Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
507 results about "Enterprise services" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method of direct communication between a business and its customers
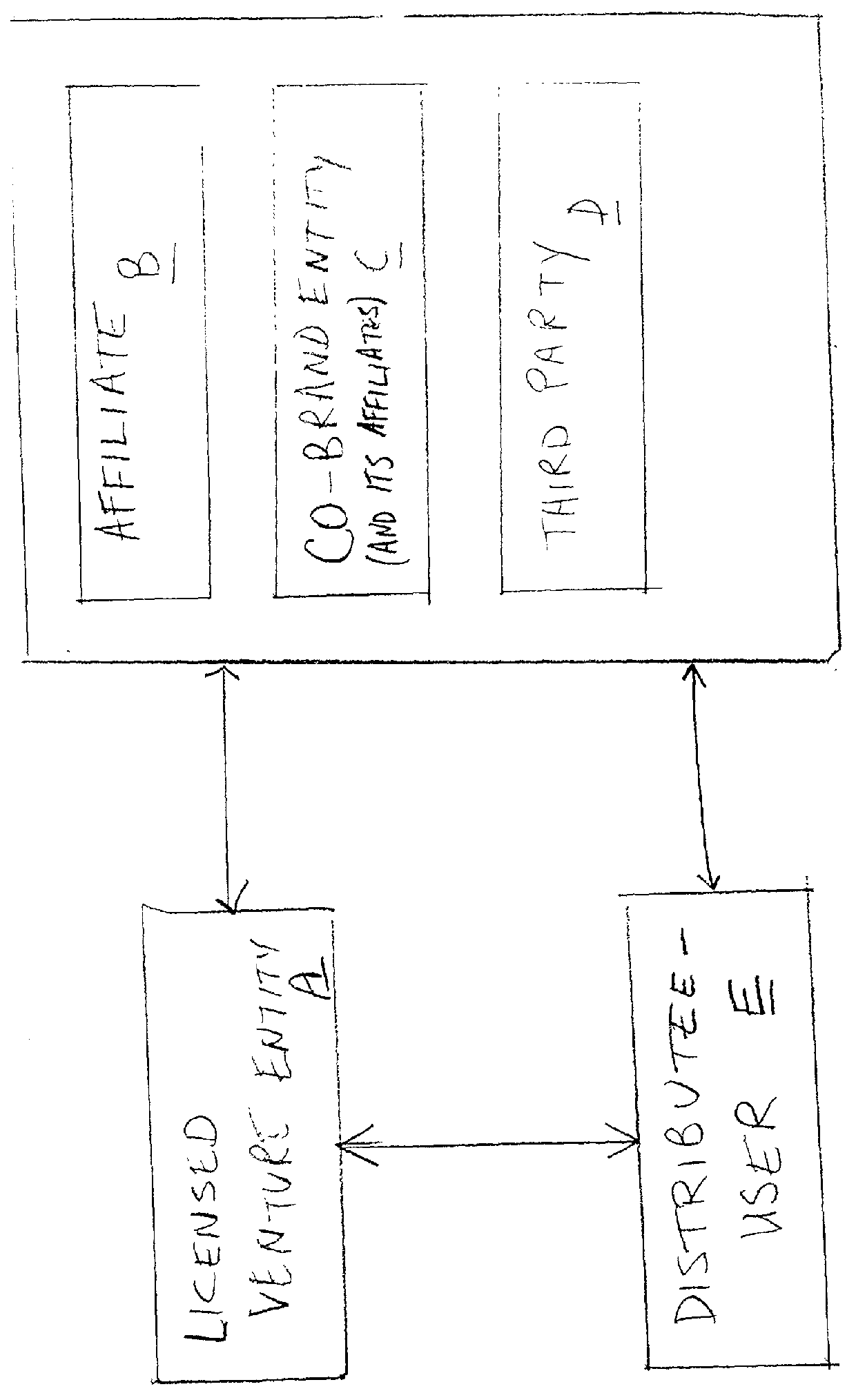
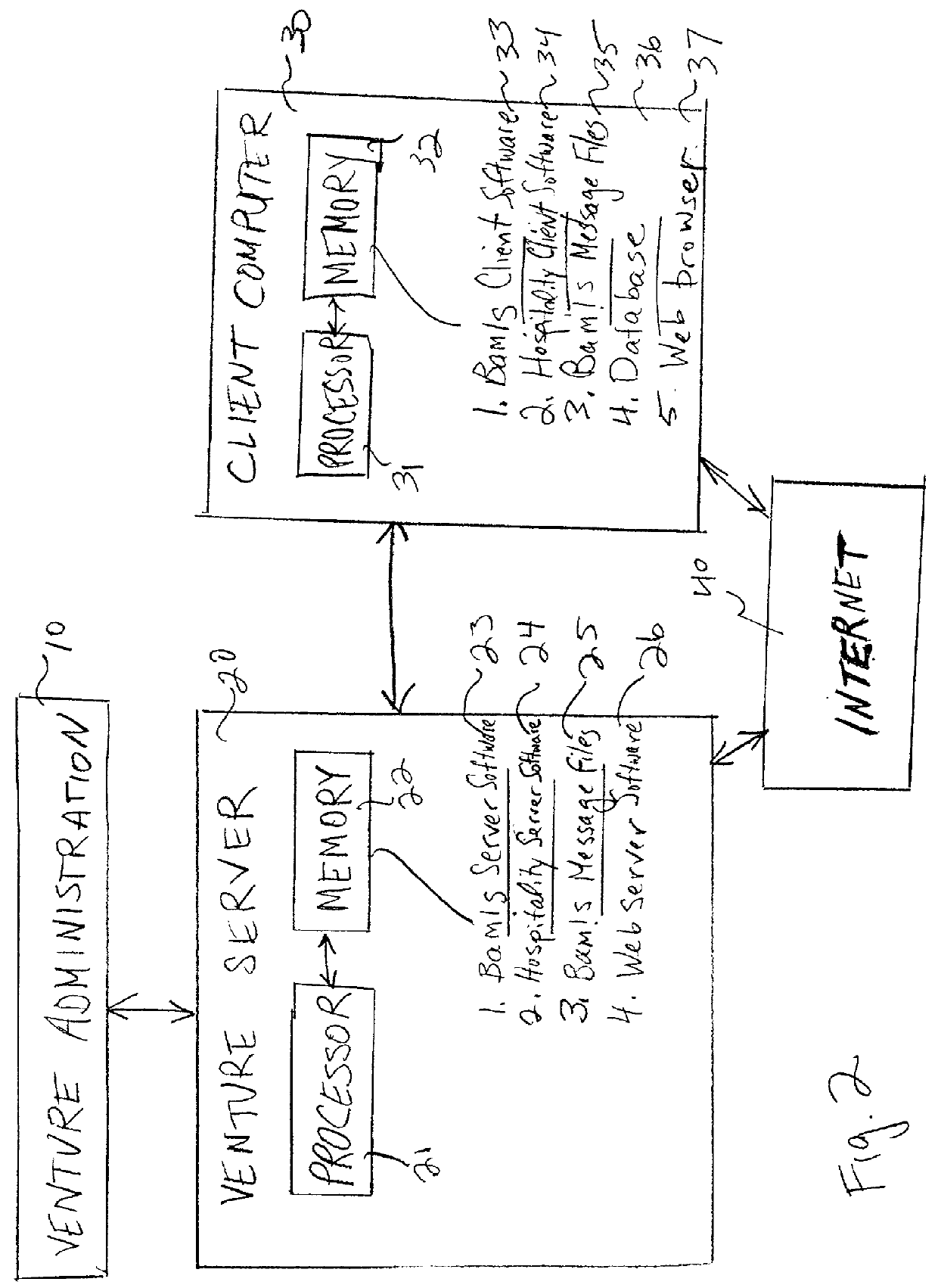
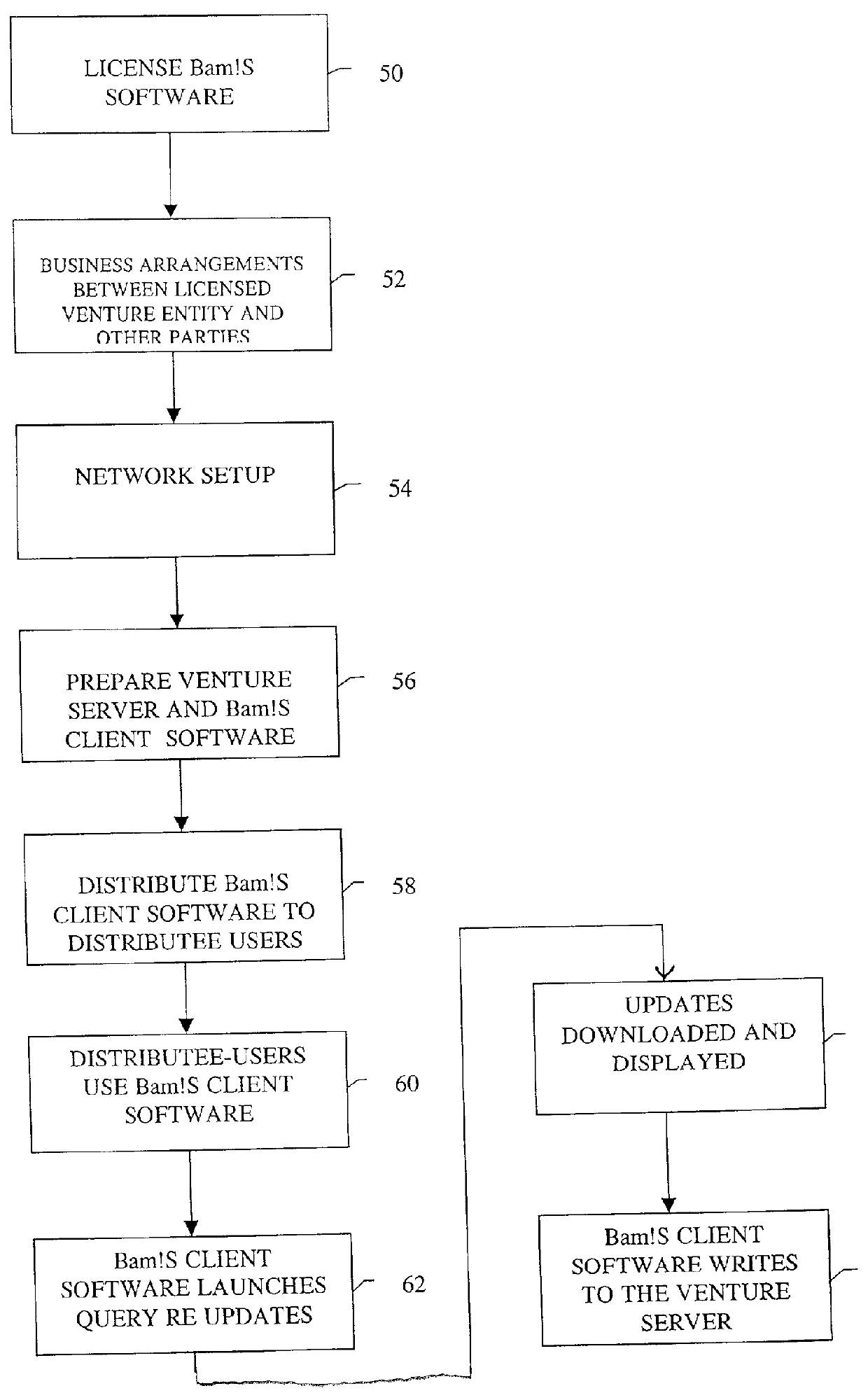
A business model, system, and method for a business entity to distribute branding, advertising, marketing, and service (BAMS) data to consumer-users is described. The business entity establishes and maintains a venture server that transmits BAMS data to client applications installed on the electronic devices of consumer-users and controls usage and display of the BAMS data at the electronic devices. The client application, which is prepared and assigned a unique identifier by the business entity, performs a useful function that requires a graphical user interface (GUI) to be displayed in the display of the user's electronic device. After receiving the BAMS data, the client application stores it, and displays it in the GUI. The client application can be written so that no user information is transmitted from the electronic device to the venture server.
Owner:INTEL CORP
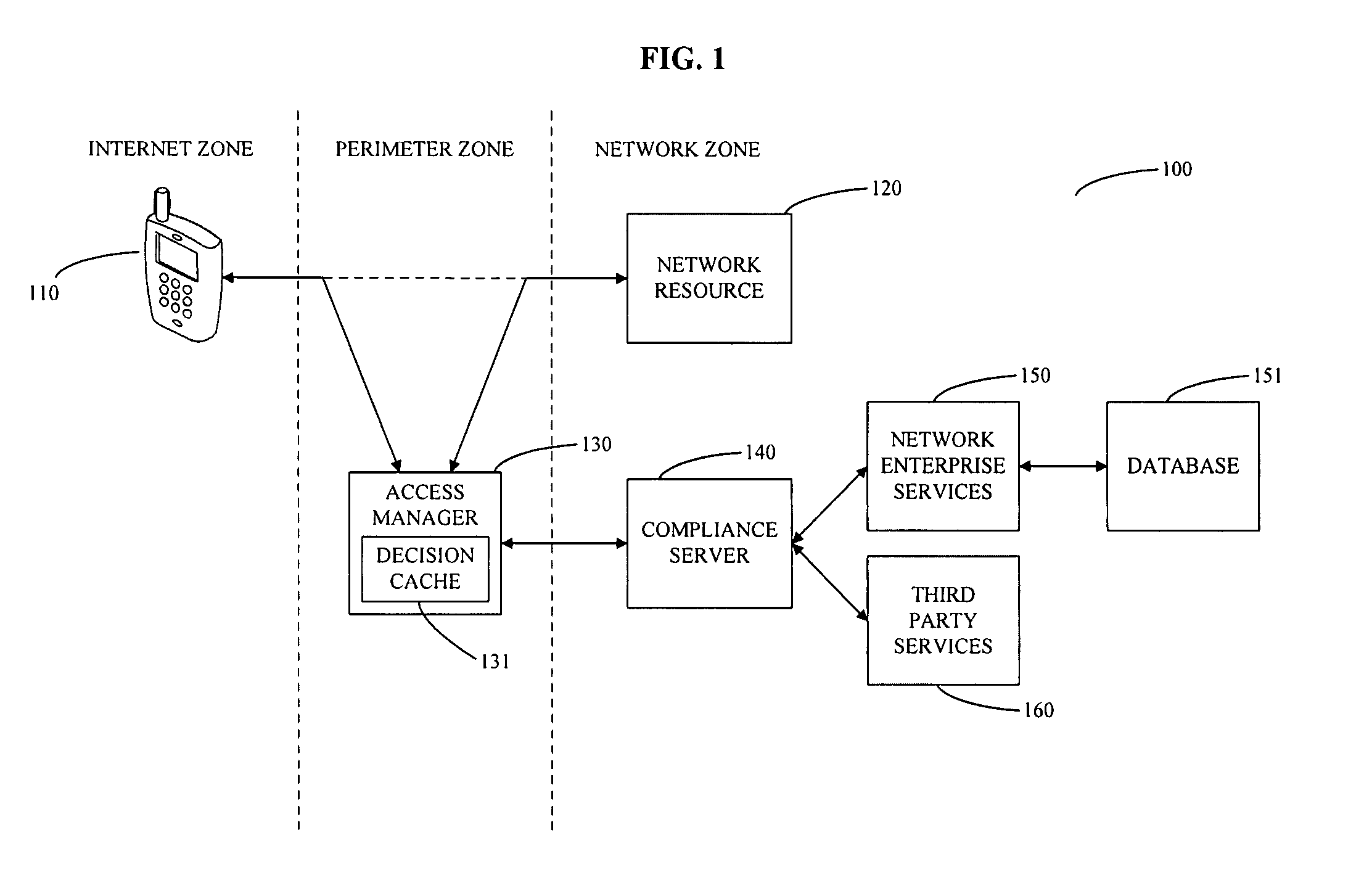
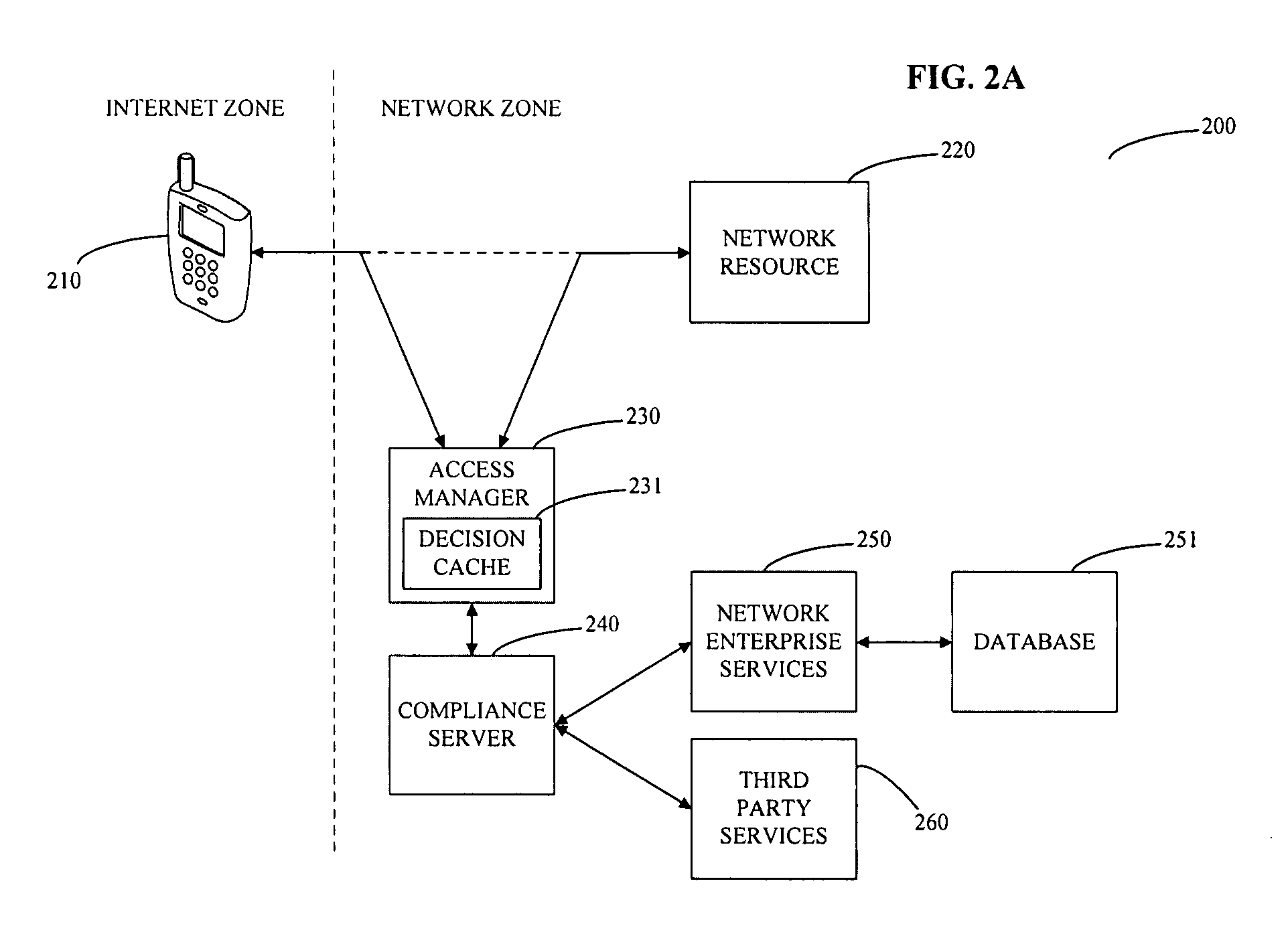
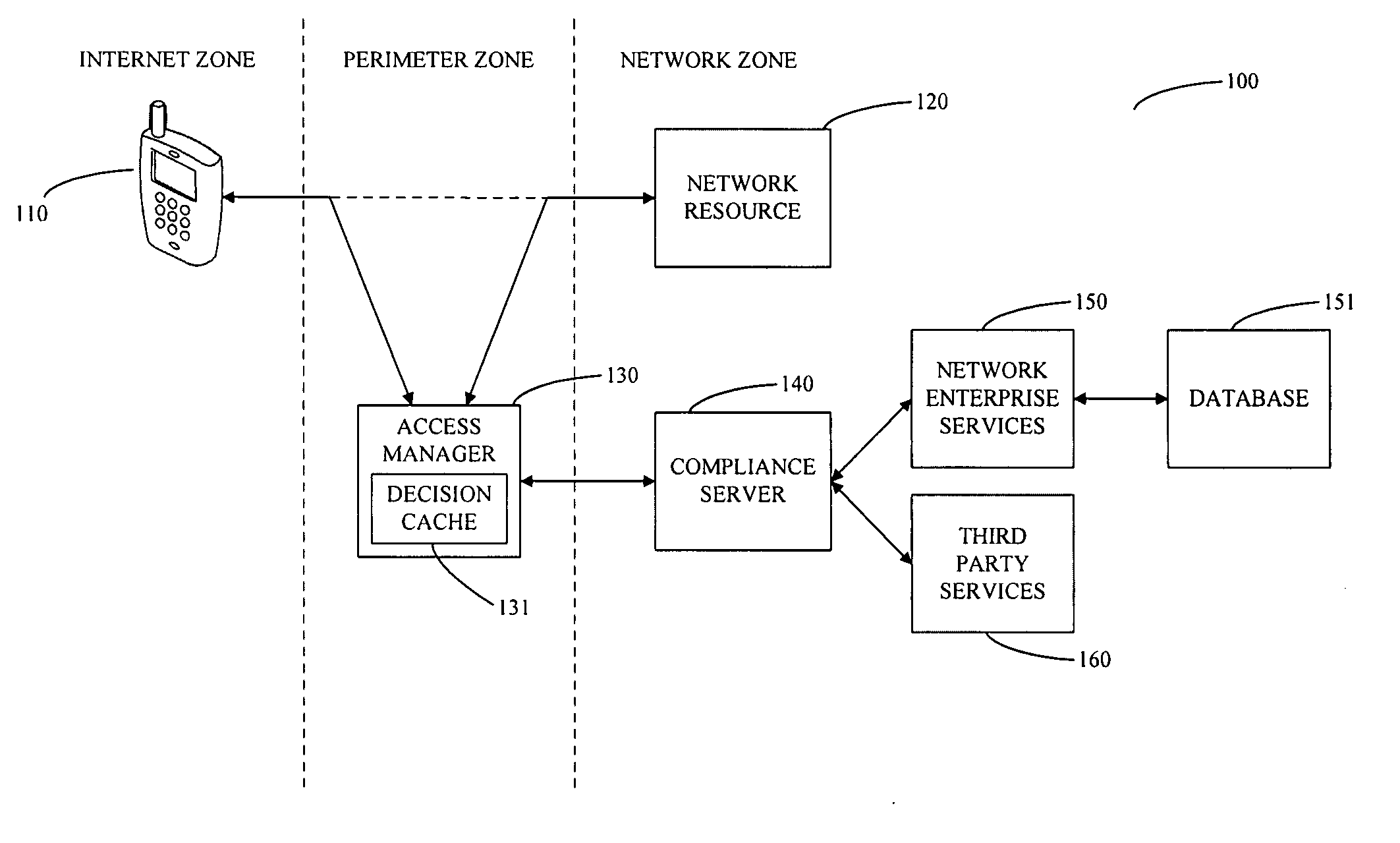
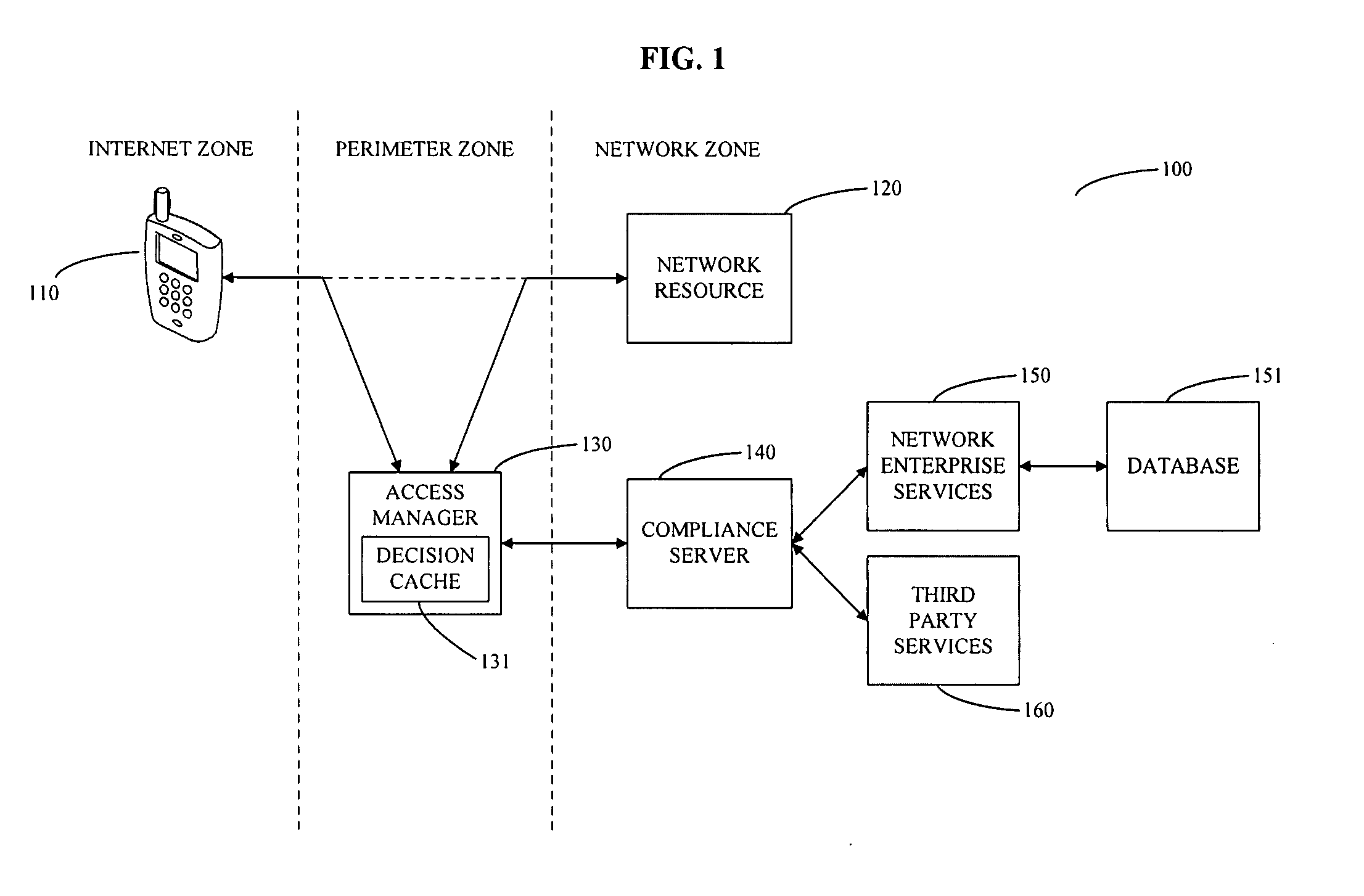
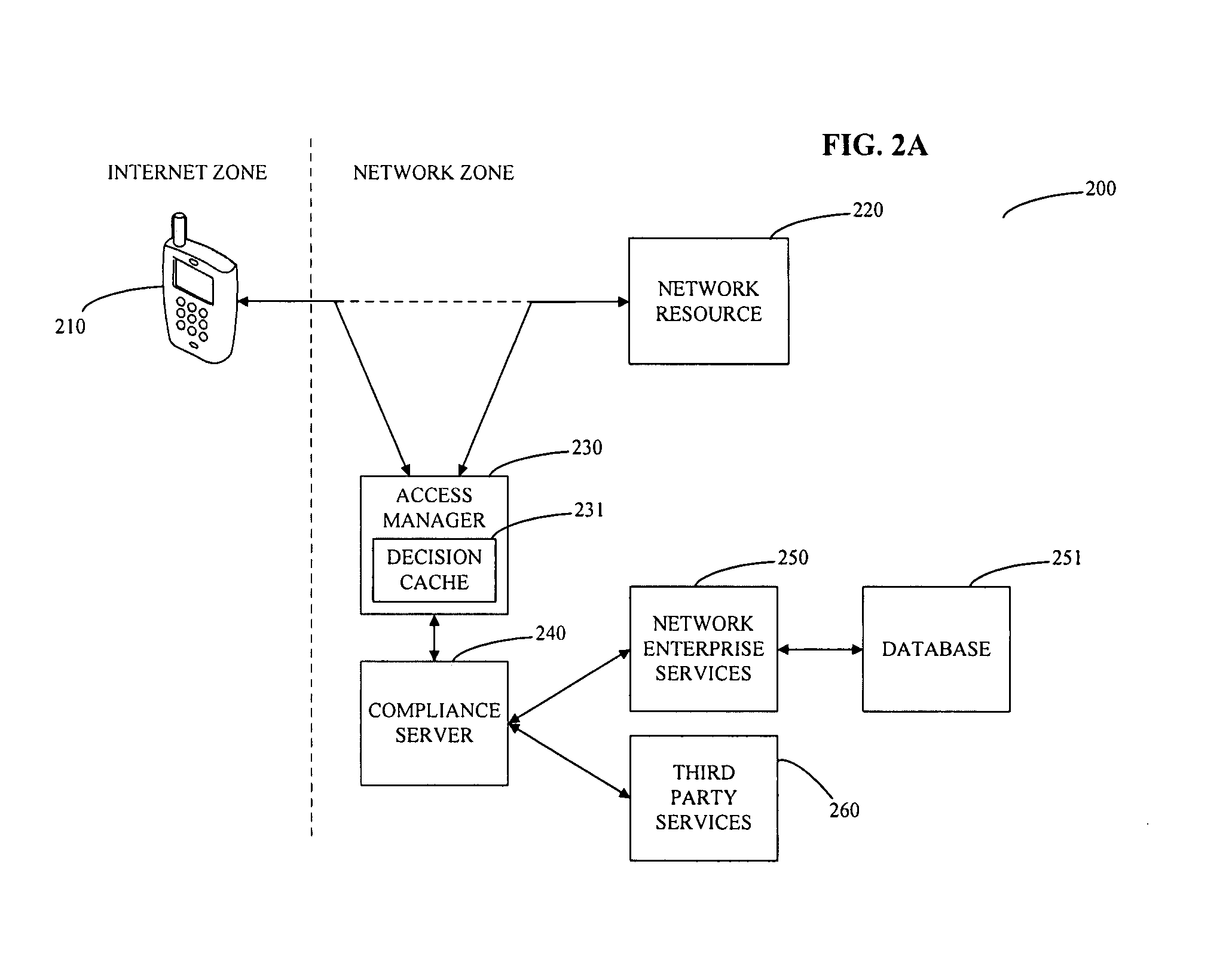
System and method for controlling mobile device access to a network
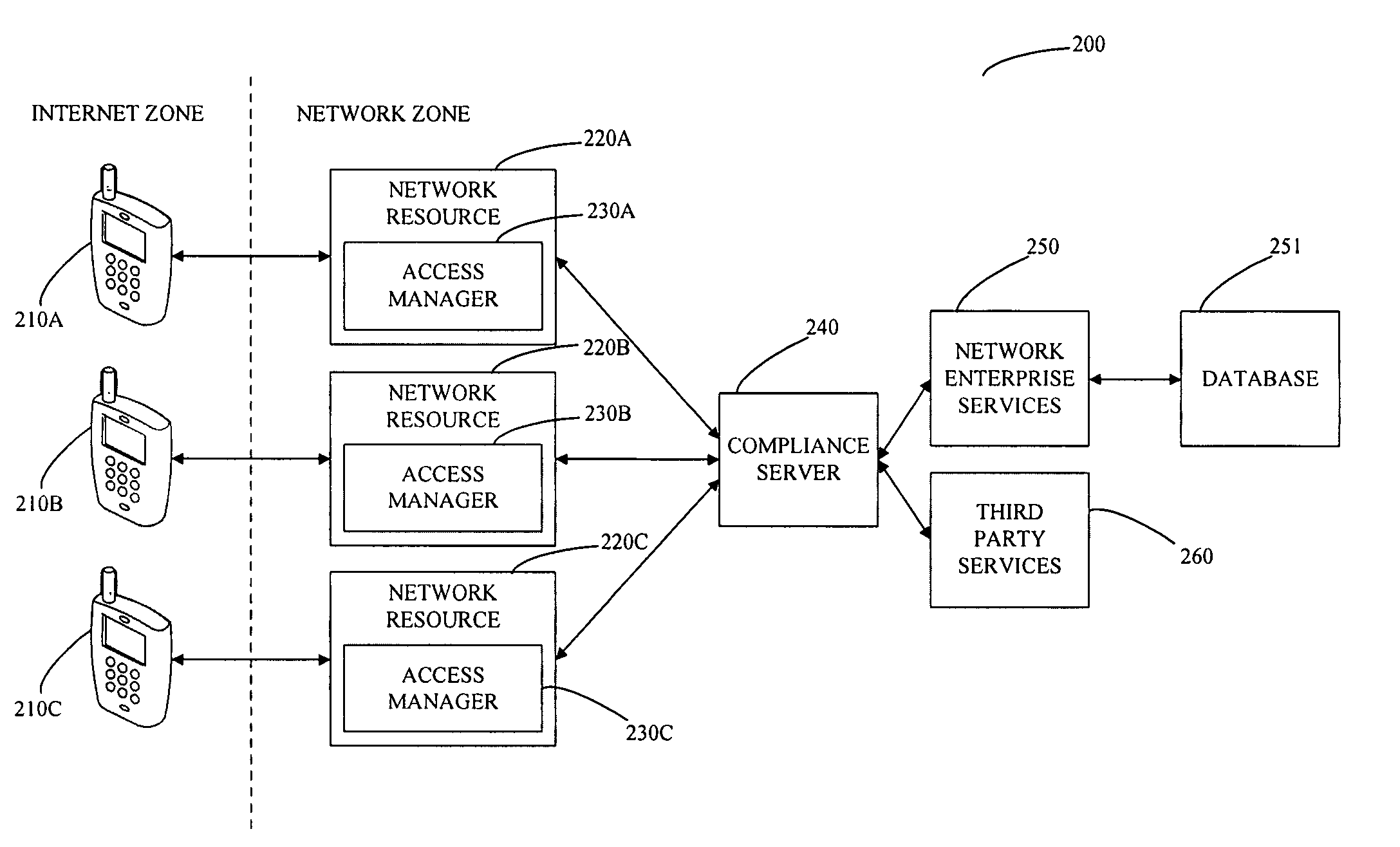
The invention provides a method for managing access to a network resource on a network from a mobile device, the method including the steps of intercepting a data stream from the mobile device attempting to access the network resource, extracting information from the intercepted data stream relating to at least one of the mobile device or a user of the mobile device, accessing at least one of enterprise service based information and third party information regarding at least one of the mobile device or the user of the mobile device, determining whether the mobile device is authorized to access the network resource, preparing an access decision that specifies whether the mobile device is authorized to access the network resource, and storing the access decision in a database on the network. The method may also include the step of enforcing the access decision by granting access to the mobile device to the network resource if the mobile device is determined to be authorized and denying access to the mobile device to the network resource if the mobile device is determined not to be authorized.
