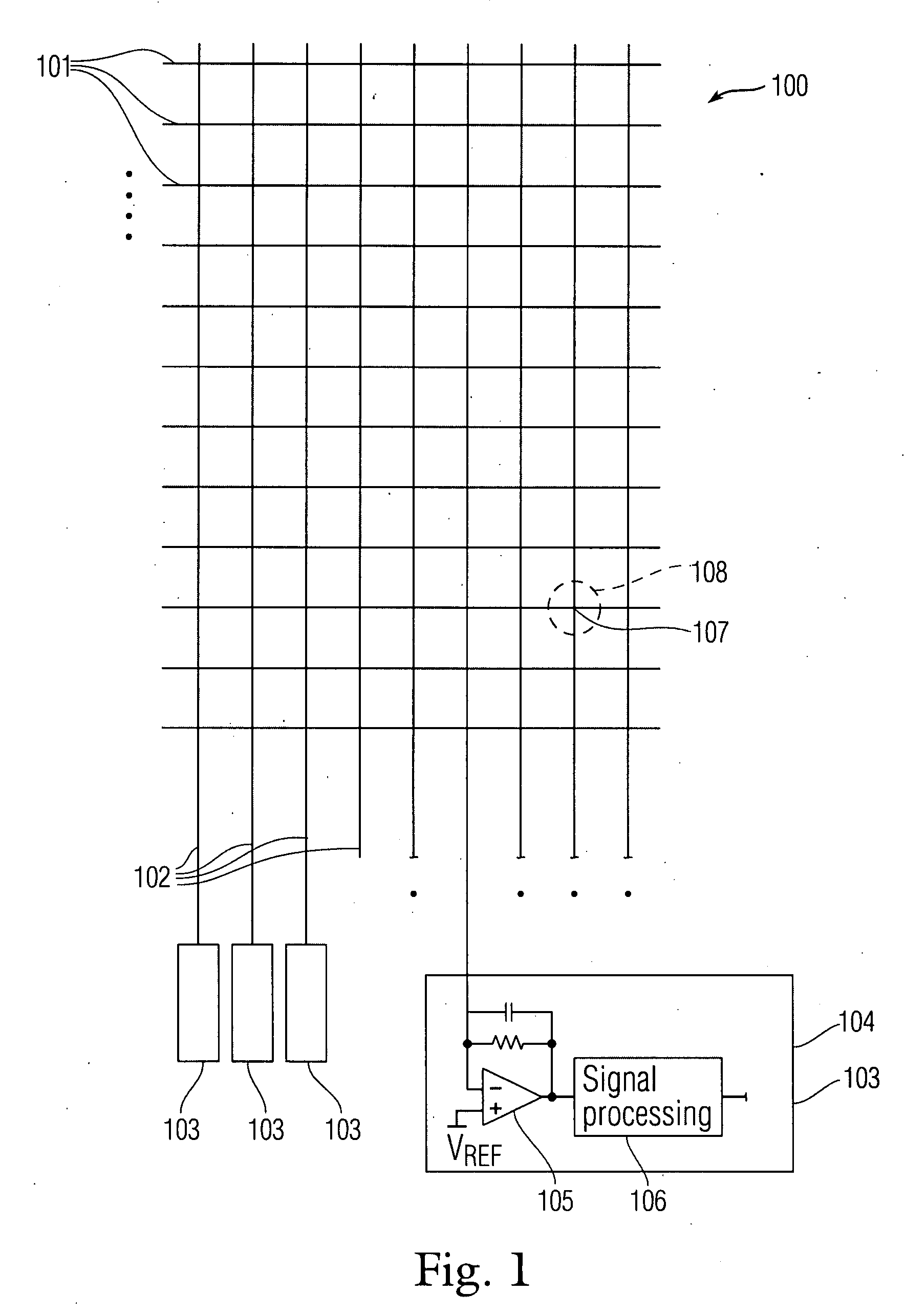
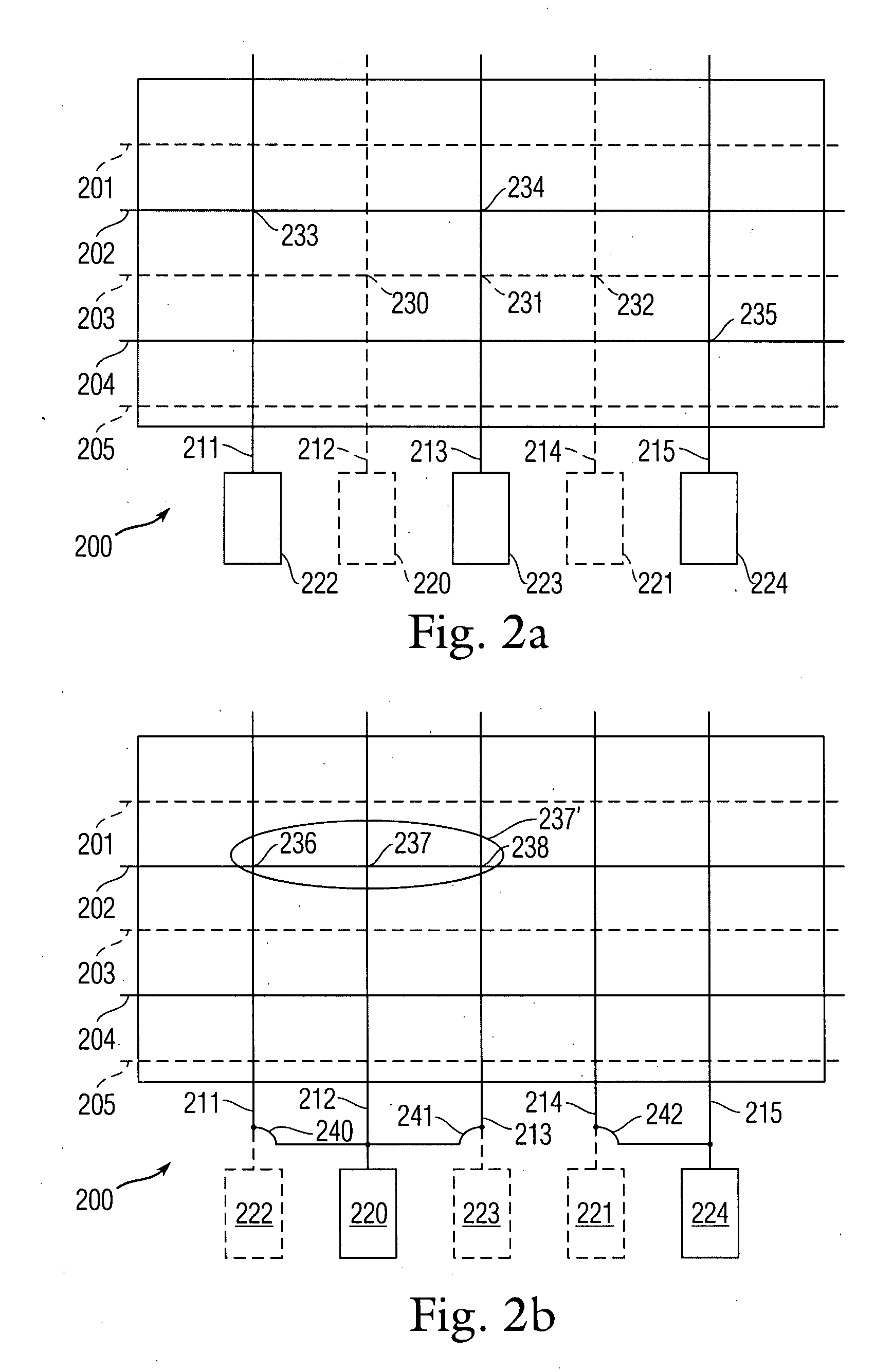
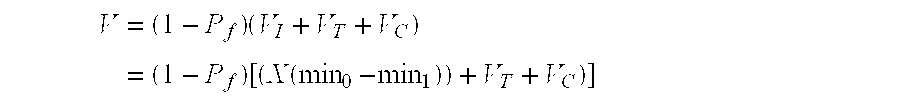Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2342results about How to "Fine granularity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
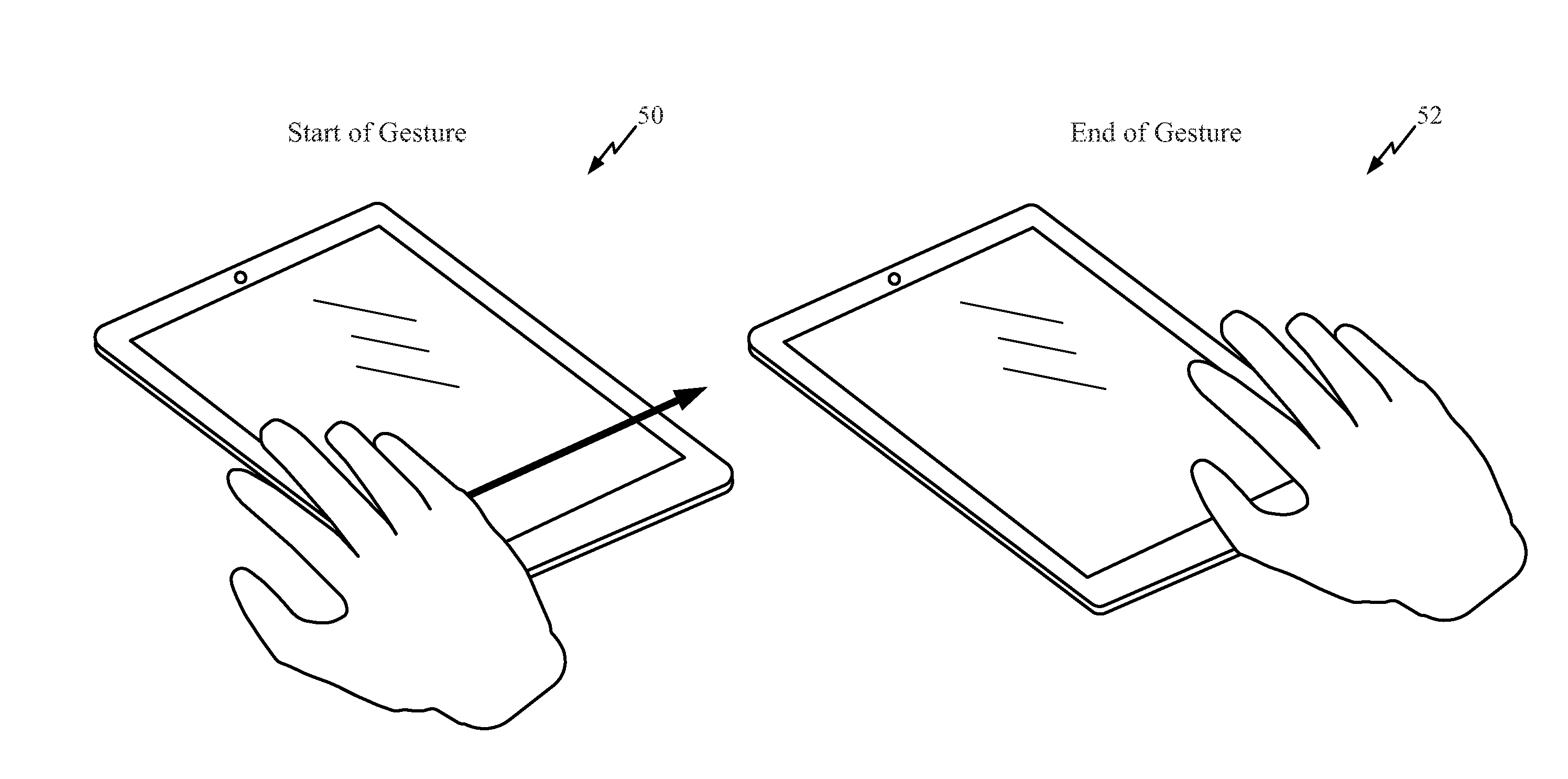
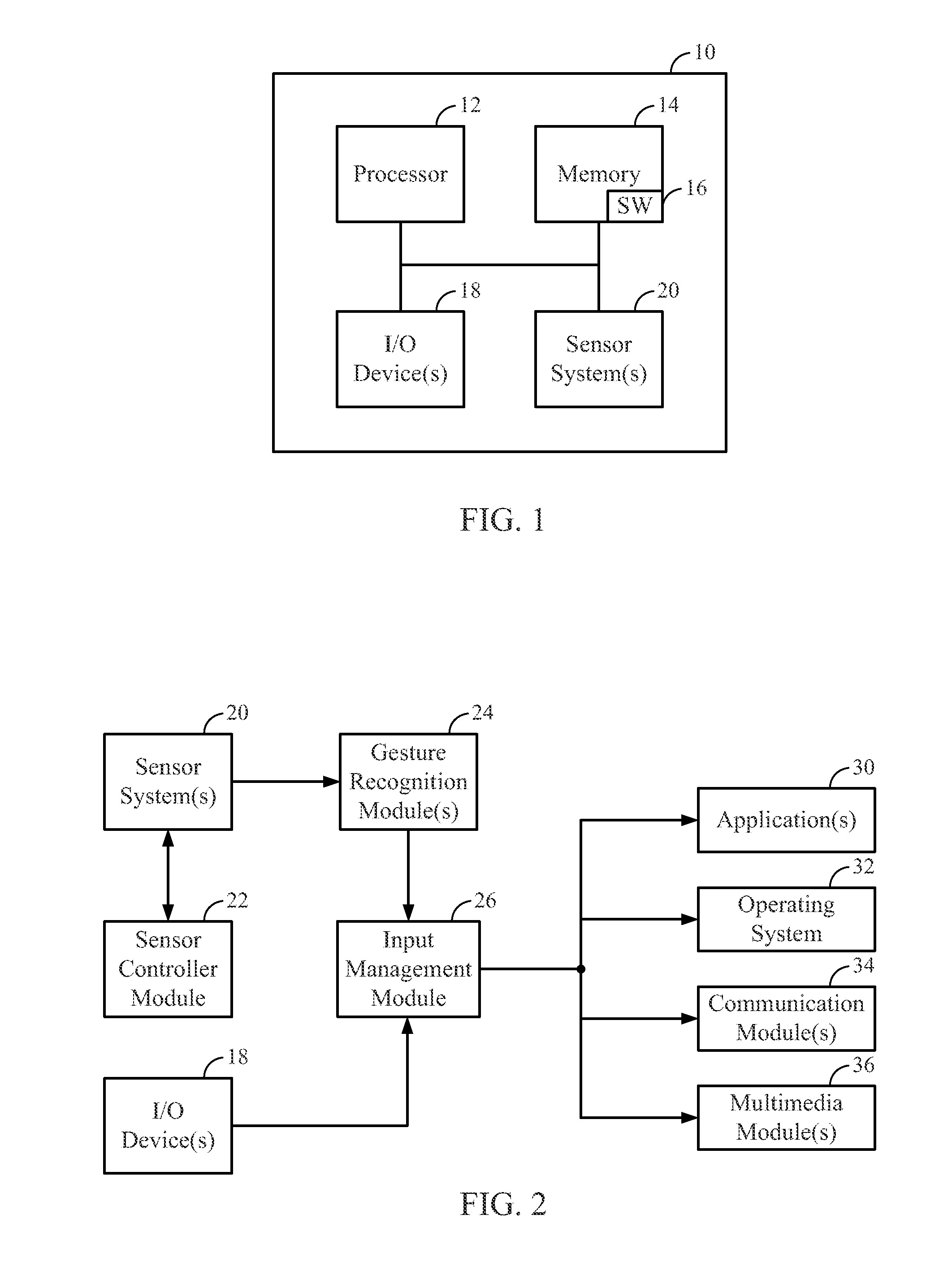
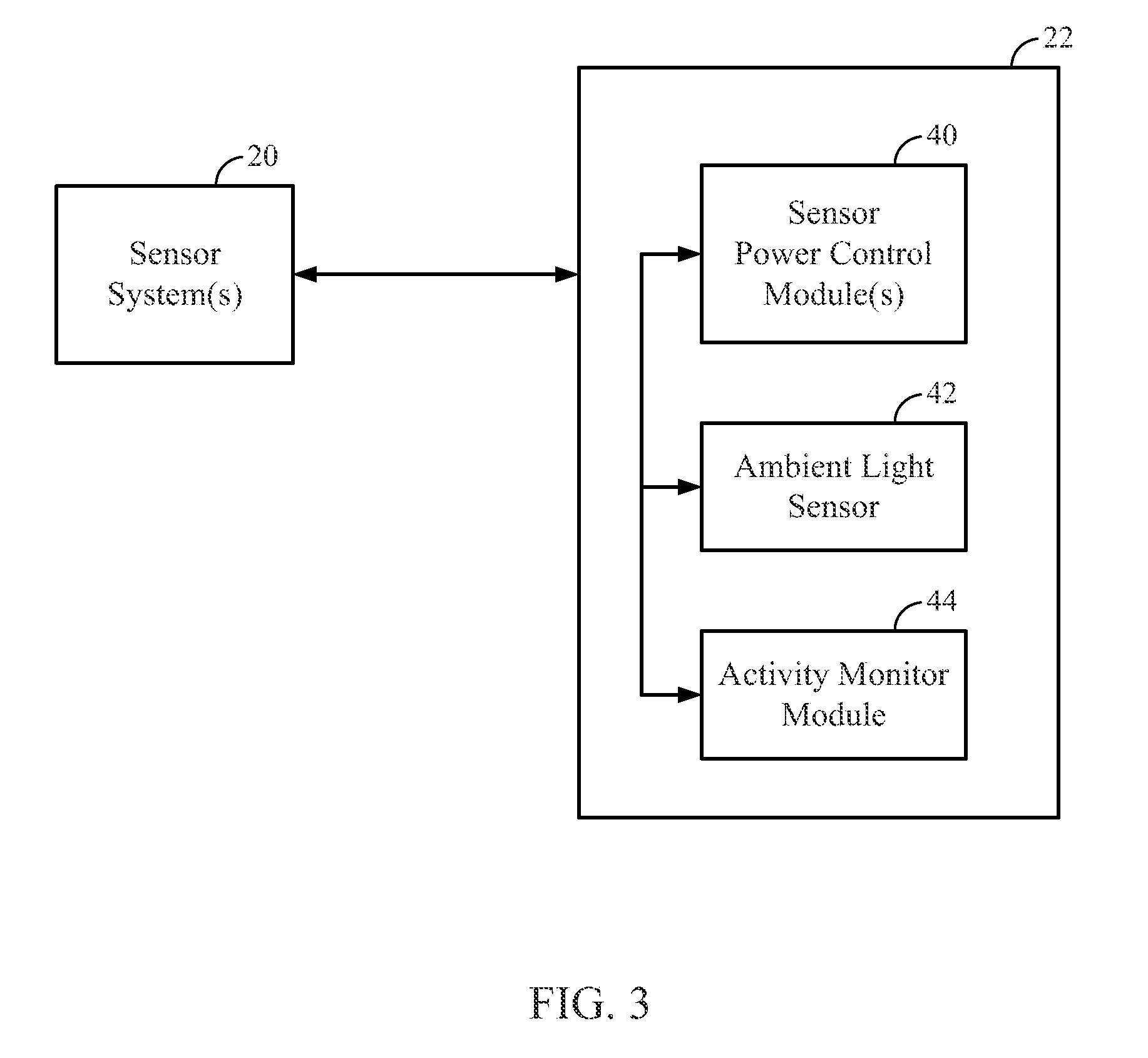
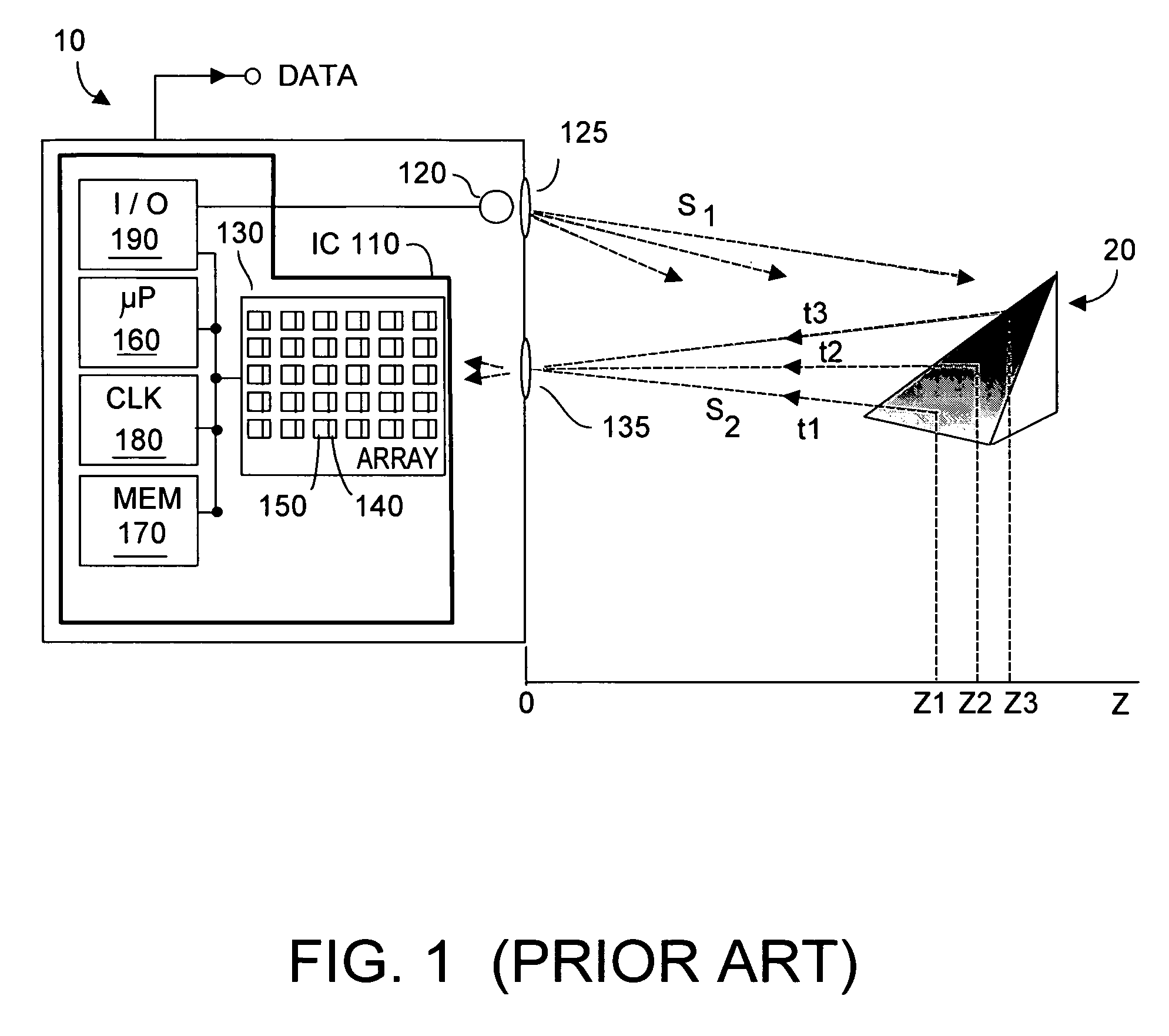
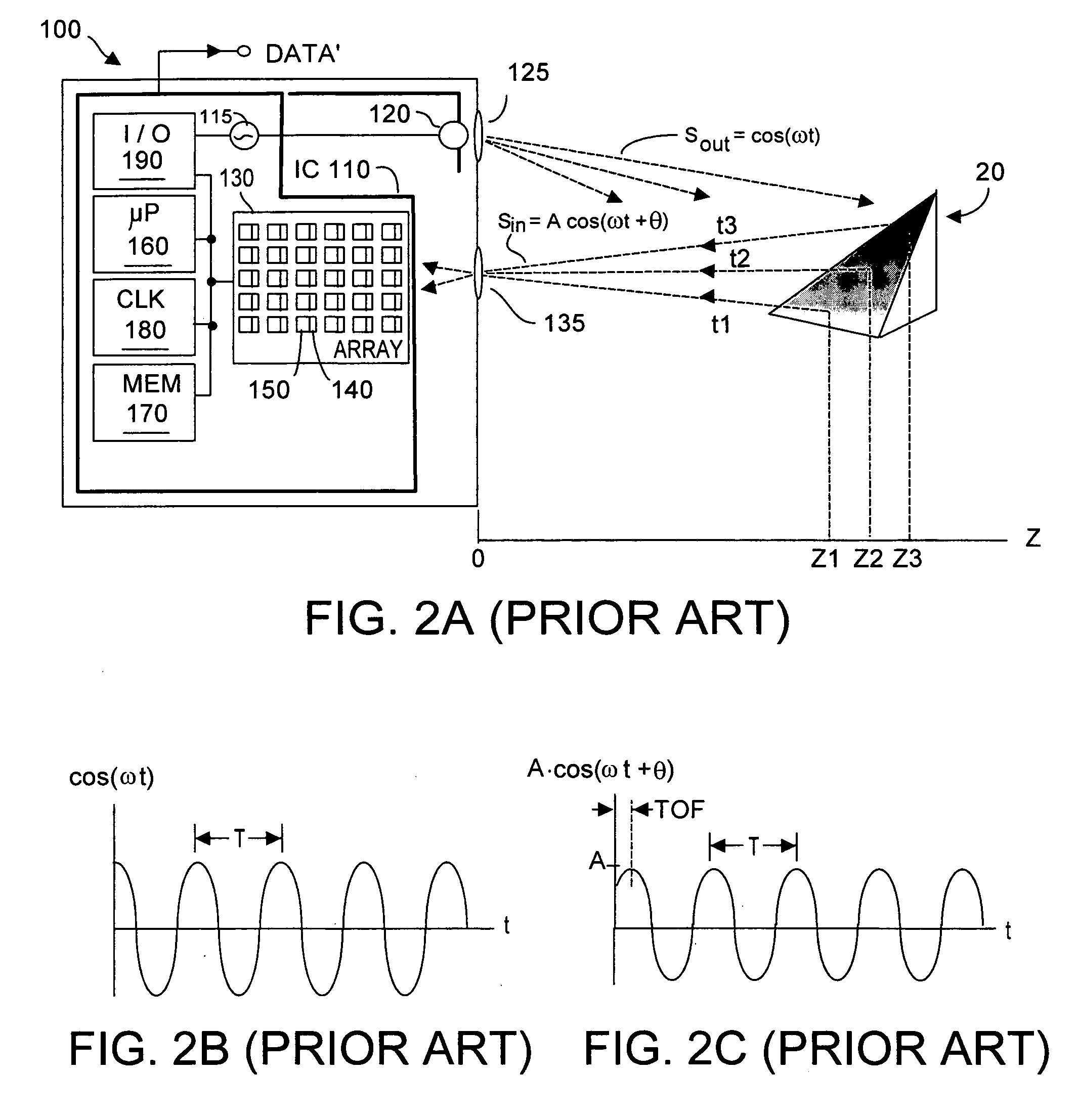
Methods and apparatus for contactless gesture recognition
InactiveUS20110310005A1Reduce wearImprove aestheticsInput/output for user-computer interactionEnergy efficient ICTProximity sensorHuman–computer interaction
Systems and methods are described for performing contactless gesture recognition for a computing device, such as a mobile computing device. An example technique for managing a gesture-based input mechanism for a computing device described herein includes identifying parameters of the computing device relating to accuracy of gesture classification performed by the gesture-based input mechanism and managing a power consumption level of at least an infrared (IR) light emitting diode (LED) or an IR proximity sensor of the gesture-based input mechanism based on the parameters of the computing device.
