Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
103results about How to "Secure distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
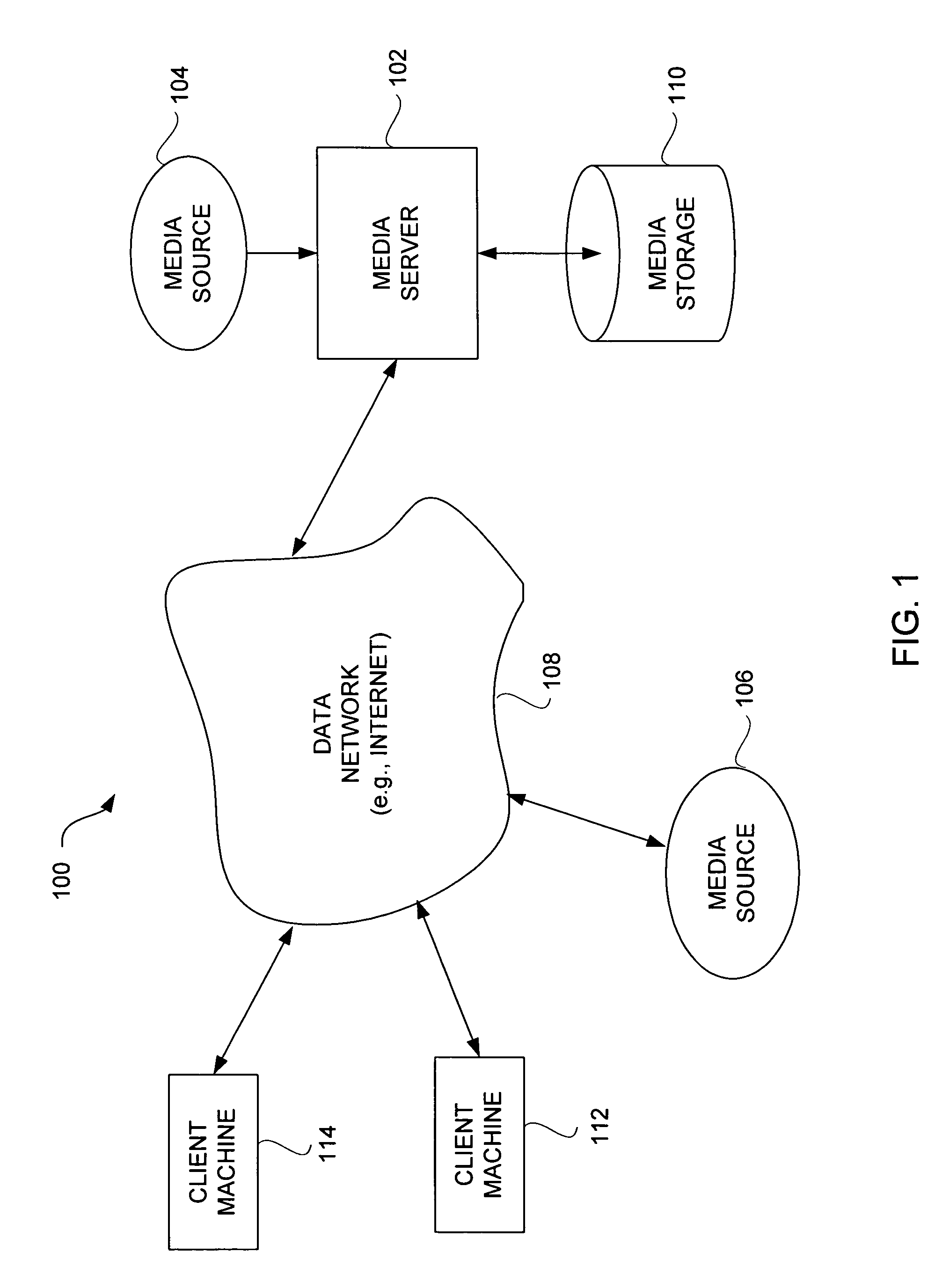
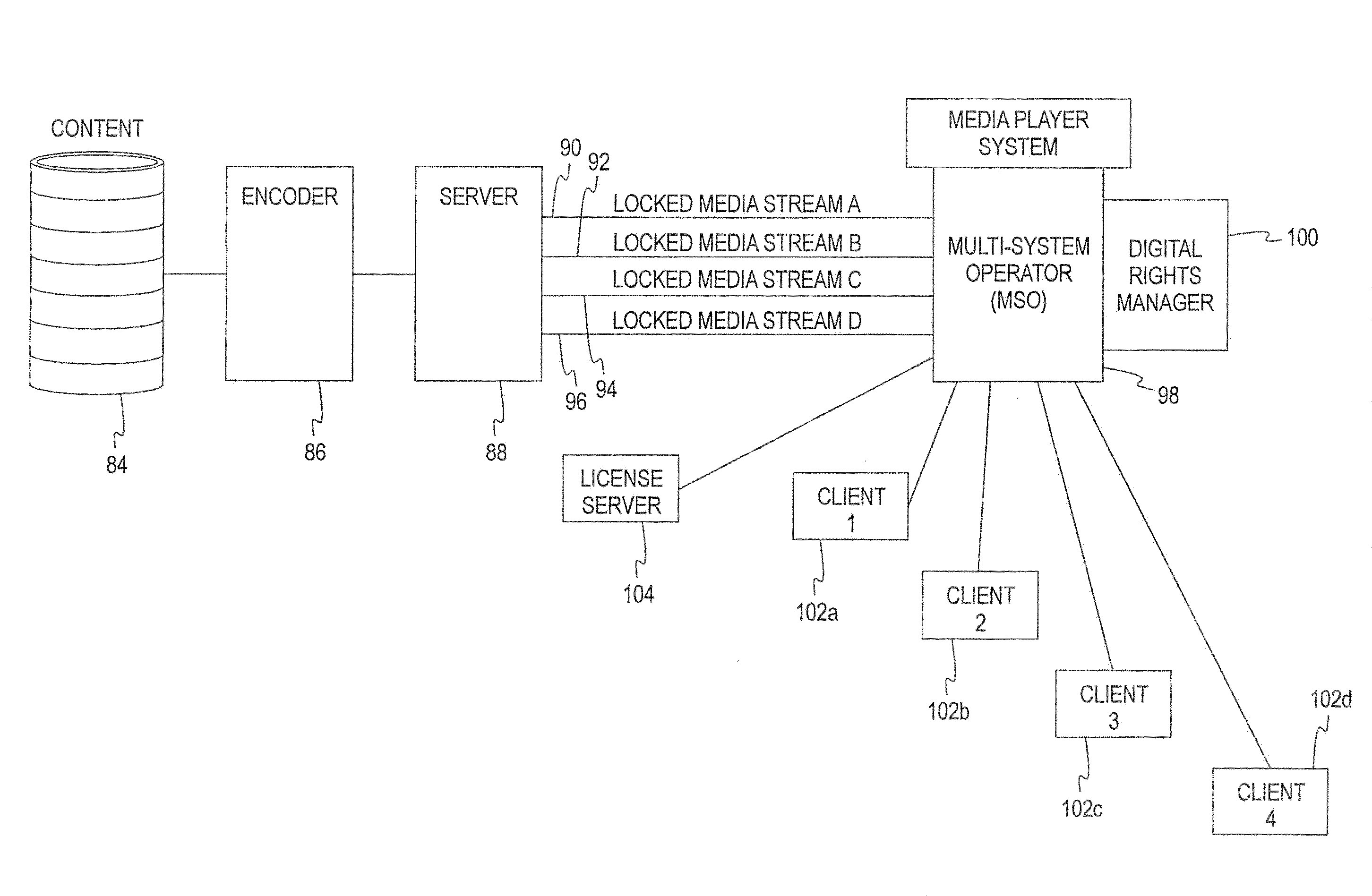
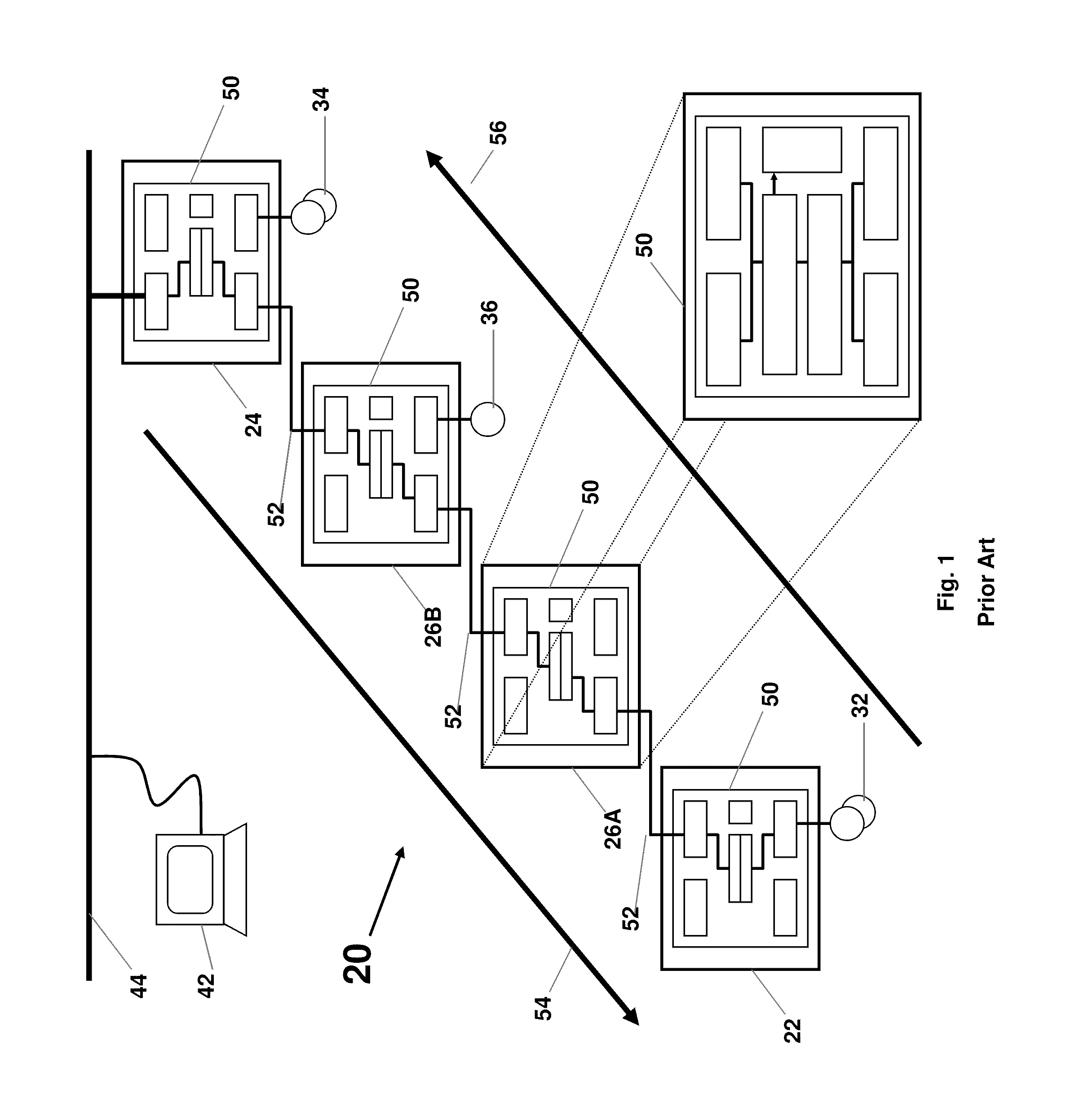
Methods and apparatus for secure distribution of software
InactiveUS6966002B1Secure distributionReduce usageDigital data processing detailsUser identity/authority verificationPaymentData file
Owner:FLEXERA SOFTWARE
Method and system for secure network-based distribution of content
InactiveUS20050050345A1Secure distributionRestricts distributionDigital data processing detailsUnauthorized memory use protection
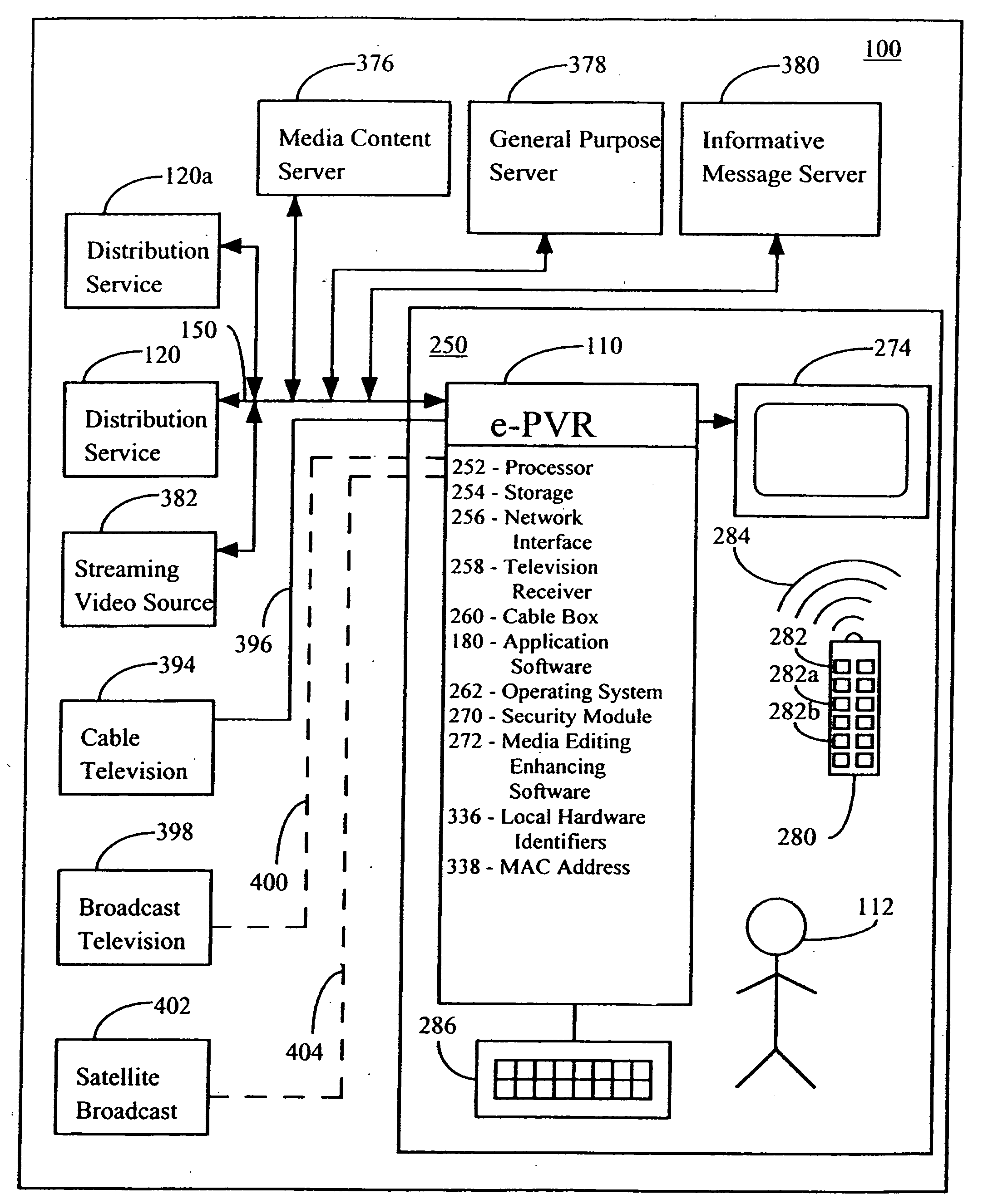
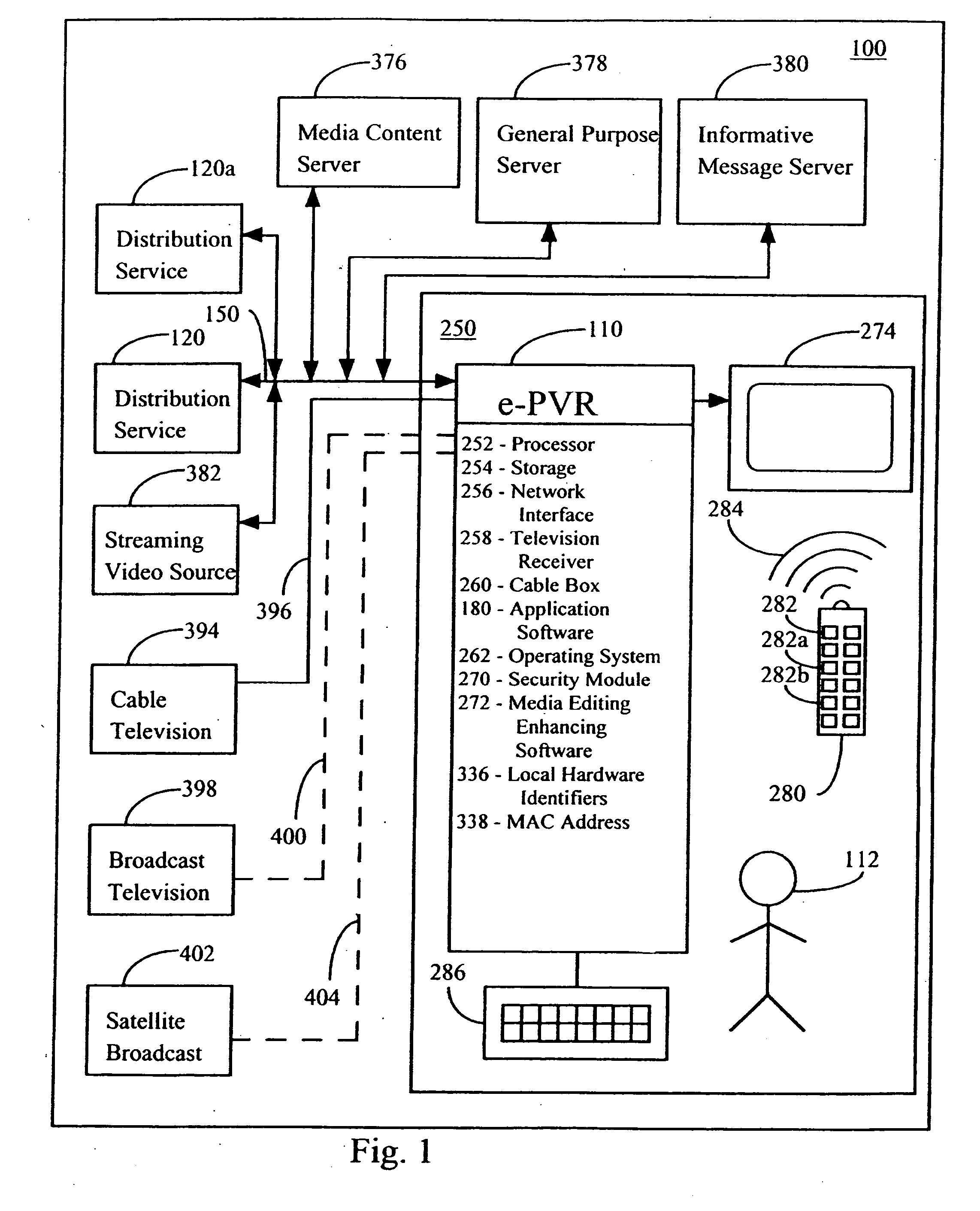
A method and system for network-based distribution of content are disclosed. The distribution of content is not only secure but also controlled. The security restricts access to content within media files during downloads as well as while stored at a server or client. In one embodiment, each media file is encrypted with a different, randomly generated key. The control over the distribution of the media file can serve to limit the subsequent distribution of media files from clients to other clients. In another embodiment, the control can permit media files to be shared on a limited number of different clients affiliated with the same user. The clients can vary with application but generally are computing devices that have memory storage. Often, the clients are personal computers or other computing devices that are capable of storing and presenting content to their users.
