Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
5744results about "Metering/charging/biilling arrangements" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
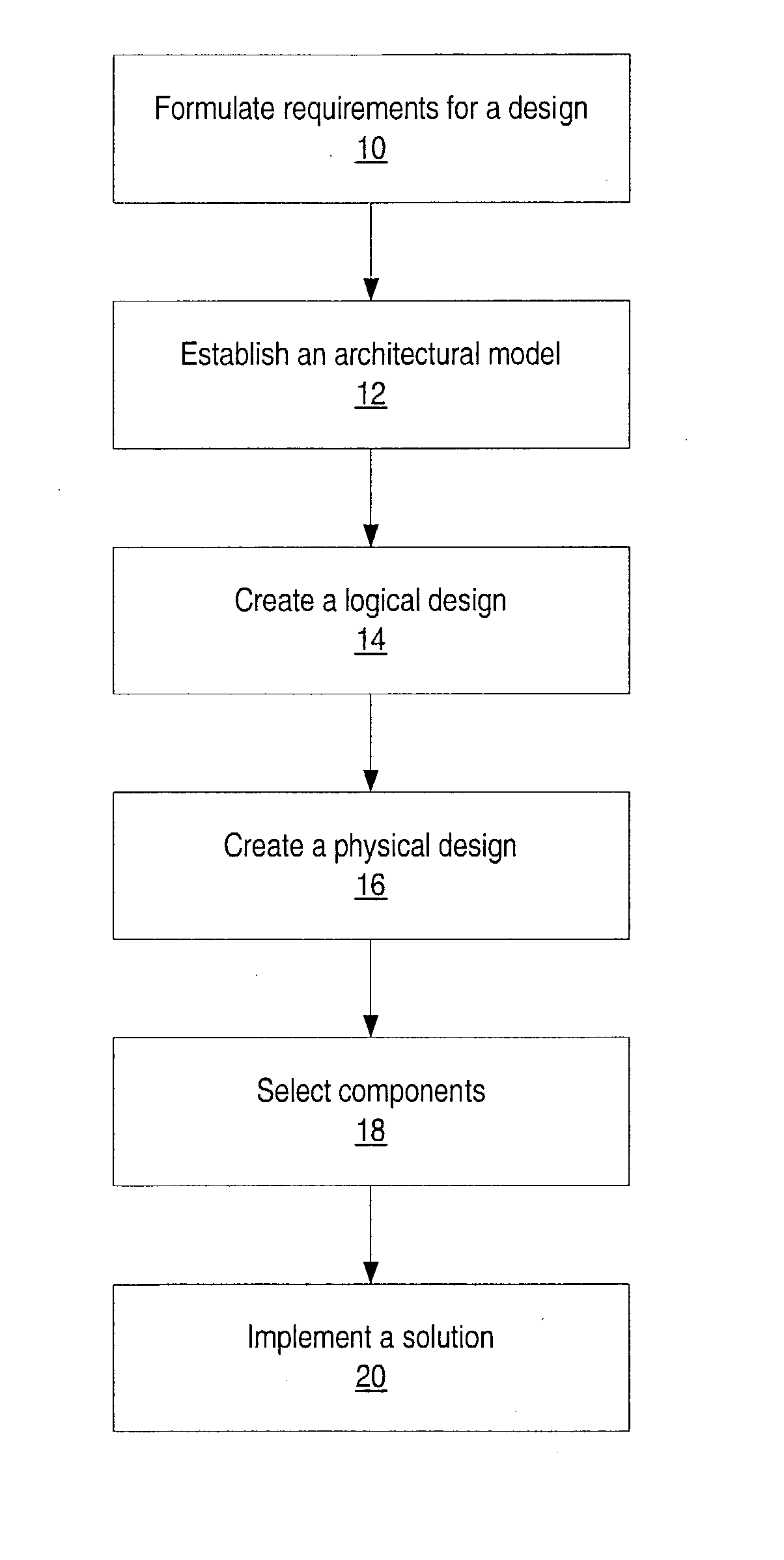
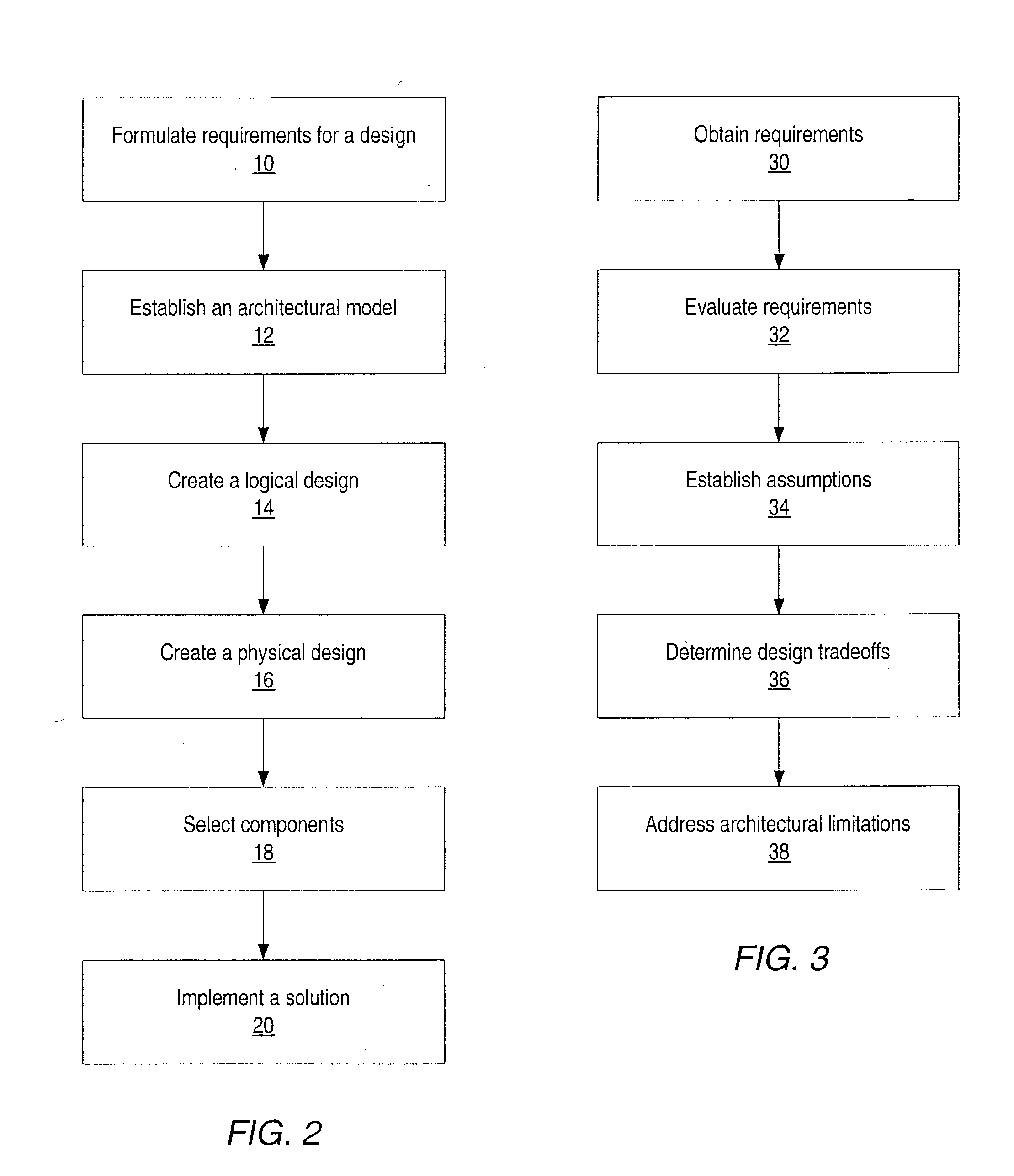
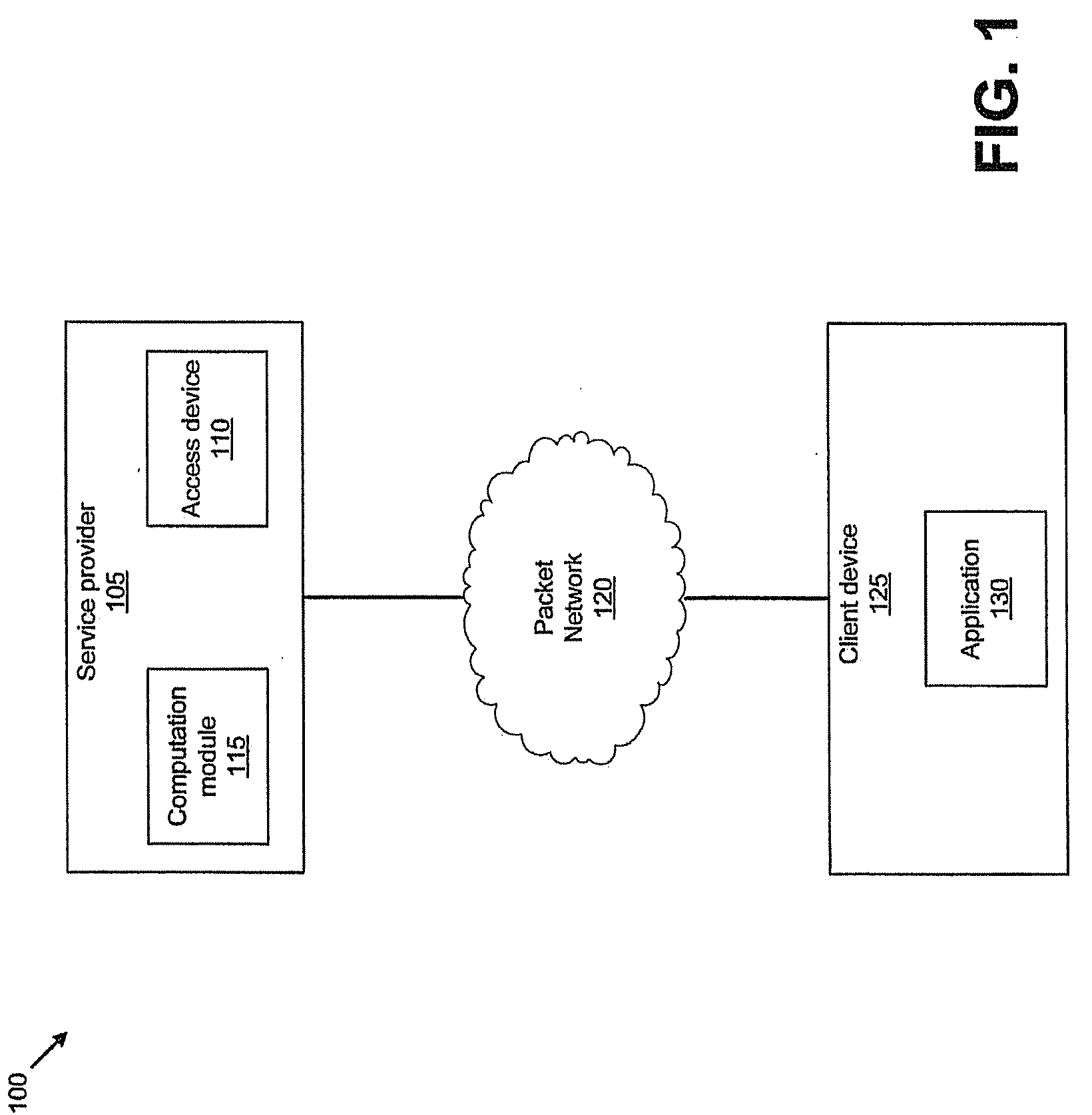
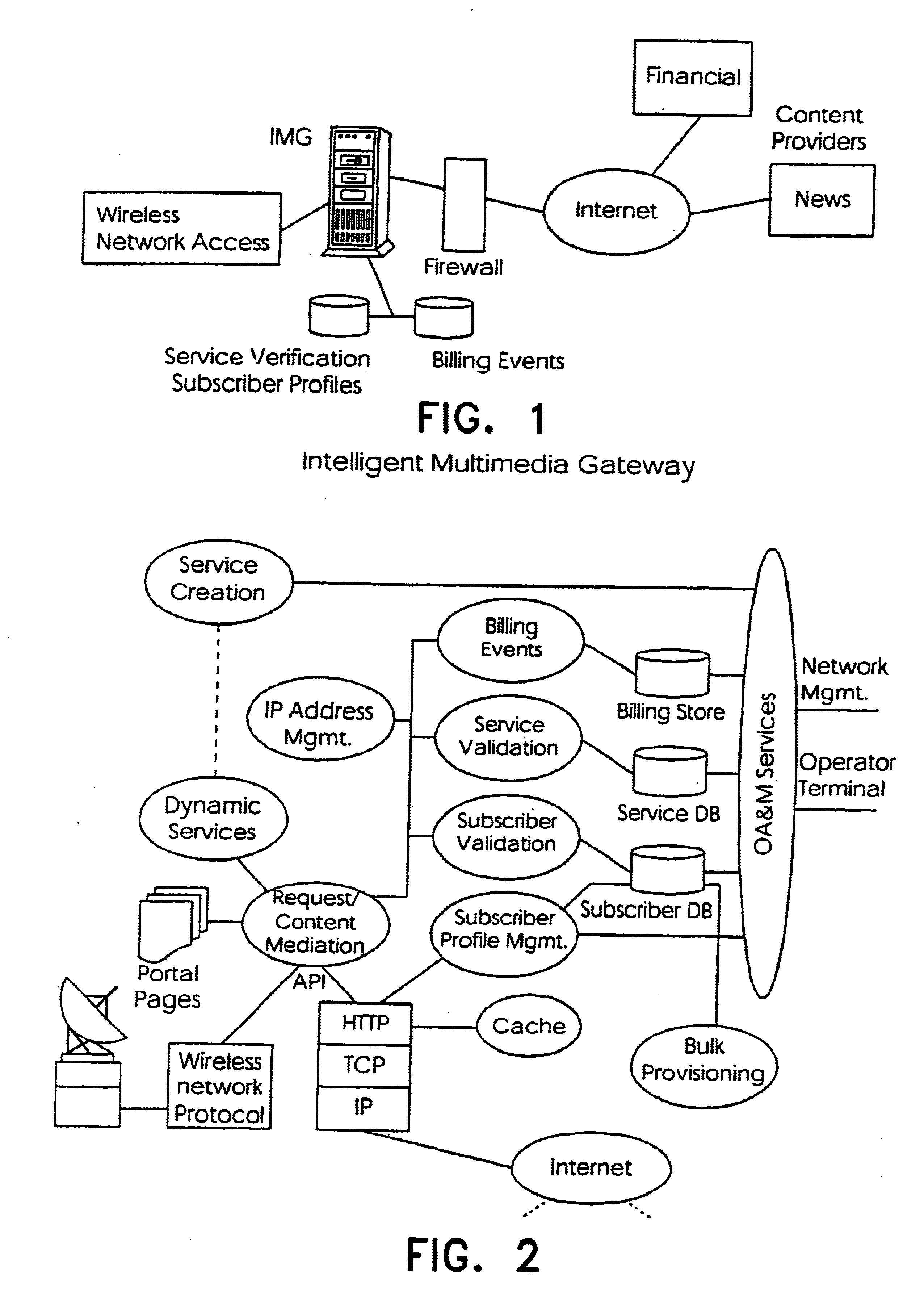
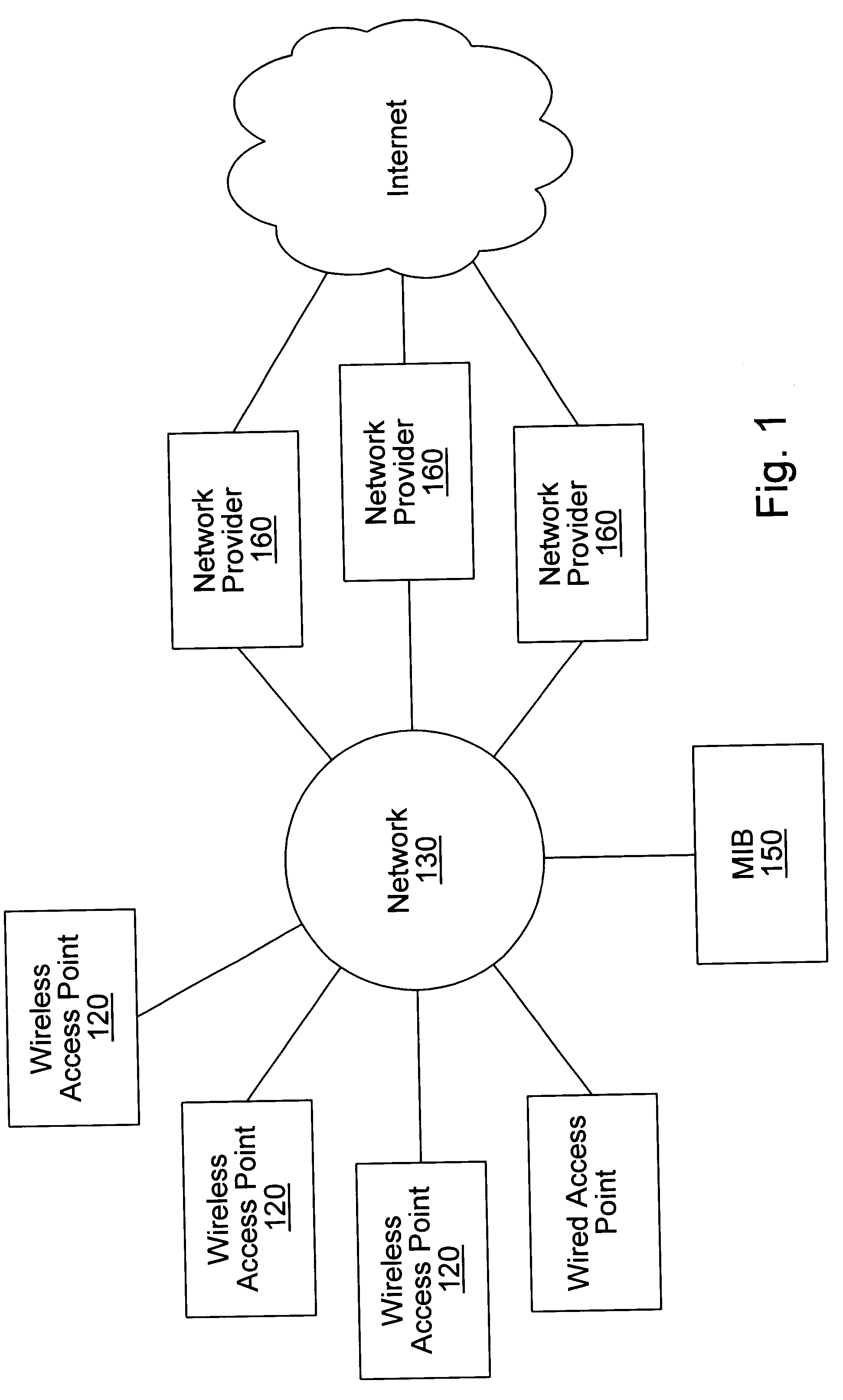
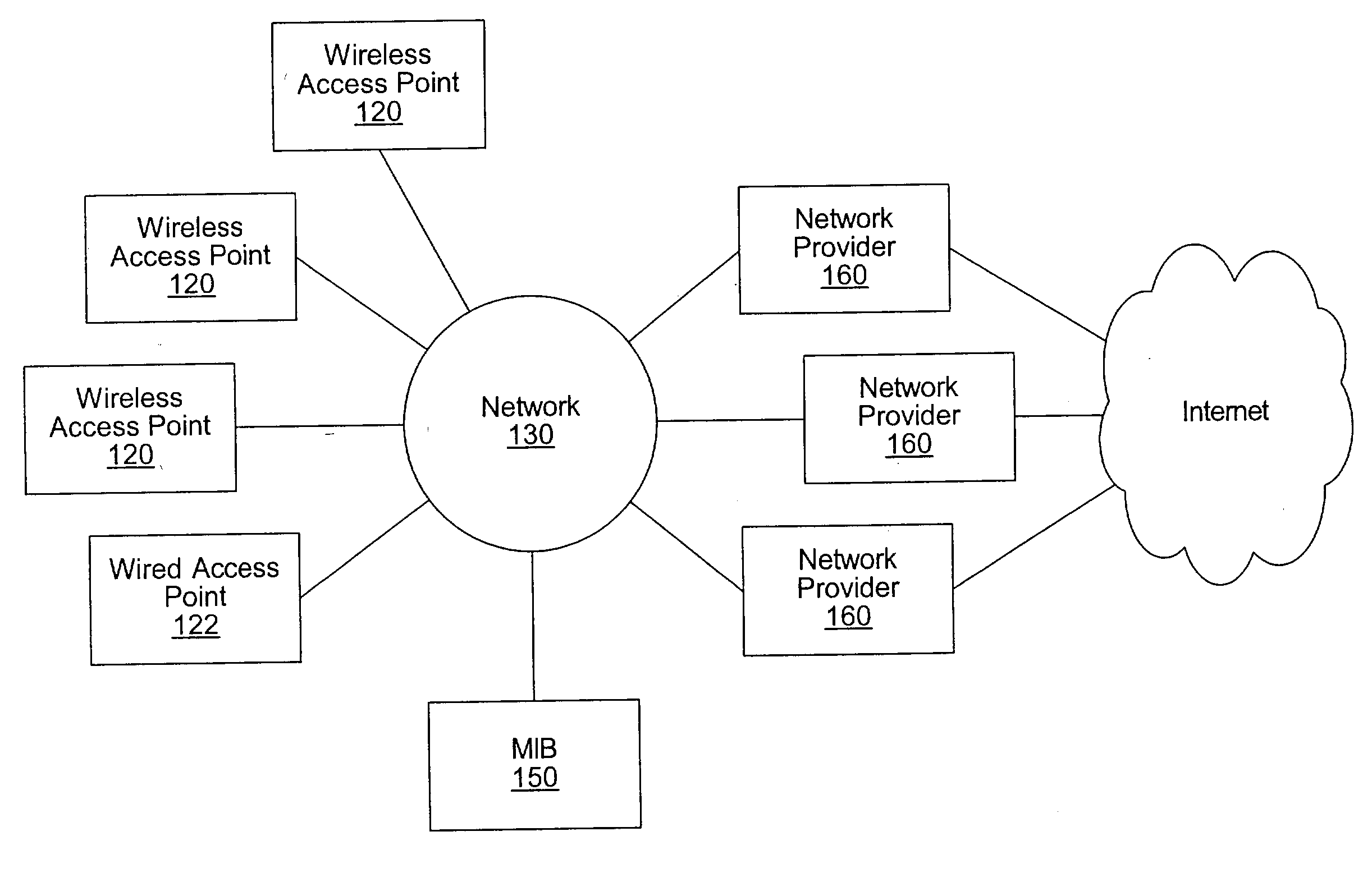
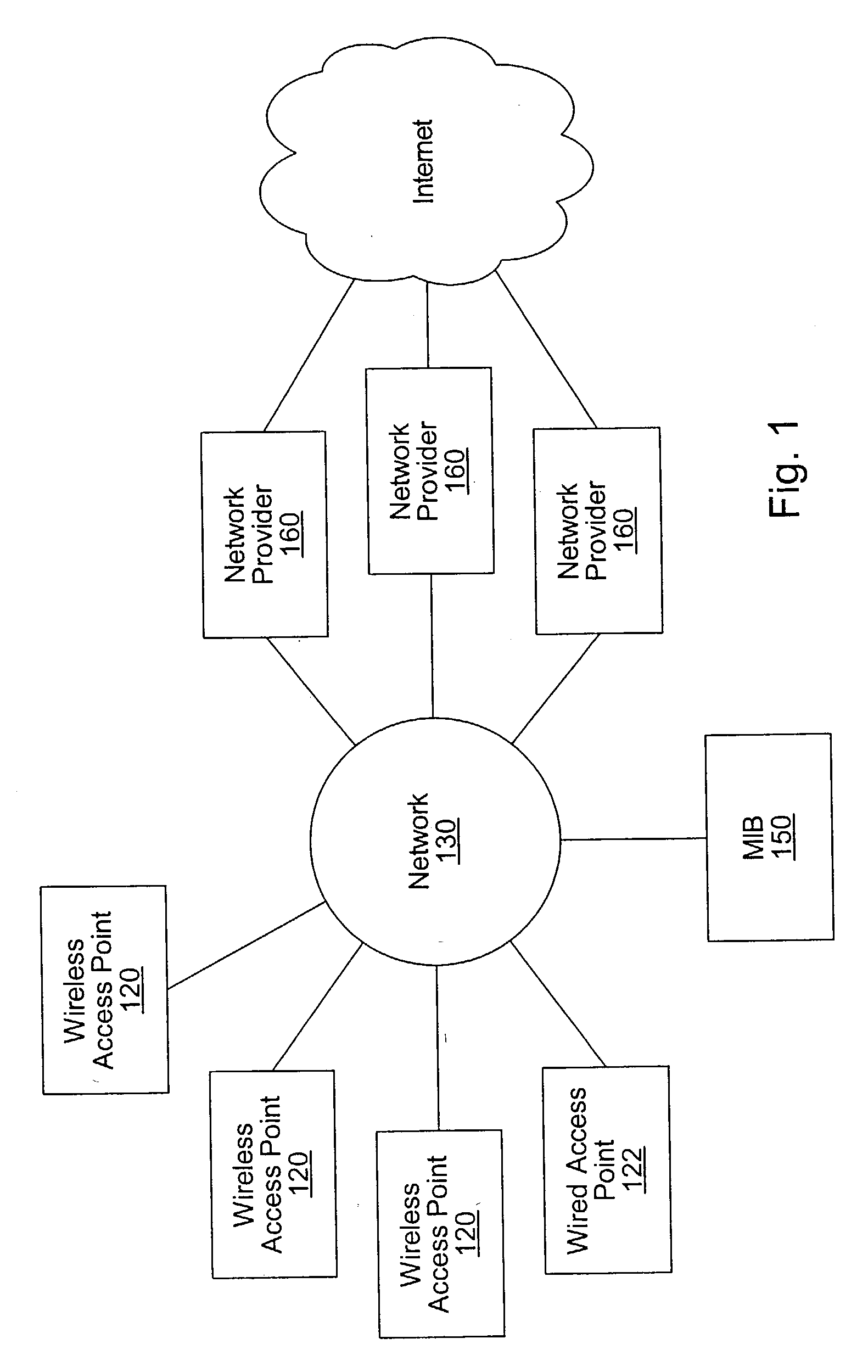
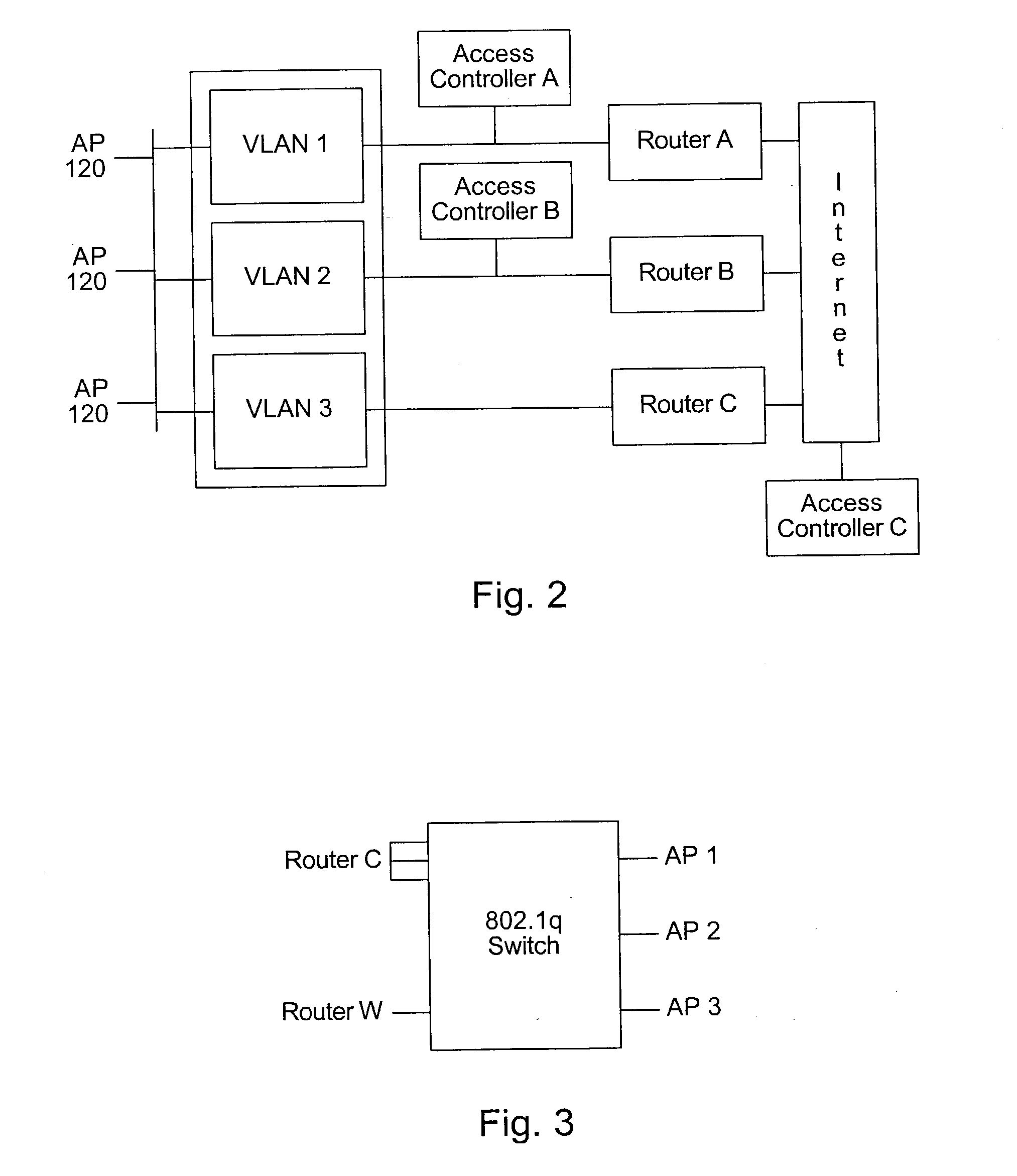
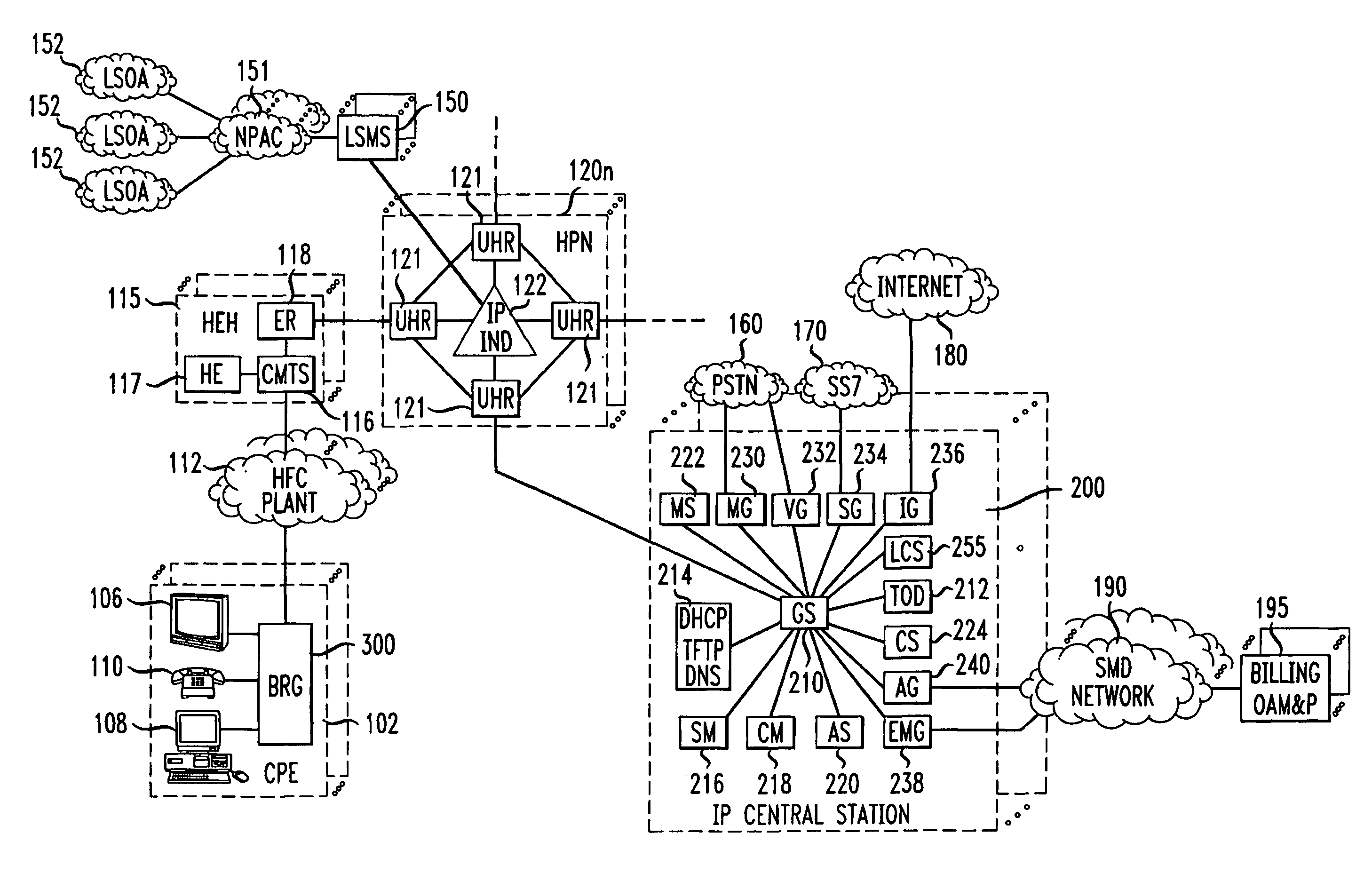
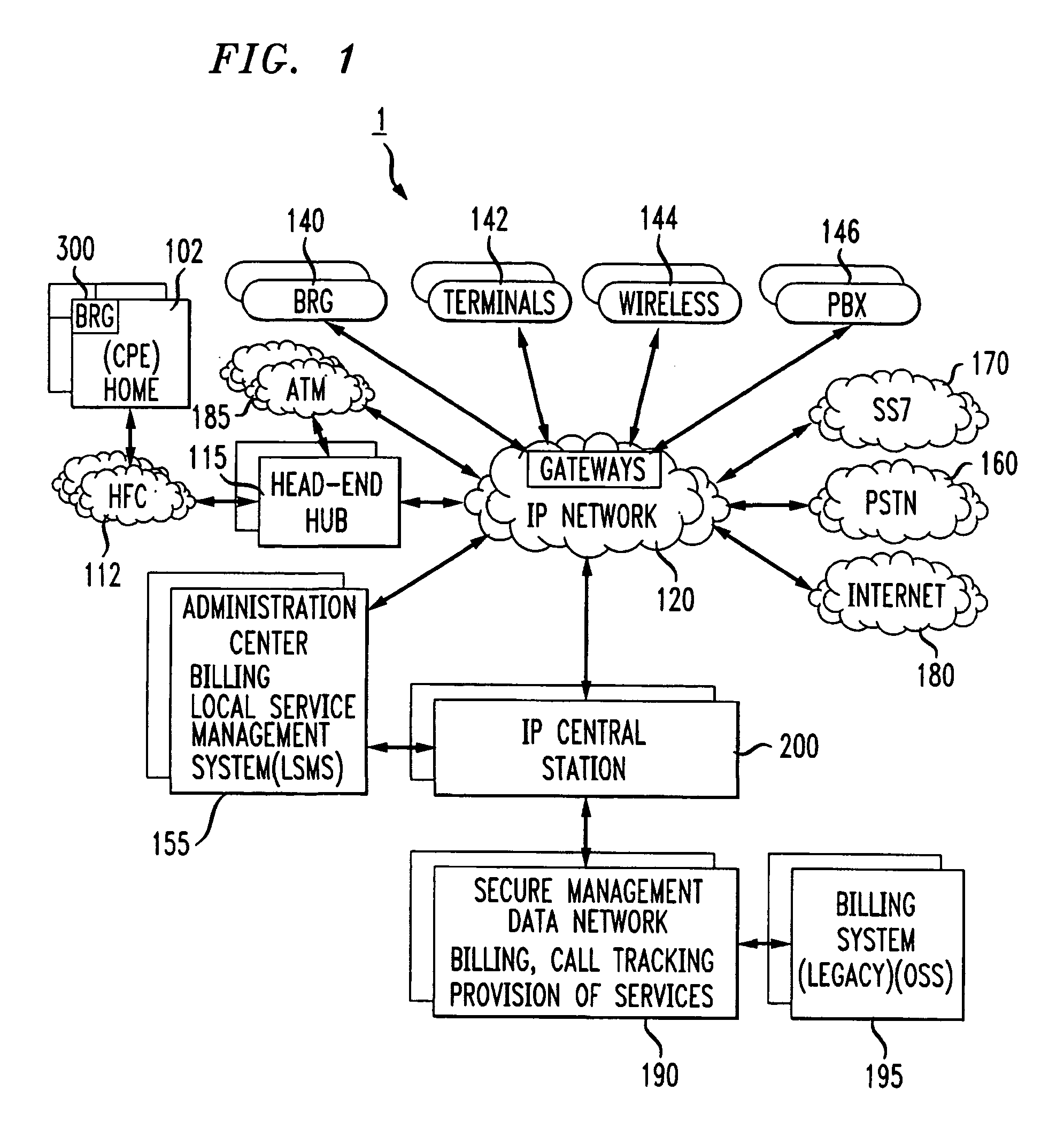
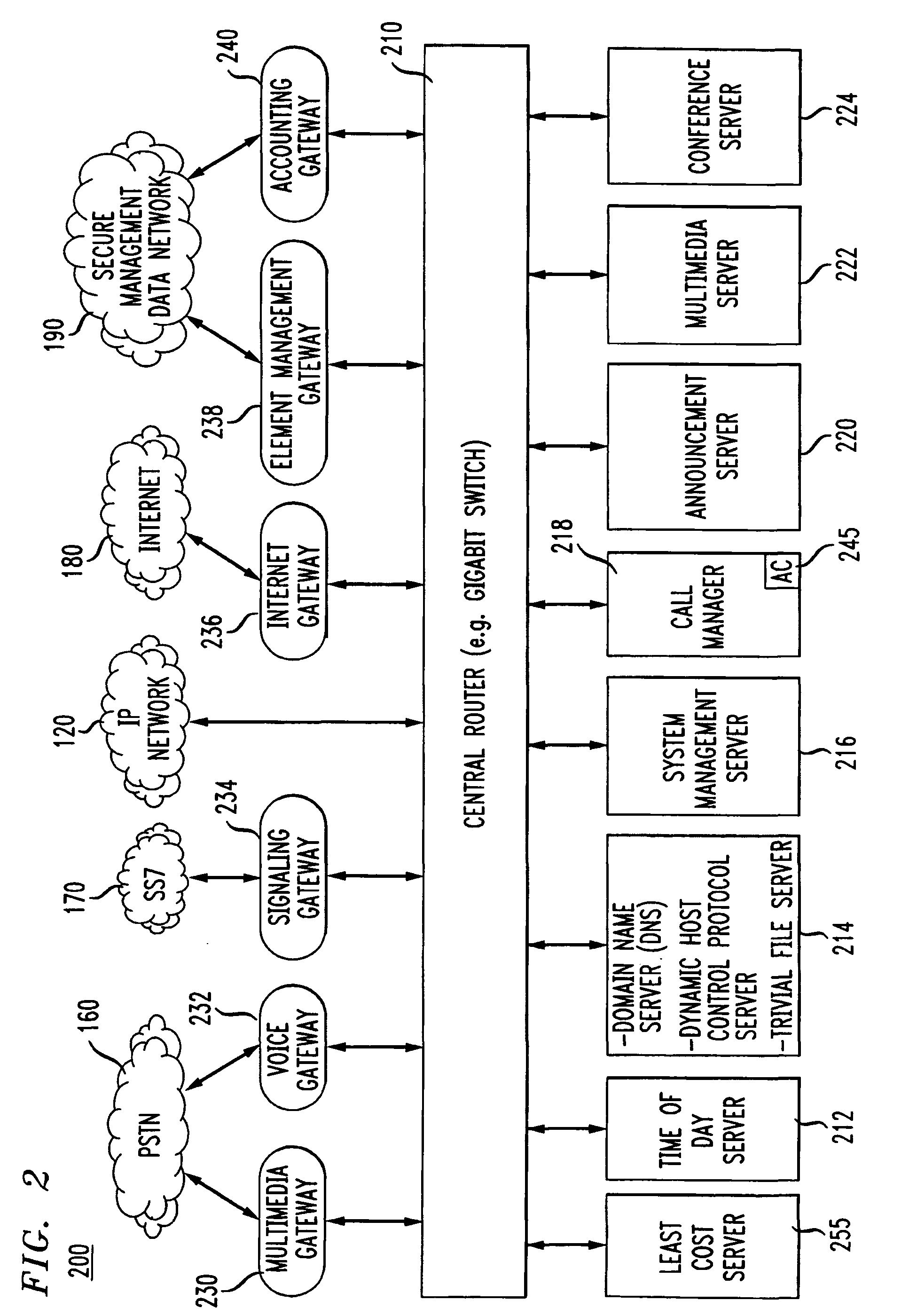
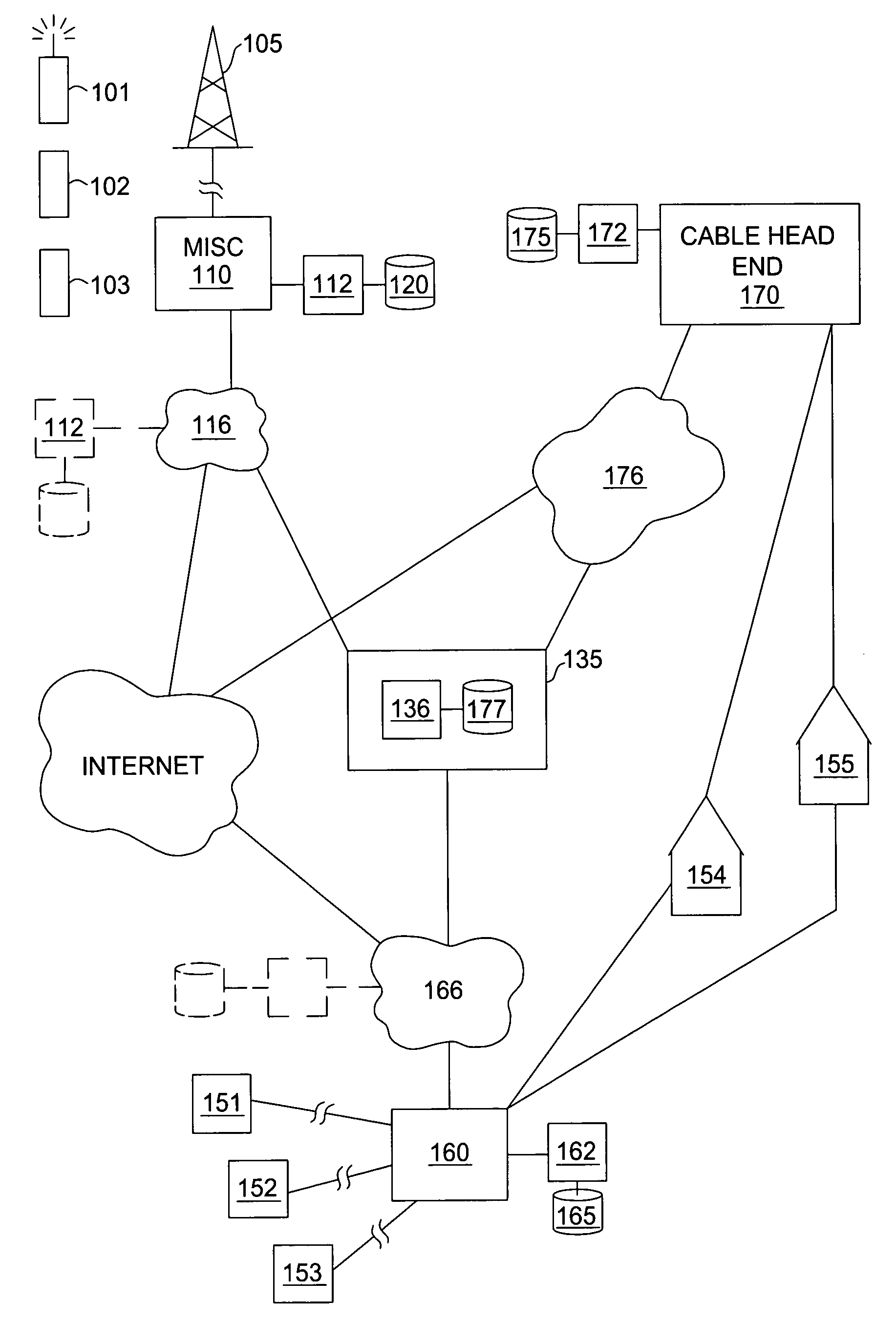
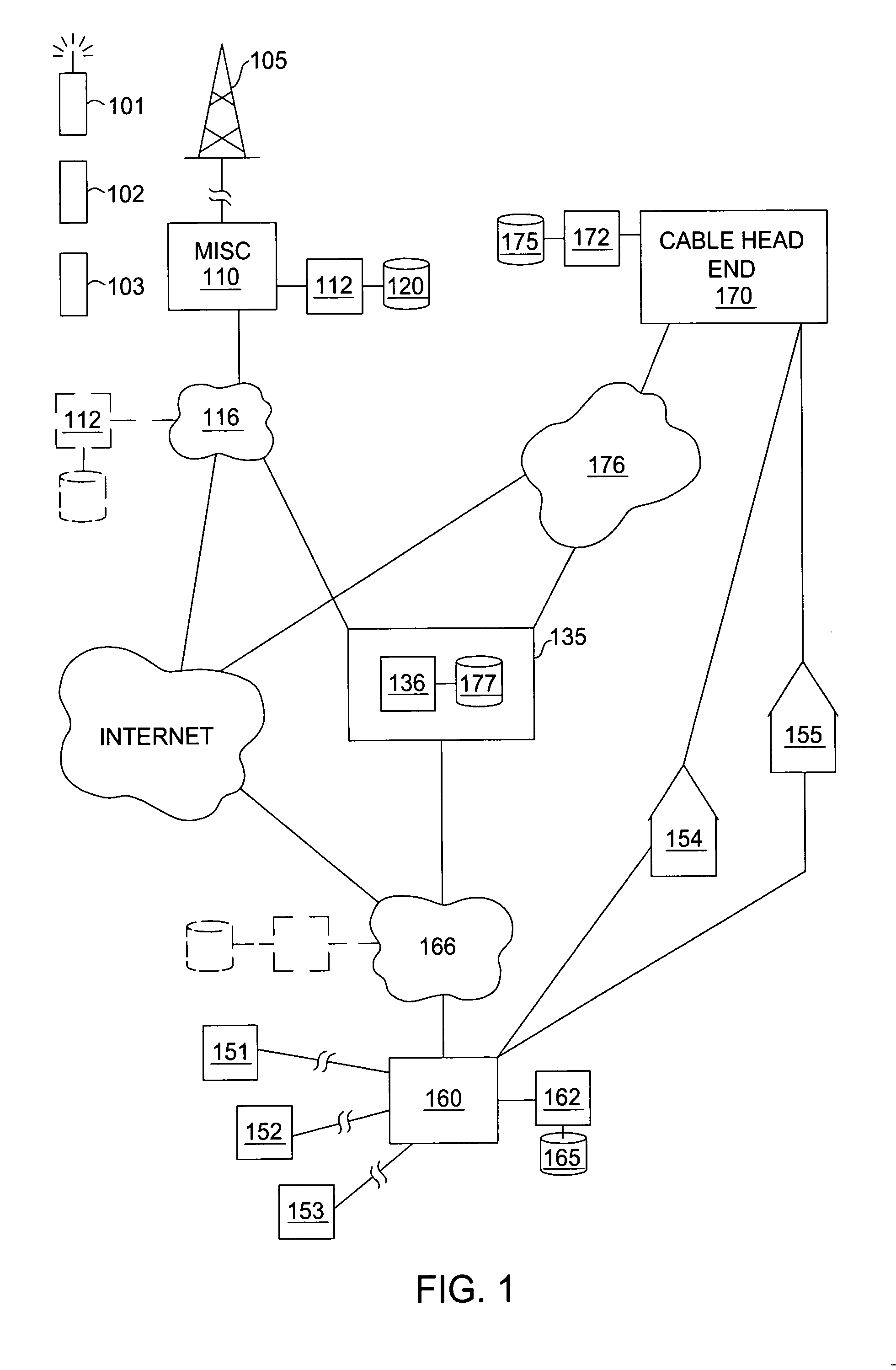
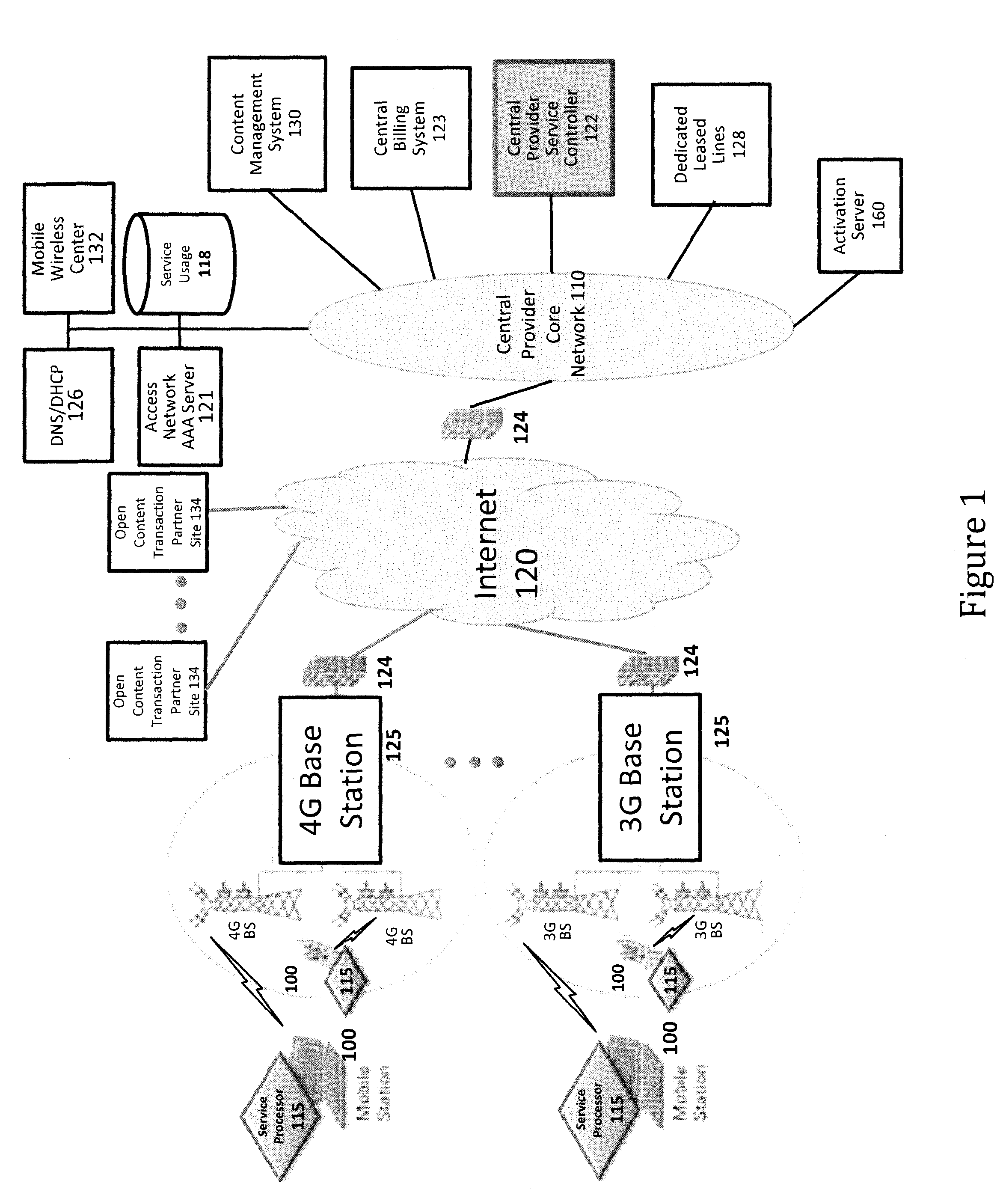
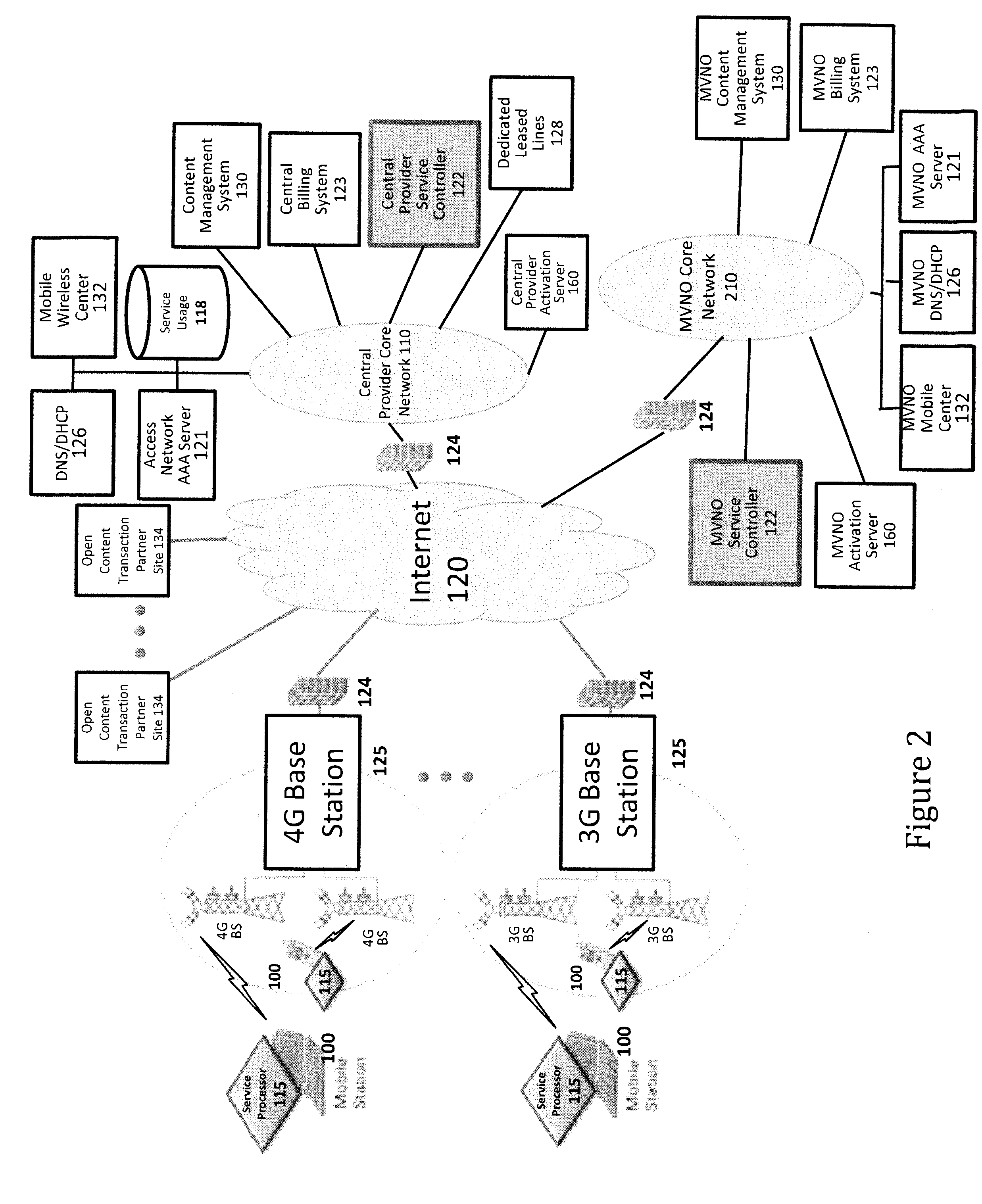
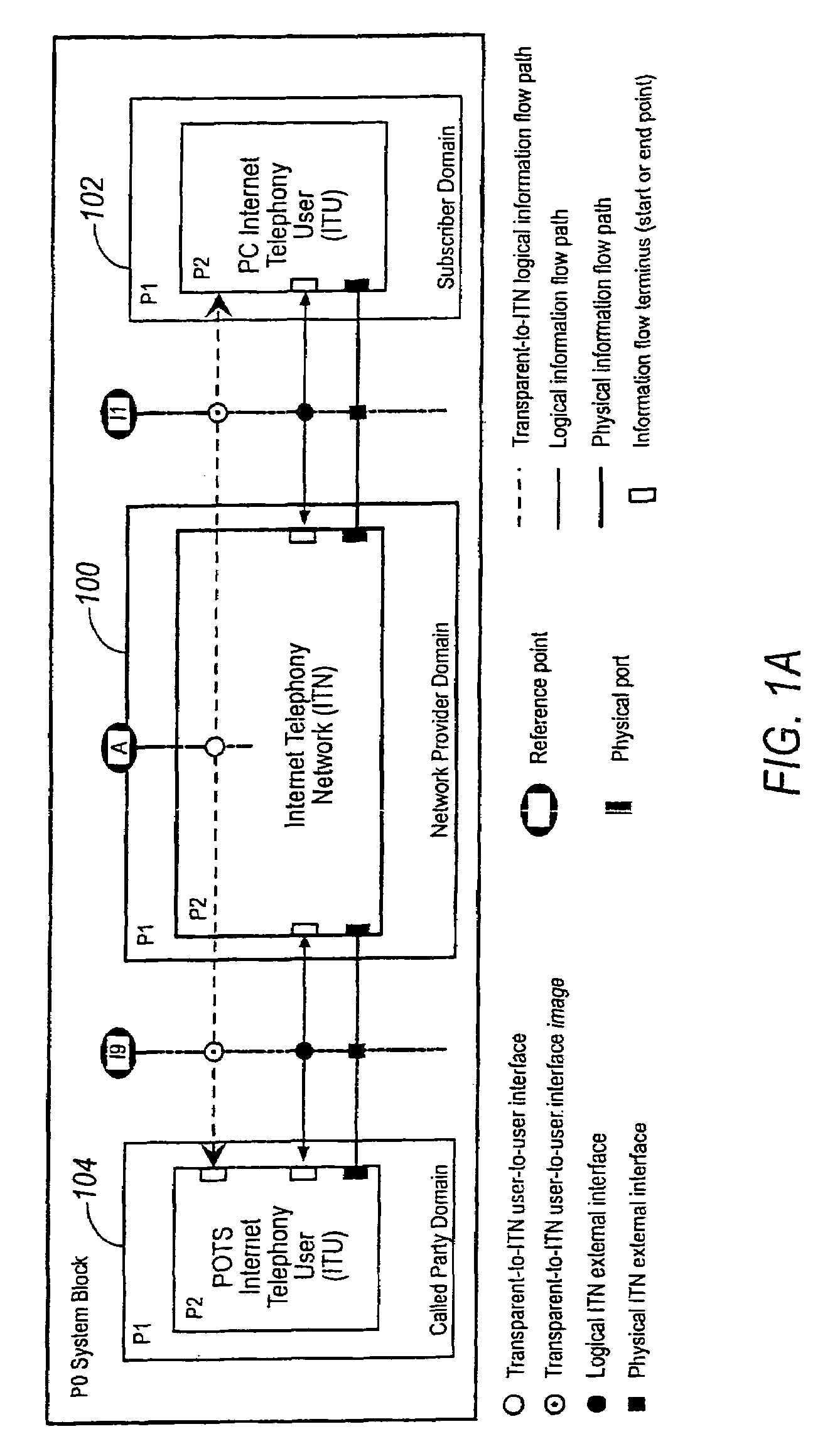
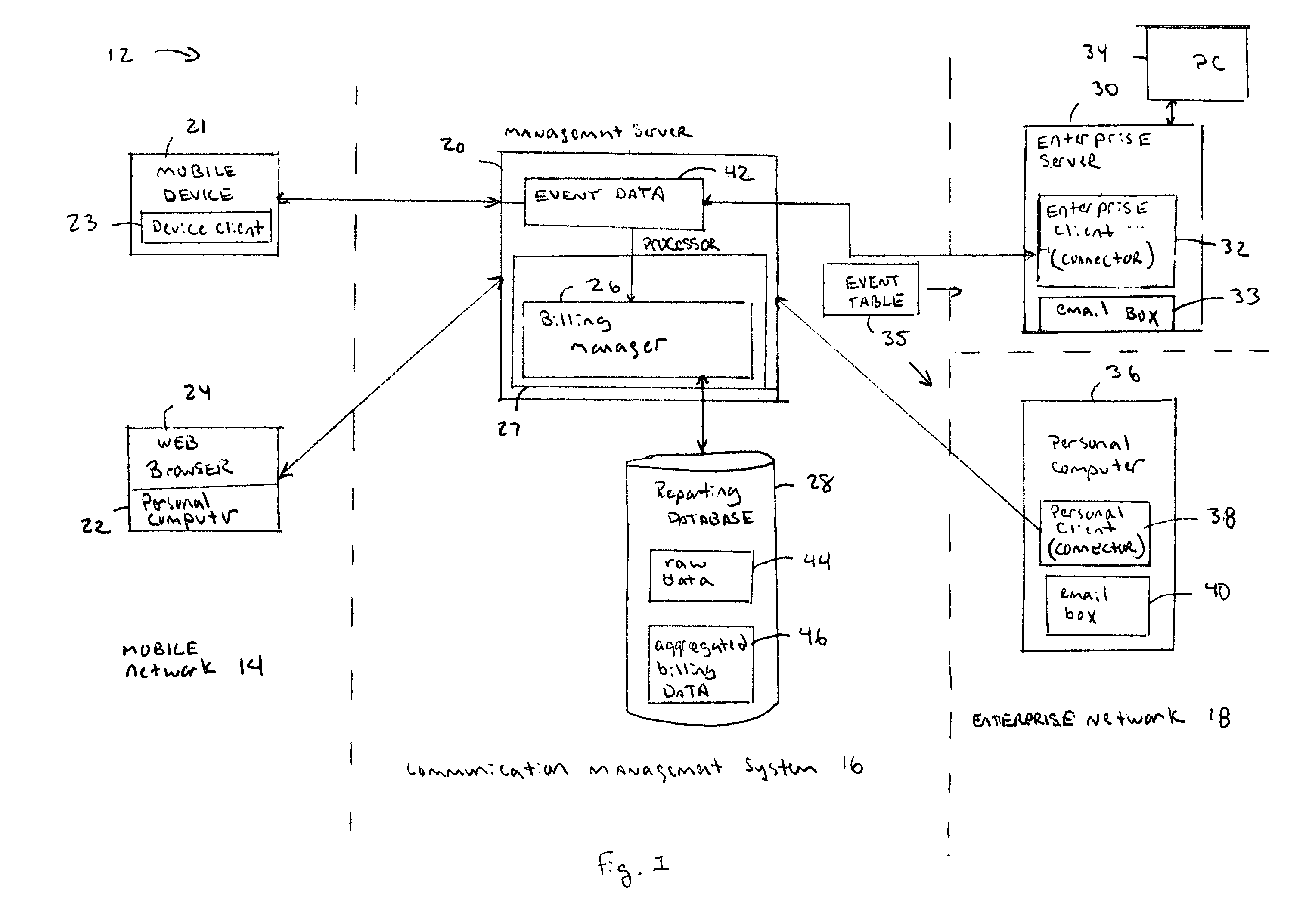
System and method for designing, developing and implementing internet service provider architectures
ActiveUS20030172145A1Metering/charging/biilling arrangementsDigital computer detailsComputer architectureService provision
System and method for designing, developing and implementing Internet Service Provider (ISP) architectures. One embodiment of a method for designing and implementing ISP architectures may include formulating a set of design requirements for an ISP architecture, establishing an architectural model for the ISP architecture using the set of design requirements, generating a logical design for the ISP architecture from the architectural model and the set of design requirements, and generating a physical design for the ISP architecture using the architectural model and the logical design. One embodiment may also include selecting one or more components of the ISP architecture and implementing the ISP architecture according to the logical design and the physical design. In one embodiment the system and method for designing, developing and implementing ISP architectures may be used to design, develop and implement an N-tiered ISP architecture.
Owner:SUN MICROSYSTEMS INC
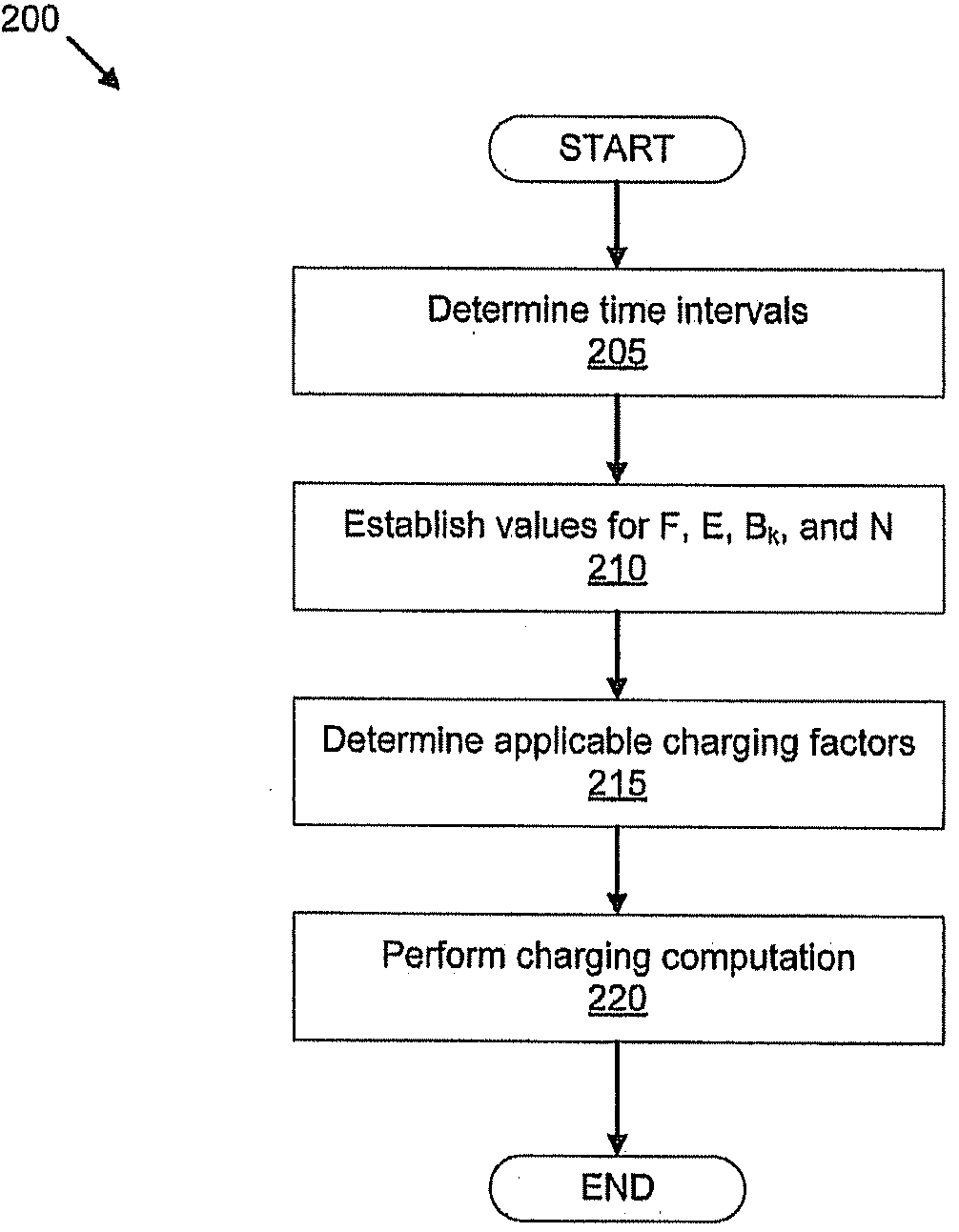
