Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2158 results about "Routing protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
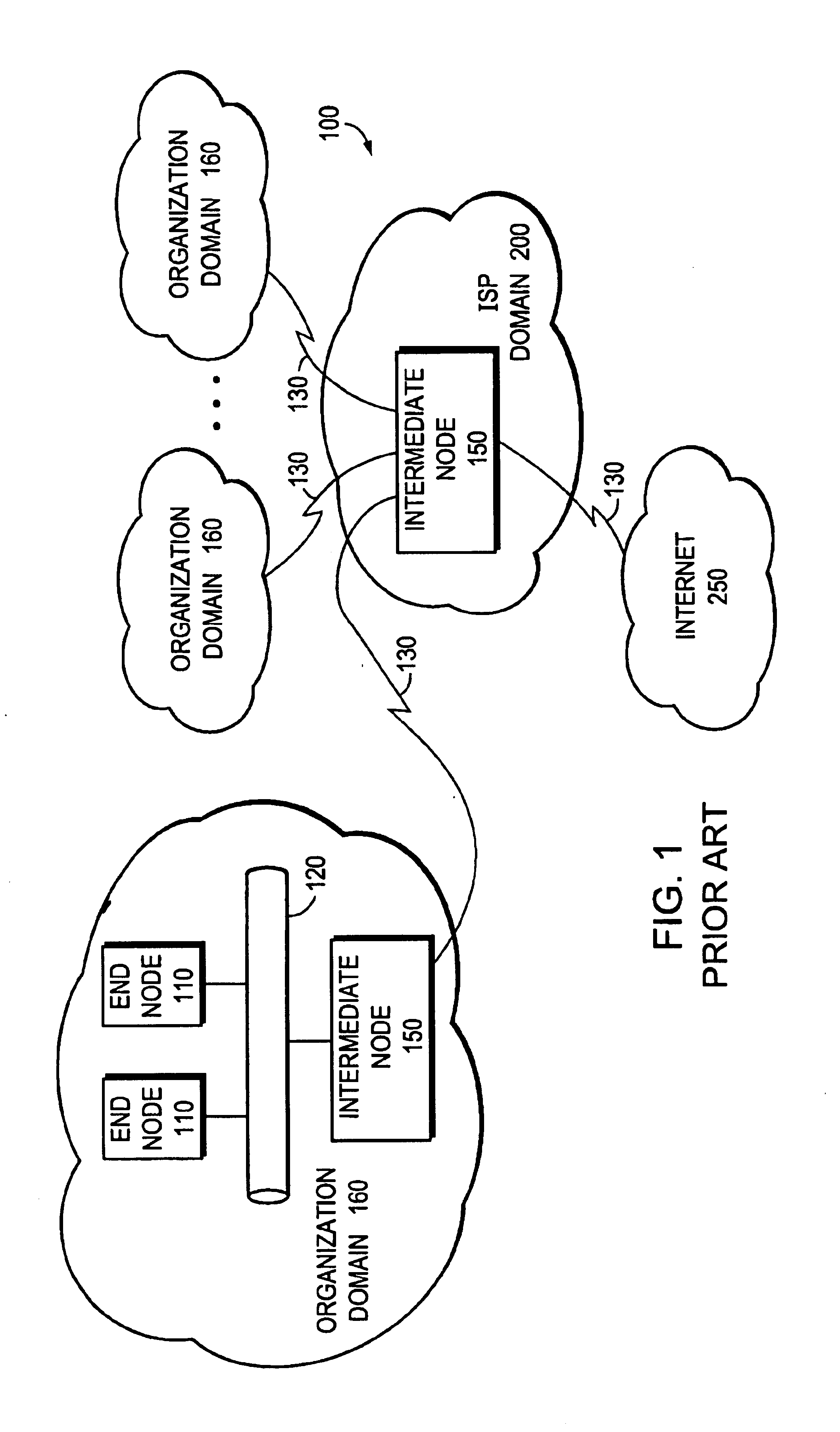
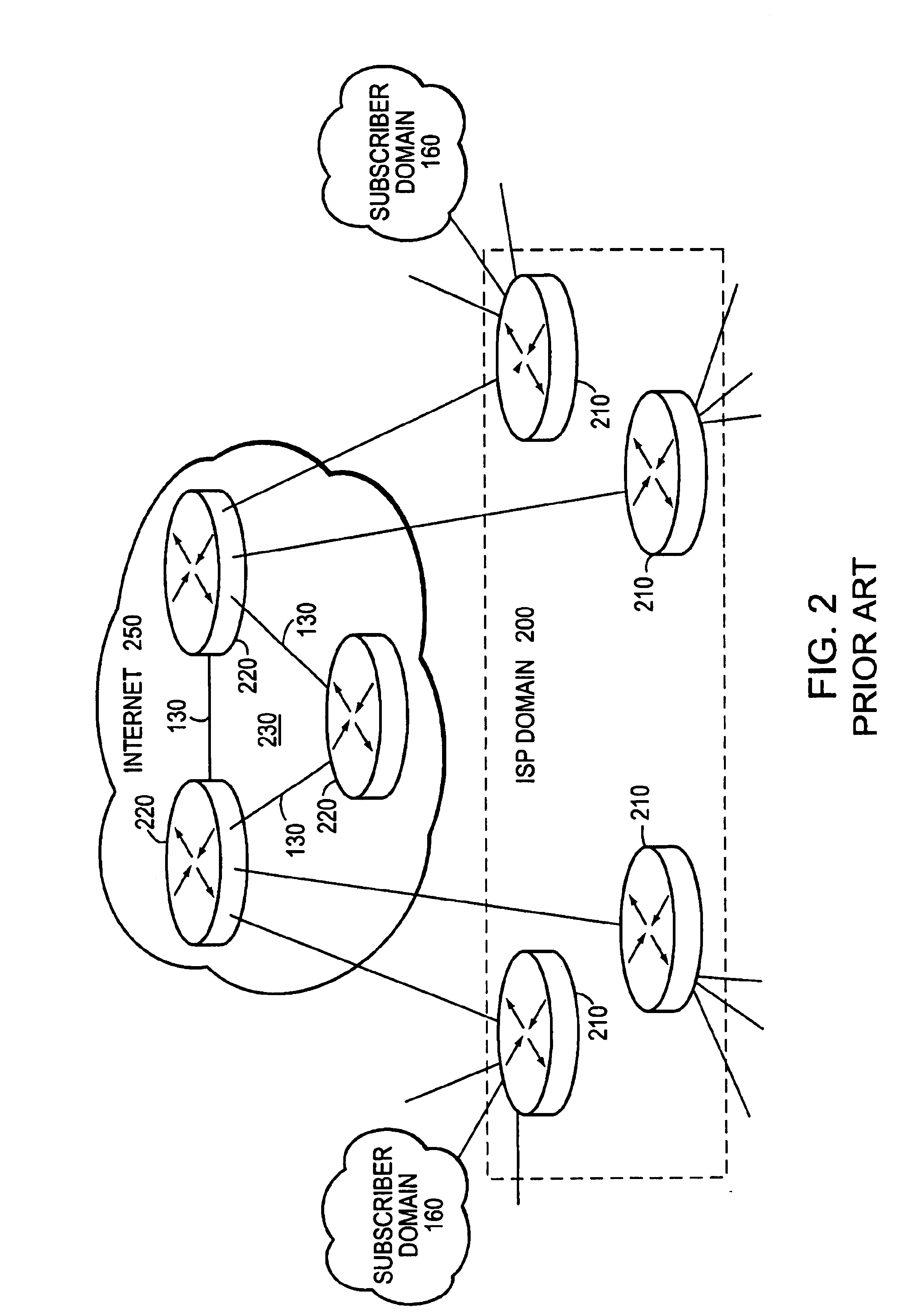
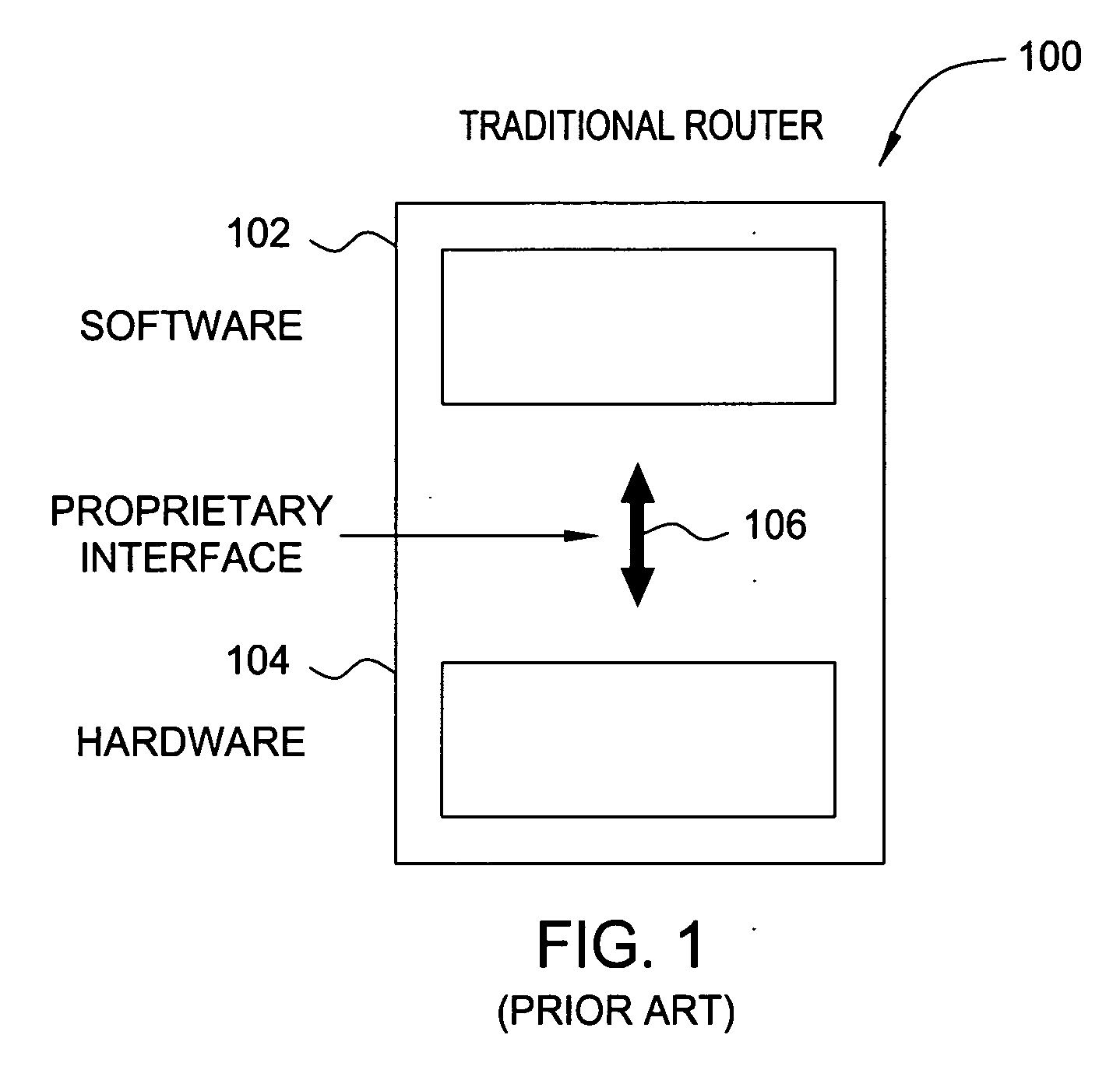
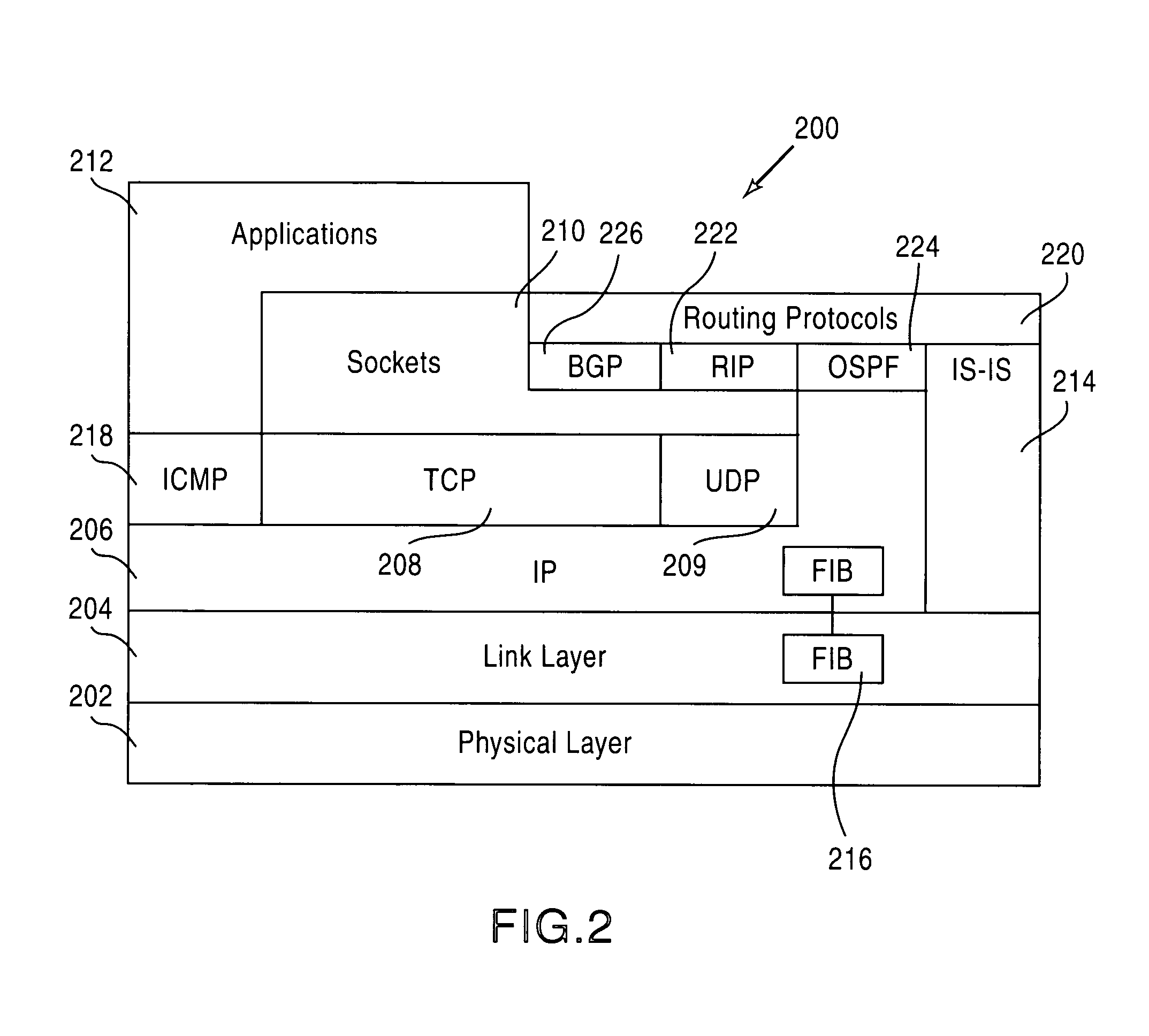
A routing protocol specifies how routers communicate with each other, distributing information that enables them to select routes between any two nodes on a computer network. Routers perform the "traffic directing" functions on the Internet; data packets are forwarded through the networks of the internet from router to router until they reach their destination computer. Routing algorithms determine the specific choice of route. Each router has a prior knowledge only of networks attached to it directly. A routing protocol shares this information first among immediate neighbors, and then throughout the network. This way, routers gain knowledge of the topology of the network. The ability of routing protocols to dynamically adjust to changing conditions such as disabled data lines and computers and route data around obstructions is what gives the Internet its survivability and reliability.
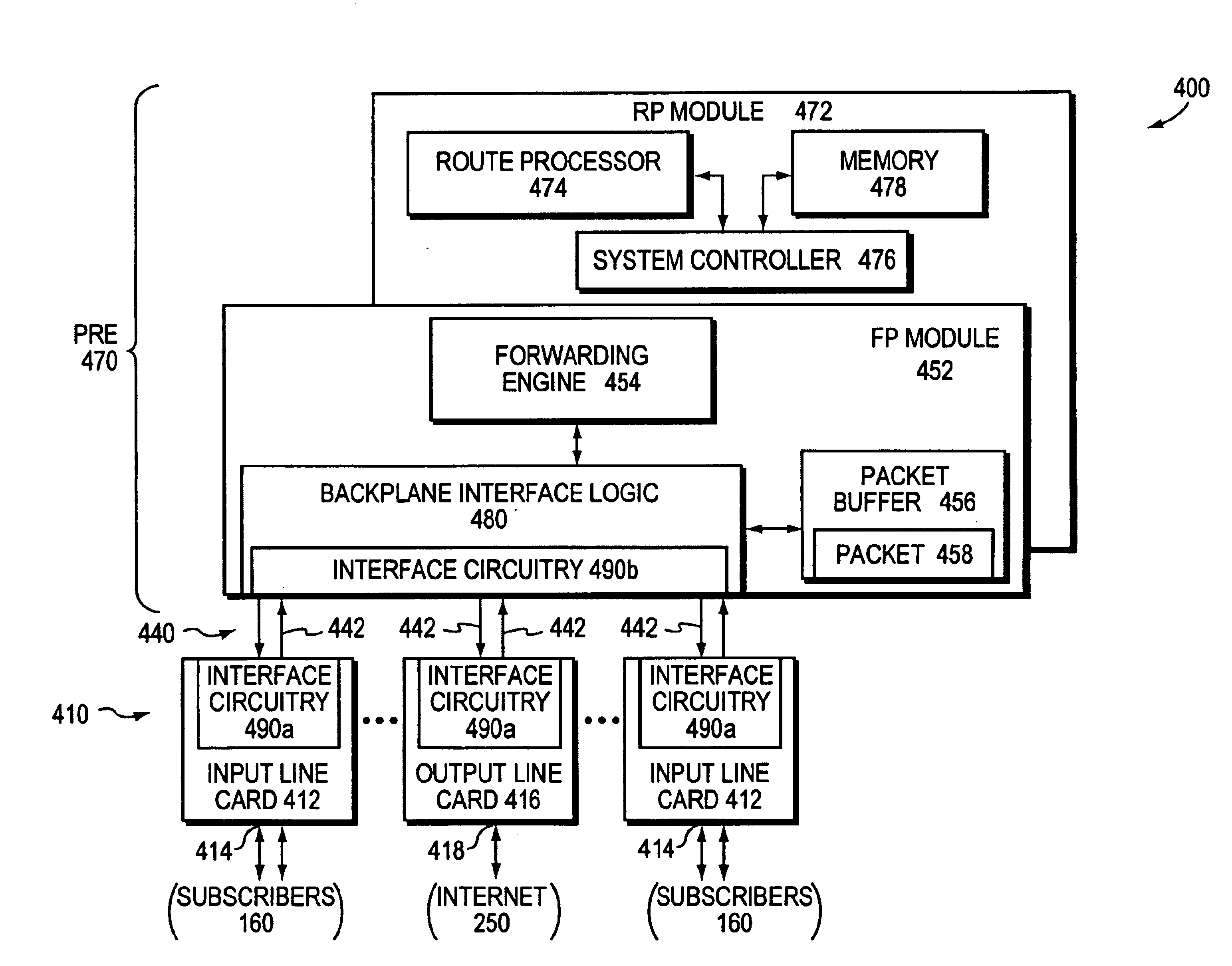
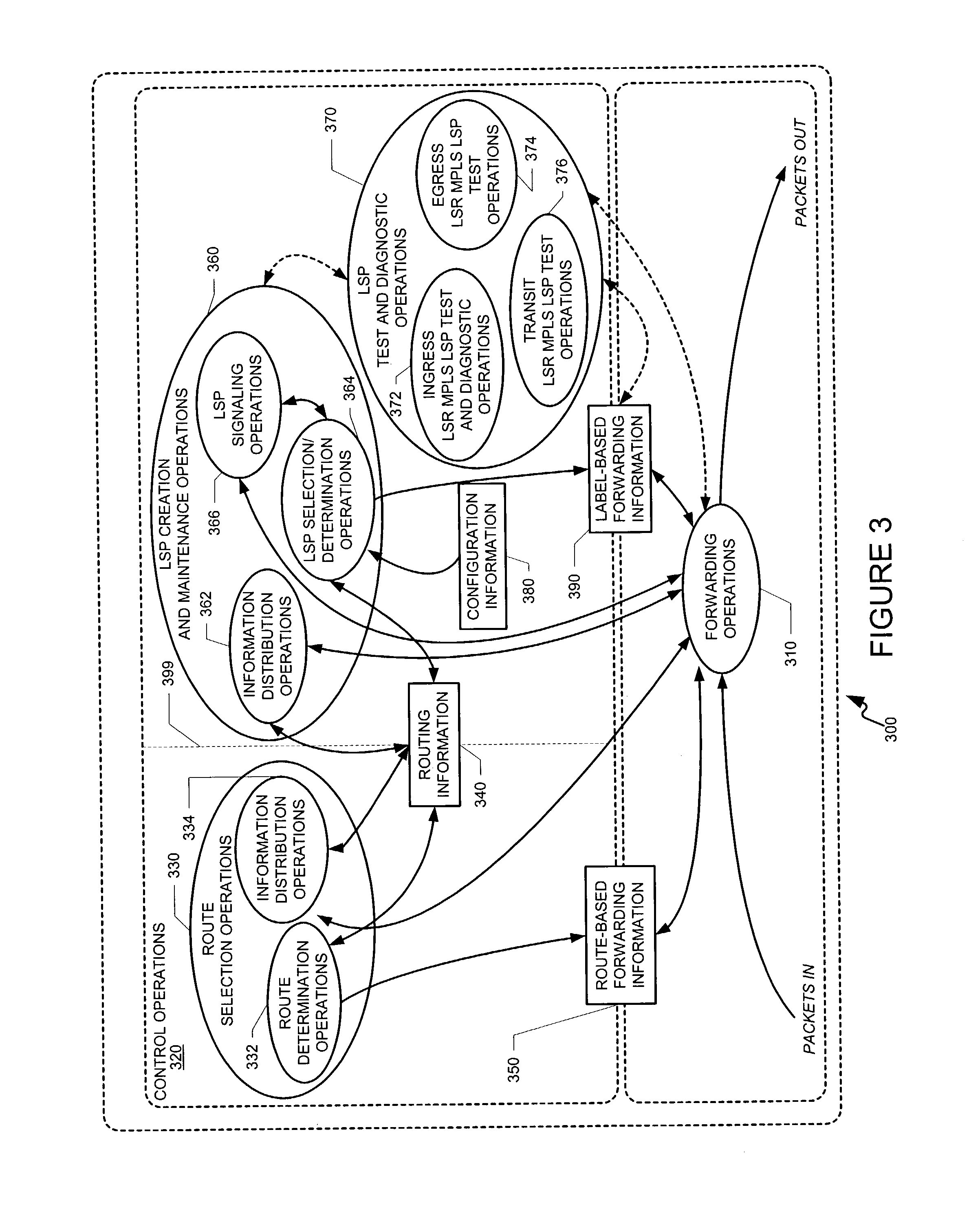
Data plane restart without state change in a control plane of an intermediate network node
A system and technique restarts a data plane of an intermediate node, such as an aggregation router, of a computer network without changing the state of a control plane in the router. The aggregation router comprises a control plane that includes a supervisor processor configured to manage traffic forwarding operations of the node. To that end, the supervisor processor maintains a current state of the control plane pertaining to, e.g., routing protocols and interface states of line cards within the router. The aggregation router further comprises a data plane that includes hardware components, such as a forwarding engine, configured to perform forwarding operations for data forwarded by the router.
