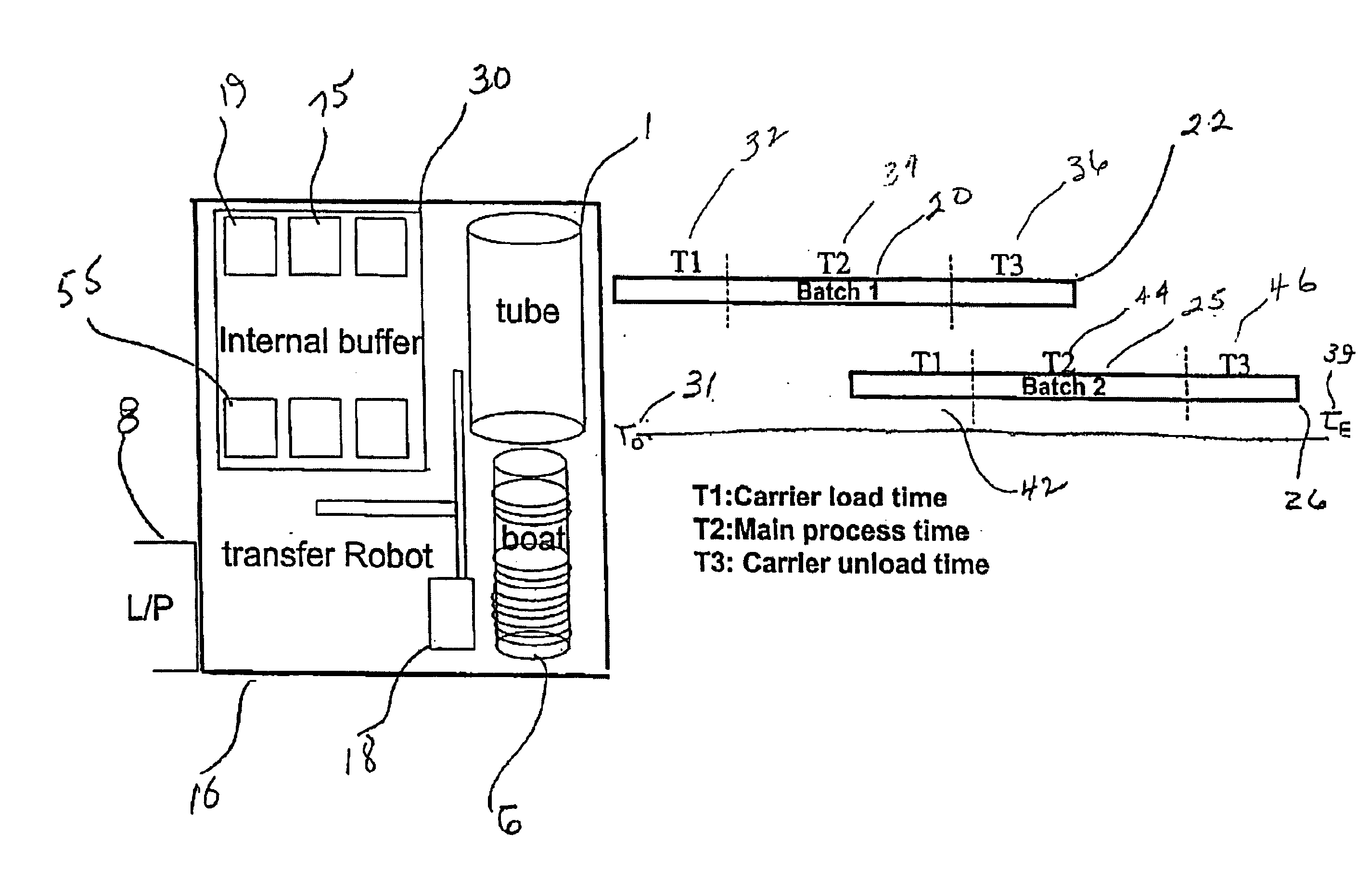
Intelligent full automation controlled flow for a semiconductor furnace tool
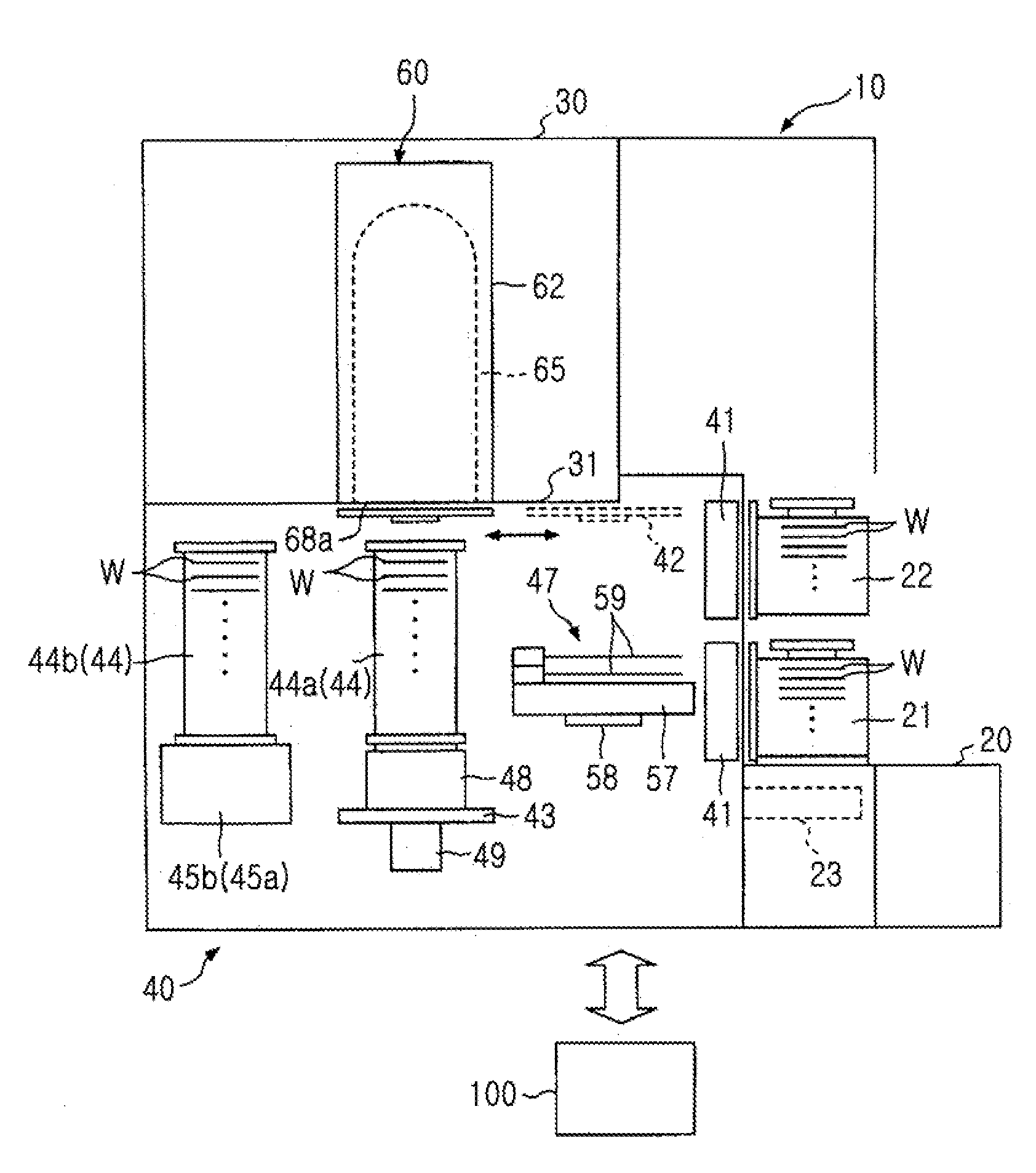
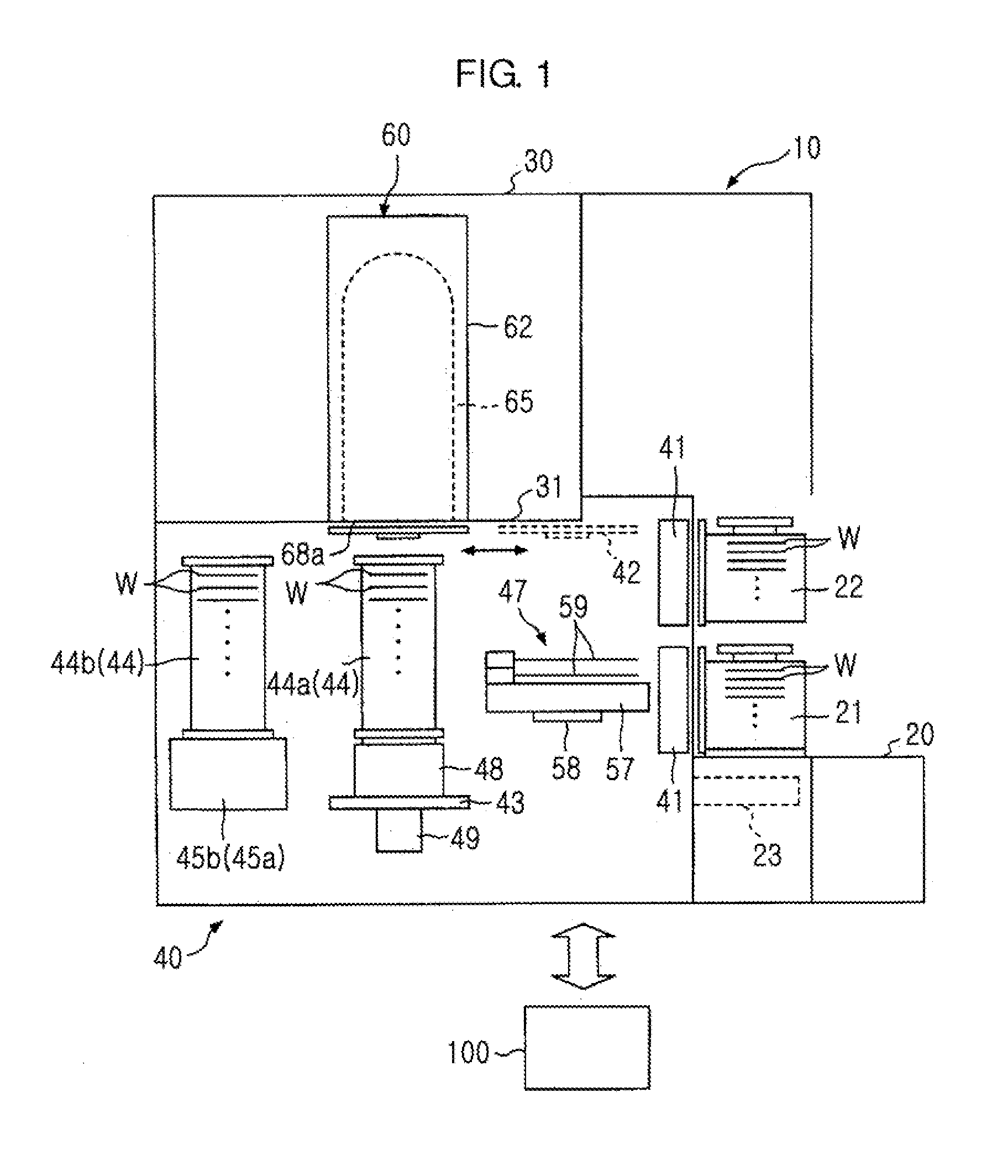
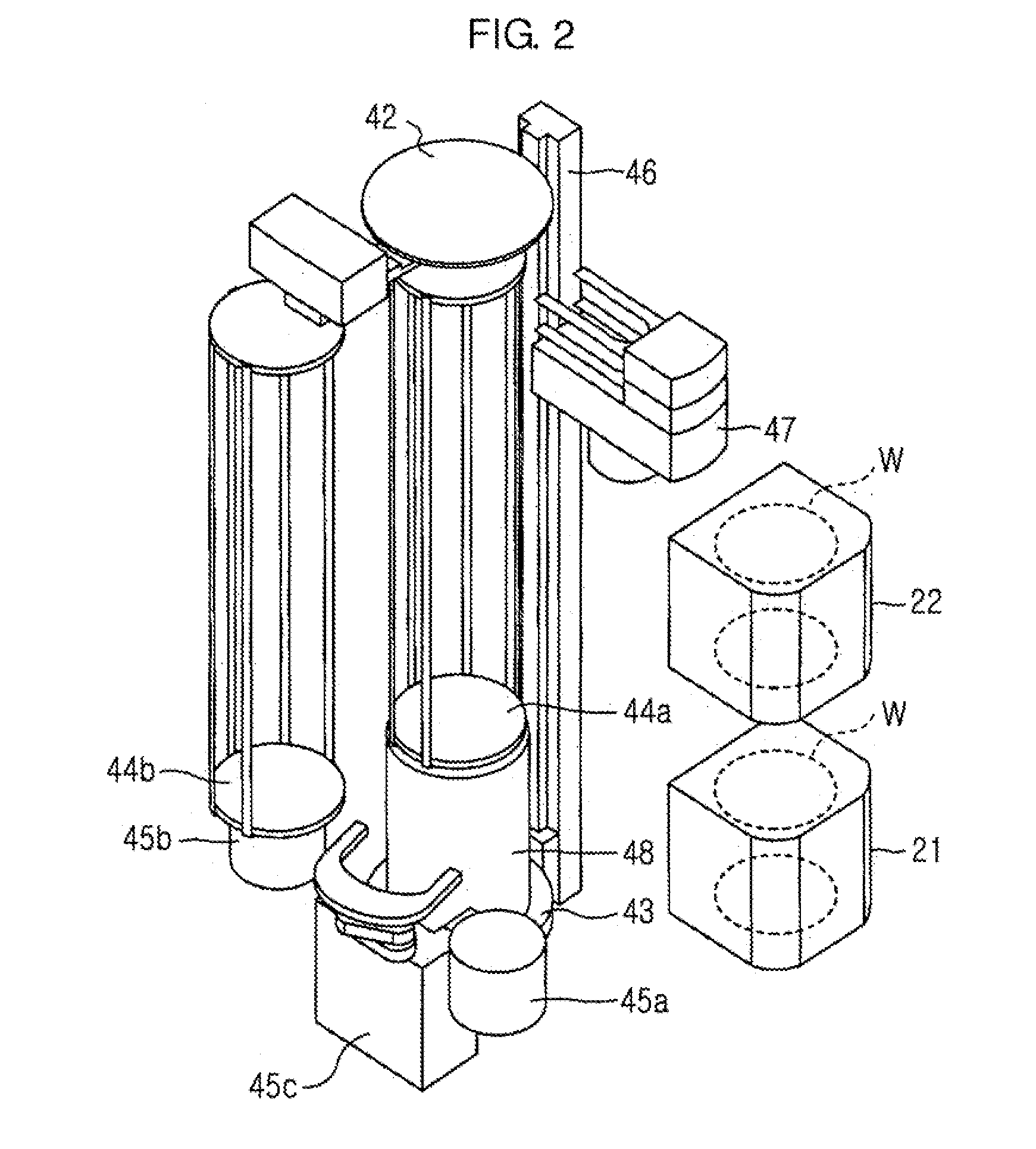
InactiveUS20050187647A1Reduce idle timeSemiconductor/solid-state device manufacturingSpecial data processing applicationsControl flowAutomatic control
The present invention relates to an apparatus and method for processing the flow of semiconductor wafers through a furnace tool having a front-opening unified pod (FOUP) material handling system. The invention provides for an automated control flow to realize greater efficiency and assure process quality. In one aspect of the invention the wafer batch completing its operation is discharged simultaneous with the charging of the next batch. Essentially the operation takes place by overlapping processing operations. An embodiment of the invention includes a process comprising the steps of: providing a first batch of semiconductor material, and loading the first batch into a carrier which transports the first batch into a semiconductor manufacturing process, and while the first batch undergoes the process, forming a second batch of semiconductor material, and pausing a second batch process operation until the first batch completes processing, to reduce the idle time of said process.
Owner:TAIWAN SEMICON MFG CO LTD
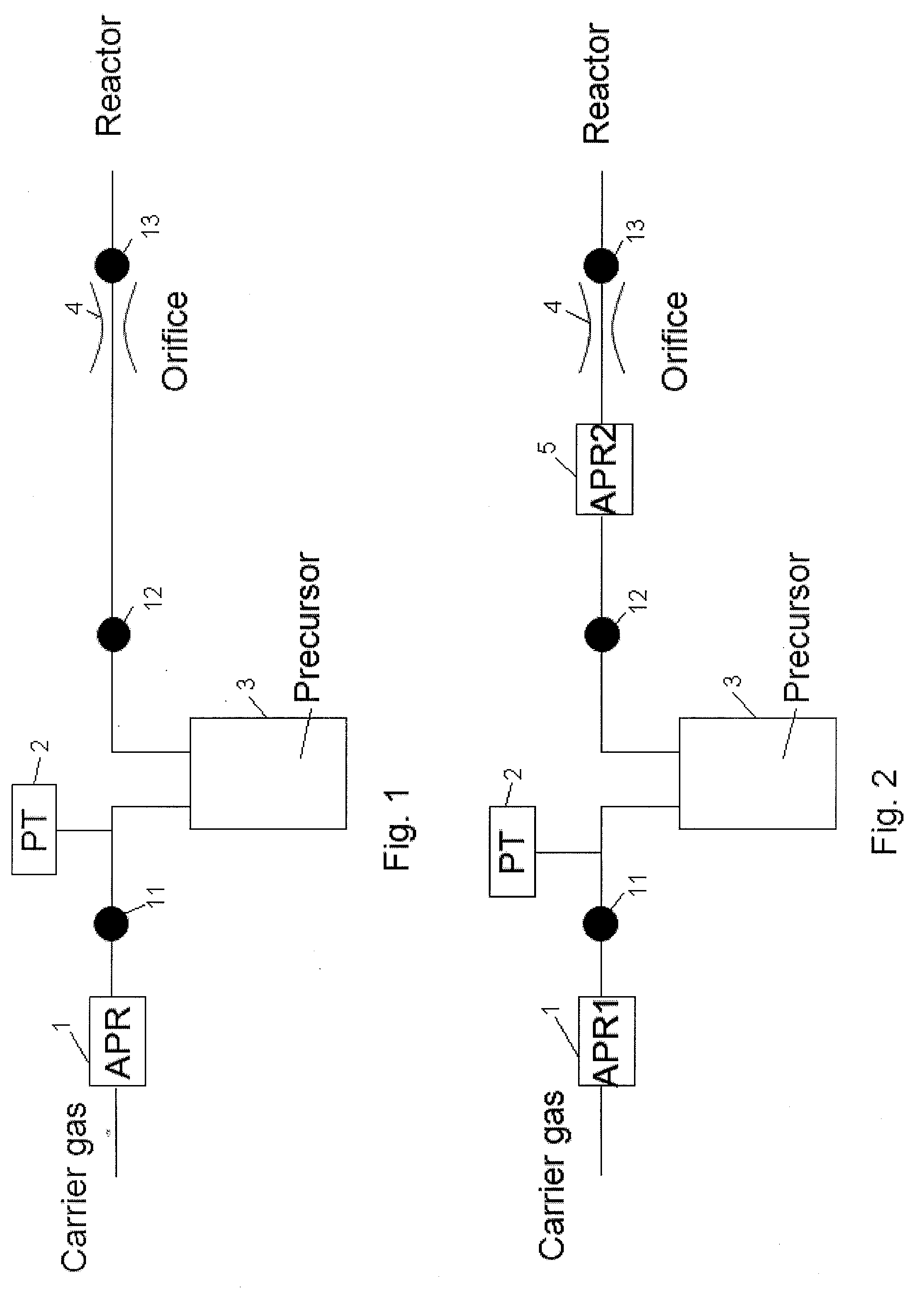
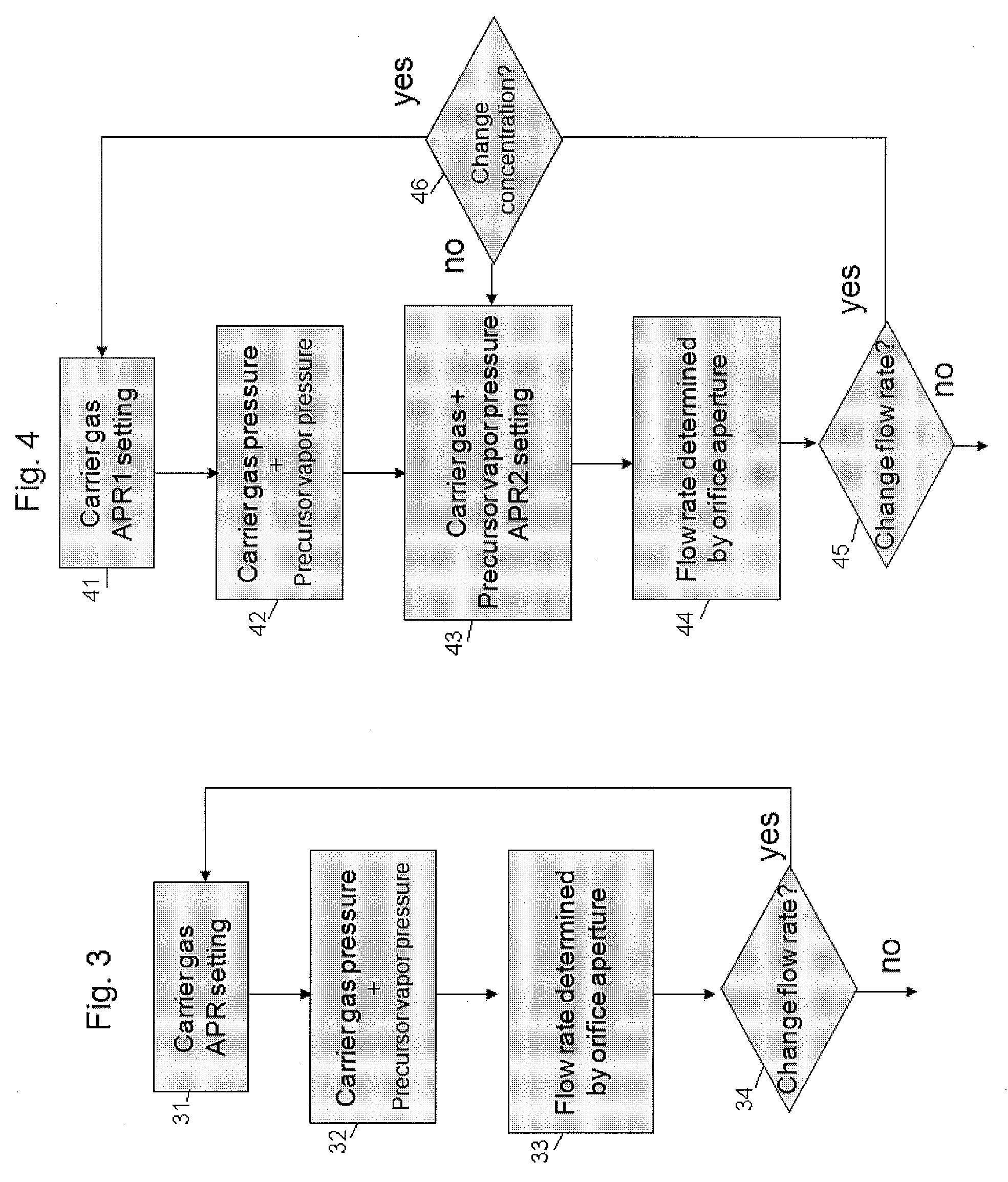
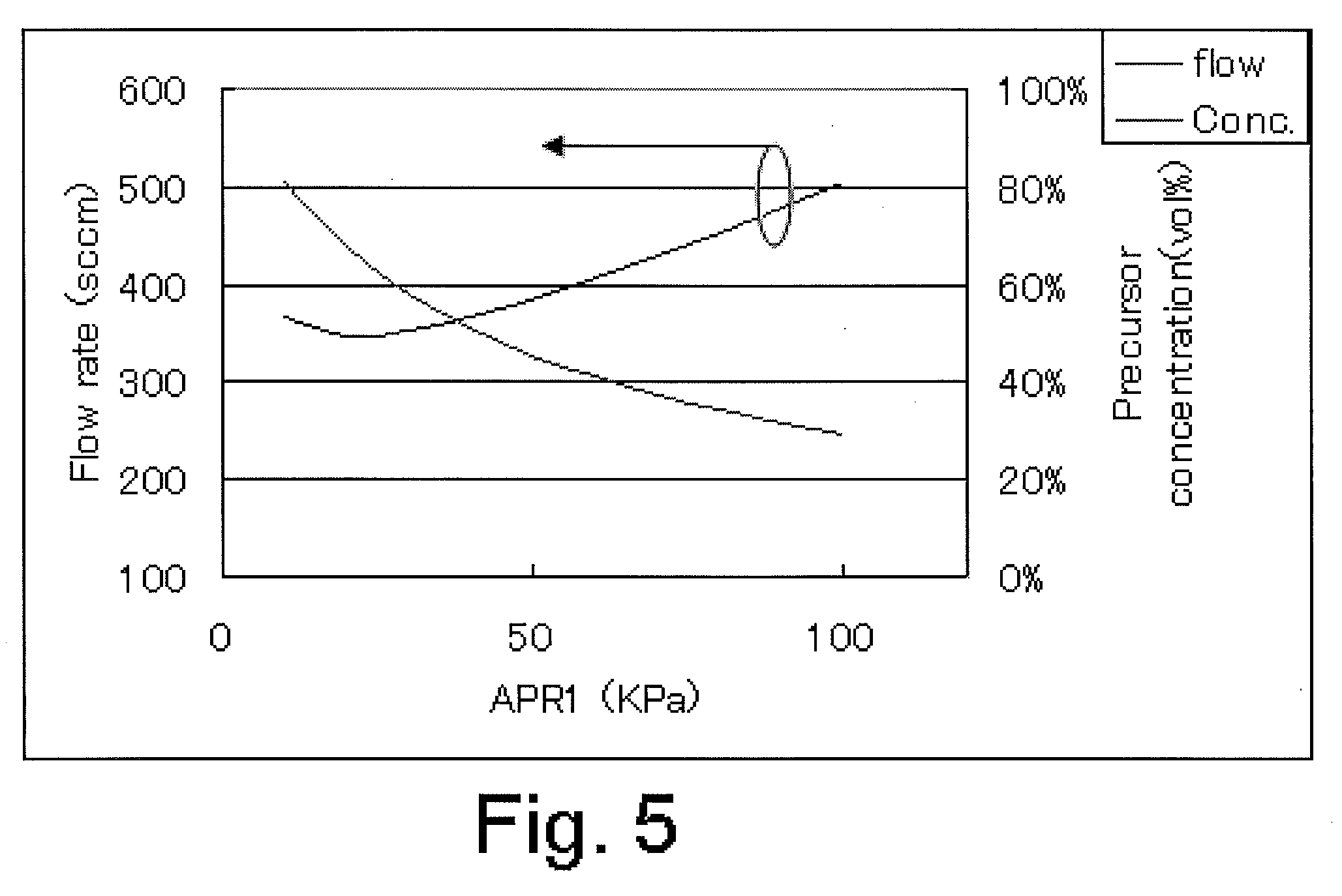
Method for controlling flow and concentration of liquid precursor
ActiveUS20100178423A1Material concentration can be controlledLine pressure can be accuratelyLiquid surface applicatorsVacuum evaporation coatingControl flowPressure regulator
A method for controlling flow and concentration of a liquid precursor includes: supplying a carrier gas to a first auto-pressure regulator and outputting therefrom the carrier gas at a first pressure to a precursor reservoir; outputting the mixture of the vaporized precursor and the carrier gas from the precursor reservoir; and supplying the mixture to a second auto-pressure regulator and outputting therefrom the mixture at a second pressure to a reactor via an orifice.
