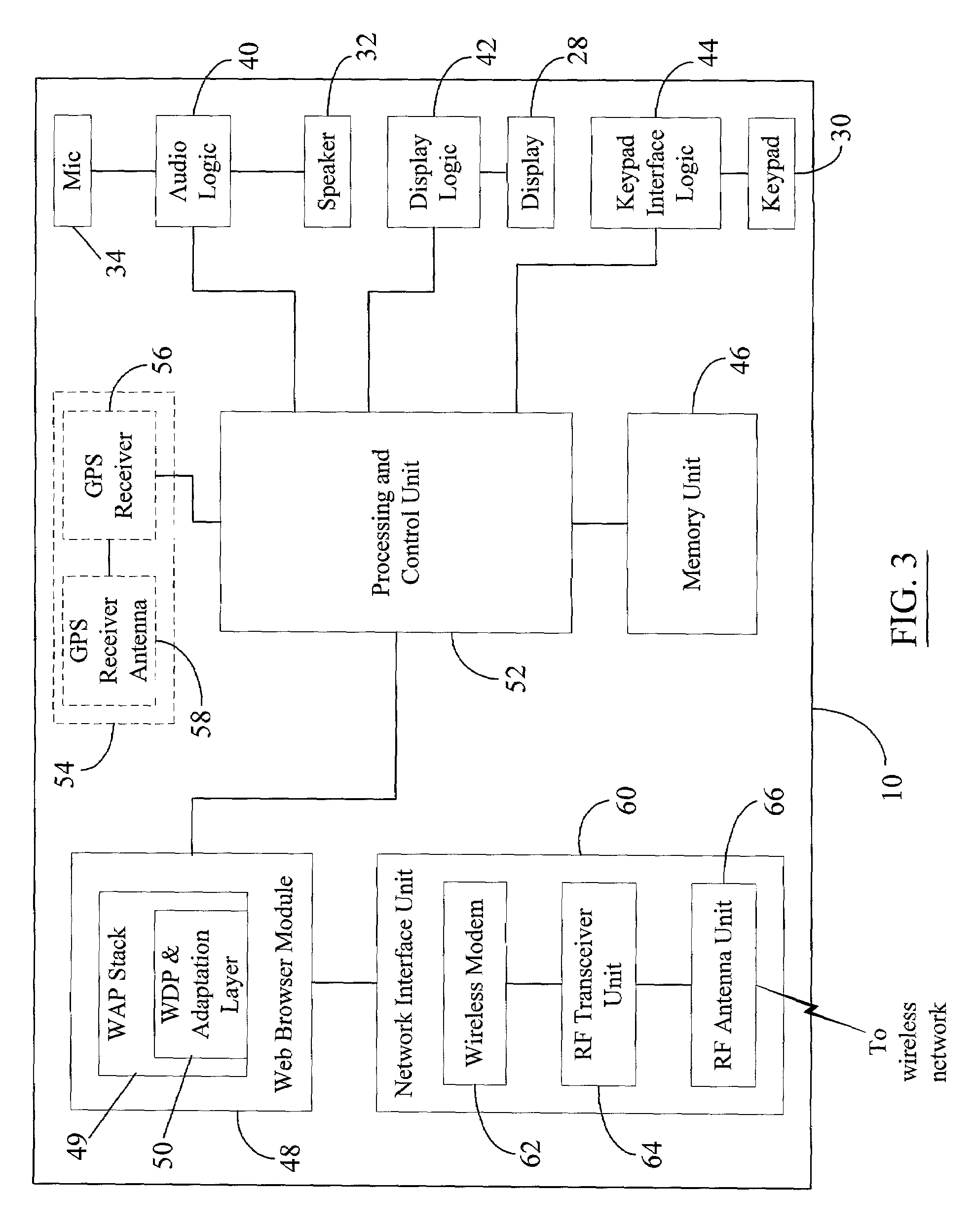
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
906 results about "Internet service provider" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An Internet service provider (ISP) is an organization that provides services for accessing, using, or participating in the Internet. Internet service providers can be organized in various forms, such as commercial, community-owned, non-profit, or otherwise privately owned.
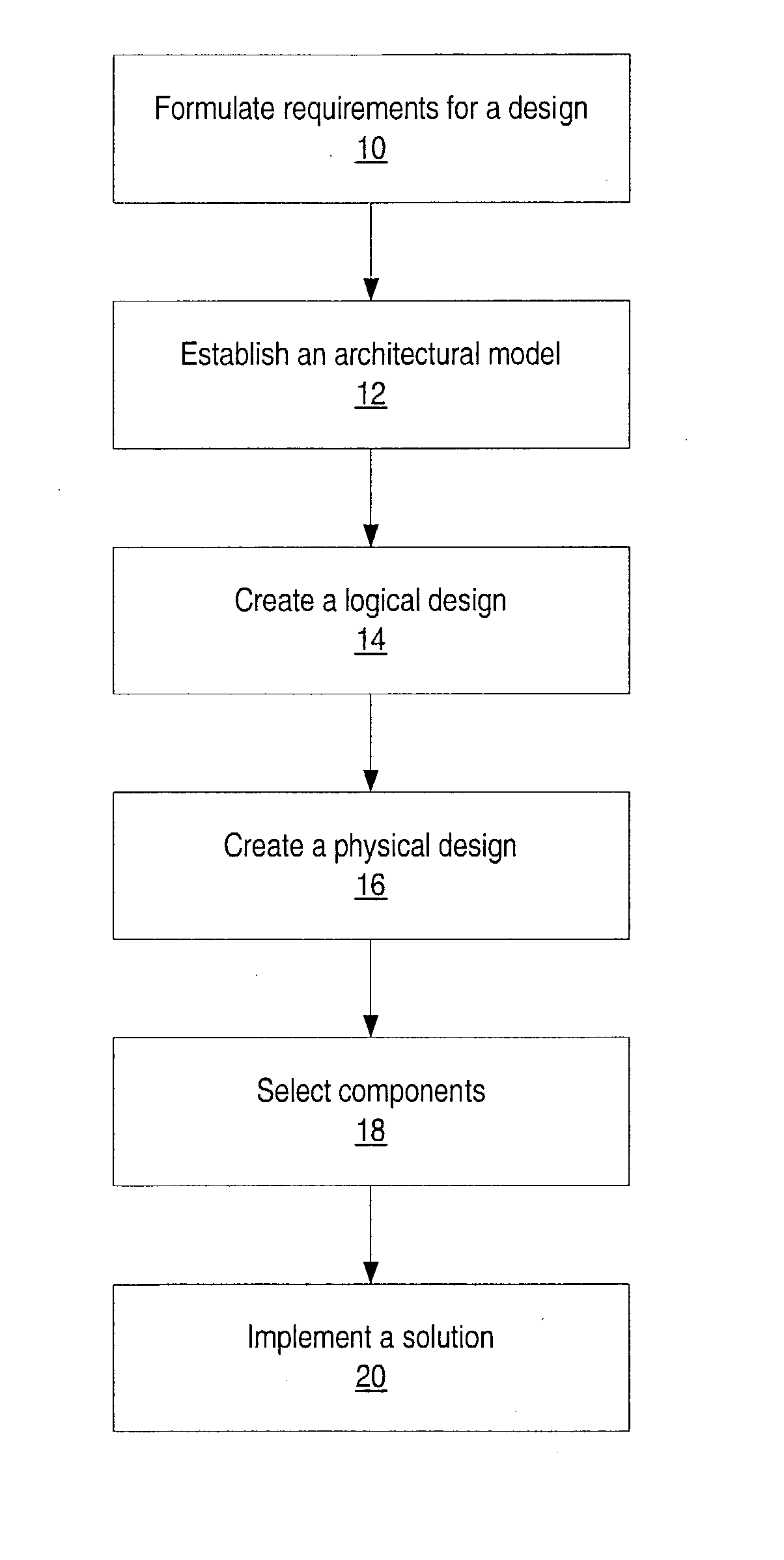
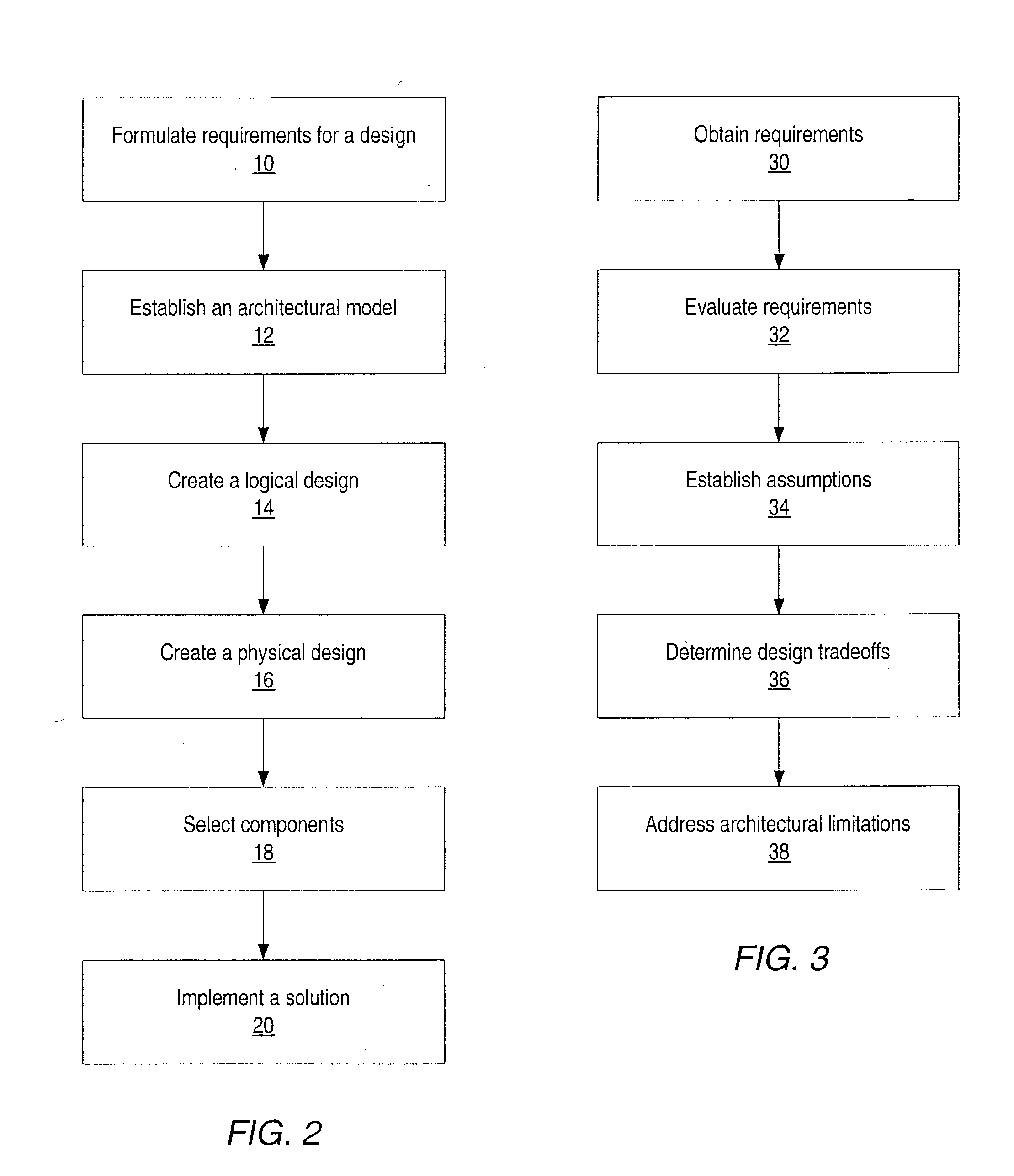
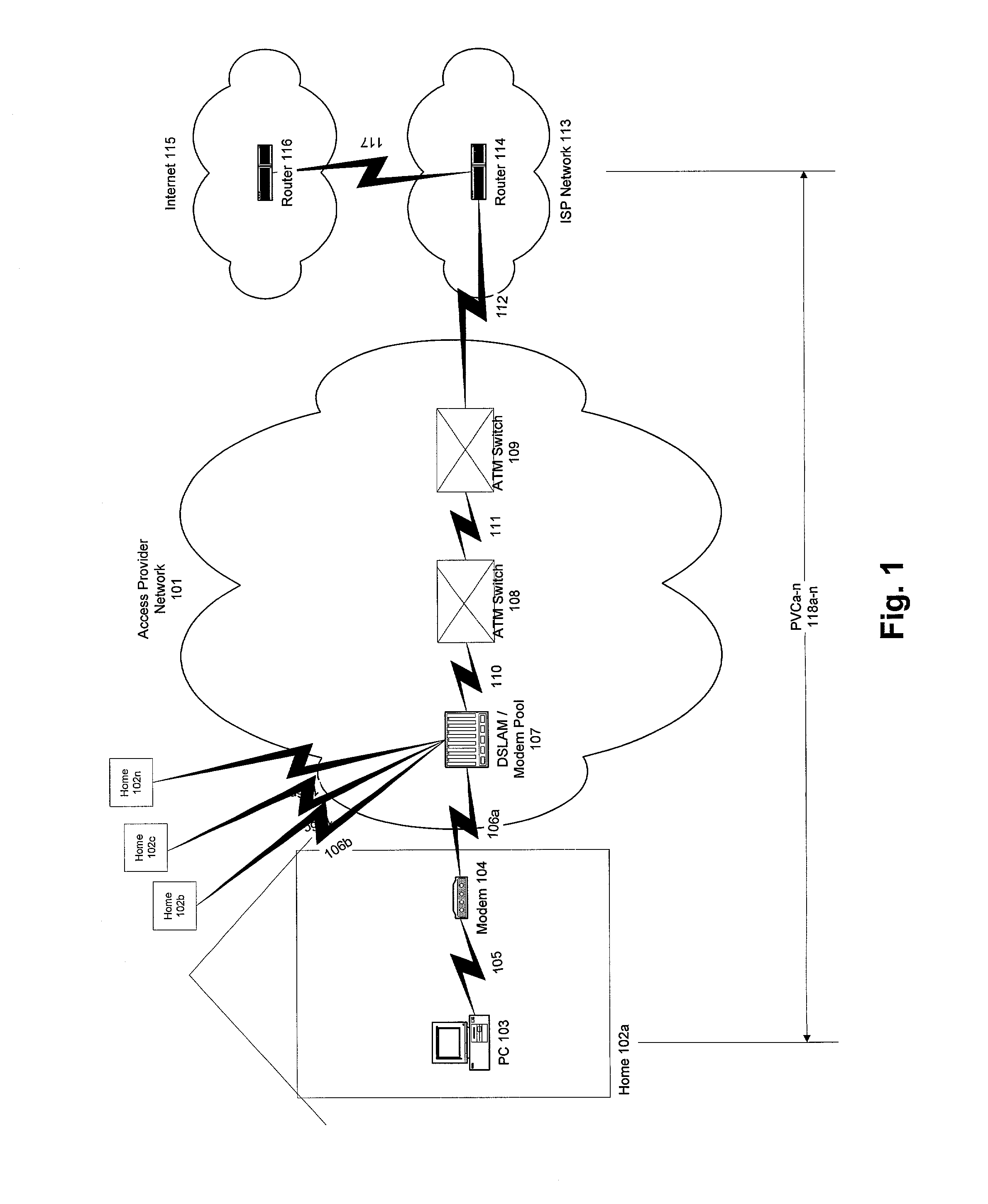
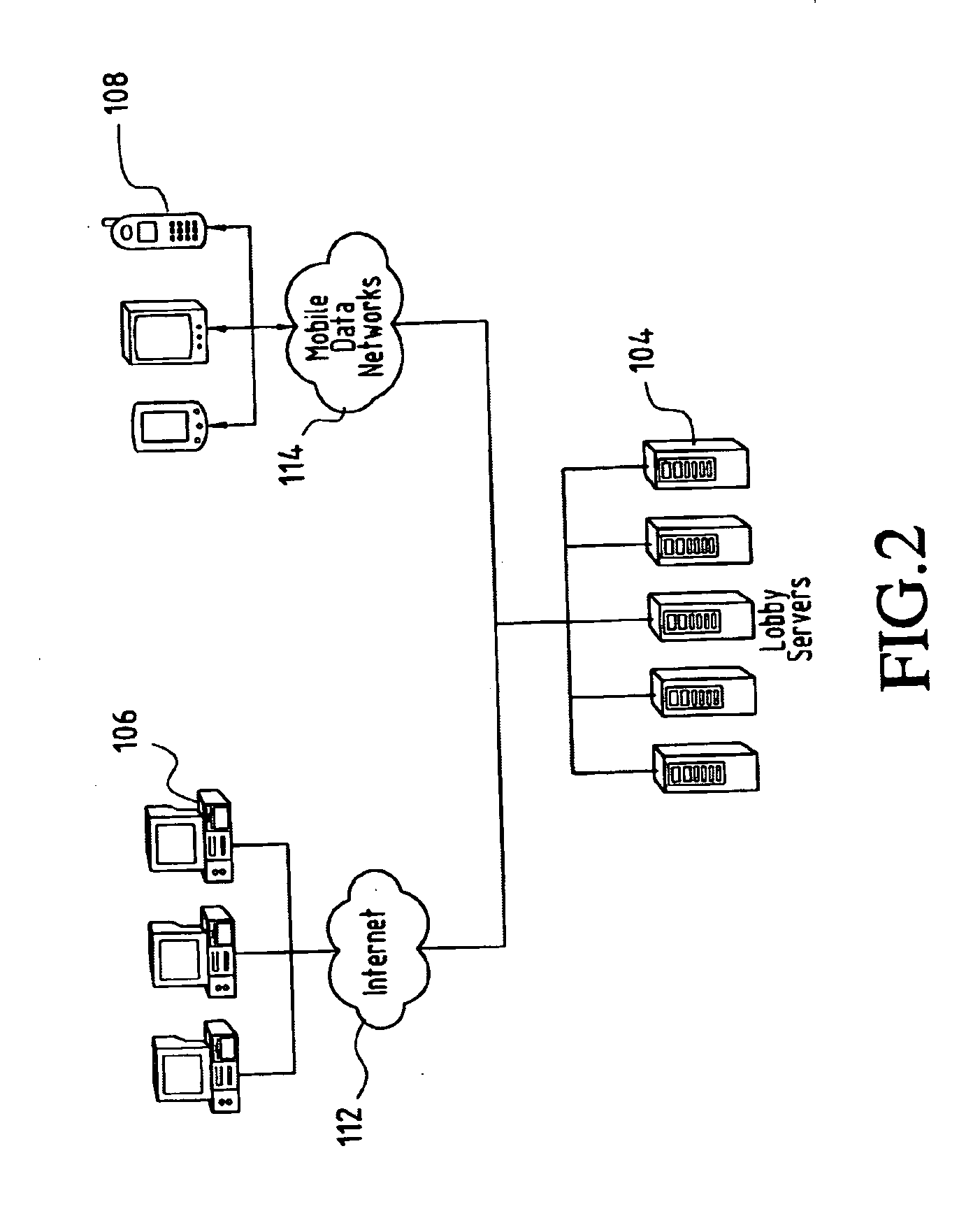
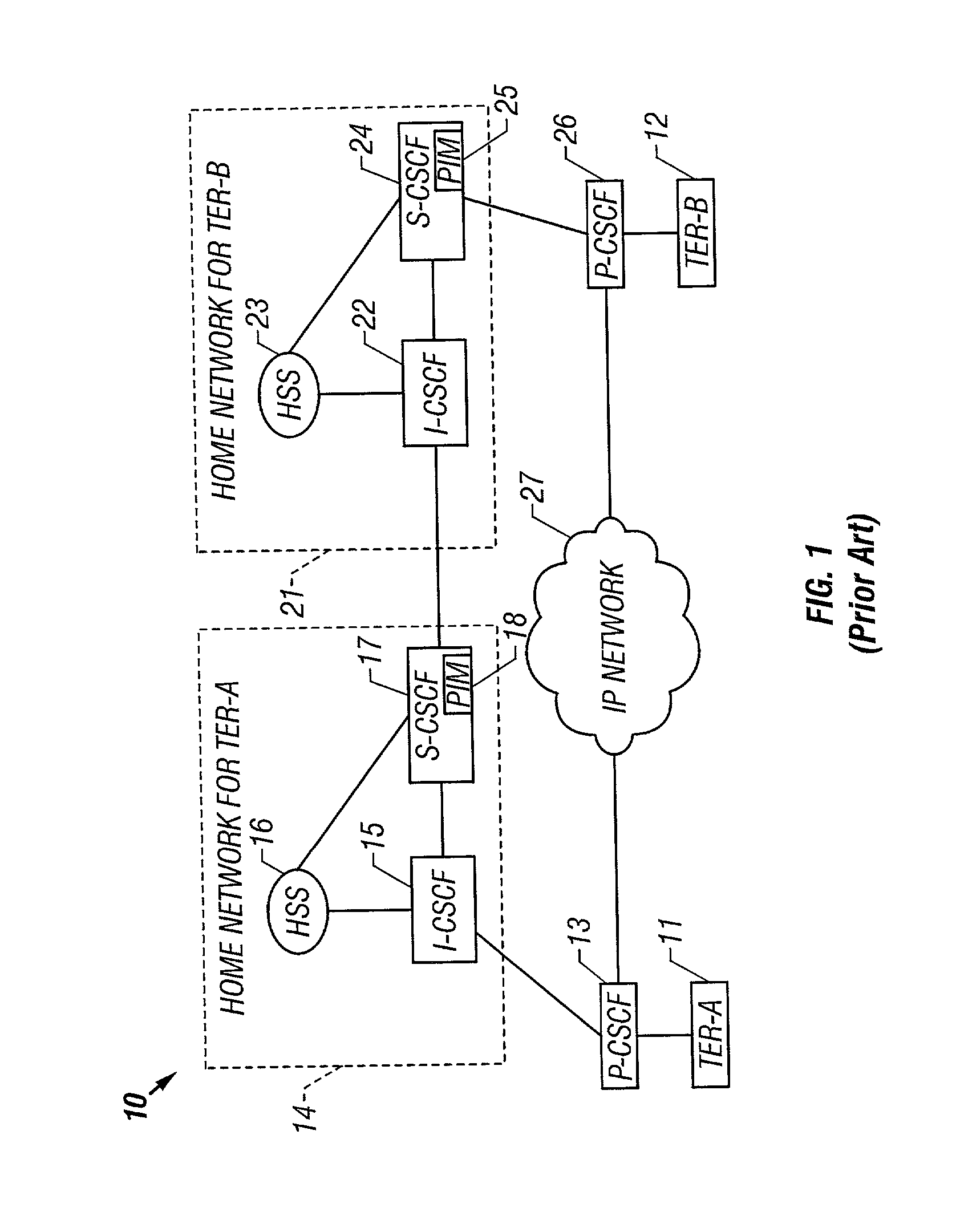
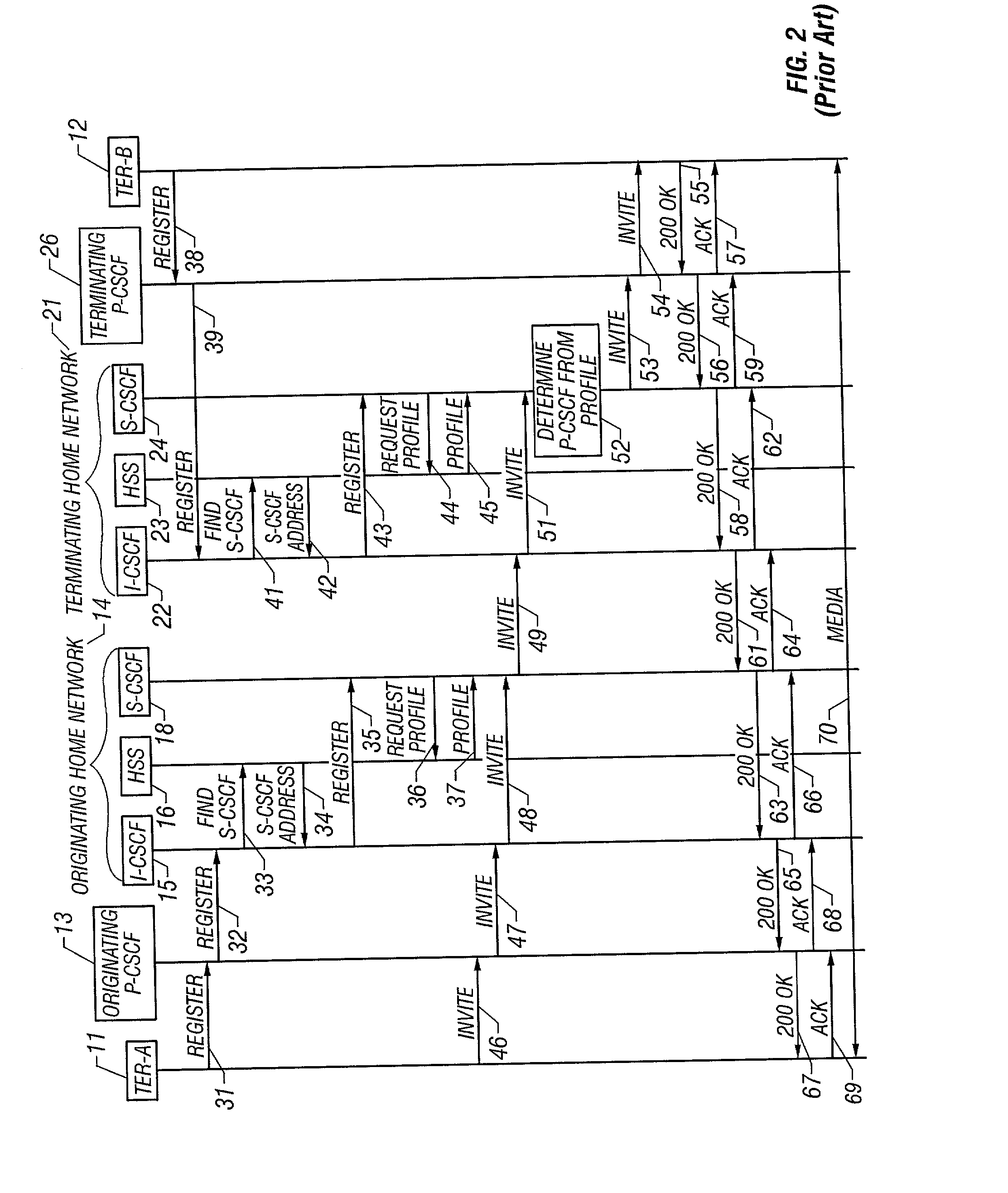
System and method for designing, developing and implementing internet service provider architectures
ActiveUS20030172145A1Metering/charging/biilling arrangementsDigital computer detailsComputer architectureService provision
System and method for designing, developing and implementing Internet Service Provider (ISP) architectures. One embodiment of a method for designing and implementing ISP architectures may include formulating a set of design requirements for an ISP architecture, establishing an architectural model for the ISP architecture using the set of design requirements, generating a logical design for the ISP architecture from the architectural model and the set of design requirements, and generating a physical design for the ISP architecture using the architectural model and the logical design. One embodiment may also include selecting one or more components of the ISP architecture and implementing the ISP architecture according to the logical design and the physical design. In one embodiment the system and method for designing, developing and implementing ISP architectures may be used to design, develop and implement an N-tiered ISP architecture.
