Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
97results about How to "Avoid hijacking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
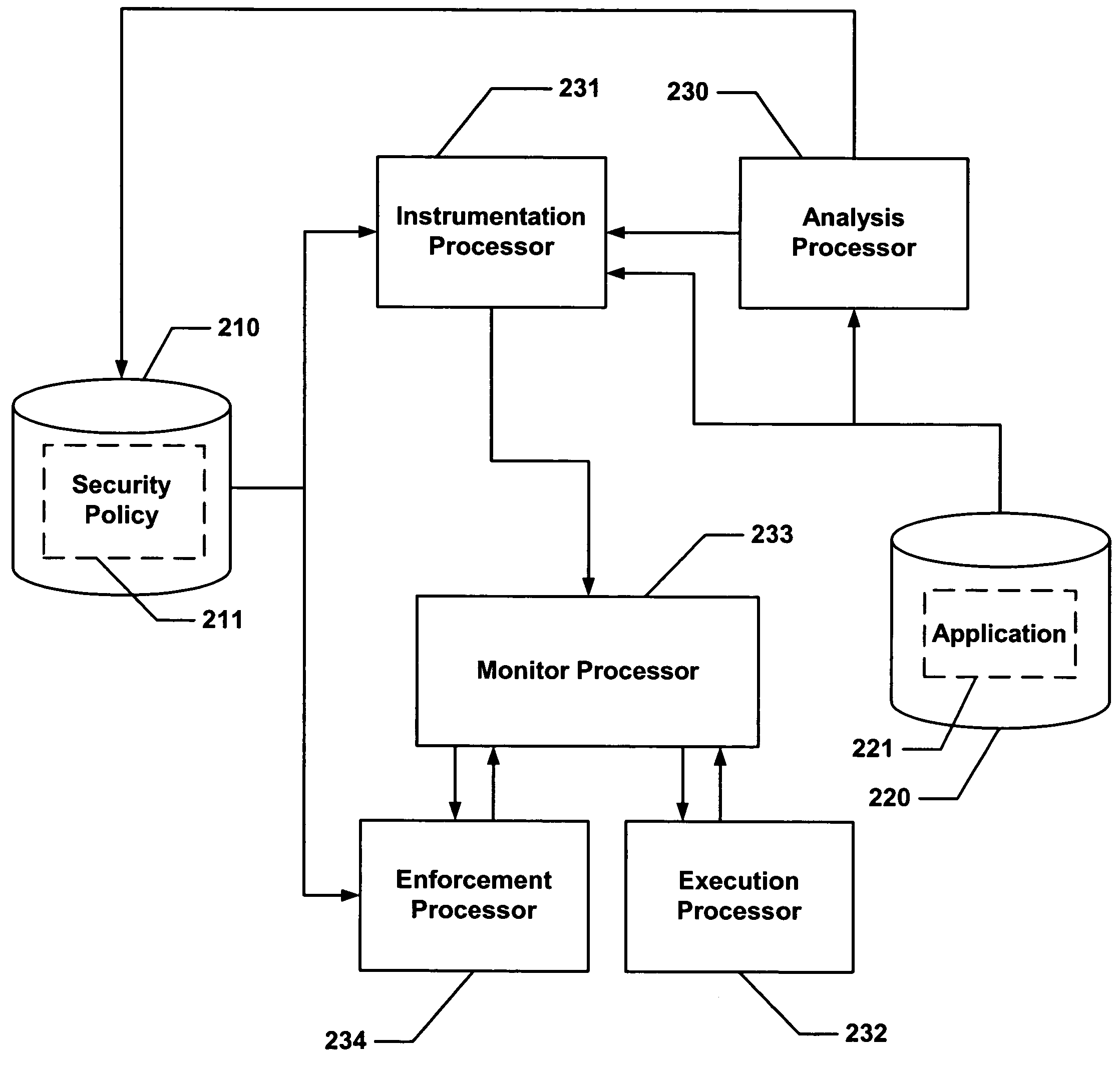
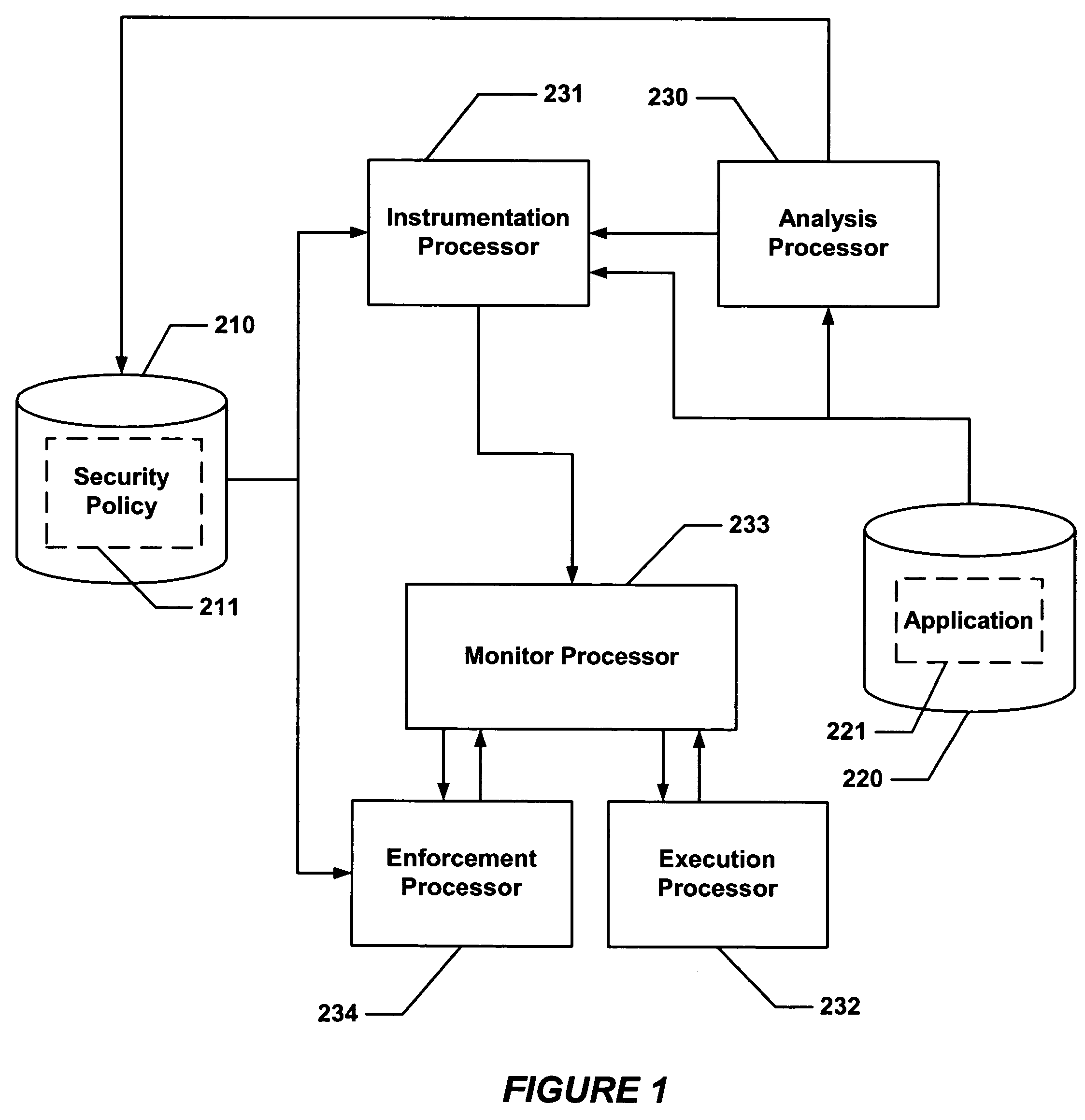
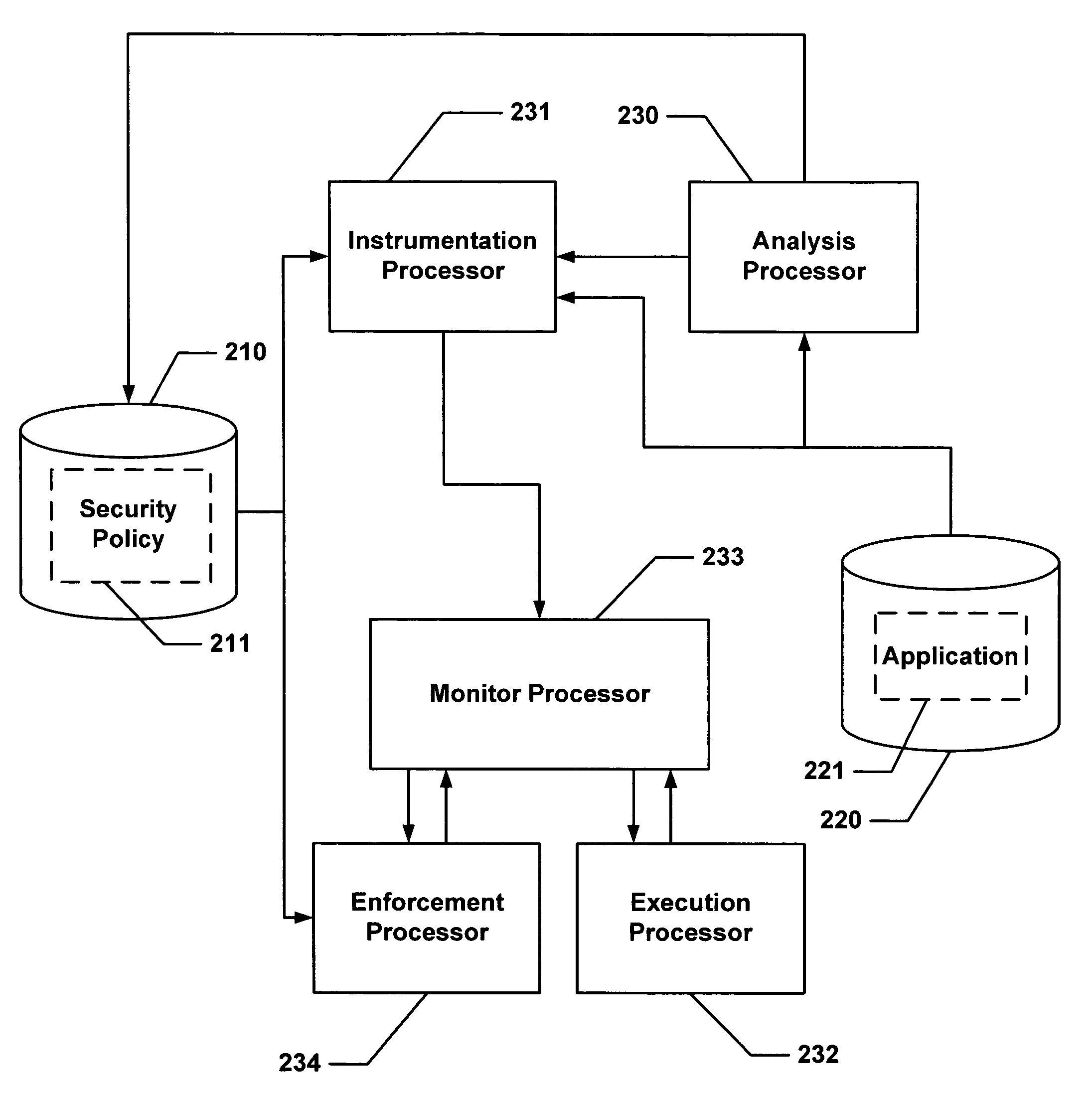
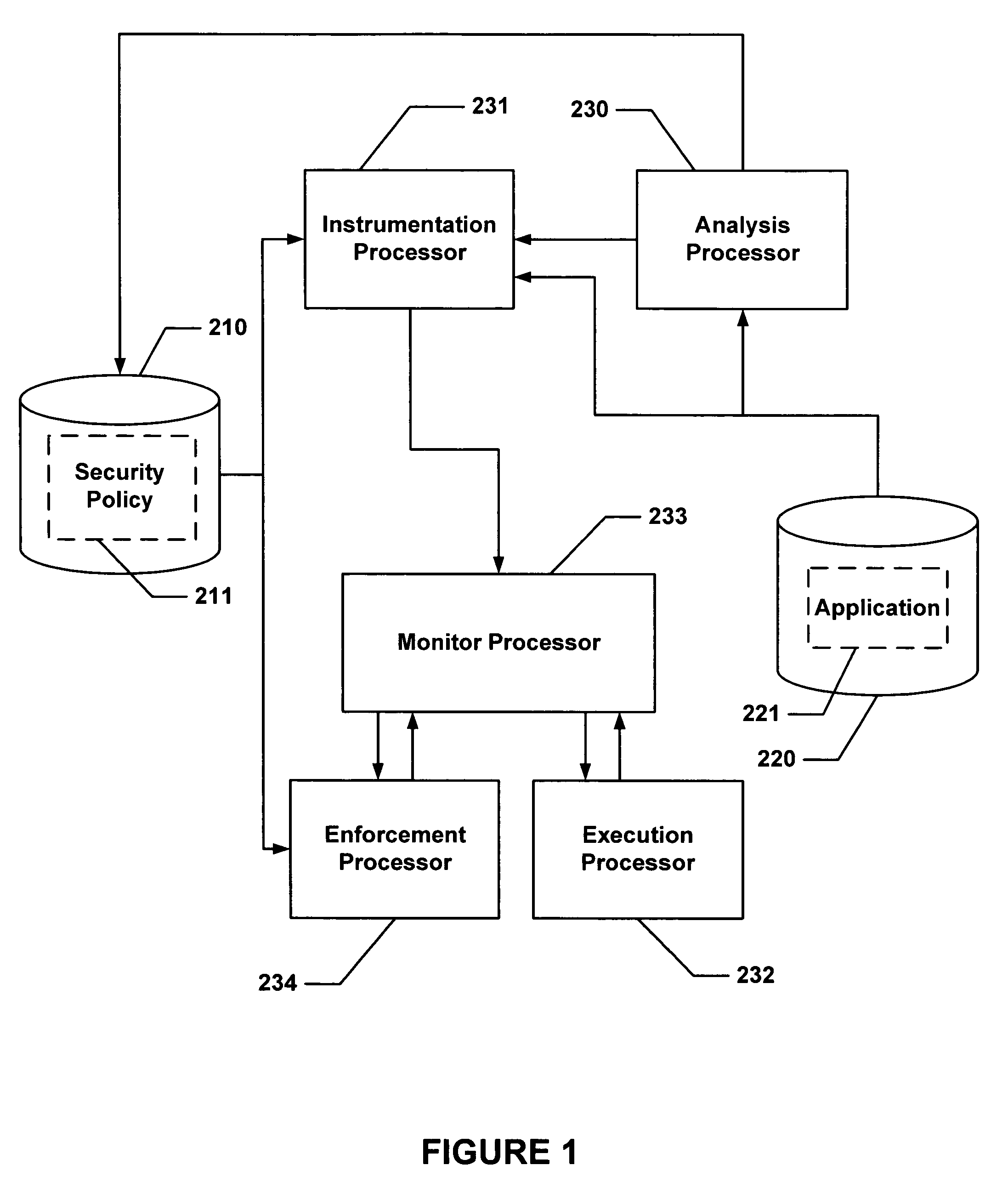
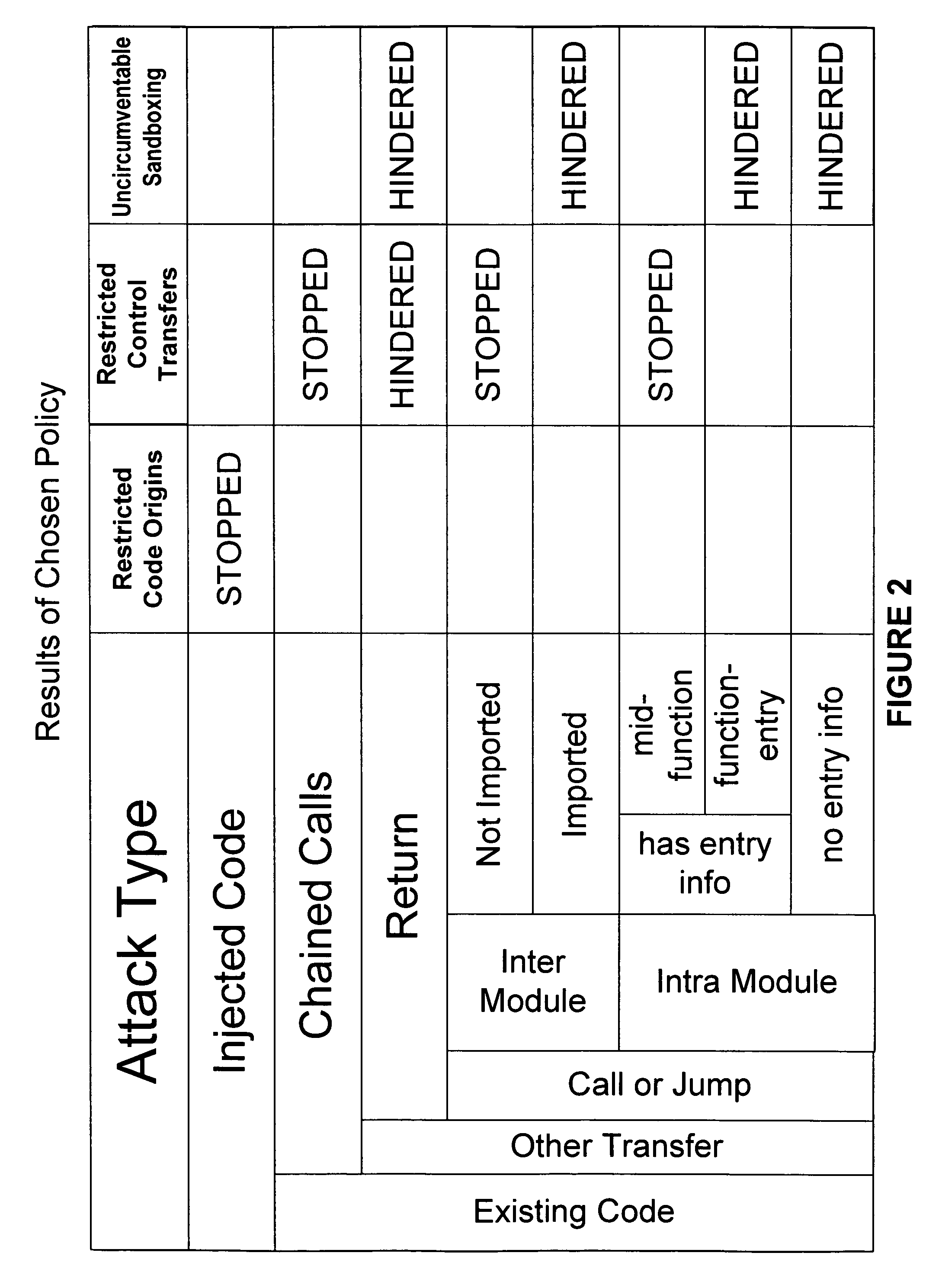
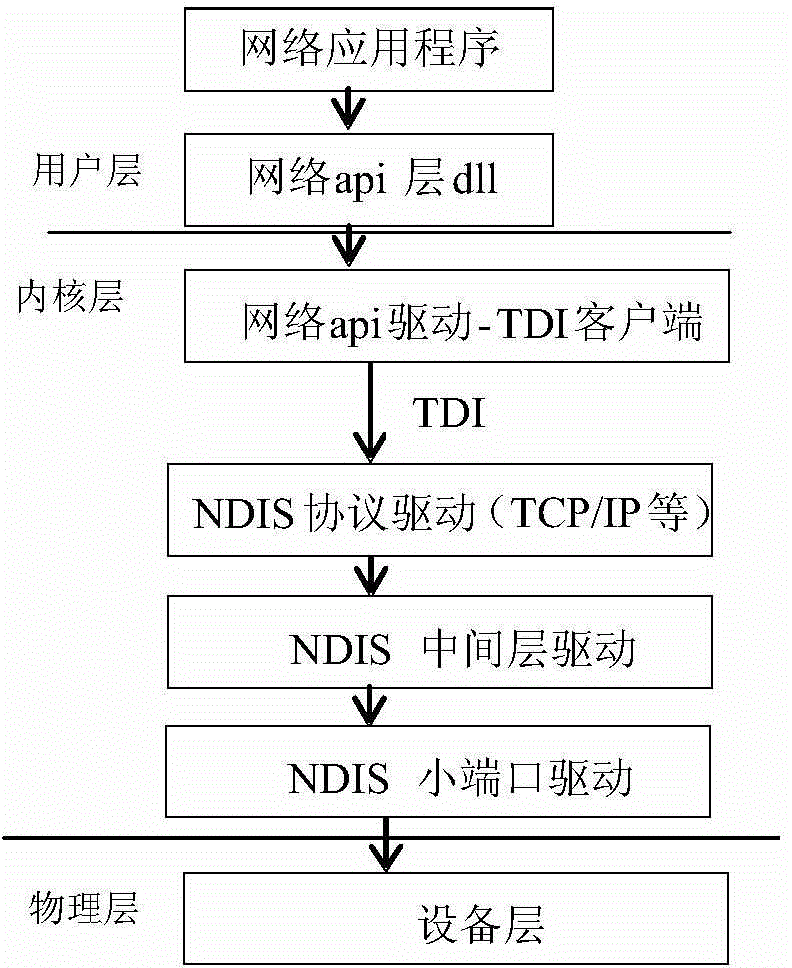
Secure execution of a computer program
ActiveUS7594111B2Avoid hijackingDigital data processing detailsUnauthorized memory use protectionControl flowApplication software
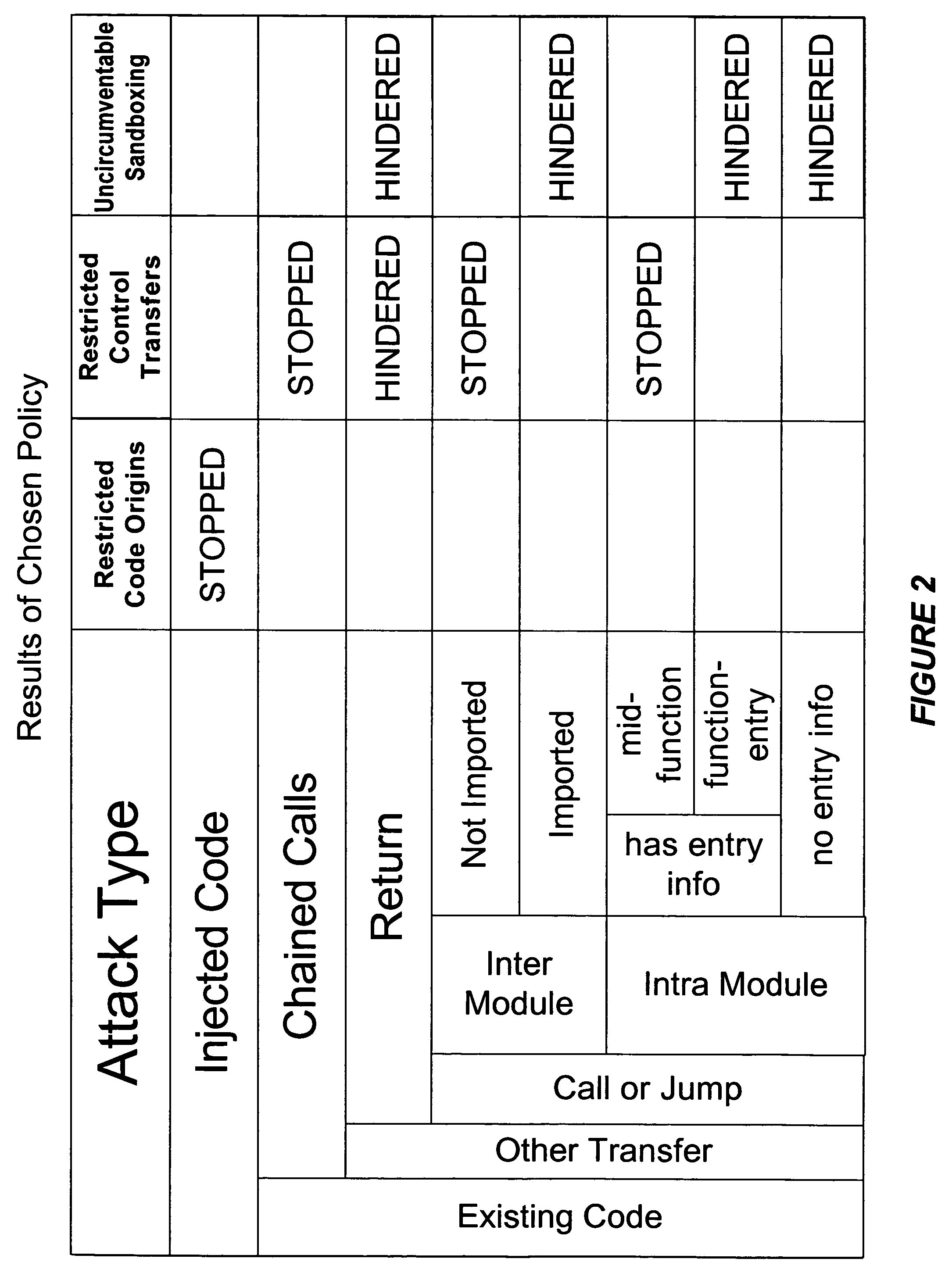
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
Secure execution of a computer program using a code cache
ActiveUS7603704B2Avoid hijackingMemory loss protectionError detection/correctionControl flowApplication software
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
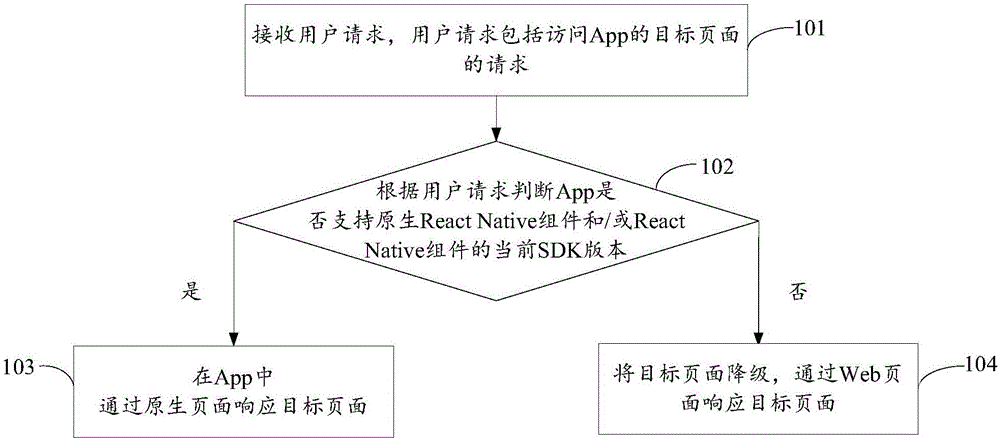
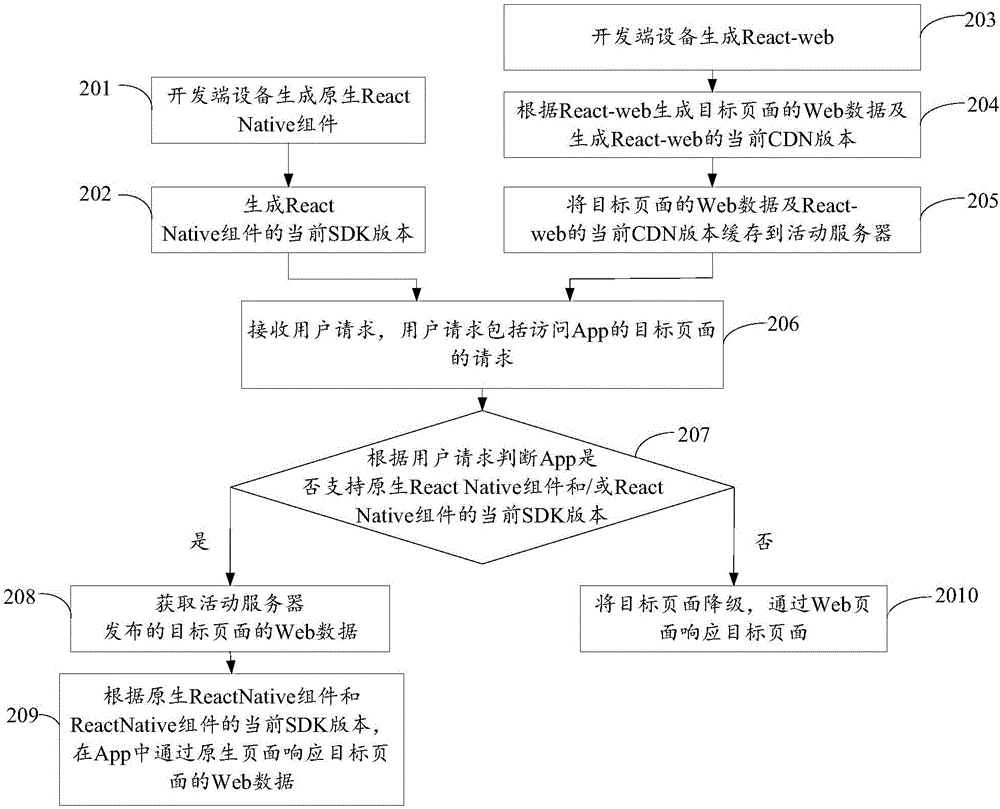
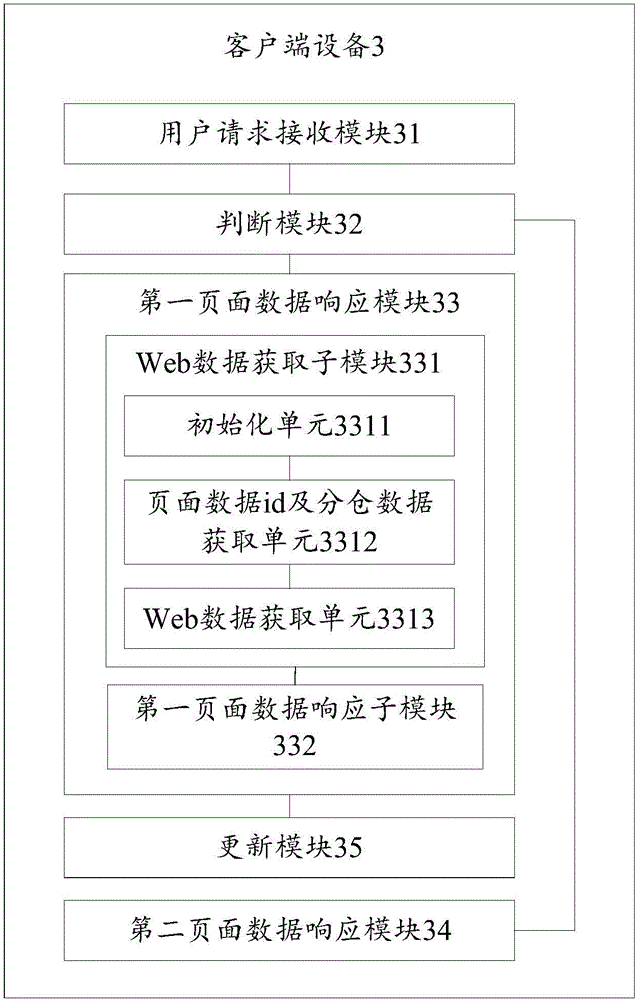
Page display method, equipment and system
ActiveCN106445583AImprove loading speedImprove performanceProgram loading/initiatingWeb pageNative page
The invention discloses a page display method, equipment and system, belonging to the field of computers. The method comprises the following steps of: receiving a user request including a request for accessing a target page of an App; according to the user request, judging whether the App supports a native React Native component and / or the current SDK edition of the React Native component or not; if so, responding to the target page through a native page at the App end; and otherwise, degrading the target page, and responding to the target page through a Web page. According to the page display method, equipment and system disclosed by the invention, when the App supports, Web data of the target page is loaded through the React Native component and / or the current SDK edition of the React Native component at the App end; therefore, the Web data of the target page can be displayed through the native page of the App; the target page access performance in the App can be improved; the user experience is improved; simultaneously, when the App does not support, the target page is degraded; the target page is responded through the Web page; and thus, the release efficiency of the target page is not influenced.