Owner:CISCO TECH INC
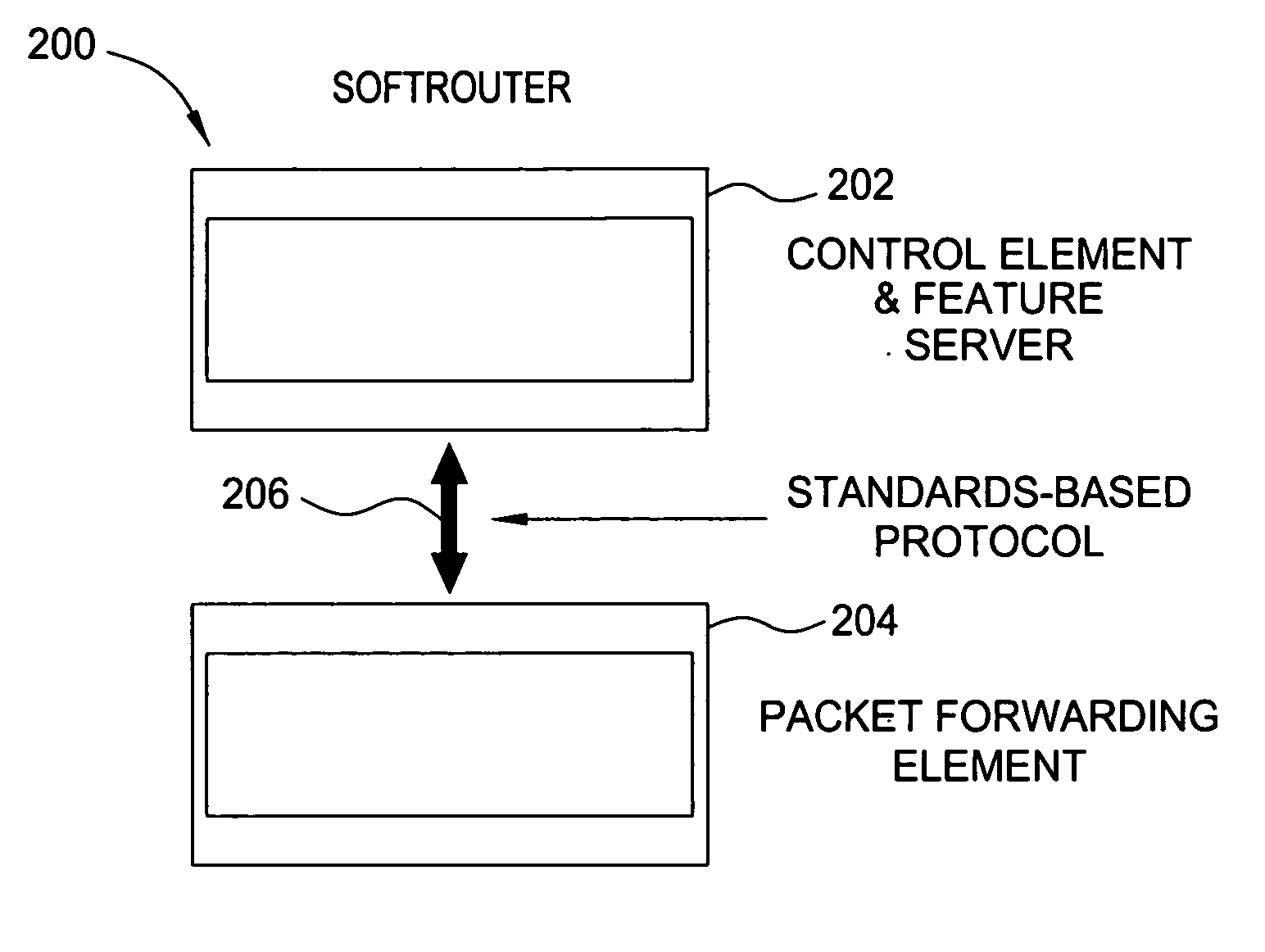
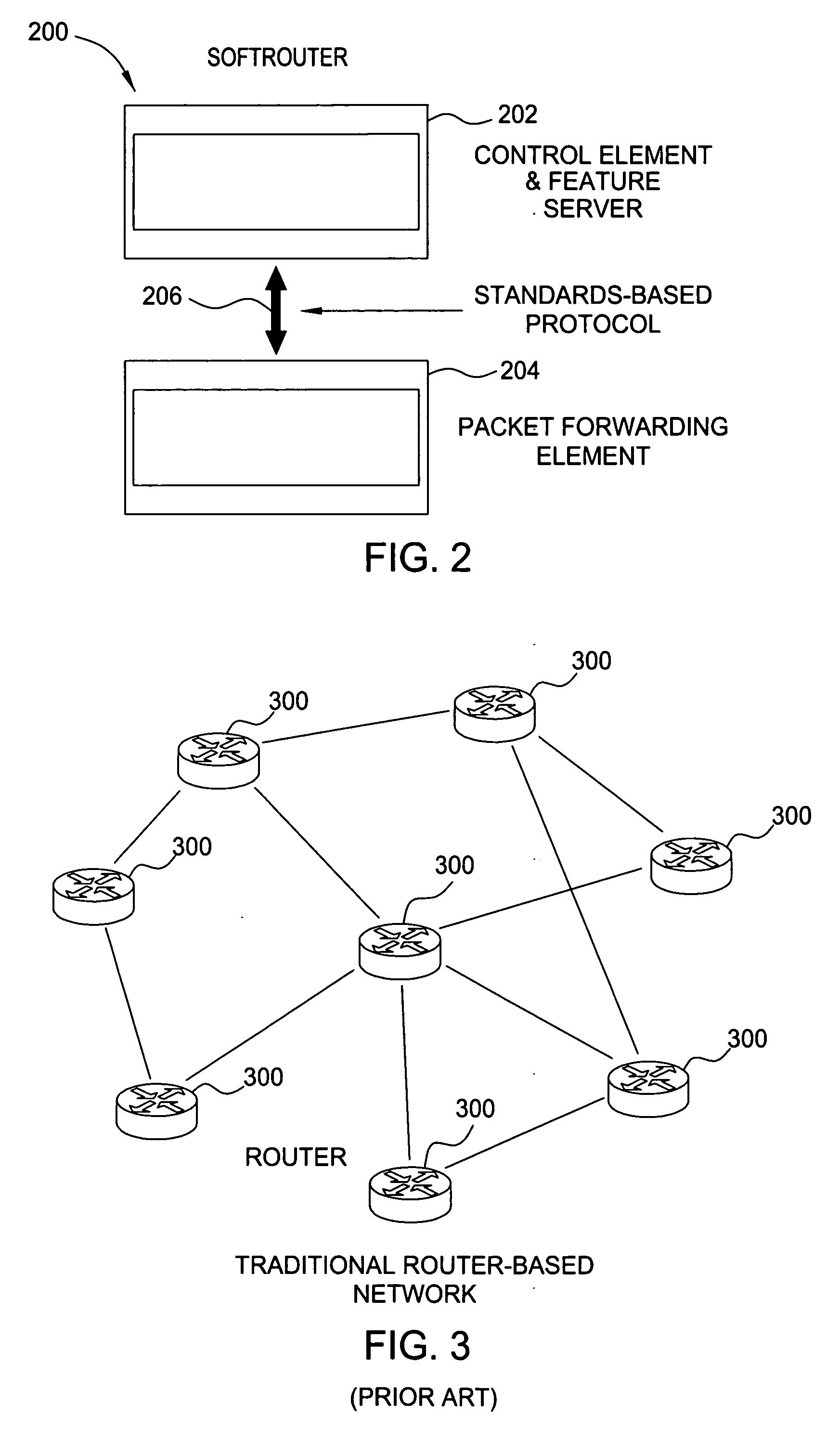
Softrouter protocol disaggregation
ActiveUS20060092940A1Data switching by path configurationSecuring communicationFailoverRate of convergence
A SoftRouter architecture deconstructs routers by separating the control entities of a router from its forwarding components, enabling dynamic binding between them. In the SoftRouter architecture, control plane functions are aggregated and implemented on a few smart servers which control forwarding elements that are multiple network hops away. A dynamic binding protocol performs network-wide control plane failovers. Network stability is improved by aggregating and remotely hosting routing protocols, such as OSPF and BGP. This results in faster convergence, lower protocol messages processed, and fewer route changes following a failure. The SoftRouter architecture includes a few smart control entities that manage a large number of forwarding elements to provide greater support for network-wide control. In the SoftRouter architecture, routing protocols operate remotely at a control element and control one or more forwarding elements by downloading the forwarding tables, etc. into the forwarding elements. Intra-domain routing and inter-domain routing are also included.
Owner:ALCATEL LUCENT SAS
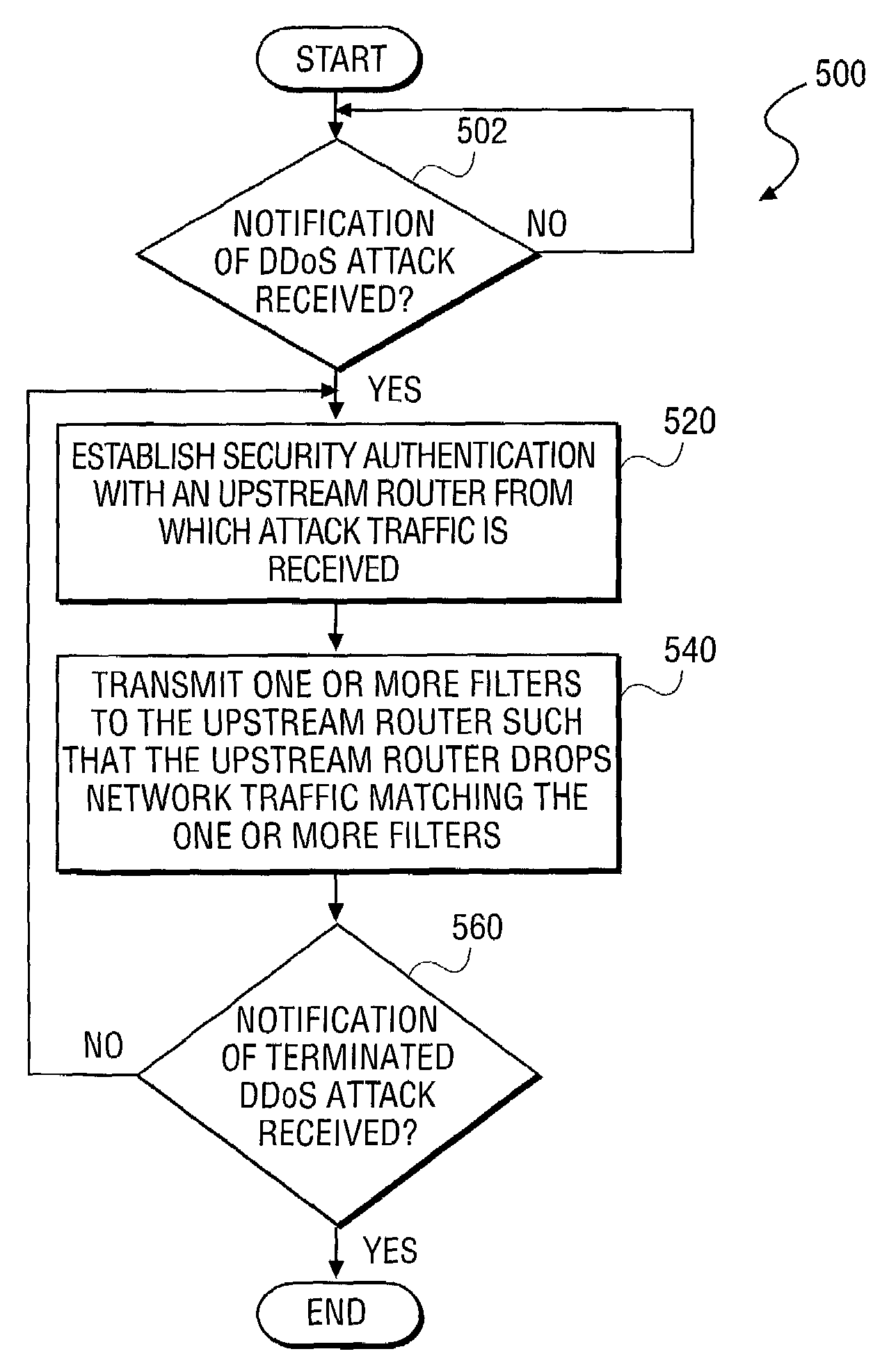
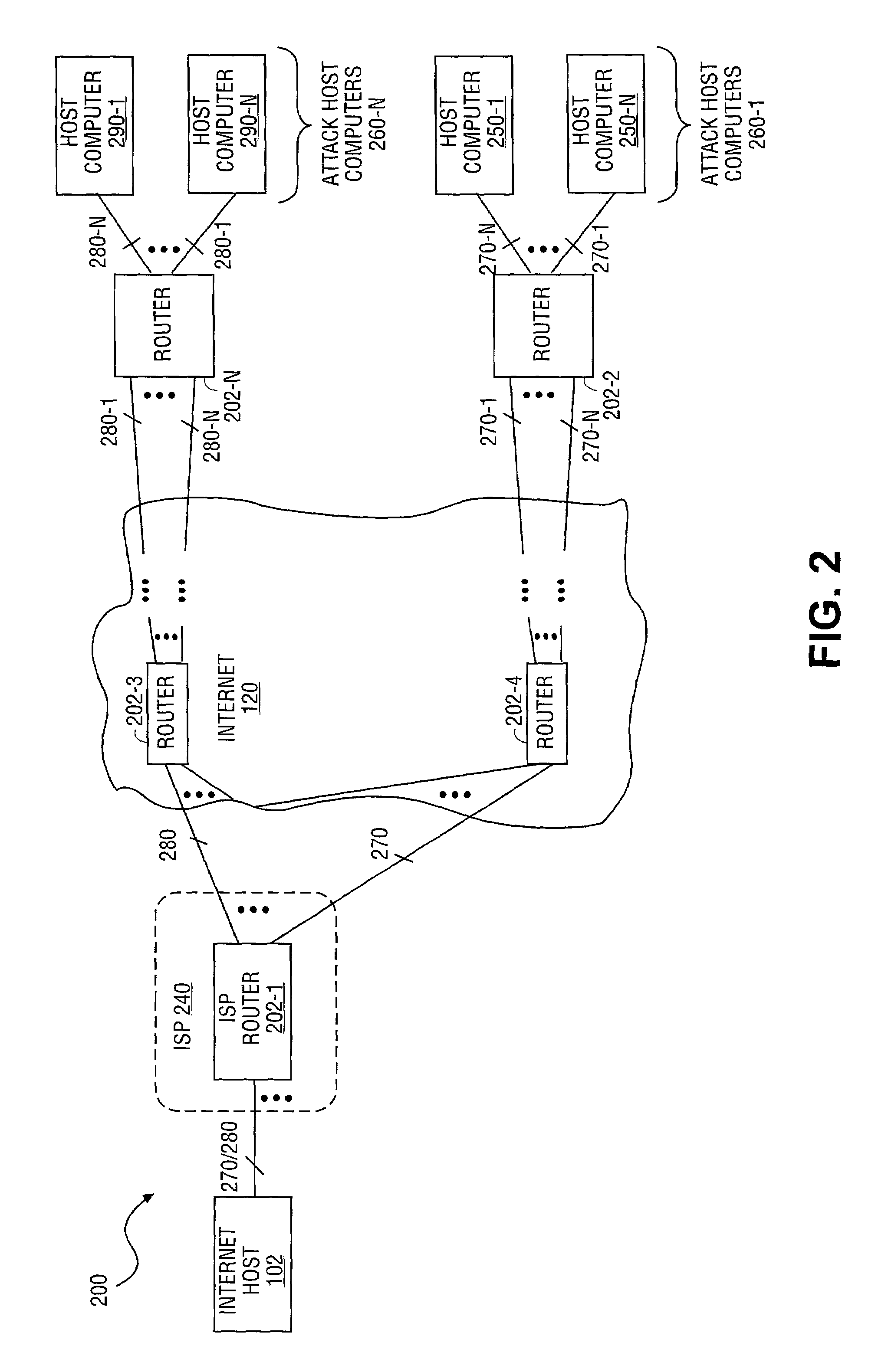
Apparatus and method for secure, automated response to distributed denial of service attacks
InactiveUS7028179B2Memory loss protectionError detection/correctionThe InternetSecurity authentication
An apparatus and method for secure, automated response to distributed denial of service (DDoS) attacks are described. The method includes notification of a DDoS attack received by an Internet host. Once received by an Internet host, the Internet host establishes security authentication from an upstream router from which the attack traffic, transmitted by one or more host computers, is received. The Internet host then transmits filter(s) to the upstream router generated based upon characteristics of the attack traffic. Once installed by the upstream router, the attack traffic is dropped to terminate a DDoS attack. In addition, the router may determine upstream router(s) coupled to ports from which attack traffic is received, and securely forward the filter(s) to the upstream routers as a routing protocol updated in order to drop the attack traffic at a point closer to a source of the DDoS attack.
Owner:INTEL CORP
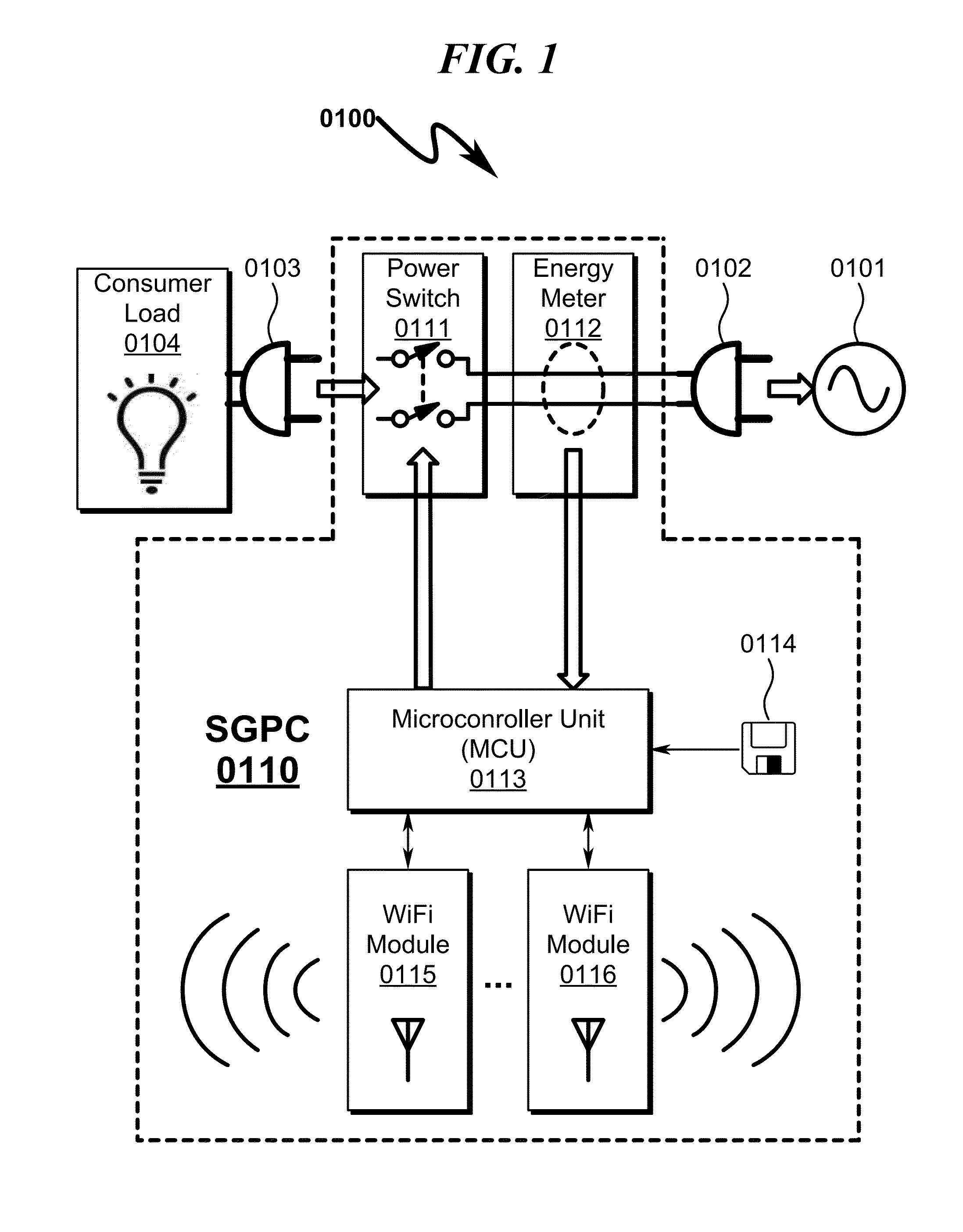
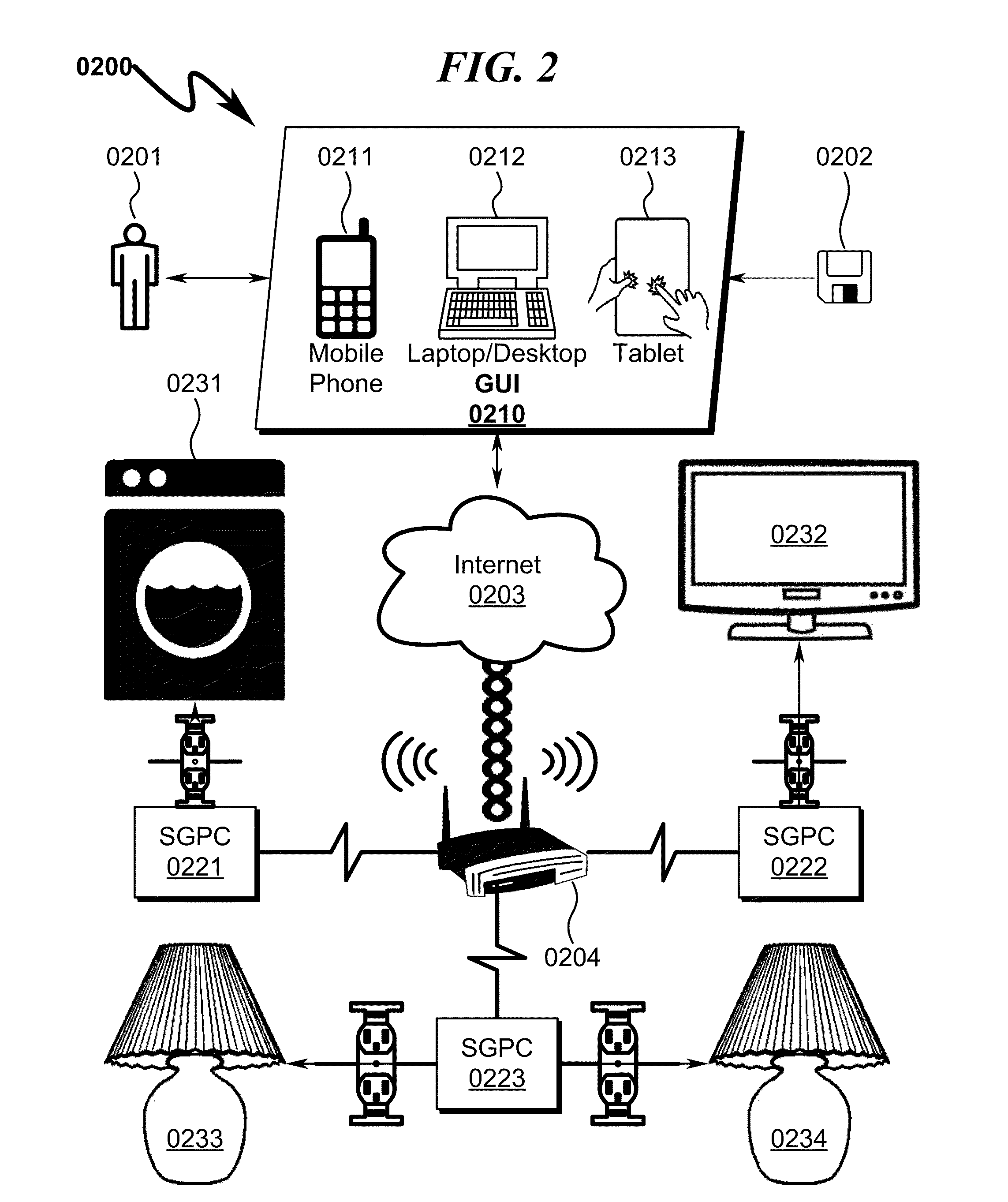
Power distribution system and method
ActiveUS20130261821A1Easy accessMechanical power/torque controlLevel controlTablet computerDistribution power system
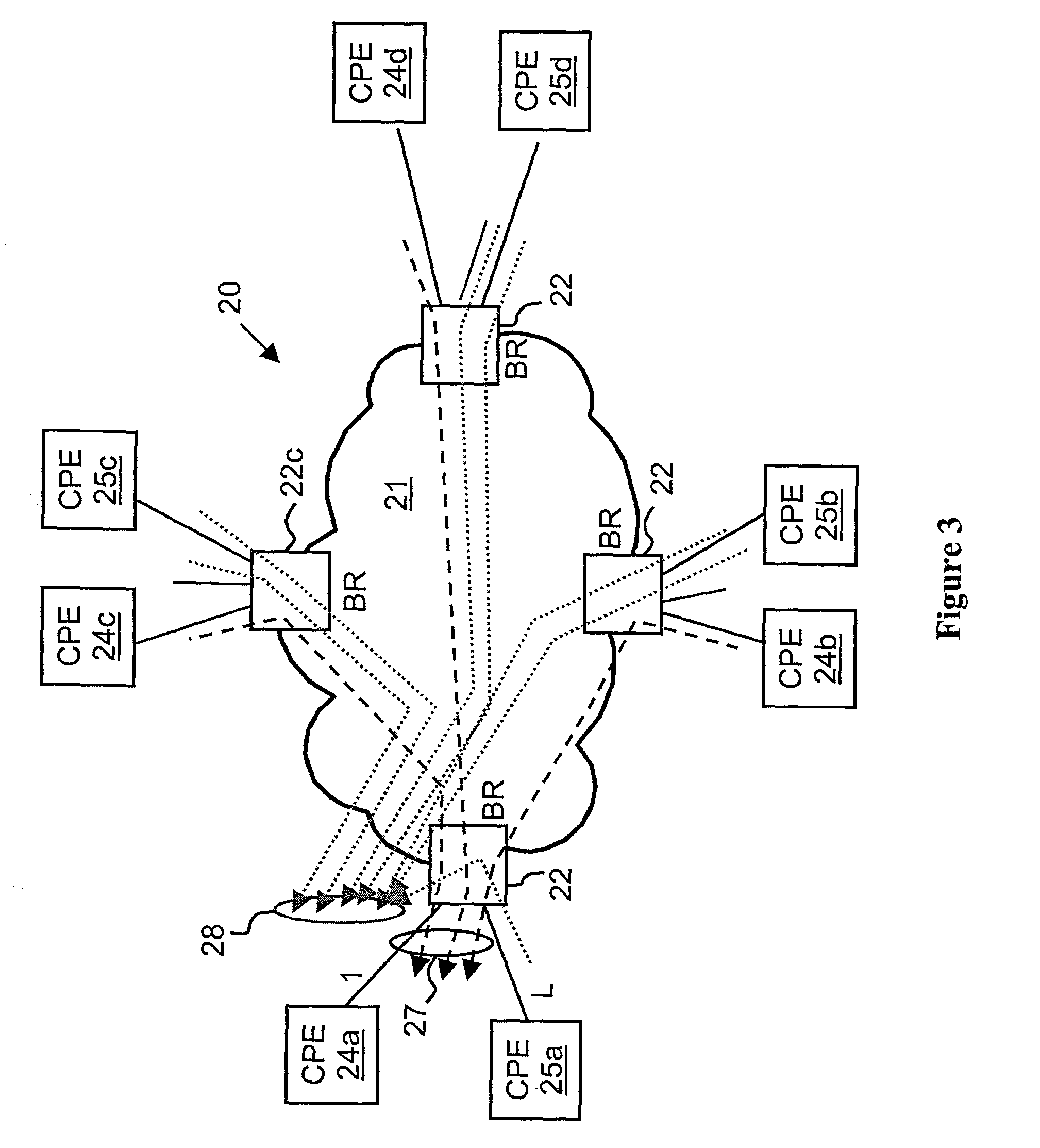
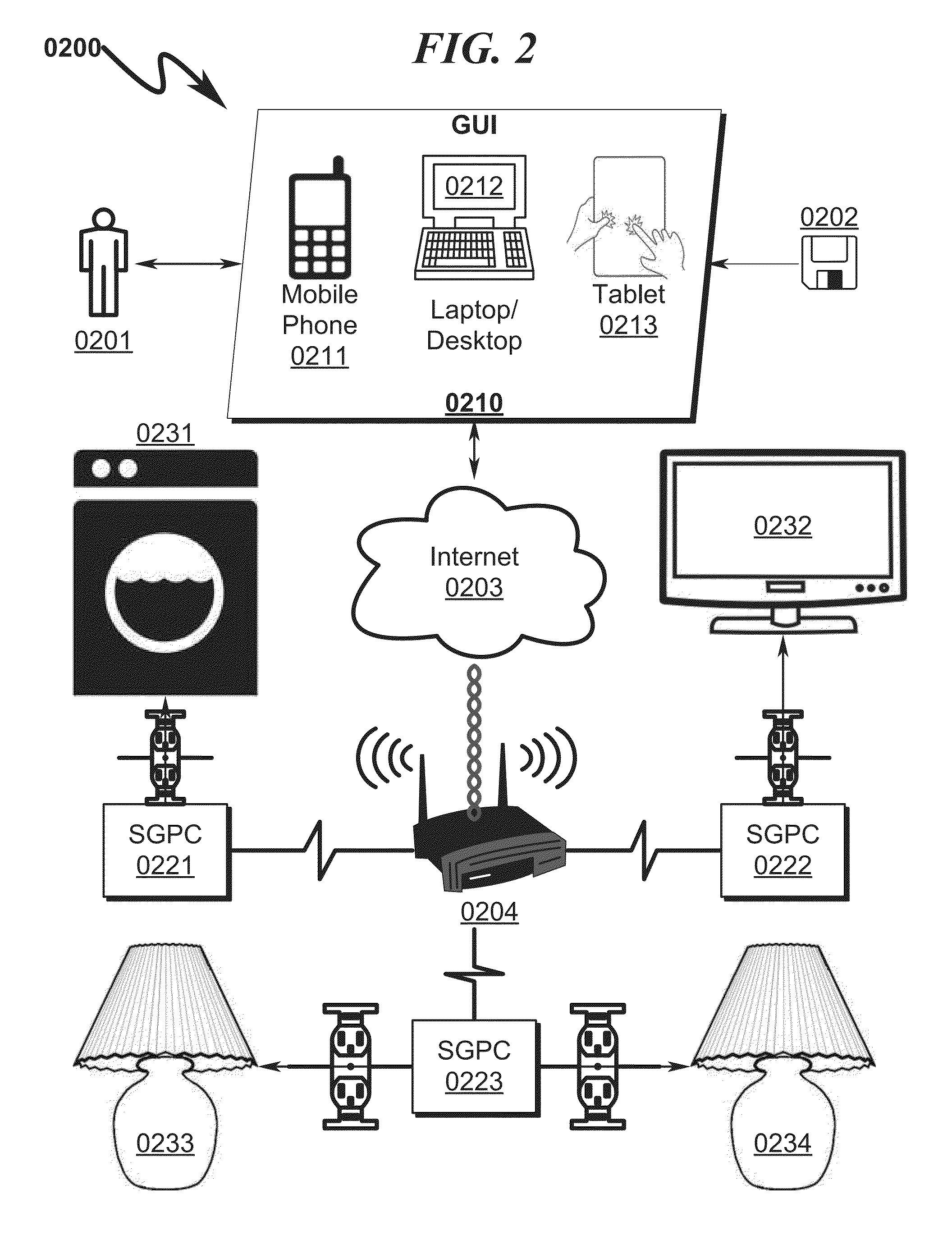
A power distribution system / method implementing Internet based access to hybrid home automation networks is disclosed. The system utilizes a smart gateway power controller (SGPC) configured for single / multi-gang wallplate installation to selectively switch an AC power source to a load device under switched control and / or local / remote network commands that may be routed through a variety of network interfaces and protocols present within a home or other structure-local communications network. SGPC configurations may be nested within a home automation network to permit separation of control for load devices within a common home automation environment. Present invention methods may include routing protocols between disparate home automation networks as well as remote access protocols that permit control of disparate home automation networks via the Internet using a wide variety of remote access interfaces including mobile devices, tablet computers, laptops, desktop computers, and the like.