Owner:APPLE INC
File format method and apparatus for use in digital distribution system
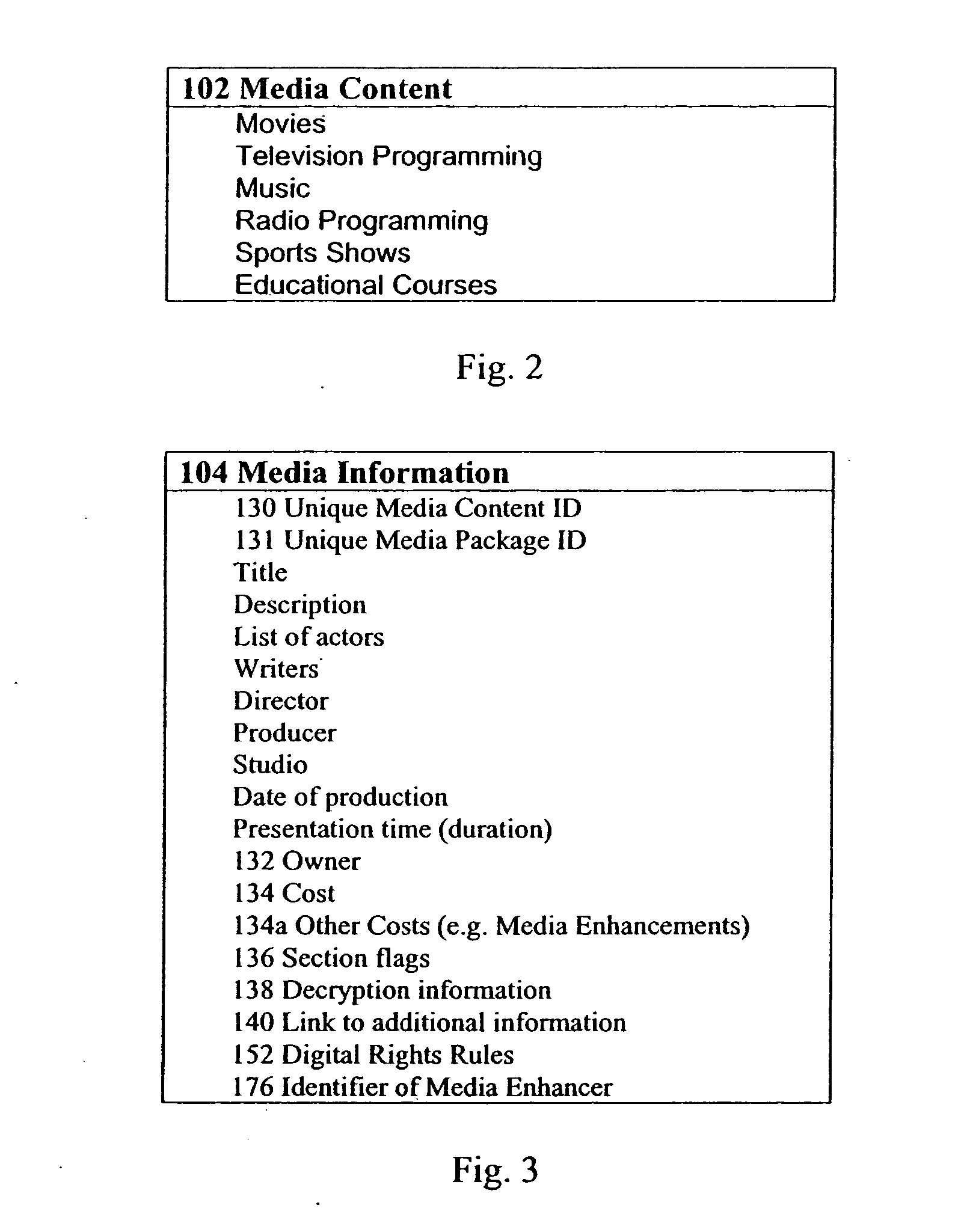
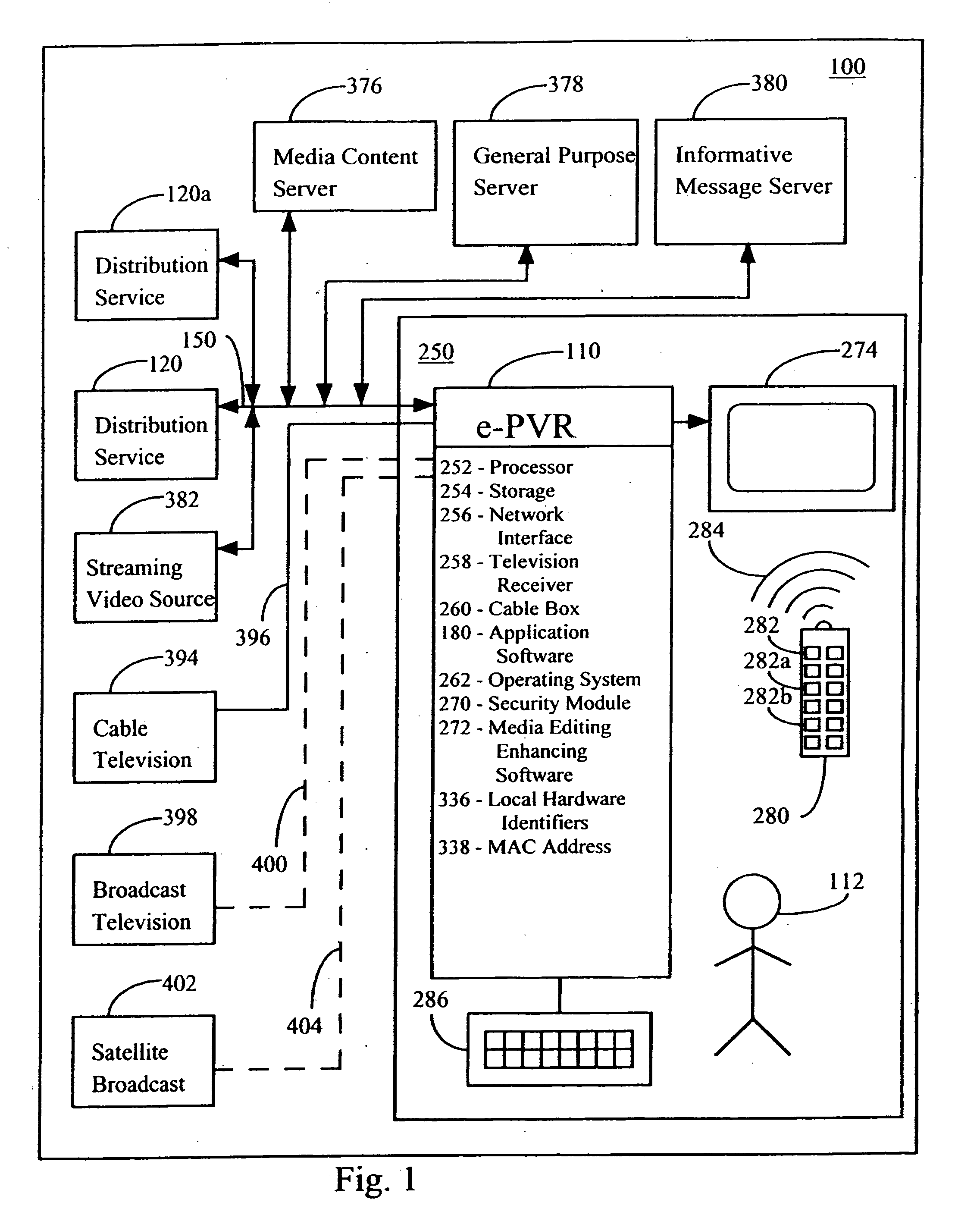
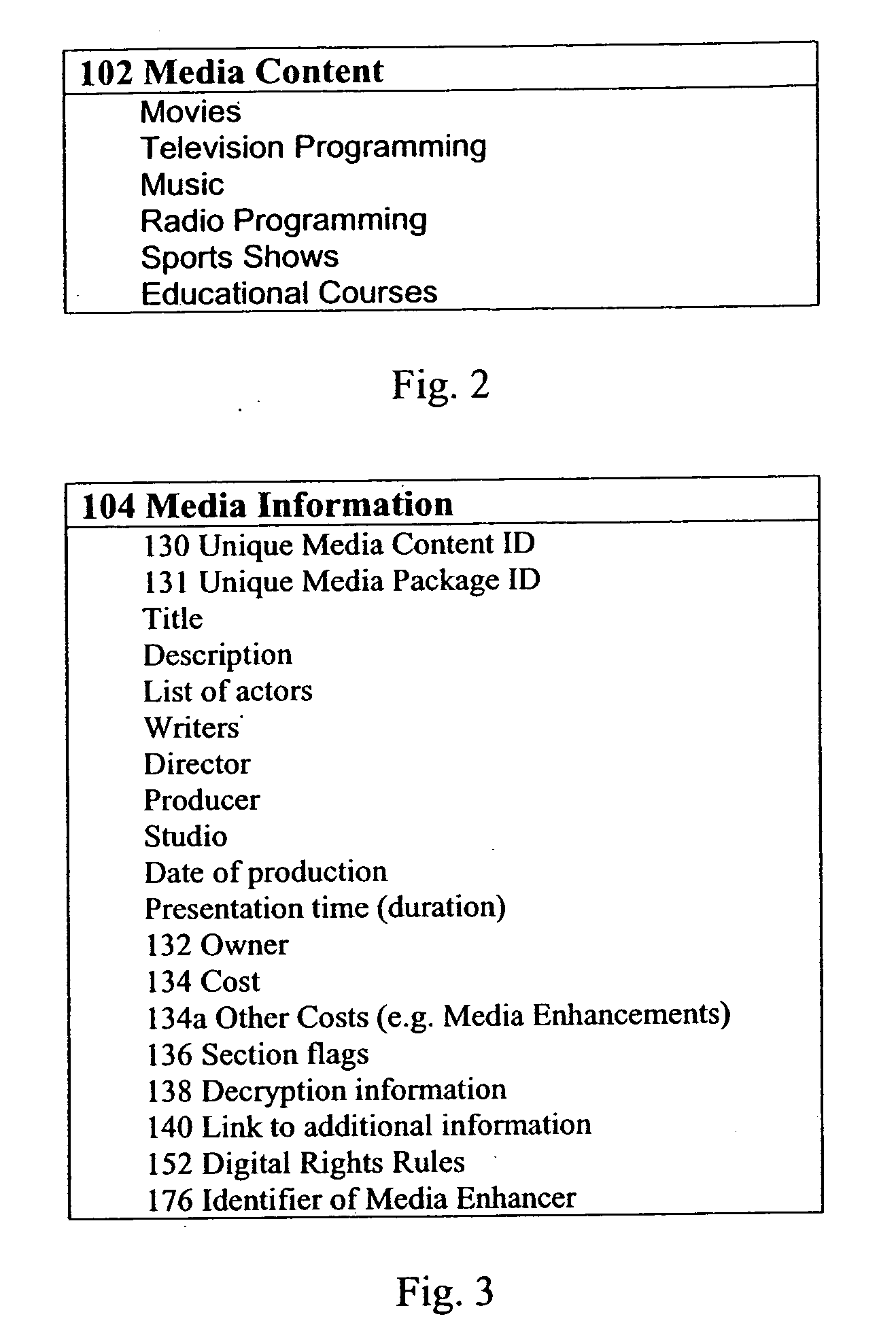
InactiveUS20060282864A1Improve security levelNew kinds of servicesAnalogue secracy/subscription systemsTwo-way working systemsDistribution systemMedia content
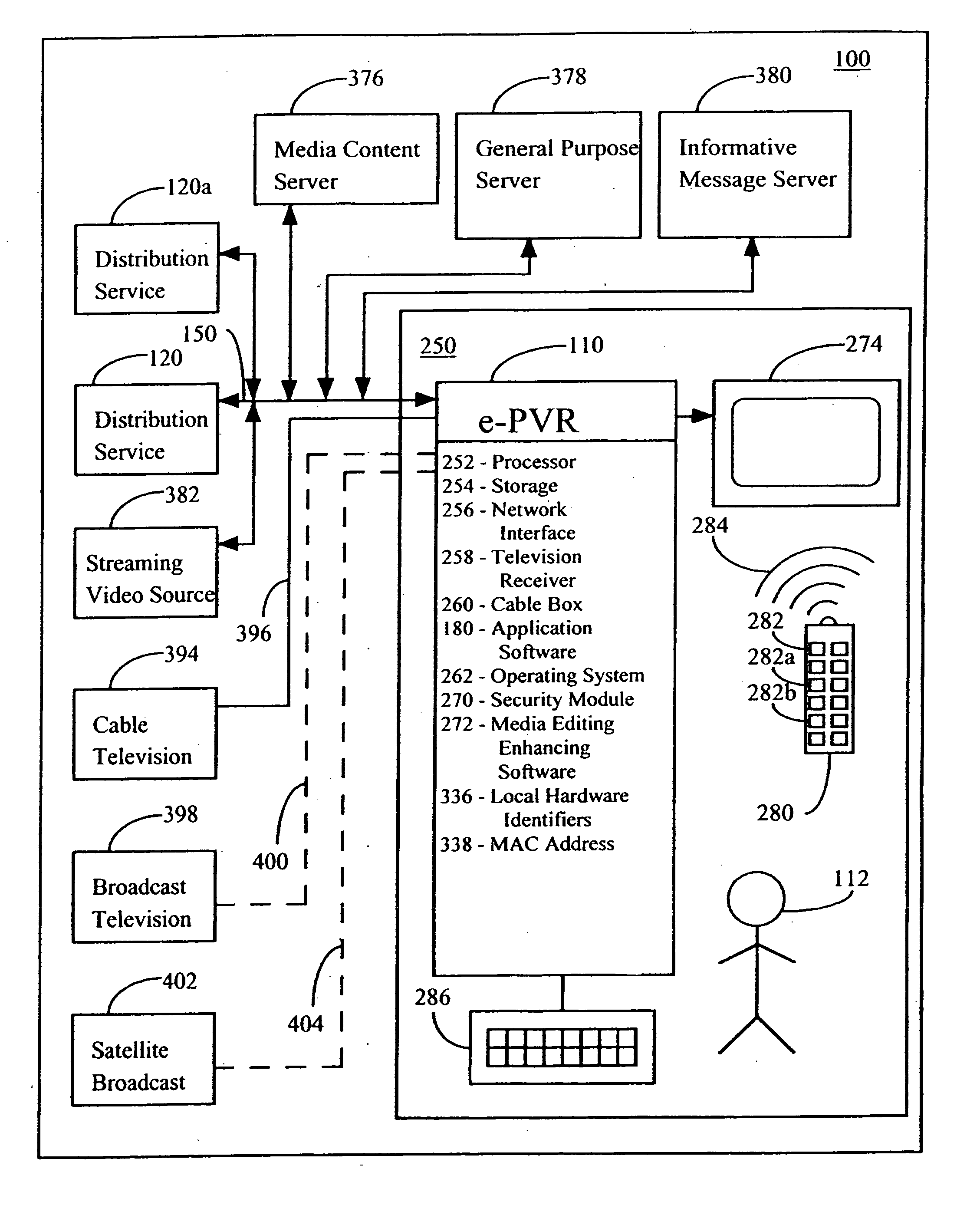
A method of distributing media content and associated media information as a media package in a file format embodied as a data structure. A method of presenting media content such as Audio or Video including segmenting the media content into sections and storing data and information about the sections as part of media information with the media content in a media package. The presentation program uses information about the users preferences / profile and location and compares it to section information in order to present certain sections and skip others during the presentation. During presentation, informative messages are inserted between sections if sponsor supported presentation is chosen. Any part of the media content or media information can be embedded in the file or can be linked to from the file and can also be determined using a script or program.
Owner:GUPTE ANIRUDDHA
Digital content delivery and viewing system and method
ActiveUS20050010963A1Eliminate needSecure distributionAnalogue secracy/subscription systemsBroadcast information monitoringComputer networkDigital content
A media distribution system is provided whereby devices on a network are provided with native-mode, optimized content viewers adapted to receive and present digital content provided elsewhere on the network. An agent is downloaded to a device, where it gathers information regarding the device environment and uses that information to identify the appropriate application for that device. The appropriate application for a particular device is then downloaded to the device to enable the device to present the content to a user.
Owner:VIDEO FURNACE INC
Enhanced media method and apparatus for use in digital distribution system
InactiveUS20060282847A1Improve security levelNew kinds of servicesAnalogue secracy/subscription systemsComputer security arrangementsDistribution systemWorld Wide Web
A method to protect the financial rights of tiered media content providers including the original media content owner and media enhancers who add enhancements as additional media information or additional media content to be presented in conjunction with the media content when chosen by user.
Owner:GUPTE ANIRUDDHA
Computer network security system employing portable storage device
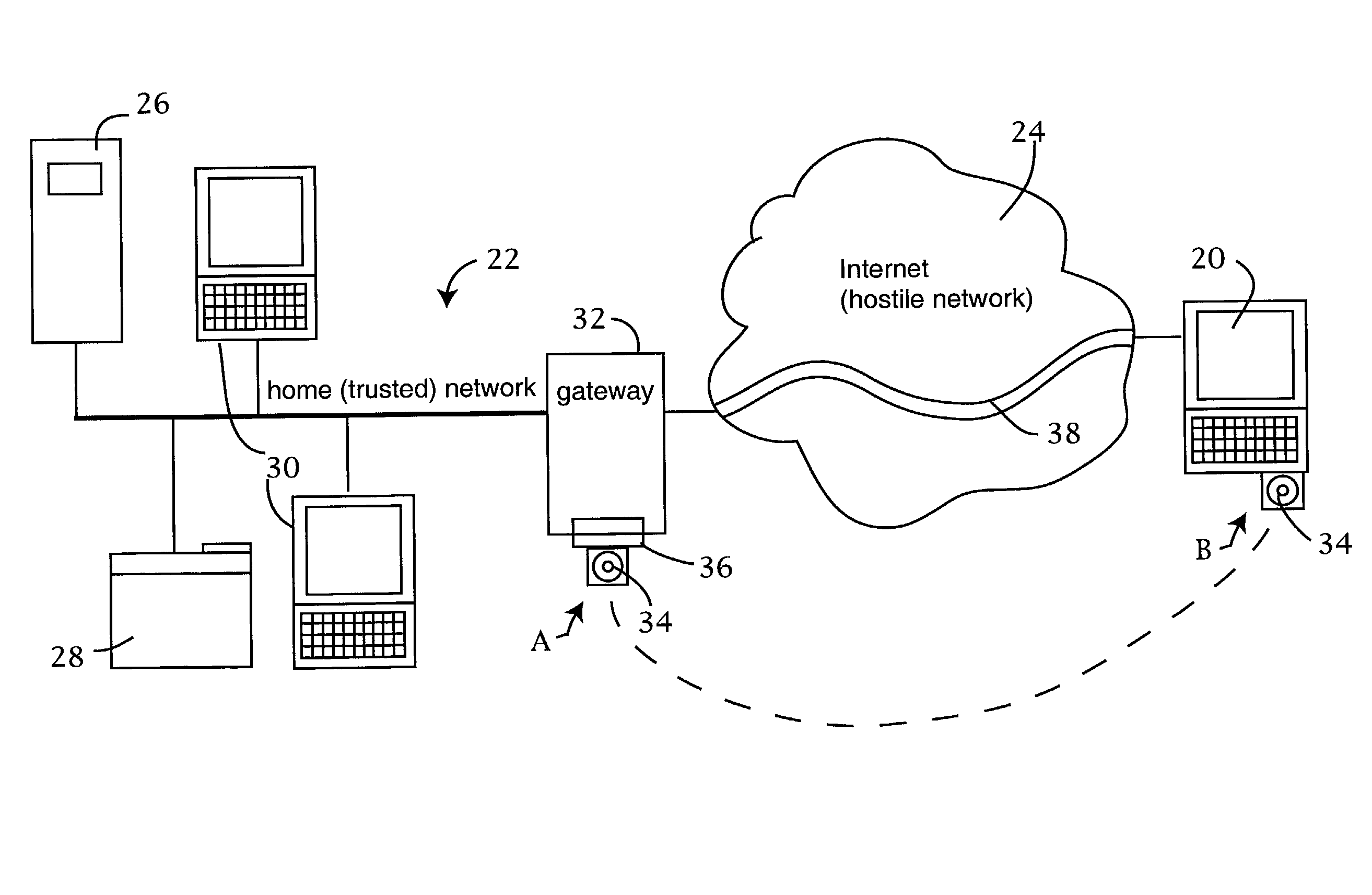
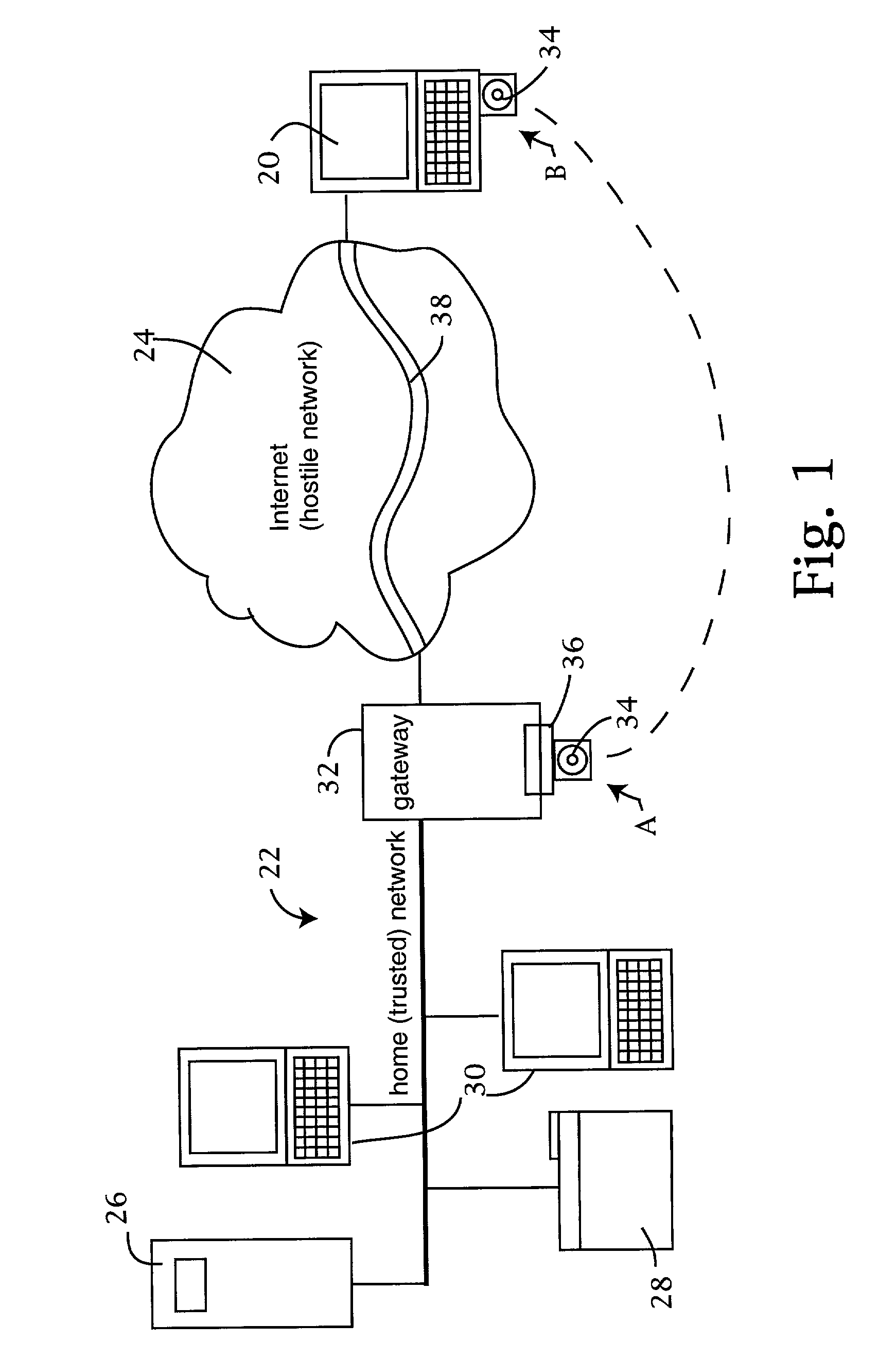
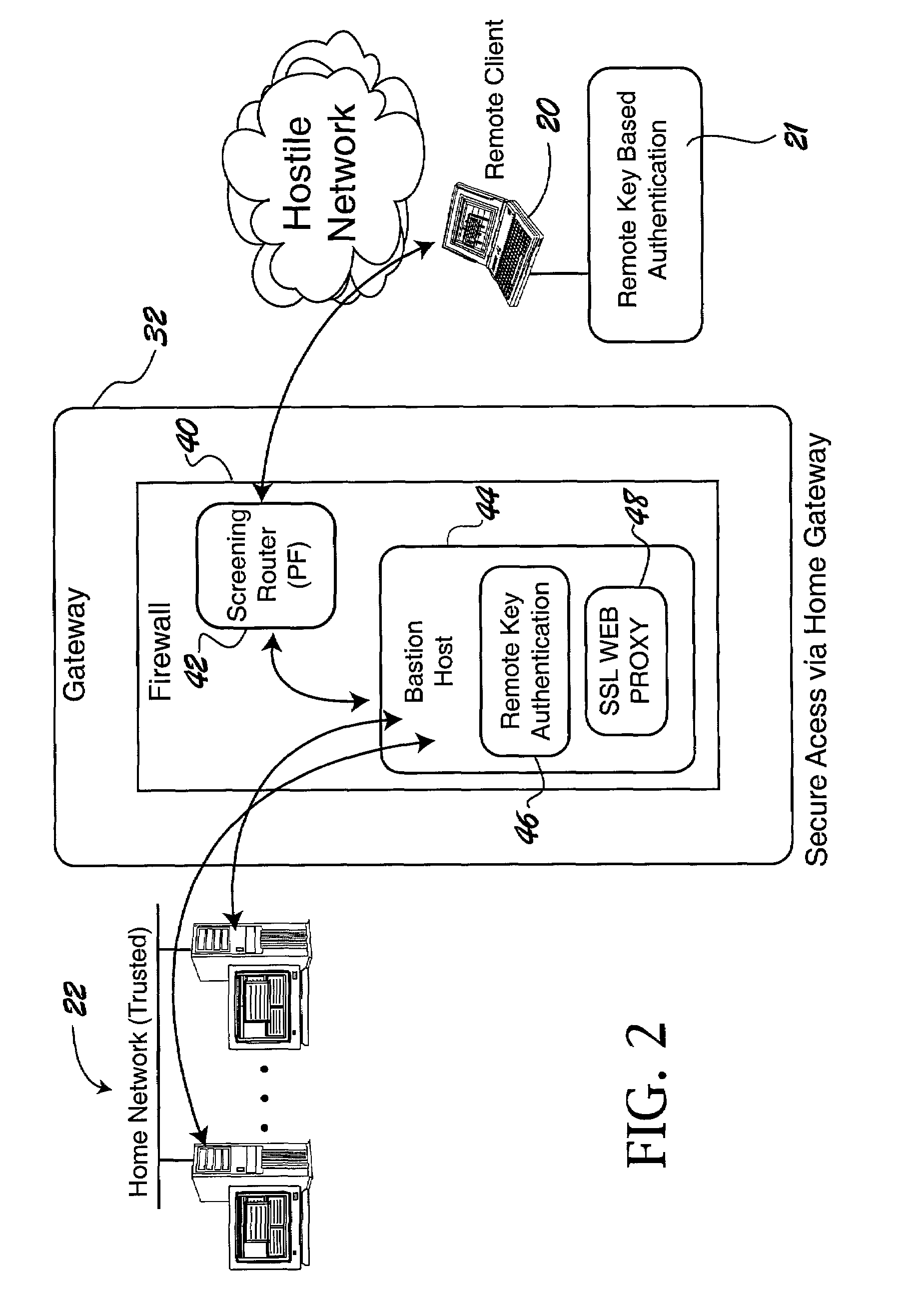
ActiveUS7228438B2Easy to useRaise security concernsUser identity/authority verificationUnauthorized memory use protectionUniform resource locatorClient machine
The trusted computer network is protected behind a gateway that includes a bastion host and screening router which blocks all URLs associated with the trusted network. The bastion host includes a remote client authentication mechanism and web proxy component that verifies and translates incoming URL requests from authenticated remote clients. Authentication is performed using one-time passwords that are stored on a portable storage device. The user configures the portable storage device by operating configuration software from the protected side of the gateway. The portable storage device also stores plug-in software to enable the client computer to properly retrieve the one-time password and exchange authentication messages with the bastion host. Further security is obtained by basing the one-time password on an encrypted version of the user's PIN. A symmetric key used to encrypt the PIN is stored in a protected area within the portable storage device.
