Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
678 results about "Control transfer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
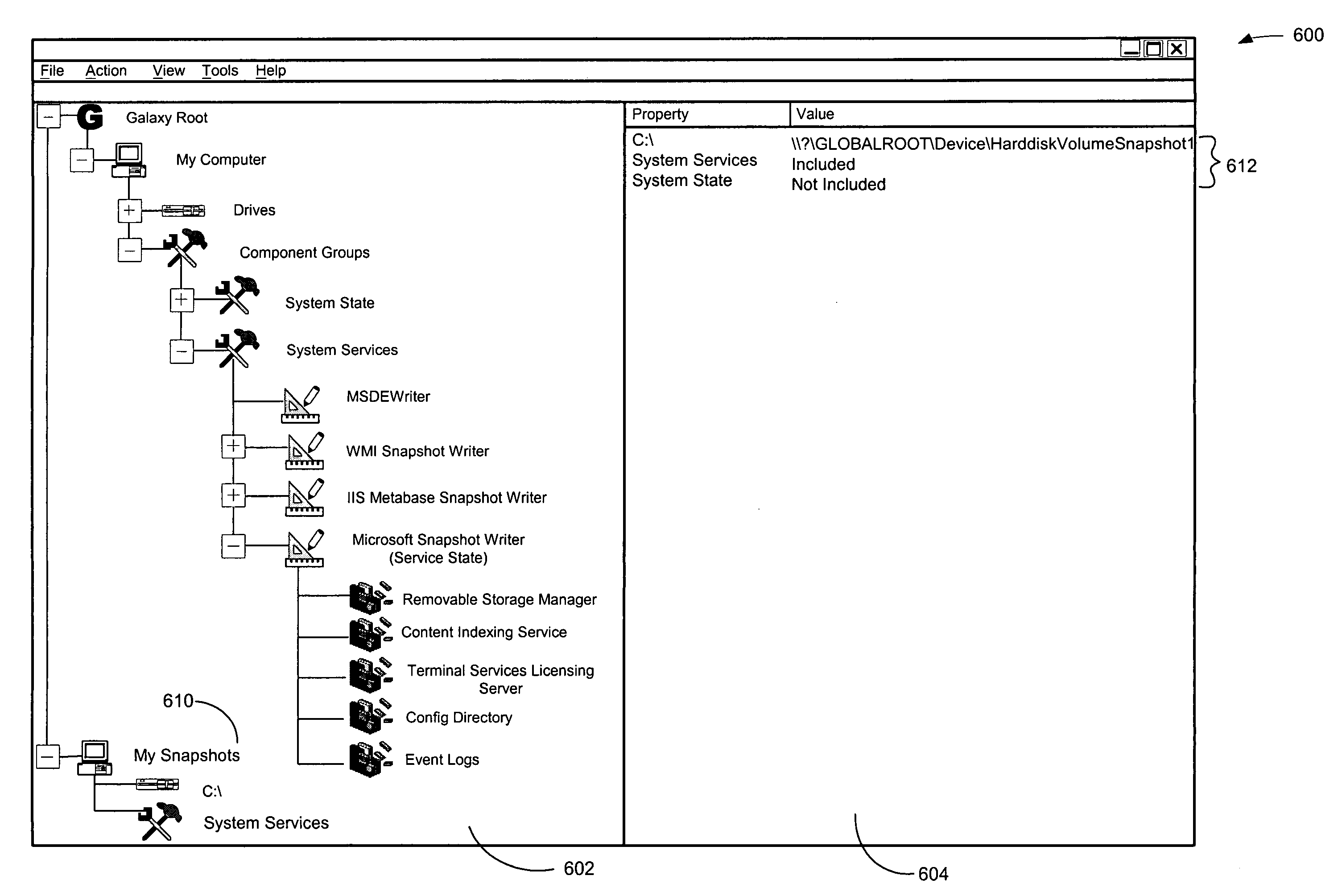
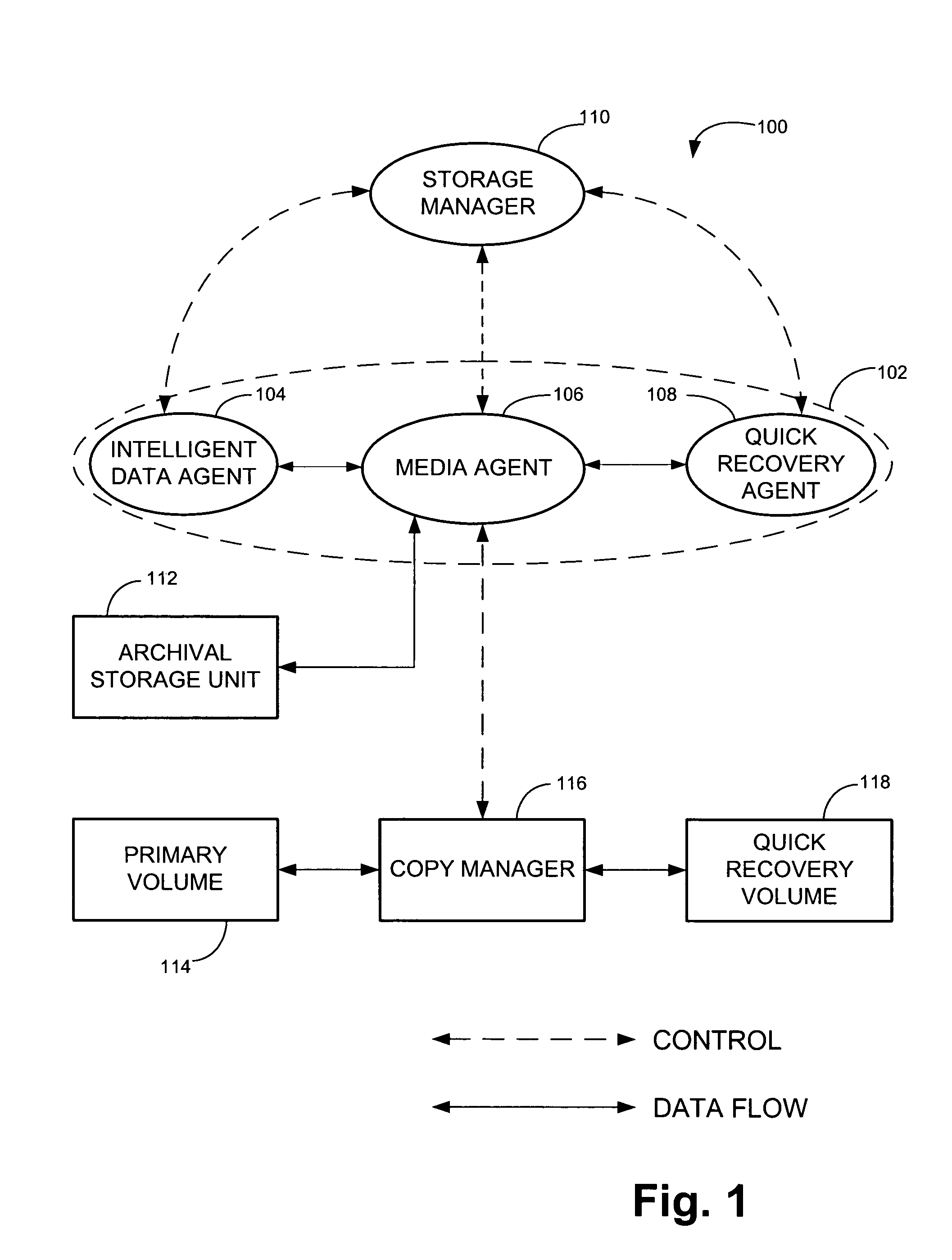
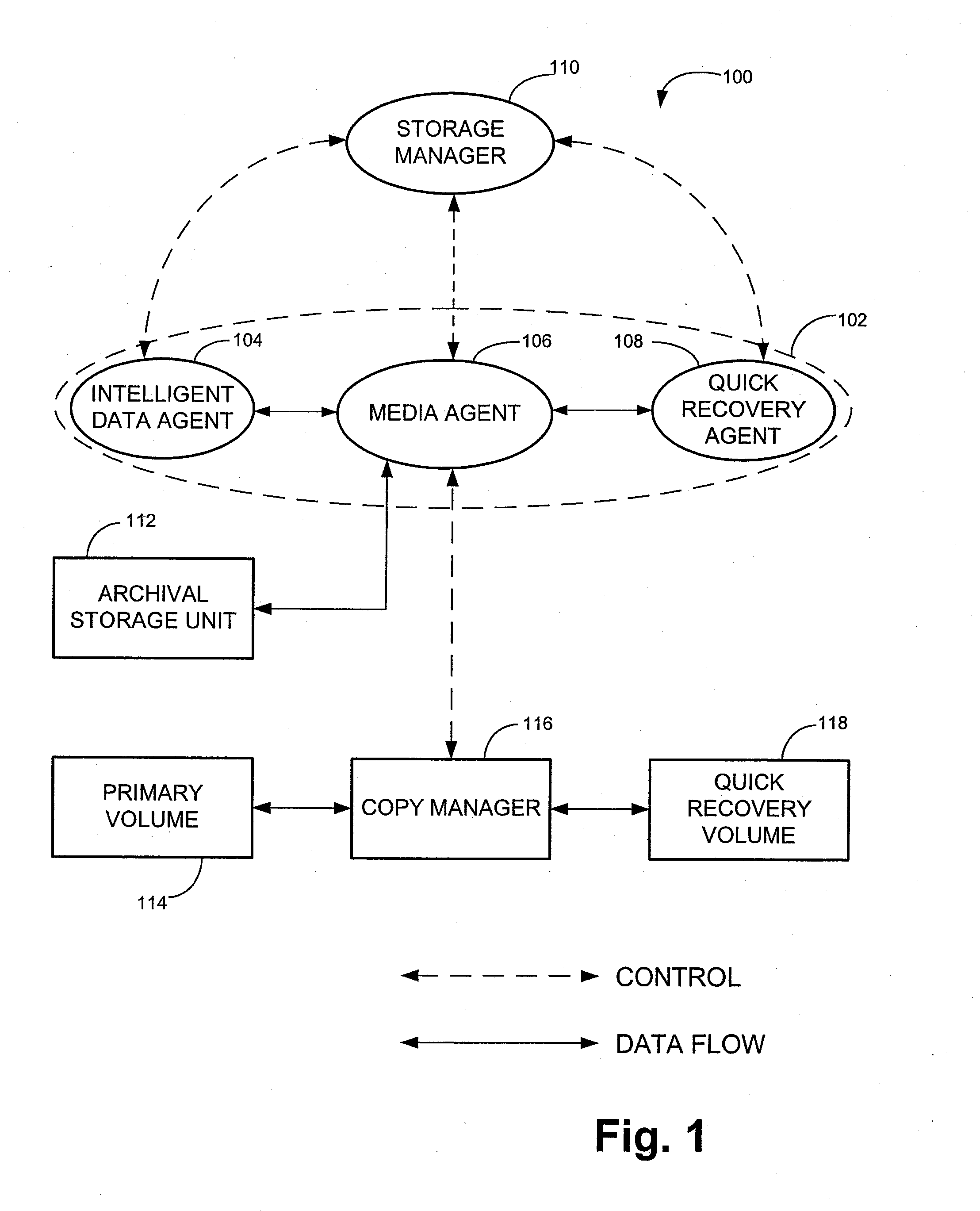
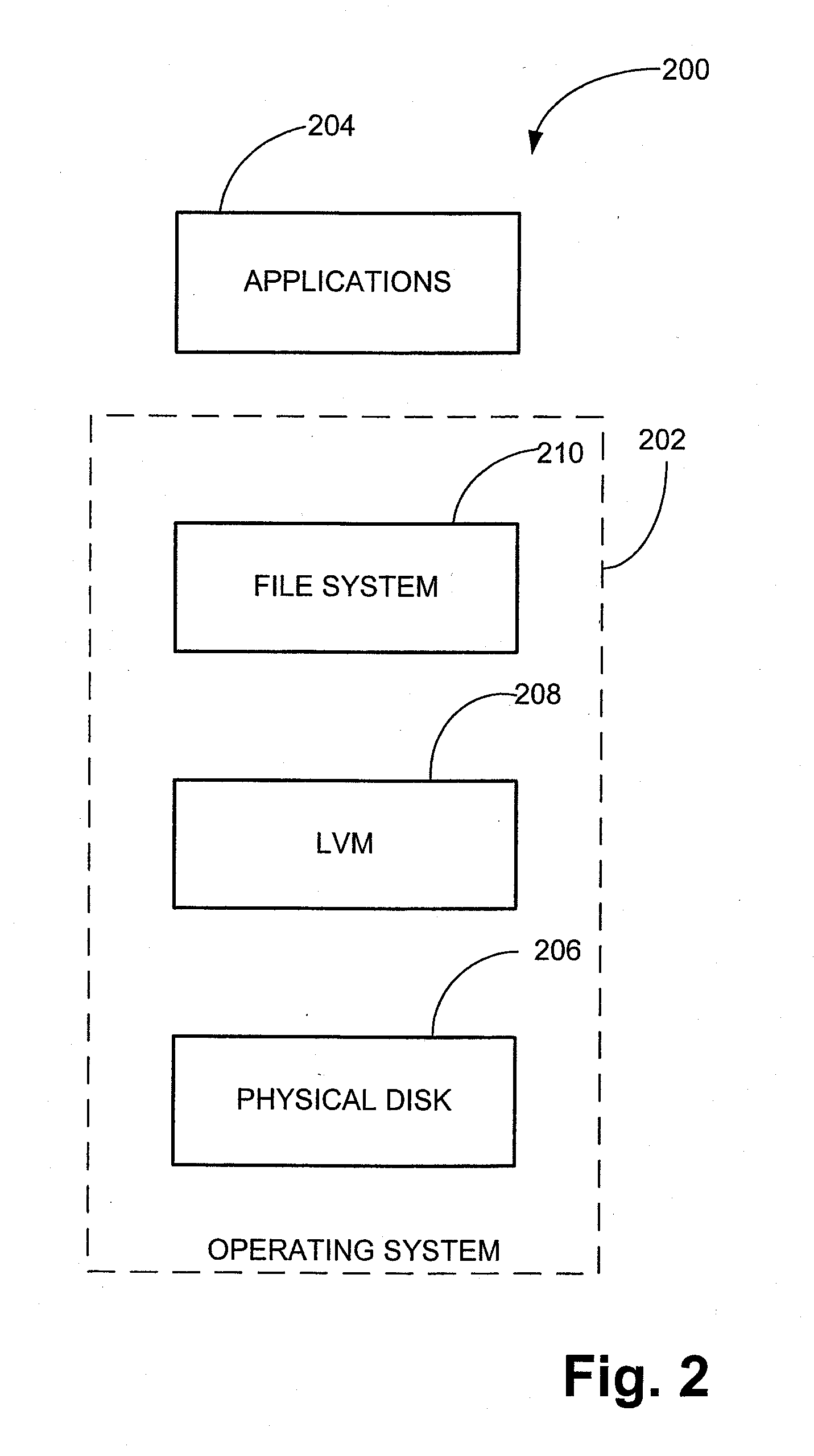
System and method for generating and managing quick recovery volumes
InactiveUS7346623B2Efficient creation and management and recoveryInput/output to record carriersData processing applicationsData setApplication software
The invention relates to computer readable medium storing program code which when executed on a computer causes the computer to perform a method for creating a quick recovery volume of a primary data set used by a first computer in a backup storage system, which includes identifying a snapshot image of the primary data set generated by a snapshot application, creating the quick recovery volume of the primary data set from the snapshot image of the primary data set and controlling transfer of data from the first computer to an archival storage unit. In one embodiment, the invention provides a method for creating a quick recovery volume of a primary data set that includes creating a snapshot image of the primary data set and creating a quick recovery volume of the primary data set from the snapshot image of the primary data set. In another embodiment, the invention provides a user interface screen enabling browser style browsing and recovery of quick recovery volumes and snapshot images.
Owner:COMMVAULT SYST INC
Method for Voice Activation of a Software Agent from Standby Mode
InactiveUS20140214429A1Save energyPower managementDigital data processing detailsDialog systemBiological activation
A method for voice activation of a software agent from a standby mode. In one embodiment, an audio recording (2) is buffered in an audio buffer (6) and at the same time, the audio recording is input to a secondary voice recognition process (7) which is economical in terms of energy and has an increased false positive rate. When a keyword is recognized, a primary voice recognition process (8) is activated from an inactive state, which converts the audio buffer to text and inputs it to a dialog system (9) which analyzes as to whether there is a relevant question made by the user. If this is the case, the user gets an acoustic reply (3), and if this is not the case, the dialog system and the primary voice recognition process immediately return to the inactive state and transfer the control to the secondary voice recognition process.
Owner:INODYN NEWMEDIA
Device for controlling processing system, method for controlling processing system and computer-readable storage medium stored processing program
ActiveUS8055378B2Production of product can be suppressedIncrease productionProgramme controlDigital data processing detailsProcess moduleComputer module
A processing system includes process modules, load lock modules, an equipment controller, and a machine controller. The equipment controller controls transfer and processing of wafers in the processing system. A transfer destination determining portion determines the transfer destination of each wafer such that each wafer is sequentially transferred to a normally operating process module. When an abnormality occurs in a process module, an evacuation portion temporarily evacuates to a cassette stage the wafer determined is to be transferred to the abnormal process module and that has not yet been transferred to the abnormal process module. When a new transfer destination of the evacuated wafer is determined, if a process that is performed immediately before processing the evacuated wafer in the processing module as the new transfer destination satisfies a predetermined condition, a transfer inhibition portion inhibits the transfer of the evacuated wafer to the new transfer destination.
