Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2384 results about "Packet forwarding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
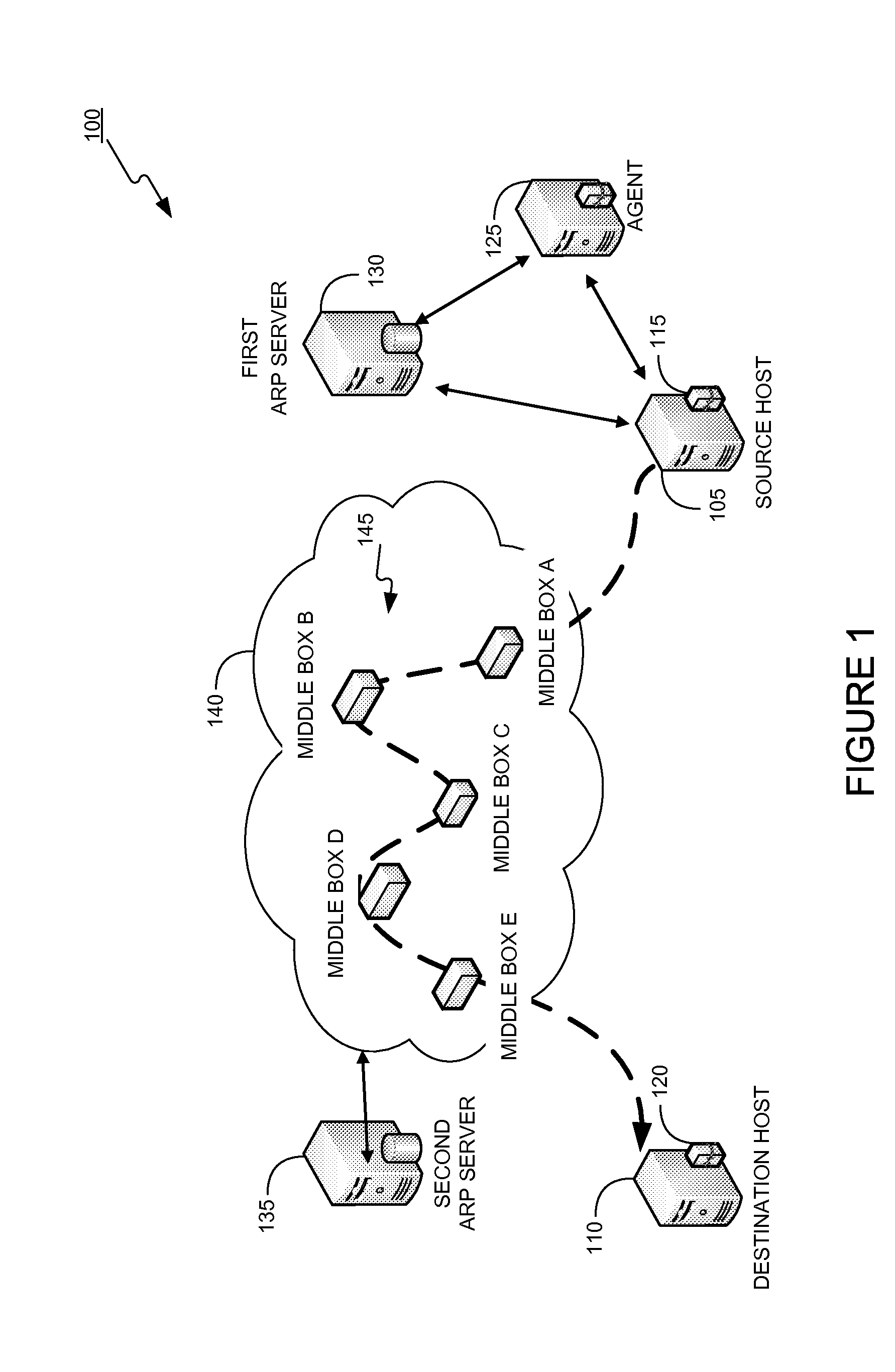
Packet forwarding is the relaying of packets from one network segment to another by nodes in a computer network. The network layer in the OSI model is responsible for packet forwarding.
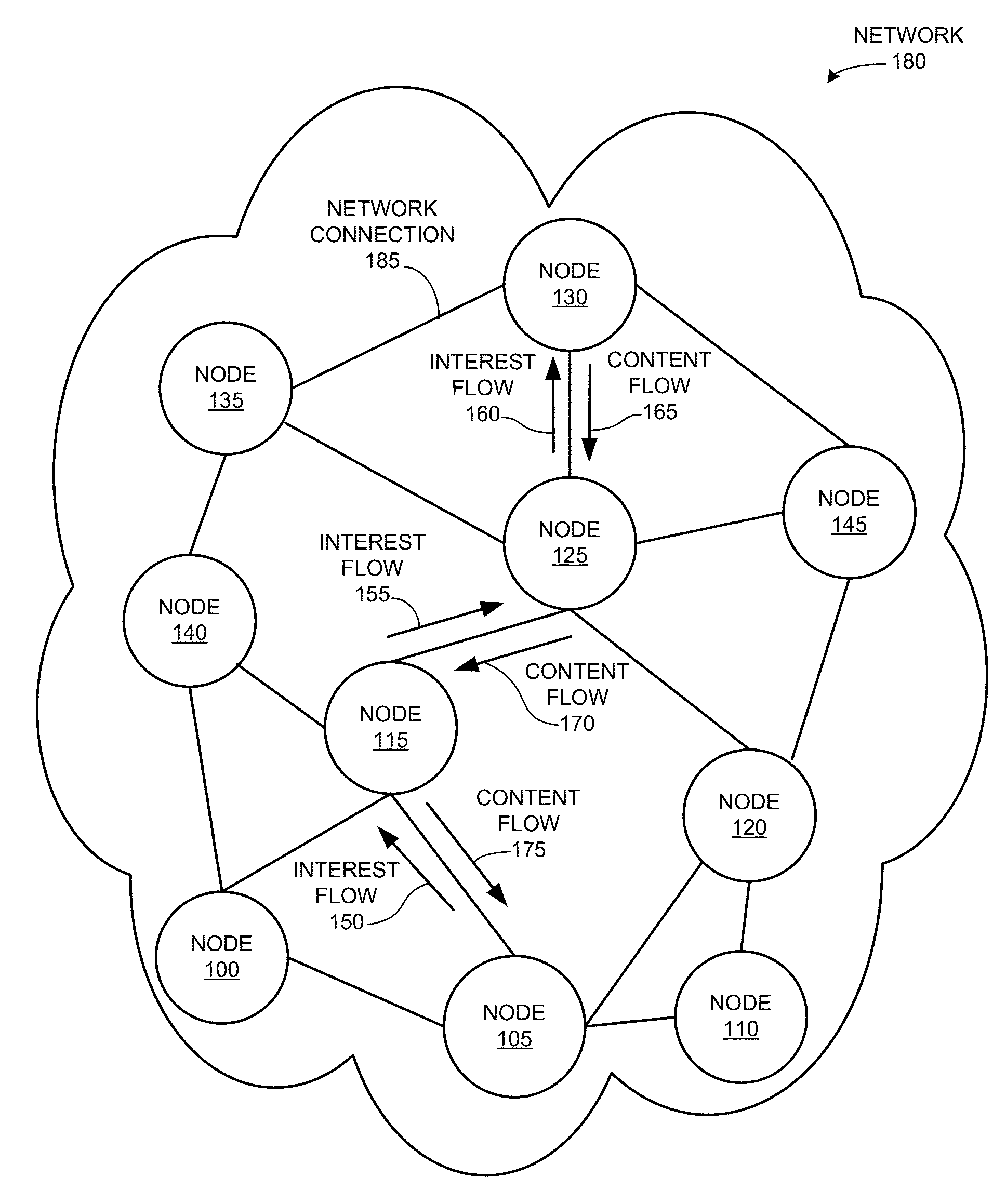
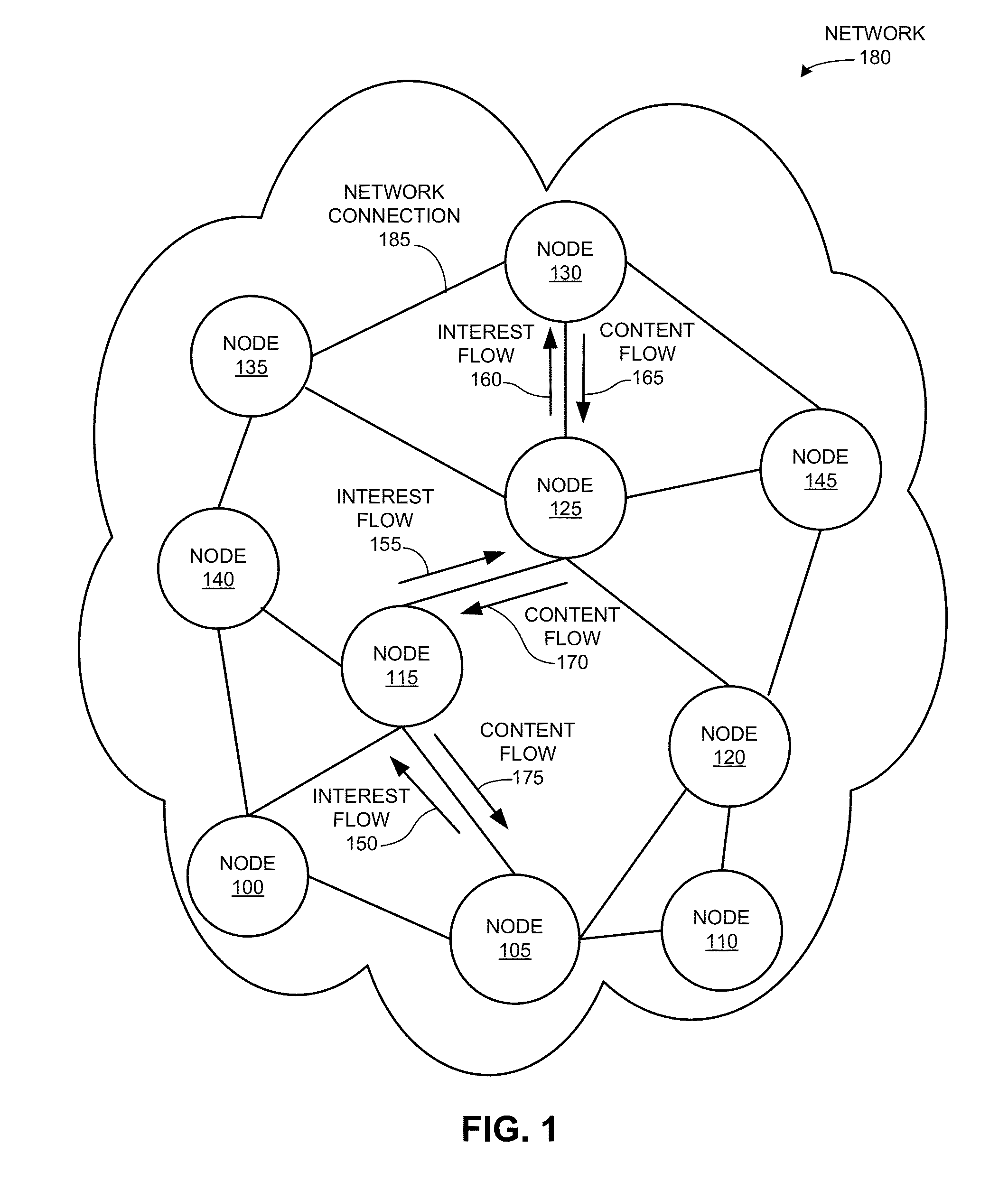
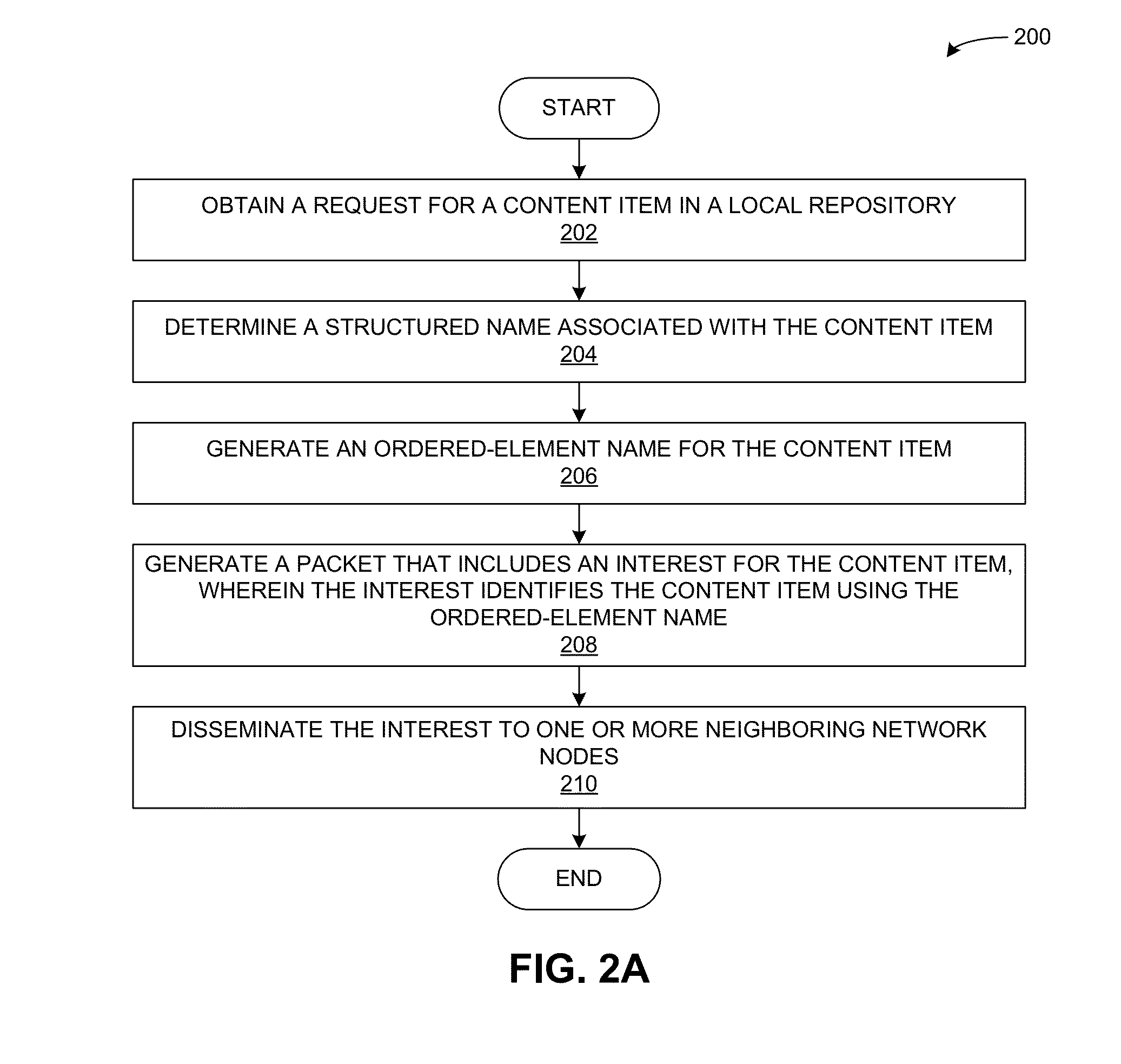
Ordered-element naming for name-based packet forwarding
ActiveUS20140289325A1Easy to determineEasy pairingDigital data processing detailsDigital computer detailsComputer scienceFixed length
A name-based content-forwarding system generates an ordered-element name for a content item, and can process an interest to identify and perform an action that satisfies the interest. To generate the ordered-element name, the system generates one or more fixed-length elements for a content item, such that each fixed-length element of the ordered-element name is mapped to the content item or to a context associated with the content item. The system then generates the ordered-element name to include the one or more fixed-length elements so that the name elements are ordered from a highest matching priority to a lowest matching priority. The system can also generate a packet that includes the ordered-element name for the content item, and sends the packet to a target location that corresponds to the ordered-element name.
Owner:CISCO TECH INC
Dynamically provisioning middleboxes
Hybrid security architecture (HSA) provides a platform for middlebox traversal in the network. The HSA decouples the middlebox control from network forwarding. More specifically, such embodiments may receive a data packet having a packet header including an Ethernet header identifying source and destination addresses in the network. A traffic type of the data packet is determined. Then, layer-2 forwarding information, which encodes a set of non-forwarding network service provider middleboxes in the network to be traversed by the data packet, is determined based on the traffic type. The layer-2 forwarding information is inserted into the Ethernet header and the data packet is forwarded into the network. The data packet will then traverse, according to the layer-2 forwarding information, a sequence of the middleboxes in the network, wherein at least one non-forwarding network service will be provided by each of the middleboxes to the data packet in a sequence.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
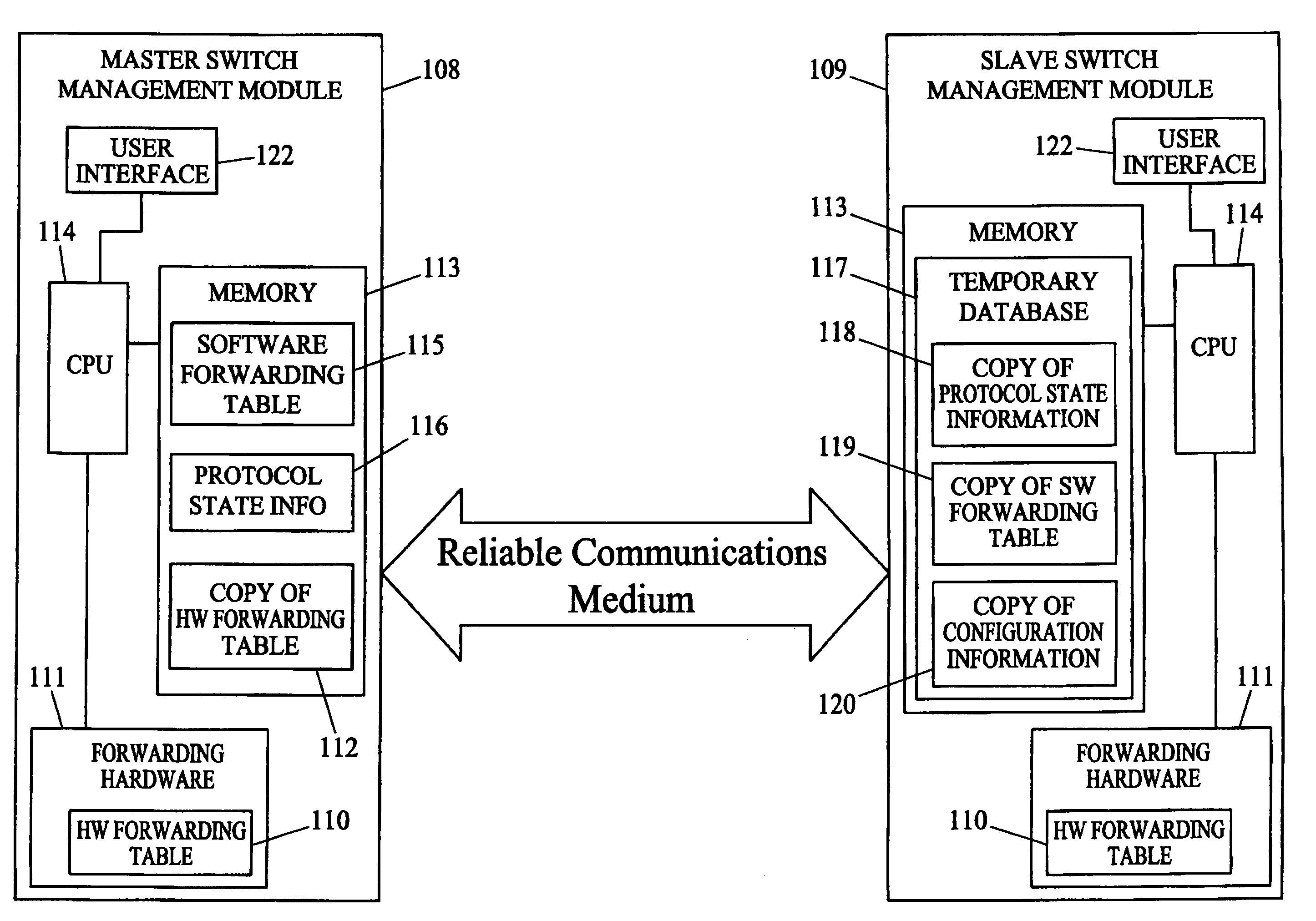
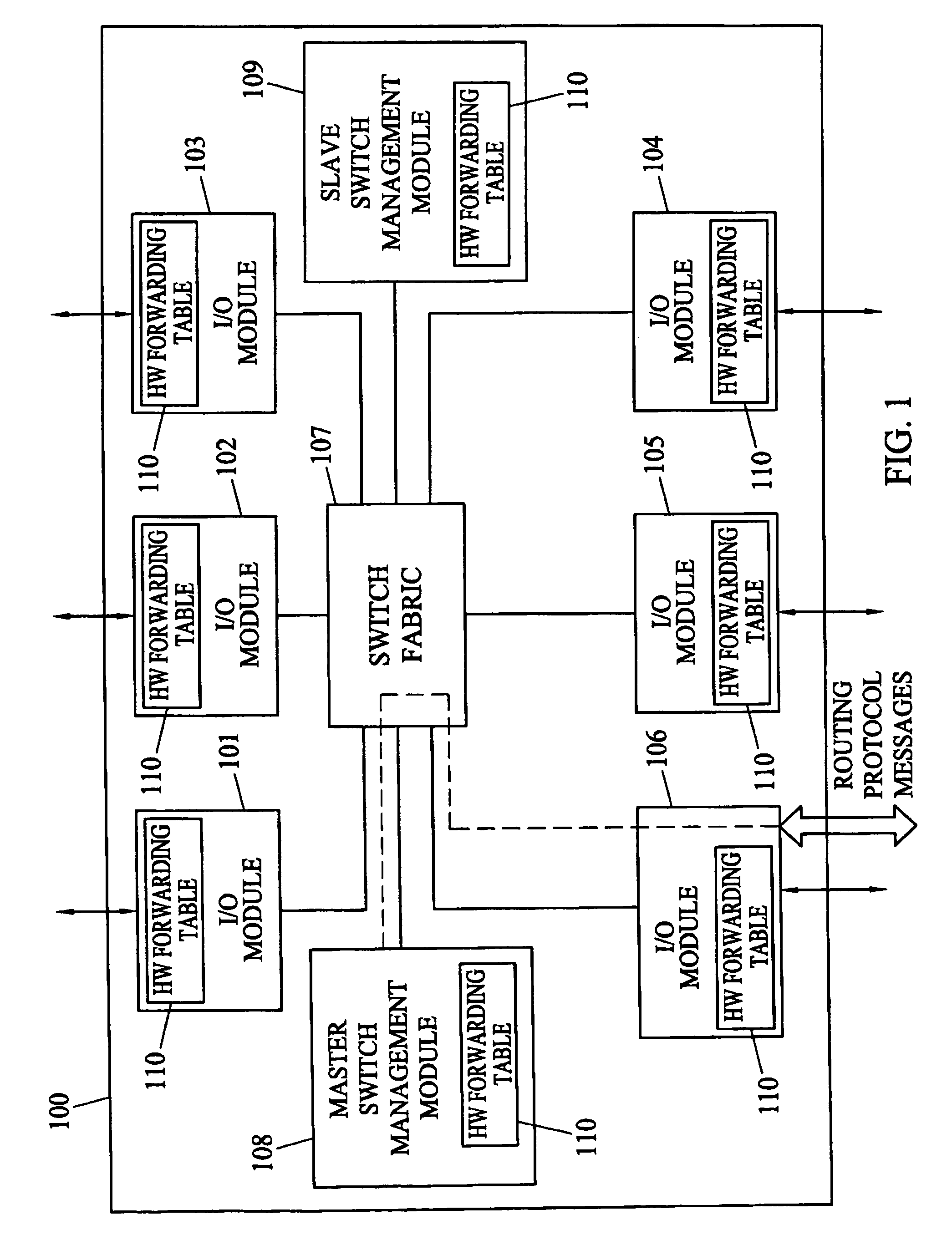
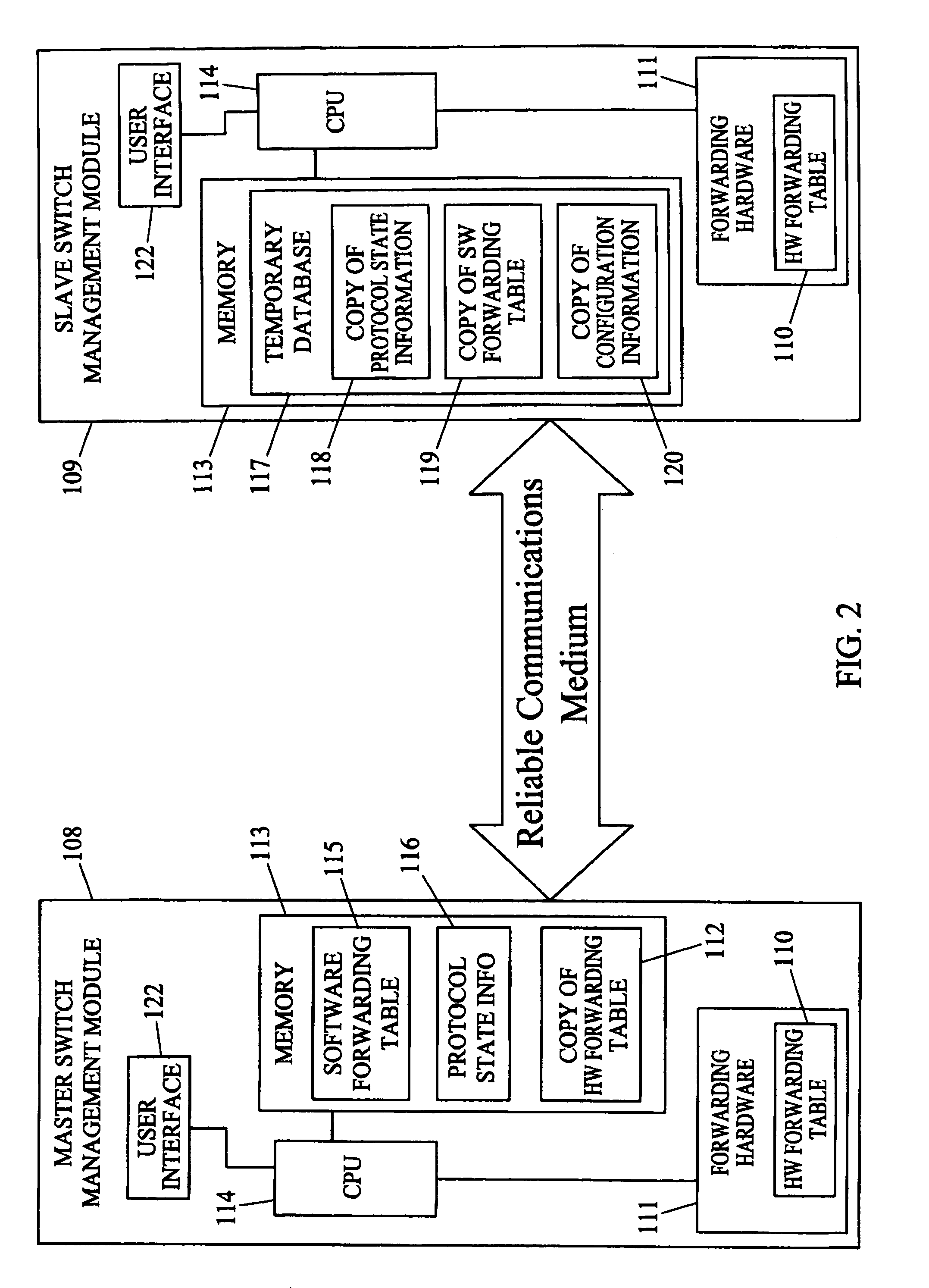
Methods and systems for hitless switch management module failover and upgrade
Methods and systems for hitless switch management module failover and upgrade are disclosed. According to one method, a master switch management module participates in network protocols and performs packet forwarding operations. The master switch management module distributes protocol state and packet forwarding information to the slave switch management module. The slave switch management module continuously monitors the operational state of the master switch management module. In response to detecting failure of the master switch management module or a forced failover initiated by the user interface on the master switch management module, the slave switch management module begins network protocol operation in the master mode in a state where the master switch management module last operated correctly.