Owner:SKYHIGH SECURITY LLC
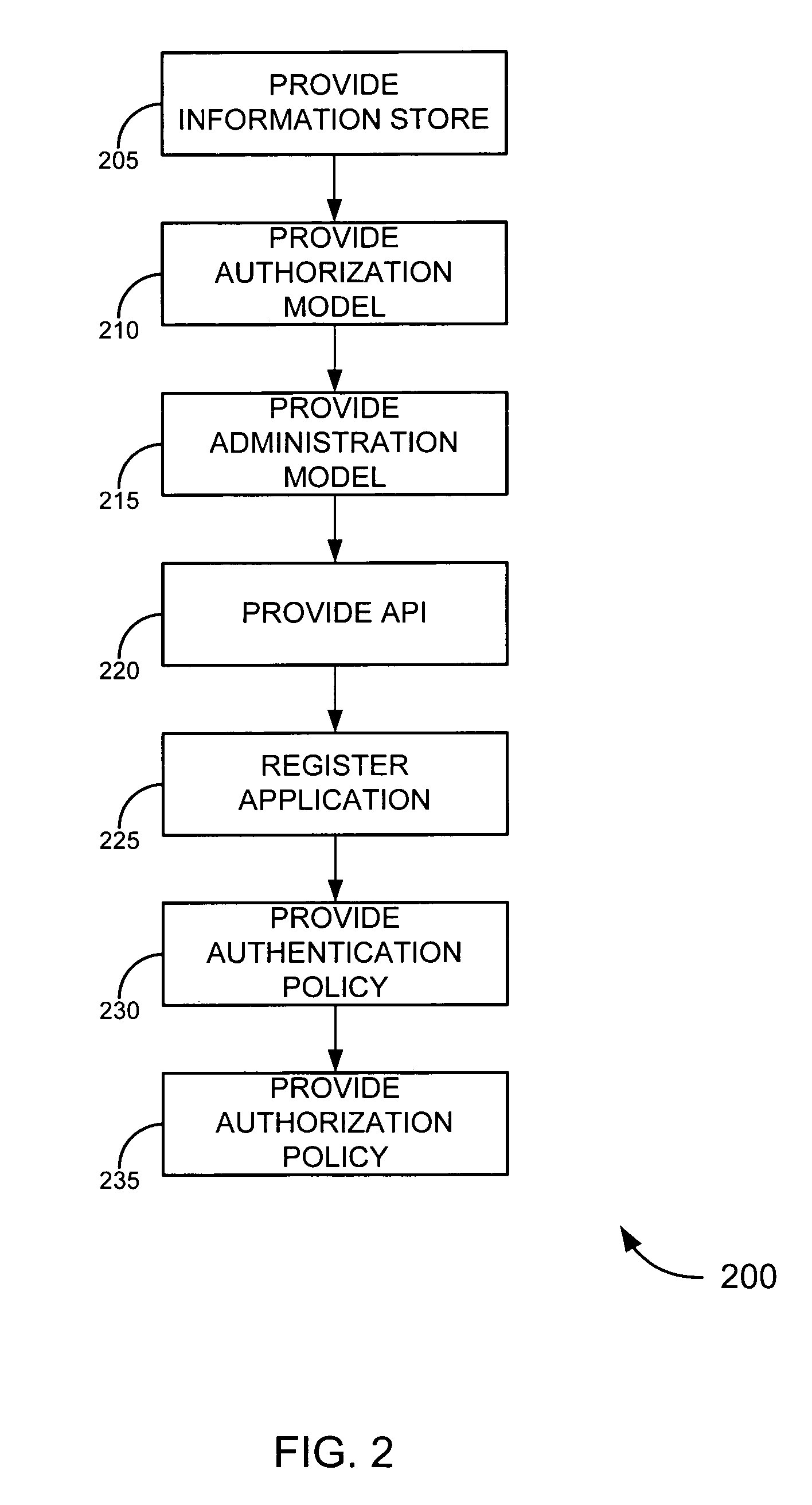
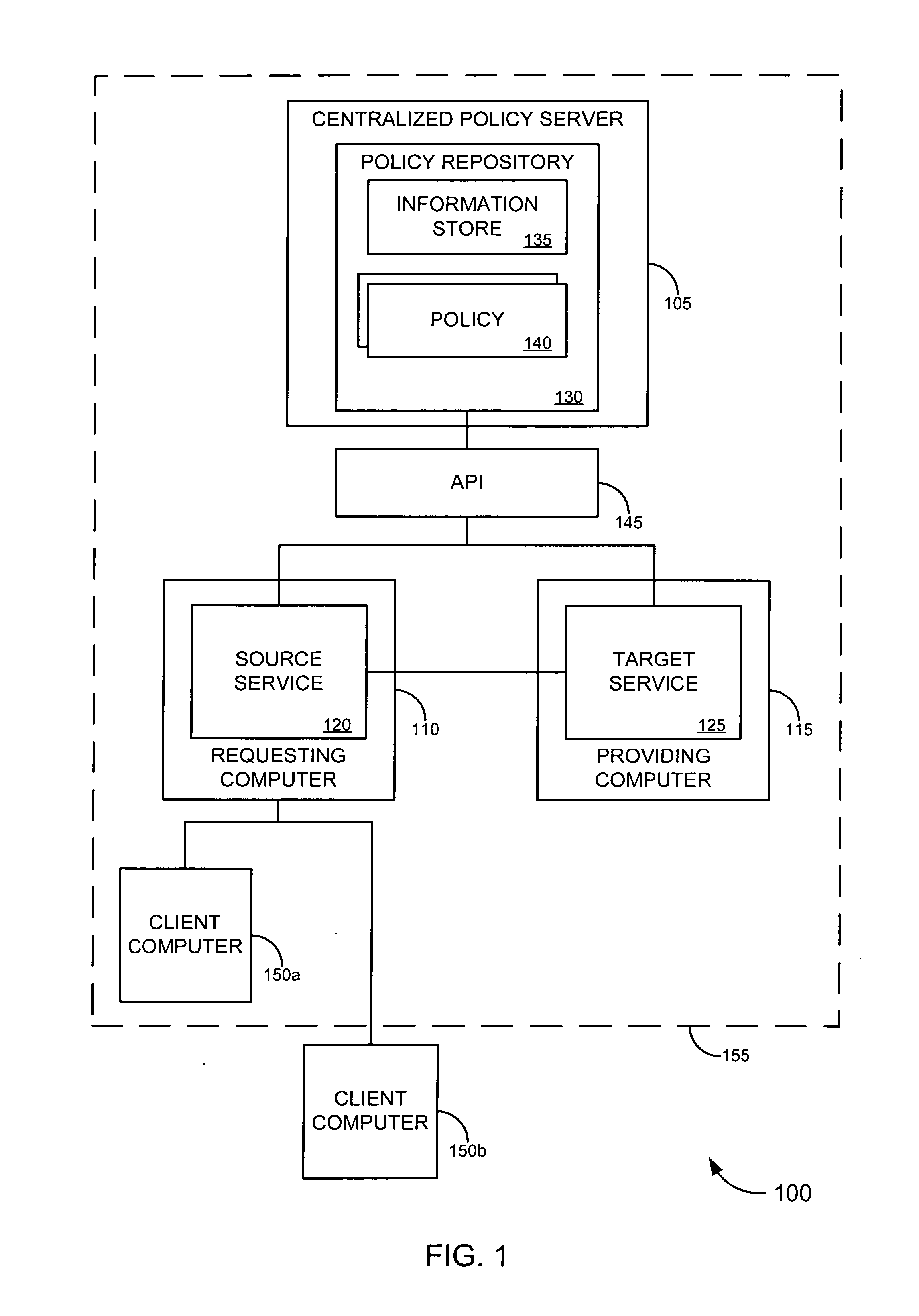
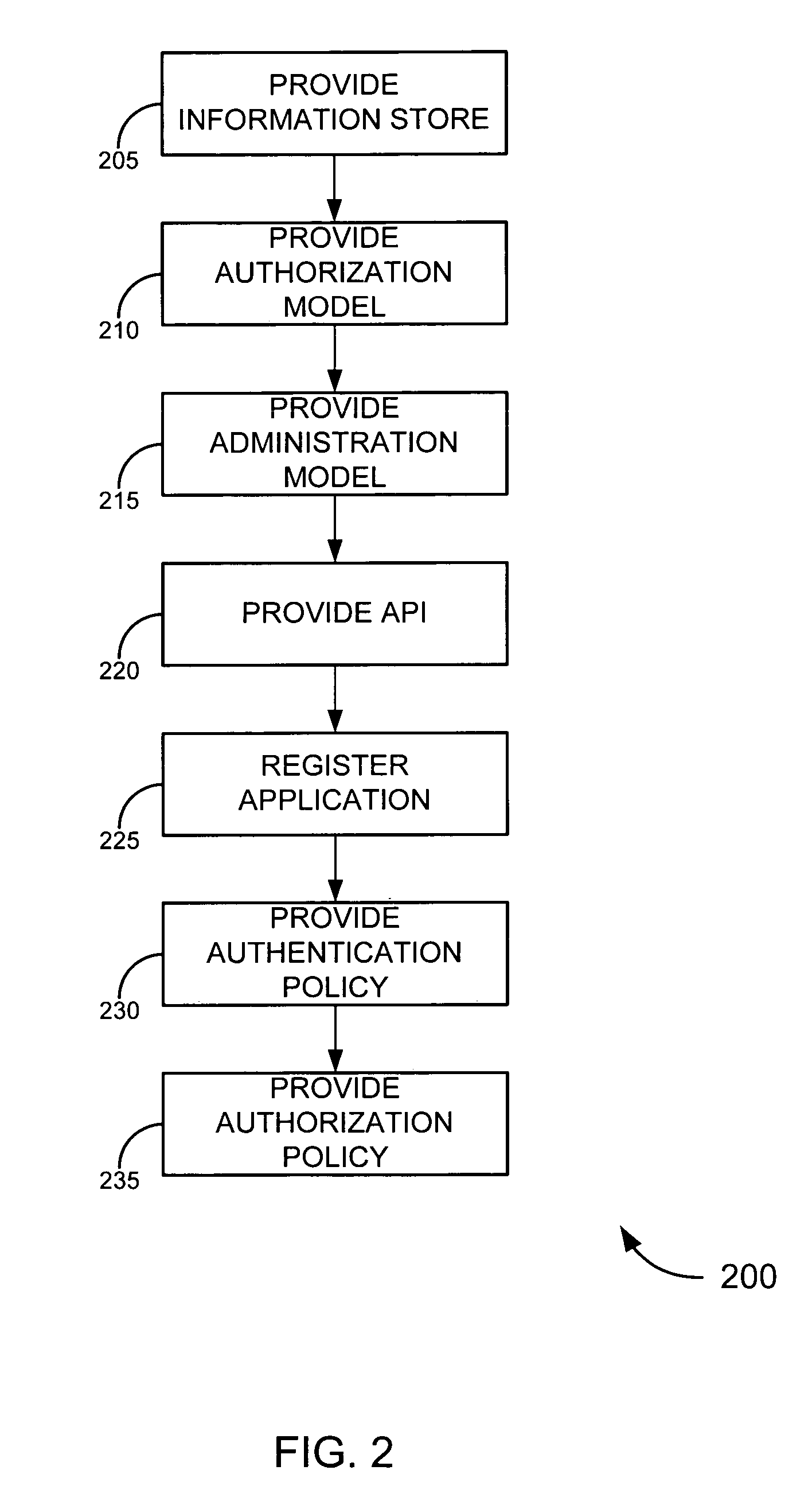
Enterprise service-to-service trust framework
ActiveUS7721322B2Improve manageabilityImprove securityDigital data processing detailsMultiple digital computer combinationsEnterprise servicesInformation security
Embodiments of the invention provide a trust framework for governing service-to-service interactions. This trust framework can provide enhanced security and / or manageability over prior systems. Merely by way of example, in some cases, an information store can be used to store information security information (such as trust information, credentials, etc.) for a variety of services across an enterprise. In other cases, the trust framework can provide authentication policies to define and / or control authentication between services (such as, for example, types of authentication credentials and / or protocols are required to access a particular service—either as a user and / or as another service—and / or types of authentication credentials and / or protocols a service may be enabled to use to access another service). Alternatively and / or additionally, the trust framework can provide authorization policies to define and / or control authorization between services.
Owner:ORACLE INT CORP
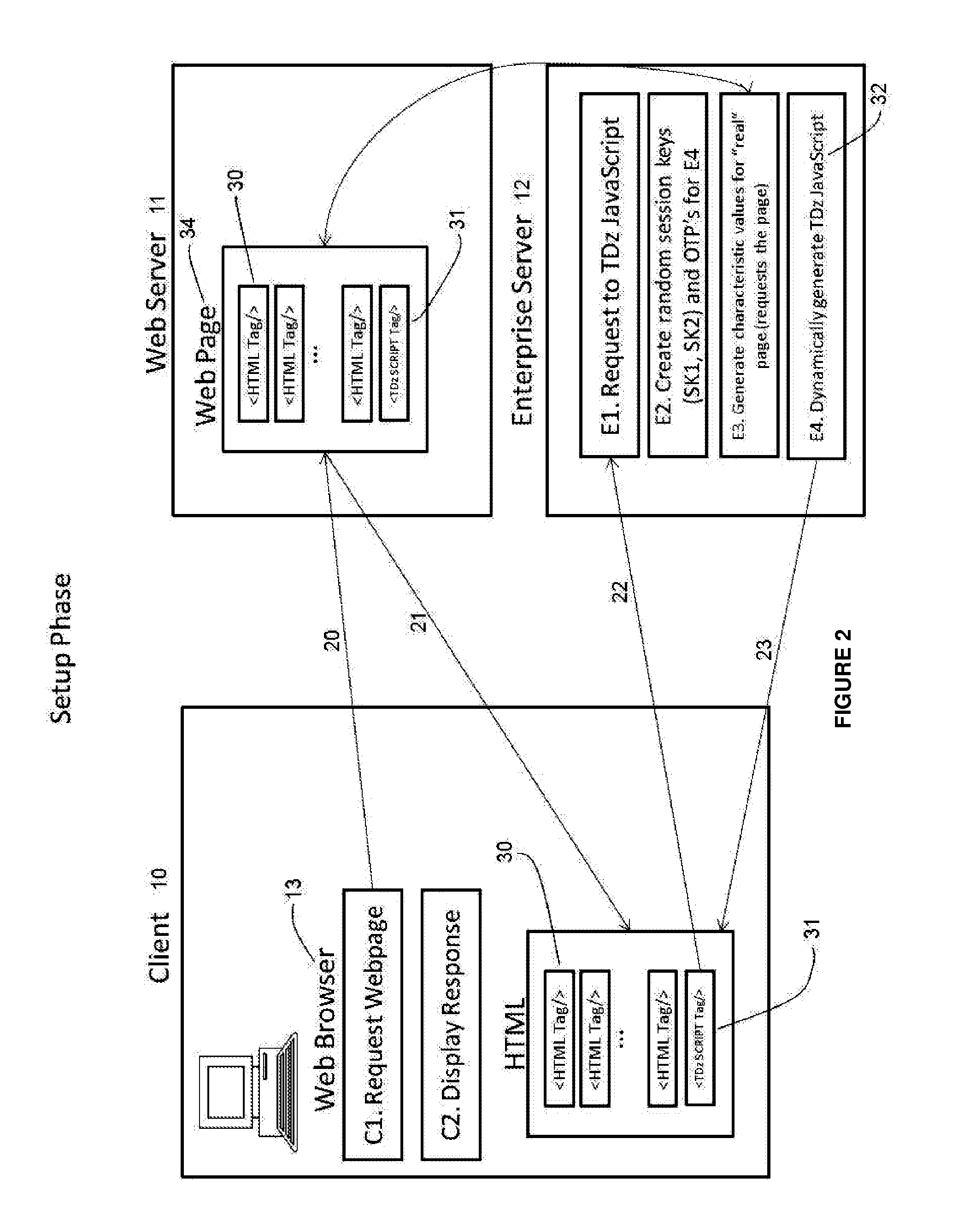
Methods and systems to detect attacks on internet transactions
ActiveUS20120198528A1Memory loss protectionDigital data processing detailsWeb serviceOne-time password
A method and system are disclosed for detecting interference with a remote visual interface, such as a HTML webpage, at a client computer, particularly to determine if a malicious attack such as at HTML attack has occurred. When the web server receives a request for a page, a script is embedded in the page, and as a consequence the client computer requests at least one session key and at least one one time password from an enterprise server. The client computer also performs a check of the HTML interface present on the client computer, which an attack of this type would change. The result of the interface check, encrypted with the session key and one time password, is sent to the enterprise server, so that a comparison with the expected value for the website can be performed.
Owner:SYMBIOTIC TECH
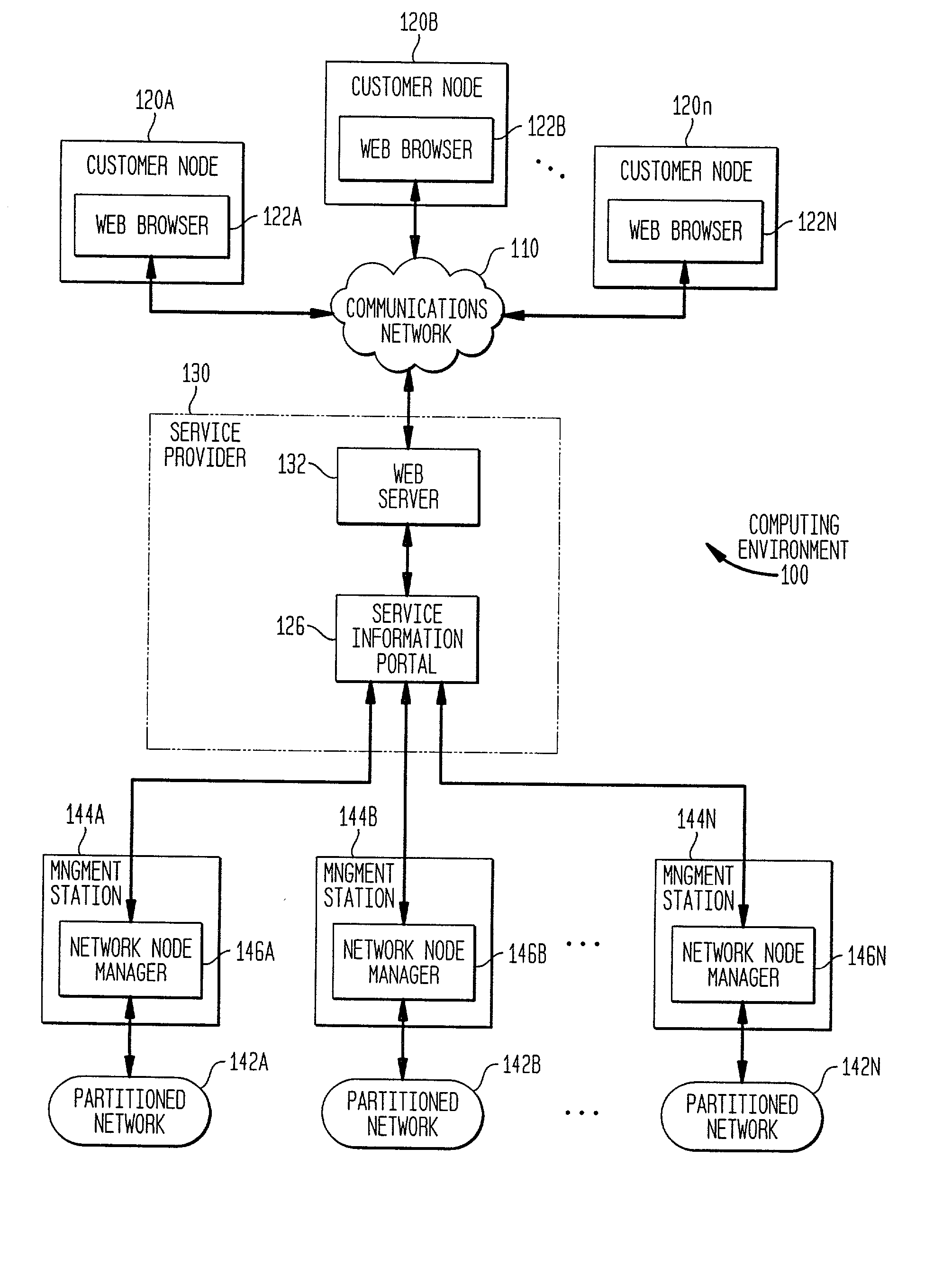
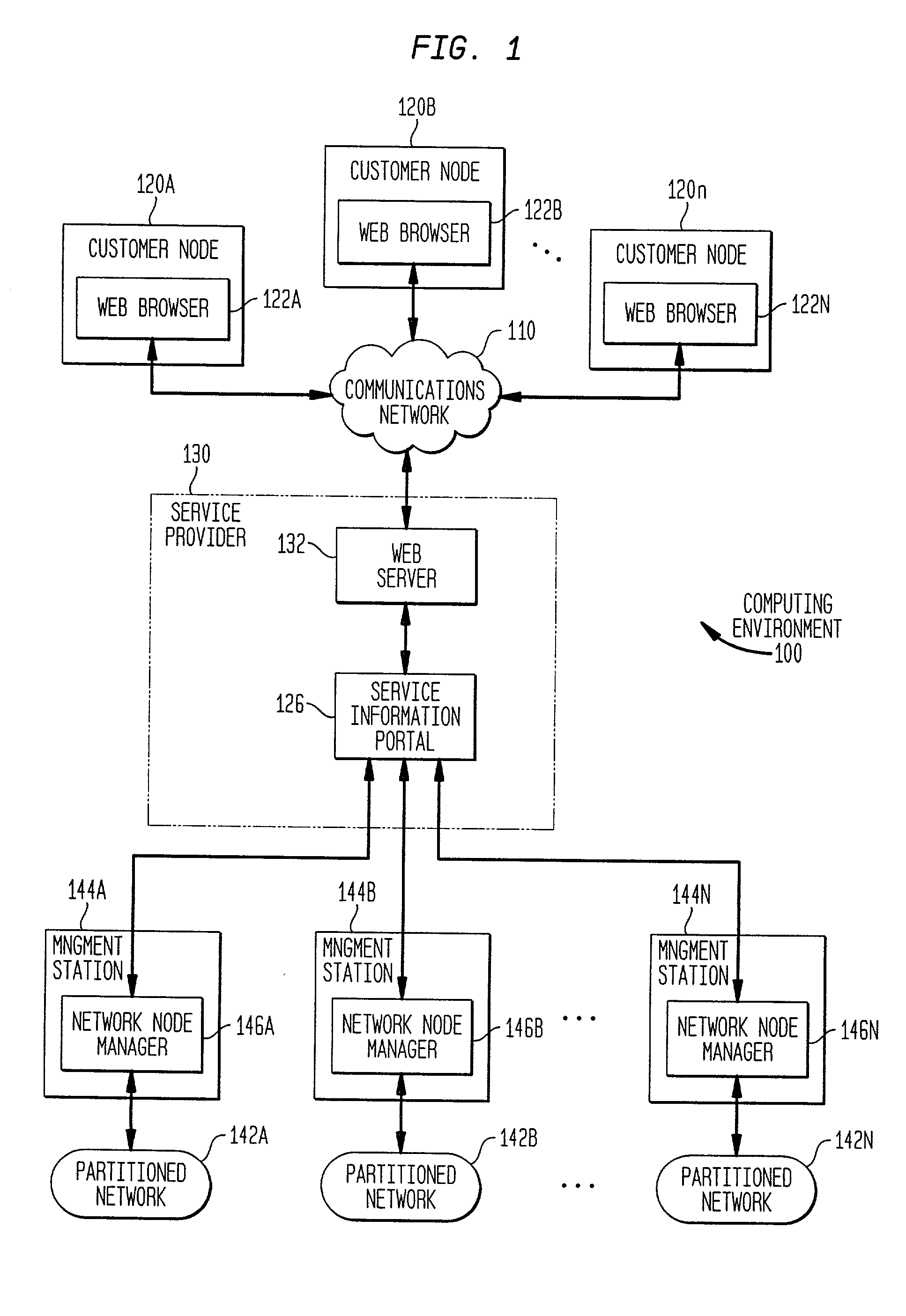
Portal system and method for managing resources in a networked computing environment
InactiveUS20020158899A1Easy to manageEliminate needDigital computer detailsData switching networksWorld Wide WebSoftware
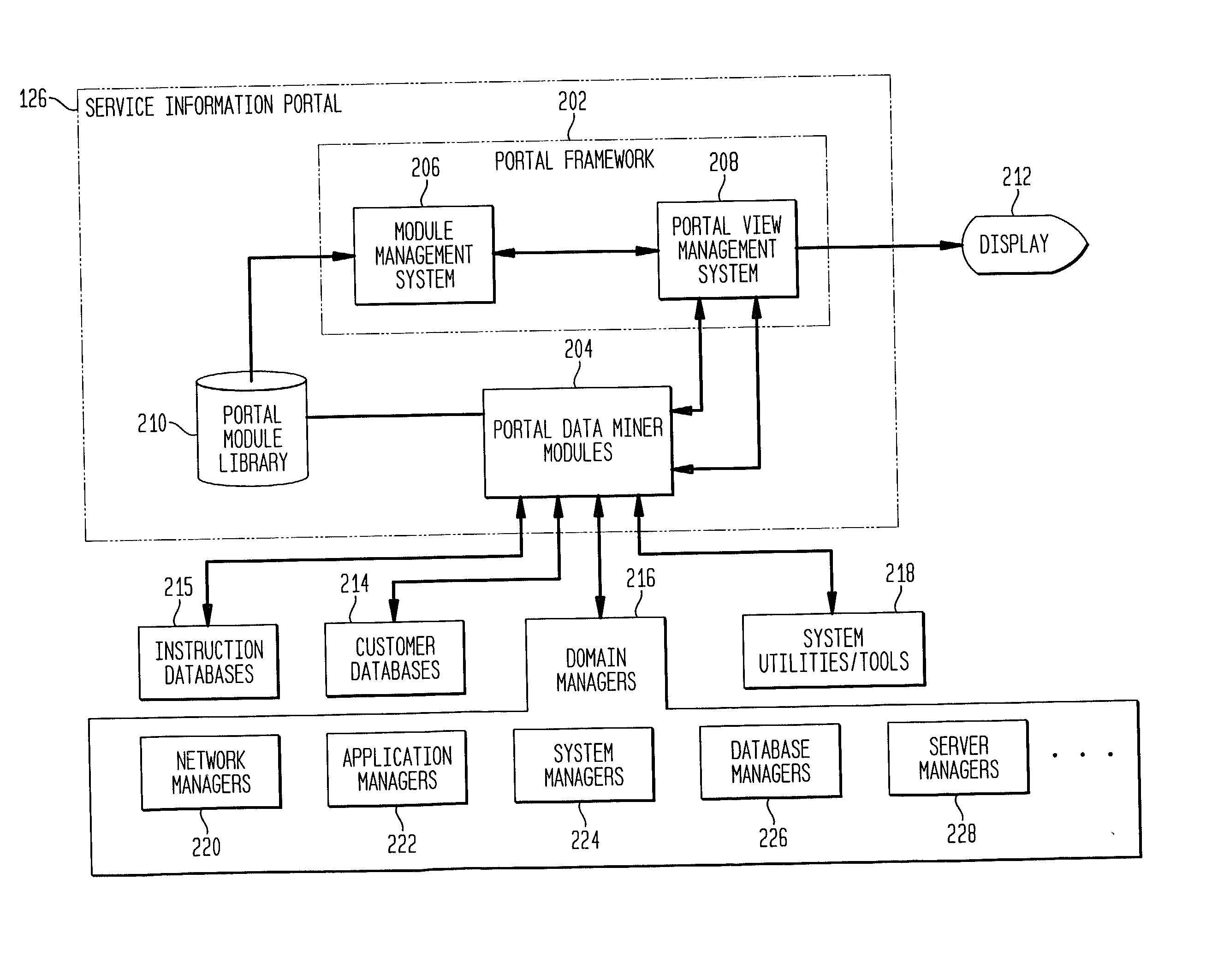
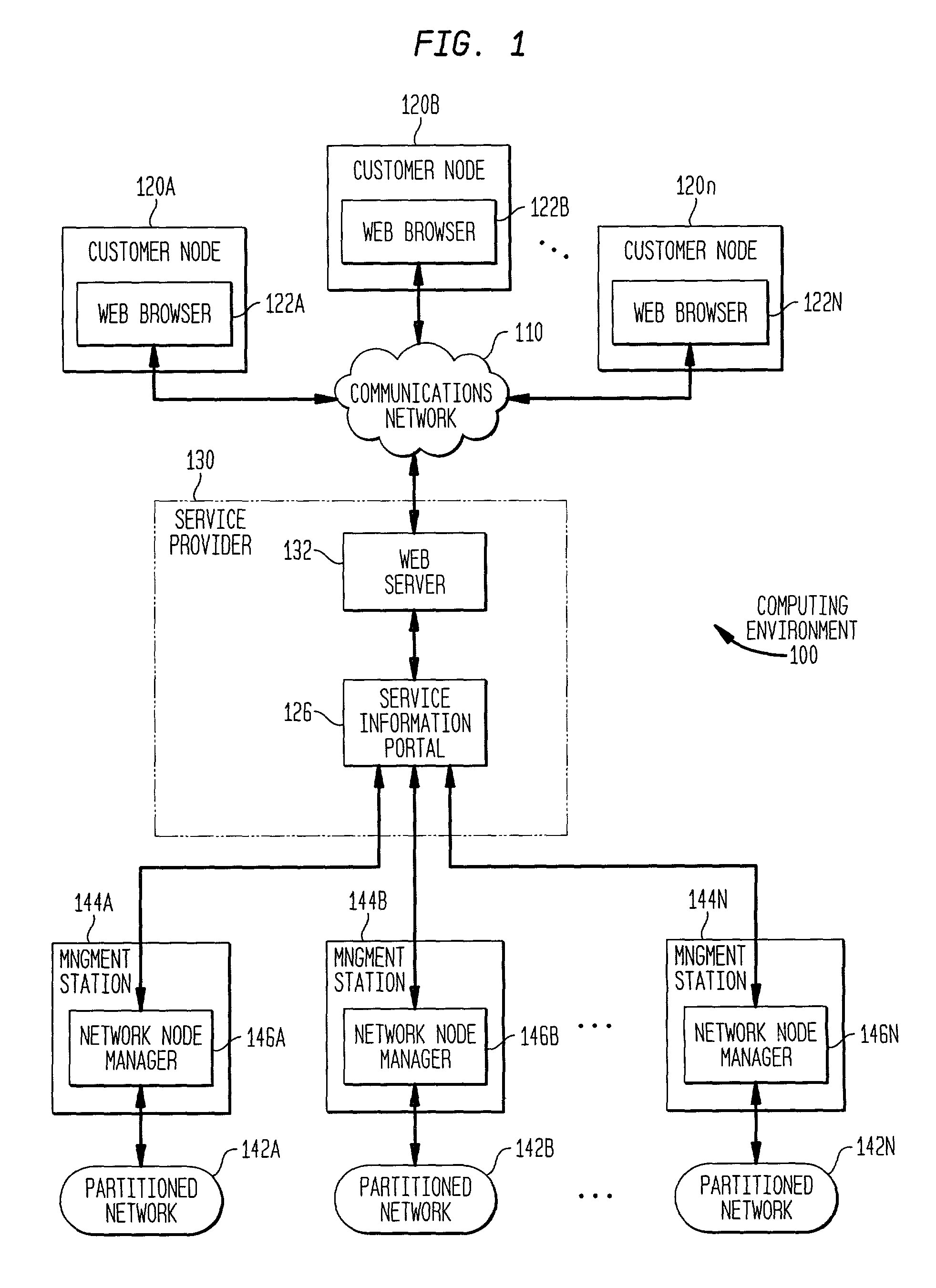
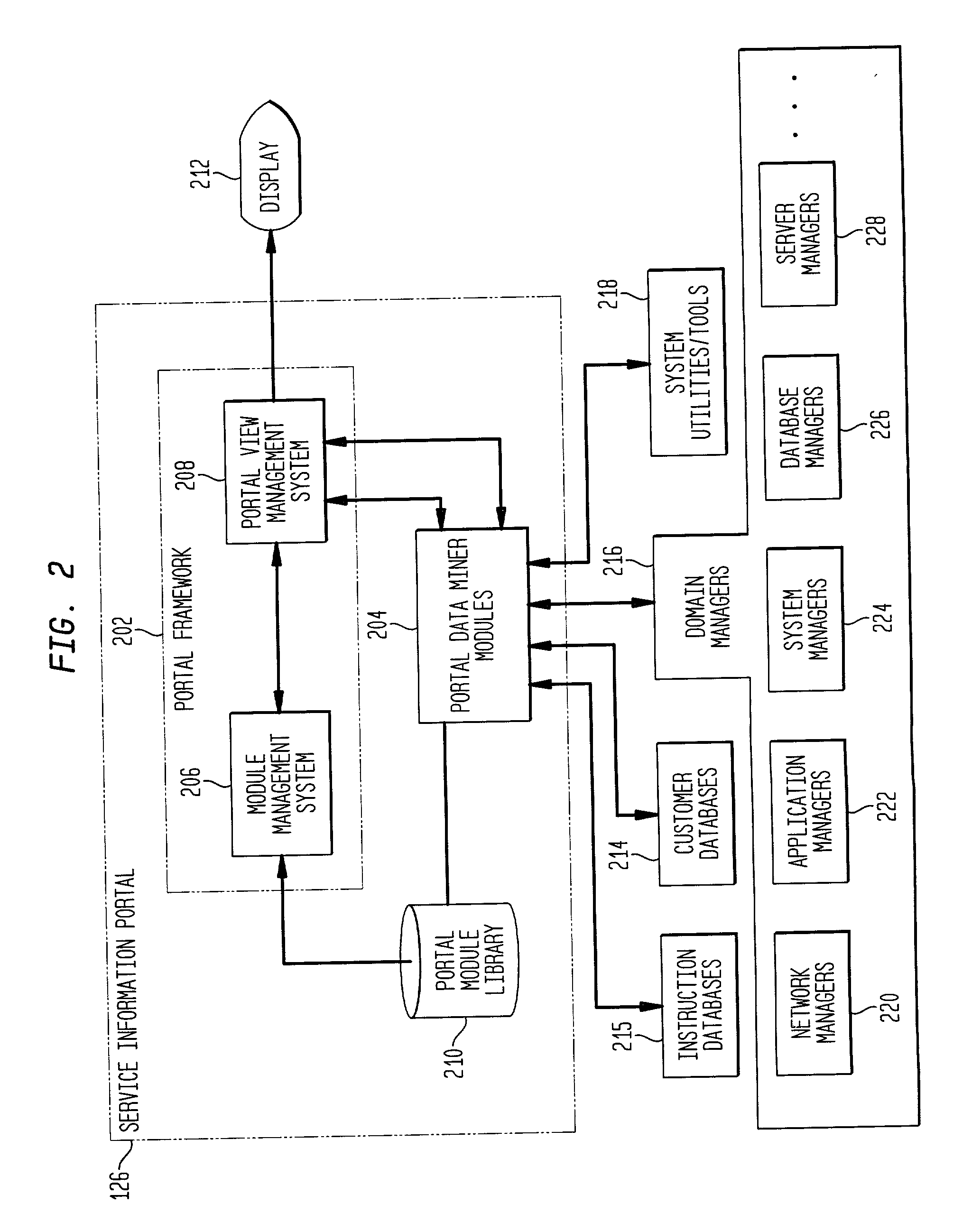
A service information portal (SIP) and associated methodology for providing customer-based management information of networked computing environments for Internet service providers (ISPs), outsourcers, and enterprise service providers ("service providers"). The invention enables such service providers to provide the network administrators / users / customers / network managers / network operators ("network administrators") they serve with flexible, extensible, tailored, in-depth views of hosted computing environments in an intuitive graphical format. Generally, the invention extracts from relevant computing environment entities specified information for managing the outsourced computing environment. The specified information is presented on a customized display for consideration and interaction by the network administrator. Specifically, aspects of the invention include a database of executable portal view profiles each designed for and / or by a particular network administrator. Each such portal view profile references one or more portal data miner modules included in a library of such modules. When a portal view profile is invoked, the referenced data miner modules are executed to access hardware and / or software entities in the computing environment for information that is displayed to assist a network administrator manage the outsourced computing environment.
