Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
171results about How to "Prevent impersonation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
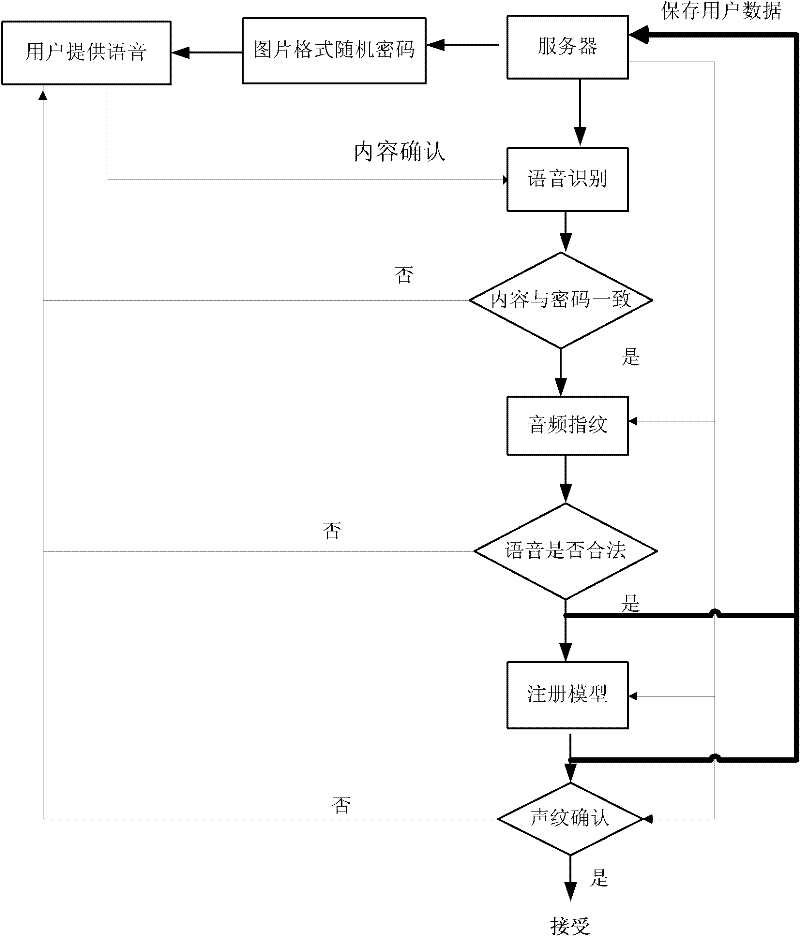
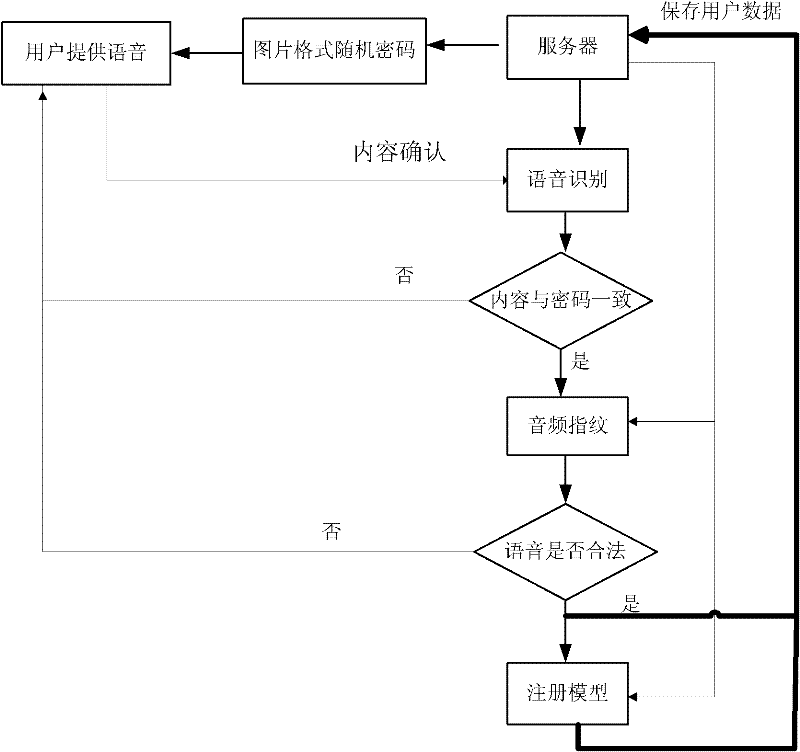
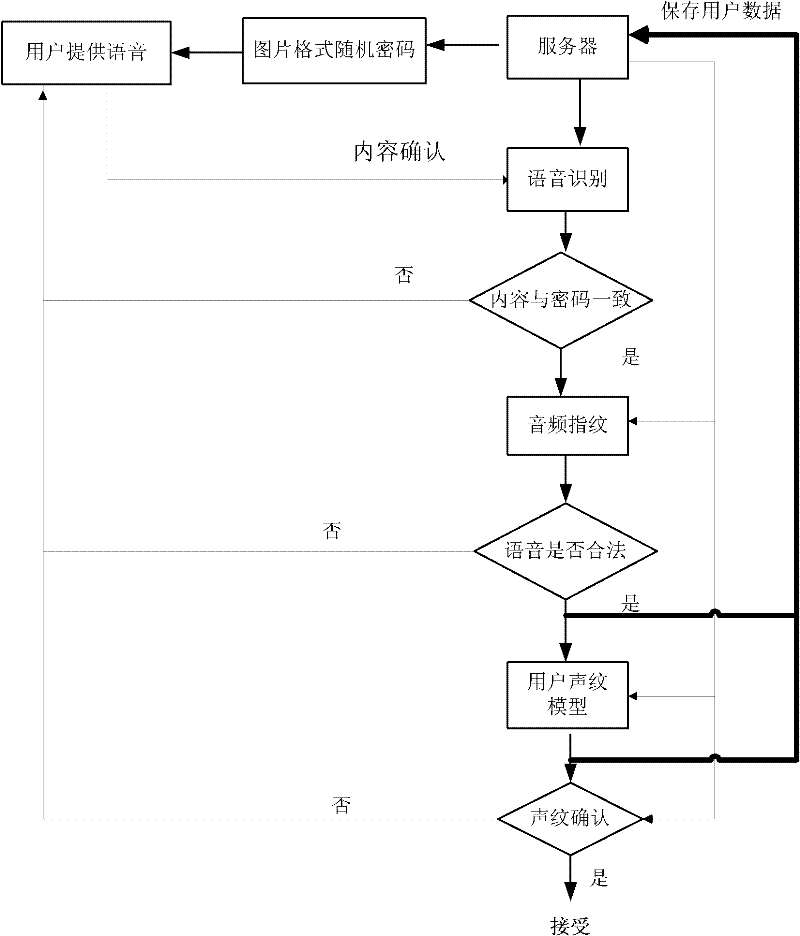
Online voiceprint recognition system and implementation method thereof
InactiveCN102543084APrevent recording attack problemImprove accuracySpeech analysisTransmissionPasswordAuthentication server
The invention discloses an online voiceprint recognition system and an implementation method thereof. The online voiceprint recognition system comprises a user recording module and an online voiceprint recognition server, and the implementation method comprises the following steps of: (1) providing generated password content for a user through the online voiceprint recognition server; (2) recording the voice of the user by utilizing the user recording module and providing the voice for a voice recognition module; (3) performing mode matching analysis on voice content provided by the user and the password content through the voice recognition module; (4) judging whether an audio fingerprint of the voice provided by the user is of the legal voice or not through an audio fingerprint recognition module; and (5) inspecting the matching degree between the voice provided by the user and a voiceprint module established by the registered user through a voiceprint recognition module, and regarding login is the real user login and receiving the login of the user if the degree achieves a set value. According to the online voiceprint recognition system and the implementation method thereof, disclosed by the invention, simple, easy-to-use and high-efficient online identity authentication can be realized.
Owner:SHENGLE INFORMATION TECH SHANGHAI
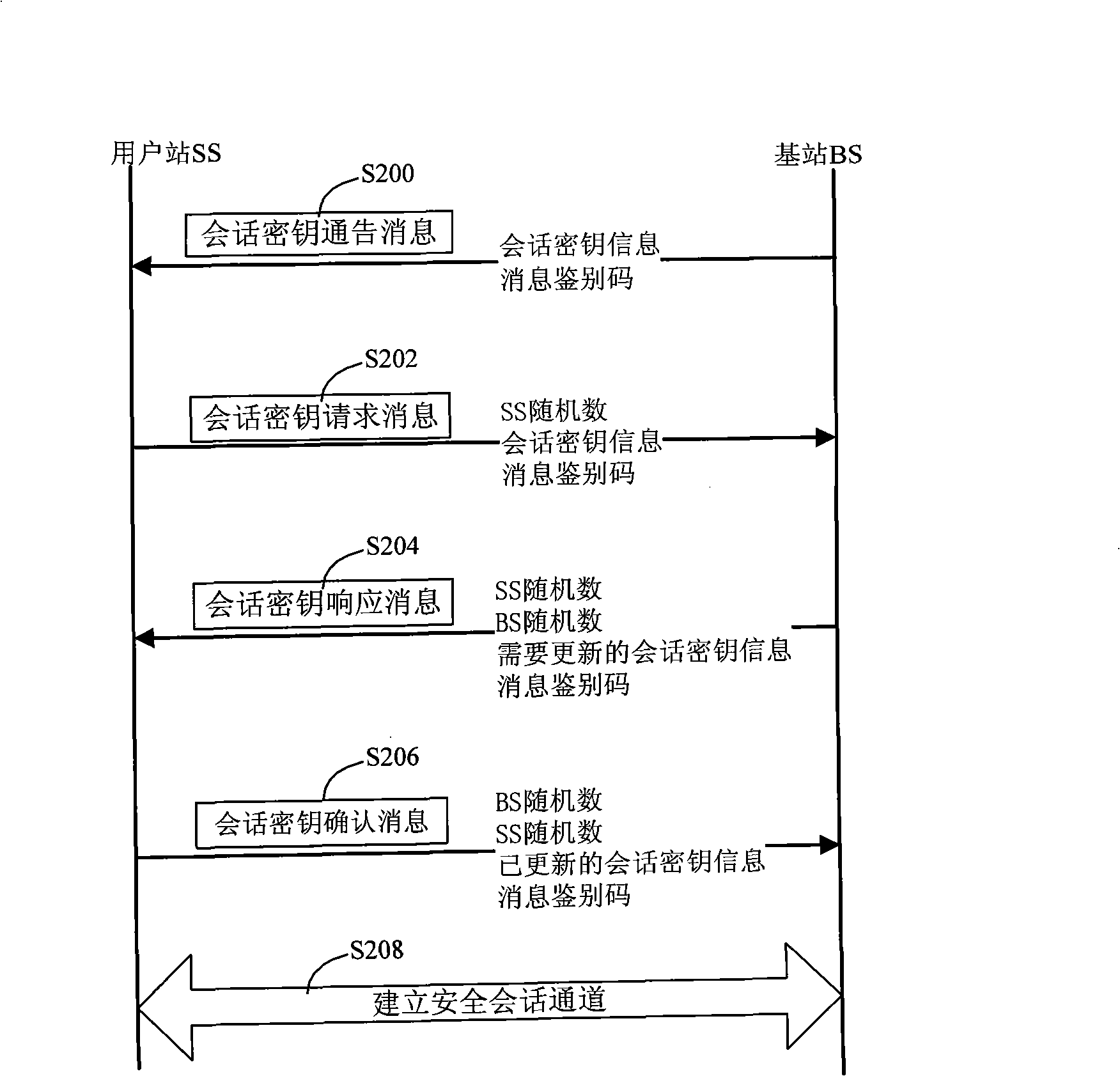
Safety access method of wireless metropolitan area network
InactiveCN101272616AReduces the possibility of crackingRealize AuthenticationUser identity/authority verificationRadio/inductive link selection arrangementsDigest access authenticationAccess method
The invention relates to a method for safe accessing of a wireless metropolitan area network, which comprises an authenticating step and a session key negotiating step. The authenticating step comprises that: a subscriber station SS sends a request message for access authentication to a base station BS; the BS sends a request message for certificate authentication to an authentication server AS; the AS verifies the request message for certificate authentication and sends a response message for certificate authentication to the BS; the BS verifies the validity of the identity of the SS according to the response message for certificate authentication; if the SS is valid, the BS sends the response message for access authentication to the SS; the SS verifies the validity of the BS according to the response message for access authentication; if the BS is valid, the SS uses the encryption certificate key of the SS to decrypt the material of authentication key. The SS signing certificate in the proposal is used for stating the identity and the SS encrypting certificate is used for encrypting and decrypting the material of authentication key so as to reduce the risk that the key is decrypted; through verifying the certificates of the BS and the SS by the AS, authentication for the subscriber station SS and the base station BS is realized and security level is improved.
Owner:GCI SCI & TECH
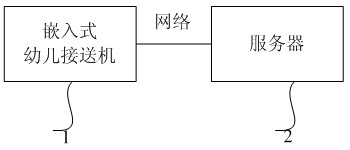
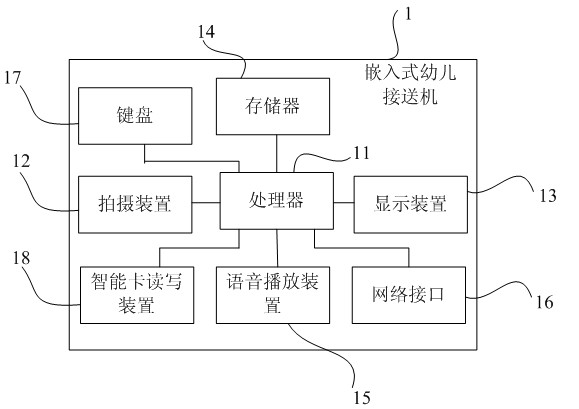
Child picking and sending system on basis of face identification and control method thereof
InactiveCN102073859AStrengthen security managementPrevent impersonationCharacter and pattern recognitionMessaging/mailboxes/announcementsText messagingMobile phone
The invention belongs to the field of face identification and provides a child picking and sending system on the basis of face identification. The child picking and sending system comprises an embedded child picking and sending machine and a server, wherein the embedded child picking and sending machine is used for registering first information of a plurality of picking and receiving people for each child in advance, storing the first information in a storage of the embedded child picking and sending machine, identifying a field picking or sending person through face identification according to the first information and sending identification record information comprising an identity of the picked or sent child to the server through a network after the identification is successful; and the server is used for sending a mobile phone prompting short message to other picking and sending people of the picked or sent child except for the field picking or sending person according to the received identification record information and second information of the child picking and sending people, which is prestored at the end of the server. The child picking and sending system provided by the invention prevents a lawless person from falsely picking up the child by carrying out face identification on the picking and sending person, sends the mobile phone prompting short message to parents of the child, who are registered in advance, when the child is picked up, so as to strengthen safety management of picking up and sending the child.
Owner:HANVON CORP
Express item collecting and dispatching method of logistics
InactiveCN104361479AAvoid lossPrevent impersonationApparatus for meter-controlled dispensingLogisticsLogistics managementData library
The invention discloses an express item collecting and dispatching method of logistics. The express item collecting and dispatching method comprises the following steps that express item posting information is recorded in a database system, and a two-dimensional code and a freight note are generated; the collected express item is scanned, and the two-dimensional code is sent to a client at the same time; the express item is dispatched and scanned, and the express item dispatching information is sent to the database system; a self-service express cabinet sends an express item storage request and scans and sends the two-dimensional code to the database system, the database system controls the self-service express cabinet to be opened, and after the express item is stored, the database system sends express item picking reminding information to the client; the self-service express cabinet sends an express item picking request and scans and sends the two-dimensional code of the client to the database system, and the database system controls the self-service express cabinet to finish express item picking; if the express item is not picked, the database system regularly sends the express item picking reminding information to the client, if the express item is not picked within the set period, the database system informs a postman to pick back the parcel and try to dispatch the parcel, and the express item is withdrawn if dispatching still fails. The dispatching speed is high, self-service express item picking is achieved, personal information of the client can be prevented from being leaking, safety is high, and operation is easy.