Owner:EXTREME NETWORKS INC
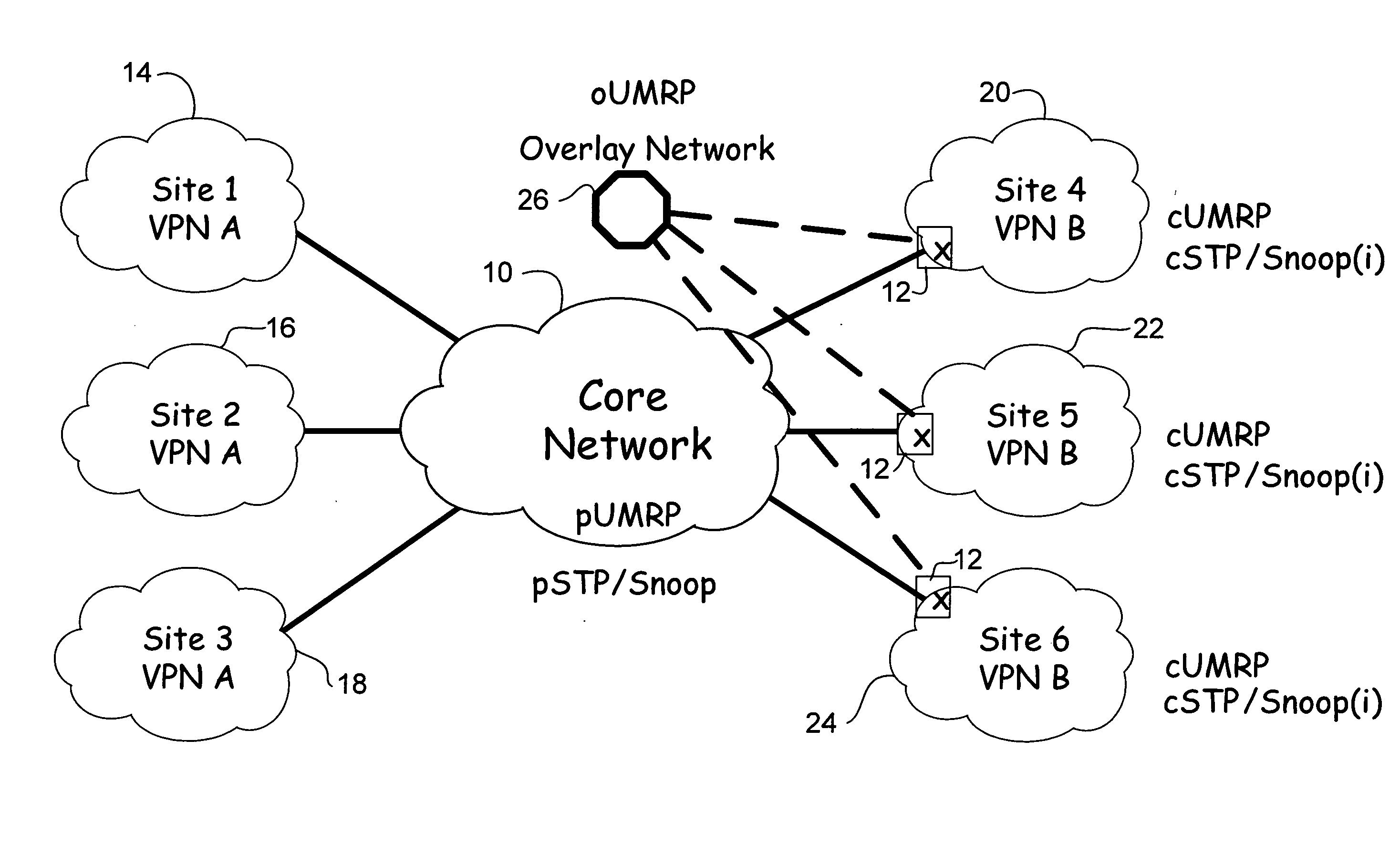
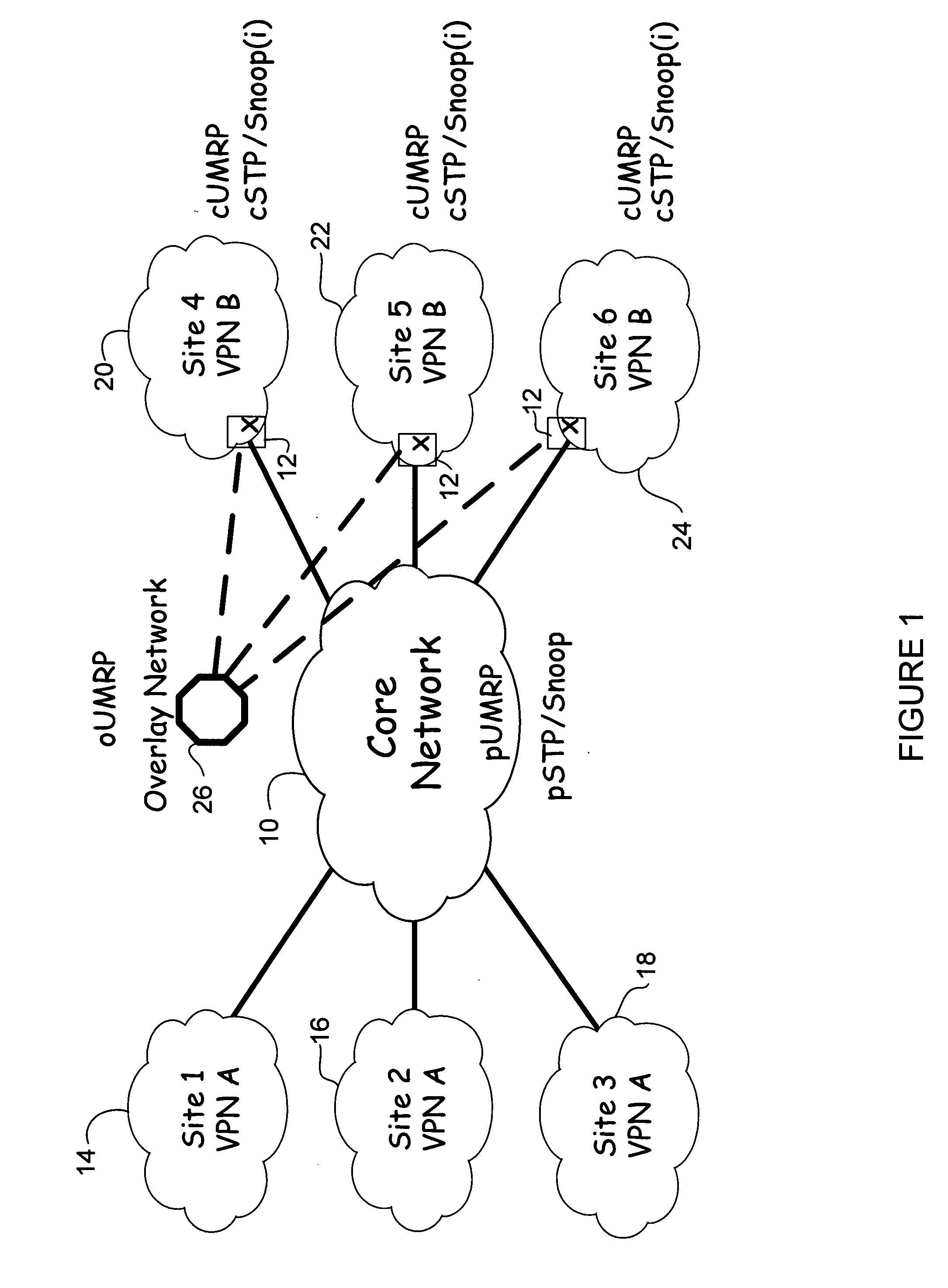
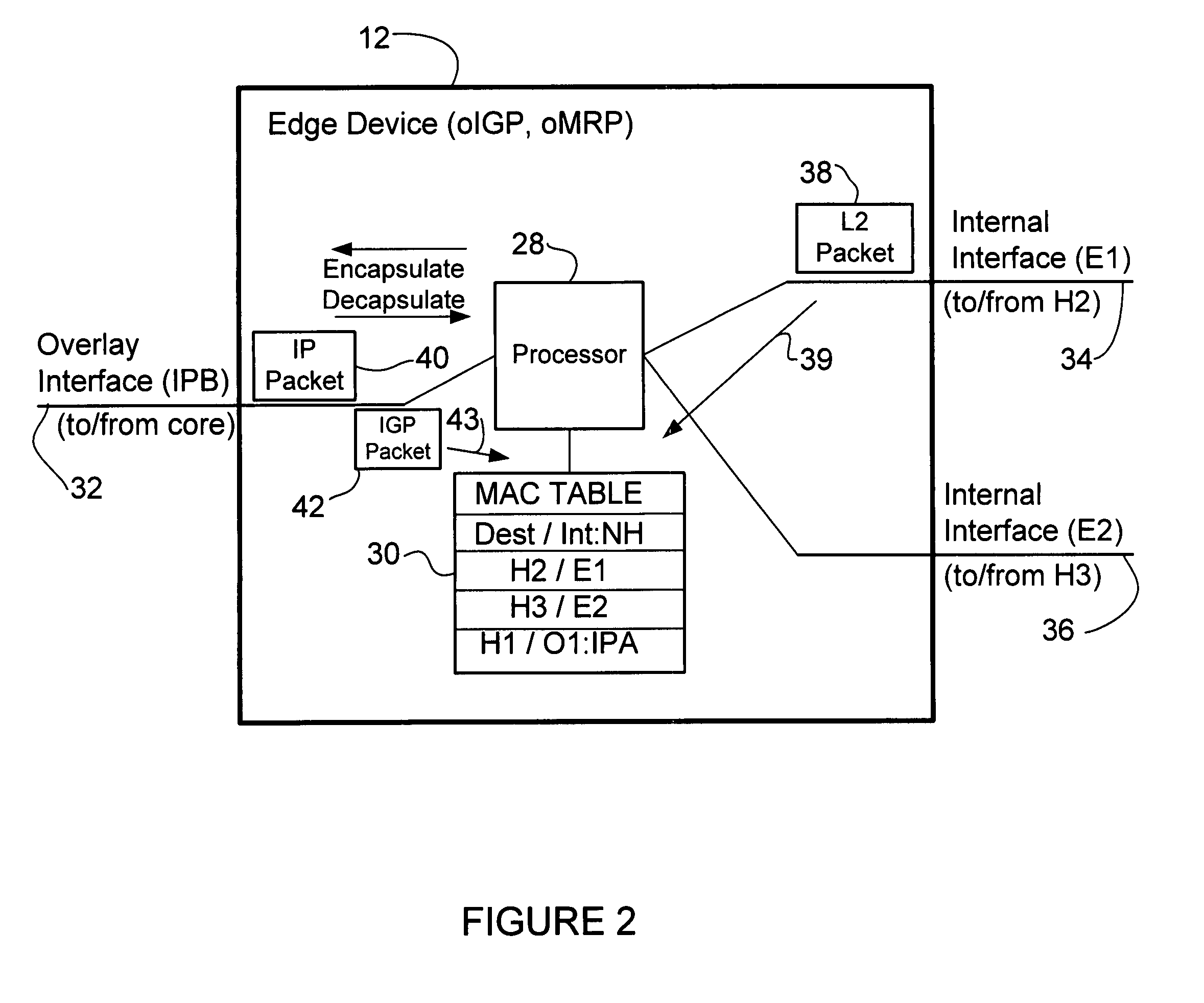
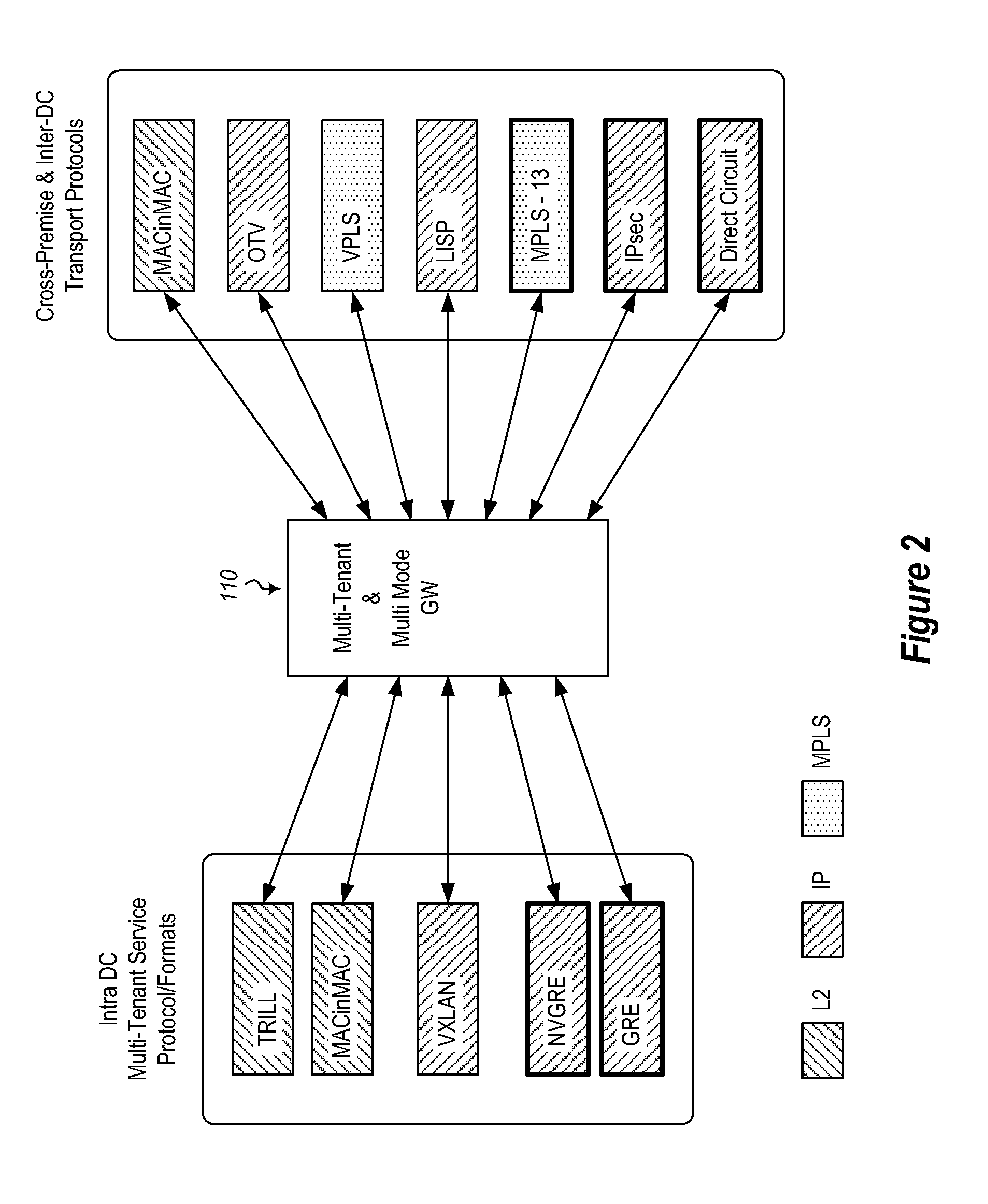
Overlay transport virtualization
ActiveUS20090037607A1Data switching by path configurationMultiple digital computer combinationsVirtualizationEdge device
In one embodiment, an apparatus includes one or more internal interfaces in communication with one or more network devices in a first network site through a Layer 2 link, an overlay interface in communication through a Layer 3 link with a core network connected to one or more other network sites, and a table mapping addresses for network devices in the other network sites to addresses of edge devices in the same network site as the network device. The apparatus further includes a processor operable to encapsulate a packet received at one of the internal interfaces and destined for one of the network devices in the other network sites, with an IP header including a destination address of the edge device mapped to the destination network device, and forward the encapsulated packet to the core network.
Owner:CISCO TECH INC
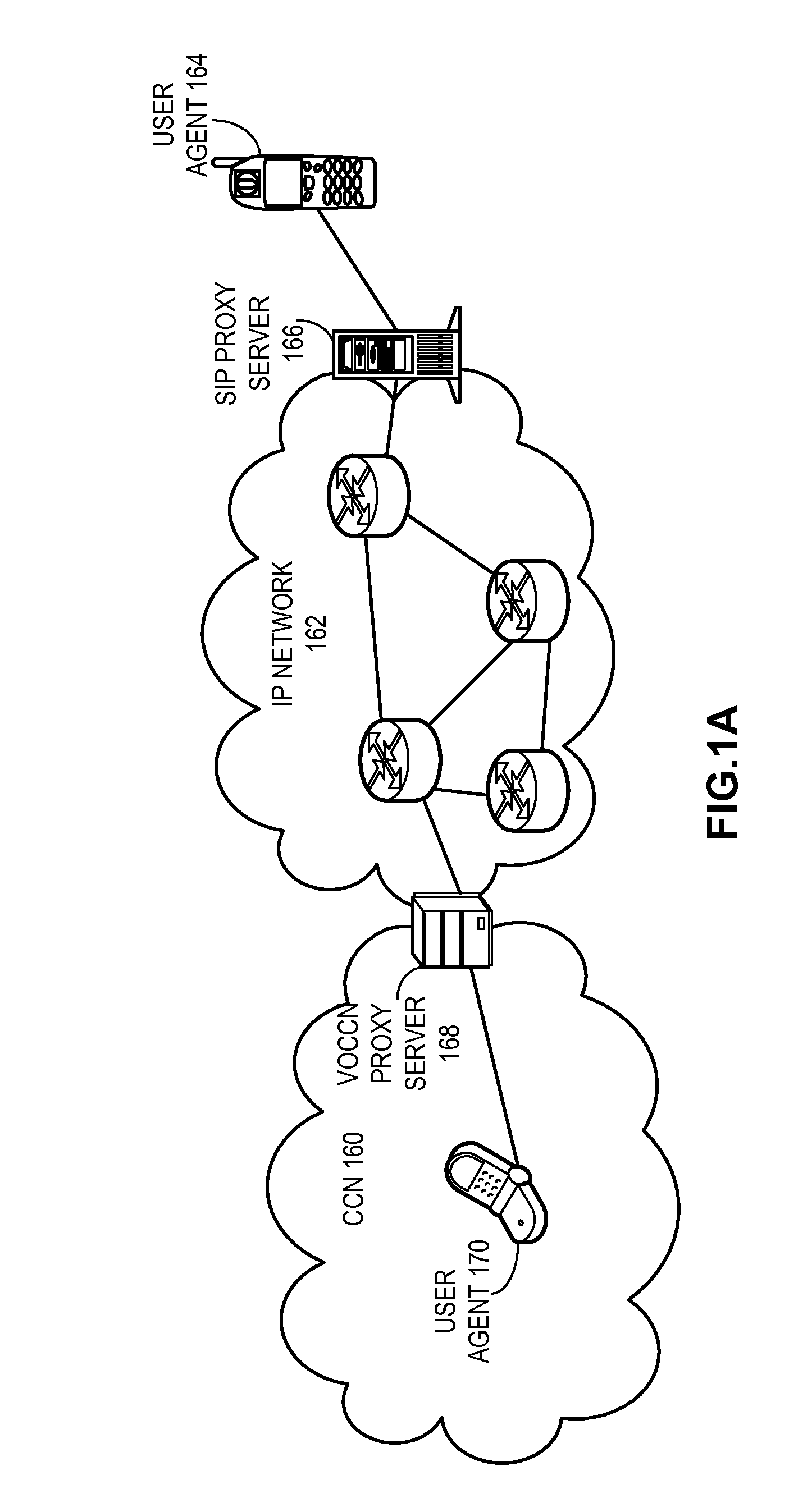
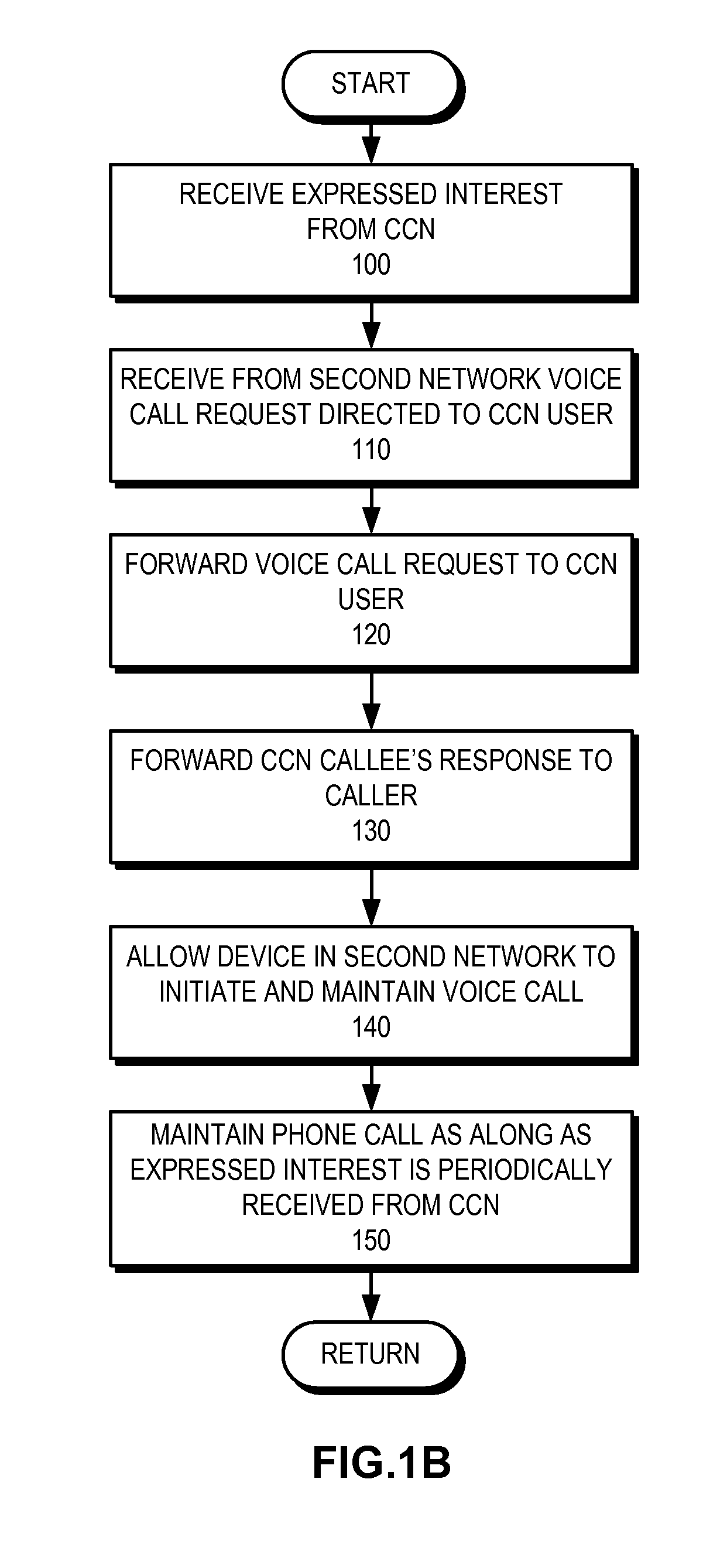
Voice over content centric networks
ActiveUS20090285209A1Special service for subscribersData switching by path configurationContent IdentifierComputer network
A system for facilitating voice calls over a content centric network (CCN) receives from a CCN user an expressed interest in receiving voice calls directed to the CCN user, wherein information in the CCN can be addressed, located, and disseminated by its content identifier and wherein data packets in the CCN are self-authenticating. Next, the system receives from a second network a packet for a voice call directed to the CCN user. The system then forwards to the CCN user the packet received from the second network with a CCN identifier corresponding to the interest expressed by the CCN user and forwards a packet from the CCN user for the voice call to the second network.