Owner:HEWLETT PACKARD DEV CO LP
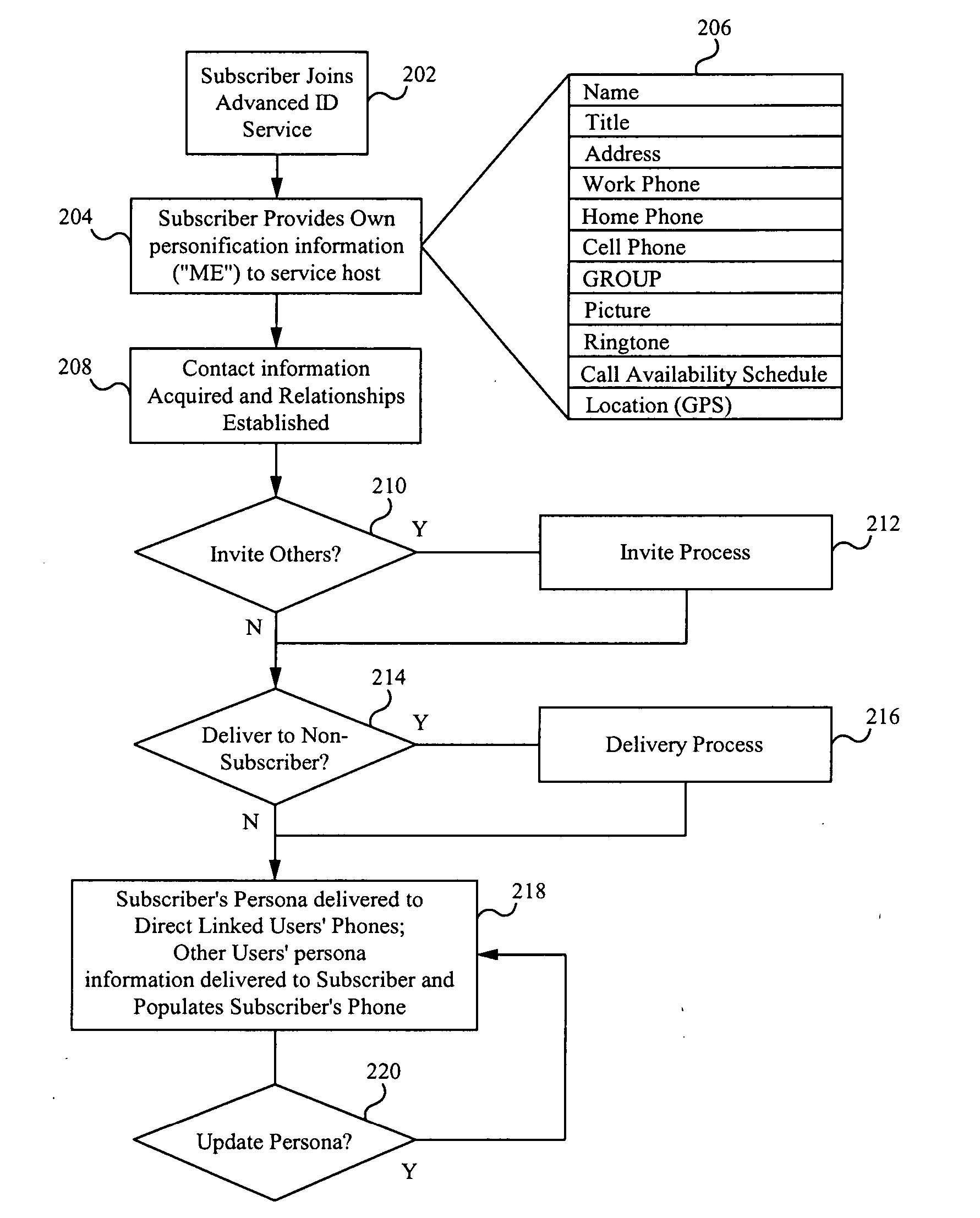
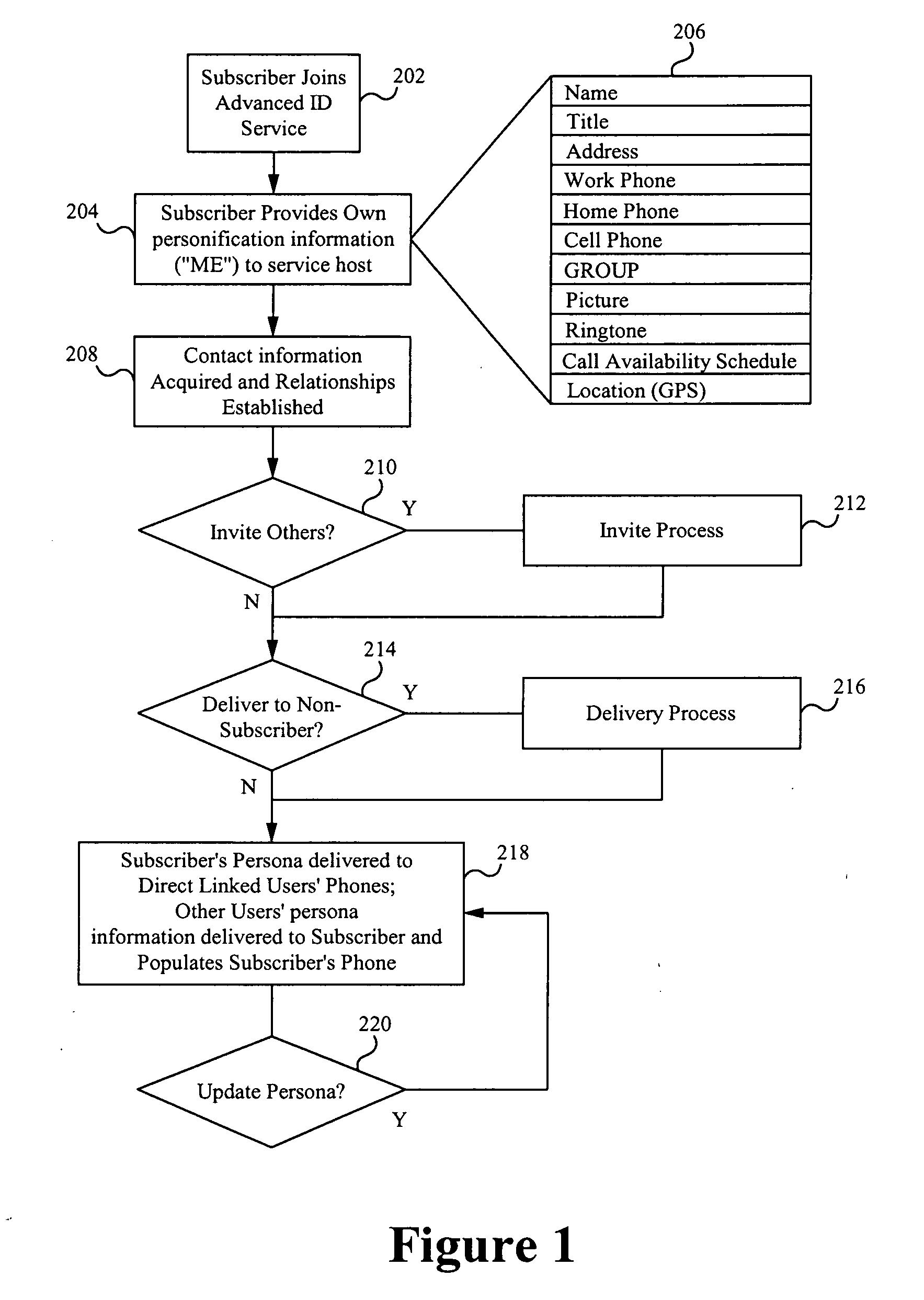
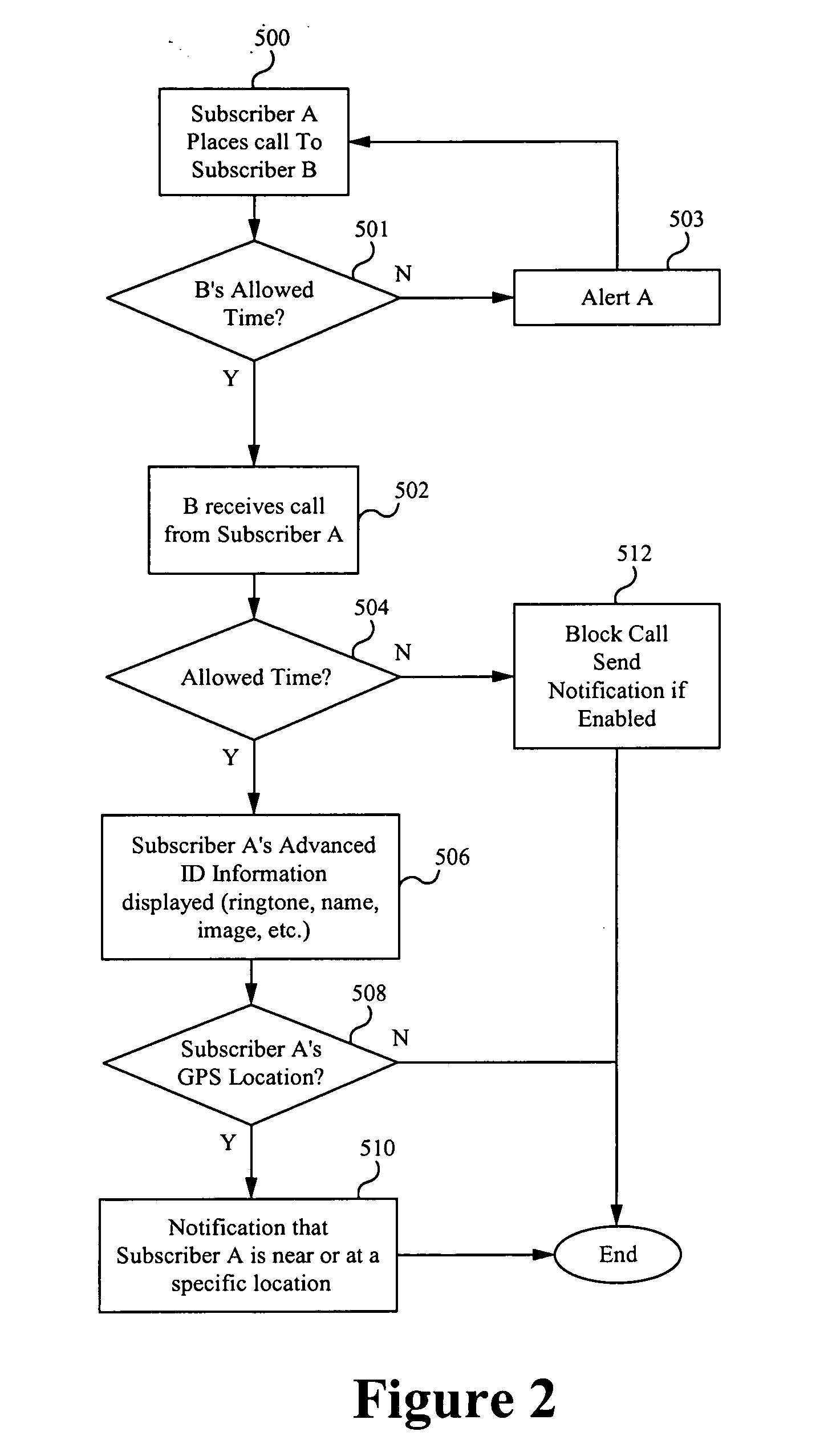
Monetization of an advanced contact identification system
An advanced contact identification system in a wireless communication network is configurable to increase subscribership and revenues for an enterprise service provider and vendors and to increase sales of content. A personal brand having a popular ringtone, graphic or other content may be widely shared among subscribers of the advanced contact identification system. Various configurations of a monetization scheme for subscribers to share popular and incentivized content drive sales for such content and increase revenue.
Owner:SYNCHRONOSS TECH
System and method for controlling mobile device access to a network
ActiveUS20080137593A1Error preventionFrequency-division multiplex detailsThird partyComputer network
The invention provides a method for managing access to a network resource on a network from a mobile device, the method including the steps of intercepting a data stream from the mobile device attempting to access the network resource, extracting information from the intercepted data stream relating to at least one of the mobile device or a user of the mobile device, accessing at least one of enterprise service based information and third party information regarding at least one of the mobile device or the user of the mobile device, determining whether the mobile device is authorized to access the network resource, preparing an access decision that specifies whether the mobile device is authorized to access the network resource, and storing the access decision in a database on the network. The method may also include the step of enforcing the access decision by granting access to the mobile device to the network resource if the mobile device is determined to be authorized and denying access to the mobile device to the network resource if the mobile device is determined not to be authorized.
Owner:SKYHIGH SECURITY LLC
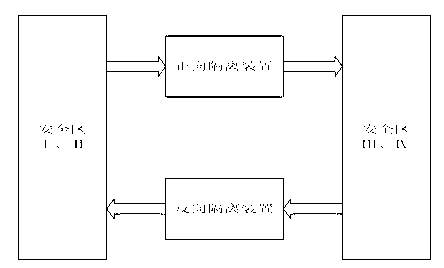
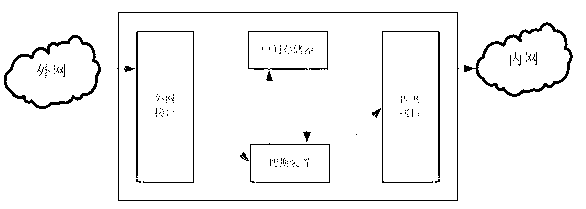
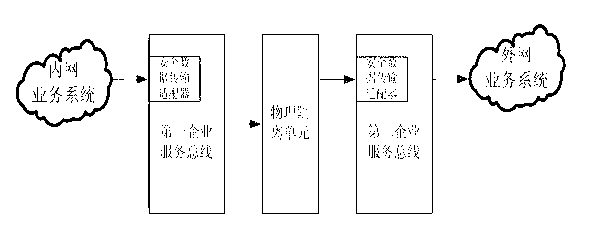
Cross-physical isolation data transparent transmission system and method between intranet and extranet
ActiveCN102843352ARetrofit smallEasy to deployUser identity/authority verificationBus networksEnterprise servicesWorkload
The invention relates to a cross-physical isolation data transparent transmission system between an intranet and an extranet. The system comprises a first enterprise service bus and a second enterprise service bus which are respectively arranged on the two sides of physical isolation, wherein a first safety data transmission adapter and a second safety data transmission adapter are respectively deployed on the first and second enterprise service buses, the physical isolation is arranged between gateways of the intranet and the extranet for performing network safety area isolation, the first and second enterprise service buses are used for respectively providing calling interfaces and simultaneously communicating with the physical isolation, and the first and second safety data transmission adapters are respectively responsible for safety certification and calibration of integrity and effectiveness of data of the intranet and the extranet. The invention further relates to a cross-physical isolation data transparent transmission method of the system. Improvement of data transmission can be performed under a physical isolation environment through the system and the method, the difficulty in transformation and the workload of the service system can be simplified, and the safety in data transmission can be further enhanced through the safety data transmission adapters.
