Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
492 results about "Access key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
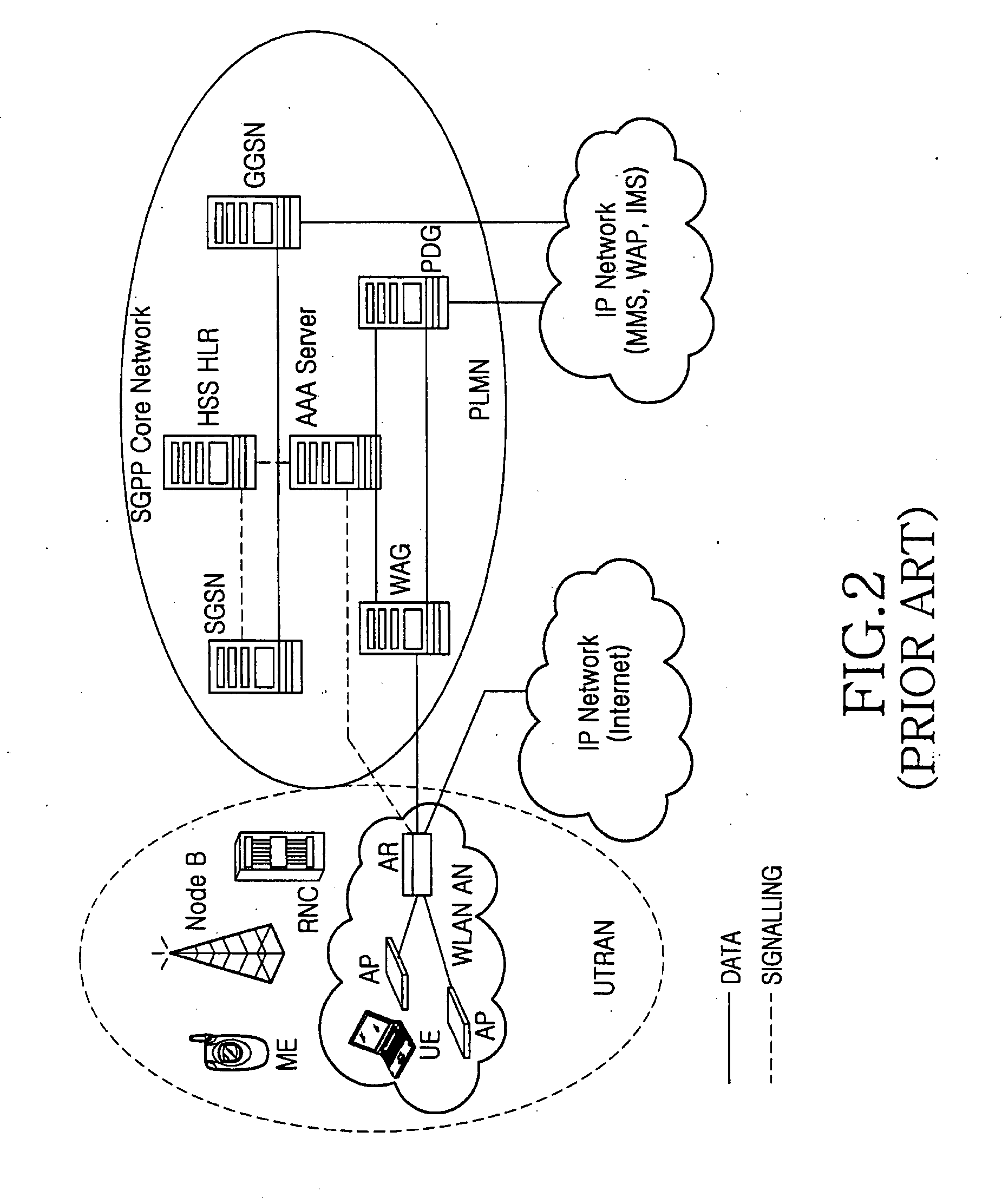
In a web browser, an access key or accesskey allows a computer user to immediately jump to a specific part of a web page via the keyboard. They were introduced in 1999 and quickly achieved near-universal browser support.
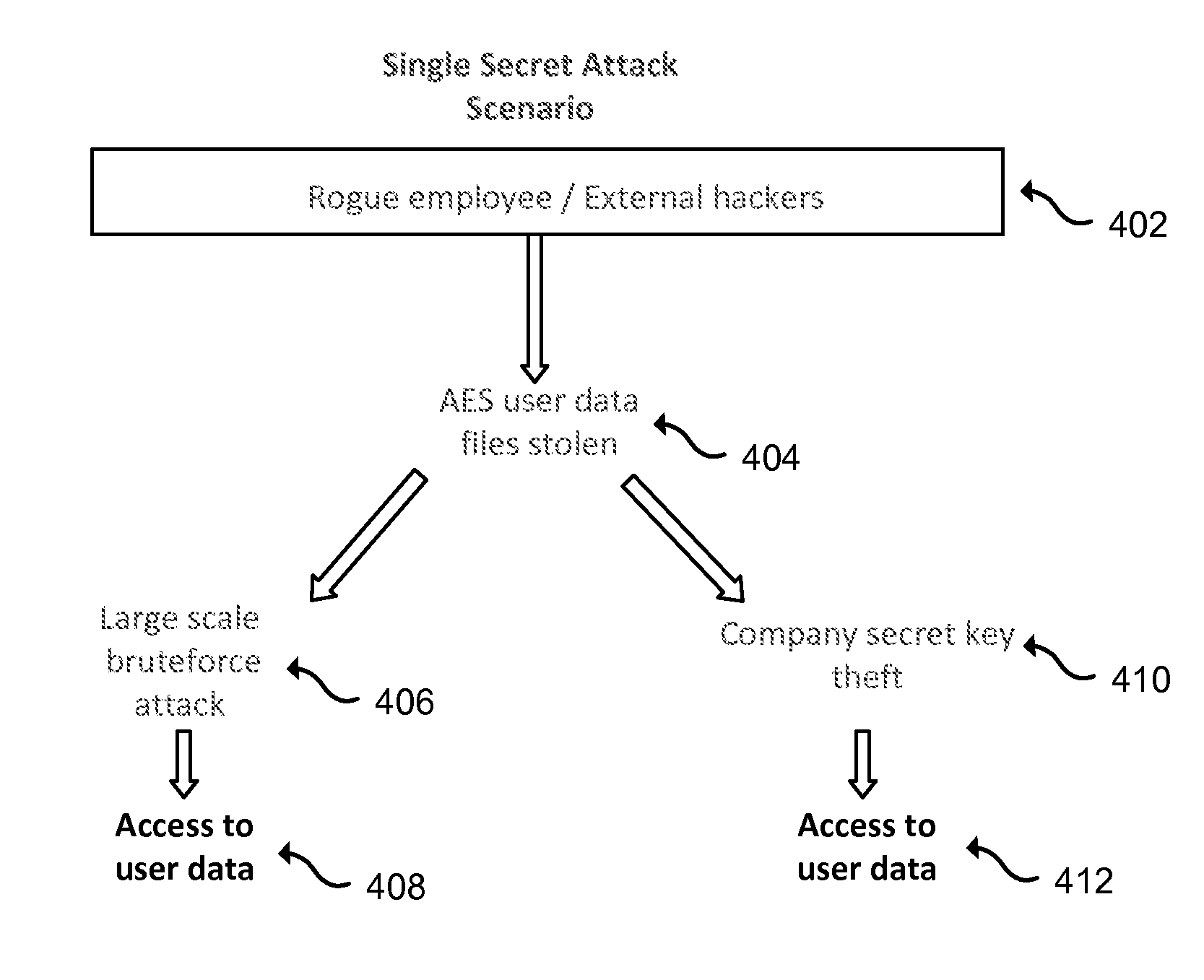
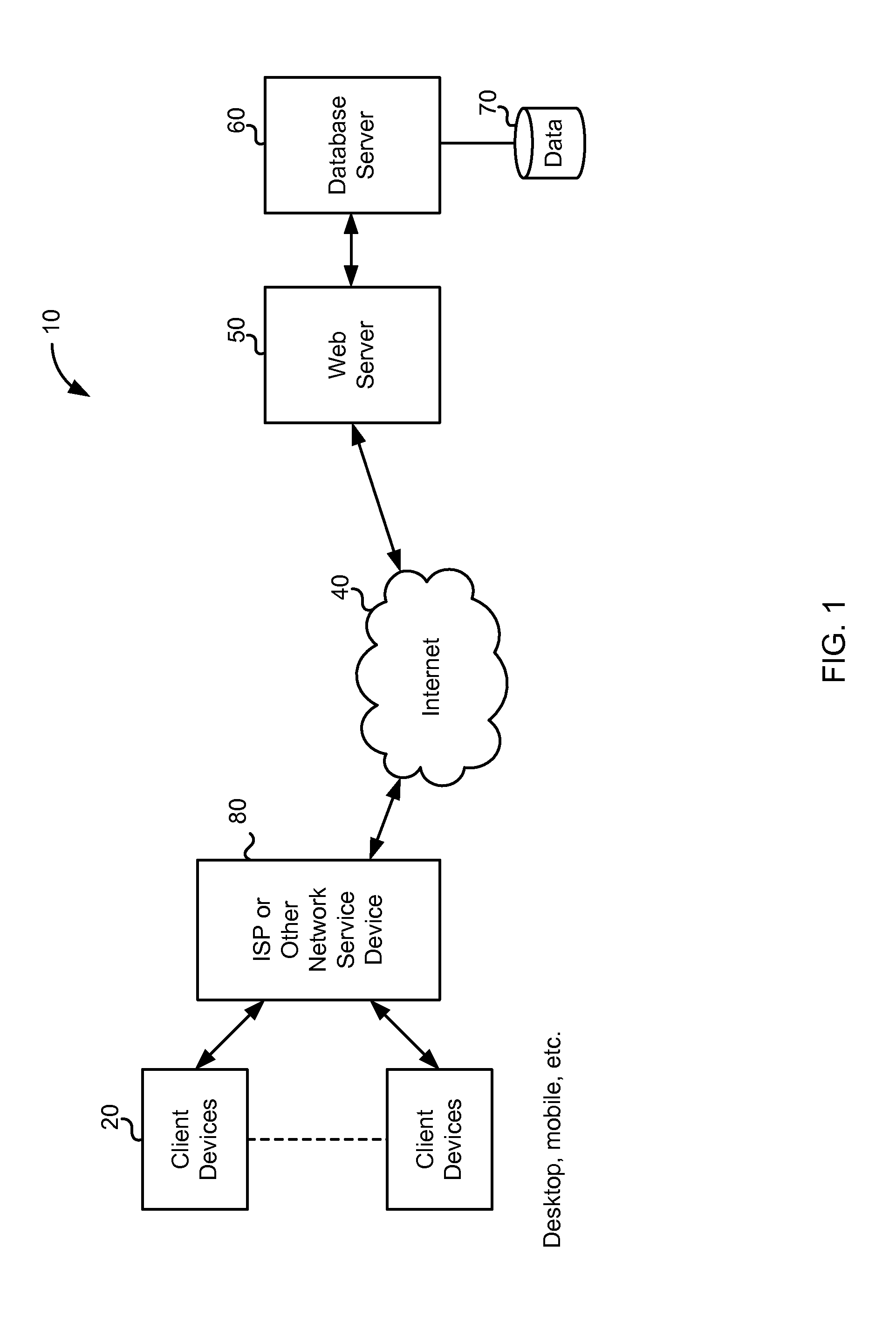
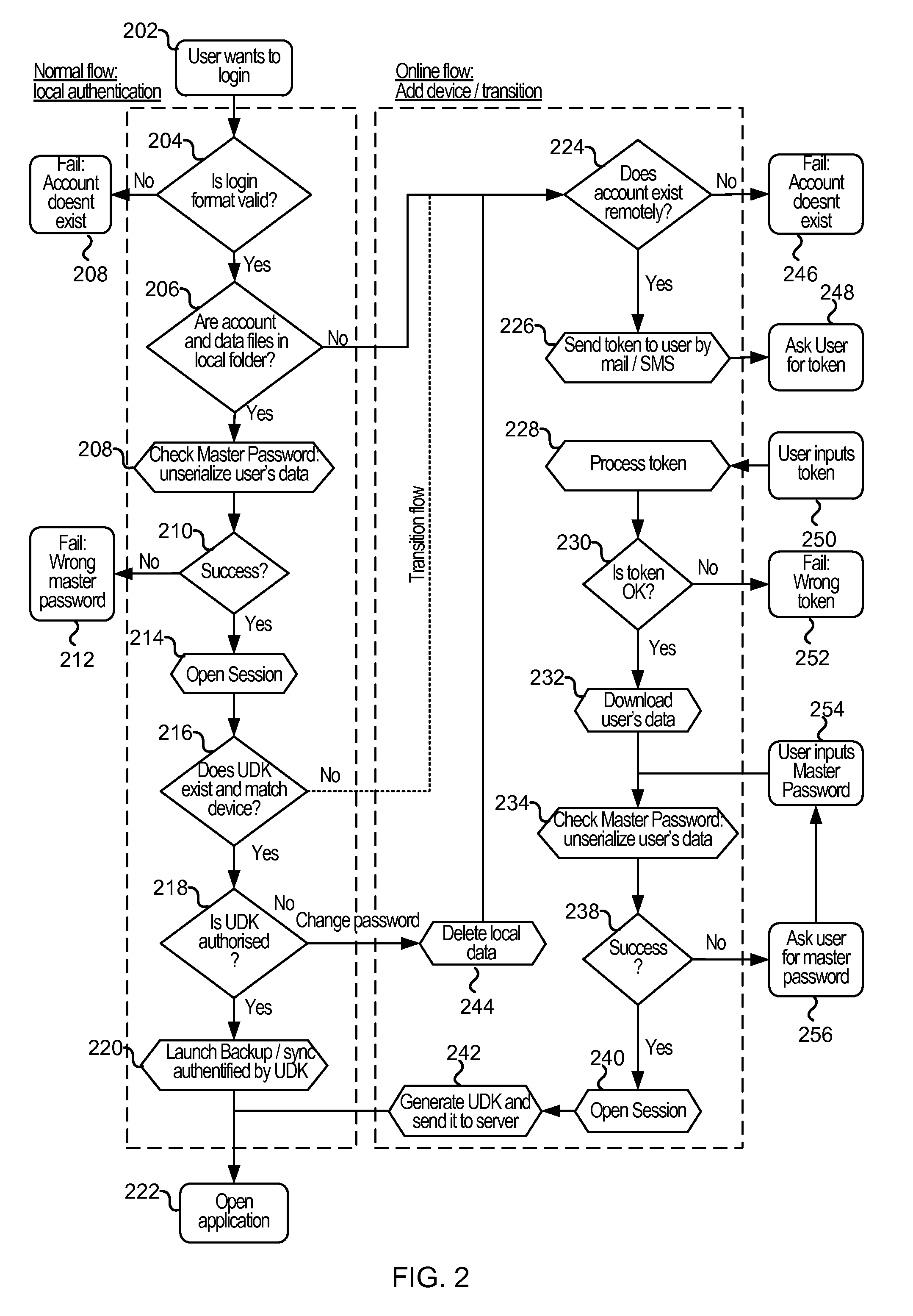
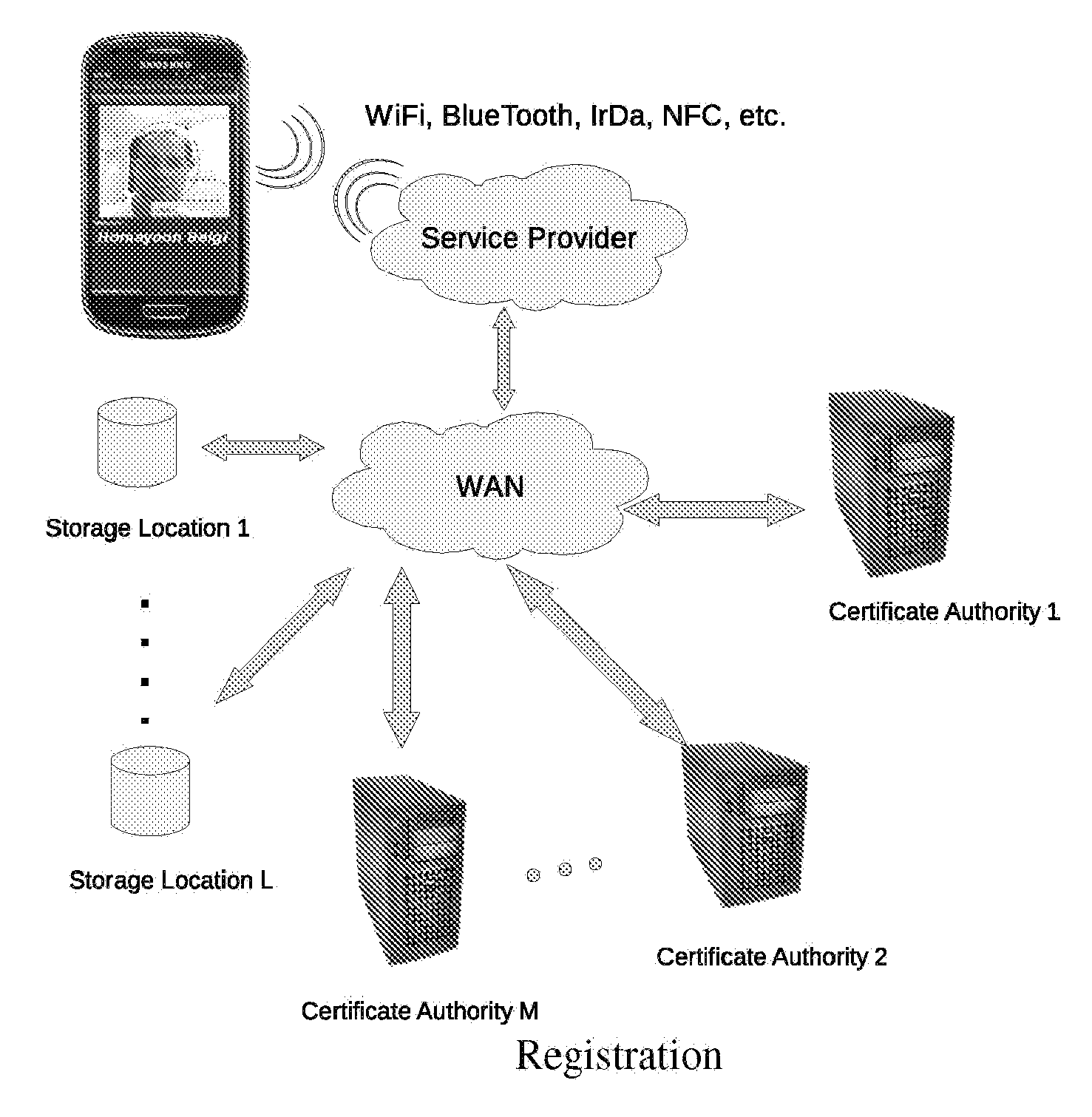
Cloud-based data backup and sync with secure local storage of access keys
ActiveUS20130145447A1Digital data processing detailsMultiple digital computer combinationsThree levelUser device
Methods and systems are provided for secure online data access. In one embodiment, three levels of security are provided where user master passwords are not required at a server. A user device may register with a storage service and receive a user device key that is stored on the device and at the service. The user device key may be used to authenticate the user device with the storage service. As data in the storage service is encrypted with a master password, the data may be protected from disclosure. As a user master key or derivative thereof is not used in authentication, the data may be protected from a disclosure or breach of the authentication credentials. Encryption and decryption may thus be performed on the user device with a user master key that may not be disclosed externally from the user device.
Owner:DASHLANE
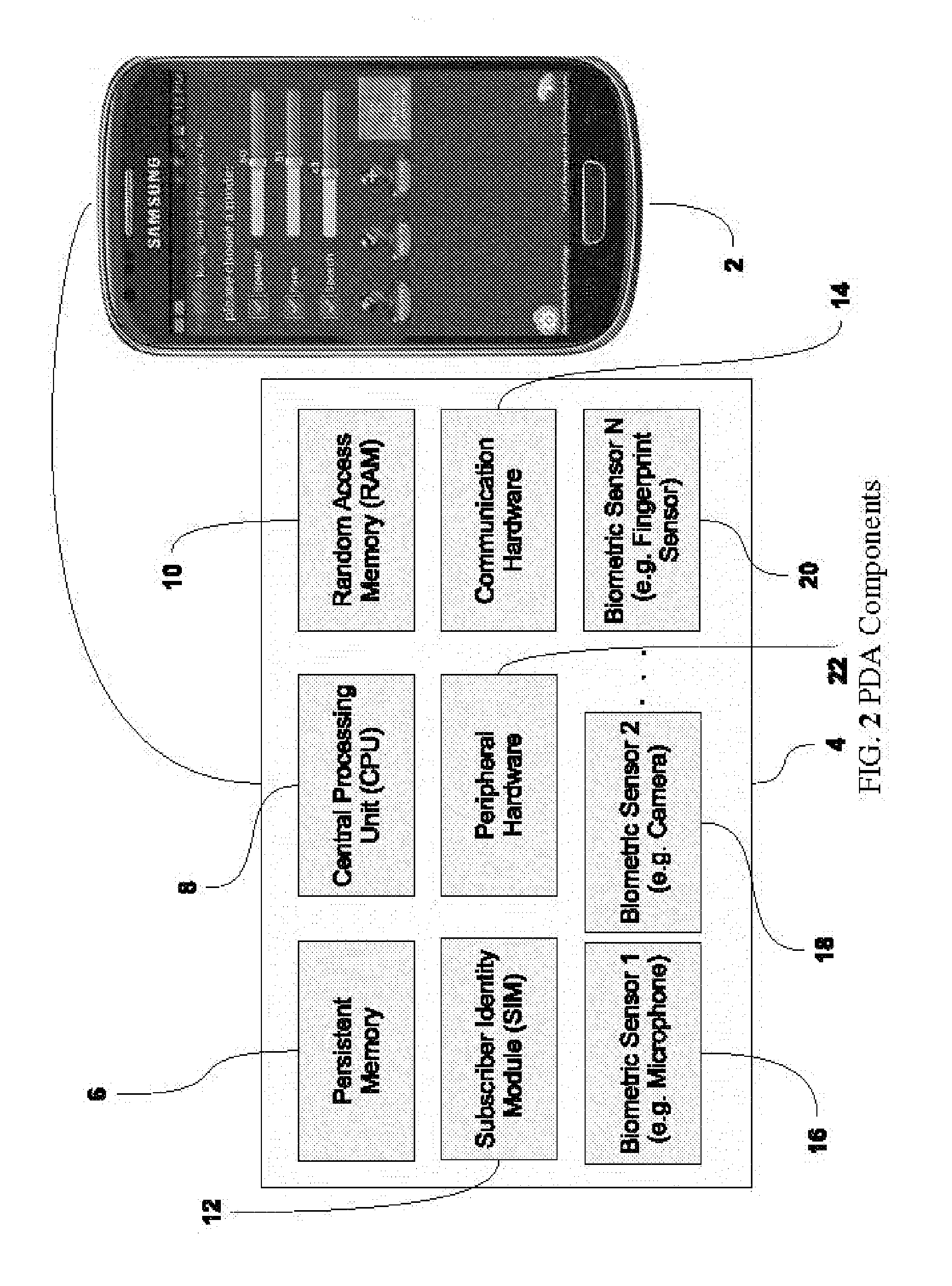
Access Control Through Multifactor Authentication with Multimodal Biometrics
ActiveUS20150347734A1Safe storageImprove securityDigital data processing detailsUser identity/authority verificationThe InternetFinancial transaction
A system is provided in which a person may use a Cellular (Mobile) Telephone, a PDA or any other handheld computer to make a purchase. This is an example only. The process may entail any type of transaction which requires authentication, such as any financial transaction, any access control (to account information, etc.), and any physical access scenario such as doubling for a passport or an access key to a restricted area (office, vault, etc.). It may also be used to conduct remote transactions such as those conducted on the Internet (E-Commerce, account access, etc.). In the process, a multifactor authentication is used.
Owner:BEIGI HOMAYOON
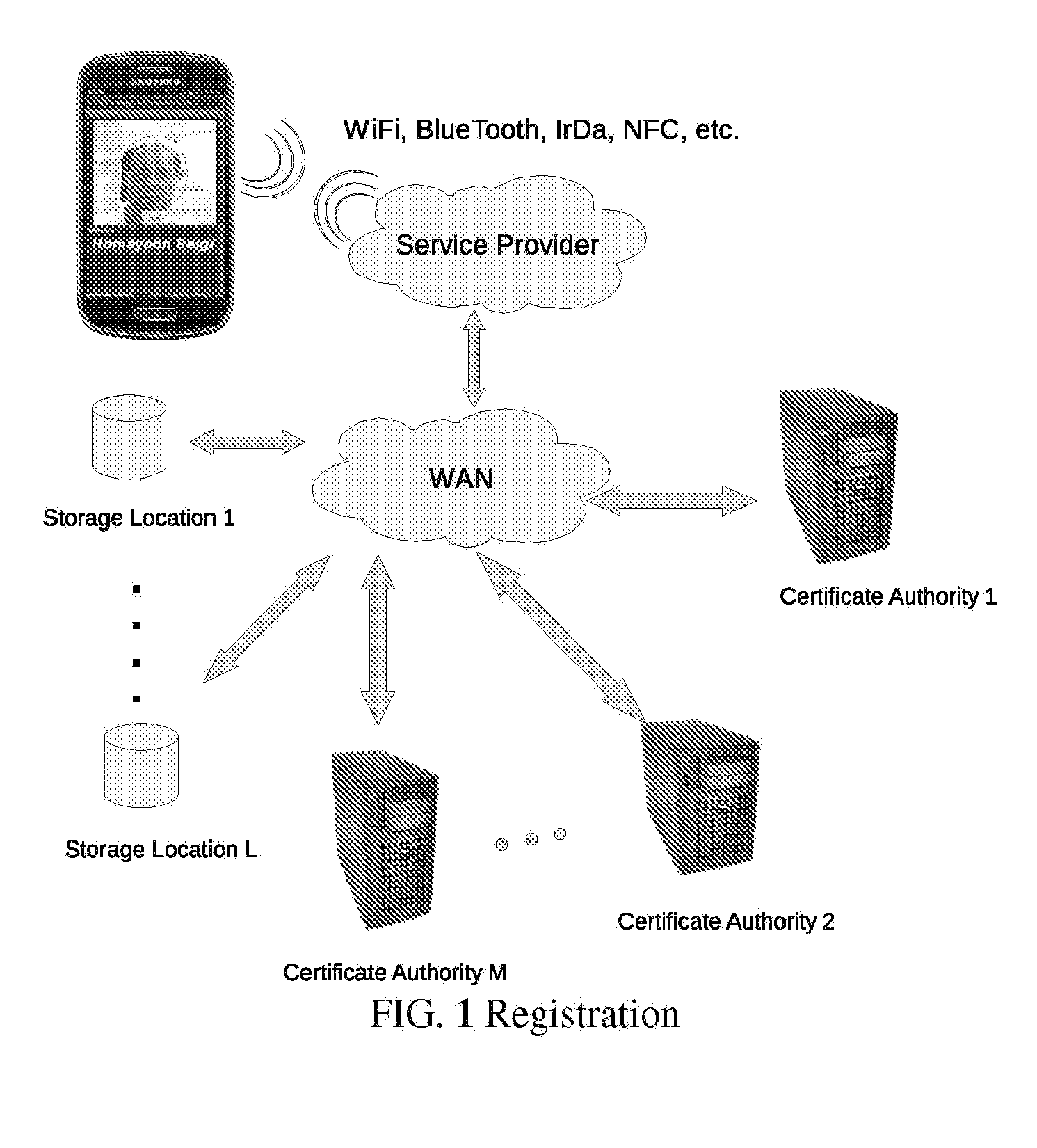
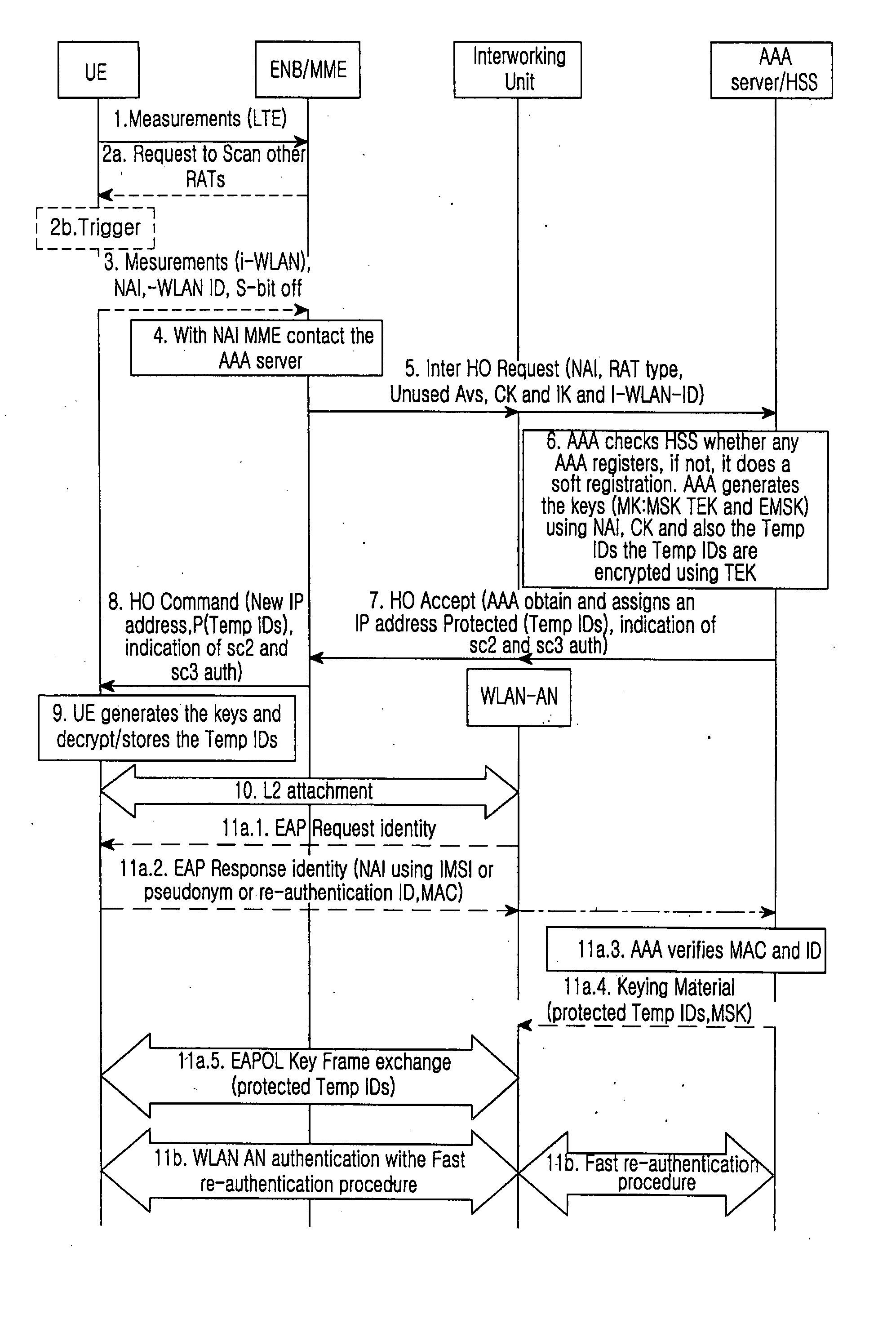
System and method for optimizing authentication procedure during inter access system handovers
ActiveUS20070249352A1Quickly perform re-authenticationUnauthorised/fraudulent call preventionEavesdropping prevention circuitsEngineeringUser equipment
Disclosed is a method and system of deriving new keys for accessing a new system. The method enables an optimized authentication procedure during handover form an existing system to a new system by using the existing system access keys. The user equipment that is accessing the new system receives a temporary ID during handover preparation which enables the user equipment to perform a fast re-authentication. The method uses existing system access keys to derive system access keys for the new network.