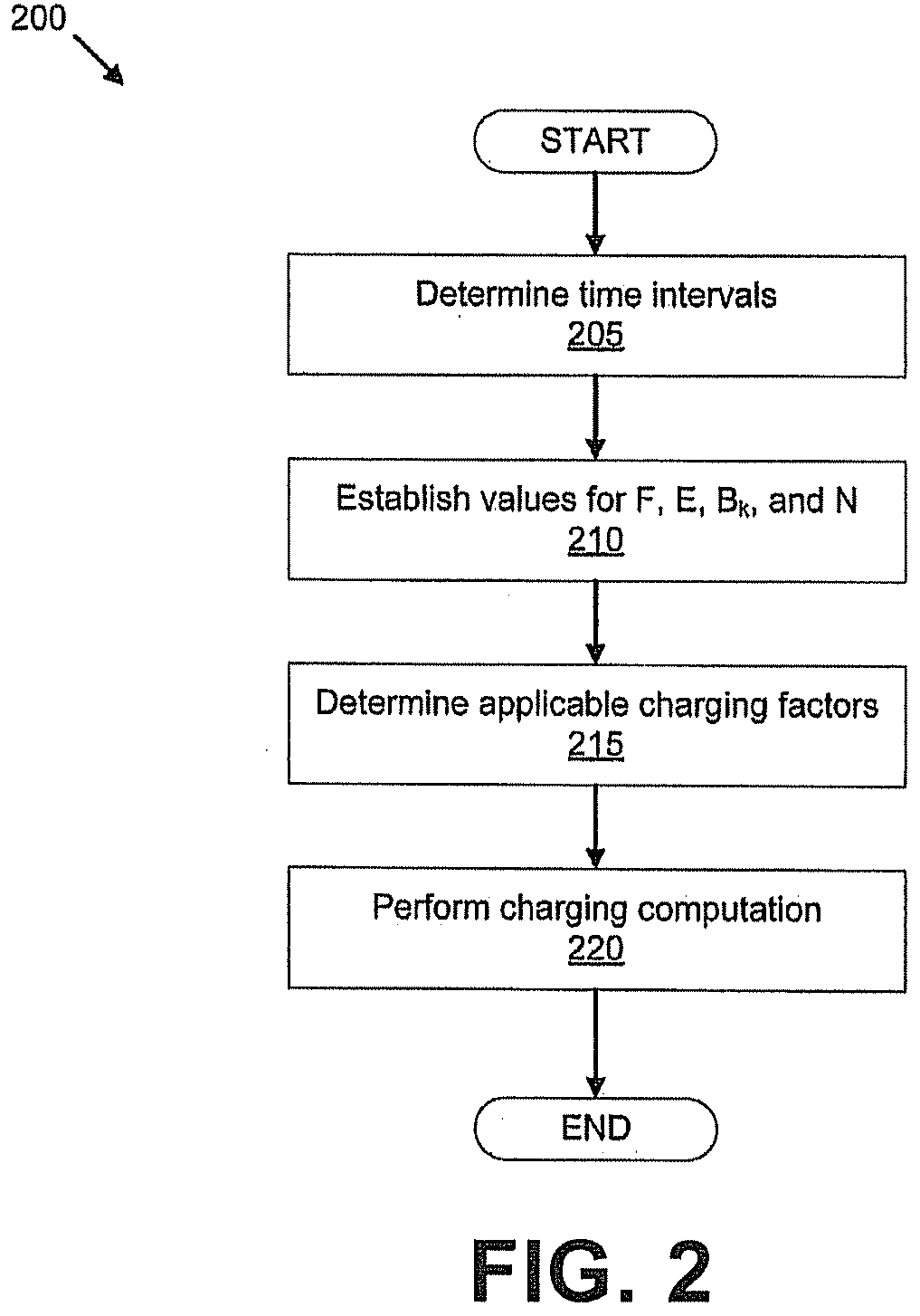
Data metering
InactiveUS20090132400A1Complete banking machinesMetering/charging/biilling arrangementsStart timeData transmission
A charging factor is determined applicable to each time interval in a period of time during which at least one data transfer was conducted. An amount of data transferred during each time interval is determined. A total charge applicable to the at least one data transfer is computed based at least in part on the charging factor applicable to each time interval and the amount of data transferred. Alternatively or additionally, a plurality of potential start times and an amount of data for a data transfer are identified. A set of time intervals associated with each of the potential start times are determined. For each of the potential start times, an estimated charge applicable to the data transfer is computed based at least in part on a charging factor applicable to each of one or more time intervals associated with the potential start time and the amount of data estimated to be transferred.
Owner:VERIZON PATENT & LICENSING INC
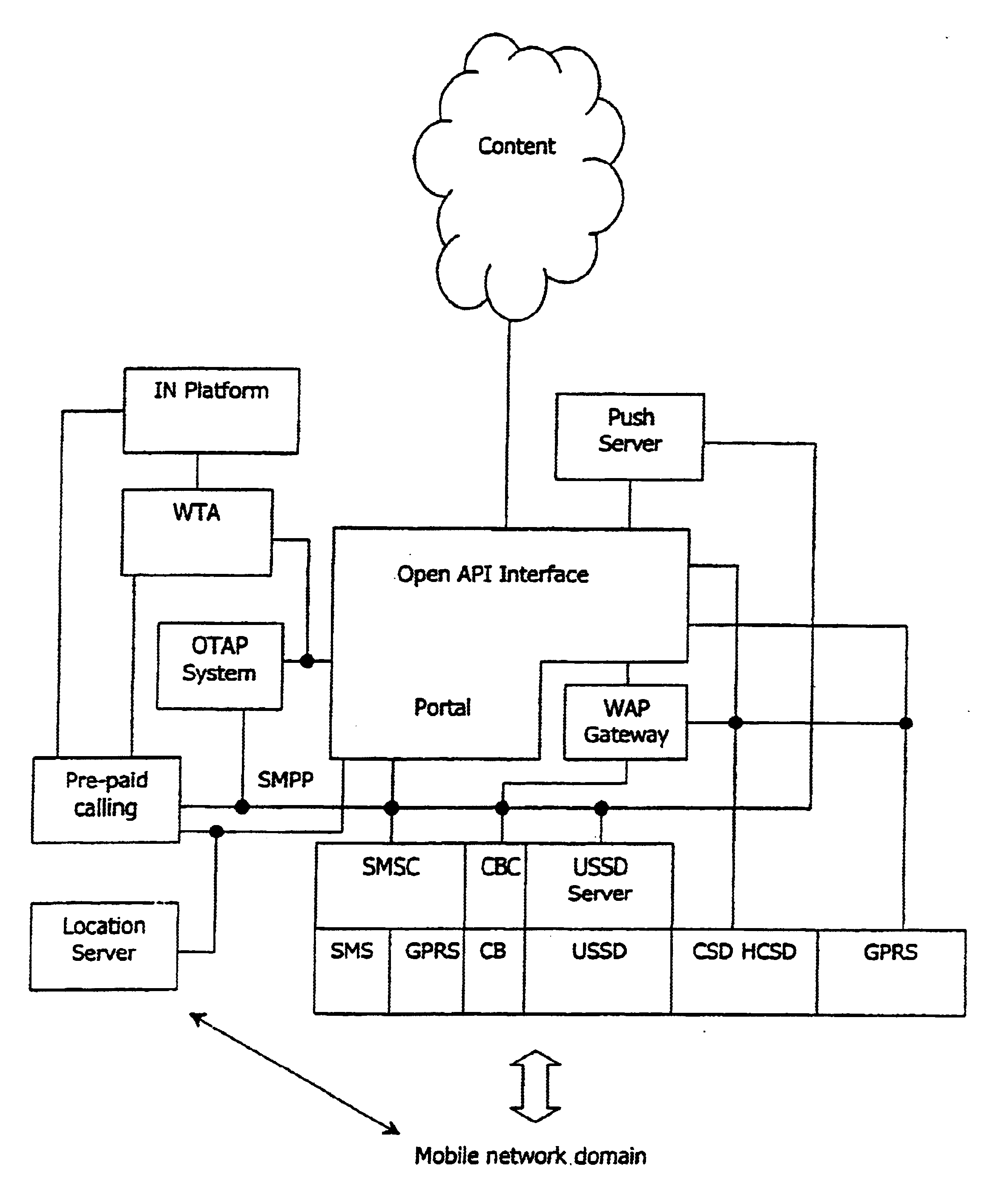
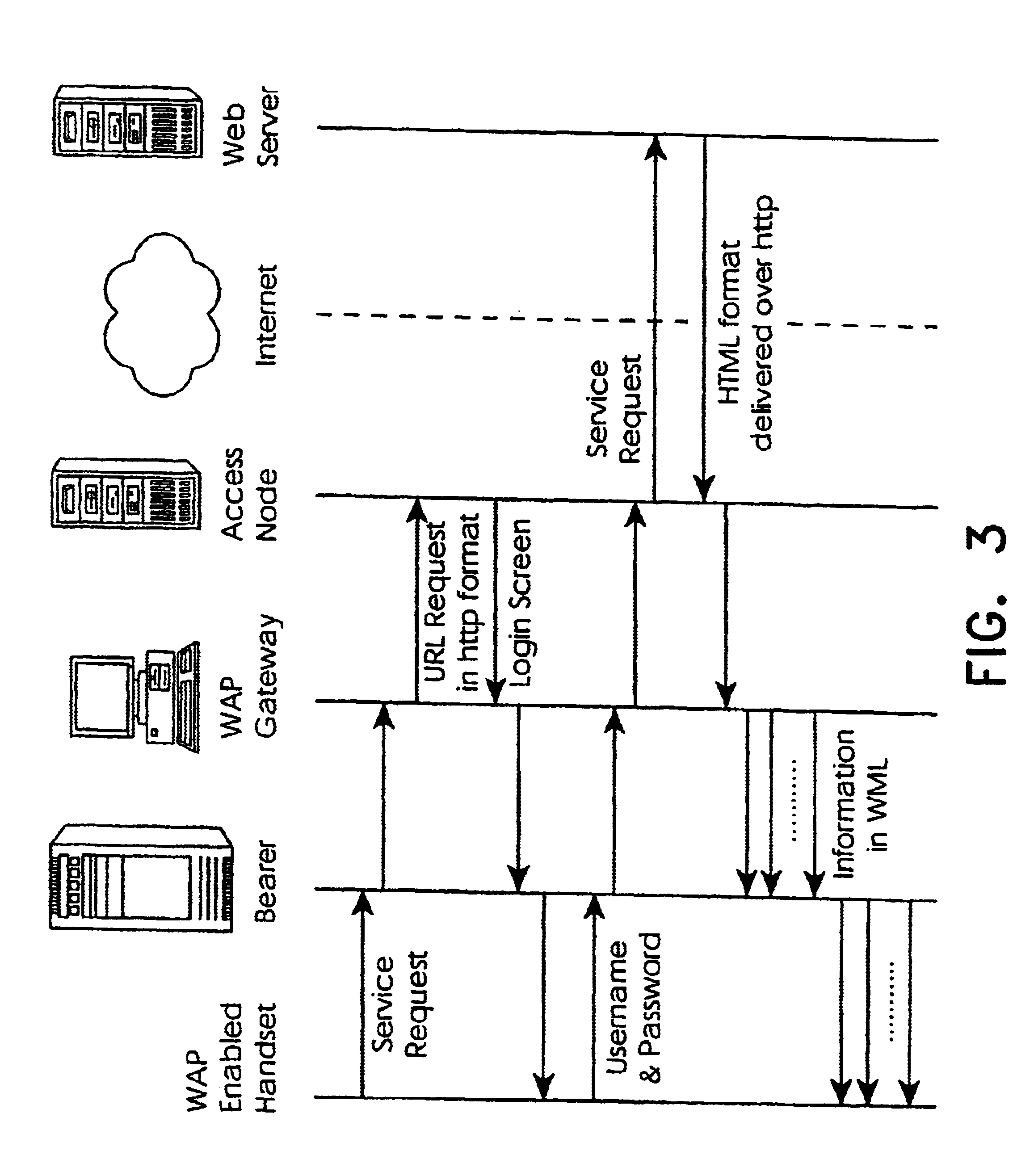
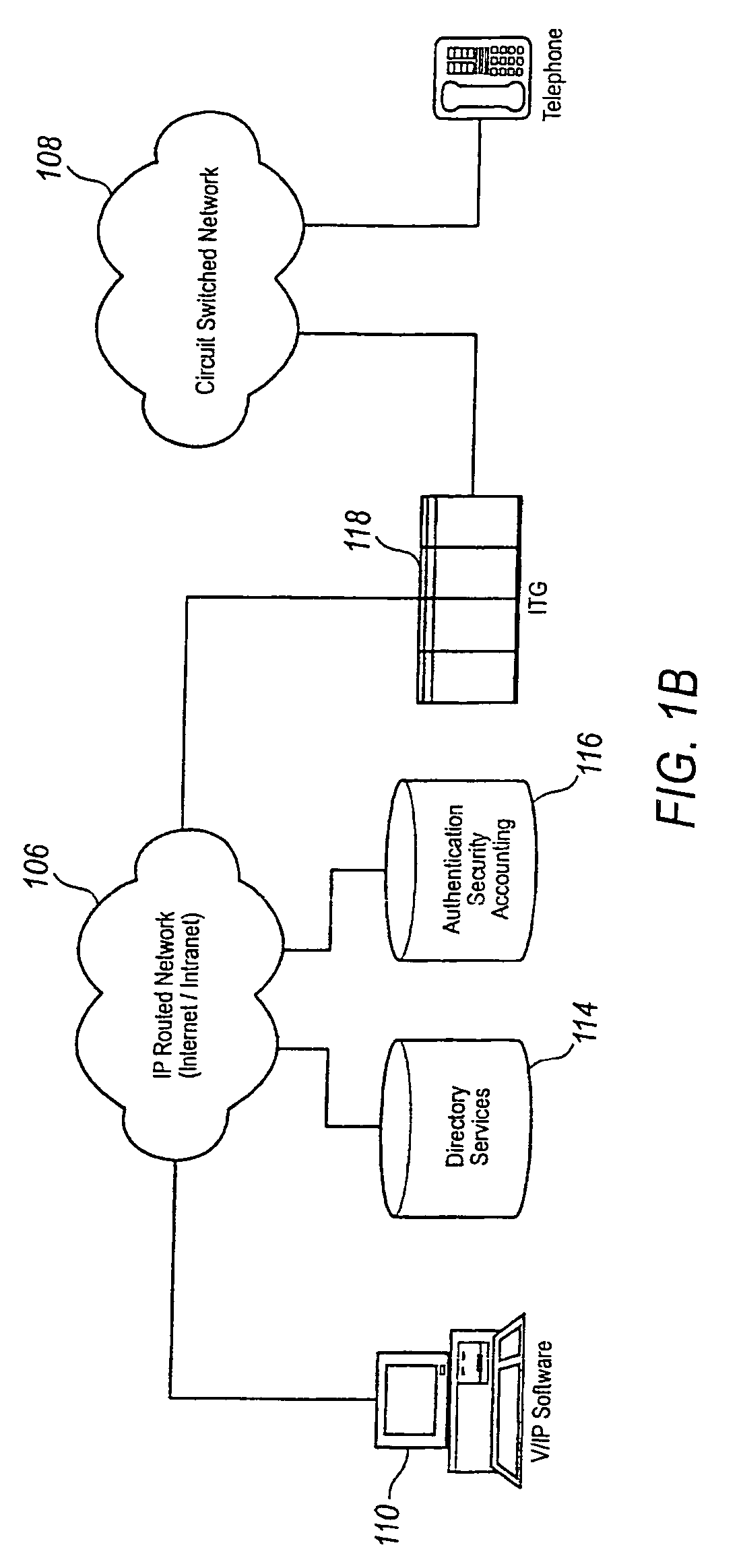
WAP service personalization, management and billing object oriented platform
InactiveUS6640097B2Metering/charging/biilling arrangementsAccounting/billing servicesPersonalizationThe Internet
An access node has a portal which performs interfacing between a wireless network domain and content / service providers in the Internet. On the wireless side the portal is linked with an SMSC, a CBC, and a USSD server for interfacing with and management of bearer stacks. Service functionality includes modular systems including a Push server, a Pre-paid calling server, and a location server in addition to internal portal functions. The latter provide for subscriber self-provisioning, customer care provisioning, subscriber device provisioning, and service provisioning. Thus, the node caters for both particular subscriber service and mobile device requirements.