Owner:TOKYO ELECTRON LTD
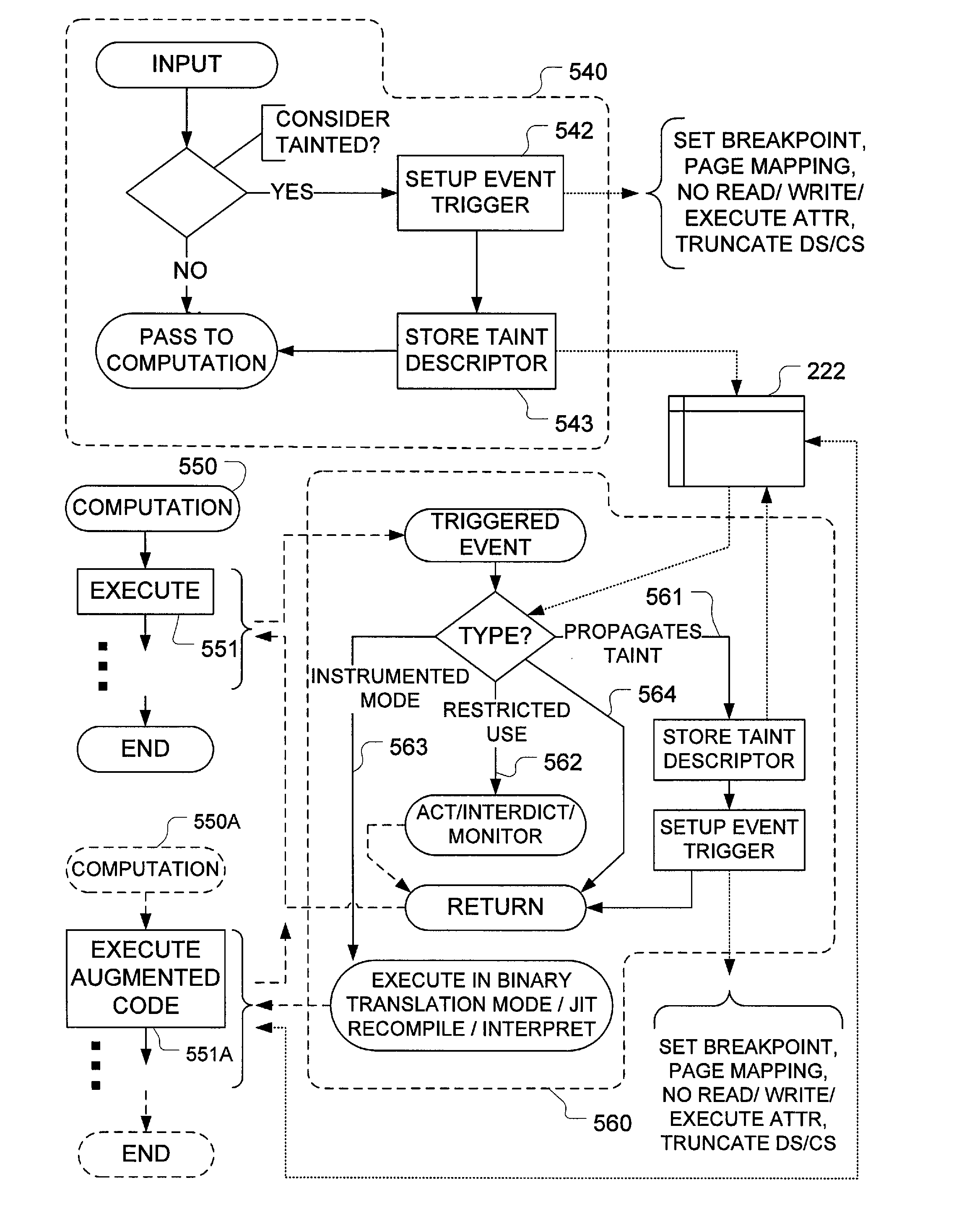
Taint tracking mechanism for computer security
ActiveUS8510827B1Easy to trackAvoid modificationMemory loss protectionDigital data processing detailsInformation dispersalOperation mode
Mechanisms have been developed for securing computational systems against certain forms of attack. In particular, it has been discovered that, by maintaining and propagating taint status for memory locations in correspondence with information flows of instructions executed by a computing system, it is possible to provide a security response if and when a control transfer (or other restricted use) is attempted based on tainted data. In some embodiments, memory management facilities and related exception handlers can be exploited to facilitate taint status propagation and / or security responses. Taint tracking through registers of a processor (or through other storage for which access is not conveniently mediated using a memory management facility) may be provided using an instrumented execution mode of operation. For example, the instrumented mode may be triggered by an attempt to propagate tainted information to a register. In some embodiments, an instrumented mode of operation may be more generally employed. For example, data received from an untrusted source or via an untrusted path is often transferred into a memory buffer for processing by a particular service, routine, process, thread or other computational unit. Code that implements the computational unit may be selectively executed in an instrumented mode that facilitates taint tracking. In general, instrumented execution modes may be supported using a variety of techniques including a binary translation (or rewriting) mode, just-in-time (JIT) compilation / re-compilation, interpreted mode execution, etc. Using an instrumented execution mode and / or exception handler techniques, modifications to CPU hardware can be avoided if desirable.
Owner:VMWARE INC
Secure execution of a computer program
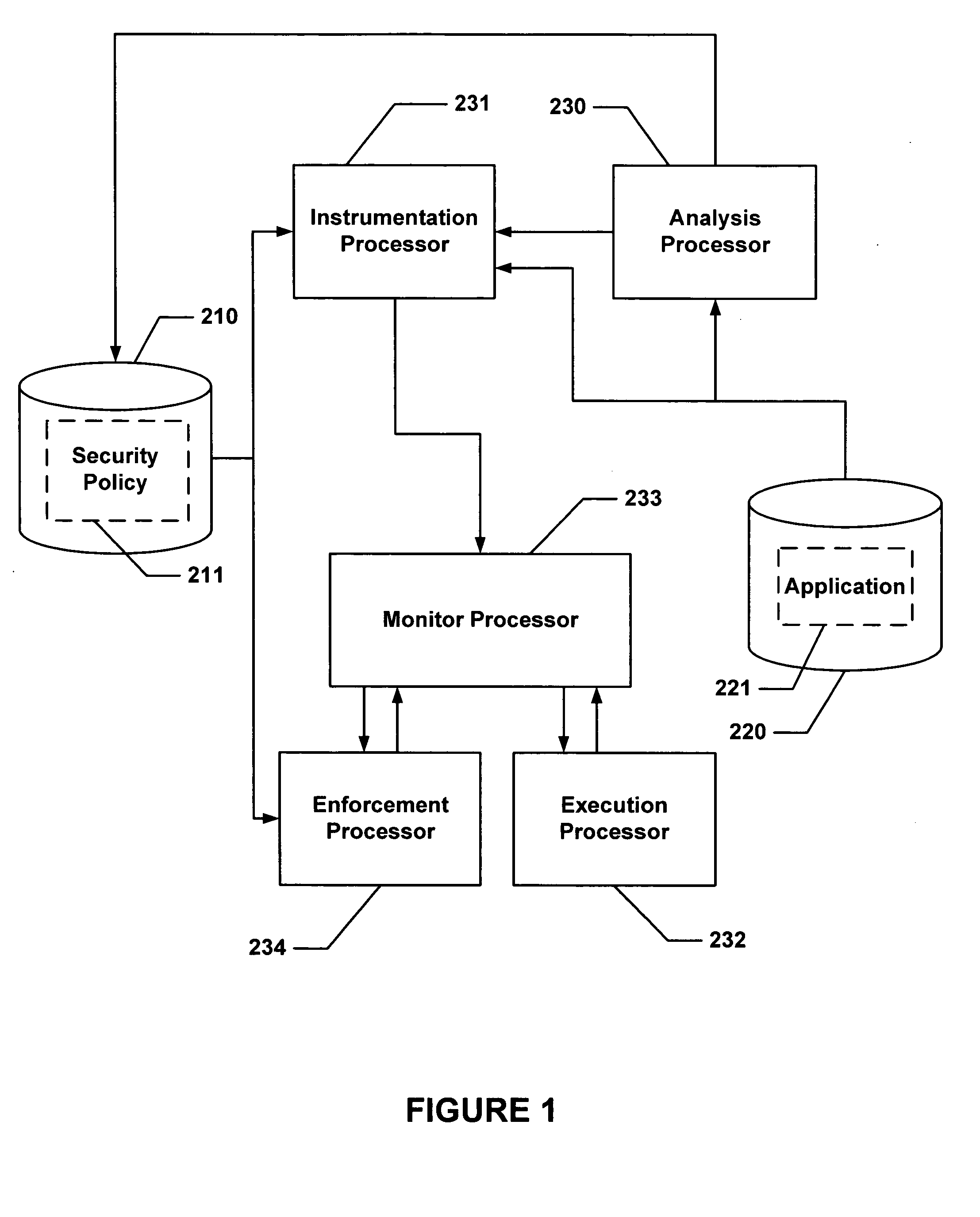
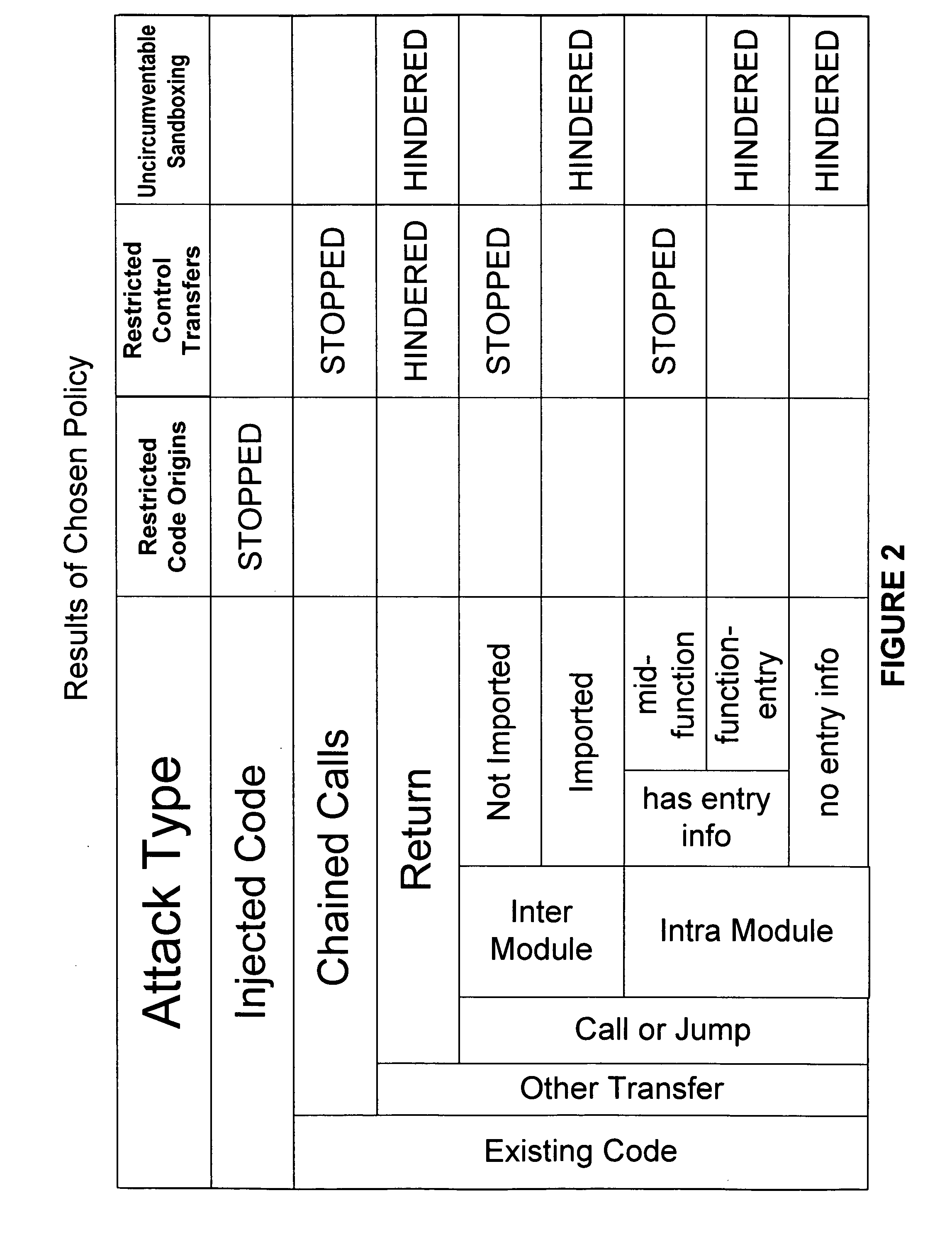
ActiveUS20040133777A1Digital data processing detailsUnauthorized memory use protectionControl flowApplication software
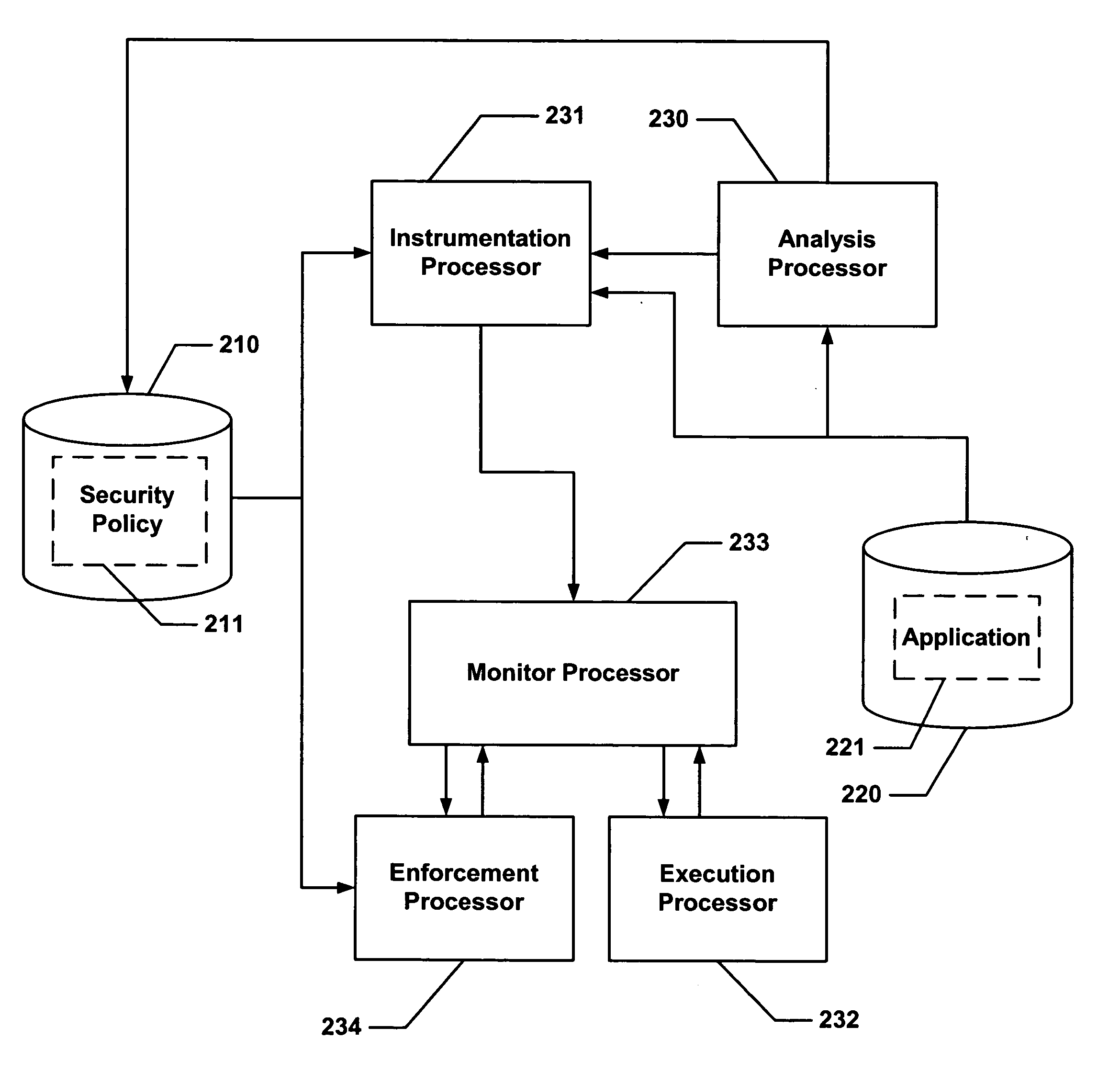
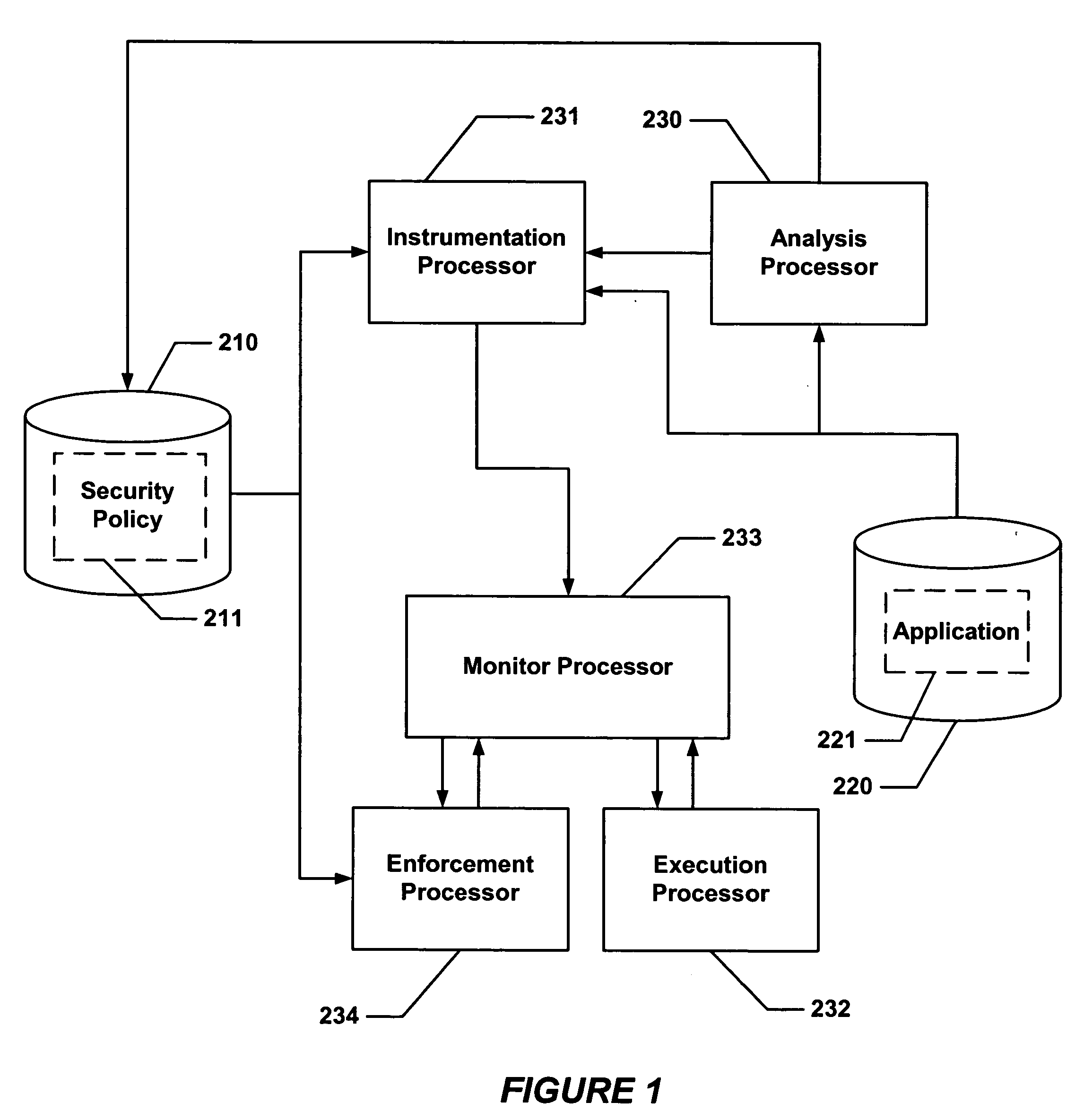
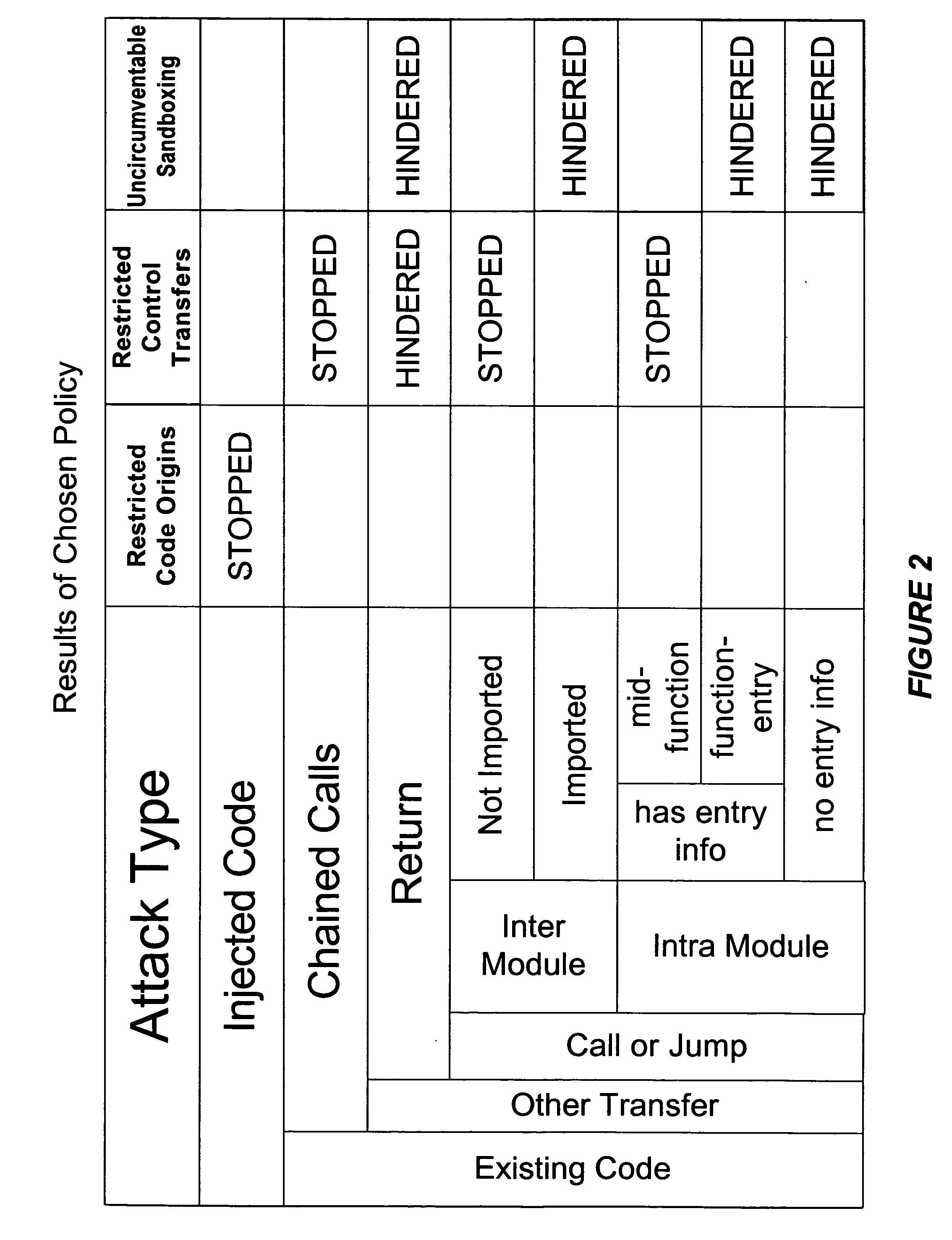
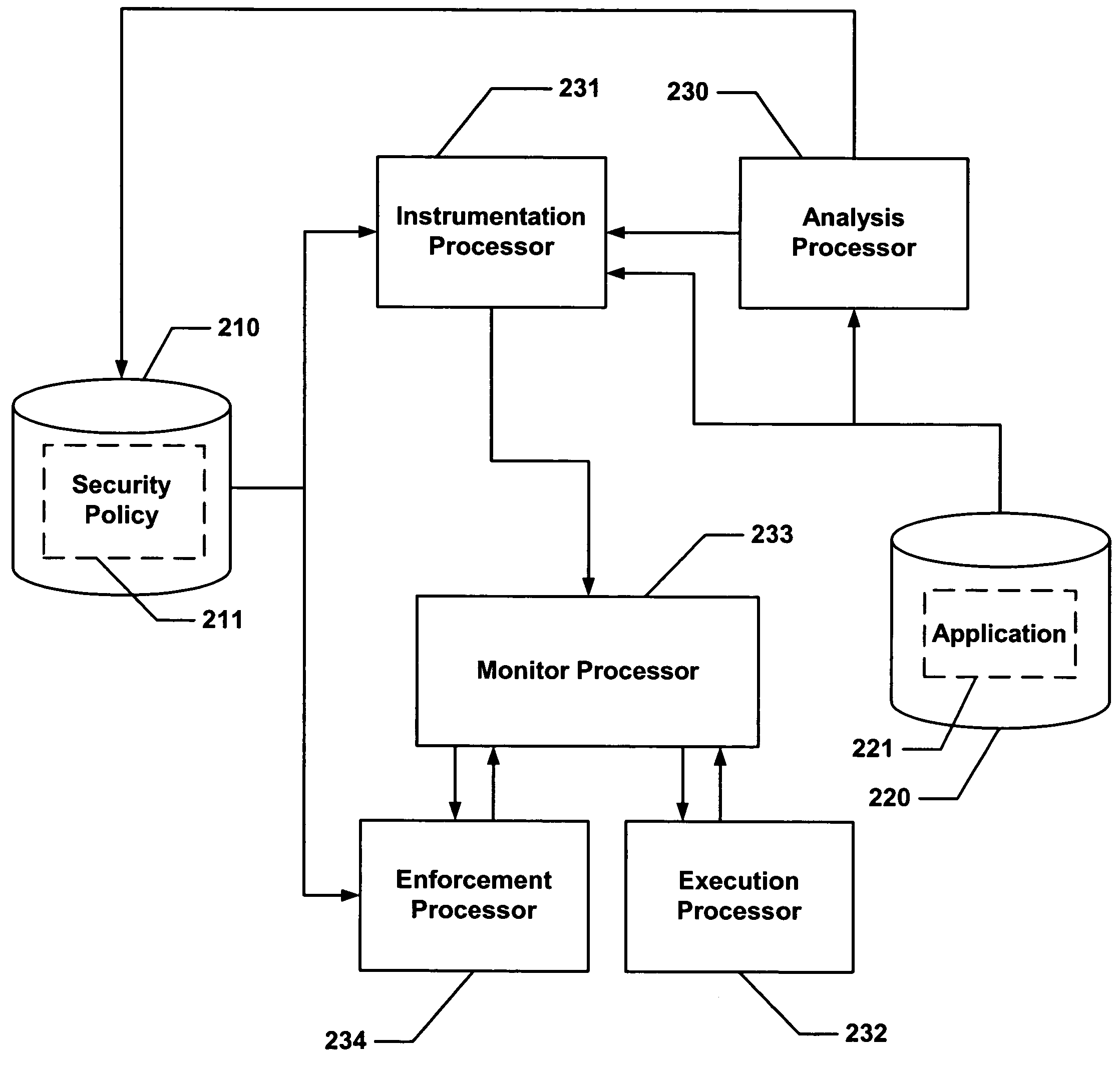