Owner:SUN MICROSYSTEMS INC
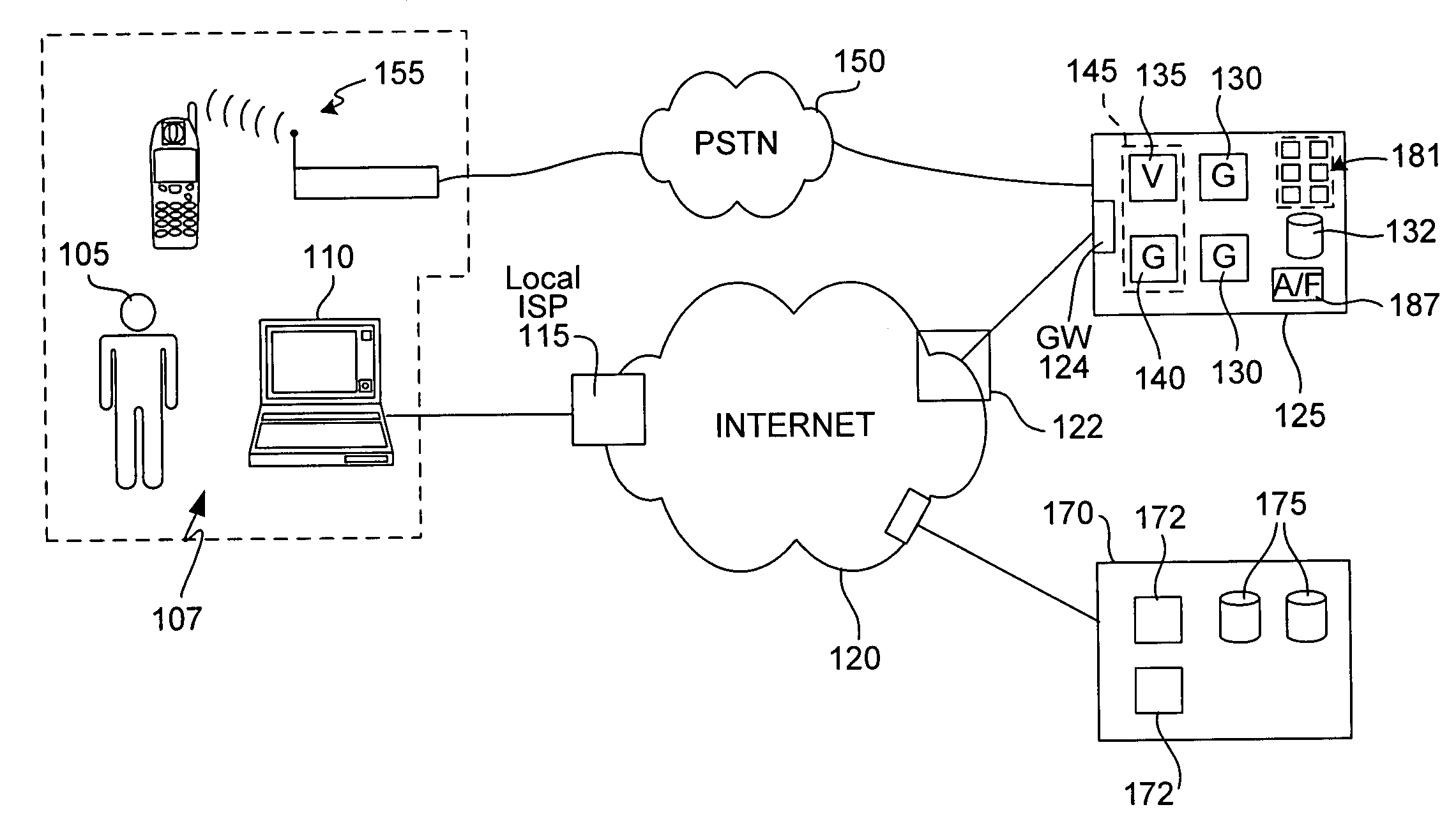
Method and apparatus for acquiring, maintaining, and using information to be communicated in bar code form with a mobile communications device
InactiveUS6736322B2Convenient acquisition and maintenance and useCharacter and pattern recognitionIndividual entry/exit registersBarcodeCommunication device
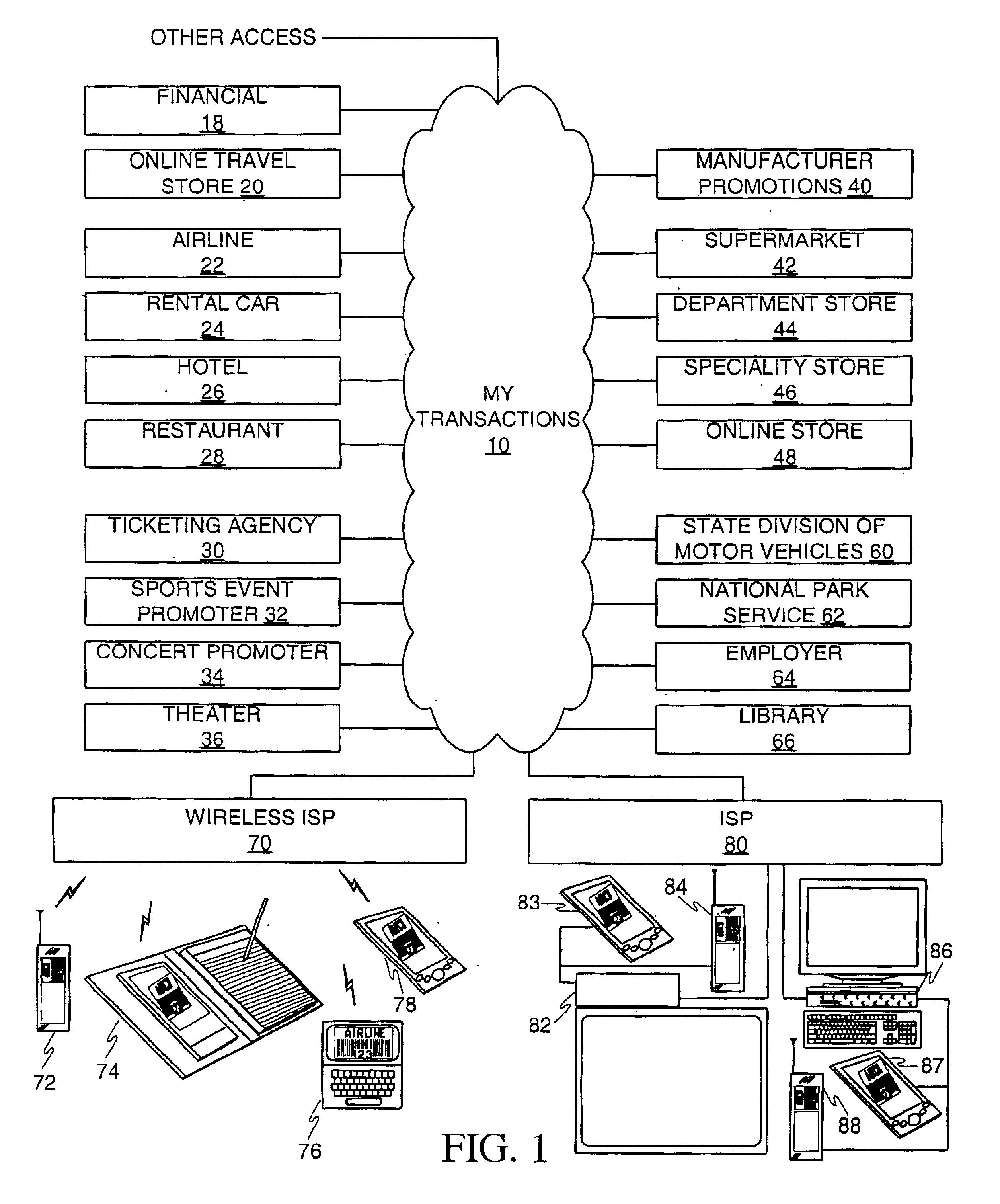
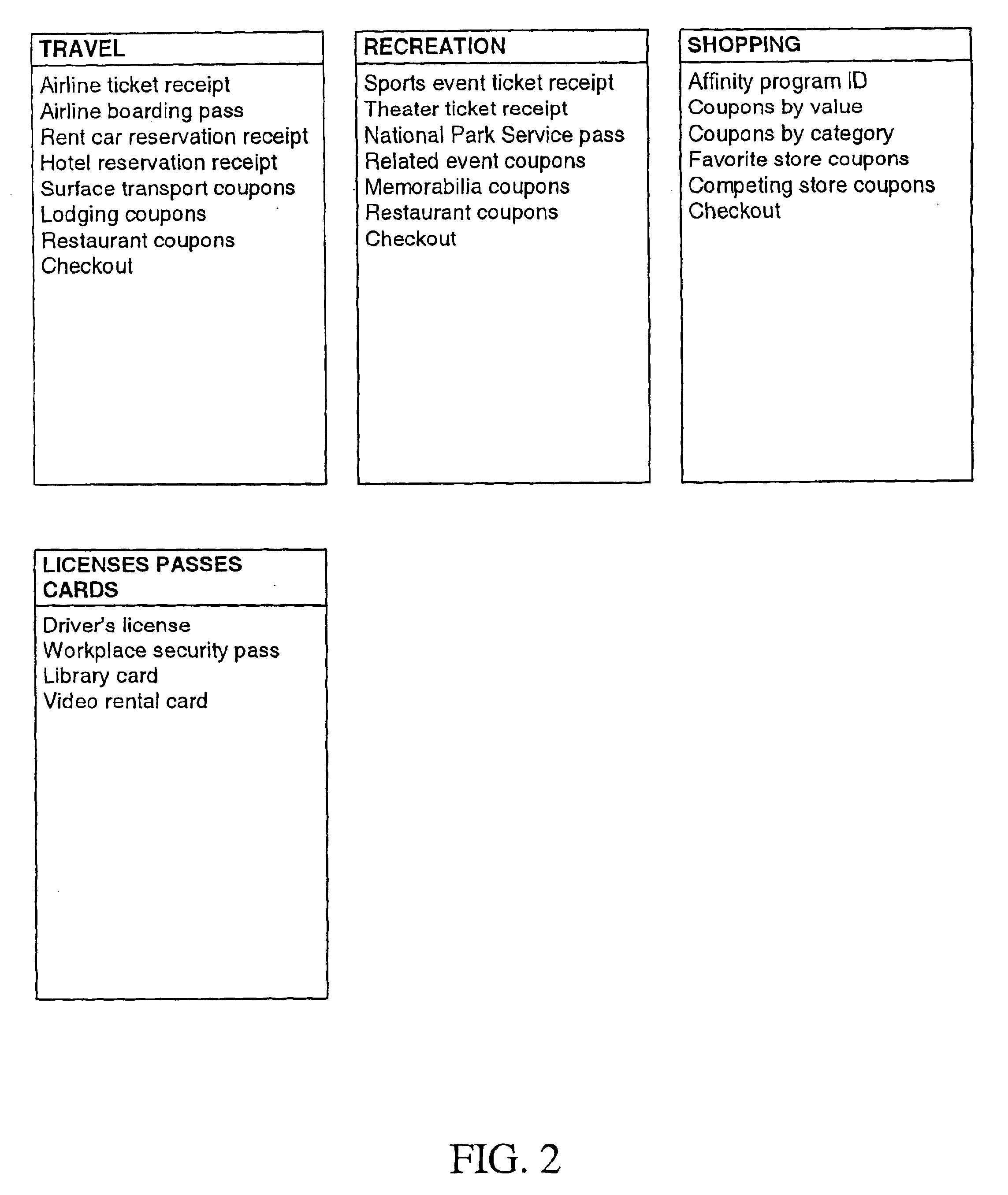
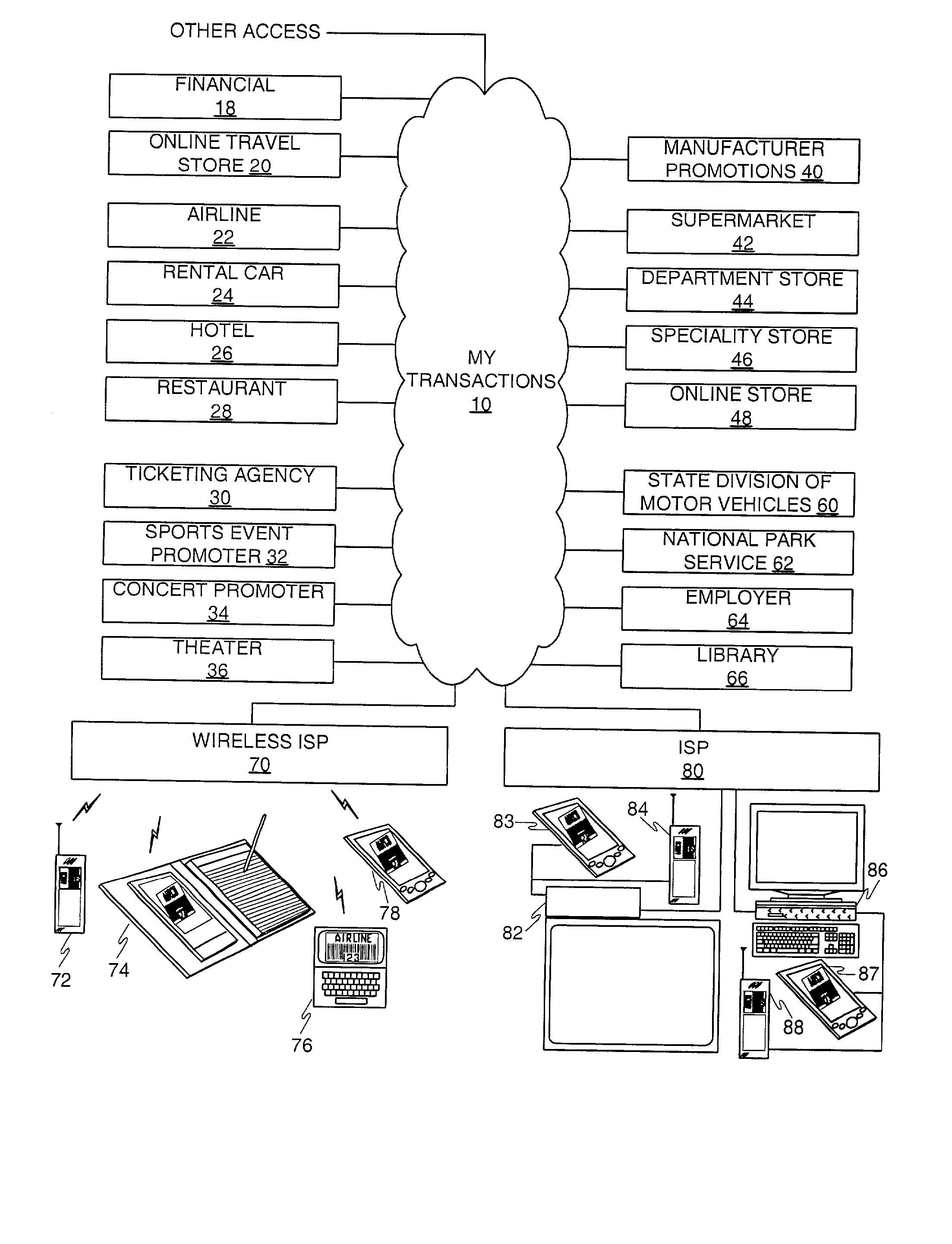
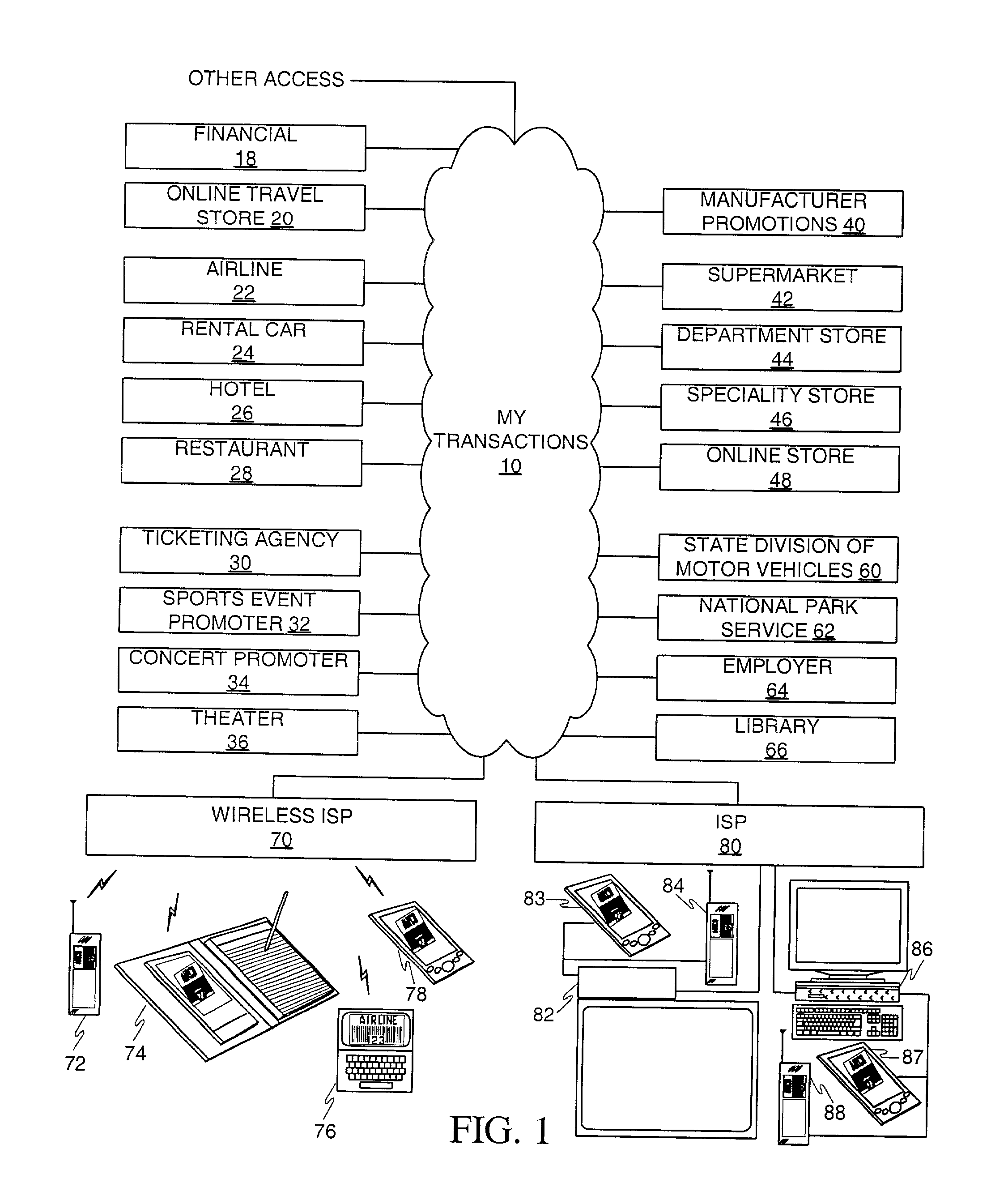
A user is provided with a secure database containing information in diverse categories that relates to the user and that may be represented at least in part in bar code form and communicated with light from a mobile communications device. The diverse information is obtained from any combination of a variety of vendor and governmental computer systems, internet service providers, and communications devices. The user has access to the database using a mobile communications device for displaying, managing, and entering information, and for communicating information in bar code form with light. The user first selects the category that contains the specific item of information, and then selects the specific item of information. The specific item of information then is communicated in bar code form with light from the mobile communications device for scanning by a bar code scanner to obtain the desired good or service.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for acquiring, maintaining, and using information to be communicated in bar code form with a mobile communications device
InactiveUS20020060246A1Convenient acquisition and maintenance and useCharacter and pattern recognitionIndividual entry/exit registersBarcodeCommunication device
A user is provided with a secure database containing information in diverse categories that relates to the user and that may be represented at least in part in bar code form and communicated with light from a mobile communications device. The diverse information is obtained from any combination of a variety of vendor and governmental computer systems, internet service providers, and communications devices. The user has access to the database using a mobile communications device for displaying, managing, and entering information, and for communicating information in bar code form with light. The user first selects the category that contains the specific item of information, and then selects the specific item of information. The specific item of information then is communicated in bar code form with light from the mobile communications device for scanning by a bar code scanner to obtain the desired good or service.
Owner:SAMSUNG ELECTRONICS CO LTD
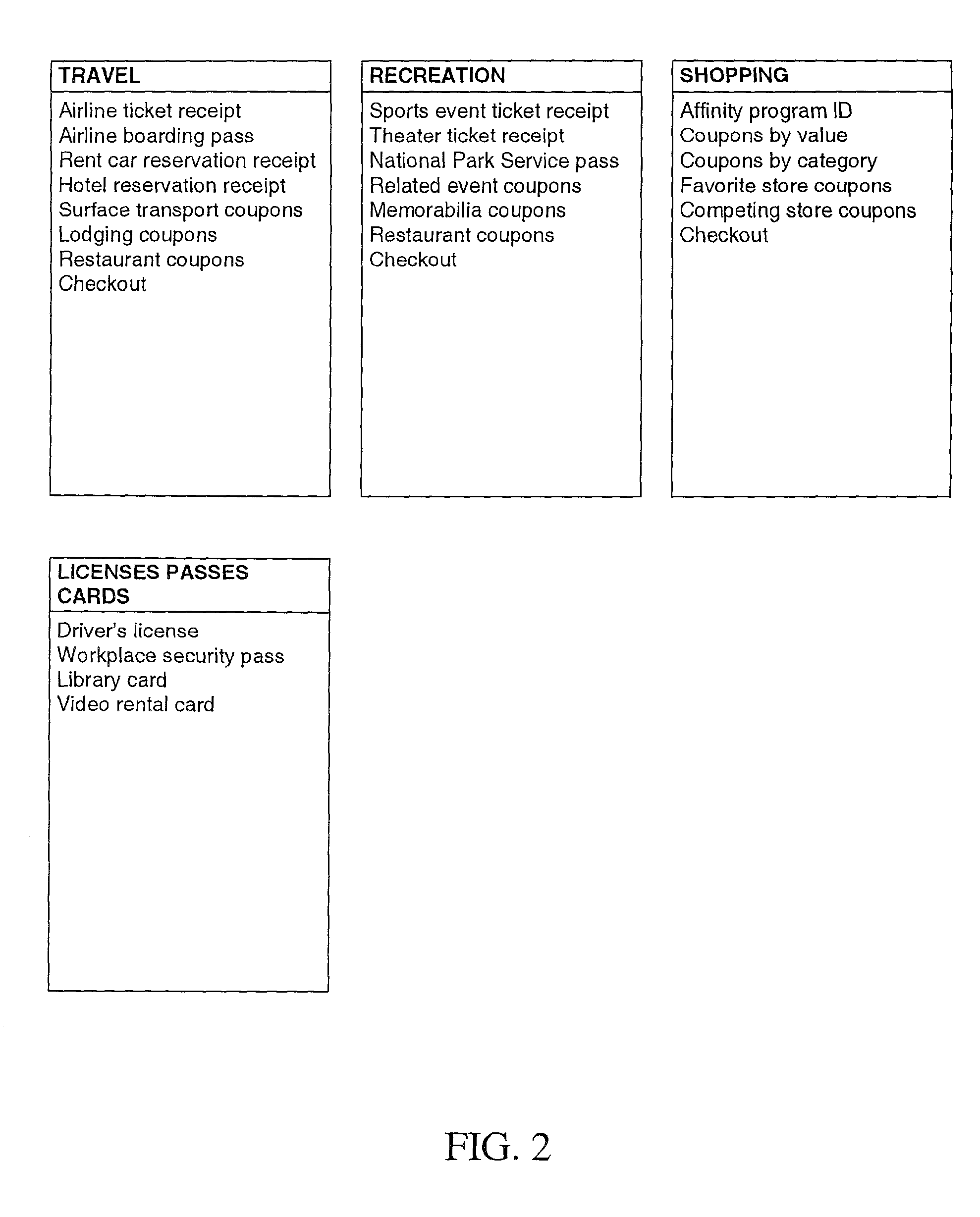
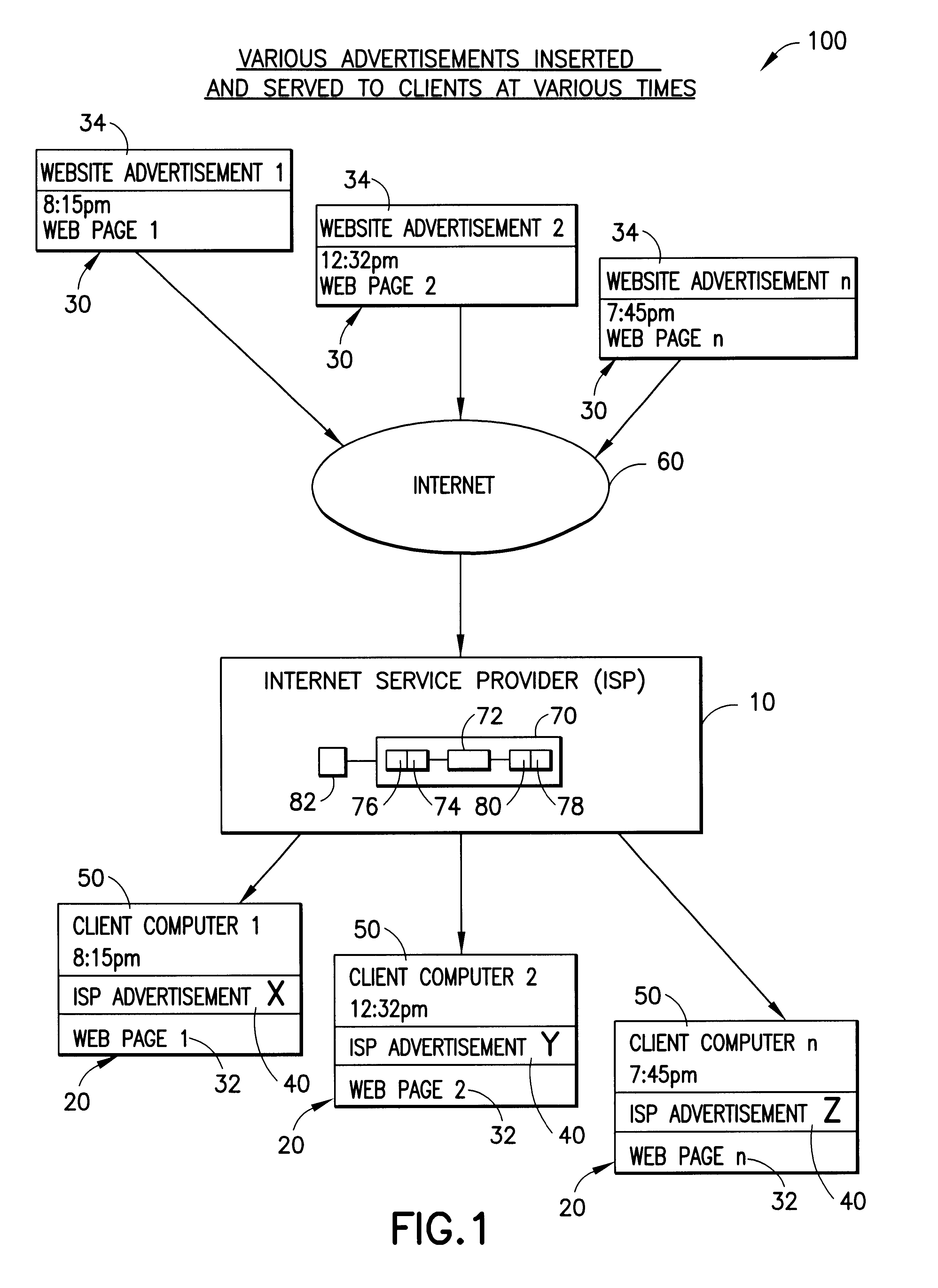
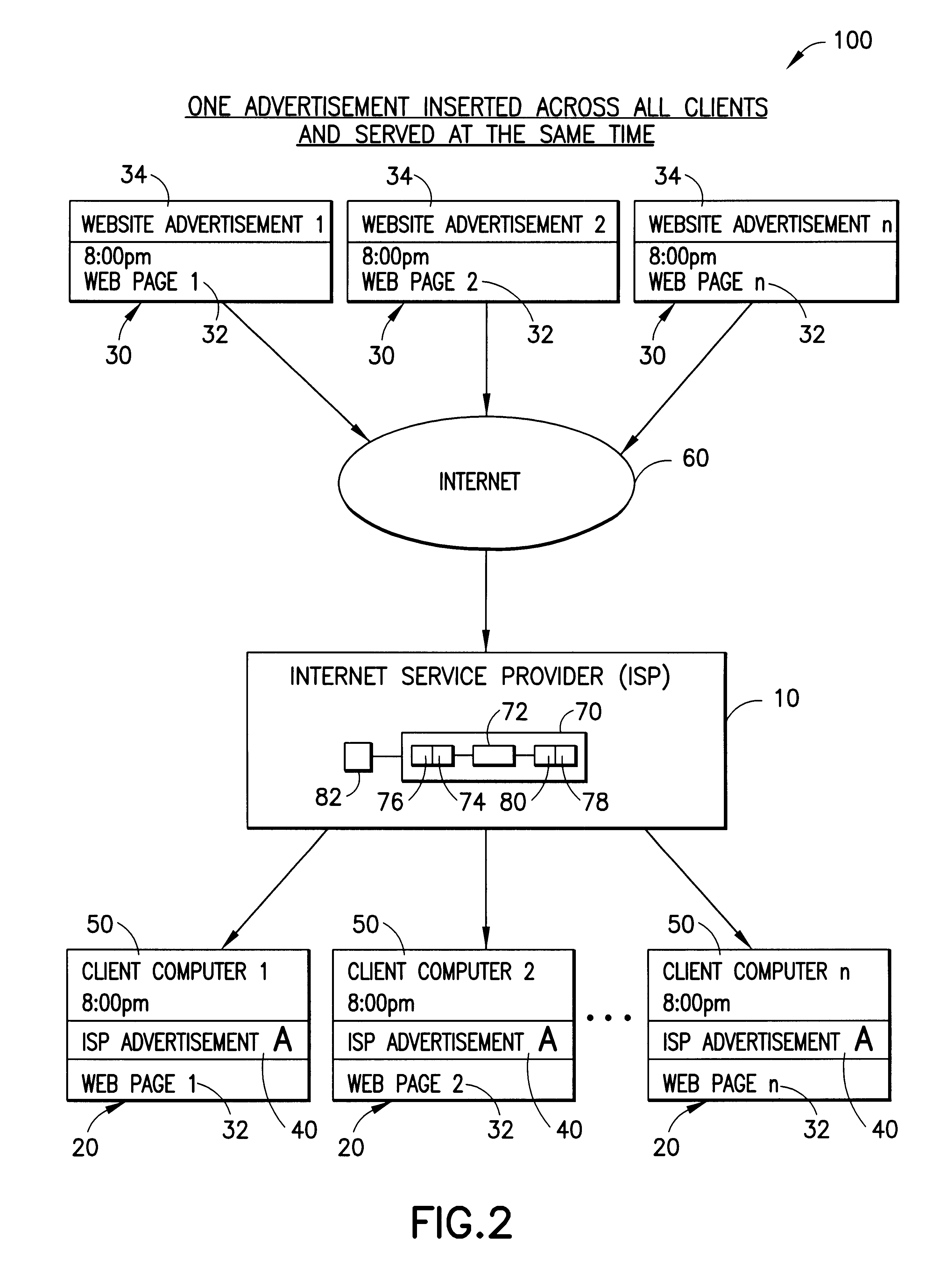
Internet service provider advertising system
InactiveUS6339761B1Advertising dollars are well-spentAdvertisementsSpecial data processing applicationsService provisionDemographic data
The present invention advantageously provides to Internet Service Providers (ISP) precise control over who receives an advertisement. Thus, in accordance with the present invention, an ISP provider may now offer advertisers precision advertising. An ISP provider has access to precise demographic data on each of the ISP's customers. The ISP provider also has access to data on the periods of usage, including the type of customers accessing the Internet during such periods of usage. With this information, which is available only to the ISP provider, a profile may be compiled by the ISP provider that provides precise information on the ISP customers (e.g., demographic data) and the periods of heaviest Internet access by the various different ISP customer groups (e.g., 20-35 year old males, retired persons, children, etc.).