Owner:MARKPORT LTD
Method and apparatus for integrating billing and authentication functions in local area and wide area wireless data networks
ActiveUS20030051041A1Metering/charging/biilling arrangementsAccounting/billing servicesNetwork ConvergenceWireless data
A converged network accessible by client terminals is provided. The converged network includes a wide area network, a local area network, and a gateway linked to the wide area and local area networks. The gateway integrates billing and authentication functions of the wide area and local area networks.
Owner:SMITH MICRO SOFTWARE INC
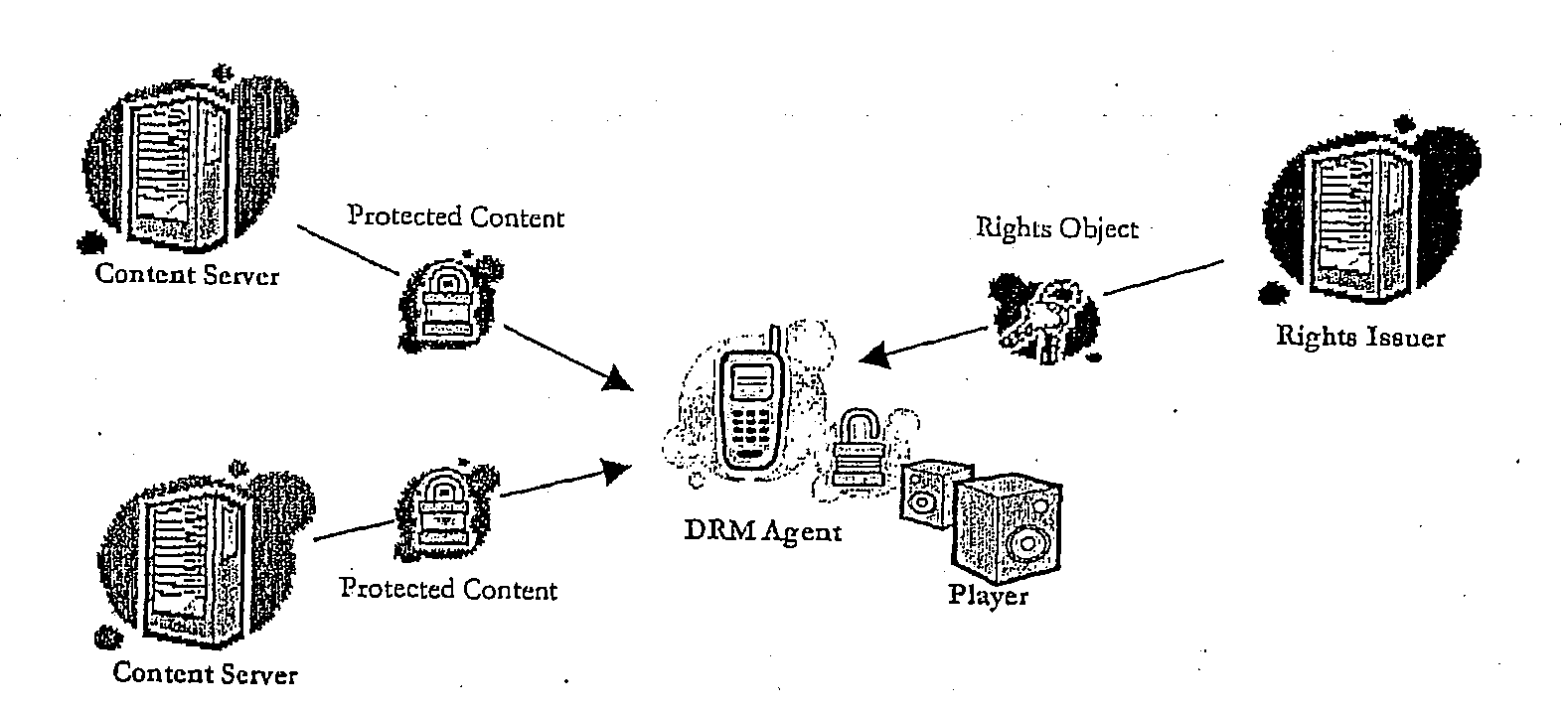
Method of Providing Digital Rights Management for Music Content by Means of a Flat-Rate Subscription
ActiveUS20100031366A1Reliable and goodEasy to manageMetering/charging/biilling arrangementsDigital data processing detailsOperational systemComputer network
The invention enables digital music content to be downloaded to and used on a portable wireless computing device. An application running on the wireless device has been automatically adapted to parameters associated with the wireless device without end-user input (e.g. the application has been configured in dependence on the device OS and firmware, related bugs, screen size, pixel number, security models, connection handling, memory etc. This application enables an end-user to browse and search music content on a remote server using a wireless network; to download music content from that remote server using the wireless network and to playback and manage that downloaded music content. The application also includes a digital rights management system that enables unlimited legal downloads of different music tracks to the device and also enables any of those tracks stored on the device to be played so long as a subscription service has not terminated.
Owner:TIKTOK PTE LTD
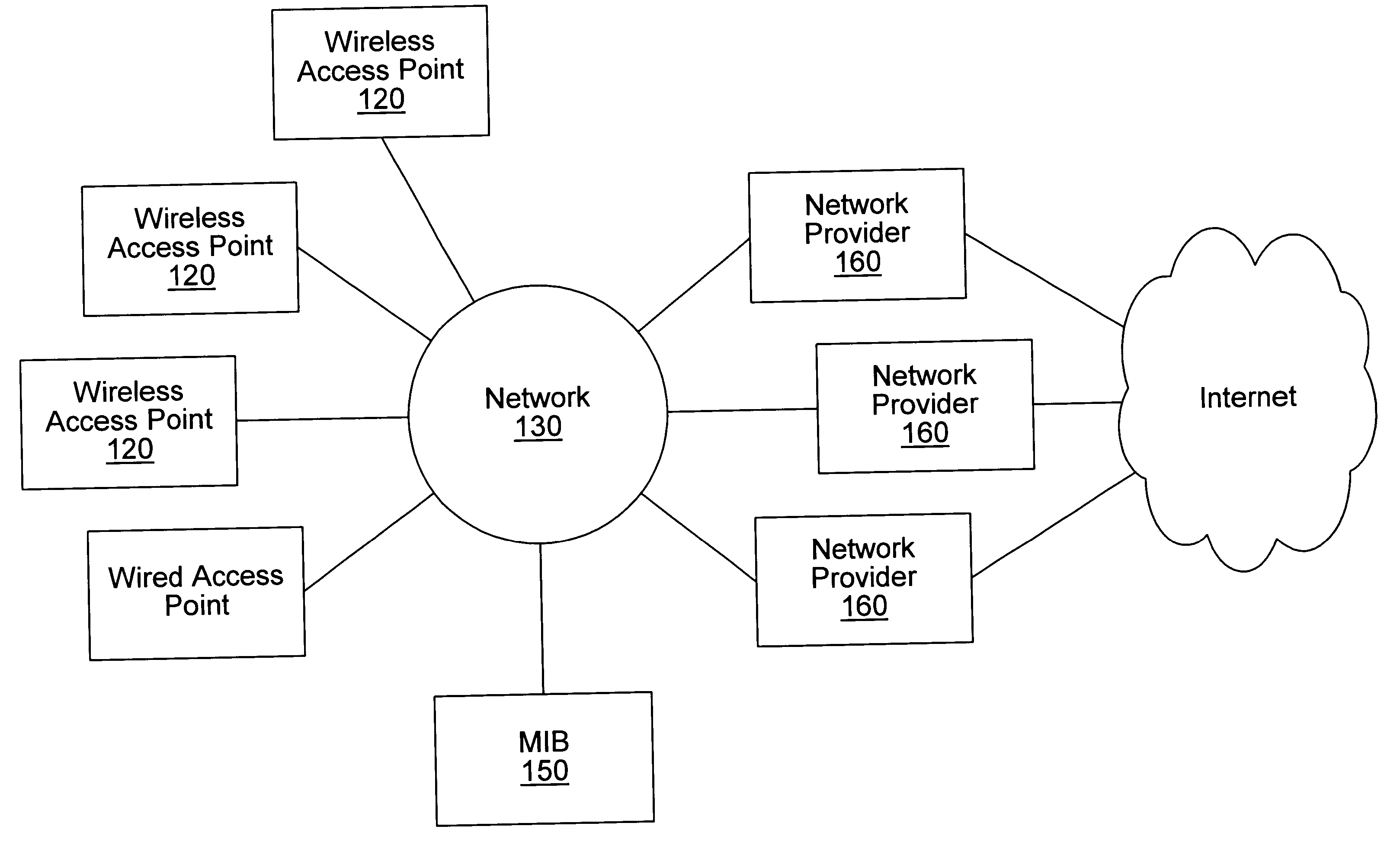
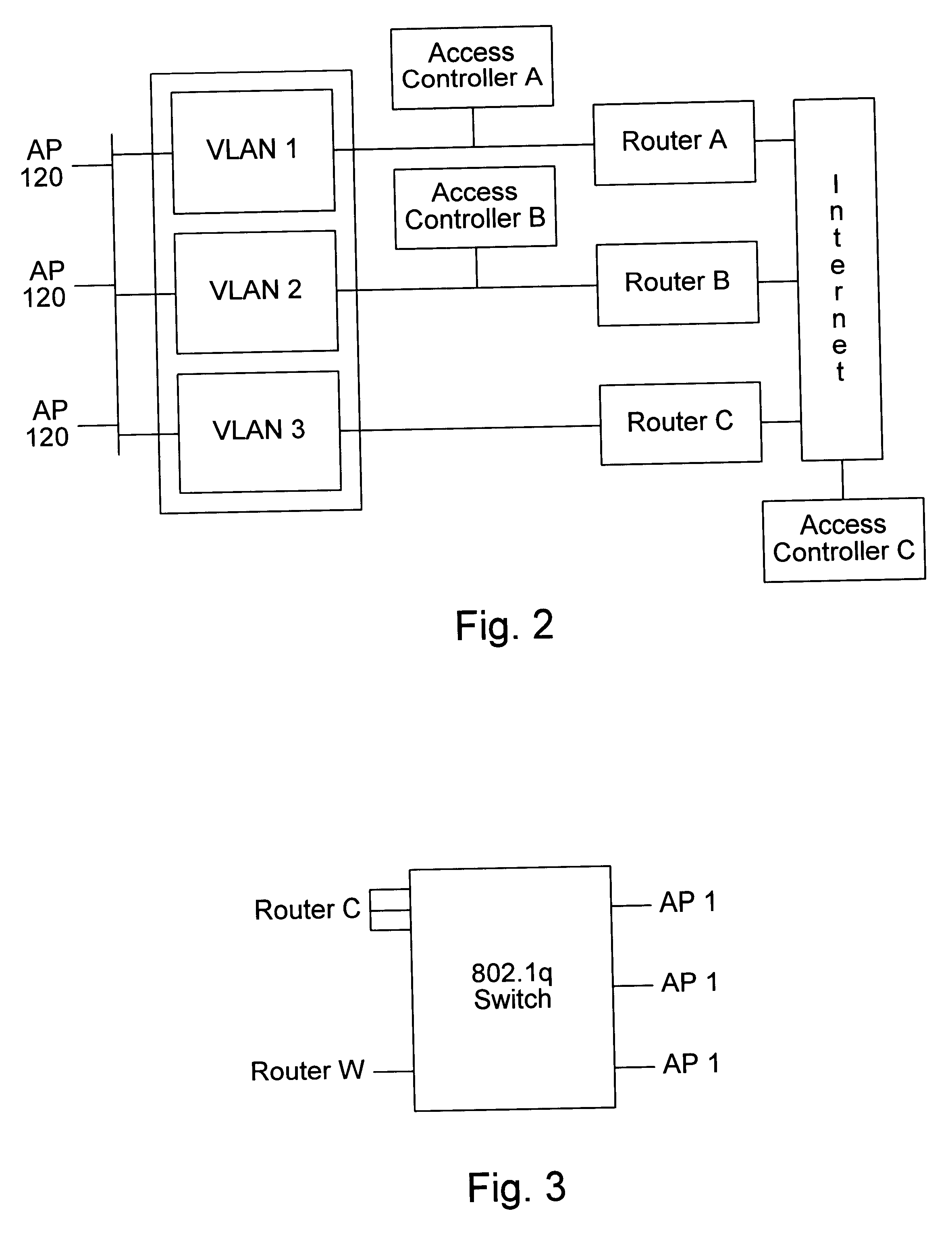
Distributed network communication system which enables multiple network providers to use a common distributed network infrastructure
InactiveUS6732176B1Metering/charging/biilling arrangementsMultiple digital computer combinationsCommunications systemNetworked system
A system and method for providing access and / or roaming features on a network system. The network system includes a plurality of wireless and / or wired access points coupled to a network. A portable computing device (PCD) of a user may store identification information which uniquely indicates a network provider of a plurality of possible network providers. The identification information may also or instead indicate an access or privilege level of the user. When the access point receives the identification information from a PCD of a user, the access point may determine the appropriate network provider for the portable computing device using the identification information. Network access may then be provided to the portable computing device through the determined network provider.
Owner:CISCO TECH INC
System and method for user access to a distributed network communication system using persistent identification of subscribers
InactiveUS20030233332A1Market predictionsMetering/charging/biilling arrangementsDevice registerCommunications system
A system and method for providing network access are disclosed. After connecting to a network at an access point, a user of a computing device registers for network access with a network provider. In response to the registration, the network provider sends a completion page to the computing device. The completion page includes a link to an embedded file such as a small, transparent GIF image. When the computing device retrieves the embedded file, the embedded file is associated with a header than includes an instruction to generate a network system identifier (e.g., a cookie). The network system identifier may be stored by the computing device and later used to identify the computing device as a registrant for network access with the network provider. The embedded file may also be sent at other times, such as after authentication of the user for network access.
Owner:WAYPORT
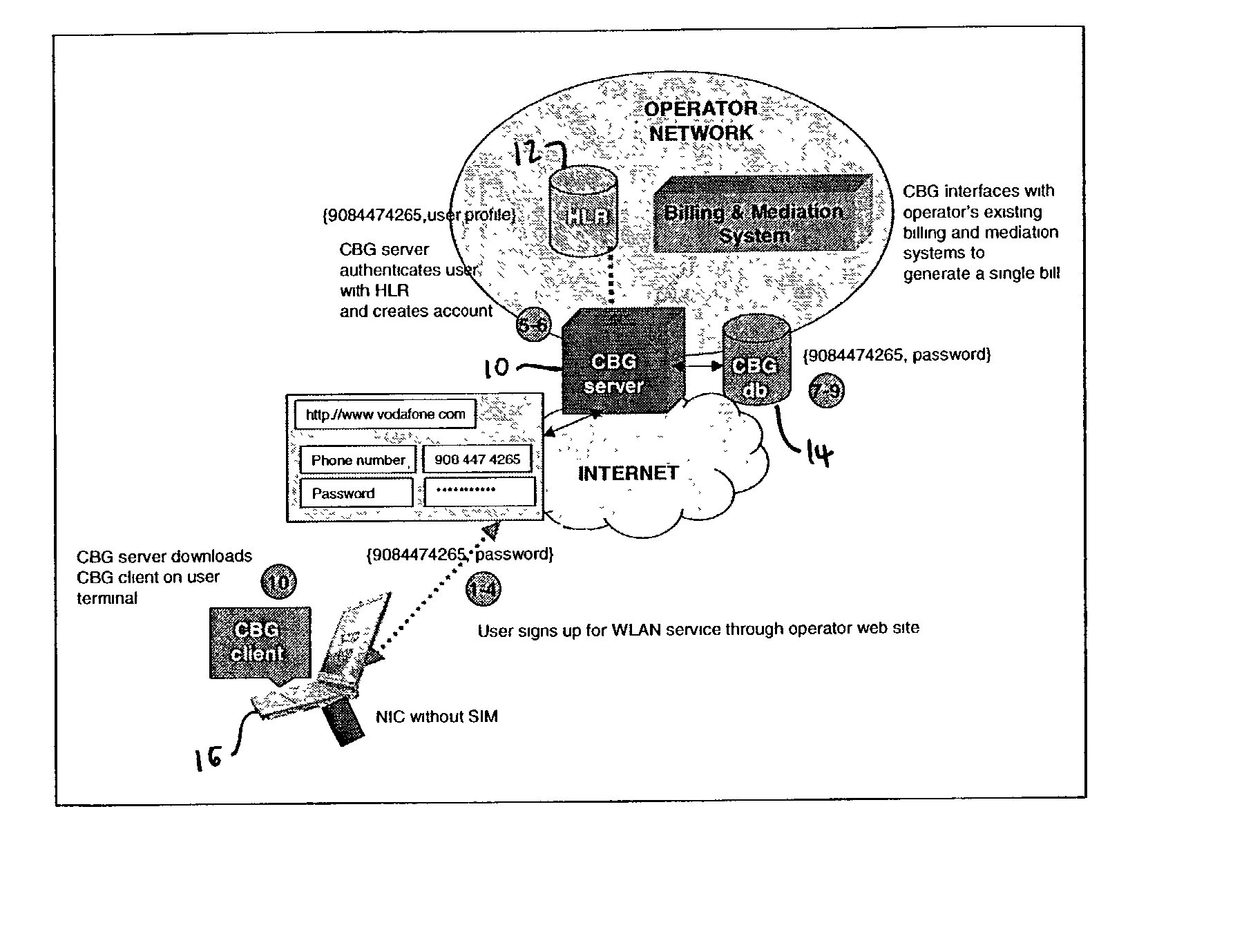
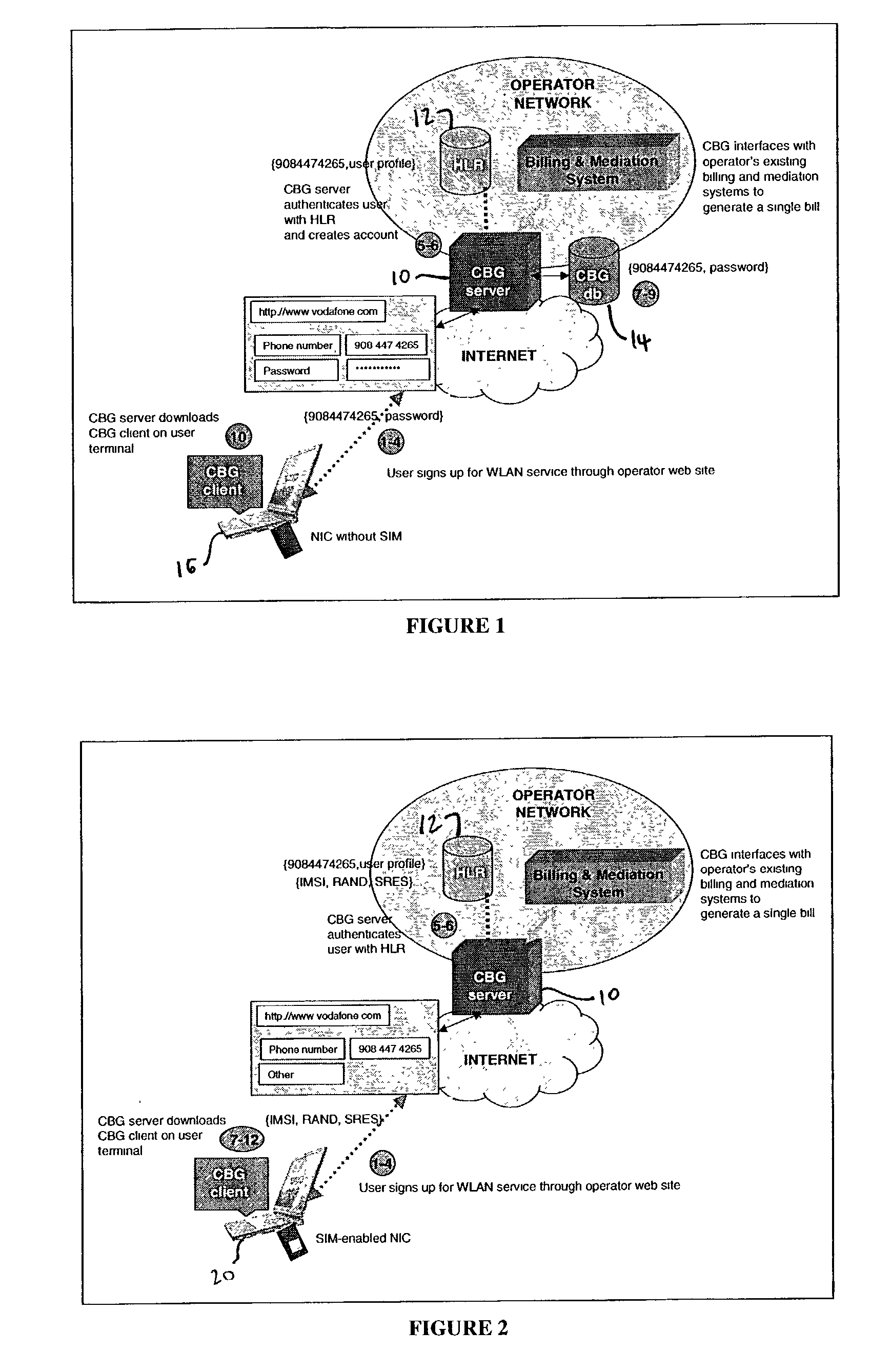
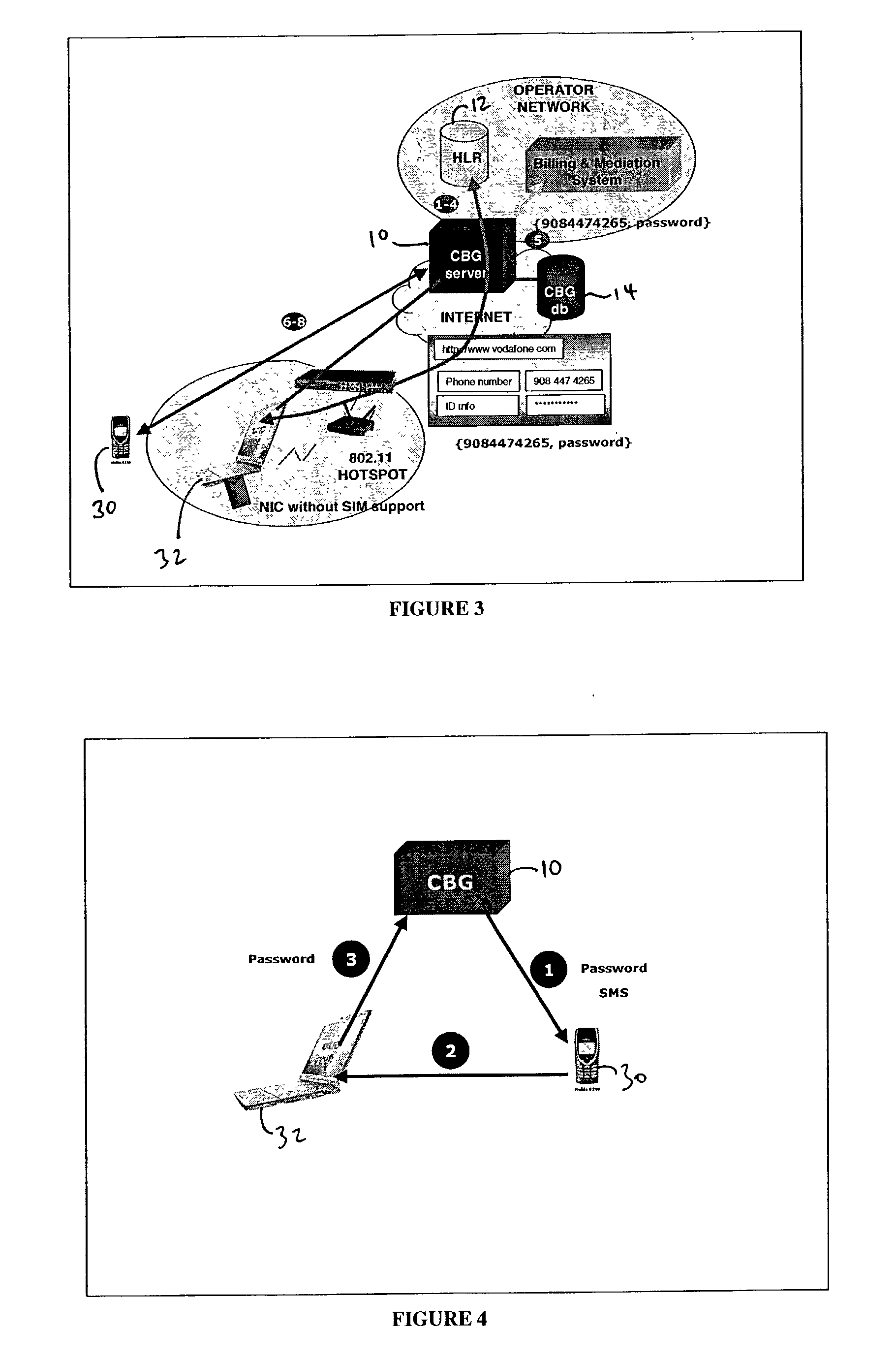
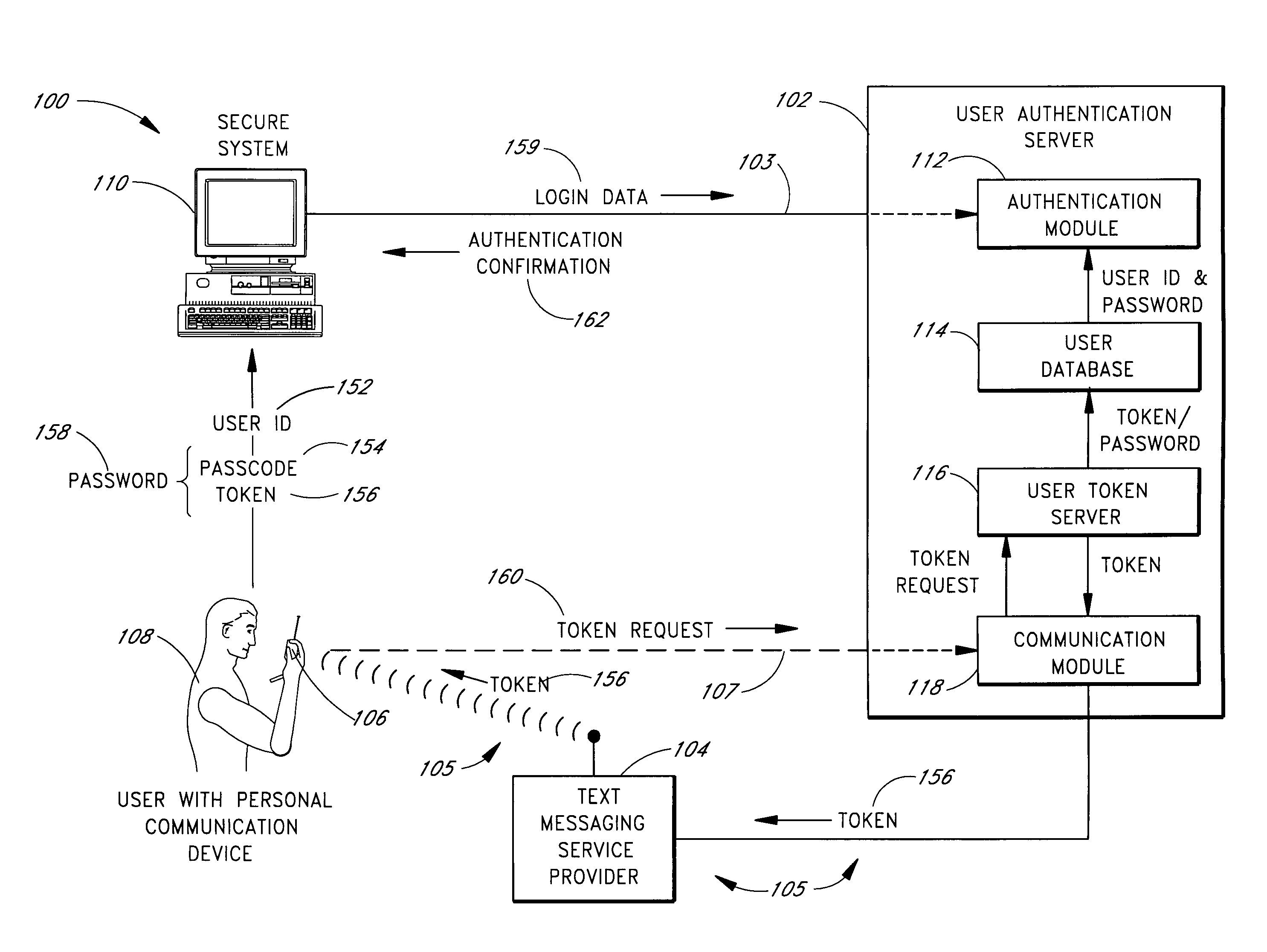
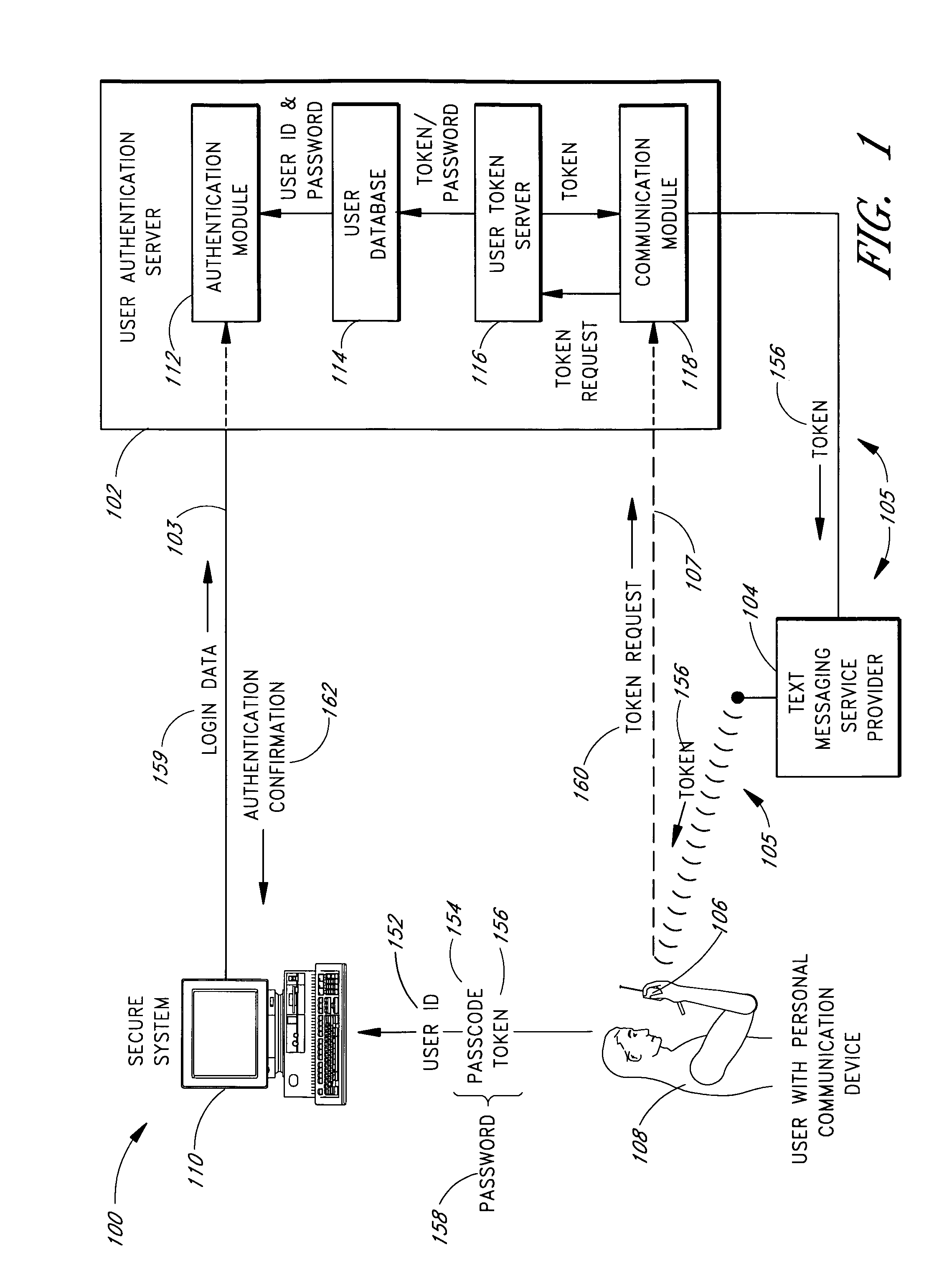
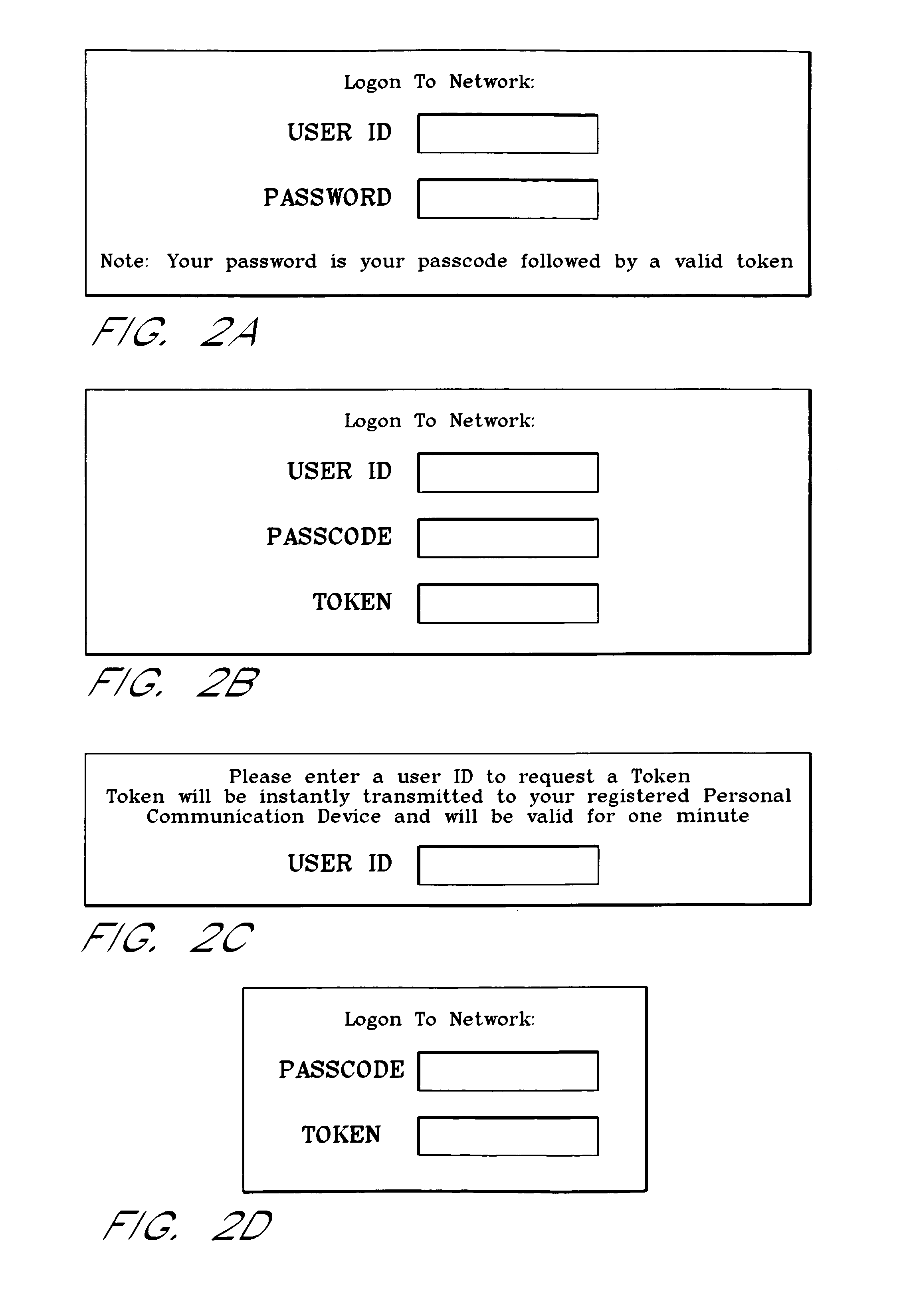
Use of personal communication devices for user authentication
InactiveUS6993658B1Metering/charging/biilling arrangementsDigital data processing detailsPagerInternet privacy
A password setting system for a secure system includes a user token server and a communication module. The user token server generates a random token in response to a request for a new password from a user. The server creates a new password by concatenating a secret passcode that is known to the user with the token. The server sets the password associated with the user's user ID to be the new password. The communication module transmits the token to a personal communication device, such as a mobile phone or a pager carried by the user. The user concatenates the secret passcode with the received token in order to form a valid password, which the user submits to gain access to the secure system. Accordingly, access to the system is based upon: nonsecret information known to the user, such as the user ID; secret information known to the user, such as the passcode; and information provided to the user through an object possessed by the user, such as the token.