Owner:SAMSUNG ELECTRONICS CO LTD
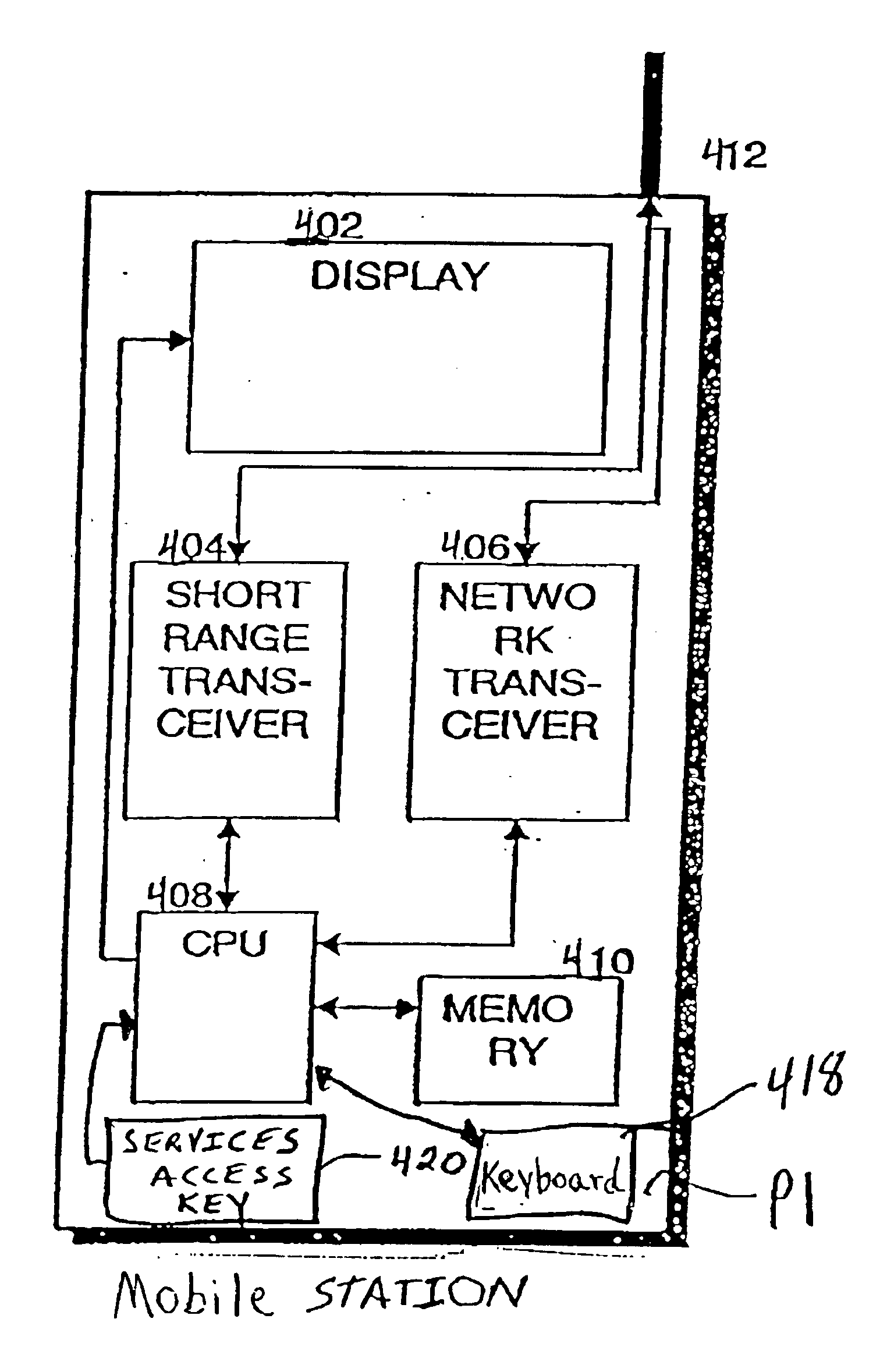
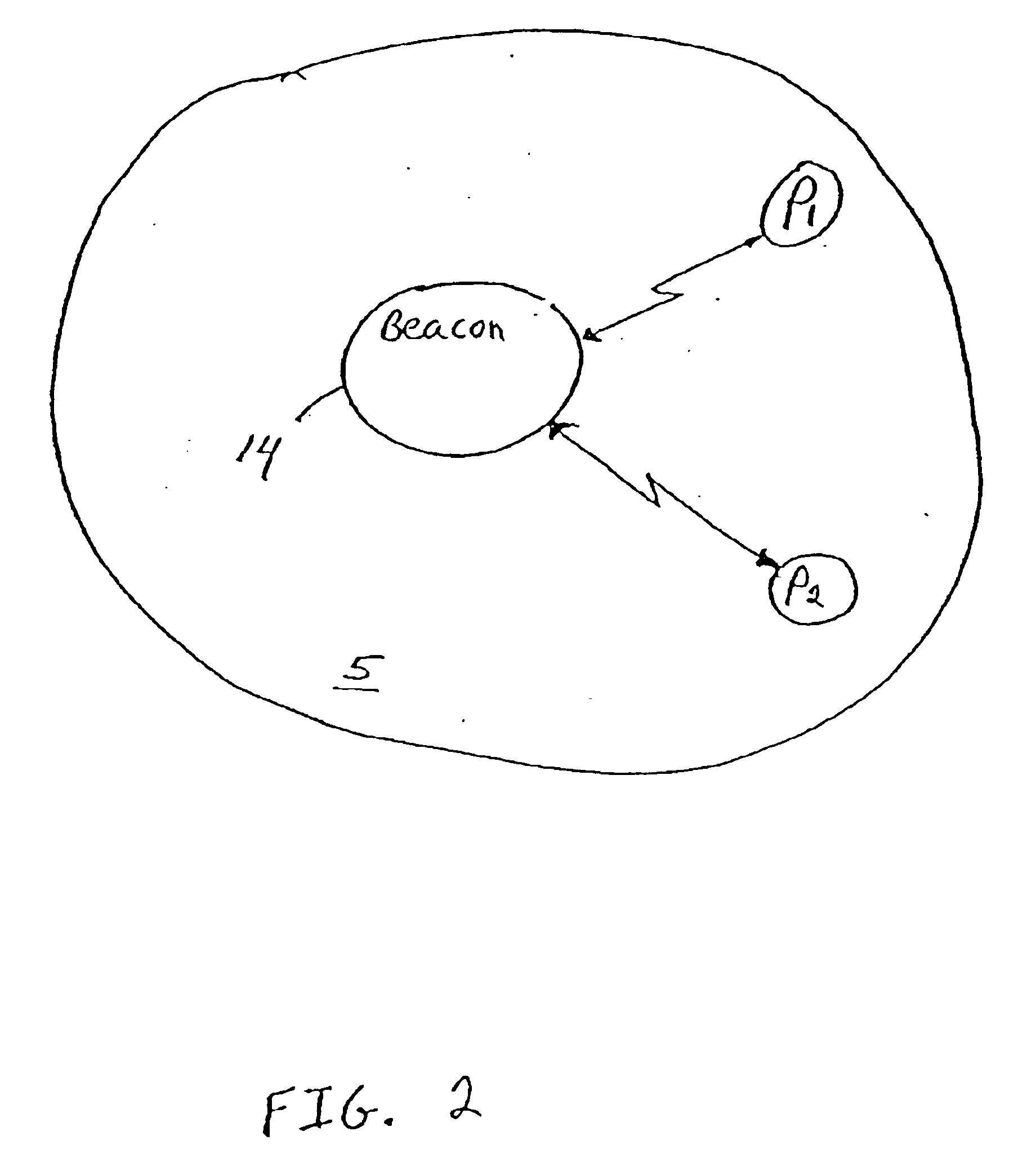
System and method for accessing local services with a mobile terminal
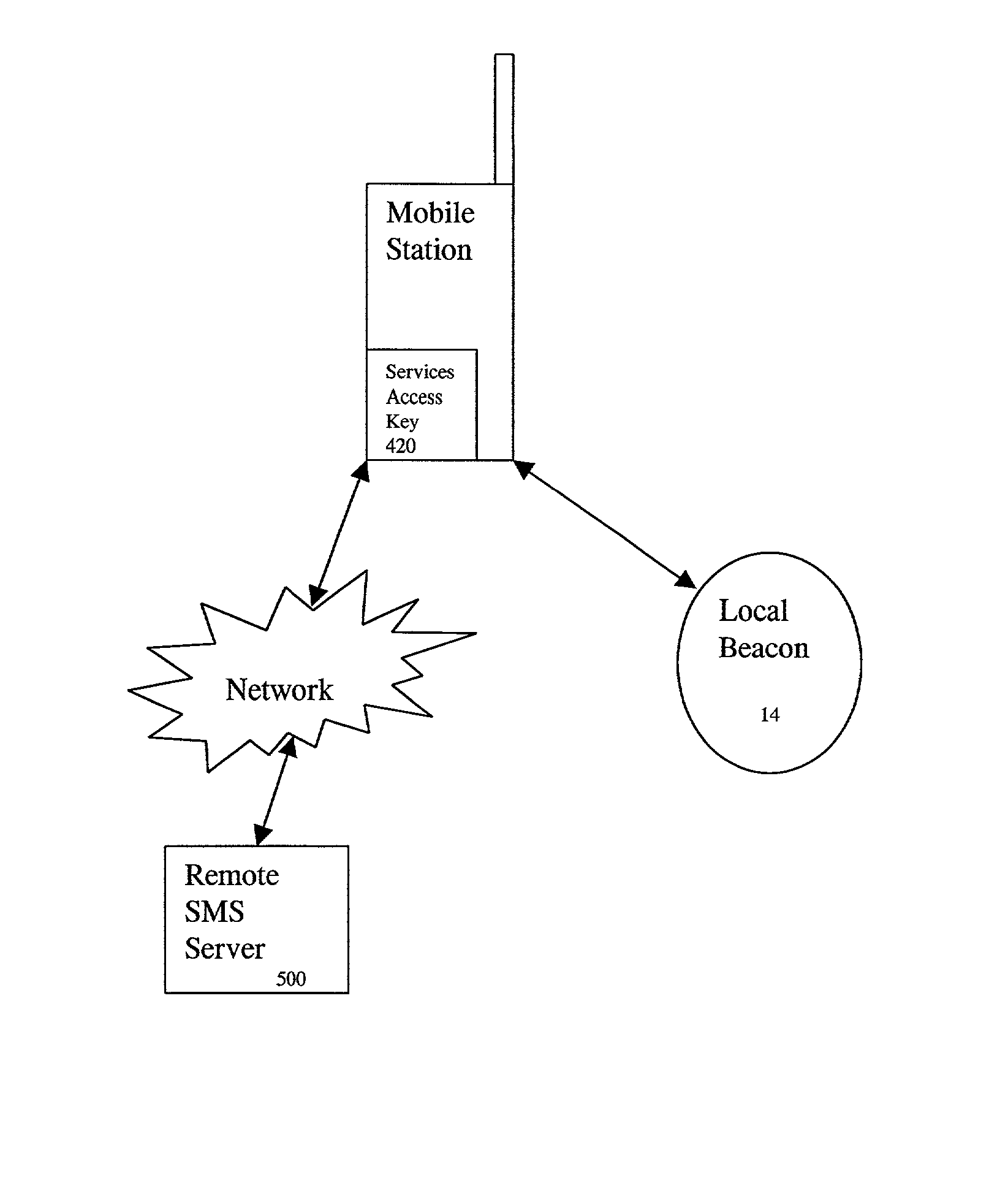
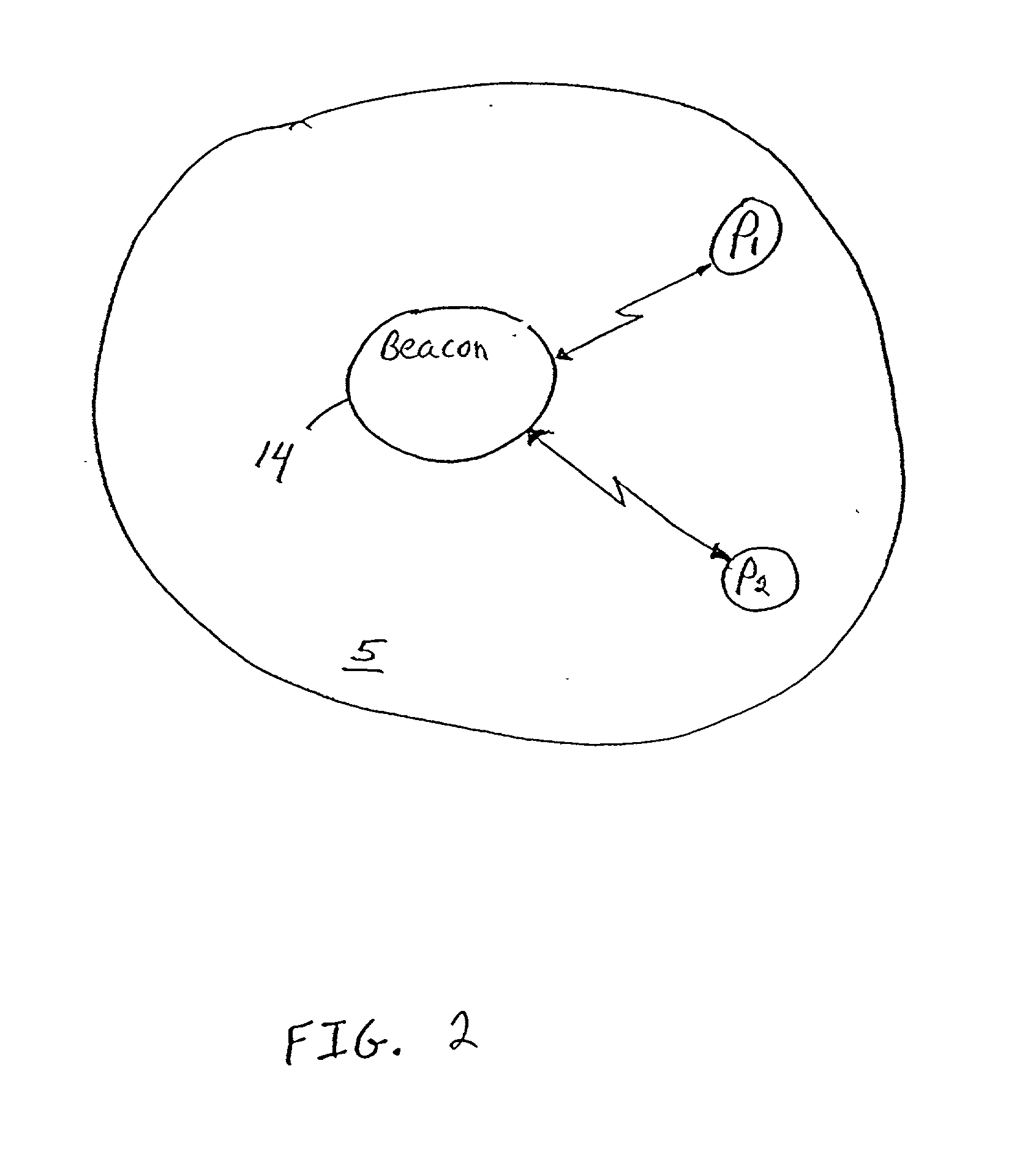
InactiveUS6847823B2Assess restrictionRadio/inductive link selection arrangementsMobile stationMobile communication systems
In a mobile communication system, a method and system for obtaining location-dependent services information by using a mobile station. An information beacon containing services information pertaining to the location of the beacon is disposed in an environment. The beacon is capable of communicating with the mobile station when the mobile station is located within the operating range of the beacon. The mobile station includes a services access key which, when selected while the mobile station is within the operating range of the beacon, will transmit a query to the beacon requesting location-based services. In response to the query, location-based services information will be transmitted to the mobile station.
Owner:NOKIA TECHNOLOGLES OY
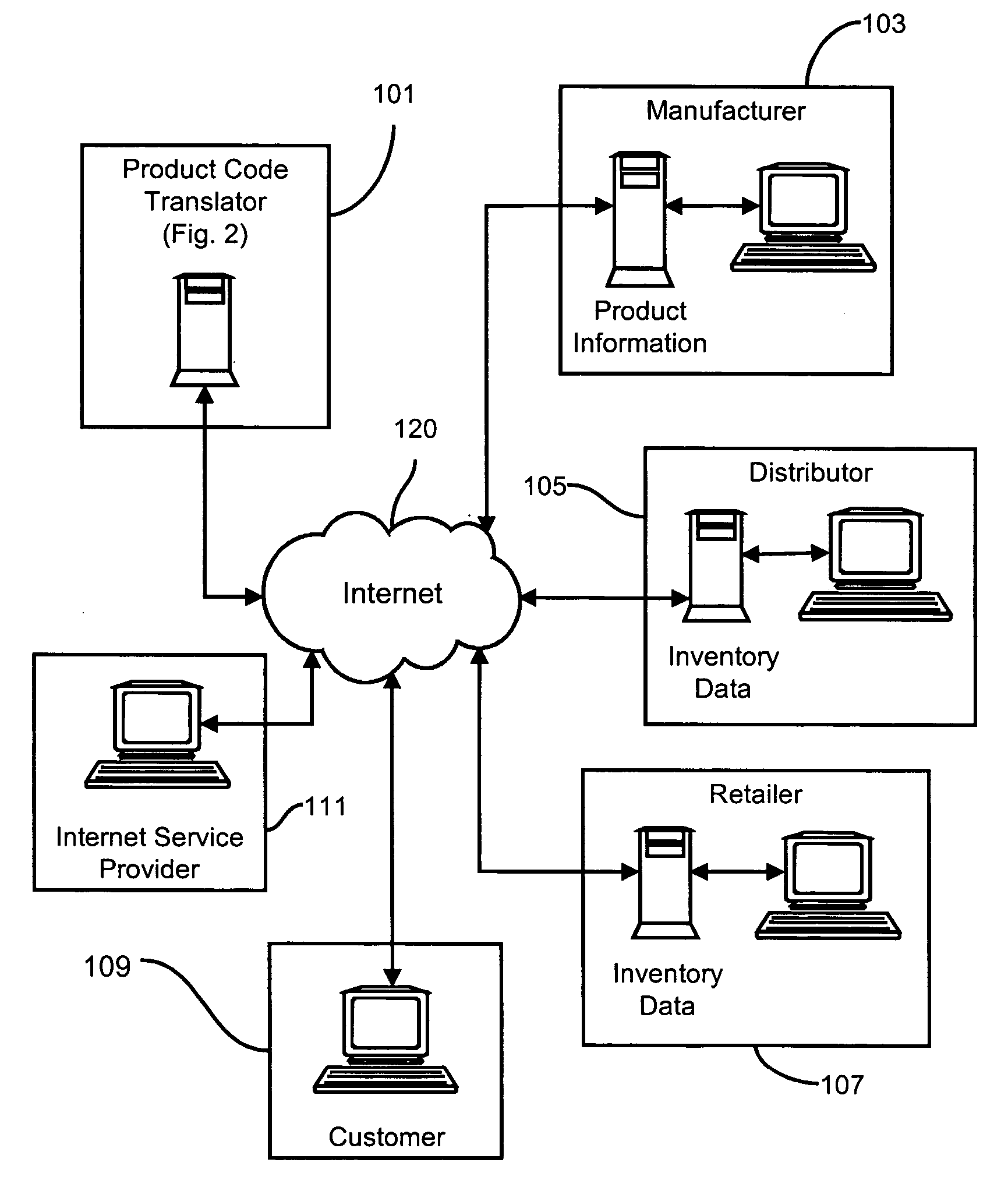
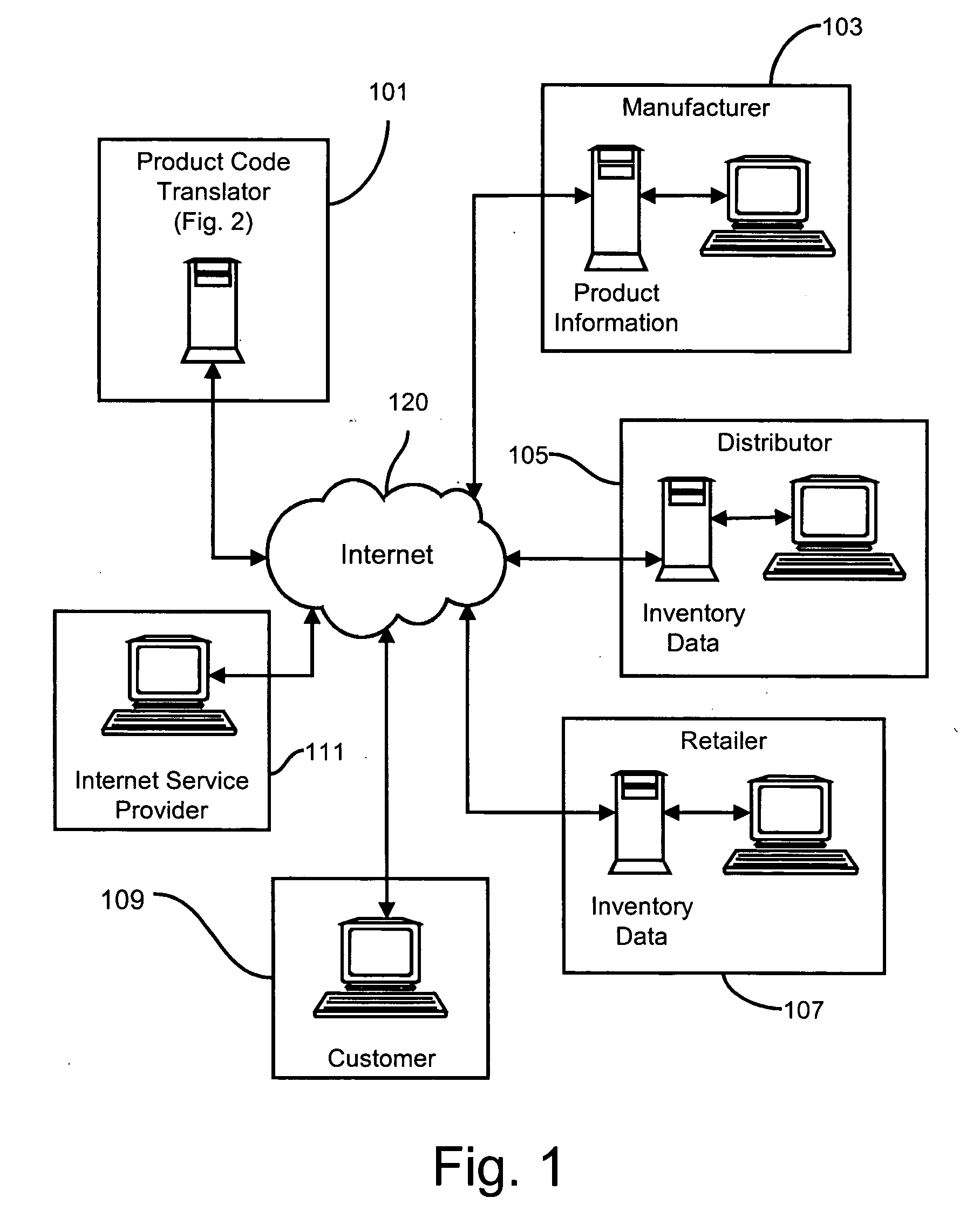
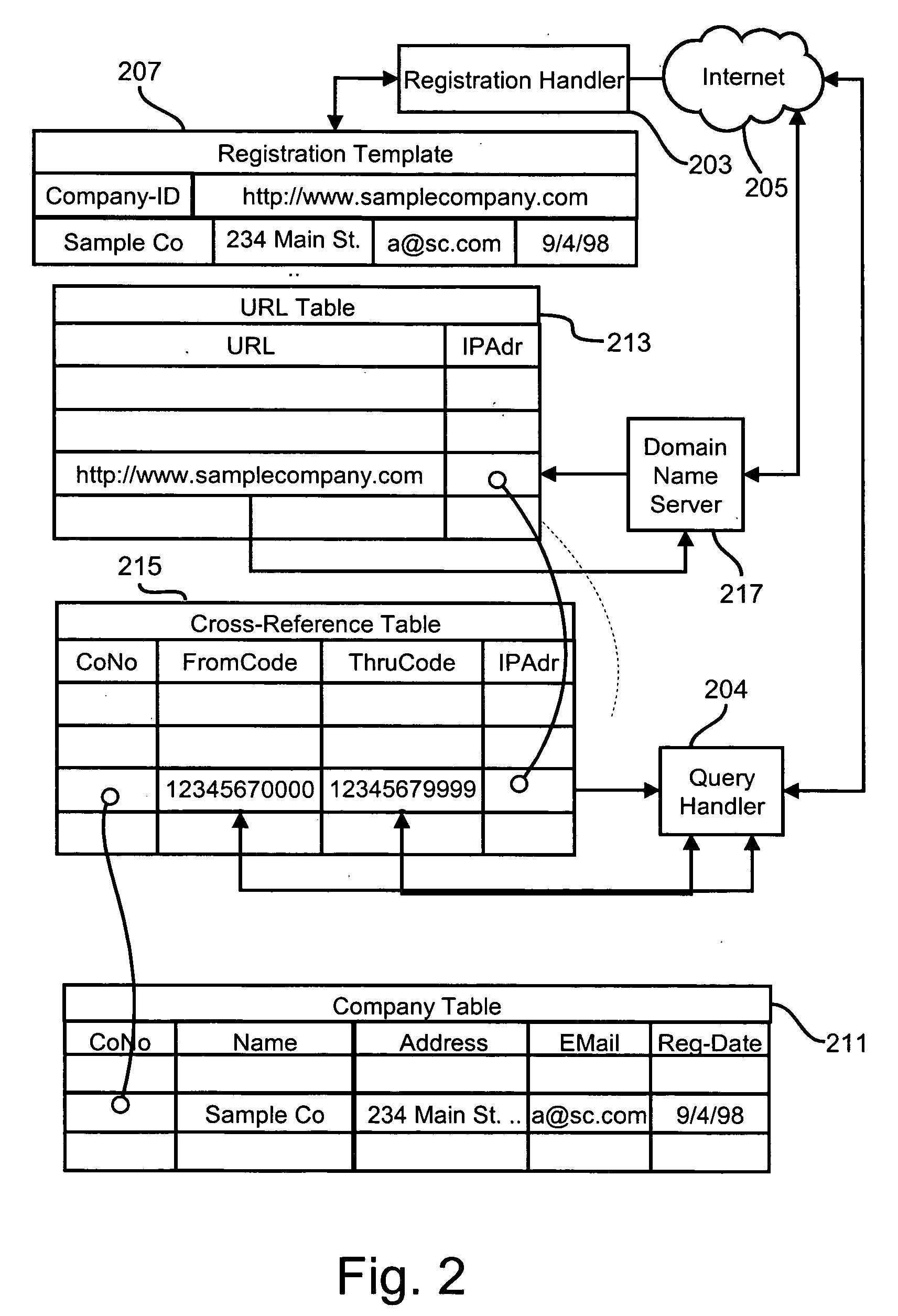
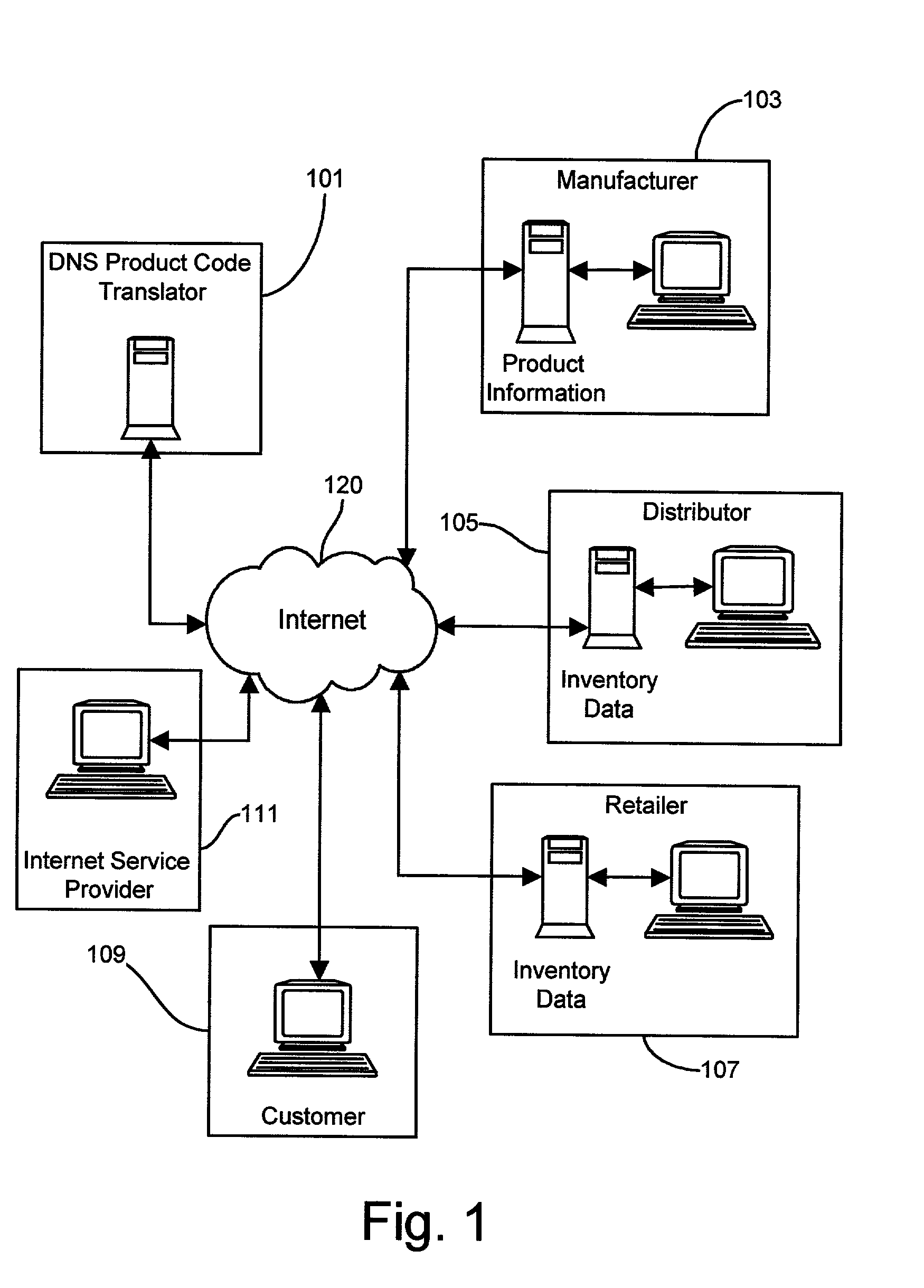
Methods and apparatus for transferring product information from manufacturers to retailers and distributors via the Internet
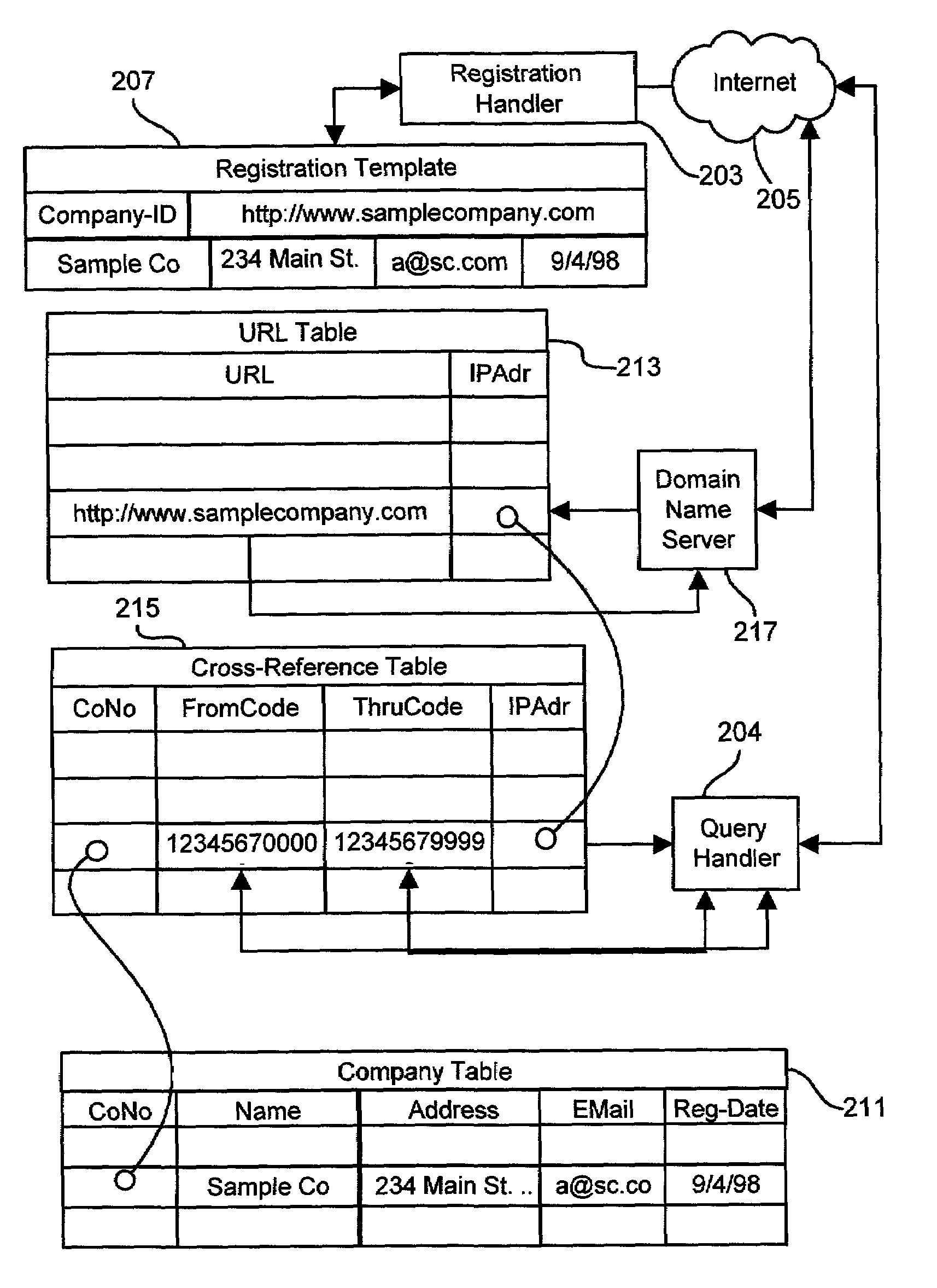
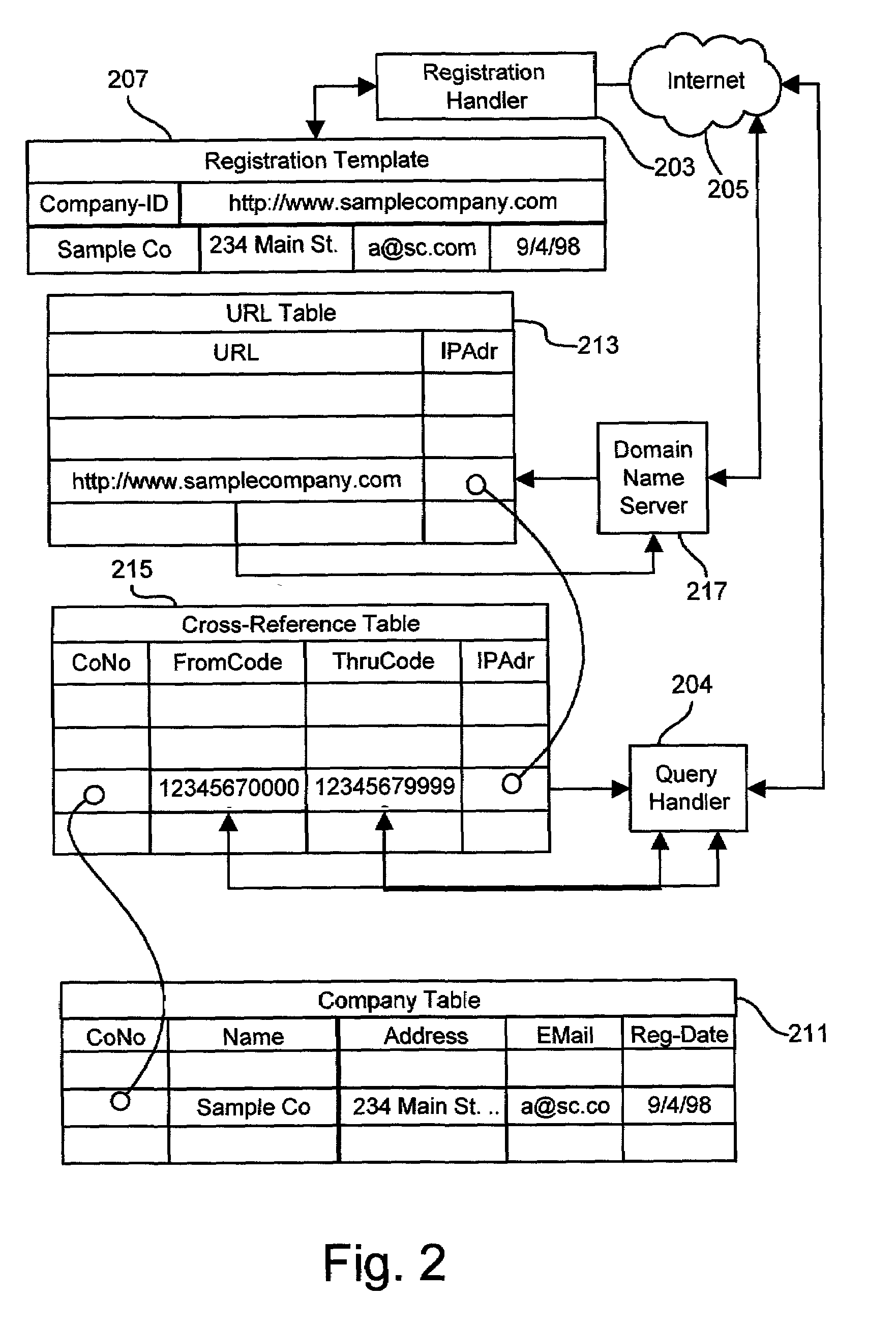
InactiveUS20060011720A1Digital data information retrievalVisual presentationUniversal Product CodeDomain name
Methods and apparatus for disseminating over the Internet product information produced and maintained by product manufacturers using existing universal product codes (bar codes) as access keys. A cross-referencing resource preferably implemented by the existing Internet Domain Name System (DNS) receives Internet request messages containing all or part of a universal product code value and returns the Internet address at which data or services relating to the identified product, or to the manufacturer of that product, may be obtained. By using preferred Web data storage formats and protocol which conform to XML, XLS, XLink, Xpointer, RDF and Web service standards specifications, product and company information may be seamlessly identified, retrieved and integrated with information from other sources. A “web register” module can be employed to provide an Internet interface between a shared sales Internet server and an otherwise conventional inventory control system, and operates in conjunction with the cross-referencing server to provide detailed product information to Internet shoppers who may purchase goods from existing stores via the Internet.
Owner:PROD ASSOC TECH LLC +1
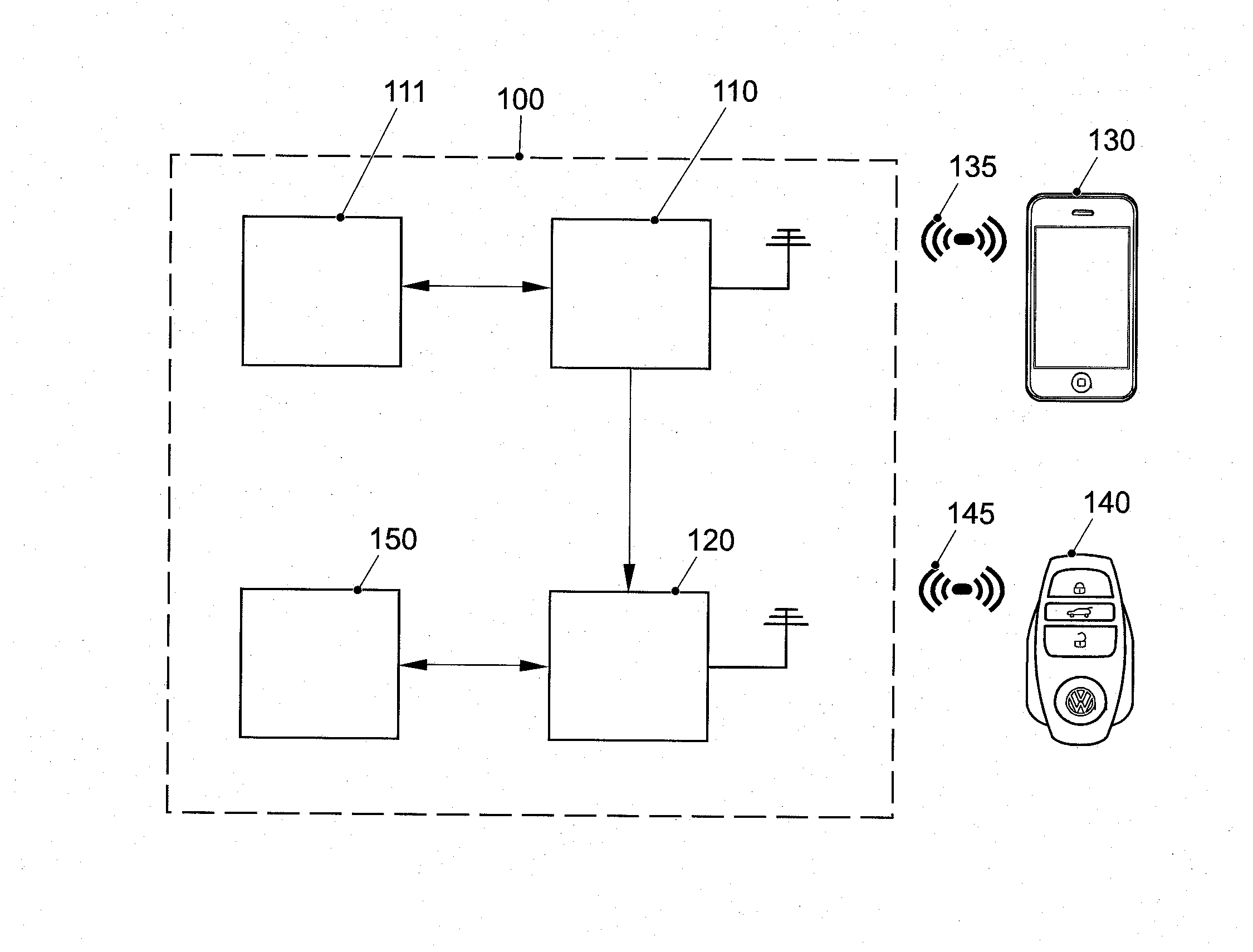
Vehicle system for activating a vehicle component