Owner:SOVEREIGN PEAK VENTURES LLC
Payment method and apparatus for use in digital distribution system
InactiveUS20060282389A1Improve security levelNew kinds of servicesComputer security arrangementsPayment architecturePaymentDistribution system
A method to distribute and monetize media content by associating media content with a cost stored in associated media information within a media package. The user can elect to pay all of the cost, a portion of the cost, or none of the cost. When the user does not pay all of the cost, informative messages paid for by sponsors can be presented as part of the presentation of media content.
Owner:GUPTE ANIRUDDHA
Digital content delivery and viewing system and method
ActiveUS7734684B2Eliminate needSecure distributionAnalogue secracy/subscription systemsMultiple digital computer combinationsDigital contentDistribution system
A media distribution system is provided whereby devices on a network are provided with native-mode, optimized content viewers adapted to receive and present digital content provided elsewhere on the network. An agent is downloaded to a device, where it gathers information regarding the device environment and uses that information to identify the appropriate application for that device. The appropriate application for a particular device is then downloaded to the device to enable the device to present the content to a user.
Owner:VIDEO FURNACE INC
Multibit Forensic Watermark with Encrypted Detection Key
InactiveUS20080310629A1Strengthen copyright protectionAlleviates, mitigates or eliminates one or more disadvantagesTelevision systemsImage watermarkingData signalAncillary data
The invention relates to embedding auxiliary data in the form of a multibit payload in a host signal, and encrypting the associated detection key. Moreover, the invention relates to extracting the auxiliary data in the form of the multibit payload from a data signal. Auxiliary data is embedded in a host signal by the following steps. First a reference watermark is provided, subsequently an encrypted detection key associated only with the reference watermark is generated. The encrypted detection key may be a scrambled version of the watermark. In a further step, the multibit watermark is generated and a multibit payload is encoded into the reference watermark. Finally, the multibit watermark is embedded into the host signal.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
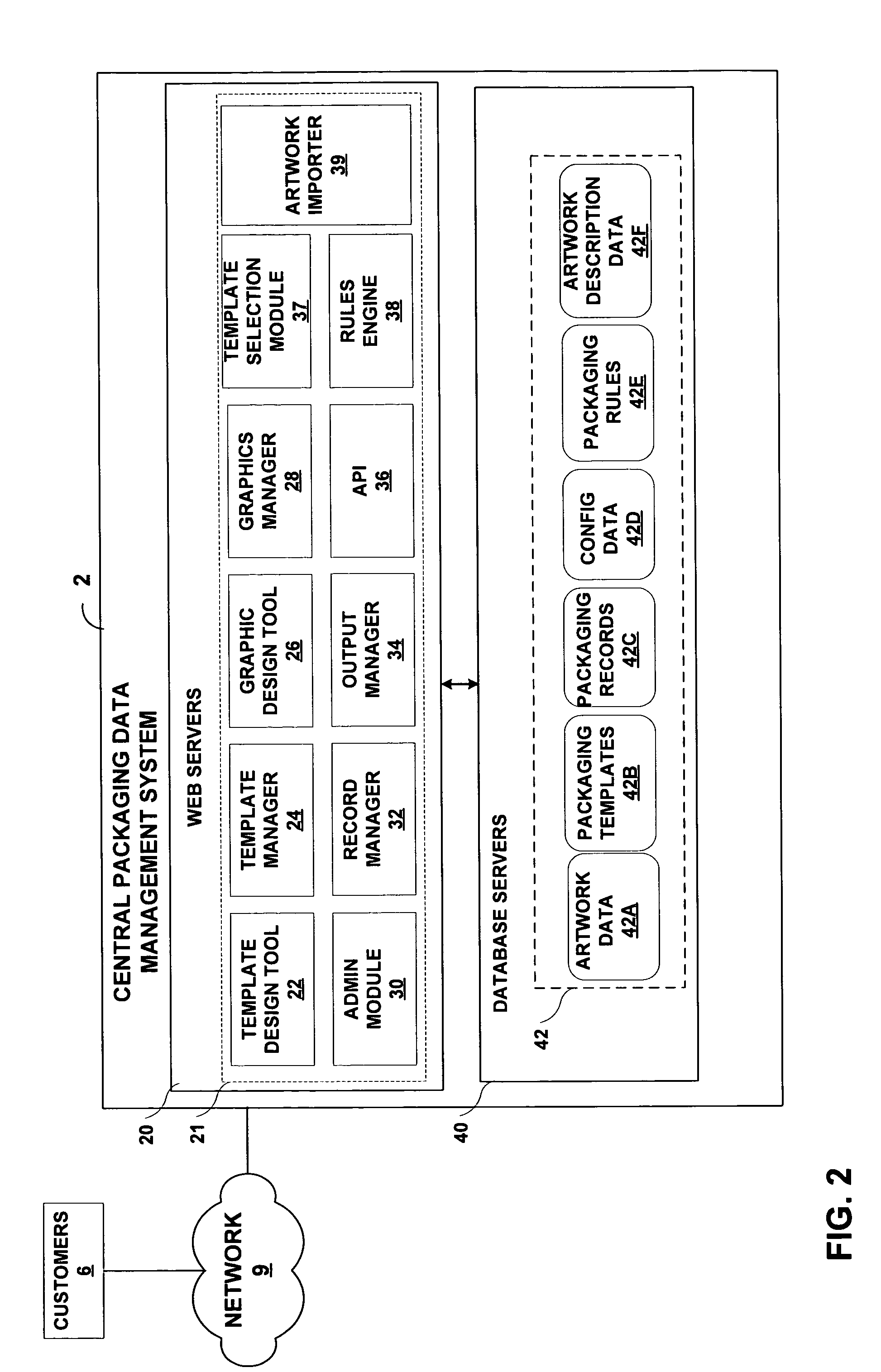
Centralized management of packaging data with artwork importation module
InactiveUS20050050052A1Easy to controlSecure distributionDigital data processing detailsExecution for user interfacesGraphicsData field
A central packaging data (CPD) management system provides an online environment in which customers manage packaging data for their respective products. The CPD management system securely distributes the packaging data to manufacturing sites or other output locations, and allows the customers to control the printed output material applied to their packaging and manufactured products. The CPD management system includes a set of packaging templates having data fields selected from a set of data field types, and an artwork importation module that processes a graphic file to identify elements of a packaging layout. The artwork importer generates metadata that associates each of the elements with a respective one of the data field types of the packaging templates. A record manager presents an interface by which a user forms packaging records based on the metadata. An output manager communicates the packaging record to an output location to control printing of packaging material.
Owner:3M INNOVATIVE PROPERTIES CO
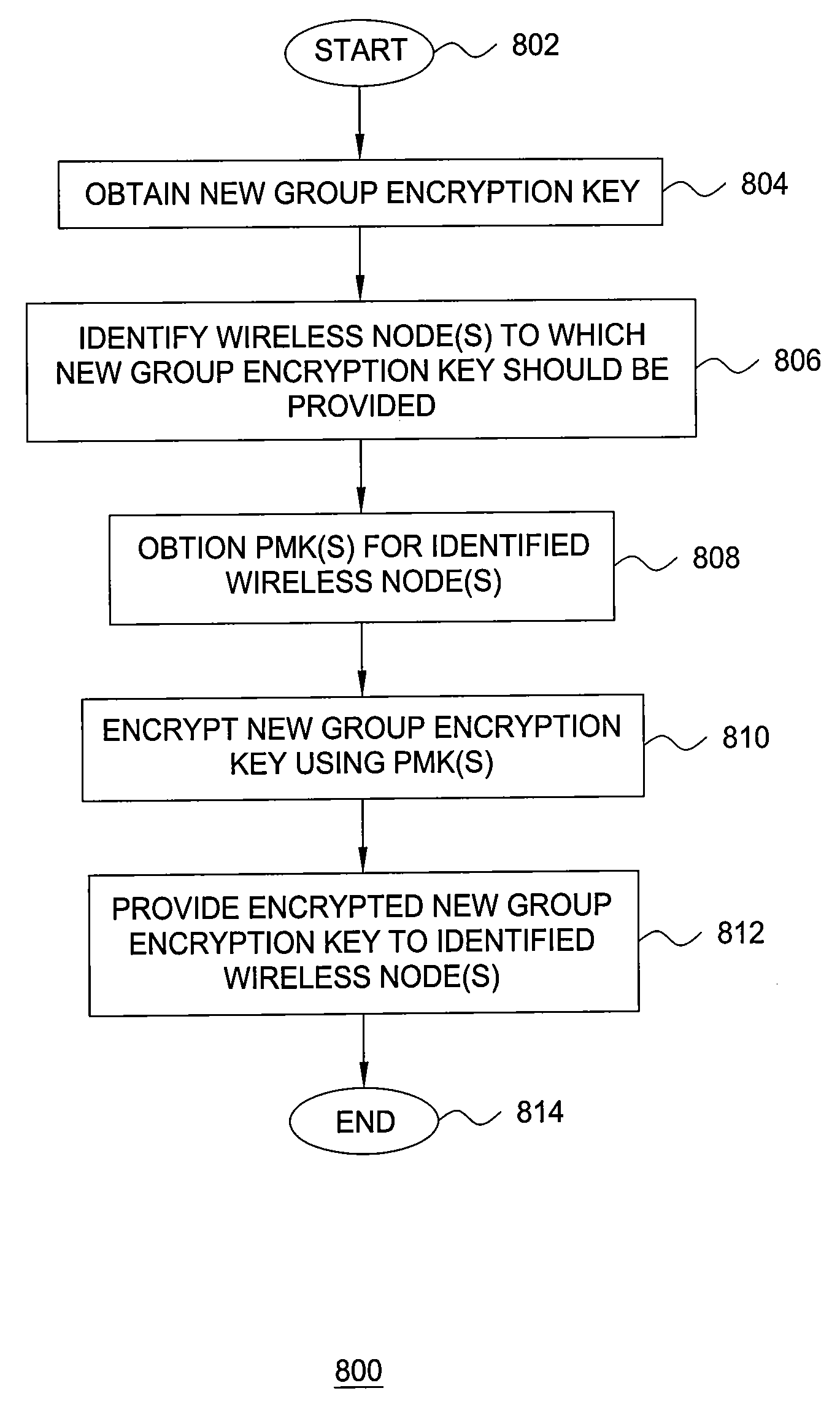
Method and Apparatus for Authenticating Nodes in a Wireless Network
ActiveUS20090086973A1Secure distributionMultiple keys/algorithms usageBroadcast service distributionMaster keyWireless network
The invention includes a method and apparatus for authenticating a wireless node requesting to join a network. A method includes receiving an authentication request from the wireless node, negotiating at least one authentication parameter with the wireless node, deriving a first encryption key using the at least one authentication parameter, encrypting a second encryption key using the first encryption key, and propagating the encrypted second encryption key toward the wireless node, wherein the wireless node independently derives the first encryption key for use in decrypting the encrypted second encryption key received from the authentication server node. The wireless node decrypts the encrypted second encryption key and stores the second encryption key for use to securely communicate with other wireless nodes of the network. In one embodiment, the present invention may be implemented using a modified version of the EAP-TLS protocol, in which rather than a Pairwise Master Key (PMK) being sent from the authentication server node to the wireless node, the authentication server node and the wireless node each derive the PMK and the authentication server node securely provides a group encryption key to the wireless node by encrypting the group encryption key using the PMK.
Owner:RPX CORP
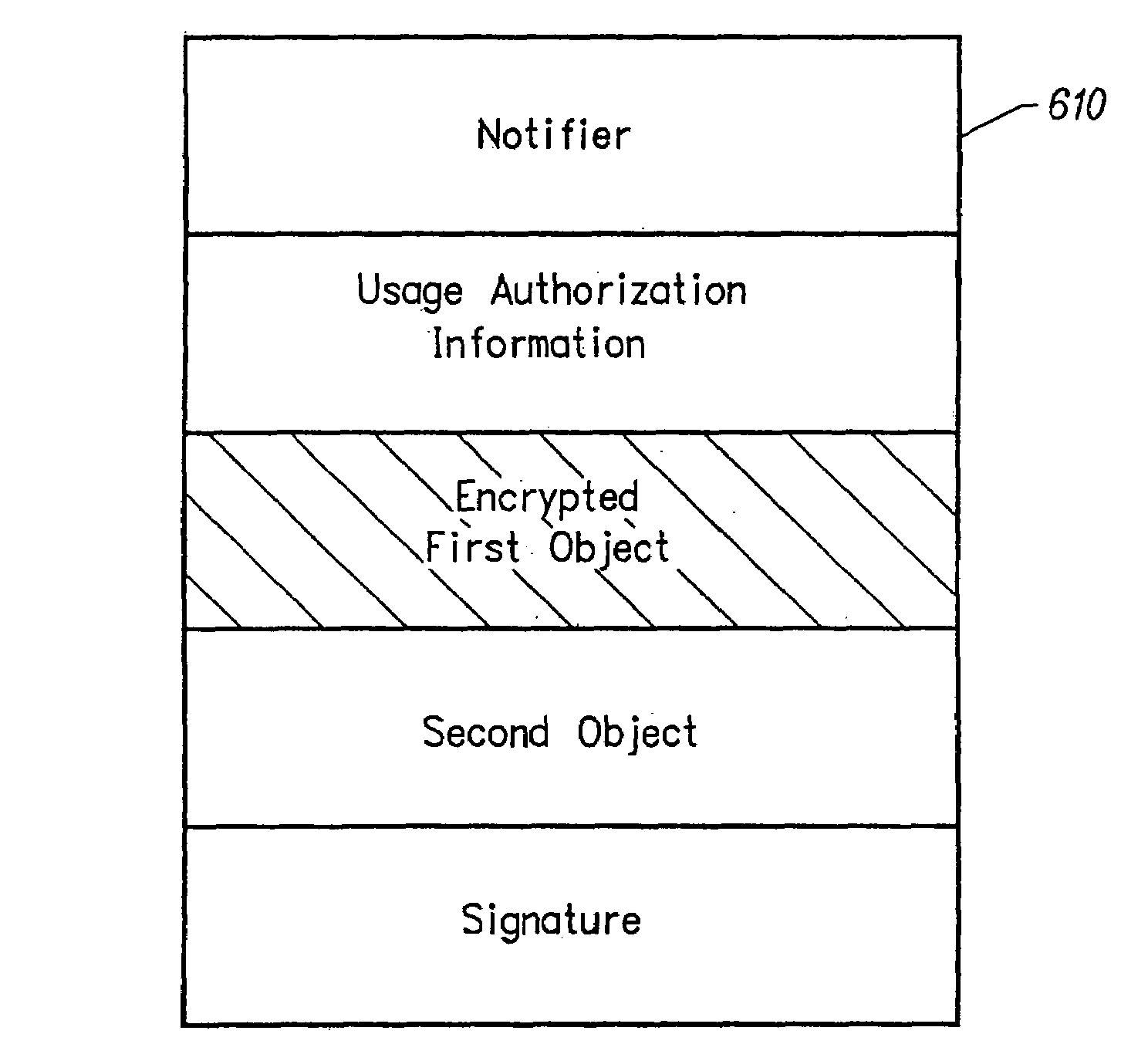
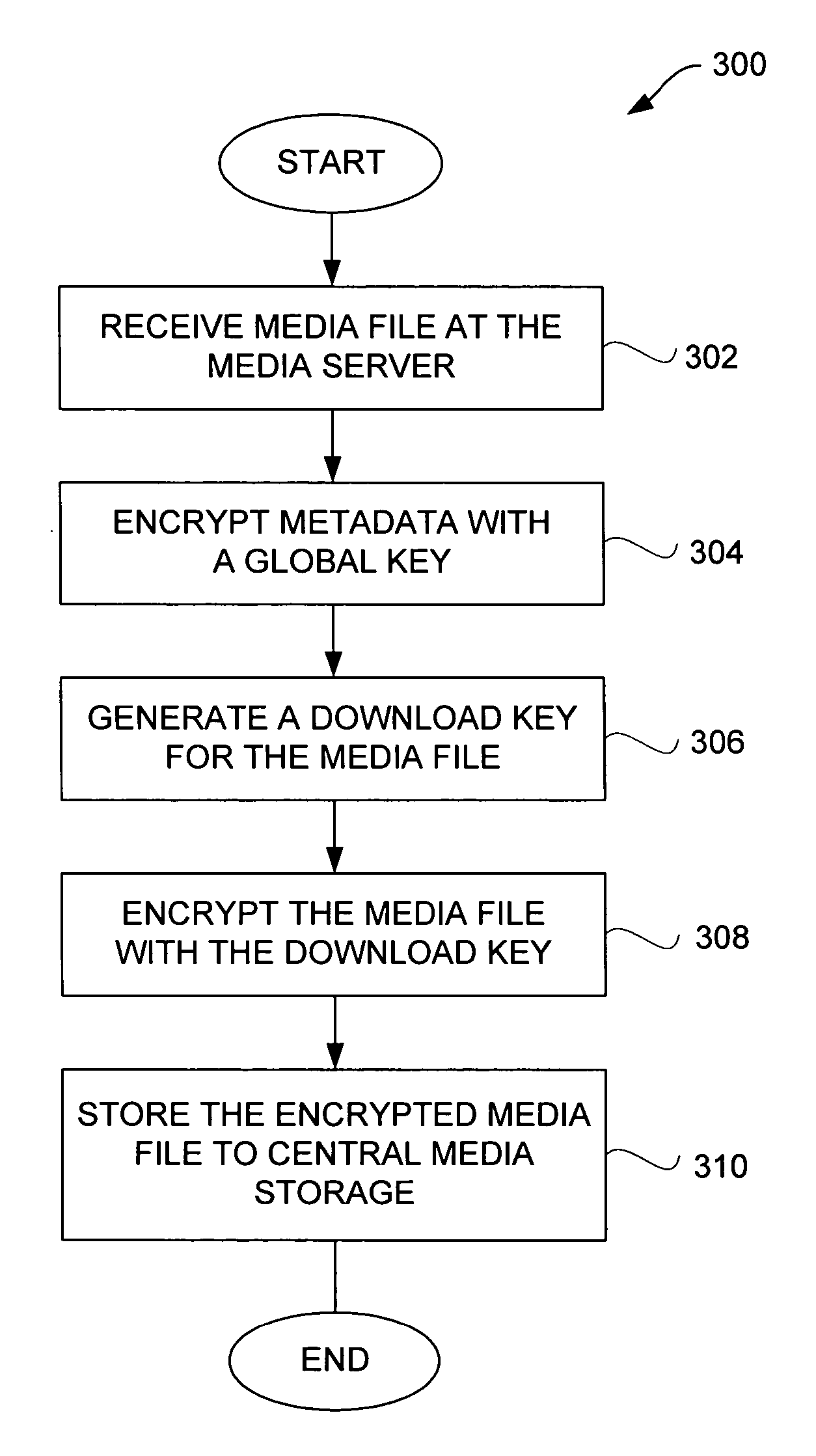
Encrypted media key management
InactiveUS7076067B2Secure distributionKey distribution for secure communicationPulse modulation television signal transmissionMedia serverClient-side
A key or licence management system for the secure online distribution of digitized audio-visual works (“media”) using encryption techniques. Encrypted media is stored on a media server while the encryption keys are stored on a media key server. Users acquire rights from online retailers to obtain from the media key server keys corresponding to the media they wish to play. The key server encrypts keys before releasing them, preferably with the user's public key using a public key encryption algorithm. Keys are stored in volatile memory at the user's client device and thus the user is in receipt of the key just in time to play the media.
