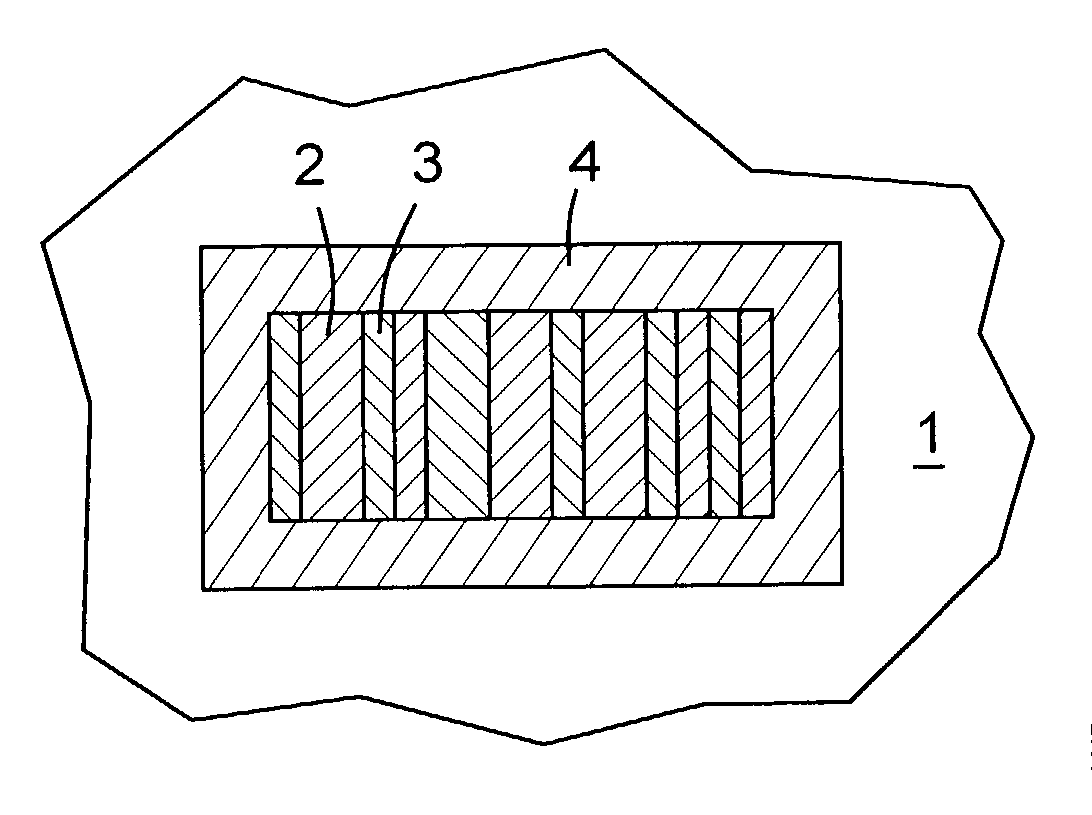
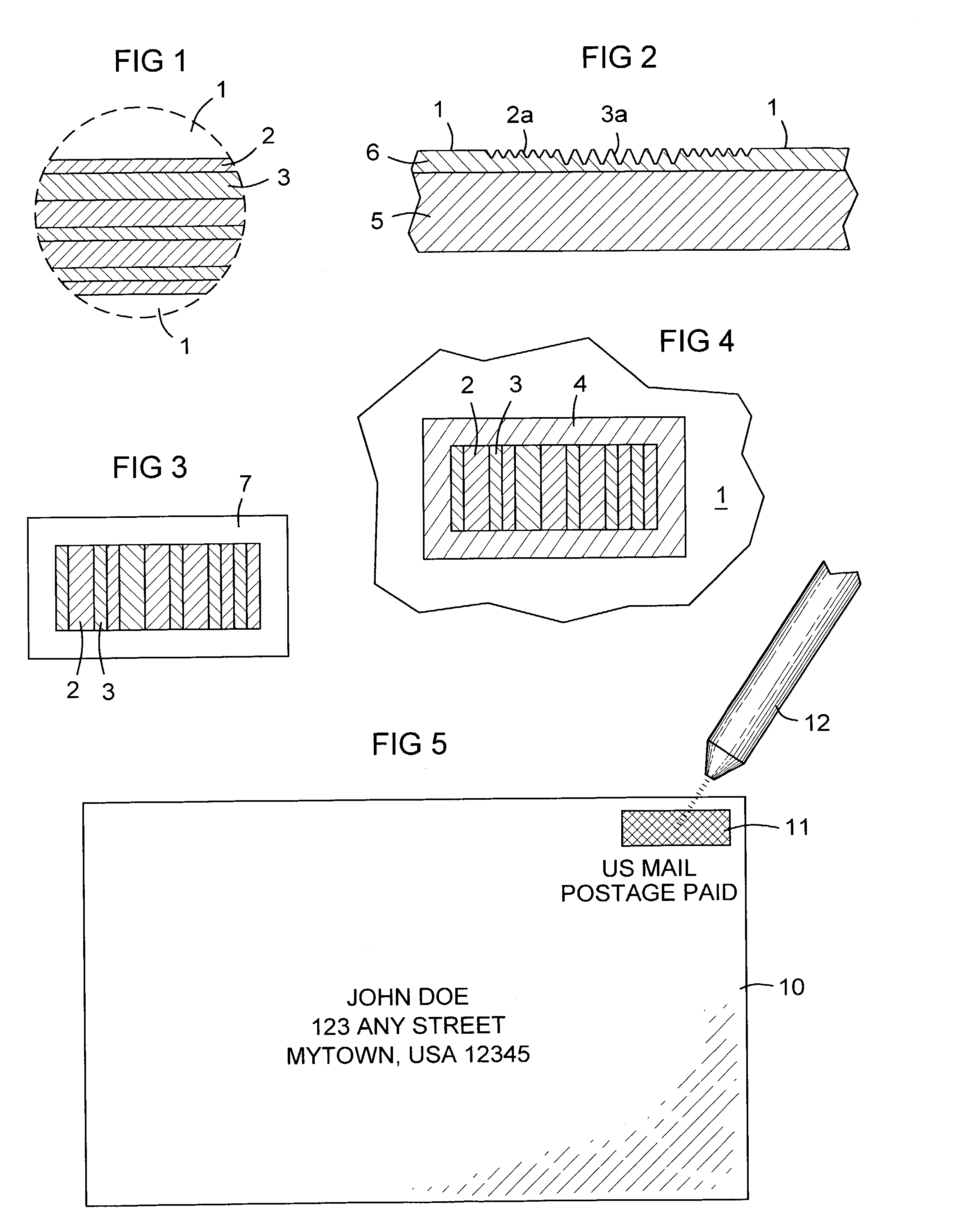
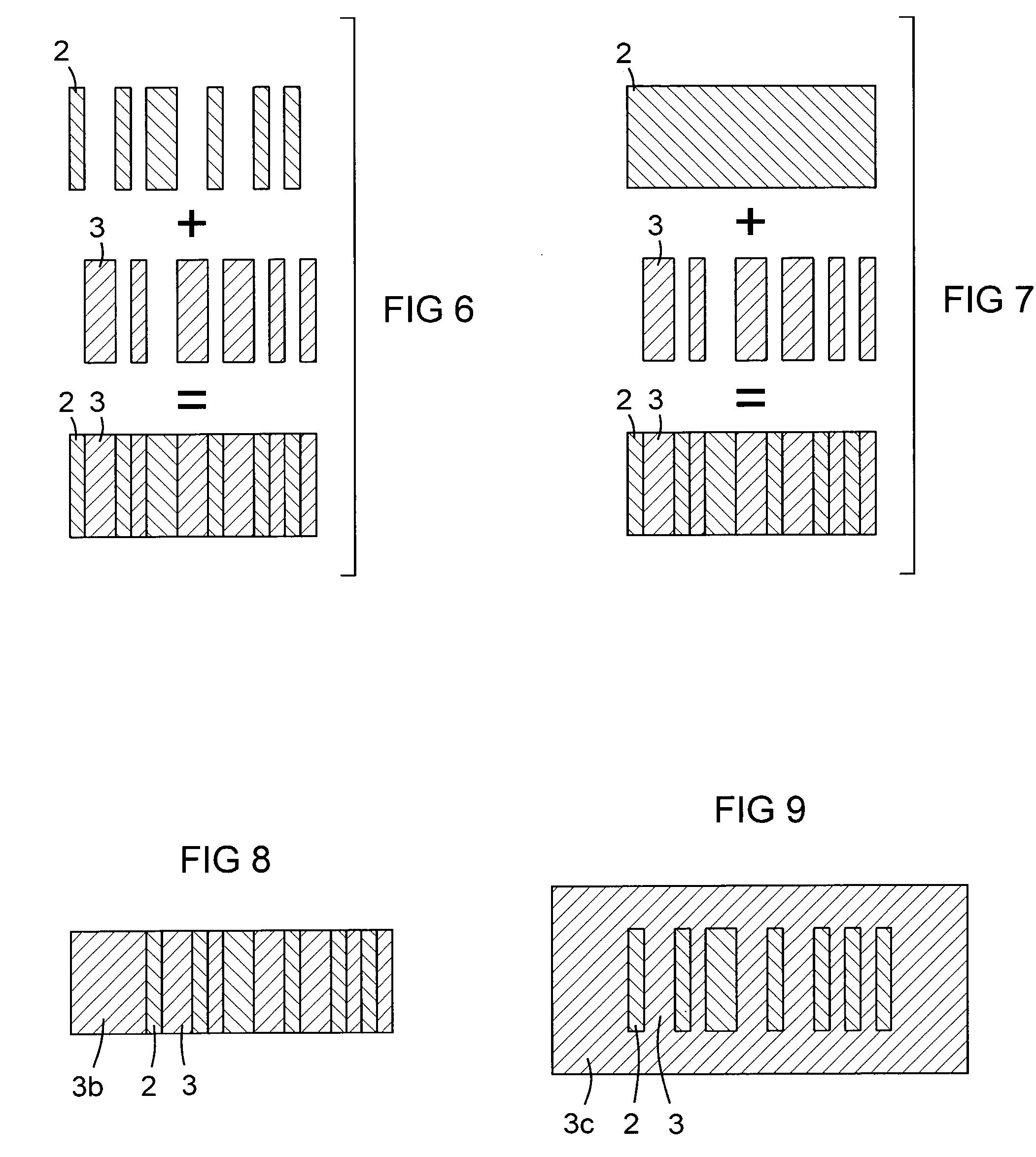
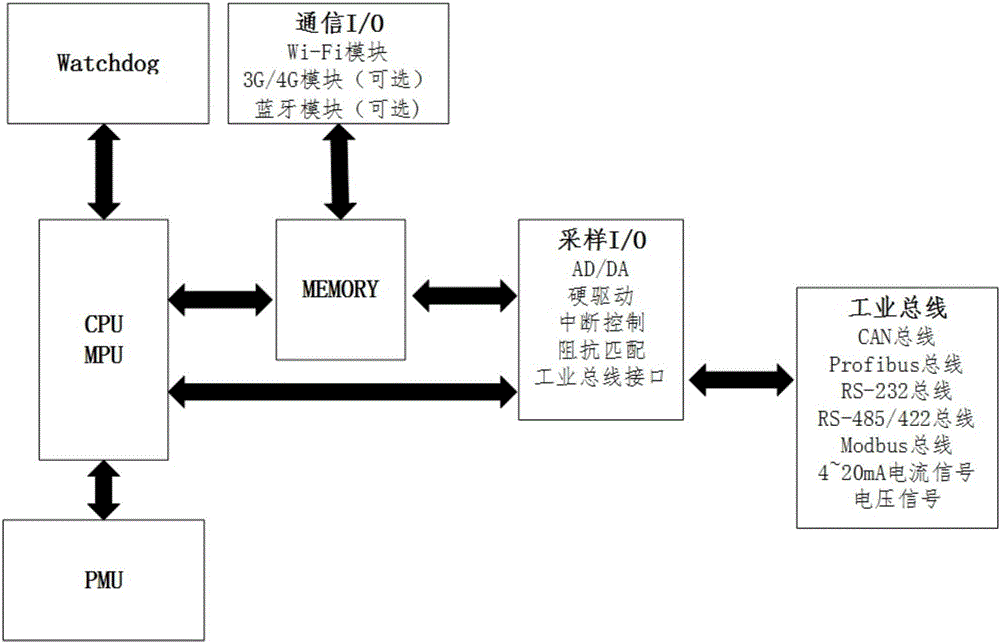
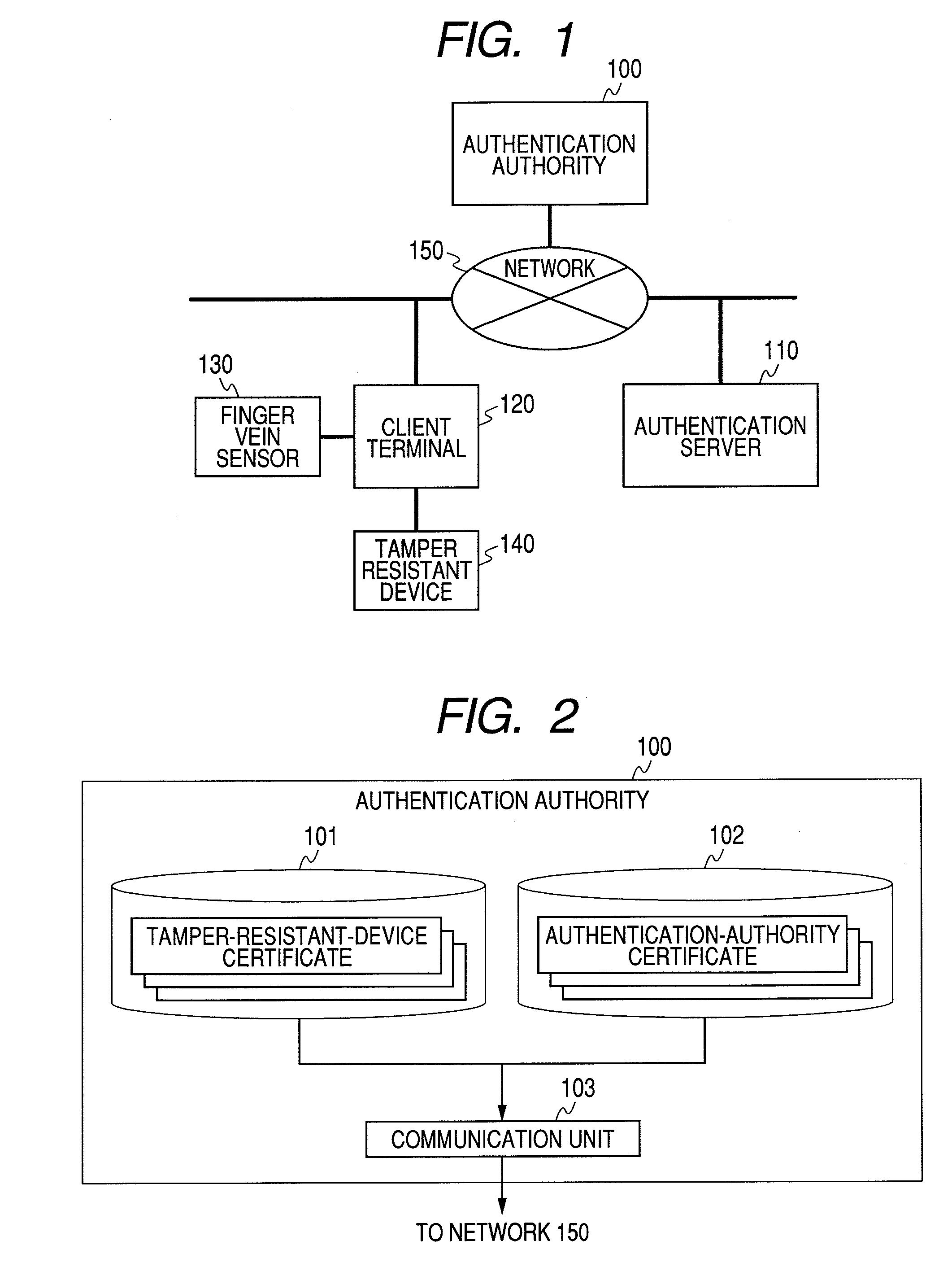
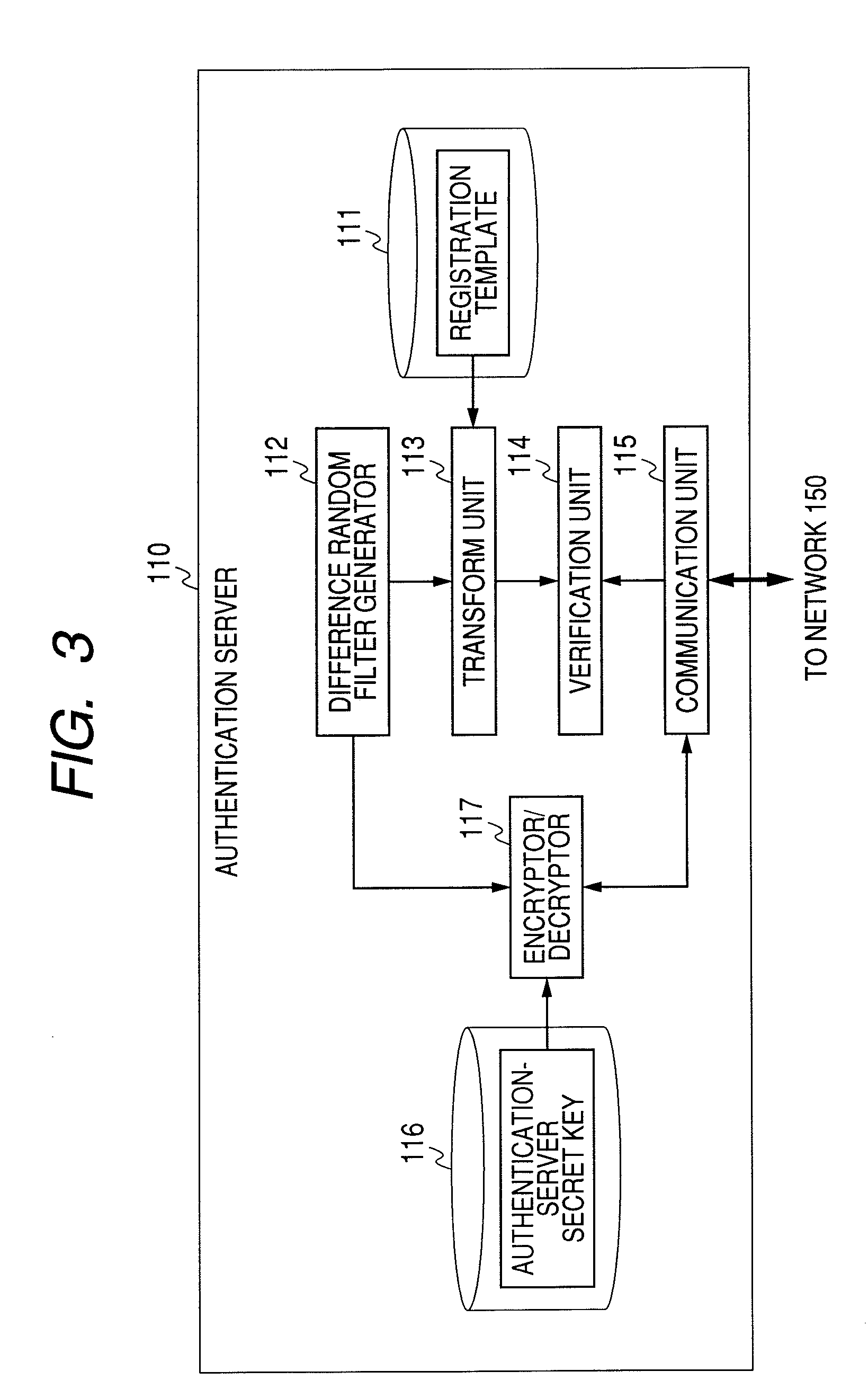
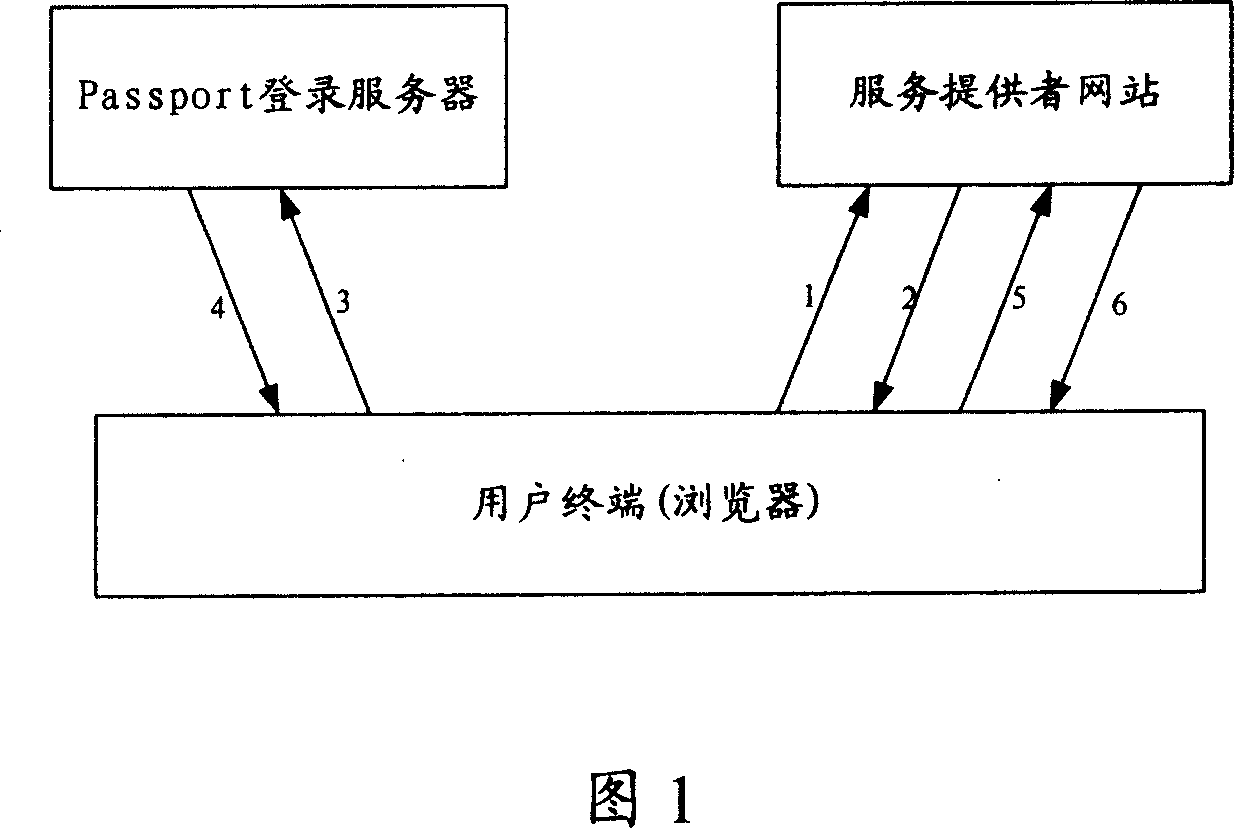
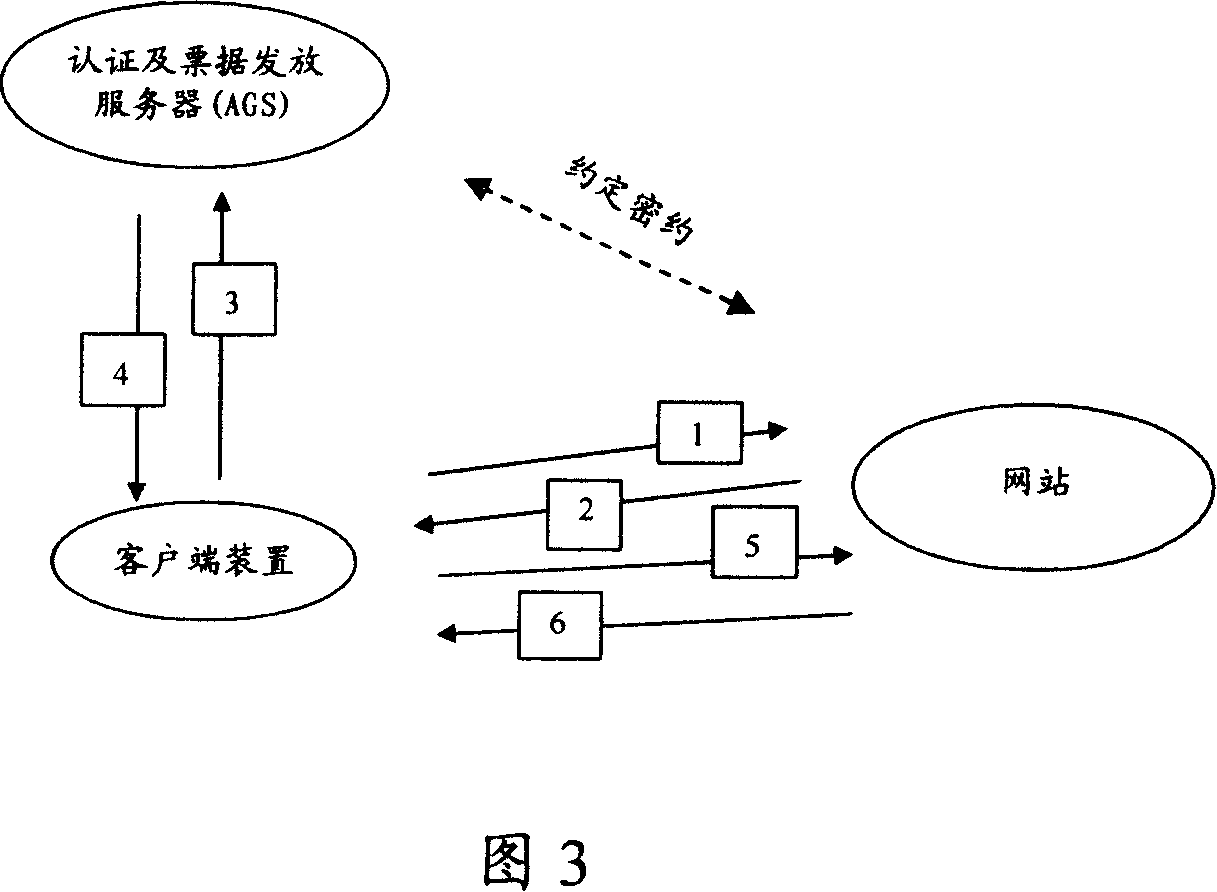
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
746results about How to "Prevent counterfeiting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
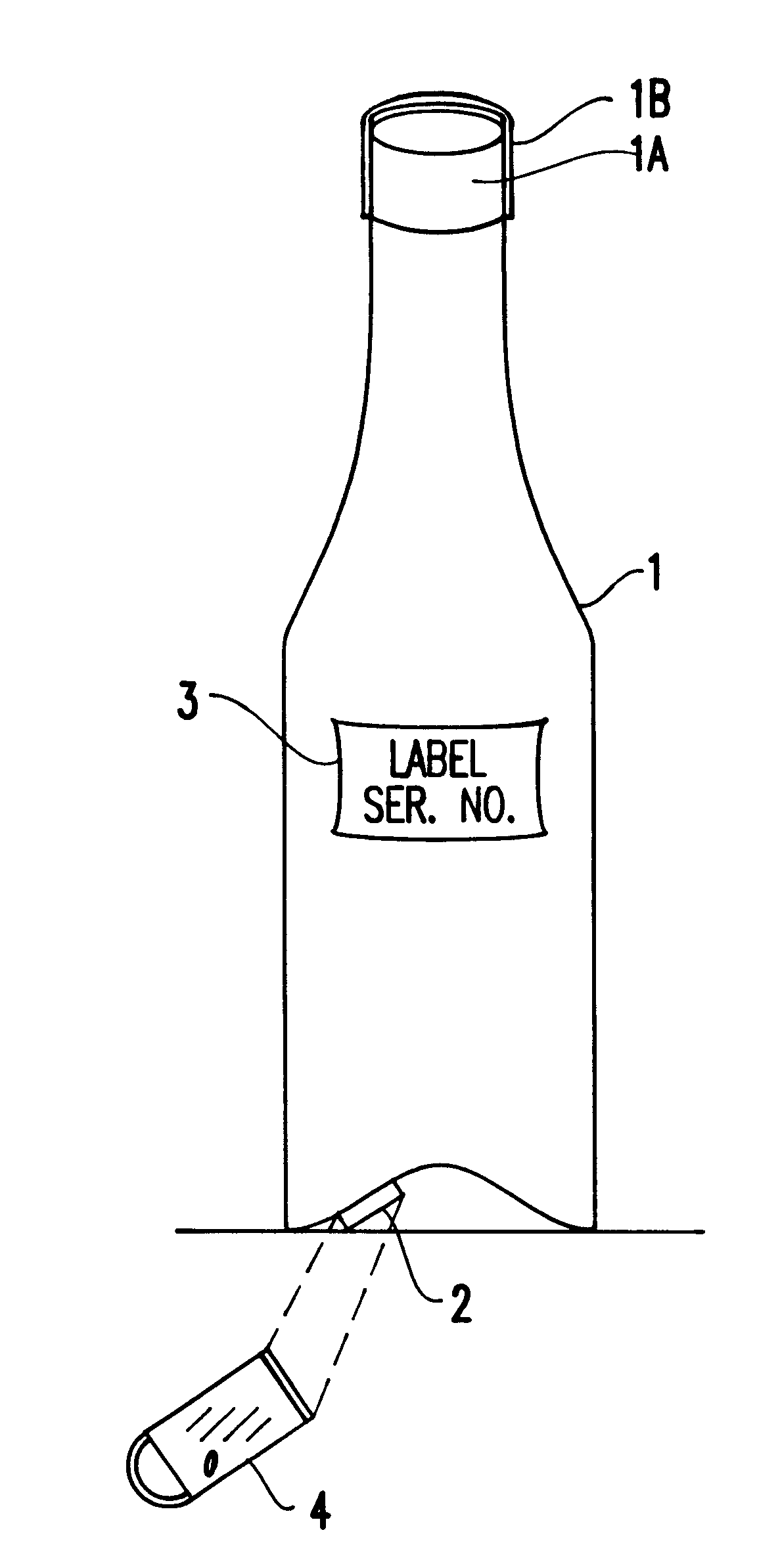
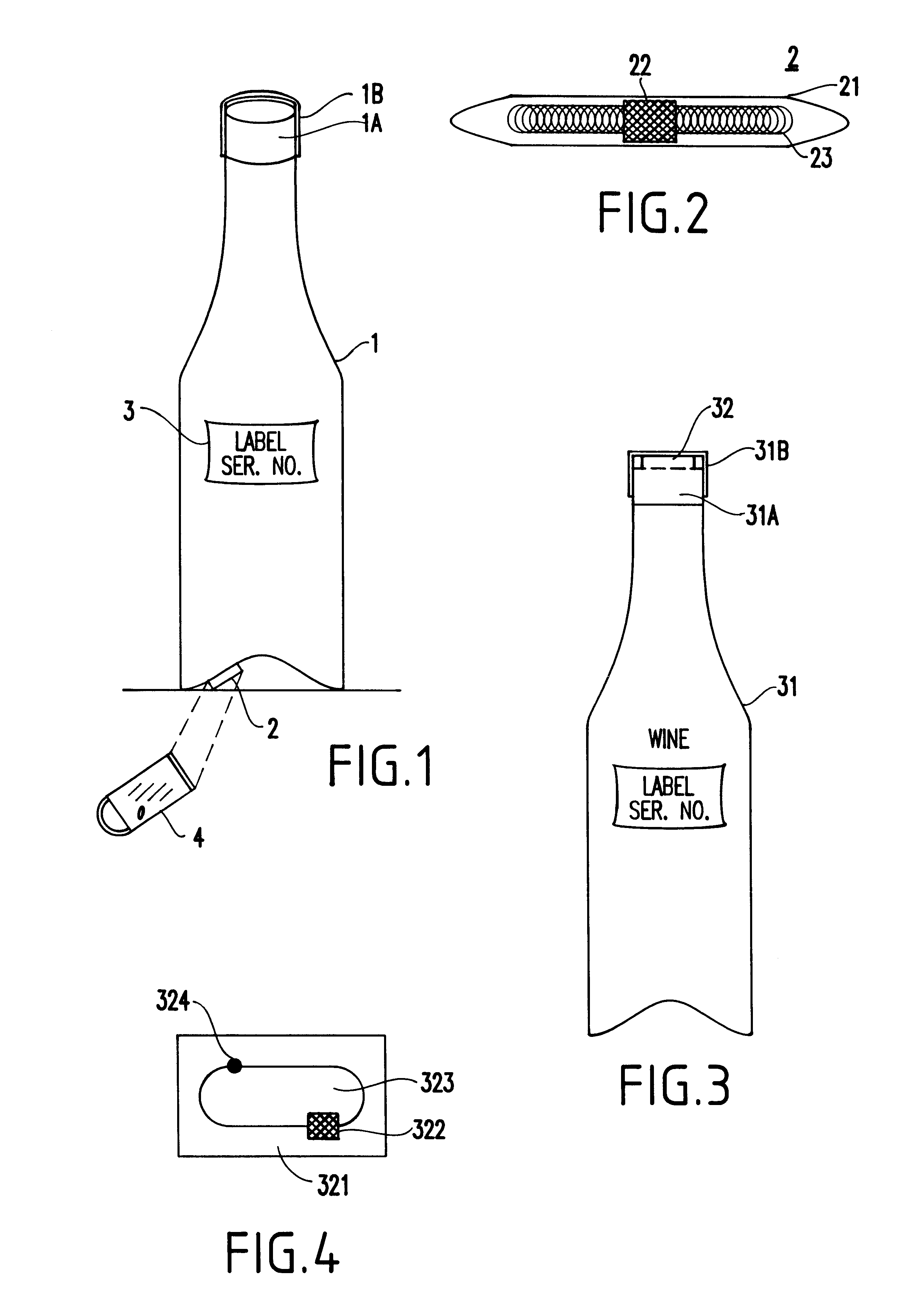
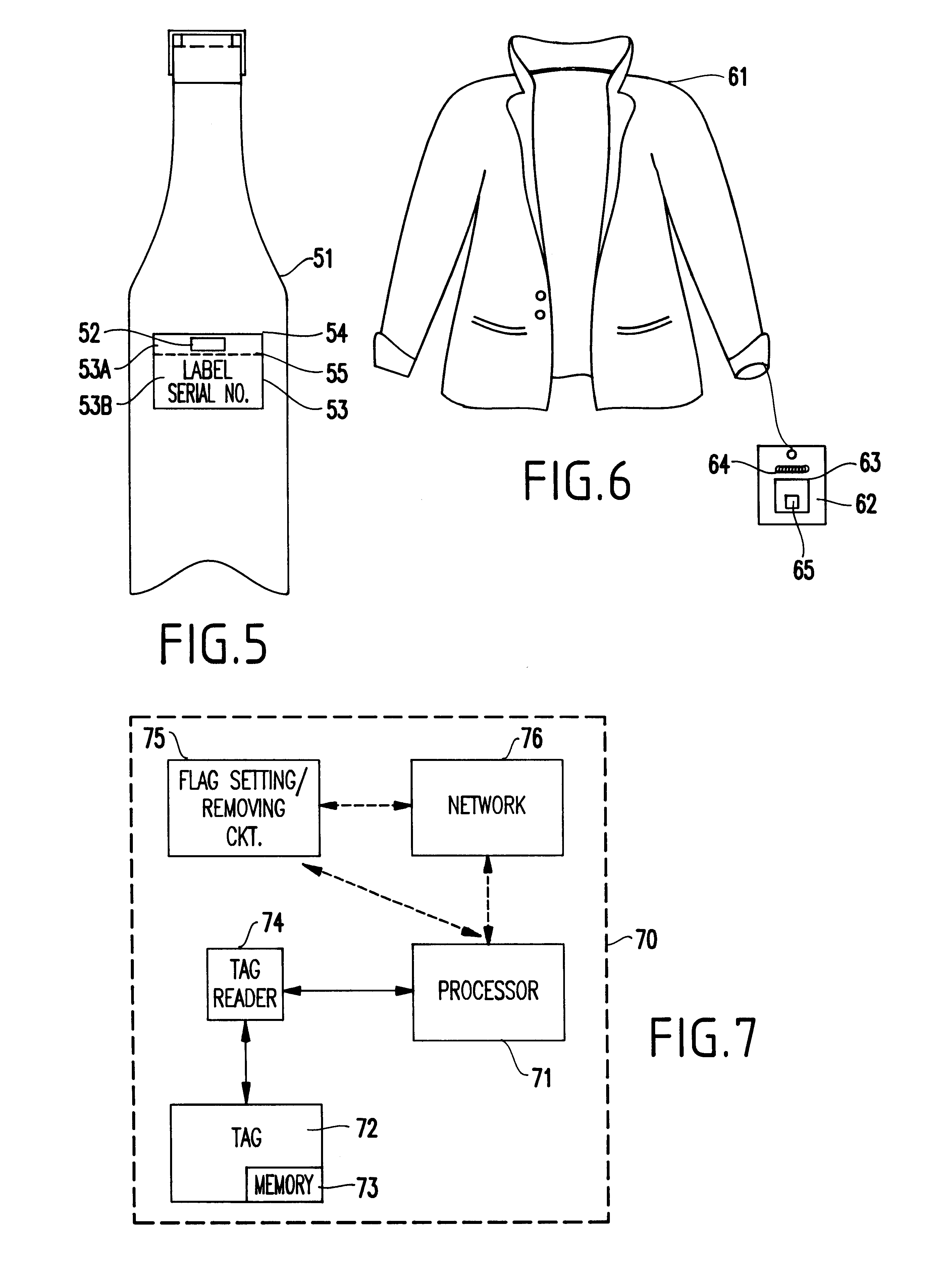
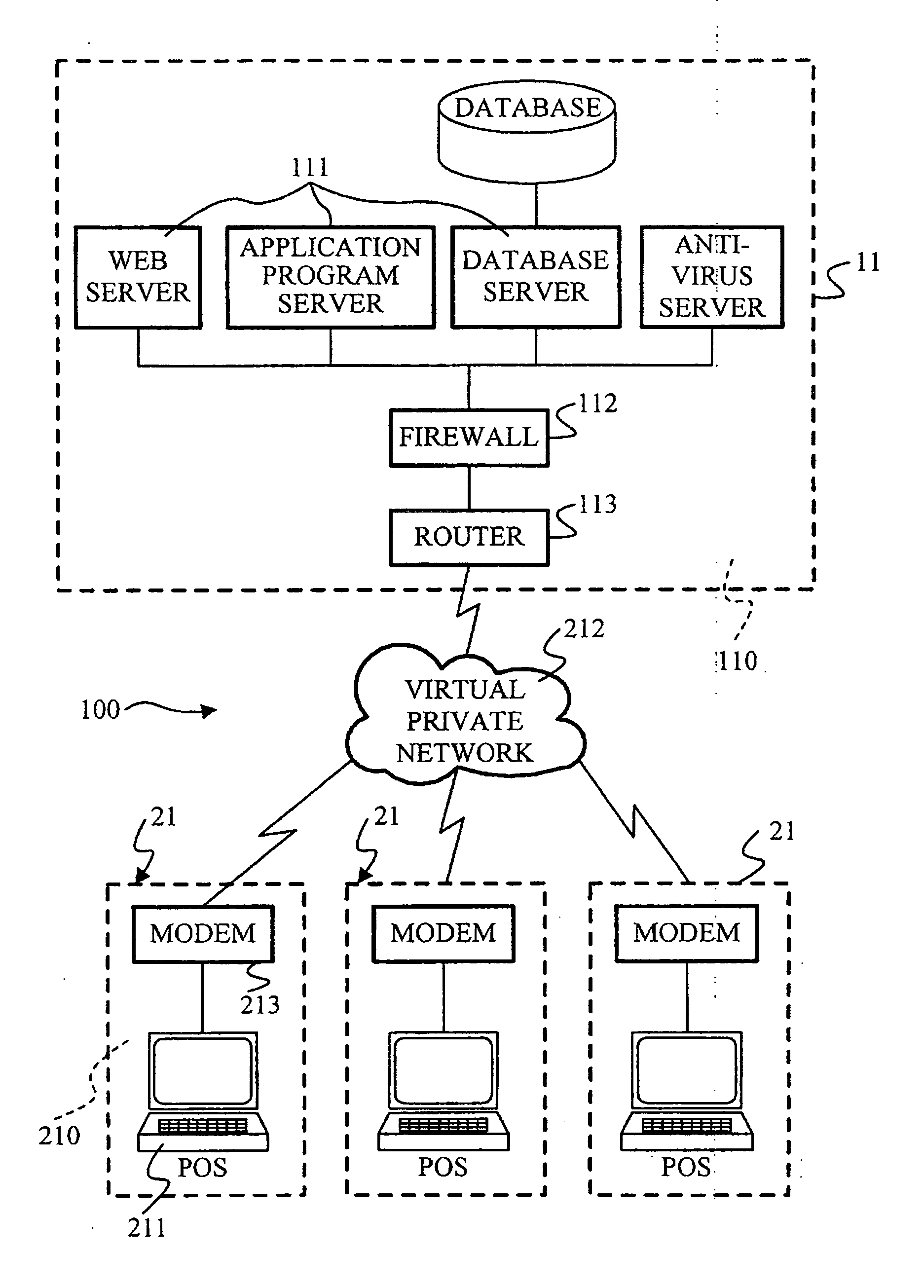
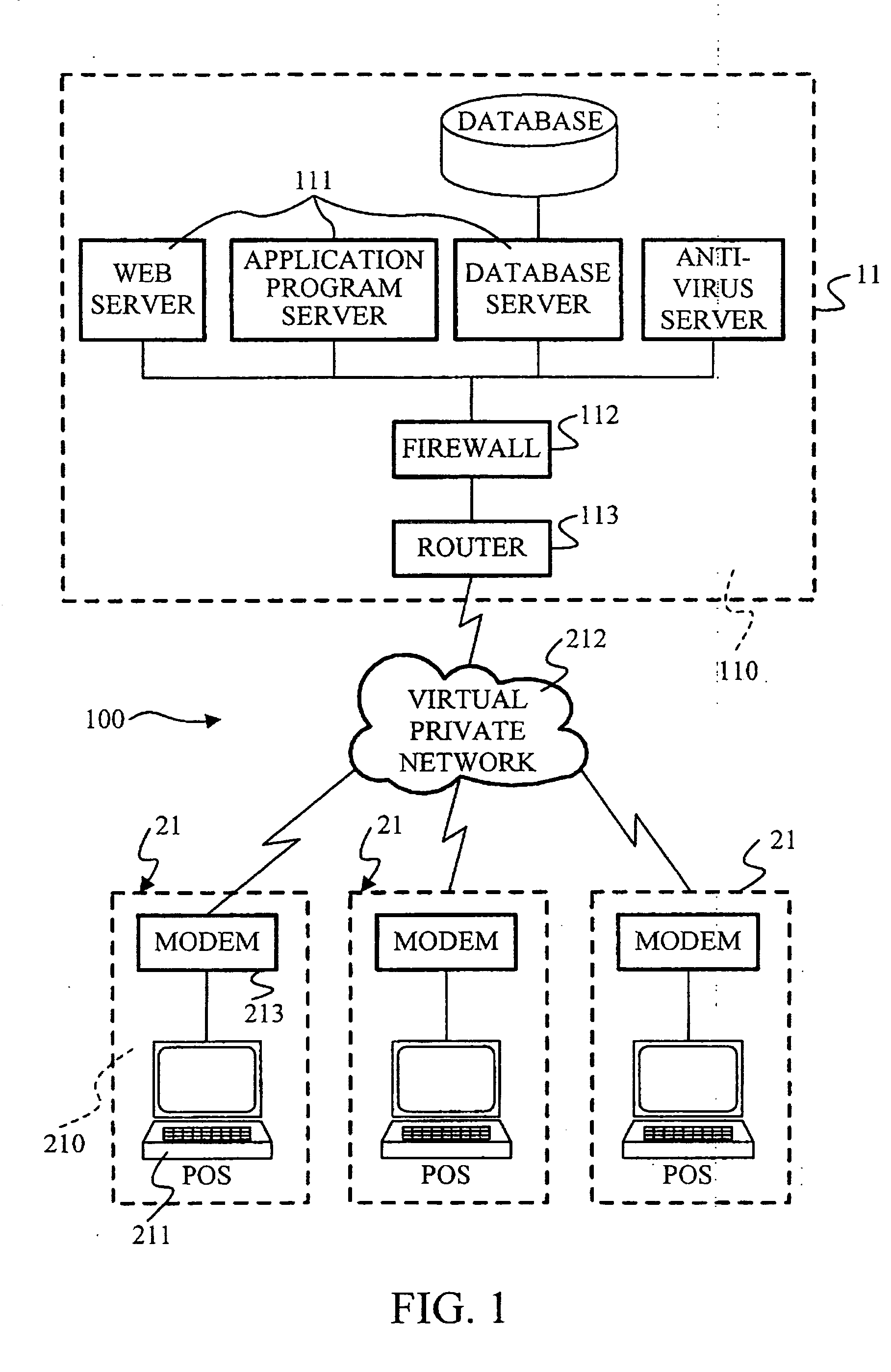
Method and system for preventing counterfeiting of high price wholesale and retail items
InactiveUS6226619B1Convenient verificationPrevent counterfeitingContainer decorationsLevel indicationsWorld Wide Web
A method and system for preventing counterfeiting of an item, include an interrogatable tag attached to the item. The item includes visible indicia for comparison with secret, non-duplicable information stored in the tag designating authenticity.
Owner:TOSHIBA GLOBAL COMMERCE SOLUTIONS HLDG
Air purifier based on filter Anti-counterfeiting identification
InactiveUS20180161716A1Guarantee product qualityPrevent counterfeitingDispersed particle filtrationTransportation and packagingAir purifiersPairing
Disclosed is an air purifier based on filter anti-counterfeiting identification, comprising a purifier body (1) in which control circuitry and a purifying chamber are provided; a filter (2) is arranged in the purifying chamber; the filters (2) are paired and coupled with the purifier body (1) via an identification unit; the identification unit comprises an identification chip configured on the filter (2) and an identifier configured on the purifier body (1); the identifier is connected with the control circuitry; the control circuitry