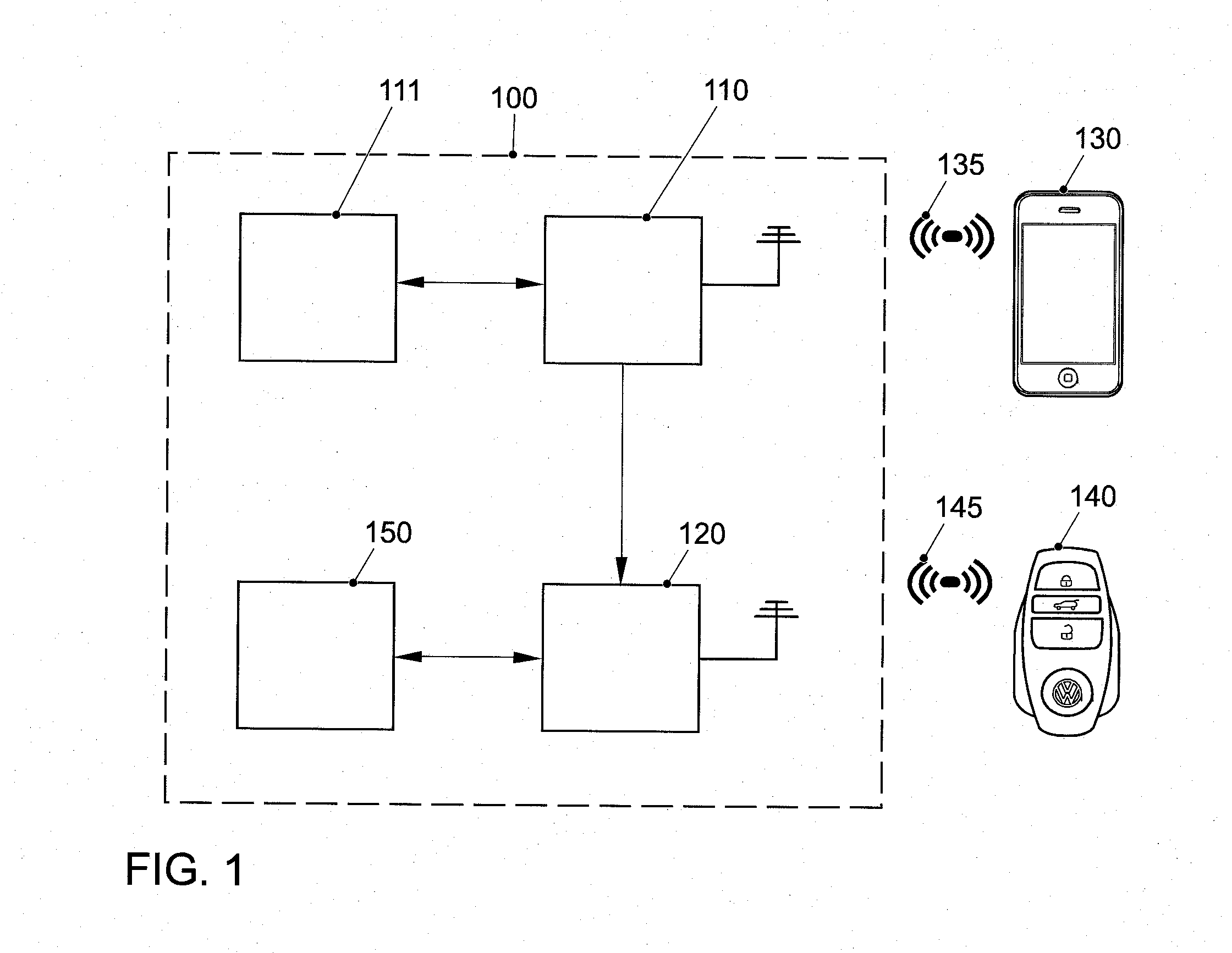
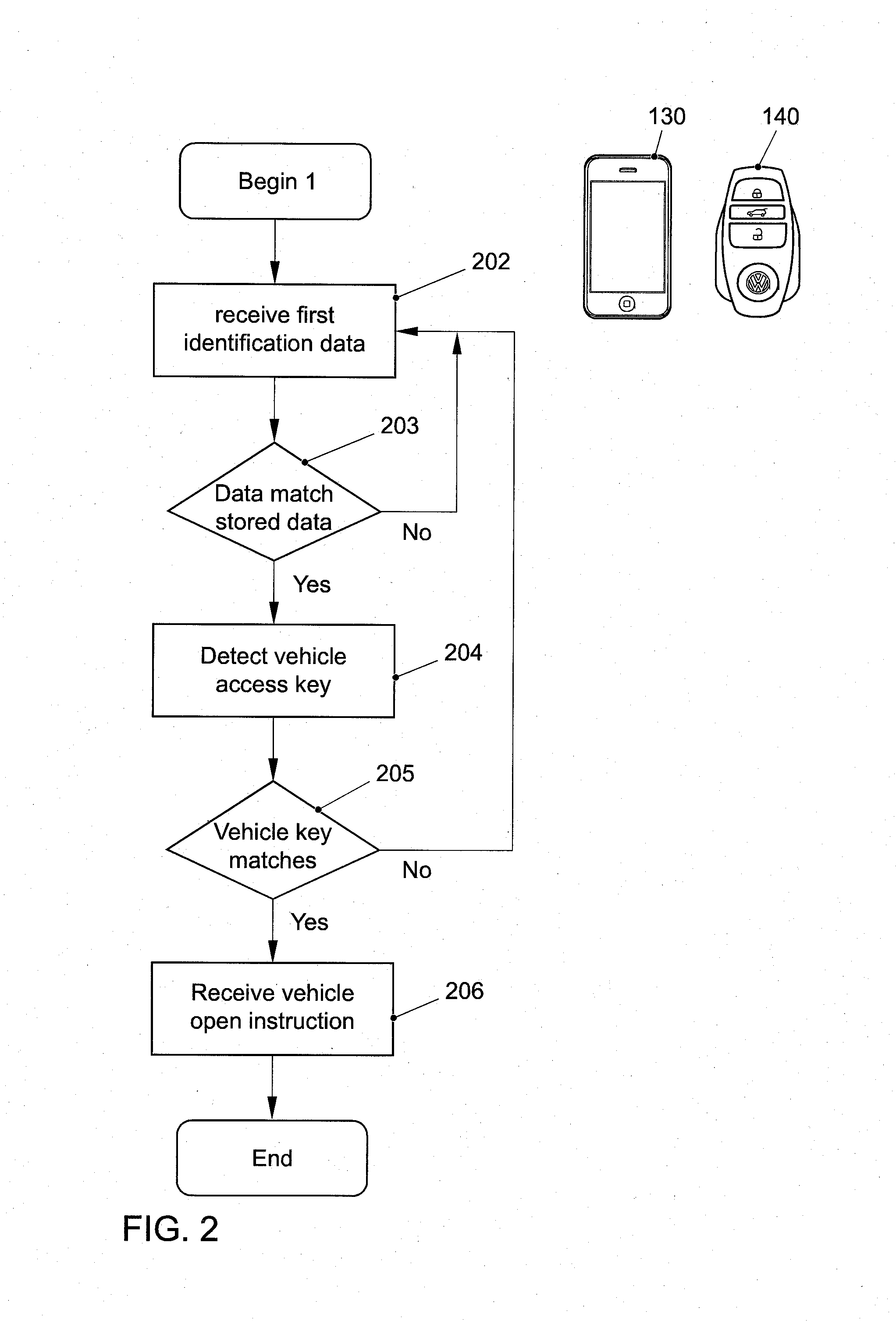
ActiveUS20150120151A1Save electricityEasy to set upElectric signal transmission systemsDigital data processing detailsData matchingEngineering
A vehicle system for activating at least one vehicle component to provide access to a vehicle. A first receiver is operative to obtain a wireless signal at least comprising first identification data of an electronic device; a memory device storing at least second identification data; at least a second receiver being operative to check the presence of a matching vehicle access key, and the at least second receiver being operative to check the presence of a matching vehicle access key if the first identification data match the at least second identification data.
Owner:VOLKSWAGEN AG +1
System and method for accessing local services with a mobile terminal
InactiveUS20020077060A1Assess restrictionRadio/inductive link selection arrangementsMobile stationMobile communication systems
In a mobile communication system, a method and system for obtaining location-dependent services information by using a mobile station. An information beacon containing services information pertaining to the location of the beacon is disposed in an environment. The beacon is capable of communicating with the mobile station when the mobile station is located within the operating range of the beacon. The mobile station includes a services access key which, when selected while the mobile station is within the operating range of the beacon, will transmit a query to the beacon requesting location-based services. In response to the query, location-based services information will be transmitted to the mobile station.
Owner:NOKIA TECHNOLOGLES OY
Method for installing a mailbox file associated with a disk storage medium
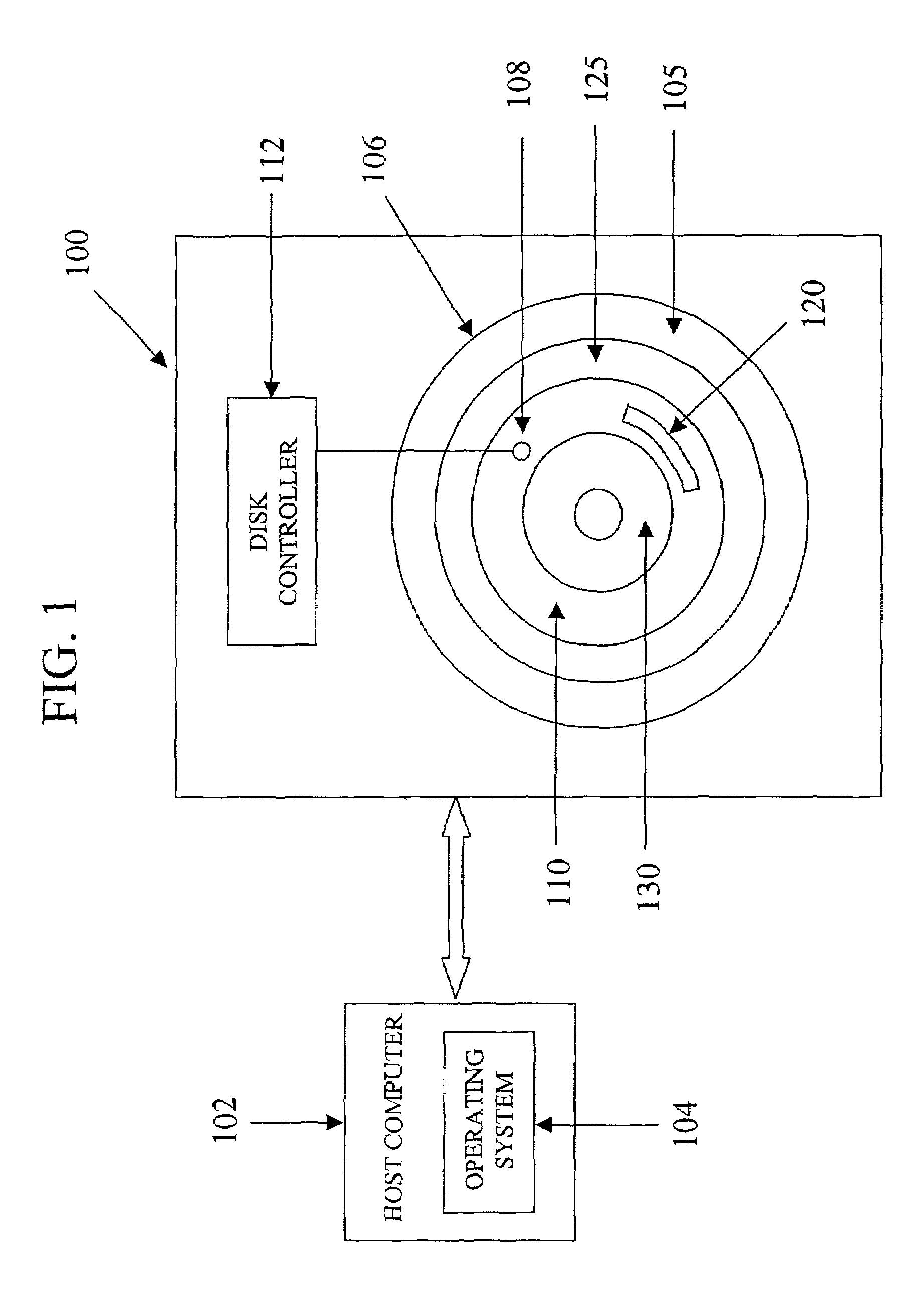
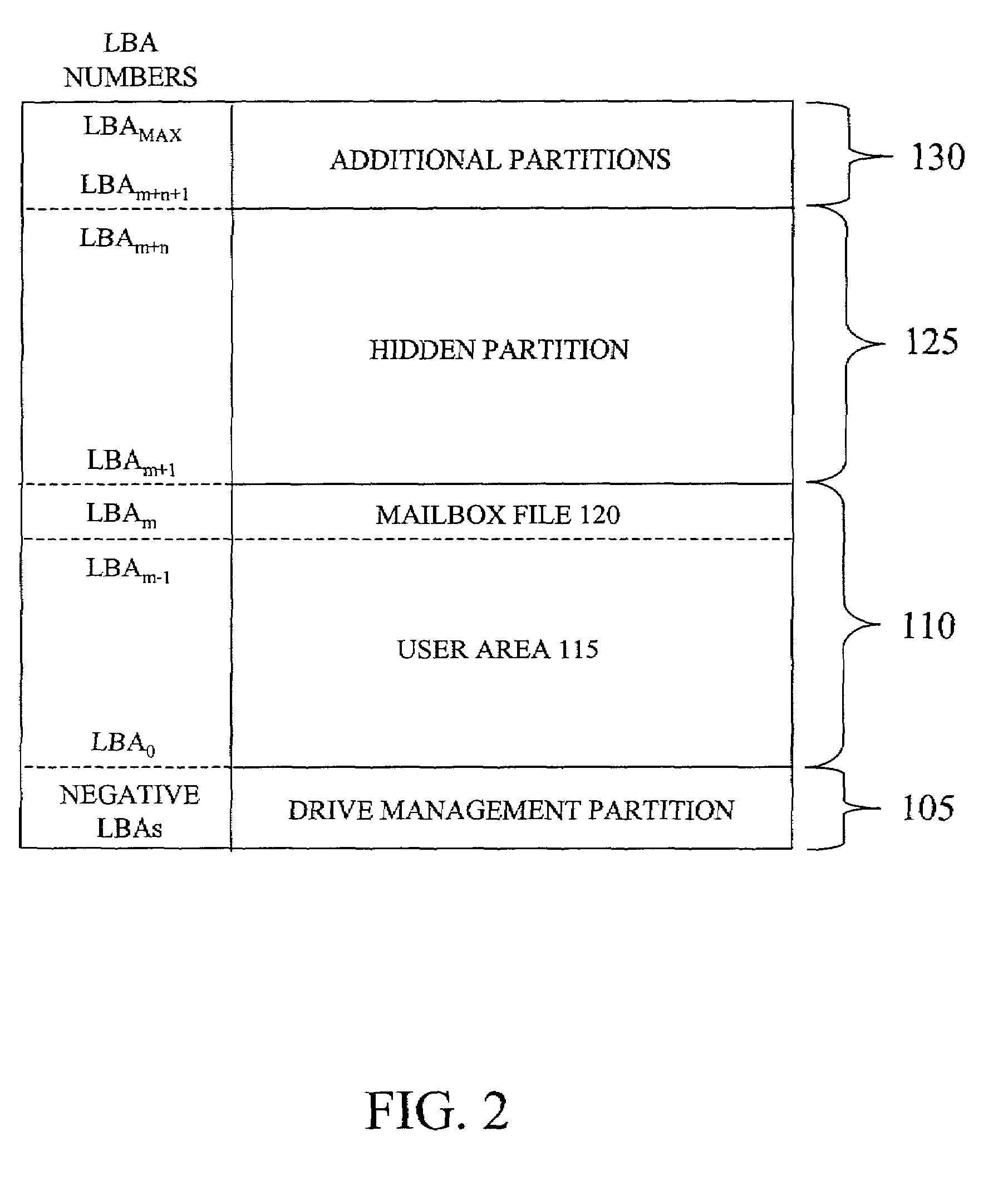
InactiveUS7543117B1Record information storageUsing detectable carrier informationComputerized systemComputer science
A method is disclosed for installing a mailbox file associated with a disk storage medium of a disk drive. In accordance with exemplary embodiments of the present invention, a computer system includes a host computer, a disk drive host interface and a disk drive having a disk storage medium with a first range of disk drive host interface addressable locations. A disk drive access key is obtained from an access key server, the access key being generated by the access key server as a function of an identifying characteristic of the disk drive. A mailbox file is created in the first range of addressable locations using the access key obtained from the access key server. The disk drive is notified of a location of the mailbox file in the first range of addressable locations such that the disk drive can perform a function characterized by contents of the mailbox file.
