Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
577results about How to "Improve manageability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
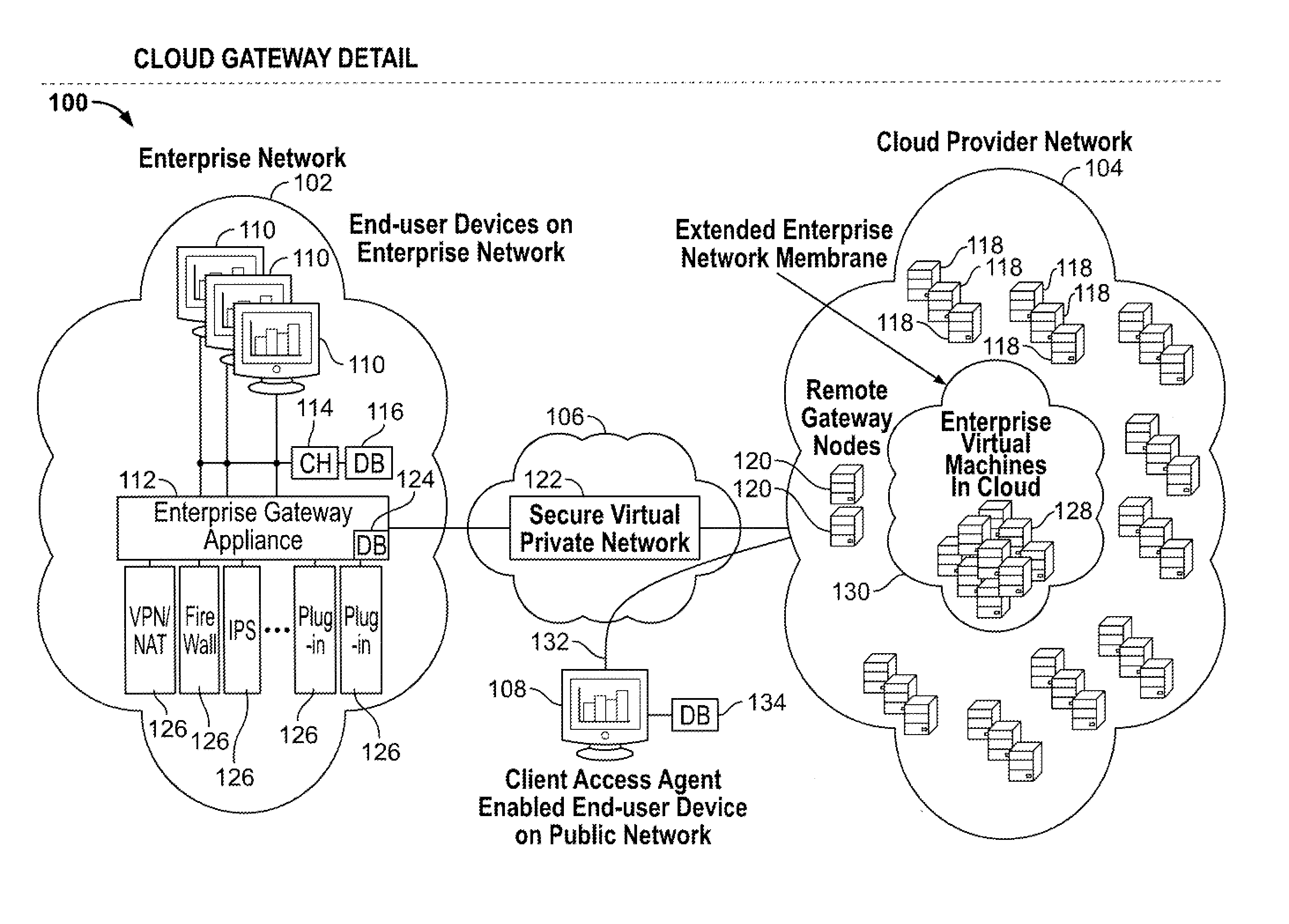
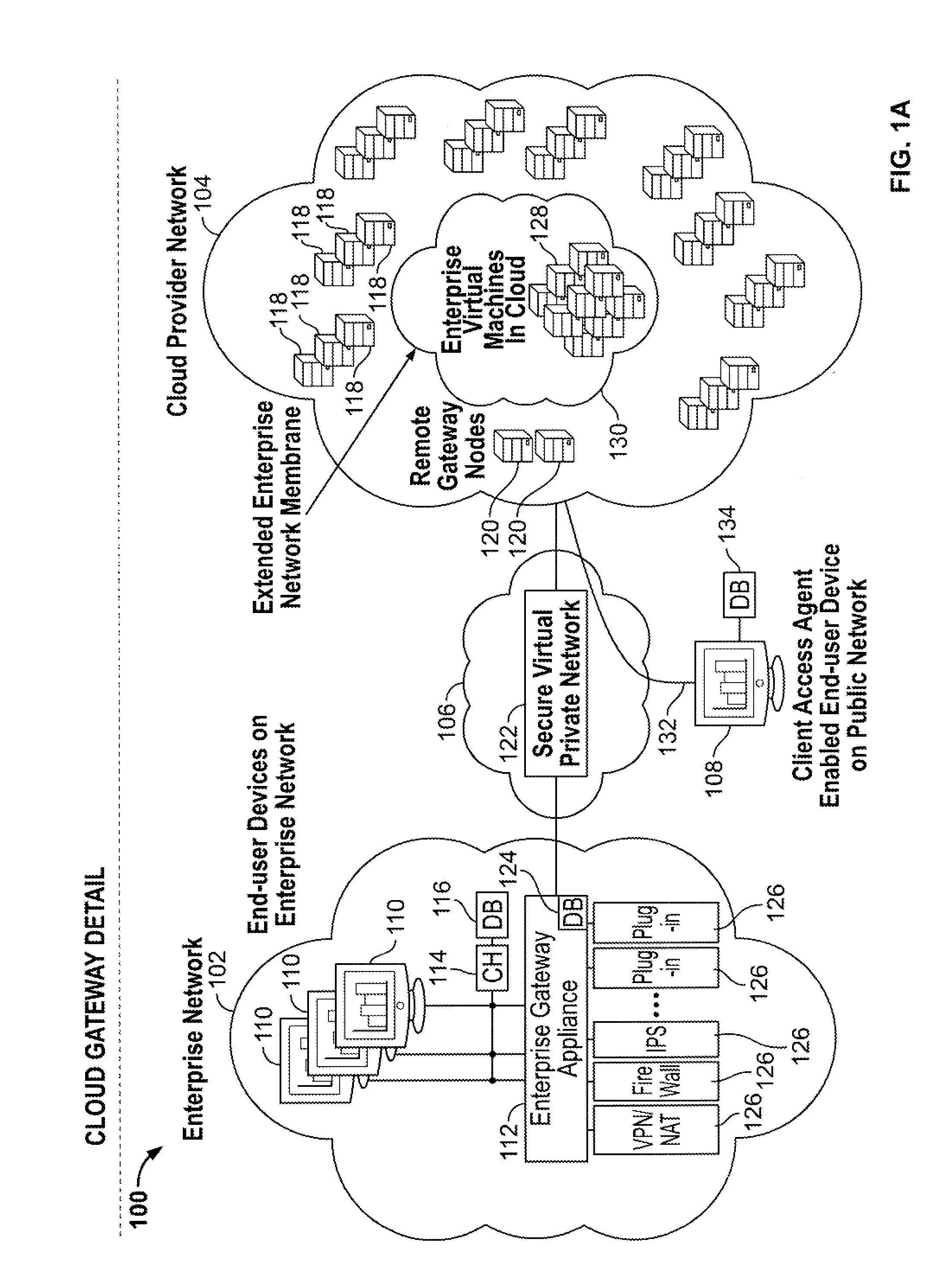
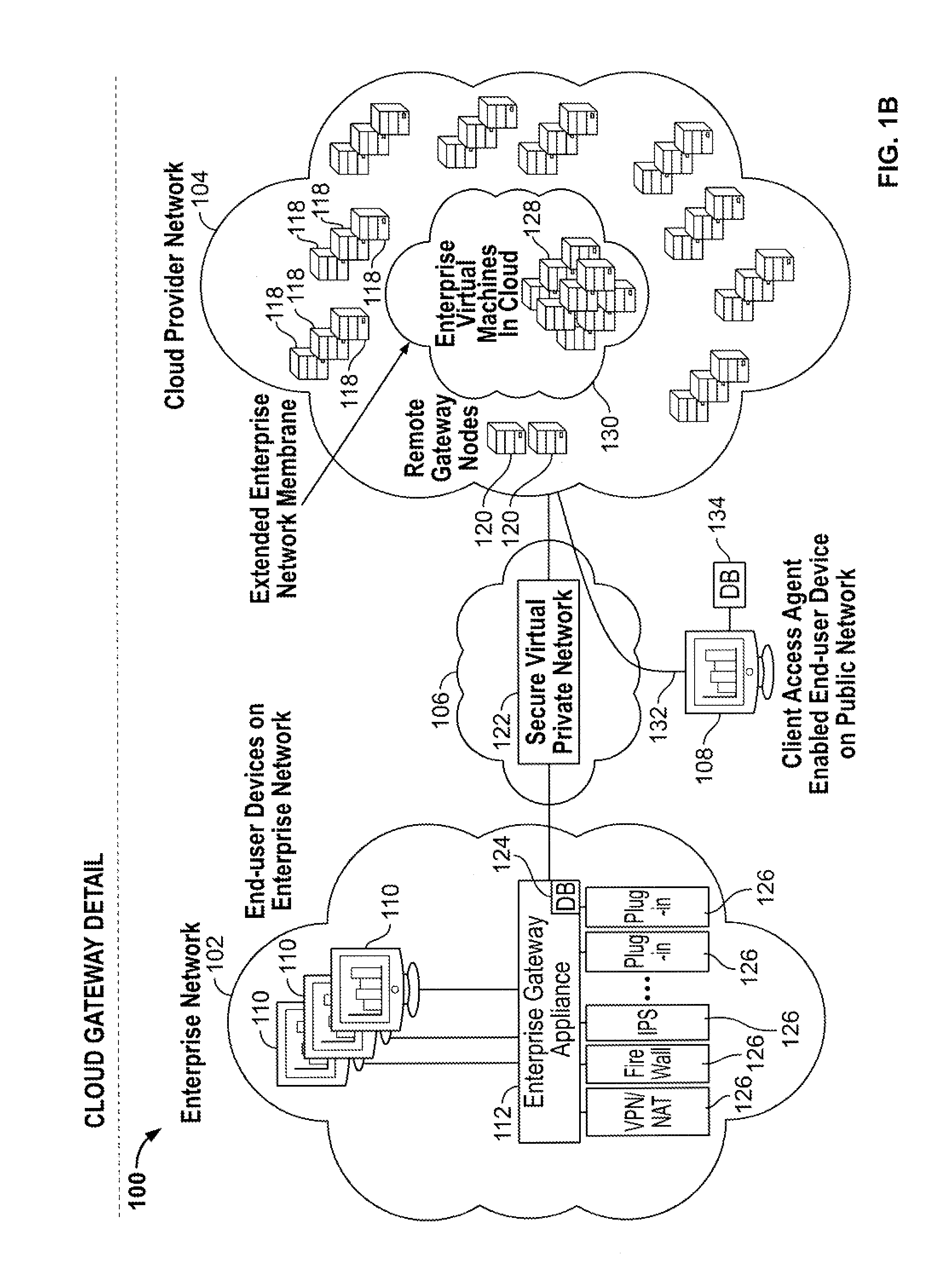
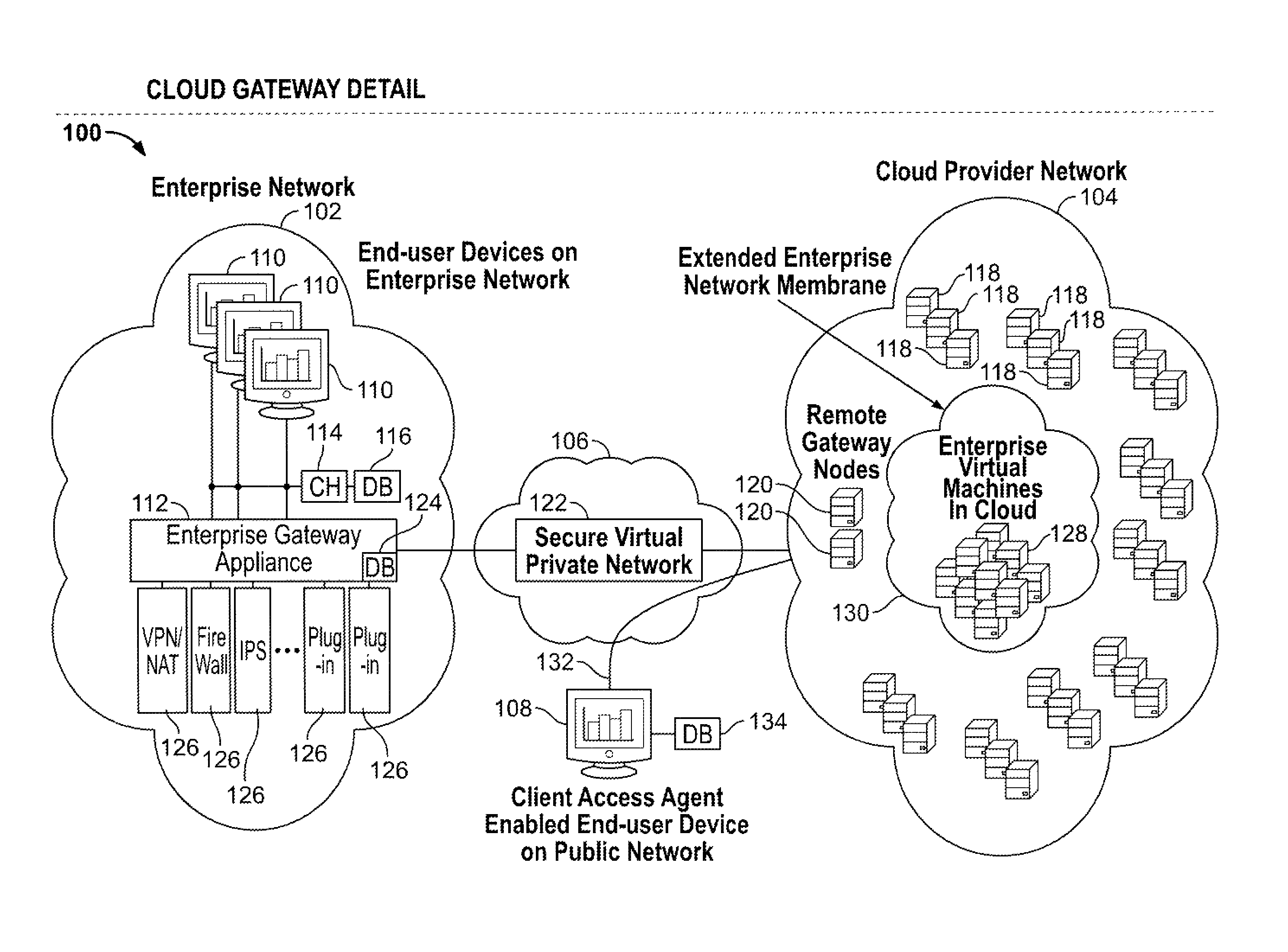
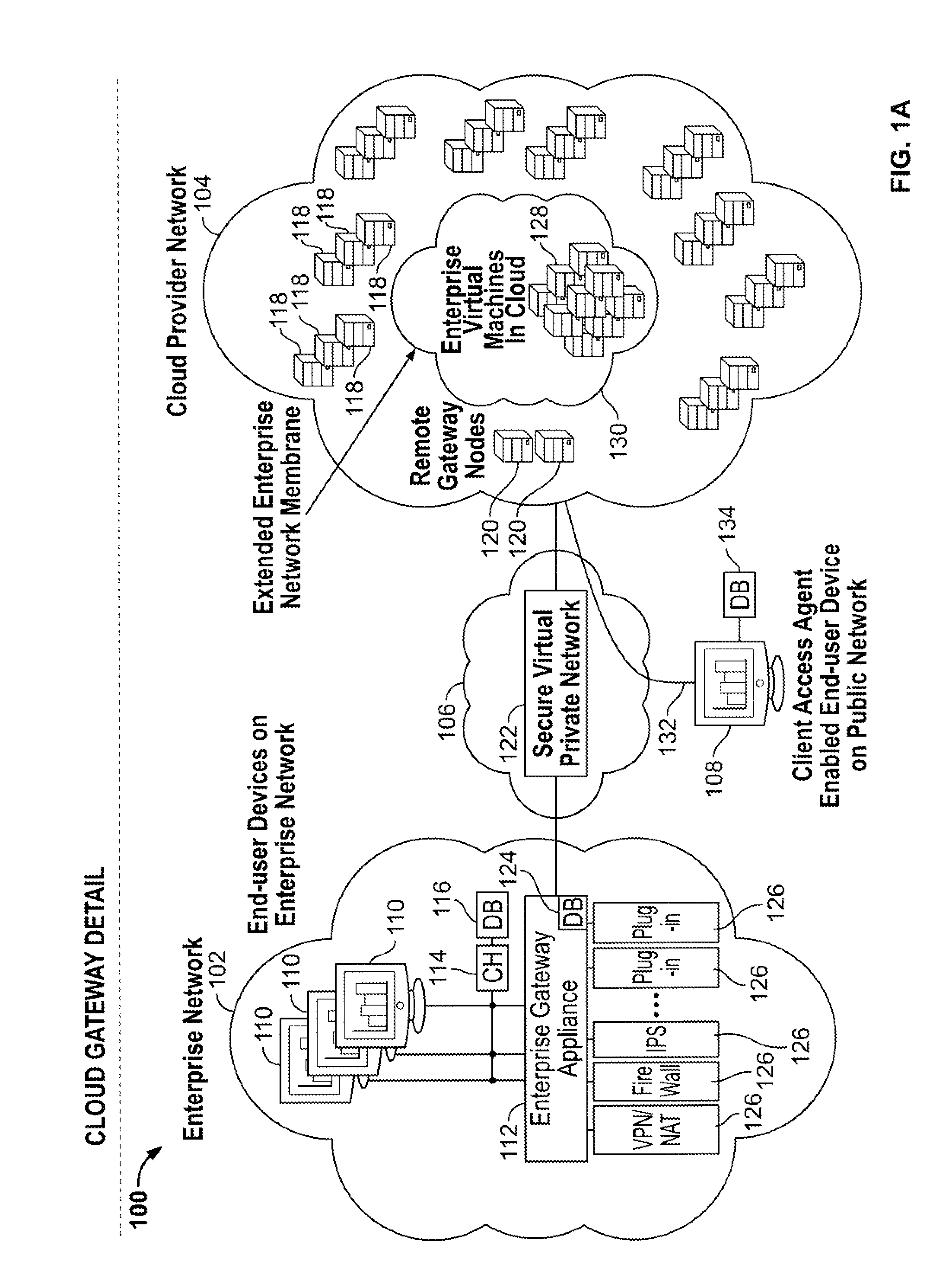
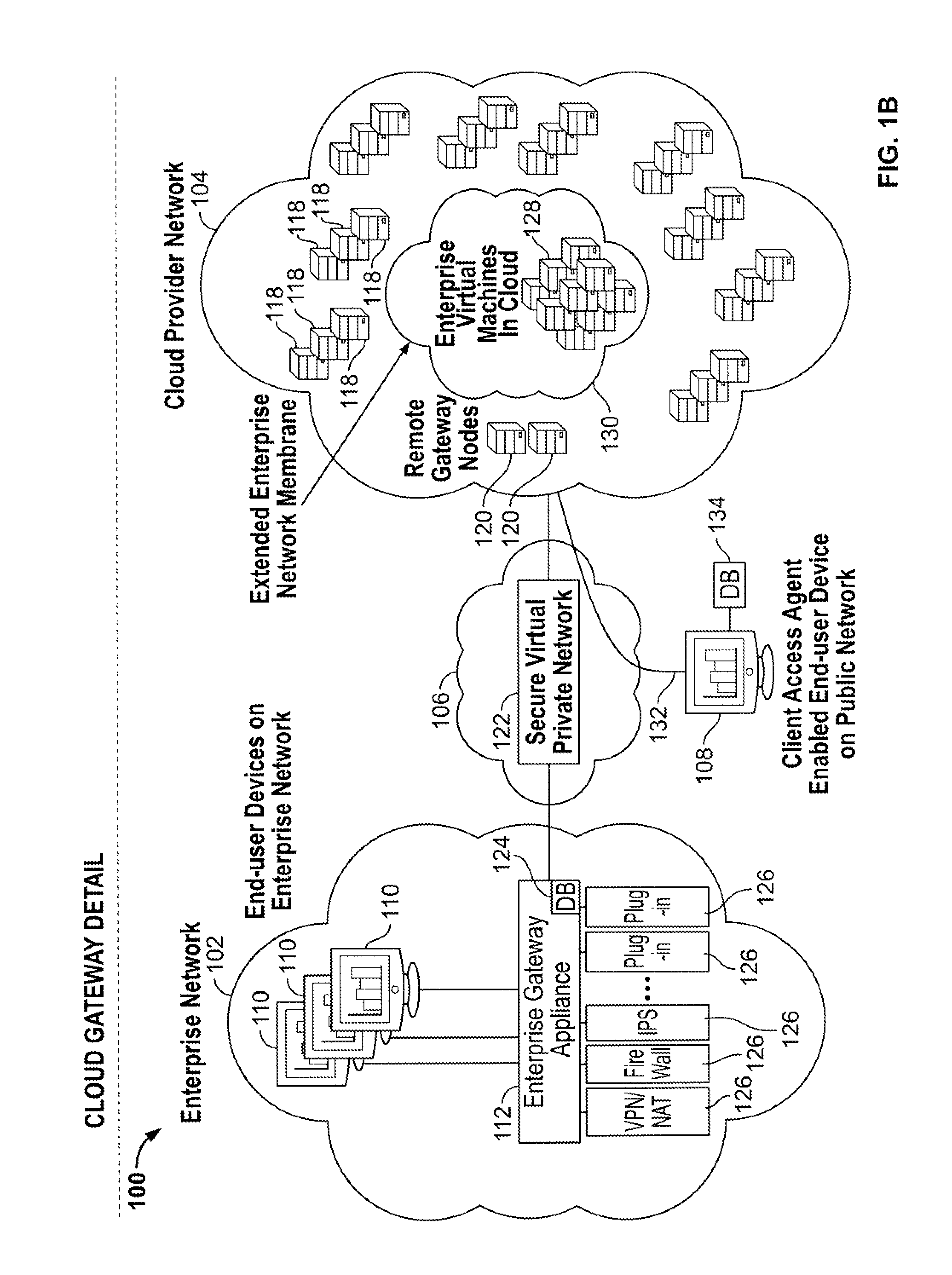
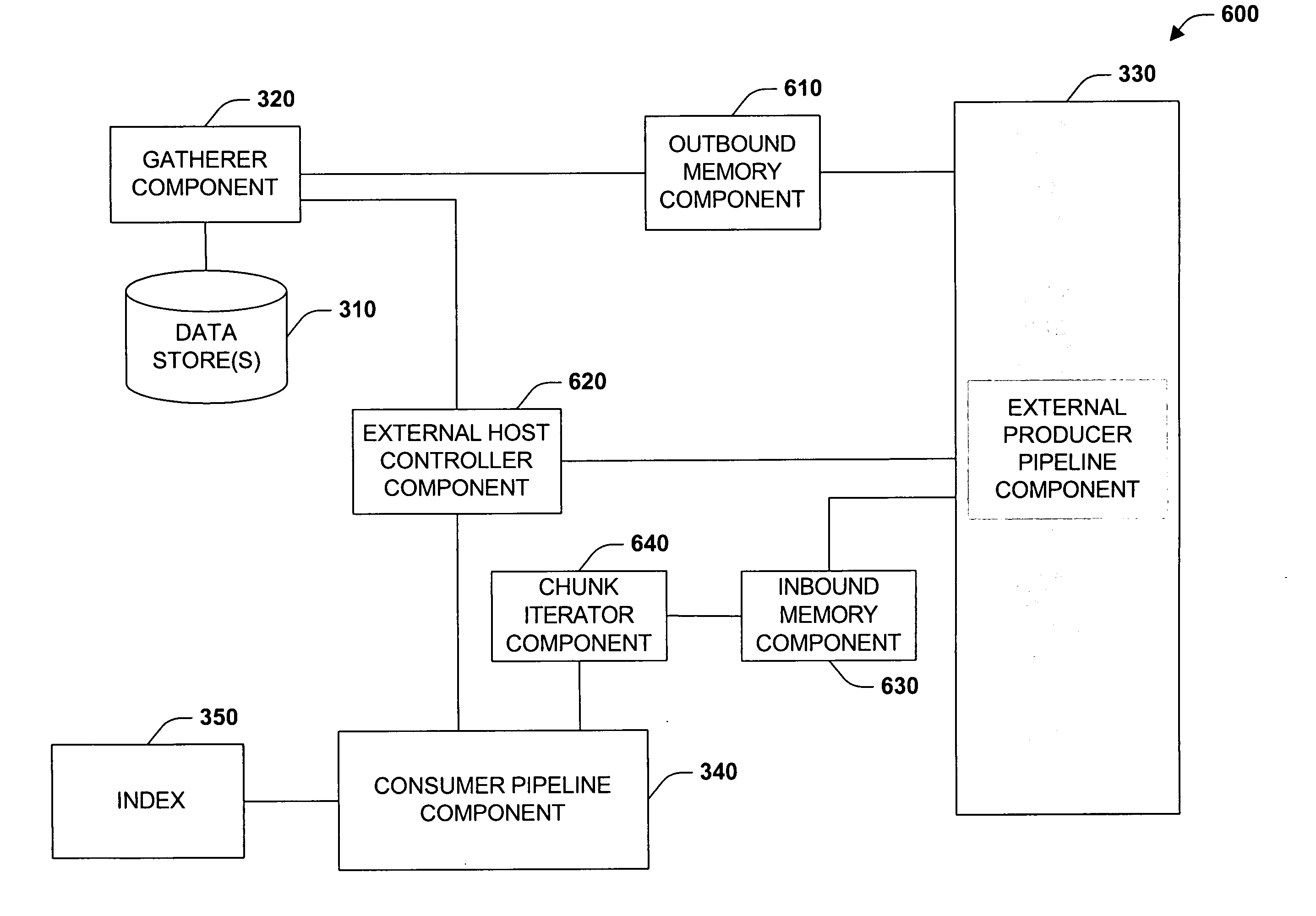
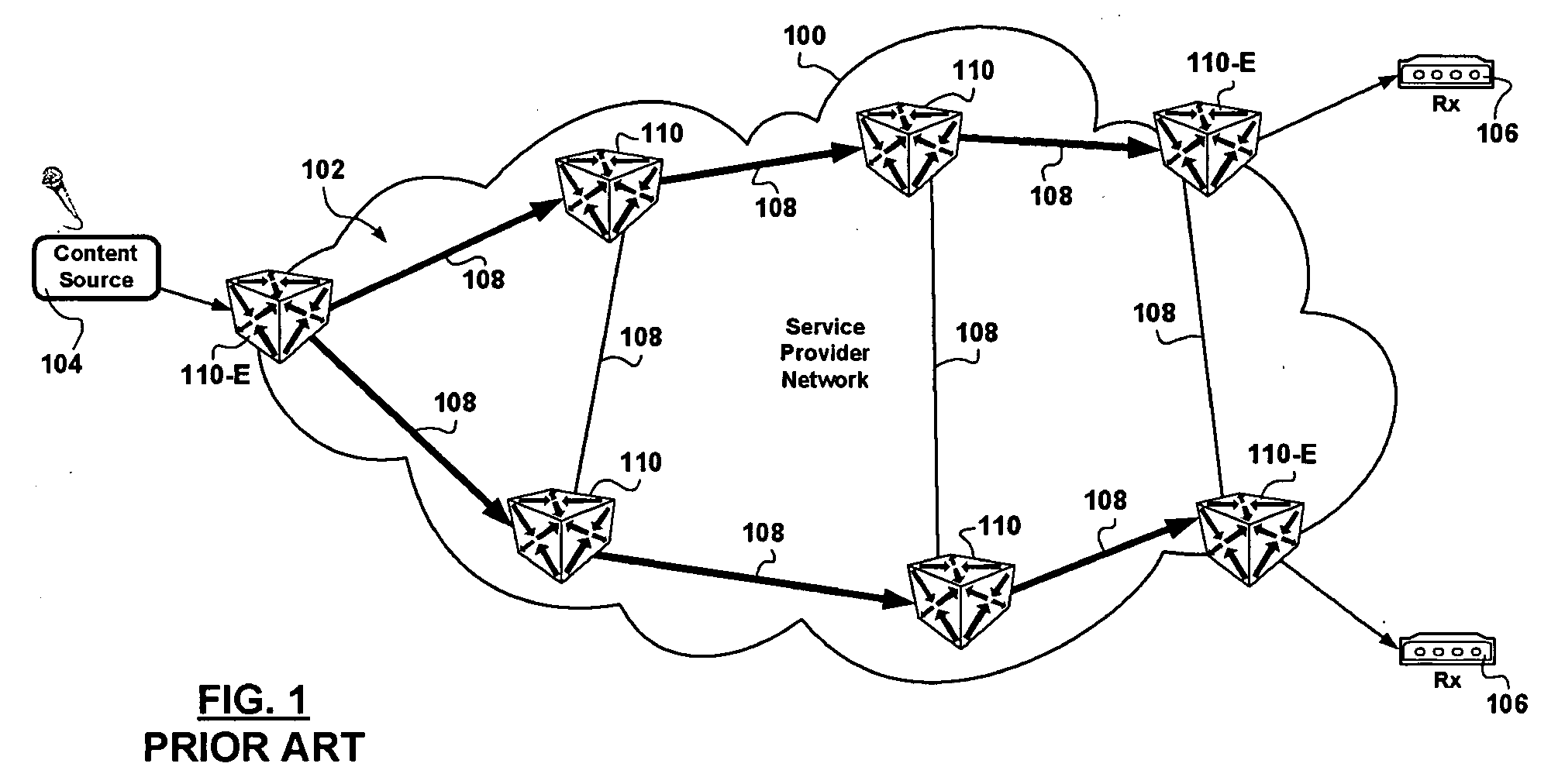
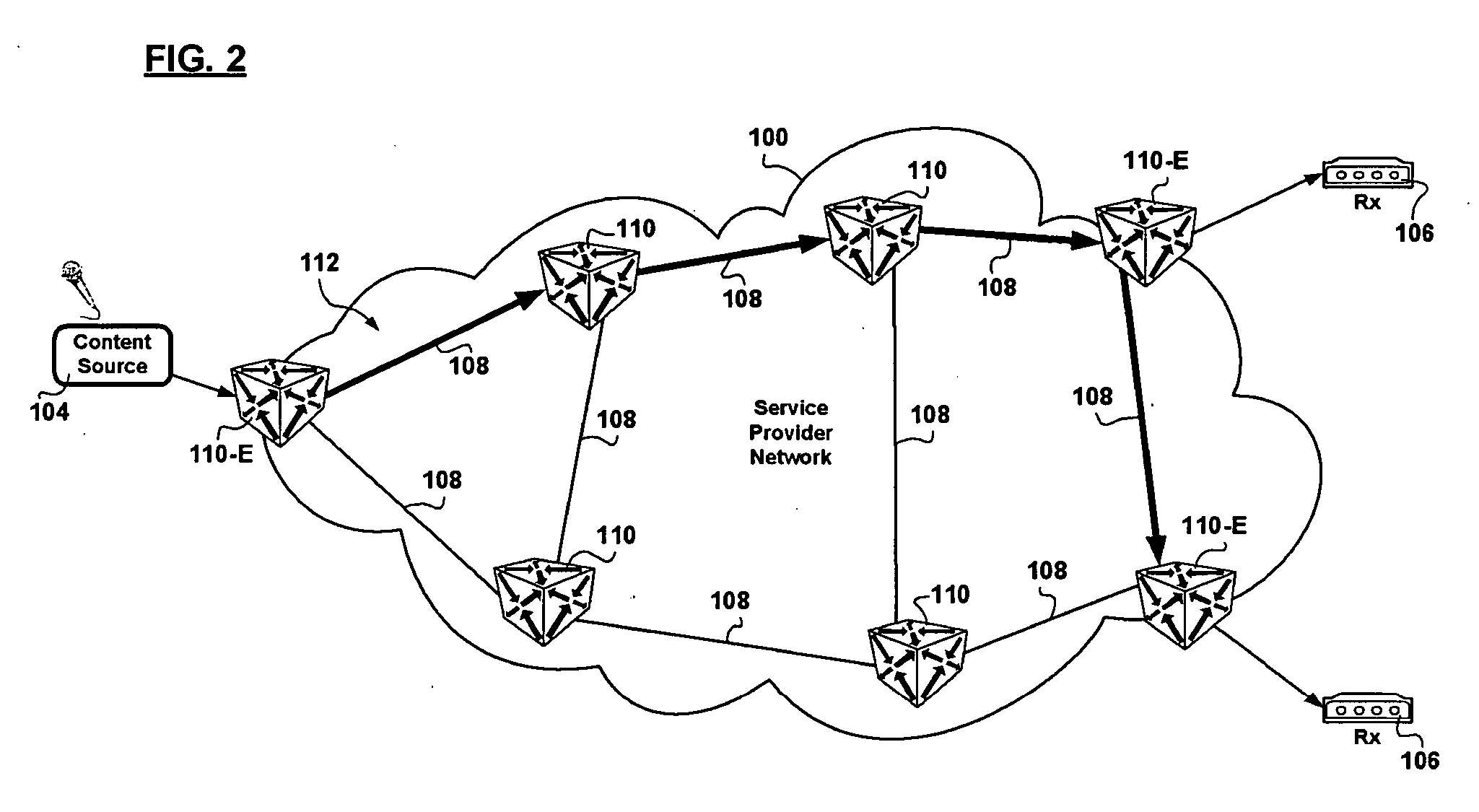
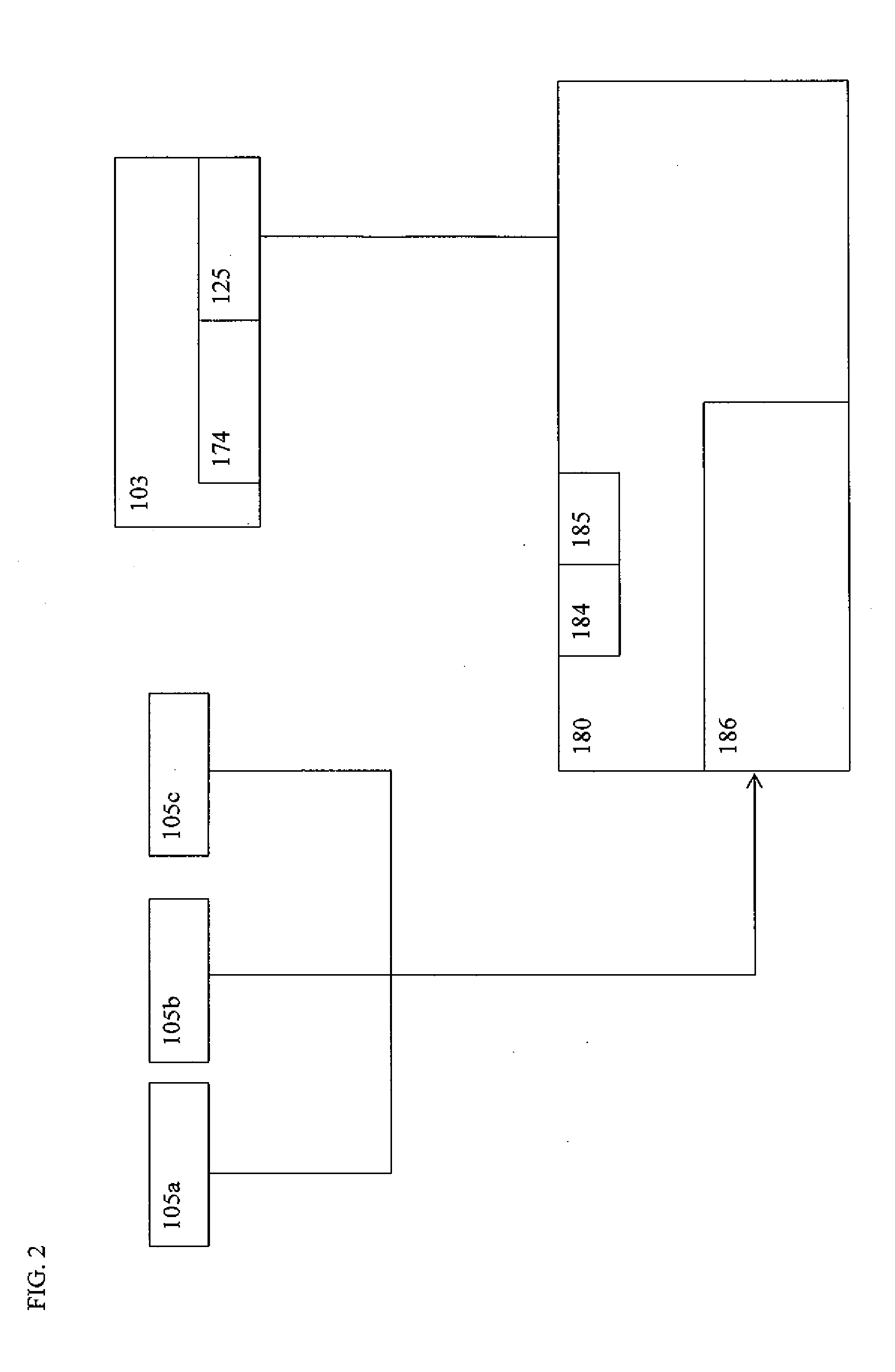
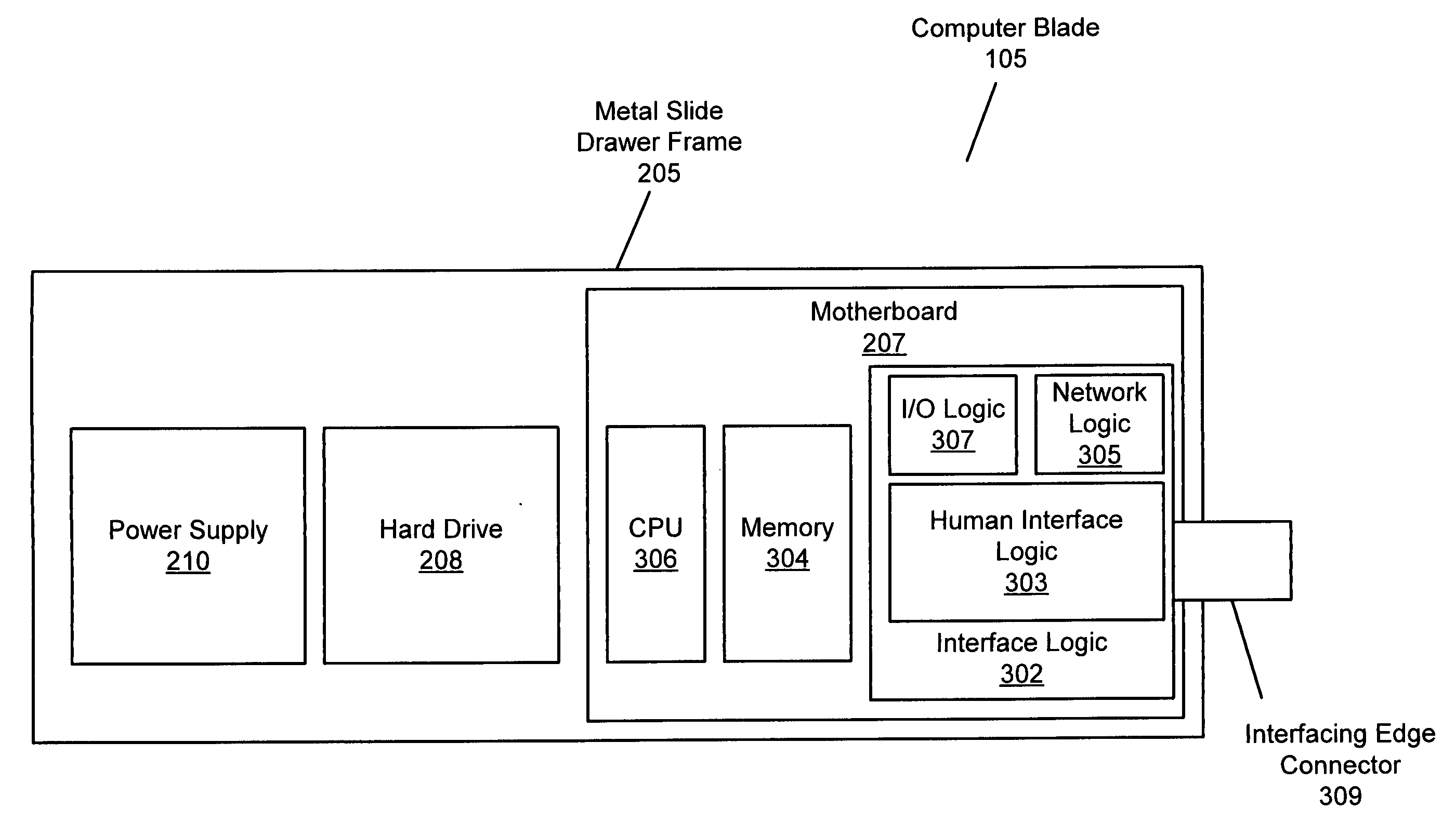
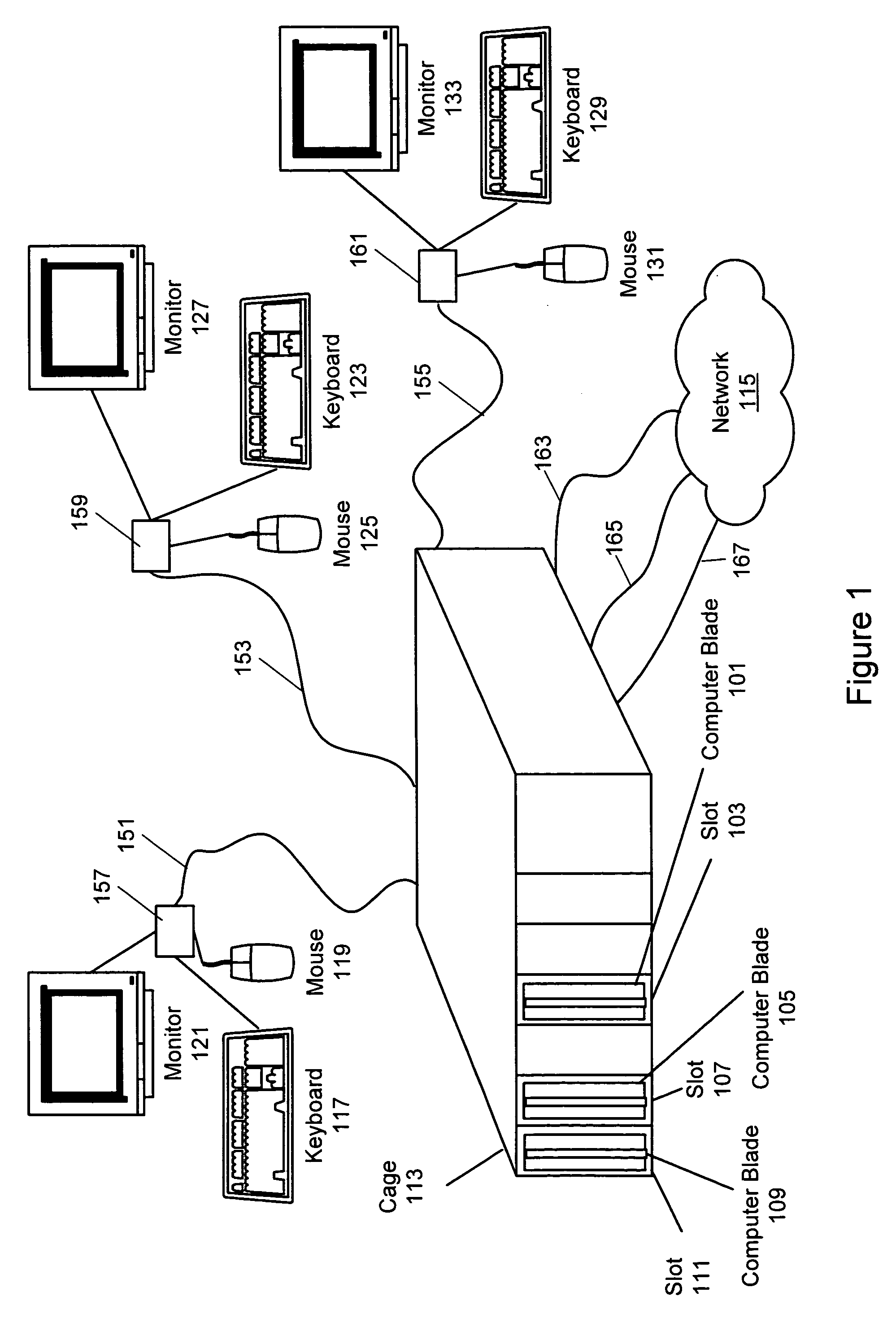
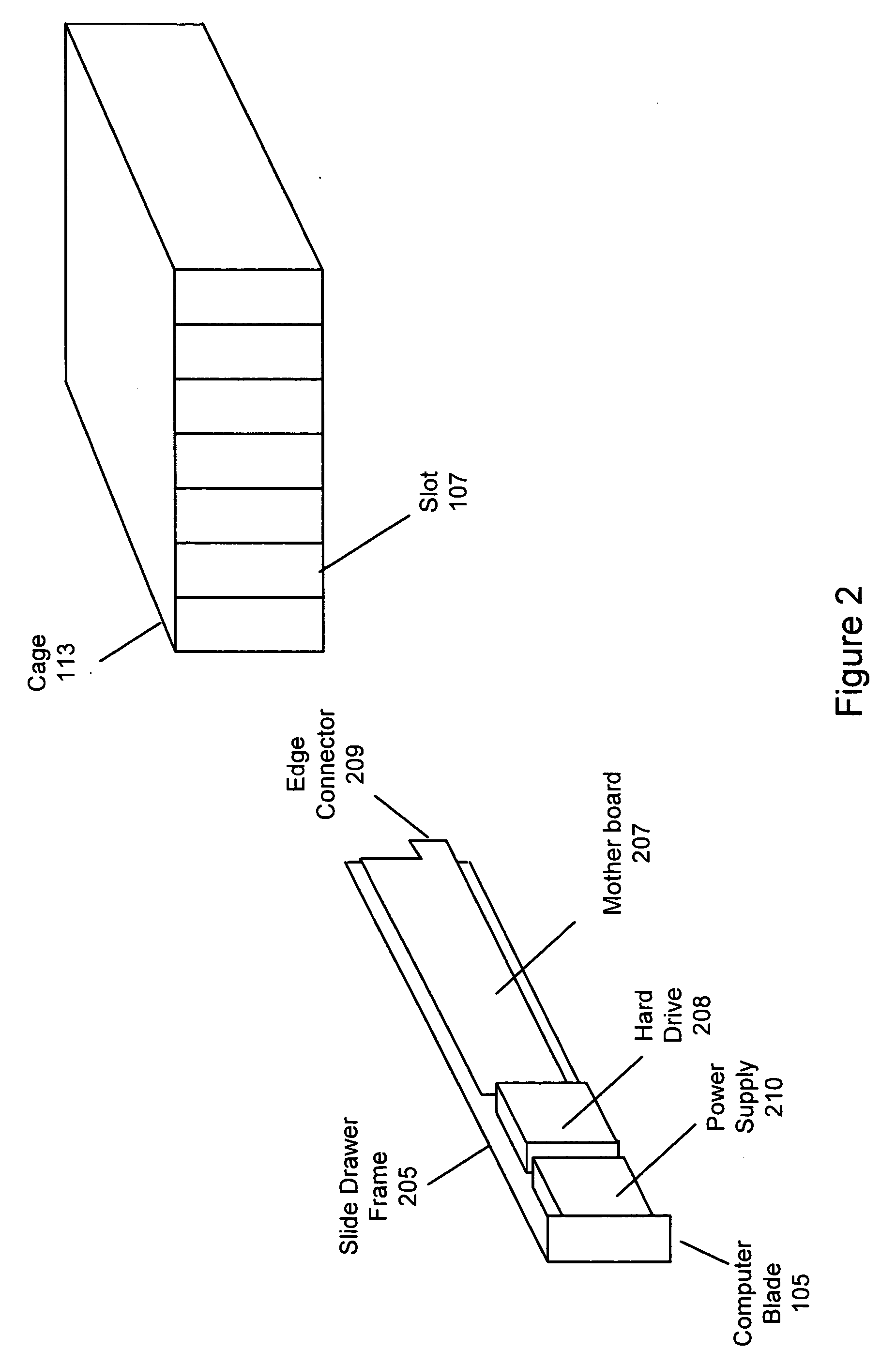
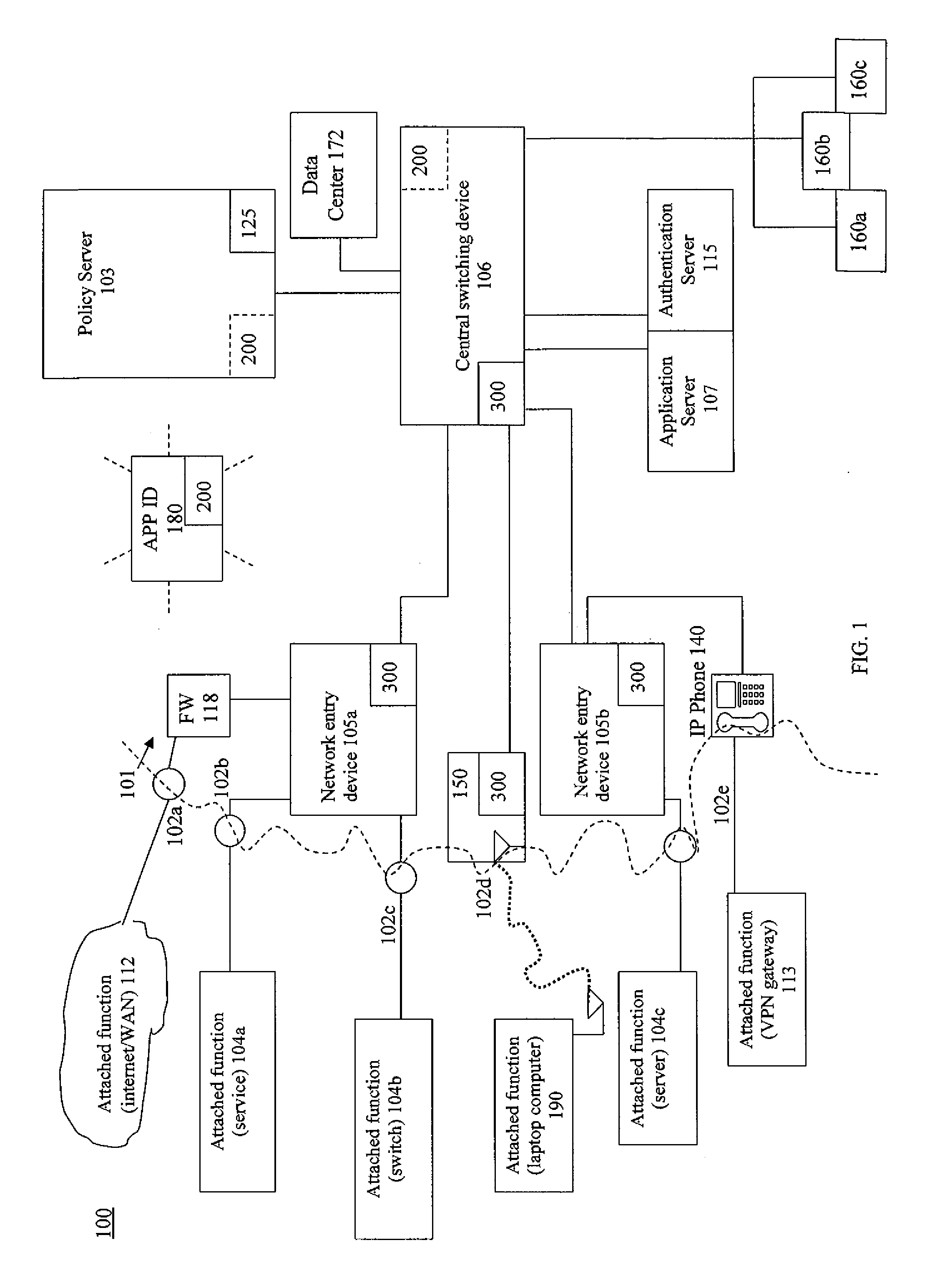
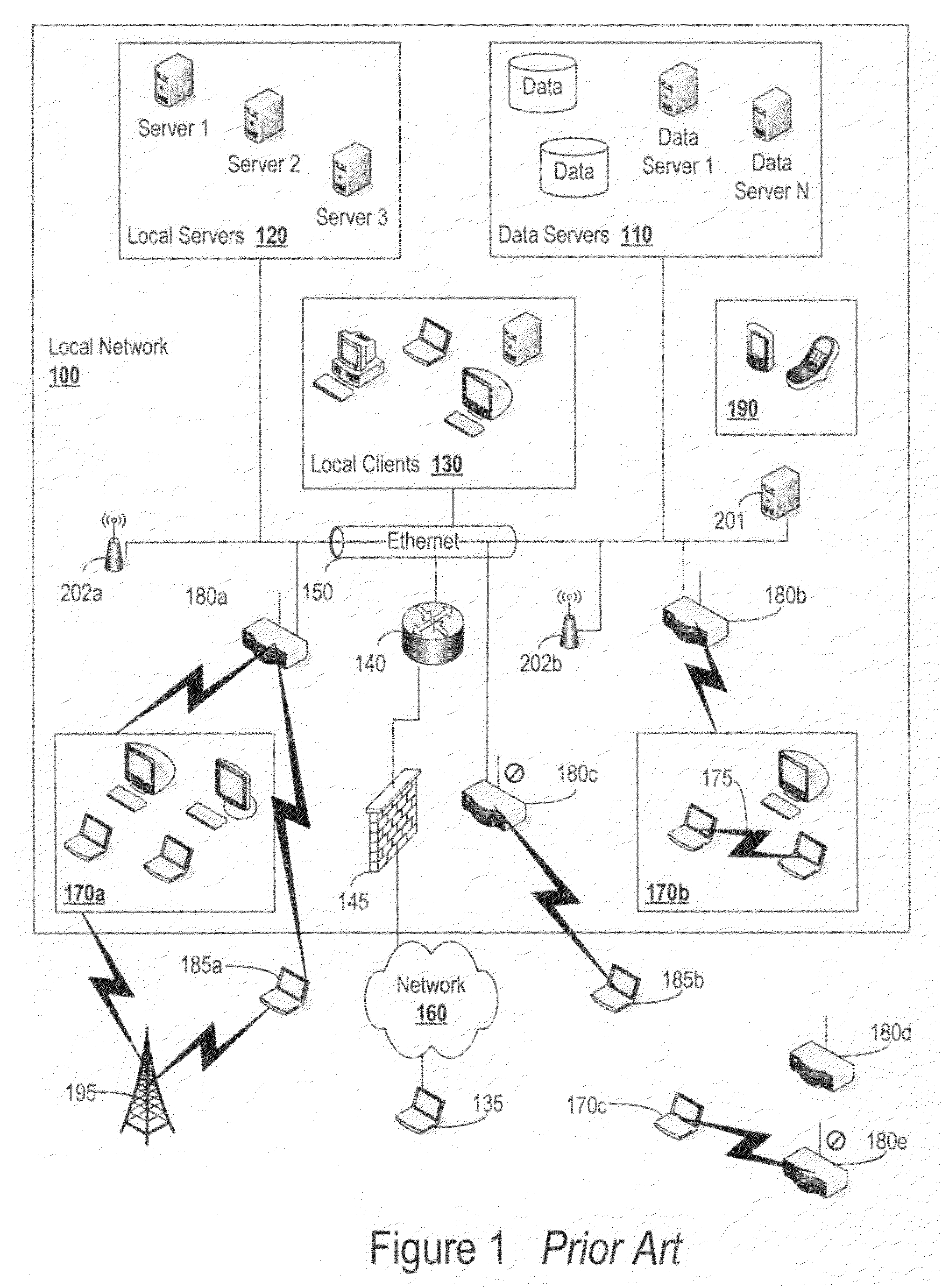
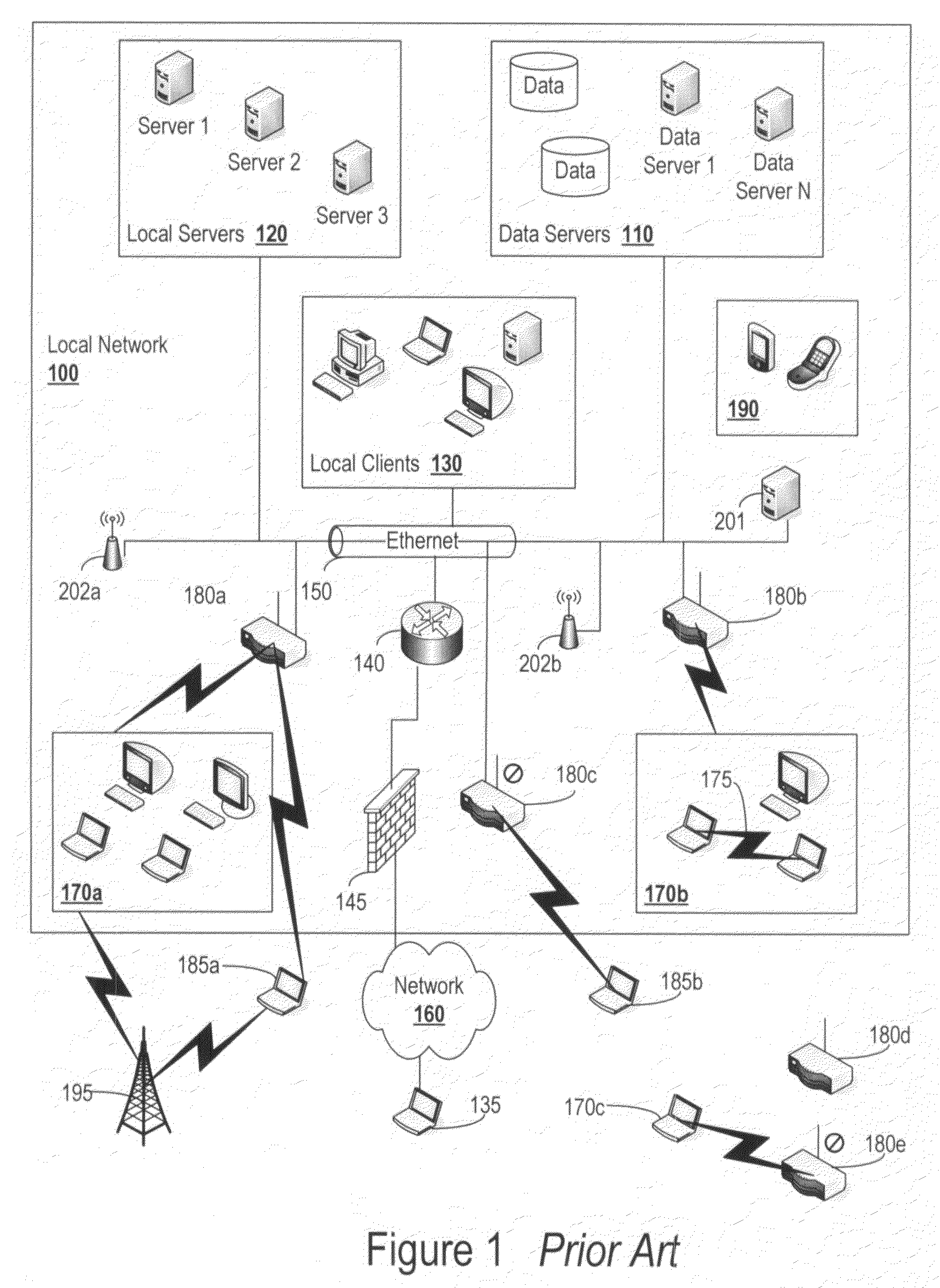
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS20100027552A1Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
Cloud computing gateway, cloud computing hypervisor, and methods for implementing same
ActiveUS8514868B2Improve manageabilityQuality improvementData switching by path configurationMultiple digital computer combinationsQuality of serviceManagement tool
Embodiments of the present invention provide a cloud gateway system, a cloud hypervisor system, and methods for implementing same. The cloud gateway system extends the security, manageability, and quality of service membrane of a corporate enterprise network into cloud infrastructure provider networks, enabling cloud infrastructure to be interfaced as if it were on the enterprise network. The cloud hypervisor system provides an interface to cloud infrastructure provider management systems and infrastructure instances that enables existing enterprise systems management tools to manage cloud infrastructure substantially the same as they manage local virtual machines via common server hypervisor APIs.