Owner:RPK NEW ZEALAND
Quantum-key distribution method between a plurality of users or groups
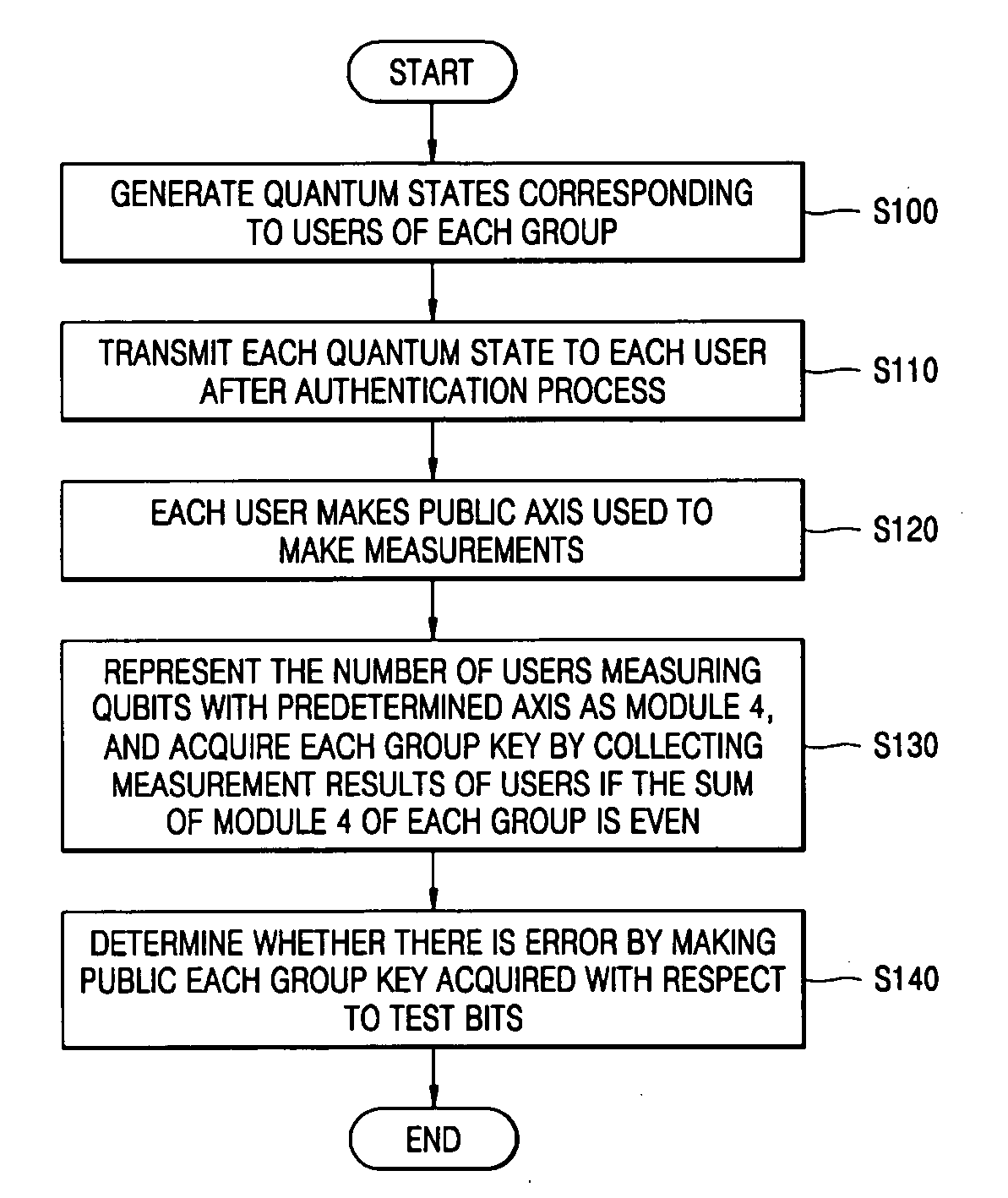
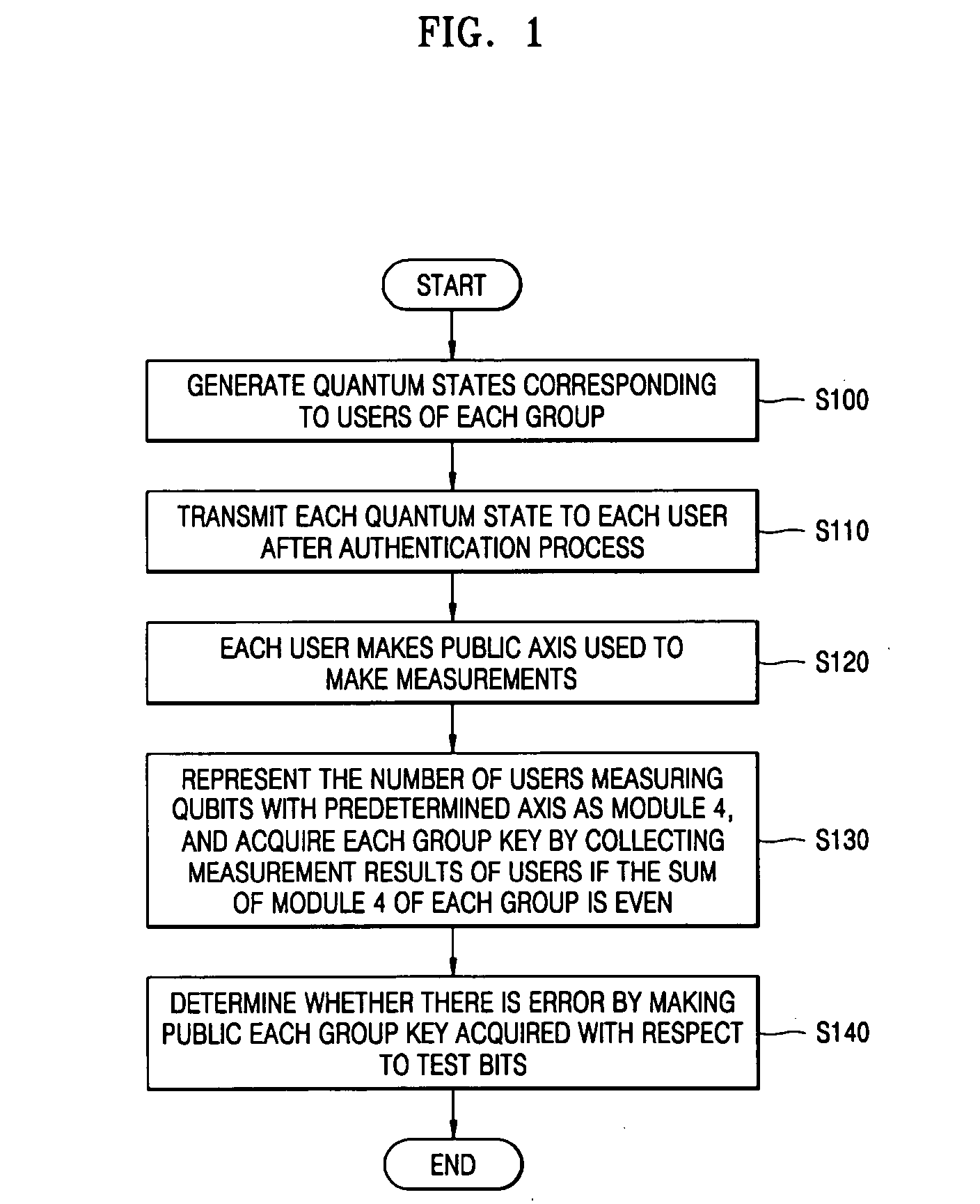
InactiveUS20050249352A1Improve securitySecure distributionKey distribution for secure communicationPump componentsComputer scienceQuantum state
There is provided a quantum-key distribution method between a plurality of users or groups. A center prepares a predetermined number of entangled states consisting of qubits equal to the number of the users, and generates quantum states consisting of the qubits belonging to each of the entangled states and corresponding to each of the users. The center transmits each of the quantum states to each of the users after an authentication process. Each of the users receiving the quantum state makes public an axis used to measure each of the qubits constituting the quantum states. The number of users in each group measuring the qubits with a predetermined axis is represented by module 4. If the sum of the module 4 of each group is even, each group collects the qubit measurement results of the users and acquires each group key. Therefore, it is possible to provide a high-security quantum-key distribution method between an unspecified number of users or groups.
Owner:ELECTRONICS & TELECOMM RES INST
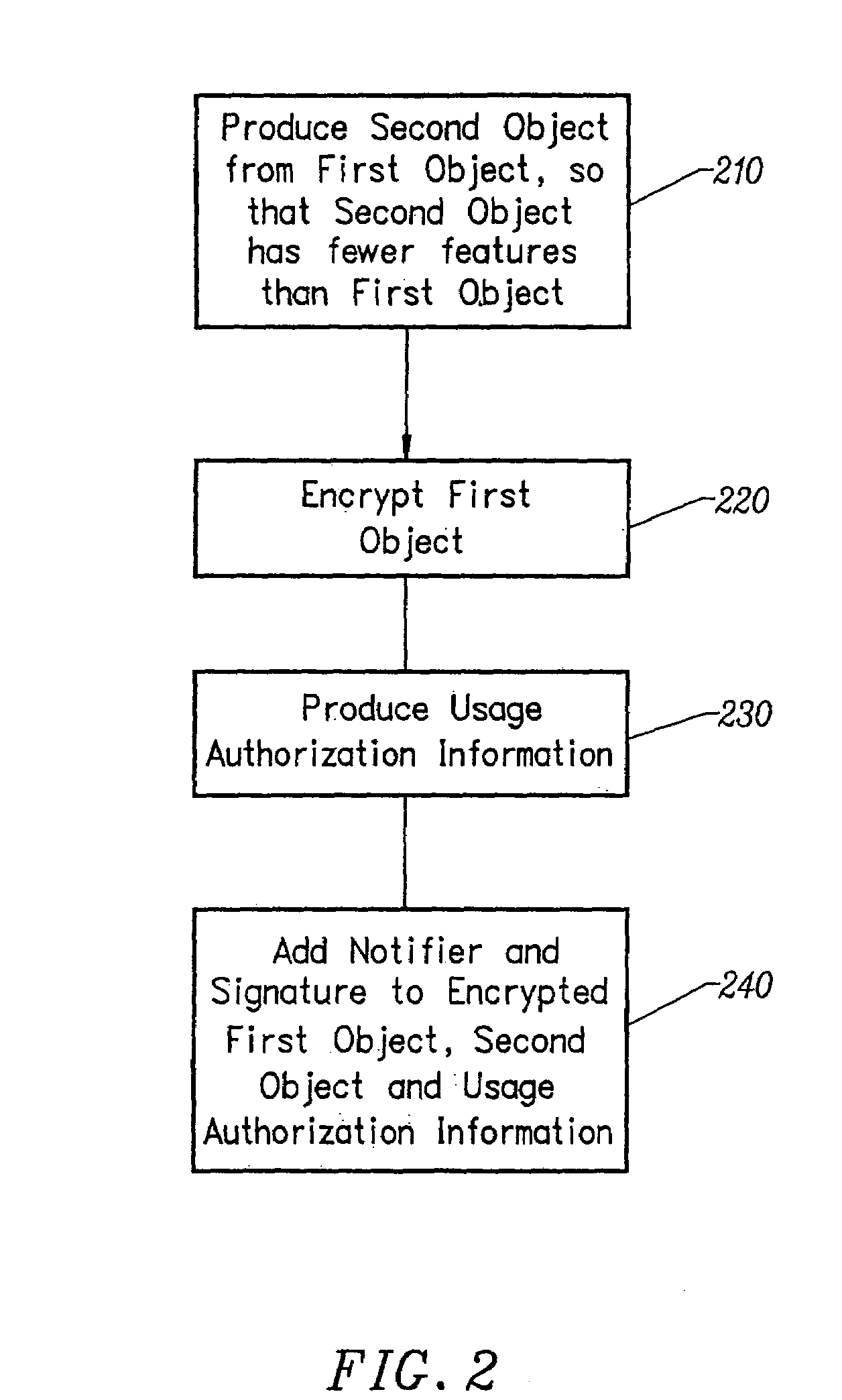
Method and apparatus for secure distribution of software
InactiveUS7360252B1Secure distributionReduce usageDigital data processing detailsUser identity/authority verificationPaymentData file
Software is securely distributed with limited usage rights. The software may be an executable program and / or one or more data files such as image or multimedia data files. The software includes an access control object which prevents at least some usage of the software without the use of a first access control code. The first access control code is produced based on selected information characteristic of the user's computer system. The access control code is produced in a server computer to which the user directs a request for the access control code. The user makes a payment to receive the access control code, which is then downloaded to the user's computer system.
Owner:FLEXERA SOFTWARE
Digital content delivery and viewing system and method
InactiveUS20100082743A1Eliminate needSecure distributionMultiple digital computer combinationsSecuring communicationDigital contentDistribution system
A media distribution system is provided whereby devices on a network are provided with native-mode, optimized content viewers adapted to receive and present digital content provided elsewhere on the network. An agent is downloaded to a device, where it gathers information regarding the device environment and uses that information to identify the appropriate application for that device. The appropriate application for a particular device is then downloaded to the device to enable the device to present the content to a user.
Owner:VIDEO FURNACE INC
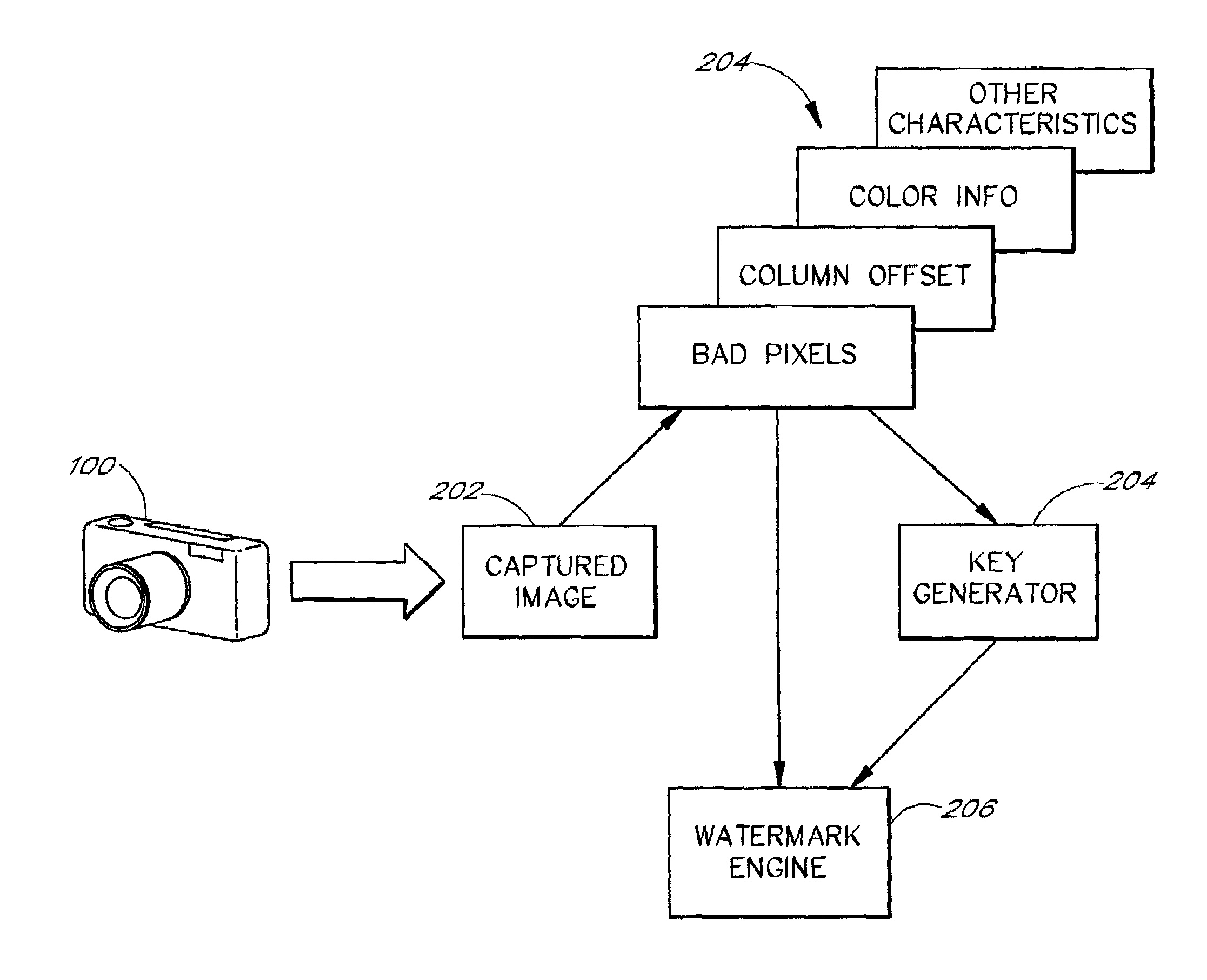
Methods and systems for embedding camera information in images
InactiveUS7663670B1Promote reproductionSecure distributionTelevision system detailsSolid-state device signal generatorsComputer scienceImage capture
The present invention is related to providing, in association with an image, information related to the image capture device used to capture the image. In one embodiment, information related to a first static camera characteristic and camera setting information related to a first captured digitized image is embedded in the first captured digitized image using a watermark. The watermarked information may be used to identify the source or owner of the picture, and / or to aid in the more accurate reproduction of the image.
Owner:GULA CONSULTING LLC +1
Encryption method and apparatus for use in digital distribution system
InactiveUS7567671B2Harder to decrypt media contentSecure distributionTelevision system detailsAnalogue secracy/subscription systemsComputer hardwarePayment
A method to securely distribute media content such as Audio or Video with associated media information as part of a media package, in a media distribution system. The media content is encrypted and can be decrypted using a code, process or algorithm called a program key which is further encrypted and stored in the media package as one or both of a service encrypted program key or a locally encrypted program key. When a payment arrangement is not required the program key can be obtained by decrypting the locally encrypted program key, but when a payment arrangement is required, the locally encrypted program key cannot be decrypted or is not present and the service encrypted program key must be decrypted using a decryption message provided by a server after the payment arrangement is made. Media content, the locally encrypted program key and the service encrypted program key are re-encrypted periodically to ensure the security of the media package.
Owner:GUPTE ANIRUDDHA
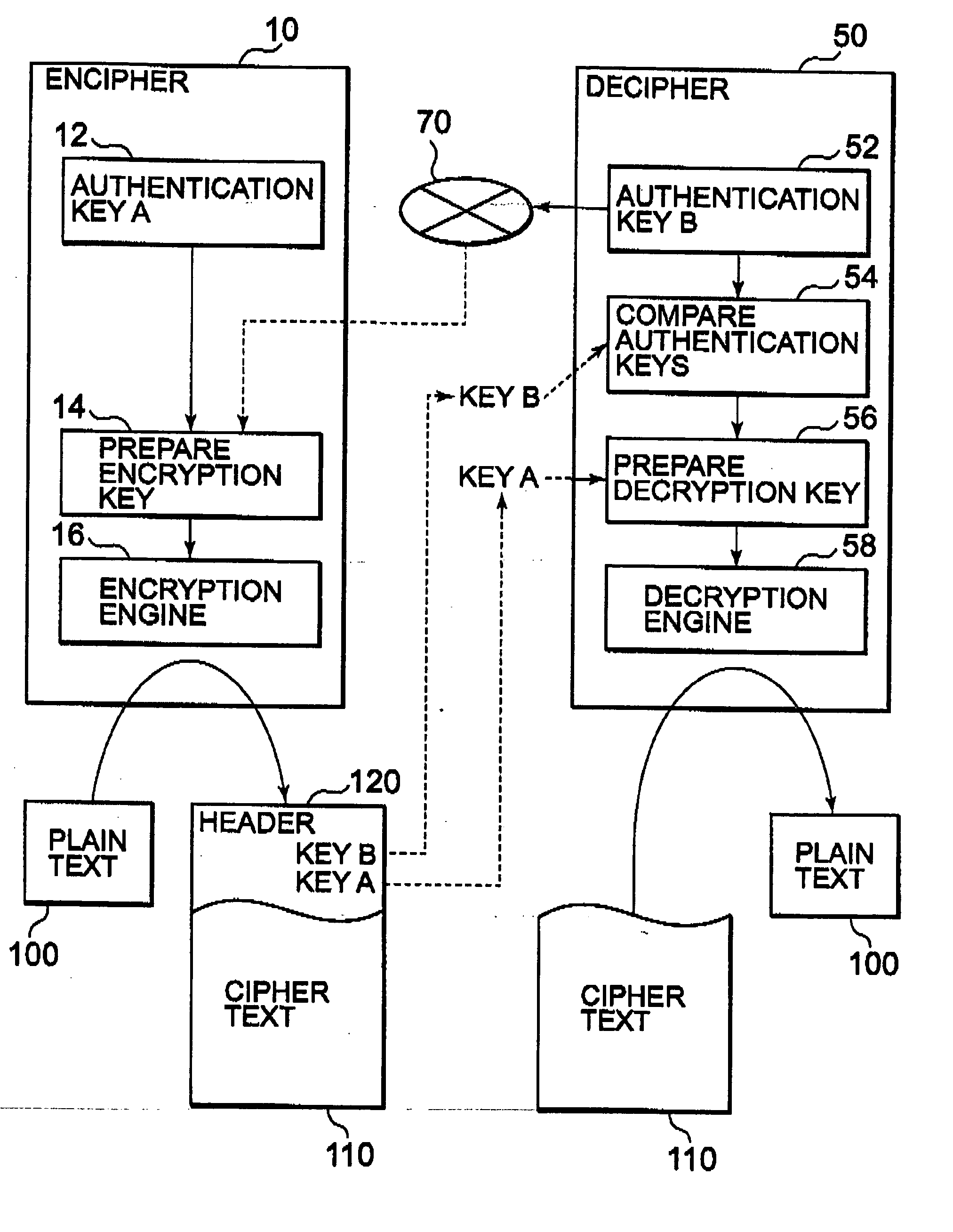
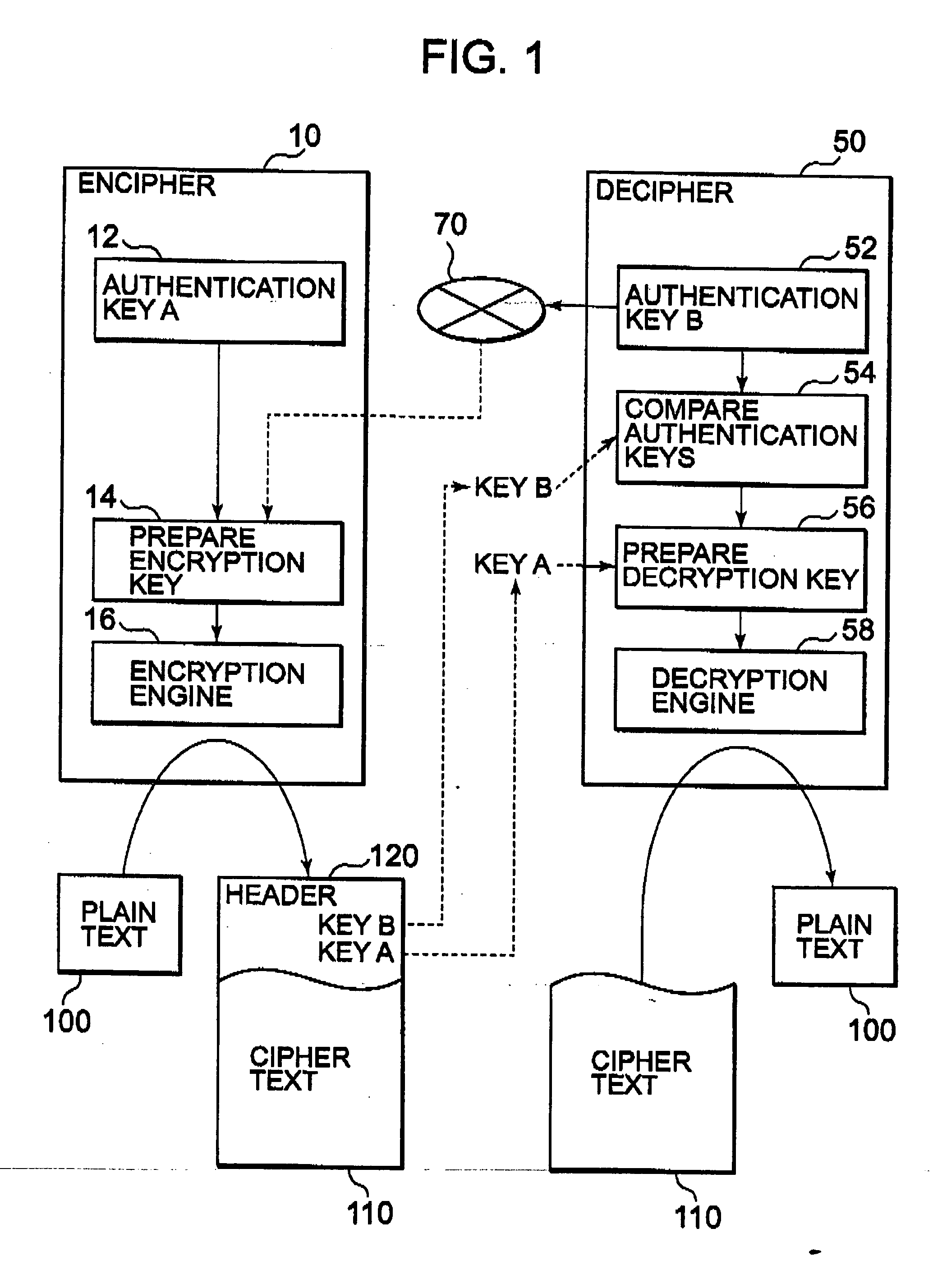
Encryption system using device authentication keys
InactiveUS20060072745A1Increase speedHigh speed machiningKey distribution for secure communicationData stream serial/continuous modificationCiphertextAuthentication
An encrypted data distributing method includes preparing cipher text which can be decrypted only by a specific trusted device, and performing encryption and decryption processing at a high speed. An encryption key is prepared using an encryption device authentication key unique to an encryption device and a decryption device authentication key unique to a decryption device, and cipher text is prepared by this encryption key. The authentication keys are also sent to the decryption device. In the decryption device, the decryption device authentication key received from the encryption device is compared with the decryption device authentication key prepared by the decryption device to perform decryption processing only when the authentication keys match.