Owner:MAOMING POWER SUPPLY BUREAU GUANGDONG POWER GRID CORP
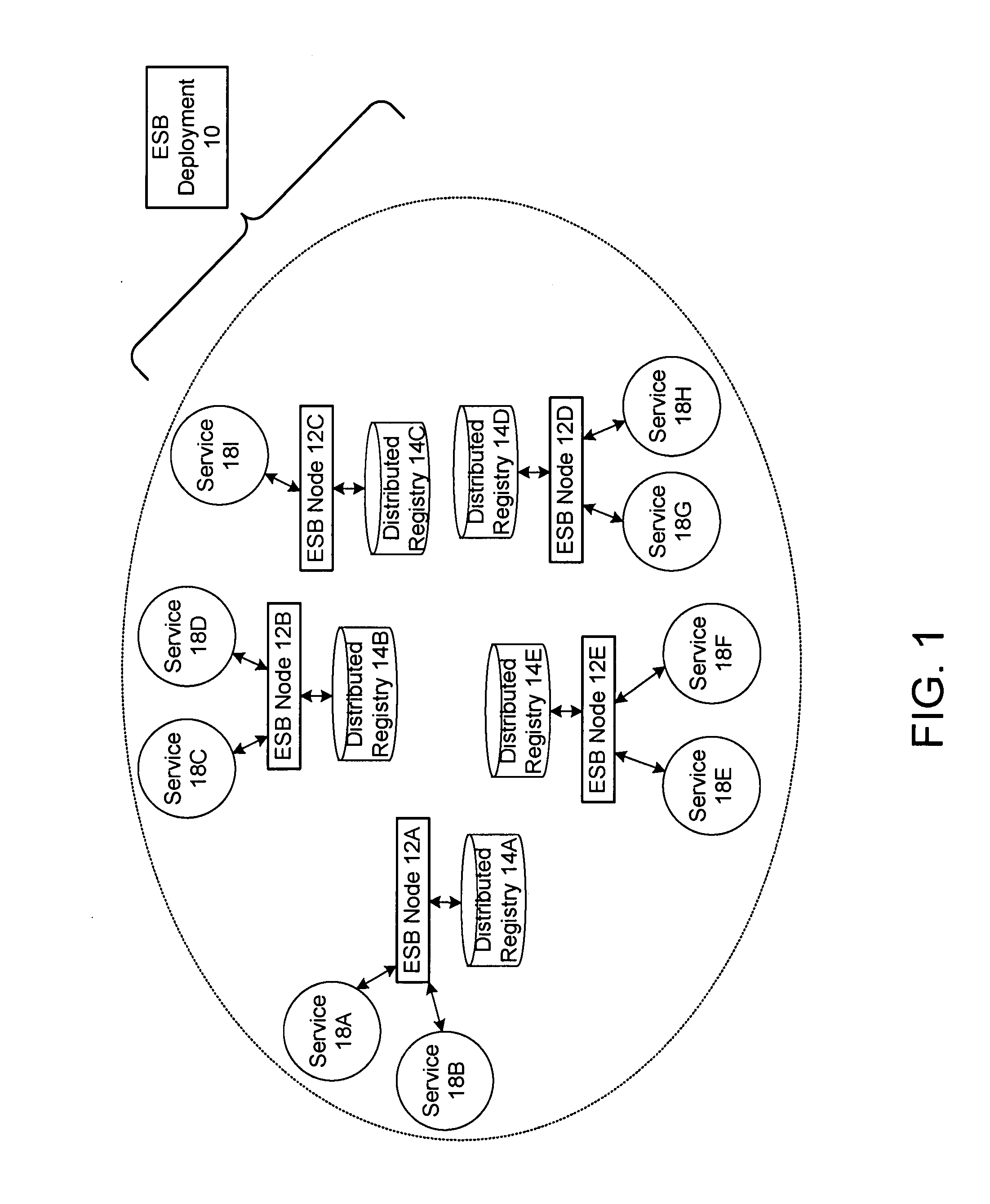
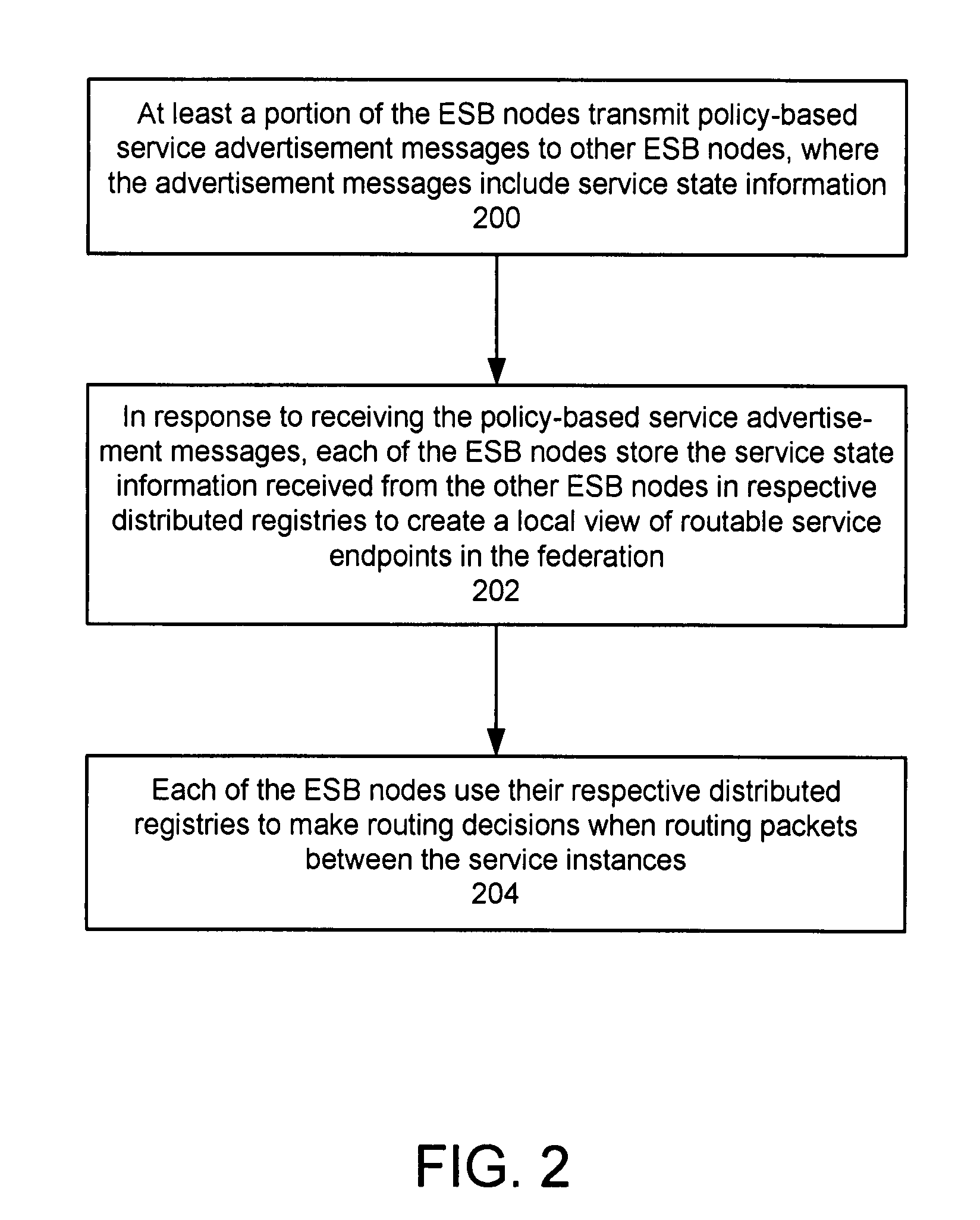
Protocol for enabling dynamic and scalable federation of enterprise service buses
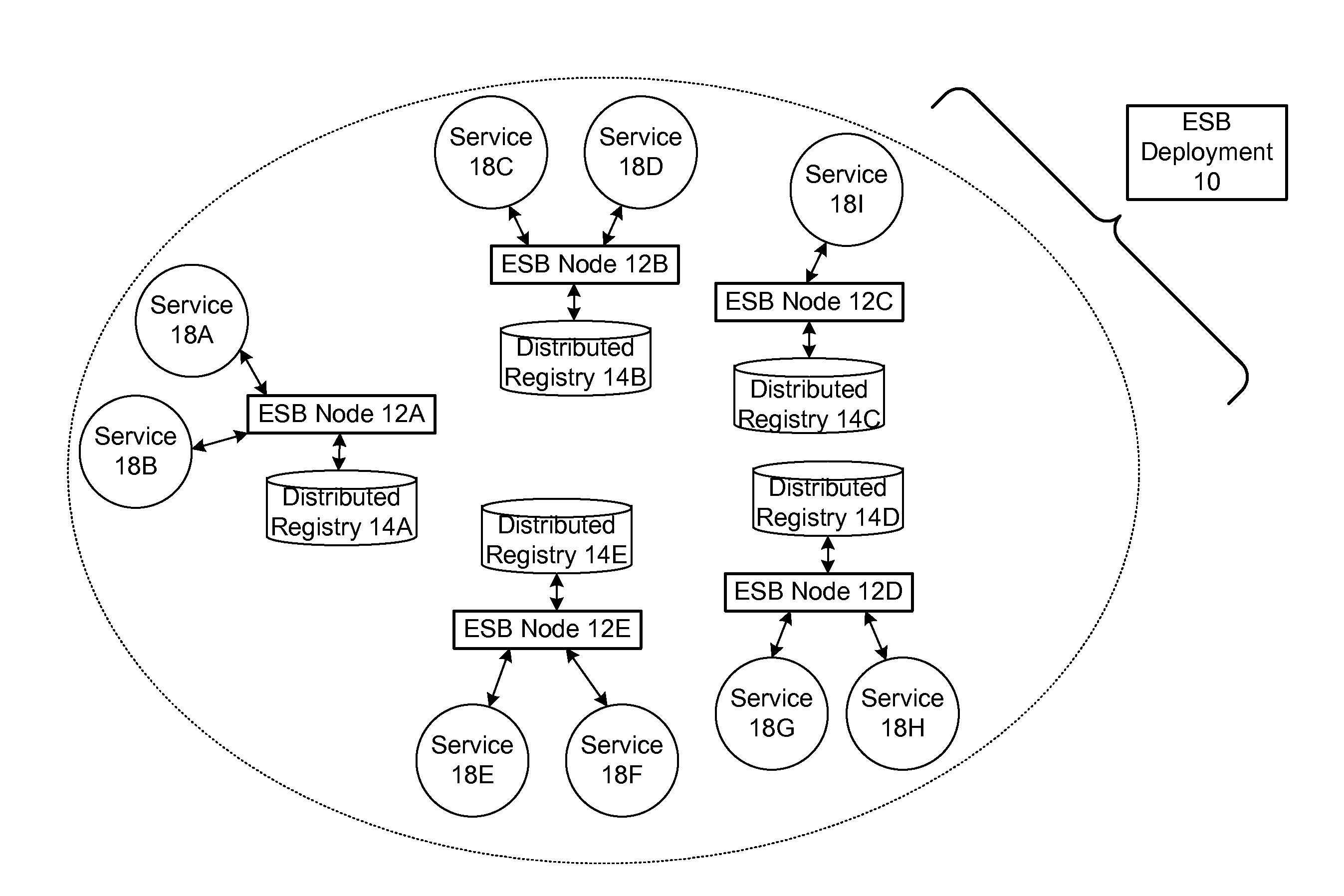
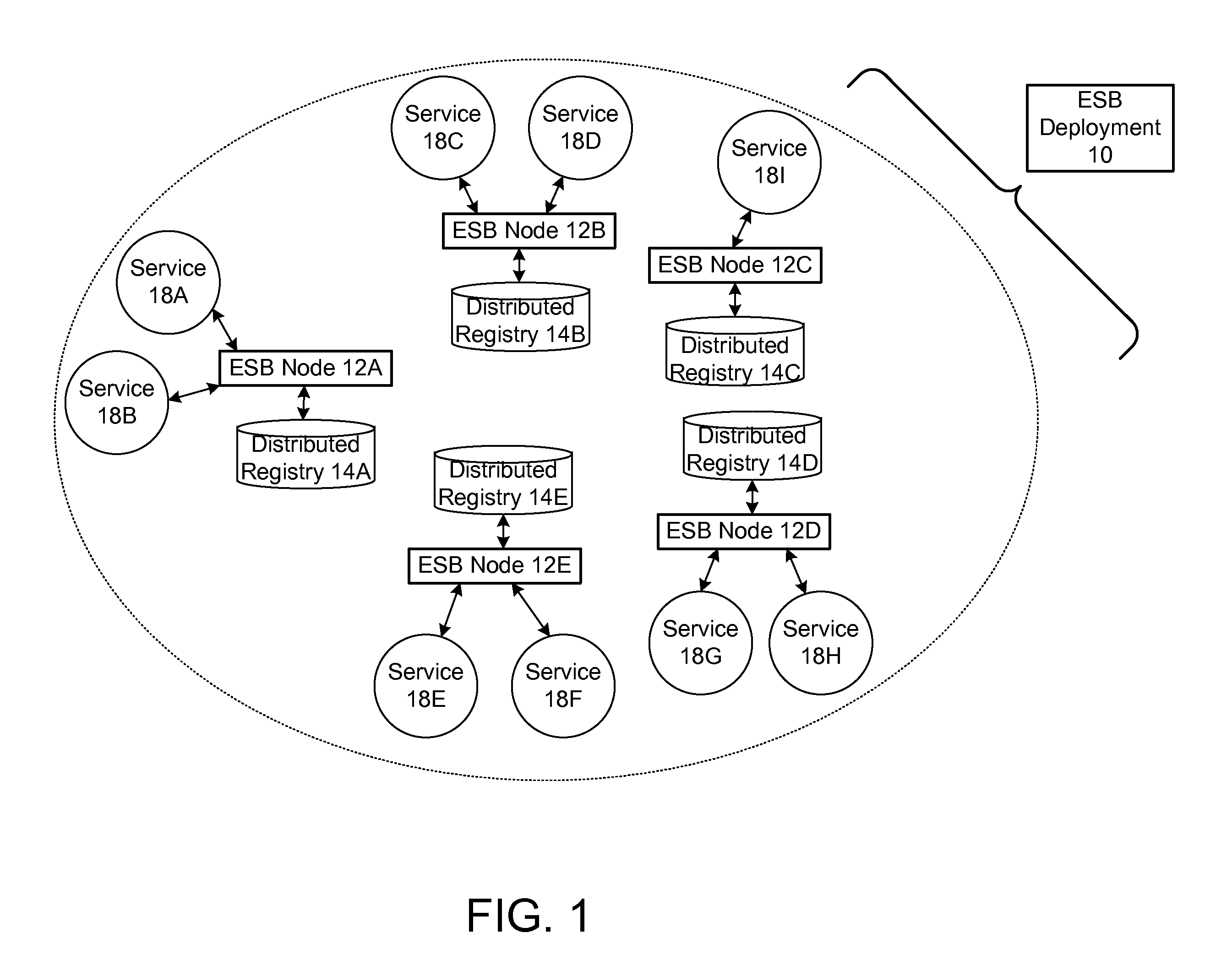
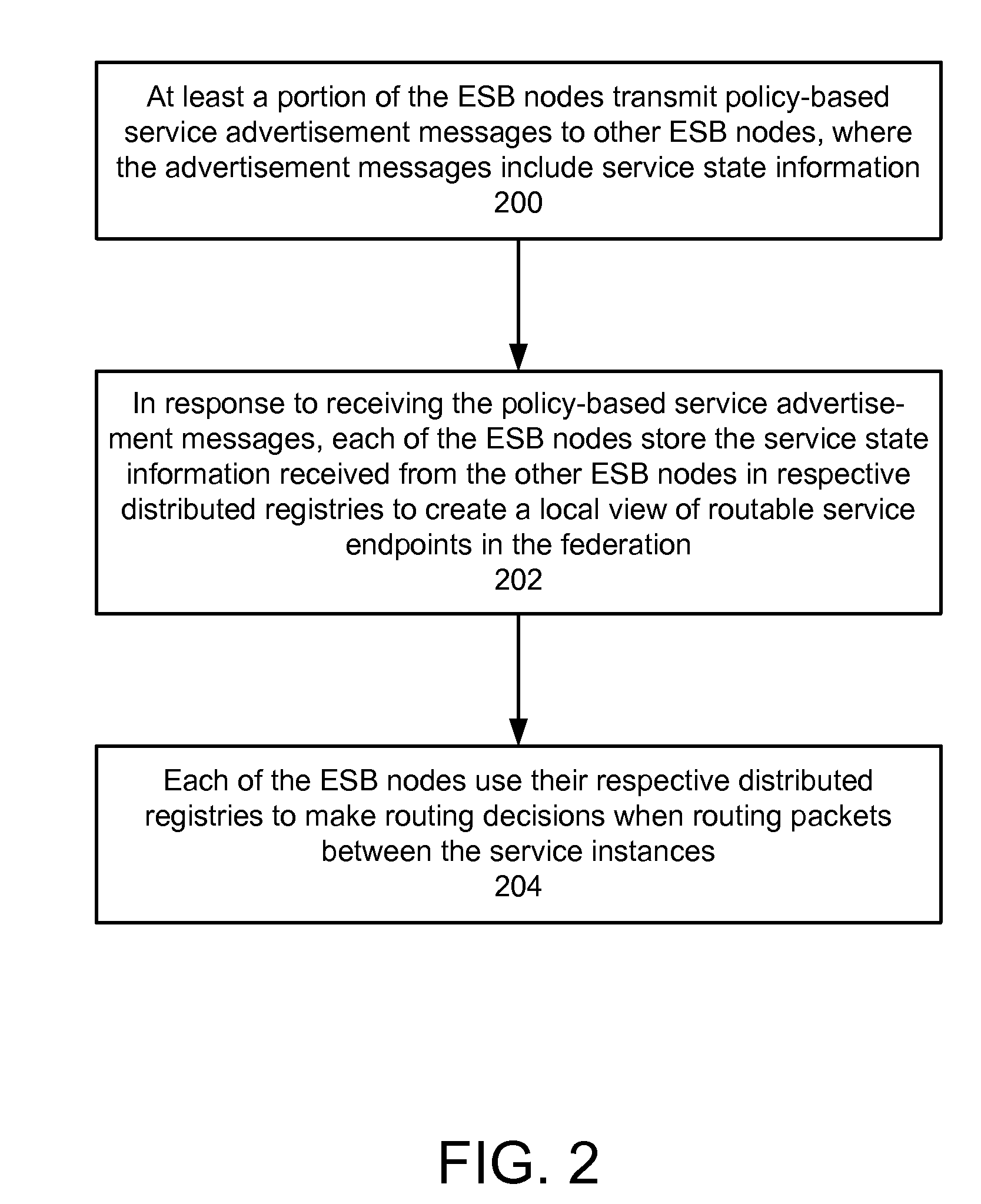
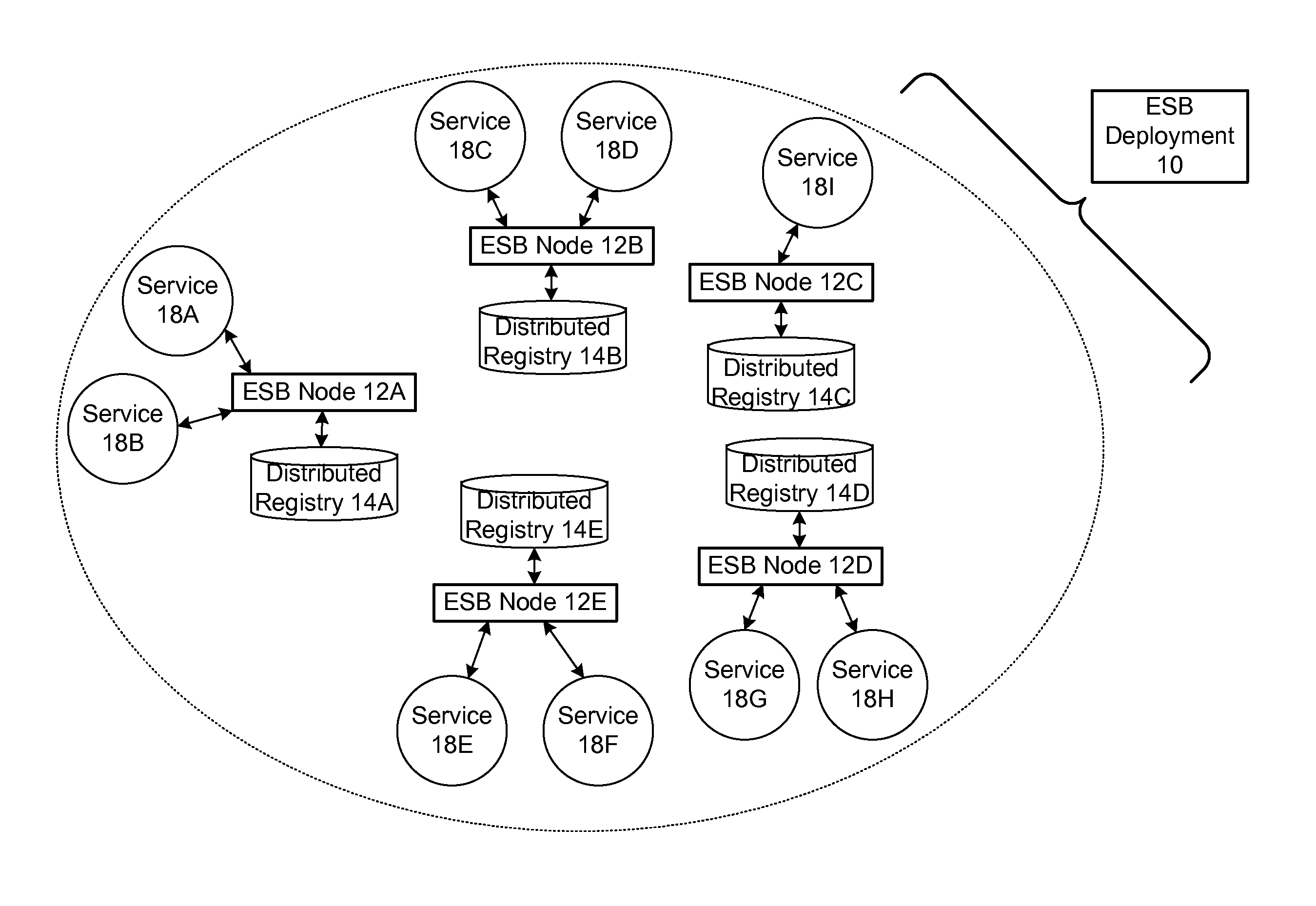
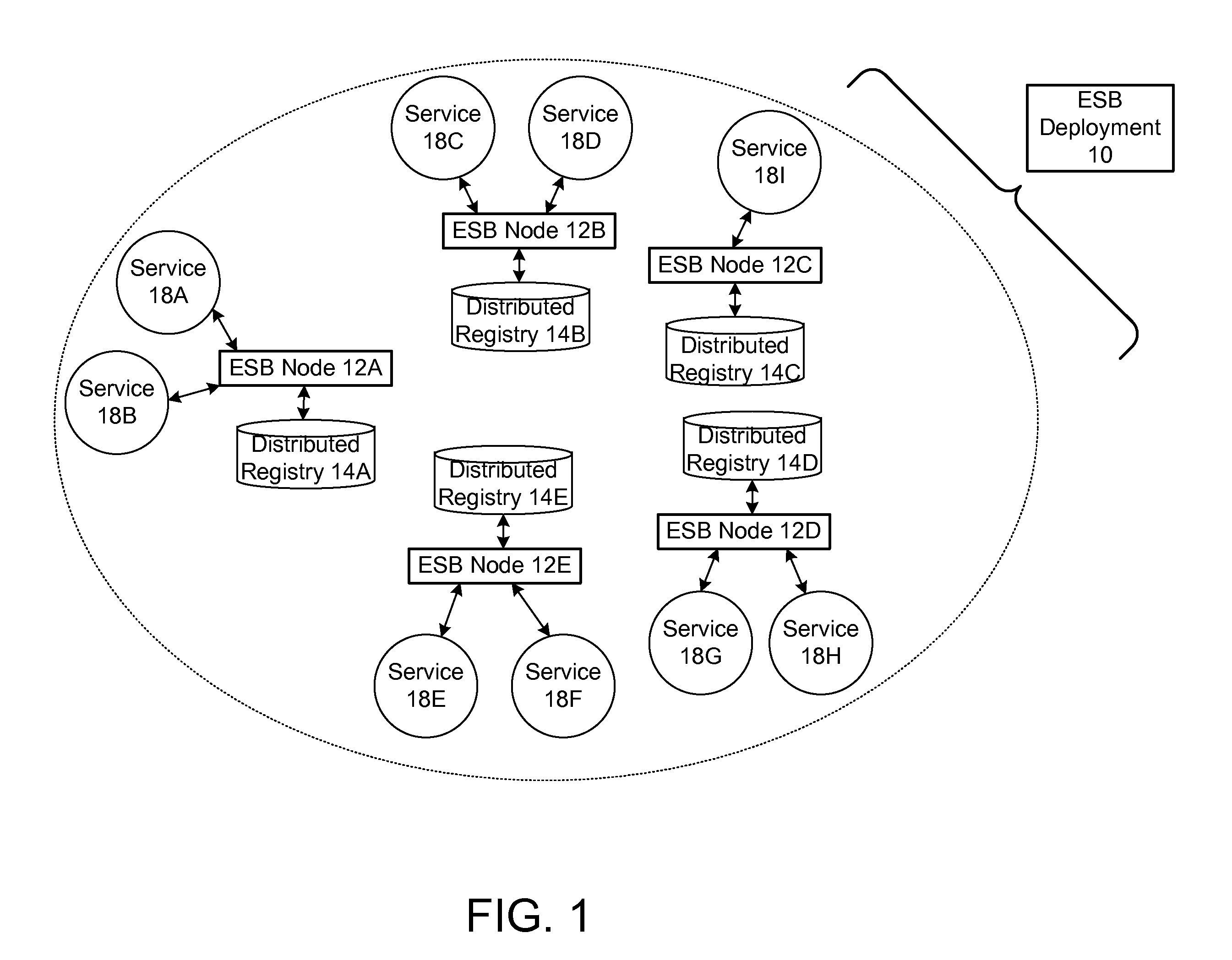
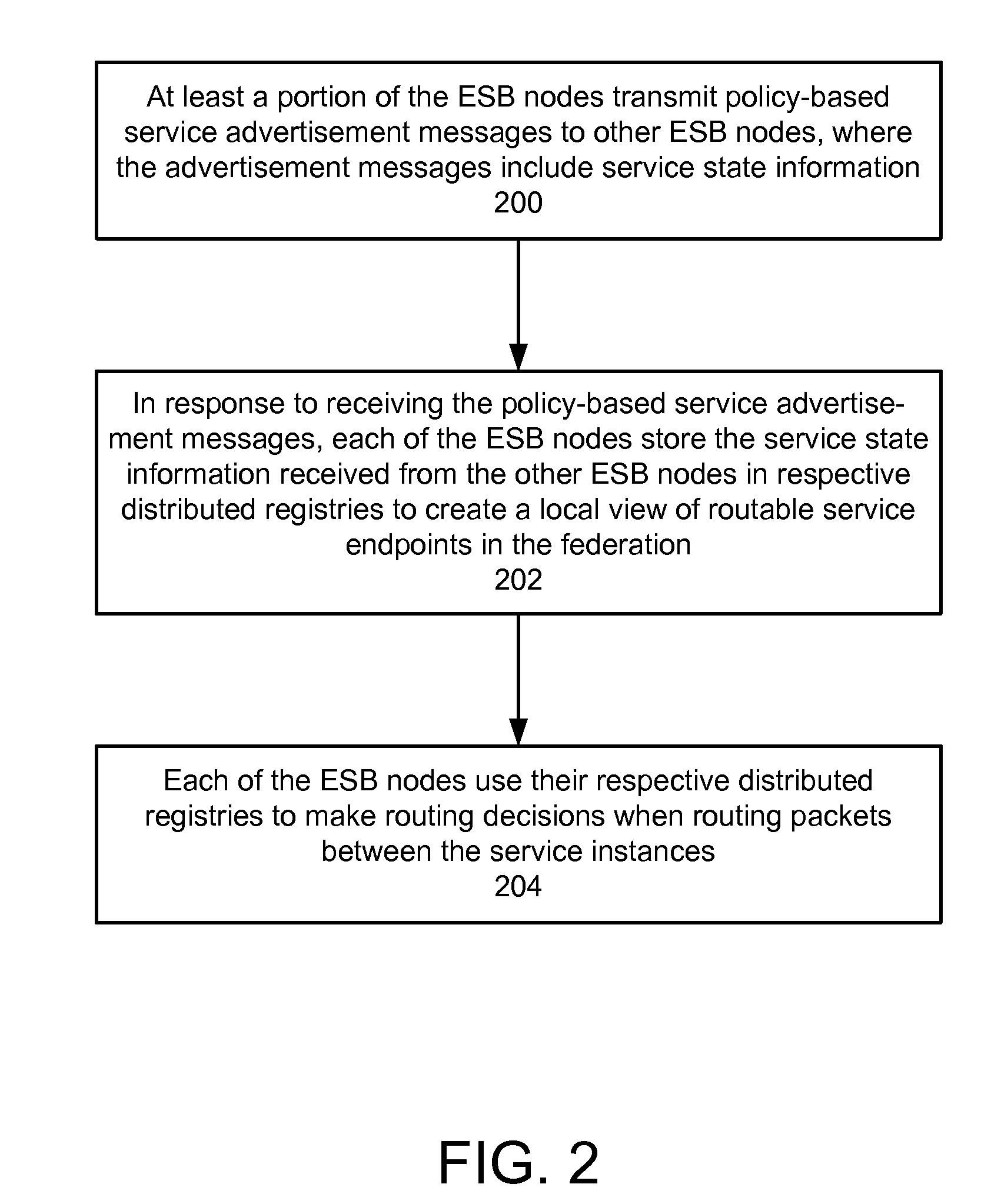
ActiveUS20090070456A1Multiple digital computer combinationsMarketingRouting decisionEnterprise services
In a method and system for creating a federation of a plurality of enterprise service buses (ESBs), a plurality of ESB nodes provide connectivity to one or more services. According to a protocol, at least a portion of the ESB nodes transmit policy-based service advertisement messages to other ESB nodes, wherein the policy-based service advertisement messages include service state information. In response to receiving the policy-based service advertisement messages, each of the ESB nodes stores the service state information received from other ESB nodes in respective distributed registries to create a local view of routable service endpoints in the federation. Each of the ESB nodes then uses its respective distributed registry to make routing decisions when routing service requests.
Owner:SERVICENOW INC
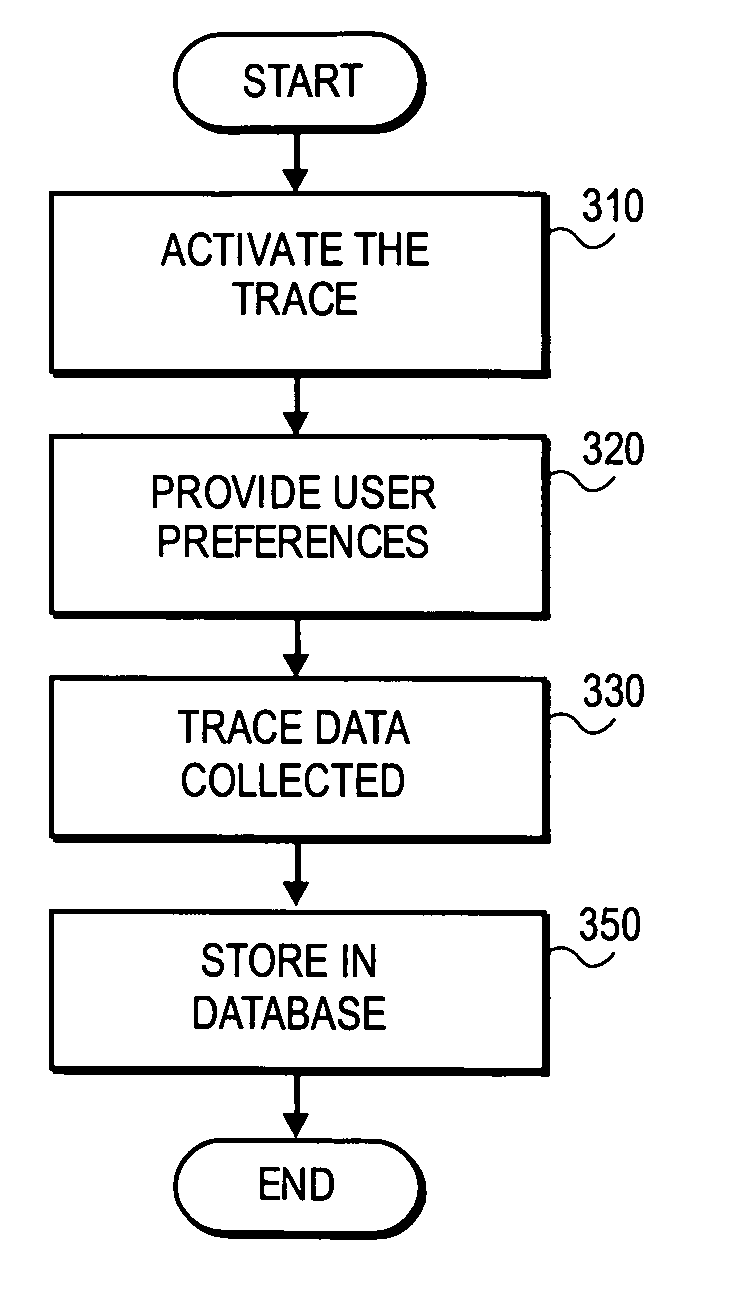
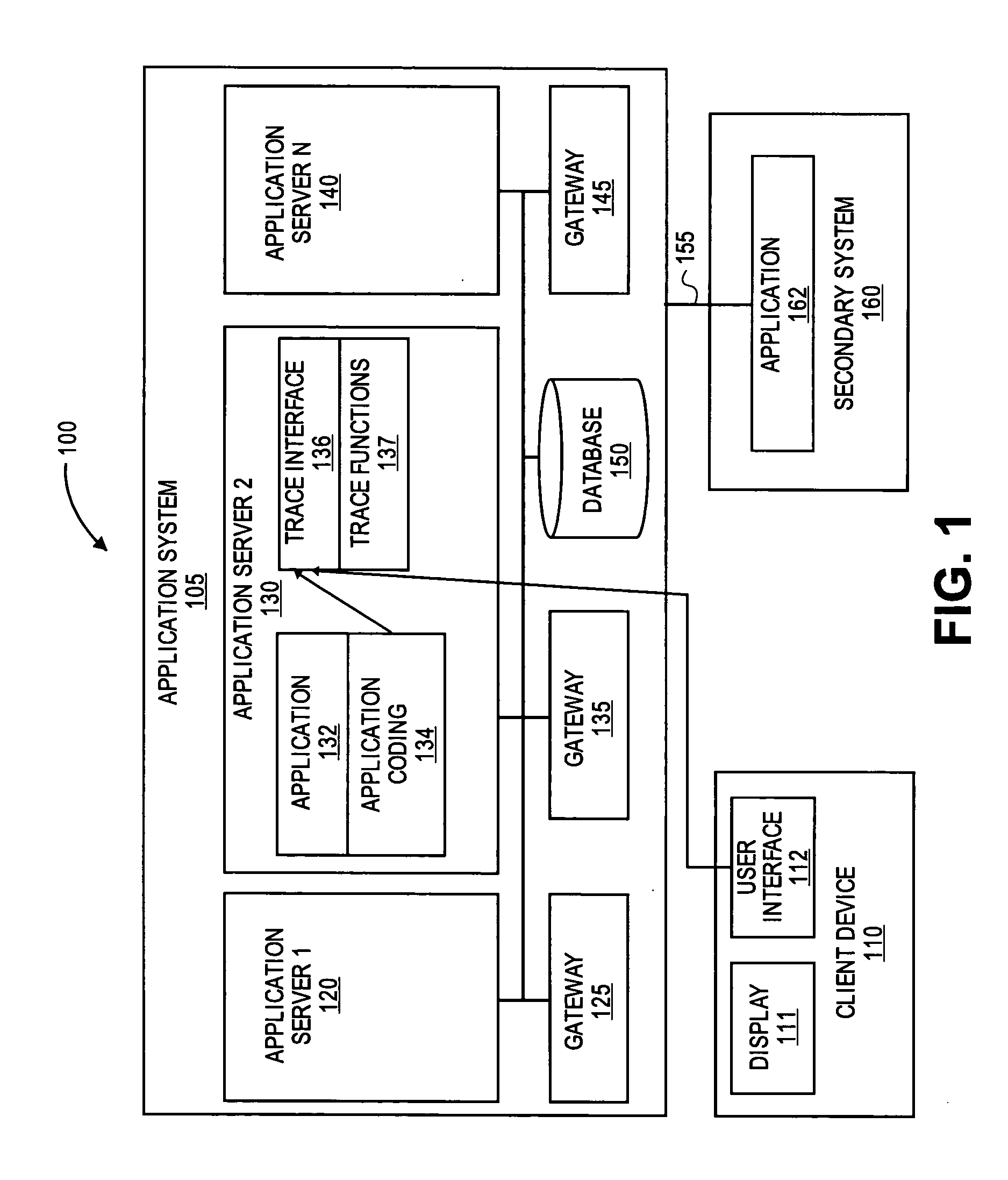
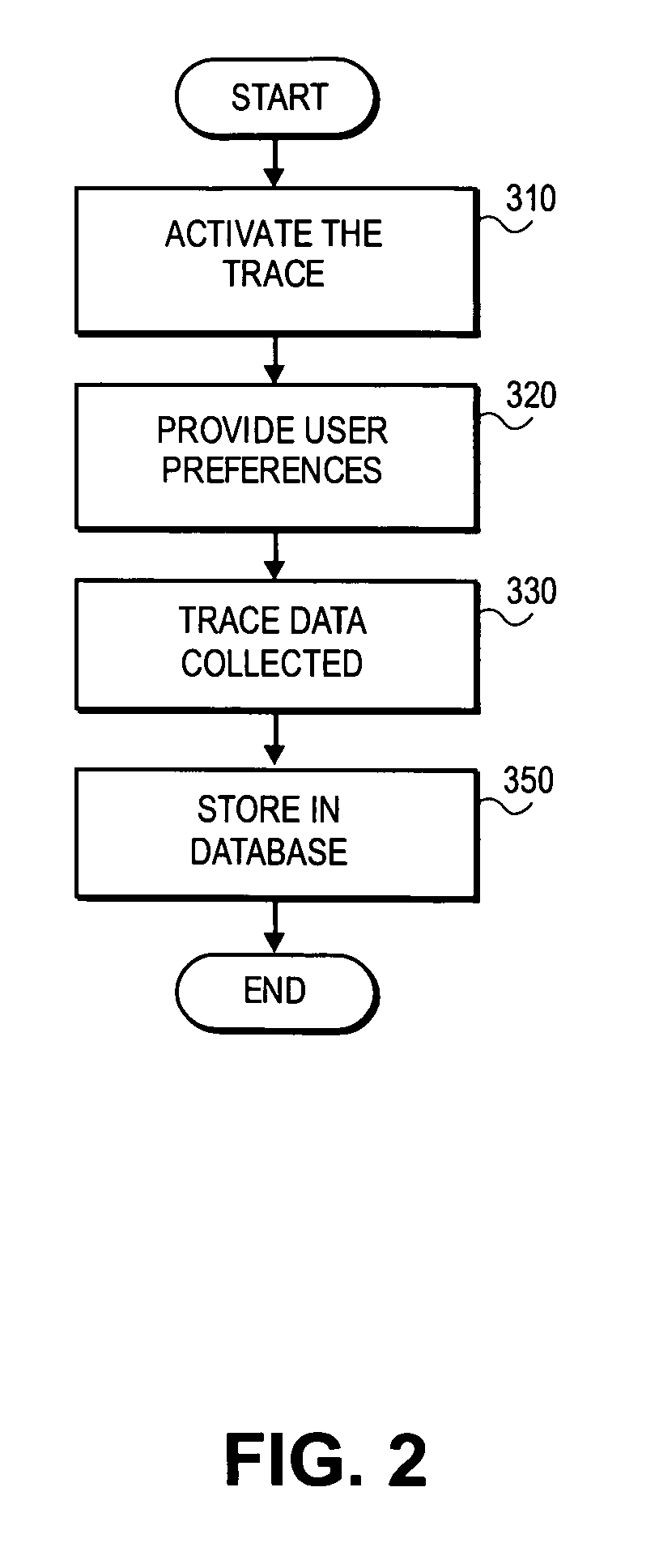
Application trace for distributed systems environment
InactiveUS20070143795A1Television system detailsError detection/correctionWeb browserEnterprise services
Methods and systems are provided for making application trace data for a local system available to others within an enterprise services network. A user at system remote to the server can specify trace data collection preferences and trace data is collected based on the user preferences. The trace data is stored in a database at the server in a standard format for web browsers and accessible to users of both SAP and non-SAP systems.
Owner:SAP AG
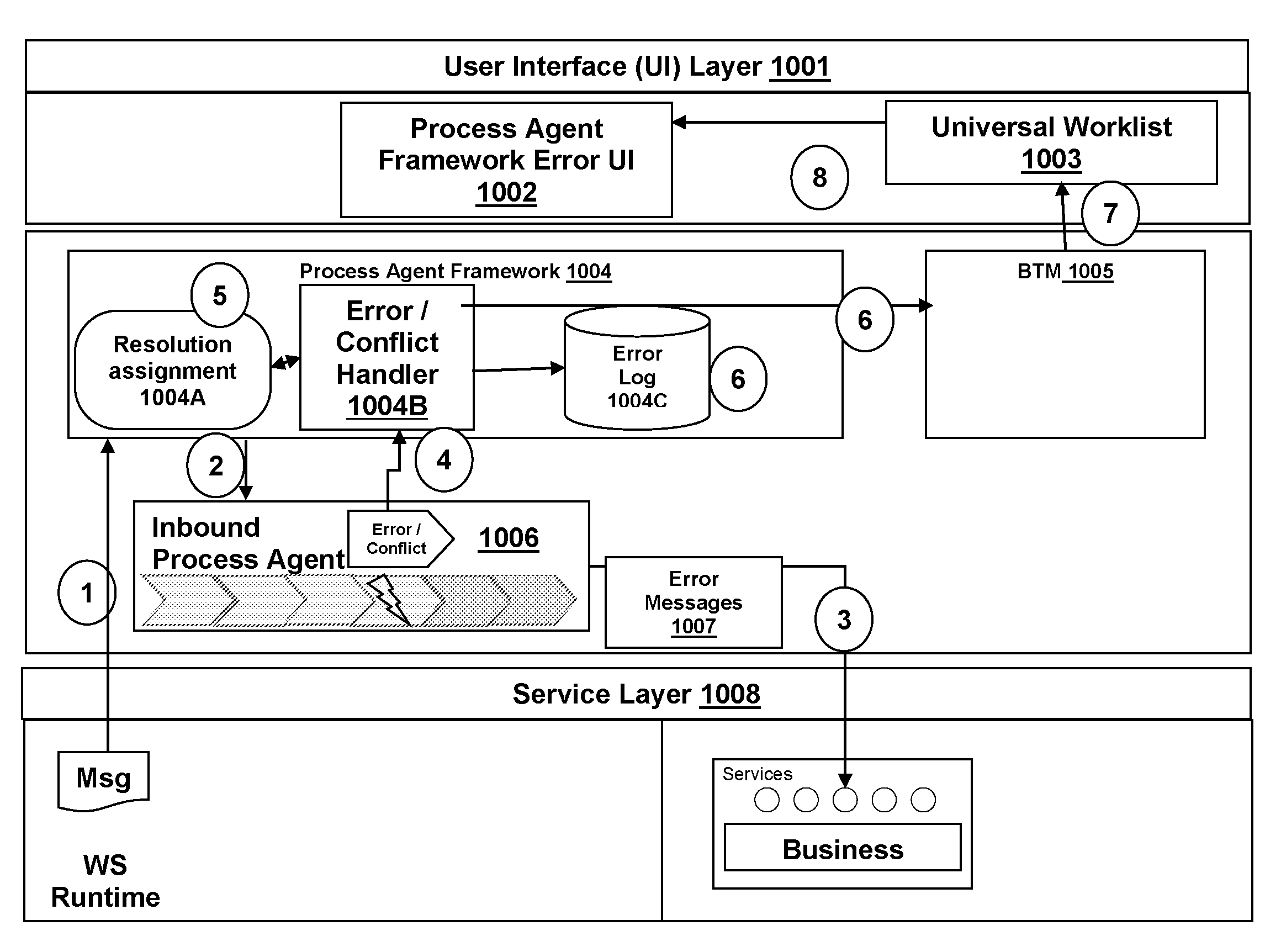
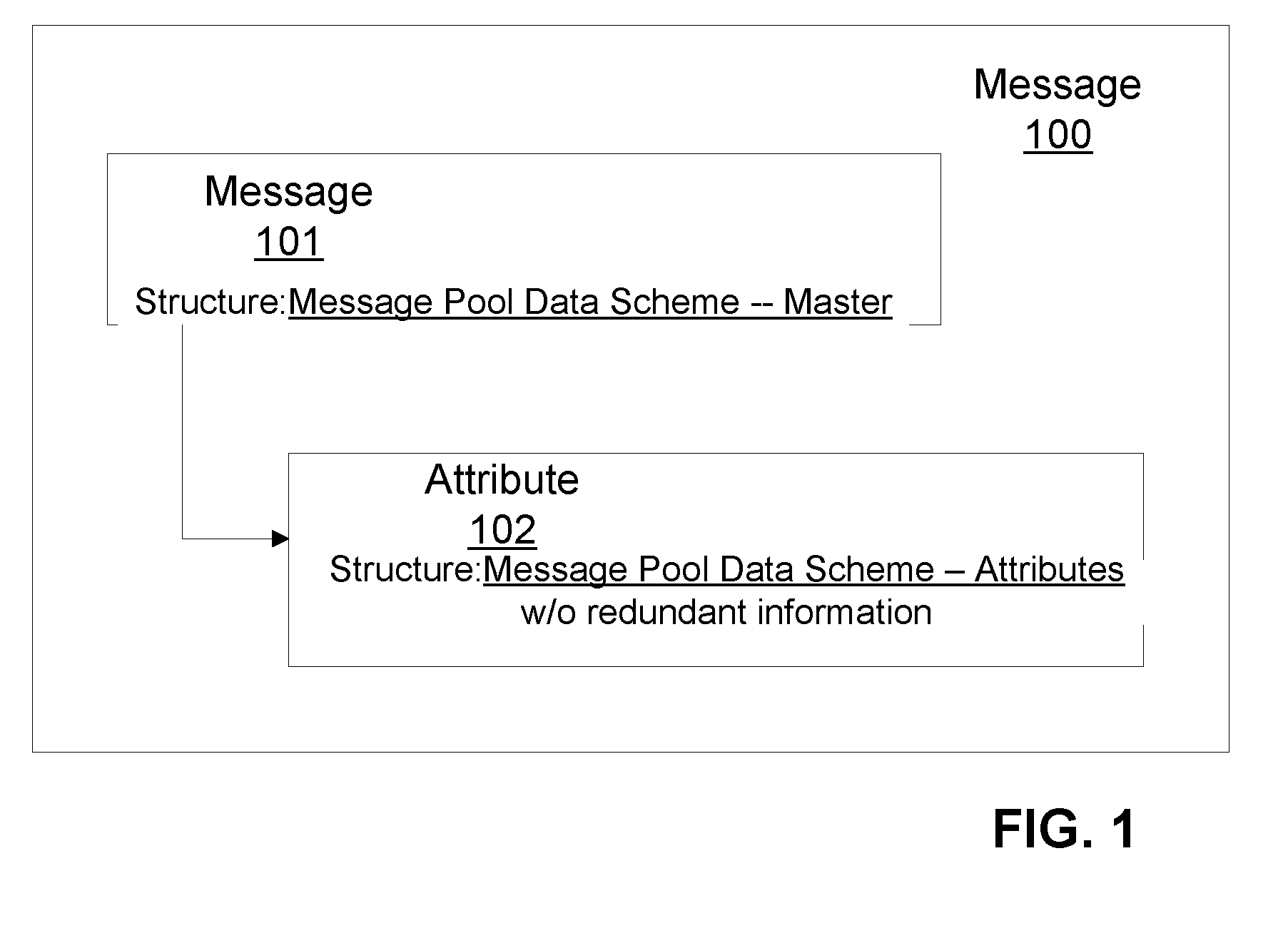
System and method for a message registry and message handling in a service -oriented business framework
InactiveUS20100001834A1Frequency-division multiplex detailsTime-division multiplexRegistry dataMessage handling
A system and method are provided for handling a notification message in an enterprise services framework, including in response to the saving of a transaction, sending a notification message to the enterprise system framework, the notification message containing an associated message class including information of message severity and message symptom. The framework includes a controller layer situated between a service management layer and a business object layer, the controller layer maintaining a message registry database which collects and stores the notification message and the information of message severity, message symptom, and message identification. A system and method is provided for the hierarchical handling of software objects, including providing software objects, each associated with a user interface message, hierarchically associating the user interface messages, and displaying those messages in a tree structure in association with each of the software objects.