Owner:CSC AGILITY PLATFORM INC
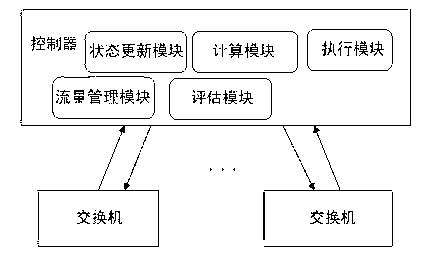
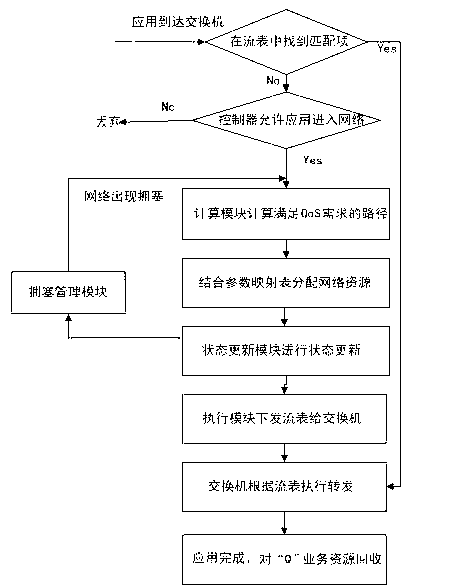
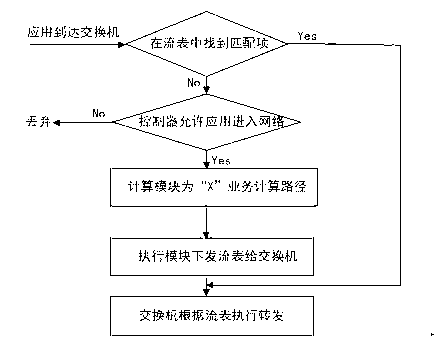
Controller for determining network state based on SDN (Software Defined Networking) and determination method thereof
The invention discloses a controller for determining a network state based on an SDN (Software Defined Networking) and a determination method thereof. The controller comprises a state updating module, a calculation module, an execution module, a flow management module and an evaluation module, wherein the state updating module is used for updating through a state and a path calculated by the calculation module; the calculation module is used for calculating a current network resource state N; the execution module is used for setting rules according to the path calculated by the calculation module and writing the path into a flow meter; the flow management module is used for carrying out congestion avoidance, flow supervision and shaping; and the evaluation module is used for carrying out synthetic judgment according to the current network resource state N calculated by the calculation module and QoS (Quality of Service) requirements of an application when receiving the application transmitted by a switch. According to the controller, the network state can be accurately controlled, a forwarding plane is precisely controlled, a 'Q+X' resource distribution mode is proposed, and the network resource is scheduled, so that the flexibility, the high efficiency, the intelligence and the optimization of a network can be realized.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
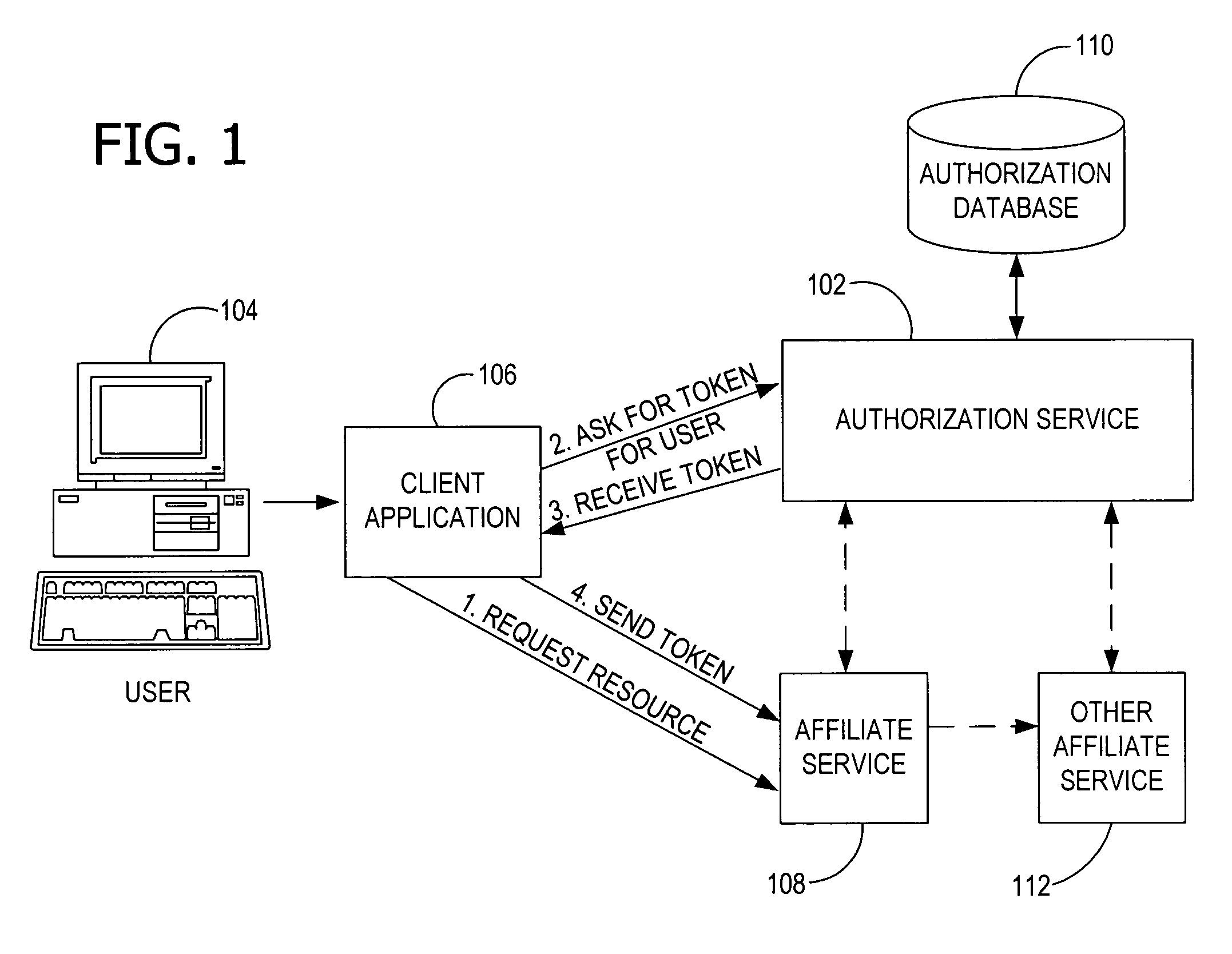
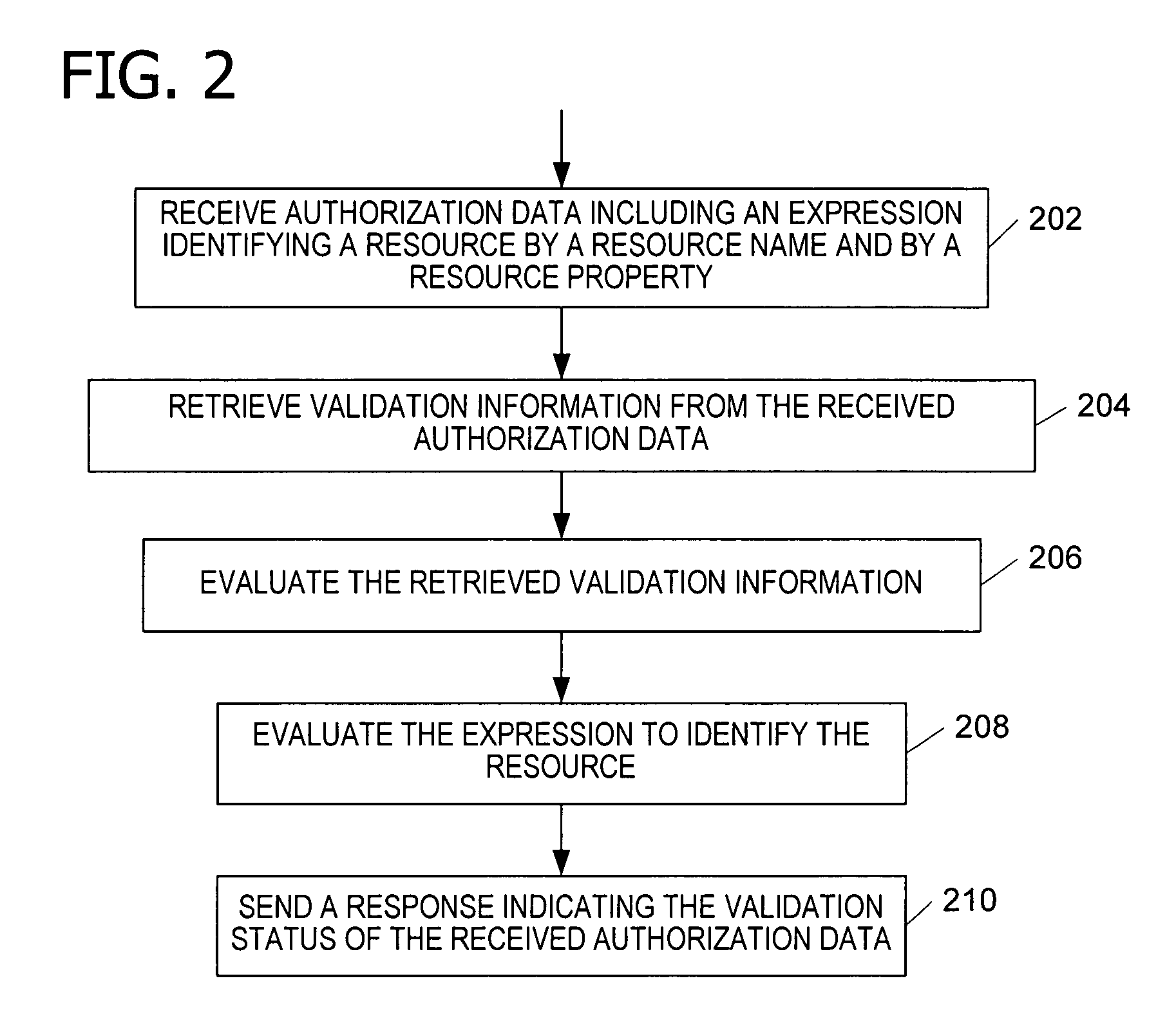
Authorization and access control service for distributed network resources
ActiveUS7685206B1Simplify access control managementEasy to implementDigital data processing detailsTransmissionMulti siteClient-side
Providing access to a resource via authorization data that conditionally defines the access by an expression that identifies the resource by name and by at least one property of the resource. An authorization service issues the authorization data (e.g., as a token) and evaluating authorization data received from a client. The authorization service evaluates the expression in the authorization data to identify the resource and determine the rights associated with the user for the resource. The authorization service implements role-based access control to control access to resources in a distributed, multi-site network.
Owner:MICROSOFT TECH LICENSING LLC
Integrated full text search system and method
ActiveUS20050222975A1Improve execution of queryEnhance manageabilityData processing applicationsWeb data indexingFull text searchMetadata
The present invention relates to an integrated full-text search architecture that integrates full text search with database server applications in a tight manner so that it becomes part of the server in all aspects including storage, metadata, query processing, back / up restore and resource management. This provides improved performance with respect to queries as well as improved manageability. Furthermore, the subject architecture is open and schema directed unlike other conventional full-text search architectures. Accordingly, the full-text search architecture enables expert users (e.g., search providers) to define their own index structures as well as ranking algorithms.
Owner:MICROSOFT TECH LICENSING LLC
Architecture and provisioning tools for managed multicast virtual private LAN trees
InactiveUS20060187950A1Simpler and reliableImprove manageabilityTime-division multiplexData switching by path configurationHigh bandwidthBroadcast service
Methods, tools, and a multicast connectivity architecture are provided for provisioning bundled high bandwidth multi-channel multimedia broadcast services over a packet switched communications network. Multicast group membership join / prune requests generated by the destination network nodes are processed on edge. Multicast tree connectivity in the core of the communications network is static and centrally provisioned based on multicast group member edge network nodes associated with subscribers, while dynamic multicasting techniques are employed over the distribution portion of the service provider's communications network to deliver requested content to each destination network node. The methods and tools compute multicast trees, configure on-tree branching network nodes, and establish Virtual Private LAN network overlays for channel bundles to convey multi-channel content in the core of the managed communications network between edge network nodes. Centralized multicast tree provisioning enables the use of efficient multicast tree topologies, while VPLS packet transport provides interoperability between disparate Layer-2 packet transport technologies employed in different portions of the communications network.
Owner:ALCATEL LUCENT SAS
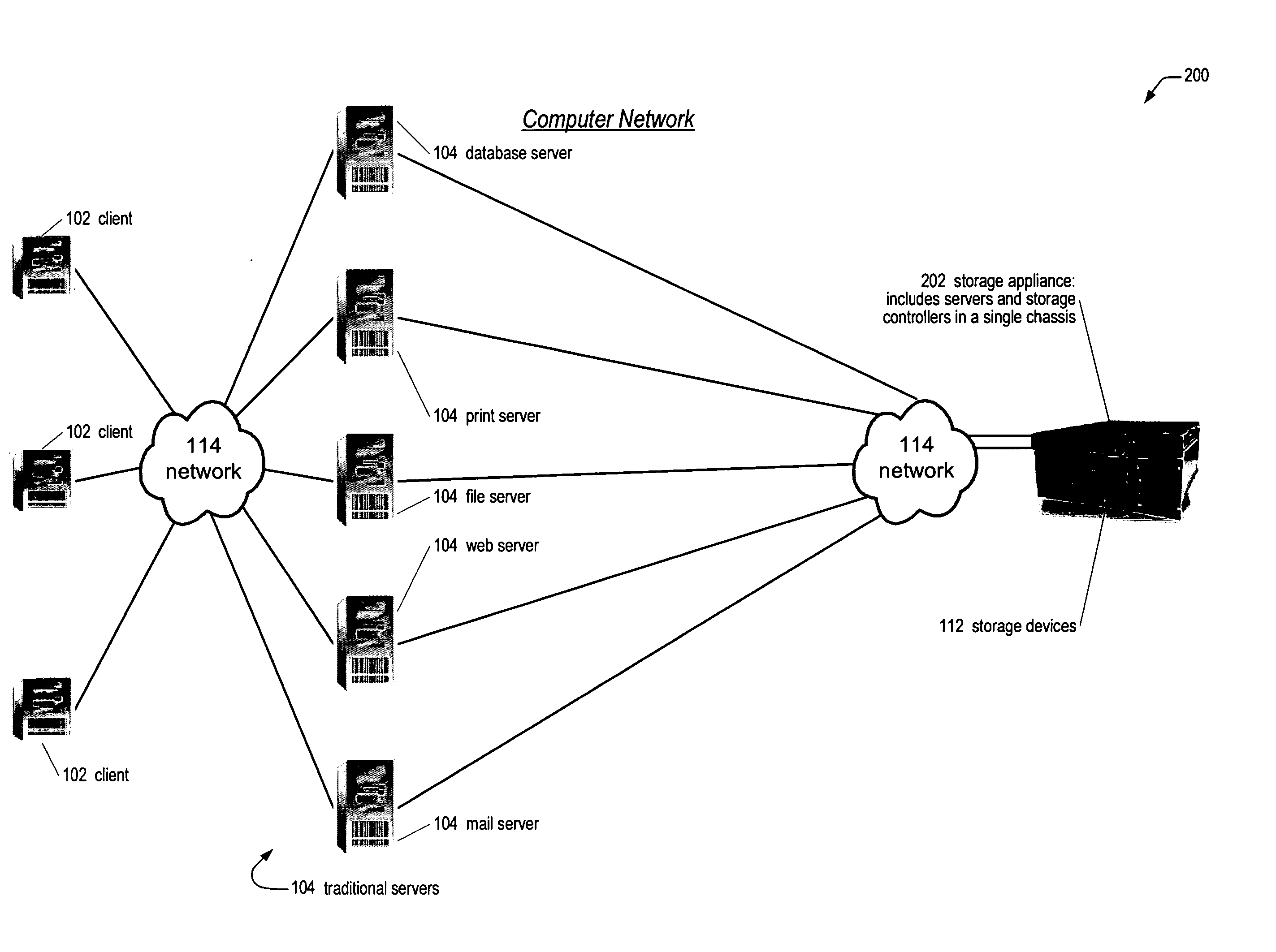
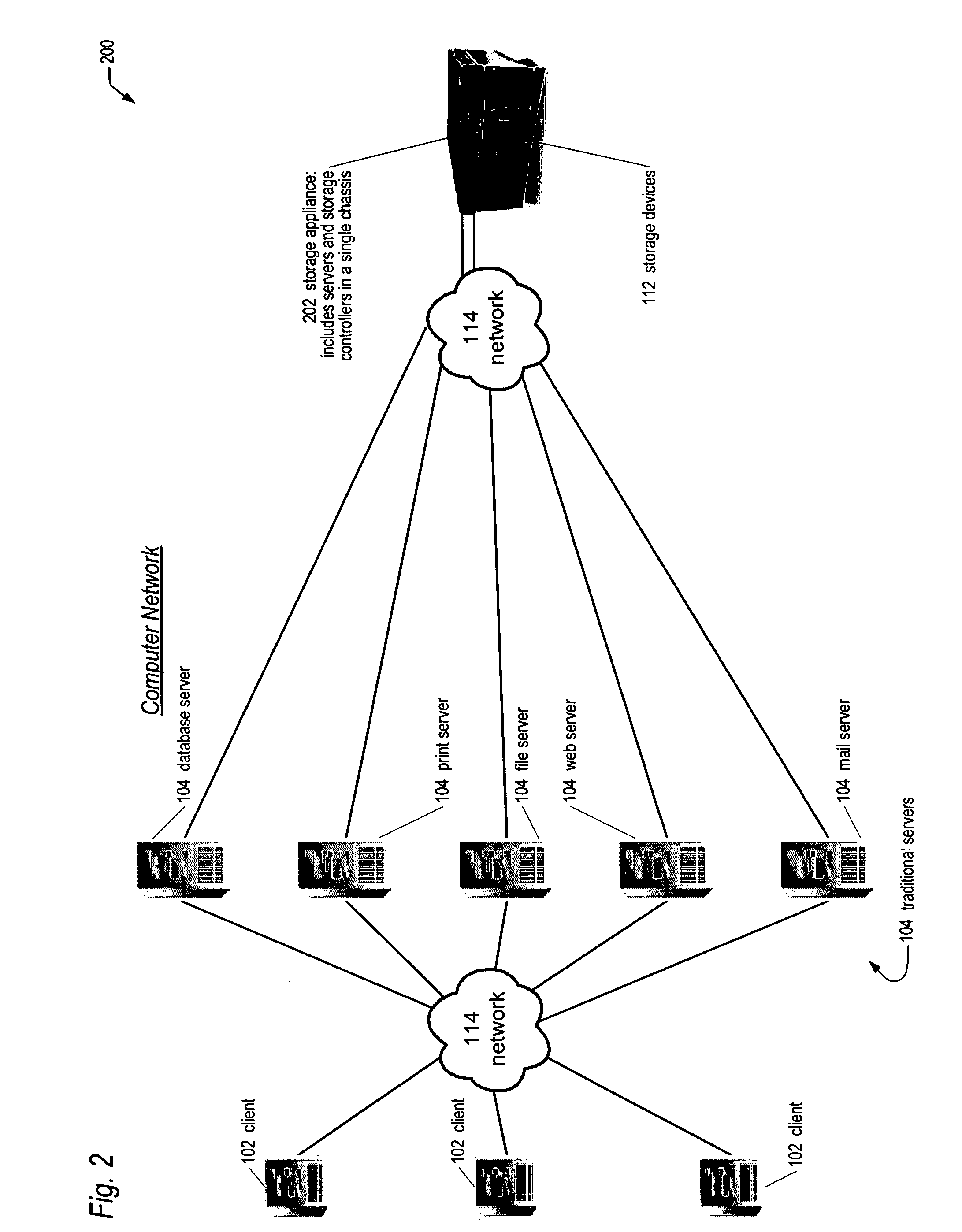
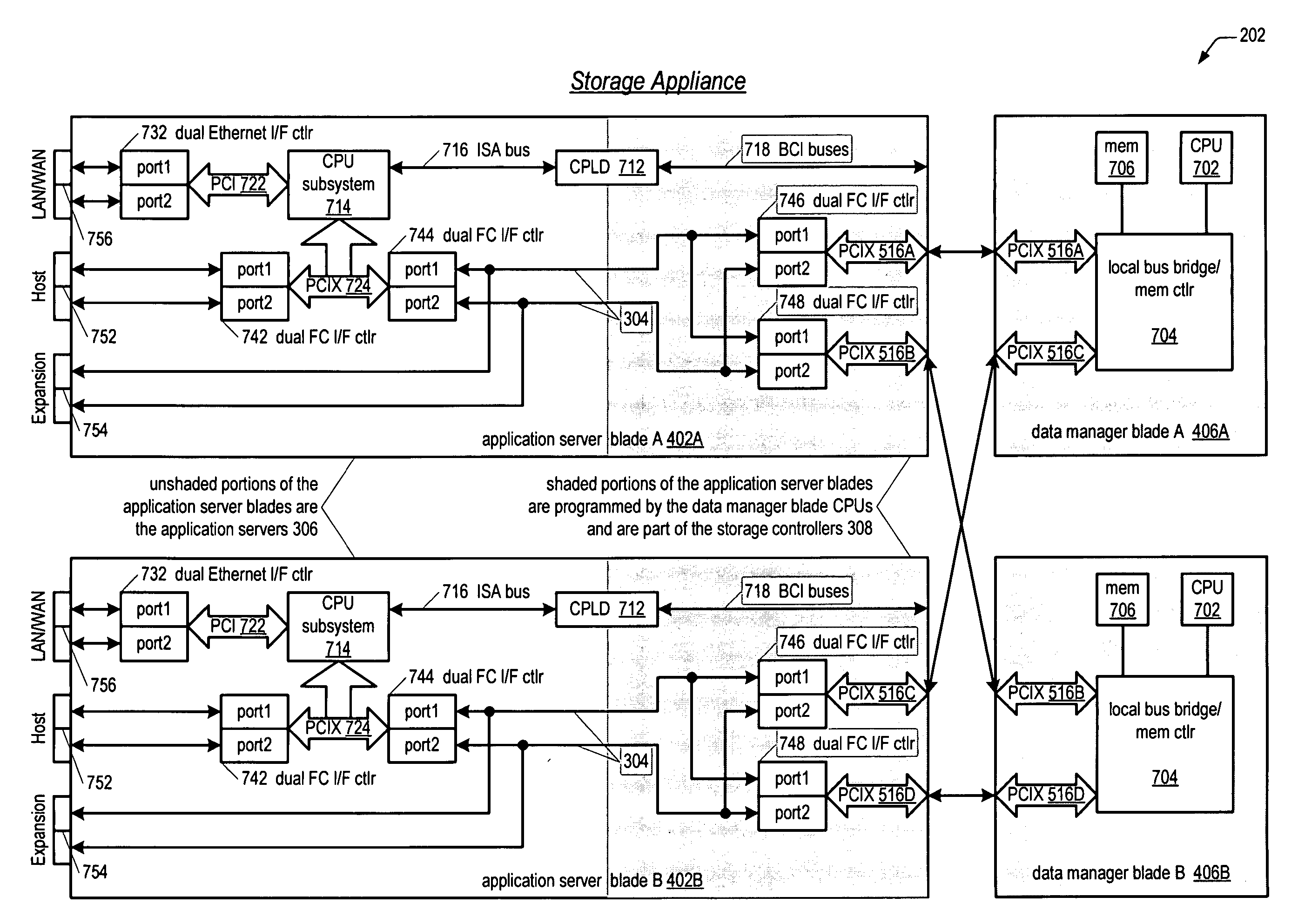
Network storage appliance with integrated redundant servers and storage controllers
ActiveUS20050021606A1Reduce needLow costInput/output to record carriersDigital data processing detailsHard disc driveOff the shelf
A network storage appliance is disclosed. The appliance includes a single chassis that encloses a plurality of servers and a plurality of storage controllers coupled together via a chassis backplane. The storage controllers control the transfer of data between the plurality of servers and a plurality of storage devices coupled to the storage controllers. The servers and storage controllers include a plurality of field replaceable unit (FRUs) hot-pluggable into the backplane such that any one of the FRUs may fail without loss of availability to the storage devices' data. In various embodiments, the chassis fits in a 19″ wide rack; is 1U high; the servers are standard PCs configured to execute off-the-shelf server applications and to facilitate porting of popular operating systems with little modification; the servers include disk-on-chip memory rather than a hard drive; local buses (e.g., PCIX) on the backplane interface the various FRUs.
Owner:DOT HILL SYST
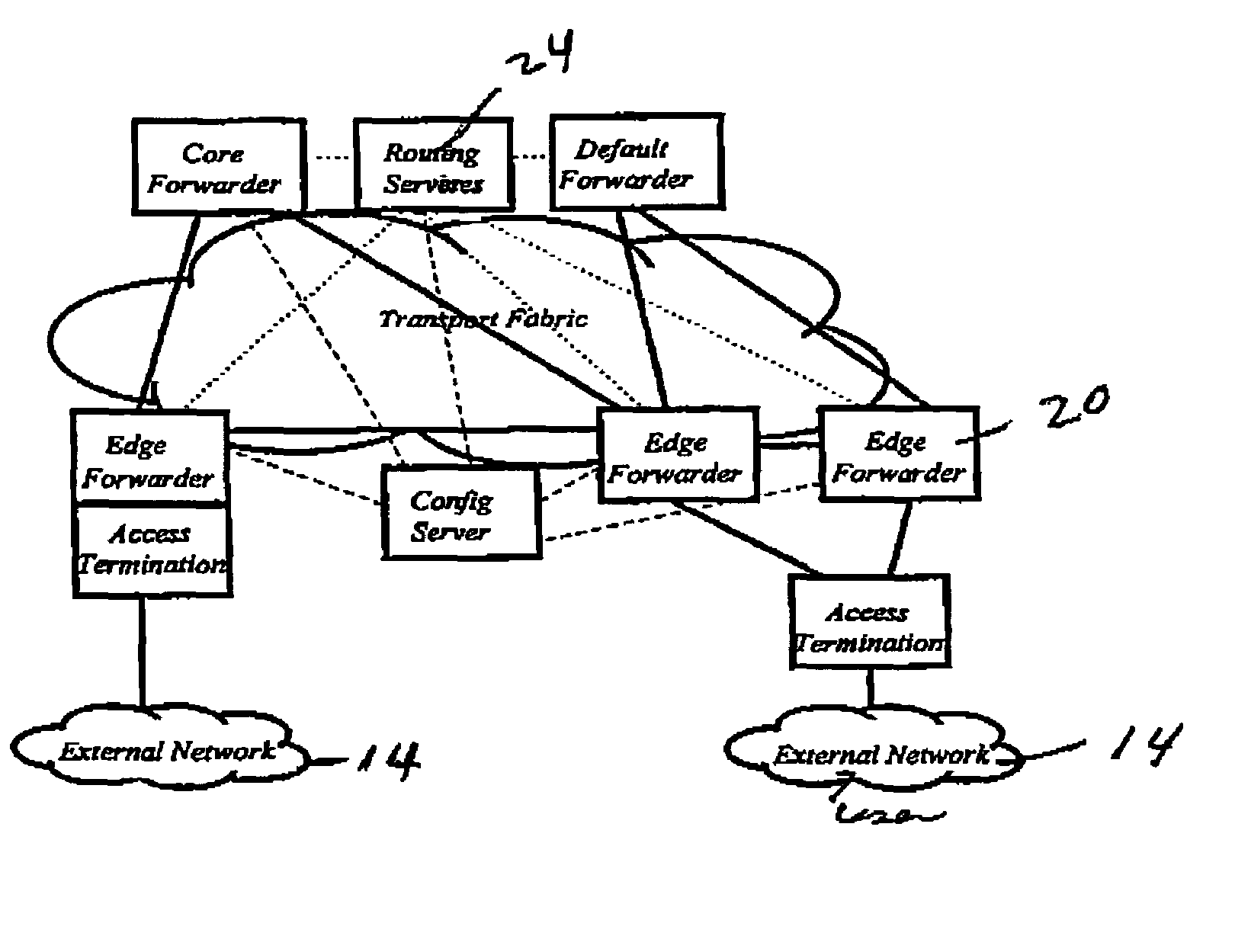
Method and apparatus for forwarding packets
InactiveUS7583665B1Reduce numberReduce managementMultiplex system selection arrangementsData switching by path configurationPhysical networkLogical partition
An internetworking system operating over an ATM backbone. The physical internetworking devices within the system are shared to provide the internetworking functions while servicing two or more distinct and isolated user networks. This is accomplished by logically partitioning the devices into distinct sub-elements which provide all or part of the internetworking functions. These sub-elements are uniquely allocated to independent realms which are then assigned to specific user networks.
Owner:ALCATEL LUCENT SAS
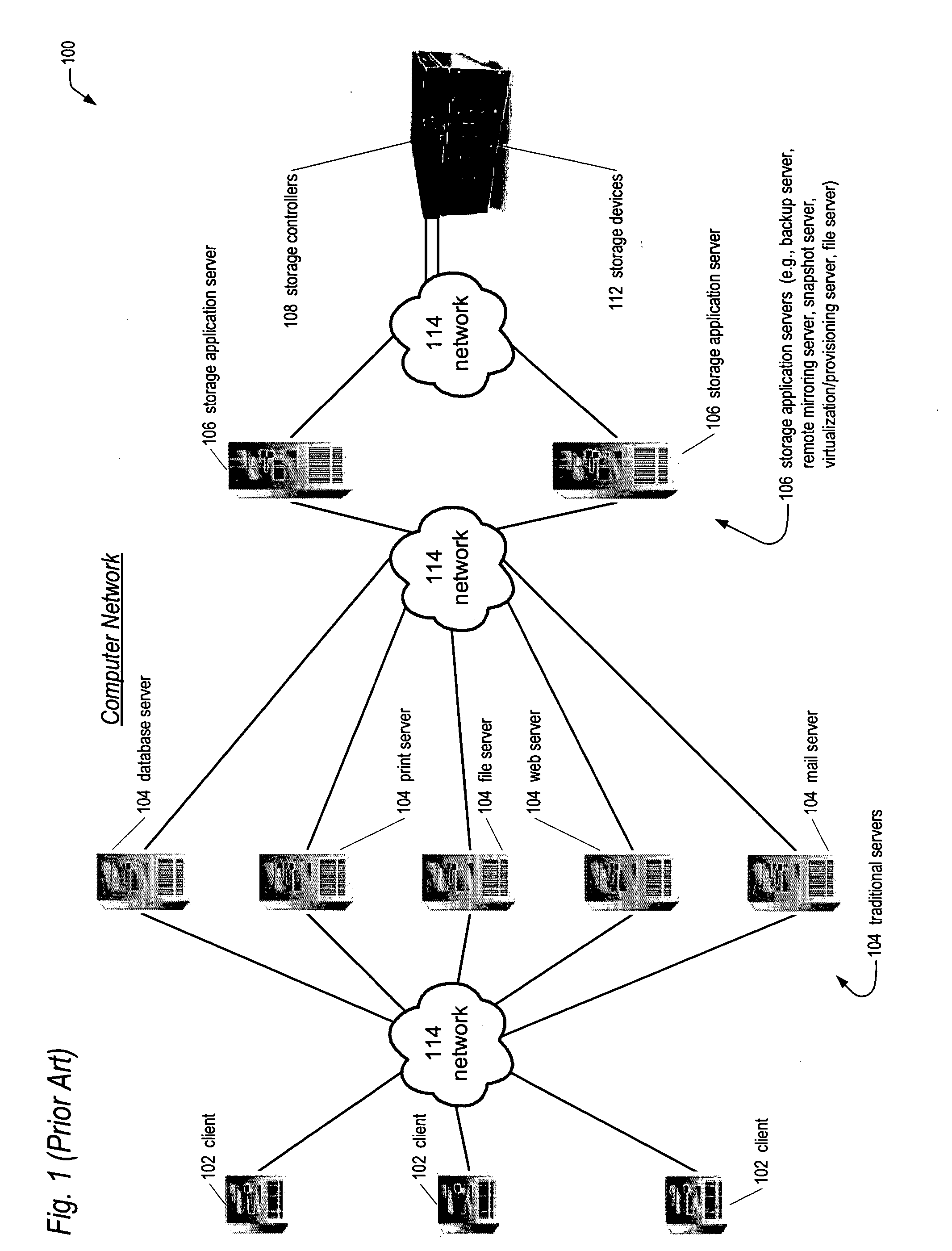
Network storage appliance with integrated server and redundant storage controllers
ActiveUS20050010715A1Improve system reliabilityImprove manageabilityInput/output to record carriersDigital data processing detailsControl storeMagnetic tape
A network storage appliance is disclosed. The appliance includes a chassis enclosing a backplane, and a server enclosed in the chassis and coupled to the backplane. The appliance also includes storage controllers enclosed in the chassis, each coupled to the backplane, which control transfer of data between the server and storage devices coupled to the storage controllers. The storage controllers also control transfer of data between the storage devices and computers networked to the appliance and external to the appliance. The storage controllers and the server comprise a plurality of hot-replaceable blades. Any one of the plurality of blades may be replaced during operation of the appliance without loss of access to the storage devices by the computers. In one embodiment, the server executes storage application software, such as backup software for backing up data on the storage devices, such as to a tape device networked to the server.
