Method for defending border gateway protocol prefix hijacking attack
A border gateway protocol and prefix technology, applied to electrical components, public keys for secure communication, transmission systems, etc., can solve problems such as inability to authenticate connectivity, incomplete security protection, and inability to prevent IP prefix hijacking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The present invention will be further described below in conjunction with accompanying drawing:
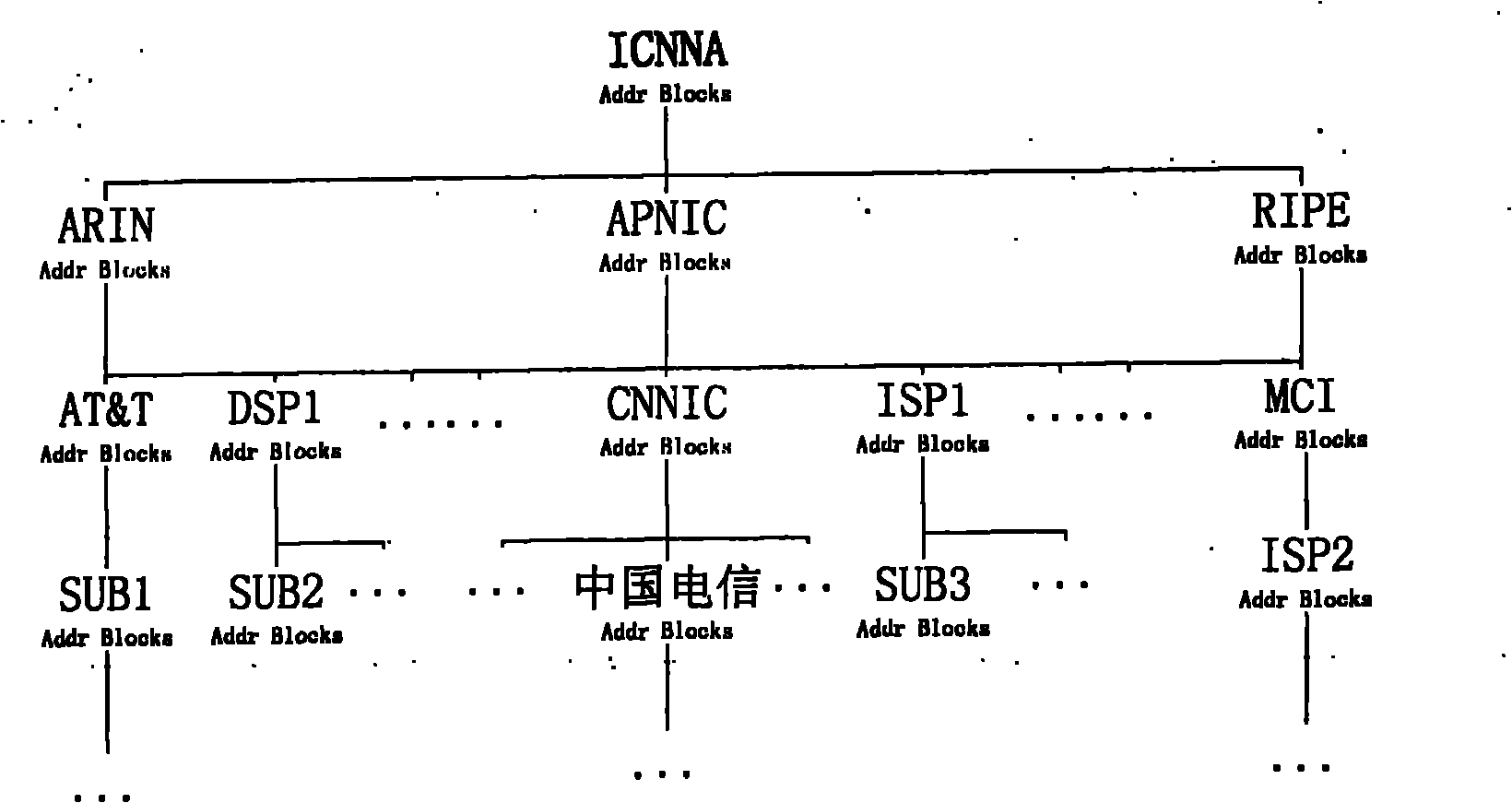
[0065] 1. Hierarchical allocation system of PKI based on IP prefix and AS number
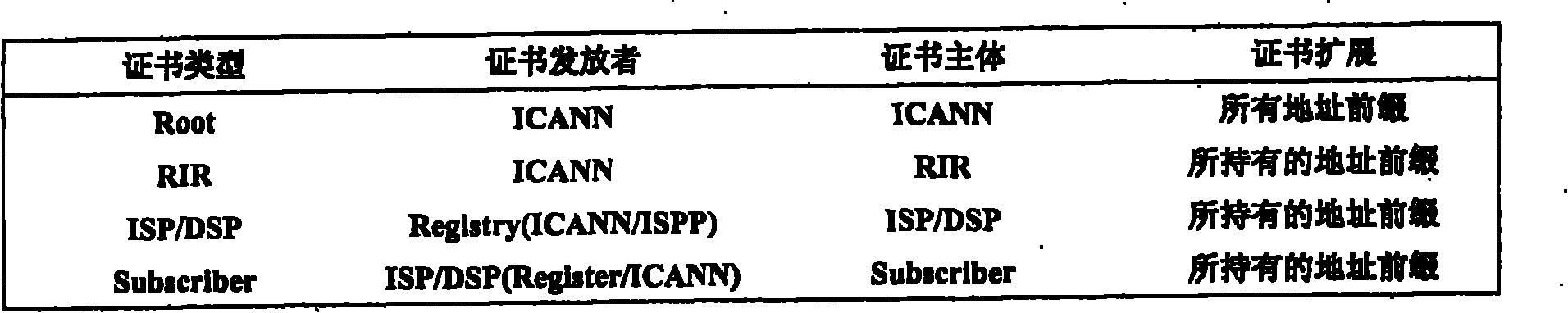
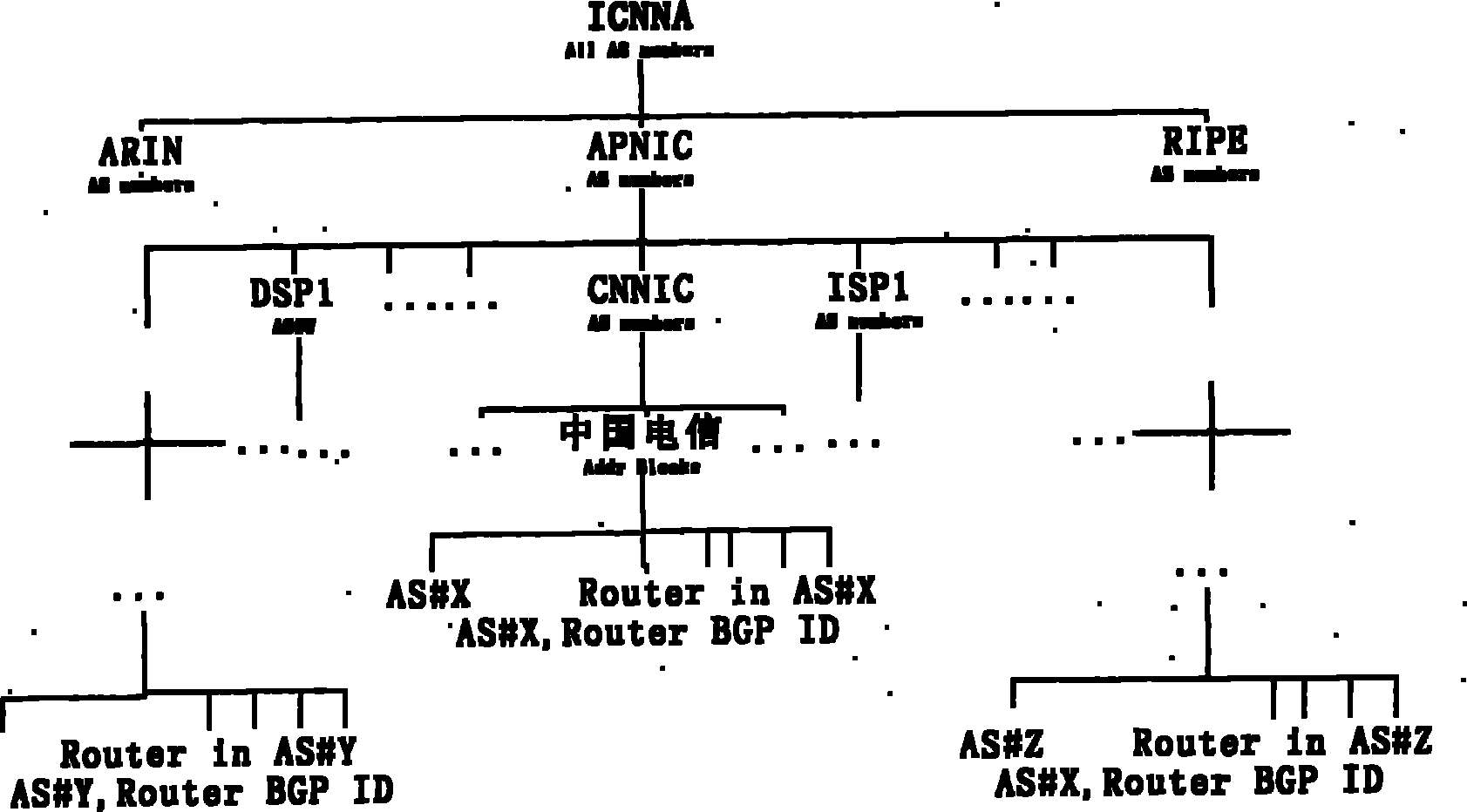
[0066] The establishment of the PKI hierarchical allocation system based on IP prefixes and AS numbers is based on the existing IP address and AS number allocation agent system, which does not consider the "trust" problem encountered at the beginning of the new PKI, which saves a lot of trouble in the creation process . This method needs to use the following two PKIs to solve the certificate distribution of IP prefixes and AS numbers, namely: one is used to distribute certificates representing the ownership of IP prefixes; the other is responsible for the distribution of certificates representing the ownership of AS numbers and the binding between AS numbers and routers certificate of relationship.
[0067] IP prefix ownership certificate distribution PKI hierarchy and certificate style are...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com