Owner:ADVANERGY
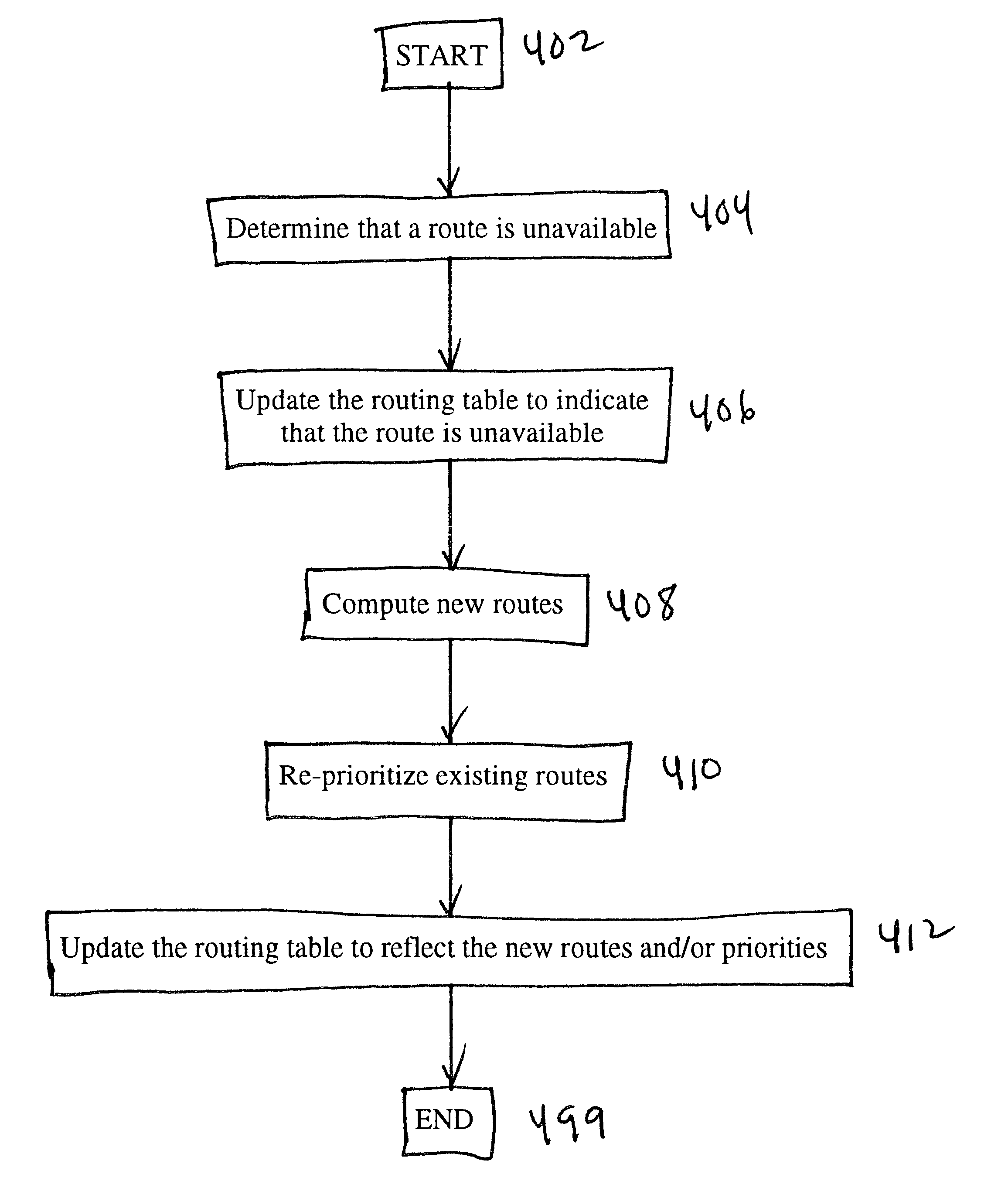
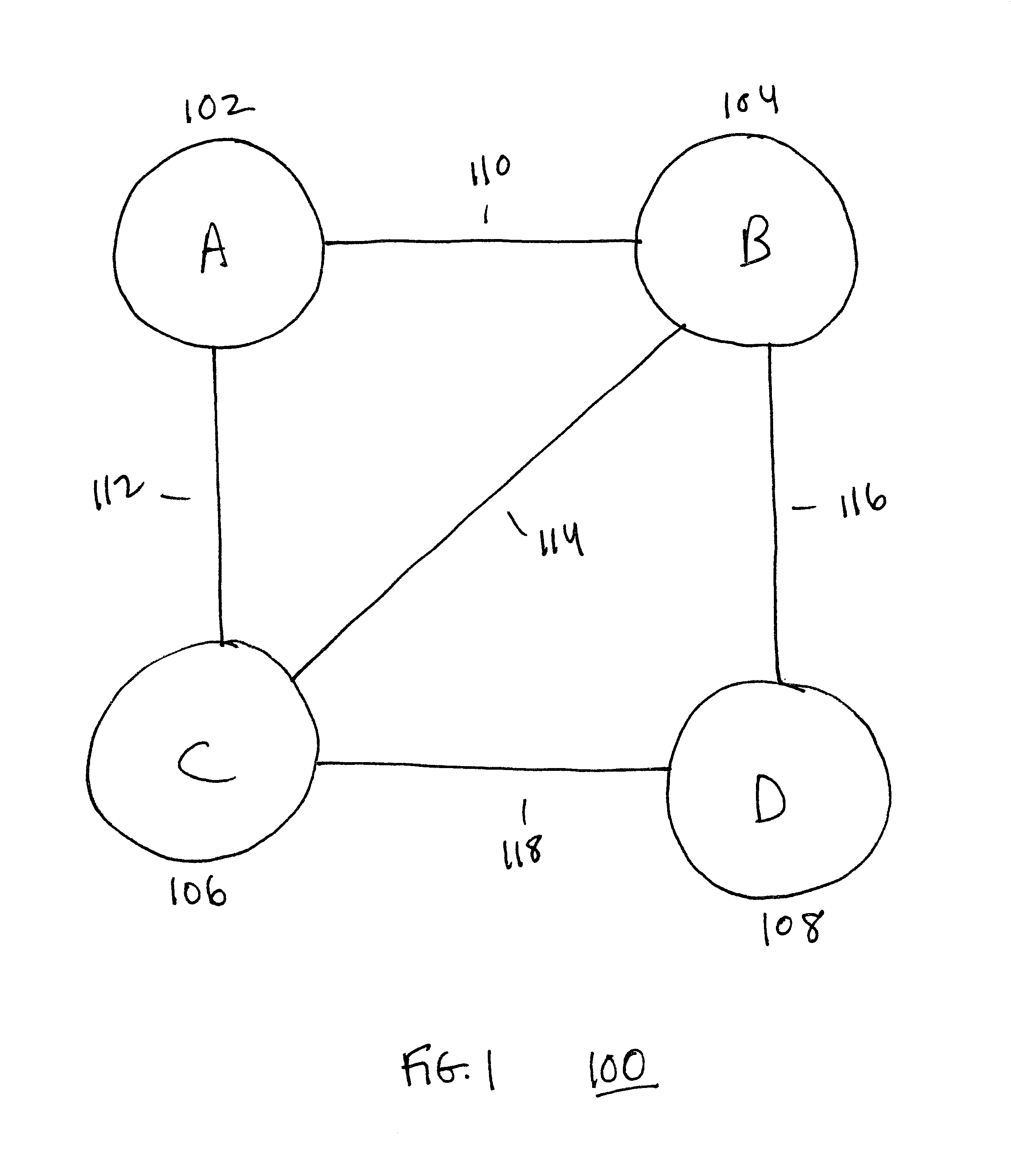
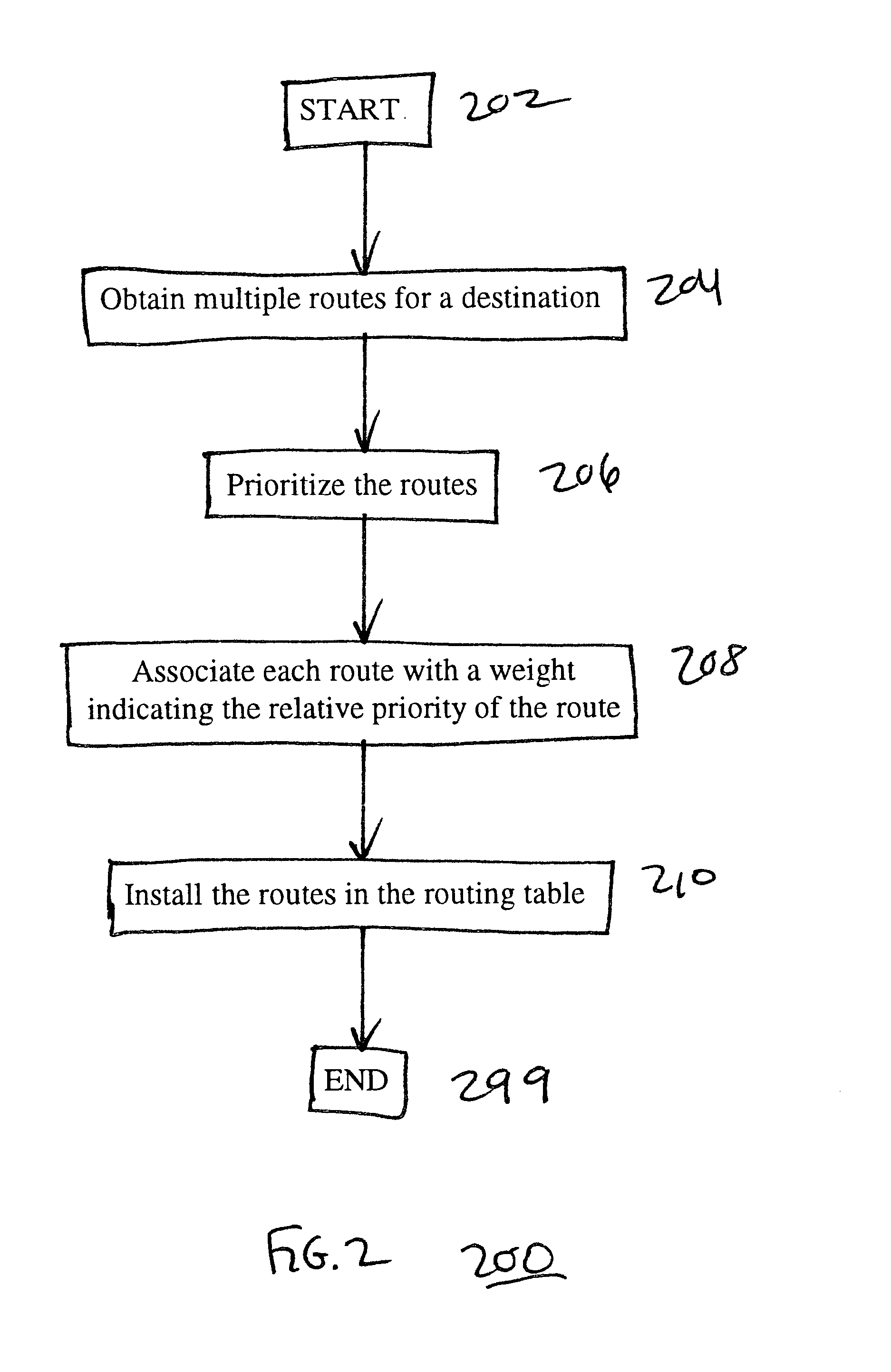
Using alternate routes for fail-over in a communication network
InactiveUS6857026B1Error detection/correctionData switching by path configurationFailoverRouting table
Using alternate routes for fail-over in a communication network involves maintaining a preferred route and an alternate route in a routing table and routing protocol messages according to the alternate route when the preferred route is unavailable. A node obtains multiple routes for a destination, prioritizes the routes, and installs multiple routes in the routing table, including at least the preferred route and the alternate route. When the node receives a protocol message, the node searches the routing table for a highest priority route that is available for routing the protocol message, and routes the protocol message according to the highest priority route that is available for routing the protocol message. When a route becomes unavailable, the node updates the routing table to indicate that the route is unavailable, and may compute new routes and / or re-prioritize existing routes.
Owner:RPX CLEARINGHOUSE
Router and routing protocol redundancy
InactiveUS6910148B1Reduce service outageReduce degradationData switching networksRedundant hardware error correctionSoftwareRouting protocol
A router and routing protocol redundancy are disclosed to reduce service outage or degradation for a network device and thus to increase service availability on a network due to software and hardware failures of the network device. A network device such as router includes a redundancy platform having an active controller system and a standby controller system. A routing protocol state change is received or generated by the active controller system. The received or generated routing protocol state change is replicated to the standby controller system. By replicating the routing protocol state change, the standby controller system can maintain the routing protocol sessions for the network device if a failure occurs in the active controller system. Furthermore, the routing protocol states are maintained in realtime to handle the dynamic changes created by routing protocols.
Owner:RPX CORP
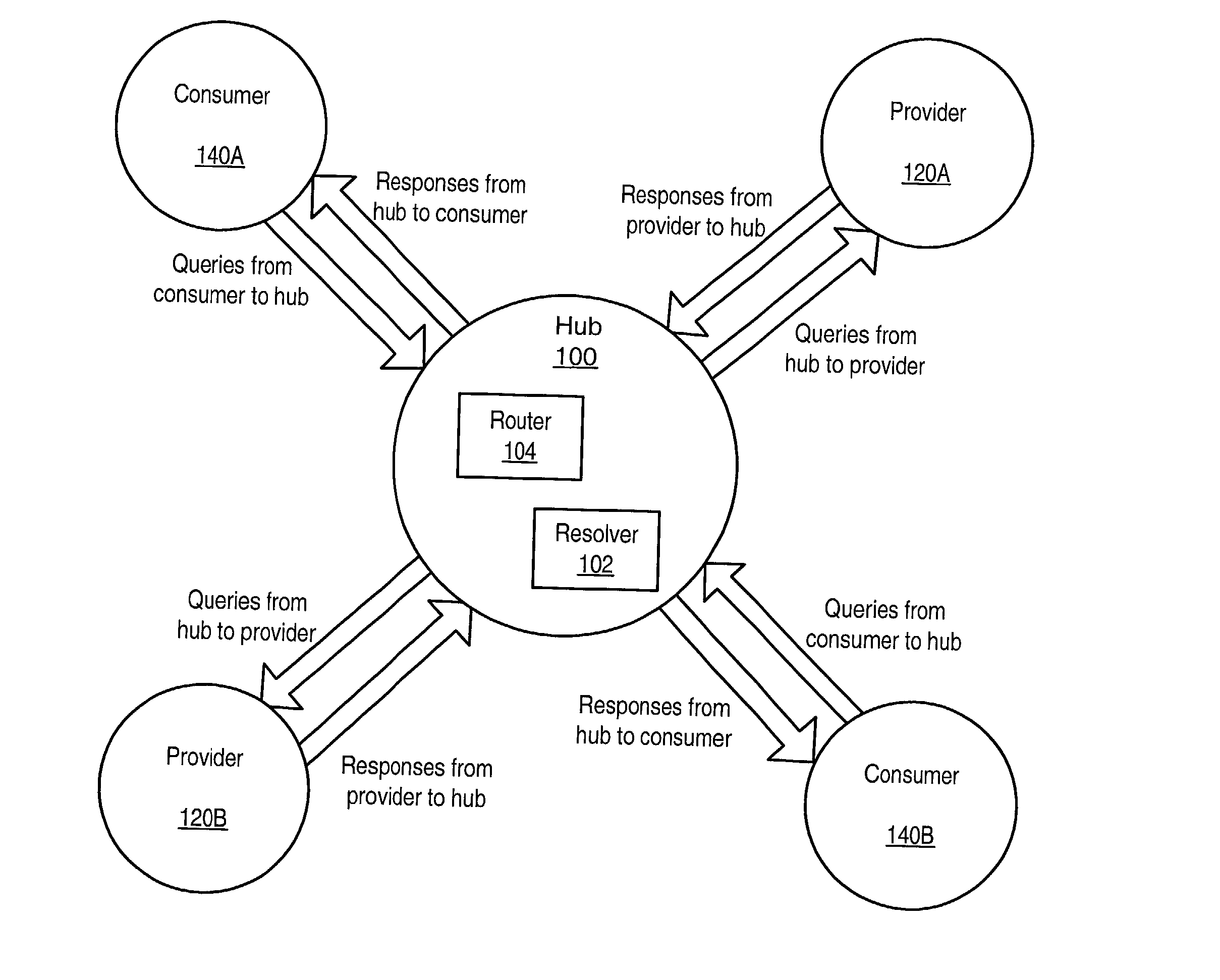
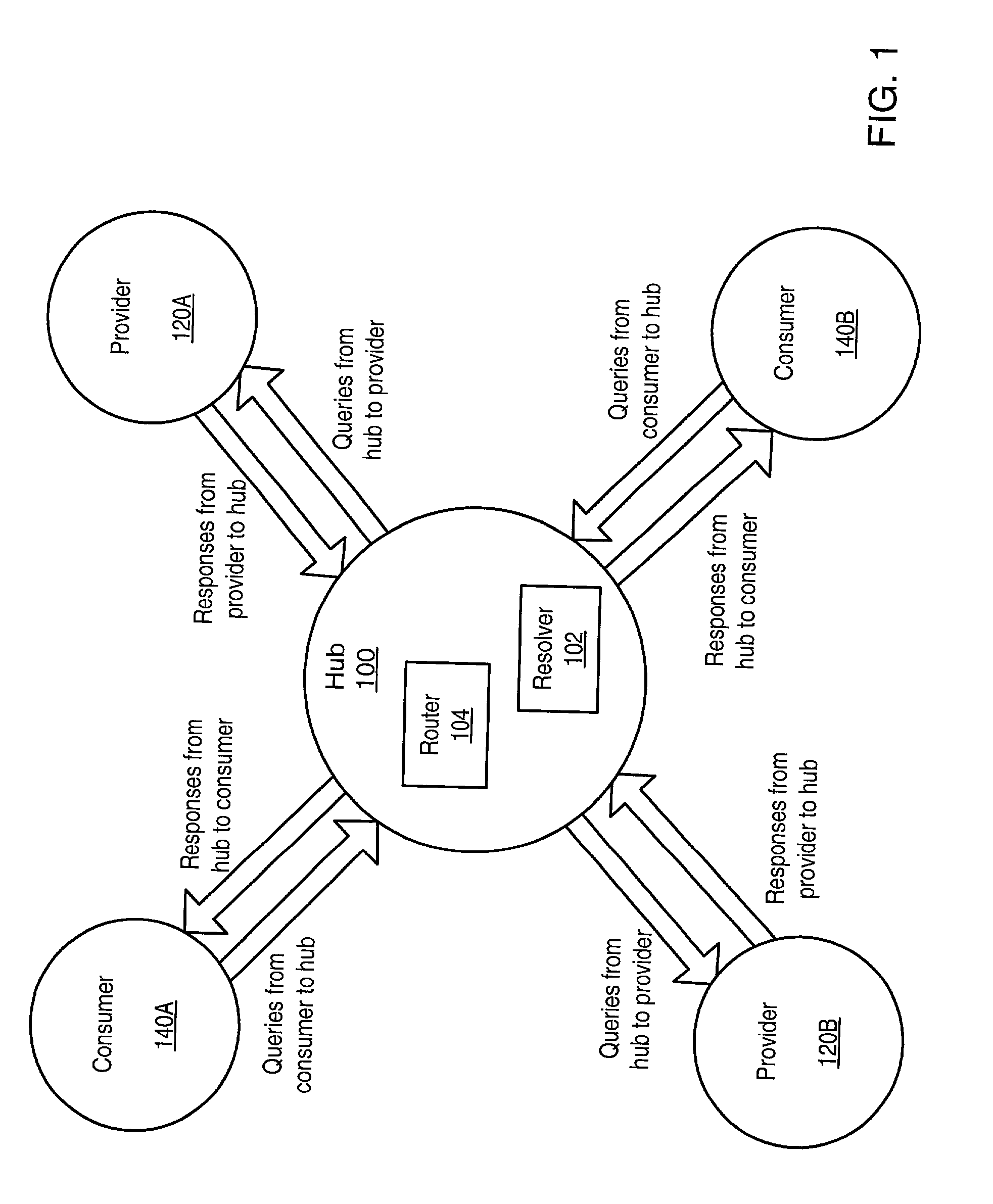
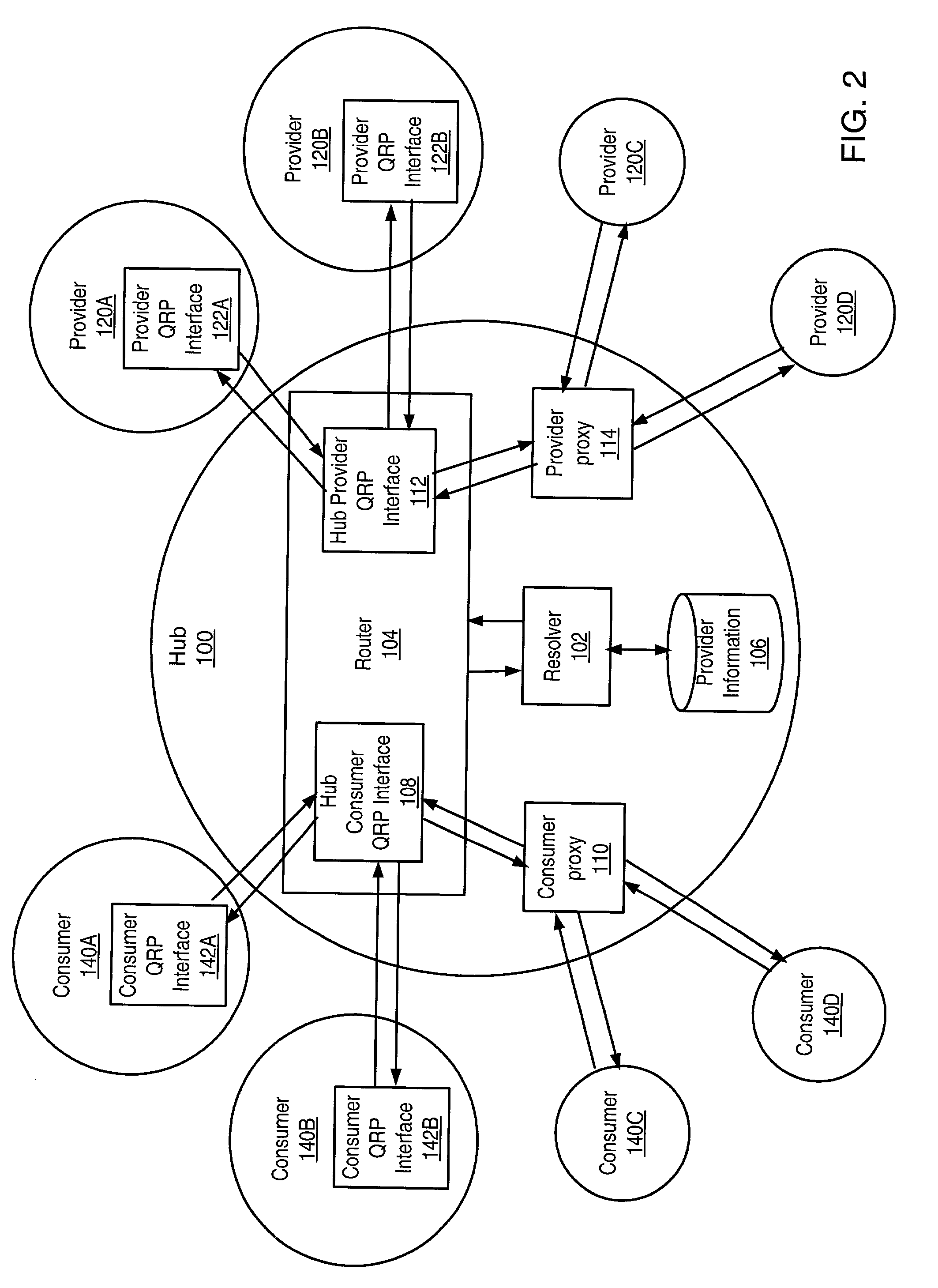
Distributed information discovery
ActiveUS20030088544A1Digital data information retrievalDigital data processing detailsWeb search queryInformation discovery
A distributed network search mechanism may be provided for consumers coupled to a network to search information providers coupled to the network. Consumers may make search requests according to a query routing protocol. A network hub may be configured to receive search requests from consumers. The hub may also receive registration requests from information providers according to the query routing protocol. Information providers register with the hub to indicate search queries in which they are interested in receiving. When a query request is received, the hub resolves the query request with a provider registration index. The hub matches search query information from the query request with provider registrations to determine which providers have registered to receive search queries like the current search query. The hub then routes the search query to matching providers according to the query routing protocol.