Owner:DOT HILL SYST
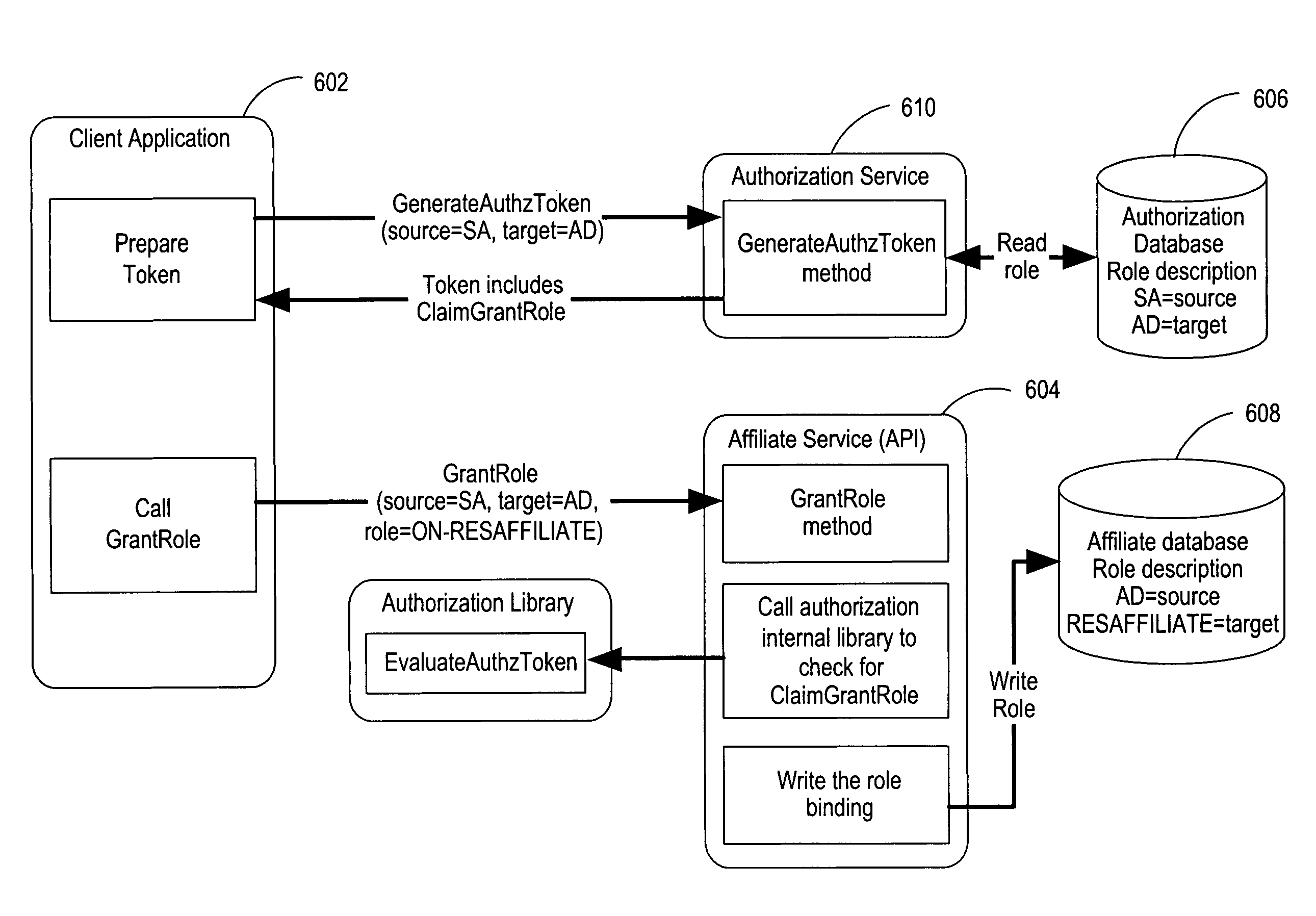
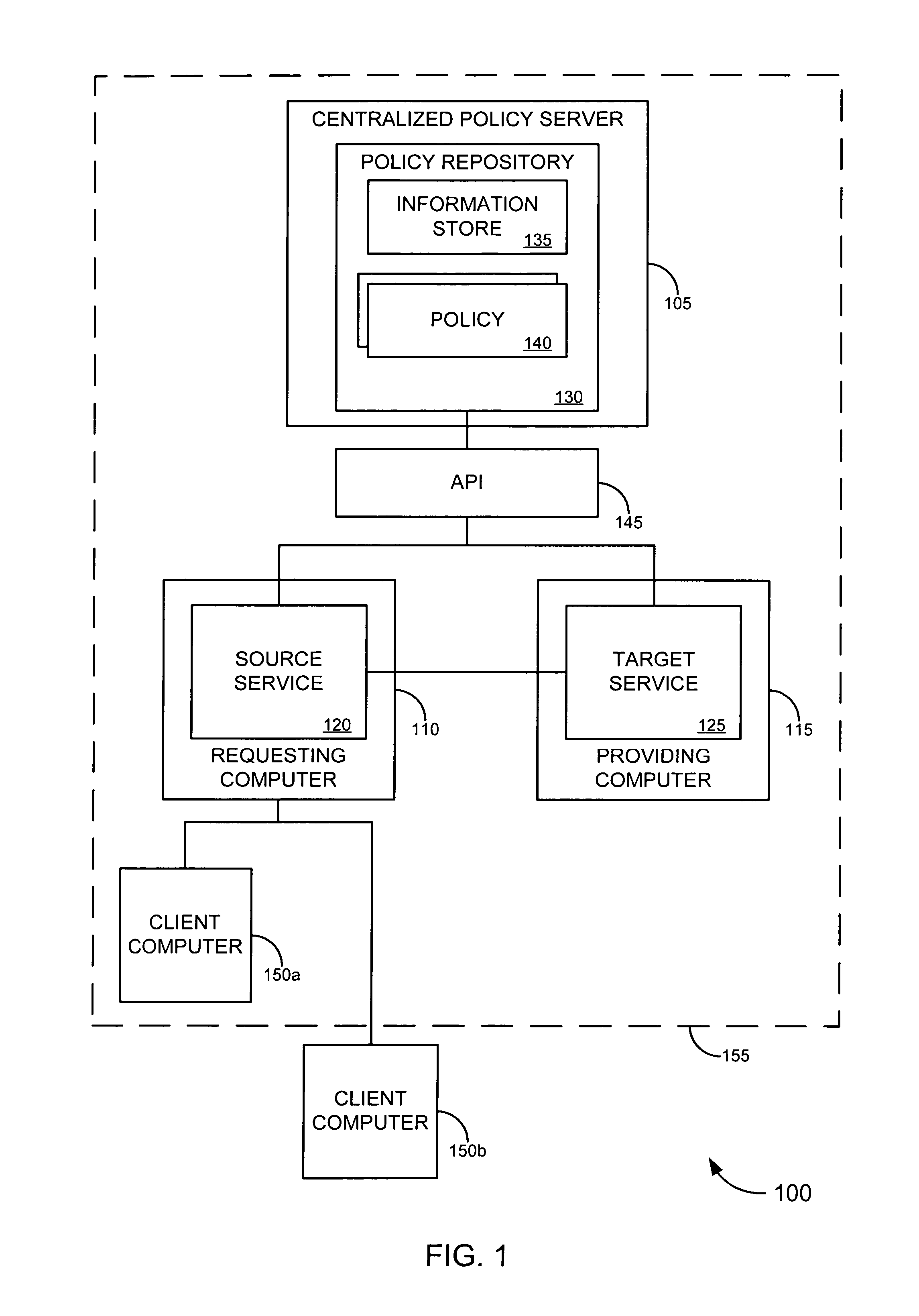
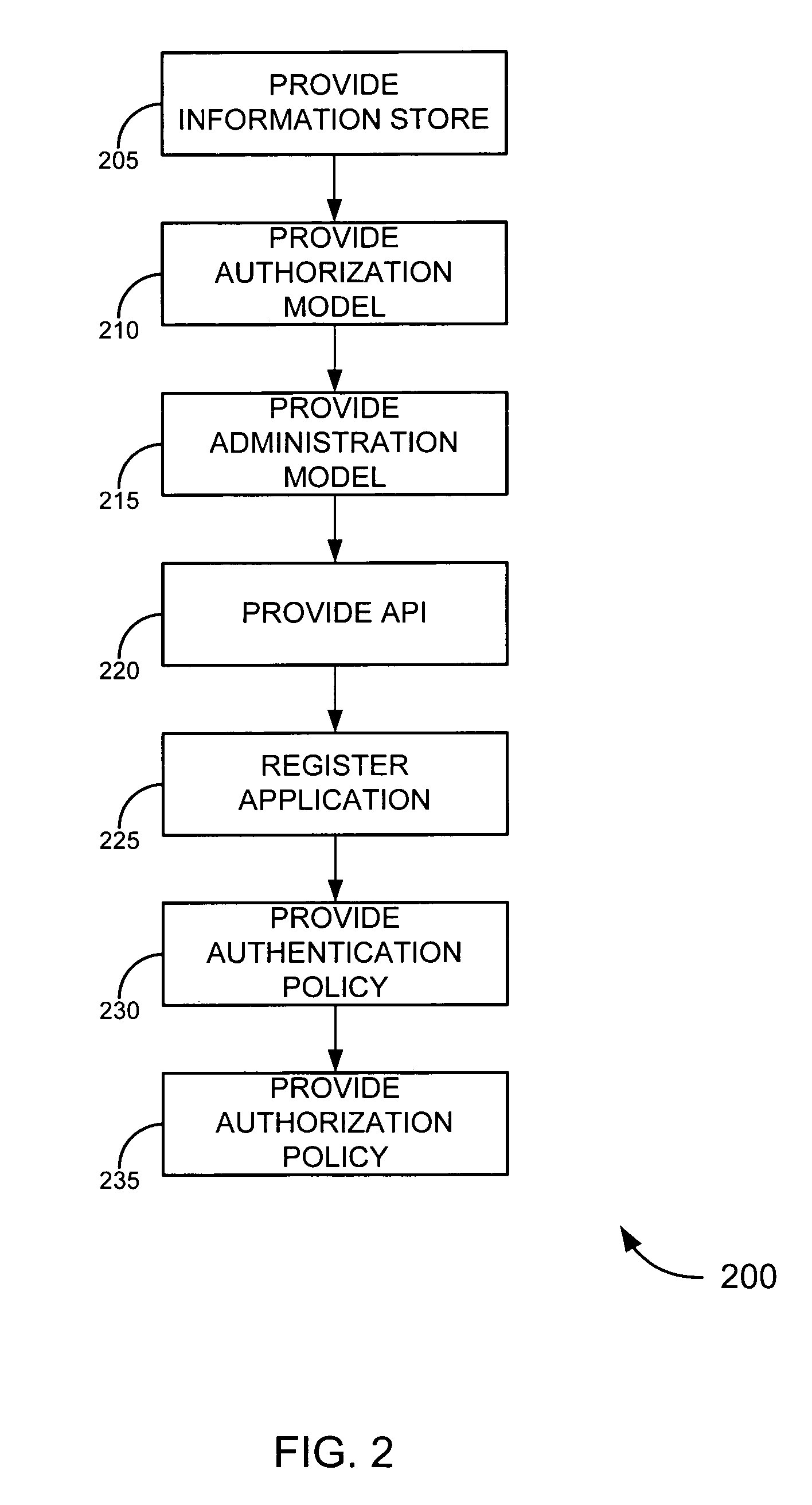
Enterprise service-to-service trust framework
ActiveUS7721322B2Improve manageabilityImprove securityDigital data processing detailsMultiple digital computer combinationsEnterprise servicesInformation security
Embodiments of the invention provide a trust framework for governing service-to-service interactions. This trust framework can provide enhanced security and / or manageability over prior systems. Merely by way of example, in some cases, an information store can be used to store information security information (such as trust information, credentials, etc.) for a variety of services across an enterprise. In other cases, the trust framework can provide authentication policies to define and / or control authentication between services (such as, for example, types of authentication credentials and / or protocols are required to access a particular service—either as a user and / or as another service—and / or types of authentication credentials and / or protocols a service may be enabled to use to access another service). Alternatively and / or additionally, the trust framework can provide authorization policies to define and / or control authorization between services.
Owner:ORACLE INT CORP
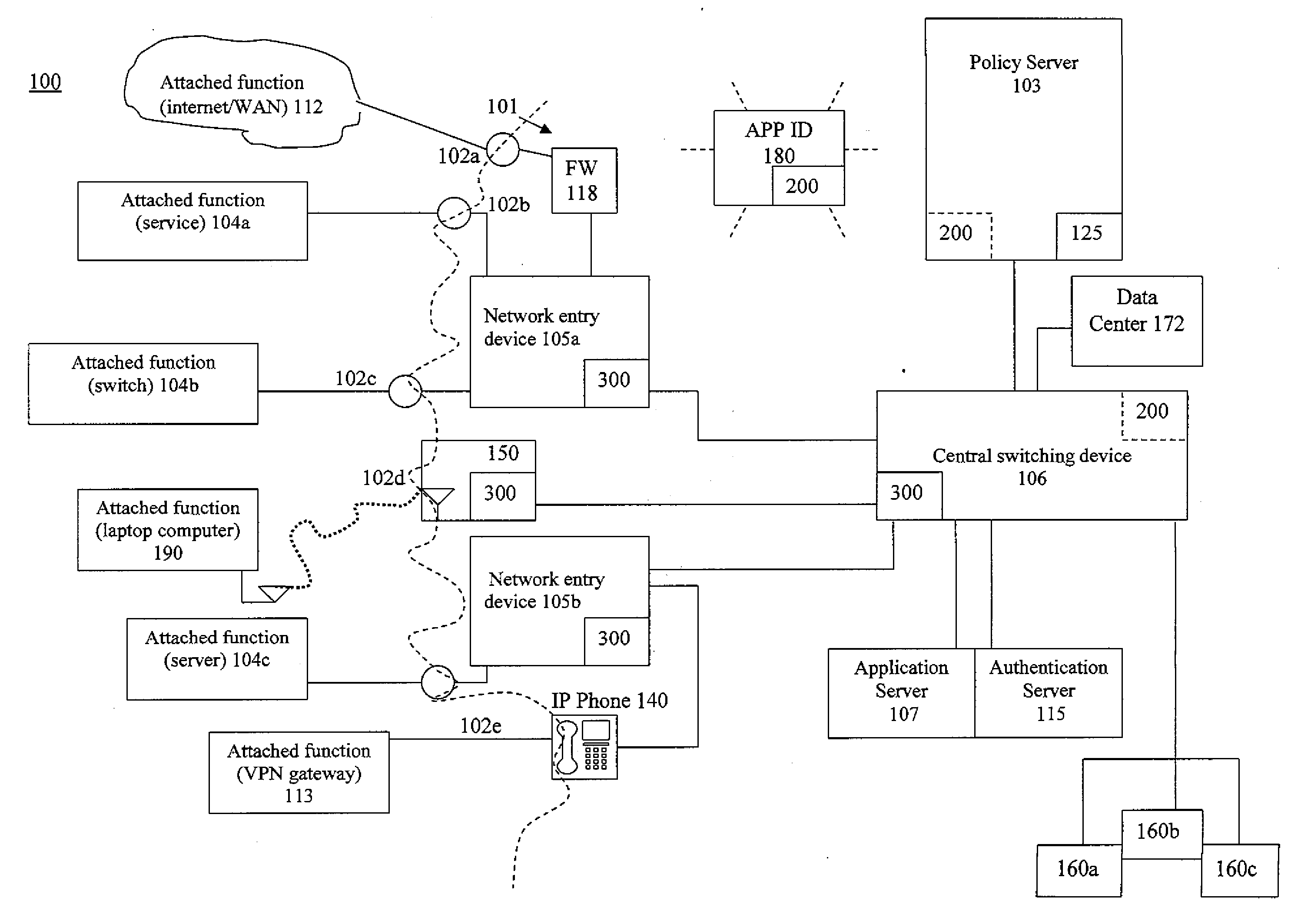
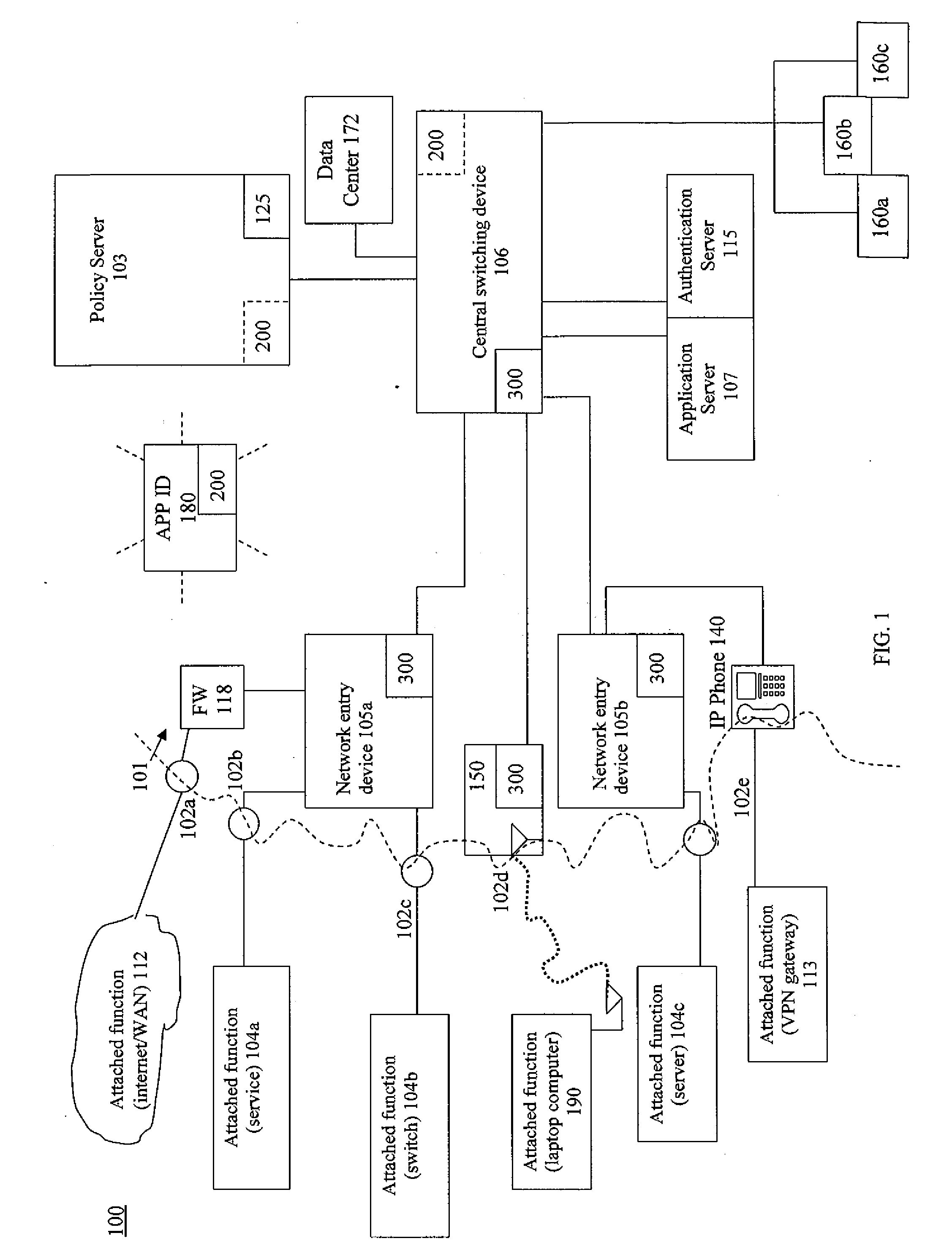
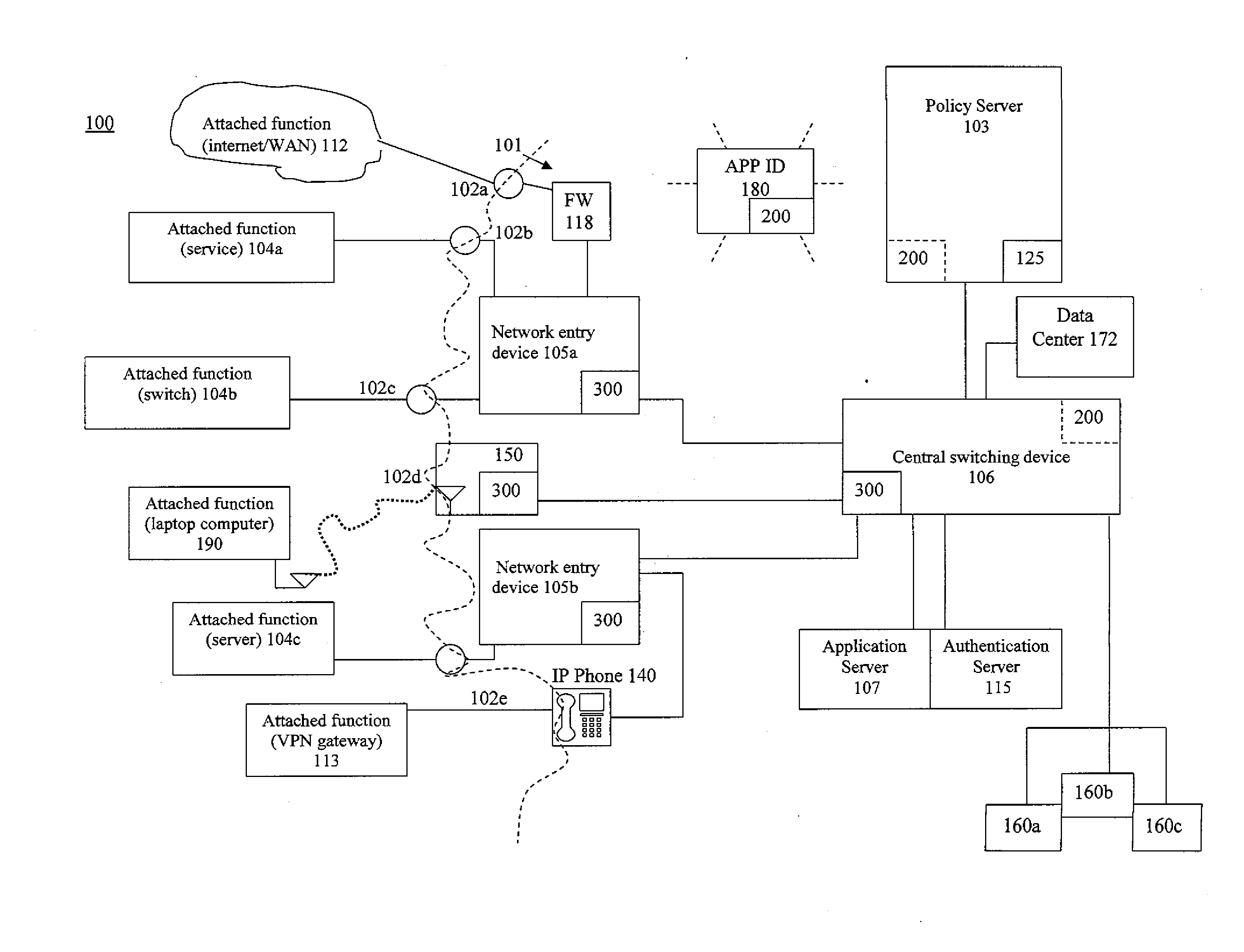
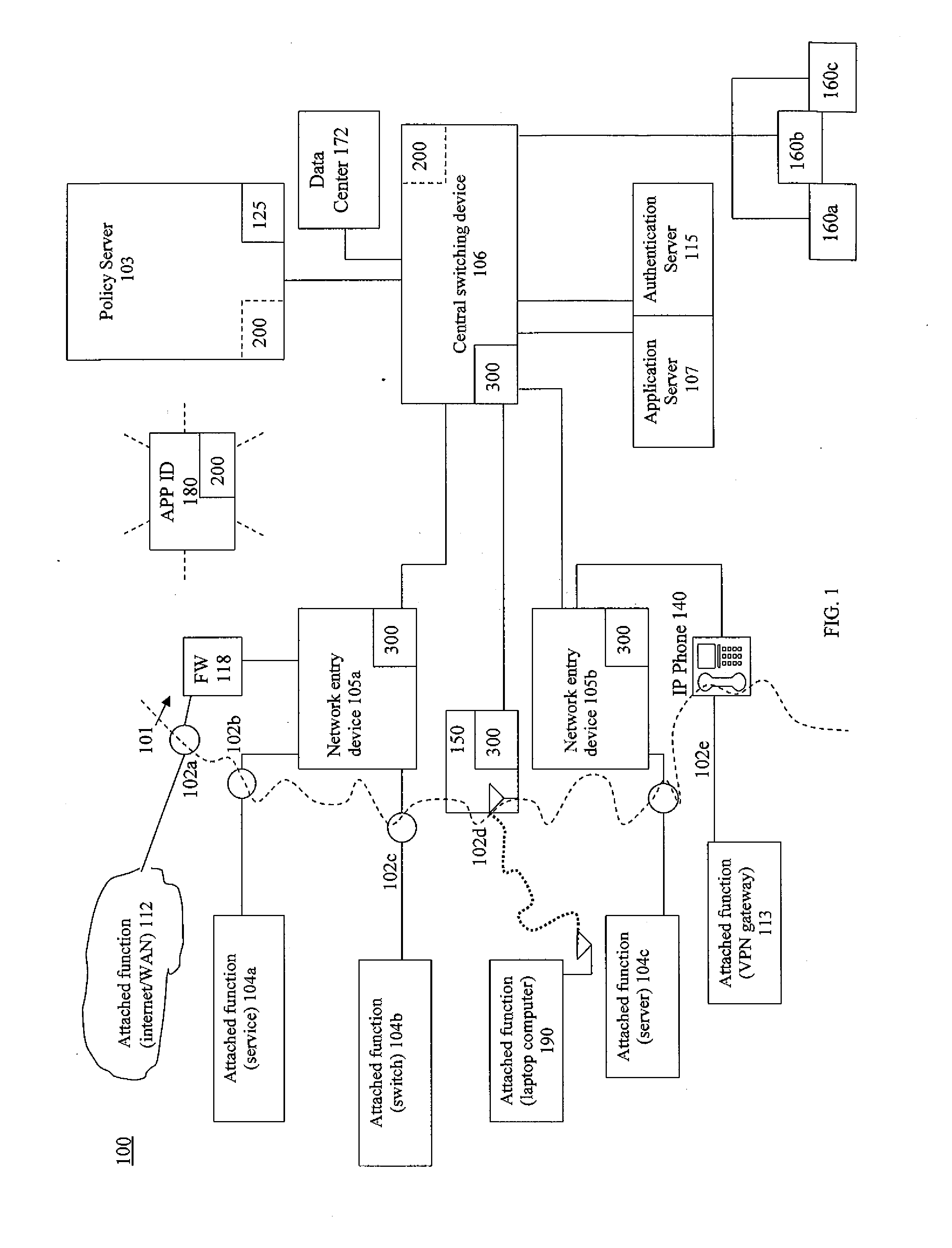
System and related method for network monitoring and control based on applications
ActiveUS20140280889A1Improving network manageabilityImprove securityDigital computer detailsData switching networksTraffic capacityVisibility
A network architecture system that expands the control network administrators have on existing networks. The system provides application identification and usage data by user, by device and network location. Dynamic traffic mirroring of the system allows for the efficient use of a tool to identify computer applications running on the network. The system includes the ability to embed the tool where needed rather than pervasively based on the use of the dynamic mirroring to bring the packets to the tool. The architecture implemented functions allow the ability to start small with a single application identification tool added to a network management server, examine flows from throughout the network (via mirroring) and upgrade policy control based on real application identification data and usage, then grow to pervasive deployment where virtually all new flows could be identified and controlled via policy. This architecture enables substantially complete application visibility and control.