is powered on and starts to operate until the pairing between the identification chip and the identifier succeeds. The identification process can identify multiple objects without manual intervention. Moreover, it responds quickly and no mechanical malfunction will happen. Thus, the air purifier can operate under harsh environment and serve for a long time. In this manner, counterfeits can be effectively prevented and quality of products can be guaranteed.
Owner:SHUNDE APOLLO AIR CLEANER
Trackable pills with electronic ID tags
InactiveUS7253716B2Prevent counterfeitingAccurate trackingMemory record carrier reading problemsPharmaceutical product form changeConstant powerEngineering
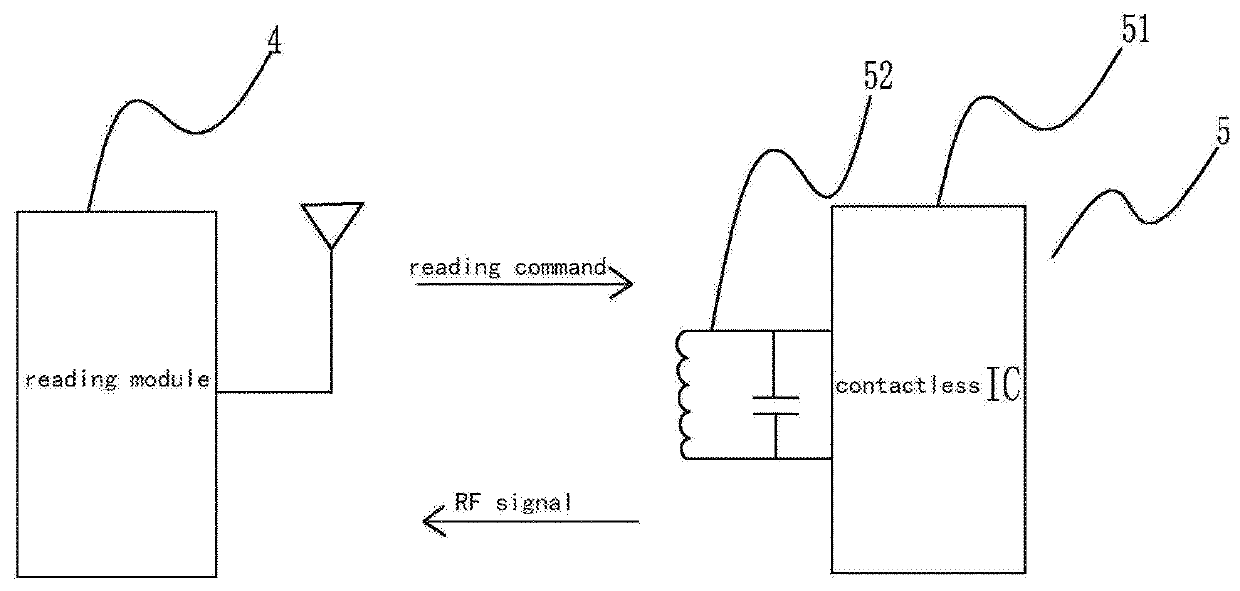
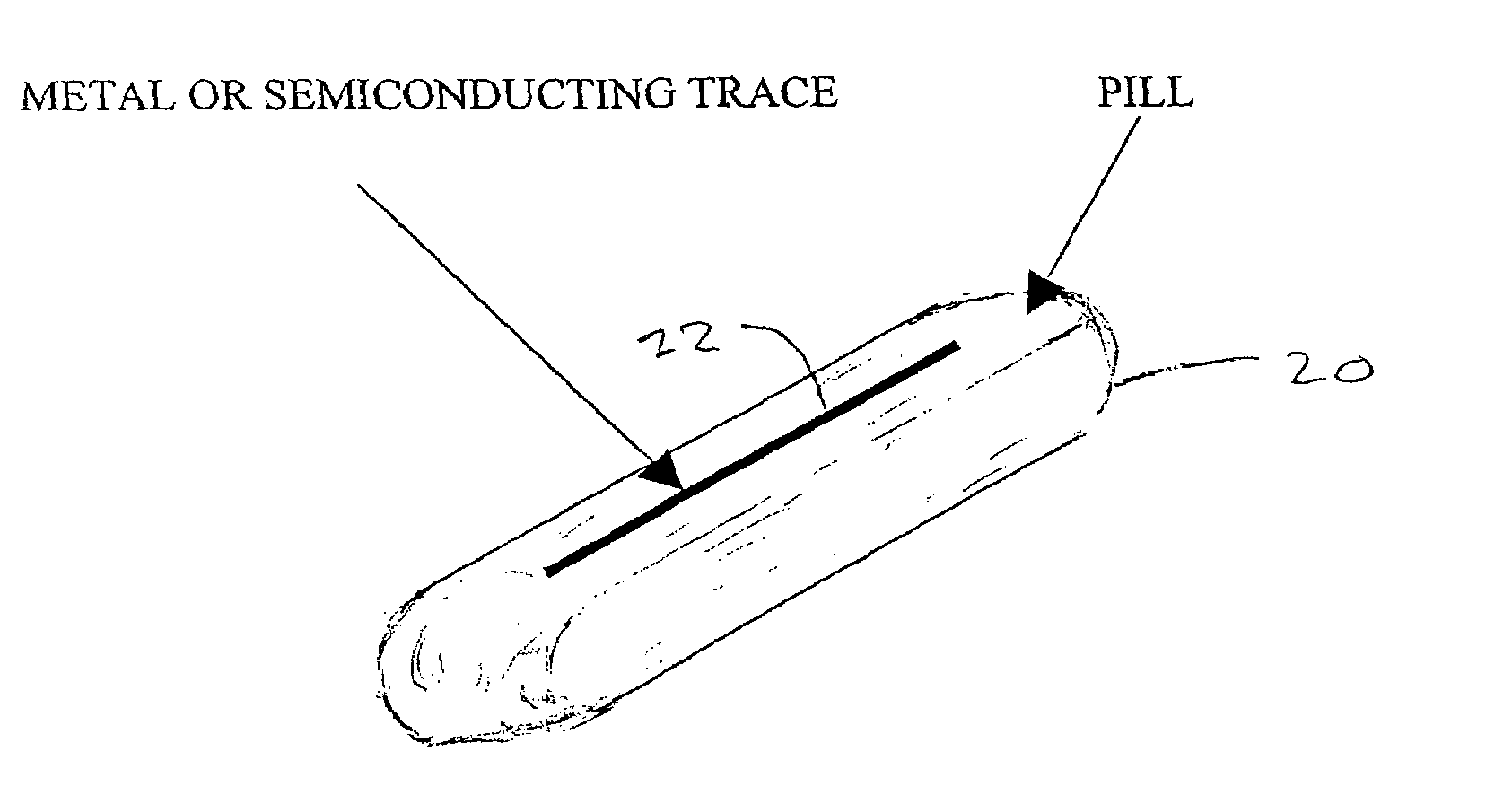
A medical pill intended for human or animal consumption includes an RF ID tag in or on the pill. The tag will respond to a nearby reader, the tag itself being without a battery or other constant power supply, capturing power from the reader's transmitted signal and storing a portion of that power in a power supply. An antenna for the RF ID tag may be integral with the tag or it may be transferred to the pill using conductive materials in the pill's coating, filler or binding agents, embedded within the pill, or printed onto the pill. If separate from the tag the antenna is electromagnetically coupled to the tag which has a small onboard antenna. The RF ID tag of each pill has data that are transmitted when the tag is interrogated by a signal from a reader. Incorporation of an ingestable ID tag is possible because of the tag's very small size compatible with ingestion and because the tag can contain an antenna within the pill that allows the tag to be read at a substantial distance. Several different methods for deactivating the RF ID tag after ingestion or use of the pill are disclosed. Medicaments other than oral pills can also have the ID tags.