Owner:ORACLE INT CORP
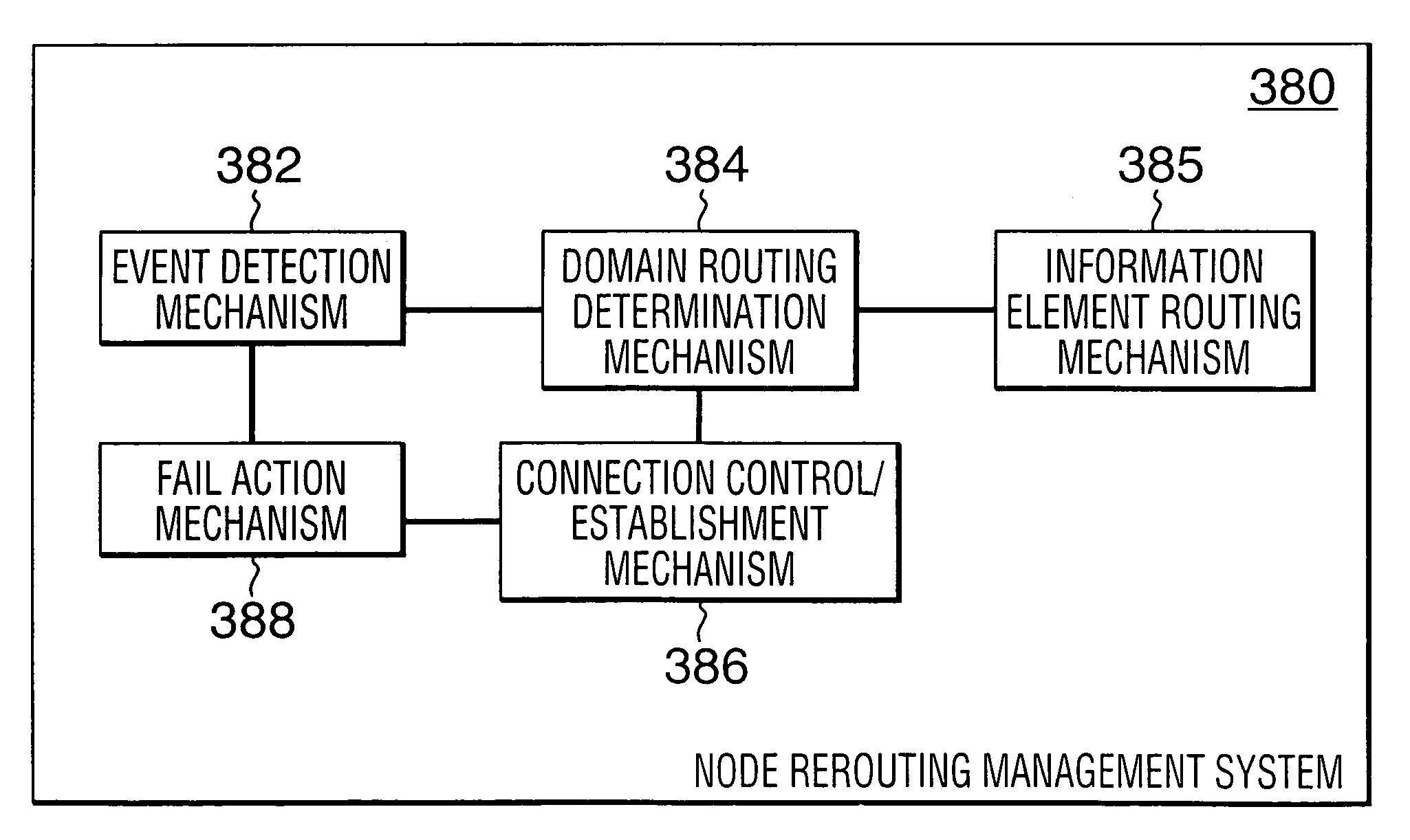
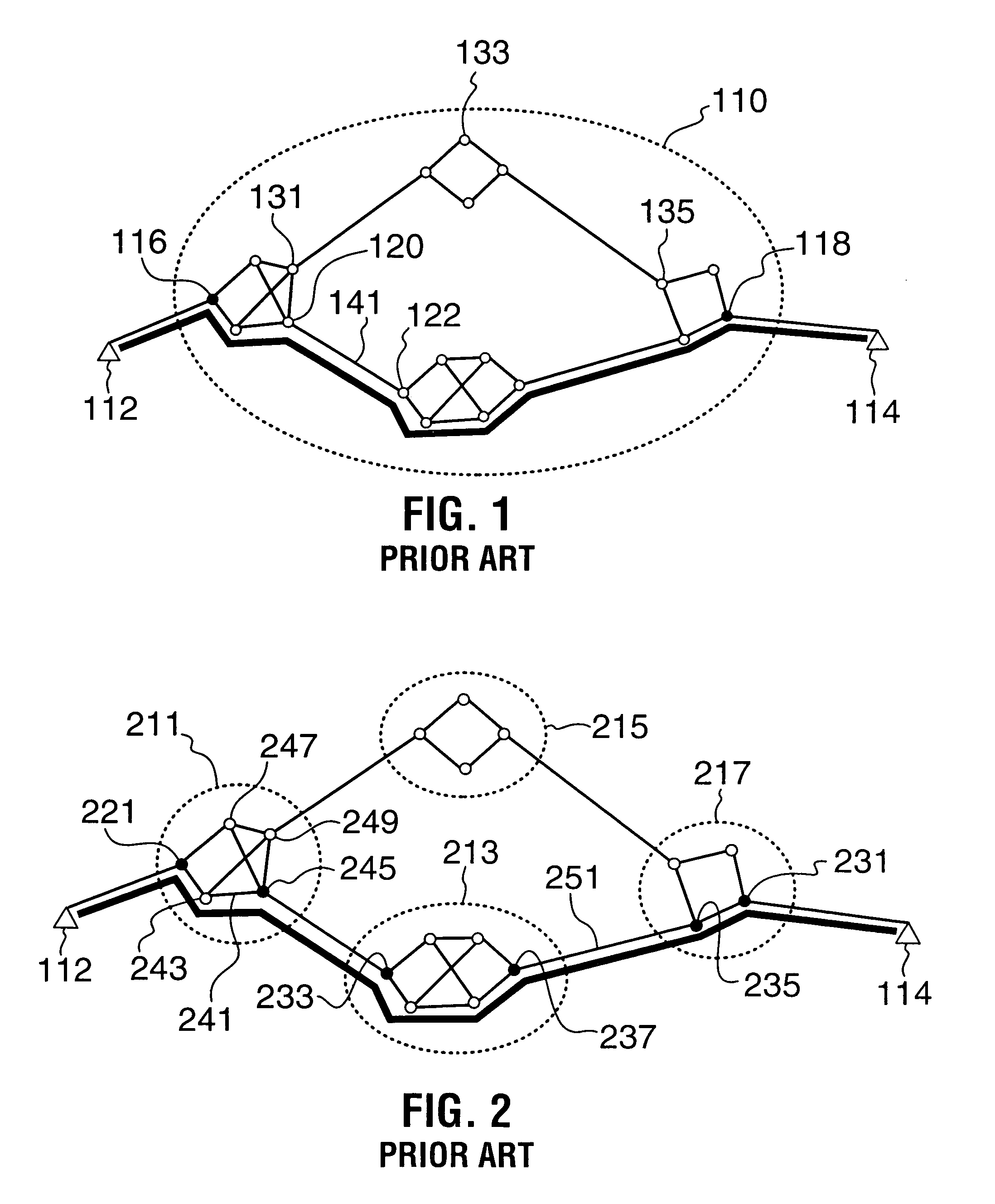
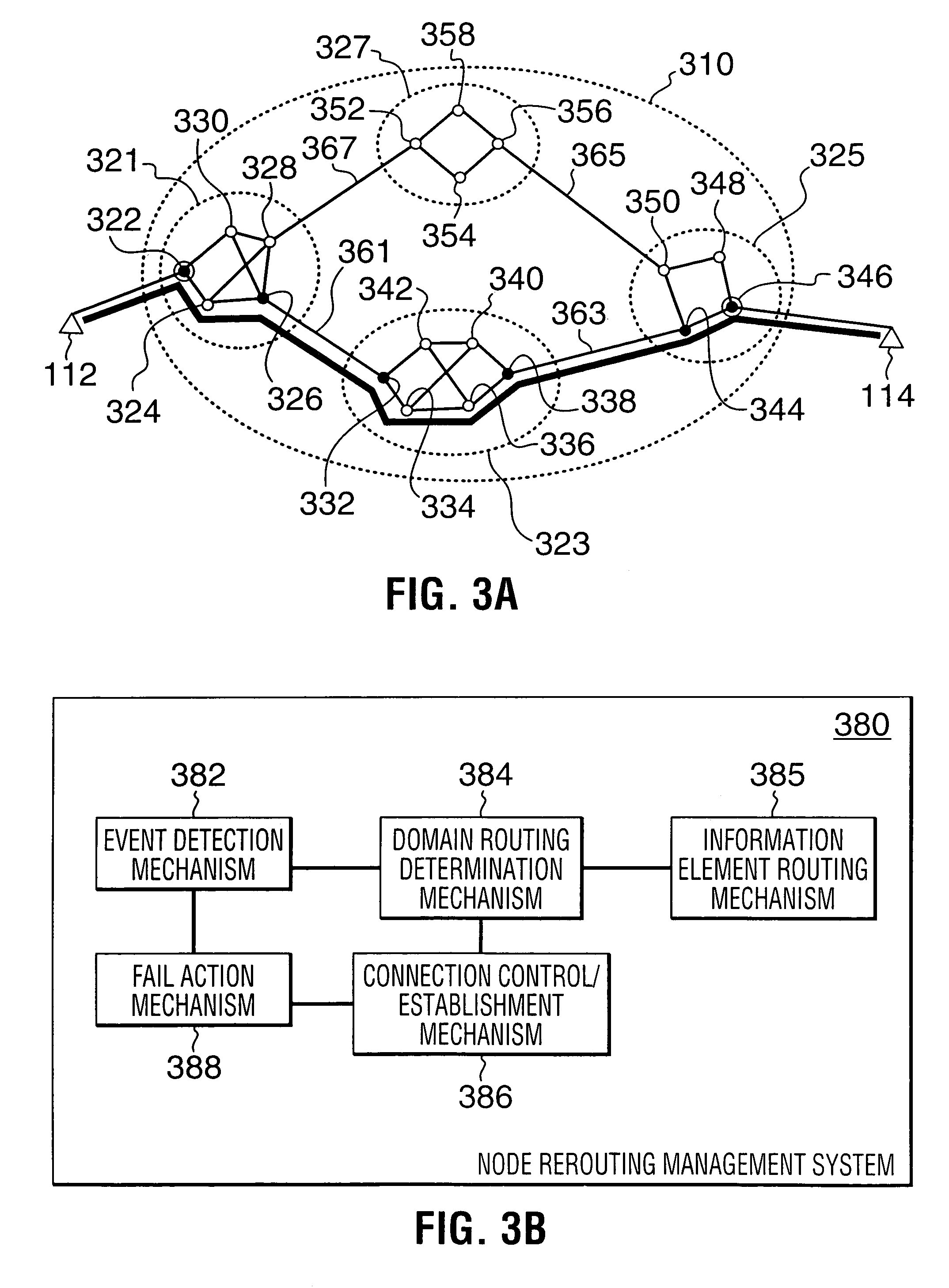
Rerouting in connection-oriented communication networks and communication systems
InactiveUS7180866B1Multiplex system selection arrangementsError preventionDouble faultCommunications system
A Private Network-Network Interface (PNNI) network including interconnected nodes is defined as a single rerouting domain (“global domain”) and the global domain is further defined by multiple divided domains (“local domains”). Each of the local domains is defined to include multiple nodes that are included in the network. Connection recovery and path optimization in the global domain (the entire PNNI network) are performed in accordance with a global rerouting protocol. The global rerouting protocol is a modification of the standard Domain-Based Rerouting (DBR) protocol, by adding information elements of domain identifier, rerouting for the global domain. The DBR protocol does not support the connection recovery from a link failure between local domains (“inter-domains”) and the global path optimization. The global rerouting method is capable of connection recovery and path optimization outside of any rerouting local domains. The global rerouting provides double fault recovery within the rerouting domain (“intra-domain”) as covered by the DBR and outside of the domains (“inter-domain”) or when the initial fault recovery within the domain has failed. Also, the global rerouting method provides maximum path optimization across all domains and within the rerouting local domain.
Owner:RPX CLEARINGHOUSE
Telecommunication routing using multiple routing protocols in a single domain
InactiveUS7177646B2Improve routing efficiencyAssess restrictionSpecial service for subscribersRouting domainNetwork addressing
Packets are routed in a communications network including an infrastructure of packet switching nodes interconnected by packet transport links, and a plurality of access nodes to which a routing path, defined by data held in packet switching nodes located along the routing path, may be directed in the infrastructure for a given network address. Different types of routing updates are used in a single routing domain.
Owner:BRITISH TELECOMM PLC
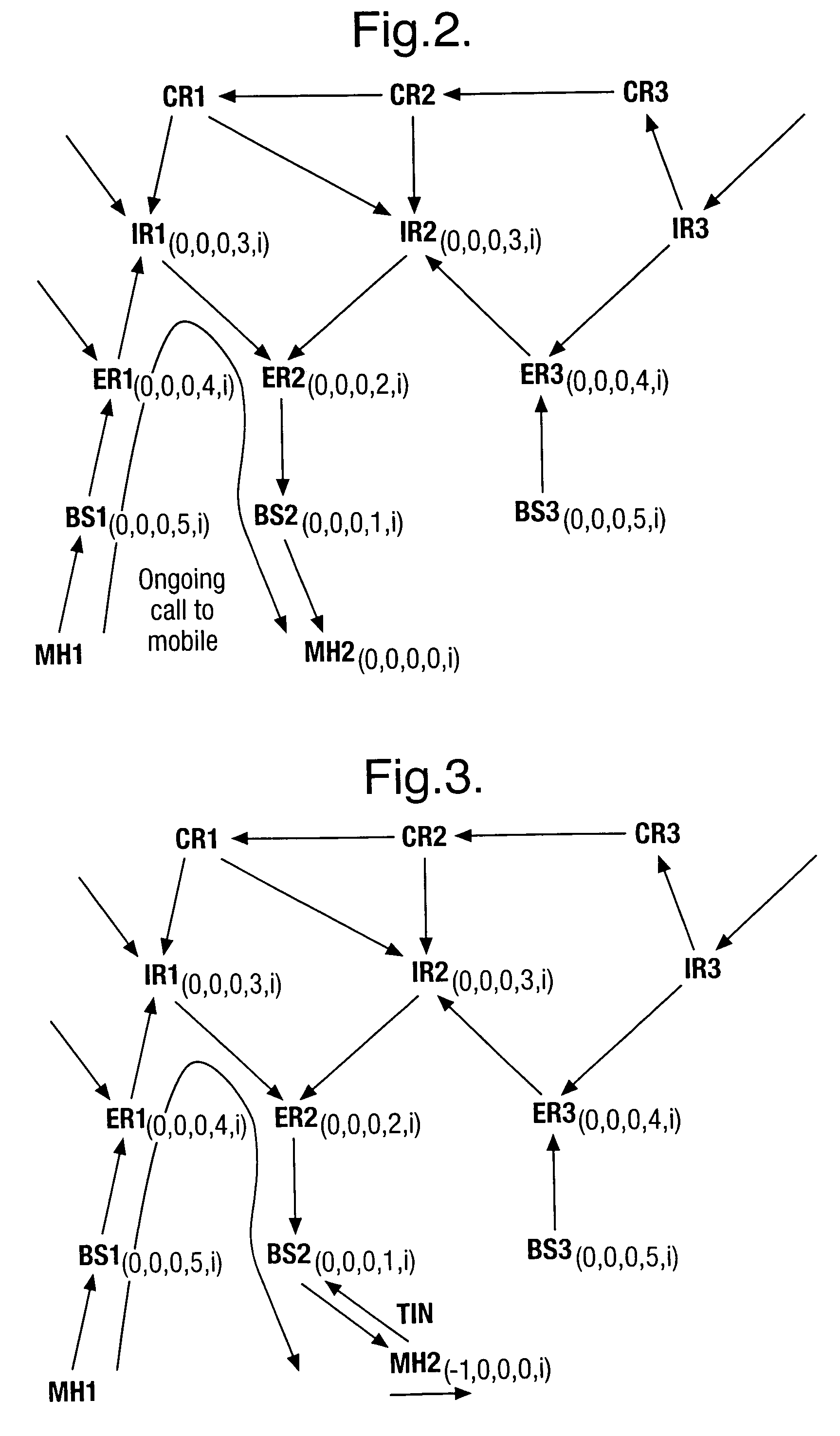
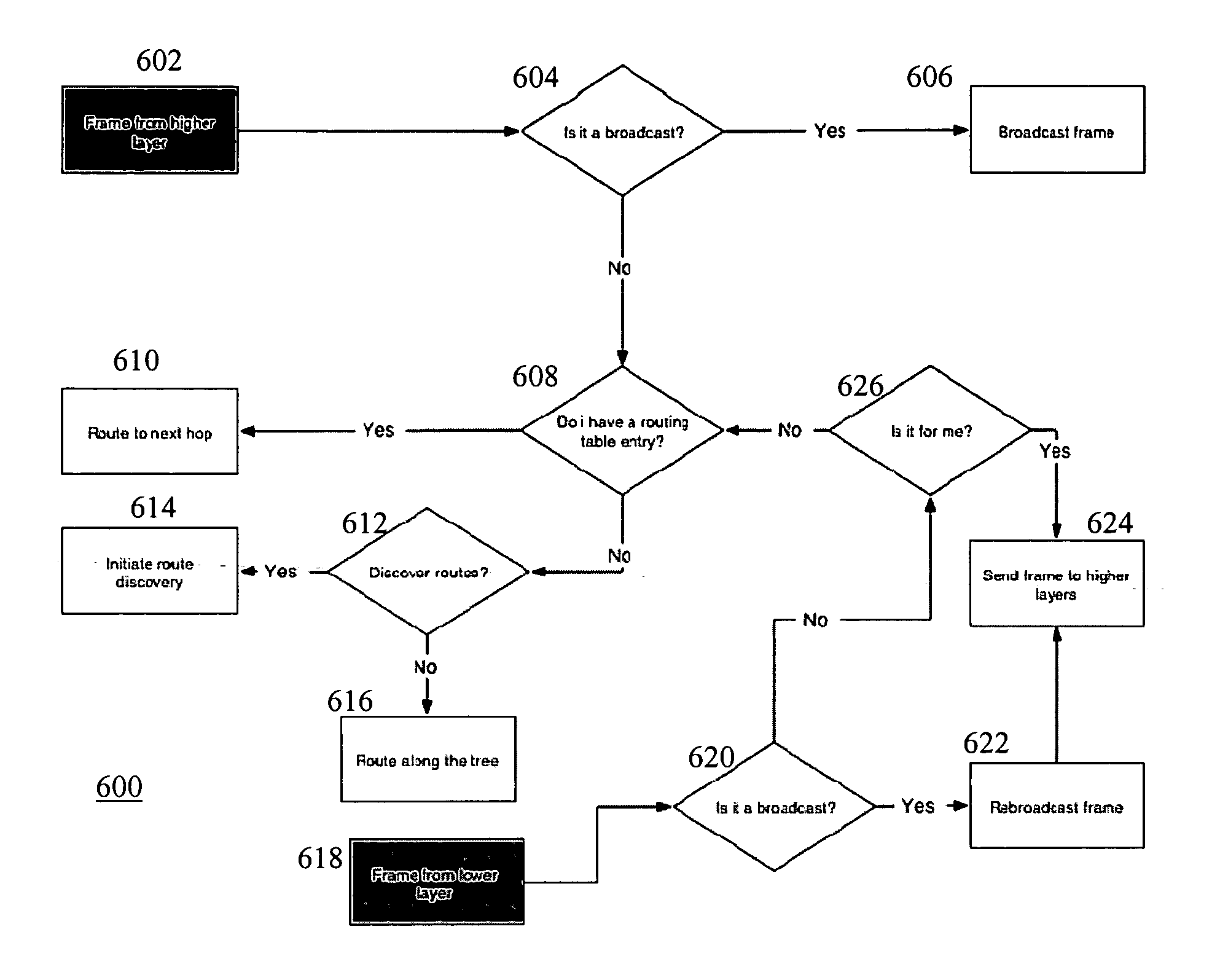
Methods and apparatuses for routing data in a personal area network
The invention is a routing method for data in a personal area network. The personal area network includes a plurality of nodes. The method includes receiving a frame at a node, determining whether the node contains a routing table entry for the frame destination, and when the node contains a routing table entry, determining a route for the frame based on a first routing protocol. The method further includes, when the node does not contain a routing table entry for the frame destination, determining whether a route should be discovered for the frame destination, and when a route should not be discovered, determining a route for the frame based on a second routing protocol.
Owner:SAMSUNG ELECTRONICS CO LTD +4
Wireless sensor network with energy efficient protocols
InactiveUS20130128786A1Small sizeReduce the overall heightPower managementEnergy efficient ICTWireless mesh networkWireless sensor network
The wireless sensor network with energy efficient protocols includes a network of external sensors in communication with a data sink. The network utilizes an algorithm integrating a modified S-MAC (an algorithm for medium access control) protocol for decreasing energy usage in operating the node and associated sensors. A routing protocol is further integrated into the algorithm, the routing protocol being based upon cluster head rotation.
Owner:KING FAHD UNIVERSITY OF PETROLEUM AND MINERALS +1
Distributed information discovery through searching selected registered information providers
InactiveUS7171415B2Digital data information retrievalMultiple digital computer combinationsWeb search queryInformation discovery
A distributed network search mechanism may be provided for consumers coupled to a network to search information providers coupled to the network. Consumers may make search requests according to a query routing protocol. A network hub may be configured to receive search requests from consumers. The hub may also receive registration requests from information providers according to the query routing protocol. Information providers register with the hub to indicate search queries in which they are interested in receiving. When a query request is received, the hub resolves the query request with a provider registration index. The hub matches search query information from the query request with provider registrations to determine which providers have registered to receive search queries like the current search query. The hub then routes the search query to matching providers according to the query routing protocol.
Owner:ORACLE INT CORP
Energy-efficient network protocol and node device for sensor networks
ActiveUS7729285B2Balanced energy consumptionEnergy efficiencyPower managementEnergy efficient ICTComputer scienceEnergy consumption
Owner:OLLNOVA TECH LTD
Hybrid mesh routing protocol
ActiveUS8467297B2Error preventionFrequency-division multiplex detailsWireless mesh networkEngineering
A method for selecting a route by a node between a source node and a destination node in a wireless mesh network by establishing the route between the source node and the destination node using media access control addresses is described. A method for a node to selecting a route to join a multicast group in a wireless mesh network using media access control addresses, is also described.
Owner:INTERDIGITAL CE PATENT HLDG
Hybrid Mesh Routing Protocol
ActiveUS20080170550A1Quality of service requirementError preventionFrequency-division multiplex detailsWireless mesh networkHybrid mesh
A method for selecting a route by a node between a source node and a destination node in a wireless mesh network by establishing the route between the source node and the destination node using media access control addresses is described. A method for a node to selecting a route to join a multicast group in a wireless mesh network using media access control addresses, is also described.