Owner:GUANGZHOU PINWEI SOFTWARE
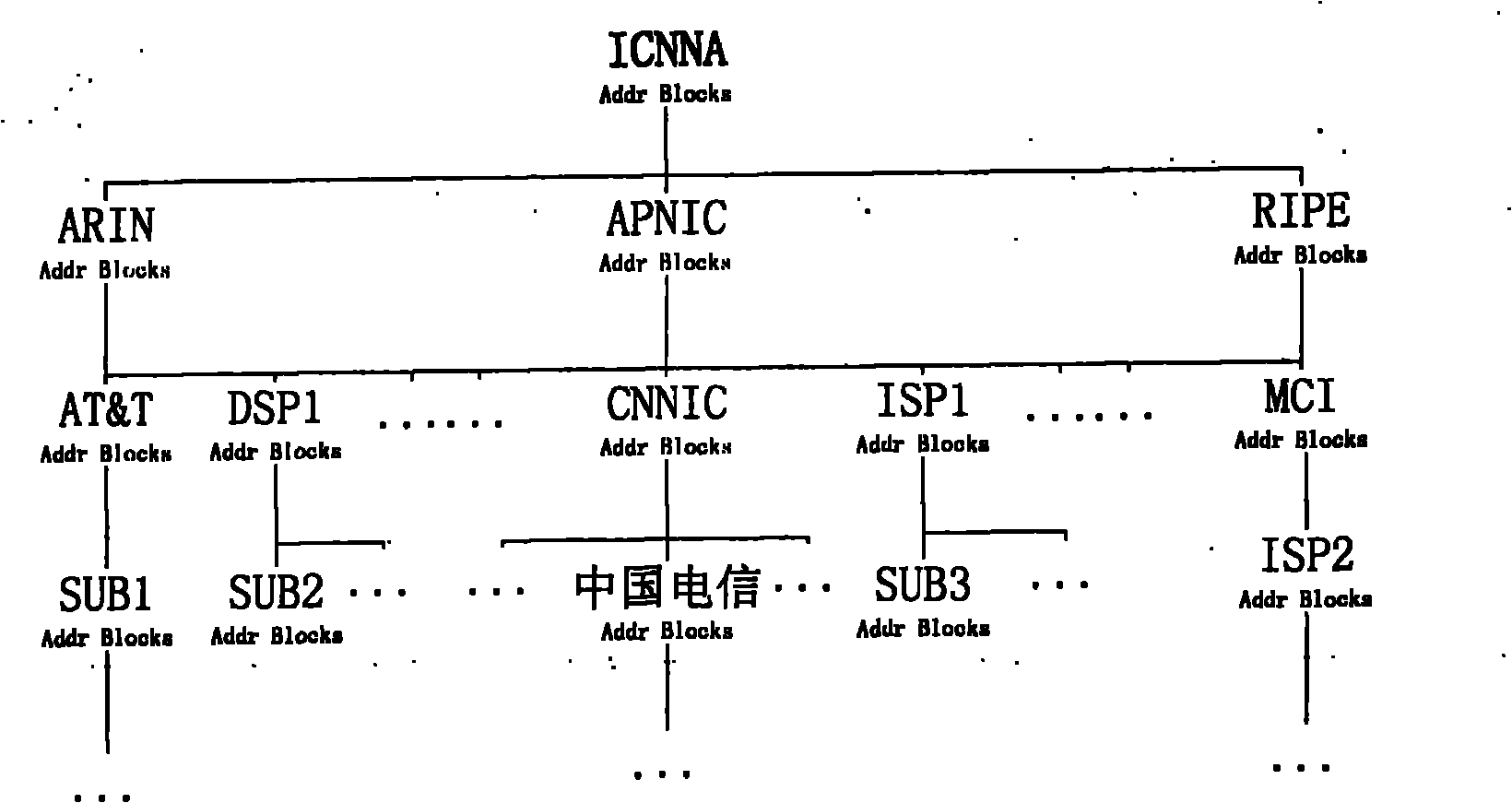
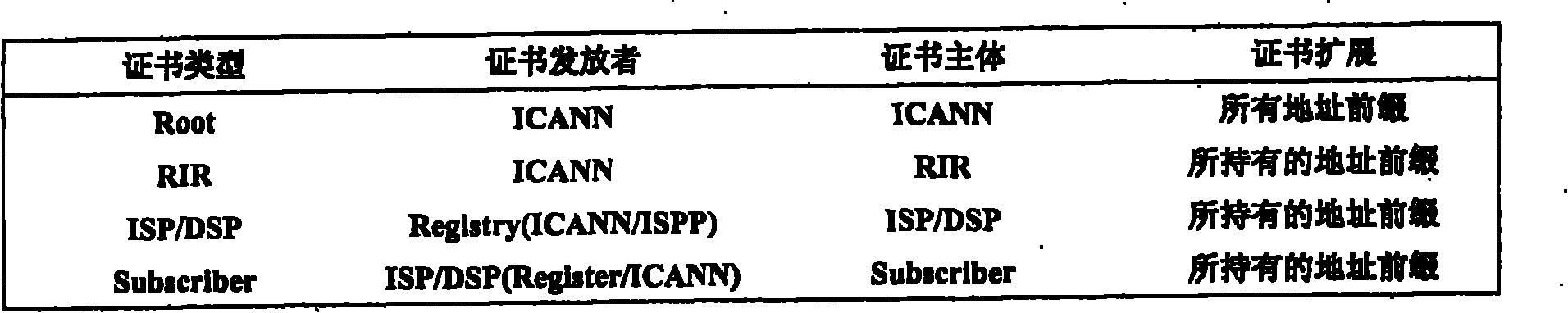
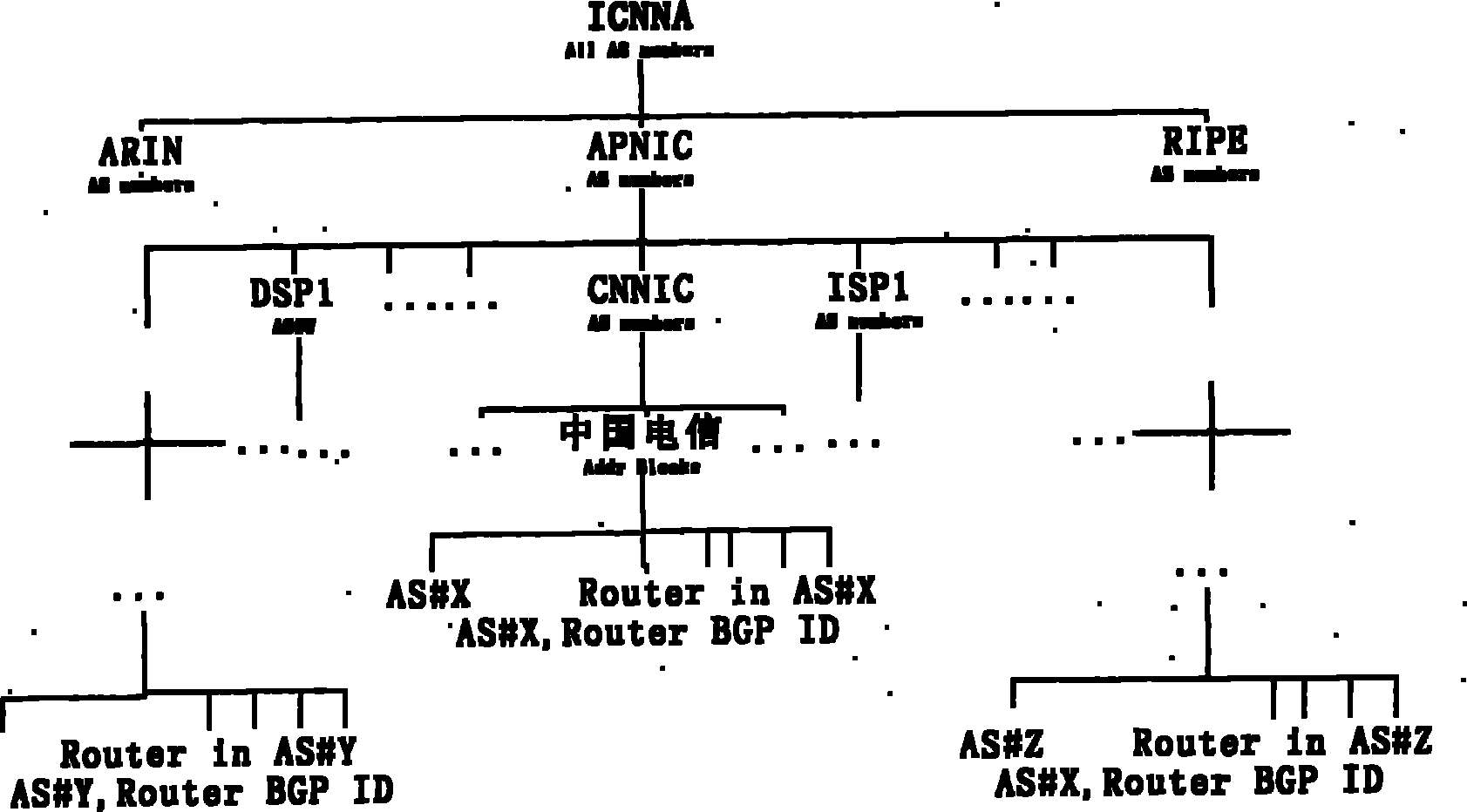
Method for defending border gateway protocol prefix hijacking attack
InactiveCN102158469AAllocation is accurateFree from hijackingPublic key for secure communicationBorder Gateway ProtocolAccreditation
The invention discloses a method for defending border gateway protocol prefix hijacking attack. Firstly, a layered dispatching system is structured according to IP (Internet Protocol) prefix and AS numbers to assign PKIs (Public Key Infrastructures), and two types of the PKIs based on the IP prefix and the AS number are assigned; the two types of PKIs respectively comprise IP prefix assignment certification and AS number assignment certification; the PKI is updated according to the assignment and revocation of the IP prefix and the AS number; the assignment of the PKI adopts the method that an ISP (Internet Service Provider) builds a assignment library; and when the IP prefix and announce messages of AS reach a router, verification is performed, a public key is validated firstly, then an assignment certificate and connectivity are validated, and the accreditation of the IP prefix or the AS number is validated. The method can protect an inter-domain routing system from the attacking of prefix hijacking, IP subnetwork prefix hijacking and particularly upper layer ISP prefix hijacking, and simultaneously can effectively prevent IP prefix AS path hijacking and IP subnetwork prefix AS path hijacking.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Domain name resolution method and device
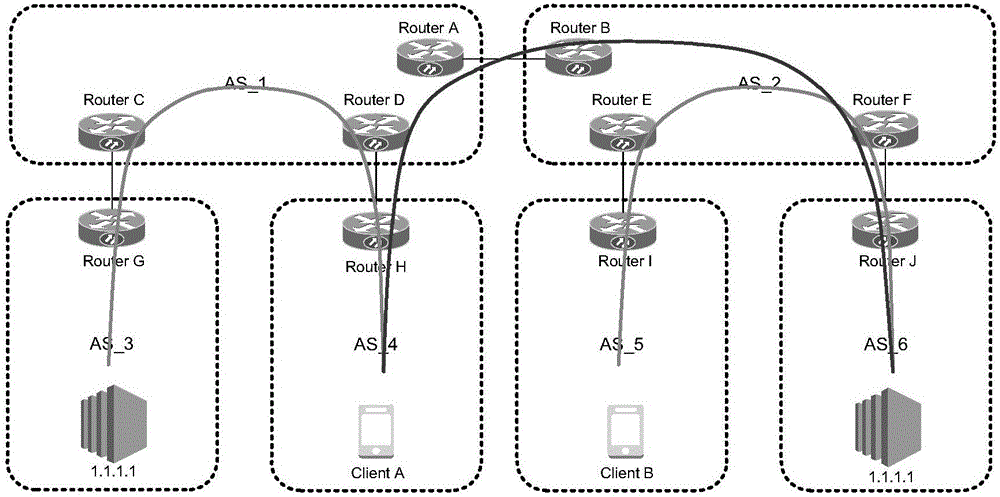
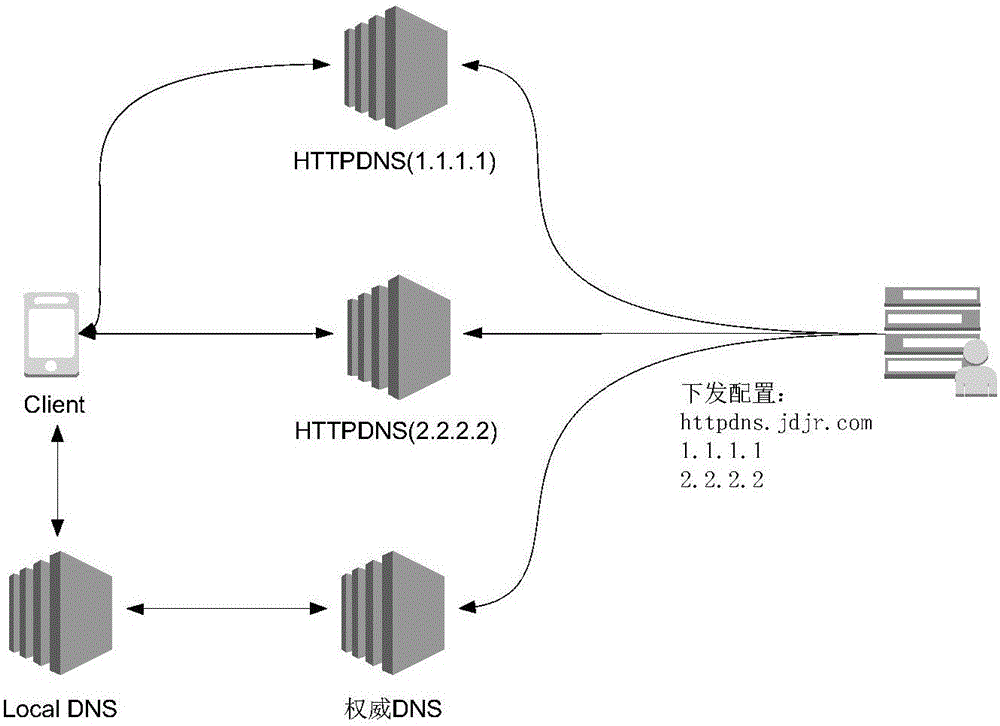
The invention discloses a domain name resolution method and a device. The method comprises the steps of configuring the address list of a hypertext transmission protocol domain name resolution server HTTPDNS capable of resolving domains to be resolved; determining the address of a target HTTPDNS from the said address; sending HTTP request having the domains to be resolved to the address of the target HTTPDNS to obtain the resolution result returned by the target HTTPDNS. The invention is advantageous in that domain resolution is conducted through the determined target HTTPDNS; based on the current safety mechanism of HTTPDNS, domain hijacking can be effectively prevented, and safety and efficiency of domain resolution can be increased.
Owner:JINGDONG TECH HLDG CO LTD
Domain name system DNS secondary recursion resolution method
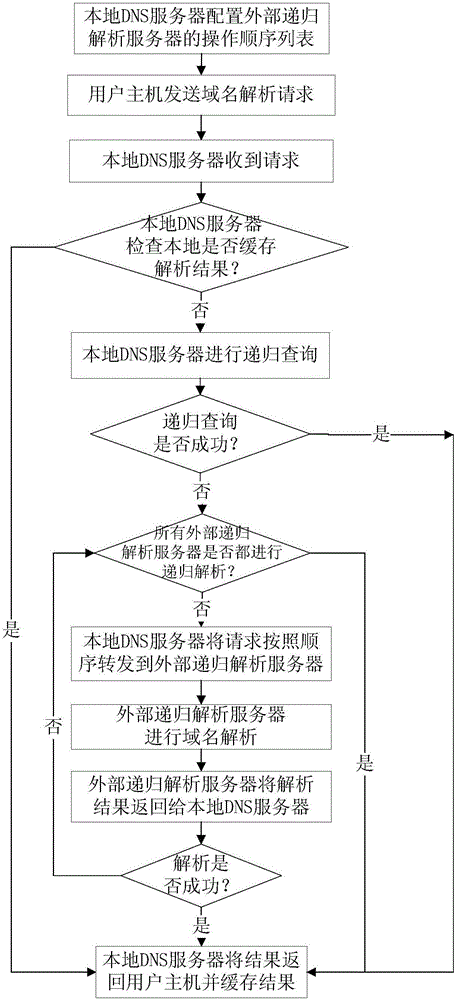
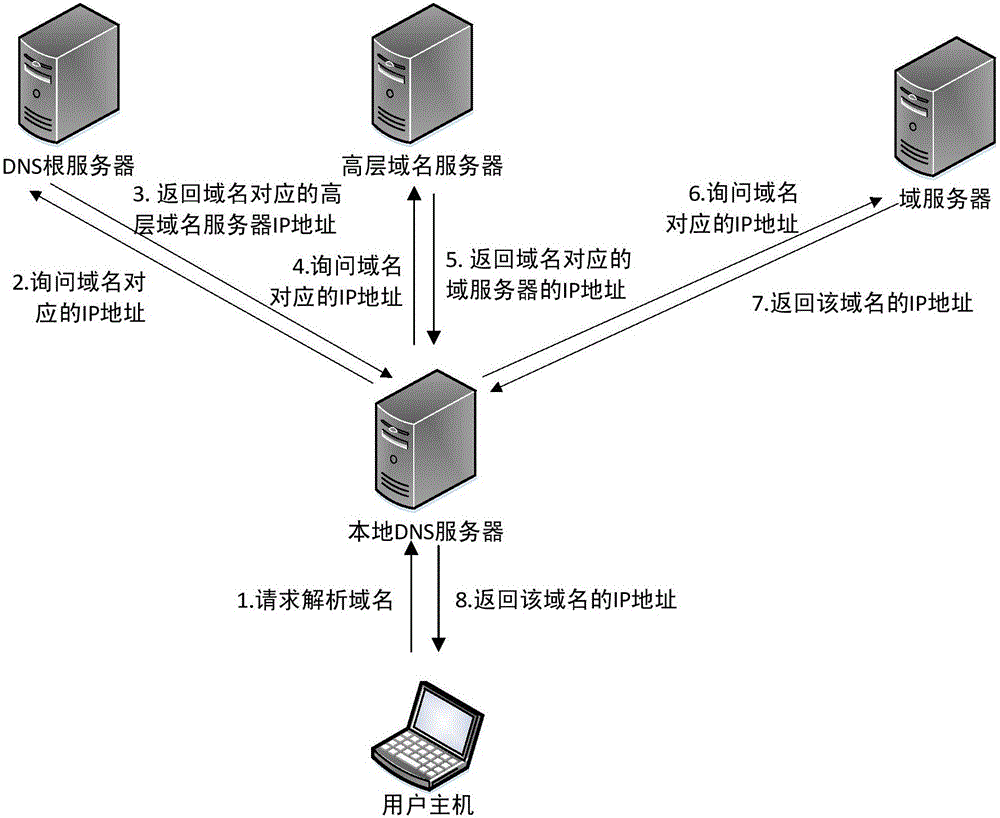
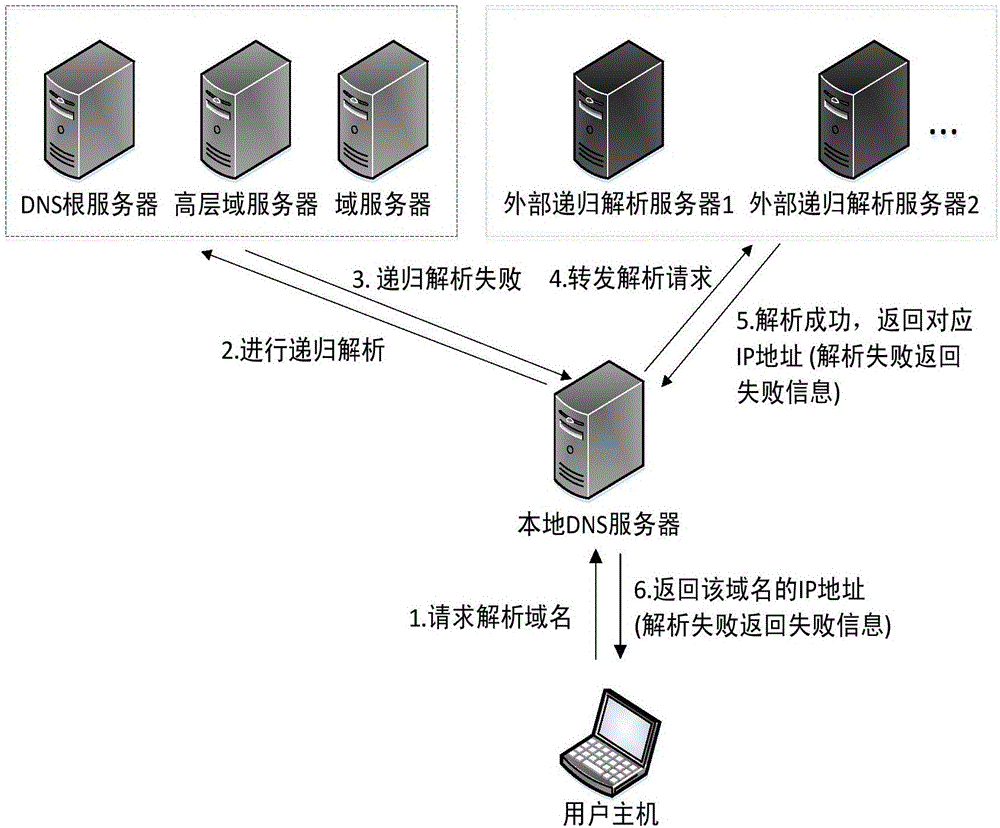
InactiveCN106790747AAvoid hijackingAvoid contamination riskTransmissionDomain nameDomain Name System
The invention discloses a domain name system DNS secondary recursion resolution method. After a local DNS server receives a domain name resolution request of a user host, whether a resolution result is cached locally or not is firstly checked, if the resolution result is cached locally, a process is directly responded and finished, if the resolution result is not cached locally, the local DNS server carries out recursion resolution, and the user host is prevented from being attacked by address pollution and domain name hijacking; only when the recursion resolution is failed, the domain name resolution request is forwarded to an external recursion resolution server for secondary resolution; and the local DNS server receives a resolution result returned by the external recursion resolution server, sends the resolution result to the user host and records a cache. The cache record is stored in the external recursion resolution server and positions of network nodes are different, so the condition that the user host cannot access a domain name due to a recursion failure resulting from an error occurring in authorized DNS configuration of a searched domain name is not liable to occur. The method provided by the invention is simple and convenient in operation steps, no hardware is increased, only functions of the local DNS server is modified, and the recursion resolution is backed up.
Owner:BEIJING WANGRUIDA TECH CO LTD
Multi-platform based unified account system
The invention relates to a multi-platform based unified account system. The multi-platform based unified account system comprises a user login process, a mailbox binding process, a user registration process, a mobile phone binding process and a mobile phone replacement process, and has a mobile phone registration request submitting function, a mobile phone short message obtaining function, a mailbox verifying mail sending function, a mailbox registration verifying address visiting function, a login network detecting function, a mobile phone replacing function, a firstly bound mailbox mail URL (Uniform Resource Locator) activating function, a bound mobile phone first submitting function and a RSA key data obtaining function. The multi-platform based unified account system can help a user to just use a set of accounts rather than using a large number of accounts in different websites; meanwhile, the purposes of safe, efficient and clear management, time conservation and use convenience for the user are realized.