Owner:TAGENT
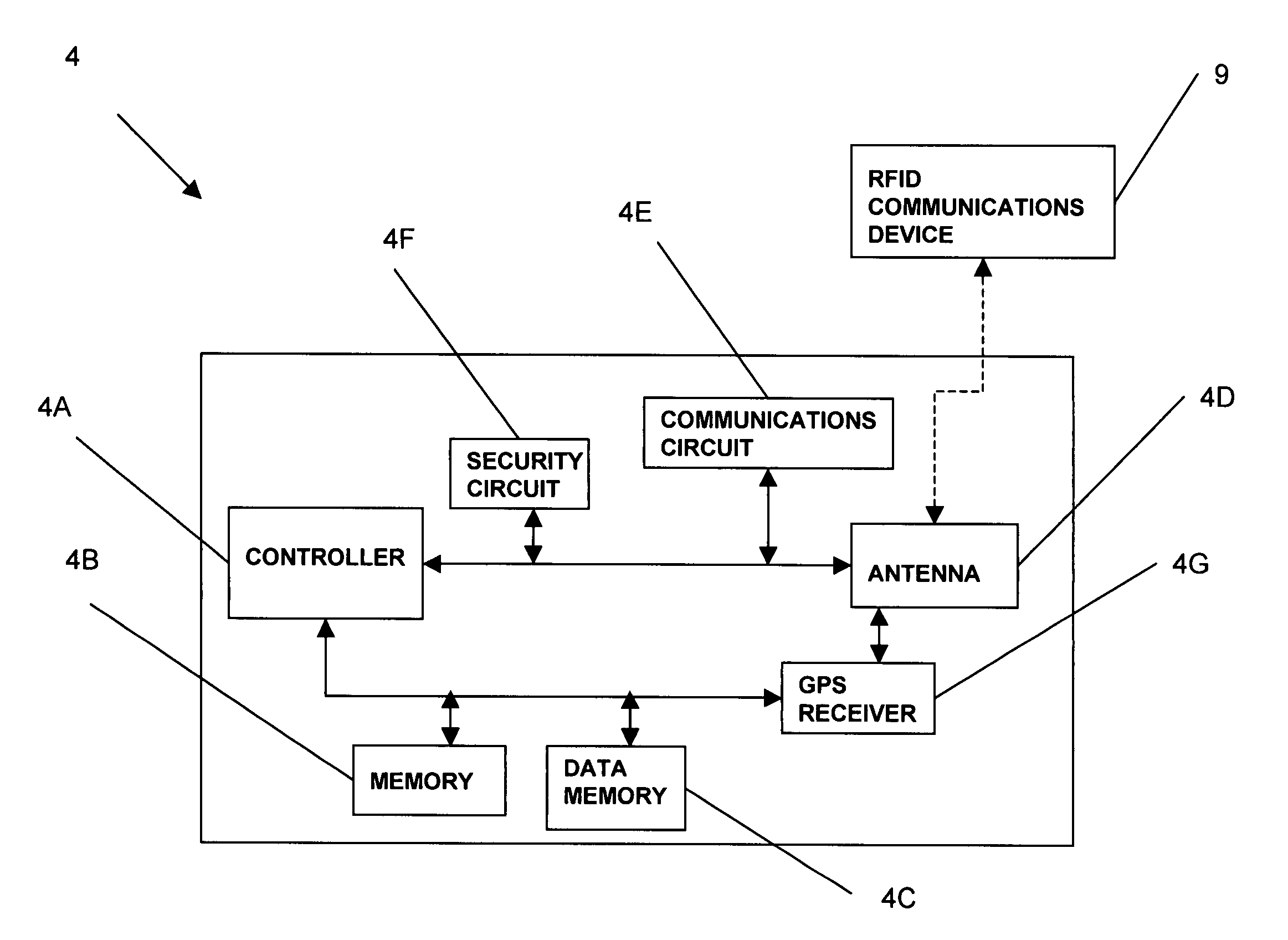
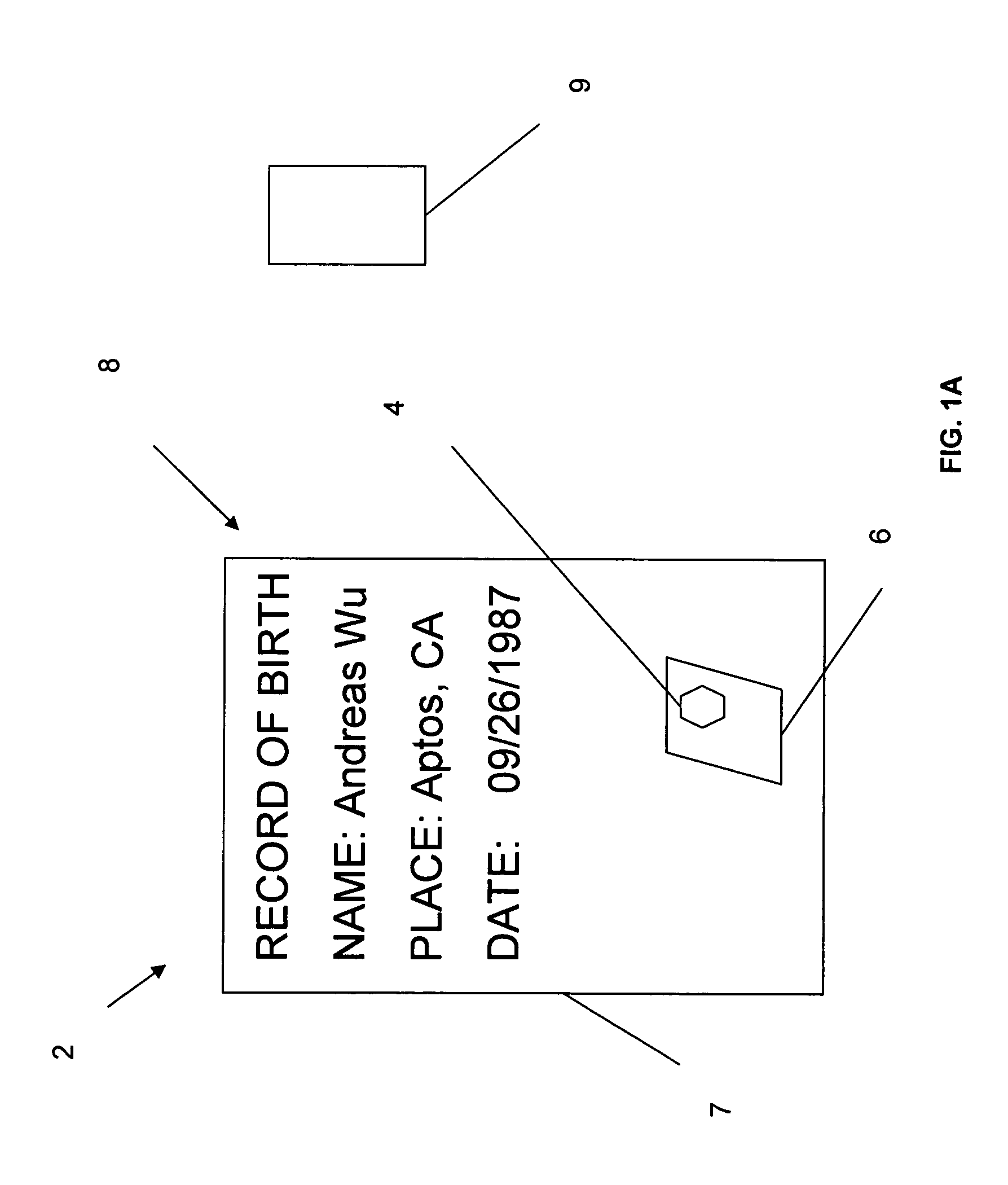
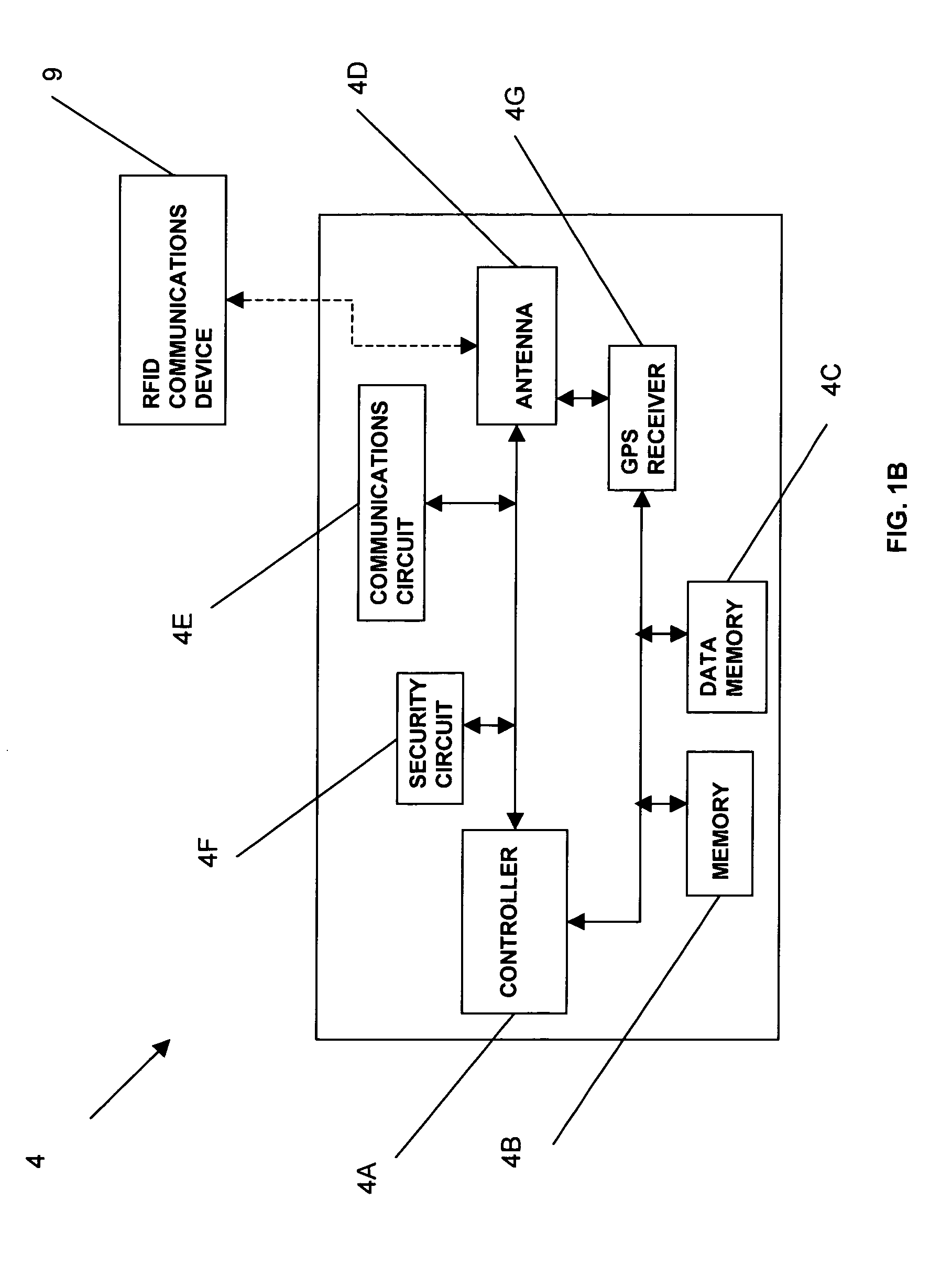
Birth and other legal documents having an RFID device and method of use for certification and authentication
InactiveUS7170391B2Prevent counterfeitingEasy to identifyElectric signal transmission systemsImage analysisElectronic documentThird party
A method and apparatus for authenticating entities to use an intelligent interactive Electronic Document Code stored in an RFID tag attached to a document as a means for third parties to ascertain a document is not counterfeit and has not been revoked or changed. In addition, such intelligent RFID tags can uniquely identify a particular document and data related to the document. The authenticating agency can utilize a public or private Electronic Document Code database as a means for the authenticating agency and third parties to authenticate documents and data in documents. The intelligent interactive Electronic Document Code can be used as an anti counterfeit mechanism enabling third parties requested to provide services, benefits or monetary payments to authenticate documents and or the data associated with the document is not counterfeit.
Owner:LANE KATHLEEN +1
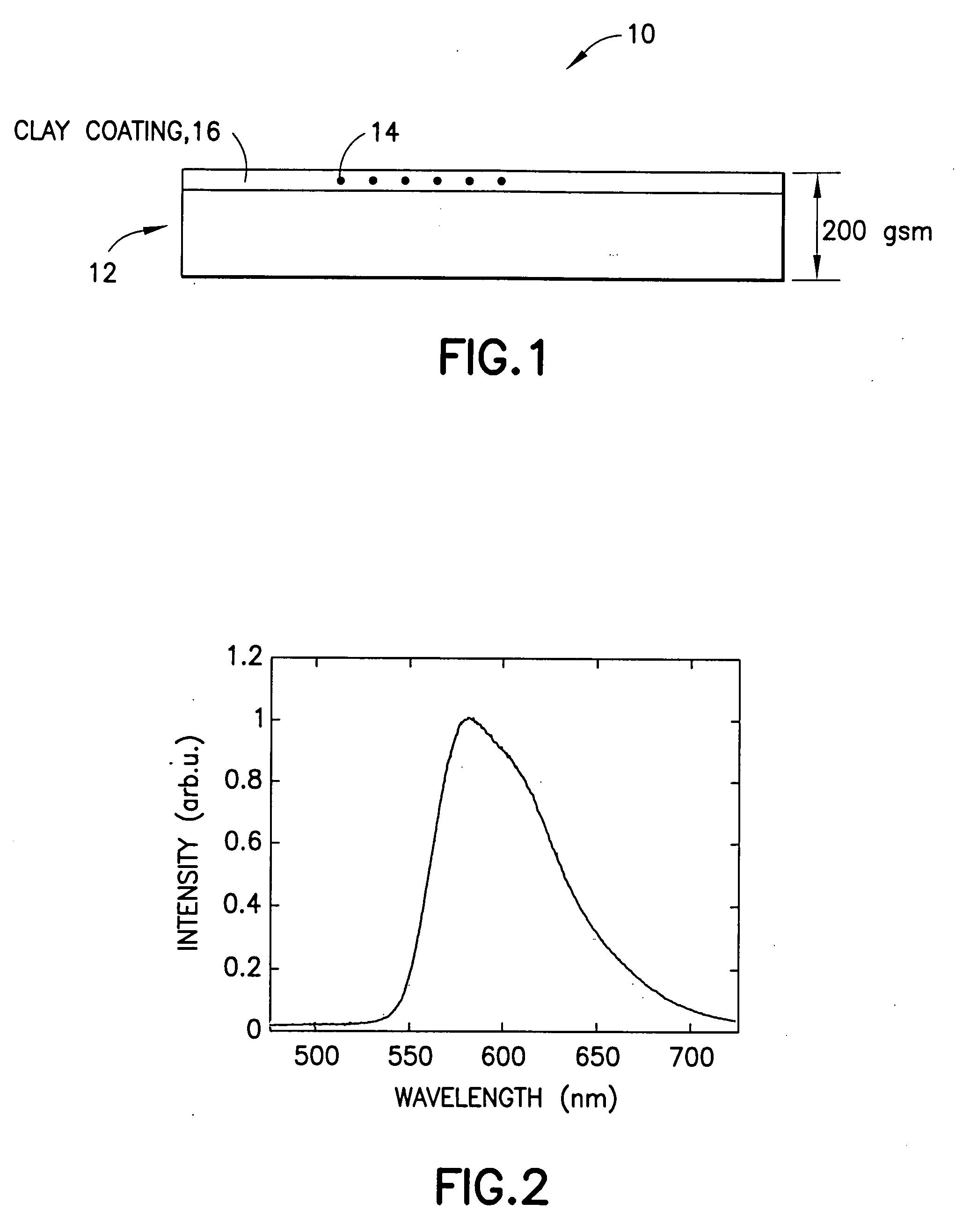
Taggant security system for paper products as a deterrent to counterfeiting
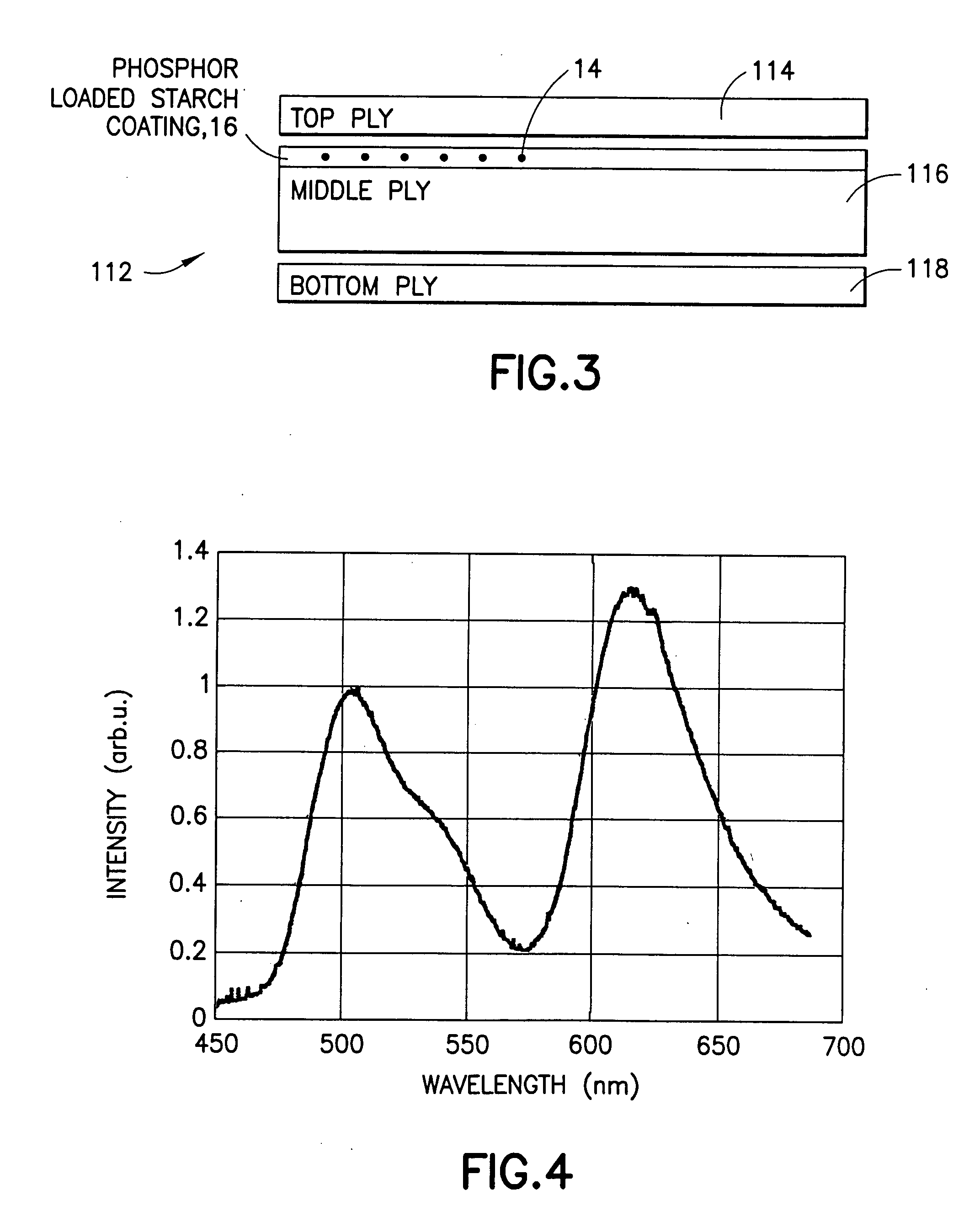
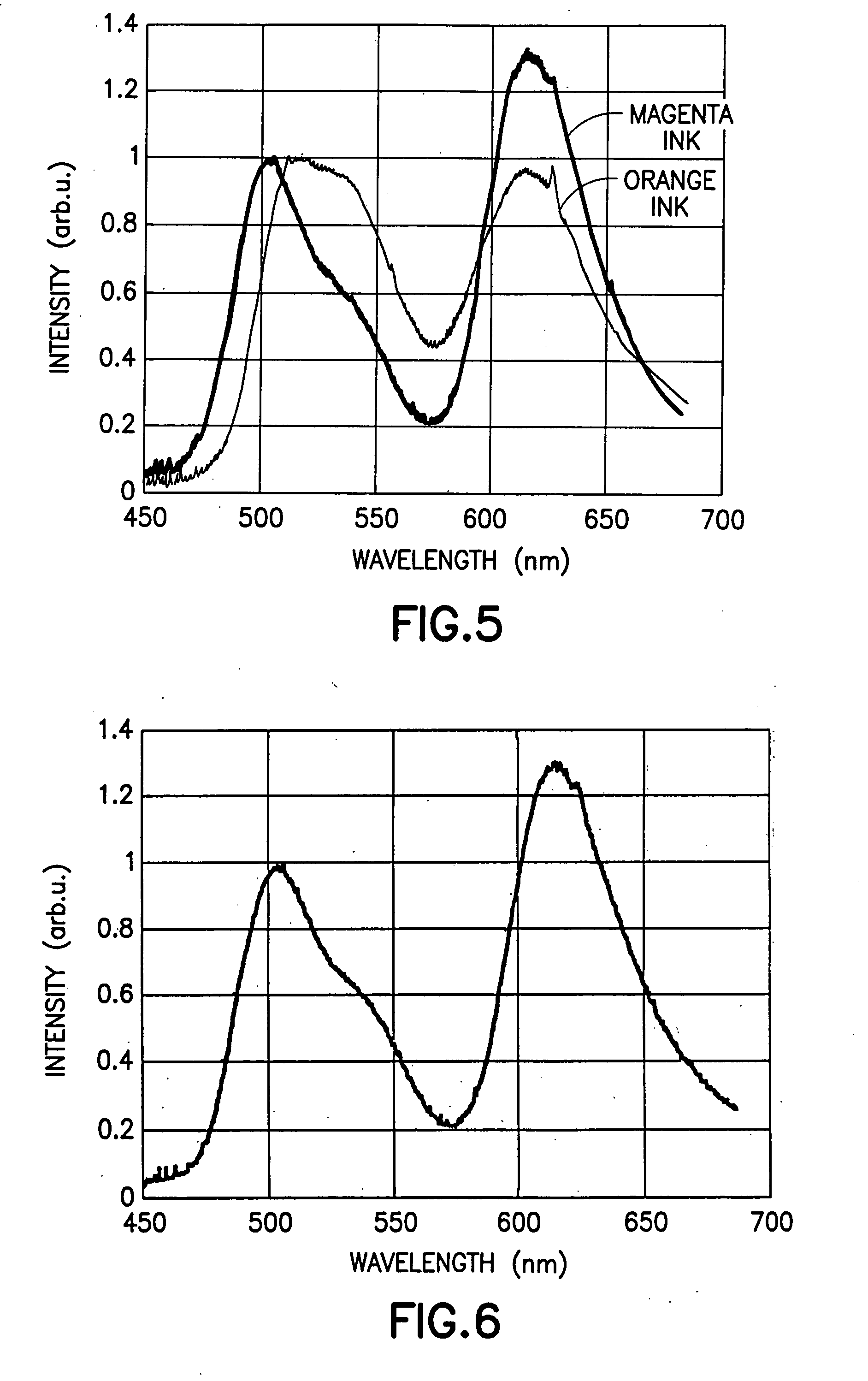
InactiveUS20050031838A1Difficult to duplicateNot easy to counterfeitNon-fibrous pulp additionOther printing matterPulp and paper industrySecurity system
A taggant security system for preventing the counterfeiting of goods associated with a paper product is provided. The taggant security system includes a paper product coating located on a paper product. The paper product coating is preferably one which is commonly used in the paper making industry. The taggant security system further includes one or more taggants incorporated within said paper product coating for authenticating said paper product. In preferred embodiments, the paper product coating is either a clay or starch coating. In addition, in preferred embodiments, the paper product is either a single or multi-ply packaging board or a label stock.
Owner:SPECTRA SYST CORP
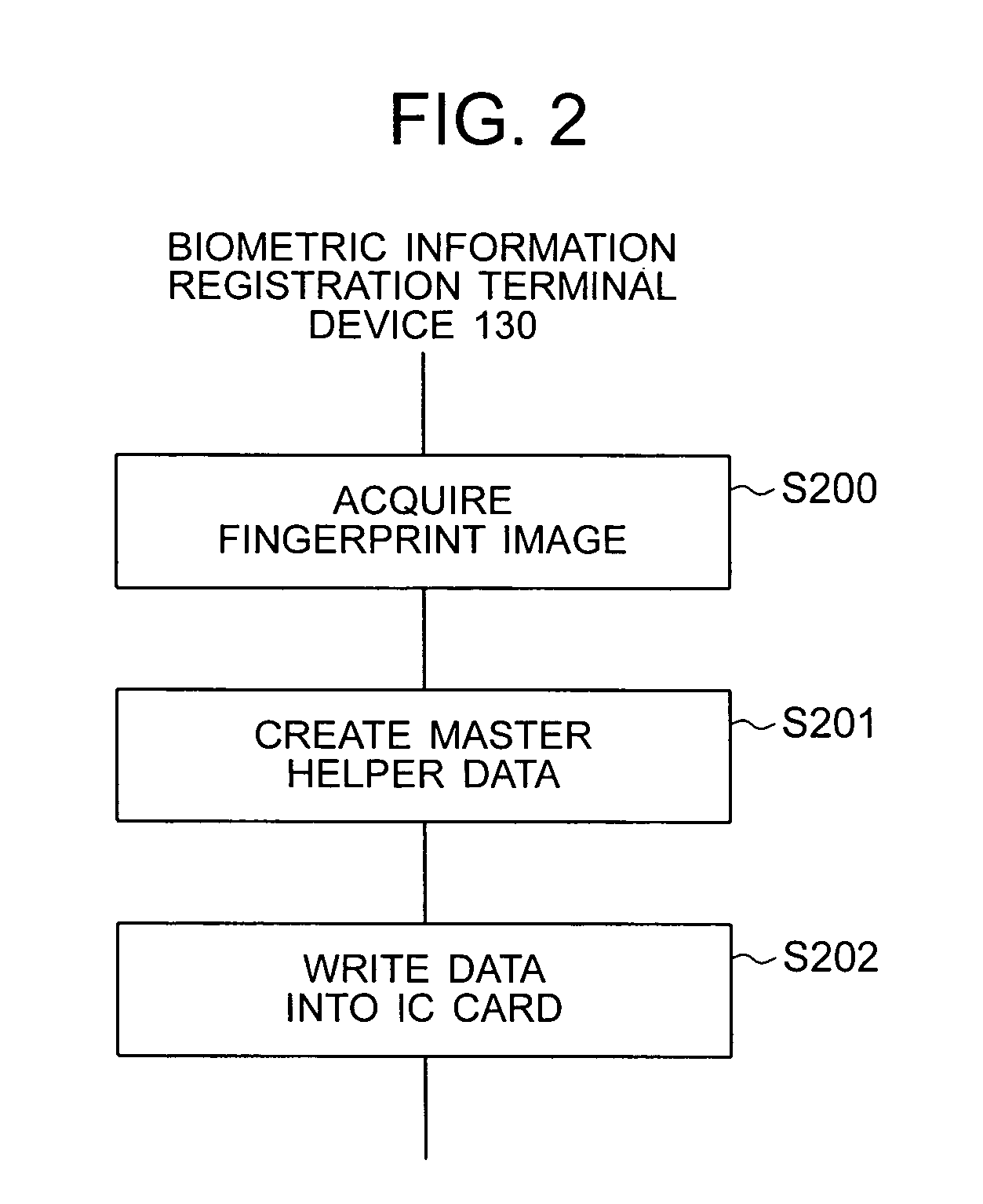
Processing device, helper data generating device, terminal device, authentication device and biometrics authentication system
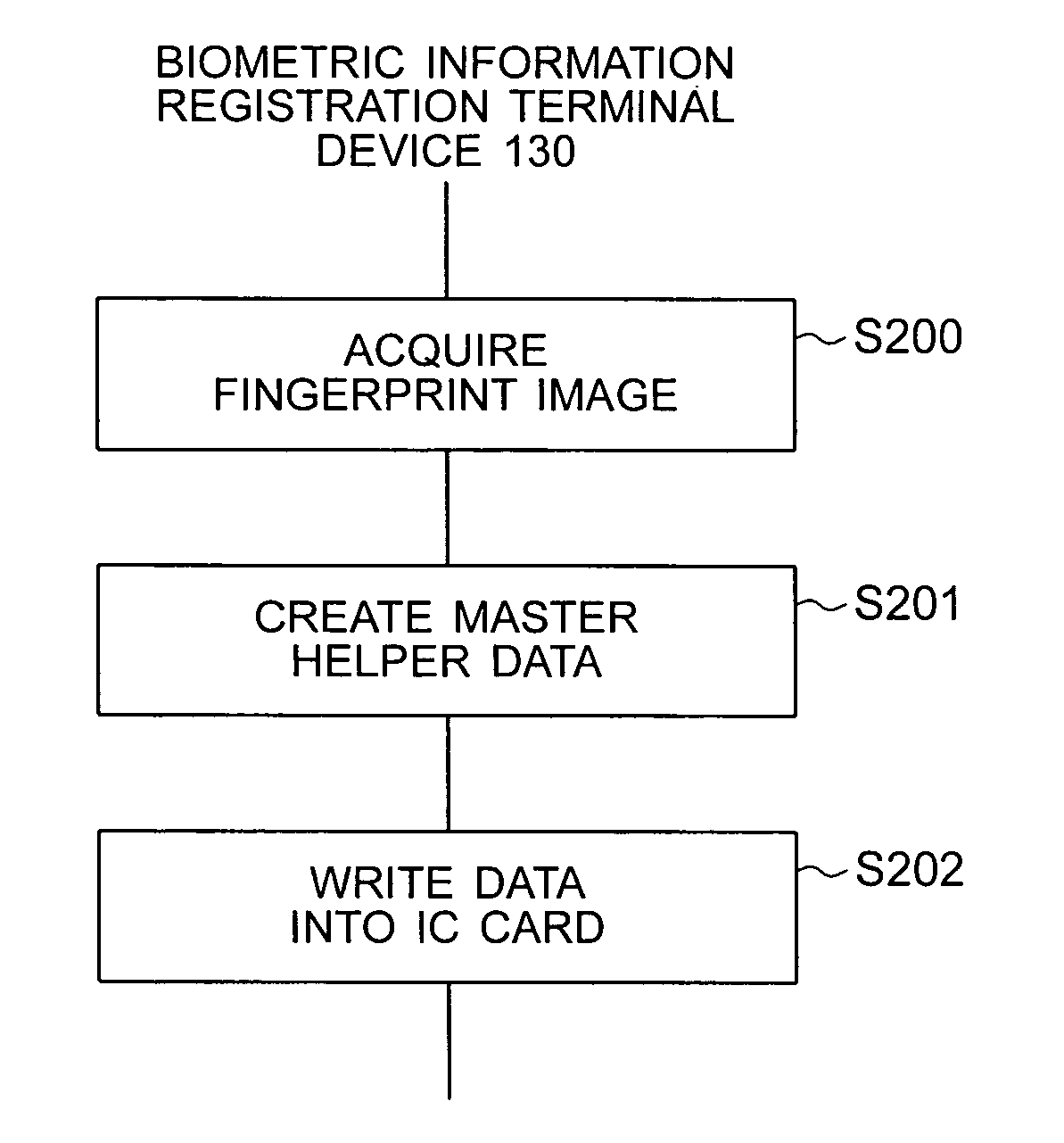
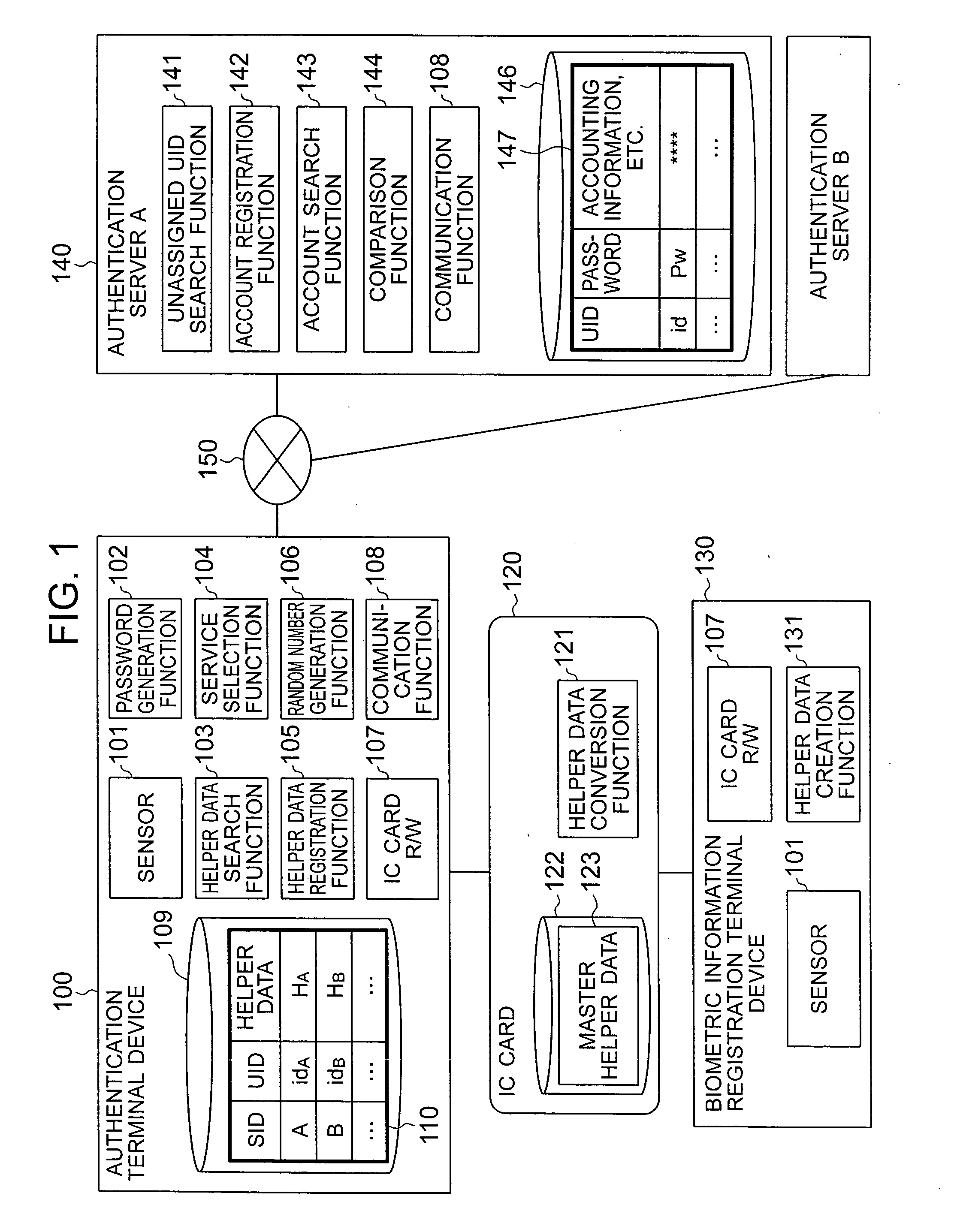
InactiveUS20070118758A1Prevent counterfeitingReducing operation codeDigital data authenticationSecret communicationPasswordTerminal equipment
When biometric information is registered, master helper data is created from user's biometric information and is saved in an IC card. When a user is registered in an authentication server, a password is created and registered in the server, the master helper data is converted to create helper data corresponding to the password, and the helper data is saved in an authentication terminal. When a user is authenticated, the authentication terminal generates an authentication password from the helper data and newly acquired user's biometric information, sends the generated authentication password to the authentication server, and the authentication server compares the authentication password with a registration password to authenticate the user.