Owner:INTERDIGITAL CE PATENT HLDG
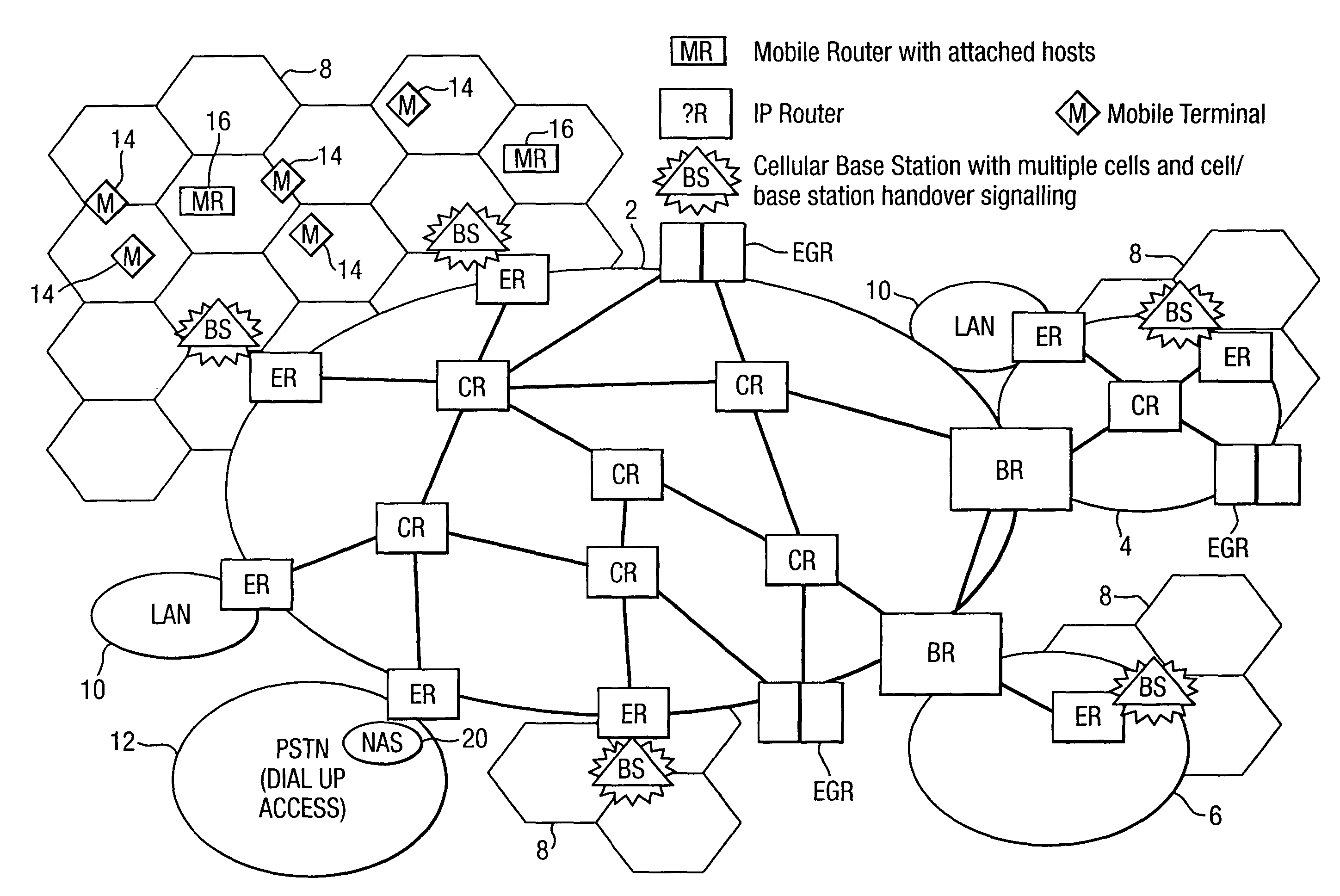
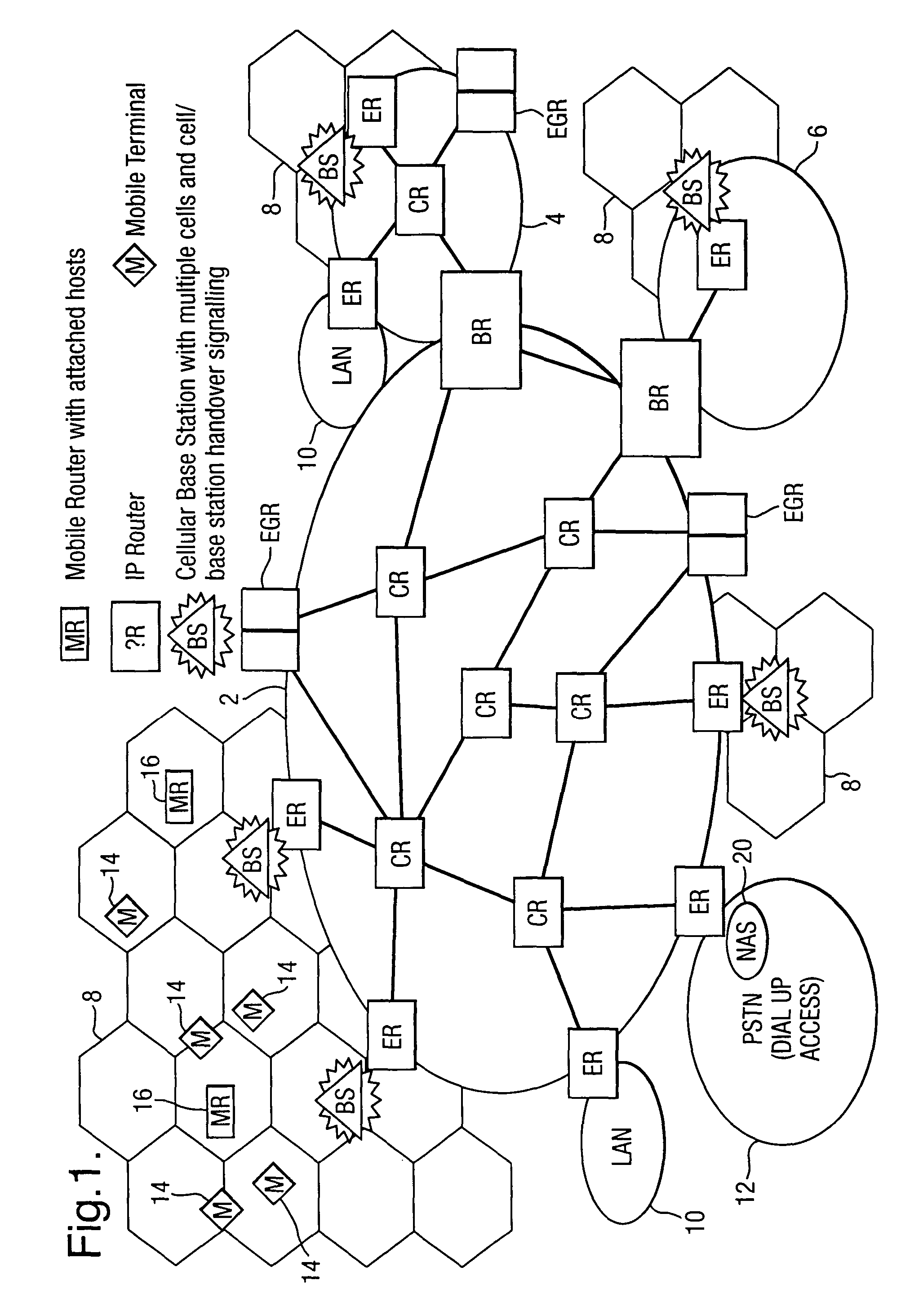
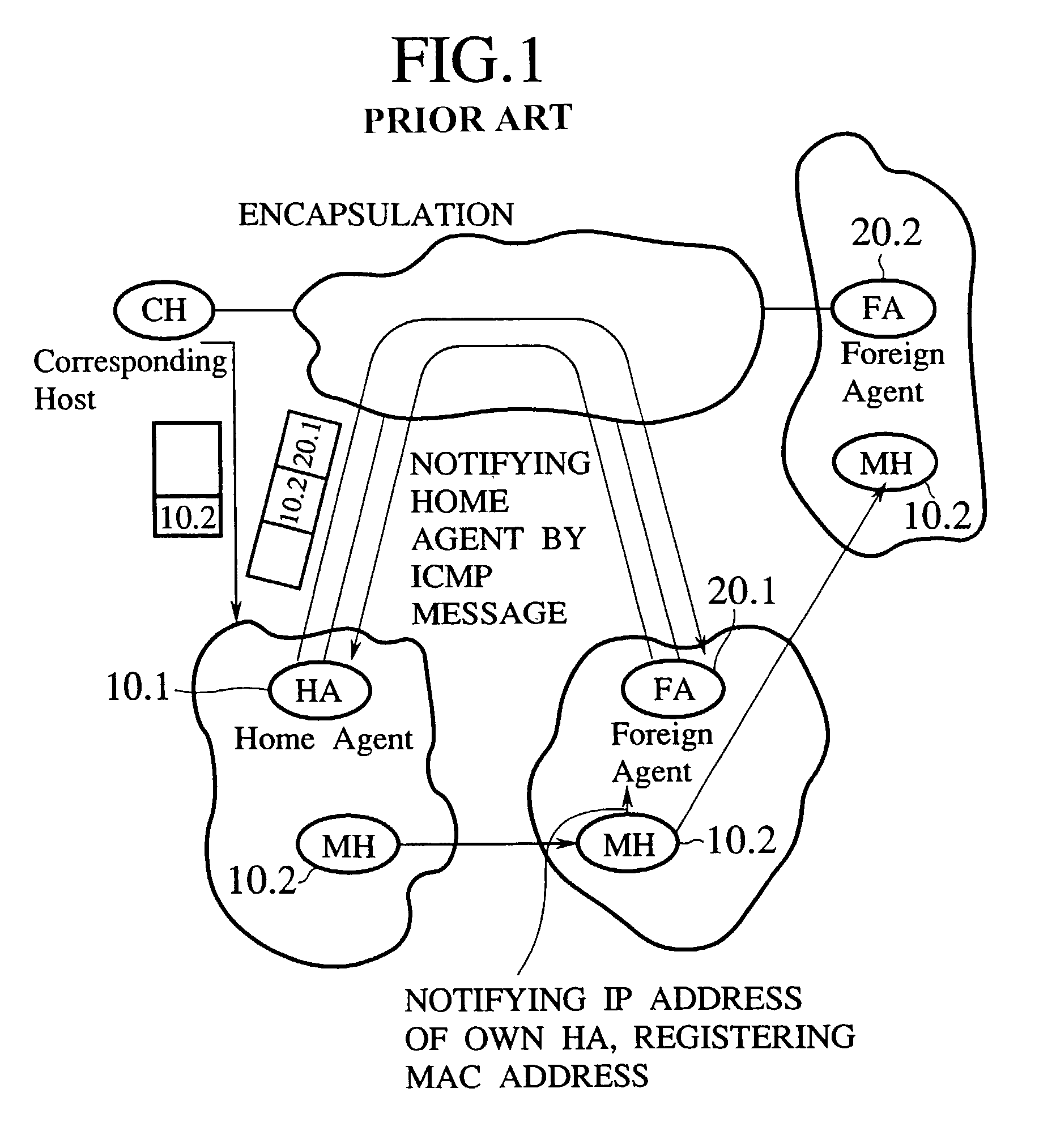
Router device, datagram transfer method and communication system realizing handoff control for mobile terminals
InactiveUS7151758B2Increase speedEasy to controlData switching by path configurationWireless network protocolsCommunications systemHandoff control
A mobile supporting router device for realizing the handoff control associated with the moving in high speed is forms by at least one first interface connected with radio base stations, each capable of accommodating at least one mobile terminal; at least one second interface connected with a wire network; an information exchanging unit for exchanging a routing protocol on a network layer, through the second interface; a memory unit for storing information regarding a routing on the network layer based on the routing protocol exchanged by the information exchanging unit; a transfer unit for transferring datagram through the first interface according to the information regarding the routing on the network layer stored in the memory unit; a moving detection unit for detecting a moving of the mobile terminal among the radio base stations; and an information updating unit for updating the information regarding the routing on the network layer stored in the memory unit when the moving of the mobile terminal is detected by the moving detection unit.
Owner:KK TOSHIBA
Network routing protocol power saving method for network elements
ActiveUS20140192677A1Energy efficient ICTData switching by path configurationDistance-vector routing protocolPath network
Methods and apparatus relating to network routing protocols to support power savings in network elements. A most utilized link path network topology for a computer network is discovered using a routing protocol such as a Spanning Tree, link-state, or distance vector routing protocol. In view of the most utilized link path network topology, links are identified as candidates for power management under which a power state of the link and associated network ports are managed to save power under applicable link conditions, such as low utilization. Link power-state change conditions are detected, and in response a corresponding change to the power state of a link is effected by changing the power-state of the network ports at the ends of the link. Power state changes include putting a link into a reduced power state, taking a link offline, and powering a link back up.
Owner:INTEL CORP
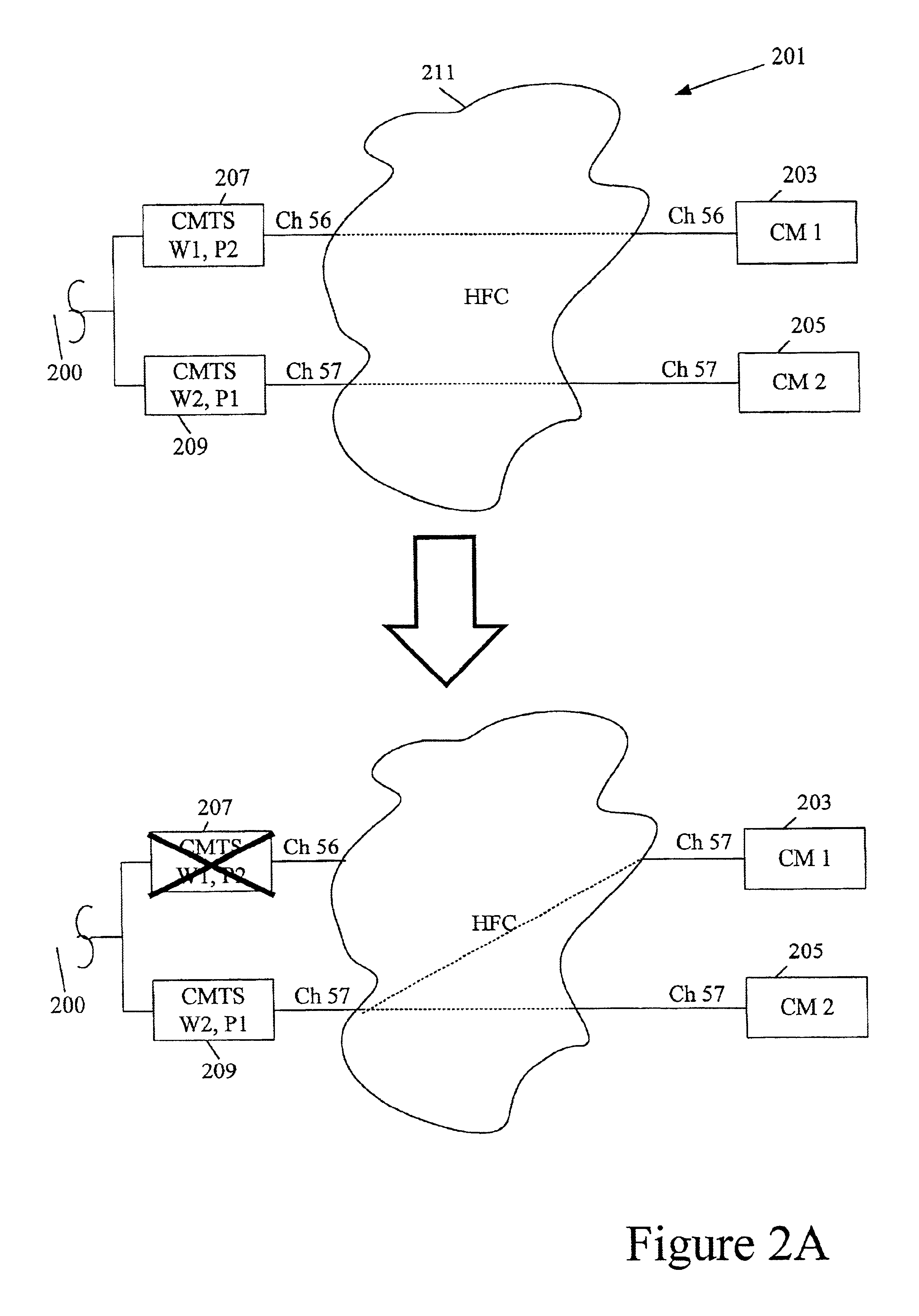
Routing protocol based redundancy design for shared-access networks
InactiveUS6839829B1Reduce delaysFew significant disruptionError preventionBroadband local area networksAccess networkModem device
A protection CMTS is available to immediately service a cable modem should that modem's service from a working CMTS fail for any reason. To speed the service transfer (cutover) from the working CMTS to the protection CMTS, the cable modem may preregister with the protection CMTS well before the cutover becomes necessary. The cable modem's registration with both the working CMTS and the protection CMTS preferably employs a single IP address, so that the cable modem need not obtain a new IP address during cutover. While the cable modem may register with both the working CMTS and the protection CMTS, the devices are designed or configured so that only the working CMTS injects a host route for the cable modem into the appropriate routing protocol. Only after cutover to the protection CMTS does the protection CMTS inject its host route.
Owner:CISCO TECH INC
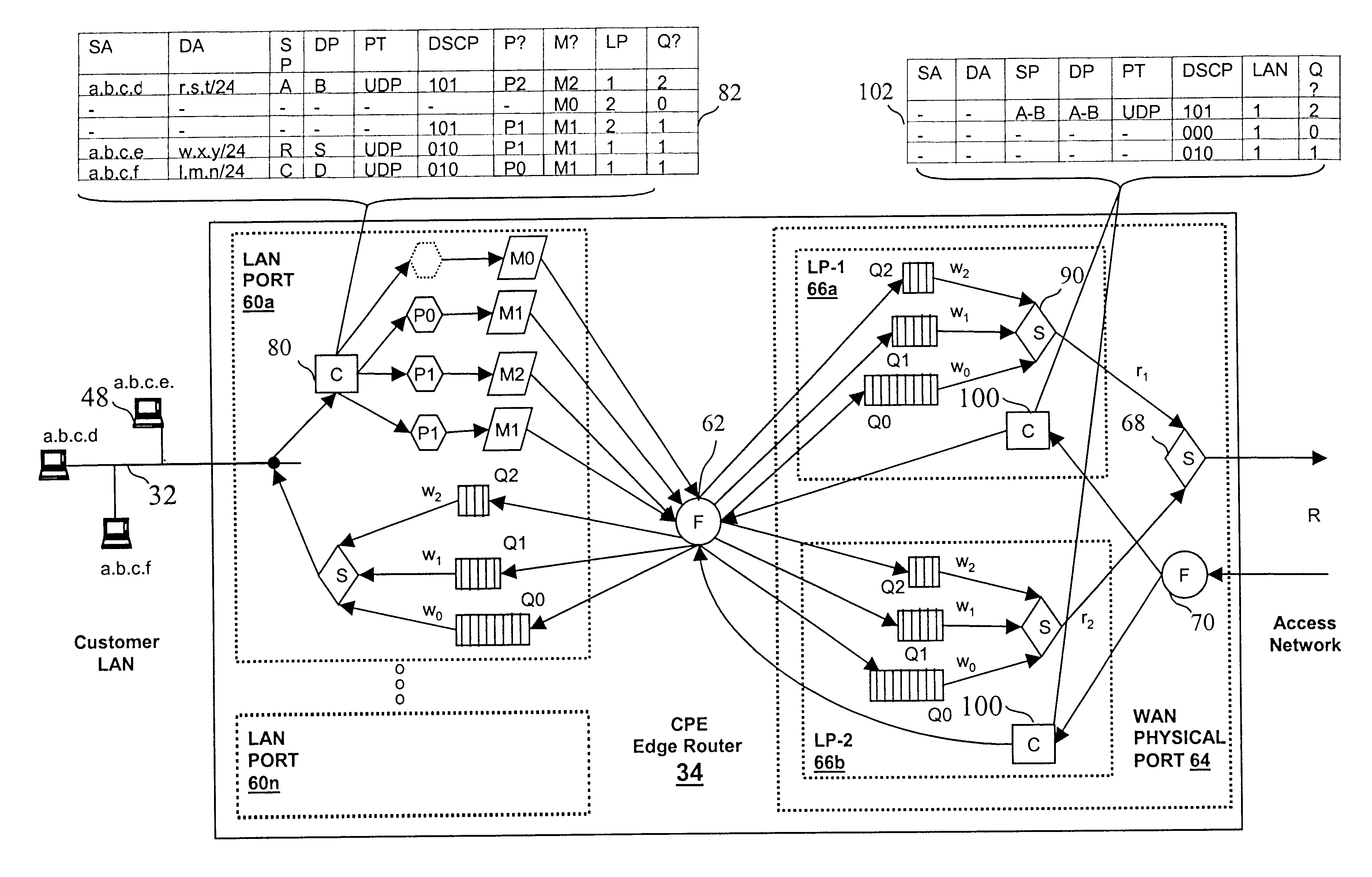
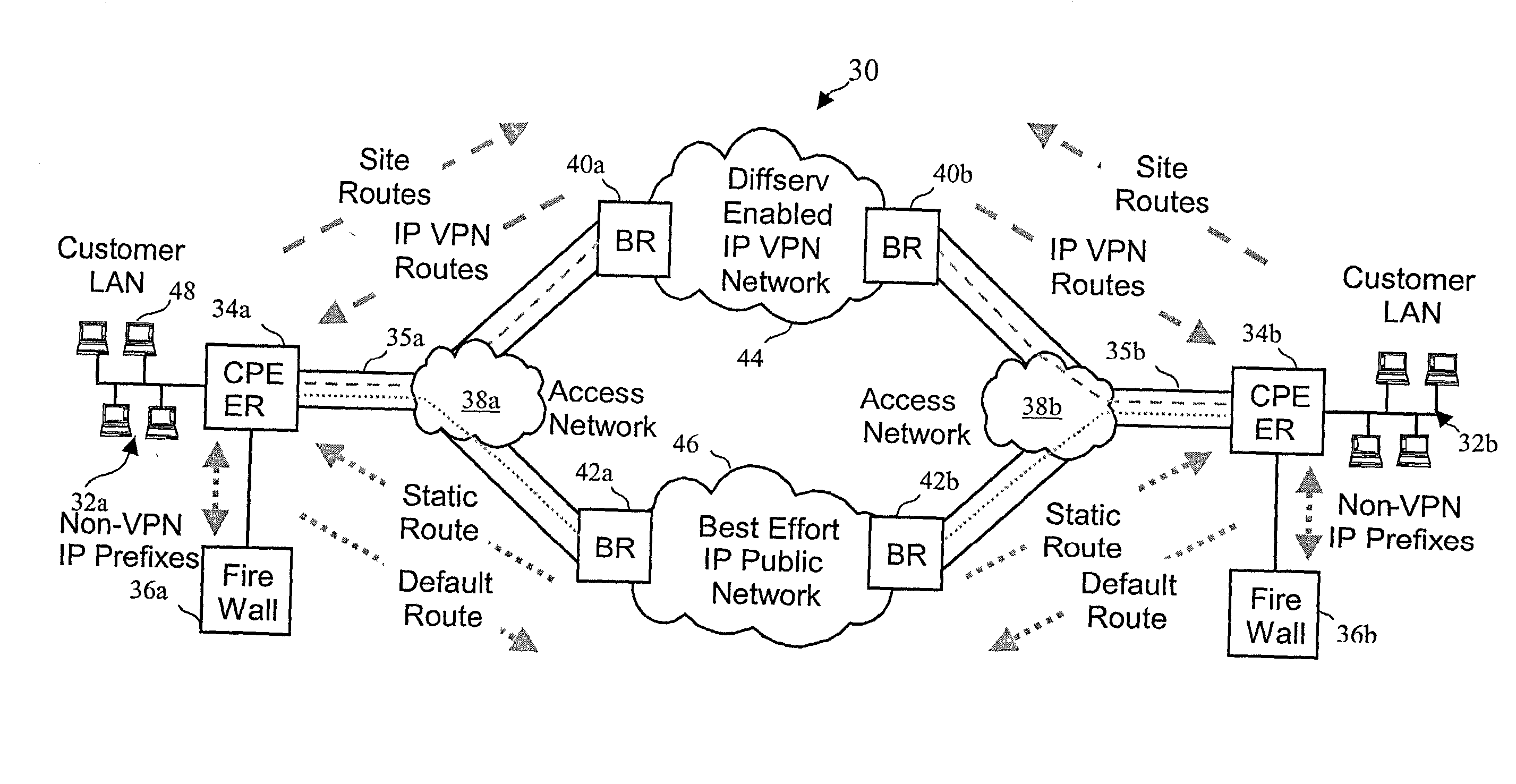
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
InactiveUS6778498B2Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
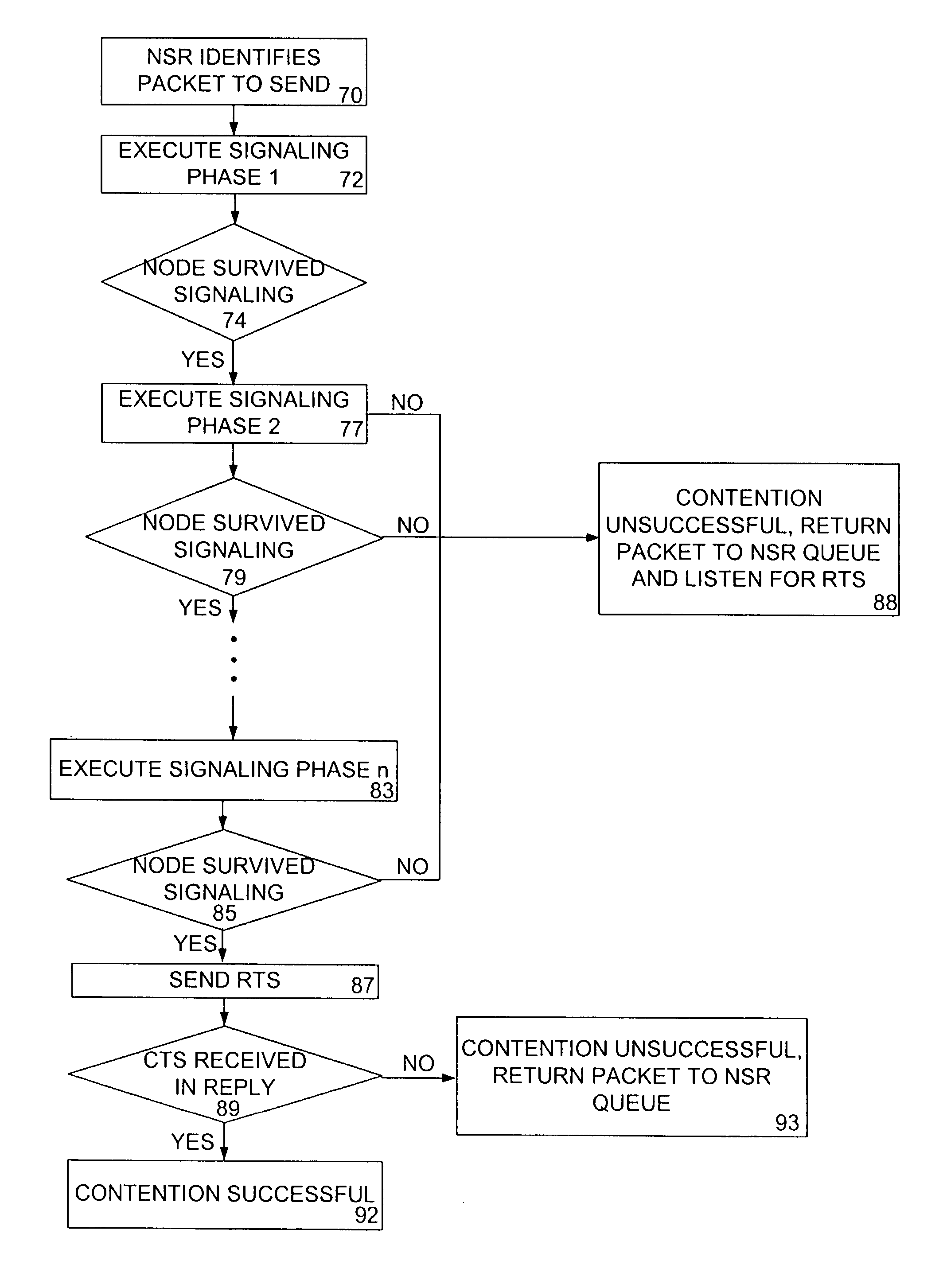
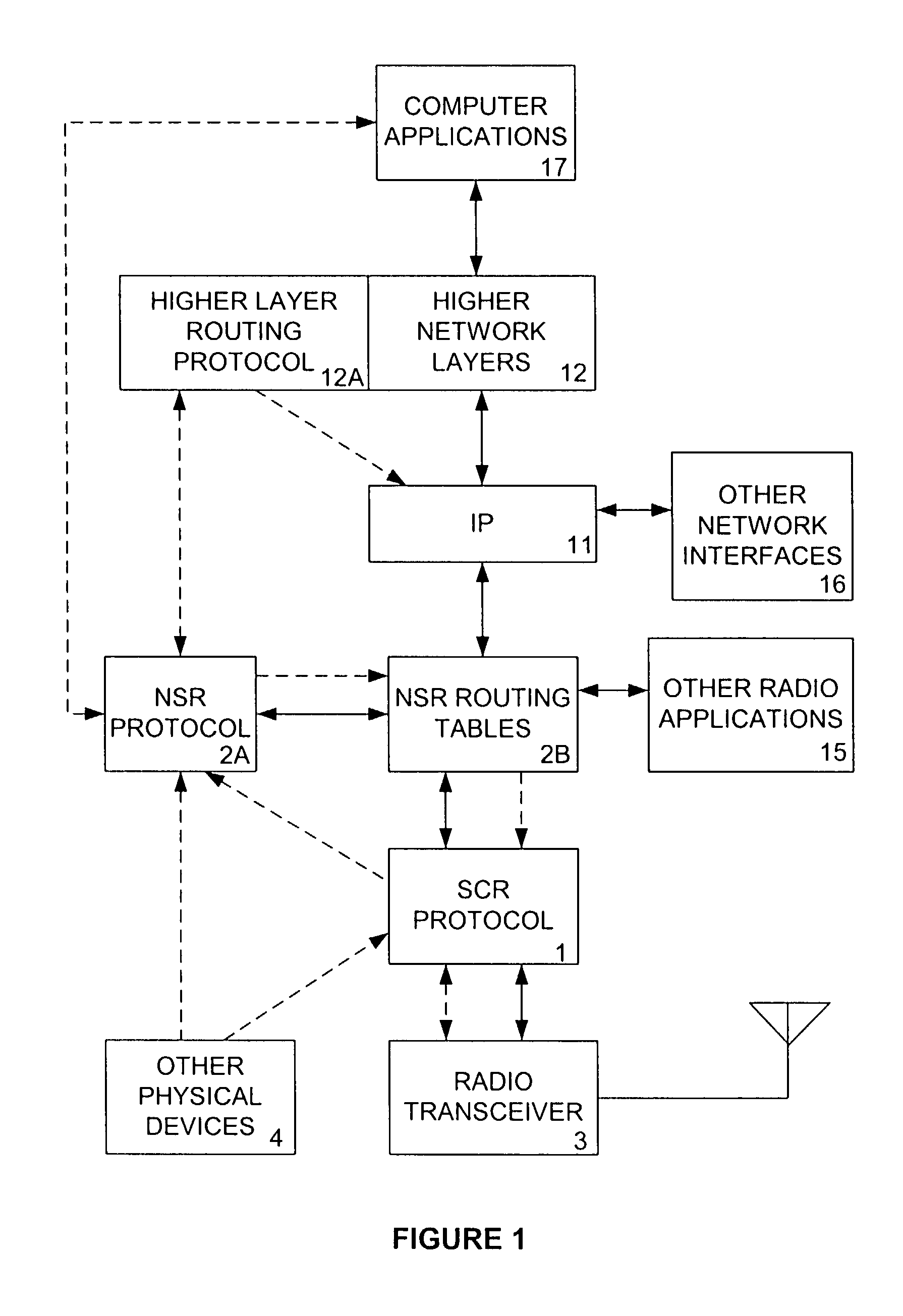
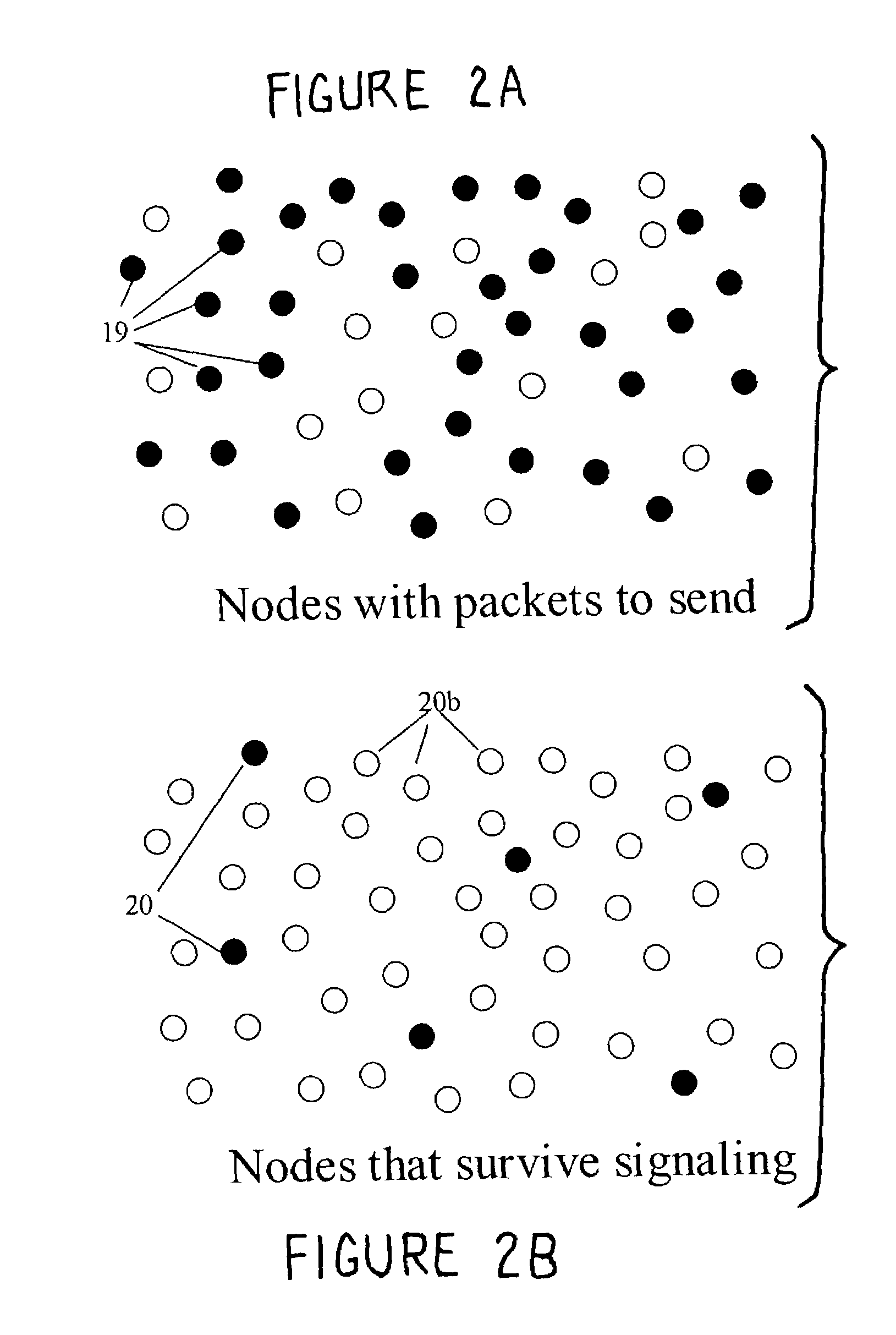
Access and routing protocol for ad hoc network using synchronous collision resolution and node state dissemination
ActiveUS7266085B2Without sacrificing performanceImprove performanceEnergy efficient ICTError preventionQuality of serviceSelf-organizing network
An ad hoc network organizes itself to provide communications without need for an a priori designated central control mechanism or base stations. Such self-organization is challenging in a multihop ad hoc network having member nodes that are highly mobile and widely distributed. A Synchronous Collision Resolution (SCR) protocol and a Node State Routing (NSR) protocol are well suited to provide efficient ad hoc network organization. SCR is an access protocol that achieves high capacity collision free access using a signaling approach that creates a random cellular-like network after each signaling period. NSR is a routing protocol that uses the dissemination of node states to predict link availability and to assign metrics to those links for the creation of optimized routes. In use, the present invention provides quality of service and supports energy conservation for the mobile nodes.