Owner:FUKAYA HIROMI
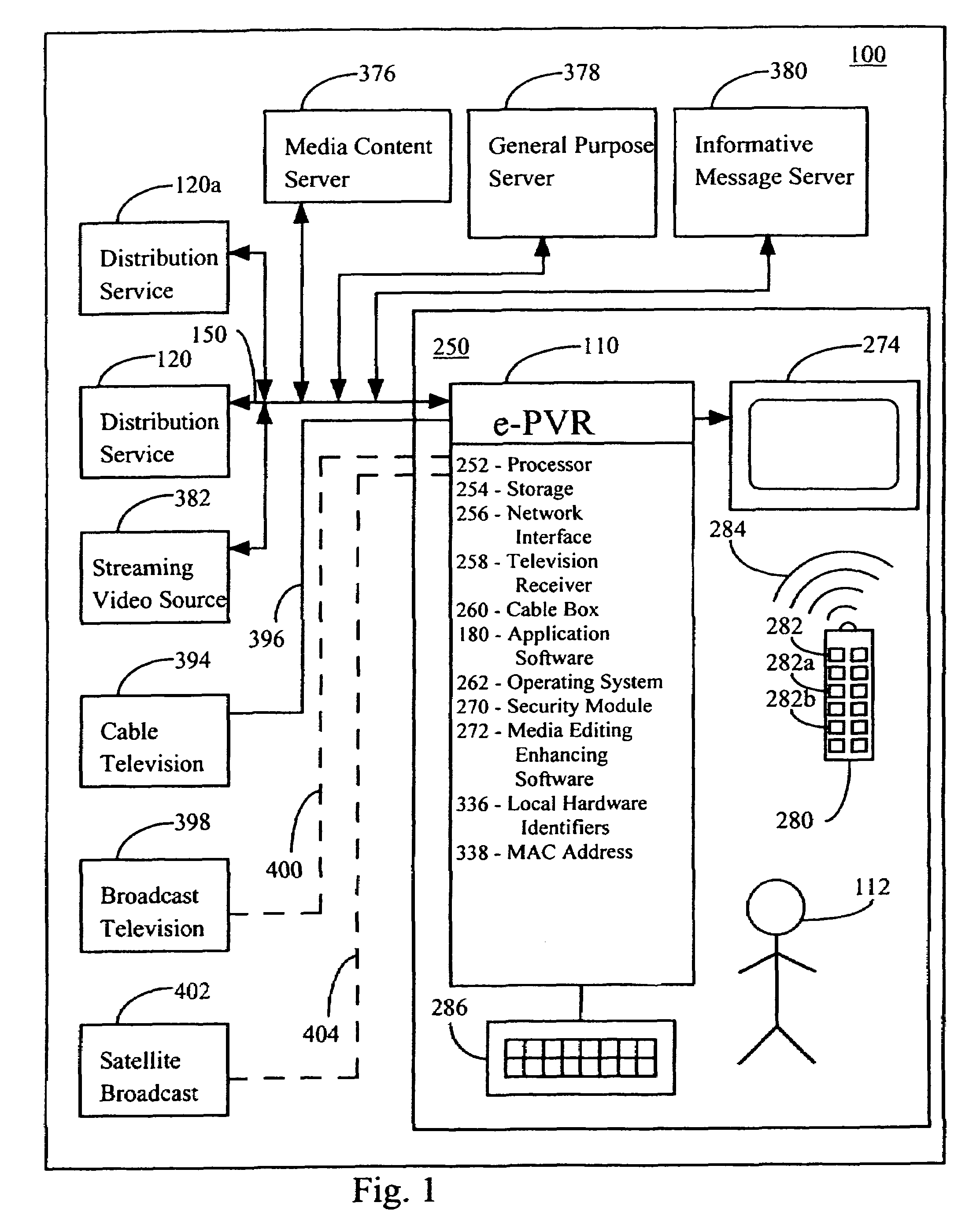
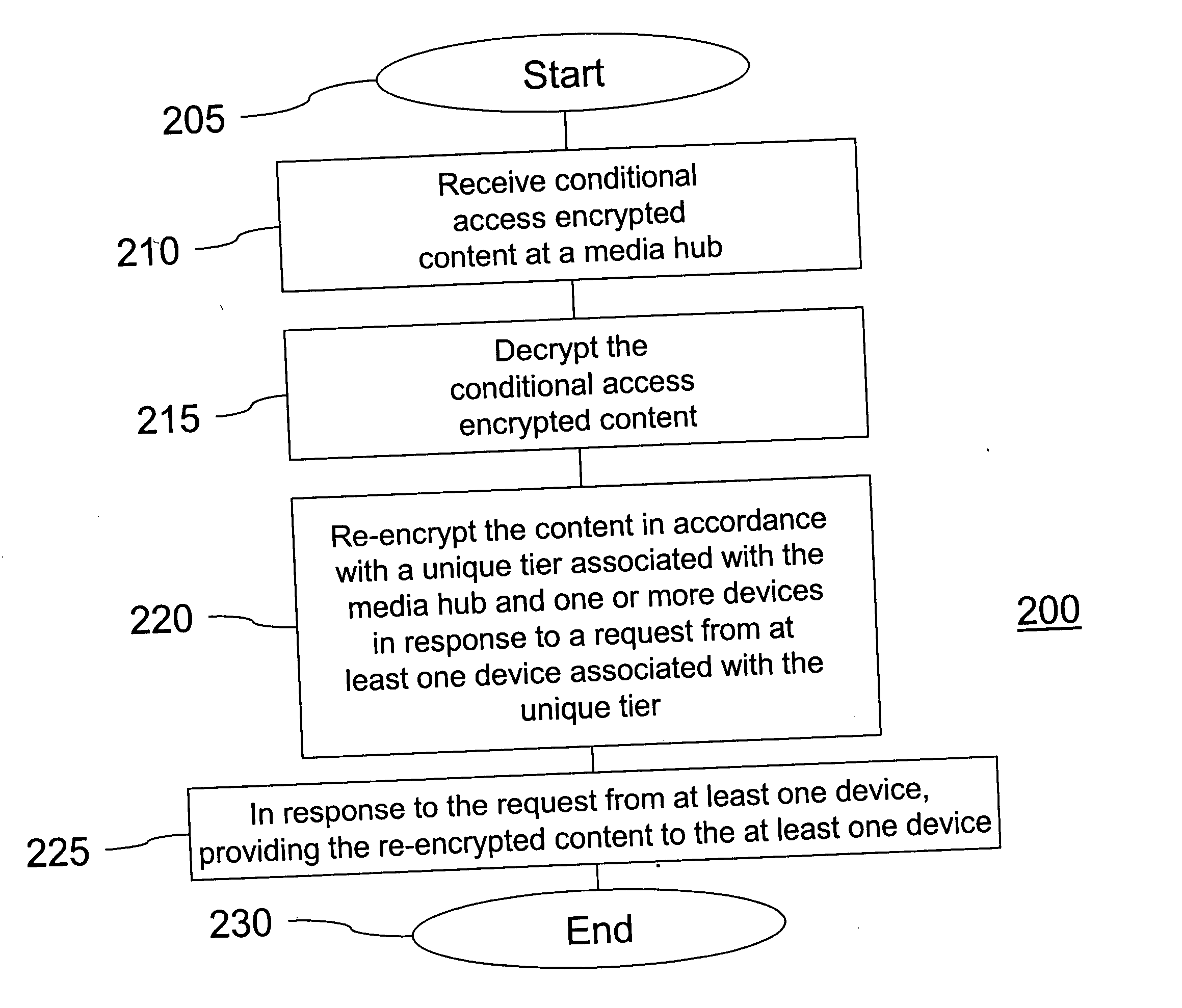
Method and apparatus for providing secured content distribution
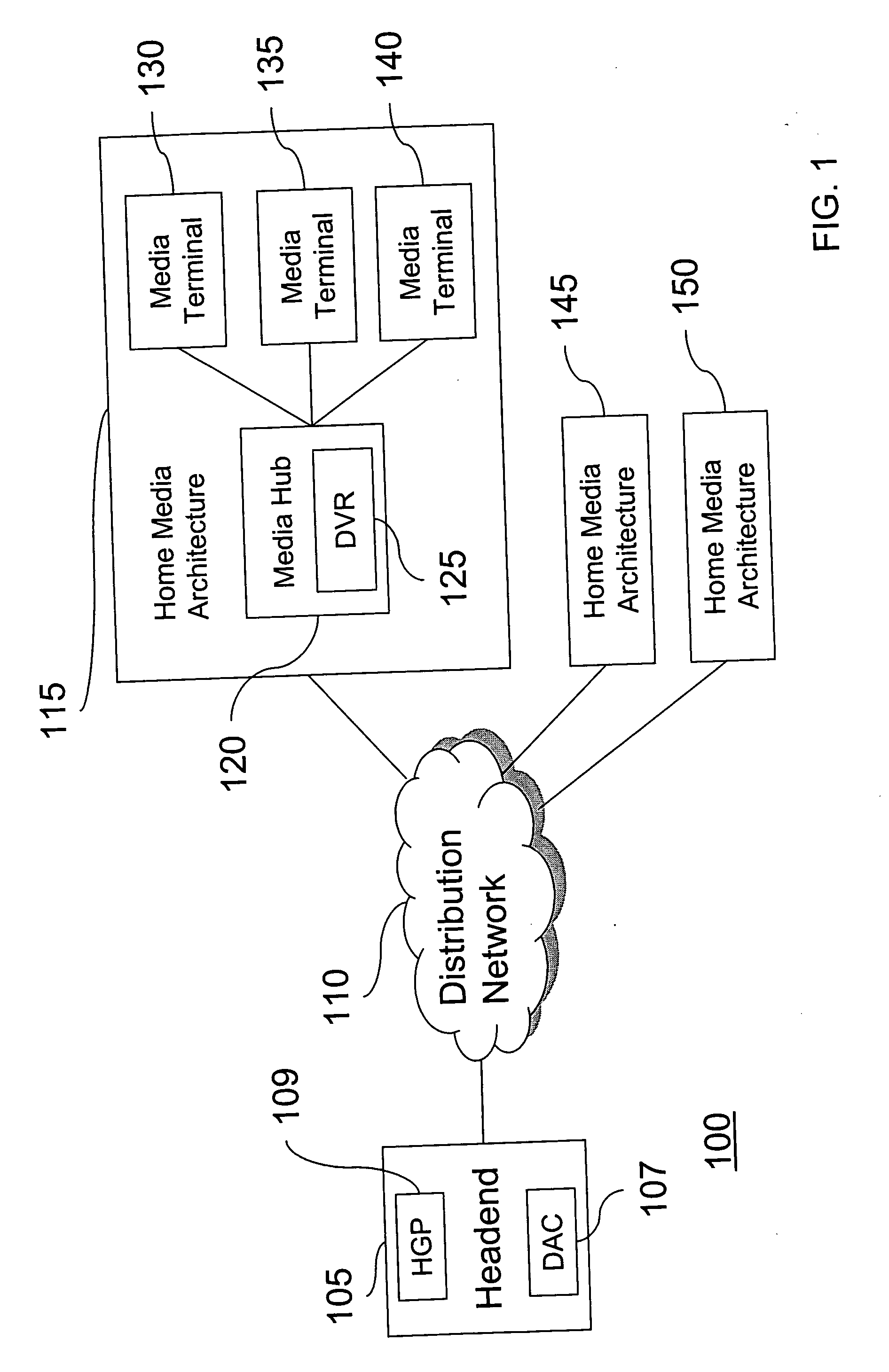
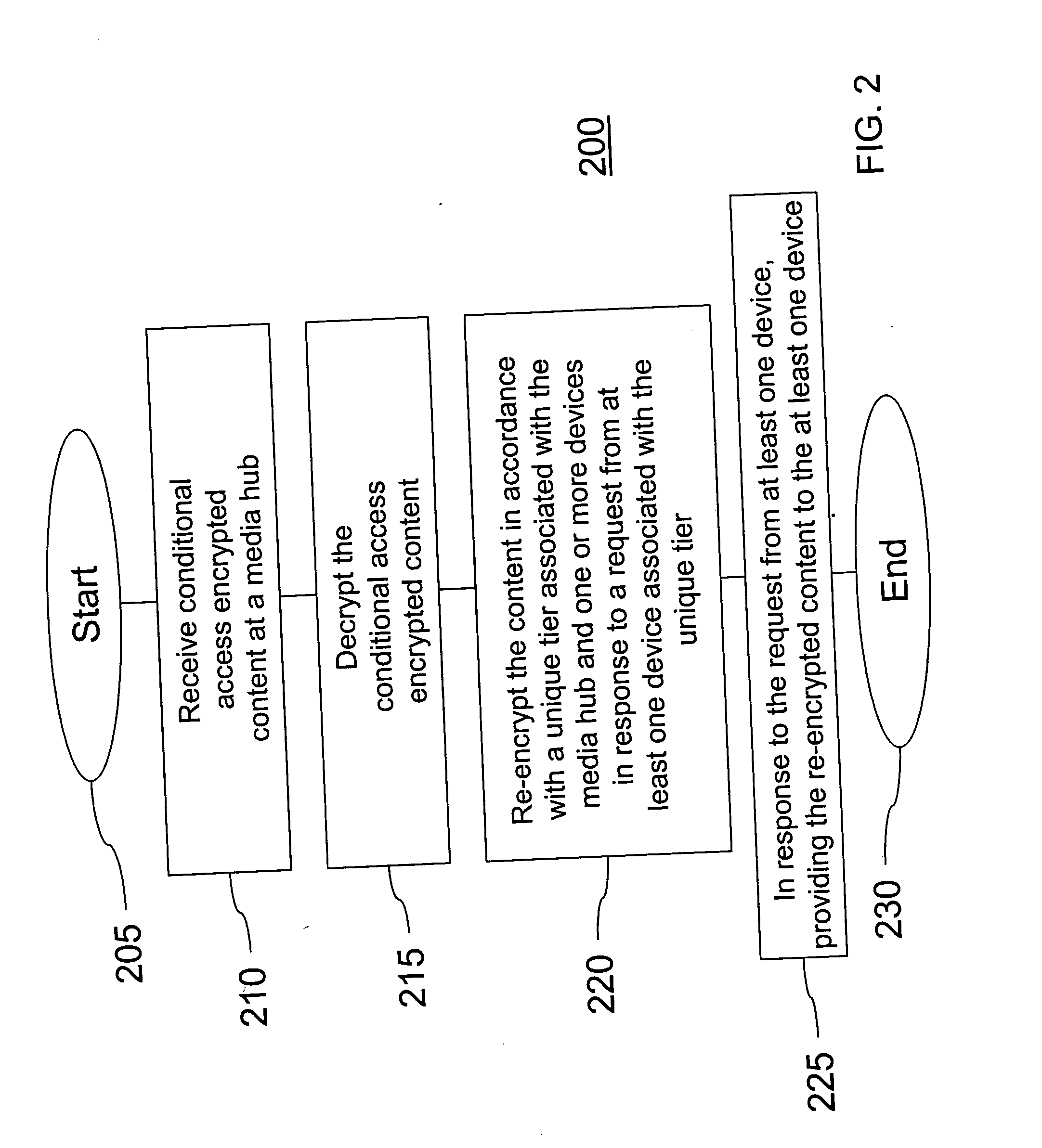
InactiveUS20060069645A1Secure distributionComputer security arrangementsTelevision systemsContent distributionConcentrator
A method and apparatus for providing secured content distribution using a media hub is disclosed. In one embodiment, conditional access encrypted content is received at the media hub. The conditional access encrypted content is decrypted. The content is re-encrypted in accordance with a unique tier associated with the media hub and one or more devices in response to a request from at least one device associated with the unique tier. The re-encrypted content is provided to the at least one device in response to the request from the at least one device associated with the unique tier. A method and apparatus for providing secured content distribution is disclosed. In one embodiment, unit addresses (UAs) of all components within a home media architecture are obtained. A unique key is generated for the home media architecture using public information from the UA of each component. A message including the unique key is distributed to each component of the home media architecture. A method and apparatus for providing secured content distribution is disclosed. In one embodiment, UAs of all decoders within a home media architecture are obtained. A unique key is generated for the home media architecture using public information from the UA of each decoder. A message including the unique key is distributed to each decoder of the home media architecture.