Owner:ASM JAPAN
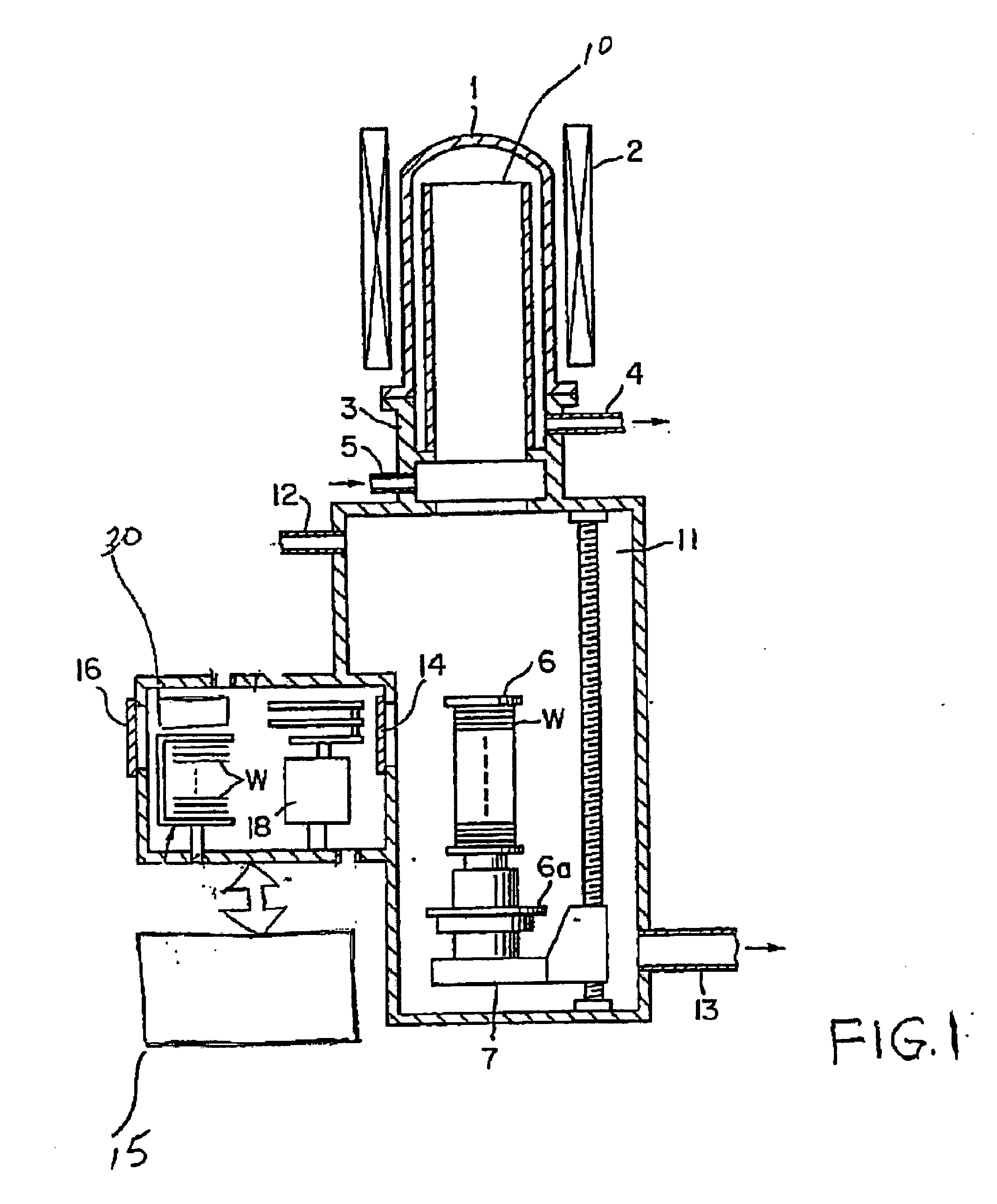
Thermal treatment apparatus, temperature control system, thermal treatment method, temperature control method, and non-transitory computer readable medium embodied with program for executing the thermal treatment method or the temperature control method
InactiveUS20130065189A1Avoid it happening againIncrease power consumptionSemiconductor/solid-state device manufacturingCharge manipulationControl flowTemperature control
A thermal treatment apparatus includes a processing container, a substrate holding unit for holding a plurality of substrates at predetermined intervals in a direction inside the processing container, a heating unit for heating the processing container, a supply unit for supplying gas, a plurality of supply ports provided respectively at different locations in the direction, and a cooling unit for cooling the processing container by supplying the gas into the processing container by the supply unit via each of the supply ports, wherein the supply unit is provided in such a way that the supply unit independently controls flow rates of the gases supplied via each of the supply ports.
Owner:TOKYO ELECTRON LTD
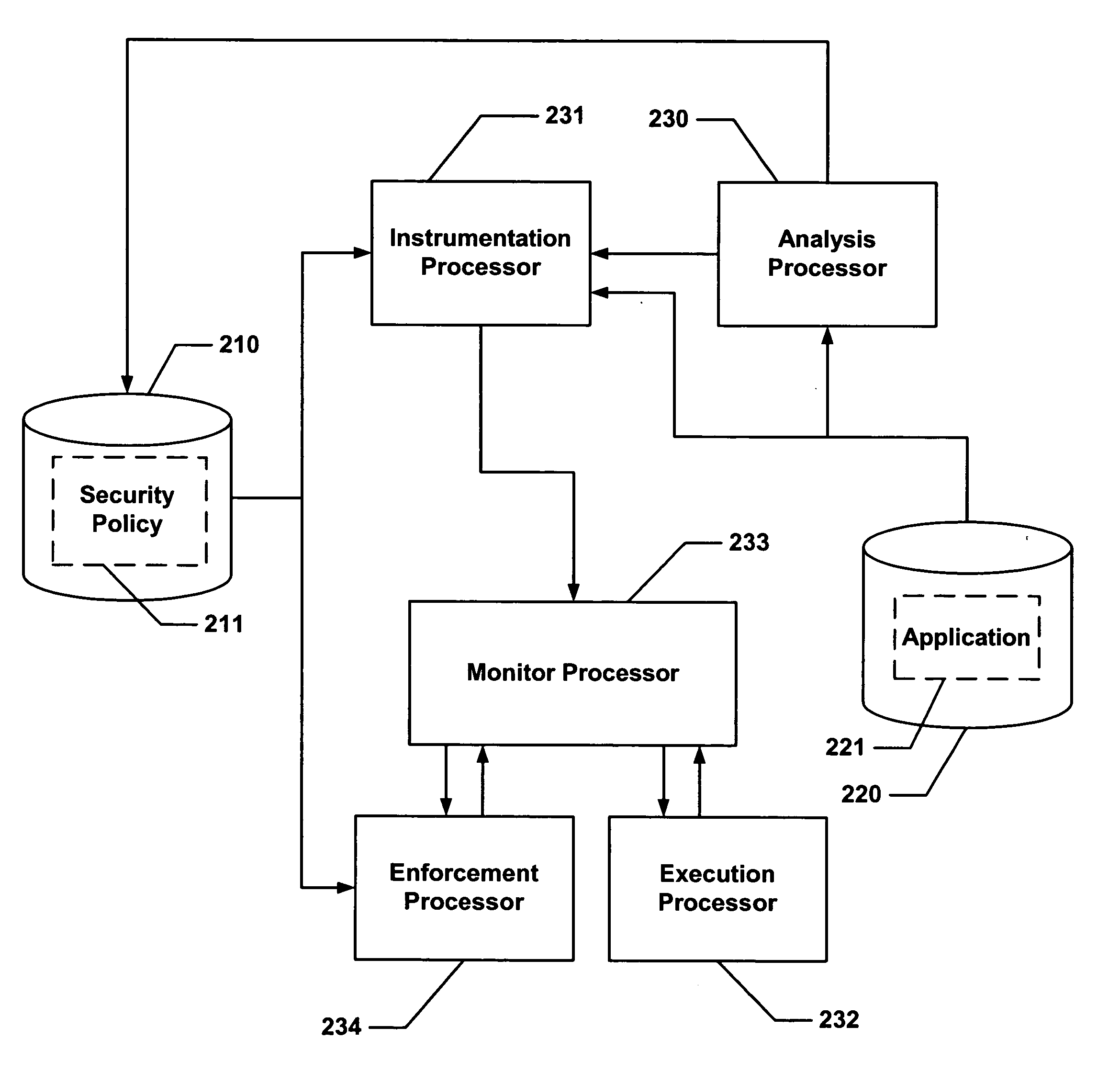
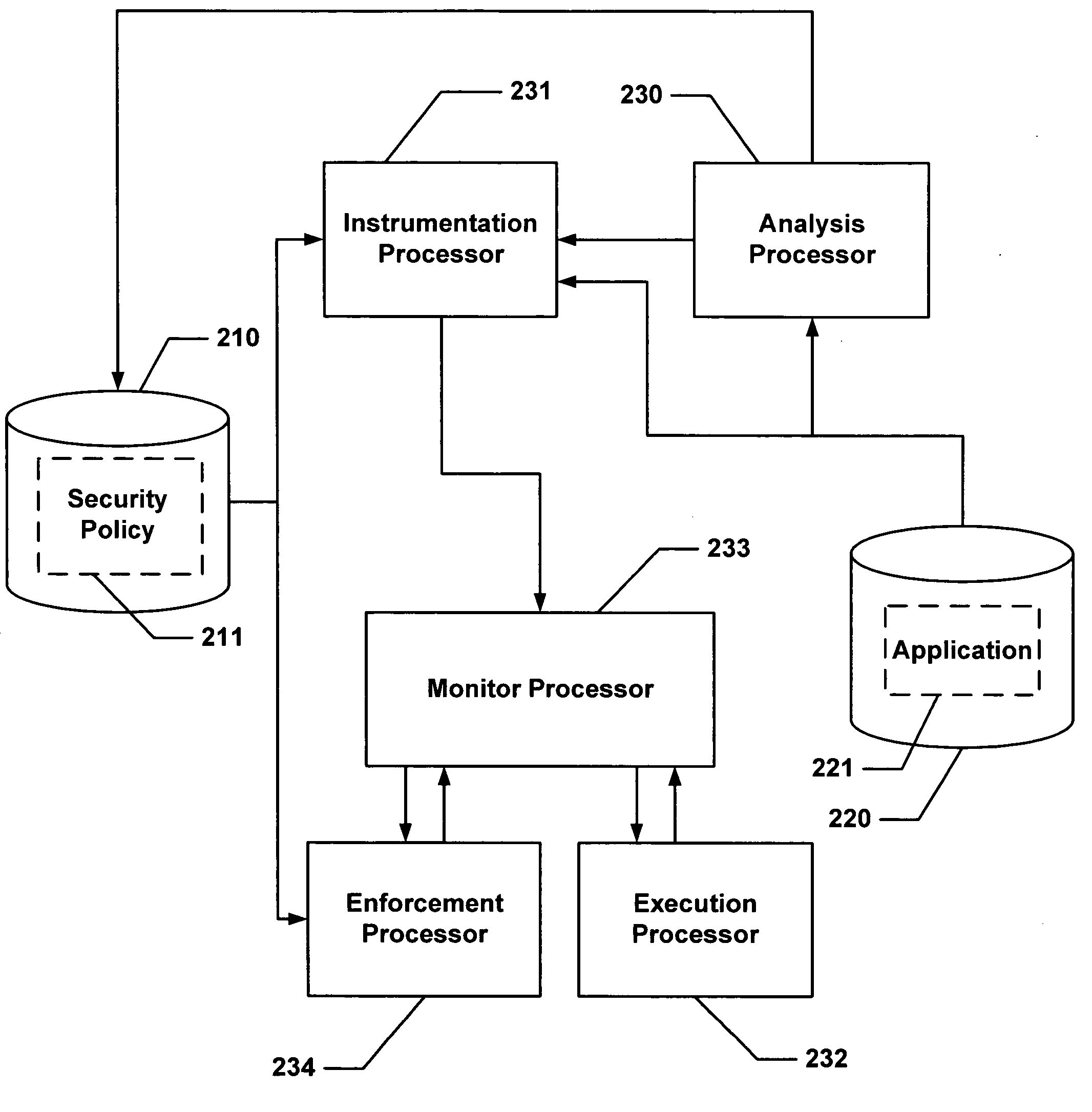
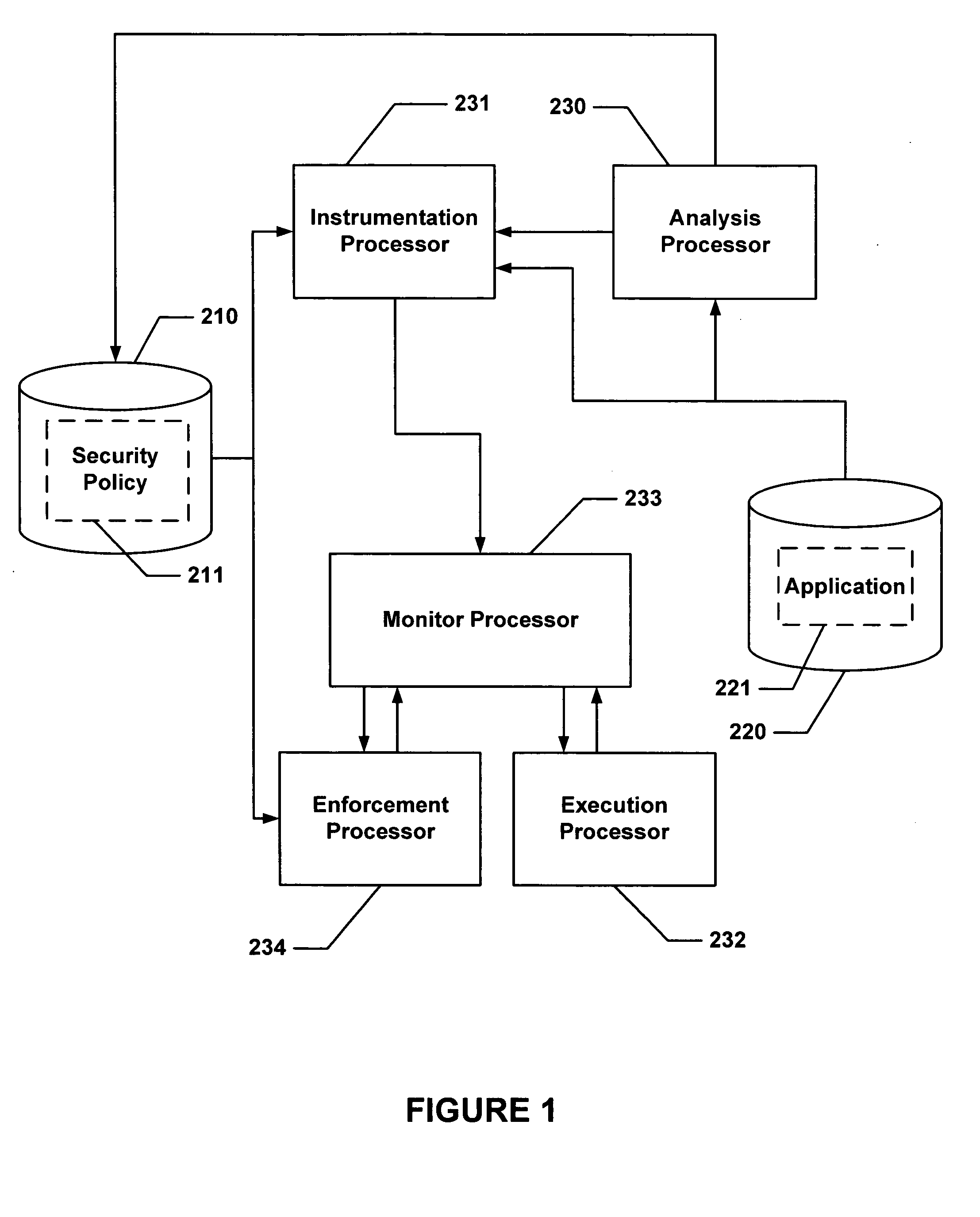
Secure execution of a computer program
ActiveUS20040133777A1Digital data processing detailsUnauthorized memory use protectionControl flowApplication software
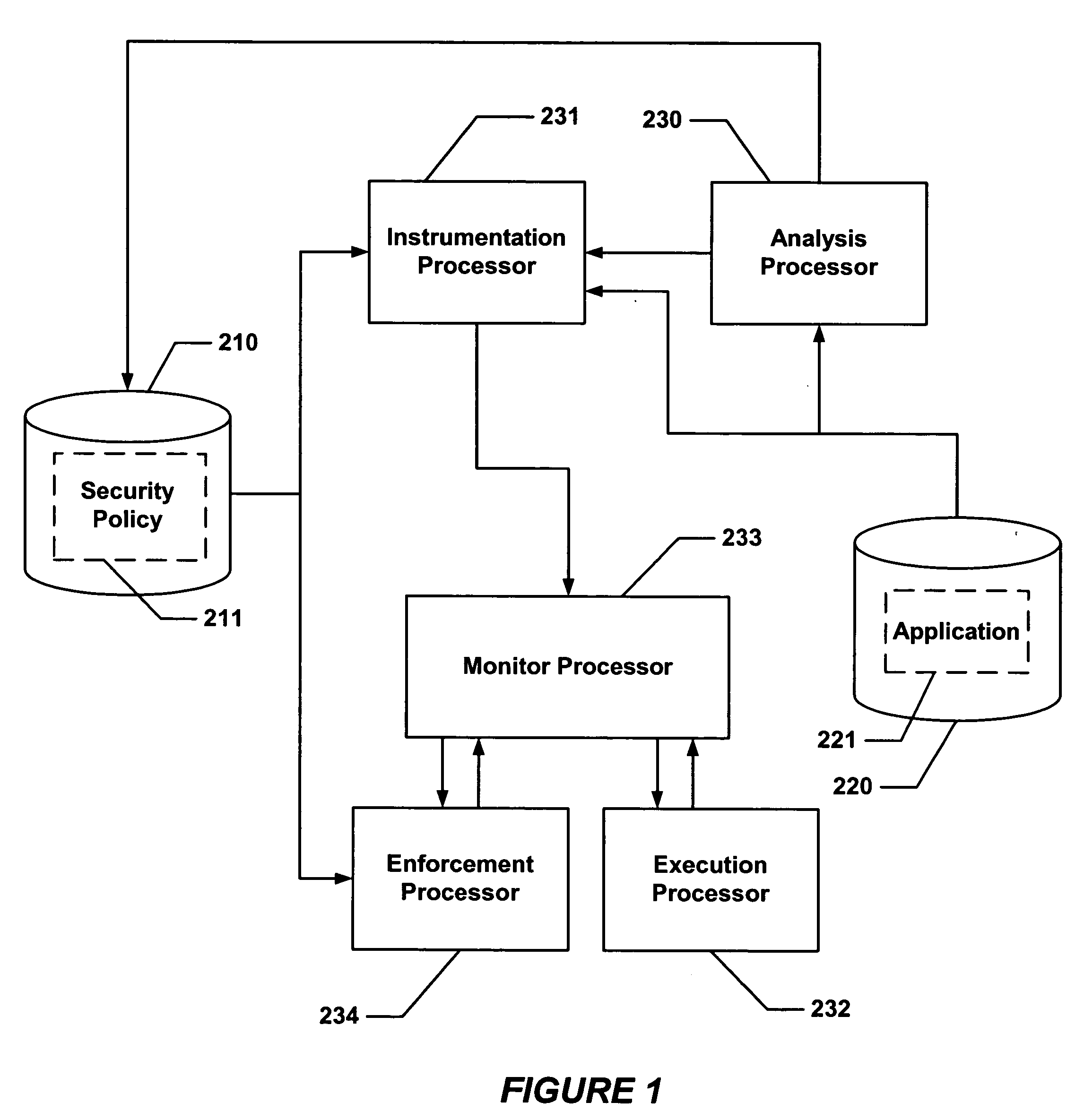
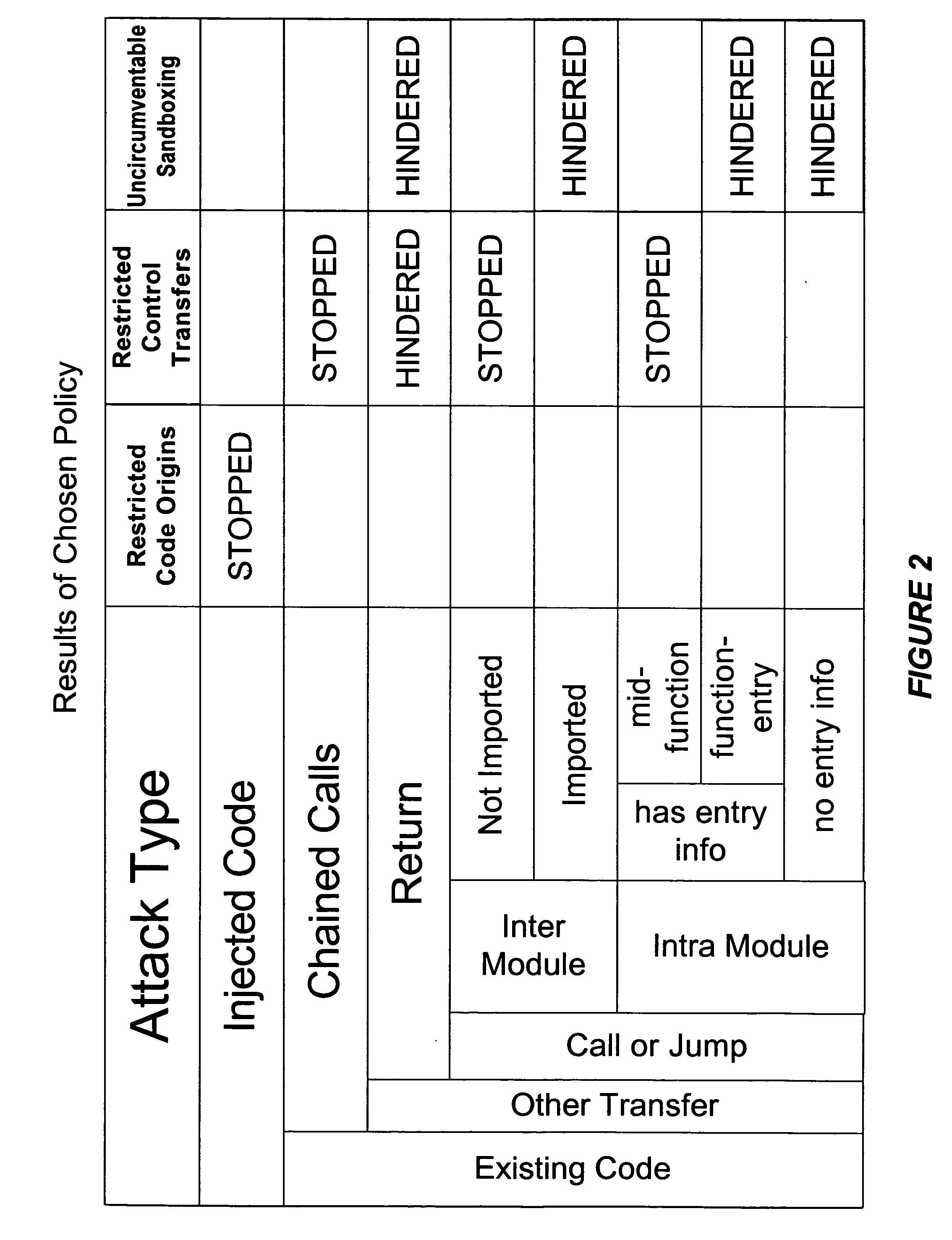
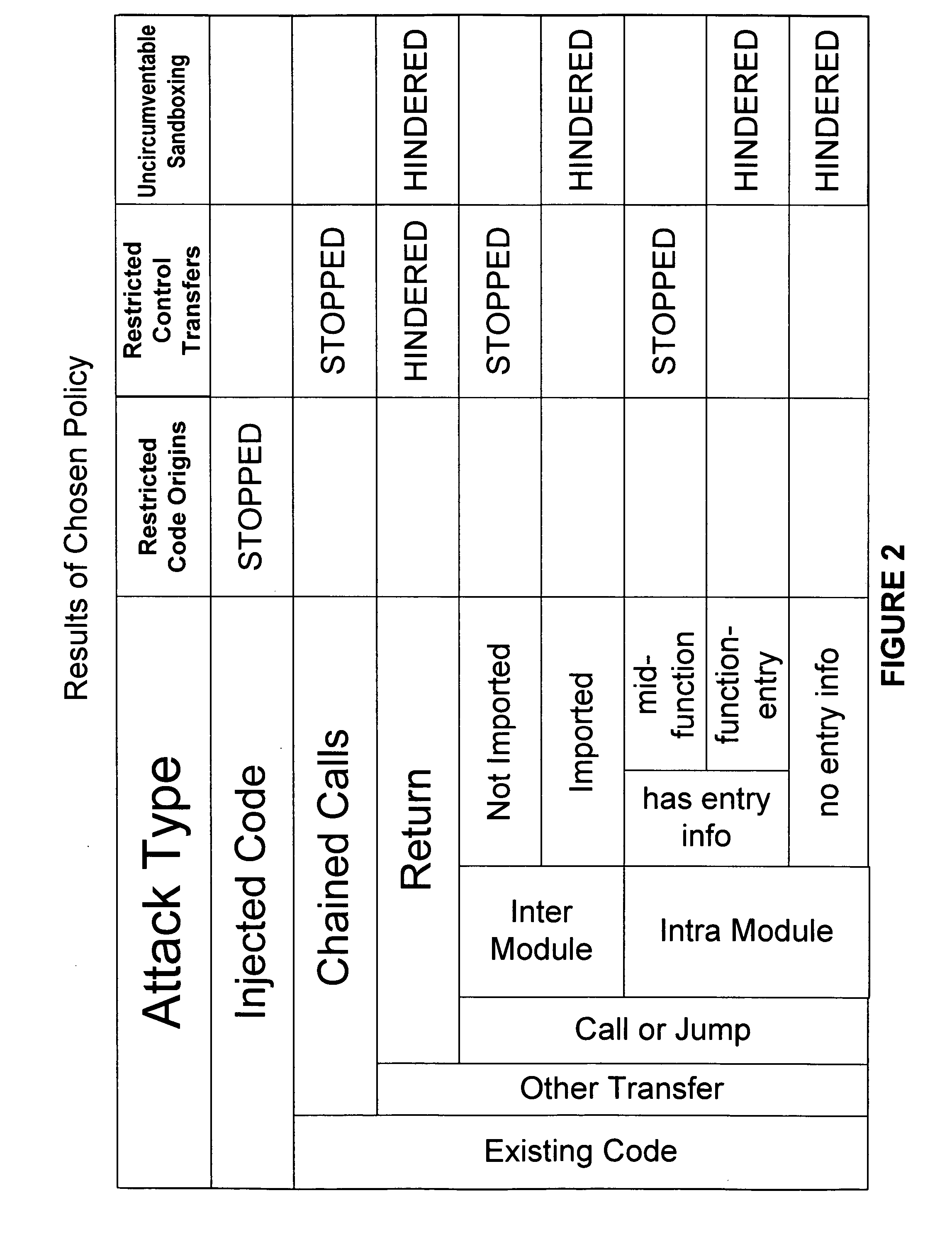
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
Collaborative derivation of an interface and partial implementation of programming code
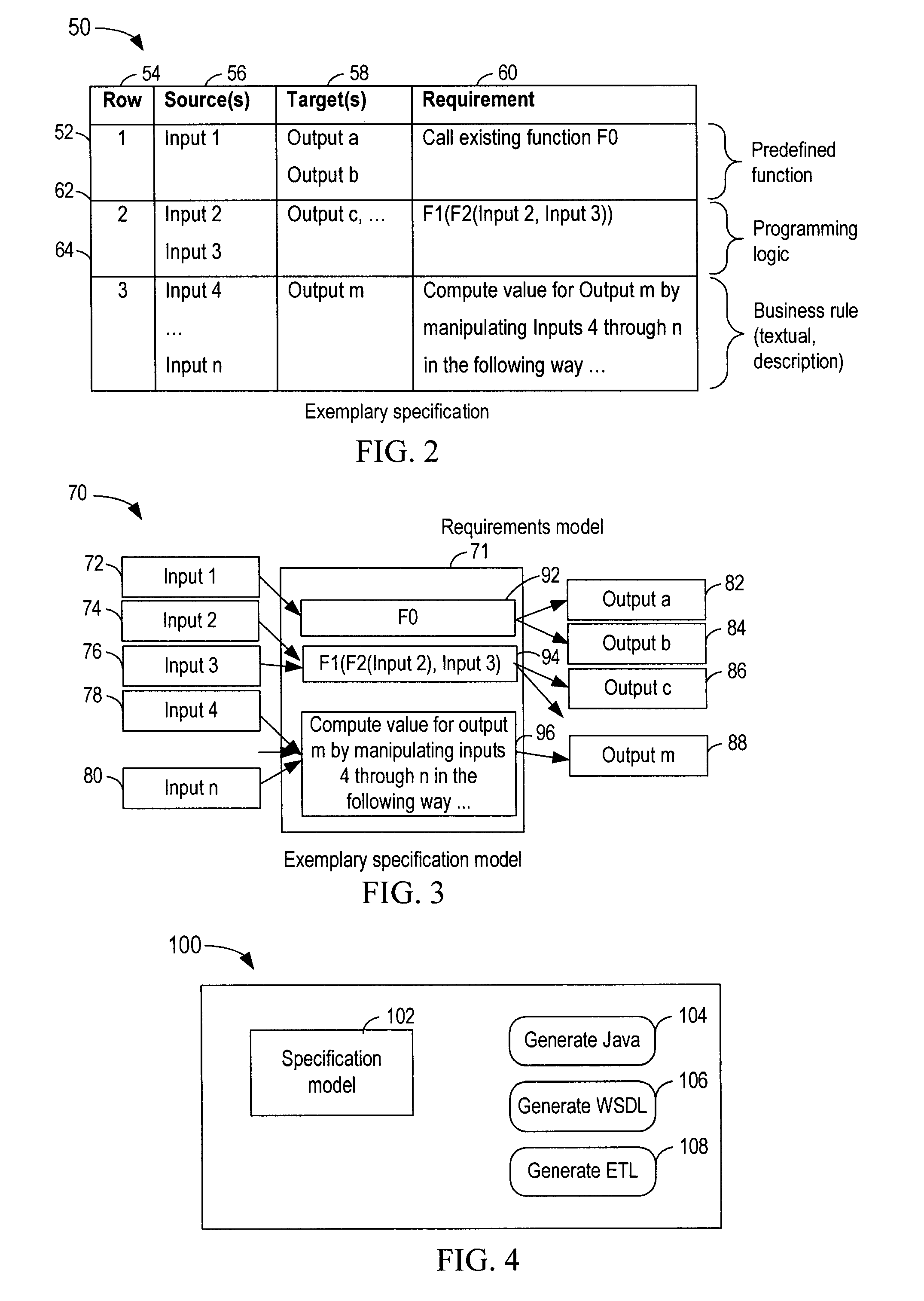
InactiveUS8176470B2Simple technologyRequirement analysisSpecific program execution arrangementsControl flowProgram code
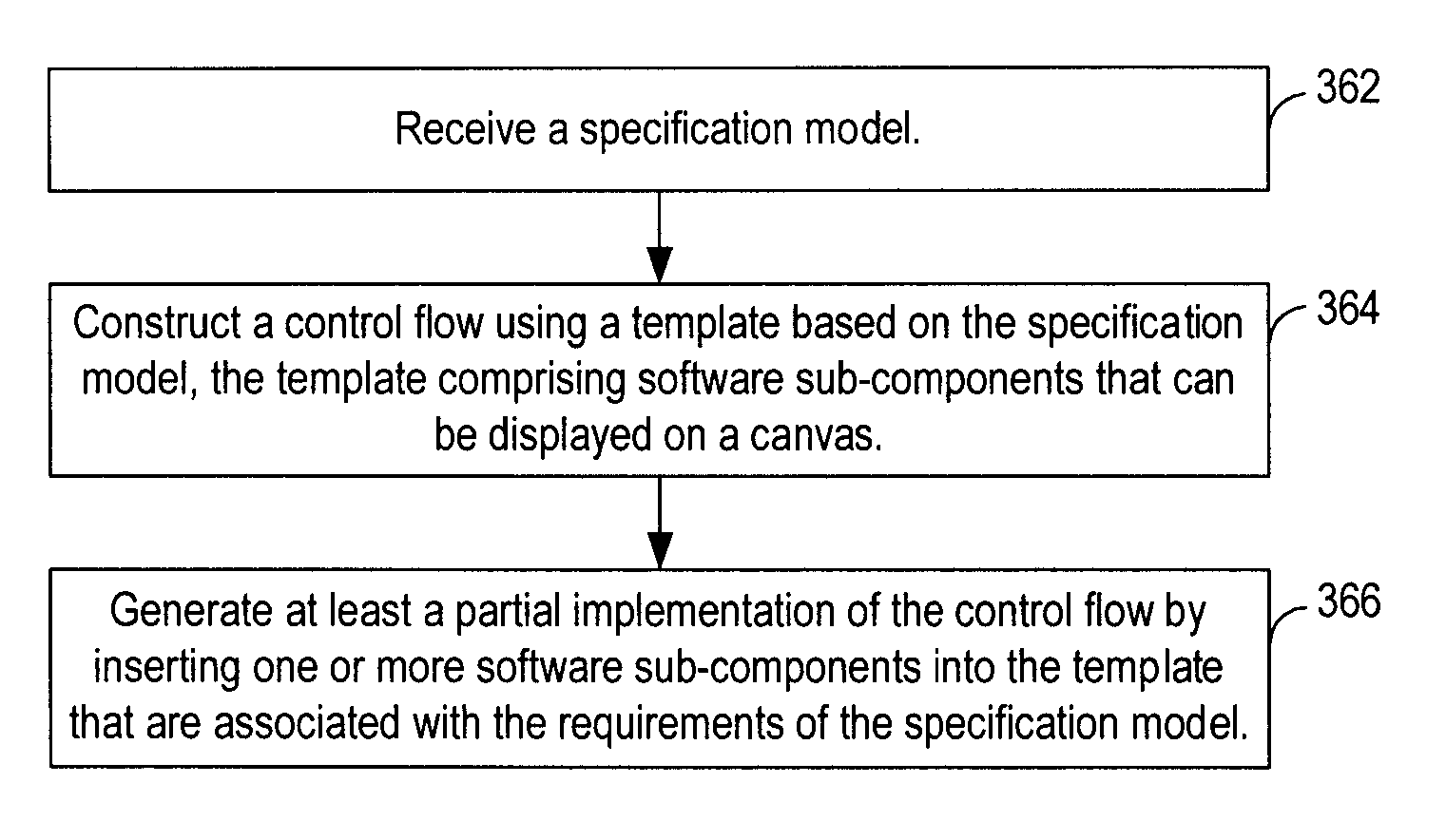
A method, system and computer program product provide an implementation of software. A control flow of a software component is constructed based on a specification model. In various embodiments, the specification model comprises at least one input and at least one requirement referencing the at least one input. At least a partial implementation of the software component is generated based on the control flow and the at least one input and the at least one requirement of the specification model. In some embodiments, the specification model further comprises at least one output, and the at least a partial implementation of the software component is also based on the at least one output.