Owner:WESTERN DIGITAL VENTURES
Method of self-service access control for frequent guests of a housing facility
InactiveUS20090066476A1Electric signal transmission systemsDigital data processing detailsPaymentTime segment
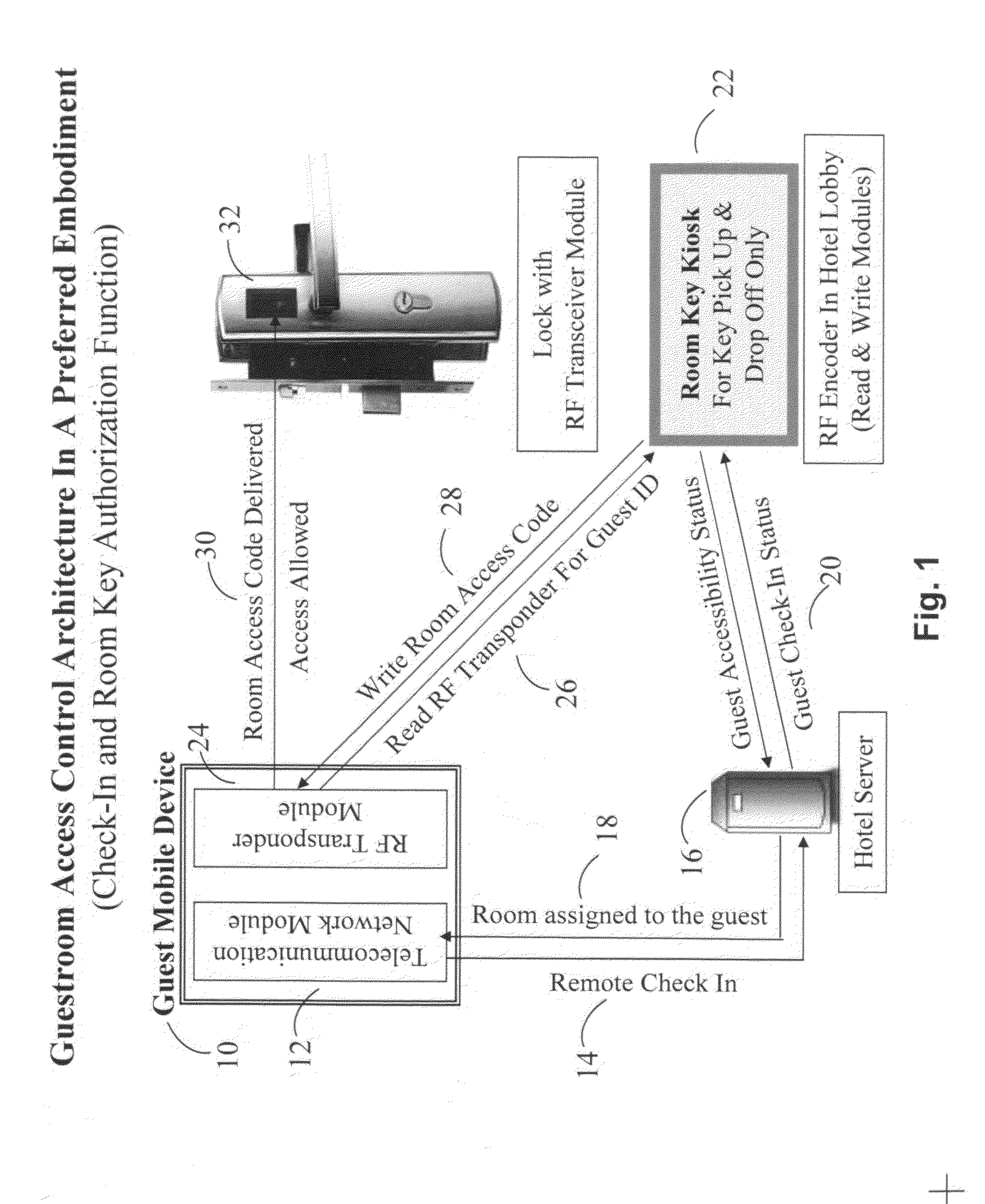
An improved electronic lock with keyless, card-less digital key system is provided for use in residential and commercial buildings. The invention describes a novel method of self-service remote assignment and access authorization to the facility for a specified period of time, and consequent contact-less operation of door locks by means of a mobile device. The method requires no interaction with the facility's front desk or reception or management for checking in, checking out, payments, or access key pick up or drop off.
Owner:FONEKEY
Methods and apparatus for using the internet domain name system to disseminate product information
InactiveUS7117227B2Digital data information retrievalDigital data processing detailsUniversal Product CodeWeb service
Methods and apparatus for disseminating over the Internet product information produced and maintained by product manufacturers using existing universal product codes (bar codes) as access keys. A cross-referencing resource preferably implemented by the existing Internet Domain Name System (DNS) receives Internet request messages containing all or part of a universal product code value and returns the Internet address at which data or services relating to the identified product, or to the manufacturer of that product, may be obtained. By using preferred Web data storage formats and protocol which conform to XML, XLS, XLink, Xpointer, RDF and Web service standards specifications, product and company information may be seamlessly identified, retrieved and integrated with information from other sources. A “web register” module can be employed to provide an Internet interface between a shared sales Internet server and an otherwise conventional inventory control system, and operates in conjunction with the cross-referencing server to provide detailed product information to Internet shoppers who may purchase goods from existing stores via the Internet.
Owner:PROD ASSOC TECH LLC
Method To Make Payment Or Charge Safe Transactions Using Programmable Mobile Telephones
InactiveUS20080091614A1Flexible systemRobustness and safetyComplete banking machinesAcutation objectsPaymentTransaction service
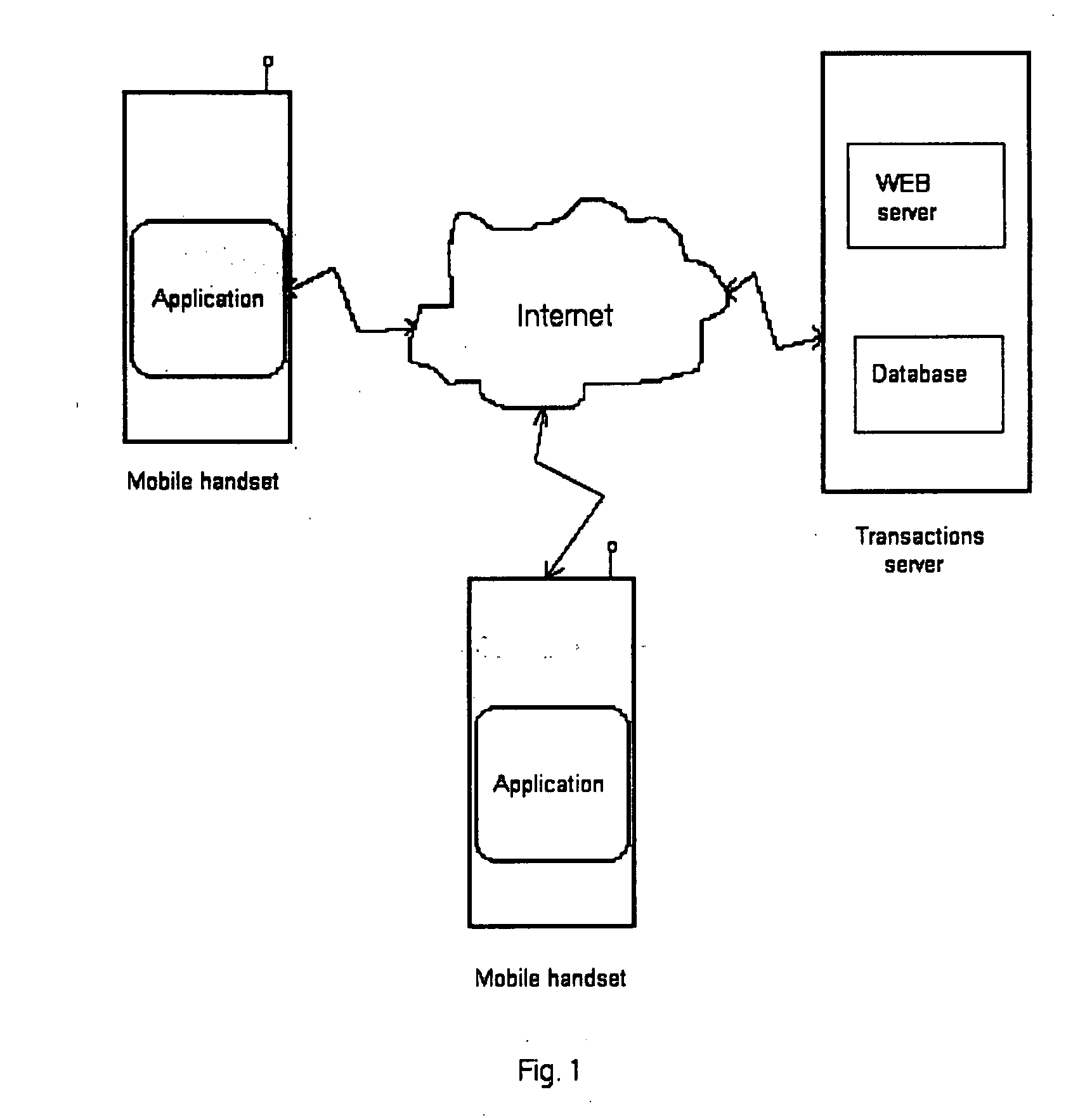
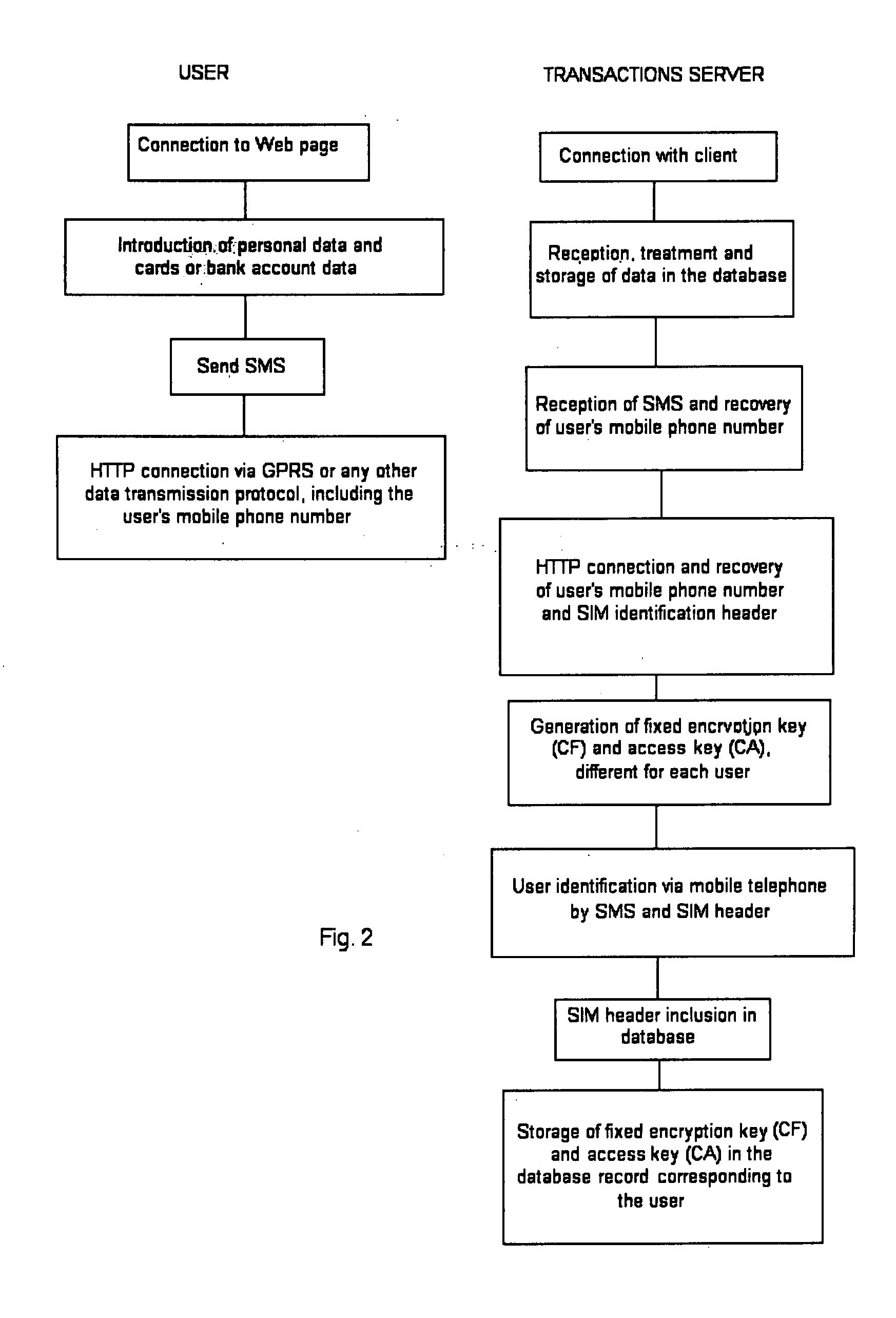
This is a method to carry out safe transactions using programmable mobile telephones. The use of programmable handsets—for example with Java technology—, to which an application is downloaded (e.g. Java application) allows people to carry out safe transactions. The application allows the buyer / seller to carry out the transaction, including the verification, with just one connection. The data that was sent is then encrypted and transmitted via GPRS or any other data transmission protocol, to a transactions server, where the transactions are verified and authorised. The security of the process is provided mainly by the use of up to five non related identification elements, including an access key unique for each user, stored in the mobile handset.
Owner:ETRANS L C
Remote monitoring system for water
InactiveUS20050009192A1Minimal disruptionFunction increaseWater treatment parameter controlControlling ratio of multiple fluid flowsControl signalMonitoring system
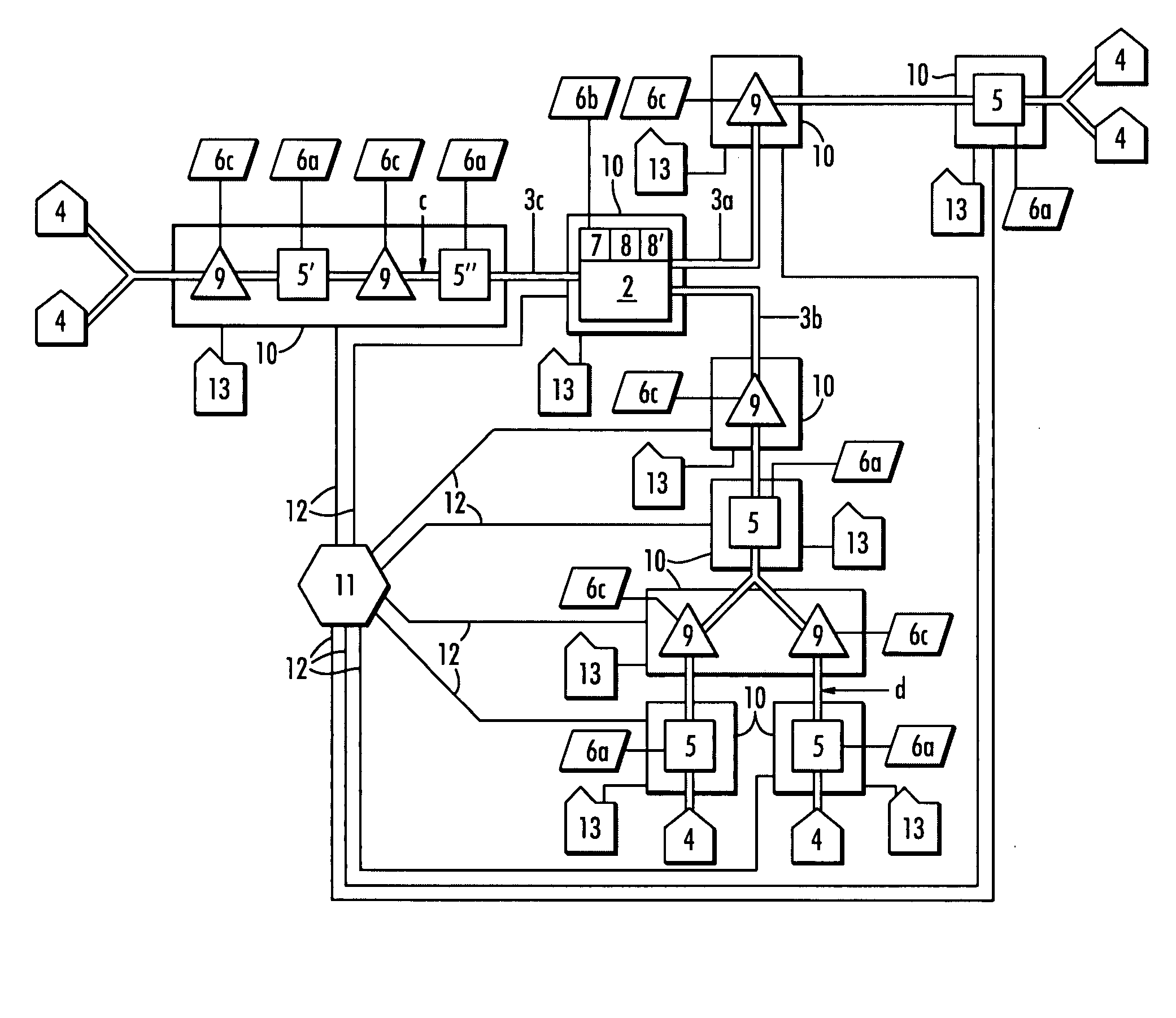
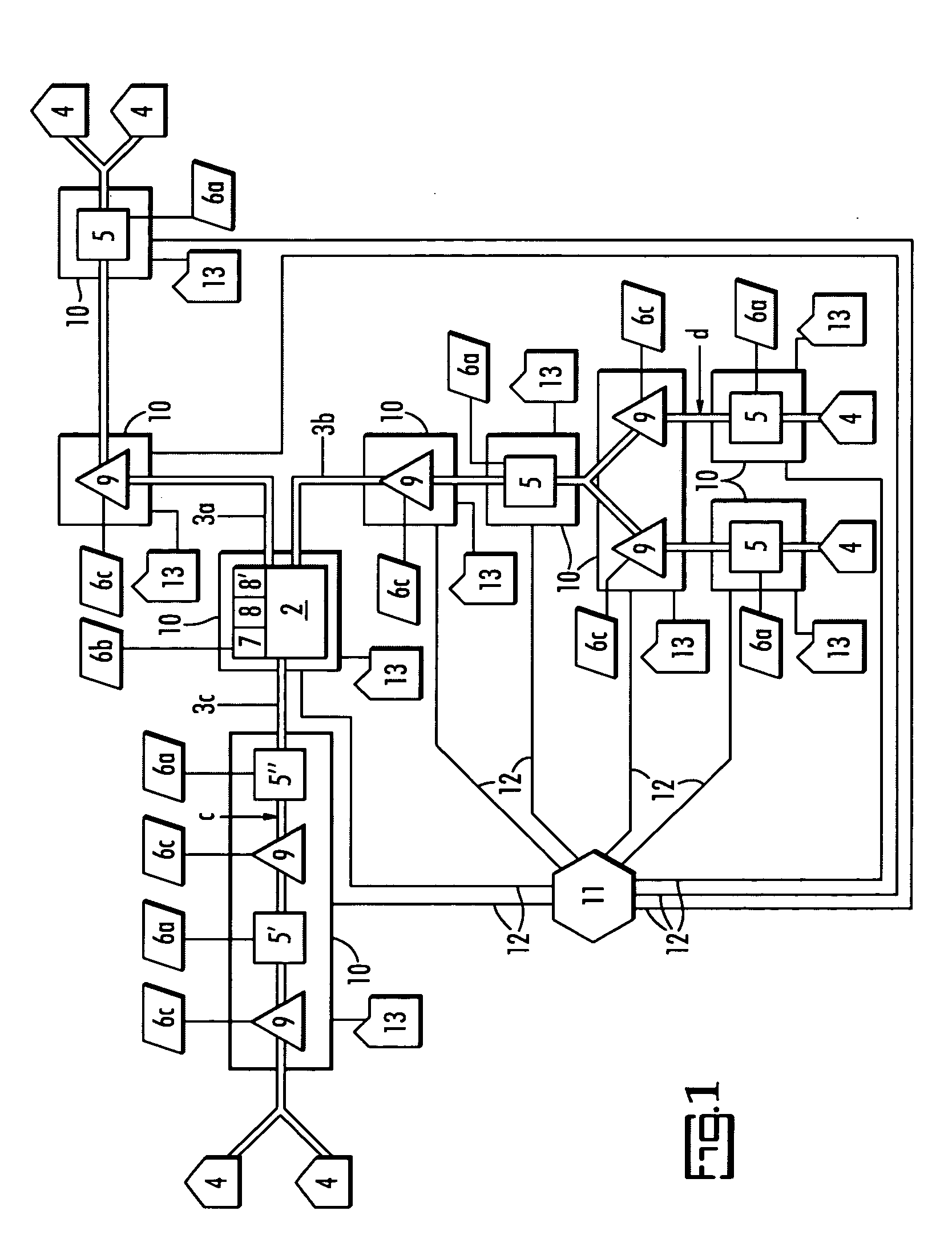
A water quality detection system for distributed water supply network. The system, 1, comprises a multiplicity of detectors, 5, wherein each detector of the detectors is capable of monitoring at least one attribute of water and providing a signal related to the attribute. A controller, 7, is provided which is capable of receiving each signal and comparing the signal to a control signal for the attribute. A response mechanism, 9, is responsive to the controller and activated when at least one signal matches the control signal. An access gate, 10, limits access to at least one of the detector, the controller or the response mechanism. An access key, 13, is provided for comparing a user attribute with a stored attribute wherein when the user attribute matches the stored attribute access is provided into the access gate.
Owner:PDA SECURITY SOLUTIONS
Mobile Device Transaction Using Multi-Factor Authentication
ActiveUS20120110341A1Reduce chanceImprove securityComputer security arrangementsPayment architectureThe InternetHand Held Computer
The following is a system in which a person may use a Cellular (Mobile) Telephone, a PDA or any other handheld computer to make a purchase. This is an example only. The process may entail any type of transaction which requires authentication, such as any financial transaction, any access control (to account information, etc.), and any physical access scenario such as doubling for a passport or an access key to a restricted area (office, vault, etc.). It may also be used to conduct remote transactions such as those conducted on the Internet (E-Commerce, account access, etc.). In the process, a multi-factor authentication is used.
Owner:BEIGI HOMAYOON
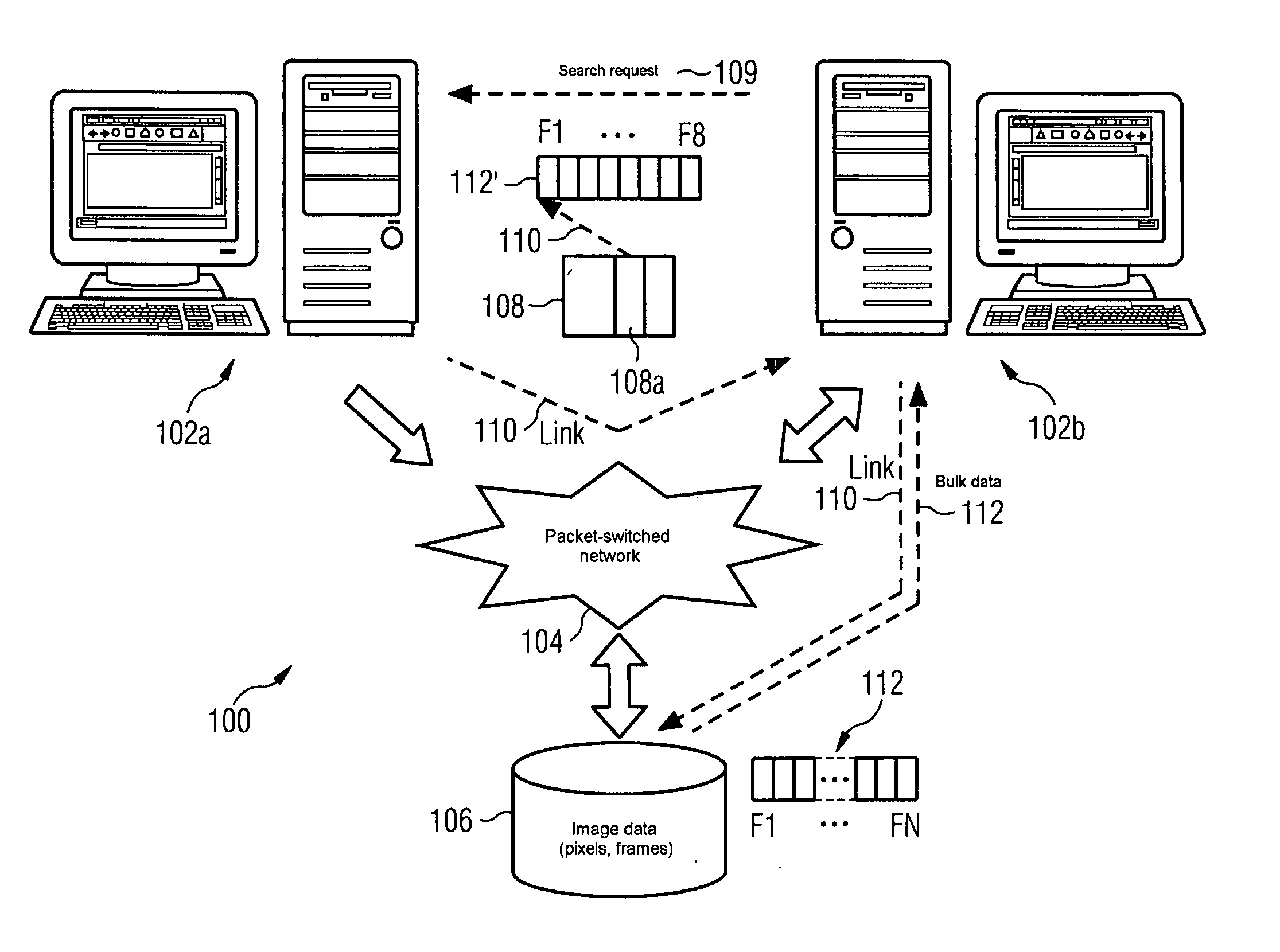
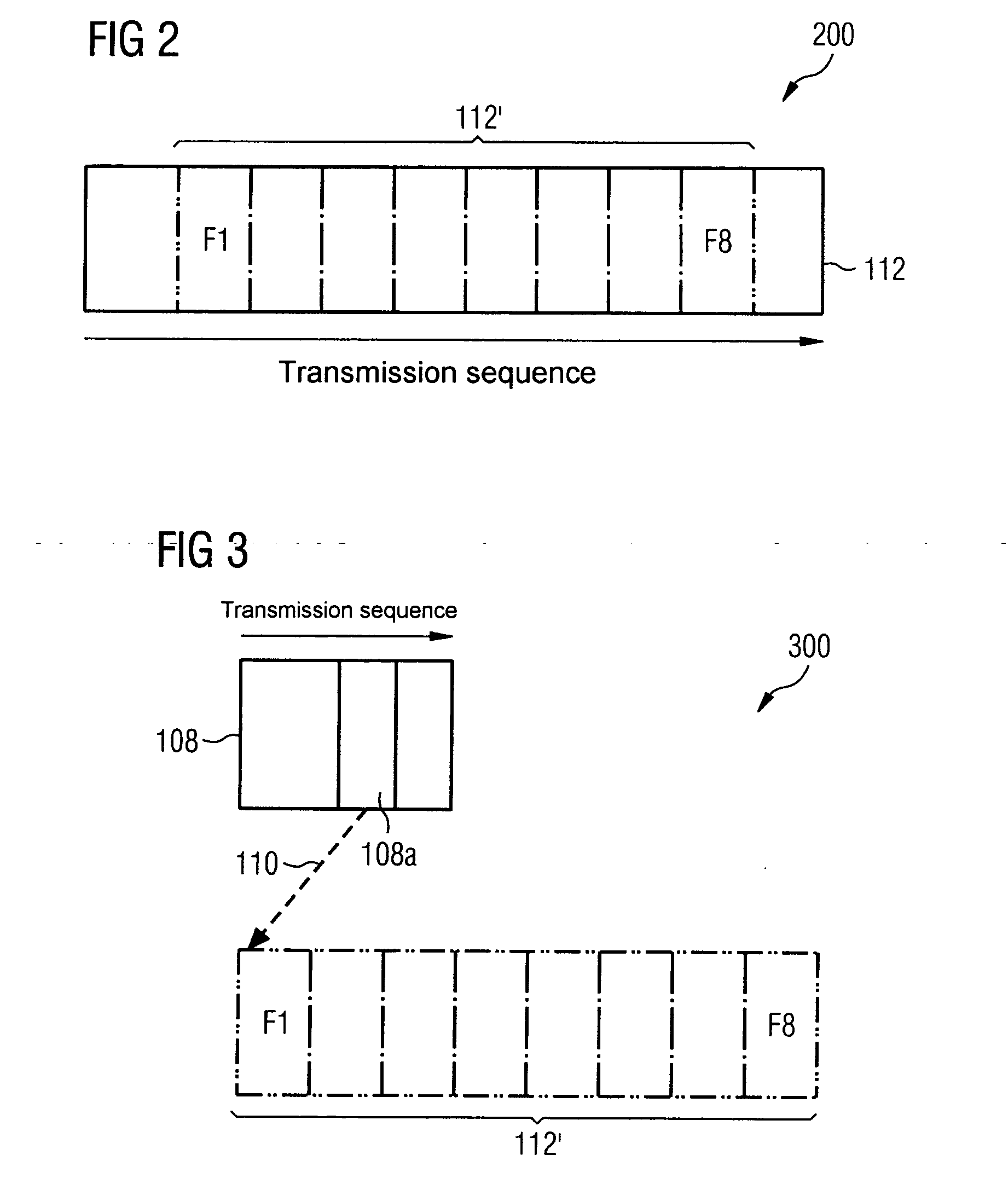
Storage and access method for an image retrieval system in a client/server environment
ActiveUS20050108365A1Reduce data volumeShorten access timeStill image data indexingMultiple digital computer combinationsData streamData field
An image retrieval system has a network server, at least one client terminal and a data archive of a multiuser file management system, spatially separated from server and client, of a file server. A reduced data stream is now transmitted between server and client and includes a header for transmitting address and meta information with an additional data field that includes an access key to the bulk data stored in the external data archive. This reduces the data volume to be transmitted during image retrieval, and thus reduces the network utilization in the transmission of the data stream occurring between server and client. As a result of this, the time period required to transfer the modified data stream between server and client terminal is correspondingly short.