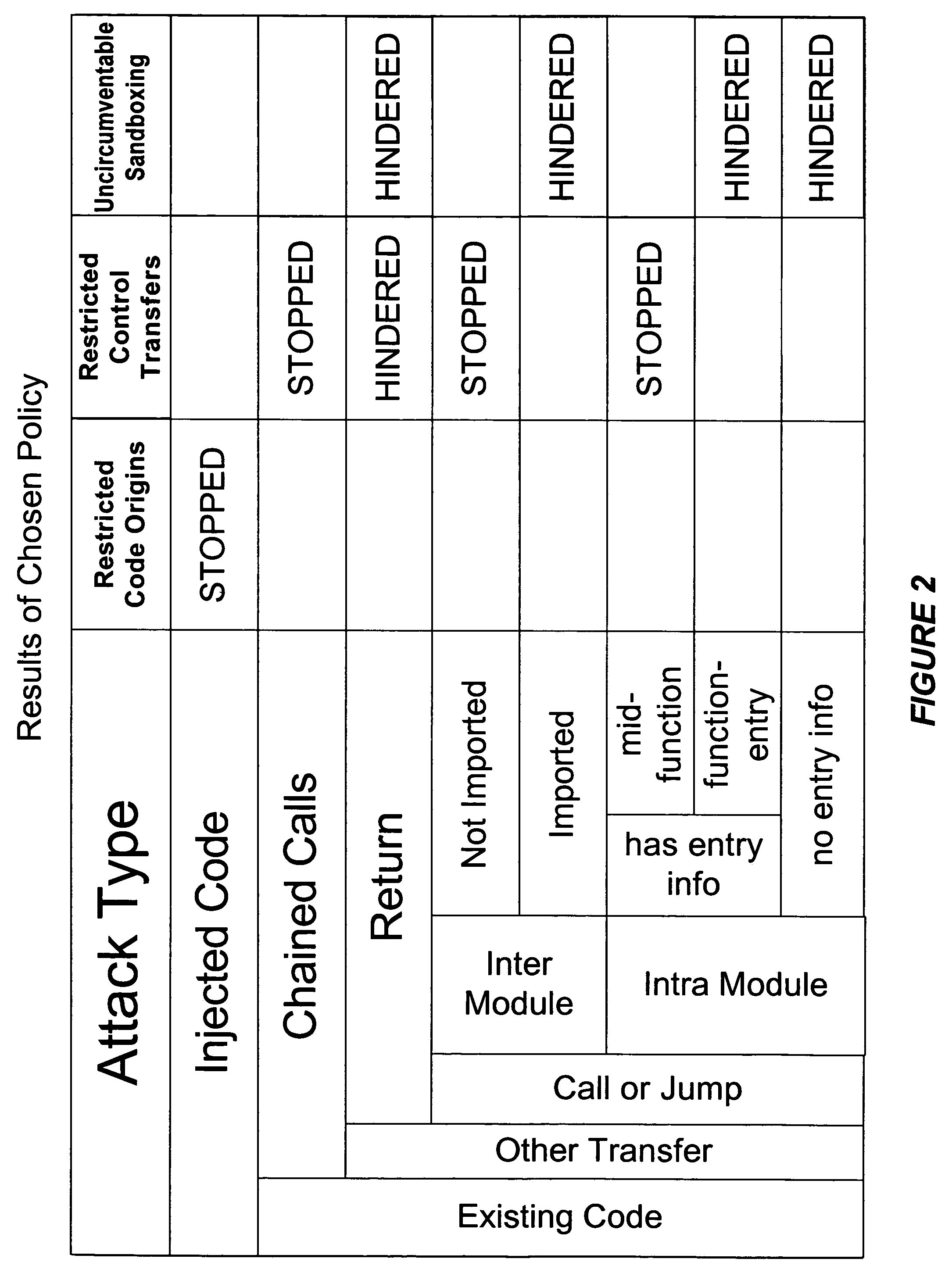
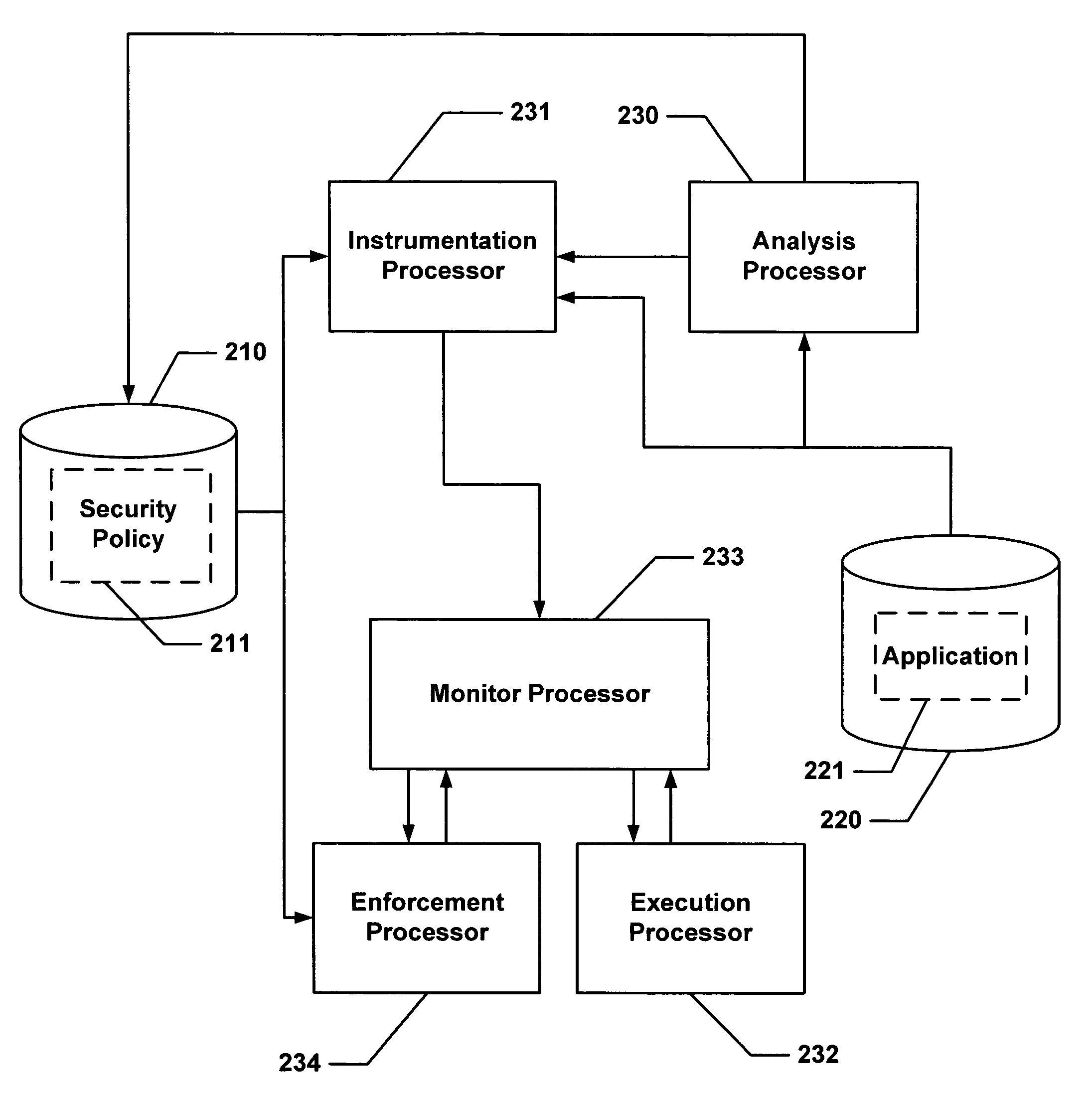
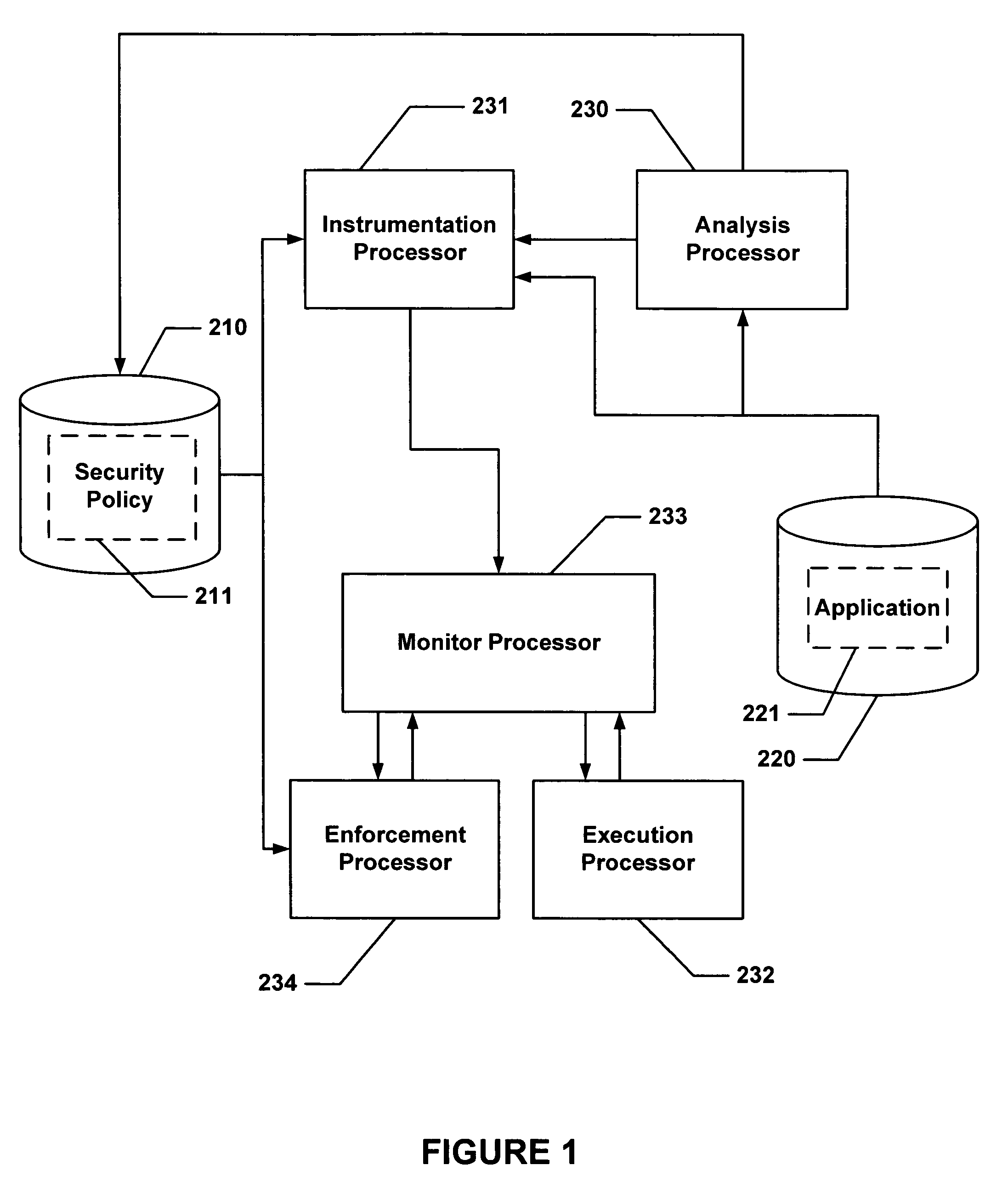
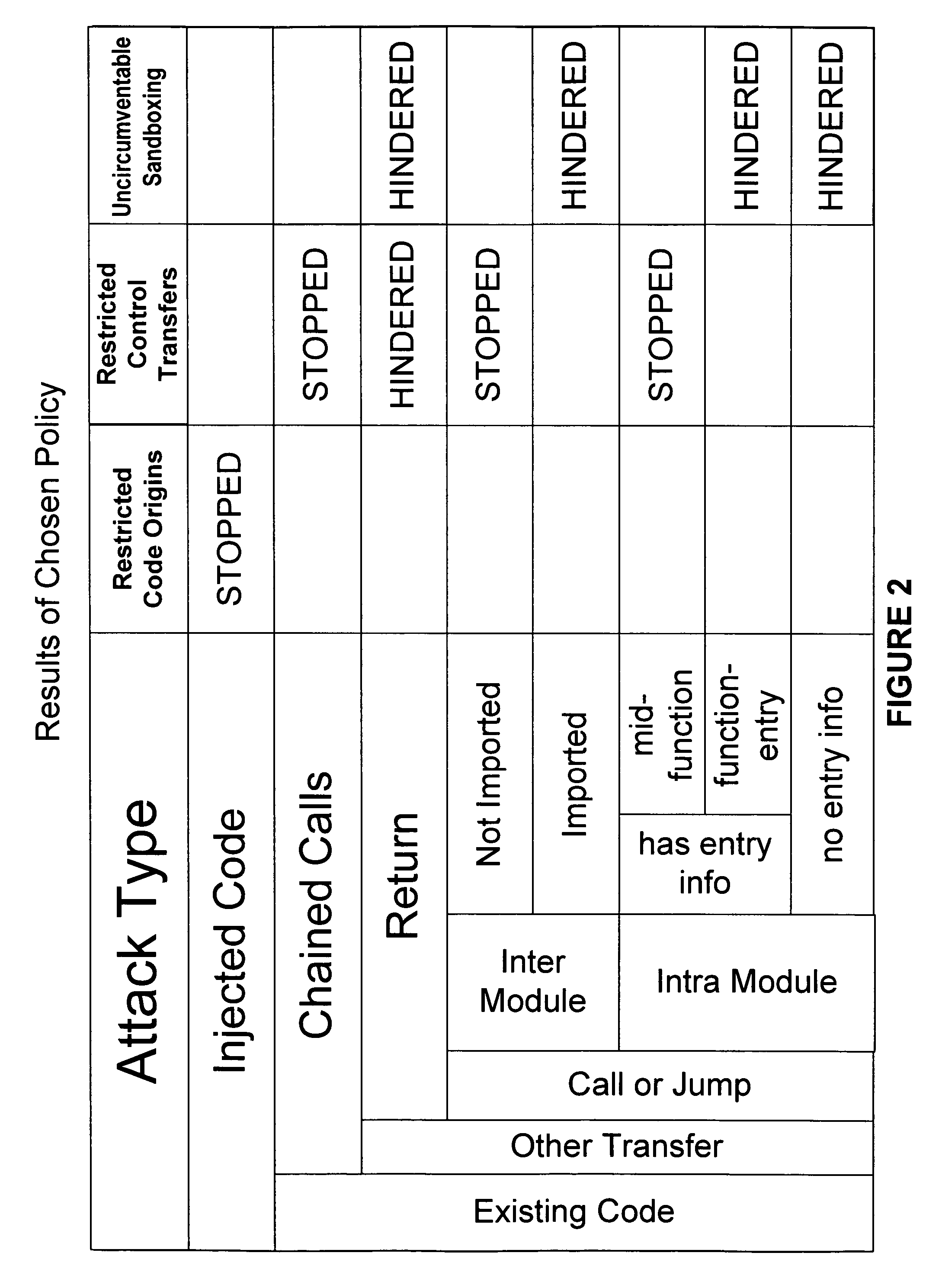
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
Adaptive pattern recognition based control system and method
A network media appliance, comprising at least one packet data network interface, adapted for communicating data packets with a data network according to an Internet Protocol; a media data interface, and a processor, having an associated memory for storing executable code, said code defining at least a remote virtual interface function, and a data transfer function for controlling transfer of data through said media data interface.
Owner:BLANDING HOVENWEEP
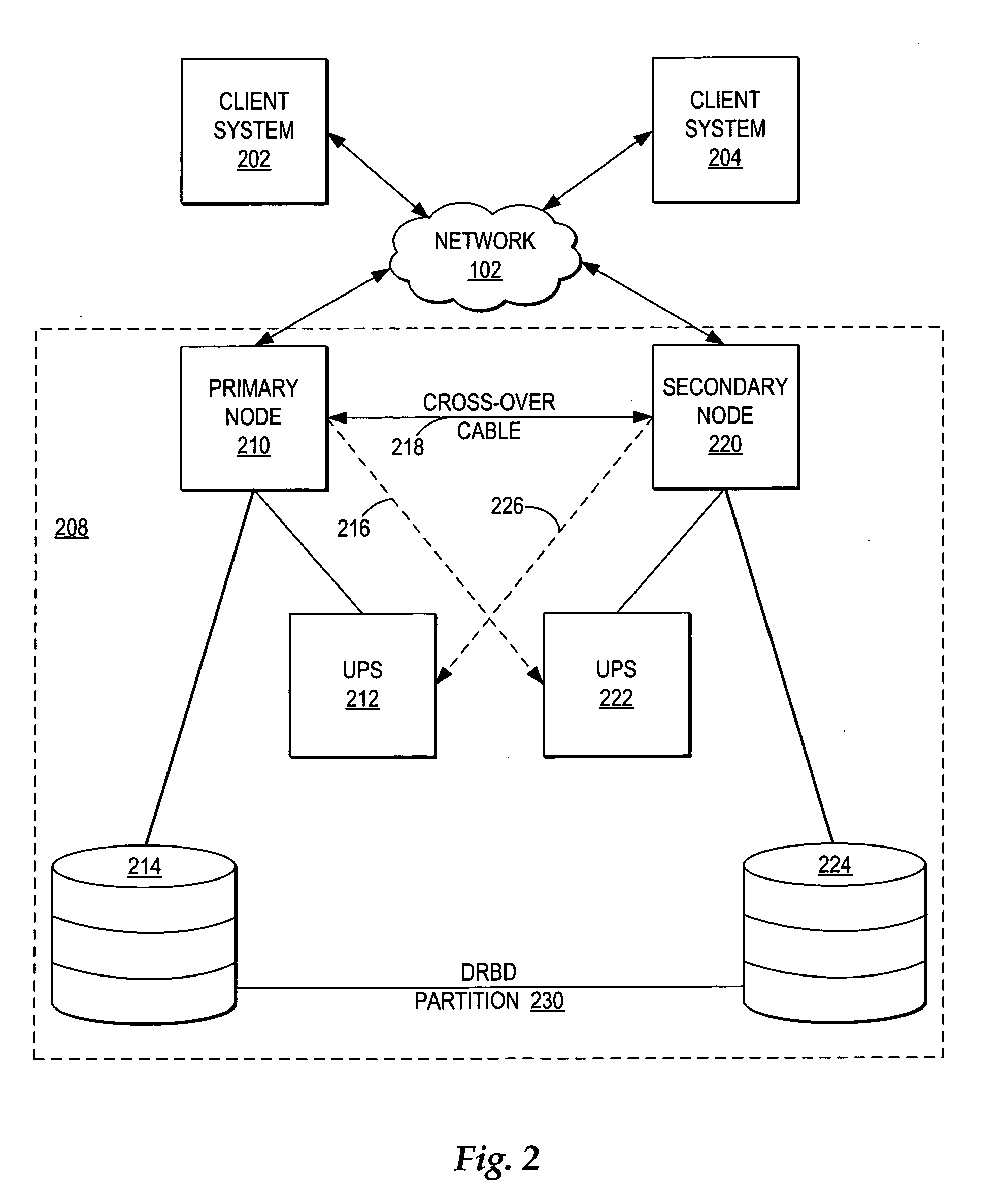
Managing failover of J2EE compliant middleware in a high availability system
InactiveUS20050172161A1Short recovery timeMinimal data lossRedundant hardware error correctionFailoverWeb application
A method, system, and program for managing failover of J2EE compliant middleware in a high availability system are provided. A primary node and a secondary node each run the same J2EE compliant middleware stack comprising layers including a load balancer, a web server, a web application server, a message control server, a monitoring server, and a database control server. In the primary node, all layers are active. In the secondary node, part of the layers are active and part of the layers are in standby. A data replication partition shared between the primary node and the secondary node includes persistent resource data accessible to a selection of the layers of the primary node. A heartbeat controller monitors each node, including the middleware stack, and upon detection of a failure, controls transfer of the services provided by the primary node to the secondary node by transferring virtual IP addresses from the primary node to the secondary node, remounting the data replication partition for access by the secondary node, and activating the standby layers which require access to the data in the data replication partition.
Owner:IBM CORP
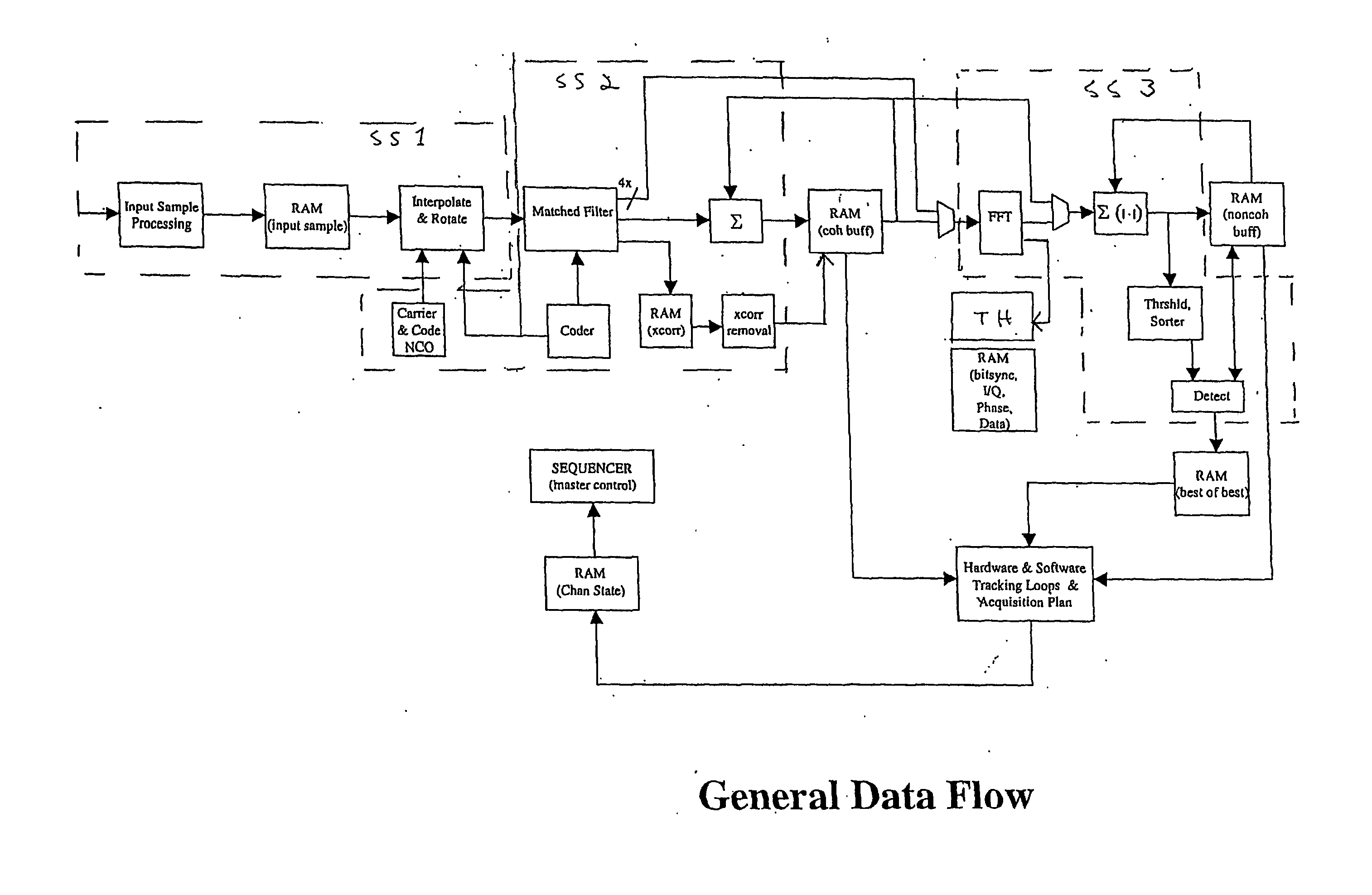
Signal Processing System for Satellite Positioning Signals
InactiveUS20110102258A1Beacon systemsSatellite radio beaconingControl signalFourier transform on finite groups