Owner:DYNAPASS IP HLDG LLC
Integrated mobile application server and communication gateway
InactiveUS20060258397A1Metering/charging/biilling arrangementsAccounting/billing servicesCommunication interfacePayment
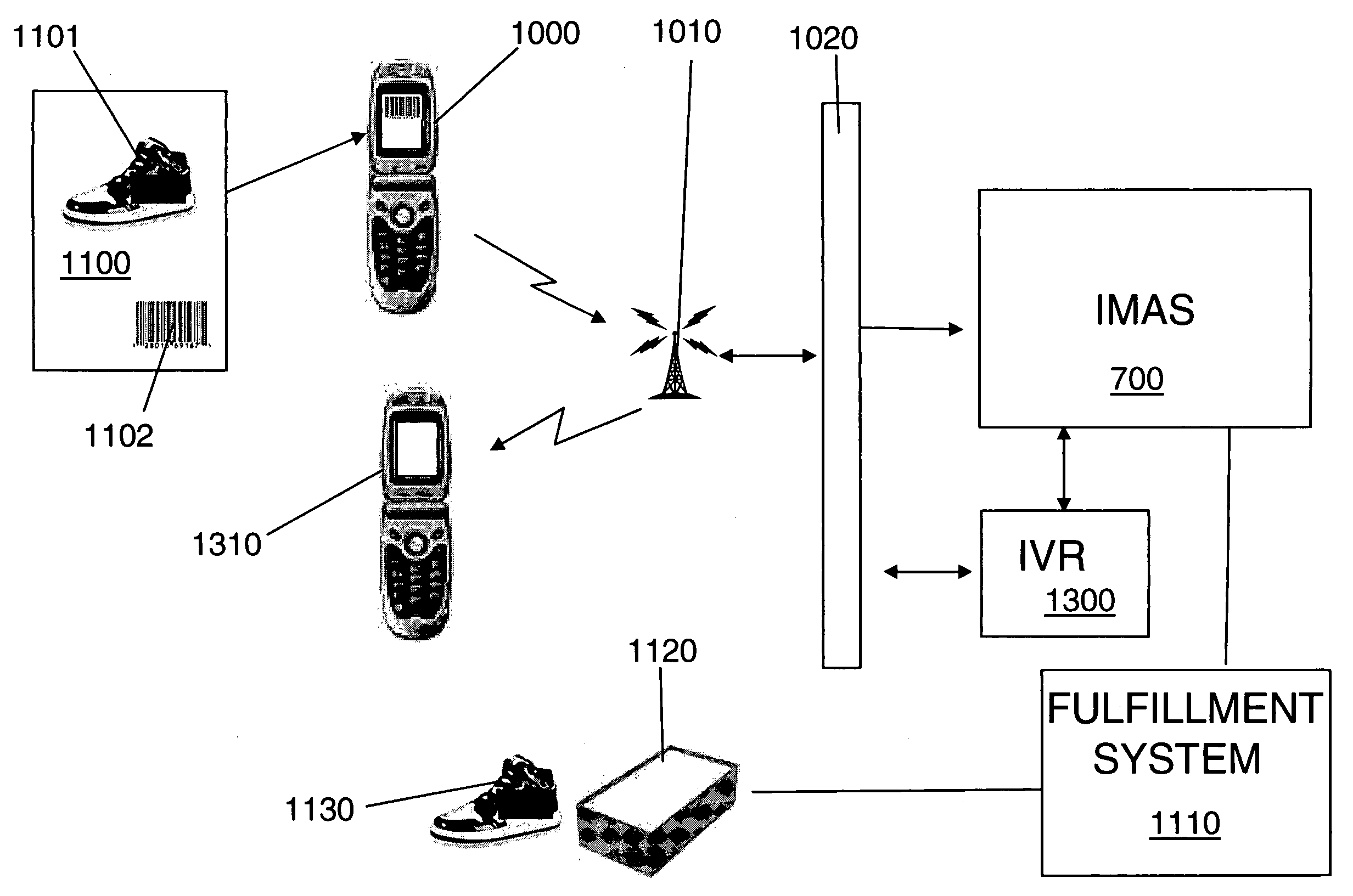
A system is provided that includes a request module adapted to receive a request from an initiation interface initiated by a user and a user profile module adapted to associate the request with a user profile of the user. The user profile includes at least a payment plan selected by the user and an identification number of the user. The system also includes a payment interface adapted to submit a payment demand to the payment plan and a mobile communication interface adapted to transmit a confirmation to a mobile communication network for transmission to a wireless device associated with the identification number. In the system, the initiation interface may be a wireless device, a magnetic swipe reader, a wireless barcode reading device, an RFID interface, a website, and / or a web banner interface. A method of operating a server is provided. A computer-readable storage medium containing a set of instructions for a processor is provided.
Owner:SHOPTEXT INC
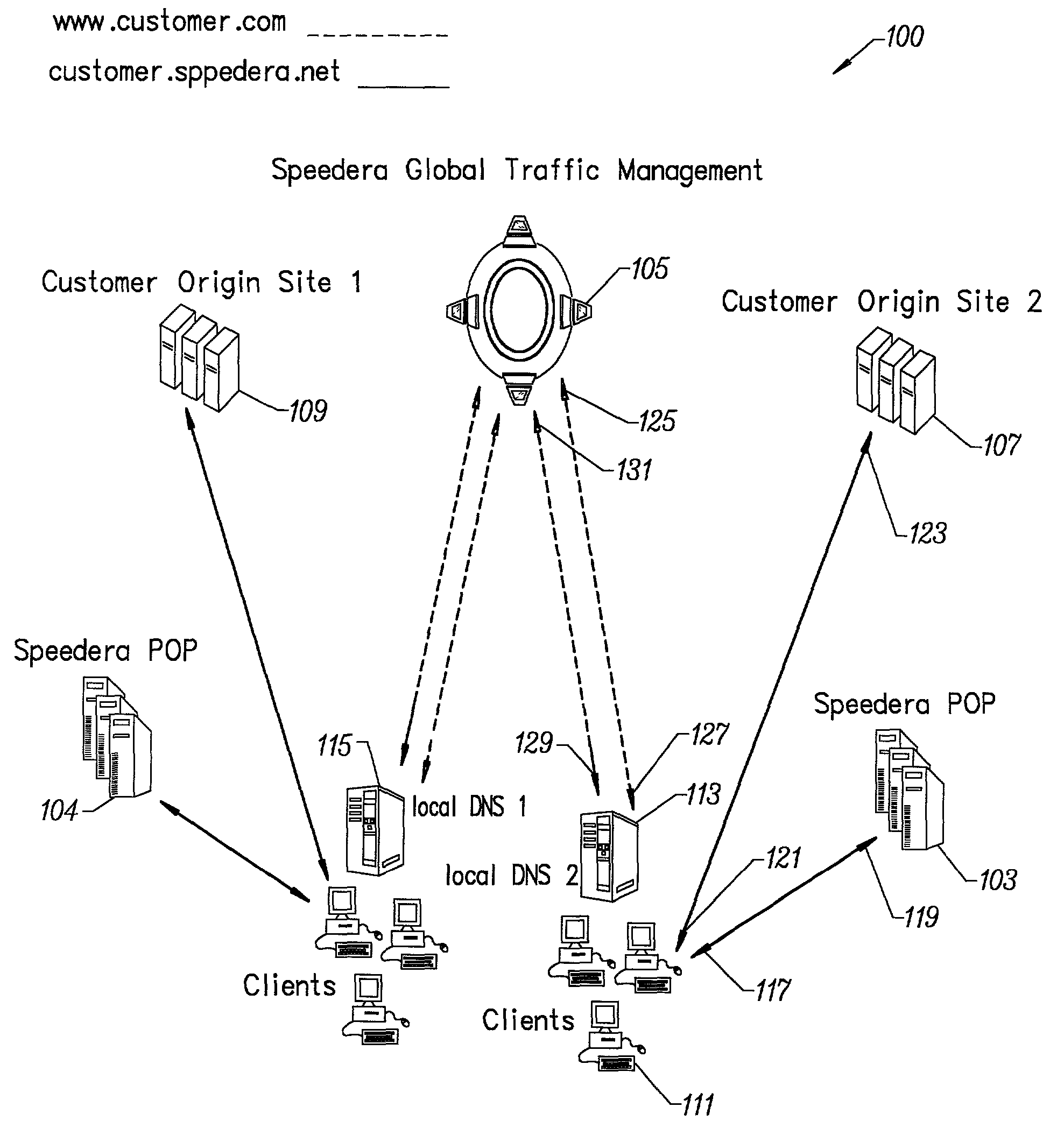
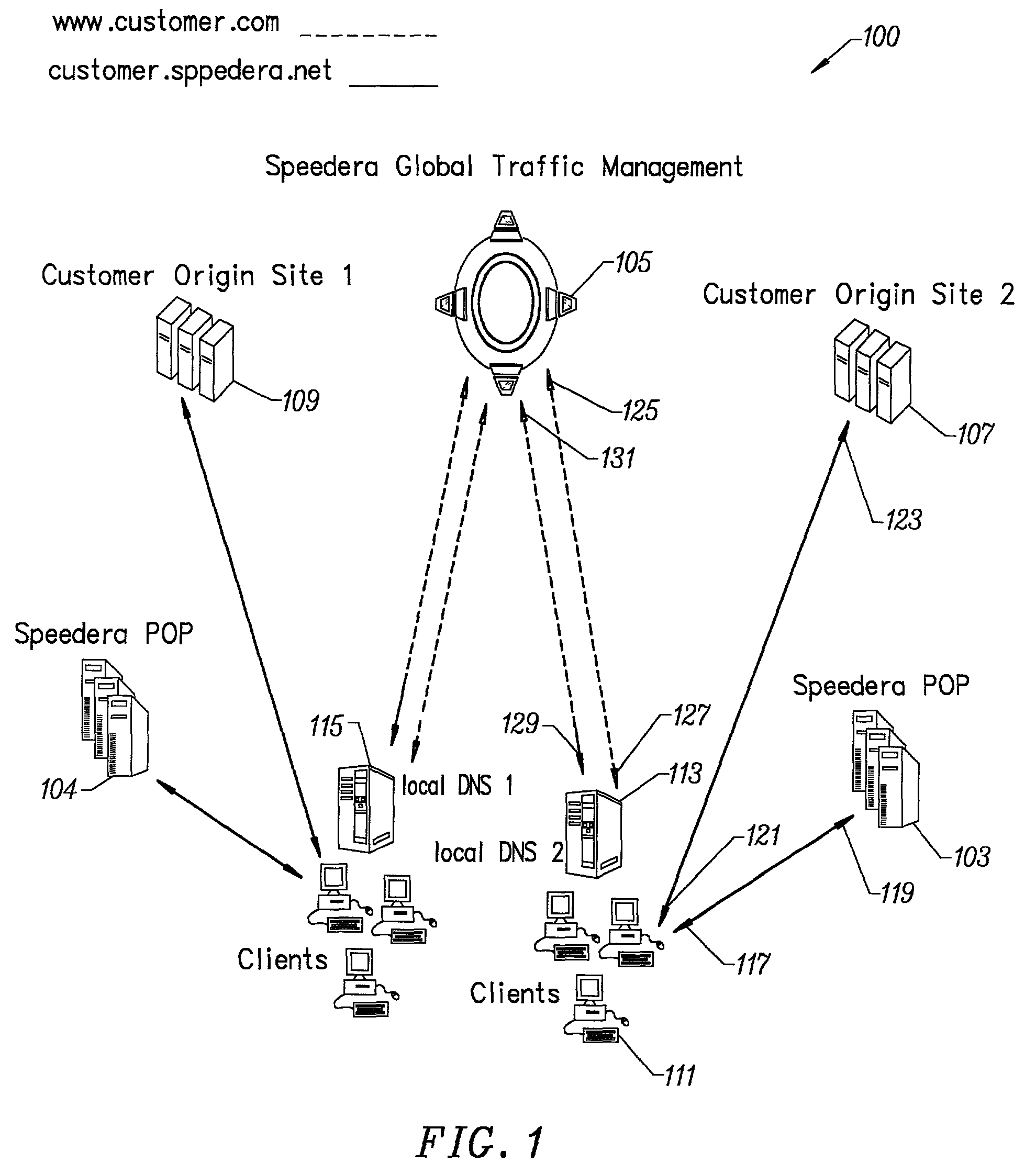
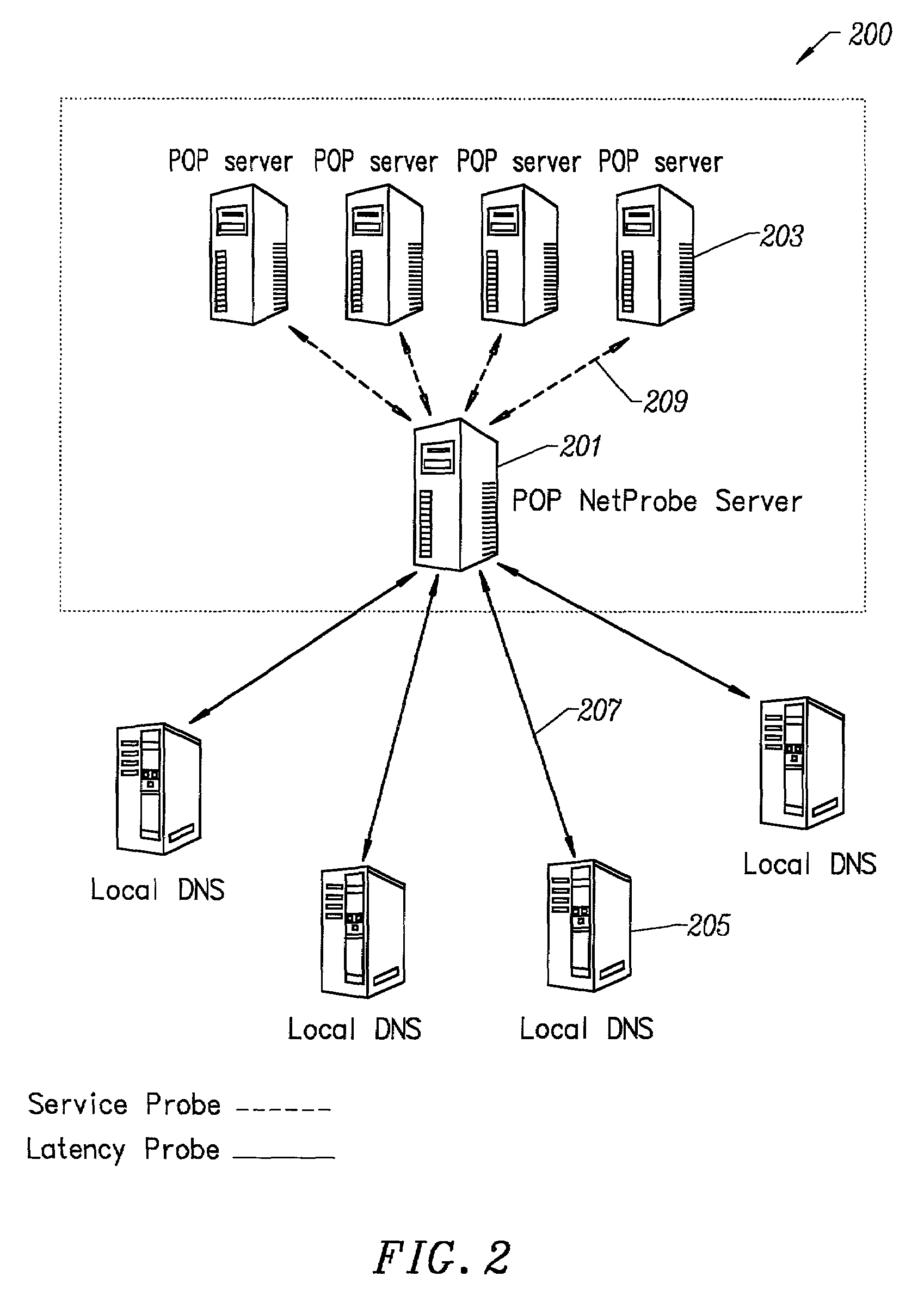
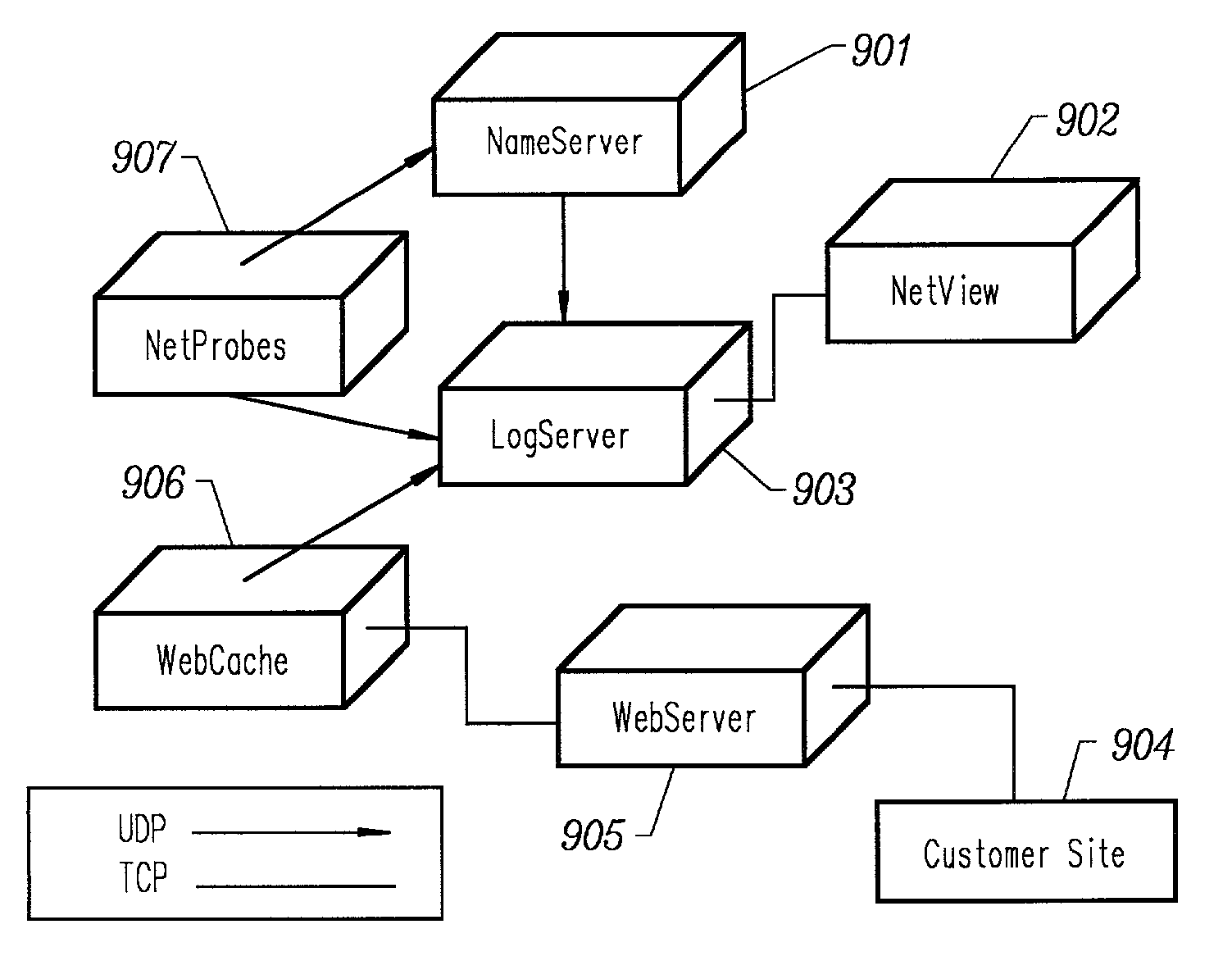
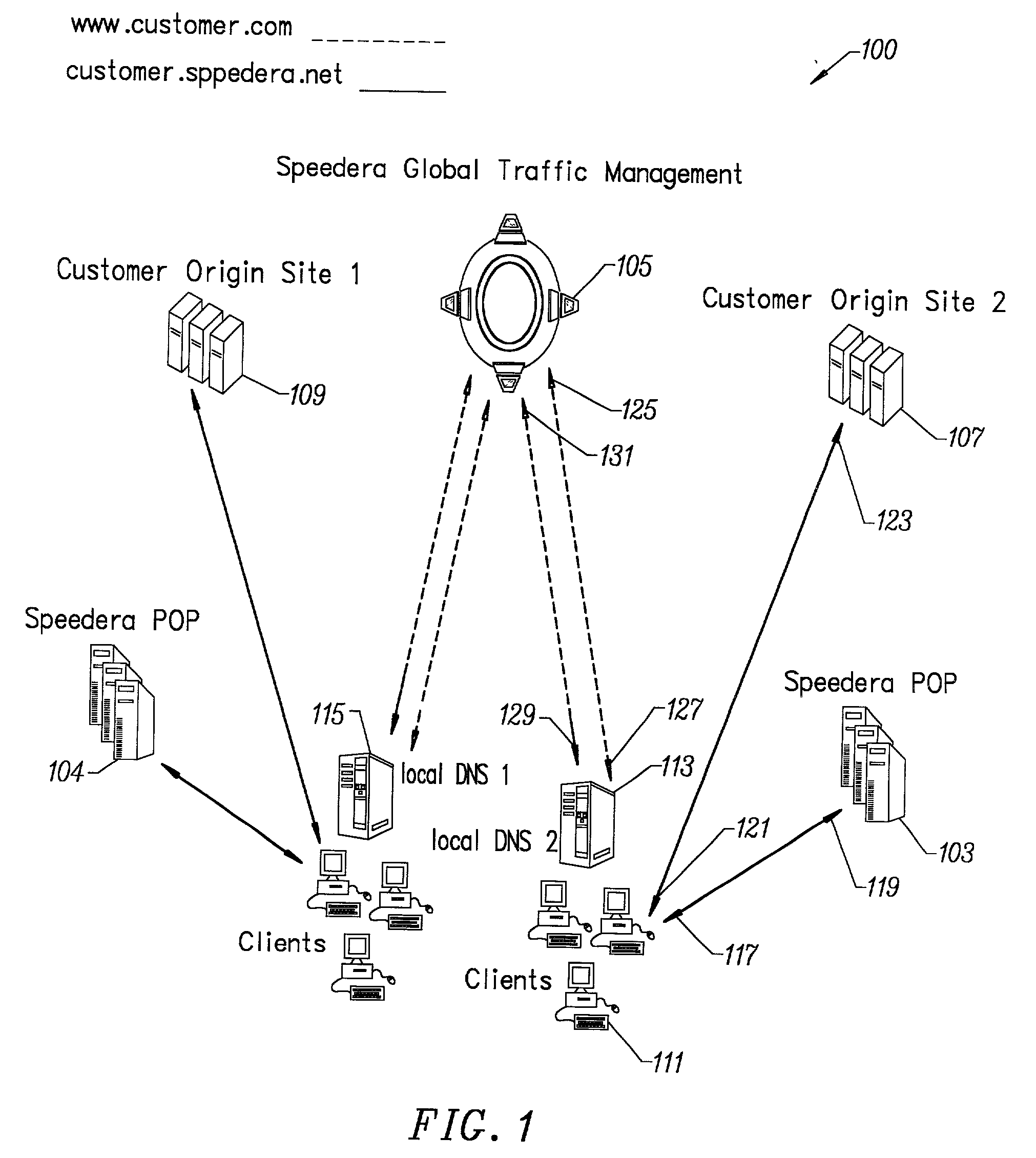
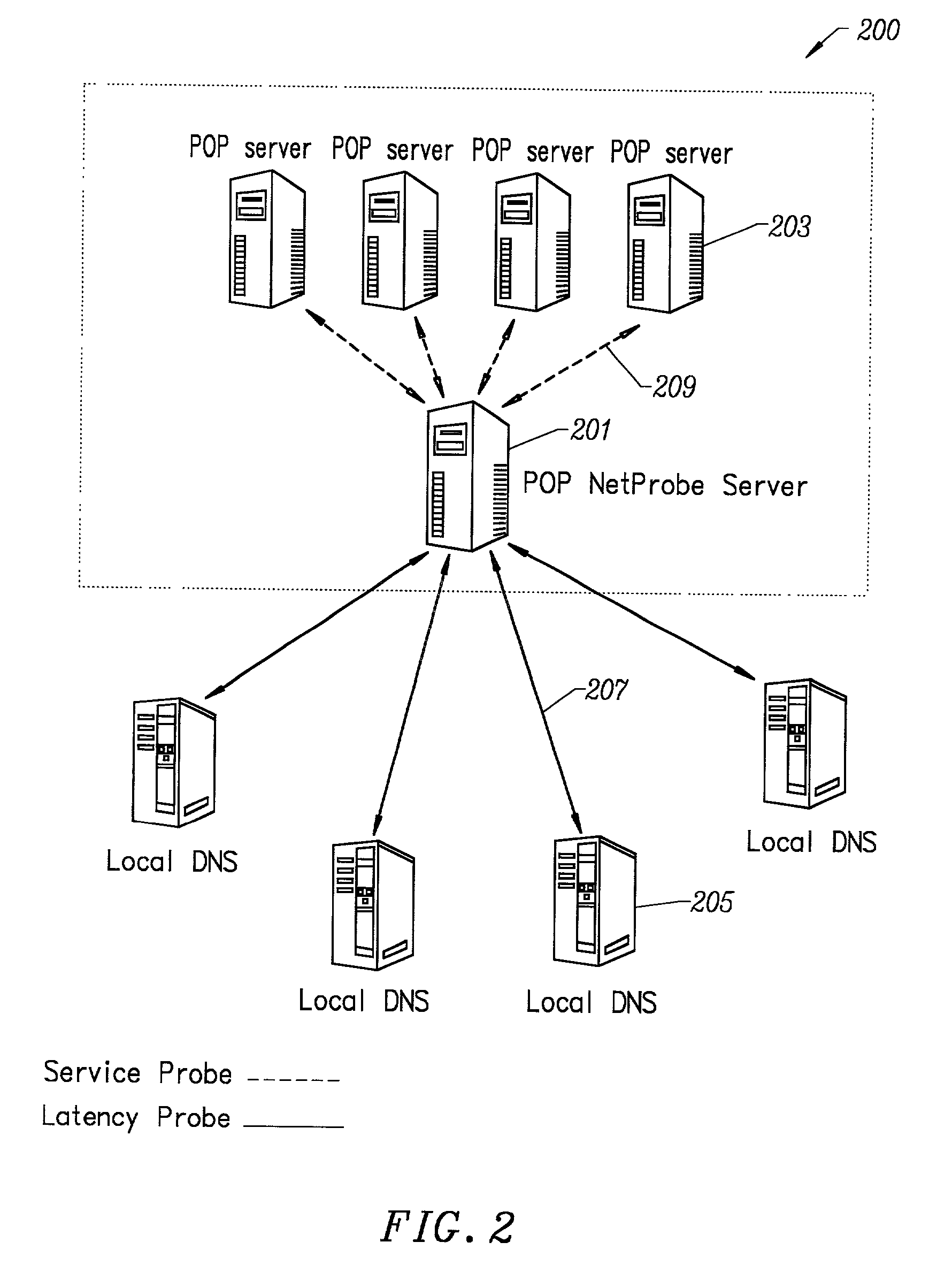
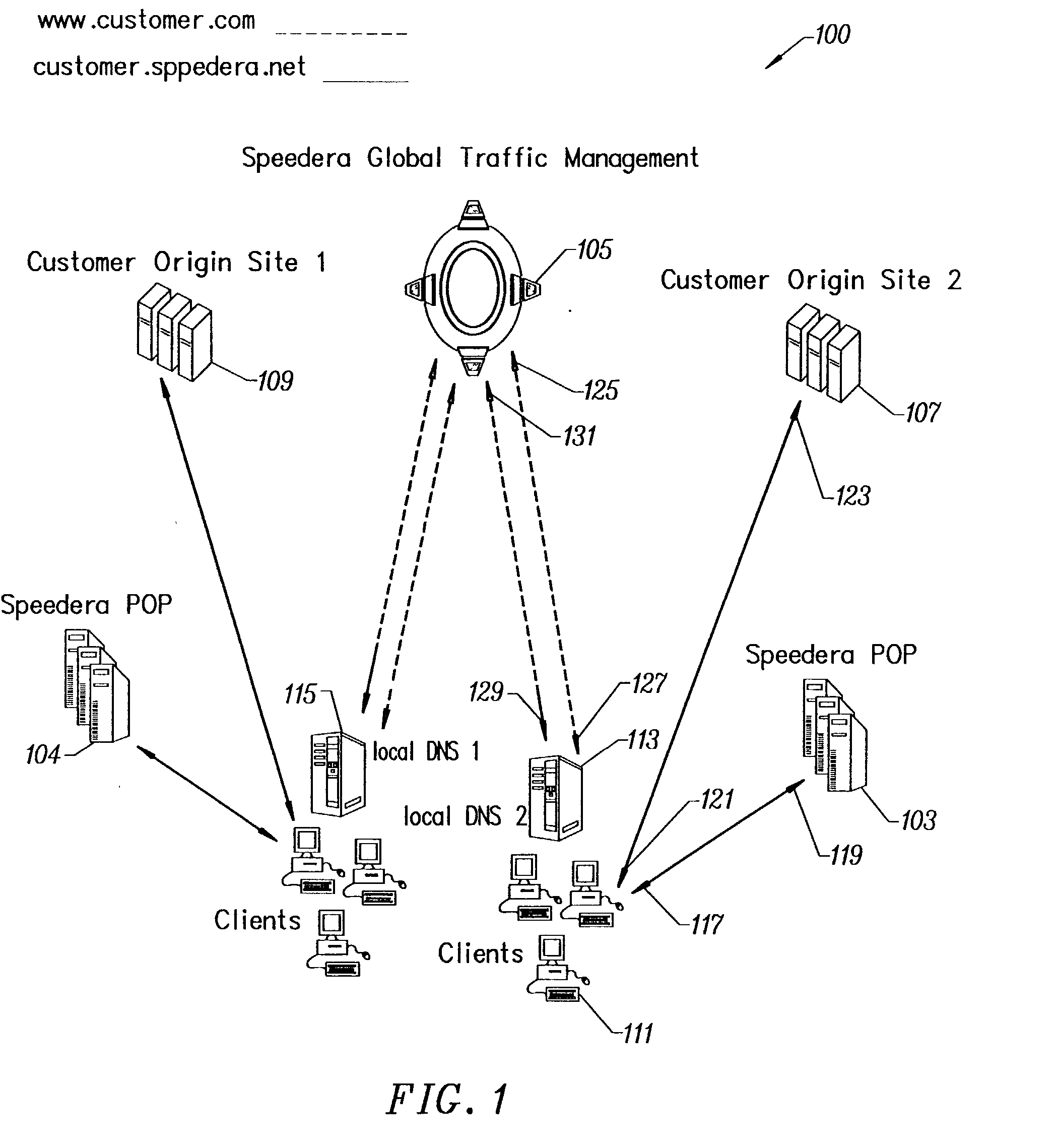
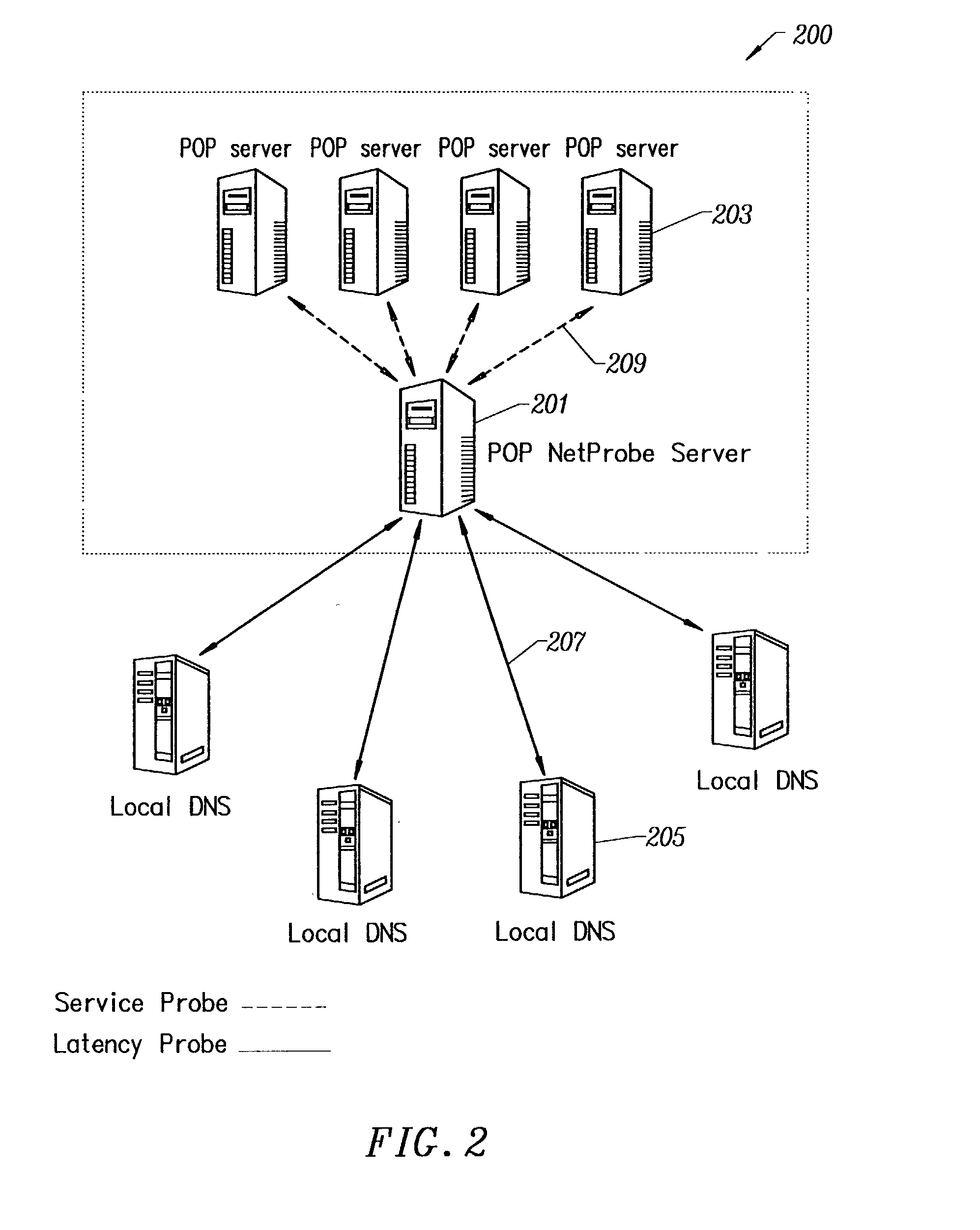
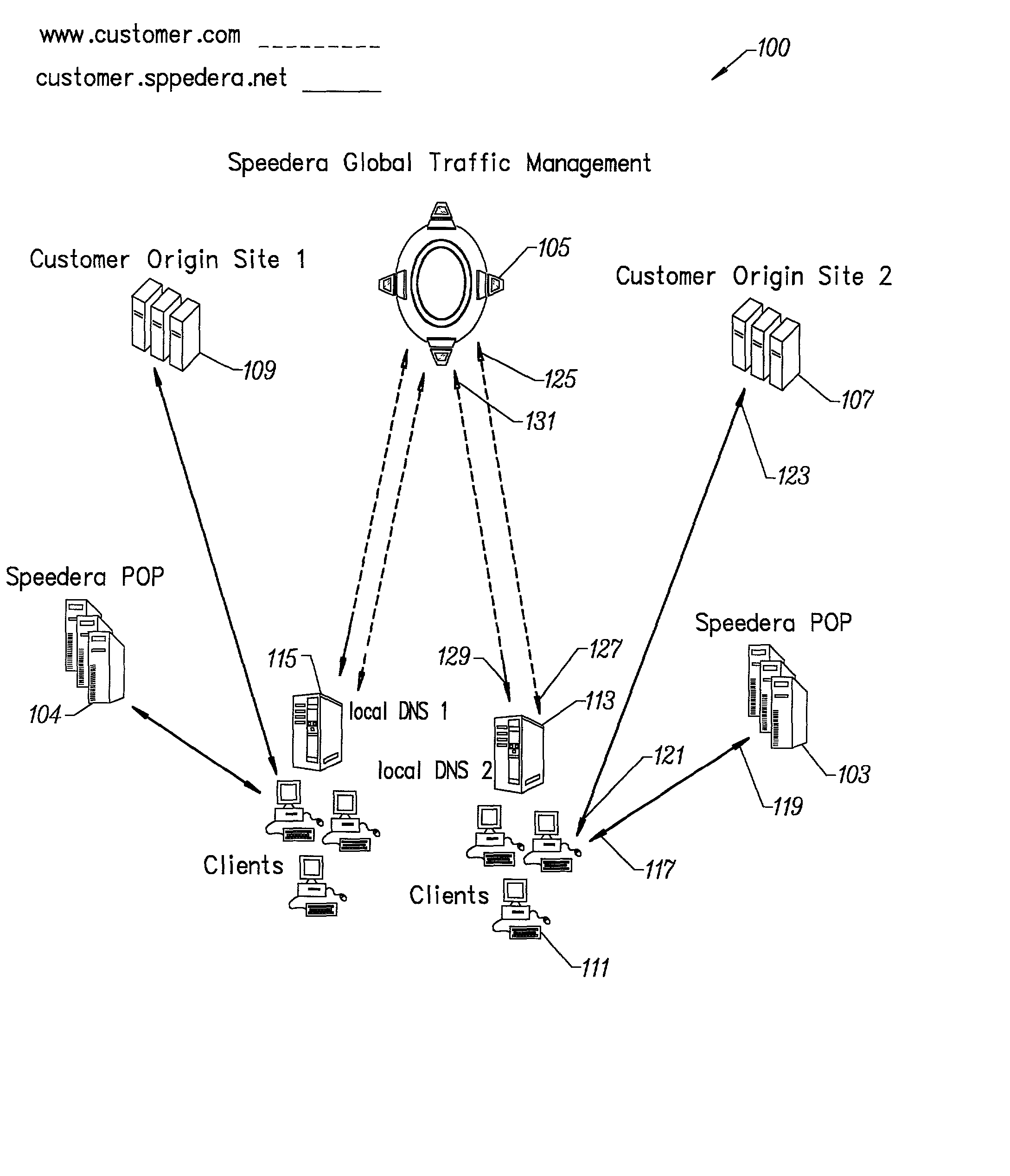
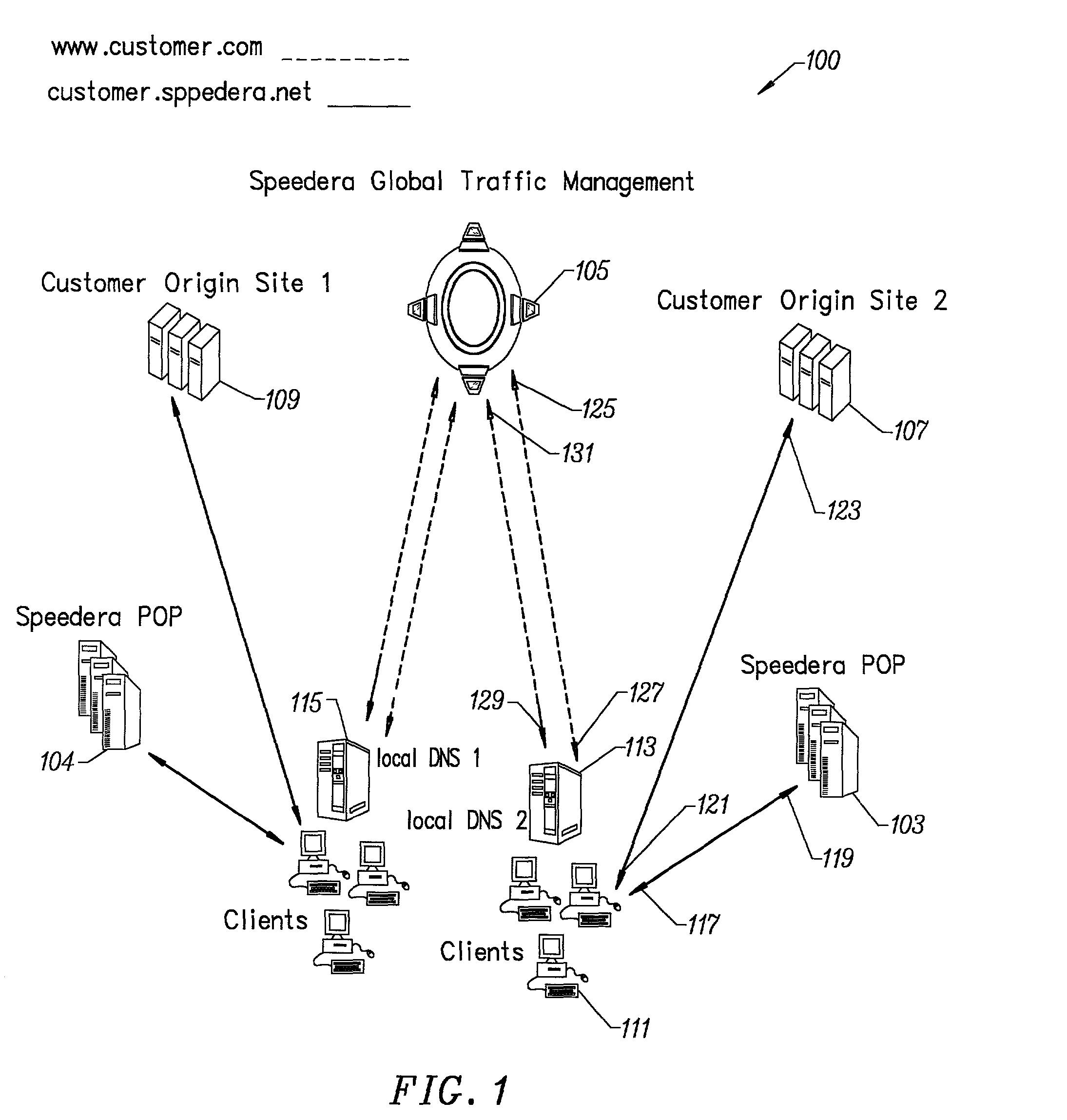
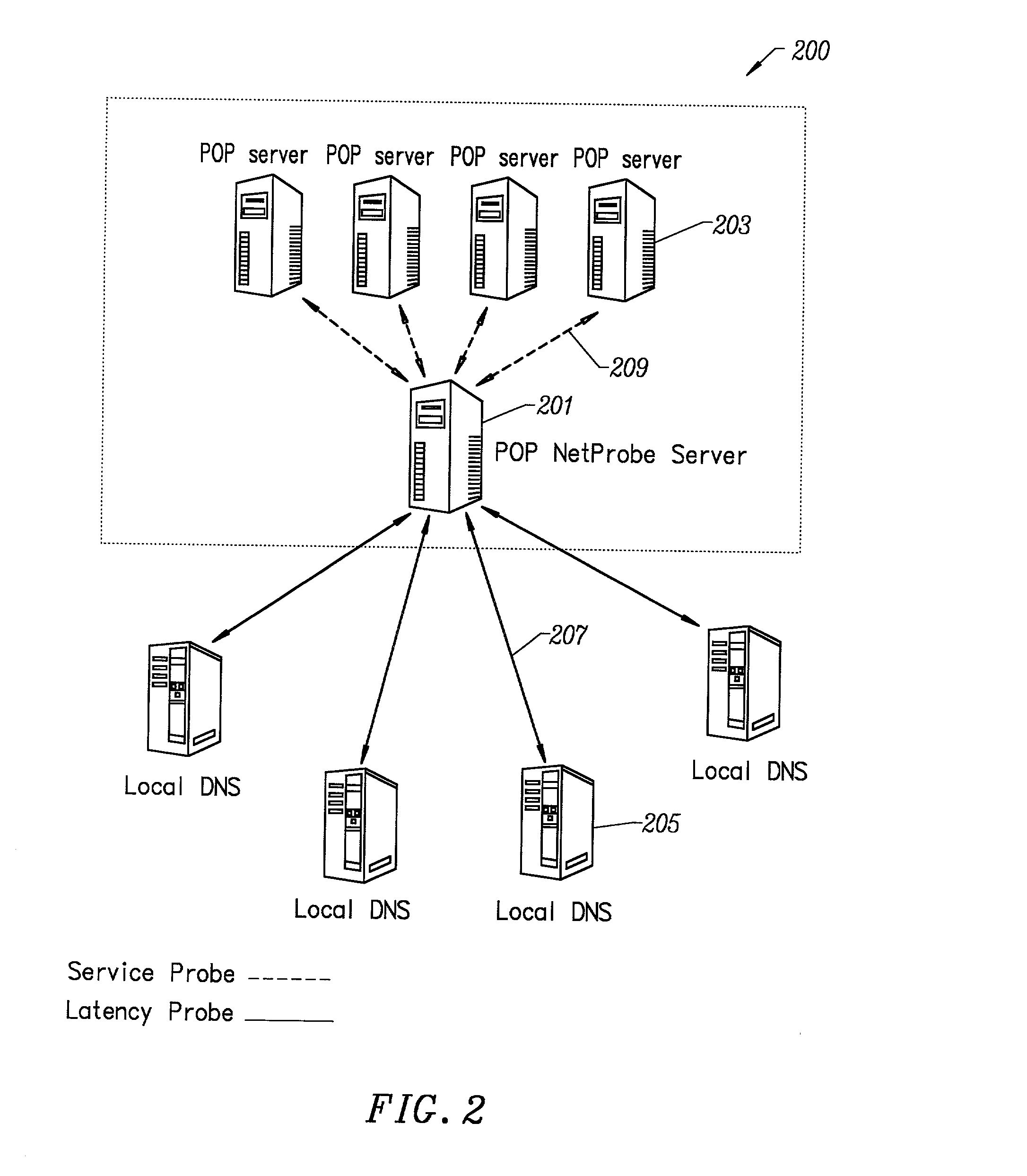
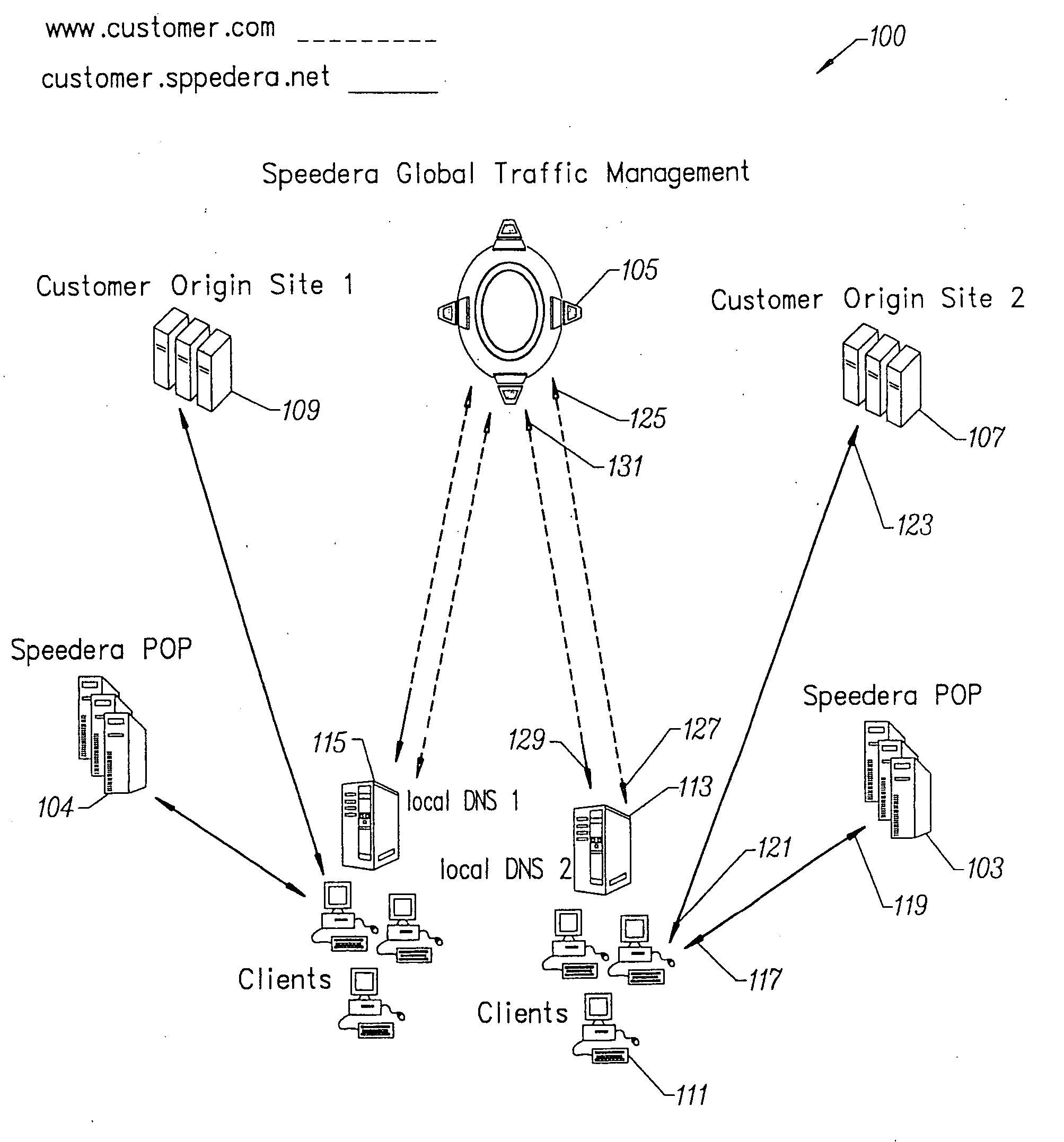
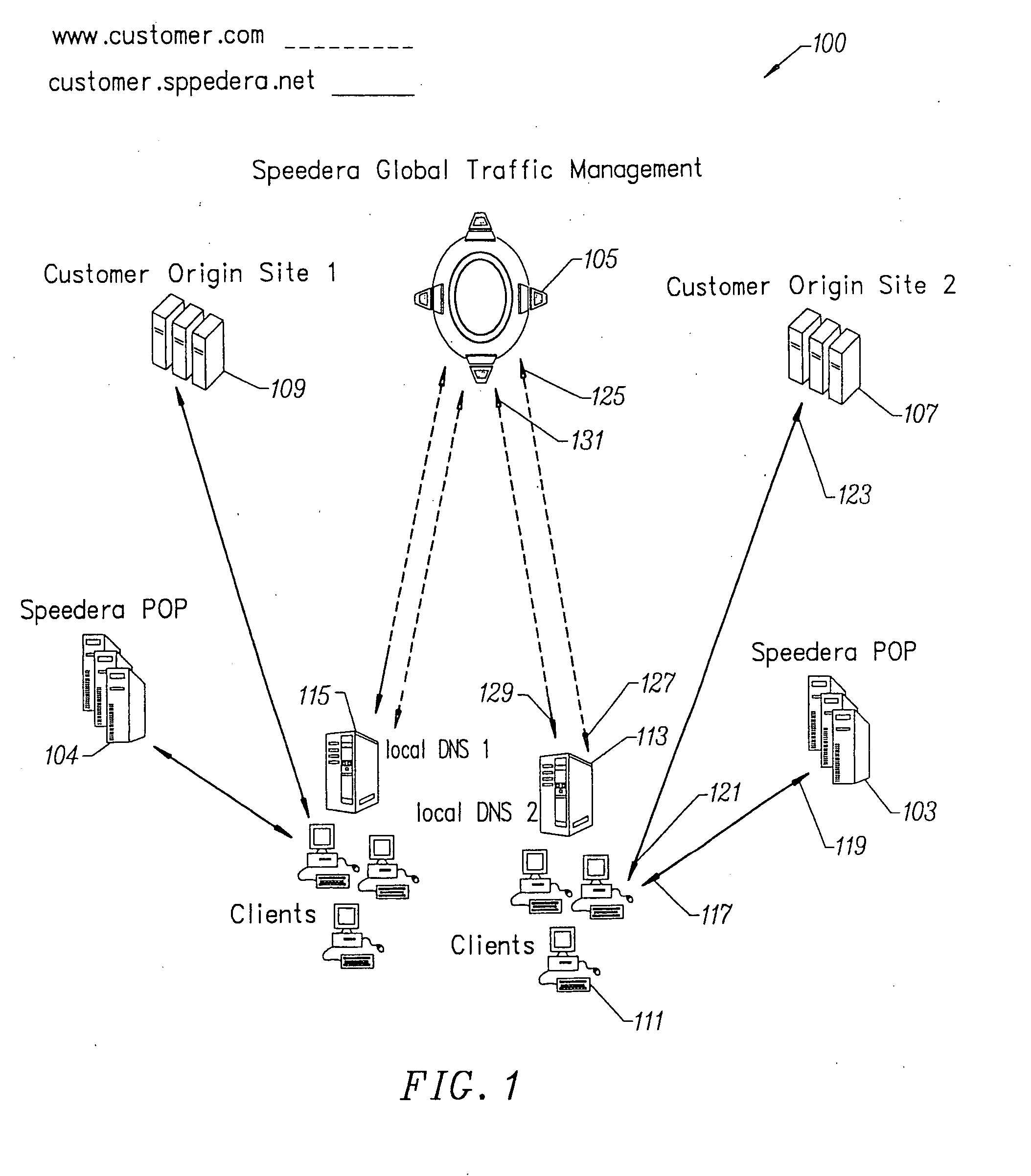
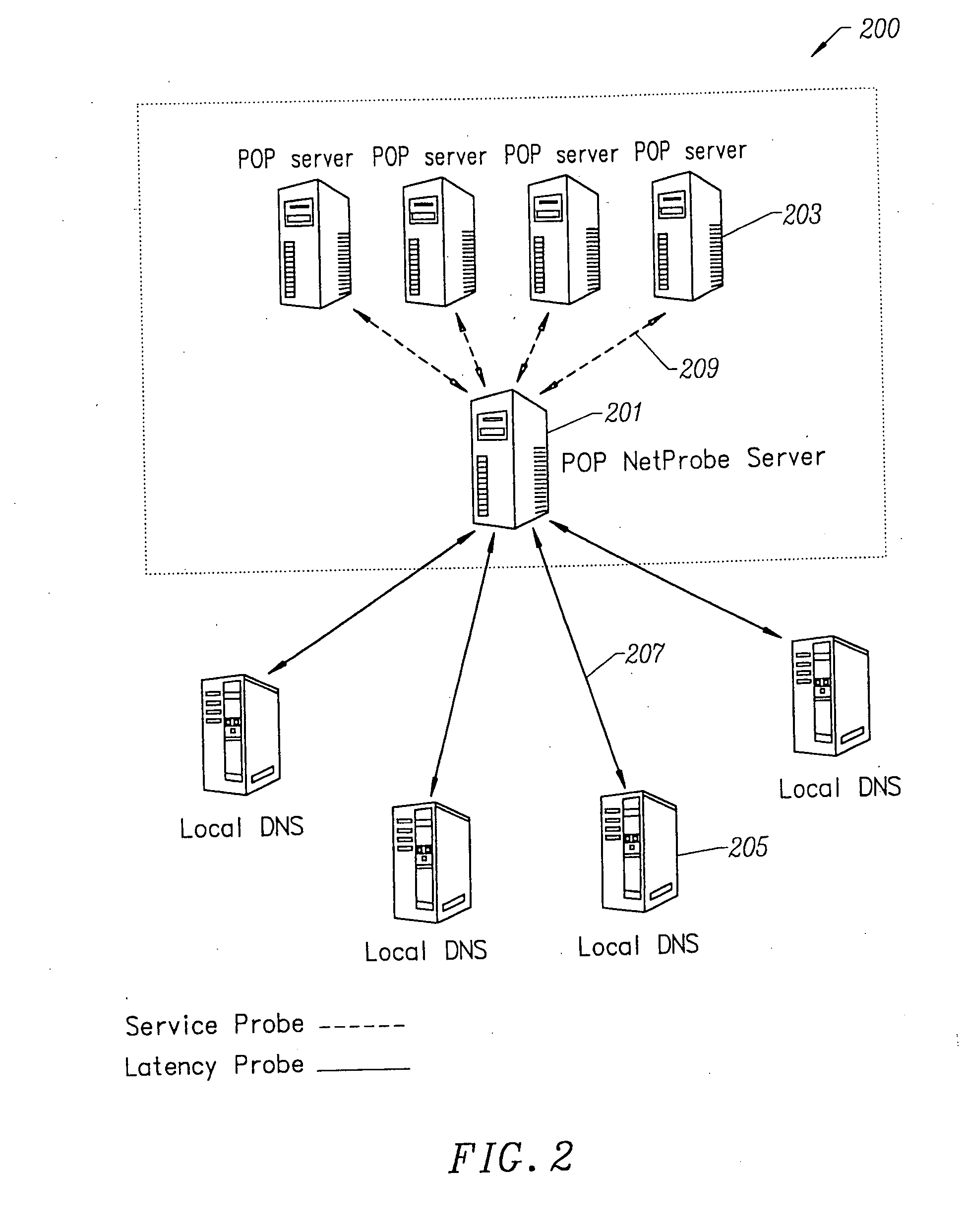
Method for determining metrics of a content delivery and global traffic management network
ActiveUS7523181B2Efficient executionMetering/charging/biilling arrangementsError preventionData packConfigfs
A method for determining metrics of a content delivery and global traffic management network provides service metric probes that determine the service availability and metric measurements of types of services provided by a content delivery machine. Latency probes are also provided for determining the latency of various servers within a network. Service metric probes consult a configuration file containing each DNS name in its area and the set of services. Each server in the network has a metric test associated with each service supported by the server which the service metric probes periodically performs metric tests on and records the metric test results which are periodically sent to all of the DNS servers in the network. DNS