Owner:SIEMENS HEALTHCARE GMBH
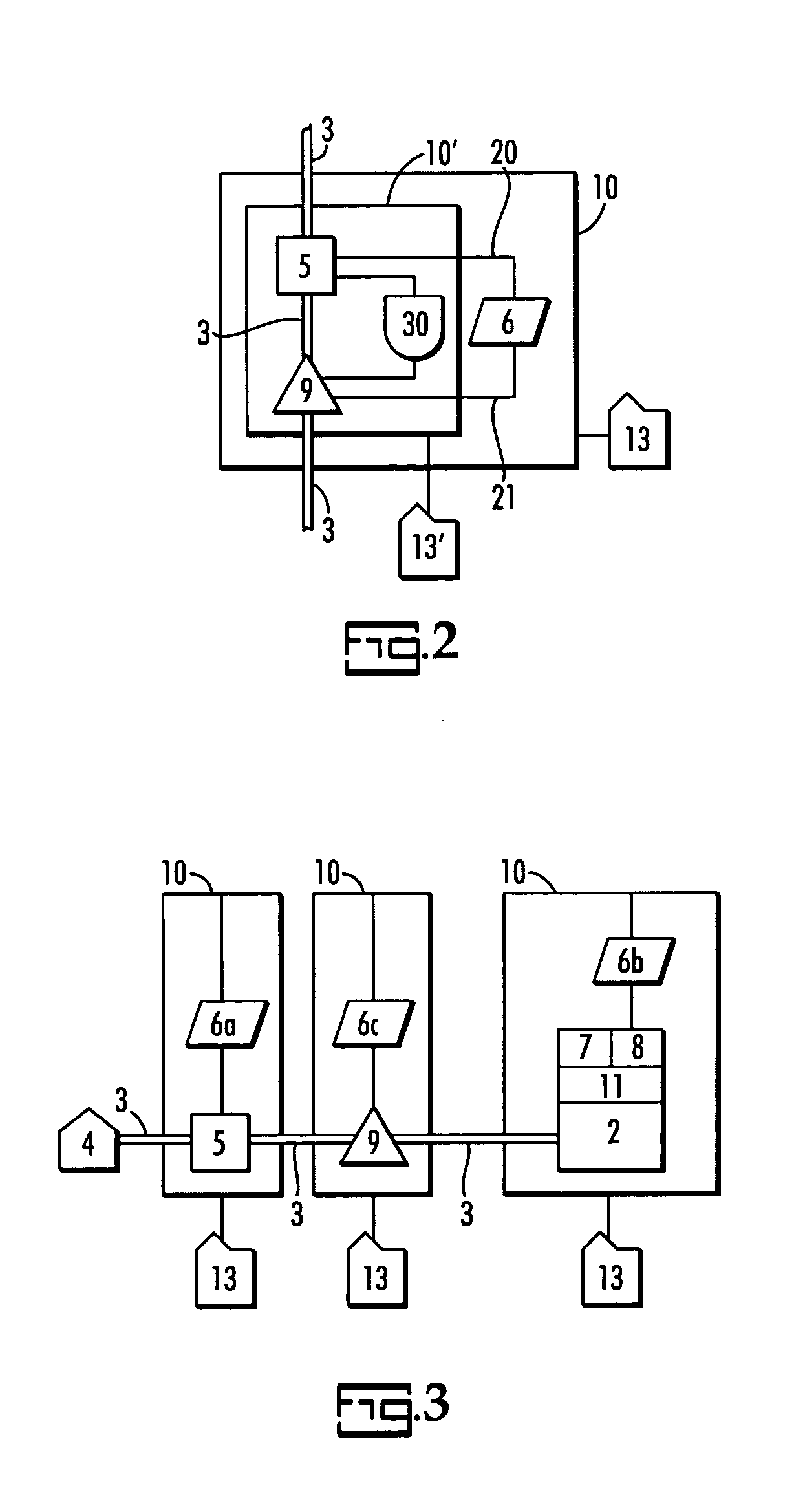
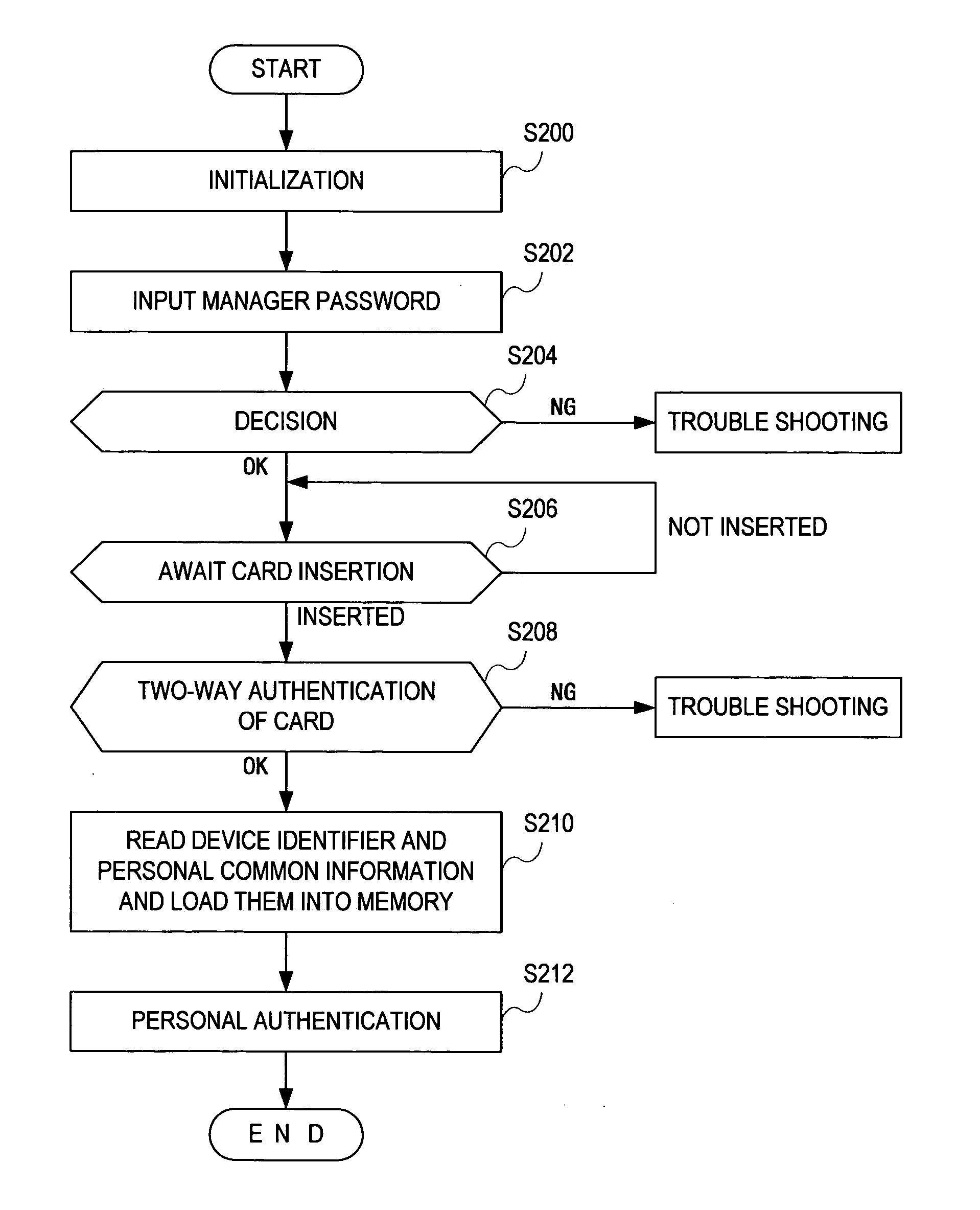
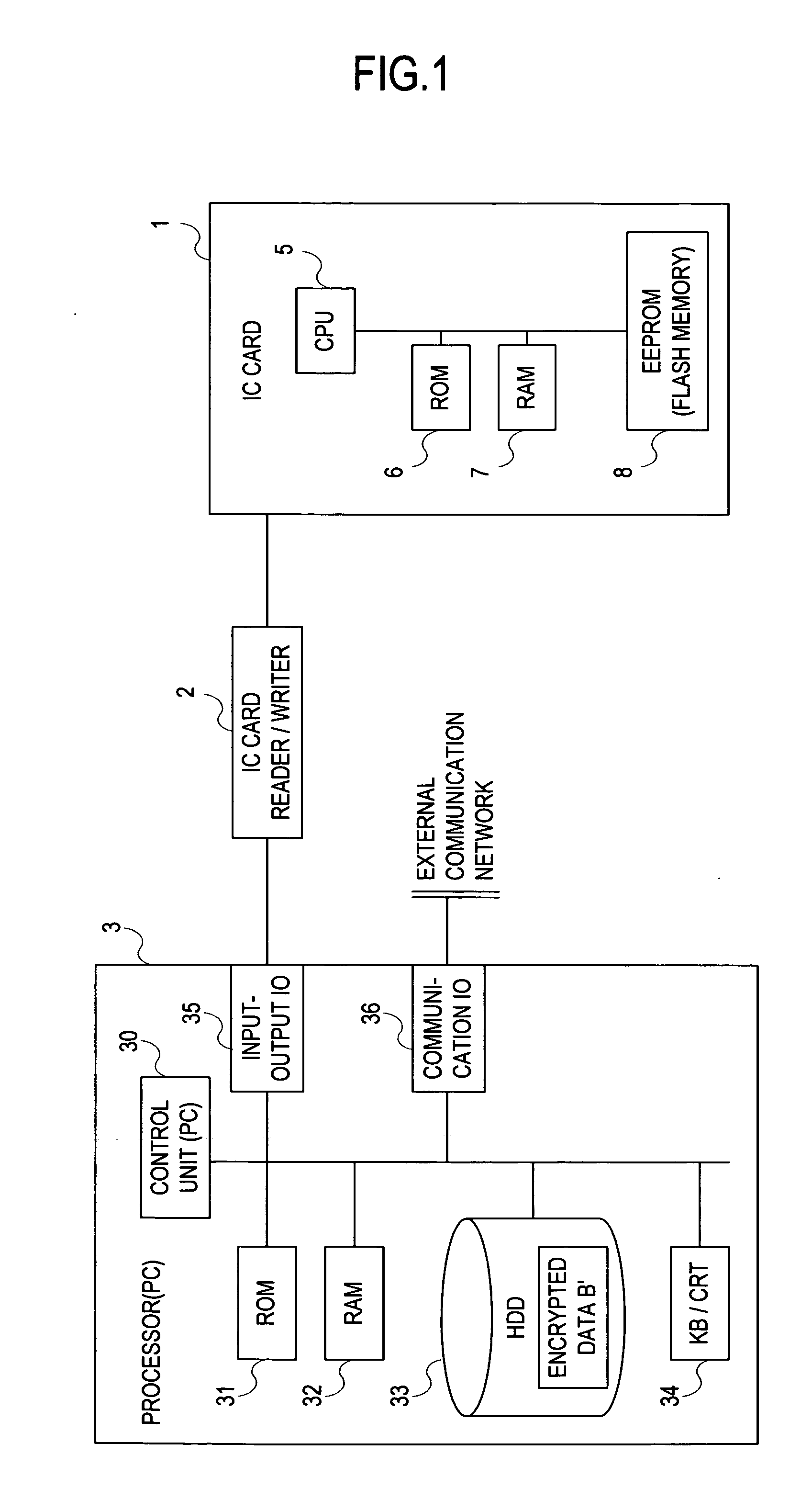
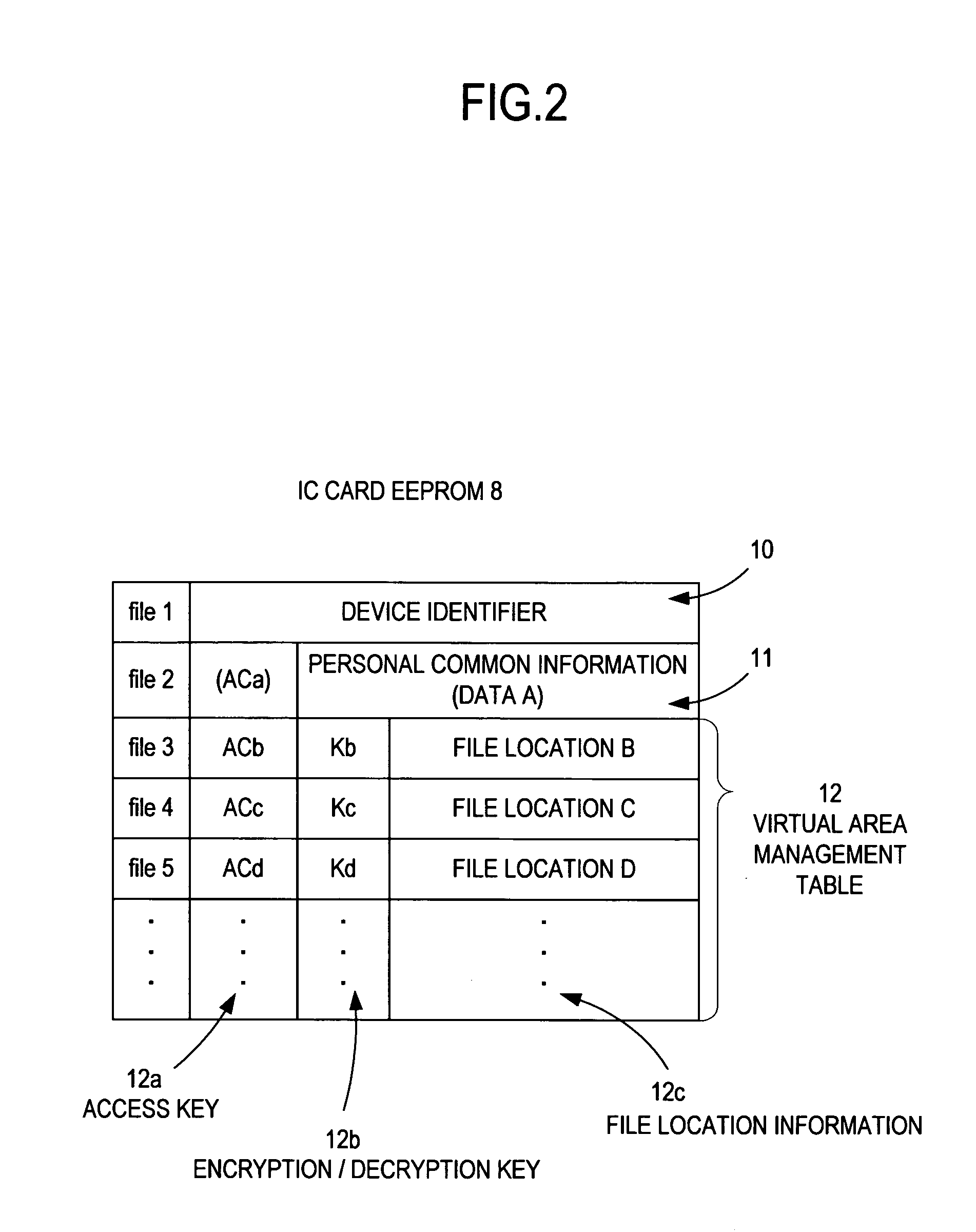
IC card system
InactiveUS20050086497A1Solve large capacityEnabling operationDigital data processing detailsUser identity/authority verificationComputer hardwareData file
An IC card system capable of increasing a storage capacity virtually and flexibly while making the best use of characteristics of the IC card, facilitating file layout, and ensuring security among applications. With personal common information (data A) and virtual area management information (access keys, encryption / decryption keys, and information indicating encrypted data file location) stored in the IC card, an application executed by a control unit of a processor loads the data A in a memory, acquires the encryption / decryption key corresponding to the retained access key and the information indicating the encrypted data file location from the IC card, reads encrypted data B′ from the acquired data file location, decrypts the acquired encryption / decryption key, and loads the data B in the memory for using the data.
Owner:SYSTNEEDS
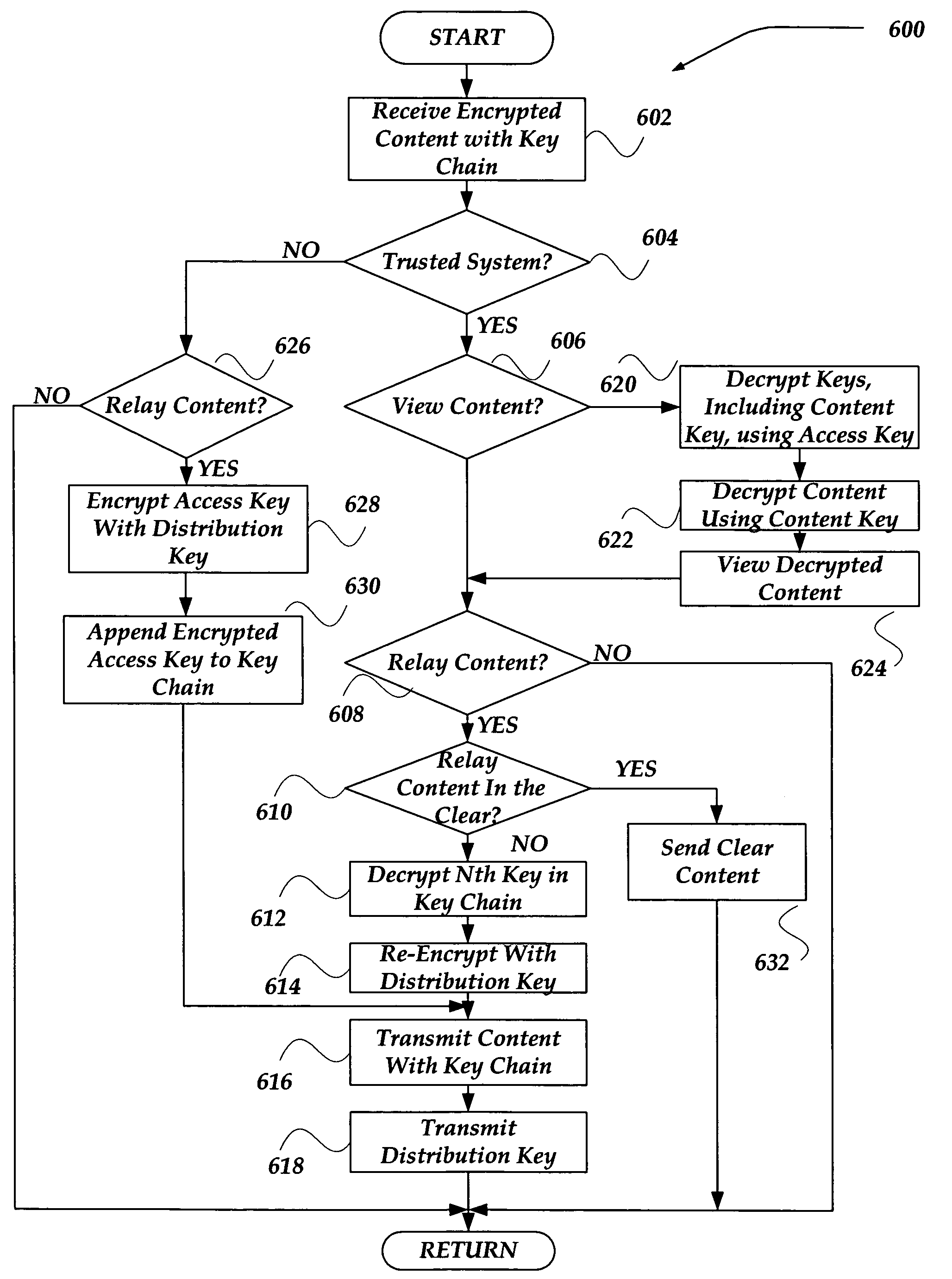
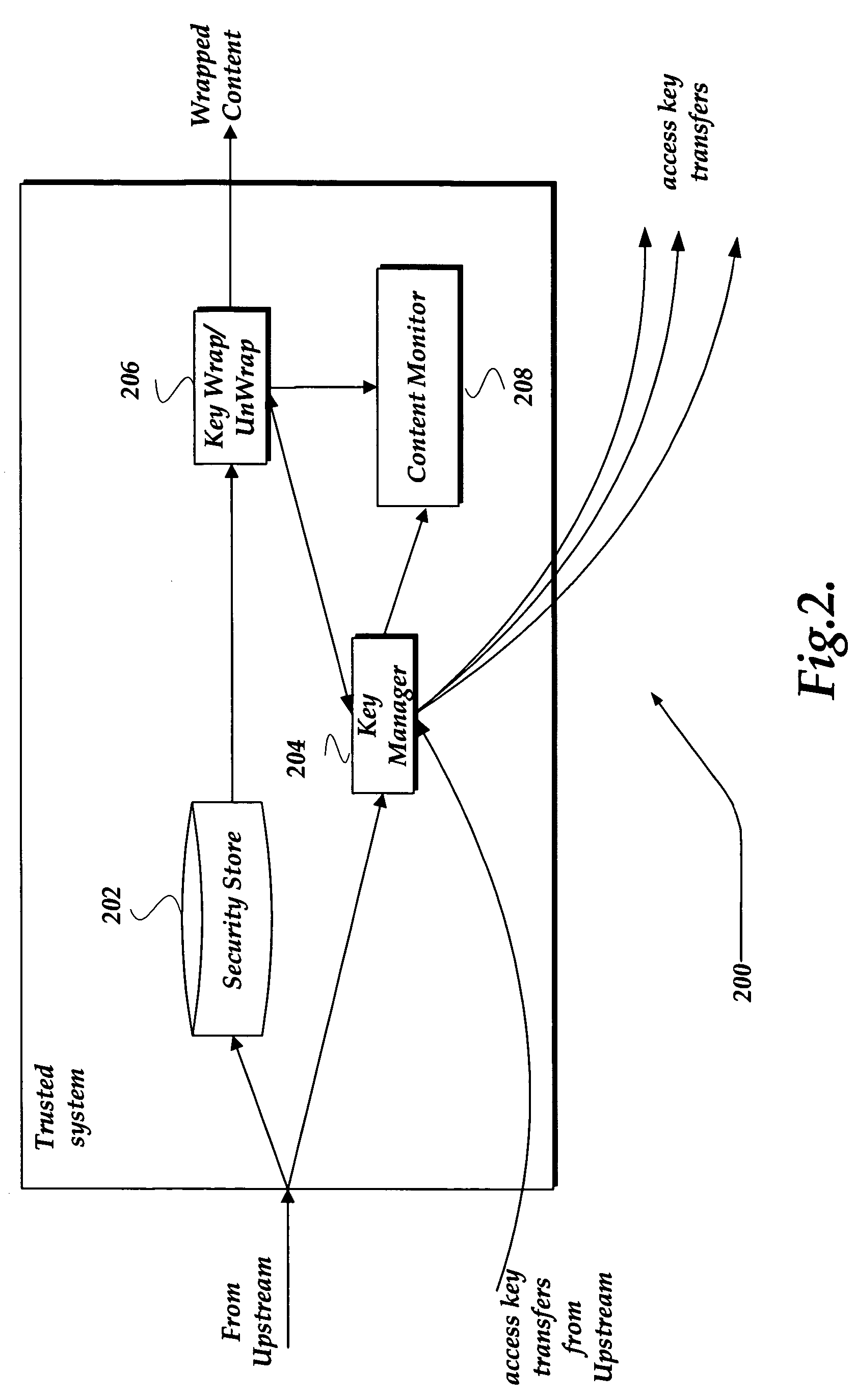
Securely relaying content using key chains
A system, apparatus, and method are directed towards generating chains of encrypted decryption keys for content in a highly distributed environment. In one embodiment, the key chain may be provided within an Entitlement Control Message (ECM). An access key that enables decryption of a current link within the chain of decryption keys may be provided to a downstream recipient using an out-of-band mechanism. Alternatively, the access key may be provided through an in-band mechanism, such as through the use of Entitlement Management Message (EMM), or the like. In one embodiment, the access key within the EMM may be further encrypted by another encryption key that may be unique to the downstream recipient.
