Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
421 results about "Physical access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Physical access is a term in computer security that refers to the ability of people to physically gain access to a computer system. According to Gregory White, "Given physical access to an office, the knowledgeable attacker will quickly be able to find the information needed to gain access to the organization's computer systems and network."
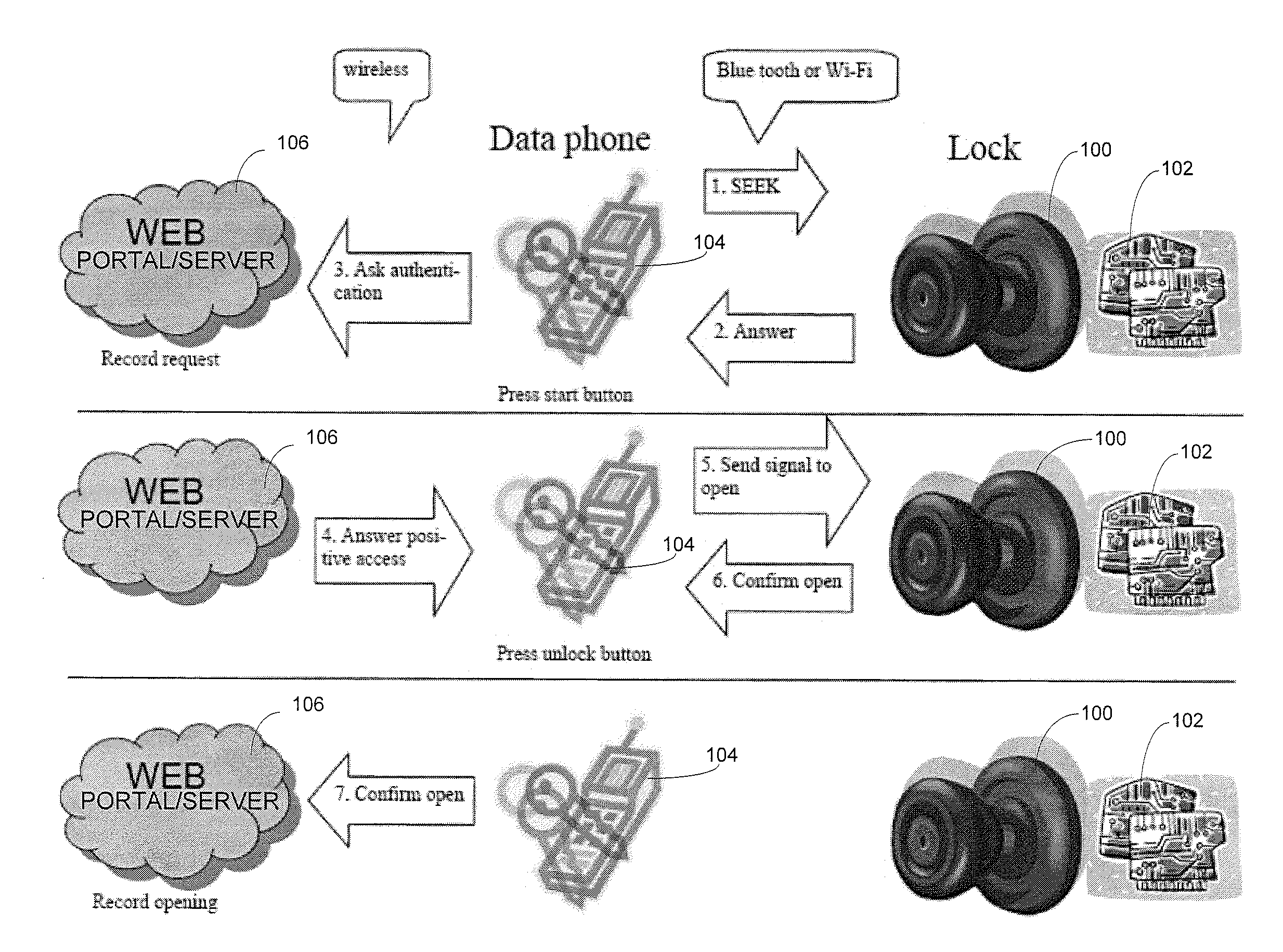
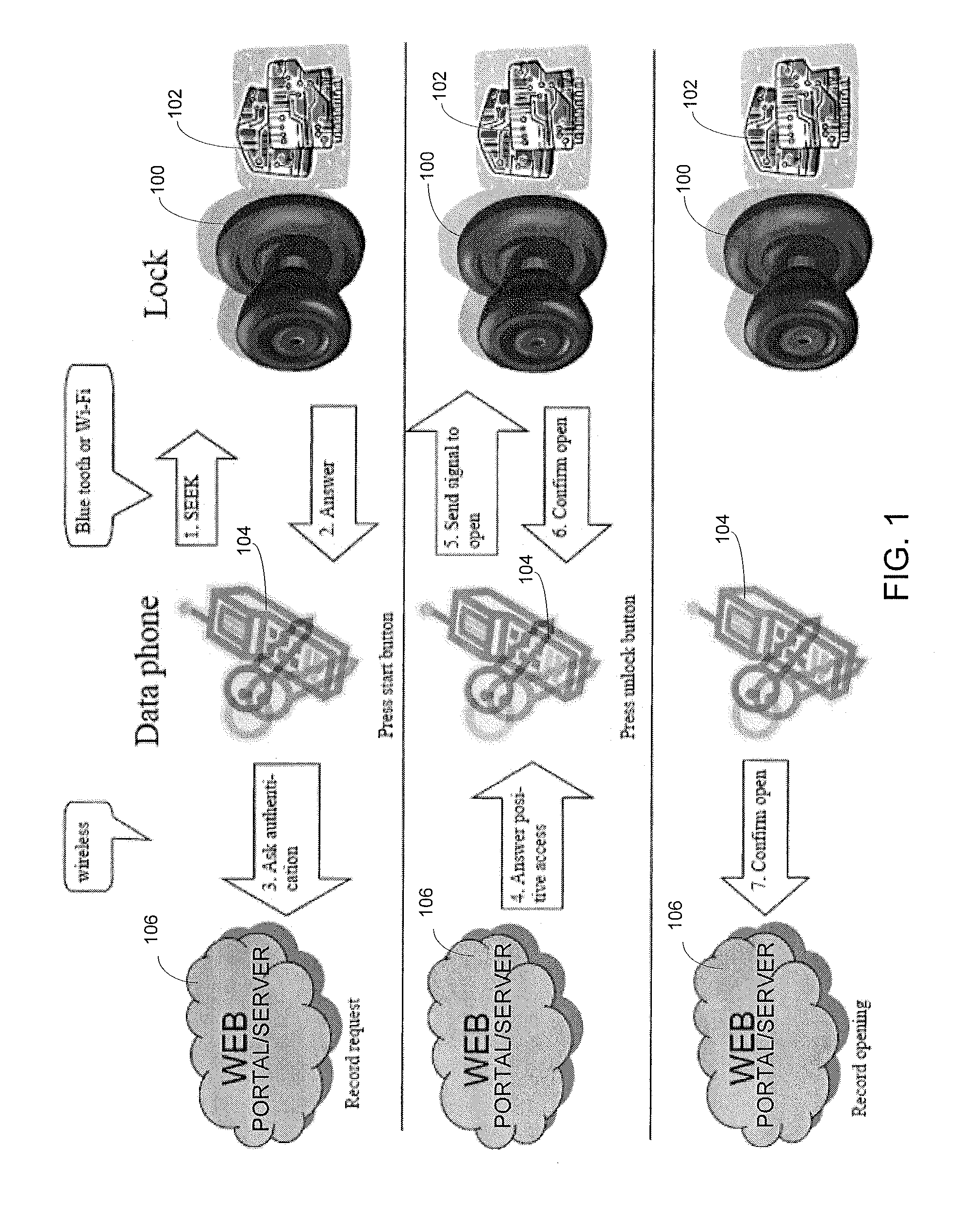
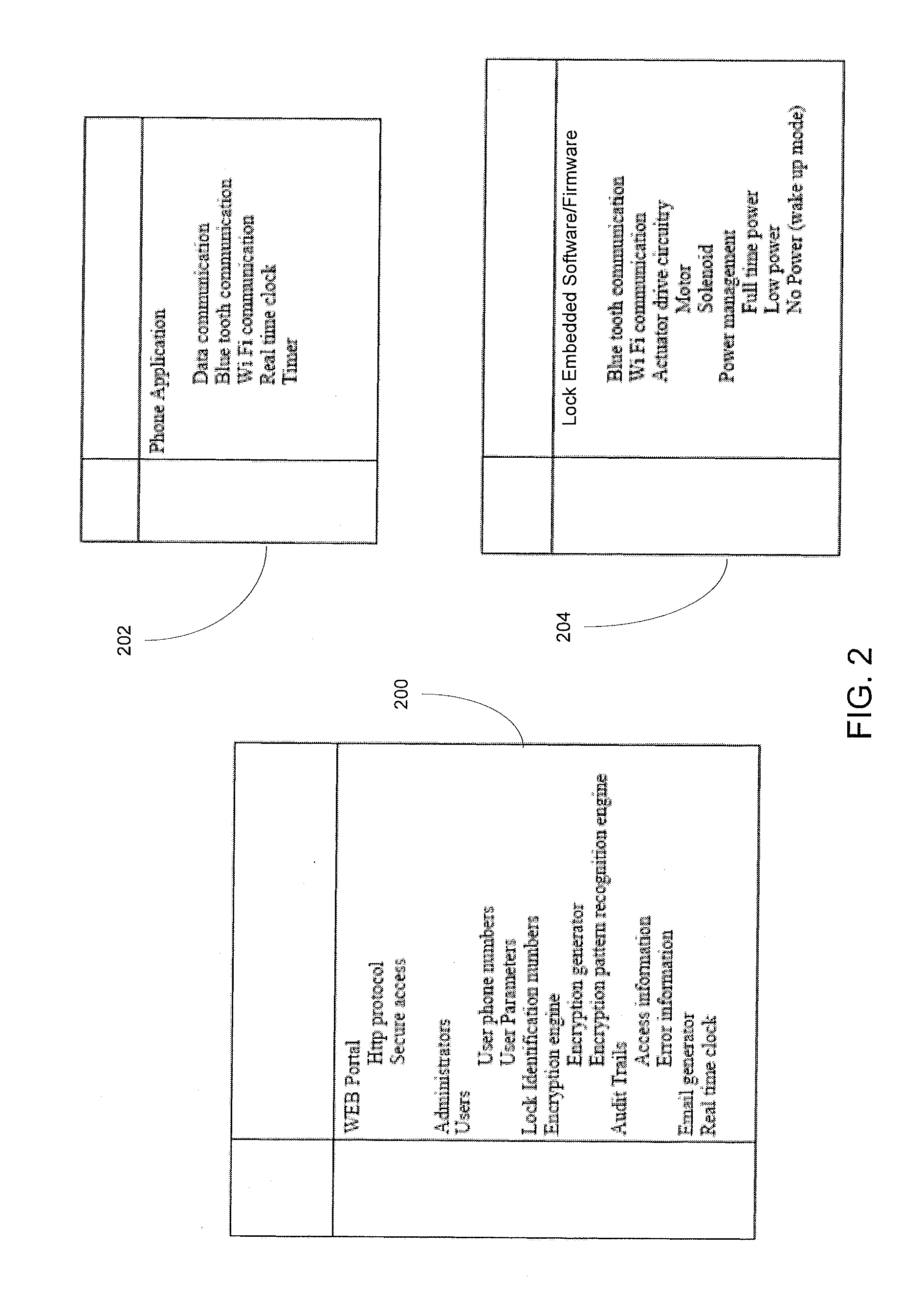
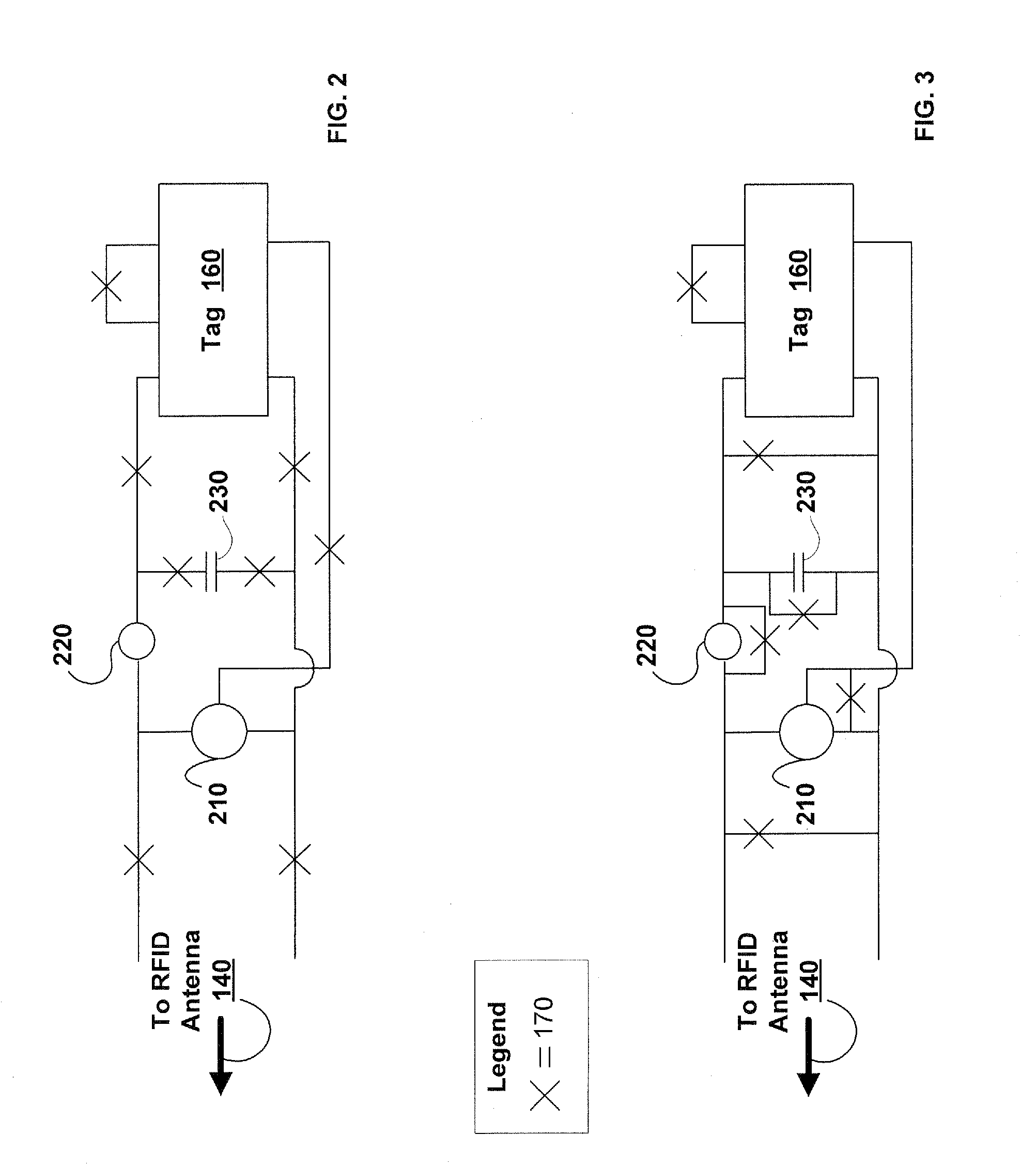
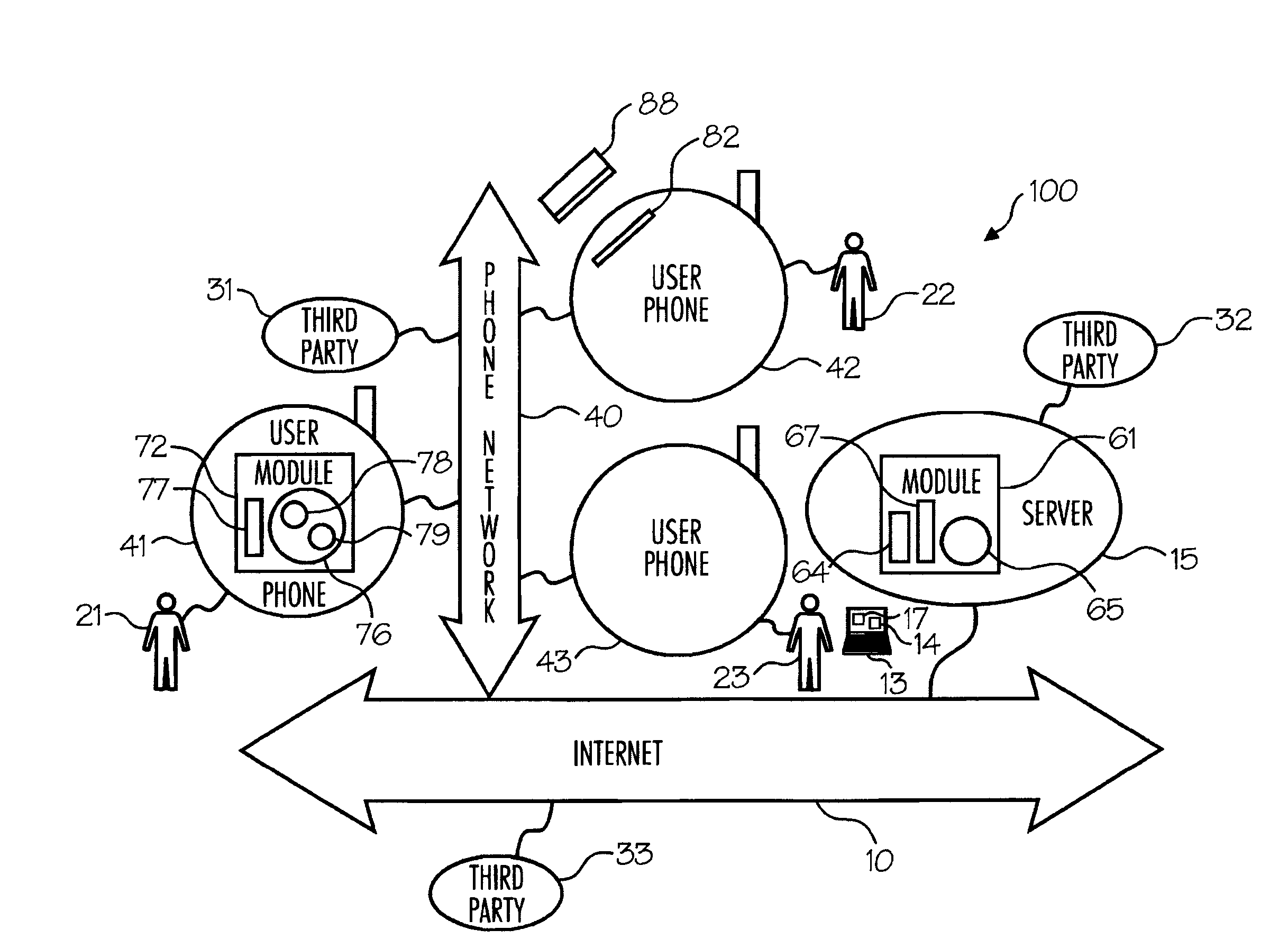
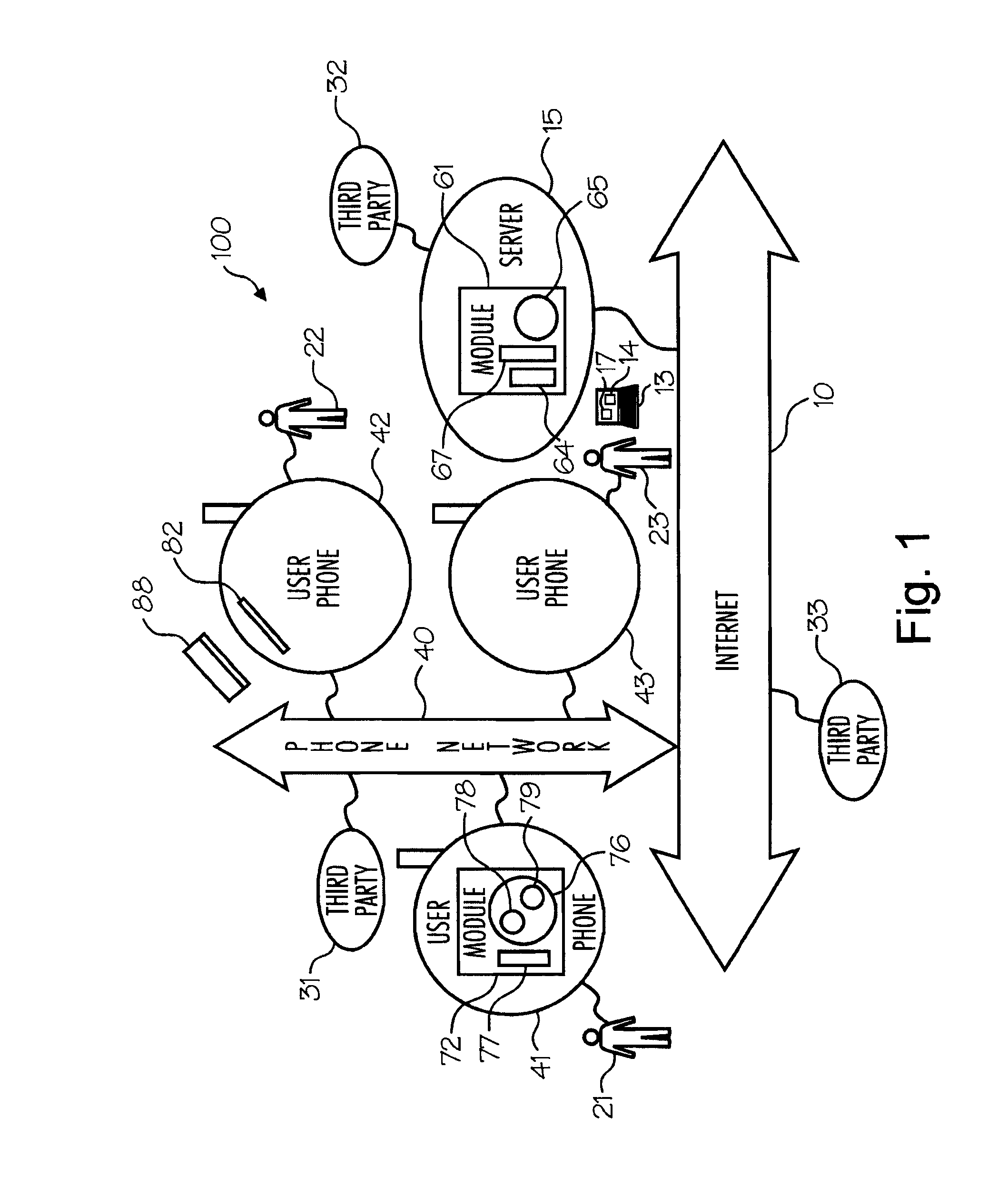
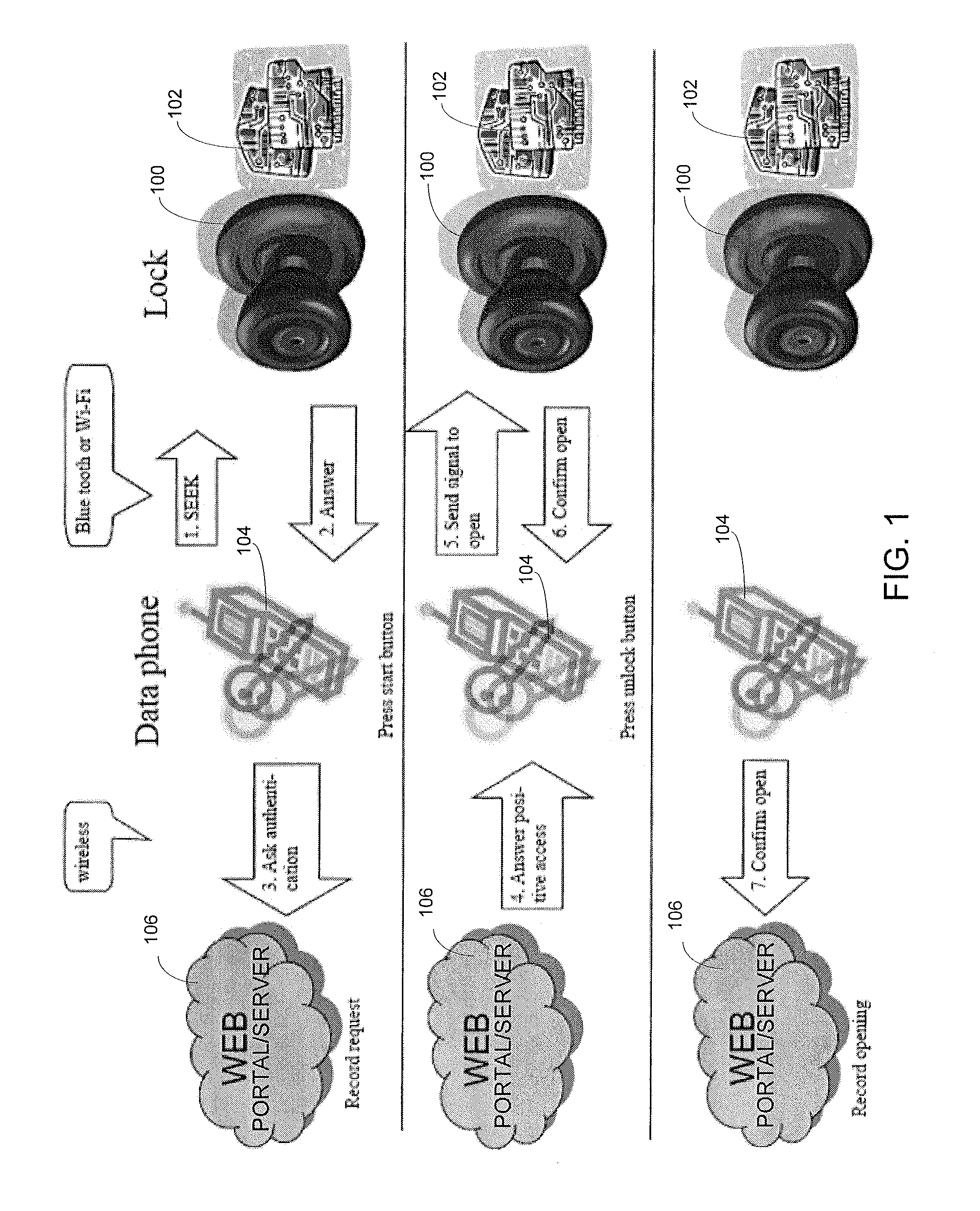
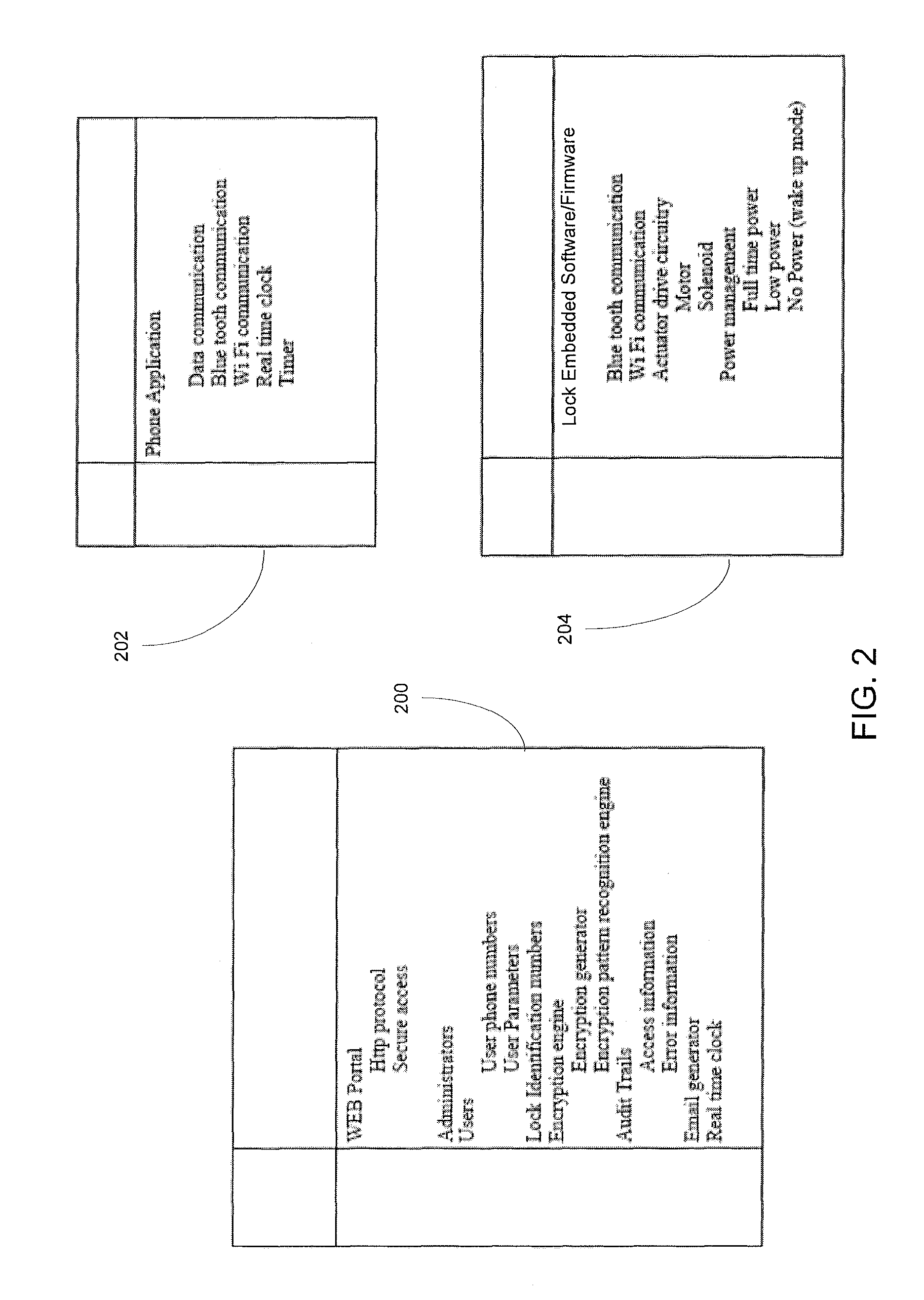
Wireless Device Enabled Locking System
ActiveUS20110311052A1Provide securityDigital data authenticationSecret communicationUnique identifierMobile device
An encrypted security system and associated methods for controlling physical access. The system includes a security server configured to receive a request for authentication from a mobile device, the request comprising information identifying the mobile device and a physical access control device. The security server forwards an encryption message comprising a plurality of unique identifiers to the physical access control device via the mobile device. The physical access control device is configured to authenticate the plurality of unique identifiers in the encryption message and operate an access control mechanism.