Owner:GENERAL INSTR CORP
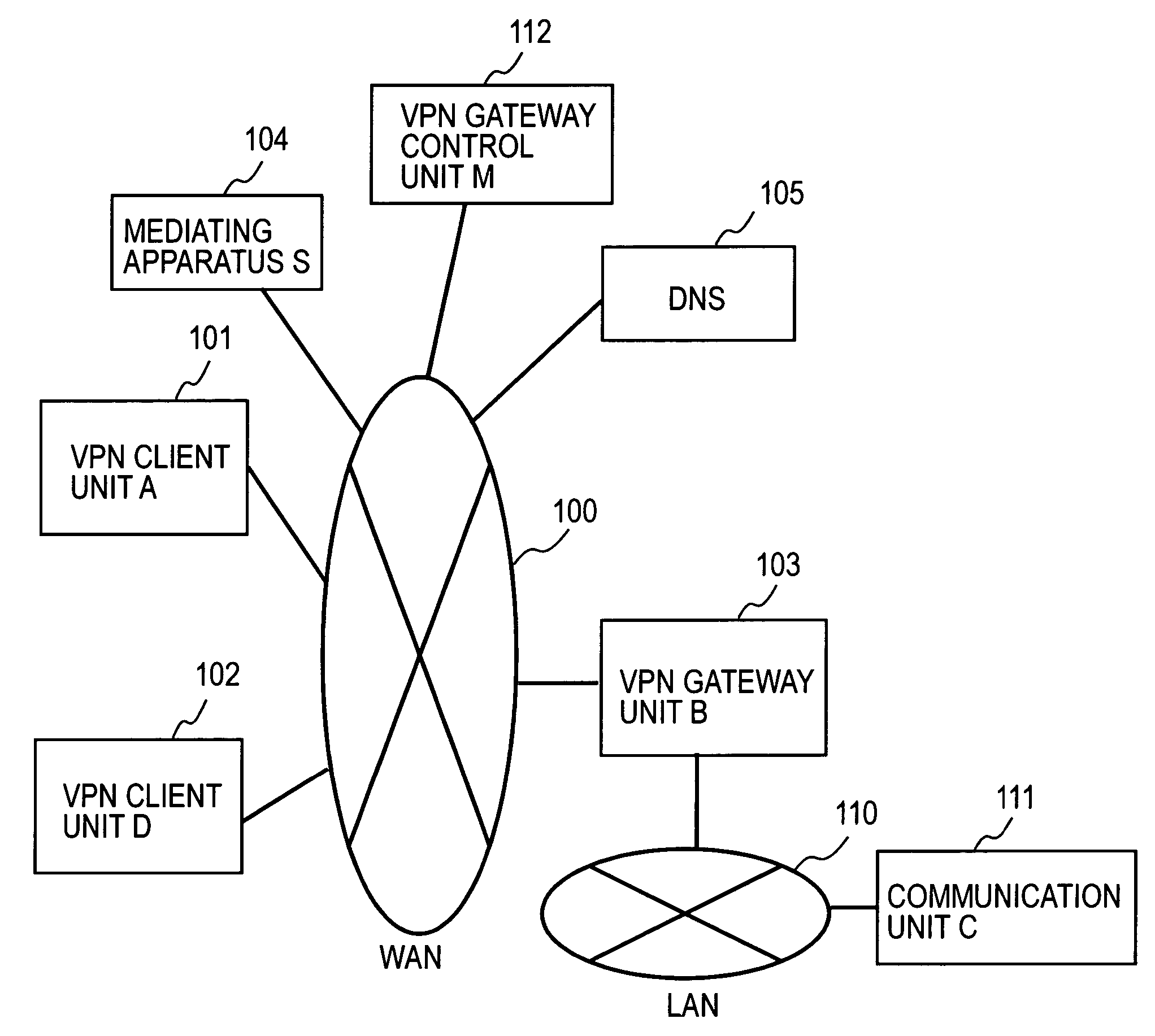
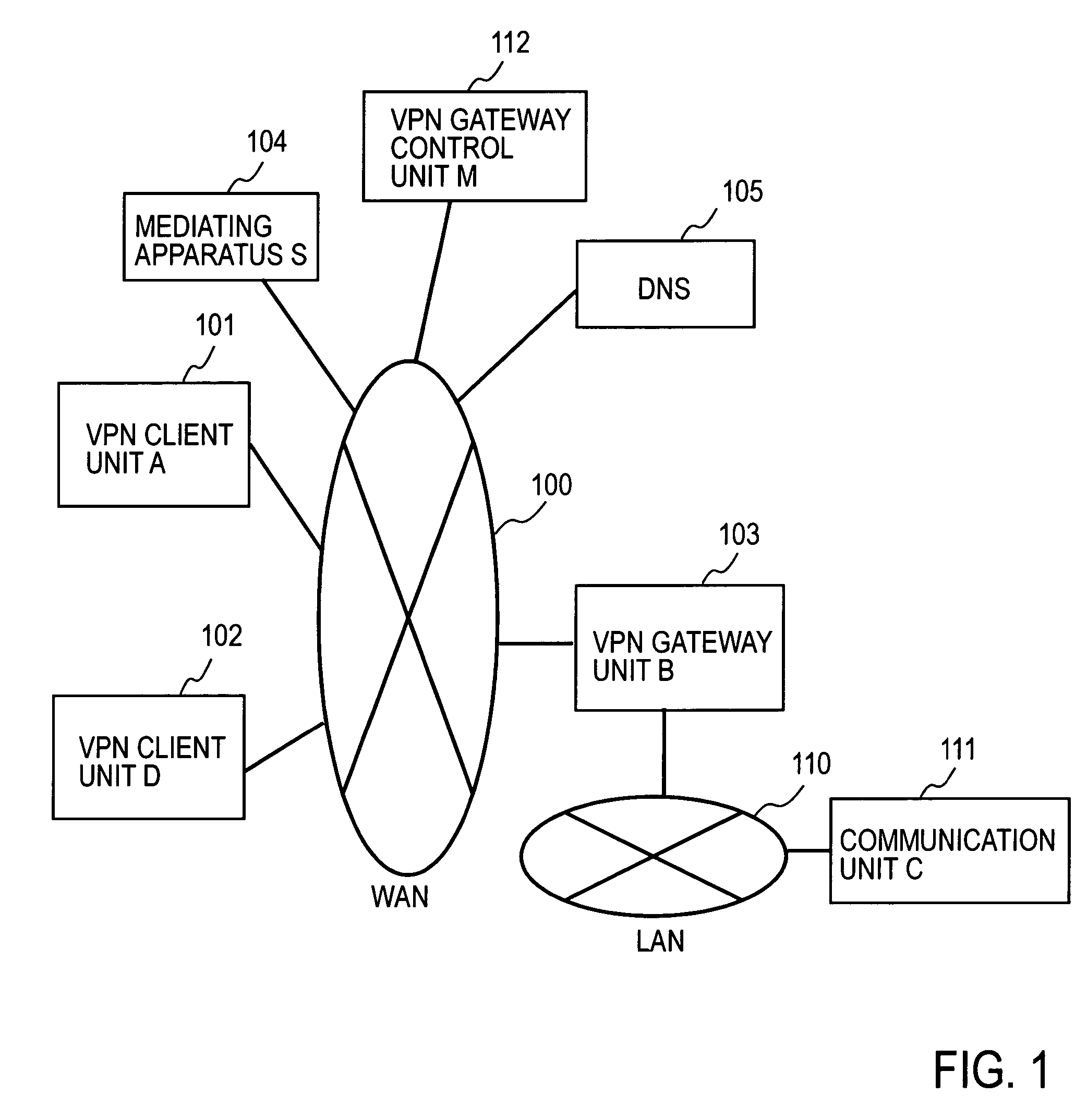
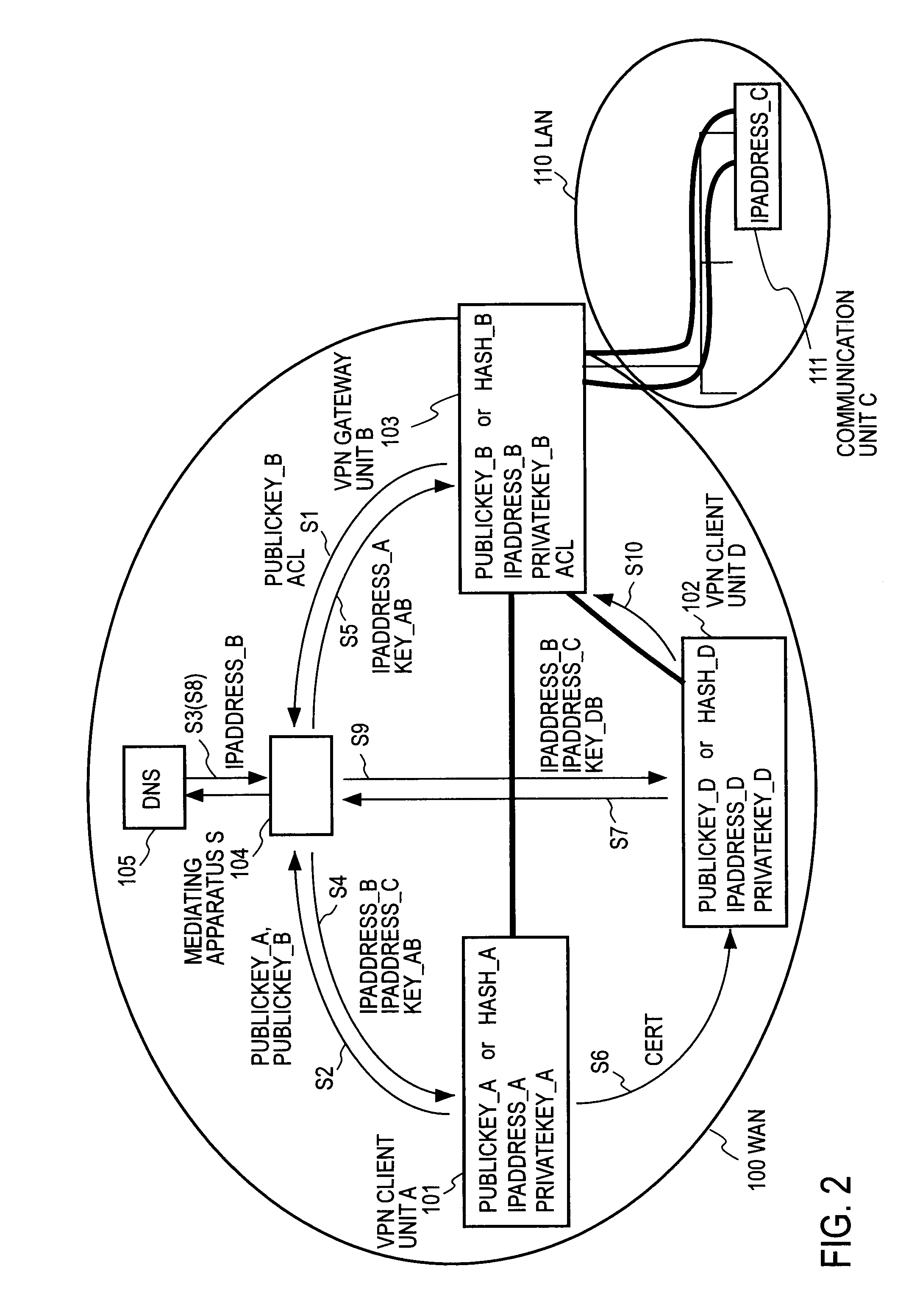
Remote access VPN mediation method and mediation device
InactiveUS7665132B2Secure distributionKey distribution for secure communicationDigital data processing detailsPrivate IPCommunication unit
A mediating apparatus is provided on an IP network, and stores an access control list (ACL) retained in a VPN gateway unit. The mediating apparatus: receives a retrieval request from a VPN client unit; acquires a private IP address of a communication unit by reference to ACL; searches DNS to acquire therefrom an IP address of the VPN gateway unit; generates a common key that is used for authentication between the VPN client unit and the VPN gateway unit and for encrypted communication therebetween; sends the IP address of the VPN gateway unit, the private IP address of the communication unit, and the common key to the VPN client unit; and sends the IP address of the VPN client unit and the common key to the VPN gateway unit.
Owner:NIPPON TELEGRAPH & TELEPHONE CORP
Method and apparatus for securing layer 2 networks
InactiveUS20090034738A1Secure distributionKey distribution for secure communicationSpecial data processing applicationsMesh networkingNetwork security
Systems and methods for using a shared key architecture to enable secure Layer 2 meshed network security.
Owner:CIPHEROPTICS
Method for creating global distributed namespace
InactiveUS8914429B2Improve communication reliabilityEasy accessDigital computer detailsSpecial data processing applicationsA domainDistributed computing
One example embodiment includes a method for constructing a unified namespace carried out by a domain manager service executing on a domain node in a domain network comprised of domain nodes. The method includes establishing a single, hierarchical domain tree that encompasses digital computers in a distributed data service network, where the domain manager service sends a request to all domain member nodes requesting that each domain node export the root of its sub-domain to the domain manager. The method also includes receiving the exported sub-domain roots. The method further includes grafting onto a domain root of the domain manager service the received exported sub-domain roots.
Owner:PITTS WILLAIM
Apparatus & methods for digital content distribution
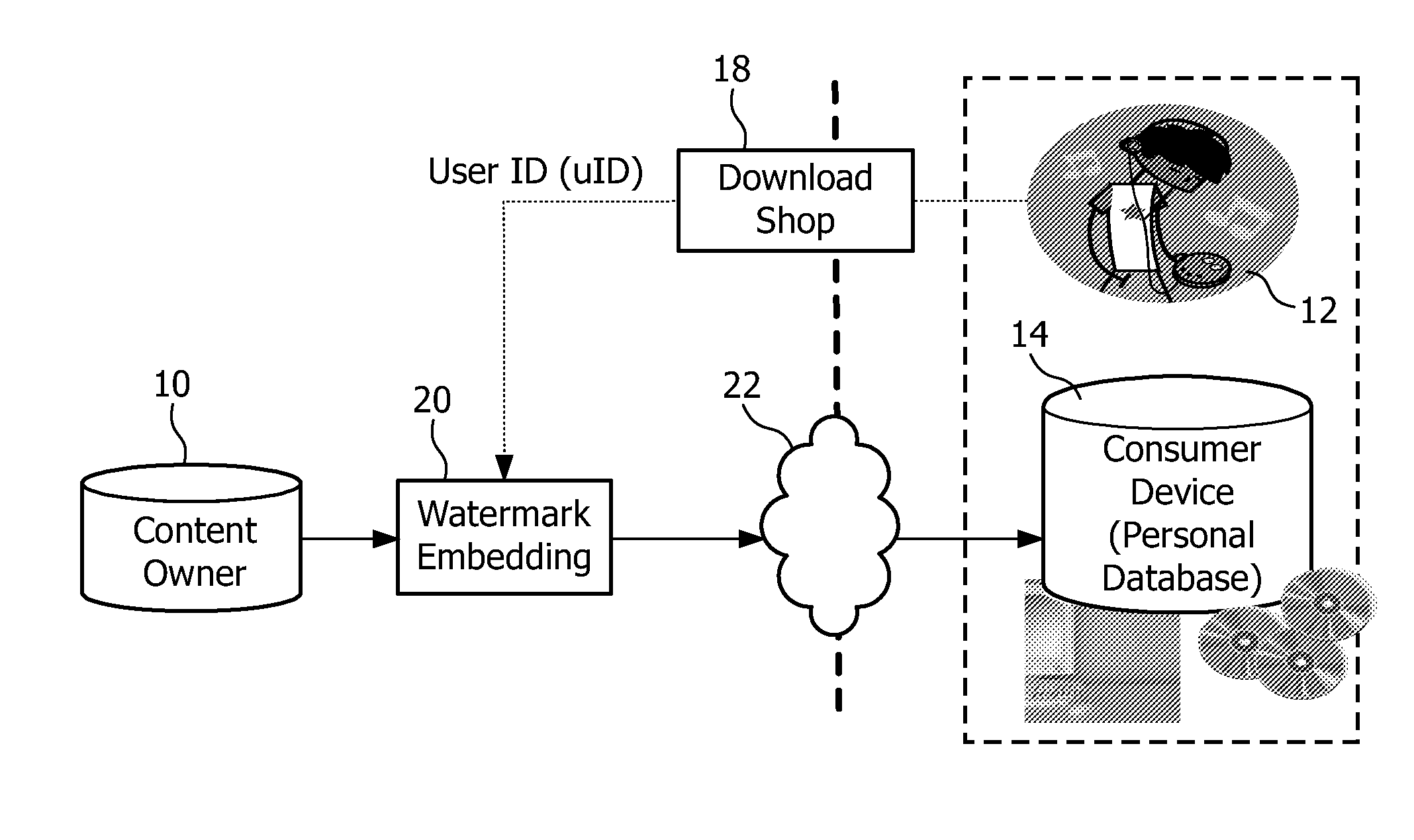
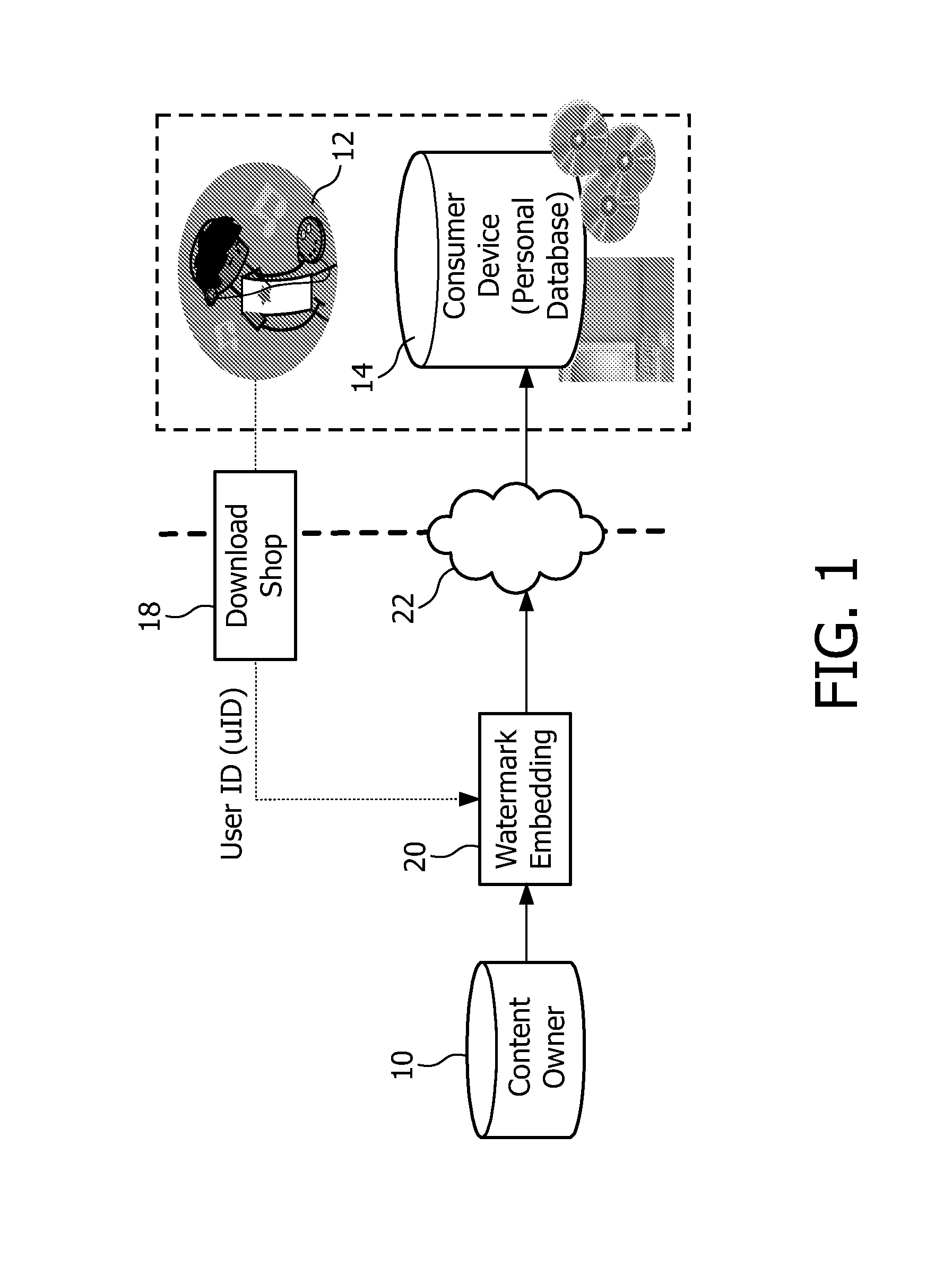
InactiveUS20100082478A1Facilitates peer-to-peer file sharing of digital contentMinimize the possibilityKey distribution for secure communicationFinanceDigital contentNumber content
The present invention relates to methods and apparatus for digital content distribution. A method of transferring digital content from a first entity (60) to a second entity (70) includes the steps of: a transfer control entity (50) transmitting a transmission key (KA) to the first entity, the first entity storing content data comprising digital content embedded with a first watermark (WA). The first entity applies the transmission key to the content data to remove the first watermark from the digital content and encrypt the digital content. The first entity transmits the encrypted digital content (CX) to the second entity. The transfer control entity transmits a receive key (KB) to the second entity and the second entity applies the receive key to the encrypted digital content to generate decrypted data comprising the decrypted digital content embedded with a second watermark (WB).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Database management for managing data distribution