Owner:GOOGLE LLC
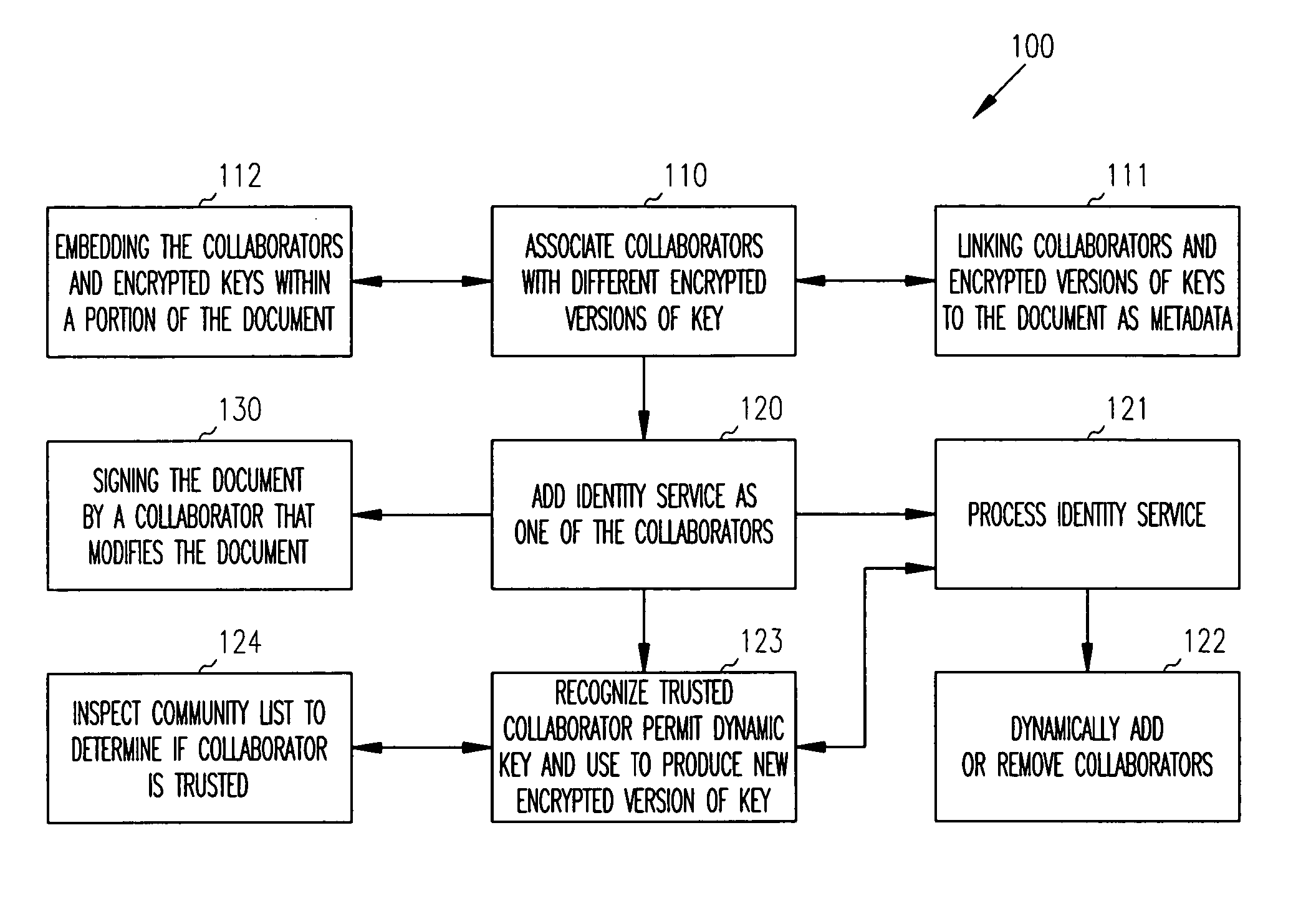
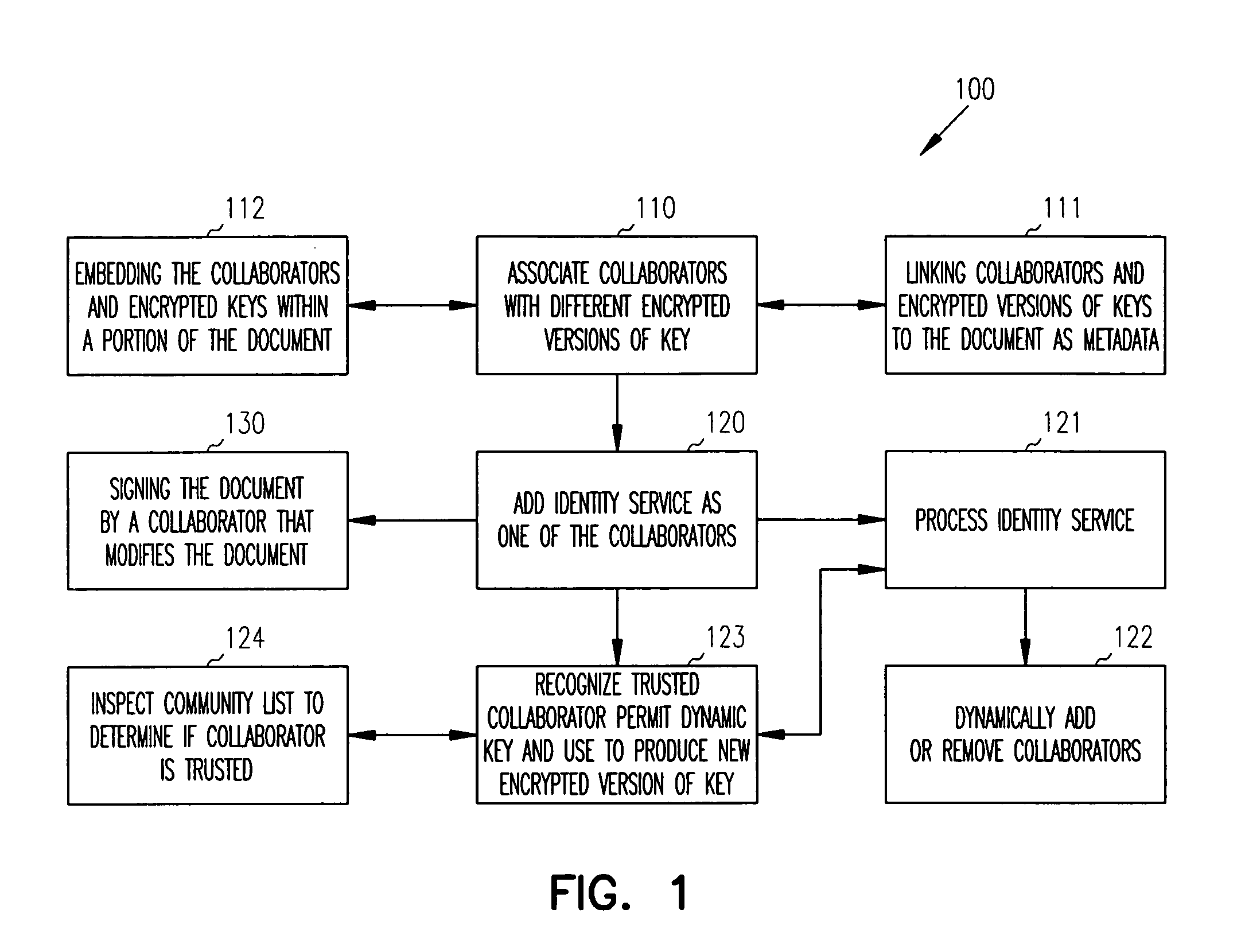
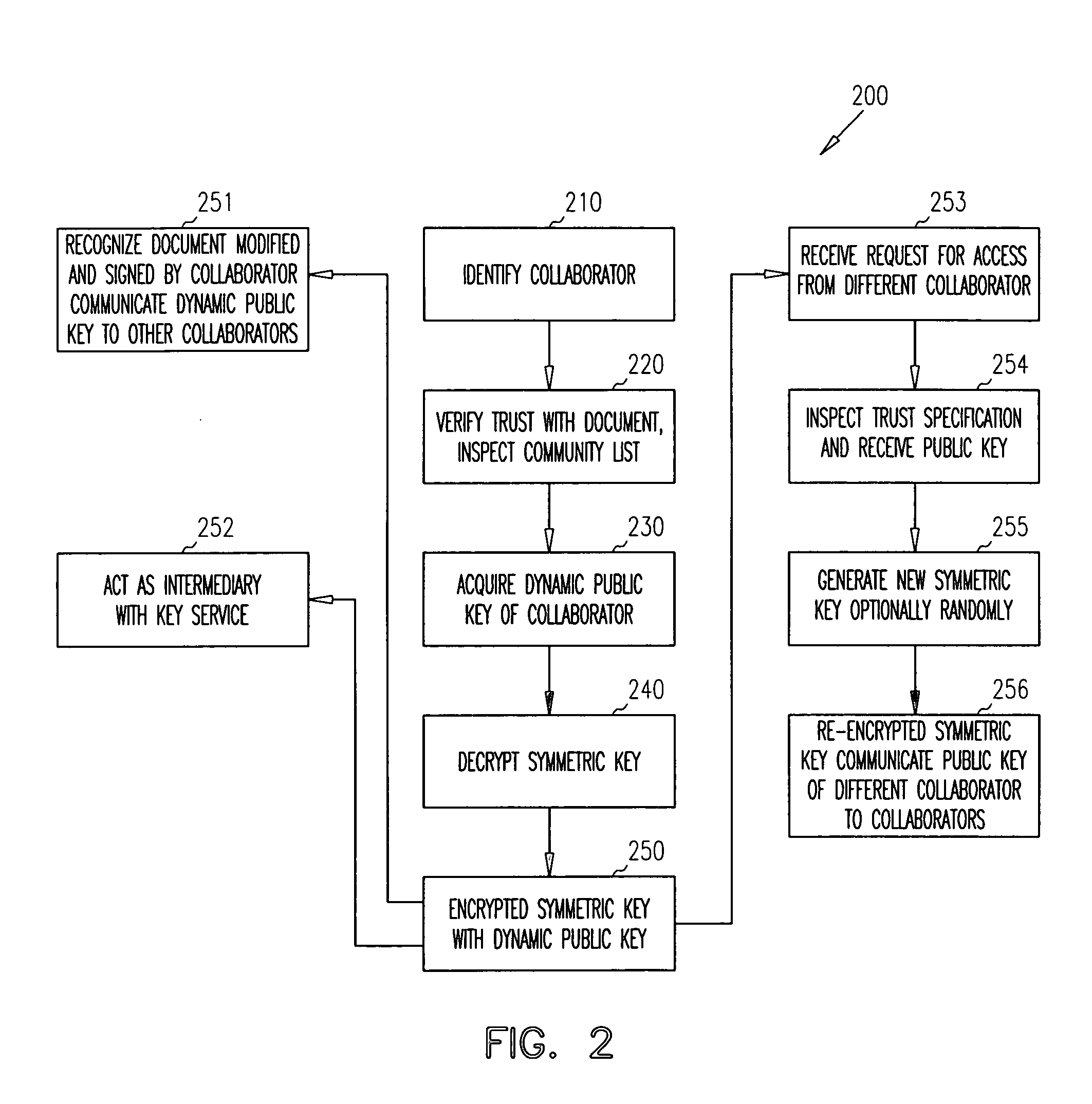
Distributed dynamic security for document collaboration
ActiveUS20050120199A1Digital data processing detailsUser identity/authority verificationPaper documentDynamic management
Techniques are provided for dynamically managing security for document collaboration. A document is associated with a list of collaborators, which can access the document. One collaborator is an identity service. The identity service is capable of dynamically encrypting versions of an access key needed by a collaborator to access the document and capable of dynamically adding or removing collaborators from the list of collaborators.
Owner:ORACLE INT CORP
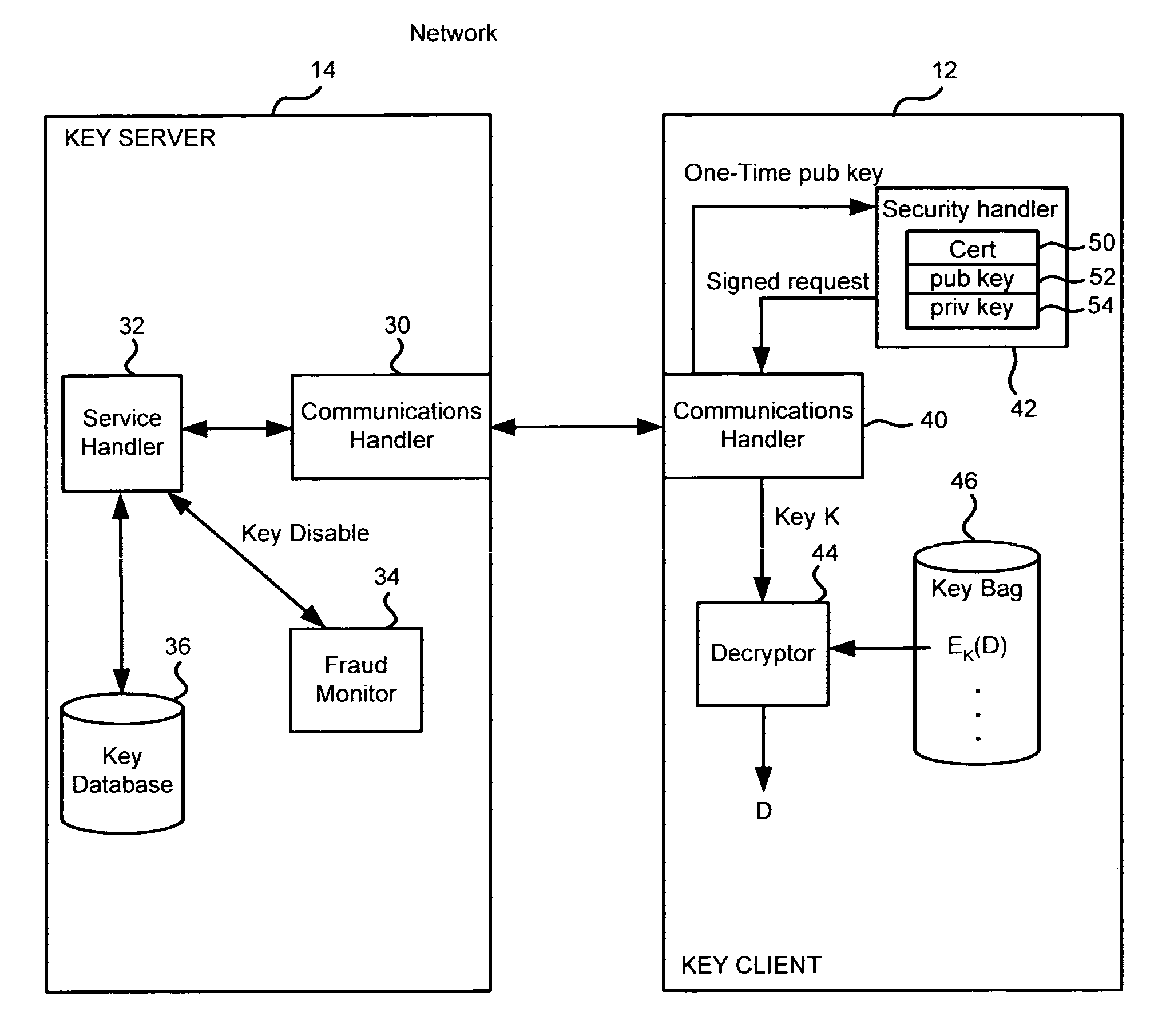
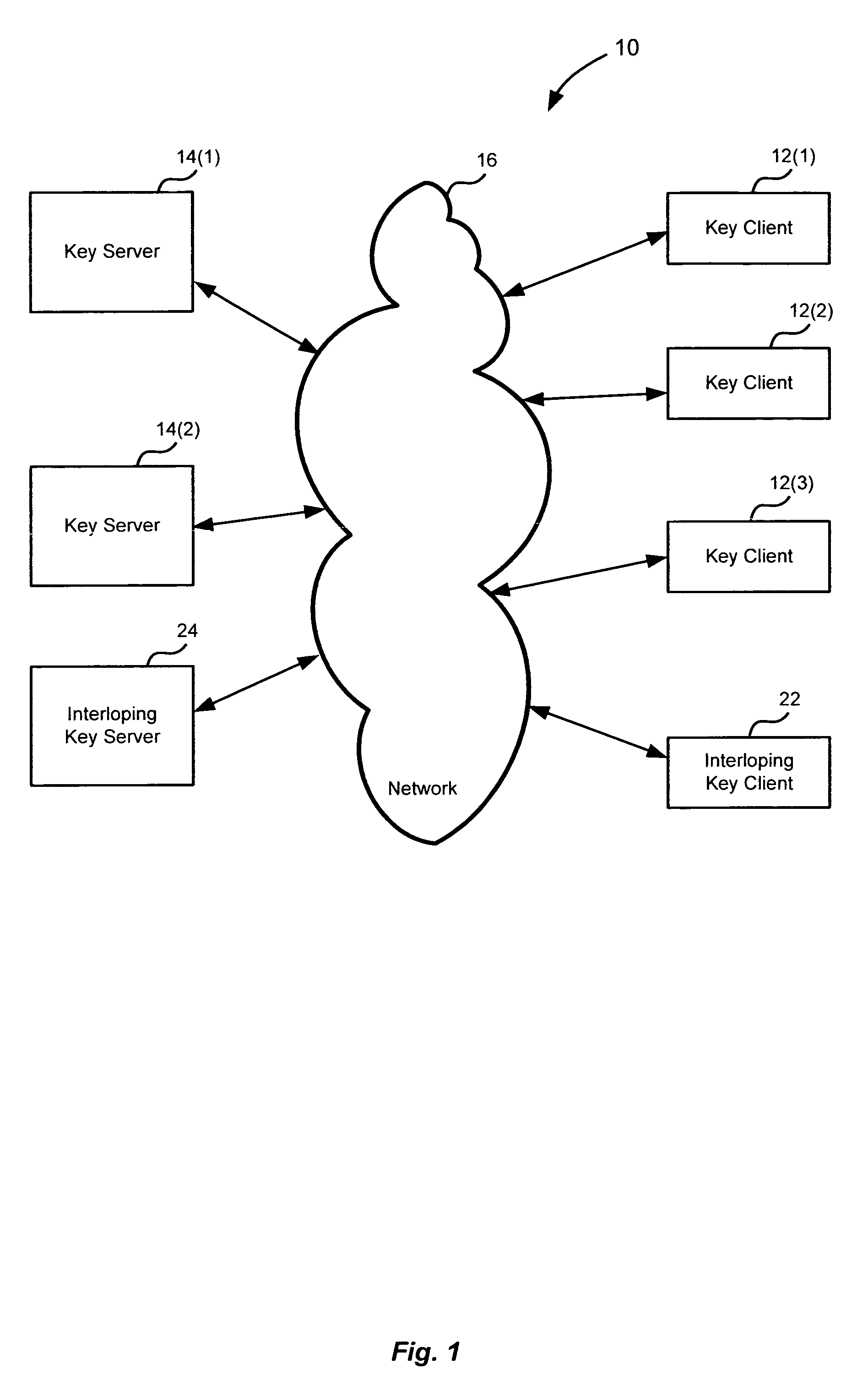
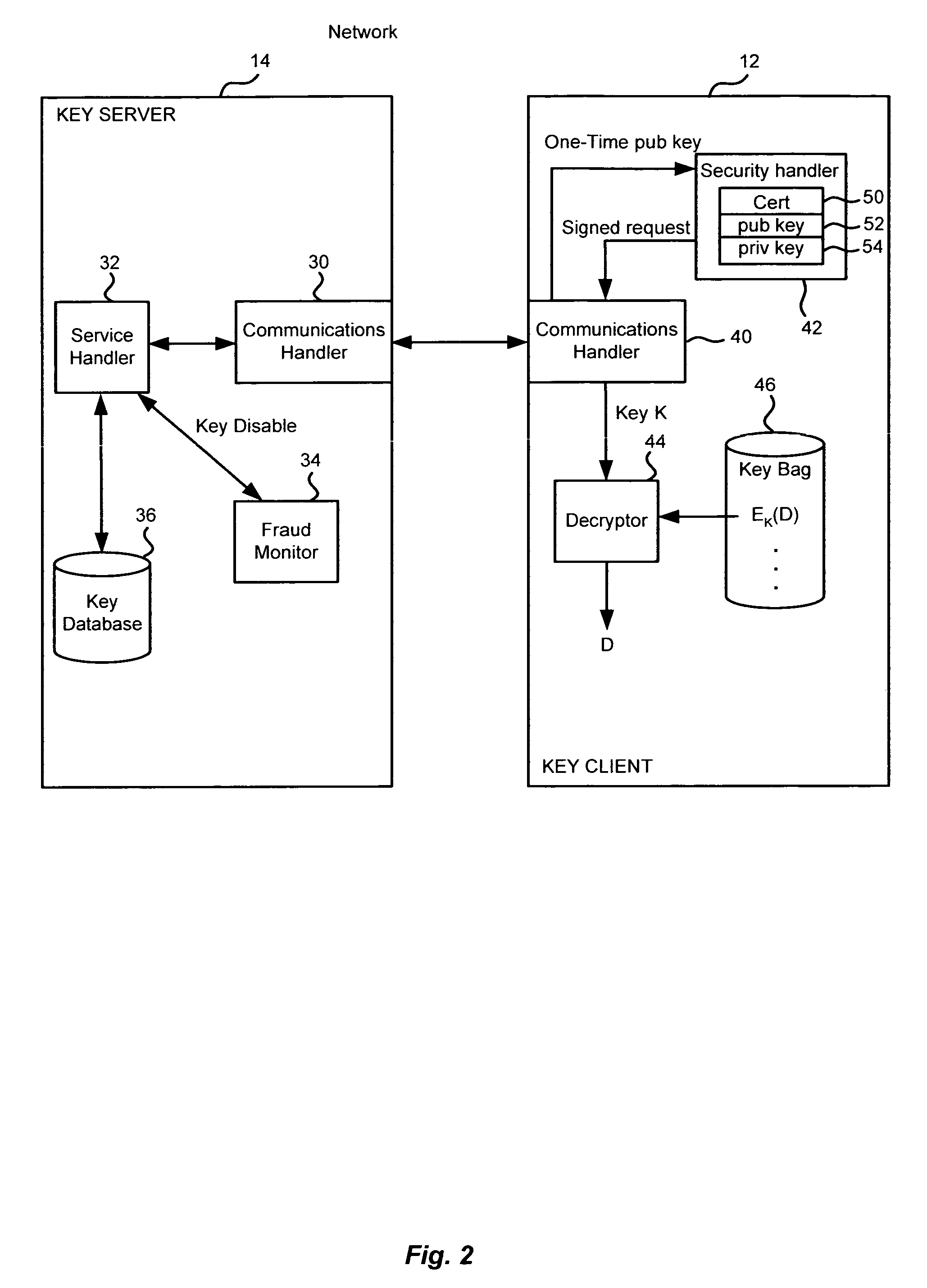
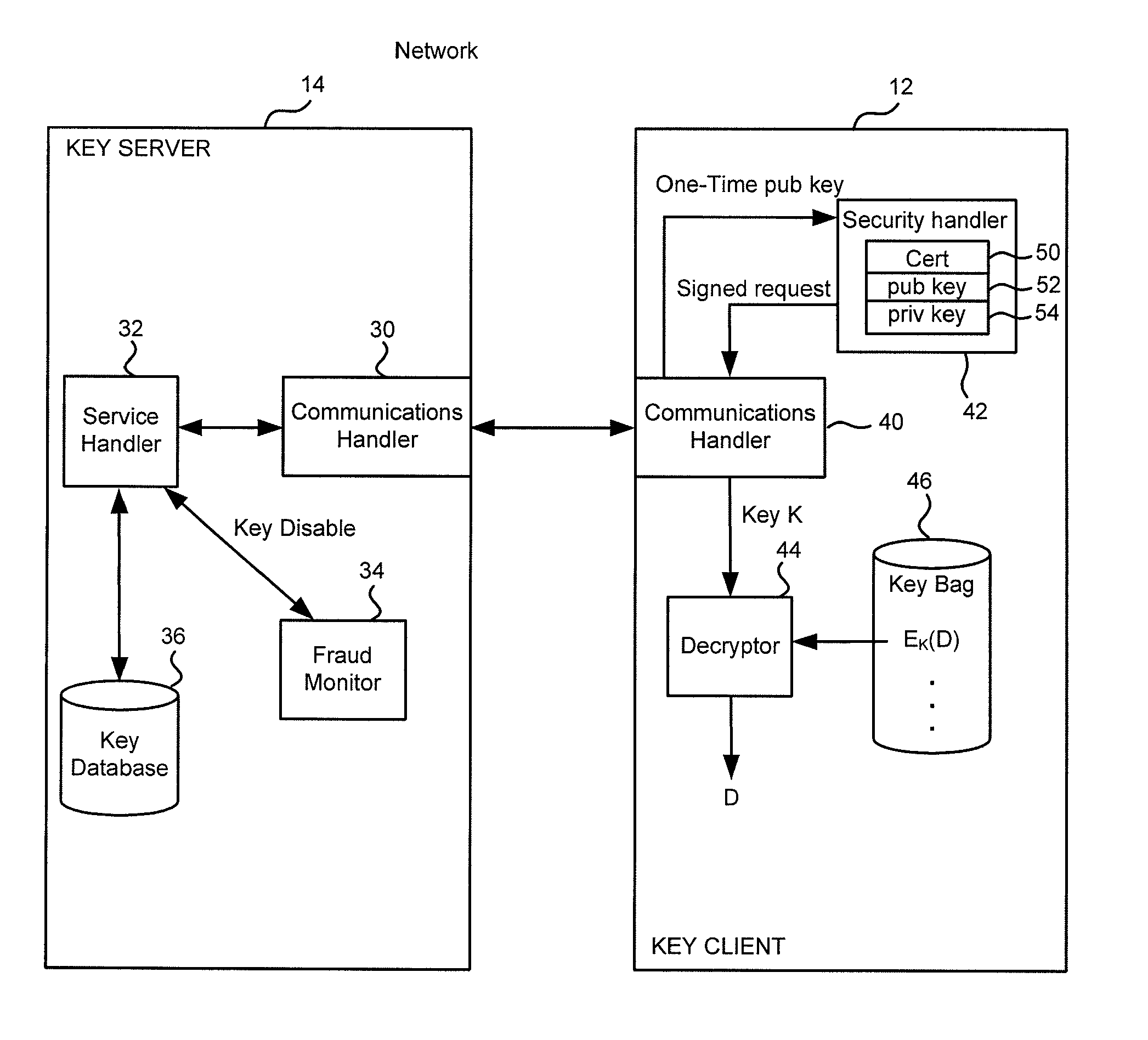
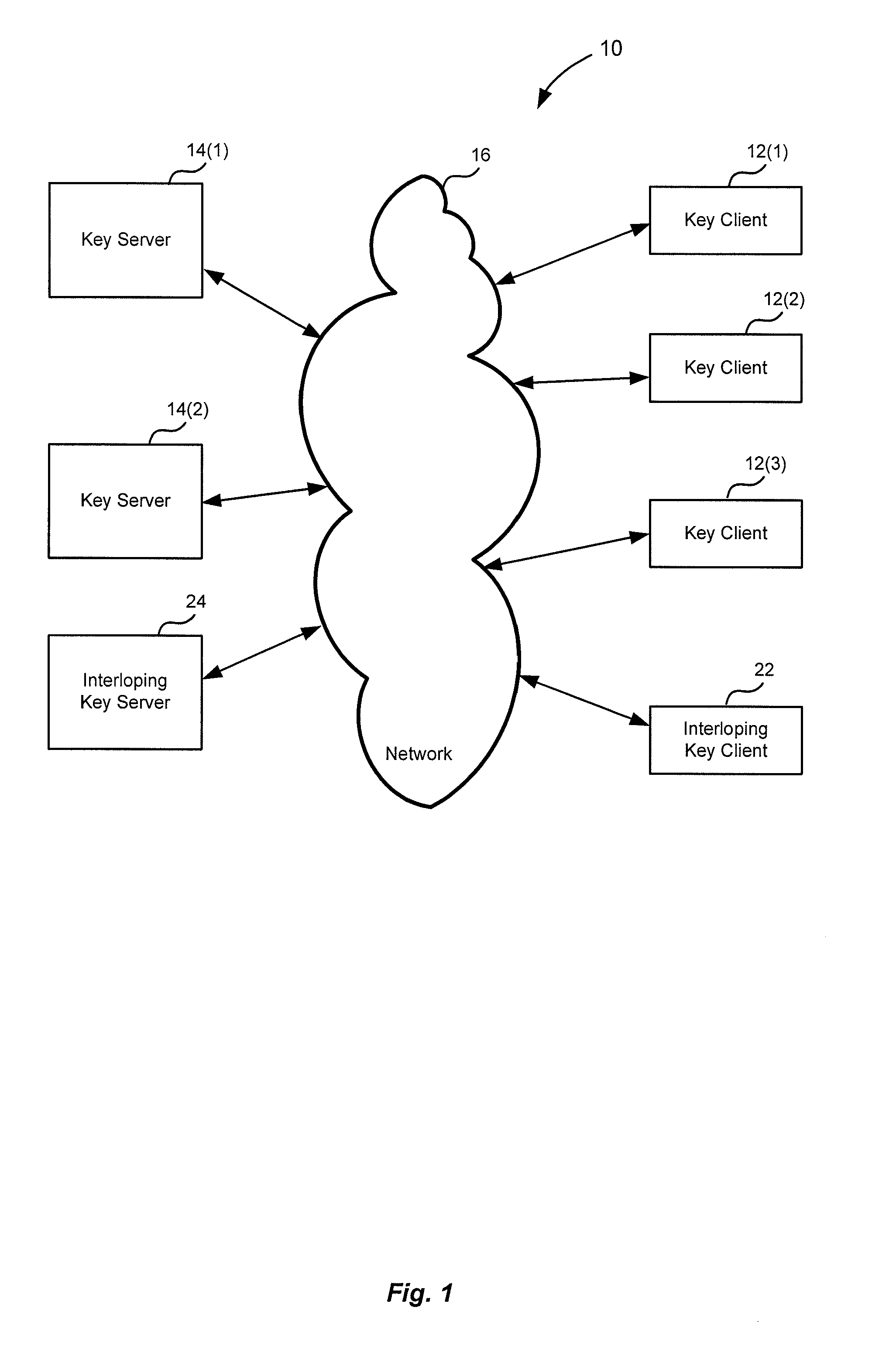
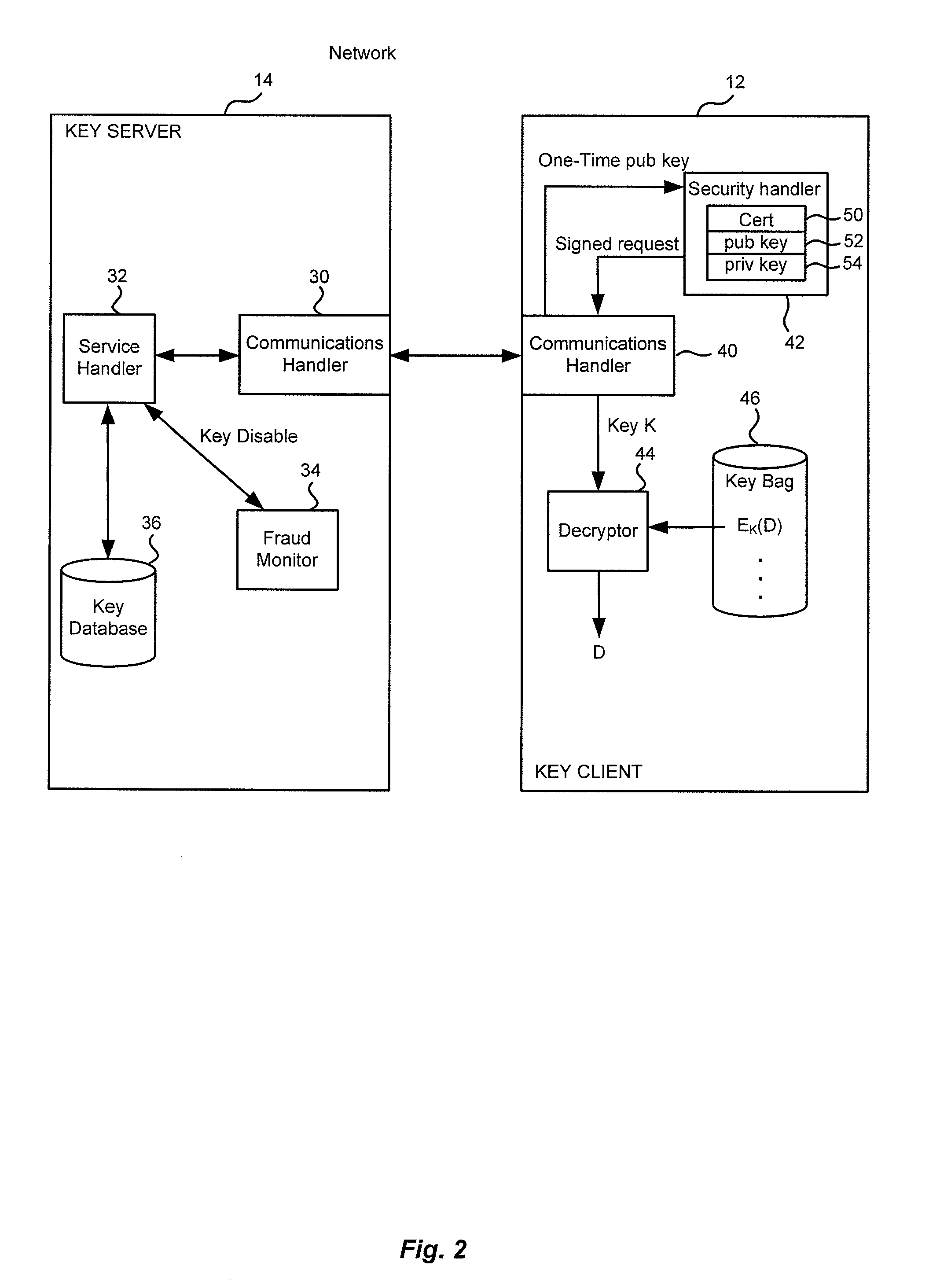
Method and apparatus for cryptographic key storage wherein key servers are authenticated by possession and secure distribution of stored keys
InactiveUS7711122B2Key distribution for secure communicationPublic key for secure communicationKey storageData storing
A key management system includes secured data stored on a first system secured by a control key stored securely on a key server. The secured data is secured against attacks such as unauthorized use, modification or access, where authorization to access the secured data is determined by knowledge of an access private key of an access key pair. When an authorized user is to access the secured data, the first system generates a request to the key server, signed with the access private key, wherein the request is for a decryption control key and the request includes a one-time public key of a key pair generated by the first system for the request. The first system can decrypt the decryption control key from the response, using a one-time private key. The first system can then decrypt the secured data with the decryption control key remaining secured in transport.