Owner:DELPHIAN SYST
Access Control Through Multifactor Authentication with Multimodal Biometrics
ActiveUS20150347734A1Safe storageImprove securityDigital data processing detailsUser identity/authority verificationThe InternetFinancial transaction
A system is provided in which a person may use a Cellular (Mobile) Telephone, a PDA or any other handheld computer to make a purchase. This is an example only. The process may entail any type of transaction which requires authentication, such as any financial transaction, any access control (to account information, etc.), and any physical access scenario such as doubling for a passport or an access key to a restricted area (office, vault, etc.). It may also be used to conduct remote transactions such as those conducted on the Internet (E-Commerce, account access, etc.). In the process, a multifactor authentication is used.
Owner:BEIGI HOMAYOON
Communication device having multiple keypads
InactiveUS20050059438A1“connection” between such elements can be somewhat indirectDevices with multiple keyboard unitsDigital data processing detailsKey pressingLoudspeaker
A communication device having a front housing and first and second independent keypad housings having respective keypads functionally connected to the front housing. The front housing has a speaker, a microphone, and a display panel. Each keypad has a key configuration that is different than the other. The front housing, first keypad housing, and second keypad housing are constructed to overlap and stack in a nested configuration in which each of the keypads is concealed by the front housing. The front housing is movable relative to each of the keypad housings from the nested configuration to an extended position in which one of the keypads is exposed and physically accessible by a user.
Owner:GOOGLE TECH HLDG LLC
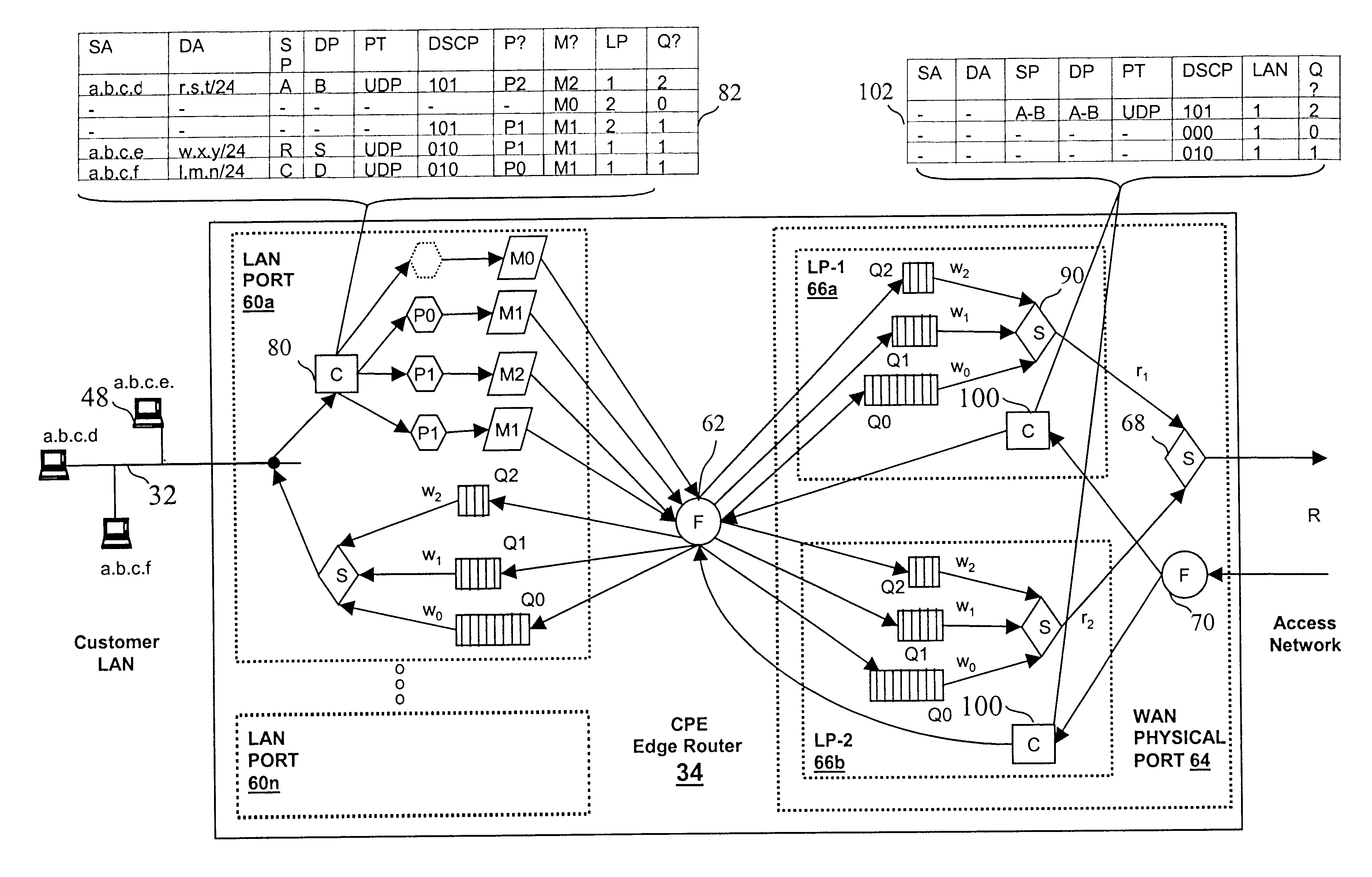
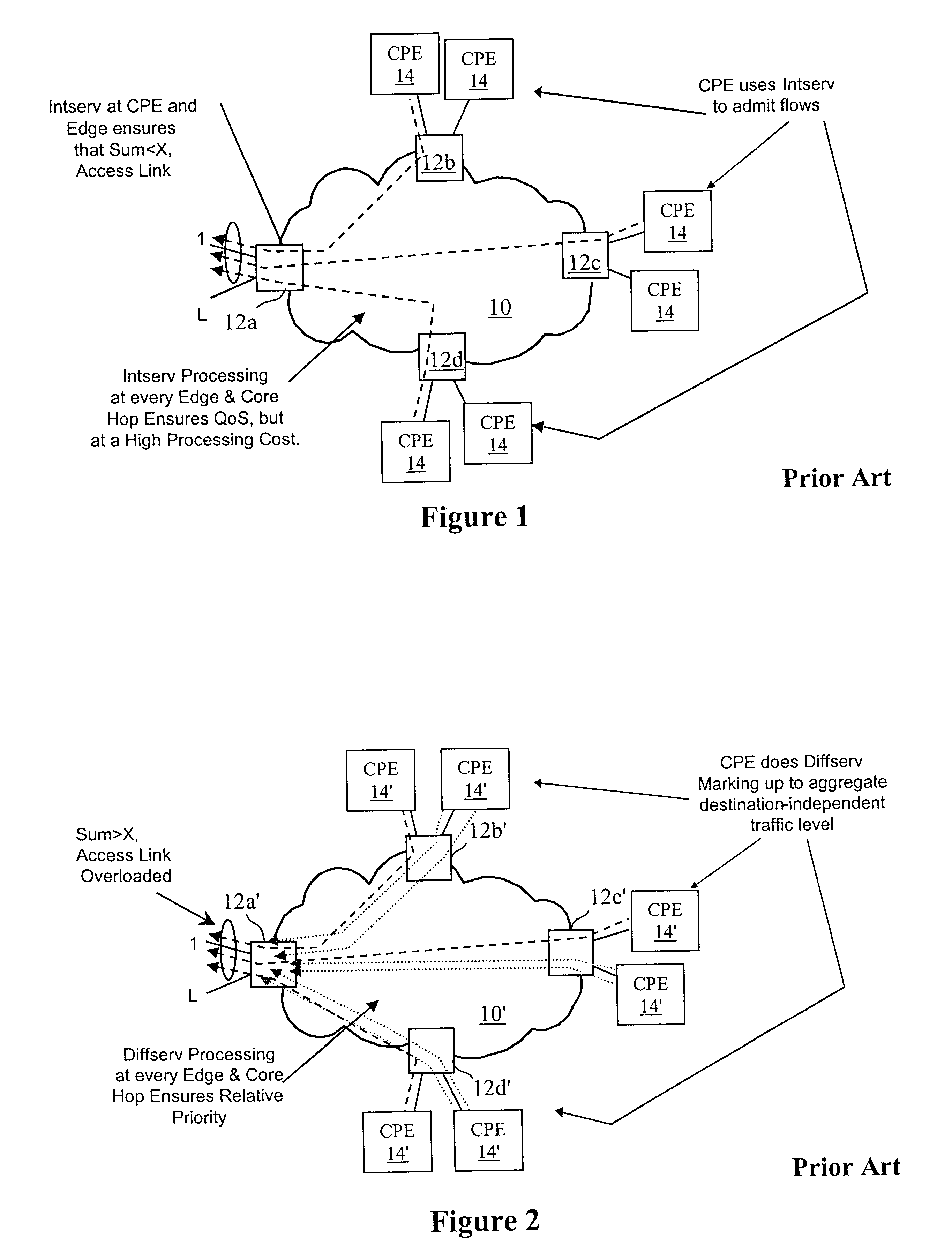
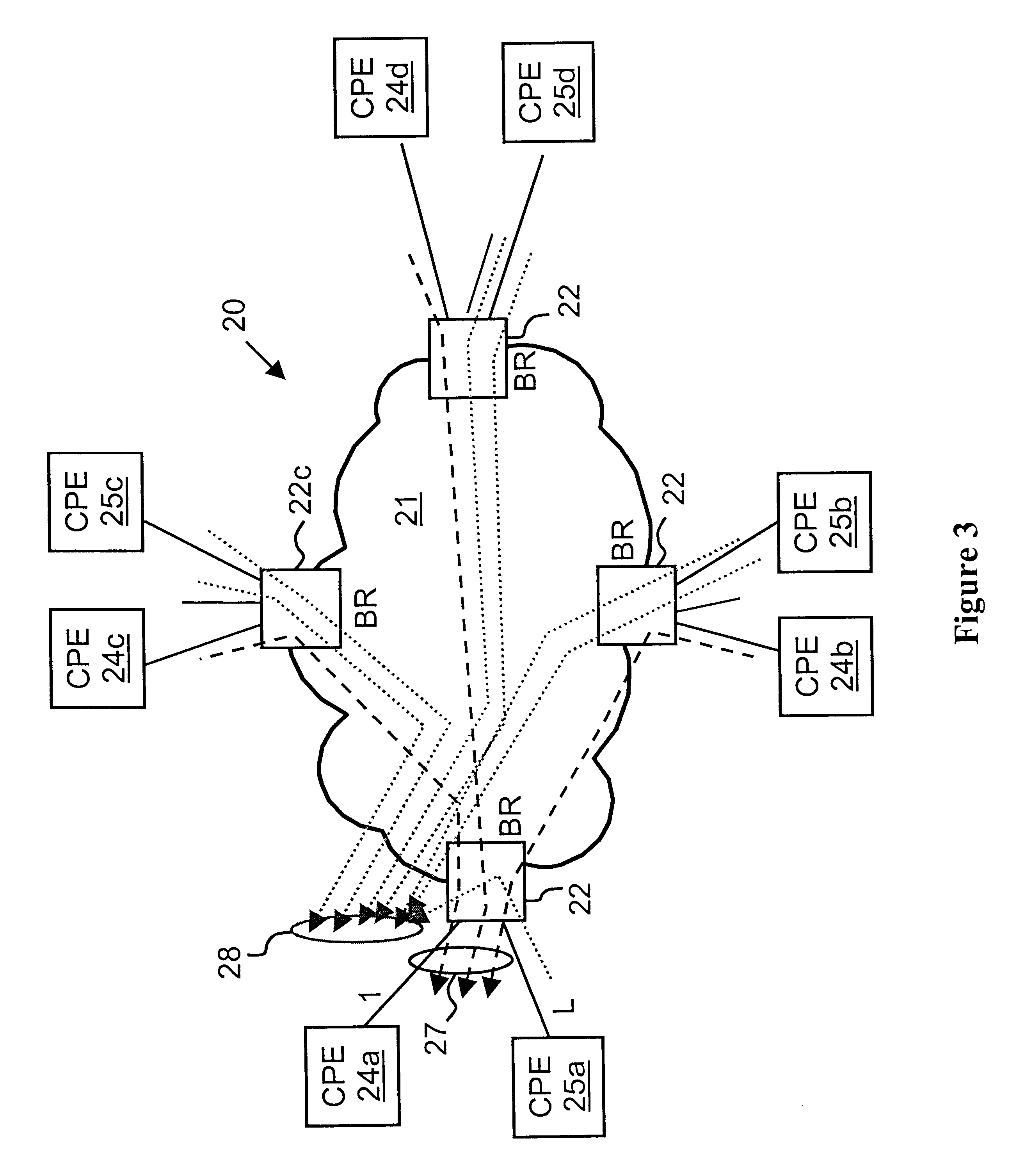
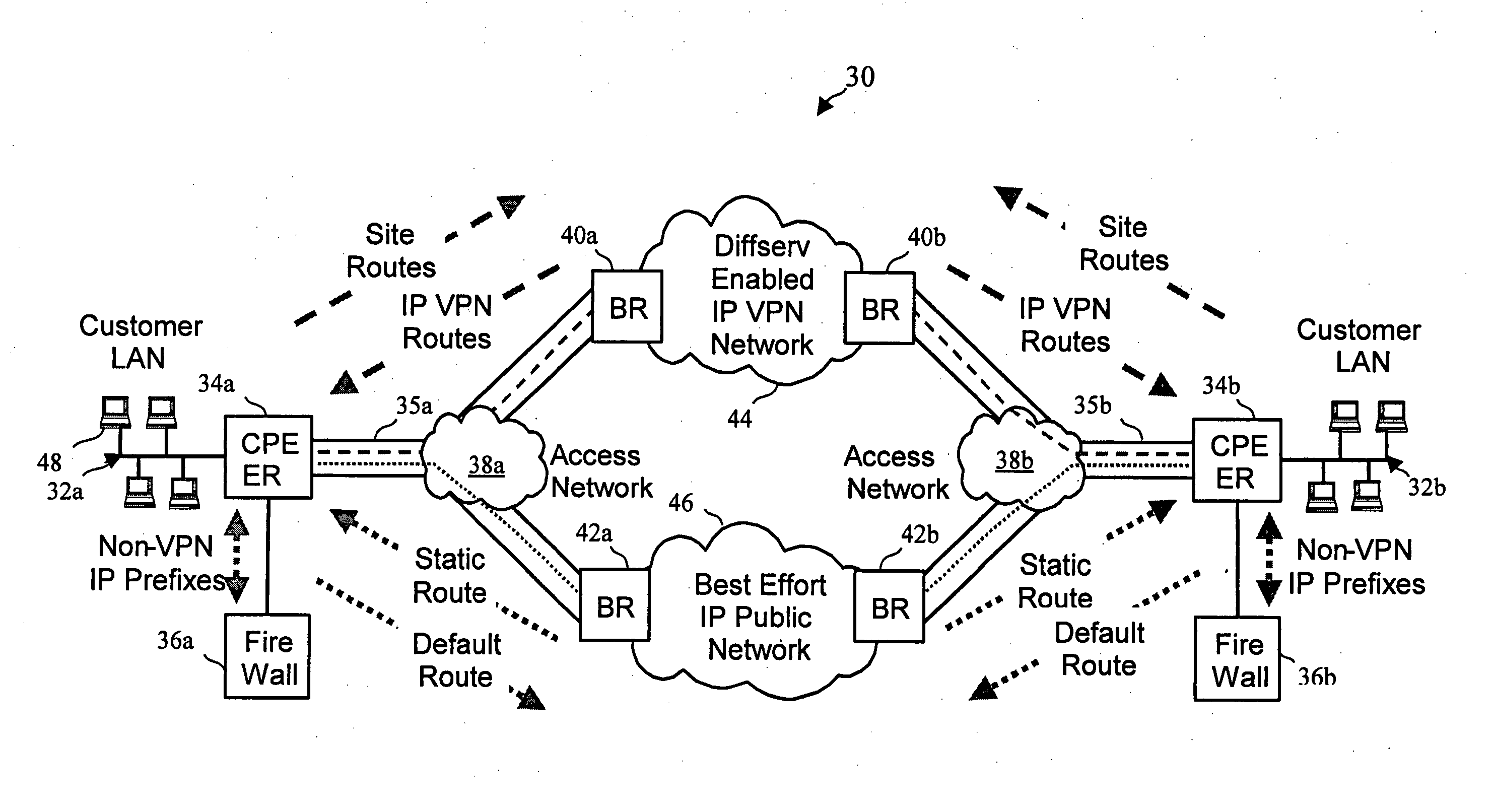
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
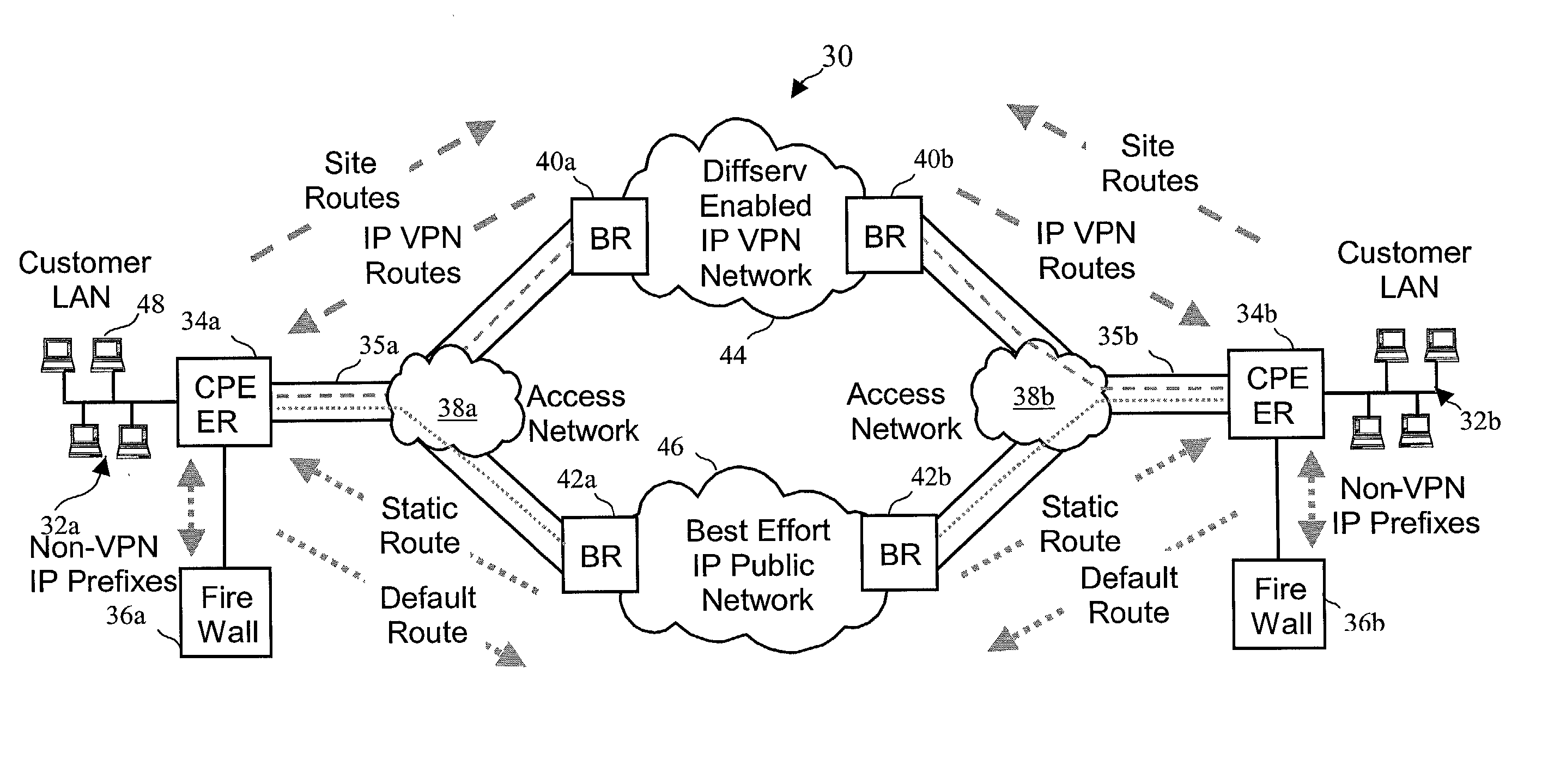
InactiveUS6778498B2Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
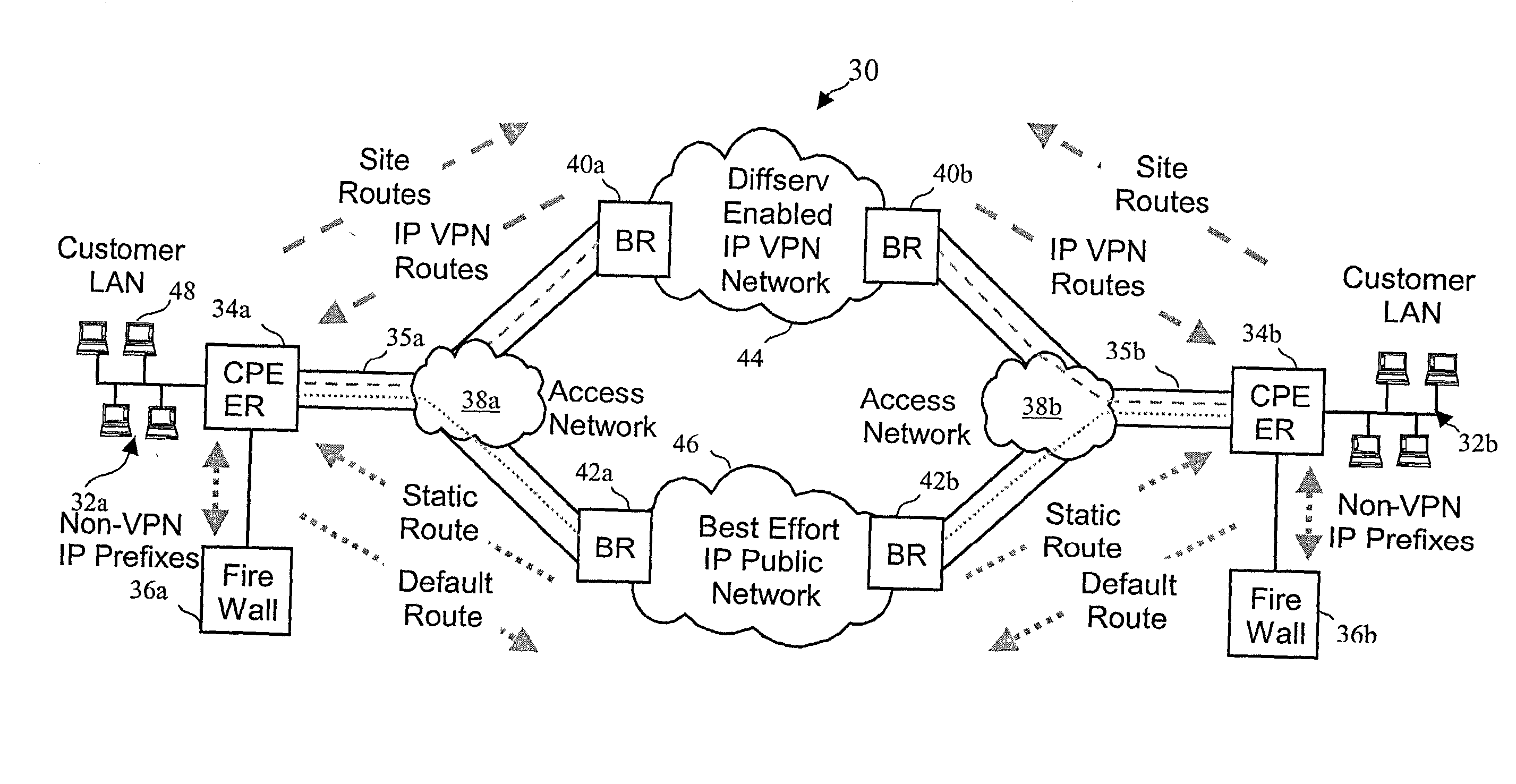
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
Secure Biometric Verification of Identity
InactiveUS20080019578A1Reduce computational complexityReduce probabilityImage analysisCharacter and pattern recognitionComputer hardwareData matching
A high security identification card includes an on-board memory for stored biometric data and an on-board sensor for capturing live biometric data. An on-board processor on the card performs a matching operation to verify that the captured biometric data matches the locally stored biometric data. Only if there is a positive match is any data transmitted from the card for additional verification and / or further processing. Preferably, the card is ISO SmartCard compatible. In one embodiment, the ISO SmartCard functions as a firewall for protecting the security processor used for storing and processing the protected biometric data from malicious external attack via the ISO SmartCard interface. In another embodiment, the security processor is inserted between the ISO SmartCard Interface and an unmodified ISO SmartCard processor and blocks any external communications until the user's fingerprint has been matched with a previously registered fingerprint. Real-time feedback is provided while the user is manipulating his finger over the fingerprint sensor, thereby facilitating an optimal placement of the finger over the sensor. The card may be used to enable communication with a transactional network or to obtain physical access into a secure area.