Owner:QUALCOMM INC
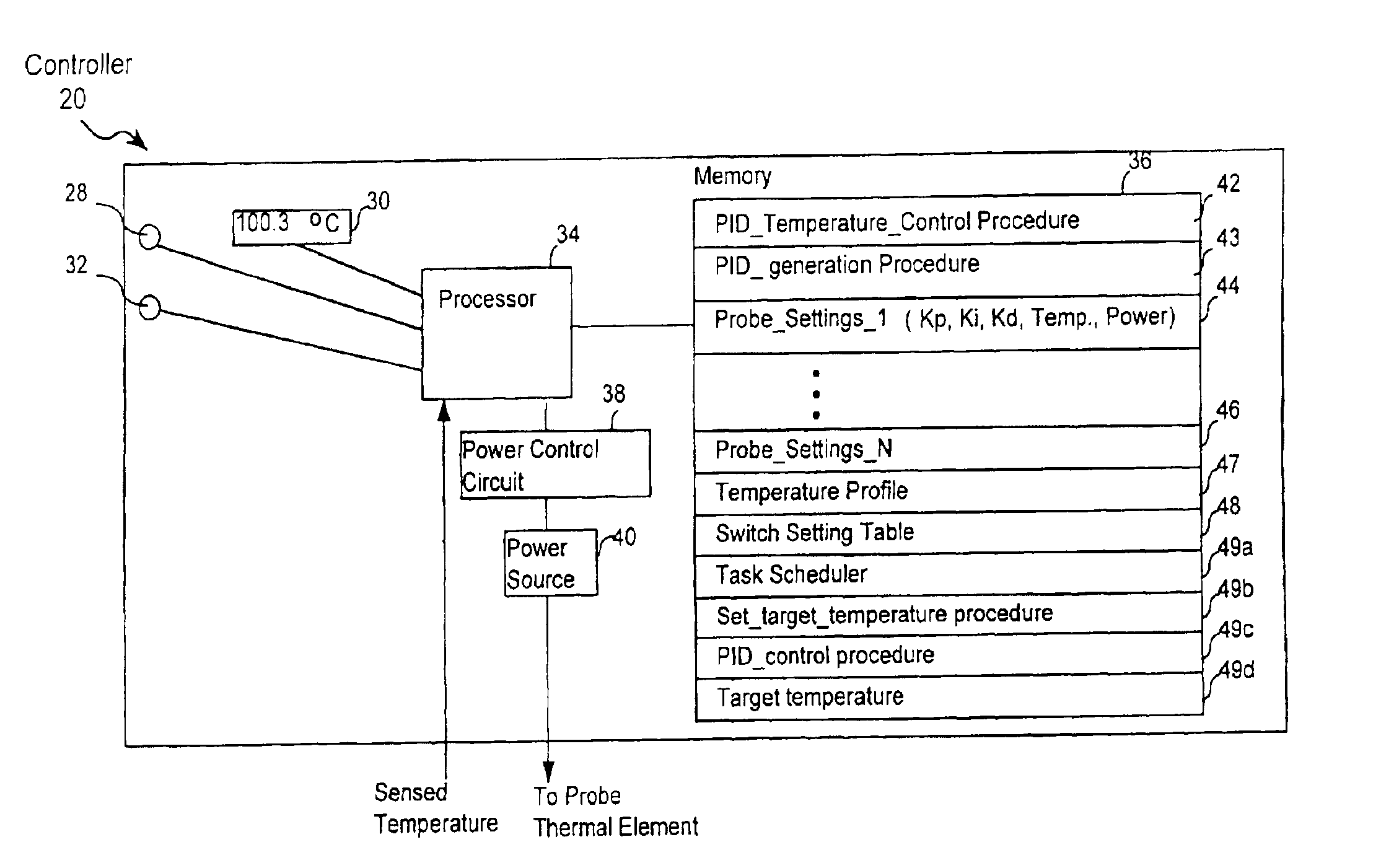
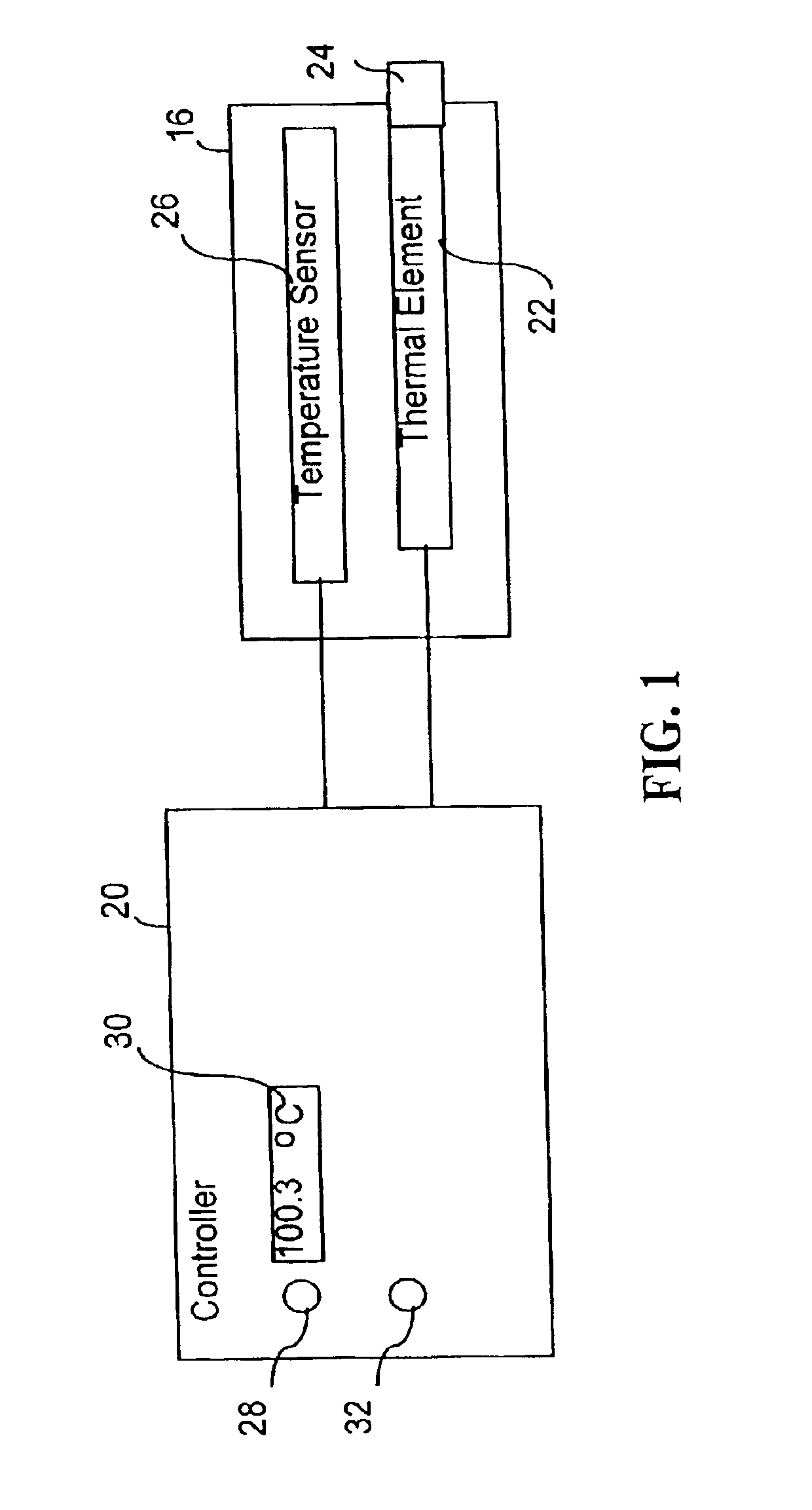
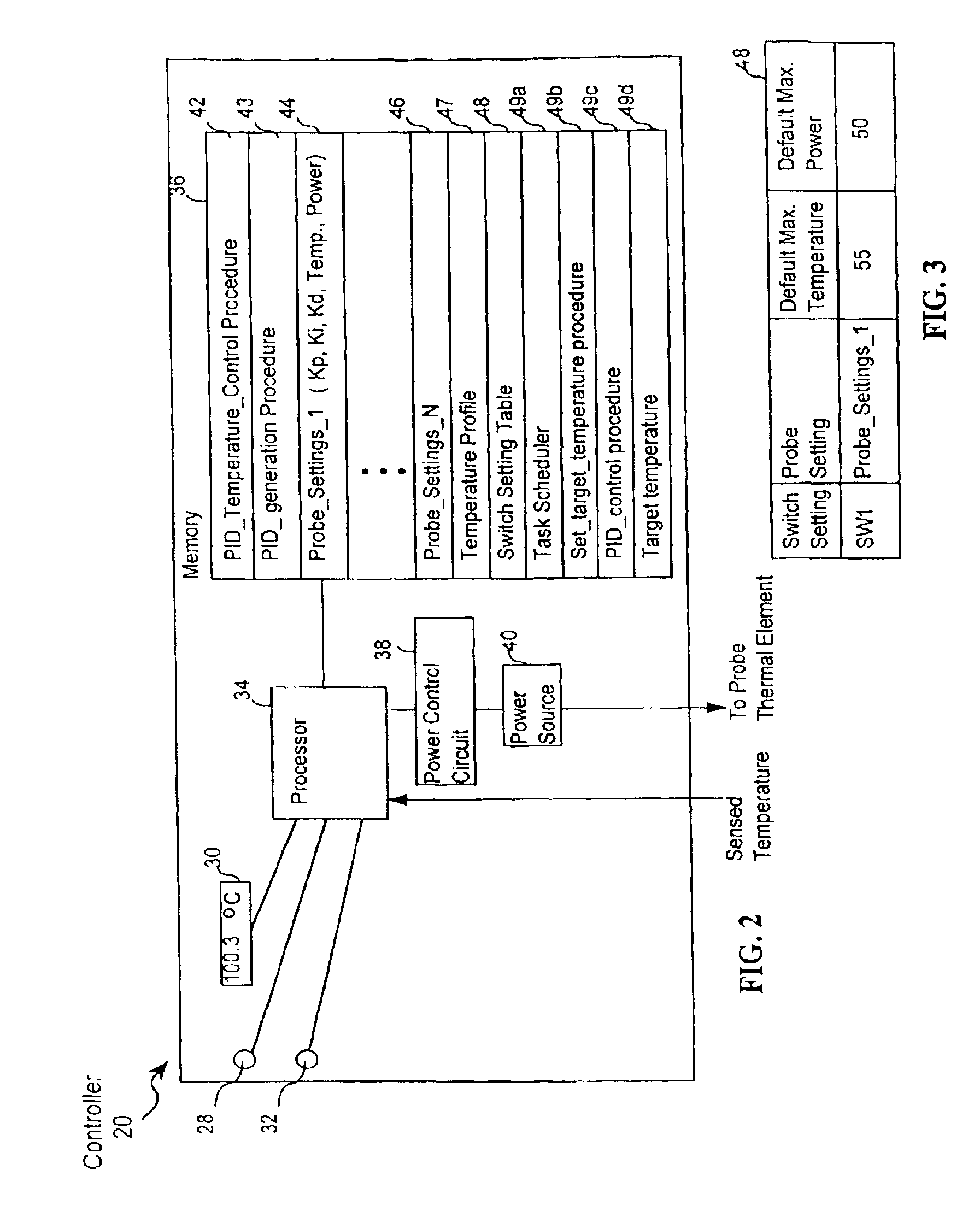
Method and apparatus for controlling a temperature-controlled probe
InactiveUS6939346B2Finer granularity of controlMinimize overshootThermometers using electric/magnetic elementsUsing electrical meansThermal energyMedicine
A thermal energy controller system useful in medical procedures includes a controller coupled to a probe, and a thermal element to vary probe temperature. The controller includes memory storing a non-continuous algorithm that permits user-selectable settings for various probe types such that controller operation is self-modifying in response to the selected probe setting. Probe output power Pout is constant in one mode to rapidly enable probe temperature to come within a threshold of a target temperature. The controller can then vary Pout dynamically using a proportional-integral-derivative (PID) algorithm Pout=Kp·P+Ki·I+Kd·D, where feedback loop coefficients Kp, Ki, Kd can vary dynamically depending upon magnitude of an error function e(t) representing the difference between a user-set desired target temperature and sensed probe temperature. Advantageously, target temperature can be rapidly attained without overshoot, allowing the probe system to be especially effective in arthroscopic tissue treatment.
Owner:ORATEC INTERVENTIONS
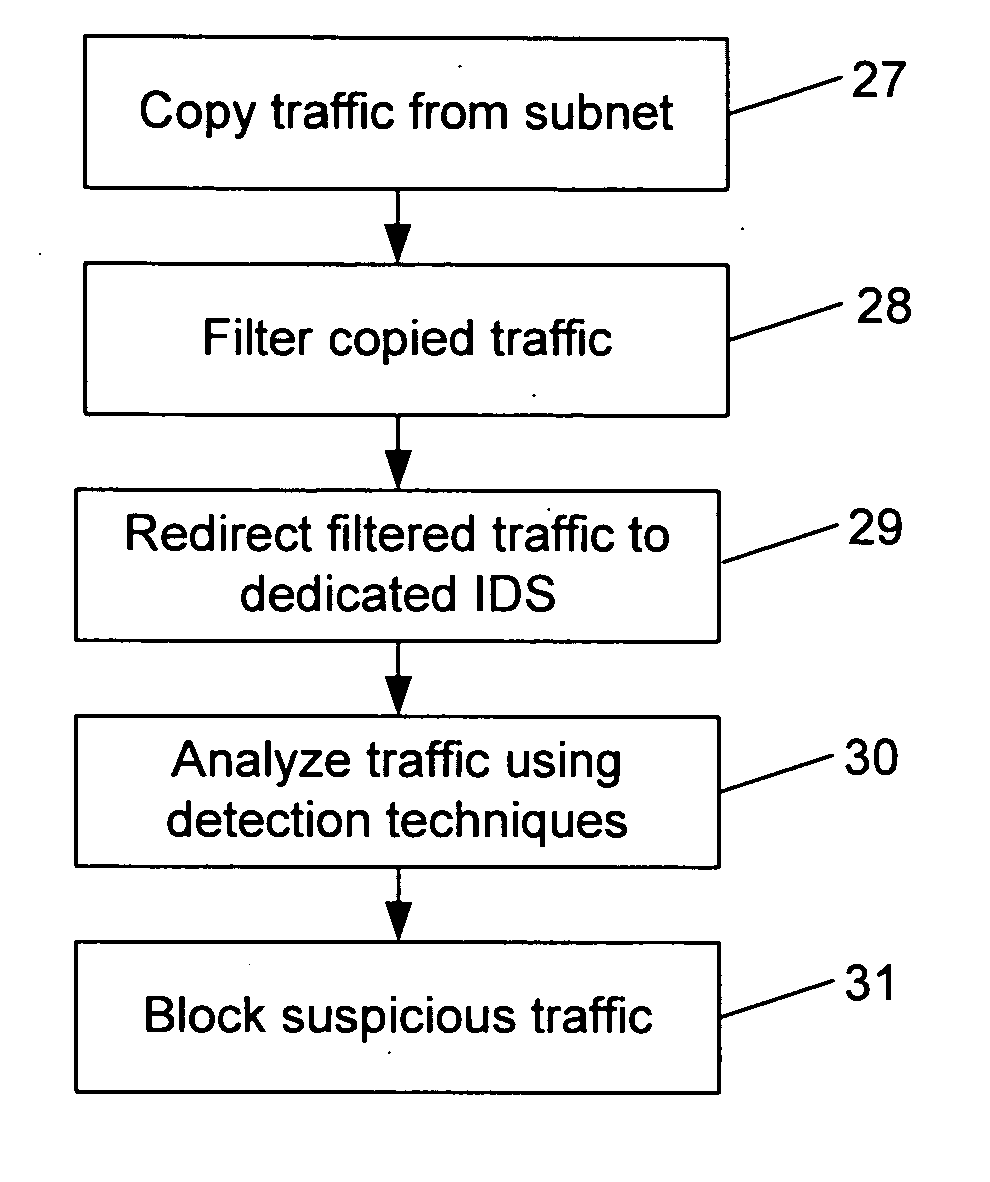
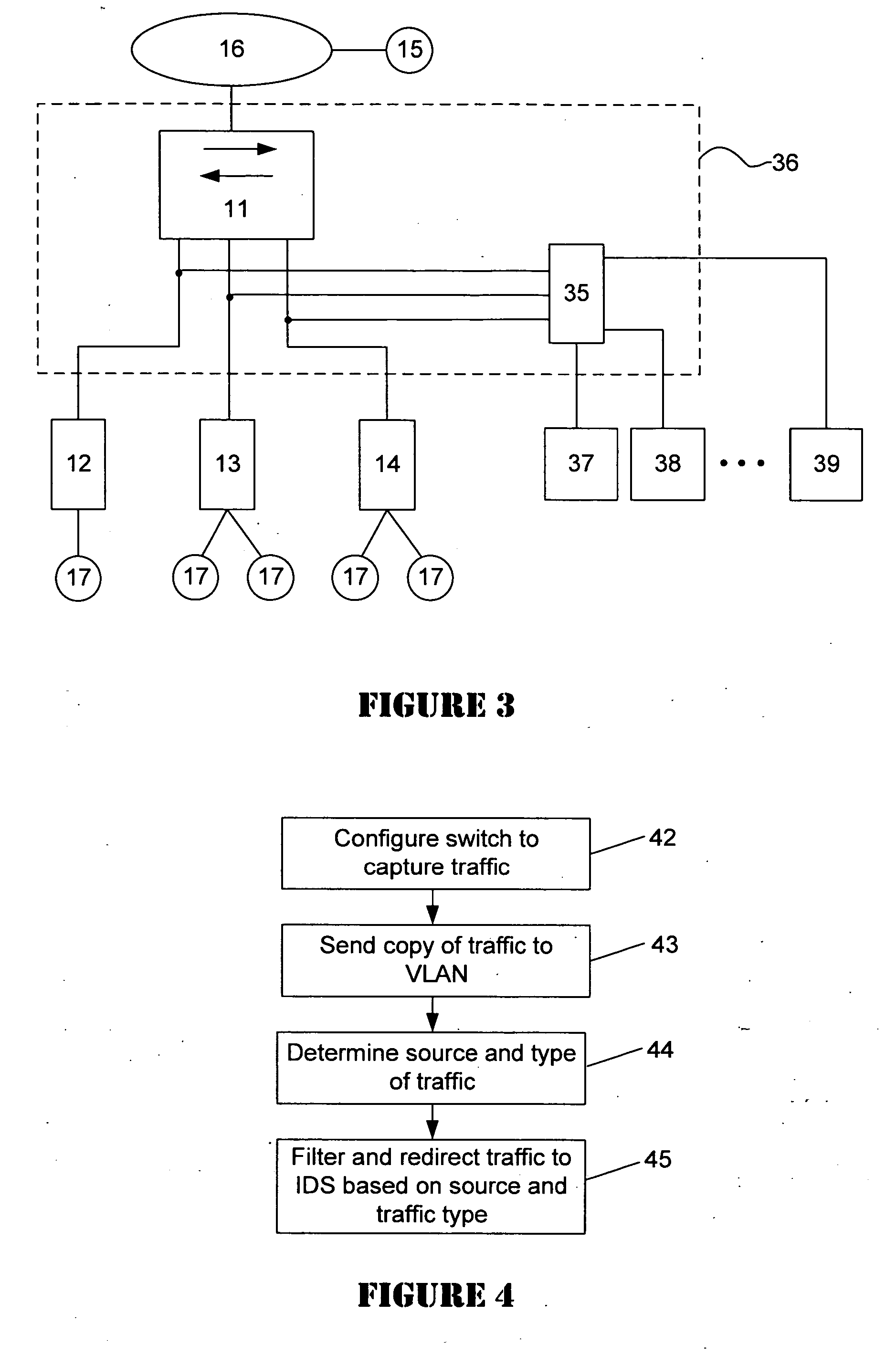
Intrusion detection in a data center environment
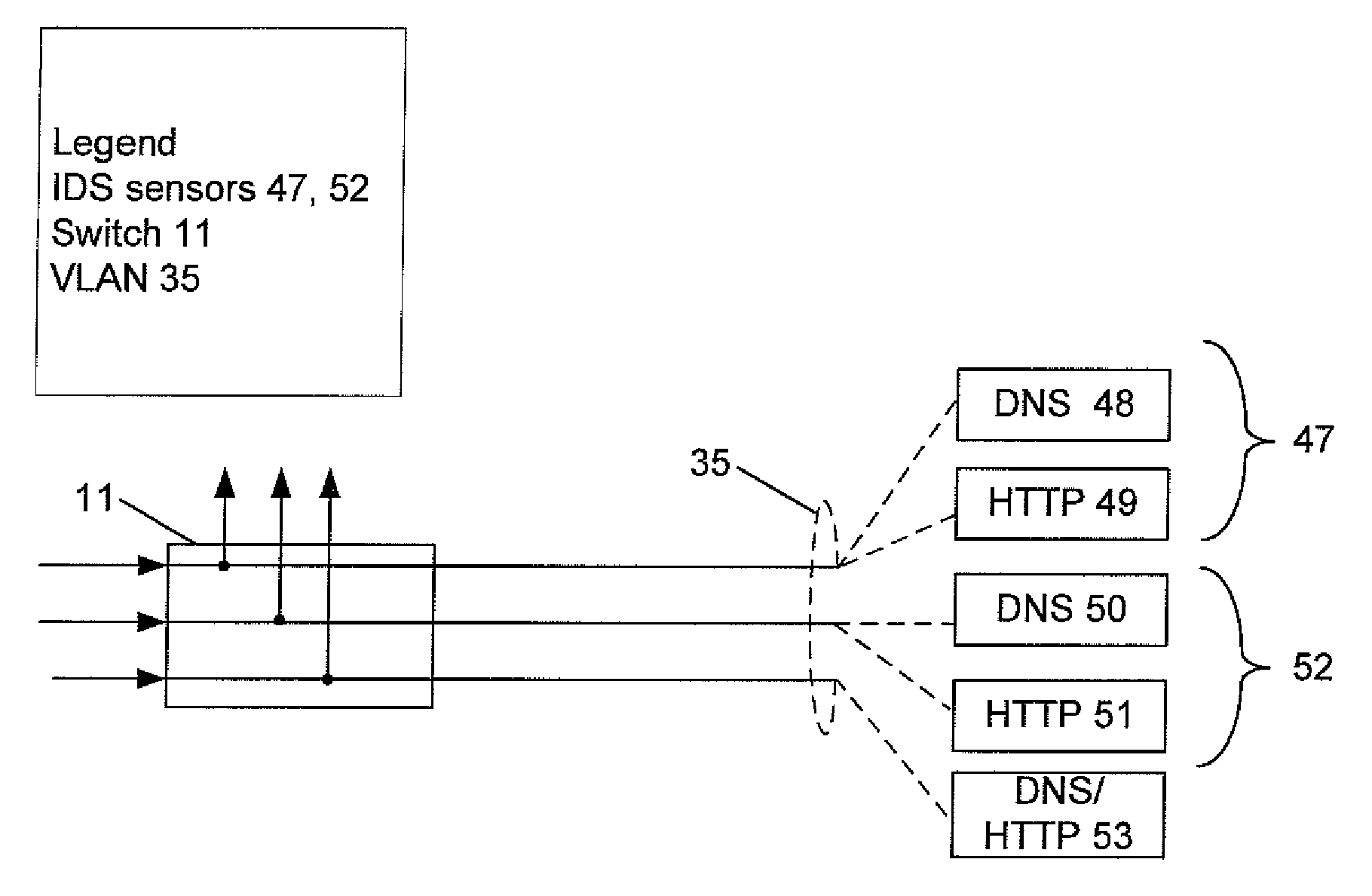
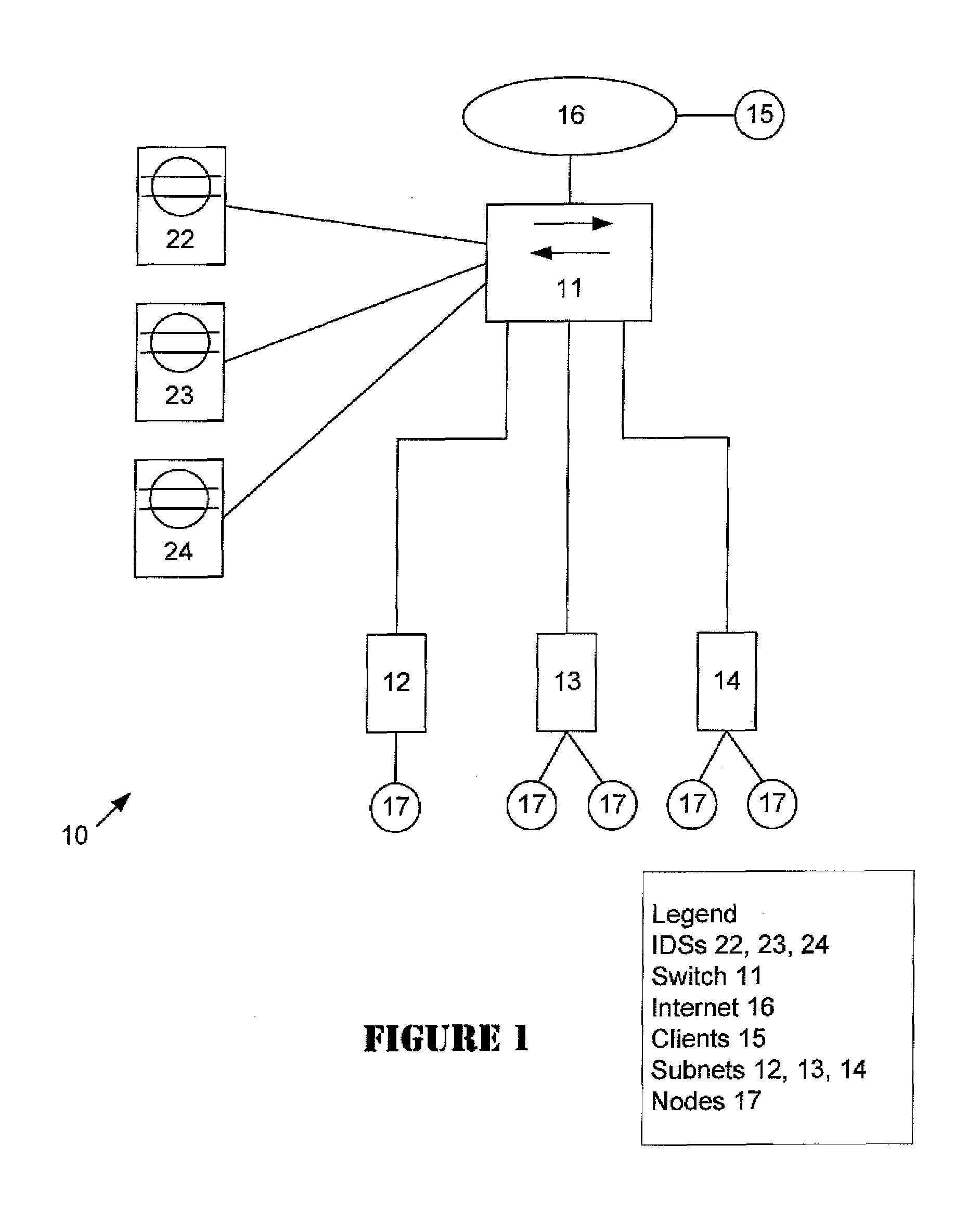
ActiveUS20060095968A1Reduce false-positivesGreat granularityError preventionTransmission systemsTraffic volumeIntrusion detection system
An intrusion detection system (IDS) is capable of identifying the source of traffic, filtering the traffic to classify it as either safe or suspect and then applying sophisticated detection techniques such as stateful pattern recognition, protocol parsing, heuristic detection or anomaly detection either singularly or in combination based on the traffic type. In a network environment, each traffic source is provided with at least one IDS sensor that is dedicated to monitoring a specific type of traffic such as RPC, HTTP, SMTP, DNS, or others. Traffic from each traffic source is filtered to remove known safe traffic to improve efficiency and increase accuracy by keeping each IDS sensor focused on a specific traffic type.
