Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
402results about How to "Strengthen security management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
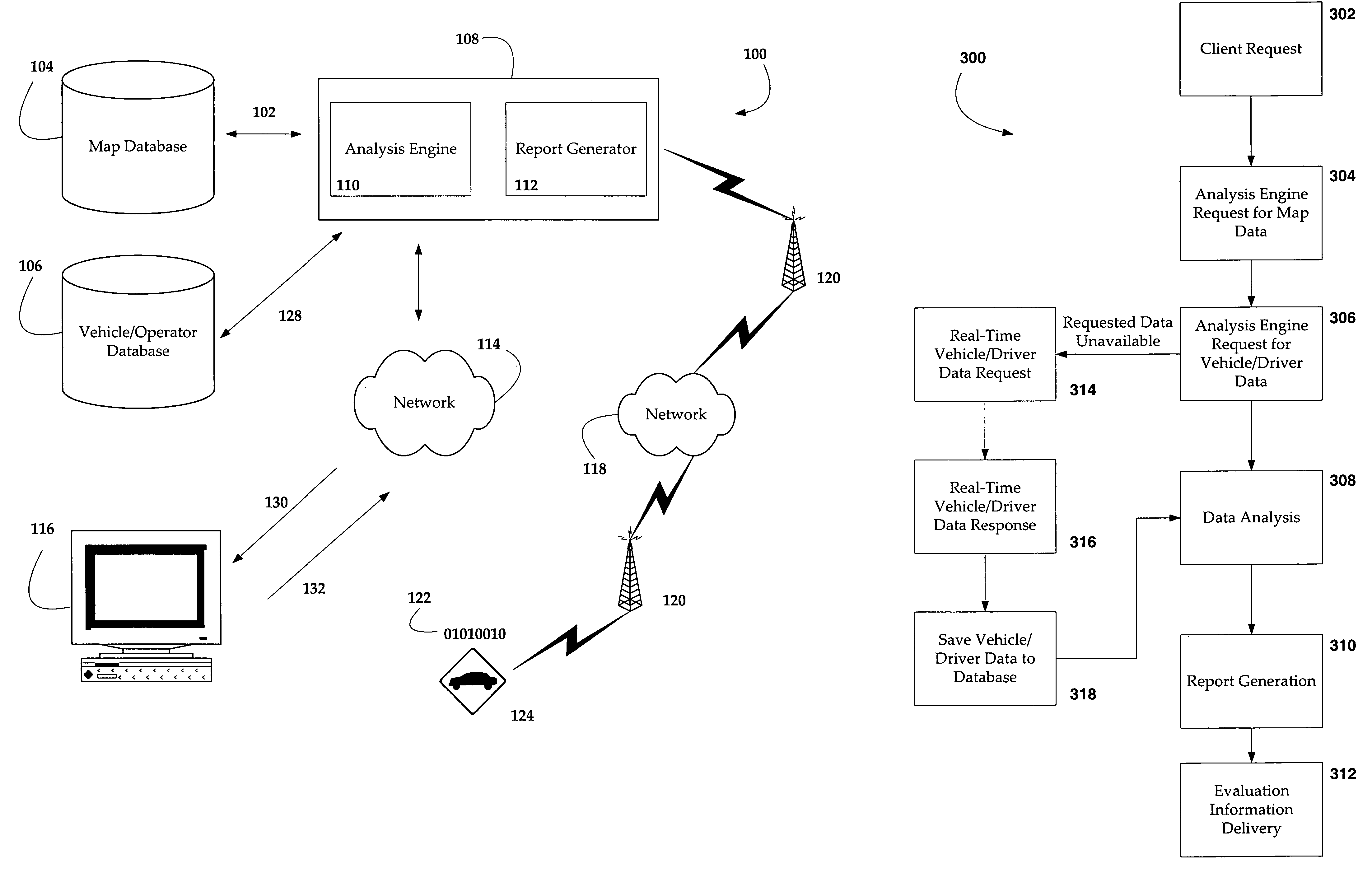
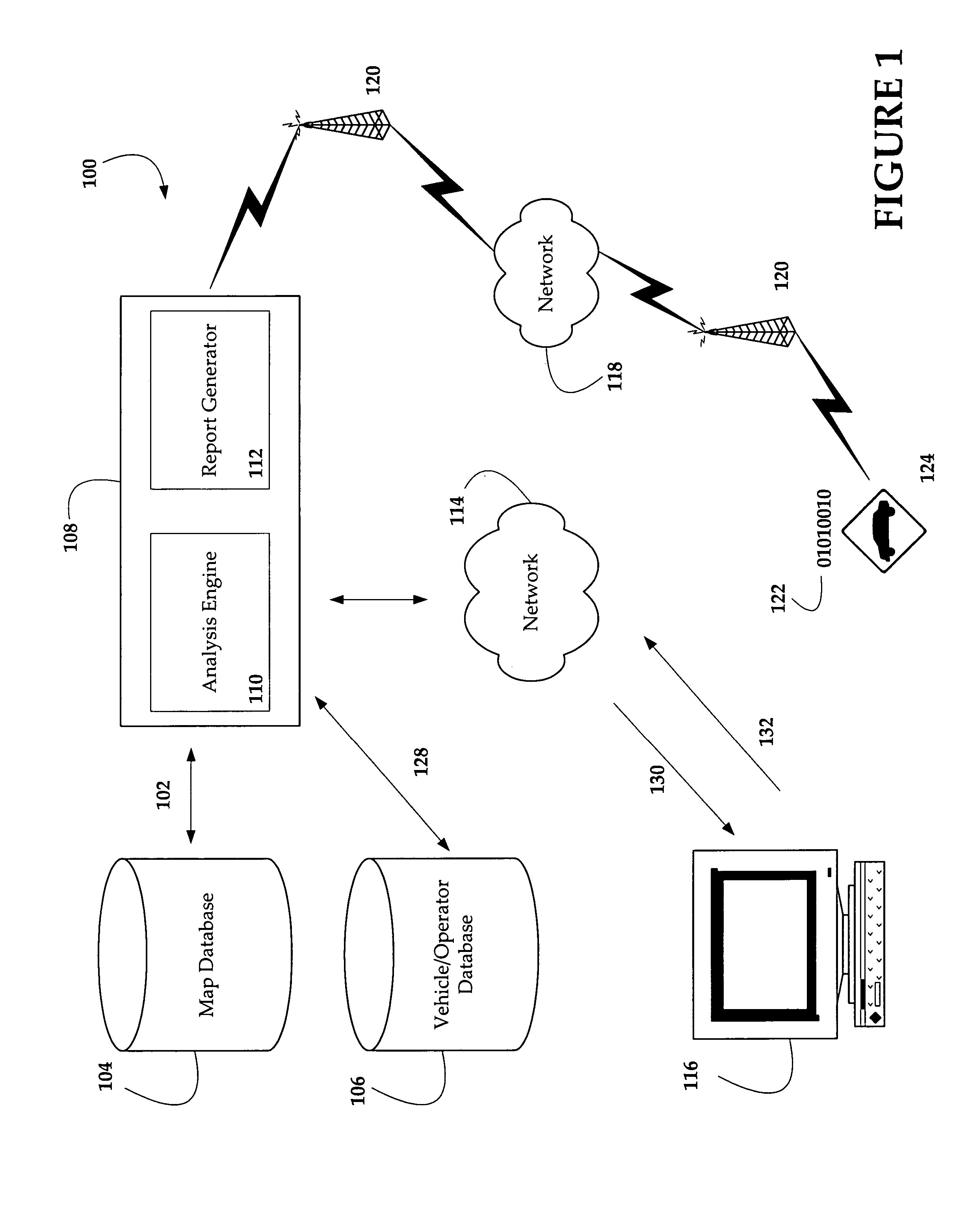
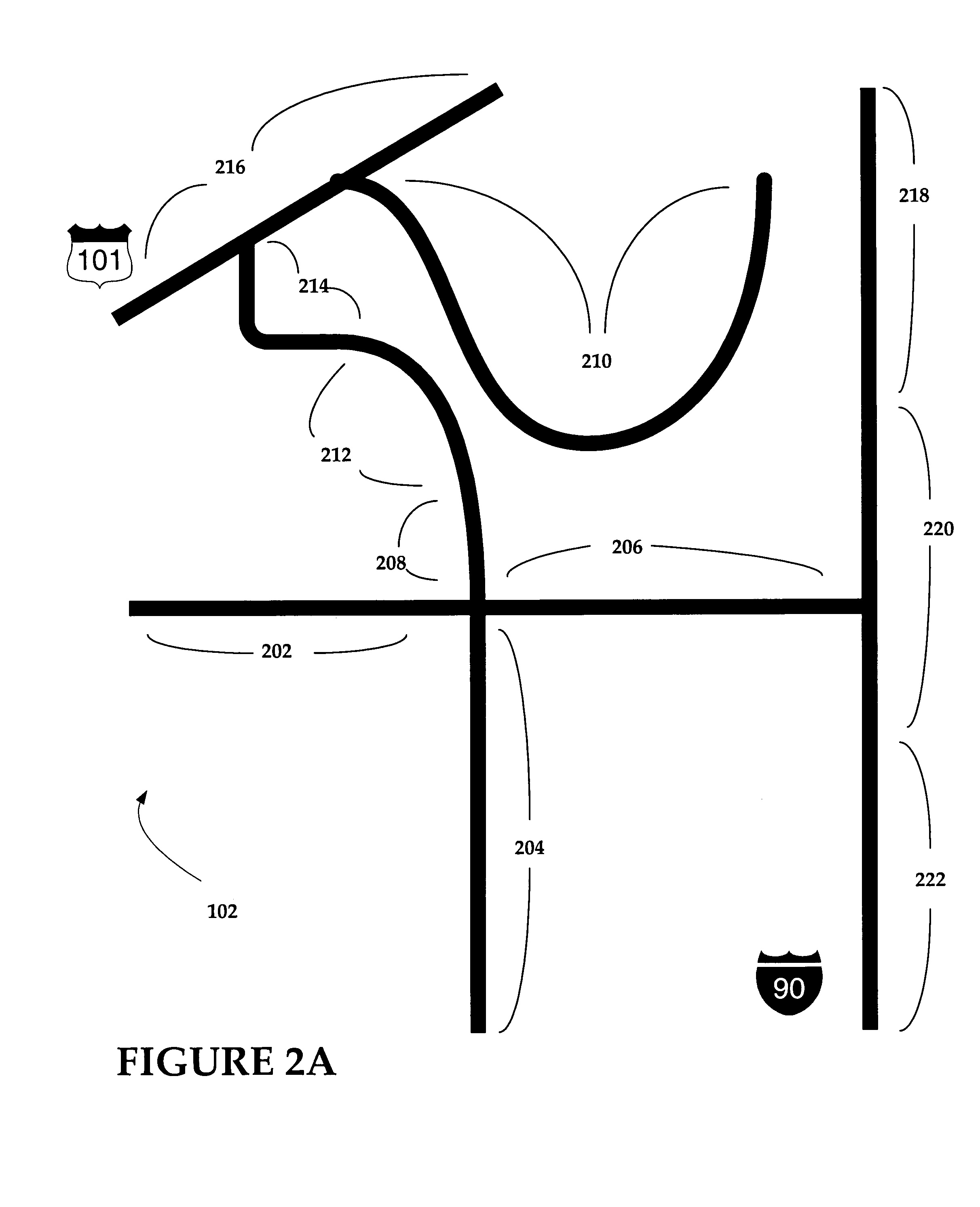
System and method for evaluating vehicle and operator performance
ActiveUS7356392B2Strengthen security managementMore speedVehicle testingArrangements for variable traffic instructionsNetwork performanceOperator performance
The present invention relates to the field of safety management of one or more vehicles, and more particularly, to a system and method for analyzing information relating to a vehicle's performance characteristics such as speed against environmental attributes such as speed limits to assess a vehicle and operator's tendency to operate according to preset or other criteria.
Owner:SPEEDGAUGE
Universal userid and password management for internet connected devices
InactiveUS6859878B1Computer security is enhancedImprove securityKey distribution for secure communicationDigital data authenticationThe InternetApplication software
An improved system, method, and computer program product is provided to manage userid / password combinations by utilizing a universally accessible Internet location. This site stores and manages an encrypted database containing the customers multiple userid and password combinations, and also acts as the repository and distribution center for the software used to access and manage the database by the customer. In one embodiment, these applications are designed to work seamlessly with the Internet connection-software (e.g. a set of buttons on a browsers tool bar). Encryption is used on both the client and / or server side to ensure security and integrity.
Owner:IBM CORP
Method and apparatus for managing communication security in wireless network
ActiveUS20060062391A1Maintain communication securityMaintaining communication securityKey distribution for secure communicationDigital data processing detailsKey generationCommunications security
A method and apparatus for managing communication security in a wireless network are provided. The method includes receiving from a station that intends to associate in the wireless network including an access point, first key generation information provided by the access point and second key generation information provided by the station, providing third key generation information, generating a security key using the first key generation information, the second key generation information, the third key generation information, and an initial key, and sending the third key generation information and the security key to the station.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for secure management or remote systems
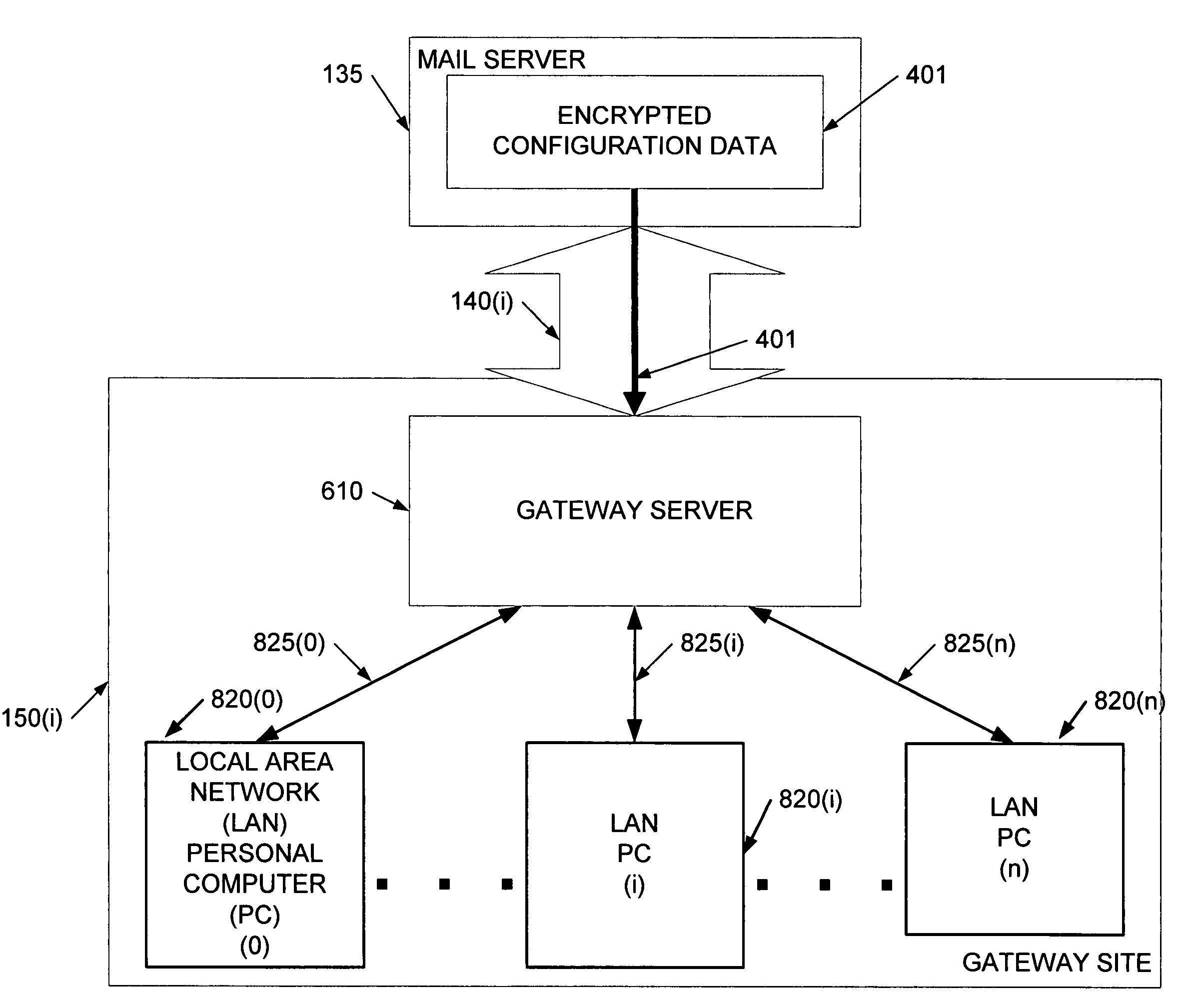
InactiveUS7222228B1Strengthen security managementDigital computer detailsData resettingComputer networkRemote system
A secure system and method for managing and monitoring remote devices preferably includes periodic pulling of configuration information from an accessible platform rather than pushing information from a central site. In one implementation, an electronic mail system is used as a staging platform in combination with a defined polling arrangement to transfer encrypted configuration information in a robust and secure method for updating remote device configurations.
Owner:NETWOLVES IP
Translation Engine for Computer Authorizations Between Active Directory and Mainframe System
InactiveUS20080263640A1Extended processing timeImproved security flexibilityDigital data processing detailsComputer security arrangementsComputer accessMainframe computer
The invention provides a method and system of implementing a high performance “non-RACF external security-manager product,” which maintains and translates a merged single source of authorizations to both mainframe and Microsoft Windows Active Directory (AD) systems. In one embodiment, a method comprises generating at a server computer access information for a mainframe computer indicative of mainframe authorization for a set of users, receiving from the mainframe computer information indicative of an authorization request, the information indicative of the authorization request identifying a user trying to access the mainframe computer, and sending at least a portion of the access information from the server computer to the mainframe computer, the portion of the access information including mainframe access information for the user.