Owner:GUANGXI UNIV
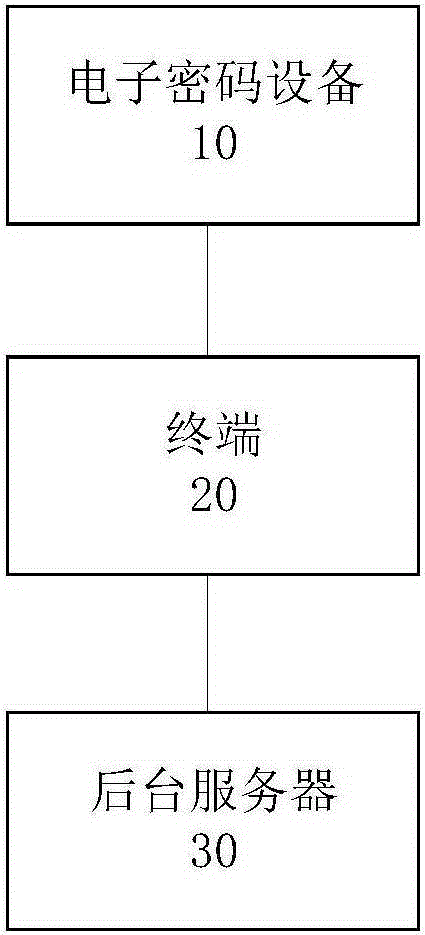
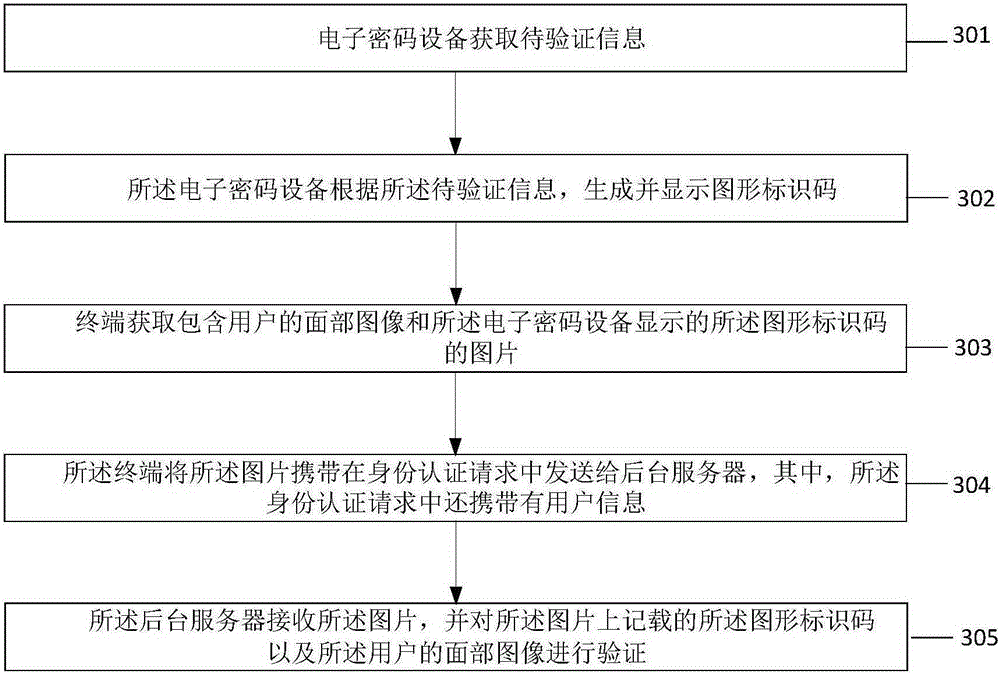
Remote identity authentication method and system and remote account opening method and system
ActiveCN105245341AGuaranteed non-repudiationWill not be tampered withUser identity/authority verificationDigital data authenticationGraphicsComputer terminal
The invention provides a remote identity authentication method and a system and a remote account opening method and a system. The remote identity authentication method comprises steps: electronic cipher equipment acquires to-be-authenticated information, a graph marking code is generated and displayed according to the to-be-authenticated information, a terminal acquires a picture comprising a facial image of the user and the graph marking code displayed by the electronic cipher equipment, the picture is sent to a backstage server, the backstage server receives the picture, and the graph marking code and the facial image of the user recorded on the picture are authenticated.
Owner:TENDYRON CORP
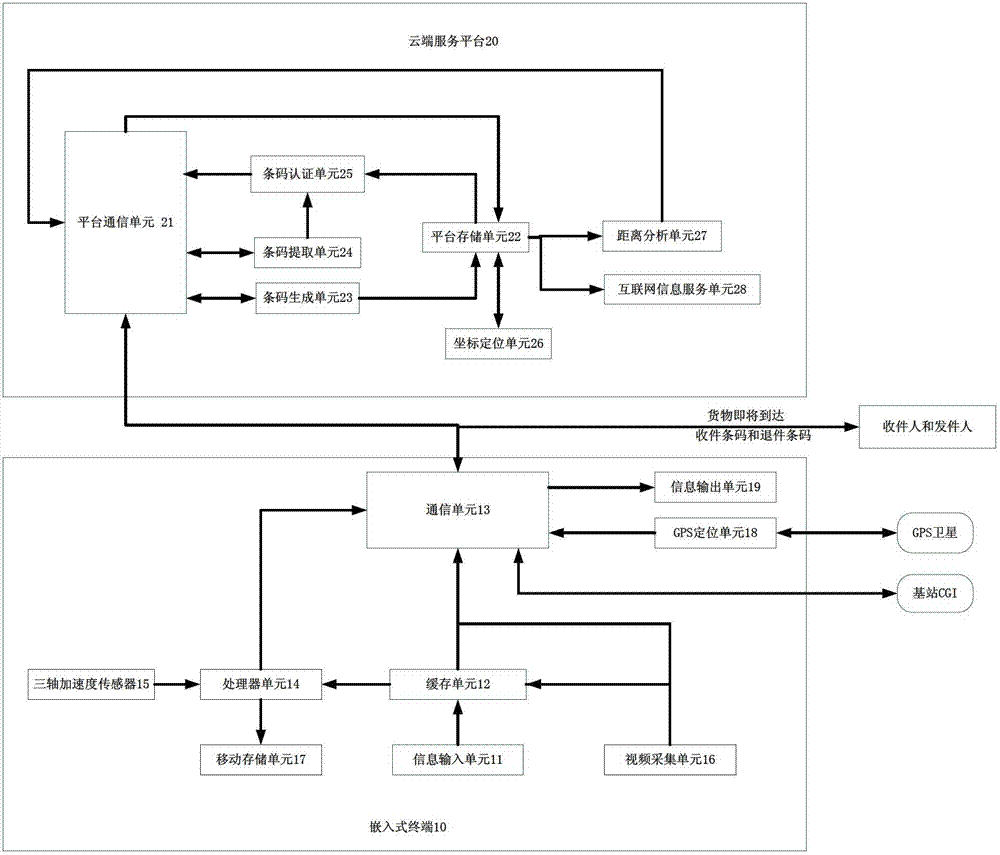
Logistics positioning, authenticating and monitoring system and working method thereof
ActiveCN102780772ASafe deliveryReduce workloadData processing applicationsLocation information based serviceGlobal systemAuthentication
The invention relates to a logistics positioning, authenticating and monitoring system and a working method of the logistics positioning, authenticating and monitoring system. The system comprises an embedded terminal on each cargo packaging bag and a cloud service platform arranged on a cloud server of an express company; each embedded terminal is provided with a sole terminal identity identification code and is connected with the cloud service platform through a communication network; when the cargo is delivered, a received / retreated pack bar code is distributed to each cargo randomly by the cloud service platform, and the received / retreated pack bar code as a pack receiving certificate is transmitted to a receiver / sender, then the received / retreated pack bar code can be used for assisting the identity authentication when the pack is received; during whole the transportation process, the cargo is positioned in an uninterrupted way by the embedded terminal through the double positioning functions of a GPS (global position system) and a GSM (global system for mobile communications) base station; the acceleration of the cargo is confirmed through a three-axis acceleration sensor, and is transmitted to the cloud service platform to be stored; images are taken by using a video acquisition unit at regular intervals; and a video differential algorithm is adopted to retain images having sudden scene change in a moving storage unit for evidence taking. The system and the method can be used in the field of express delivery logistics, and the cargo can be delivered more safely and more reliably.
Owner:LUZHOU PINCHUANG TECH CO LTD +1
Safety face identification device with high identification precision
InactiveCN107798315AImprove recognition accuracyImprove work efficiencyCharacter and pattern recognitionLifting framesEngineeringIdentification device
The present invention relates to a safety face identification device with high identification precision. The device comprises a pedestal, a support block, a camera, a lifting mechanism, a cleaning mechanism and at least two bracing pieces. The lifting mechanism comprises a first motor, a screw rod, a moving block, a pulse sensor and a spacing module. The cleaning mechanism comprises a driving module, a first connection block, a moving module, a spraying module and a connection rod. The safety face identification device with high identification precision performs living body verification by employing the lifting mechanism to prevent other people from pretending to be users for authentication, so that the reliability of the face identification device is improved, and the cleaning mechanism is employed to clean a camera to improve the definition of a lens of the camera, so that the identification precision of the face identification device is improved; and moreover, compared to a traditional cleaning mechanism, the work efficiency of the cleaning mechanism is higher, and the practicability of the face identification device is higher.
Owner:小视科技(江苏)股份有限公司
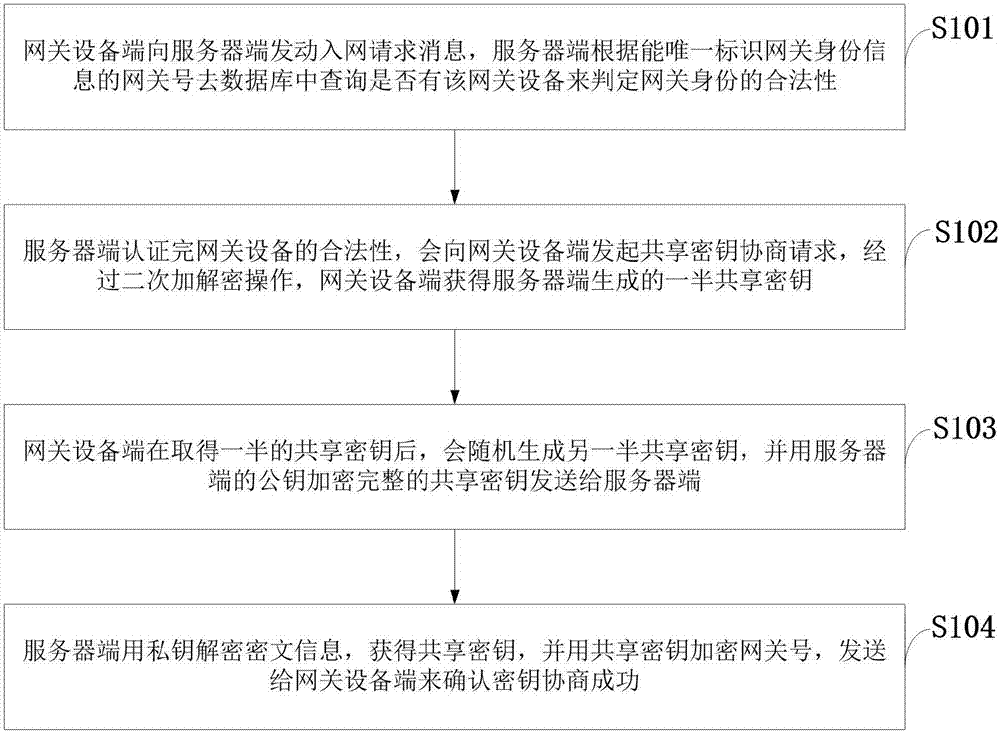
Lightweight device authentication and shared key negotiation method based on Internet-of-things platform
ActiveCN107454079ASimple calculationCalculation speedKey distribution for secure communicationData informationInternet of Things
The invention belongs to the technical field of the Internet of things, and discloses a lightweight device authentication and shared key negotiation method based on an Internet-of-things platform. The method includes the following steps: a gateway device side sends a network access request message to a server side, and the server side queries whether there is the gateway device in a database according to a gateway number which can uniquely identify gateway identity information in order to judge the legitimacy of the gateway identity; the server side authenticates the legitimacy of the gateway device, and issues a shared key negotiation request to the gateway device side, and through two encryption and decryption operations, the gateway device side obtains one half of a shared key generated by the server side; after getting the half of the shared key, the gateway device side randomly generates the other half of the shared key, uses a public key of the server side to encrypt the complete shared key, and sends the shared key to the server side; and the server side uses a private key to decrypt cipher text information to get the shared key, and sends the shared key to the network device side to confirm the success of key negotiation. The security of equipment authentication, shared key and data information is ensured.