A signal processing system for processing satellite positioning signals is described. The system comprises at least one processor and a signal processor operating under a number of operational modes. The signal processor includes at last one of a signal processing subsystem, a fast Fourier transform (FFT) subsystem, and a memory subsystem that are each dynamically and independently configurable in response to the operational modes. Further, the system includes a controller that couples to control transfer of data among the signal processing subsystem and the FFT subsystem via the memory subsystem. Configurability of the memory subsystem includes configuring the memory subsystem into regions according to the operational modes where each region is accessible in one of a number of manners according to the operational modes.
Owner:CSR TECH INC
Secure execution of a computer program using a code cache
ActiveUS20050010804A1Avoid hijackingLimit executionMemory loss protectionError detection/correctionControl flowSecurity policy
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
Managing failover of J2EE compliant middleware in a high availability system
InactiveUS7246256B2Improved high availability cluster managementShort recovery timeRedundant hardware error correctionFailoverWeb application
A method, system, and program for managing failover of J2EE compliant middleware in a high availability system are provided. A primary node and a secondary node each run the same J2EE compliant middleware stack comprising layers including a load balancer, a web server, a web application server, a message control server, a monitoring server, and a database control server. In the primary node, all layers are active. In the secondary node, part of the layers are active and part of the layers are in standby. A data replication partition shared between the primary node and the secondary node includes persistent resource data accessible to a selection of the layers of the primary node. A heartbeat controller monitors each node, including the middleware stack, and upon detection of a failure, controls transfer of the services provided by the primary node to the secondary node by transferring virtual IP addresses from the primary node to the secondary node, remounting the data replication partition for access by the secondary node, and activating the standby layers which require access to the data in the data replication partition.