Owner:IVI HLDG
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
InactiveUS20030112755A1Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
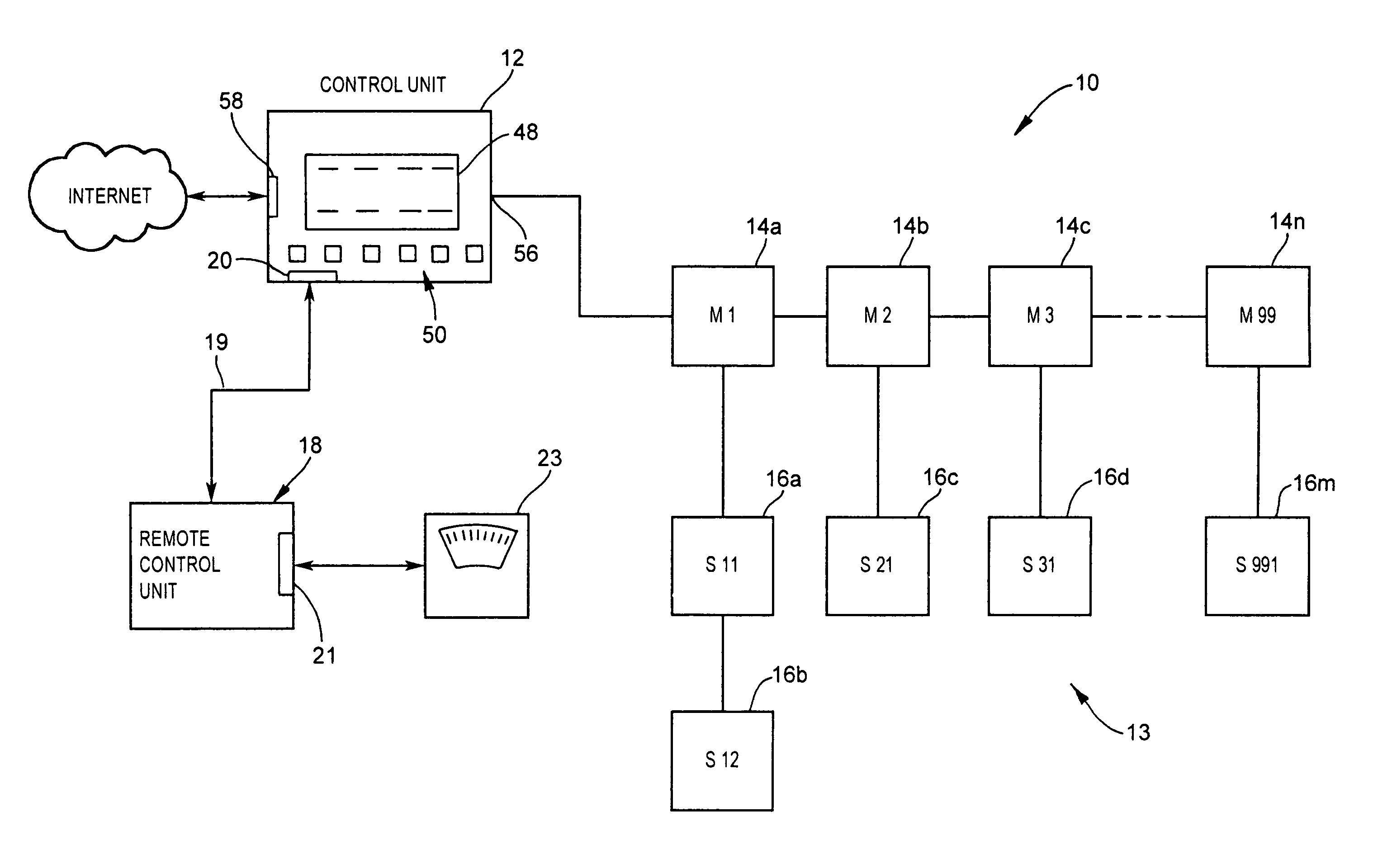
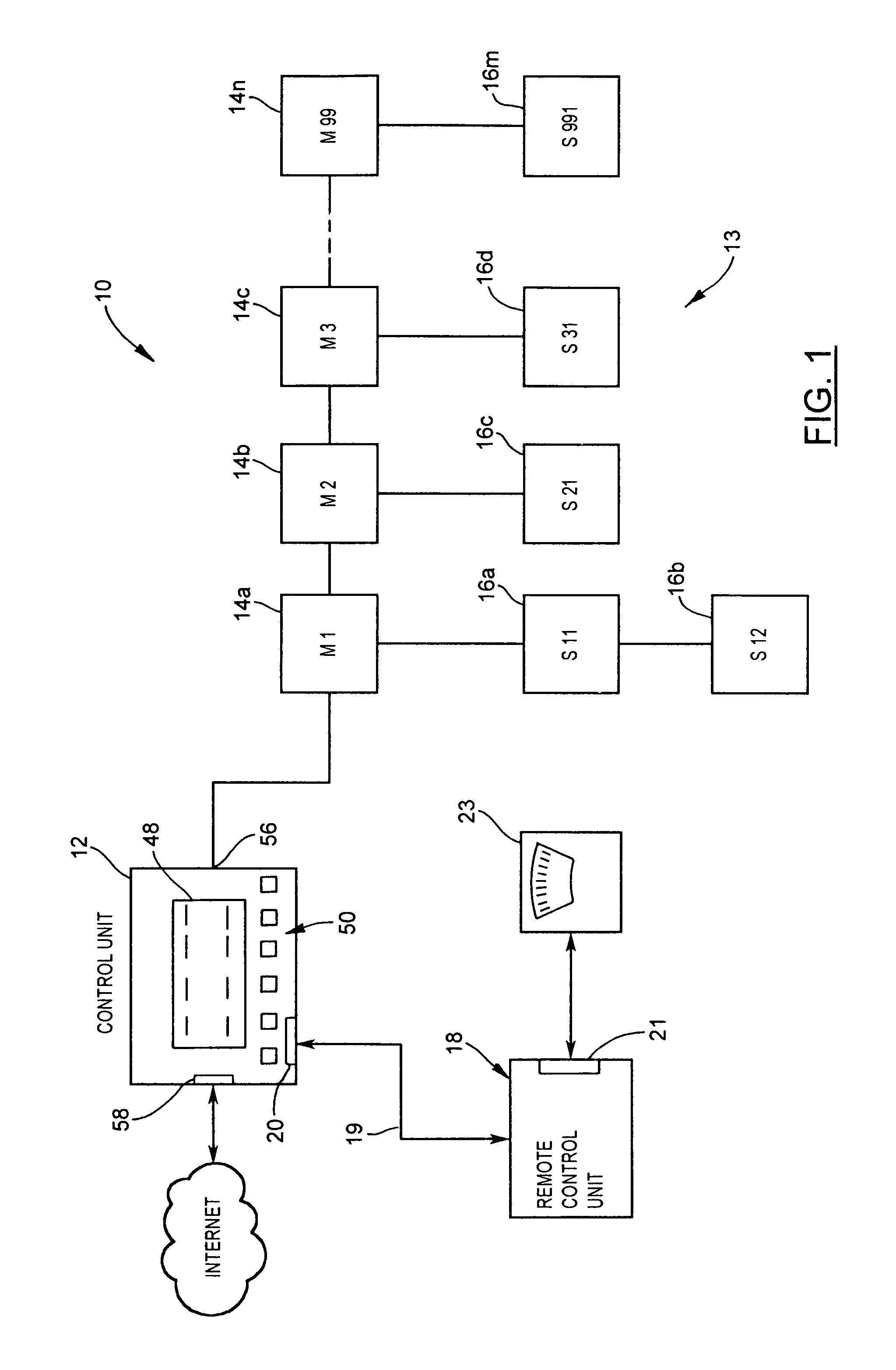
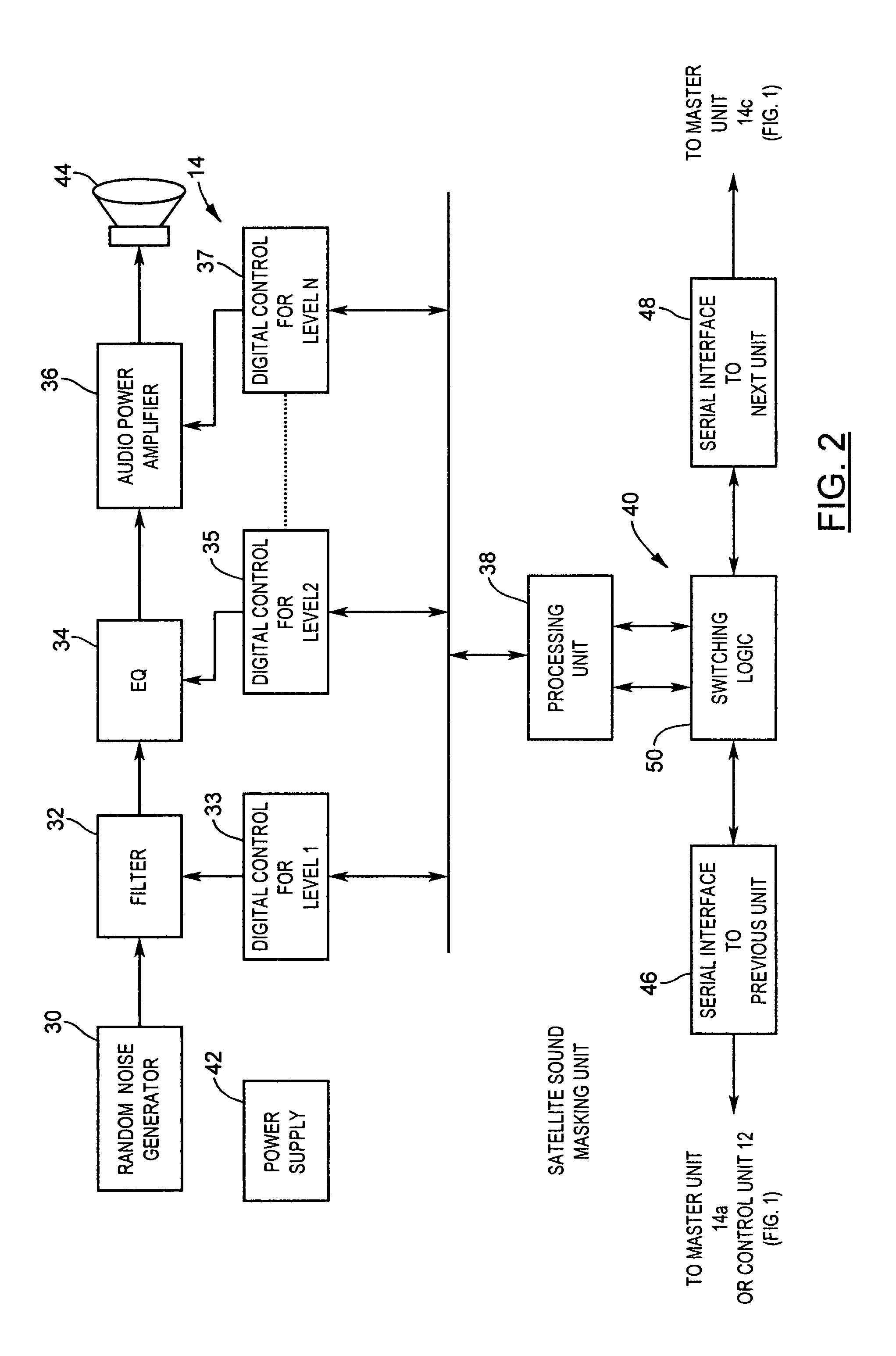
Networked sound masking system
InactiveUS8477958B2Limit its operationPublic address systemsCasings/cabinets/drawers detailsSpectral bandsRemote control
A sound masking system for shaping the ambient noise level in a physical environment. The sound masking system comprises a networked and distributed system having a number of master units coupled together and to a control unit. One or more of the master units may include satellite sound masking units which function to reproduce the sound masking signal generated by the master sound masking unit. Each of the master units is addressable over the network by the control unit enabling the control unit to program the contour, spectral band, and gain characteristics of the sound masking output signal. The system may also include a remote control unit which provides the capability to tune and adjust each master sound masking unit in situ without requiring physical access through the ceiling installation.
Owner:777388 ONTARIO
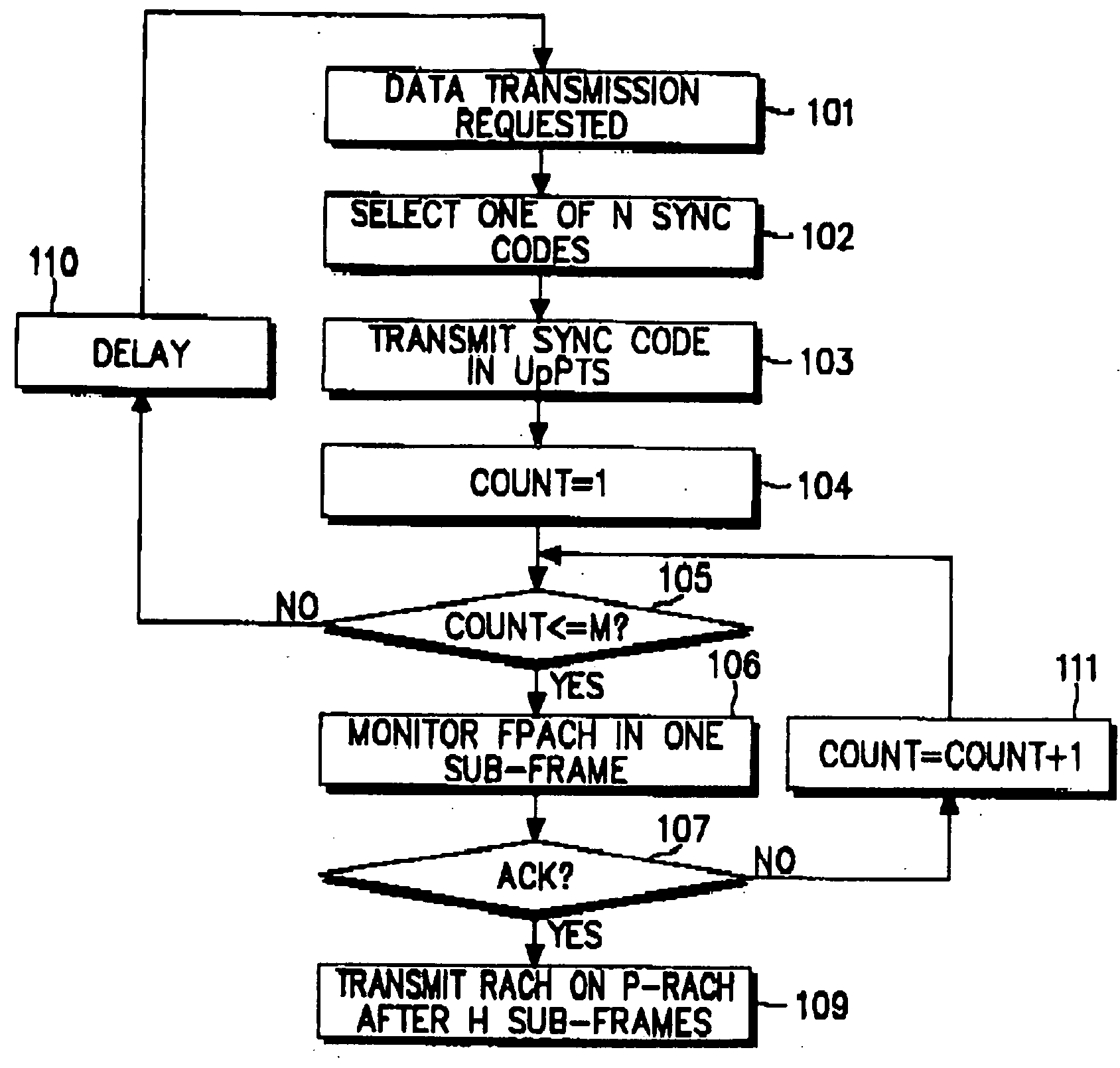
Method of assigning an uplink random access channel in a CDMA mobile communication system
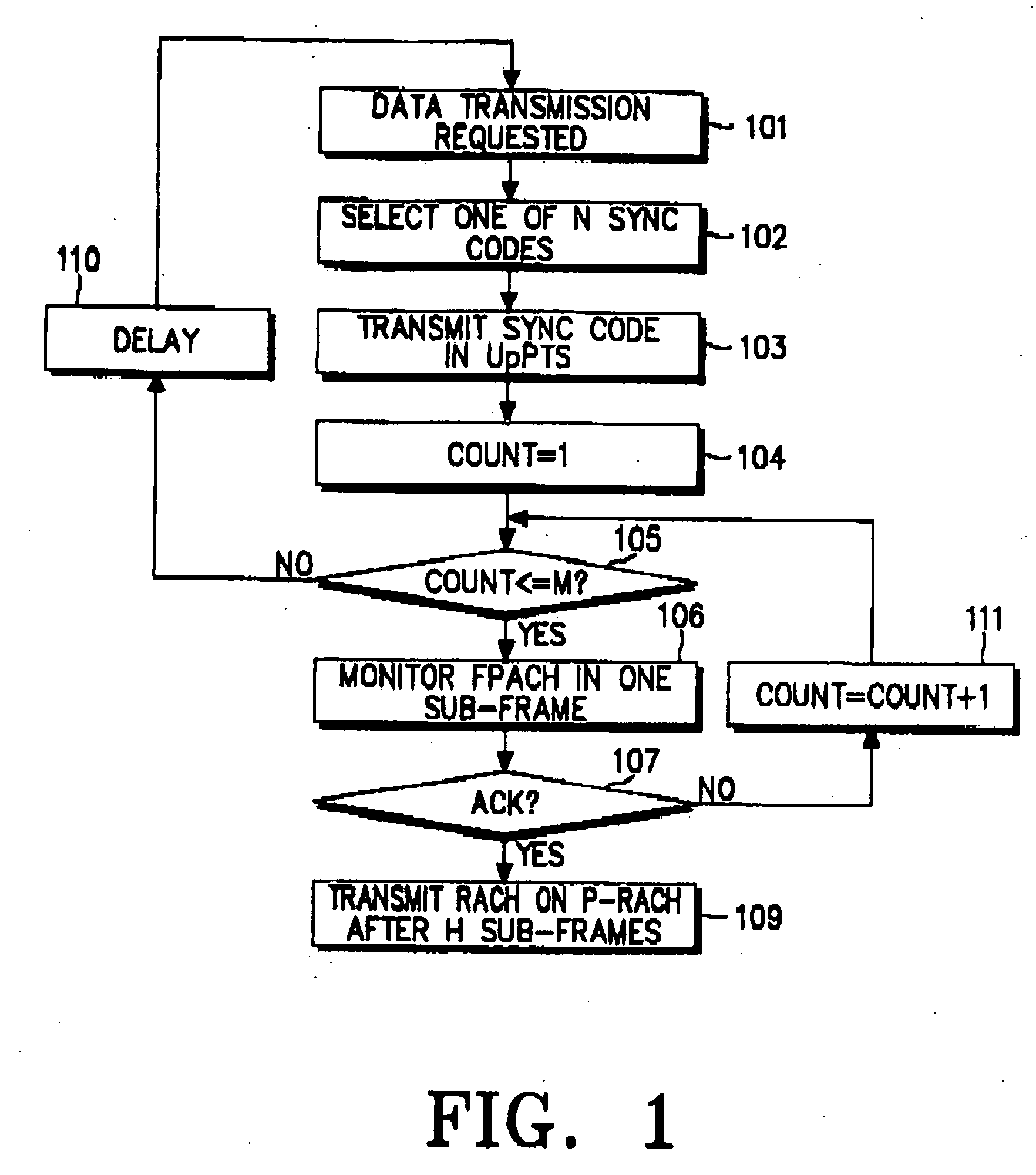
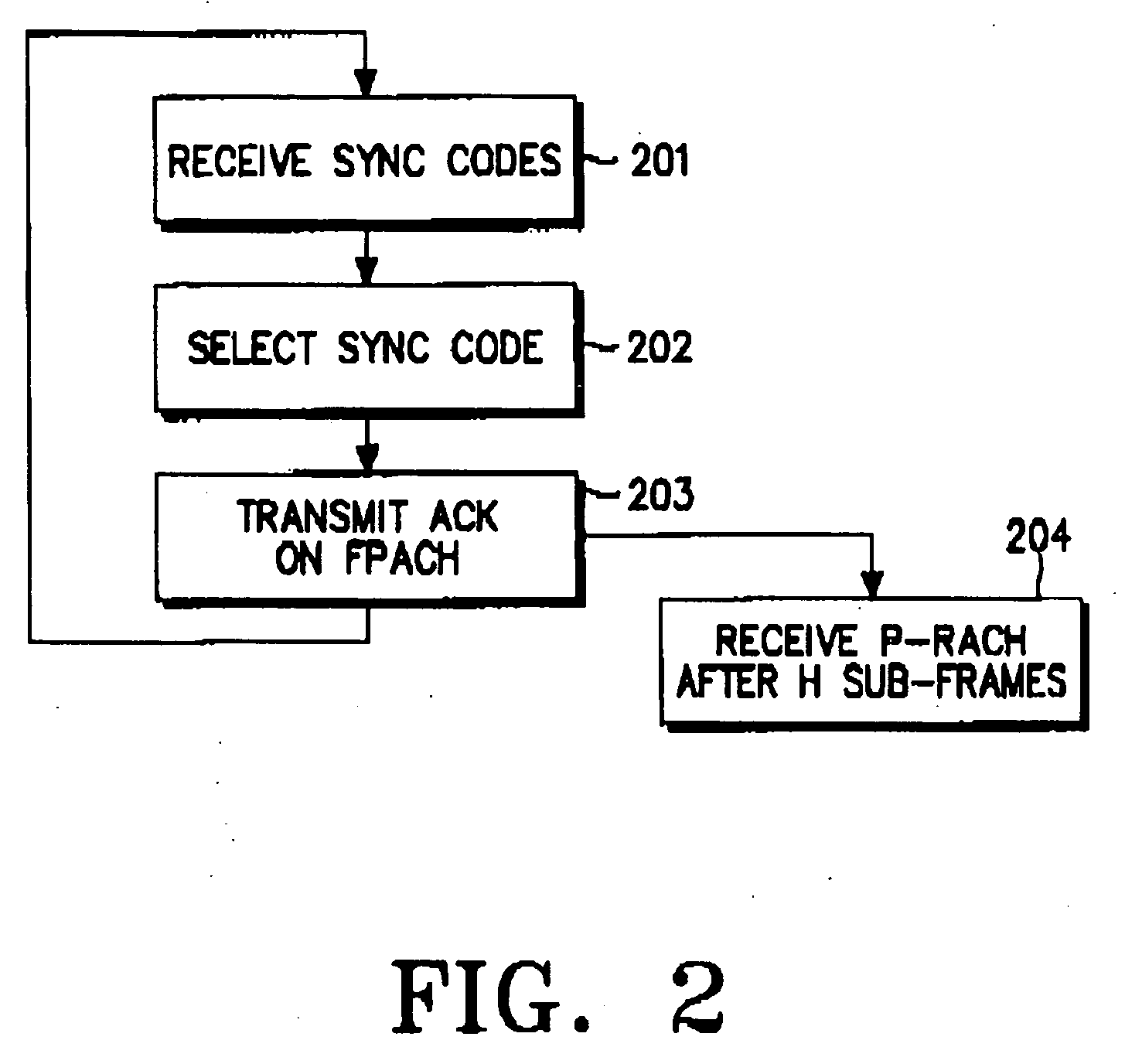
ActiveUS20070274278A1Easy to useMinimize timePower managementSynchronisation arrangementData transmission timeRandom-access channel
Disclosed is an uplink random access procedure in an NB-TDD (Narrow Band Time Division Duplexing) system. To achieve an acknowledgement for data transmission from a UTRAN (UMTS Terrestrial Radio Access Network), a UE selects one of a plurality of sync codes by which the UTRAN identifies UEs that request data transmission and transmits the selected sync code in a time slot of a sub-frame to the UTRAN. Then, the UE receives the sync code information, information about the arrival time of the sync code, time update information indicating a variation in the transmission time of data, and power information indicating an adjustment to a power gain in the UE from the UTRAN on an FPACH (Fast Physical Access Channel). The UE transmits the data on a P-RACH (Physical Random Access Channel) mapped from the FPACH according to the time update information and the power information.
Owner:SAMSUNG ELECTRONICS CO LTD
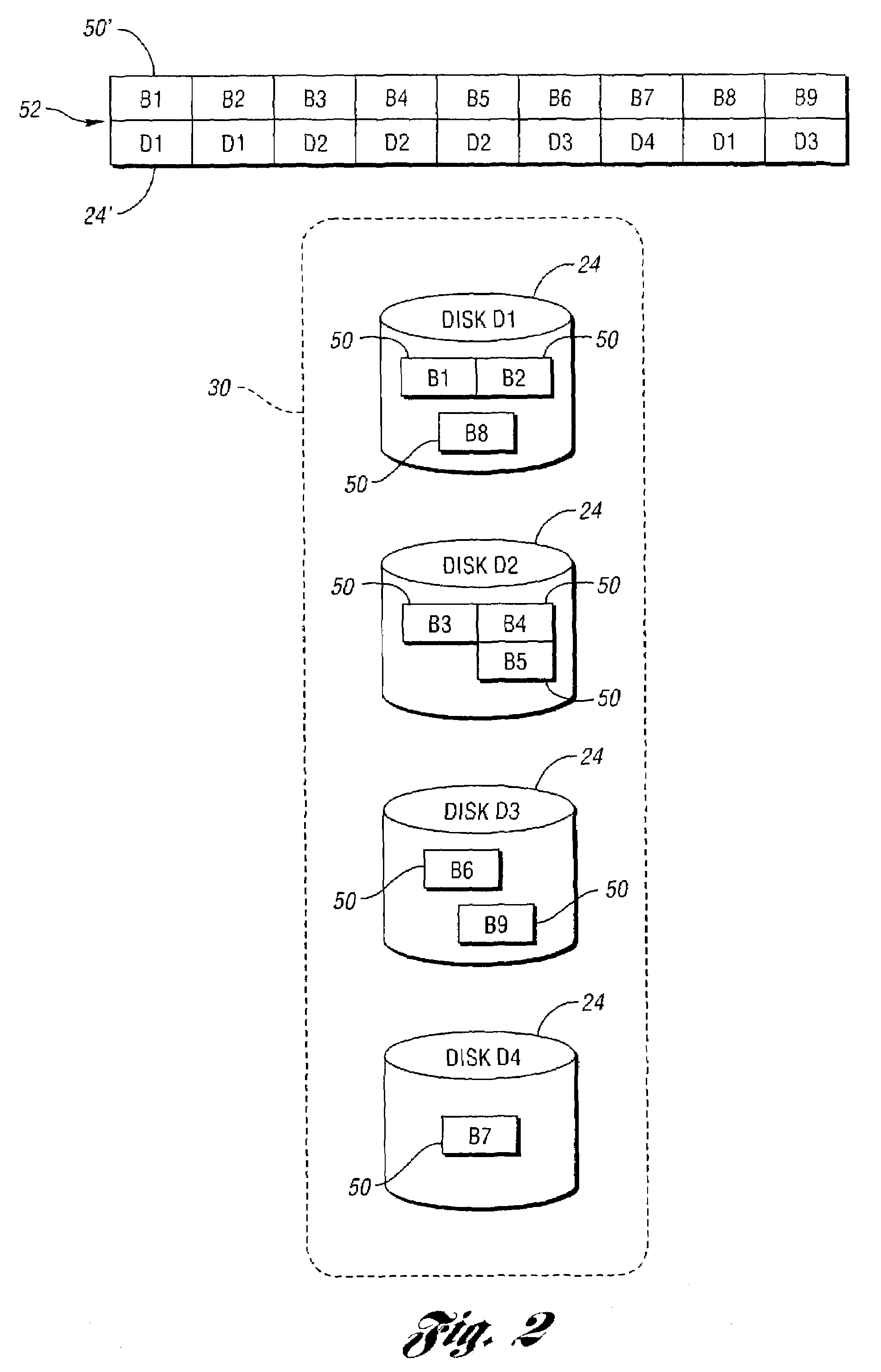
Virtual storage status coalescing with a plurality of physical storage devices
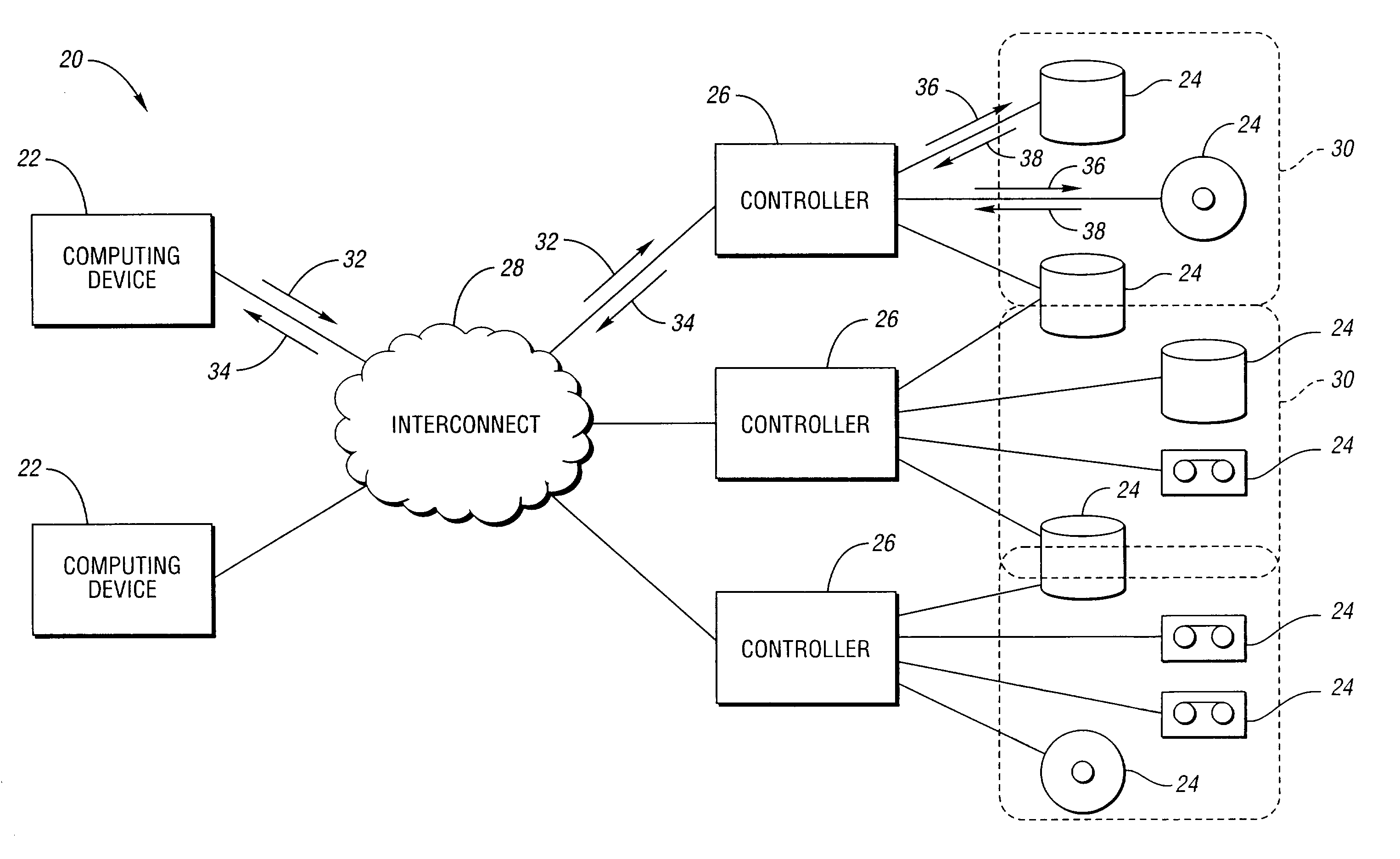
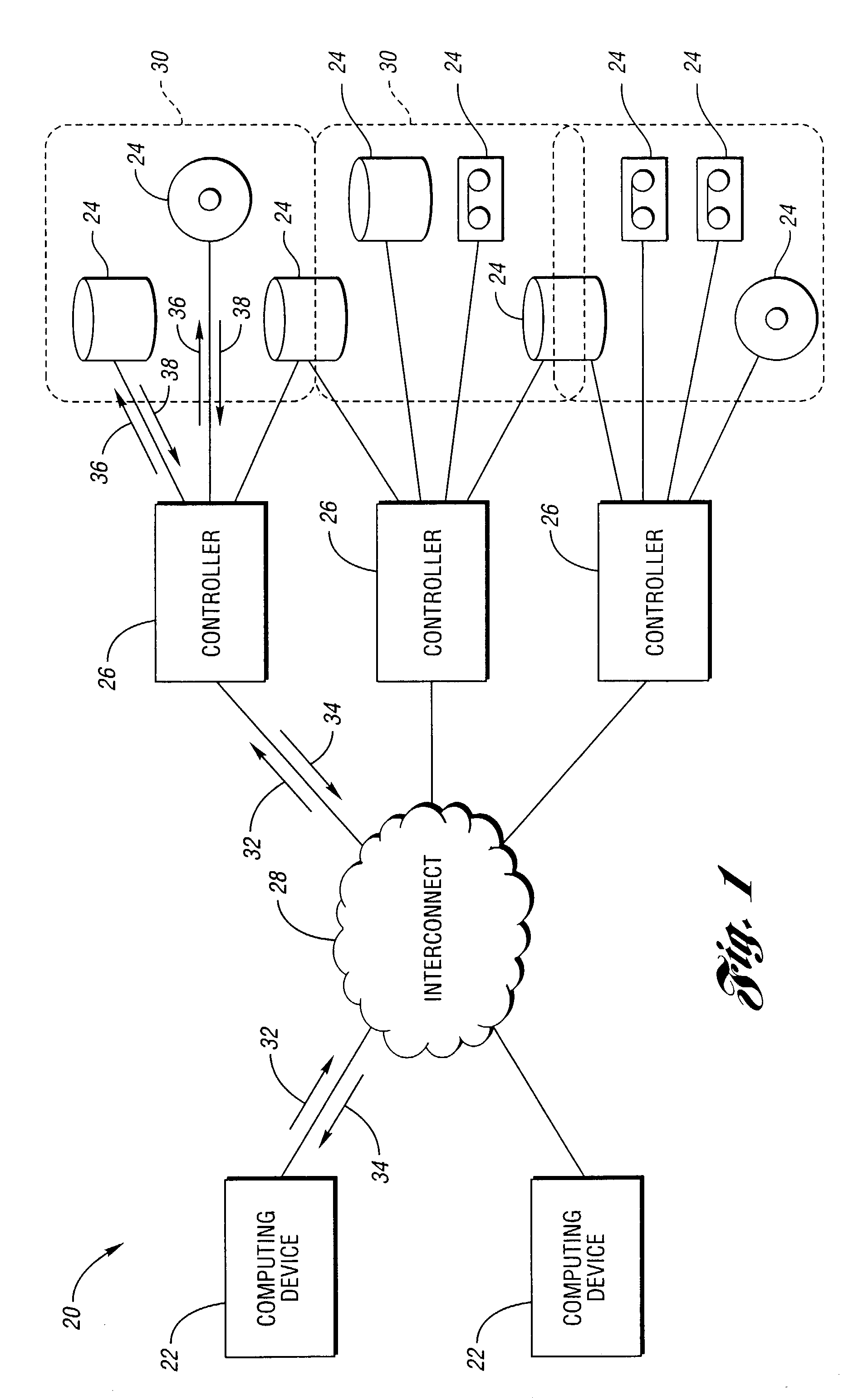
ActiveUS6990604B2Reduce difficultyNon-redundant fault processingInput/output processes for data processingData accessPhysical access
Error messages generated when accessing more then one physical storage device are handled by coalescing the status from each accessed physical storage device. A controller receives a virtual storage request from a computing device specifying a virtual data access. The virtual data access includes a plurality of blocks, each block associated with one of at least two target physical storage devices. An access sequence associating one target storage device with each block in the received virtual storage access request is determined. At least one physical access request is sent to each target storage device. At least one error message is received from a target storage device, each error message having an error type. An error response is determined based on the error message type and on the access sequence.