Owner:REDPHONE SECURITY INC
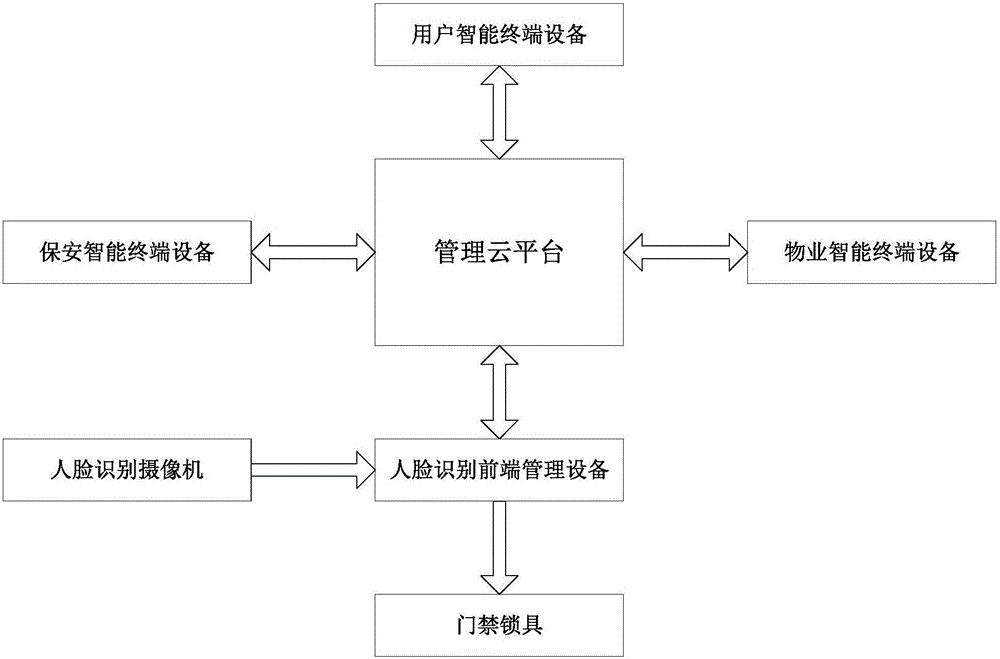
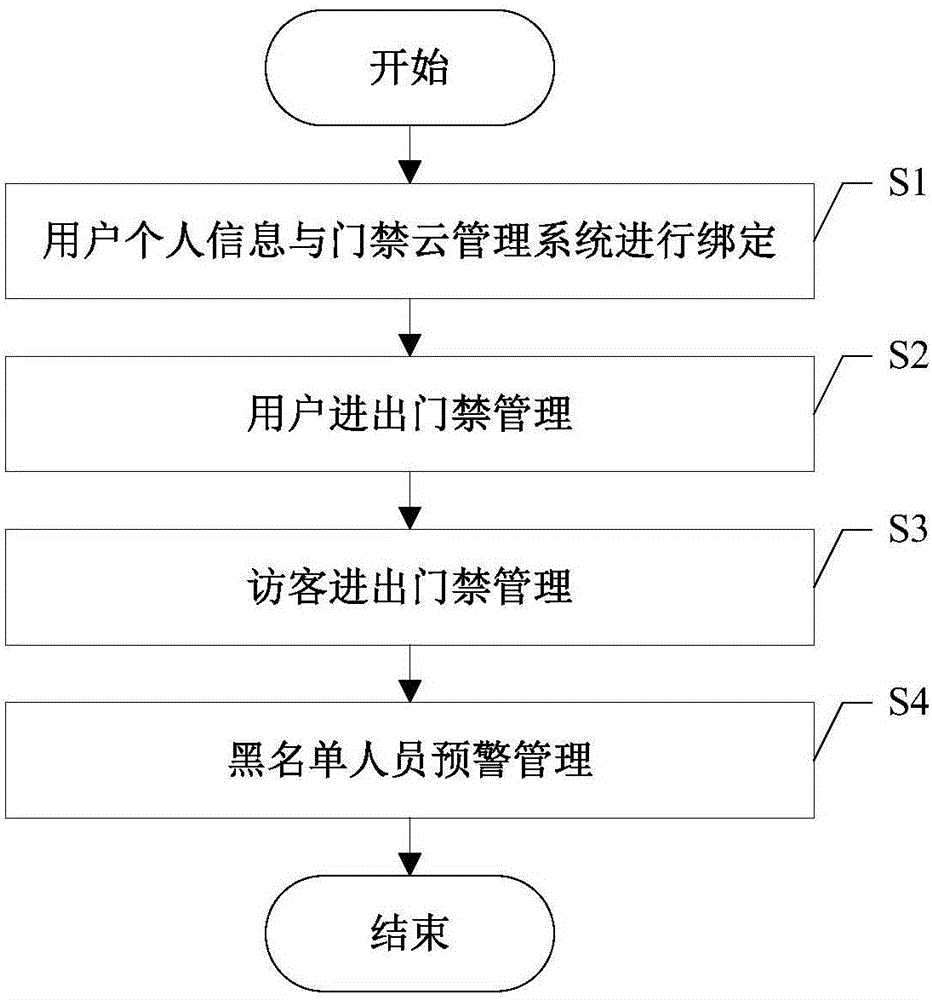
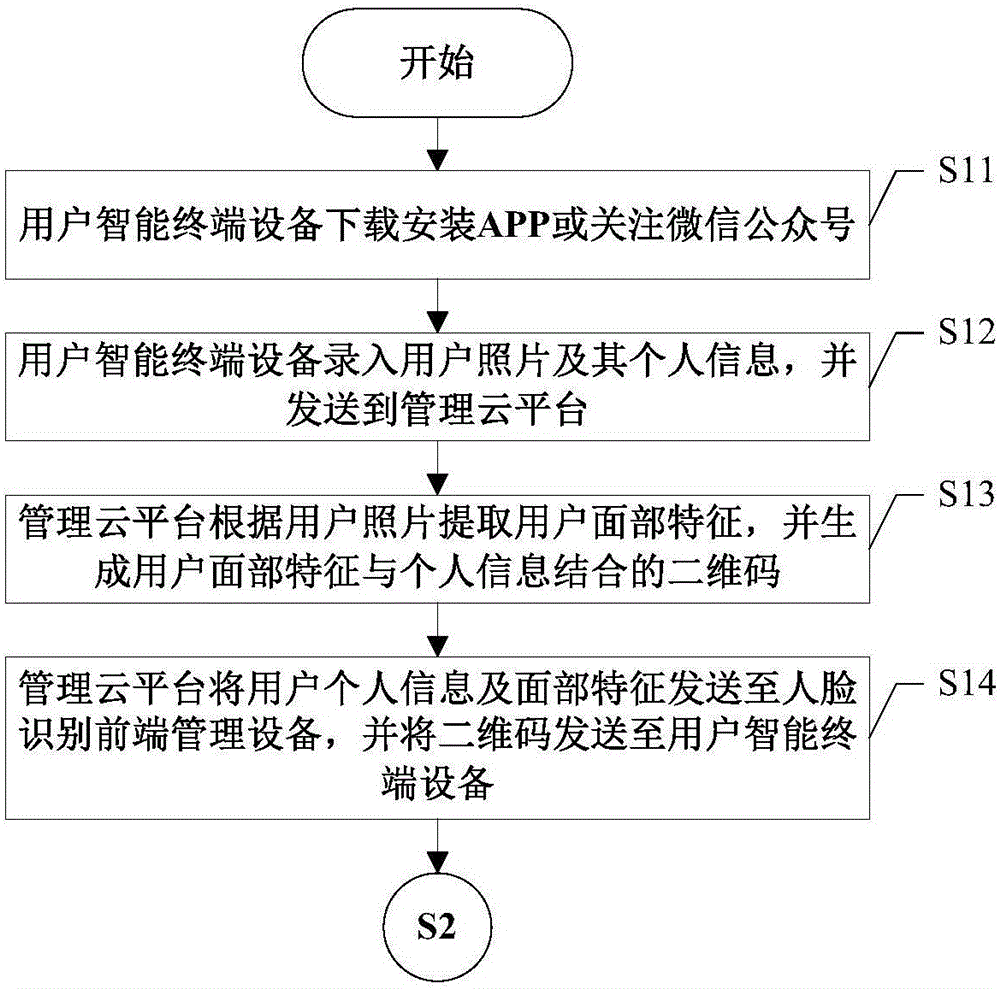
Access control cloud management system and method based on face recognition
ActiveCN105869248AHigh feasibilityImplement security managementCharacter and pattern recognitionIndividual entry/exit registersWorkloadPersonally identifiable information
The invention discloses an access control cloud management system and method based on face recognition. Through face recognition and a cloud technology thereof, a video real-time monitoring and alarming function is supplied to access control, integration of access control and video face recognition is achieved, and access control security and protection management is improved. According to the system and method, a user using threshold is low, operation is easy, the system and method can be used only by verifying personal identity information of a user, access control recognition is conducted by adopting face recognition, and therefore an access control system can easily, conveniently, rapidly and comprehensively record personnel entering and leaving information; entering and leaving of a person with the face which cannot be recognized can be forbidden, or alarming is conducted; entering and leaving information of a visitor also can be quickly generated and recorded, the security management effect can be effectively improved, and the workload of security personnel can be reduced.
Owner:CHENGDU QIANFAN TECH DEV
Multi-dimensional intelligent remote inspection system for transformer substation
ActiveCN110707823AAvoid silosExtend the cycle of comprehensive inspectionsCircuit arrangementsSustainable buildingsSmart surveillanceEmbedded system
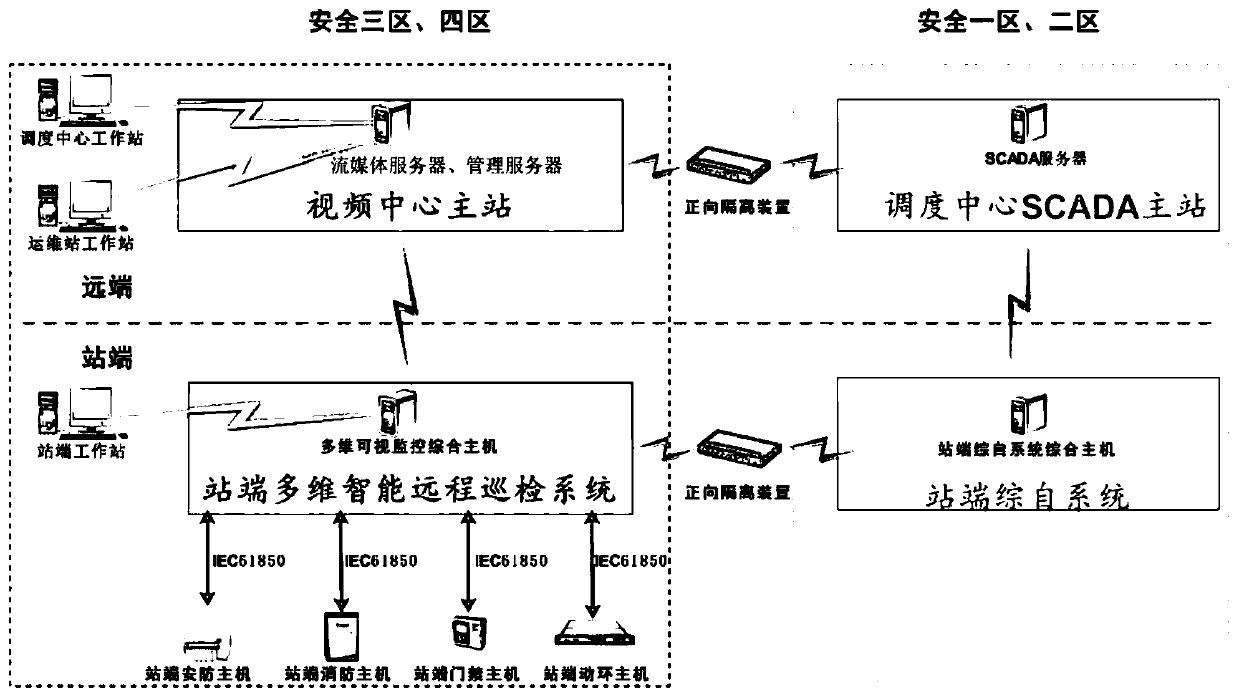
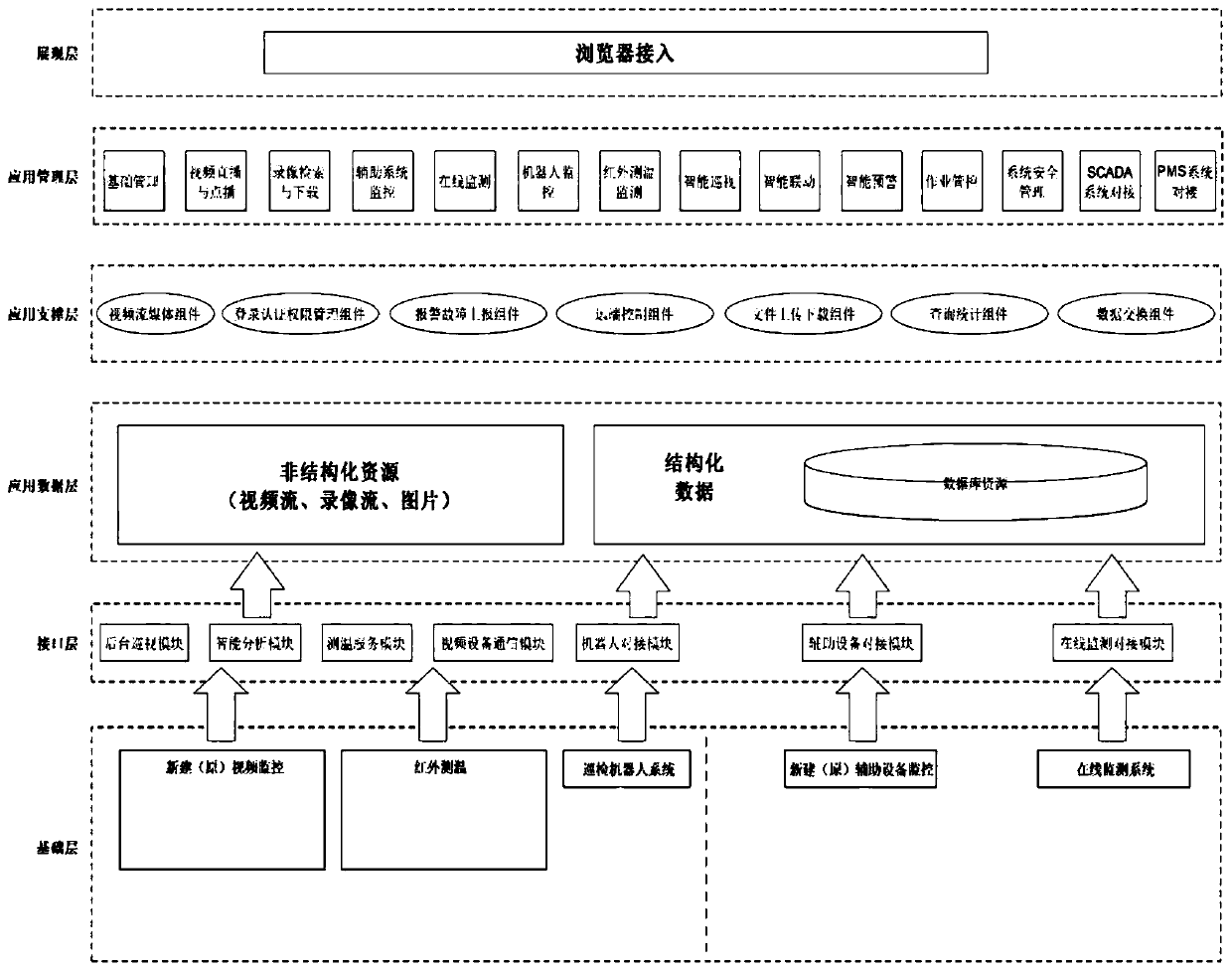
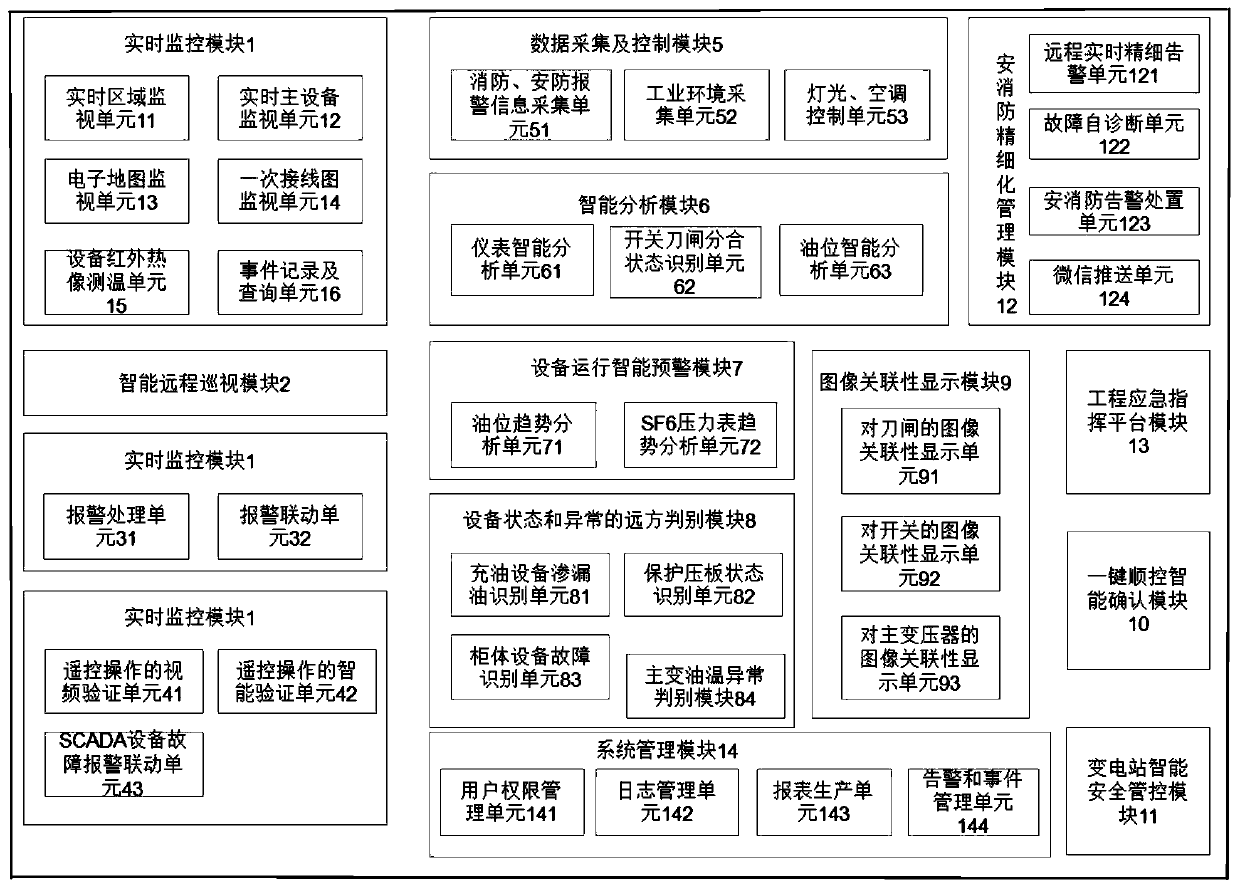
The invention discloses a multi-dimensional intelligent remote inspection system for a transformer substation, which adopts independent networking and receives various operation information of a station end integrated automation system, and is in communication connection with a video center main station to obtain remote view data, remote measurement data, remote control data and remote signaling data; the dispatching center SCADA main station system is in data communication with the station end integrated automation system and receives various kinds of operation information of the station endintegrated automation system; and the video center main station is also in data communication with the dispatching center SCADA master station system to provide real-time video verification for remotecontrol operation of the dispatching center SCADA master station system. According to the invention, a powerful intelligent monitoring and emergency command platform is provided for production linksand security links such as remote control operation and remote equipment inspection of scheduling personnel, field operation and emergency disposal of operation and maintenance personnel and the like,can be suitable for actual application of power production, and ensures safe operation of power grid production.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO
Apparatus for controlling articles in custody
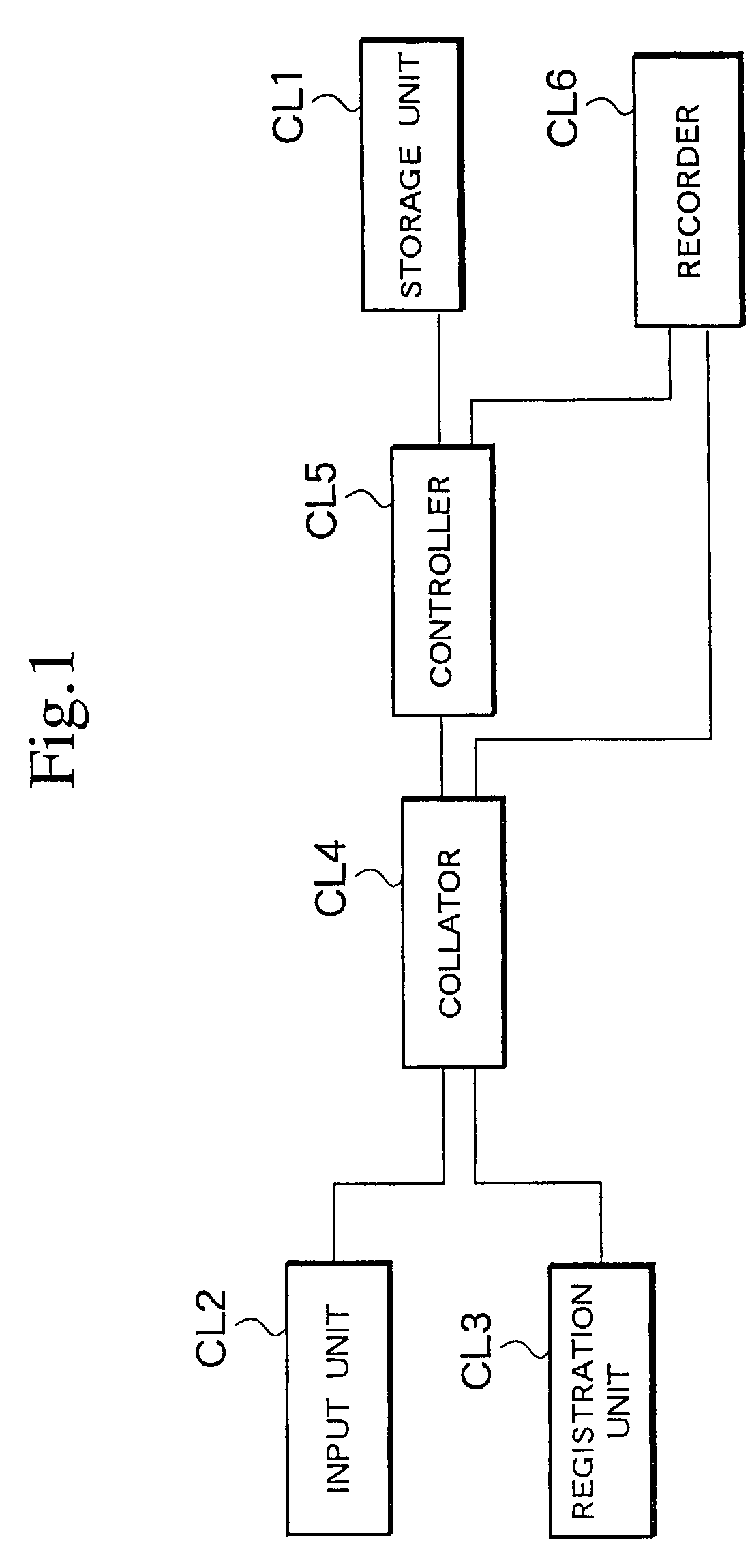
InactiveUS7129817B2Control process safetyStrengthen security managementElectric signal transmission systemsImage analysisCollationComputer security
An apparatus for reliably and easily controlling articles in custody, for example articles in a safe, has a storage unit lockable to keep the articles therein and unlockable to allow the articles to be taken out therefrom, an input unit to input biometric information for unlocking the storage unit, a registration unit to register biometric information in advance, a collator to collate the input biometric information with the registered biometric information, a controller to unlock the storage unit if the collation by the collator authenticates the input biometric information, and a recorder to record at least a person related to the authenticated biometric information in response to the unlocking of the storage unit.
Owner:UNIREC +1
High toss act evidence obtaining system based on digital image processing technology