Owner:IBM CORP
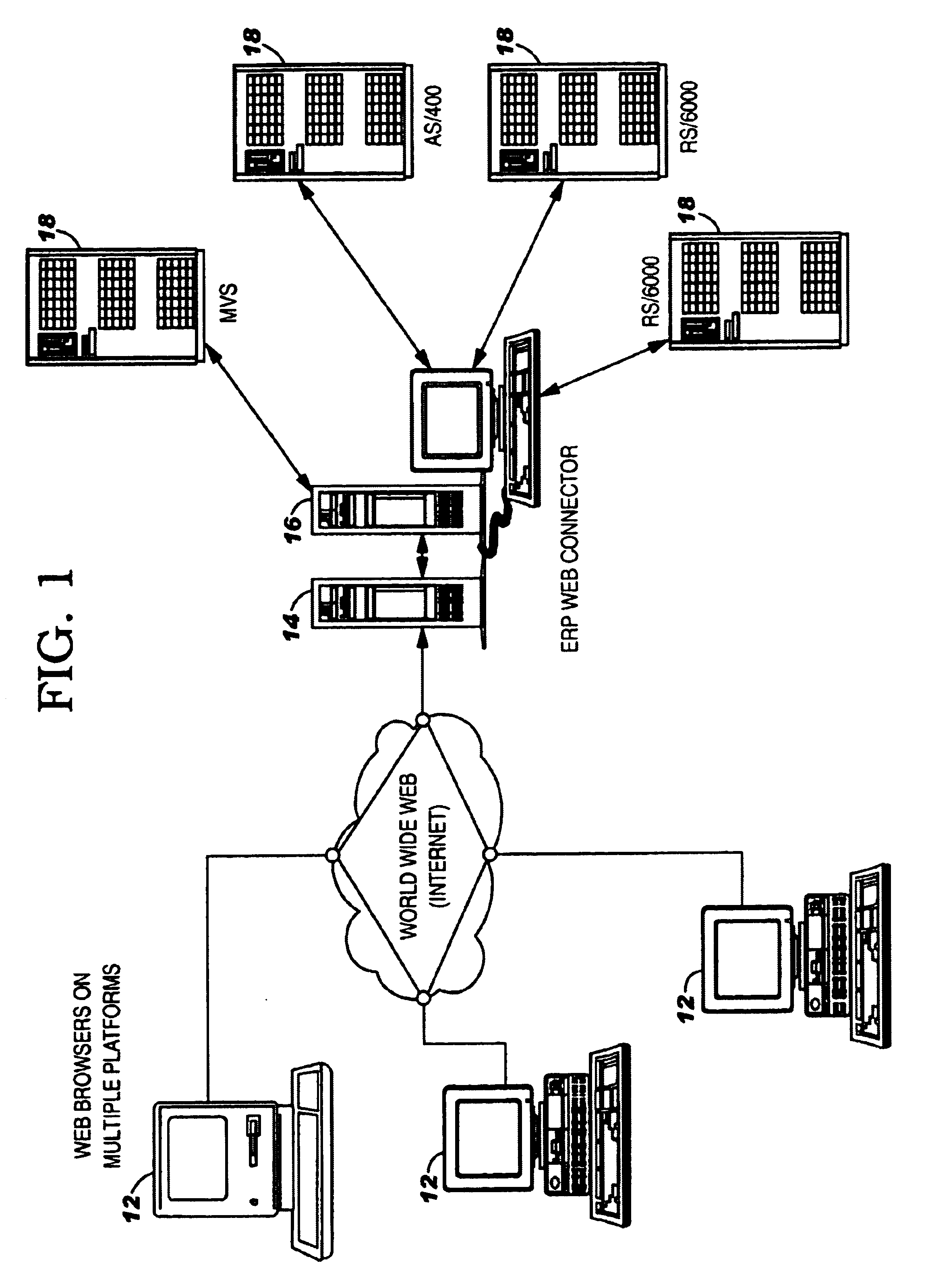
Accessing a ERP application over the internet using strongly typed declarative language files
The present invention provides a method and apparatus for executing ERP application requests in a computer-implemented ERP data processing system via a network, using the steps of:(a) transmitting a HyperText Markup Language (HTML) input form to a browser executed by a client computer in the network for display on a monitor attached thereto;(b) receiving a HyperText Transfer Protocol (HTTP) request from the browser to access the ERP System, wherein the request optionally includes data entered by the user into an HTML input form;(c) transferring any data entered by the user into the HTML input form and any data stored in the requested HTML page into the ERP application API(d) transferring control to the ERP application for execution;(e) receiving output data from the ERP application in response to the transmitted data and request;(f) merging the output data from the ERP application into a strongly typed Java object;(g) transforming the strongly typed Java objects into a transmittable format, such as XML or HTML, and(h) transmitting the HTML or XML object to the browser for display on the monitor attached to the client computer.
Owner:IBM CORP
System and method for generating and managing quick recovery volumes
InactiveUS20080183775A1Efficient creation and management and recoveryData processing applicationsDigital data information retrievalData setApplication software
The invention relates to computer readable medium storing program code which when executed on a computer causes the computer to perform a method for creating a quick recovery volume of a primary data set used by a first computer in a backup storage system, which includes identifying a snapshot image of the primary data set generated by a snapshot application, creating the quick recovery volume of the primary data set from the snapshot image of the primary data set and controlling transfer of data from the first computer to an archival storage unit. In one embodiment, the invention provides a method for creating a quick recovery volume of a primary data set that includes creating a snapshot image of the primary data set and creating a quick recovery volume of the primary data set from the snapshot image of the primary data set. In another embodiment, the invention provides a user interface screen enabling browser style browsing and recovery of quick recovery volumes and snapshot images.
Owner:COMMVAULT SYST INC
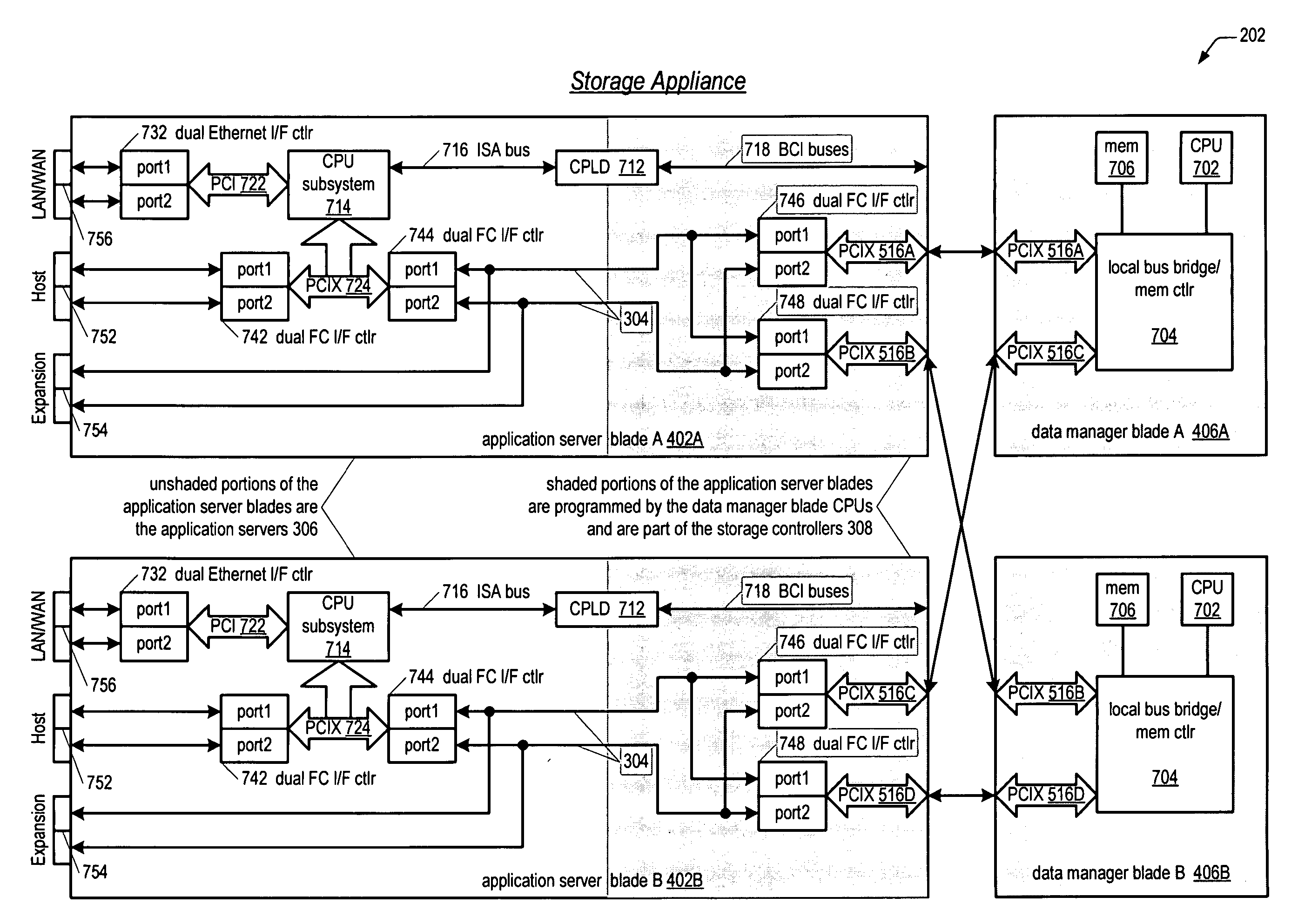
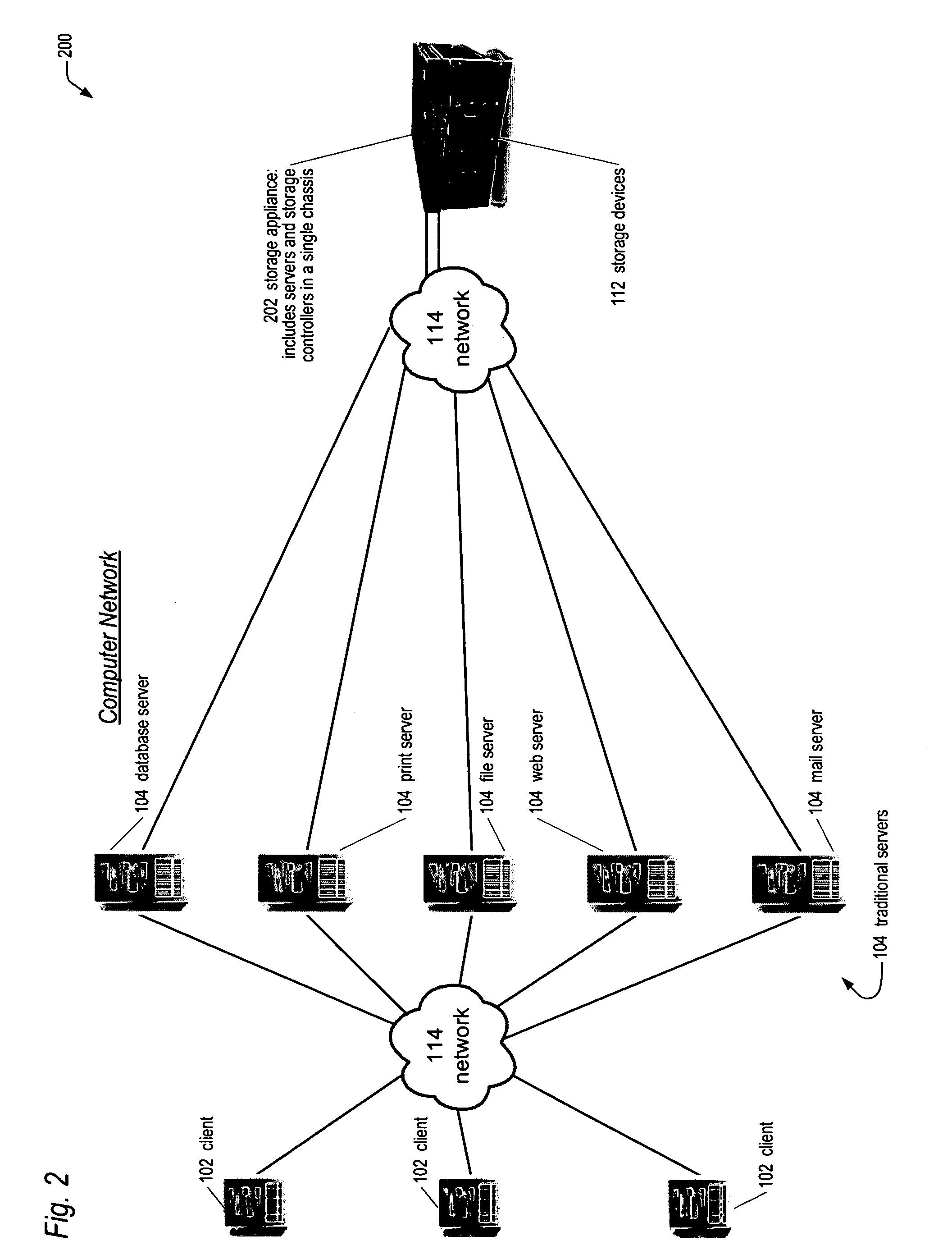
Network storage appliance with integrated server and redundant storage controllers
ActiveUS20050010715A1Improve system reliabilityImprove manageabilityInput/output to record carriersDigital data processing detailsControl storeMagnetic tape
A network storage appliance is disclosed. The appliance includes a chassis enclosing a backplane, and a server enclosed in the chassis and coupled to the backplane. The appliance also includes storage controllers enclosed in the chassis, each coupled to the backplane, which control transfer of data between the server and storage devices coupled to the storage controllers. The storage controllers also control transfer of data between the storage devices and computers networked to the appliance and external to the appliance. The storage controllers and the server comprise a plurality of hot-replaceable blades. Any one of the plurality of blades may be replaced during operation of the appliance without loss of access to the storage devices by the computers. In one embodiment, the server executes storage application software, such as backup software for backing up data on the storage devices, such as to a tape device networked to the server.
Owner:DOT HILL SYST
Secure execution of a computer program
ActiveUS7594111B2Avoid hijackingDigital data processing detailsUnauthorized memory use protectionControl flowApplication software
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
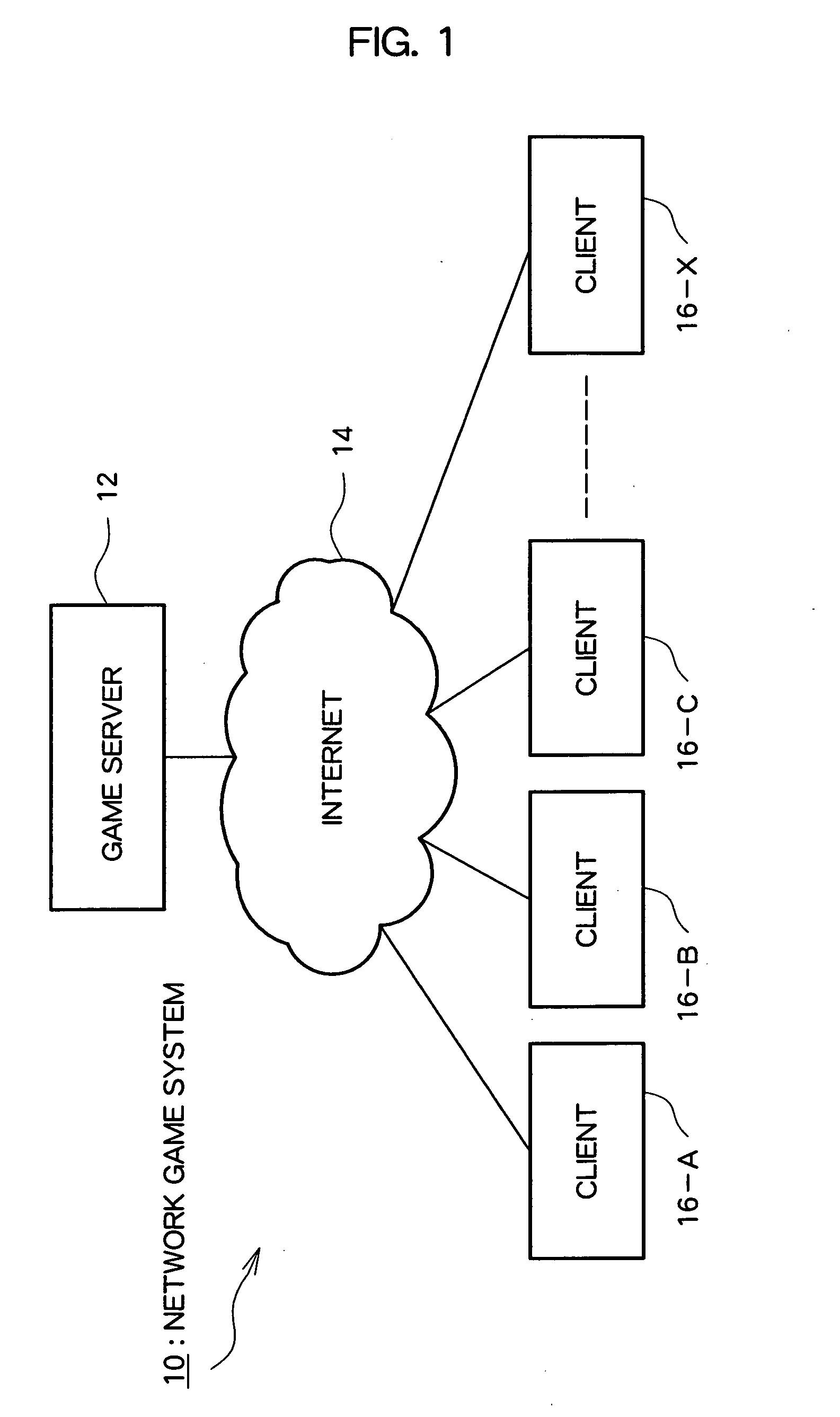
Spatial position sharing system, data sharing system, network game system, and network game client
InactiveUS20060154713A1Suppress mutationImprove accuracyData processing applicationsVideo gamesVirtual spaceClient-side
In a client (16), current position information and predicted future position information for an object that have been generated in another client (16) are received, and estimated current position information for the same object in virtual space are sequentially generated based on these items of information. A game server (12) controls transfer of position information received from non-specified clients to specified clients. Further, at the client (16), in a message input mode, current position information for an object is generated automatically or semi-automatically, and that current position information is transmitted to the game server (12).