Owner:CISCO TECH INC
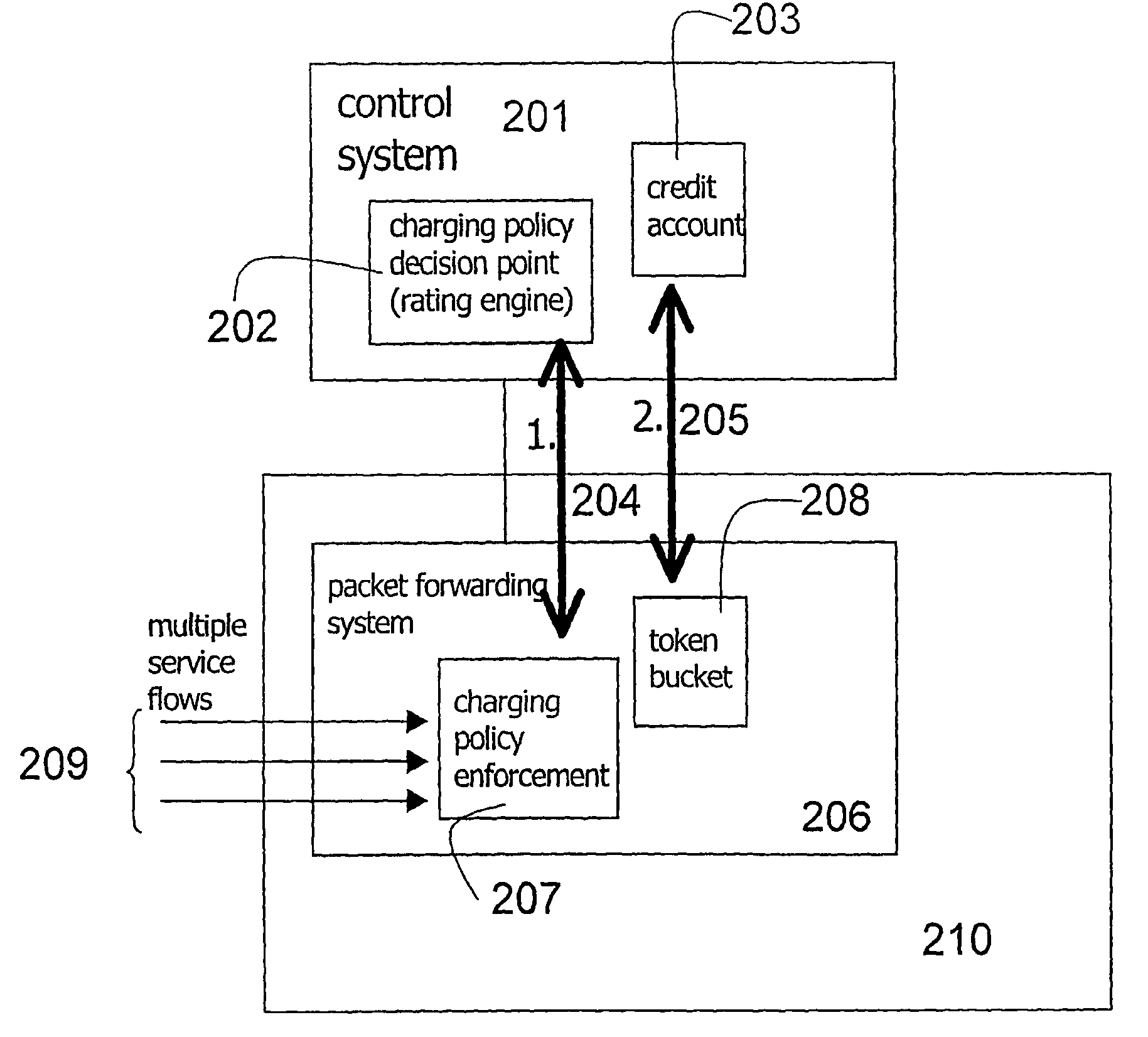
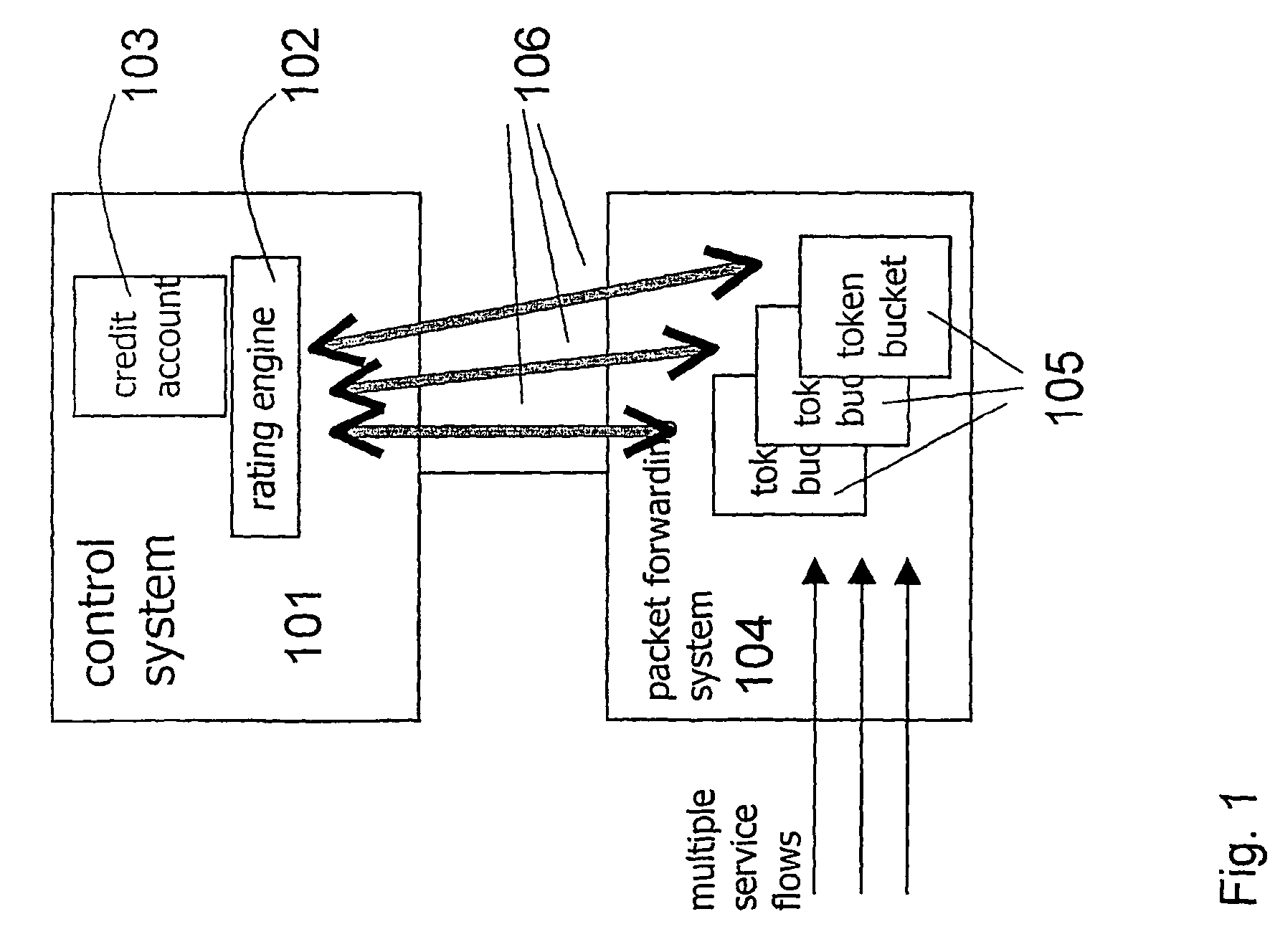
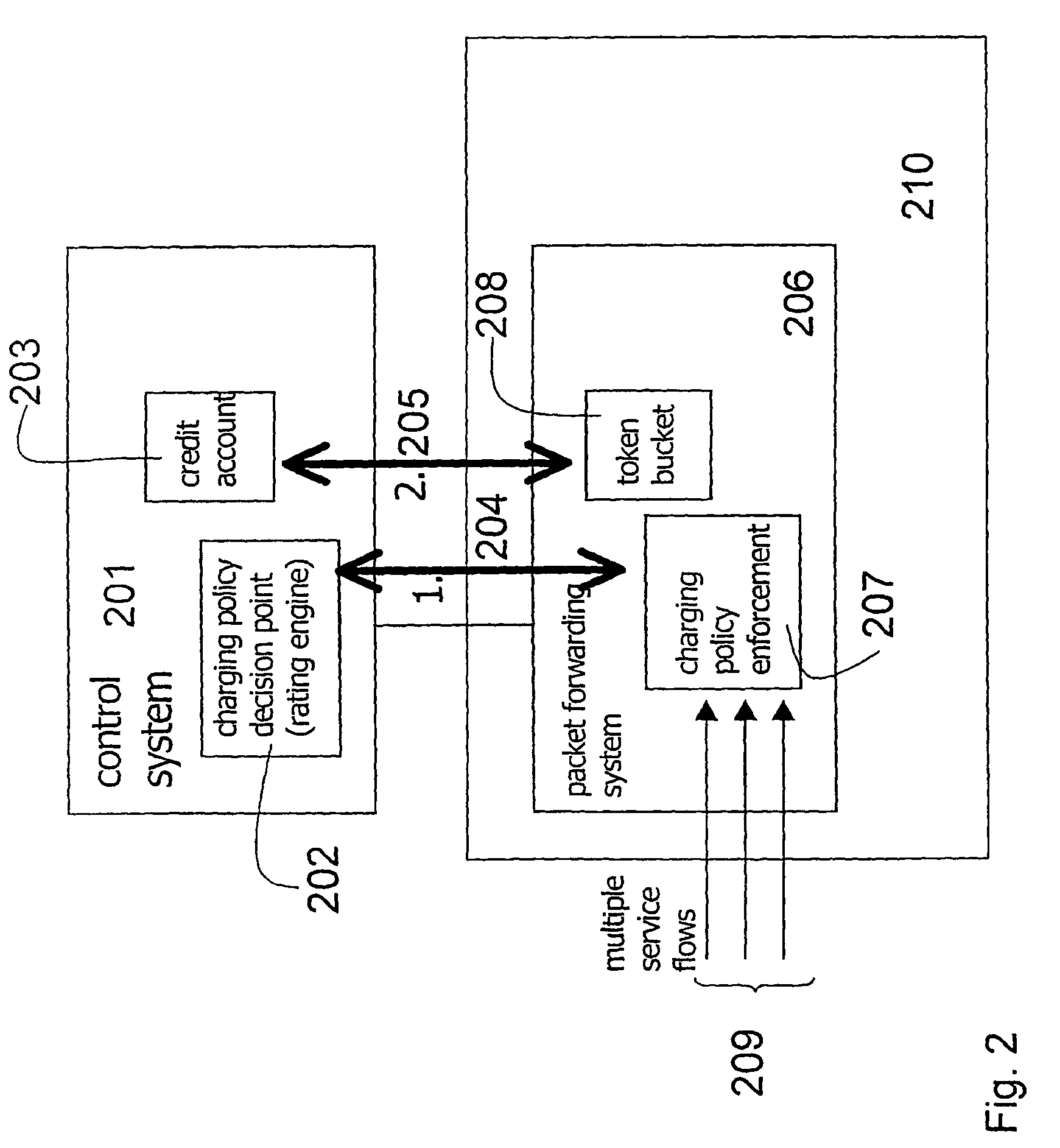
System for providing flexible charging in a network
ActiveUS7450591B2Reduce signaling loadReduce reservationMetering/charging/biilling arrangementsData switching by path configurationService flowPolicy decision
Owner:TELEFON AB LM ERICSSON (PUBL)
Global load balancing on a content delivery network
ActiveUS20100036954A1Improve performanceImprove efficiencyHybrid transportMultiple digital computer combinationsEdge serverNetwork connection
The invention relates to systems and methods of global load balancing in a content delivery network having a plurality of edge servers which may be distributed across multiple geographic locations. According to one aspect of the invention, a global load balancing system includes a first load balancing server for receiving a packet requesting content to be delivered to a client, selecting one of the plurality of edge servers to deliver the requested content to the client, and forwarding the packet across a network connection to a second load balancing server, which forwards the packet to the selected edge server. The selected edge server, in response to receiving the packet, sends across a network connection the requested content with an address for direct delivery to the client, thereby allowing the requested content to be delivered to the client while bypassing a return path through the first load balancing server.
Owner:EDGIO INC
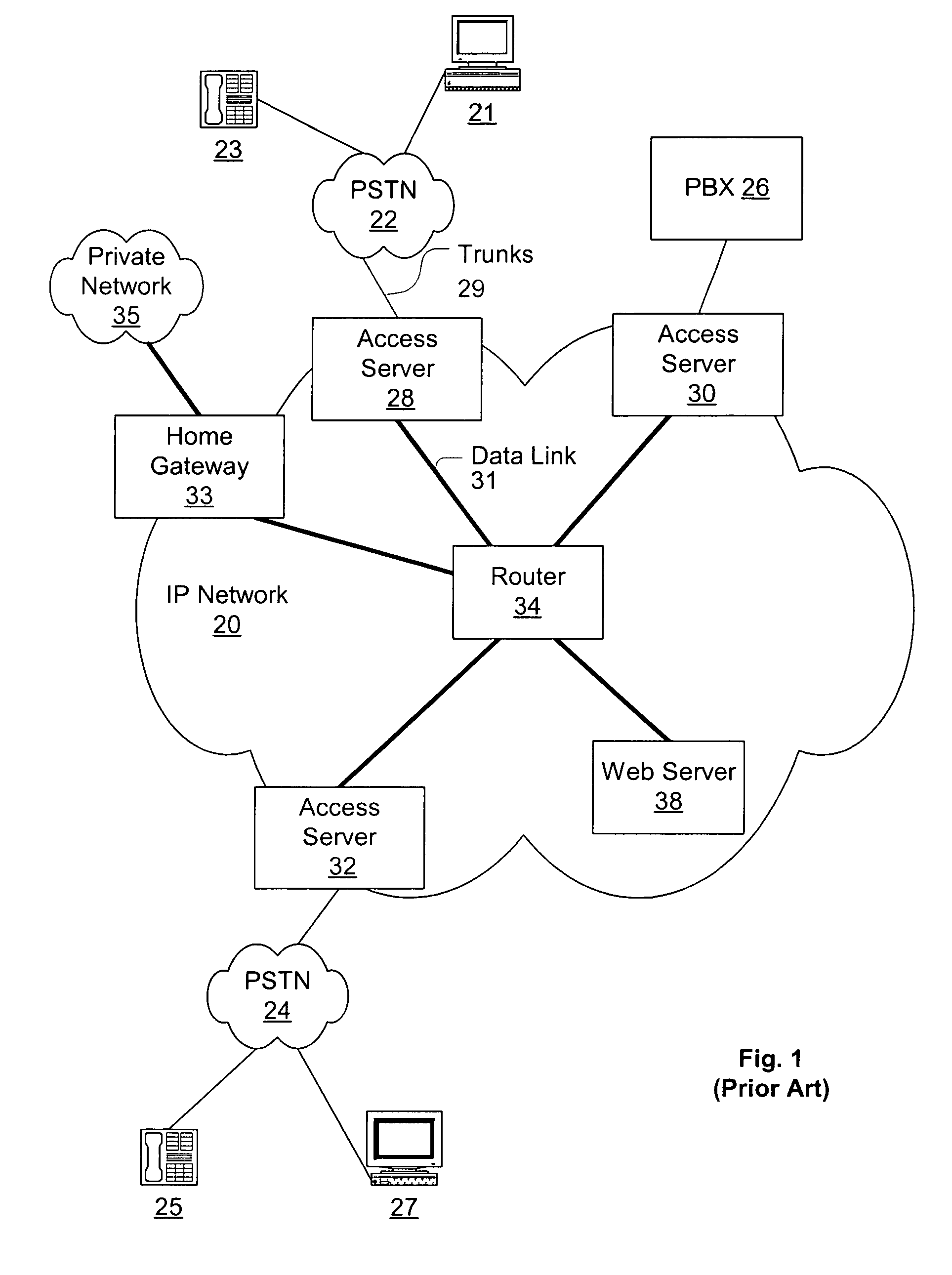
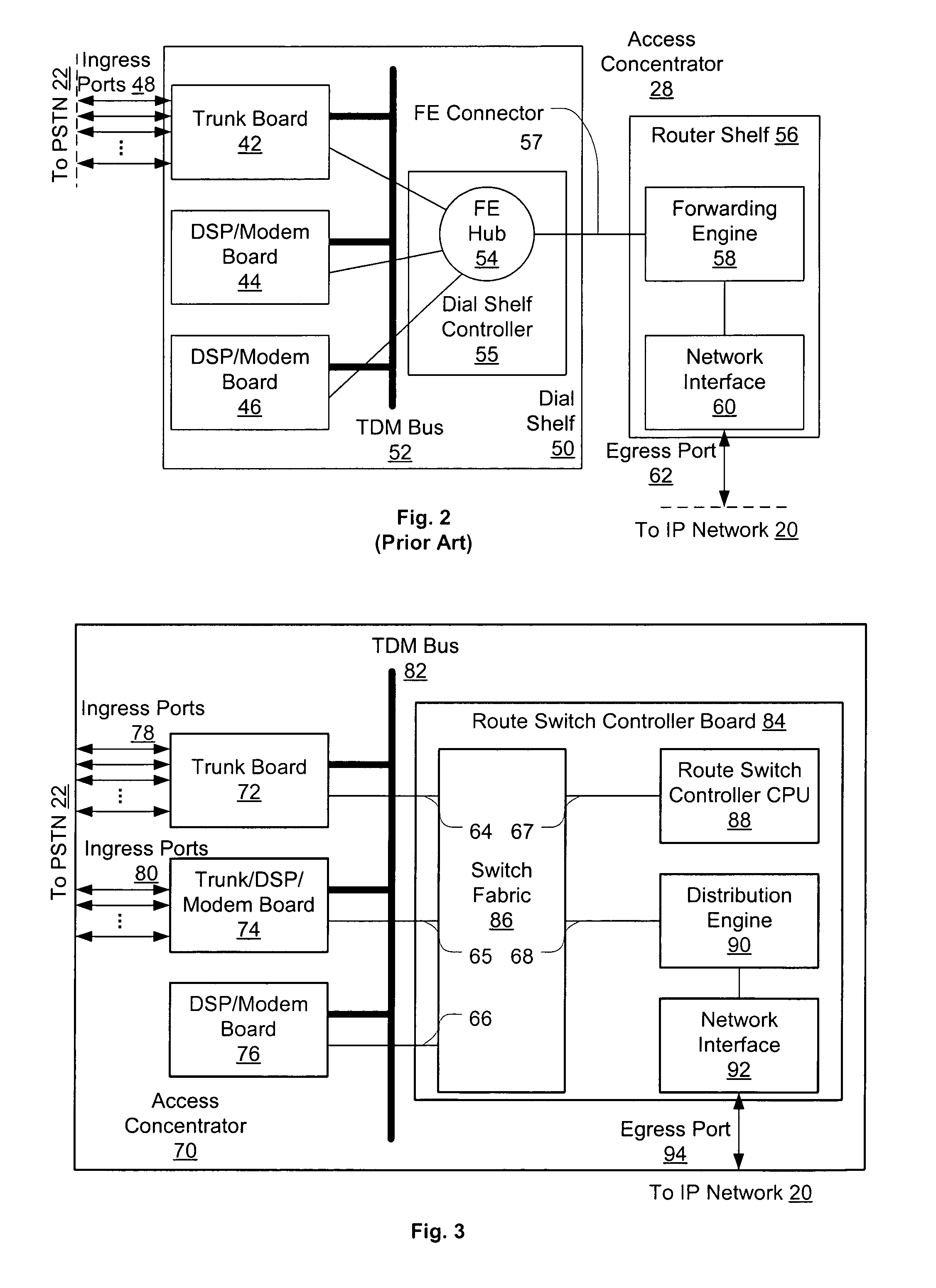
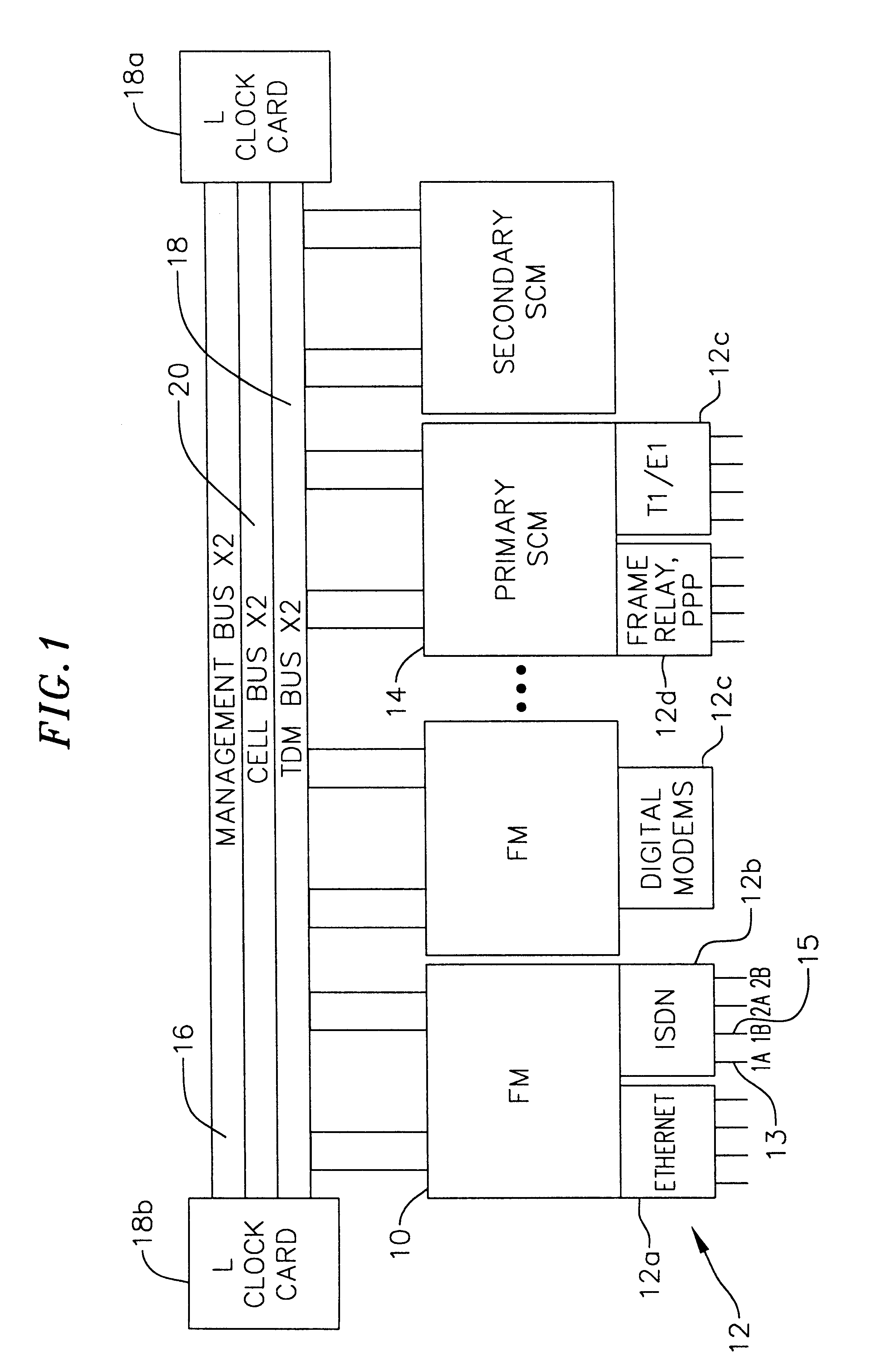
Distributed packet processing architecture for network access servers
InactiveUS6954463B1Increase the number ofRaise countData switching by path configurationNetwork access serverComputer hardware
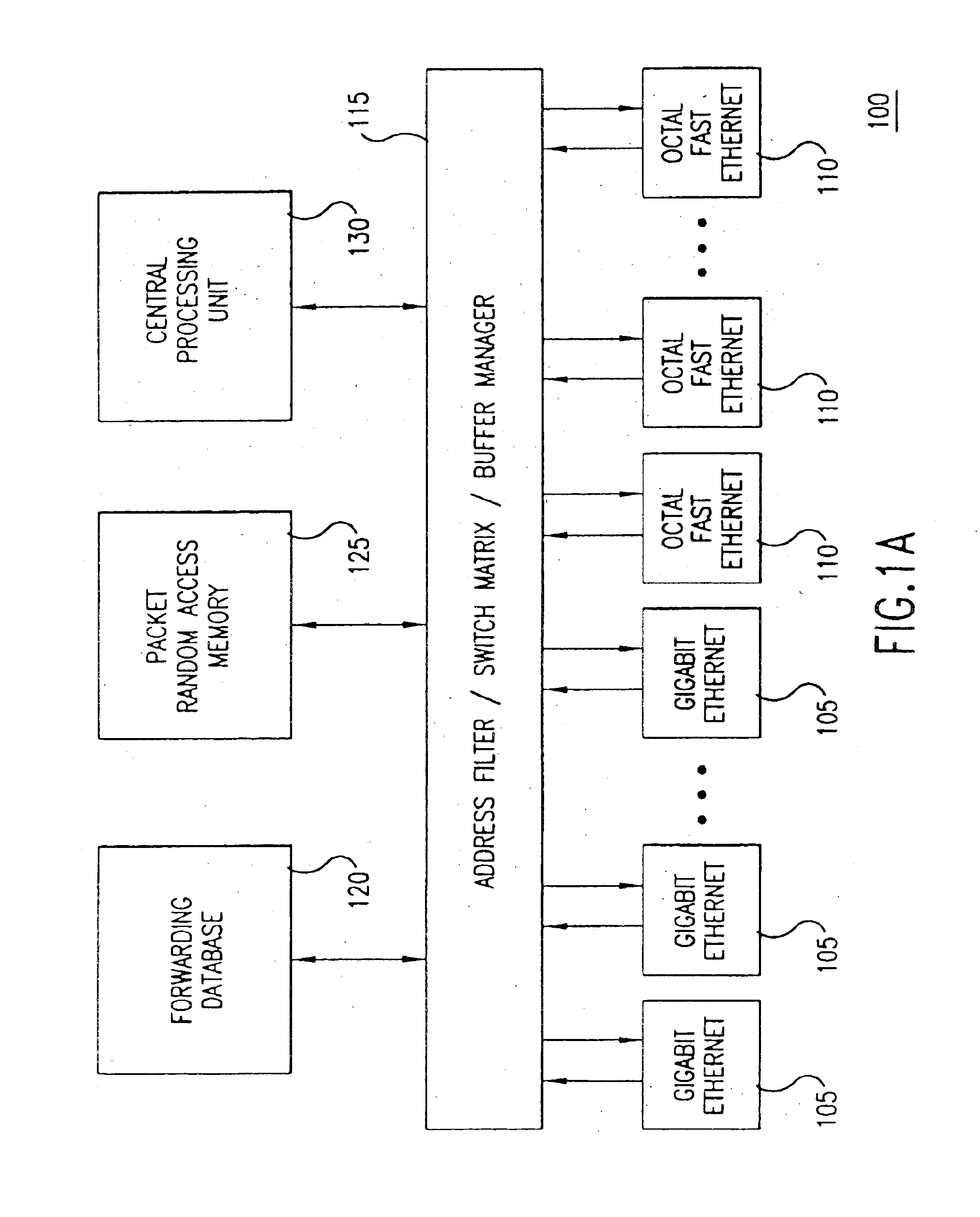
An access server architecture, and methods for use of the architecture, are disclosed. The architecture and methods are designed to increase the scalability of and balance processor load for a network access server. In this architecture, packet forwarding and packet processing are distributed amongst the cards serving the low-speed access lines, such that each line card is responsible for performing forwarding and packet processing for packets associated with the low-speed ports that line card serves. As the number of line cards expands, forwarding resources are expanded in at least rough proportion. The NAS route switch controller, and the high-speed ports, are largely relieved of packet processing tasks because the egress port uses a distribution engine that performs a cursory examination on one or more header fields on packets received—comprehending only enough information to allow each packet to be distributed to the appropriate line card for full processing.