InactiveCN105163067AStrengthen community security managementStrengthen security managementImage analysisClosed circuit television systemsData transmissionCable network
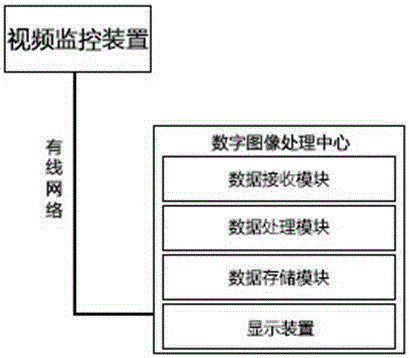
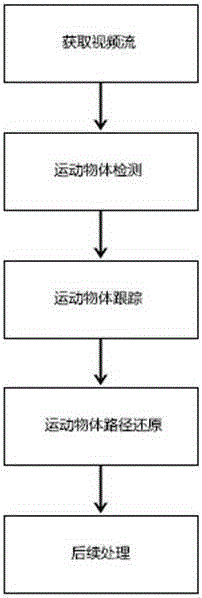
The invention discloses a high toss act evidence obtaining system based on a digital image processing technology. The system comprises a video monitoring device, a digital image processing center and a wired network. The video monitoring device is used for comprehensively and timely monitoring a district and obtaining image data. The wired network is used for performing image data transmission between the video monitoring device and the digital image processing center. The digital image processing center is used for analyzing the image data obtained by the video monitoring device and obtaining the movement track and a toss position of a thrown object. Real-time monitoring of the district is performed aiming at the high toss act. When the high toss act is detected, the moving object track tracing is performed, and the toss position of the thrown object is positioned, so that evidence obtainment for liability dispute about the high toss act is facilitated. The invention fully utilizes modern technologies of communication, digital image processing and the like, and combines monitoring videos of the high toss act of the district for providing an operable solution to high toss act evidence obtaining, so that the district security management is enhanced.
Owner:WUHAN UNIV
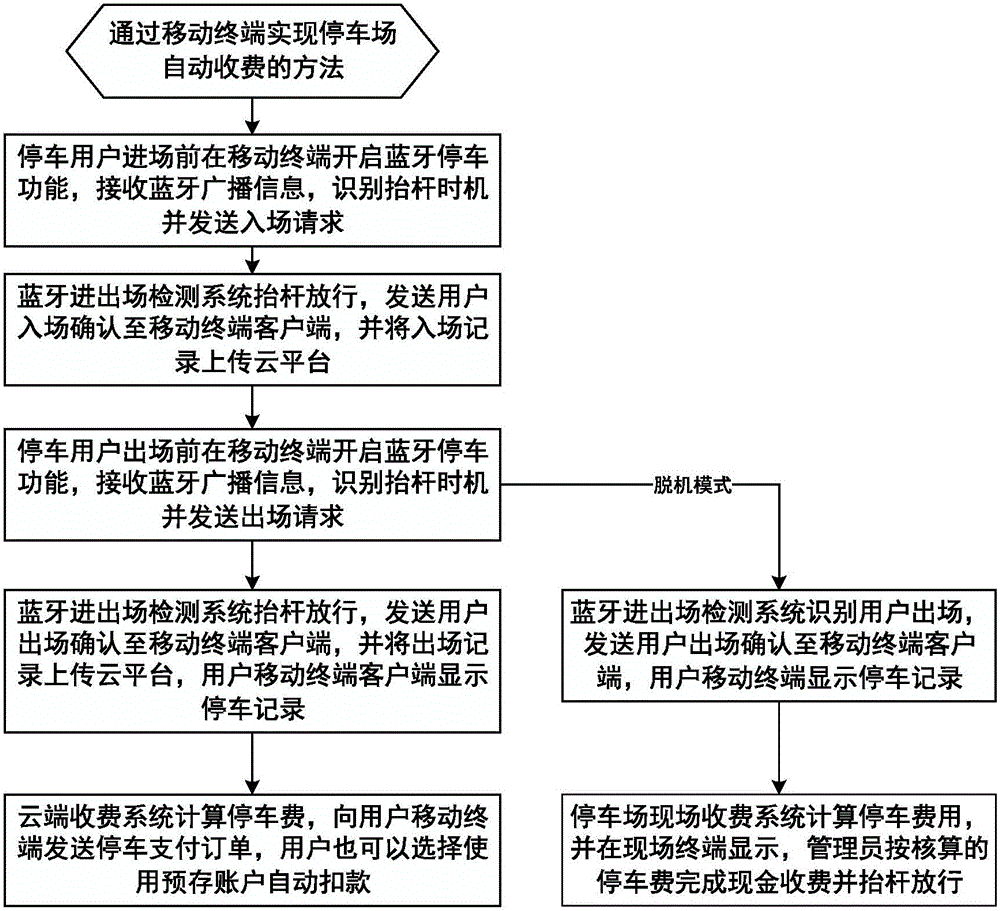
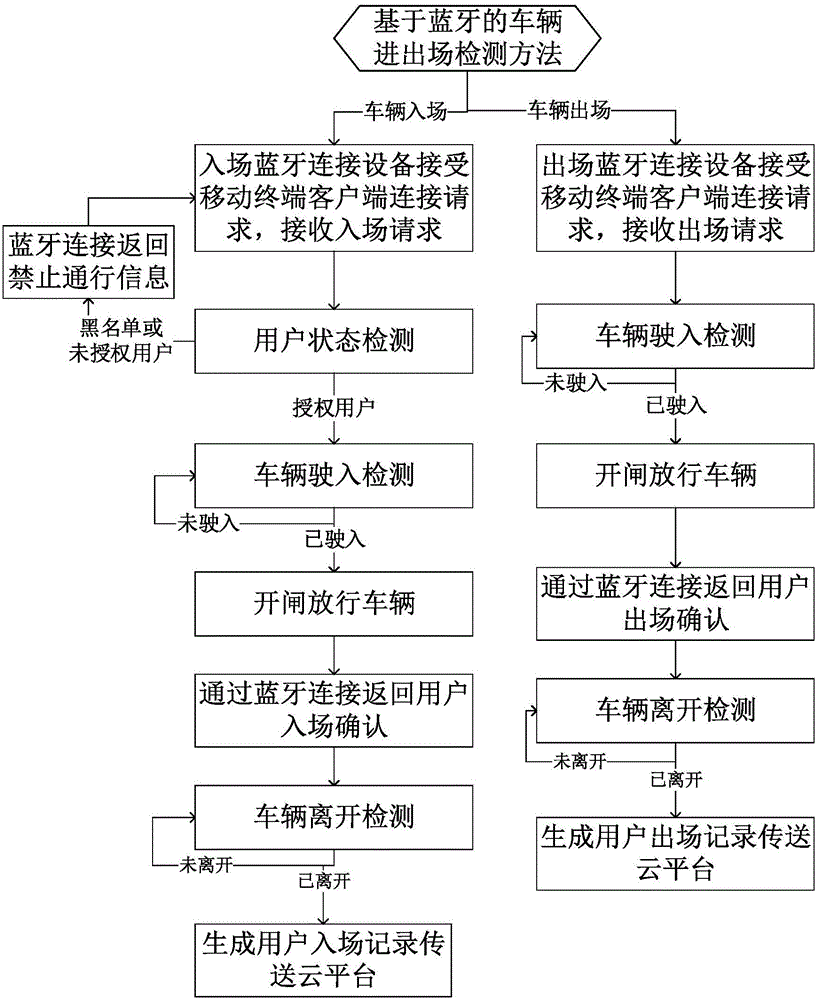
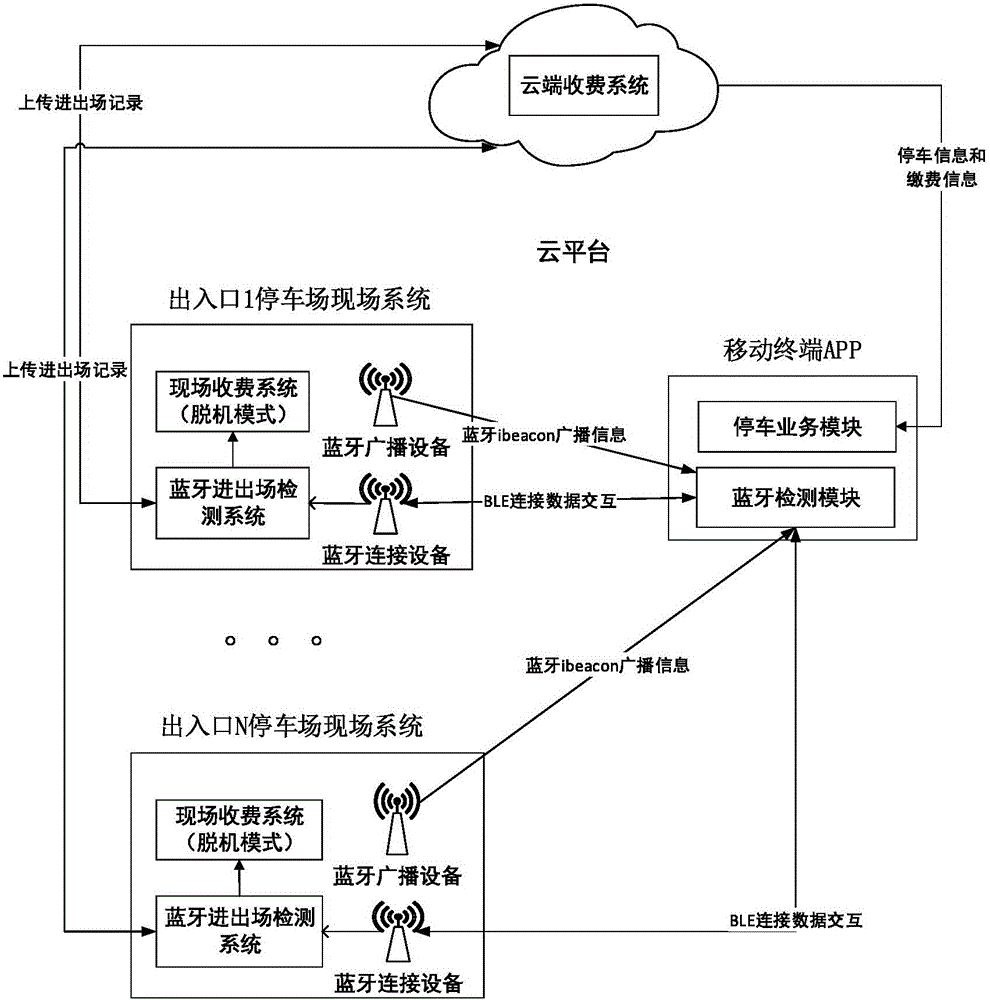
Method and system of realizing parking lot automatic charging based on bluetooth technology
ActiveCN105957159AImprove work efficiencyEntry and exit time savingsTicket-issuing apparatusNetwork connectionData exchange
The invention discloses a method and a system of realizing parking lot automatic charging based on bluetooth technology. Bluetooth broadcasting devices are disposed on an entrance gate and an exit gate of a parking lot, and are used as beacons for transmitting broadcasting information. A user mobile terminal client is used to acquire the broadcasting information, and is used to determine rod lifting information, and then is used to establish bluetooth connection with bluetooth entry / exit detection systems for data exchange, and then users can enter and leave the parking lot automatically and quickly by using the mobile terminal bluetooth technology under a condition of lack of network connection. A vehicle queuing condition caused by vehicle owners paying fees at the exit is effectively reduced, and the vehicle passing efficiency is improved, and in addition the costs are low, and the maintenance is easy. By adopting the automatic charging, a plurality of charging modes are realized, and the solving of the irregular charging phenomenon is facilitated. By adopting a cell phone parking way, the users are bound with the corresponding vehicles, and then the safety management of the vehicles and the users is facilitated, and the safety problems that the vehicle are stolen in the parking lot, and the unidentified people drive in the parking lot, and so on are effectively solved.
Owner:WISCOM SYSTEM CO LTD
An enterprise resource management system based on a block chain
ActiveCN109698752AImprove management and operation efficiencyEnsure safetyFinanceUser identity/authority verificationResource Management SystemComputer module
The invention discloses an enterprise resource management system based on a block chain. The enterprise resource management system includes a network communication layer, a network entity layer, a network entity service layer, a public support component, a security protection component, a business service layer, a command line front-end module, an API & SDK, a block link entry and management module and an application and presentation module. and various types of block chain platforms are developed and accessed based on the business service layer and the API & SDK. Compared with a traditional resource management system, the management operation efficiency can be greatly improved in the aspects of safety confirmation, input, management, query and the like, the safety of the system can be guaranteed, and the management operation efficiency can also be improved.