Owner:IBM CORP
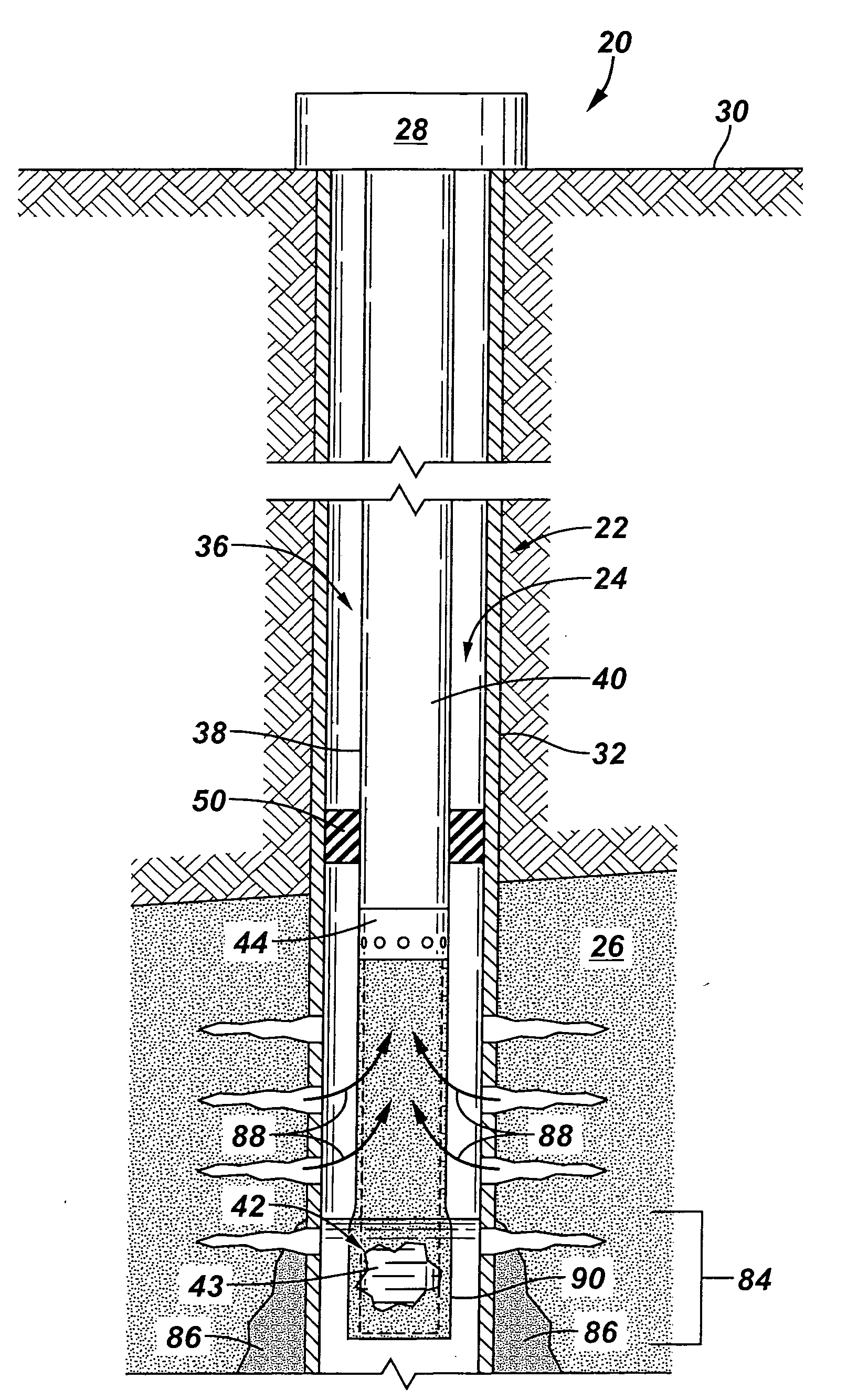
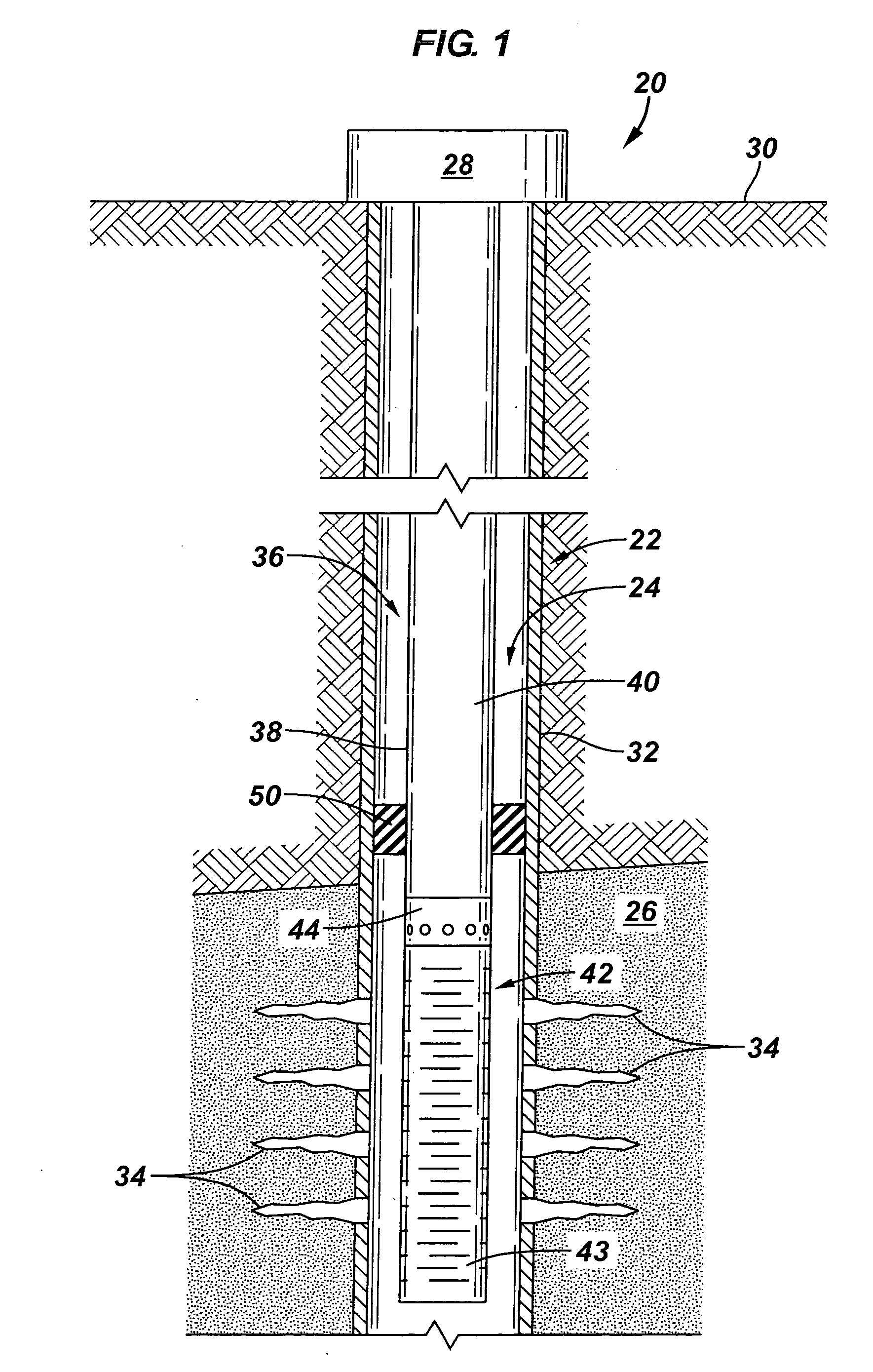
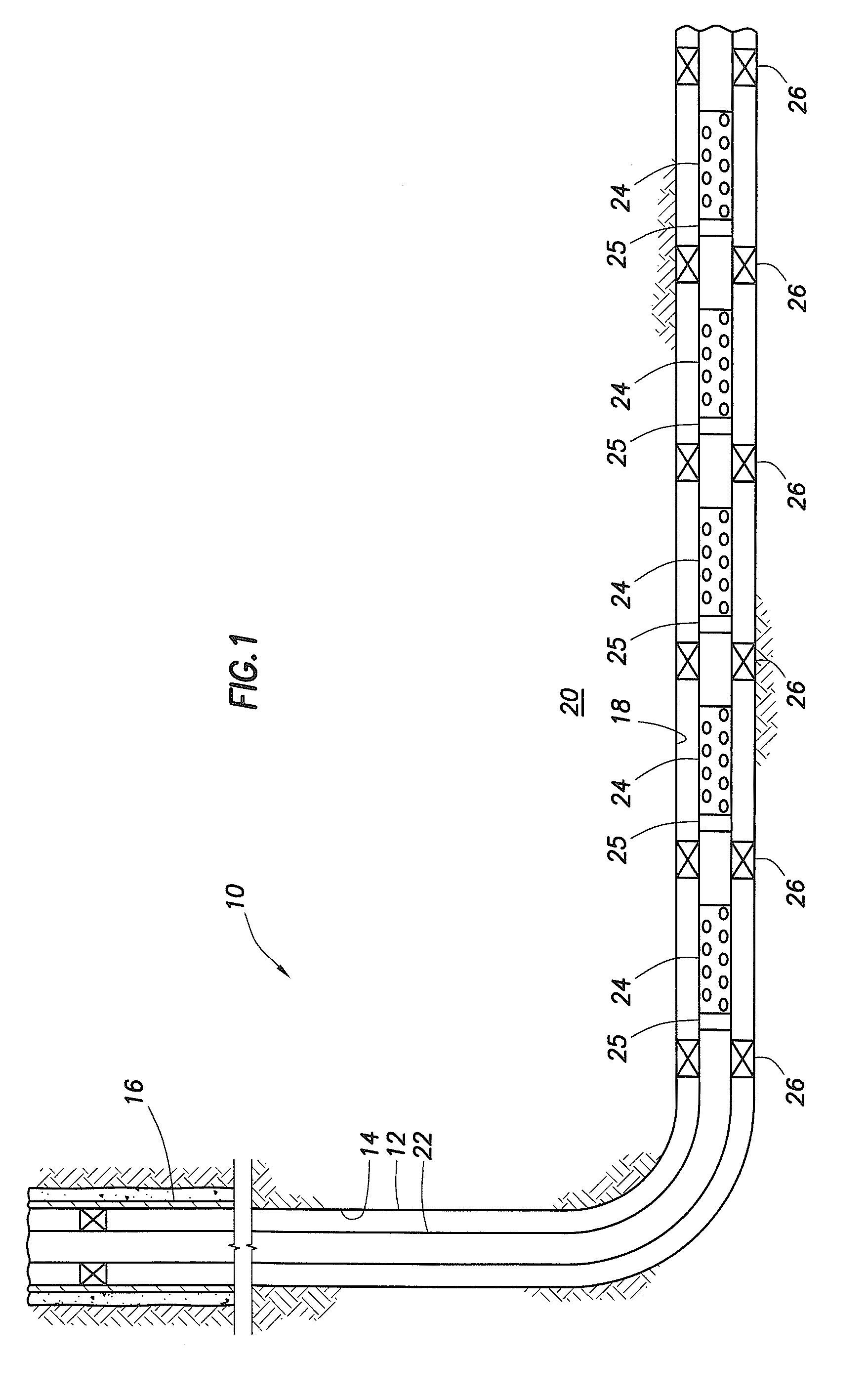
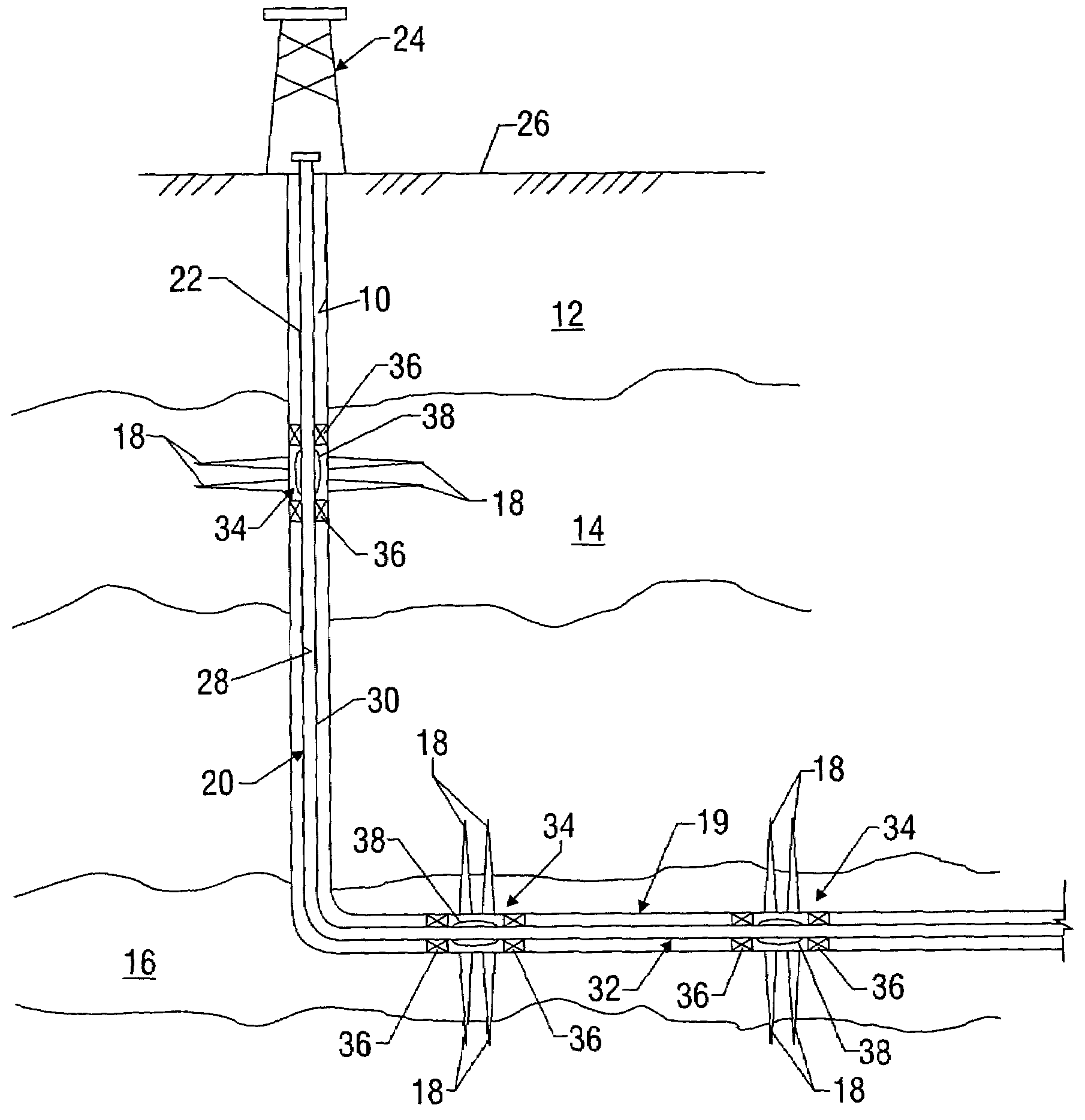
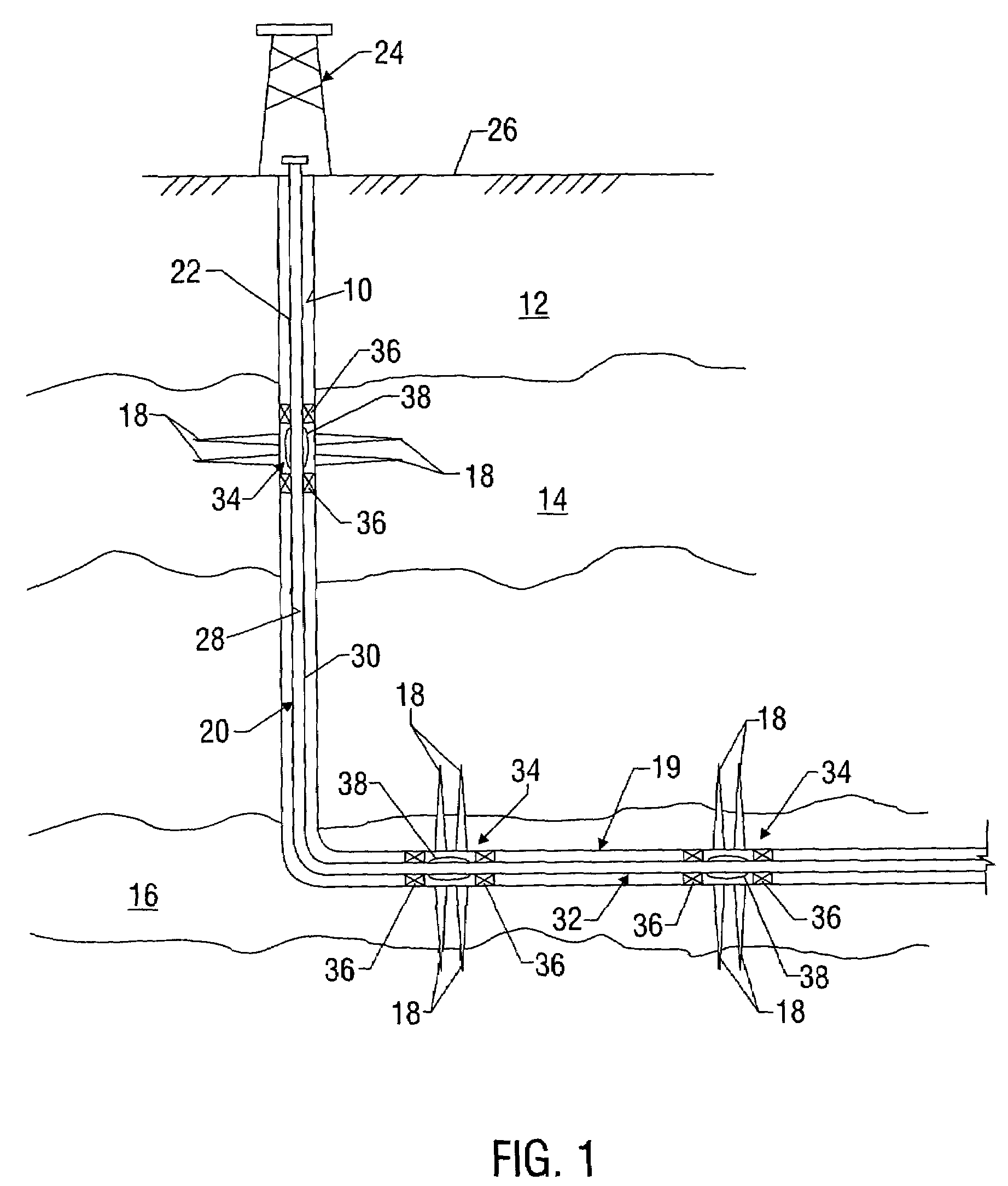
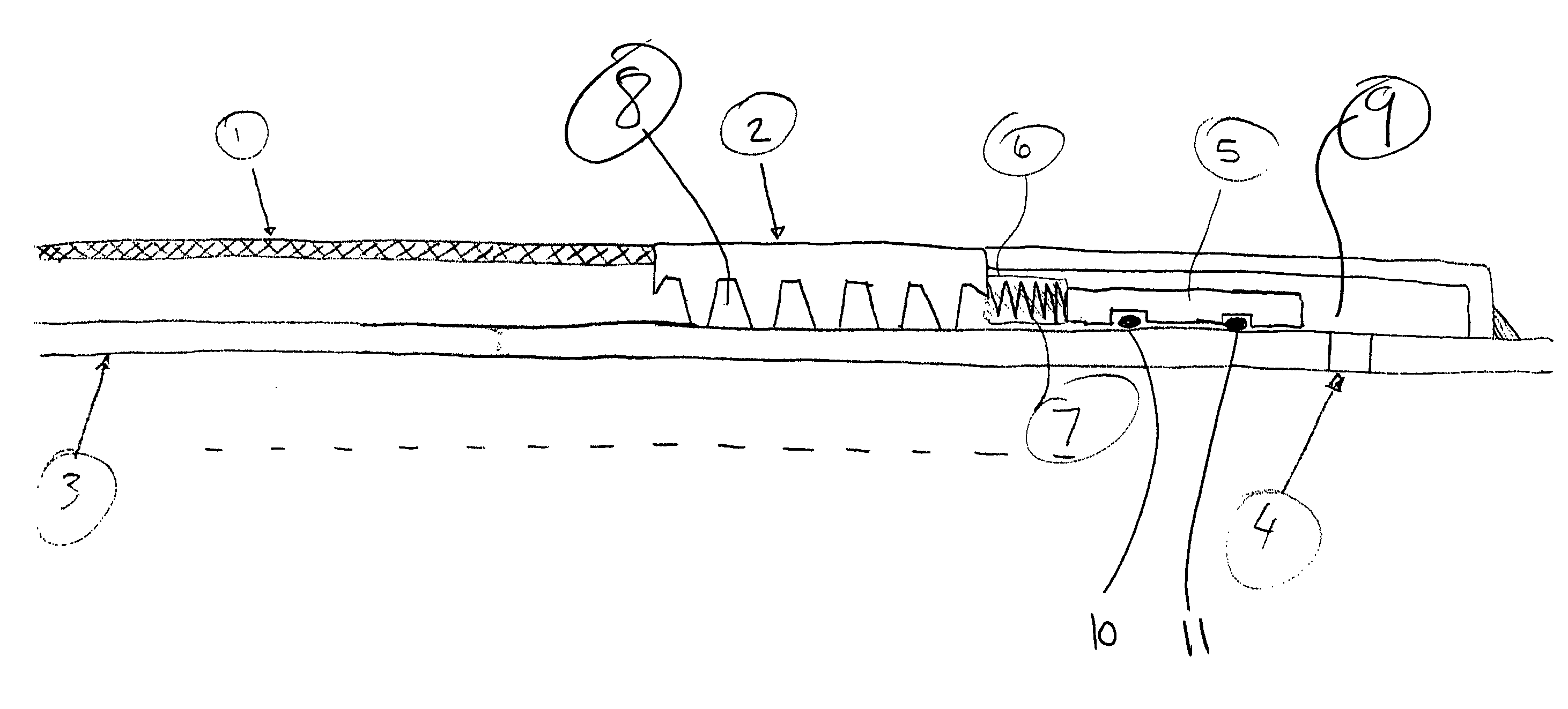
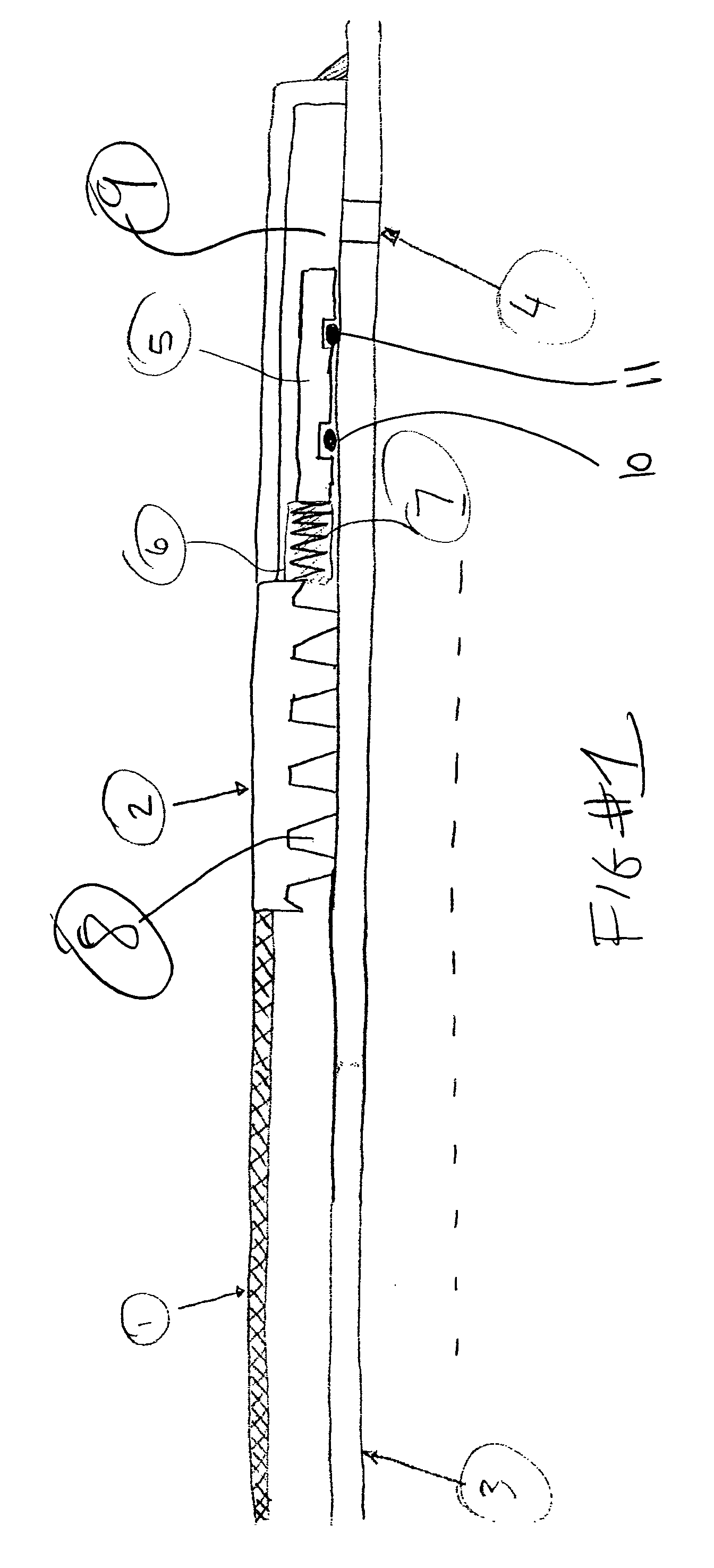
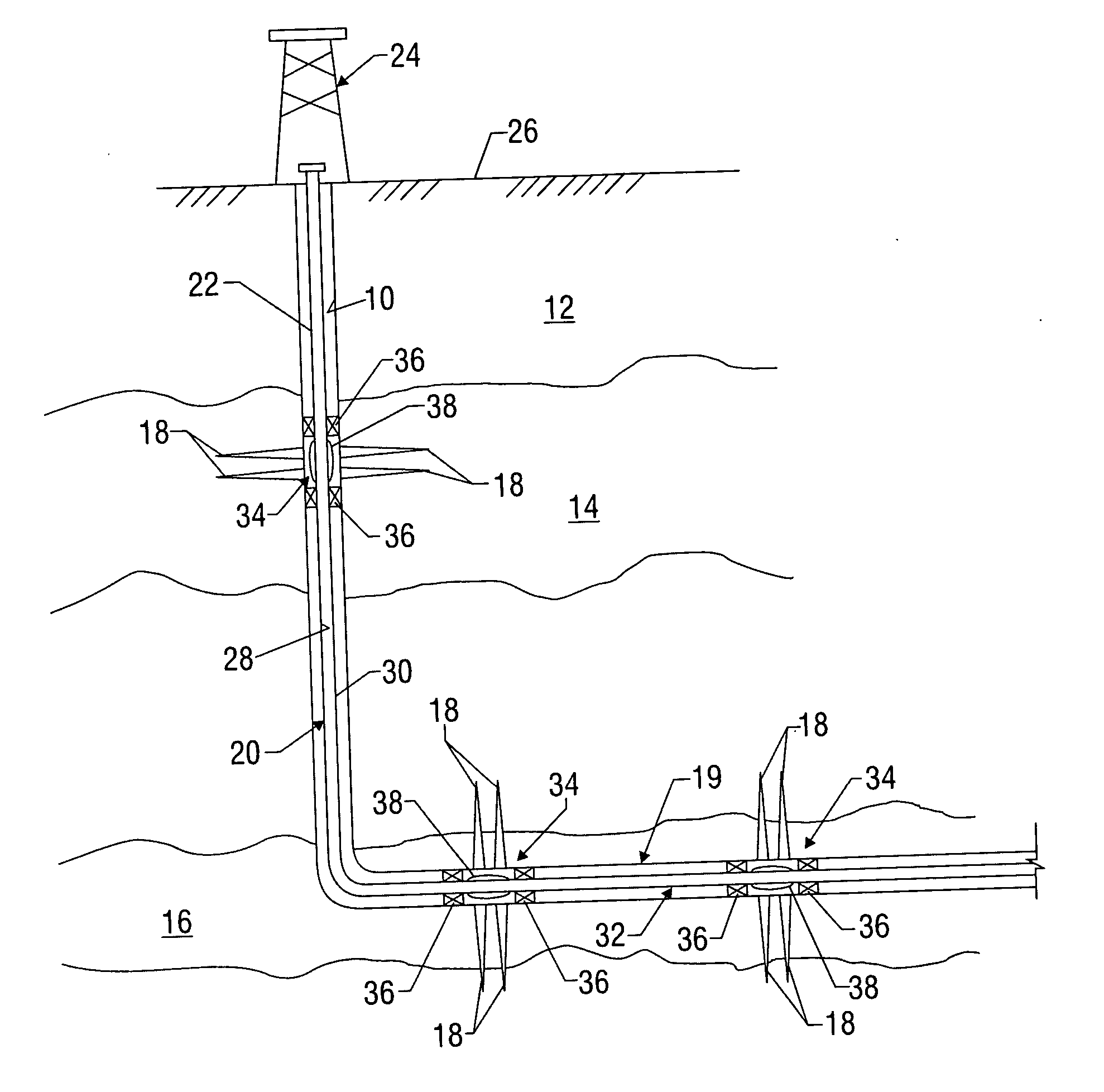
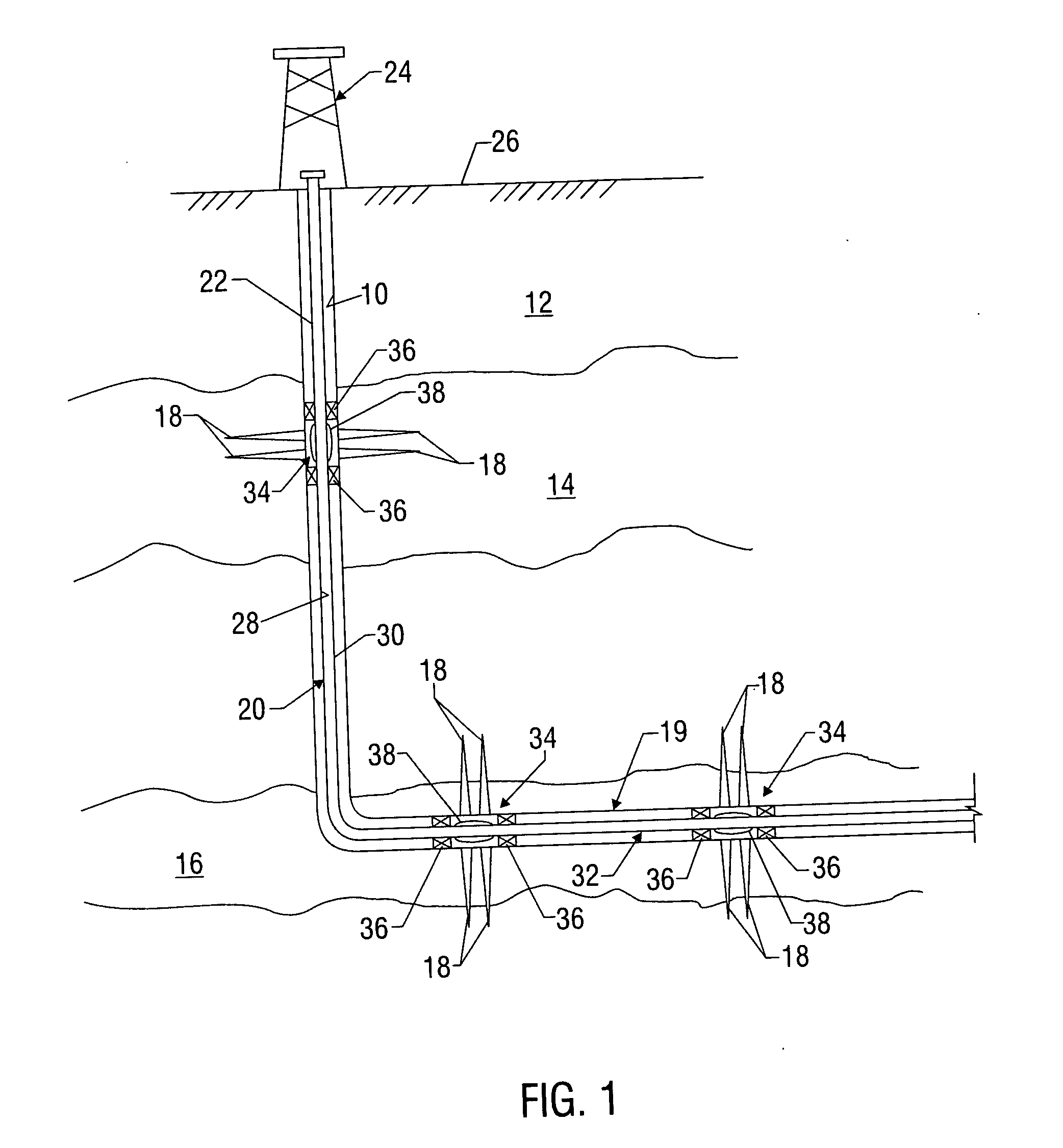
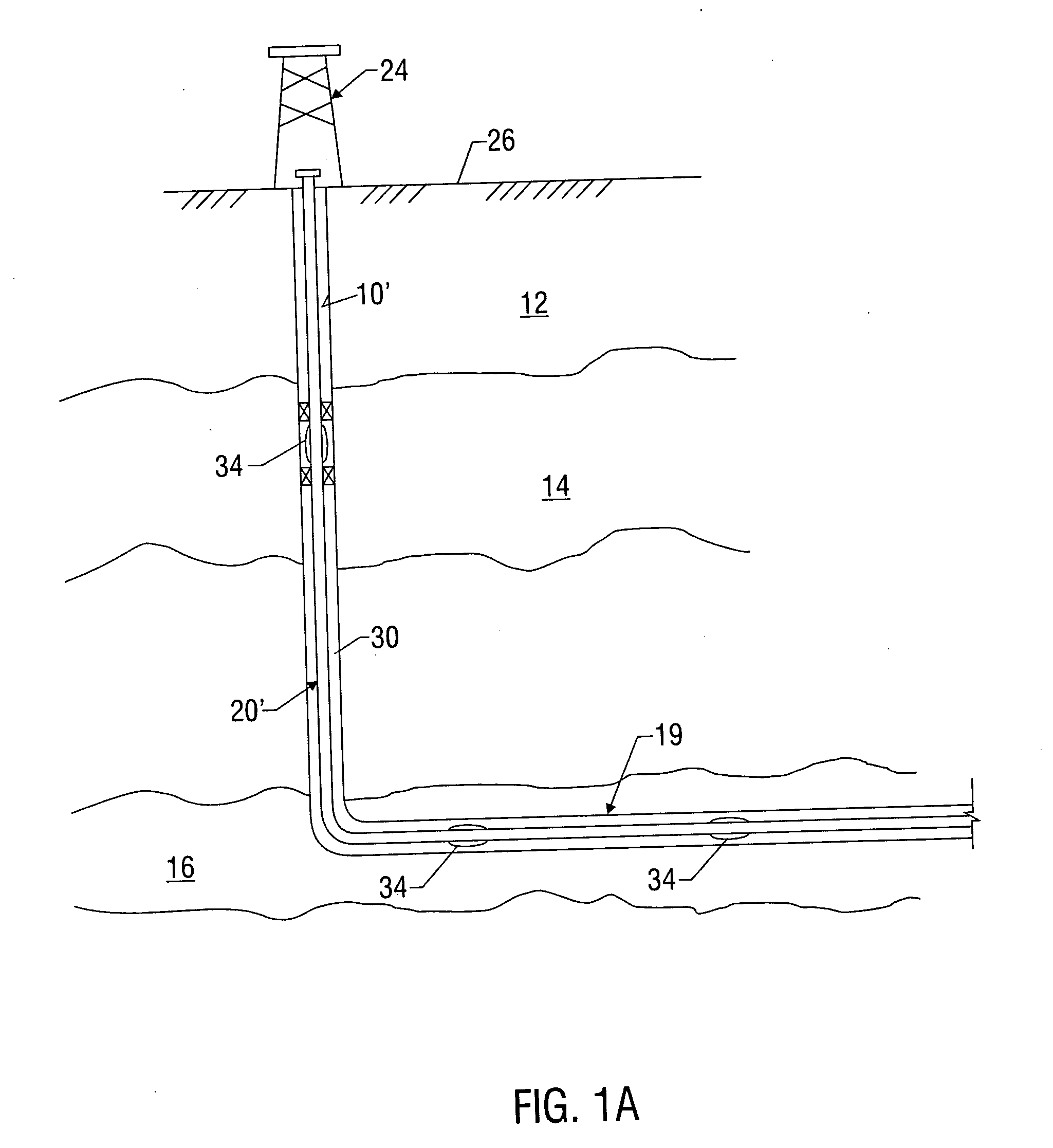
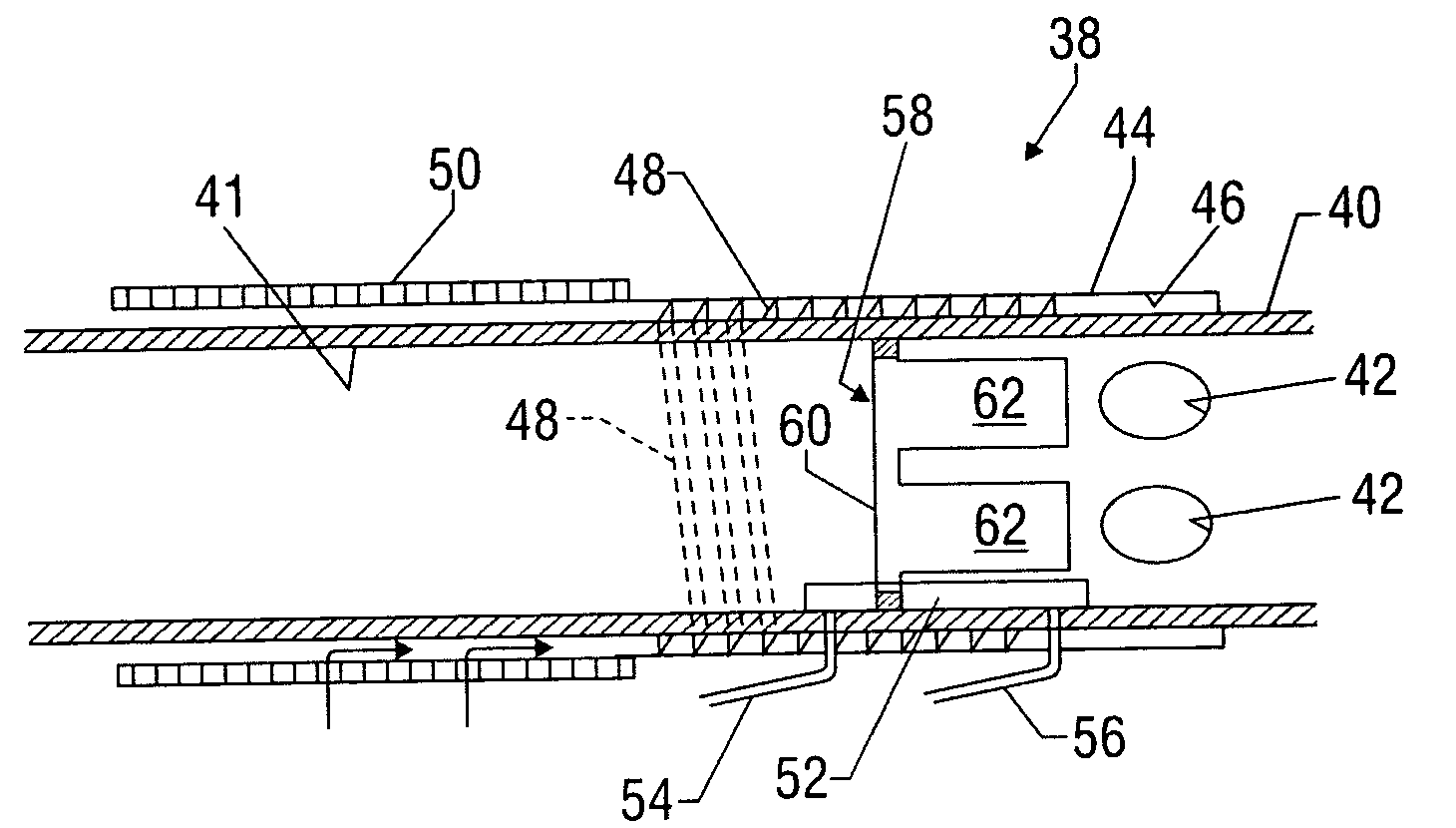
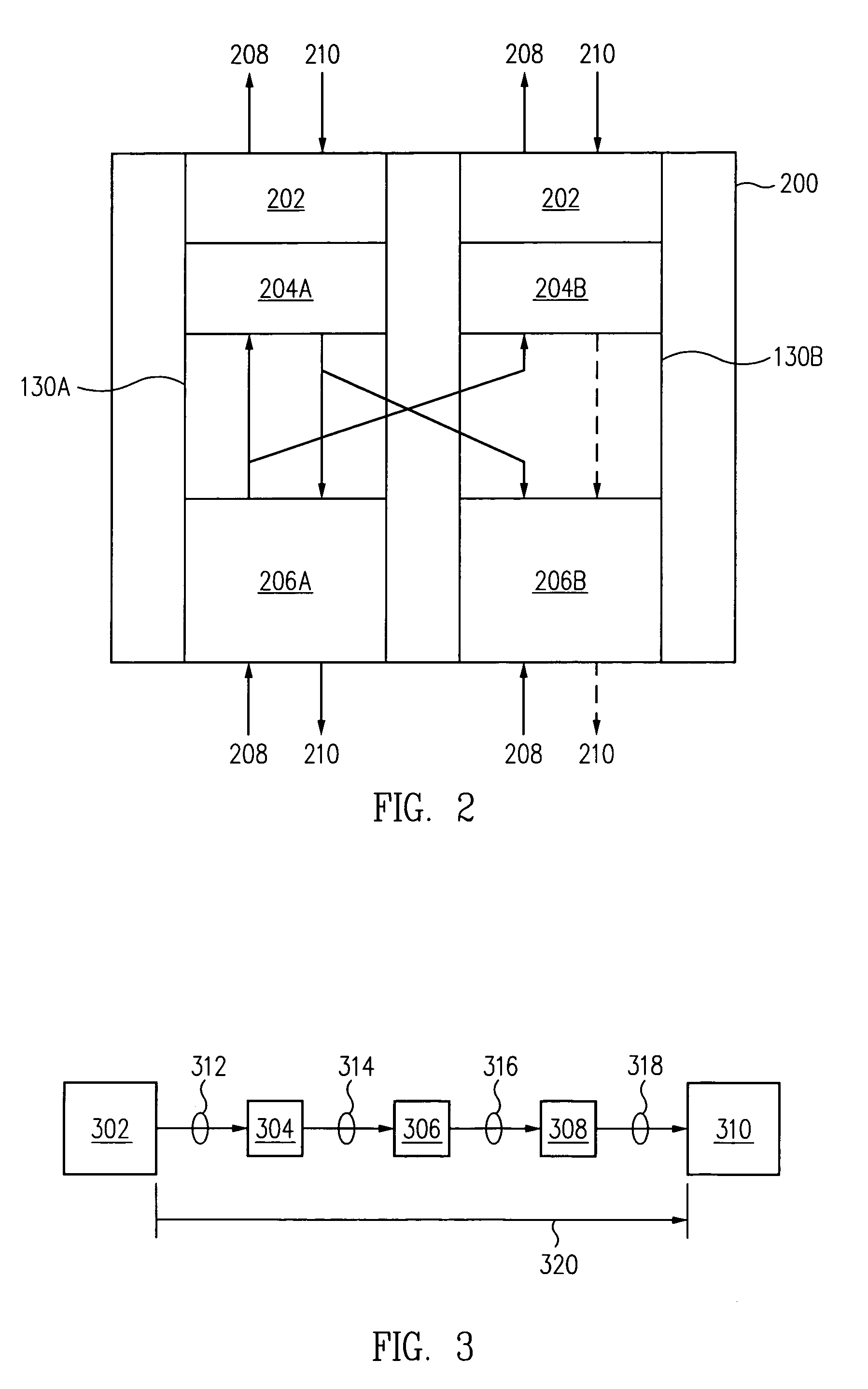
Sand control screen assembly and treatment method using the same
A sand control screen assembly (200) positionable within a production interval of a wellbore that traverses a subterranean hydrocarbon bearing formation comprises a base pipe (202) having openings (204) in a sidewall section thereof that allow fluid flow therethrough. A filter medium (210) is positioned about the exterior of at least a portion of the base pipe (202). The filter medium (210) selectively allows fluid flow therethrough but prevents the flow of particulate of a predetermined size therethrough. A seal member (218, 220, 222) is operably associated with the base pipe (202). The seal member (218, 220, 222) has a one-way valve configuration and a valve open configuration such that the seal member (218, 220, 222) controls fluid flow through the openings (204) of the base pipe (202).
Owner:HALLIBURTON ENERGY SERVICES INC
High fidelity integrated heat transfer and clearance in component-level dynamic turbine system control
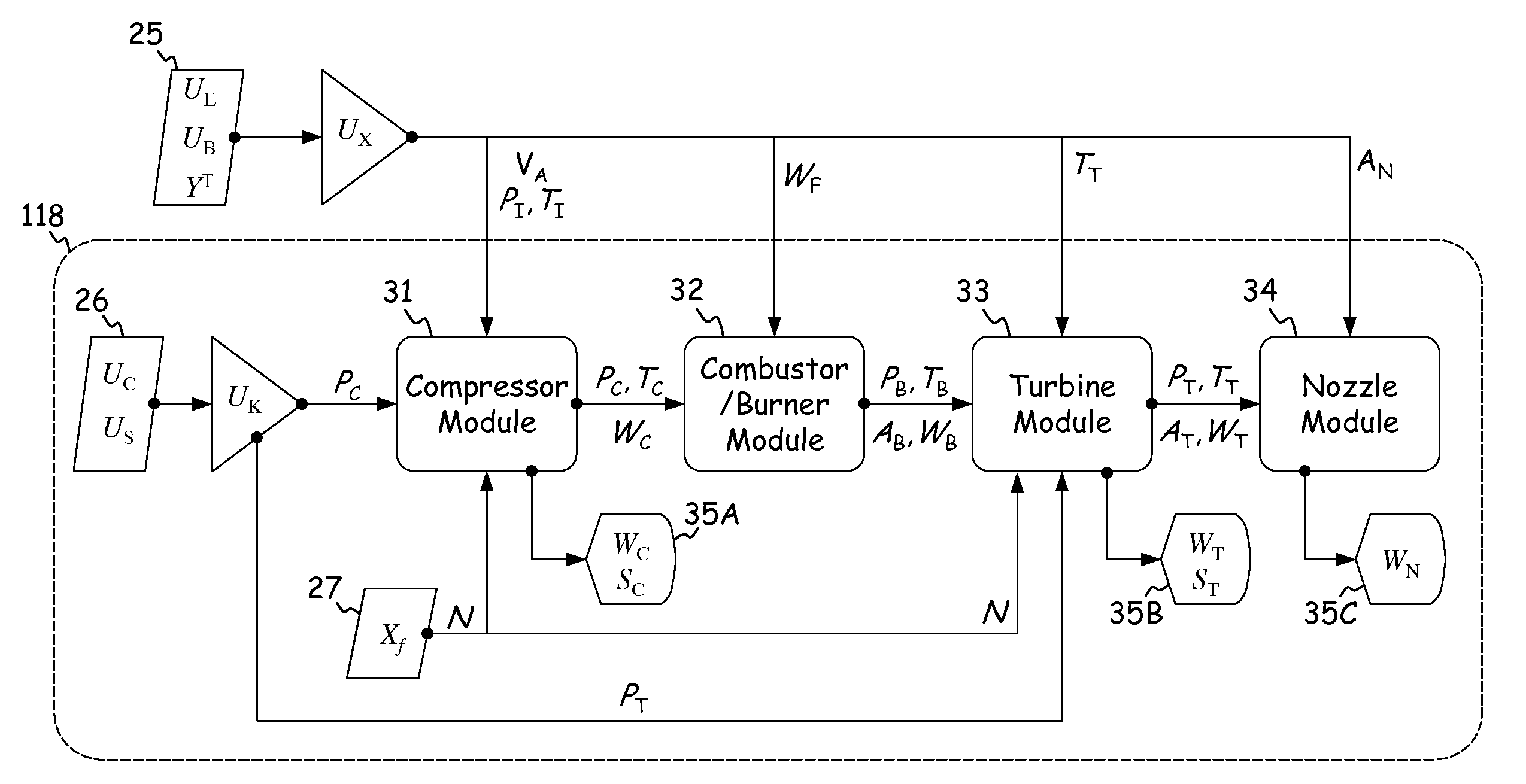
ActiveUS20110054704A1Turbine/propulsion fuel supply systemsTemperatue controlControl flowEngineering
