Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
6866 results about "Upgrade" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
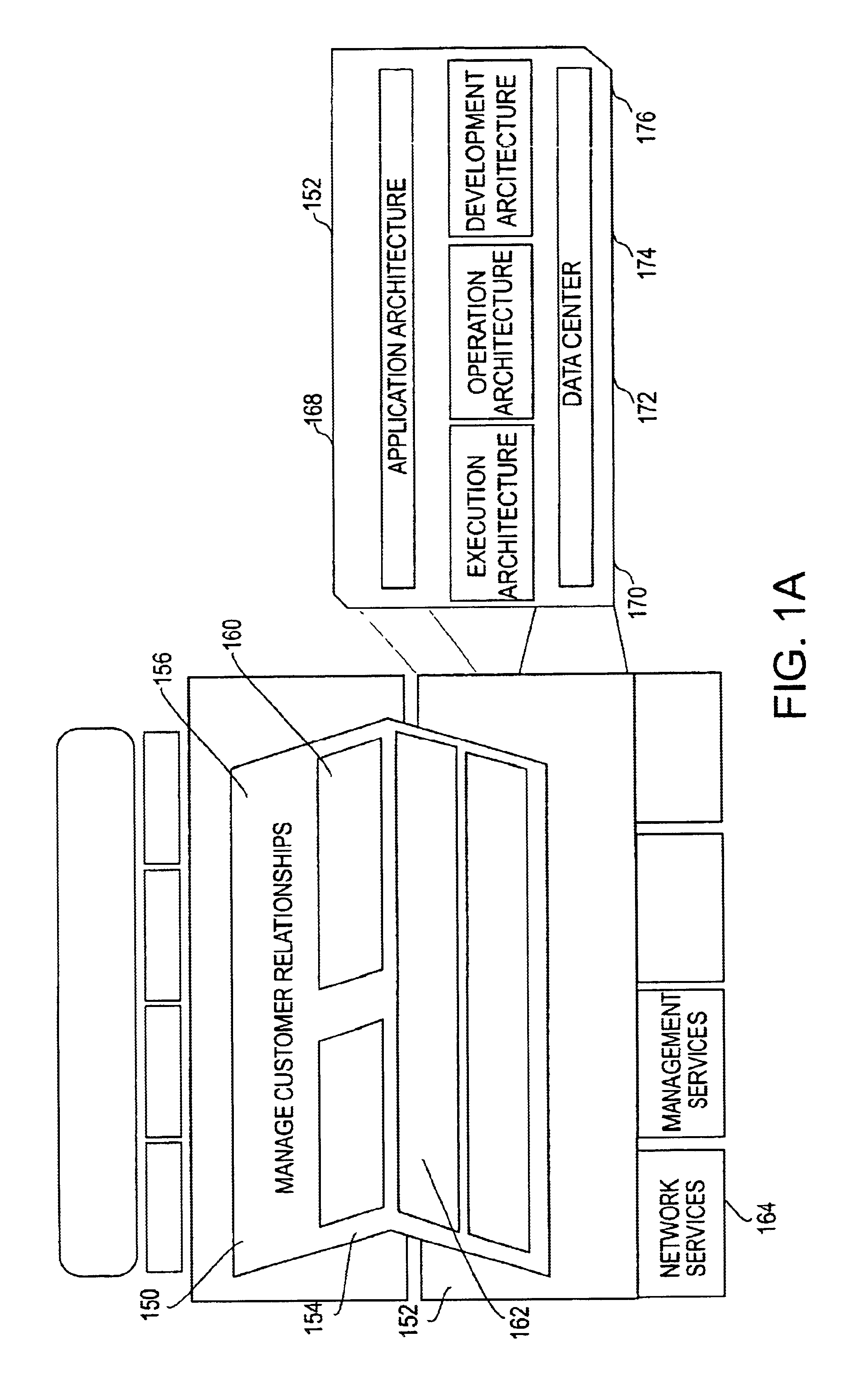
Upgrading is the process of replacing a product with a newer version of the same product. In computing and consumer electronics an upgrade is generally a replacement of hardware, software or firmware with a newer or better version, in order to bring the system up to date or to improve its characteristics.