servers use the test result updates to determine the best server to return for a given DNS name. The latency probe calculates the latency from its location to a client's location using the round trip time for sending a packet to the client to obtain the latency value for that client. The latency probe updates the DNS servers with the clients' latency data. The DNS server uses the latency test data updates to determine the closest server to a client.
Owner:AKAMAI TECH INC
Content delivery and global traffic management network system
InactiveUS20020052942A1Meet cutting requirementsReduce trafficMetering/charging/biilling arrangementsError preventionWeb serviceCache server
Owner:AKAMAI TECH INC
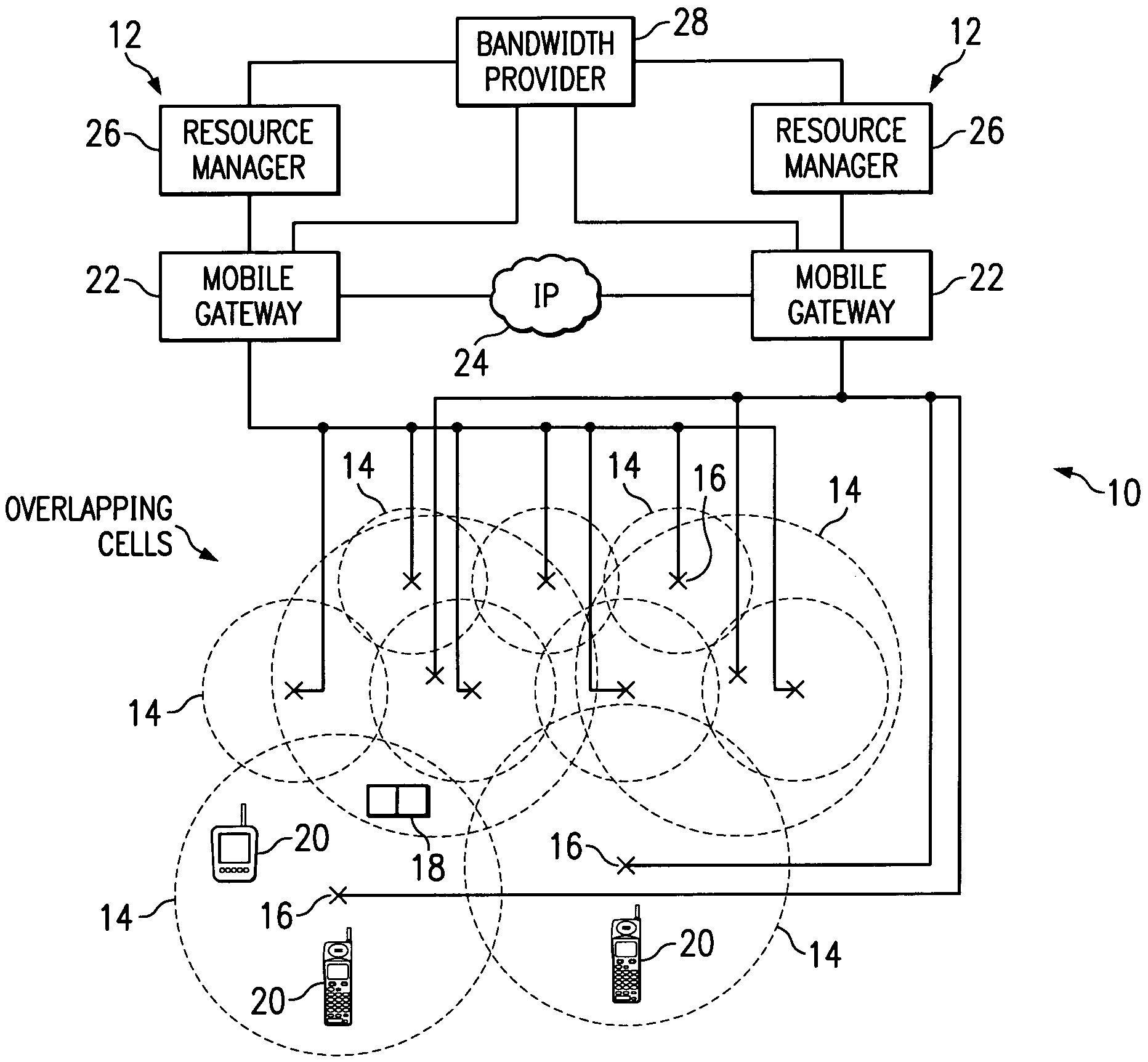
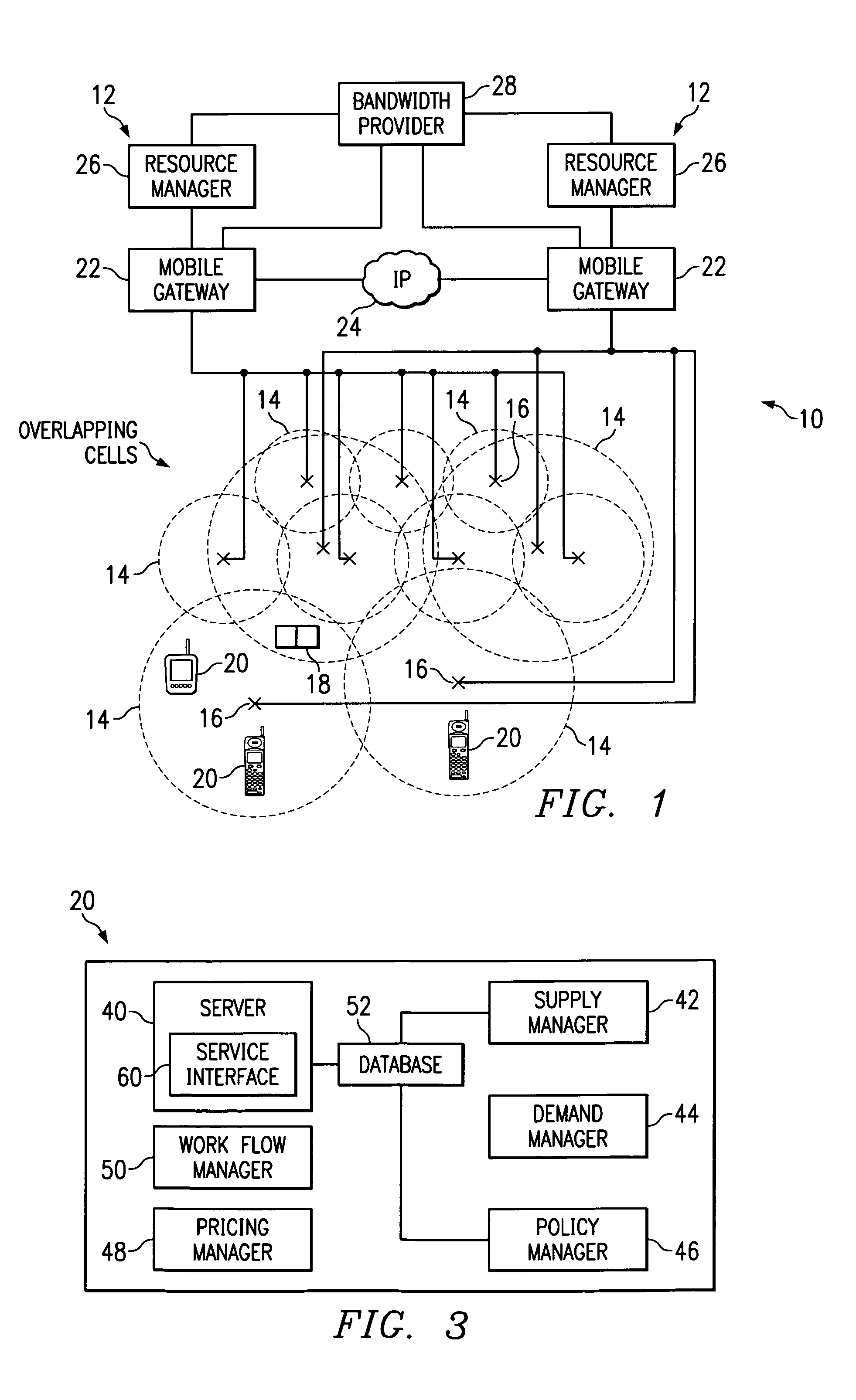
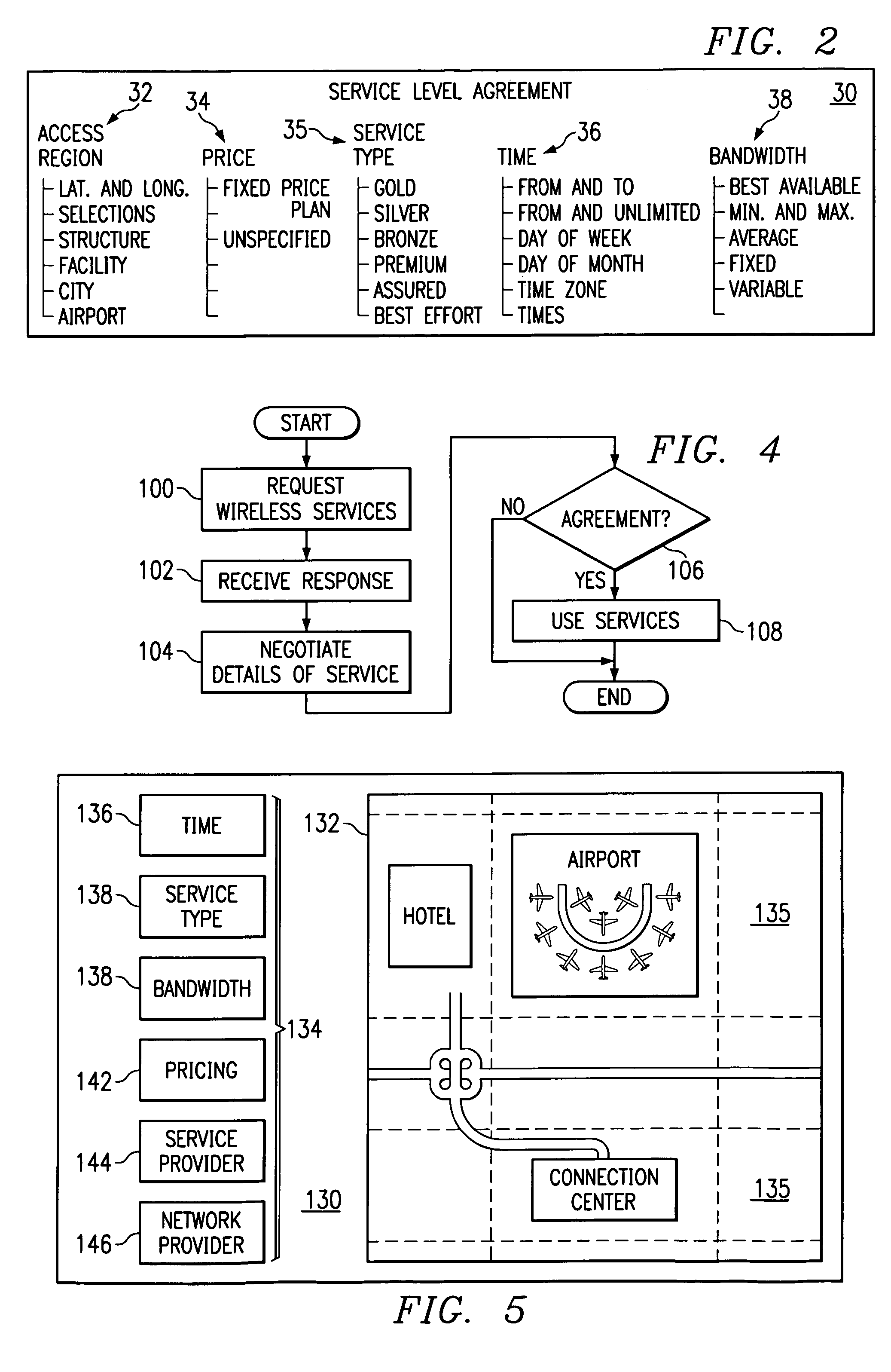
Method and system for brokering bandwidth in a wireless communications network
InactiveUS7043225B1Limit priceAdequate wireless resourceMetering/charging/biilling arrangementsTelephonic communicationGeographic regionsTelecommunications
A method and system for brokering bandwidth in a wireless communications network includes receiving a request for a wireless service at a geographic region. An availability of the wireless service is determined at the geographic region. A response to the request is generated based on the availability of the wireless service. The response includes one or more terms for the wireless service.
Owner:CISCO TECH INC
Pool-based resource management in a data network
ActiveUS7209439B2Metering/charging/biilling arrangementsInterconnection arrangementsNetworked systemResource management
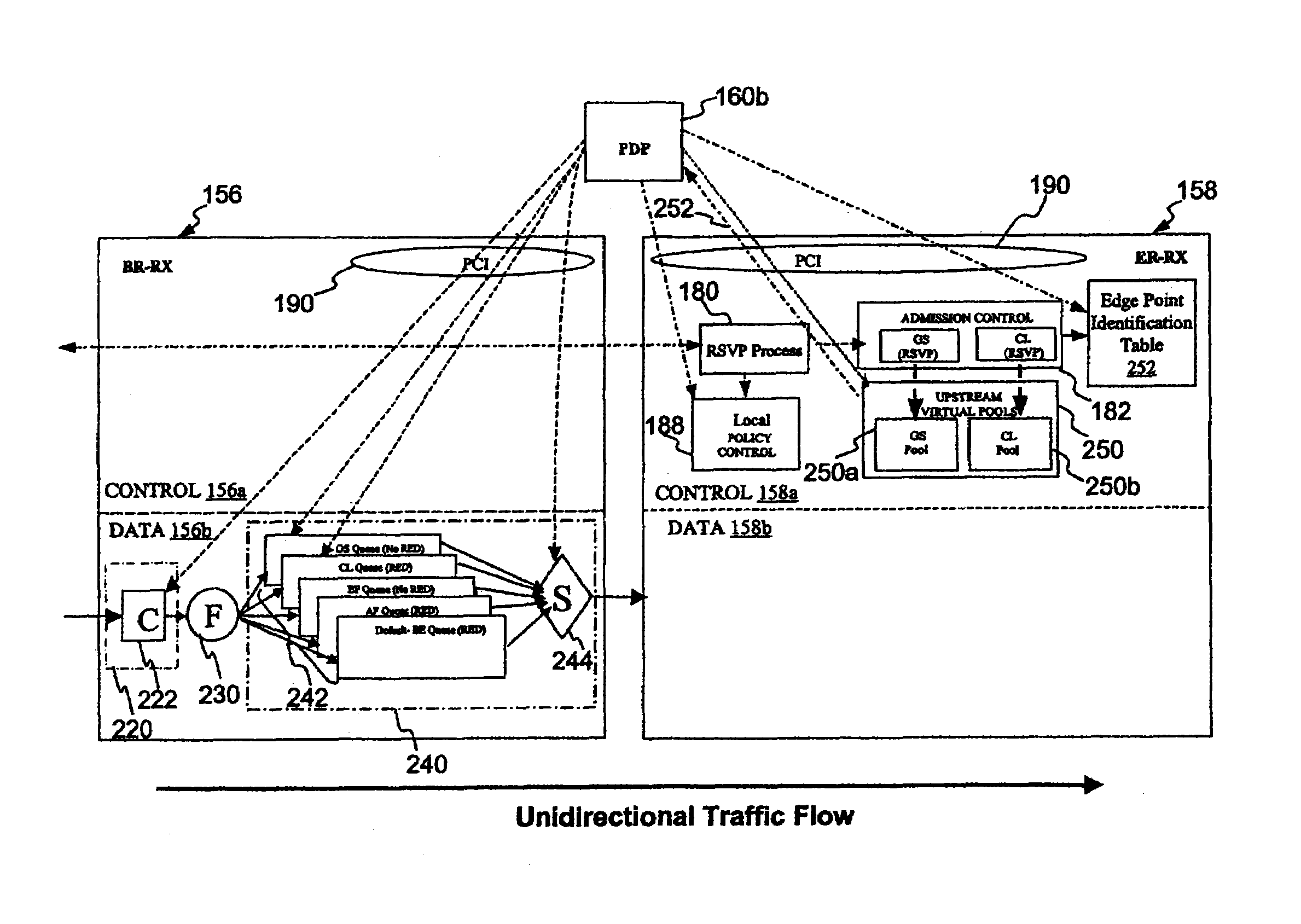
In one embodiment, a network system of the present invention includes at least a first router and a second router coupled to an upstream link to permit data flow from the first router to the second router across the upstream link. The second router includes a control plane and a data plane having an input port coupled to the upstream link and an output port connectable to a downstream link. The control plane includes a virtual pool having a capacity corresponding to a resource capacity of the first router and an admission control function. In response to a request to reserve resources for a flow through the data plane from the input port to the output port, the admission control function performs admission control for the upstream link by reference to resource availability within the virtual pool. In one embodiment, the request is a request to reserve resources for an Integrated Services flow, and the capacity of the virtual pool corresponds to a resource capacity of a Integrated Services service class supported by the first router.