Owner:ORACLE INT CORP
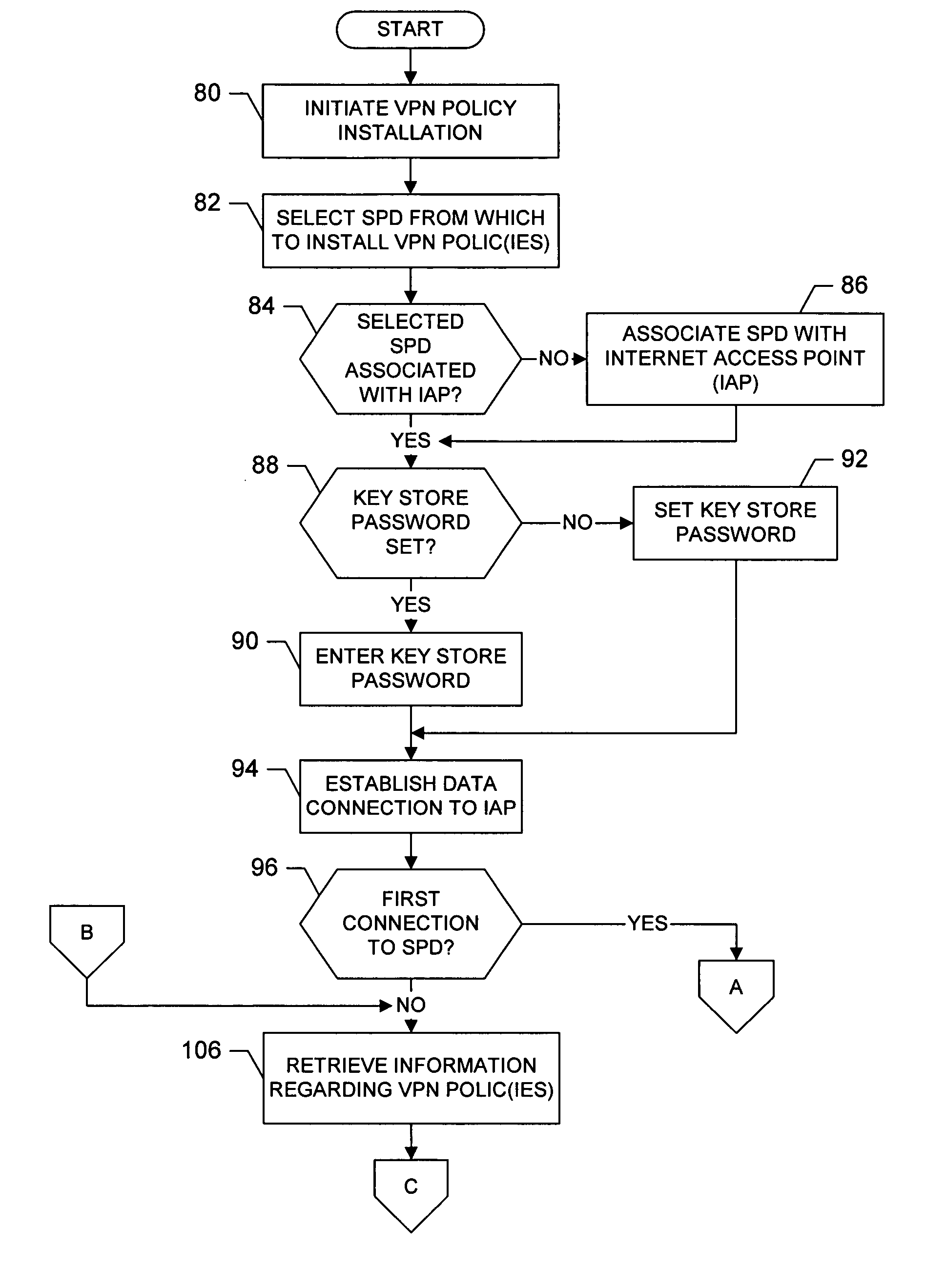
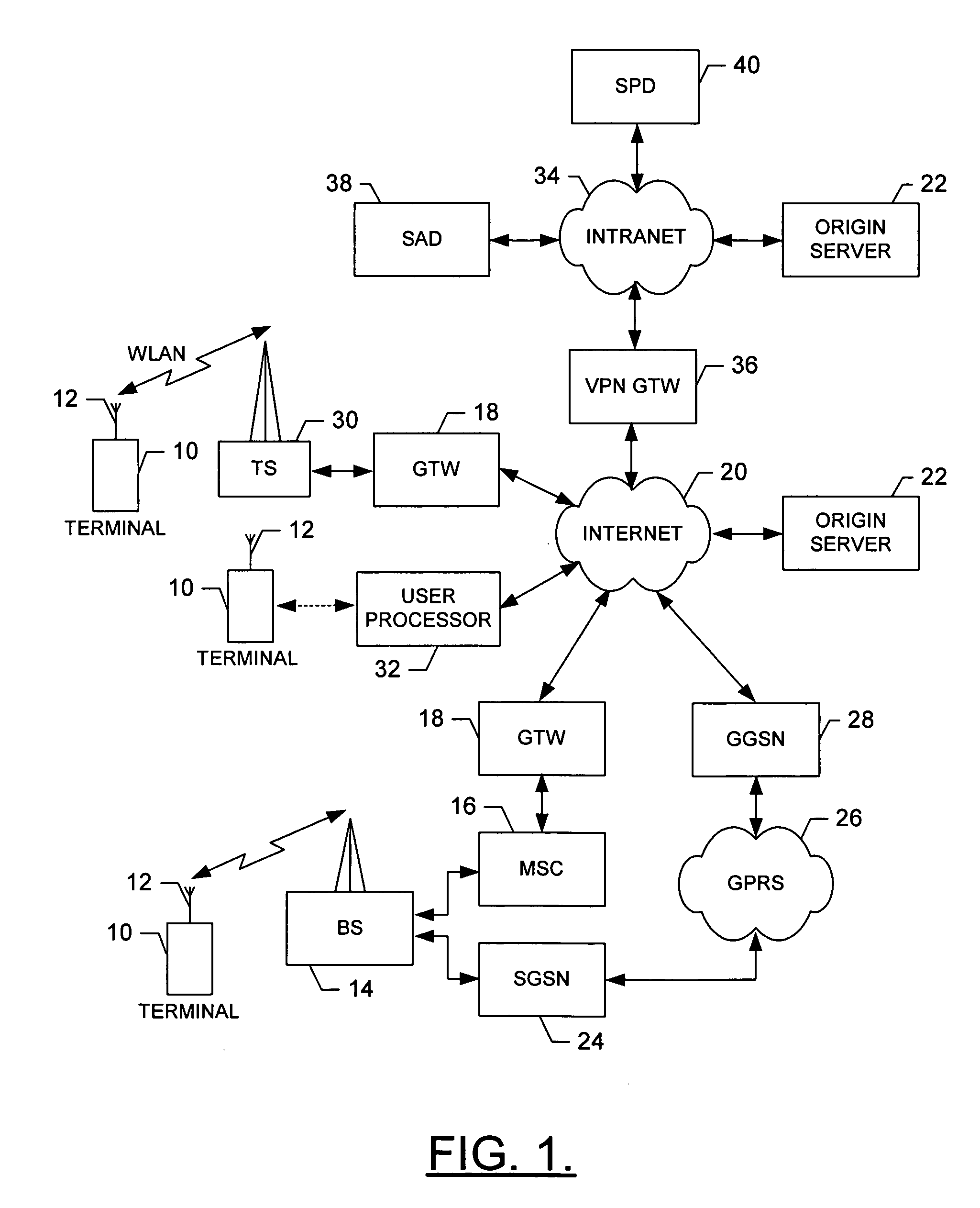
System, method and computer program product for accessing at least one virtual private network
ActiveUS20050198306A1Reduce the burden onSolve the real problemMultiple digital computer combinationsNetworks interconnectionData connectionPrivate network
A system for accessing at least one Virtual Private Network (VPN) includes a terminal, and can include at least one Security Policy Database (SPD). The terminal is capable of communicating with a VPN client and at least one application. The VPN client, in turn, is capable of defining at least one VPN access point, each VPN access point including an associated physical access point and VPN policy. Thereafter, the VPN client can access at least one VPN based upon the VPN access point(s) to thereby establish at least one data connection from at least one application across the at least one VPN. In addition, the VPN client can be capable of downloading at least one VPN policy from the SPD. A system for managing at least one Virtual Private Network (VPN) policy is also provided, where the VPN polic(ies) are for use in accessing at least one VPN.
Owner:NOKIA TECHNOLOGLES OY
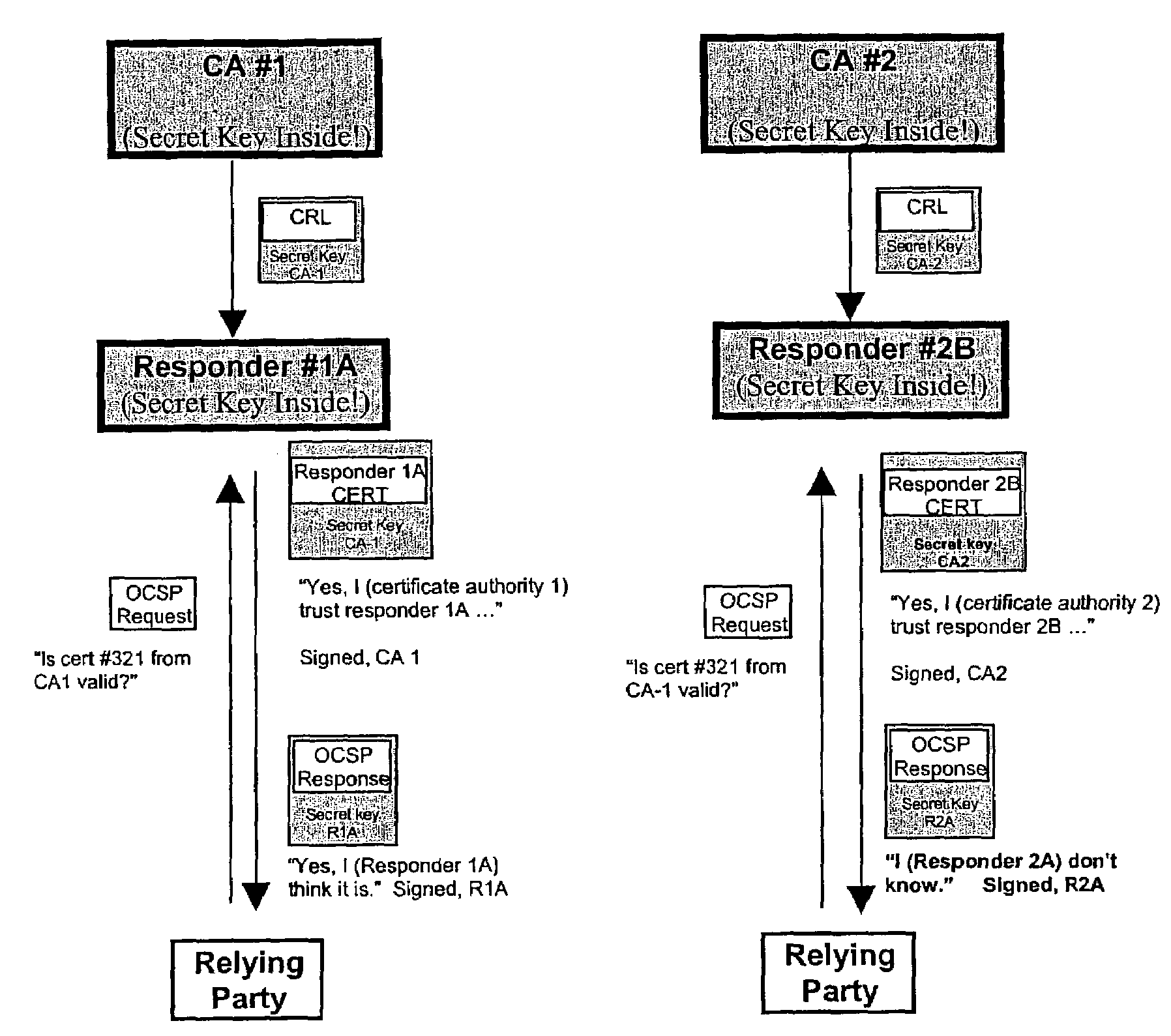
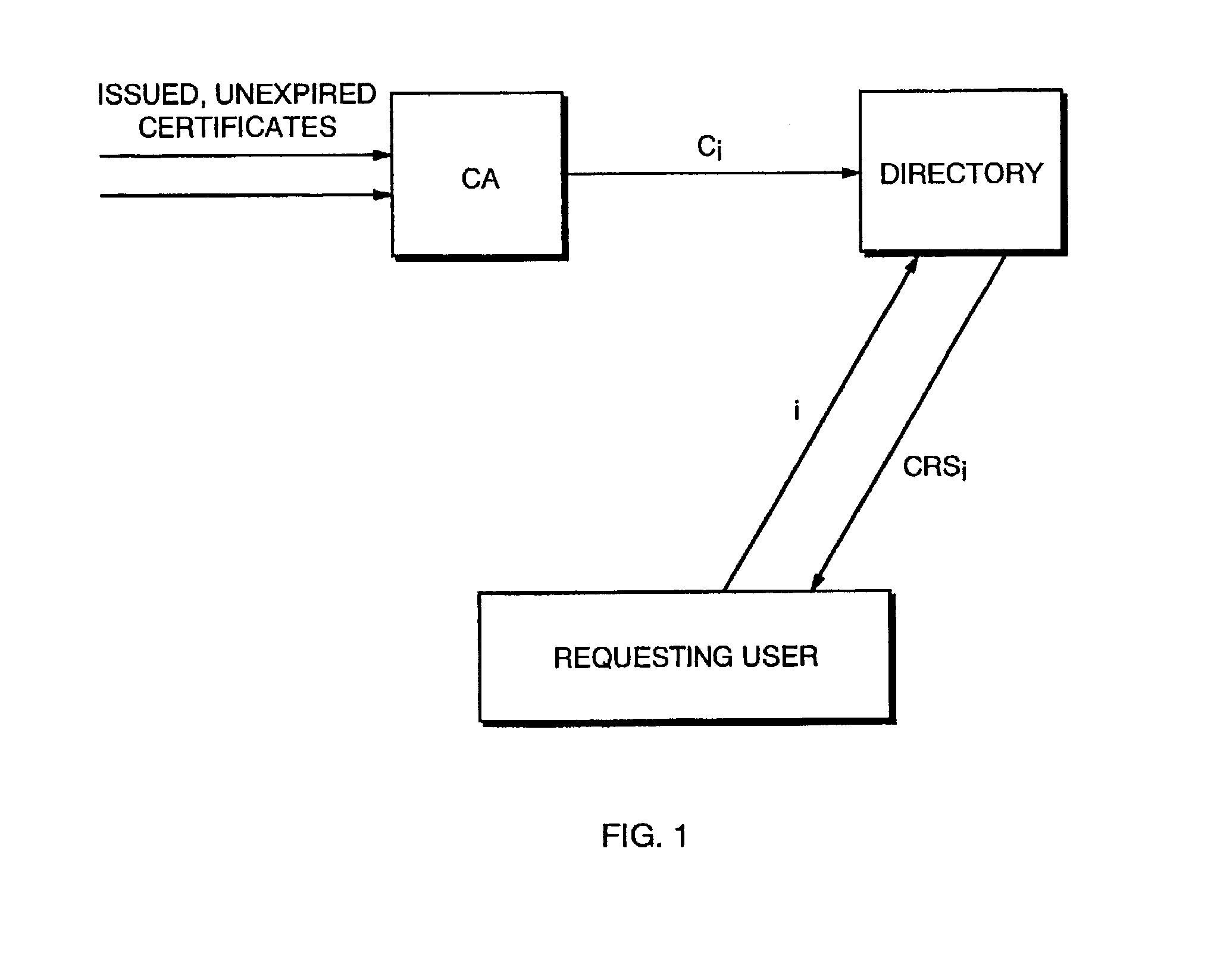
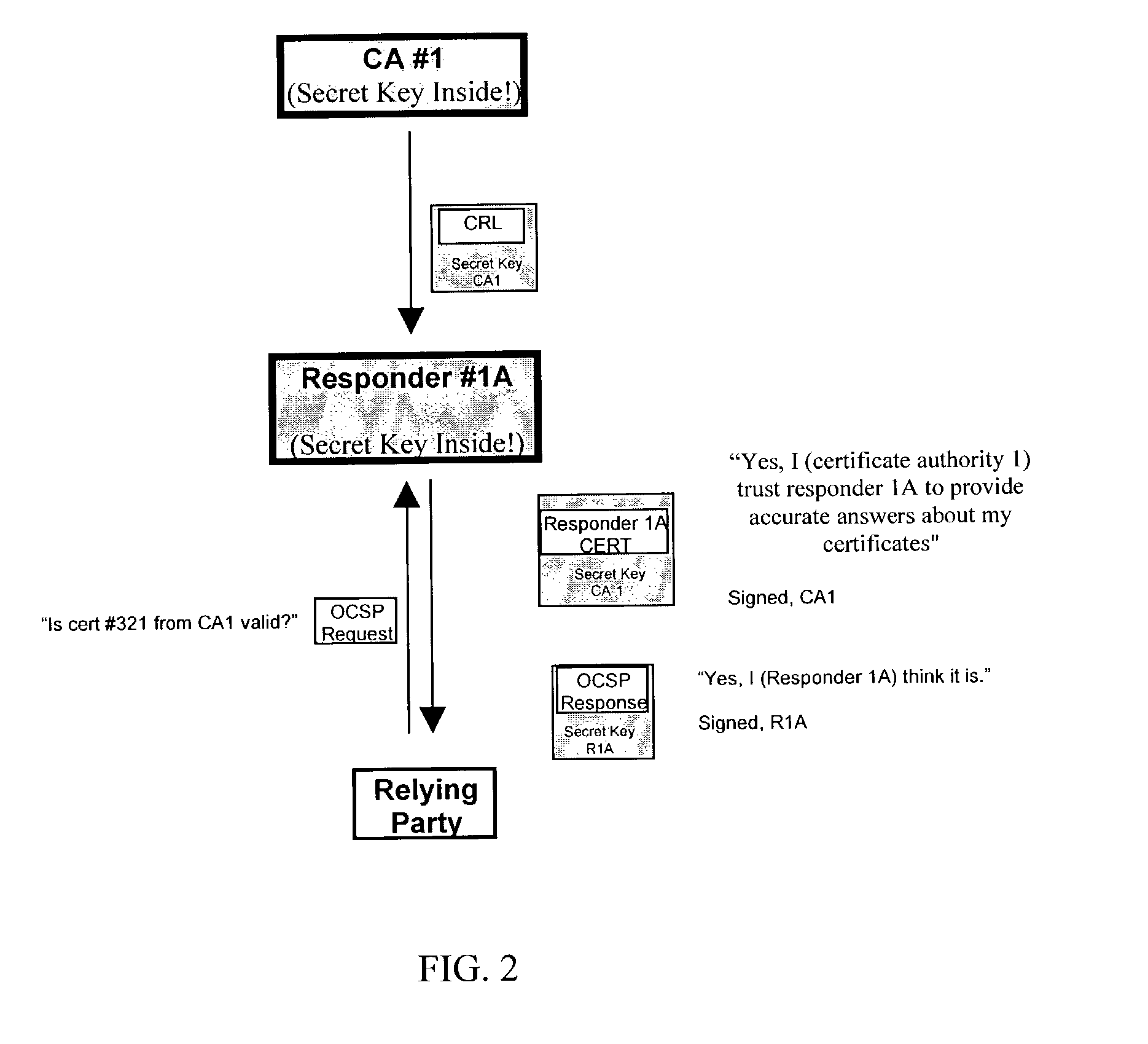
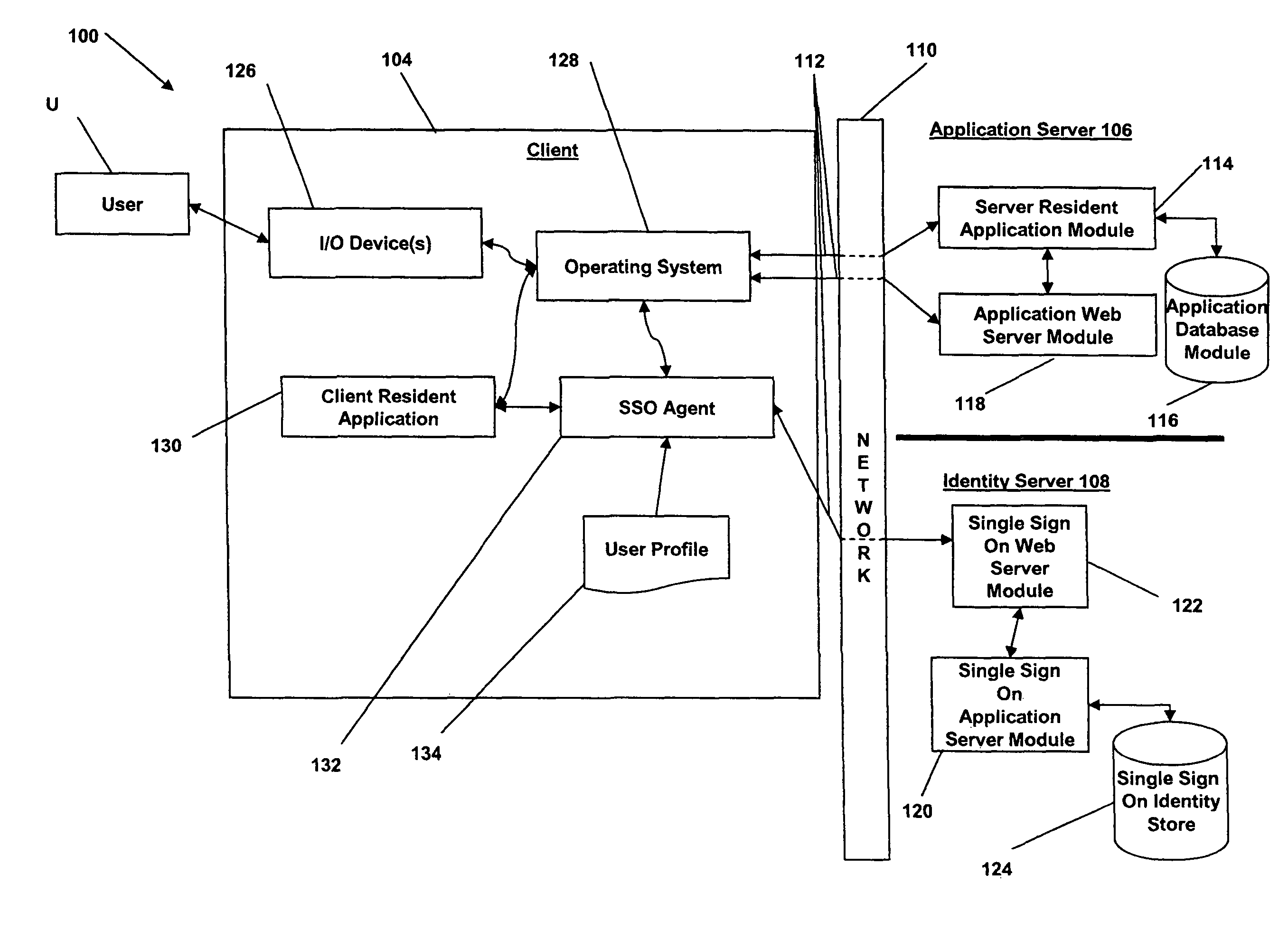
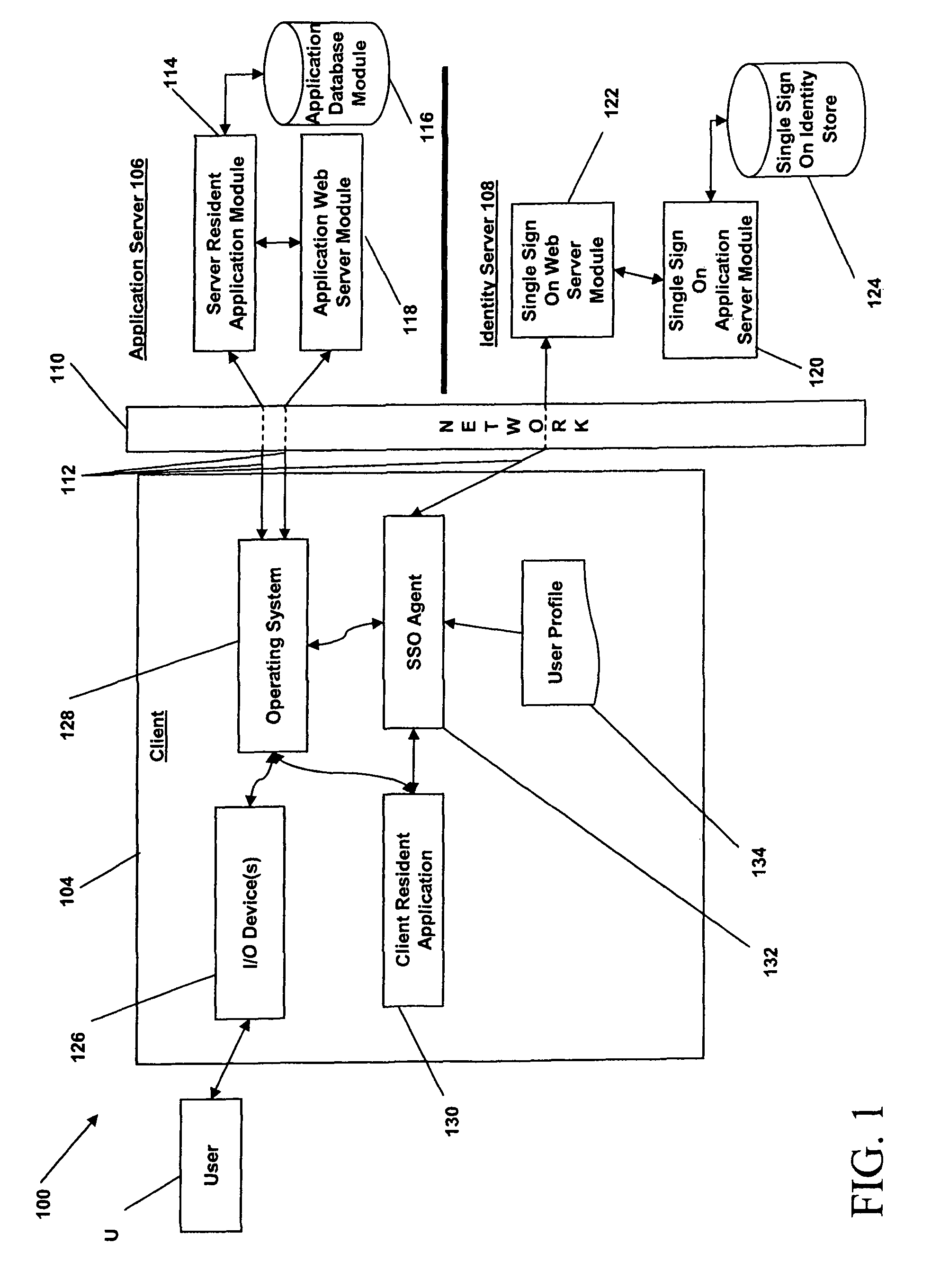
Physical access control
InactiveUS7353396B2Digital data processing detailsUser identity/authority verificationHash functionGranularity
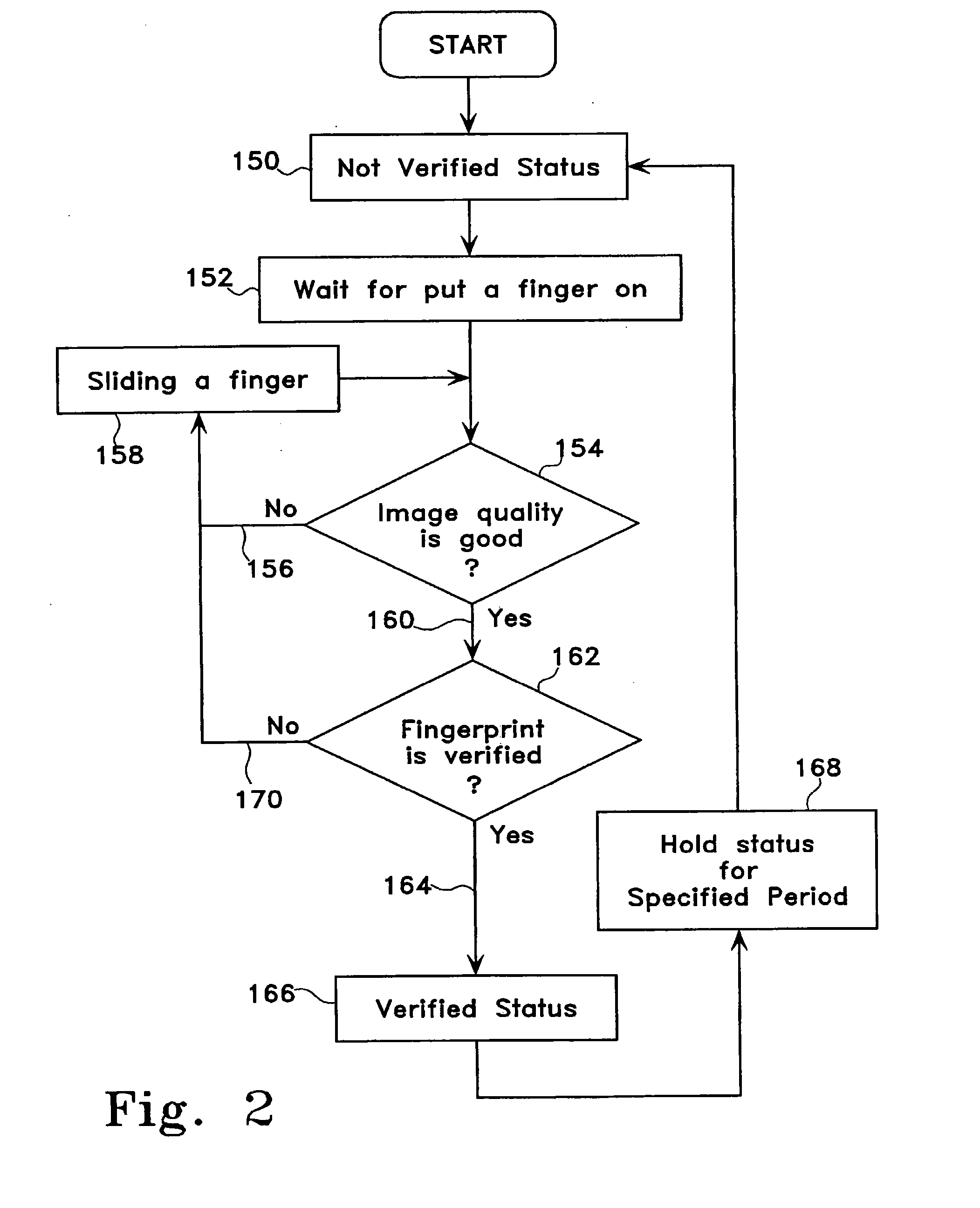
A system and method are disclosed for controlling physical access through a digital certificate validation process that works with standard certificate formats and that enables a certifying authority (CA) to prove the validity status of each certificate C at any time interval (e.g., every day, hour, or minute) starting with C's issue date, D1. C's time granularity may be specified within the certificate itself, unless it is the same for all certificates. For example, all certificates may have a one-day granularity with each certificate expires 365 days after issuance. Given certain initial inputs provided by the CA, a one-way hash function is utilized to compute values of a specified byte size that are included on the digital certificate and to compute other values that are kept secret and used in the validation process.