Owner:SHANGHAI HODE INFORMATION TECH CO LTD
Network data access method and device and electronic equipment
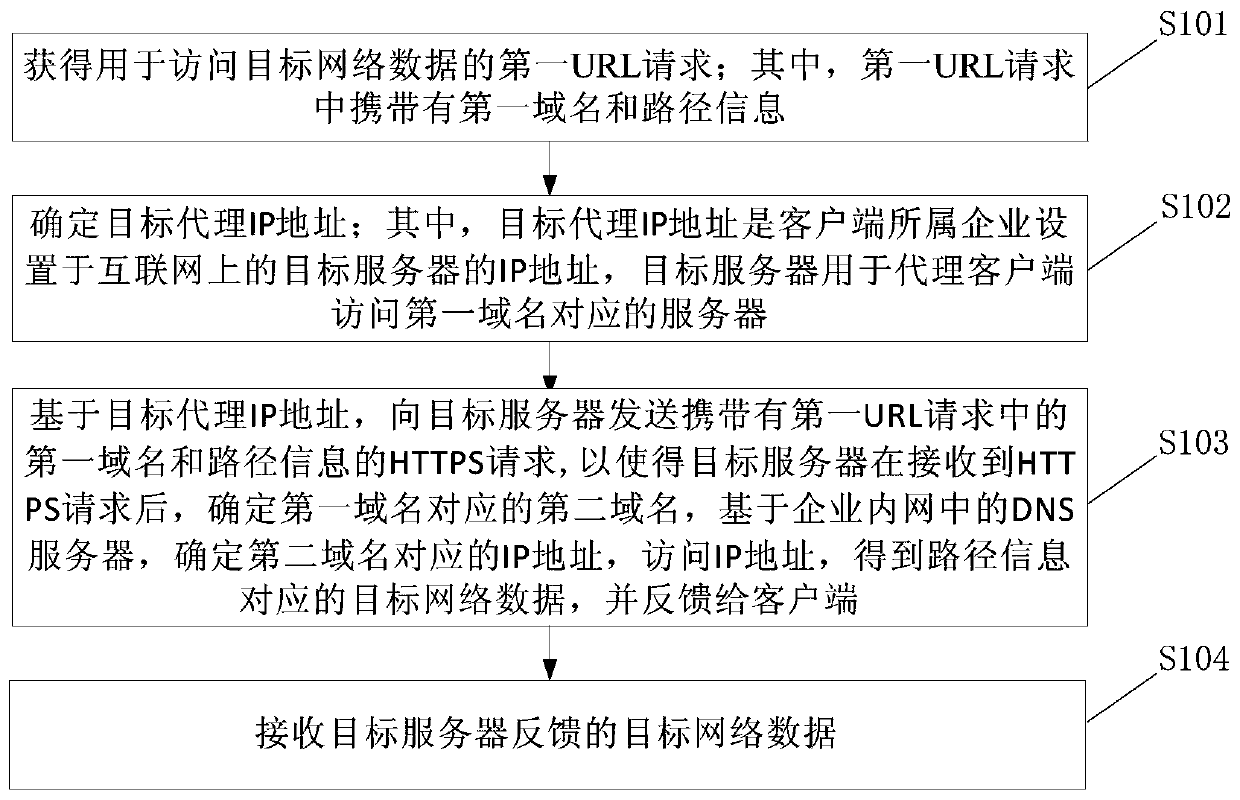
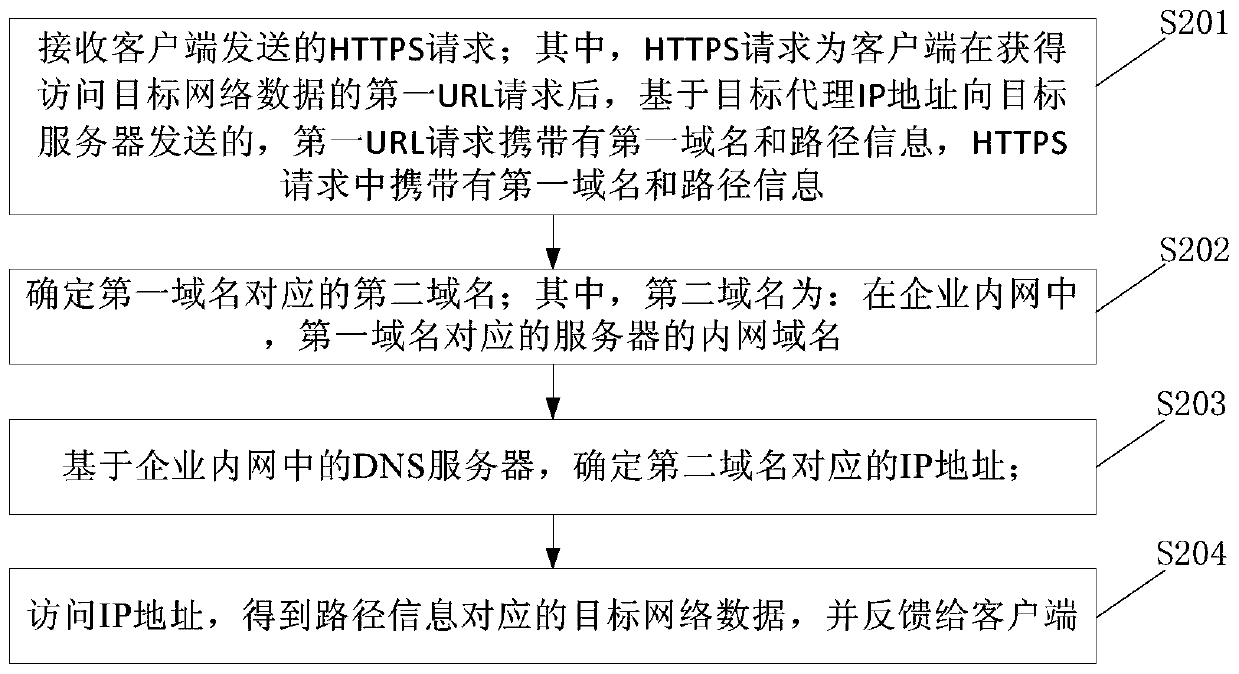
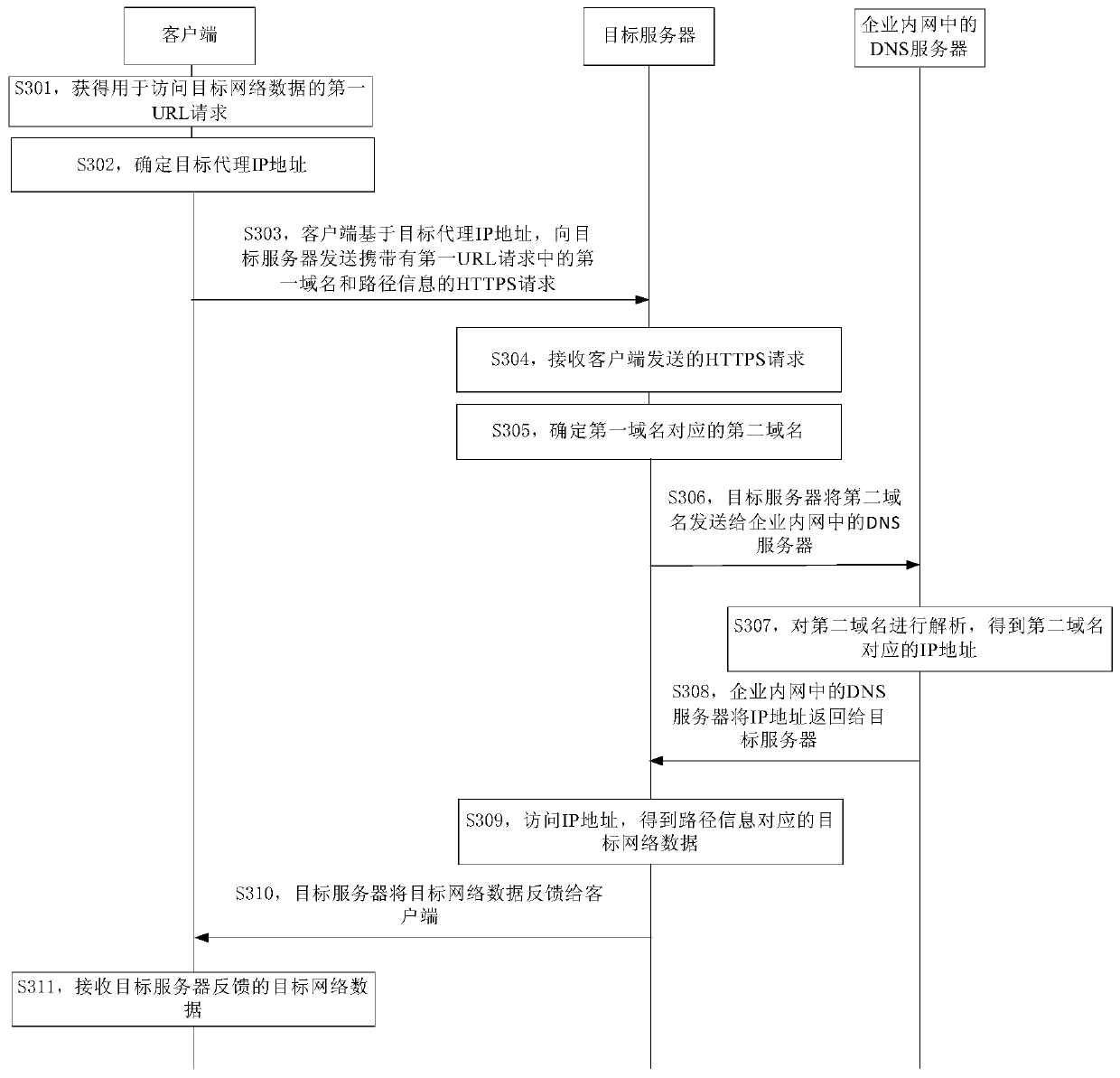
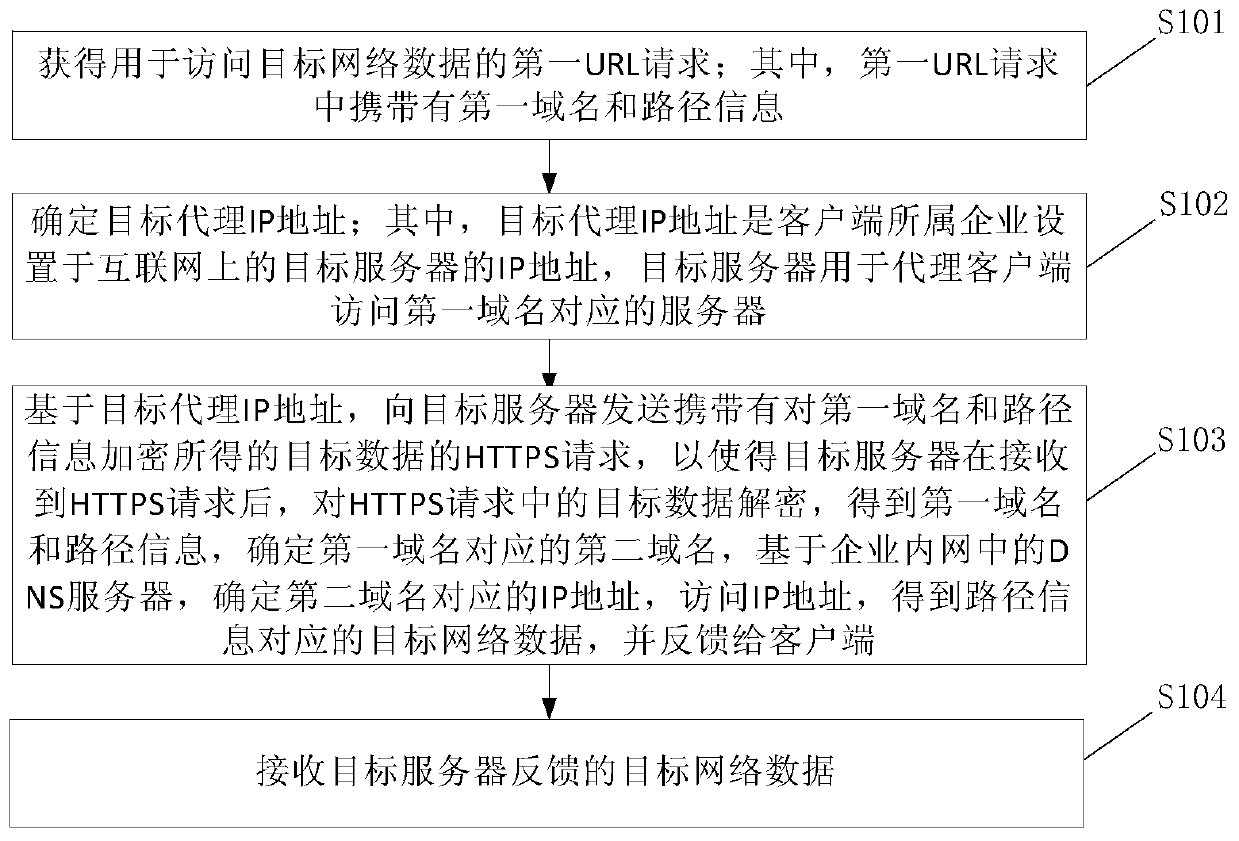
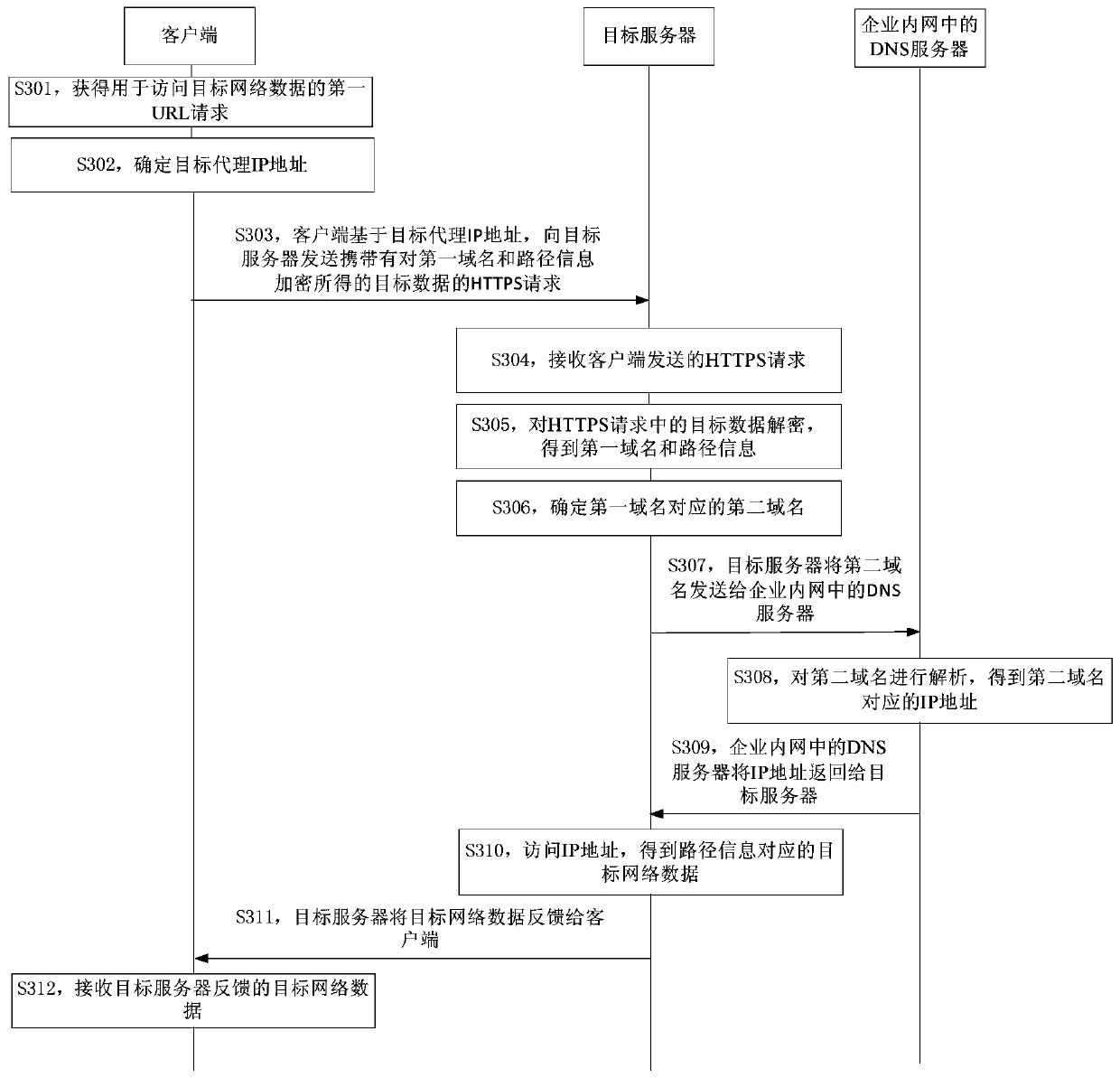
ActiveCN109787951AEfficient accessAvoid hijackingTransmissionWeb data retrieval using information identifiersClient-sideIp address
The embodiment of the invention provides a network data access method and device and electronic equipment. The method is applied to a client, and comprises the following steps: firstly, obtaining a first URL request for accessing target network data; Secondly, determining a target agent IP address; Then, based on a target agent IP address, sending an HTTPS request carrying a first domain name andpath information in the first URL request to a target server, after receiving the HTTPS request, the target server determines a second domain name corresponding to the first domain name, determines anIP address corresponding to the second domain name based on a domain name system DNS server in the enterprise intranet, accesses the IP address to obtain target network data corresponding to the pathinformation, and feeds back the target network data to the client; And finally, receiving target network data fed back by the target server. By applying the embodiment of the invention, HTTP hijacking and domain name resolution hijacking can be prevented, so that the purpose of accessing effective network data is achieved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
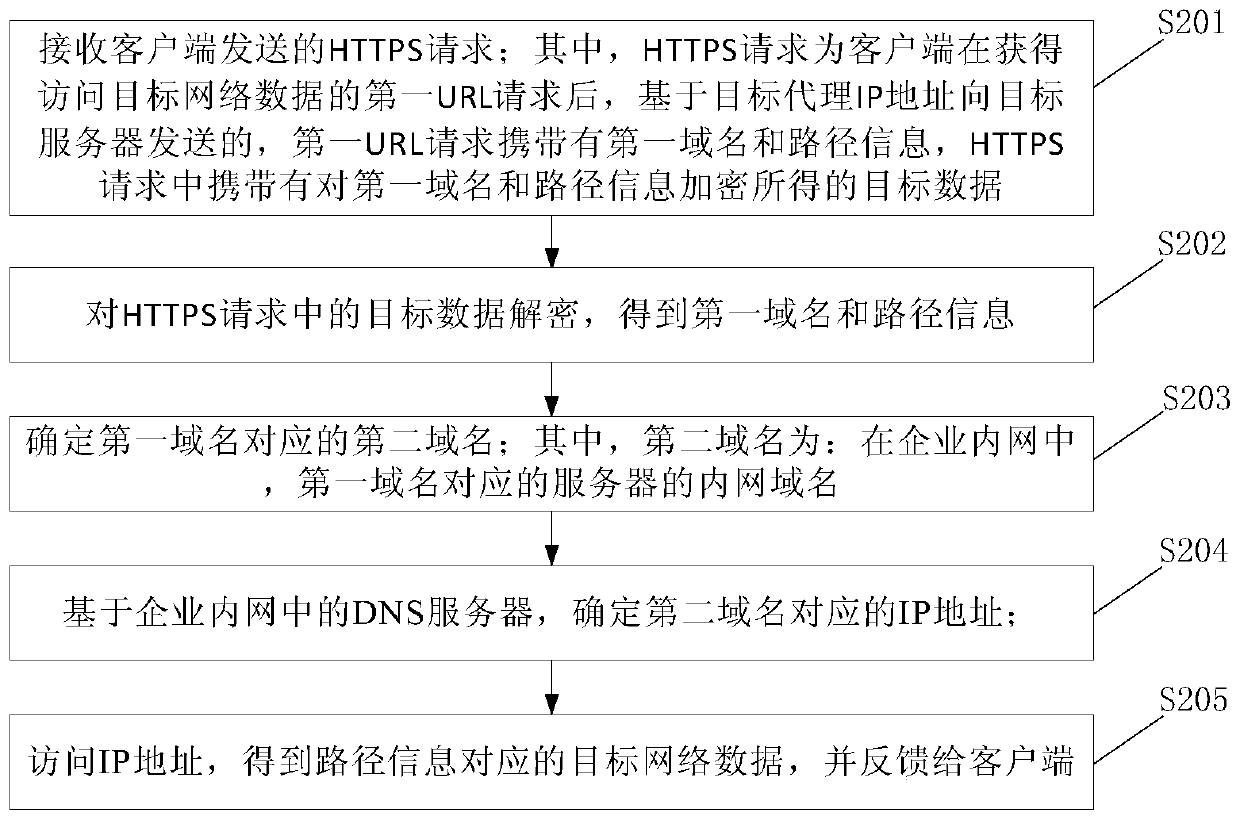
Network data access method and device and electronic equipment
The embodiment of the invention provides a network data access method and device and electronic equipment. The method is applied to a client, and comprises the following steps: firstly, obtaining a first URL request for accessing target network data; Secondly, determining a target agent IP address; Then, based on a target agent IP address, sending an HTTPS request carrying target data obtained byencrypting the first domain name and the path information to a target server, after the target server receives the HTTPS request, the target server sends the HTTPS request to the target server; decrypting the target data in the HTTPS request to obtain a first domain name and path information, determining a second domain name corresponding to the first domain name, determining an IP address corresponding to the second domain name based on a domain name system DNS server in an enterprise intranet, accessing the IP address to obtain target network data corresponding to the path information, and feeding back the target network data to the client; And finally, receiving target network data fed back by the target server.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Anti-injection method for browser, browser client and device
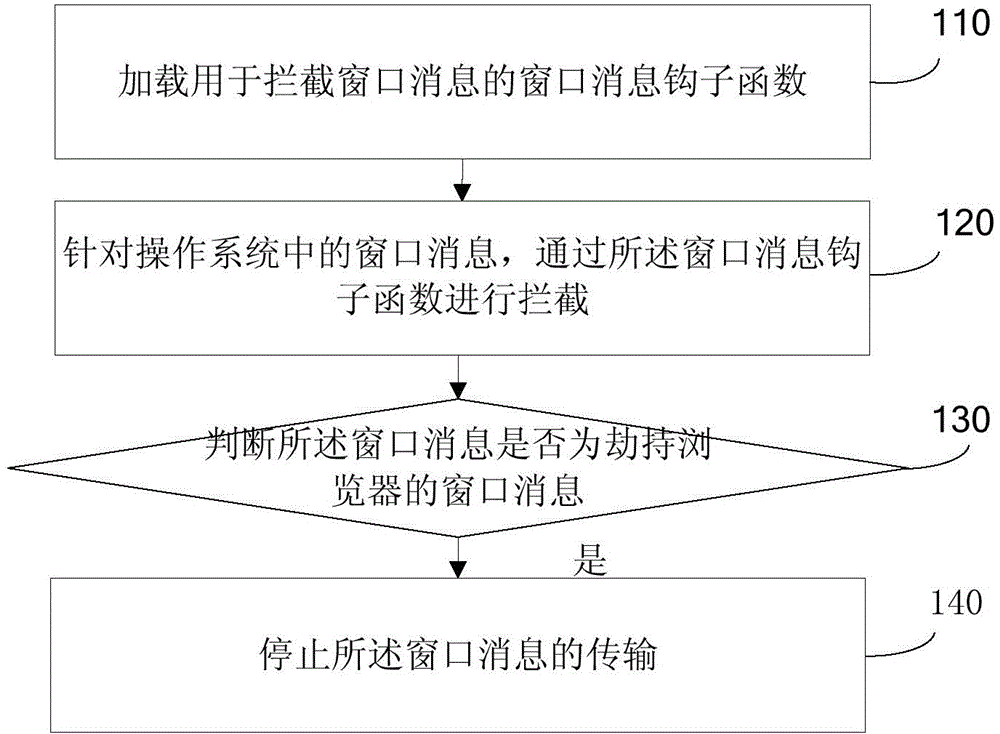
ActiveCN104539584ASolve insecurityImprove securitySecuring communicationComputer hardwareBrowser security
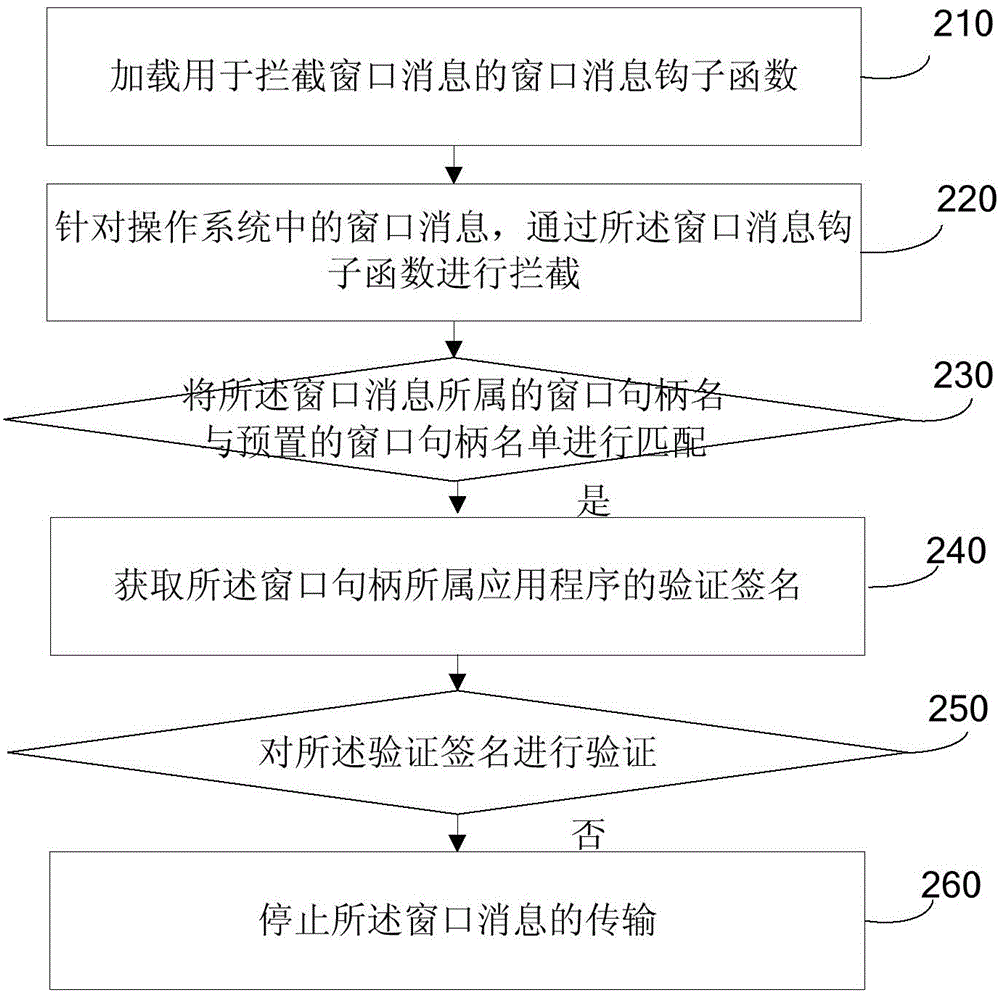
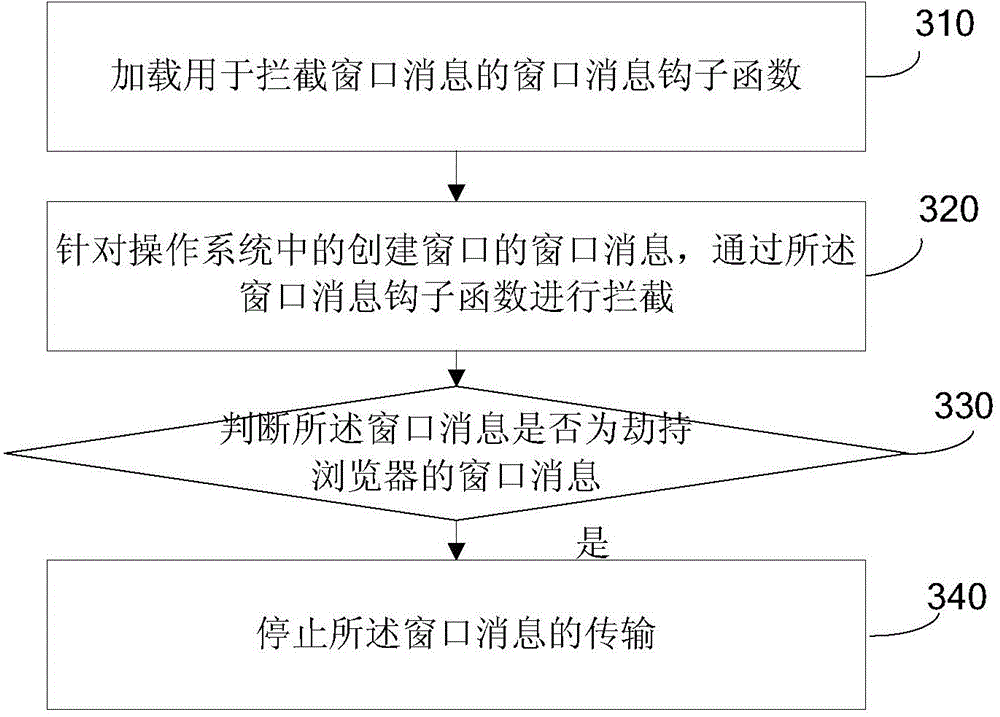
The invention discloses an anti-injection method for a browser, and relates to the technical field of browsers. The method comprises the following steps: loading a window message hook function for intercepting a window message; intercepting a window message in an operating system through the window message hook function; judging whether the window message is a browser-hijacking window message or not; and if the window message is the browser-hijacking window message, stopping transmission of the window message. According to the anti-injection method for the browser disclosed by the invention, the window message in the operating system can be intercepted by loading a global window message hook function, and a judgment on whether the window message is the browser-hijacking window message or not is made, so that the problem of unsafety of the browser due to the injection of dll into the browser through other applications is solved, and the beneficial effects of preventing the other applications from hijacking the browser by injecting unsafe dll into the browser and enhancing the safety of the browser are achieved.