Owner:GENKI
Method and a control system for controlling a work machine
ActiveUS20100332061A1Facilitate energy recoveryReduce fuel consumptionAnalogue computers for trafficSoil-shifting machines/dredgersElectric power transmissionControl system
A method is provided for controlling a work machine during operation in a repeated work cycle including controlling transfer of power to and from an energy storage arrangement in the work machine according to a predetermined control strategy, which is adapted for the characteristics of the work cycle.
Owner:VOLVO CONSTR EQUIP
Network interface device that can transfer control of a TCP connection to a host CPU
InactiveUS20050160139A1Avoid header processingAvoid data copyingMultiple digital computer combinationsData switching networksGeneral purposeFast path
An intelligent network interface card (INIC) or communication processing device (CPD) works with a host computer for data communication. The device provides a fast-path that avoids protocol processing for most messages, greatly accelerating data transfer and offloading time-intensive processing tasks from the host CPU. The host retains a fallback processing capability for messages that do not fit fast-path criteria, with the device providing assistance such as validation even for slow-path messages, and messages being selected for either fast-path or slow-path processing. A context for a connection is defined that allows the device to move data, free of headers, directly to or from a destination or source in the host. The context can be passed back to the host for message processing by the host. The device contains specialized hardware circuits that are much faster at their specific tasks than a general purpose CPU. A preferred embodiment includes a trio of pipelined processors devoted to transmit, receive and utility processing, providing full duplex communication for four Fast Ethernet nodes.
Owner:ALACRITECH
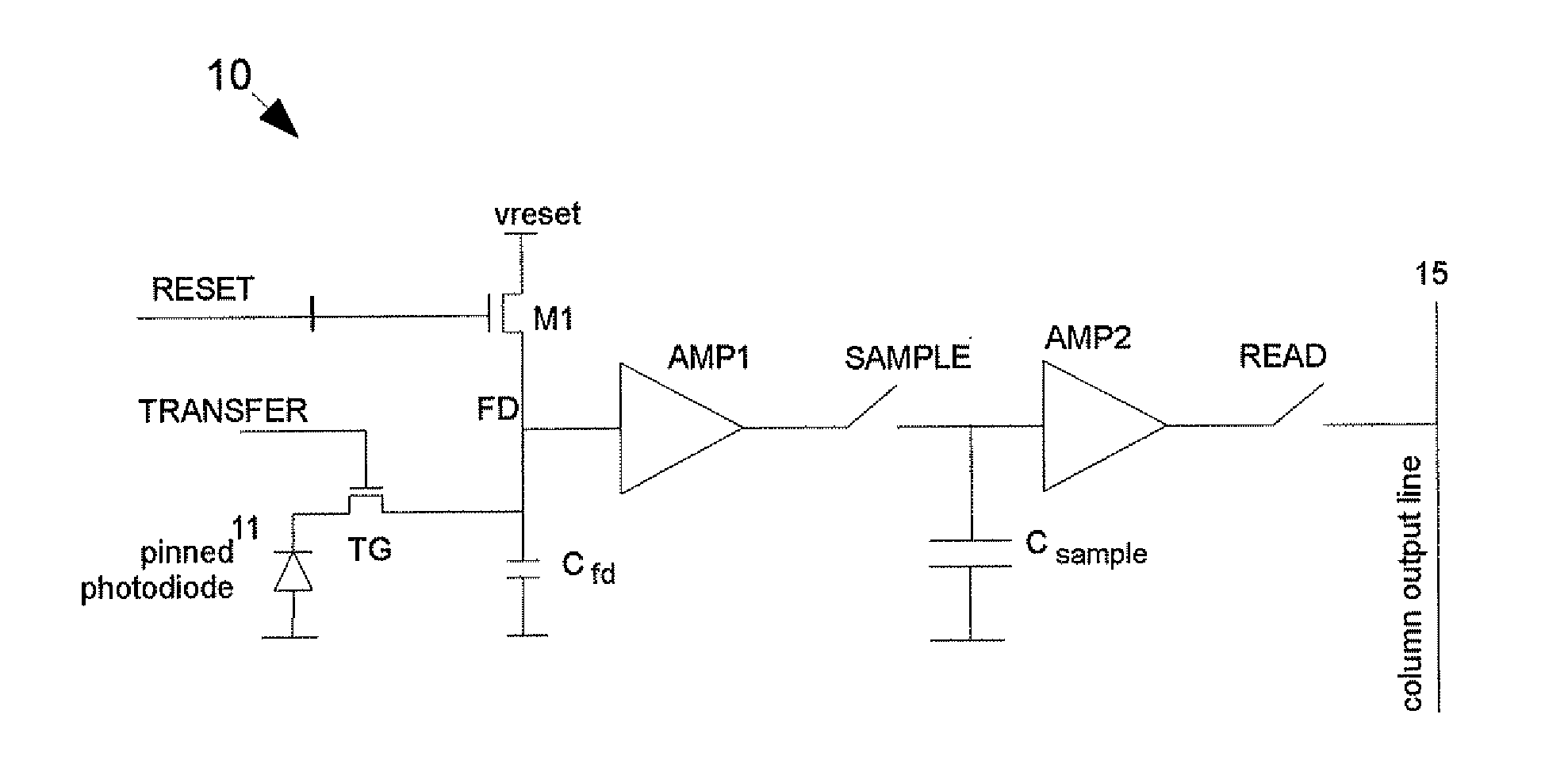
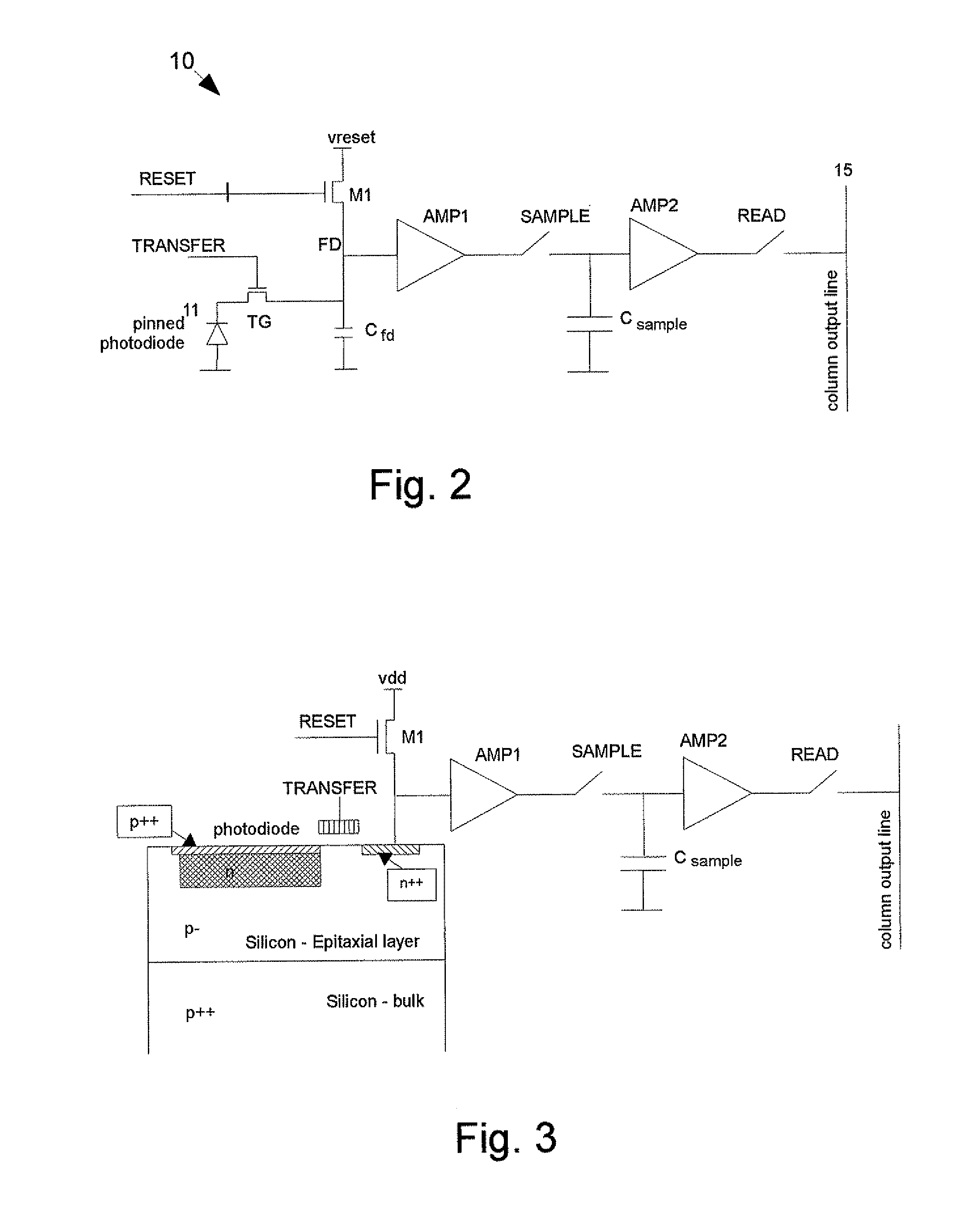
Pixel array with global shutter
ActiveUS20090256060A1Reduce in quantityOptimize layoutTransistorTelevision system detailsAudio power amplifierExposure period
A pixel comprises a photo-sensitive element for generating charges in response to incident radiation and a sense node. A transfer gate is positioned between the photo-sensitive element and the sense node for controlling transfer of charges to the sense node. A reset switch is connected to the sense node for resetting the sense node to a predetermined voltage. A first buffer amplifier has an input connected to the sense node. A sample stage is connected to the output of the first buffer amplifier and is operable to sample a value of the sense node. A second buffer amplifier has an input connected to the sample stage. Control circuitry operates the reset switch and causes the sample stage to sample the sense node while the photo-sensitive element is being exposed to radiation. An array of pixels is synchronously exposed to radiation. Sampled values for a first exposure period can be read while the photo-sensitive element is exposed for a second exposure period.
Owner:CMOSIS
Low noise charge pump method and apparatus
ActiveUS20050052220A1Reduce noiseSimple designAc-dc conversionApparatus without intermediate ac conversionCapacitanceLow noise
A charge pump method and apparatus is described having various aspects. Noise injection from a charge pump to other circuits may be reduced by limiting both positive and negative clock transition rates, as well as by limiting drive currents within clock generator driver circuits, and also by increasing a control node AC impedance of certain transfer capacitor coupling switches. A single-phase clock may be used to control as many as all active switches within a charge pump, and capacitive coupling may simplify biasing and timing for clock signals controlling transfer capacitor coupling switches. Any combination of such aspects of the method or apparatus may be employed to quiet and / or simplify charge pump designs over a wide range of charge pump architectures.
Owner:PSEMI CORP
Images with high speed digital frame transfer and frame processing
ActiveUS20080309810A1Television system detailsTelevision system scanning detailsRolling shutterMemory controller
A digital frame transfer imager having an image sensor and frame memory in the same chip. The image sensor has an integrated memory controller for controlling transfers of data between the sensor and the memory array. The imager utilizes a rolling shutter and multiple groups of analog-to-digital processing circuitry to readout data from the sensor and to output digital images substantially free from image smear, kT / C noise and other unwanted image artifacts.
Owner:APTINA IMAGING CORP
Secure execution of a computer program using a code cache
ActiveUS7603704B2Avoid hijackingMemory loss protectionError detection/correctionControl flowApplication software
Hijacking of an application is prevented by monitoring control flow transfers during program execution in order to enforce a security policy. At least three basic techniques are used. The first technique, Restricted Code Origins (RCO), can restrict execution privileges on the basis of the origins of instruction executed. This distinction can ensure that malicious code masquerading as data is never executed, thwarting a large class of security attacks. The second technique, Restricted Control Transfers (RCT), can restrict control transfers based on instruction type, source, and target. The third technique, Un-Circumventable Sandboxing (UCS), guarantees that sandboxing checks around any program operation will never be bypassed.
Owner:MASSACHUSETTS INST OF TECH
Detecting conditions for transfer of execution from one computer instruction stream to another and executing transfer on satisfaction of the conditions
InactiveUS8121828B2Efficiently tailoredEasy to operateGeneral purpose stored program computerSoftware simulation/interpretation/emulationInstruction pipelineInstruction stream
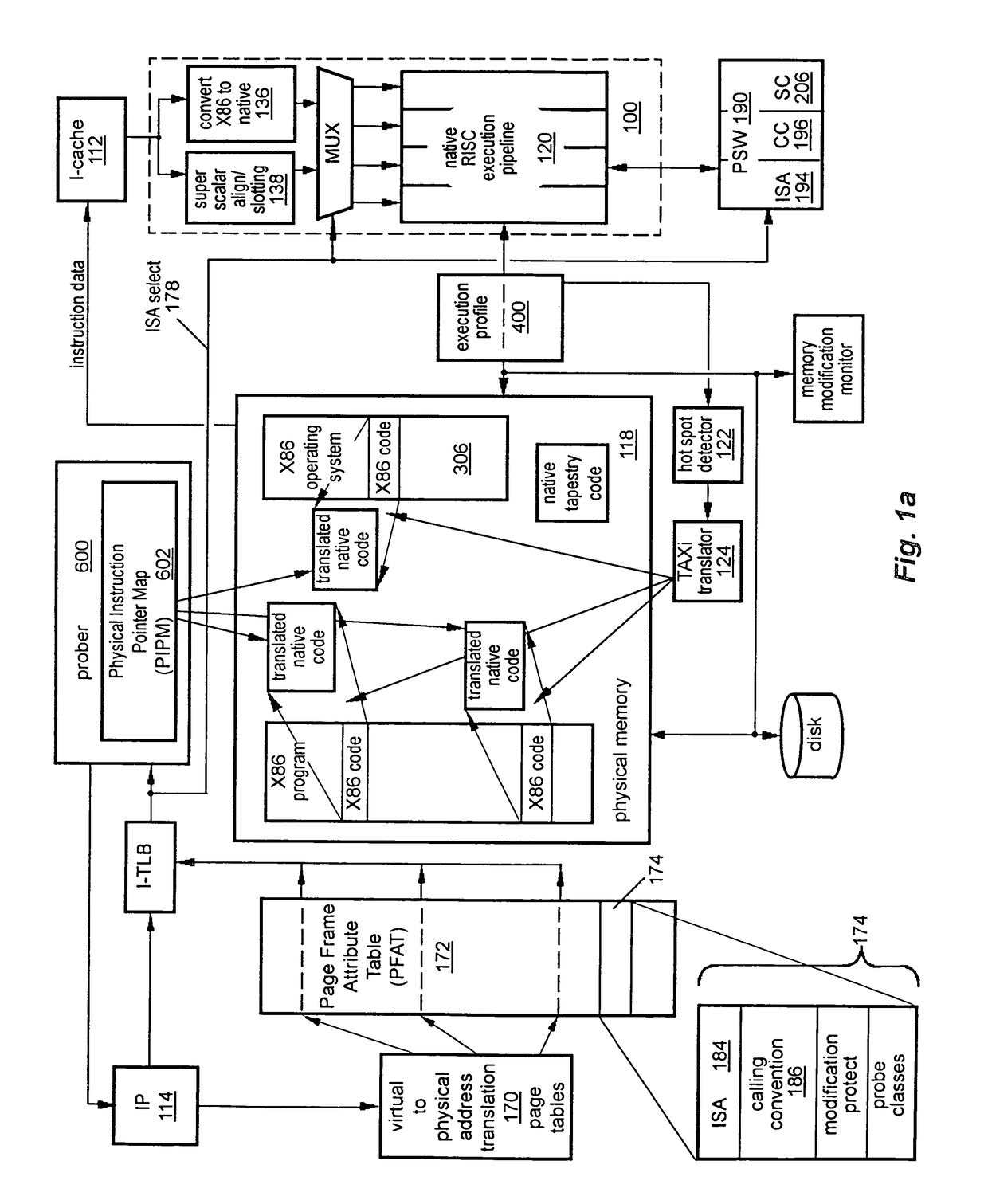
A computer has instruction pipeline circuitry capable of executing two instruction set architectures (ISA's). A binary translator translates at least a selected portion of a computer program from a lower-performance one of the ISA's to a higher-performance one of the ISA's. Hardware initiates a query when about to execute a program region coded in the lower-performance ISA, to determine whether a higher-performance translation exists. If so, the about-to-be-executed instruction is aborted, and control transfers to the higher-performance translation. After execution of the higher-performance translation, execution of the lower-performance region is reestablished at a point downstream from the aborted instruction, in a context logically equivalent to that which would have prevailed had the code of the lower-performance region been allowed to proceed.