A system comprises a rotary apparatus, a control law and a processor. The rotary apparatus comprises a rotor and a housing forming a gas path therebetween, and the control law controls flow along the gas path. The processor comprises an output module, a plurality of temperature modules, a thermodynamic module, a comparator and an estimator. The output module generates an output signal as a function of a plurality of rotor and housing temperatures defined along the gas path, and the temperature modules determine time derivatives of the rotor and housing temperatures. The thermodynamic module models boundary conditions for the gas path, and the comparator determines errors in the boundary conditions. The estimator estimates the rotor and housing temperatures based on the time derivatives, such that the errors are minimized and the flow is controlled.
Owner:RTX CORP
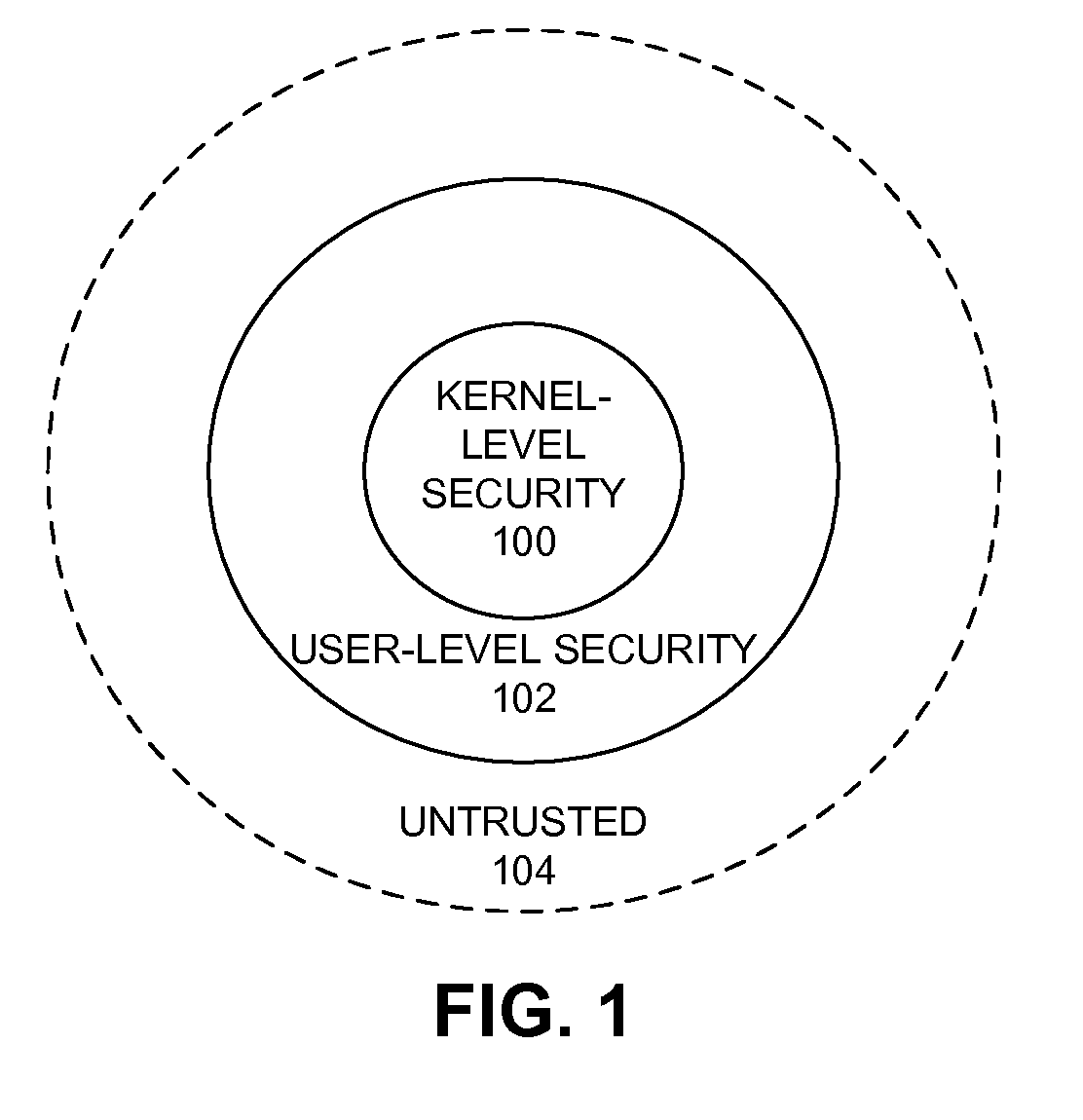
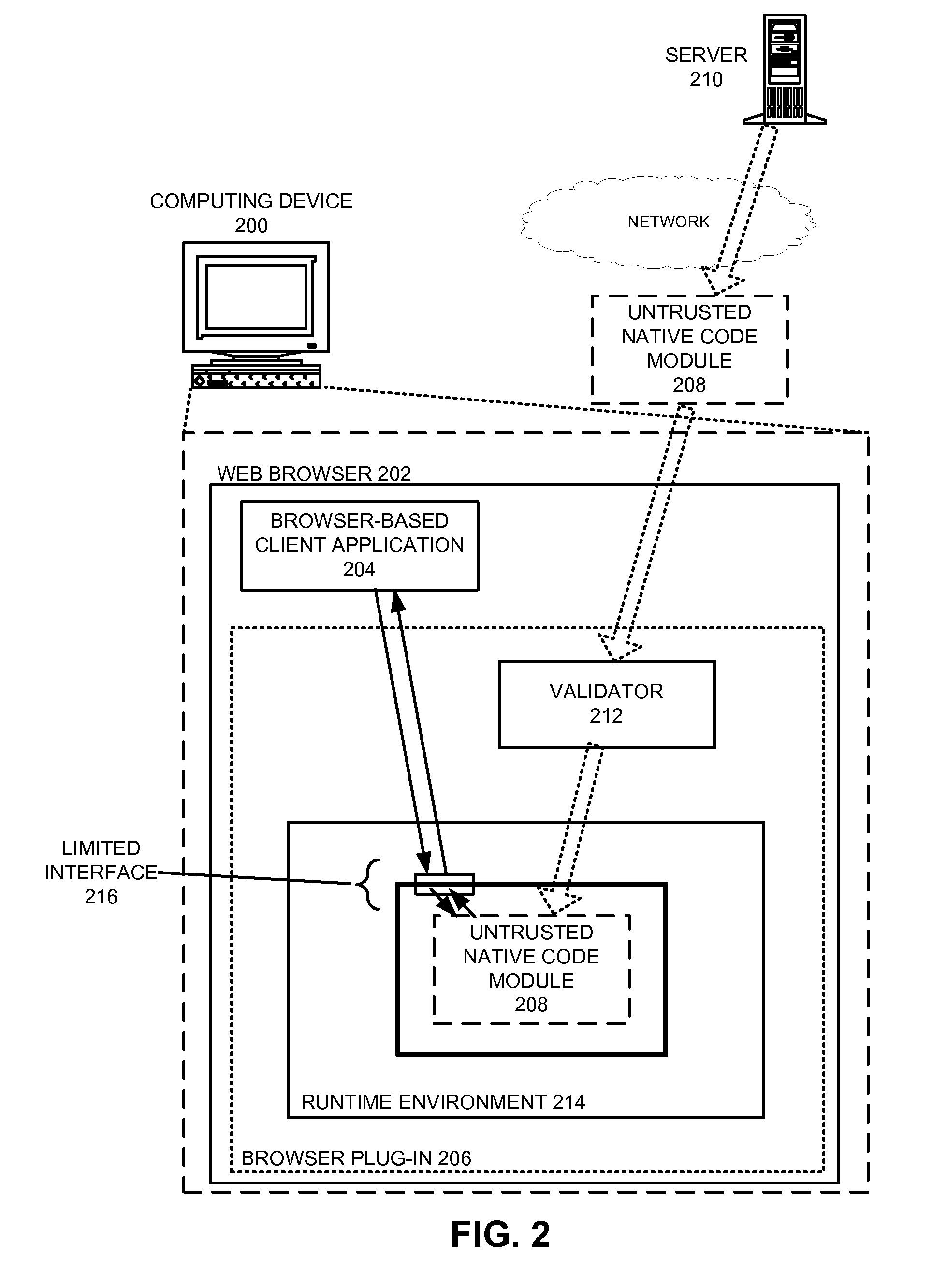
Method for validating an untrusted native code module
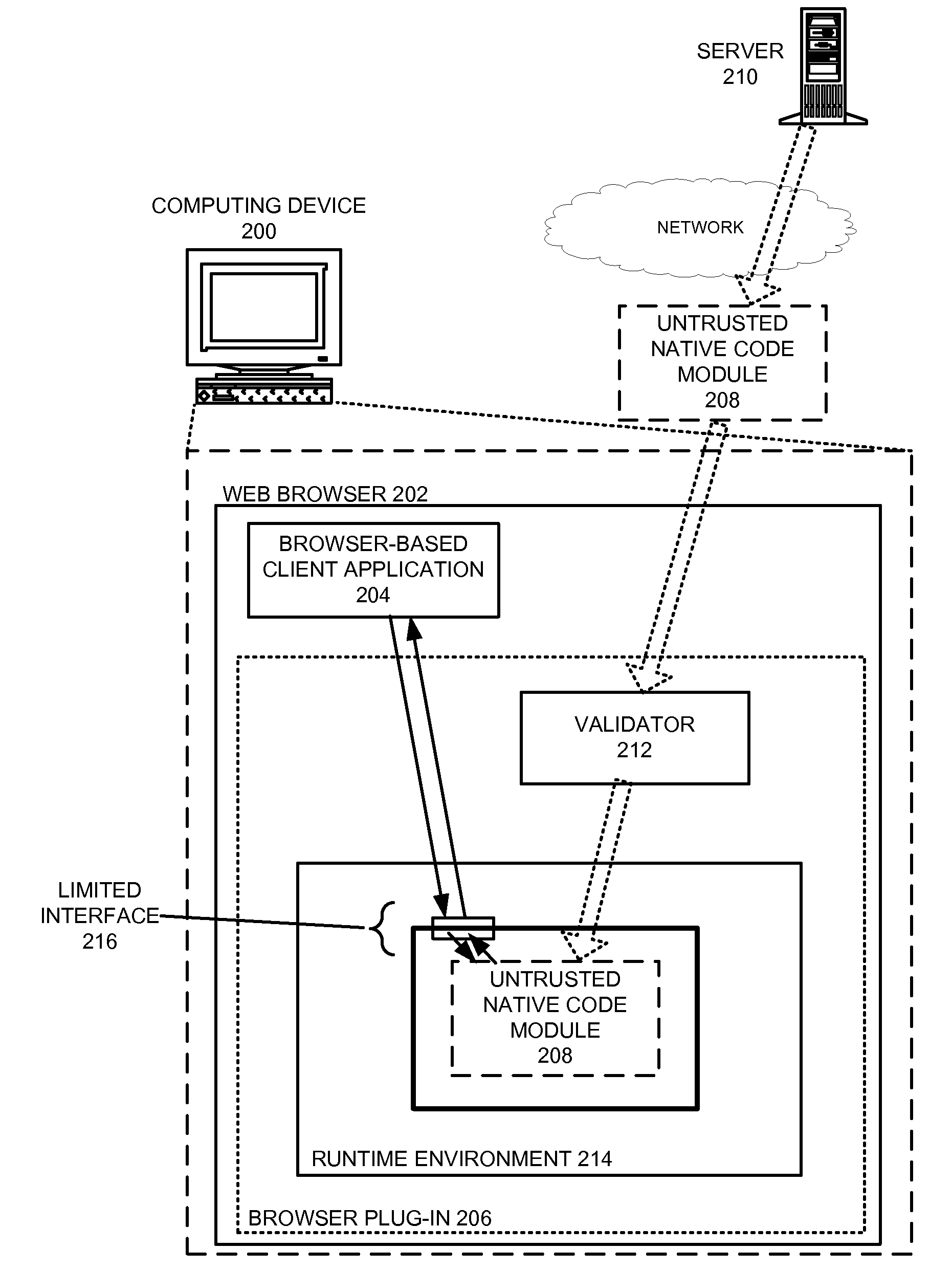
ActiveUS20090282477A1Facilitates safely executingWithout significant risk of unwanted side effectMemory loss protectionError detection/correctionCode moduleControl flow
A system that validates a native code module. During operation, the system receives a native code module comprised of untrusted native program code. The system validates the native code module by: (1) determining that code in the native code module does not include any restricted instructions and / or does not access restricted features of a computing device; and (2) determining that the instructions in the native code module are aligned along byte boundaries such that a specified set of byte boundaries always contain a valid instruction and control flow instructions have valid targets. The system allows successfully-validated native code modules to execute, and rejects native code modules that fail validation. By validating the native code module, the system facilitates safely executing the native code module in the secure runtime environment on the computing device, thereby achieving native code performance for untrusted program binaries without significant risk of unwanted side effects.