Owner:NARI INFORMATION & COMM TECH
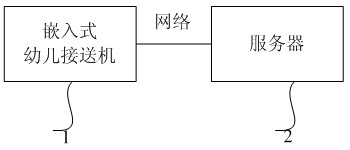
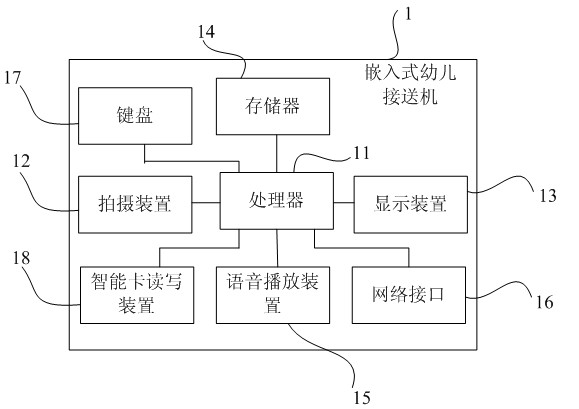
Child picking and sending system on basis of face identification and control method thereof
InactiveCN102073859AStrengthen security managementPrevent impersonationCharacter and pattern recognitionMessaging/mailboxes/announcementsText messagingMobile phone
The invention belongs to the field of face identification and provides a child picking and sending system on the basis of face identification. The child picking and sending system comprises an embedded child picking and sending machine and a server, wherein the embedded child picking and sending machine is used for registering first information of a plurality of picking and receiving people for each child in advance, storing the first information in a storage of the embedded child picking and sending machine, identifying a field picking or sending person through face identification according to the first information and sending identification record information comprising an identity of the picked or sent child to the server through a network after the identification is successful; and the server is used for sending a mobile phone prompting short message to other picking and sending people of the picked or sent child except for the field picking or sending person according to the received identification record information and second information of the child picking and sending people, which is prestored at the end of the server. The child picking and sending system provided by the invention prevents a lawless person from falsely picking up the child by carrying out face identification on the picking and sending person, sends the mobile phone prompting short message to parents of the child, who are registered in advance, when the child is picked up, so as to strengthen safety management of picking up and sending the child.
Owner:HANVON CORP
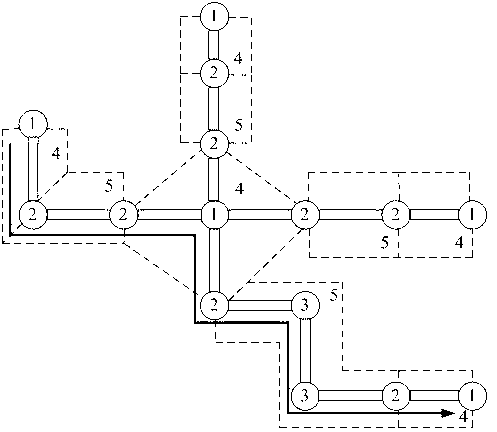
Airport surface road network model and airport surface collision detection critical alarm algorithm
InactiveCN103310661AStrengthen security managementAvoid exhaustionAircraft ground controlCollision detectionRoad networks
The invention provides an airport surface road network model, wherein an airport aircraft ground moving path is divided into fork components, taxi track components, runway components and taxi track component ports. The invention further provides an airport surface collision detection critical alarm algorithm which comprises the following steps of: for each aircraft, firstly computing the time when the aircraft enters into and leaves away from all the components according to the ground path of the aircraft and the speed of the aircraft; and for each fork component and each taxi track component, determining whether or not the component has a collision risk. After the airport surface road network model and the airport surface collision detection critical alarm algorithm provided by the invention are used, the safety detecting efficiency of an airport can be observably improved, the running instantaneity can be guaranteed, so that the airport surface road network model and the airport surface collision detection critical alarm algorithm provided by the invention are better in stability and robustness.
Owner:CIVIL AVIATION FLIGHT UNIV OF CHINA
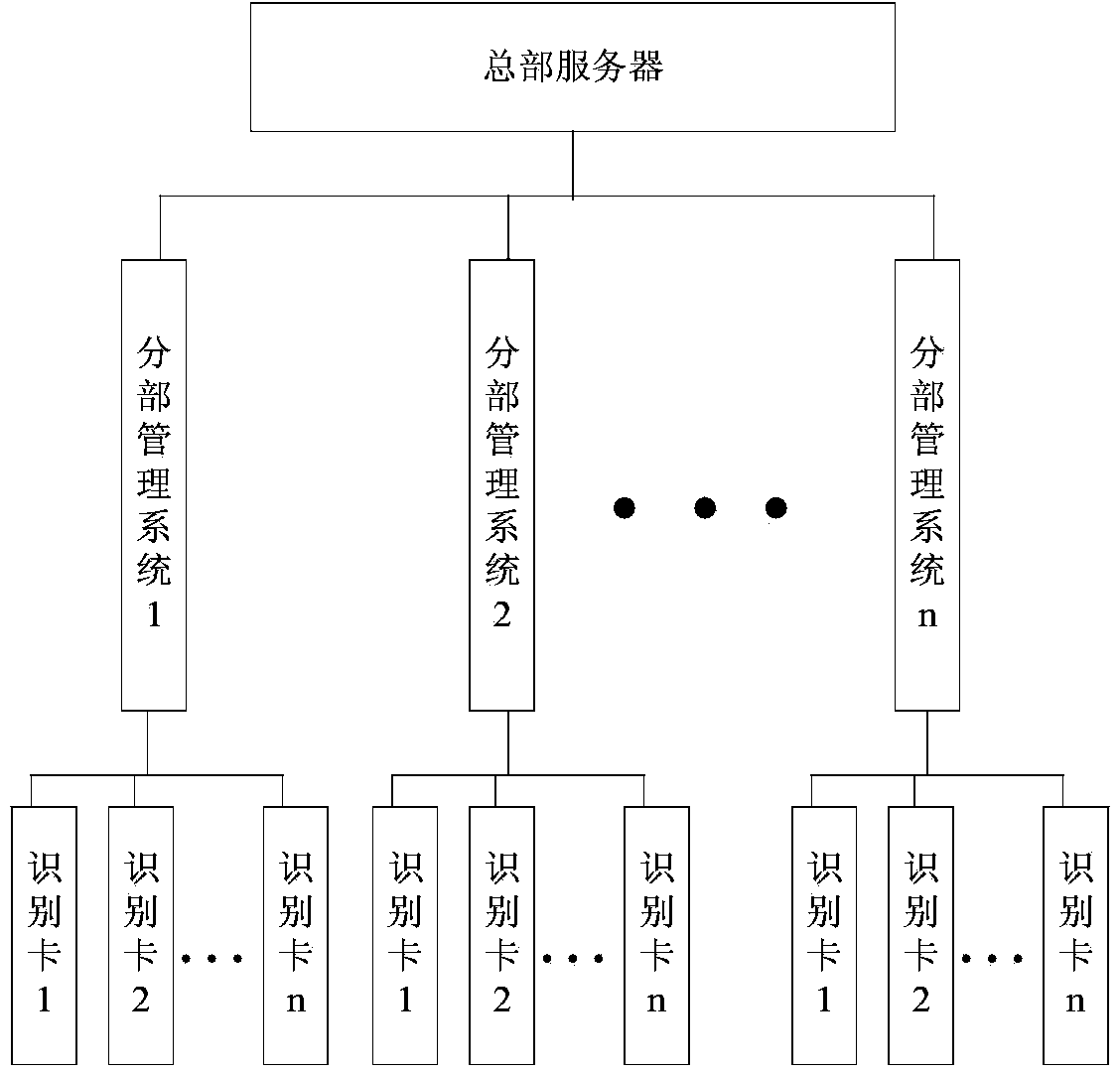
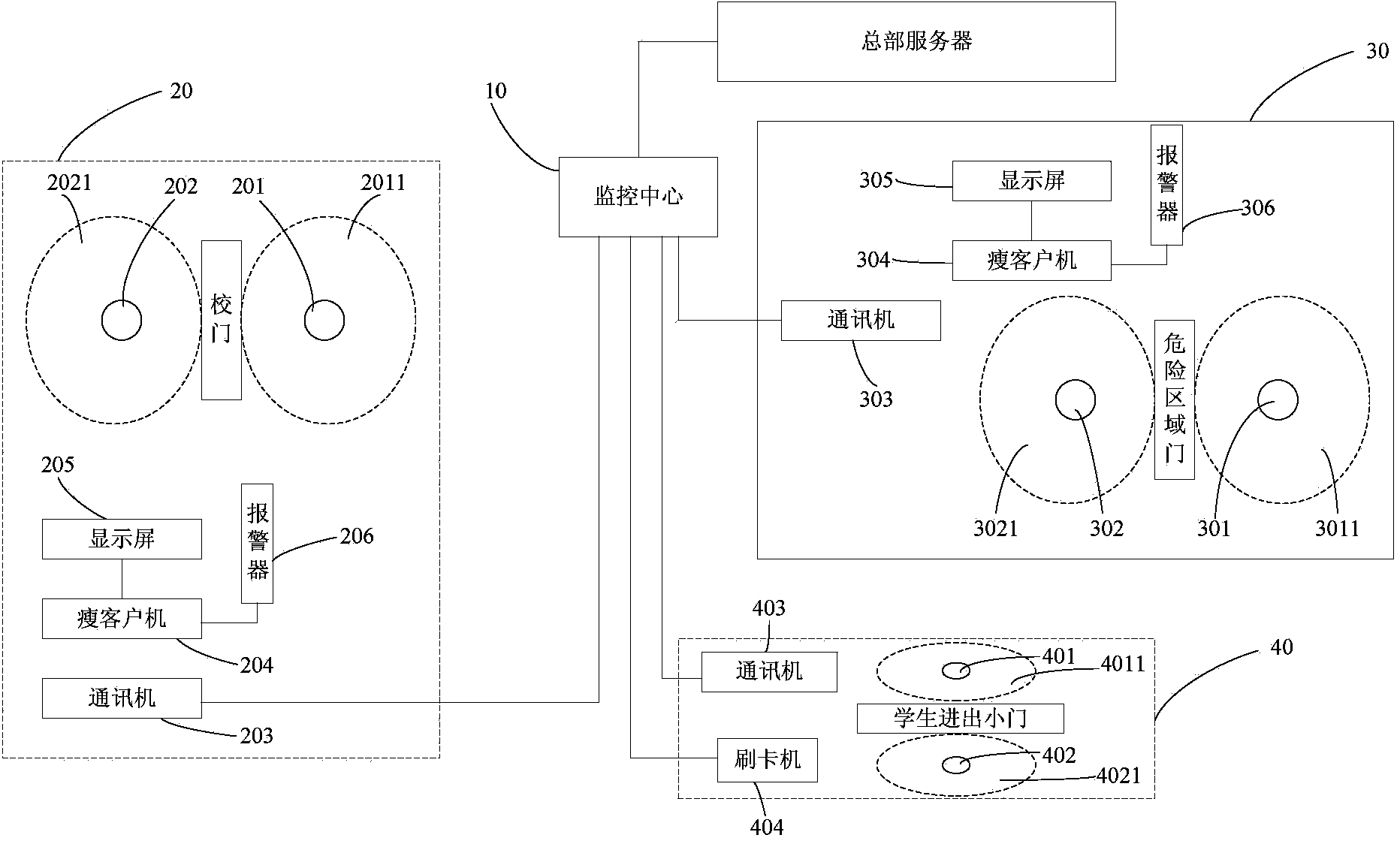
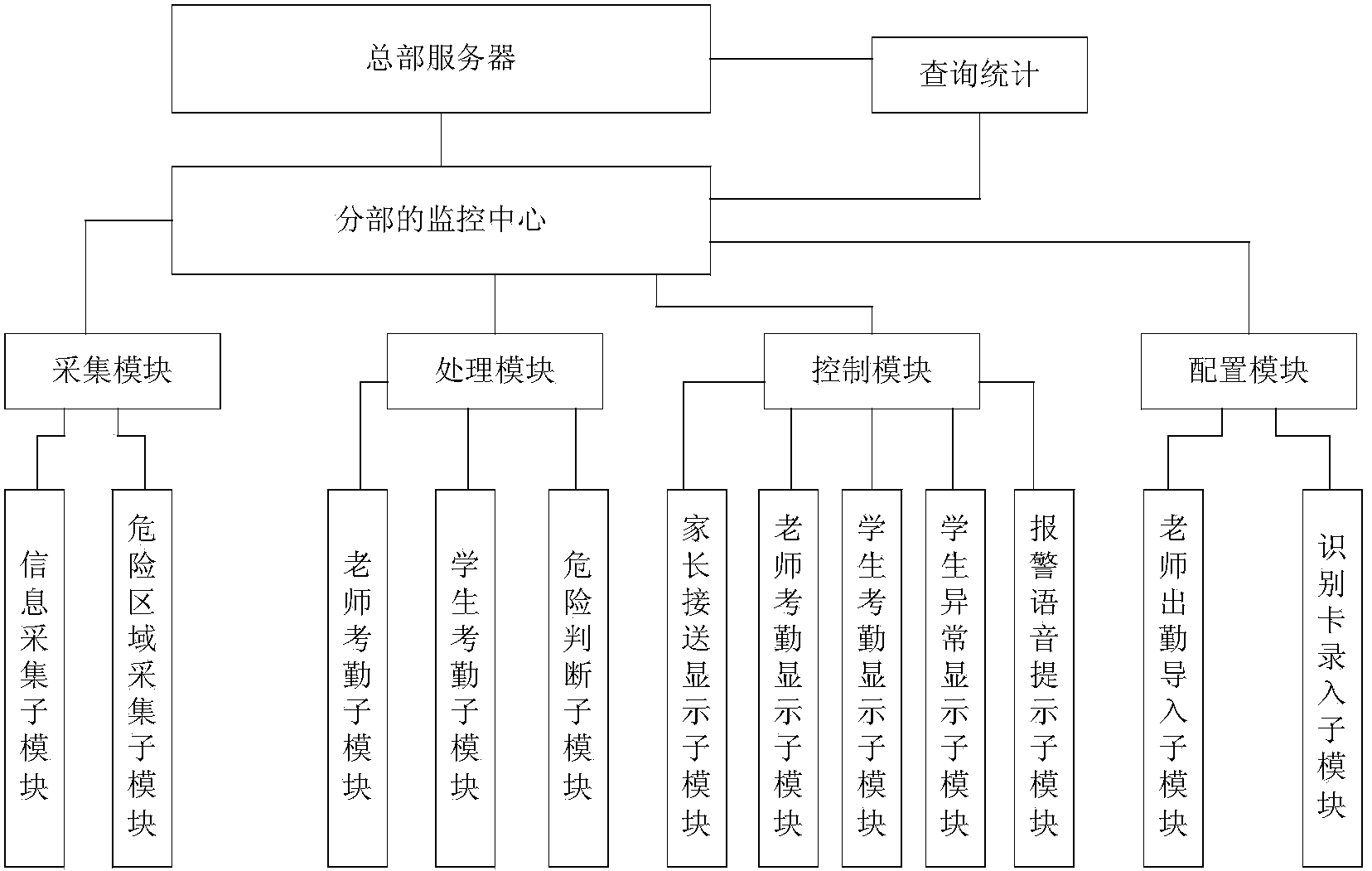
Campus security management system
ActiveCN103729923ARealize automatic identificationImprove securityIndividual entry/exit registersSafety management systemsSecurity management
The invention relates to a campus security management system. The campus security management system comprises a headquarter server, a segment management system and an identification card worn on each user, wherein the identification card is used for recording the identity information of the user; the segment management system activates the identification card entering in a designated region of the campus and receives the identity information sent by the identification card, so as to realize security management by combination of the designated region and the identity information and send the security management information to the headquarter server; the headquarter server receives the security management information sent by the segment management system and carries out statistical recording on the security management information. The campus security management system has the functions of giving an alarm when a student enters a hazardous area, automatic displaying when parents take the student, automatically recording attendance by teachers, carrying out inquiry statistics and the like.