Owner:CISCO TECH INC
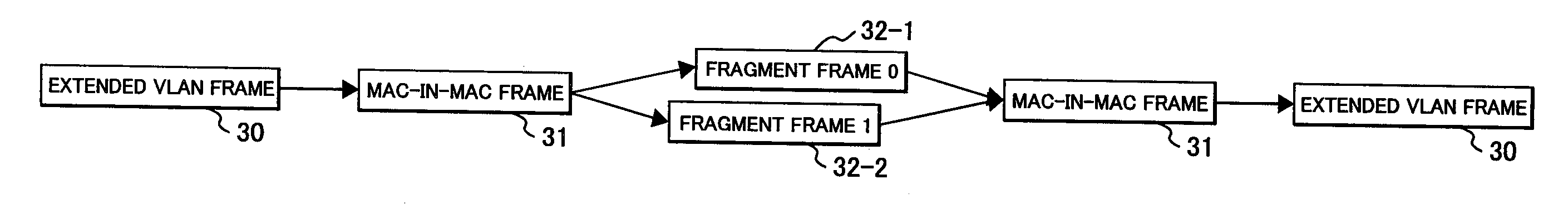
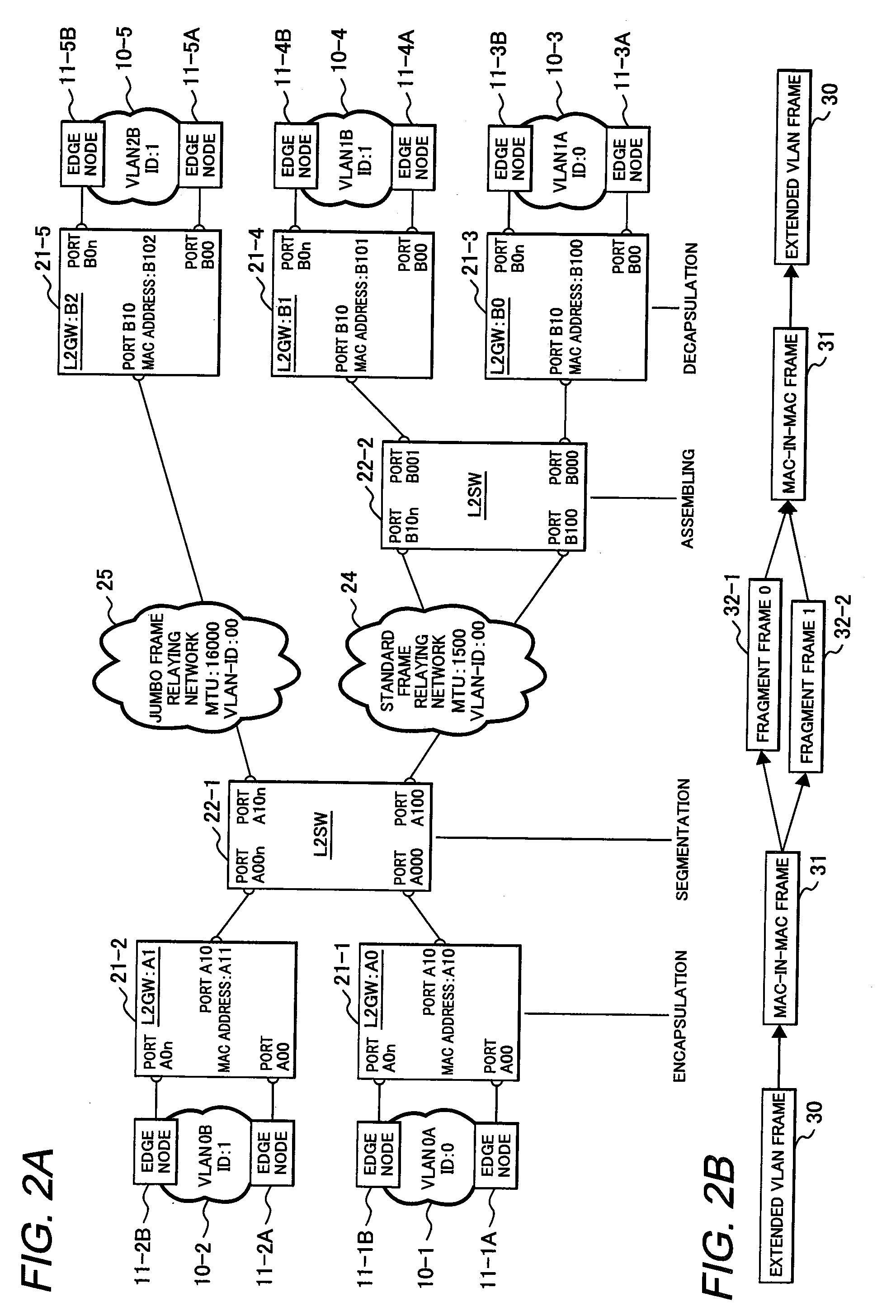
Packet forwarding apparatus suitable for forwarding extended frame
InactiveUS20090067429A1Efficient forwardingTime-division multiplexNetworks interconnectionEthernet framePacket forwarding
A packet forwarding apparatus (L2SW) having a frame segmentation function of converting a extended Ethernet frame such as a MAC-in-MAC frame into a plurality of fragment frames when a payload length of the received frame exceeds a standard MTU size communicable in an Ethernet network to be a forwarding destination, by segmenting the received frame into a plurality of data blocks having a size not longer than the MTU size, and a frame assembling function of restoring an original extended frame from a series of fragment frames received from the Ethernet network.
Owner:HITACHI LTD
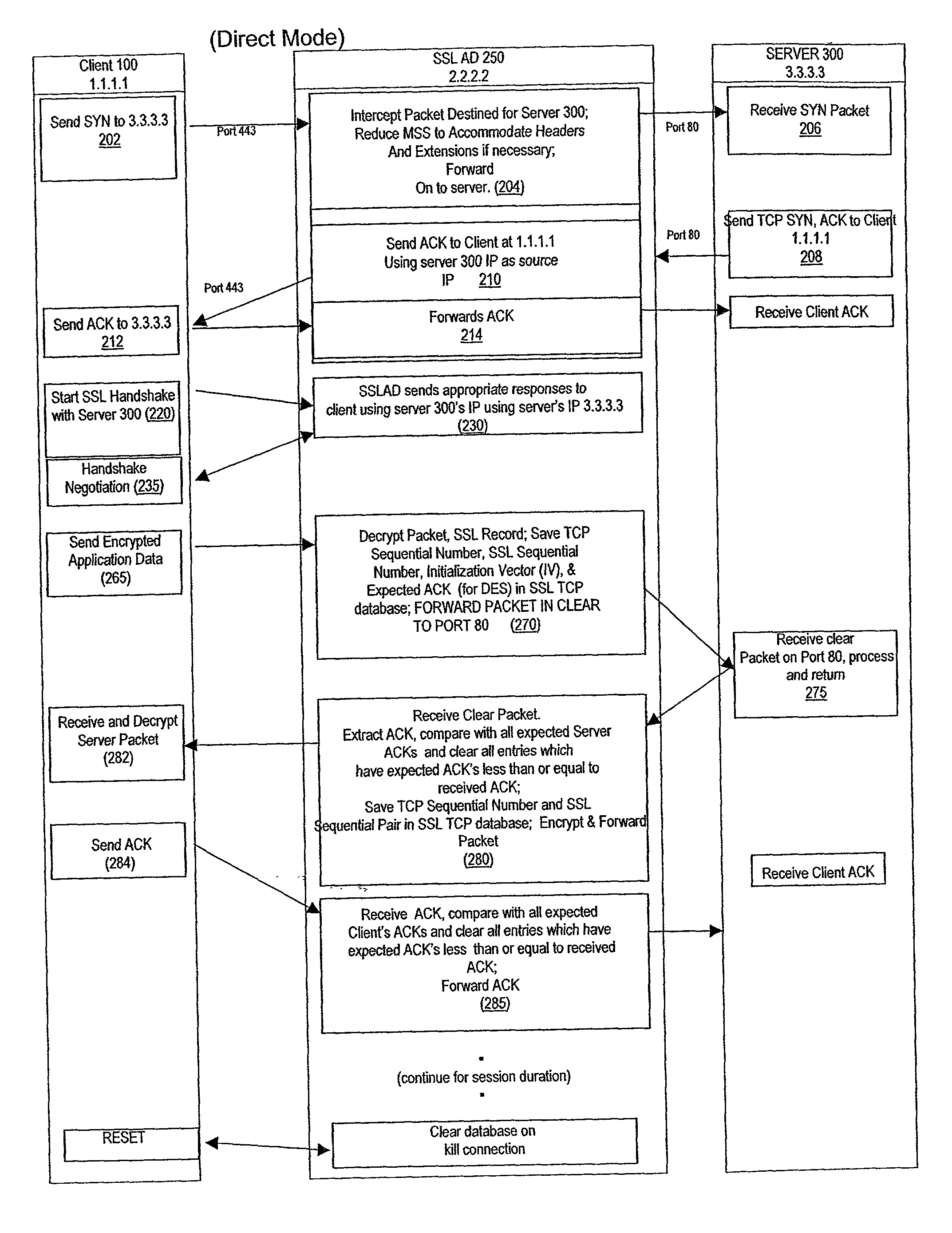
Secure sockets layer cut through architecture
ActiveUS20030014623A1Low hardware requirementsLower latencyDigital data processing detailsUser identity/authority verificationSecure communicationSession management
A method for secure communications between a client and a server. The method includes the steps of managing a communications negotiation between the client and the server; receiving encrypted data packets from the client; decrypting each encrypted packet data; forwarding unencrypted data packets to the server; receiving data packets from the server; encrypting the data packets from the server; and forwarding encrypted data packets to the client. In a further embodiment, an apparatus communicating with a client via a public network and communicating with one of a plurality of servers via a secure network is disclosed. The apparatus includes a network communications interface, at least one processor, programmable dynamic memory, and a communications channel coupling the processor, memory and network communications interface. In addition, the apparatus includes a client / server open communications session manager, a client secure communication session manager, a client / server secure communications session tracking database; and a data packet encryption and decryption engine.
Owner:NEXSI SYST
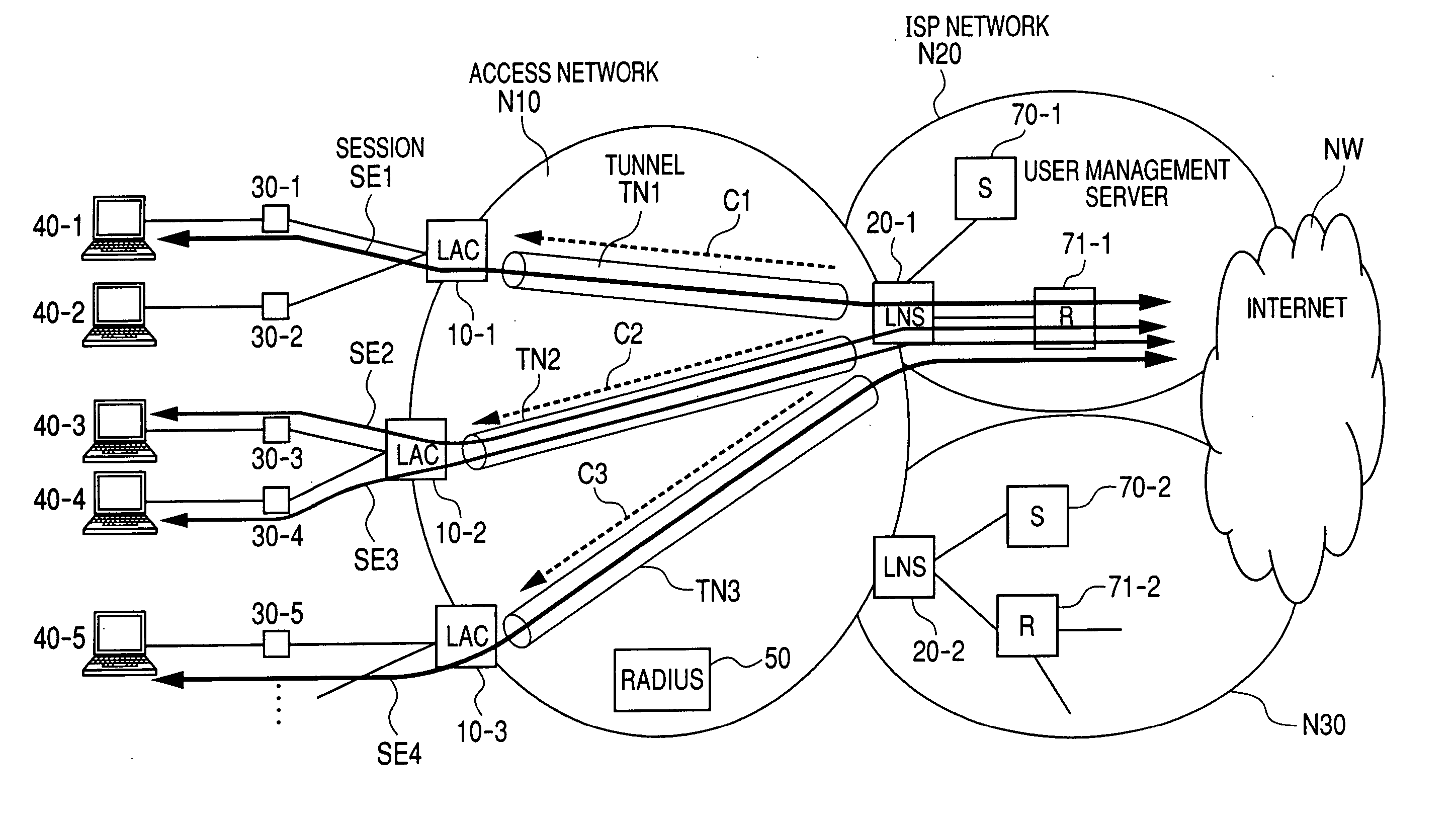
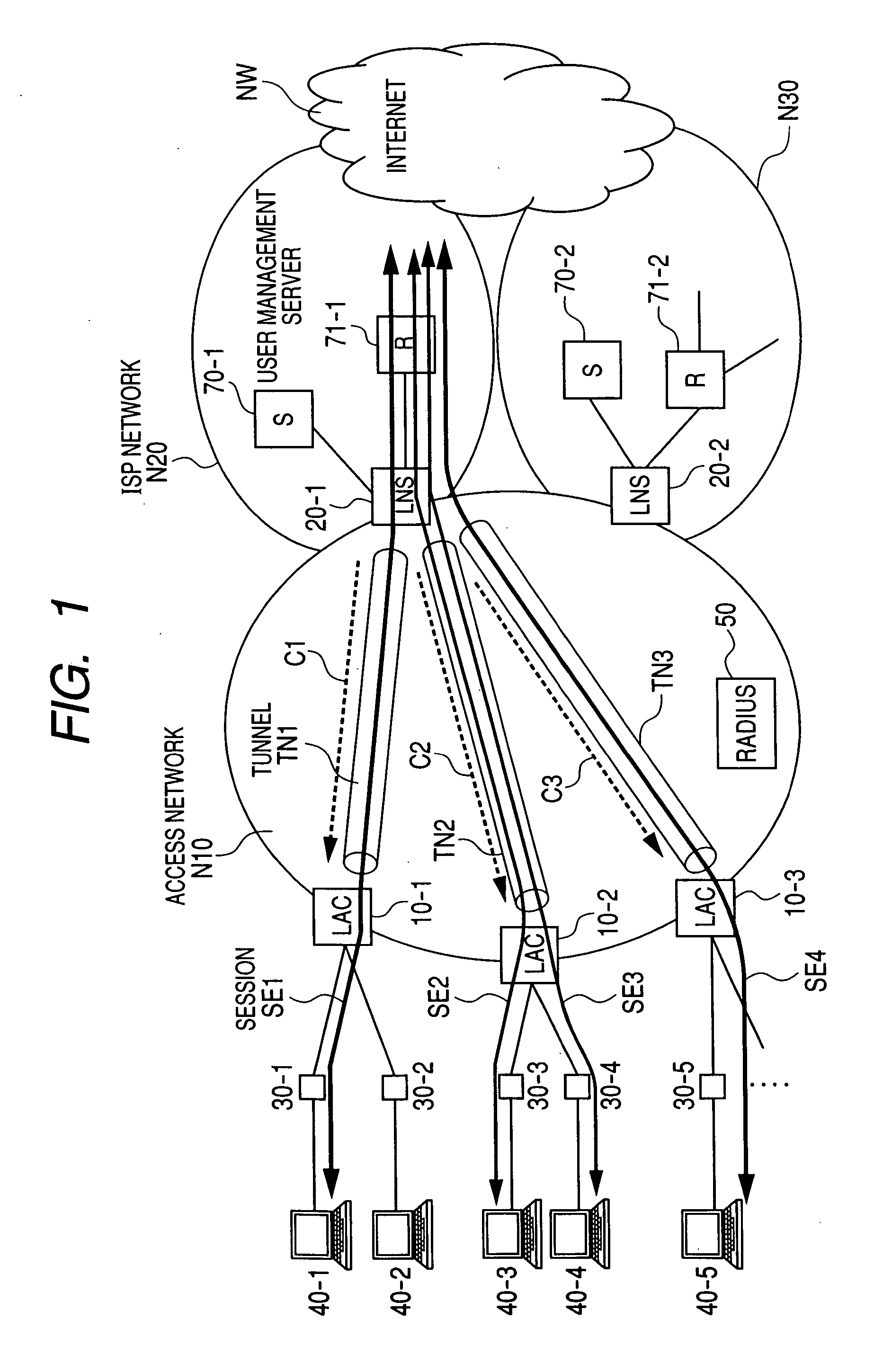
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS20040032856A1Fast protection re-routingEfficient multicastingData switching by path configurationPrivate networkOSI model
A packet forwarding method for optimizing packet traffic flow across communications networks and simplifying network management. The invention provides look-up-free and packet-layer-protocol transparent forwarding of multi-protocol packet traffic among Layer-N (N=2 or upper in the ISO OSI model) nodes. The invention enables flexible and efficient packet multicast and anycast capabilities along with real-time dynamic load balancing and fast packet-level traffic protection rerouting. Applications include fast and efficient packet traffic forwarding across administrative domains of Internet, such as an ISP's backbone or an enterprise virtual private network, as well as passing packet traffic over a neutral Internet exchange facility between different administrative domains.