Owner:HITACHI LTD
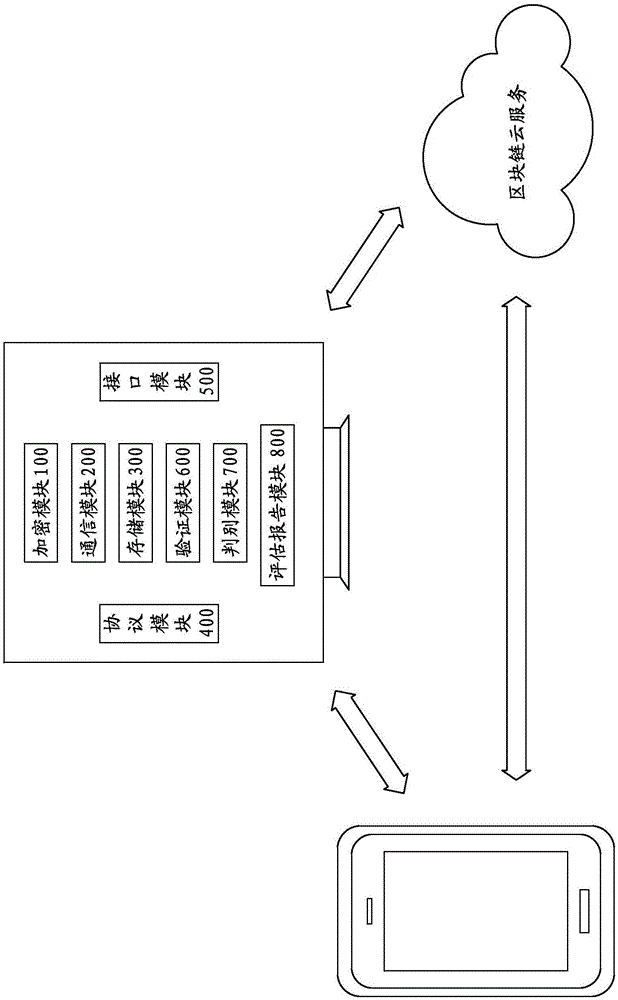
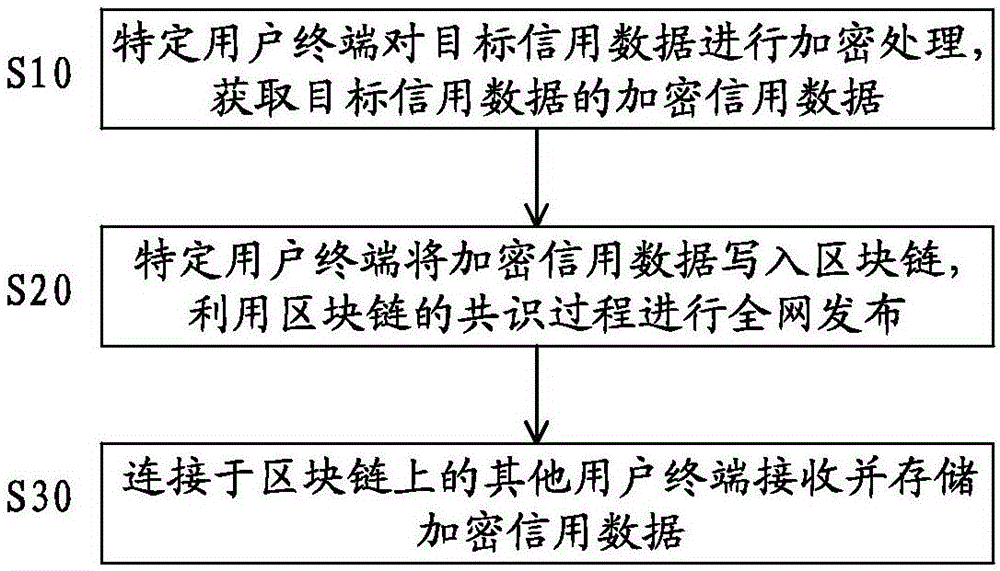
Credit recording system and method based on block chain
ActiveCN106485167AWide variety of sourcesReduce complexityDigital data protectionExtensibilityComputer terminal
The invention discloses a credit recording system and method based on a block chain. The credit recording system comprises a plurality of user terminals which are connected to the block chain and used for acquiring and verifying credit data, wherein each user terminal is installed with an encryption module for encrypting target credit data to be transmitted to form encrypted credit data, a communication module for transmitting the encrypted credit data together with the block chain, and a storage module for storing the target credit data of the user terminal and other encrypted credit data transmitted by the block chain. The credit data are wide in sources, independent, reliable and real; the cleaning and sieving complexity of the credit data are lowered greatly; and the credit recording system and method have flexible and diverse application scenes and high extensibility.
Owner:CENTRIN DATA SYST
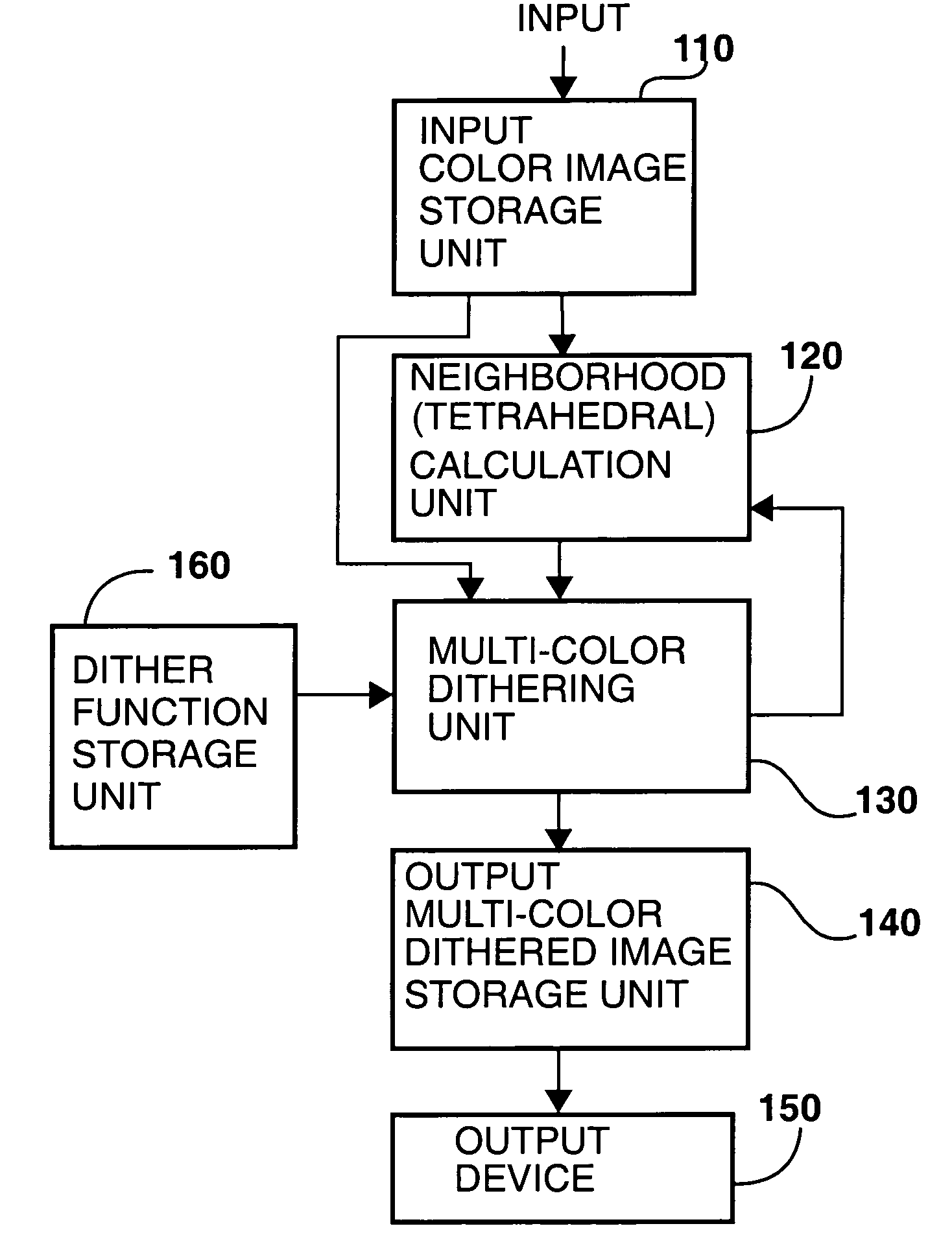
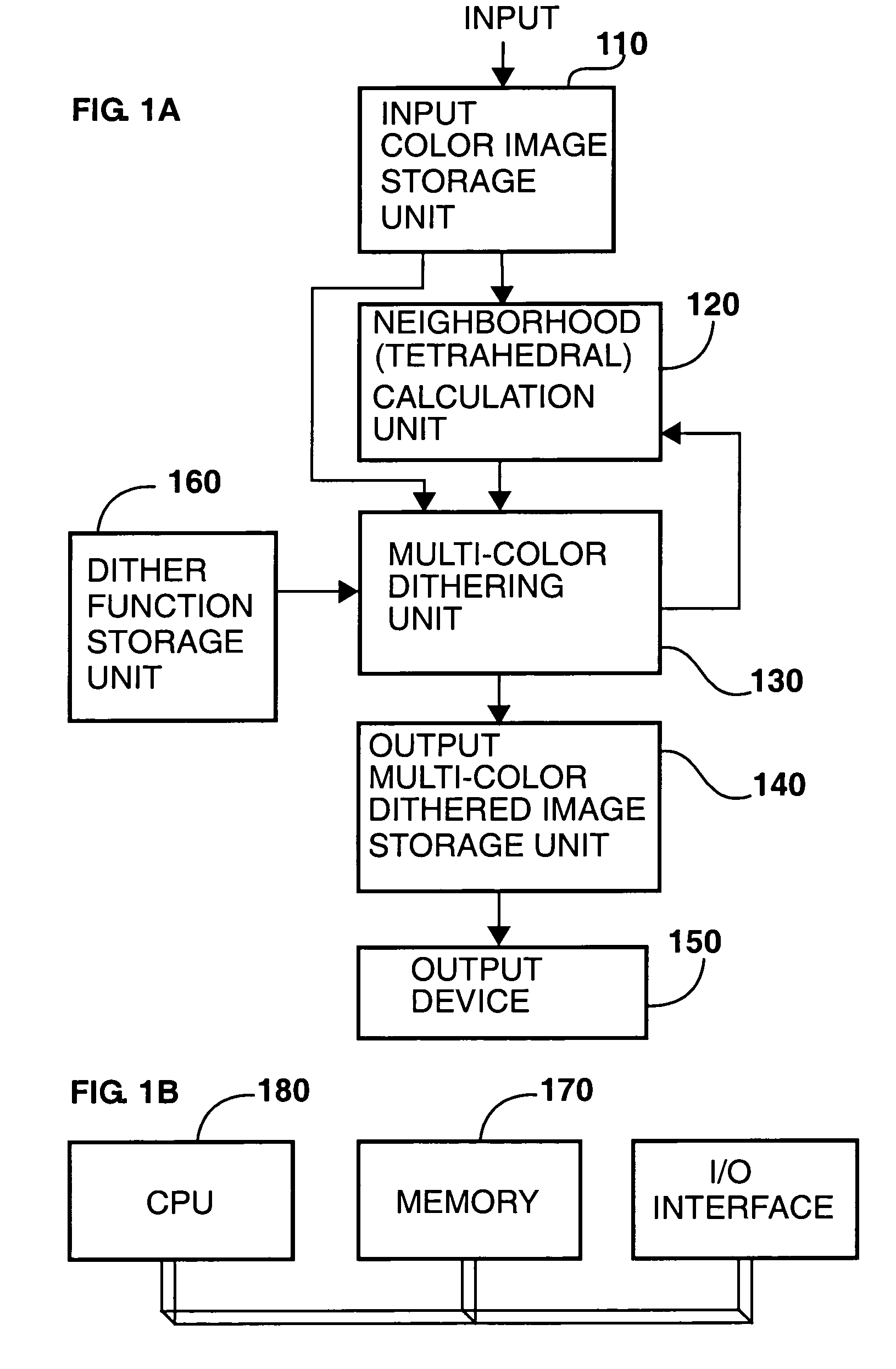
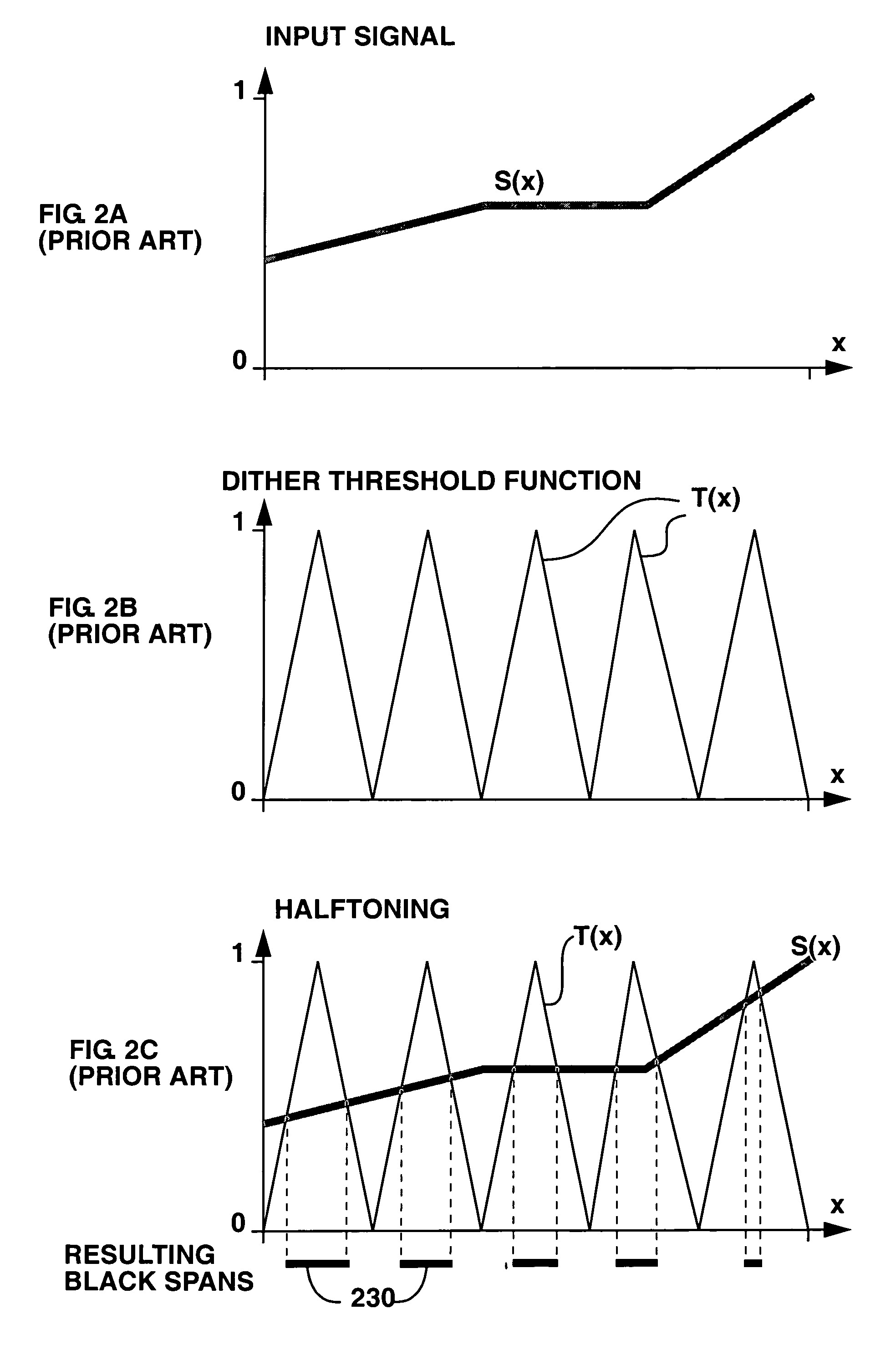
Method and apparatus for generating digital halftone images by multi color dithering
InactiveUS7054038B1Efficient solutionImprove registration accuracyVisual presentationPictoral communicationColor imageEffective solution
The invention provides a method and apparatus for the reproduction of color images by multi-color dithering. Multi-color dithering is an extension of bi-level dithering for halftoning an input image using as primary colors an arbitrary number of inks. The inks may comprise standard inks or non-standard inks such as non-process color inks, opaque inks, metallic inks, variable color inks and fluorescent inks. Multi-color dithering provides a solution for creating artistic multi-color dithered images, whose screen elements are made of artistic color screen shapes such as micro-letters, symbols and ornaments. When printed at high resolution and at high registration accuracy, multi-color dithering using large dither arrays incorporating artistic dither shapes provides an effective solution for preventing counterfeiting. The use of non-standard inks offers additional protection. Multi-color dithering also offers a solution for printers requiring that all inks are printed side by side, without overlaps.
Owner:ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE (EPFL)
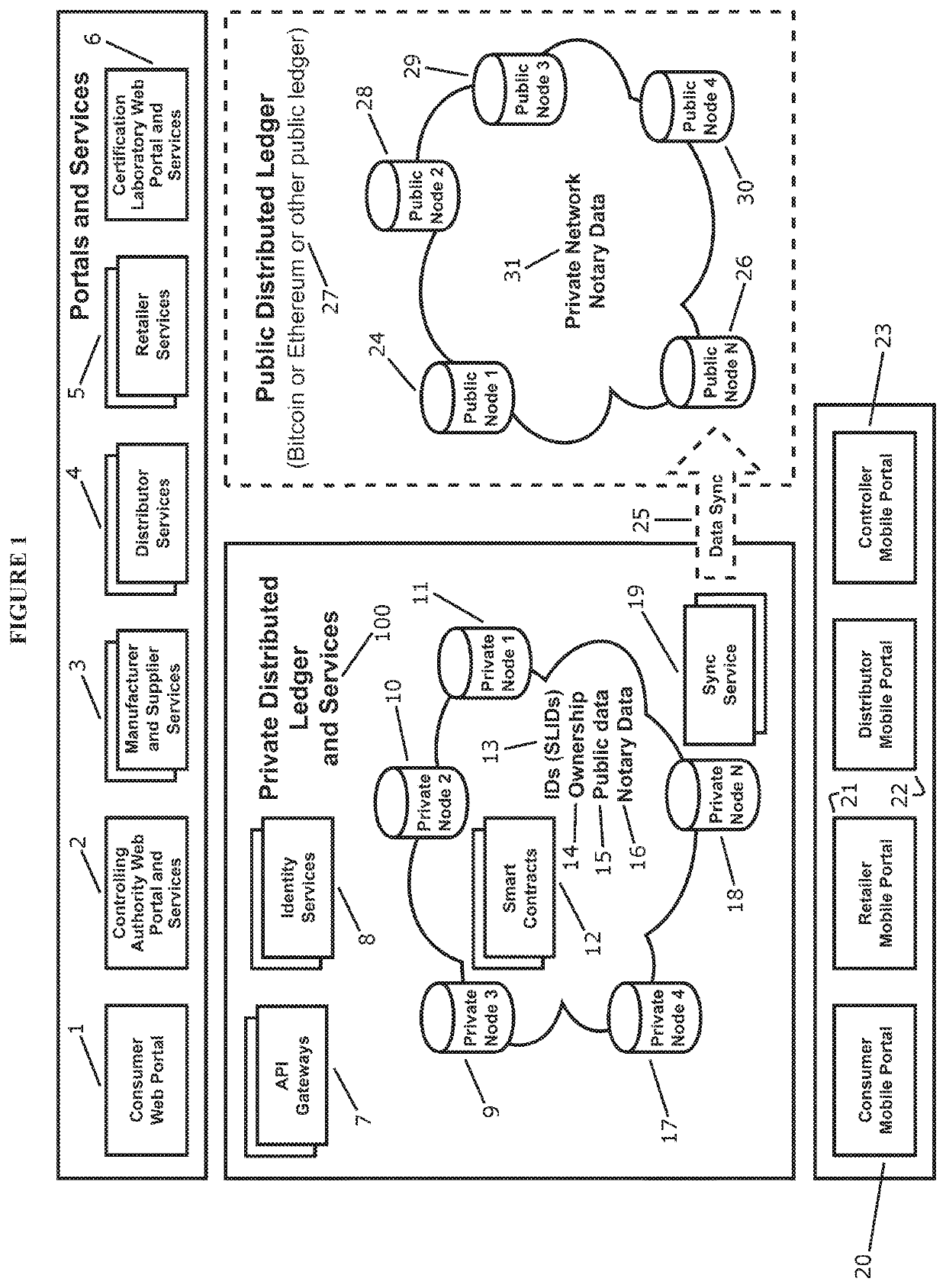
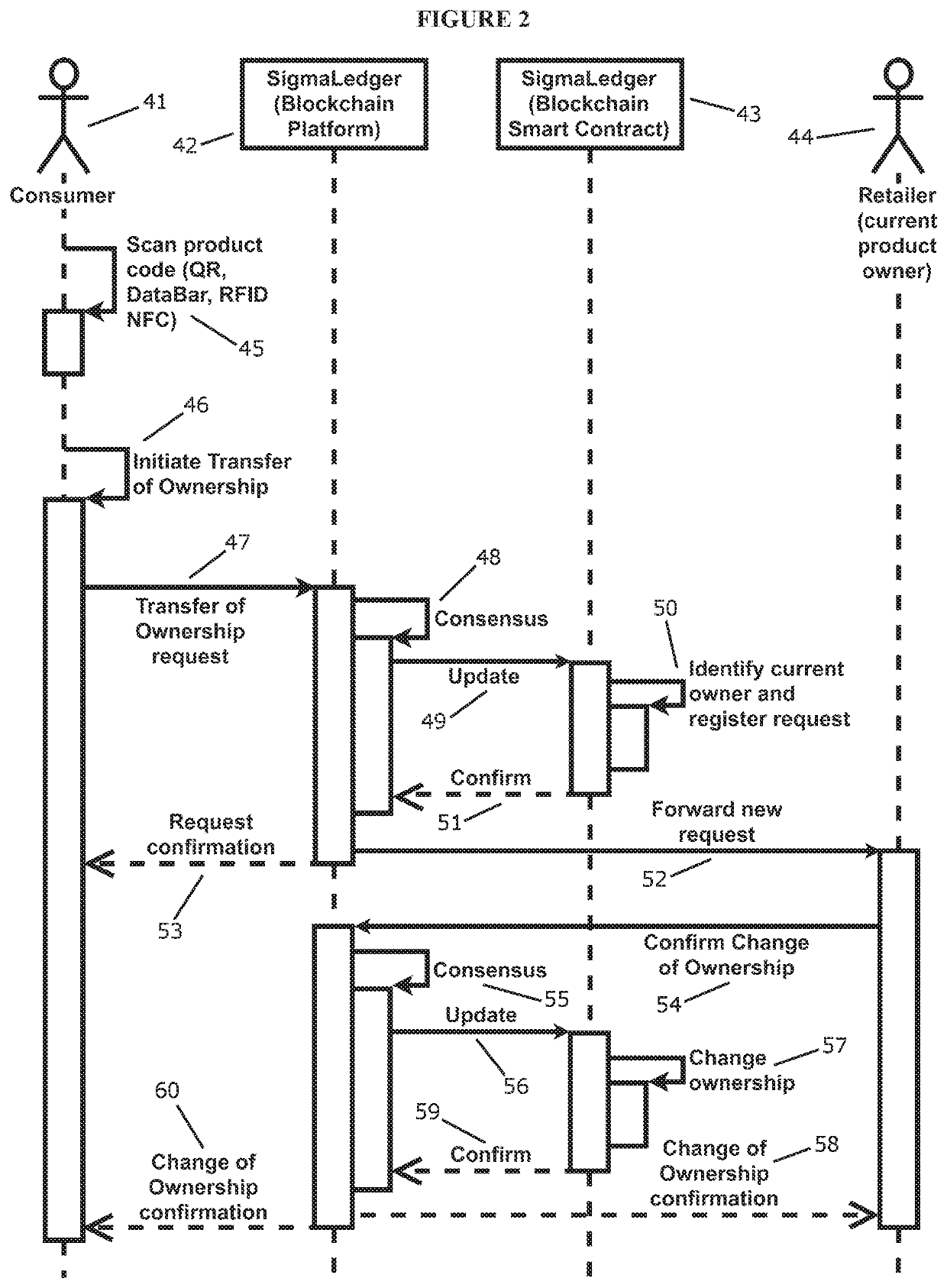
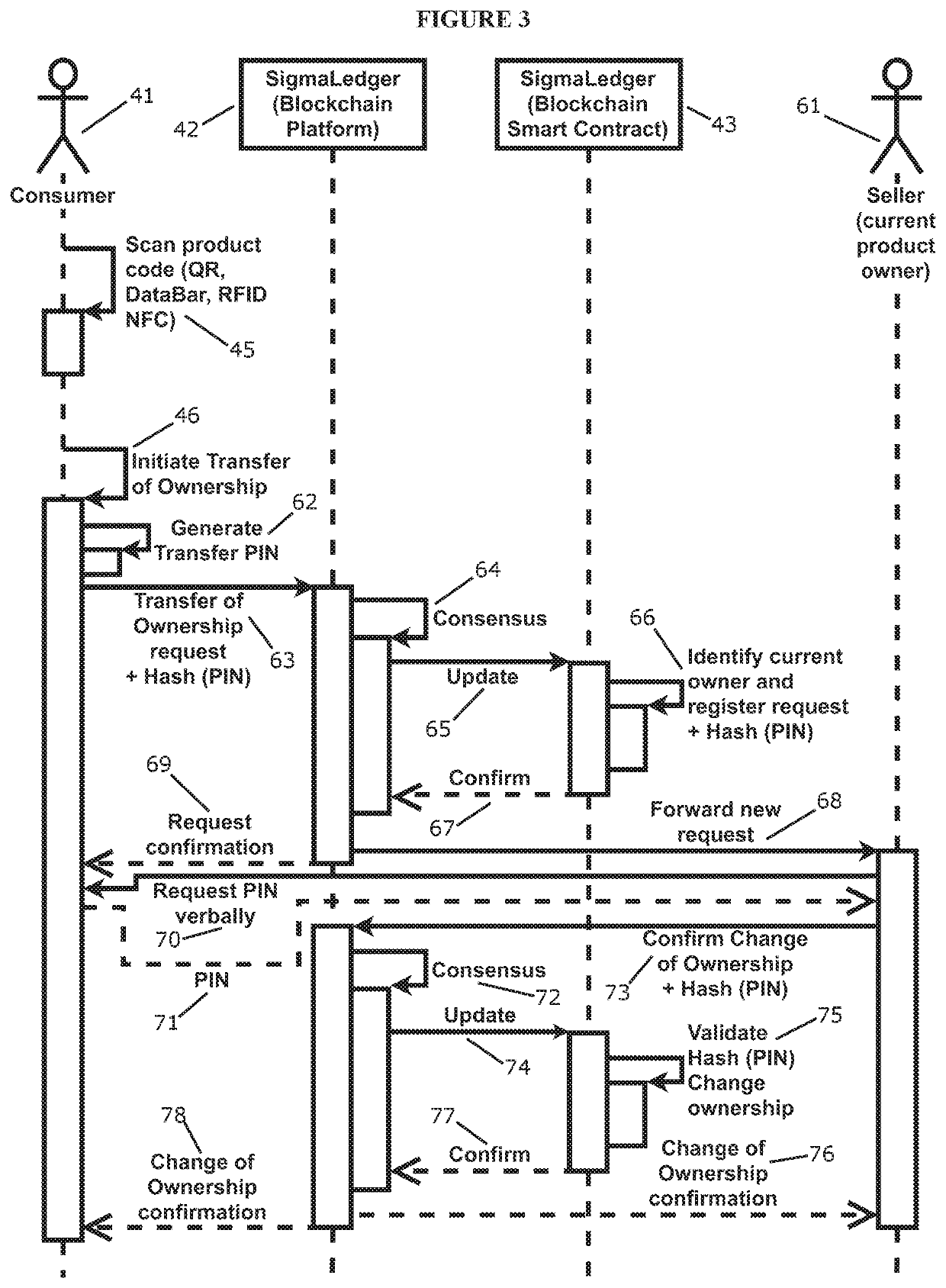
System and method for verifying authenticity of the products based on proof of ownership and transfer of ownership
PendingUS20190340623A1Reduce riskPrevent illegal transactionsDatabase updatingDigital data protectionProduct baseVerification system
A system for determining and verifying authenticity of a product unit comprising: a ledger system comprising at least two nodes; at least one product code attached to said product unit, said product code having an entry in said at least two nodes, said entry defining at least a current owner and a hash of product information; said system capable of self-executing computer code for providing a request for transfer of ownership of said product unit by initiating a request from a portal, and accessing a first node of the at least two nodes; quantifying a consensus of the product information from the first node to a second node; engaging a self-executed computer code via confirming said ownership between said first and second nodes; and forwarding a request to an owner; upon approval by the owner confirming a change of ownership by registering and confirming a change within said first and second nodes.