Owner:GOOGLE LLC
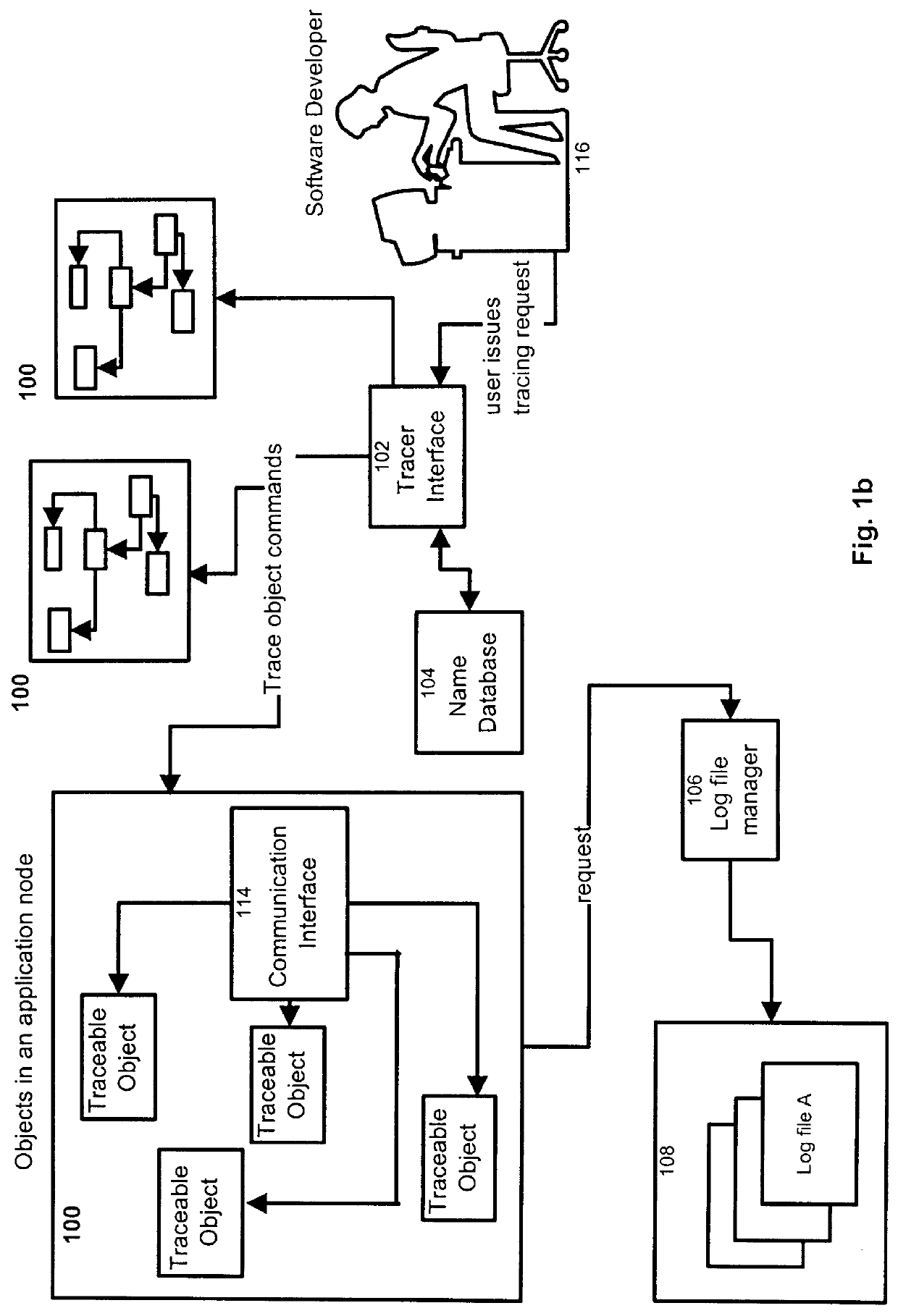
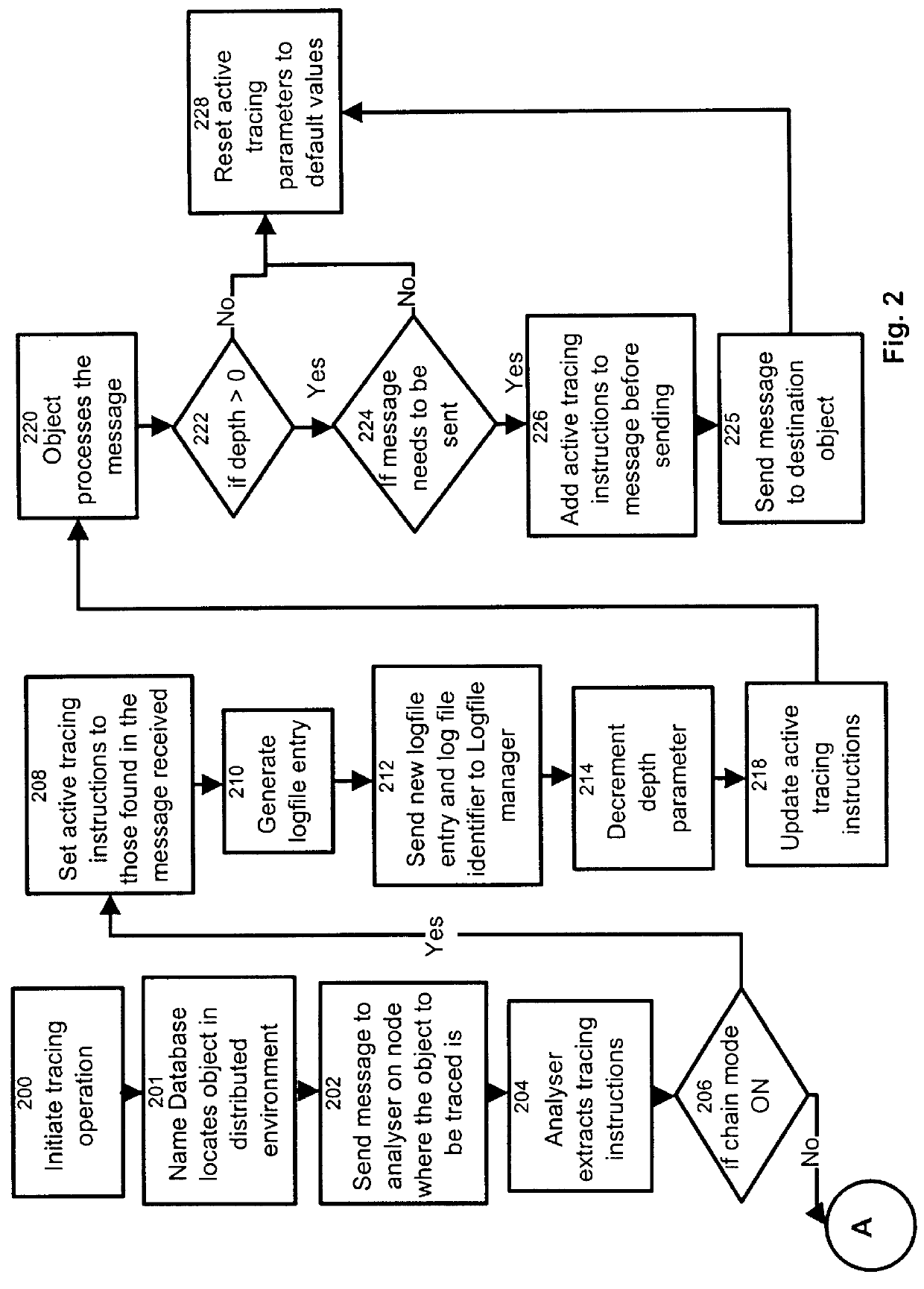
Process and apparatus for tracing software entities in a distributed system
InactiveUS6083281AHardware monitoringSoftware testing/debuggingControl flowDistributed Computing Environment
The invention relates to a process and apparatus for tracing software entities, more particularly a tracing tool providing tracing capabilities to entities in an application. The object-tracing tool provides software components to allow tracing the execution of an application. Tracing software entities is important for software developers to permit the quick localization of errors and hence facilitate the debugging process. It is also useful for the software user who wishes to view the control flow and perhaps add some modifications to the software. Traditionally, software-tracing tools have been confined to single node systems where all the components of an application run on a single machine. The novel tracing tool presented in this application provides a method and an apparatus for tracing software entities in a distributed computing environment. This is done by using a network management entity to keep track of the location of the entities in the system and by using a library of modules that can be inherited to provide tracing capabilities. It also uses a log file to allow the program developer or user to examine the flow, the occurrence of events during a trace and the values of designated attributes. The invention also provides a computer readable storage medium containing a program element to direct a processor of a computer to implement the software tracing process.
Owner:RPX CLEARINGHOUSE
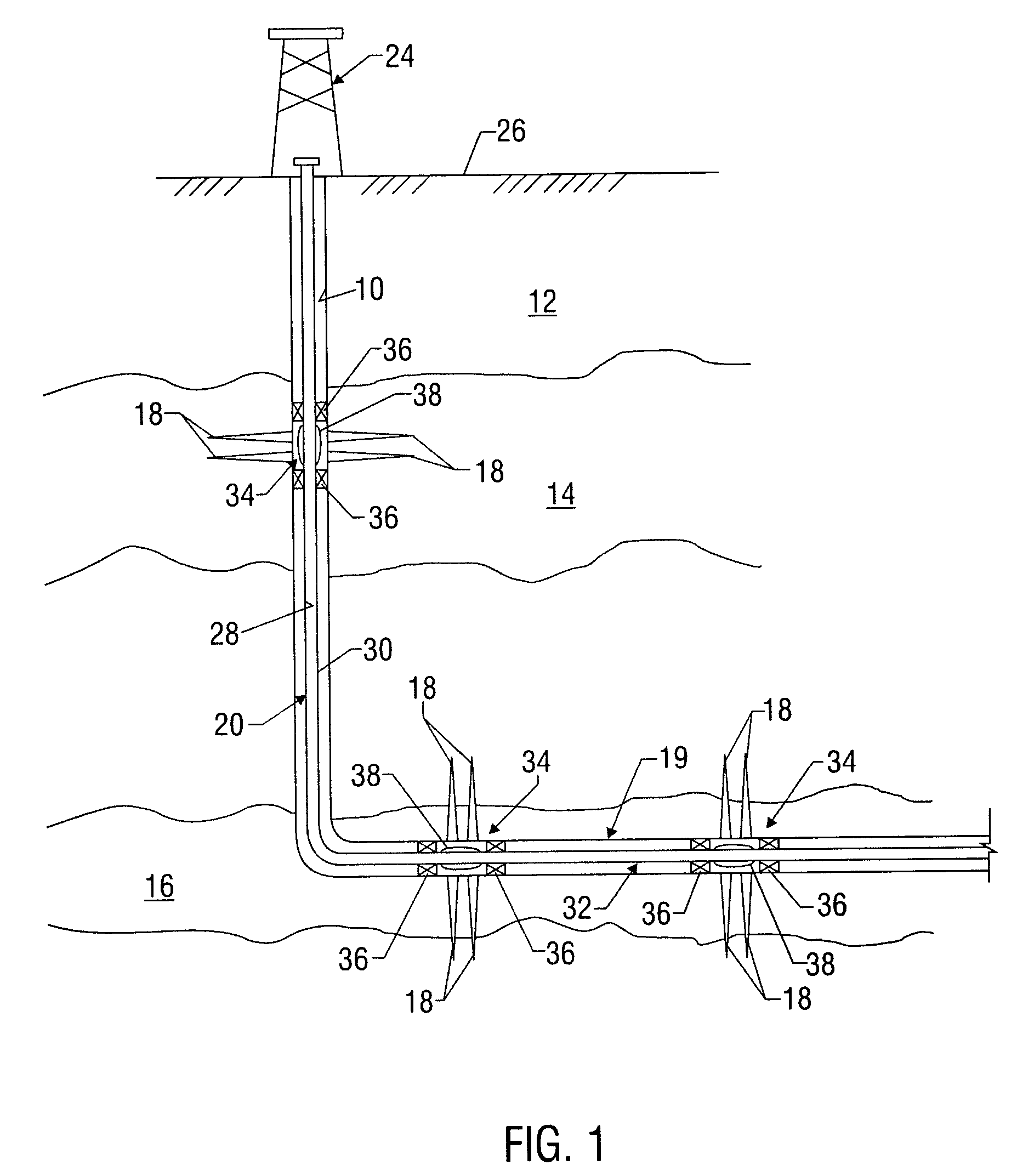
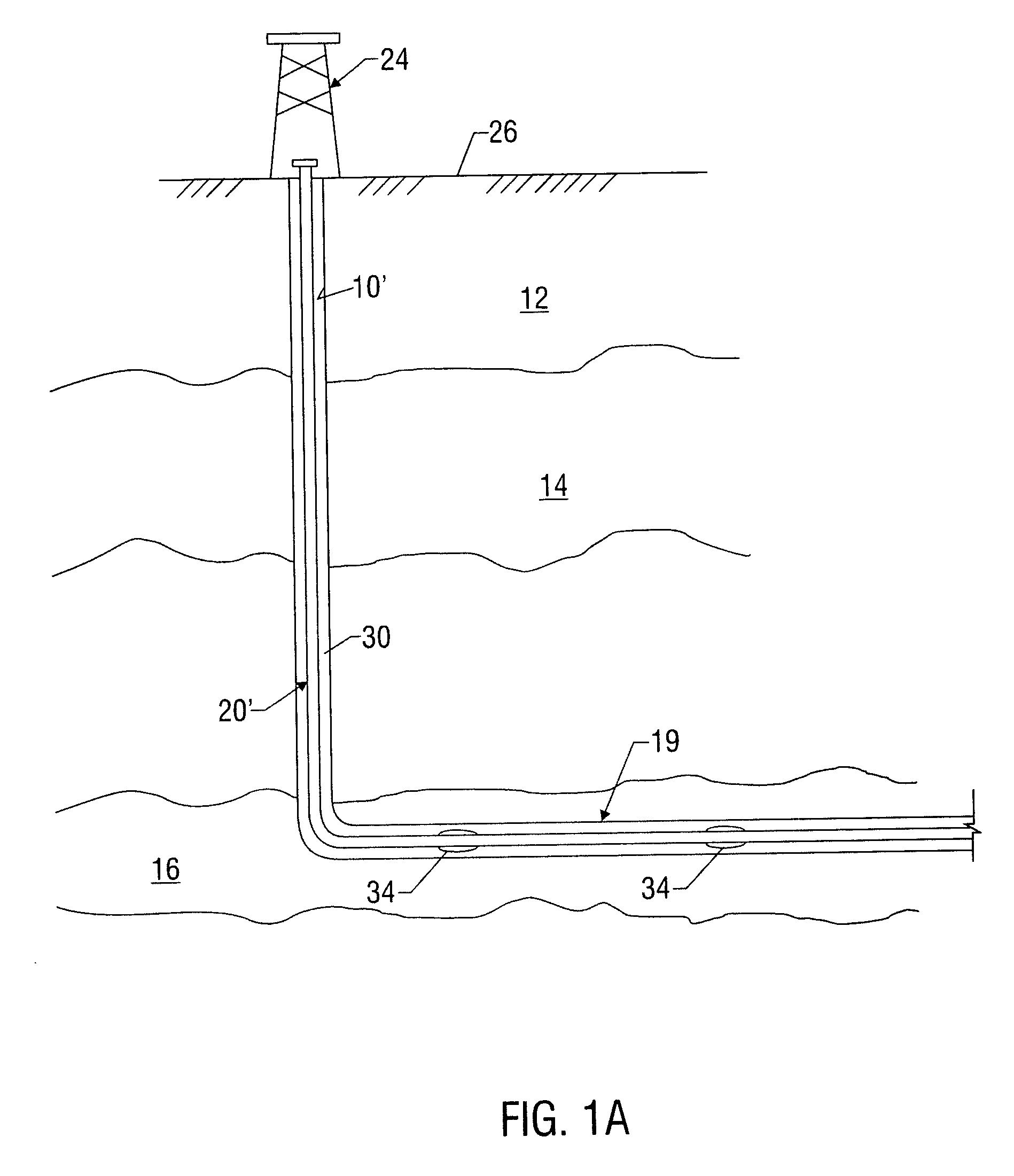
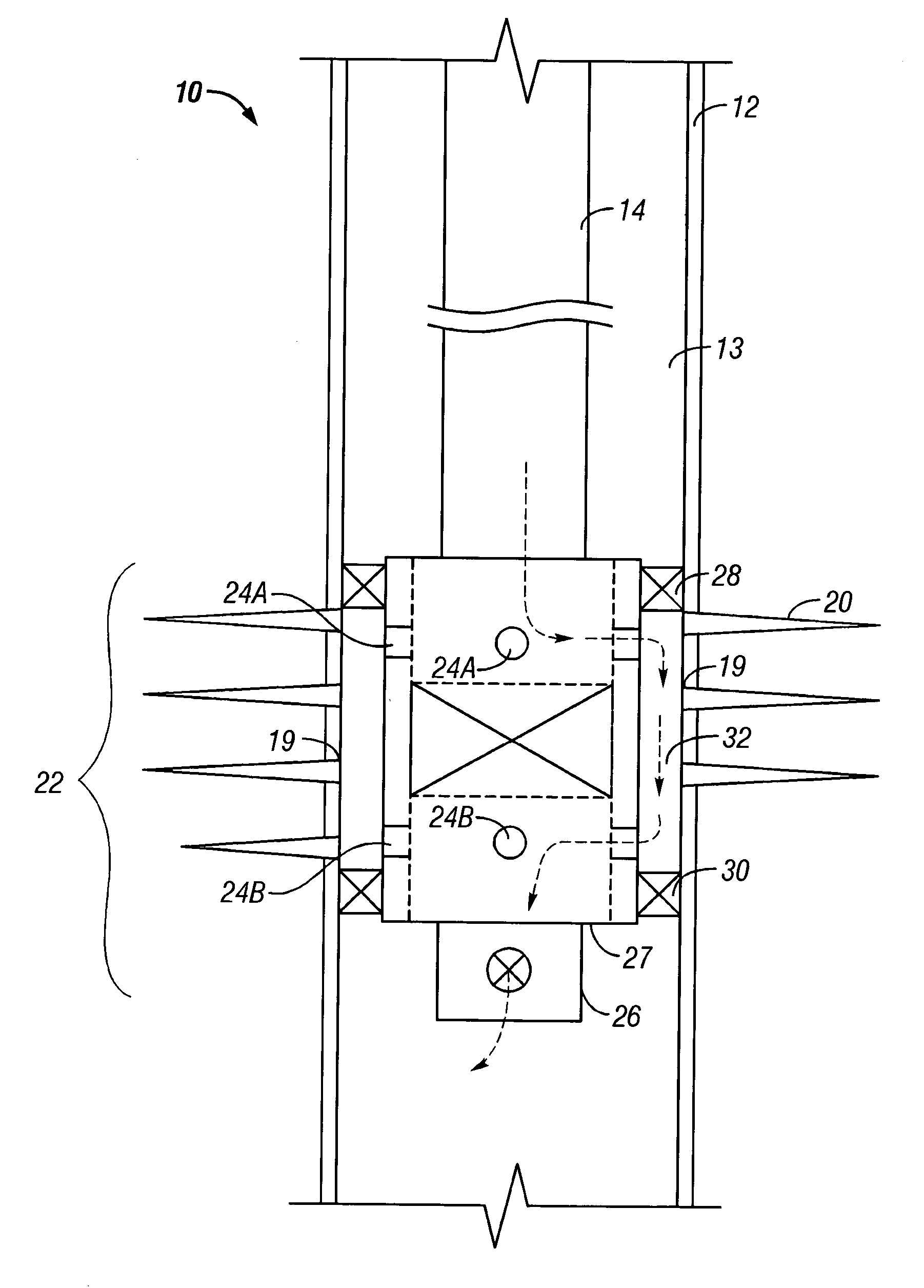
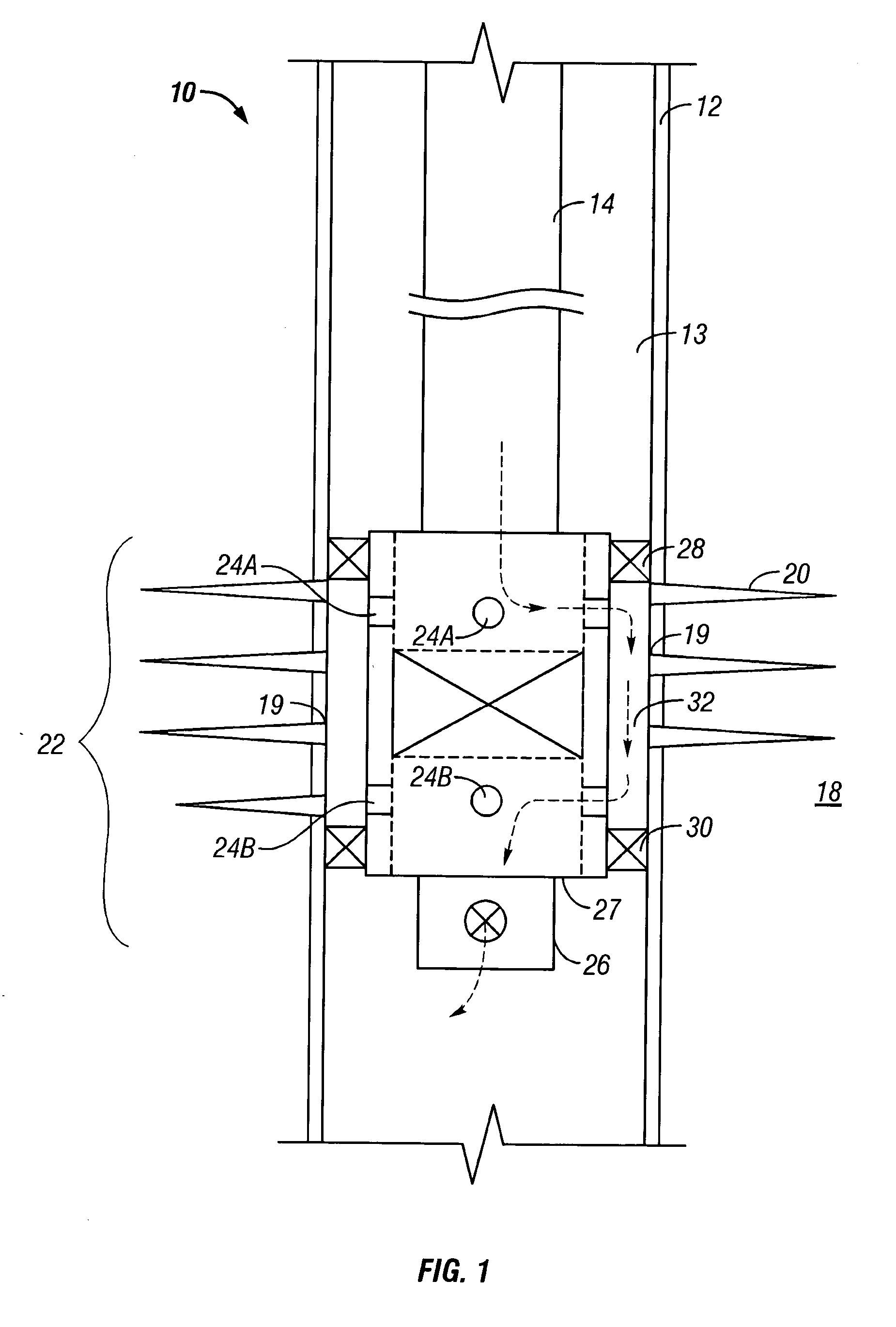
Water shut off method and apparatus
A technique is provided to control flow in subterranean applications, such as hydrocarbon fluid production applications. The technique utilizes an material formed, at least in part, of material that swell in the presence of a specific substance or substances. The material is deployed as a membrane outside a base pipe to desired subterranean locations. Once located, the material allows the flow of hydrocarbon fluids but swells upon contact with the specific substance or substances to limit inflow of undesirable fluids.