Owner:BEIJING QIHOO TECH CO LTD +1
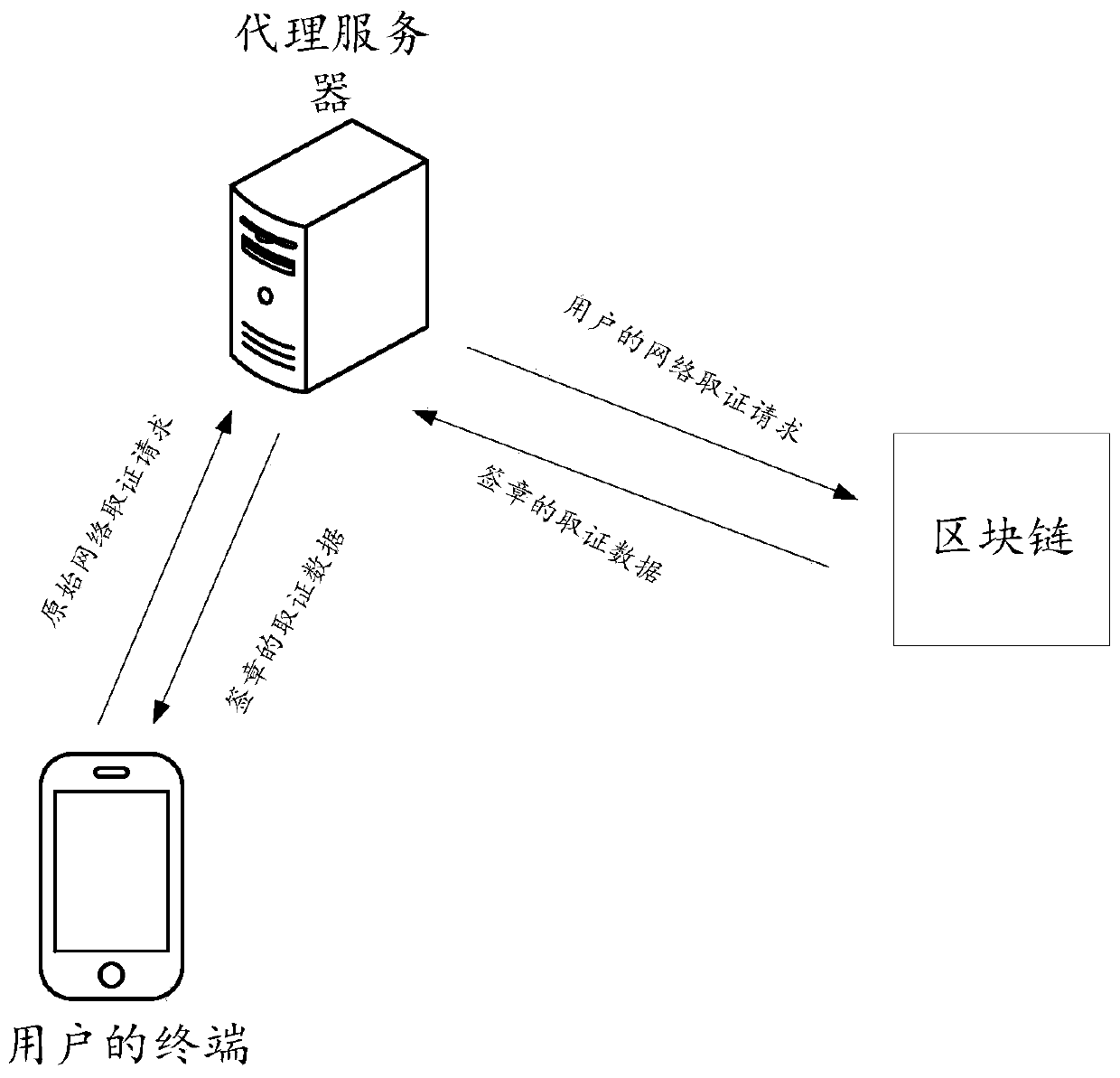
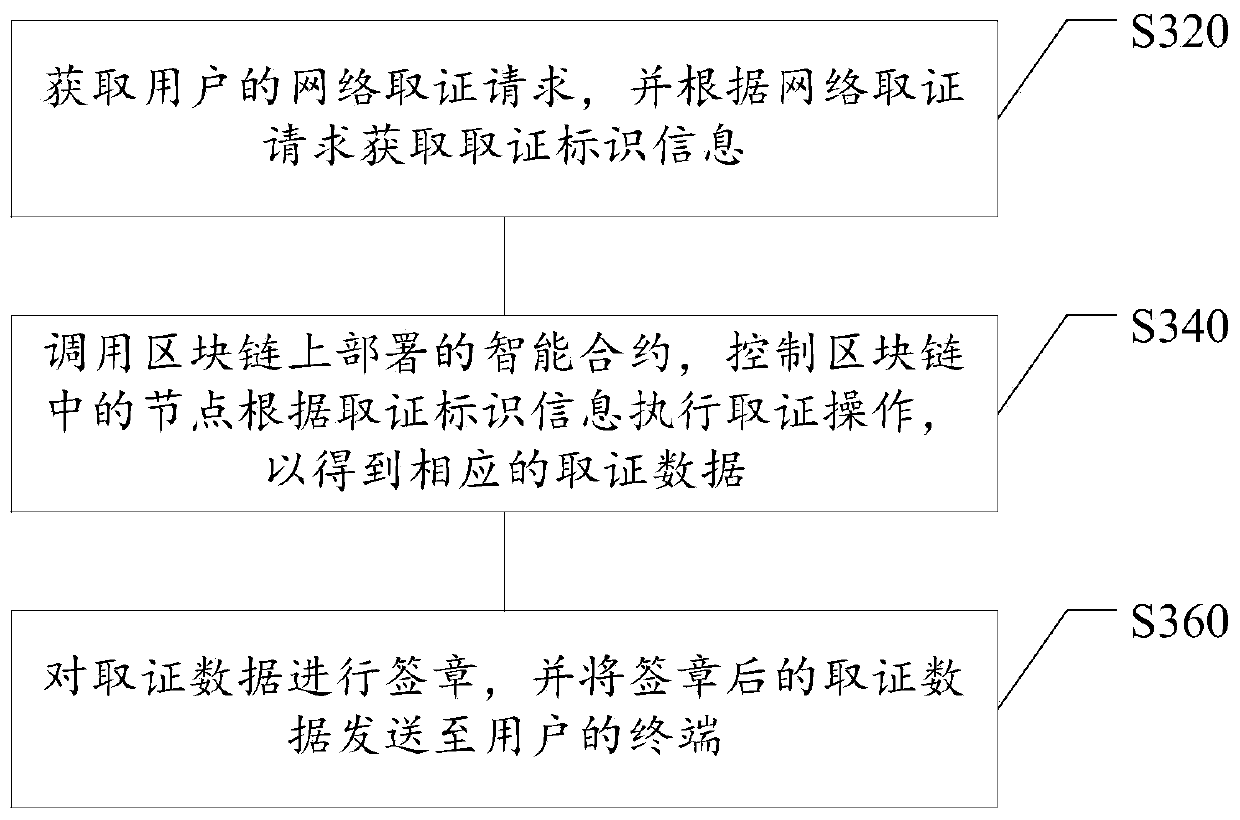
Evidence obtaining method and device based on block chain
PendingCN110009336AShorten the time for obtaining evidenceImprove forensics efficiencyPayment protocolsTransmissionData miningNetwork forensics
Owner:ADVANCED NEW TECH CO LTD
Credible electronic transaction method and transaction system
InactiveCN101482957APrevent man-in-the-middle attacksPrevent transaction sensitive information leakageTransmissionCommerceTransaction serviceAuthorization
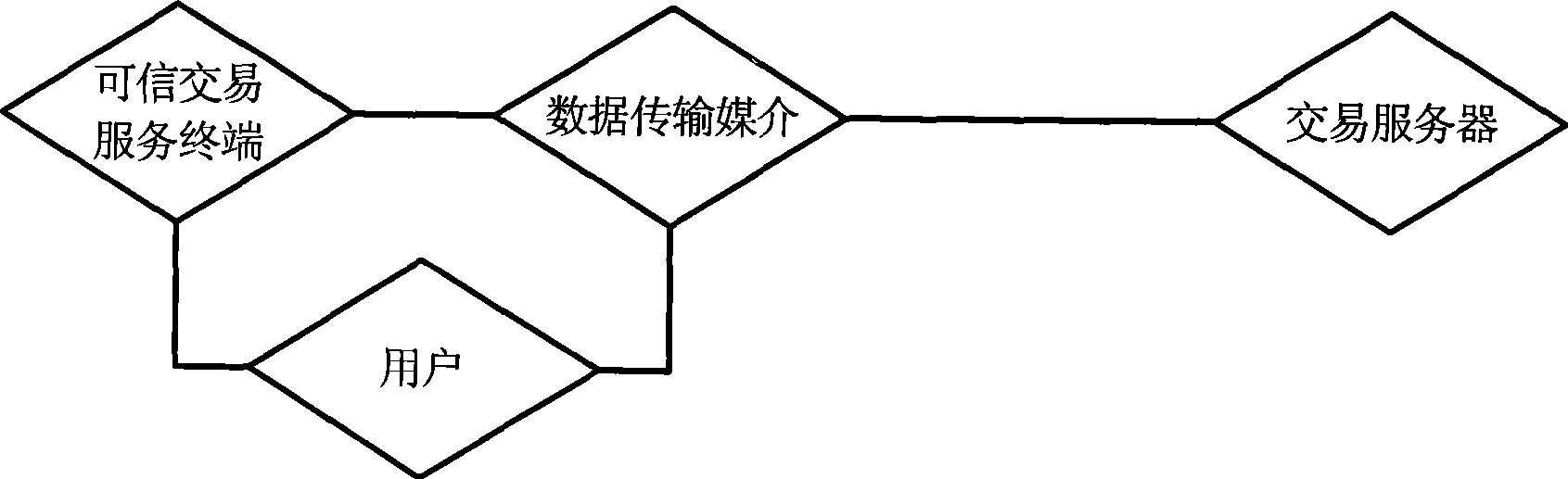
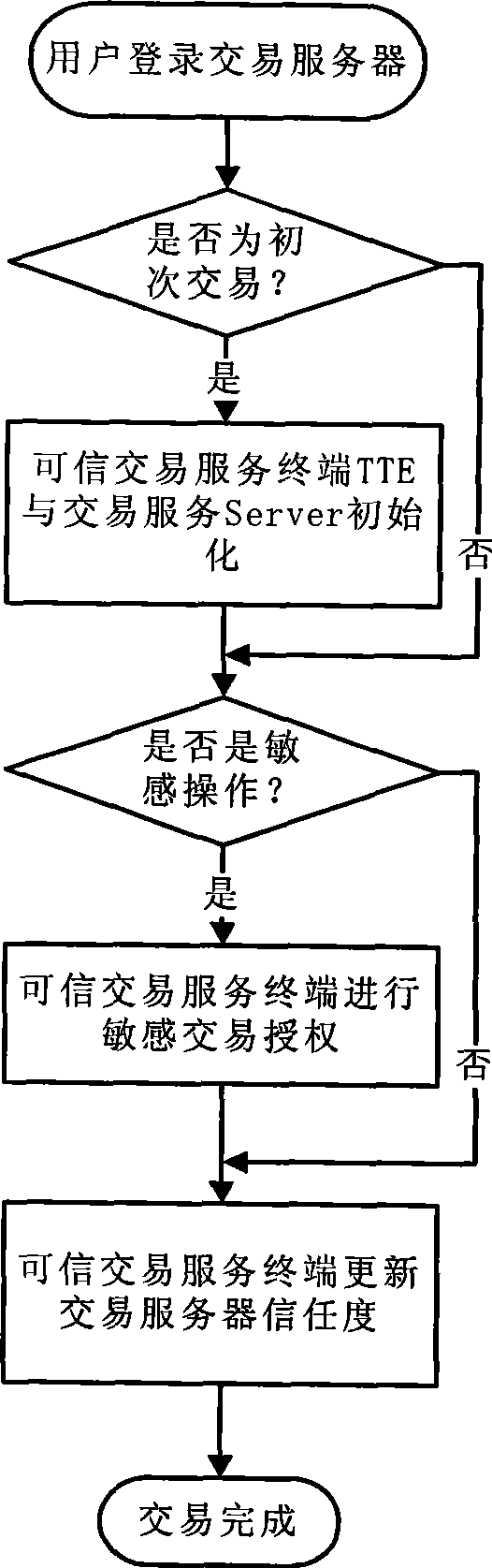
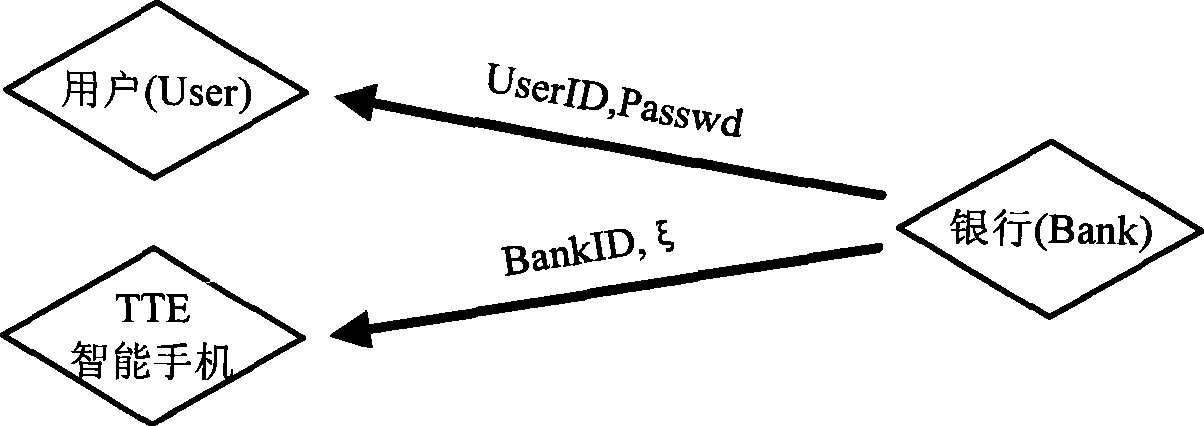
The invention discloses a credible electronic trading method and a trading system thereof, belonging to the technical field of information security. The inventive trading method comprises the following steps: a user logs in a trading server through an information transmission medium; initializing between a credible trading service terminal and a trading server through the information transmission medium, and setting up security connection; the credible trading service terminal displays trading information of the electronic trading in a way capable of being understood by the user, and the trading information is validated through the credible trading service terminal if the user confirms the trading information is right; the credible trading service terminal authorizes the trading server to trade through the information transmission medium. The inventive trading system comprises a personal computer and the credible trading service terminal. Compared with the prior art, the invention solves security problems of network angling, authorization hijack and the like existing in electronic payment and network trading through the credible trading service terminal, and related authentication and encryption protocols.
Owner:PEKING UNIV
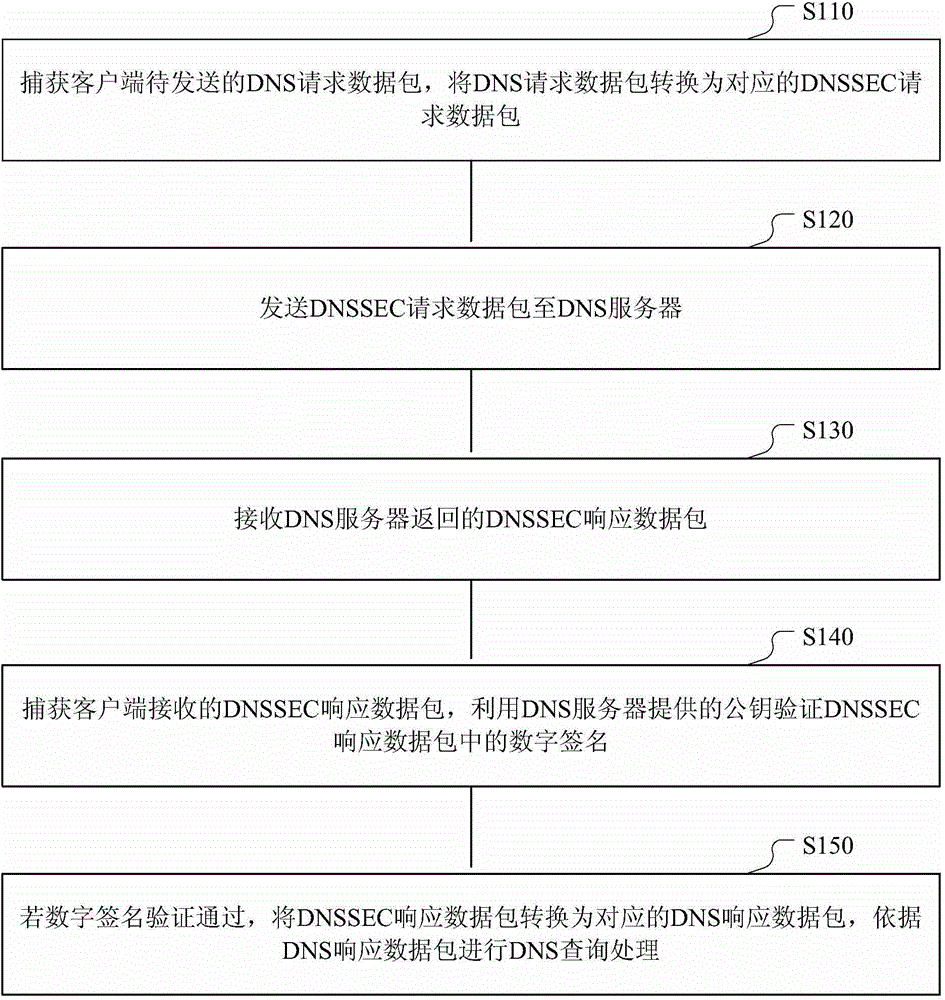
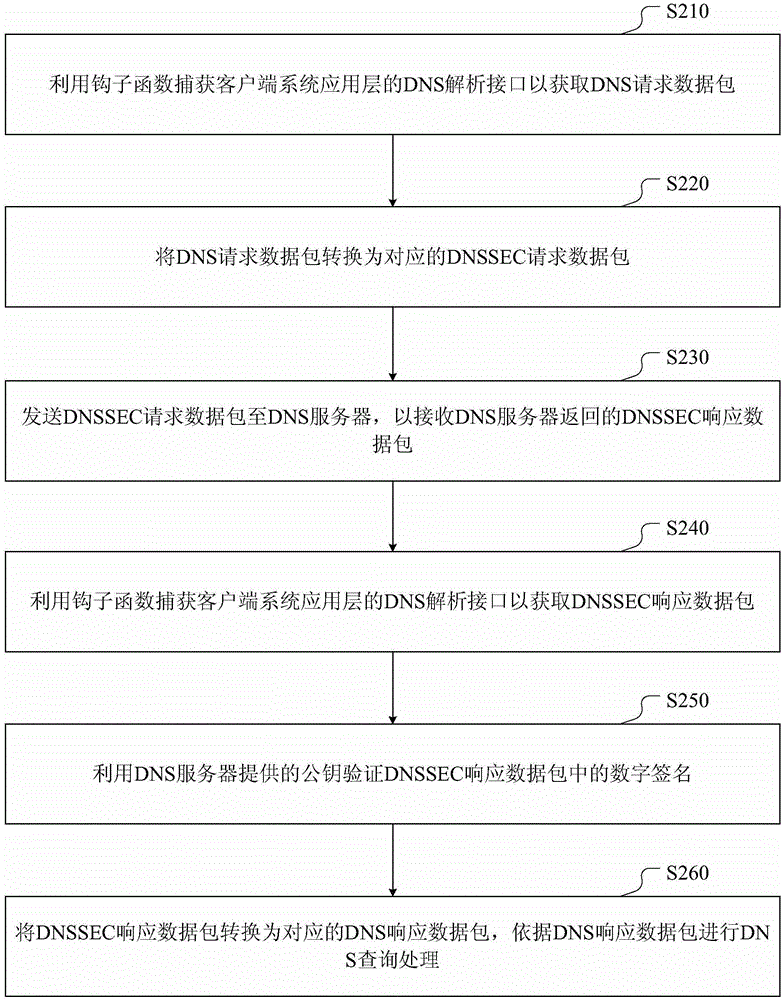
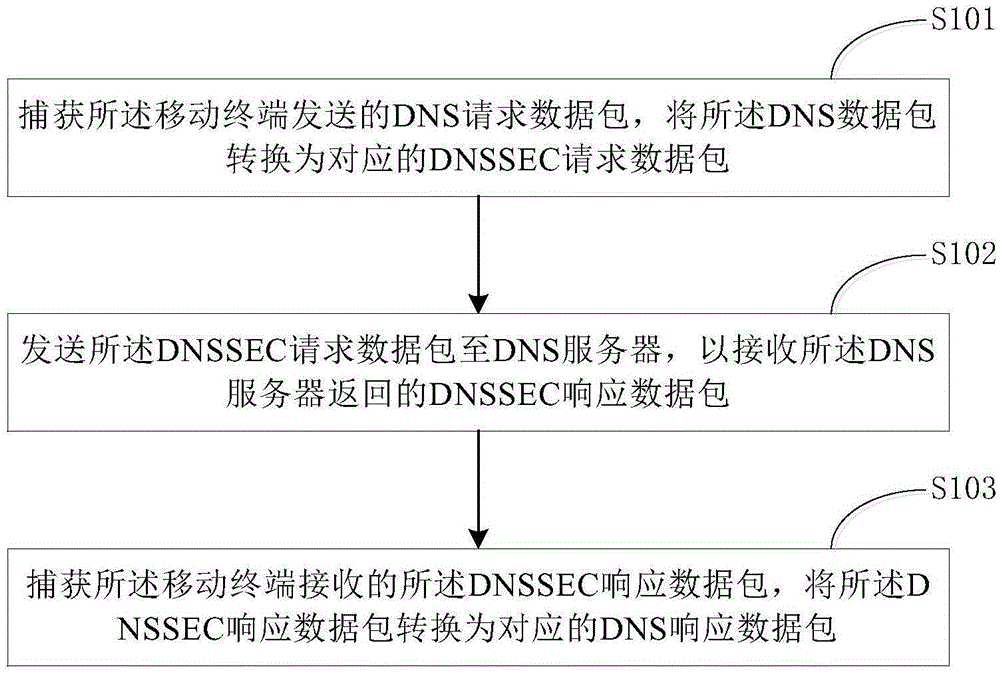
DNS (Domain Name Server) safety querying method and device
The invention discloses a DNS (Domain Name Server) safety querying method and device. The method comprises the steps of capturing a DNS request data packet to be sent by a client; converting the DNS request data packet into a corresponding DNSSEC (Domain Name System Security Extensions) request data packet; sending the DNSSEC request data to a DNS server to receive a DNSSEC response data packet returned by the DNS server; capturing the DNSSEC response data packet received by the client; verifying to a digital signature in the DNSSEC response data packet through a public key provided by the DNS server; if passing the digital signature passes the verification, converting the DNSSEC response data packet into the corresponding DNS response data packet; performing DNS querying processing according to the DNS response data packet. According to the scheme, the method has the advantages that the DNSSEC verification process is applied to the client, and a trust relationship between the client and the closest DNS server is configured, so as to form a complete trust chain with the DNS servers at each level; the truth and integrity of the data can be verified through the client, and thus the problems of DNS hijacking and cheating can be further avoided.
Owner:三六零数字安全科技集团有限公司
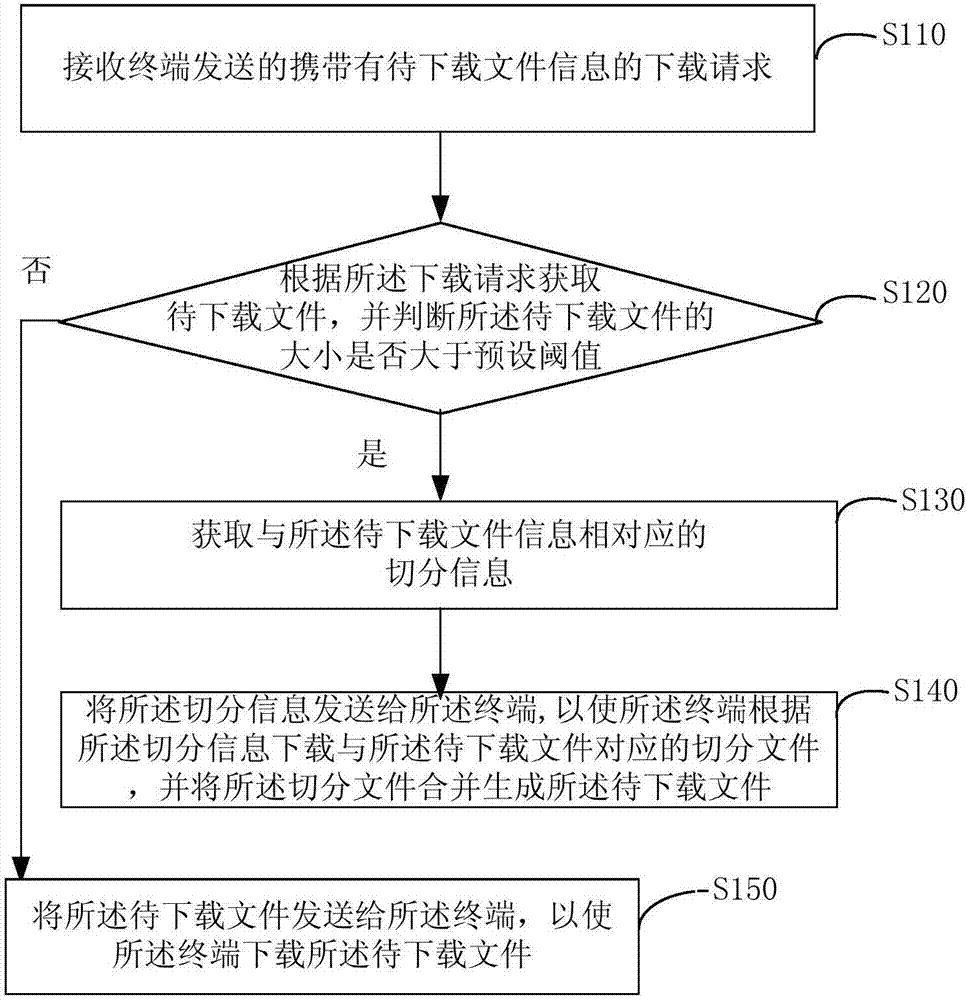
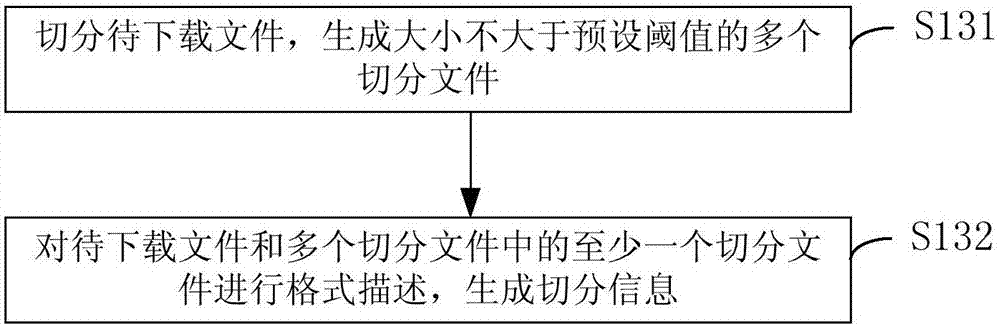
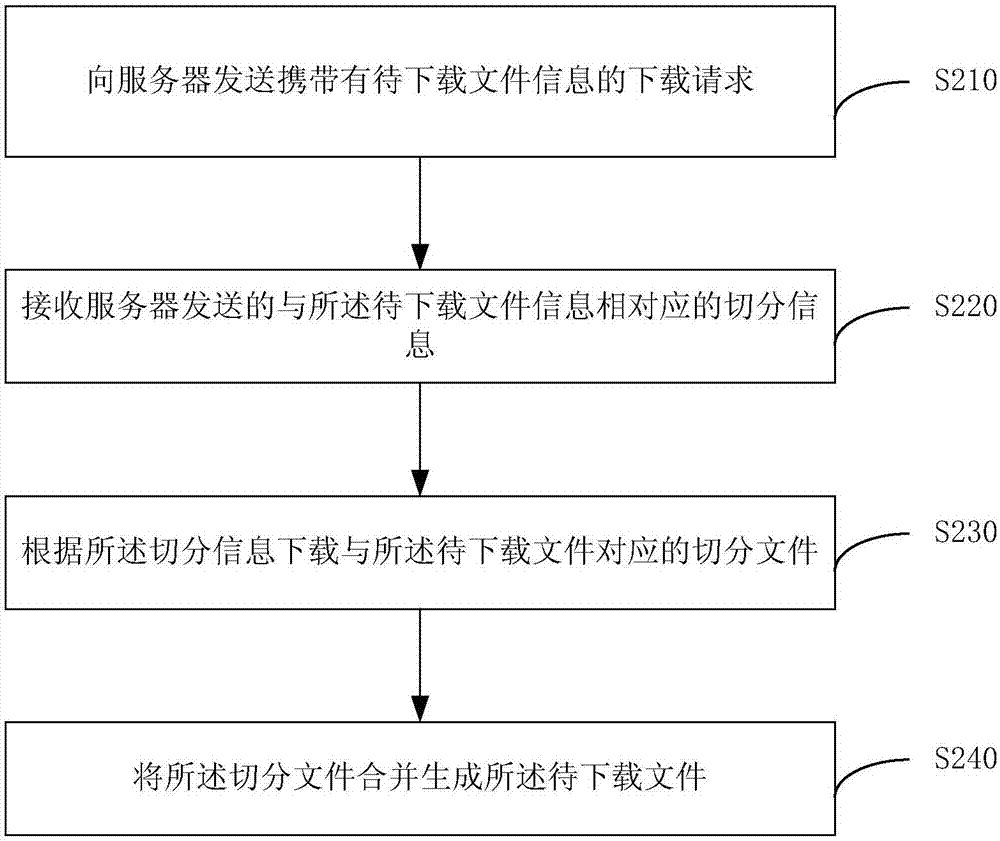
File downloading method, device, server and terminal
The embodiment of the invention provides a file downloading method, a file downloading device, a server and a terminal. The file downloading method is applied to the server. The method comprises the following steps of receiving a downloading request which is sent by a terminal and carries the information of a to-be-downloaded file; acquiring the to-be-downloaded file according to the downloading request, and judging whether the size of the to-be-downloaded file is larger than a preset threshold value or not; if the size of the to-be-downloaded file is judged to be larger than the preset threshold value, acquiring the segmentation information corresponding to the information of the to-be-downloaded file; sending the segmentation information to the terminal to enable the terminal to segment the to-be-downloaded file according to the segmentation information; and merging segmented files to generate the to-be-downloaded file. According to the technical scheme of the invention, a user is prevented effectively from being hijacked by an operator when the user downloads the file. Therefore, the file downloading success rate is improved, and the user experience is improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
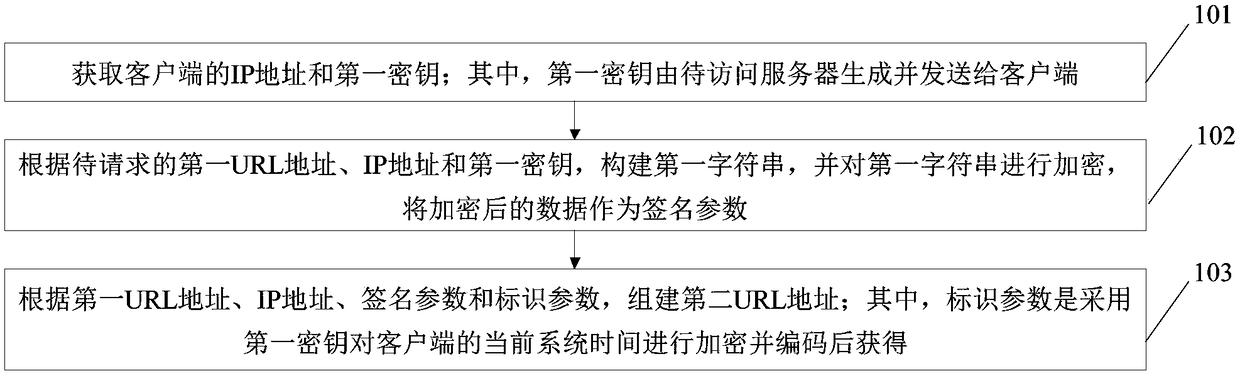
The invention relates to a method for establishing and verifying a live broadcast link address and a corresponding device
InactiveCN109040079AImprove the effectiveness of anti-theftImprove timelinessTransmissionValidation methodsIp address
The invention discloses a method for establishing and verifying a live broadcast link address and a corresponding device. The method comprises the following steps: obtaining an IP address of a clientend and a first key, wherein the first key is generated by the server to be accessed and sent to the client; forming a first string according to a first URL address, an IP address and a first key to be requested, encrypting the first string, the encrypted data being taken as a signature parameter; forming a second URL address according to the first URL address, the IP address, the signature parameter and the identification parameter, wherein the identification parameter is obtained by encrypting and encoding the current system time of the client using the first key. The second URL address hasthe capability of anti-theft chain. Compared with the existing anti-theft chain technology, the technical scheme of the invention is more suitable for network live broadcast, so that the anti-theft chain has timeliness, hijacking and tampering are prevented, and the anti-theft effectiveness of the live link address is improved.