Owner:CISCO TECH INC
Certificate-based search
InactiveUS20080005086A1Fine granularityImprove reusabilitySpecial data processing applicationsSecuring communicationGranularityReusability
The systems and methods disclosed herein provide for authentication of content sources and / or metadata sources so that downstream users of syndicated content can rely on these attributes when searching, citing, and / or redistributing content. To further improve the granularity and reusability of content, globally unique identifiers may be assigned to fragments of each document. This may be particularly useful for indexing documents that contain XML grammar with functional aspects, where atomic functional components can be individually indexed and referenced independent from a document in which they are contained.
Owner:MOORE JAMES F
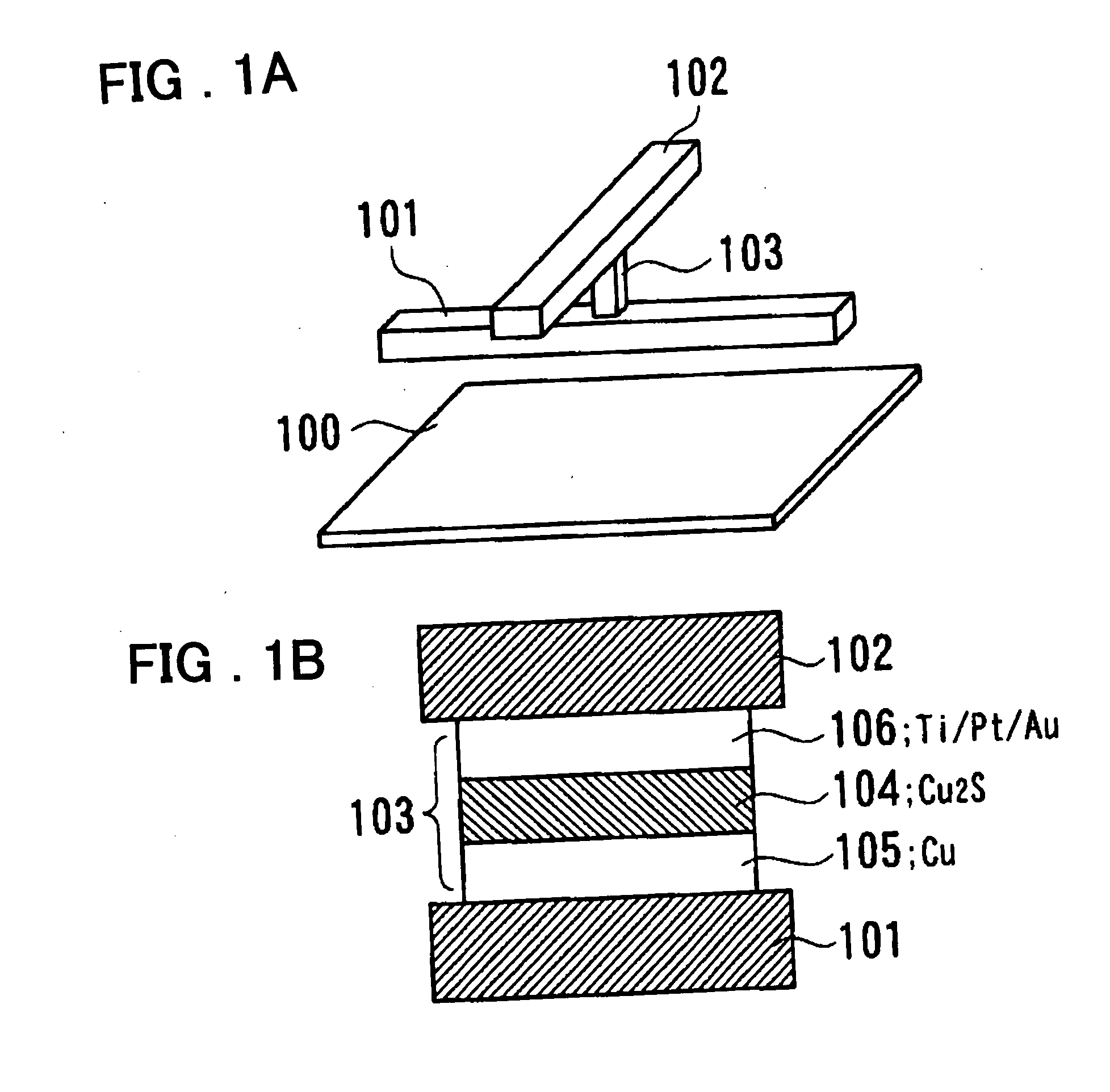
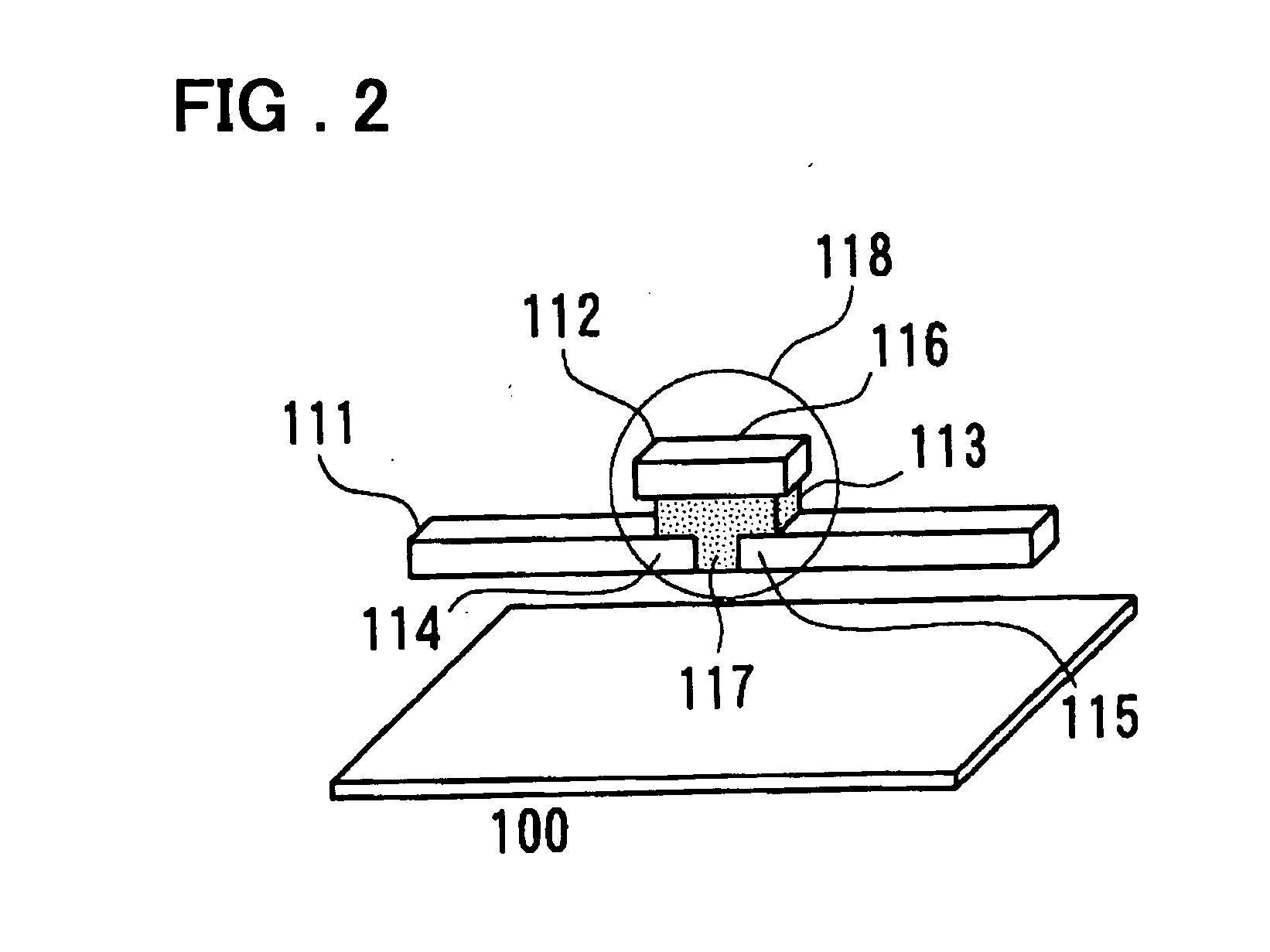
Semiconductor device
InactiveUS20050045919A1Increase the areaFine granularitySemiconductor/solid-state device detailsSolid-state devicesDevice materialEngineering
A programmable semiconductor device has a switch element in an interconnection layer, wherein in at least one of the inside of a via, interconnecting a wire of a first interconnection layer and a wire of a second interconnection layer, a contact part of the via with the wire of the first interconnection layer and a contact part of the via with the wire of the second interconnection layer, there is provided a variable electrical conductivity member, such as a member of an electrolyte material. The via is used as a variable electrical conductivity type switch element or as a variable resistance device having a contact part with the wire of the first interconnection layer as a first terminal and having a contact part with the wire of the second interconnection layer as a second terminal. By varying the electrical conductivity of the switch element, the state of connection of the via with the wire of the first interconnection layer and the state of connection of the via with the wire of the second interconnection layer may be variably set to a shorted state, an open-circuited state or to an intermediate state A two-state switch element includes an ion conductor for conducting metal ions interposed between the first and second electrodes. The second electrode is formed of a material lower in reactivity than the first electrode. The electrical conductivity across the first and second electrodes is changed by the oxidation-reduction reaction of the metal ions. There are provided first and second transistors of opposite polarities, connected to the first electrode, and third and fourth transistors of opposite polarities, connected to the second electrode.
Owner:NEC CORP
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
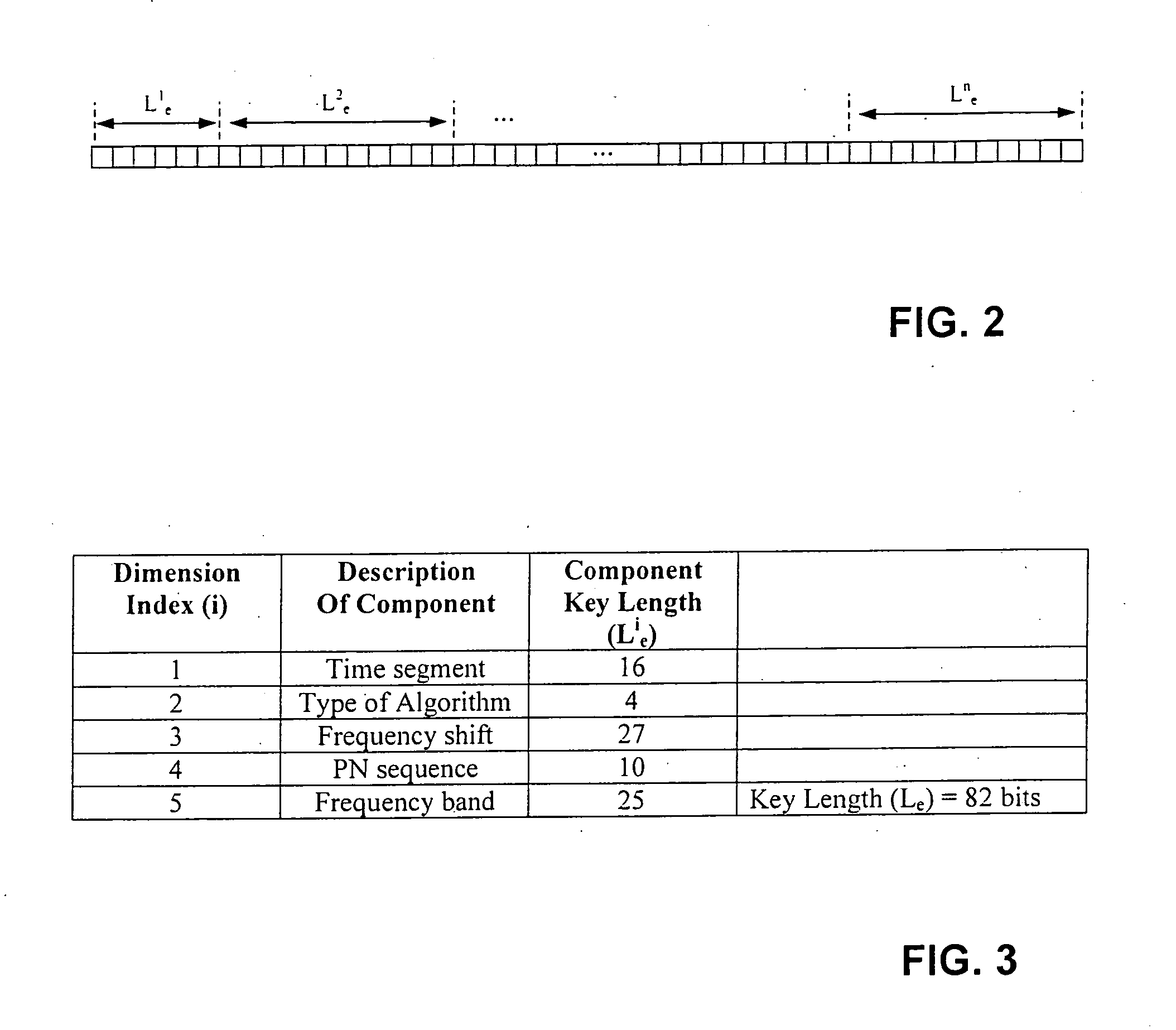
ActiveUS7287275B2Speeding routingFine granularityError preventionFrequency-division multiplex detailsData streamNetwork packet
Disclosed herein are methods and systems for transmitting streams of data. In one embodiment, a method comprises the steps of: receiving a stream of data; organizing the stream of data into a plurality of packets; generating a packet watermark associated with the stream of data; combining the packet watermark with each of the plurality of packets to form watermarked packets; and transmitting at least one of the watermarked packets across a network. The present invention also relates to: receiving at least one packet that has been transmitted across a network; analyzing at least one packet for a watermark; and authenticating the at least one packet using at least a portion of the watermark. The present invention also relates to generating packet watermarks and packet watermark keys.
Owner:WISTARIA TRADING INC
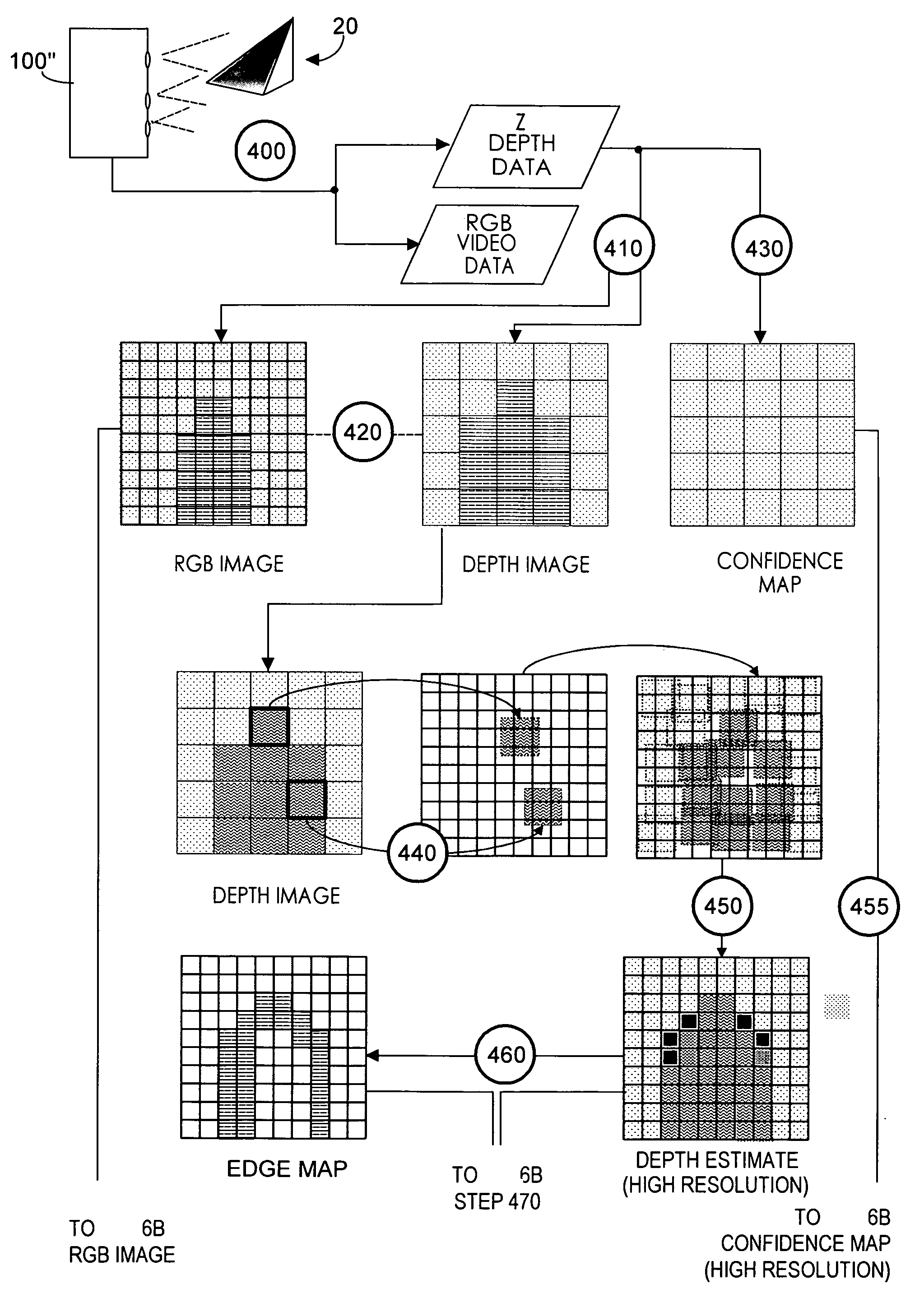
Video manipulation of red, green, blue, distance (RGB-Z) data including segmentation, up-sampling, and background substitution techniques
ActiveUS20110285910A1Improve resolutionEasy to processTelevision system detailsOptical rangefindersImage resolutionSignal characteristic
RGB-Z imaging systems acquire RGB data typically with a high X-Y resolution RGB pixel array, and acquire Z-depth data with an array of physically larger Z pixels having additive signal properties. In each acquired frame, RGB pixels are mapped to a corresponding Z pixel. Z image resolution is enhanced by identifying Z discontinuities and identifying corresponding RGB pixels where the Z discontinuities occur. Thus segmented data enables RGB background substitution, which preferably blends foreground pixel color and substitute background color. The segmented data also enables up-sampling in which a higher XY resolution Z image with accurate Z values is obtained. Up-sampling uses an equation set enabling assignment of accurate Z values to RGB pixels. Fixed acquisition frame rates are enabled by carefully culling bad Z data. Segmenting and up-sampling enhanced video effects and enable low cost, low Z resolution arrays to function comparably to higher quality, higher resolution Z arrays.
Owner:MICROSOFT TECH LICENSING LLC
Selective stimulation systems and signal parameters for medical conditions
Devices, systems and methods are provided for targeted treatment of a variety of conditions, particularly conditions that are associated with or influenced by the nervous system, such as pain. Targeted treatment of such conditions is provided with minimal deleterious side effects, such as undesired motor responses or undesired stimulation of unaffected body regions. This is achieved by directly neuromodulating a target anatomy associated with the condition while minimizing or excluding undesired neuromodulation of other anatomies.