Owner:ASSA ABLOY AB
Mobile Device Transaction Using Multi-Factor Authentication
ActiveUS20120110341A1Reduce chanceImprove securityComputer security arrangementsPayment architectureThe InternetHand Held Computer
The following is a system in which a person may use a Cellular (Mobile) Telephone, a PDA or any other handheld computer to make a purchase. This is an example only. The process may entail any type of transaction which requires authentication, such as any financial transaction, any access control (to account information, etc.), and any physical access scenario such as doubling for a passport or an access key to a restricted area (office, vault, etc.). It may also be used to conduct remote transactions such as those conducted on the Internet (E-Commerce, account access, etc.). In the process, a multi-factor authentication is used.
Owner:BEIGI HOMAYOON
Process and appliance for data processing and computer program product
InactiveUS20060129745A1Mutual interaction can be avoidedSimple interfaceMemory loss protectionUnauthorized memory use protectionDigital dataFile system
The present invention concerns an appliance, a process and a computer program product for the processing of unstructured or semi-structured digital data in a file system. In order to create an appliance, a process and a computer program product which allow simple, reliable, high-performance and purpose oriented management of every manner of digital, stored, unstructured data, it is proposed that, when accessing data, logical access be carried out jointly with physical access and, when doing so, a particularly transparent, common access mechanism be implemented for both types of access.
Owner:SMAPPER TECH
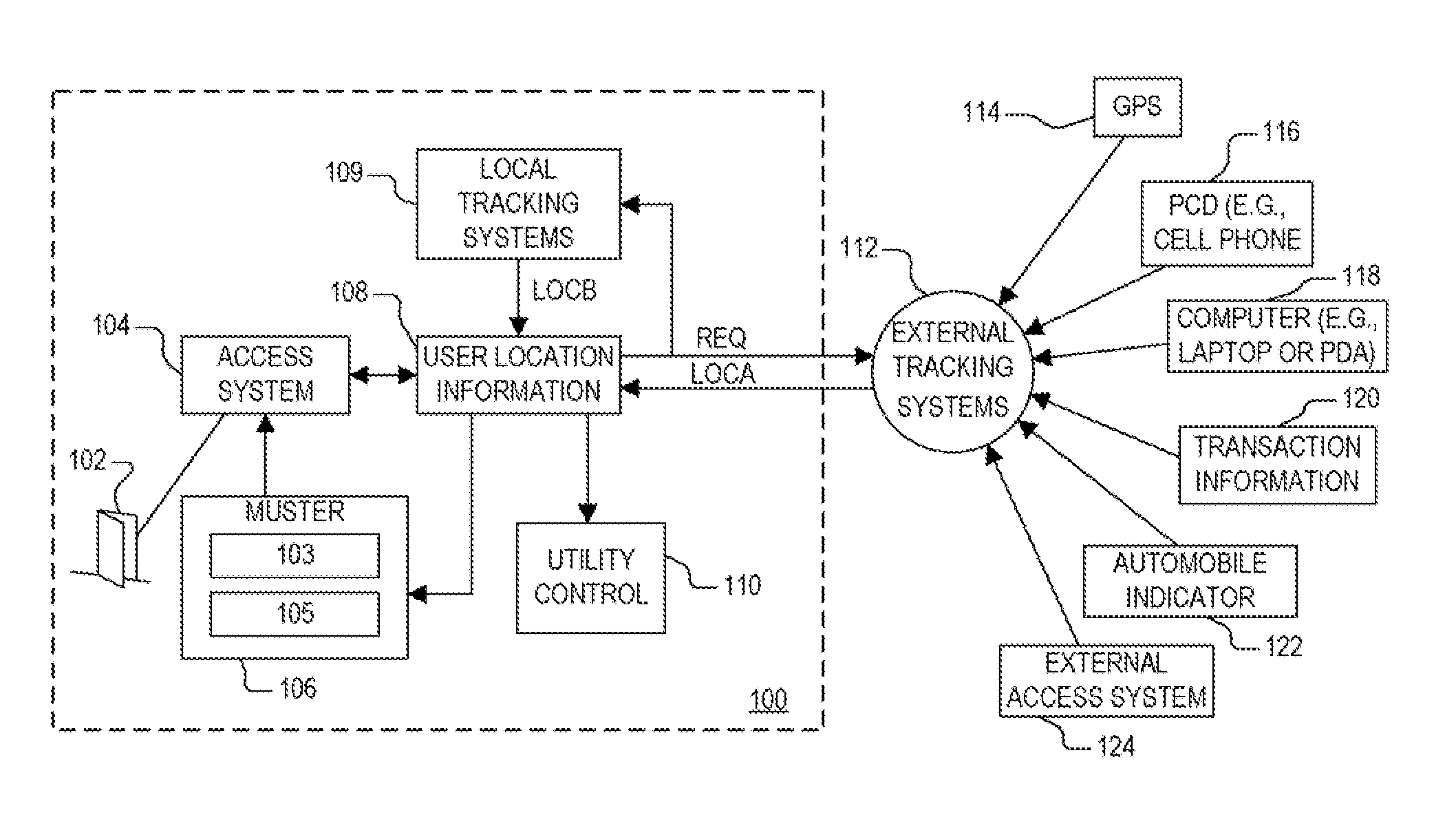
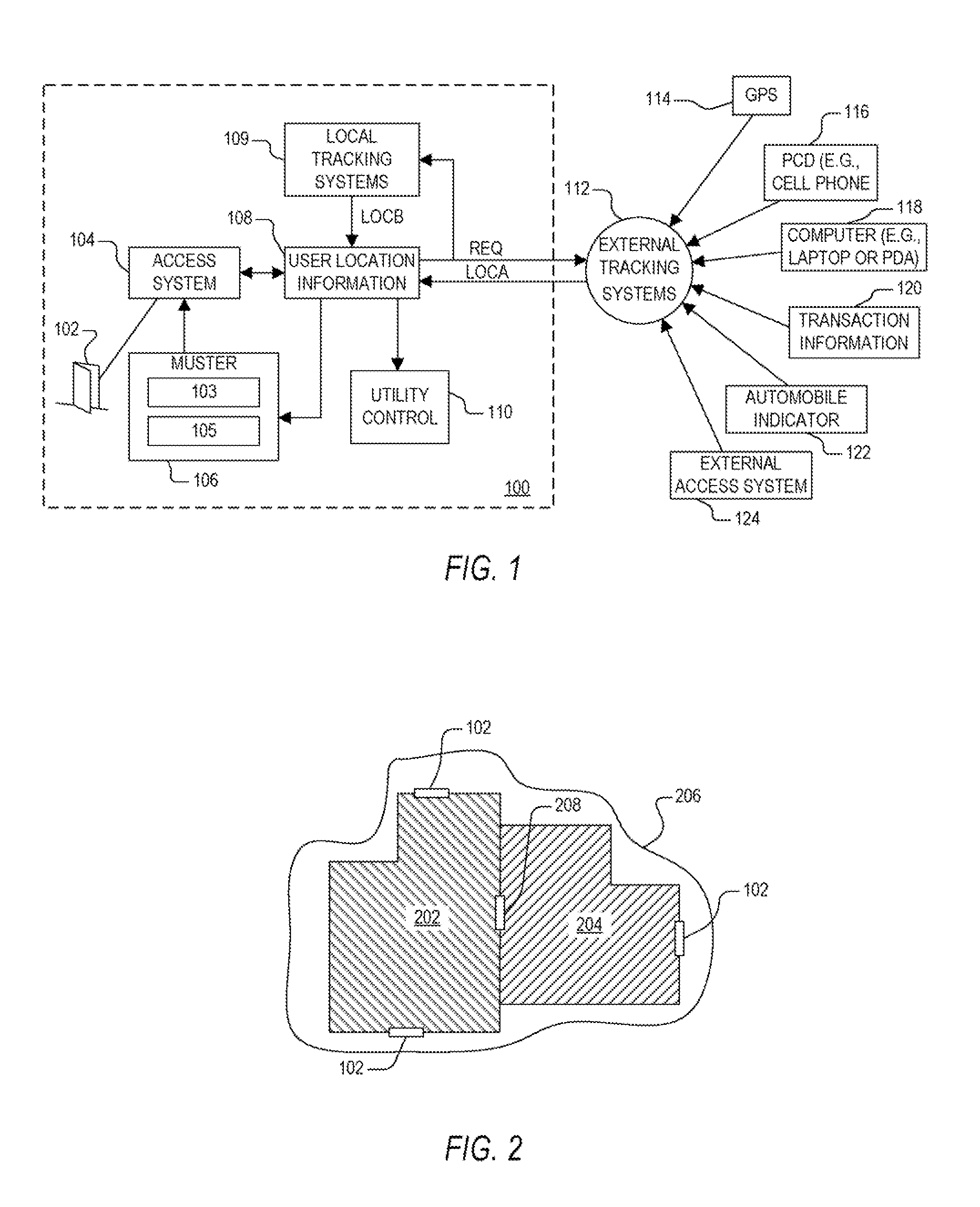
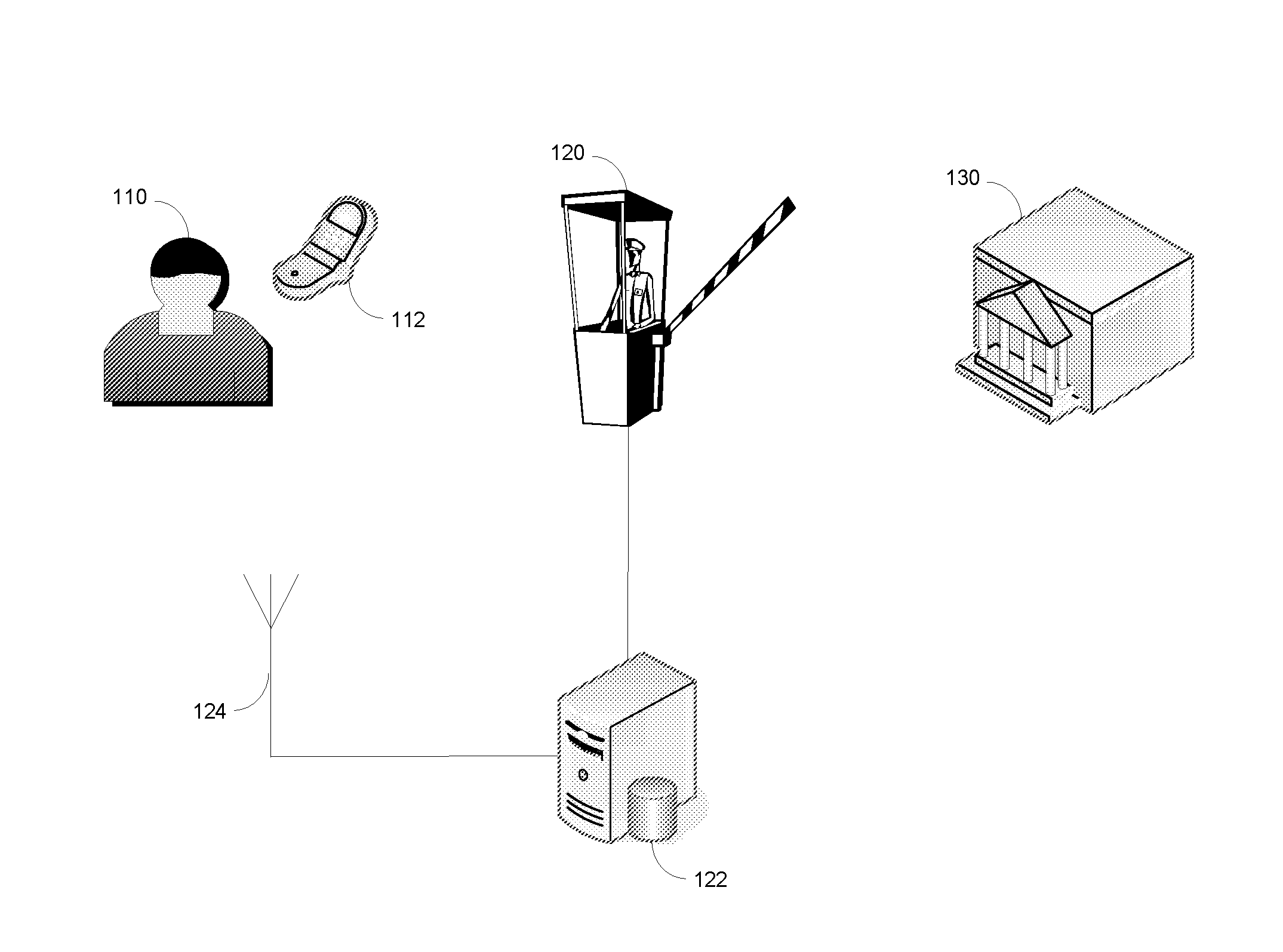
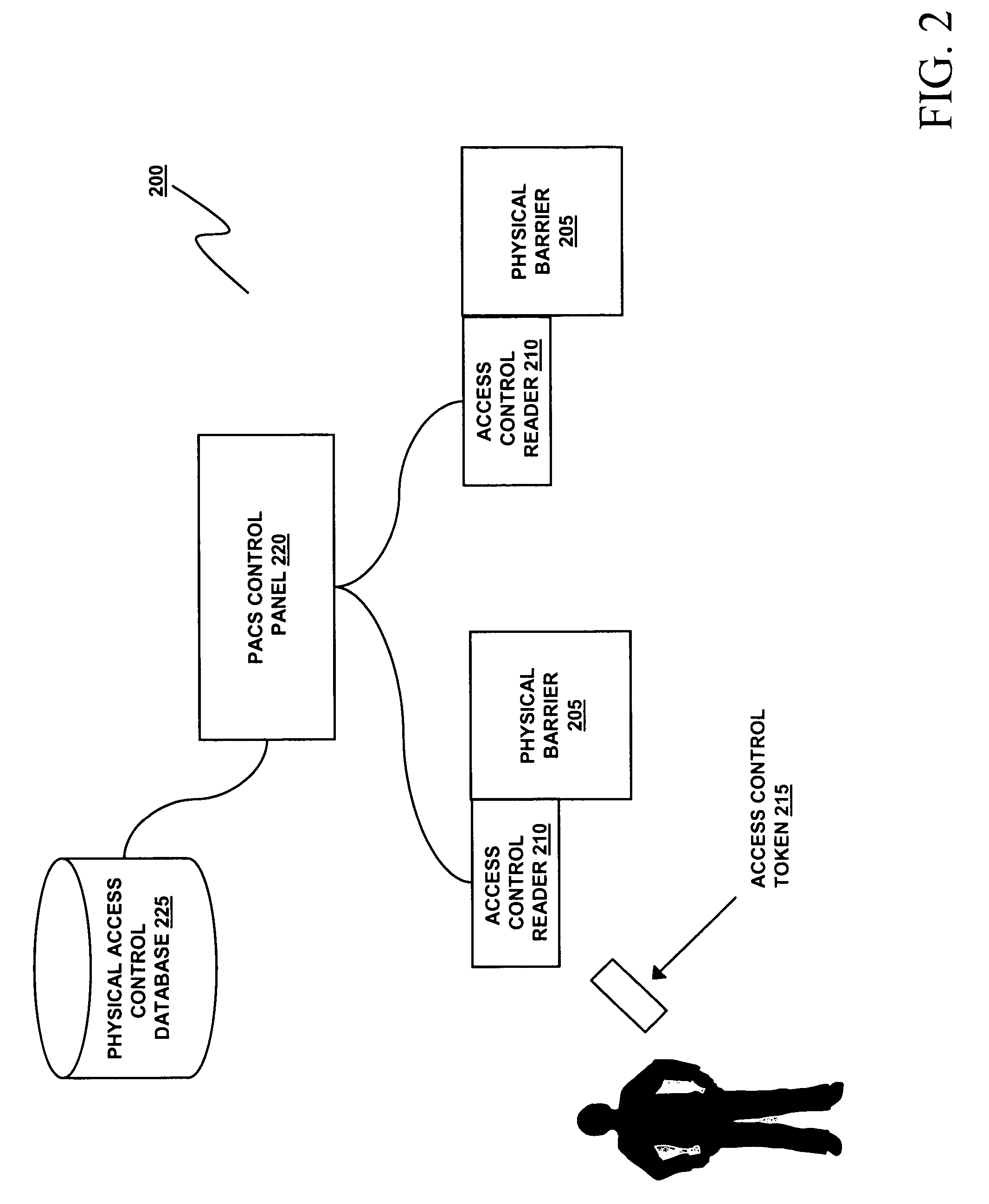
Access control system and method using user location information for controlling access to a restricted area
A method of controlling access to a restricted area including receiving location information from at least one supplemental tracking source which tracks location of an authorized user, and controlling access by the authorized user to a restricted area based on the location information. The method may further include maintaining a muster based on the location information. A physical access control system for controlling access to a restricted area including a user location information system and an access system which controls access based on the location information. The user location information system may further maintain a muster based on the location information. The user location information system receives location information indicating location of an authorized user from at least one supplemental tracking source.
Owner:PRECISION EDGE ACCESS CONTROL
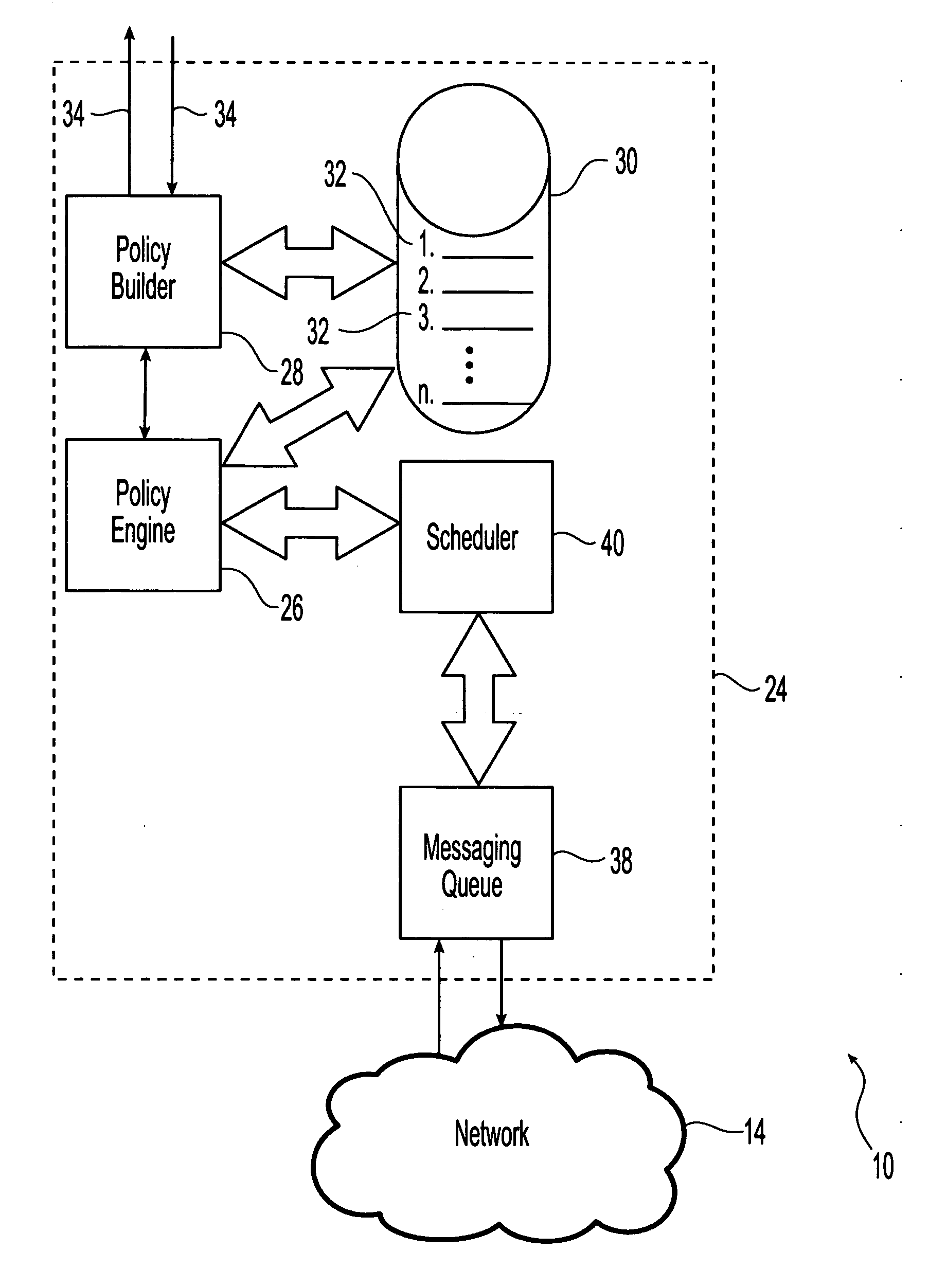
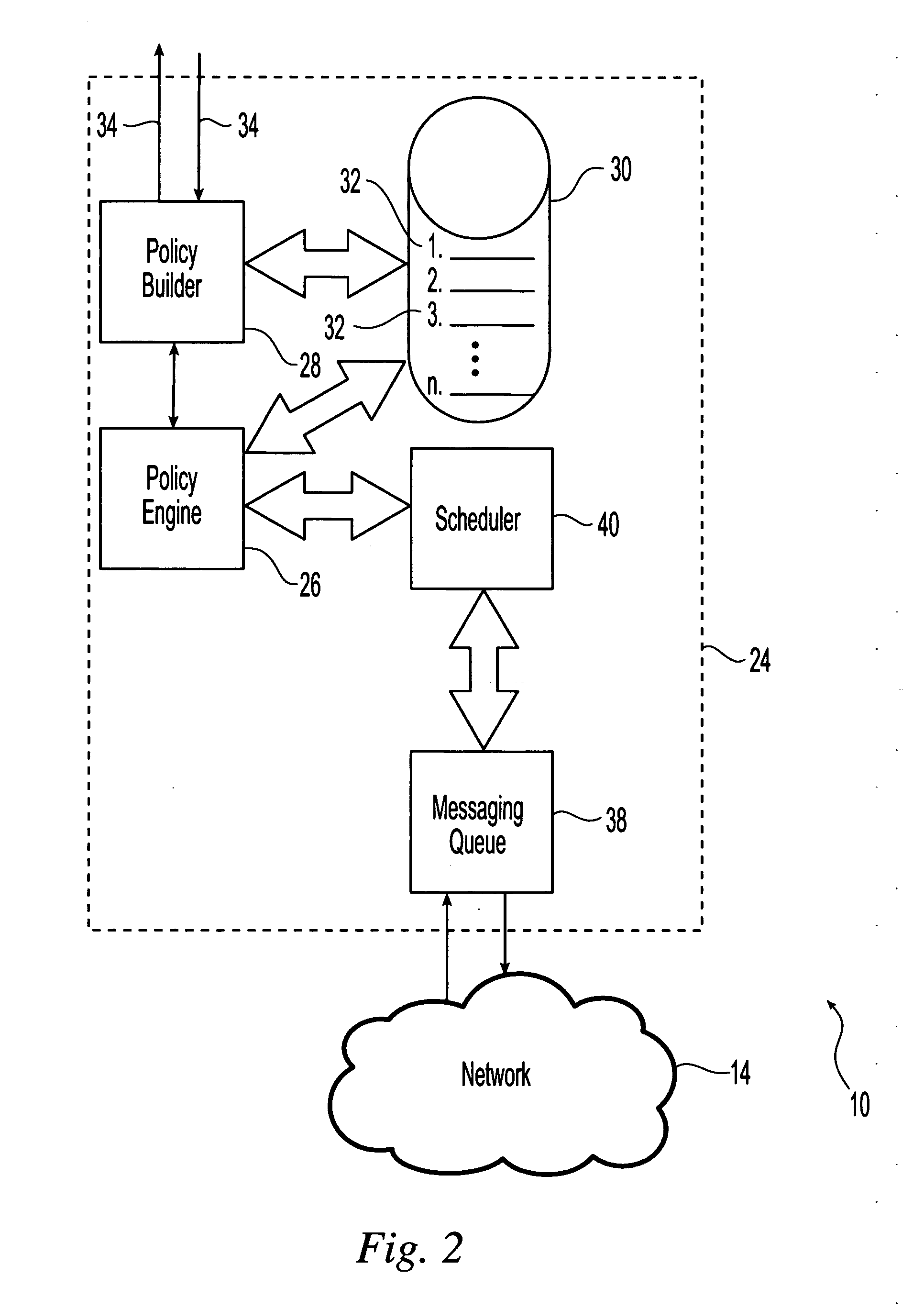
System and method for policy enforcement and token state monitoring
InactiveUS20060059548A1Broaden applicationEasily scalable, extensible and reliableDigital data processing detailsUser identity/authority verificationMonitoring systemCombined use
Systems and methods for monitoring the state of a token and communication exchanges between the token containing an embedded integrated circuit chip and a system are provided. Communications between the token and the system are established and the exchanged of commands and responses between the token and the system are monitored and evaluated for compliance with an identified policy. The identified policy contains lists of impermissible commands, responses and content, and delivery of the commands and responses is contingent upon compliance with the identified policy. The token is in communication with a token reader which communicates with the system using token reader driver software. Either the token reader driver software or the token itself is adapted to provide for the desired monitoring, evaluation and policy enforcement. Systems and methods are also provided that enforce policies at access points within a physical access system. The physical access system can be used in combination with tokens.