Owner:VERIZON PATENT & LICENSING INC
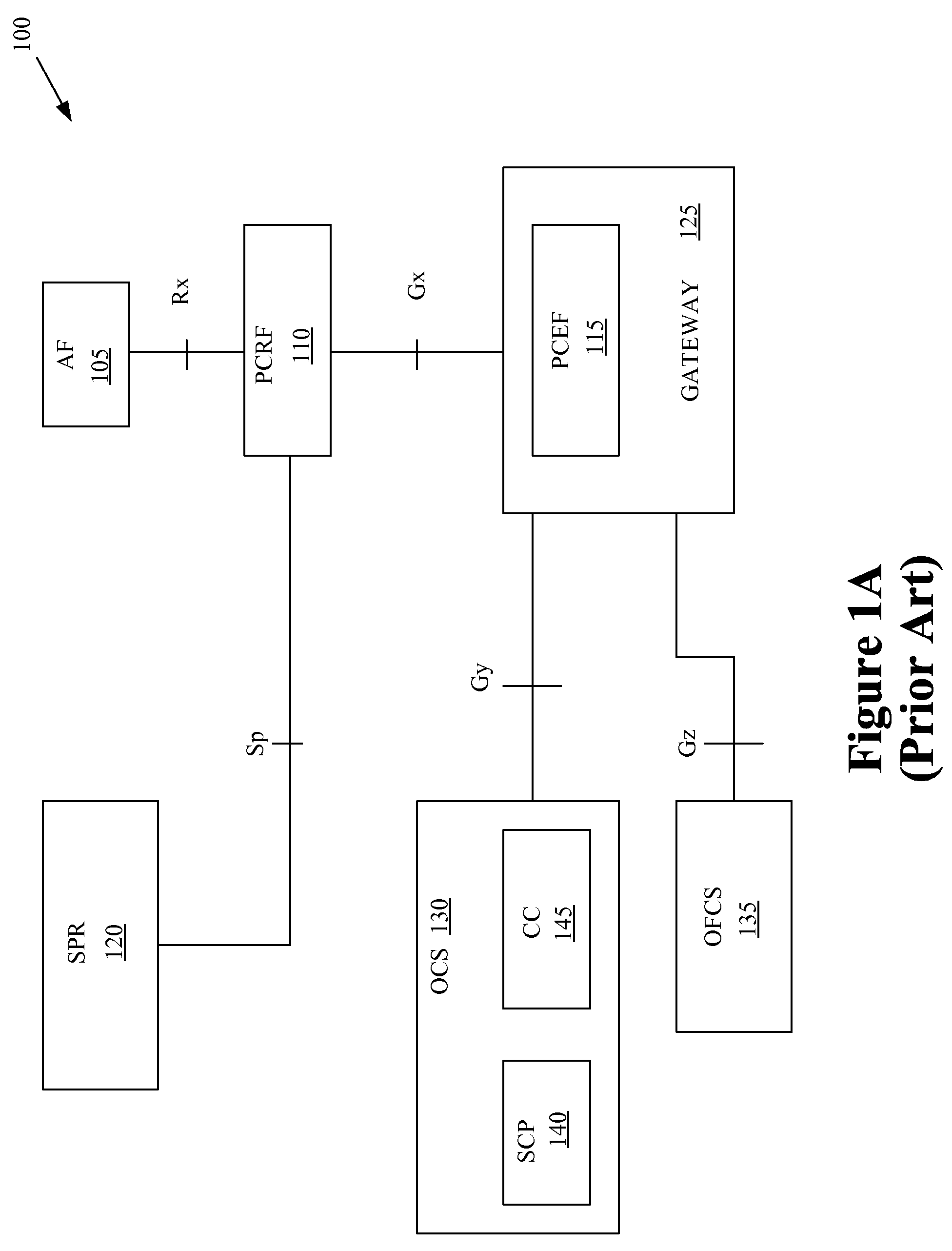
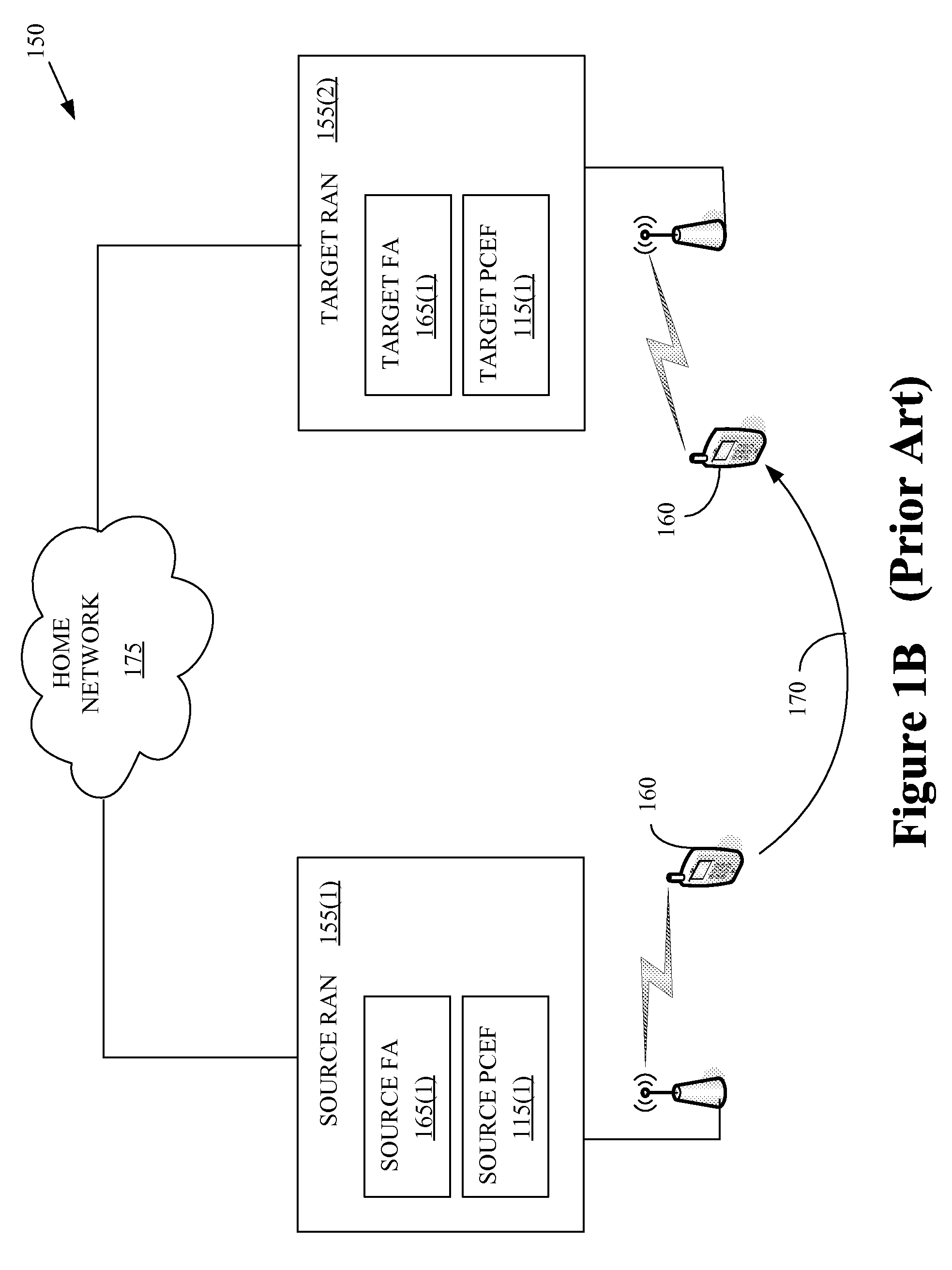
Mobility Aware Policy and Charging Control in a Wireless Communication Network
ActiveUS20080229385A1Metering/charging/biilling arrangementsTelephonic communicationAccess networkCommunications system
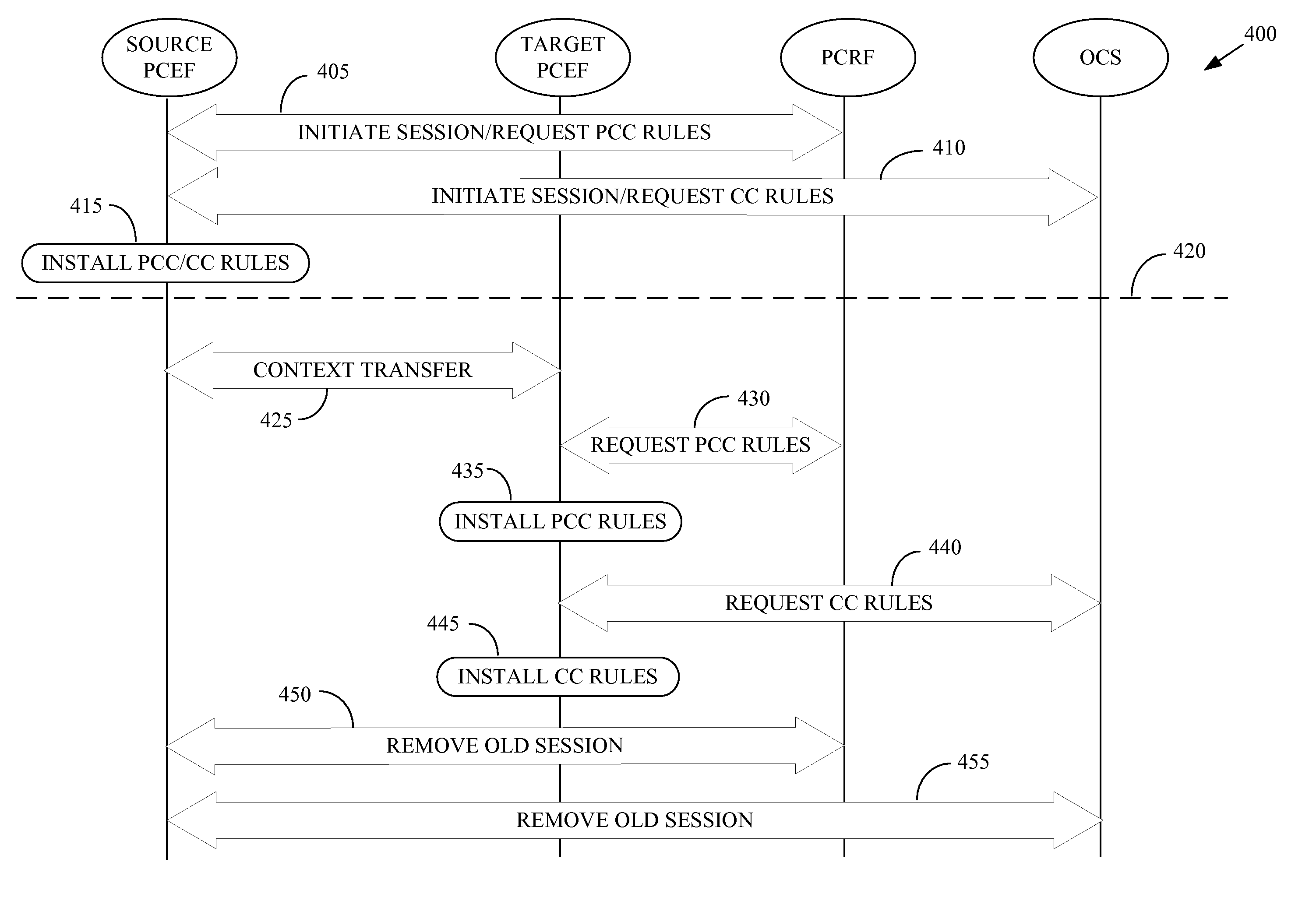
One embodiment of the present invention provides a method for implementation in a policy control and charging rules functional entity in a wireless communication system. The method includes receiving, from at least one of a source policy and charging enforcement function in a source access network or a target policy and charging enforcement function in a target access network, information indicative of a mobile unit that has handed off from the source access network to the target access network. The method also includes establishing a first session for communicating policy and charging rules associated with the mobile unit. The first session is concurrent with a second session for communicating policy and charging rules associated with the mobile unit. The second session was previously established with the source policy and charging enforcement function in the source access network. The method further includes transmitting at least one policy and charging rule to the target policy and charging enforcement function using the first session.
Owner:NOKIA TECHNOLOGLES OY
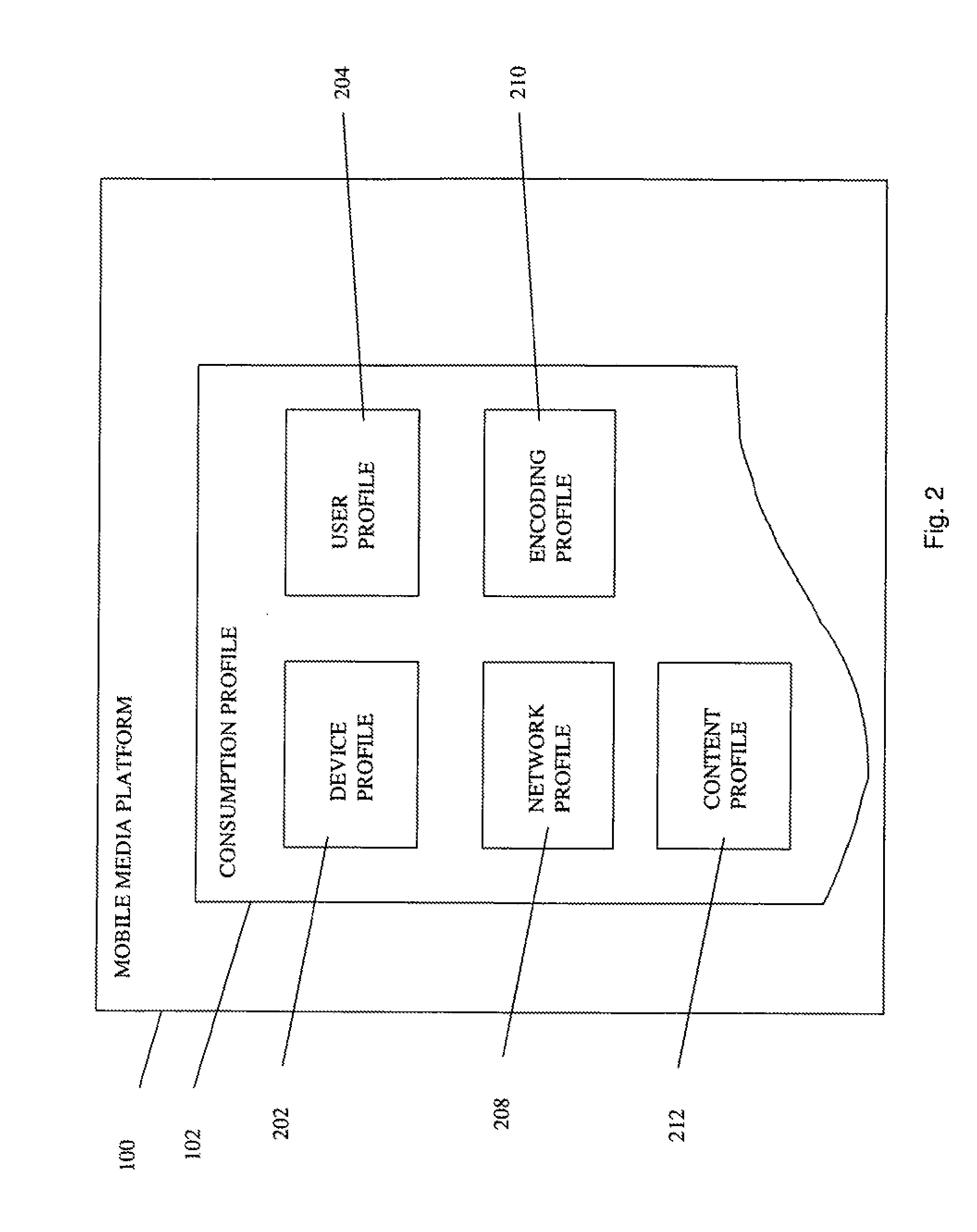
Media Processor
InactiveUS20130166580A1Efficiently provideMetering/charging/biilling arrangementsAdvertisementsData miningMedia processor
In embodiments, the present invention provides method and system for determining if an existing pass log may be reused. The method may include associating an existing pass log with an encoding profile. The method may further include computing with a processor a signature for the encoding profile and for a target encoding profile. The method may include comparing with the processor at least a portion of the two signatures and based on a result of the comparing, storing in a processor accessible memory at least one of an indication that the pass log file may be used in conjunction with the target encoding profile and an indication that the pass log file cannot be used in conjunction with the target encoding profile.
Owner:THE DIRECTV GROUP
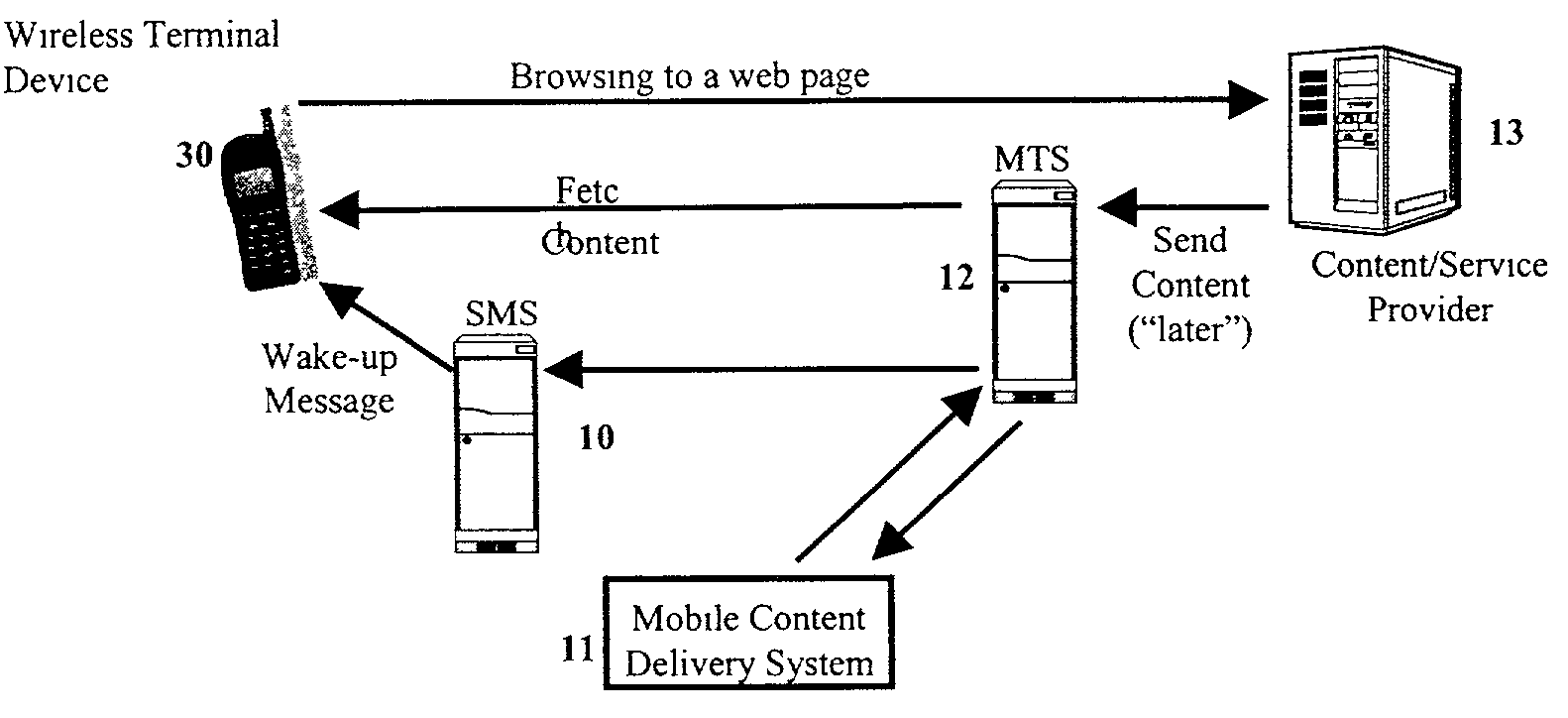
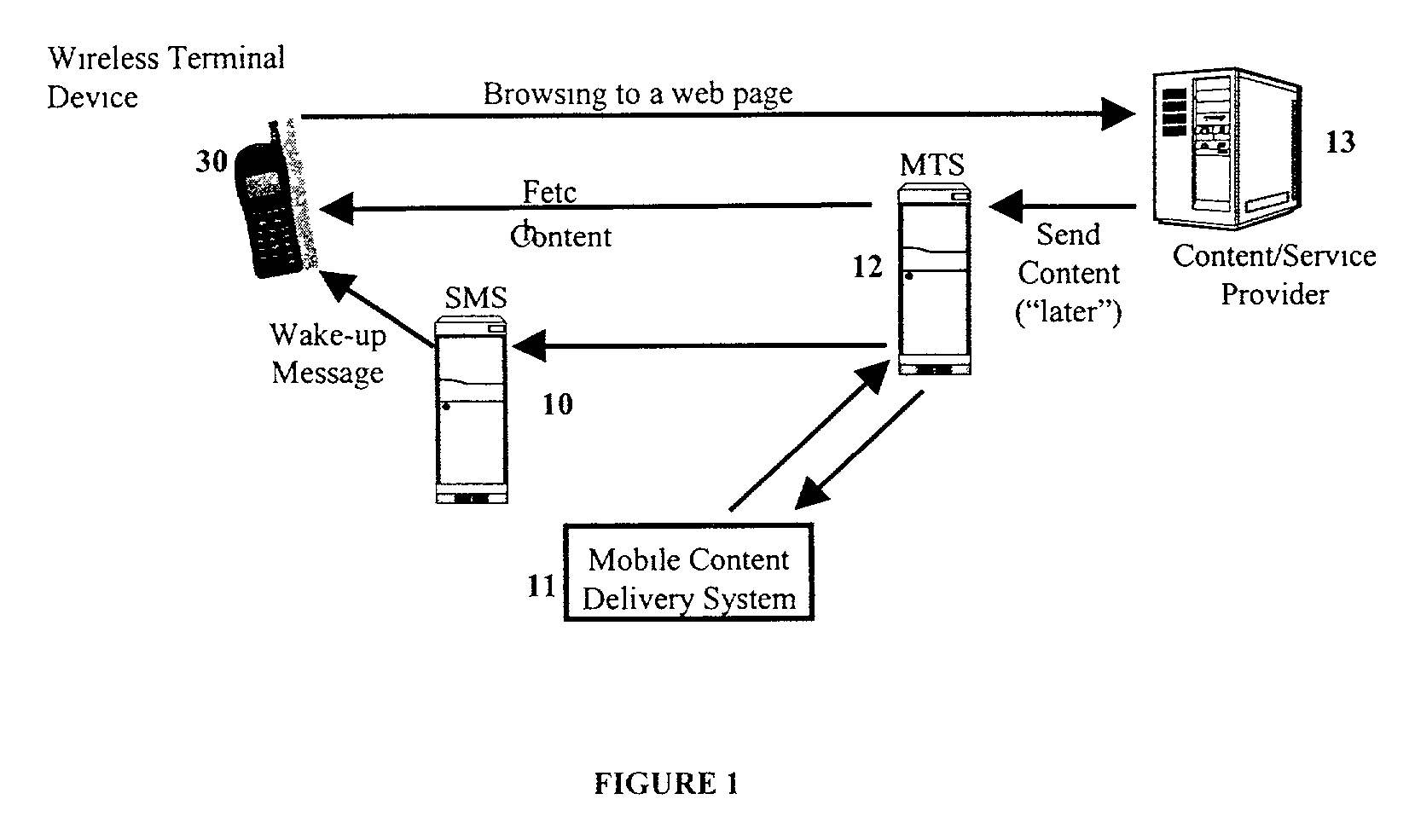
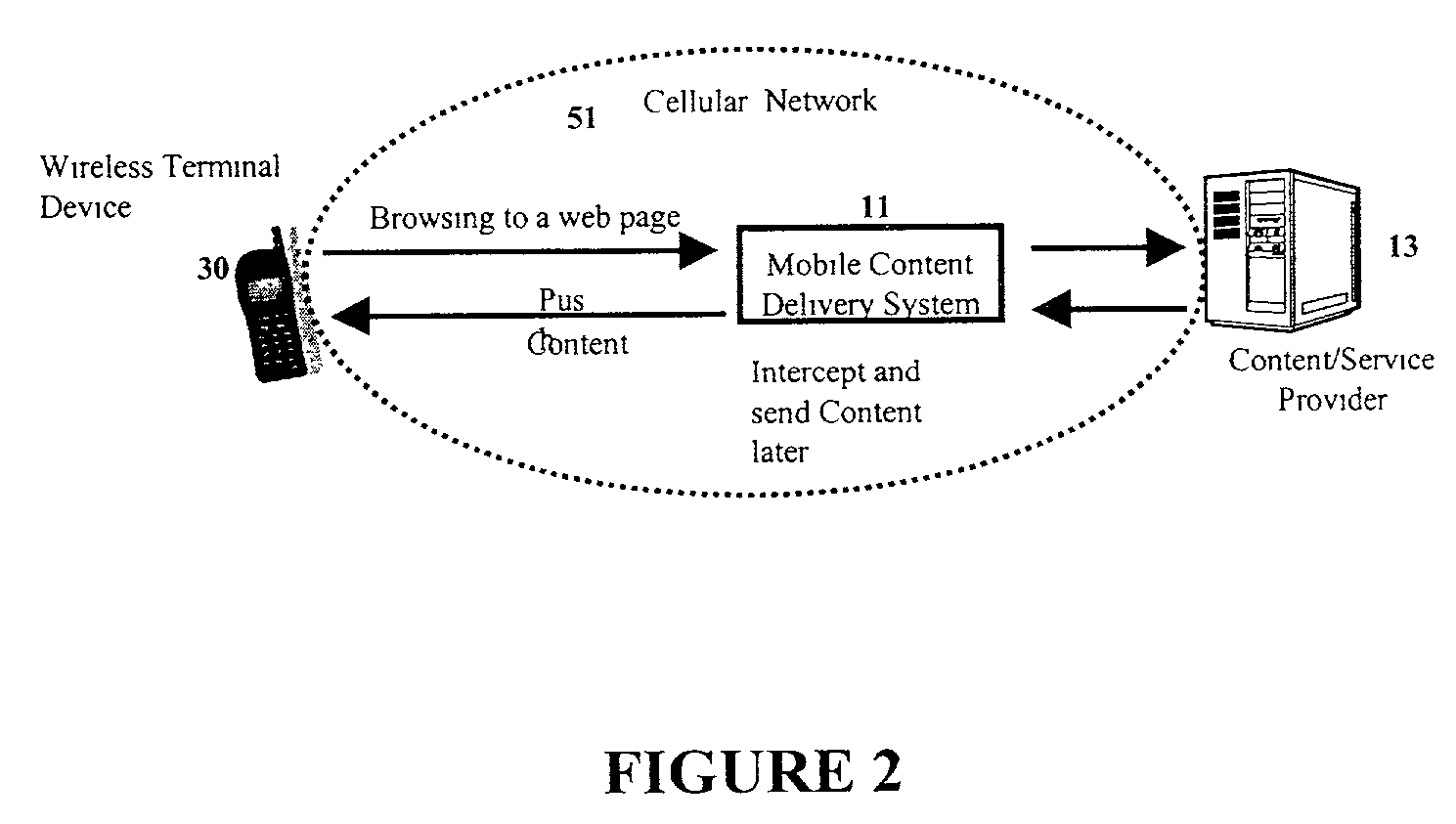
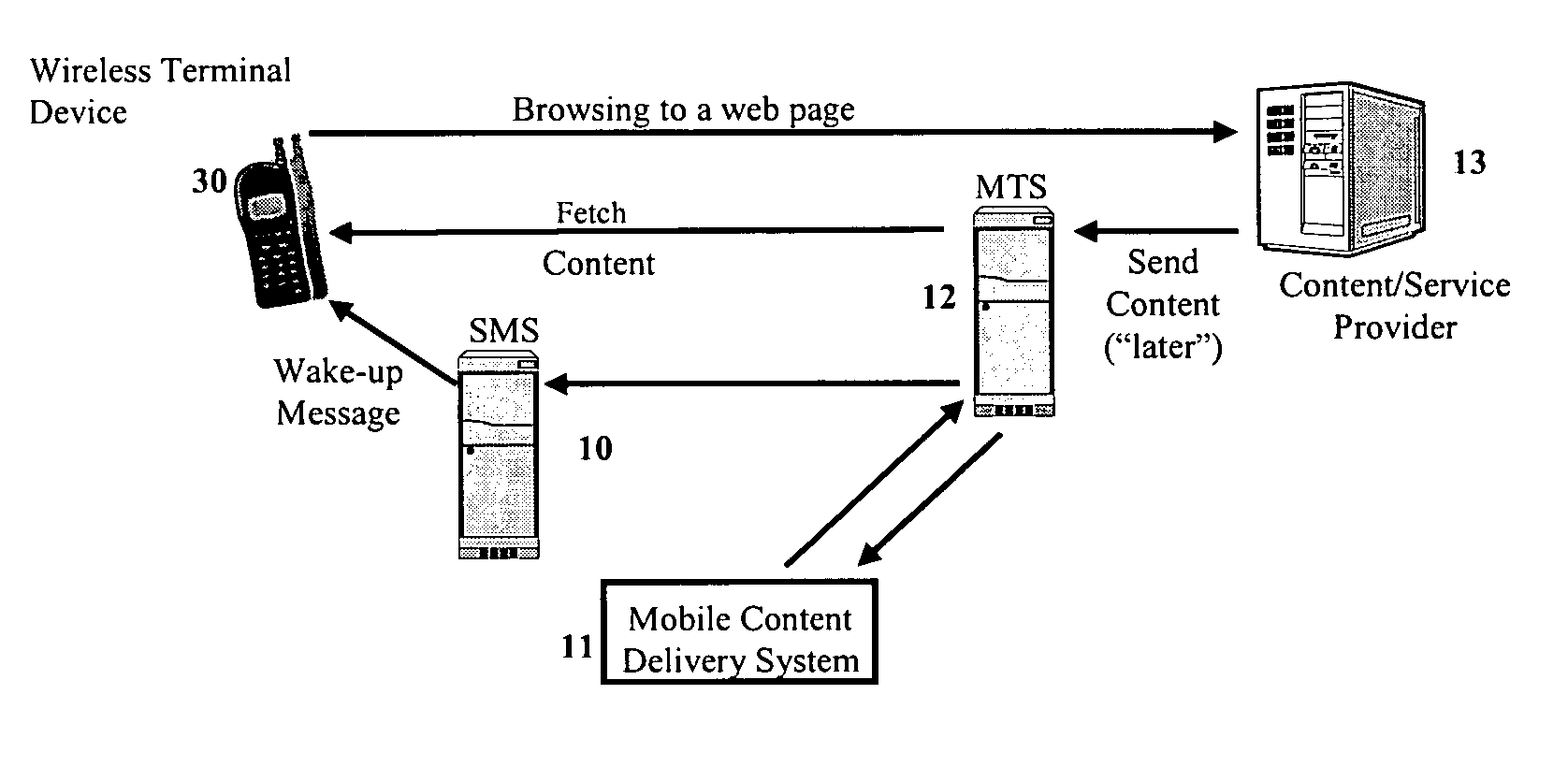
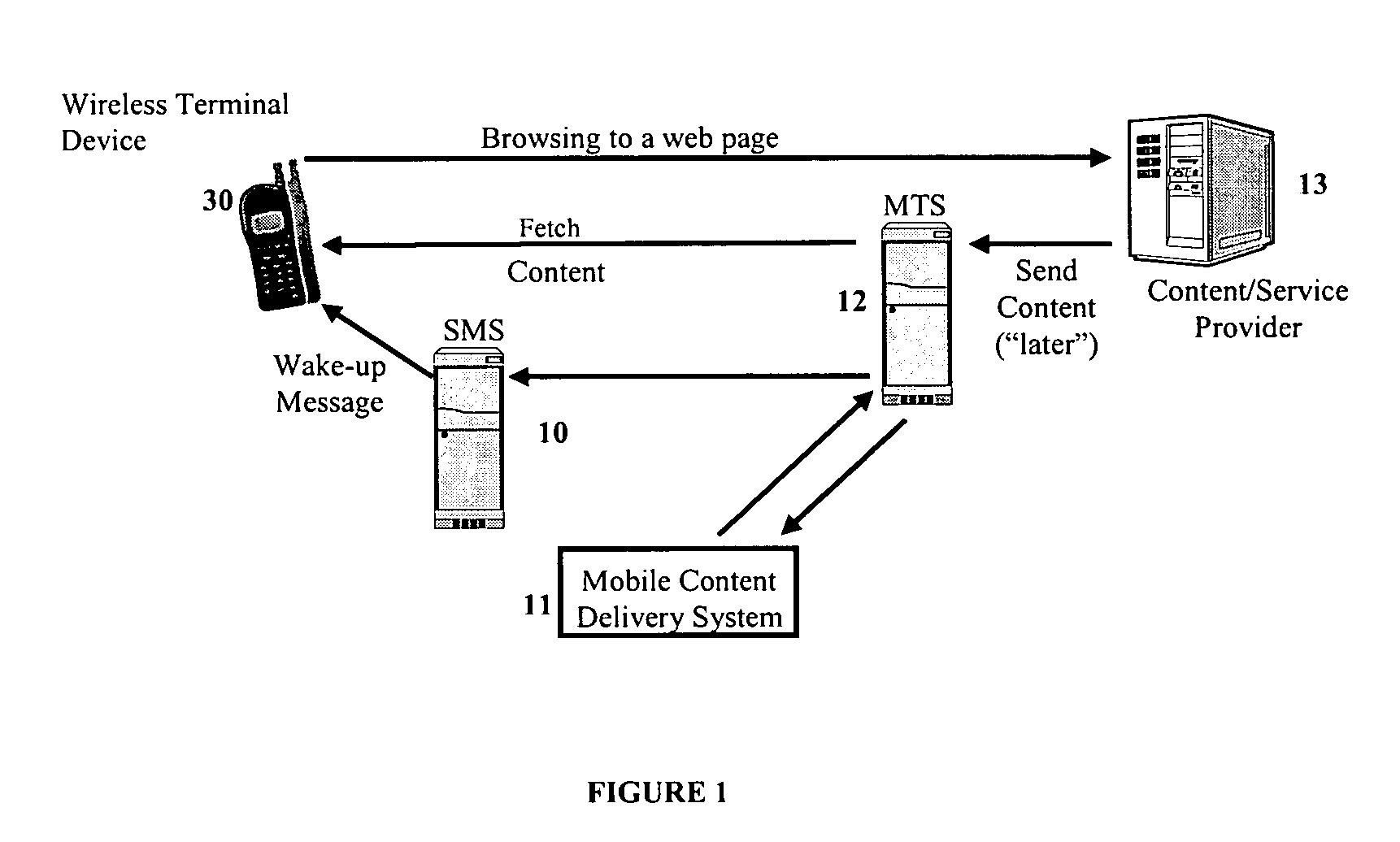
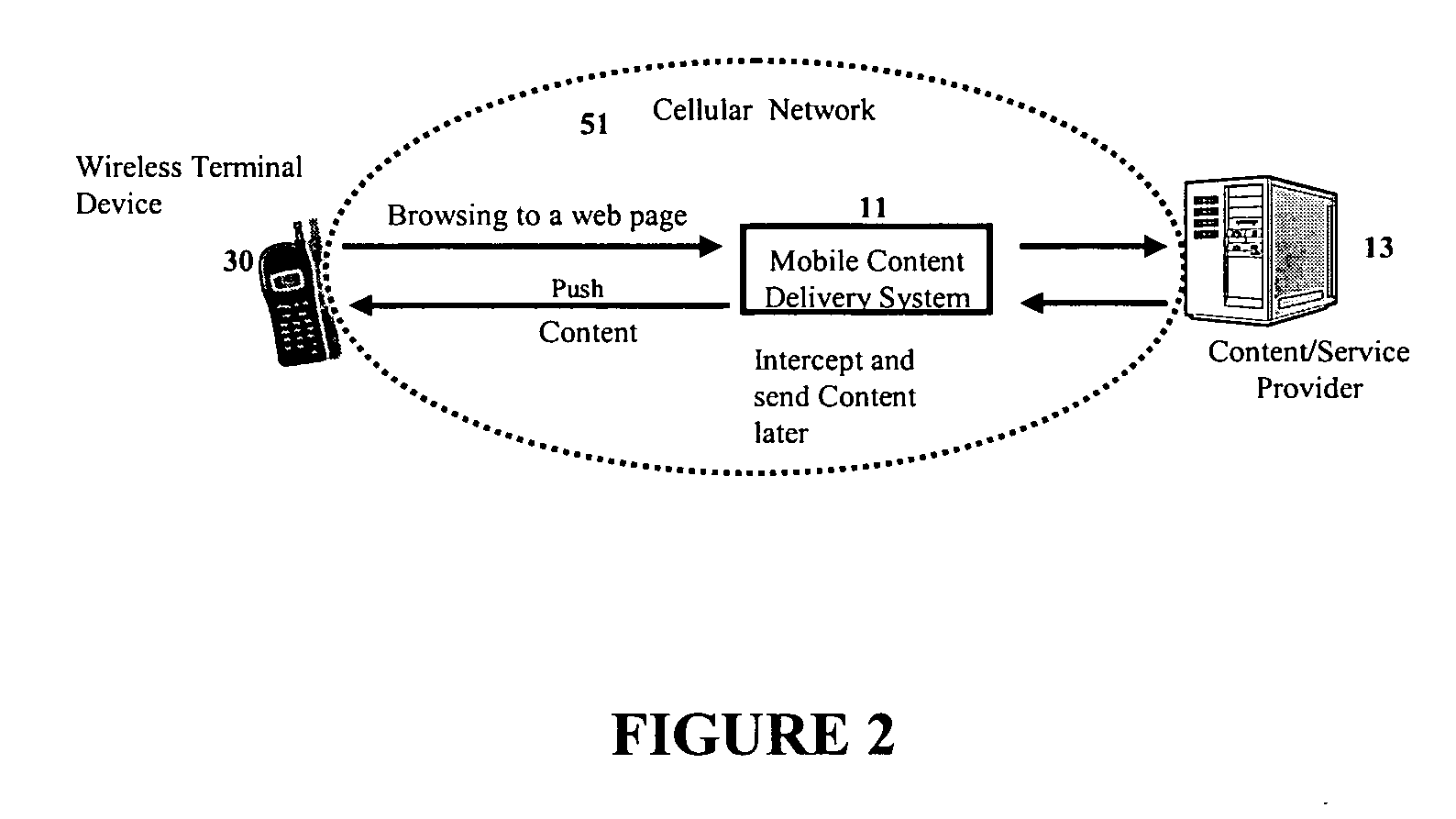
Mobile content delivery system
InactiveUS6996393B2Attracting more userImprove network throughputMetering/charging/biilling arrangementsSpecial service for subscribersRadio networksMobile content
A mobile content delivery system that optimizes the delivery of especially bandwidth-consuming content (or the flow of any peak-hour data traffic) in a way that best utilizes the free capacity in the radio network, thus enabling considerably more efficient usage of the radio capacity. It also allows new services and pricing structures to be used in the cellular network, that otherwise would not be possible. The class of delivery of message content can be selected by the user on a transaction basis, or subscription-based and pre-defined in a user profile. By choosing a scheduled delivery the user can receive the content at a fraction of the price compared to instant delivery, since the content is sent at a time when the network is least utilized.