Owner:TC1 LLC
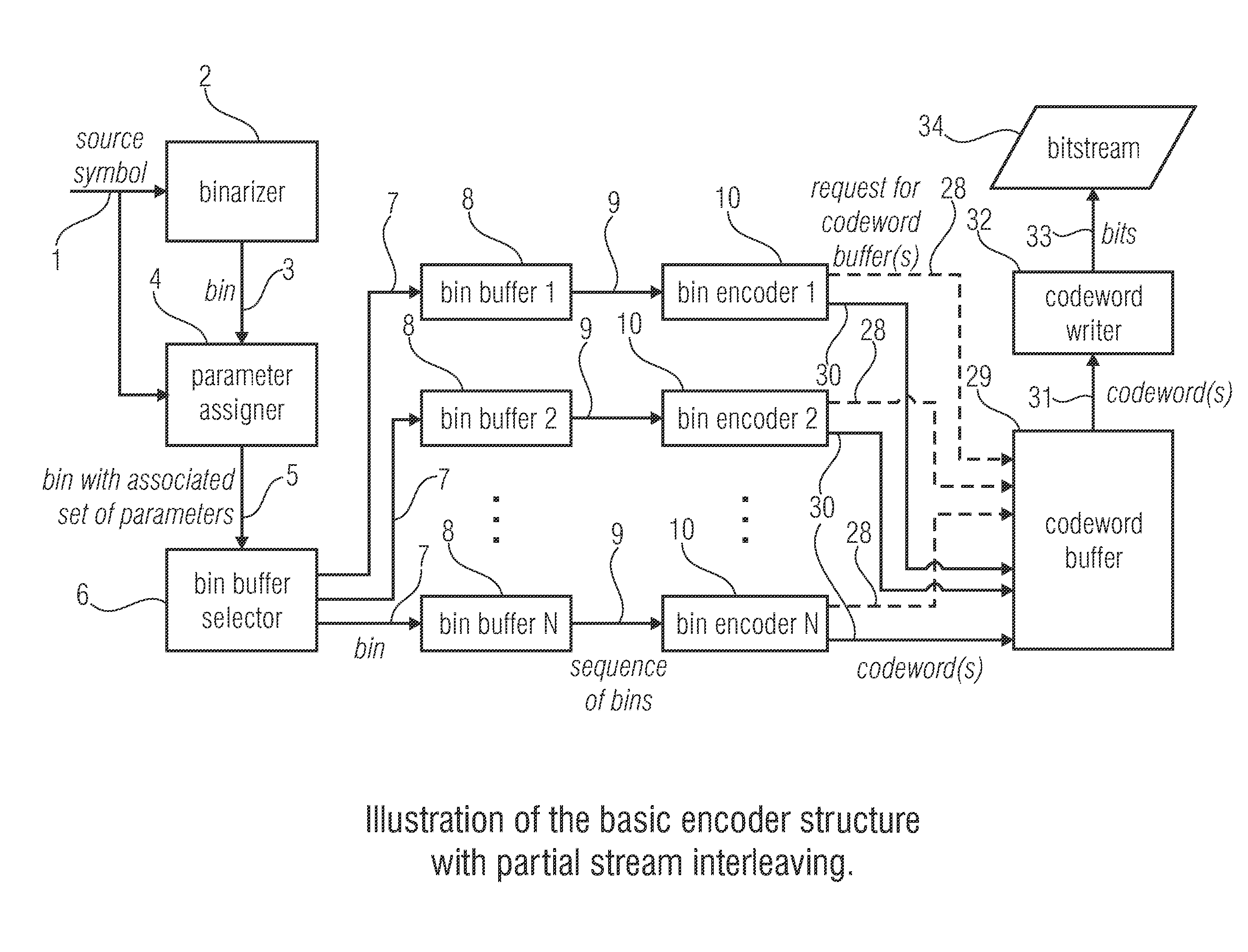
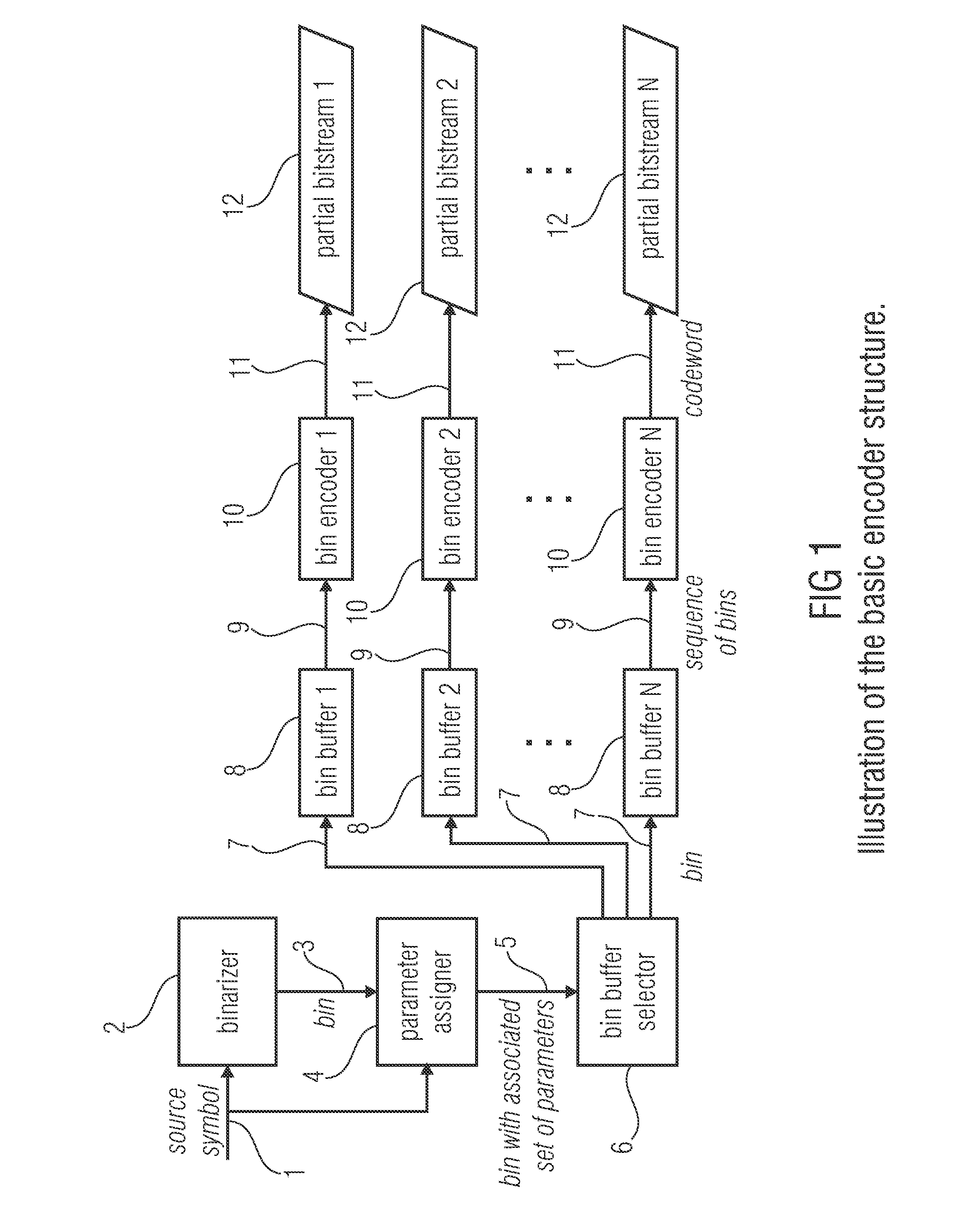
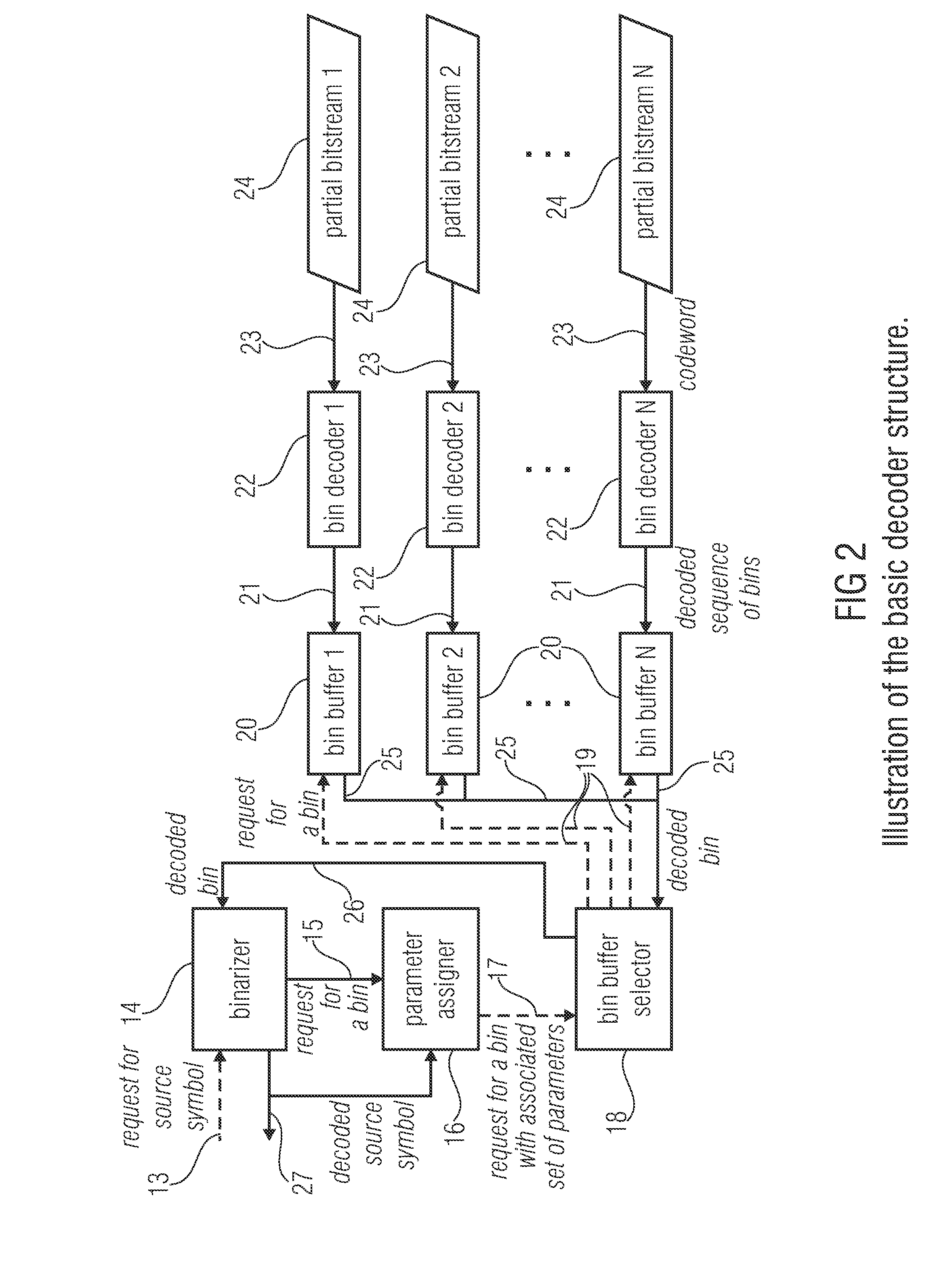
Entropy coding
ActiveUS20130027230A1Reduce complexityOverhead for transmitting the partial bitstream can be kept smallCode conversionDigital video signal modificationEntropy encodingComputer science
An encoder for encoding a sequence of symbols is described which includes an assigner configured to assign a number of parameters to each symbol of the sequence of symbols based on information contained within previous symbols of the sequence of symbols; a plurality of entropy encoders each of which is configured to convert the symbols forwarded to the respective entropy encoder into a respective bitstream; and a selector configured to forward each symbol to a selected one of the plurality of entropy encoders, the selection depending on the number of parameters assigned to the respective symbol.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
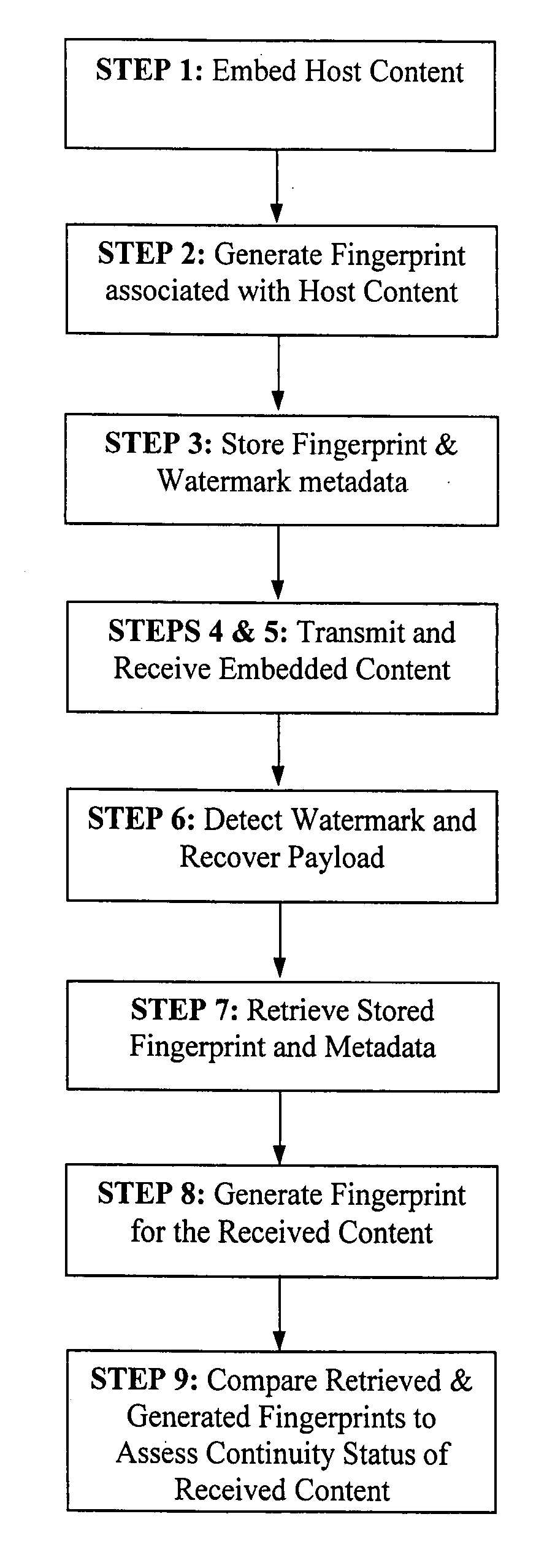
System reactions to the detection of embedded watermarks in a digital host content
InactiveUS20060239503A1Increase payload capacityIncreased payload capacityUser identity/authority verificationSpeech analysisSystem requirementsSystem recovery
Methods for adapting the operation of a system in response to the detection of embedded watermarks from a digital host content are provided. A digital host content is received and examined for the presence of watermarks. In response to the detection of embedded watermarks and in accordance with the value, type, density or spacing of the detected watermarks, one or more system reactions may take place. These reactions include conditionally allowing the system to resume its normal operation, prohibiting the system from resuming its normal operation, degrading the quality of the digital host content or changing the security status of the digital host content. In response to the extraction of weak watermarks that do not meet the desired system requirements, the extraction operation may be modified or extended to enable the detection of strong watermarks.
Owner:IP ACQUISITIONS LLC
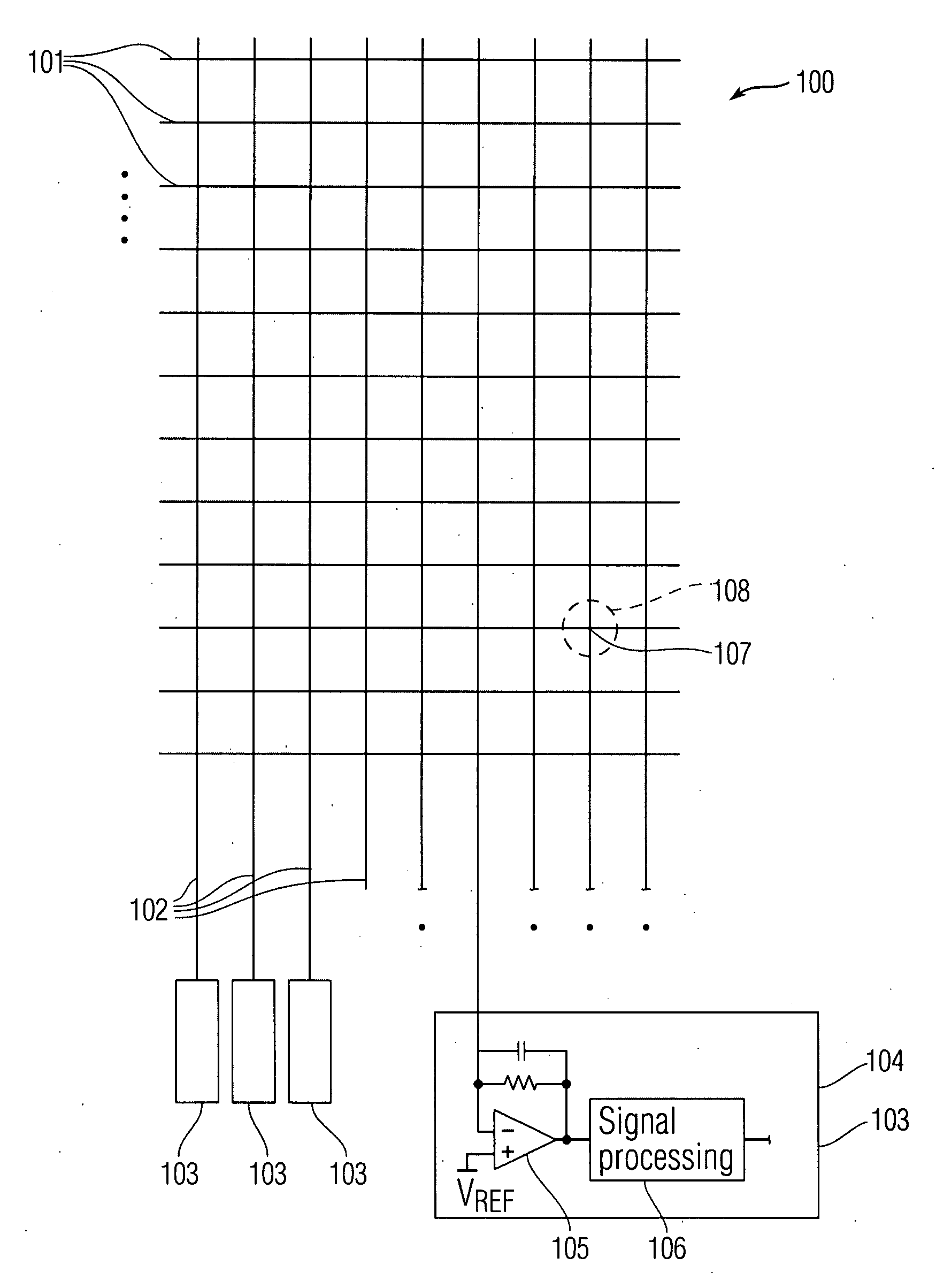
Integrated multi-touch surface having varying sensor granularity
ActiveUS20080309631A1Easy inputFine granularityDigital data processing detailsSubstation equipmentGranularityComputer science
This relates to an event sensing device that includes an event sensing panel and is able to dynamically change the granularity of the panel according to present needs. Thus, the granularity of the panel can differ at different times of operation. Furthermore, the granularity of specific areas of the panel can also be dynamically changed, so that different areas feature different granularities at a given time. This also relates to panels that feature different inherent granularities in different portions thereof. These panels can be designed, for example, by placing more stimulus and / or data lines in different portions of the panel, thus ensuring different densities of pixels in the different portions. Optionally, these embodiments can also include the dynamic granularity changing features noted above.
Owner:APPLE INC
Communications system and method
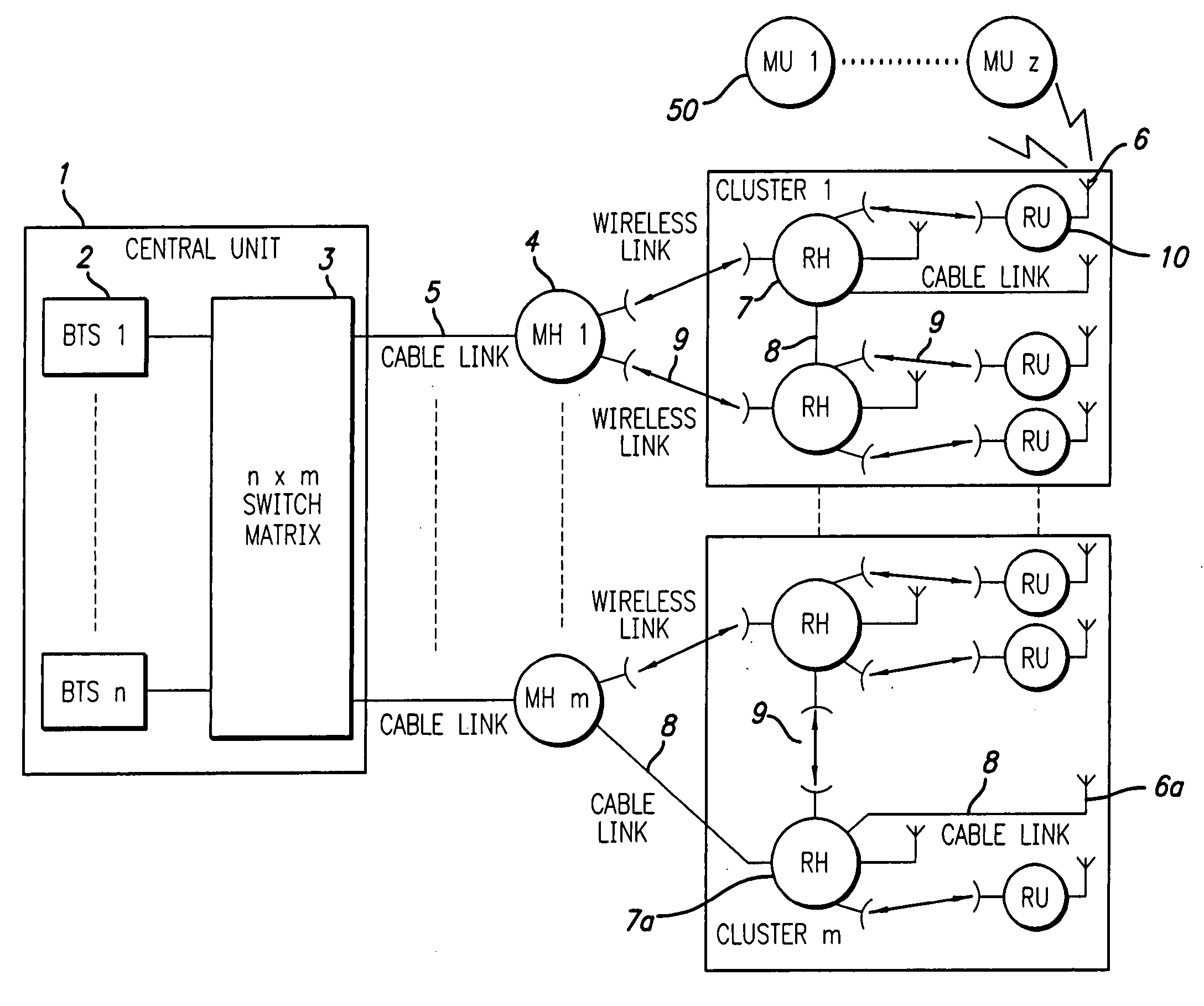
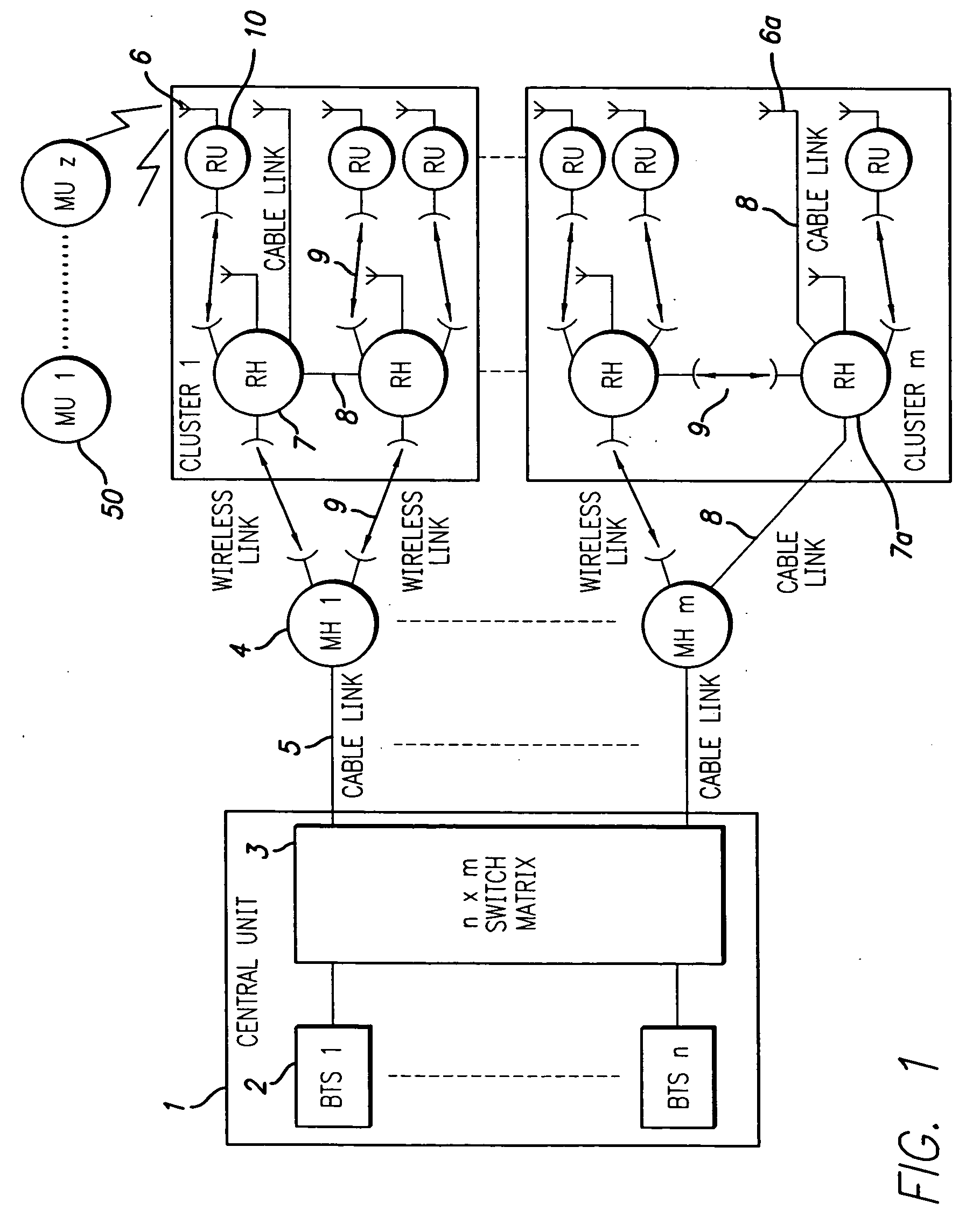
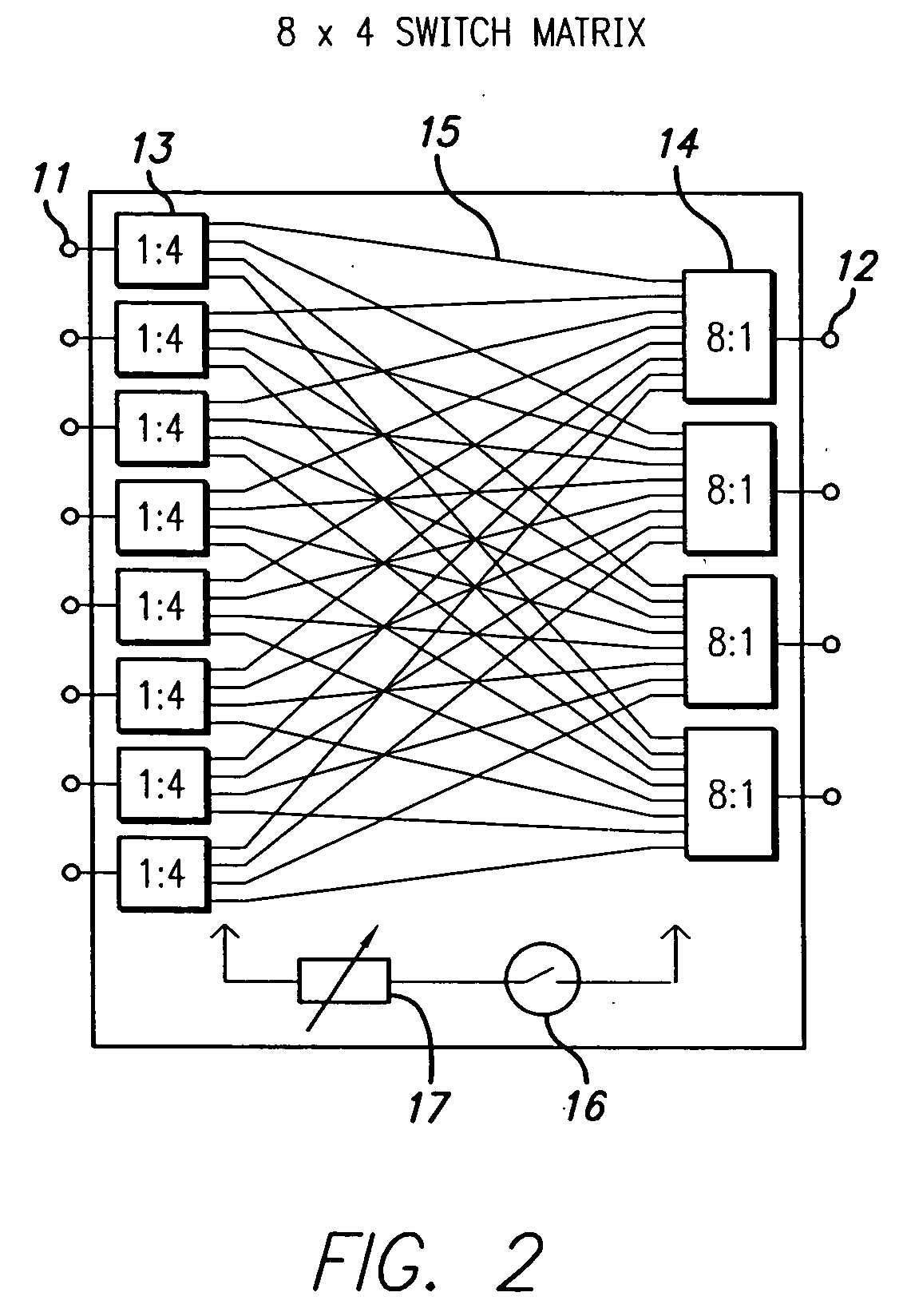
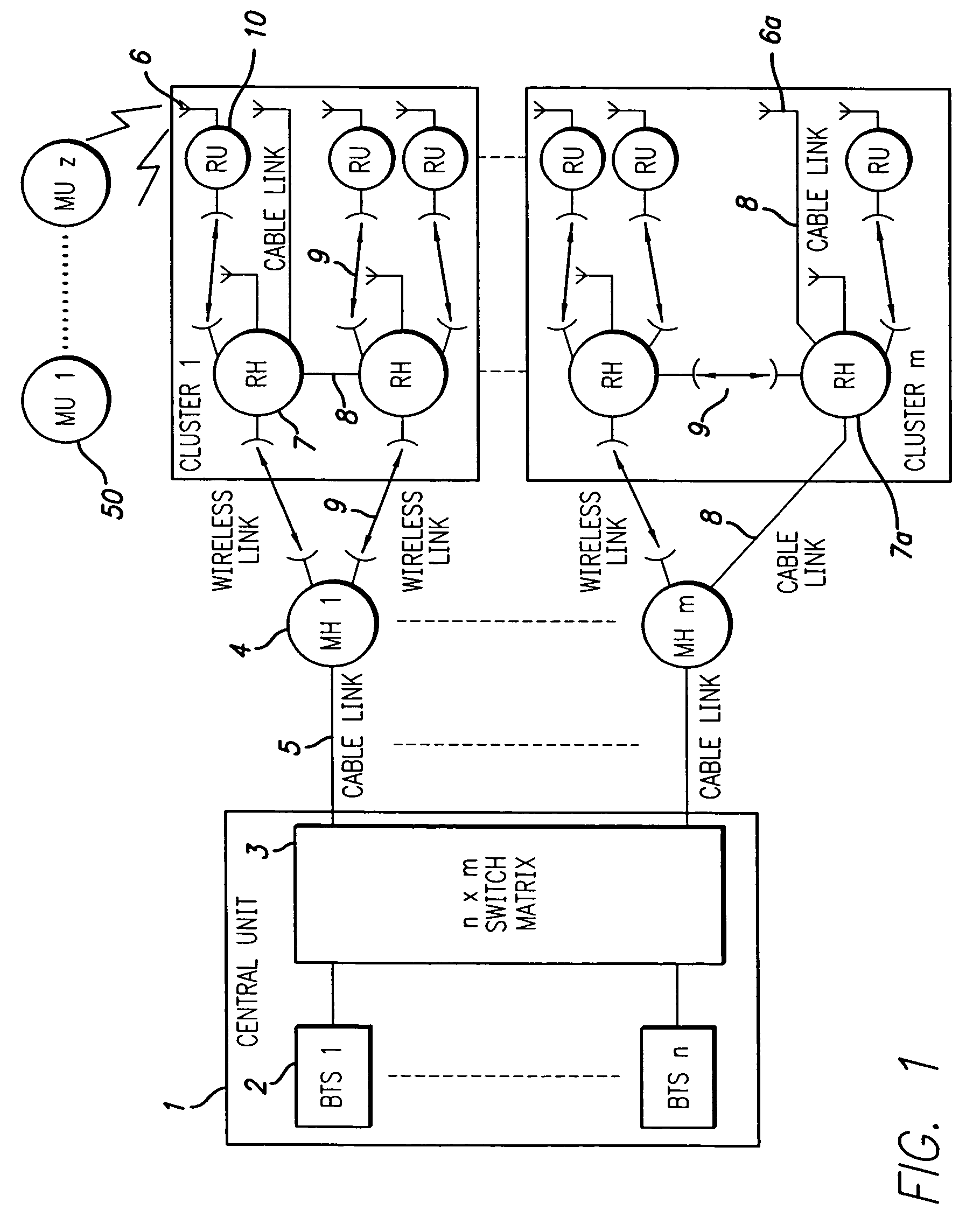
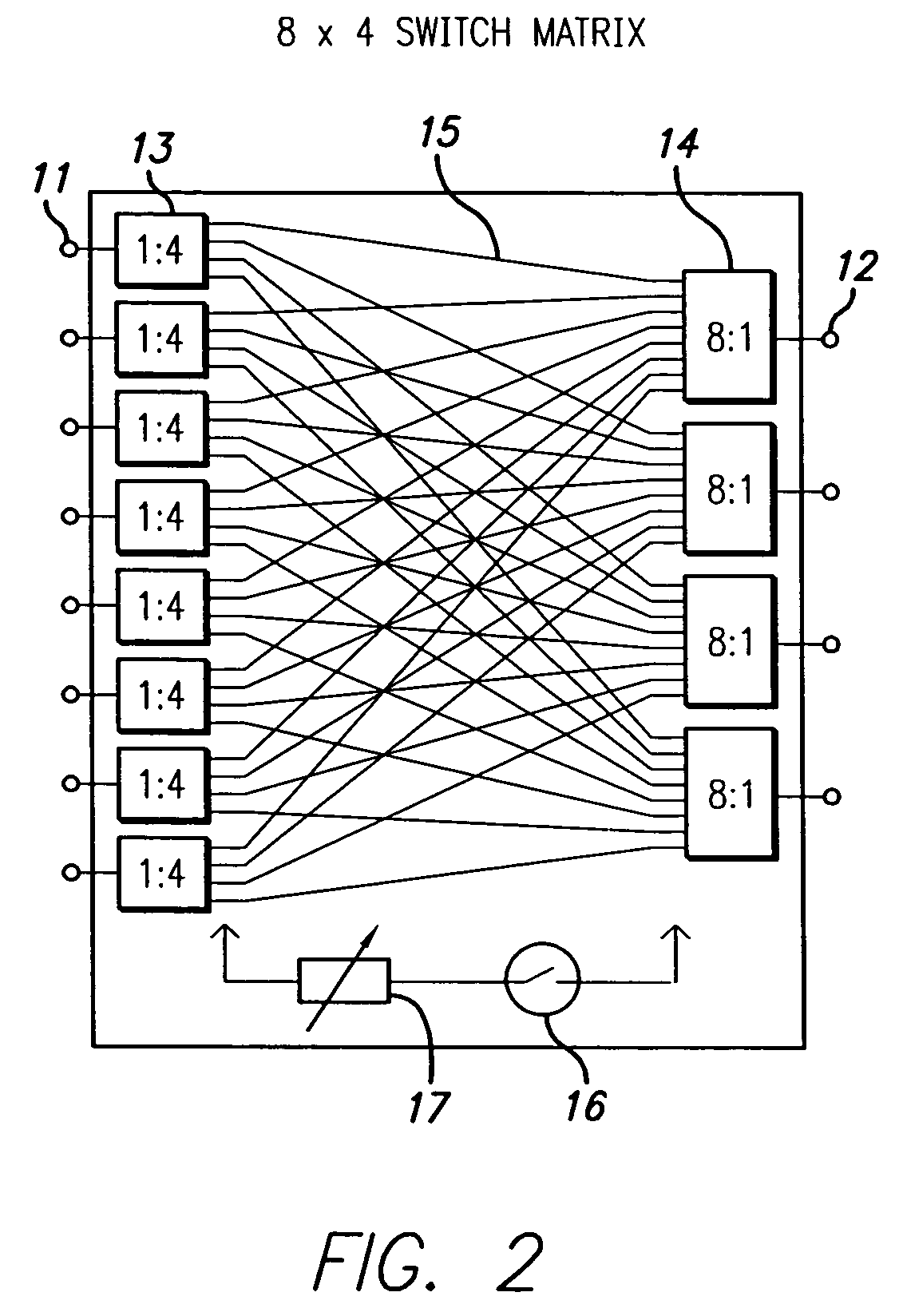
ActiveUS20060094470A1Finer granularityFine granularityRadio/inductive link selection arrangementsSubstation equipmentDistribution systemBase station
A signal distribution system for distributing signals, such as for outdoor wireless networks, comprises a number of remote hubs, each of which can direct wireless signals to a number of antennas. The antennas are used to provide wireless service to the service users, such as mobile units, within their geographic coverage area. The remote hubs are connected to main hubs, which are usually located centrally. Each main hub can support a number of remote hubs. The main hubs are connected to a number of base stations (again usually located centrally) in a flexible and re-configurable manner using a switch matrix. Some remote hubs may also include switched matrices for a further level of signal routing.