Owner:EXTREME NETWORKS INC
System and communication method of IP telecommunication network and its application
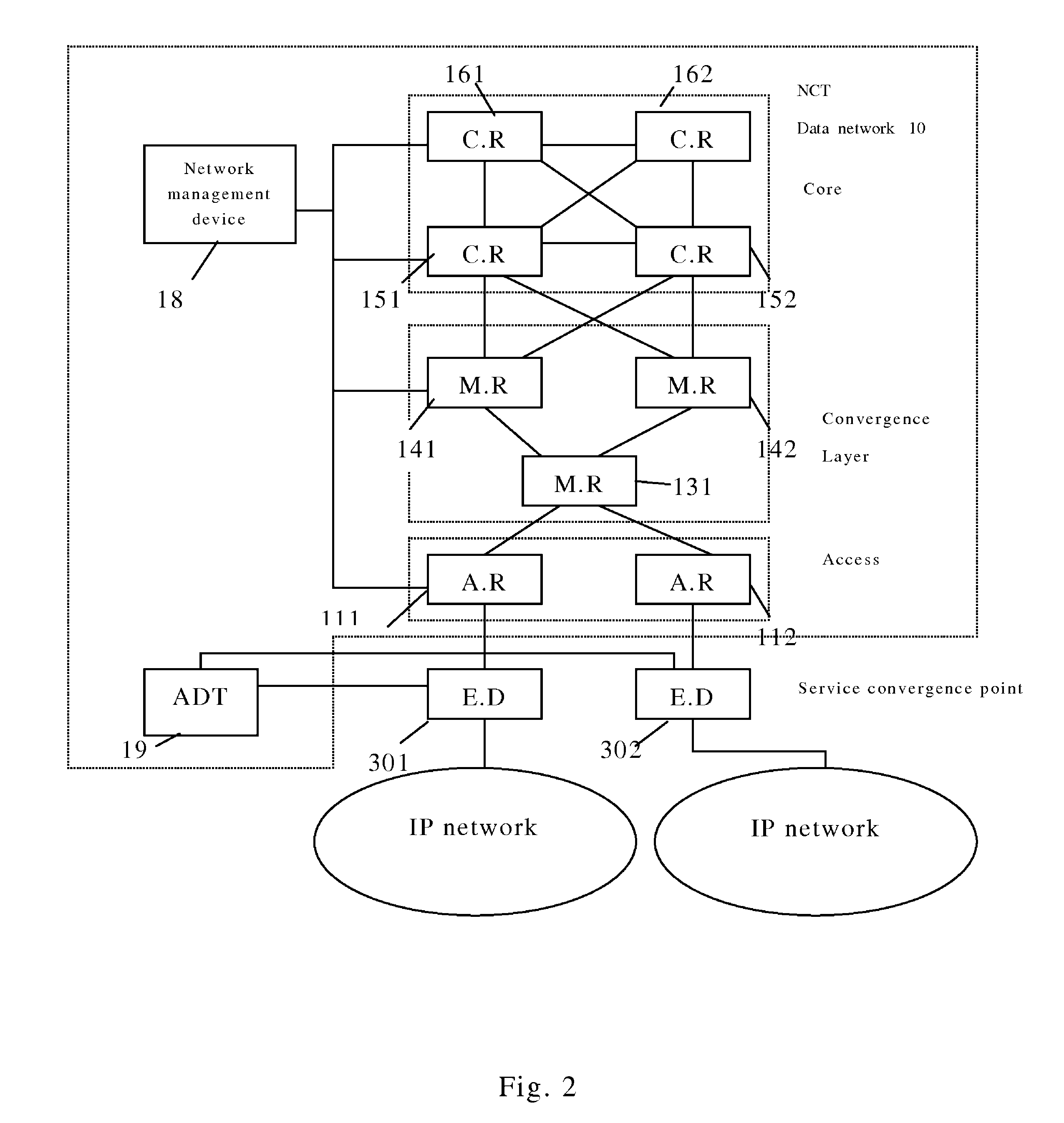
ActiveUS7894458B2Improve reliabilityImprove stabilitySpecial service provision for substationNetworks interconnectionTelecommunications networkIp address
Owner:BEIJING JIAXUN FEIHONG ELECTRICAL +2
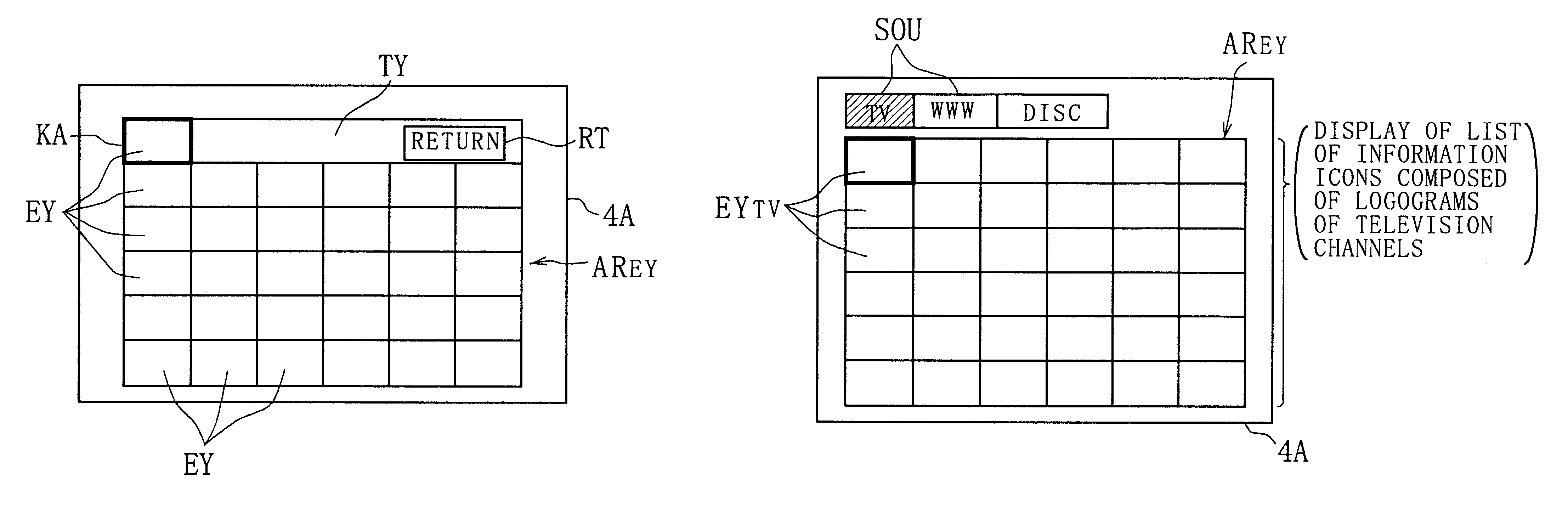
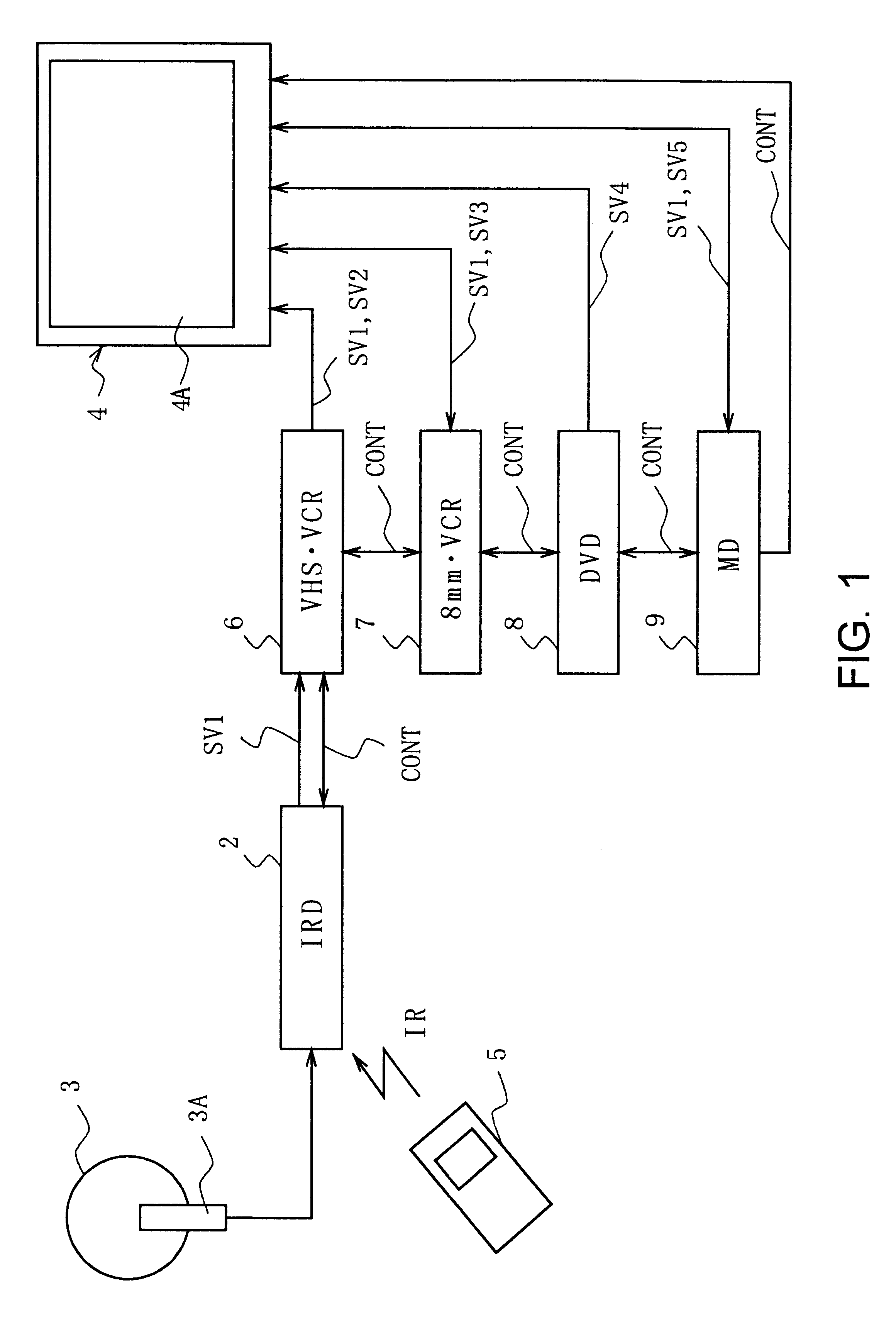
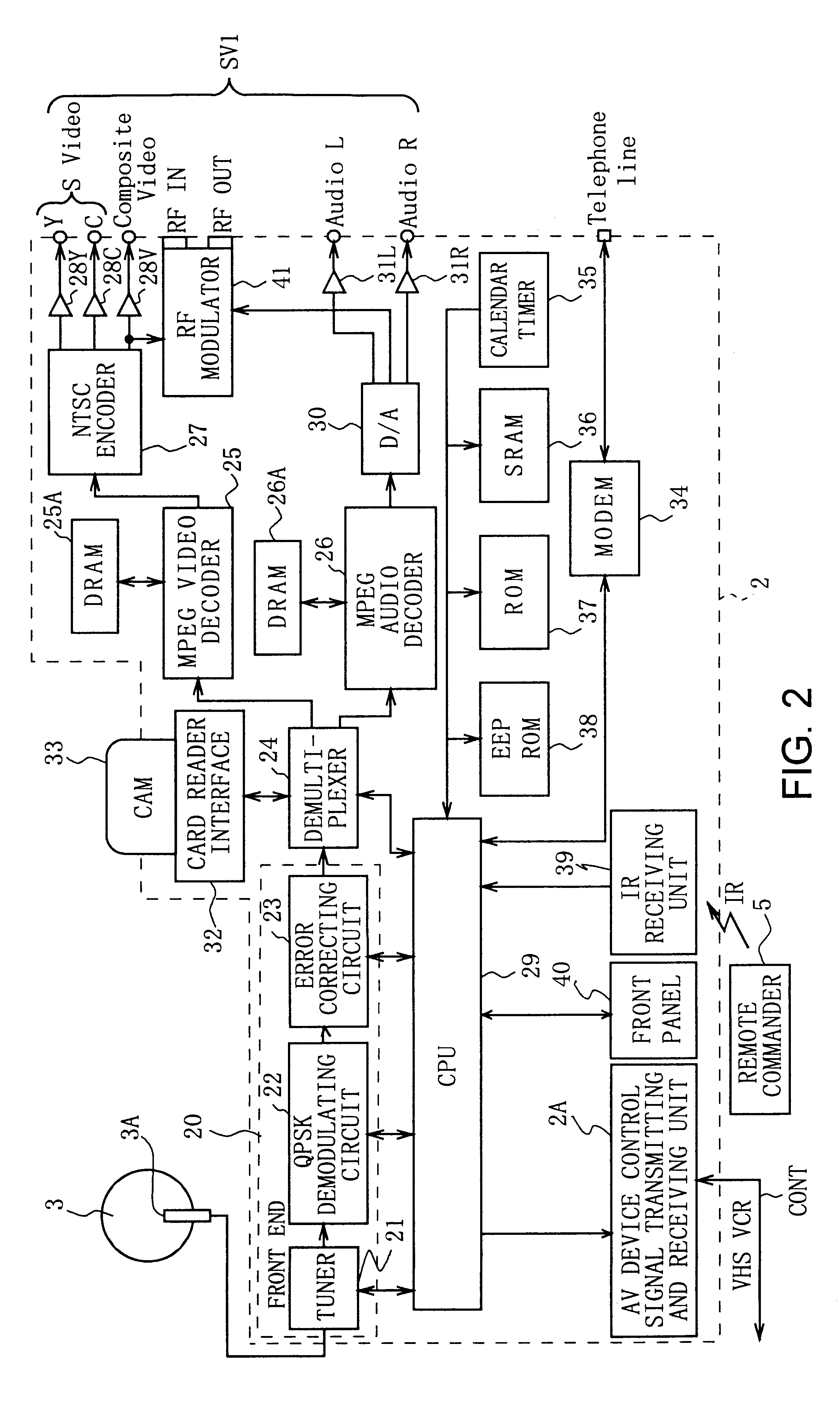
Information display method
InactiveUS6344880B1Improve manageabilityTelevision system detailsColor television detailsComputer scienceMultimedia
Owner:SATURN LICENSING LLC
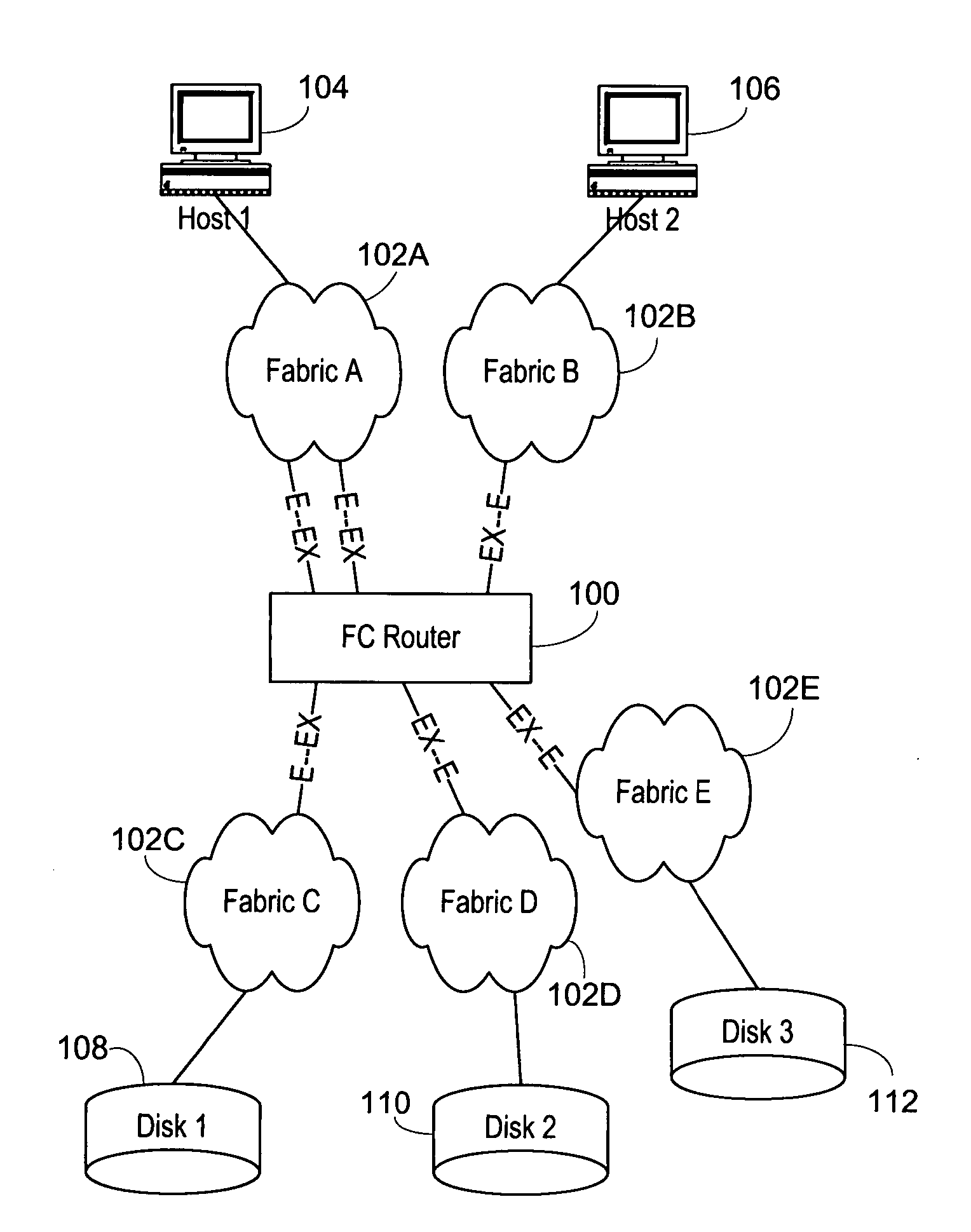
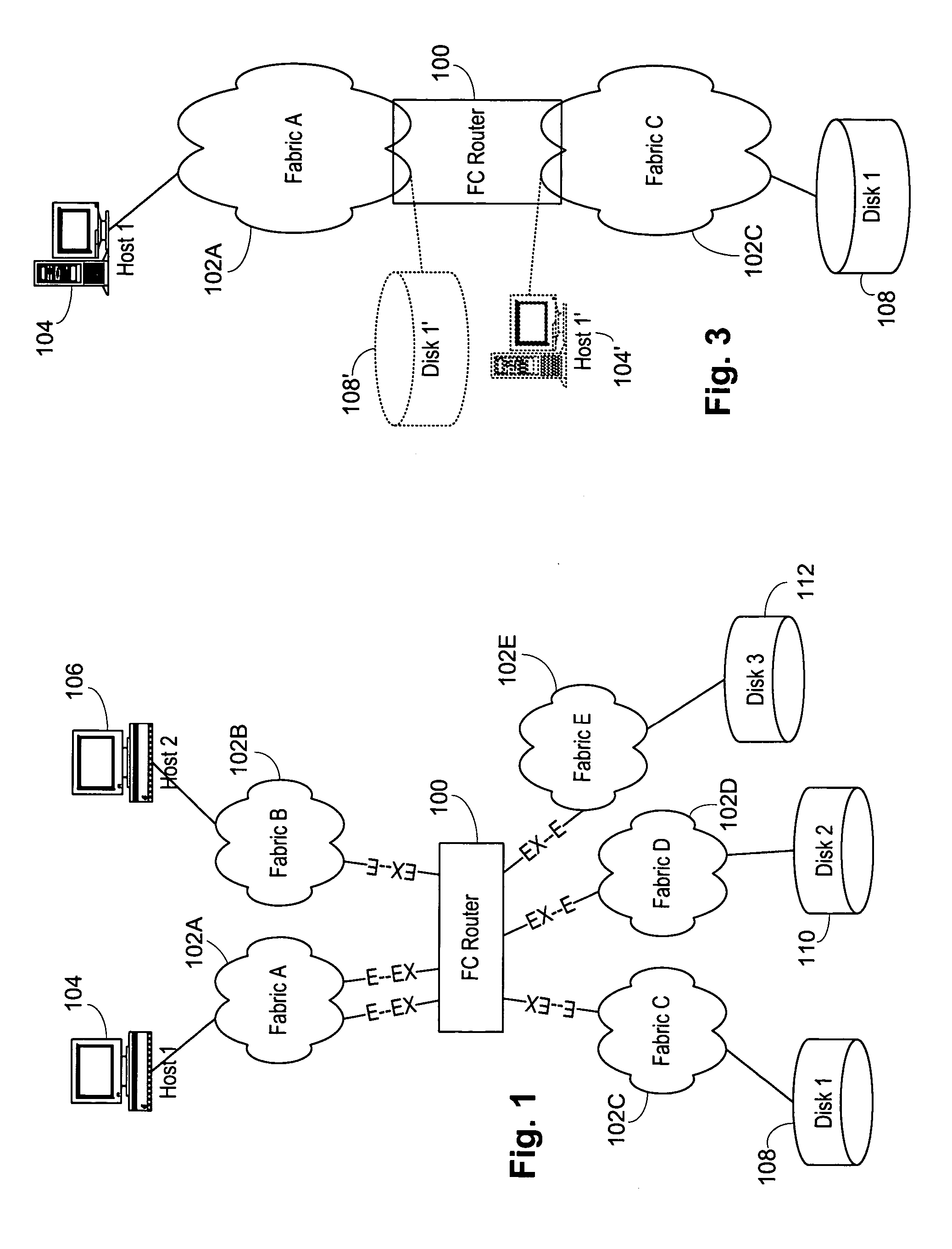
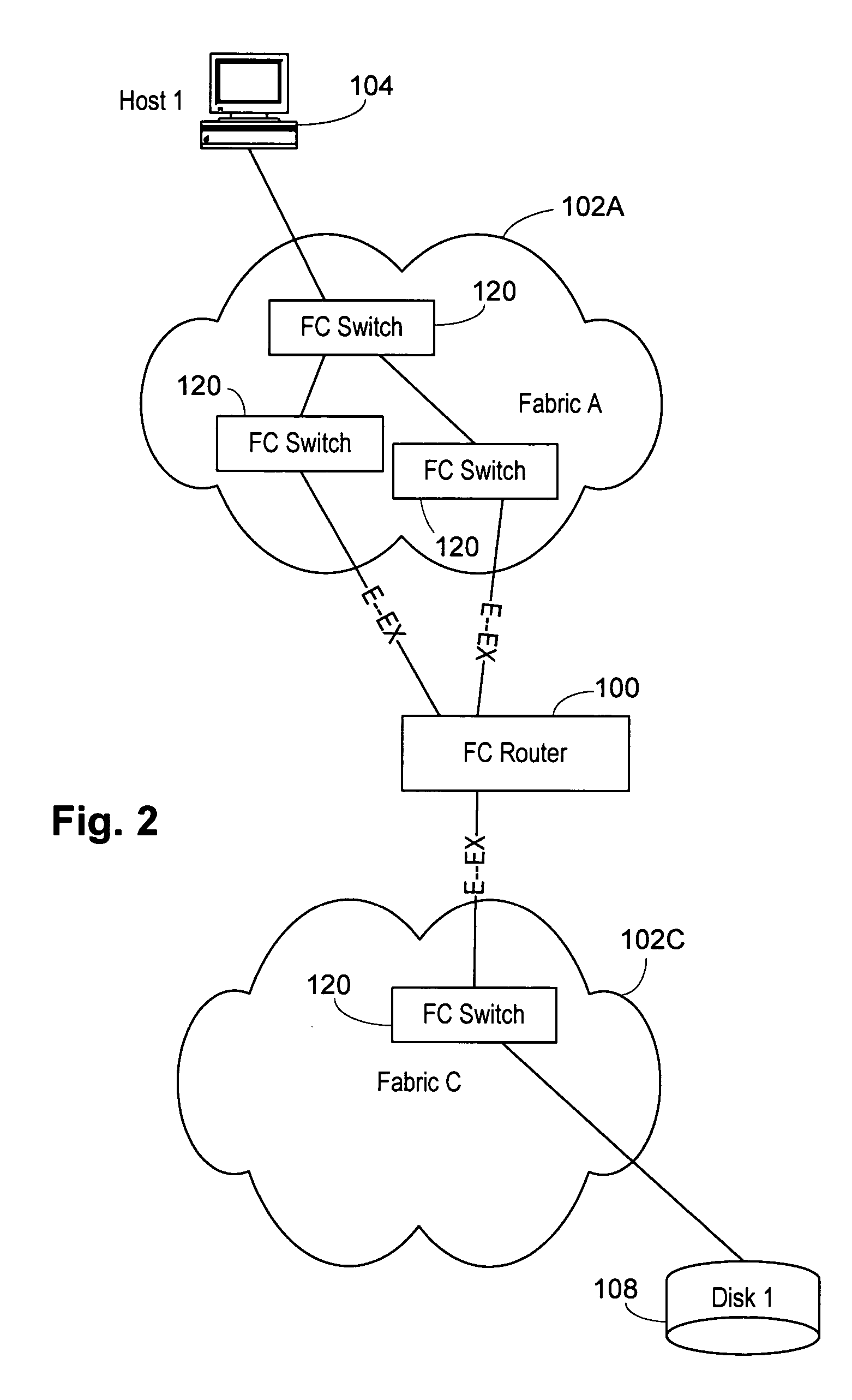
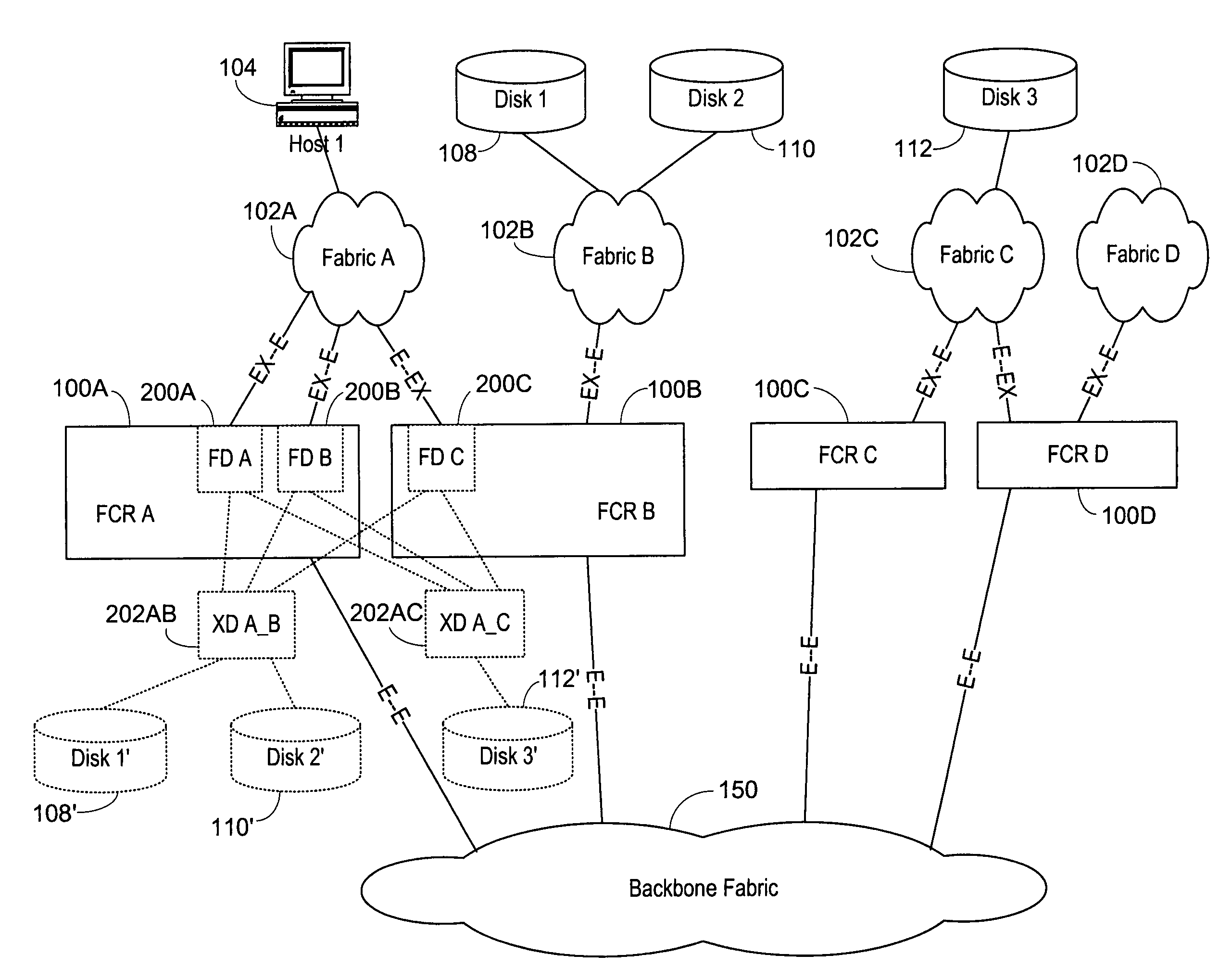
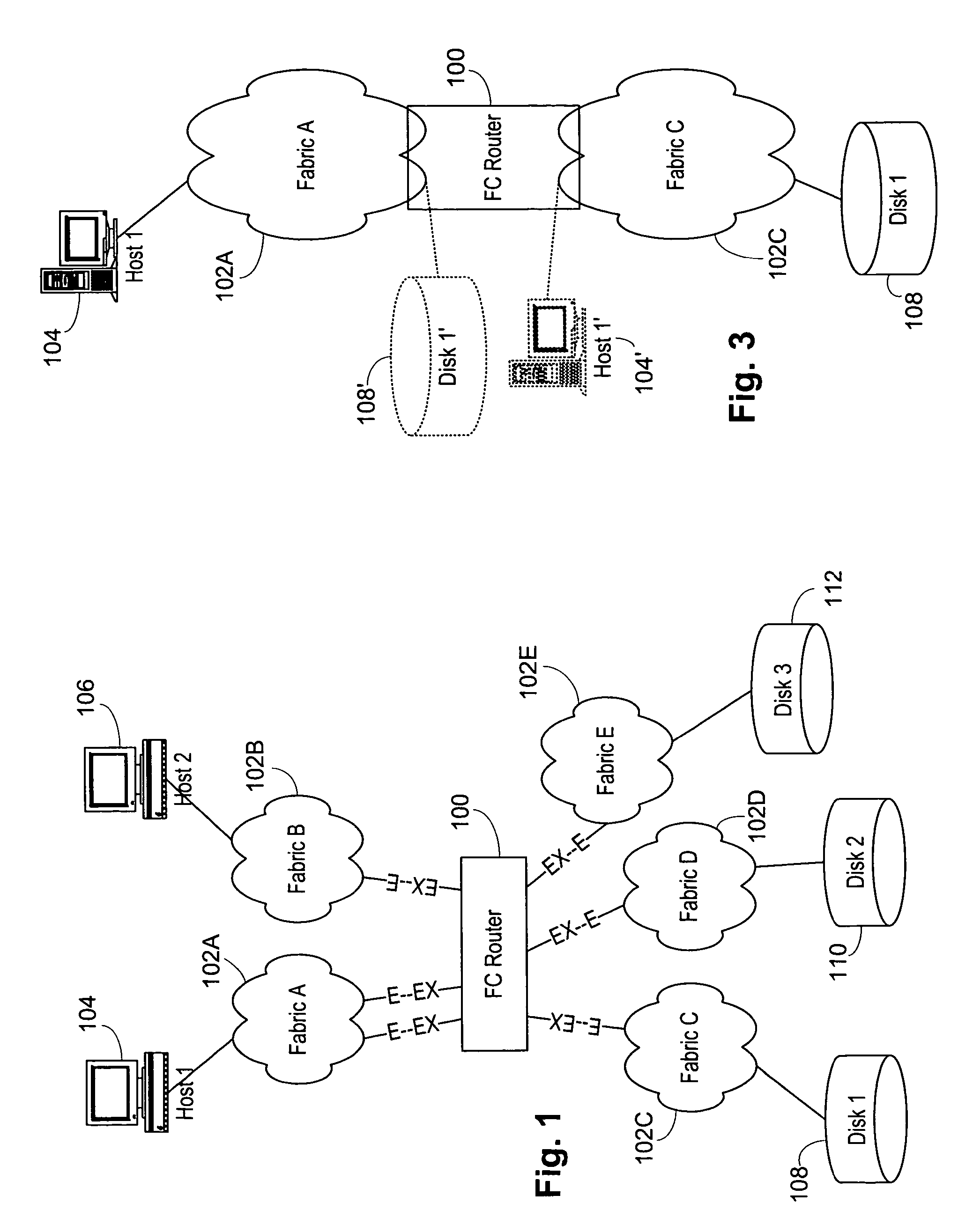
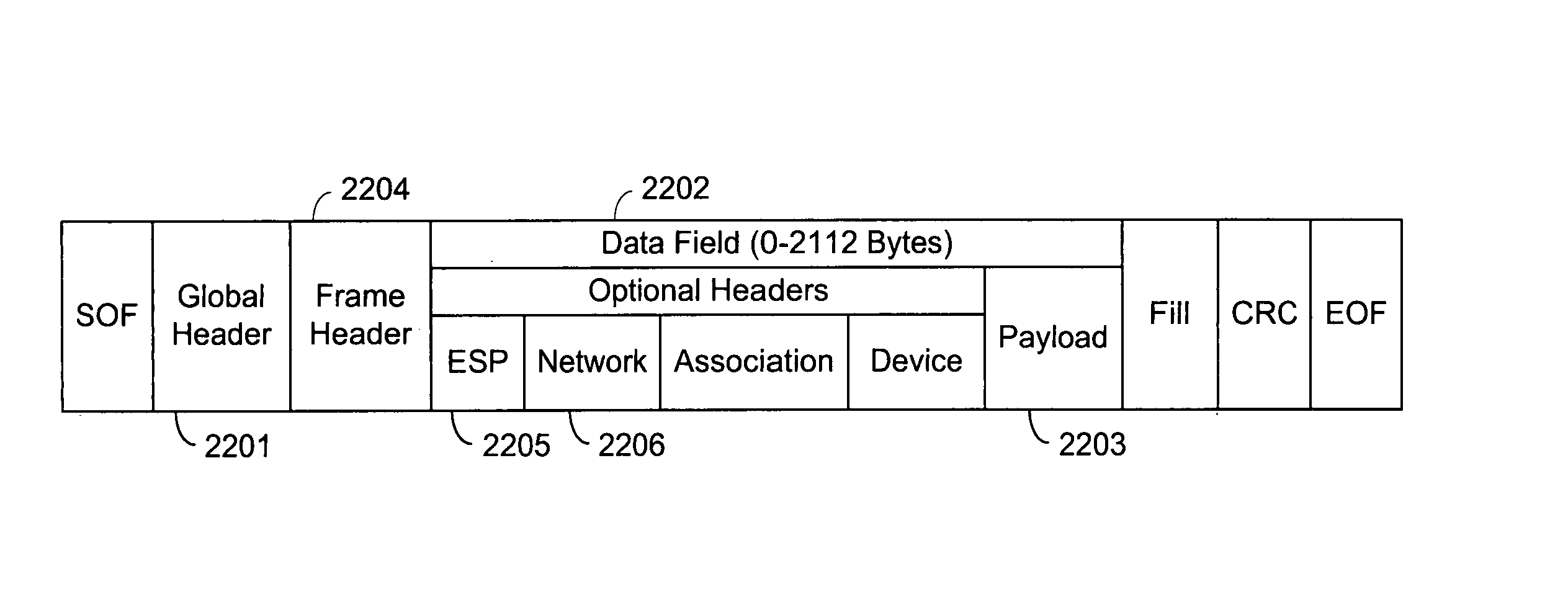
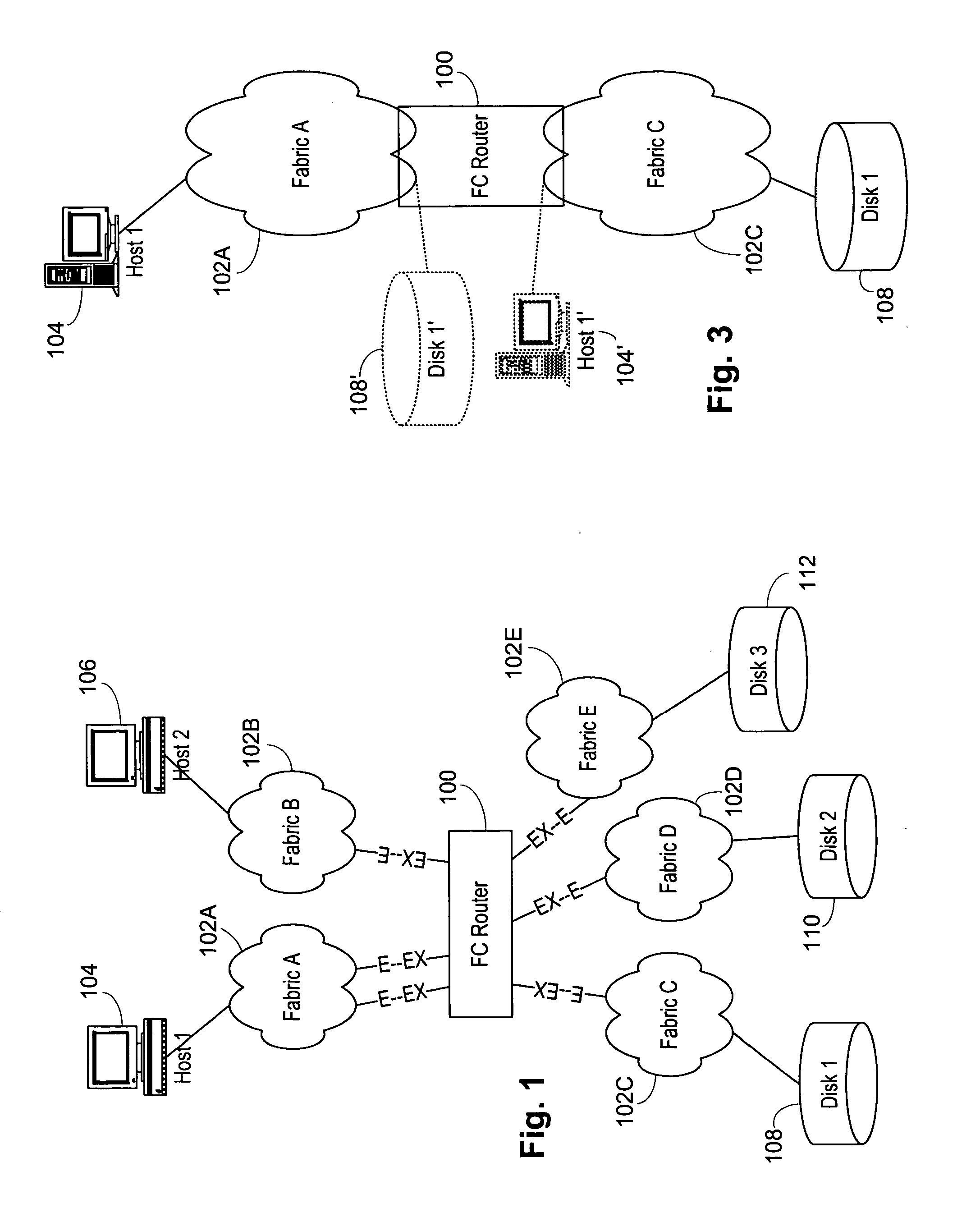
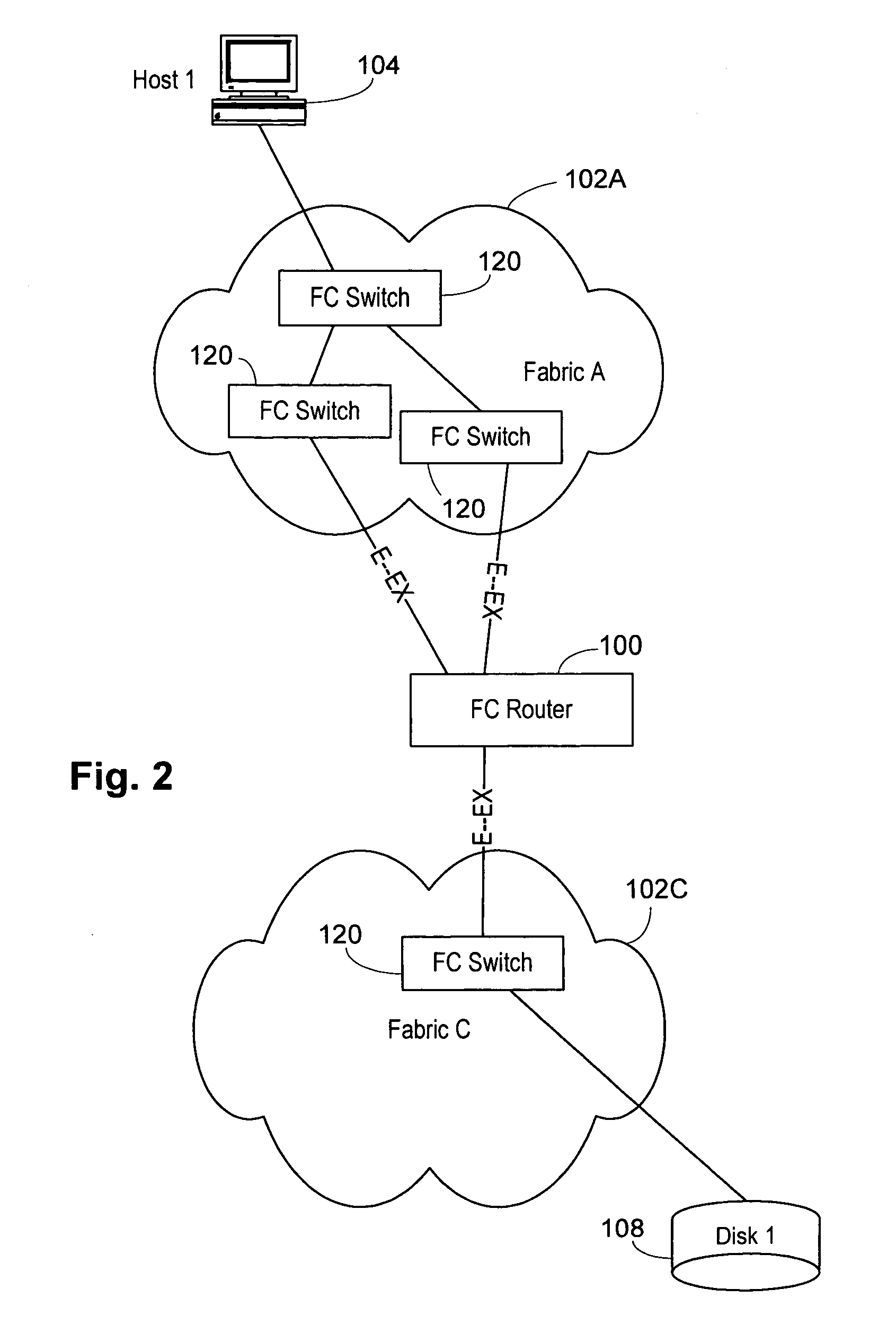
Interfabric routing header for use with a backbone fabric
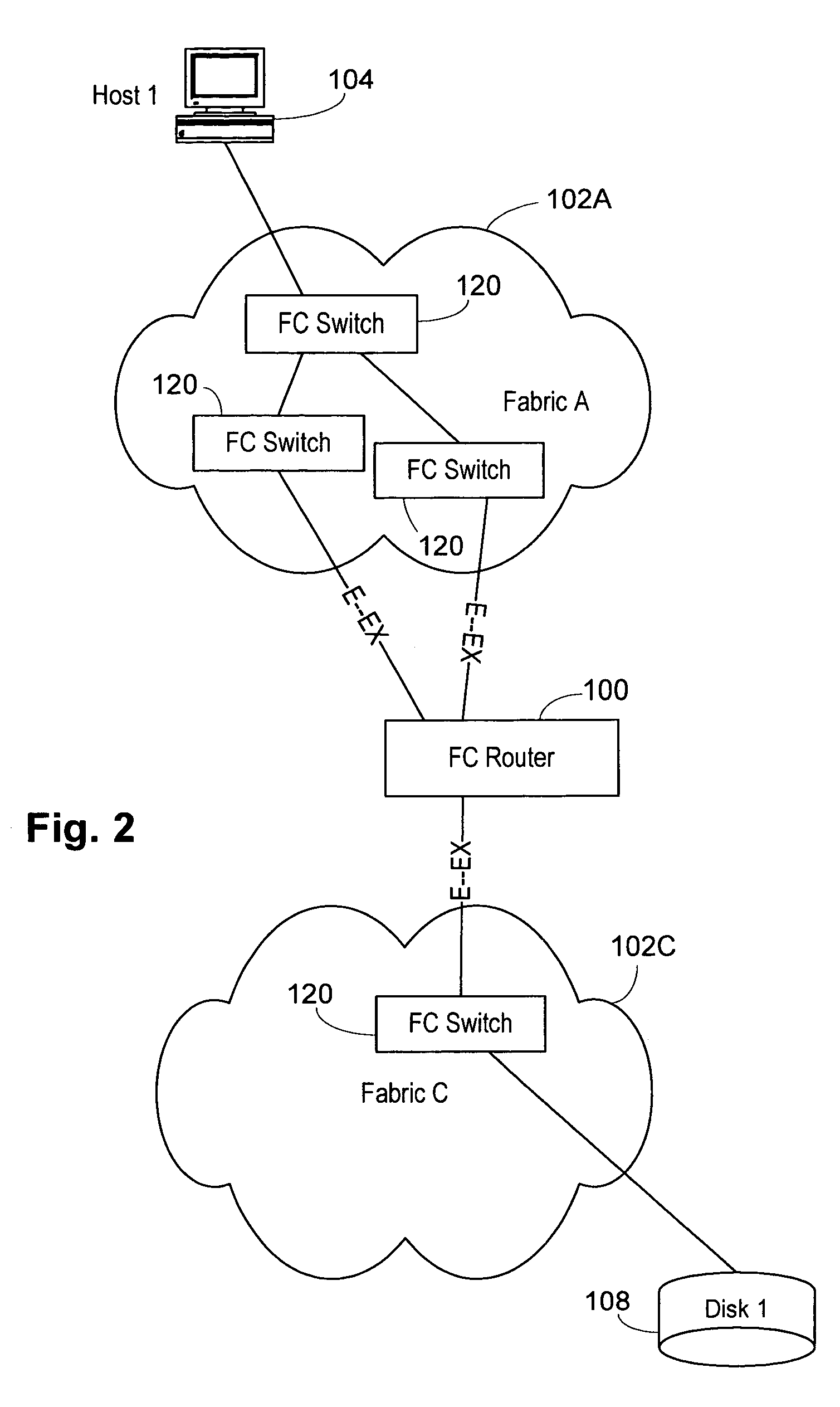
ActiveUS20060023708A1Easy interconnectionImprove manageabilityData switching by path configurationFiberTelecommunications
A Fibre Channel router used to join fabrics. EX_ports are used to connect to the fabrics. The EX_port joins the fabric but the router will not merge into the fabric. Ports in the Fibre Channel router can be in a fabric, but other ports can be connected to other fabrics. Fibre Channel routers can be interconnected using a backbone fabric. Global, interfabric and encapsulation headers are developed to allow routing by conventional Fibre Channel switch devices in the backbone fabric and simplify Fibre Channel router routing. Phantom domains and devices must be developed for each of the fabrics being interconnected. Front phantom domains are present at each port directly connected to a fabric. Each of these is then connected to at least one translate phantom domain. Zoning is accomplished by use of a special LSAN zoning naming convention. This allows each administrator to independently define devices are accessible.