Owner:SHANGHAI YUHE IND
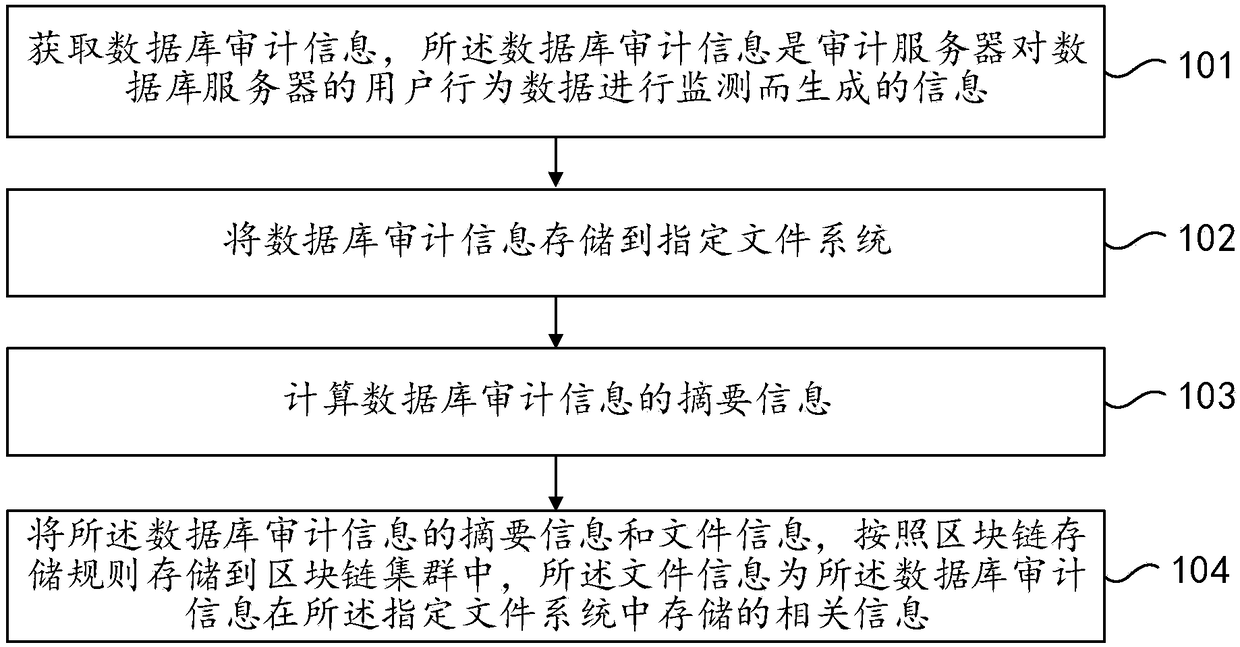
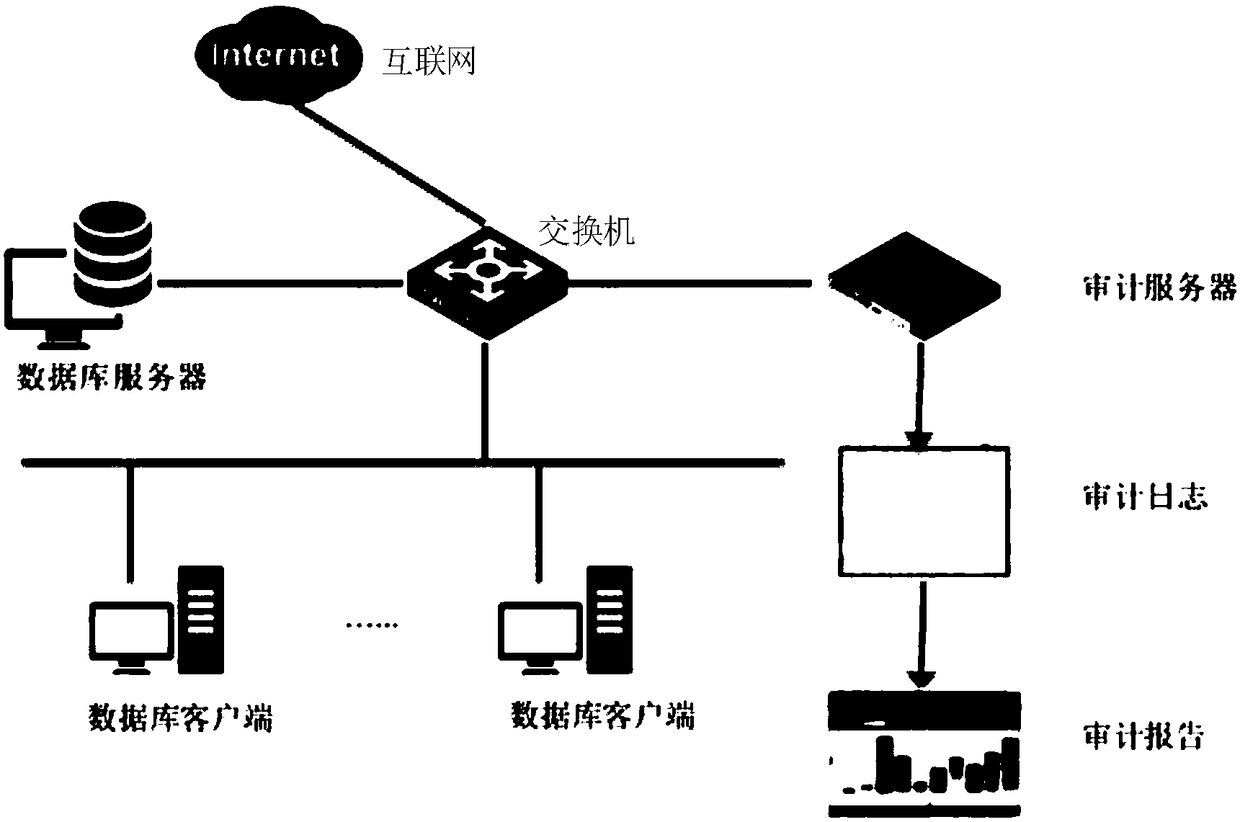
Database auditing method and device based on block chain
ActiveCN108446407AStrengthen security managementPrevent tamperingSpecial data processing applicationsDatabase design/maintainanceCalculated dataBlockchain
The embodiment of the invention provides a database auditing method and a database auditing device based on a block chain. The method comprises the steps of acquiring database auditing information; storing the database auditing information in a specified file system; calculating abstract information of the database auditing information; and storing the abstract information and the file informationof the database auditing information into a block chain cluster according to a block chain storage rule, wherein the file information is relevant information of the database auditing information in the specified file system. The database auditing information is stored in the specified file system, the abstract information of the database auditing information is stored in the block chain cluster,the data volume stored in the block chain cluster is small, the abstract information and the file information of the auditing information can be prevented from tampering by use of a consensus mechanism of the block chain cluster to achieve the purpose of preventing the auditing information and the abstract information thereof from tampering, thereby being beneficial to performing safety managementon a database.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
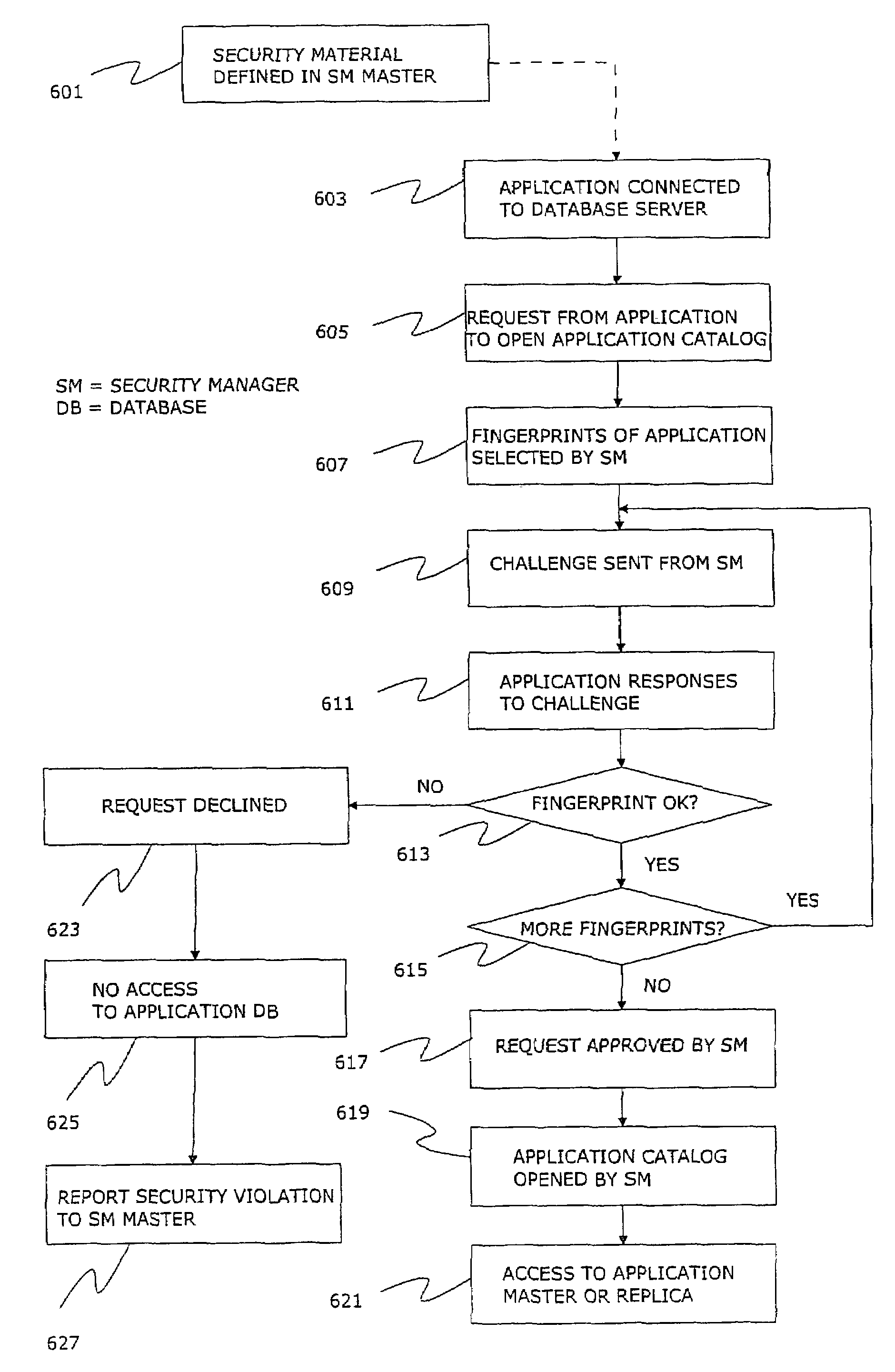
Method and system for managing security material and services in a distributed database system
InactiveUS7266702B2Strengthen security managementSecure distributionData processing applicationsUser identity/authority verificationApplication softwareDatabase server
A method and system for managing security material and security services, and for securely distributing them in a distributed database system where one or multiple distributed applications operate on distributed data. One database hosted by database server contains master version of the security data of databases hosted by database servers. The database hosted by database server has a global view of the security material for managing security of the other databases. A special database is responsible of providing security services to application database of a database server. The system and method control application programs access to data of a database in a database server, and also facilitates the security management issues of complex database topologies, such as multitier hierarchies or multi-master topologies.
Owner:SOLID INFORMATION TECH
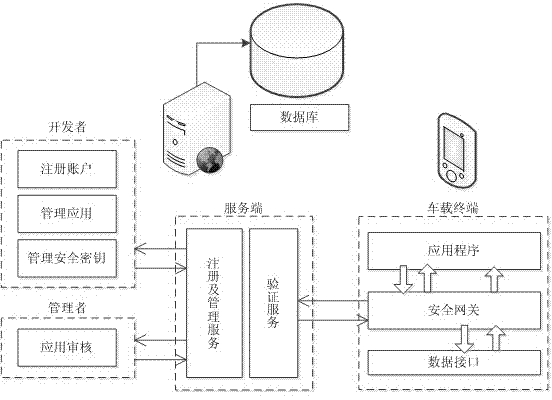
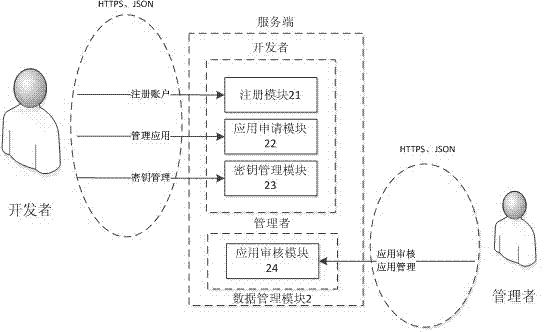
Security management method and system for vehicular mobile Internet
The invention discloses a security management method and a system for the vehicular mobile Internet. When an application program accesses a vehicular terminal, the vehicular terminal judges the authorization of the application program. When the authorization of the application program is the runtime authorization of a local access, the application program directly accesses the vehicular terminal information. When the authorization of the application program is the remote authorization of a remote access, the vehicular terminal authenticates the access authority of the application program through a server side. If the authorization is passed, the application program accesses the vehicular terminal information. The server side provides register, application, safe key management and application audit service for application developers of a third party, and the application access authority of the third party is saved in the server side. Through the interaction of the vehicular terminal and the server side and the own management of the vehicular terminal, the method and the system adopt a high-efficiency authentication mechanism and an encryption communication mechanism, so that the safety management of vehicular application is easily realized, and the critical data of the vehicular terminal cannot be embezzled by illegal application. Thus, a car accesses the mobile Internet to share the convenience and fast of the network, and while the privacy data of users cannot be stolen.
Owner:SOUTH CHINA UNIV OF TECH
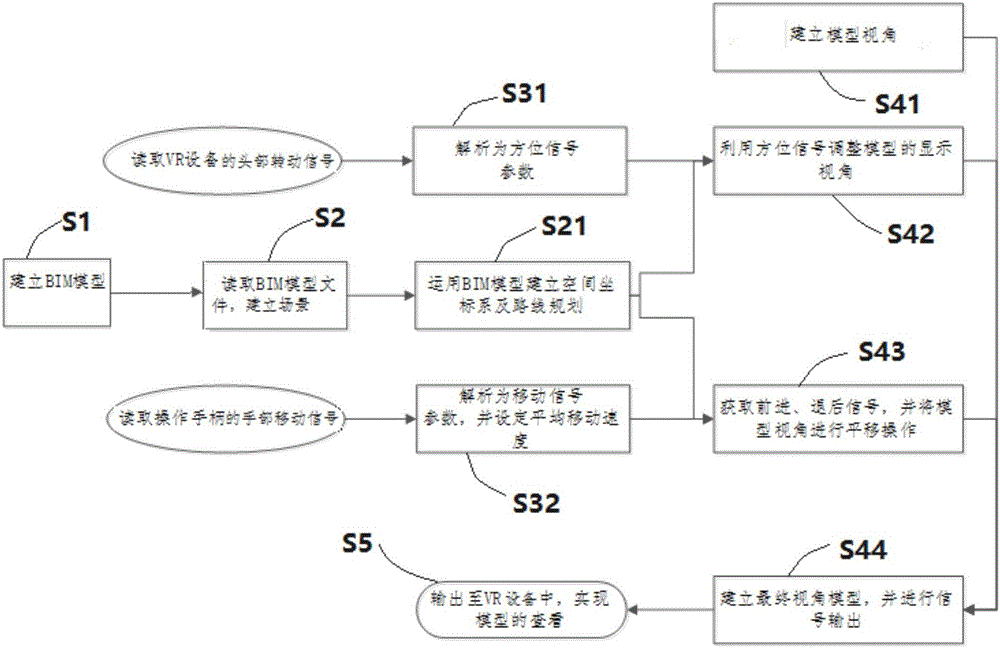
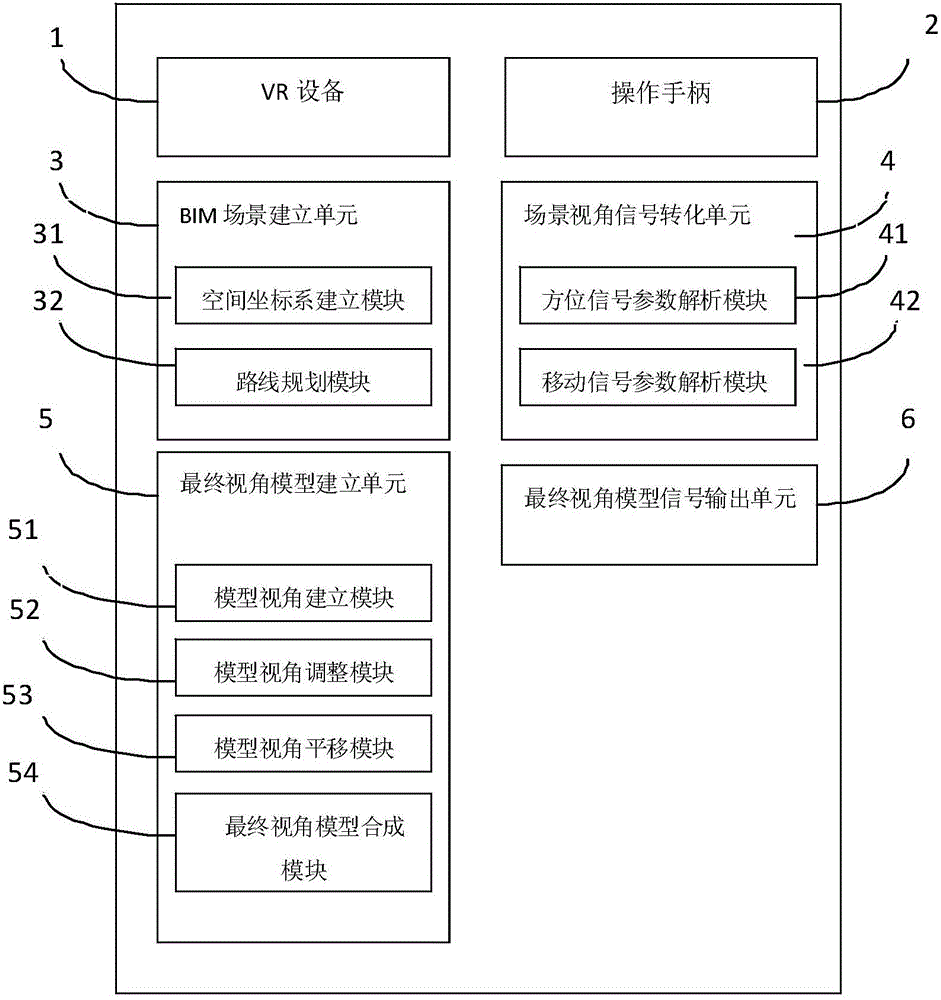
Virtual engineering experience method and virtual engineering experience device based on VR (Virtual Reality) and BIM (Building Information Model)
InactiveCN106569595AStrengthen security managementReduce engineering changesInput/output for user-computer interactionGraph readingVirtual engineeringVirtual reality
The invention discloses a virtual engineering experience method and a virtual engineering experience device based on VR (Virtual Reality) and a BIM (Building Information Model). The device comprises VR equipment, an operating handle, a BIM scene establishment unit, a scene vision angle signal conversion unit, a final vision angle model establishment unit and a final vision angle model signal output unit. According to the method and the device, an engineering model is established by employing a BIM technology, dynamic roaming is realized by combining the VR equipment, and implementation of whole engineering and various scenes can be simulated in virtuality, so that an experience person can personally experience the various scenes; unpredictable problems in an implementation process of the engineering can be effectively found and early solved; engineering change can be reduced; engineering investment can be controlled; in addition, waste in a construction process of the engineering can be reduced; a material can be saved; the efficiency can be improved; and a concept of green construction can be met.
Owner:SHANGHAI URBAN CONSTR DESIGN RES INST GRP CO LTD
Intersection pass early warning method based on computer vision
ActiveCN106373430AControl facilitation measuresAutomatic and Efficient SupervisionInternal combustion piston enginesAnti-collision systemsVideo imageVisual perception
The invention discloses an intersection pass early warning method based on computer vision. The method comprises the following steps: S1) collecting video images of an intersection in real time and capturing close-up images of vehicles; S2) extracting moving objects according to the video images, generating moving object driving information and extracting complete vehicle license plate information according to the close-up images; S3) carrying out classification on the moving objects to obtain a classification result; S4) calculating driving speed of each vehicle according to the classification result and the driving information; S5) storing information of the vehicles passing through the intersection, and predicating the center-of-mass coordinate of each moving object at the next-moment position according to the driving speed and driving information of the vehicle; and S6) according to the driving information, the driving speed and the center-of-mass coordinate of the moving object at the next-moment position, generating an early warning signal and displaying the early warning information for the situations meeting abnormal conditions. The method can carry out analysis on construction intersection pass abnormity conditions through the video image analysis technology and output the early warning signal, and is high in stability and accuracy.