Owner:XENOGENIC DEV LLC
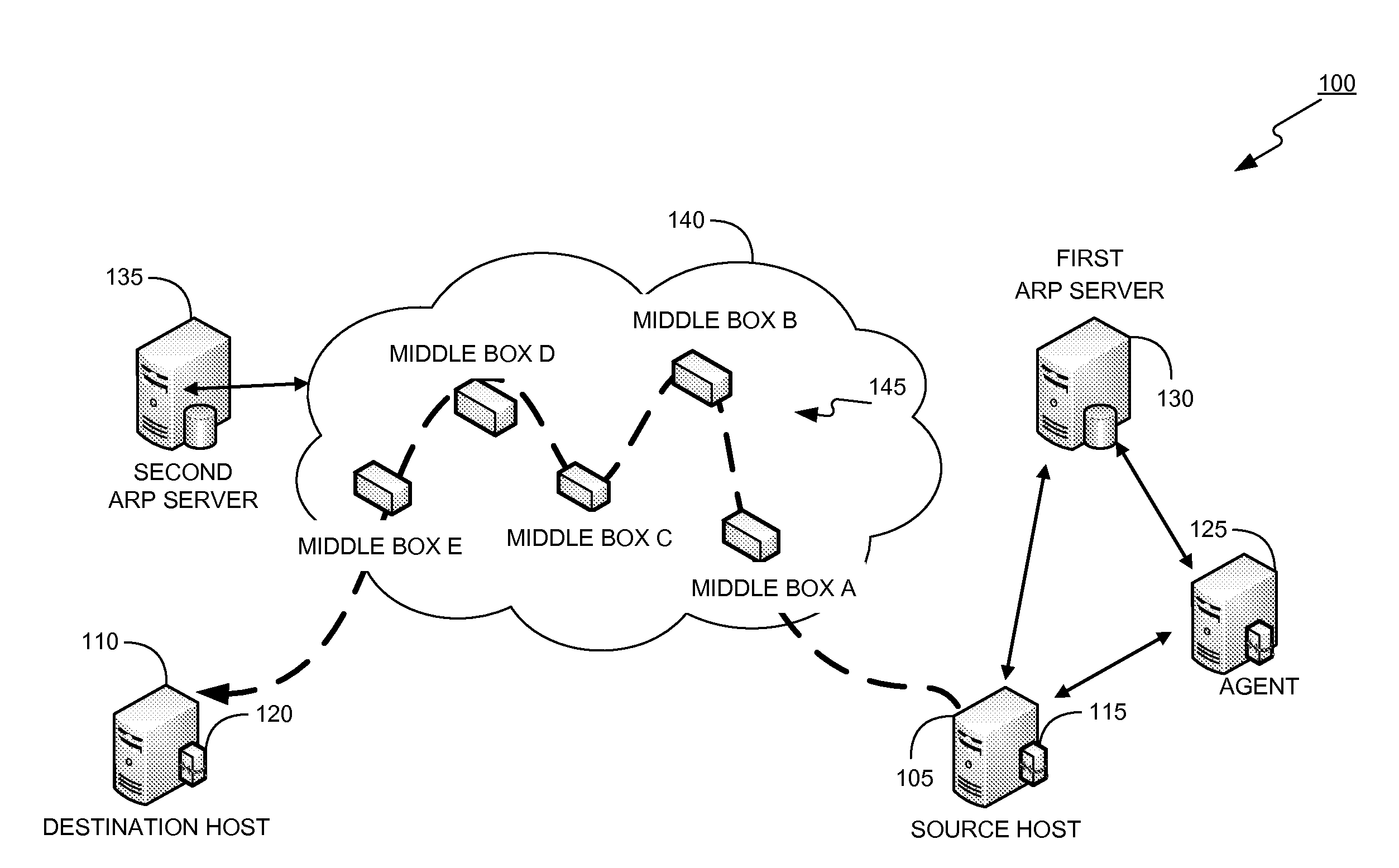
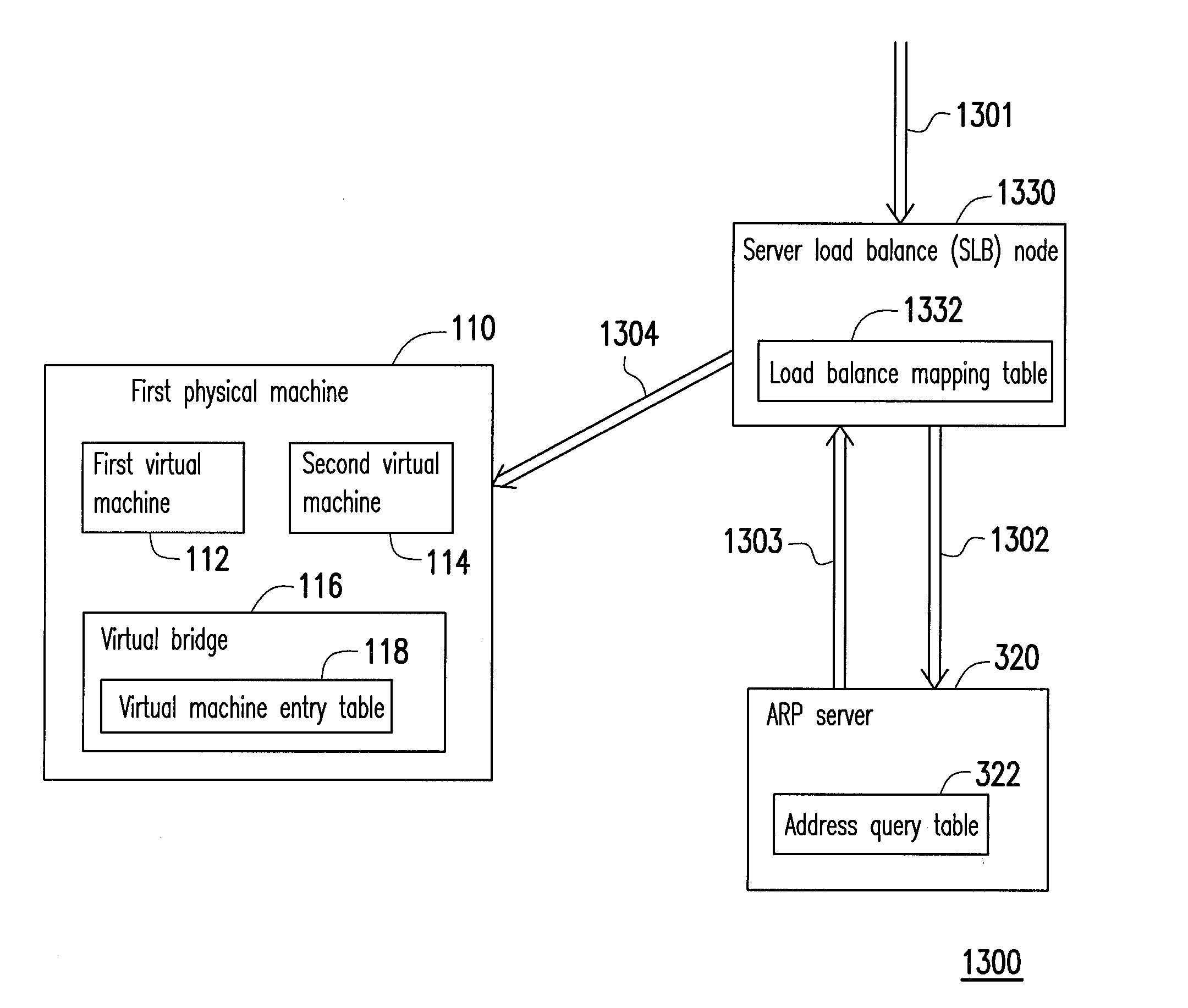
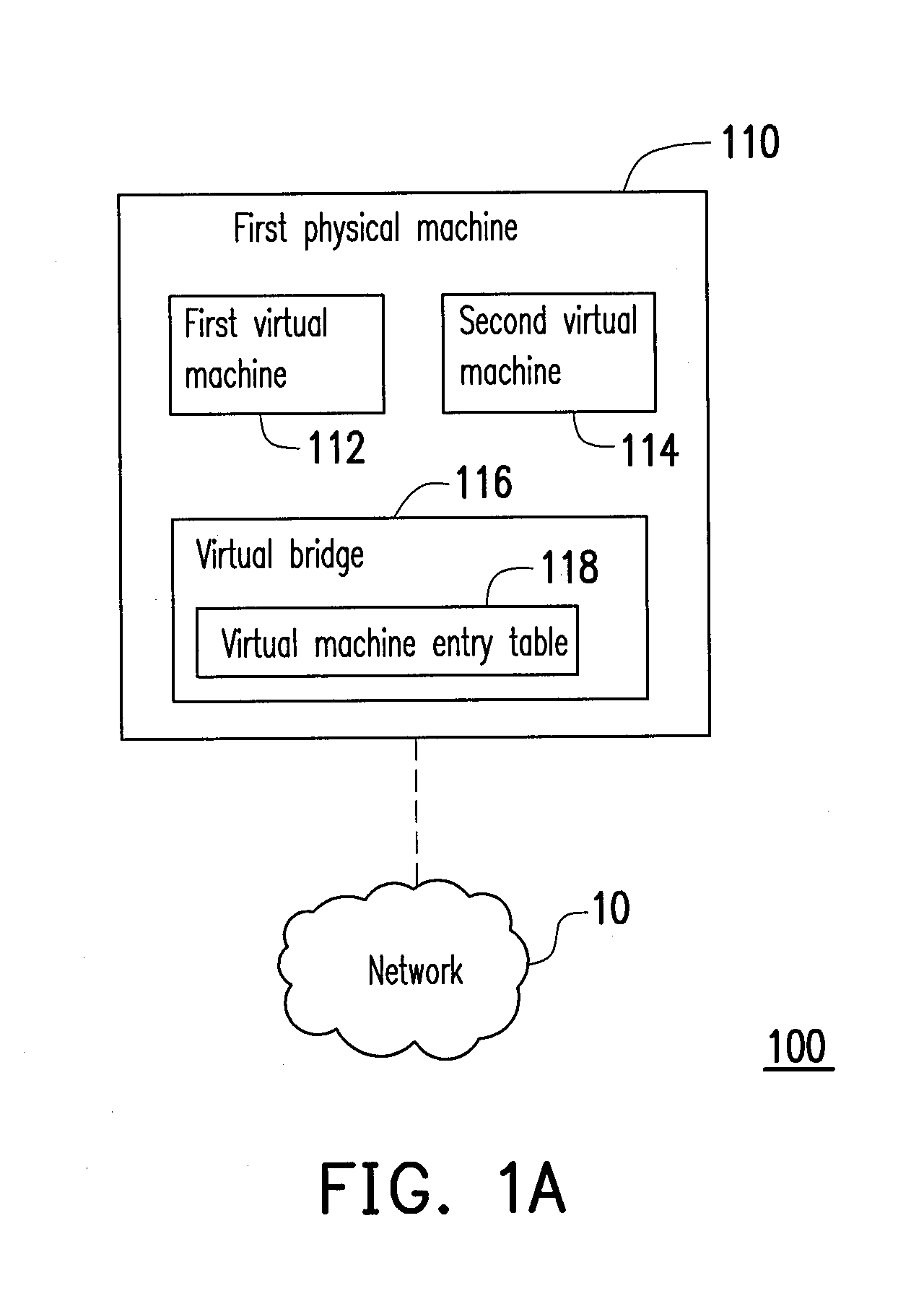
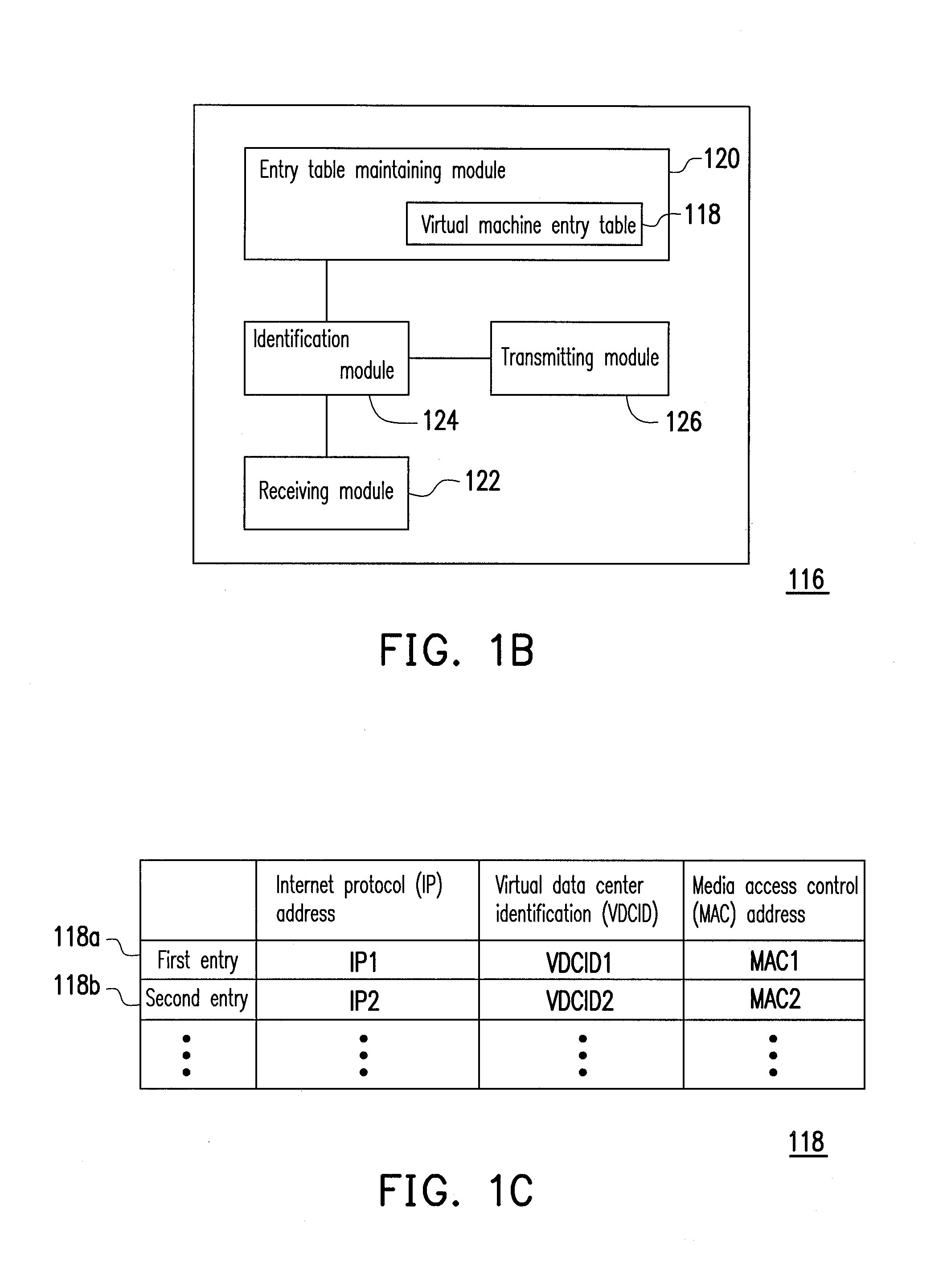
Data center network system and packet forwarding method thereof
ActiveUS20130136126A1Efficient solutionData switching by path configurationProgram controlPrivate IPAddress Resolution Protocol
A data center network system and a packet forwarding method thereof are provided. The data center network system includes a virtual bridge and an address resolution protocol (ARP) server. The virtual bridge intercepts an ARP request having an identification field and a destination IP address field and adds a corresponding virtual data center identification to the identification field of the ARP request and redirecting the ARP request to the ARP server. Additionally, the ARP server queries a corresponding MAC address according to an IP address recorded in the destination IP address field of the ARP request and the corresponding VDCID recorded in the identification field of the ARP request, and transmits the corresponding MAC address in response to the ARP request. Accordingly, the same private IP address can be reused in the data center network system.
Owner:IND TECH RES INST
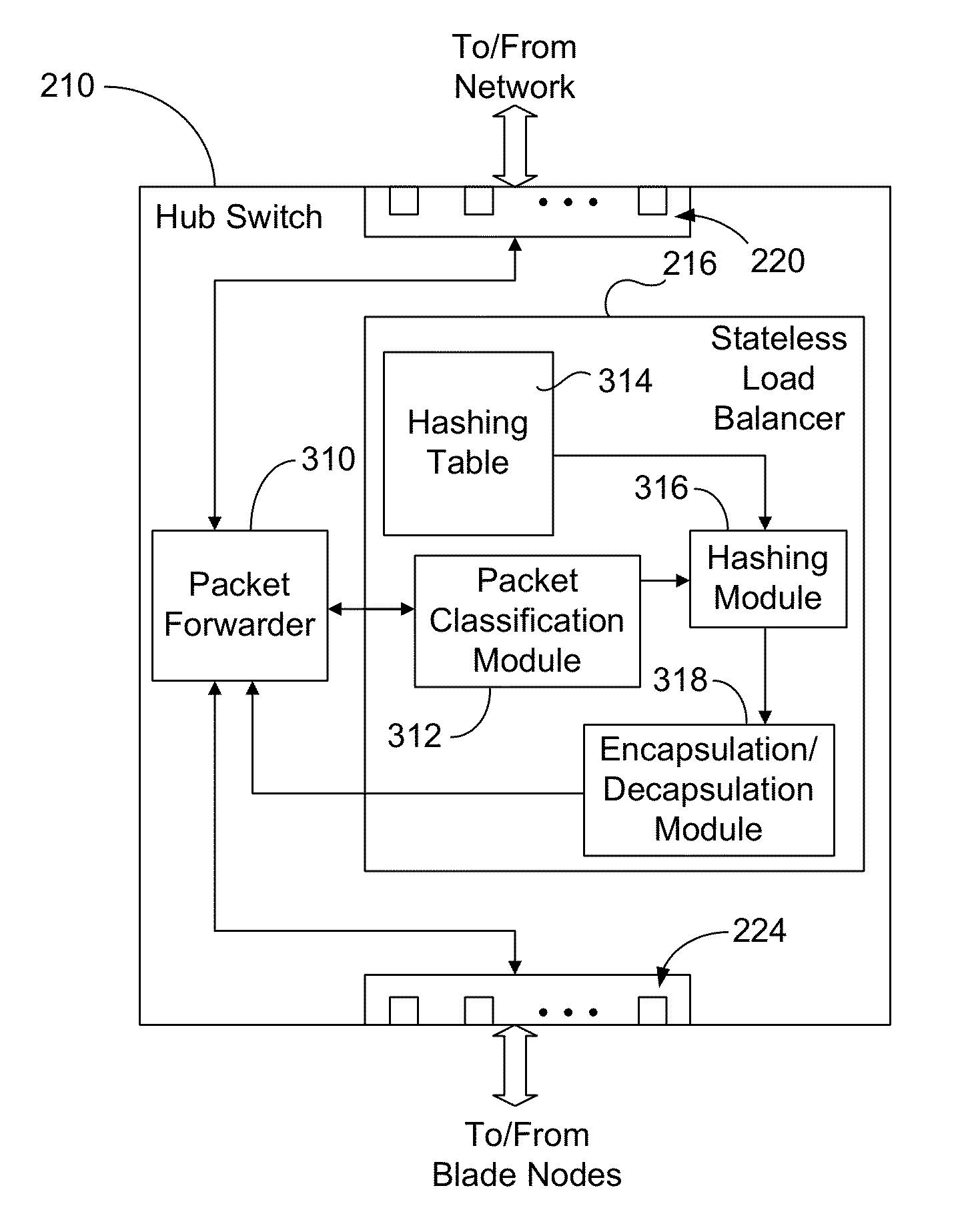
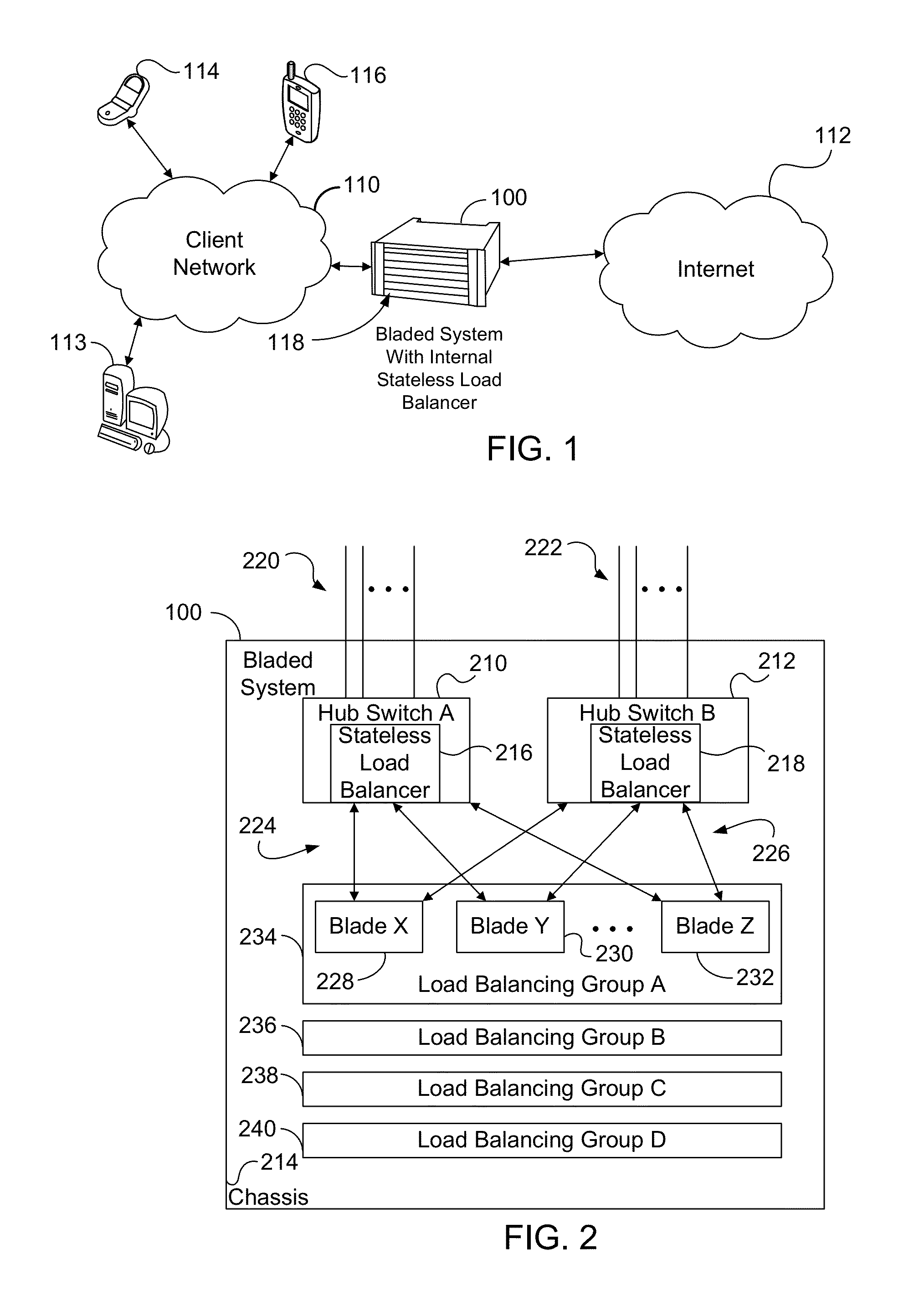
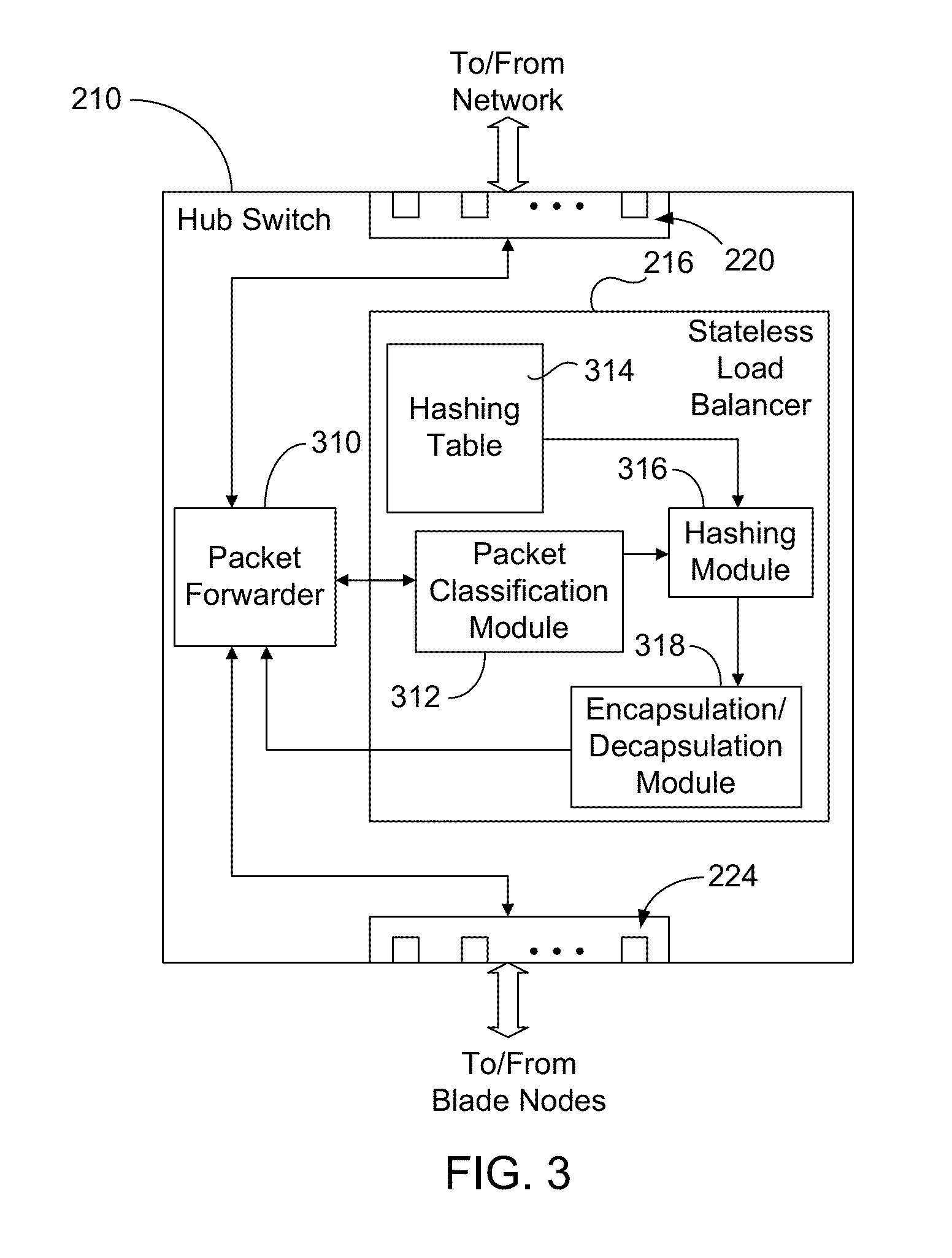
Stateless load balancer in a multi-node system for transparent processing with packet preservation
Stateless load balancing of network packets within a system avoids detection by a network client or end user for deep packet inspection or other bump-in-the-wire applications. At least one header field of a received packet is used in generating a hash value. The hash value is used to identify a processing resource within the system for processing the received packet. Before being sent to the identified resource, the received packet is encapsulated with a new header that includes an indication of ingress port. The encapsulation does not modify the original packet. On a return path from the identified processing resource, the ingress port is determined from the encapsulated packet, the encapsulated packet is decapsulated to obtain a recovered packet that is identical to the received packet, and the recovered packet is forwarded to the network through an egress port as determined from the recovered ingress port.
Owner:RADISYS CORP
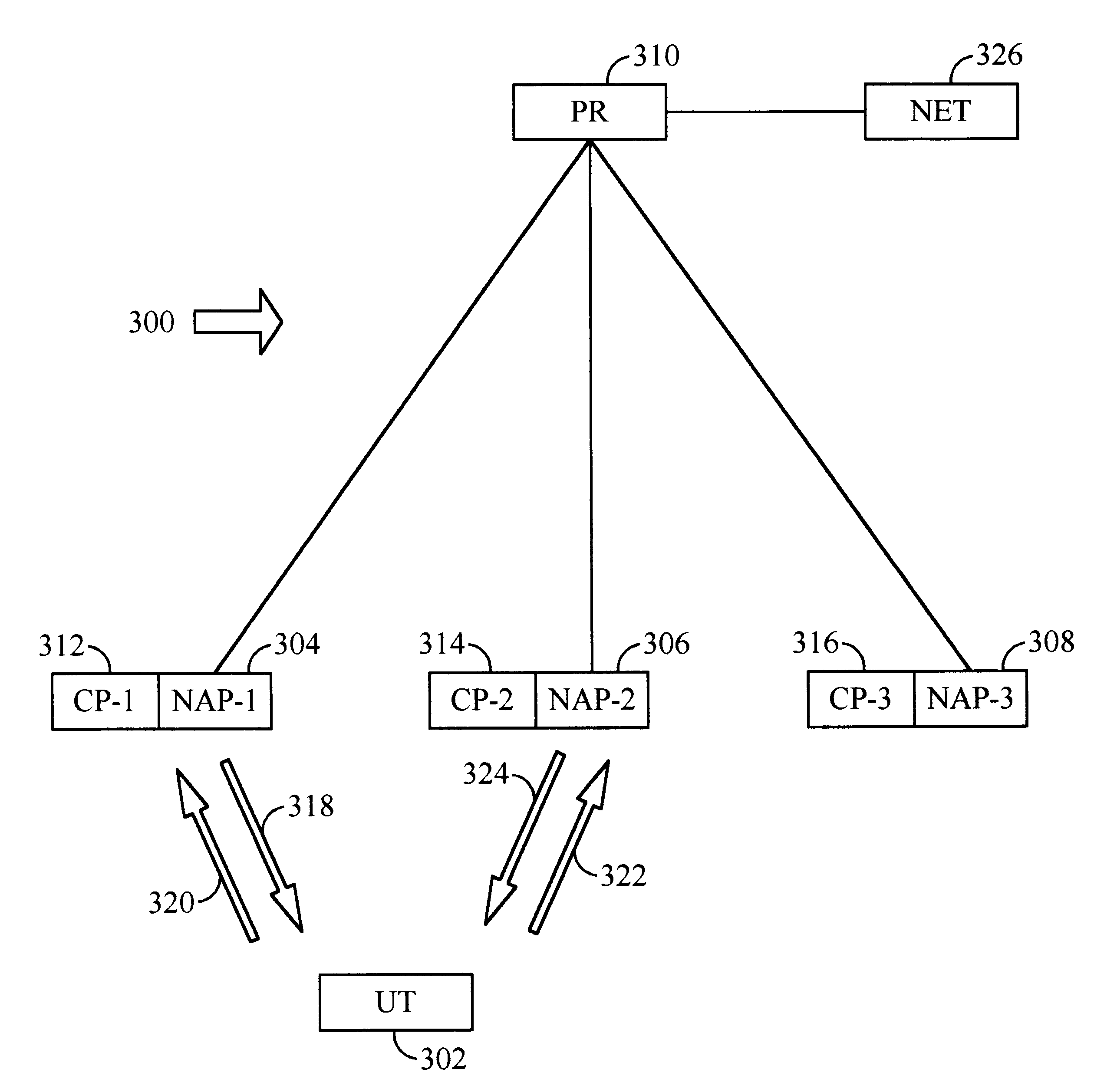
Distributed infrastructure for wireless data communications
InactiveUS6215779B1Wireless network protocolsRadio/inductive link selection arrangementsForeign agentWireless data
A mobile user terminal 402 accesses a packet data network 450 through one or more of several network access points 404-412. One or more control points 432-440 determines which network access point or points the user terminal is to access. Control may be retained in the current control point, or transferred to another control point, whenever it is convenient. There are preferably several routers, each having an associated home agent 418-420 which determines which foreign agents need to be accessed on behalf of each user terminal. There are several foreign agents 422-430, which forward packets received from a user terminal's home agent to the control point currently controlling communications with the user terminal.