Owner:SLINGSHOT TECH LLC
Location and user identification for online gaming
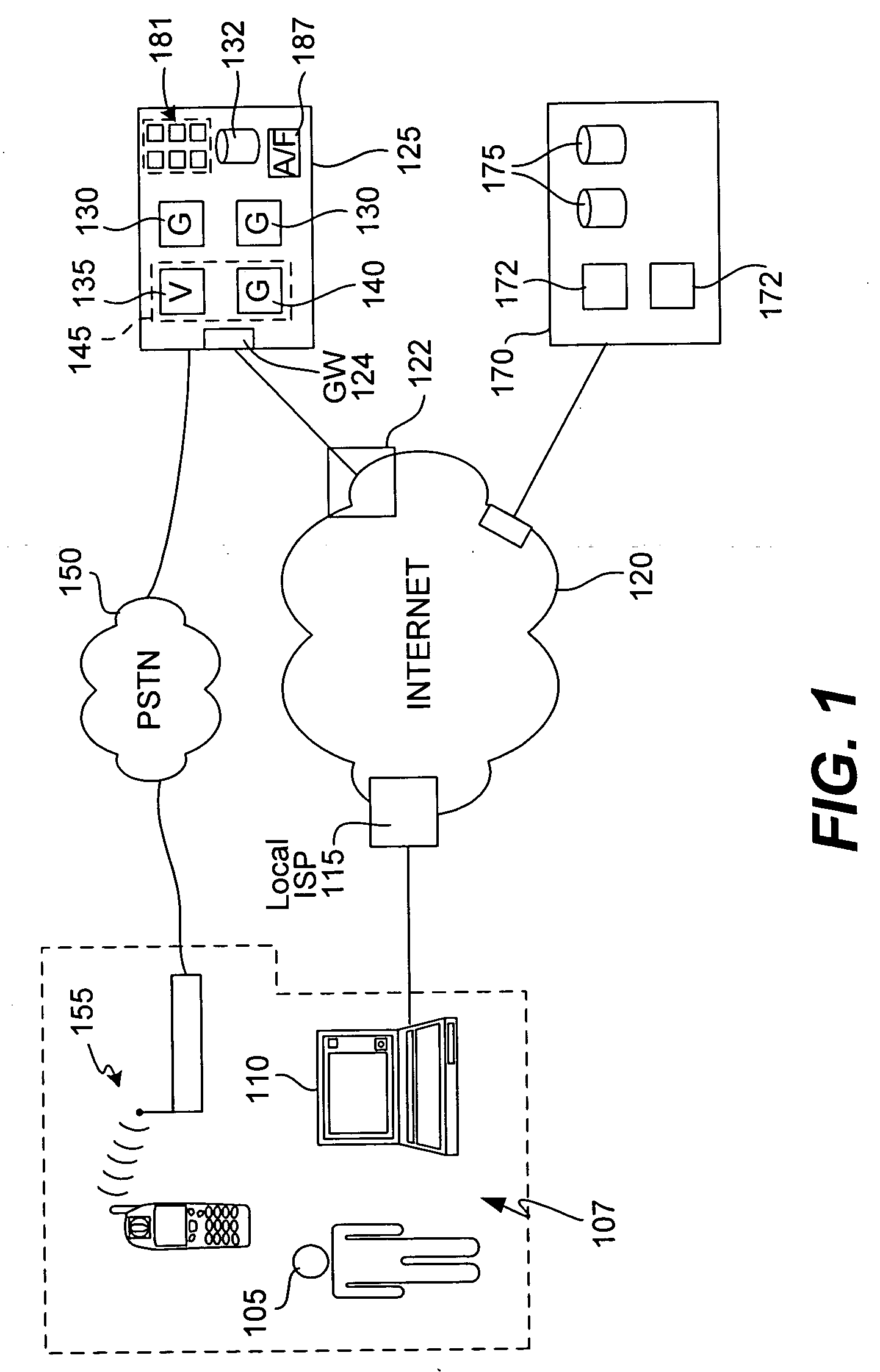
ActiveUS20060095790A1Digital data processing detailsComputer security arrangementsUser inputTelephone network
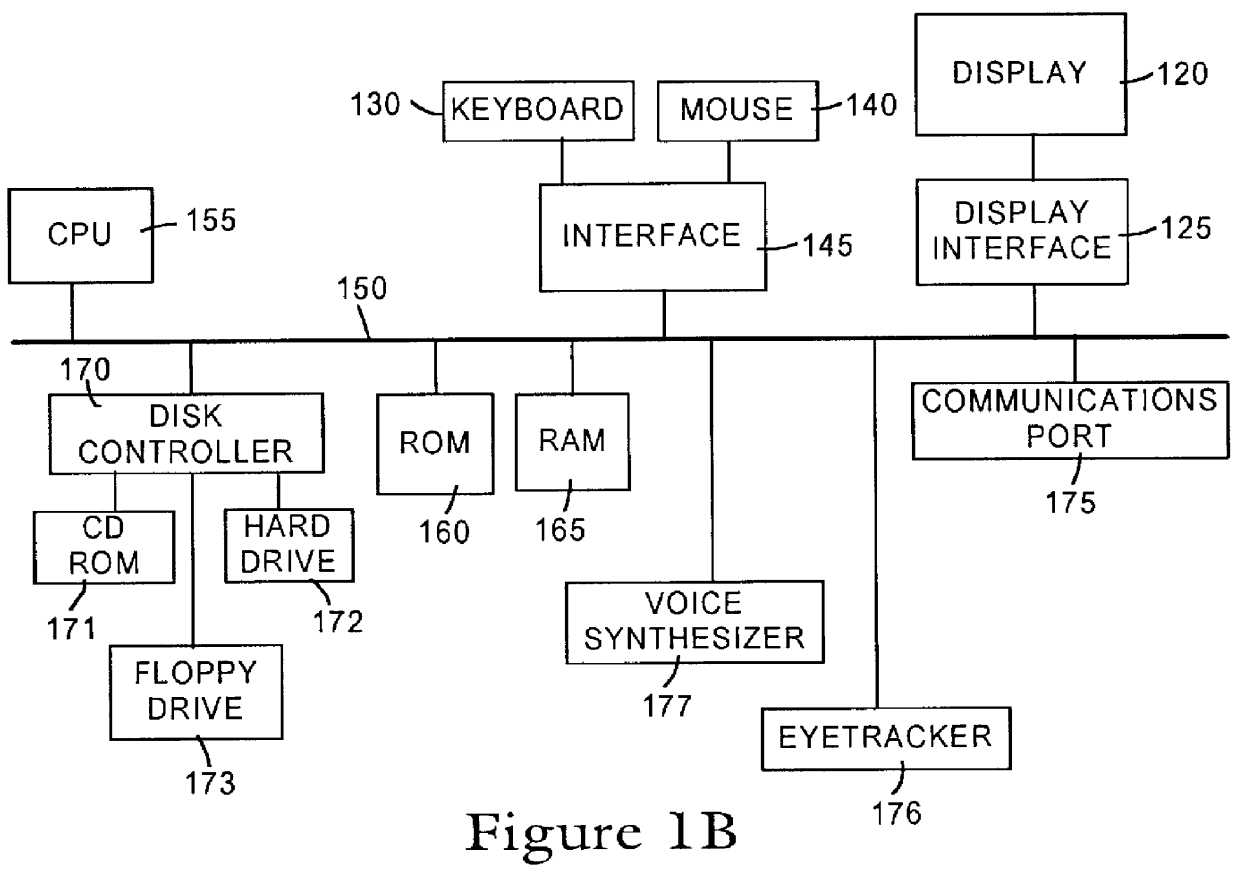
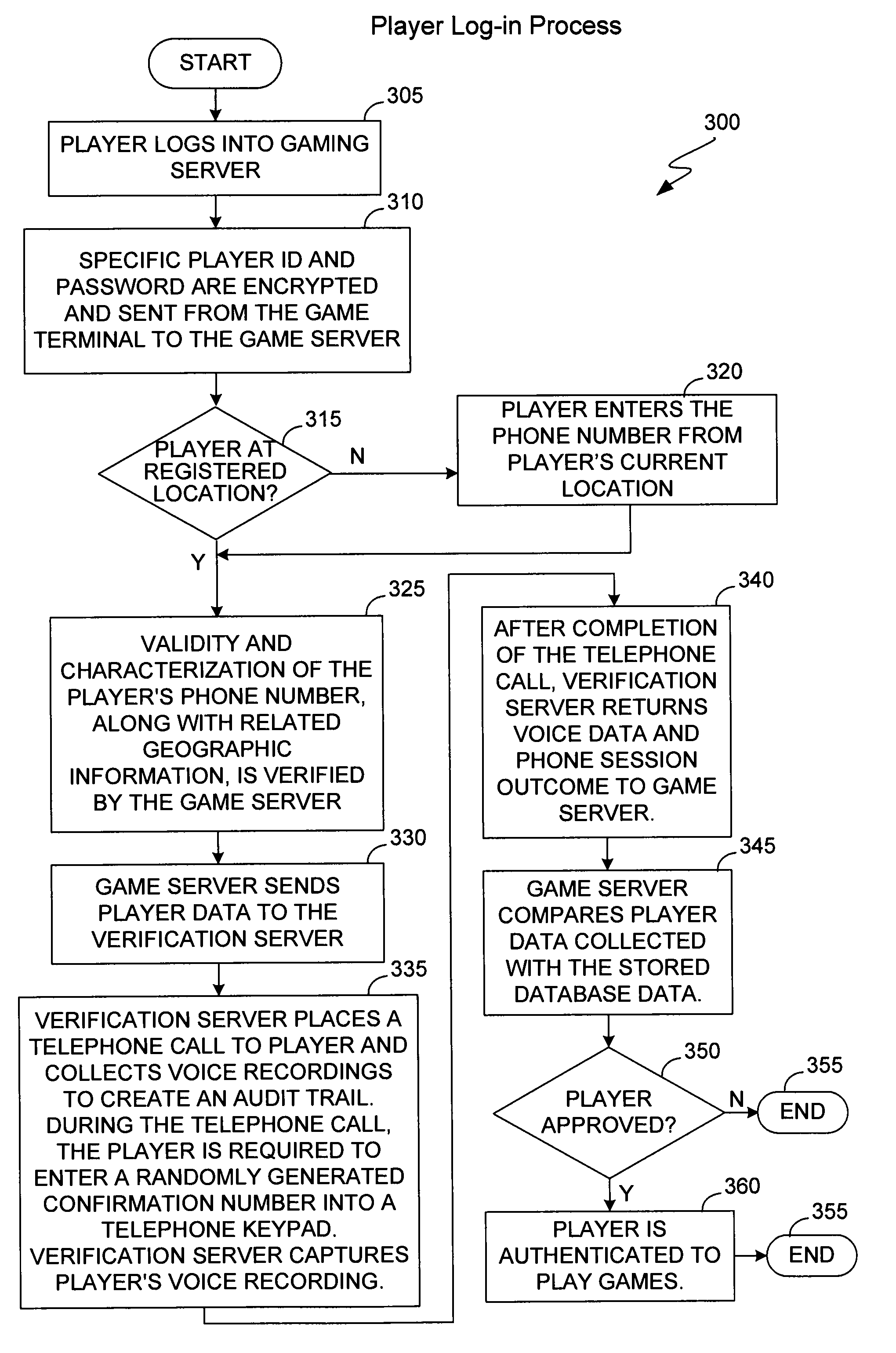
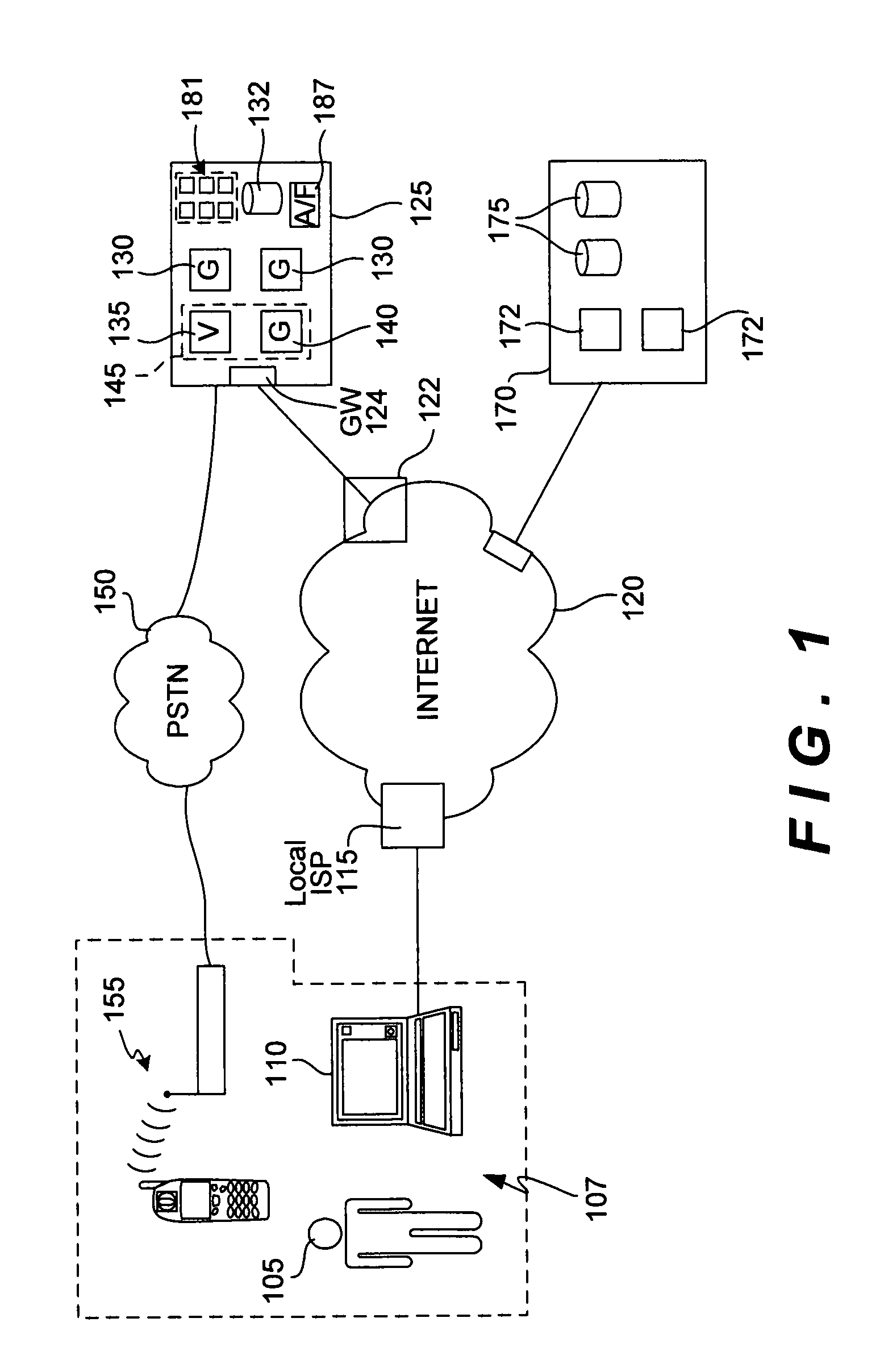
The present invention provides methods and devices for determining the location, identity and age of a user who desires to initiate a gaming session from an uncontrolled environment such as a home, a gaming kiosk or a hotel room. In some implementations, the user's location is determined in part by reference to a database of land telephone lines and corresponding addresses. The location may be verified by reference to a location determined by other methods, e.g., by determining the location of an Internet service provider's network device that is near a user's host device. In other implementations, the user's location is determined by information provided by a cellular telephone network. The user may be asked to input a confirmation number and / or make an oral response during a telephone call to a telephone number associated with the uncontrolled environment. These the oral response may be analyzed to verify the user's identity. The user may also be prompted to make statements verifying his or her identity, age, a maximum amount available for wagering or other statements, which are preferably recorded and stored.
Owner:IGT
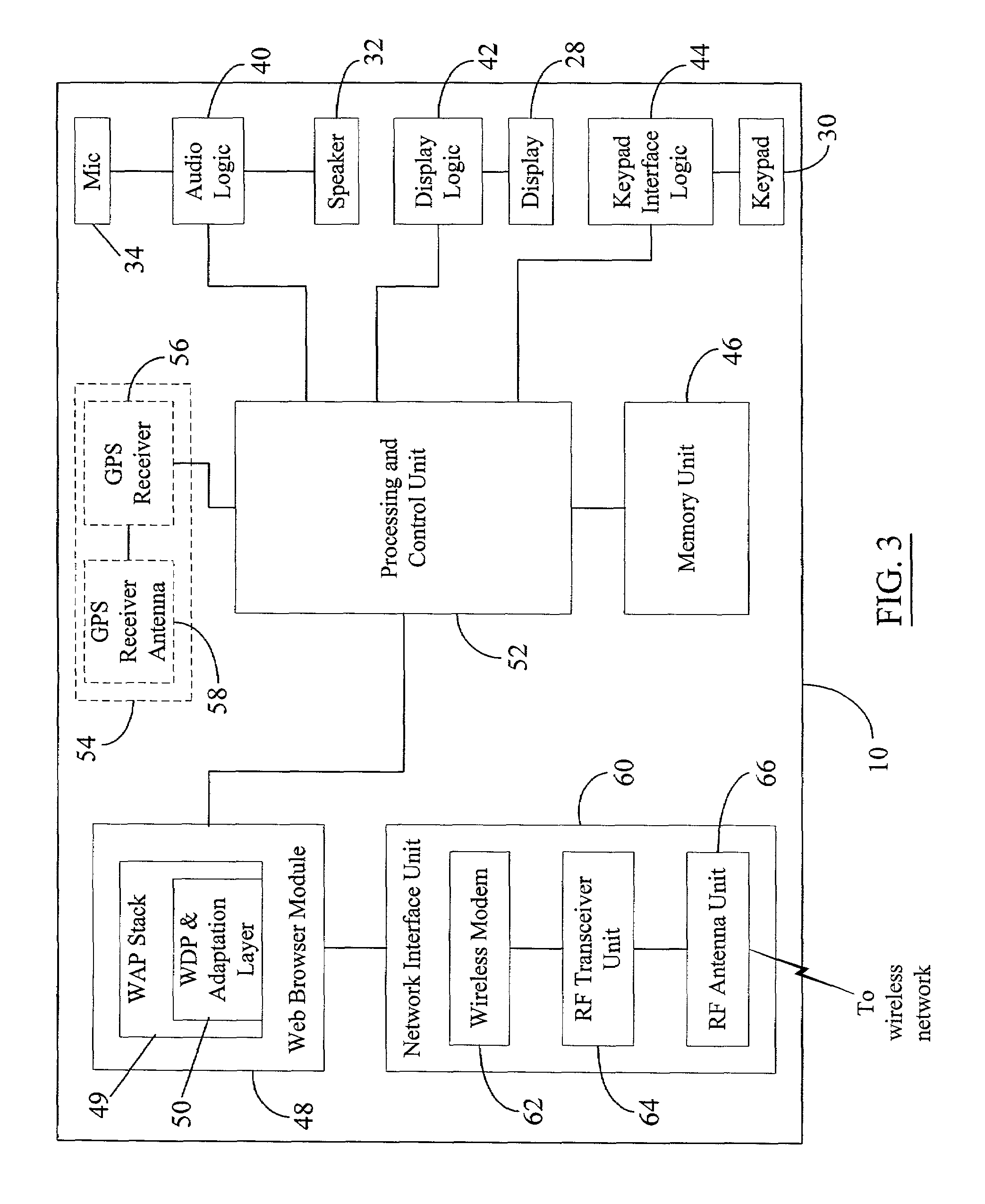
Hand-held portable WWW access terminal with visual display panel and GUI-based WWW browser program integrated with bar code symbol reader
InactiveUS6027024ACharacter and pattern recognitionSensing by electromagnetic radiationModem deviceService provision
A portable hand-held WWW access terminal for accessing HTML-encoded documents located on the WWW. The terminal includes a bar code symbol reader in a hand-supportable housing for reading URL-encoded symbols specifying the location of HTML-encoded documents stored in information servers connected to the Internet and supporting the TCP / IP standard. A computing platform is provided for supporting a GUI-based WWW browser program integrated with the bar code symbol reader in the hand-supportable housing. A telecommunication modem is operably connected to the computing platform in order to establish a two-way telecommunication link between the GUI-based WWW browser and an Internet service provider (ISP) connected to the Internet. In response to reading a URL-encoded bar code symbol, the WWW browser program automatically accesses a corresponding HTML-encoded document on the Internet, for display on a visual display panel integrated with hand-supportable housing. A keypad is also integrated with the hand-supportable housing for manually providing information to the WWW browser program.
Owner:METROLOGIC INSTR
Mobile valet
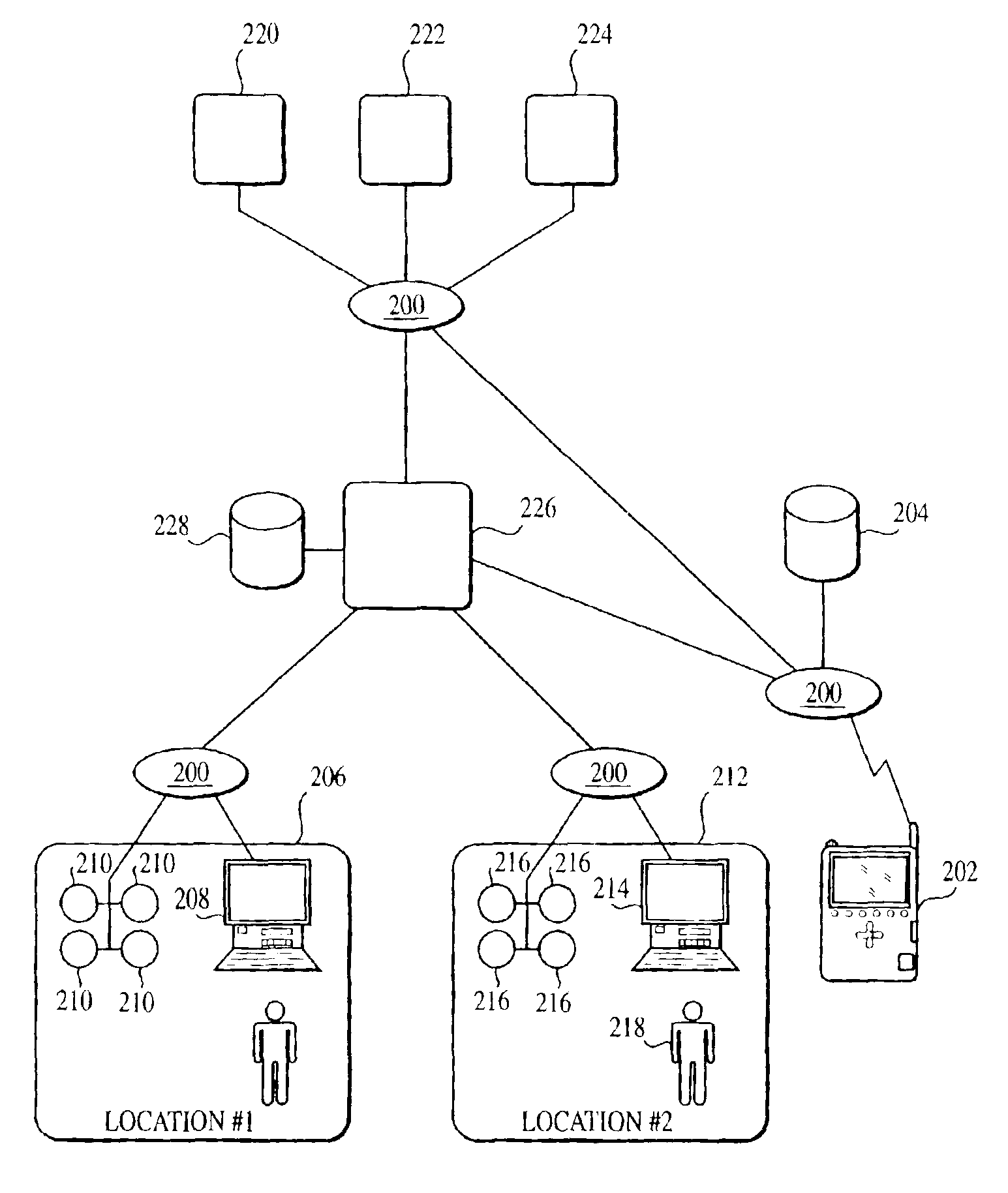
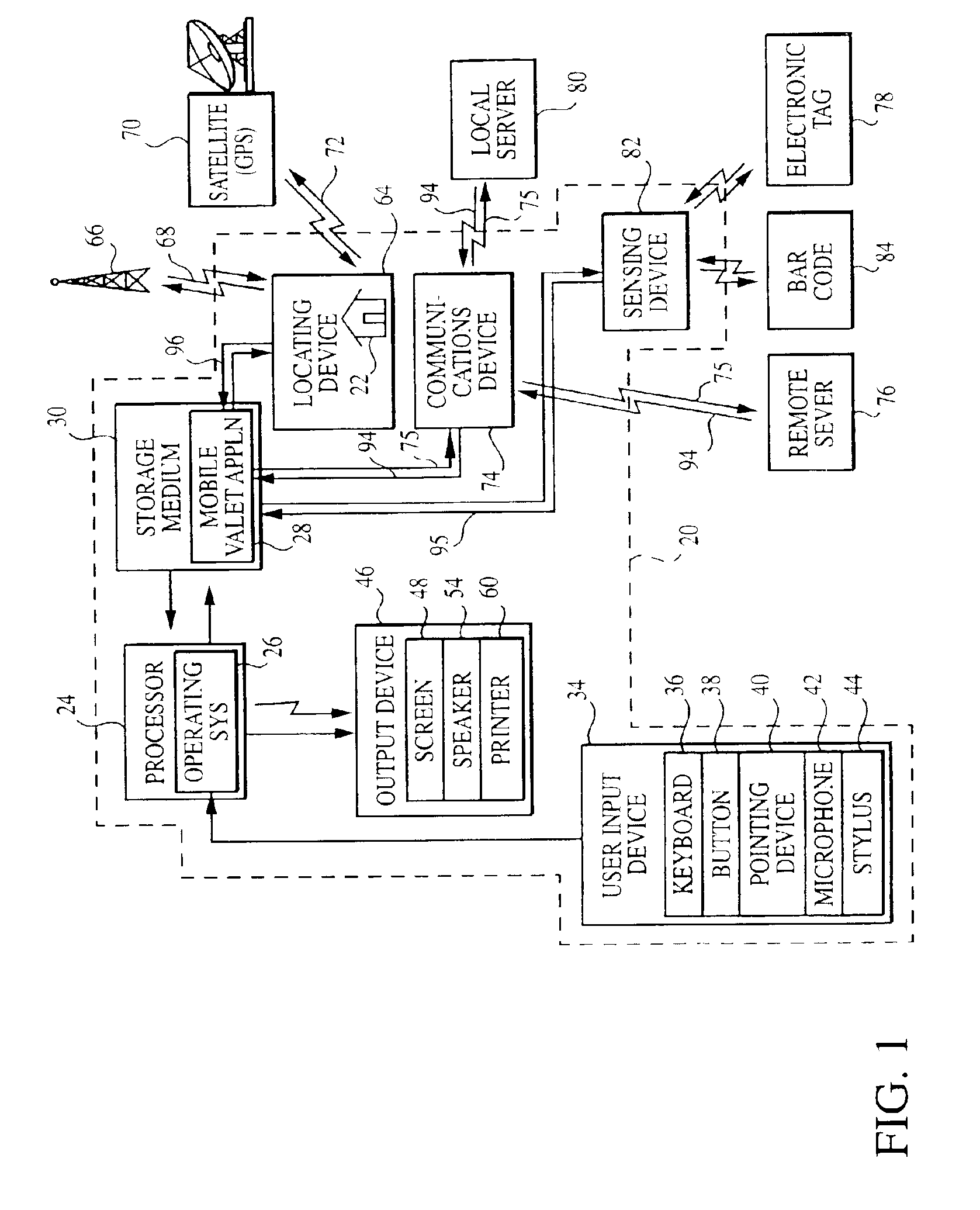
InactiveUS6957393B2Enhances overall experience and effectivenessIncrease richnessPosition fixationDigital computer detailsWireless mobile devicesContext based
Enhanced delivery of services are provided through a wireless mobile device and one or more location service channels, preferably at the direction of the user of the mobile device requesting the desired service through common context-based user interfaces. The mobile device communicates with local and remote service providers. The context is determined by accessing information in the user profile, by sensors on the mobile device identifying items of interest, or by identifying the location of the mobile device. An aggregator server maintains a registry of location service channels and manages the access to the channels by the mobile device users and the service providers.
Owner:ACCENTURE GLOBAL SERVICES LTD
Home agent management apparatus and method
InactiveUS7626957B2Raise countTime-division multiplexData switching by path configurationComputer networkAnalysis data
A home agent management apparatus and method for routing a packet using a home network equipment as a home agent in a mobile Inter Protocol version 6 (IPv6) are provided. The home agent management apparatus includes a packet analyzer, which receives a packet and analyzes the packet; a database, which stores information indicating whether a home agent of a home network operates normally according to the result of the analysis; and a home agent function executor, which performs a home agent function in place of the home agent when the home agent does not operate normally. Accordingly, a load concentrated on a home agent of an Internet Service Provider (ISP) can be split.