Owner:HILDRE ERIC ARNOLD +1
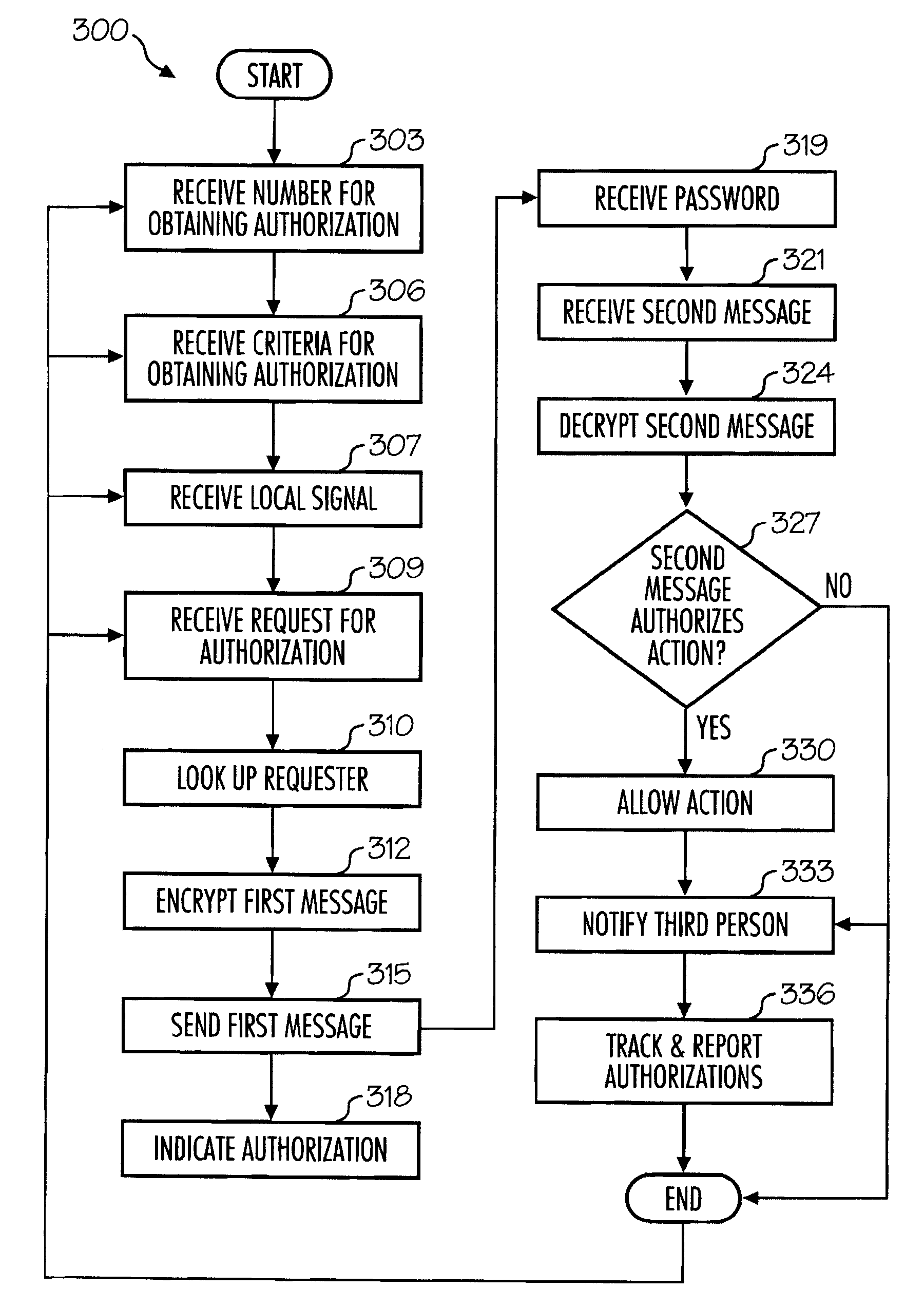
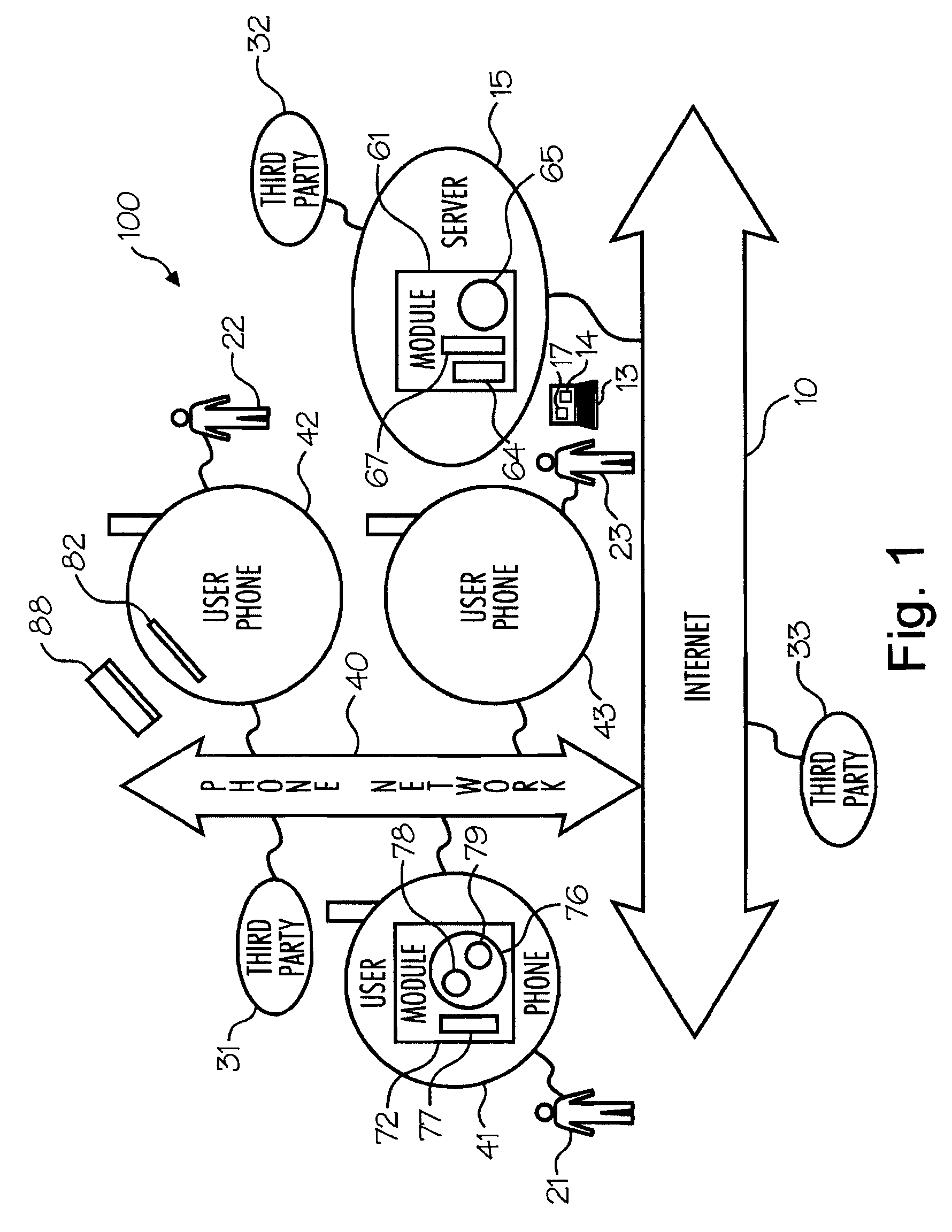
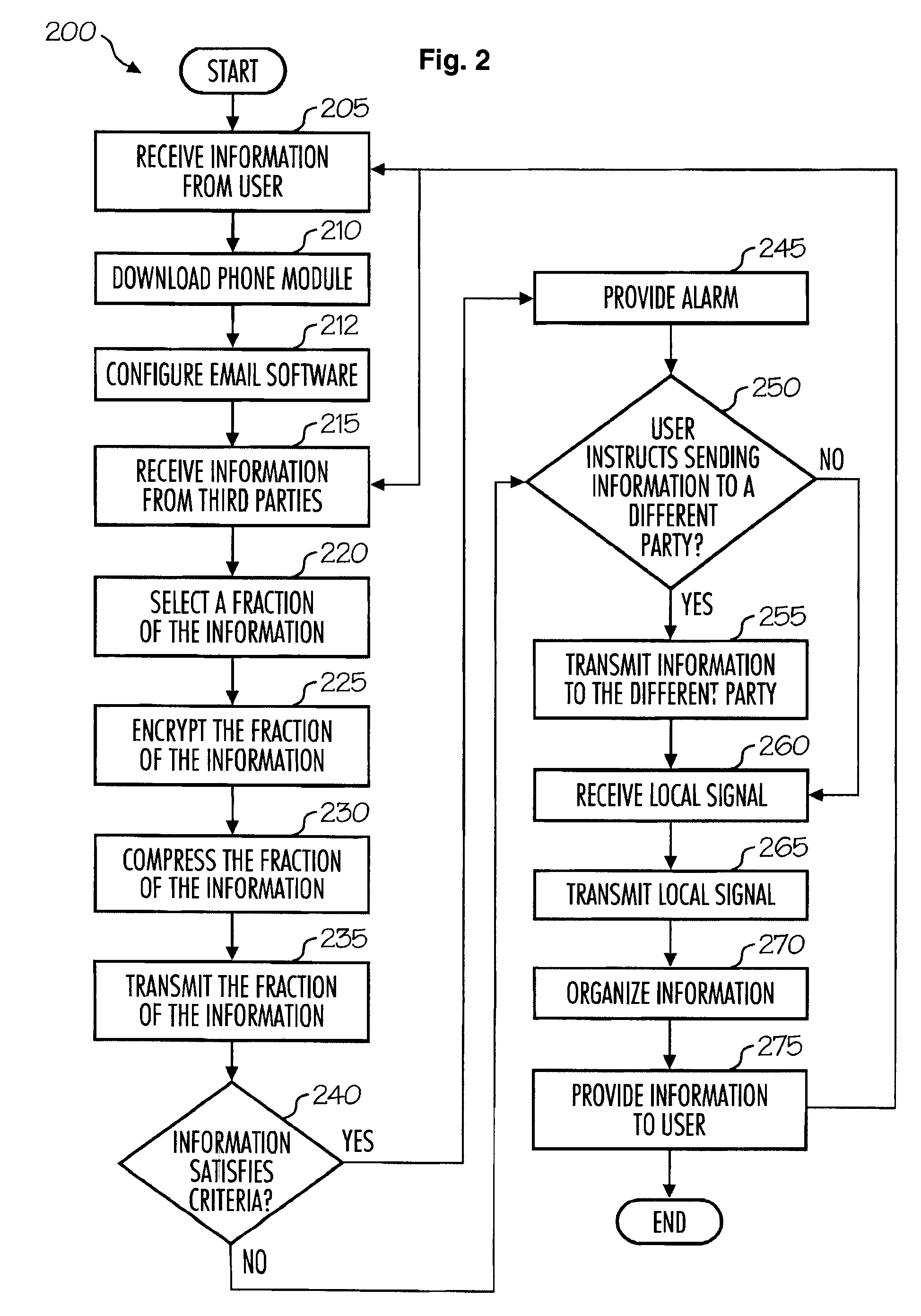
Methods of authorizing actions
ActiveUS20080108324A1Improve the level ofEasy to useUnauthorised/fraudulent call preventionEavesdropping prevention circuitsThe InternetFinancial transaction
Methods for authorizing actions using mobile phones. Embodiments include receiving from a person having authorize the action, an identification of a phone number for obtaining authorization for the action, receiving from a person seeking the action a request for authorization of the action, sending an automated first message through a mobile phone network to the mobile phone, including a description of the action for which authorization is requested, and receiving, from the first mobile phone, a second message, which authorizes the action. Actions that are authorized, in different embodiments, include computer access, physical access, and financial transactions. In various embodiments, the phone number may be received through the mobile phone network through the Internet, through a local signal, or directly from the user.
Owner:CELLTRUST CORP
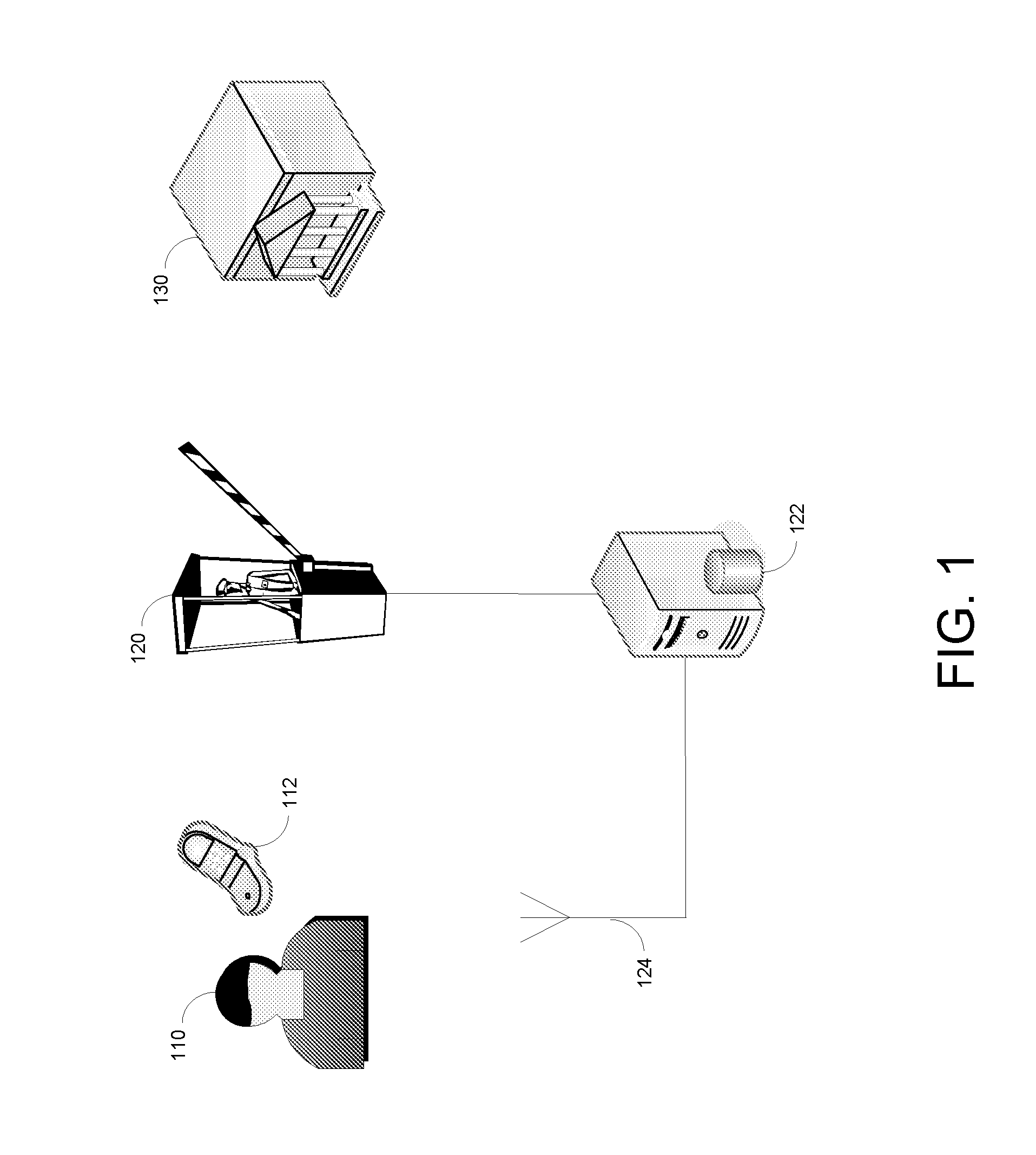
Wireless Encrypted Control of Physical Access Systems
InactiveUS20110291798A1Safety issue is lessenedImprove securityElectric signal transmission systemsTicket-issuing apparatusComputer hardwareDigital signature
Physical access systems and methods securely grant physical access to restricted areas in high-volume applications. An electronic device, such as a smartphone, stores a digitally signed physical access rights file. An individual uses this rights file to gain access to a restricted area only after self-authenticating to the device. A physical access control system receives the rights file, validates it, and determines whether to permit passage through a physical barrier. The determination may be made by a physical barrier system, or by a remote access control headend. An access control gateway, which may be an access control headend, may either unlock the physical barrier system when the electronic device is near the physical barrier, or it may transmit an authorization code to the electronic device and the physical barrier system, whereby passage is only permitted if the barrier system subsequently receives the authorization code from the electronic device using near field communications.
Owner:SURIDX
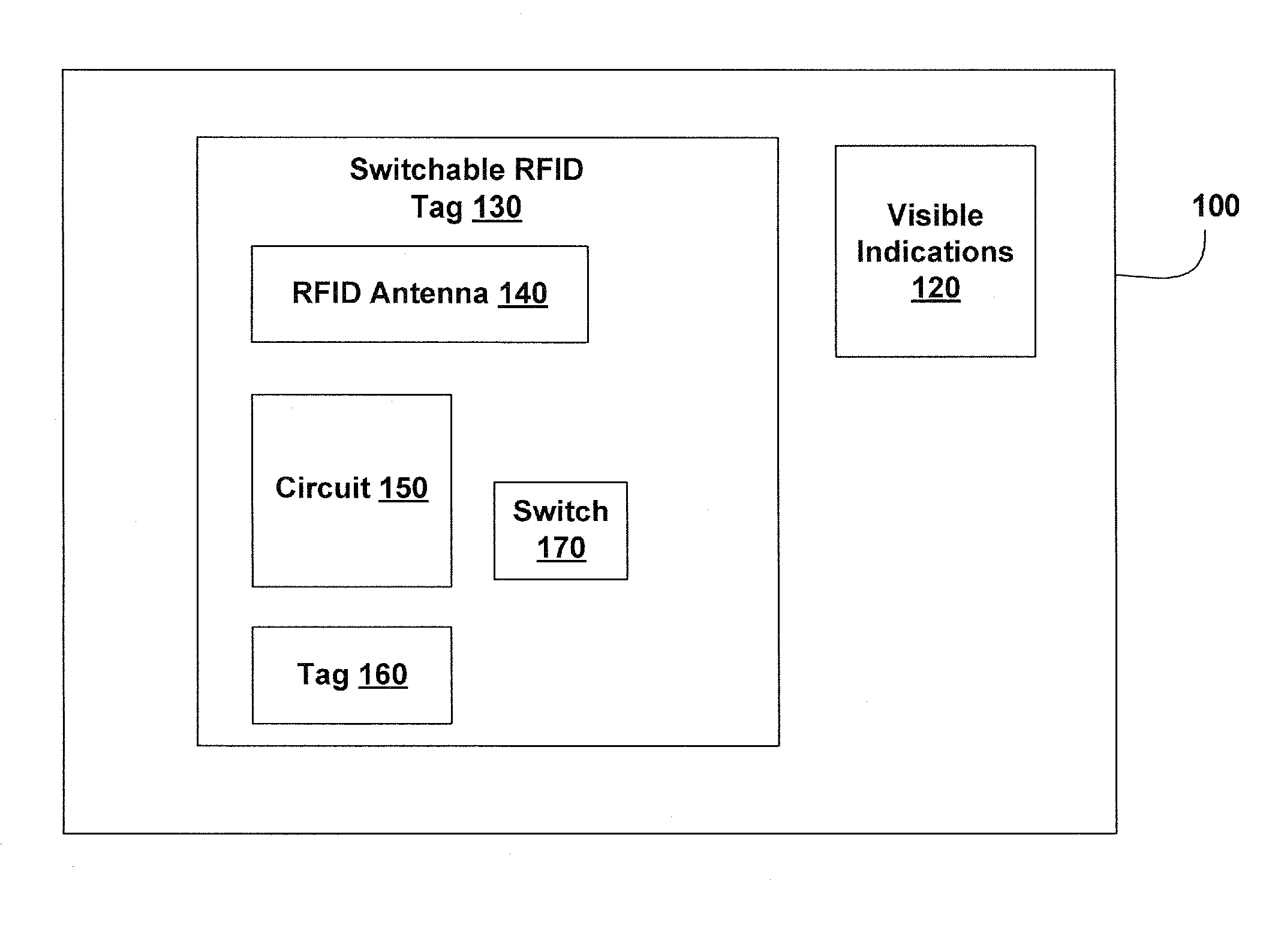
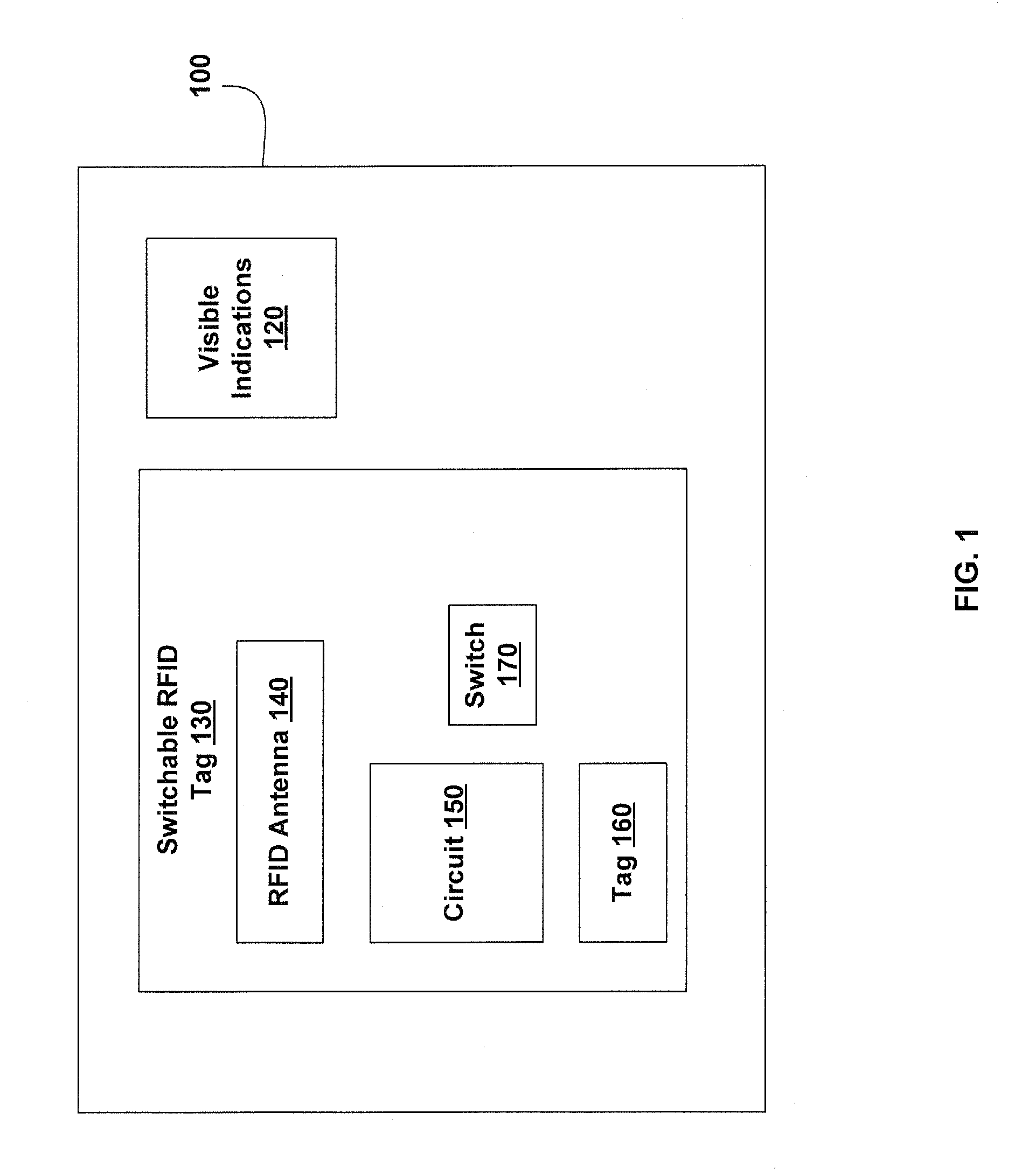
RF Powered Remote Control
InactiveUS20060267737A1Subscribers indirect connectionRecord carriers used with machinesRemote controlRadio frequency
Various passive remote control devices are disclosed. These passive remote control devices may include one or more RFID tags and one or more switches. In various embodiments, the passive remote control devices include identity devices, financial devices remote controls, and the like. The devices controlled may include electronic devices, televisions, computers, locks, physical access systems, or the like. In some embodiments, switches are configured to enter data into a switchable RFID device, for example to select a financial account.