Owner:NEXTG NETWORKS INC
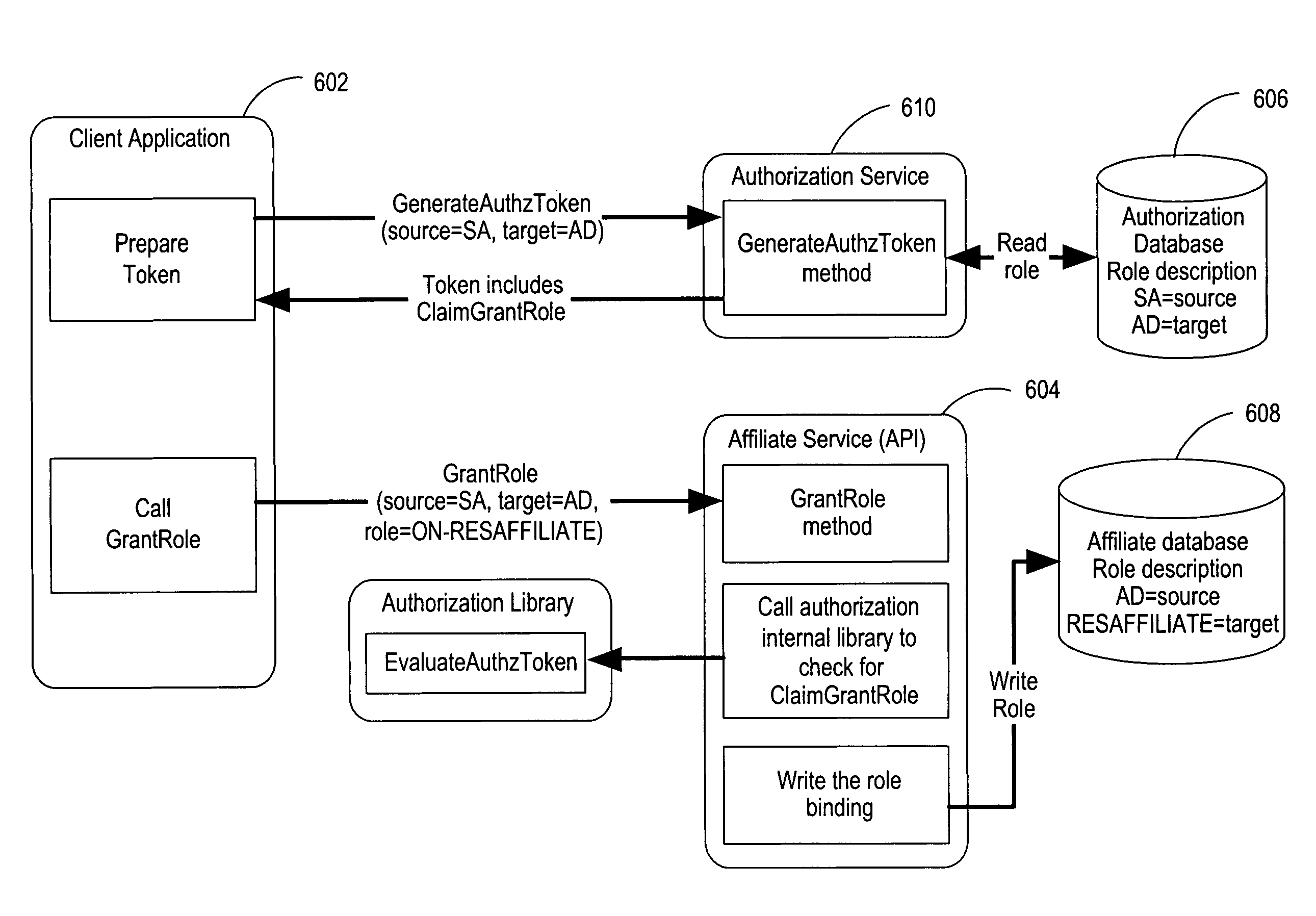
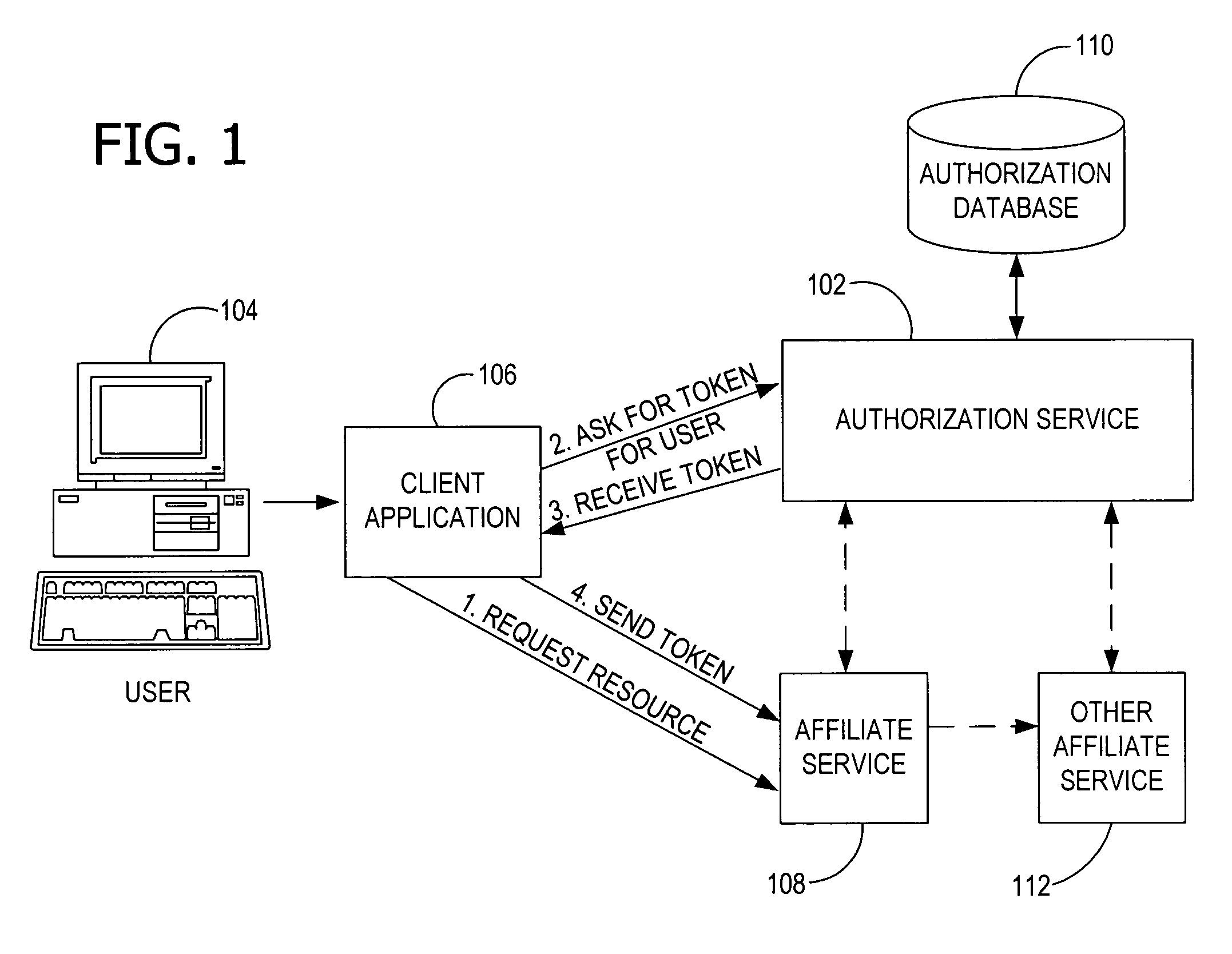
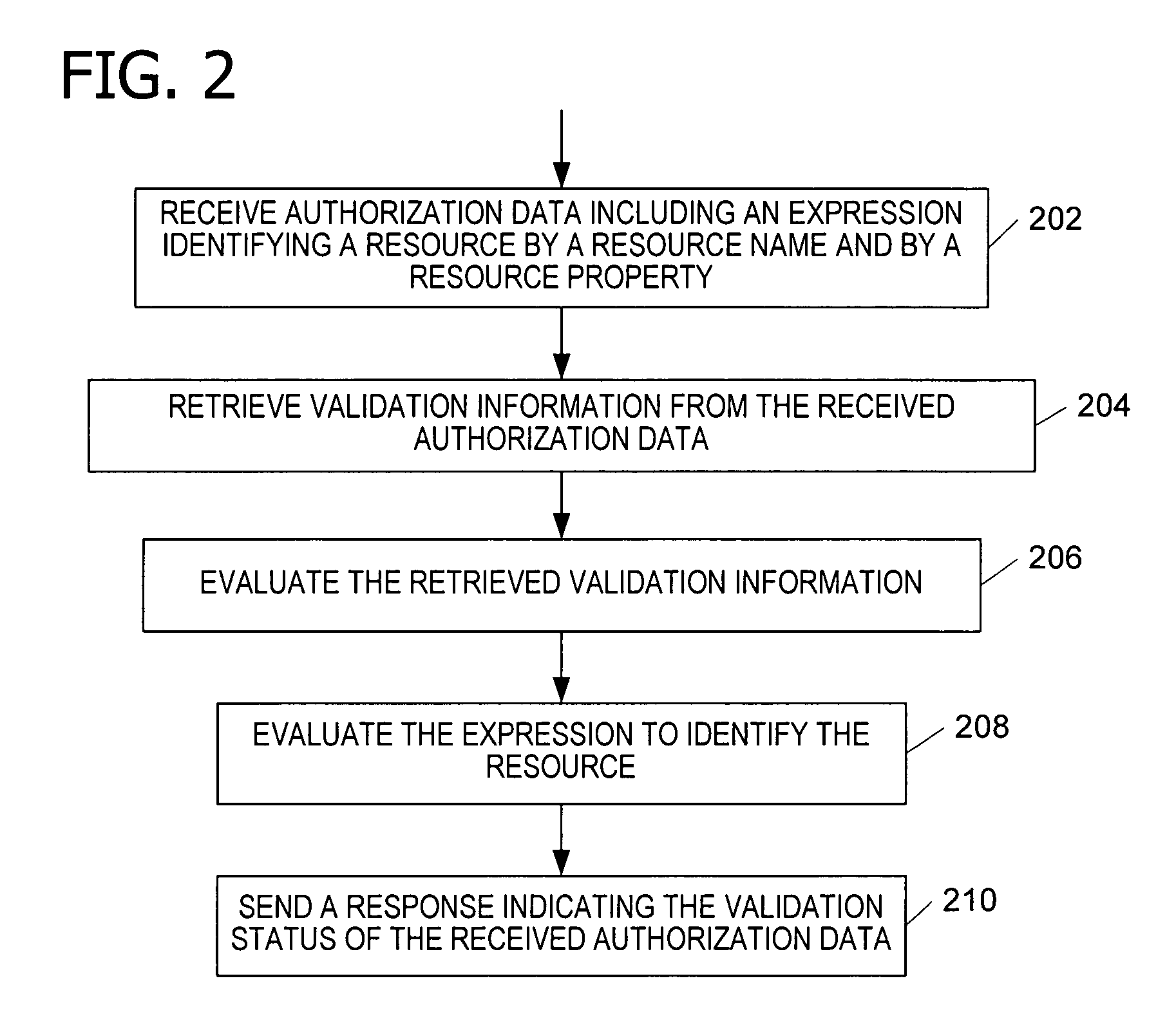
Authorization and access control service for distributed network resources
ActiveUS7685206B1Simplify access control managementEasy to implementDigital data processing detailsTransmissionMulti siteClient-side
Providing access to a resource via authorization data that conditionally defines the access by an expression that identifies the resource by name and by at least one property of the resource. An authorization service issues the authorization data (e.g., as a token) and evaluating authorization data received from a client. The authorization service evaluates the expression in the authorization data to identify the resource and determine the rights associated with the user for the resource. The authorization service implements role-based access control to control access to resources in a distributed, multi-site network.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus to apply aggregate access control list/quality of service features using a redirect cause
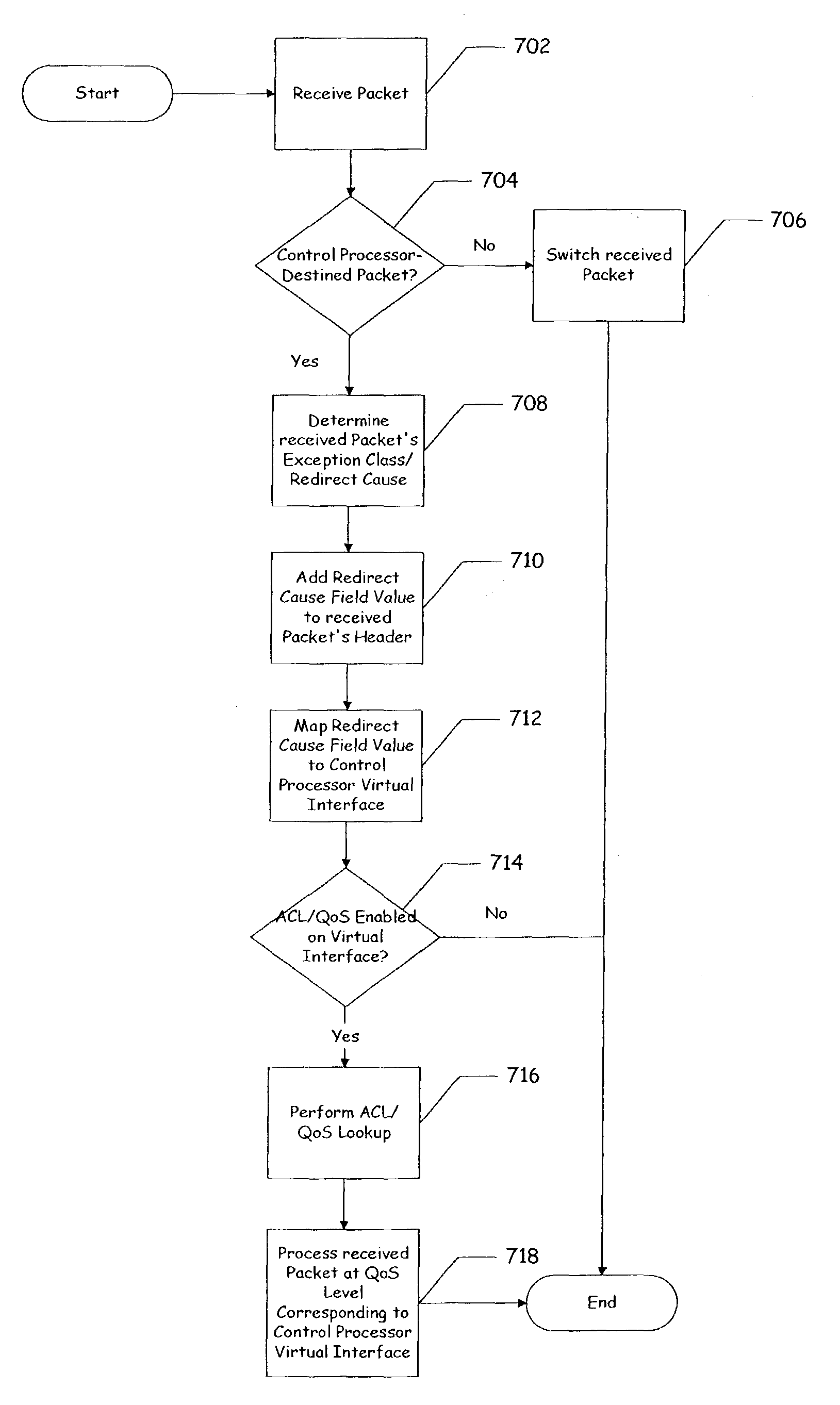
ActiveUS7953885B1Fine granularityDigital computer detailsData switching by path configurationQuality of serviceDistributed computing
A method and apparatus to apply aggregate ACL / QoS features using a redirect cause is disclosed. According to one embodiment of the present invention, a control processor configured to support a plurality of virtual interfaces is provided, wherein each of the plurality of virtual interfaces is associated with a quality of service level. According to another embodiment, each quality of service level is associated with a processing bandwidth of the control processor. According to yet another embodiment, a control processor interface is provided coupled to the control processor which is configured to select a virtual interface of the plurality of virtual interfaces using data of a received data unit, and to transfer the received data unit to the selected virtual interface.
Owner:CISCO TECH INC
Communications system and method
ActiveUS7313415B2Fine granularityReduce congestionSubstation equipmentTransmissionSignal routingCommunications system
A signal distribution system for distributing signals, such as for outdoor wireless networks, comprises a number of remote hubs, each of which can direct wireless signals to a number of antennas. The antennas are used to provide wireless service to the service users, such as mobile units, within their geographic coverage area. The remote hubs are connected to main hubs, which are usually located centrally. Each main hub can support a number of remote hubs. The main hubs are connected to a number of base stations (again usually located centrally) in a flexible and re-configurable manner using a switch matrix. Some remote hubs may also include switched matrices for a further level of signal routing.
Owner:NEXTG NETWORKS INC
Network system
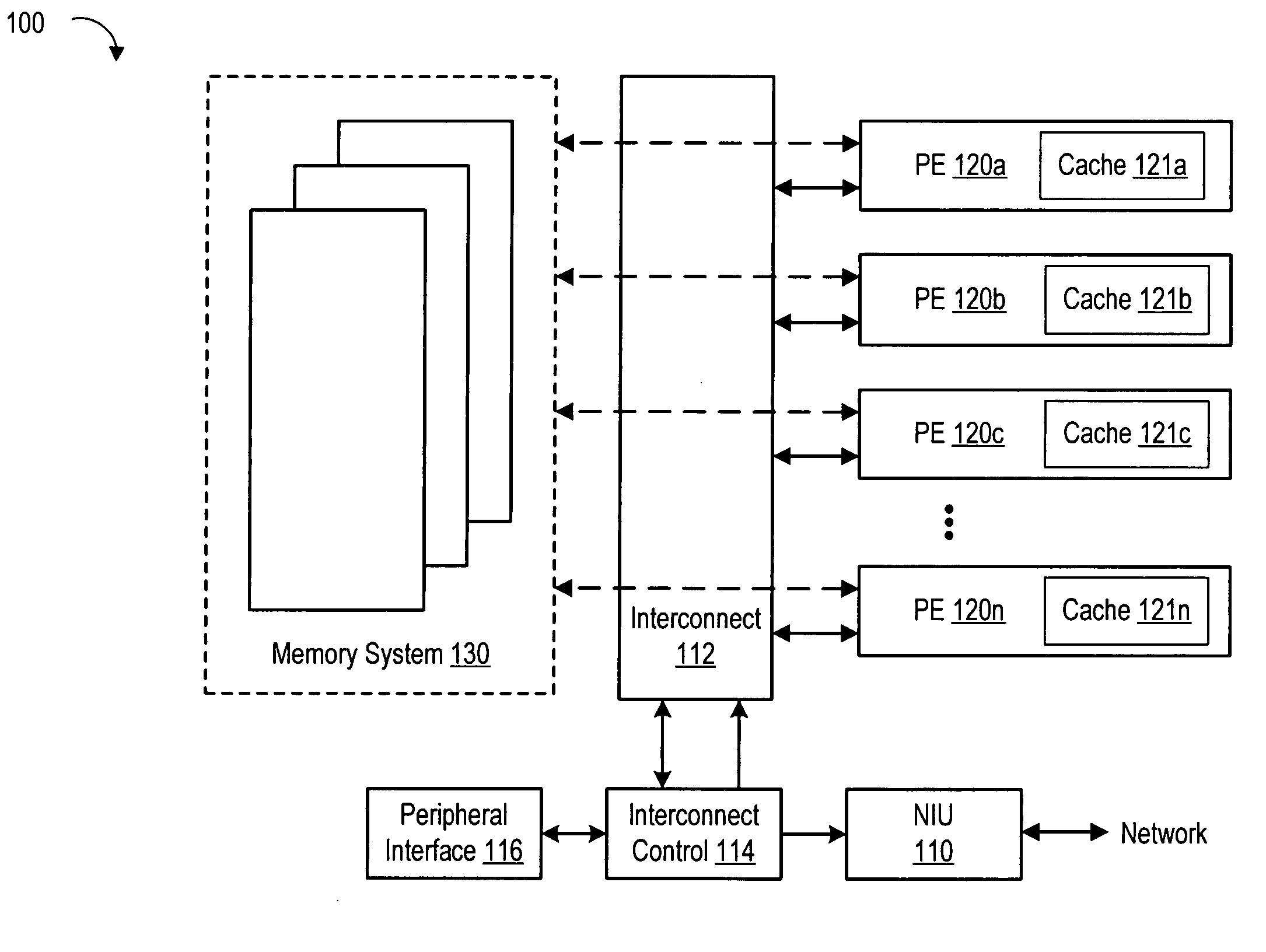
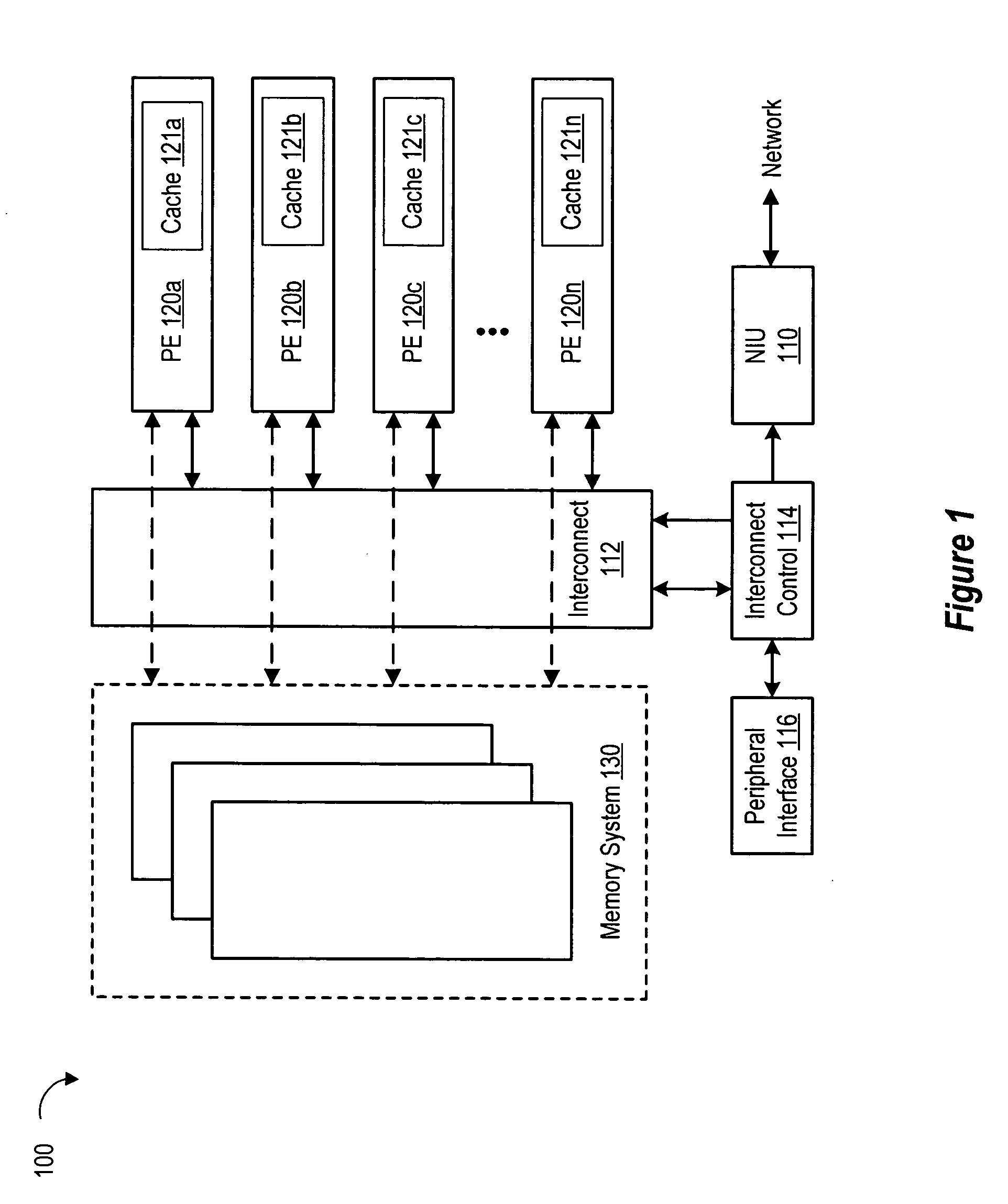
ActiveUS20060251109A1Lower DMA latencyIncrease DMA bandwidthNetwork connectionsNetworked systemNetwork interface controller
A network system which includes a plurality of processing entities, an interconnect device coupled to the plurality of processing entities, a memory system coupled to the interconnect device and the plurality of processing entities, a network interface unit coupled to the plurality of processing entities and the memory system via the interconnect device. The network interface includes a memory access module and a packet classifier. The memory access module includes a plurality of parallel memory access channels. The packet classifier provides a flexible association between packets and the plurality of processing entities via the plurality of memory access channels.