Owner:SIGMALEDGER INC
Apparatus and method for security tag detection
InactiveUS20070023521A1Improve securityPrevent fraudMaterial analysis by optical meansRecord carriers used with machinesAlcoholDrug product
The present invention relates, in general, to the field of securing, prevention of fraud, or theft of products such as pharmaceuticals, cigarettes, alcohol and other high value often counterfeited products. In particular the invention teaches an apparatus and method to encode packaging of the protected goods using a near infrared luminescing compound and detecting the compound through recognition of a characteristic spectral signature of its emission.
Owner:AUTHENTIX INC
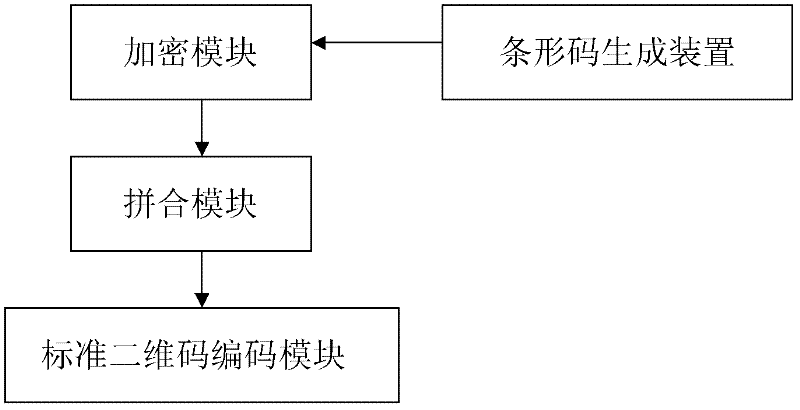
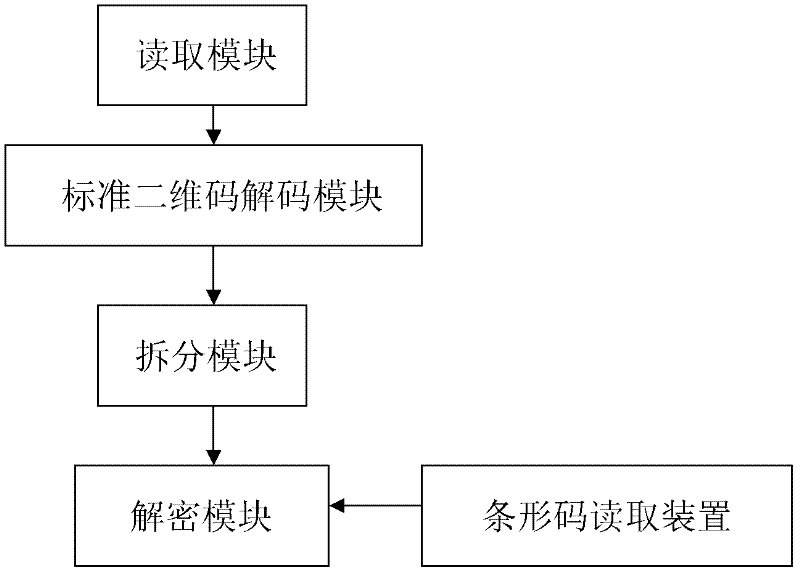
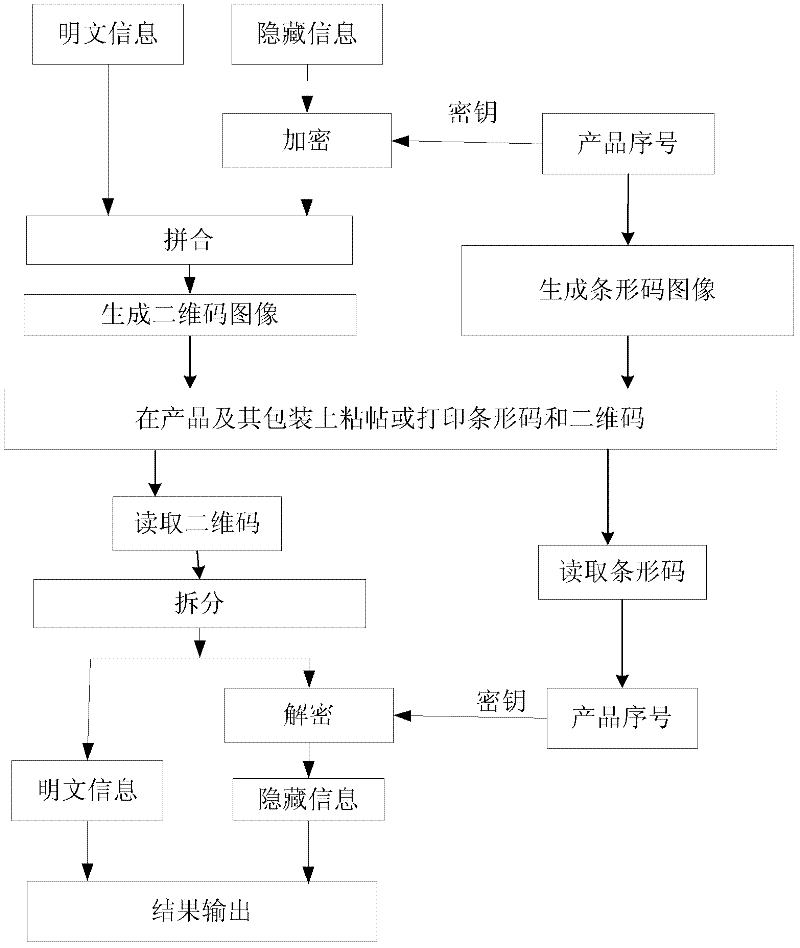
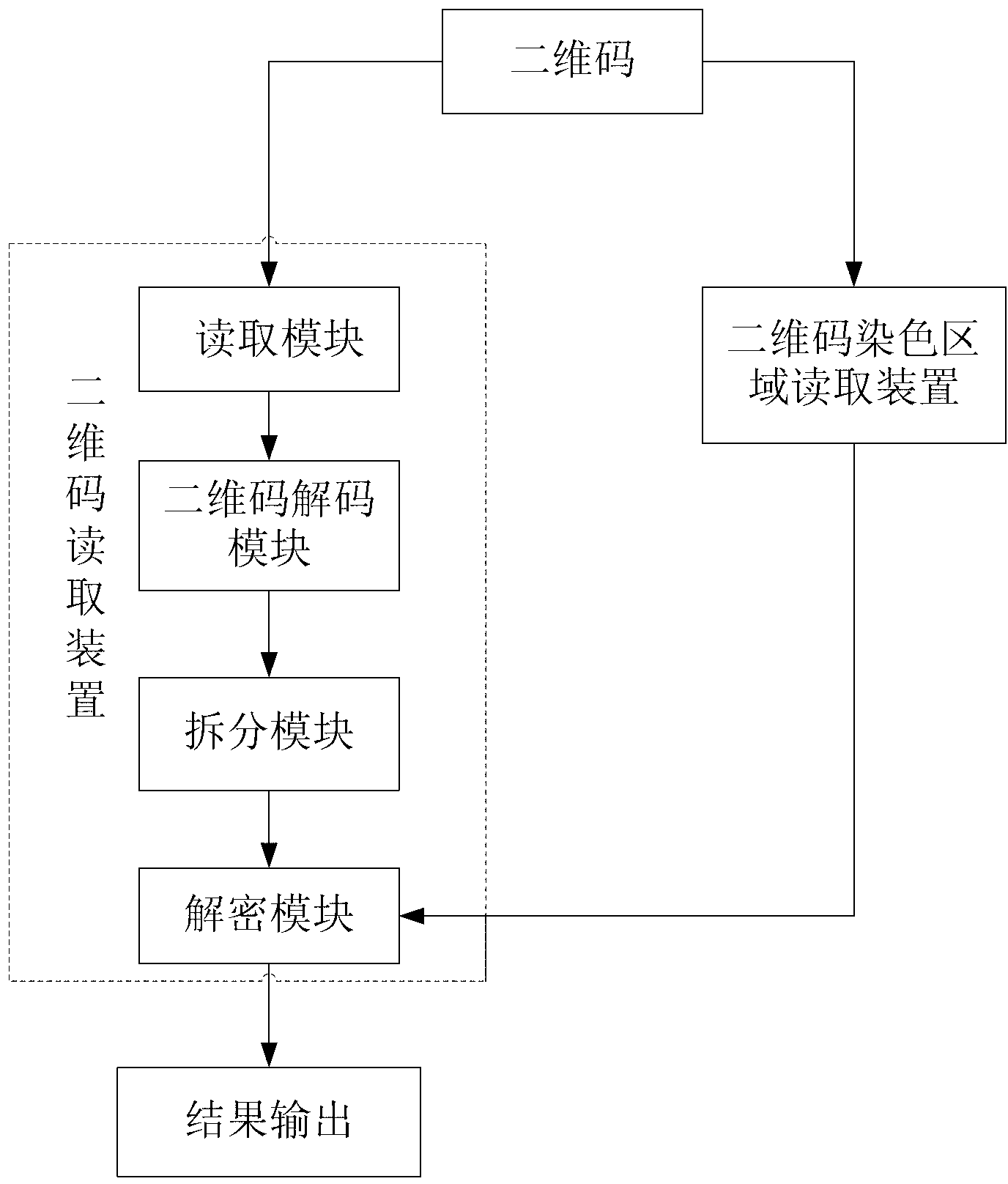
Mixed encoding and decoding method and device of barcode and two-dimensional code
InactiveCN102270294AIntegrity guaranteedEnsure safetySensing by electromagnetic radiationDecoding methodsConfidentiality
The invention discloses a coding method for mixing barcodes and two-dimensional codes, which comprises the following steps: (1) generating barcode images through barcode algorithms through barcode data; Encrypting as a key to obtain two-dimensional code generation information; (3) generating a two-dimensional code image by using the two-dimensional code generation information obtained in step (2) through a two-dimensional code generation algorithm. The invention also discloses a decoding method and an encoding and decoding device of the encoding method. On the one hand, the present invention can use naked eyes to identify products, certificates or bills through the barcode, and on the other hand, the two-dimensional code reading device of the present invention can be used to read the information hidden in the two-dimensional code, ensuring the integrity of the two-dimensional code Safety, security and confidentiality, and enable the two-dimensional code to carry hidden information, strengthen the anti-counterfeiting and uniqueness of the two-dimensional code, and open up a new application field of the two-dimensional code as a data label.
Owner:SOUTH CHINA AGRI UNIV
Information encoding on surfaces by varying spectral emissivity
InactiveUS7044386B2Prevent counterfeitingEnhanced informationRecord carriers used with machinesDigital marking by printing code marksSpectral emissionEmissivity
A method for applying surface modifications in at least two patterns that differ in spectral emissivity by known amounts. The patterns form an information-encoding sequence of transitions of differential emissivity along a scan path over the patterns, that encodes a set of information. This information is decoded by a scanner sensitive to emissivity in the given portion of the electromagnetic spectrum, and sensitive to transitions in emissivity of the known amounts, when scanned along the scan path, combined with knowledge of the expected emissivity values of the patterns. This provides secure informational marking of articles and documents, including mail. The patterns may be visible, or hidden, but the emissivity values are not duplicated by standard office equipment, so authenticity of the patterns can be determined using the special emissivity scanner.
Owner:BERSON WILLIAM
Land change investigation information management system of three-checking unification
InactiveCN107516282APrevent counterfeitingPlay the role of supervision and guidanceData processing applicationsGeographical information databasesLand basedLand change
The invention discloses a land change investigation information management system of three-checking unification. The system comprises a server-side data superposition analysis system, a front-end information management query system and a mobile terminal information acquisition system. The server-side data superposition analysis system processes and analyzes pattern spot information and a land base database, and carries out storage and shares to a server through the front-end information management query system. The mobile terminal information acquisition system downloads data in an on-line mode, carries out real-time positioning and field-operation non-paper information acquisition, and returns to the server. The front-end information management query system is used to realize management and query, uploading and audit, and analysis and statistics of pattern spot data. In the invention, a pattern spot flow function of departments at all levels, in which patrol, investigation and checking are integrated into one body, is realized; a traditional flow is optimized and recombined; whole-course on-line operation of pattern spots is realized; and operating efficiency of investigation work is increased and a great safety meaning of the data is guaranteed.
Owner:青岛市房地产信息与交易资金监管中心 +1
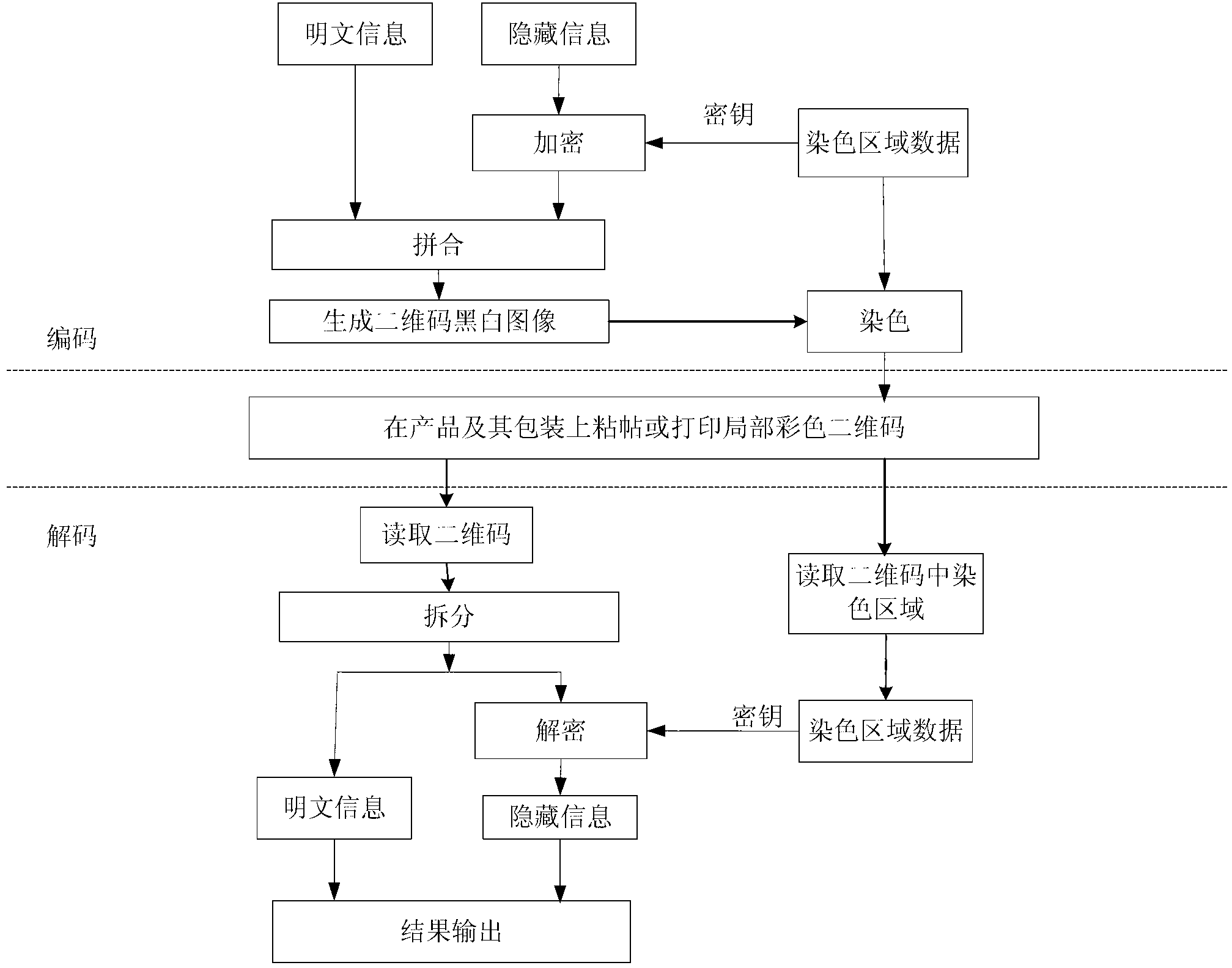
Two-dimension code coding and decoding method and device based on local color verification
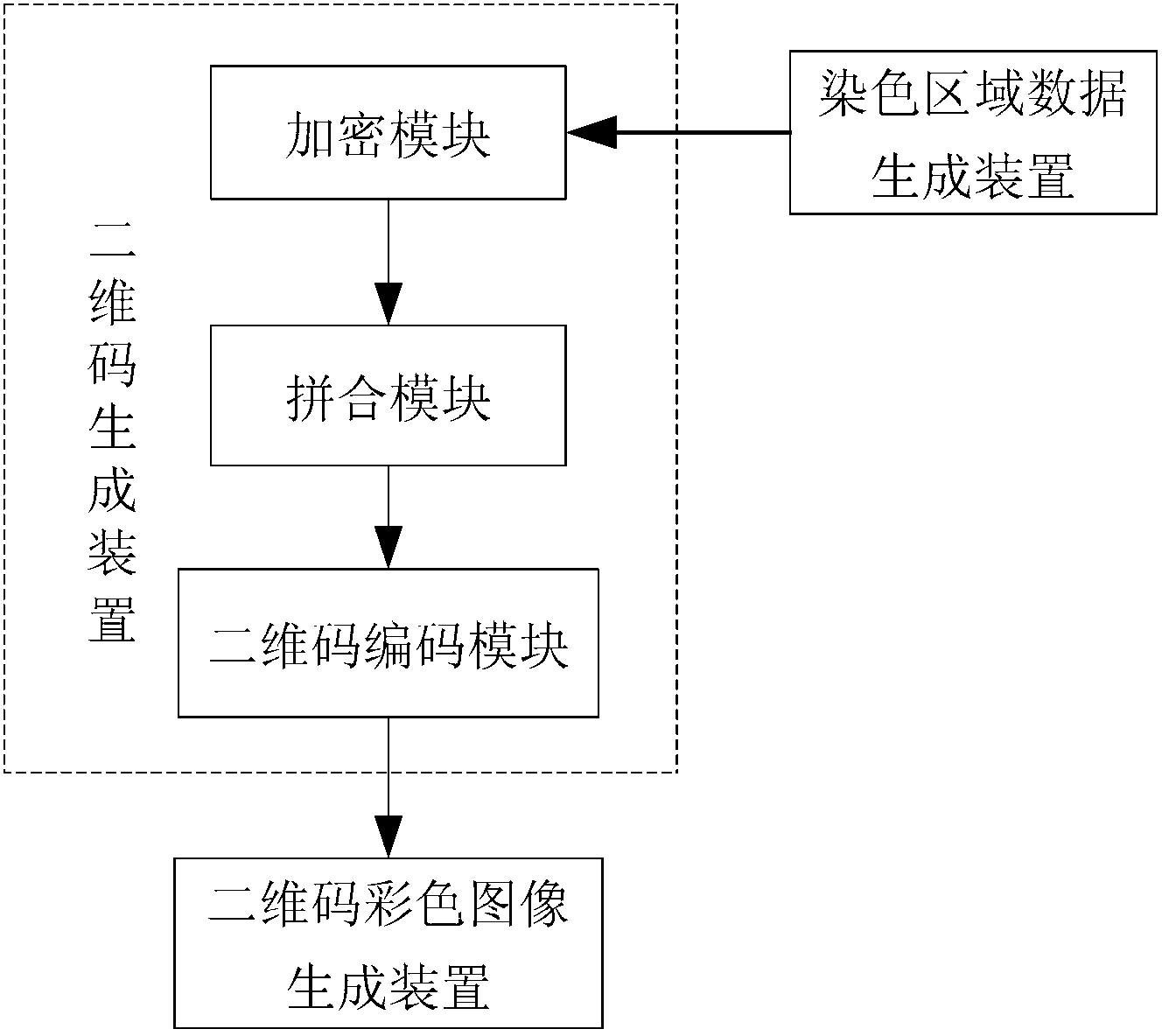
ActiveCN102916804ARealize monitoringRealize regulationEncryption apparatus with shift registers/memoriesRecord carriers used with machinesPattern recognitionCode space
The invention discloses a two-dimension code coding and decoding method and devices based on local color verification. The coding method comprises the following steps of: generating coloring region data randomly according to a predefined coloring region coding and decoding table, and taking the generated coloring region data as a secret key to perform encryption so as to obtain two-dimension code generation information; generating two-dimension code black-and-white images by a two-dimension code generation algorithm; and finally coloring the generated two-dimension code black-and-white images according to the coloring region data to obtain local colored two-dimension code images. The decoding method comprises the following steps of: reading the coloring region data on the two-dimension code images, and using a standard two-dimension code decoding algorithm to decode; and performing decryption on the decoded information by taking the coloring region data as the secret key via a decipherment algorithm to obtain original information of the two-dimension cod images. By using the invention based on original black and white colors, the coloring region information is increased, coding space of two-dimension codes can be expanded, and counterfeited difficulty is increased.
Owner:SOUTH CHINA AGRI UNIV
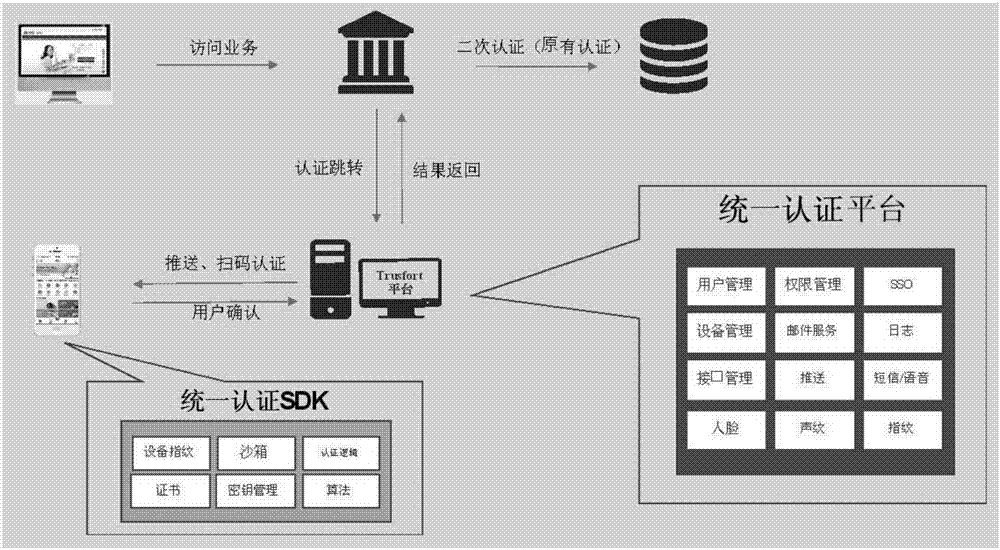
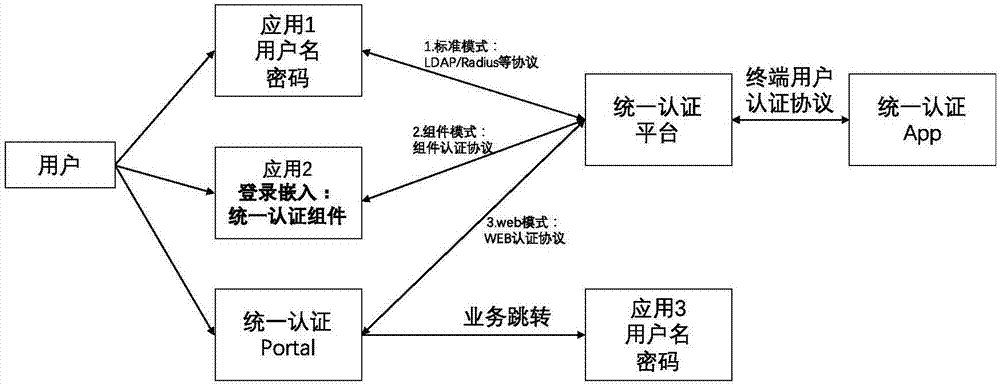
System and method for multi-system authentication and synchronization in mobile equipment
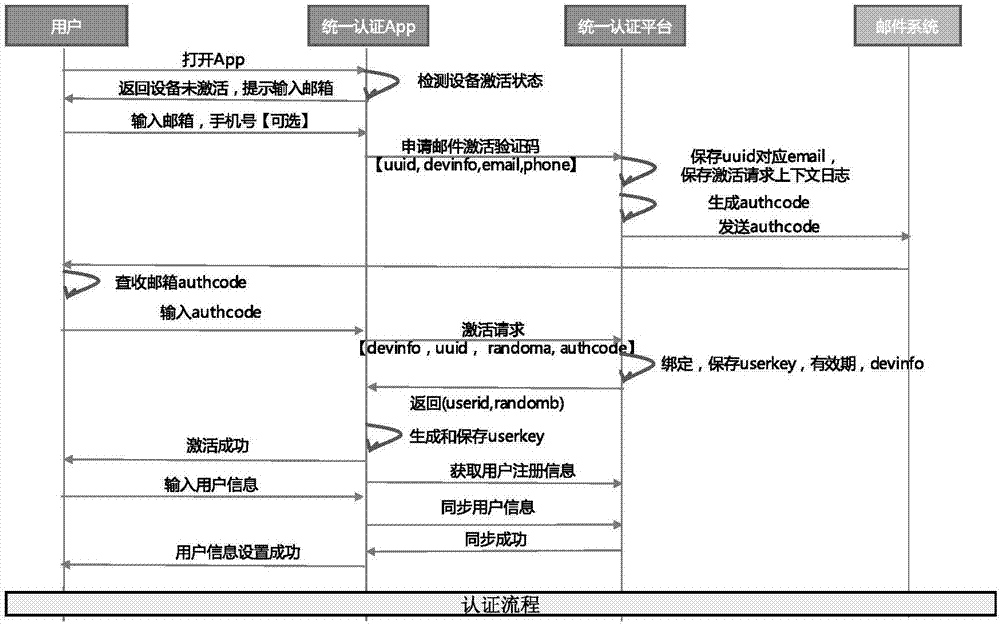
ActiveCN107172008AGuaranteed experienceAvoid enteringEncryption apparatus with shift registers/memoriesUser identity/authority verificationMobile endBiological activation
The invention discloses a system and method for multi-system authentication and synchronization in mobile equipment. The system is composed of a unified authentication assembly SDK and a unified authentication platform, wherein the unified authentication assembly SDK comprises an equipment fingerprint module, a sandbox module, a certificate module, a secret key management module, an algorithm module and an authentication logic module; and the unified authentication platform comprises a user management module, an authority management module, an SSO module, an equipment management module, a mail service module, a log module, an interface management module, a push module, a text message / voice module, a face module, a voiceprint module and a fingerprint module. The system and method can be applied to service scenes where existing enterprise services migrate to mobile ends, provide authentication and state synchronization on the mobile ends for enterprise users, through an innovative equipment fingerprint generation algorithm, a matching algorithm and a system activation process, the users can bind their mobile phones with enterprise accounts, and thus the enterprise accounts can realize login and state synchronization on the mobile equipment.