Owner:SOUTH CHINA UNIV OF TECH
Door control system capable of conferring opening authority to visitors and door control management method
PendingCN106355708ASolve unmanageable problemsImprove convenienceIndividual entry/exit registersControl systemOperations management
The invention relates to a door control system capable of conferring opening authority to visitors and a door control management method. The authority of users is managed by a door control management server, so that the users can confer the opening authority to the visitors, owners have visitor management authority, after the owners identify identities of the visitors, then the opening authority is given to the visitors, and therefore, management safety of the door control system is greatly improved. Meanwhile, after the opening authority is conferred to the visitors, the visitors can voluntarily open doors, inconvenience that the user permits visiting of the visitors is avoided, and opening convenience of the visitors is improved.
Owner:BEIJING UPVALUE INTPROP CONSULTANTSCO
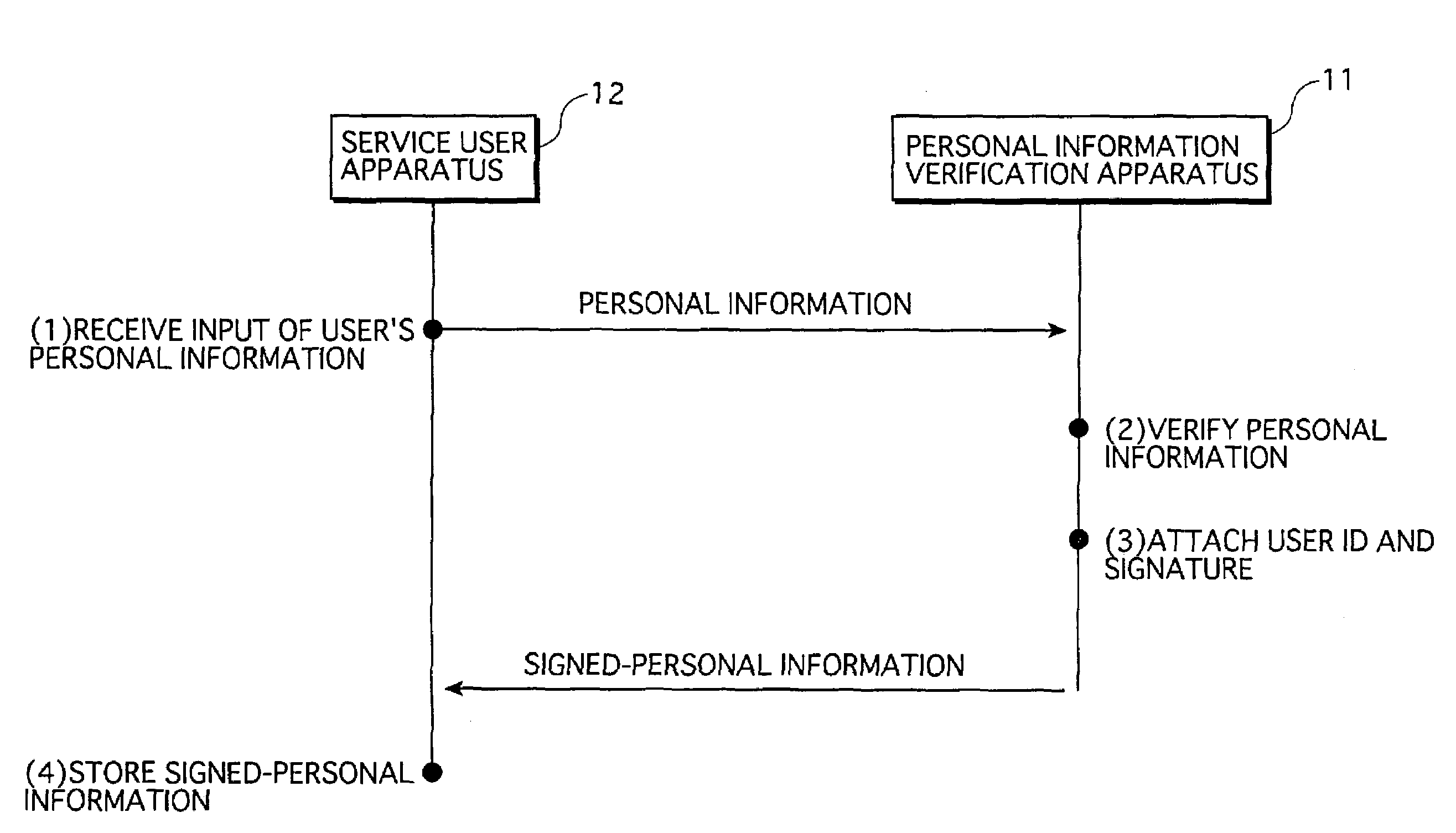
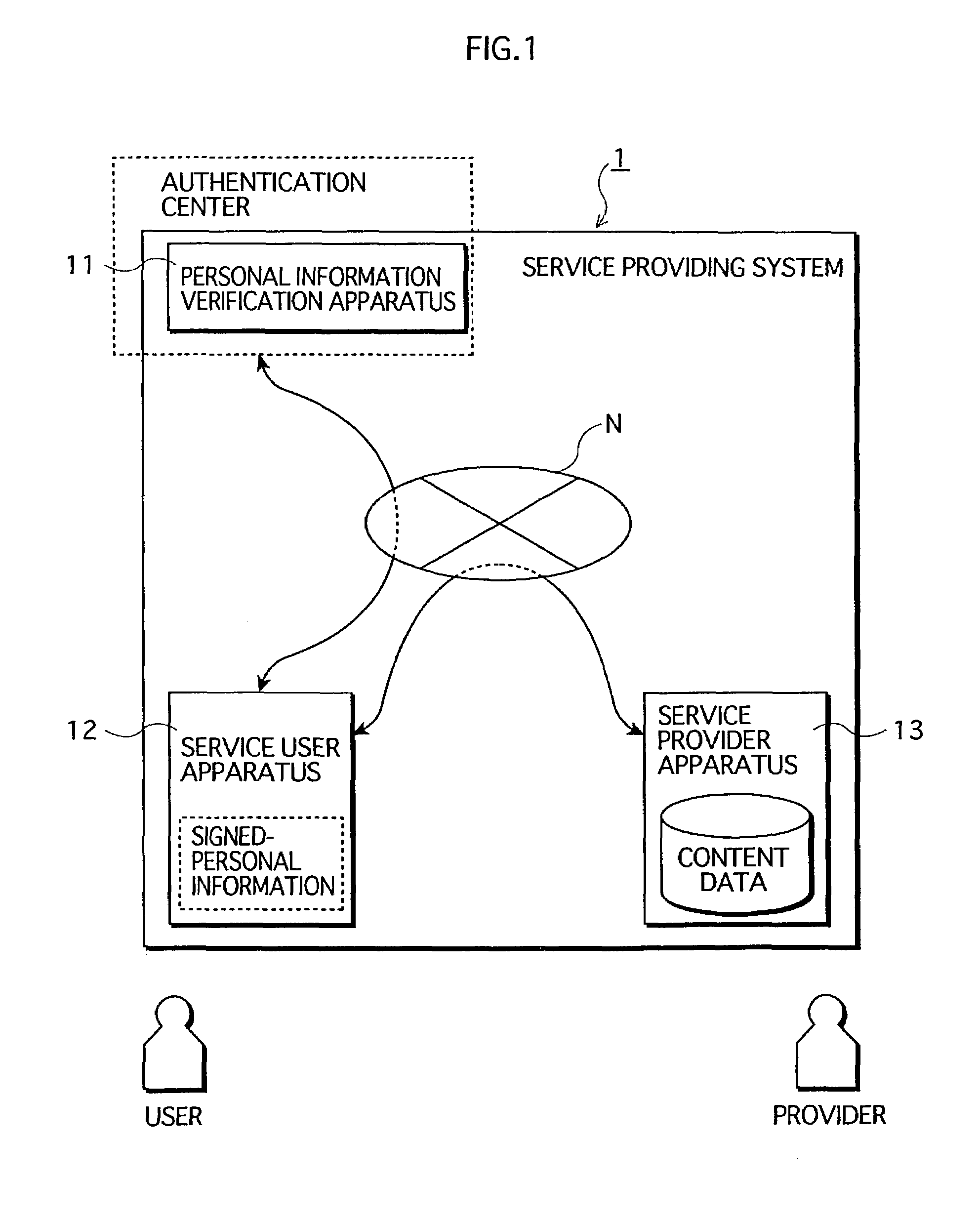
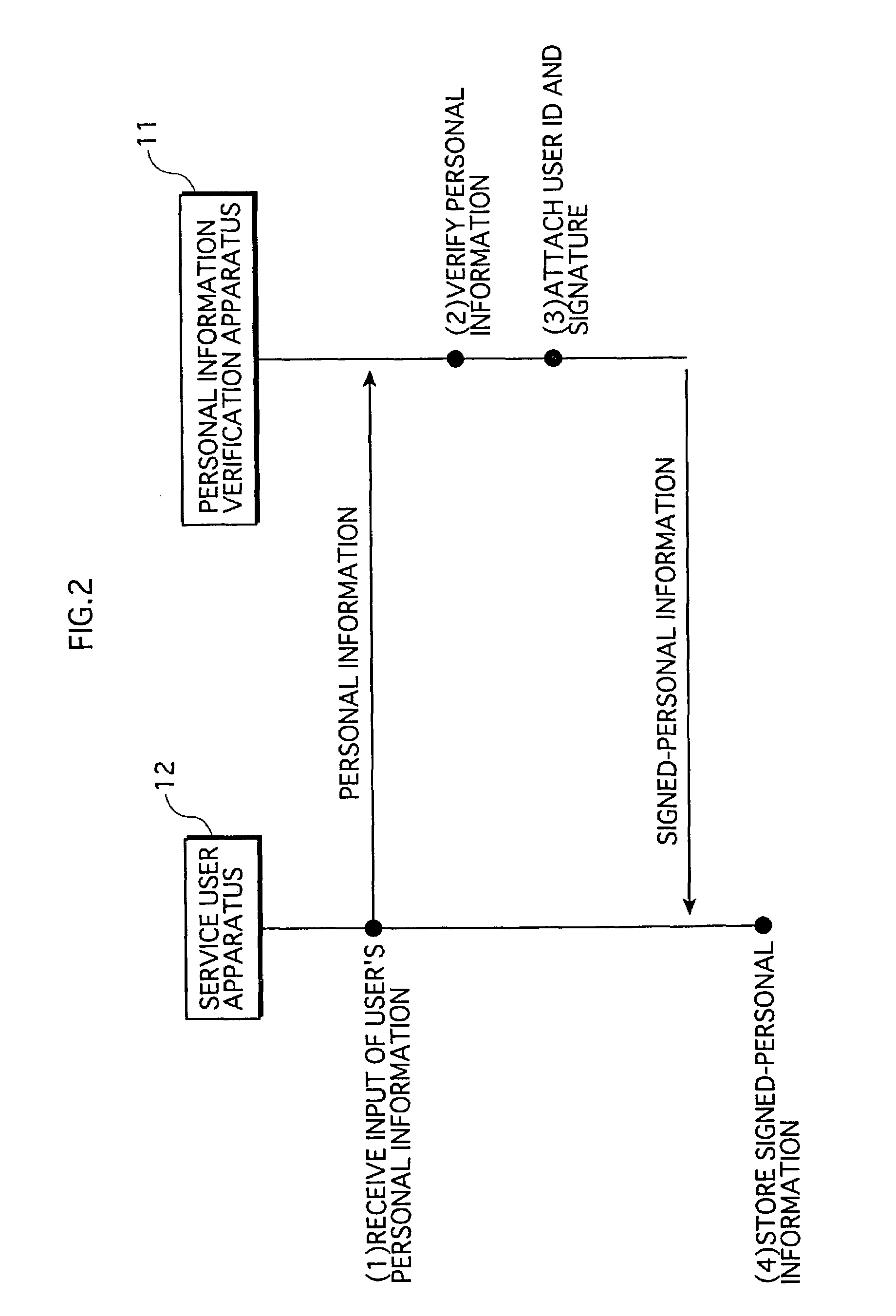
Service providing system in which services are provided from service provider apparatus to service user apparatus via network
ActiveUS7254705B2Strengthen security managementImprove reliabilityUser identity/authority verificationDigital data protectionDigital signatureService provision
A service user's personal information that has been verified and to which a digital signature has been attached by a personal information verification apparatus (signed-personal information) is stored in a highly secure form within a service user apparatus. For receiving services, the service user apparatus transmits the signed-personal information stored there into a service provider apparatus. The service provider apparatus verifies the signed-personal information based on the digital signature, and then provides services based on the personal information.
Owner:SOVEREIGN PEAK VENTURES LLC
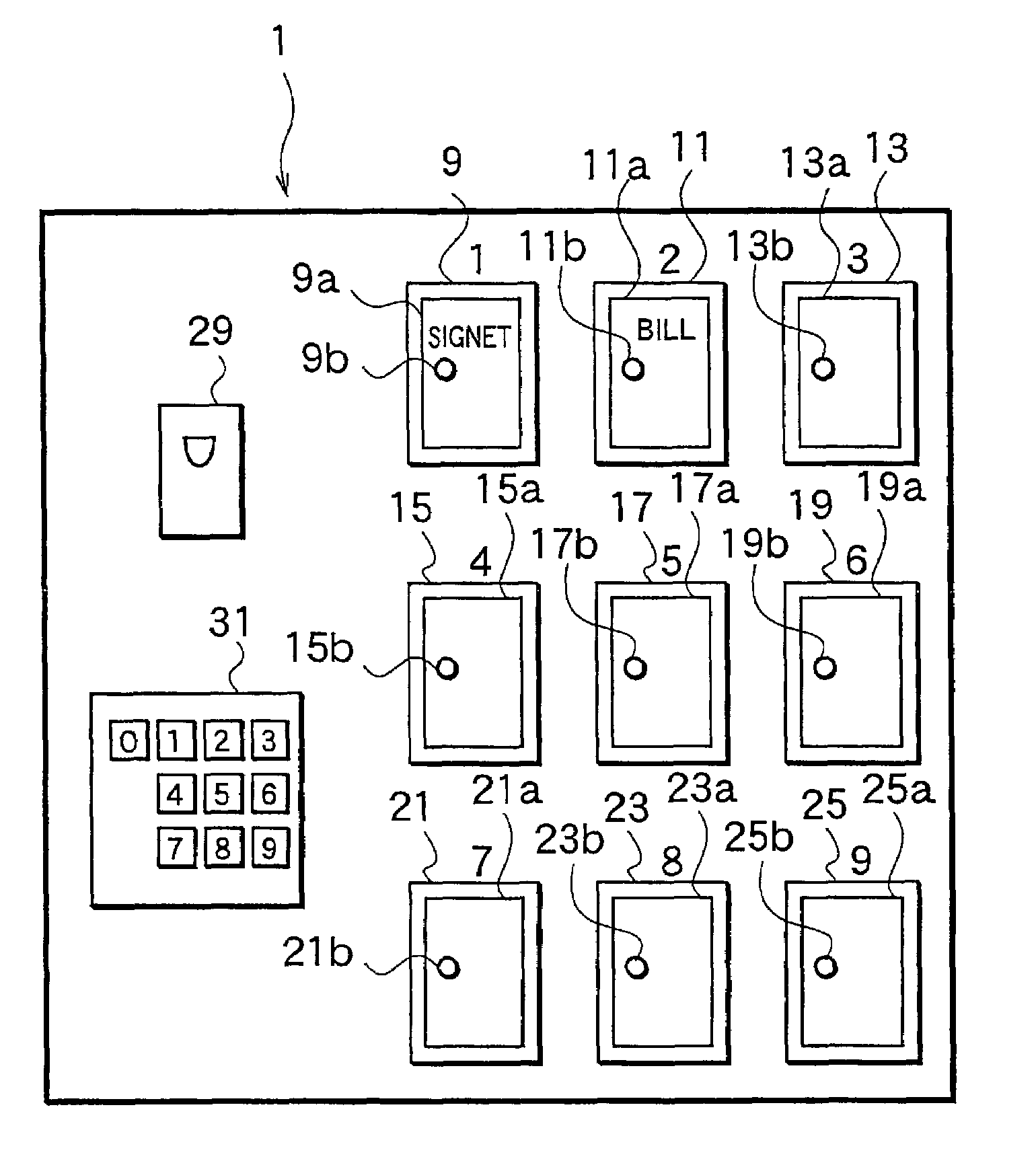
Dynamic coded lock management and control system
InactiveCN104318650AStrengthen security managementImprove management efficiencyIndividual entry/exit registersManagement processControl system
The invention relates to the field of electronic locks and in particular relates to a dynamic coded lock management and control system. The system comprises a management end and an electronic lock end and also comprises a handheld terminal, wherein the management end is used for storing and managing information of an operator, information of a handheld terminal and information of the electronic lock end and is also used for generating and recording an unlocking task with a dynamic unlocking code, wherein the dynamic unlocking code corresponds to a dynamic electronic lock end code generated by the electronic lock end; the electronic lock end is used for generating the dynamic electronic lock end code and receiving and verifying the input dynamic unlocking code; and the handheld terminal is used for acquiring the unlocking task from the management end and acquiring the dynamic unlocking code in the unlocking task. According to the system disclosed by the invention, the information of all the electronic lock ends, the information of the handheld terminal and the information of the operator are managed, so that the management safety of the electronic lock is greatly enhanced, the potential safety hazards are eliminated, all the unlocking information lockset states can be taken in a glance at the management end, the management efficiency of the electronic lock is greatly improved, and the safety in the management process is enhanced.