Owner:ADVANCED SILICON TECH
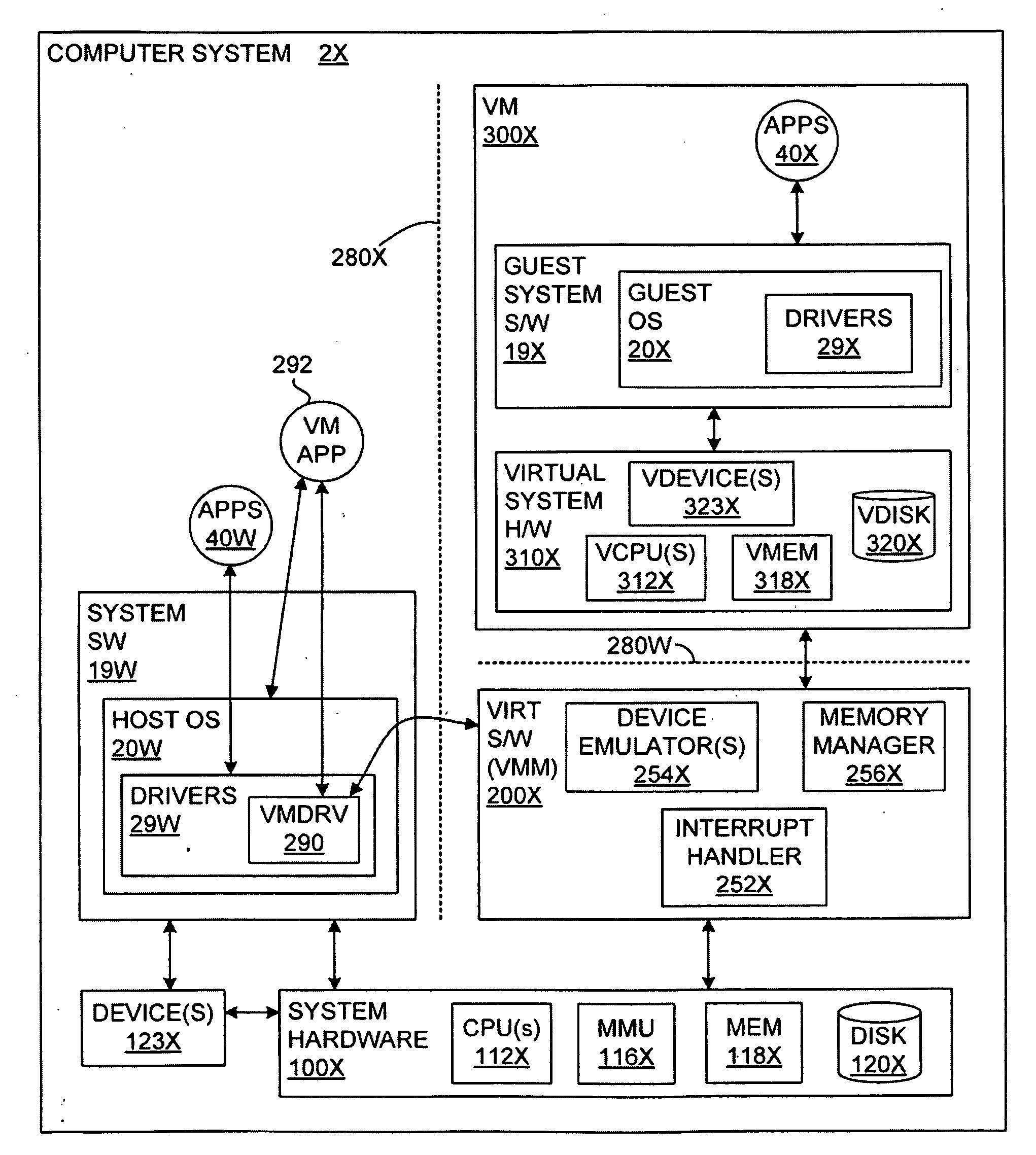
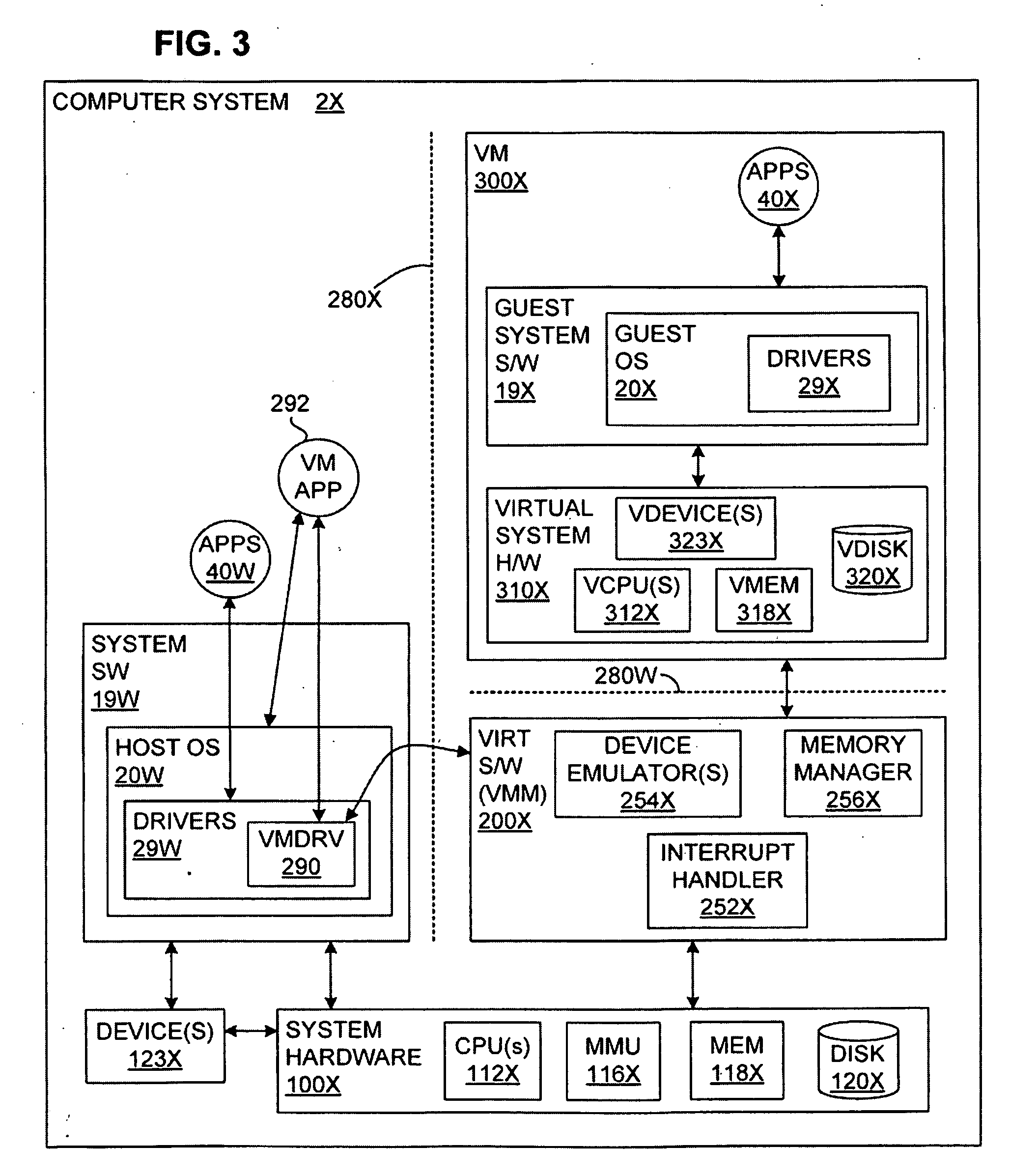
Transparent VMM-Assisted User-Mode Execution Control Transfer
ActiveUS20090113424A1Privacy protectionImprove integrityMemory architecture accessing/allocationError detection/correctionOperational systemExecution control
A virtual-machine-based system provides a control-transfer mechanism to invoke a user-mode application handler from existing virtual hardware directly, without going through an operating system kernel running in the virtual machine. A virtual machine monitor calls directly to the guest user-mode handler and the handler transfers control back to the virtual machine monitor, without involving the guest operating system.
Owner:VMWARE INC
System, method, and apparatus for a wireless hard disk drive
InactiveUS20060072241A1Maximum physical isolationMaximized physical isolationDigital data processing detailsUndesired vibrations/sounds insulation/absorptionHard disc driveTemperature control
A sealed Hard Disk Drive filled with an inert gas mixture of air, helium, and / or nitrogen provides a wireless data encrypted interface to facilitate data and control transfer with a host system. The wireless interface additionally allows power transfer through Radio Frequency (RF) propagation or electromagnetic induction. Extended measures for vibration, shock, and temperature control are made possible through the use of the wireless interface. Immersion of the HDD into a viscous gel, or other damping material, provides vibration and shock control, while heating / cooling coils provide temperature control.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV
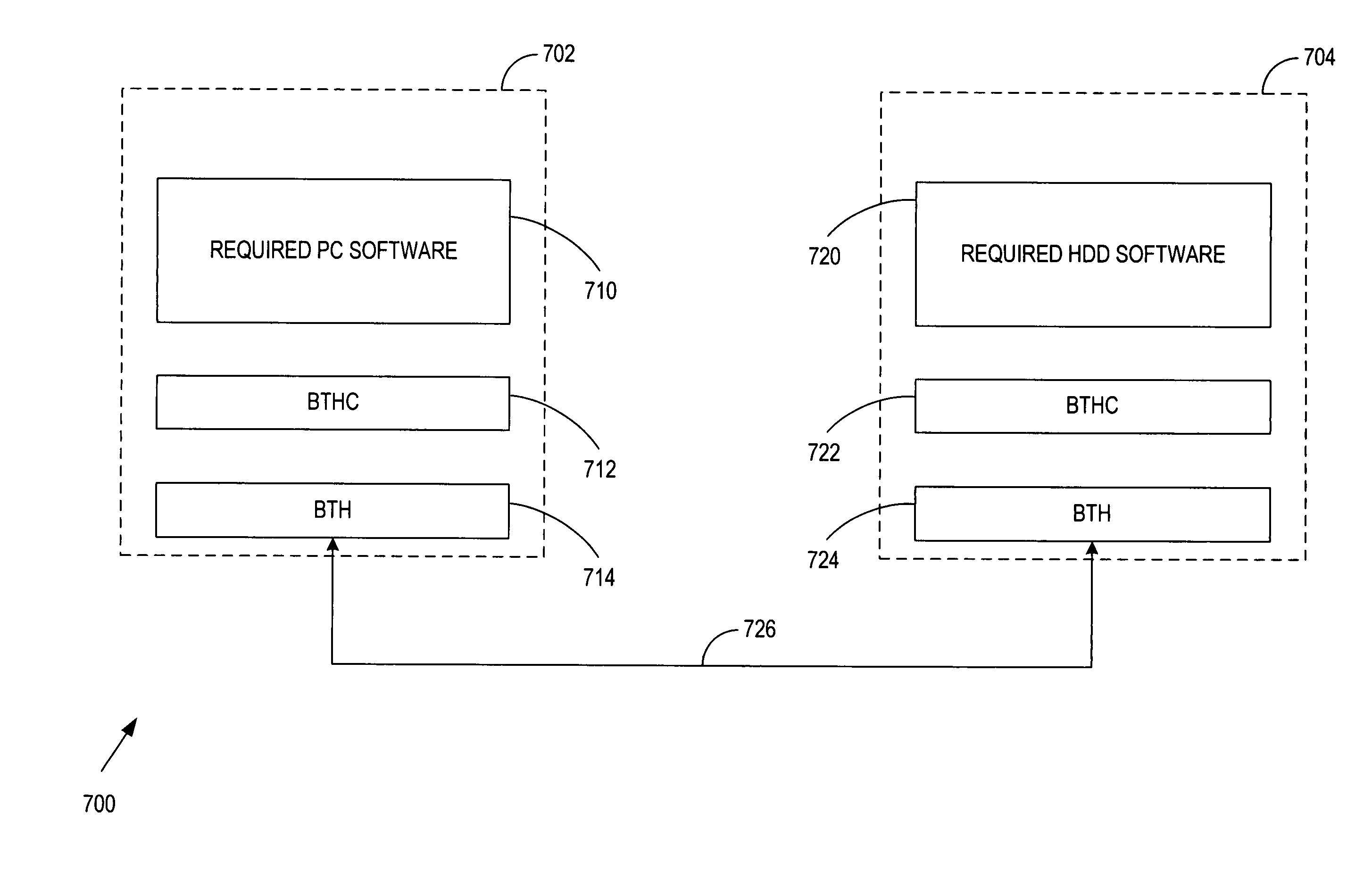
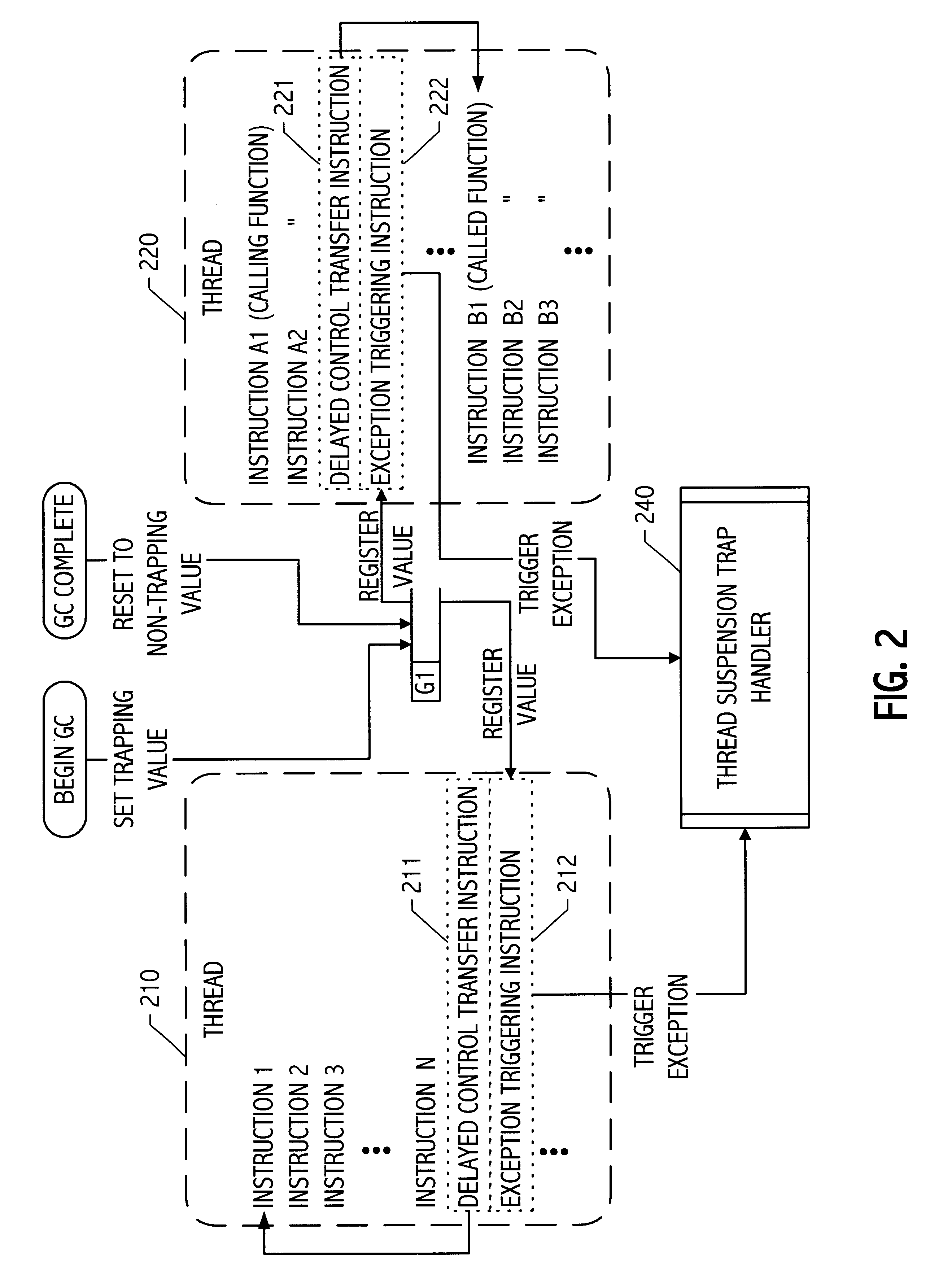
Thread suspension system and method using trapping instructions in delay slots
InactiveUS6308319B1Data processing applicationsProgram initiation/switchingWaste collectionDelay slot
By encoding an exception triggering value in storage referenced by an instruction in the delay slot of a delayed control transfer instruction coinciding with a safe point, an efficient coordination mechanism can be provided for multi-threaded code. Because the mechanism(s) impose negligible overhead when not employed and can be engaged in response to an event (e.g., a start garbage collection event), safe points can be defined at call, return and / or backward branch points throughout mutator code to reduce the latency between the event and suspension of all threads. Though particularly advantageous for thread suspension to perform garbage collection at safe points, the techniques described herein are more generally applicable to program suspension at coordination points coinciding with calls, returns, branches or calls, returns and branches therein.