Owner:CA TECH INC
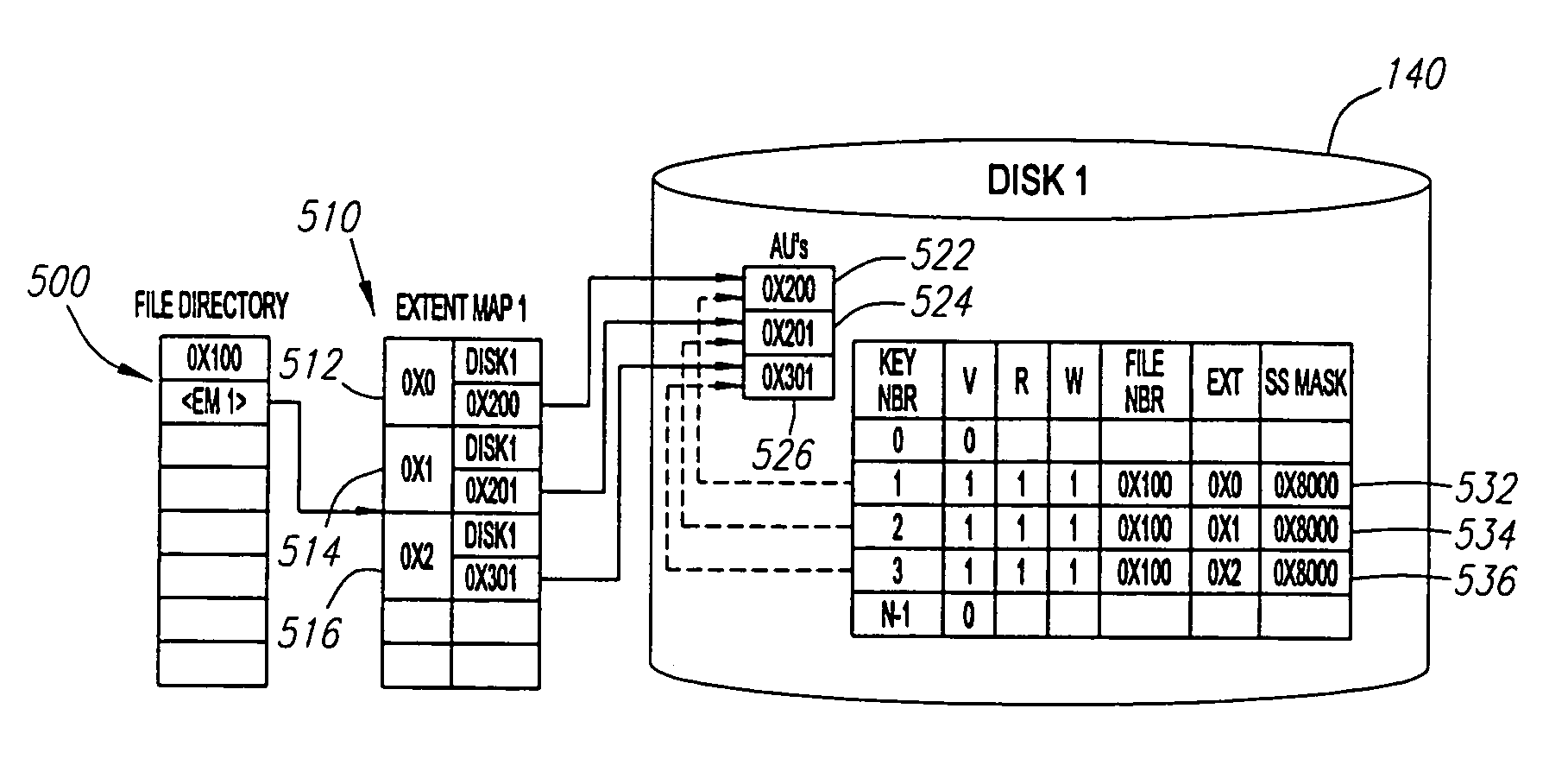
Storage access keys
InactiveUS7152148B2Data processing applicationsInput/output to record carriersFile systemData storing
Methods are provided for communicating with and regulating access to a storage system contained within a file system. Storage access keys are used to communicate to the file system changes in location of data stored in the storage system. Fence keys are used to regulate access to the storage system.
Owner:ORACLE INT CORP
System for regulating access to a resource
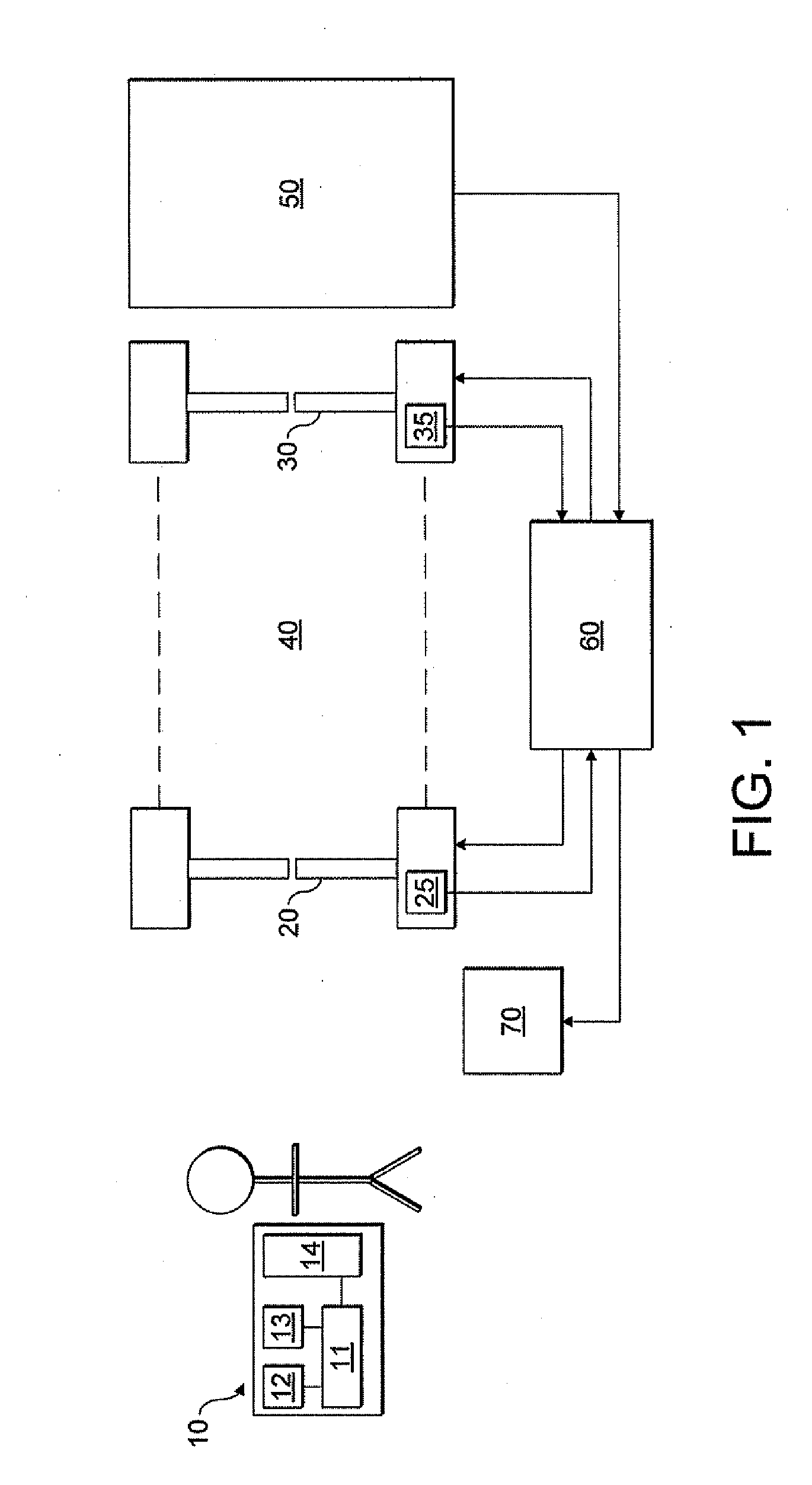
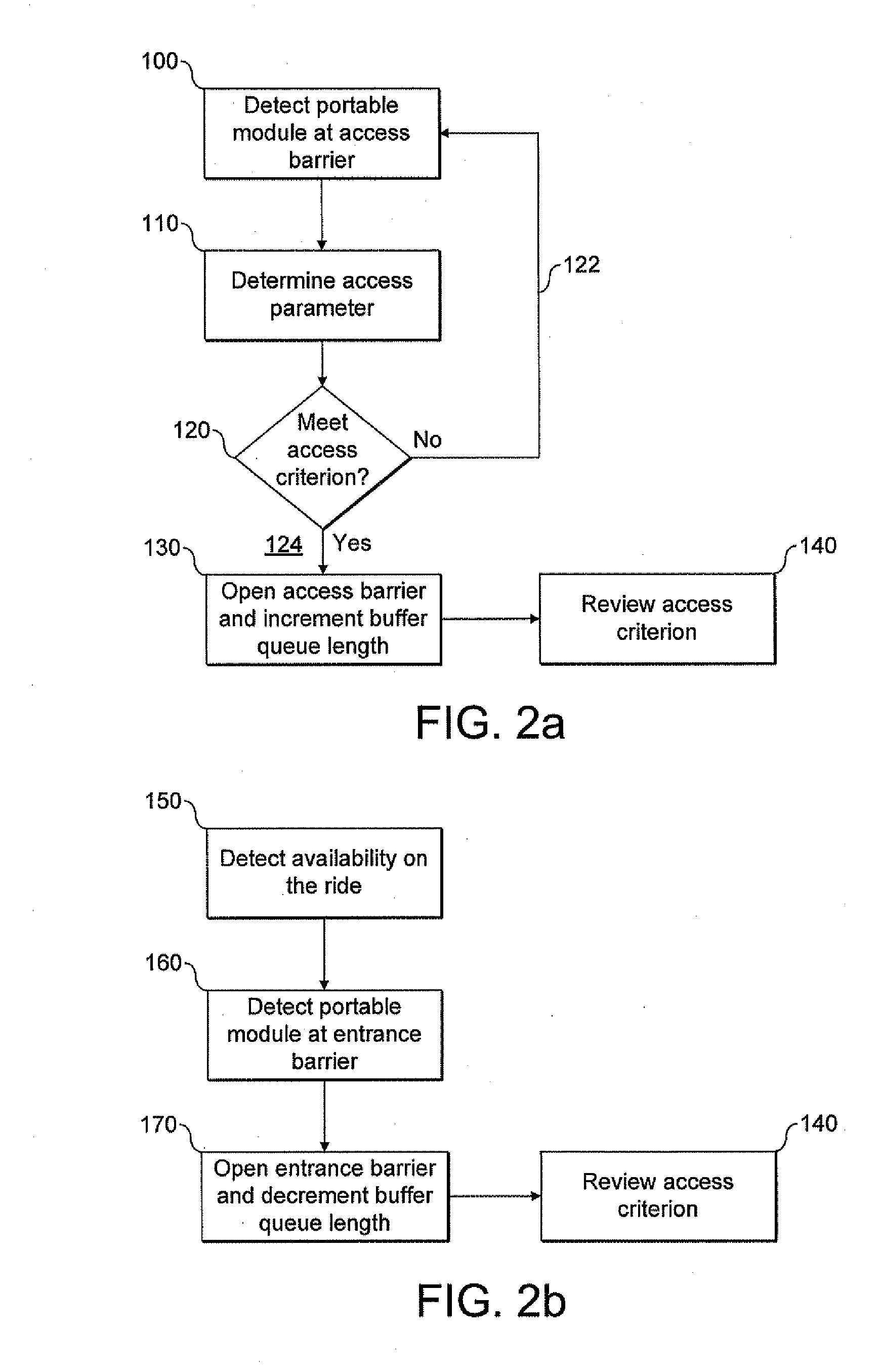
ActiveUS20100277276A1Reduce complexityLow costElectric signal transmission systemsMultiple keys/algorithms usageClosed stateAccess key
A system for regulating access to a resource by a plurality of users is provided. The system comprises: a plurality of portable access keys, each being provided to one of the users and having an associated variable access parameter; an access barrier, having an open state allowing passage through and a closed state denying access to the resource, and defining an access queue; a sensor that determines an access queue characteristic related to a number of users in the access queue; a controller, which sets an access criterion based on the determined access queue characteristic; and a detector, located at the access barrier and which determines the variable access parameter of a portable access key when it is brought into the vicinity of the detector. The controller sets the access barrier in its open state if the variable access parameter determined by the detector meets the access criterion.
Owner:LO Q
Method, apparatus, and system for protecting memory
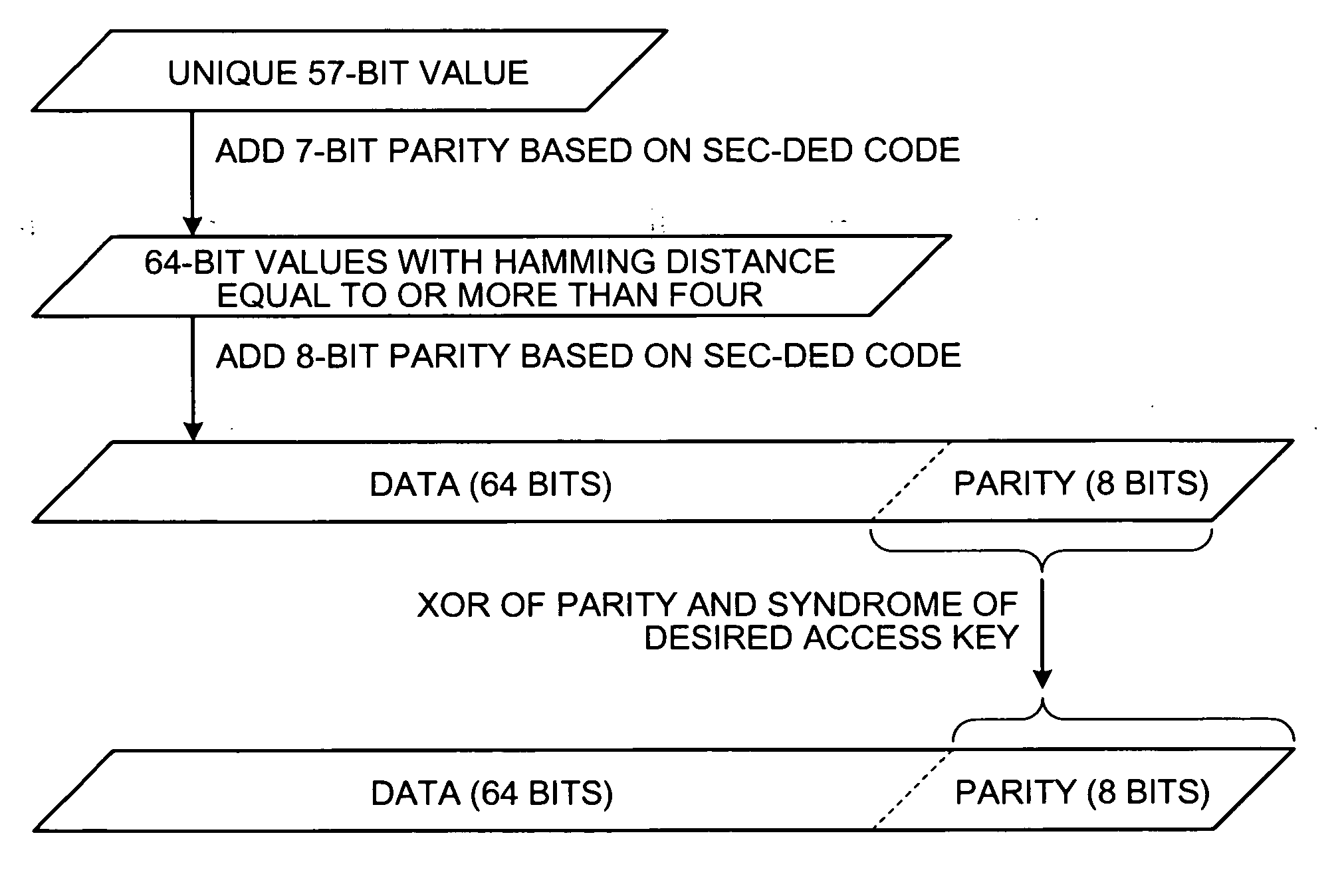
InactiveUS20070124557A1Error detection/correctionUnauthorized memory use protectionCalculatorComputer security
A parity adder obtains a second data by adding a parity for first data to be written to a memory to the first data. An access-key register holds an access key unique to a source of request. A first operating unit obtains a third data by calculating an XOR between the second data and the access key, the access key being set by the source of request for writing data to the memory. A second operating unit obtains a fourth data by calculating an XOR between the access key and the third data. A syndrome calculator calculates a syndrome from the third data, the access key being set by the source of request for reading data from the memory. A determining unit determines whether to output the third data as the first data, based on calculated syndrome.
Owner:KK TOSHIBA
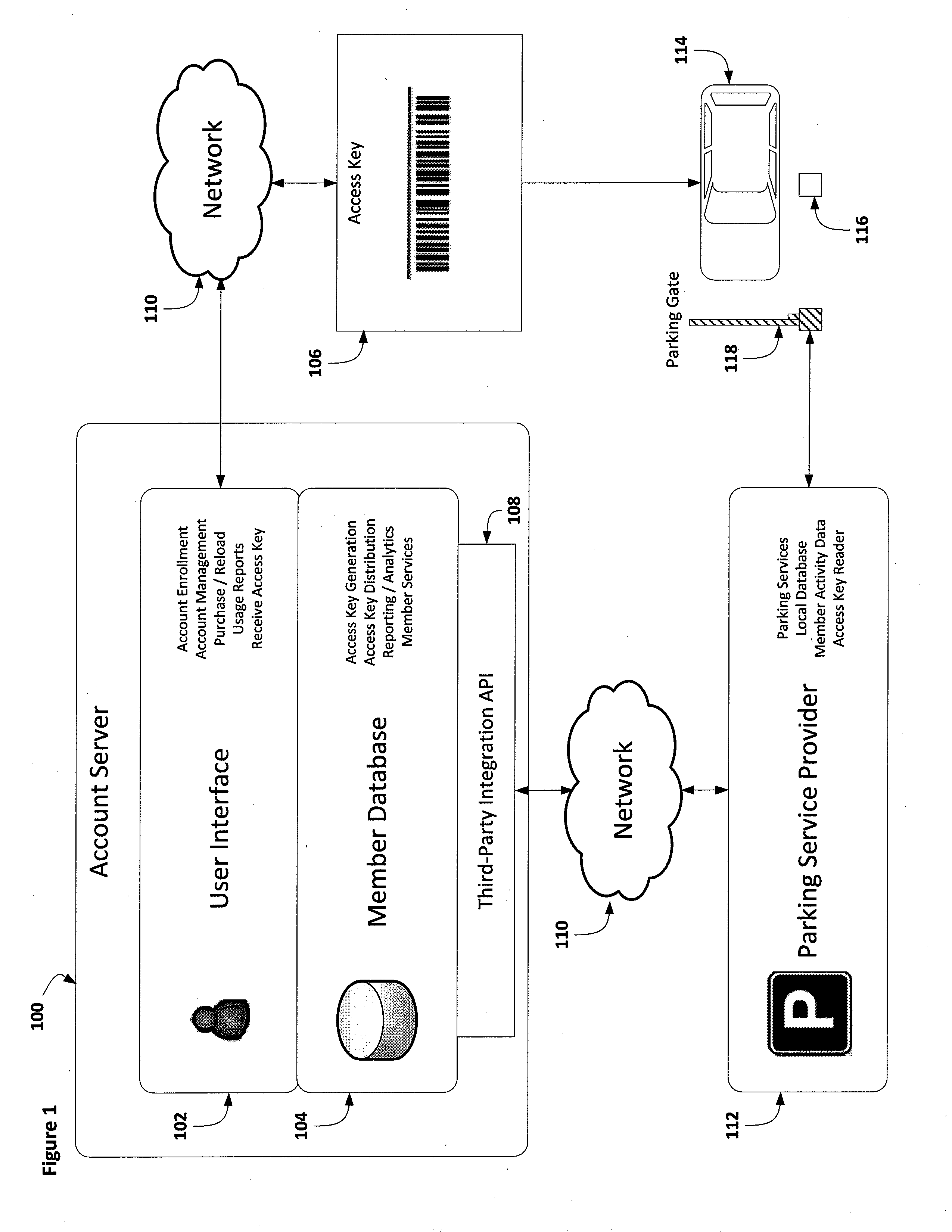
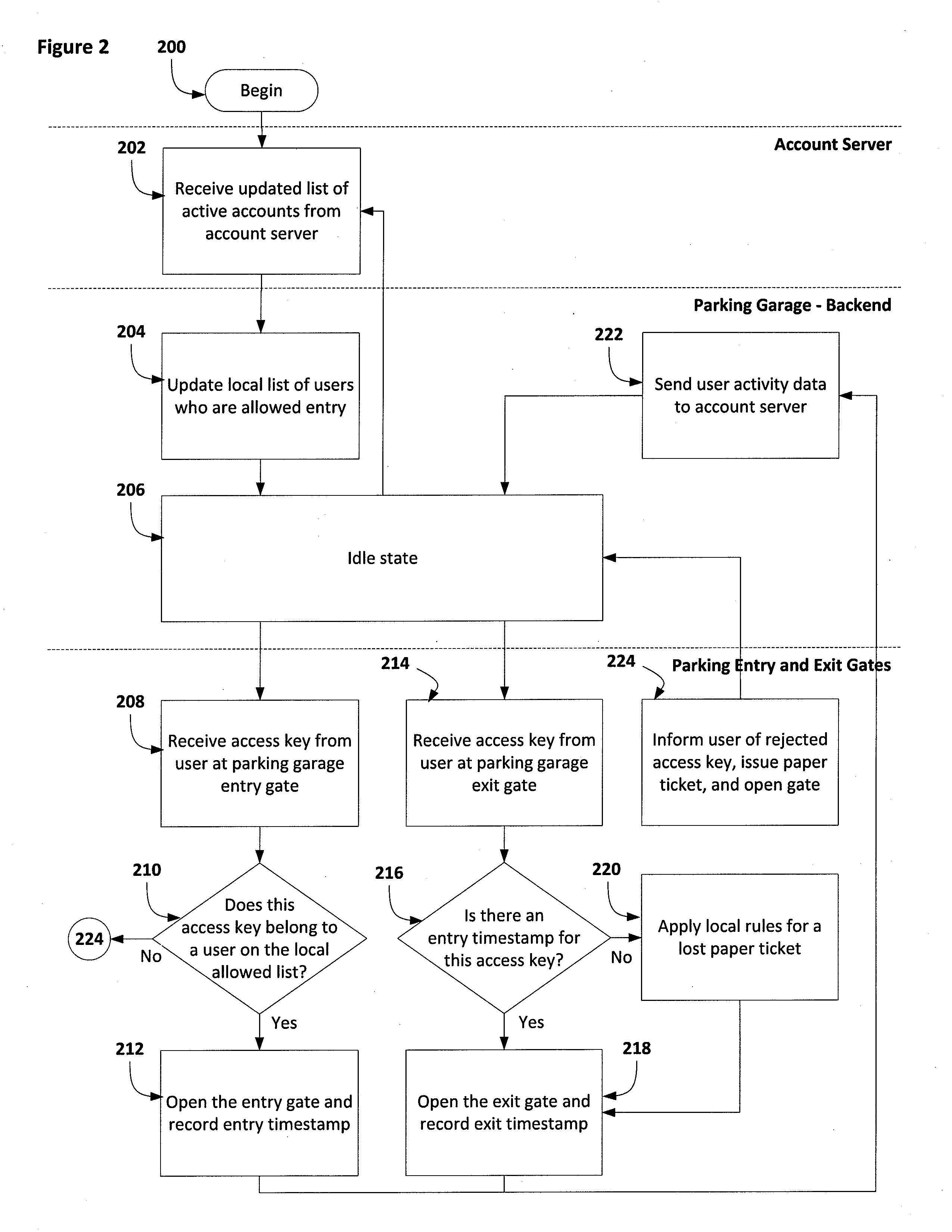
Systems and methods for an automated parking facility
InactiveUS20140232518A1Electric signal transmission systemsTicket-issuing apparatusBarcodeReal-time computing
Systems and methods for automated parking facilities are described herein. Users may purchase self-parking and / or valet parking with an access key. The access key may comprise various formats, such as, a barcode, a machine-readable representation of data, PIN code, or the like. The access key may be distributed via a print medium or a mobile computing device. The automated parking facility system may be interface with multiple parking facilities and / or may provide accounts across multiple parking facilities. The automated parking facility system may be configured to wirelessly open entrance and / or exit gates of parking facilities.
Owner:CAH TECH
Apparatus and method for a secure broadcast system
ActiveUS20050010774A1Key distribution for secure communicationMultiple keys/algorithms usageBroadcast serviceBroadcast system
Apparatus and method for provisioning an access key used for a controlled access broadcast service is disclosed. In one aspect, a method for secure processing in a device that securely stores a secret key comprises receiving a plurality of challenges from a network, generating a plurality of ciphering keys based on the secret key and the plurality of challenges, and generating an access key based on the plurality of ciphering keys.