Owner:ORACLE INT CORP
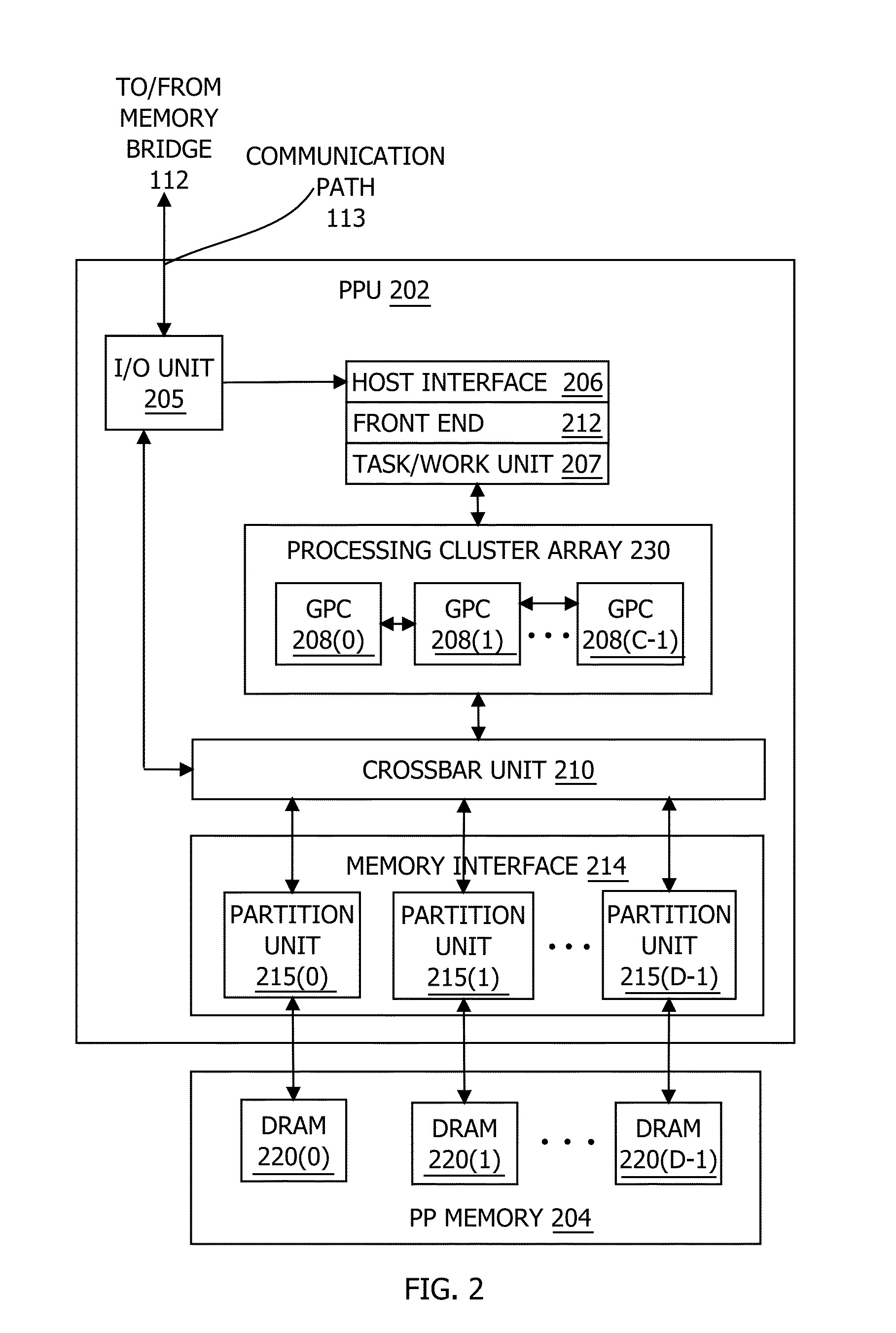
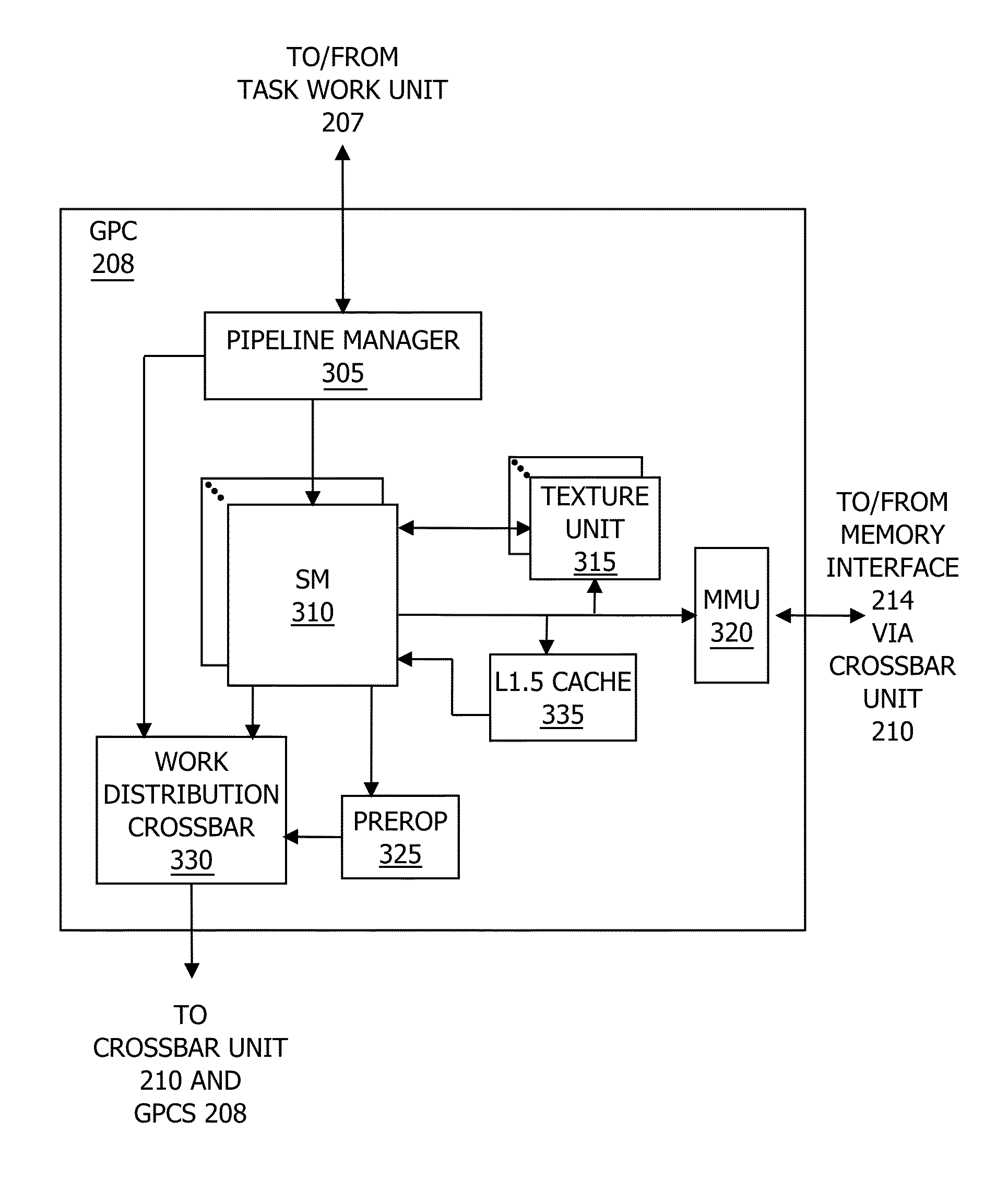
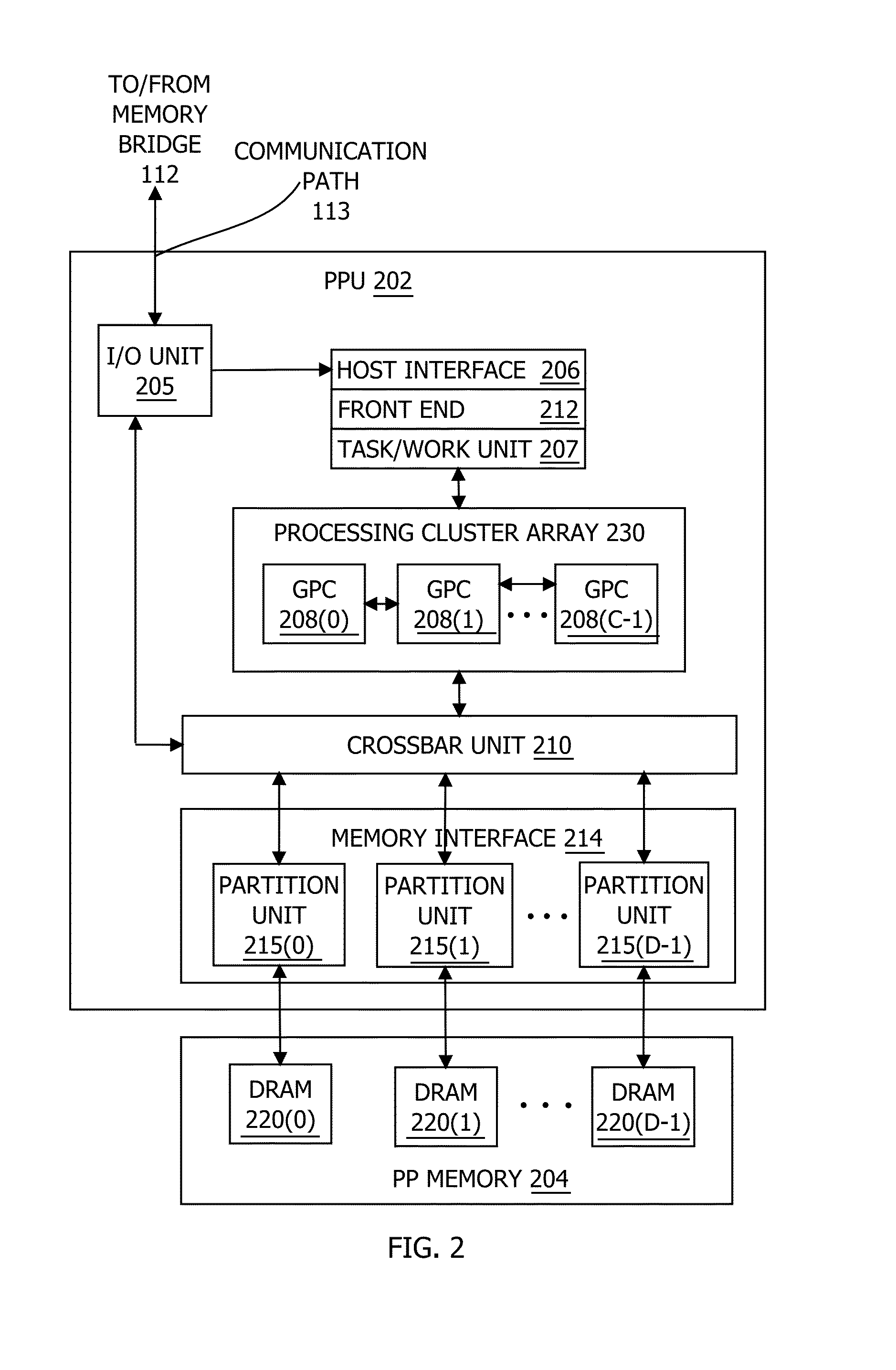
Adaptive shading in a graphics processing pipeline
ActiveUS20150170408A1Fine granularityConsumes less powerProcessor architectures/configurationImage generationGraphicsGranularity
One embodiment of the present invention includes a parallel processing unit (PPU) that performs pixel shading at variable granularities. For effects that vary at a low frequency across a pixel block, a coarse shading unit performs the associated shading operations on a subset of the pixels in the pixel block. By contrast, for effects that vary at a high frequency across the pixel block, fine shading units perform the associated shading operations on each pixel in the pixel block. Because the PPU implements coarse shading units and fine shading units, the PPU may tune the shading rate per-effect based on the frequency of variation across each pixel group. By contrast, conventional PPUs typically compute all effects per-pixel, performing redundant shading operations for low frequency effects. Consequently, to produce similar image quality, the PPU consumes less power and increases the rendering frame rate compared to a conventional PPU.
Owner:NVIDIA CORP
Signal continuity assessment using embedded watermarks
ActiveUS20080002854A1Fine granularitySpeech analysisCharacter and pattern recognitionWatermark methodVolumetric Mass Density
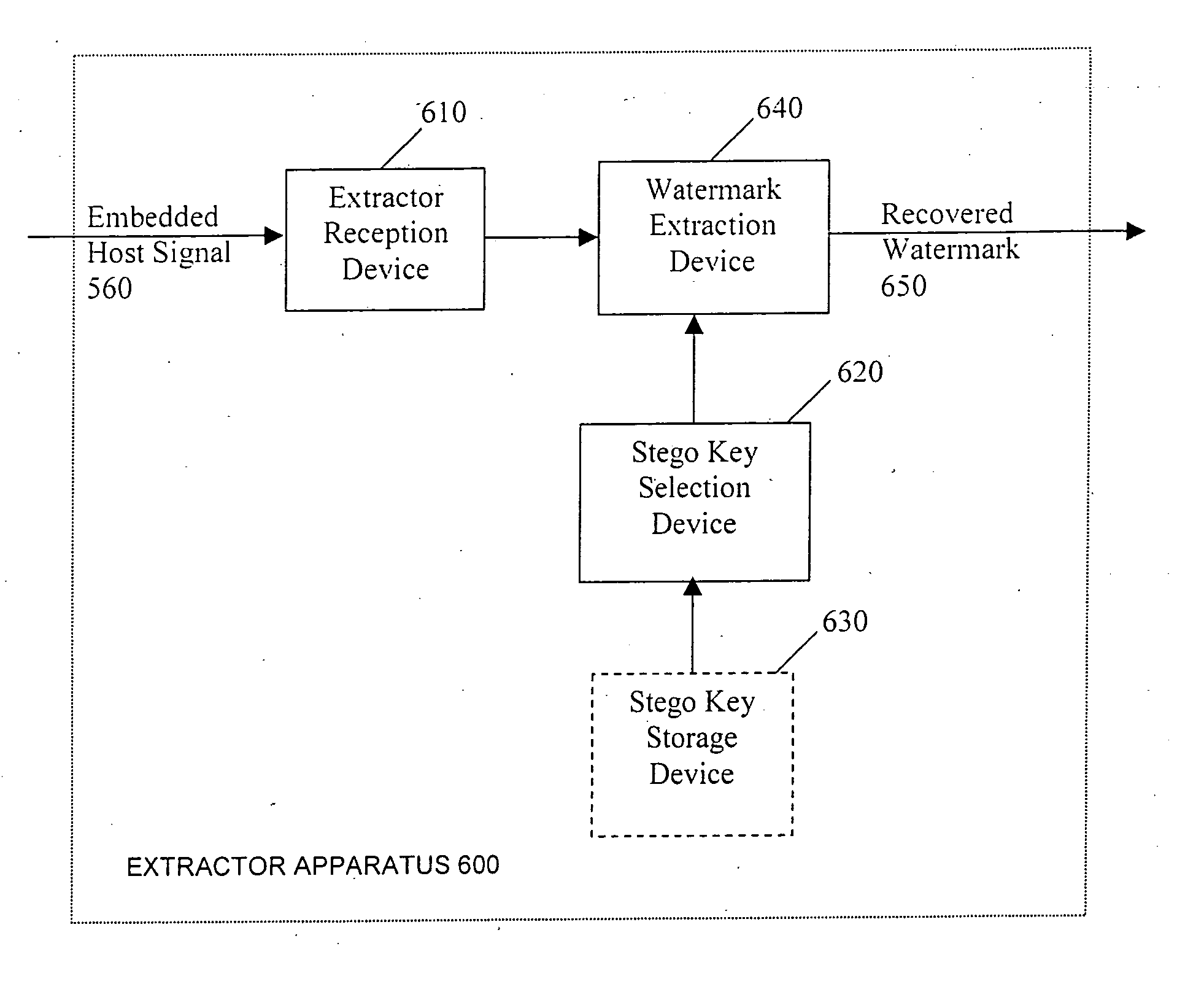
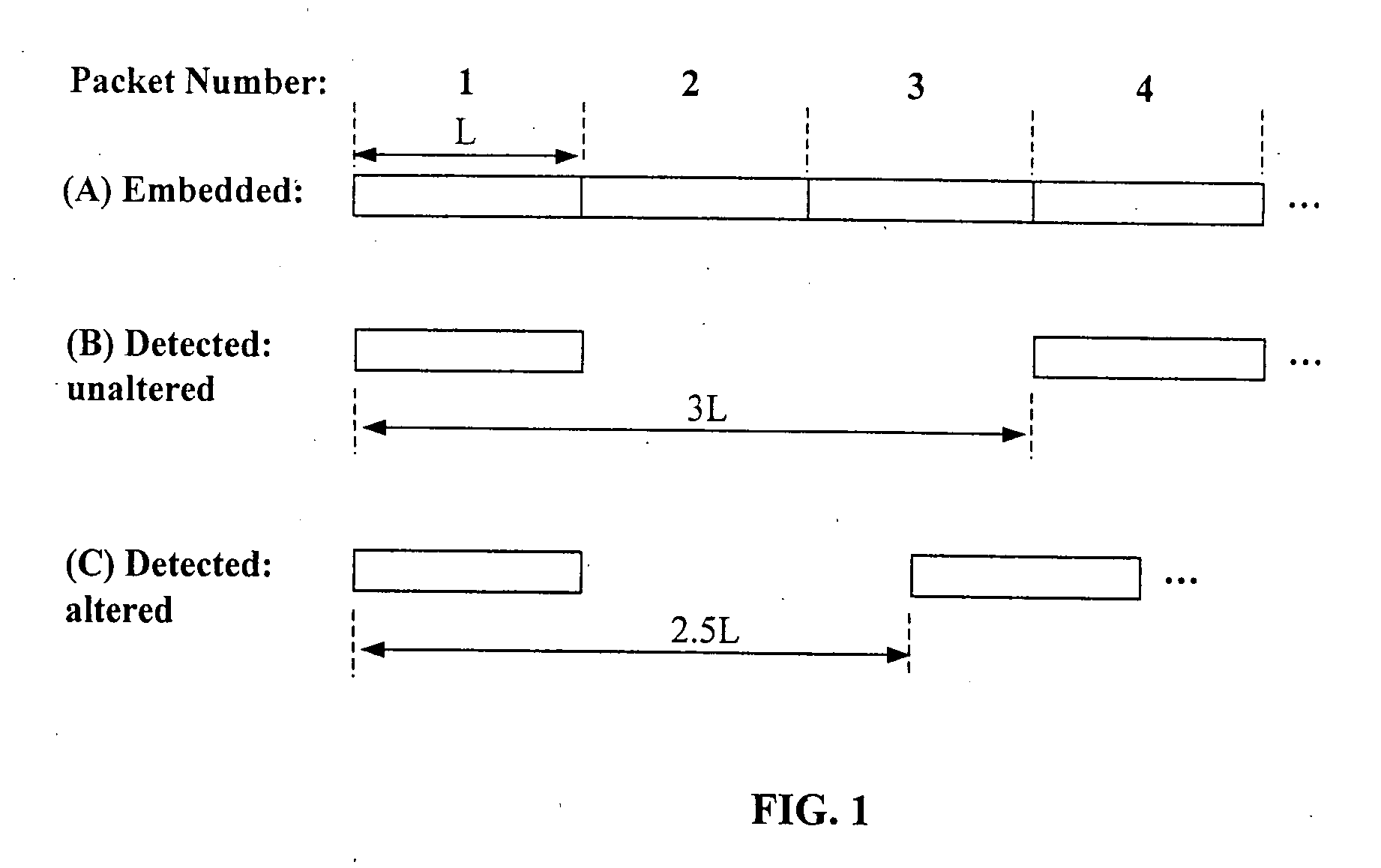
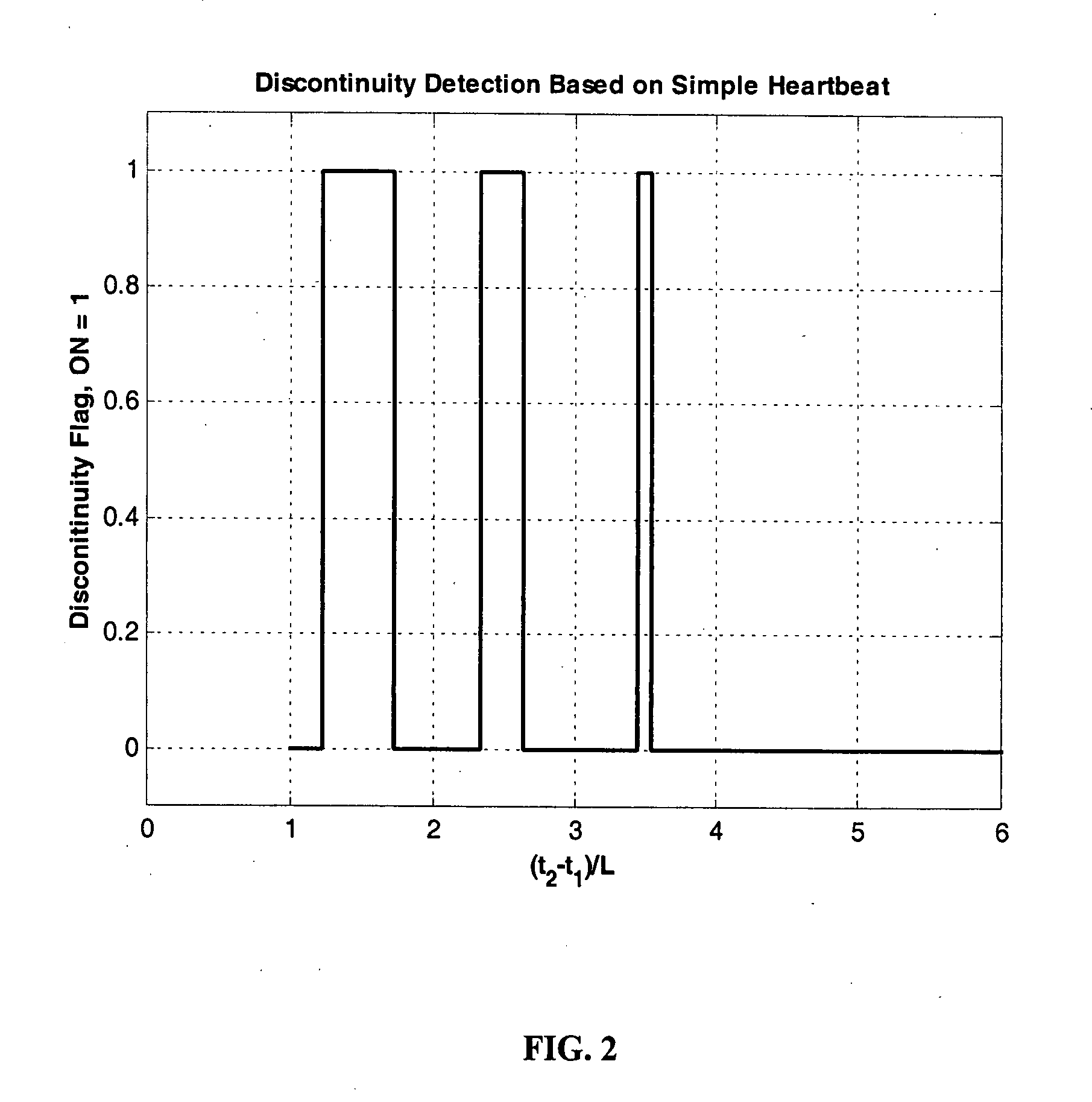
Methods, apparatus, and systems for signal continuity assessment using embedded watermarks are provided. The embedded watermarks are recovered from the content and one or more attributes associated with the recovered watermarks are identified. A continuity of the content can then be assessed in accordance with the one or more attributes. The continuity assessment may be based on a variety of factors, including but not limited to a determined heartbeat of the recovered watermarks, a density, separation, location, or extent, of the recovered watermarks, as well as information associated with the watermarks, such as a stego key, channel bits, packet numbers, a fingerprint, or the like.
Owner:IP ACQUISITIONS LLC
Adaptive shading in a graphics processing pipeline
ActiveUS20150170409A1Fine granularityConsumes less power3D-image renderingComputational scienceGraphics
One embodiment of the present invention includes a parallel processing unit (PPU) that performs pixel shading at variable granularities. For effects that vary at a low frequency across a pixel block, a coarse shading unit performs the associated shading operations on a subset of the pixels in the pixel block. By contrast, for effects that vary at a high frequency across the pixel block, fine shading units perform the associated shading operations on each pixel in the pixel block. Because the PPU implements coarse shading units and fine shading units, the PPU may tune the shading rate per-effect based on the frequency of variation across each pixel group. By contrast, conventional PPUs typically compute all effects per-pixel, performing redundant shading operations for low frequency effects. Consequently, to produce similar image quality, the PPU consumes less power and increases the rendering frame rate compared to a conventional PPU.