Owner:ORACLE INT CORP
Electronic payment system
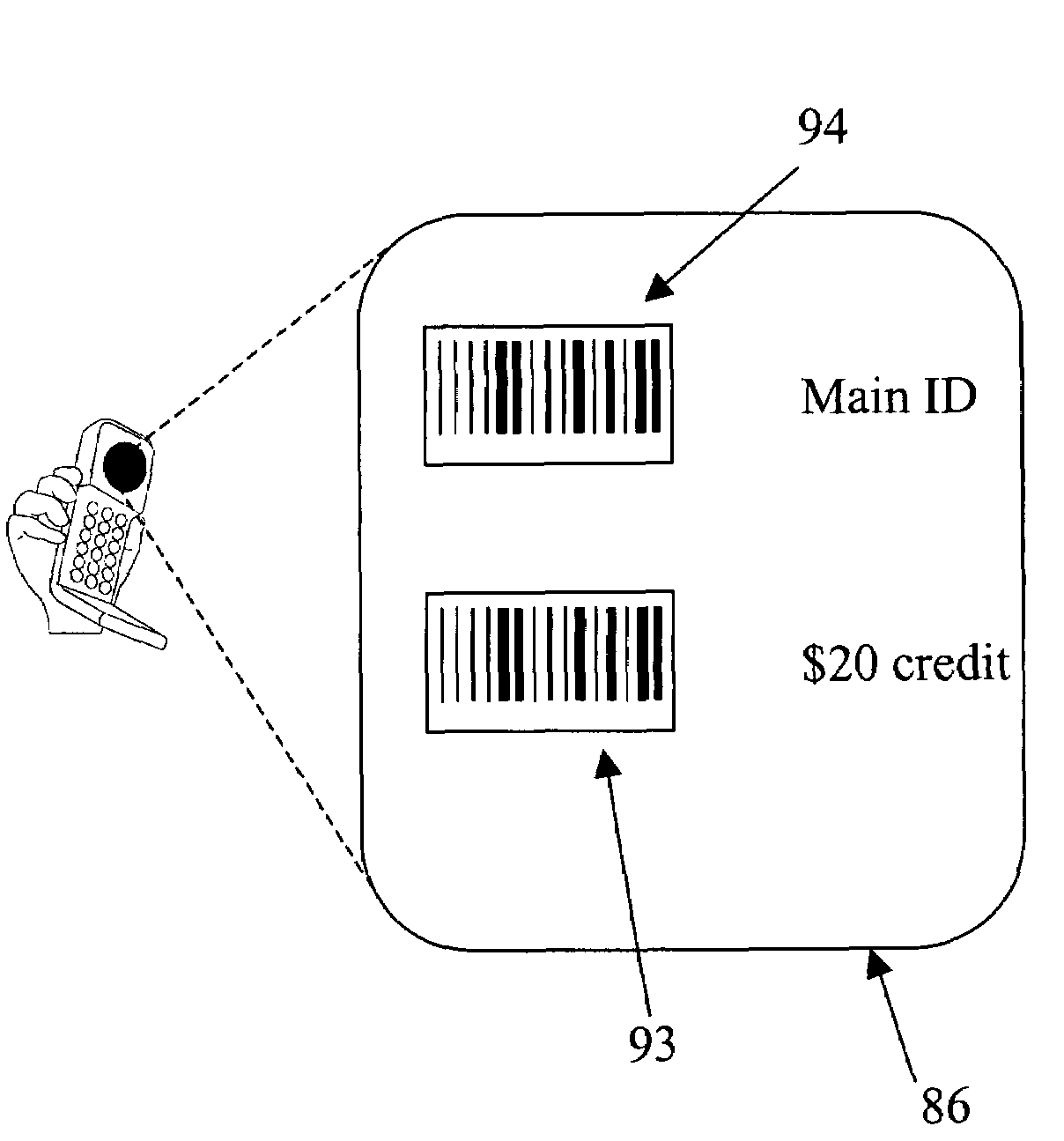
An electronic payment system and method facilitates electronic commerce through controlled transfer of identification and value representations to wireless devices. The system includes a payment collection apparatus and a transaction apparatus, and provides for representation of user and transaction information via machine-readable indicia. In one embodiment, the machine-readable indicia is a barcode. The present invention is useful in such example applications as credit transactions, lottery system operations, and mobile top up applications.
Owner:GTECH RHODE ISLAND CORP
Method and apparatus for suppressing duplicative prefetches for branch target cache lines
ActiveUS20060242365A1Digital computer detailsSpecific program execution arrangementsParallel computingDelay slot
A system that suppresses duplicative prefetches for branch target cache lines. During operation, the system fetches a first cache line into in a fetch buffer. The system then prefetches a second cache line, which immediately follows the first cache line, into the fetch buffer. If a control transfer instruction in the first cache line has a target instruction which is located in the second cache line, the system determines if the control transfer instruction is also located at the end of the first cache line so that a corresponding delay slot for the control transfer instruction is located at the beginning of the second cache line. If so, the system suppresses a subsequent prefetch for a target cache line containing the target instruction because the target instruction is located in the second cache line which has already been prefetched.
Owner:ORACLE INT CORP
Circuit and method for a fully integrated switched-capacitor step-down power converter
ActiveUS7907429B2Effective regulationEasy to adjustAc-dc conversionApparatus without intermediate ac conversionDc dc converterVoltage control
A circuit and method for providing a fully integrated DC-DC converter using on-chip switched capacitors is disclosed. A switched capacitor matrix is coupled as a digitally controlled transfer capacitor. A pair of non-overlapping, fixed frequency clock signals is provided to a switched capacitor circuit including the switched capacitor matrix and a load capacitor coupled to the output terminal. A DC input voltage supply is provided. A hysteretic feedback loop is used to control the voltage at the output as a stepped-down voltage from the input by digitally modulating the transfer capacitor using switches in the switch matrix to couple more, or fewer, transfer capacitors to the output terminal during a clock cycle. A coarse and a fine adjustment circuit are provided to improve the regulation during rapid changes in load power. A method of operating the regulator is disclosed.
Owner:TEXAS INSTR INC
Control module for flywheel operated hand tool
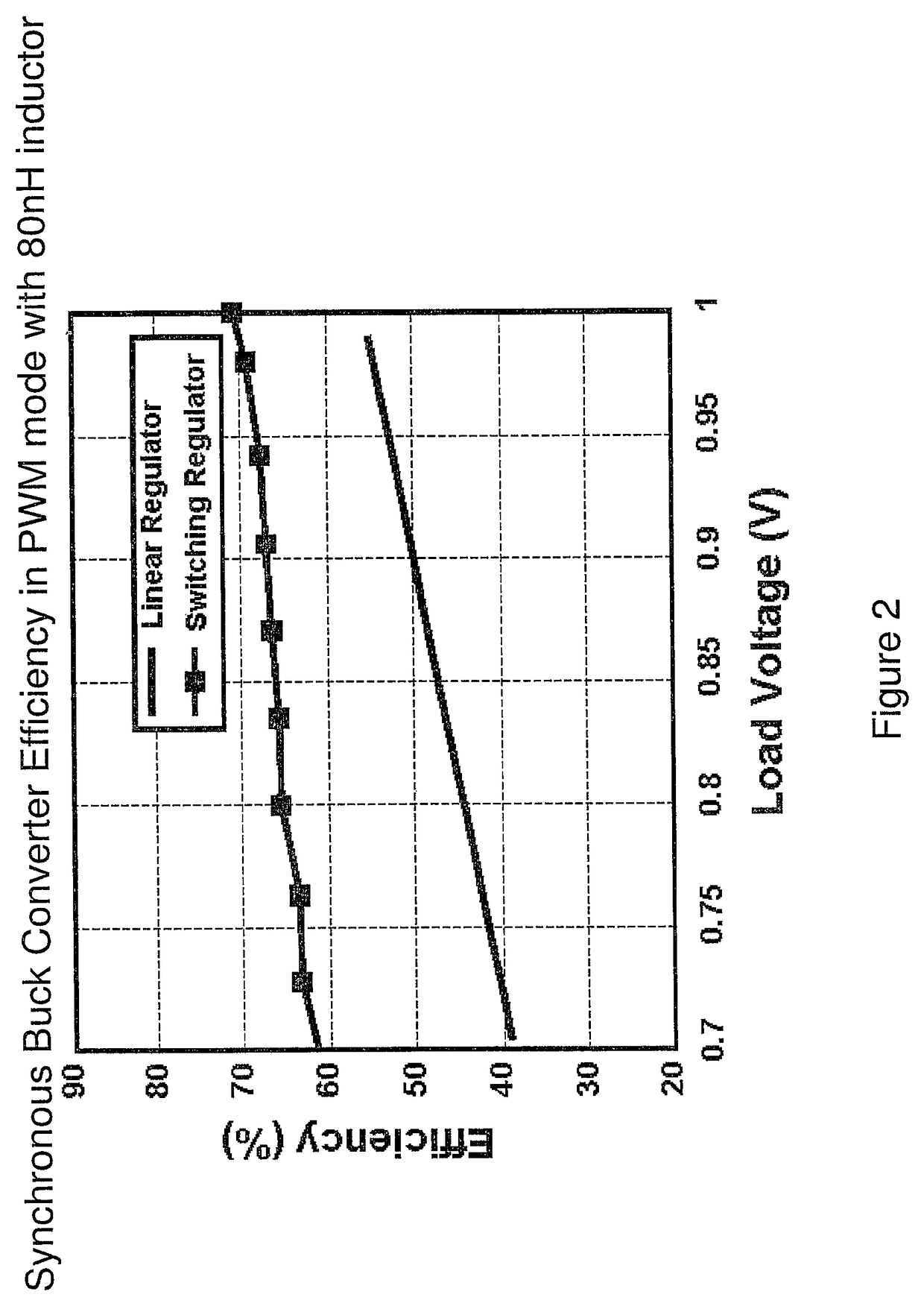
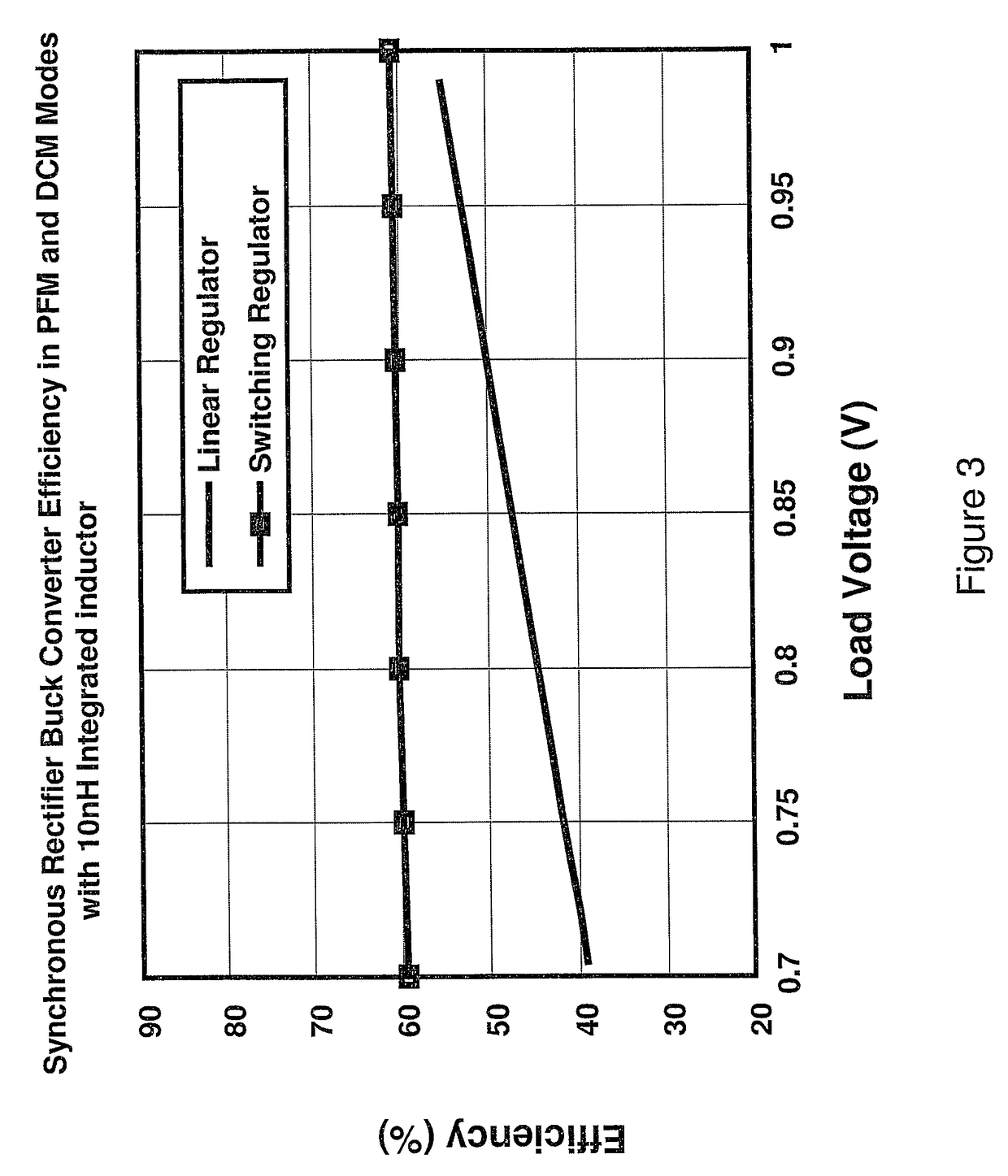
InactiveUS6974061B2Avoid mistakesConsistent controlStapling toolsAC motor controlControl engineeringMembrane switch
A control module advantageously reduces cost and enhances reliability, design flexibility, ease of assembly, and performance of a flywheel operated hand tool. The control module includes a thin film printed circuit with non-contact speed sensing of a flywheel to more accurately set the target speed and control transfer kinetic energy thereof to a fastener, achieving a desired depth regardless of variations in component performance and battery voltage. The printed circuit also includes long service life thin film switches for responding to trigger and safety inputs. Furthermore, the control module responds to a user speed selection and to preset speed selection ranges to reconfigure the controls as appropriate to constraints of a fastener drive assembly and to user preferences.
Owner:SENCO BRANDS
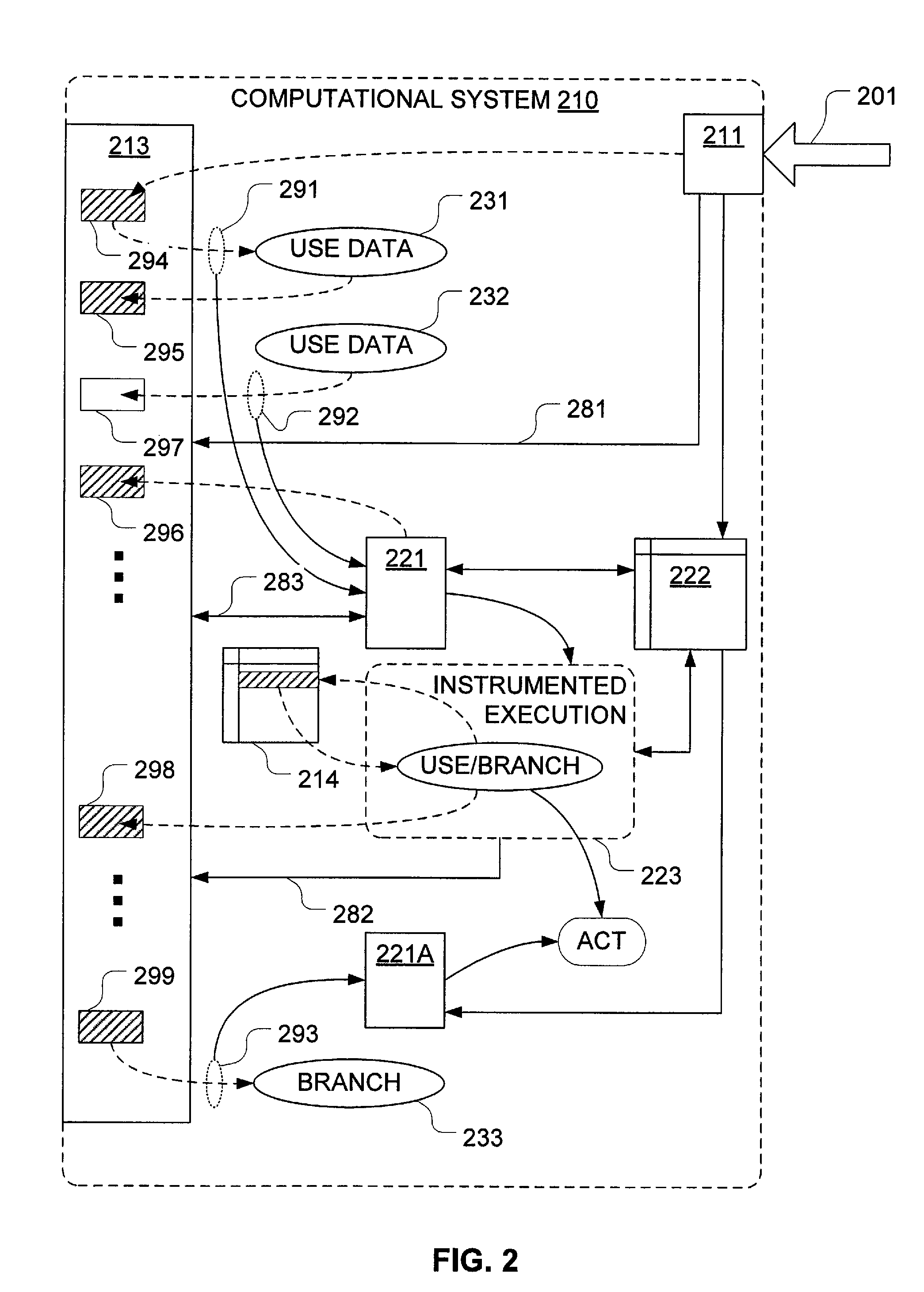
Computational system including mechanisms for tracking propagation of information with aging
ActiveUS7958558B1Control overheadEasy to trackMemory loss protectionError detection/correctionInternet privacyControl transfer
Mechanisms have been developed for securing computational systems against certain forms of attack. In particular, it has been discovered that, by maintaining and selectively propagating taint status for storage locations in correspondence with information flows of instructions executed by a computing system, it is possible to provide a security (or other appropriate) response if and when a control transfer (or other restricted use) is attempted based on tainted data. By employing aging in decisions to propagate, it is possible limit overheads associated with such tracking. In some embodiments, a decay oriented metric is applied and further propagation of taints is interrupted once aging reaches a predetermined decay threshold. In some embodiments, more generalized labels may be maintained and selectively propagated based on an aging metric. For example, in some embodiments, labels may be employed to code source designation or classification, aging, popularity / frequency of access or taint.
Owner:VMWARE INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com