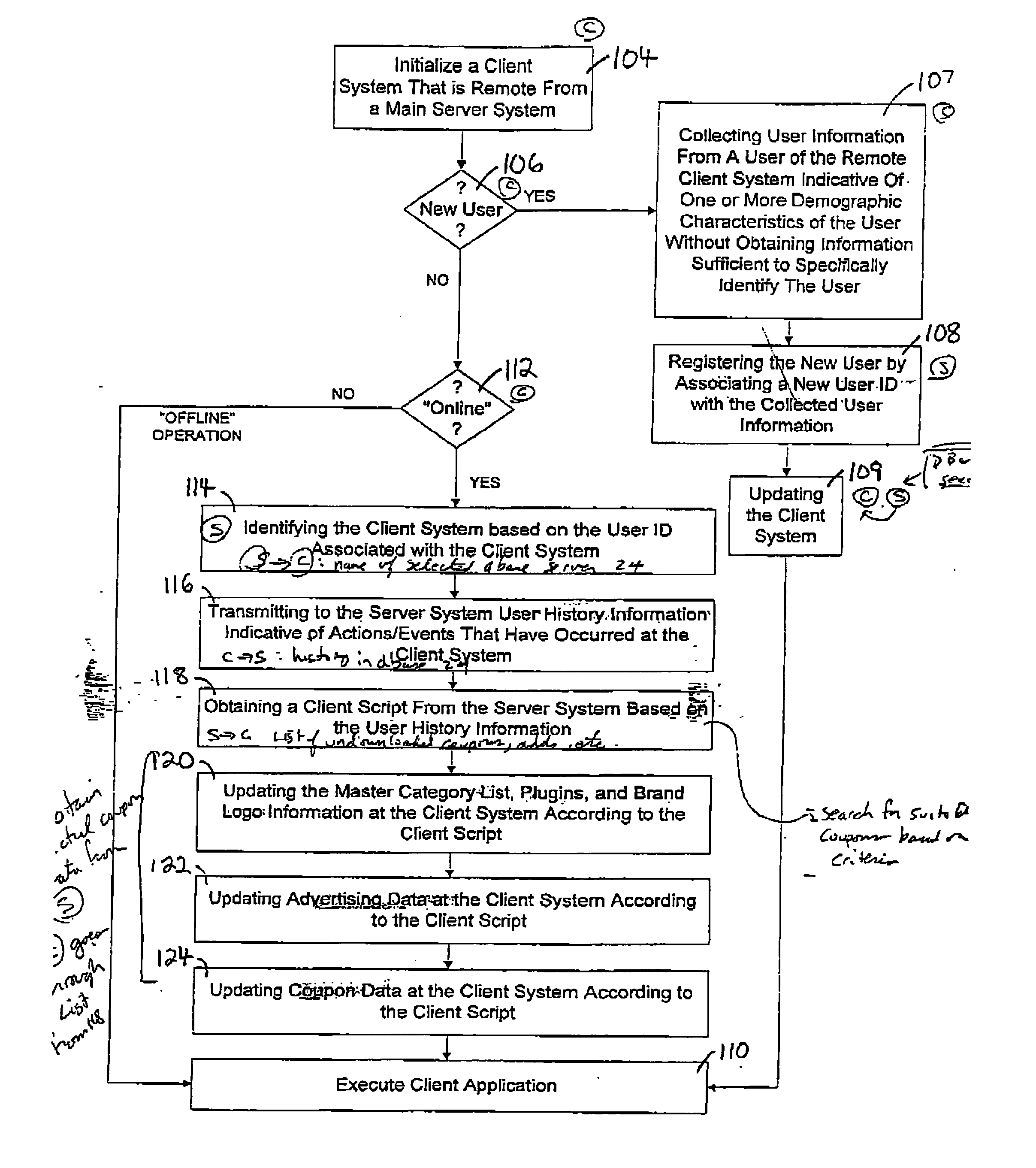
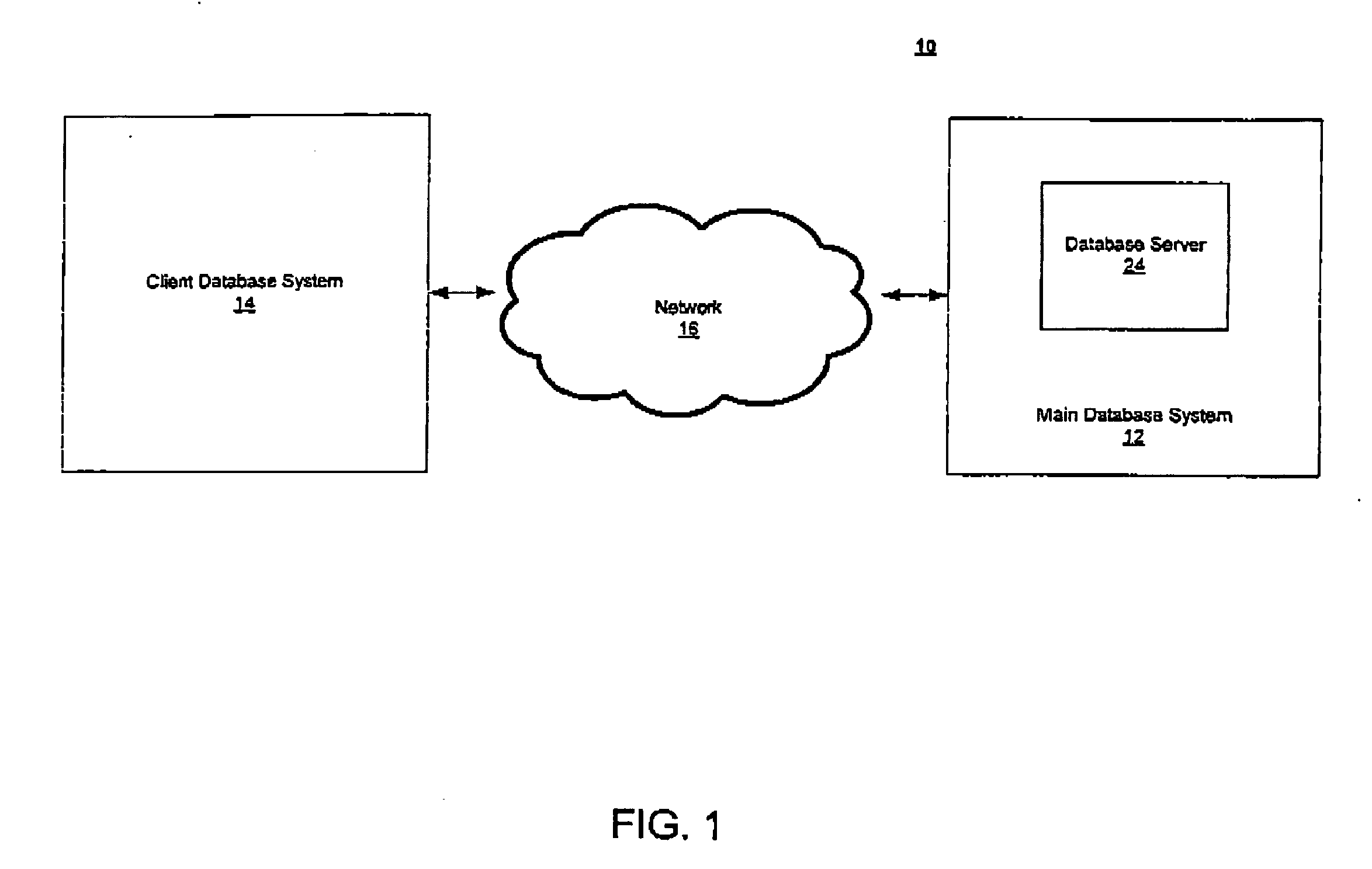
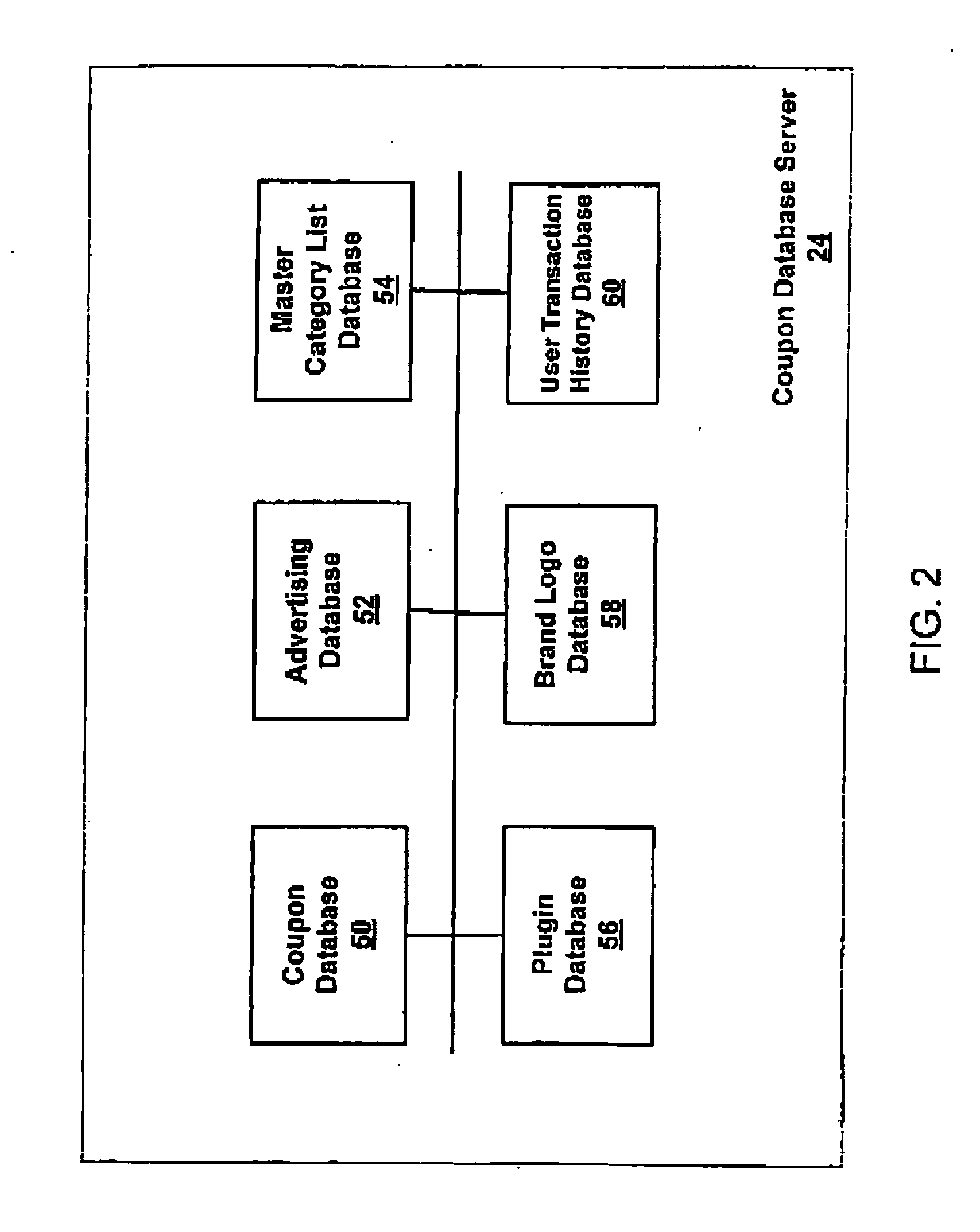
InactiveUS20070244745A1Ensuring user privacySecure distributionDiscounts/incentivesClient-sideDatabase
A system and method of distributing electronic coupon securely are disclosed, which includes a main database system, and a client system interconnected by a distributed computer network. Coupon data and advertising data can be encrypted to reduce the likelihood that such data may be misused, such as by unauthorized duplication. In addition, the client database system can be identified by a user identification that is allocated and associated with the user information collected from the user of the client database system. The user information can be indicative of one or more demographic characteristics of the user without being sufficiently and personally identify the user, thus preserving privacy. An icon can be provided to alert the user that new coupons are available.
Owner:QUOTIENT TECH INC
Session key management for public wireless lan supporting multiple virtual operators
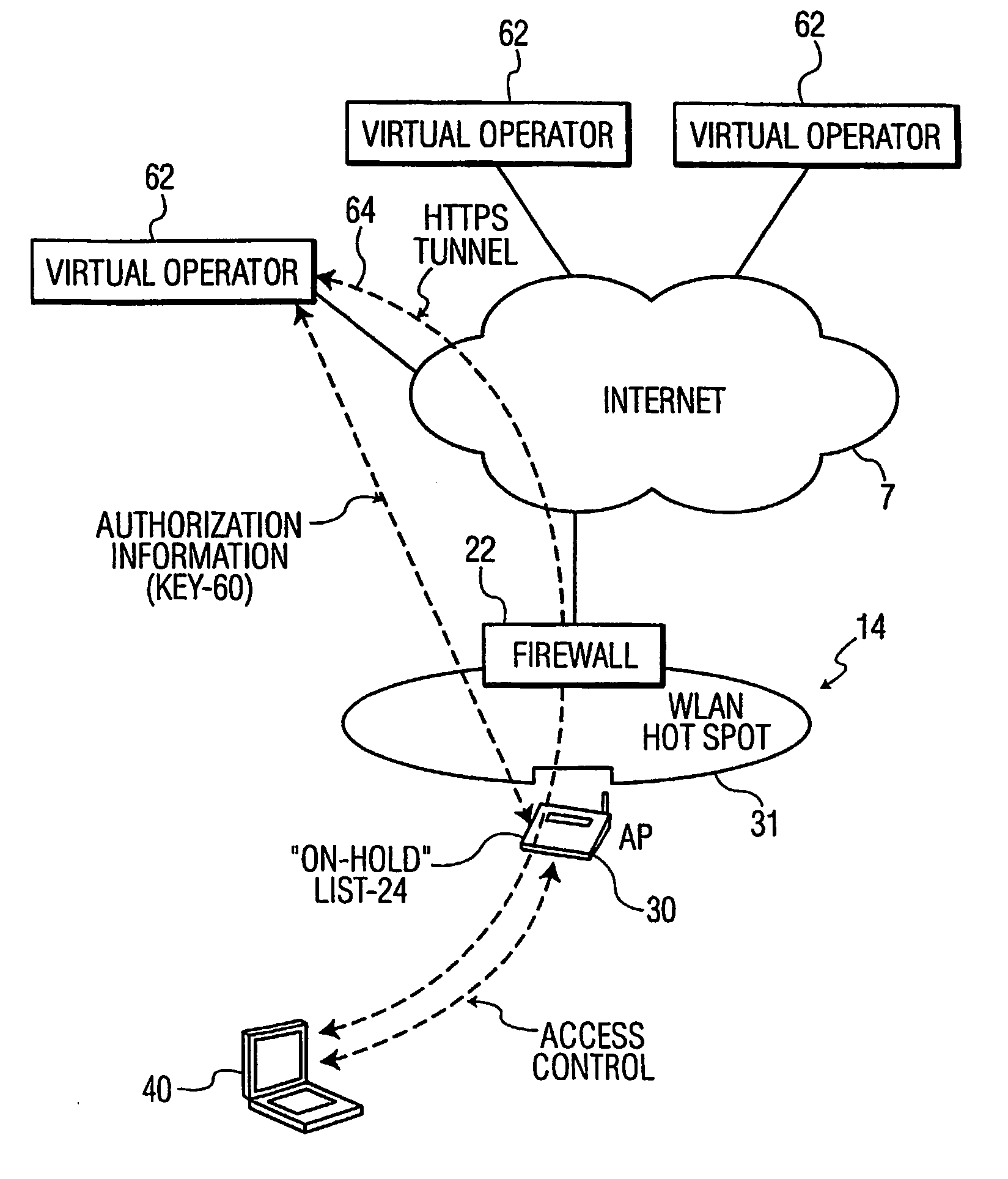
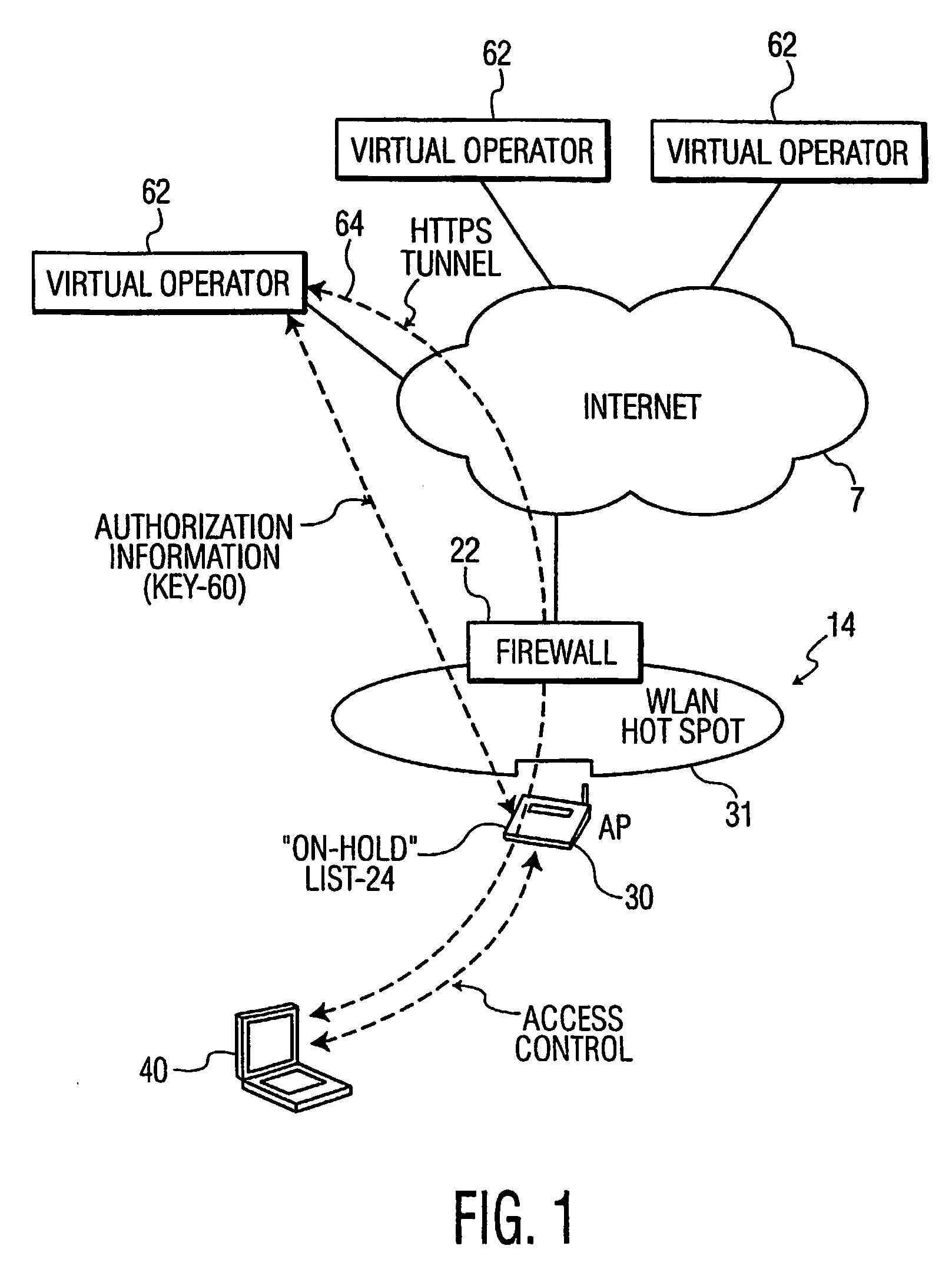
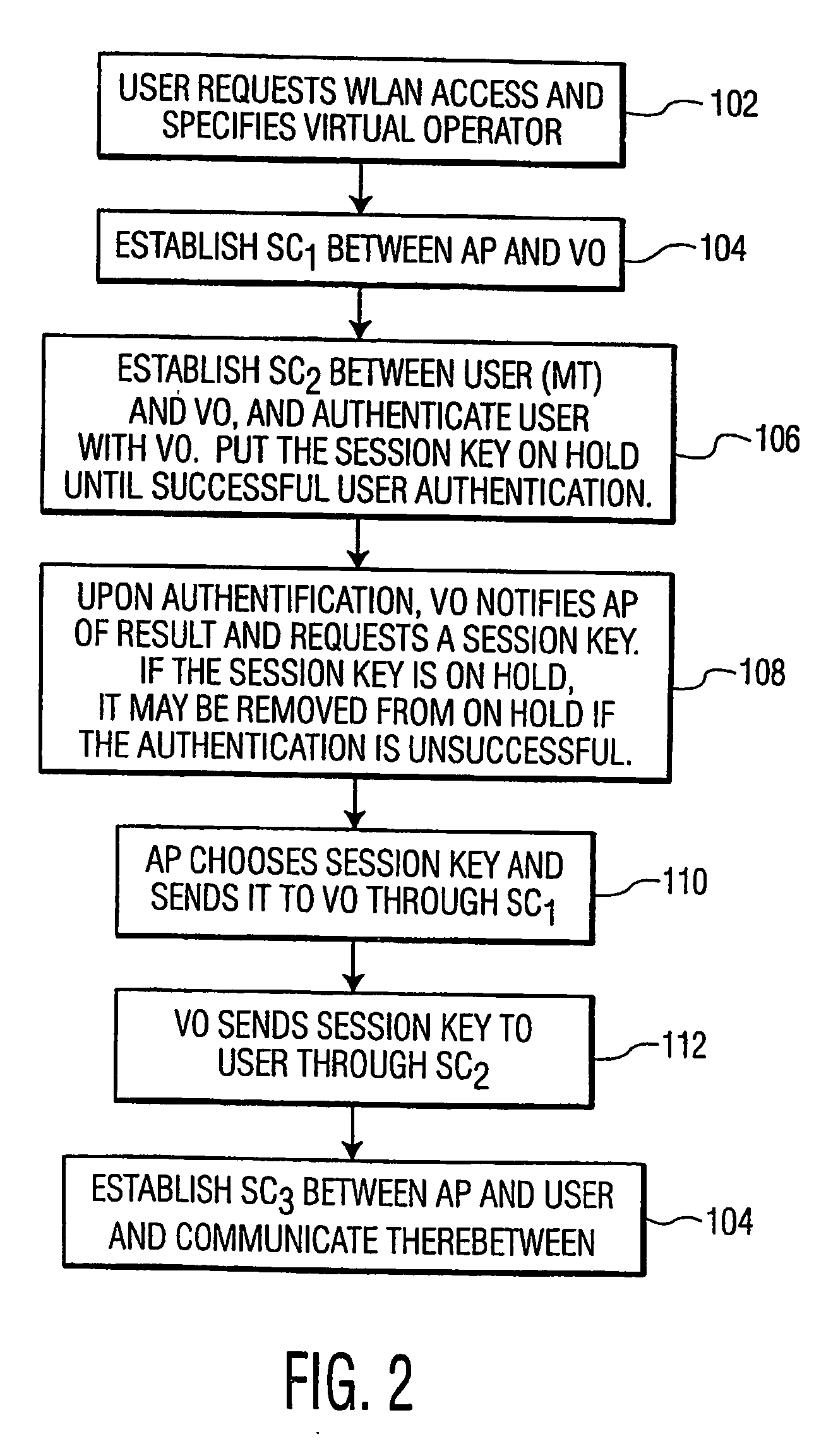
InactiveUS20060161771A1Efficient and effectiveSecure distributionKey distribution for secure communicationUnauthorised/fraudulent call preventionComputer networkWireless lan
A method and apparatus for managing a session key for allowing a mobile terminal to access a wireless local area network (WLAN). The invention provides for establishing a first secure channel between an access point and a virtual operator, and suggesting a session key to the virtual operator from the access point. A second secure channel is established between the virtual operator and a user, and the session key is sent to the user via the second secure channel upon successful user authentication. The mobile terminal accesses the WLAN using the session key.
Owner:INTERDIGITAL CE PATENT HLDG
Method for automatically generating list of meeting participants and delegation permission
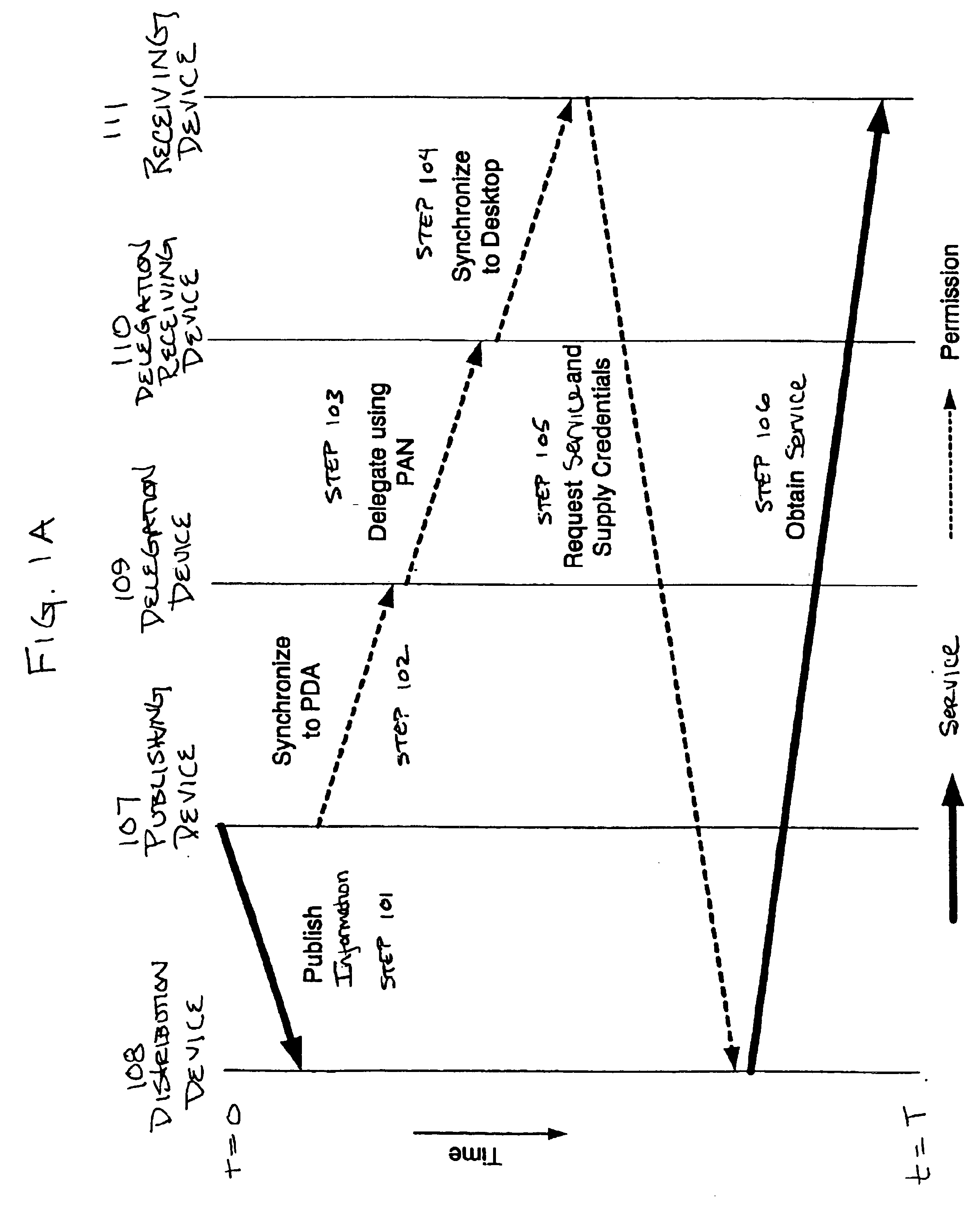
InactiveUS6885388B2Secure and convenient distributionImprove securityCathode-ray tube indicatorsMultiple digital computer combinationsAccess control matrixWorld Wide Web
A method and system automatically generate a list of participants physically present at a meeting and distribute permission to the participants. Identity and key information is collected from the participants during the meeting using at least one personal area network. The identity and key information is stored on a delegation device. Permission to access the services is distributed to the participants over at least one personal area network using the delegation device. The delegation device may include an access control matrix or moveable icons for organizing and distributing participant and permission information.