Owner:SCR NETWORKS LLC
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
InactiveUS20030112755A1Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
Power Control System and Method
ActiveUS20130085620A1Easy accessLevel controlEmergency protective arrangements for automatic disconnectionTablet computerPower control system
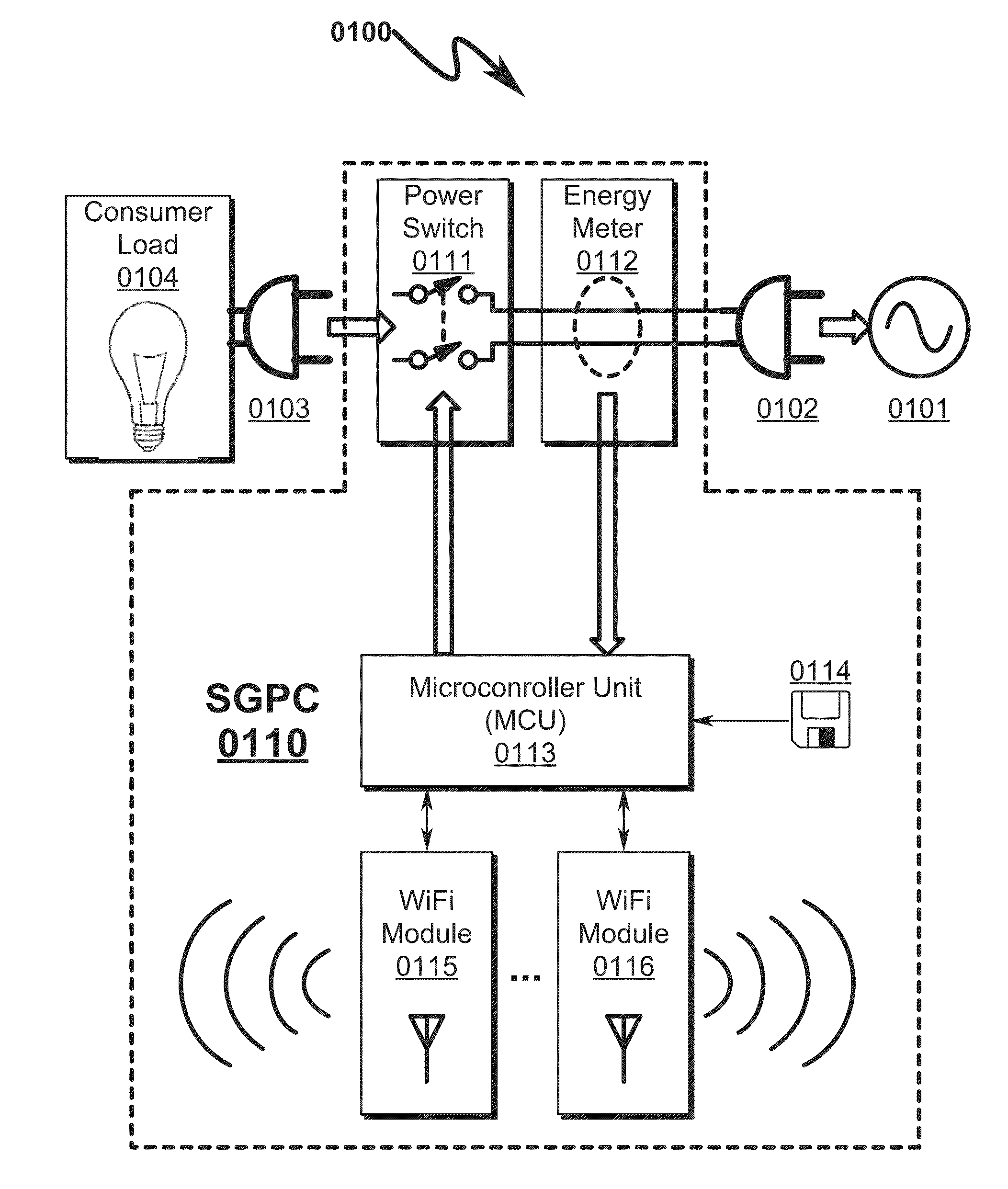
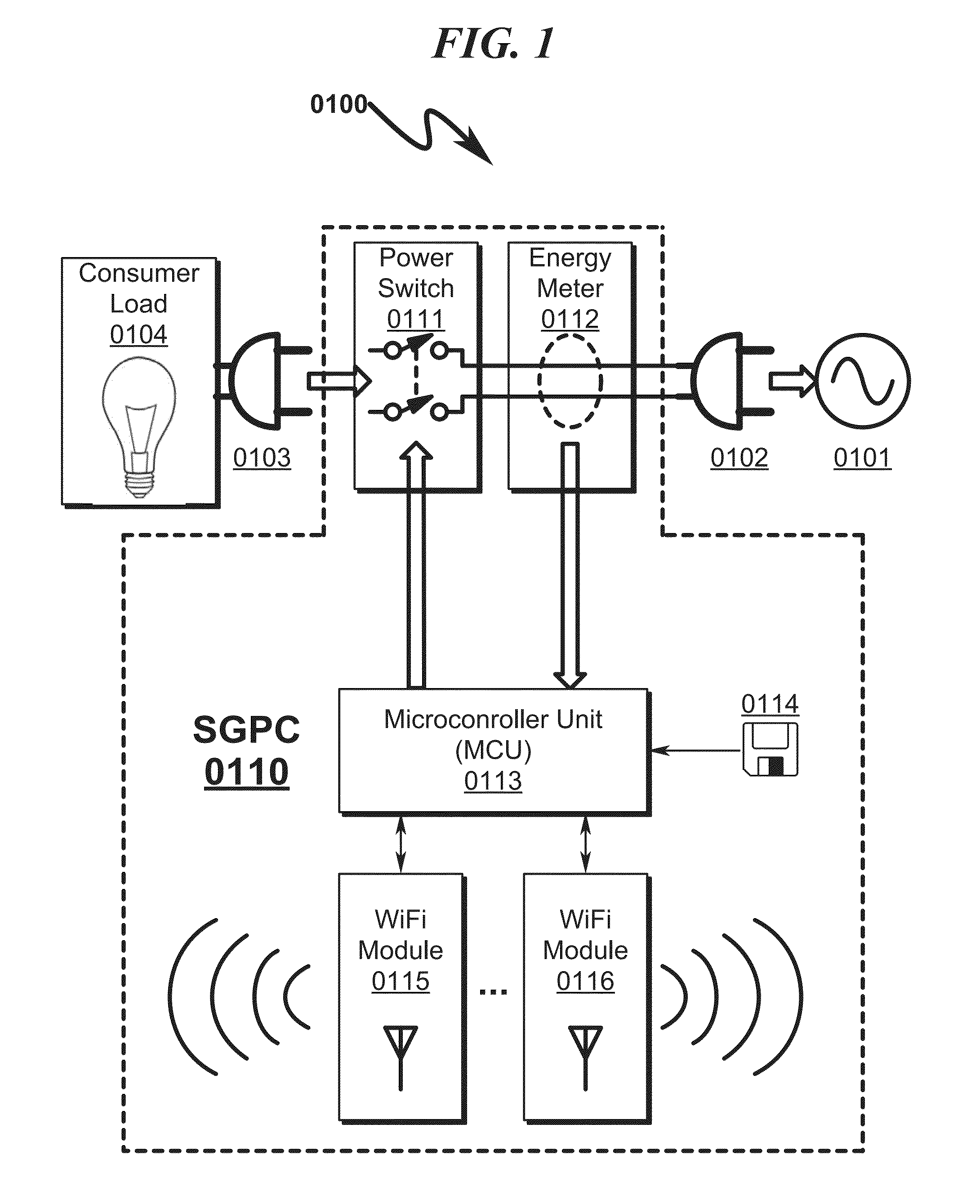
A power control system / method implementing Internet based access to hybrid home automation networks is disclosed. The system utilizes a smart gateway power controller (SGPC) to selectively switch an AC power source to a load device under control of local or remote network commands that may be routed through a variety of network interfaces and protocols present within a home or other structure-local communications network. SGPC configurations may be nested within a home automation network to permit separation of control for load devices within a common home automation environment. Present invention methods may include routing protocols between disparate home automation networks as well as remote access protocols that permit control of disparate home automation networks via the Internet using a wide variety of remote access interfaces including mobile devices, tablet computers, laptops, desktop computers, and the like.
Owner:ADVANERGY
Router and routing protocol redundancy
InactiveUS20050265346A1Reduce service outage and degradationImprove service availabilityData switching by path configurationSoftwareRouting protocol
A router and routing protocol redundancy are disclosed to reduce service outage or degradation for a network device and thus to increase service availability on a network due to software and hardware failures of the network device. A network device such as router includes a redundancy platform having an active controller system and a standby controller system. A routing protocol state change is received or generated by the active controller system. The received or generated routing protocol state change is replicated to the standby controller system. By replicating the routing protocol state change, the standby controller system can maintain the routing protocol sessions for the network device if a failure occurs in the active controller system. Furthermore, the routing protocol states are maintained in realtime to handle the dynamic changes created by routing protocols.
Owner:RPX CORP
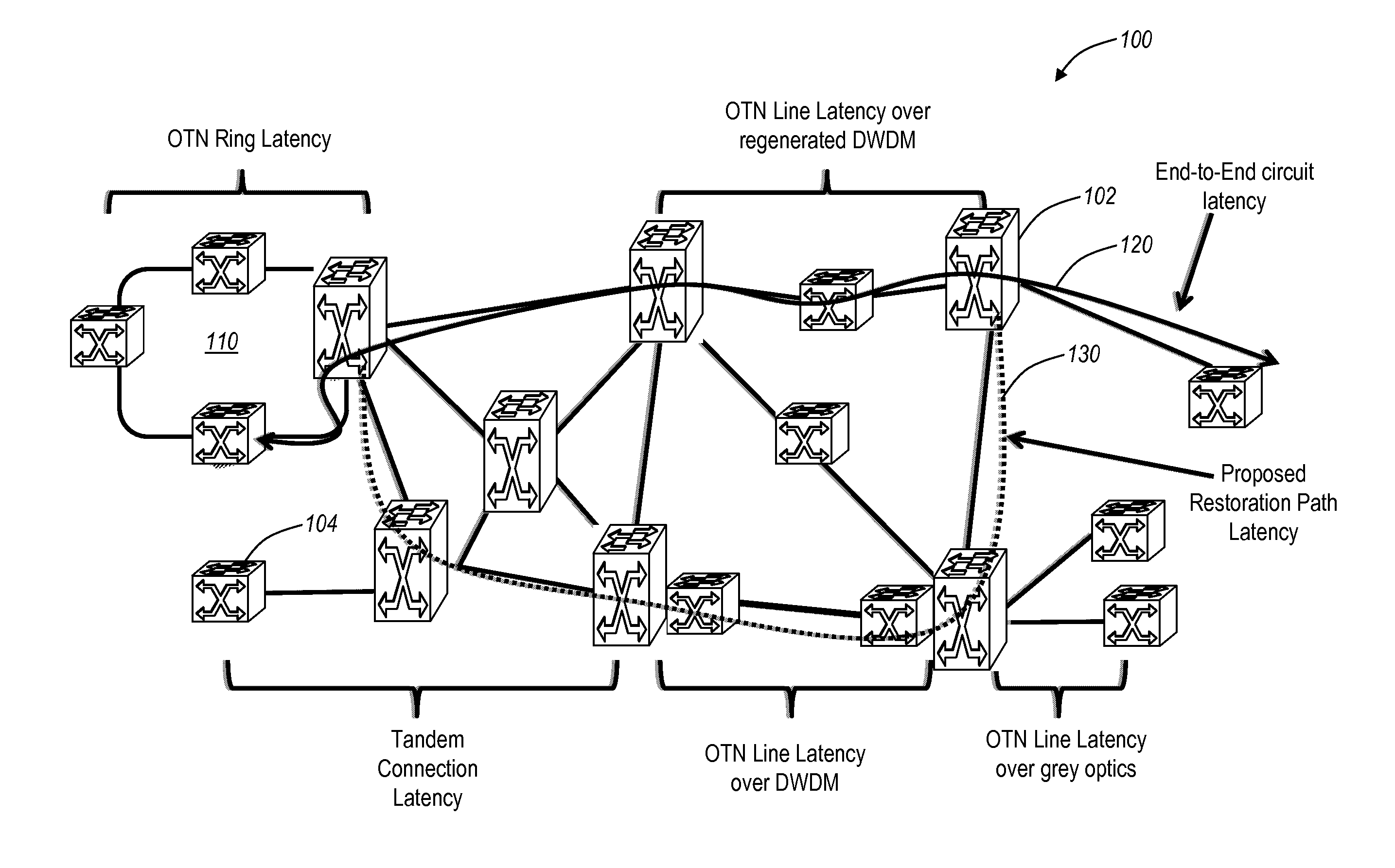
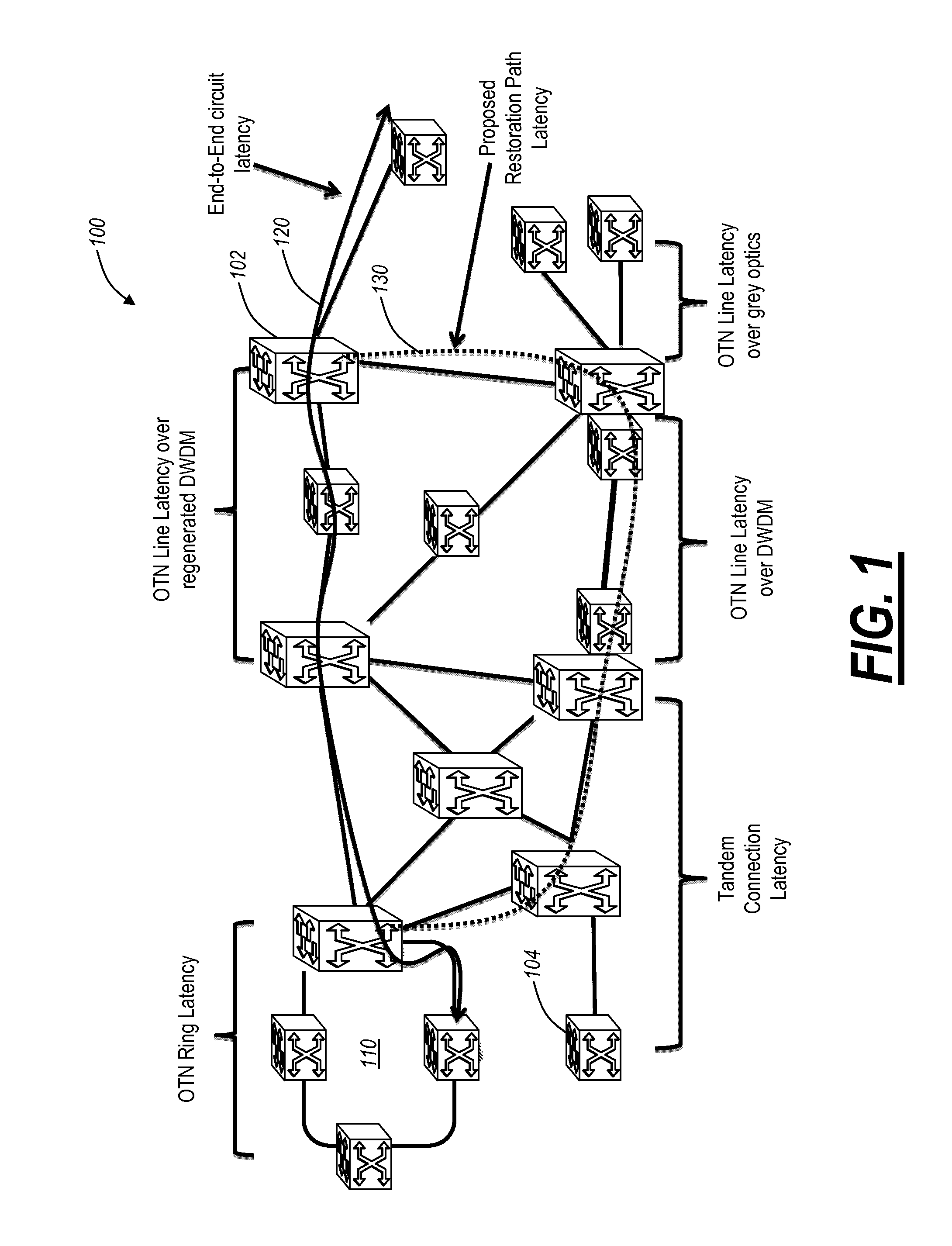
Systems and methods of measuring latency and routing thereon in optical networks
ActiveUS20110170860A1Preventing mesh restorationMultiplex system selection arrangementsTime-division multiplexNODALMaximum latency
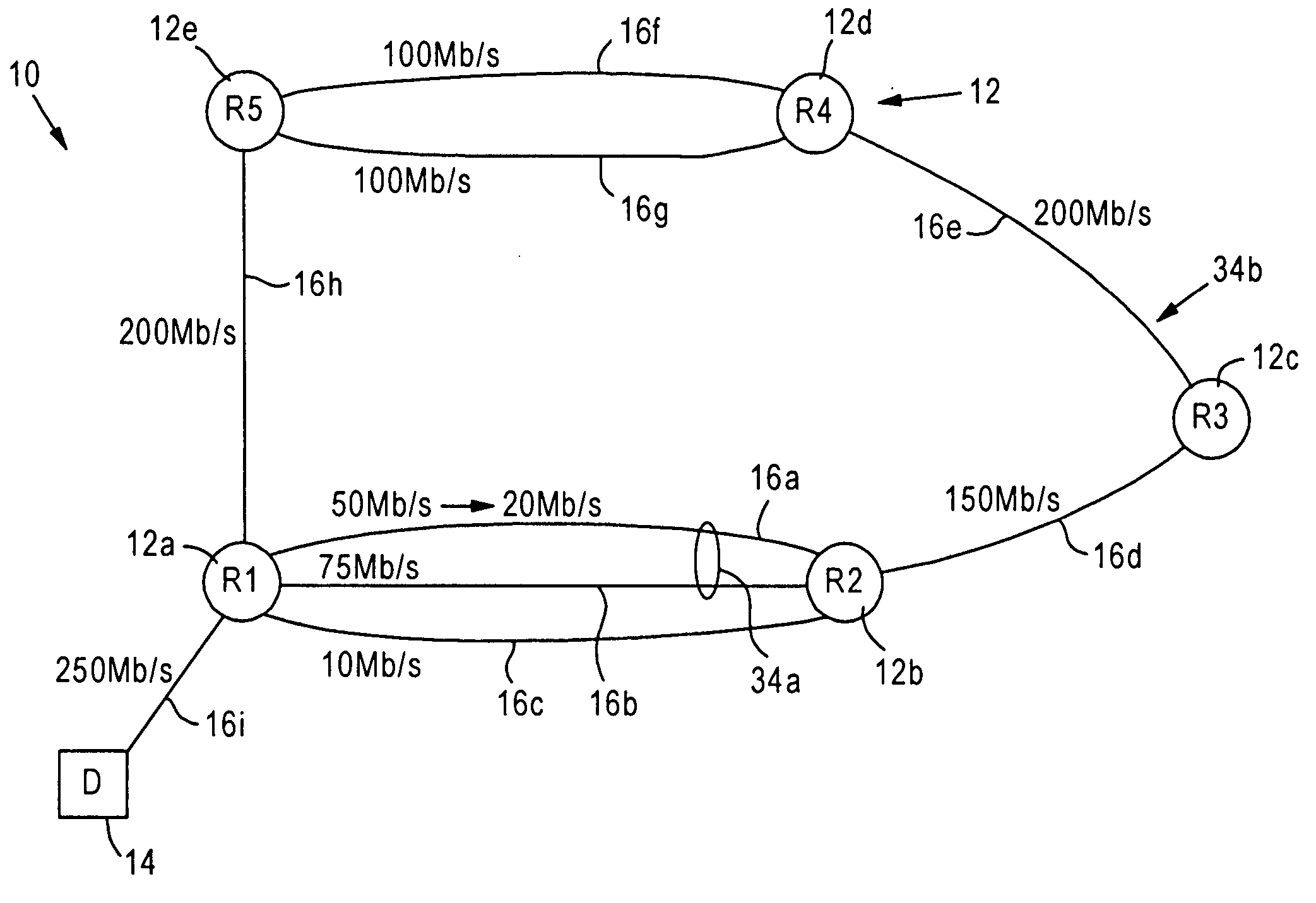
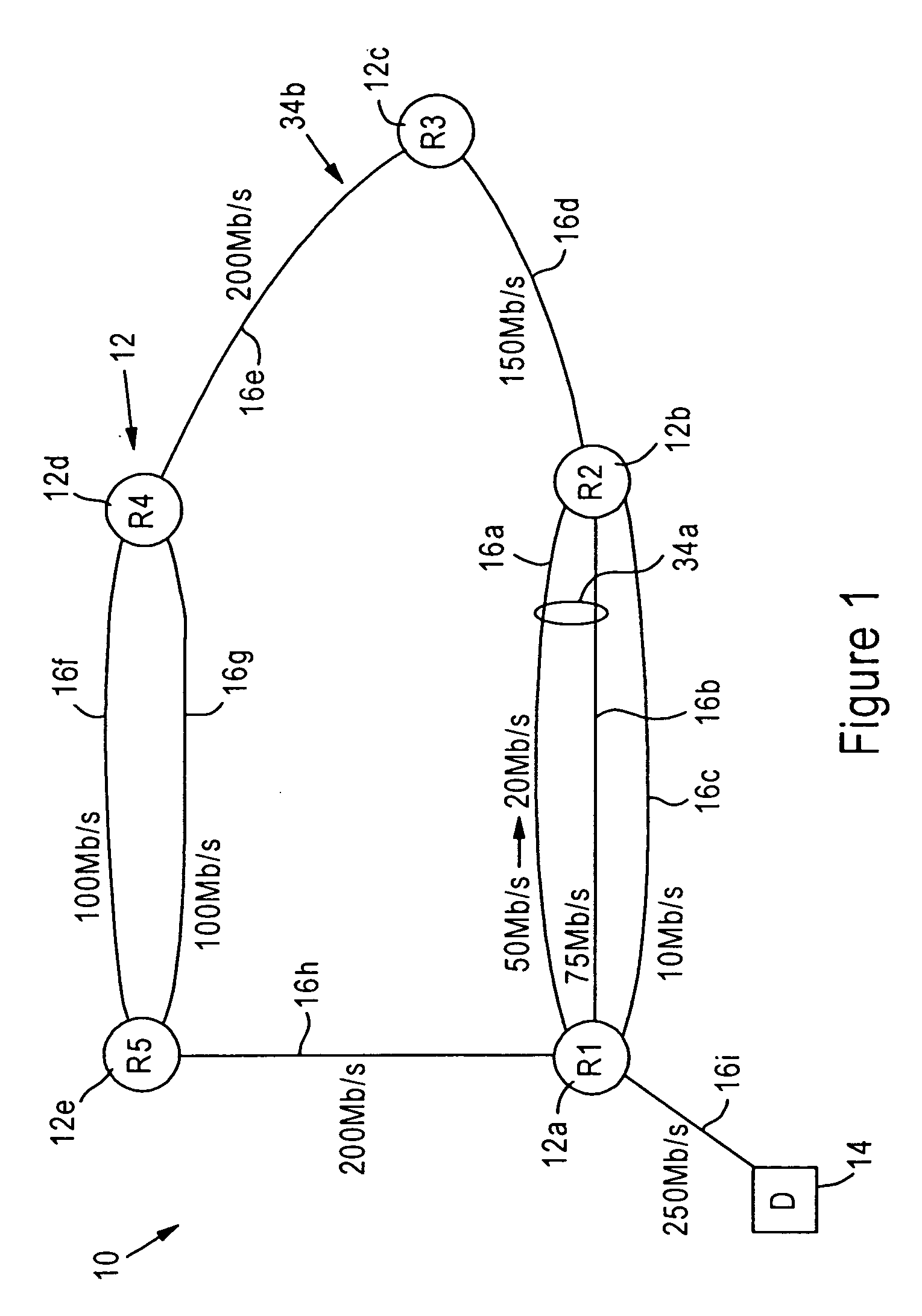
The present disclosure provides systems and methods for making latency measurements and using these measurements in routing in optical networks. In an exemplary embodiment, a method is defined whereby two nodes sharing a line automatically determine whether both nodes are capable of making a latency measurement and then which node will initiate and which node participates in making the latency measurement. In another exemplary embodiment, an on-demand latency measurement may be made between any two arbitrary nodes within a domain. Routing messages may be used to disseminate the latency of links via a signaling and routing protocol. Advantageously, the present invention provides measurement of latency and latency variation of customer circuits (i.e., SNCs) using an in-band, non-intrusive calculation with a high-degree of accuracy. Furthermore, the present invention may consider these calculations for circuit routing based on the latency and circuit acceptance based on maximum latency restrictions.