Owner:SAMSUNG ELECTRONICS CO LTD
Voice-over-IP enabled chat
InactiveUS7039040B1Avoid the needSpecial service provision for substationMultiplex system selection arrangementsCredit cardData connection
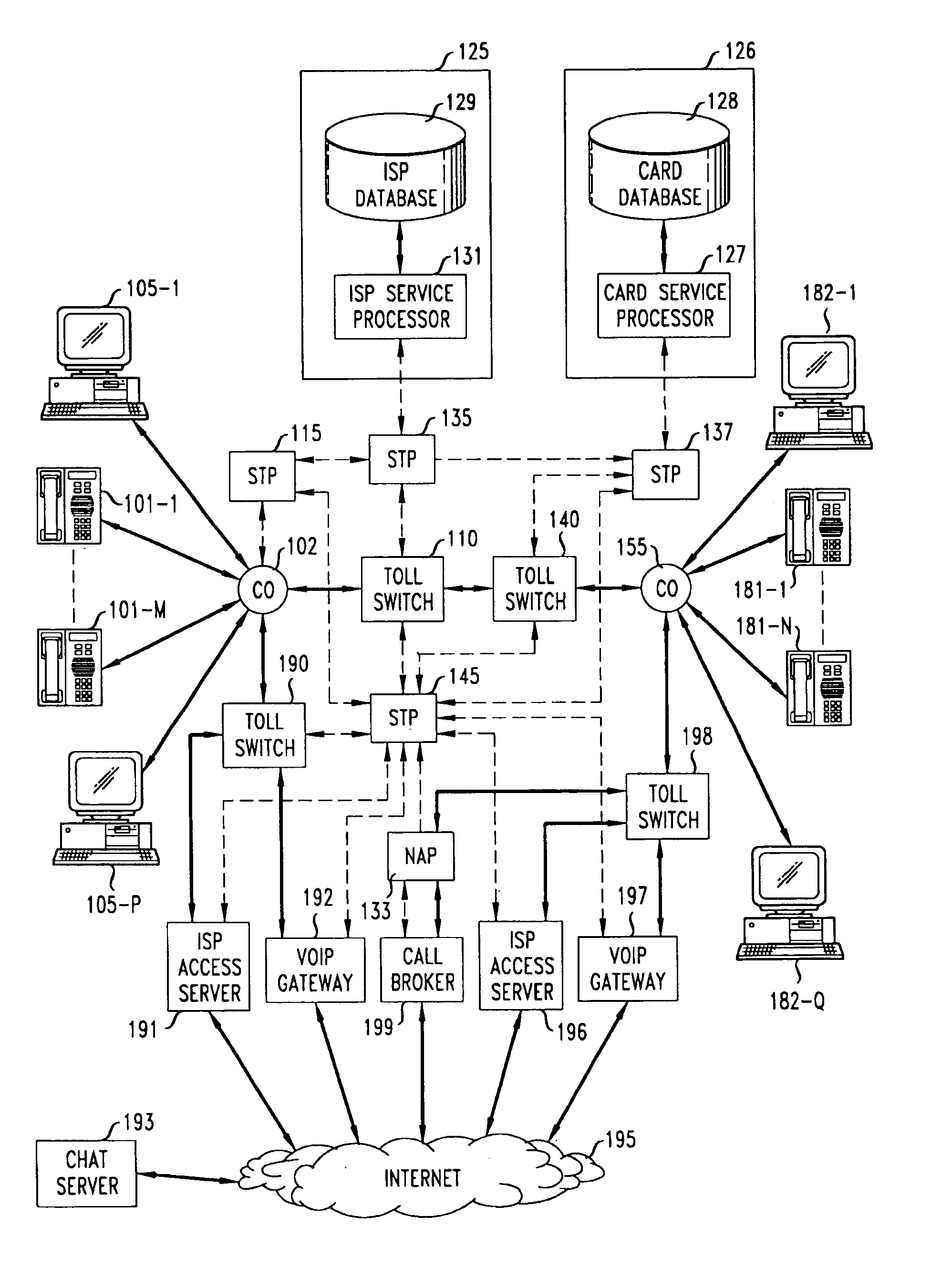
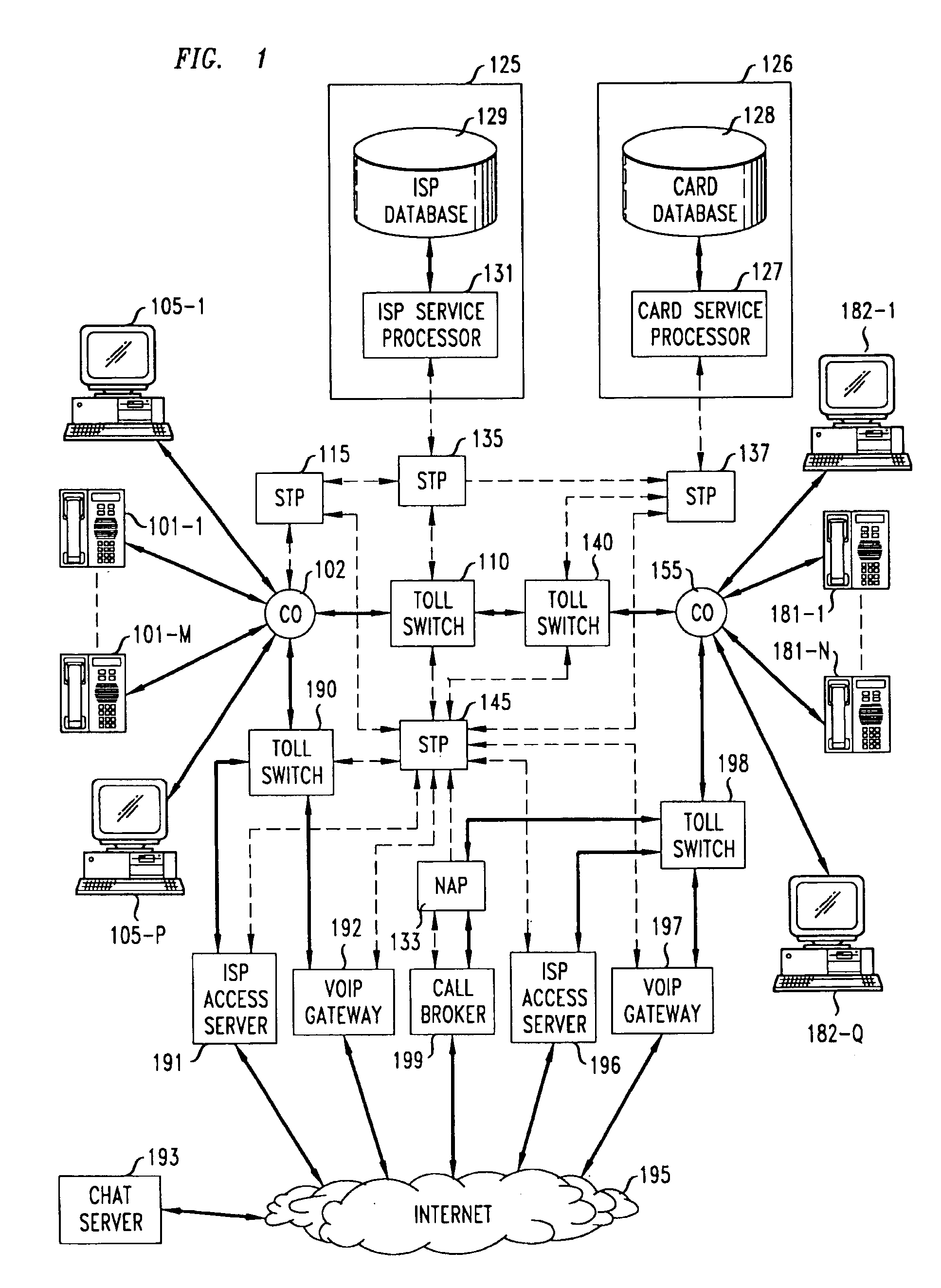
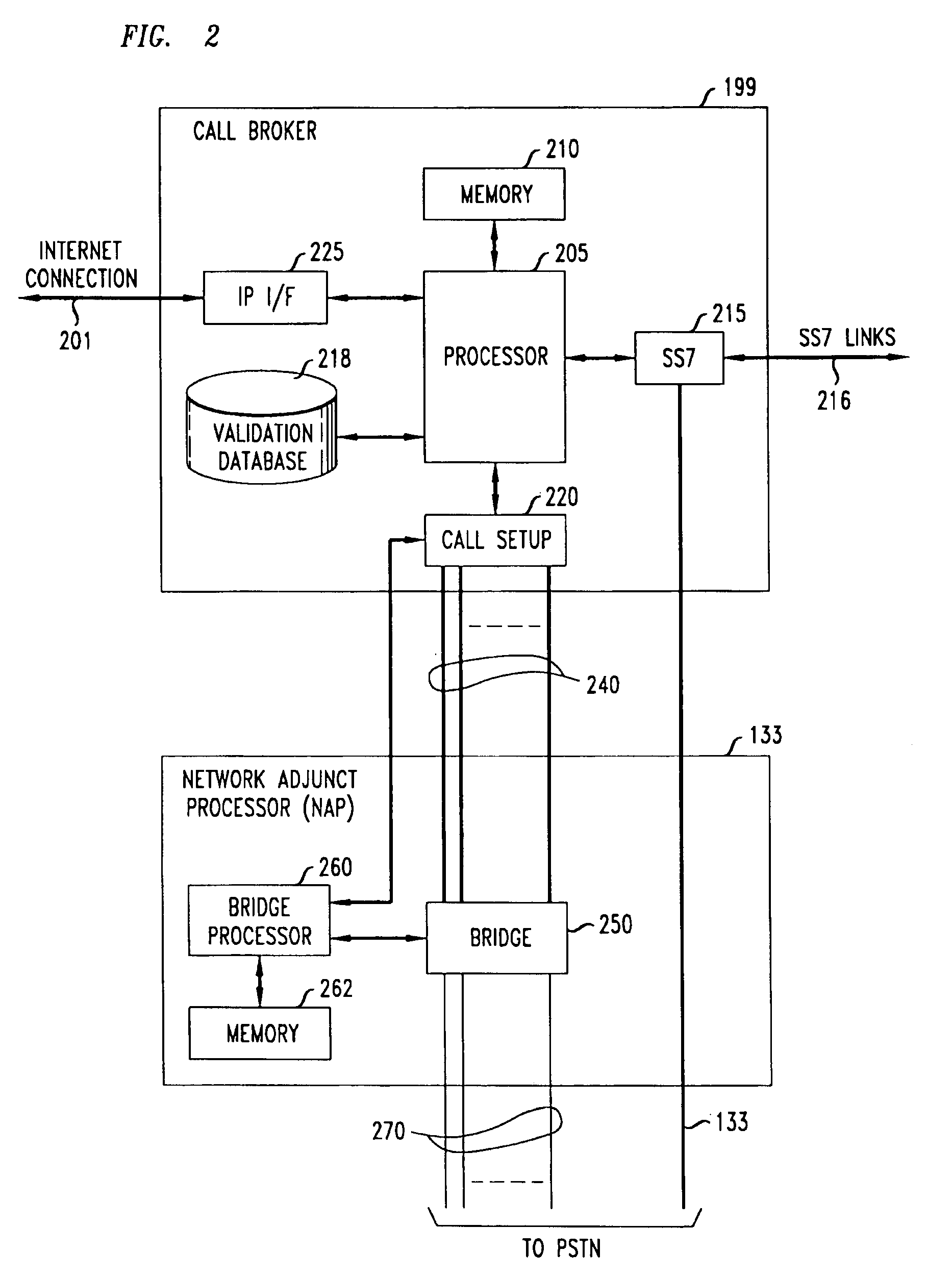
A network-based system and method for providing anonymous voice communications using the telephone network and data communications links under the direction of a Call Broker and associated network elements. A user (the call initiator) present in a text chat room session establishes a data connection to Call Broker and, after qualifying for access (e.g., using credit card information) and providing a callback number, receives voice session information and participant access codes for each desired participant in a voice call. The initiator causes session information and participant codes to be passed to one or more selected chat participants in the current text chat room. When a selected participant uses the received session information, and enters the received participant code and a callback number, the Call Broker in cooperation with a Network Adjunct Processor (NAP) completes voice links to the initiator and the selected participant(s). The need for each party to have a second subscriber line is advantageously avoided by having the Call Broker arrange to have one or more voice links completed through a VoIP link, and further reduces the need for second lines for participants by forwarding a Call Broker—placed call to a busy participant line to the participant's Internet Service Provider (ISP), which then sends a message to the participant announcing one or more options for receiving the incoming call, including receiving the incoming call through a VoIP link.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
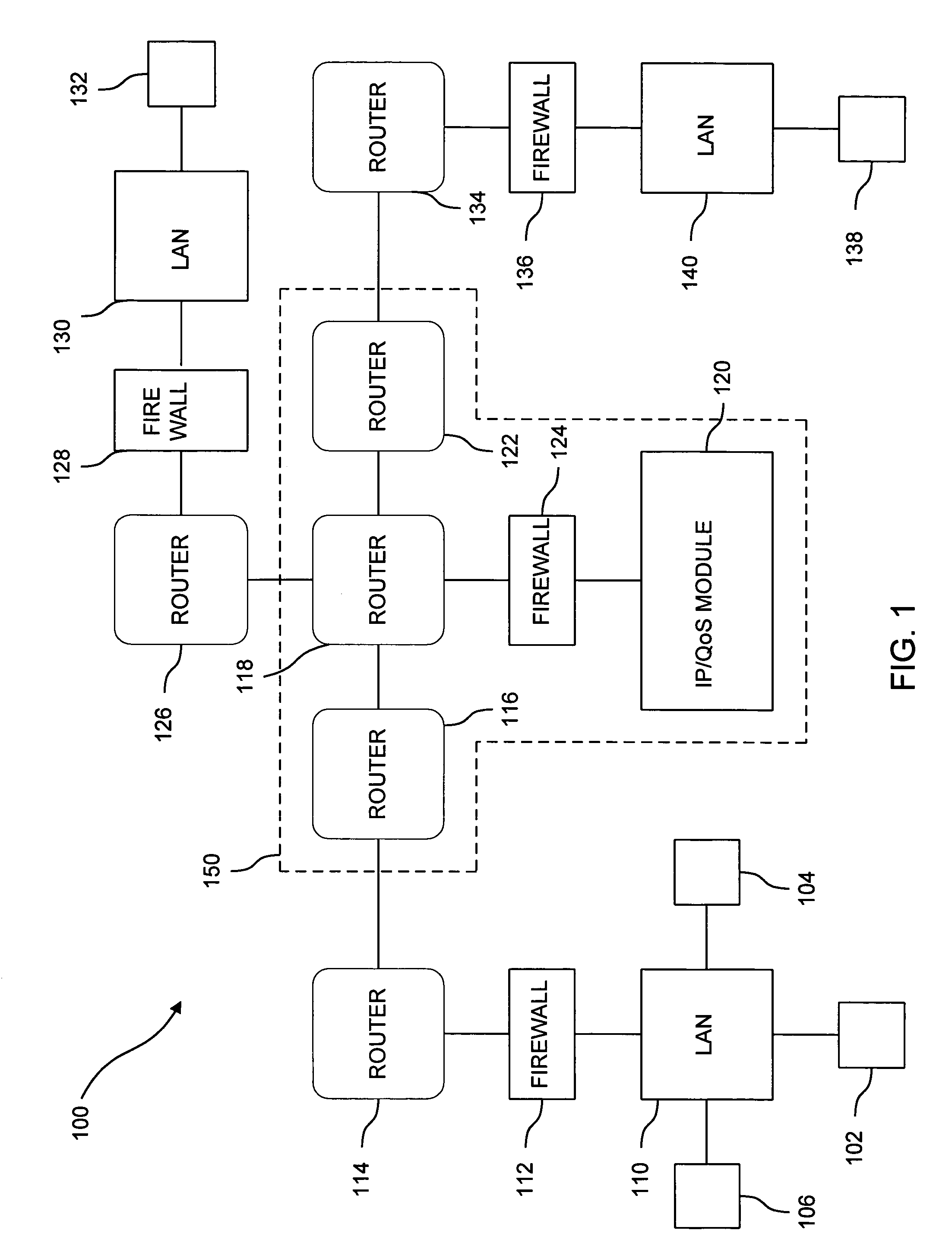
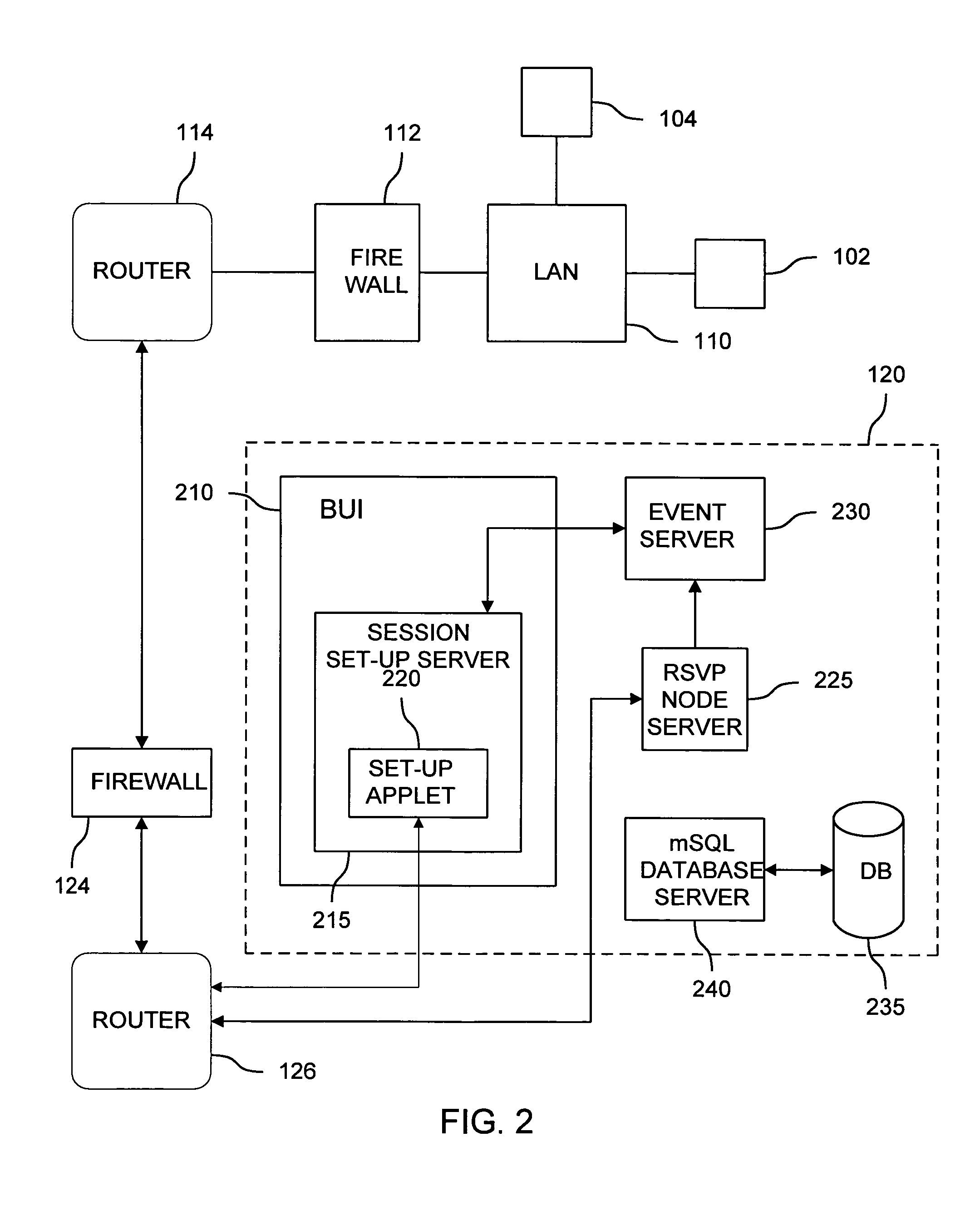
Secure network architecture with quality of service
InactiveUS7283561B1Maintain securityDigital computer detailsTime-division multiplexQuality of serviceAccess network
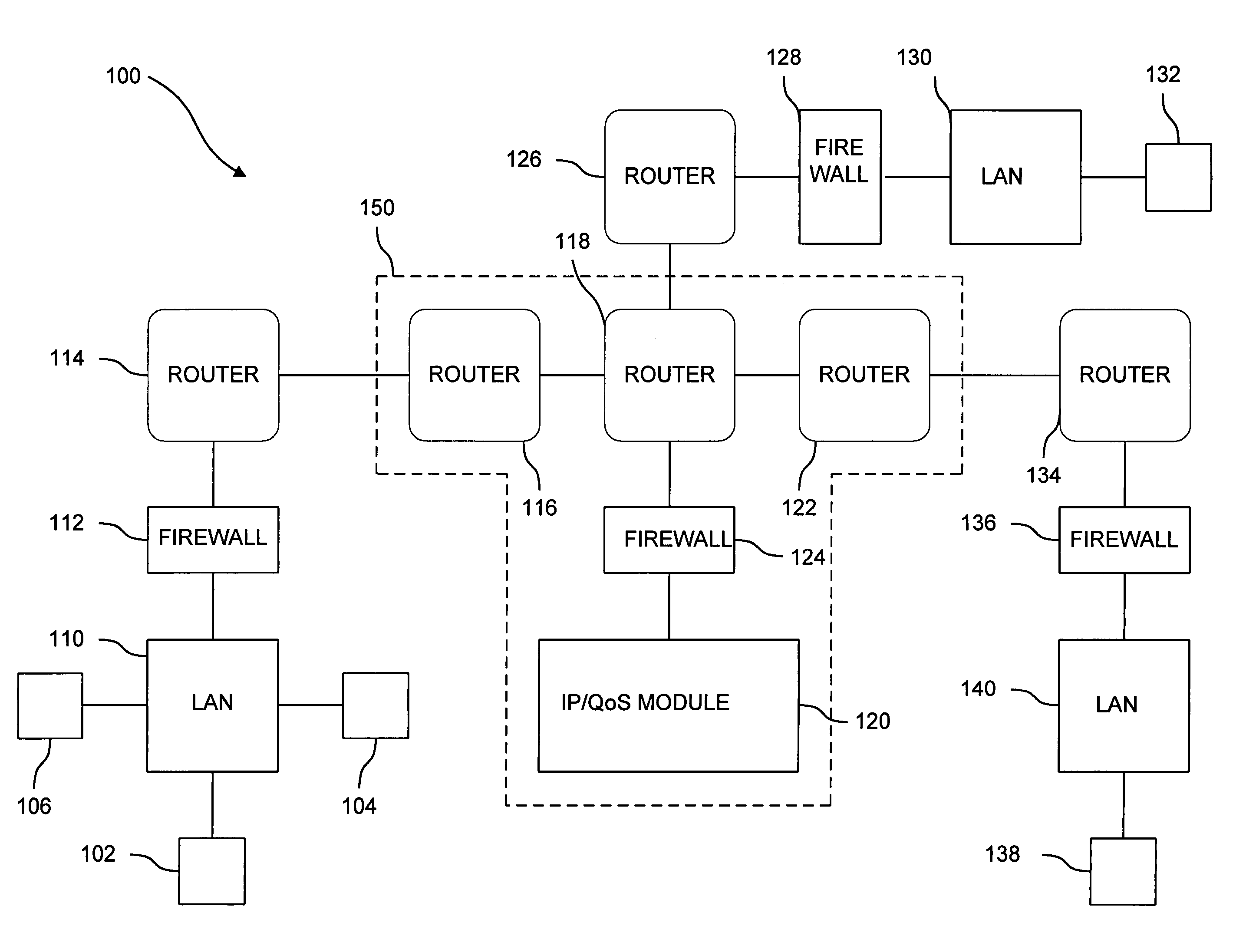
In a wide area network arrangement composed of some number of secure local networks and an Internet service provider (ISP) back-bone, LAN hosts are able to indirectly access network routers, through an ISP quality of service (QoS) module, to request that information transmitted during certain specified sessions be given priority treatment by the network.
Owner:LEVEL 3 COMM LLC
System and method for providing network and service access independent of an internet service provider
InactiveUS7099944B1Multiple digital computer combinationsNetwork connectionsTraffic capacityService provision
Systems and methods for providing personalized internet protocol (IP) services to an IP enabled device residing on a local area network (LAN) are disclosed. The systems and methods utilize an access device in communication with an access provider network, and involve communicating a first IP address to the access device, the first address allowing the access device to communicate with a first plurality of IP service devices through an Internet service provider (ISP), and communicating a second IP address to the access device, the second address allowing the access device to communicate with a second plurality of IP service devices in the access provider network. When the access device receives IP traffic from the IP enabled device it determines whether the IP traffic is addressed to one of the second IP service devices. If yes, the IP traffic is forwarded to the one of the second IP service devices with the second address as a return address. Otherwise, the IP traffic is forwarded to the ISP with the first address as the return address.
Owner:BELLSOUTH INTPROP COR
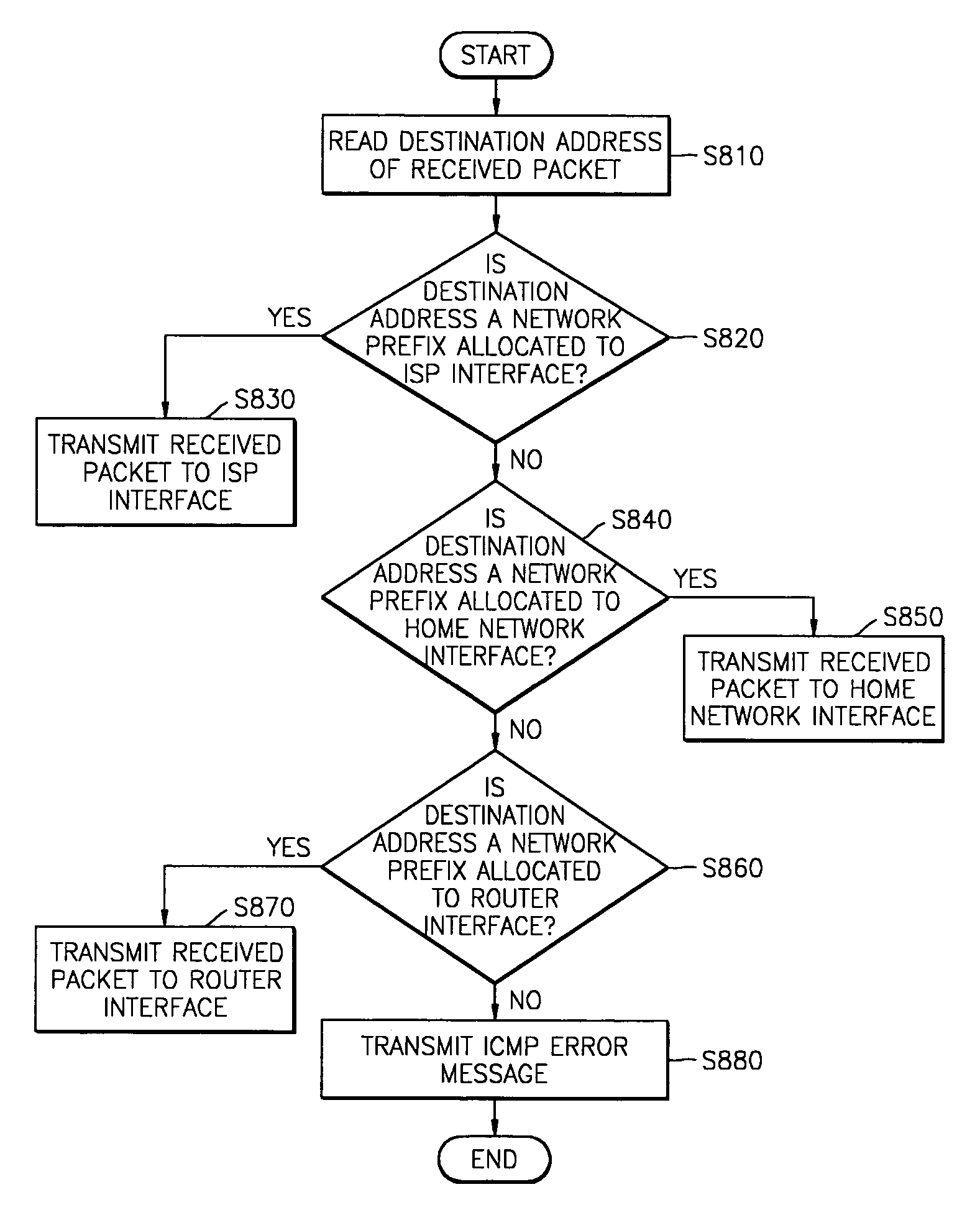
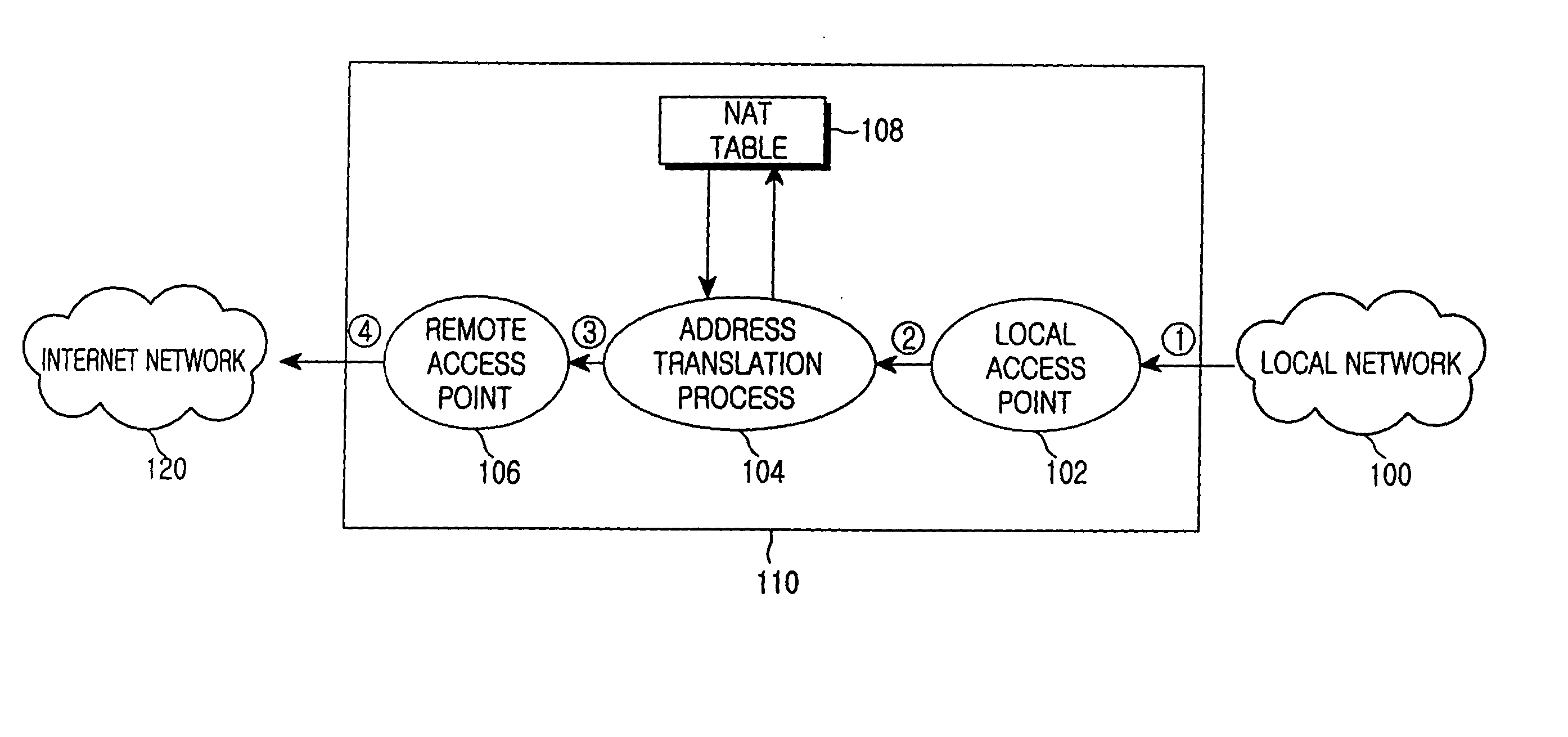
Internet protocol address allocation device and method
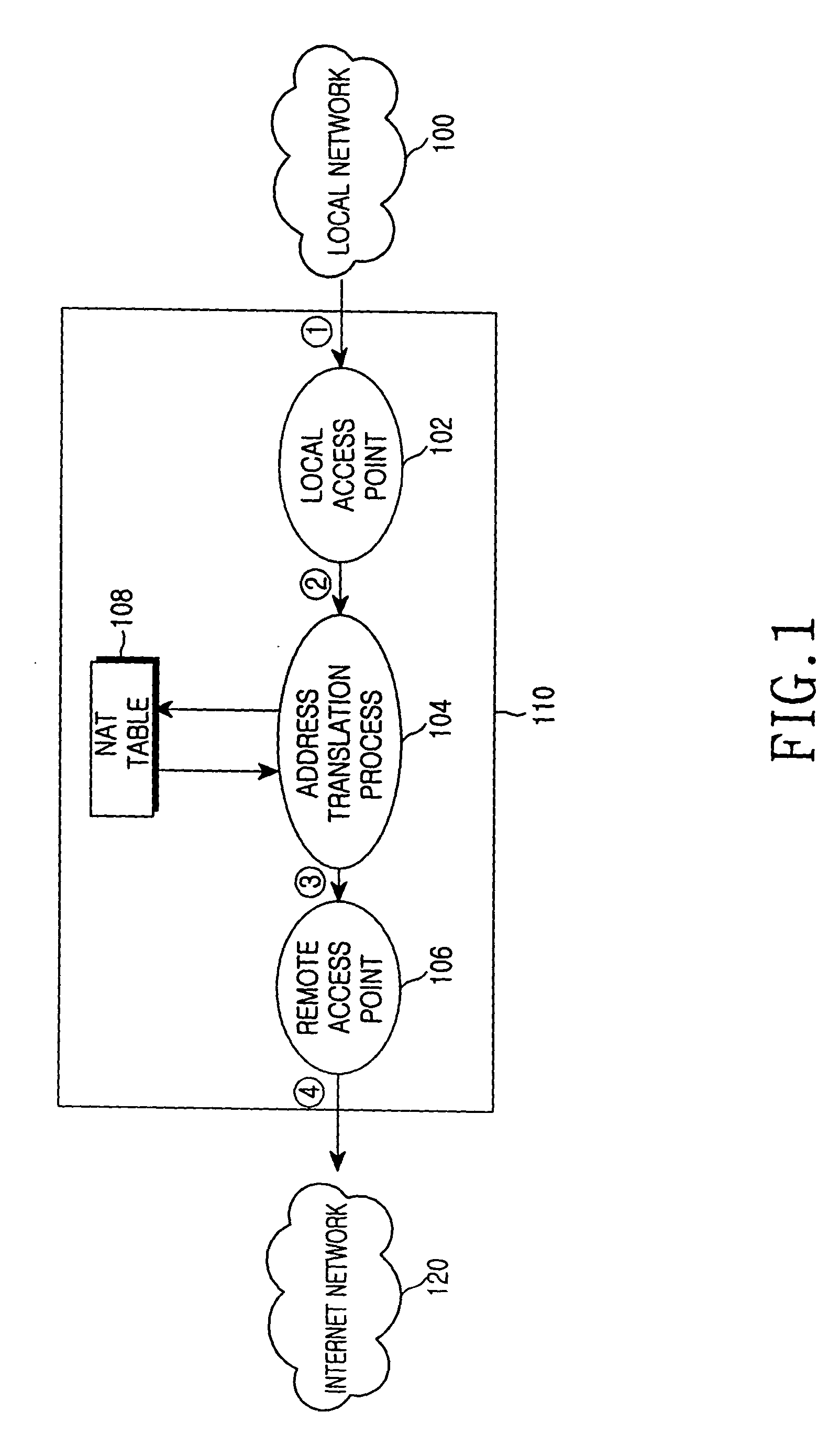
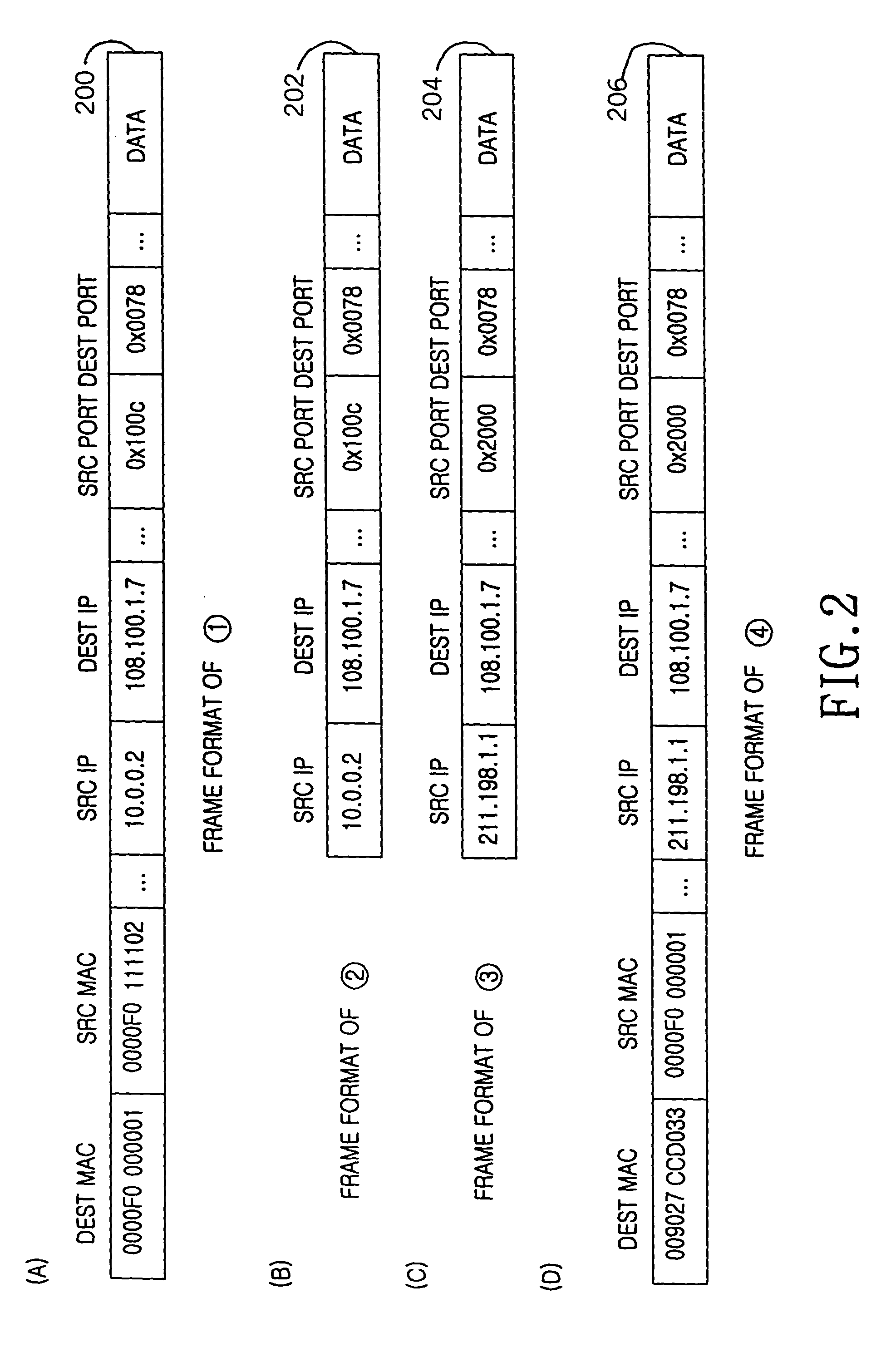
InactiveUS20040052216A1Error preventionFrequency-division multiplex detailsService provisionInternet access
A device and method for allocating the same Internet protocol (IP) address to all information terminals or hosts connected to a specific local network, which allows the hosts in the local network to gain access to the Internet while the hosts share a single IP address. The device includes a dynamic host configuration protocol (DHCP) client, a local access point, and a DHCP server spoofer. The DHCP client is allocated an IP address through a DHCP message communication with an Internet service provider. The Internet service provider includes a DHCP server for allocating IP addresses to the hosts and an Internet access gateway. The local access point includes a hardware address port translation (HAPT) module and a local IP address translation (LIAT) module. The HAPT module modifies a source medium access control (MAC) II address and port number of a frame received from each host, stores the modified result in a HAPT table, and recovers a destination MAC address and port number of a frame received from the Internet service provider, referring to the HAPT table. The LIAT module prevents a collision occurring because the hosts have the same public IP address. The DHCP server spoofer implements a DHCP server function to allocate an IP address to each host.