Owner:COLBY TRUST STEVEN M +1
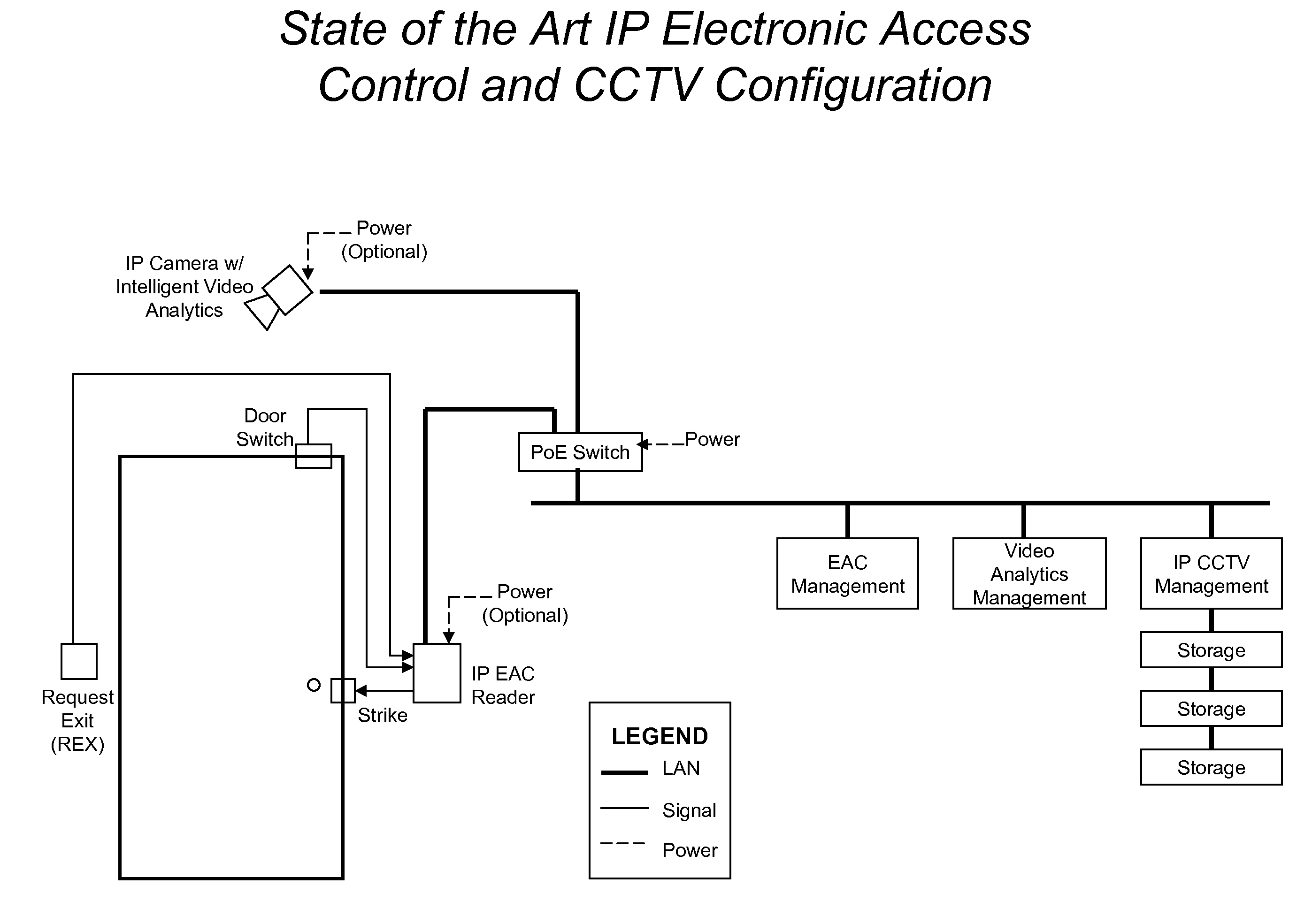
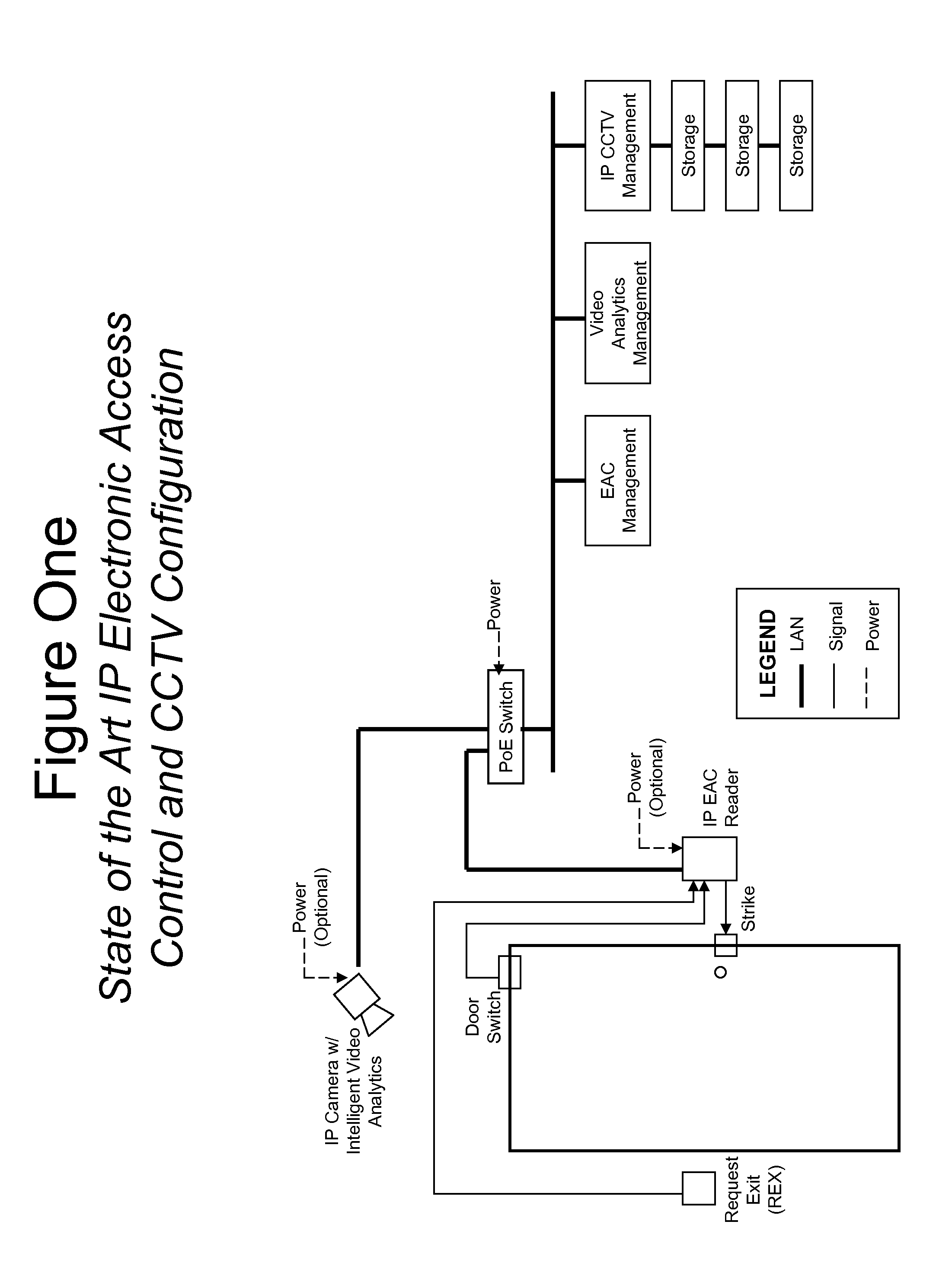
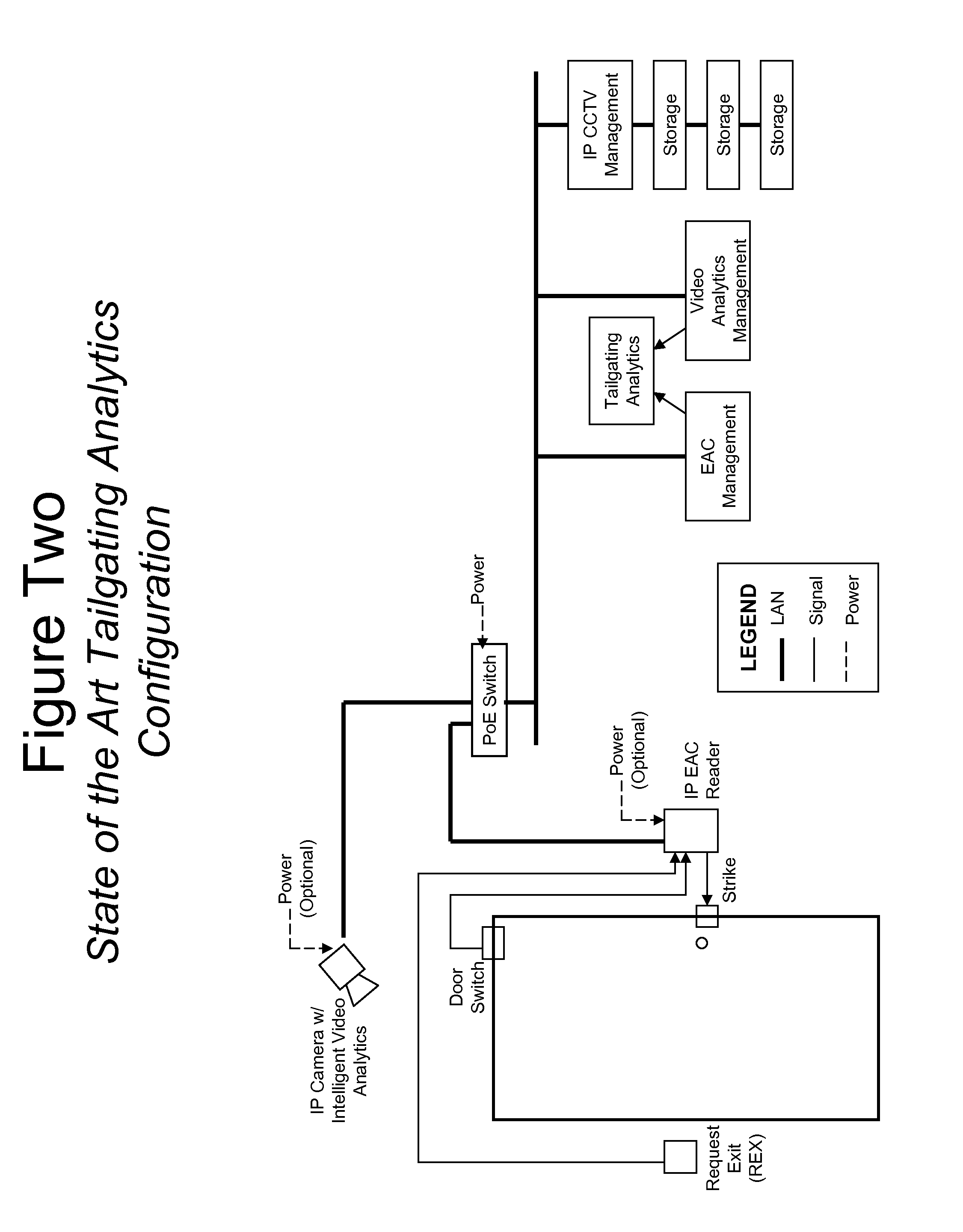
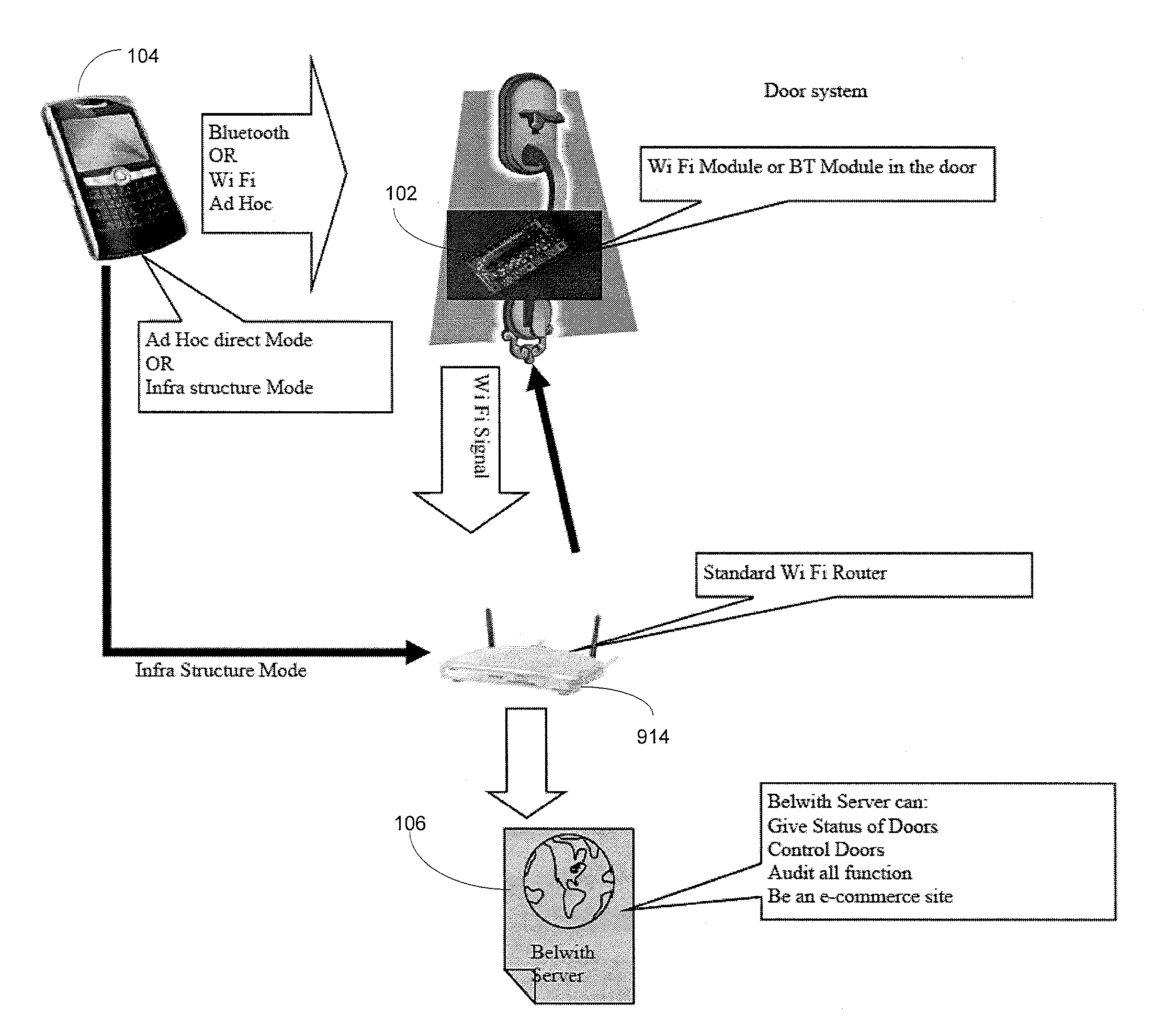
Device for electronic access control with integrated surveillance
ActiveUS20090115570A1Electric signal transmission systemsMultiple keys/algorithms usageElectronic accessComputer network
Described is a device for electronic access control (EAC) and surveillance. The device includes an EAC module and an imager integrated in a single unit. The EAC module controls physical access through a secure portal and the imager maintains surveillance of an observation area near the portal. A data signal is provided at a data port proximate to the EAC module and imager. The data signal includes EAC data for the portal, image or video data of the observation area and optional audio data. The device can be configured to communicate with a remote server and database over an IP data network. The device can also include one or more analytical modules for real-time computation and processing of data and generation of metadata for transmission over the data network. Correlating and combining current and historical data from multiple devices results in powerful real time threat detection and forensic search capability.
Owner:CUSACK JR FRANCIS JOHN
Virtual private network (VPN)-aware customer premises equipment (CPE) edge router
ActiveUS20040208122A1Metering/charging/biilling arrangementsError preventionPrivate networkNetwork architecture
A network architecture includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
System and method for wireless network security
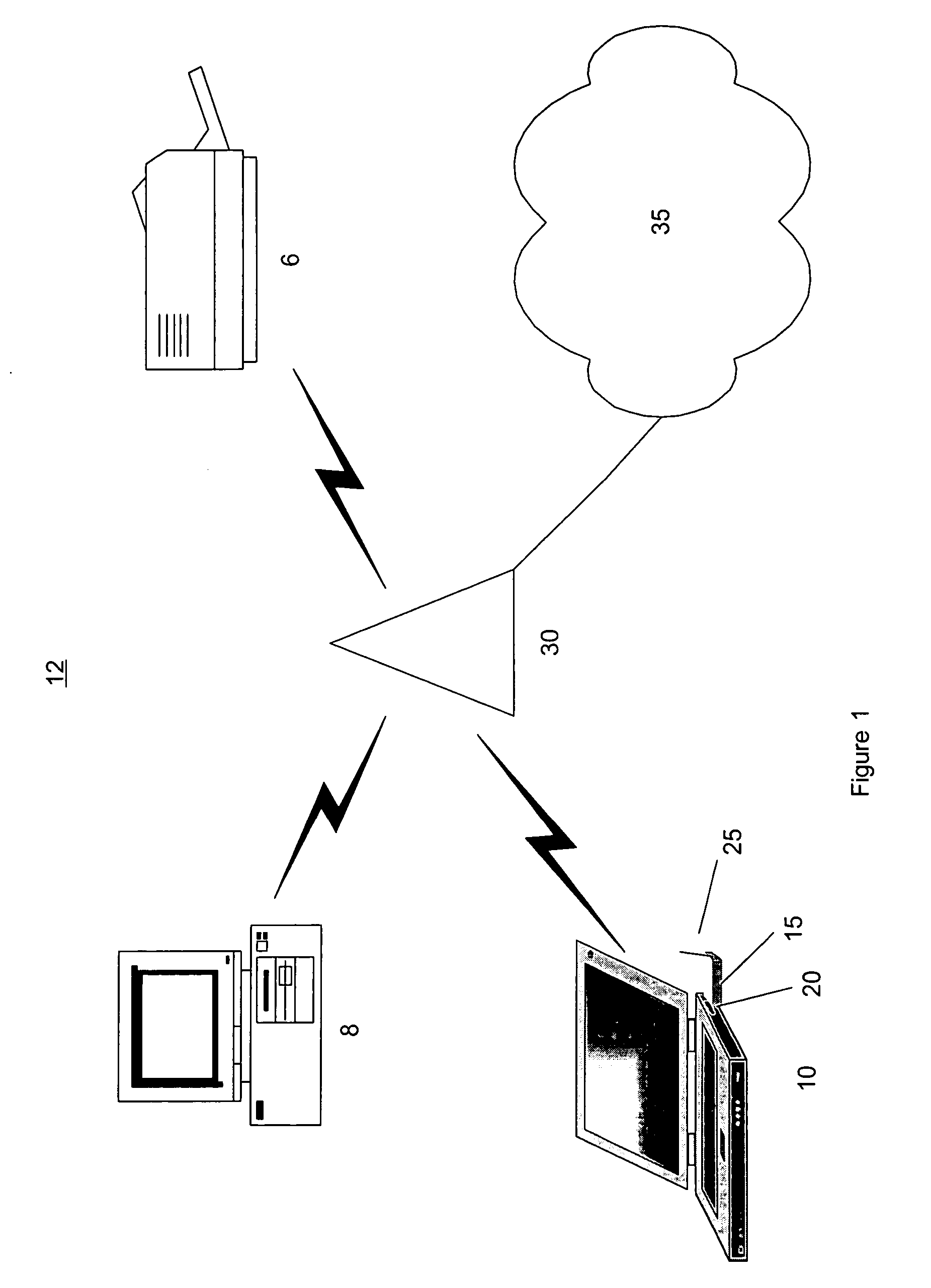
InactiveUS20050245235A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsPhysical accessWireless access point
Described are a system and method for a wireless network security. The system may include a wireless electronic device and a wireless access point. The access point includes a memory and is capable of wirelessly communicating with the device. The memory stores an access scheme which defines an authentication procedure for allowing the wireless communications between the electronic device and the further asset. The authentication procedure utilizes data as defined by the access scheme. The access point is situated in a location accessible to an authorized user and provides access for the electronic device to a further asset. The access point allows the wireless communications between the electronic device and the further asset only when the authentication procedure is successful. Before the authentication procedure, the data is transferred between the device and the access point via a physical access to at least one of the access point and the electronic device.
Owner:SYMBOL TECH INC
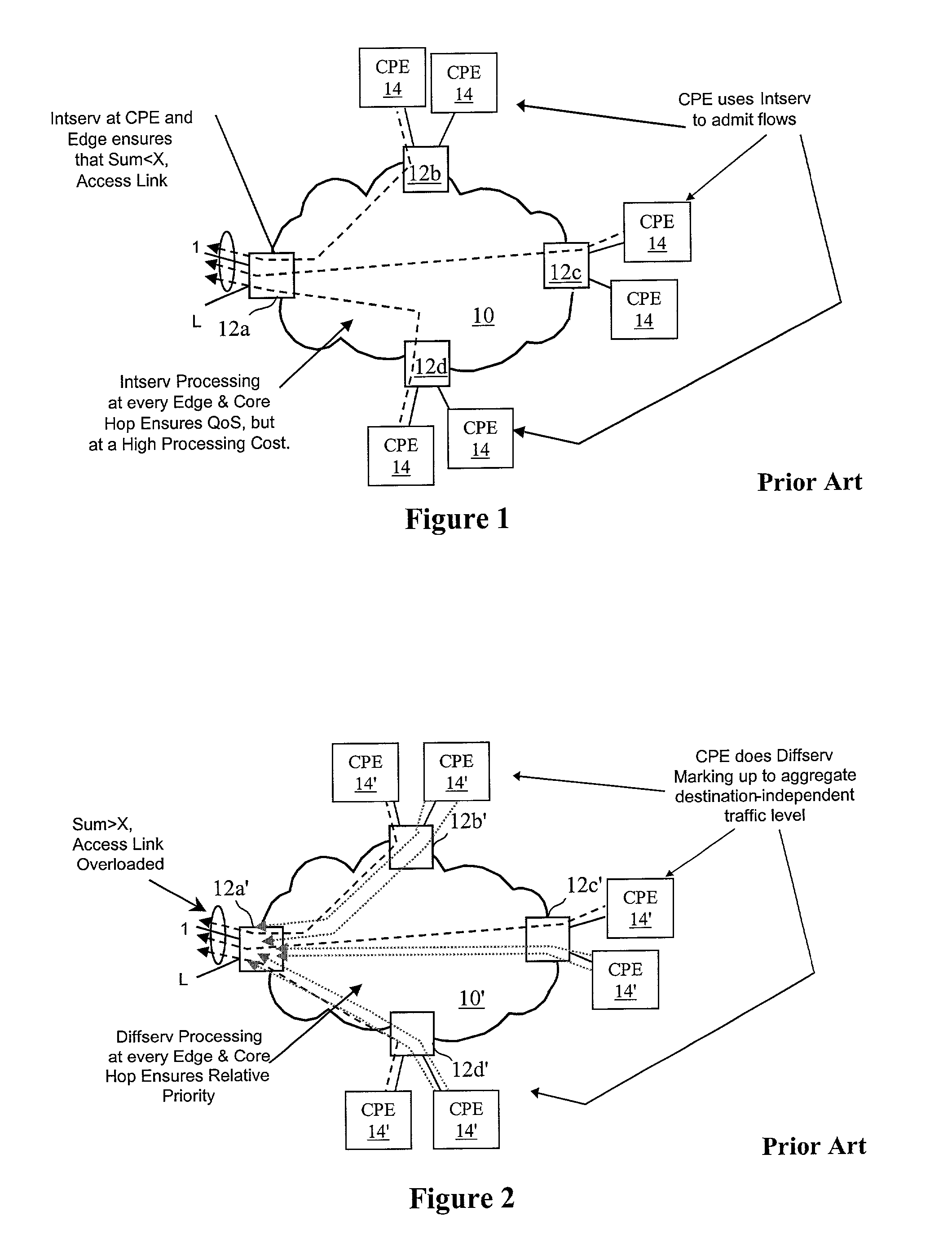
System, method and apparatus that employ virtual private networks to resist IP QoS denial of service attacks
InactiveUS20030115480A1Error detection/correctionVolume/mass flow measurementPrivate networkThe Internet
A network architecture in accordance with the present invention includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails special configuration of network elements and protocols, including partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and the configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
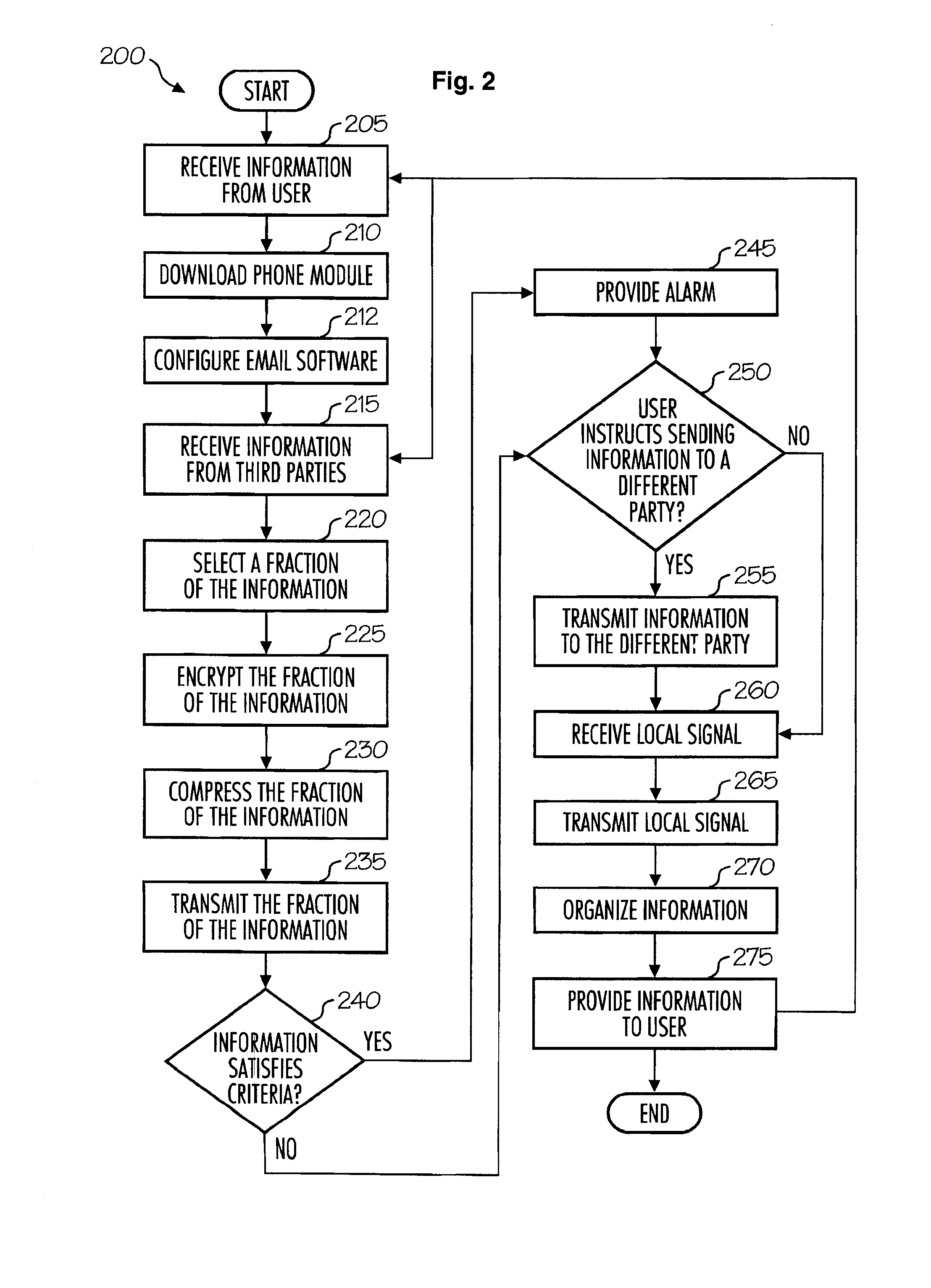
Methods to authenticate access and alarm as to proximity to location
ActiveUS20080133930A1Easy to trackImprove security levelUser identity/authority verificationPayment architectureResidencePassword
Methods for authenticating access and proving positional awareness using mobile phones. Embodiments for authenticating access include receiving identification indicia from a person seeking access, sending a message to a person having authority for access, and receiving either a second message indicating that the person has taken an affirmative action to indicate authorization, or a password that was provided in the first message. Access may be computer access or physical access, as examples. Methods of providing positional awareness include obtaining or storing location coordinates, monitoring the location of a mobile phone, and providing an alarm, for example, through a second mobile phone. In a number of embodiments, location coordinates are automatically obtained from Internet websites. In some embodiments, parents can monitor the location of their children to make sure they do not get too close to a reported residence of a registered sex offender, for instance.
Owner:CELLTRUST CORP
Wireless device enabled locking system
An encrypted security system and associated methods for controlling physical access. The system includes a security server configured to receive a request for authentication from a mobile device, the request comprising information identifying the mobile device and a physical access control device. The security server forwards an encryption message comprising a plurality of unique identifiers to the physical access control device via the mobile device. The physical access control device is configured to authenticate the plurality of unique identifiers in the encryption message and operate an access control mechanism.