Owner:CIENA
Router configured for outputting update messages specifying a detected attribute change of a connected active path according to a prescribed routing protocol
ActiveUS20050195835A1Easy to routeEfficient sharingEnergy efficient ICTData switching by path configurationData streamComputer science
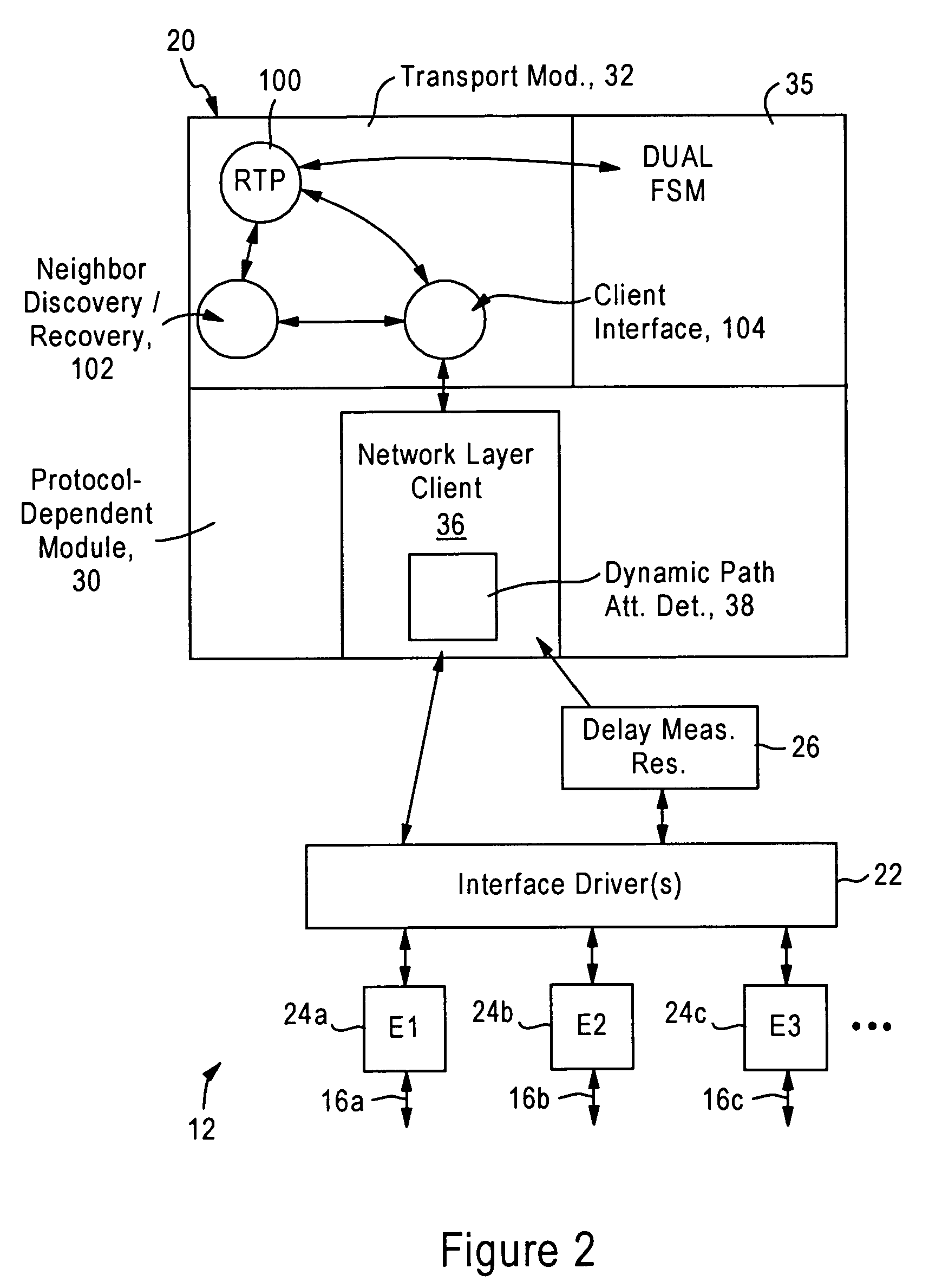
A first router is configured for monitoring prescribed attributes of an active path connected to the first router, and supplying an update message to a second router, according to a prescribed routing protocol such as Enhanced Interior Gateway Routing Protocol (EIGRP), that specifies a detected change by the first router in at least one of the prescribed attributes of the connected active path. Hence, the second router, in response to receiving the update message, can update an internal topology table based on the detected change in the active path connected to the first router, and selectively adjust an internal routing table based on the detected change relative to queuing policies for prescribed data flows.
Owner:CISCO TECH INC
Detecting data plane liveliness of a label-switched path
ActiveUS7463591B1Error preventionFrequency-division multiplex detailsForwarding equivalence classNetwork packet
Detecting if a label-switched path (LSP) is functioning properly. To test that packets that belong to a particular Forwarding Equivalence Class (FEC) actually end their MPLS LSP on an label switching router (LSR) that is an egress for that FEC, a request message carrying information about the FEC whose LSP is being verified may be used. The request message may be forwarded like any other packet belonging to that FEC. A basic connectivity test as well as a fault isolation test are supported. In a basic connectivity test mode, the packet should reach the end of the LSP, at which point it is sent to the control plane of the egress LSR. The LSR then verifies that it is indeed an egress for the FEC. In a fault isolation test mode, the packet is sent to the control plane of each transit LSR, which performs various checks that it is indeed a transit LSR for the LSP. The transit LSR may also return further information that helps check the control plane against the data plane, i.e., that forwarding matches what the routing protocols determined as the path. A reliable return path is used for the reply.
Owner:JUMIPER NETWORKS INC
Routing protocol for ad hoc networks
InactiveUS20050030921A1Enabling detectionSpecial service provision for substationError prevention/detection by using return channelRouting protocol
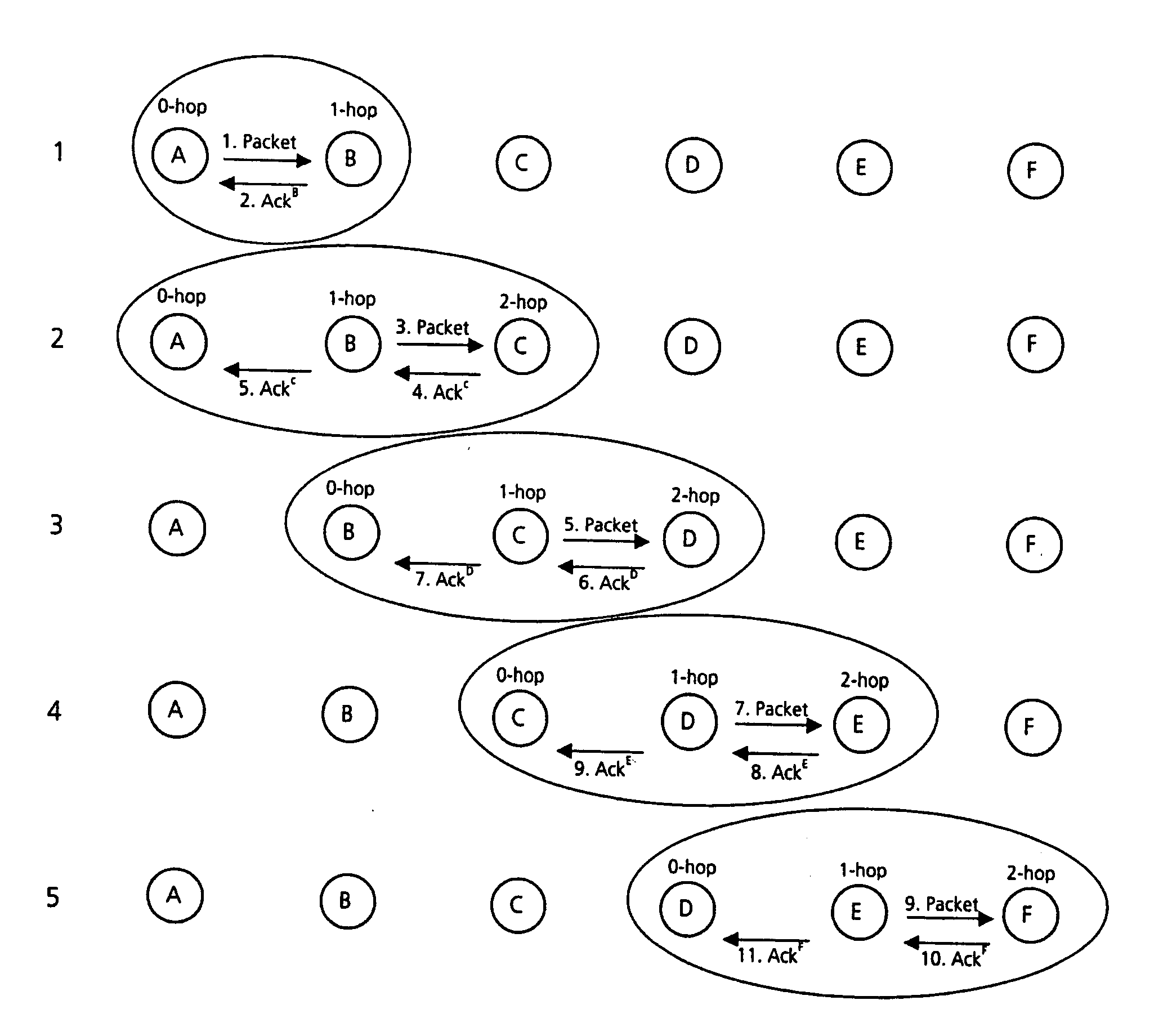
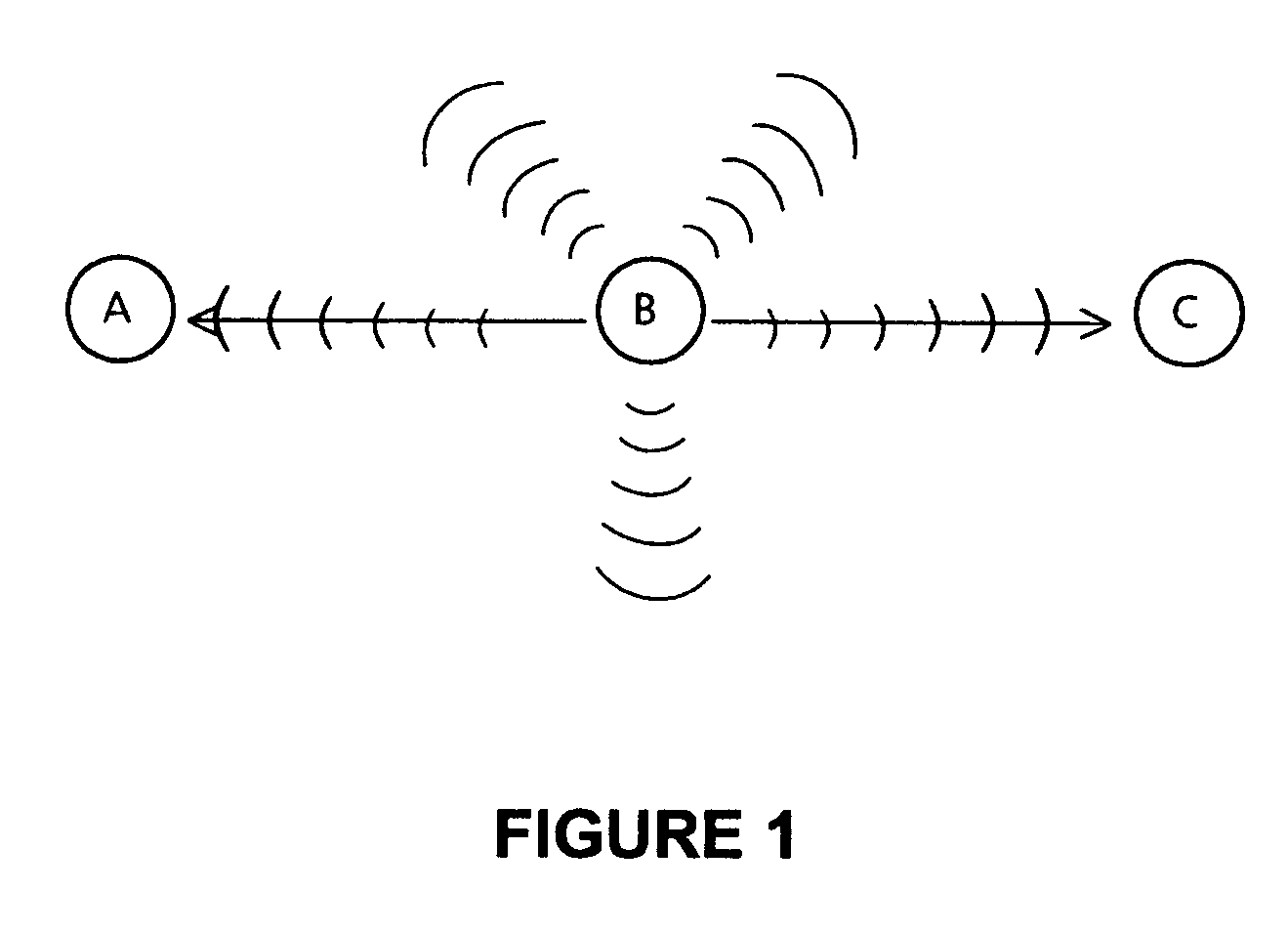
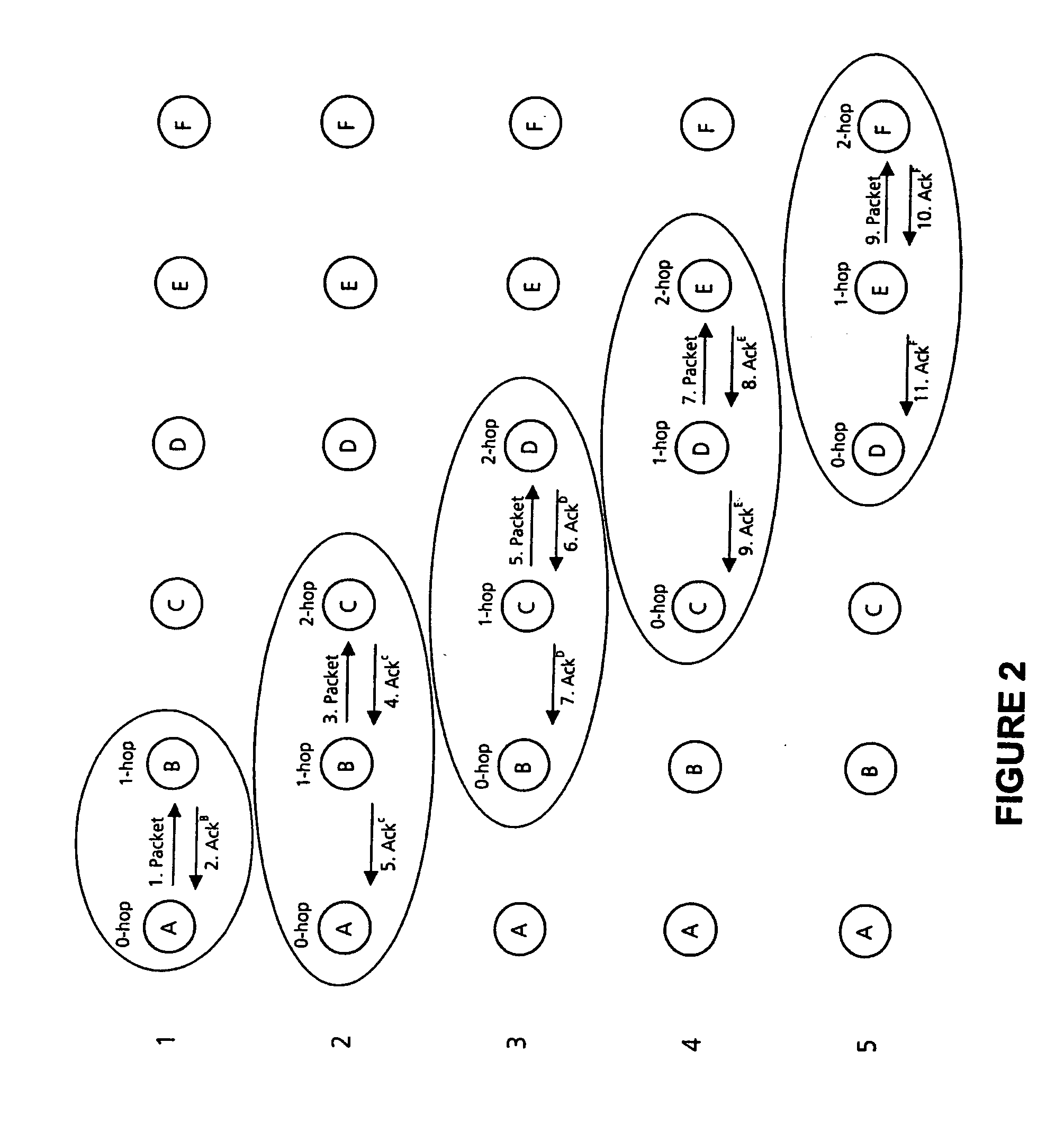
A routing method for an ad hoc network is disclosed, the network comprising two or more nodes (A, B, C, D, E, F), and the method comprising: sending a message from a start node (A) to a finish node (F) via one or more intermediate nodes (B, C, D, E); each of the start node (A) and intermediate nodes (B, C, D, E) receiving an acknowledgement signal (AckB, AckC, AckD, AckE, AckF) from a one-hop neighbouring node when the one-hop neighbouring node receives the message from the start node (A;F) or intermediate nodes (B, C, D, E) and, in the case of the one-hop neighbouring node not being the finish node (F), the start node and intermediate nodes receiving an acknowledgement signal (AckC, AckD, AckE, AckF) from a two-hop neighbouring node when the two-hop neighbouring node receives the message from the one-hop neighbouring node.
Owner:ROYAL HOLLOWAY UNIV OF LONDON +1
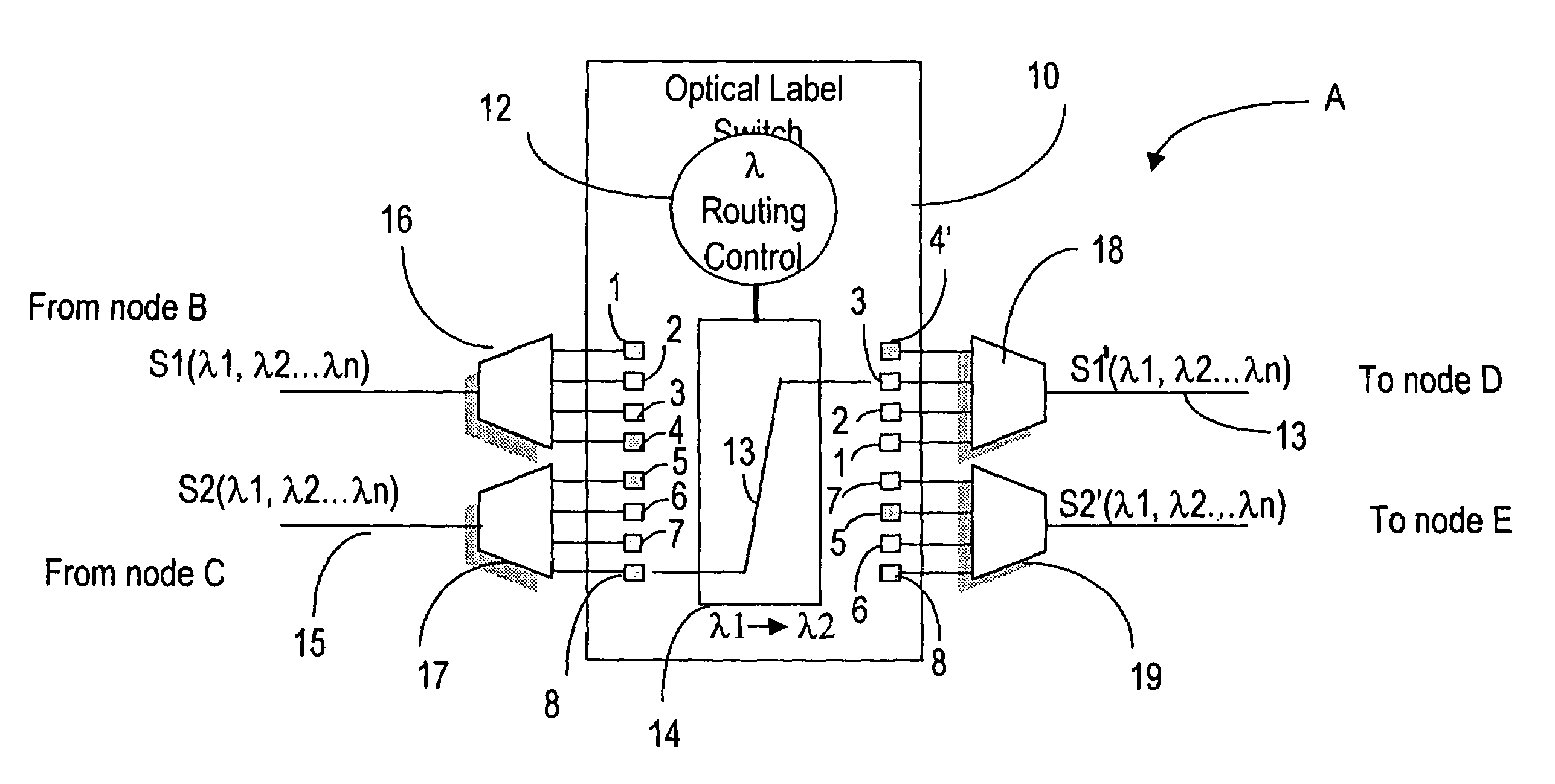
MPLS application to optical cross-connect using wavelength as a label
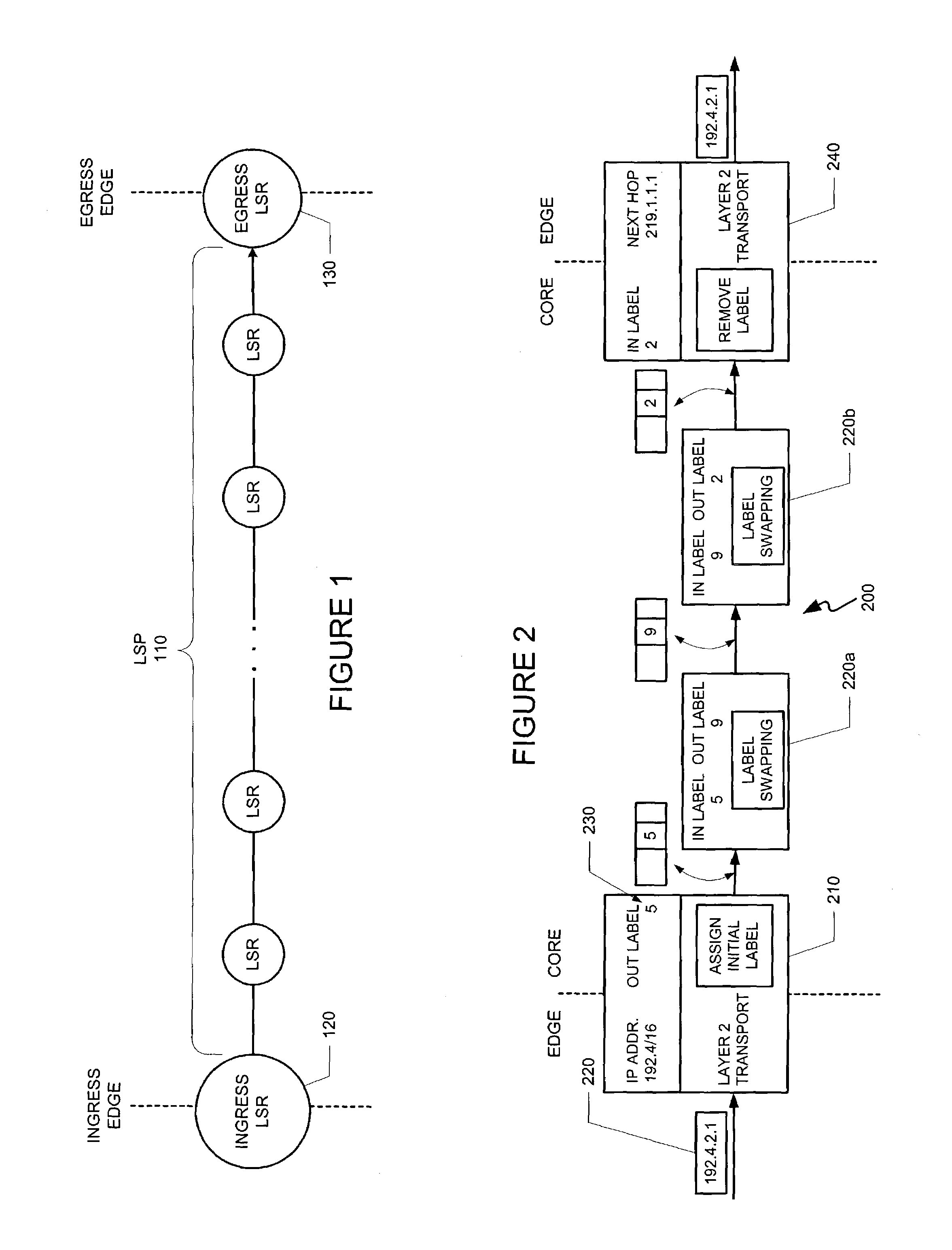
InactiveUS7031607B1Easy networkingMultiplex system selection arrangementsOptical multiplexCross connectionMulti protocol
A label switching routing protocol for establishing a datapath as a sequence of locally unique labels in an optical communications network, is provided. A wavelength on an optical cross-connect is considered as a label, or one portion of a label. Timeslots may be assigned to designated wavelengths so as to form the second portion of a composite label. An optical / time cross-connect (OTXC) capable of wavelength conversion from an input to an output interface creates the datapath based on wavelength to wavelength substitution, under the control of a multi-protocol label switching (MPLS) protocol.