Owner:XIDIAN UNIV
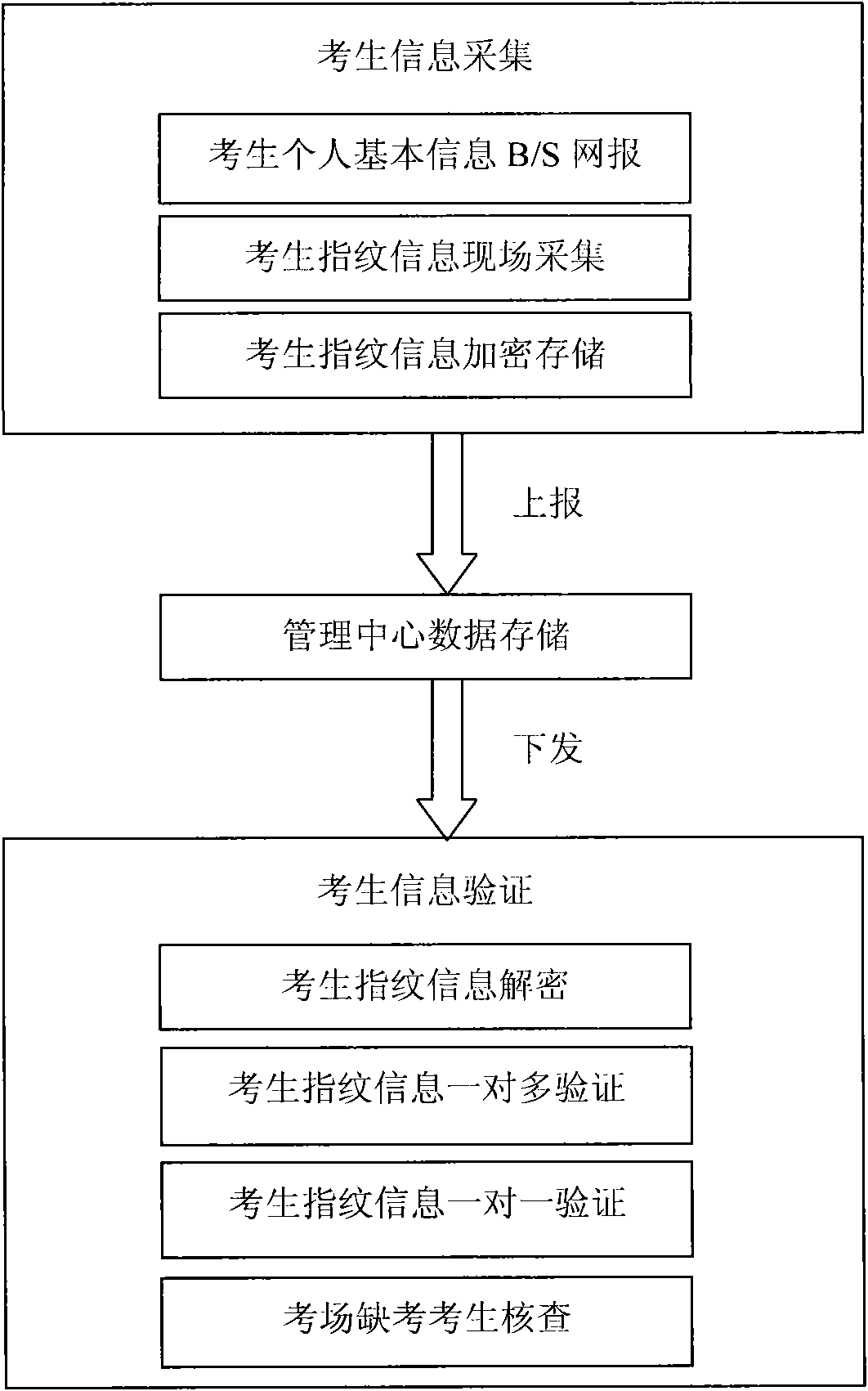
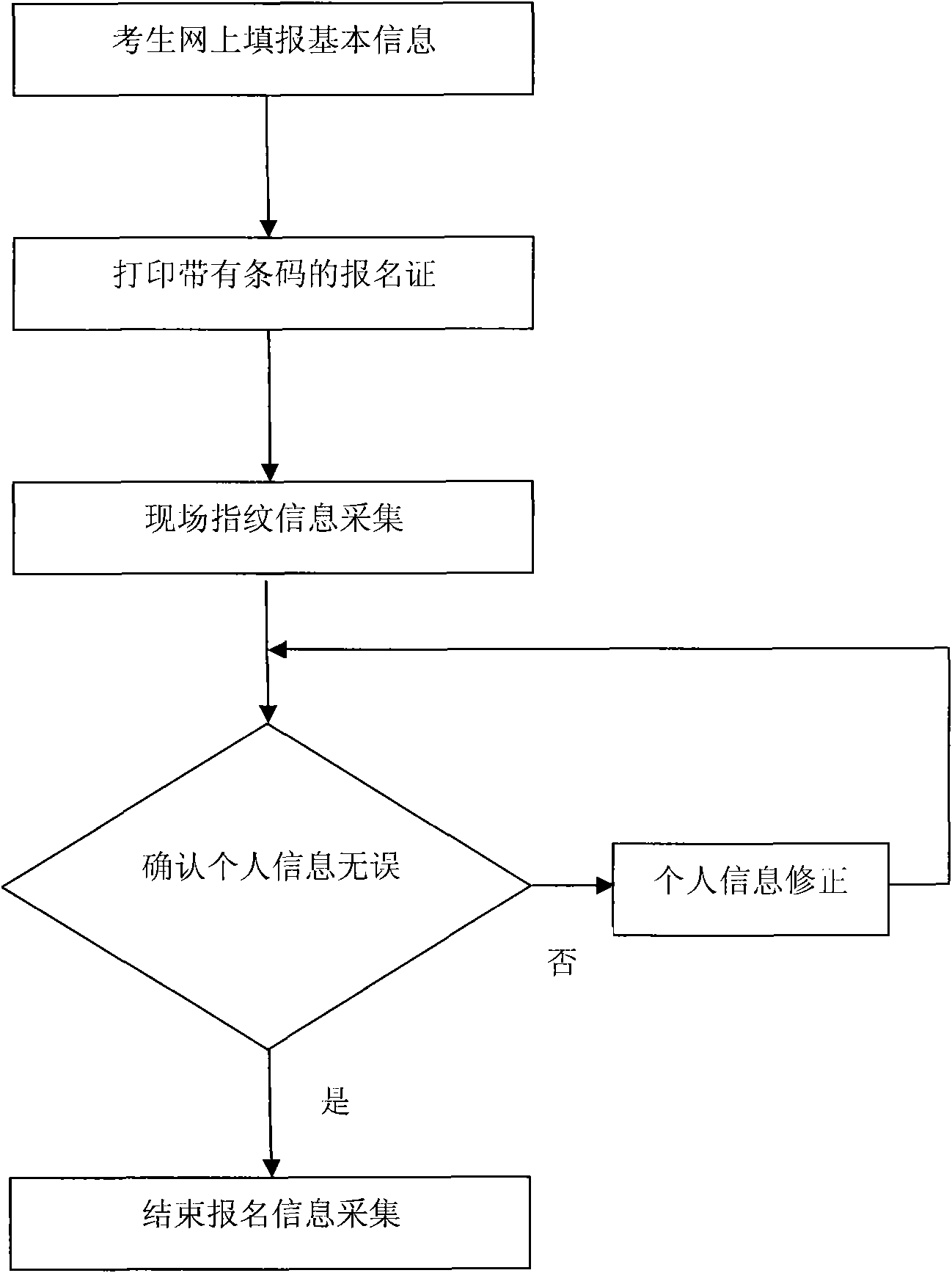
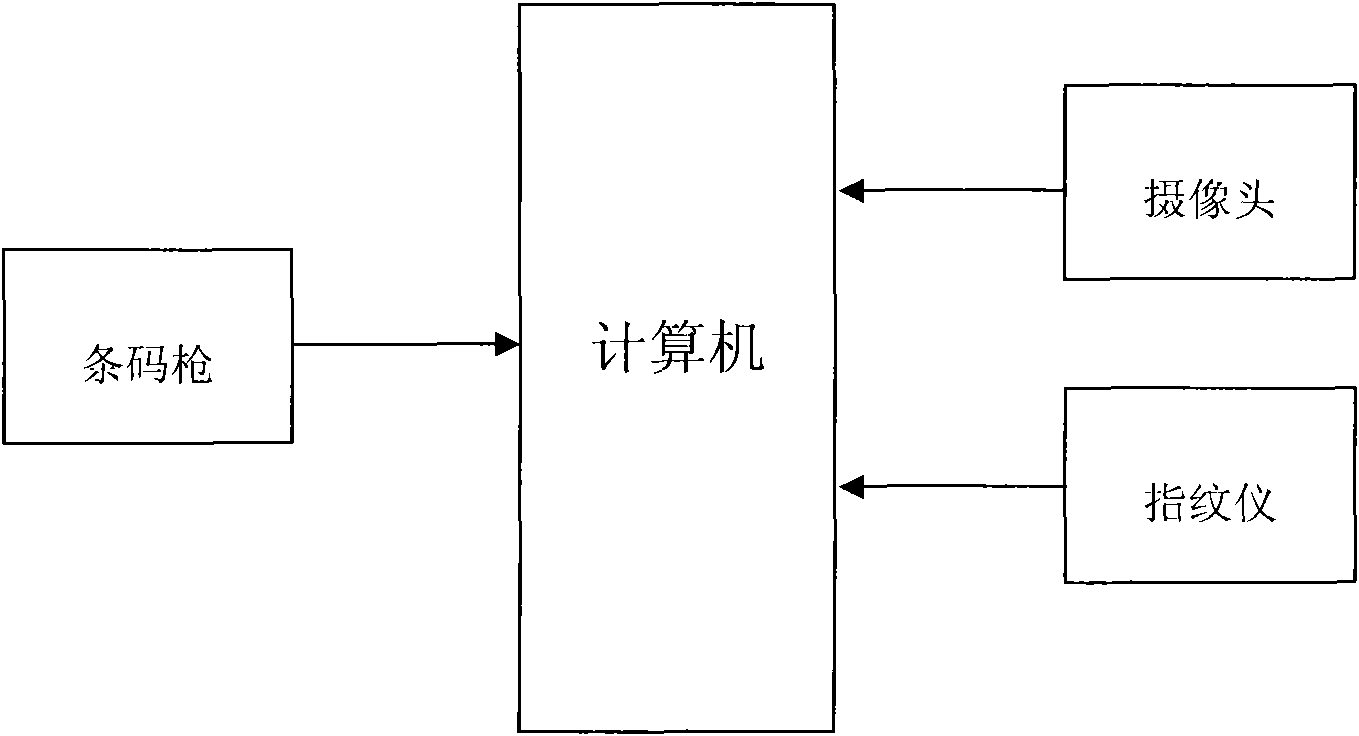
Large-scale test-oriented examinees identity fingerprint verification system
InactiveCN101615246AAccurately determineEnsure safetyCharacter and pattern recognitionIndividual entry/exit registersTest takerValidation methods
Owner:HARBIN ENG UNIV
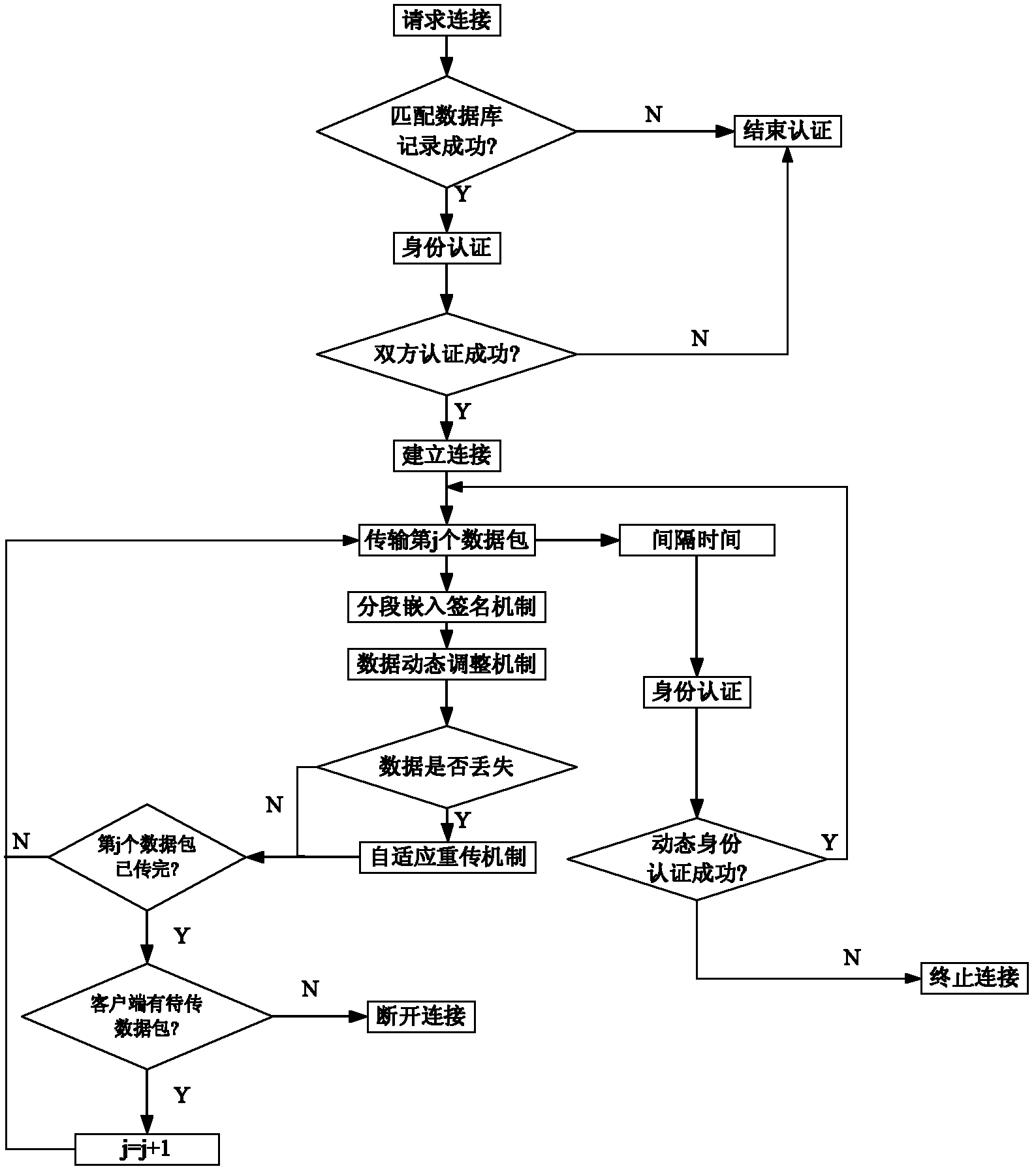
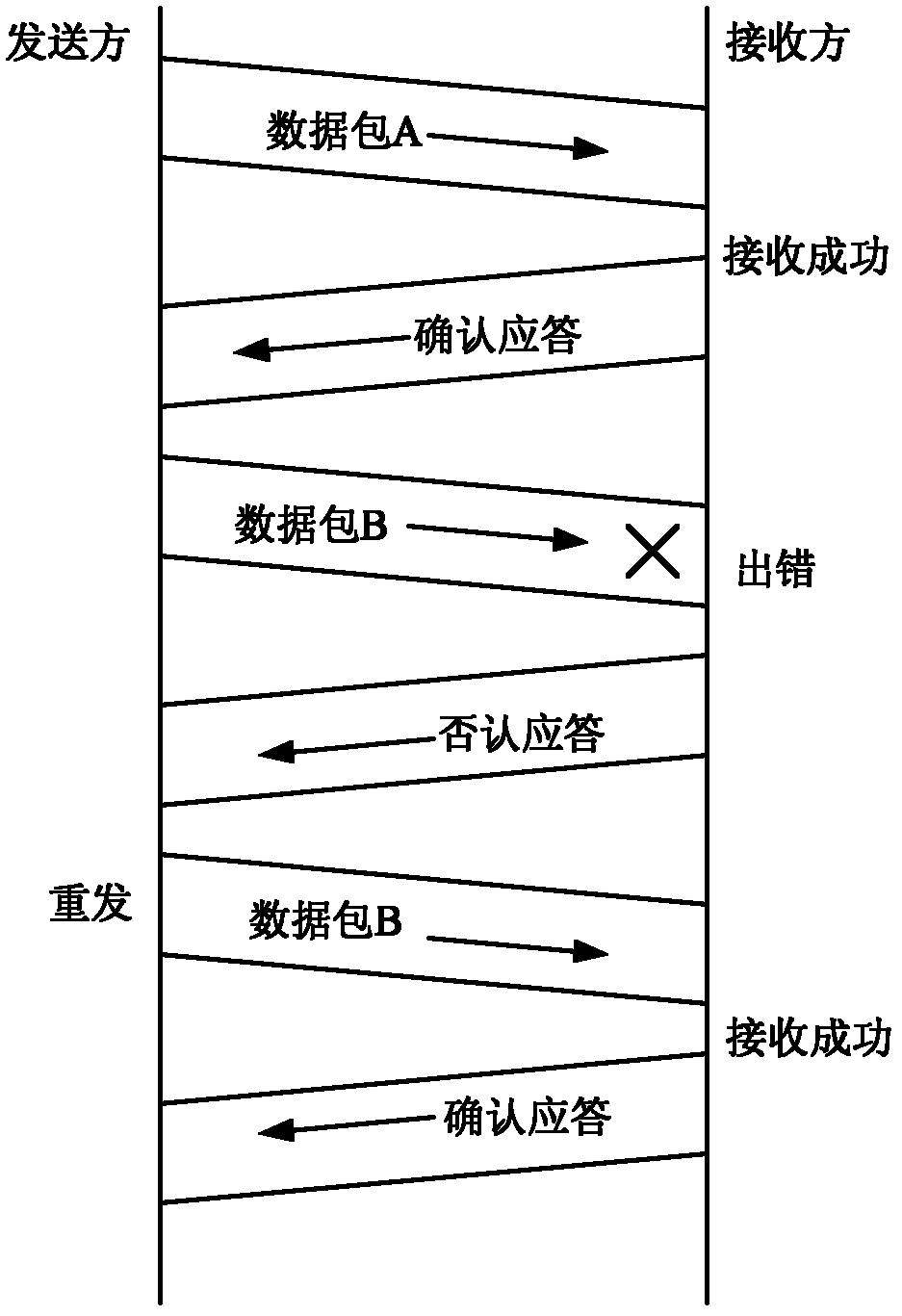
Adaptive retransmission and signature segmented embedding data transmission method
InactiveCN102664893AIntegrity guaranteedFirmly connectedError prevention/detection by using return channelUser identity/authority verificationSelf adaptiveData transmission
The invention discloses an adaptive retransmission and signature segmented embedding data transmission method, which is characterized by comprising the following steps of: matching the identity information of a user in a safety database by using a server, and finishing the method if the identity information of the user fails to be matched; performing mutual identity authentication on the user and the server, and finishing the method if the mutual identity authentication of the user and the server fails; and performing data transmission, and in a data transmission process, performing the steps of performing dynamic identity authentication on the server and the user at random time intervals, terminating connection if the dynamic identity authentication of the server and the user fails, embedding a signature in a segmented way, judging whether transmitted data has an error or is lost or not in an acknowledgement way, performing data retransmission if the transmitted data has the error or is lost, judging whether the data transmission is finished or not, and terminating the connection when the data transmission is finished.