Owner:AVAGO TECH INT SALES PTE LTD
System and method for providing proxy and translation domains in a fibre channel router
InactiveUS7466712B2Great interconnectionImprove manageabilityData switching by path configurationFiberComputer network
Owner:AVAGO TECH INT SALES PTE LTD
Device and related method for establishing network policy based on applications
ActiveUS20140282823A1Improving network manageabilityImprove securityTransmissionSpecial data processing applicationsTraffic volumeTraffic capacity
A function is provided in a network system for adjusting network policies associated with the operation of network infrastructure devices of the network system. Network policies are established on network devices including packet forwarding devices. The network has a capability to identify computer applications associated with traffic running on the network. A network policy controller of the network is arranged to change one or more policies of one or more network devices based on computer application information acquired. The policies changed may be network policies as well as mirroring policies. An example policy to change is direct a network device to mirror traffic to an application identification appliance for the purpose of identifying applications running on the network through a plurality of mechanisms. The function may be provided in one or more devices of the network.
Owner:EXTREME NETWORKS INC
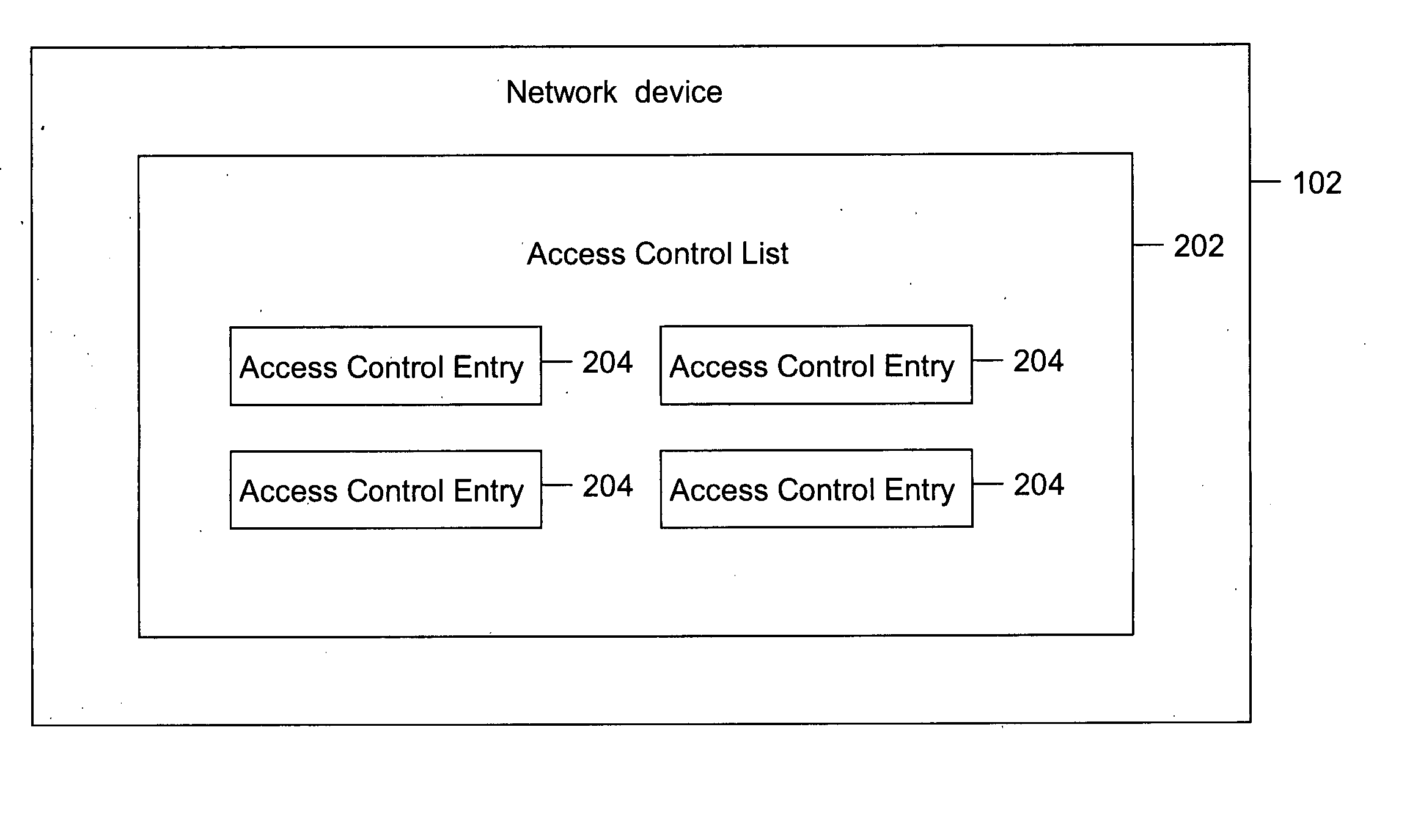
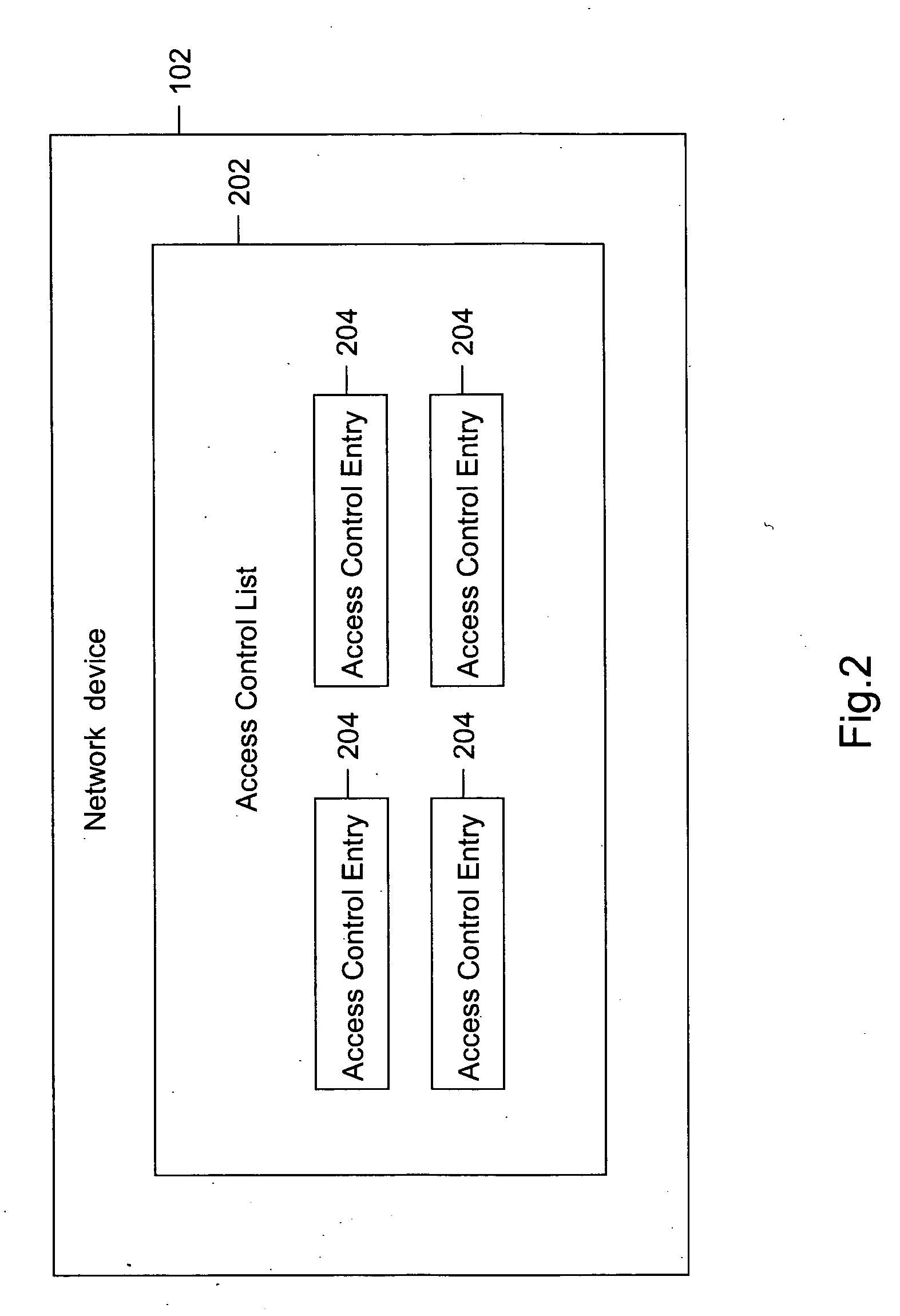
Method and system for removing dead access control entries (ACEs)
ActiveUS20070223487A1Improve manageabilitySave processing timeData switching by path configurationInformation repositoryTime limit
Methods and systems have been provided for removing dead Access Control Entries (ACEs) in an Access Control List (ACL). In one embodiment, the dead ACEs can be detected for an egress as well as an ingress ACL. The ACEs that have a hit count above a user-specified hit count are checked for their validity. The validity of the ACE is checked, using the information based on a Forwarding Information Base (FIB). If an ACE is found to be invalid, it is considered dead. The dead ACEs are referred as candidates for removal from the ACL. If the ACE is found to be a candidate for removal, a system administrator can either warn the network administrator about the candidate for removal or delete the ACE from the ACL after a pre-defined time limit.
Owner:CISCO TECH INC
Method and apparatus for enhancing manageability of software catalog, abstracting software configuration, and desired state management
ActiveUS20060253849A1Improve manageabilityProgram loading/initiatingMemory systemsData centerState management
A method, apparatus, and computer instructions are provided for enhancing software catalog manageability, providing abstract software configuration, and desired state management. A first mechanism is provided for enhancing software catalog manageability. The first mechanism includes a software model that separates metadata of software from actual binaries of the software. A second mechanism is provided for abstracting software configuration for automation. The second mechanism includes a hierarchical software resource template structure that specifies parameters, dependencies between parameters, features, options, and parameters that cannot be predefined. The template is consumed by user defined workflows to create actual software resources during deployment. A third mechanism is provided for desired state management and patch compliance assessments. The third mechanism checks against a server template or software resource in a data center model against what is installed on actual machines to determine compliance.
Owner:TWITTER INC
Method and device for processing data in online business processing
InactiveCN101566986AReduce space consumptionReduce congestionSpecial data processing applicationsMaintainabilityOnline business
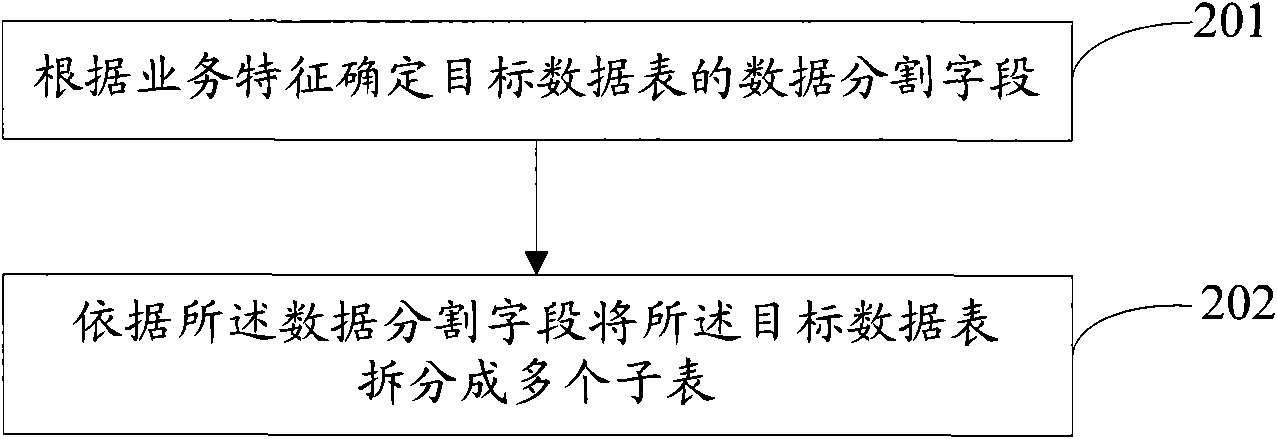
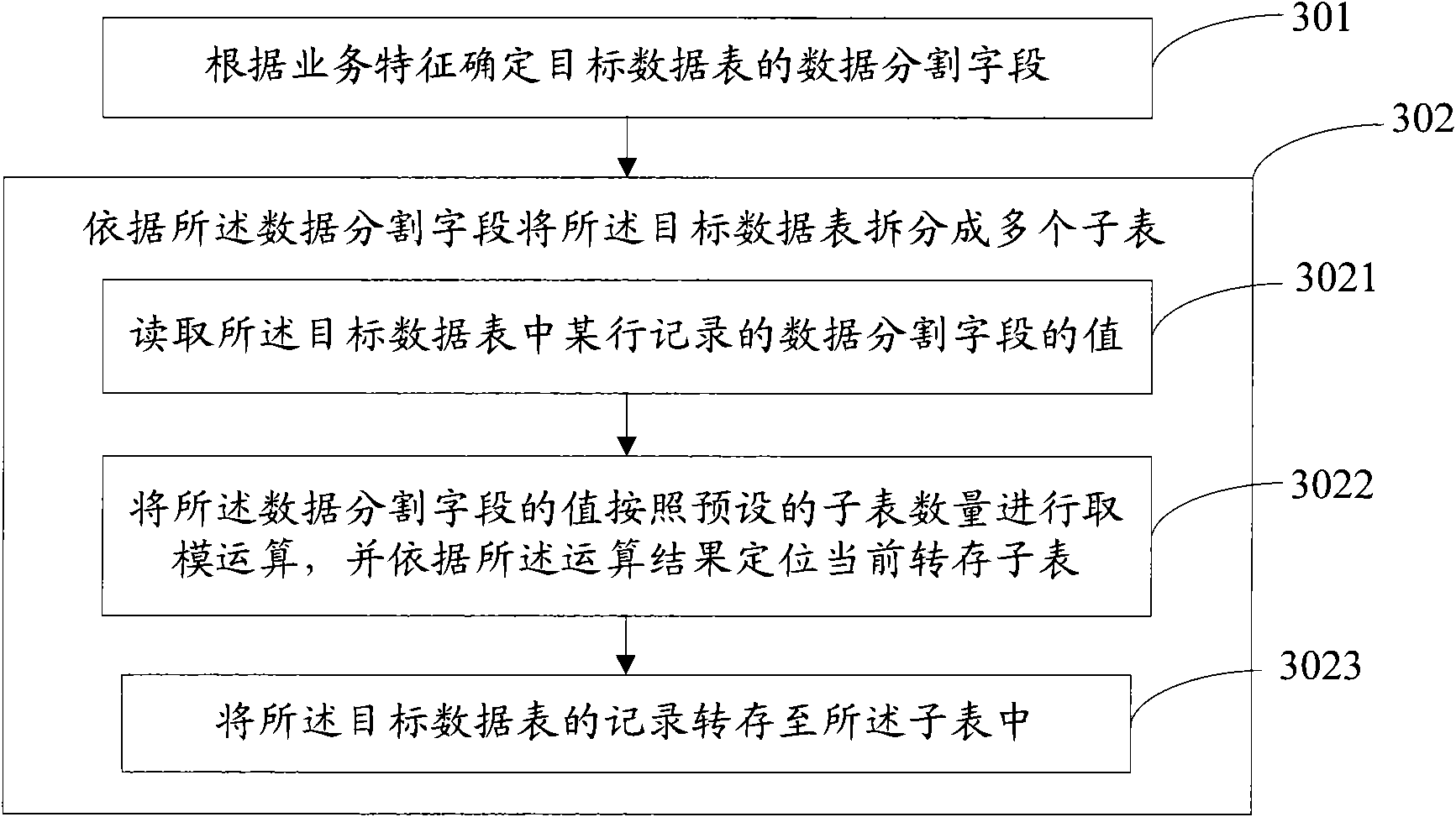
The invention discloses a method for processing data in online business processing, which comprises the following steps: a data partitioning field of a target data table is confirmed according to a business characteristic; and the target data table is divided into a plurality of subtables according to the data partitioning field. The invention uses the method that the core data table in an online business processing system is divided into a plurality of subtables to enable the data amount of the subtables after division to be lower than that of the original core data table. When DDL operation is carried out to the subtables, the occupied space of the temporary table is small, and blocked talks are few, thus the pressure born by the system is greatly reduced, and the maintainability and the manageability of the core data table of the database are improved.
Owner:ALIBABA GRP HLDG LTD
Distributed computing infrastructure including small peer-to-peer applications
ActiveUS20050060432A1Dense configurationImprove manageabilitySpecial service provision for substationInterprogram communicationWhiteboardDistributed computing infrastructure
Systems and methods are disclosed for a distributed computing infrastructure on a computer network comprising a plurality of computers. The distributed computing infrastructure (DCI) provides a software platform for creating, running, and managing distributed applications. DCI may include XML-capable software applications on a peer-to-peer network. DCI may include small, network-unaware applications called peerlets. DCI may include a system and method for creating complex distributed applications using pre-complied binaries. DCI may include a capability for multiple, independent collaborative sessions for distributed collaborative applications (e.g., chat, instant messaging, shared whiteboard, etc.). DCI may include systems and methods for reducing interactions between users and applications to archivable form and then playing back the interactions. DCI may include a system and method for automatic software retrieval on a peer-to-peer network.
Owner:GOOGLE LLC
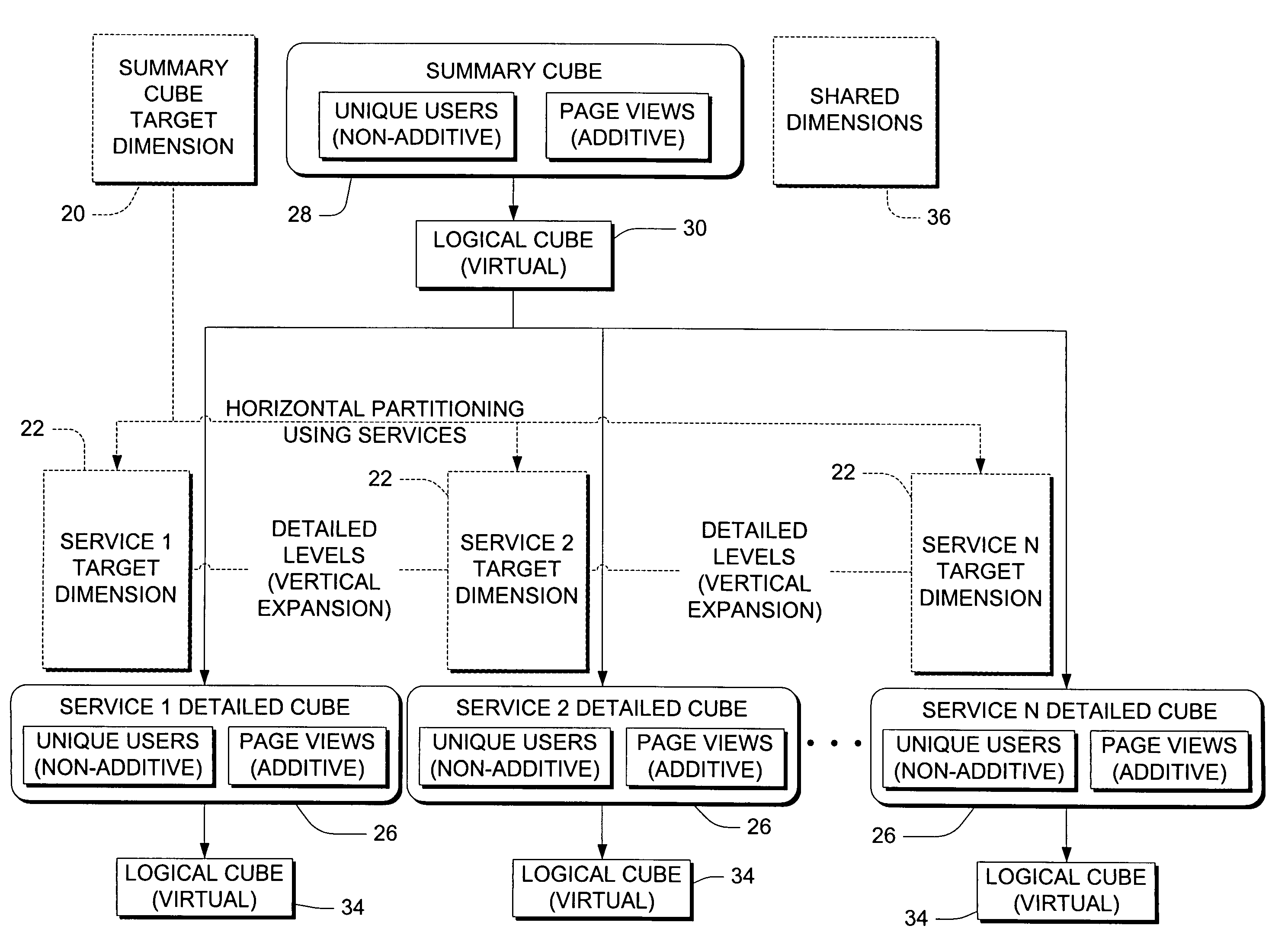
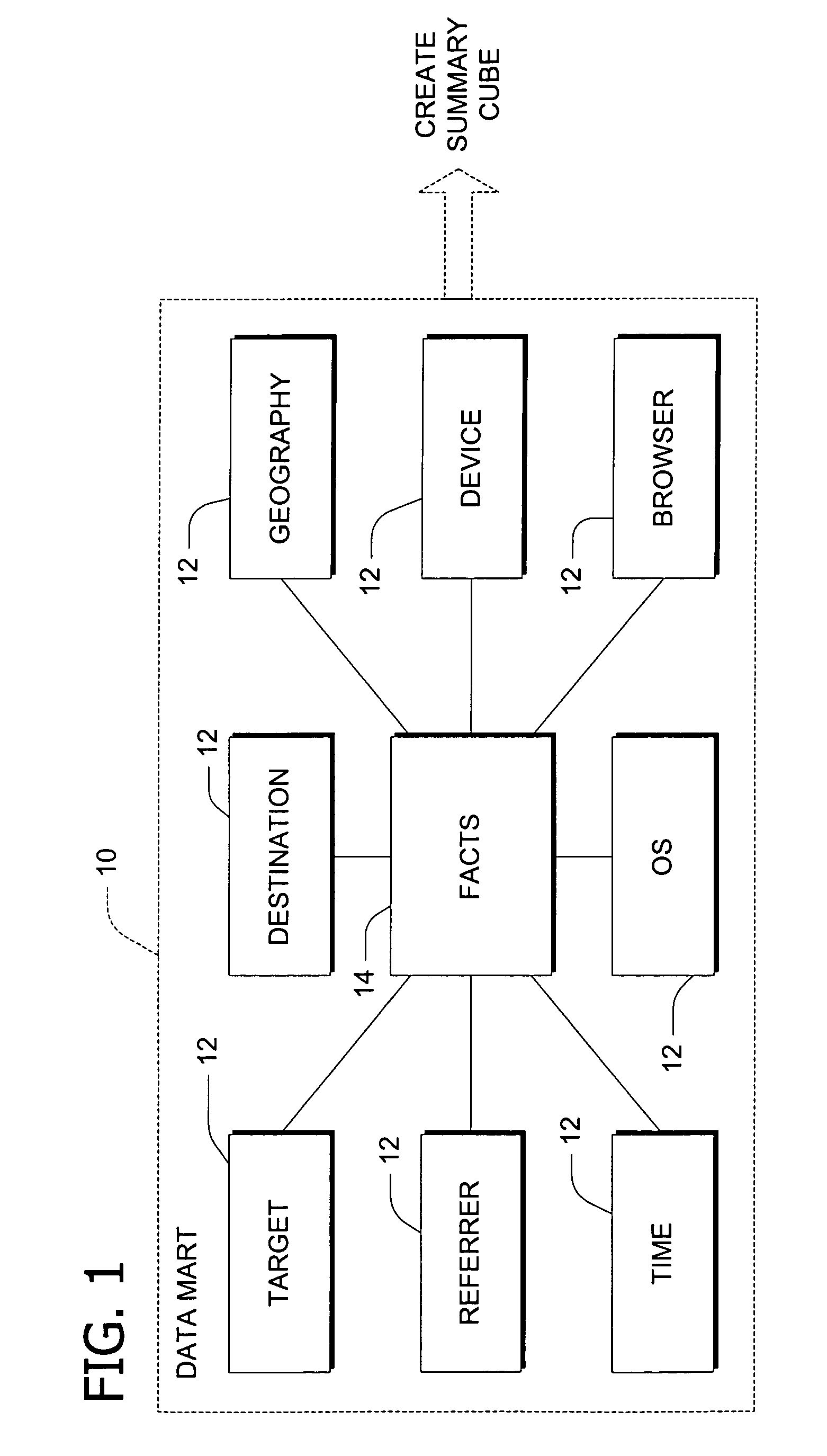
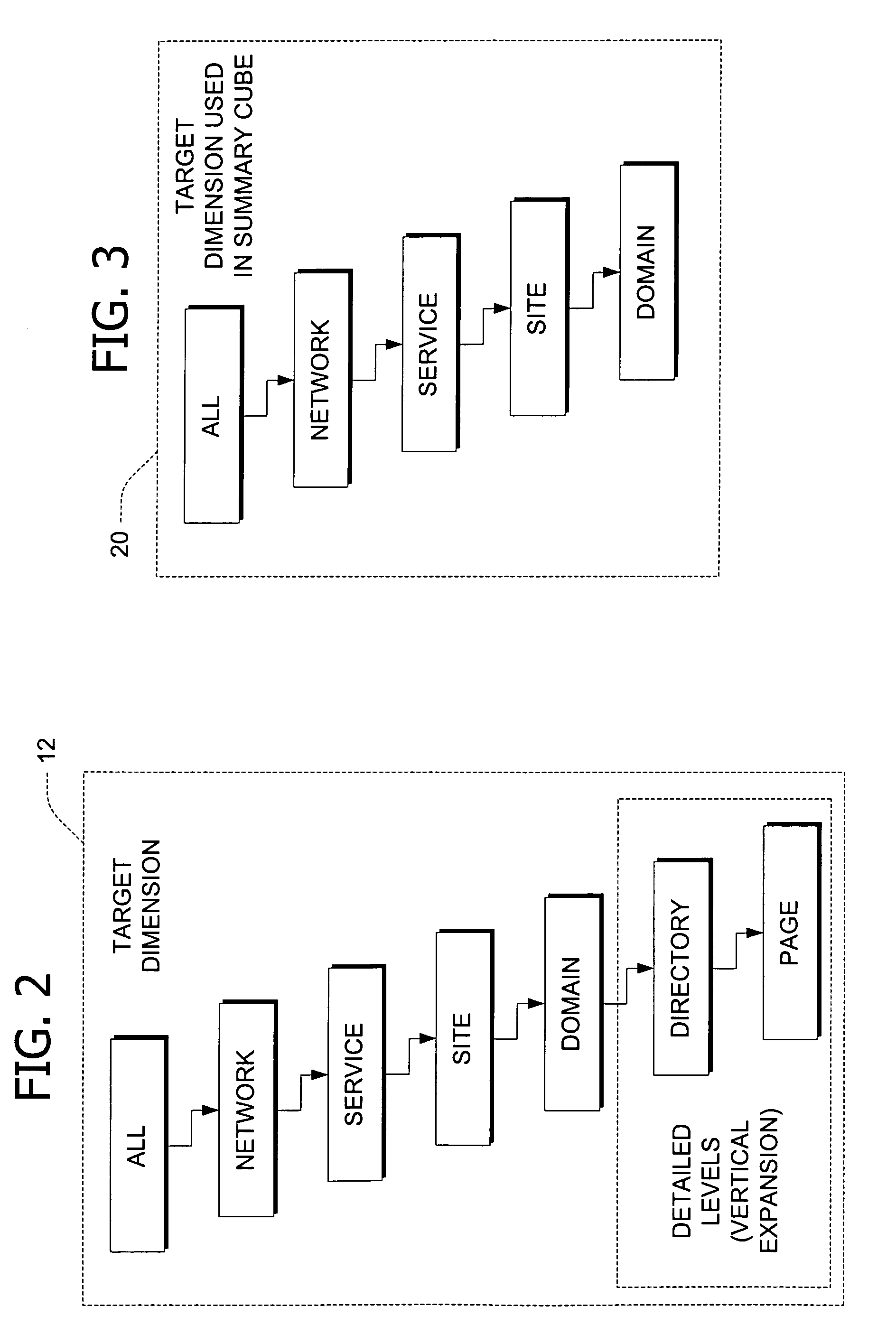
Summary-detail cube architecture using horizontal partitioning of dimensions
InactiveUS6980980B1Reduce decreaseReduce processing timeData processing applicationsMulti-dimensional databasesData setWeb usage analysis
A database architecture and method for processing data in a multidimensional database, including performing Web usage analysis. A summary cube contains the members of an upper level of a dimension and a detail cube contains a subset of the members of a lower level of the dimension partitioned therefrom based on a selected member of the upper level of the dimension. The detail cube also includes one or more sub-cubes containing aggregations of the first subset of the lower level members. An XML template implements a workflow to automatically create a second detail cube partitioned from the dimension based on another selected member of the upper level. Using XML metadata, the invention implements zoom in / zoom out events to navigate between information in the summary cube and information in the detail cubes.