Owner:WIDEPOINT CYBERSECURITY SOLUTIONS CORP
Method and system for secure distribution of subscription-based game software
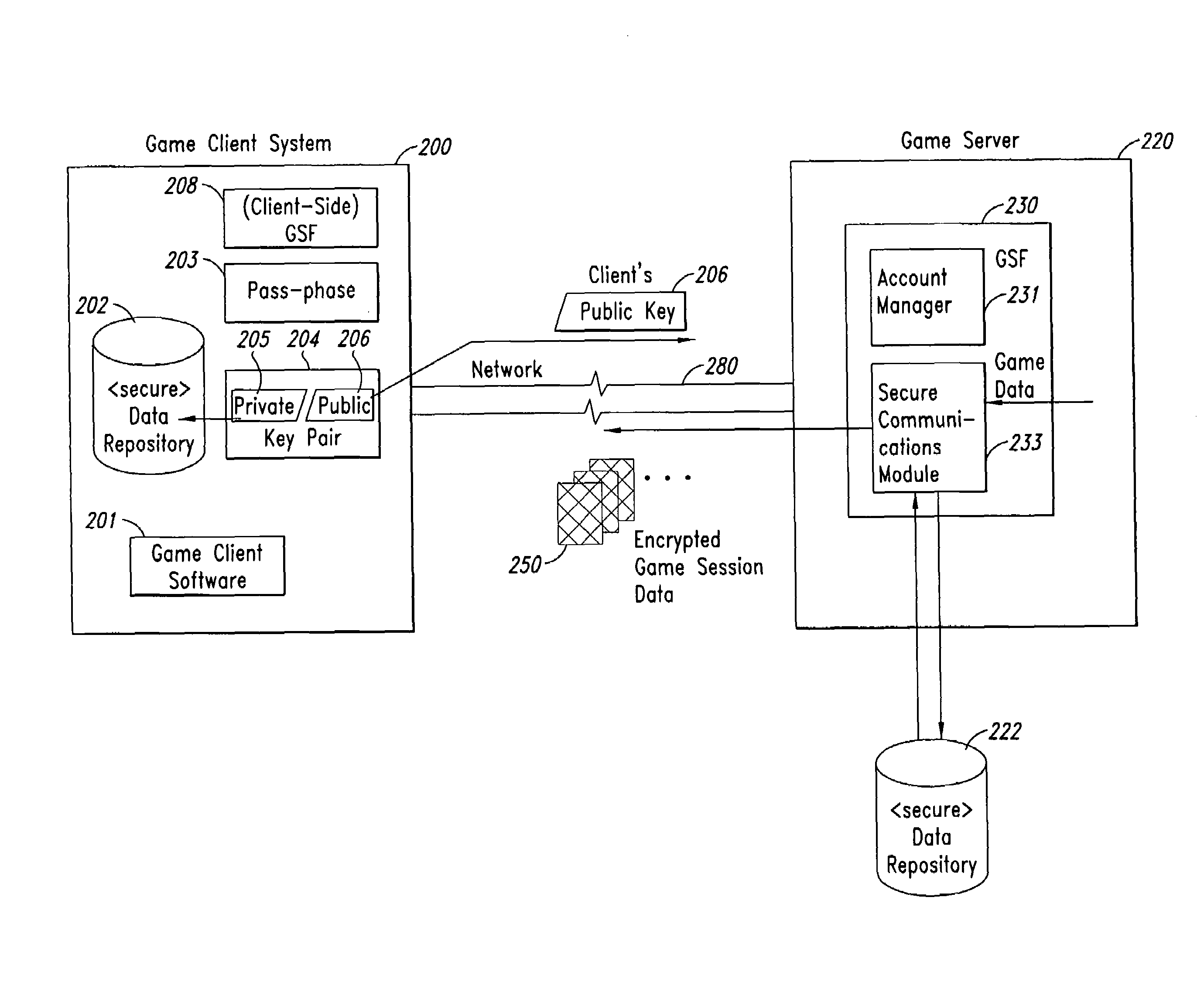
ActiveUS7409061B2Secure distributionCommunication securityKey distribution for secure communicationPublic key for secure communicationGame serverCopying
Methods and Systems for securely distributing software in a subscription-based environment are provided. In an example embodiment, a Game Security Facility (“GSF”) associated with a game server is used to manage secure communications with game clients. The GSF typically manages secure communication of the accounting and billing information and secure communication of game session data. In typical operation, the game client generates a pass-phrase that transparently includes a unique identifier of the machine upon which the subscription software will reside. RSA-type key pairs that are then generated using this pass-phrase will be associated uniquely with both the game player and with the machine upon which the software resides, thus preventing unauthorized copying to another machine or unauthorized use by a third party. A public key generated using this pass-phrase is forwarded to the GSF, which uses it to generate a unique one-time random session key (for use as a symmetric key) for each session with the game client. The session key is then encrypted for the game client using the public key of the client. Session data, including the original game files downloaded upon successfully subscribing, are then transmitted between the game server and the game client using encrypted versions of the session key. In one embodiment, the game client can upgrade the machine upon which the subscription data resides, cause the session keys to be reissued using a new public key, and retain access to previously downloaded data.
Owner:CLOUDROCK LLC
Peer-to-peer content distribution
InactiveUS20110125849A1Easy to liftSecure distributionMultiple digital computer combinationsTransmissionClient-sideDistribution system
A method is described for distributing content using a P2P distribution system. The distribution system comprises a P2P network connected to a server system, wherein the server system is configured to divide the content in pieces and to provide the P2P network with piece variants of one or more pieces. The method comprises the steps of: providing a communication session between a client and the server system; the client sending a content request to the server system; the client receiving in response to the content request one more piece variant identifiers and distribution information comprising integrity information of all piece variants provided by the server system.
Owner:IRDETO ACCESS
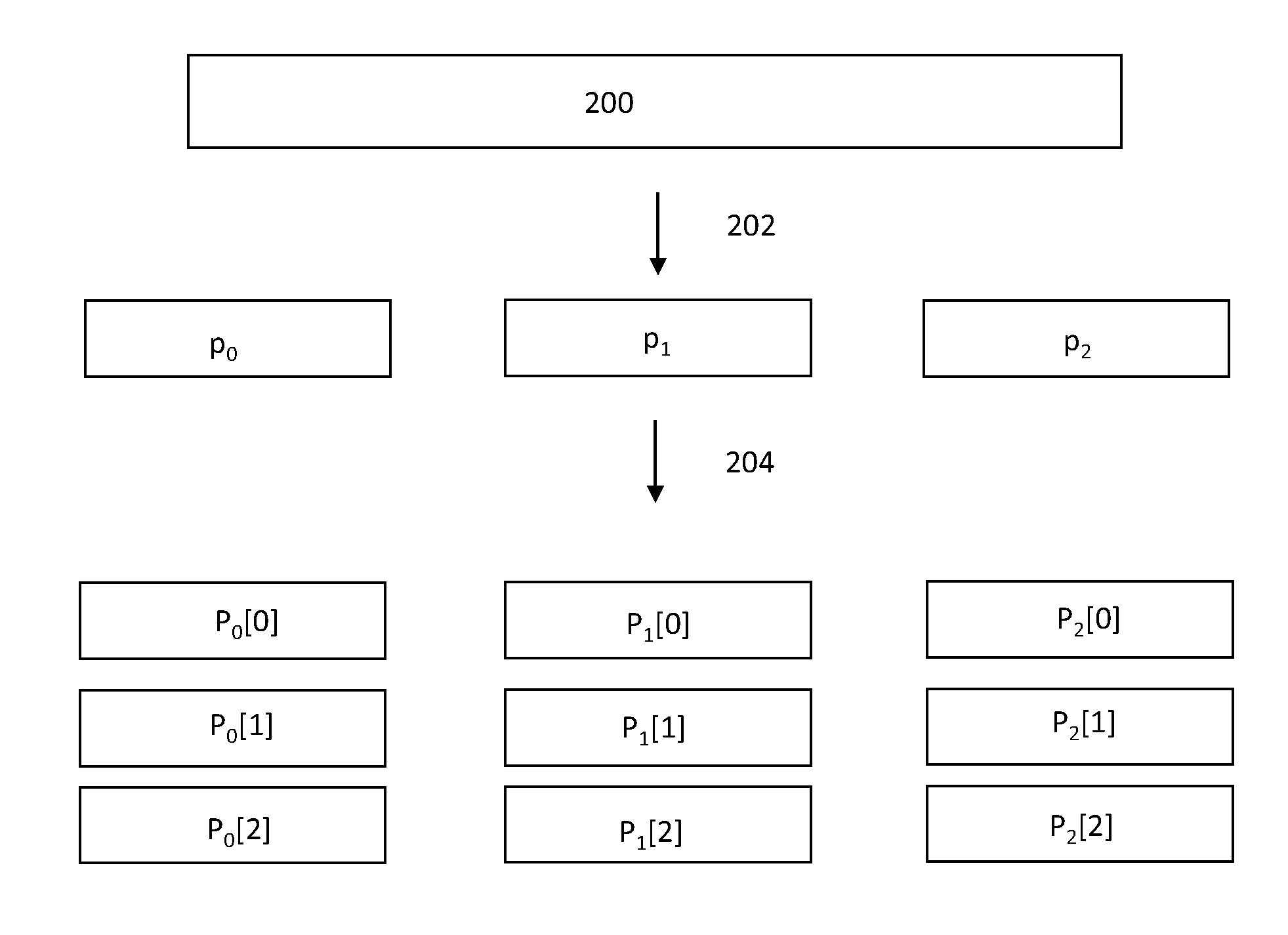
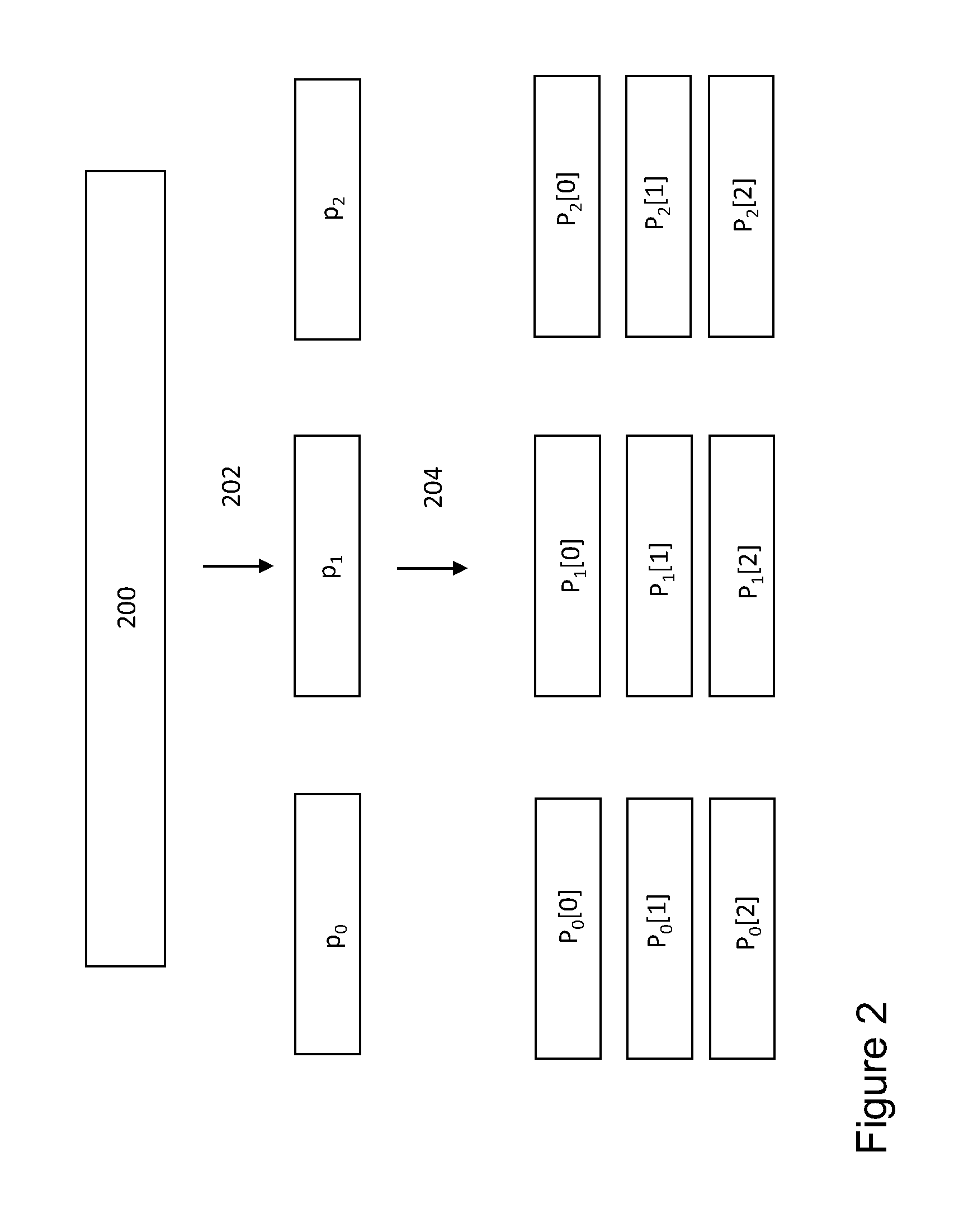
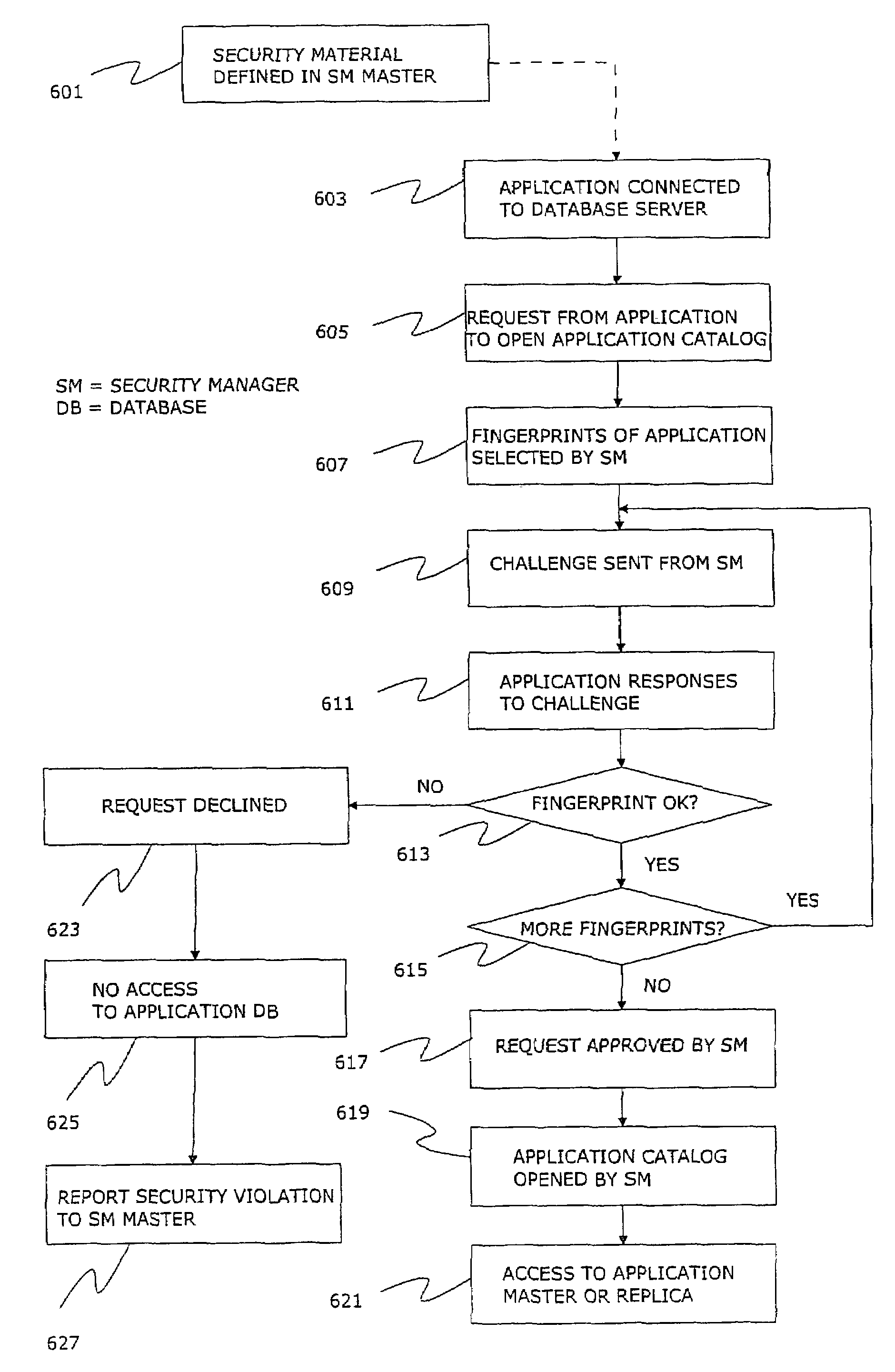
Method and system for managing security material and services in a distributed database system
InactiveUS7266702B2Strengthen security managementSecure distributionData processing applicationsUser identity/authority verificationApplication softwareDatabase server
A method and system for managing security material and security services, and for securely distributing them in a distributed database system where one or multiple distributed applications operate on distributed data. One database hosted by database server contains master version of the security data of databases hosted by database servers. The database hosted by database server has a global view of the security material for managing security of the other databases. A special database is responsible of providing security services to application database of a database server. The system and method control application programs access to data of a database in a database server, and also facilitates the security management issues of complex database topologies, such as multitier hierarchies or multi-master topologies.
Owner:SOLID INFORMATION TECH
Method for controlling the distribution of software code updates
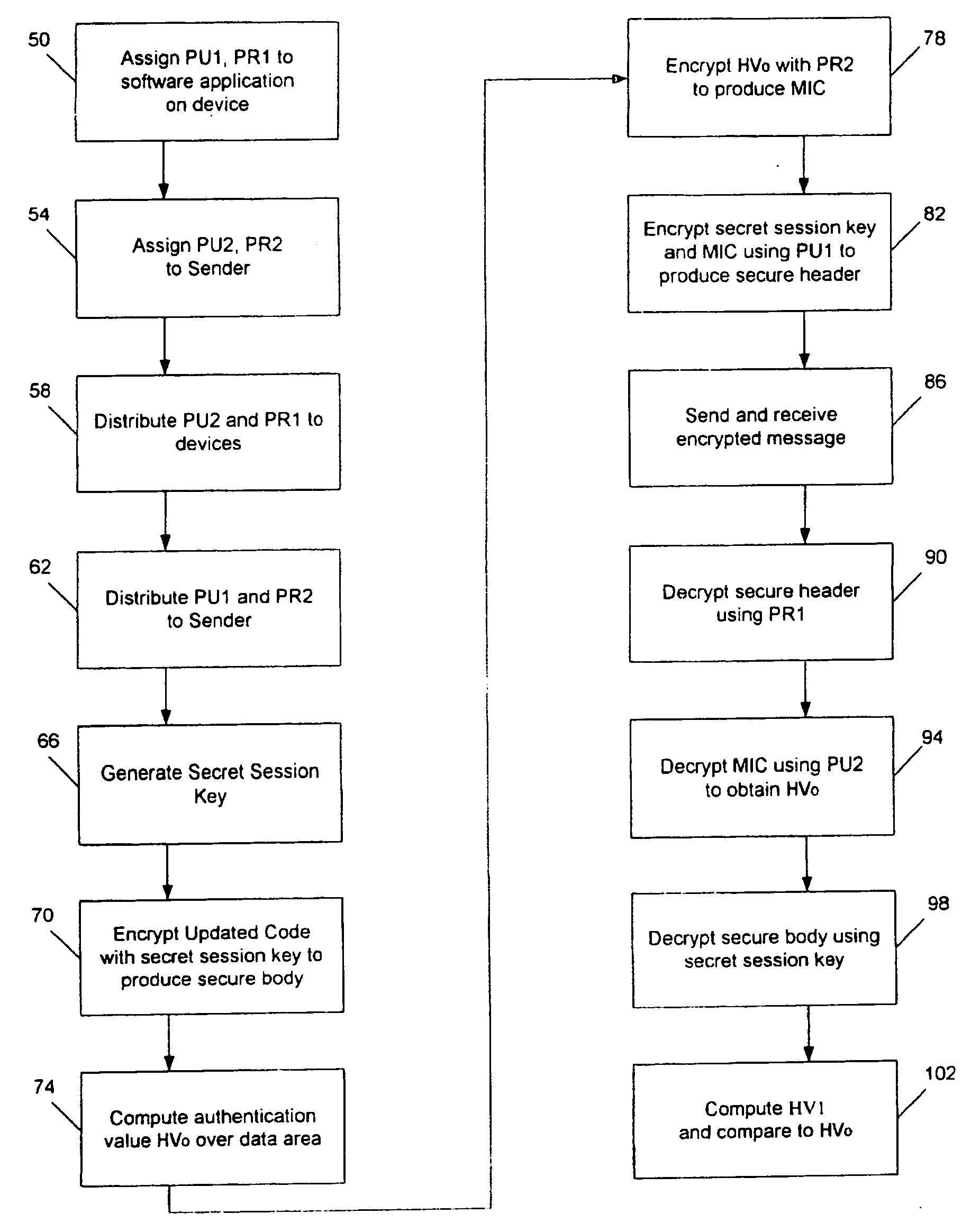
InactiveUS20060101454A1Secure distributionKey distribution for secure communicationUser identity/authority verificationComputer hardwareEmbedded software
A method is described for controlling the distribution of a software code update for an embedded software application on a device. The method includes the steps of assigning an asymmetric key pair to the software application and another asymmetric key pair to the sender of the software code update. The software code update is sent in a secure manner to one or more devices while preventing devices not possessing to the appropriate keys from obtaining the software code update.
Owner:LEXMARK INT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com