Owner:CHONGQING UNIV OF TECH
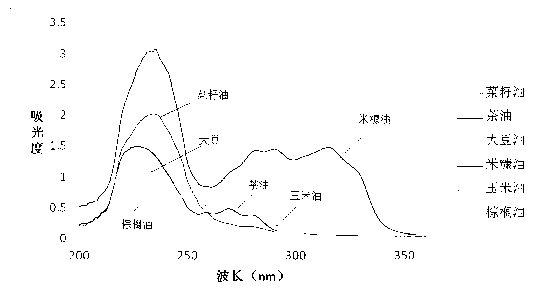
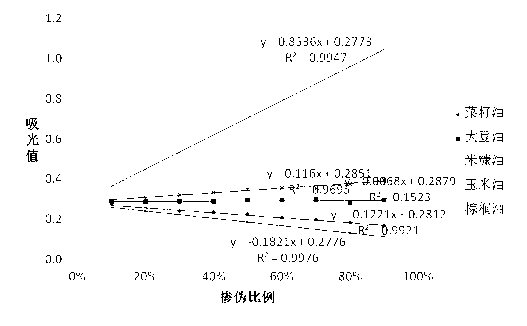
Detection method for adulterated tea oil
ActiveCN103217393APrevent impersonationProtect interestsColor/spectral properties measurementsFull waveRefractive index
The invention relates to the technical field of edible oil, and provides a method for detecting the adulterated tea oil. The method comprises the following steps of: firstly, establishing a refractive index, an iodine value, a saponification value and an oleic acid content adulteration detection model, determining the adulteration type by detecting the sample, then, determining an adulteration quantity model through ultraviolet spectrum full-wave scanning, and comparing the data to obtain the determined adulteration quantity. According to the method provided by the invention, not only can the adulteration type for the tea oil be identified, but also the adulteration quantity can be detected, so that cheap edible oil can be prevented from being used for personating expensive tea oil. The method provided by the invention has the characteristics of being economical and simple, excellent in repeatability and high in accuracy, and the like, can be practically used for the teal oil adulteration detection work, and can guarantee and safeguard the benefits of consumers.
Owner:SOUTH CHINA AGRI UNIV
Method for rapidly confirming express delivery receiver
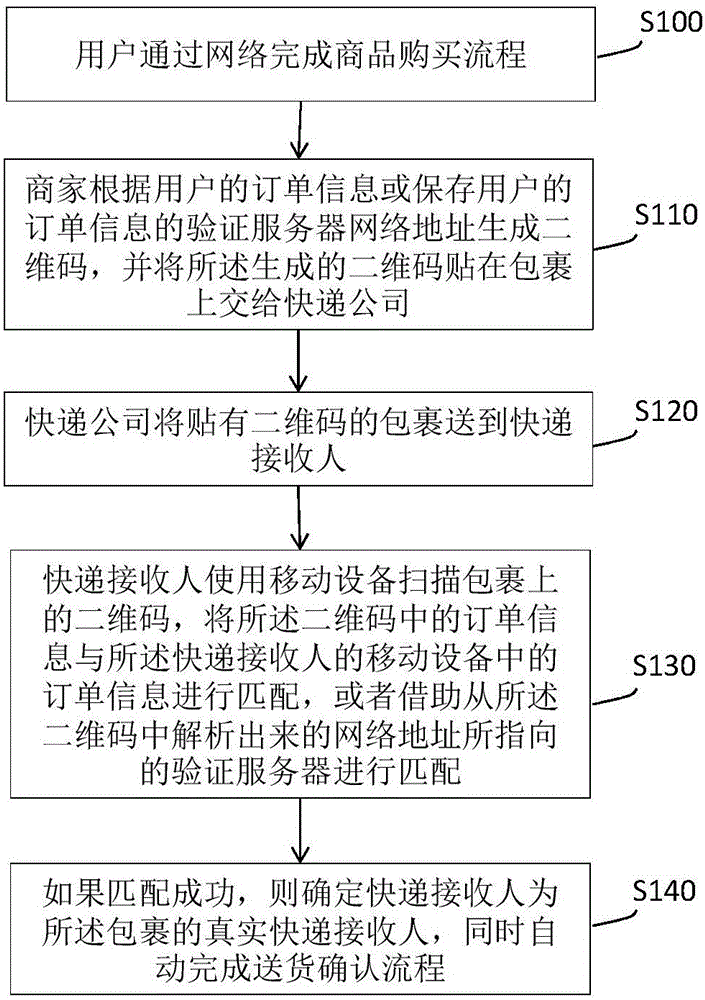
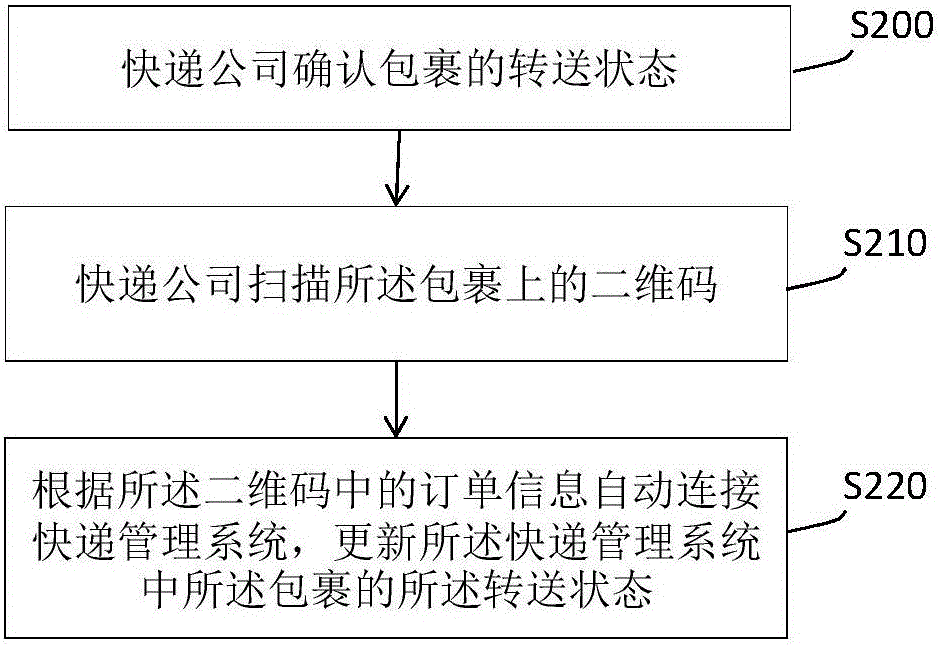
InactiveCN105825421ALive UpdatePrevent impersonationBuying/selling/leasing transactionsLogisticsNetwork addressingNetwork address
The invention discloses a method for rapidly confirming an express delivery receiver. A user finishes a goods purchasing process through a network, a trade company, according to order information of the user or a verification server network address storing the order information of the user, generates a two-dimensional code, adheres the generated two-dimensional code to a package, handles the package to an express delivery company, the express delivery company sends the package to the express delivery receiver, the express delivery receiver scans the two-dimensional code on the package by use of a mobile device, matches the order information in the two-dimensional code with order information in the mobile device, or performs matching by means of a verification server directed by the network address analyzed from the two-dimensional code, if the matching succeeds, it is confirmed that the express delivery receiver is a real express delivery receiver of the package, and at the same time, a delivery confirmation process is automatically completed. By using the scheme provided by the invention, an express delivery conveying state can be updated rapidly in real time, the package can be prevented from being fraudulently taken by others, the express delivery management, dispatching and signing receiving efficiency and safety are improved, the cost is saved for the express delivery company, and user experience is improved.
Owner:BEIJING SHEJIYUE TECH CO LTD
Method for making fingerprint encryption certificates and cards
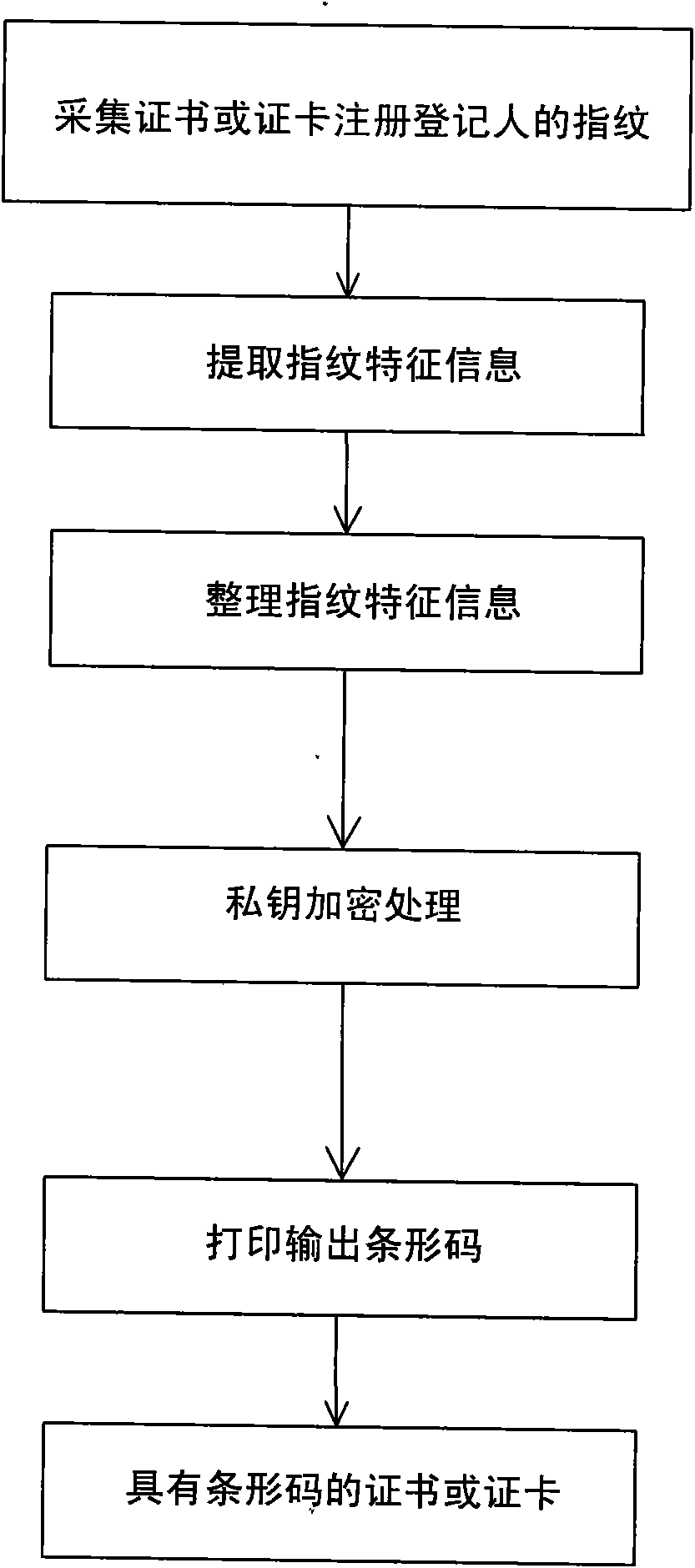
InactiveCN101596820AImprove the level of anti-counterfeiting technologyPrevent counterfeitingOther printing matterVisual presentation using printersBarcodeHigh intensity
The invention relates to a method for making fingerprint encryption certificates and cards, mainly comprising the following steps: a fingerprint scanner is adopted to collect the fingerprint characteristic information of registers registered on the certificates or the cards and transmit the fingerprint characteristic information to a PC machine; and after the PC machine clear up the fingerprint characteristic information by corresponding software, the PC machine encrypts the fingerprint characteristic information by special private key encryption equipment and then prints out the encrypted fingerprint characteristic information on the certificates or the cards in a bar code mode by a print-out device and can also transfer the bar codes to a photographic film or a film to cover and adhere the bar codes on the certificates or the cards. The method can fundamentally enhance the anti-forgery technology level of the certificates and the cards, enables the traditional certificates and cards to have functions of digital break resistance, forgery prevention, obliteration prevention, demagnetization prevention, electric rewrite prevention, the locking of personal biological characteristics of the registers registered on the certificates or the cards, and the like, can simply, fast and authoritatively verify the fact or fiction of the held certificates or cards of the registers and has a high-strength safety anti-forgery function.