Owner:MICROSOFT TECH LICENSING LLC
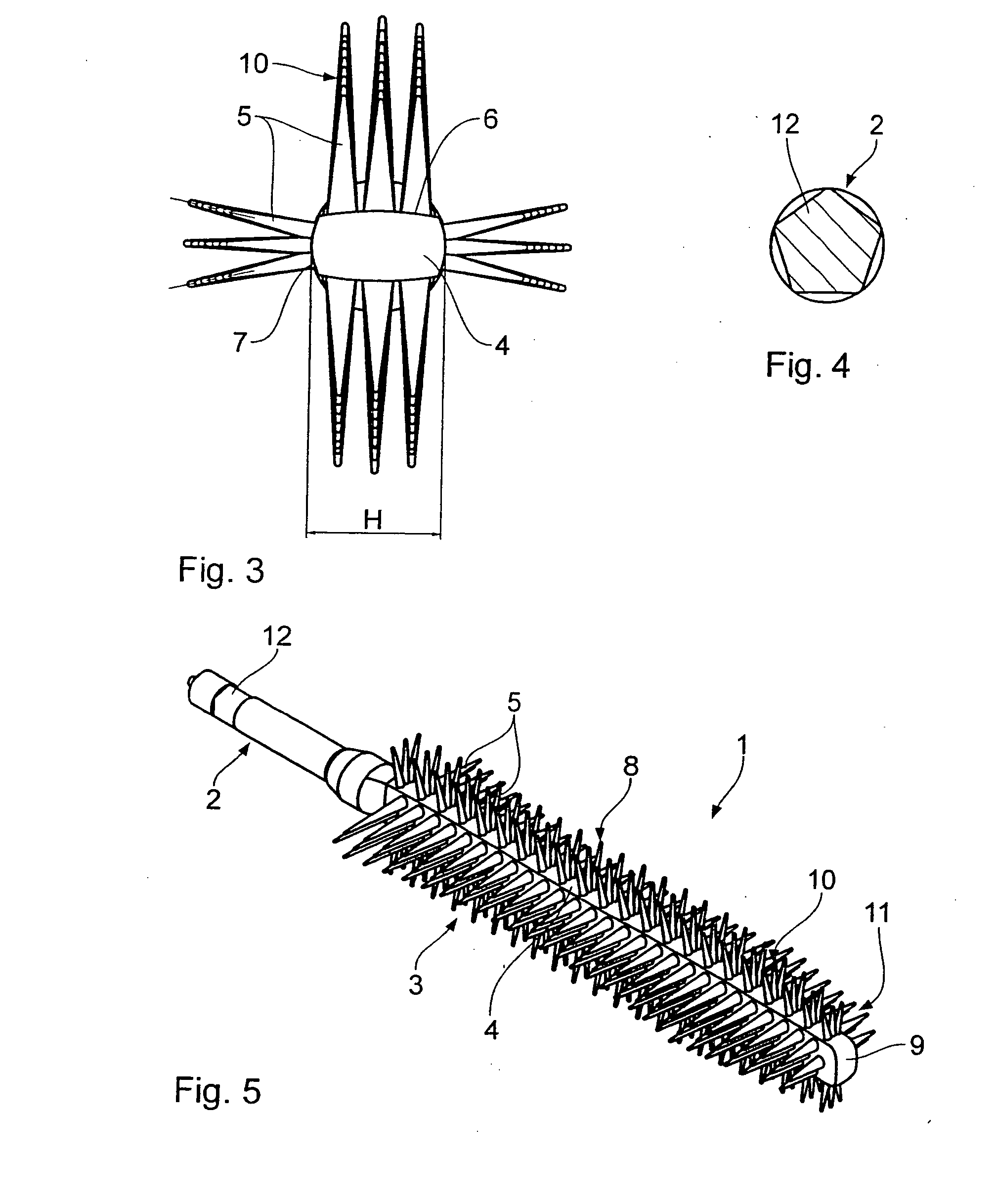
Brush for applying cosmetic substances
ActiveUS20070033759A1Broaden applicationOptimal combing propertyBrush bodiesBristleBristleEngineering
In a brush for applying cosmetic substances, especially a mascara brush or hair coloring brush, which is injection-molded from plastic as one piece and comprises a first section for connection to a rod and a second section, said second section having a main body from which a plurality of bristles protrude radially outward, provision is made for the main body to be designed as a polygon in cross section.
Owner:GEKA
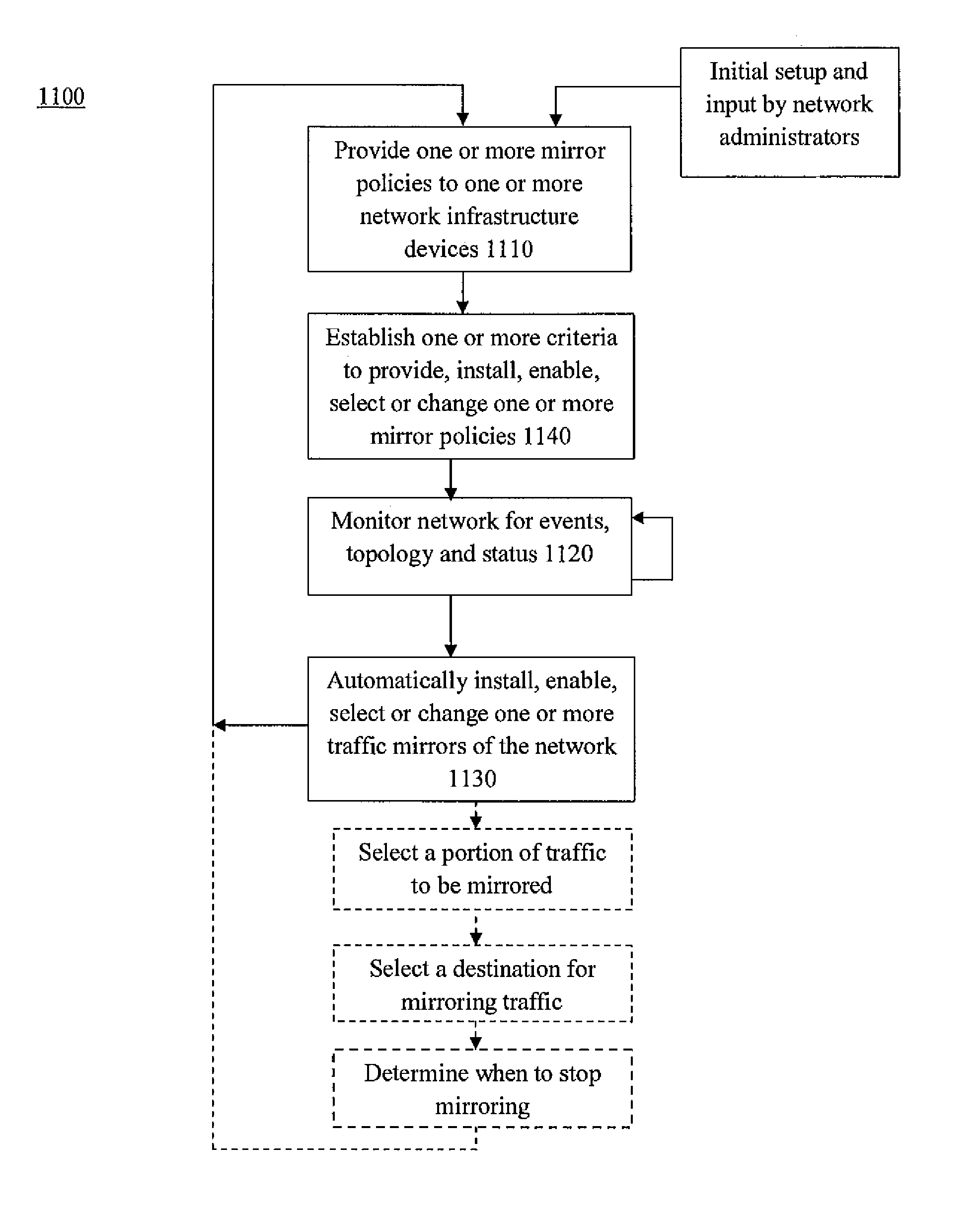
Device and related method for dynamic traffic mirroring
ActiveUS9172627B2Improve efficiencyImprove manageabilityData switching networksTraffic capacityDevice type
A function is provided in a network system for the dynamic mirroring of network traffic for a variety of purposes including the identification of characteristics of the traffic. Multiple criteria are established for when, what and where to mirror the traffic. The criteria include what frames of traffic to mirror, what portions of the selected frames to mirror, one or more portals through which to mirror the selected frames, a destination for the mirroring and the establishment of a mirror in a device to carry out the mirroring. The criteria may also include when to stop the mirroring. The mirroring instructions can be changed based on the detection of a triggering event, such as authentication, device type or status, ownership of an attached function attached to the device, flow status, but not limited to that. The function may be established in one or more devices of the network.
Owner:EXTREME NETWORKS INC
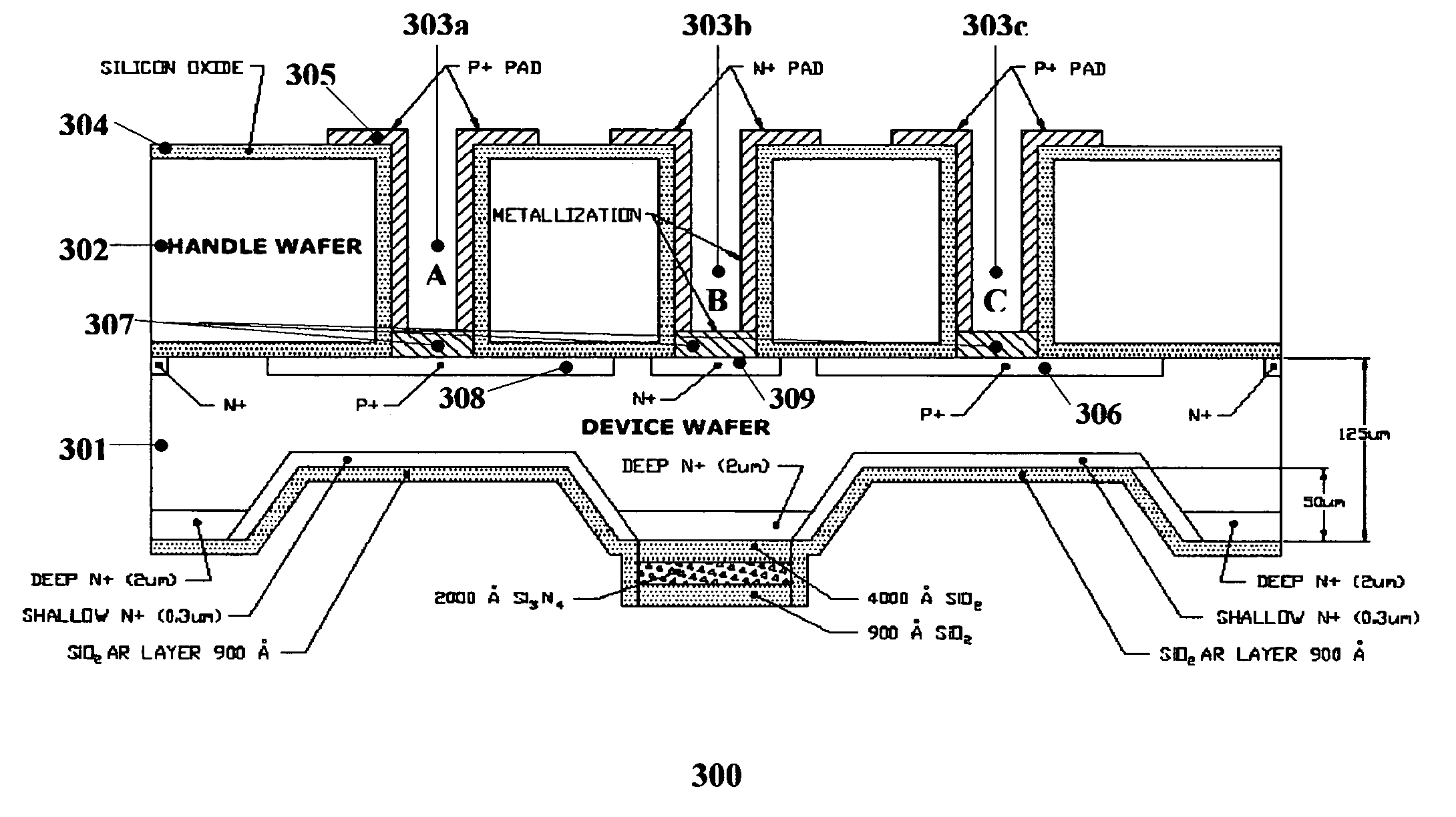
Thin wafer detectors with improved radiation damage and crosstalk characteristics
InactiveUS7242069B2Reduces its damage susceptibilityImprove application flexibilitySolid-state devicesMaterial analysis by optical meansEtchingShortest distance
The present invention provides for reduced radiation damage susceptibility, decreased affects of crosstalk, and increased flexibility in application. In one embodiment, the present invention includes a back side illuminated photodiode array with a back side etching that minimizes the active area layer, thereby decreasing the affects of crosstalk. The back side etching is preferably, but by no way of limitation, in the form of “U” or “V” shaped grooves. The back side illuminated with back side etching (BSL-BE) photodiodes are implemented in an array and have superior performance characteristics, including less radiation damage due to a thinner active area, and less crosstalk due to shorter distances for minority carriers to diffuse to the PN junction.
Owner:OSI OPTOELECTRONICS
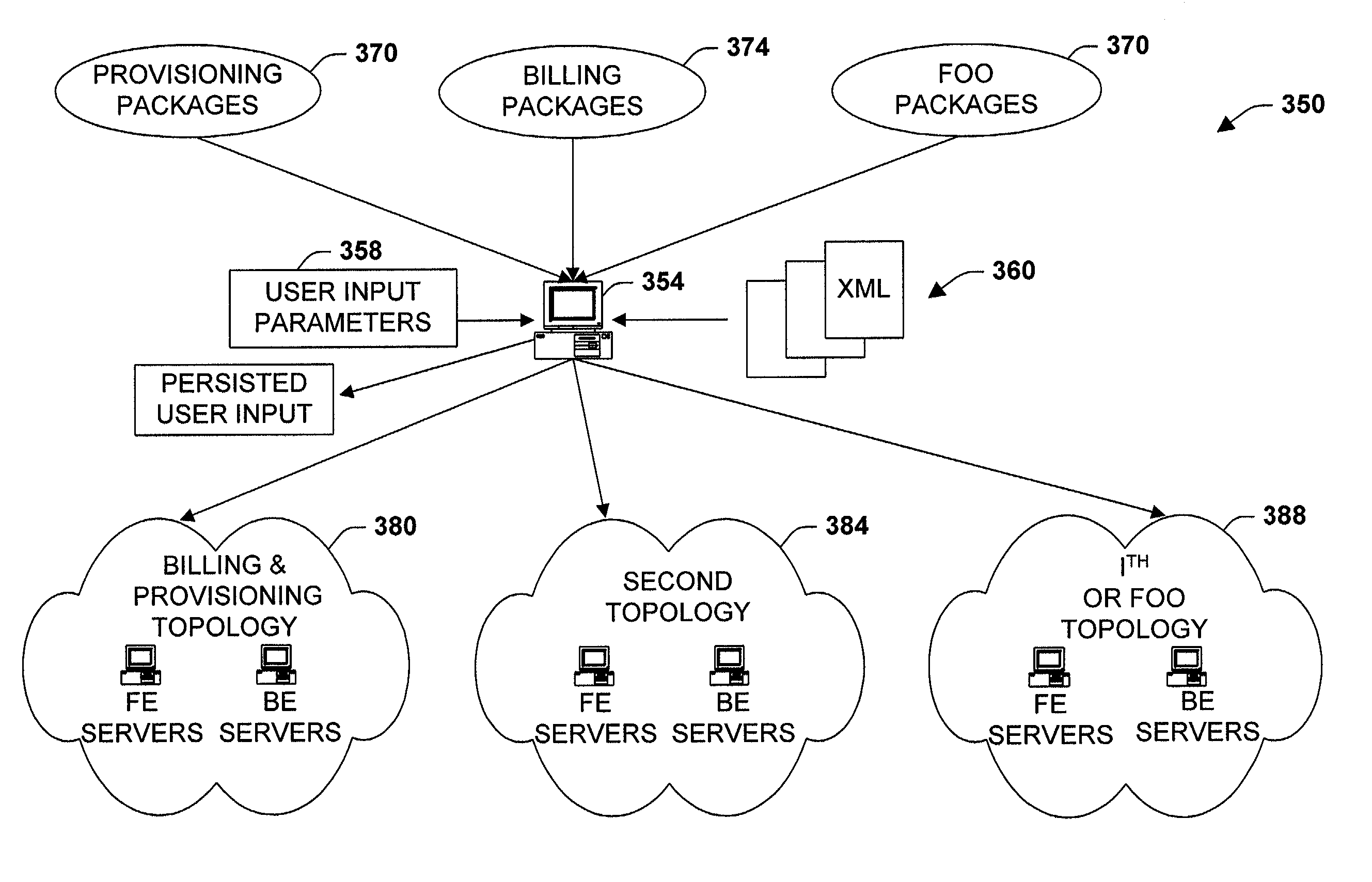
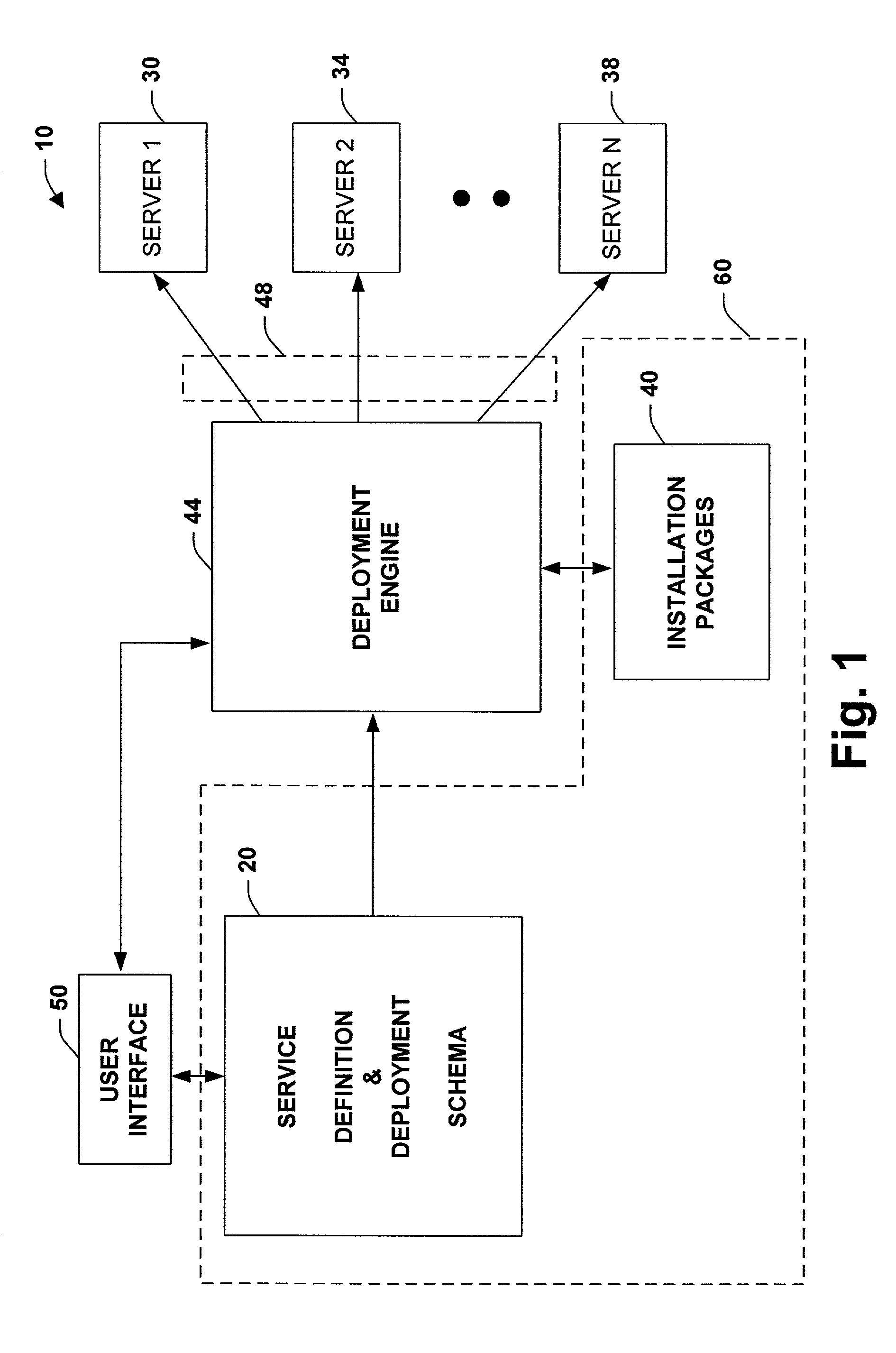
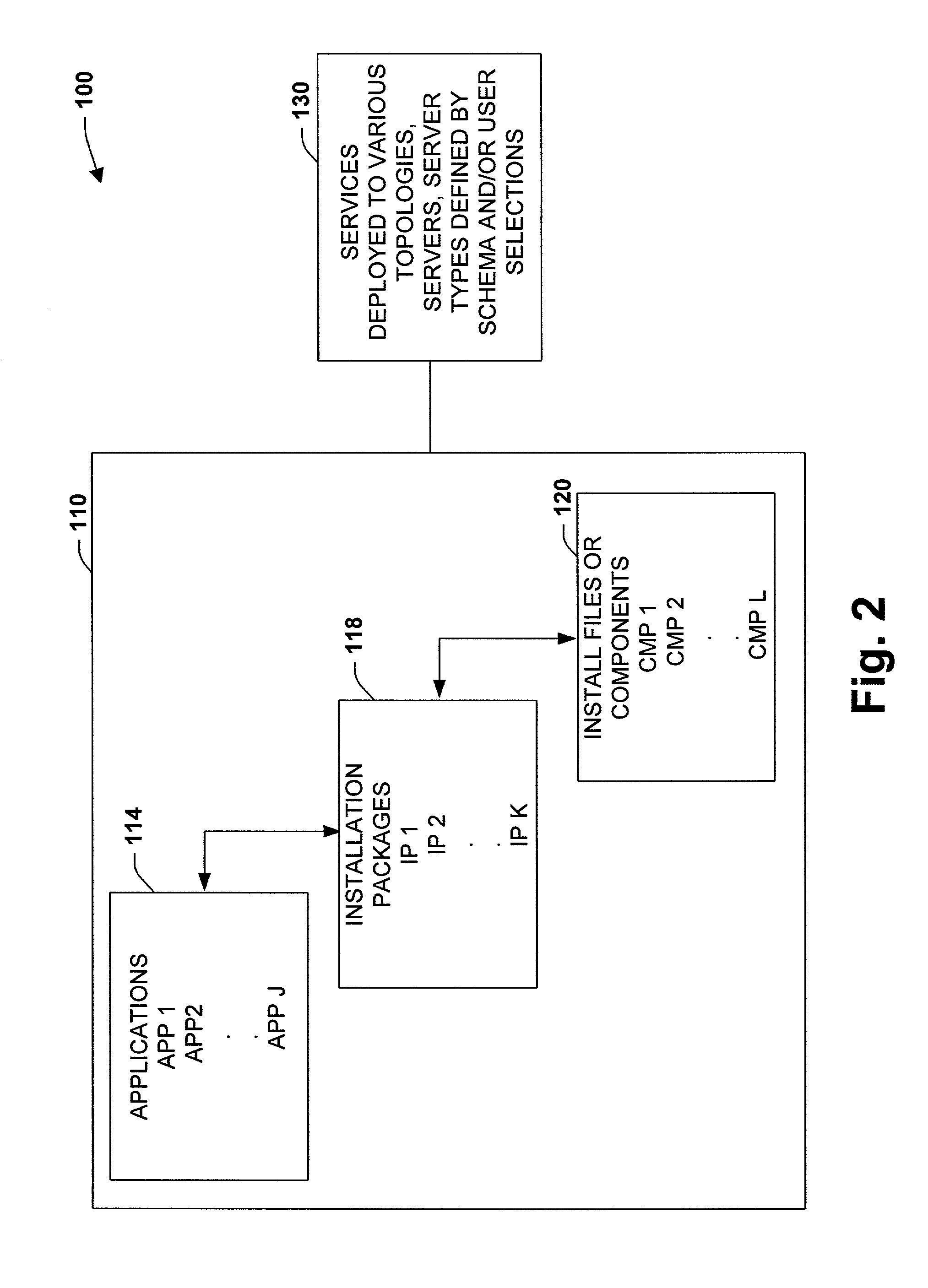
System and method to facilitate manageable and agile deployment of services in accordance with various topologies
ActiveUS7340520B1Mitigates extrapolationImprove manageabilityDigital computer detailsBilling/invoicingUser inputUser interface
The present invention relates to a system and methodology to facilitate service deployment in a distributed computing and applications environment. A schema is provided that describes various components of a service and various topologies for execution of the services, wherein a deployment engine utilizes the schema in conjunction with user inputs to determine one or more destination locations for the service. The topologies relate to various machine and / or machine types defined for various groups or individuals that employ the service. A user interface can be provided to receive user inputs for topological selections and to facilitate various parametric configurations associated with service deployment and subsequent execution thereof.
Owner:MICROSOFT TECH LICENSING LLC
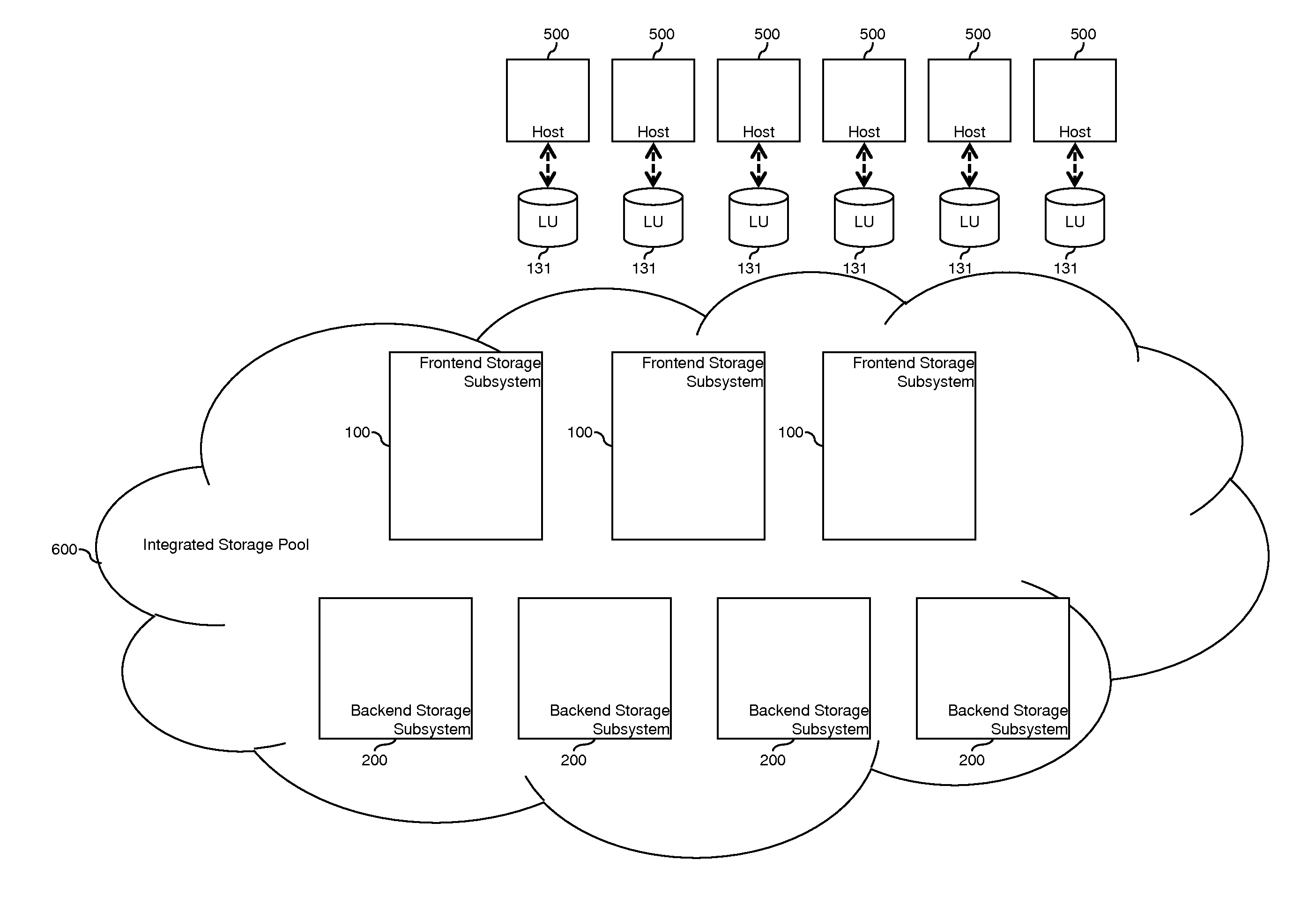
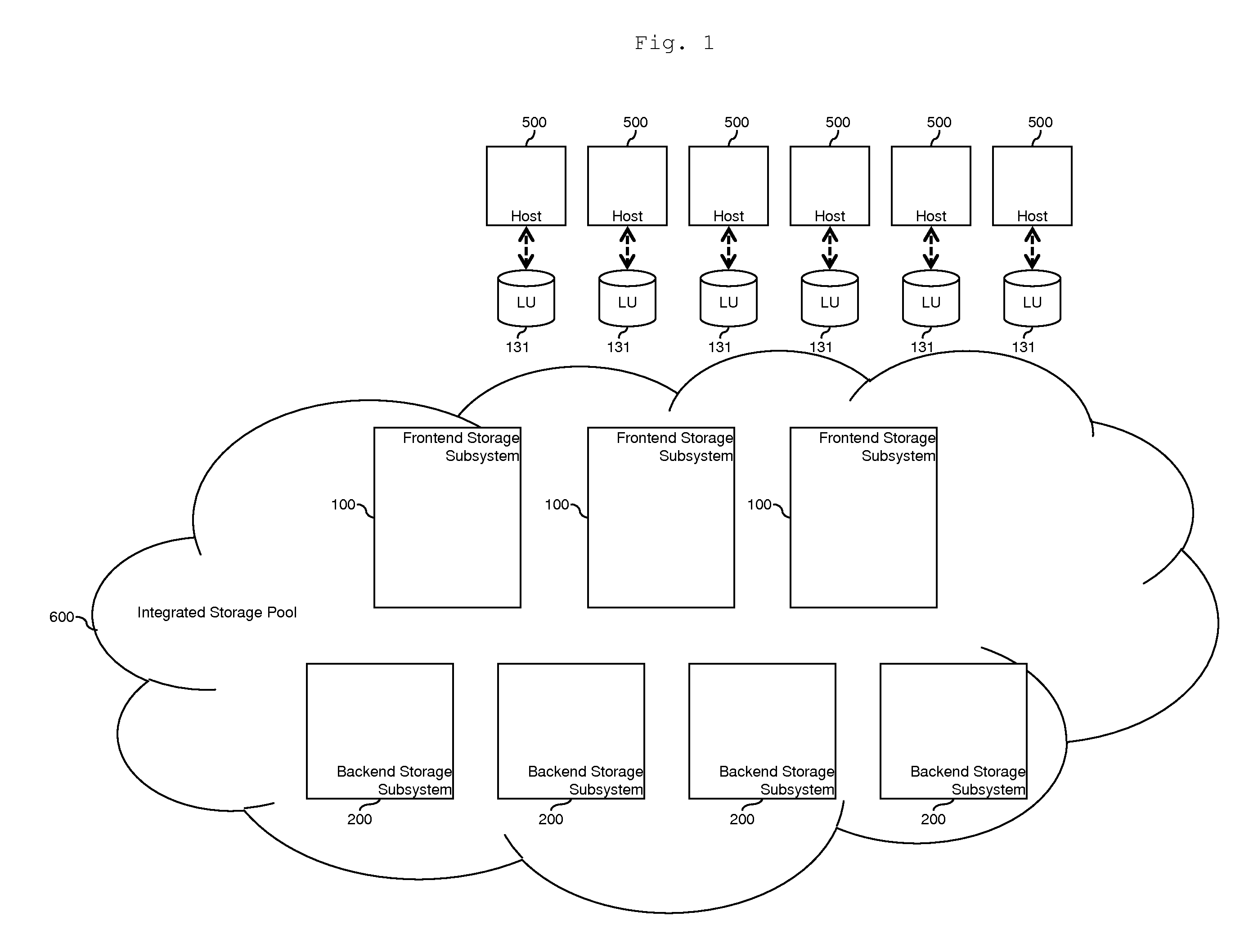
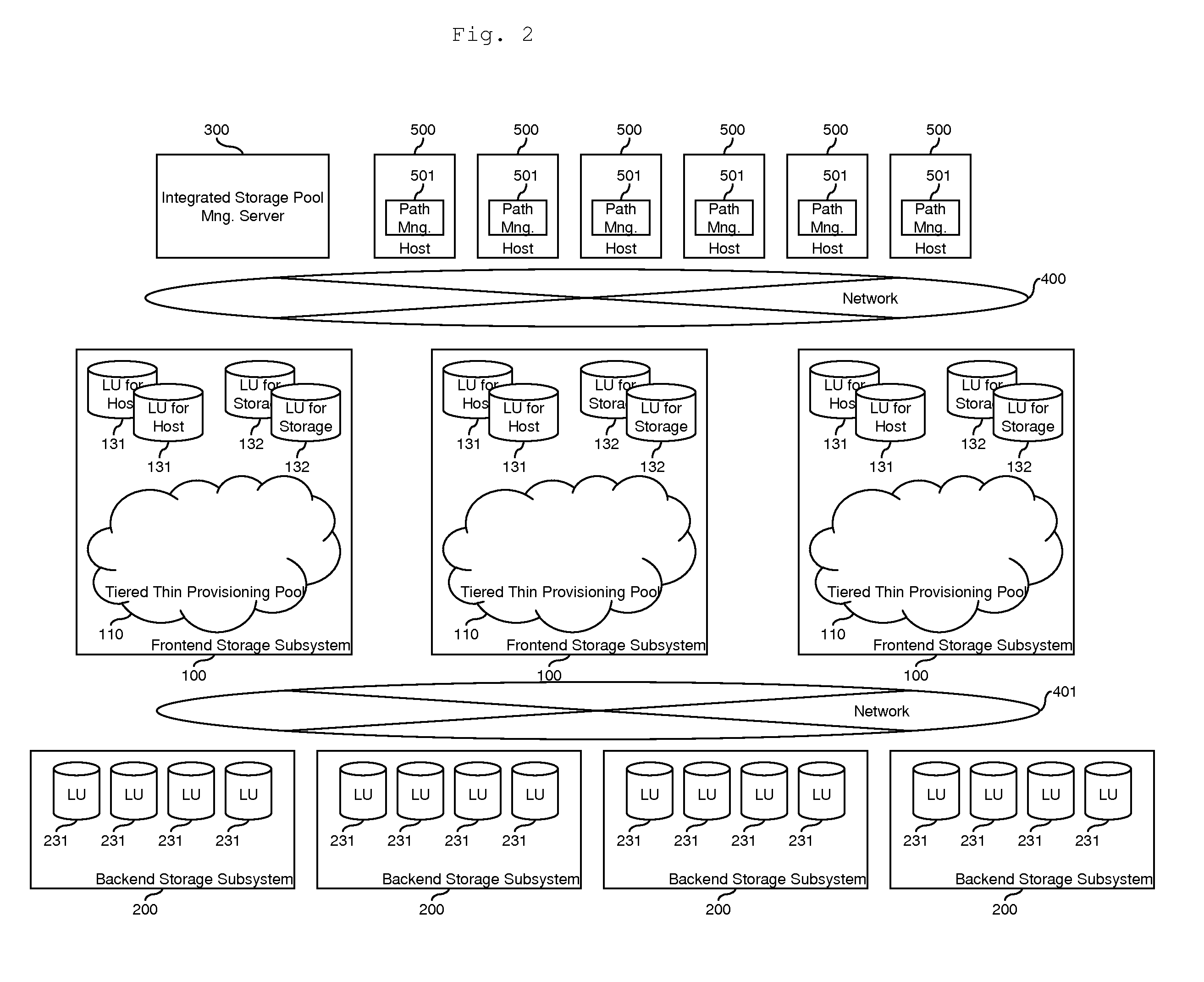
Tiered storage pool management and control for loosely coupled multiple storage environment
ActiveUS20120047346A1Improve manageabilityEasy to controlMemory adressing/allocation/relocationInput/output processes for data processingControl storeEngineering
A system comprises a first storage system including a first storage controller, which receives input / output commands from host computers and provides first storage volumes to the host computers; and a second storage system including a second storage controller which receives input / output commands from host computers and provides second storage volumes to the host computers. A first data storing region of one of the first storage volumes is allocated from a first pool by the first storage controller. A second data storing region of another one of the first storage volumes is allocated from a second pool by the first storage controller. A third data storing region of one of the second storage volumes is allocated from the first pool by the second storage controller. A fourth data storing region of another one of the second storage volumes is allocated from the second pool by the second storage controller.