Owner:广东省南方数字电视无线传播有限公司
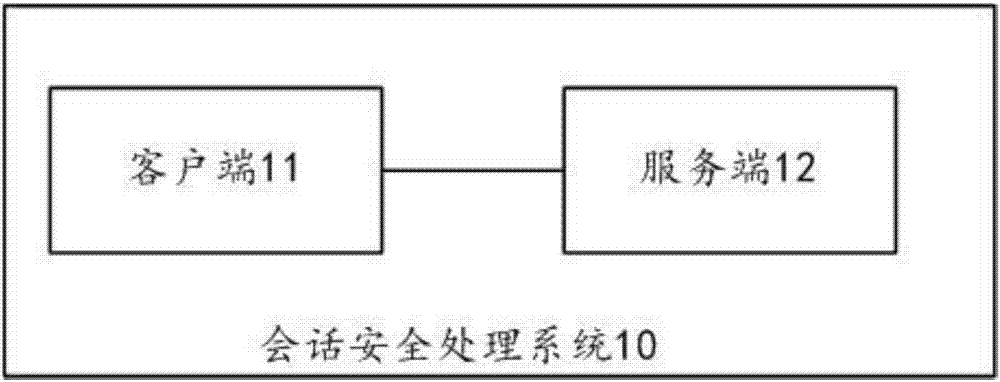
Session security processing system, equipment, device, and method
The invention discloses a session security processing system, equipment, device, and method. The session security processing system comprises a client and a server; the client respectively encrypts user authentication information and a generated random key according to a set algorithm and a locally stored public key certificate at the session authentication stage, generates ciphertext information that contains the user authentication information and the random key, sends the ciphertext information to the server, receives encrypted session information transmitted by the server containing a session identifier and a session key, and decrypts the session information to acquire the session identifier and the session key; and the client encrypts transmitted data according to the session key in the received session information at the session communication stage, and generates a ciphertext data packet containing the session identifier and the transmitted data and transmits the ciphertext data packet to the server. The scheme provided by the invention can improve the session security.
Owner:ALIBABA (CHINA) CO LTD
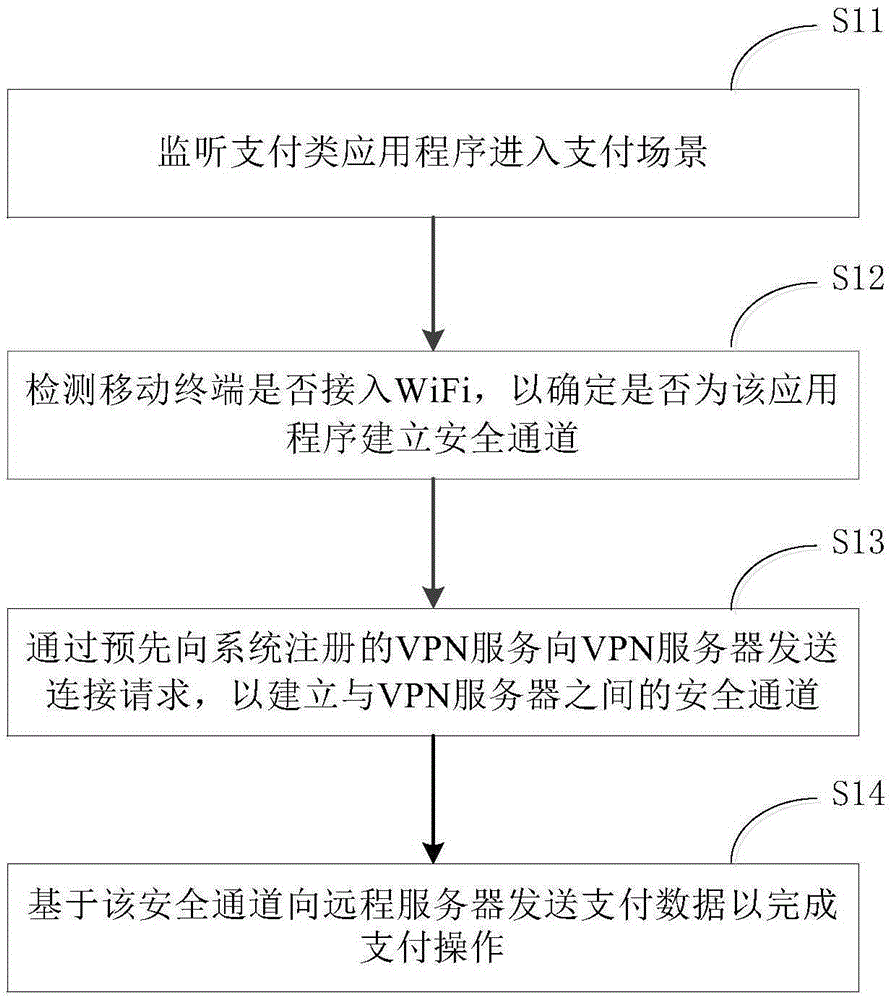
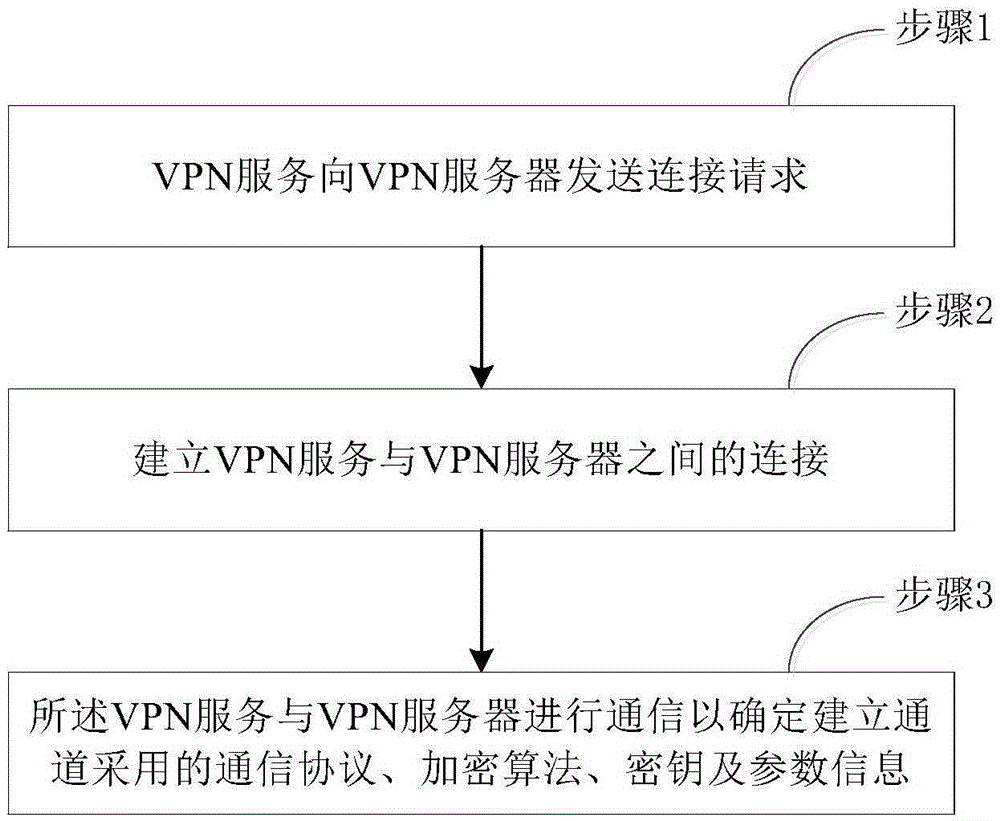
Security payment method and apparatus for mobile terminal payment application
InactiveCN106888184AEnsure safetyPrevent theftTransmissionProtocol authorisationPaymentComputer terminal
The invention provides a security payment method for a mobile terminal payment application. The method includes steps: monitoring the entrance of the payment application into a payment scenario; detecting whether a mobile terminal is accessed to WiFi to determine whether a security channel is established for the application; sending a connection request to a VPN server through a VPN service pre-registered at a system to establish the security channel with the VPN server; and sending payment data to a remote server based on the security channel to accomplish payment operation. Besides, the invention also provides a security payment apparatus for the mobile terminal payment application, and the apparatus comprises a monitoring module, a security channel establishing module, and a payment module. According to the method or apparatus, the security channel is established, security interaction between the payment application program and the server is realized, the security of user information in a transmission process is guaranteed, and privacy data of users is prevented from being stolen.
Owner:BEIJING QIHOO TECH CO LTD +1
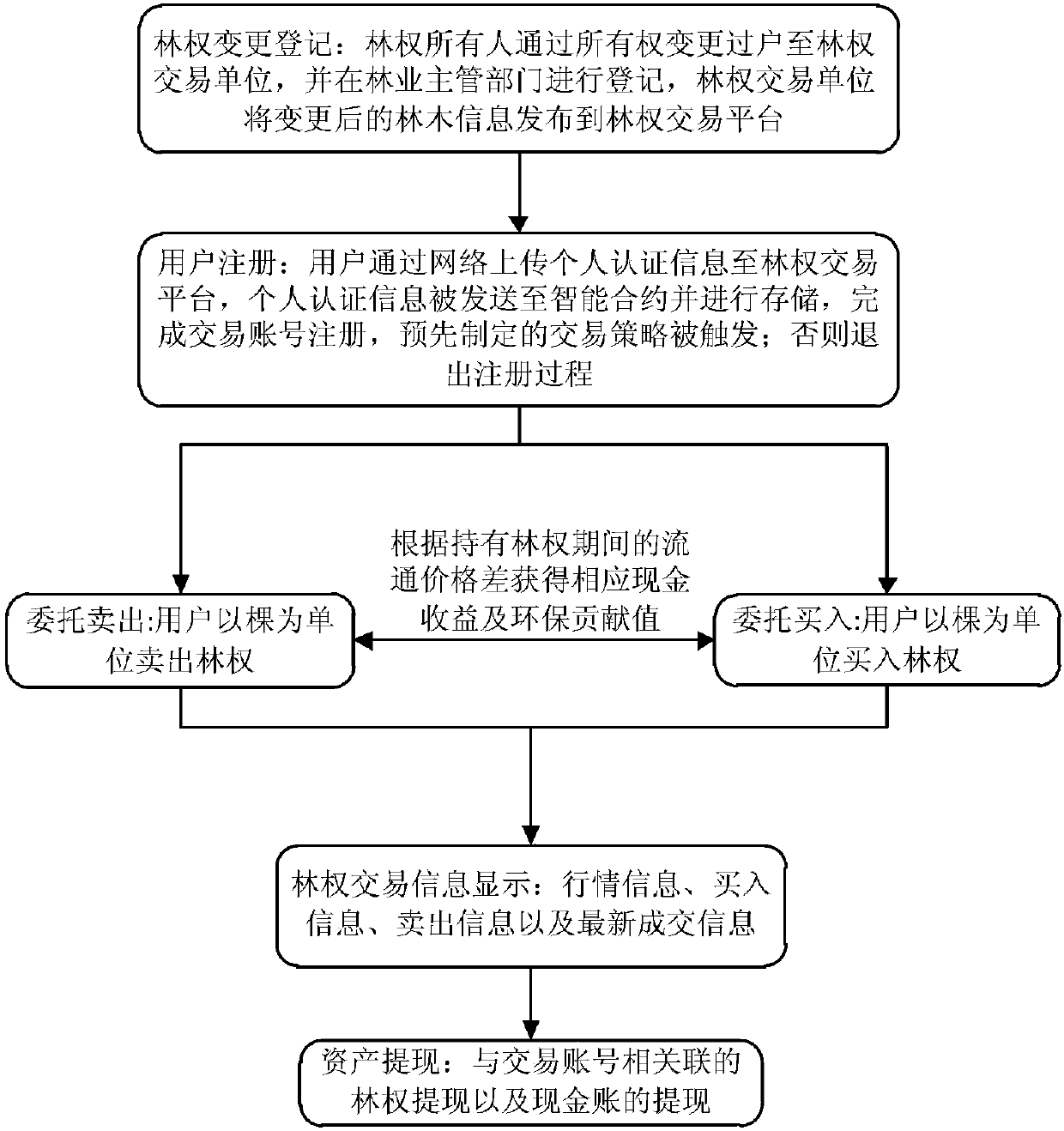
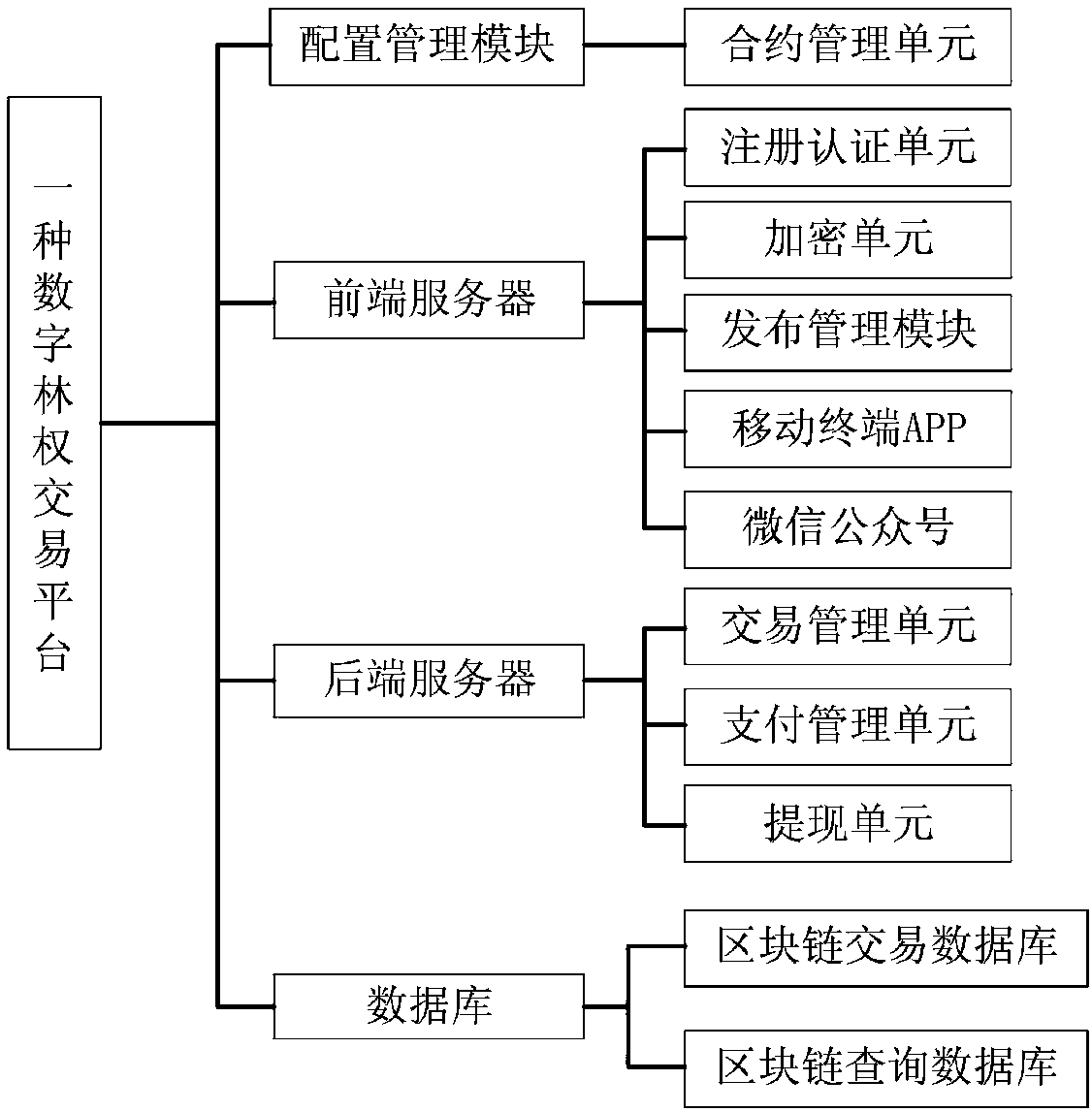
Digital forest right exchange method and platform
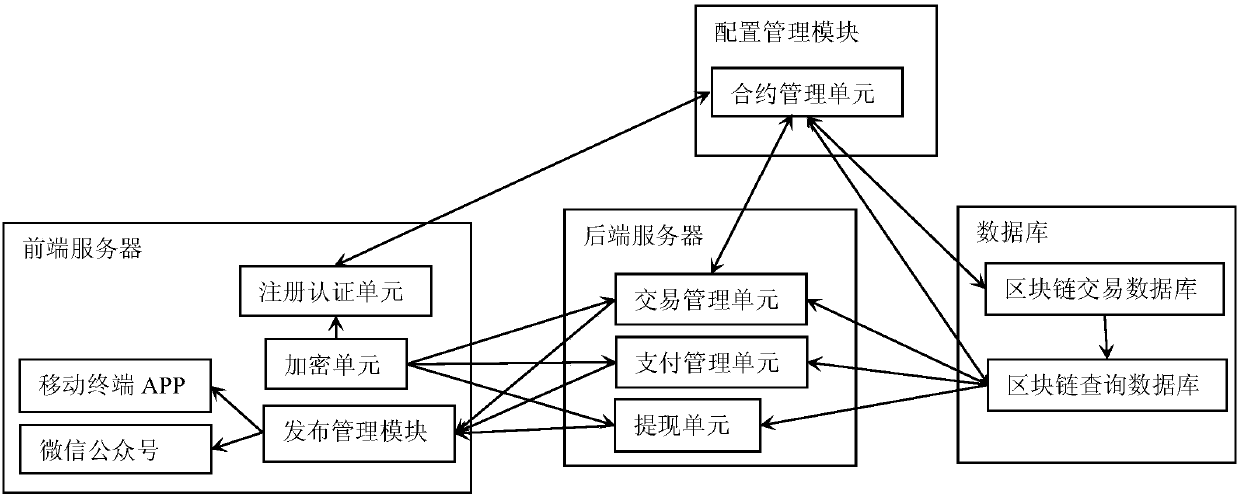
InactiveCN107742252AGuarantee rights and interests cashing mechanismPrevent leakageFinanceConcurrency controlDeforestation
The invention discloses a digital forest right exchange method. The method comprises the steps of forest right change registration, user registration, sell entrusting and buying entrusting, forest right exchange information display and asset withdrawing. A digital forest right exchange platform comprises a configuration management module, a front-end server, a back-end server and a database, and the platform meets the security protection and concurrency control requirements of exchange data. In the digital forest right exchange method and platform, a traditional forest right with mu as a unitis upgraded into the digital forest right with piece as a unit, so that the thresholds of individual participation and forest protection are greatly reduced, and meanwhile, the deforestation rate is greatly reduced. Ordinary users can by the ownership of trees with piece as the unit through the platform so as to obtain the economic benefits brought by tree growth, and while technological forest protection is achieved, the appreciation, value maintenance and deposit withdrawing functions of the forest right of the users are achieved.
Owner:浙江时间林农业有限公司
Anti-hijack communication method of DNS (Domain Name System)
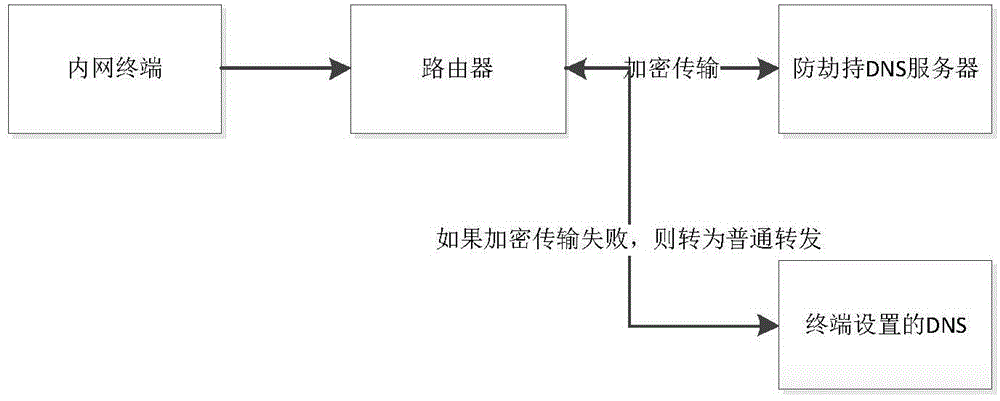
ActiveCN104135471AGuaranteed not to be hijackedAvoid being hijackedTransmissionDomain nameDomain Name System
The invention provides an anti-hijack communication method of a DNS (Domain Name System), which relies on a router and has excellent security. The anti-hijack communication method comprises the following processes that: a user sends a domain name resolution request, after the router receives the request, the router does not directly forward outwards, instead, the following judgments are made, if the router has no DNS cache or the DNS cache has no relevant record, and an anti-hijack DNS server is arranged in the router, the router is communicated with the anti-hijack DNS server, and a communication process is as follows: if the router and the anti-hijack DNS server perform safety communication handshake, the following process is executed; otherwise, the safety communication handshake is established firstly; and the router and the anti-hijack DNS server both utilize keys established by the safety communication handshake to encrypt and decrypt sending information and receiving information respectively so as to carry out communication, the information, which is sent to the anti-hijack DNS server by the router, at least comprises a requested domain name, and the information, which is sent to the router by the anti-hijack DNS server, is information fed back by the information, which is sent to the anti-hijack DNS server by the router.