Owner:北京中维华盾科技发展有限公司
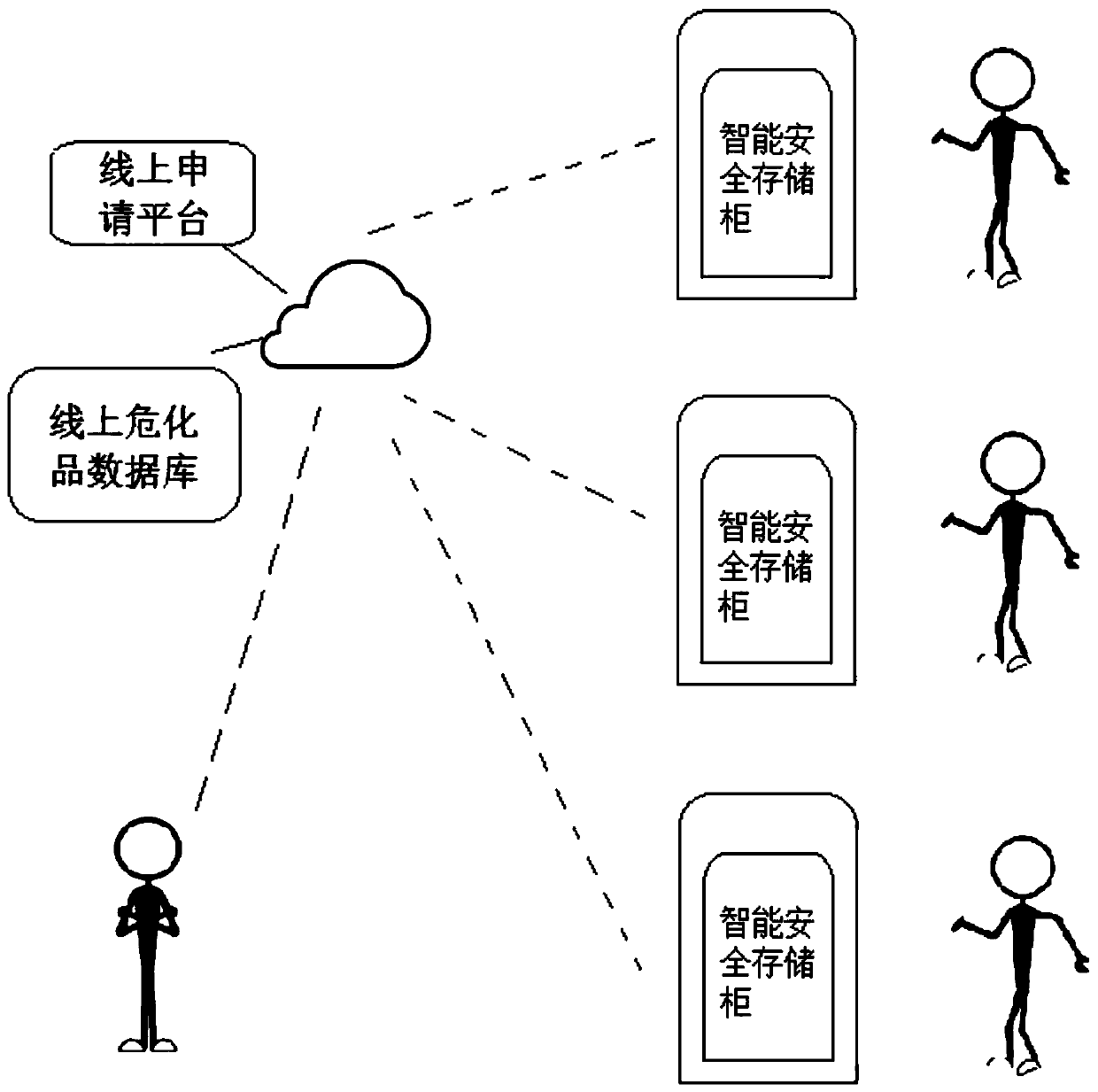
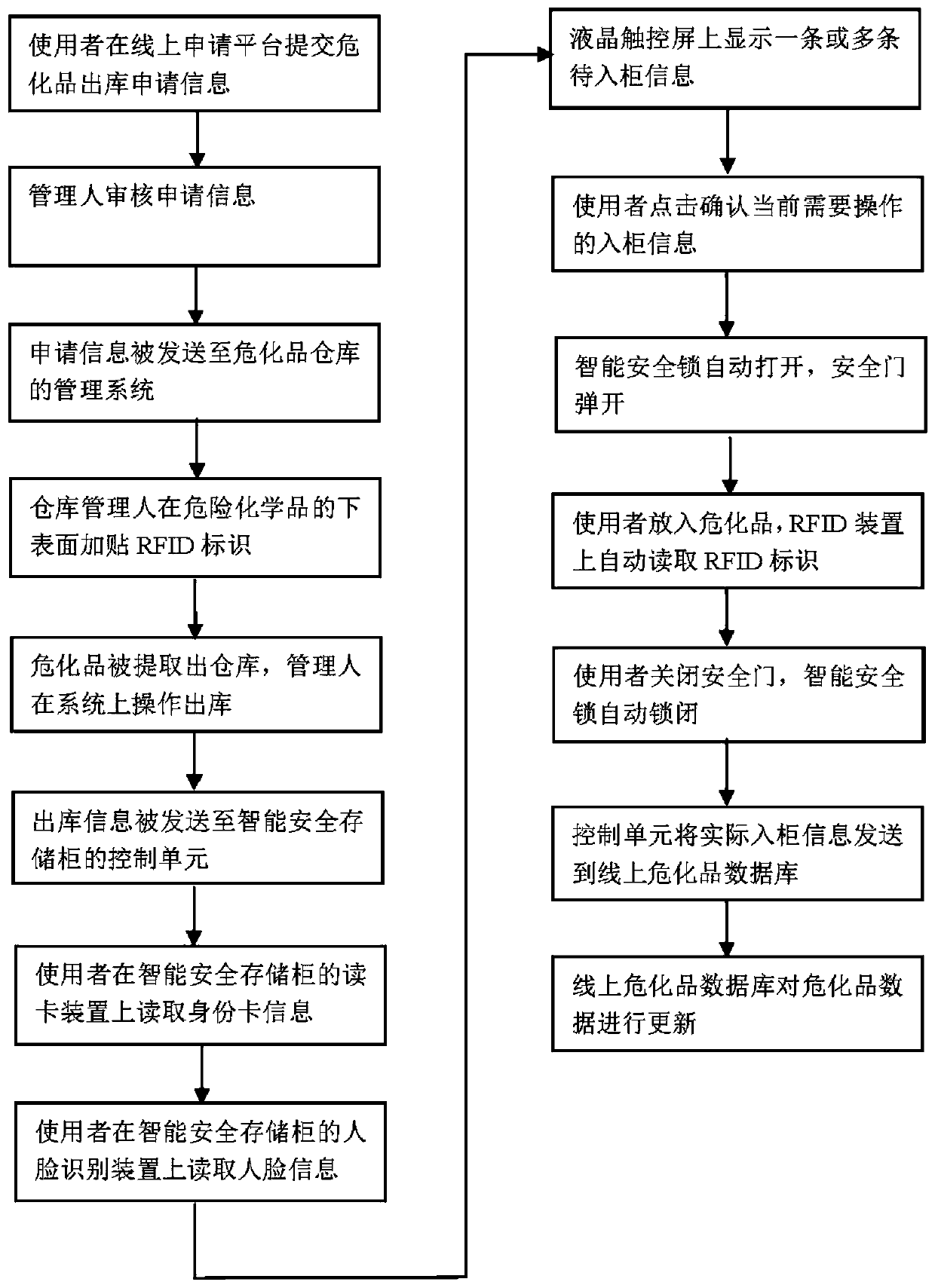
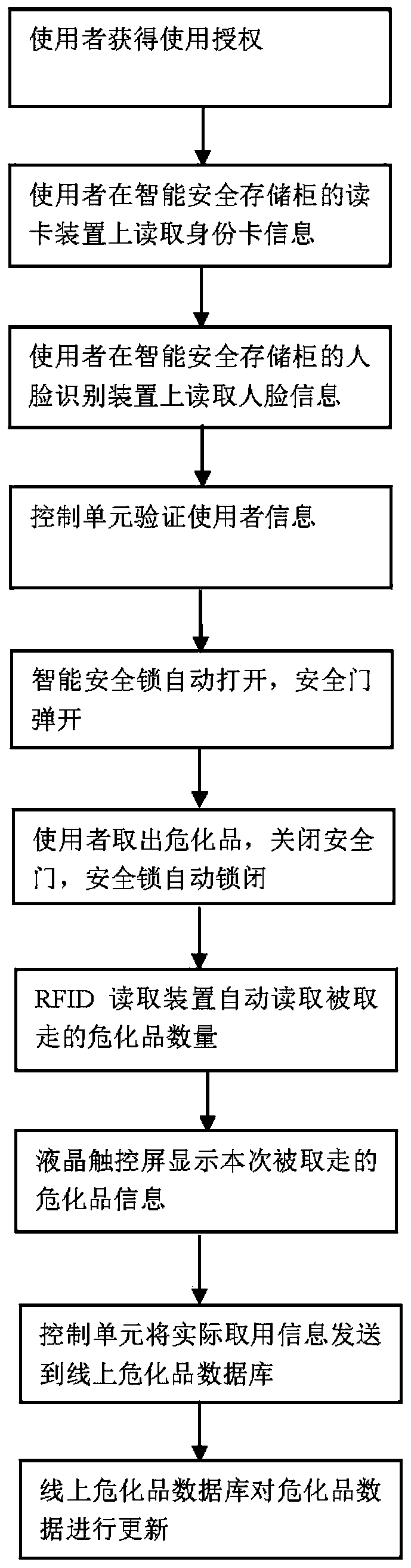
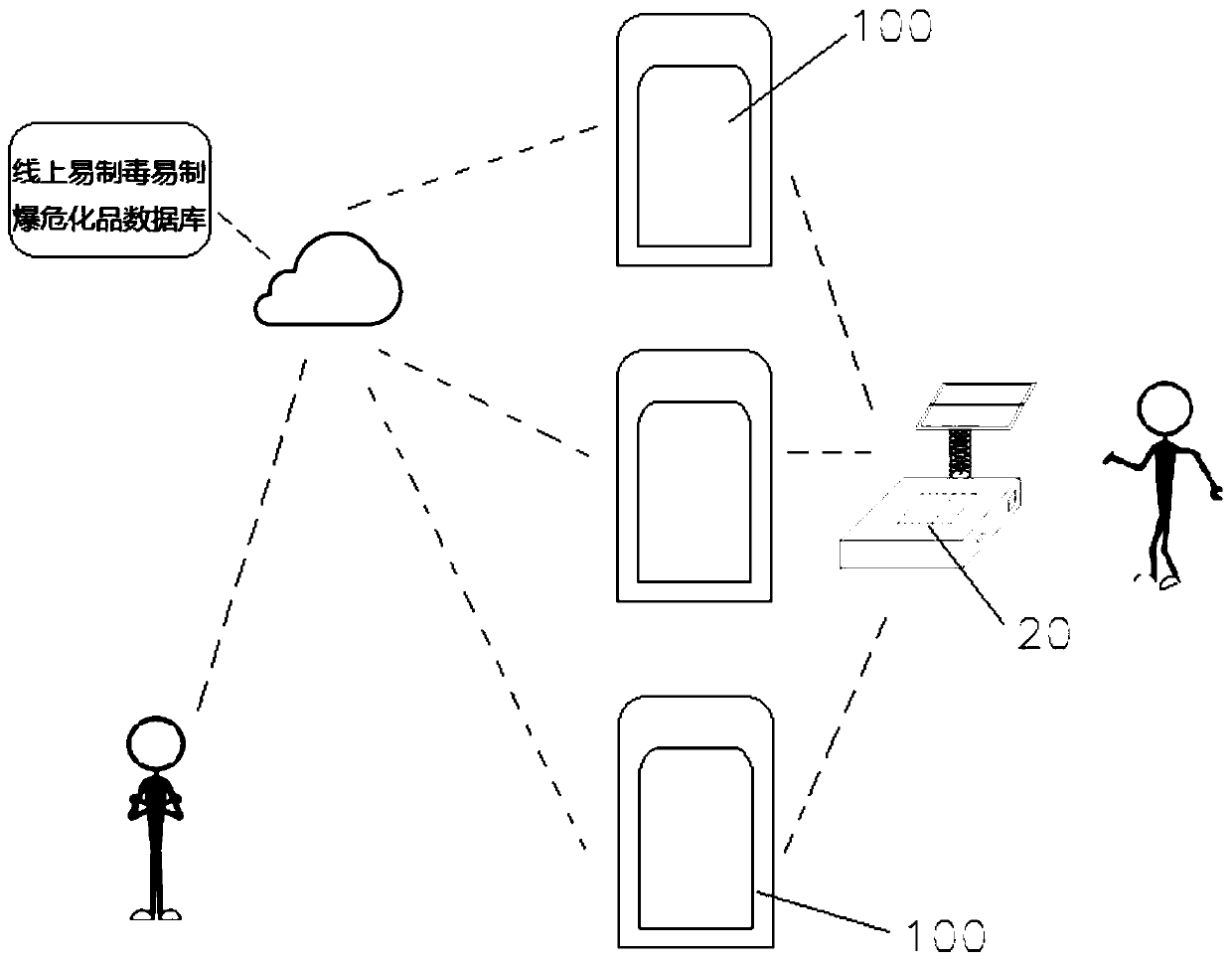
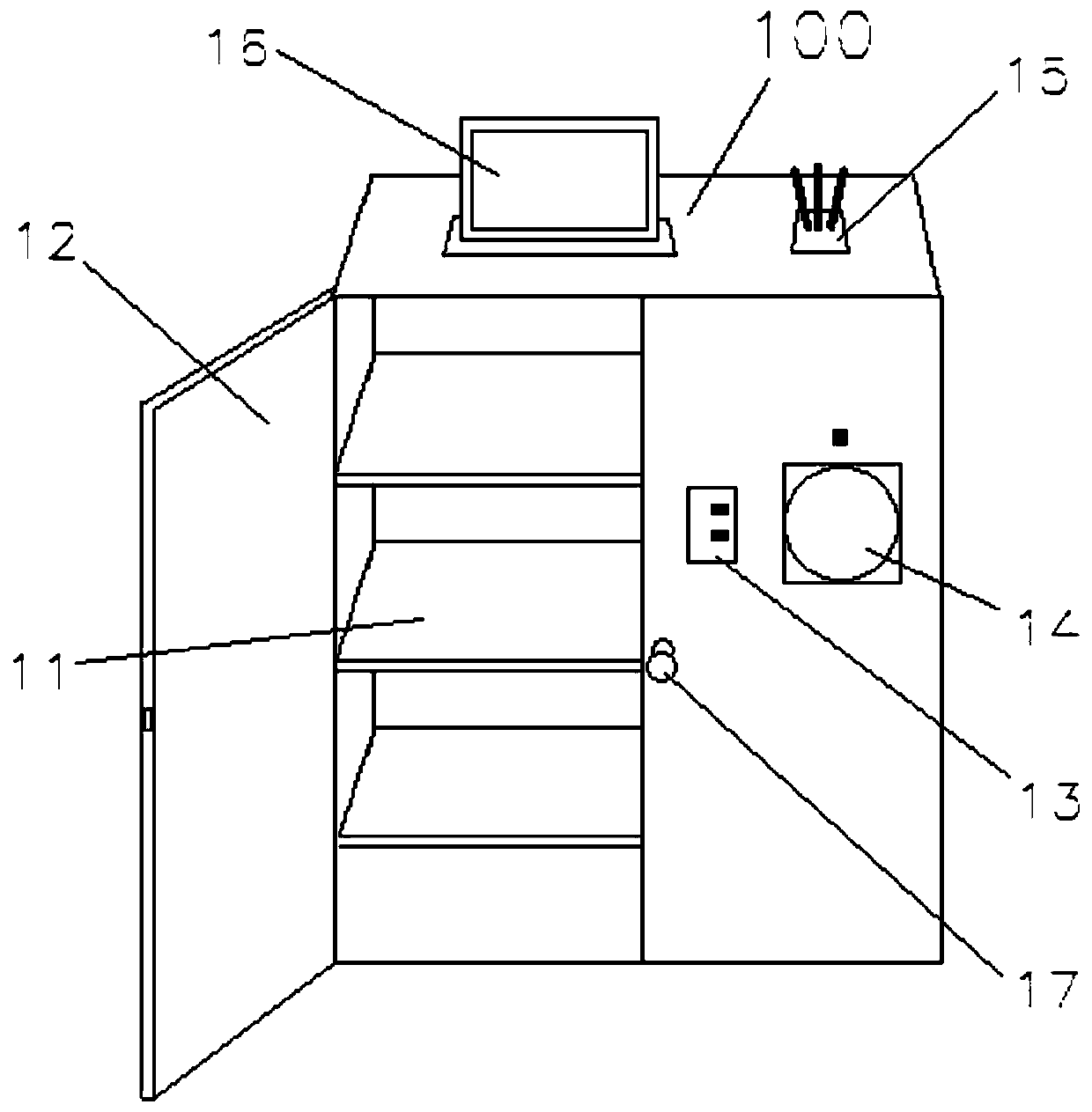
Hazardous chemical substance management system and method
PendingCN110889662AImplement usage tracking managementPrevent impersonationLogisticsData connectionInformatization
The invention relates to a hazardous chemical substance management system and method. The management system comprises an online application platform, an online hazardous chemical substance database and an intelligent safety storage cabinet. The online application platform is used for submitting the warehouse-out application information of the hazardous chemical substances, the online hazardous chemical substance database is used for recording and updating the hazardous chemical substance information, and the intelligent safety storage cabinet is provided with a safety door, an RFID reading device, a card swiping device, a face recognition device, a communication module or an intranet and a control unit. The RFID reading device is used for reading the RFID identifiers of the hazardous chemical substances, the card swiping device is used for reading the identity card information, the face recognition device is used for reading the face information, and the communication module is used for being in data connection with the online application platform and the online hazardous chemical database. According to the invention, through the combination of software and hardware, the omnibearing and full-platform informatization management is carried out on purchase, sale and storage of the hazardous chemical substances, a complete record report of the hazardous chemical substances from thewarehouse delivery to each use is formed, and the permanent query and traceability are formed.