Owner:BEIJING TRUSFORT TECH CO LTD
Payment and identity authentication systems based on biometric feature recognition
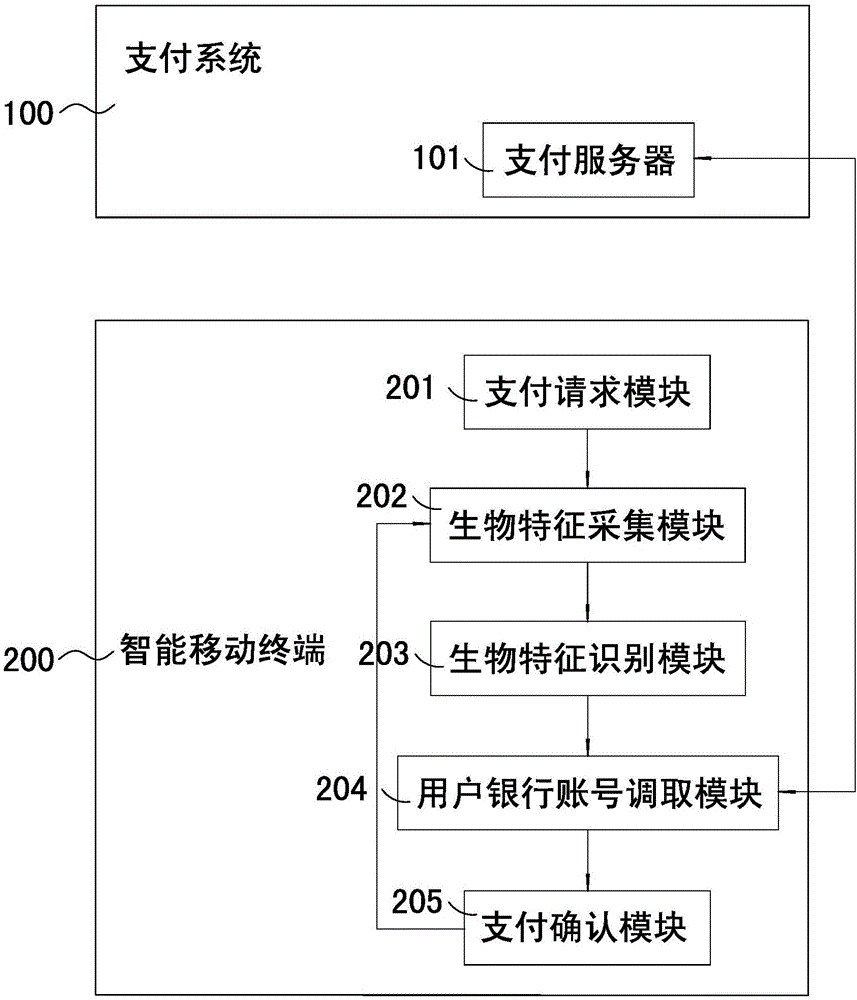
InactiveCN106296199AImprove accuracyImprove reliabilityBiometric pattern recognitionProtocol authorisationPalm printBank account
The invention discloses payment and identity authentication systems based on biometric feature recognition. The payment system based on the biometric feature recognition comprises a payment system and a smart mobile terminal, wherein the payment system comprises a payment server for storing user bank account information which is bound with biometric feature information of a user; and the smart mobile terminal comprises a payment request module, a biometric feature acquisition module, a biometric feature recognition module, a user bank account calling module and a payment confirmation module. The payment system based on the biometric feature recognition has the effects that when the payment system is used for making a payment, the user can make a rapid payment by inputting a voiceprint, irises, a palm print, a vein, ears, a gait or retinas without carrying any cash, bank card, consumer card or mobile phone no matter where the user is, so that a conventional payment mode is broken, and the restraints of the cash, cards and electronic equipment are broken. A checker can rapidly check user identity information by using the identity authentication system, and the user does not need to take out any identity card, so that high practicability and a good use effect are achieved.
Owner:刘洪文
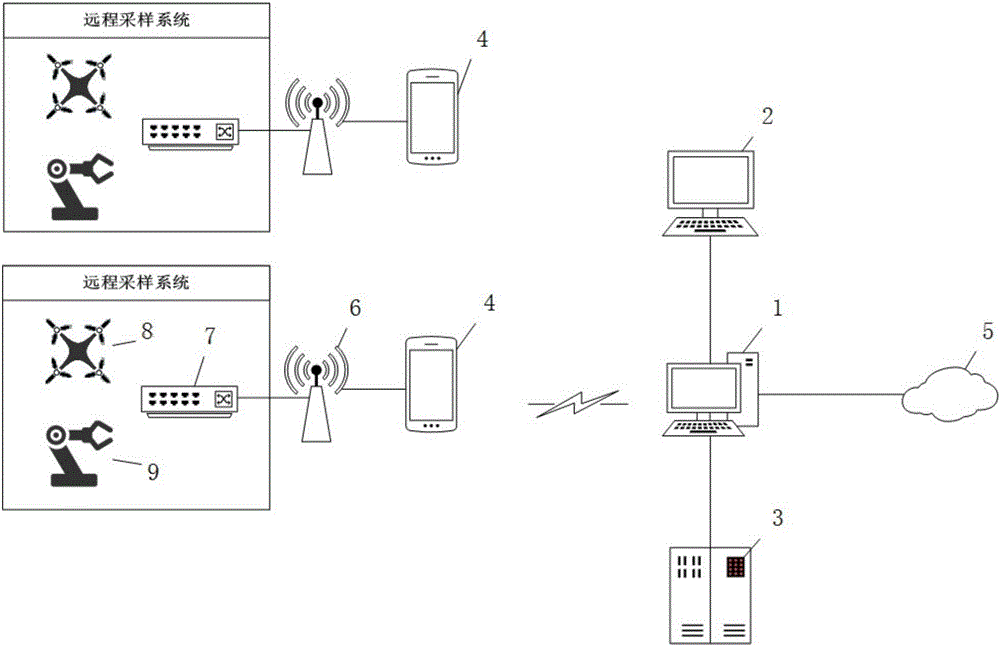
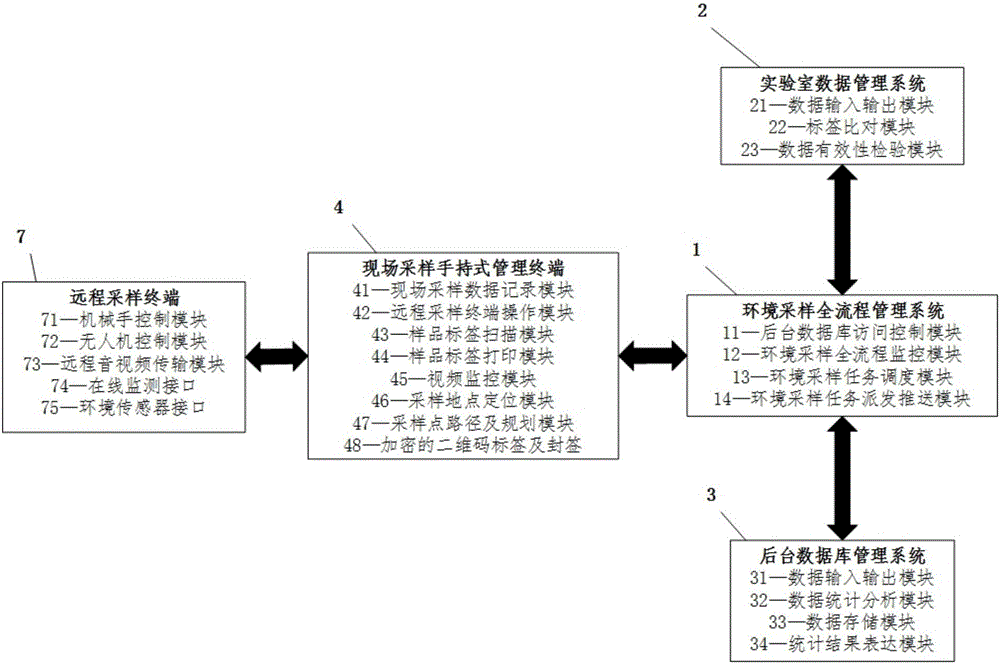
Whole process management and control-based environment sampling management system and method
The invention discloses a whole process management and control-based environment sampling management system and method. The system comprises an environment sampling whole process management system, a laboratory data management system, a background database management system, one or more embedded system secondary development-based field sampling handheld management terminals, one or more cloud information distribution systems, one or more directed wireless data reception / transmission ends, one or more remote sampling terminals and one or more remote sampling tools, wherein the one or more cloud information distribution systems are supplied to the public for accessing environment sampling test data and reports, and the one or more directed wireless data reception / transmission ends are used for field short-distance data transmission. According to the system and method disclosed by the invention, the whole process management and control in an environment sampling process can be realized by utilizing technological means such as real-time video uploading, two-dimensional code encryption and task pushing.
Owner:北京南科大蓝色科技有限公司 +1
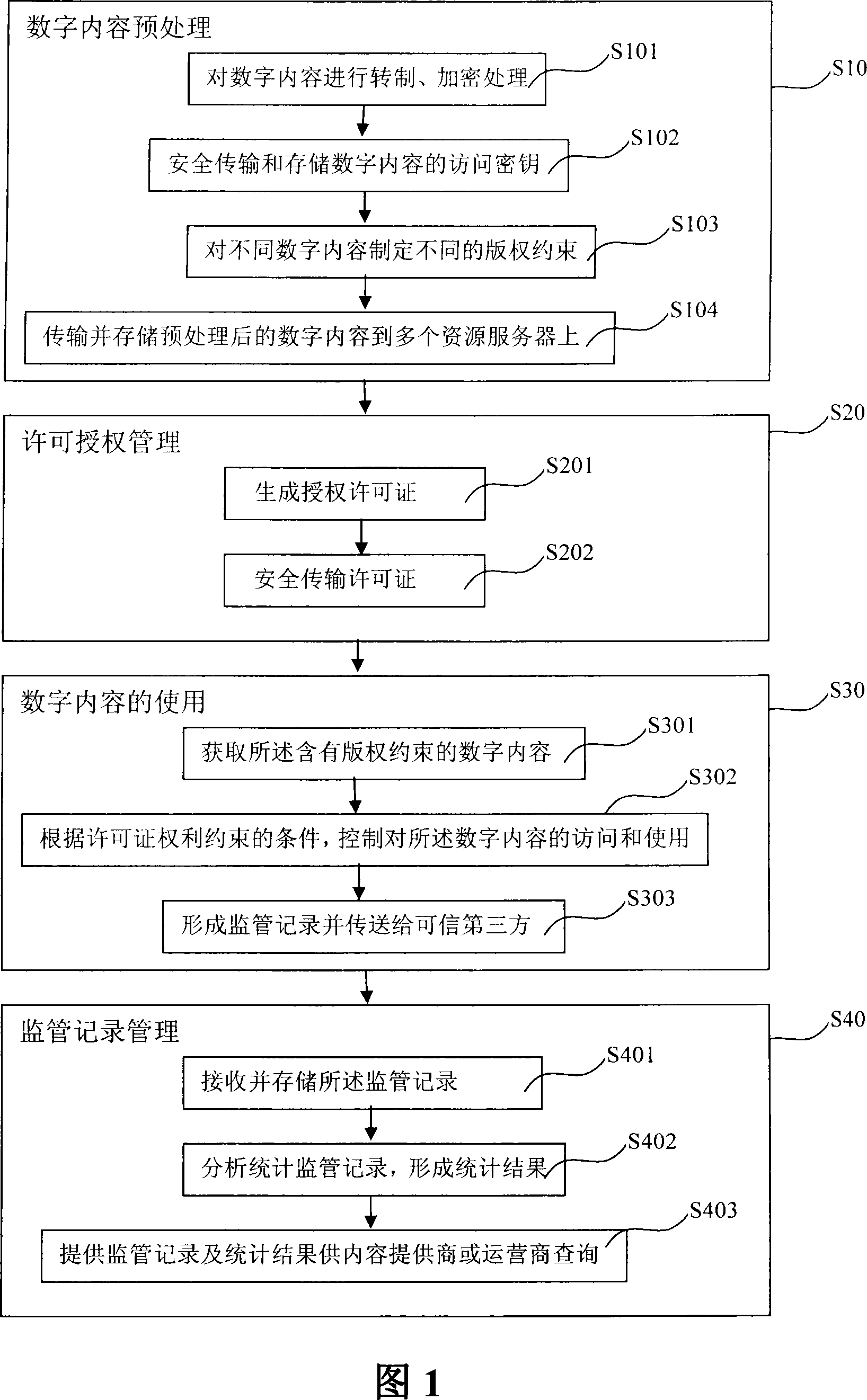
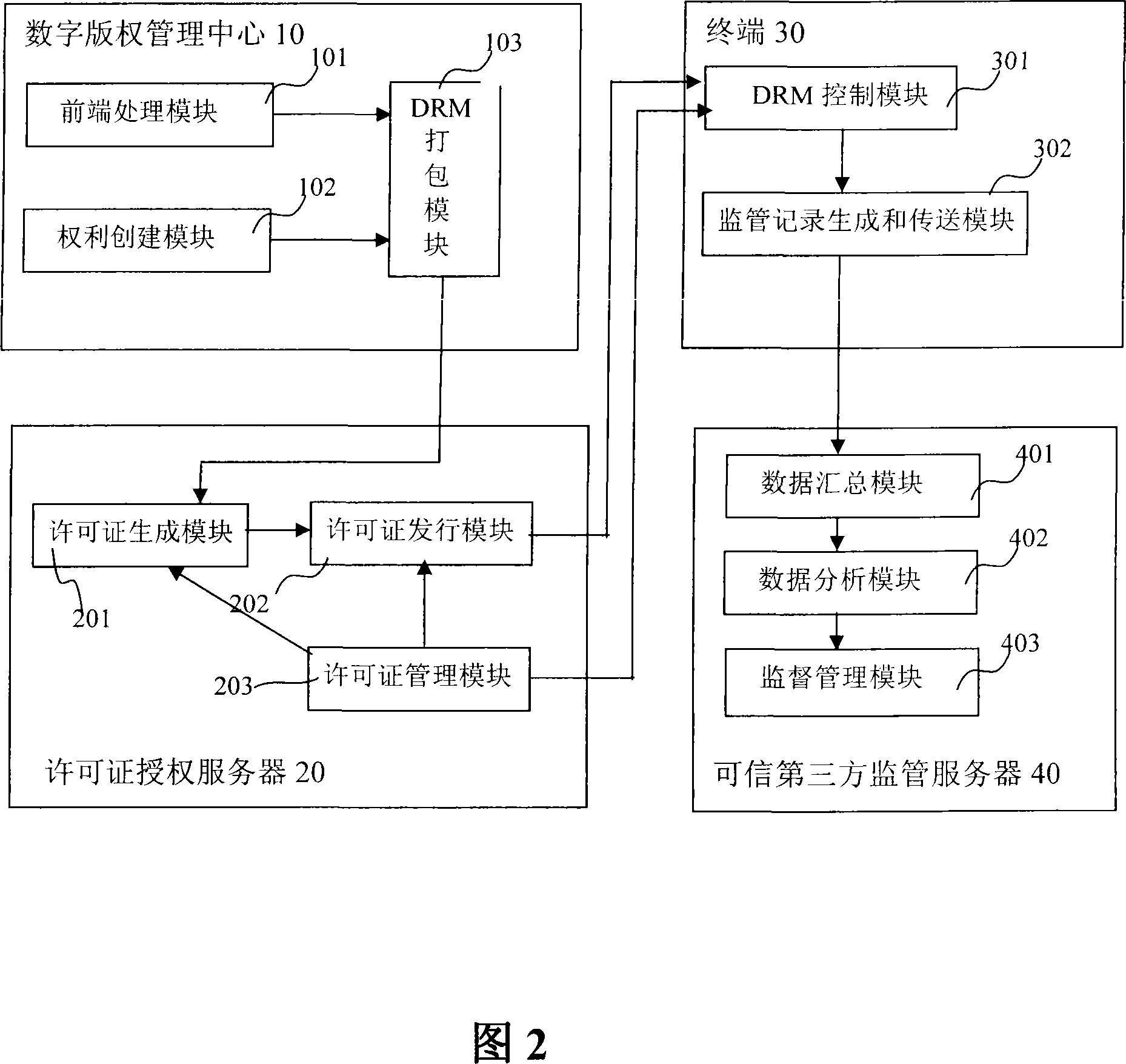
A digital copyright protection method and system
ActiveCN101216871AAchieve protectionRealize the use effectKey distribution for secure communicationCommerceThird partyDigital content
The invention discloses a digital copyright protection method and a system. The method comprises the following steps: performing pretreatment on the original digital content provided by a content supplier before distribution and operation; conducting management of copyright constraints on the pretreated digital content through a mode of an authorized license; accessing and using the digital content containing the copyright constraints via a terminal in accordance with corresponding right constraints, and sending supervision records formed by the usage and the access to a credible third-party supervision server; and managing the supervision records which are formed by accessing and using the digital content containing the copyright constraints via the terminal with the credible third-party supervision server. The invention realizes balance constraints of all roles in a value chain of the digital content, which are required by the digital copyright protection system, so as to truly protect legitimate rights of a digital content copyright holder.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
A secure communication method between nodes in vehicular network
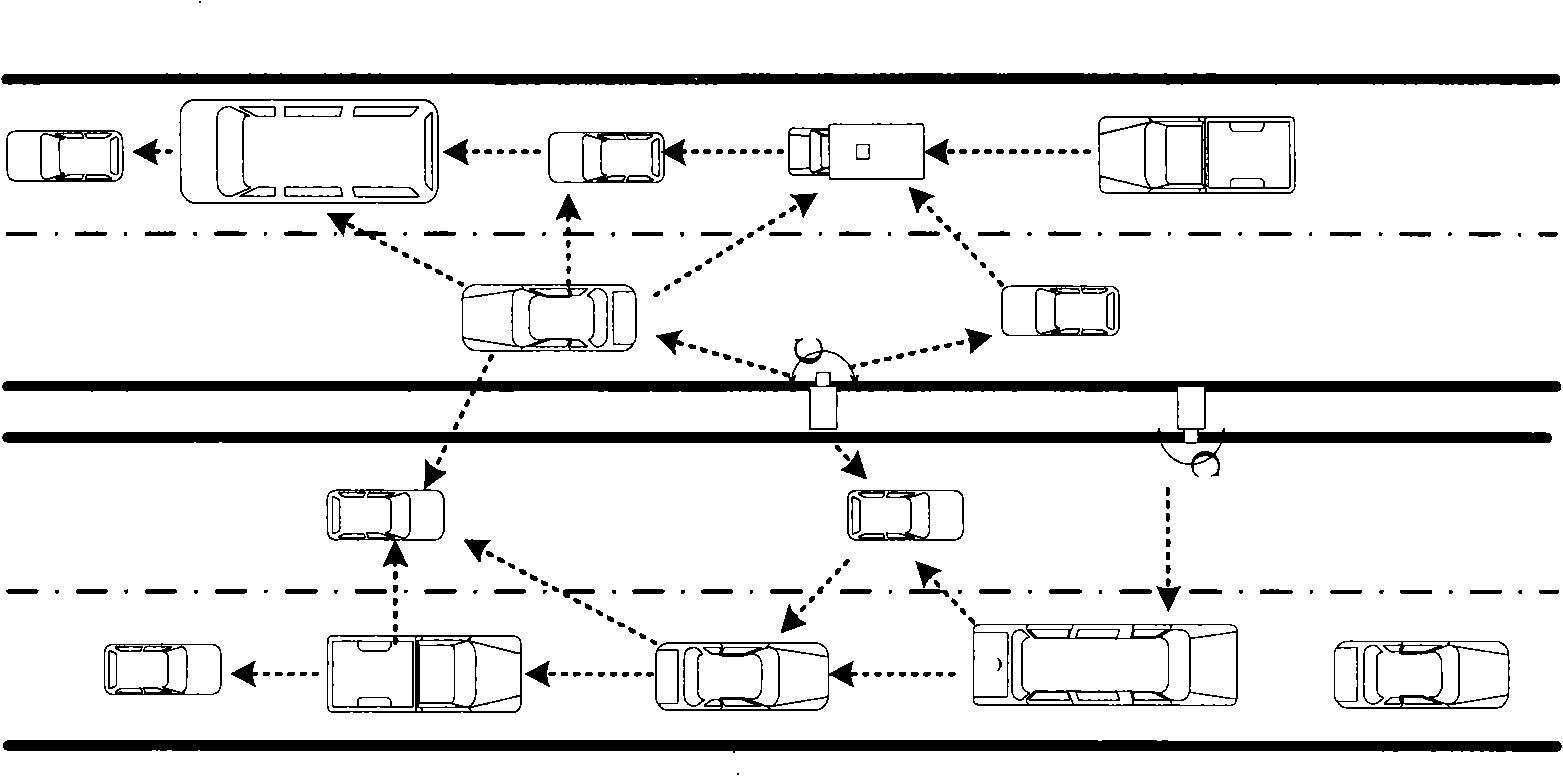
InactiveCN101262333APrevent counterfeitingImprove security strengthKey distribution for secure communicationParticular environment based servicesKey exchangeSecure communication
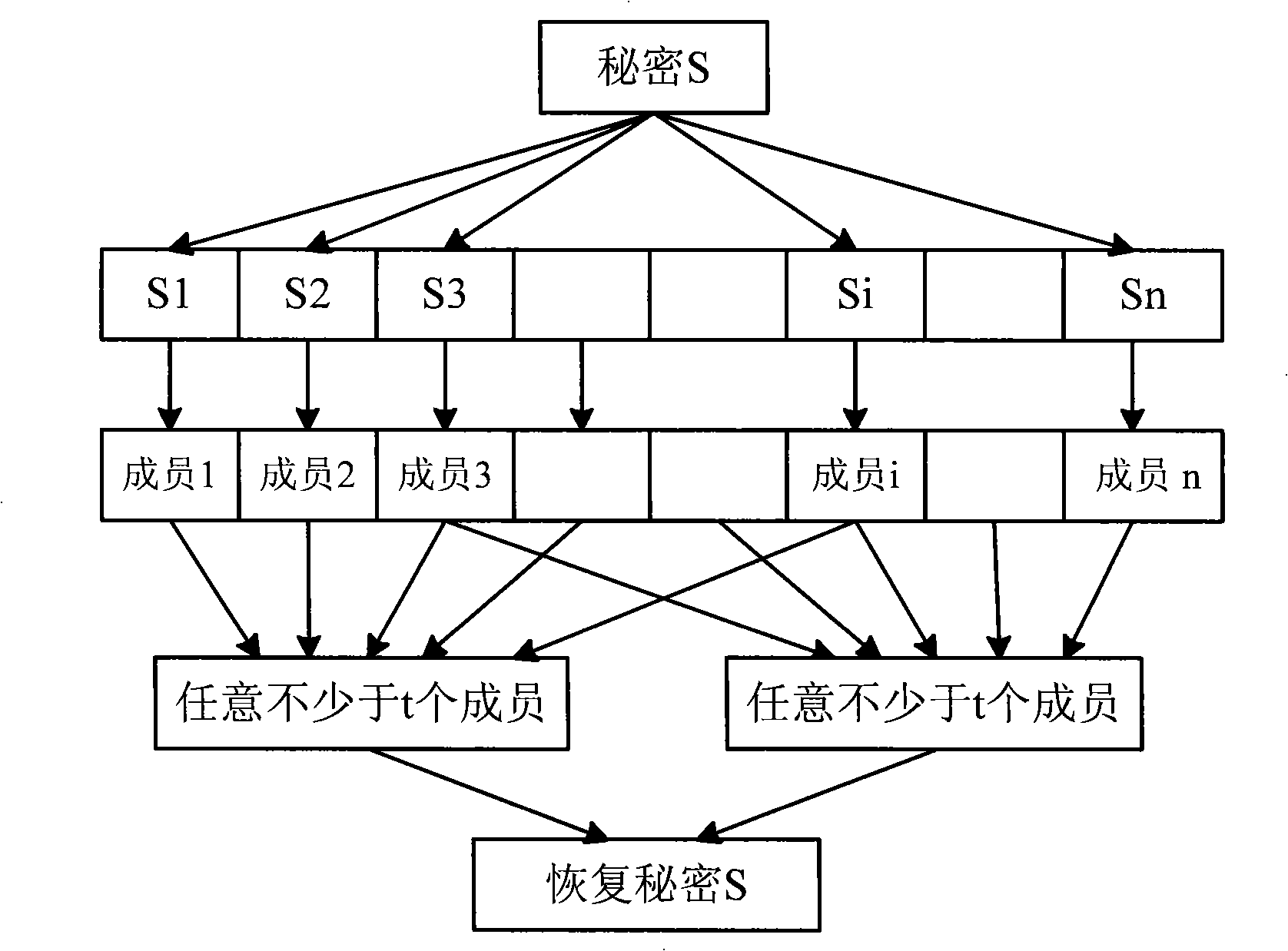
The invention discloses a safe communication method between nodes in a vehicular network. The method provides a disperse trust and security system based on elliptic curves. Before communicating, communication nodes are two-way indentified by a (t, n) threshold authentication proposal to prevent hostile nodes from personating legal nodes and t-1 members in a network from counterfeiting certificates. Meanwhile, a key exchange based on password authentication is carried out to ensure that all conventioneers consult about a key by a safe approach, and therefore, a strong session key is generated to provide message discrimination, confidentiality and integrality for communication nodes in a vehicular network. The method of the invention adopts an elliptic curve encryption scheme and the (t, n) threshold authentication proposal, thereby being characterized by small calculated amount, low complexity, high safety, small key space, high speed, needing no authentic certificate authority and having great application value in vehicular networks.
Owner:SHANGHAI UNIV
Identification and business management for network user
InactiveCN1510862ASolve multicast businessSolving Bandwidth Business ProblemsUser identity/authority verificationData switching networksBusiness managementBroadband
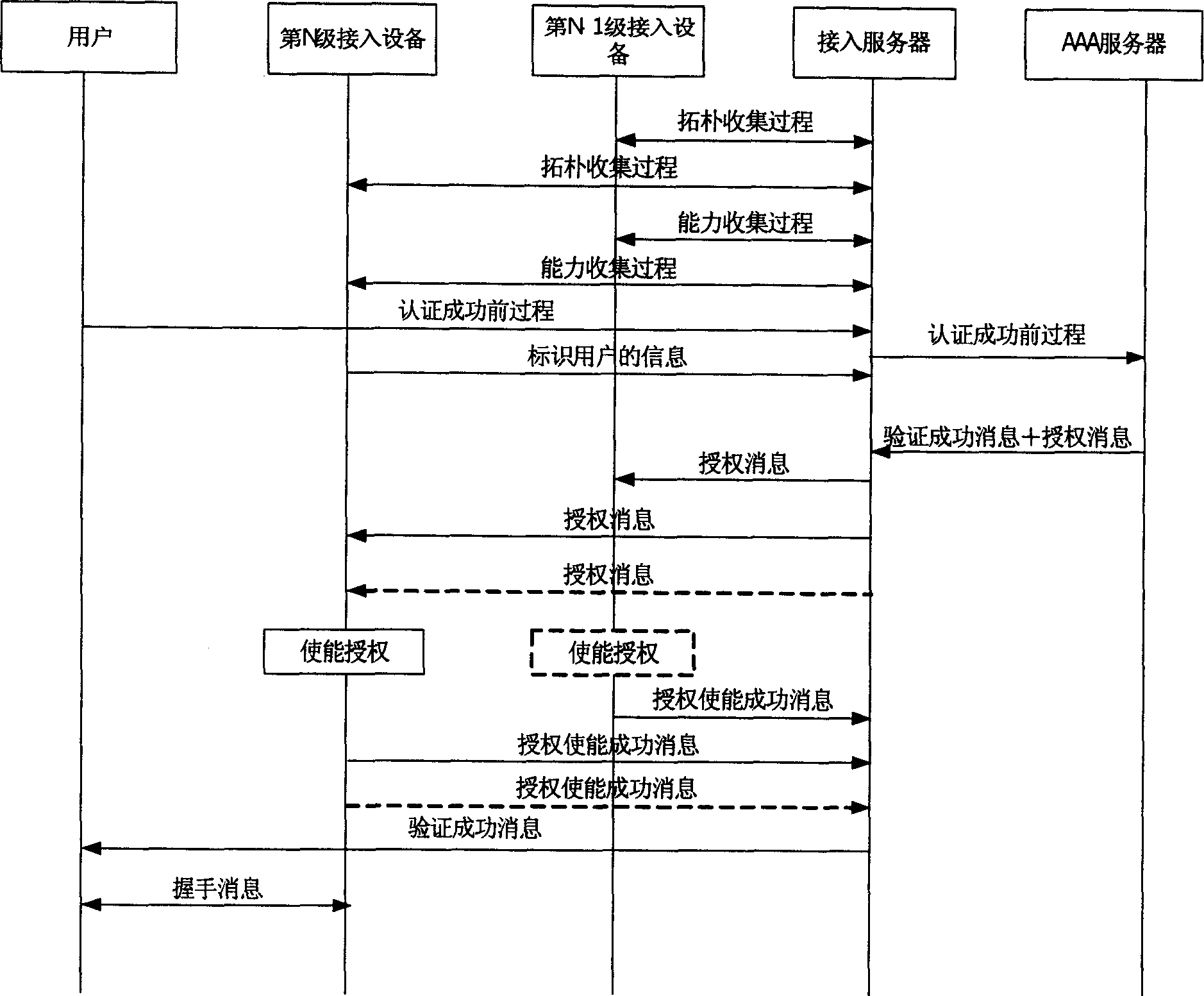
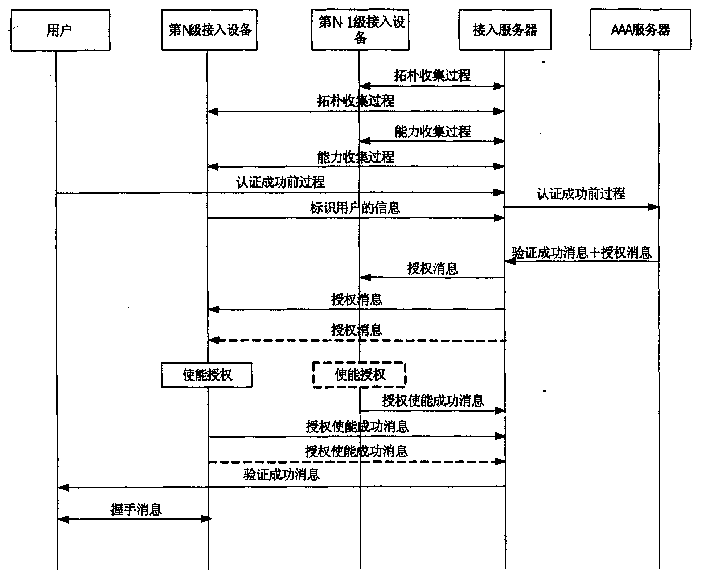
This invention relates to broadband access field, specially relates to a method by which can make certification to network users and carry out operational management, first build up the network analysis situs of access equipment on the access server, and register the capacity of access equipment; the access equipment sends the basic information of users to the access sever, the access server sends the certification information of users to AAA server, the AAA server confirms this certification of users has passed, sends the passing information and authorization message to the access equipment, after the access equipment receives the authorization message, completes stated action, implements the certification and operational management to users. This method can complete the control for multicast, broadband operation on the bottom layer access equipment.