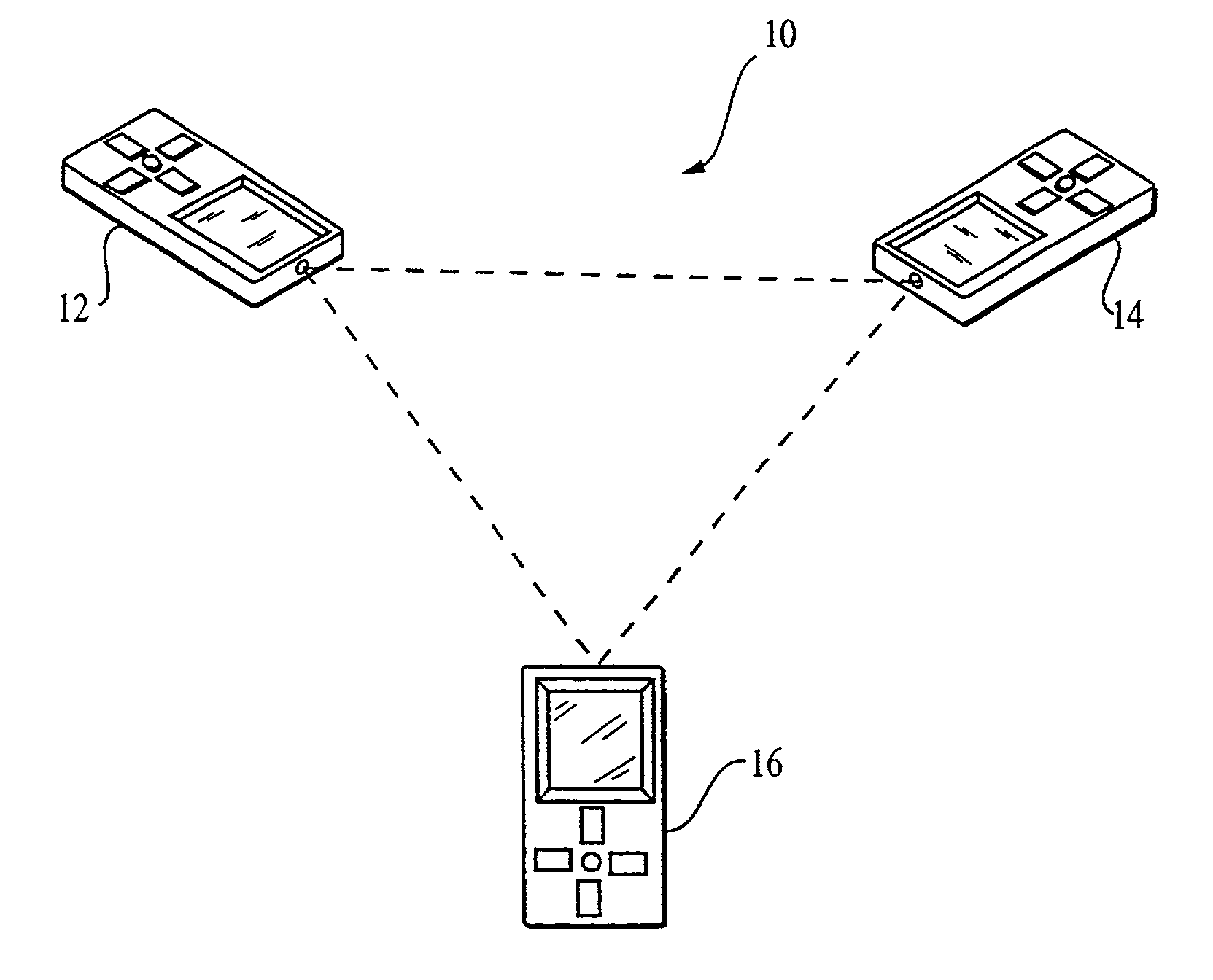
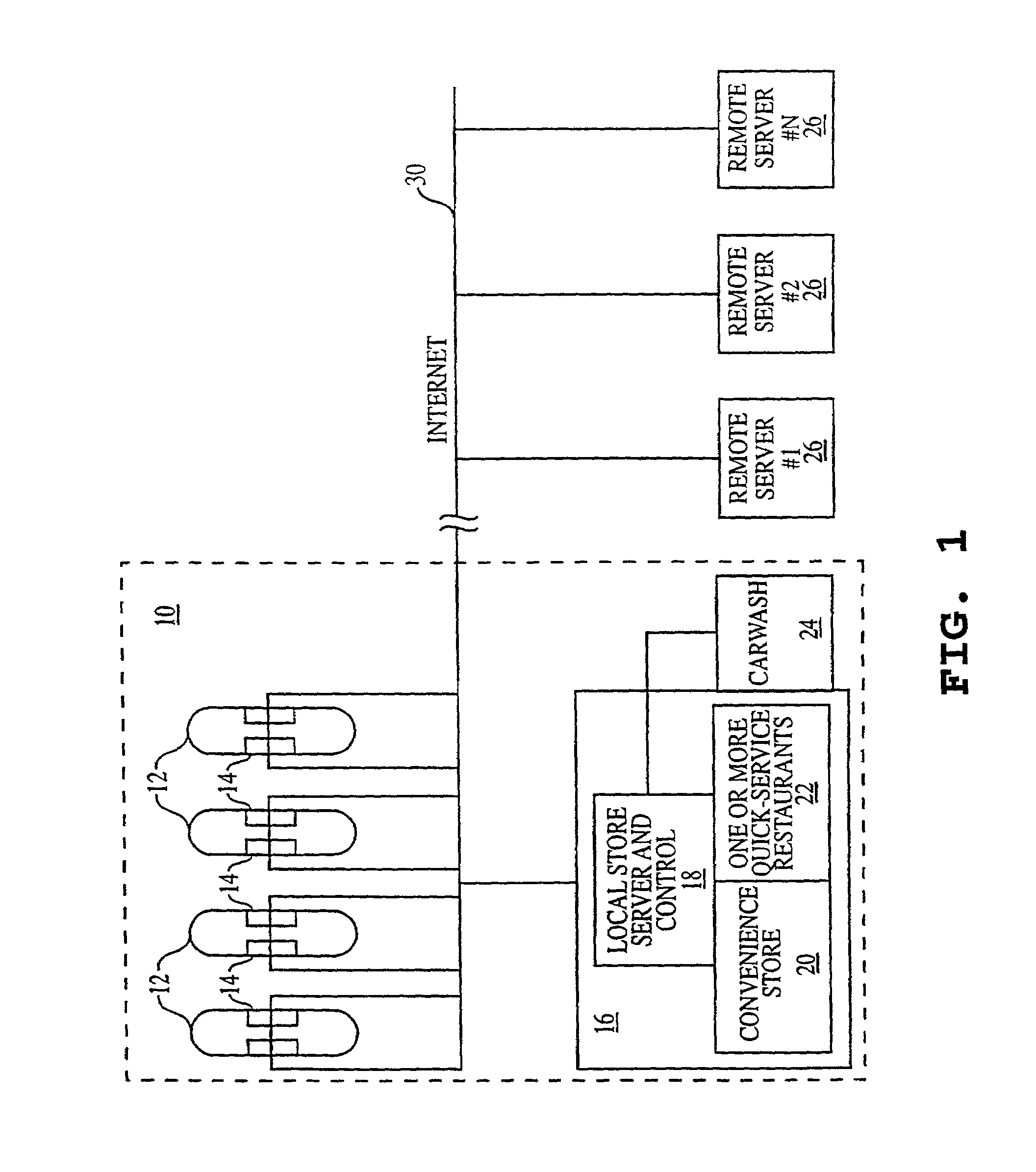
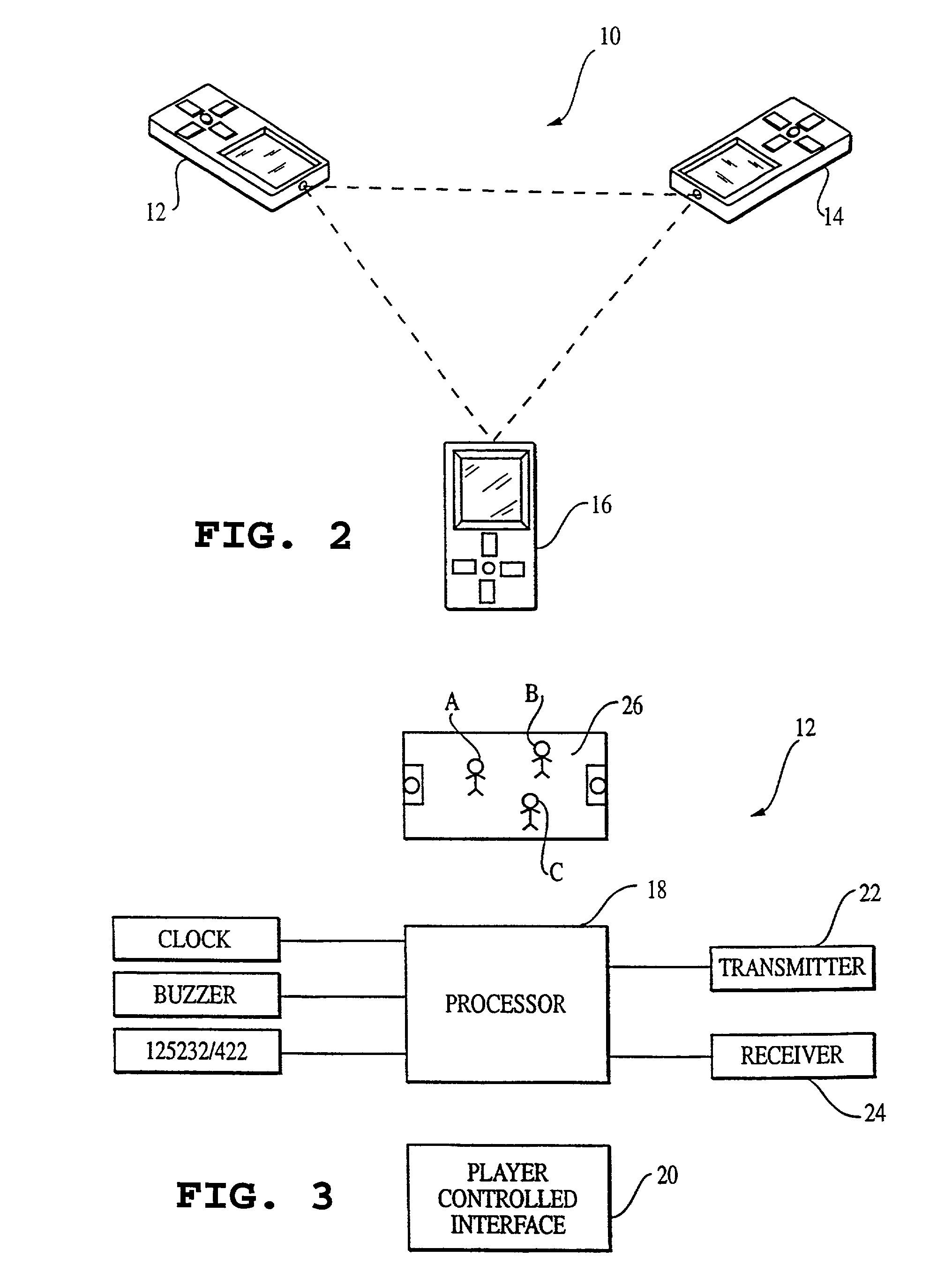
Slim terminal gaming system
InactiveUS6409602B1Minimizing unavailabilityReduce hardware and software costsData processing applicationsBoard gamesClient-sideUpgrade
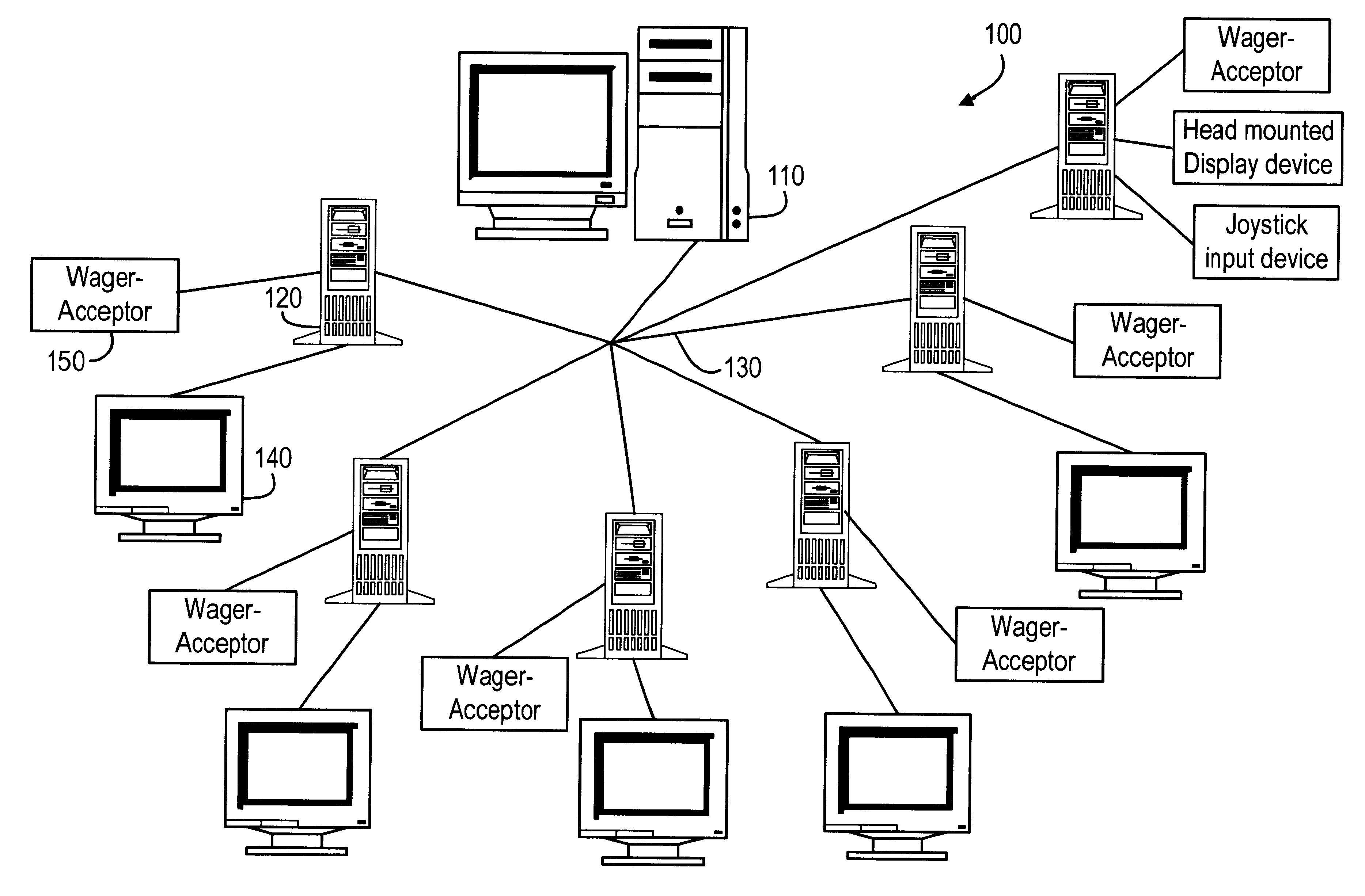