Owner:SHENZHEN JUNWU TECH
System and method for on-line separation and recovery of electronic documents
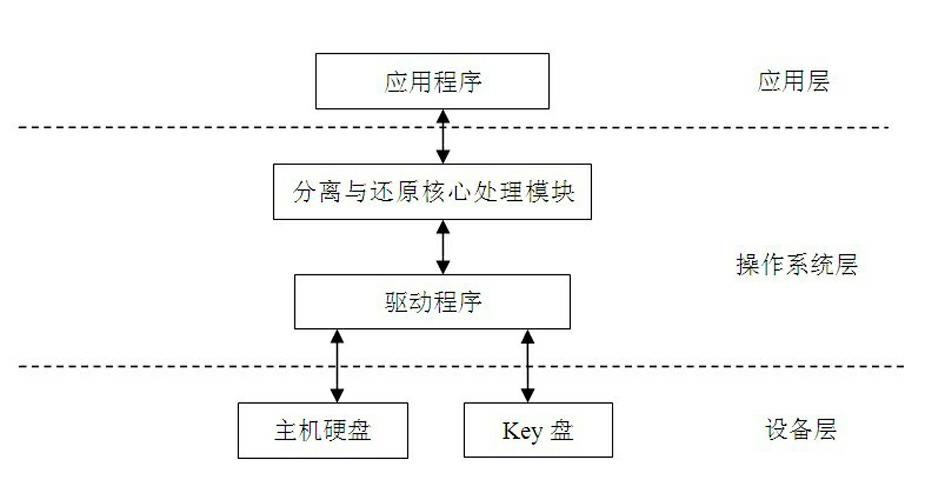
ActiveCN102693399APrevent leakageImprove protection strengthDigital data protectionElectronic documentManagement tool
The invention discloses a system and a method for on-line separation and recovery of electronic documents, and aims to realize automatic separation storage and recovery of electronic documents during the editing and using processes without any influence on thespecific document editing system. The method comprises the steps of binding a part storage area of a management terminal and a part storage area of a special key board (customized by the system) to form a logic storage space, namely, ''separation storage area''; when preserving the file in the separation storage area, effectively separating and storing information to two different mediums, namely, the management terminal and the special key board; when reading the file in the separation storage area, acquiring recovered original document by document fragment information on two mediums. Compared with the traditional encryption management, the method is more safe, convenient and reliable, so that the method can provide a safety management tool with super strength for terminal-level electronic documents.
Owner:南京伍安信息科技有限公司
Document management method, document management system, and computer program product
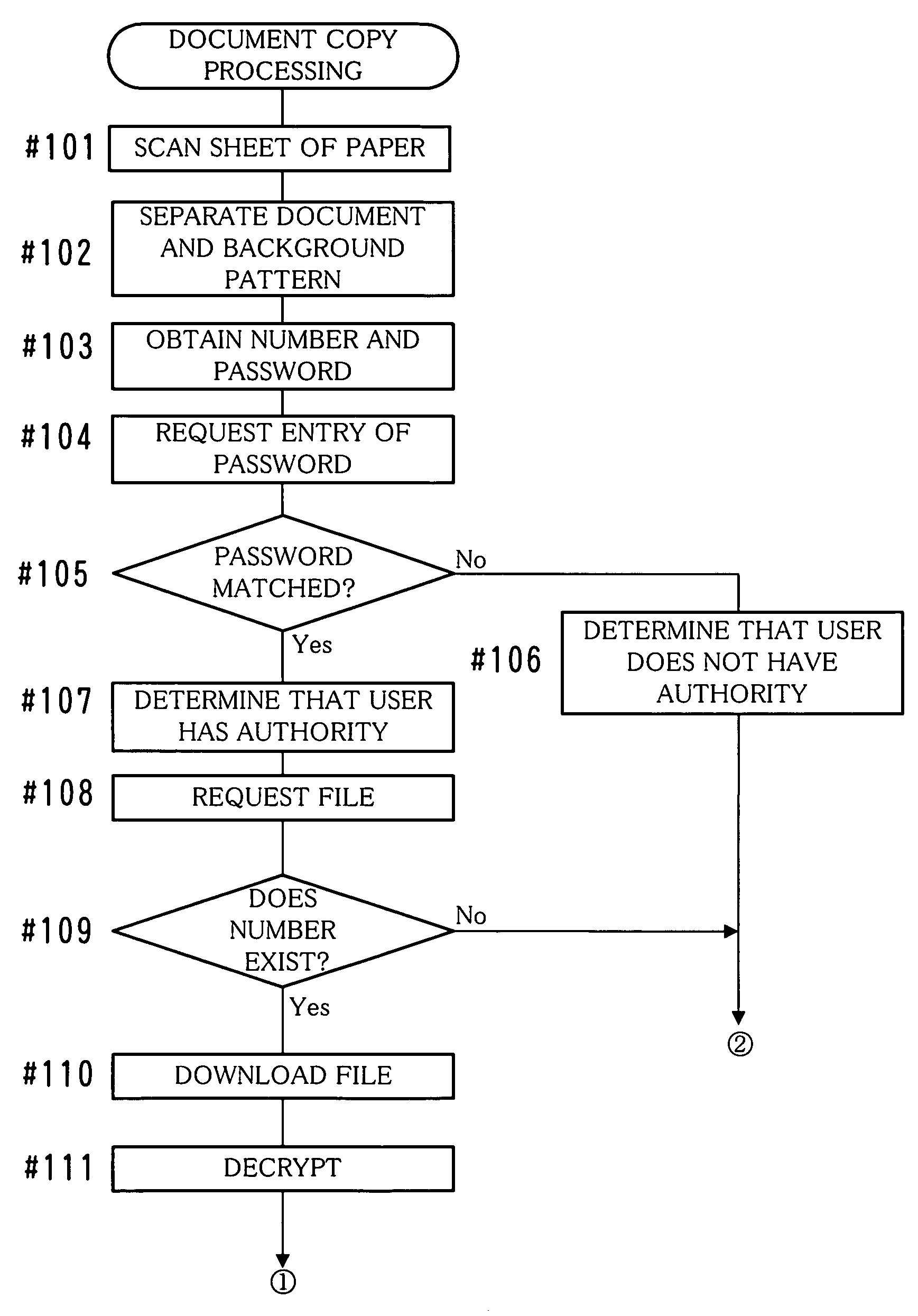
ActiveUS20070223955A1Strengthen security managementEasy to manageElectrographic process apparatusPasswordComputer vision
The image of a document is depicted on a sheet of paper together with a background pattern image expressing a password, and the password is notified to a person having authority to duplicate the document. A requestor requesting duplication of the document is caused to enter a password (#104), and the document image and the background pattern image are obtained by scanning the sheet (#101). Then, it is determined whether the requestor has the above-described authority, based on the entered password and the password expressed by the obtained background pattern image (#105). When it is determined that the requestor has the authority, a different password is issued. The document image is printed on a separate sheet of paper together with a background pattern image expressing the different password, and the different password is notified to a person having authority to duplicate the document printed on the separate sheet of paper.
Owner:KONICA MINOLTA BUSINESS TECH INC
An identity-enhanced authentication and authentication method and device
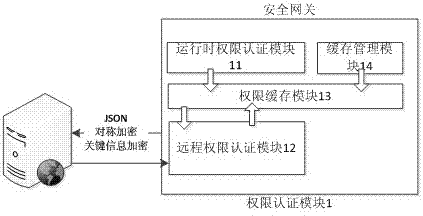
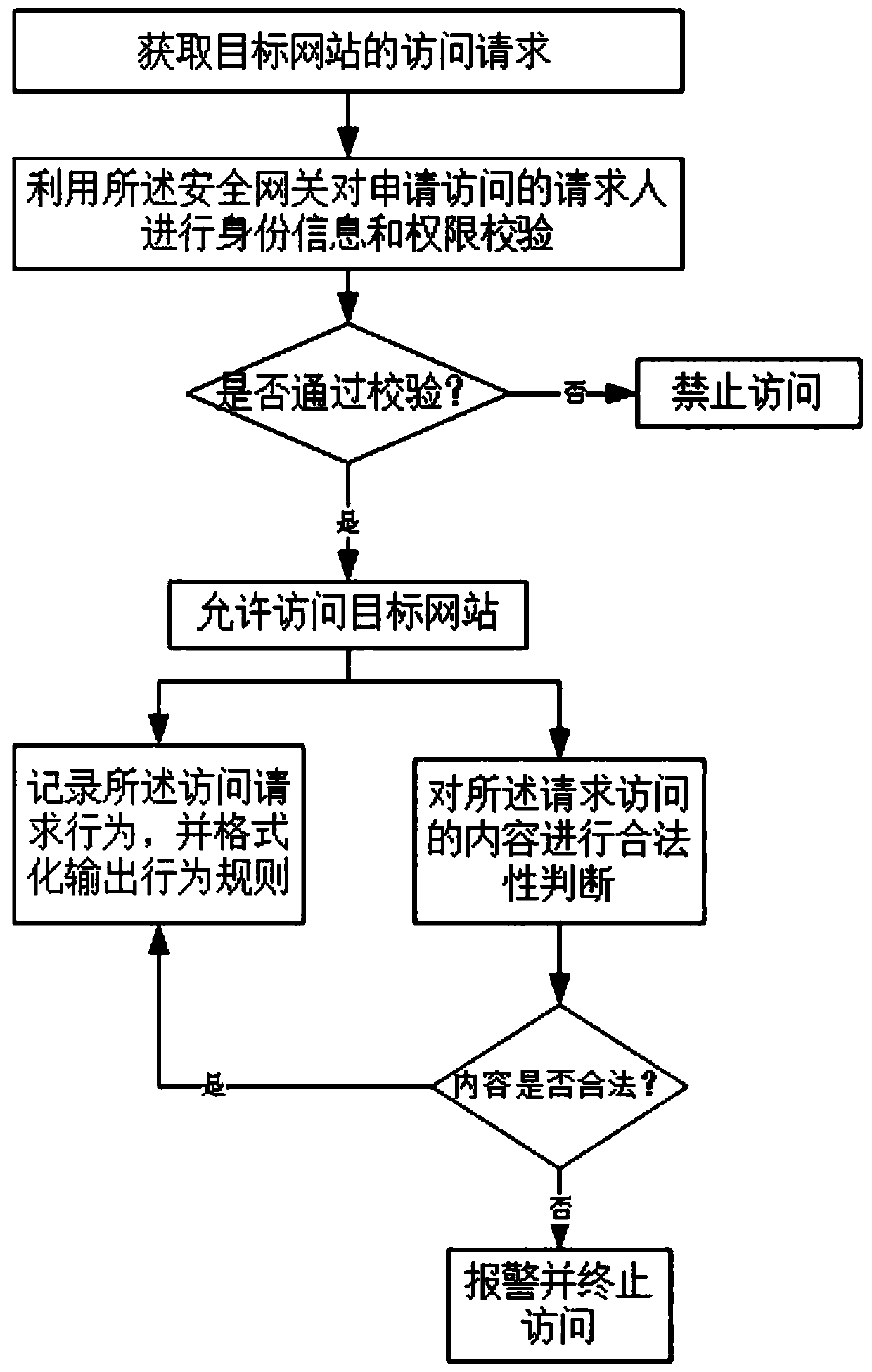
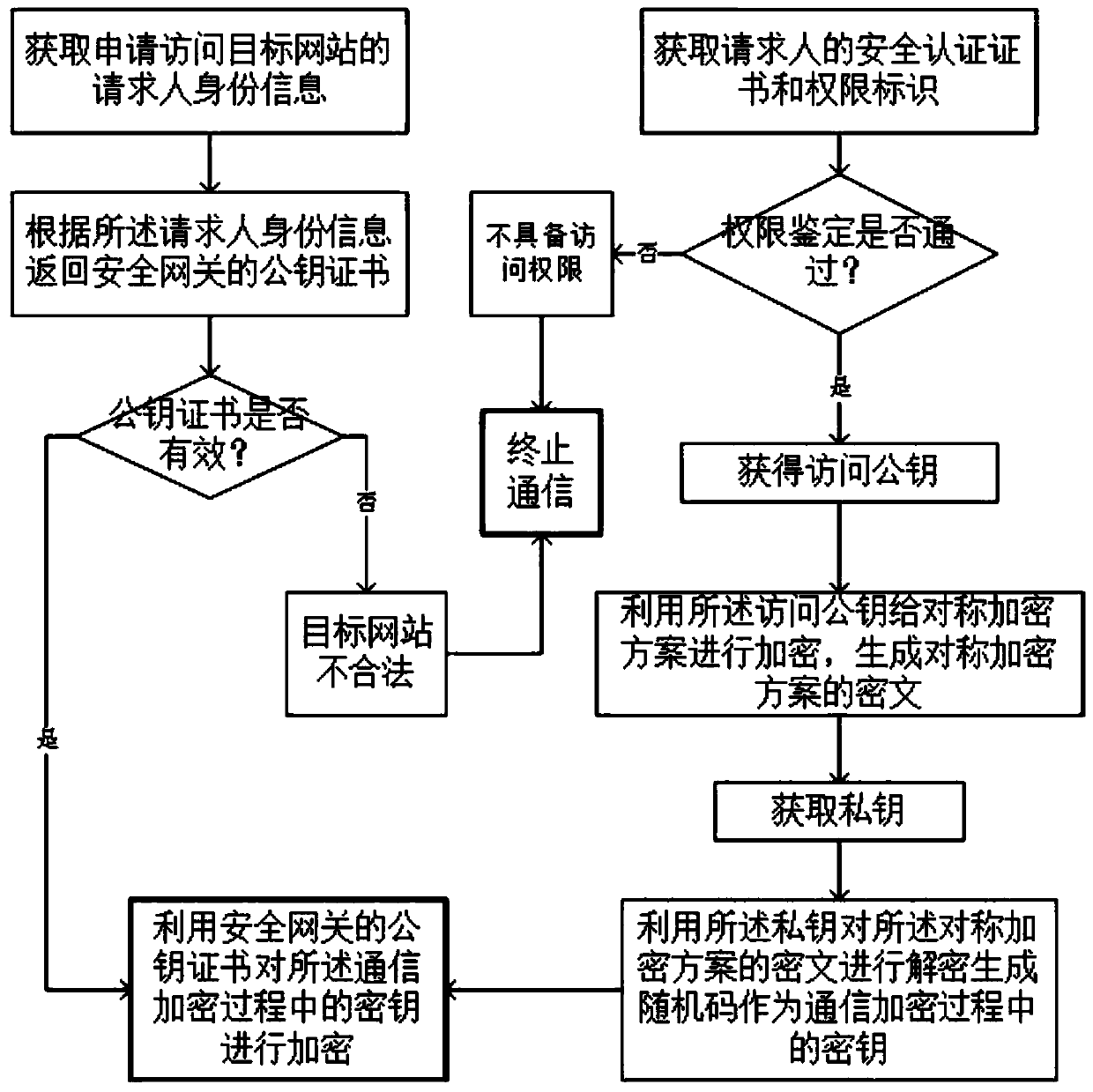
ActiveCN109787988AImprove safety management efficiencyStrong deployment compatibilityTransmissionService systemClient-side
The invention discloses an identity-enhanced authentication and authentication method and device, and the method comprises the steps: deploying a security gateway at an access entrance of a target website, and obtaining an access request of the target website through encrypted communication; Utilizing the security gateway to carry out identity information and authority verification on a requesterapplying for access; Recording the access request behavior, and formatting and outputting a behavior rule; Legality judgment is conducted on the content requested to be accessed, an alarm is given toillegal content, and access is terminated. A security gateway is deployed at an access entrance of a target website; a security authentication certificate is deployed on the PC client; A mode of verifying a certificate and a certificate identity permission identifier by using a security website is adopted; Under the condition that an enterprise does not change a network structure and a service system code, the access authority of the employee client side identity to the target service system is controlled, the defects of authentication and other safety aspects of traditional login based on a user name / password mode are effectively overcome, and the enterprise information safety is effectively improved.
Owner:杭州恩牛网络技术有限公司
Construction method of prefabricated wallboard
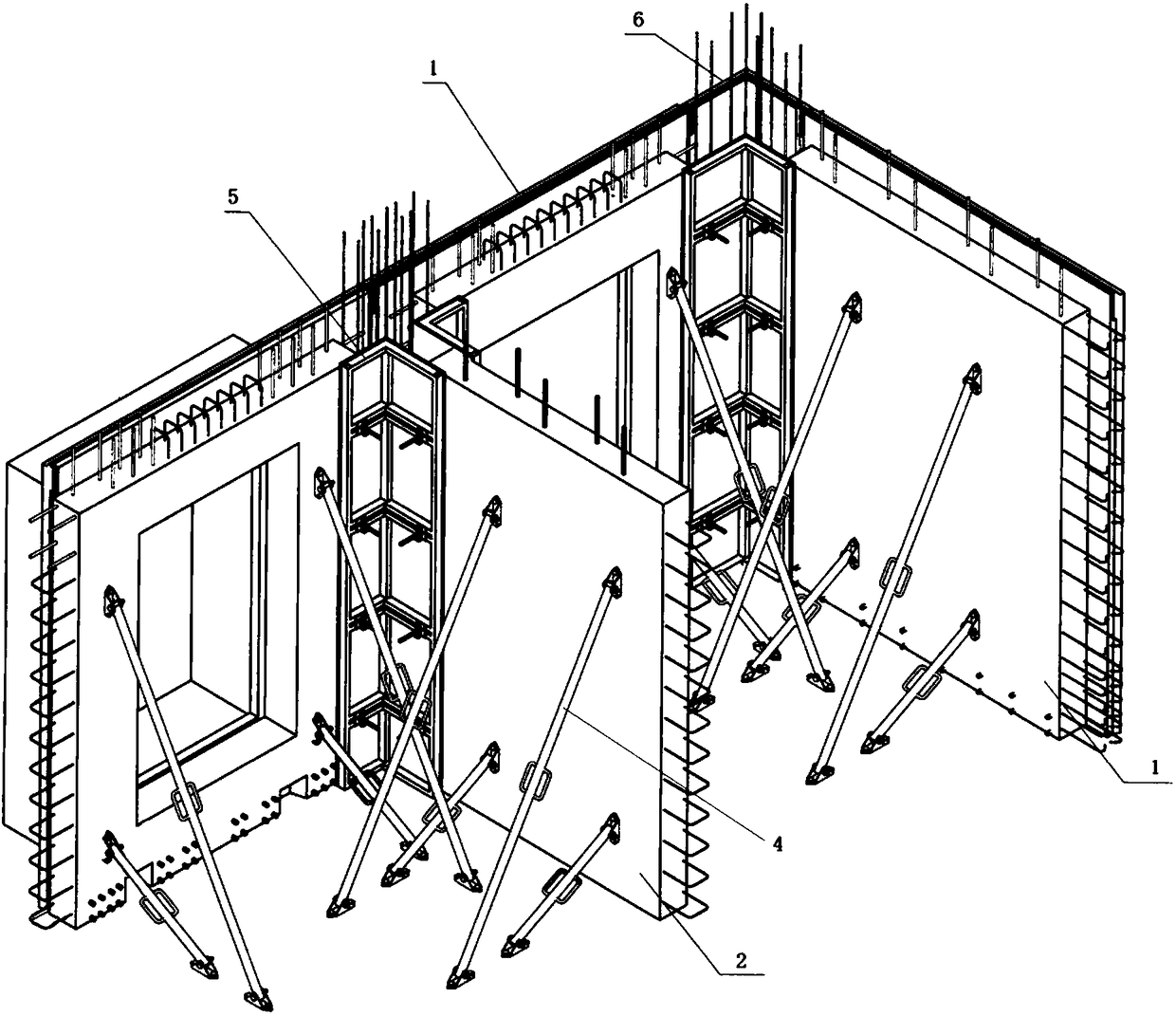
InactiveCN108118900AImprove construction qualitySpeed up the progress of the projectBuilding material handlingTower craneWall plate
The invention discloses a construction method of a prefabricated wallboard. The construction method of the prefabricated wallboard comprises the following steps of 1, numbering the prefabricated wallboard after the wallboard is prefabricated in a factory, and transporting the prefabricated wallboard to a site; 2, checking components and confirming the number; 3, before hoisting, constructing the bottom laying position of the prefabricated wallboard; 4, hoisting and installing the prefabricated wallboard, wherein before the prefabricated wallboard is hoisted, upper and lower supporting end bases of an inclined strut are firstly installed, after the prefabricated wallboard is hoisted, the prefabricated wallboard is adjusted in position and is connected with the inclined strut to be fixed, then a tower crane hook is unhooked, the perpendicularity of the prefabricated wallboard is adjusted, finally, the periphery of the prefabricated wallboard is sealed, and a grouting sleeve is utilized to conduct mortar injecting. By means of the construction method of the prefabricated wallboard, a component assembly mode is adopted, a structural wallboard is divided into multiple blocks, after being prefabricated in the factory, the prefabricated wallboard is hoisted and installed on spot, and certain construction treatment is conducted, which helps to improve the construction quality, accelerate the engineering progress, and improve the building quality.