Owner:耀客明道物联网(武汉)有限公司
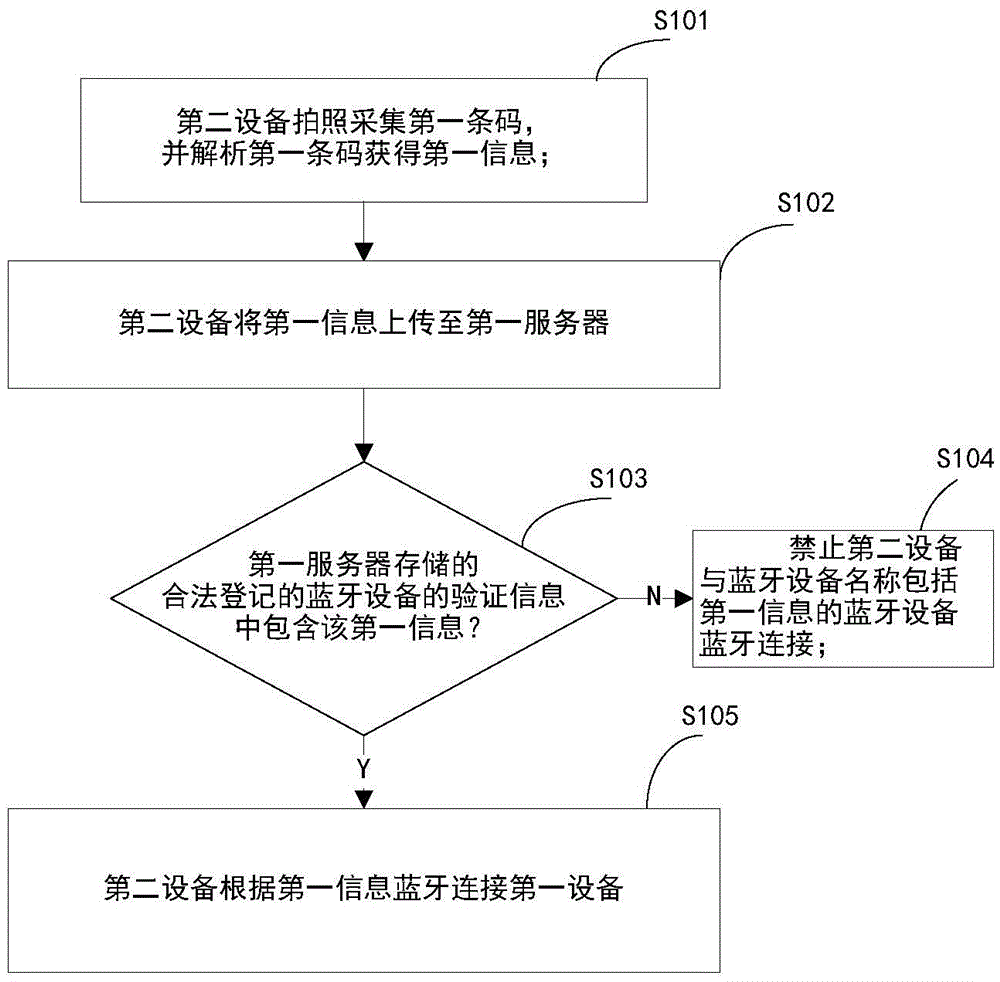
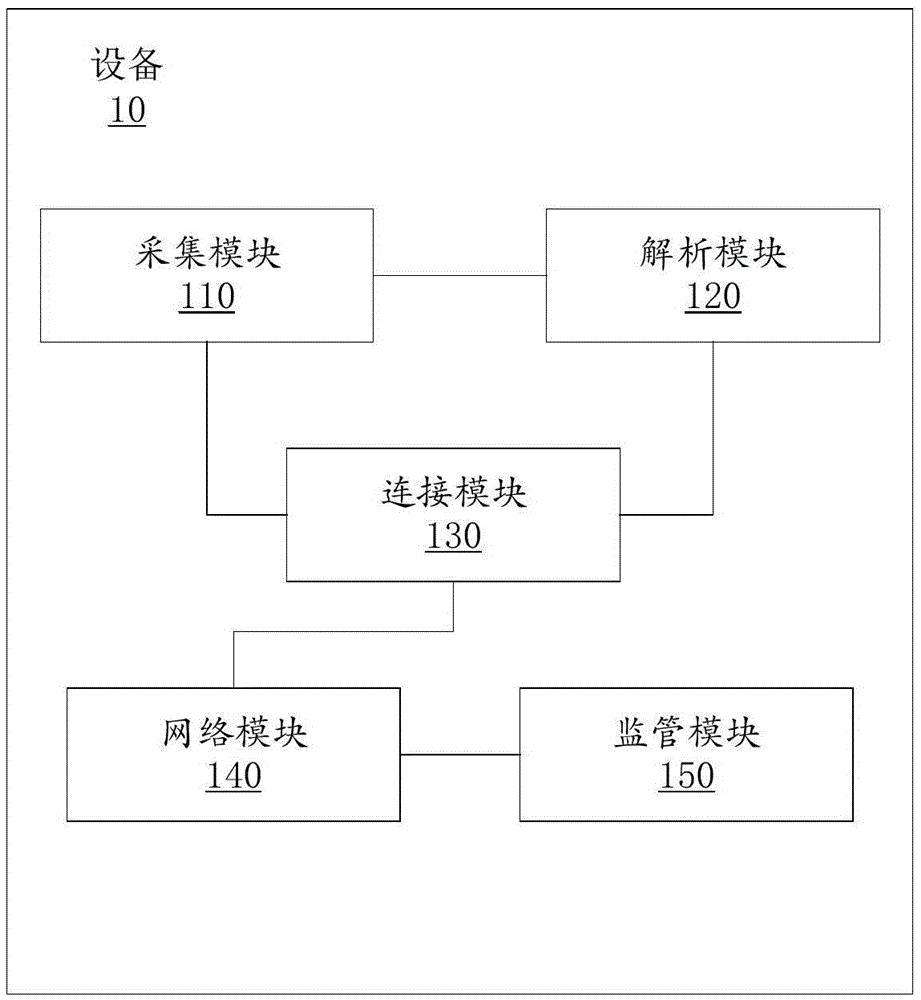
Method, master device, slave device and system for achieving code scanning automatic bluetooth connection
InactiveCN105554908ARaise the possibilityFirmly connectedConnection managementSensing by electromagnetic radiationComputer hardwareBluetooth
The inventor provides a method, master device, slave device and system for achieving code scanning automatic bluetooth connection, which solve the safety and automatic connection problems of bluetooth connection. The invention relates to a method for achieving connection of bluetooth devices, particularly rapid and automatic connection of the bluetooth devices. The method provided by the invention comprises the following steps: a first graphic code is corresponding to a first device, and a second device takes pictures to collect the first graphic code and analyzes the first graphic code to obtain first information; the second device uploads the first information onto a first server, and the first server stores verification information of legally registered bluetooth devices; if the verification information of the legally registered bluetooth devices which is stored in the first server does not contain the first information, then the second device is prohibited from being connected with a bluetooth device, whose name contains the first information, through bluetooth; if the verification information of the legally registered bluetooth devices which is stored in the first server contains the first information, then the second device is connected with the first device through bluetooth according to the first information.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
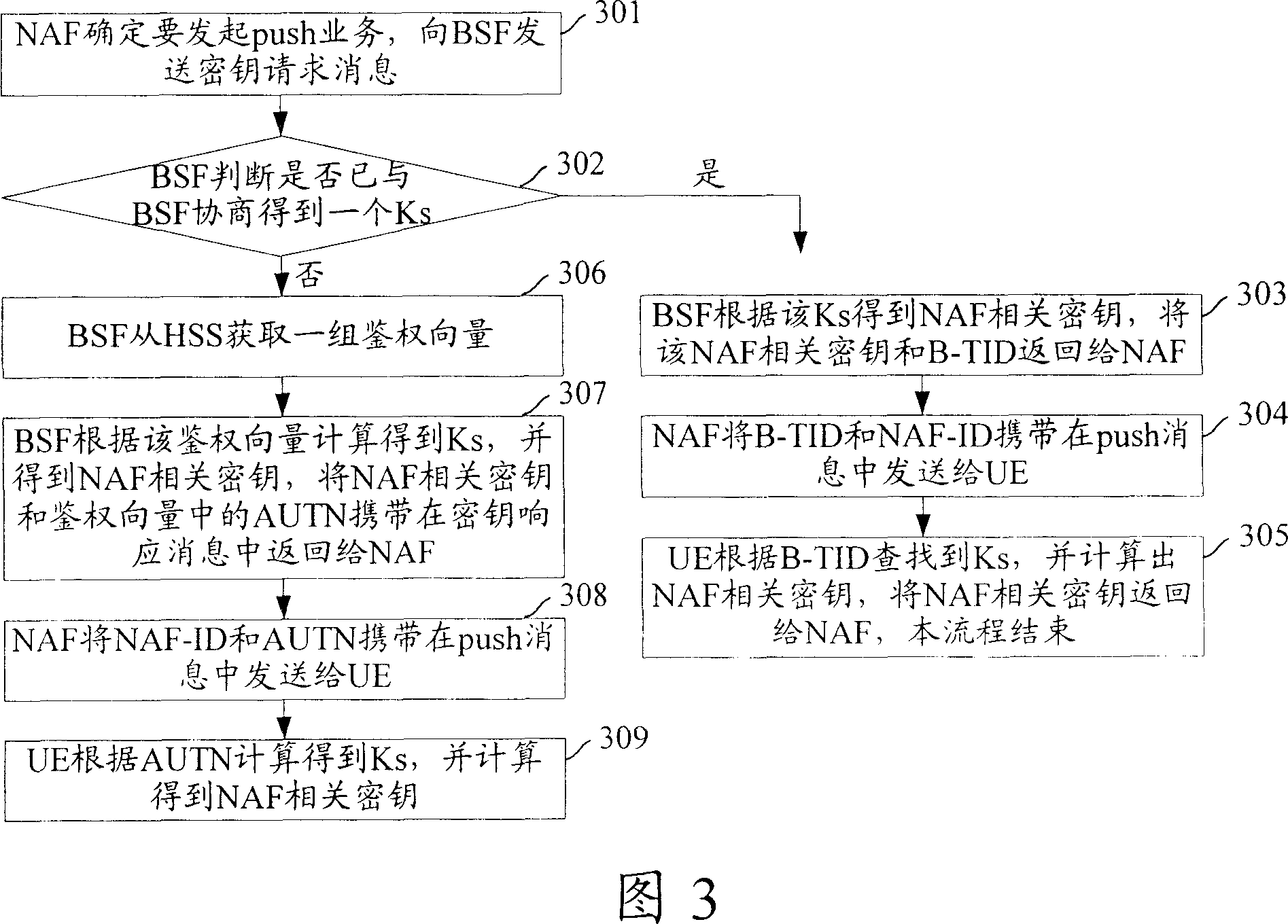
Method for getting service key
ActiveCN101090513AReduce usagePrevent impersonationPublic key for secure communicationRadio/inductive link selection arrangementsAuthorizationStart up
This invention discloses a method for obtaining service keys including: NAF determines services to be initiated to send a push service key request to BSF, which applies the key computation method to compute the obtained push service key based on the obtained push service key and returns it to the NAF to send the push information to UE, which computes to get the push service key. This invention can differentiate the service key initiated actively by NAF and that initiated by UE by altering the computation formula of the service key started up by UE or adding a push service authorization label parameter for the push service key so as to avoid that NAF not ordering the push service uses the service.
Owner:HUAWEI TECH CO LTD
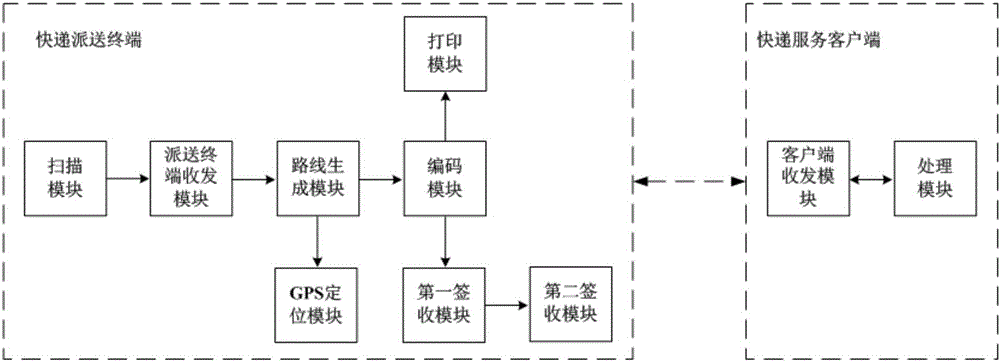
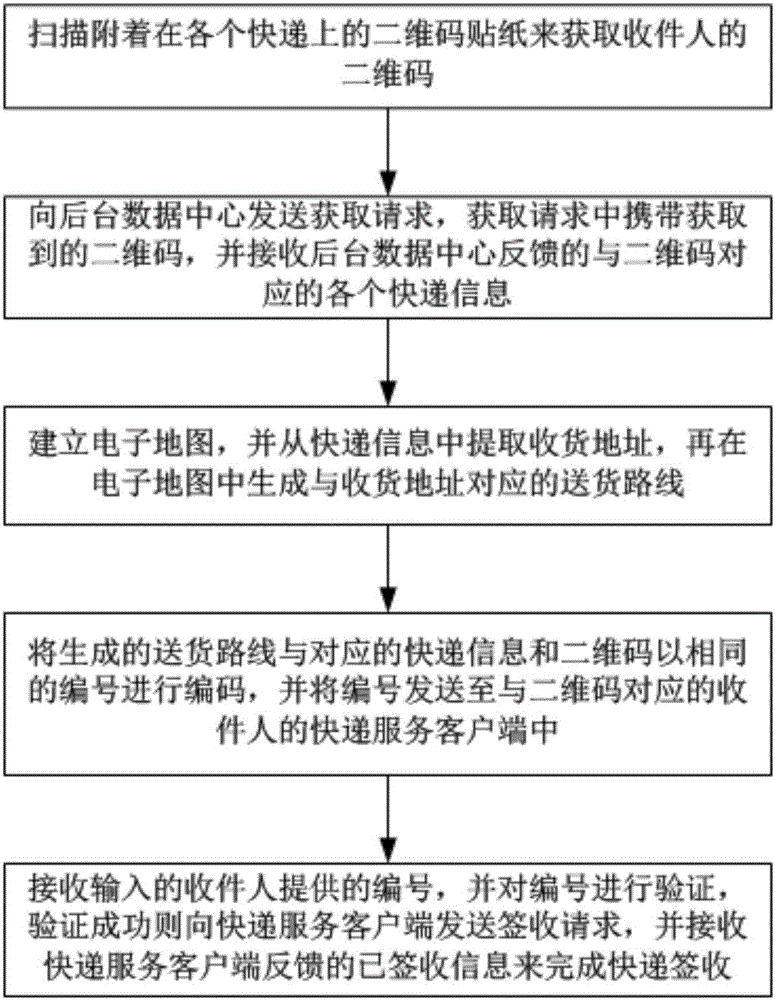
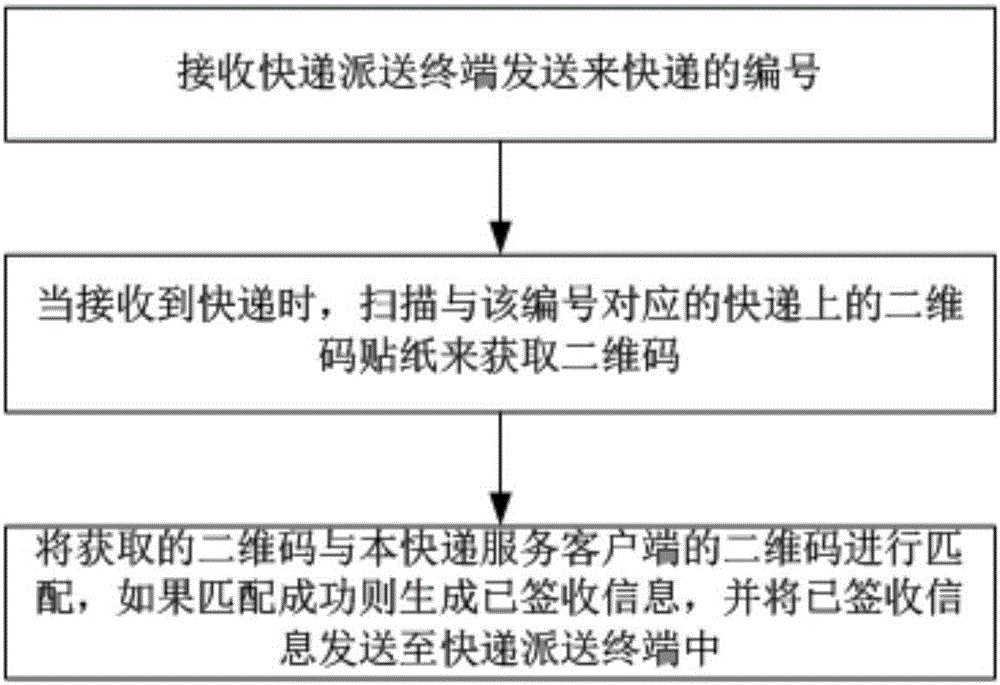
Two-dimensional code based express delivery dispatching terminal, service client and method
The invention provides a two-dimensional code based express delivery dispatching terminal, service client and method. The method of the express delivery dispatching terminal comprises the following steps: obtaining a two-dimensional code through a two-dimensional code patch on an express package; obtaining express delivery information corresponding to the two-dimensional code from a background server; generating a delivery route in an electronic map; encoding the generated delivery route, the corresponding express delivery information and the two-dimensional code through the same number; and according to the number, performing verification, and receiving receipt information of the express delivery client so as to complete express delivery receipt. According to the invention, the two-dimensional code information and the express delivery information can be obtained through the two-dimensional code patch, and the delivery route is generated in the electronic map; the number enables a delivery man to find the corresponding express package conveniently and can also well prevent the express package from being wrongly given or falsely claimed; and the express delivery receipt is completed by receiving the receipt information through the express delivery client and a two-dimensional code mode is employed, such that the utilization rate of an express delivery sheet is also greatly reduced, and client information is also prevented from leakage to a quite great extent.