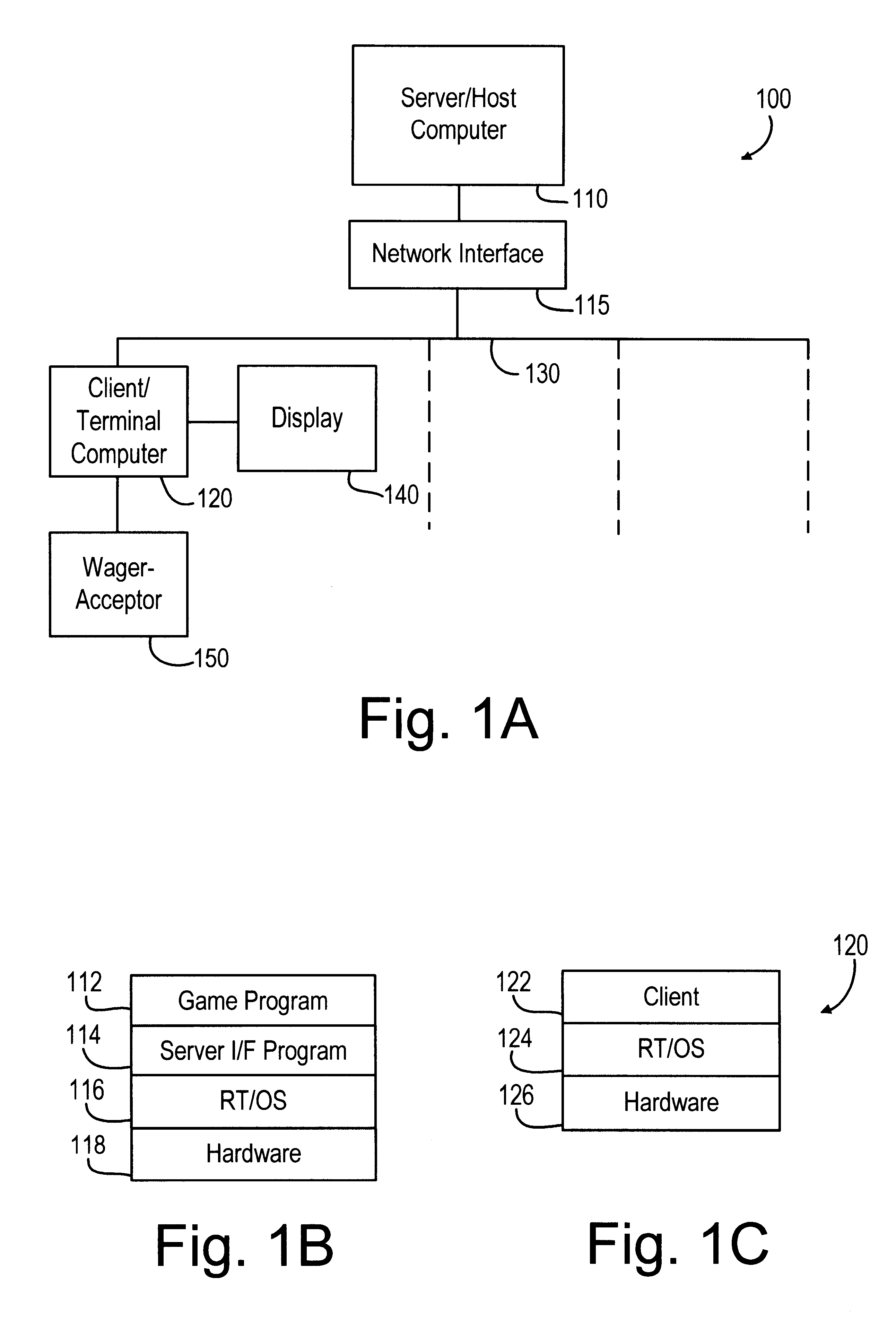
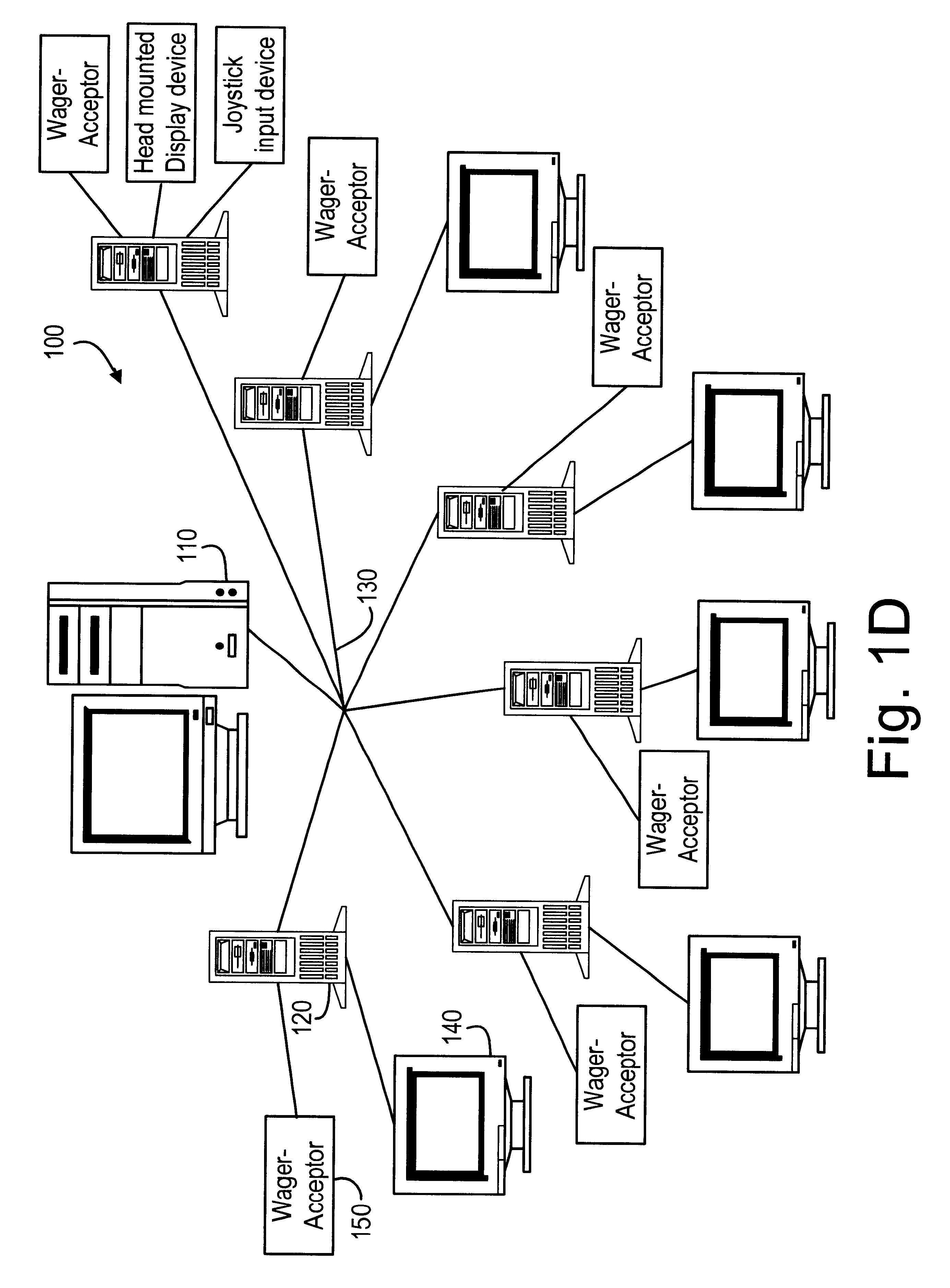
A computer gaming system and method of operation thereof are provided that both drastically reduce the cost of gaming stations and allow contemporaneous access to multiple game programs from a single gaming station. The