Owner:NVIDIA CORP
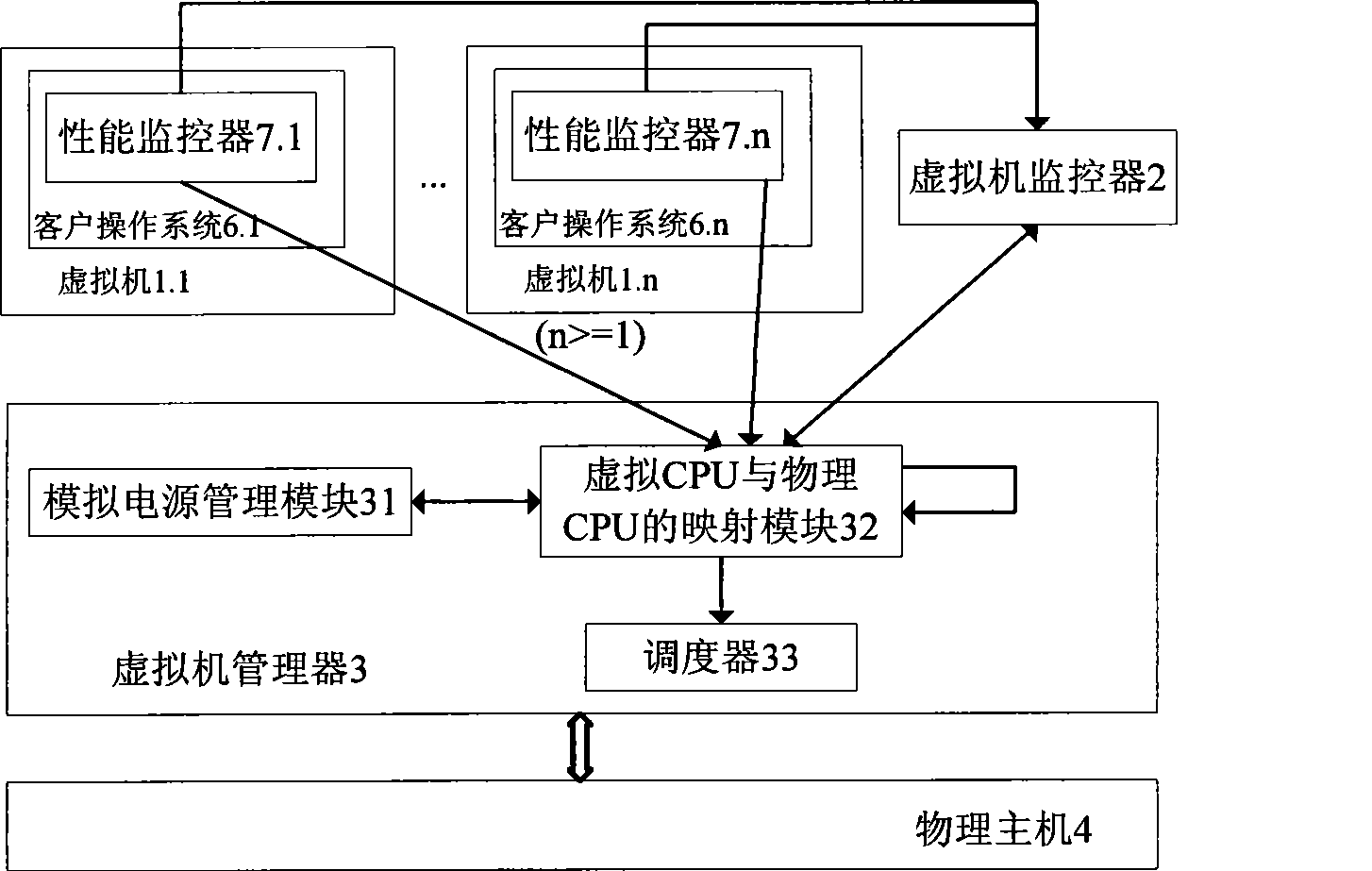
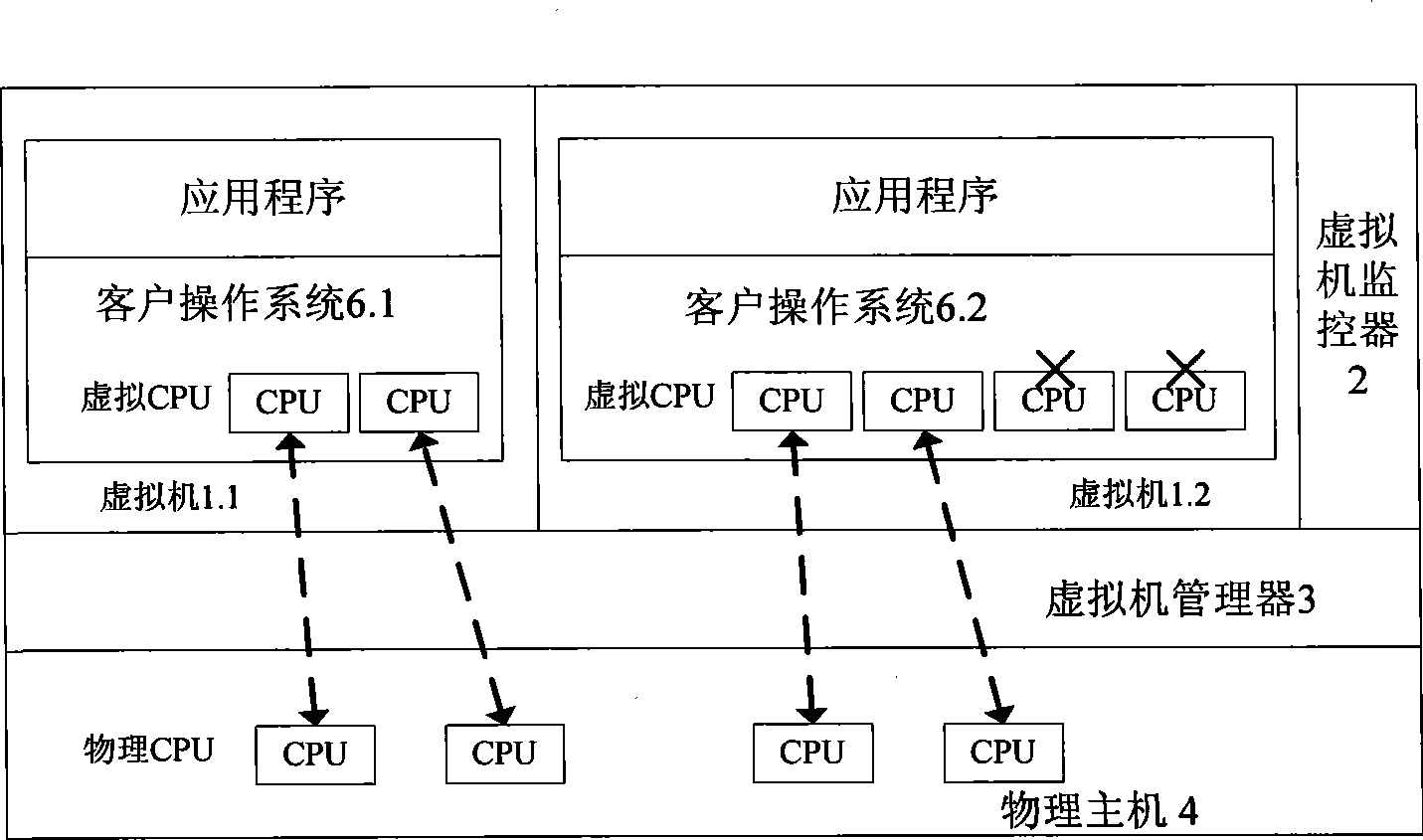
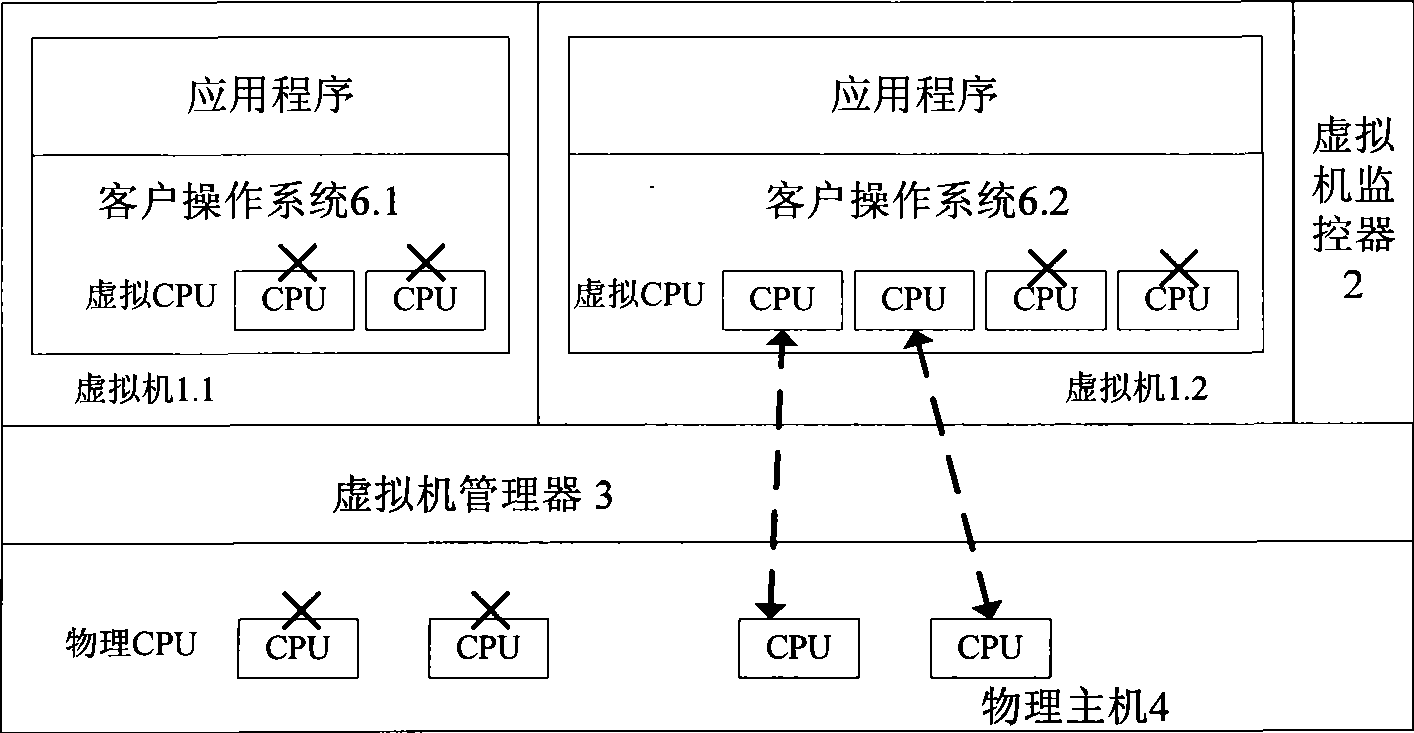
Multi-core computing resource management system based on virtual computing technology
InactiveCN101488098AReasonable distributionImprove management abilityEnergy efficient ICTResource allocationMulti core computingResource Management System
The invention relates to a multi-core system computer resource management system based on a virtual computer technology. The system comprises a plurality of virtual machines, a virtual machine monitor and a virtual machine manager. The virtual machine monitor monitors the load condition and the operation state of the virtual machine at real time. The virtual machine manager is a bond for communication between a virtual machine and a physical host. The virtual machine operates on the virtual machine manager and provides the user with a virtual platform. At the same time, the invention divides the virtual machine into three general categories, and different resource adjusting strategies are adopted for each category of the virtual machine respectively. The invention provides a practical and feasible way for the dynamic adjusting and distributing problem of multi-core computer resource and realizes the maximization of energy saving and resource utilization.
Owner:HUAZHONG UNIV OF SCI & TECH
Intrusion detection in a data center environment
ActiveUS7610375B2Network degradationRemove noiseError preventionTransmission systemsTraffic capacityData center
Owner:CISCO TECH INC
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
InactiveUS20080005572A1Fine granularityEffective distributionError preventionFrequency-division multiplex detailsData streamDigital signature
Disclosed herein are methods and systems for transmitting streams of data. The present invention also relates to generating packet watermarks and packet watermark keys. The present invention also relates to a computerized system for packaging data for transmission to a user. The system may utilize computer code to generate a bandwidth rights certificate that may include: at least one cryptographic credential; routing information for the transmission; and, optionally, a digital signature of a certificate owner; a unique identification code of a certificate owner; a certificate validity period; and pricing information for use of bandwidth. The present invention also relates to an electronic method and system for purchasing good and services by establishing an account whereby a customer is credited with a predetermined amount of bandwidth usage, and then charges are assessed against the account in an amount of bandwidth usage which corresponds to the agreed upon purchase value for the selected item.
Owner:WISTARIA TRADING INC
Error propagation tree technology
A method and system for providing condition information associated with an entity being analyzed. The method includes presenting nodes corresponding to components of the entity according to a tree-like configuration, and providing condition information associated with at least one of the components using the nodes.
Owner:TRIVENI DIGITAL
Methods, systems and devices for packet watermarking and efficient provisioning of bandwidth
ActiveUS20080005571A1Fine granularityEffective distributionUser identity/authority verificationDigital data protectionComputer networkDigital signature
Disclosed herein are methods and systems for transmitting streams of data. The present invention also relates to generating packet watermarks and packet watermark keys. The present invention also relates to a computerized system for packaging data for transmission to a user. The system may utilize computer code to generate a bandwidth rights certificate that may include: at least one cryptographic credential; routing information for the transmission; and, optionally, a digital signature of a certificate owner; a unique identification code of a certificate owner; a certificate validity period; and pricing information for use of bandwidth. The present invention also relates to an electronic method and system for purchasing good and services by establishing an account whereby a customer is credited with a predetermined amount of bandwidth usage, and then charges are assessed against the account in an amount of bandwidth usage which corresponds to the agreed upon purchase value for the selected item.
Owner:WISTARIA TRADING INC
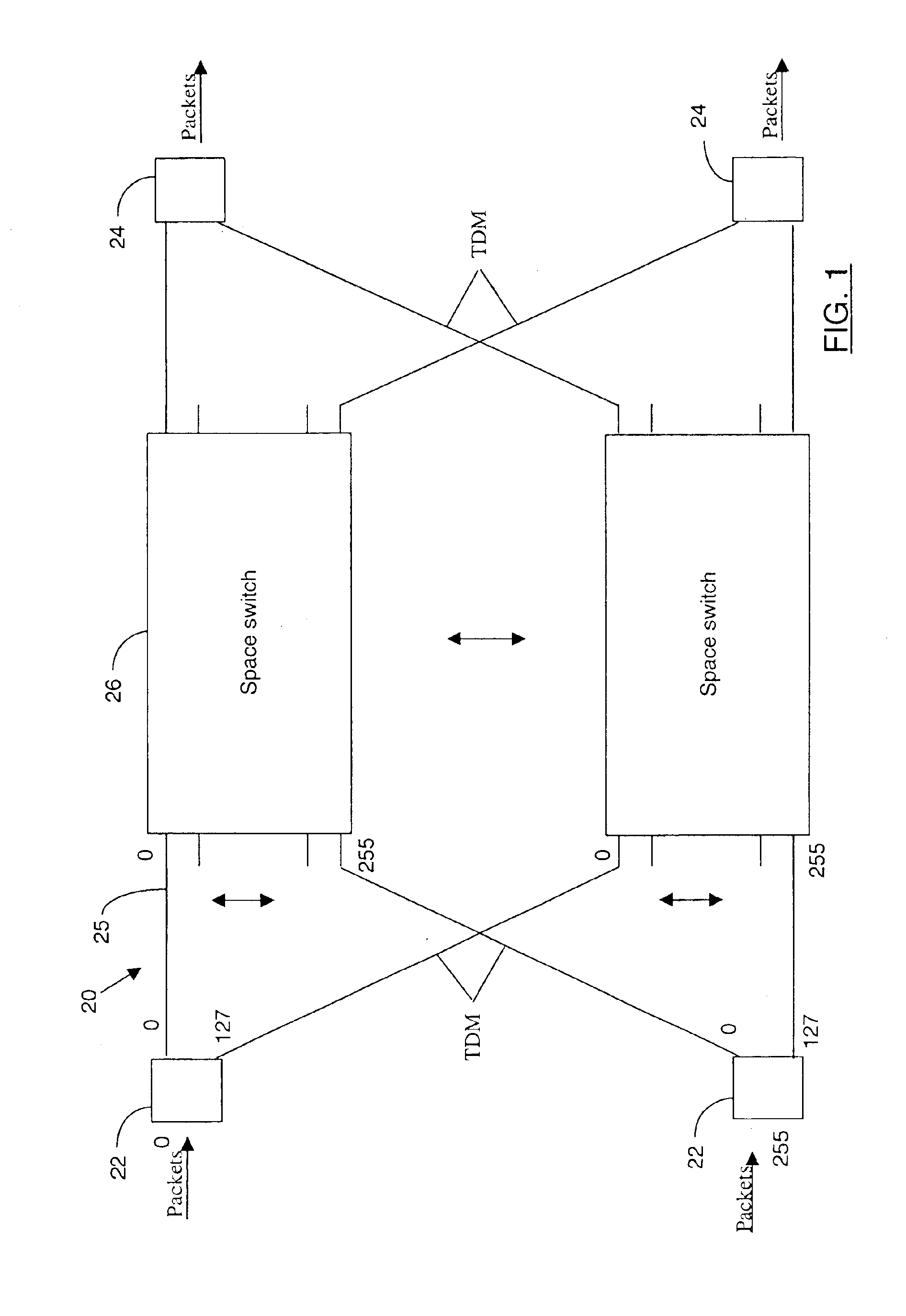
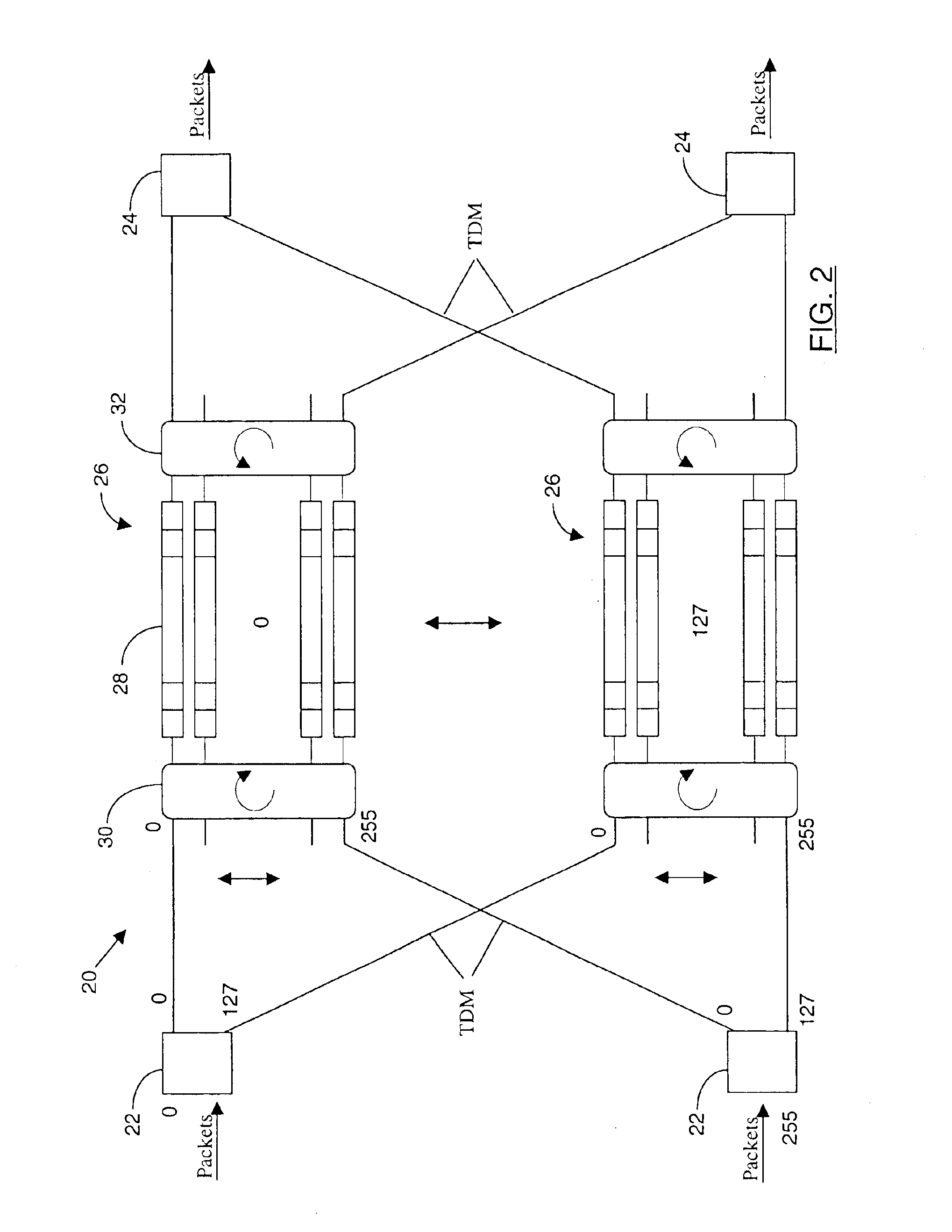
High-capacity WDM-TDM packet switch
InactiveUS6876649B1Fine granularityReduces and eliminates requirementMultiplex communicationCircuit switching systemsHigh bandwidthTera-
A self-configuring distributed packet switch which operates in wavelength division multiplexed (WDM) and time division multiplexed (TDM) modes is described. The switch comprises a distributed channel switching core, the core modules being respectively connected by a plurality of channels to a plurality of high-capacity packet switch edge modules. Each core module operates independently to schedule paths between edge modules, and reconfigures the paths in response to dynamic changes in data traffic loads reported by the edge modules. Reconfiguration timing between the packet switch modules and the channel switch core modules is performed to keep reconfiguration guard time minimized. The advantage is a high-capacity, load-adaptive, self-configuring switch that can be distributed to serve a large geographical area and can be scaled to hundreds of Tera bits per second to support applications that require, very high bandwidth and a guaranteed quality of service.
Owner:CIENA
Auto mapping through location based triggers
InactiveUS20070129082A1Fine granularityHigh frequencyInstruments for road network navigationRoad vehicles traffic controlNavigation systemMobile device
An automated map generator that can be used for creating new maps for uncharted areas, augmenting uncompleted maps, or creating maps for areas that are changing dynamically. One or more mobile devices include location based technology that operates to identify a current location for the mobile device and report that location to the map creation application. If the location of the mobile device is within an active mapping region, the map creation device can instruct the mobile device to report its location on a more frequent basis and then commence to map out the route to the mobile device. As the route is mapped out, a new map of the territory is created. As subsequent devices enter into that area (including navigational systems), the updated mapping information is provided to the device and can then be augmented by future location readings or can simply be used by the device.