Owner:JIAXING CHENXIANG INFORMATION TECH
Method and device for preventing traffic hijacking of advertisement operator, equipment and storage medium
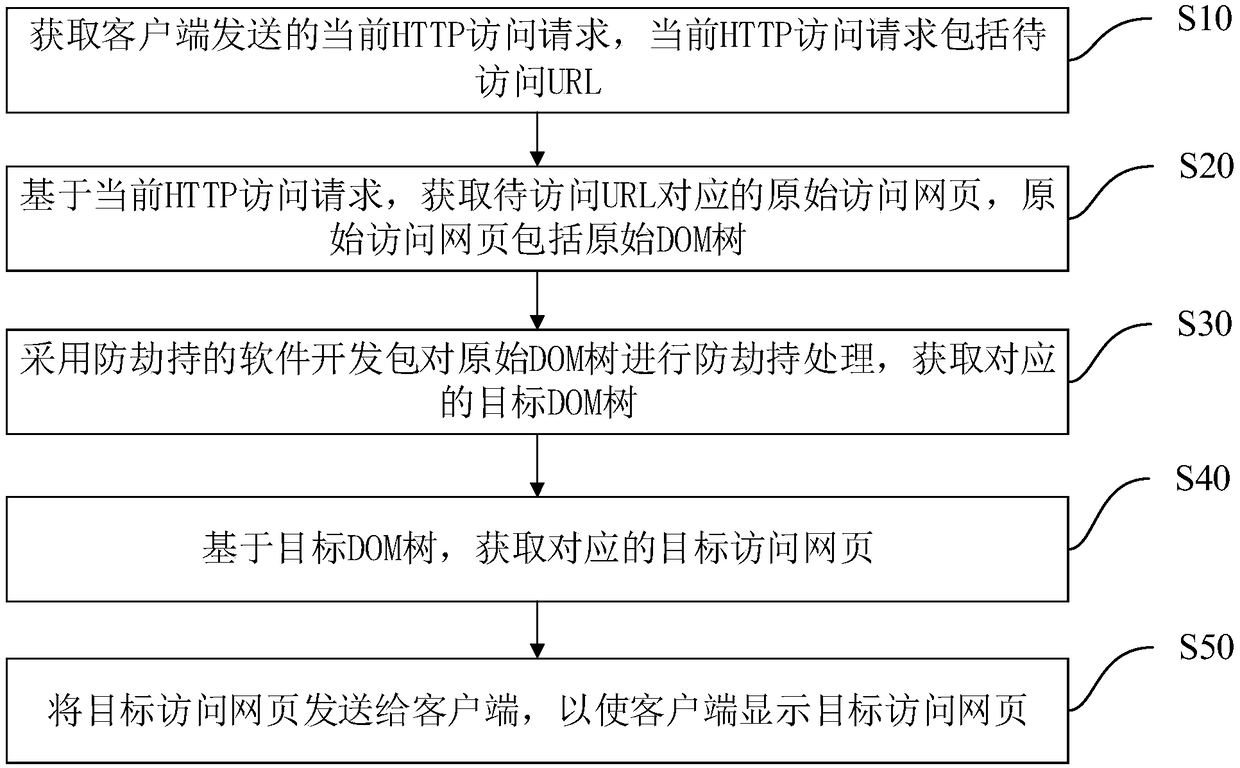
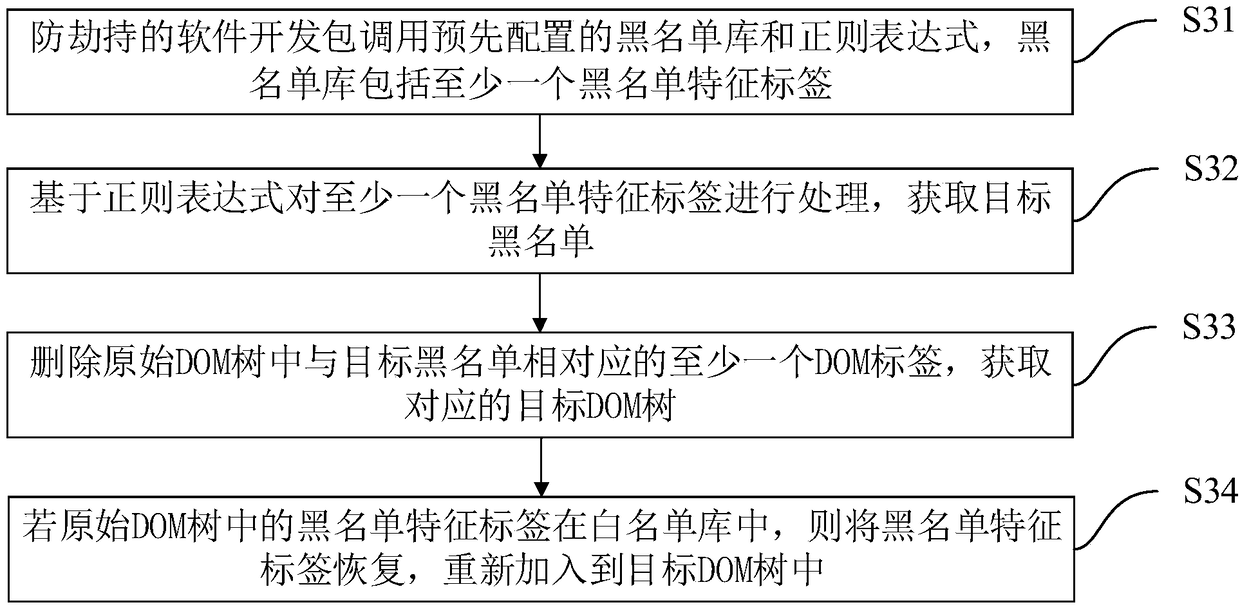
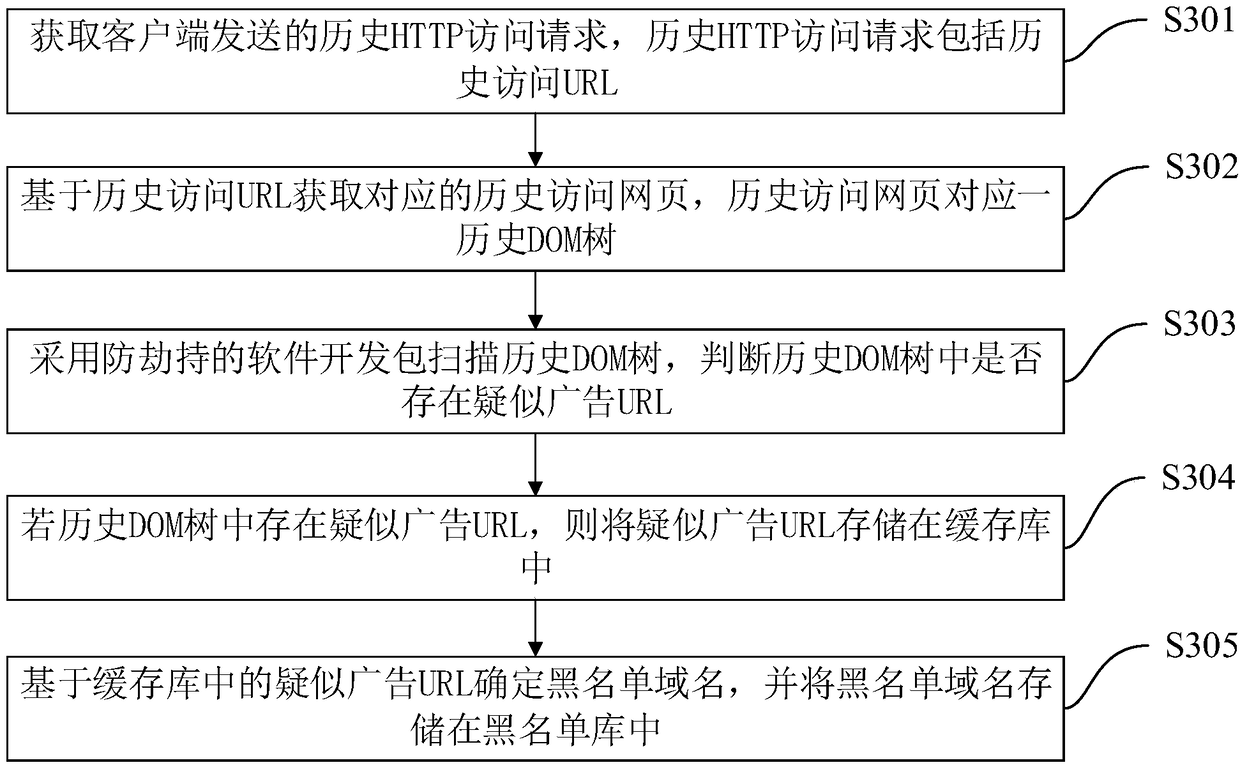
The invention discloses a method and a device for preventing traffic hijacking of an advertisement operator, equipment and a storage medium. The method comprises the following steps of acquiring a current HTTP access request sent by a client, wherein the current HTTP access request comprises a URL to be accessed; acquiring an original access webpage corresponding to the URL to be accessed on the basis of the current HTTP access request, wherein the original access webpage comprises an original DOM tree; adopting an anti-hijacking software development kit for carrying out anti-hijacking processing on the original DOM tree to acquire a corresponding target DOM tree; acquiring a corresponding target access webpage based on the target DOM tree; and sending the target access webpage to the client in order to make the client display the target access webpage. According to the method, the target access webpage rendered by the target DOM tree does not display webpage resource information inserted by the advertisement operator, only the normal webpage resource information is displayed, so that a purpose of better preventing the advertisement operator from carrying out traffic advertisementhijacking is achieved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Method and device for full-text protection and verification of feedback data
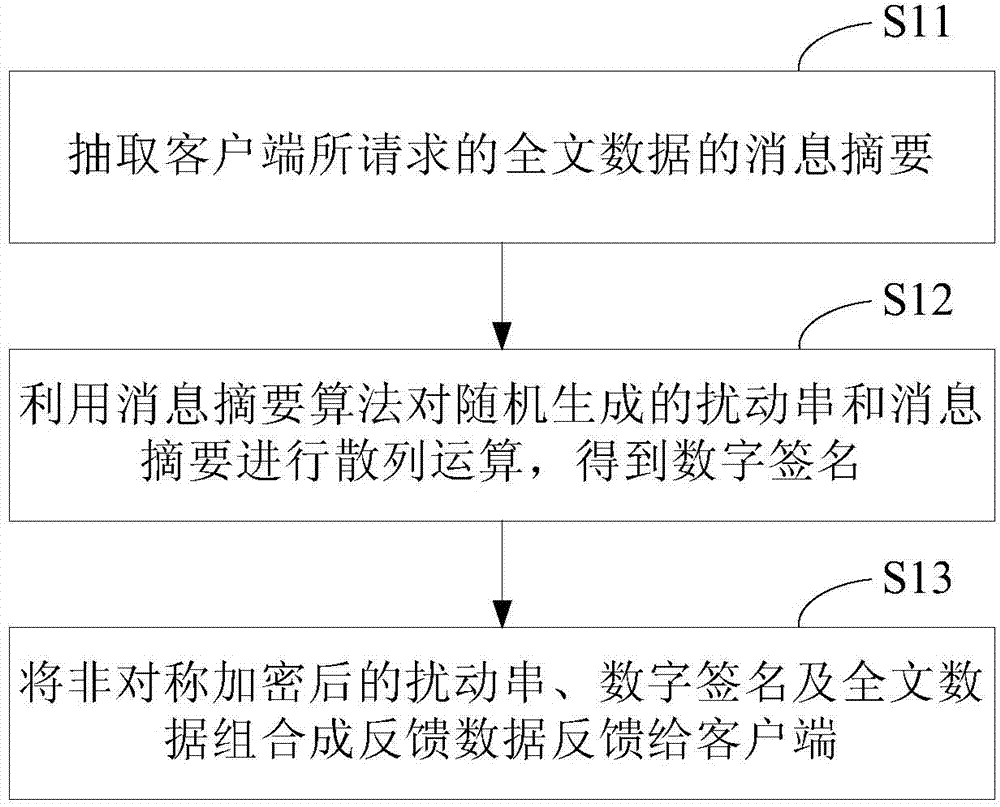
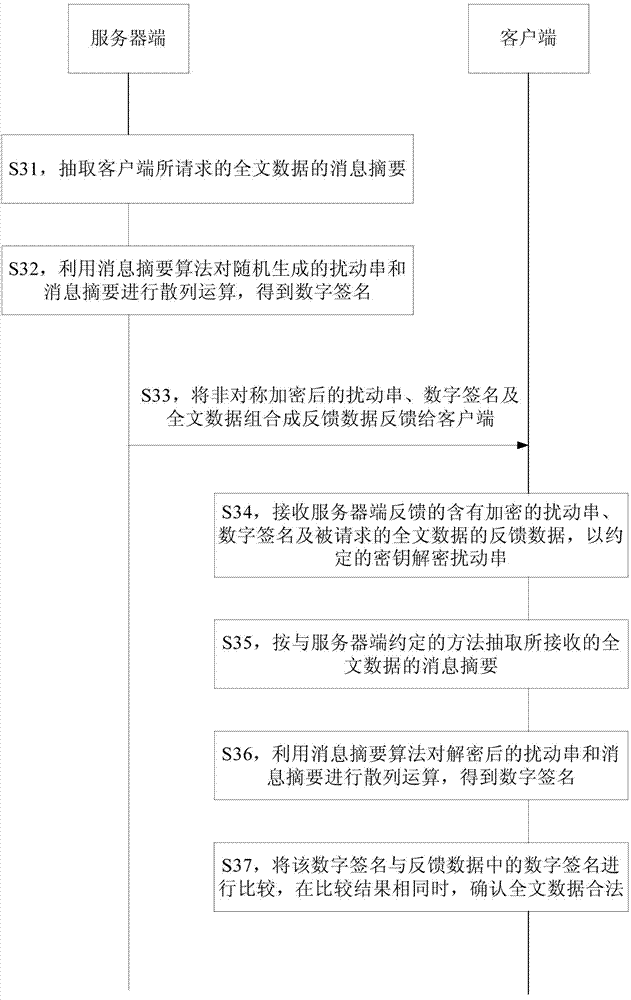
InactiveCN104243171AQuick checkAccurate CalibrationUser identity/authority verificationDigital signatureComputer security
The invention provides a method and a device for full-text protection and verification of feedback data. The method comprises the following steps: a server extracts the message abstract of full-text data requested by a client; hash operation is performed on a randomly generated disturbance string and the message abstract by use of a message abstract algorithm to obtain a digital signature; the asymmetrically encrypted disturbance string, the digital signature and the full-text data are combined into the feedback data for feeding back to the client; the client receives the feedback data and decrypts the disturbance string by use of an appointed key; the message abstract of the received full-text data by use of a method appointed with the server; hash operation is performed on the decrypted disturbance string and the message abstract by use of the message abstract algorithm to obtain a digital signature, and then the digital signature is compared with the digital signature in the feedback data, and then the comparison result indicates that the two digital signatures are the same, the full-text data are confirmed to be legal. The invention also provides a device corresponding to the method. The method for full-text protection and verification of feedback data is capable of performing quick and accurate verification on the authenticity of the full-text data.
Owner:BEIJING QIHOO TECH CO LTD +1
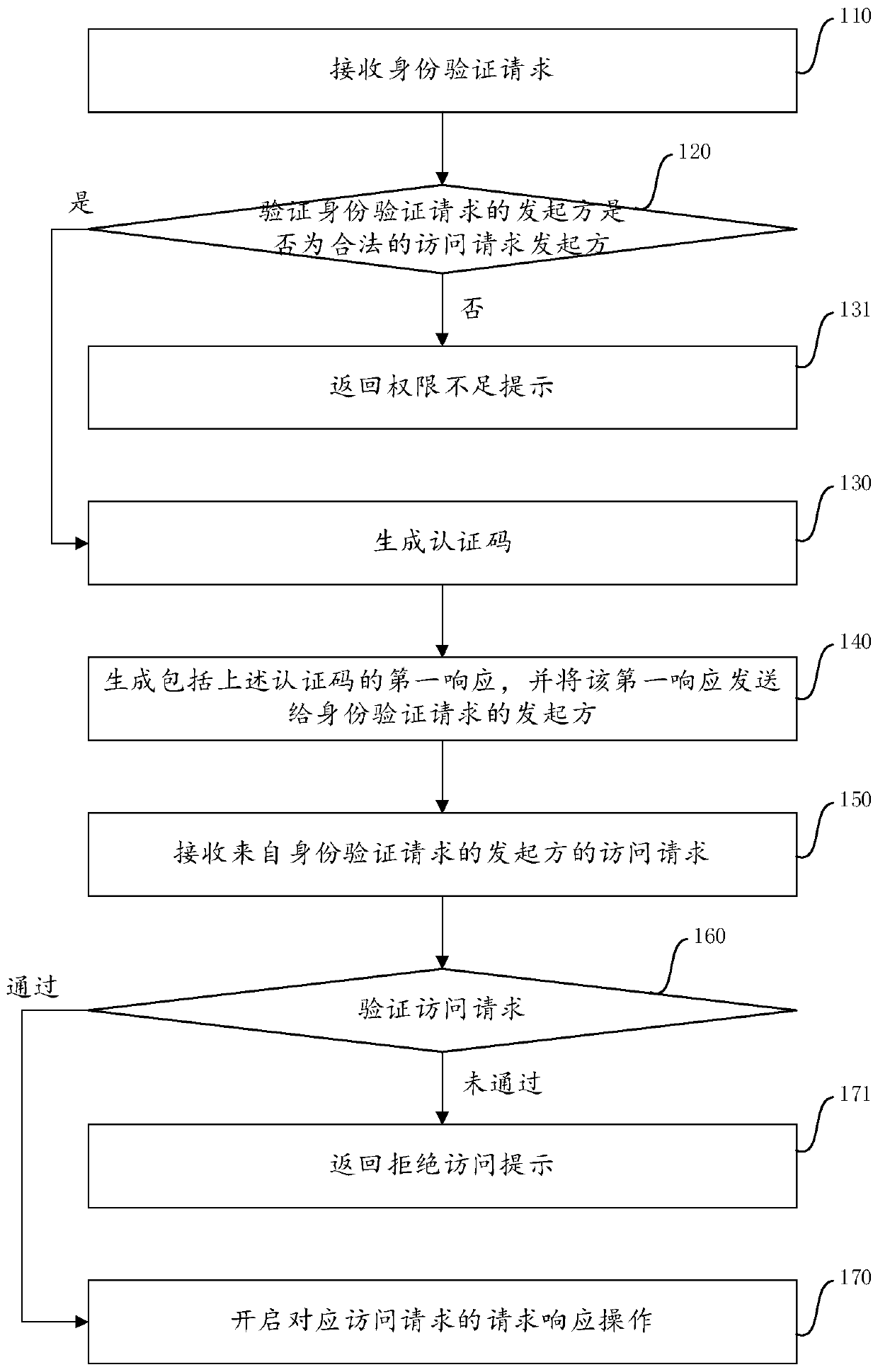
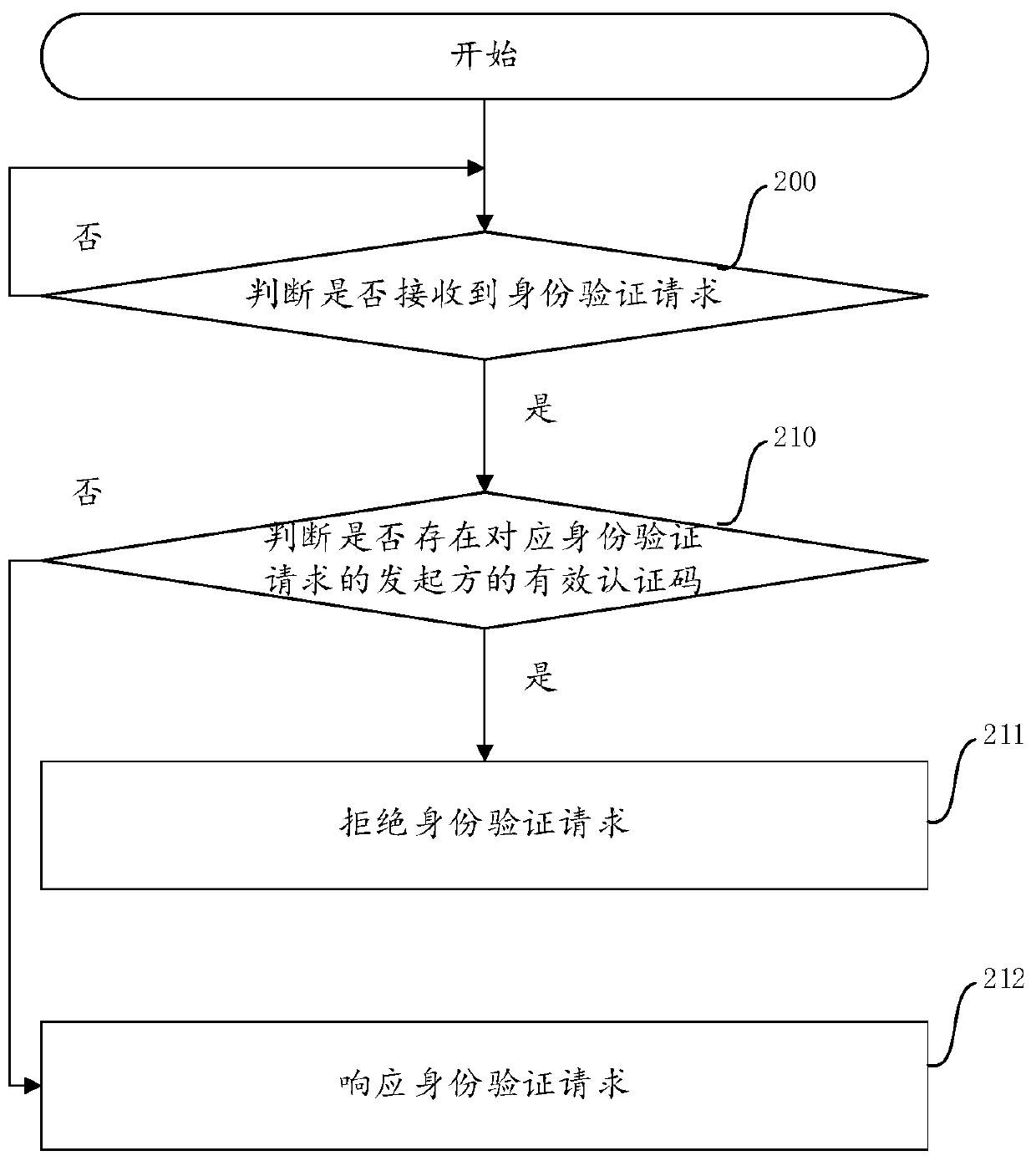
Access request response method and device and electronic equipment
The embodiment of the invention provides an access request response method, electronic equipment and a computer storage medium. The access request response method comprises the following steps: receiving an identity verification request; verifying whether the initiator of the identity verification request is a legal access request initiator or not; when the initiator passes the verification, generating a single valid authentication code corresponding to the initiator; generating a first response including the authentication code, and sending the first response to the initiator; receiving an access request including the authentication code from the initiator; verifying the access request, and verifying the authentication code included in the access request; and when the access request passes the verification, starting a request response operation corresponding to the access request. According to the method provided by one embodiment of the invention, a single effective authentication code is adopted, so that the permission stealing of an illegal intruder to a legal access request initiator is effectively prevented, and the possibility that the target equipment is remotely and illegally intruded is greatly reduced.
Owner:HUAWEI TECH CO LTD
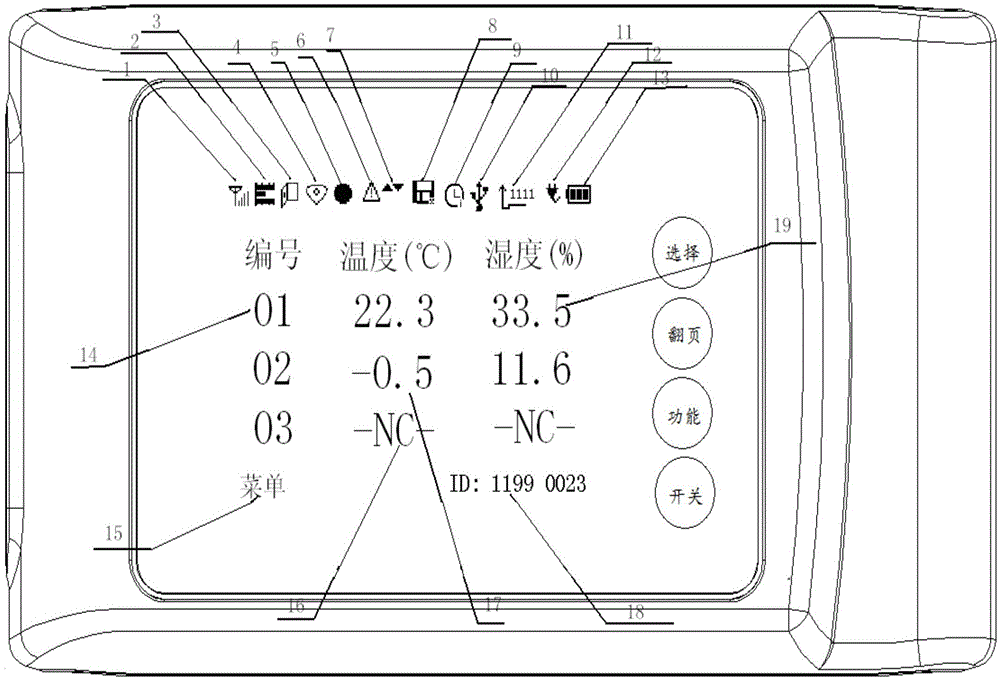
Refrigerator car or warehouse multipoint monitoring and data returning device
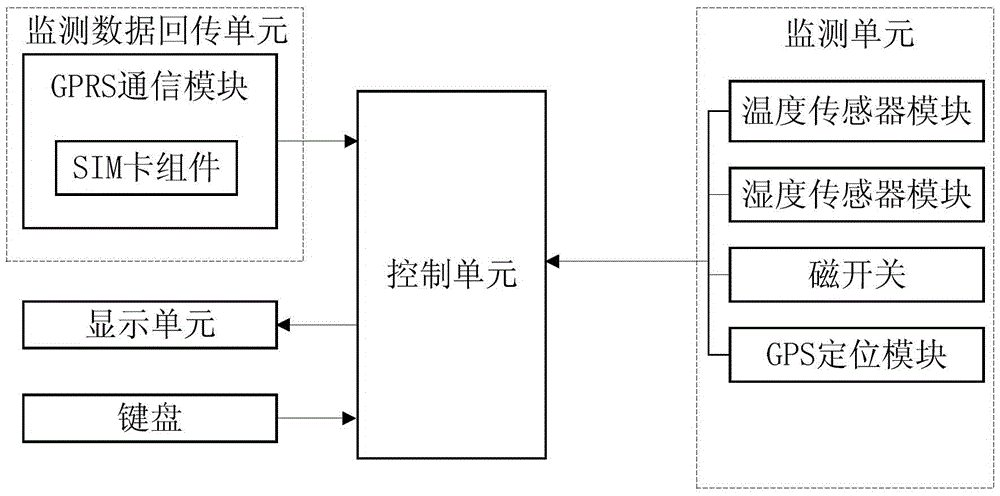
InactiveCN105607559AGuarantee quality and safetyComprehensive monitoring of environmental parametersProgramme controlComputer controlCold chainRefrigerator car
The invention discloses a refrigerator car or warehouse multipoint monitoring and data returning device. The refrigerator car or warehouse multipoint monitoring and data returning device comprises a monitoring unit, a monitoring data returning unit, a display unit, a keyboard and an alarm unit, wherein the monitoring unit, the monitoring data returning unit, the display unit, the keyboard and the alarm unit are connected with a control unit. Multiple temperature and humidity monitoring points are arranged in a refrigerator car or a warehouse, environment parameters in a compartment or the warehouse can be monitored in an omni-directional manner, when humiture is higher than a preset upper value or lower than a preset lower value, acousto-optic alarm signals are emitted, real-time monitoring data is transmitted to a background management server or a specified mobile phone through a GPRS wireless network, and monitoring personnel is prompted timely to take remedy measures, such that quality safety of vaccines, biological agents, food and the like which are transported by the refrigerator car in a cold chain transport process or quality safety of medicine, food and the like in the warehouse can be fully guaranteed.