Owner:HITACHI LTD
Multifabric global header
InactiveUS20060023751A1Improve manageabilityGreat interconnectionTime-division multiplexData switching by path configurationFibre Channel switchComputer network
A Fibre Channel router used to join fabrics. EX_ports are used to connect to the fabrics. The EX_port joins the fabric but the router will not merge into the fabric. Ports in the Fibre Channel router can be in a fabric, but other ports can be connected to other fabrics. Fibre Channel routers can be interconnected using a backbone fabric. Global, interfabric and encapsulation headers are developed to allow routing by conventional Fibre Channel switch devices in the backbone fabric and simplify Fibre Channel router routing. Phantom domains and devices must be developed for each of the fabrics being interconnected. Front phantom domains are present at each port directly connected to a fabric. Each of these is then connected to at least one translate phantom domain. Zoning is accomplished by use of a special LSAN zoning naming convention. This allows each administrator to independently define devices are accessible.
Owner:AVAGO TECH INT SALES PTE LTD
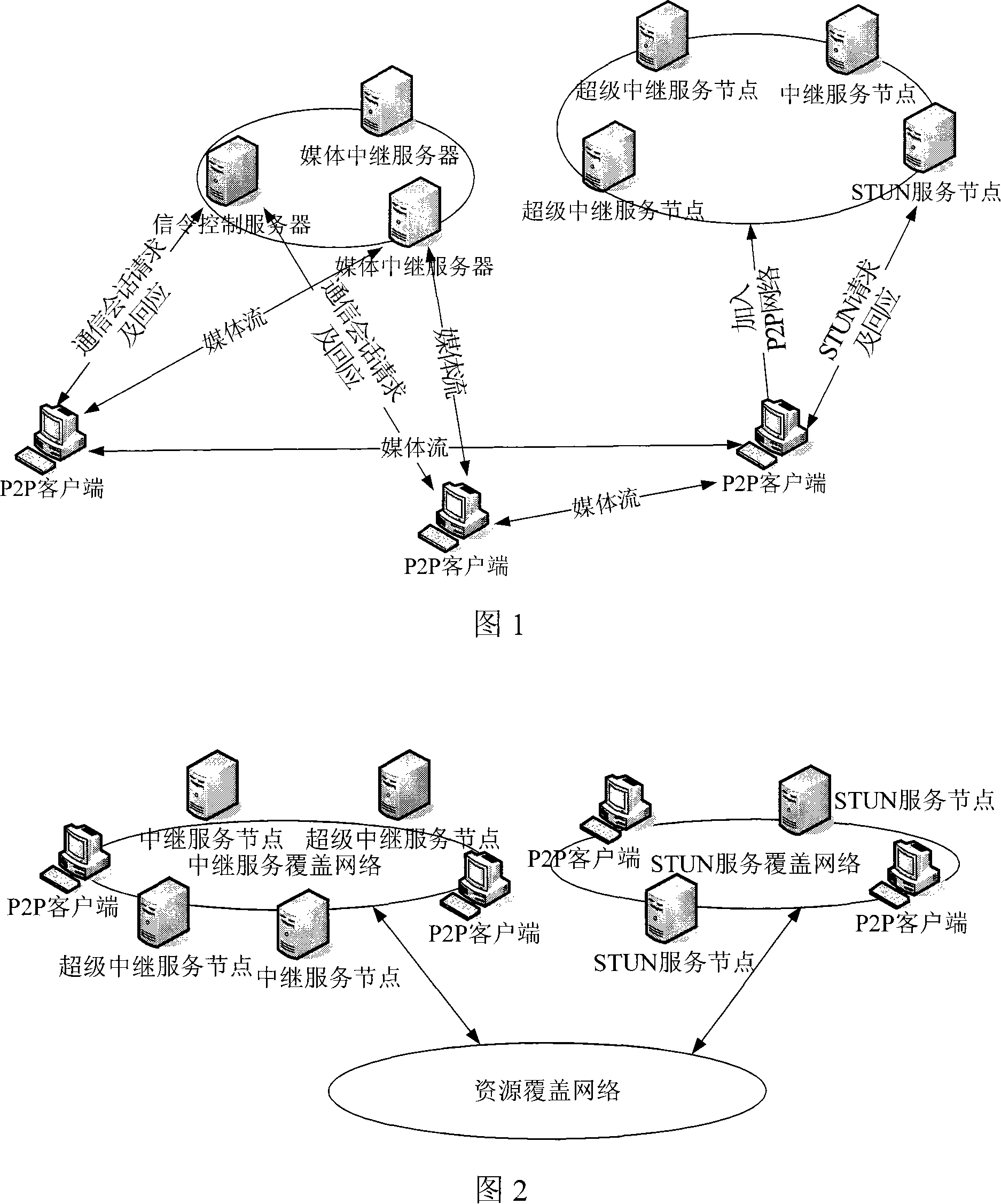
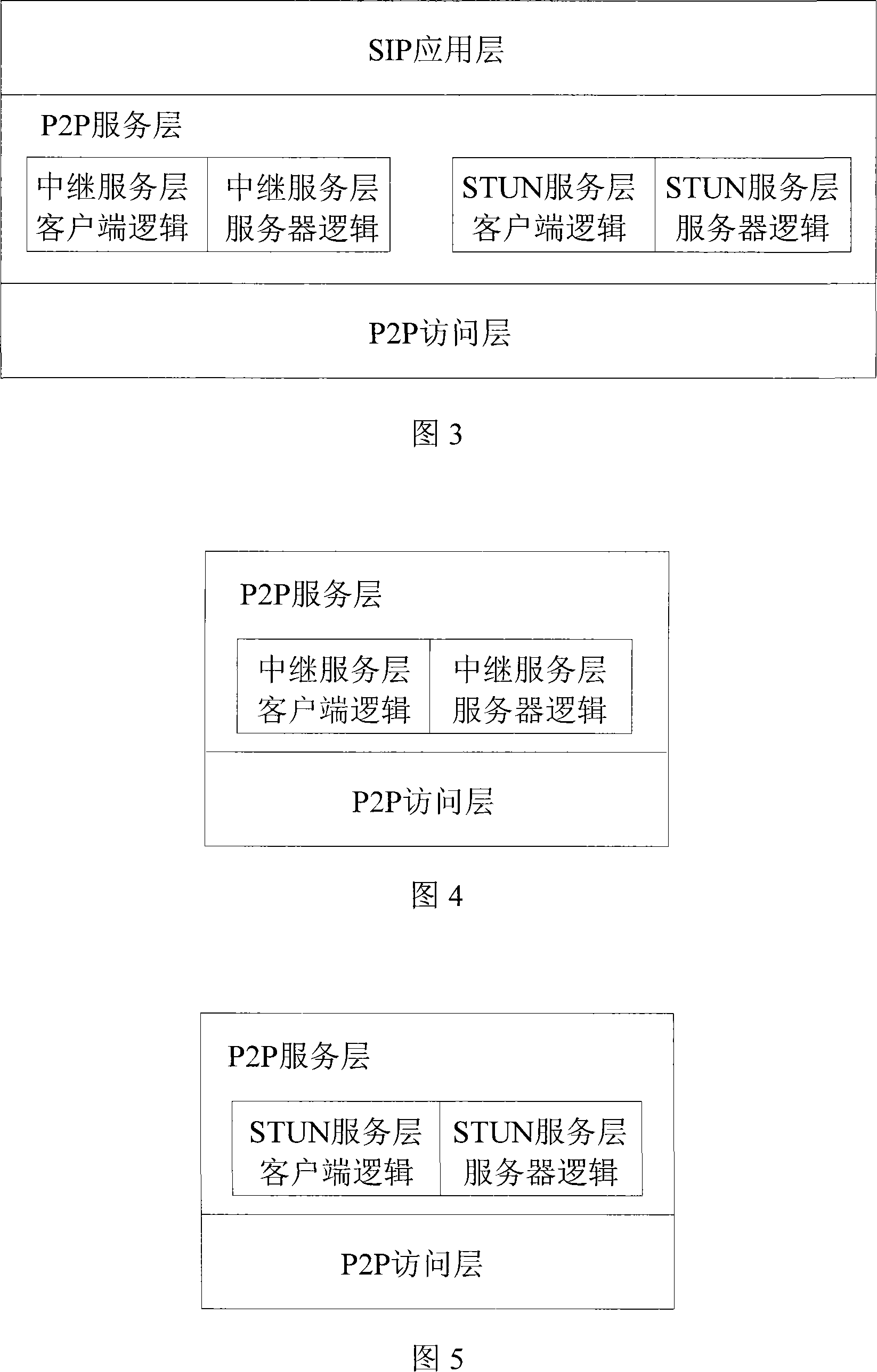
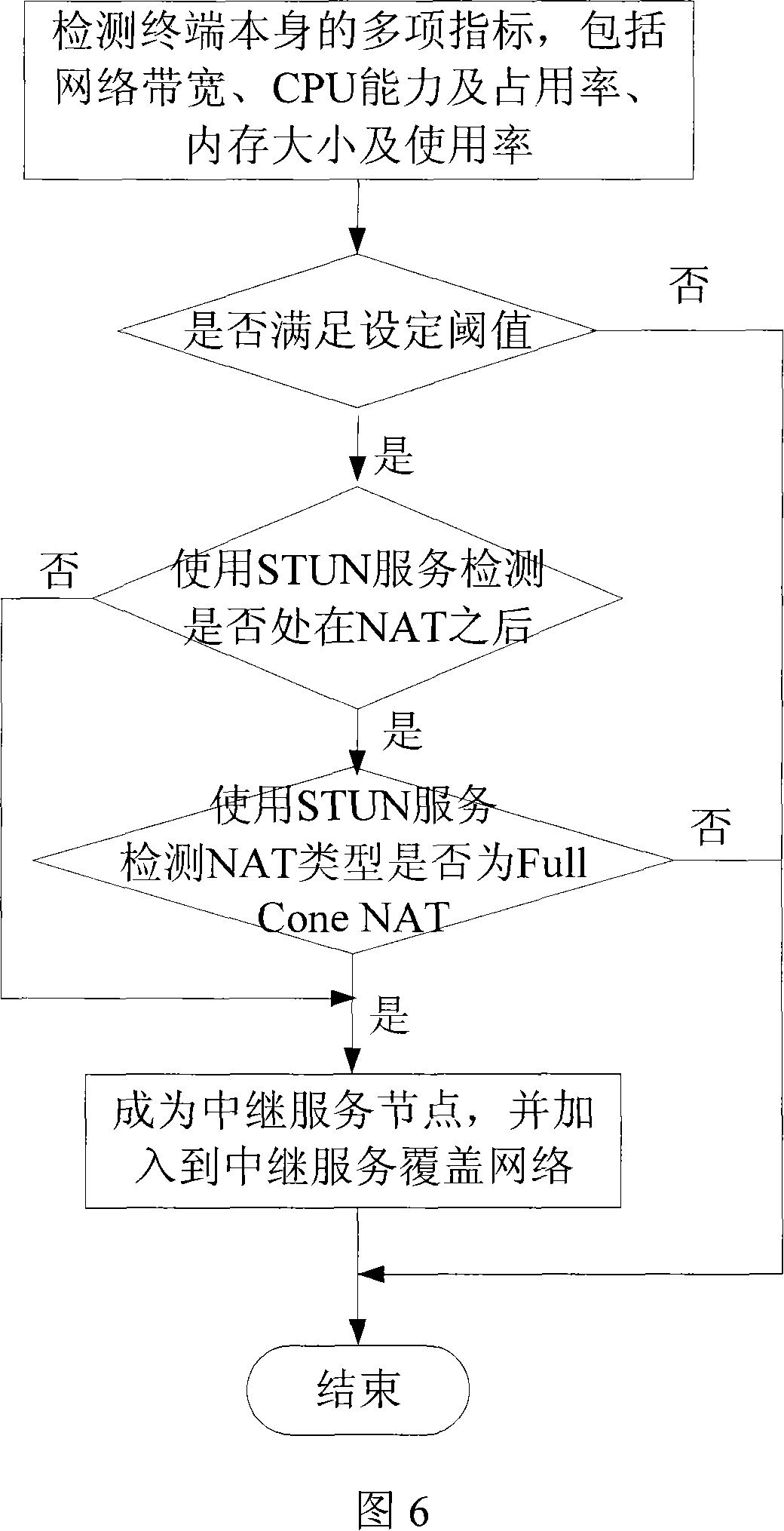
SIP soft switching system supporting P2P media transmission and its implementation method
ActiveCN101102310AGood manageability and controllabilityGood compatibilityData switching networksClient-sideService coverage
The system thereof comprises: a signaling controlling server, a media relay server, a supper relay serving node; a STUN serving node and some P2P client sides or some normal client sides. It uses an expanded SIP protocol as the communication protocol of the signaling control layer; the signaling controlling server located at the center of the system is used for processing the relaying of signaling. The method comprises: initializing system; making registration to the signaling controlling server; P2P client side is connected to the relay service coverage network and the STUN service coverage network; making self estimation; establishing the communication session between client sides; when current transmission path fails to cause the interruption of call; both P2P client sides are switched to the standby media transmission path.
Owner:SHENYANG CALCULATION TECH INST CHINESE ACAD OF SCI
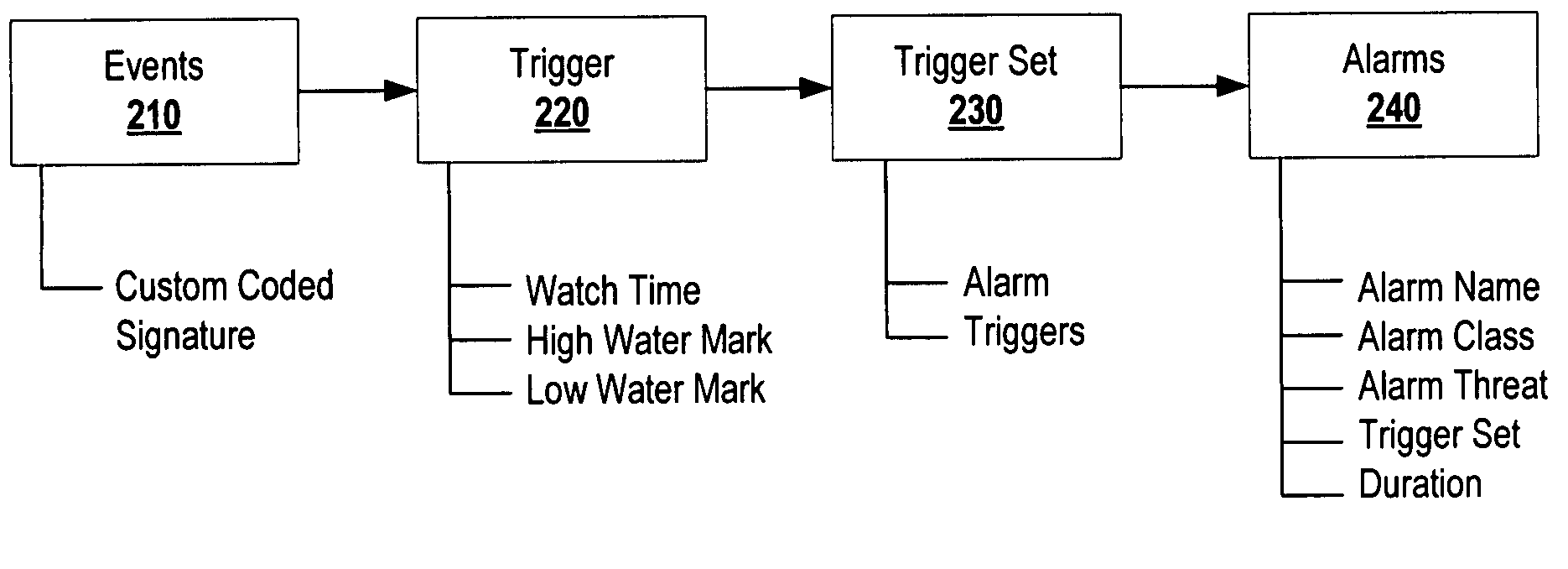
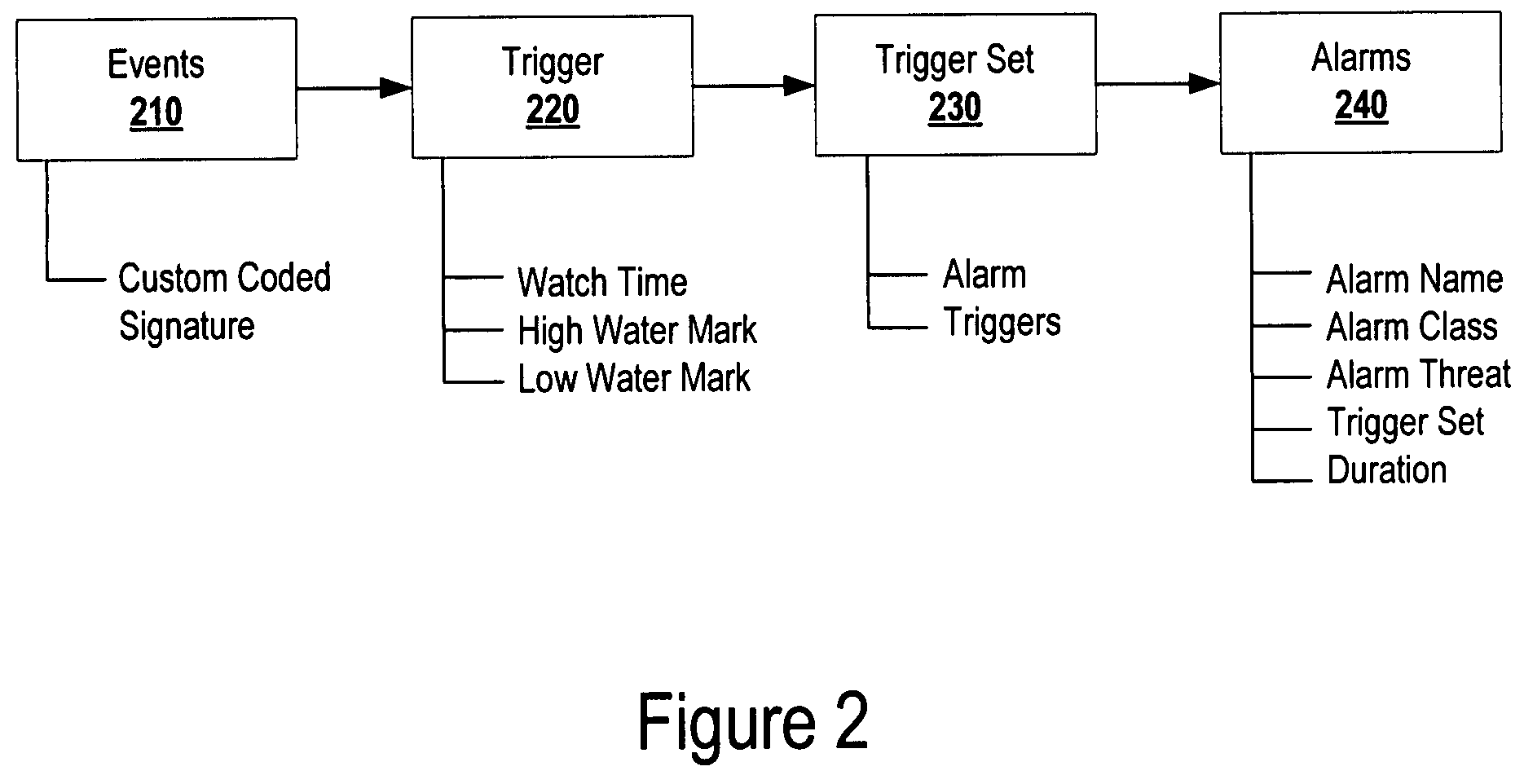
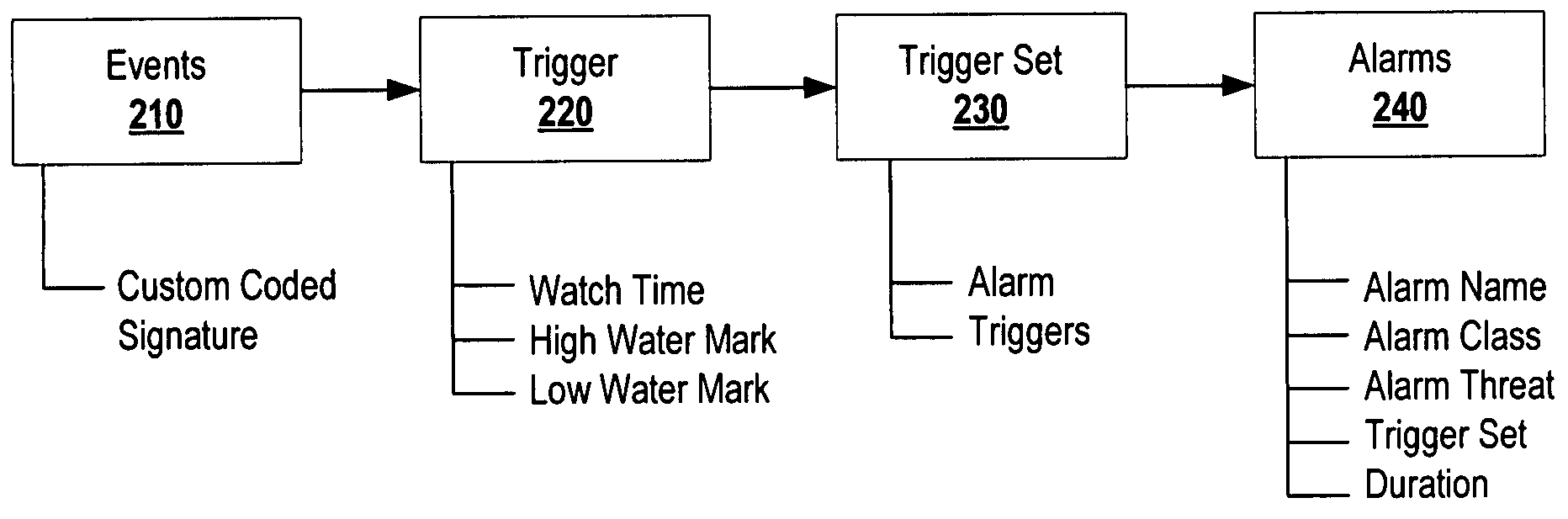
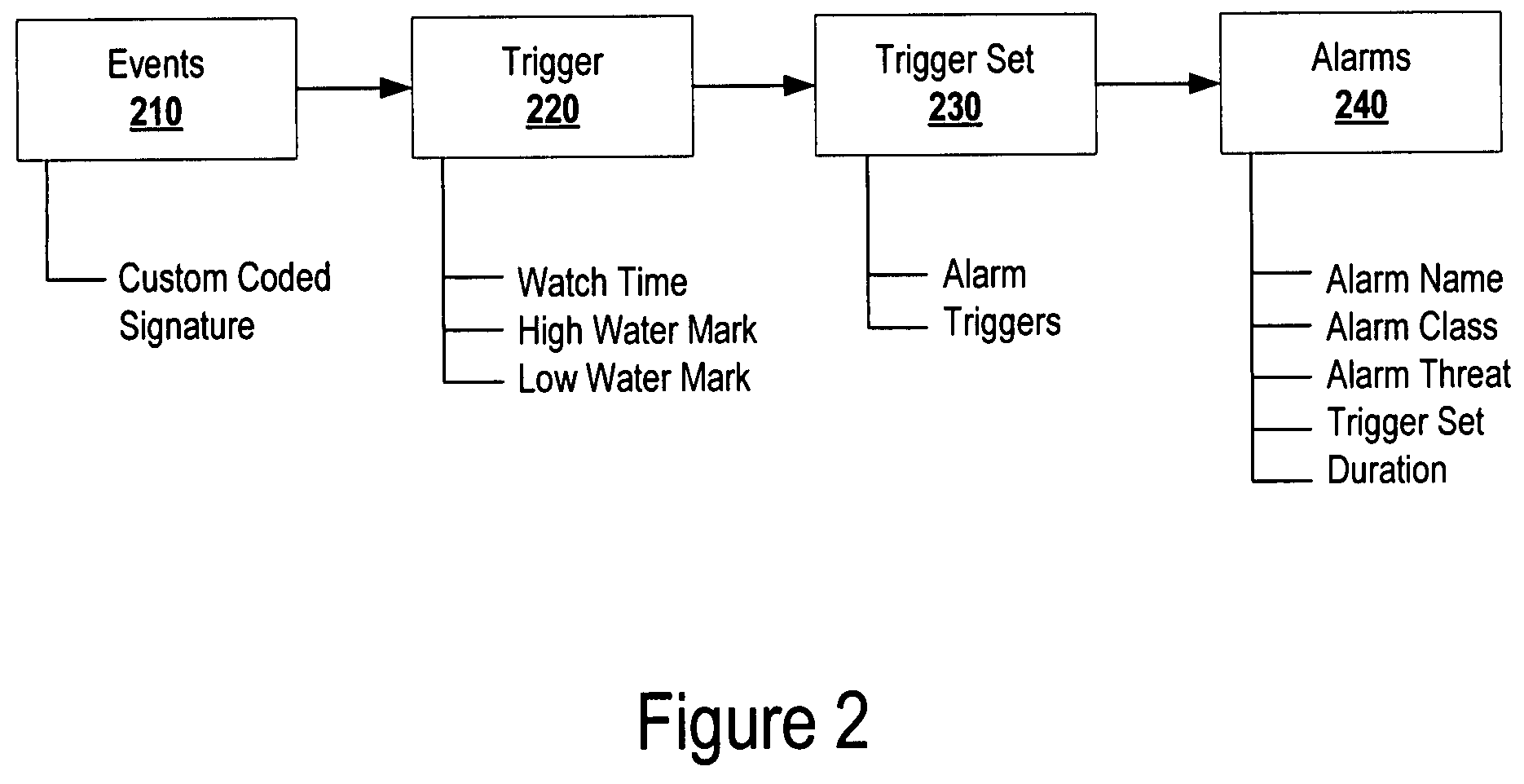
Systems and methods for generating, managing, and displaying alarms for wireless network monitoring
ActiveUS8205244B2Lower the volumeImprove manageabilityMemory loss protectionDigital data processing detailsNetwork monitoringComputer science
The present disclosure is directed to systems and methods for generating, managing, and displaying alarms associated with monitoring a wireless network. Advantageously, the present disclosure provides one alarm per security event, and the ability to see an event in context over time and aggregate information. This results in a significant reduction in alarm volume for wireless monitoring which increases manageability and reduces storage requirements. Further, this provides better security by avoiding the “needle in the haystack” problem where you see few actionable alarms rather than being flooded by multiple copies of the same event over time. Finally, the present disclosure provides improved system scalability with large deployments by managing alarms through lesser alarm volume, and through visual representation.
Owner:EXTREME NETWORKS INC
Systems and methods for generating, managing, and displaying alarms for wireless network monitoring
ActiveUS20080209517A1Reduction in alarm volumeImprove manageabilityMemory loss protectionDigital data processing detailsNetwork monitoringVisual perception
The present disclosure is directed to systems and methods for generating, managing, and displaying alarms associated with monitoring a wireless network. Advantageously, the present disclosure provides one alarm per security event, and the ability to see an event in context over time and aggregate information. This results in a significant reduction in alarm volume for wireless monitoring which increases manageability and reduces storage requirements. Further, this provides better security by avoiding the “needle in the haystack” problem where you see few actionable alarms rather than being flooded by multiple copies of the same event over time. Finally, the present disclosure provides improved system scalability with large deployments by managing alarms through lesser alarm volume, and through visual representation.
Owner:EXTREME NETWORKS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com