Owner:沈海峰
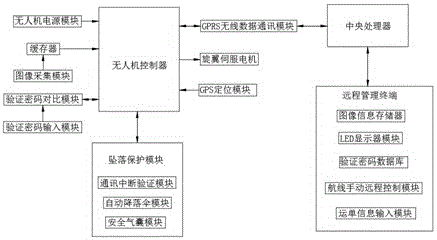
Automatic transmission and delivery system and method based on unmanned aerial vehicle
InactiveCN106228319ASimple structureGuarantee property securityRemote controlled aircraftFranking apparatusWireless dataImage acquisition
The invention discloses an automatic transmission and delivery system based on an unmanned aerial vehicle (UAV), comprising an UAV controller, an image acquisition module, a verification password input module, a UAV power supply module, and a GPS positioning module. The input end of the UAV power supply module is electrically connected with the input end of the UAV controller; the GPS positioning module is in signal connection with the input end of the UAV controller; the output end of the verification password input module is electrically connected with the input end of a verification password contrast module; the verification password contrast module and the UAV controller are electrically connected in a two-way mode; the UAV controller is in two-way signal connection with a central processing unit through a GPRS wireless data communication module; and the central processing unit is in two-way signal connection with a remote management terminal. The system is simple in structure and principle, is of high stability and high safety, and is suitable for promotion.
Owner:张阳康
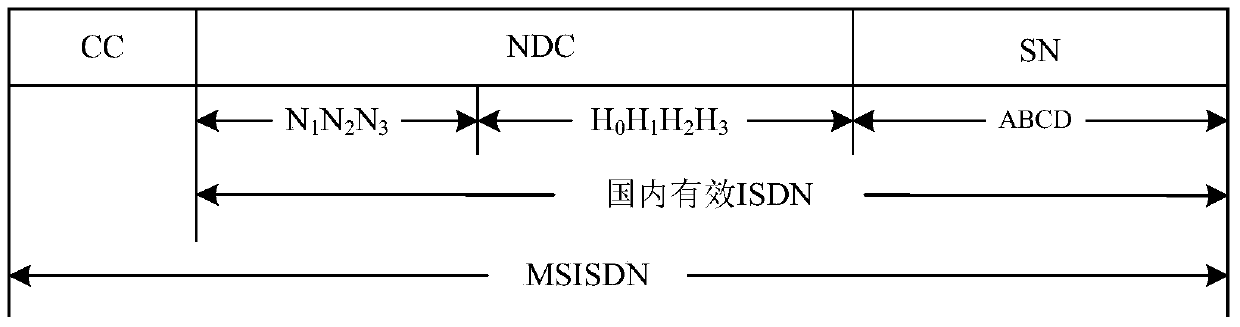
Method and user device for sending user identity authentication information
InactiveCN104219650AImprove protectionEnhanced authenticationSecurity arrangementNetwork data managementThird partyProcessor register
The invention discloses a method and a user device for sending user identity authentication information, a method for confirming a home location register and a visitor location register, and a method for confirming a user legal identity and the home location register. The method for sending the user identity authentication information includes steps: receiving a user identity information request sent by the visitor location register; generating a random serial number according to the user identity information request; using a first secret key stored in the user device to encrypt a serial number formed by connecting the random serial number and an IMSI (international mobile subscriber identification number) in series, and then obtaining an encrypted serial number; returning the user identity authentication information including first information obtained according to the IMSI, second information obtained according to MSISDN, the random serial number and the encrypted serial number to the visitor location register. In exceptional circumstances, the user identity authentication information returned when the user device responds to the user identity information request does not include the IMSI, and therefore risk caused by direct plaintext transmission of the IMSI is reduced. Furthermore, the method and the user device for sending the user identity authentication information are used in combination during the encryption and decryption process, and thereby can prevent a malicious third party from pretending to be a legal user, and strengthen protection and authentication for user identities.
Owner:BEIJING ELECTRONICS SCI & TECH INST
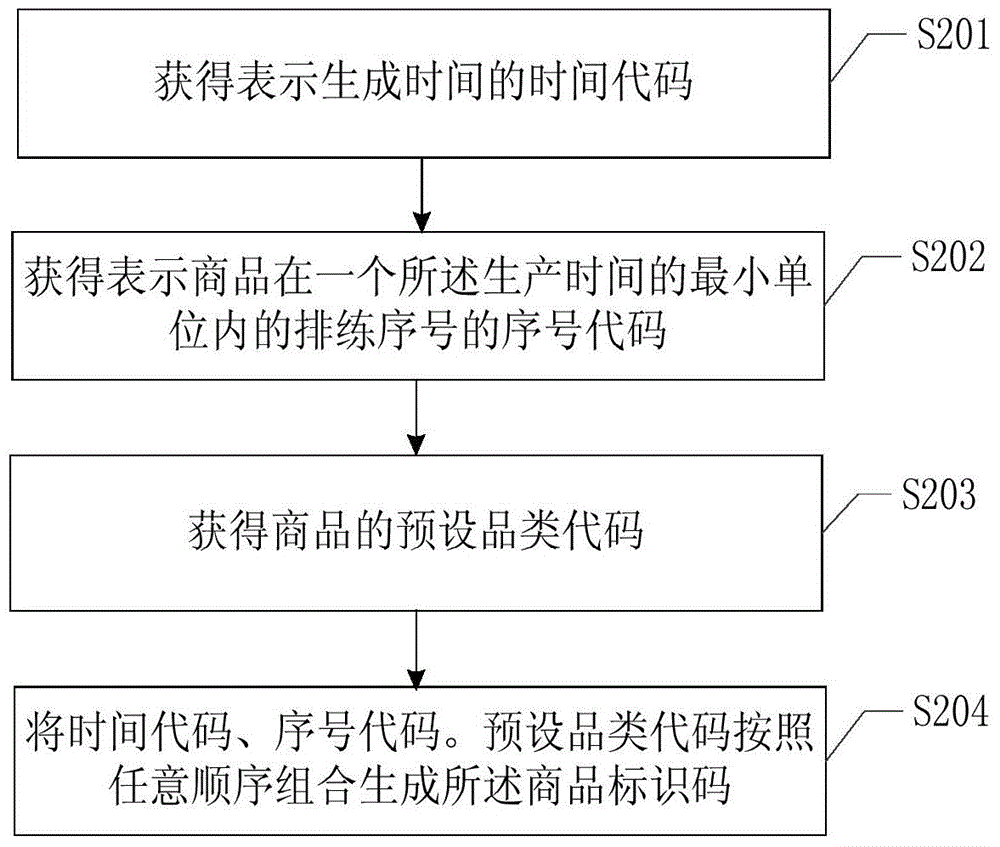
Method for generating commodity identification code, commodity with commodity identification code, packaging can and production technology for canned commodities
InactiveCN105139057AEasy to traceConvenient queryCoverings/external coatingsRecord carriers used with machinesComputer engineeringTime codes
Owner:许泽人
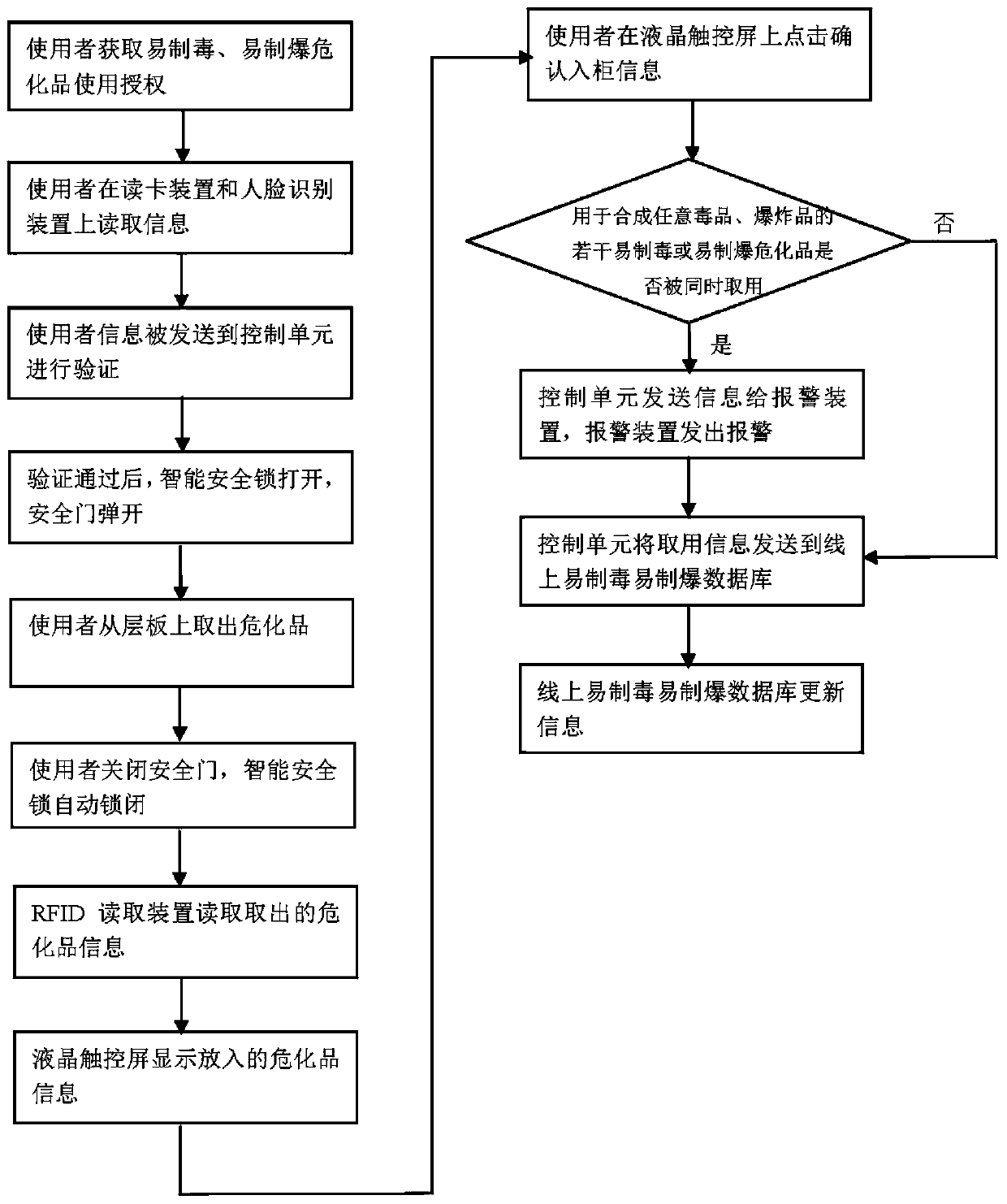
System and method for managing hazardous chemicals easy to produce poison and explode
PendingCN110956566AImplement usage tracking managementPrevent impersonationData processing applicationsCo-operative working arrangementsSingle useSafe storage
The invention relates to a system and method for managing hazardous chemicals easy to produce poison and explode. The system for managing hazardous chemicals easy to produce poison and explode comprises an online database for hazardous chemicals easy to produce poison and explode, an electronic scale and an intelligent safe storage cabinet, wherein the online database for hazardous chemicals easyto produce poison and explode is used for recording and updating names, types, quantity, service life, out-of-cabinet and in-cabinet information of hazardous chemicals easy to produce poison and explode and formula combination information of synthetic drugs or explosives of hazardous chemicals easy to produce poison and explode. The intelligent safe storage cabinet comprises a cabinet body, wherein the cabinet body is provided with a safety door, an RFID reading device, a card swiping device, a face recognition device, a communication module and a control unit. According to the system and themethod, the upper limit value of the single use of the hazardous chemical substances which are easy to produce poison and easy to produce explosion and the single use of the hazardous chemical substances which are easy to produce poison and easy to produce explosion at the same time are monitored by combining software and hardware, so that the hazardous chemical substances which are easy to produce poison and easy to produce explosion are prevented from being illegally used and excessively used, and potential safety hazards caused by illegal use are reduced.
Owner:耀客明道物联网(武汉)有限公司
Source tracing system and method for marine products
The invention discloses a source tracing system and method for marine products. The system comprises a daemon module for storing source tracing information in a data server, an information input module for inputting fishing-boat offshore catching tracks, fishing-boat arrival sorting procedures, box sealing and cooling protection information and marine-product track records of logistics transportation information and an inlet query module for supplying query an interface to the source tracing information through a WEB server. The method includes the steps that the source tracing information is stored in the data server, and the query request of the source tracing information is responded through an application server; the fishing-boat offshore catching tracks, the fishing-boat arrival sorting procedures, box sealing and cooling protection information and marine-product track records of logistics transportation information are input; the interface is supplied to the source tracing information through the WEB server. As the source tracing system is adopted, corresponding seafood is fresh marine products caught by a fish coat just now or marine products replaced with frozen marine products or stale marine products can be queried in a scanning mode, the quality of food is fully guaranteed, the due rights and interests of a consumer are safeguarded, and ecology of the marine products is improved.
Owner:宁波海上鲜信息技术股份有限公司
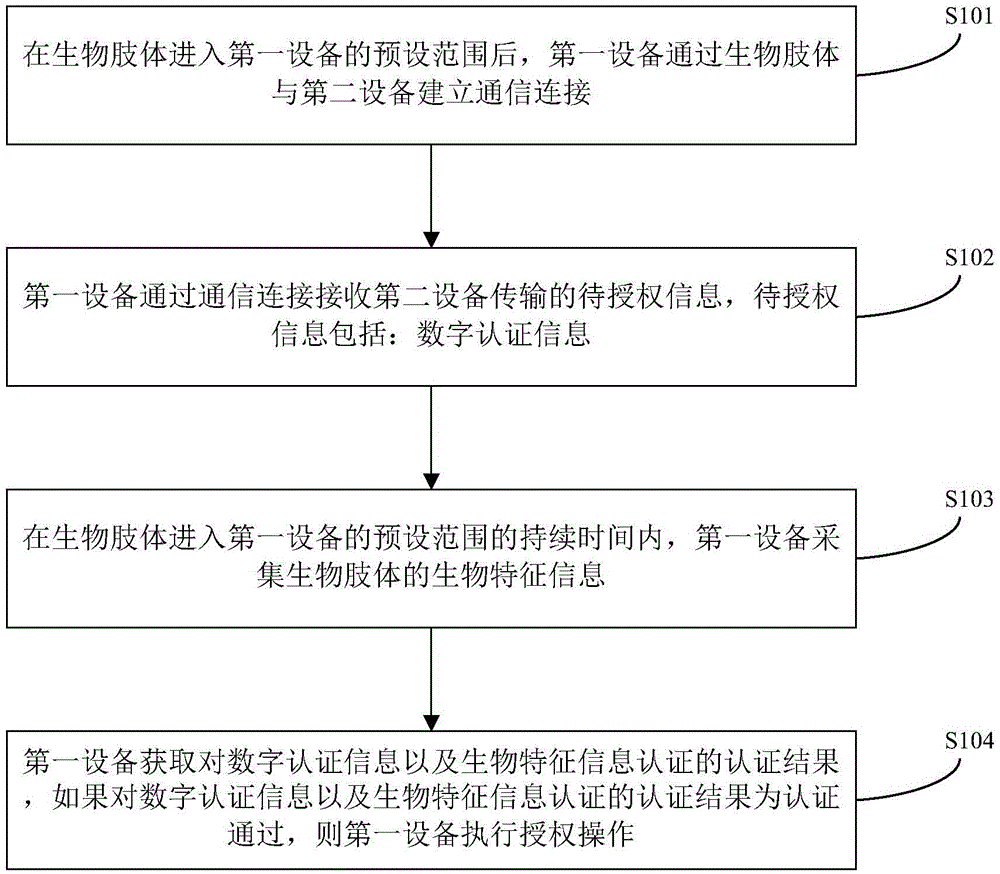
Authorization authentication method, device and system
InactiveCN105991654APrevent impersonationGuaranteed relevanceTransmissionElectric equipmentAuthorization
The invention provides an authorization authentication method, device and system. The authorization authentication method comprises the steps that first equipment establishes communication connection with second equipment through a biological limb after the biological limb enters the preset range of the first equipment; the first equipment receives information under authorization transmitted by the second equipment through communication connection, wherein the information under authorization includes digital authentication information; the first equipment acquires biological characteristic information of the biological limb in time duration when the biological limb enters the preset range of the first equipment; and the first equipment acquires an authentication result of the digital authentication information and the biological characteristic information, and the first equipment performs authorization operation if the authentication result of authentication of the digital authentication information and the biological characteristic information indicates passing of authentication. With application of the authorization authentication method, the behavior of other people of pretending to be the user to pass authorization through wristwatches and other electronic equipment can be prevented so that the security of information and property can be guaranteed.