Owner:SAP AG
Presence-based hybrid peer-to-peer communications
ActiveUS20070067443A1Improves flow of data trafficReduce loadMultiplex system selection arrangementsSpecial service provision for substationBusiness enterpriseEnterprise services
A method and an apparatus are disclosed for improving the flow of data traffic between clients and servers by determining, in an enhanced hybrid peer-to-peer network, when a client telecommunications terminal should share its data with one or more peers, instead of transmitting that data to the servers. A “super-peer” client terminal in the hybrid peer-to-peer network is responsible for determining when to share data with peers and when to transmit data to the servers. The telecommunications terminal (i) shares data with other terminals when a particular user's presence has changed and (ii) transmits data to the enterprise servers when the overall group's presence that corresponds to the terminal's peer group has changed. The system of the illustrative embodiment aggregates presence and routes communications via peer-to-peer networking, instead of via client-to server-to peer networking, thereby reducing the load on the enterprise servers and lessening the occurrences of single points-of-failure.
Owner:AVAYA INC
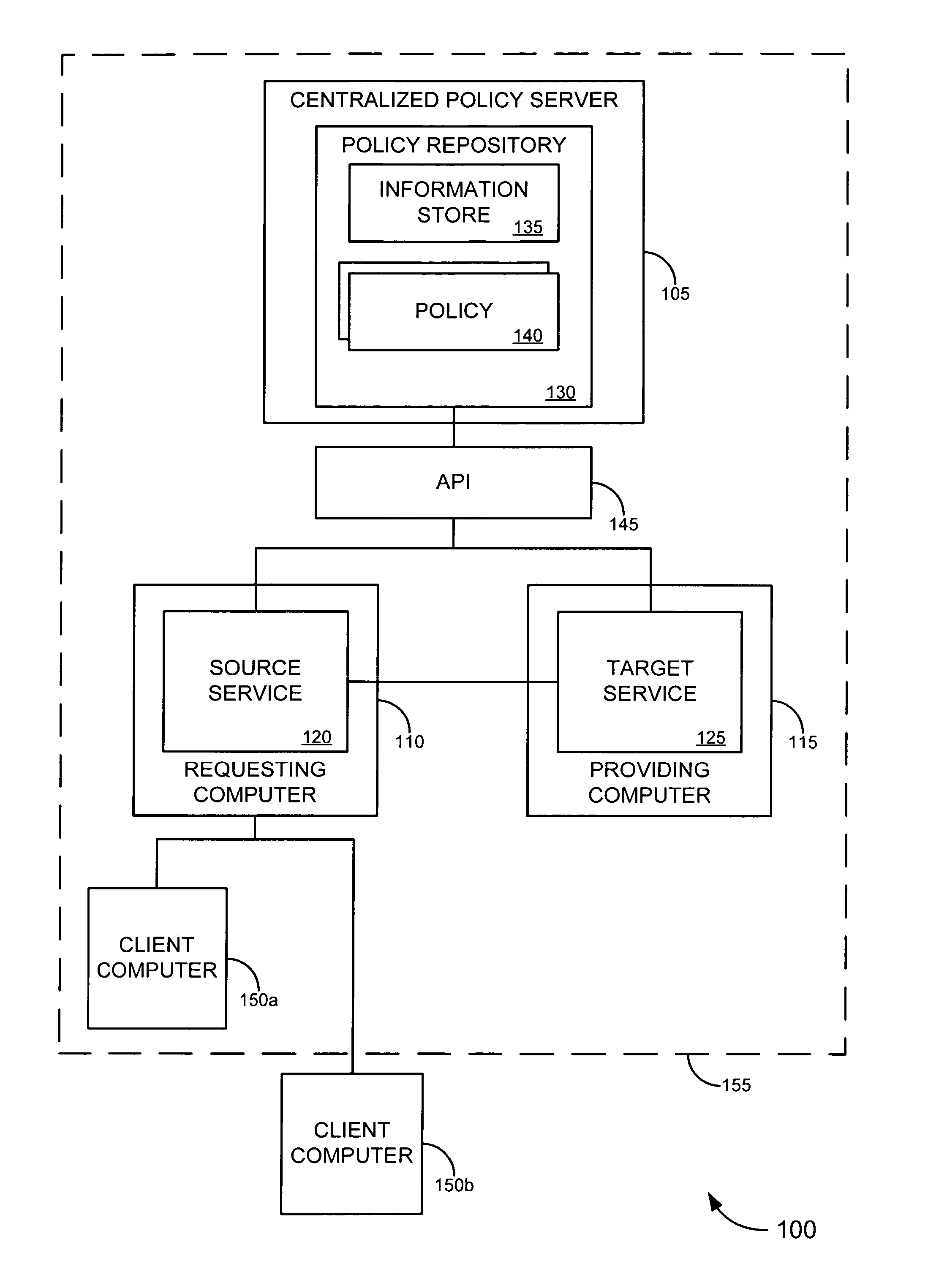
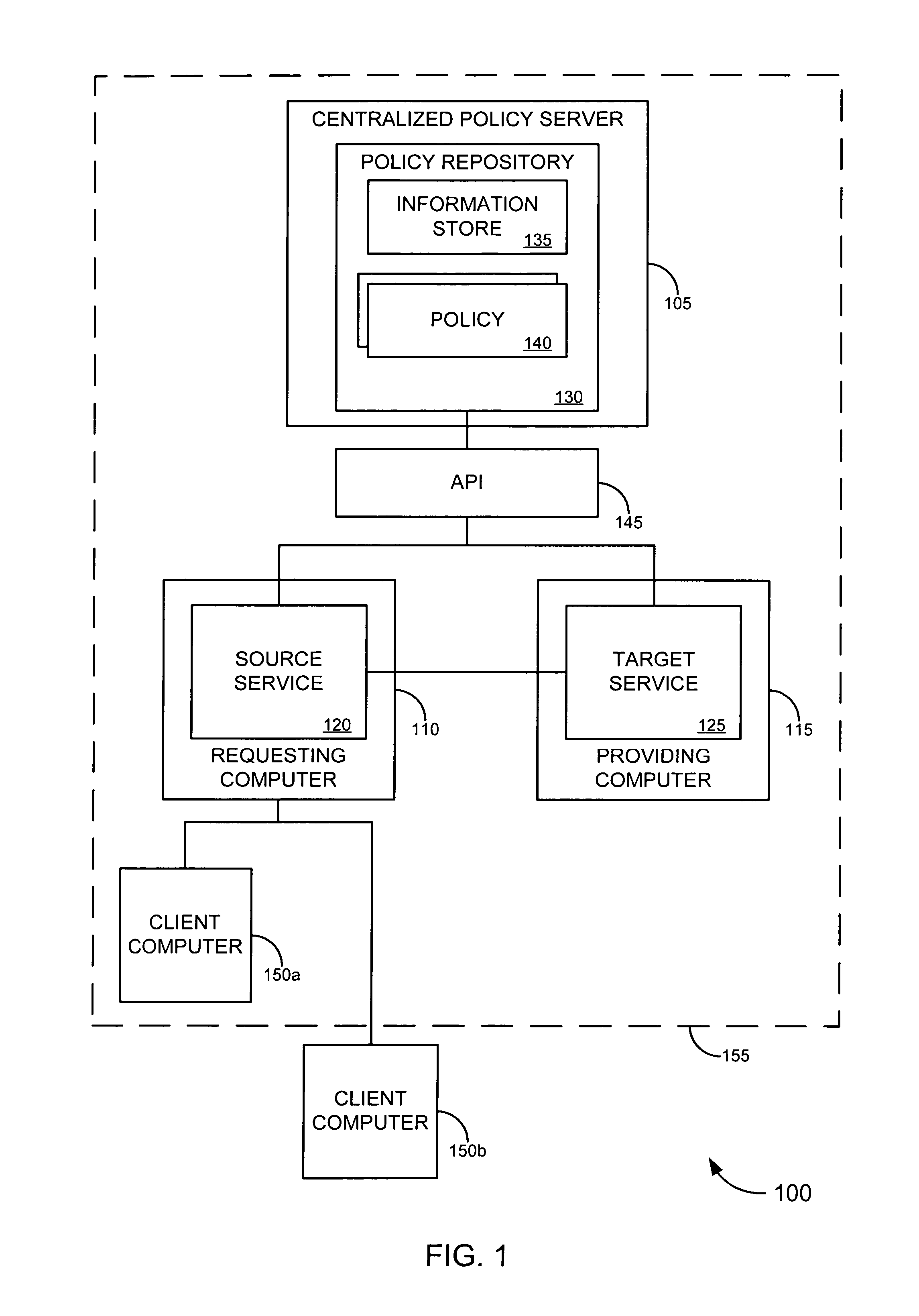
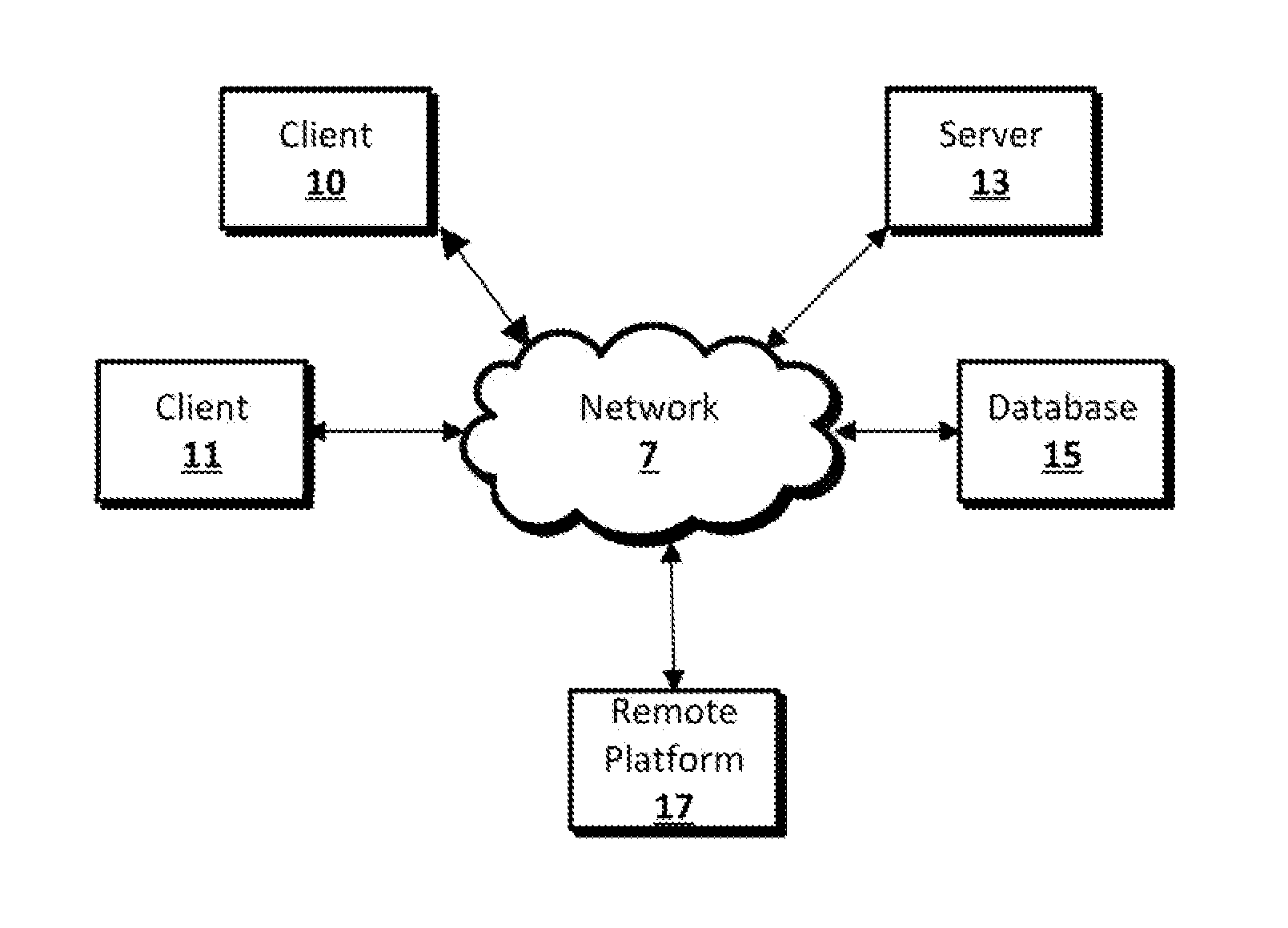
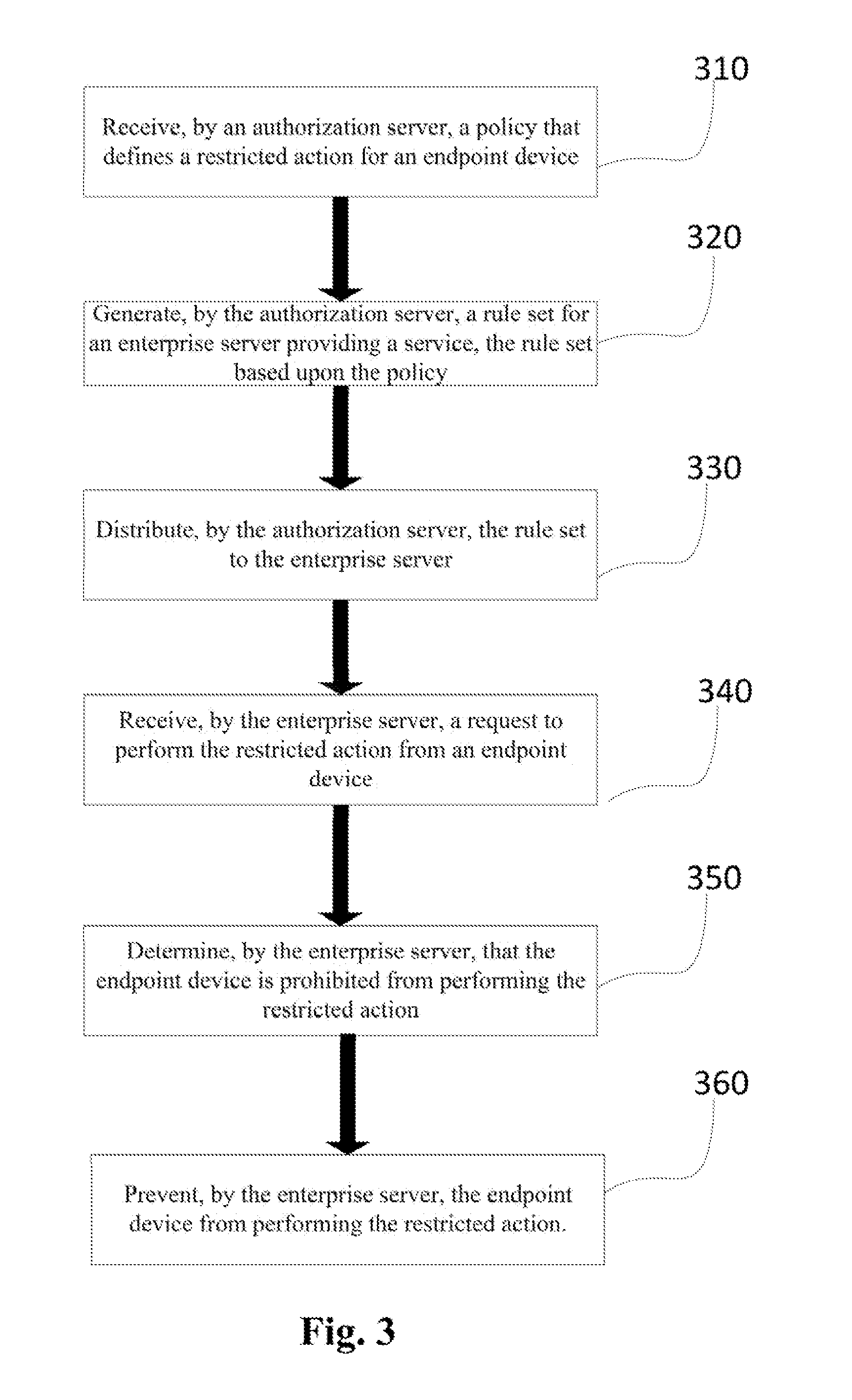
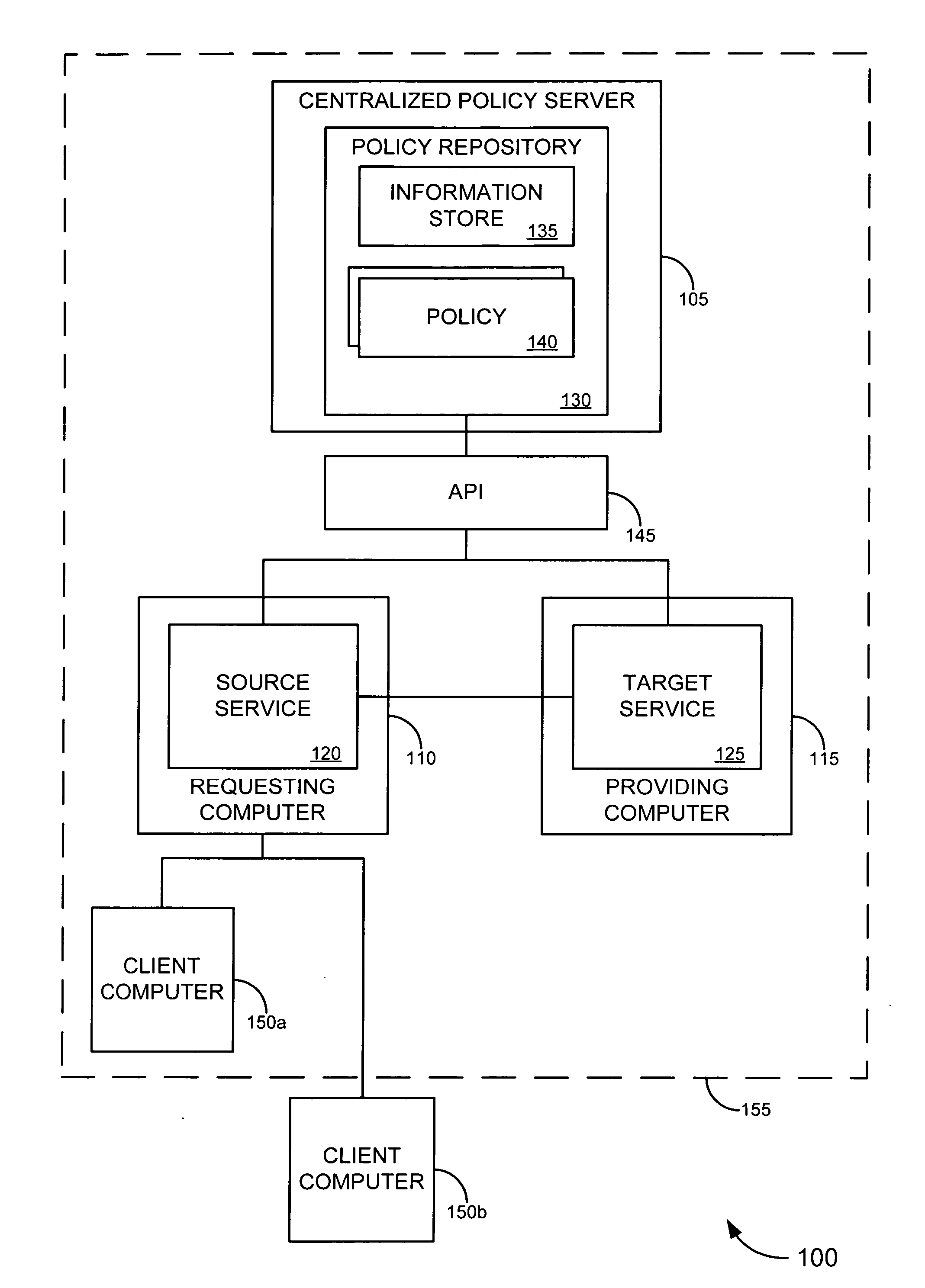
Authorization server access system
Systems and techniques are provided for authorizing restricted action (e.g., data access) requests using a tiered arrangement. A rule set is generated based on a policy received by an authorization server and is transmitted to a broker associated with an enterprise server. A restricted action request is received by an agent associated with the enterprise server and is provided to the broker associated with the enterprise server. The broker analyzes the request in view of the rule set and determines if the restricted action request should be granted or denied. The policy and / or rule set are updated based on activities and / or events within the system and a new rule set is generated based on the updated policy.
Owner:CA TECH INC
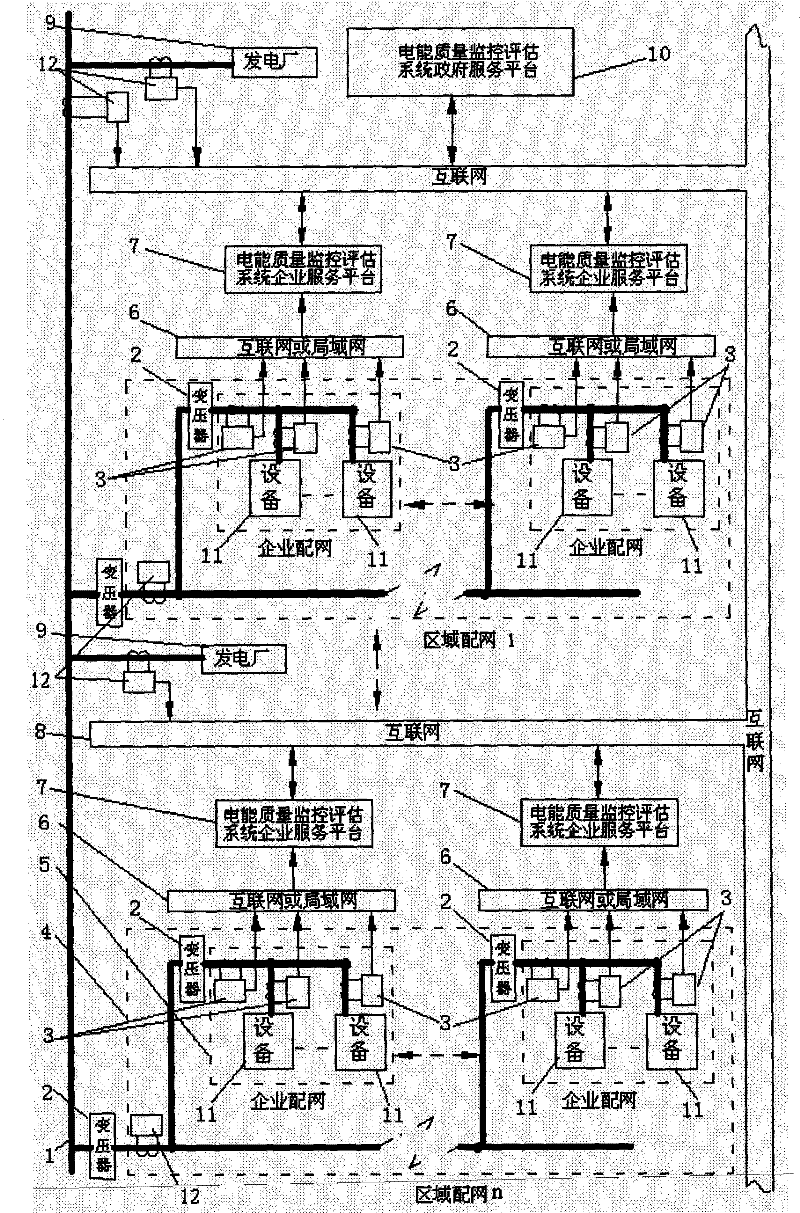
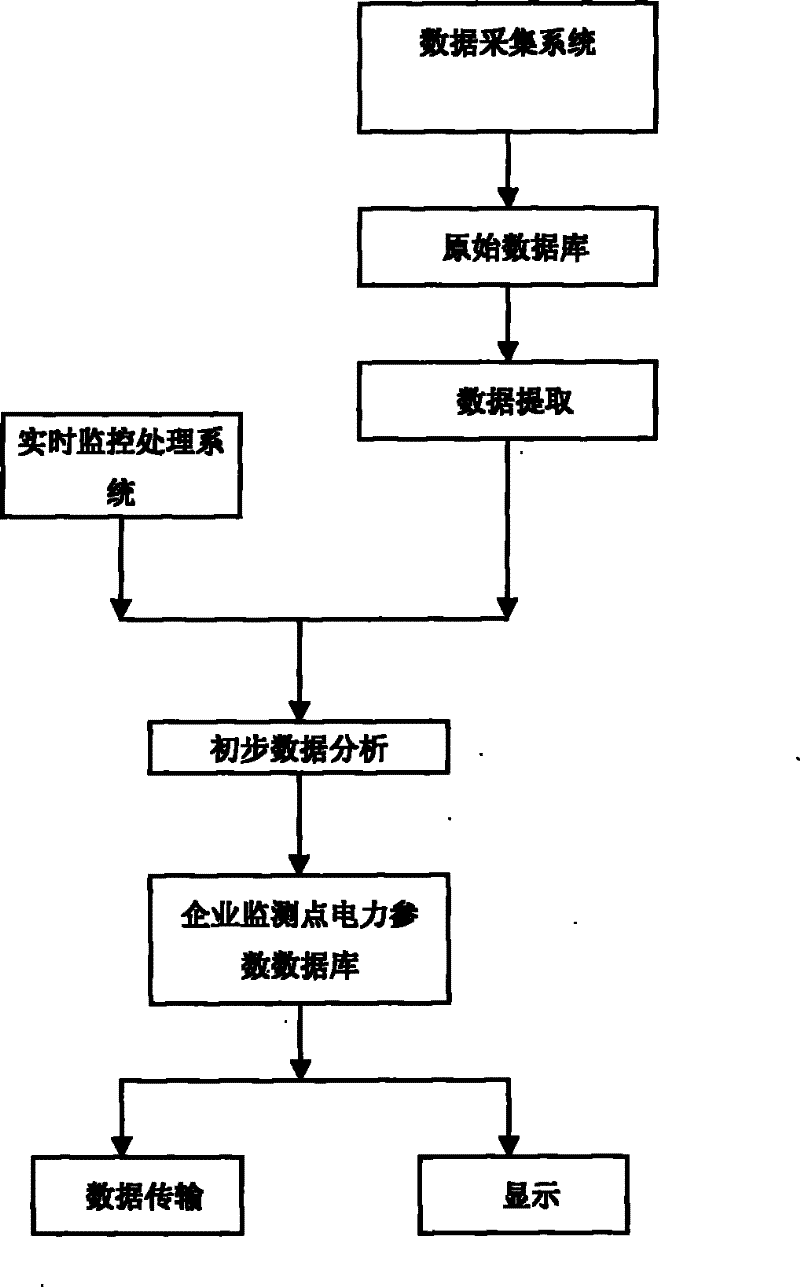
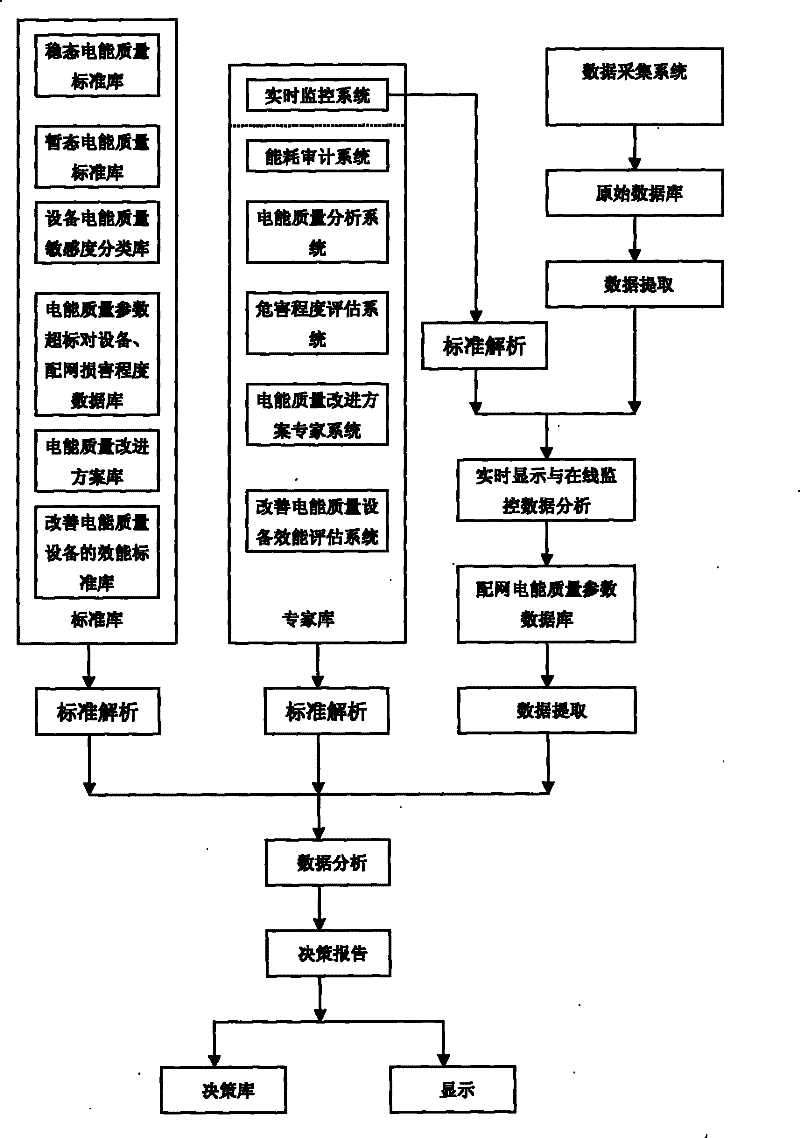
Electrical energy quality monitoring and evaluating system
InactiveCN101750561ARealize real-time monitoring functionTimely governanceSpectral/fourier analysisCurrent/voltage measurementPower qualityTransient state
The invention discloses an electrical energy quality monitoring and evaluating system, which comprises a plurality of electrical energy monitors, a communication network, a plurality of enterprise service platforms and a government service platform, wherein the enterprise electrical energy monitors are connected to the enterprise service platforms through the communication network, and the independent electrical energy monitors and the enterprise service platforms are connected with the government service platform through the communication network; the enterprise service platforms are used for receiving basic electric power parameters acquired by the enterprise electrical energy monitors at monitoring points inside the enterprises, displaying the change conditions of the electric power parameters of enterprise distribution networks, and transmitting data to the government service platform at certain time intervals; and the government service platform is used for receiving the electric power parameters of the enterprise distribution networks transmitted by the enterprise service platforms and the parameters transmitted by the independent electrical energy monitors at the monitoring points in the regional distribution networks, and performing energy consumption audit, transient and stable electrical energy quality analysis, electrical energy quality level evaluation, harm extent evaluation and evaluation of providing the corresponding electrical energy quality improvement scheme and electrical energy quality improvement effect.
Owner:SUZHOU TAIGU ENERGY MANAGEMENT
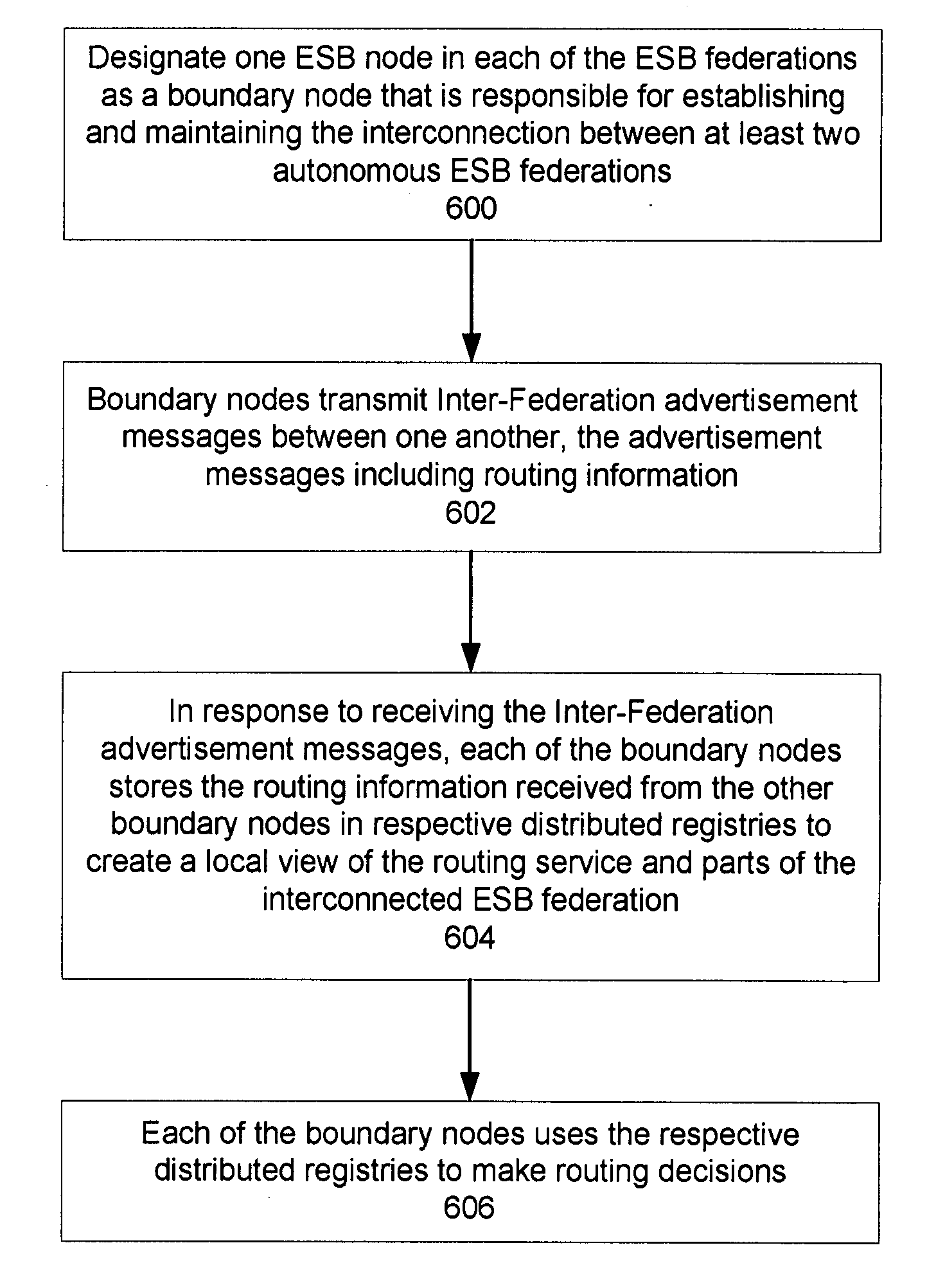
Protocol for enabling dynamic and hierarchical interconnection of autonomous federations of enterprise service buses
InactiveUS20090077251A1Multiple digital computer combinationsTransmissionRouting decisionInterconnection
In a method and system for creating an interconnection between autonomous enterprise service buses (ESB) federations, each one of the ESB federations comprise at least one ESB deployment, which further include a plurality of ESB nodes that provide connectivity to one or more services. According to a protocol, a first ESB node is designated in each of the ESB federations as a boundary node that is responsible for establishing and maintaining an interconnection between at least two of the ESB federations. Advertisement messages are transmitted between the boundary nodes that include routing information. In response to receiving the advertisement messages, each of the boundary nodes store the routing information received from other boundary nodes in respective distributed registries to create a local view of routable service endpoints in the federation. Each of the boundary nodes then use the respective distributed registries to make routing decisions when routing service requests.