Owner:SAMSUNG ELECTRONICS CO LTD
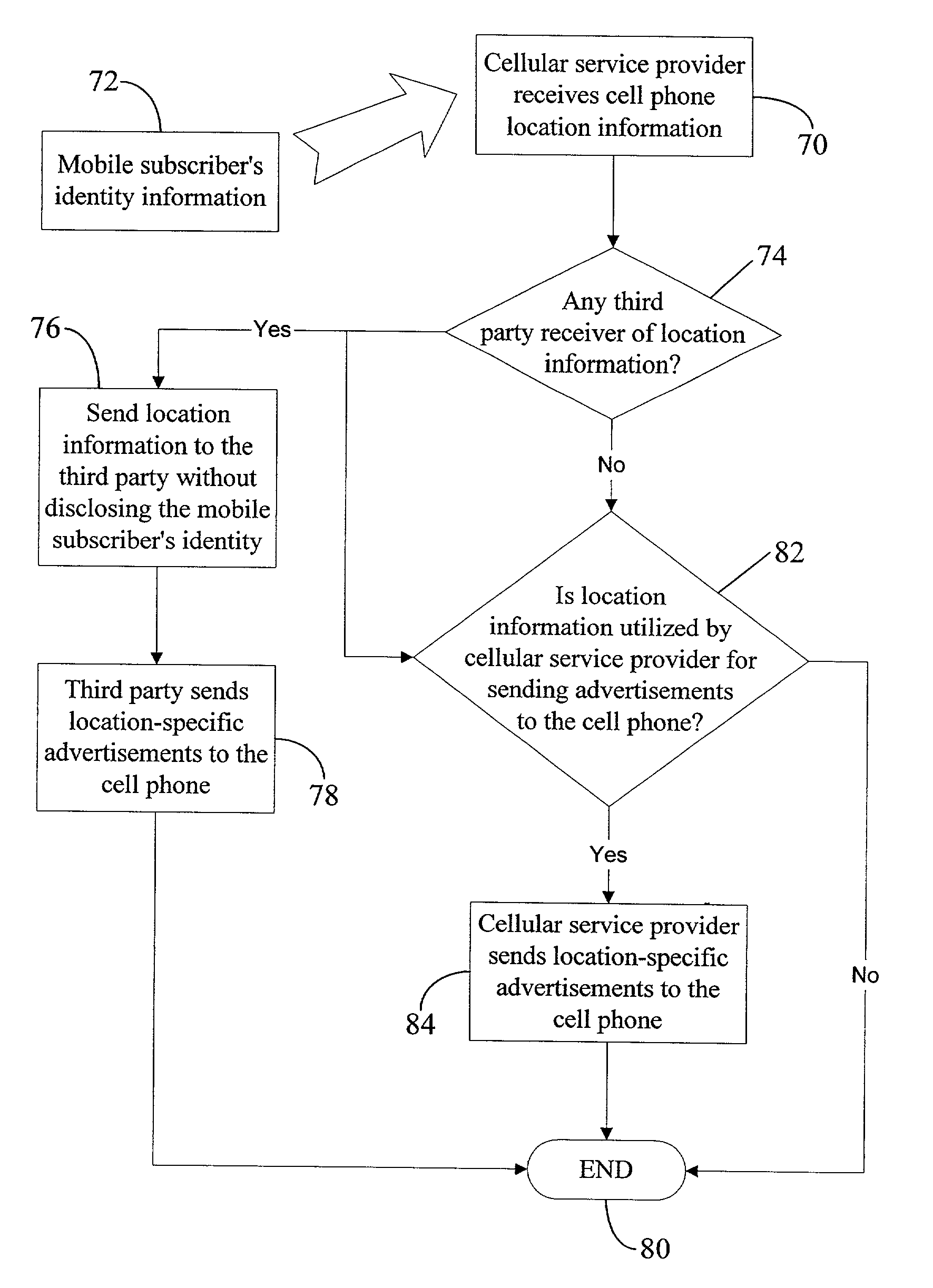
Identity blocking service from a wireless service provider
InactiveUS7110749B2Special service provision for substationUnauthorised/fraudulent call preventionOnline advertisingCellular telephone
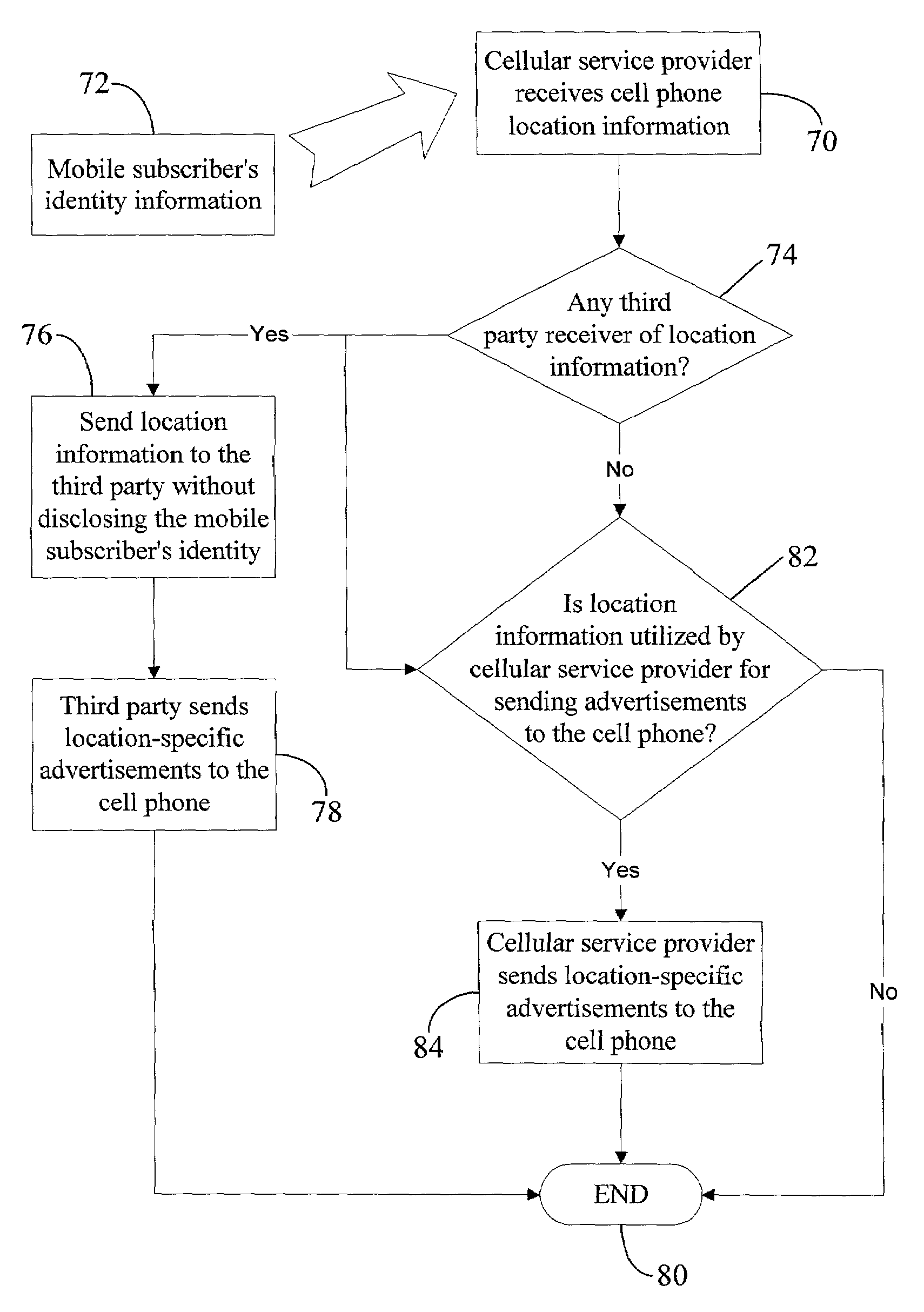
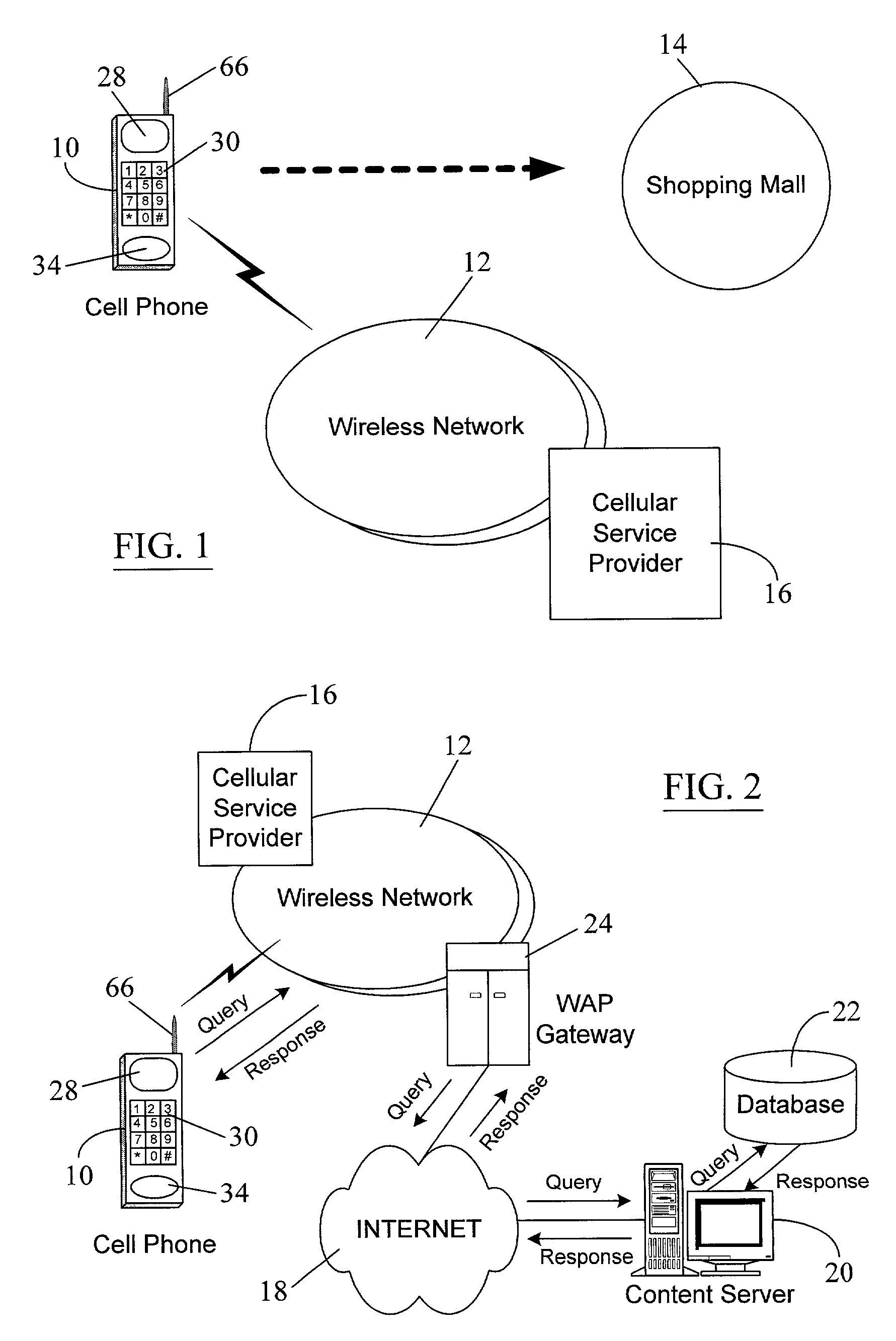
Location-blocking and identity-blocking services that can be commercially offered by a service promoter, e.g., a cellular service provider or a web advertiser. In the identity-blocking service, the service promoter may disclose the current physical location of a mobile subscriber (i.e., a cellular phone operator) to a third party (e.g., a web advertiser) subscribing to the identity-blocking service. However, the service promoter may not send any identity information for the mobile subscriber to the third party. On the other hand, in the location-blocking service, the service promoter may disclose the mobile subscriber's identity information to the third party, but not the current physical location of the mobile subscriber. Blocking of the mobile subscriber's identity or location information may be desirable for privacy reasons, to comply with a government regulation, or to implement a telecommunication service option selected by the mobile subscriber. However, in the case of the mobile subscriber requesting emergency help, the service promoter may not block identity and / or location information. Instead, the service promoter may send all such information to the emergency service provider (e.g., the police or a hospital).
Owner:GOOGLE LLC
Electronic Mail Communications System with Client Email Internet Service Provider (ISP) Polling Application and Related Methods
An electronic mail (email) communications system may include a mobile wireless communications device, a wireless communications network connected to the Internet, and an Internet Service Provider (ISP) server connected to the Internet for receiving emails for a given user. The system may further include an email proxy server connected to the Internet for pushing emails from the ISP server to the mobile wireless communications device via the wireless communications network. A user computer may be connected to the Internet and may include a client email application for periodically polling the ISP server to detect new emails. The client email application may also send new email notifications to the email proxy server upon detection of new emails to cause the email proxy server to push the new emails to the mobile wireless communications device.
Owner:MALIKIE INNOVATIONS LTD
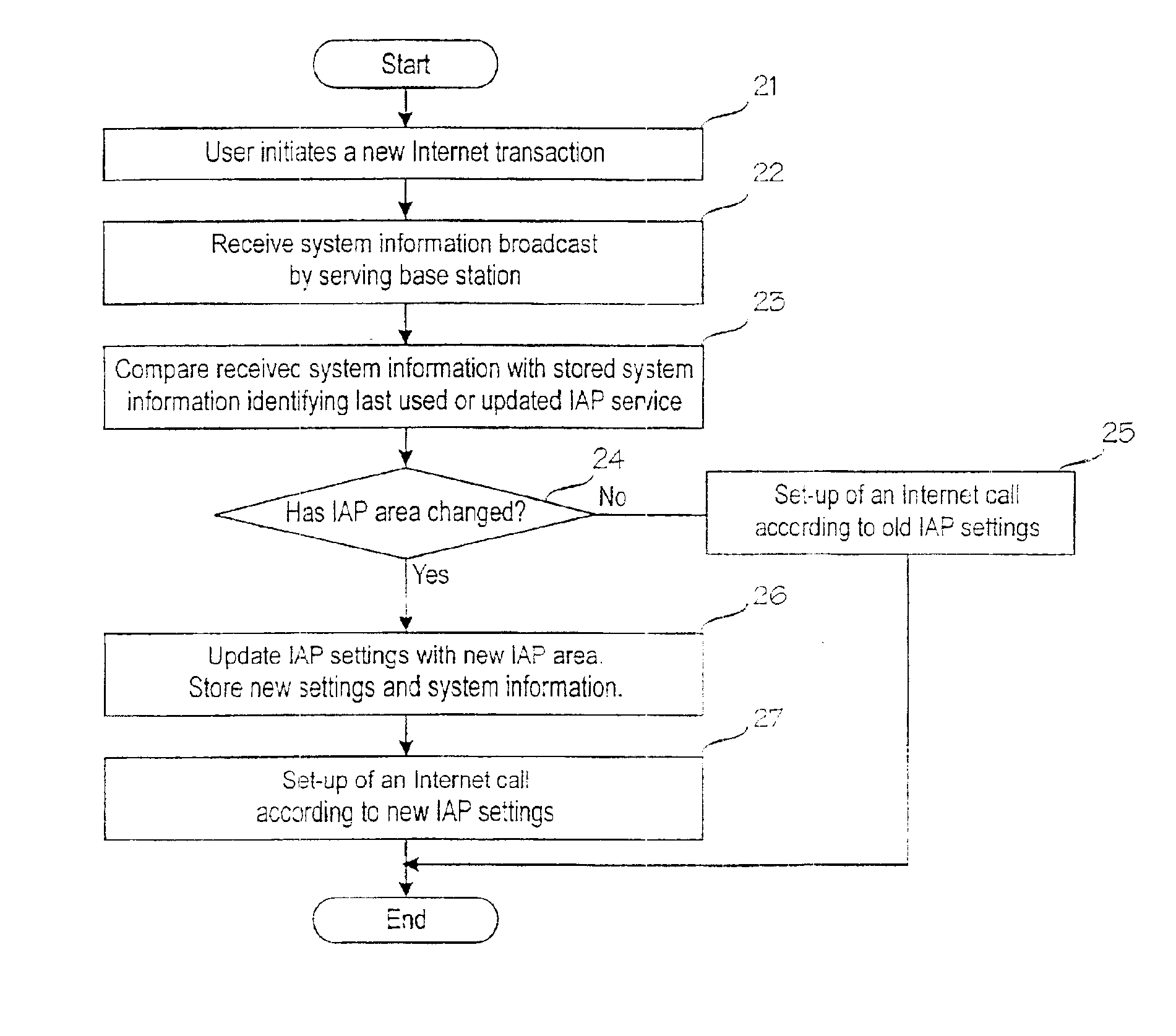
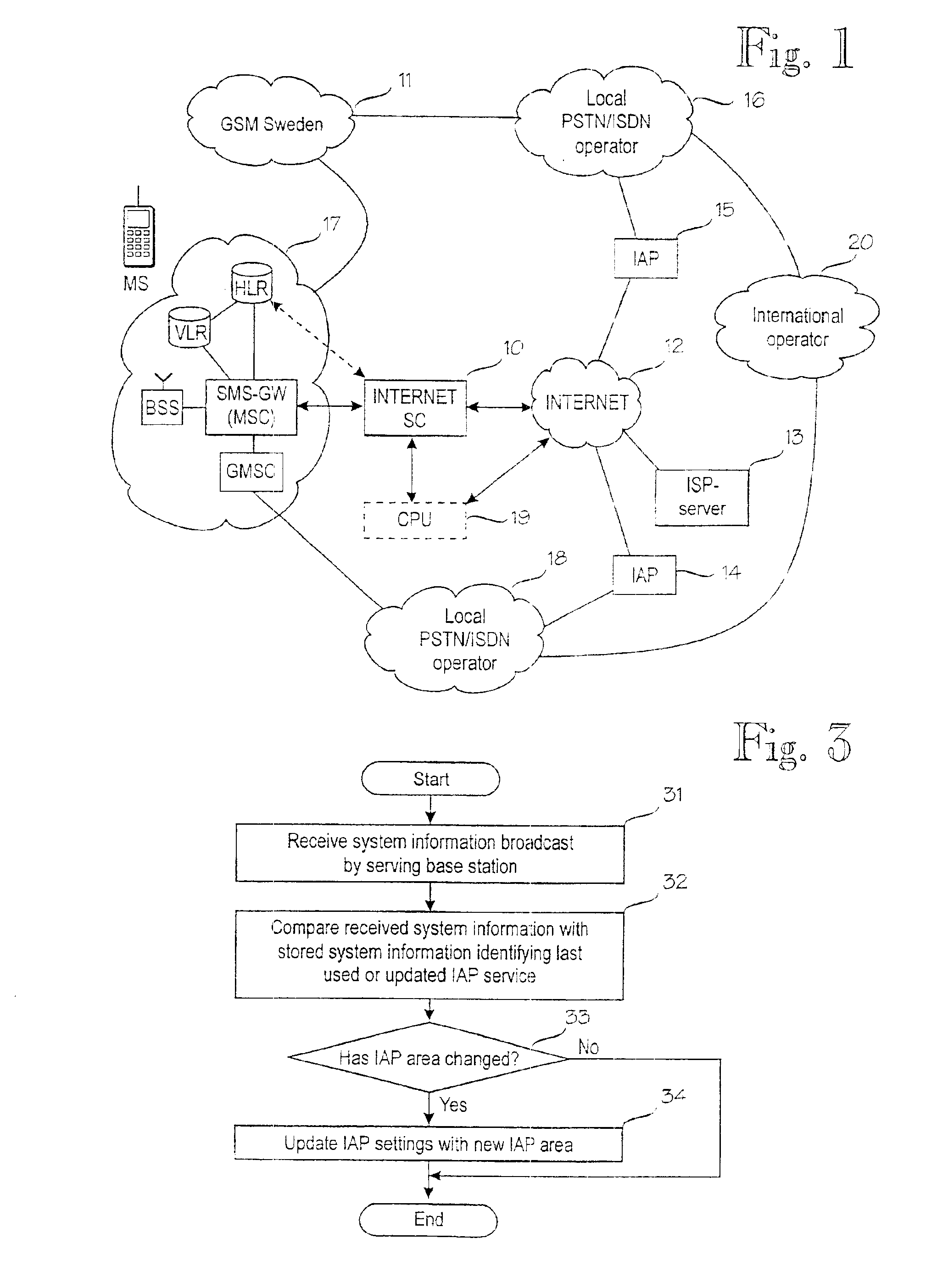
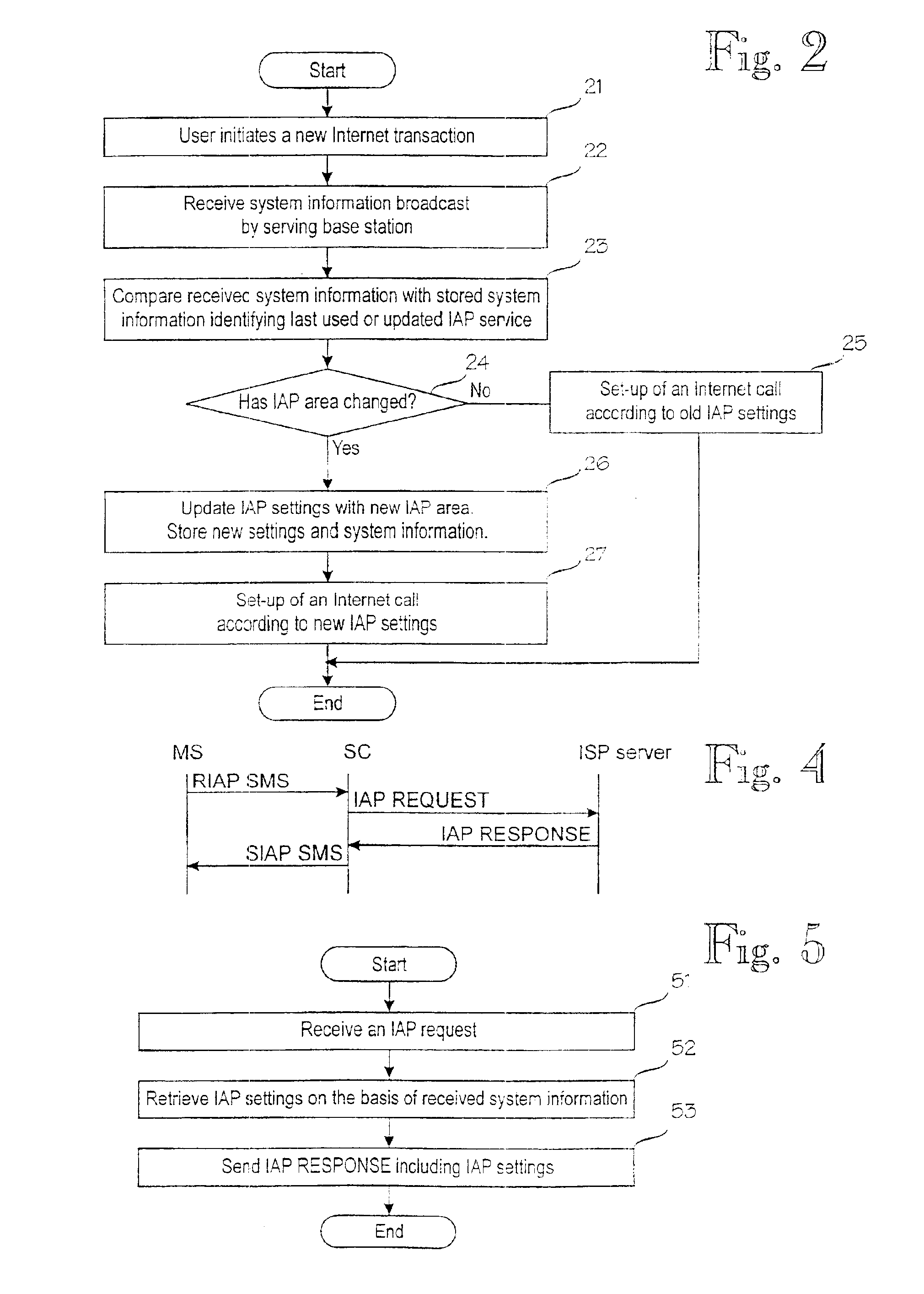
Updating of internet access point settings in a mobile communication system
InactiveUS6904026B1Reduce call costsMinimal amount of workBroadcast service distributionRadio/inductive link selection arrangementsClosest pointInternet access
A digital mobile communication system is provided with a facility by means of which it can establish a connection to the Internet network (12) via an Internet access point (14, 15). IAP settings needed for establishing a connection are stored in a mobile station (MS). When a mobile station (MS) roams, the closest point may, however, change, and IAP settings should be updated in the mobile station (MS). The invention comprises dividing the mobile communication system into IAP areas, which are given preferred IAPs. An IAP area may be e.g. a mobile communication network (11, 17). Mobile communication networks broadcast system information on the basis of which a mobile station may detect that the IAP area has changed and start a procedure for updating IAP settings. Updating may comprise retrieval of IAP settings from a special server (13) in the network maintained by an Internet service provider. Retrieval can be done e.g. via a short message service center (10). In one embodiment the mobile communication network broadcasts messages giving recommended IAP settings to mobile stations.