Owner:SCHLUMBERGER TECH CORP
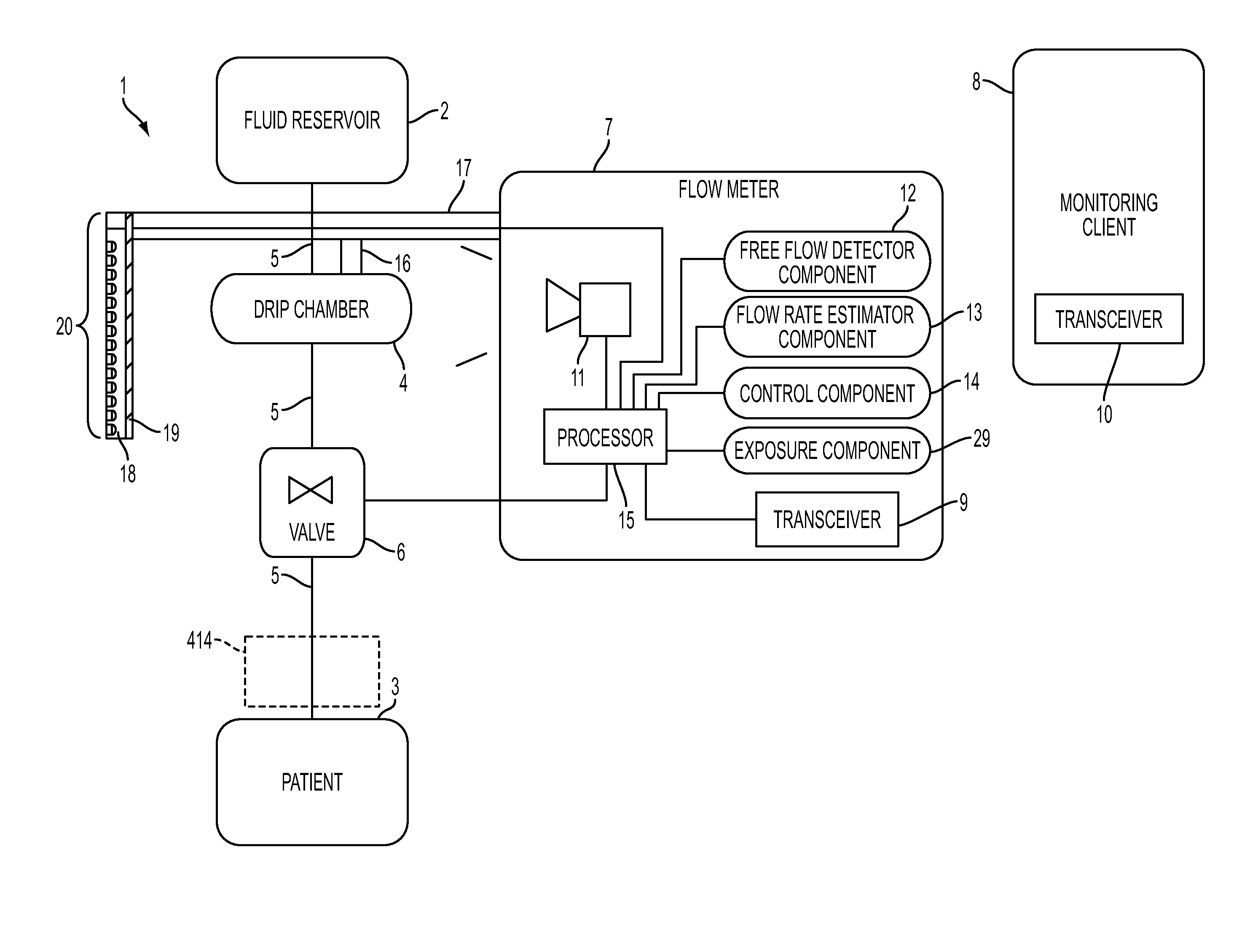
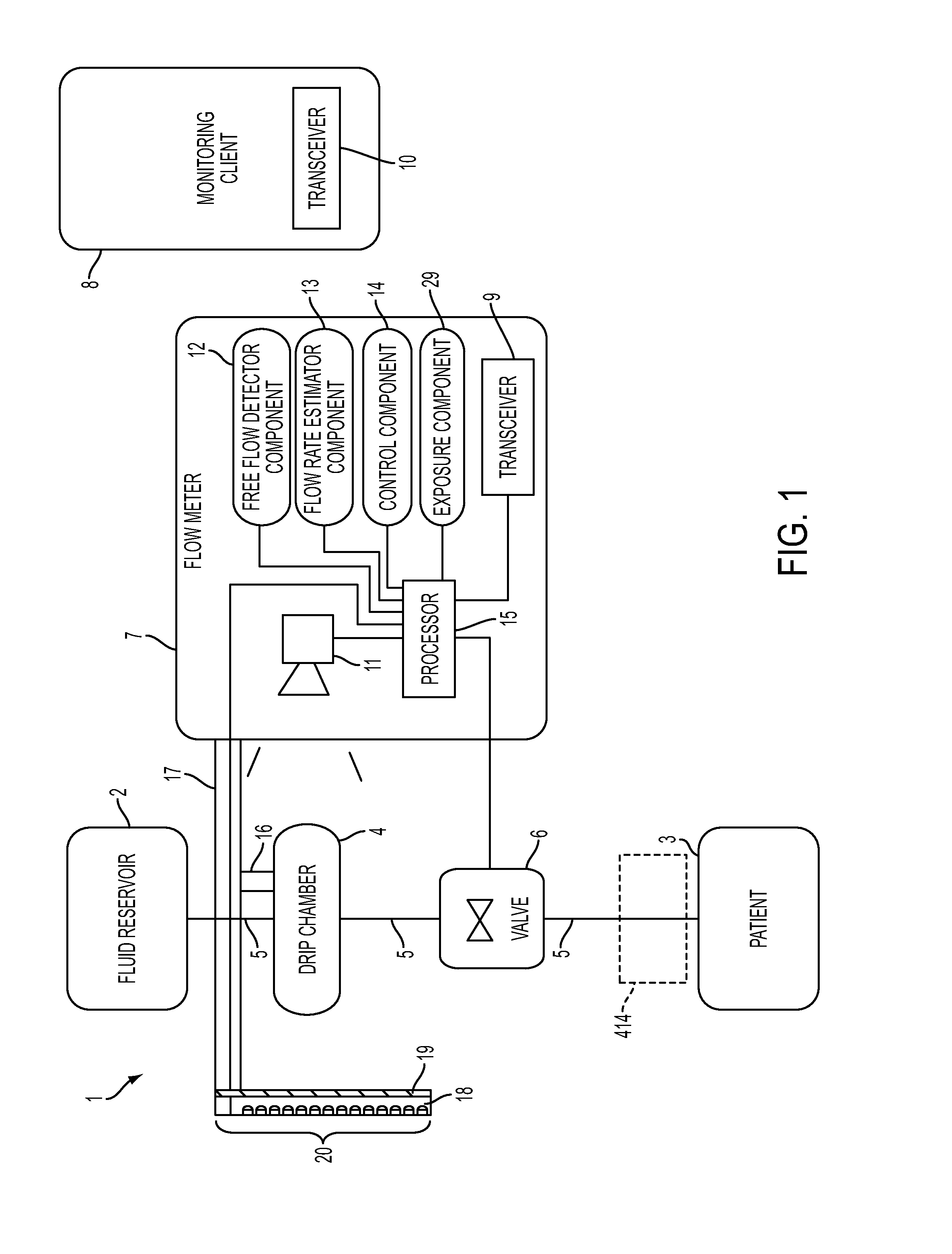
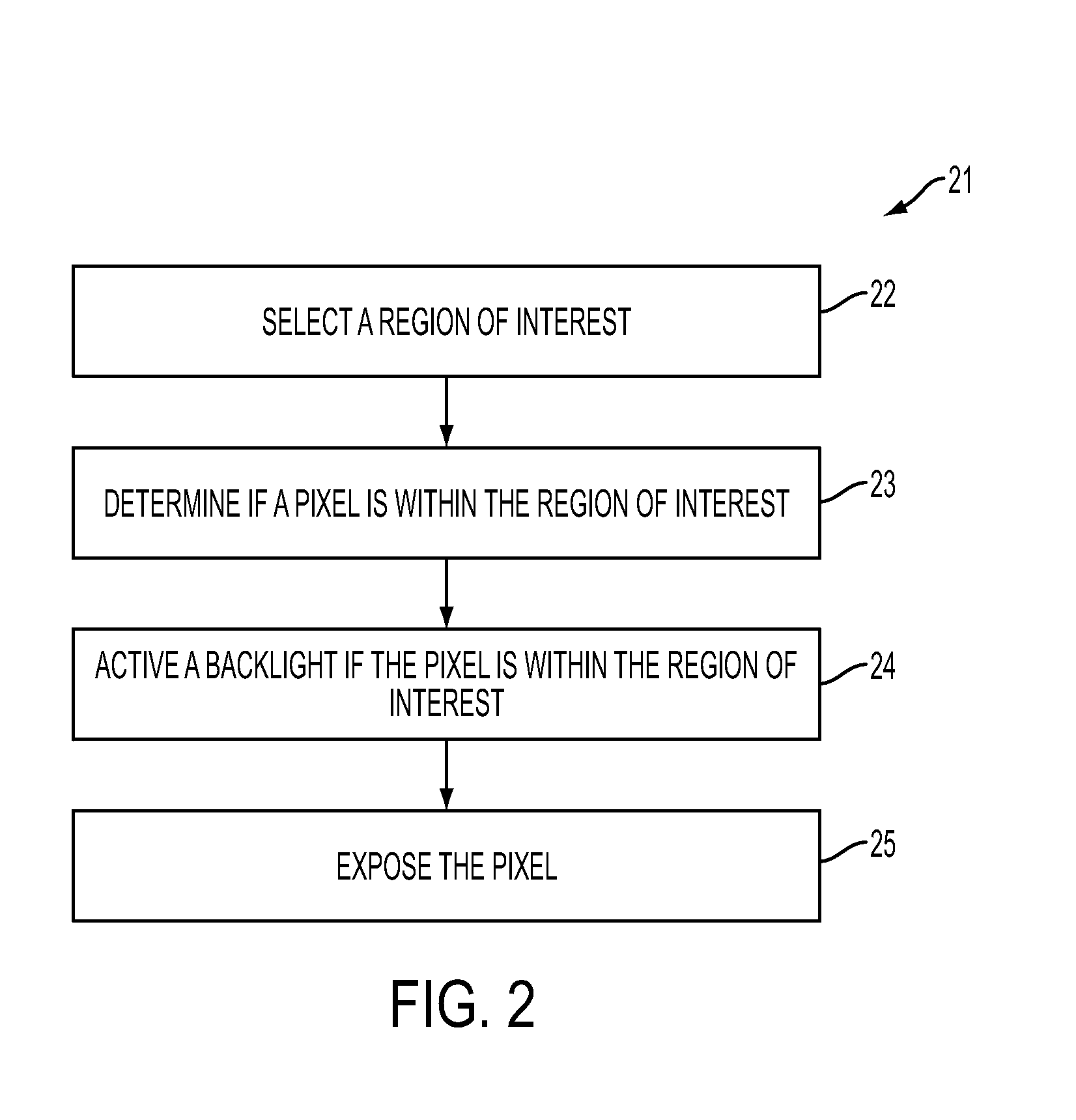
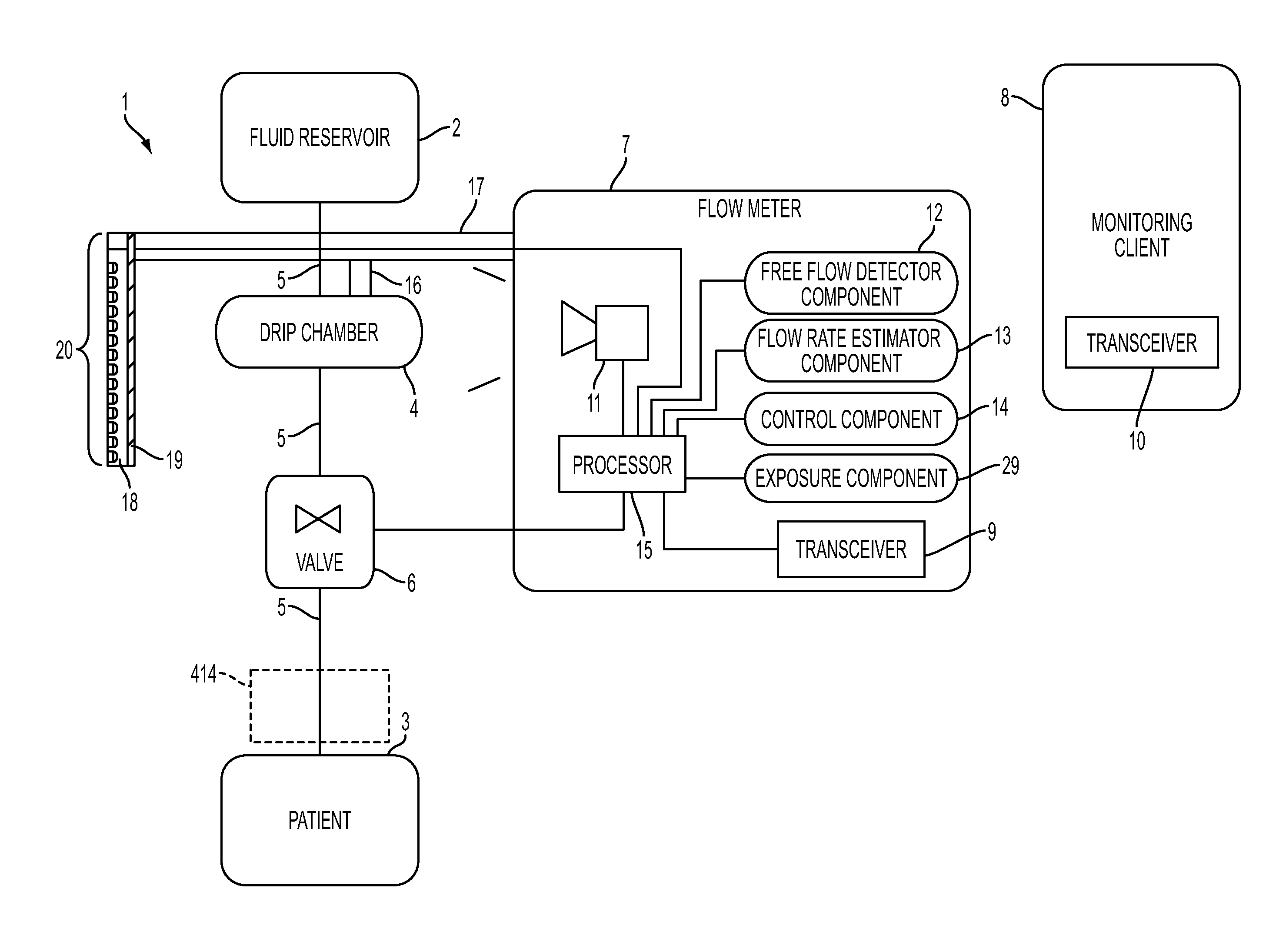
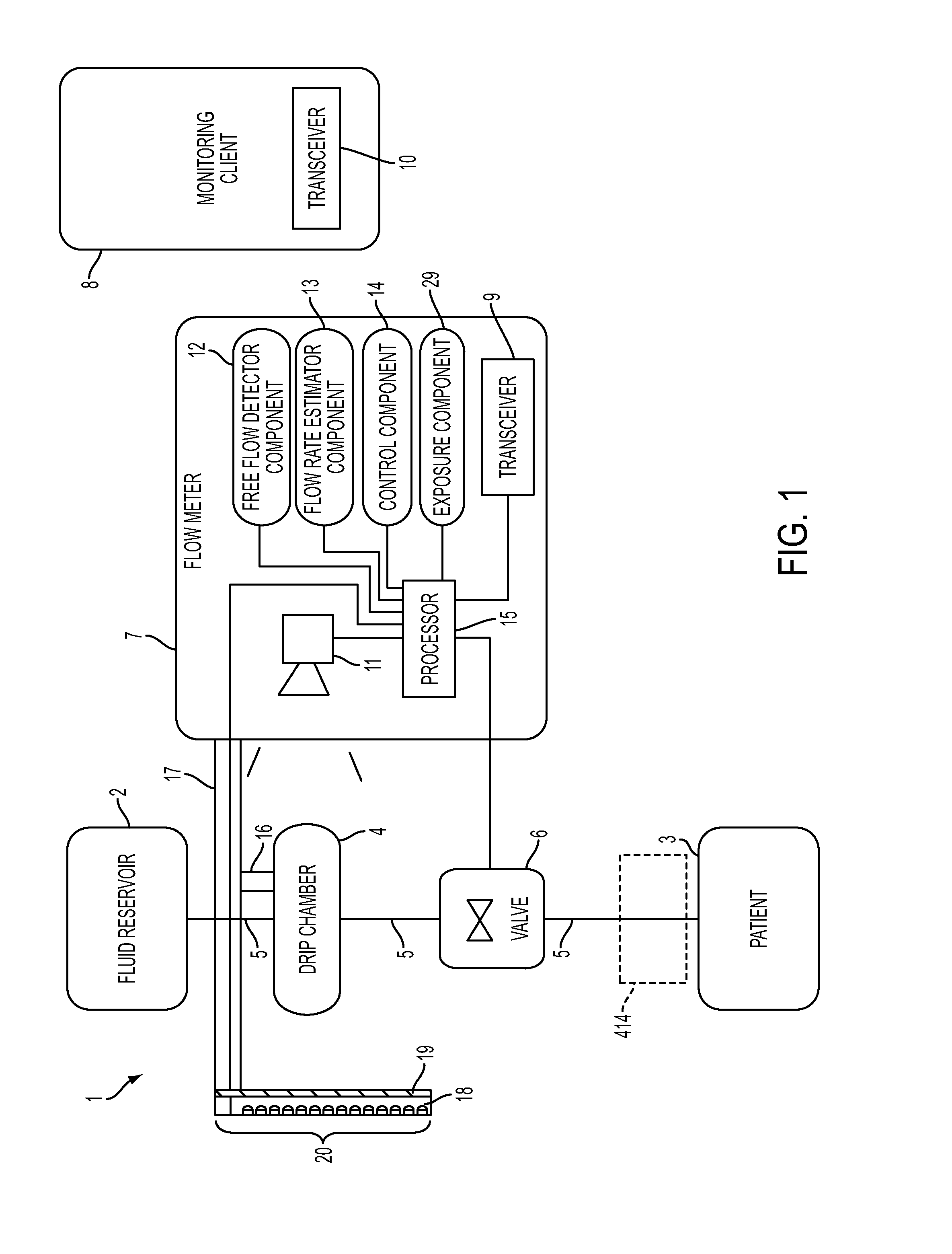
System, Method, and Apparatus for Monitoring, Regulating, or Controlling Fluid Flow
ActiveUS20140318639A1Reduce internal volumeAmount being removedEngine diaphragmsDrug and medicationsControl flowEngineering
An apparatus, system and method for regulating fluid flow are disclosed. The apparatus includes a flow rate sensor and a valve. The flow rate sensor uses images to estimate flow through a drip chamber and then controls the valve based on the estimated flow rate. The valve comprises a rigid housing disposed around the tube in which fluid flow is being controlled. Increasing the pressure in the housing controls the size of the lumen within the tube by deforming the tube, therefore controlling flow through the tube.
Owner:DEKA PROD LLP
Method and apparatus for autonomous downhole fluid selection with pathway dependent resistance system
An apparatus is described for controlling flow of fluid in a tubular positioned in a wellbore extending through a subterranean formation. A flow control system is placed in fluid communication with a main tubular. The flow control system has a flow ratio control system and a pathway dependent resistance system. The flow ratio control system has a first and second passageway, the production fluid flowing into the passageways with the ratio of fluid flow through the passageways related to the characteristic of the fluid flow. The pathway dependent resistance system includes a vortex chamber with a first and second inlet and an outlet, the first inlet of the pathway dependent resistance system in fluid communication with the first passageway of the fluid ratio control system and the second inlet in fluid communication with the second passageway of the fluid ratio control system. The first inlet is positioned to direct fluid into the vortex chamber such that it flows primarily tangentially into the vortex chamber, and the second inlet is positioned to direct fluid such that it flows primarily radially into the vortex chamber. Undesired fluids, such as natural gas or water, in an oil well, are directed, based on their relative characteristic, into the vortex primarily tangentially, thereby restricting fluid flow when the undesired fluid is present as a component of the production fluid.
Owner:HALLIBURTON ENERGY SERVICES INC
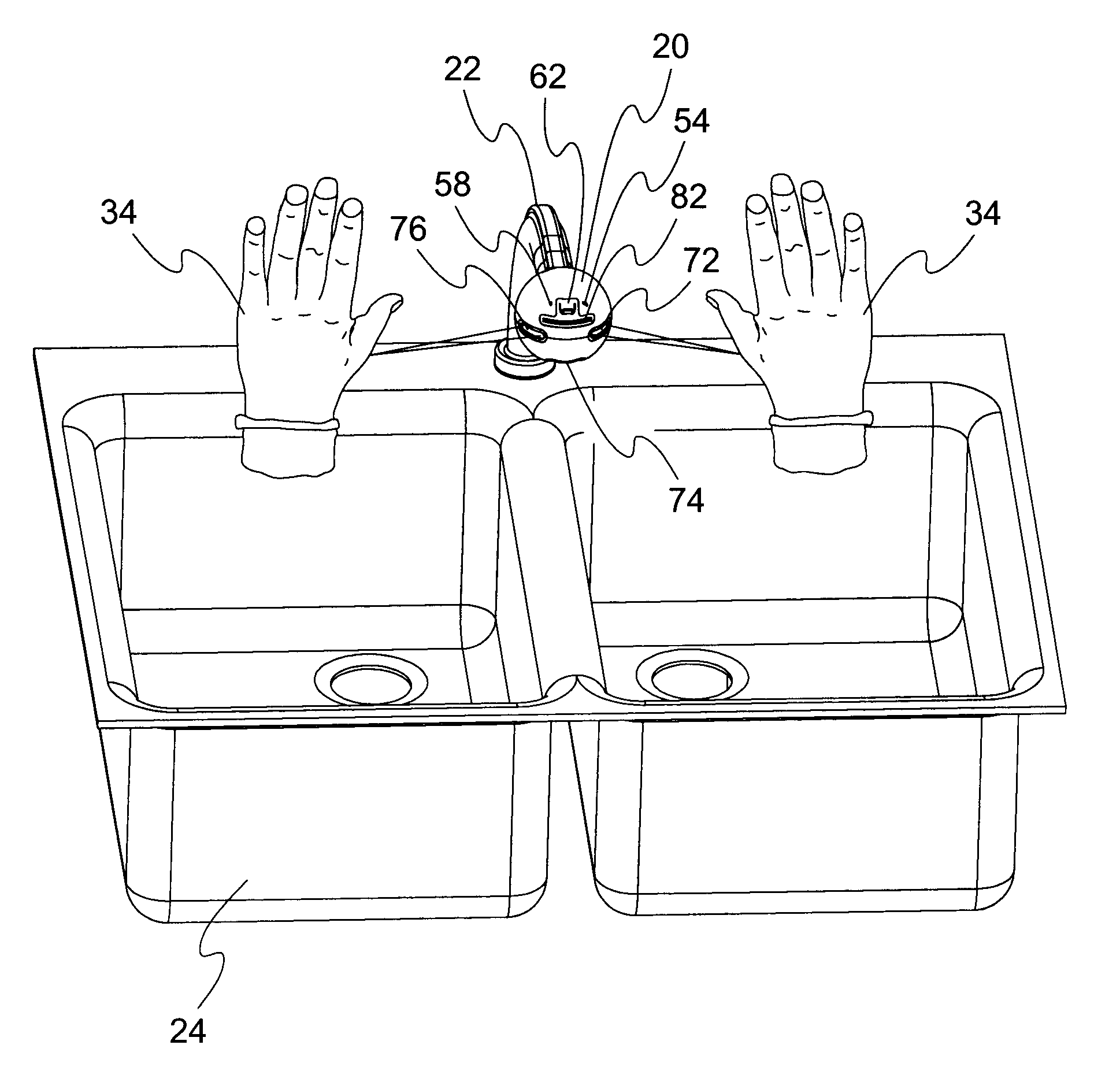
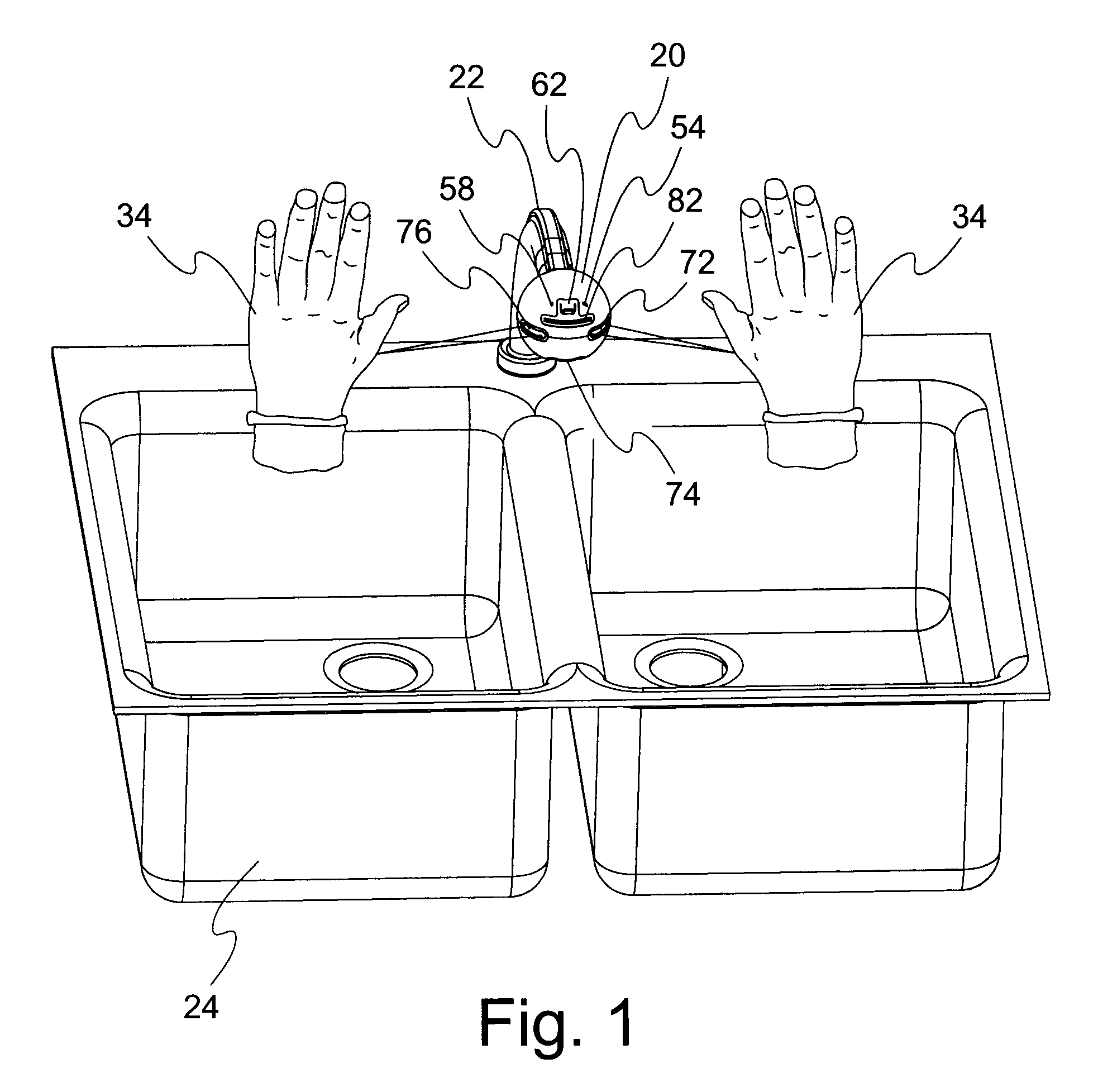
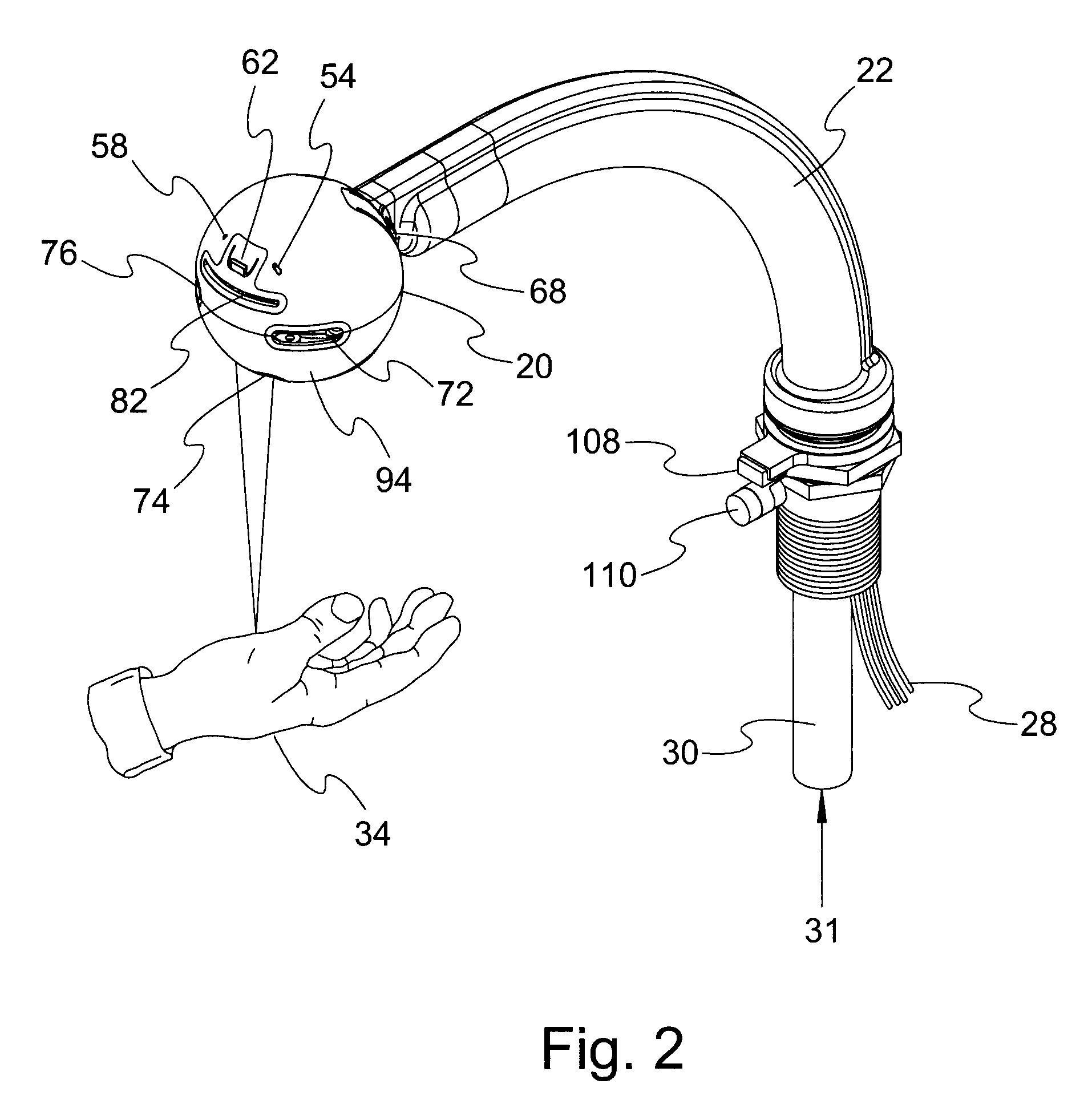
Electronic Faucet with Voice, Temperature, Flow and Volume Control
An ergonomic water conserving faucet assembly that pivots around a cognitive central point providing touchless water temperature, flow rate, volume control and spray pattern adjustment through multiple, hygienic means. The assembly comprises a pivotable, ergonomic, ball-shaped spout that may be used statically or hand held; a retractable water delivery hose connecting the spout to a water source; a water mixing valve at the water source delivering water of preselected temperature; solenoid valves controlling flow; proximity and object detection sensors mapping the sink area and detecting input signals; speech sensors with microphone for voice control; an LED display of water temperature; internal speakers delivering audible prompts; and an electronic controller recognizing speech and supervising operations.