Owner:BEIJING URBAN CONSTR NORTH CONSTR
Vehicle violation monitoring system based on radio-frequency license plate with function of communication
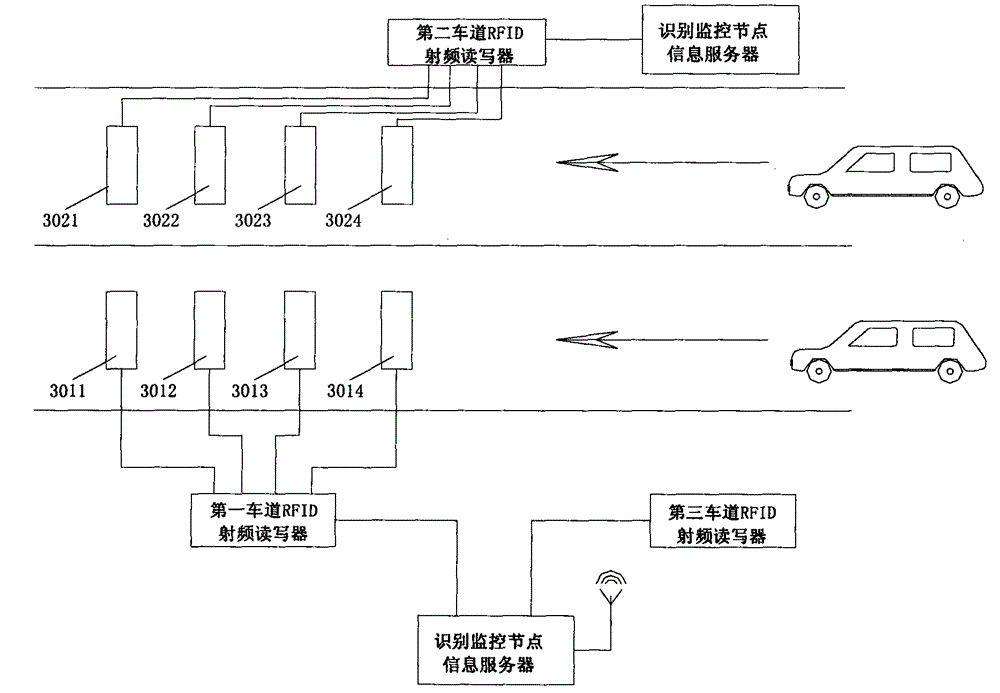
InactiveCN104821088APay attention to driving safetyPay attention to civilized drivingRoad vehicles traffic controlCo-operative working arrangementsMonitoring systemReader writer
The invention discloses a vehicle violation monitoring system based on a radio-frequency license plate with a function of communication, and the system is characterized in that the system comprises RFID license plate recognition monitoring nodes of a plurality of divided lanes; each RFID license plate recognition monitoring node consists of a divided underground buried antenna assembly, a divided lane RFID reader-writer, a recognition monitoring node information server, and a divided lane camera; the divided lane RFID reader-writers achieves the information reading of RFID license plates with the function of communication of different passed vehicles through the plurality of divided underground buried antenna assemblies, and are connected with the recognition monitoring node information servers; the recognition monitoring node information servers are connected with the divided lane camera of all lanes, and the information data of the recognition monitoring node information servers is connected with a traffic management information center, thereby forming the system.
Owner:SHENZHEN JG TECH IND
Encryption and decryption system based on medium security protection of IPTV platform
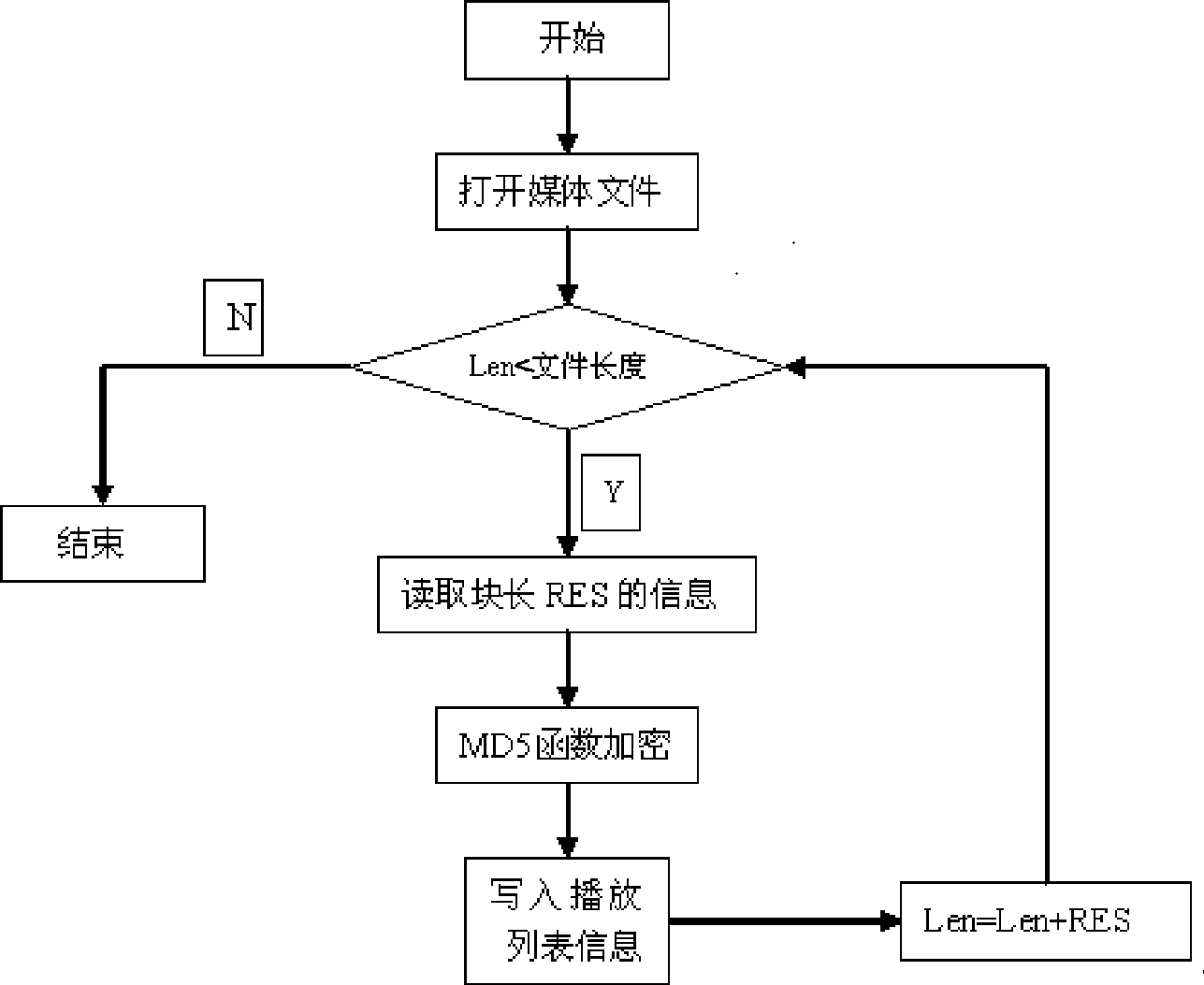
InactiveCN101521818AEnsure safetyStrengthen security managementKey distribution for secure communicationPulse modulation television signal transmissionMD5Value of information
The invention discloses an encryption and decryption system based on the medium security protection of an IPTV platform. On a platform end in the method, each sub-block of a media file is firstly carried out with MD5 operation, then a section of information is combined by the MD5 values obtained from the sub-blocks, the information is carried out with MD5 operation again, an obtained result is placed in a playlist, and finally, the playlist is encrypted. On a terminal, firstly, the playlist is decrypted, MD5 values of information abstracts of the media file, which are obtained from the playlist, are compared with the MD5 of information abstracts combined by all the sub-blocks of an operation file; if the two MD5 values are not identical, the play is prohibited; if the two MD5 values are identical, the MD5 of each sub-block is compared, if identical, the information is placed in a buffer area to by played; and if else, the play is stopped. The method has high speed and high safety factor.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Application of 2-bromide-isovanillin for the manufacture of a medicament for anti-cancer or/and radiation/chemotherapy sensitization
ActiveUS20080221221A1Induce apoptosisHigh sensitivityBiocideAldehyde active ingredientsSide effectTherapeutic effect
Use of 2-bromo-isovanillin in the preparation of an anticancer medicament and / or radio- and chemotherapy sensitizing medicament is disclosed. The medicament for the treatment of cancers and / or for radio- and chemotherapy sensitization comprising 2-bromo-isovanillin as active ingredient provided herein has the following features: (1) low toxicity, without evident adverse effects; (2) significant therapeutic effect, with remarkable proliferation inhibiting and pro-apoptotic effects in tumor cells; (3) a broad-spectrum anticancer activity; (4) suitable to be used in combination with antimetabolites, to enhance the effects and meanwhile lower the toxicity, and also to reduce multi-drug resistance; (5) convenient and safe administration, the main route being oral.
Owner:INST OF RADIATION MEDICINE ACAD OF MILITARY MEDICAL SCI OF THE PLA
Helmet-based engineering construction potential safety hazard management system and method
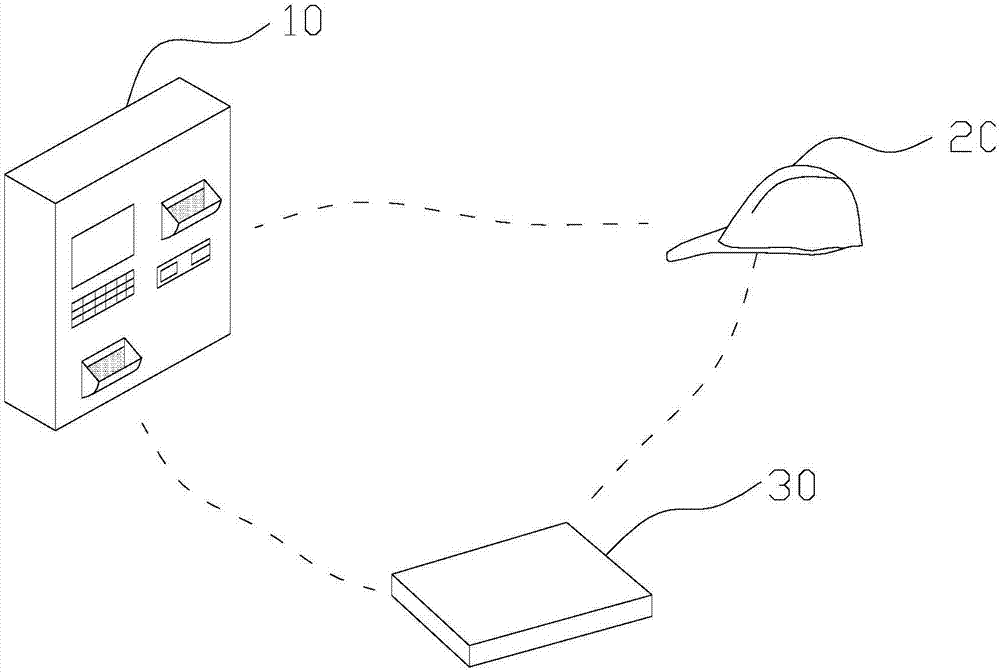
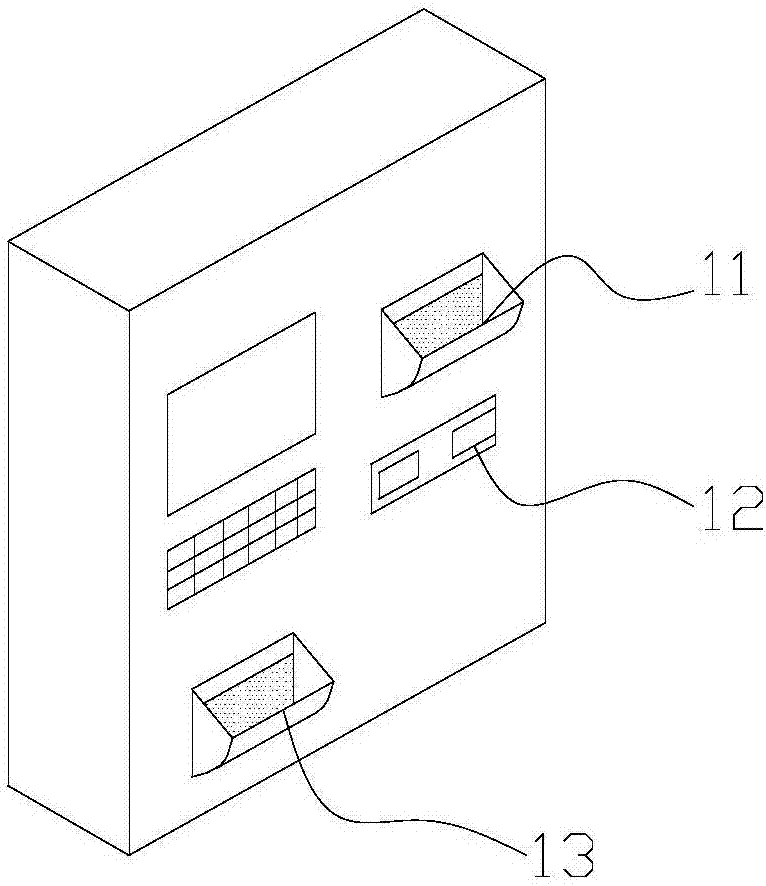
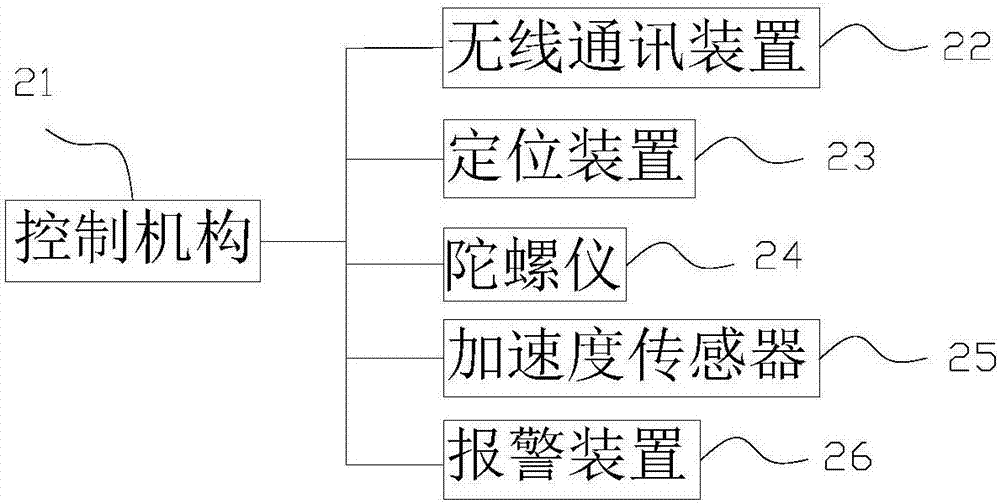
InactiveCN107358670AReal-time capture of working statusHigh precisionRegistering/indicating time of eventsData processing applicationsGyroscopeEngineering
The invention relates to a helmet-based engineering construction potential safety hazard management system. The system comprises a helmet storing mechanism, a helmet and a cloud server, a helmet storing port is formed in the upper end of the helmet storing mechanism, a helmet outlet is formed in the lower end of the helmet storing mechanism, and an authentication device is arranged on the helmet storing mechanism; a control mechanism, a wireless communication device, a positioning device, a gyroscope, an acceleration sensor and an alarm device are arranged on the helmet; the control mechanism is interconnected with the helmet storing mechanism and cloud server data separately through a wireless communication device; a management subsystem is integrated in the helmet storing mechanism. Accordingly, the positioning device, an employee status monitoring sensor and the like are implanted into the helmet, the working status of employees is captured in real time conveniently, attendance of the employees is recorded and evaluated through the helmet storing mechanism, the accuracy of engineering construction management is enhanced, and the phenomenon that oversight or absenteeism occurs due to artificial management is avoided.
Owner:四川博易达工程咨询有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com