Owner:IBM CORP
Enterprise server for communication for a supervisory control and data acquisition (SCADA) System
An enterprise server for communication for a supervisory control and data acquisition (SCADA) system, comprising: configurable server software running on memory in a computer; a configurable server interface adapted to receive at least one client request from at least one client application for specific device status data and providing those requests to the server software; a configurable protocol interface with the server software for building a message for the specific device using a device protocol; a configurable connection interface for connecting to the specific device and enabling the message to be transmitted to the specific device and receiving the specific device status data from the specific device and transmitting the status data to the server interface using the device protocol; and caching the status data on the memory in the computer as cached data from the configurable server interface.
Owner:DOUGLAS C OSBURN III +1
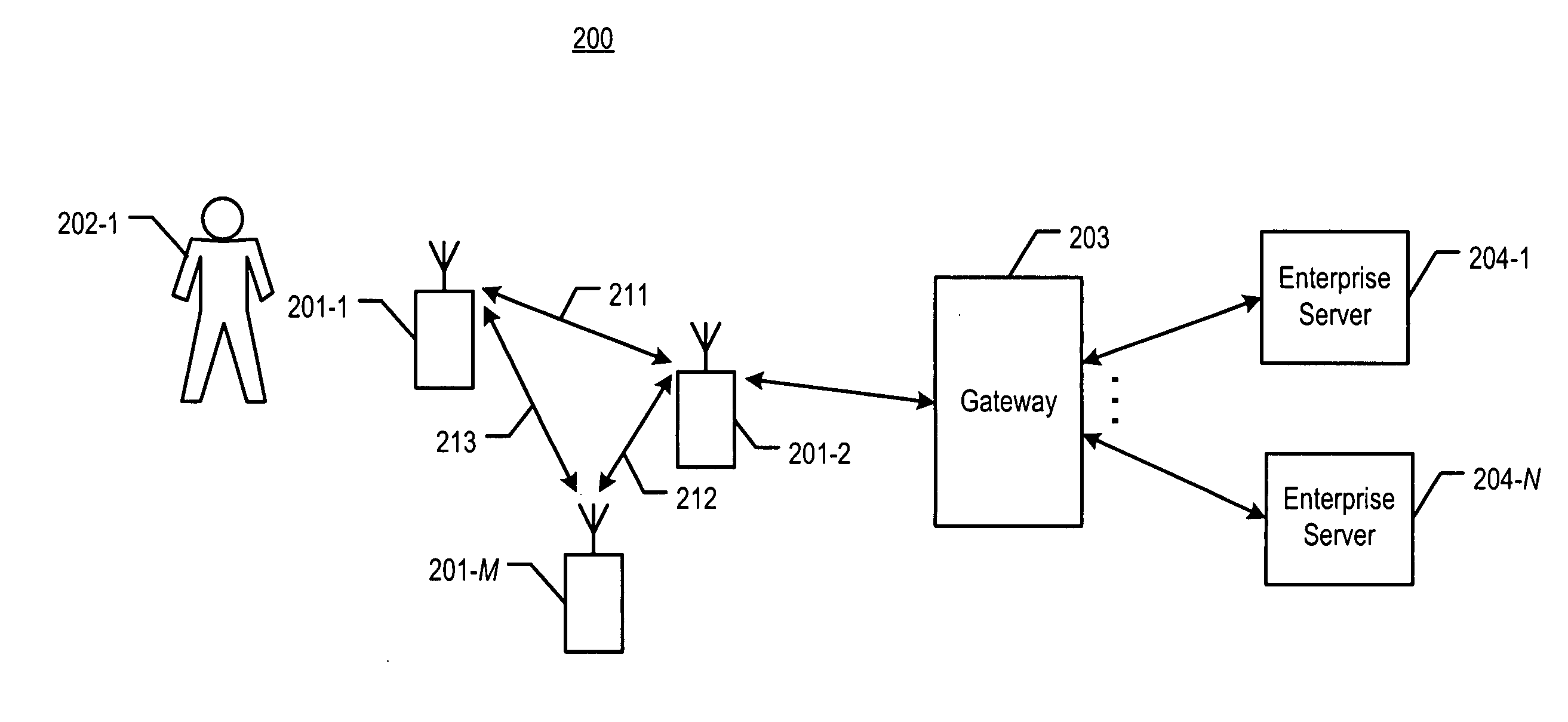
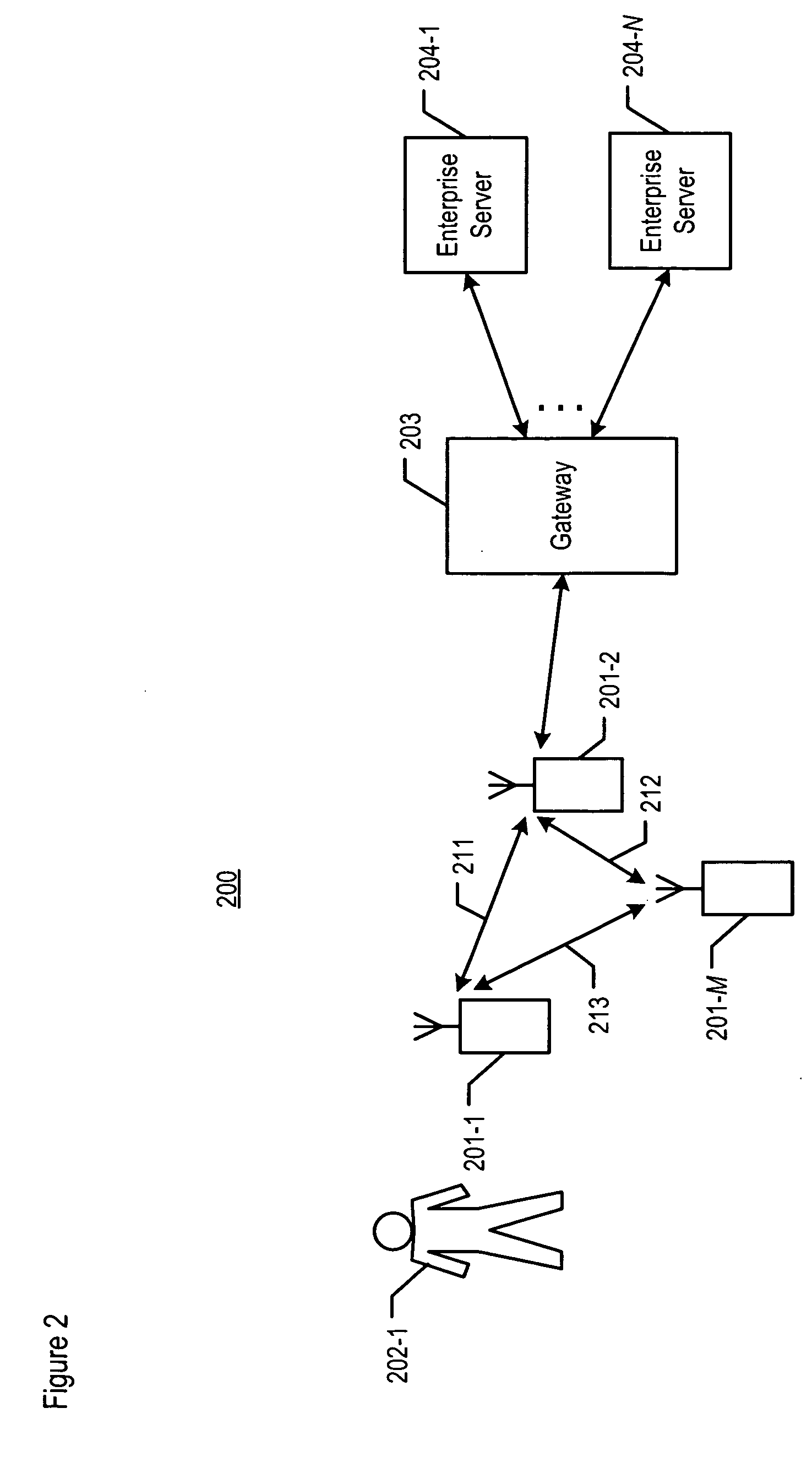
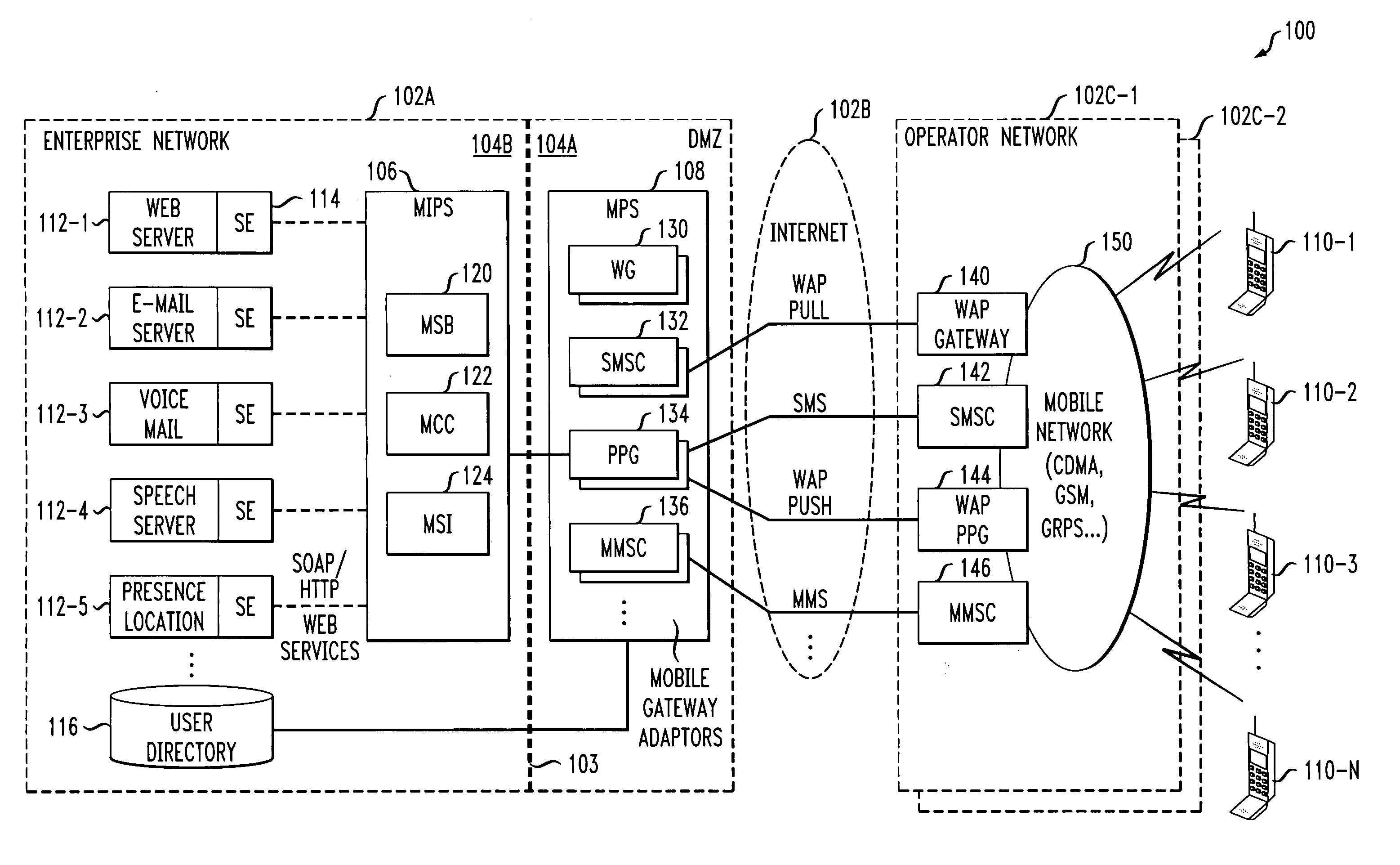
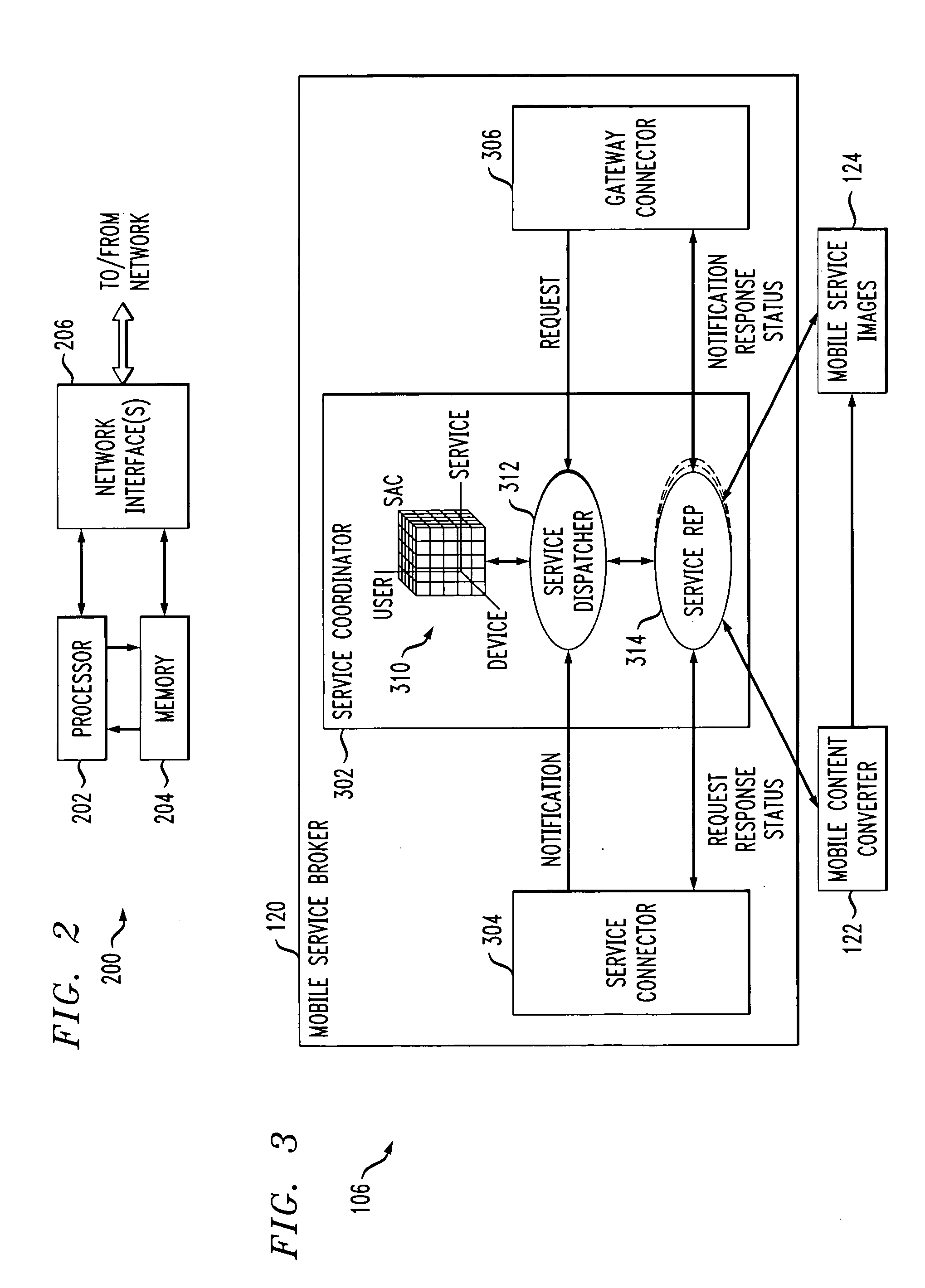
Mobile gateway for secure extension of enterprise services to mobile devices
ActiveUS20050266836A1Unauthorised/fraudulent call preventionDigital data processing detailsCommunications systemEnterprise services
Controlled access to enterprise services is provided for a mobile device in a communication system, via a mobile gateway having a first server and a second server. The first server of the gateway is arranged behind a firewall of the enterprise network and is coupled between the second server and one or more enterprise servers of the enterprise network. The second server is arranged in front of the enterprise firewall and is configured for communication with an operator network associated with the mobile device. The gateway controls interaction between the mobile device and the one or more enterprise servers such that access to one or more associated enterprise services is provided in a secure manner.
Owner:AVAYA INC
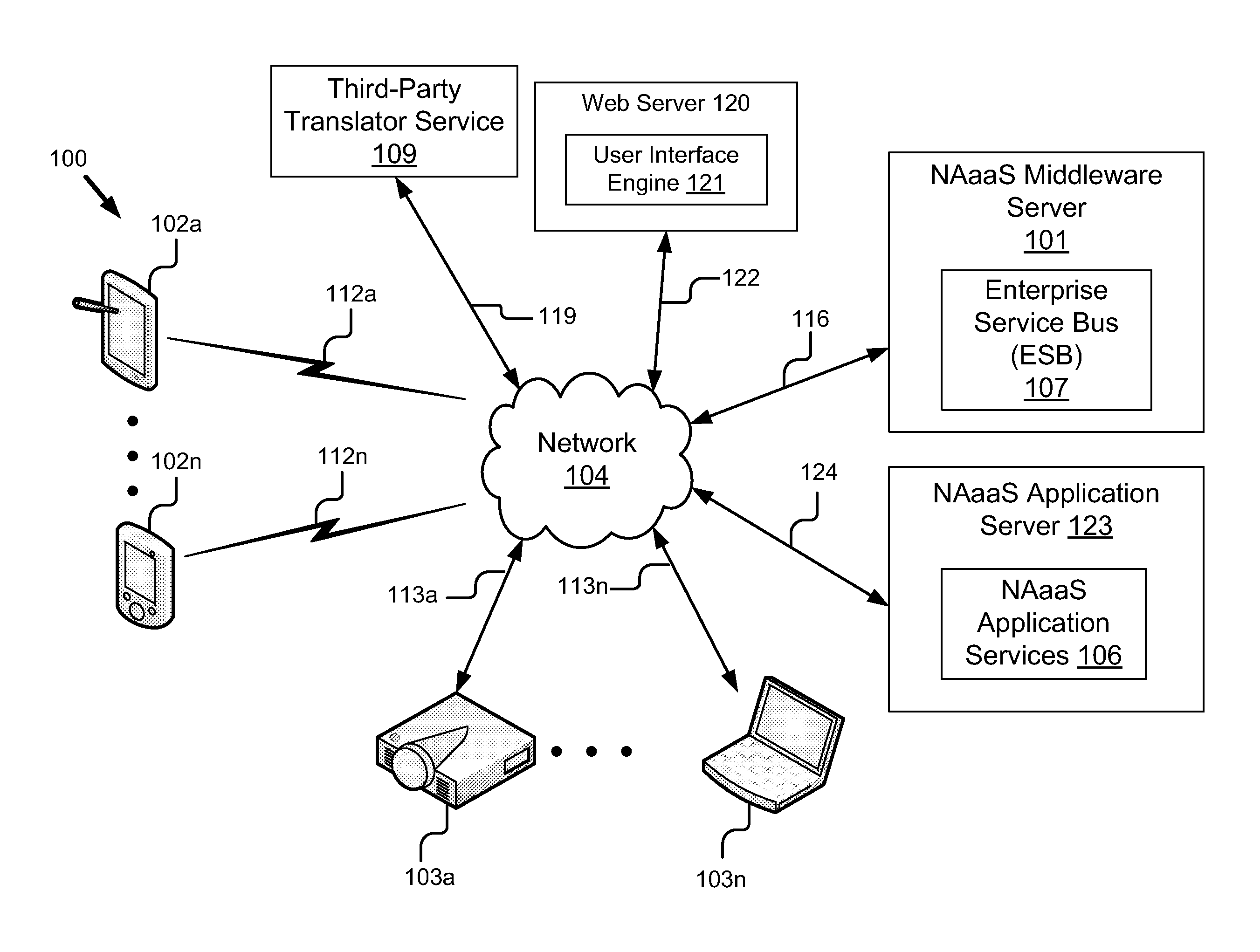
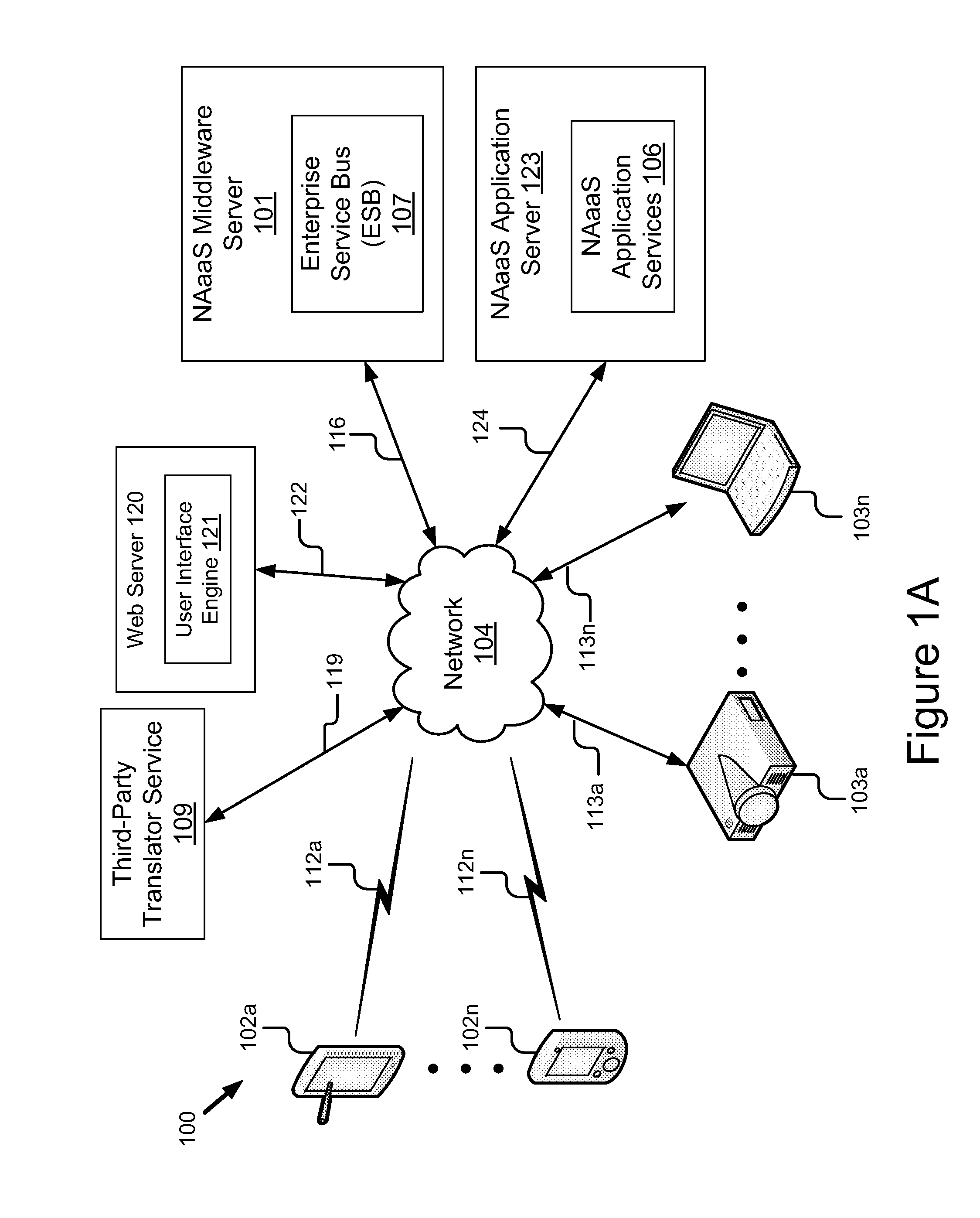
System and Method for Translating Content between Devices
ActiveUS20140157113A1Overcome deficienciesNatural language translationSpecial data processing applicationsEnterprise servicesApplication software
A system and method for translating and reformatting content are described. The system includes an enterprise service bus configured to receive a request from a first device to transmit media to a second device, the media including content in a first language. The system also includes network appliance as a service server-side application including a translation service and a formatting service. The translation service receives the request from the enterprise service bus, determines a second language for translation, determines the content for translation and translates the content to the second language. The formatting service generates a new version of the media including the content in the second language, the new version being formatted in a layout similar to an original version of the image. The enterprise services bus transmits the new version of the media to the second device for display.
Owner:RICOH KK
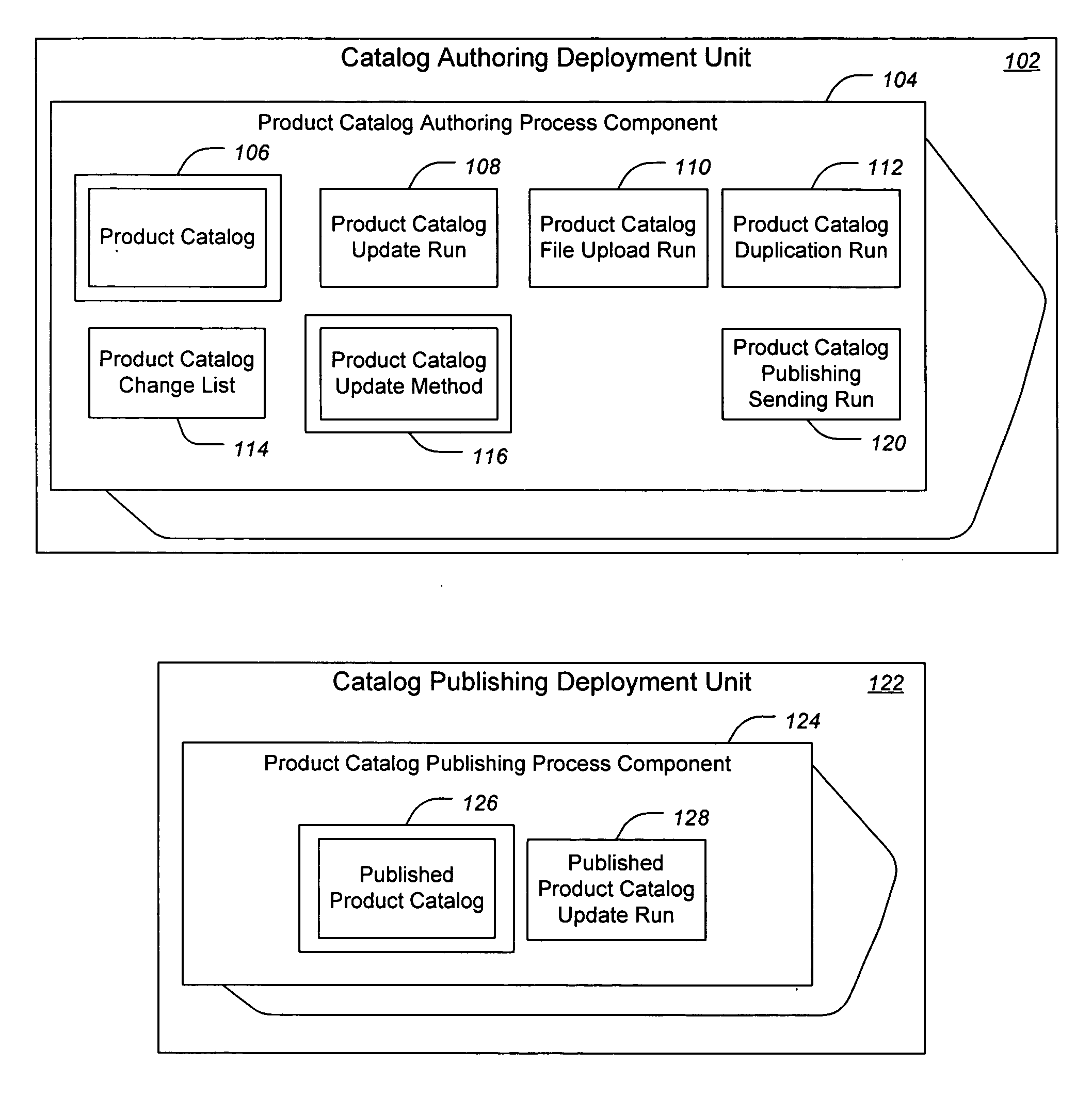
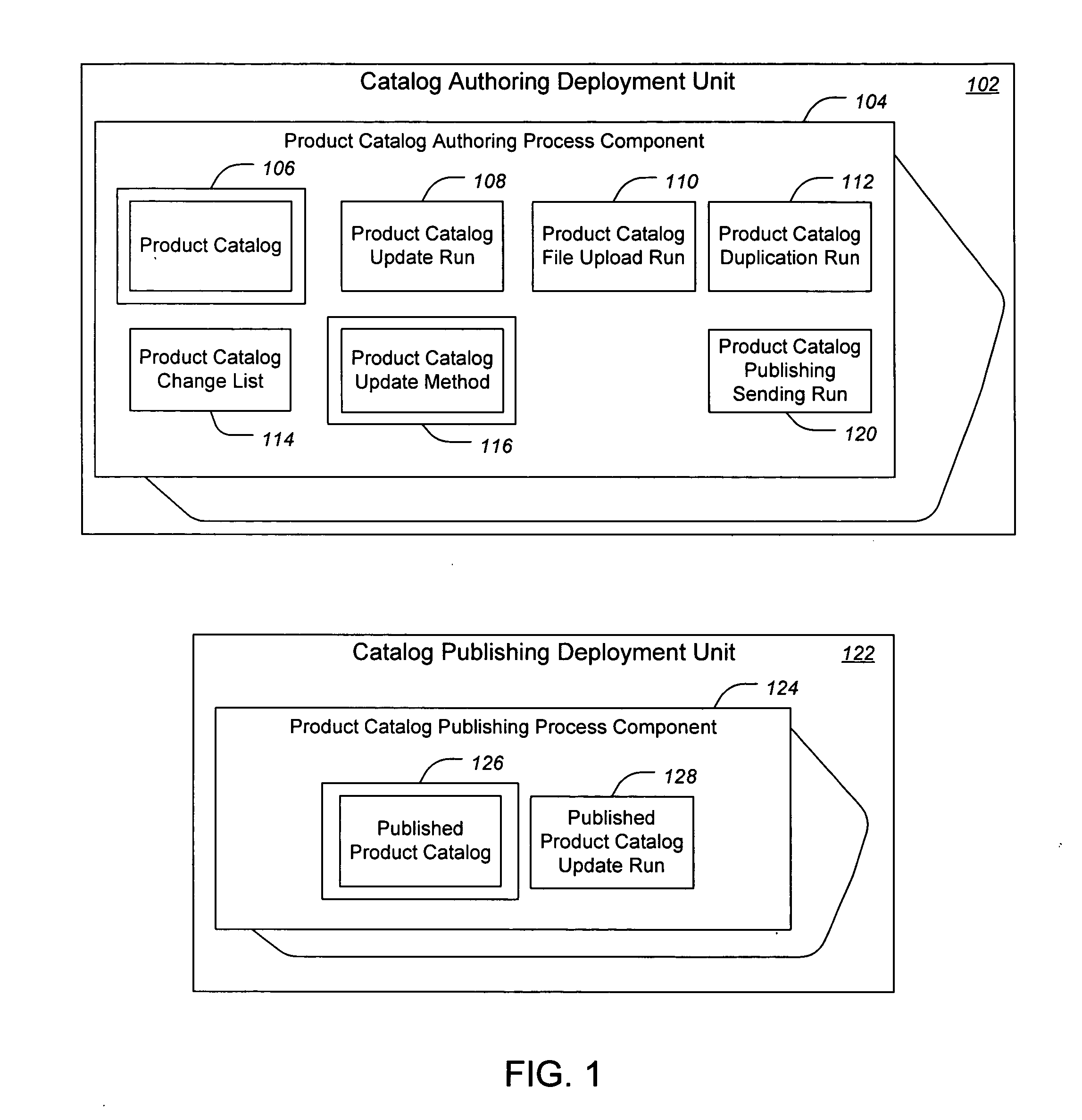
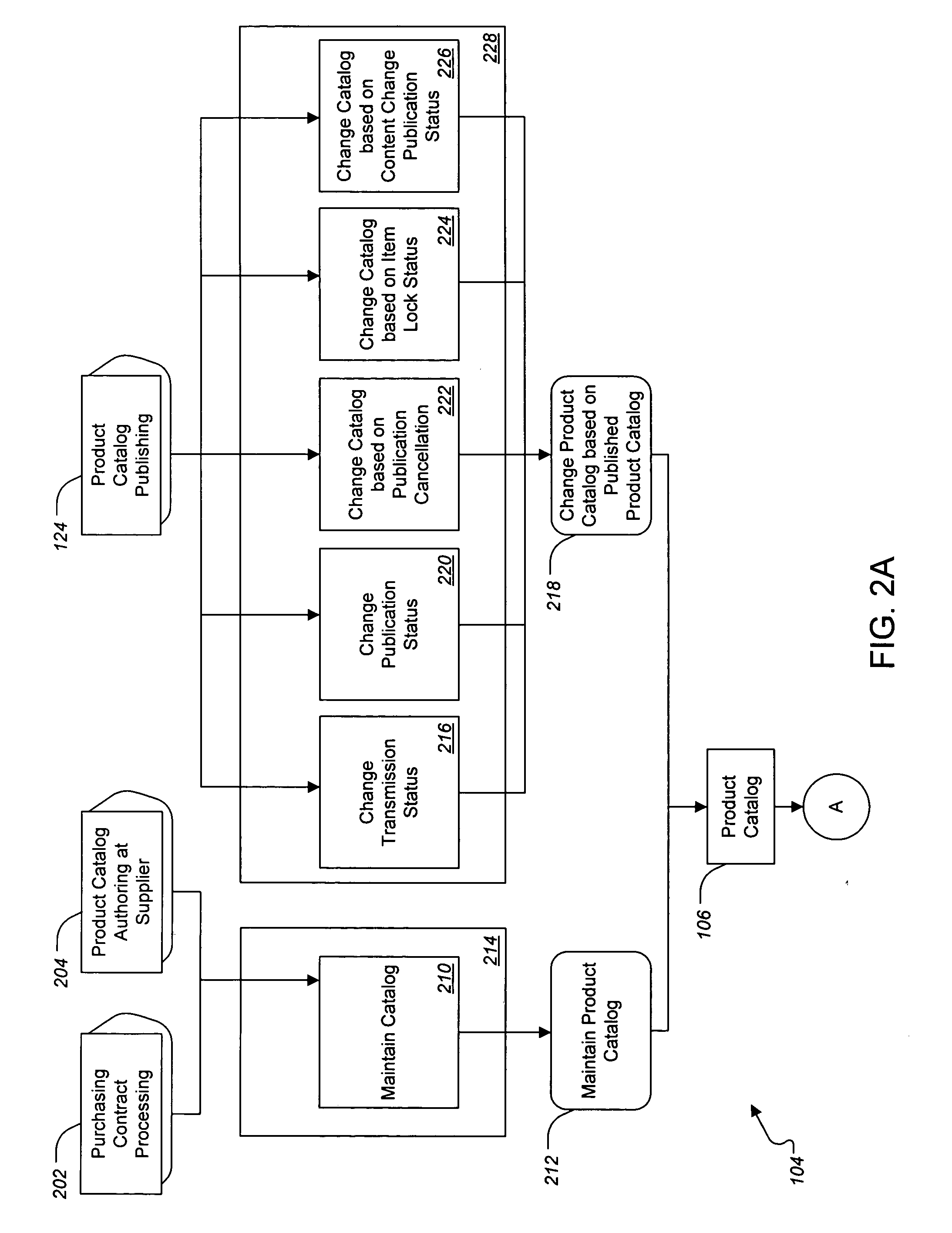
Providing product catalog software application as enterprise services
ActiveUS20070233581A1Reliable implementationDesigned can be scalableBuying/selling/leasing transactionsSpecial data processing applicationsEnterprise servicesApplication software
Methods and apparatus, including systems and computer program products, for a services architecture design that provides enterprise services having product catalog functionality at the level of an enterprise application. The design includes a set of service operations, process components, and optionally deployment units. Suitable business objects are also described.