Owner:QUALCOMM INC
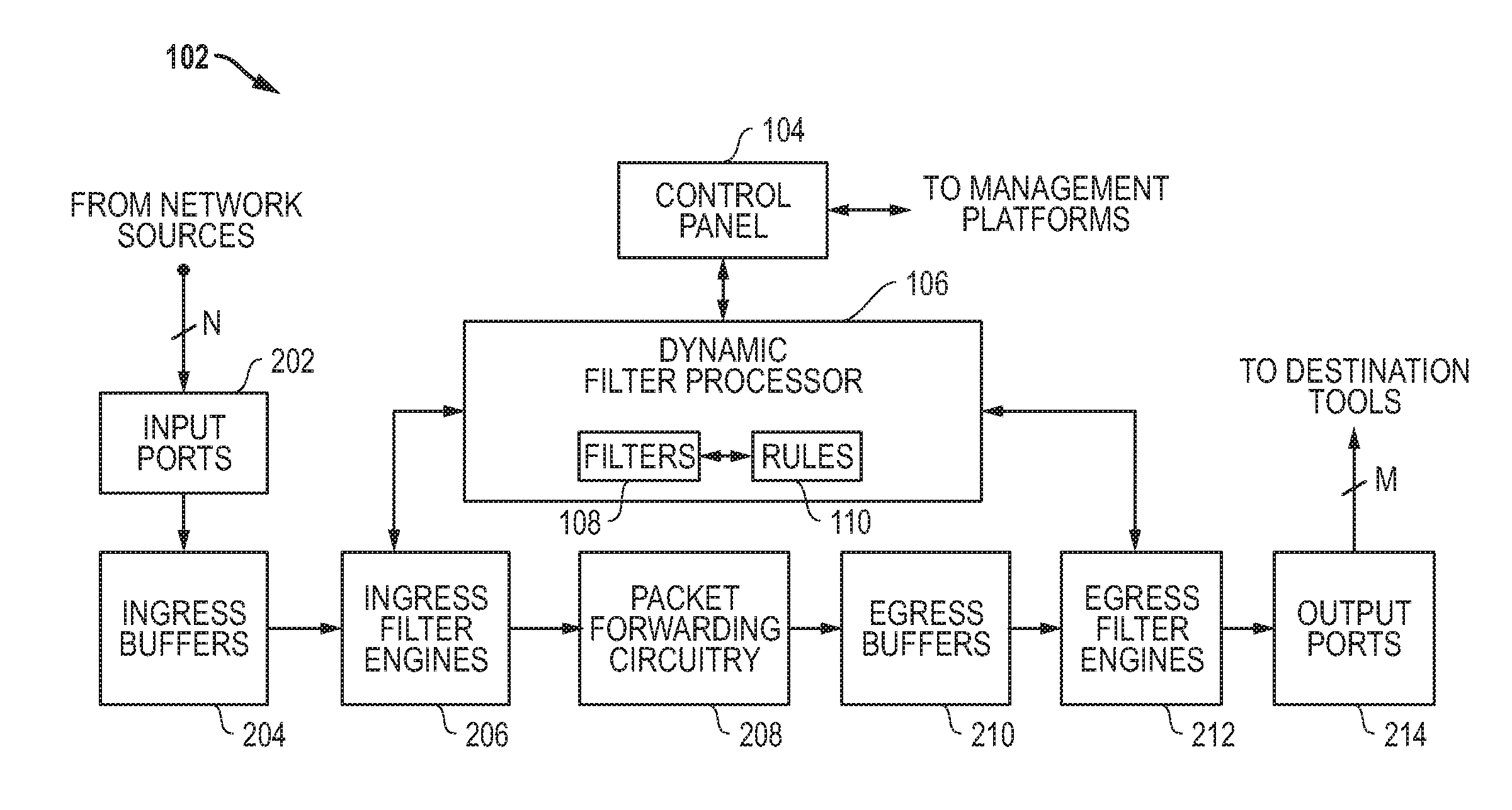
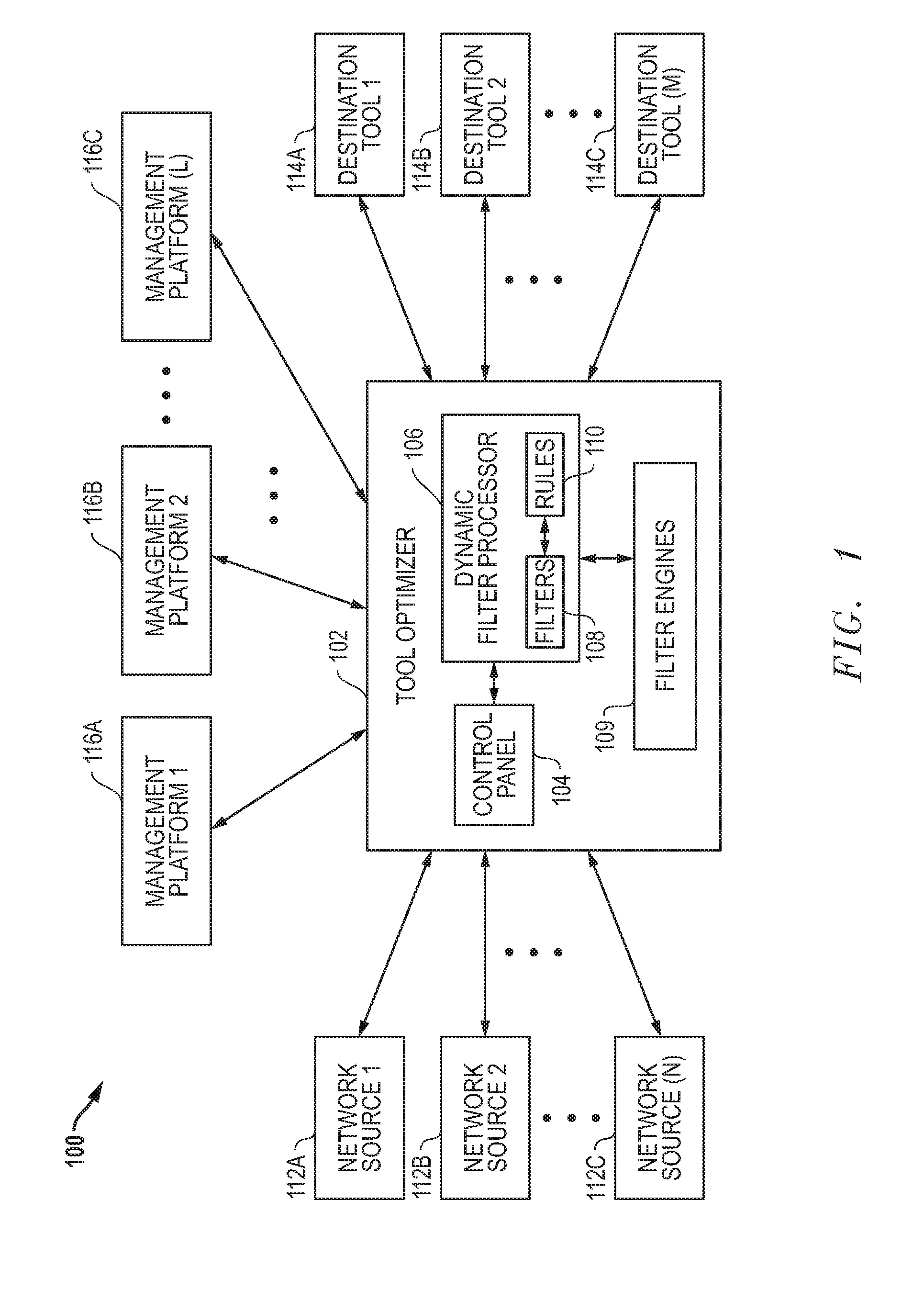
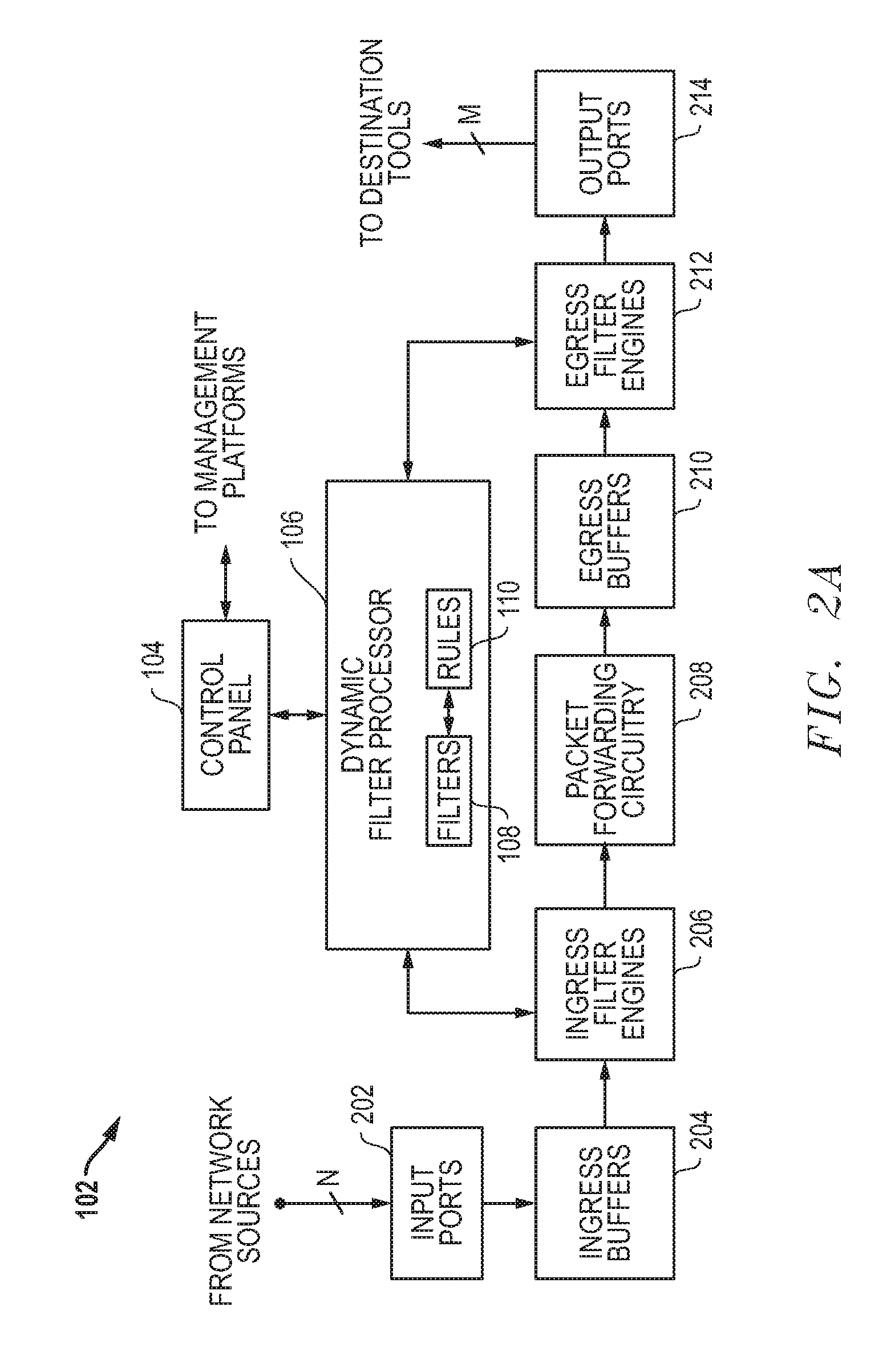
Superset packet forwarding for overlapping filters and related systems and methods
ActiveUS20120106354A1Improved management and controlImproved packet forwardingError preventionTransmission systemsNetwork monitoringIngress filtering
Systems and methods are disclosed that allow for improved management and control of packet forwarding in network systems. Network devices and tool optimizers and a related systems and methods are disclosed for improved packet forwarding between input ports and output ports. The input ports and output ports are configured to be connected to source devices and destination devices, for example, network sources and destination tools in a network monitoring environment. The network devices and tool optimizers disclosed can use superset packet forwarding, such that ingress filter engines are configured with ingress filter rules so as to forward a superset of packets to output ports associated with overlapping filters. Egress filter engines are configured with egress filter rules to then determine which of the superset packets are actually sent out the output ports.
Owner:KEYSIGHT TECH SINGAPORE (SALES) PTE LTD
Method for implementing virtual network and virtual network
ActiveCN102857416ALoad balancingEfficient use ofHybrid transportNetworks interconnectionTraffic capacityMulti path
The embodiment of the invention provides a method for implementing a virtual network and the virtual network. The method comprises the following g steps: step (1), obtaining a transfer type, a source and a destination of a data packet sent by a host computer by a controller of the virtual network; step (2), formulating a forwarding strategy according to the transfer type, a port identifier of the source and a target identifier of the destination; and step (3), sending the forwarding strategy to each virtual access exchanger and each middle exchanger through which the data packet is to be passed, and executing the forwarding strategy to the received data packet received by the virtual access exchanger and the middle exchanger. In the forwarding process of the data packet, the controller can obtain various attributes of the data packet as target identifiers, formulate the forwarding strategy according to the target identifiers and forward the data packet more intensively and flexibly; and multi-user and multi-path forwarding is supported, flow load is balanced, and network resources are utilized more efficiently.
Owner:ZTE CORP
Policy-based weighted random early detection method for avoiding congestion in internet traffic
InactiveUS6996062B1Error preventionFrequency-division multiplex detailsTraffic capacityRandom early detection
A method and apparatus for avoiding network congestion. An exemplary packet forwarding device may apply policy rules to incoming packets to assign relative drop probabilities to the packets based on the priority of the packets. In times of network congestion, packets may be selectively dropped according to their associated drop probability.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Multi-hop error recovery
Methods, apparatus and network architectures relating to the use of a Hop-by-Hop packet forwarding technique using “stepping stone” switches. The network architectures include use of stepping stone switches interspersed with non-stepping stone switches such as conventional network switches comprising network elements such switches, routers, repeaters, etc. The stepping stone switches are configured to route packets as multiplexed flows along tunneled sub-paths between stepping stone switches in a hop-by-hop manner with error recovery, as opposed to conventional routing under which packets are routed from a source to a destination using an arbitrary path or along a (generally) lengthy flow-based path. Accordingly, packets from a source endpoint are routed to a destination endpoint via multiple sub-paths connecting pairs of stepping stone switches, with each sub-path traversing one or more conventional switches and constituting a logical Hop in the Hop-by-Hop route.
Owner:INTEL CORP
Tcp/udp acceleration
ActiveUS20040111523A1Special service provision for substationInput/output to record carriersComputer hardwareComputer science
A method for accelerating TCP / UDP packet switching. The method involves determining whether exception processing is necessary; if not, the packet is forwarded to a special stack for expedited processing. Packets requiring exception processing are forwarded to the conventional stack.
Owner:ORACLE INT CORP
Transparent, look-up-free packet forwarding method for optimizing global network throughput based on real-time route status
ActiveUS7254138B2Improve performanceFast and efficient packet-level traffic protection re-routingError preventionTransmission systemsPrivate networkOSI model
Owner:XENOGENIC DEV LLC
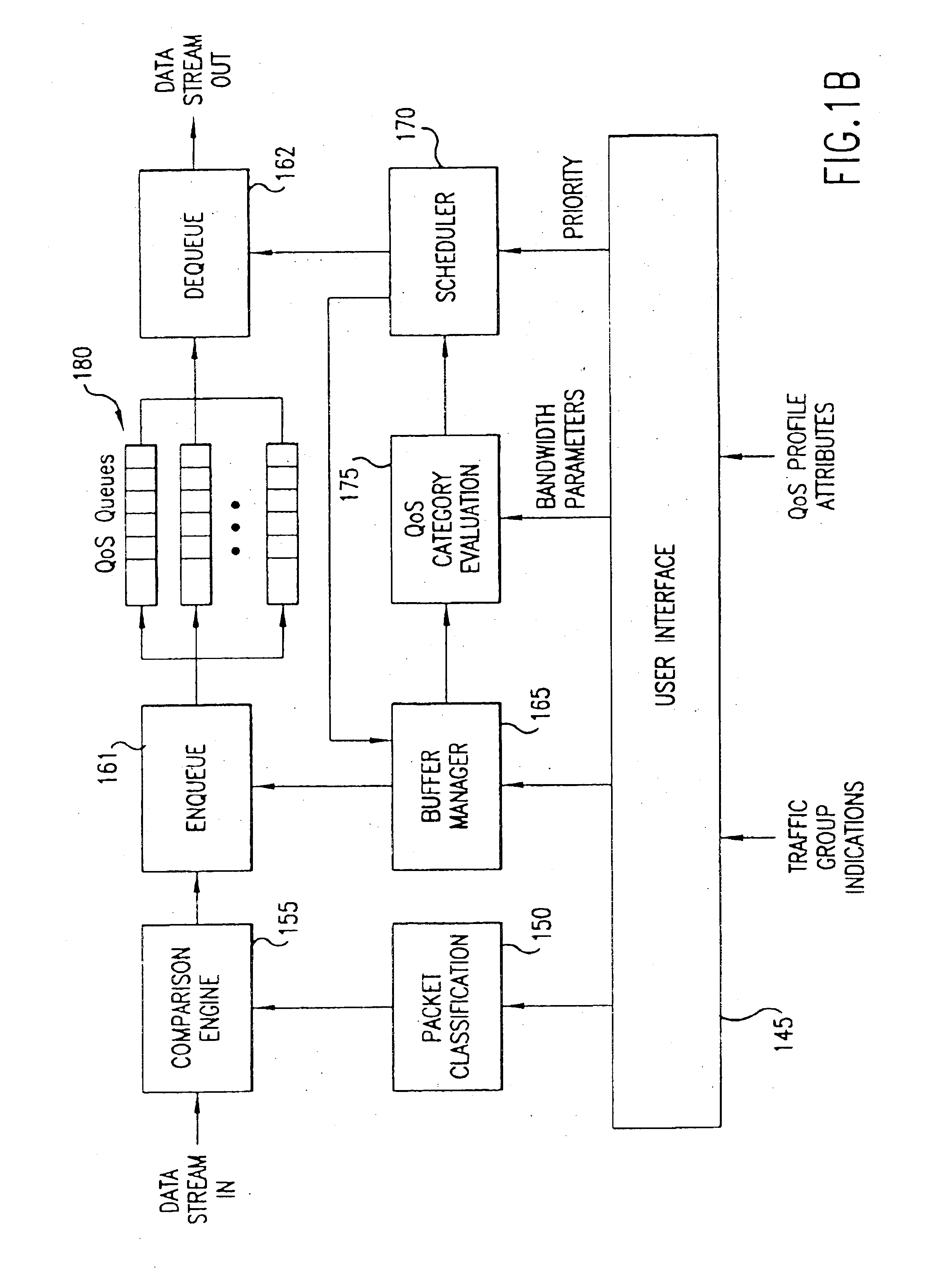
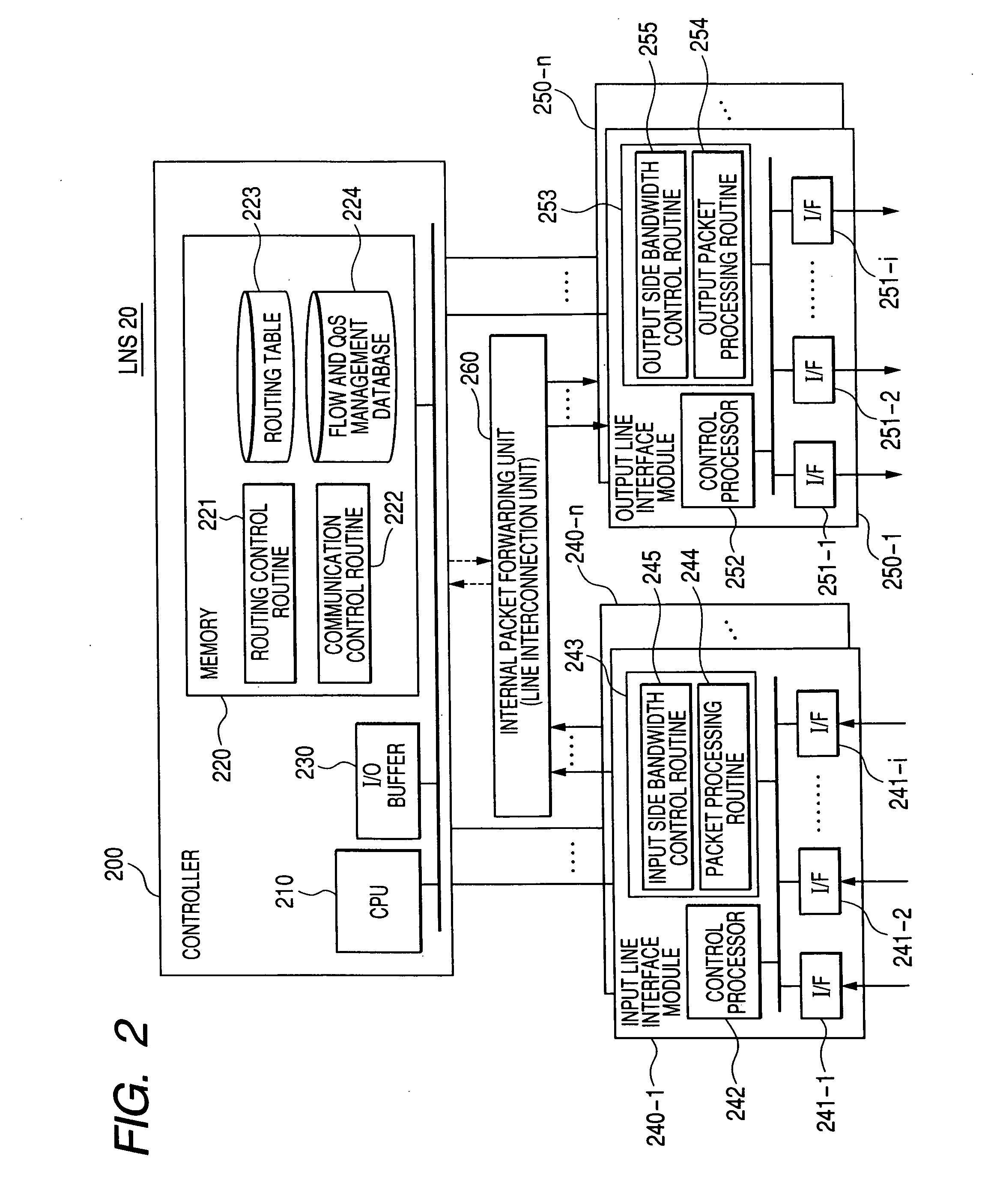
Policy based quality of service
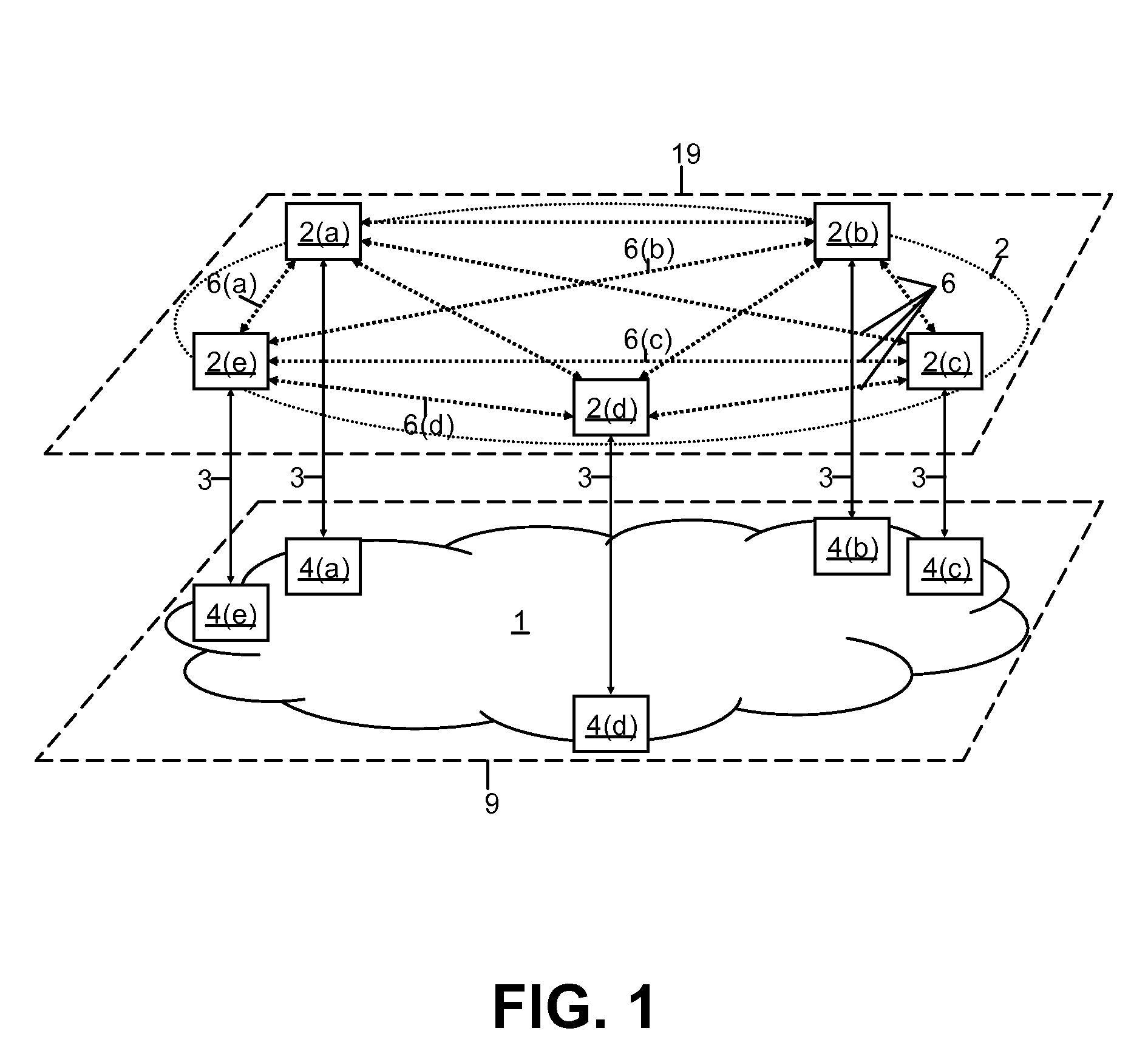
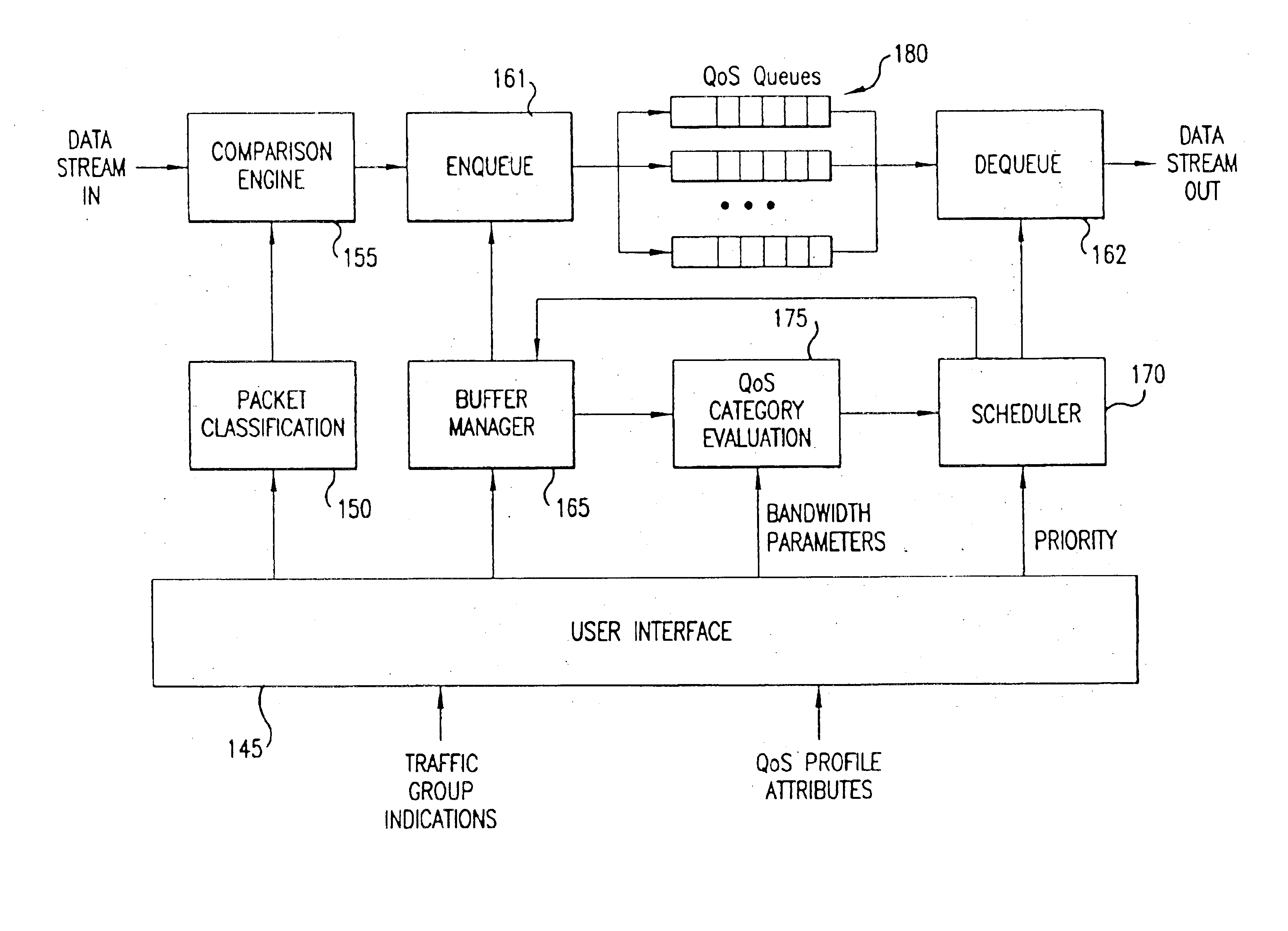
A flexible, policy-based, mechanism for managing, monitoring, and prioritizing traffic within a network and allocating bandwidth to achieve true quality of service (QoS) is provided. According to one aspect of the present invention, a method is provided for managing bandwidth allocation in a network that employs a non-deterministic access protocol, such as an Ethernet network. A packet forwarding device receives information indicative of a set of traffic groups, such as: a MAC address, or IEEE 802.1p priority indicator or 802.1Q frame tag, if the QoS policy is based upon individual station applications; or a physical port if the QoS policy is based purely upon topology. The packet forwarding device additionally receives bandwidth parameters corresponding to the traffic groups. After receiving a packet associated with one of the traffic groups on a first port, the packet forwarding device schedules the packet for transmission from a second port based upon bandwidth parameters corresponding to the traffic group with which the packet is associated. According to another aspect of the present invention, a method is provided for managing bandwidth allocation in a packet forwarding device. The packet forwarding device receives information indicative of a set of traffic groups. The packet forwarding device additionally receives information defining a QoS policy for the traffic groups. After a packet is received by the packet forwarding device, a traffic group with which the packet is associated is identified. Subsequently, rather than relying on an end-to-end signaling protocol for scheduling, the packet is scheduled for transmission based upon the QoS policy for the identified traffic group.