Owner:WOLF JAMES L +1
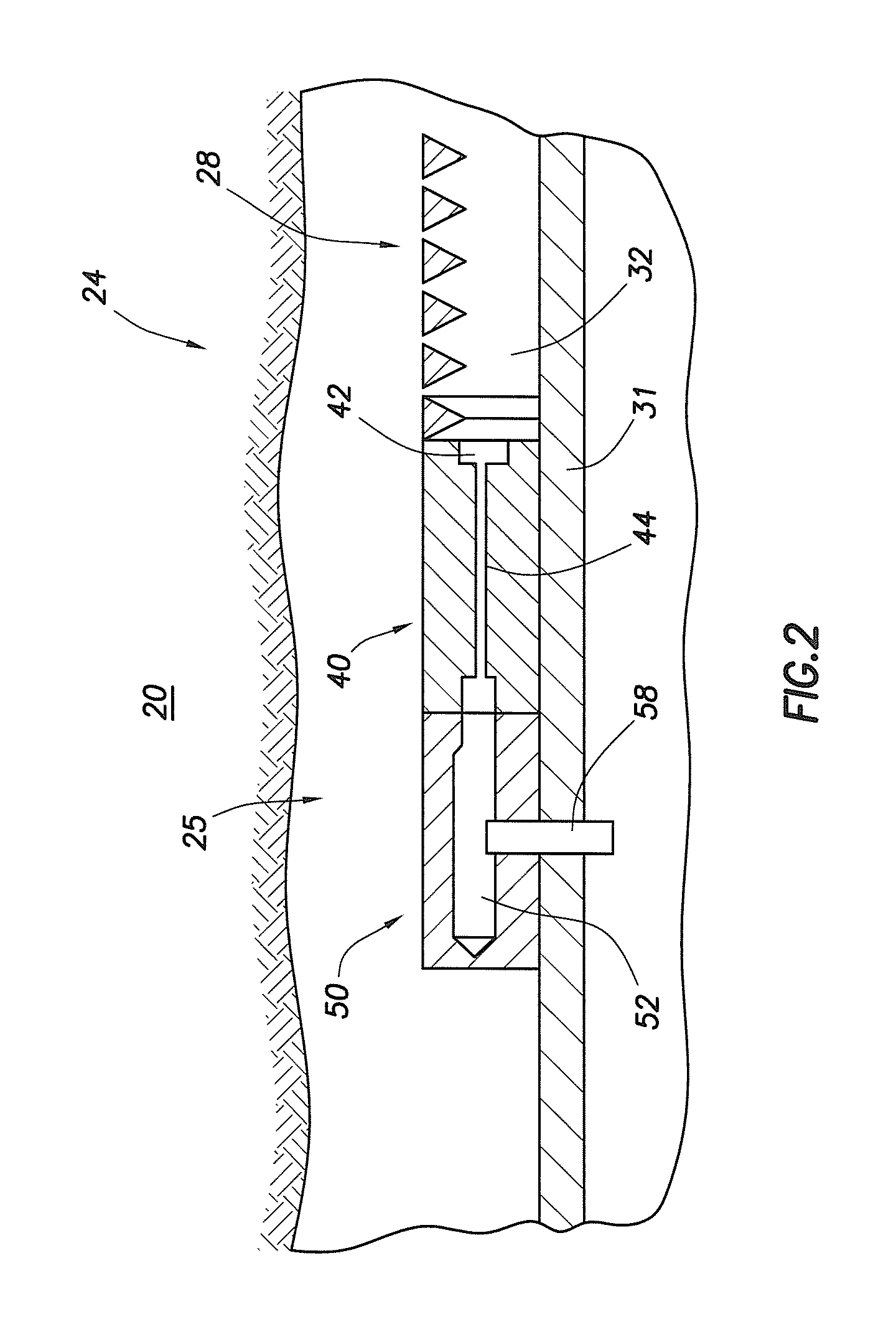
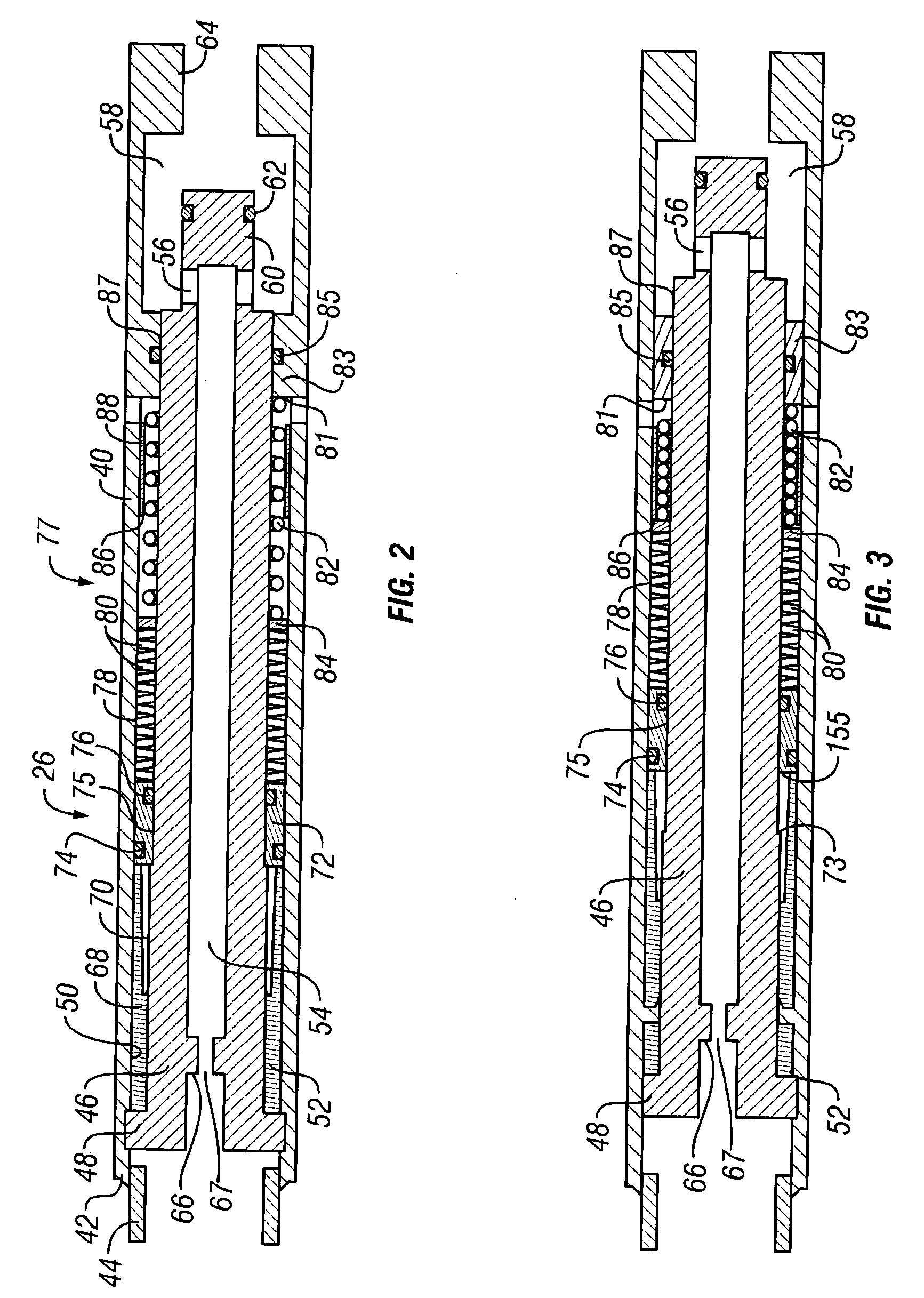
Inflow control device with passive shut-off feature
InactiveUS7290606B2Reduce gas flowConsistent service lifeSurveyConstructionsControl flowControl signal
Devices and methods for control flow of formation fluids respect to one or more selected parameter relating to the wellbore fluid. In one embodiment, a flow control device for controlling fluid flow into the production tubular uses a flow restriction member that is actuated by a character change of the formation fluid, such as liquid to gas or oil to water. The flow restriction member can be sensitive to a change in density of the formation fluid. The flow restriction member is passive, self-regulating and does not need any power source or control signal to control fluid flow. In one embodiment, the flow control device automatically rotates into a predetermined orientation upon being positioned in the wellbore. A seal disposed on the flow control devices expands into sealing engagement with an enclosure after the flow control device assumed the desired predetermined position.
Owner:BAKER HUGHES INC
Material sensitive downhole flow control device
A screen section has a valve assembly to control flow through it. The valve is open and has a closure spring held compressed by a shape memory material that responds to the presence of a specific well fluid or fluids so that its property changes to allow the spring to deliver the stored potential energy to the valve member to close it when the specific well fluid or fluids are detected. The preferred material is a shape memory polymer that, for example, is sensitive to the presence of water or methane and gets softer to release the potential energy source to operate the downhole tool.
Owner:BAKER HUGHES INC
Secure execution of a computer program using a code cache
ActiveUS20050010804A1Avoid hijackingLimit executionMemory loss protectionError detection/correctionControl flowSecurity policy
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
Method and apparatus for topology and path verification in networks
InactiveUS20150249587A1Error preventionFrequency-division multiplex detailsControl flowTraffic capacity
A method and apparatus are disclosed herein for topology and / or path verification in networks. In one embodiment, a method is disclosed for use with a pre-determined subset of network flows for a communication network, where the network comprises a control plane, a forwarding plane, and one or more controllers. The method comprises installing forwarding rules on the forwarding elements for identification of network information, wherein the forwarding rules are grouped into one or more separate control flows, where each of the one or more control flows makes a closed loop walk through at least a portion of the network according to the forwarding rules of said each control flow, injecting traffic for one or more control flows onto the forwarding plane, and identifying the network information based on results of injecting the traffic.
Owner:NTT DOCOMO INC
System, method, and apparatus for monitoring, regulating, or controlling fluid flow
An apparatus, system and method for regulating fluid flow are disclosed. The apparatus includes a flow rate sensor and a valve. The flow rate sensor uses images to estimate flow through a drip chamber and then controls the valve based on the estimated flow rate. The valve comprises a rigid housing disposed around the tube in which fluid flow is being controlled. Increasing the pressure in the housing controls the size of the lumen within the tube by deforming the tube, therefore controlling flow through the tube.
Owner:DEKA PROD LLP
Inflow control device with passive shut-off feature
InactiveUS20060076150A1Reduce gas flowConsistent service lifeSurveyConstructionsControl flowStream flow
Devices and methods for control flow of formation fluids respect to one or more selected parameter relating to the wellbore fluid. In one embodiment, a flow control device for controlling fluid flow into the production tubular uses a flow restriction member that is actuated by a character change of the formation fluid, such as liquid to gas or oil to water. The flow restriction member can be sensitive to a change in density of the formation fluid. The flow restriction member is passive, self-regulating and does not need any power source or control signal to control fluid flow. In one embodiment, the flow control device automatically rotates into a predetermined orientation upon being positioned in the wellbore. A seal disposed on the flow control devices expands into sealing engagement with an enclosure after the flow control device assumed the desired predetermined position.
Owner:BAKER HUGHES INC
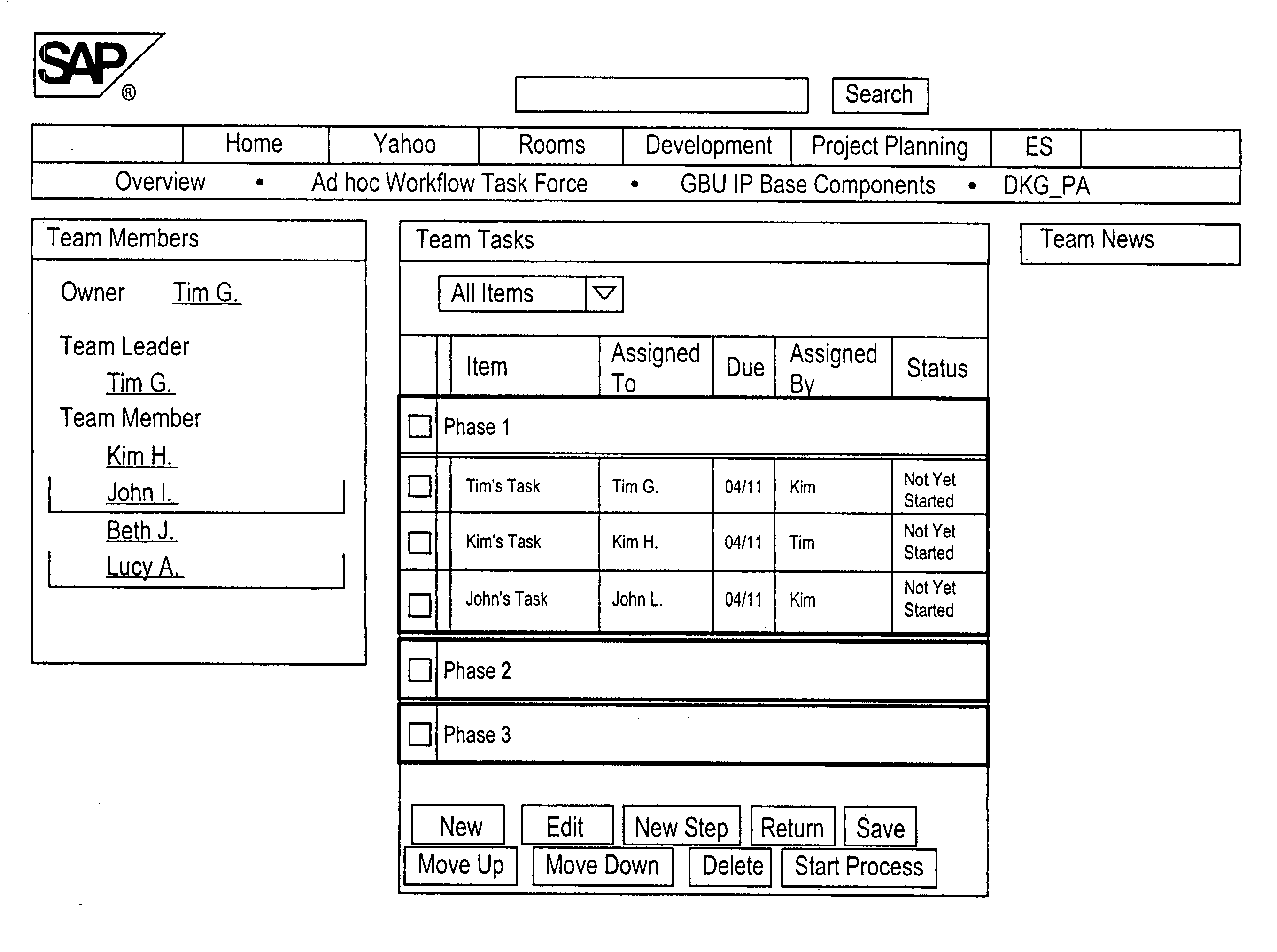
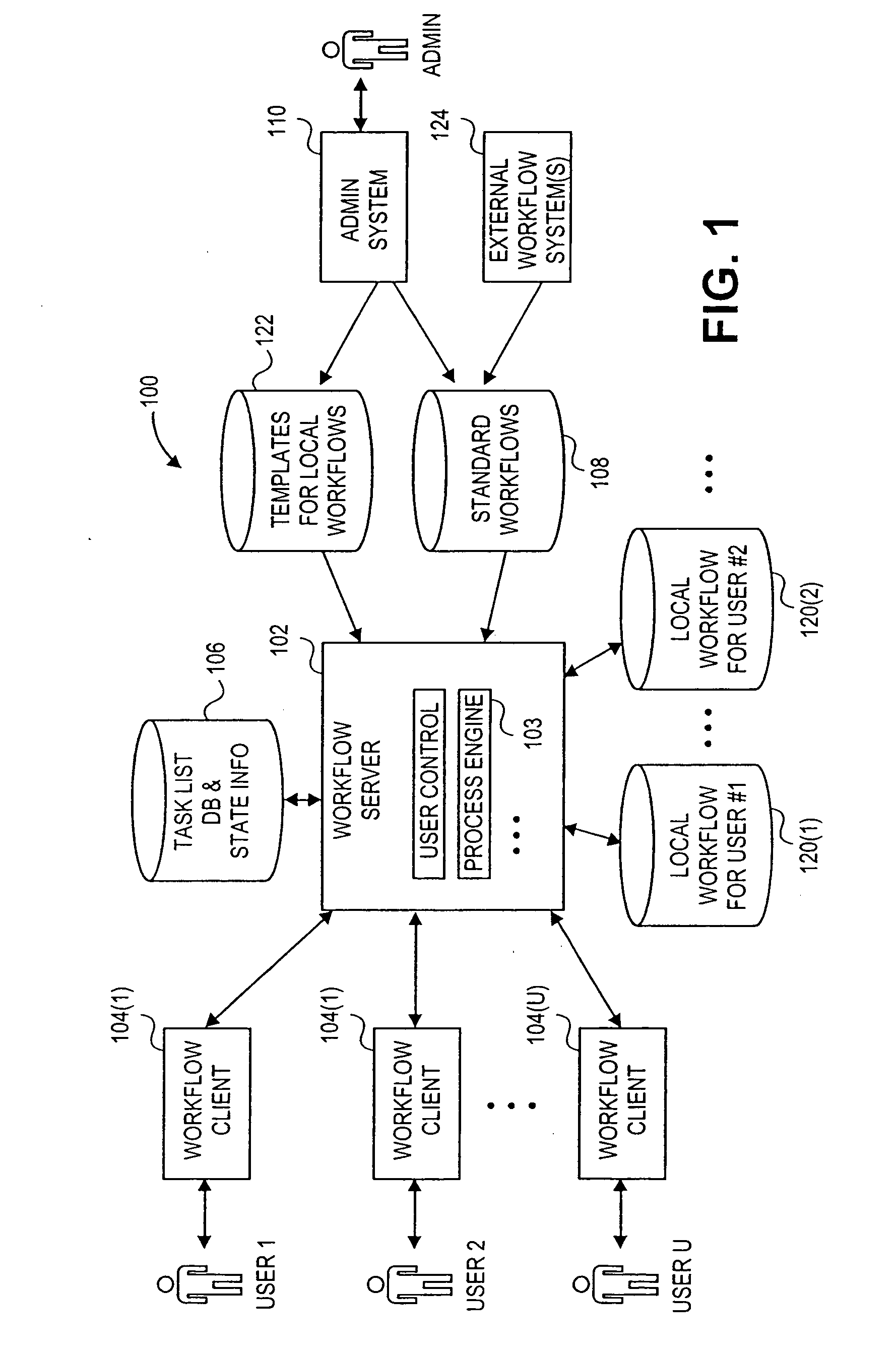
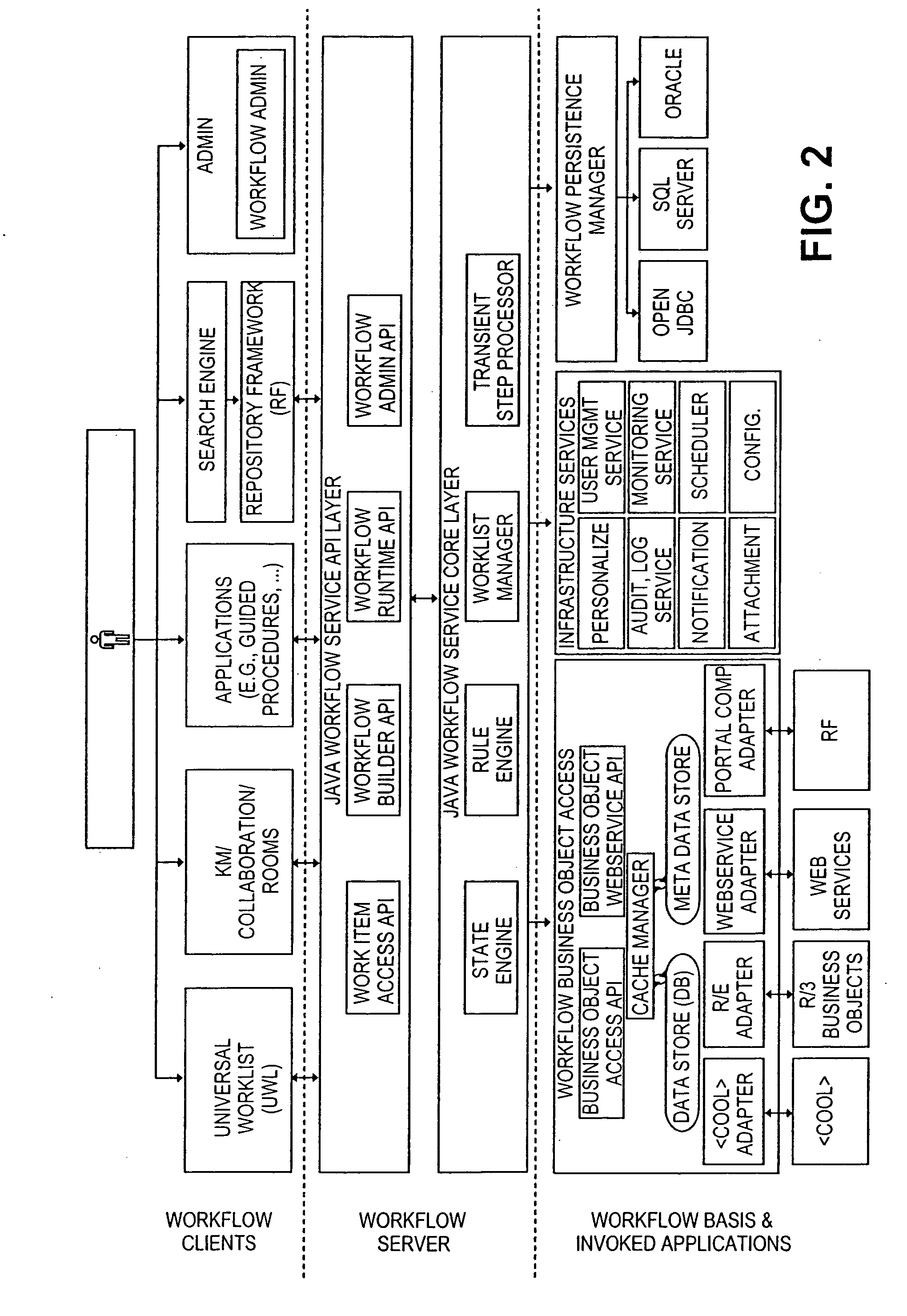
End user oriented workflow approach including structured processing of ad hoc workflows with a collaborative process engine
ActiveUS20050027585A1Multiple digital computer combinationsOffice automationControl flowExecution control
In a structured workflow system, a configurable workflow engine provides mechanisms for executing and scheduling the work items in a defined way. End users use their discretion and define their own “local” processes and “local” rules for processing work items, or deviate from predefined processes. The configurable workflow engine might be installed at a server to organize workflows and business processes where end users can define processing steps for incoming work items by setting up rules and defining workflows as part of a local workflow structure. By defining these rules and workflows, the further processing steps of future incoming work items can be automated. When an administrator directs the workflow engine to move from a current phase to a next phase, the workflow engine deals with the incomplete items by allowing the administrator to carry over work items (or might do it automatically). End -user consultation might be included in the carry-over decisions. The carried over work items are added as parallel activities to the next phase. The workflow engine handles imposing and executing control flow dependencies between tasks, thus providing a smooth transition from totally unstructured work to semi-structured or completely structured work. When the workflow engine encounters semantically correlated work items / tasks, the process engine assumes that these work items / tasks belong to the same process instance.