Owner:SAP AG
Enterprise mobility
ActiveUS20080144637A1Efficient and effectiveGood serviceUser identity/authority verificationData switching by path configurationApplication serverEnterprise services
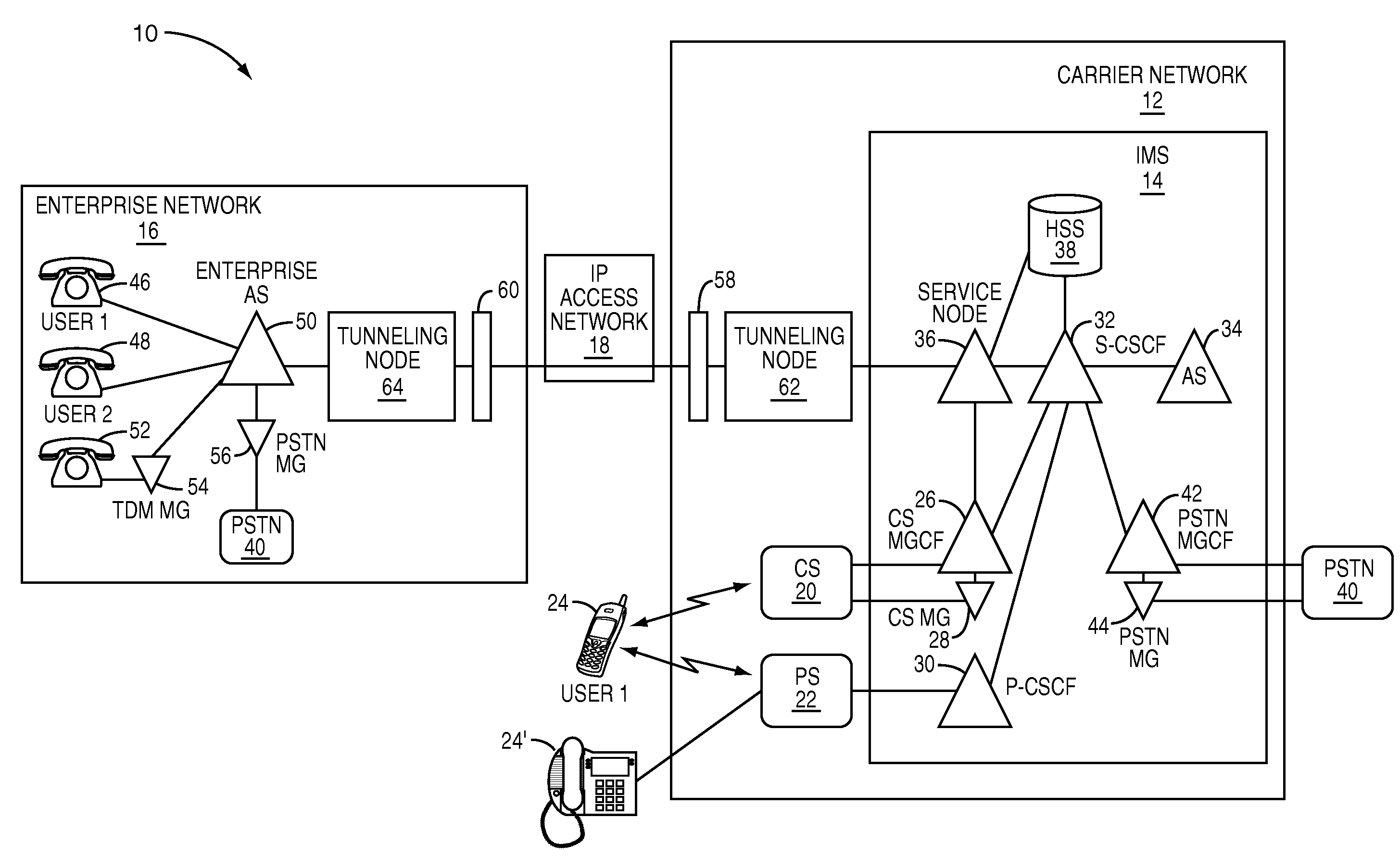
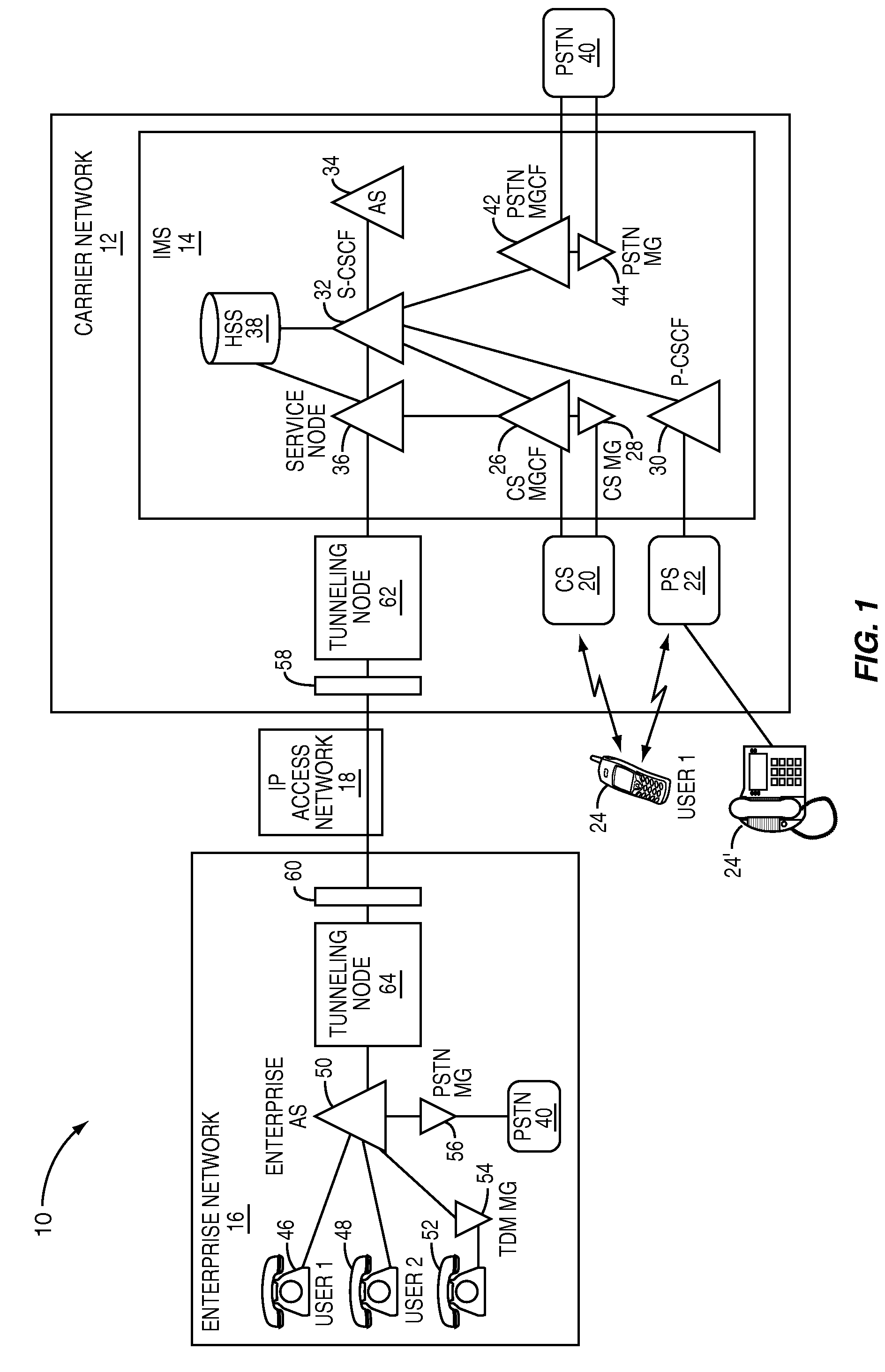
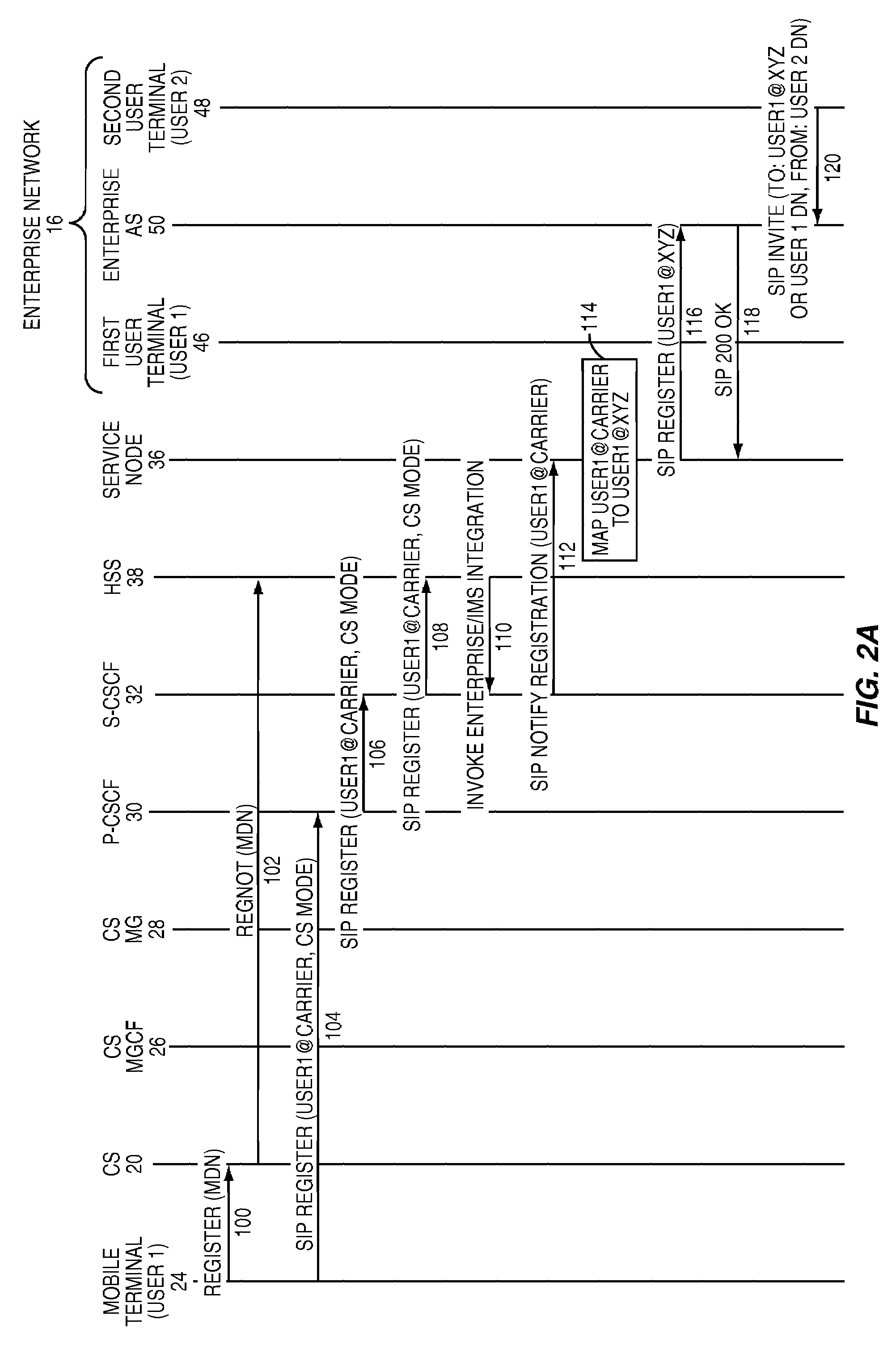
The present invention provides a service node, which extends the services of a carrier's multimedia subsystem (MS), such as an IP multimedia subsystem (IMS), to enterprise networks in an efficient and effective manner. As such, MS subscribers gain access to enterprise services in addition to the carrier's services provided via the carrier's circuit switched subsystems (CS) and packet subsystems (PS). The service node acts as a liaison between enterprise application servers and the MS, such that the enterprise application servers appear as MS application servers to the MS. The service node provides user identifier and protocol translation between enterprise and MS user identifiers and protocols, respectively. As such, enterprise application servers can access the MS as well as be accessed by the MS to support user mobility, with continuity of services, between the enterprise and carrier networks.
Owner:GENBAND US LLC
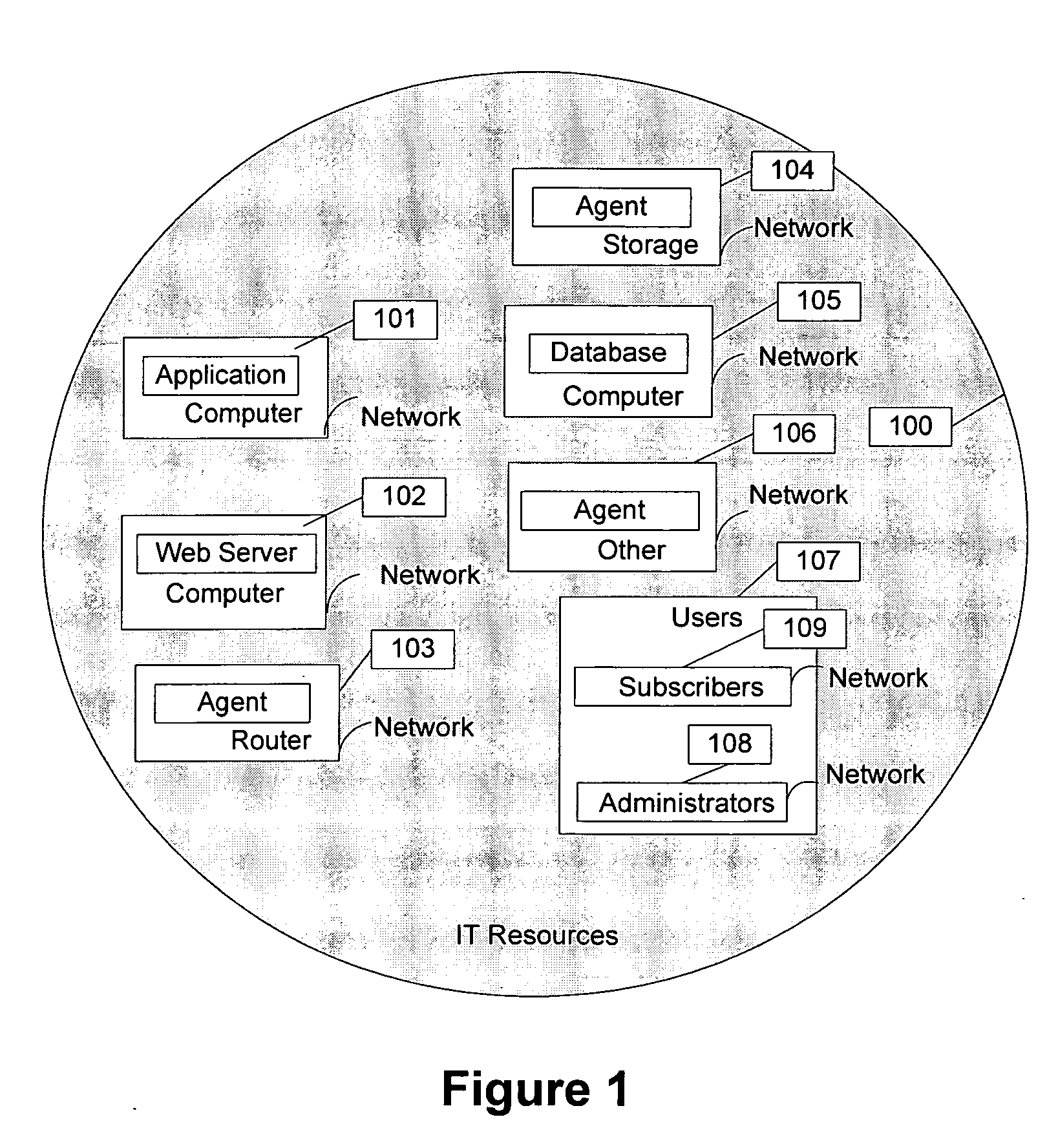
Enterprise service management unifier system
InactiveUS20080021918A1Improve scalabilityLong-term viabilityDigital computer detailsWebsite content managementService-level agreementWeb service
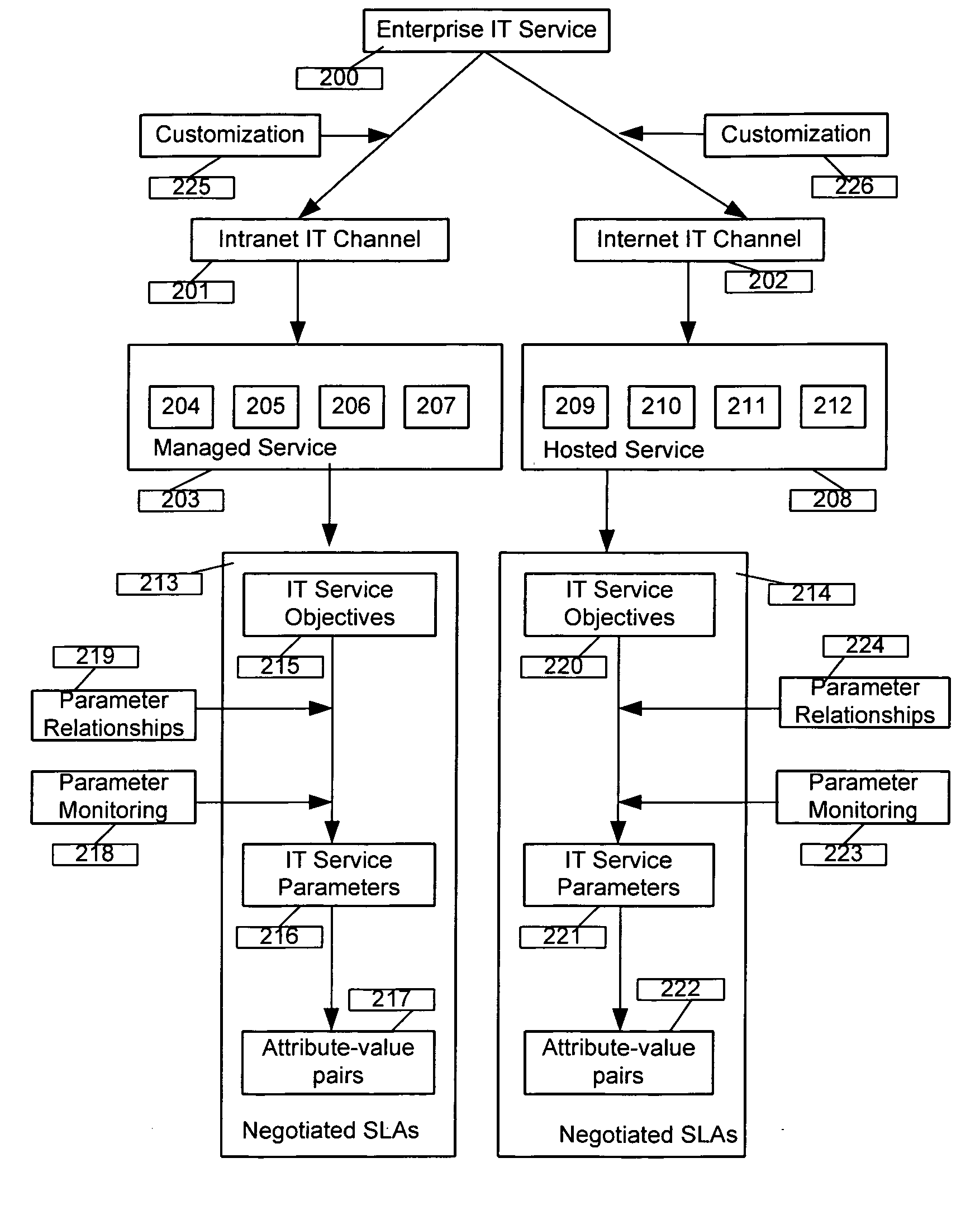
The invention is directed to an architecture and method for managing multiple resources and services in an Information Technology (IT) environment. The invention particularly provides an enterprise service management unifier system for leveraging and unifying heterogeneous IT resource management systems and their services offered by multiple vendors. The system architecture provides web services based communication framework for one or more producers to publish resource management capabilities as services and one or more consumers to avail published services. The framework consists of service negotiation and customization stacks to discover, negotiate, customize, and manage services based on service level agreements mutually acceptable between producer and consumer. Layered stacks allow state persistence with additional flexibility to reengineer services in modular fashion. The method includes steps to build consumer services by accessing one or more producer services, grouping producer managed resources into logical service channels, customizing channel resource parameters, and aggregating channels into enterprise IT services. Method also includes techniques to inspect events generated by producer service(s), correlate events based on rules, and forward events to appropriate users and enterprise service components.
Owner:RAO VISWANATHA HEMOJI
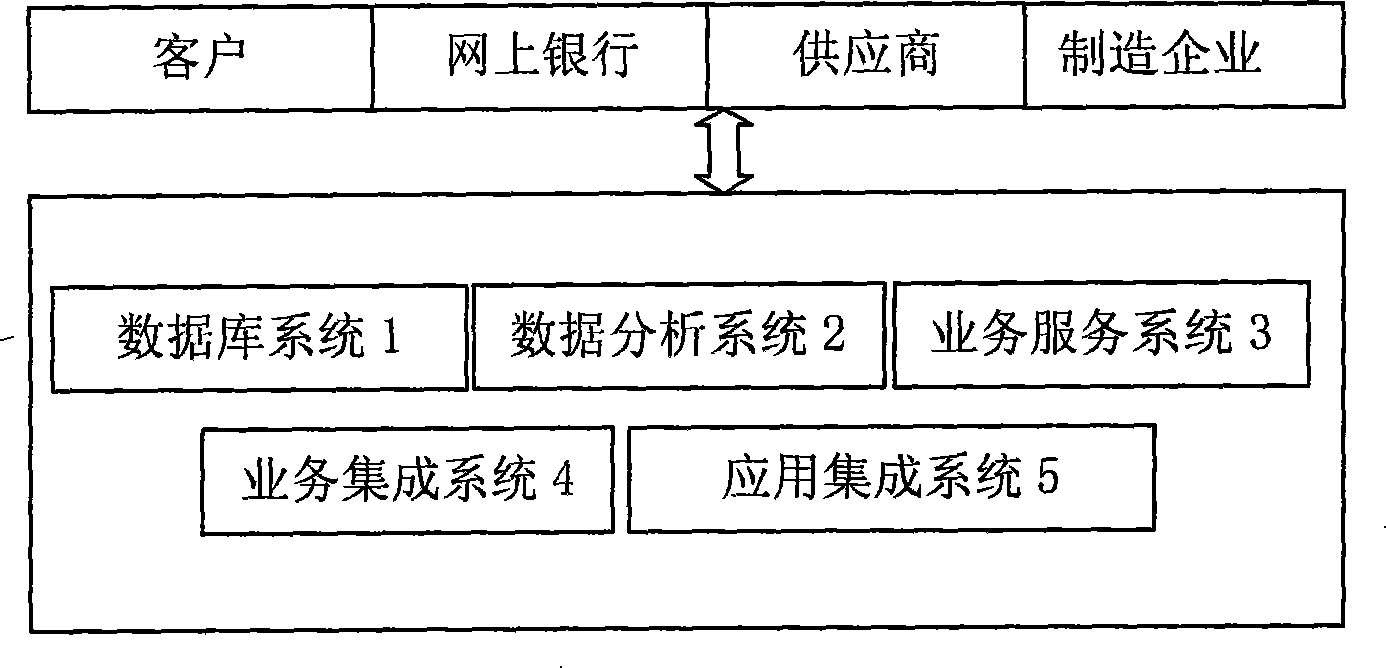
Public platform of collaborative electronic commercial system oriented to business service
A public platform facing synergic electronic business system with database system for collection, calling and storage data, the data analysis system abstracting, classifying and analyzing and digging the data, providing data to the service system, which receives the data for service processing and sealing each service for management, service accumulation system integrating the system organically, realizing the exchange accumulation of the electronic business application system that integrate the basic structure platform of the enterprise service, basic service component, specific service module. It effectively combines the data information, to allow the service exchange of manufacturing enterprise, customer, supplier and bank to improve working efficiency.
Owner:NANJING UNIV OF FINANCE & ECONOMICS
Enterprise service-to-service trust framework
ActiveUS20070118878A1Improve manageabilityImprove securityRandom number generatorsUser identity/authority verificationInternet privacyEnterprise services
Embodiments of the invention provide a trust framework for governing service-to-service interactions. This trust framework can provide enhanced security and / or manageability over prior systems. Merely by way of example, in some cases, an information store can be used to store information security information (such as trust information, credentials, etc.) for a variety of services across an enterprise. In other cases, the trust framework can provide authentication policies to define and / or control authentication between services (such as, for example, types of authentication credentials and / or protocols are required to access a particular service—either as a user and / or as another service—and / or types of authentication credentials and / or protocols a service may be enabled to use to access another service). Alternatively and / or additionally, the trust framework can provide authorization policies to define and / or control authorization between services.
Owner:ORACLE INT CORP
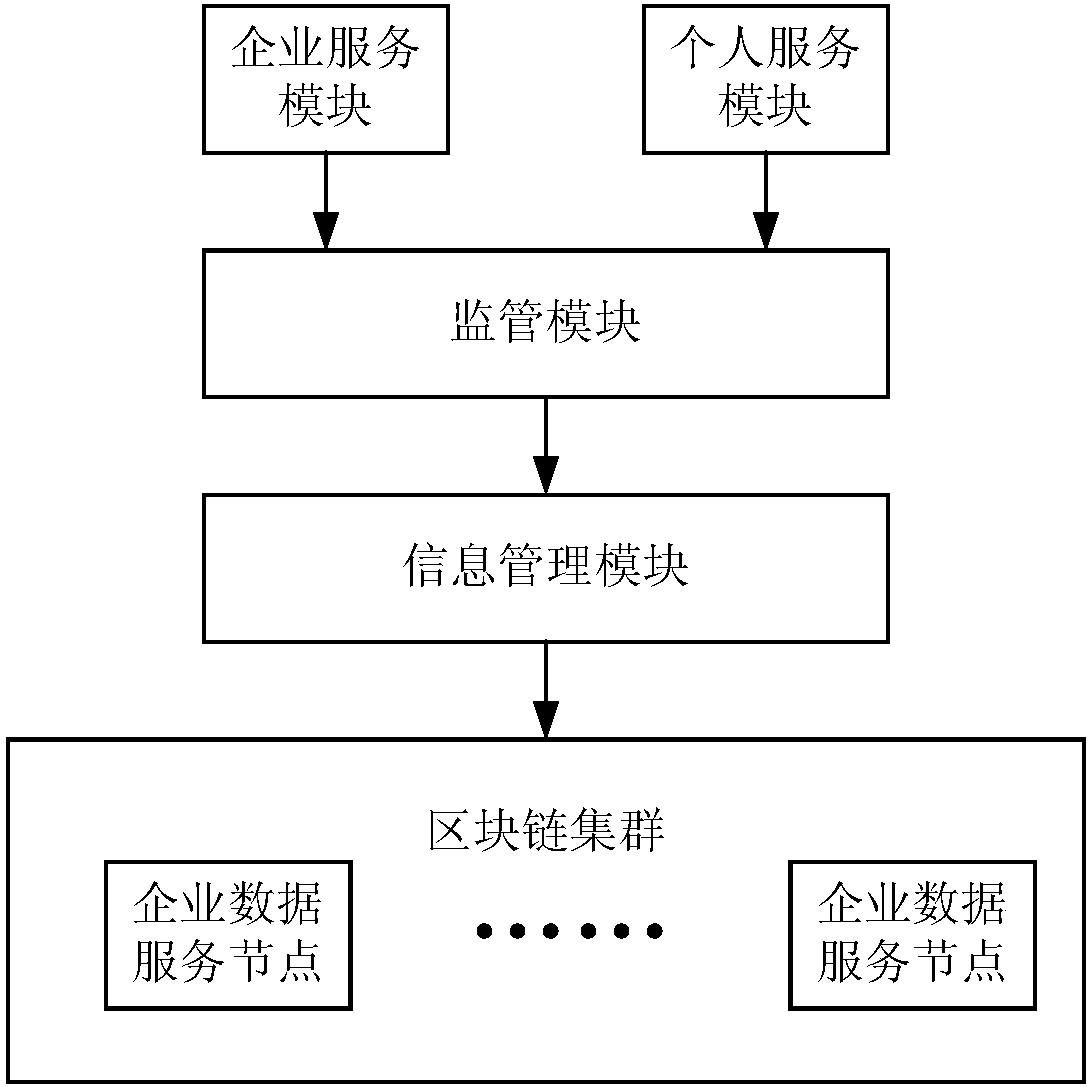
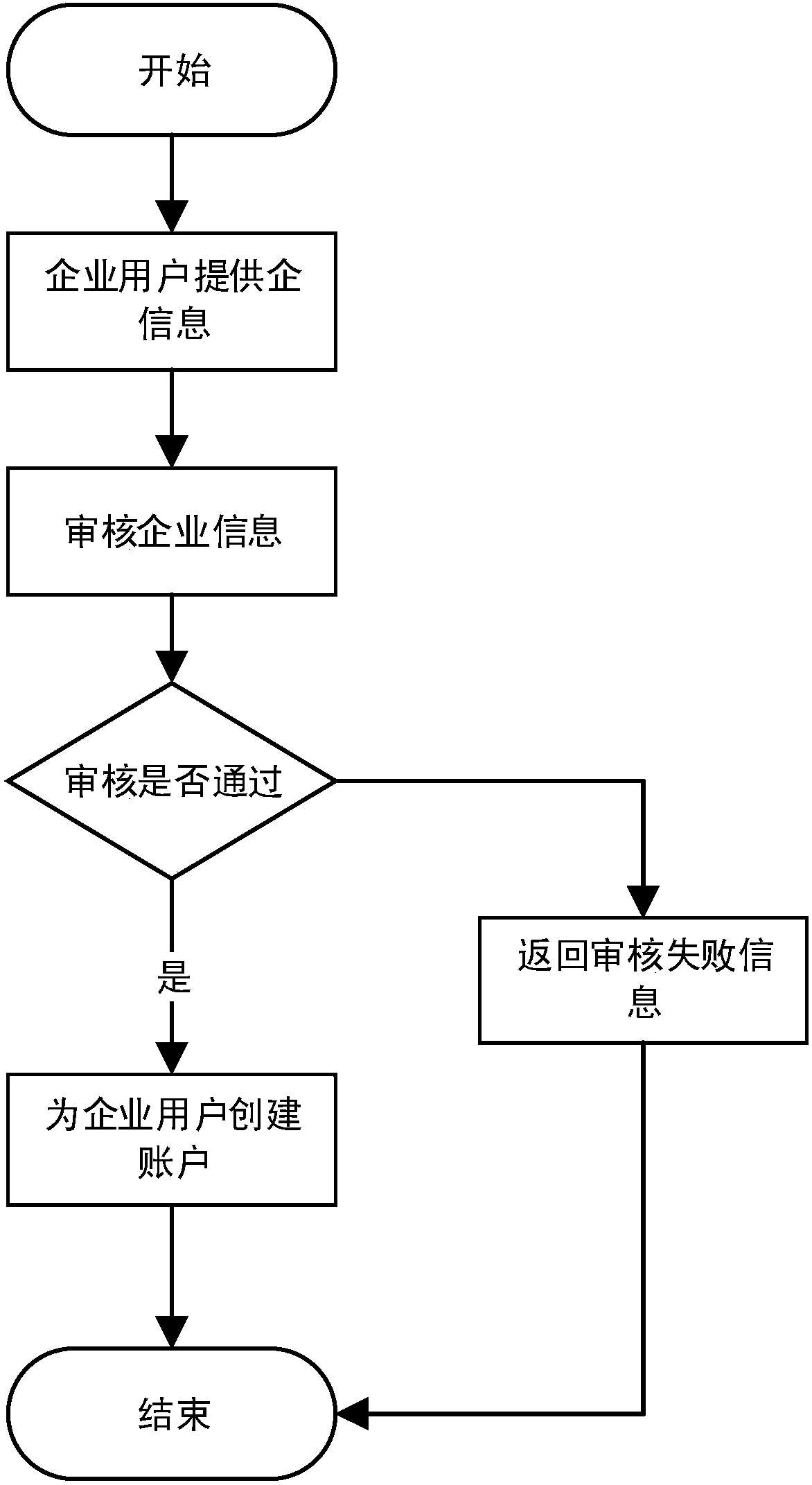
Personal credit information sharing system and method based on block chain
InactiveCN108234478ATrusted Shared ServiceExpress Sharing ServiceUser identity/authority verificationEnterprise servicesE-commerce
The invention discloses a personal credit information sharing system and method based on a block chain. The personal credit information sharing system based on the block chain comprises a block chaincluster, an enterprise service module, a personal service module, an information management module and a supervision module. The system is characterized in that the information management module is used for carrying out user information management comprising real-name authentication according to identity card information of a personal user and generation of a unique identity ID of the personal user through a hash algorithm and BASE64 code, creating assets on the block chain cluster, managing the assets on the block chain cluster and carrying out real-name authentication on the personal user; the enterprise service module is used for carrying out authentication on an enterprise user and distributing a login credential to an authenticated enterprise while providing relevant operation of thepersonal information for the enterprise user according to the authority provided by the supervision module, wherein the login credential comprises a private key and a digital certificate. The system and the method can be widely applied to the fields of banks, credit, games, electronic commerce and the like.