Owner:ARISTA NETWORKS
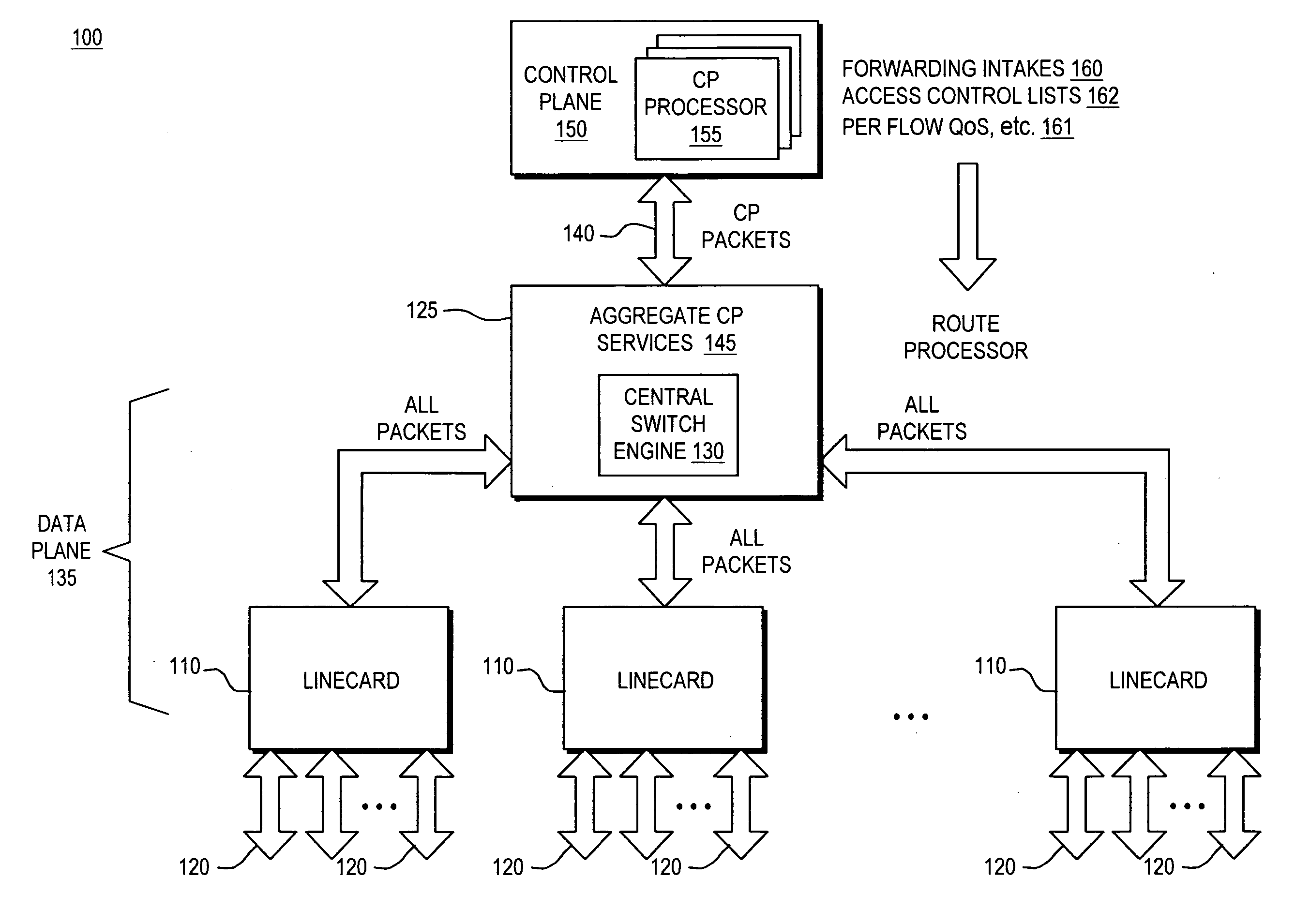
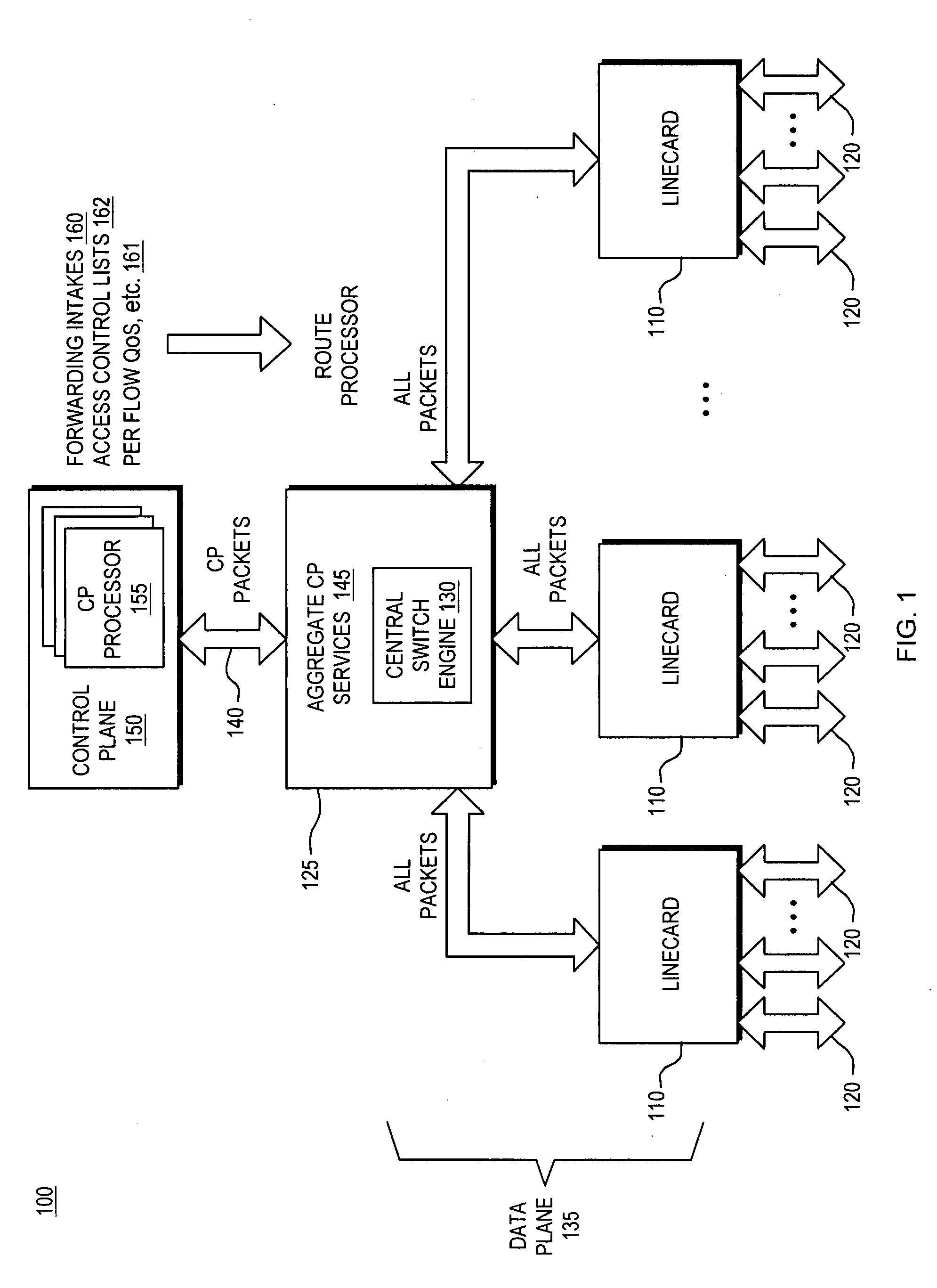
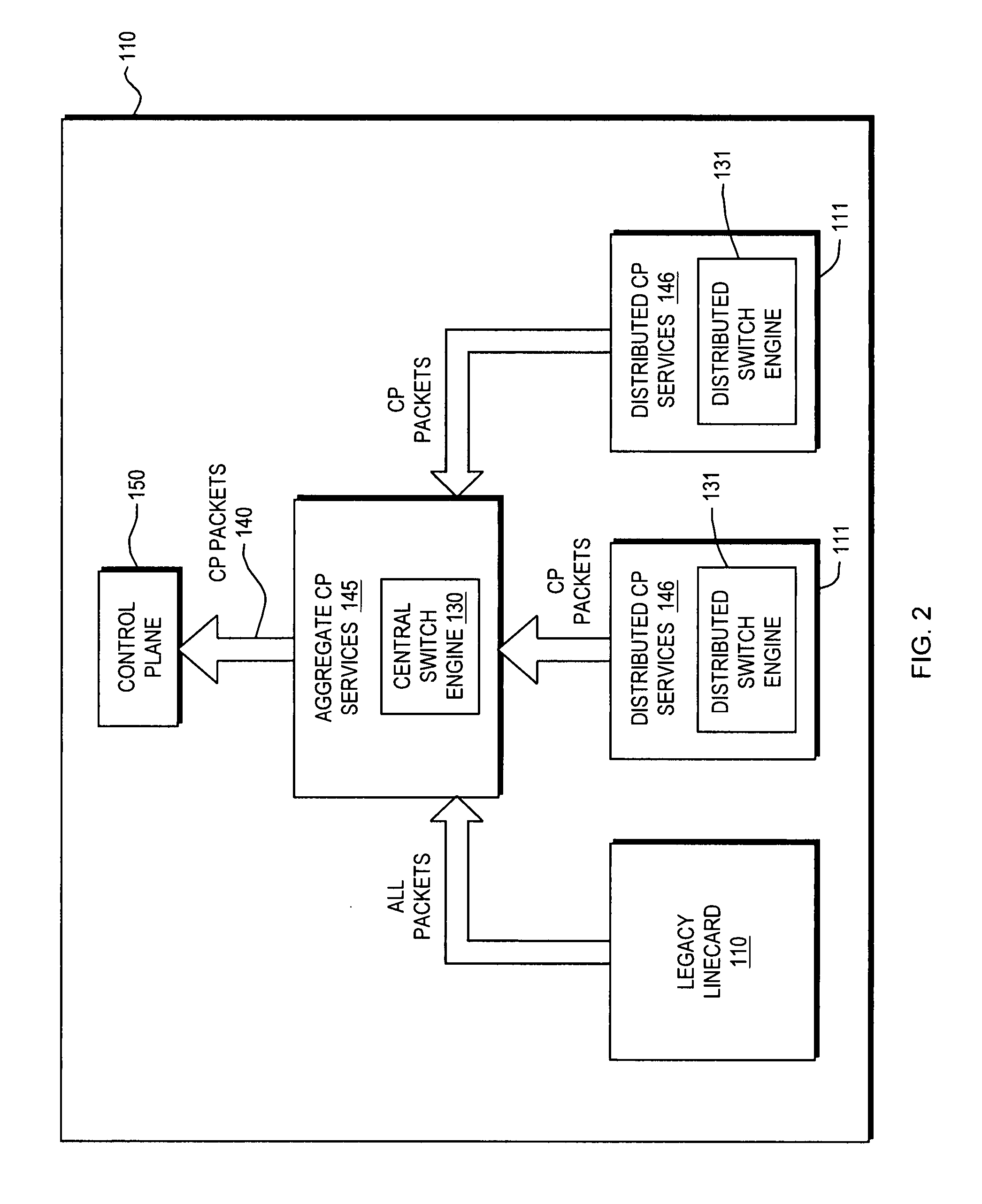
Control plane security and traffic flow management
InactiveUS20070201357A1Improve immunityImprove service qualityMultiplex system selection arrangementsInterconnection arrangementsTraffic capacityQuality of service
An internetworking device that provides improved immunity to Denial of Service attacks, and in general, improved Quality of Service (QoS). An internetworking element or other route processor is composed of two main parts, including a data forwarding plane and a control plane; the control plane runs routing, signaling and control protocols that are responsible for determining the packet forwarding behavior by the data plane. Independent control plane processes may be provided; however, they are considered to be a single network entity that is a uniquely addressable port. Packets thus intended for the control plane always pass through a designated point. As a result, a set of port services unique to the control plane may be applied to the control plane port. These control plane port services thus can be utilized to control all packet traffic entering and exiting the control plane processes as a whole.
Owner:CISCO SYSTEMS INC
Connecting on-premise networks with public clouds
A computer system for encapsulating a packet between a customer premise for delivery to customer resources within a public cloud data center. The computer system comprises a shim gateway. The shim gateway comprises a plurality of customer specific shim components. The shim gateway is configured to receive a packet from a customer premise. The packet has a VLAN tag. The packet identifies a tenant within a designated virtual network for the customer. The designated virtual network is within the public cloud data center. The shim gateway is further configured to encapsulate the packet into an encapsulated packet. Encapsulation includes mapping the VLAN tag to a destination network address of a tenant gateway for the customer. The tenant gateway is in the designated virtual network. The shim gateway is further configured to forward the encapsulated packet to the tenant gateway in the designated virtual network for delivery to the identified tenant.
Owner:MICROSOFT TECH LICENSING LLC
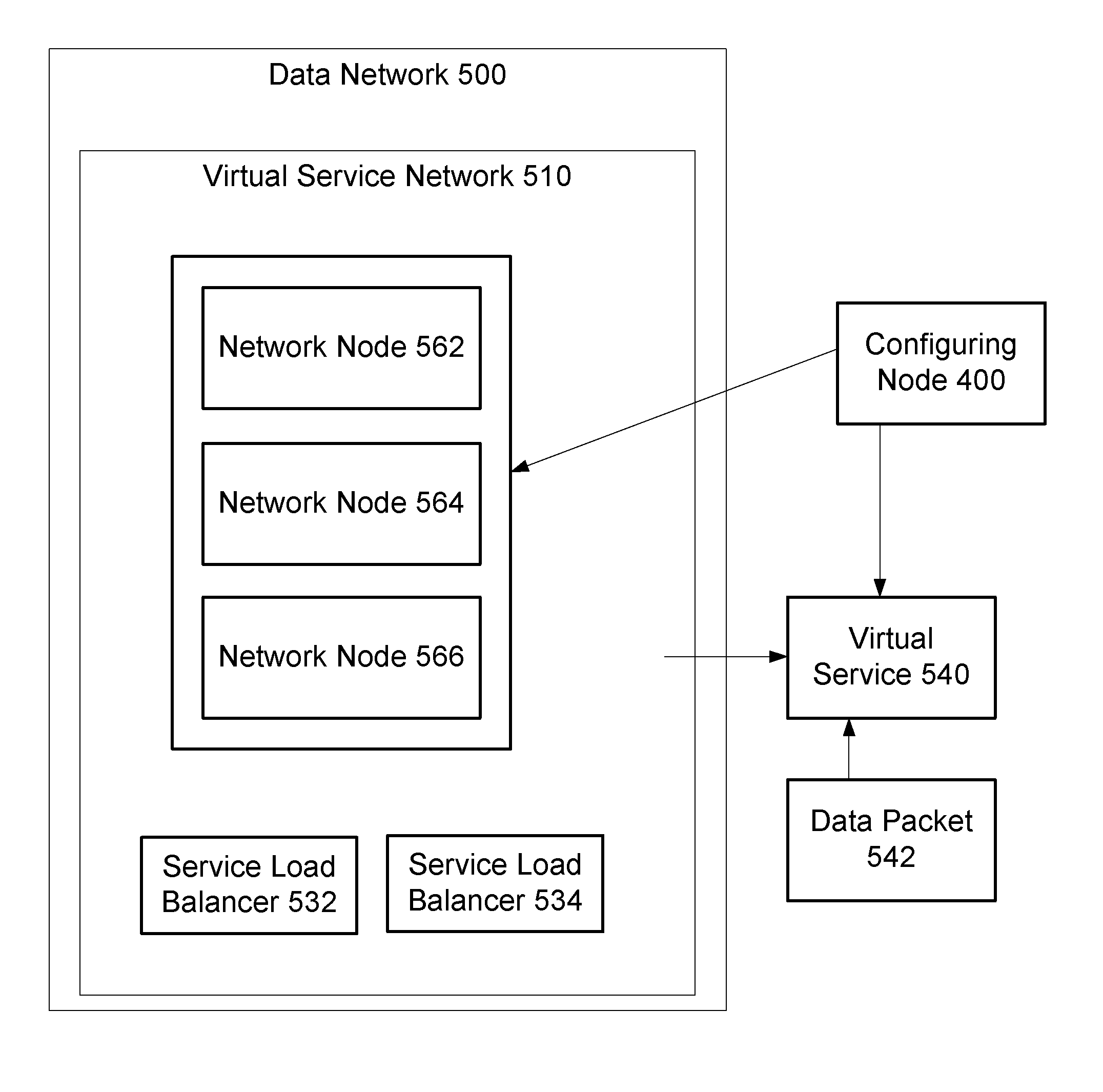
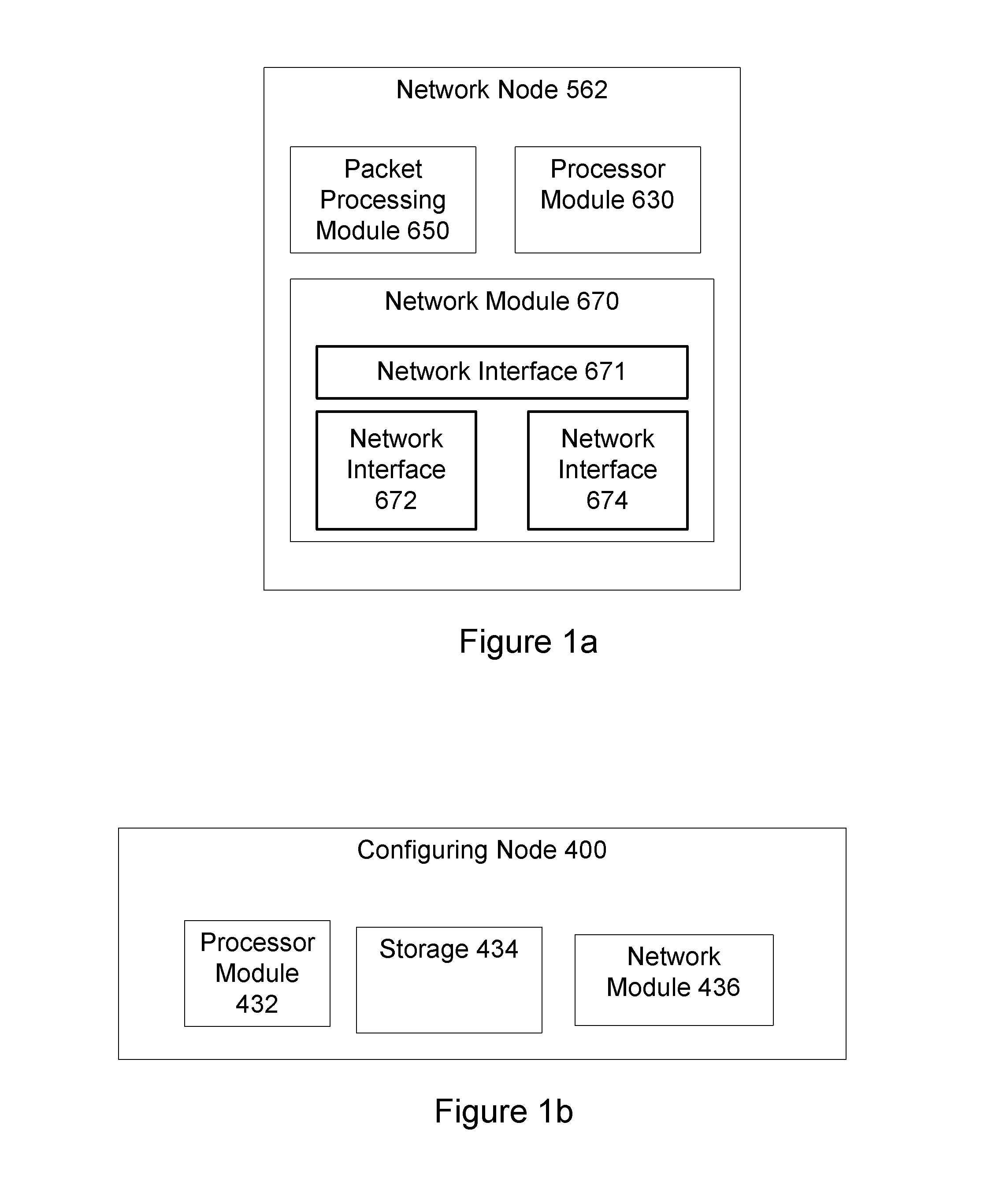
Configuration of a virtual service network
ActiveUS20140169168A1Error preventionFrequency-division multiplex detailsDistributed computingPacket forwarding
Configuration of a virtual service network by a configuring node includes: determining that the virtual service is to be configured; determining a configuration associated with the virtual service and including packet forwarding policies associated with the virtual service, each packet forwarding policy including a virtual service network address and a destination; and sending the packet forwarding policies in the configuration to a network node. The network node: stores the packet forwarding policies; receives a data packet for the virtual service and including a virtual service network address; determines a match between the virtual service network address in the data packet with the virtual service network address in a given packet forwarding policy of the stored packet forwarding policies; obtains a given destination in the given packet forwarding policy; and sends the data packet to a service load balancer associated with the given destination by the network node.