Owner:HUAWEI TECH CO LTD
System and method for pregnant woman and infant retracing and certificate storage based on blockchain technology
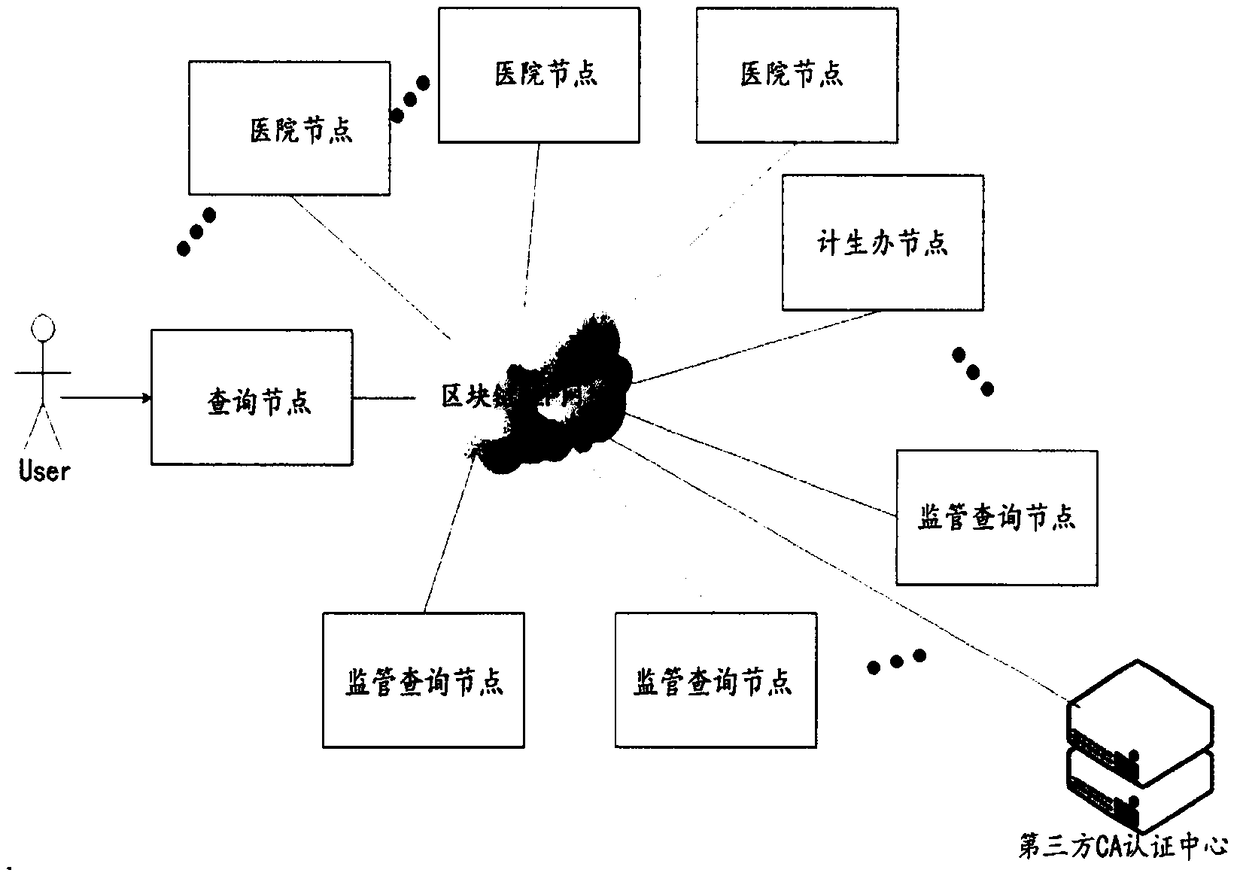
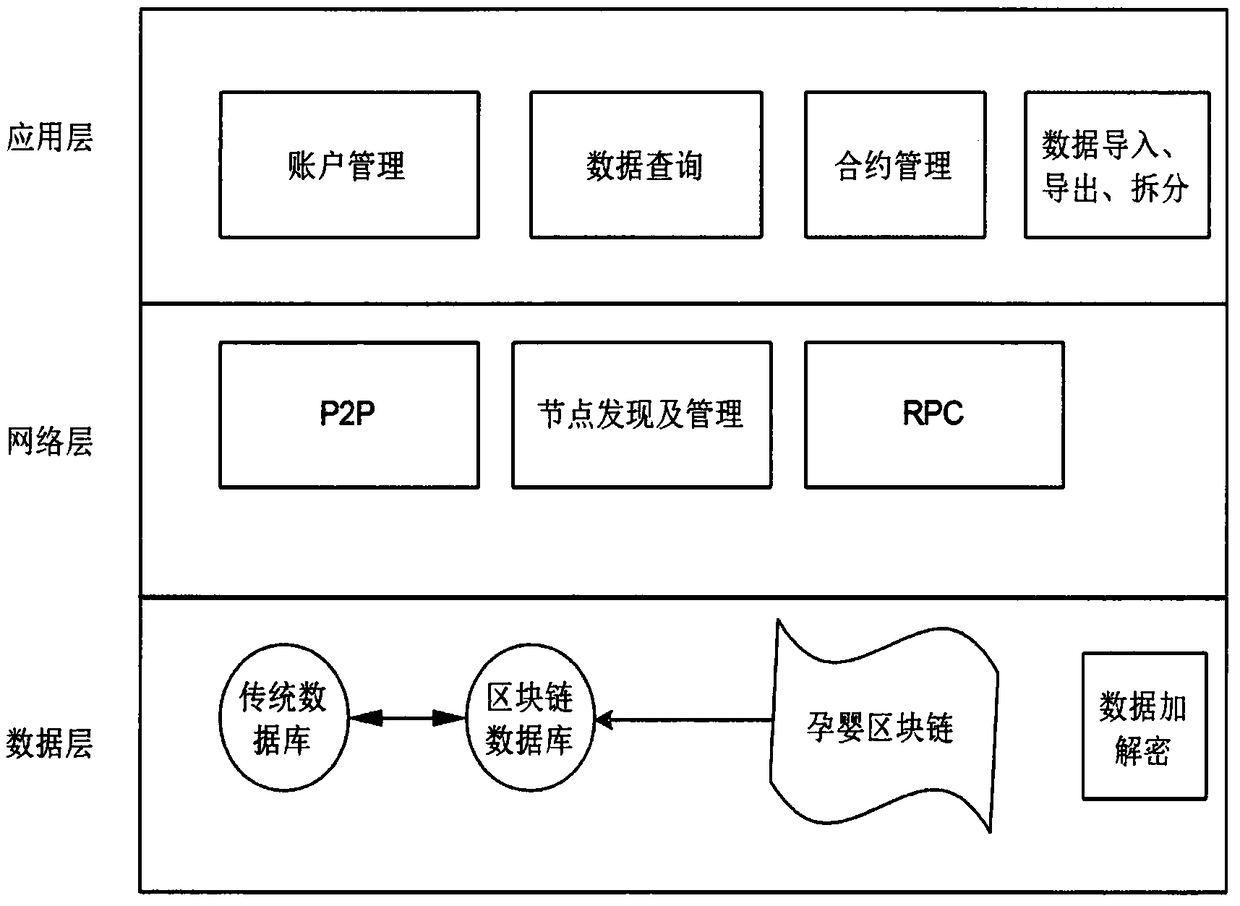
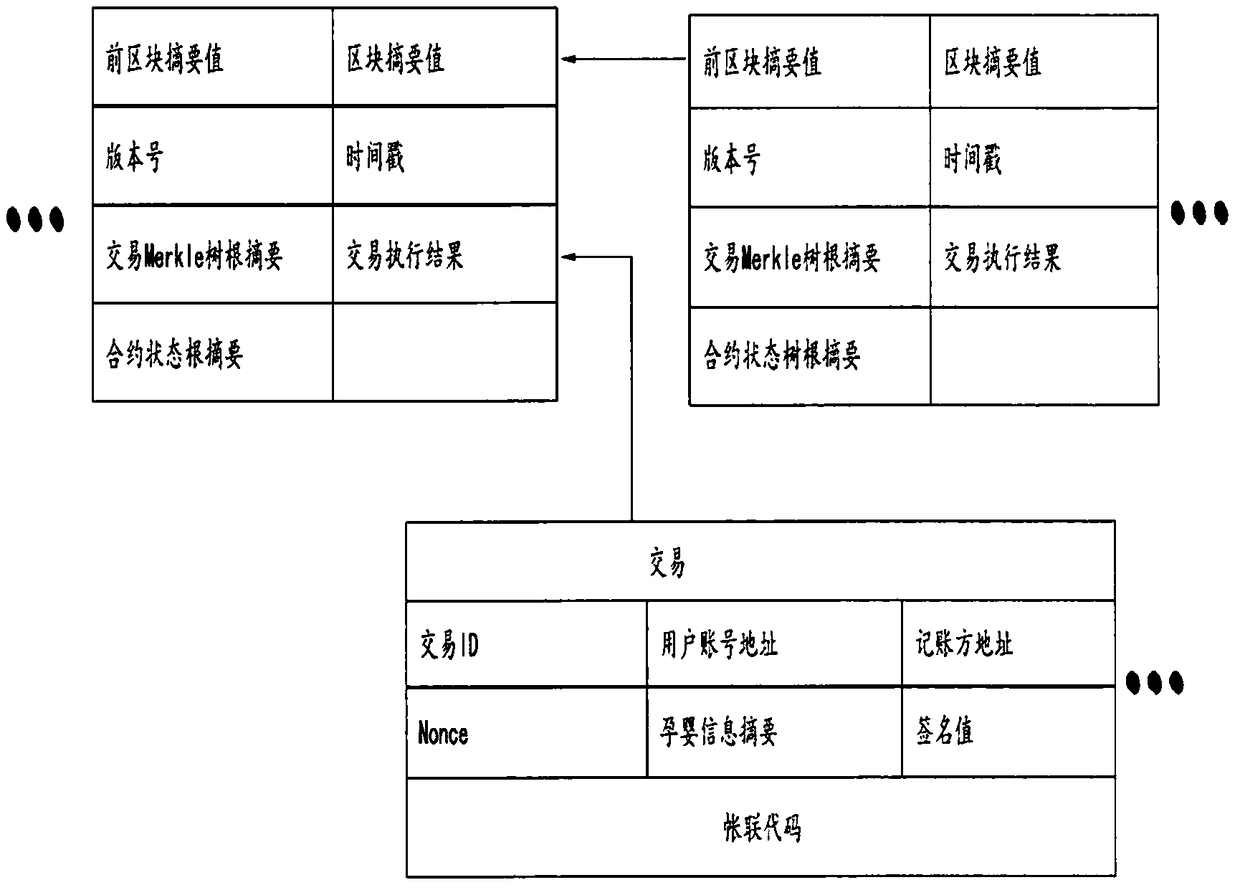
InactiveCN108389615APrevent information falsificationIncrease data interoperabilityDigital data protectionHealthcare resources and facilitiesBlockchainNetwork layer
The invention provides a system and a method for pregnant woman and infant retracing and certificate storage based on blockchain technology. The system includes a data layer, a network layer and an application layer. The system and the method are used for recording information of pregnant women and infants in all medical activities, each piece of information is stored in a block manner and is broadcast to all management nodes through aP2P network; each management node audits and records this data to a locally generated blockchain. The system and the method combine the personal information of the pregnant and the infant, the hospital and the regulatory institution by establishing a blockchain, provide a decentralized data storage scheme compared with the traditional centralized or storage method, and can also realize retracing and certification of information in a secure and encrypted manner, so as to effectively prevent information fraud.
Owner:罗梅琴 +2
Certificate false-proof verification method base on identification authentication technology
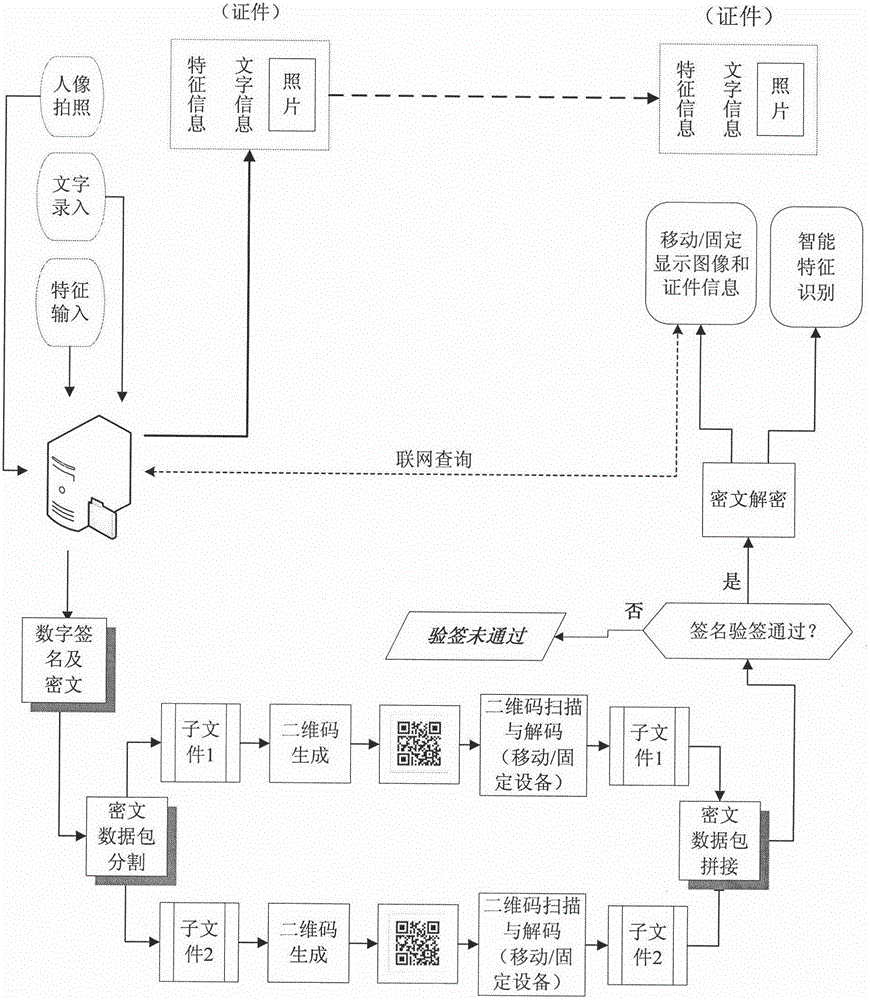
InactiveCN104021482ANot easy to tamper withPrevent counterfeitingUser identity/authority verificationMarketingCiphertextDigital signature
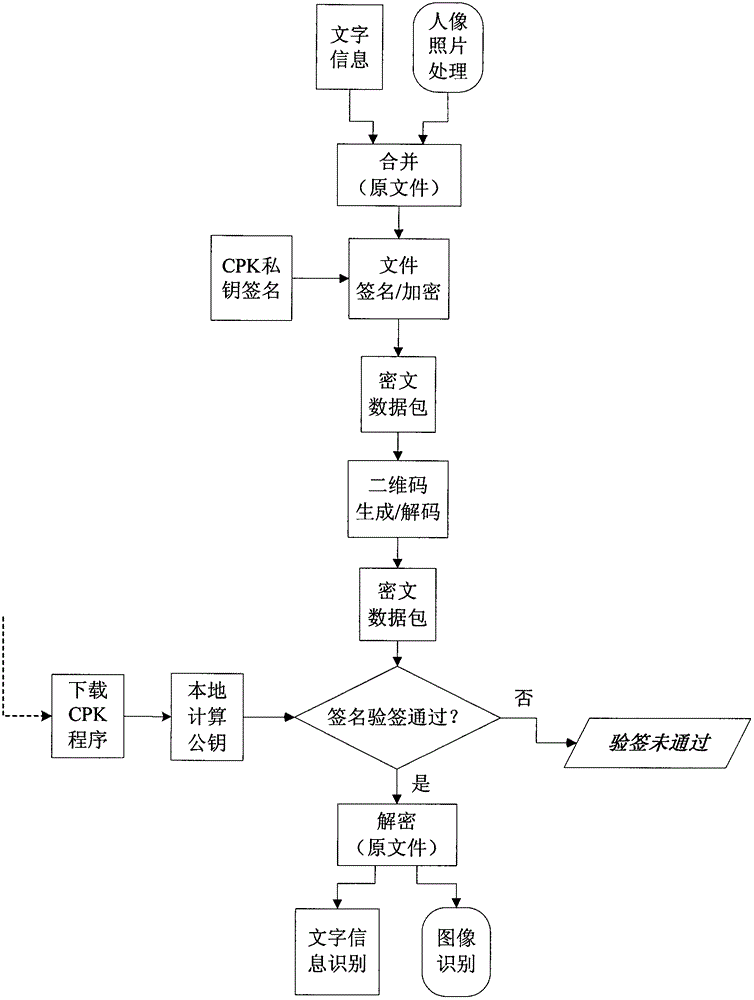
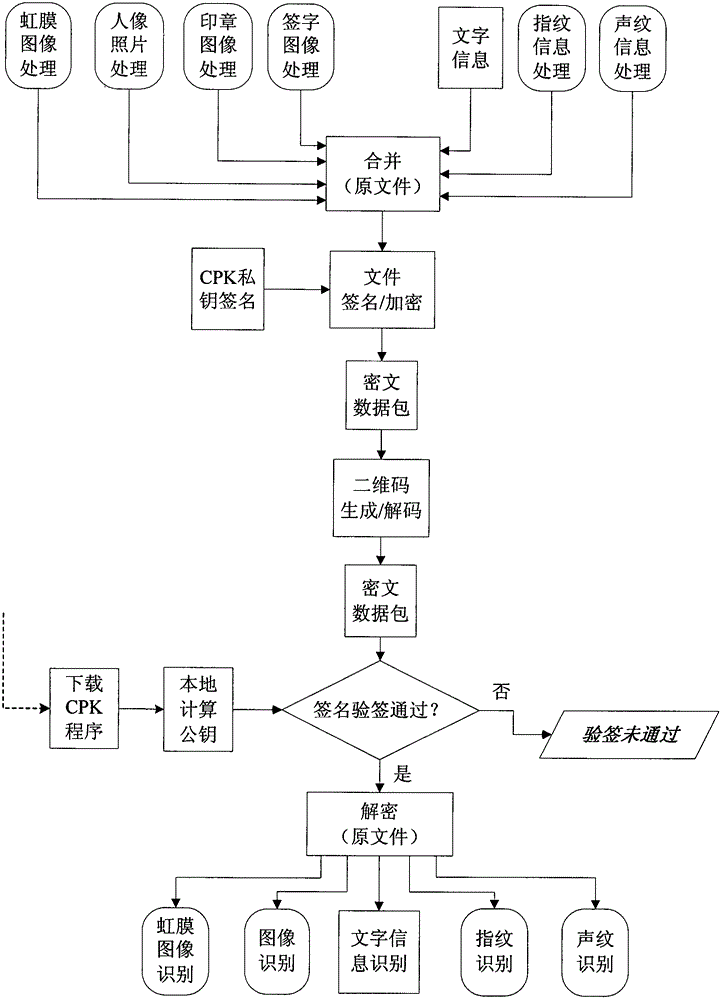
The invention discloses a certificate false-proof verification method base on an identification authentication technology; a picture, words, a stamp, a signature and bioinformation of the certificate are processed to generate a file; a CPK identification private key based on identification authentication can be used to carry out digital signature and encrypt the file, and a cryptograph containing the digital signature is recorded on the certificate through a two dimension code; in certificate identification, a CPK identification public key based on identification authentication is used to carry out label verification, and the certificate information can be restored after the label verification is done so as to carry out comparison verification; if the cryptograph is over large, the cryptograph can be cut into more than two sub files respectively generating a two dimension code, and the two dimension codes can be decoded so as to splice into a complete cryptograph. A CPK identification public key for label verification can be obtained by local calculation, so connecting to a CA data base is not needed for signature verification and decoding the cryptograph; a smart phone, a laptop or a notebook computer can be used to realize verification in an offline mode; certificate detail information can be obtained through connecting to the internet so as to carry out certificate authentication, thereby completing false-proof and verification of the certificate.
Owner:CHENGDU EHENGXIN TECH
Near field communication payment method authenticated by both sides of deal
InactiveCN103116844ARealize identificationAvoid card swipingUser identity/authority verificationPayment architectureBank accountComputer science
The invention discloses a near field communication payment method authenticated by both sides of the deal. The method includes steps that 1, a binding relationship of one-to-one and one-to-many of a cell phone number and a bank account is established; 2, identity authentication on both sides of the deal through a cell phone is performed when a near field communication deal is needed; 3, after authenticating, the payee inputs amount collected to the cell phone, submits a collection request to a deal server, and the deal server generates a trade order and sends the order number to the payee; 4, the payee chooses a payer to trade, and sends the order number to the payer by means of near field communication; 5, the payer downloads the order information from the deal server, identifies the order information, inputs a payment code to the cell phone, and submitting a payment request; 6, information verification is performed, the trade is carried on when the verification is successful, otherwise, the trade is not carried on. The method of identity authentication is high in safety and reliability and easy to achieve based on the uniqueness of the cell phone number and background server.
Owner:李锦风 +2
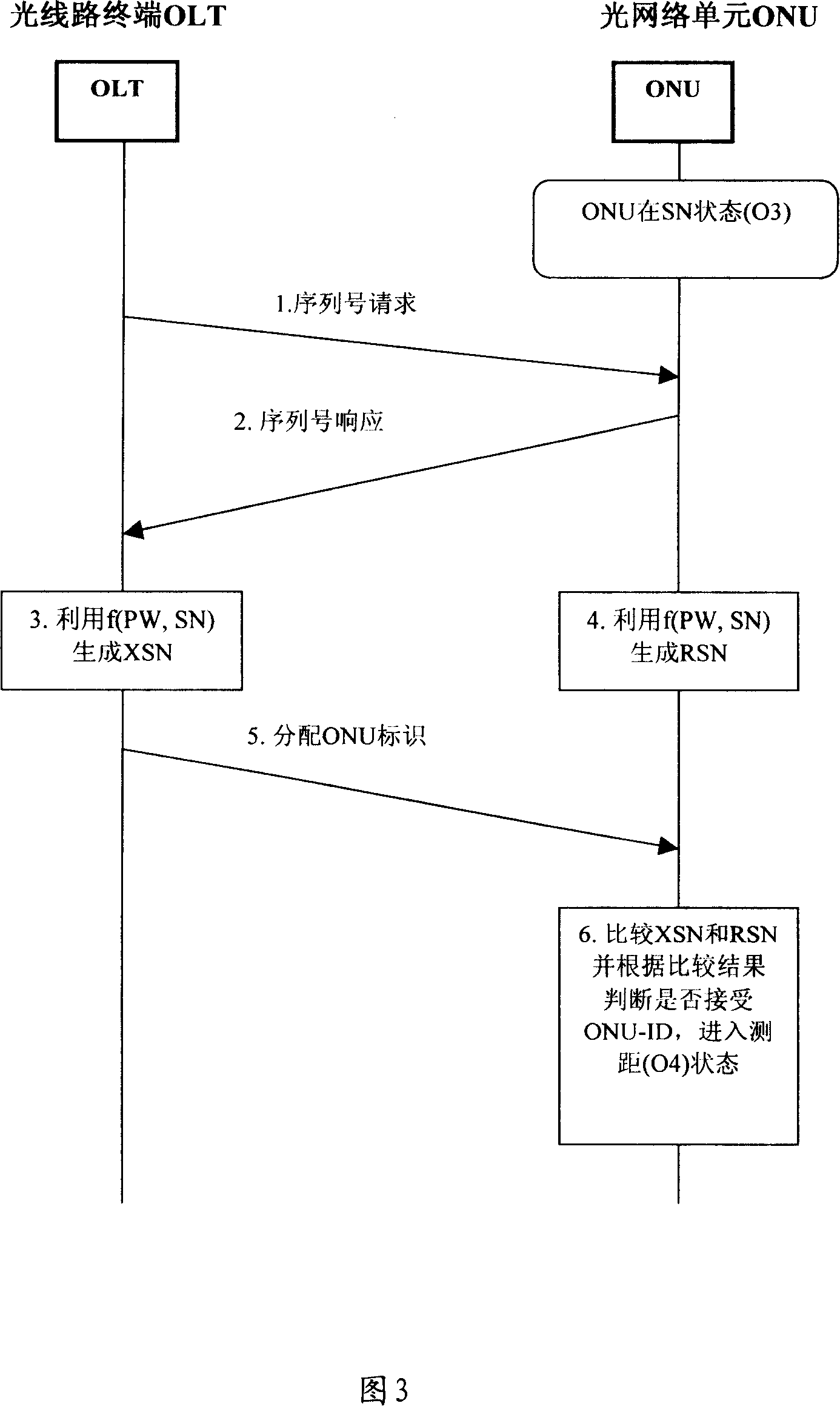
A method, system and device for preventing optical network unit in passive optical network from being counterfeiting
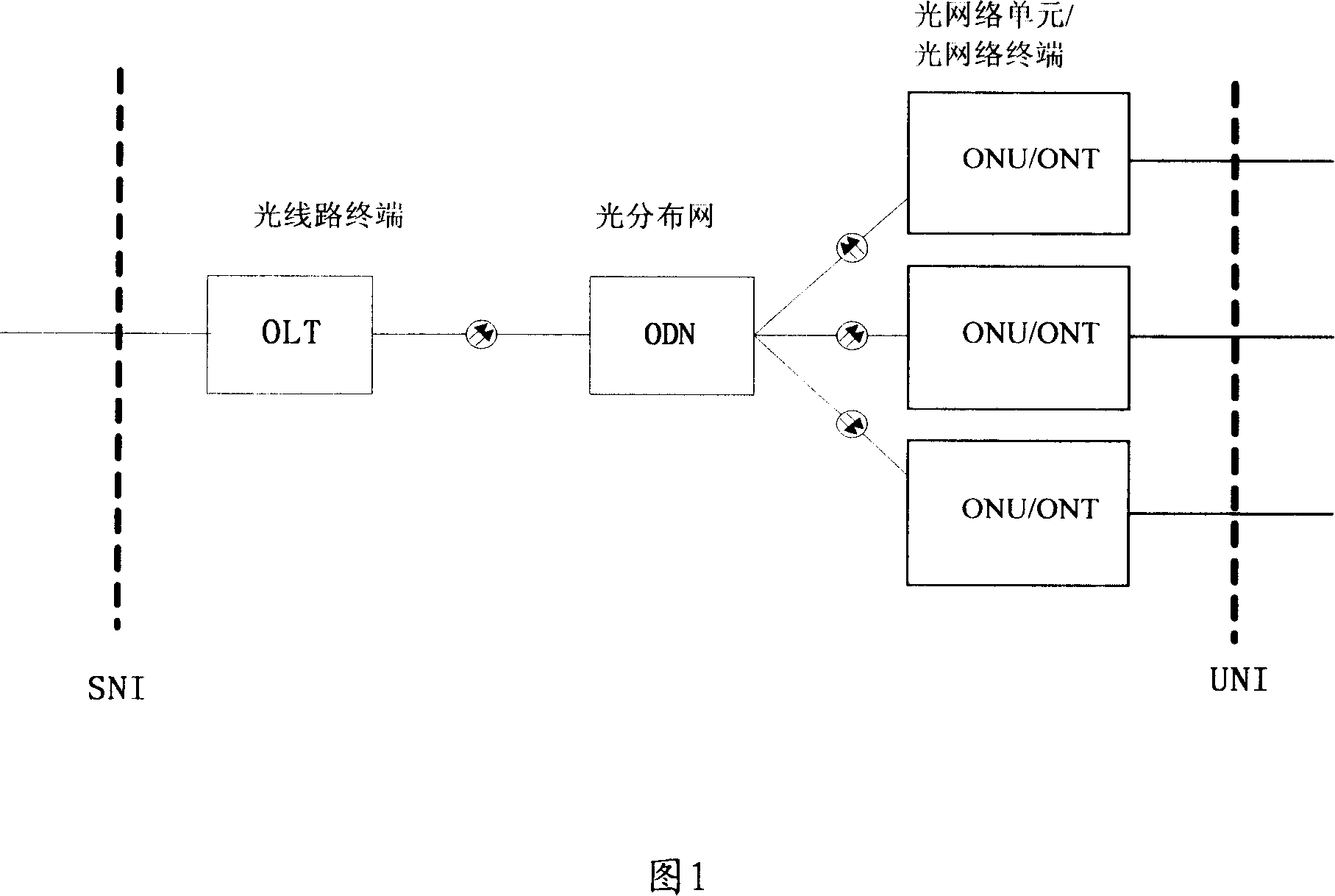
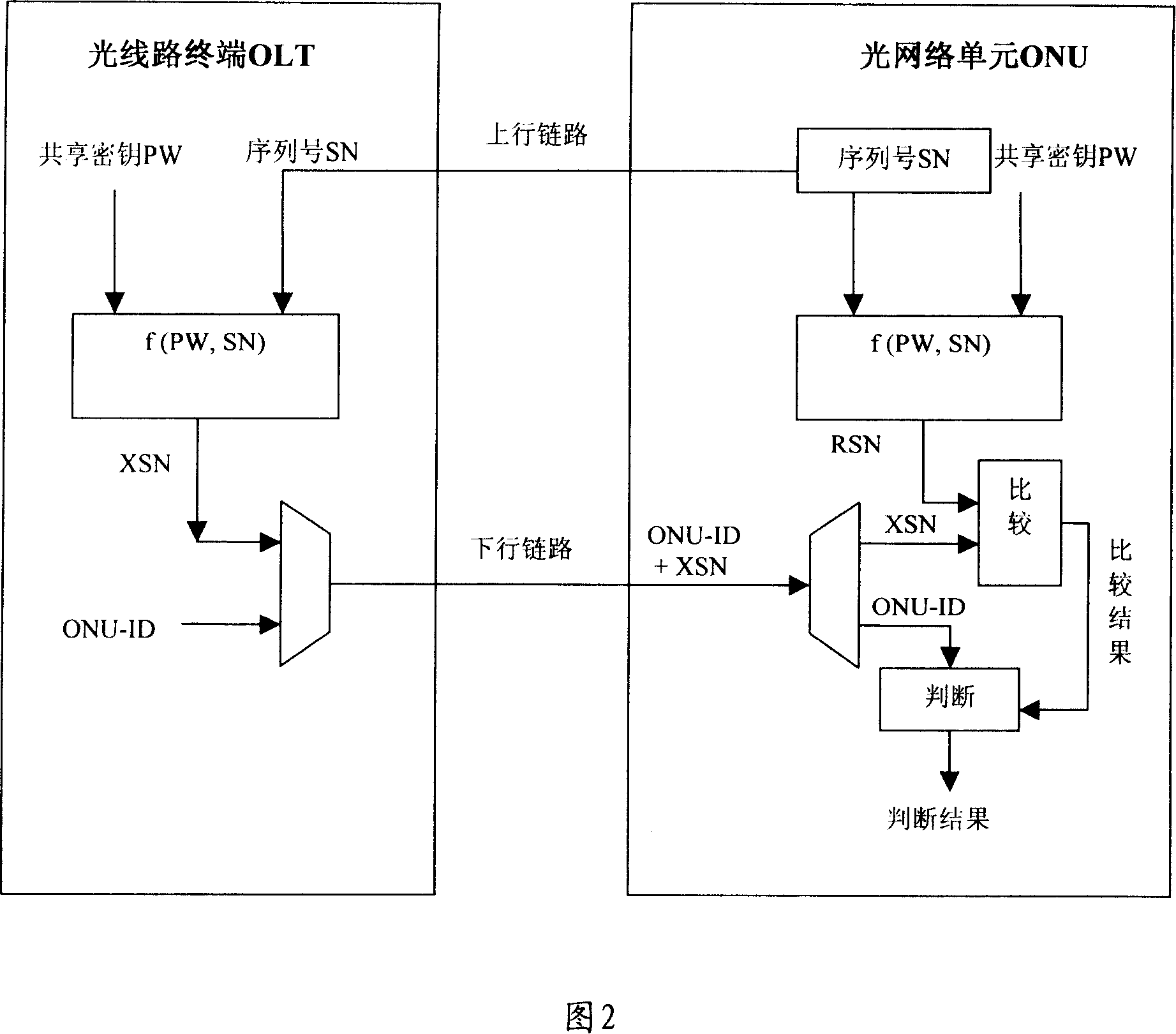
InactiveCN101150391APrevent counterfeitingElectromagnetic transmission optical aspectsData switching networksTerminal equipmentOptical network unit
This invention relates to a method, a system and a device for preventing imitating optical network units in a passive optical network system, in which, the method includes: A, an OLT utilizes a ciphered key to cipher the identification information of an ONU and sends a result to the ONU, B, the ONU gets the indentification information of the ONU from the result. This invented system includes: a management module of the OLT key and an authentication module of ONU, which includes a management module of ONU key and a comparison / judgement module. This invented device includes: an OLT device and an ONU device in a passive optical network.