Owner:DISCRETE WIRELESS
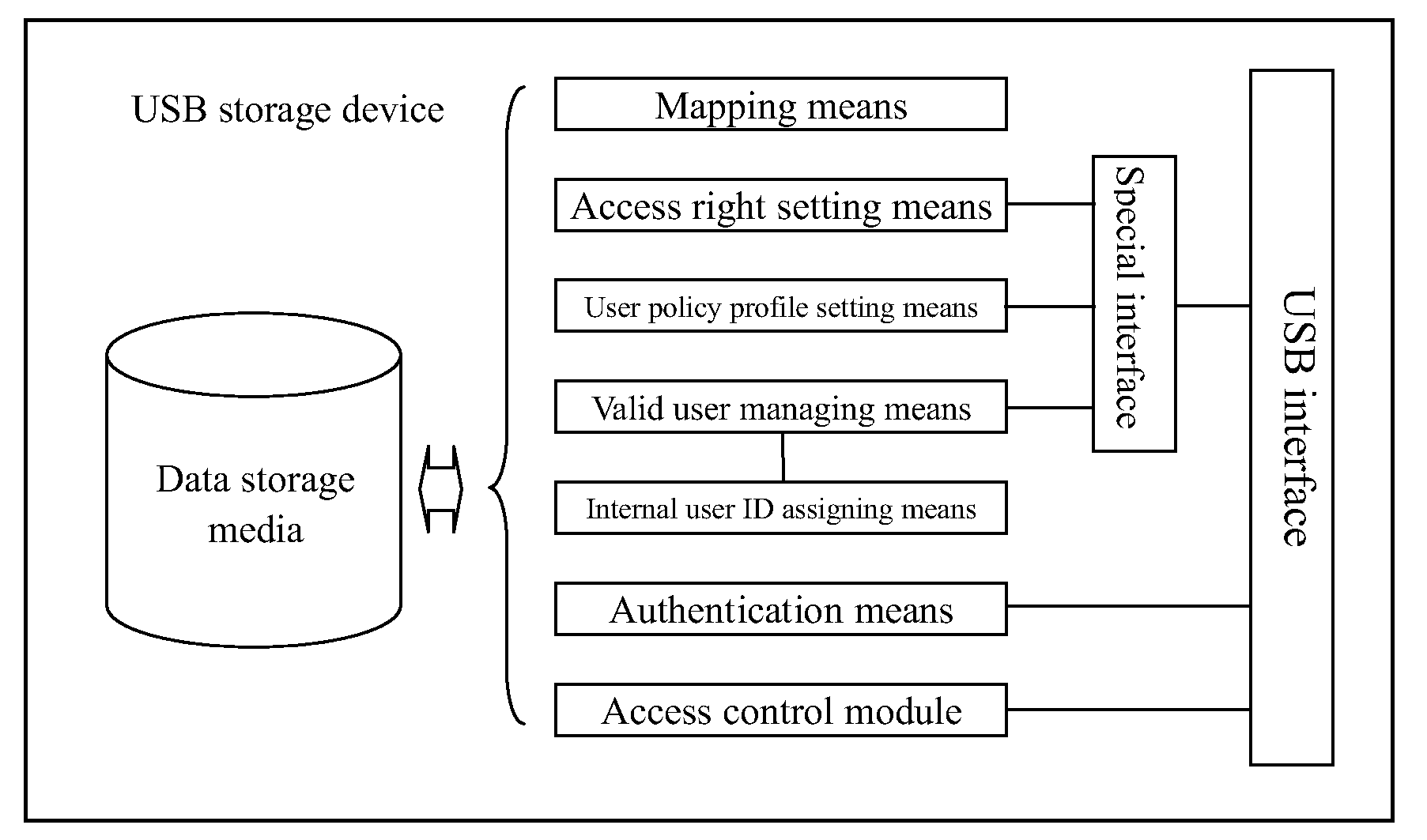
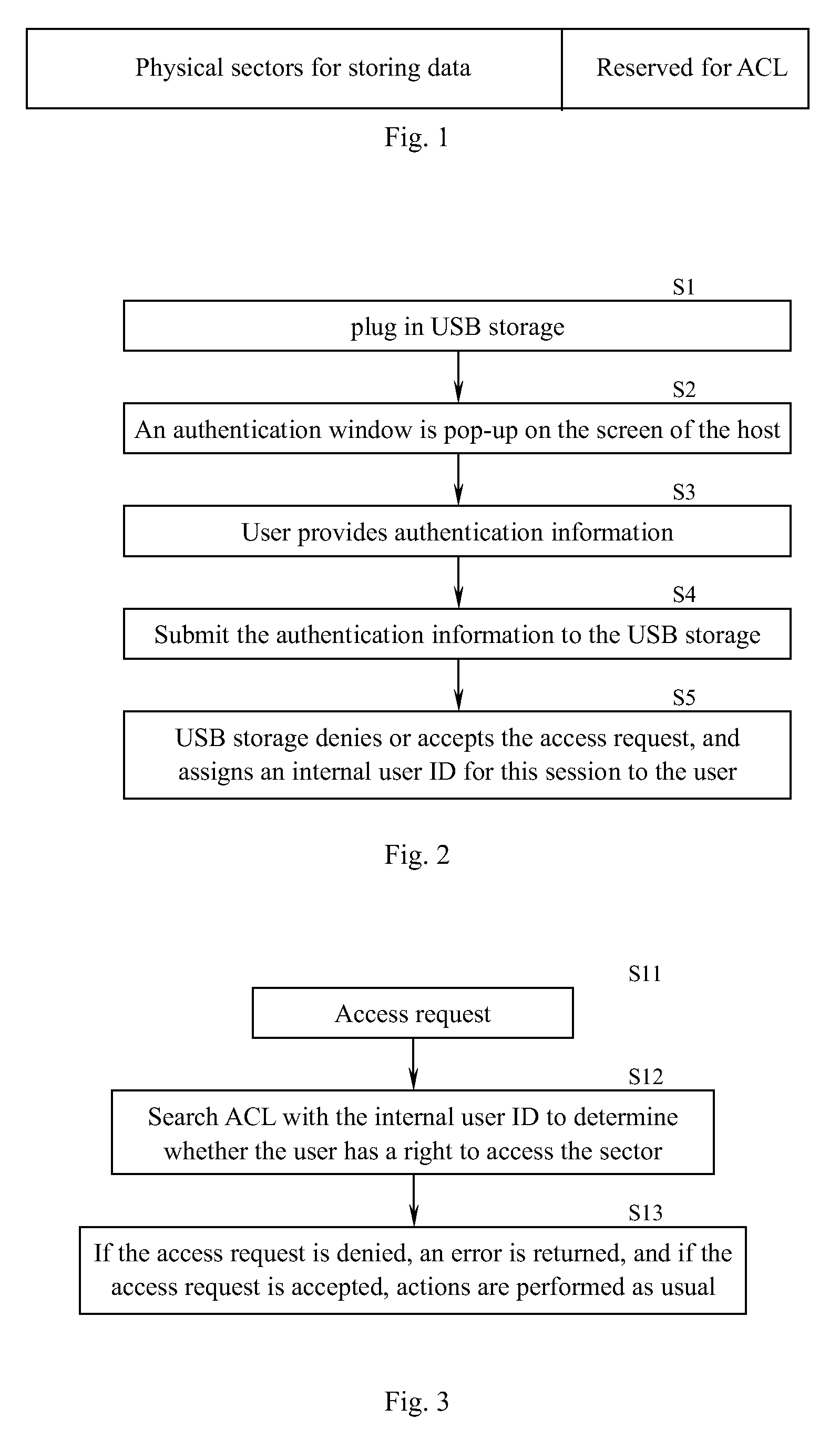
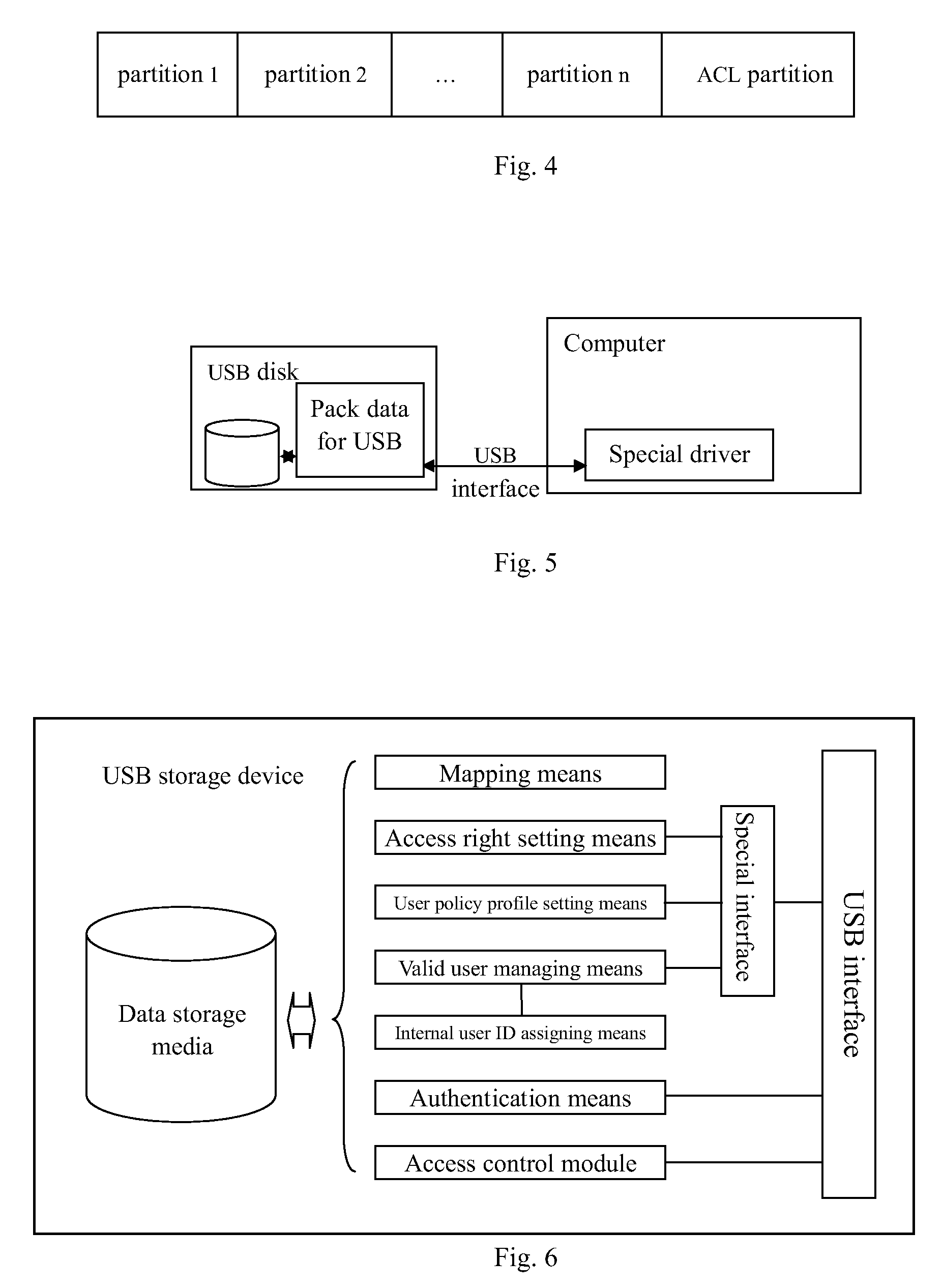
Universal serial bus (USB) storage device and access control method thereof
InactiveUS20090300710A1Fine granularityDigital data processing detailsUnauthorized memory use protectionUSBData store
The invention provides a USB storage device and an access control method thereof. An access control module is provided on the USB storage device. The storage space is divided into at least one data storage entity. Each user's access right to each data storage entity is set and stored in the USB storage device as an access control list. The process between the USB storage device's being connected with a USB host and its being disconnected from the USB host is one session. When a session is established, the user provides authentication information for the USB device to authenticate him / her, and saves the user information used in the current session. In the current session, when the host of the user issues an access request for the data storage entity on the USB storage device, the access control module queries the access right list based on the user information in the current session to determine whether the user has an access right to the requested data storage entity. When the user does not have the access right to the data storage entity, the access control module denies the user's access request for the data storage entity.
Owner:IBM CORP
Location-aware service proxies in a short-range wireless environment
InactiveUS7224979B2Fine granularityParticular environment based servicesNetwork topologiesLocation awareShort range wireless
Owner:REEFEDGE
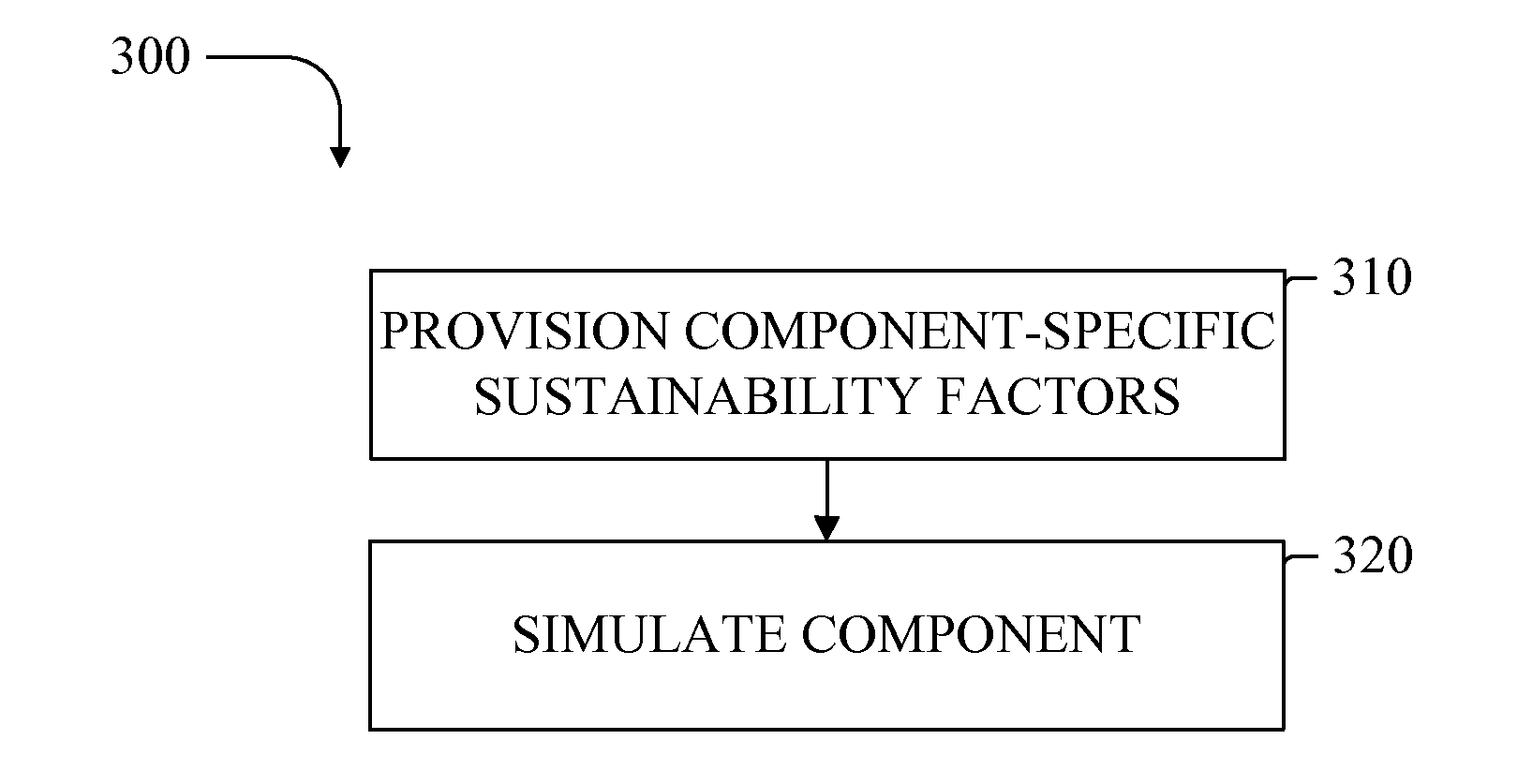
Process simulation utilizing component-specific consumption data
ActiveUS20100274367A1Low costStable supportLevel controlVolume/mass flow measurementGranularityParallel computing
Methods and apparatuses are provided for simulating components and processes using discrete, variable-granularity, component-specific data relating to energy consumption or other sustainability factors. Simulations can be analyzed and optimized to facilitate forecasting of sustainability factors and determine advantageous modifications to the components or processes.
Owner:ROCKWELL AUTOMATION TECH
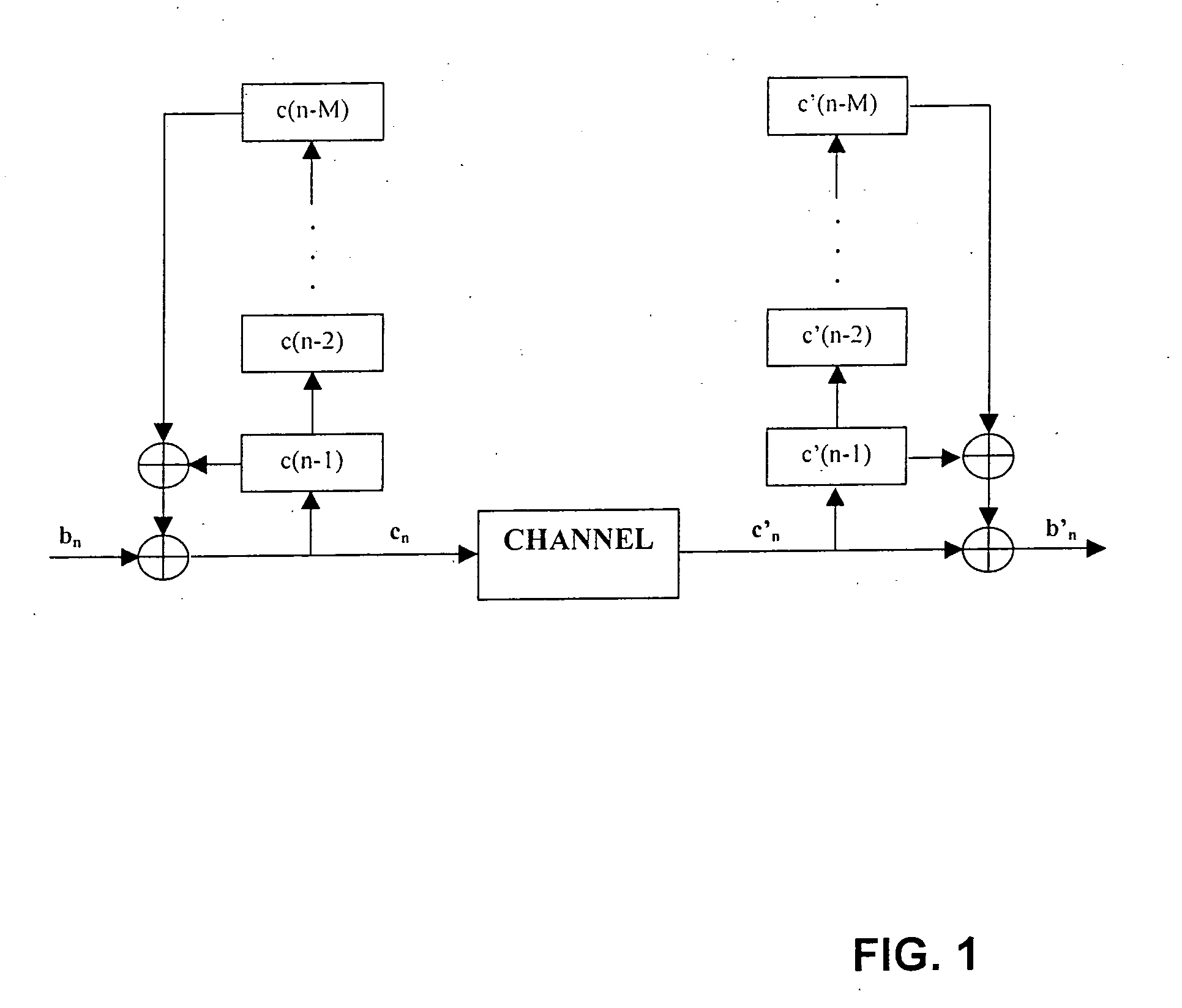
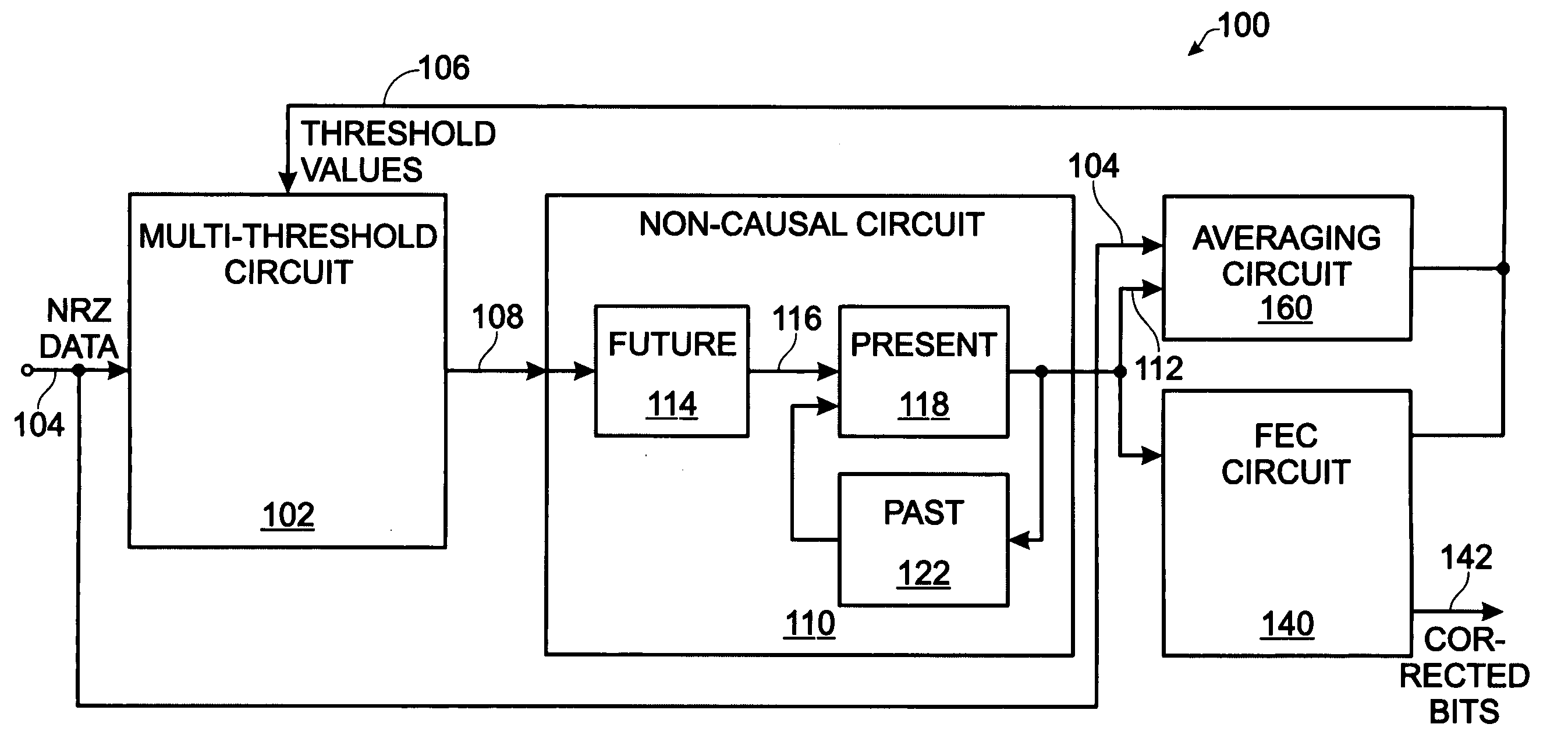
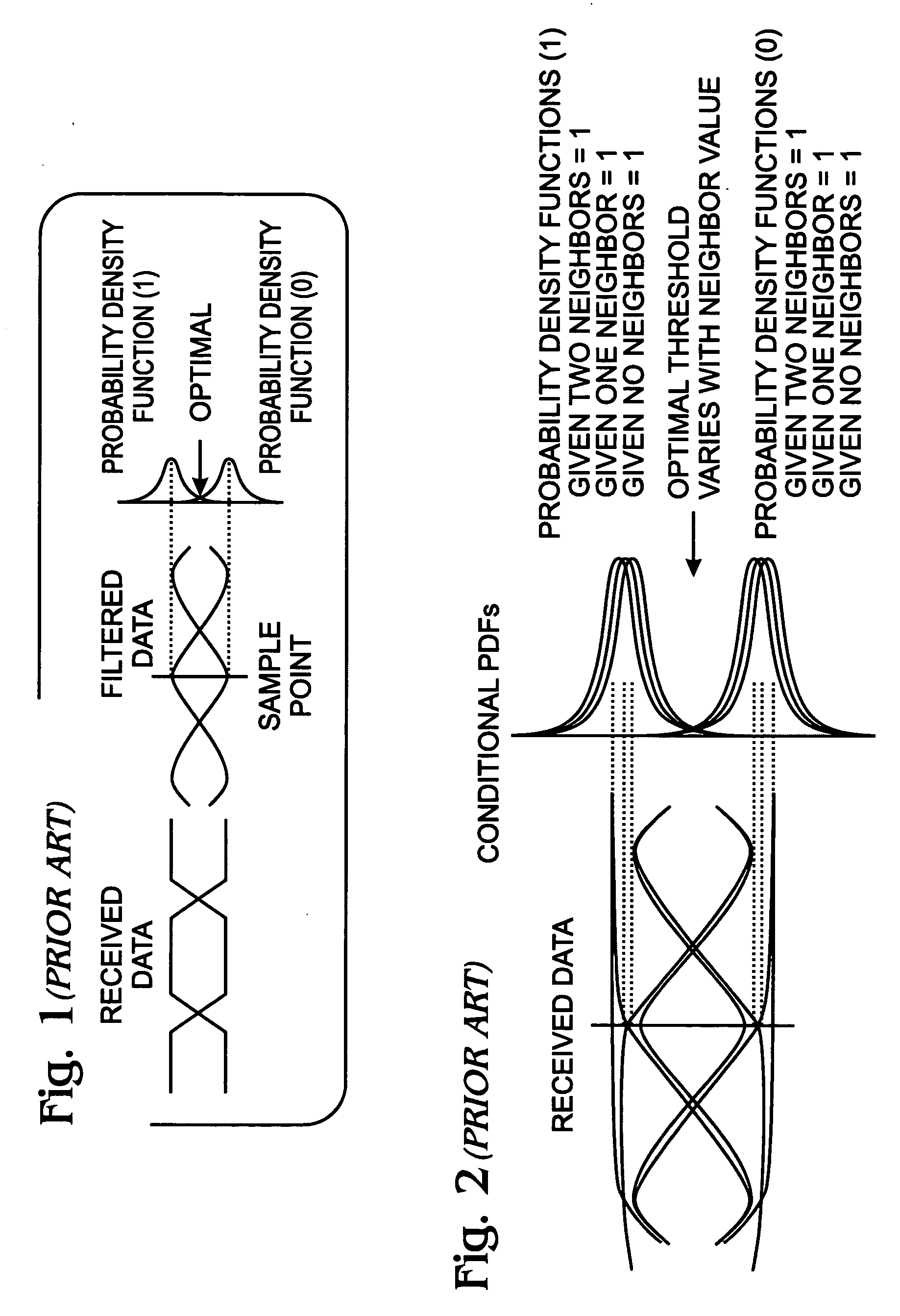
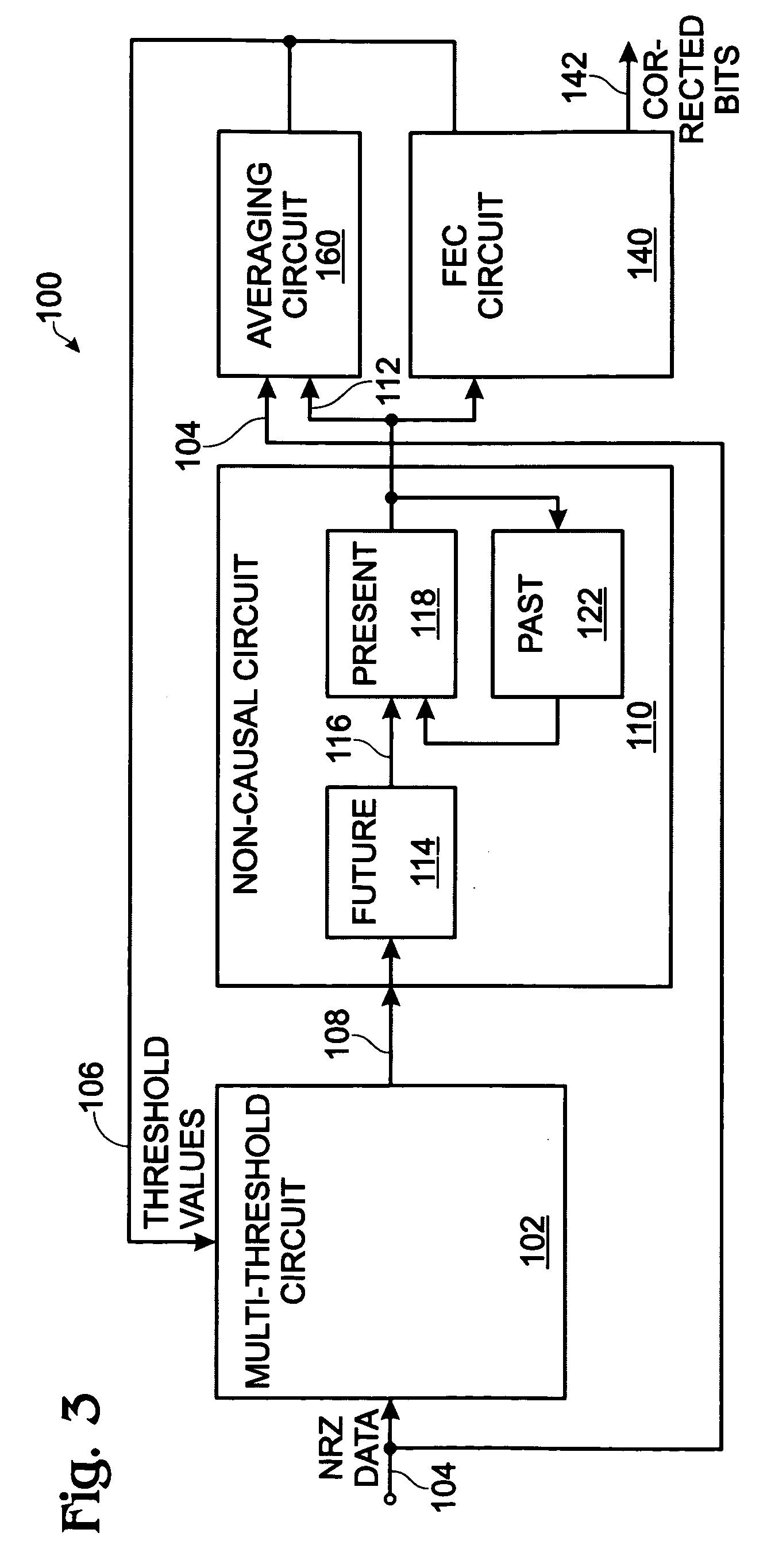
System for five-level non-causal channel equalization
InactiveUS20060256891A1Reduce impactOptimal mitigationError preventionCode conversionCommunications systemData stream
A system and method are provided for five-level non-causal channel equalization in a communications system. The method comprises: receiving a non-return to zero (NRZ) data stream input; establishing a five-level threshold; comparing the first bit estimate to a second bit value received prior to the first bit; comparing the first bit estimate to a third bit value received subsequent to the first bit; and, in response to the comparisons, determining the value of the first bit. Establishing a five-level threshold includes: establishing thresholds to distinguish a first bit value when the second and third bit values are a “1” value, when the second bit value is a “1” and the third bit value is a “0”, when the second bit value is a “0” and the third bit value is a “1”, when the second and third bit values are a “0” value, and an approximate midway threshold.
Owner:APPLIED MICRO CIRCUITS CORPORATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com