Owner:CIENA
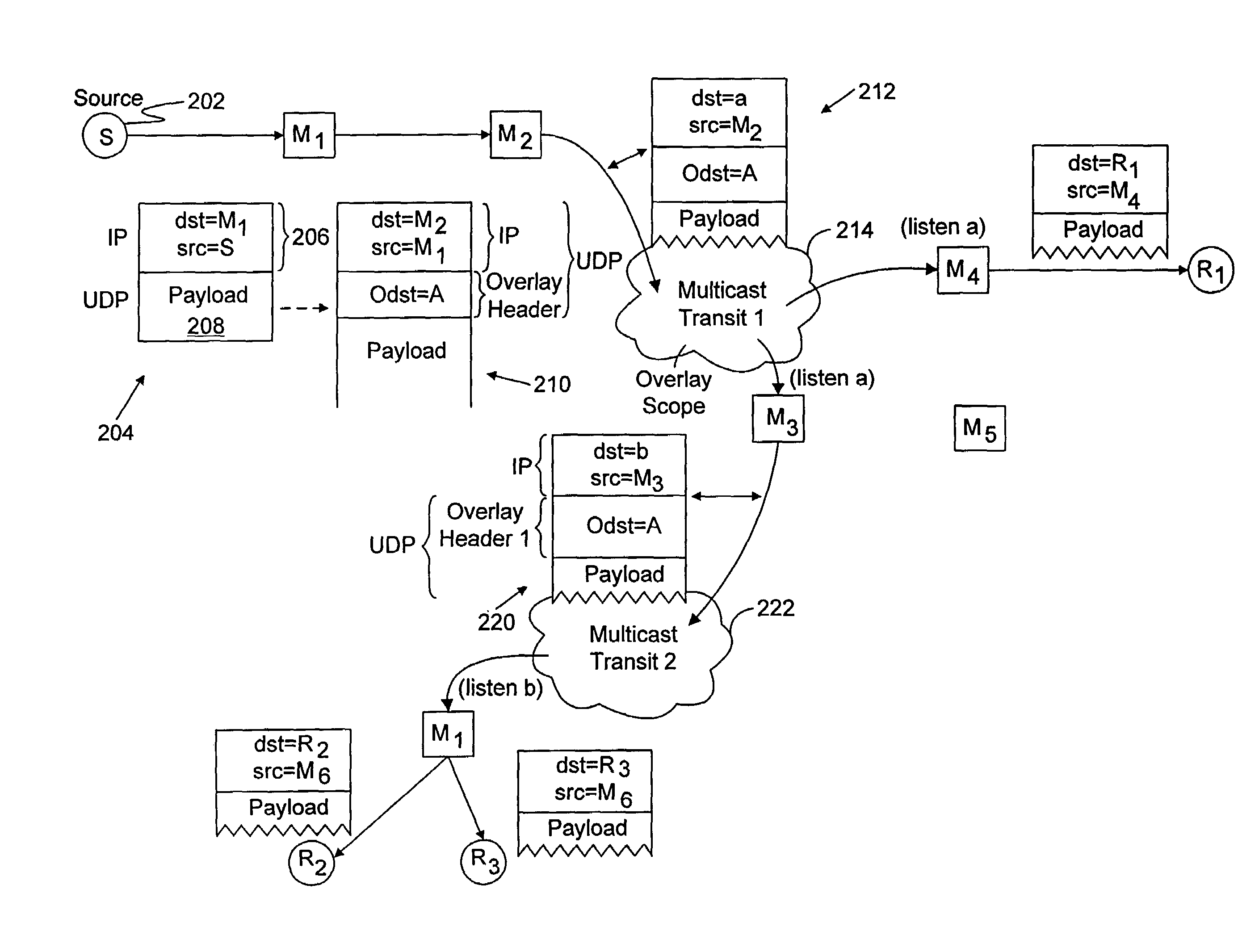
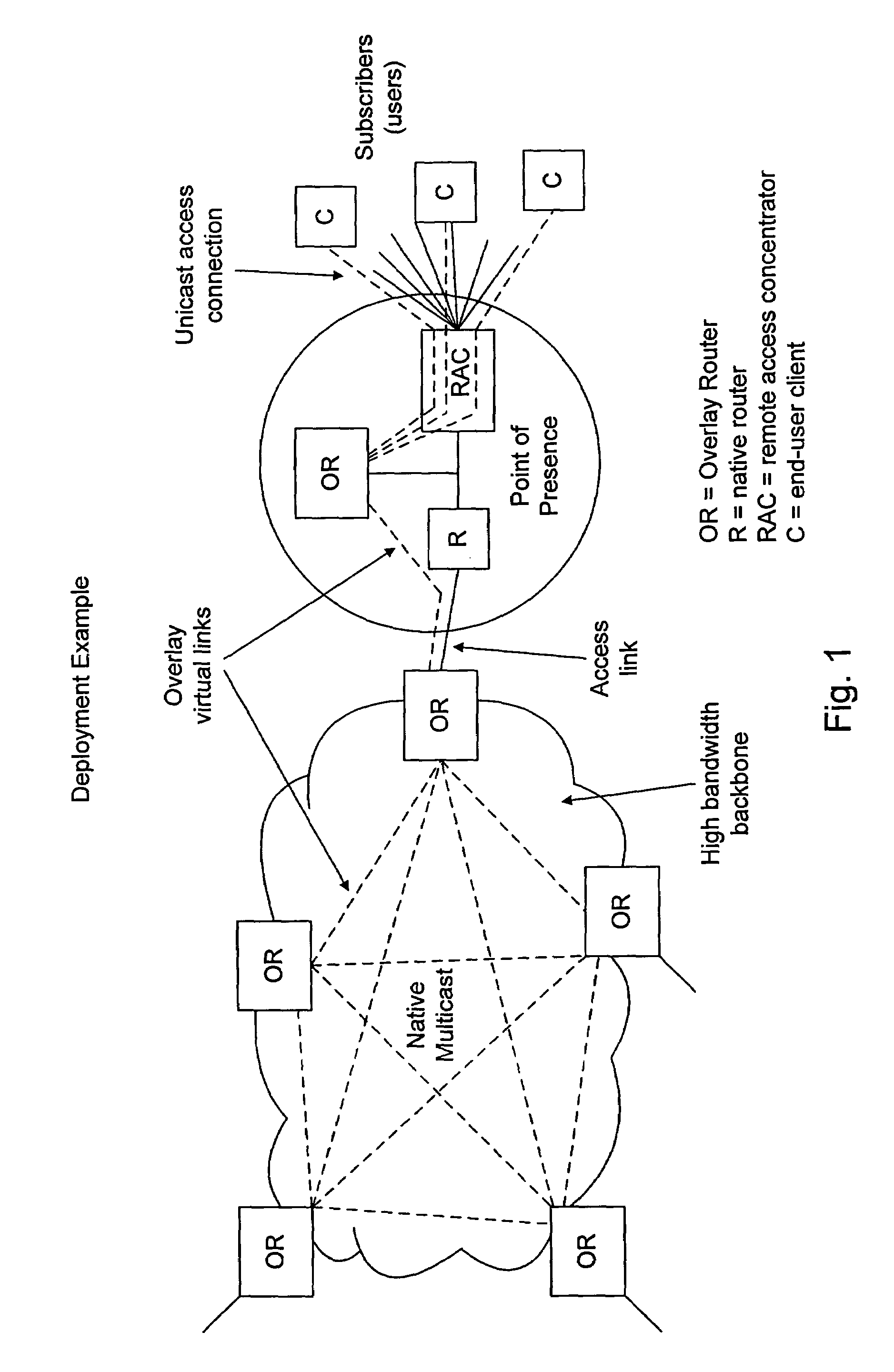
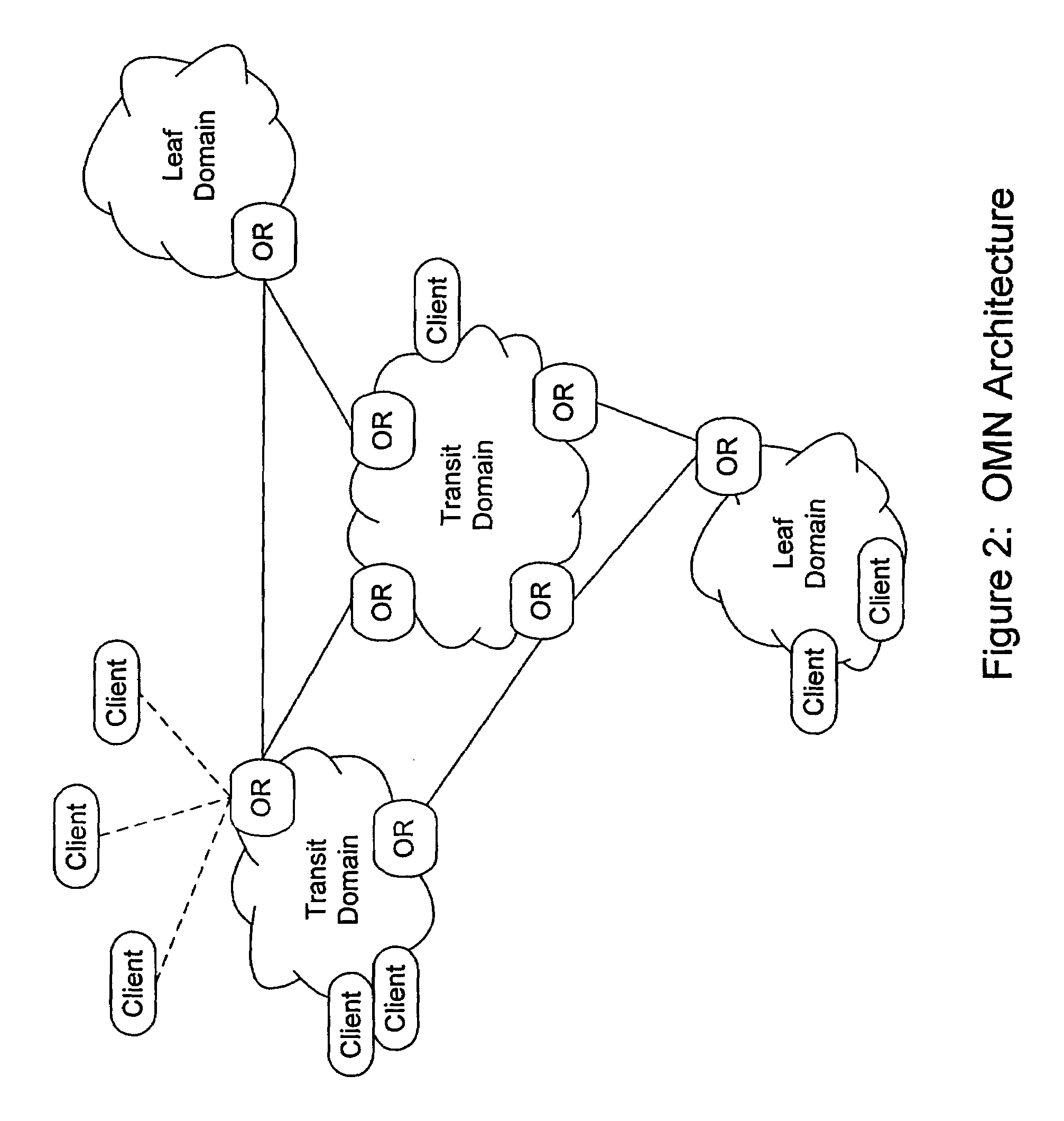
Performing multicast communication in computer networks by using overlay routing
InactiveUS7133928B2Efficient managementSpecial service provision for substationDigital computer detailsRouting tableMulticast network
An overlay protocol and system for allowing multicast routing in the Internet to be performed at the application level. The overlay protocol uses “native” Internet multicast and multicast routing protocols to route information, according to overlay routing tables. Overlay groups are mapped to native multicast groups to exploit native multicasting in regional or local forwarding domains. Use of the overlay protocol allows overlay distribution to be handled in a more intelligent and bandwidth-managed fashion. Overlay routers are placed at each of several local area networks, Internet service provider's point of presence, enterprise, or other cohesively-managed locations. The overlay computers are configured according to bandwidth and security policies, and perform application-level multicast distribution across the otherwise disjoint multicast networks by using the overlay routing. The result is an overlay multicast network that is effectively managed according to local network management policies. Application-level control can be applied to the transferred data at the overlay routers.
Owner:GOOGLE LLC
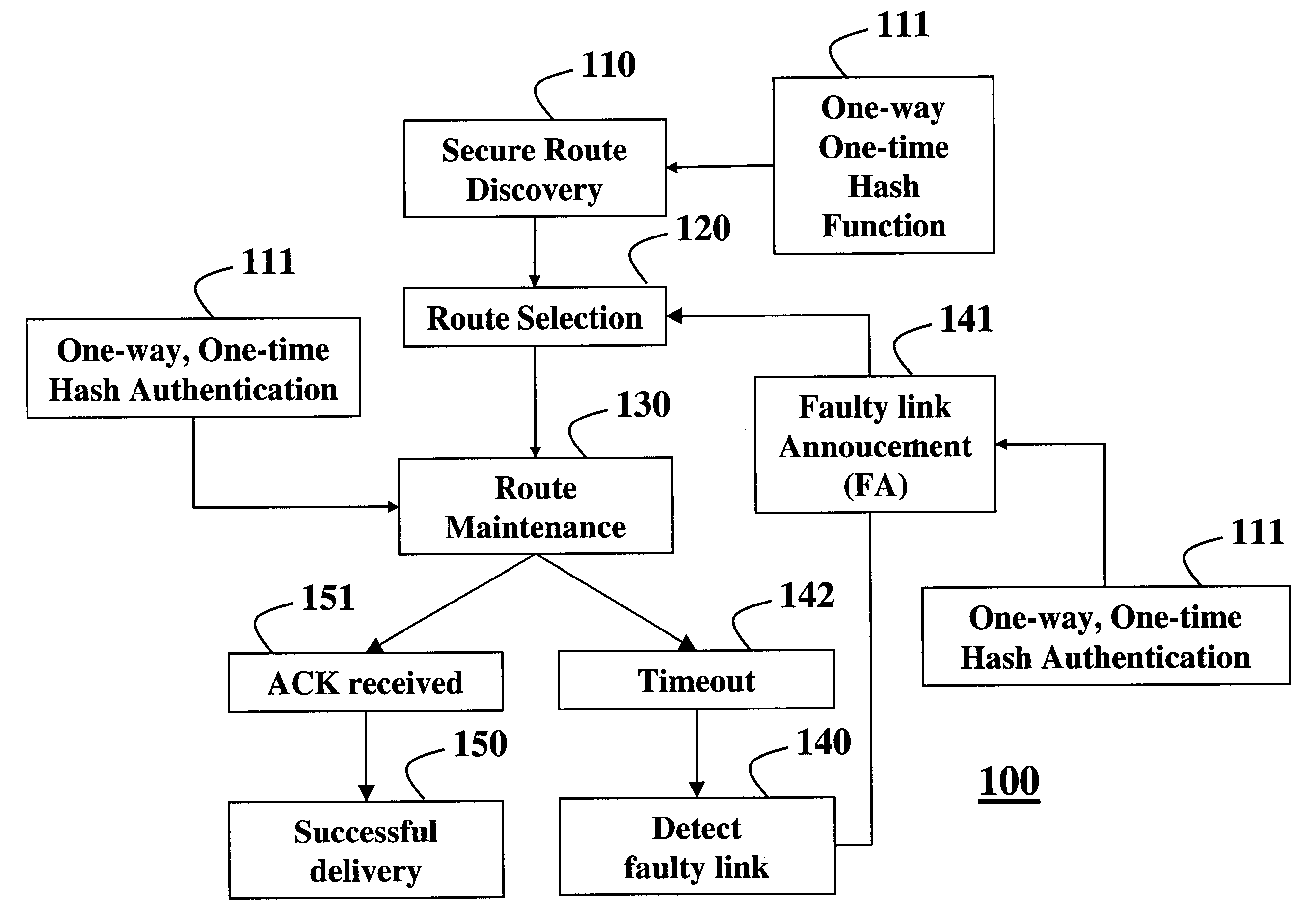
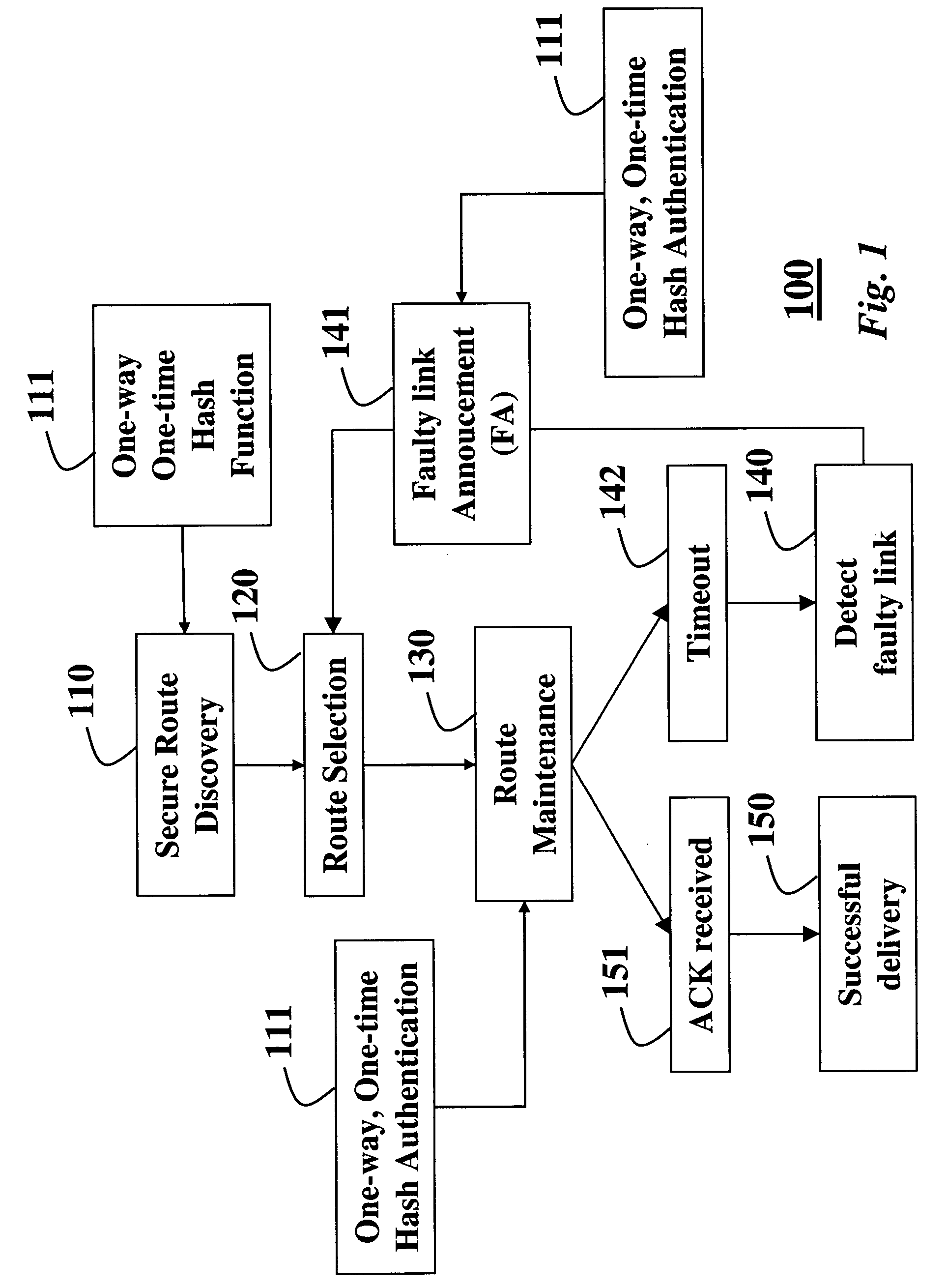
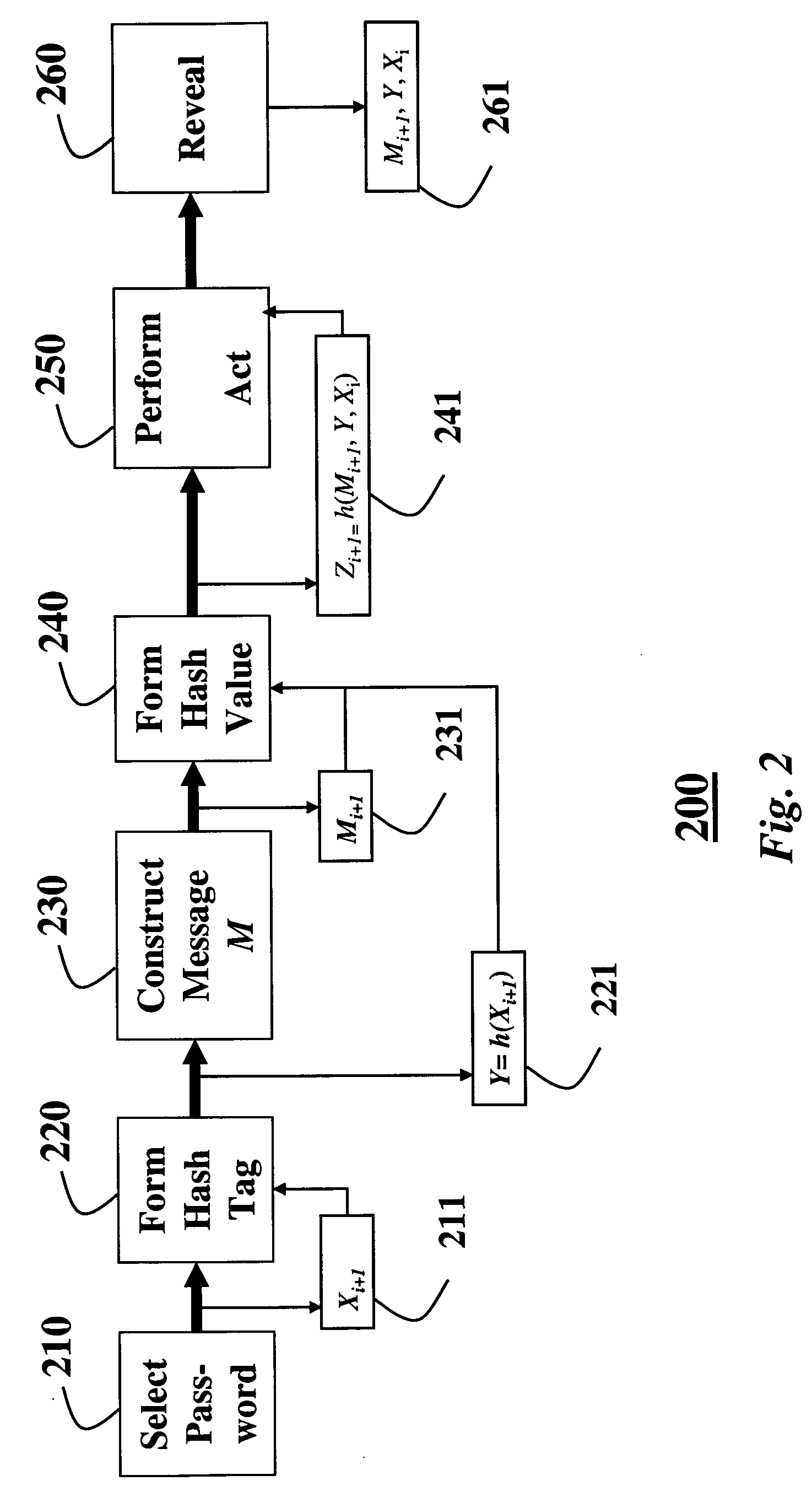
Secure routing protocol for an ad hoc network using one-way/one-time hash functions
InactiveUS20050036616A1User identity/authority verificationDigital data authenticationData packSerial transfer
A method authenticates packets that are transmitted serially in a network. A current password is selected for a current packet to be transmitted. The current packet includes current data. A one-way / one-time hash function is applied to the current password to form a current tag. A next password is selected for a next packet that includes next data, and the one-way / one-time hash function is applied to the next password to form a next tag. The one-way / one-time hash function is then applied to the next data, the next tag, and the current password to obtain a hashed value. The current packet is then transmitted to include the hash value, the current data, the current tag, and a previous password of a previous transmitted packet to authenticate the current data.
Owner:MITSUBISHI ELECTRIC INFORMATION TECH CENT AMERICA ITA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com