Owner:DELPHIAN SYST
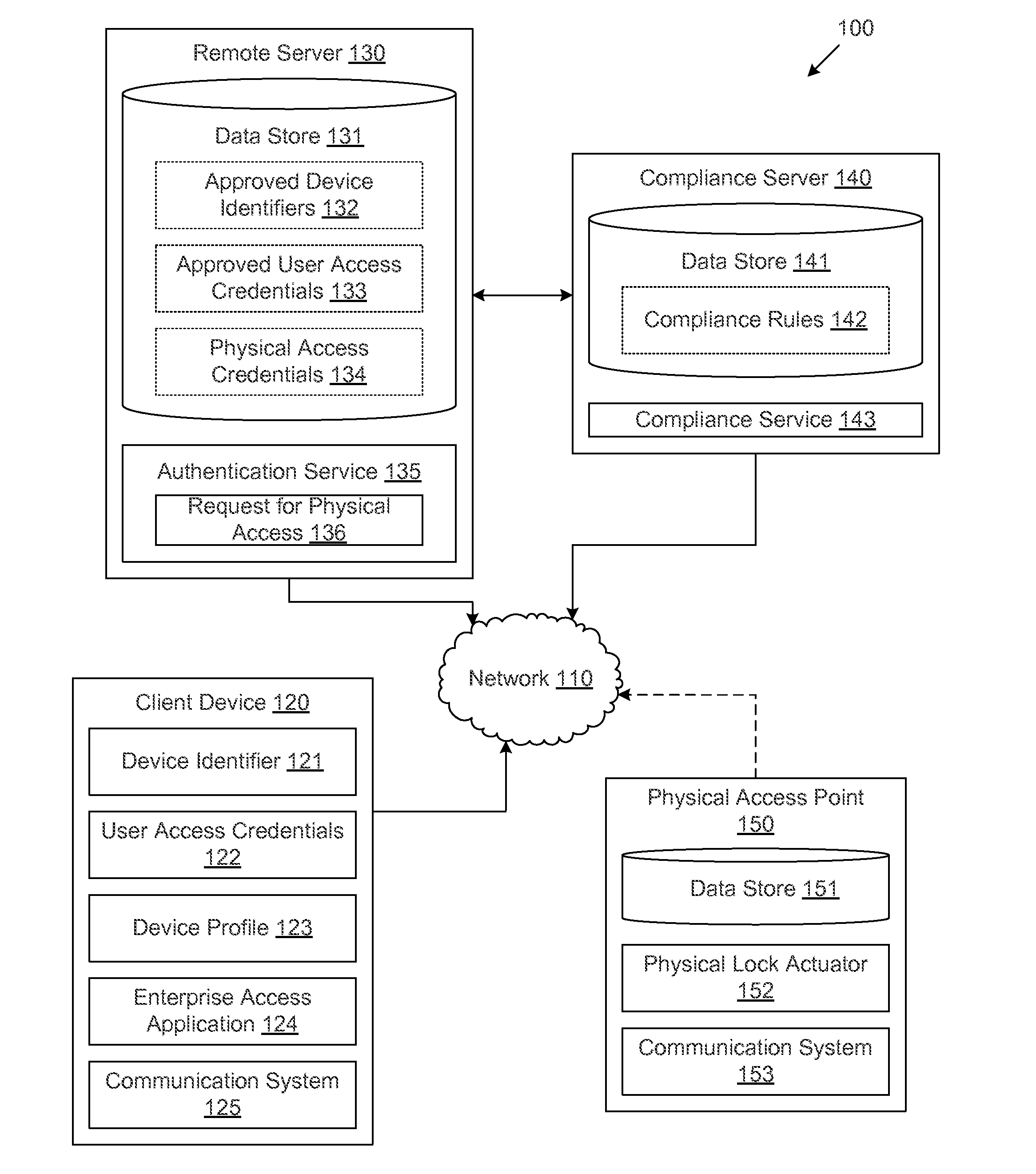
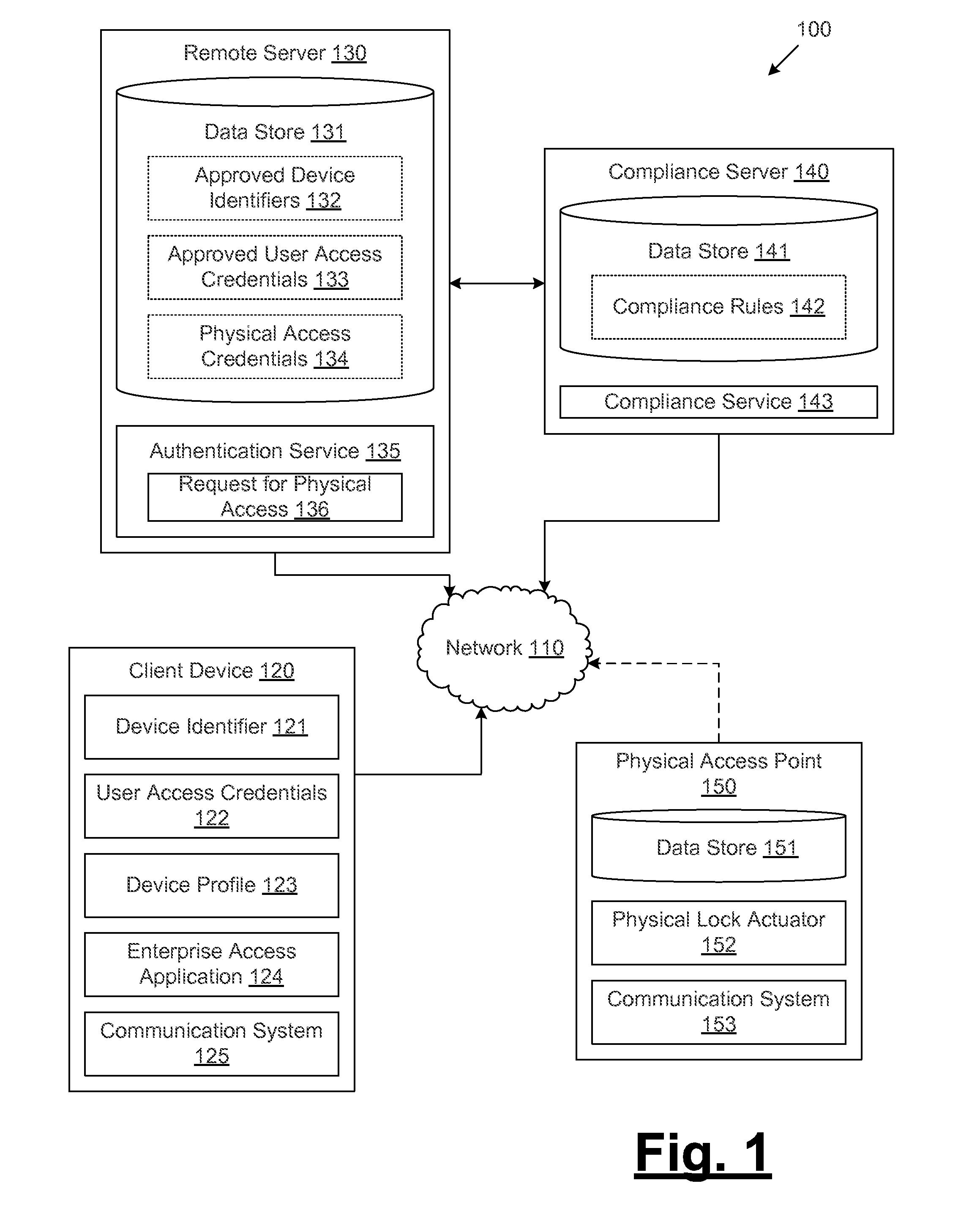
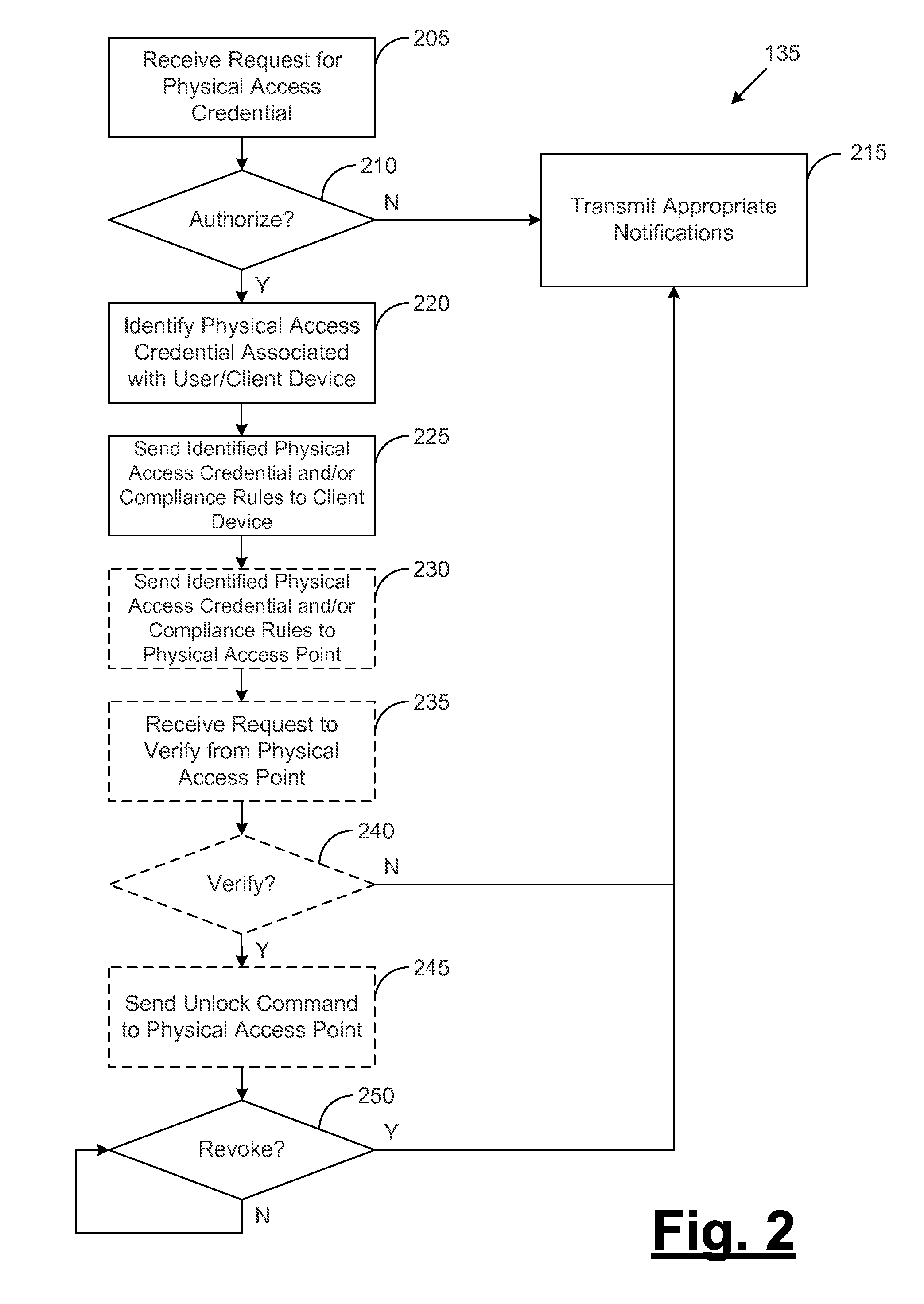
Controlling physical access to secure areas via client devices in a networked environment
ActiveUS20140282929A1Digital data processing detailsMultiple digital computer combinationsClient-sidePhysical access
A method is disclosed for providing physical access credentials to a client device. The method may include receiving a request for a physical access credential, where the first request includes at least one user access credential and at least one physical access point identifier. The method may also include determining whether the request should be granted based at least in part on the at least one user access credential. The method may further include, in response to determining that the request should be granted, sending the physical access credential associated with the physical access point.
Owner:AIRWATCH
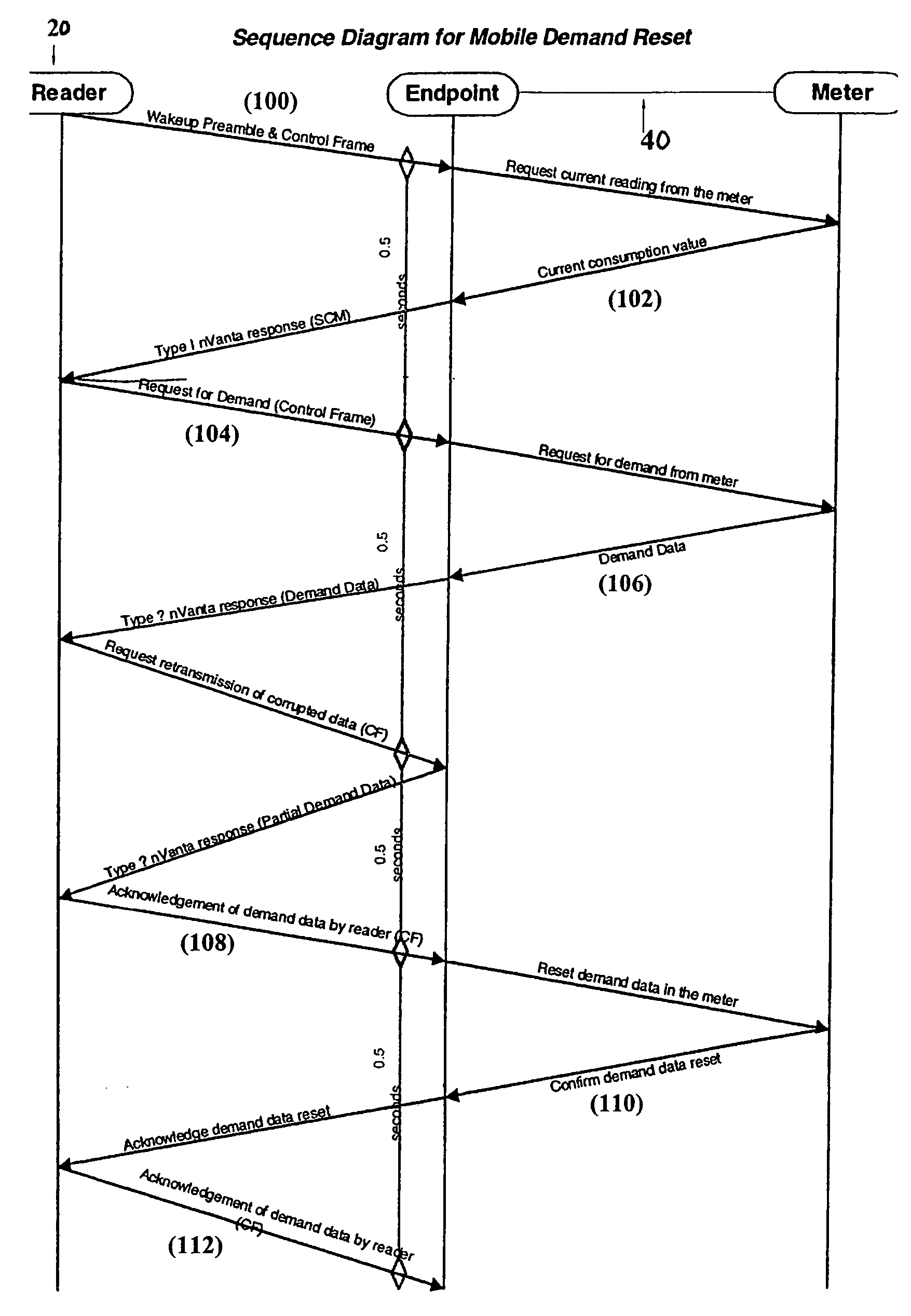
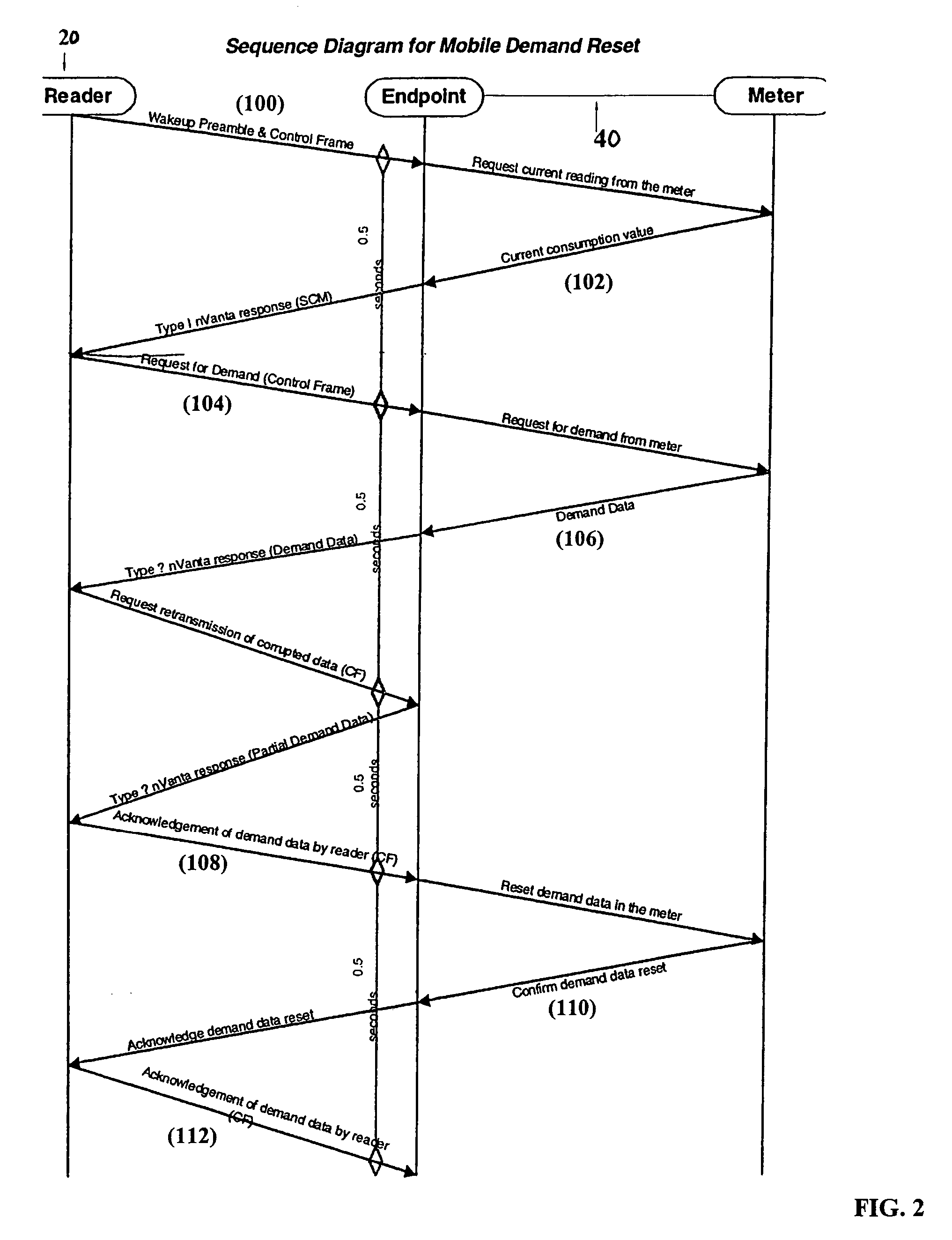
System and method for automatic meter reading with mobile configuration
ActiveUS7116243B2Eliminate needEfficient and reliable storageElectric signal transmission systemsUtility meters data arrangementsPhysical accessComputer science
An automatic meter reading (AMR) system and a method of operating an AMR system are disclosed. The AMR system stores and transfers consumptive data, demand data, and data archives. The system and method can also provide a demand reset to reduce or eliminate the need to physically visit a remote endpoint device, for example a residential utility meter, to directly connect to the endpoint device for the collection of data. The system and method provide two-way wireless communication between at least one reader and a plurality of remote endpoint devices and are adapted for use with mobile readers. The AMR system and method therefore provide efficient and reliable storage and transfer of data, including high volumes of data, at mobile read rates.
Owner:ITRON
Systems and methods for multi-factor authentication
ActiveUS9118656B2User identity/authority verificationElectric digital data processingControl systemPrivate network
Requests to gain access to secure resources are adjudicated according to authentication policies that include rules based on user-states derived from multiple heterogeneous access-control systems. Comprehensive user authentication and access control based on rules and policies that encompass a user's status in multiple access-control systems, including both logical access (e.g., Active Directory, RADIUS, Virtual Private Network, etc.) as well as physical access (e.g., card-based) control systems, may be realized.
Owner:IMPRIVATA
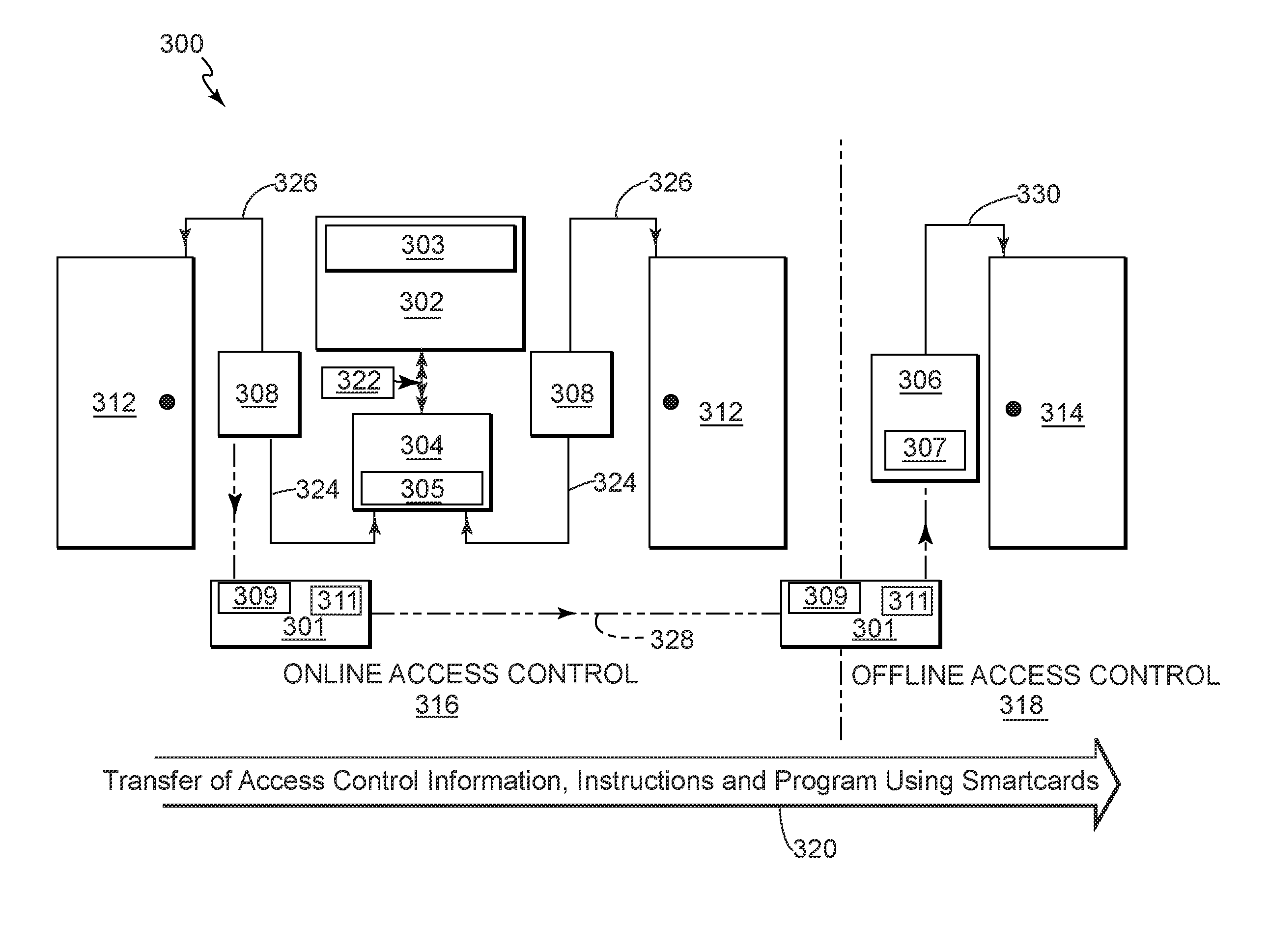
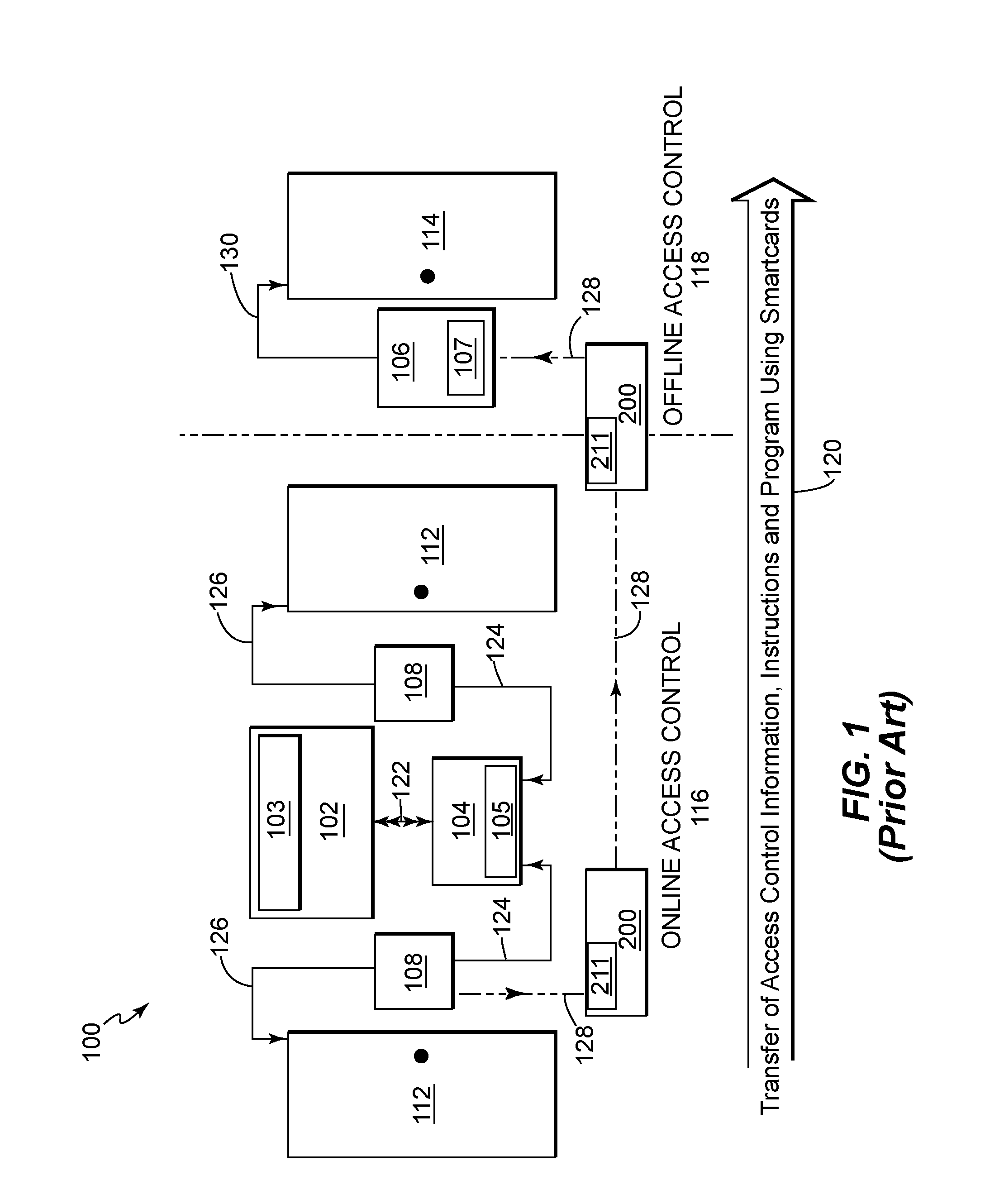
Physical access control system with smartcard and methods of operating
ActiveUS20100077474A1Avoid updatingCost and ease of deploymentDigital data processing detailsUser identity/authority verificationControl systemSmart card
An improved physical access control system has an online portion and an offline portion. A smartcard is configurable to transport access control information between the online portion and offline portion. The smartcard is further configurable to receive an offline reader identifier from an offline reader, and to control access of the smartcard holder to an offline entry / exit point. The smartcard is further configurable to carry a revoked list that is transmitted to each offline reader accessed. Methods of operating the improved physical access control system are also disclosed.
Owner:UTC FIRE & SECURITY AMERICAS CORPORATION INC
System and method for intelligent database backup
Systems and methods are provided for backing up database storage. A protection policy for database storage is activated at a remote host, wherein the database storage is not physically accessible by the computing device, such that the out-of-band storage is not in communication with the remote host through the computing device. A backup request is transmitted to the remote host comprising data indicative of a volume on the database storage to back up according to the protection policy. A response to the backup request is received comprising staging disk requirements including a required size for a staging disk. A staging disk is determined based on the response. The staging disk is presented to the remote host so that the remote host can perform a backup of the volume to the staging disk using a database backup tool provided by a vendor of the database storage.
Owner:GOOGLE LLC
System and Method for Physical Access Control
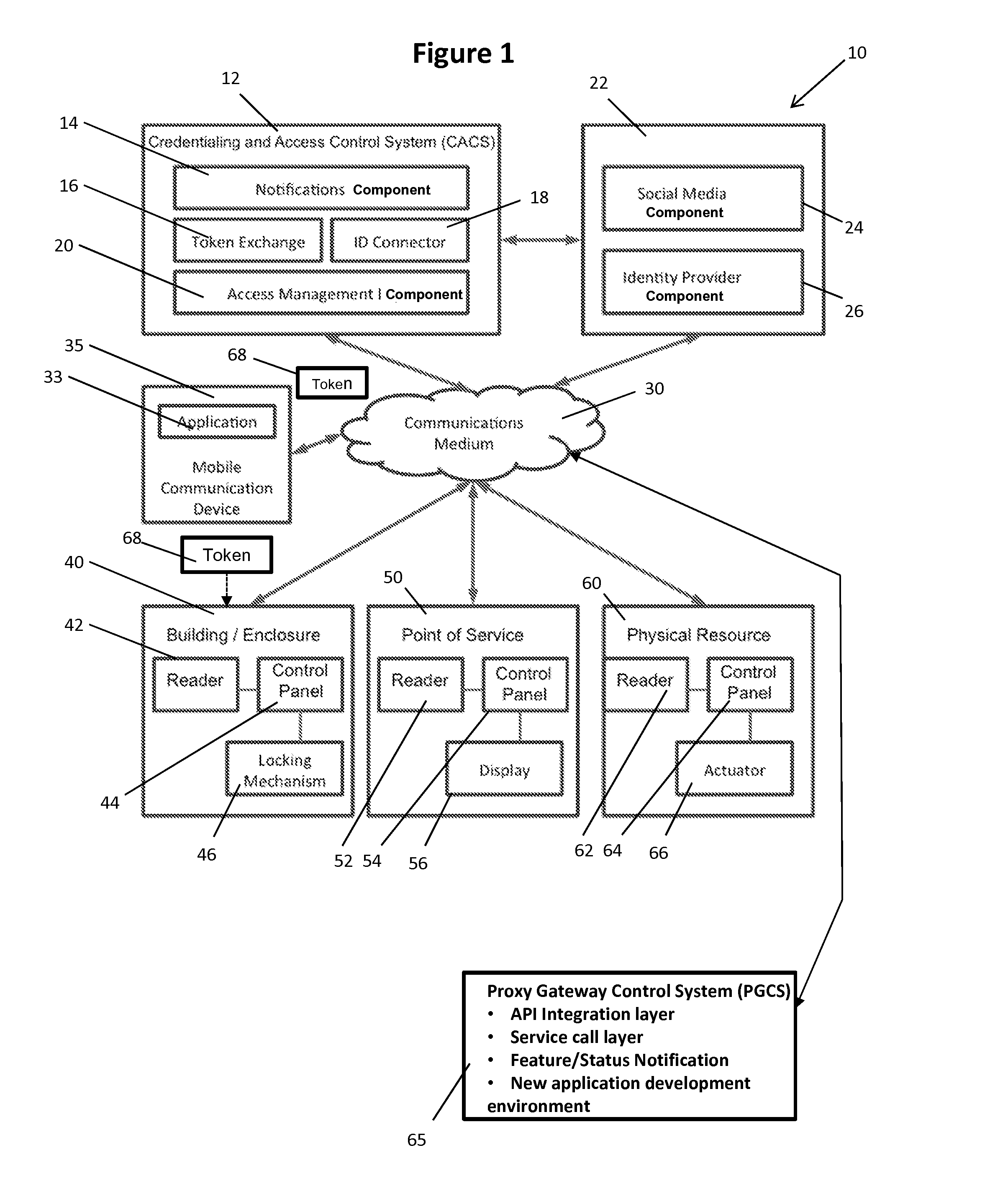
ActiveUS20140282993A1Minimize duplicationImprove consistencyDigital data processing detailsMultiple digital computer combinationsIdentity providerSocial web
The present invention provides, in one aspect, a system and method for managing authentication tokens that operate across multiple types of physical resources binding the tokens to one or more external electronic Identity Providers; generating tokens; authenticating the tokens at multiple physical resources; managing access to physical resources by linking the tokens to the electronic identities; translating the tokens to the appropriate physical token type based on infrastructure services available at the point of service; validating tokens at the physical resource; tracking and conveying usage information; and making use of social group relationships and other data defined by individual usage to, among other things, simplify the process of granting user-generated credentials to persons connected to a given individual via the Identity Provider or an external social network, for example.
Owner:BRIVO SYST LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com