Owner:HUAWEI TECH CO LTD
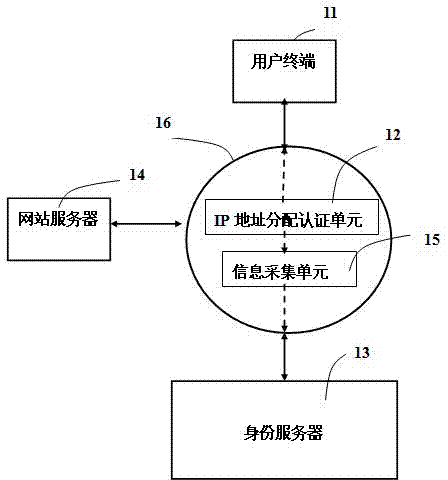
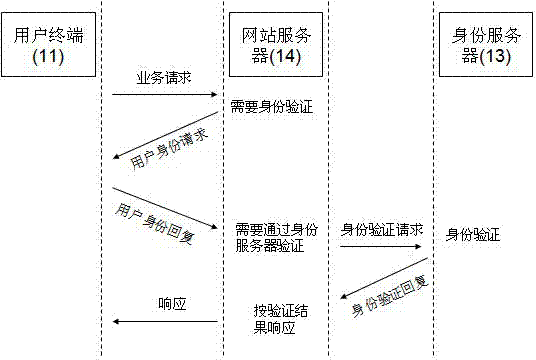
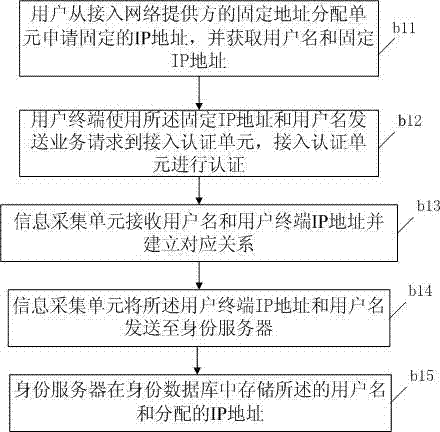
System and method for internet user authentication
InactiveCN102882853ASimple stepsPrevent counterfeitingUser identity/authority verificationUser verificationIp address
The invention discloses a system for internet user authentication and a method for internet user authentication. The system for the internet user authentication comprises a user terminal, a website server, an internet protocol (IP) address distribution identifying unit, an information collecting unit and an identification server. The identification server obtains a corresponding relationship between the IP address of the user terminal and the user identification information; the website server sends the terminal IP address to the identification server, obtains the user identification information corresponding to the IP address, and compares the user identification information with a verification method and registration data used when the user is registered; if the user identification information is in accordance with the association between the verification method used when the user is registered and the user identification information used when the data is registered, then the user verification is successful. The authentication method provided by the invention is simple, and high in accuracy and safety, wide in applicablescope.
Owner:孙银海
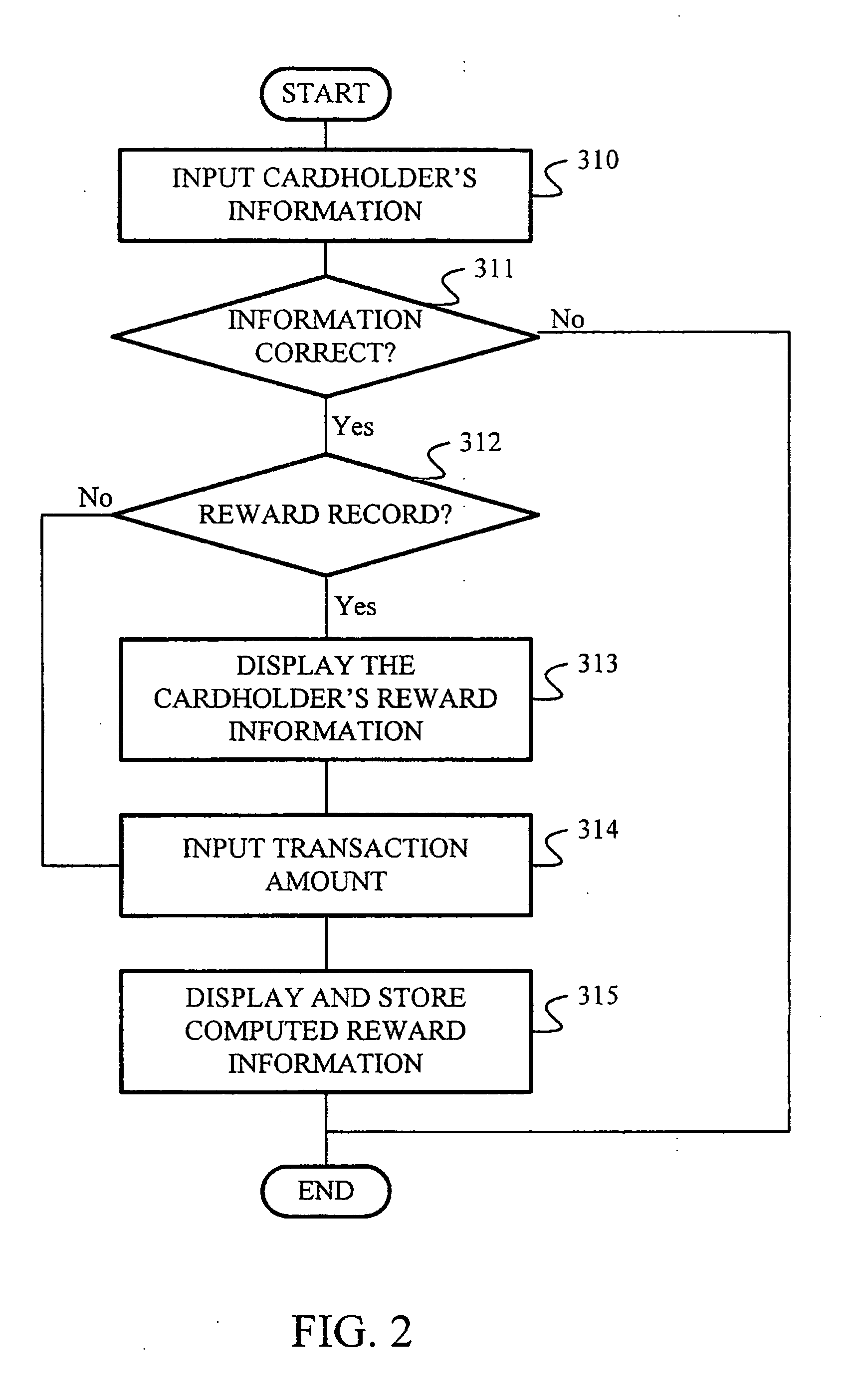
Method and system for calculating reward earned from transactions for voucher or stored value for transactions and method of redeeming the voucher or stored value
InactiveUS20050049965A1Prevent counterfeitingAvoid misappropriationFinancePayment architectureVoucherFranchise
This invention relates to a method and system for exchanging reward earned from transactions for voucher or stored value for transactions and method of redeeming the voucher or stored value, the system including a primary unit provided at a place where a service provider is located, and a secondary unit provided at where a franchisee is located. When a purchase is made by the consumer at a franchisee designated by the service provider, reward will accumulate and the reward may be exchanged for voucher or stored value when the reward is accumulated to a predetermined amount. In exchanging for the voucher or stored value, the voucher or stored value must be registered at the primary unit of the service provider or deposited in a stored value account. During redemption of the voucher or stored value, the validity of the voucher or balance of the stored value is first automatically affirmed to deter counterfeiting activities.
Owner:JEN I CHENG
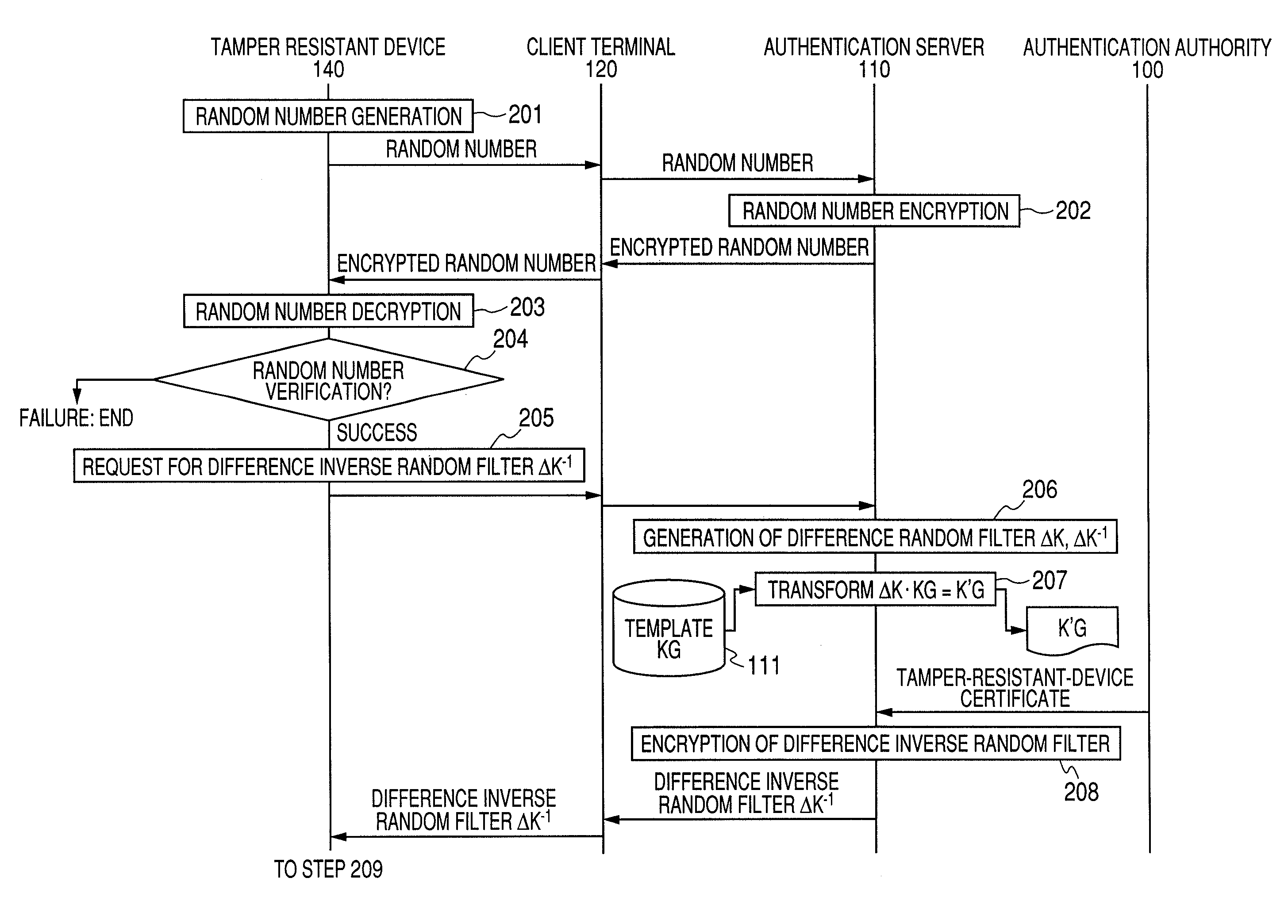
System, Server, Terminal and Tamper Resistant Device for Authenticating a User
InactiveUS20080178002A1Improve securityImprove protectionDigital data processing detailsUser identity/authority verificationTransformation parameterAuthentication server
The authentication server authenticated by a public key certificate at the time of authentication generates a difference parameter, transforms a template by the difference parameter to create a temporary registration template, and transmits the difference parameter to a tamper resistant device. The tamper resistant device generates a temporary parameter from the held transformation parameter and the difference parameter. A client terminal transforms feature using the temporary parameter, and generates temporarily-transformed feature. An authentication server receives the temporarily-transformed feature, and verifies whether the temporary registration template is in agreement with the temporarily-transformed feature.
Owner:HITACHI LTD
Network log-in authorization method and authorization system
ActiveCN101047504AKnow exactly when the event will take placePrevent counterfeitingUser identity/authority verificationClient-sideAuthentication system
A authentication method of network login includes issuing login request to network station (NS) by client device to obtain NS identification information returned back from NS, providing user account number and cipher as well as NS identification information to AGS for carrying out right-certification, generating service note for logging in NS and conversation cipher key by AGS according unique enciphering key appointed with NS, using said service note and said conversation cipher key to log in NS by client end. The authentication system used for realizing said method is also disclosed.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
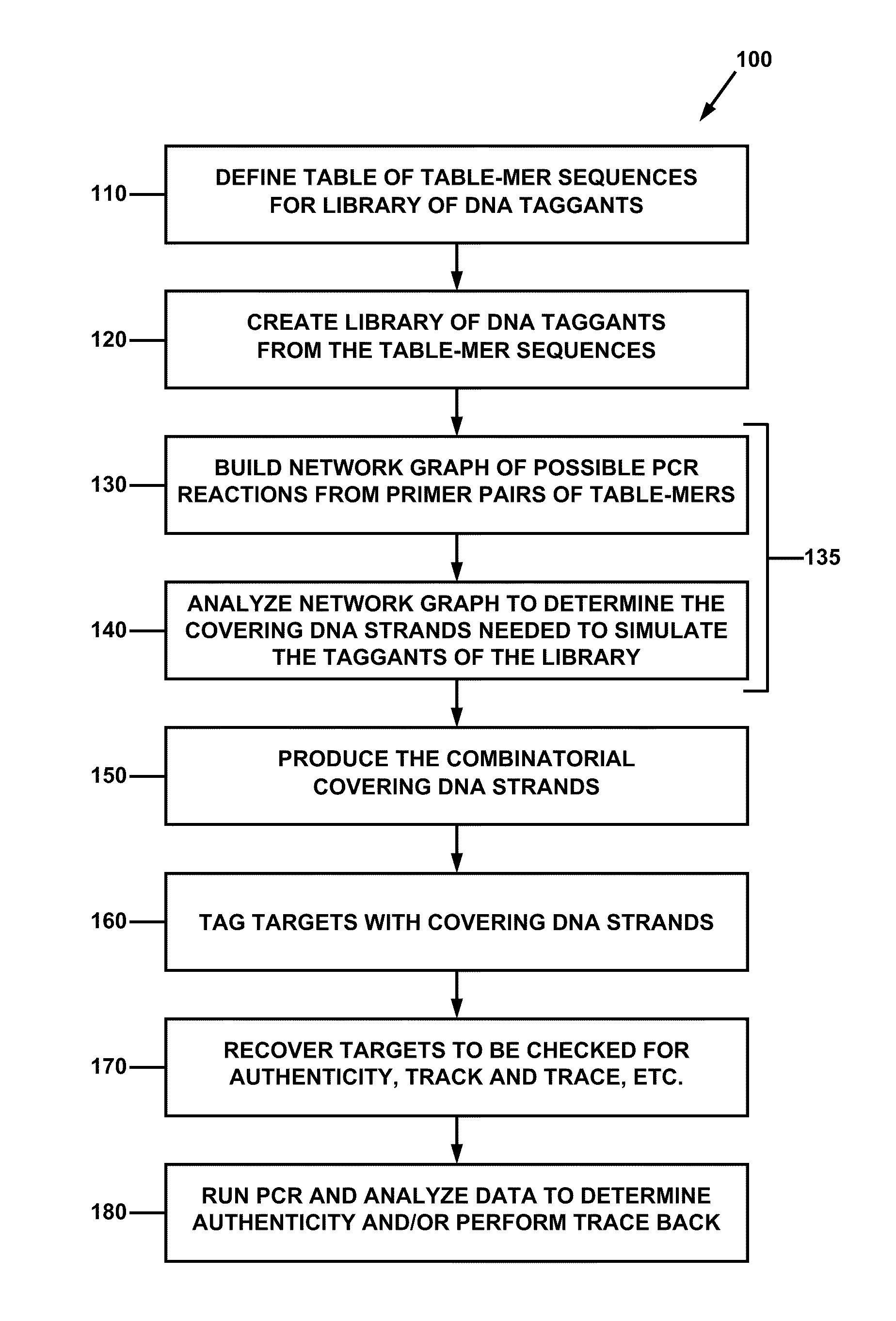
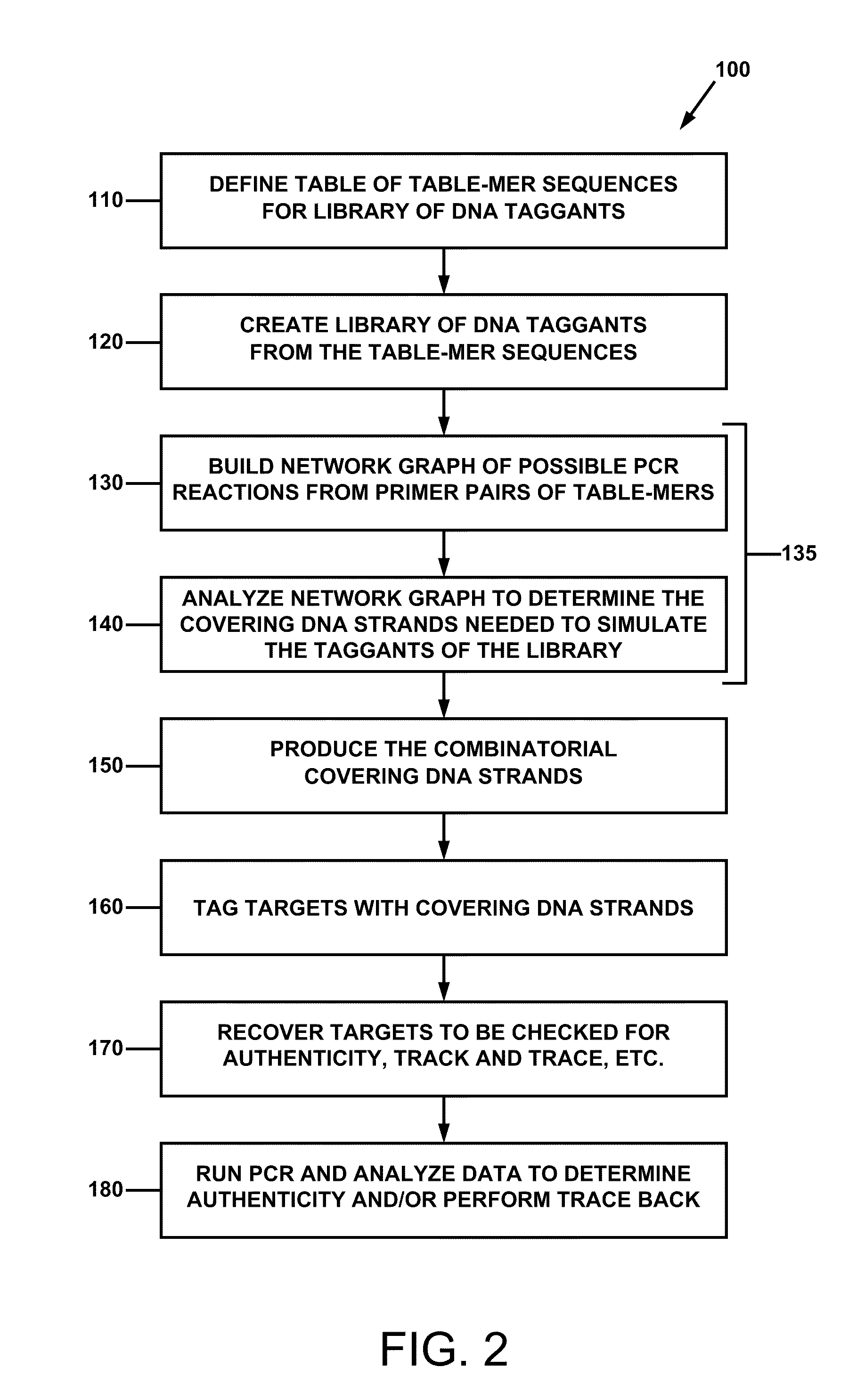
Combinatorial DNA taggants and methods of preparation and use thereof
ActiveUS20110165569A1Prevent counterfeitingAuthentication processSugar derivativesMicrobiological testing/measurementNucleotide sequencingBiology
DNA taggants in which the nucleotide sequences are defined according to combinatorial mathematical principles. Methods of defining nucleotide sequences of the combinatorial DNA taggants, and using such taggants for authentication and tracking and tracing an object or process are also disclosed.
Owner:PATENT INNOVATIONS
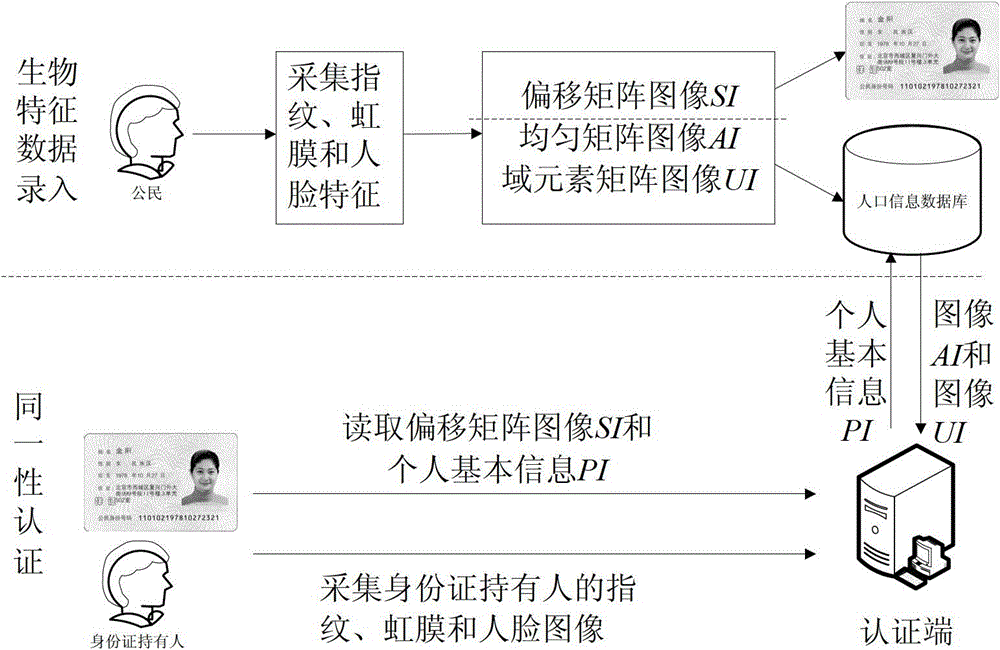
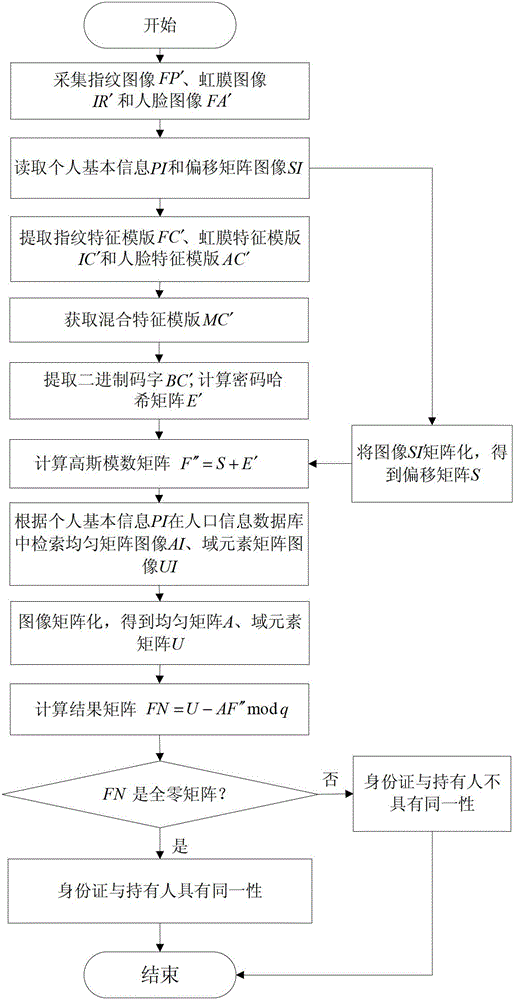
Identity authentication method of identity card and holder based on multi-biological characteristics
InactiveCN102722696APrevent forgeryPrevent counterfeitingCharacter and pattern recognitionCard holderA domain
The invention provides an identity authentication method of an identity card and a holder based on multi-biological characteristics. The invention mainly assists in solving potential safety hazard problems existing in a cross-application process in the prior art. An embodiment comprises the steps that: when identity card registration transaction is carried out, characteristics of fingerprints, iris information and face image of a citizen are acquired; a uniform matrix image AI, a domain element matrix image UI and an offset matrix image SI are acquired and saved respectively in a population information database and an identity card chip; when authentication is carried out, an authentication terminal acquires characteristics of the fingerprints, the iris information and the face image of an identity card holder; the uniform matrix image AI and the domain element matrix image UI are searched for in the population information database based on personal basic information PI; and identity authentication of the identity card and the holder is carried out by using three biological characteristics of the fingerprints, the iris information and the face image, the uniform matrix image AI, the domain element matrix image UI and the offset matrix image SI. According to the invention, an authentication accuracy rate and overall authentication system safety are improved and potential safety hazard existing in the cross-application process is effectively reduced.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com