Owner:李明
Express cabinet picking-up method, express information system, and express cabinet
InactiveCN107358753AThe pick-up method is convenient and quickEasy to useApparatus for meter-controlled dispensingIndividual entry/exit registersPattern recognitionMobile phone
The invention discloses an express cabinet picking-up method, an express information system and an express cabinet. The express cabinet picking-up method includes: a forward step: acquiring addressee information, determining if an addressee is a special addressee or not according to the addressee information, and reading first recognition information which is stored in advance by the addressee if the addresses is the special addressee; and a picking-up step: acquiring second recognition information provided by a consignee, comparing the second recognition information and the first recognition information, opening a corresponding grid opening of the expresses cabinet if the second recognition information matches the first recognition information, otherwise, prompting an error. The express cabinet picking-up method is convenient and fast; the addresses does not have to carry a mobile phone while picking up an express, and can pick up the express by using the pre-stored information such as fingers and voice; and the method can eliminate constraint of the mobile phone, is safe, and can prevent fraudulent picking. The express information system and the express cabinet have those effects, and are easy to use.
Owner:SHENZHEN HIVE BOX TECHNOLOGY CO LTD
Fingerprint identification device and fingerprint identification method
InactiveCN106778674AEnsure safetyPrevent impersonationPrint image acquisitionDetecting live finger characterPattern recognitionRadiology
The invention provides a fingerprint identification device and a fingerprint identification method. The fingerprint identification device comprises a first detection module and a second detection module, wherein the first detection module is used for detecting an attribute of a touch object; the second detection module is used for identifying line information of the touch object; the first detection module is used for obtaining color information of the touch object pressed on the fingerprint identification device; the color information comprises a first pigment coordinate; when the first pigment coordinate is not in a first threshold range, the attribute of the touch object is a living body and an indicator signal is output to the second detection module; and the second detection module starts and senses a fingerprint image of the touch object according to the indicator signal. The fingerprint identification device is relatively low in energy consumption.
Owner:MEIZU TECH CO LTD
Method for implementing lifelong anti-counterfeiting of commodities
InactiveCN104691127ARealize lifelong anti-counterfeitingProtect interestsStampsPattern printingEpoxyMass ratio
The invention provides a method for implementing lifelong anti-counterfeiting of commodities. The method comprises the following steps: mixing an epoxy resin glue A, an epoxy resin glue B or other commercial glues (such as PP glue and PVC glue) and rare-earth up-converting luminescent micro / nano-materials according to a mass ratio of 3: 1: (0.2-1.5) or 1: (0.2-1.5) to obtain anti-counterfeiting materials; coating or 3D printing the anti-counterfeiting materials onto surfaces of commodities in need of counterfeiting so as to form various patterns, curing the commodities to obtain commodities with patterns; exciting the commodities with patterns with adoption of 980 nm near-infrared light, and judging the authenticity of the commodities in a way that the patterns with particular colors are visible to naked eyes or the wavelengths of emitted lights are detected by an instrument. According to the method, the anti-counterfeiting materials can be coated or 3D printed onto the metal, glass, leather, wood, plastics, ceramics, textiles, paper and other interfaces; the method can implement the lifelong anti-counterfeiting of commodities, is simple in operation, and is good in anti-counterfeiting effect.
Owner:CAPITAL NORMAL UNIVERSITY
Authentication apparatus and method for controlling the authentication apparatus, electronic device, controlling program, and recording media
InactiveCN101043336AConvenience guaranteedPrevent impersonationUser identity/authority verificationCharacter and pattern recognitionComputer hardwareEngineering
The invention provides a certification device and a control method, which comprises an electronic device with a certification device, a control program of the certification device and a recording medium recorded with the program. The certification device avoids false claim in certification effectively and maintains consumer convenience. In a facial certification (30) of a mobile telephone, the fitting degree is calculated through the checking by a facial image checking part (32) on the facial image of a certification object gotten from a facial image taking part (31) through a filming part (13) and the facial property information contained in a facial property data base (40) of a storage part (21). On the other side, threshold value is decided through the searching and evaluation of a data base (41) by a threshold value determining part (35), as per the positional information of the device gotten from a positional information taking part (33) through a GPS receiving part (14). The facial certification can be decided to be successful or not by comparing the fitting degree calculated by the facial image checking part (32) of a certification part (36) and the threshold value decided by the threshold value determining part (35).
Owner:ORMON CORP
Login verification method and device, and login method and device
PendingCN106302339APrevent impersonationImprove securitySpeech recognitionSecuring communicationText independentValidation methods
The invention relates to a login verification method and device. The method comprises the following steps: receiving a login request sent by a terminal, wherein the login request contains a user identifier; generating a brand new verification text according to the login request, and returning the brand new verification text to the terminal; receiving to-be-verified voice corresponding to the user identifier and uploaded by the terminal; employing a text-independent voice recognition algorithm to carry out voice verification on the to-be-verified voice; converting the to-be-verified voice into a text after the voice verification is passed; and comparing whether the text converted by the to-be-verified voice is consistent with the verification text, allowing login if the to-be-verified voice is consistent with the verification text, and otherwise, refusing the login. The invention further provides a login method and device. According to the login verification method and device provided by the invention, the personation based on the situation that the voice of users is recorded by phishing sites is well avoided, and thus the login security is effectively improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data transmission method for communication of intelligent electric meters
ActiveCN102903226AGuaranteed confidentialityIntegrity guaranteedElectric signal transmission systemsUser identity/authority verificationComputer hardwareCiphertext
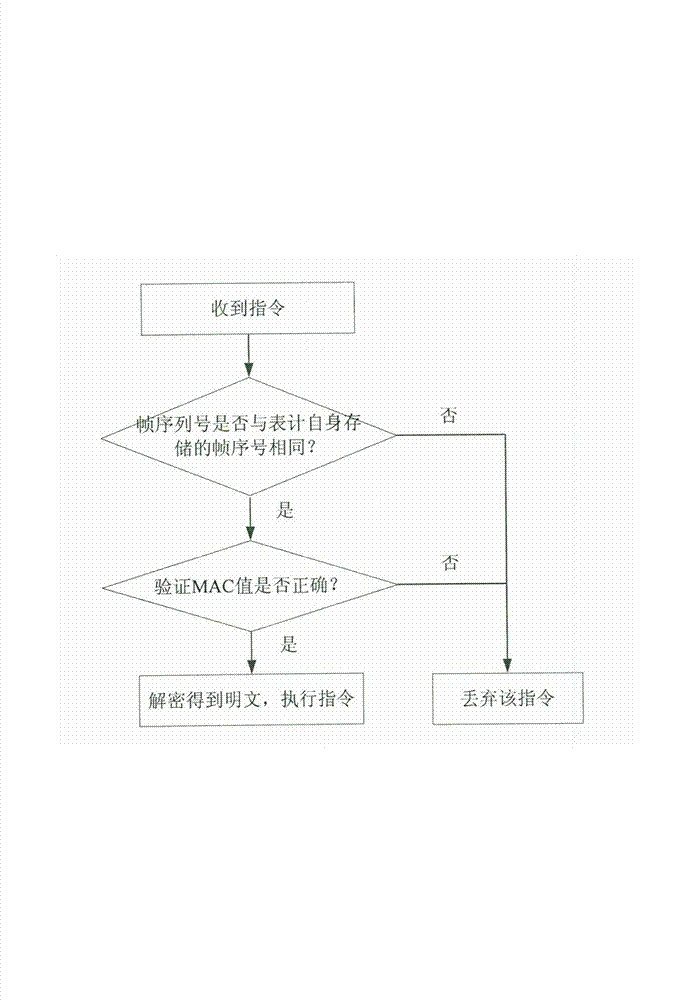
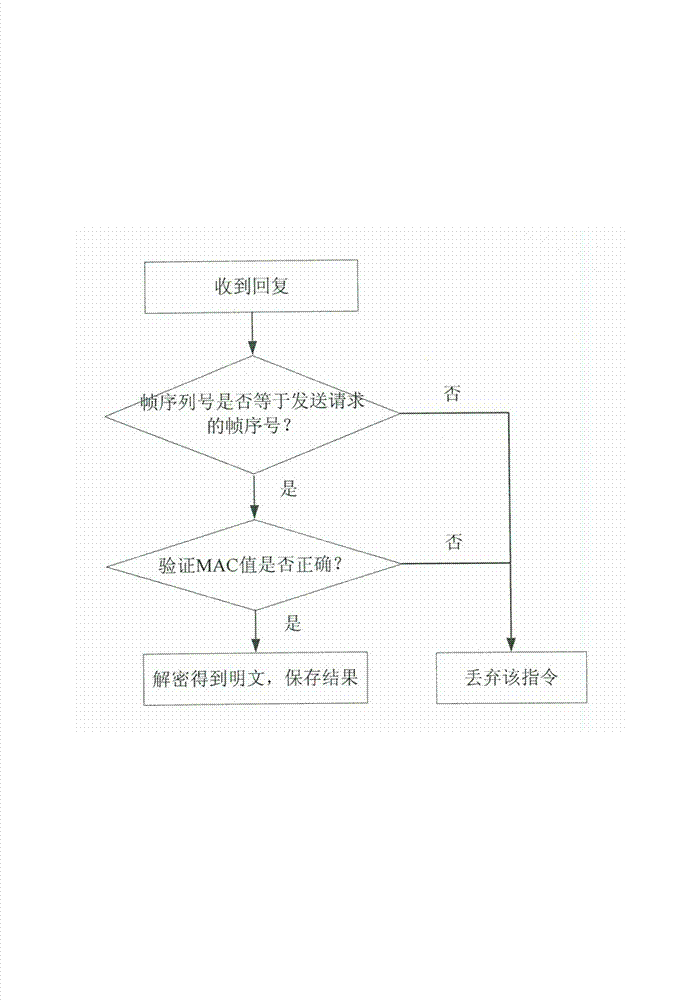
The invention relates to a data transmission method for communication of intelligent electric meters, and aims to guarantee the safety of data transmission during communication of the meters. According to the technical scheme, the data transmission method comprises the following steps that: (a) a client-side encrypts a command to be sent and then transmits the command to a meter; (b) the meter judges whether a frame number is the same as a frame number stored in the meter, and a (c) step is carried out if the frame number is the same as the frame number stored in the meter; (c) a media access control (MAC) value is tested and verified, and a (d) step is carried out if the MAC value is correct; (d) the meter decrypts the command to obtain a plaintext command, the plaintext command is carried out, and 1 is added to the frame number stored in the meter; (e) the client-side judges whether the frame number is equal to the frame number when the command is transmitted after the client-side receives ciphertext replied data of the meter, and a (f) step is carried out if the frame number is equal to the frame number when the command is transmitted; (f) the MAC value is tested and verified, and a (g) step is carried out if the MAC value is correct; (g) the client-side decrypts the replied data to obtain plaintext replied data, and the plaintext replied data are stored; and (h) the client-side adds 1 to the frame number and the (a) step is carried out again. The initialization vector of an encryption algorithm comprises the identity information and the frame number of a sender. The data transmission method is applicable to communication of the intelligent electric meters.
Owner:HEXING ELECTRICAL
Package additional information interaction system and method based on two-dimensional code
InactiveCN105809377AImplement encapsulationImprove interactivityLogisticsInteraction systemsRelevant information
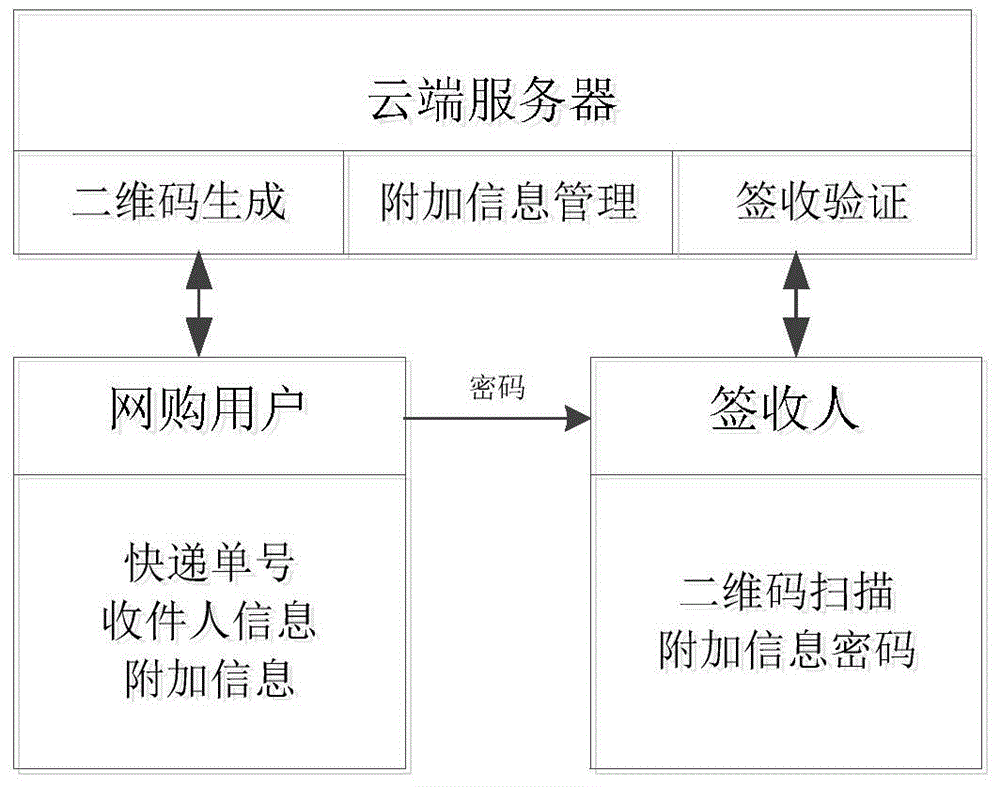
The invention belongs to the technical field of virtual reality, and specifically relates to a package additional information interaction system and method based on a two-dimensional code. The system comprises a two-dimensional code generating unit, a password setting unit, an information management unit, a code scanning unit, a signing verification unit and an additional information management unit. The method comprises the steps of generating a two-dimensional code according to order information and a courier number, and taking a password set by a user as an extraction password of a URL (Uniform Resource Locator) web page associated with the two-dimensional code; when scanning the two-dimensional code added to a package, linking the URL web page associated with the two-dimensional code; displaying relevant information after the password is verified, and sending order receiving information according to the courier number. After the URL web page is associated to the two-dimensional code, the secondary password is verified, and information stored in the additional information management unit is displayed after the verification passes. According to the system and the method, the recipient signs the package by scanning the code with a mobile phone, so that the situation of fraudulent reception in the package mailing process, particularly when the package is signed by others is avoided.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com