Owner:COMCAST CABLE COMM LLC
Method and apparatus for managing hardware address resolution
InactiveUS20070248085A1Data switching by path configurationAddress Resolution ProtocolAddress resolution
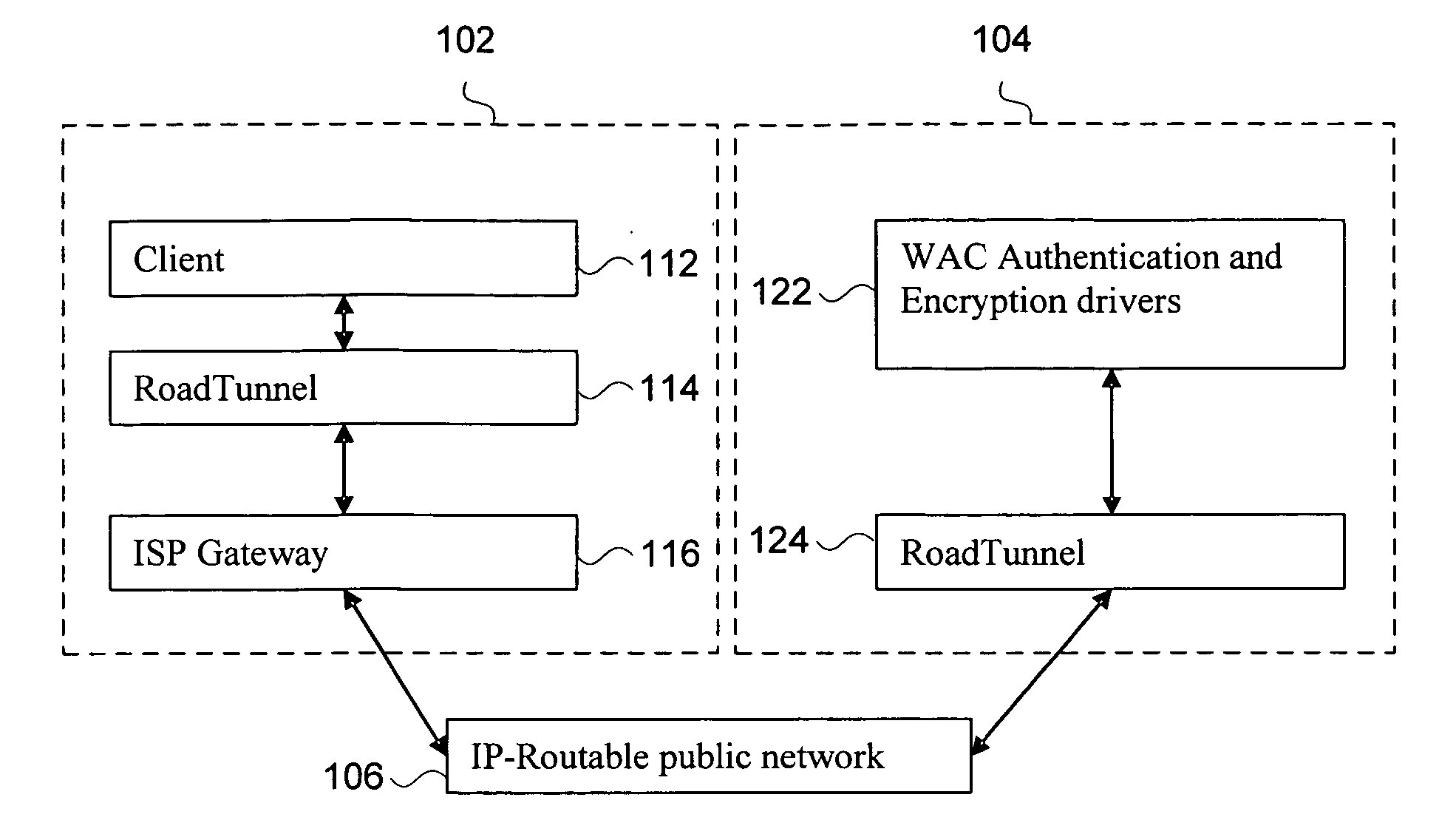
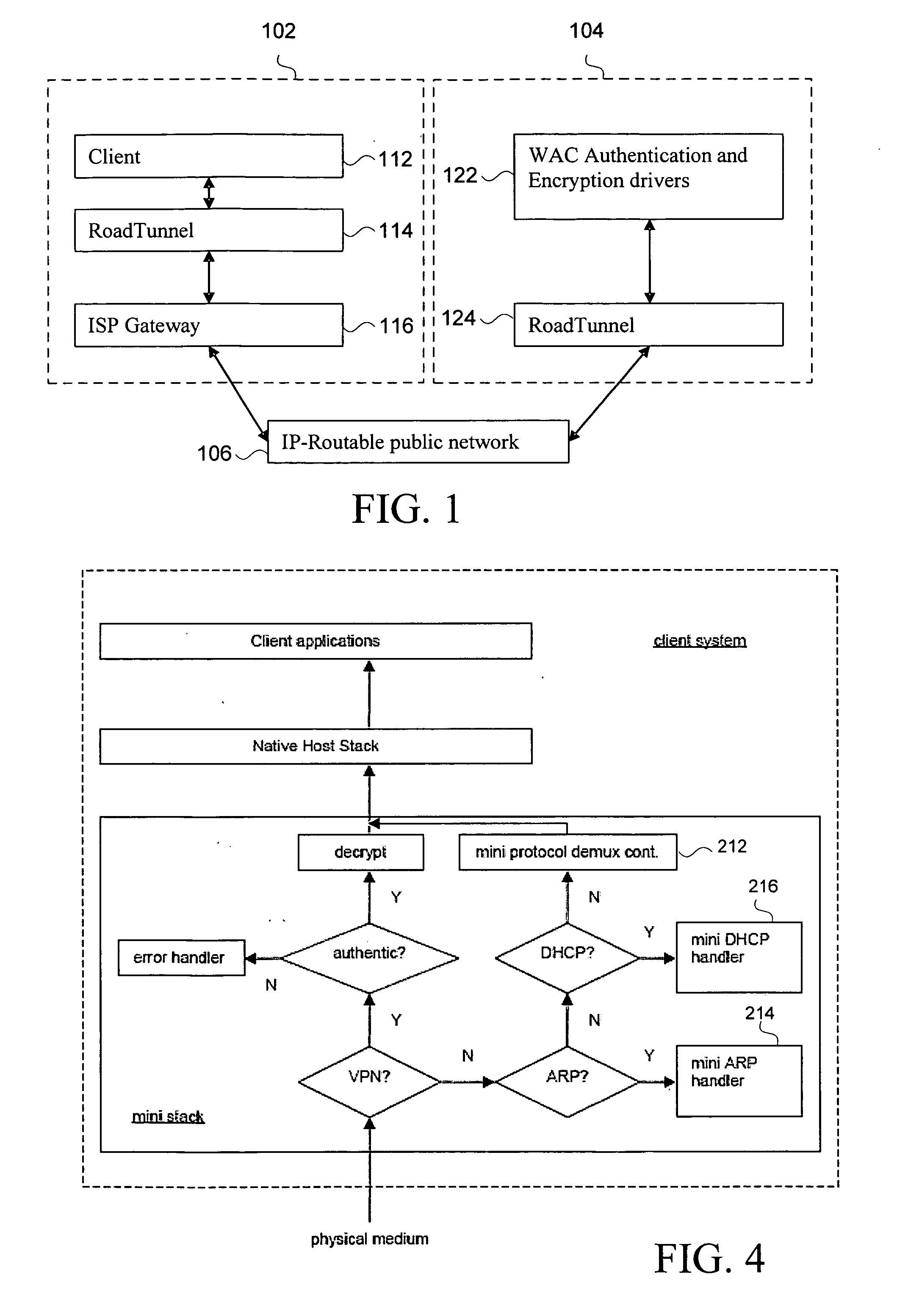
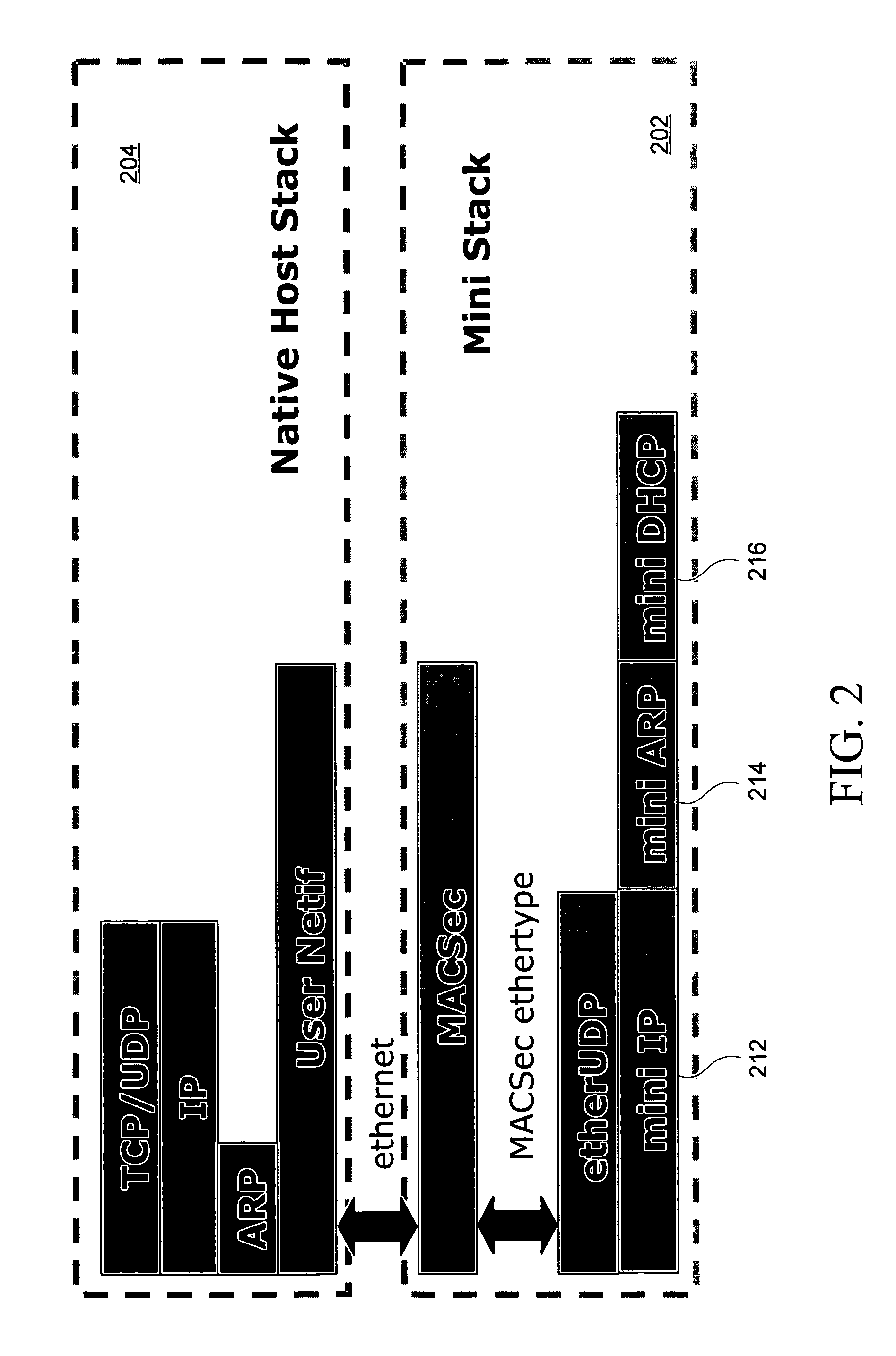
Disclosed herein is a network device, such as a host computer, that simultaneously has two IP identities: a local IP identity on a local network (e.g., a non-virtual private network) to which the host computer is connected; and a remote IP identity on a second network (e.g., virtual private network) that is remote to the host. Only the remote IP identity is visible to the host operating system's network stack. Each IP identity has its own ARP cache and Address Resolution Protocol (ARP). The local ARP cache is managed with respect to a connection of the host to a local subnet (e.g., an Internet Service Provider (ISP) subnet) and the remote ARP cache is managed with respect to a remote subnet reachable through a gateway on the local subnet.
Owner:E COLT SYST INC
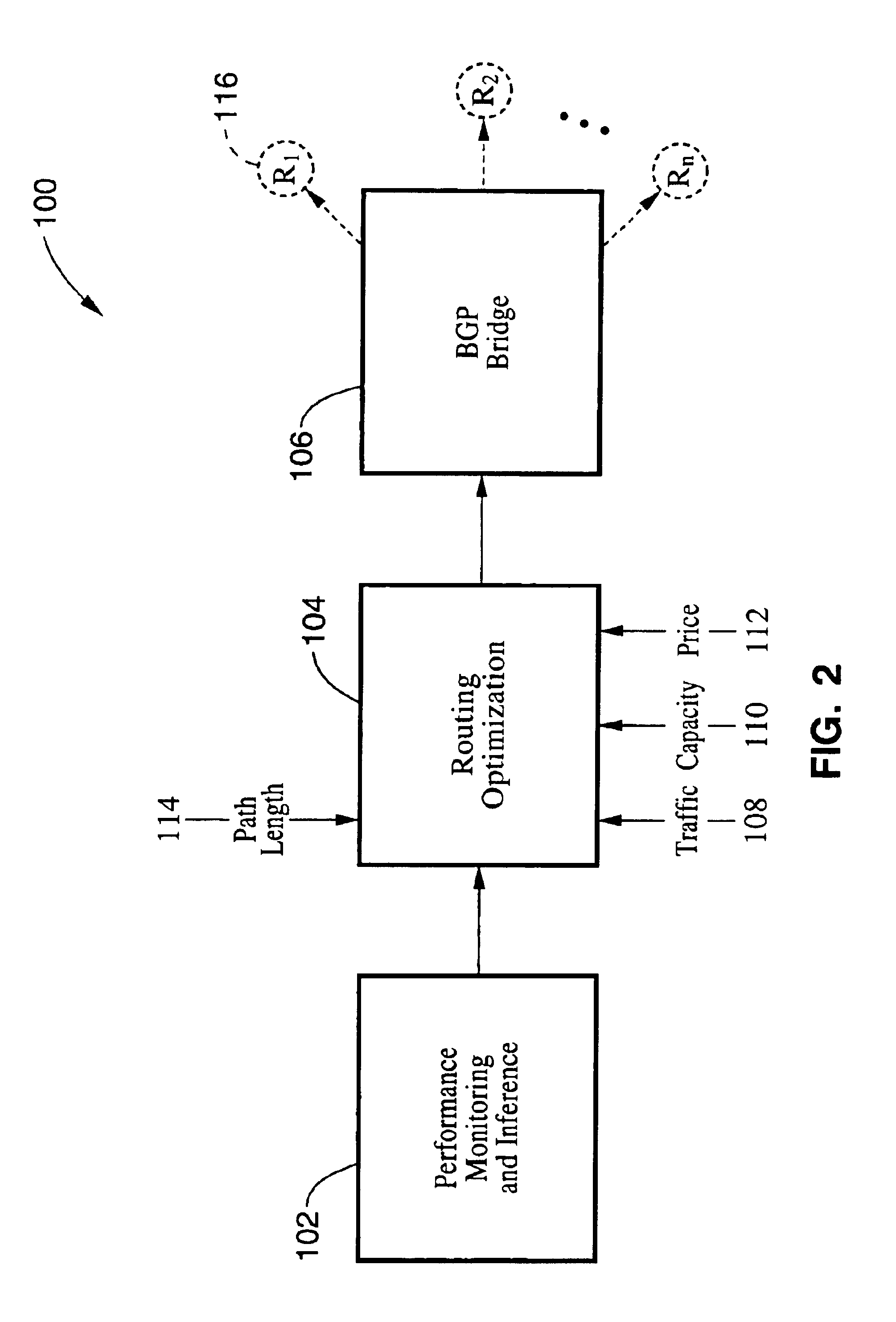
Method and system for optimizing routing through multiple available internet route providers
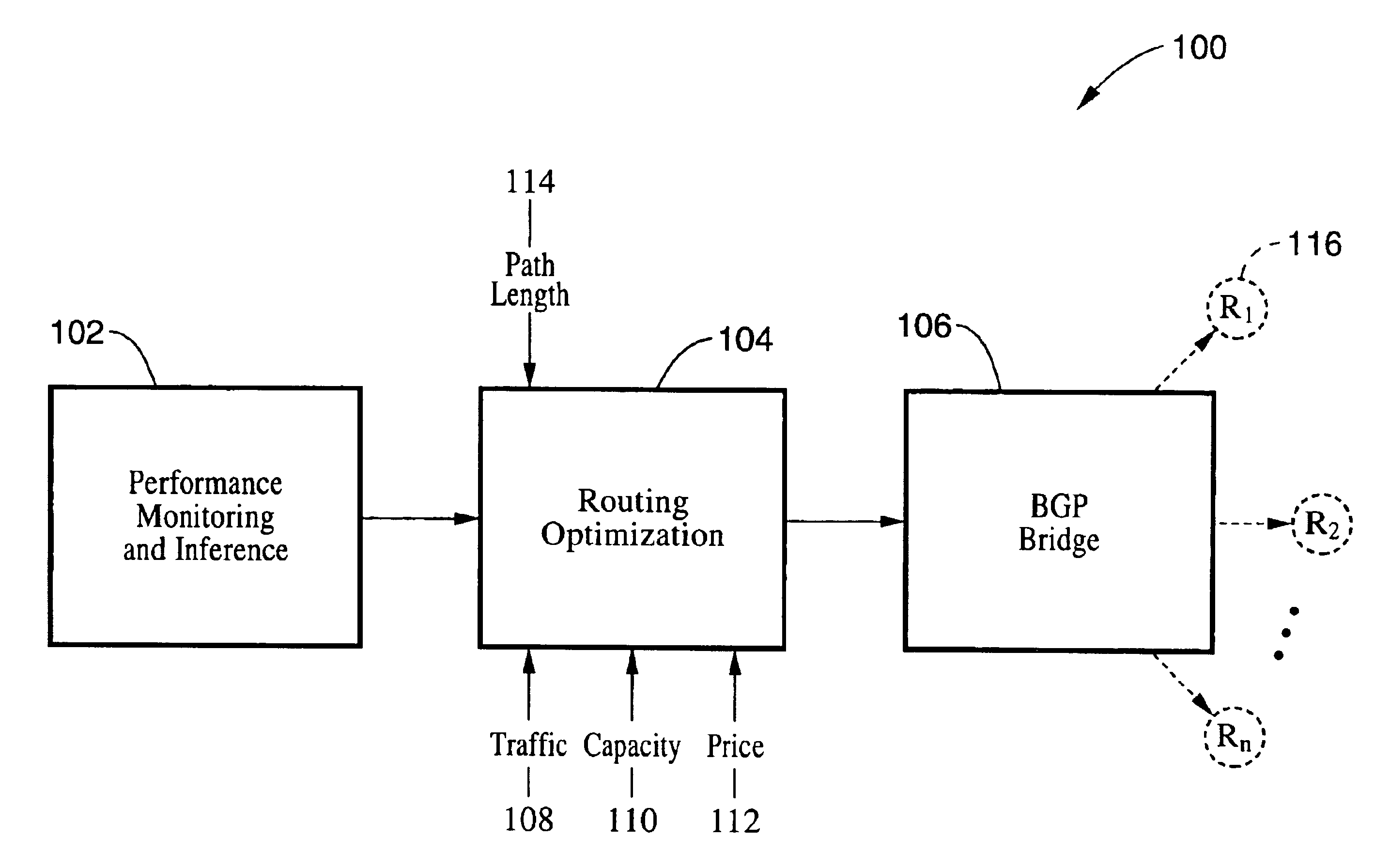
InactiveUS6981055B1Optimize route selectionInability to overcomeDigital computer detailsData switching by path configurationTraffic capacityRouting table
A method and system for optimizing routing traffic to a destination when multiple routes are available. A performance monitoring and inference component measures the performance of the available paths to a large set of subnetworks, and uses those measurements to infer the performance of all available paths to an even larger set of subnetworks. A routing optimization component uses a cost function that assigns a cost to a routing table based on information from the performance monitoring and inference component, as well as other path characteristics, and further uses a minimization methodology to find a routing table with a very low cost, as defined by the cost function. A BGP bridge takes the routing table generated by the routing optimization component and communicates that information to the routers using BGP, thereby ensuring that the routers will route traffic in accordance with the routing table.
Owner:INTERNAP HLDG LLC
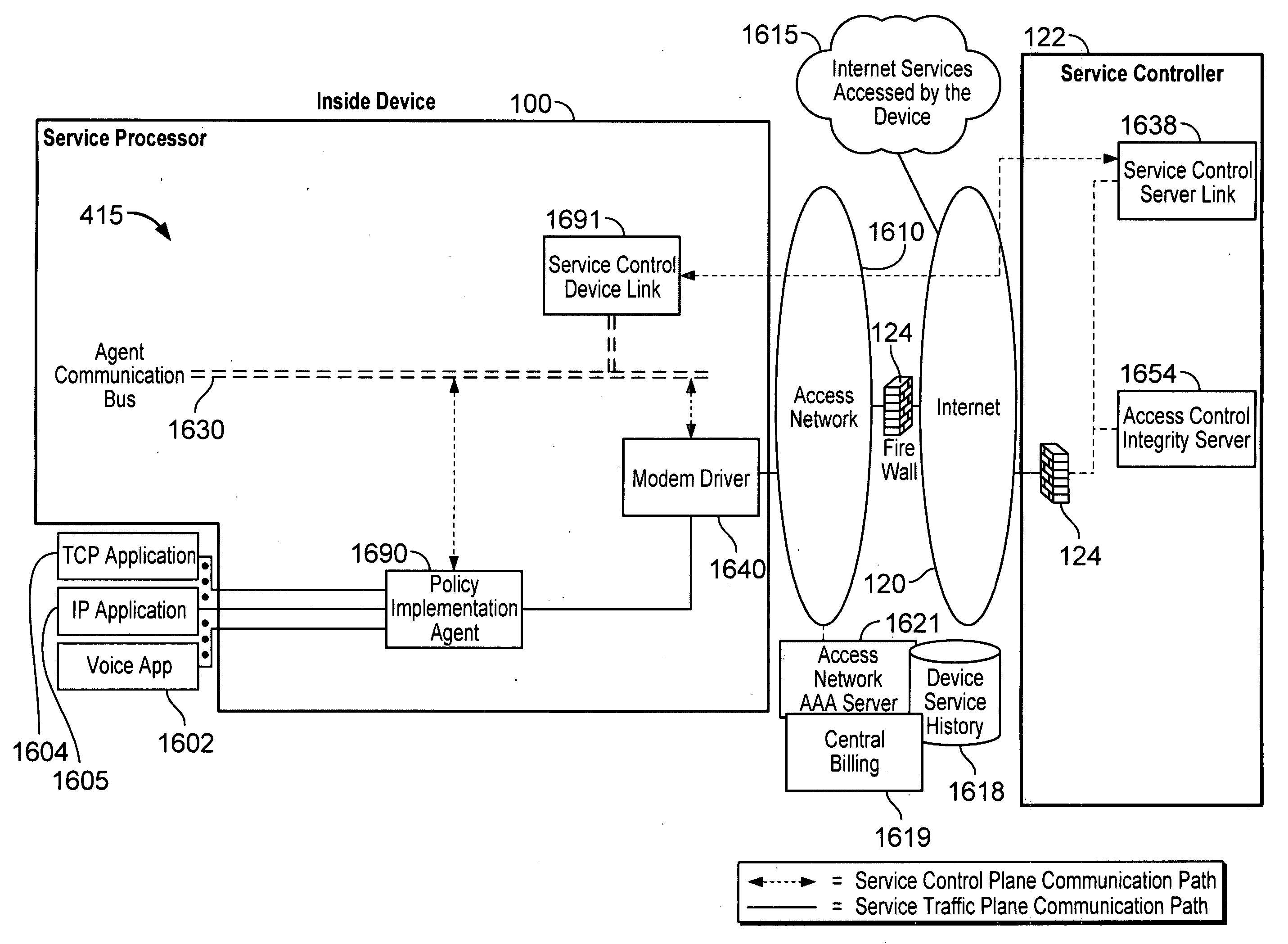
Virtual service provider systems
InactiveUS20100192207A1Digital data processing detailsTechnology managementCommunications systemService provision
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a network device executes a service controller for a plurality of device groups, in which the service controller includes a capability to securely partition one or more device group database partitions, each device group partition includes service controller system settings, and each device group includes a plurality of communication devices controlled by a virtual service provider.
Owner:HEADWATER RES LLC
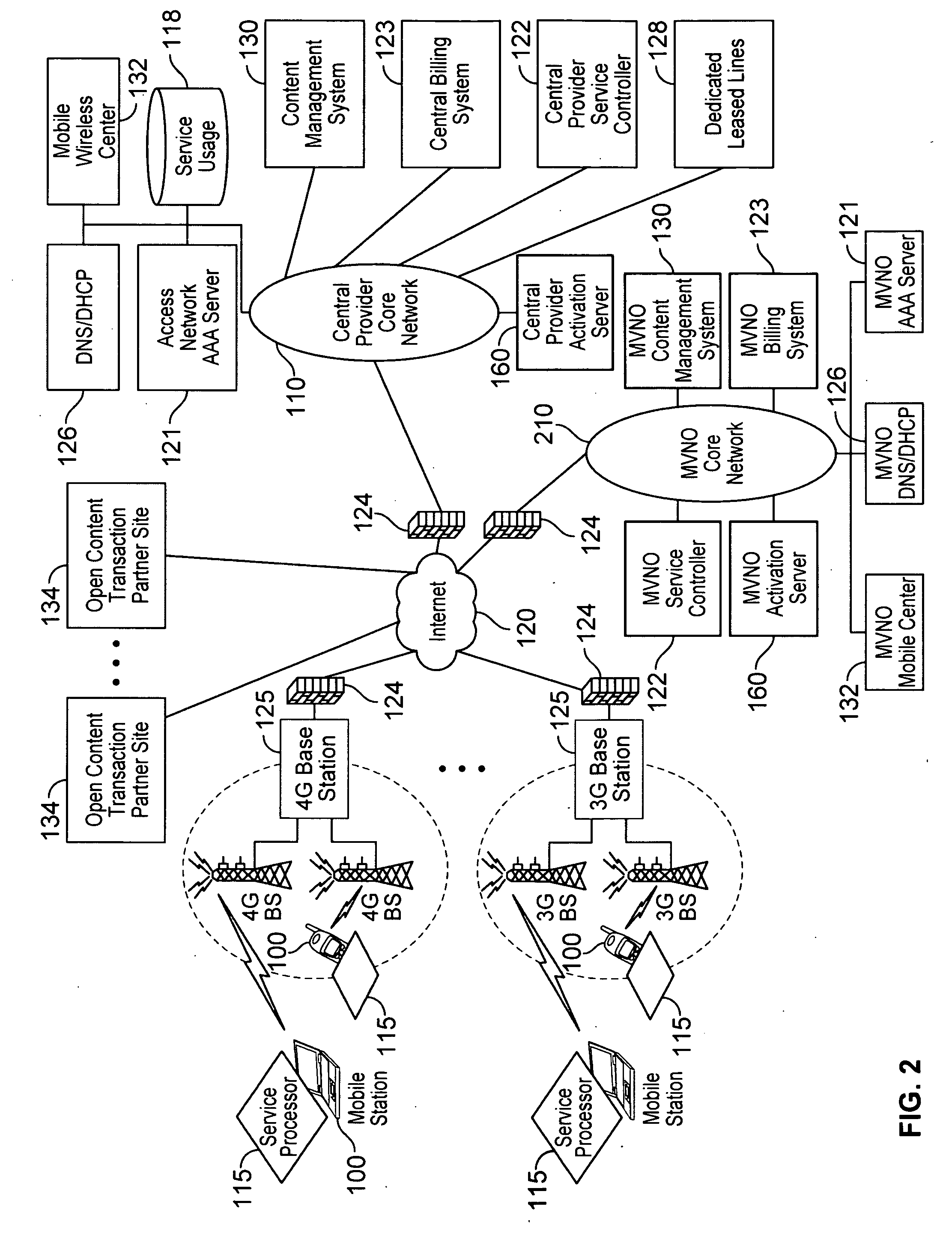
Mobile internet access system and method mapping mobile to internet service provider
InactiveUS6553219B1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsOperator IDCable Internet access
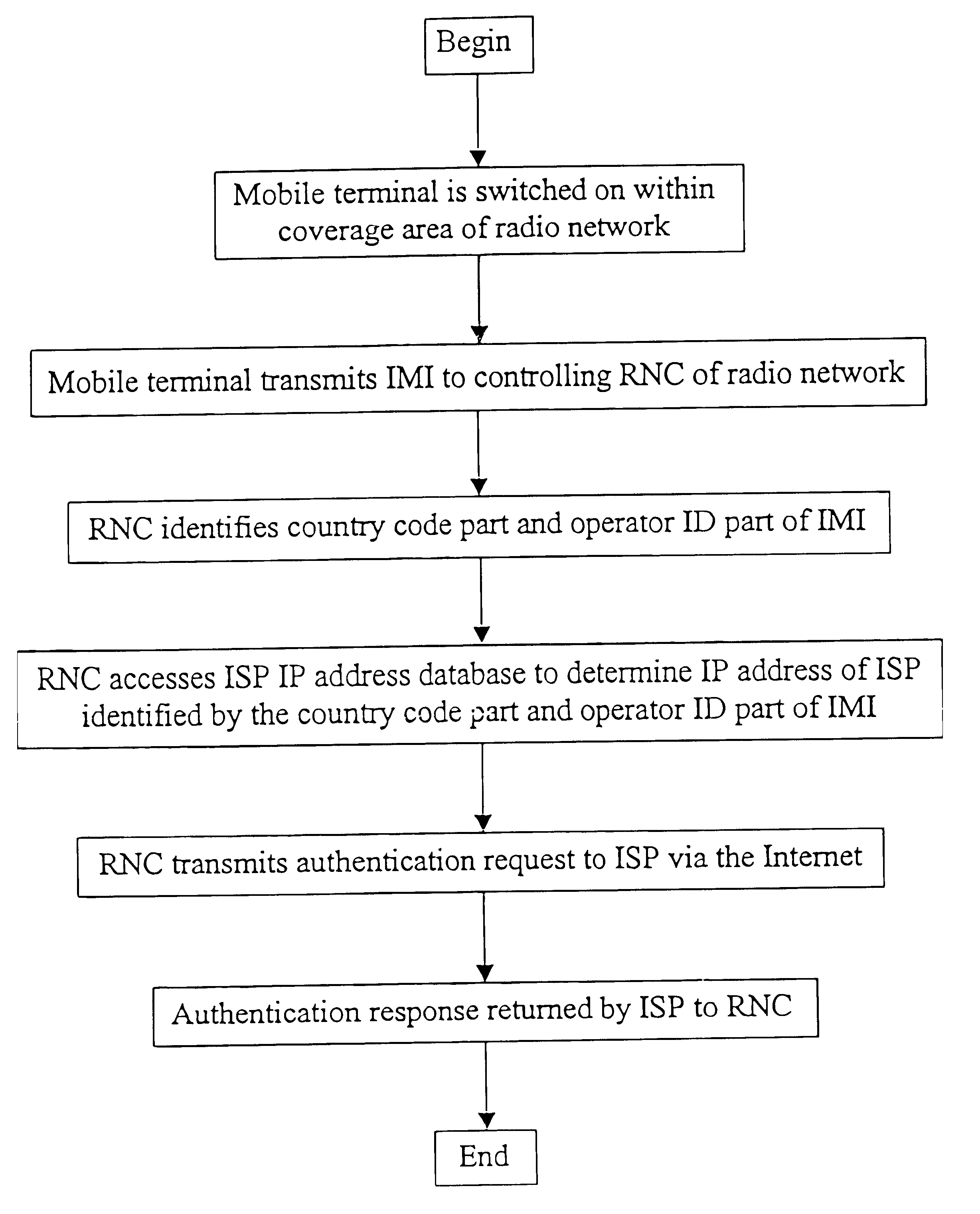
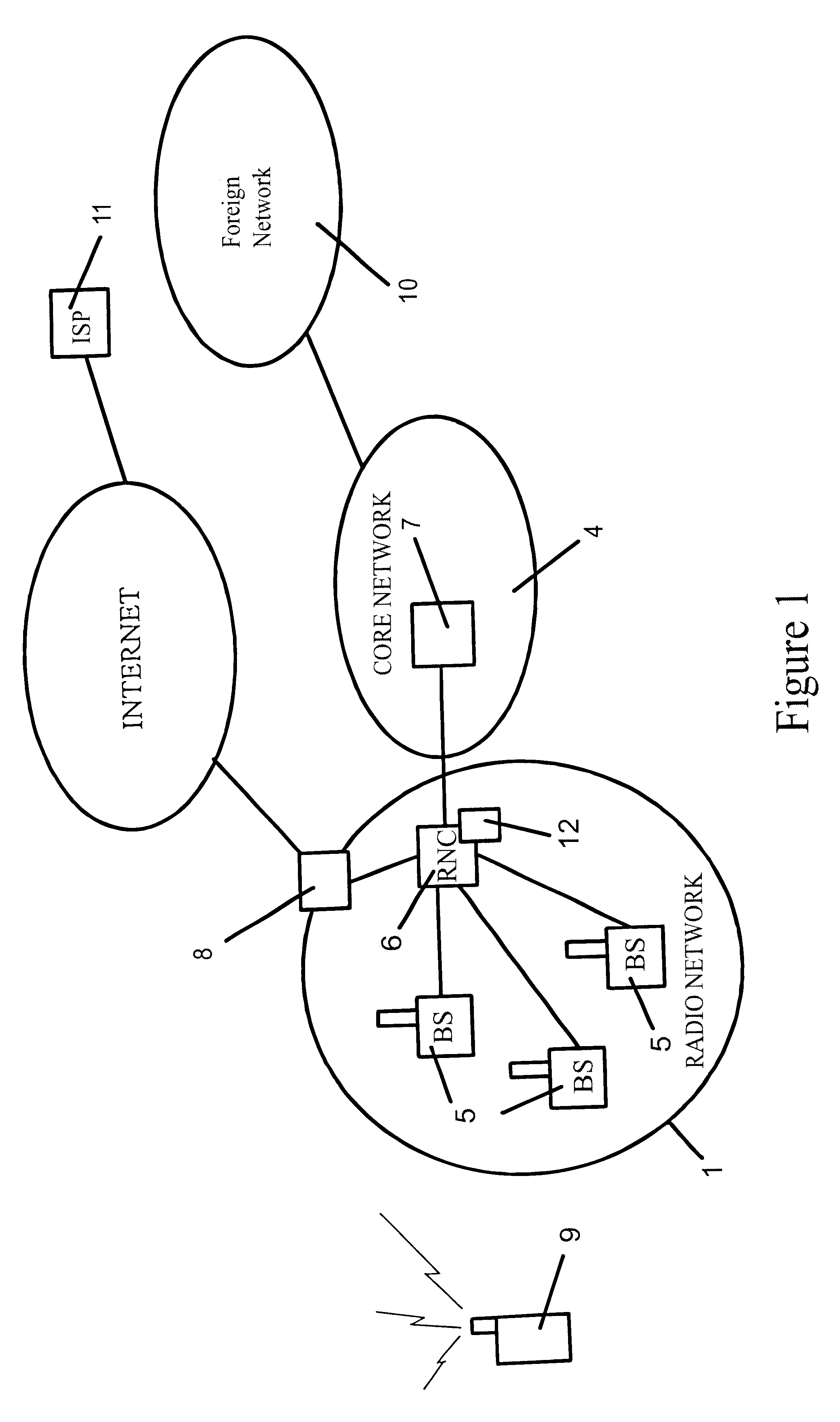
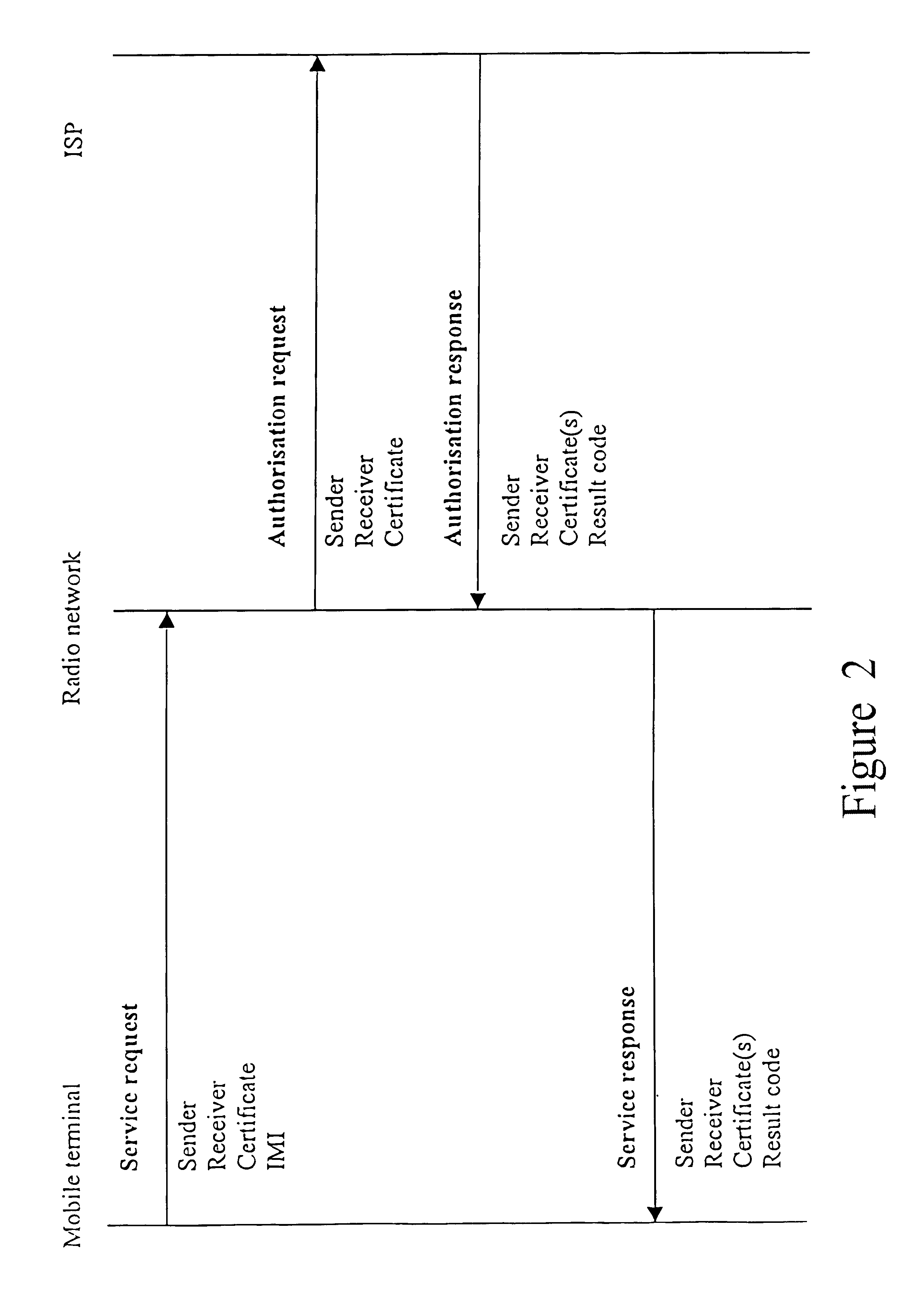
A method of authenticating a mobile wireless terminal 9 in a mobile telecommunications network, the terminal 9 being a subscriber of an Internet Service Provider (ISP) 11 rather than of a mobile network. The terminal 9 is allocated an International Mobile Identity (IMI) which is transmitted from the terminal 9 to a mobile network when the terminal 9 wishes to register with the network. A country code part and an operator ID part of the IMI are used by the network to determine the Internet Protocol (IP) address of the terminal's home ISP 11, which is then contacted by the network over the Internet to authenticate the mobile terminal 9.