Owner:NOKIA CORP
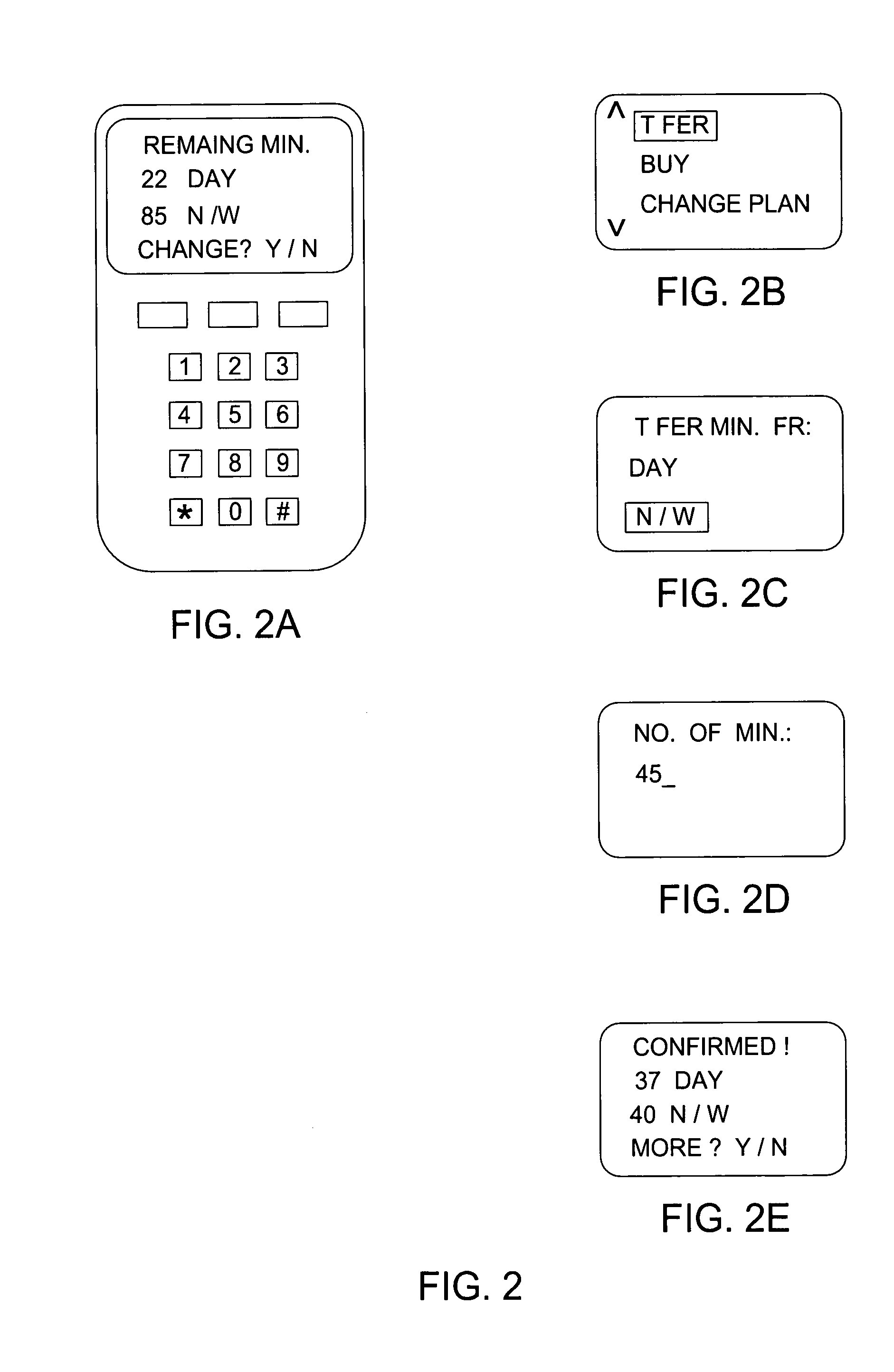
Method for billing IP broadband subscribers
InactiveUS7289489B1Least costMetering/charging/biilling arrangementsTelephonic communicationQuality of serviceLeast cost
A method of billing a variable bit rate communication between a first terminal and a distant terminal to a broadband subscriber permits changing billing parameters during a call in real time in response to user inputs including user requested changes in quality of service, changes in data rate and changes in preferred service provider. A variable bit rate communication to be billed has a variable quality of service related to the degree of utilization of a plurality of different networks. The billing method comprises the steps of i.) receiving user identification data at a first terminal and data representing a required bit rate and a default quality of service selected by the user, ii.) verifying the user identification data to be associated with the broadband service subscriber, iii.) determining least cost alternative network resources available for achieving the communication at the user selected default quality of service and the required bit rate, iv.) determining cost data associated with the network resources, v.) outputting to the user a least cost for the communication according to their selected default quality of service and alternative least cost network resources, vi.) coupling the first terminal and the distant terminal via the least cost determined network resources at the default quality of service and the required bit rate responsive to user authorization and vii.) billing for the communication at the default quality of service and according to the required bit rate after the termination of the communication.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Interactive communication service account management system
InactiveUS7450927B1Function is disabledDifferent sizeMetering/charging/biilling arrangementsUnauthorised/fraudulent call preventionWireless internet accessCommunication device
A system and method permit a customer obtaining communication services to modify account parameters governing terms on which that service is provided. Customer account parameters are stored in one or more databases and accessed by one or more servers. The customer, upon accessing the communication service, is provided with an opportunity to modify the account parameters via automated interactive communication with the server. The invention can applied to wireless communication services such as wireless telephone service, wireless internet access, paging, or other forms of interactive wireless communication; to telephone or other wired interactive communication; to cable services; and to any other form of interactive subscriber communications. The invention may be implemented using existing equipment, and can be optimized for the type of communication device at issue.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
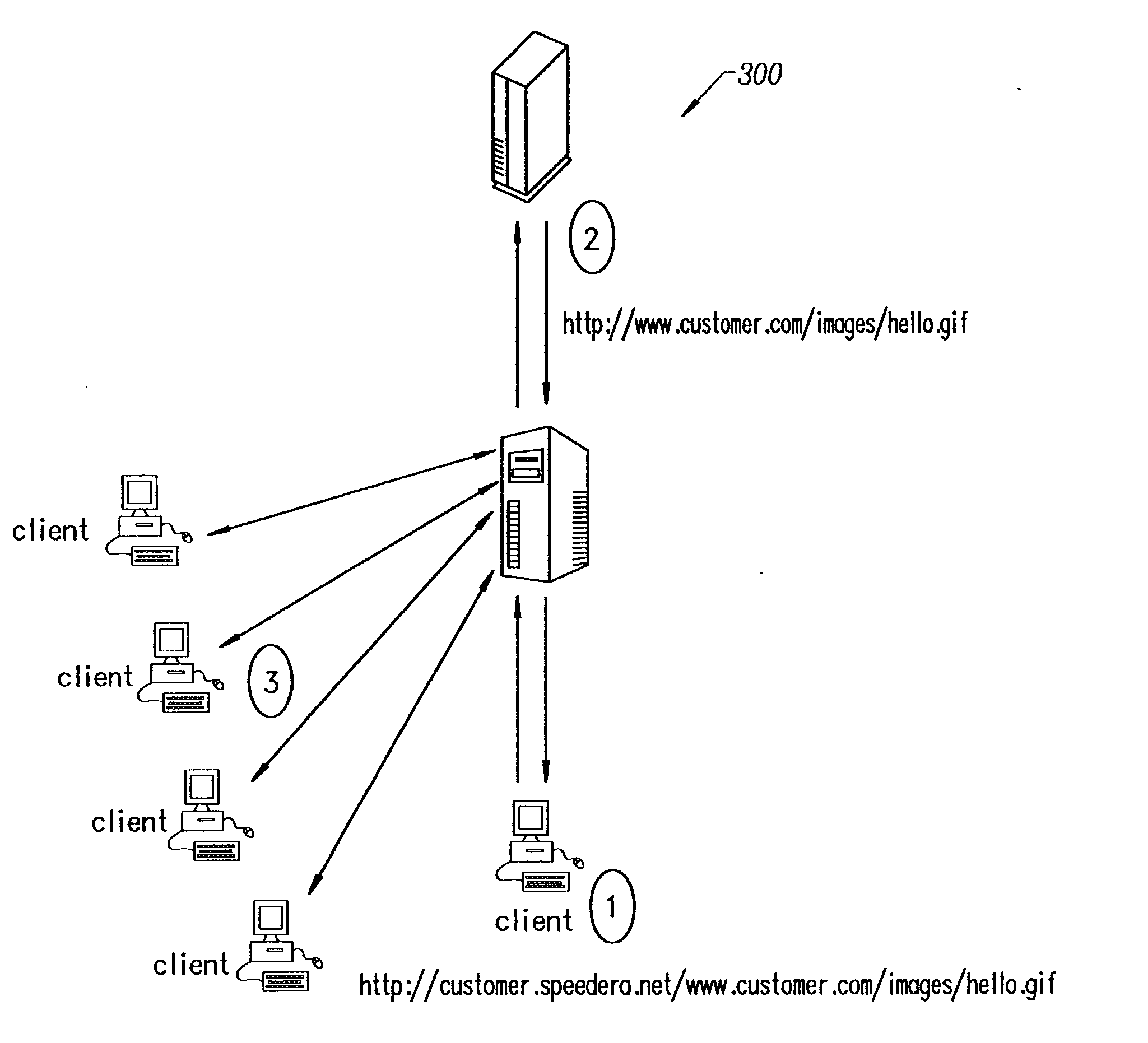
Secure content delivery system
InactiveUS20030097564A1Metering/charging/biilling arrangementsUser identity/authority verificationExpiration TimeRelevant information
A secure streaming content delivery system provides a plurality of content servers connected to a network that host customer content that can be cached and / or stored, e.g., images, video, text, and / or software. The content servers respond to requests for customer content from users. The invention load balances user requests for cached customer content to the appropriate content server. A user makes a request to a customer's server / authorization server for delivery of the customer's content. The authorization server checks if the user is authorized to view the requested content. If the user is authorized, then the authorization server generates a hash value using the authorization server's secret key, the current time, a time-to-live value, and any other information that the customer has configured, and embeds it into the URL which is passed to the user. A content server receives a URL request from the user for customer content cached on the content server. The request is verified by the content server creating its own hash value using the customer server's secret key, the current time, a time-to-live value, and any other related information configured for the customer. If the hash value from the URL matches the content server's generated hash value, then the user's request is valid and within the expiration time period and the content server delivers the requested content to the user.
Owner:AKAMAI TECH INC
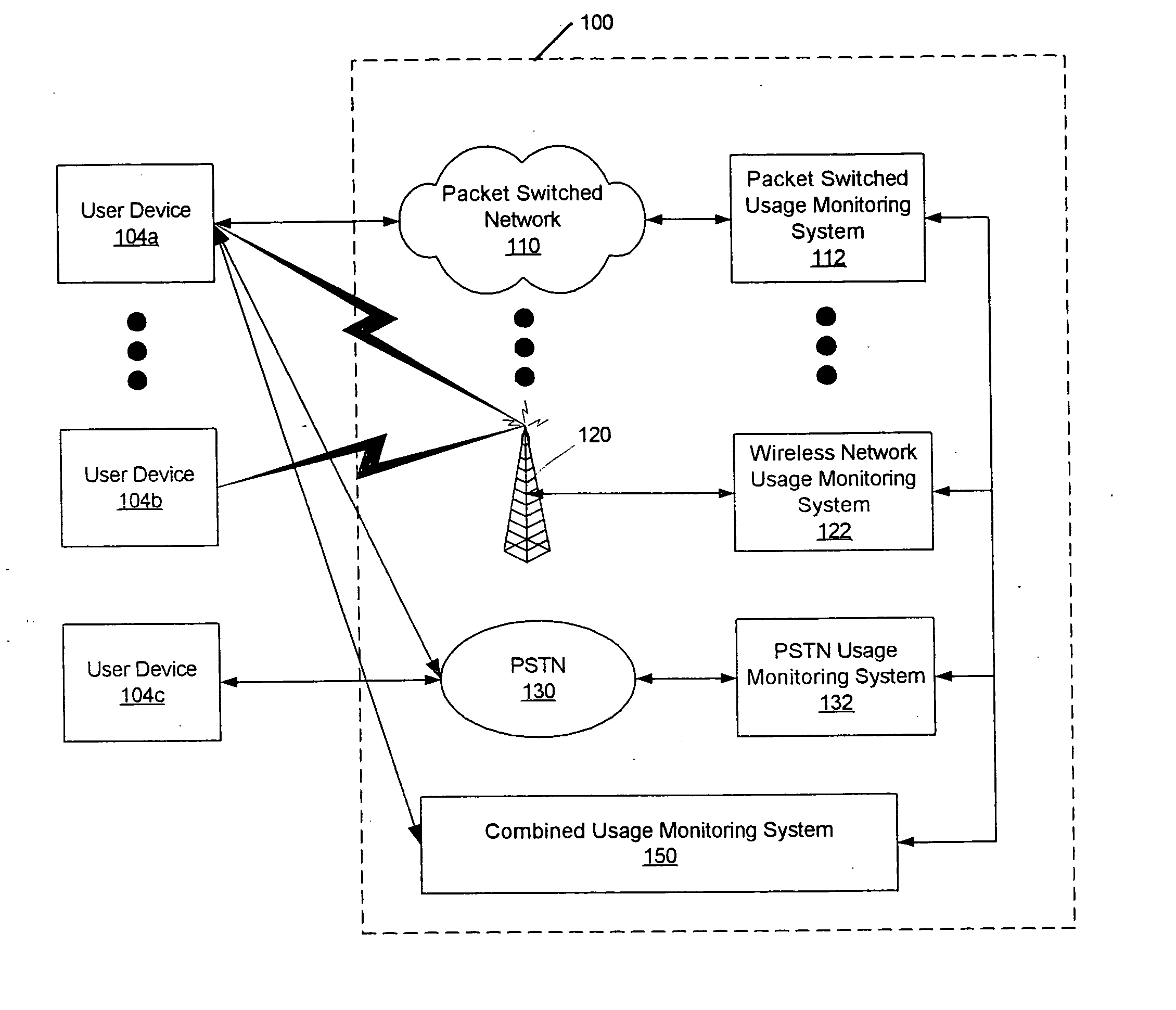
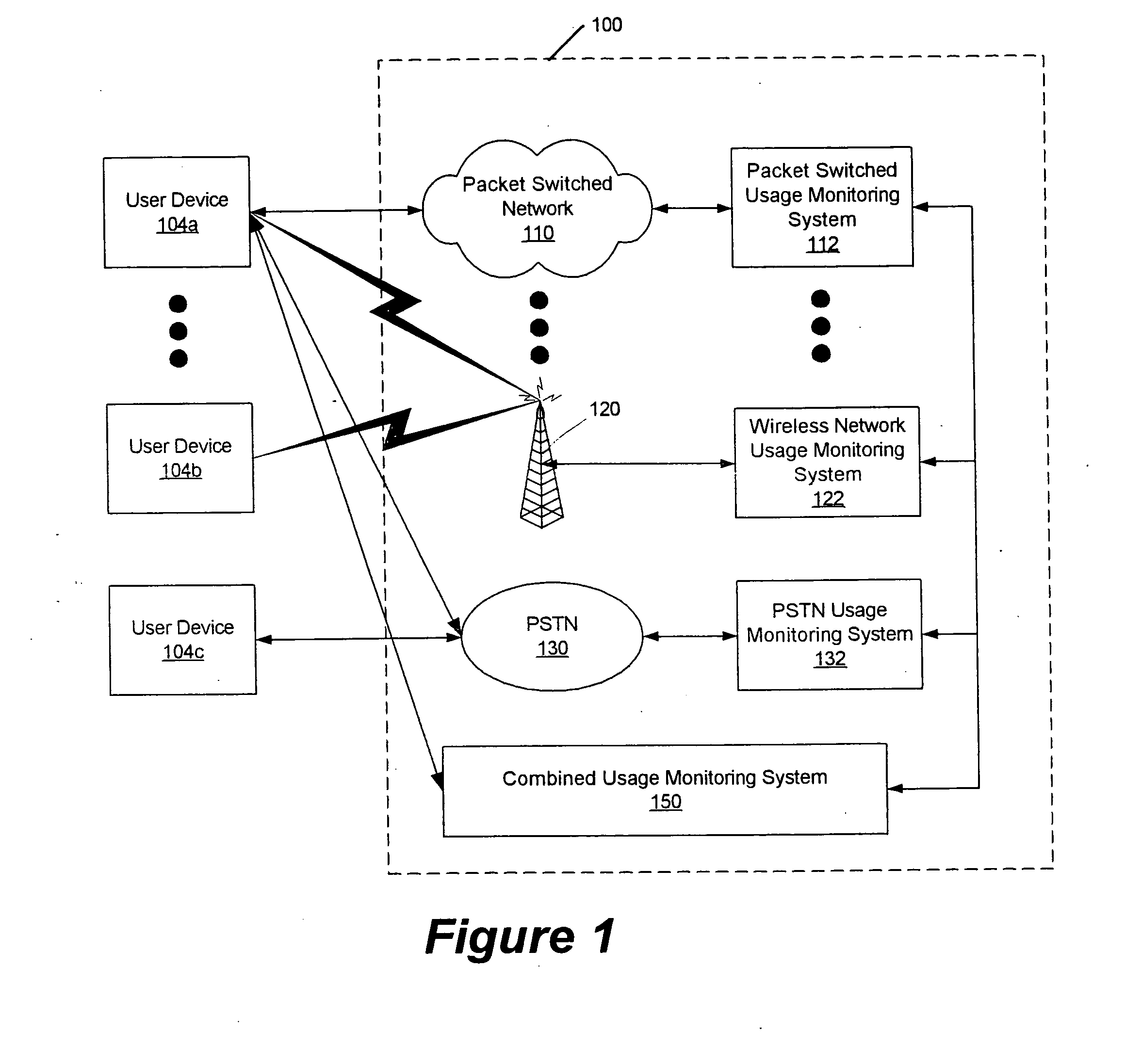
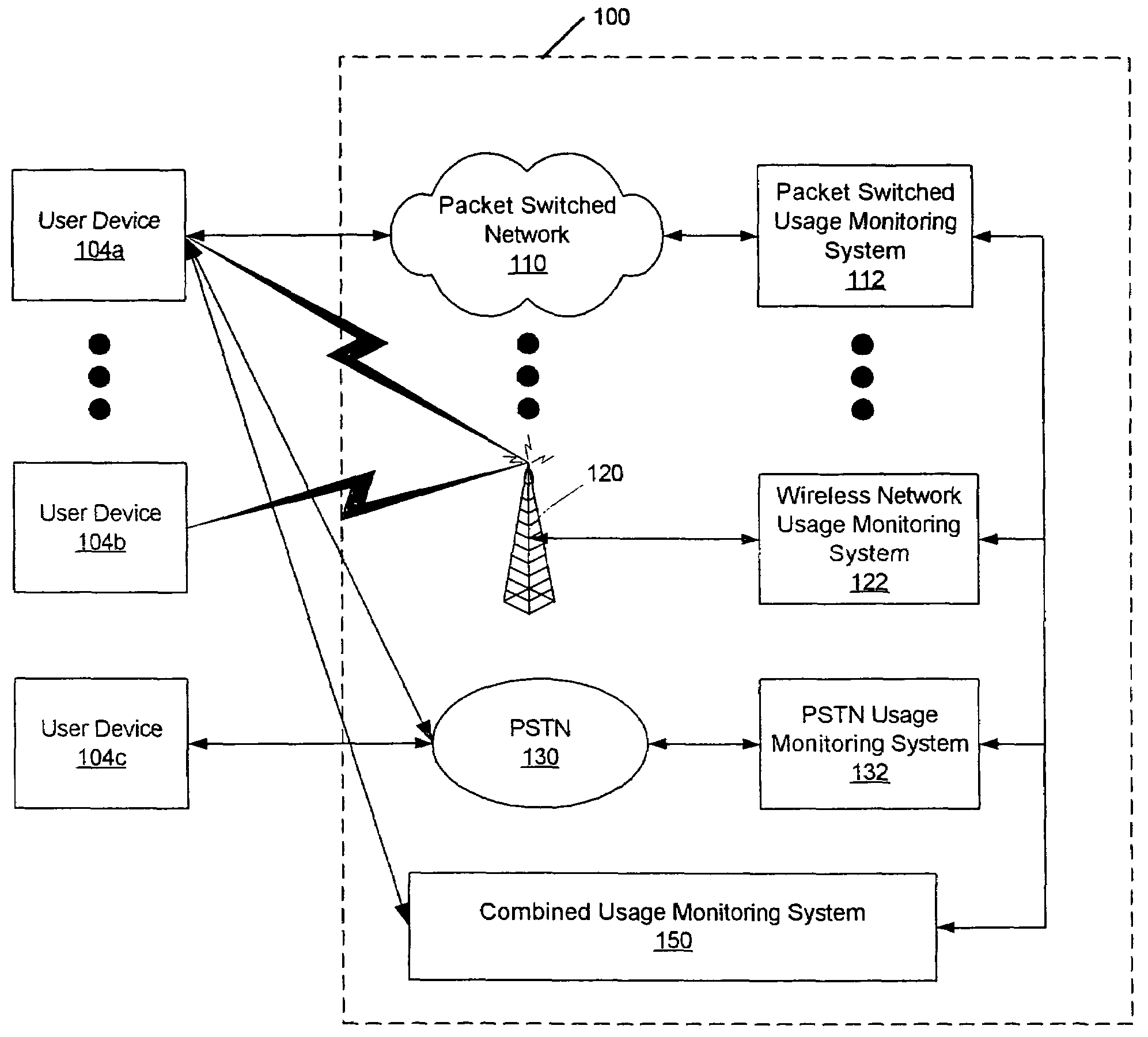
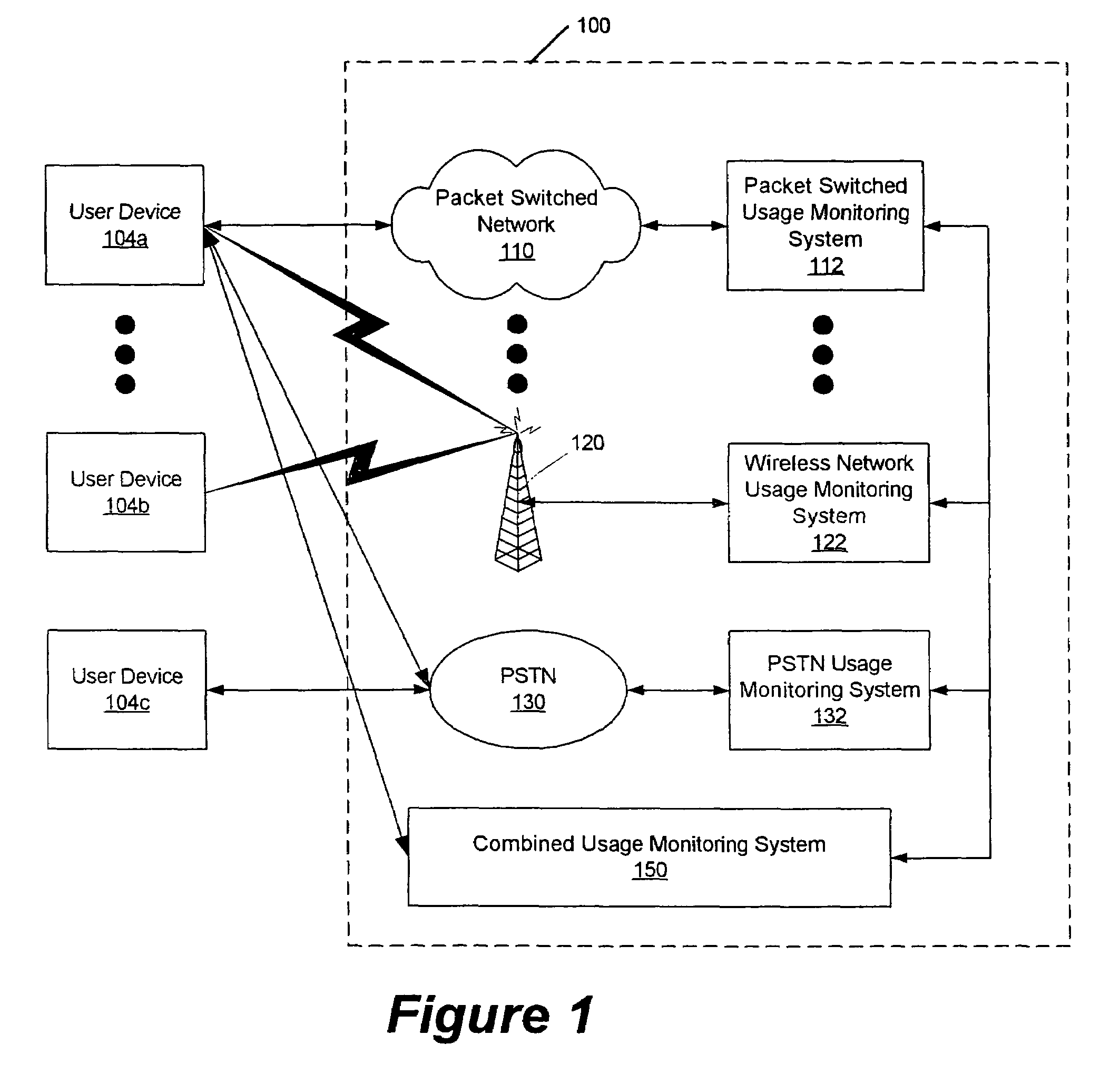
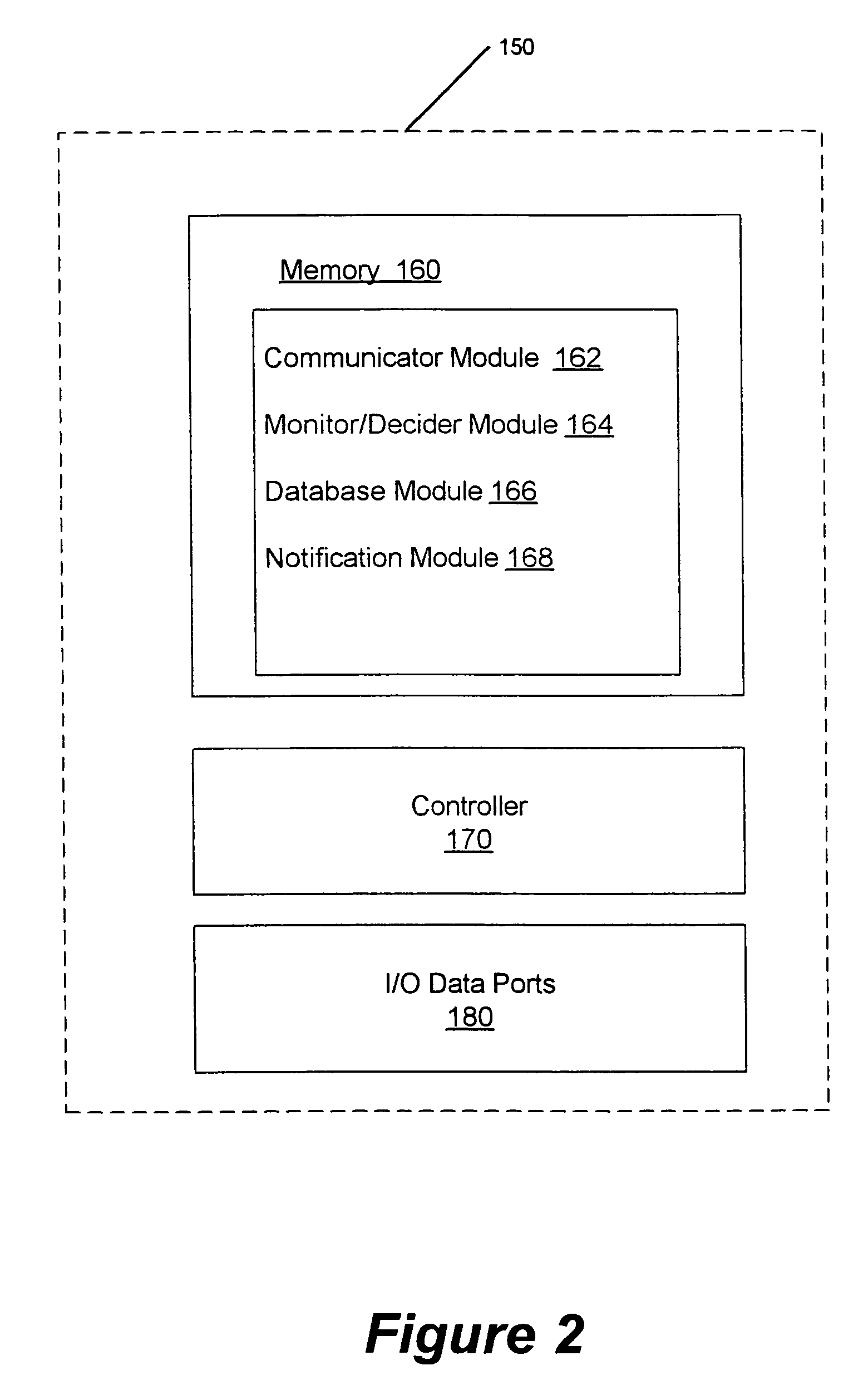
Methods, systems and computer program products for monitoring service usage
InactiveUS20060045245A1Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemUse of services
Monitoring criteria is received that corresponds to a usage quantity for a plurality of services. Each of the plurality of services is provided over ones of a plurality of different communication systems. Actual service usage information is received for the plurality of services. The actual service usage information and the monitoring criteria are compared. An electronic notification message is sent when the monitoring criteria for one or more of the plurality of services is satisfied.
Owner:AT&T INTPROP I L P
Method for determining metrics of a content delivery and global traffic management network
ActiveUS20030065763A1Metering/charging/biilling arrangementsError preventionTraffic capacityNetwork packet
Owner:AKAMAI TECH INC
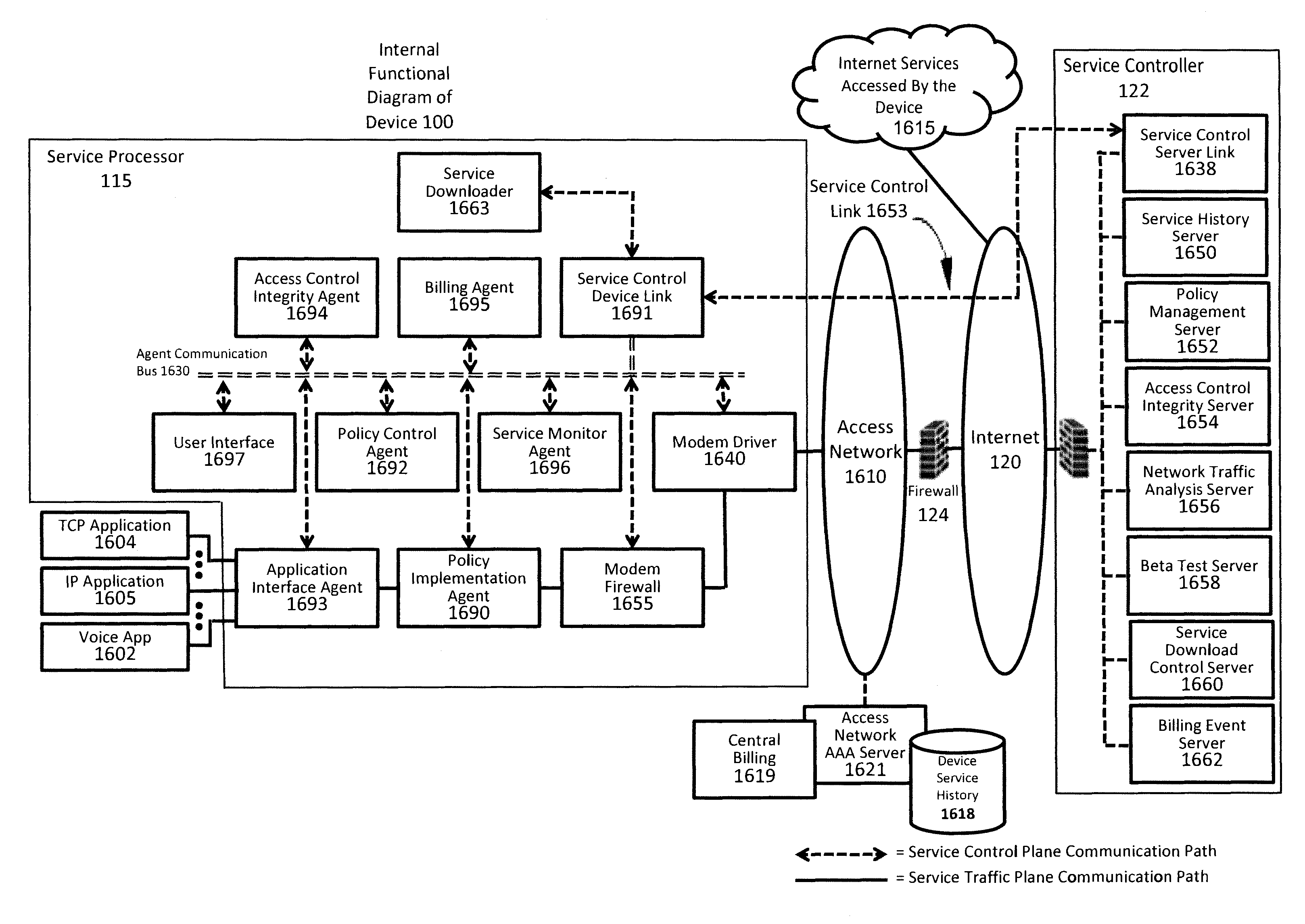
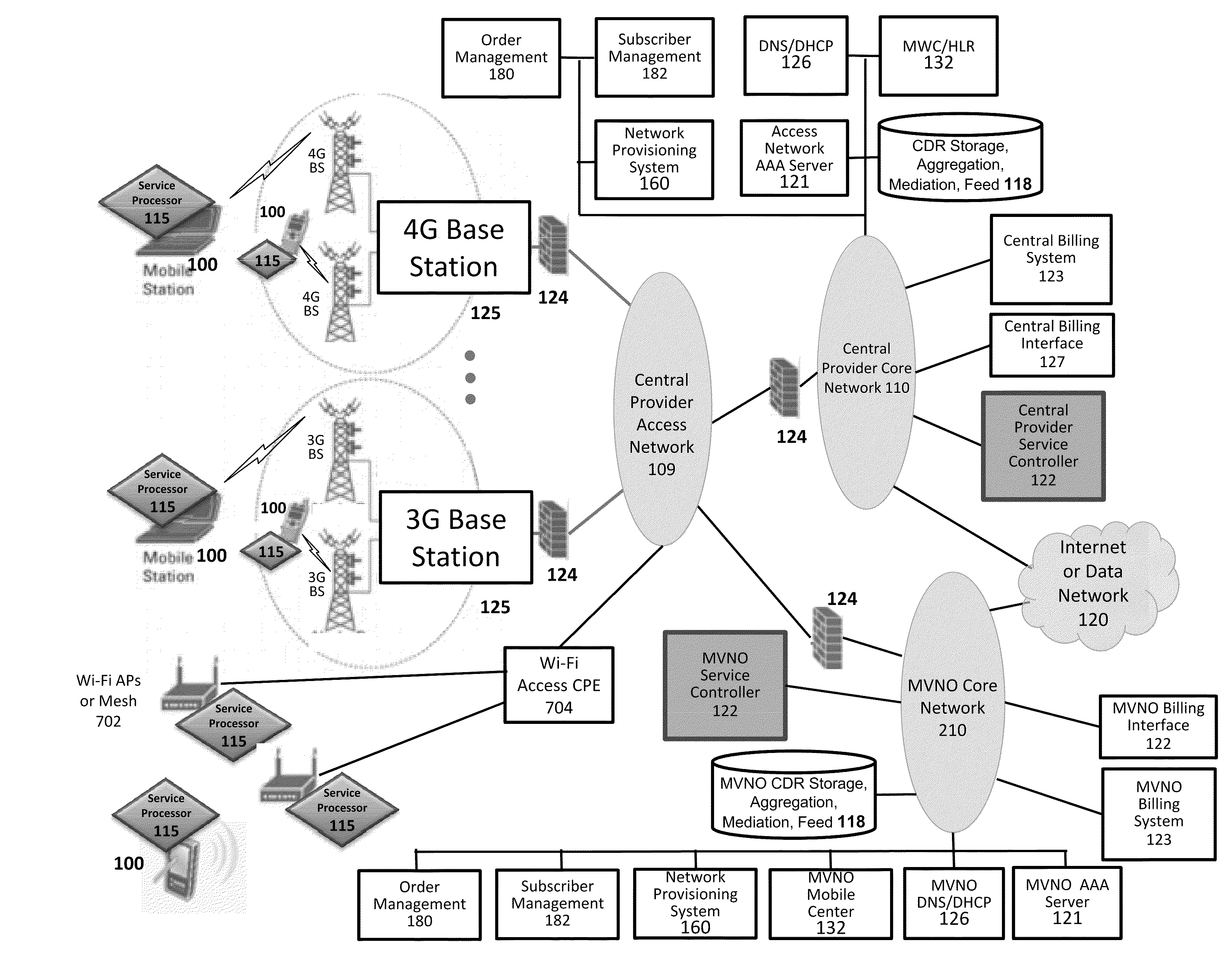
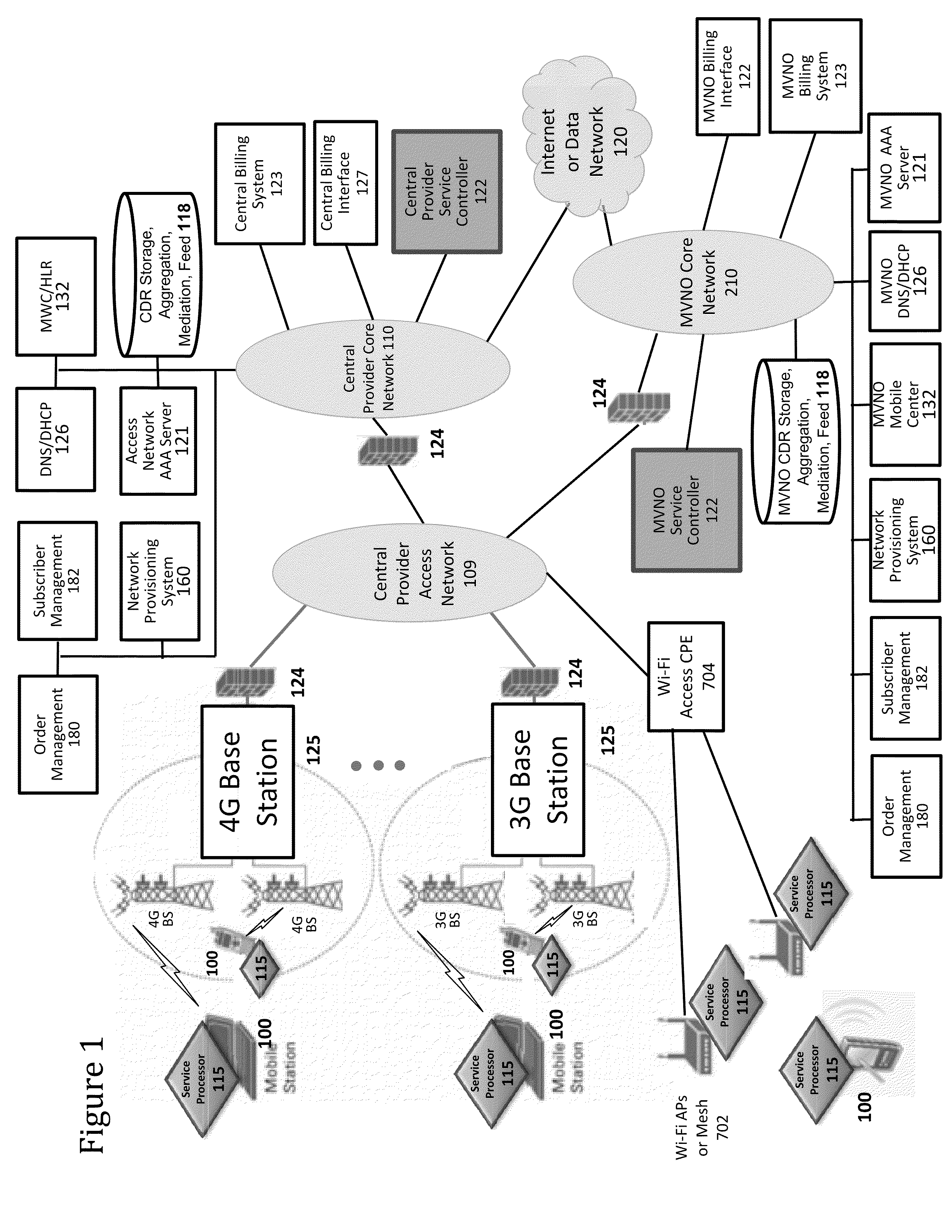
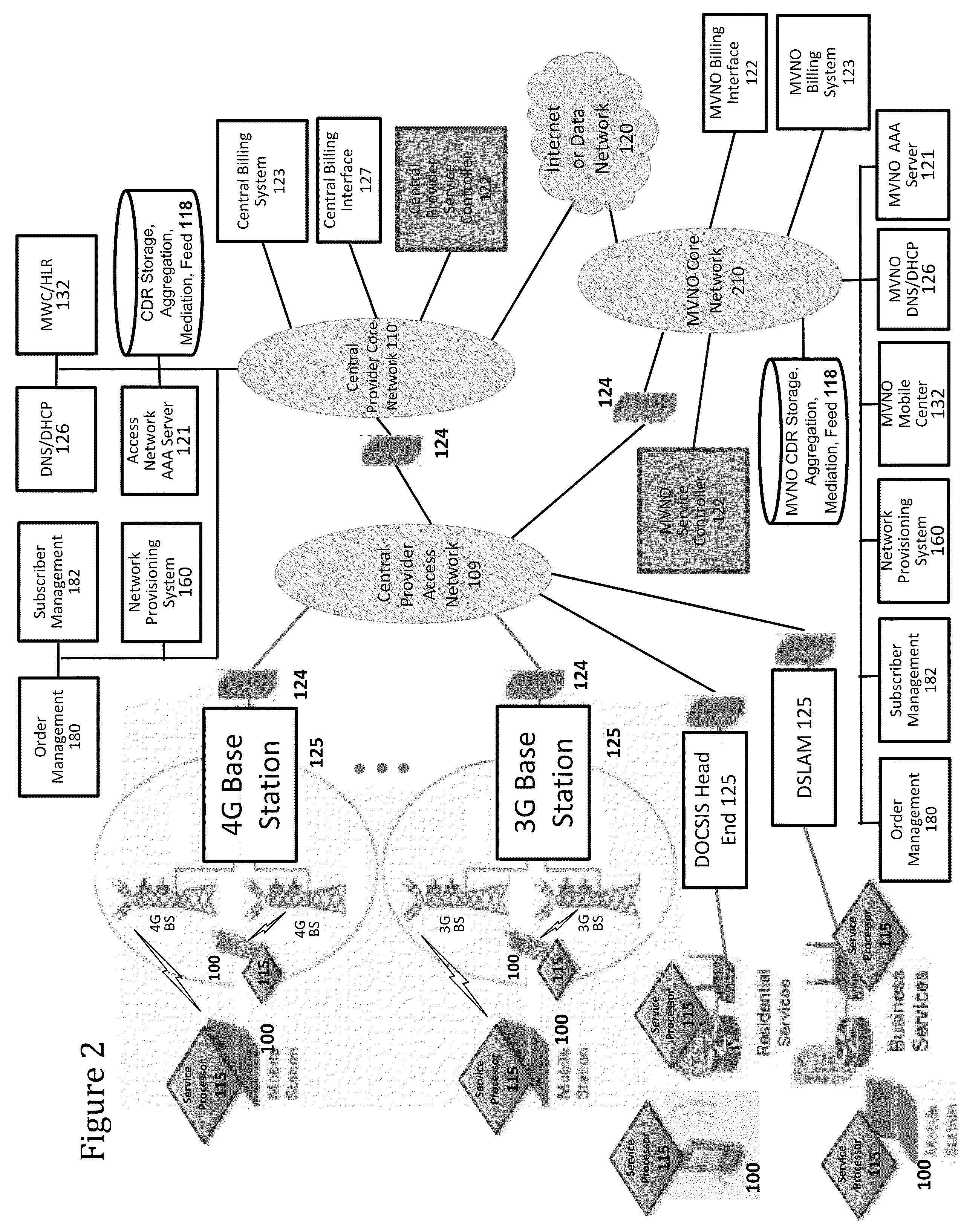
Verifiable device assisted service usage billing with integrated accounting, mediation accounting, and multi-account
ActiveUS8351898B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemService usage
Various embodiments are disclosed for a services policy communication system and method. In some embodiments, a communications device implements a service policy for assisting billing for the communications device use of a service on a network; and monitors use of the service based on the service policy, in which a local service usage is synchronized with a network based service usage.