Owner:A10 NETWORKS
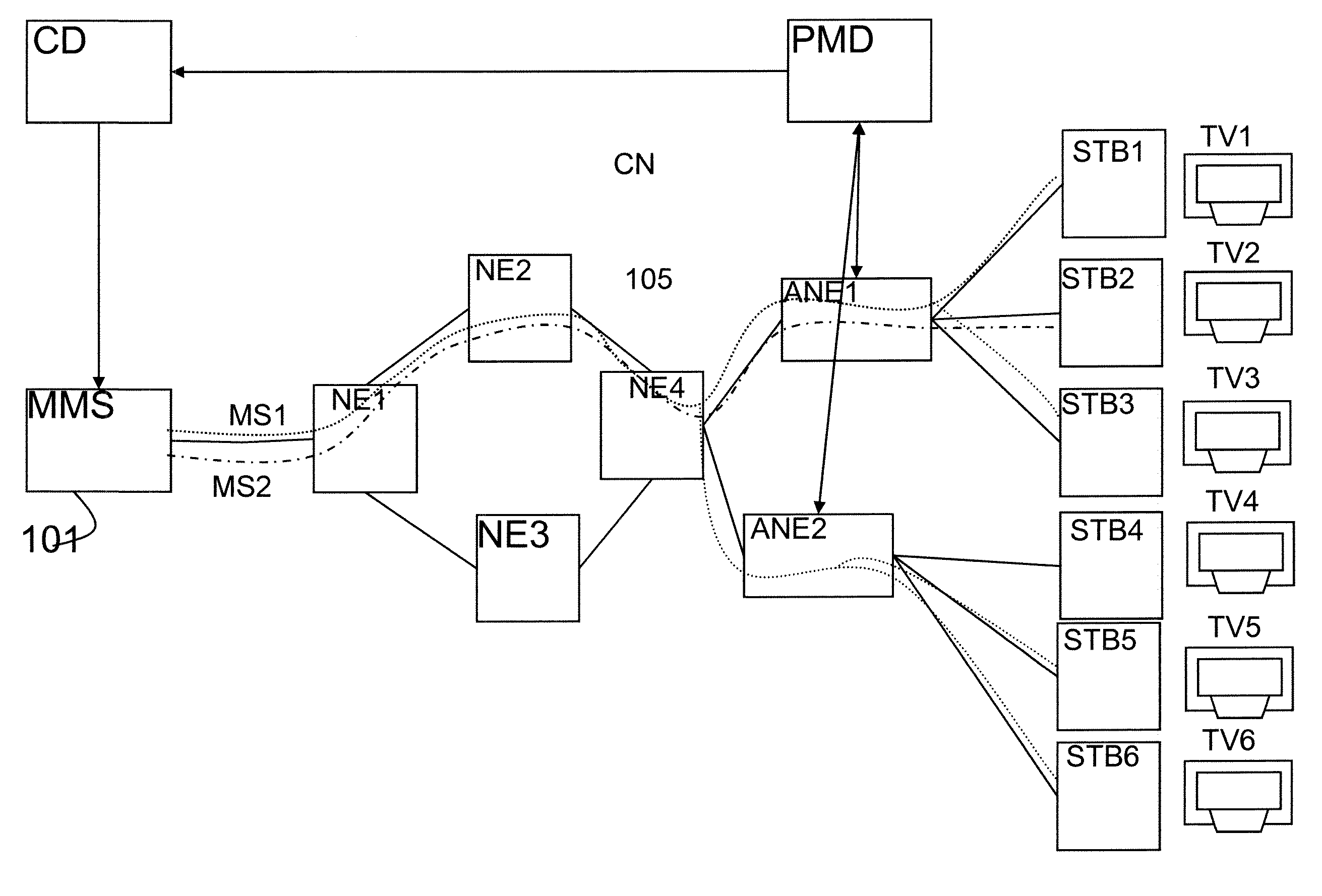
Method for forwarding packets a related packet forwarding system, a related classification device and a related popularity monitoring device
InactiveUS8503455B2Low experience requirementEfficient solutionData switching by path configurationSelective content distributionMultimedia streamsComputer network
The present invention relates to a method and related system and related devices for forwarding packets of a plurality of multimedia streams where the packets of the plurality of multimedia streams being forwarded from a multimedia source towards a plurality of multimedia endpoints over a communications network, where the method comprises a step of classifying the packets of the plurality of multimedia streams based on the usage of each of the multimedia streams.
Owner:ALCATEL LUCENT SAS
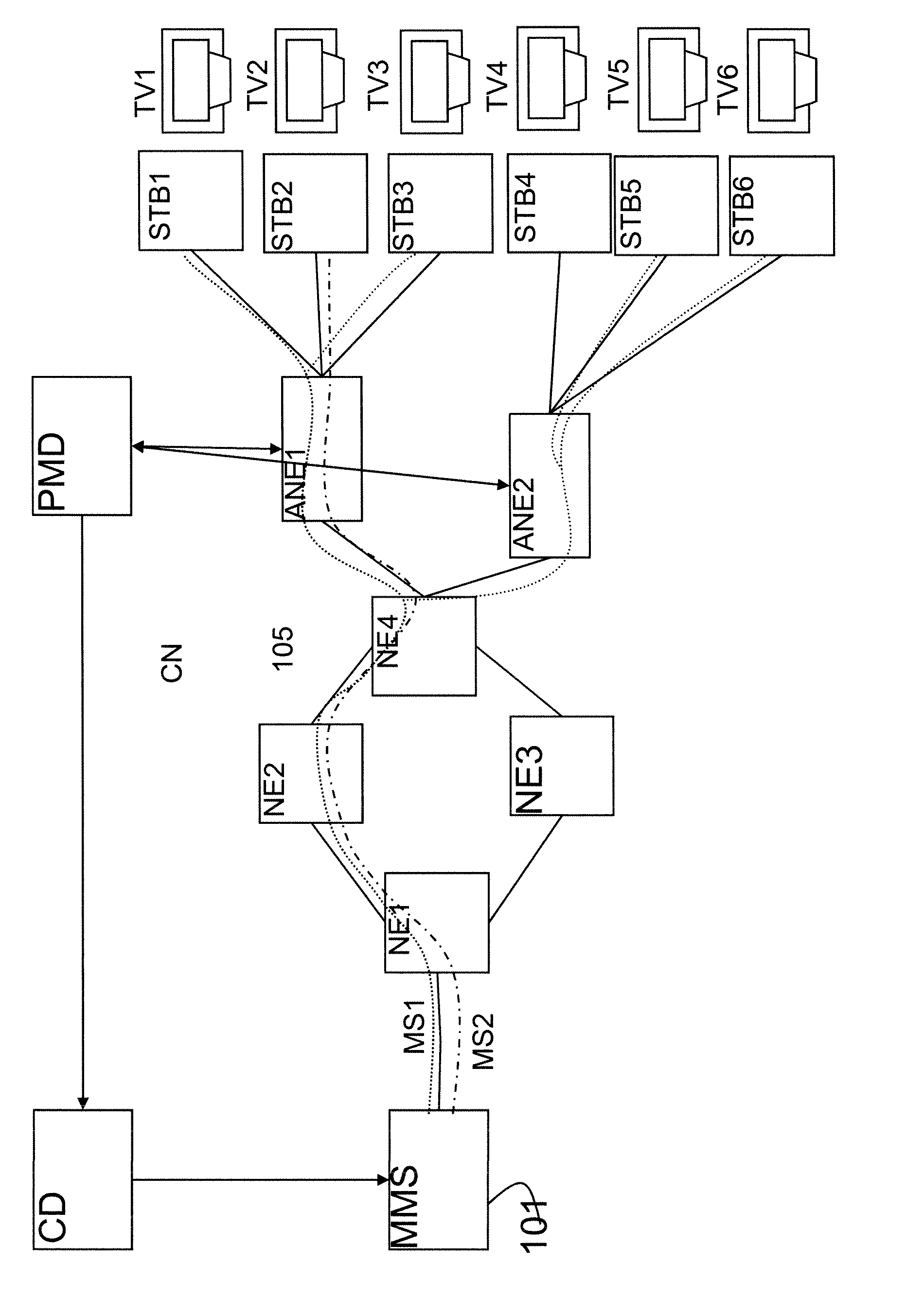
Packet forwarding apparatus and communication bandwidth control method
InactiveUS20060187942A1Data switching by path configurationStore-and-forward switching systemsTerminal equipmentEdge node
In a network for forwarding user packets by a tunneling protocol, an egress edge node to which tunnels concentrate from a plurality of ingress edge nodes allocates a bandwidth to each of sessions multiplexed through each of the tunnels and notifies each of the ingress edge nodes of the allocated bandwidth, and the ingress node notifies private routers or terminal devices of the allocated bandwidth.
Owner:HITACHI LTD
System and method for hardware accelerated packet multicast in a virtual routing system
ActiveUS7266120B2Special service provision for substationData switching by path configurationExternal storageMulti processor
A packet-forwarding engine (PFE) of a multiprocessor system uses an array of flow classification block (FCB) indices to multicast a packet. Packets are received and buffered in external memory. In one embodiment, when a multicast packet is identified, a bit is set in a packet descriptor and an FCB index is generated and sent with a null-packet to the egress processors which generate multiple descriptors with different indices for each instance of multicasting. All the descriptors may point to the same buffer in the external memory, which stores the multicast packet. A DMA engine reads from the same buffer multiple times and egress processors may access an appropriate transform control block (TCB) index so that the proper headers may be installed on the outgoing packet. The buffer may be released after the last time the packet is read by setting a particular bit of the FCB index.
Owner:FORTINET
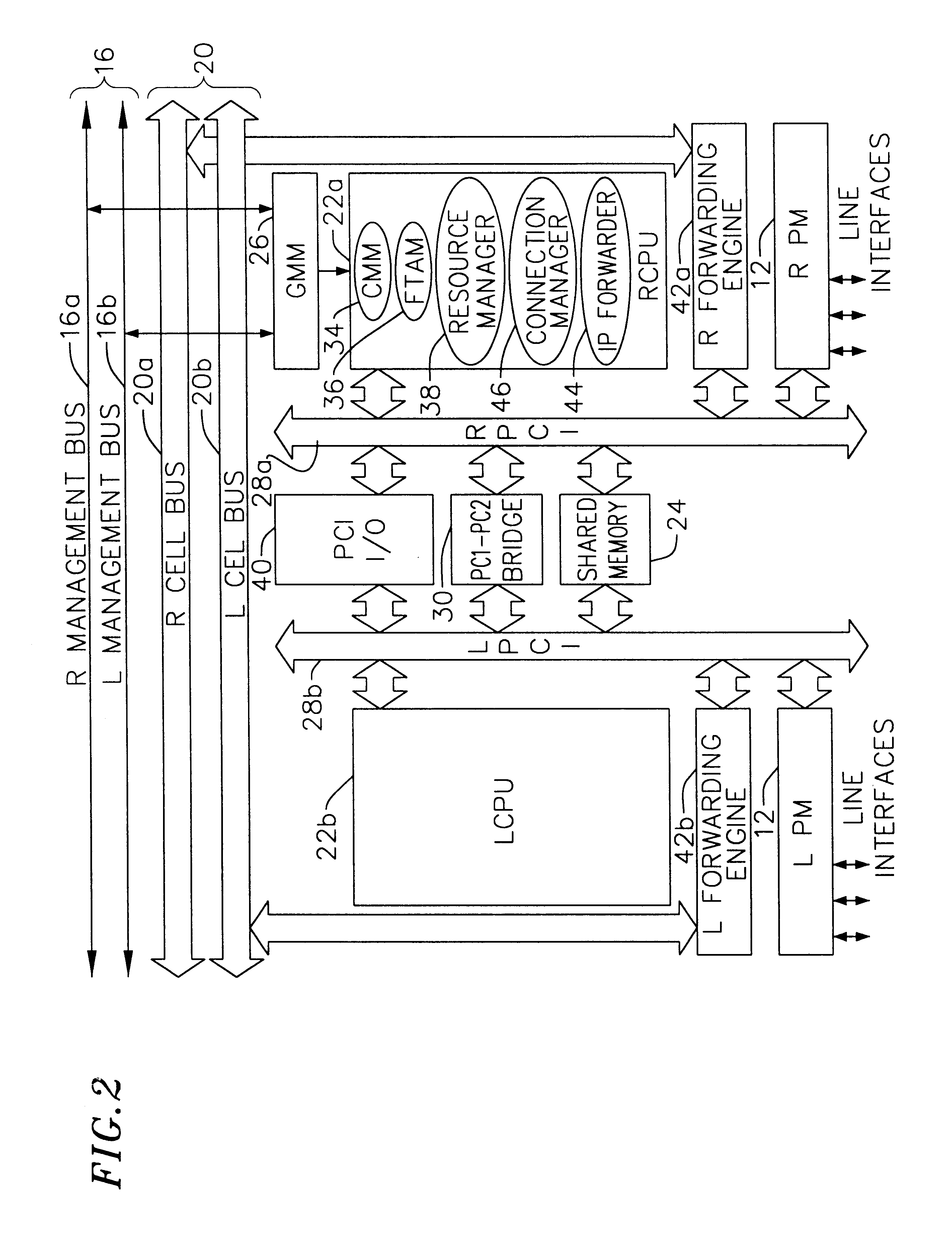
Multi-service network switch
InactiveUS6850531B1Raise priorityReduce dependenceData switching by path configurationStore-and-forward switching systemsDomain nameModem device
A multi-service network switch capable of providing multiple network services from a single platform. The switch incorporates a distributed packet forwarding architecture where each of the various cards is capable of making independent forwarding decisions. The switch further allows for dynamic resource management for dynamically assigning modem and ISDN resources to an incoming call. The switch may also include fault management features to guard against single points of failure within the switch. The switch further allows the partitioning of the switch into multiple virtual routers where each virtual router has its own set of resources and a routing table. Each virtual router is further partitioned into virtual private networks for further controlling access to the network. The switch supports policy based routing where specific routing paths are selected based on a domain name, a telephone number, and the like. The switch also provides tiered access of the Internet by defining quality of access levels to each incoming connection request. The switch may further support an IP routing protocol and architecture in which the layer two protocols are independent of the physical interface they run on. Furthermore, the switch includes a generic forwarding interface software for hiding the details of transmitting and receiving packets over different interface types.
Owner:ALCATEL LUCENT SAS
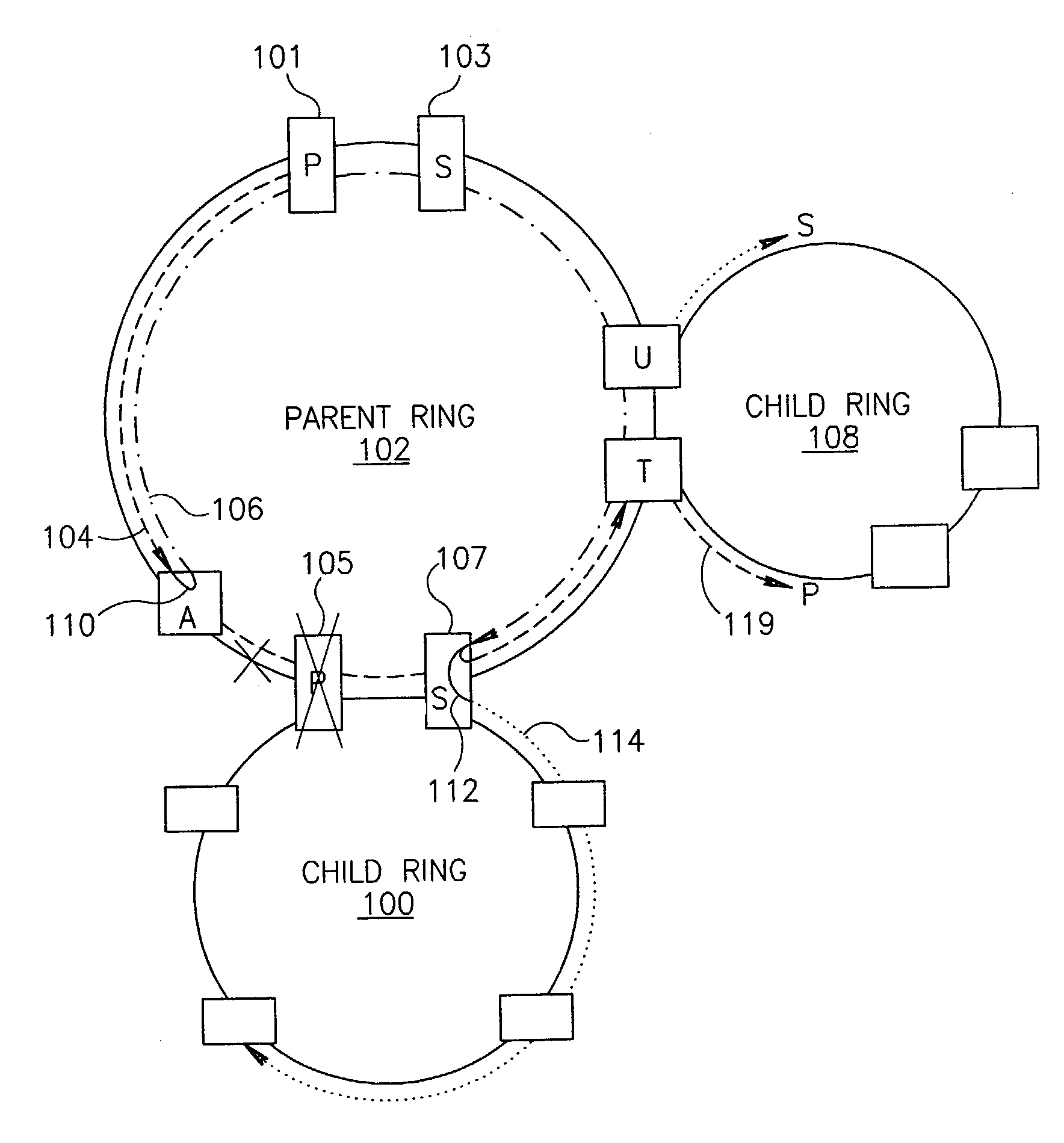
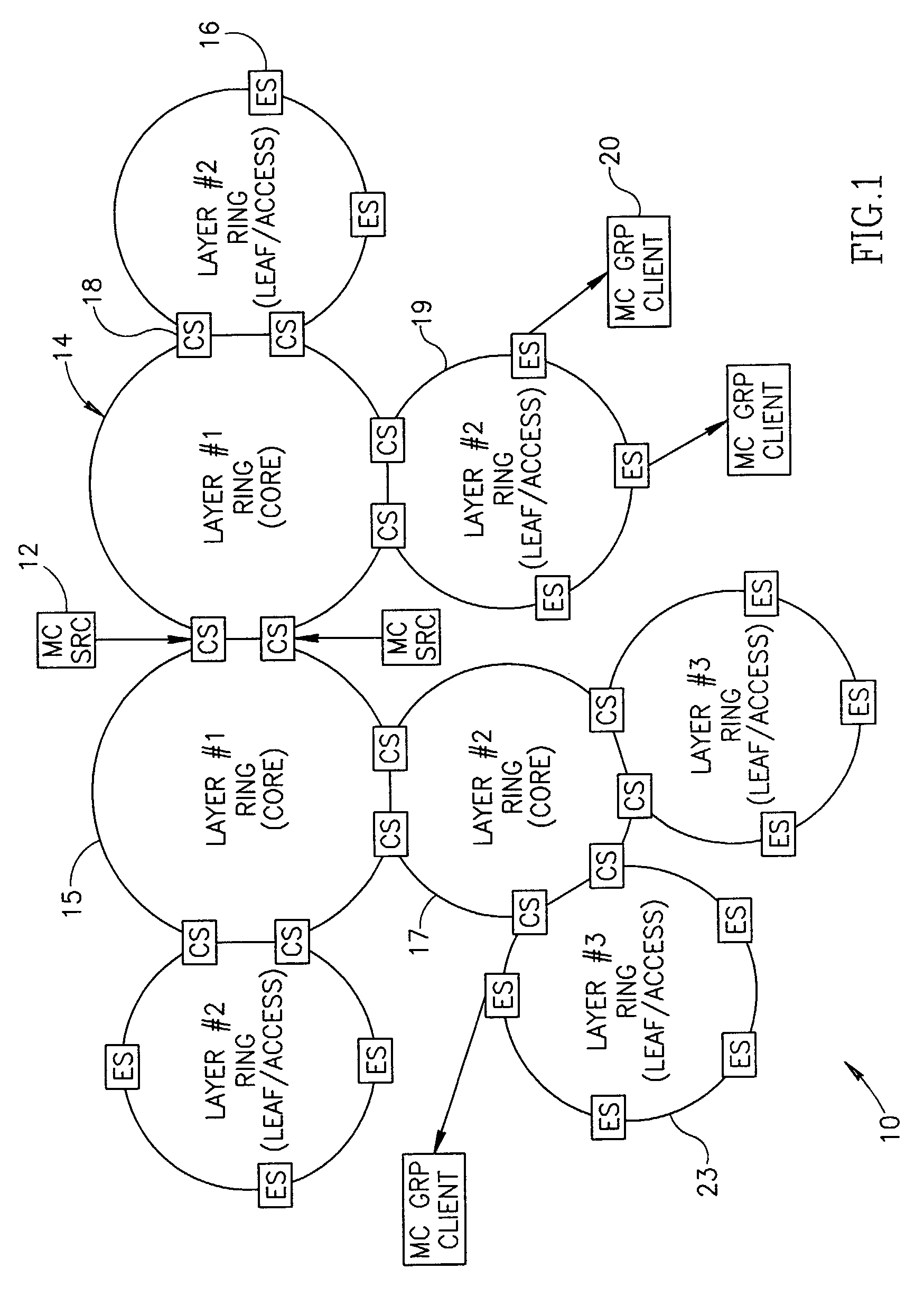
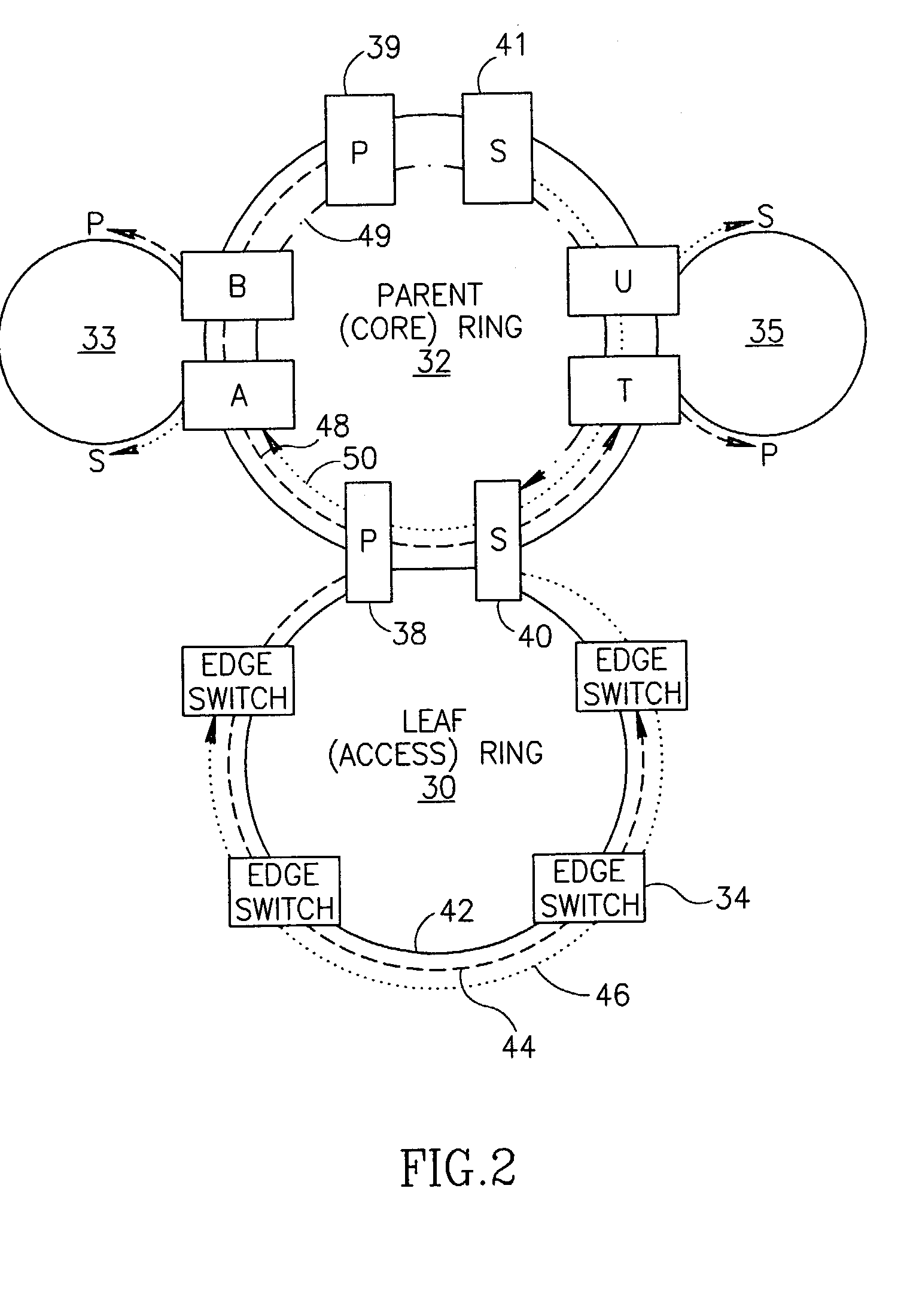
Scalable protection mechanism for hierarchical multicast service in ring based networks
ActiveUS7545735B1Reduce in quantityFrequency-division multiplex detailsTransmission systemsTraffic capacityProtection mechanism
A novel fast and scalable protection mechanism for protecting hierarchical multicast service in ring based networks. The mechanism of the present invention is especially suitable for use in Multi-Protocol Label Switching (MPLS) ring based networks such as Metro Ethernet Networks (MENs). The mechanism provides fast protection for MPLS based point-to-multipoint (P2MP) Label Switched Paths (LSPs) in a scalable manner. Each multicast connection on each ring in the network is split into two sub-LSPs: a primary P2MP sub-LSP originating on a primary node and a secondary P2MP sub-LSP originating on a secondary node traveling opposite to the primary path. For each node to be protected, a point-to-point protection tunnel is provisioned from that node to a secondary node that forwards the packets to the secondary path on all child rings connected to that parent ring through the protected node and that are provisioned to receive the specific multicast connection. In the event of a failure, all the multicast traffic on that ring is directed through the protection tunnel to the secondary node. Upon exiting the protection tunnel, the packets are forwarded to the secondary LSP on the child rings for which this node is the secondary node and also continue along the primary LSP on the parent ring and along all child rings for which this node is the primary node.
Owner:NOKIA SIEMENS NETWORKS ETHERNET SOLUTIONS +1
Enhanced switchover for MPLS fast reroute
ActiveUS20050097219A1Digital computer detailsData switching networksForwarding equivalence classDistributed computing
A Fast Reroute implementation where switchover time to backup tunnels upon failure of a protected network element is independent of a number of entries corresponding to forwarding equivalence classes forwarding over LSPs using that element. During normal operation of a packet forwarding device, adjacency information for a received packet is retrieved from a forwarding table based on a look-up of the packet's forwarding equivalence class. Upon failure of a link or node, the appropriate entries in this forwarding table are rewritten to implement the switchover to preconfigured backup tunnels. The switchover is effective even before the rewrite process has completed. Upon detection of the failure, forwarding processing shifts to a fix-up mode. During the fix-up mode, the look-up to the previously mentioned forwarding table is followed by a look-up to a backup tunnel adjacency table based on a pointer retrieved from the forwarding table. Operations relating to use of this backup tunnel adjacency table increase forwarding time somewhat but only during the special fix-up mode.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com