Owner:重庆小犀智能科技有限公司
Protocol for enabling dynamic and scalable federation of enterprise service buses
In a method and system for creating a federation of a plurality of enterprise service buses (ESBs), a plurality of ESB nodes provide connectivity to one or more services. According to a protocol, at least a portion of the ESB nodes transmit policy-based service advertisement messages to other ESB nodes, wherein the policy-based service advertisement messages include service state information. In response to receiving the policy-based service advertisement messages, each of the ESB nodes stores the service state information received from other ESB nodes in respective distributed registries to create a local view of routable service endpoints in the federation. Each of the ESB nodes then uses its respective distributed registry to make routing decisions when routing service requests.
Owner:SERVICENOW INC
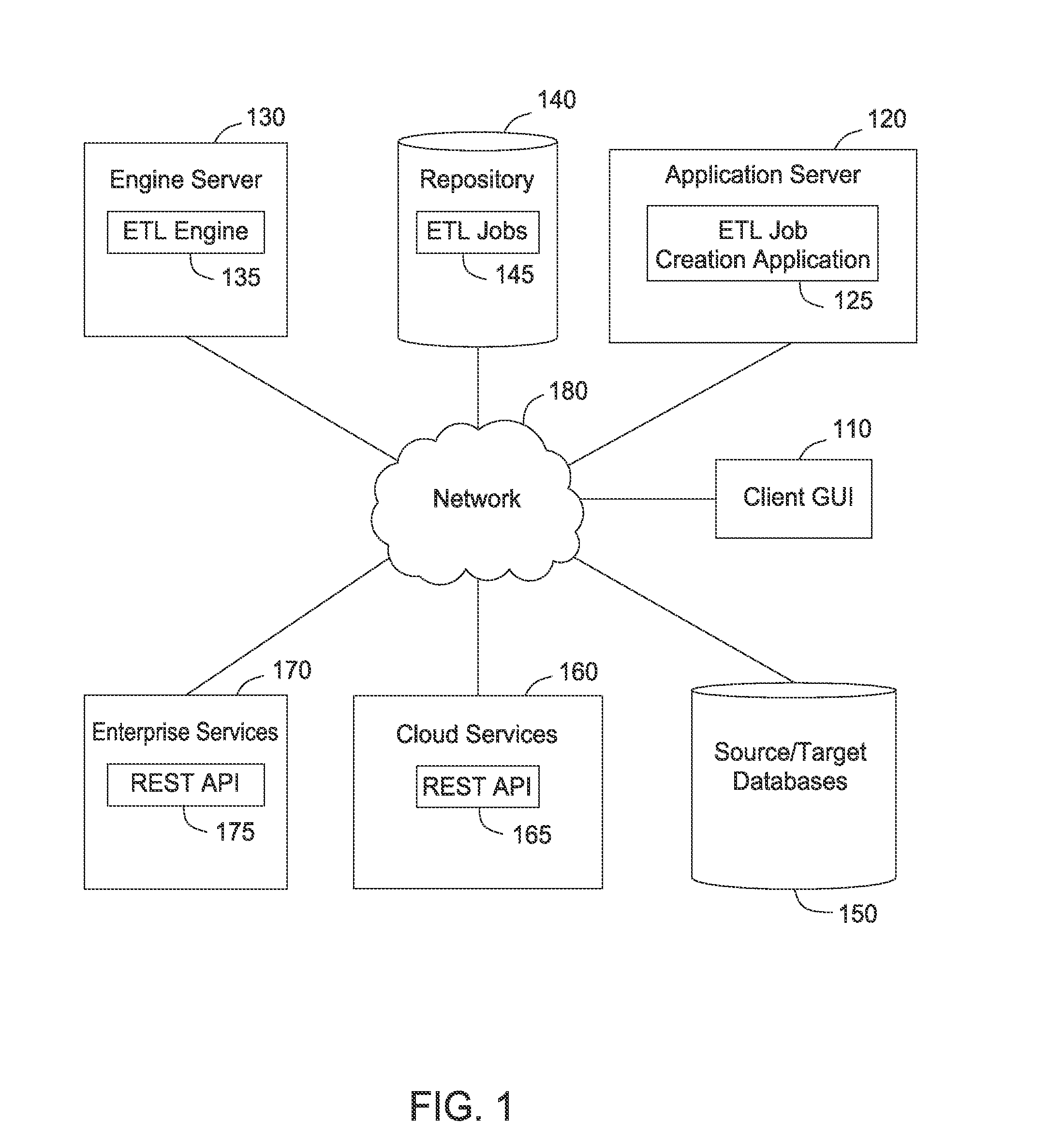
System and method of consuming and integrating with rest-based cloud and enterprise services
ActiveUS20150347541A1Digital data processing detailsWebsite content managementGraphicsRepresentational state transfer
Techniques are disclosed for consuming and integrating with representational state transfer (REST) based services. In one embodiment, a multiple-step extract, transform, load (ETL) job includes one or more REST steps. Each step in the ETL job performs a particular well-defined task, and the REST step in particular constructs REST requests, invokes REST services, and retrieves REST responses. The REST step may be mapped to a vector of inputs such that multiple REST service calls are made for each of the inputs. Further, a reusable connection may be employed so that one connection can be used to make multiple REST service calls. URLs used to make REST service calls may be dynamically constructed based on input data parameters and ETL job parameters. Additionally, a graphical user interface (GUI) allows users to configure aspects of a REST step.
Owner:IBM CORP
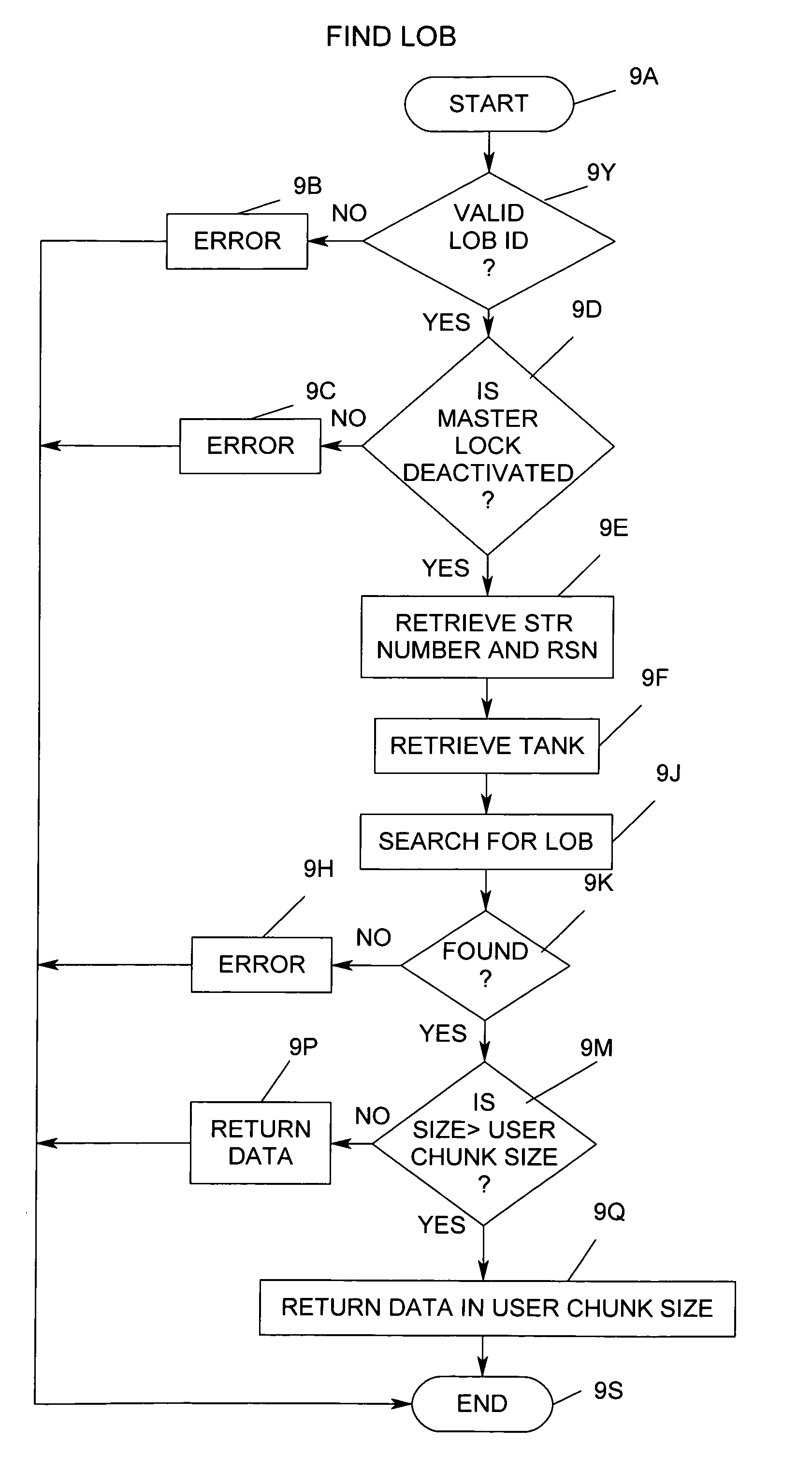
System and method to manipulate large objects on enterprise server data management system
ActiveUS7467163B1Data processing applicationsDigital data information retrievalData managementKilobyte
An Enterprise Server Data Management System provides for the handling of large data objects (LOB) according to the data size required for the large object. Methods are provided to find a particular object that is stored or to delete such an object. But particularly the method arranges for data storage of Large Objects in a structured database, depending on the number of kilobytes forming the Large Object (LOB).
Owner:UNISYS CORP
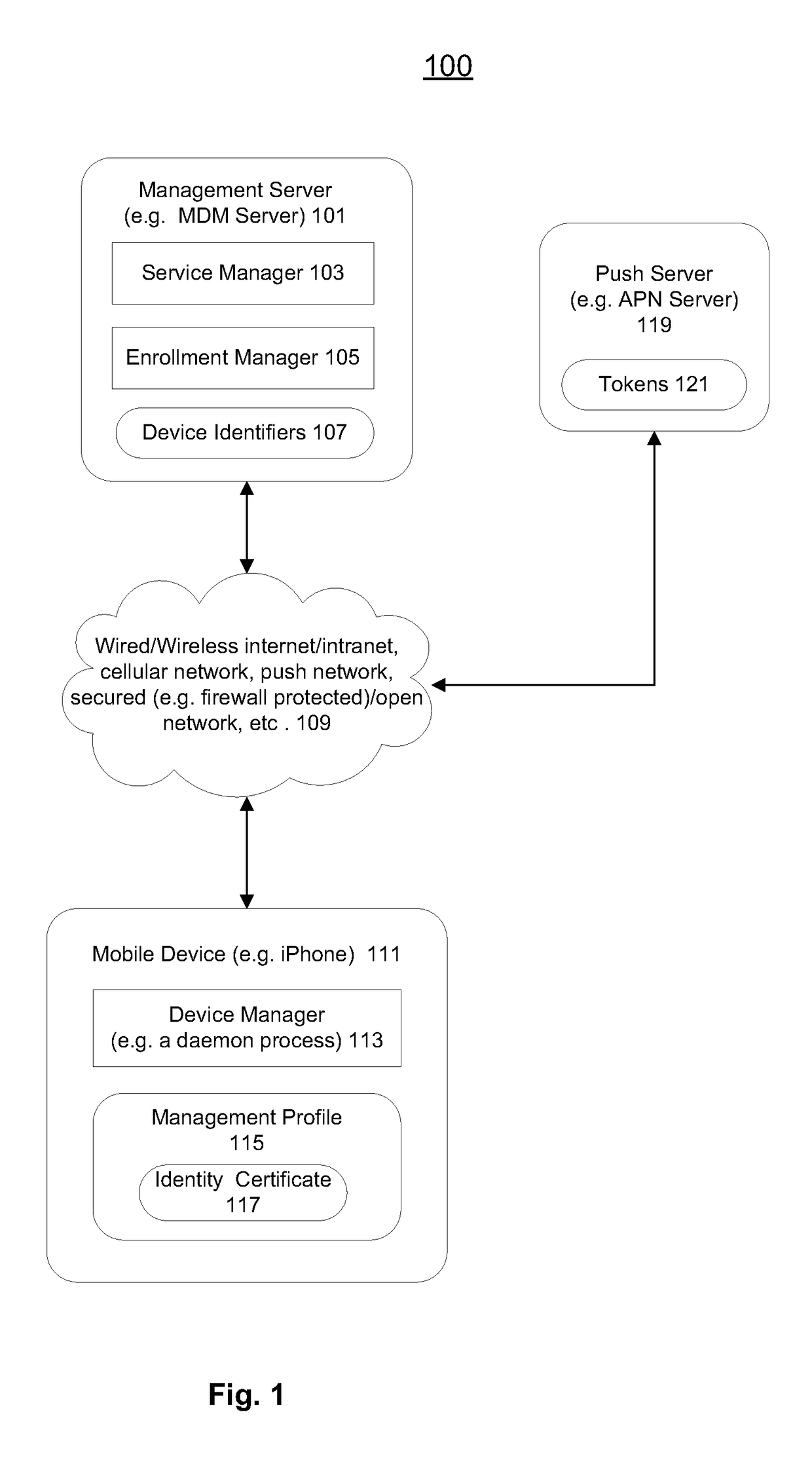
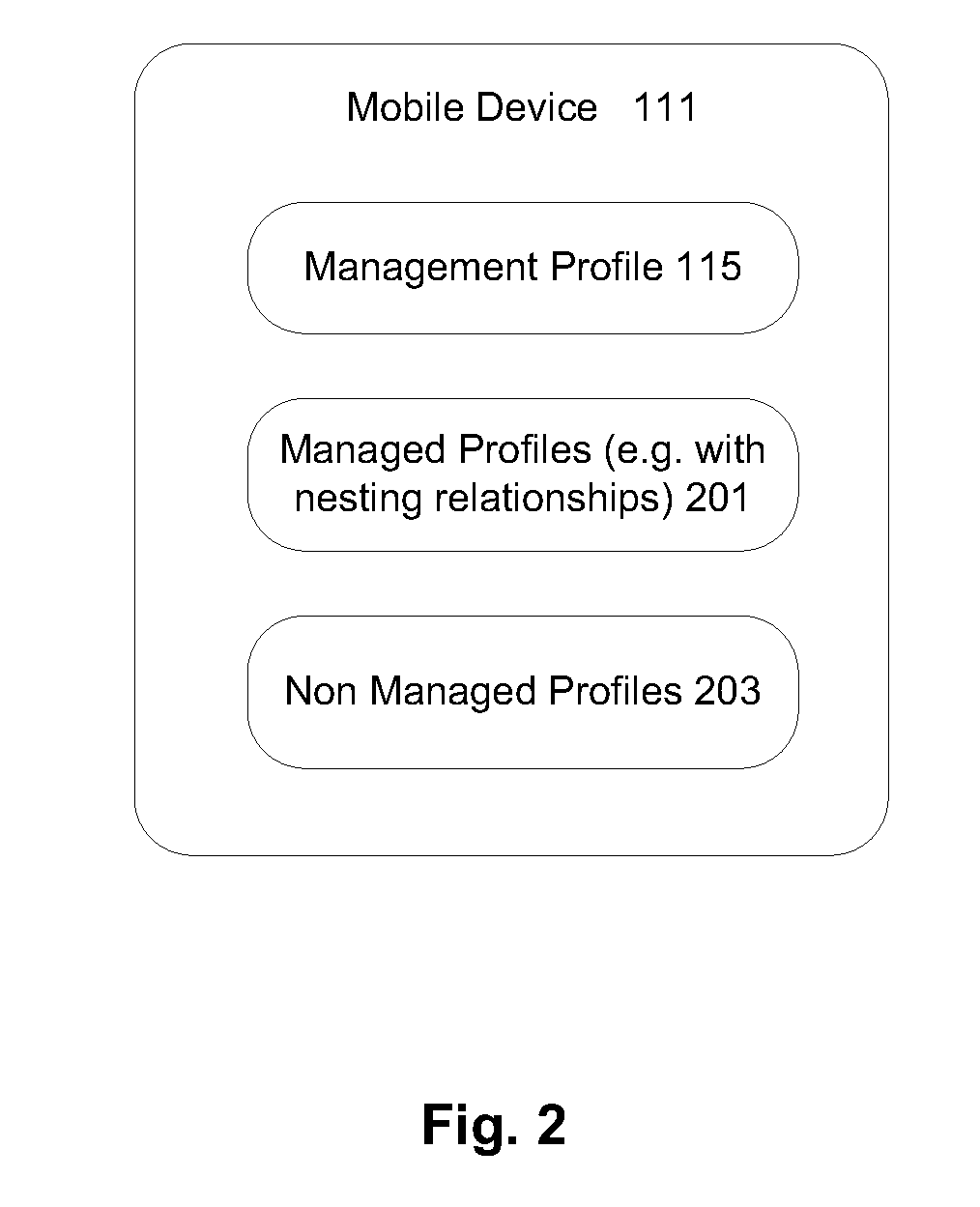
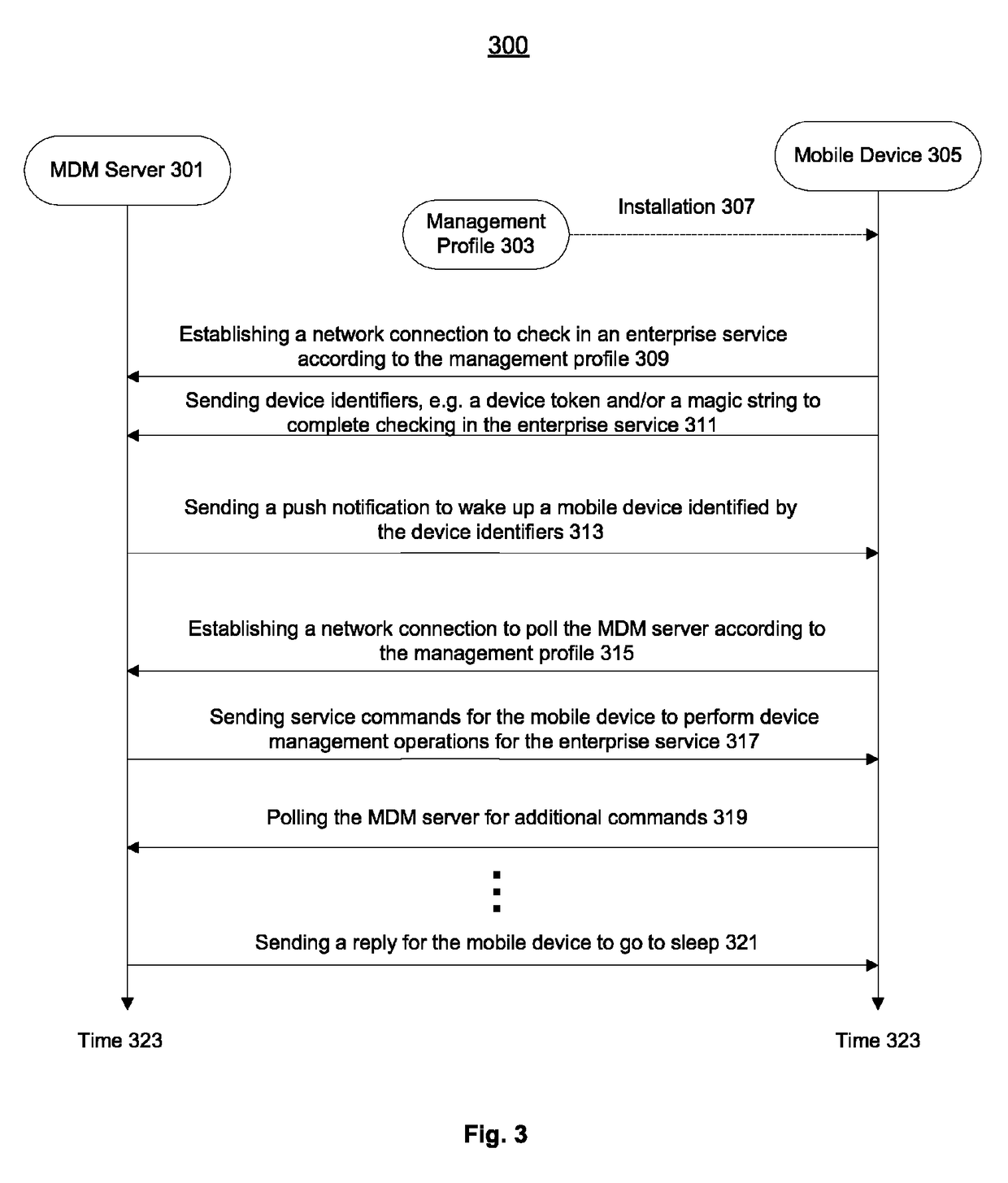
Mobile device management
ActiveUS8473743B2ExtensibilityFlexibilityDigital data processing detailsUser identity/authority verificationComputer networkEnterprise services
Methods and apparatuses that enroll a wireless device into an enterprise service with a management server addressed in a management profile are described. The enrollment may grant a control of configurations of the wireless device to the management server via the management profile. In response to receiving a notification from the management server, a trust of the notification may be verified against the management profile. If the trust is verified, a network session may be established with the management server. The network session may be secured via a certificate in the management profile. Management operations may be performed for management commands received over the secure network session to manage the configurations transparently to a user of the wireless device according to the control.
Owner:APPLE INC
System and method for multi-system authentication and synchronization in mobile equipment
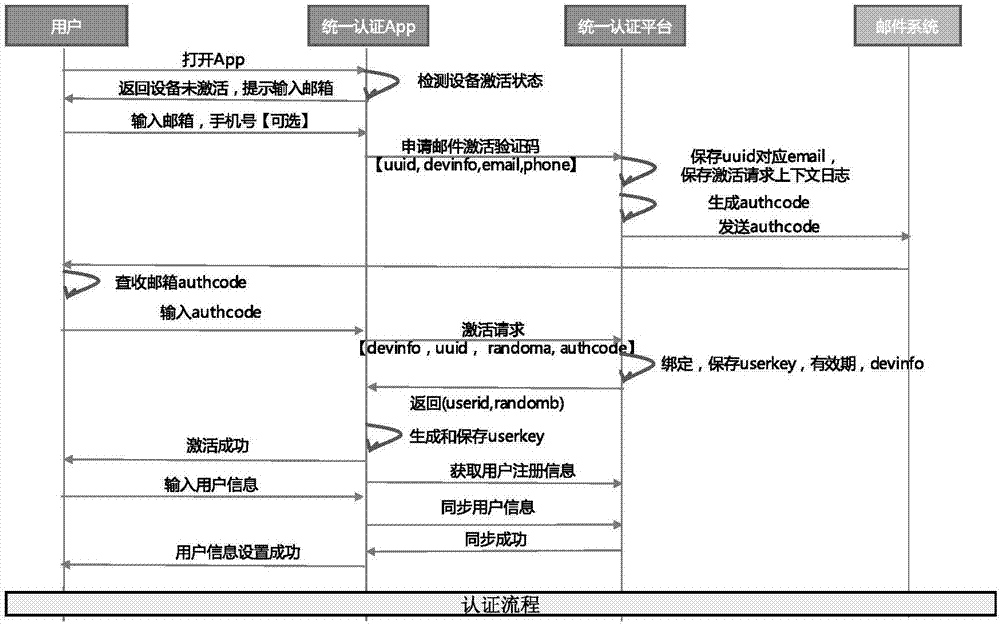
ActiveCN107172008AGuaranteed experienceAvoid enteringEncryption apparatus with shift registers/memoriesUser identity/authority verificationMobile endBiological activation
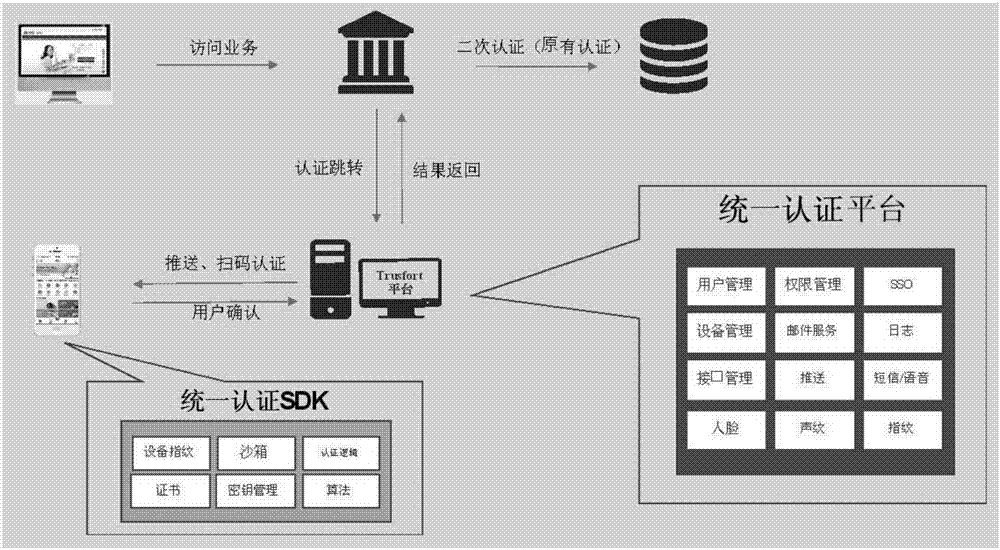
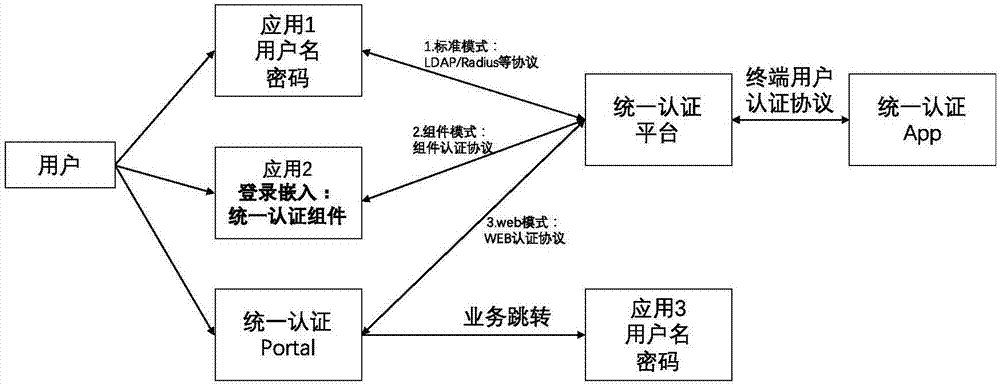
The invention discloses a system and method for multi-system authentication and synchronization in mobile equipment. The system is composed of a unified authentication assembly SDK and a unified authentication platform, wherein the unified authentication assembly SDK comprises an equipment fingerprint module, a sandbox module, a certificate module, a secret key management module, an algorithm module and an authentication logic module; and the unified authentication platform comprises a user management module, an authority management module, an SSO module, an equipment management module, a mail service module, a log module, an interface management module, a push module, a text message / voice module, a face module, a voiceprint module and a fingerprint module. The system and method can be applied to service scenes where existing enterprise services migrate to mobile ends, provide authentication and state synchronization on the mobile ends for enterprise users, through an innovative equipment fingerprint generation algorithm, a matching algorithm and a system activation process, the users can bind their mobile phones with enterprise accounts, and thus the enterprise accounts can realize login and state synchronization on the mobile equipment.
Owner:BEIJING TRUSFORT TECH CO LTD
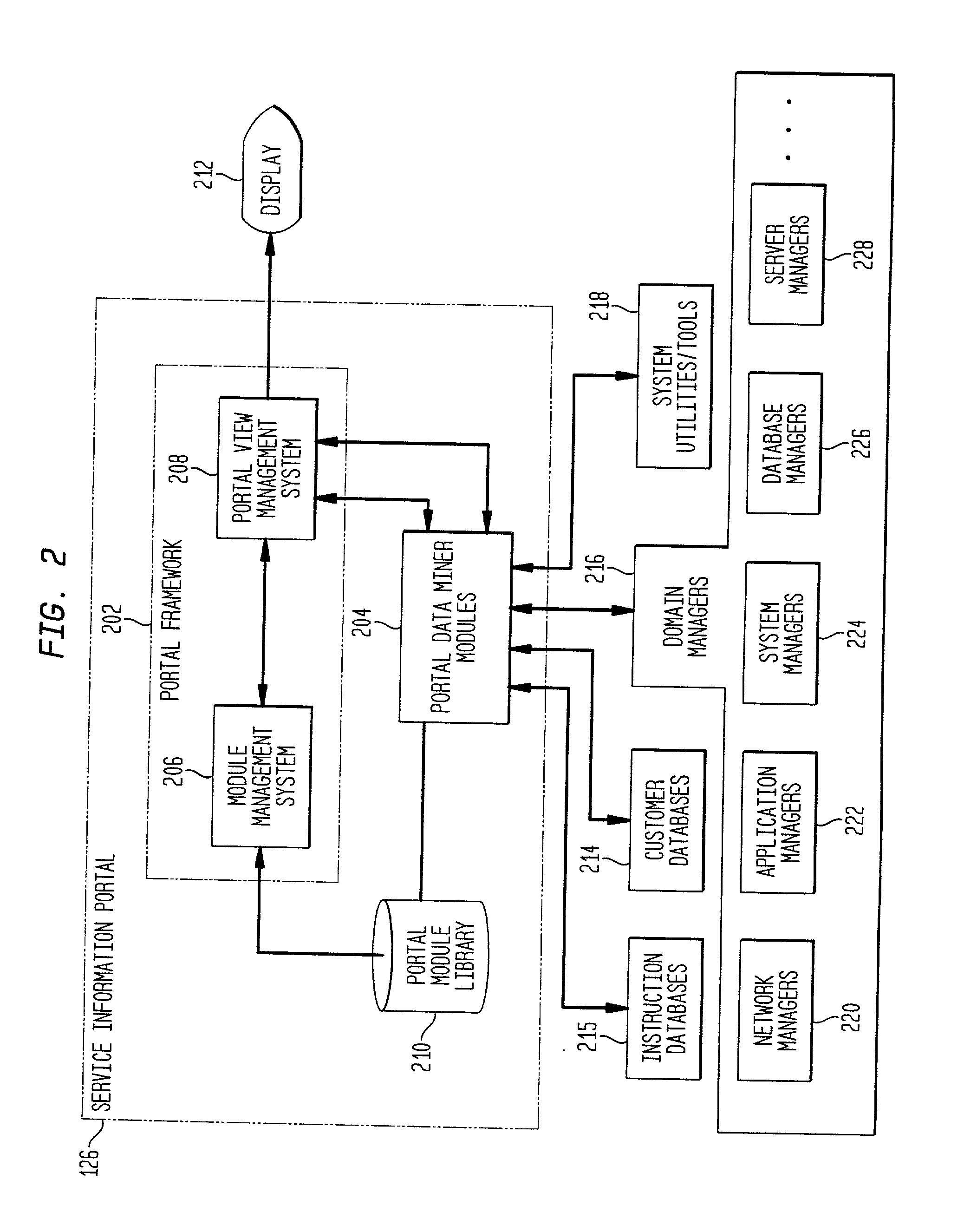
System and method for managing data miner modules in an information network system
InactiveUS20020161876A1Digital computer detailsMultiprogramming arrangementsCyber operationsDisplay device
A service information portal (SIP) and associated methodology for providing customer-based management information of networked computing environments for Internet service providers (ISPs), outsourcers, and enterprise service providers ("service providers"). The invention enables such service providers to provide the network administrators / users / customers / network managers / network operators ("network administrators") they serve with flexible, extensible, tailored, in-depth views of hosted computing environments in an intuitive graphical format. Generally, the invention extracts from relevant computing environment entities specified information for managing the outsourced computing environment. The specified information is presented on a customized display for consideration and interaction by the network administrator. The SIP includes a module management system for obtaining management information from the computing environment. The module management system includes a library of data miner modules each configured to access hardware and / or software entities in the computing environment for management information. A library of module registration files each defining an implementation of a data miner module is included in the SIP. A module manager provides access to each data miner module stored in the library of data miner modules for which the library of registration files includes a registration file.
Owner:HEWLETT PACKARD DEV CO LP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com