Owner:QUALCOMM INC
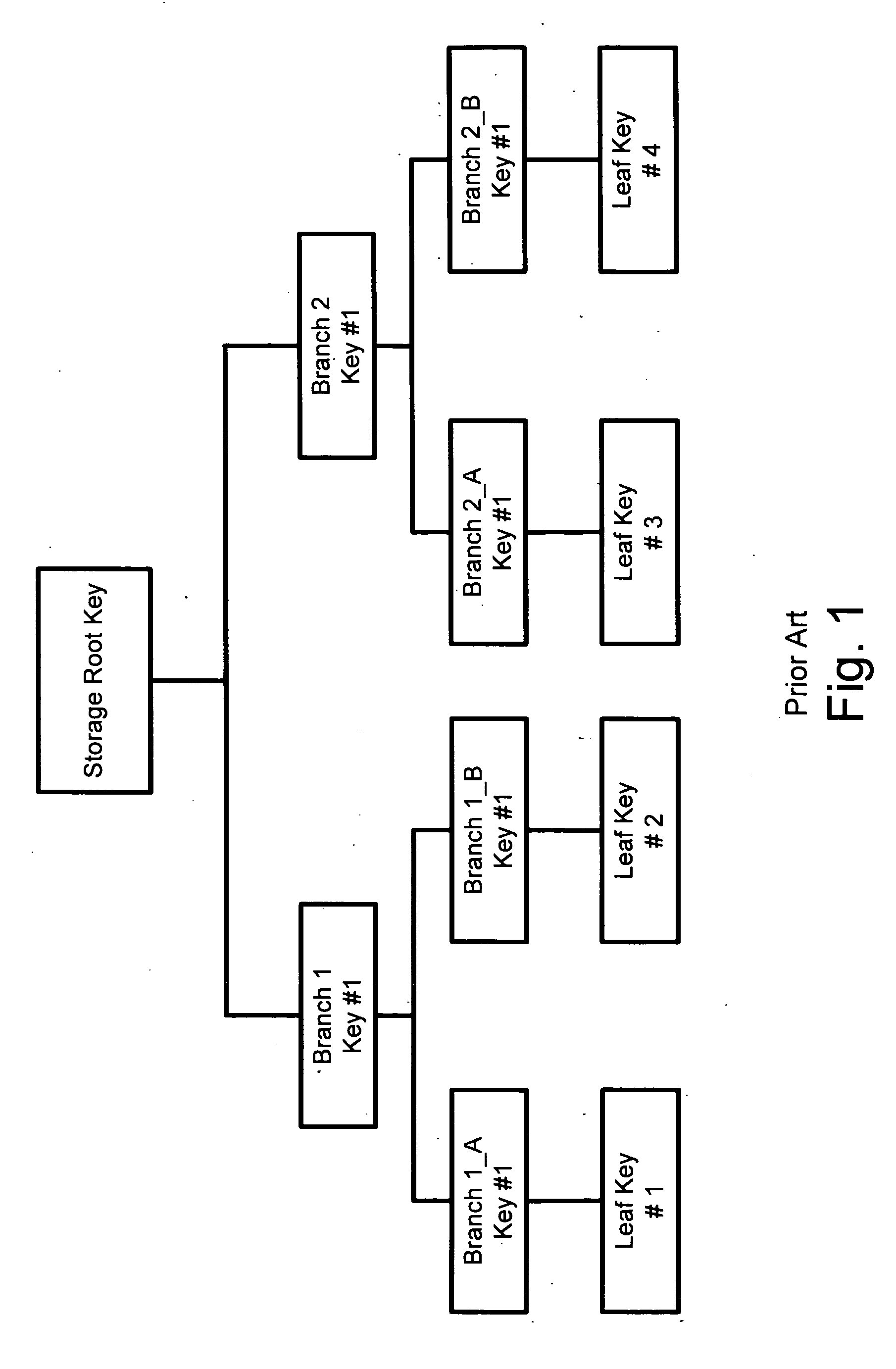
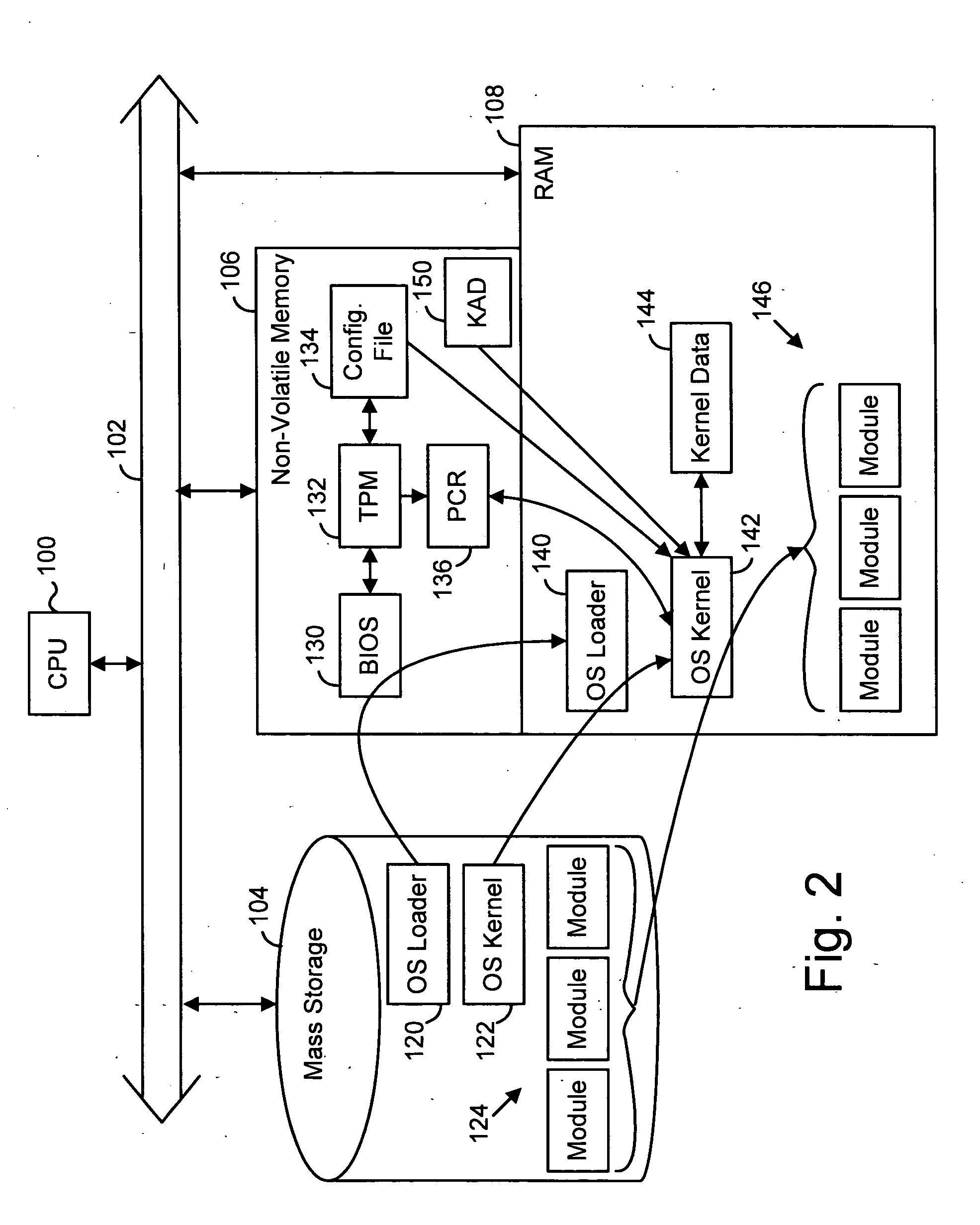
Use of kernel authorization data to maintain security in a digital processing system
InactiveUS20060015718A1Platform integrity maintainanceSecuring communicationData fieldHandling system
A system to manage and control usage rights for cryptographic keys. A kernel process is provided with secure and exclusive authorization to access certain keys in a key hierarchy. Special authorization is required for other processes or users to access keys used by the kernel. A persistent storage area is used to hold a Kernel Authorization Data field for the root key and / or other keys used by the kernel or other specialized processes. The authorization data, and the keys it protects, can be used to protect other portions of, or the entire, key structure. The persistent storage area is reserved in a TPM or similar security hardware.
Owner:SONY ELECTRONICS INC +1
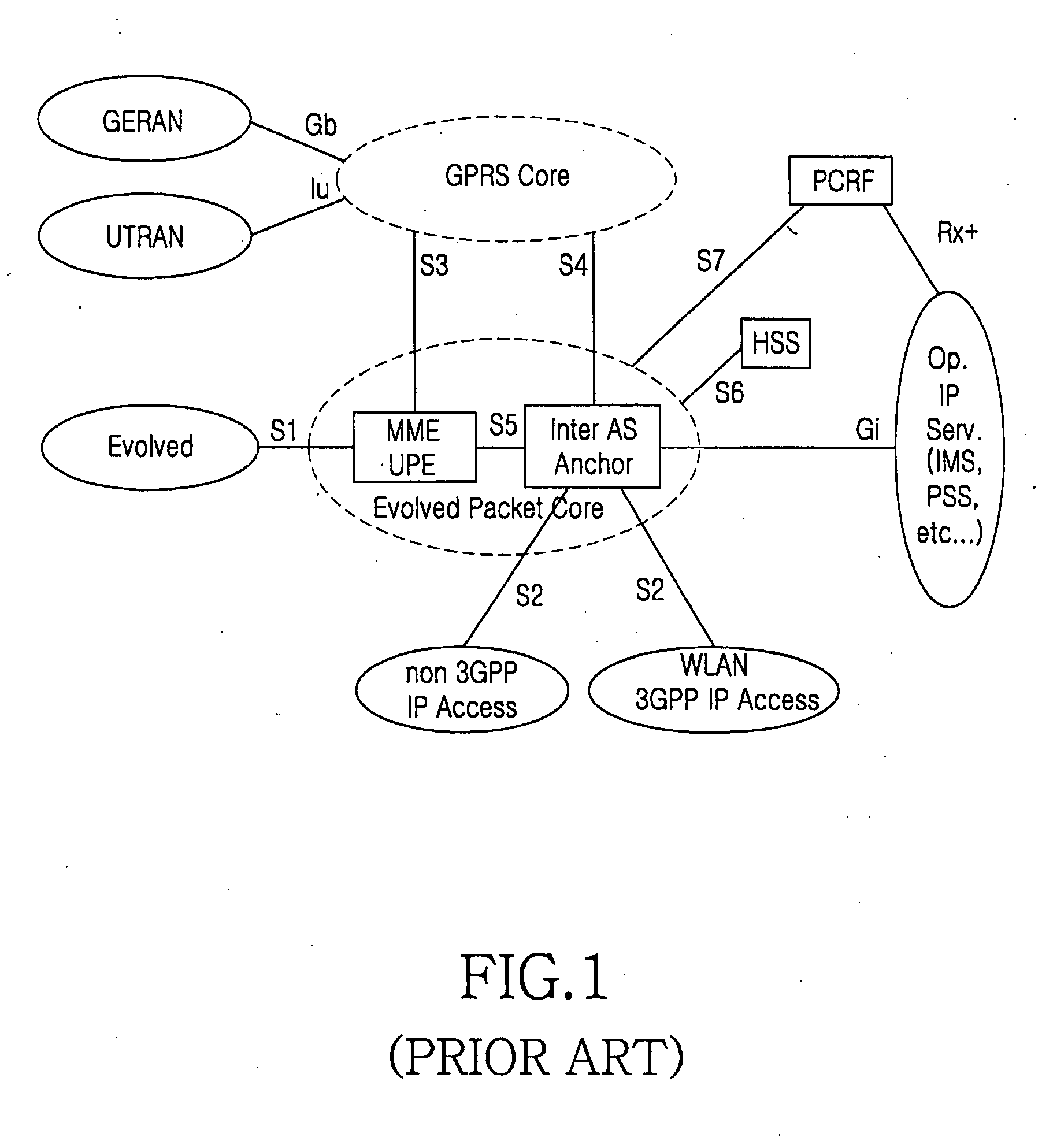
Method for operating a network, a system management device, a network and a computer program therefor
ActiveUS20110197064A1Minimizing communicational requirementMinimize computation requiredKey distribution for secure communicationUser identity/authority verificationSystems managementDistributed computing
The present invention relates to a method for operating a network comprising communicating devices representing nodes of the network. More precisely, the invention relates to a method for operating a network (1), comprising a node (D1) and a system management device (3), the system management device comprising a root keying material being a set of alpha-secure functions having a degree of complexity of, and the node being provided with a node keying material share of degree of complexity α derived from the root keying material. The method comprises the following steps, upon receipt at the system management device of a request for an external user (4) to gain access to the node (D1): the system management device generates an external user keying material share of degree of complexityα from the root keying material and an access identifier, the system management device generates an access keying material of degree of complexity less than α, from the external user keying material share and an identifier of the node, the system management device provides the external user with the access keying material share and the access identifier, the external user derives a key from the access keying material share, and transmitting this key and the access certificate to the node, the node computes a key from the access identifier and the node keying material share, and the node compares the key transmitted by the external user and the key computed by the node, so as to authenticate the external user.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Program Store for Updating Electronic Devices
InactiveUS20130073672A1Multiple digital computer combinationsTransmissionGoal systemOperating system
A system includes a central program store location having a memory storing a plurality of access keys and programs.A communication network connects the program store location and a host system. A communication channel connects the host system and a target system.The program store a first program and a second program to the host system. The host system then tries to download the second program to the target system. If the target system authenticates the second program signatures and / or keys, the second program and / or keys is downloaded.The first program and the second program enable the host system and the target system to exchange information.
Owner:OPTIMA DIRECT LLC
Method and apparatus for cryptographic key storage wherein key servers are authenticated by possession and secure distribution of stored keys
InactiveUS20100172504A1Key distribution for secure communicationPublic key for secure communicationKey serverKey storage
A key management system includes secured data stored on a first system secured by a control key stored securely on a key server. The secured data is secured against attacks such as unauthorized use, modification or access, where authorization to access the secured data is determined by knowledge of an access private key of an access key pair. When an authorized user is to access the secured data, the first system generates a request to the key server, signed with the access private key, wherein the request is for a decryption control key and the request includes a one-time public key of a key pair generated by the first system for the request. The first system can decrypt the decryption control key from the response, using a one-time private key. The first system can then decrypt the secured data with the decryption control key remaining secured in transport.
Owner:CA TECH INC
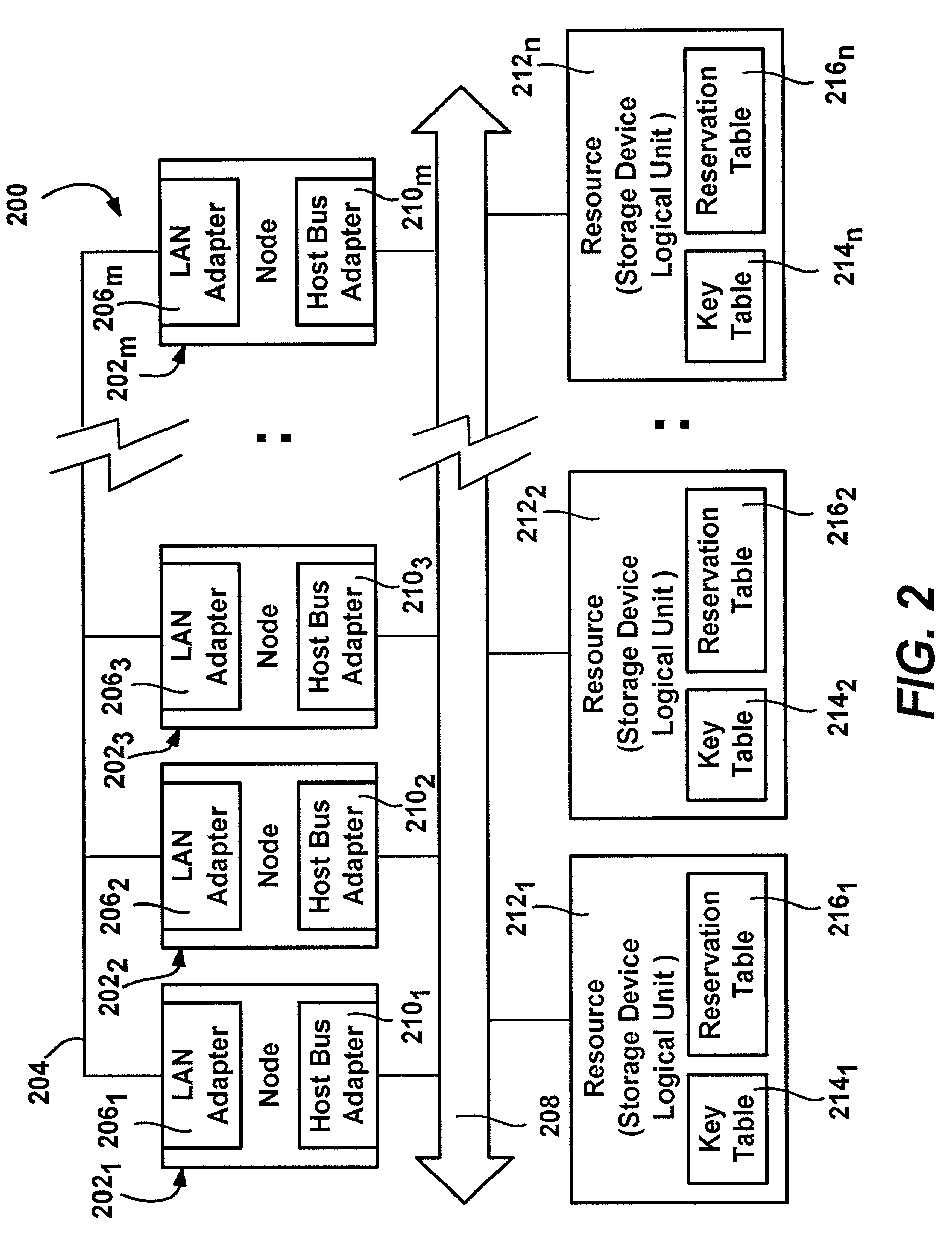
Distributed system resource protection via arbitration and ownership
InactiveUS7277952B2Resource allocationMultiple digital computer combinationsResource protectionExtensibility
In a distributed system, a resource such as a storage device is protected by an owner node's exclusive access to it, wherein exclusive access is established via a persistent reservation on the resource. A persistent reservation is never removed, however the owner node's persistent reservation may be challenged in an arbitration process, to take it away from a failed owner node. A challenger node challenges by changing an owner's access key (that establishes the persistent reservation) to a challenge key, delaying, and determining whether the owner restored the owner's access key during the delay, because a properly operating owner replaces a challenge key with its owner access key. If the owner fails to restore its owner access key, the challenger node becomes the new resource owner by replacing the challenge key with an owner access key of the challenger node. The key may include additional information to provide extensibility.
Owner:MICROSOFT TECH LICENSING LLC
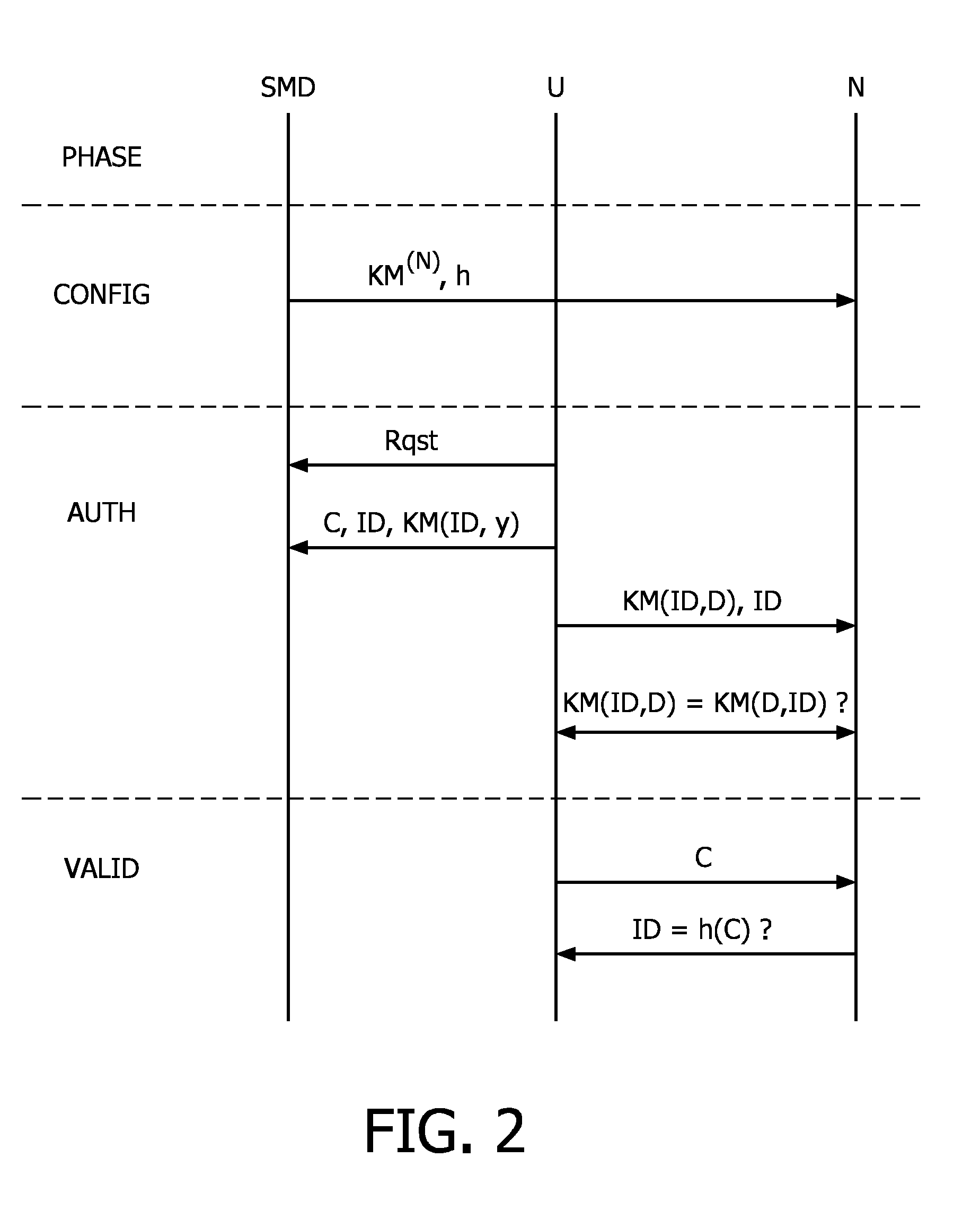
Method and system for authentication of units in a communications network
InactiveUS7020456B2Secure distributionSave capacityUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunications systemCommunication device
A method of granting, to a user communications device, access to a service provided by a plurality of service communications devices where an access key code is generated during an initial communications session between the user communications device and one of the service communications devices. The established access key code is subsequently stored in the user communications device and made available to the service communications devices for use in subsequent communications sessions between the user communications device and any one of the service communications devices. The invention further relates to a communications system and a user communications device.
Owner:TELEFON AB LM ERICSSON (PUBL)
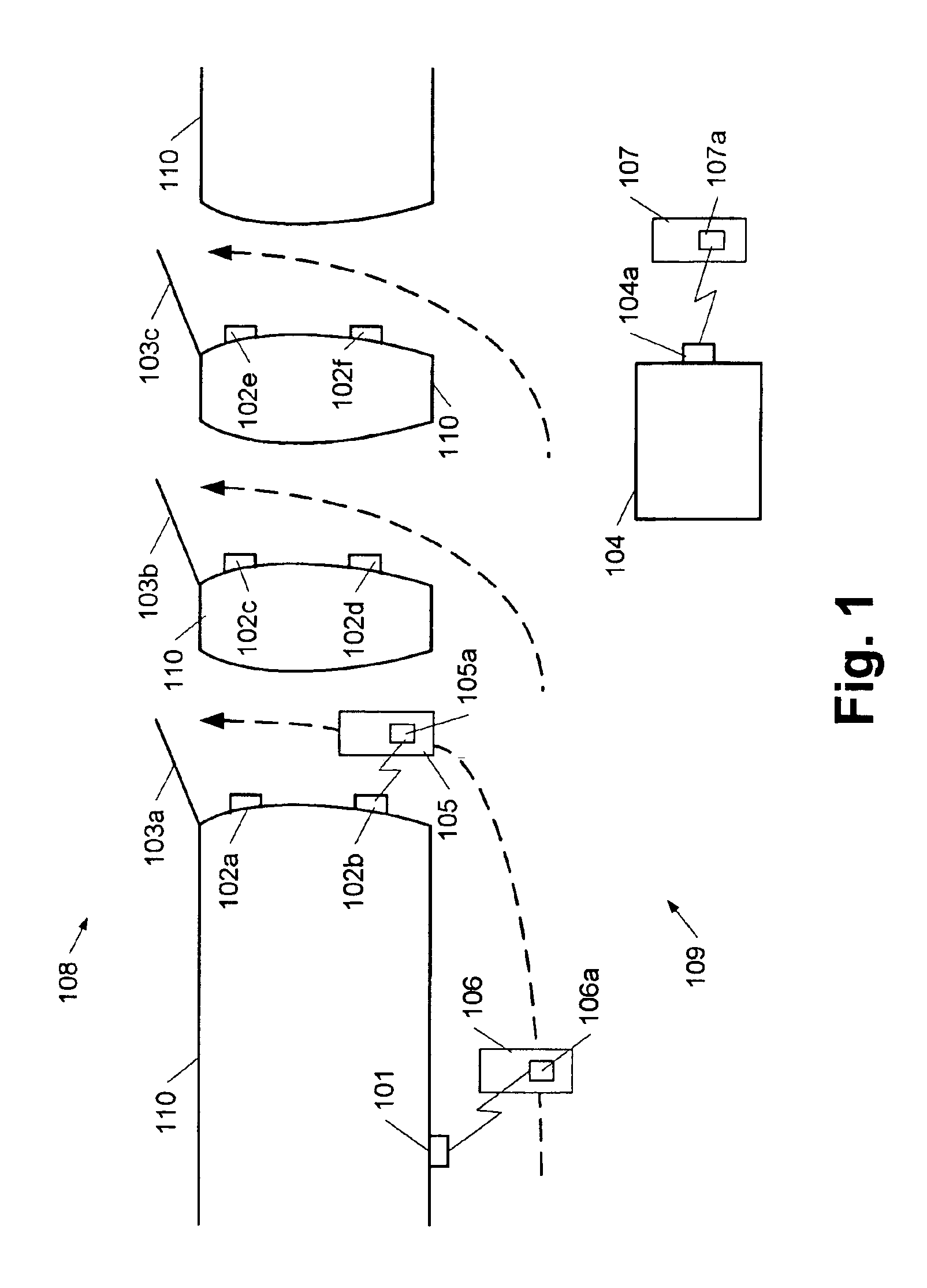
Method and apparatus for personally controlled sharing of medical image and other health data
InactiveUS20110022414A1Data processing applicationsDigital data processing detailsSubject matterComputer science
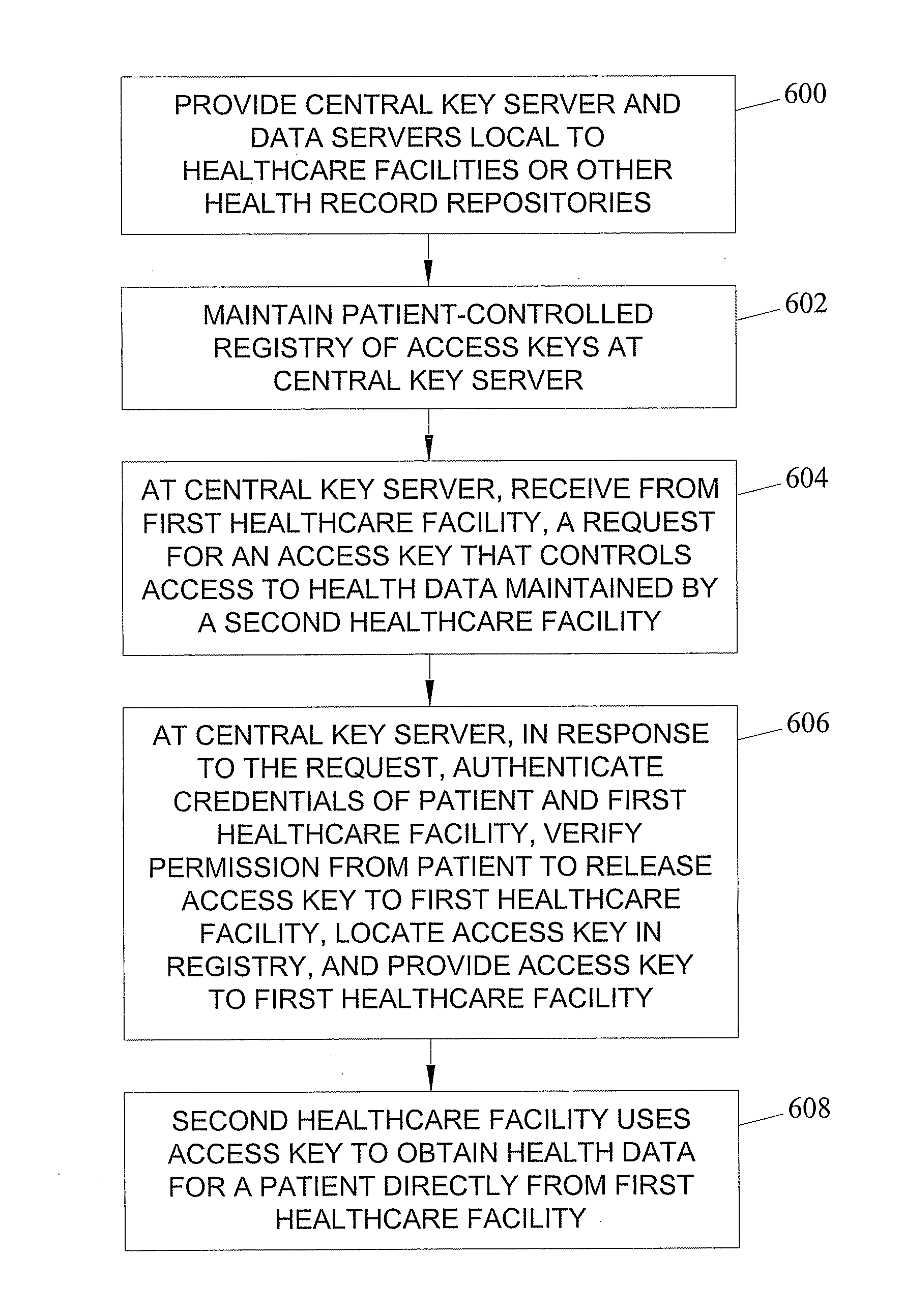
A method and apparatus for personally controlled sharing of medical image and other health data are disclosed. According to one aspect, the subject matter described herein includes a method for patient mediated access to patient health information maintained by different healthcare facilities and other health record repositories. The methods includes, using a central key server and a plurality of data servers local to healthcare facilities and other health record repositories. At the central key server, a patient controlled registry of access keys that control access to patient health information maintained by different healthcare facilities is provided. The central key server receives, from a data server of a first healthcare facility, a request for an access key that controls access to health information for a patient maintained by a second healthcare facility. In response to the request, the central key server authenticates credentials of the patient and the first healthcare facility, verifies permission from the patient to release the access key to the first healthcare facility, locates the access key for the health information for the patient at the second healthcare facility, and provides the access key to the first healthcare facility. The access key is used by the data server of the first healthcare facility to obtain health information for the patient directly from the data server of the second healthcare facility after successful authentication and verification by the second healthcare facility.
Owner:WAKE FOREST UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com