Owner:TELEFON AB LM ERICSSON (PUBL)
Probabilistic web link viability marker and web page ratings
InactiveUS6163778AData processing applicationsDigital data information retrievalThird partyService provision
Hypertext information links are typically contained in documents accessible by networks. Data is gathered regarding the results of attempted access to documents identified by these links. The link's viability is calculated based on the number of successful attempts resulting in successful access in order to provide a measure of link viability. The display of the document is altered based on the measure of link viability. An average of link viability for all links on the document, and on the site, is used to calculate document viability and site viability which can be used to rate the document and site, respectively. These viability measures are displayed along with the corresponding link, document, and site. Display of results retrieved by conventional search engines may be sorted based on link, document or site viability, and displayed accordingly. Links contained in bookmark lists are also measured for viability to cull out bookmarks with low link viability to, or low document viability of, the bookmarked document. Viability calculations may be made by a user computer device, an Internet Service Provider, a third party service, and / or a server on which a document resides.
Owner:ORACLE INT CORP
Location and user identification for online gaming
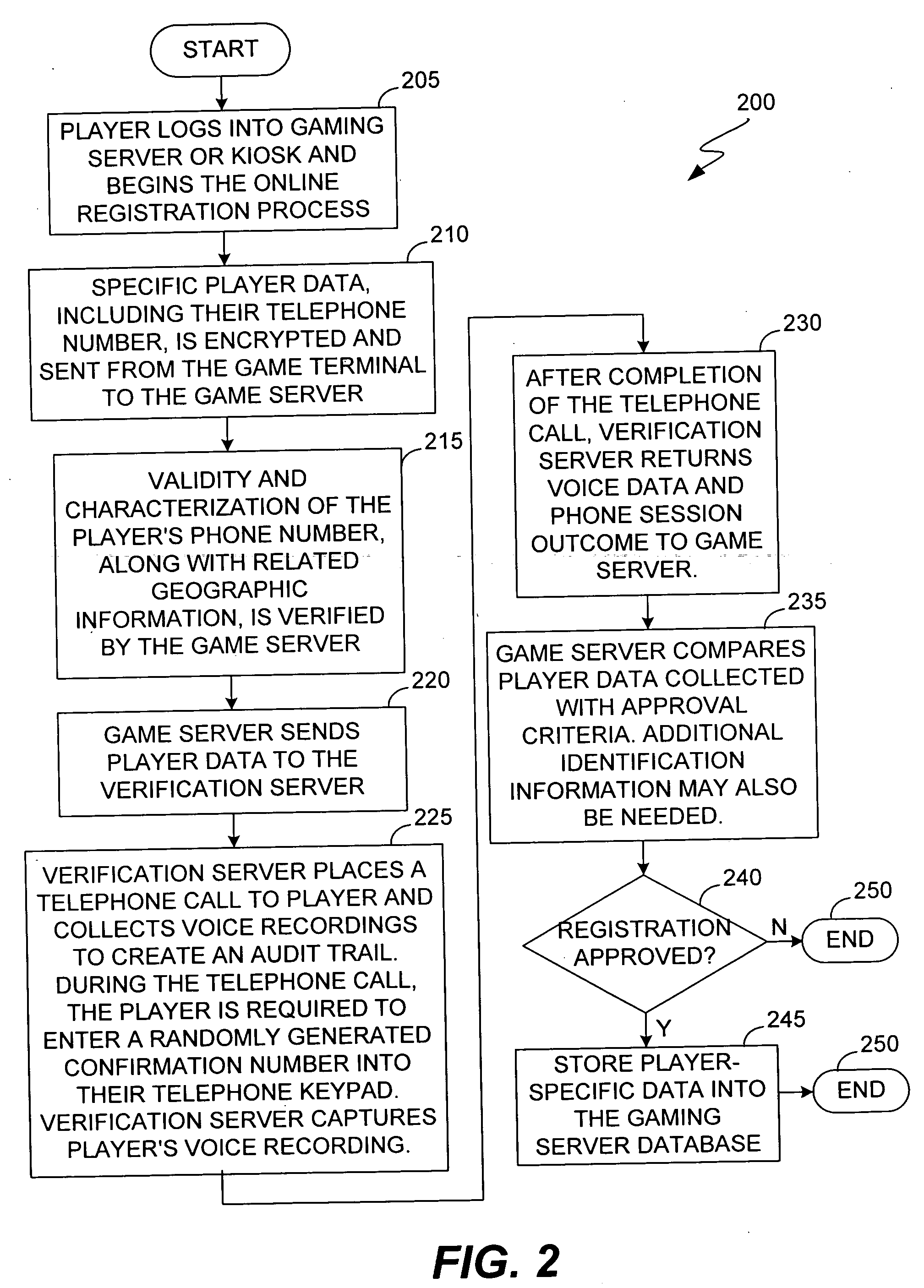
ActiveUS7577847B2Digital data processing detailsComputer security arrangementsHotel roomCellular telephone
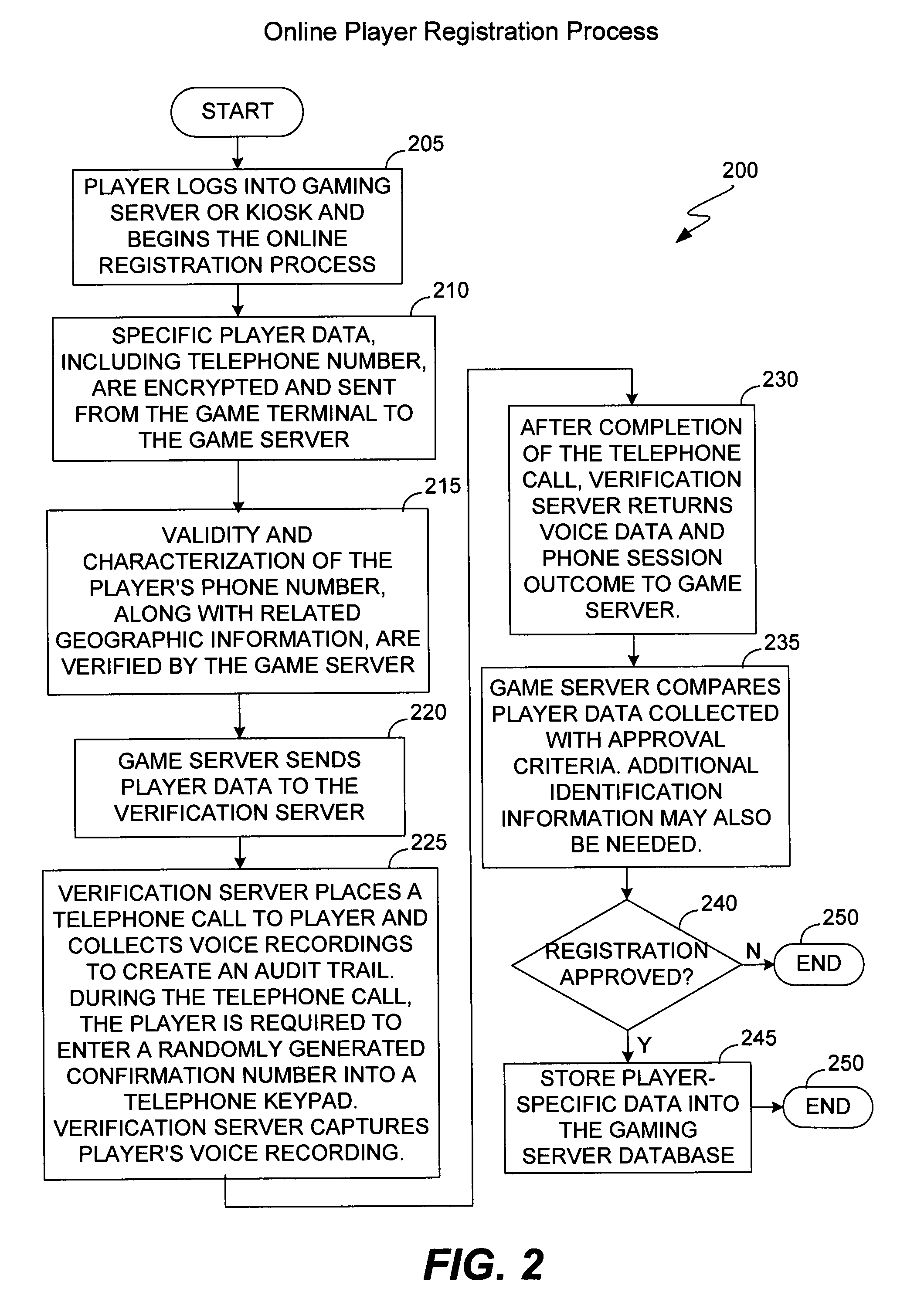
The present invention provides methods and devices for determining the location, identity and age of a user who desires to initiate a gaming session from an uncontrolled environment such as a home, a gaming kiosk or a hotel room. In some implementations, the user's location is determined in part by reference to a database of land telephone lines and corresponding addresses. The location may be verified by other methods, e.g., by determining the location of an Internet service provider's network device that is near a user's host device or via a cellular telephone network. The user may be asked to input a confirmation number and / or make an oral response during a telephone call to a telephone number associated with the uncontrolled environment. The user may also be prompted to make statements verifying his or her identity, age, a maximum amount available for wagering or other statements.
Owner:IGT
Game server system and method for generating revenue therewith
InactiveUS20050277472A1Metering/charging/biilling arrangementsApparatus for meter-controlled dispensingStart timeService provision
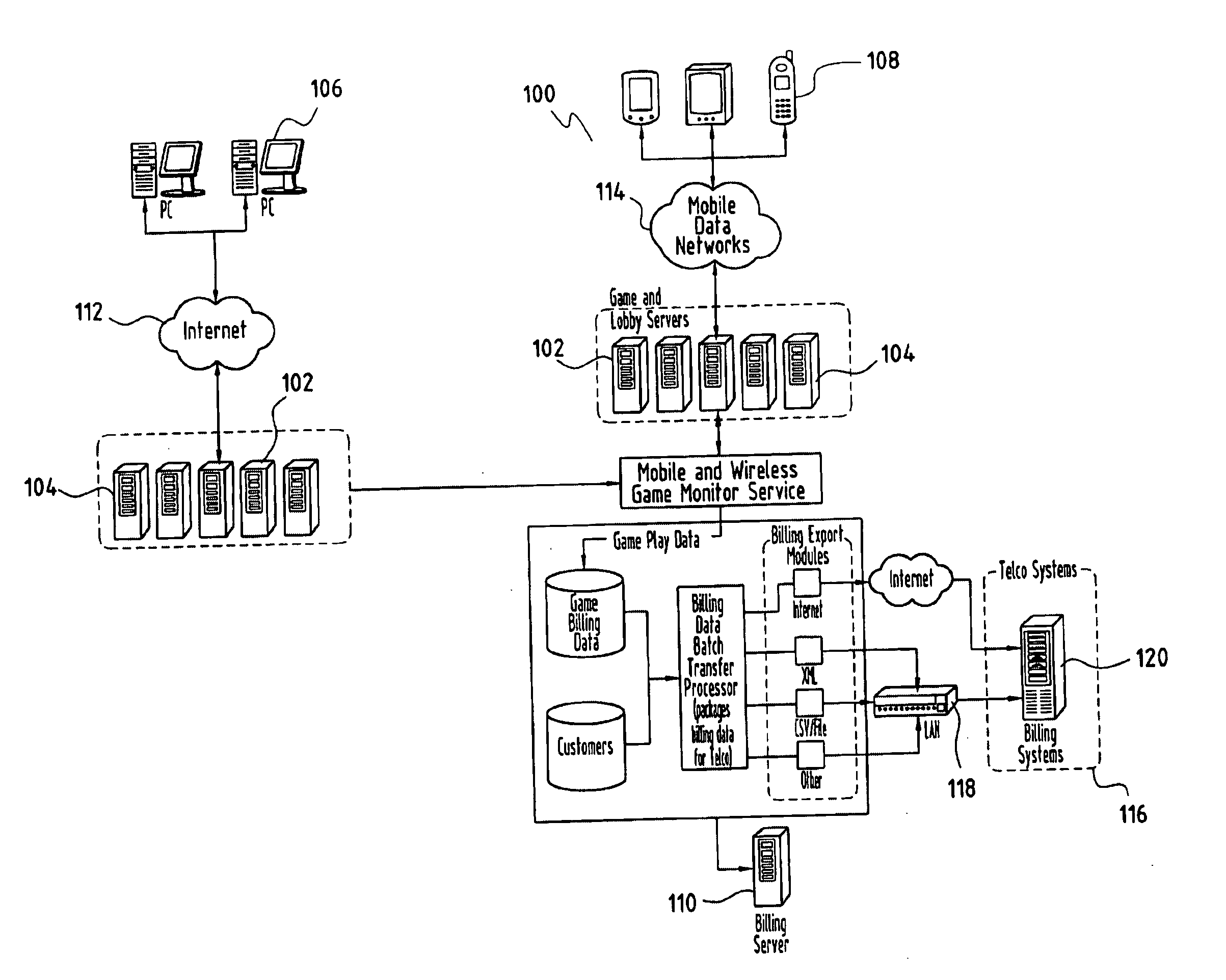
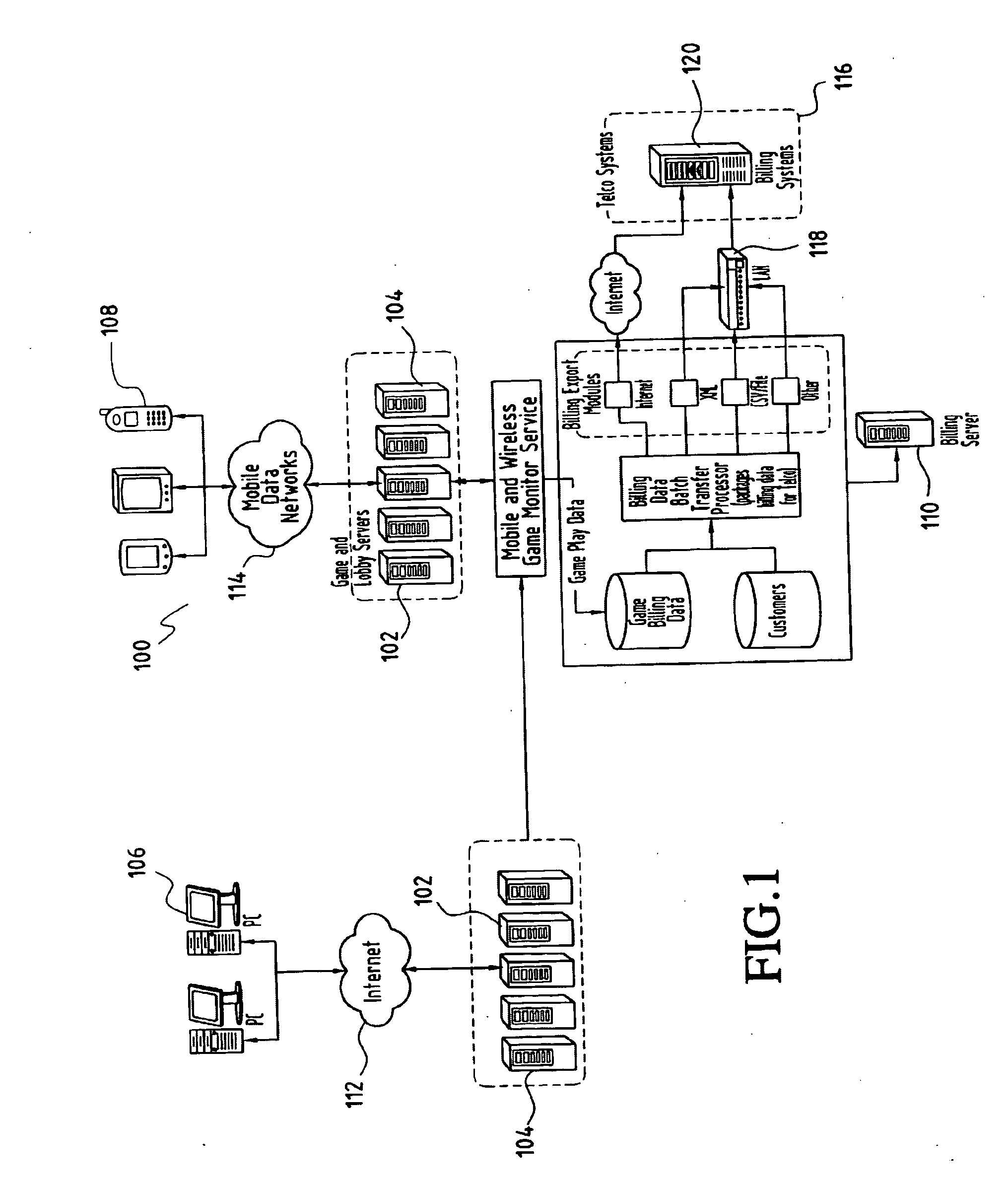
The present invention provides a system and method for generating revenue to a game provider from users using a gaming system. Games are provided to users by the game provider and played over the Internet or a mobile network. The system and method includes providing Internet or wireless services to the users having a computer or mobile device for playing a game. User activity is recorded by the system including the start time and end time of the game. A total game time is calculated and used as a basis for sharing revenue generated from the user's network use between the game provider and an Internet service provider or wireless network provider.
Owner:UPFRONT TECH
Internet service login using preexisting services
ActiveUS20080134343A1Digital data processing detailsAnalogue secracy/subscription systemsClient-sideInternet service provider
Embodiments of the present invention provide a system and method for logging a client into an internet service using a preexisting service. In order to login, the user may select a link that triggers the service to send login information to the user via a preexisting service, such as instant messaging or email. In some embodiments, the user is sent a link via their preexisting service. The user then logs into the service by selecting the link.
Owner:RED HAT
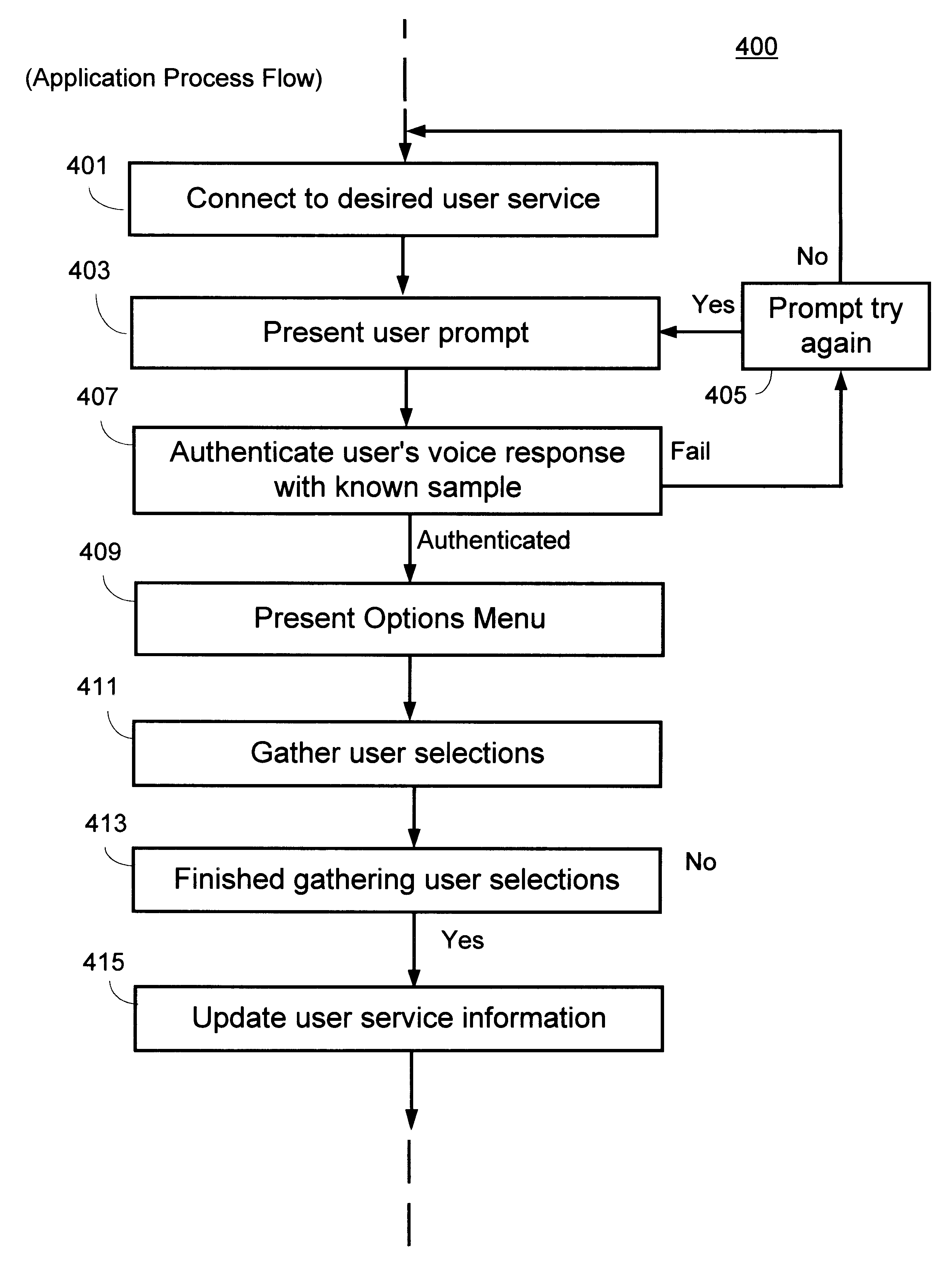
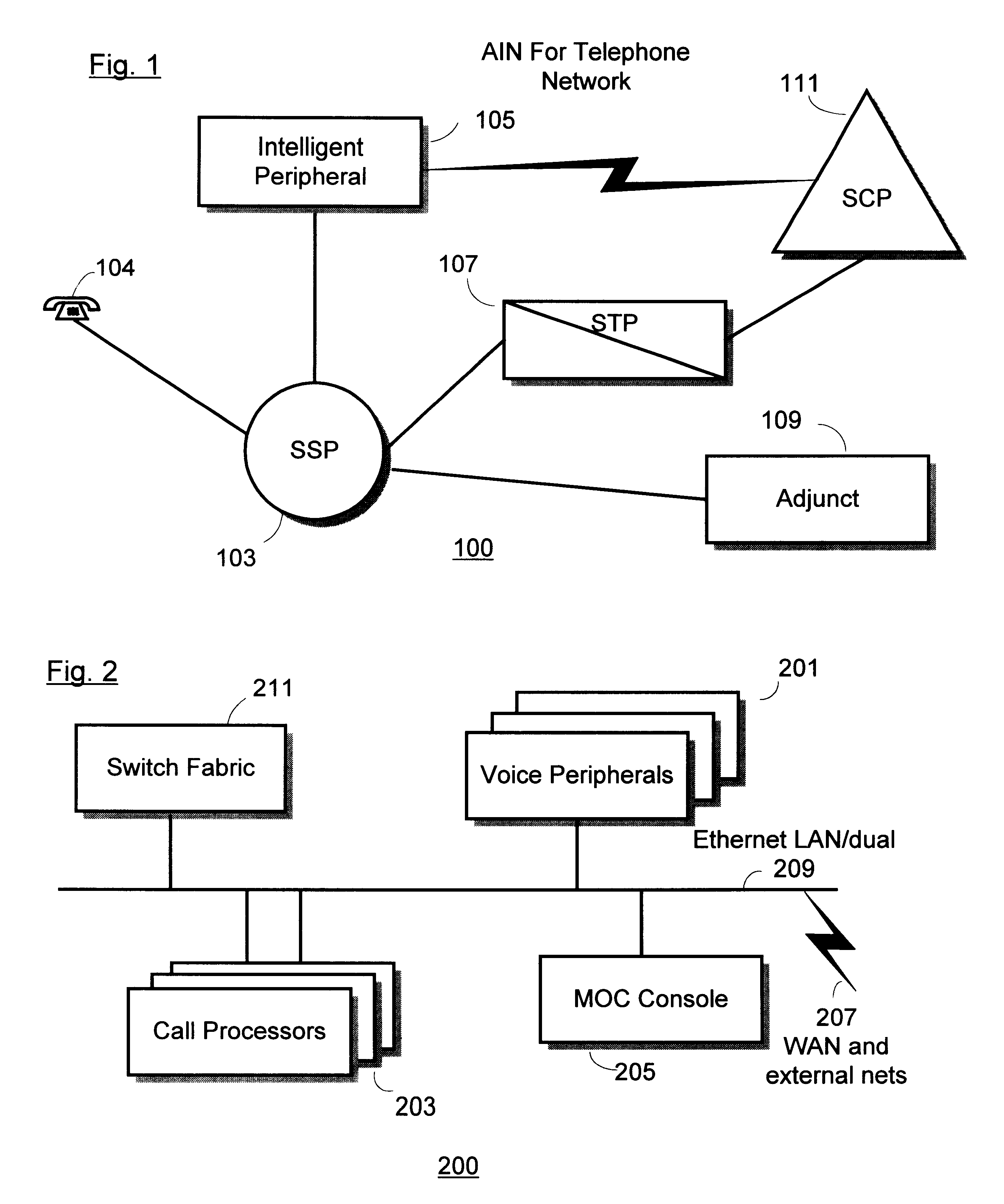
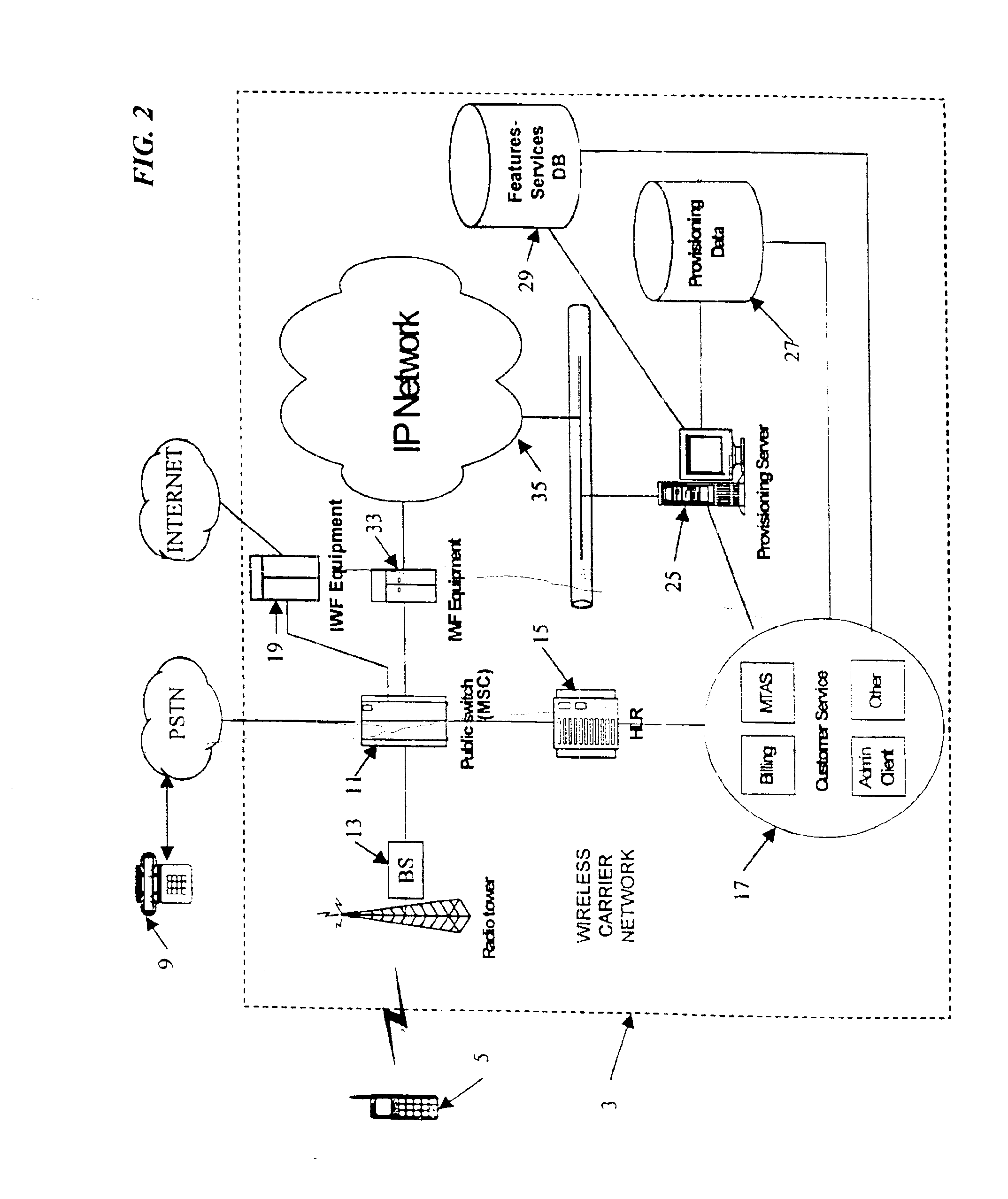
Speaker verification for authorizing updates to user subscription service received by internet service provider (ISP) using an intelligent peripheral (IP) in an advanced intelligent network (AIN)
InactiveUS6337899B1Multiplex system selection arrangementsSpecial service provision for substationFrequency spectrumMatch algorithms
A method for controlling subscription services delivered to a user by an Internet Service Provider (ISP) coupled to an Automated Intelligent Network (AIN) telephone system with at least one central office switching system. An intelligent peripheral subsystem is connected to the central office switching system, via a call connection channel. The intelligent peripheral subsystem providing at least one auxiliary call processing capability via the call connection channel and provides a telephony speaker authentication method for selectively authorizing updates to user subscription services types provided by the ISP, wherein each of the subscription services types include one or more service options. The method for controlling subscription services including: a) prompting for a voice response; b) authenticating a user's voice response pattern by performing a speaker-dependent cepstrum matching algorithm with previously stored samples of the user's voice response, and if the user's voice response pattern is positively authenticated with previously stored samples, then performing the steps of: c) presenting a menu of user subscription types, each with available AIN service options; and d) responding to a user selection of at least one user subscription types, each with service option, by activating a service option selected by the user, wherein the service option is governed by said ISP by regulating one or more Uniform Resource Locator (URL) addresses received by a user subscriber device from said ISP over a telecommunication line.