Owner:北京华海隆科技有限公司
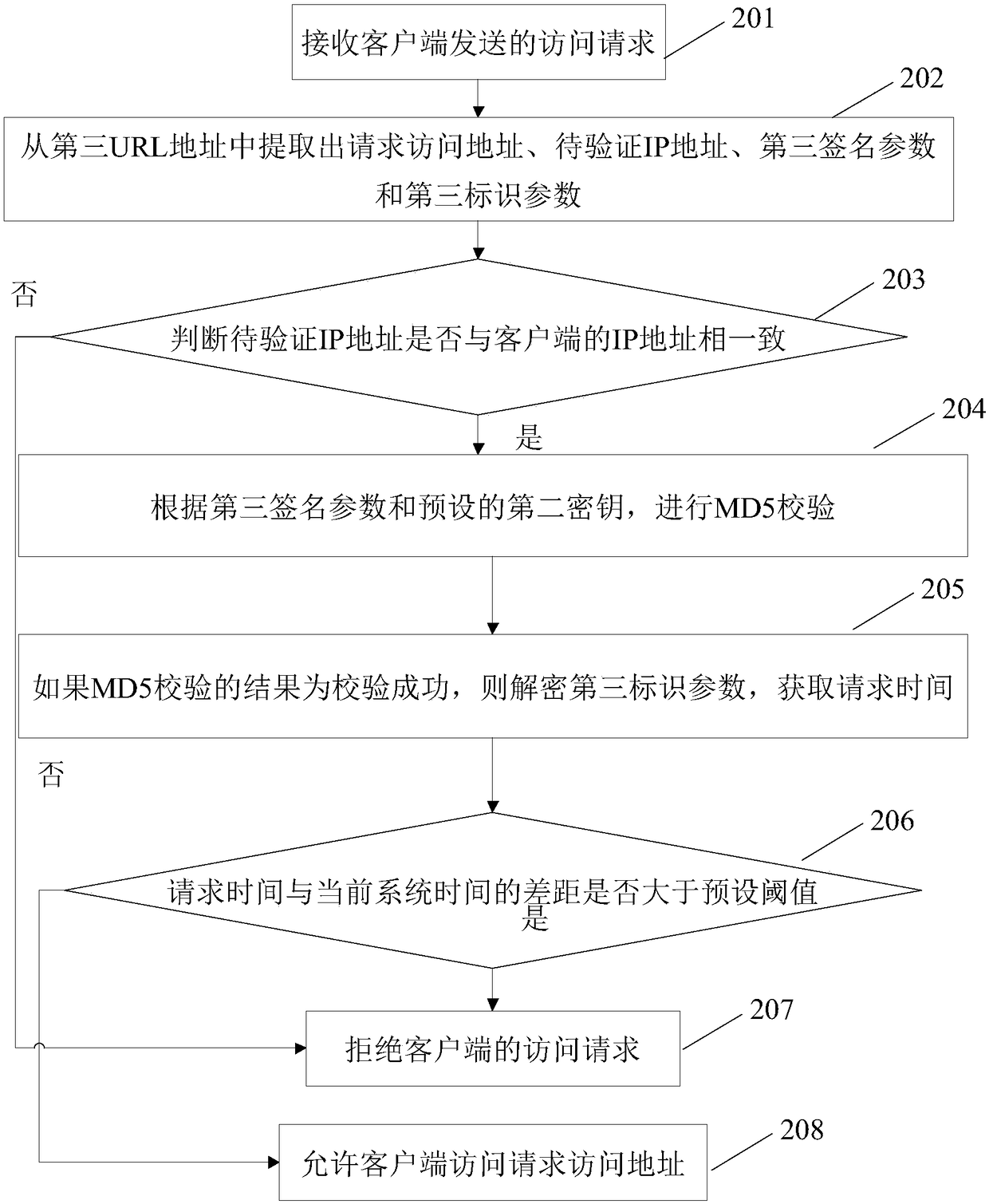
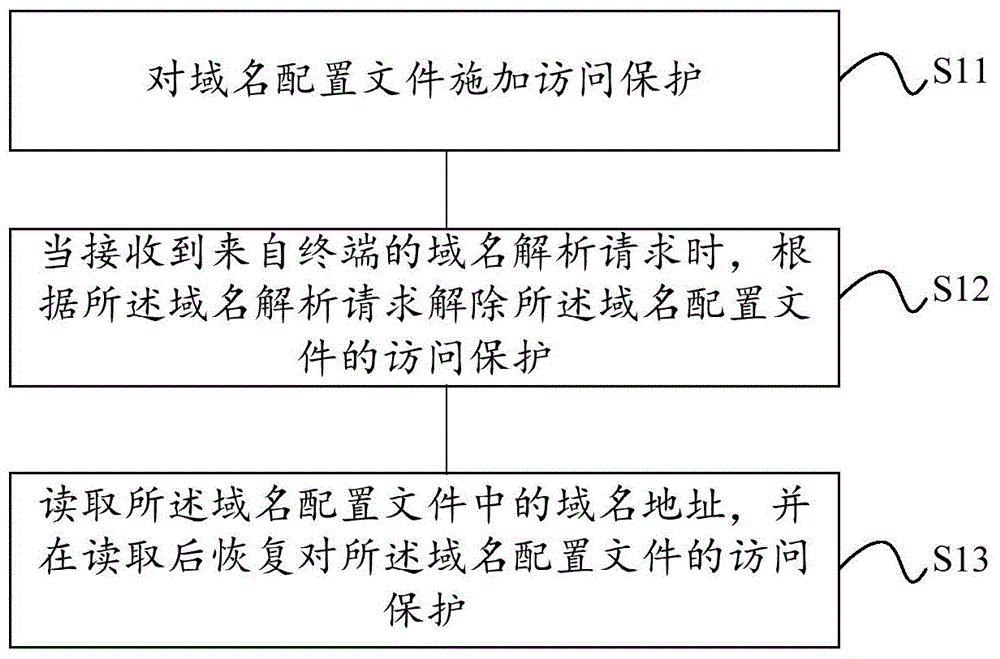
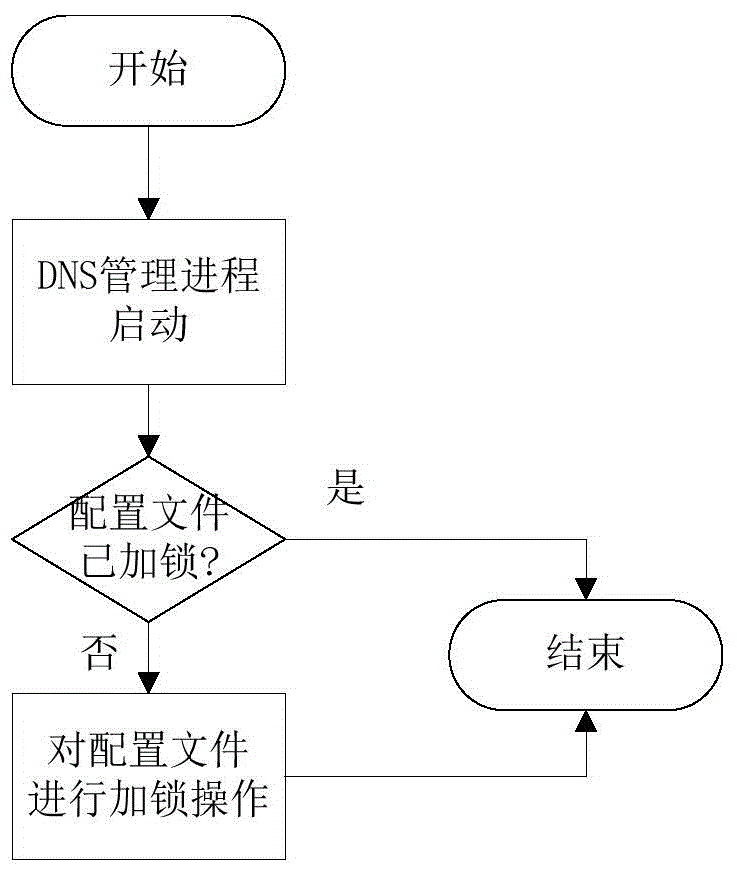
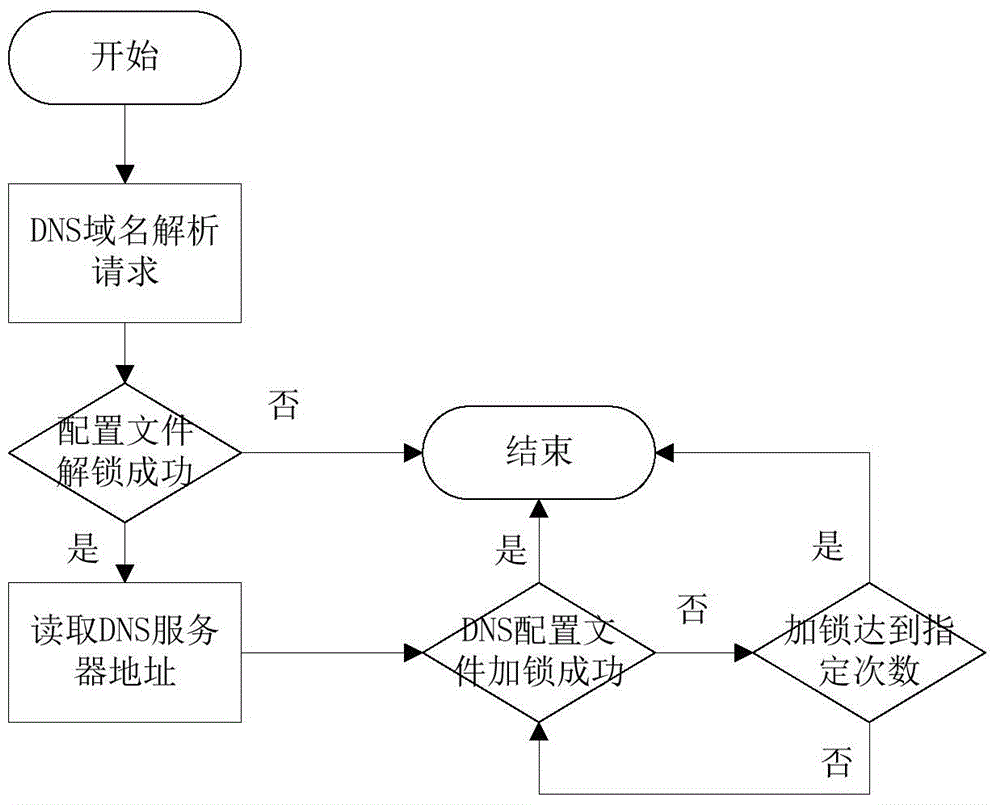
Method and device for preventing form domain name hijacking
The present invention discloses a method and device for preventing form domain name hijacking, and relates to the field of the communication technology. The objective of the invention is to solve the problems that the method for preventing DNS from being hijacked is low in safety and bad in effect in the prior art. The method comprises: applying access protection of a domain name configuration files; when a domain name analysis request from a terminal is received, releasing the access protection of the domain name configuration file according to the domain name analysis request; and reading the domain name address in the domain name configuration file, and recovering the access protection of the domain name configuration file after reading.
Owner:ZTE CORP
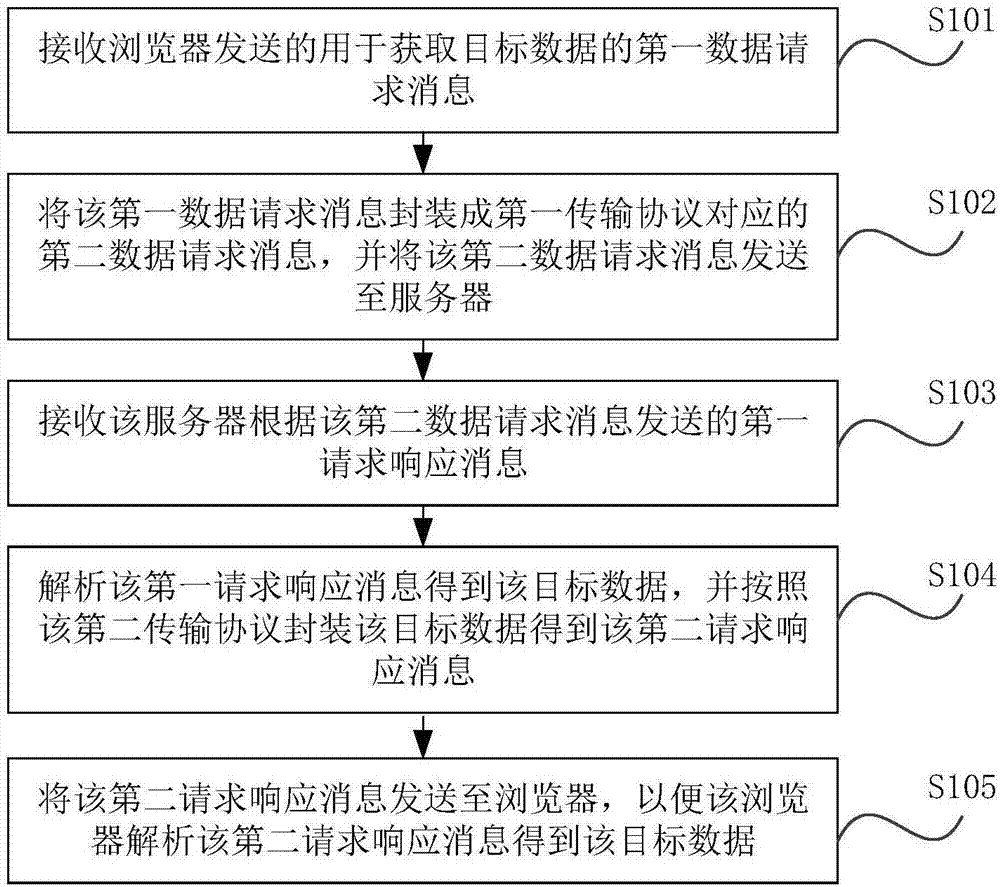
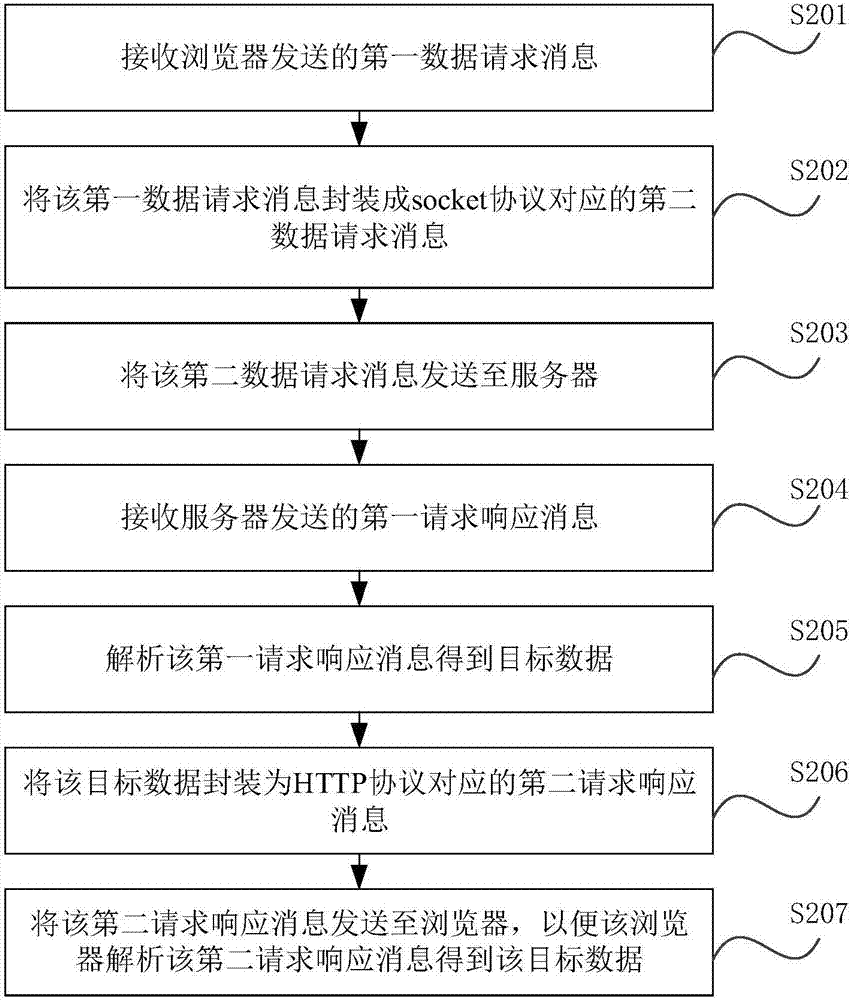
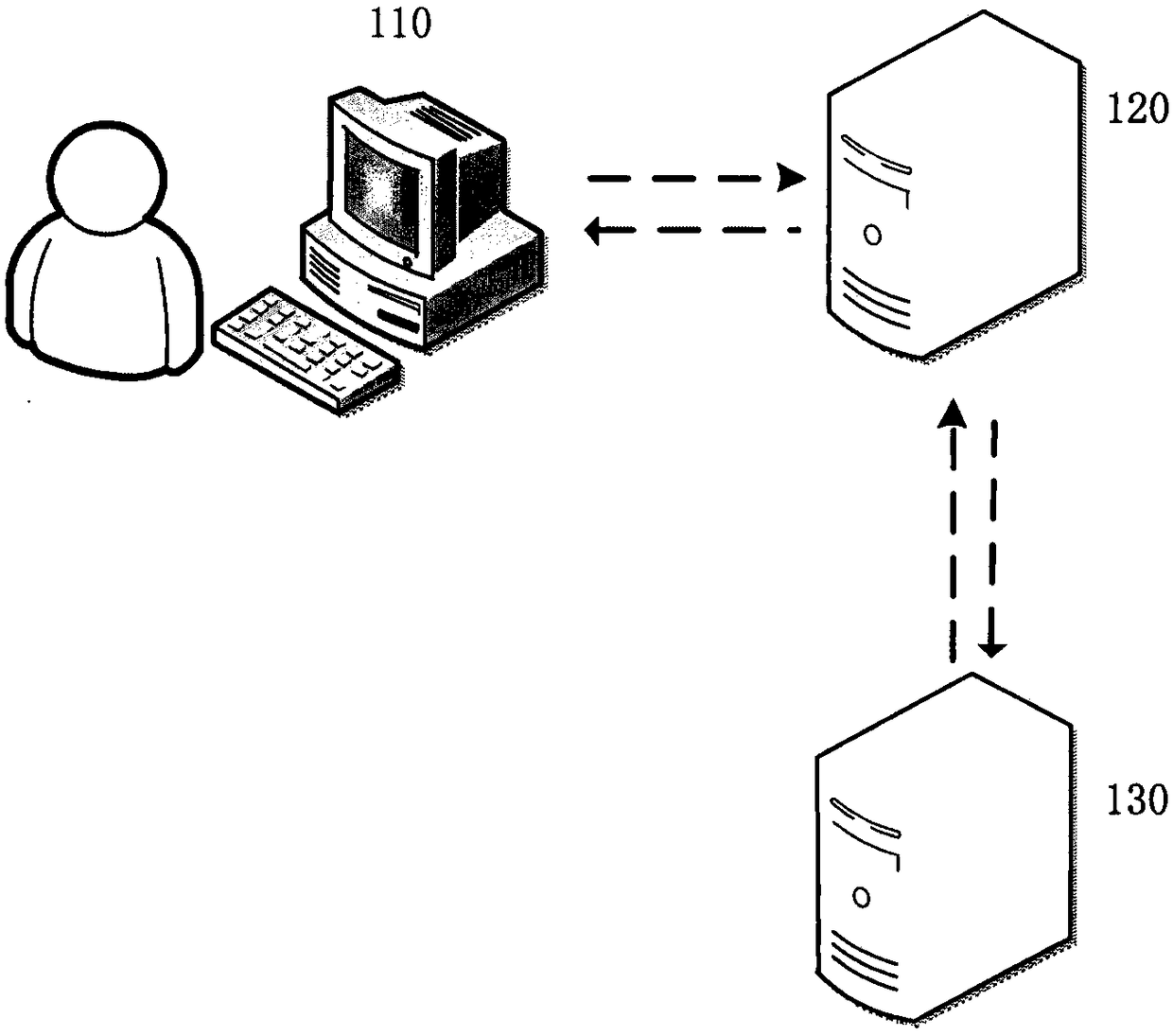
Data requesting method, device, storage medium and electronic equipment
The invention relates to a data requesting method, device, a storage medium and electronic equipment. The method comprises steps: a first data requesting message sent by a browser for requesting to acquire target data is received; the first data requesting message is packaged to a second data requesting message corresponding to a first transmission protocol, and the second data requesting messageis sent to a server, wherein the first transmission protocol is a lower layer protocol for an application layer protocol; a first request response message sent by the server according to the second data requesting message is received; the first request response message is analyzed to obtain the target data, and the target data are packaged according to a second transmission protocol, and a secondrequest response message is obtained, wherein the second transmission protocol is the application layer protocol; and the second request response message is sent to the browser, and thus, the browseranalyzes the second request response message to obtain the target data.
Owner:NEUSOFT CORP
Website monitoring method and device thereof
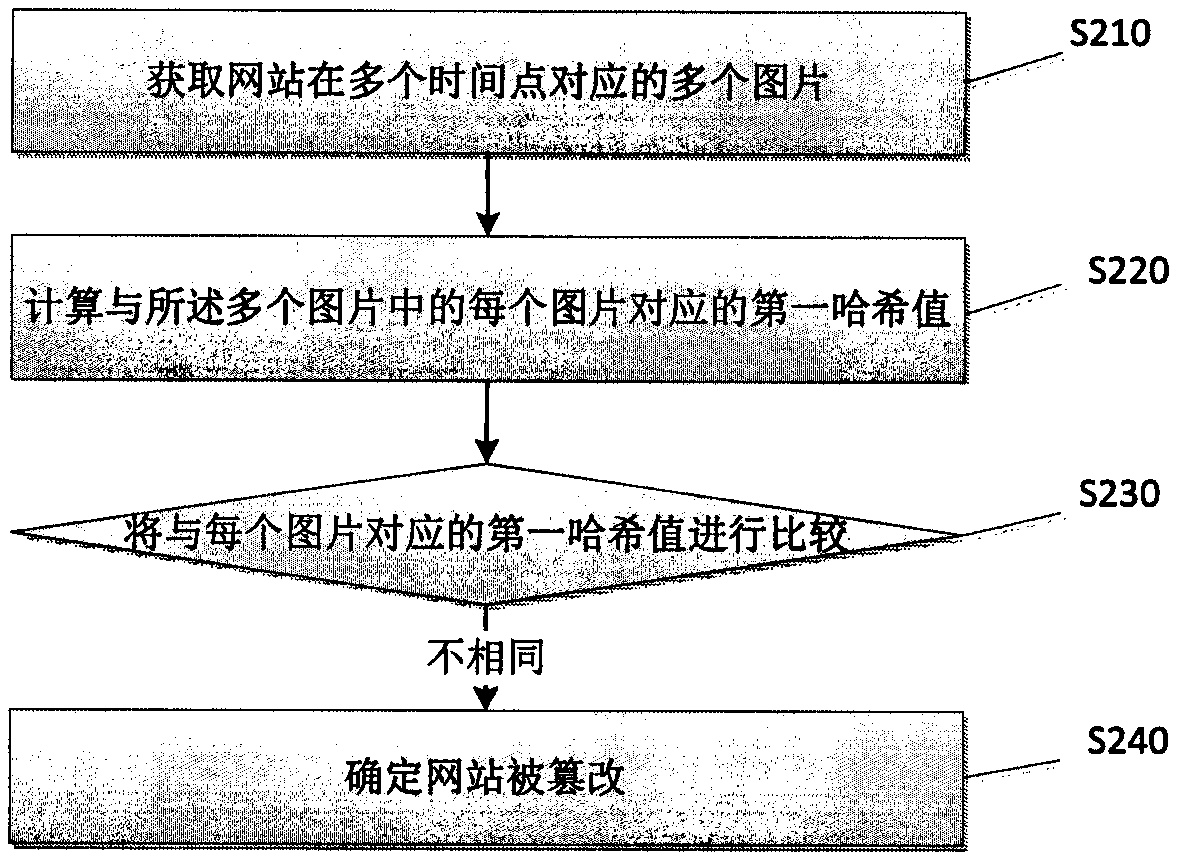
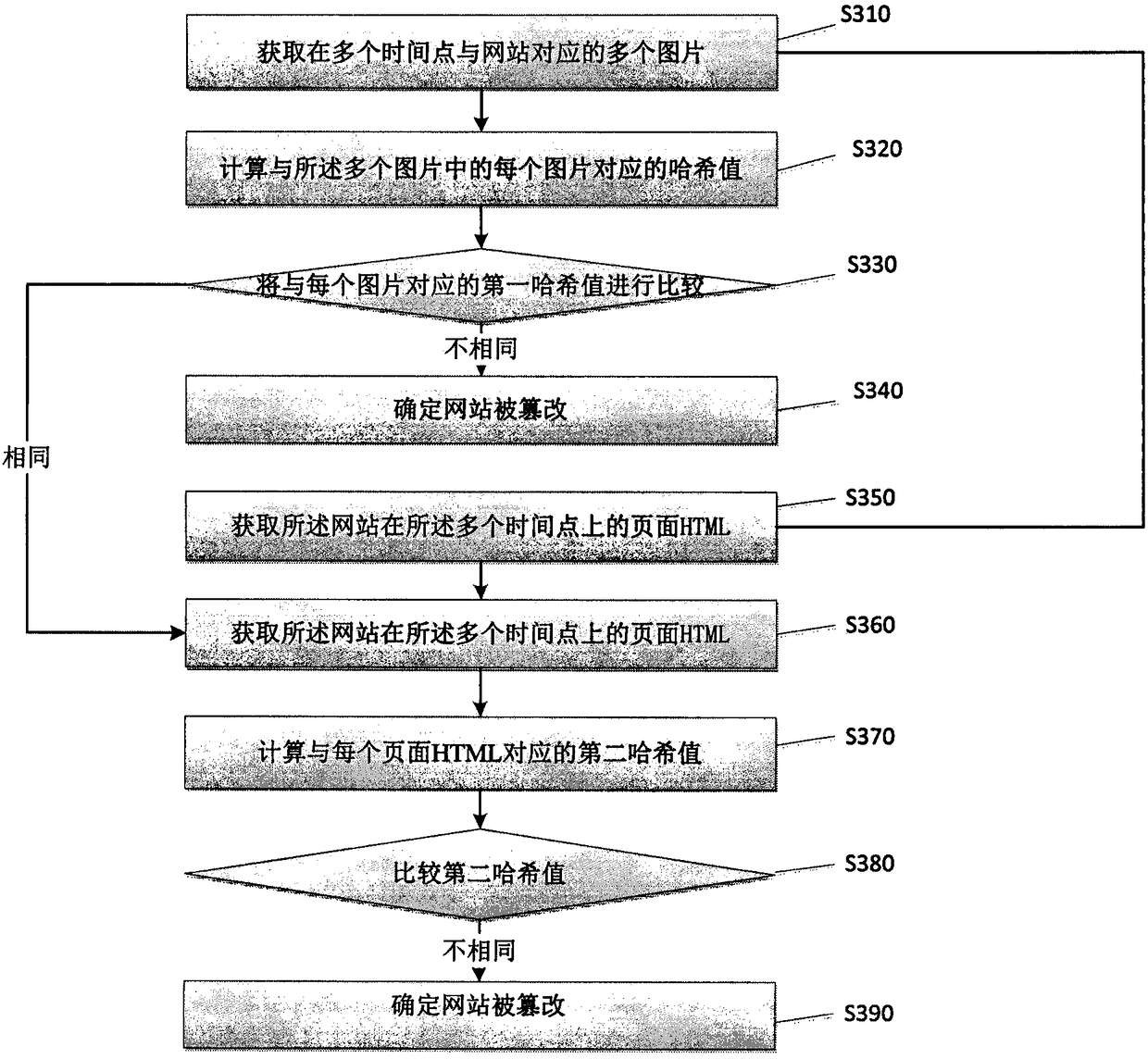
ActiveCN108809943APrevent traffic from being hijackedWide range of applicationsTransmissionData miningData science
The disclosure relates to a website monitoring method and a device thereof. The method includes the following steps: obtaining multiple pictures corresponding to a website at multiple time points; calculating a hash value corresponding to each picture among the multiple pictures; comparing the first hash values corresponding to each picture; and if the first hash values are different, determiningthat the website is tampered with. According to the website monitoring method and the device thereof provided by the embodiment of the disclosure, whether the website is tampered with can be determined by using the hash values of the pictures corresponding to the website, additional setting conditions are not required, and thus the website monitoring is simple and effective.