Owner:SAP AG
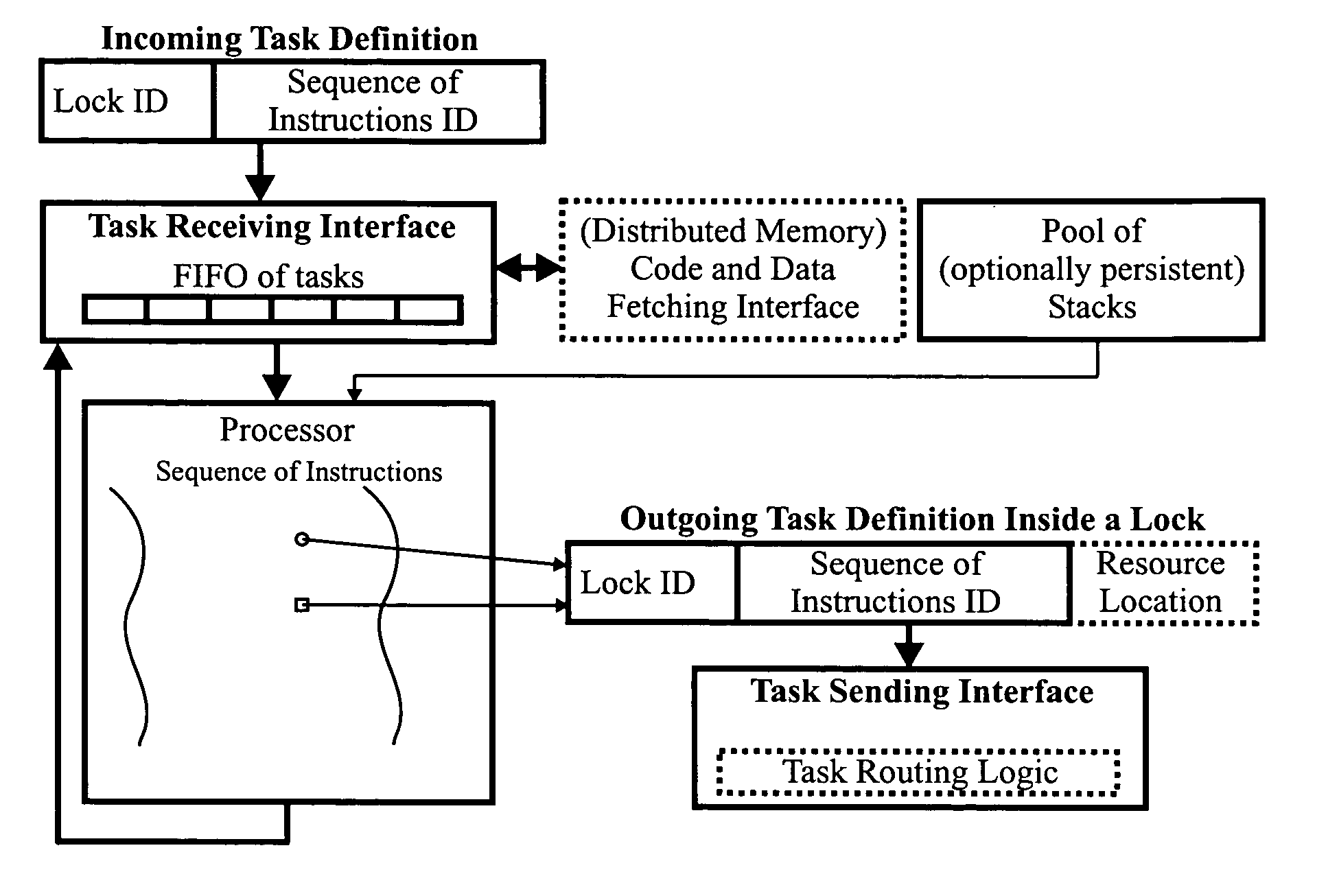
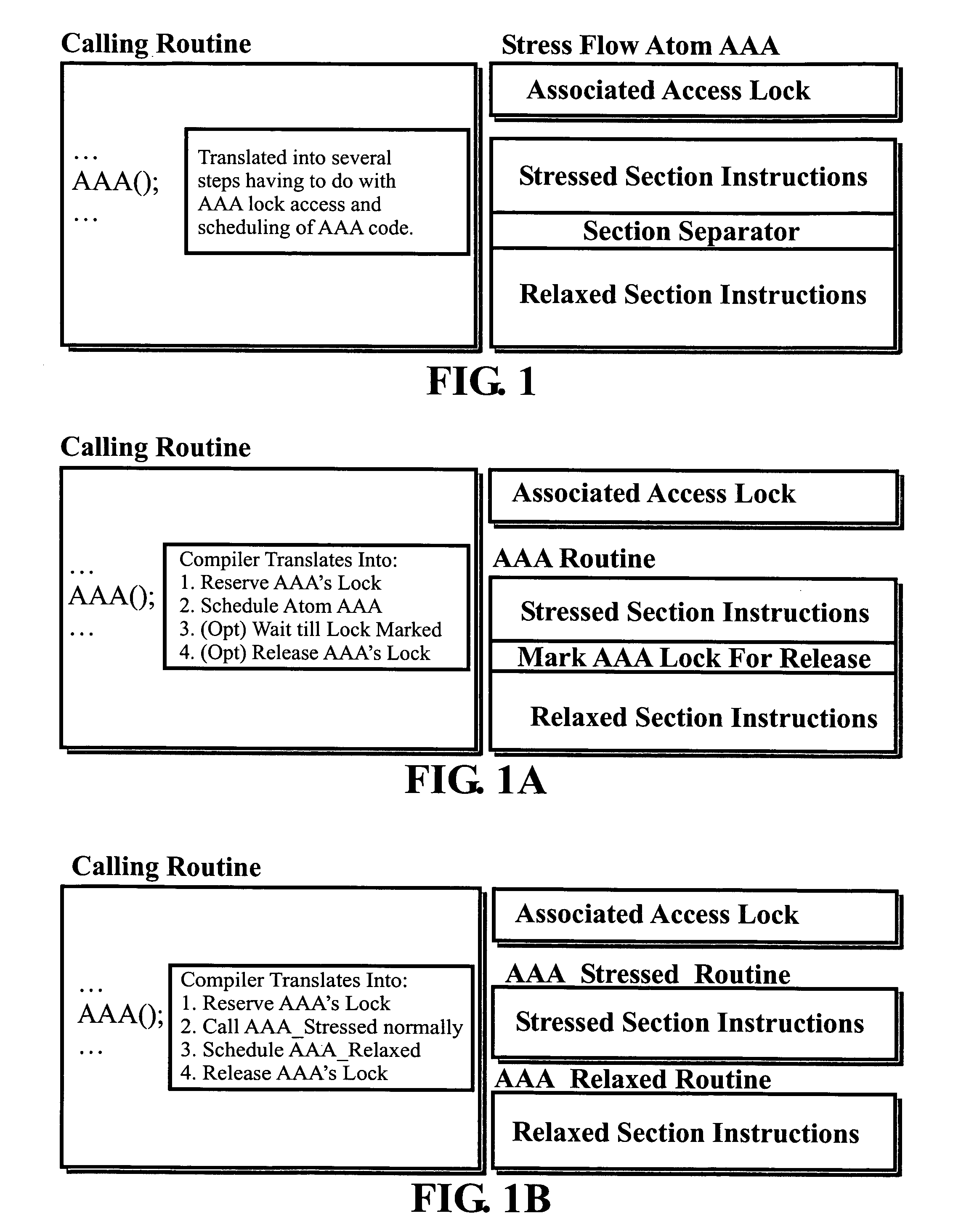
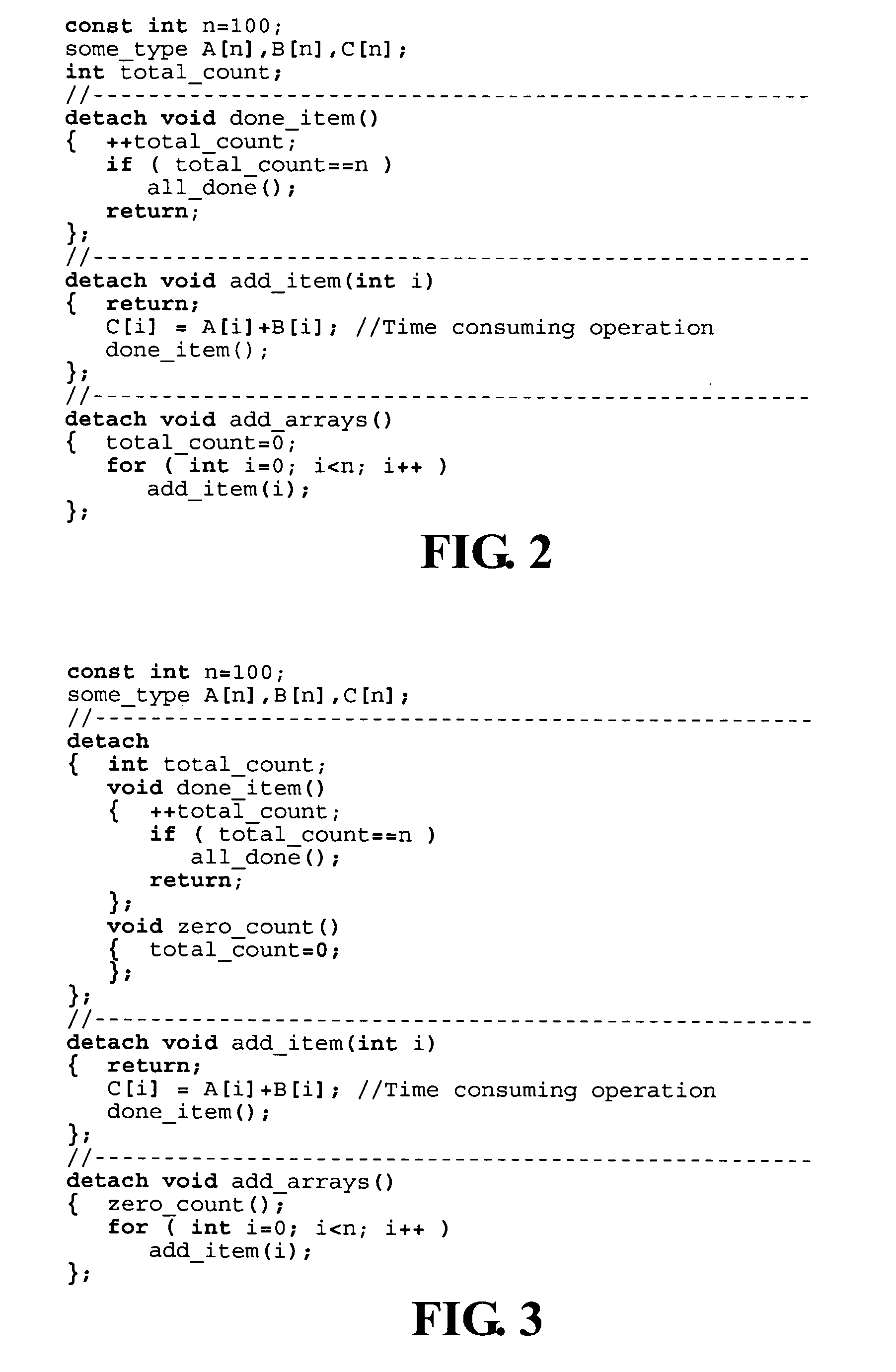
Object-oriented, parallel language, method of programming and multi-processor computer
This invention relates to architecture and synchronization of multi-processor computing hardware. It establishes a new method of programming, process synchronization, and of computer construction, named stress-flow by the inventor, allowing benefits of both opposing legacy concepts of programming (namely of both data-flow and control flow) within one cohesive, powerful, object-oriented scheme. This invention also relates to construction of object-oriented, parallel computer languages, script and visual, together with compiler construction and method to write programs to be executed in fully parallel (or multi-processor) architectures, virtually parallel, and single-processor multitasking computer systems.
Owner:JANCZEWSKA NATALIA URSZULA +2
Downhole inflow control device with shut-off feature
InactiveUS20060113089A1Fluid removalWell/borehole valve arrangementsControl flowChemical composition
A system and method for controlling inflow of fluid into a production string. In aspects, the invention provides a downhole sand screen and inflow control device with a gas or water shut-off feature that can be operated mechanically or hydraulically from the surface of the well. The device also preferably includes a bypass feature that allows the inflow control device to be closed or bypassed via shifting of a sleeve. In embodiments, the flow control device can be adaptive to changes in wellbore conditions such as chemical make-up, fluid density and temperature. Exemplary adaptive inflow control devices include devices configured to control flow in response to changes in gas / oil ratio, water / oil ratio, fluid density and / or the operating temperature of the inflow control device. In other aspects of the present invention, inflow control devices are utilized to control the flow of commingled fluids drained via two or more wellbores.
Owner:BAKER HUGHES INC
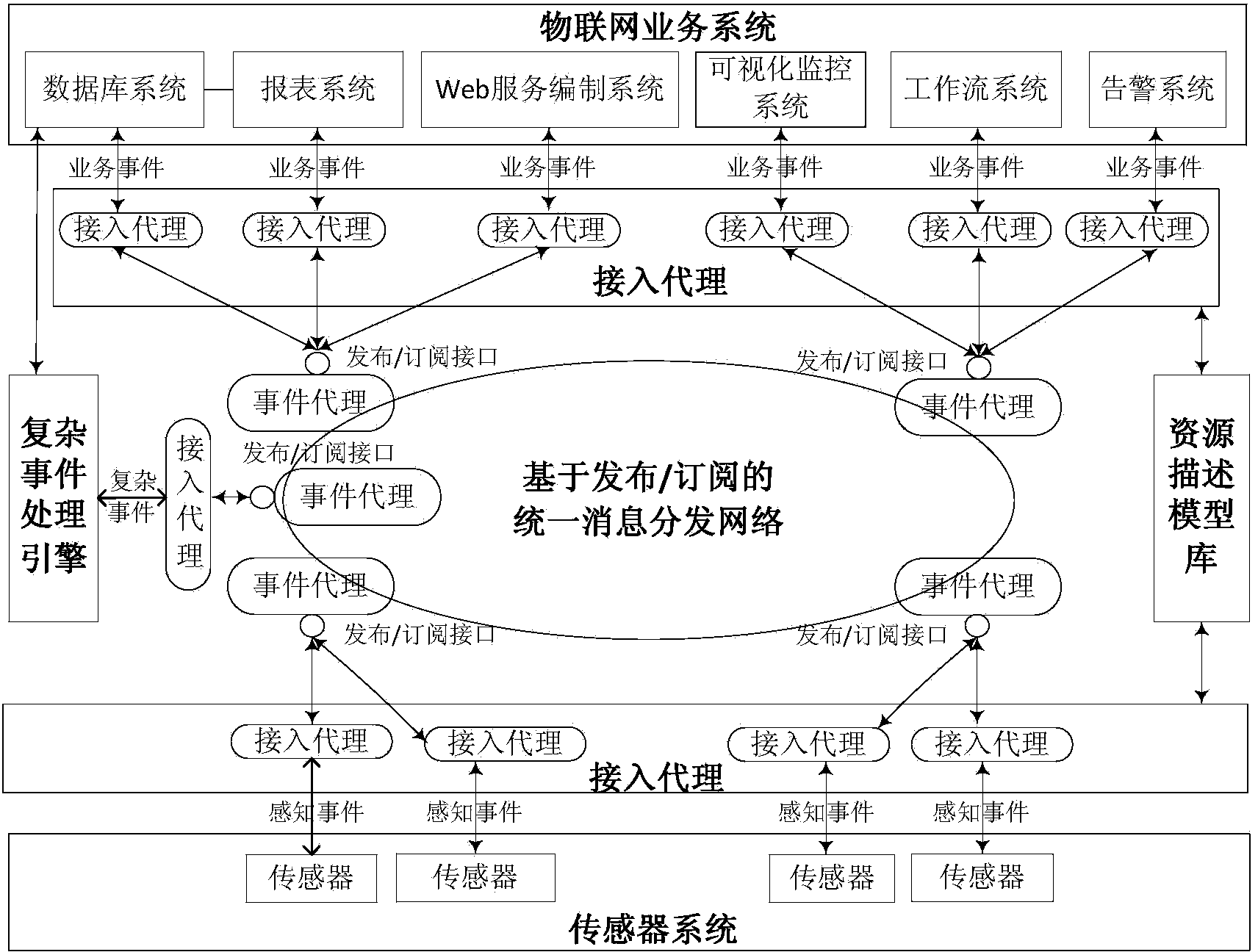
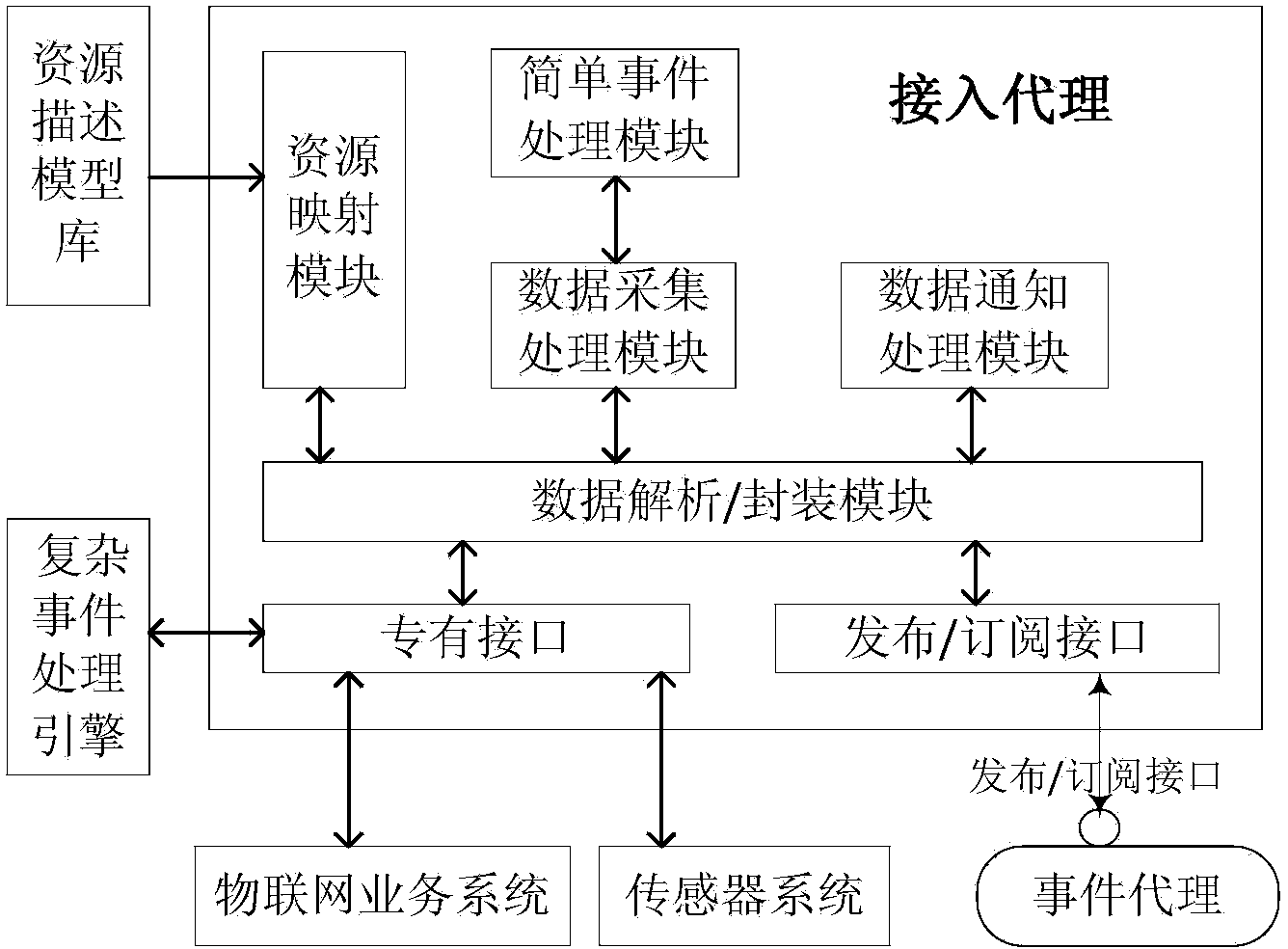
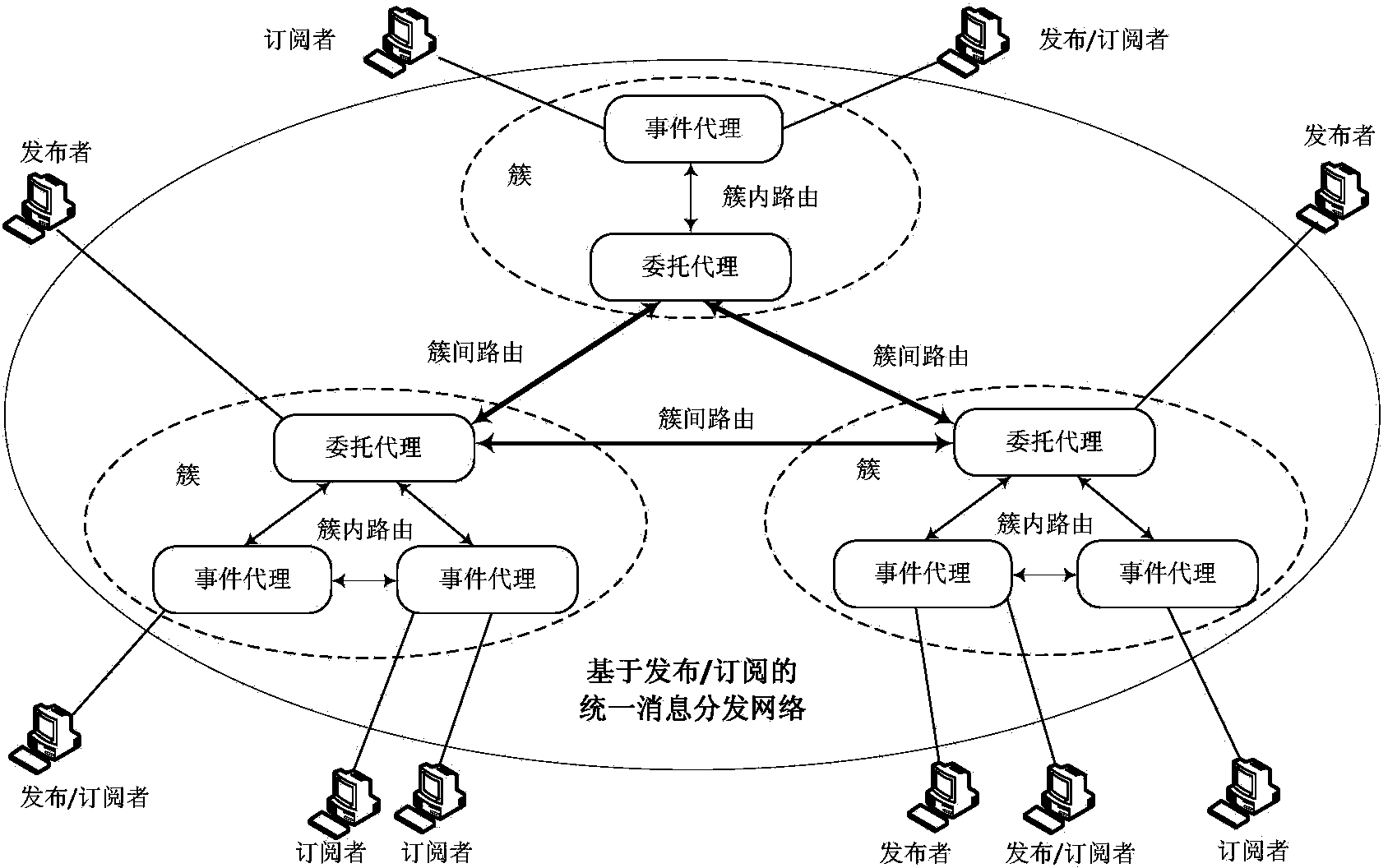
System for providing services of event-driven service-oriented internet of things and working method thereof
ActiveCN103458033ASupport on-demand distributionQuick responseData switching by path configurationComplex event processingDistributed Computing Environment
The invention provides a system for providing services of an event-driven service-oriented internet of things and a working method of the system. The system is composed of a plurality of parts of an internet of things service system, an access agent, a unified message distribution network based on a publish-subscribe mechanism, a complex event processing engine, a resource descriptive model base and a sensor system. The system and the working method solve the problems that an existing system for providing the services of the internet of things can not process large-scale sensing information in a distributed mode, events in a physical world can not be processed, effective cross-business-domain and cross-organization coordination is difficult to achieve by different enterprise business processes. According to the system, sensing information is effectively distributed in the open and distributed computing environment, various pieces of sensing information can be conveniently and quickly distributed as required among different internet of things heterogeneous service systems, event-driven cross-business-domain and cross-organization service dynamic coordination is achieved, time, space and control flow uncoupled network services are provided, and quick response to change of the physical world can be flexibly and dynamically achieved in real time.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Optical network restoration
A method for protecting the flows of traffic against, and for restoring them from, a failure in a multifunctional, hybrid broadband access-and-transport network system includes the provisioning of at least two Virtual Flows (“VFs”) of traffic between each pair of ingress and egress (“I / E”) nodes in the system. The at least two VFs are provisioned such that each takes a different physical path from the other. The VFs taking the same physical path are then respectively grouped into two “Path Protection Groups” (“PPGs”). Each of the PPGs has a dedicated “Management Control Flow” (“MCF”) provisioned within it that is carried in the at least one VF contained therein. The detection of a fault in the traffic in an “active” PPG results in the generation of a protection switching signal (“PSS”) being generated and sent by the nodes detecting the fault along the MCF of the affected PPG to the relevant “protection switching entities” (“PSEs”), i.e., the affected I / E nodes, which responsively effect a protection switch of either the reception, or both the transmission and the reception, of the affected traffic from the affected “active” PPG to the associated “protect” PPG to thereby restore path and traffic continuity within the system. The method is independent of the transport layer and can thus be used to protect traffic in networks having transport systems other than SONET.
Owner:WHITE OAK GLOBAL ADVISORS
Multi-cycle dump valve
InactiveUS20040084190A1Less timePrevent siphonFluid removalWell/borehole valve arrangementsControl flowFree falling
A flow responsive dump valve mechanism for a straddle packer tool and has a valve controlled flow passage from which underflushed fluid, typically well treatment slurry, in a conveyance and fluid supplying tubing string can be dumped into a well casing. The dump valve mechanism incorporates a ratcheting power piston, an indexing mechanism and high and low load energy storage systems to accomplish open, closed and intermediate dump valve positions. The intermediate position increases the functionality of the tool by preventing accidental closure either due to the free fall of fluid through the coiled tubing or during flushing of the tool and permits the flow rate to be increased for thorough cleaning of the straddle tool and coiled tubing. For energy storage, a light compression spring provides power to cycle the indexing mechanism. Heavier load disc springs (Bellville Washers) are used to provide power for the ratcheting power piston to open the valve.
Owner:SCHLUMBERGER TECH CORP
Modular multi-port manifold and fuel delivery system
InactiveUS20050139286A1Prevent openingLiquid transferring devicesPipeline systemsControl flowNuclear engineering
A modular multi-port manifold and fuel delivery system includes a plurality of ports in fluid communication with corresponding compartments of a fuel delivery vehicle, a collector conduit common to the ports, a control valve associated with each port to control flow of the fuel product from the associated compartment to the collector conduit to deliver the product, and a control system for operating each of the control valves.
Owner:DELAWARE CAPITAL FORMATION
Cooling system and method minimizing power consumption in cooling liquid-cooled electronics racks
InactiveUS20110060470A1Reduce power consumptionOvercomes shortcomingMechanical power/torque controlEnergy efficient ICTControl flowPower dissipation minimization
A cooling system and method are provided for facilitating cooling of a liquid-cooled electronics rack. The cooling system includes a coolant flow controller, a modular cooling unit and a pressure controller. The flow controller is associated with a respective electronics rack and controls flow of coolant through that electronics rack based on its changing cooling requirements. The cooling unit includes an adjustable coolant pump for facilitating supply of coolant to the rack. The pressure controller is associated with the cooling unit for controlling pressure of coolant at an output of the cooling unit via control of pump speed of the pump. Responsive to adjusting coolant flow through the electronics rack, the pressure controller automatically adjusts pump speed of the adjustable pump to maintain pressure about a constant coolant pressure set point at an output of the cooling unit, thereby conserving power while still cooling the liquid-cooled electronics rack.
Owner:IBM CORP
Reconfigurable processing
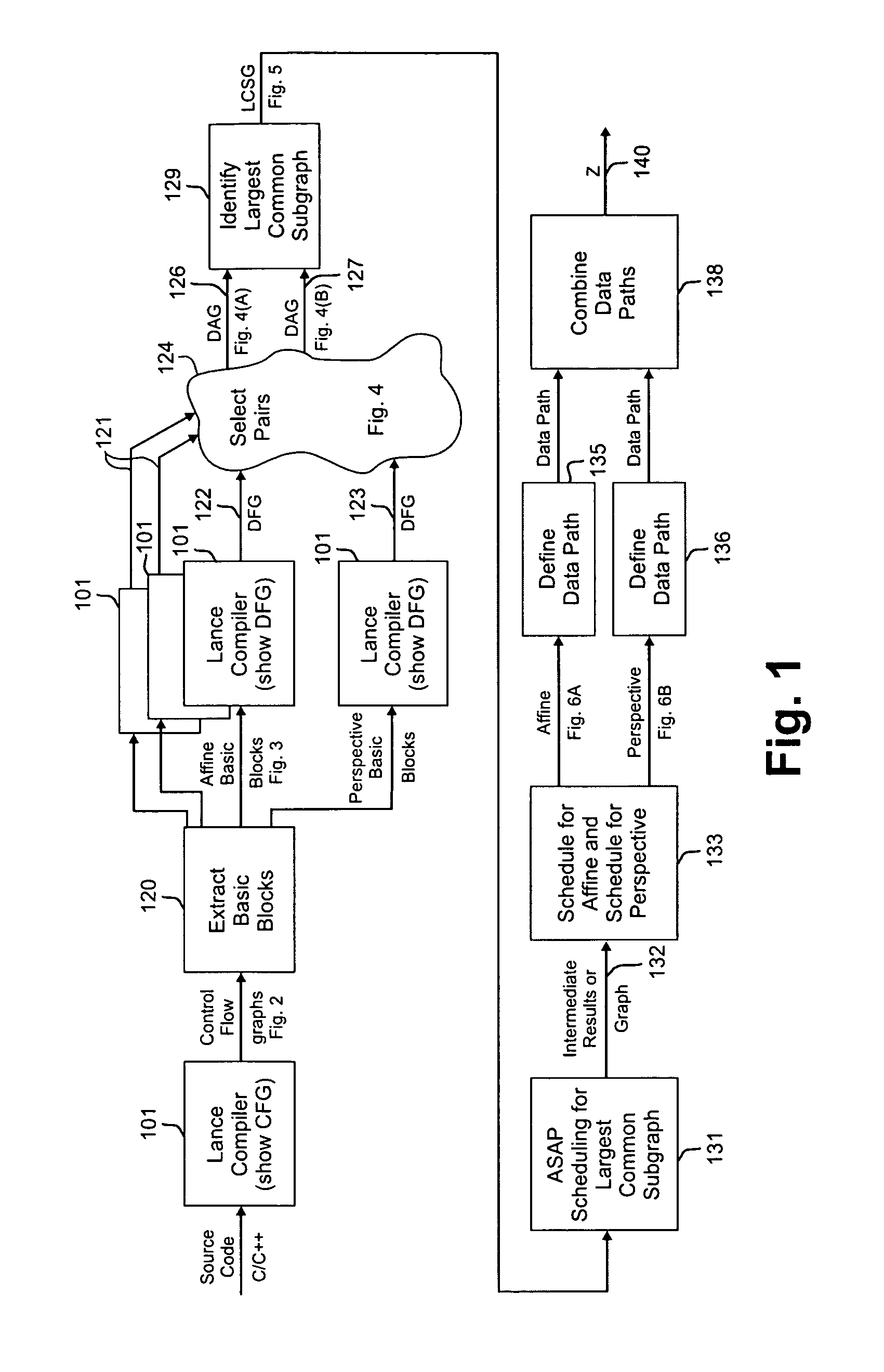
ActiveUS8281297B2Reduce the amount requiredQuick switchEnergy efficient ICTSoftware engineeringControl flowProcessing element
A method of producing a reconfigurable circuit device for running a computer program of moderate complexity such as multimedia processing. Code for the application is compiled into Control Flow Graphs representing distinct parts of the application to be run. From those Control Flow Graphs are extracted basic blocks. The basic blocks are converted to Data Flow Graphs by a compiler utility. From two or more Data Flow Graphs, a largest common subgraph is determined. The largest common subgraph is ASAP scheduled and substituted back into the Data Flow Graphs which also have been scheduled. The separate Data Flow Graphs containing the scheduled largest common subgraph are converted to data paths that are then combined to form code for operating the application. The largest common subgraph is effected in hardware that is shared among the parts of the application from which the Data Flow Graphs were developed. Scheduling of the overall code is effected for sequencing, providing fastest run times and the code is implemented in hardware by partitioning and placement of processing elements on a chip and design of the connective fabric for the design elements.
Owner:ARIZONA STATE UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com