Owner:IBM CORP
Location blocking service from a wireless service provider
InactiveUS7224978B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyOnline advertising
Location-blocking and identity-blocking services that can be commercially offered by a service promoter, e.g., a cellular service provider or a web advertiser. In the identity-blocking service, the service promoter may disclose the current physical location of a mobile subscriber (i.e., a cellular phone operator) to a third party (e.g., a web advertiser) subscribing to the identity-blocking service. However, the service promoter may not send any identity information for the mobile subscriber to the third party. On the other hand, in the location-blocking service, the service promoter may disclose the mobile subscriber's identity information to the third party, but not the current physical location of the mobile subscriber. Blocking of the mobile subscriber's identity or location information may be desirable for privacy reasons, to comply with a government regulation, or to implement a telecommunication service option selected by the mobile subscriber. However, in the case of the mobile subscriber requesting emergency help, the service promoter may not block identity and / or location information. Instead, the service promoter may send all such information to the emergency service provider (e.g., the police or a hospital).
Owner:GOOGLE LLC
Mobile station internet messaging
InactiveUS6856804B1Multiplex system selection arrangementsData switching by path configurationTelecommunicationsInternet service provider
A wireless communications network provides the power status for mobile stations served by the wireless communications network to Internet service providers. Internet service providers make the power status for mobile stations available to Internet service provider subscribers. By knowing the power status of a particular mobile device, Internet service provider subscribers can send messages to the mobile device or may call the mobile device, knowing that it is activated and will receive the call.
Owner:CELLO PARTNERSHIP DBA VERIZON WIRELESS
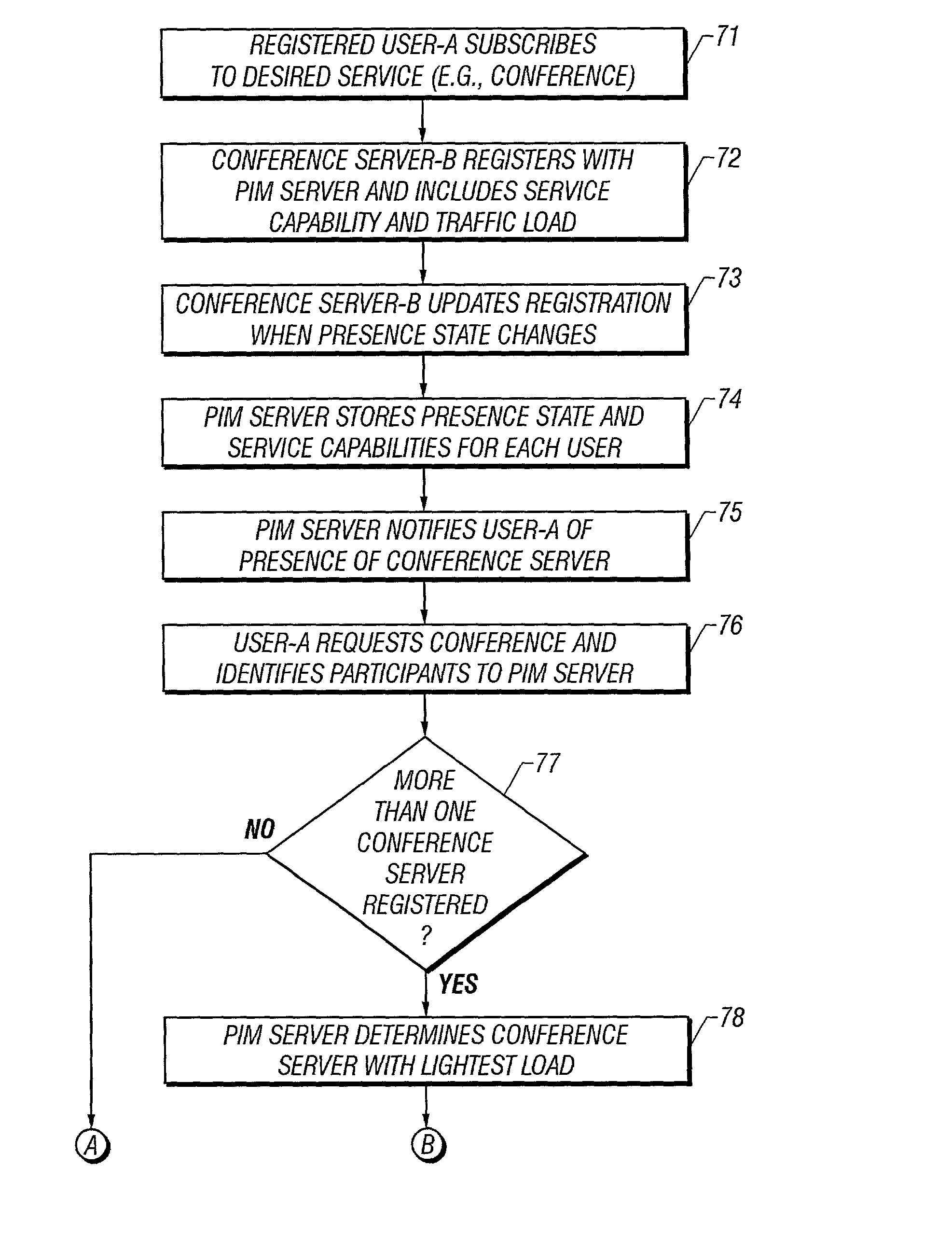
Service access system and method in a telecommunications network
ActiveUS20030108000A1Multiplex system selection arrangementsSpecial service provision for substationSession Initiation ProtocolControl signal
A system and method of providing a subscriber service to service users in a telecommunications network. In networks utilizing Session Initiation Protocol (SIP) control signaling for call setup and control, the SIP REGISTER message is modified to indicate service capability information and optionally a traffic load indication for service providers. The REGISTER message is sent to a modified Presence and Instant Messaging (PIM) server that stores presence information and the service capability information for registered service providers. The PIM server then notifies subscribing service users of the identity of the service provider that is registered on the network. The PIM server may utilize the traffic load information to balance the traffic load between service providers by providing users with the identity of the service provider that is the most lightly loaded.
Owner:TELEFON AB LM ERICSSON (PUBL)
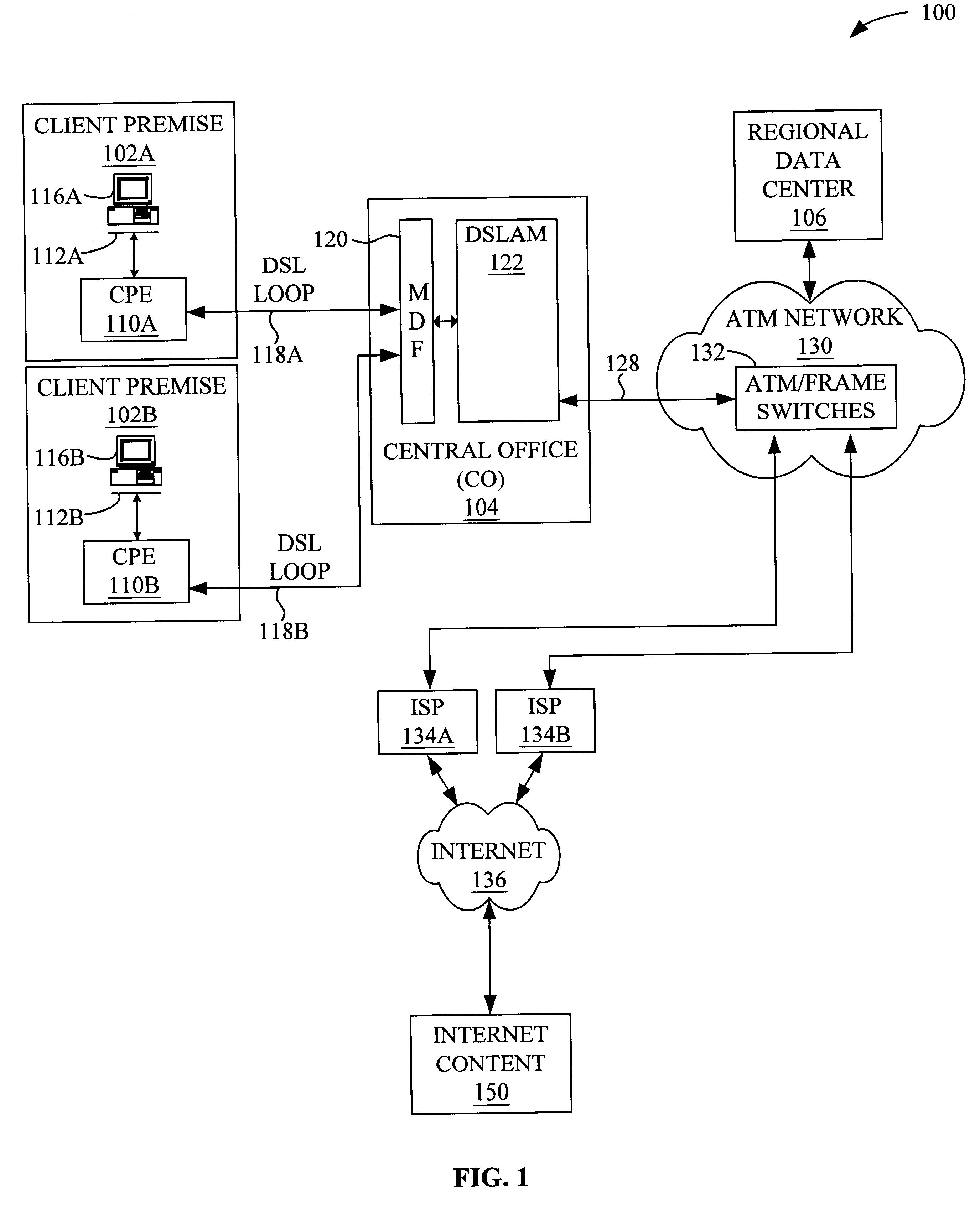
System and method for providing broadband content to high-speed access subscribers
InactiveUS6286049B1Multiple digital computer combinationsData switching networksClient dataData traffic
Systems and methods for providing broadband content to high-speed access subscribers with layer 4-7 switching are disclosed. The system generally comprises an enhanced services complex (ESC) having at least one content server having Internet content stored or cached therein and a broadband access gateway (BAG) in communication with the ESC and to at least one Internet service provider (ISP), where the BAG is configured to transmit and receive data traffic to and from a client premise equipment (CPE) at a client premise, respectively. The BAG is configured to selectively route data traffic received from the CPE to an ESC content server or the ISP based on multiple instances of the content destination address. The method generally comprises routing client data packets from a CPE to a BAG in communication with at least one ISP and an ESC having at least one content server, selectively routing each client data packet from the BAG to the ESC or the Internet, and routing content data packets from the Internet content or the content server to the CPE.
Owner:GC PIVOTAL LLC
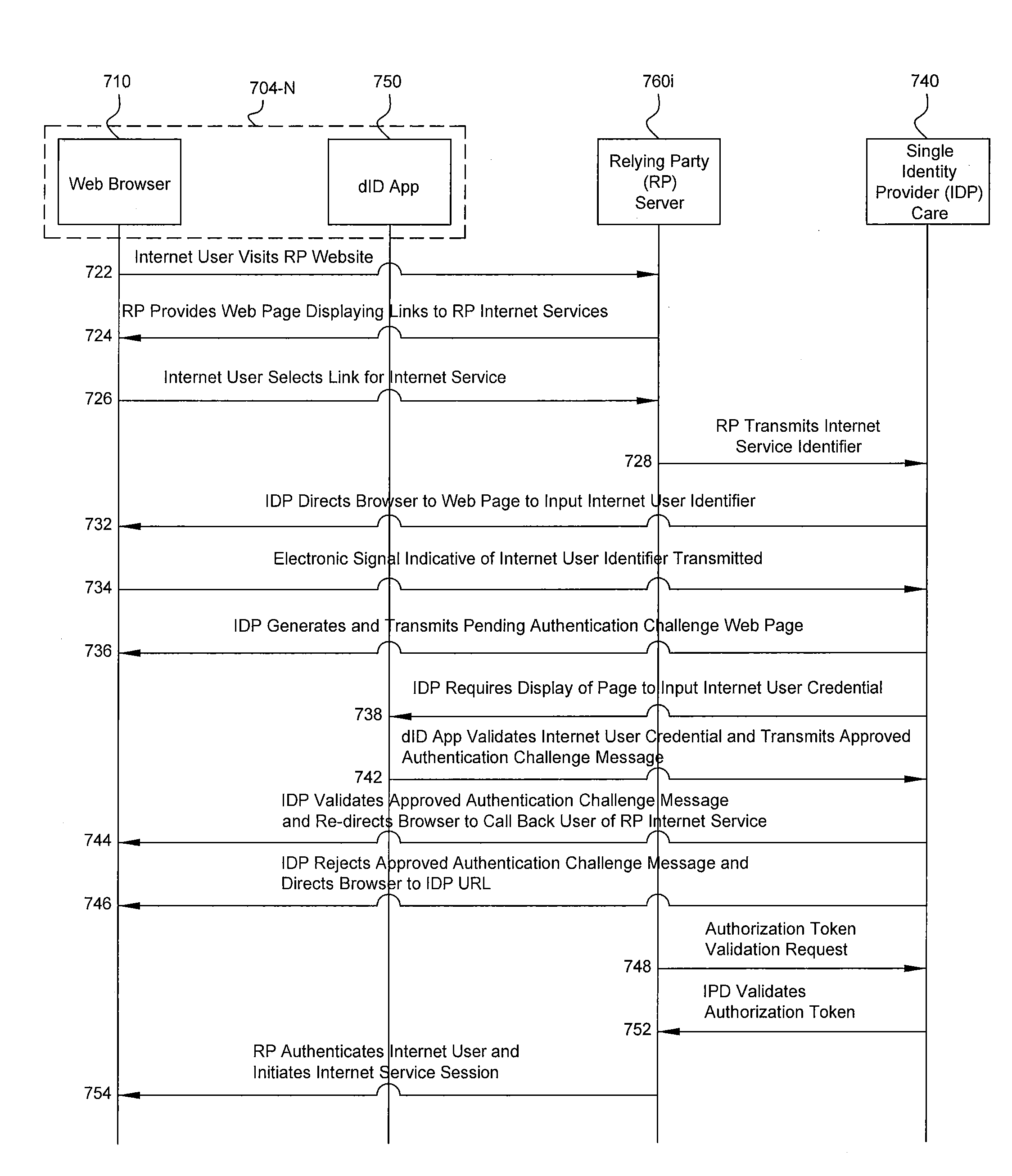
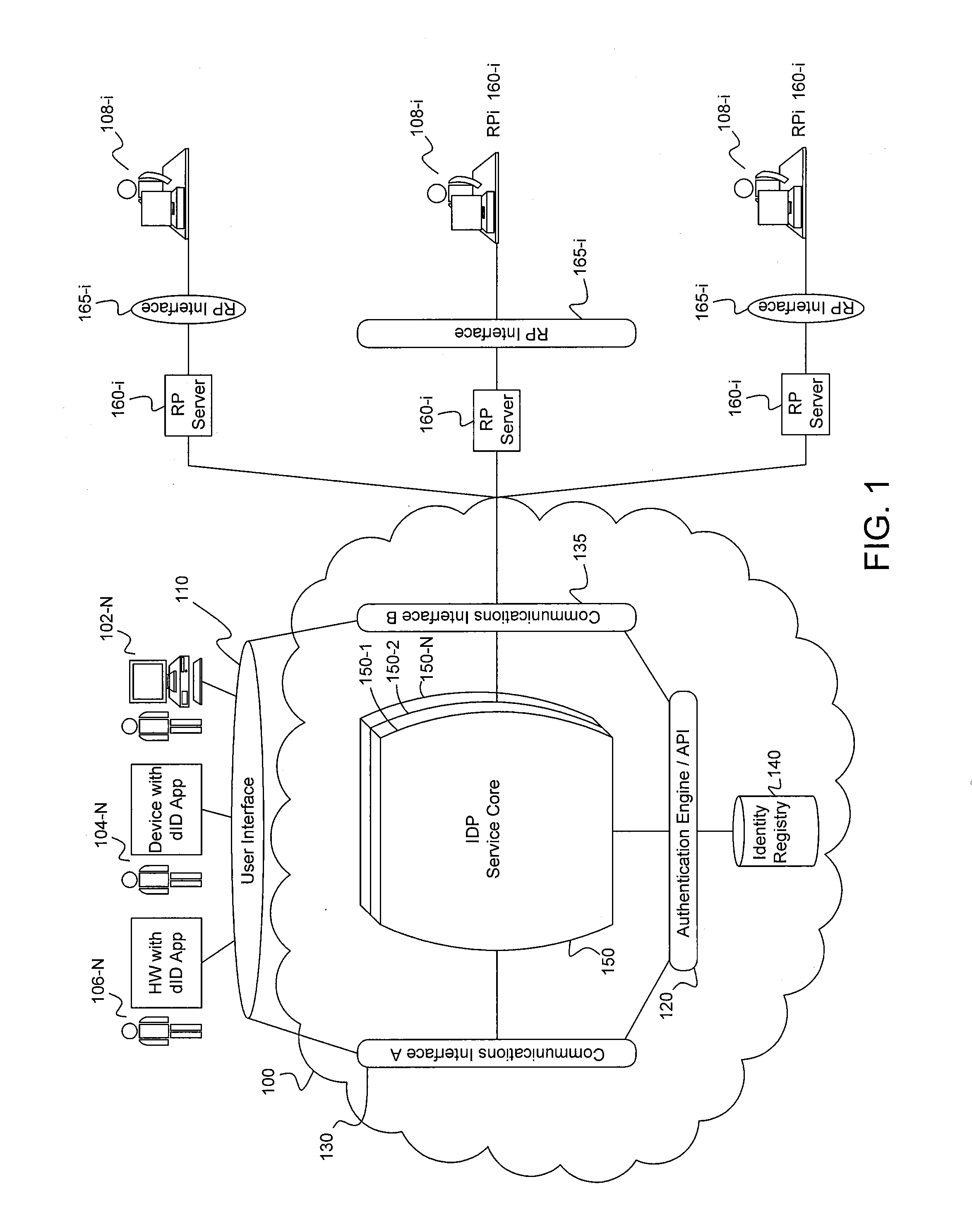
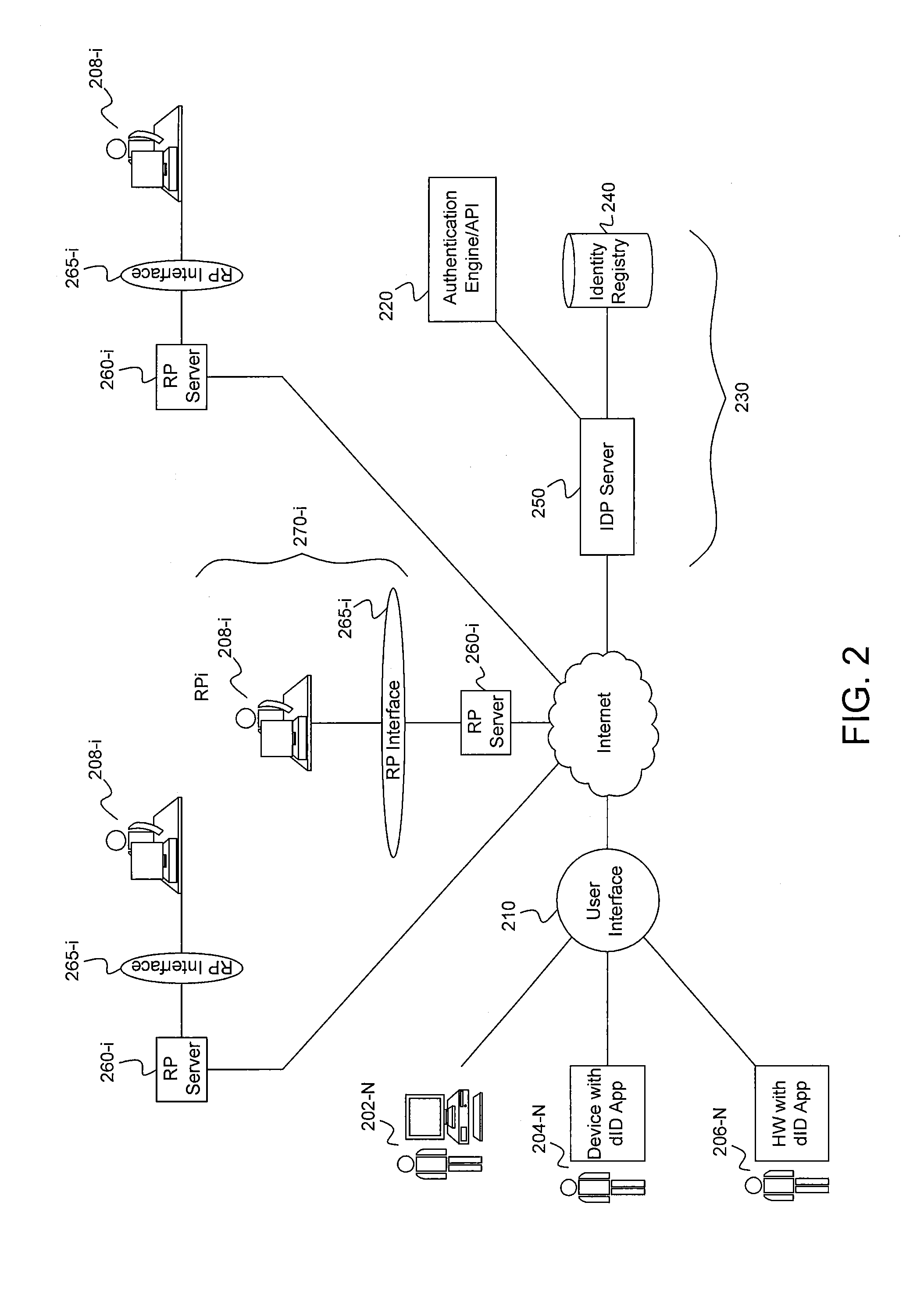
Computer-implemented systems and methods of device based, internet-centric, authentication
ActiveUS20160134599A1User identity/authority verificationDigital data authenticationInternet usersIdentity provider
Systems and computer-implemented methods for authorizing respective access by each of a plurality of Internet users to a respective one or more Internet services provided by each of a plurality of Internet service providers. A system includes a processor, and non-transient computer readable storage media, at a single identity provider. The storage media is encoded with program code executable by the processor for requiring an identity provider application residing on each of a plurality of devices to create a respective authentication token that is specific to a respective identifier and user credential of a respective Internet user, a respective device identifier, and the respective identity provider application, and for authorizing respective access by the plurality of Internet users to a respective requested one of the Internet services provided by each Internet service provider using the respective created authentication tokens and respective identifiers for each of the respective requested Internet services.
Owner:PRIVAKEY INC
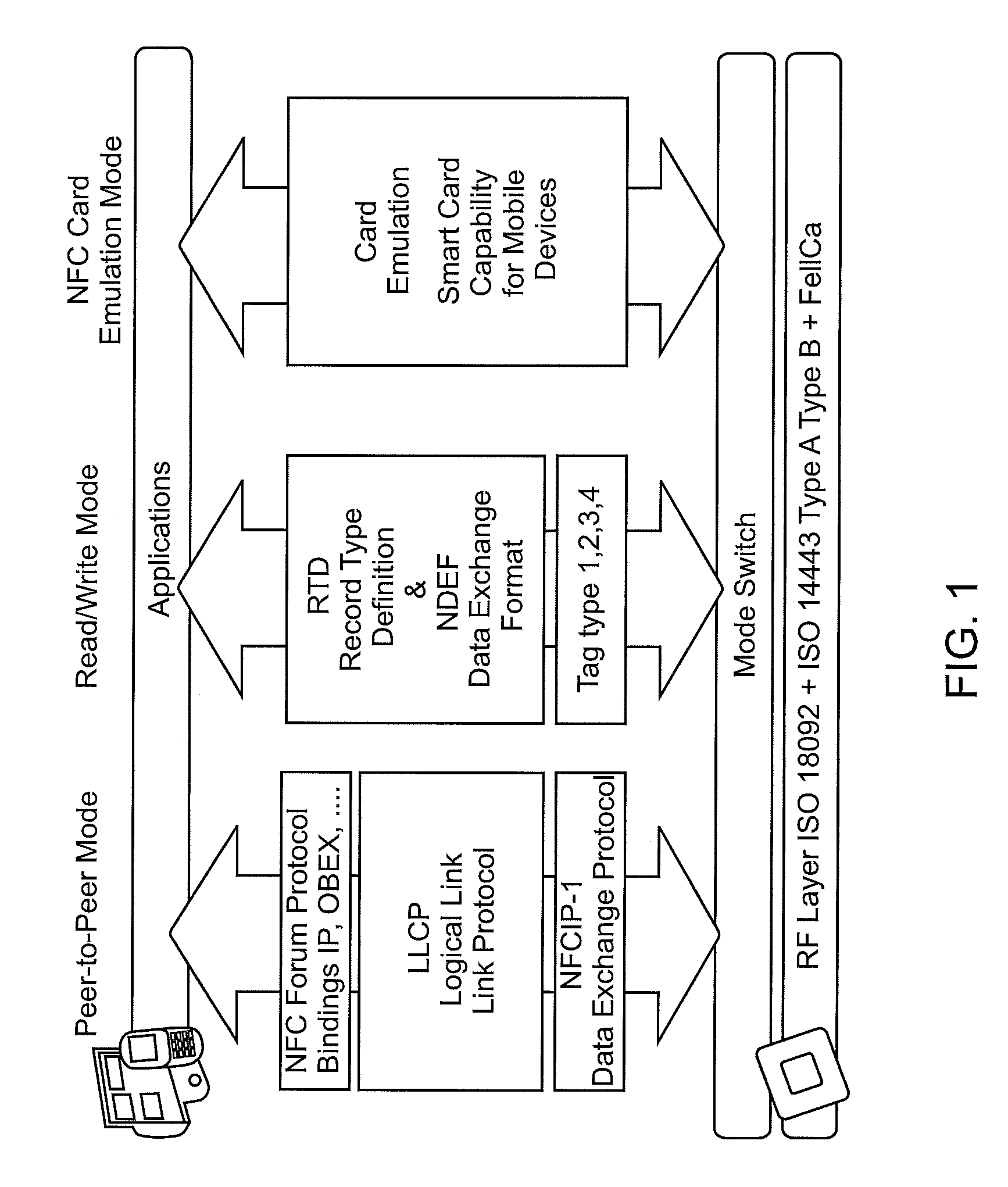
One step near field communication transactions
A one step method for transferring money from a sender to a recipient includes entering information relating to the transfer into a near field communication (NFC) enabled data communication device of the sender and then placing the sender's device in close proximity to a NFC enabled data communication device of the recipient. The sender's device is operable when placed in contact with or close proximity to the recipient's device to 1) establish an NFC link between the two devices, 2) gather information relating to the recipient from the recipient's device via the NFC link, and 3) transmit the information relating to the transfer and the recipient to a third party service provider via another network, such as the Internet, and thereby cause the service provider to transfer the money from a funding account of the sender to a receiving account of the recipient.
Owner:PAYPAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com