Owner:SUZHOU WINNDOO NETWORK TECH CO LTD
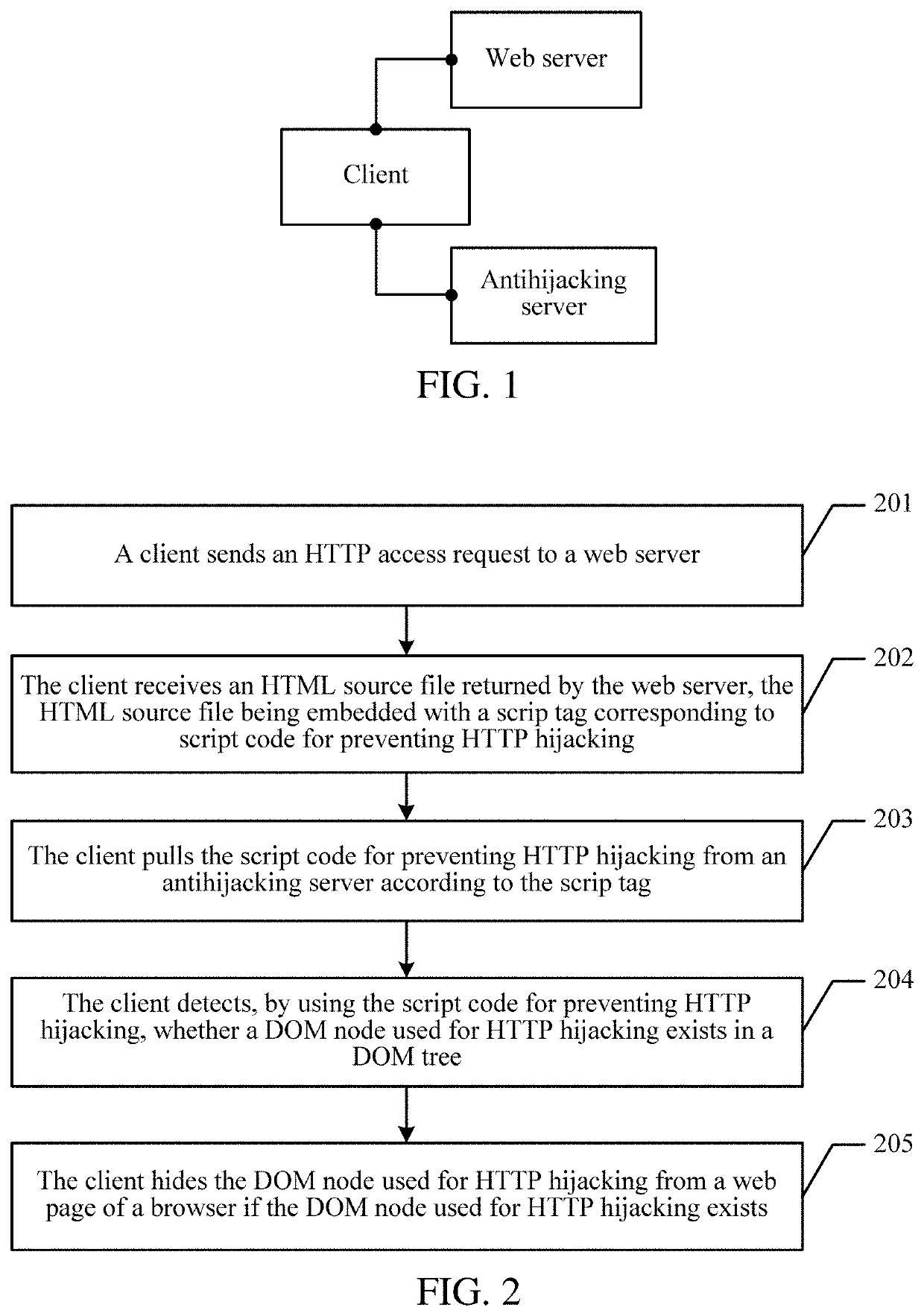
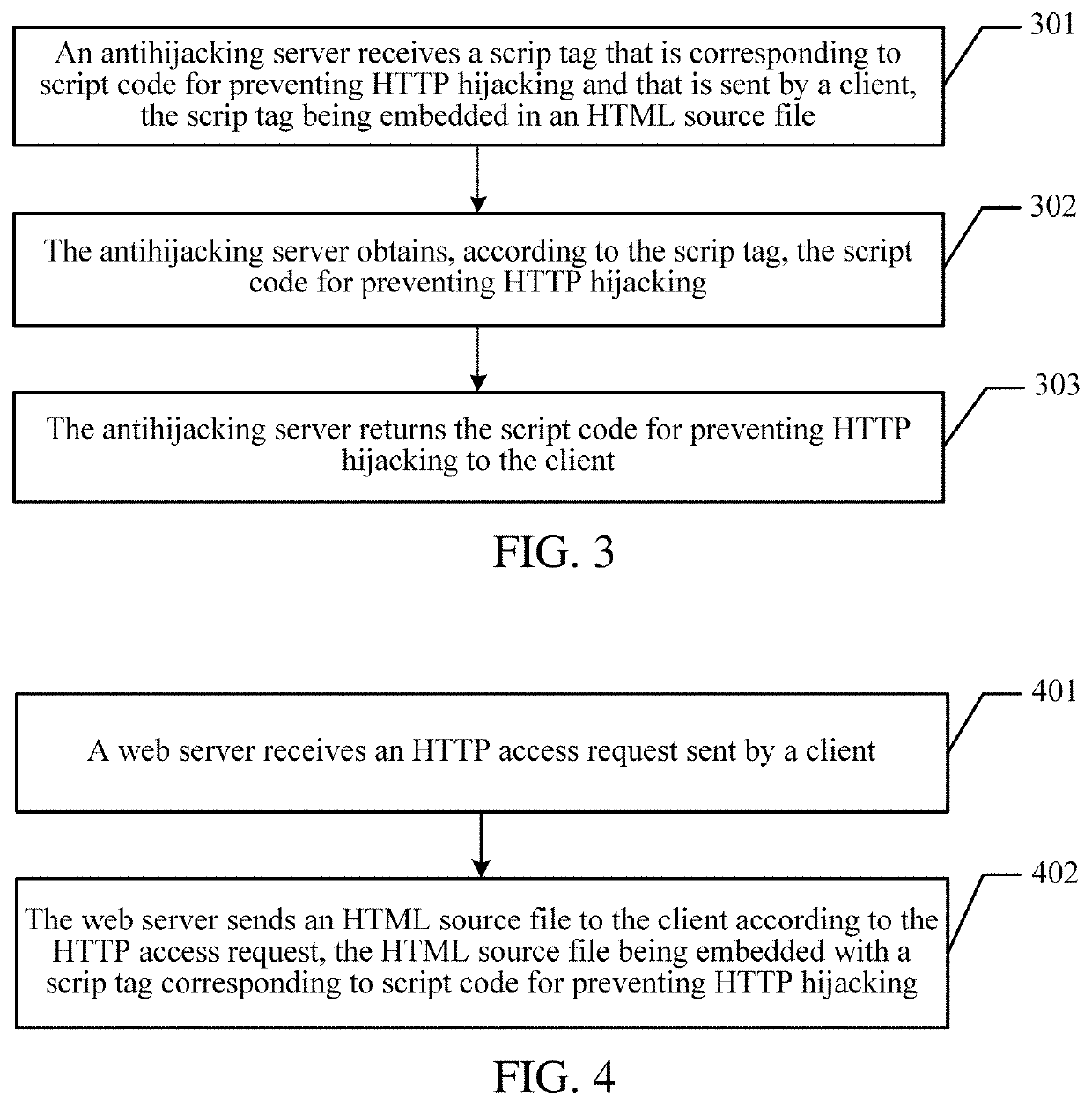
Method, client, and server for preventing web page hijacking
ActiveUS20190342334A1Prevent hijackingAvoid hijackingComputer security arrangementsTransmissionWeb serverDocument Object Model
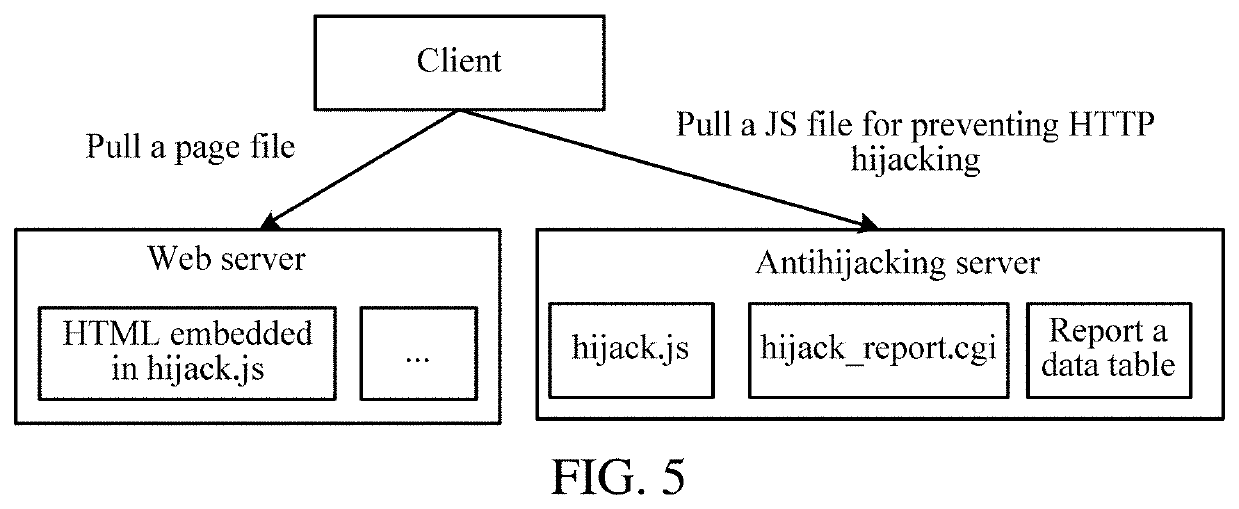
A method for preventing hijacking of a web page is provided. A HyperText Markup Language (HTML) source file is received from a web server in response to a HyperText Transfer Protocol (HTTP) access request, the HTML source file being embedded with a script tag corresponding to script code for preventing HTTP hijacking. The script code for preventing HTTP hijacking is pulled from an antihijacking server according to the script tag. It is detected, based on the script code for preventing HTTP hijacking, whether a document object model (DOM) node used for HTTP hijacking exists in a DOM tree. The DOM node used for HTTP hijacking is hidden from a web page of a browser in response to detecting that the DOM node used for HTTP hijacking.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and sever for downloading application program
InactiveCN105302617AAvoid hijackingImprove experienceComputer security arrangementsProgram loading/initiatingApplication softwareComputer network
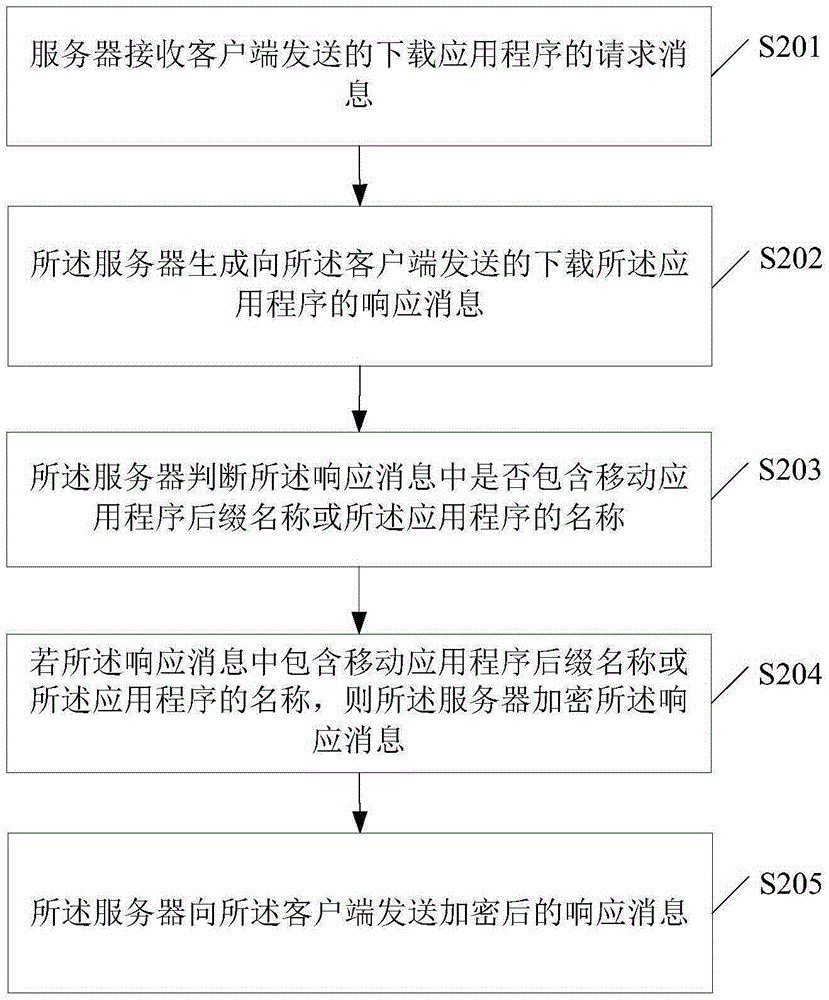
The embodiment of the invention discloses a method and a server for downloading an application program. The method comprises the following steps: receiving request information for downloading an application program, sent by a client; generating response information for downloading the application program, sent by the client; judging whether the response information contains the suffix name of a moving application program or the name of the application program; if the response information contains the suffix name of the moving application program or the name of the application program, encrypting the response information; sending the encrypted response information to the client. The implementation of the embodiment of the invention is favorable for reducing the possibility that an operator recognizes the feature information in the application downloading request to prevent the operator to hijack the application program, so that the application downloading safety and user experience are promoted.
Owner:MEIZU TECH CO LTD
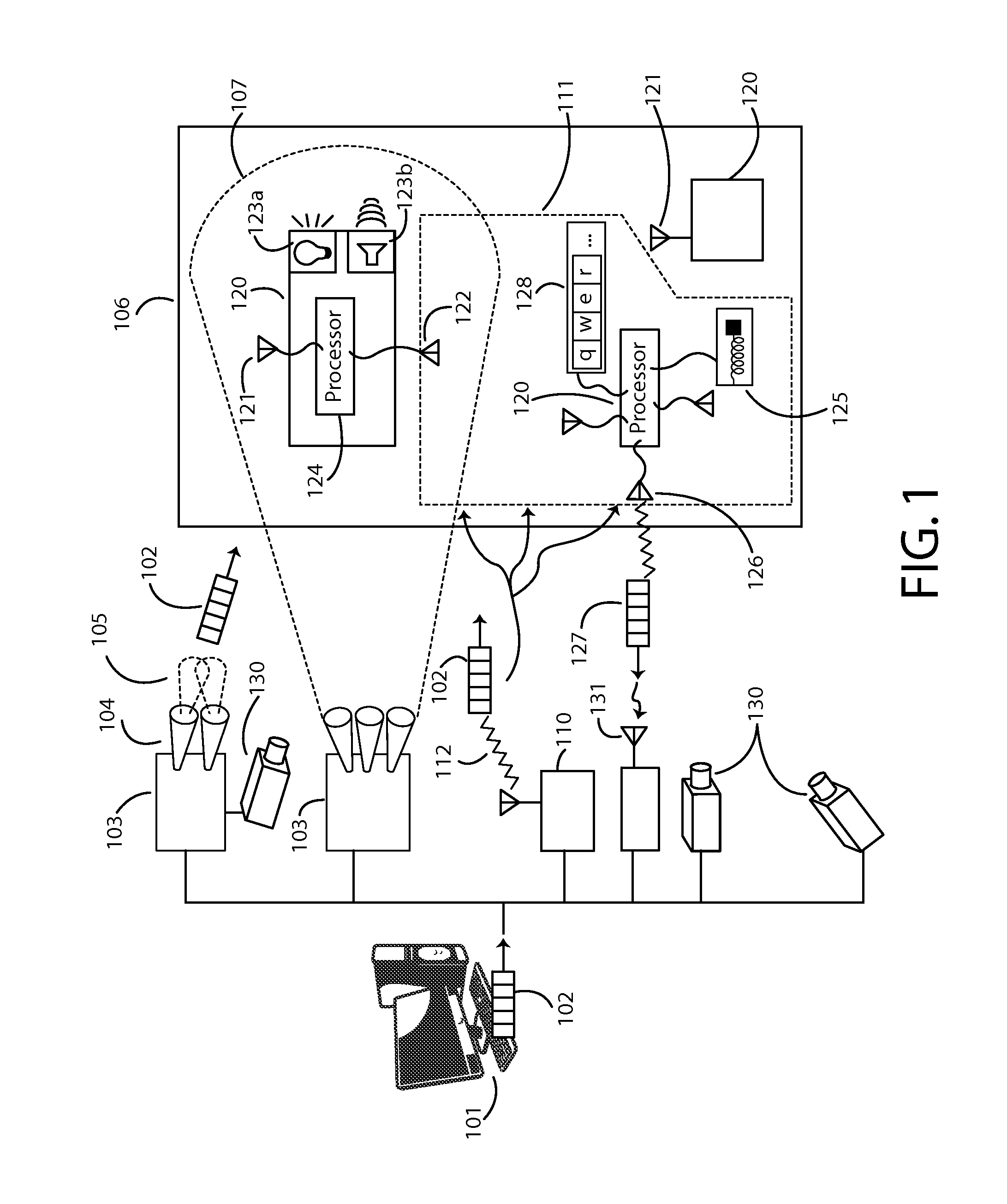
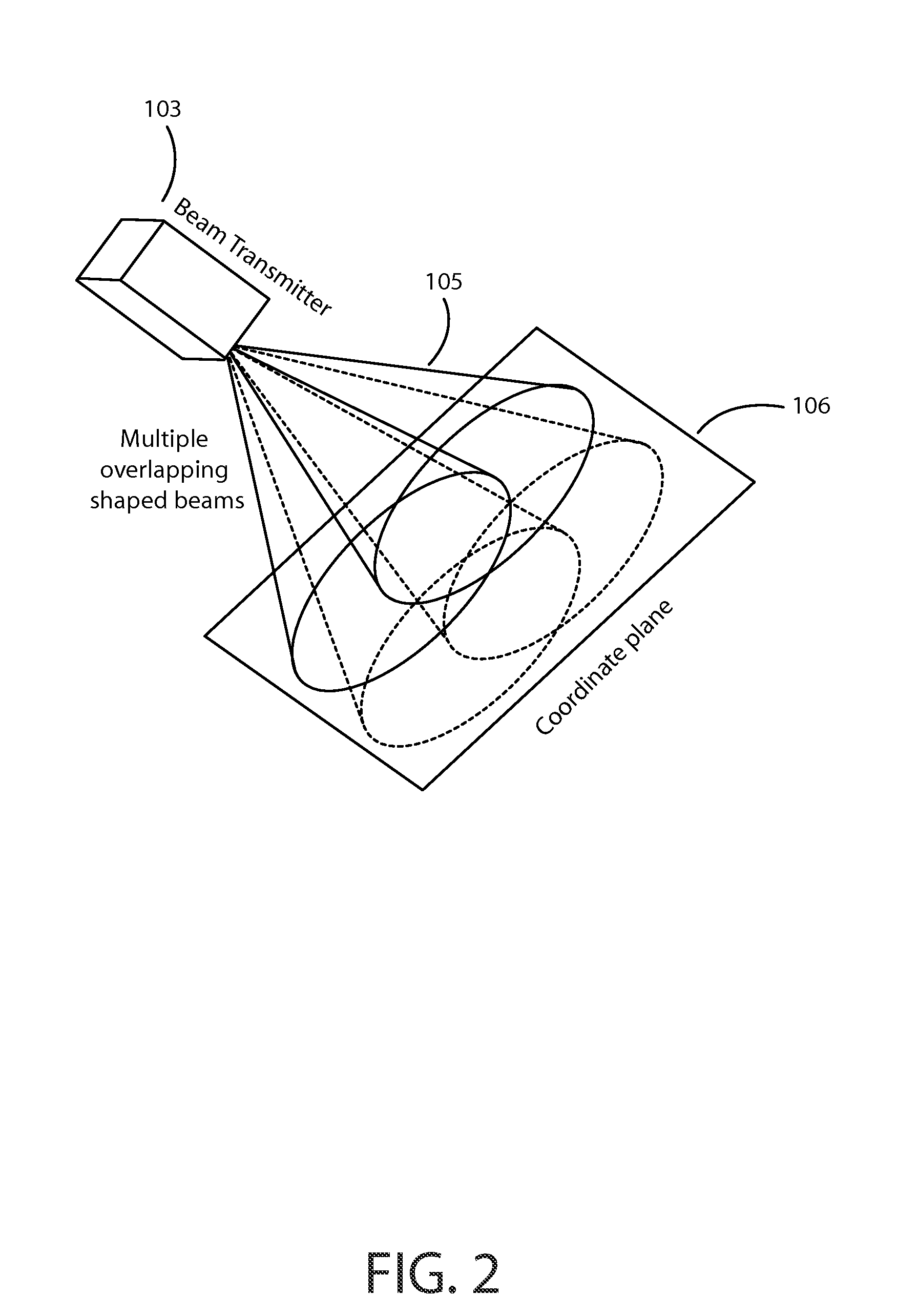
Local positioning and response system
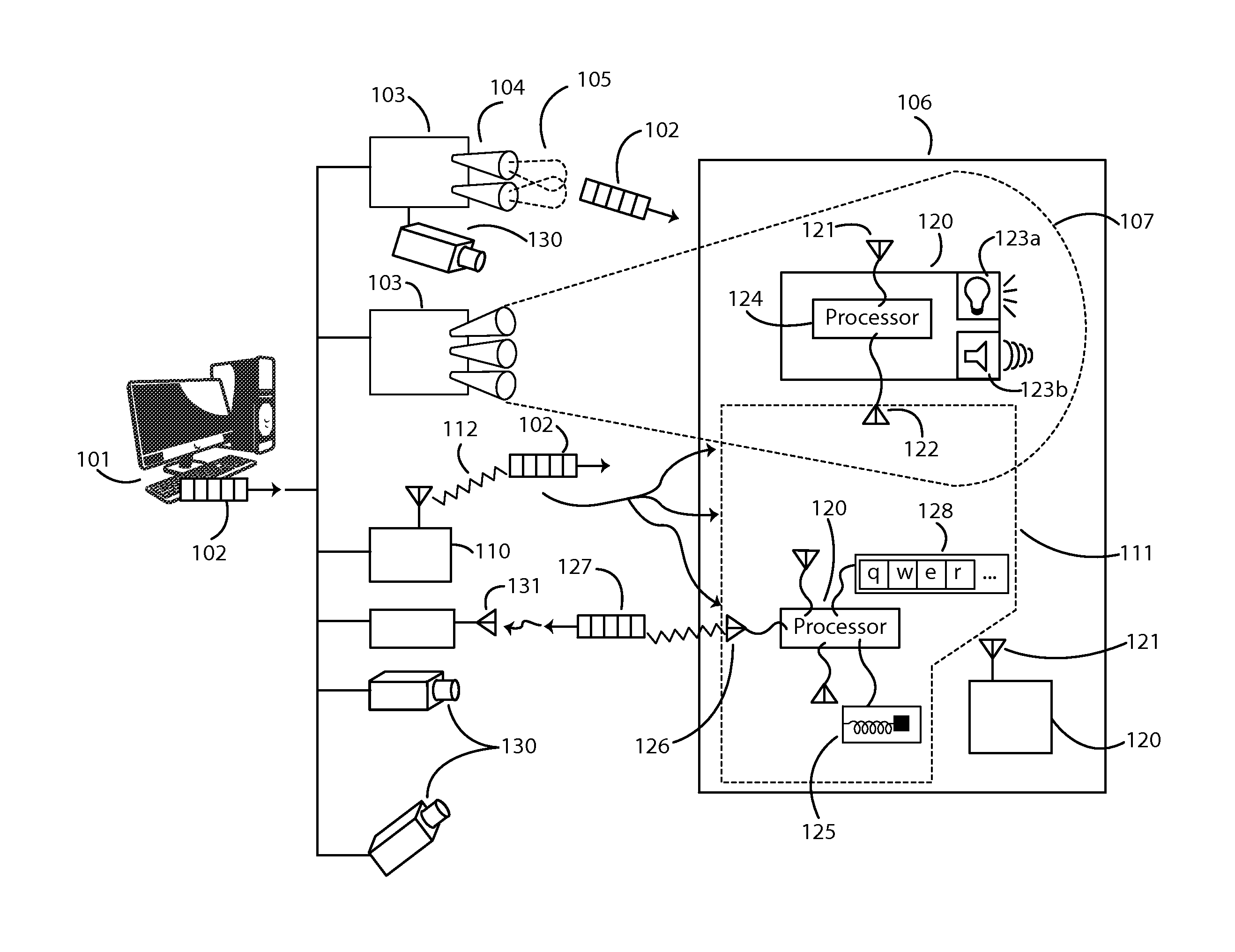
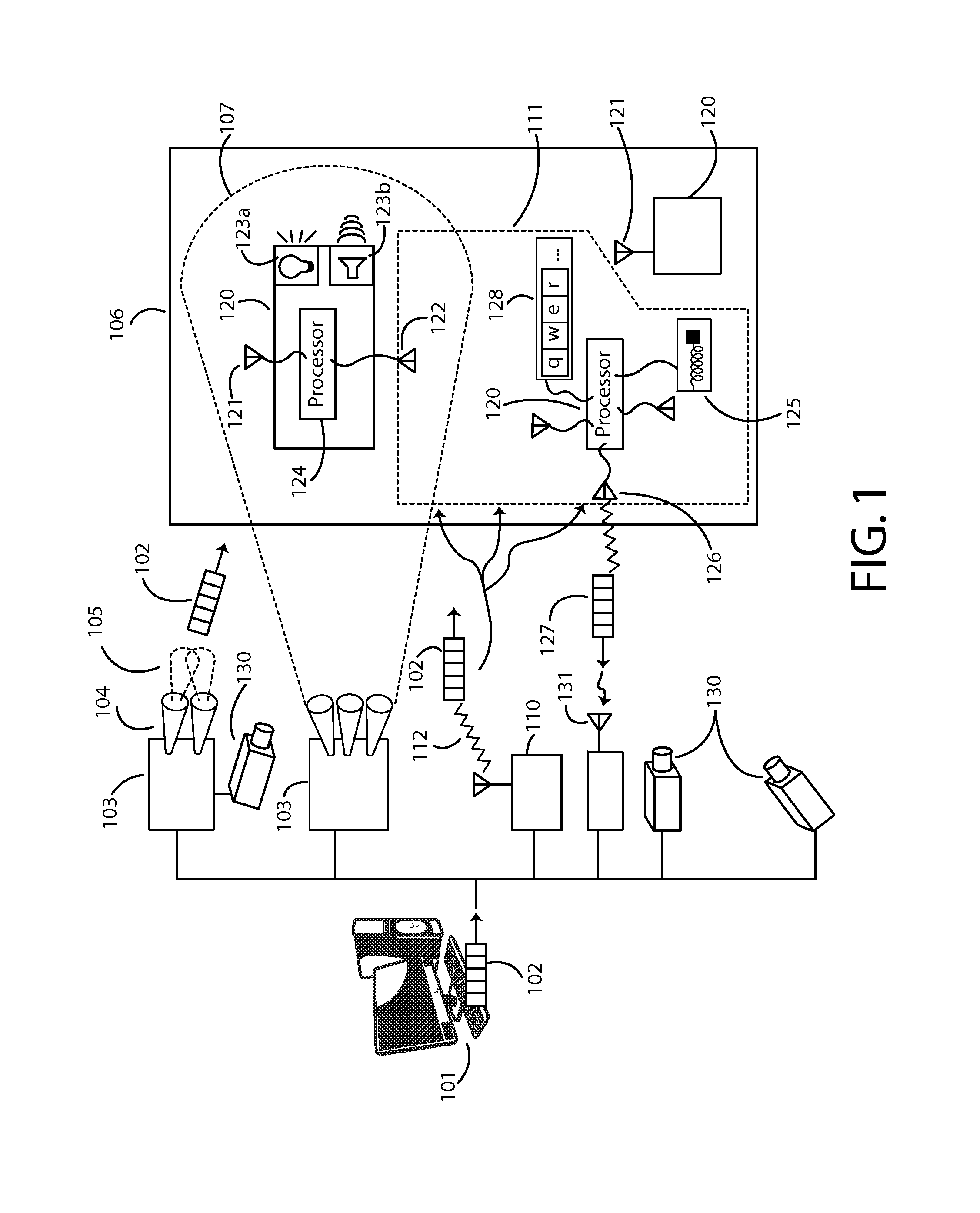
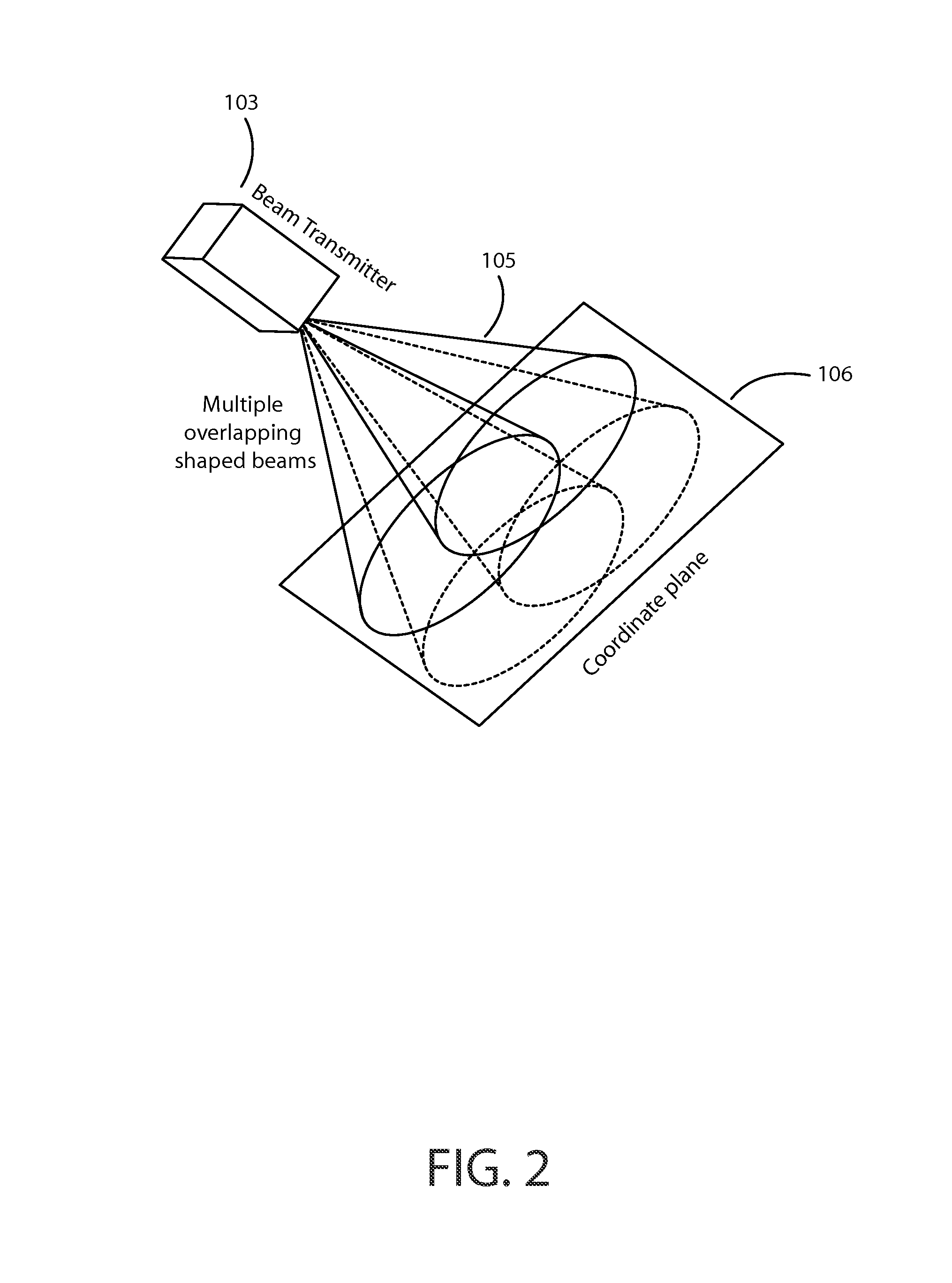
ActiveUS9060346B1Efficient and effectiveSimple calculationPosition fixationSubstation equipmentGraphicsShaped beam
Enables a local positioning and response system that allows devices in a defined area to determine their local positions in the area, and to generate individual responses based on their positions, for example based on broadcast messages. Responses can include light, sound, shock, vibration, temperature or any other physical signal. Positioning may use overlapping shaped beam signals that permit each device to determine its local position. Response to broadcast messages with local position dependency enables efficient communication with potentially thousands or millions of response units over limited bandwidth channels. Efficient communication may also be supported by messages containing high-level graphical primitives, with devices determining their individual contributions to an aggregate image. The system may also provide correction for image distortions. Applications include stadium light or sound shows, virtual fences, feedback on performance that requires specific motions or positions, and contests for event spectators.
Owner:RYPPLZZ INC
Local positioning and response system
ActiveUS20150156745A1Efficient and effectiveSimple calculationPosition fixationBeacon systemsGraphicsShaped beam
Enables a local positioning and response system that allows devices in a defined area to determine their local positions in the area, and to generate individual responses based on their positions, for example based on broadcast messages. Responses can include light, sound, shock, vibration, temperature or any other physical signal. Positioning may use overlapping shaped beam signals that permit each device to determine its local position. Response to broadcast messages with local position dependency enables efficient communication with potentially thousands or millions of response units over limited bandwidth channels. Efficient communication may also be supported by messages containing high-level graphical primitives, with devices determining their individual contributions to an aggregate image. The system may also provide correction for image distortions. Applications include stadium light or sound shows, virtual fences, feedback on performance that requires specific motions or positions, and contests for event spectators.
Owner:RYPPLZZ INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com