Owner:HEADWATER RES LLC
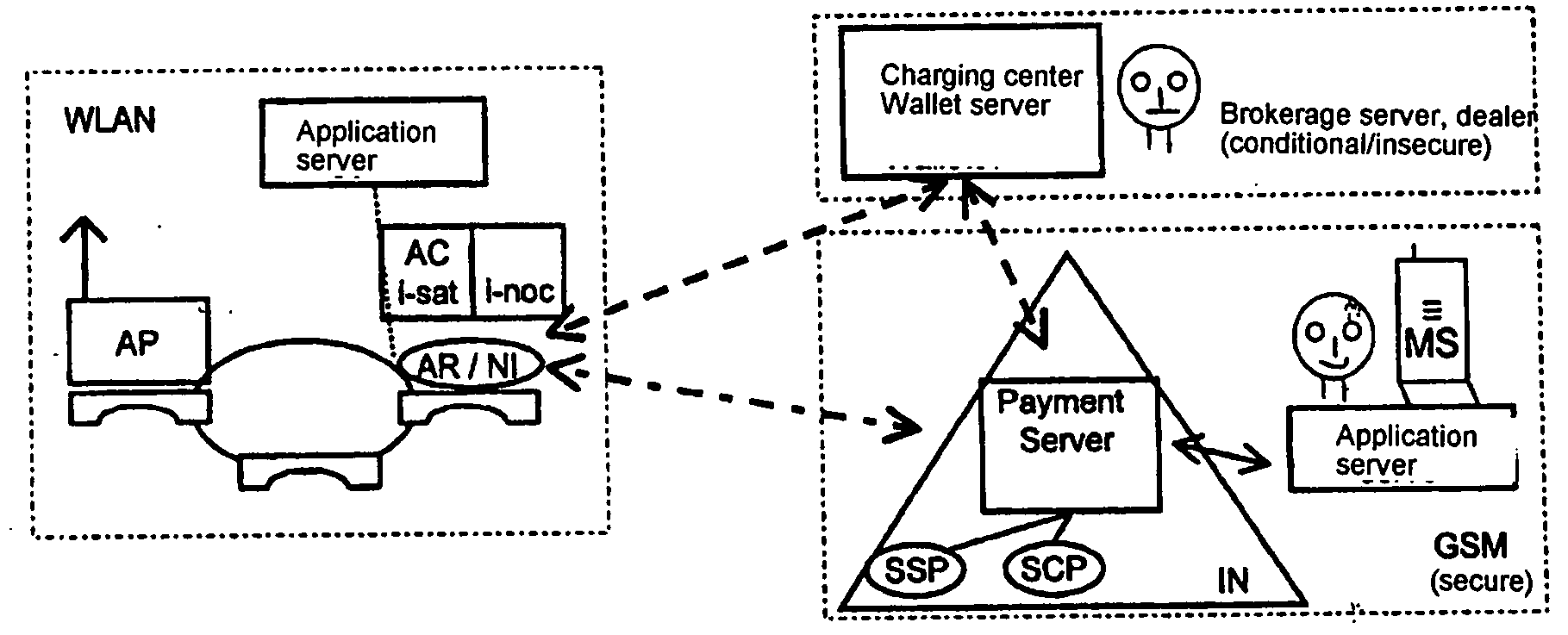
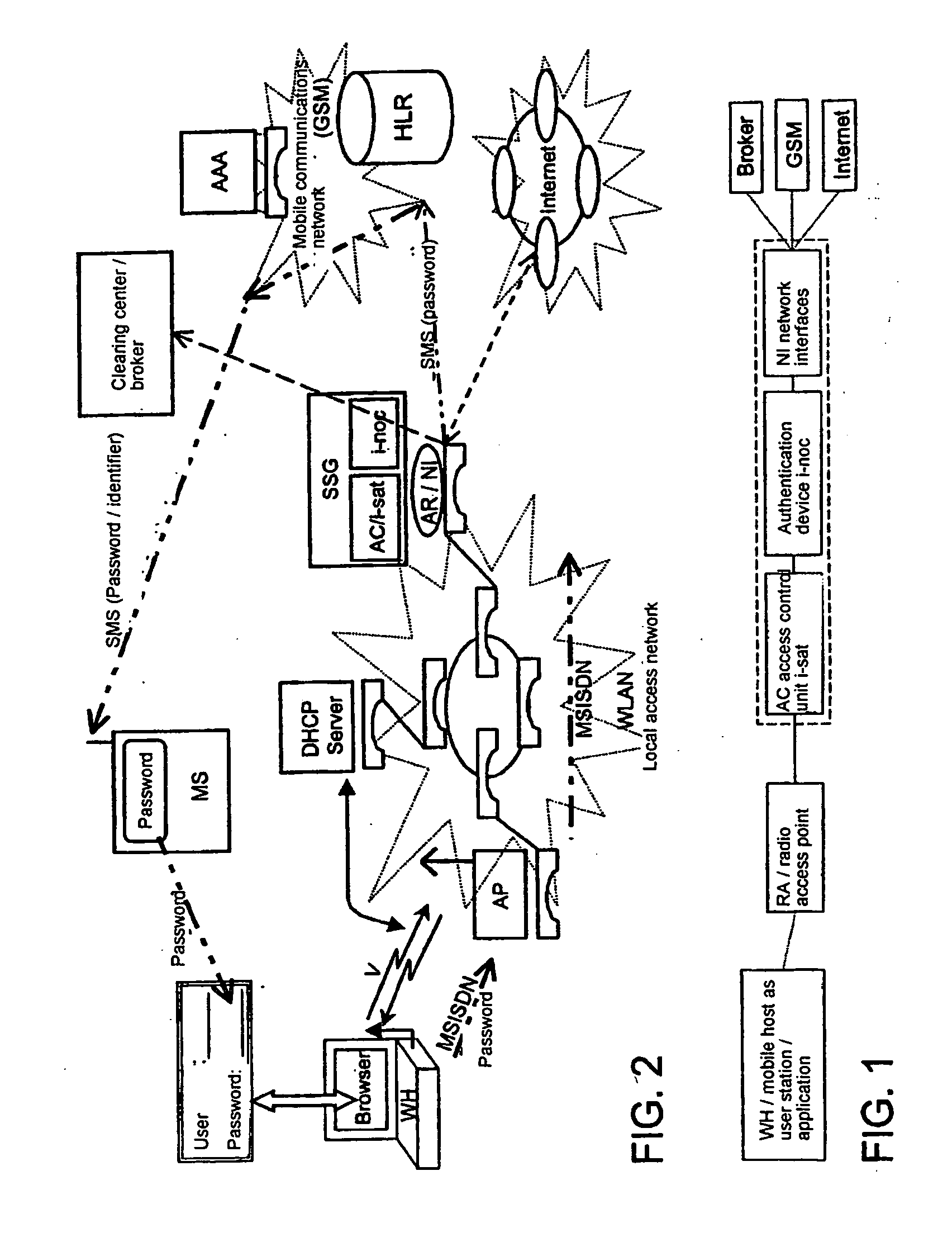
Method and device for authenticated access of a station to local data networks in particular radio data networks
ActiveUS20050048950A1Authentication is simpleEasy to chargeMetering/charging/biilling arrangementsUnauthorised/fraudulent call preventionRadio equipmentCommunications system
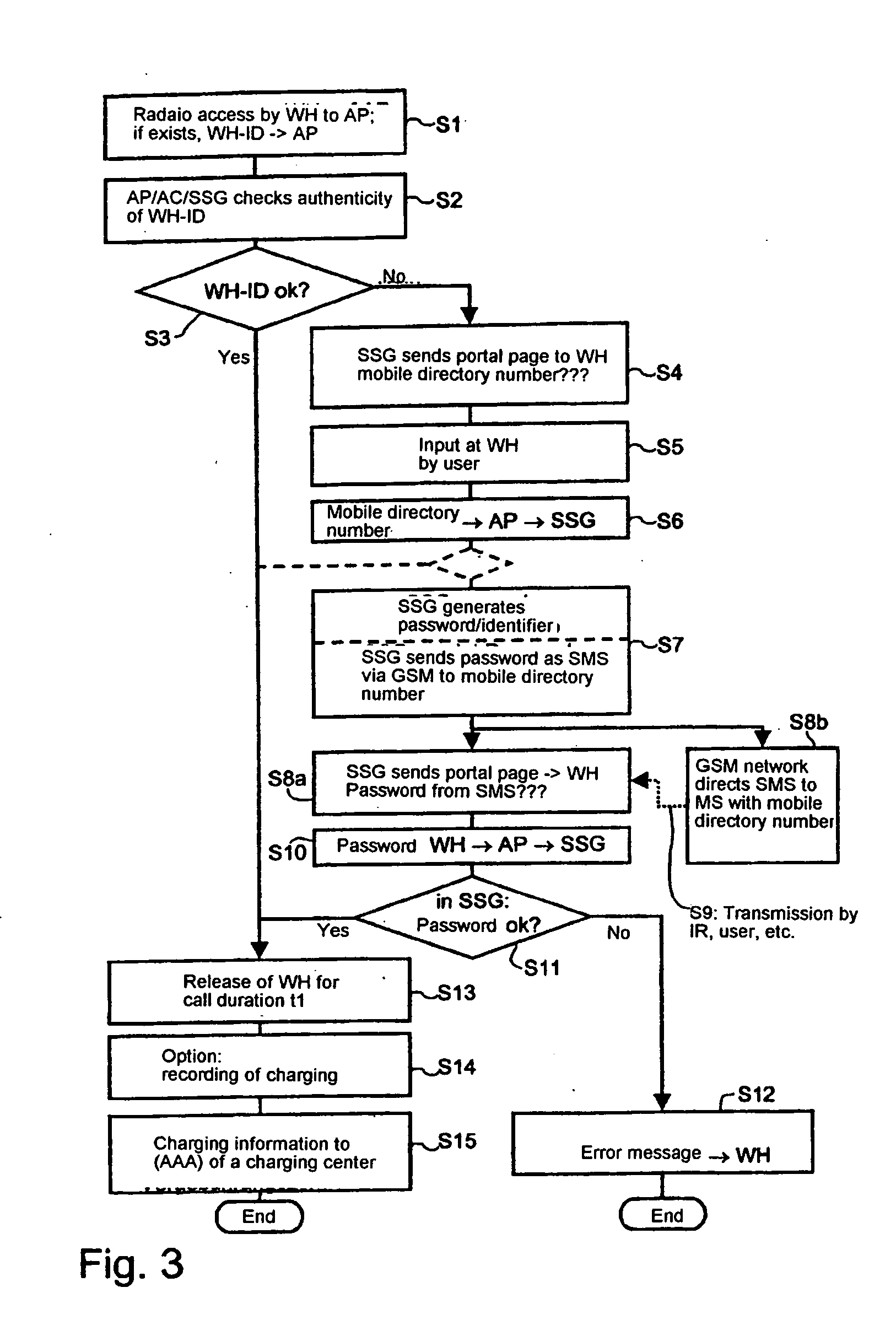
The invention relates to methods, devices and systems for the authenticated access to a data network by means of a station (WH) compatible with a data network (WLAN), which permit an authentication of the station and user. A device, for example a mobile radio device, is used for the above, which is authenticated in another system. In addition to the authentication, in particular a charging of services in a data network or another communication system (GSM) which is accessible by means of the data network is thus possible.
Owner:MONARCH NETWORKING SOLUTIONS LLC
Content delivery and global traffic management network system
InactiveUS20070174426A1Effective distributionFast response timeMetering/charging/biilling arrangementsMultiprogramming arrangementsBalancing networkWeb service
A content delivery and global traffic management network system provides a plurality of caching servers connected to a network. The caching servers host customer content that can be cached and stored, and respond to requests for Web content from clients. If the requested content does not exist in memory or on disk, it generates a request to an origin site to obtain the content. A DNS Server load balances network requests among customer Web servers and directs client requests for hosted customer content to the appropriate caching server. The customer pays a service that provides the content delivery and global traffic management network system a fee for usage of the content delivery and global traffic management network system.
Owner:AKAMAI TECH INC
Methods, systems and computer program products for monitoring service usage
InactiveUS7620162B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemUse of services
Monitoring criteria is received that corresponds to a usage quantity for a plurality of services. Each of the plurality of services is provided over ones of a plurality of different communication systems. Actual service usage information is received for the plurality of services. The actual service usage information and the monitoring criteria are compared. An electronic notification message is sent when the monitoring criteria for one or more of the plurality of services is satisfied.
Owner:AT&T INTPROP I LP
Network session management
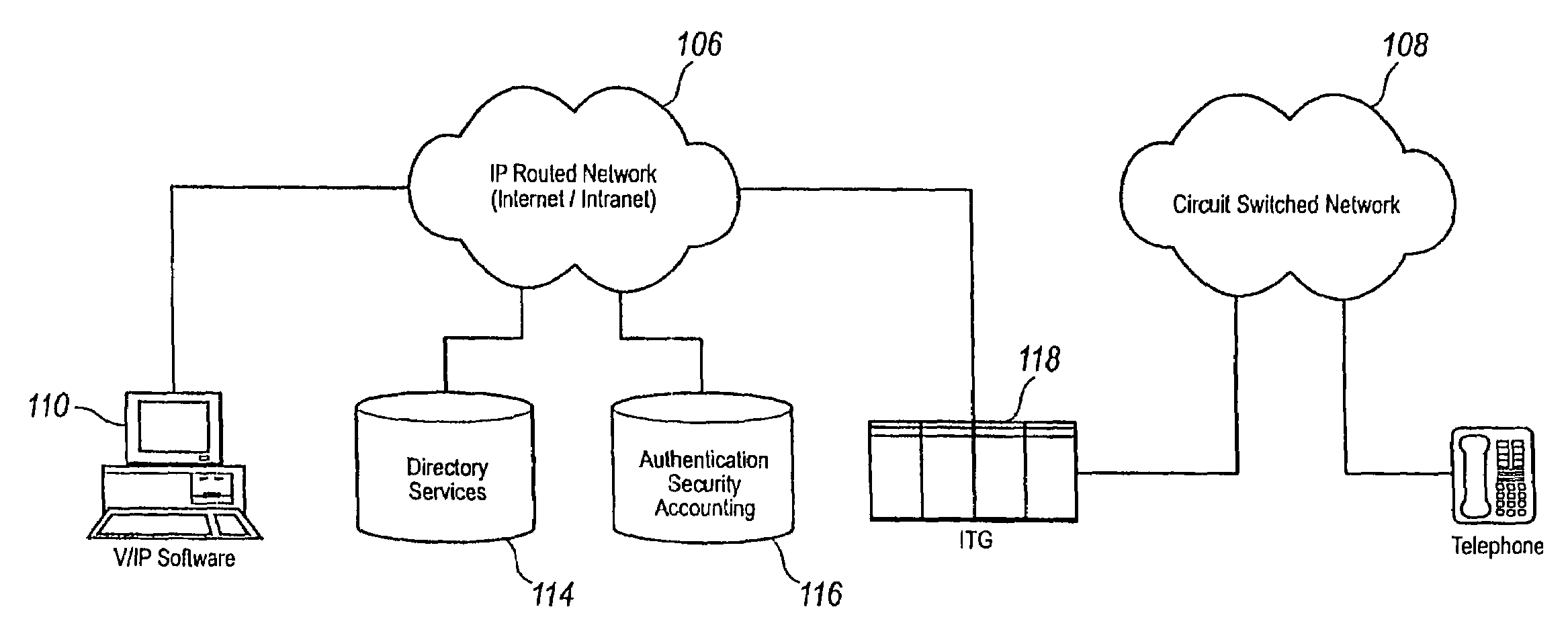
InactiveUS7948968B2Easy accessPrevent overrunningInterconnection arrangementsMetering/charging/biilling arrangementsTime informationThe Internet
A communication system providing telephony communication across combined circuit switched and packet switched networks, such as a telephone network and the Internet, which are connectable to terminals, such as telephones and computers, for selective communication therebetween. The communication system includes an authorization and account control object in the packet switched network, multiple gateways between the circuit switched and packet switched networks providing controlled connectivity between those networks, and an information retrieval object in the packet switched network, wherein the authorization and account control object maintains a substantially real time record of user accounts and usage, and the information and retrieval object provides substantially real time retrieval of selected information from the authorization and account control object. The retrieval object provides on demand to terminals which provide authentication for access to an identified account information regarding that account. The information regarding the account is substantially real time information including information with respect to communications in progress, which are chargeable to the account which has been authenticated. The authorization and account control object is preferably a unitary logical object having distributed instances thereof handling multitudinous accounts of widely separated terminals. The retrieval object provides isolation of the authorization and account control object permitting simultaneous multitasking by the authorization and account control object and the retrieval object respectively.
Owner:VERIZON PATENT & LICENSING INC
Mobile content delivery system
InactiveUS20060073810A1New data serviceMore serviceMetering/charging/biilling arrangementsSpecial service for subscribersRadio networksMobile content
Owner:NOKIA CORP
Device assisted CDR creation, aggregation, mediation and billing
ActiveUS8275830B2Complete banking machinesMetering/charging/biilling arrangementsNetwork Communication ProtocolsSyntax
Device assisted CDR creation, aggregation, mediation and billing is provided. In some embodiments, device assisted CDR creation, aggregation, mediation and billing for a wireless network includes collecting device generated service usage information for one or more devices in wireless communication on the wireless network; and providing the device generated service usage information in a syntax (e.g., a device assisted charging data record (CDR)) and a communication protocol (e.g., 3GPP, 3GPP2, or other communication protocols) that can be used by other network devices to augment or replace network generated service usage information for the one or more devices in wireless communication on the wireless network.
Owner:HEADWATER RES LLC
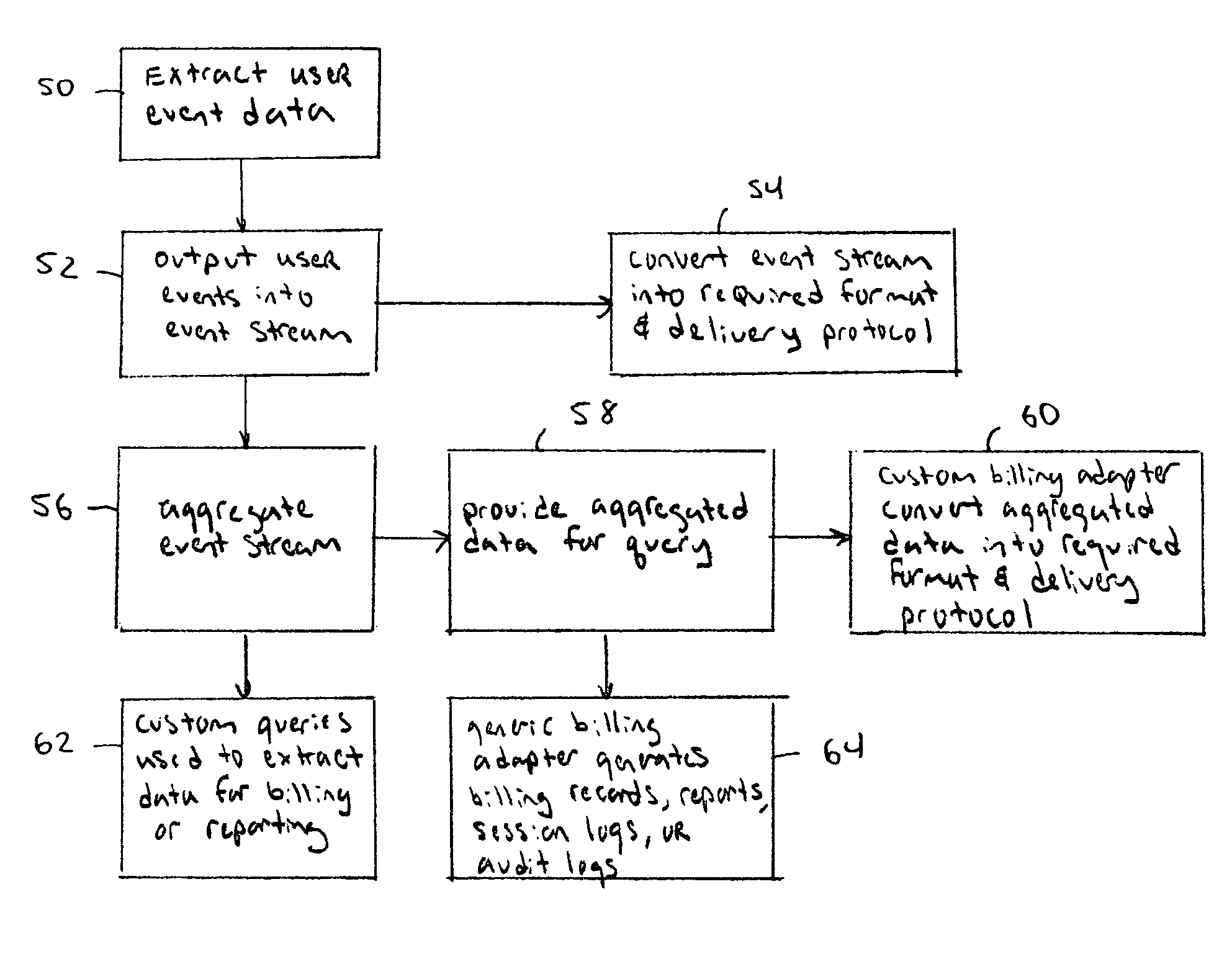
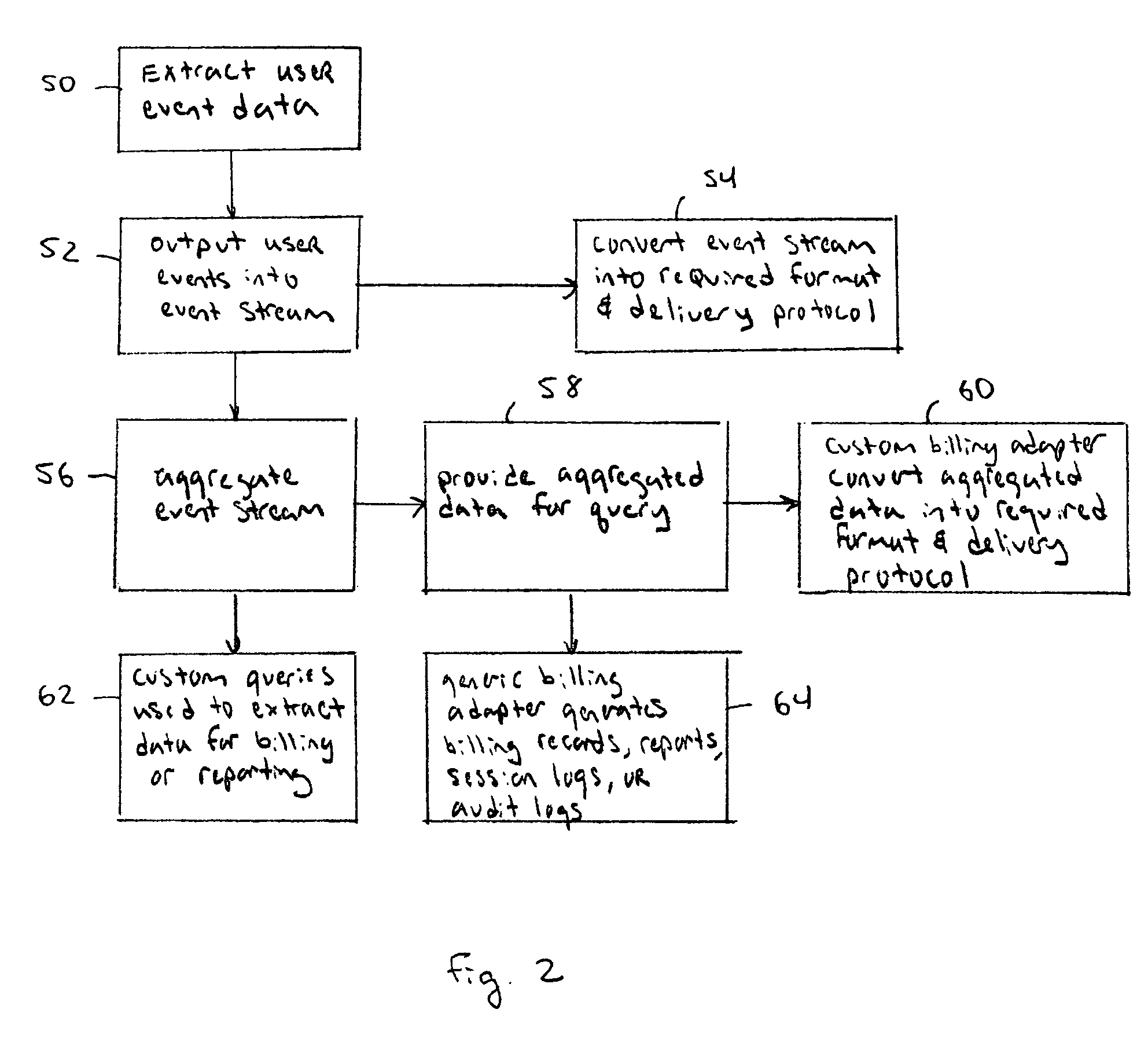
Flexible billing architecture
InactiveUS8010082B2Metering/charging/biilling arrangementsAccounting/billing servicesCommunications systemData access
A flexible billing system captures communication events on a more granular level then current communication systems. The captured communication events can then be aggregated into different event categories and combined with other event parameters to provide a wider variety of billing options to mobile network operators. The flexible billing system can be integrated with existing billing and provisioning systems. Thus, subscribers can be billed for enabled data access services and services are only enabled for billable entities.
Owner:SEVEN NETWORKS INC
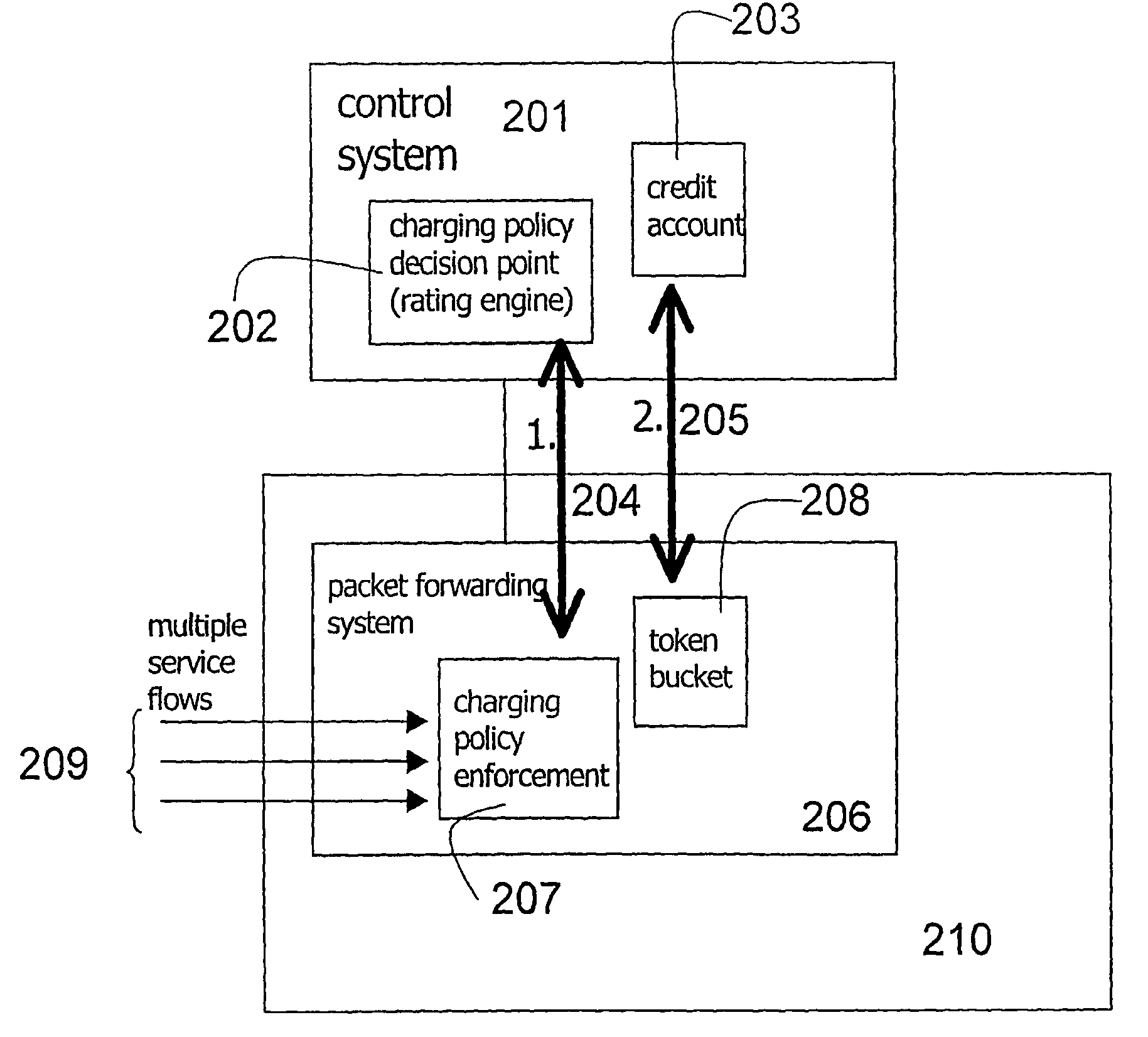
System for providing flexible charging in a network
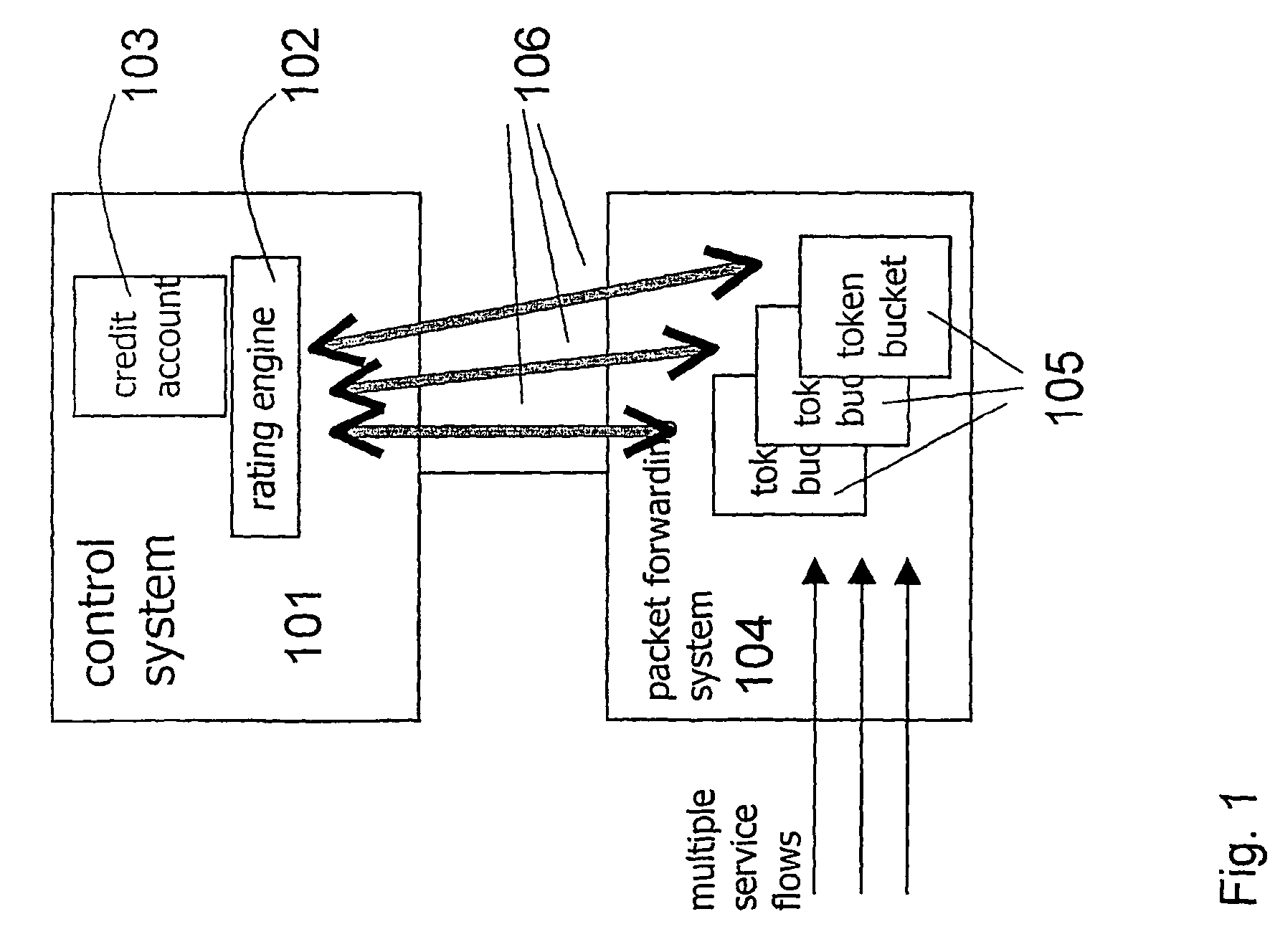
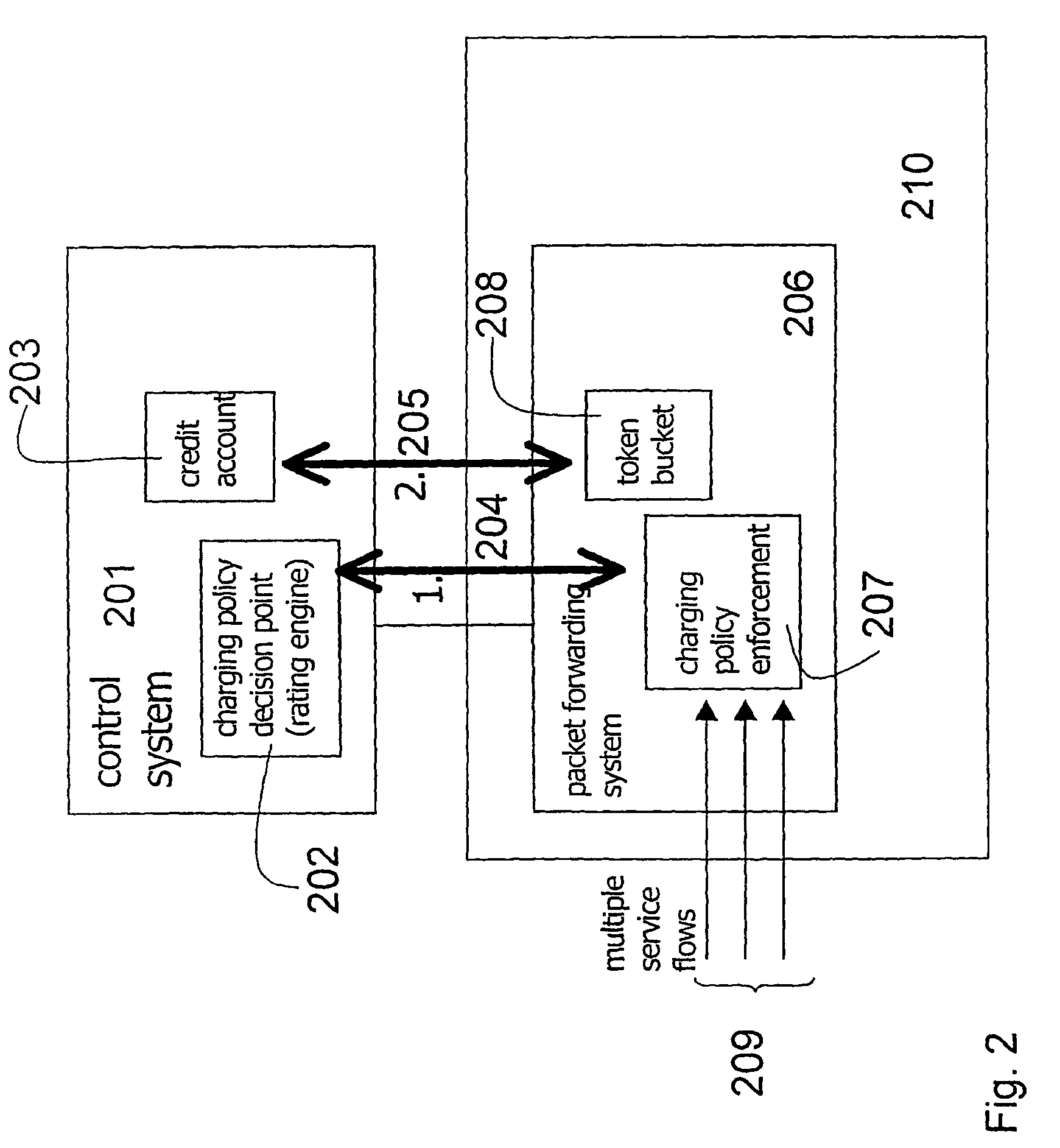
ActiveUS7450591B2Reduce signaling loadReduce reservationMetering/charging/biilling arrangementsData switching by path configurationService flowPolicy decision
Owner:TELEFON AB LM ERICSSON (PUBL)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com