computer gaming system of the present invention allows for transparent modifications and upgrades to the gaming programs by executing gaming programs on a server / host computer connected to a plurality of client / terminal computers via communication pathways. Each client / terminal computer comprises a client / terminal program that allows input and output streams of the gaming program executed on the server / host computer to be separated and redirected to the client / terminal computers. Since the gaming programs are executed entirely on the server / host computer, with only wagering input and display output operations being executed on the client / terminal computers, the cost of the hardware and software required for each client / terminal computer is greatly reduced. A patron of a client / terminal computer can access any of the gaming programs executed on the server / host computer. Modifications and upgrades of the gaming programs only need to be performed on the server / host computer. By using a stereo head-mounted display together with a joystick input device and wireless communication pathways, the present invention allows a patron to participate in a mobile gaming environment.
Owner:NEW MILLENIUM GAMING
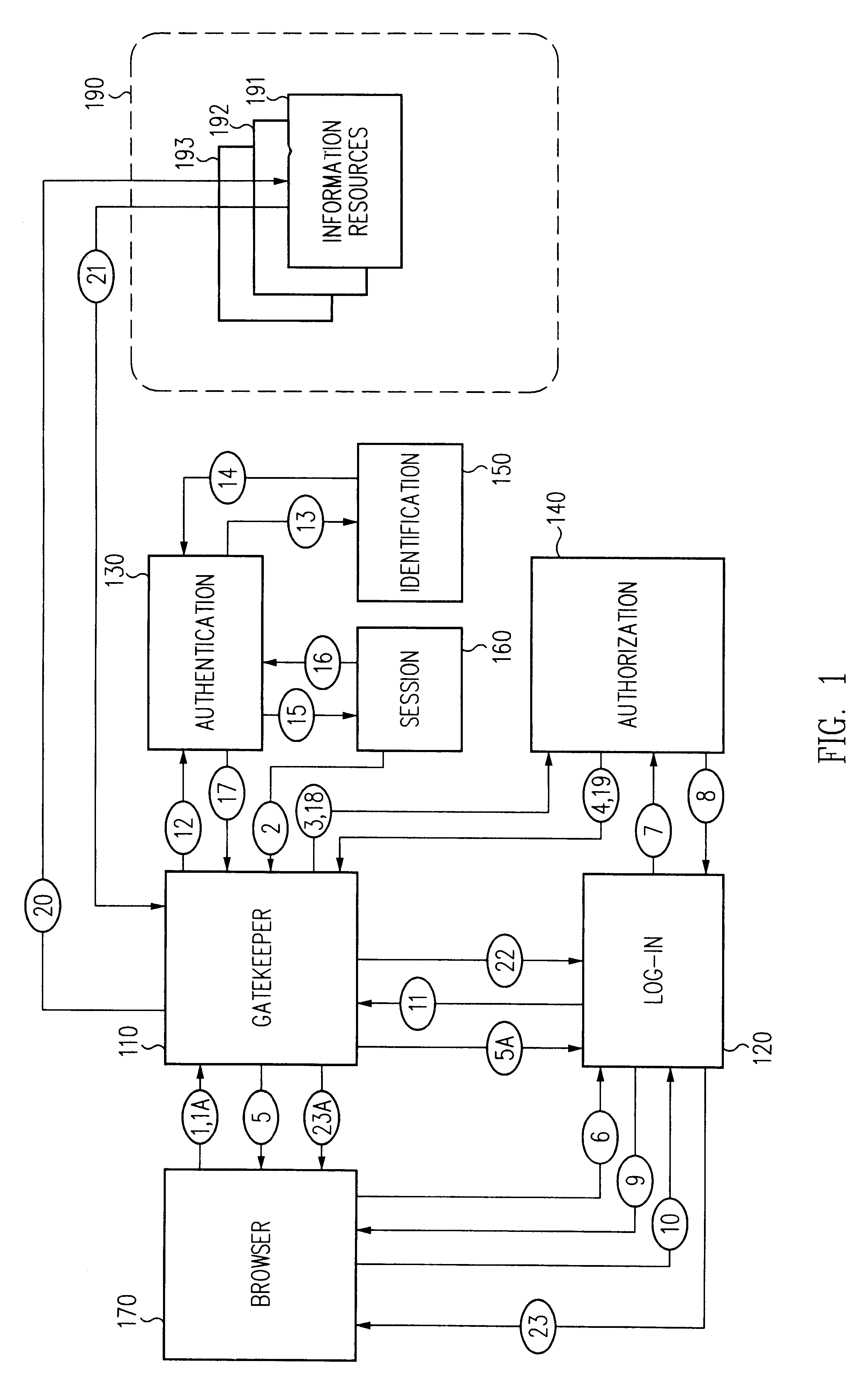
Log-on service providing credential level change without loss of session continuity
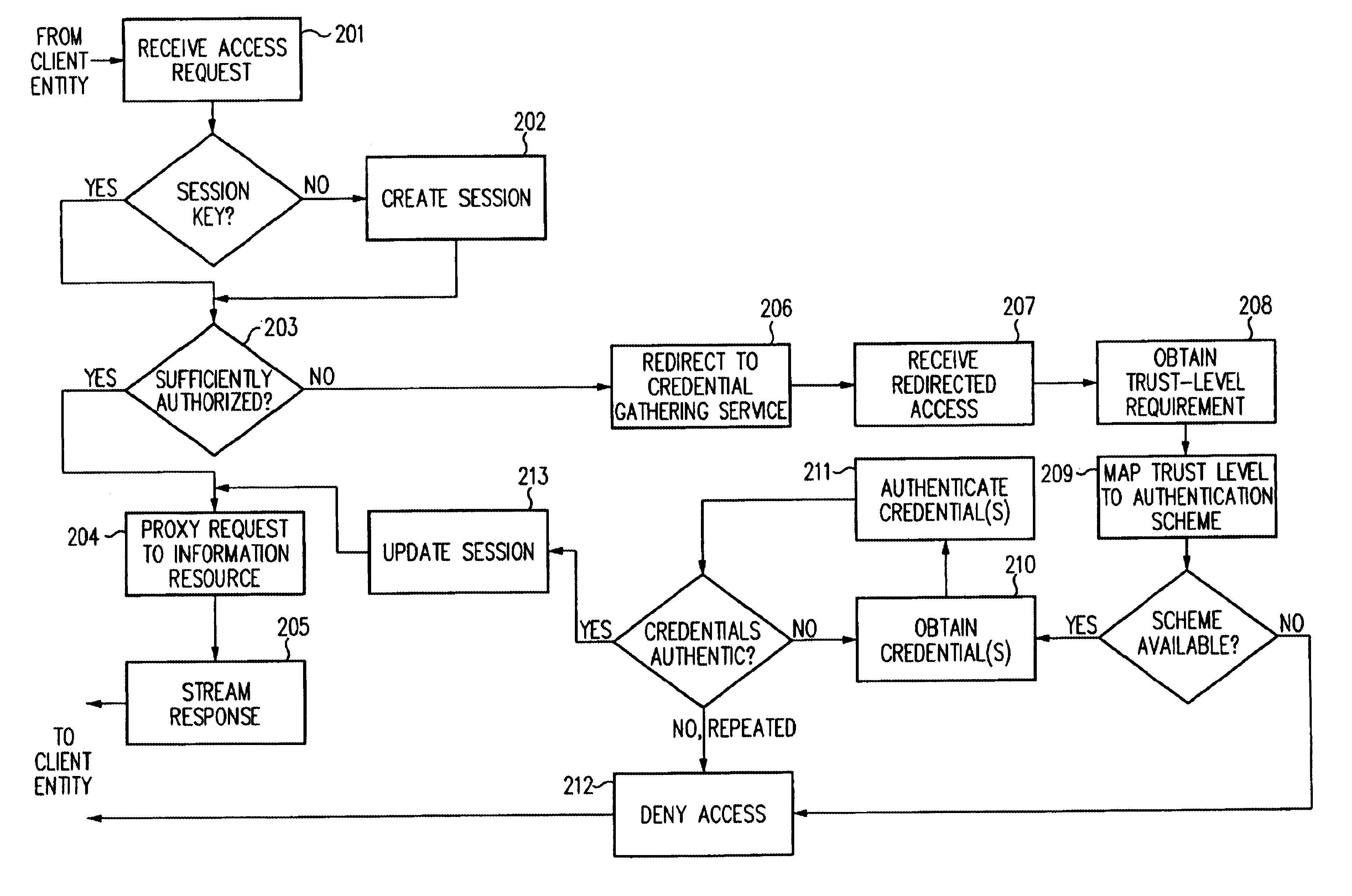
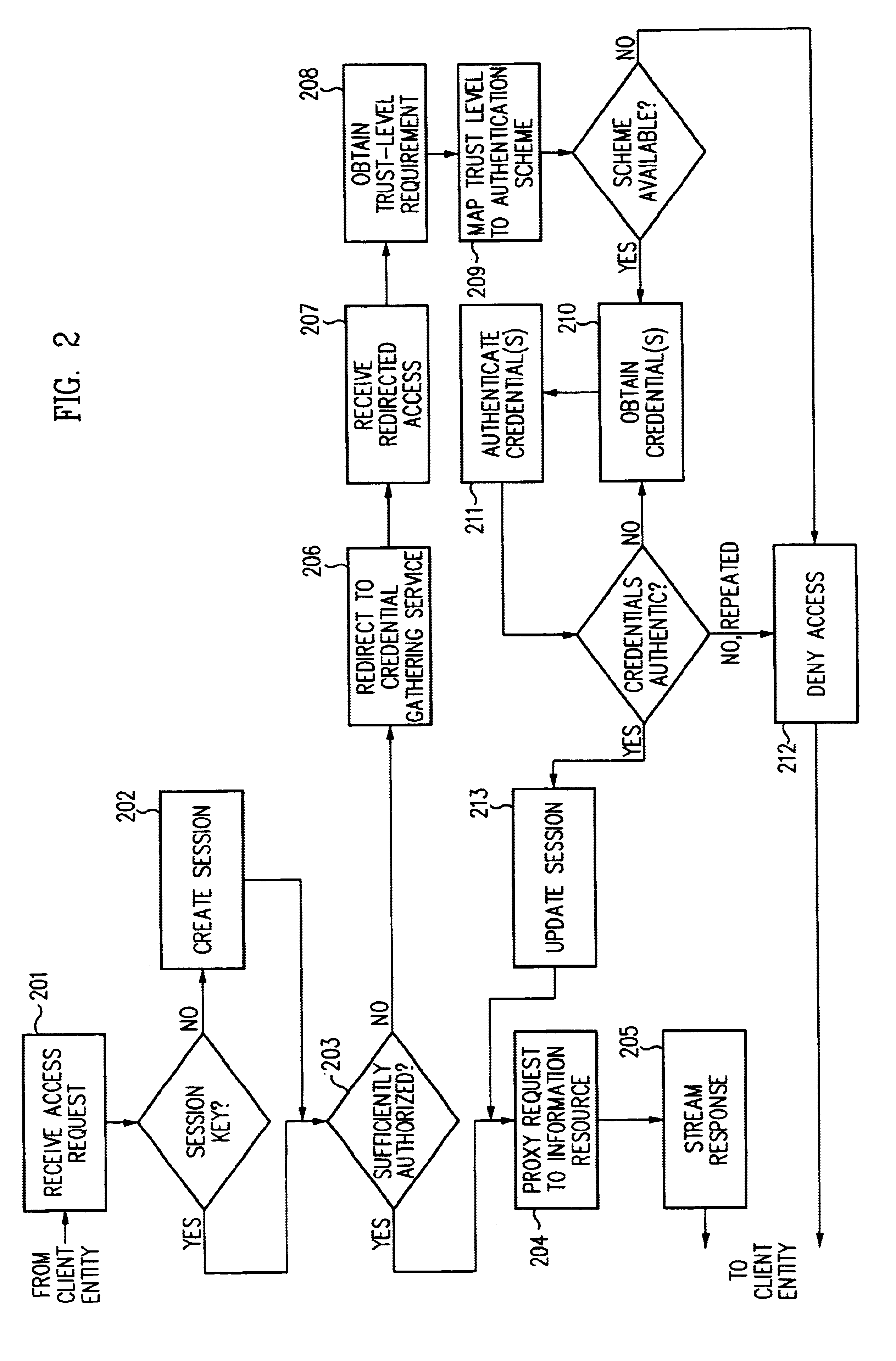
InactiveUS6609198B1Volume/mass flow measurementMultiple digital computer combinationsInformation resourceTrust level
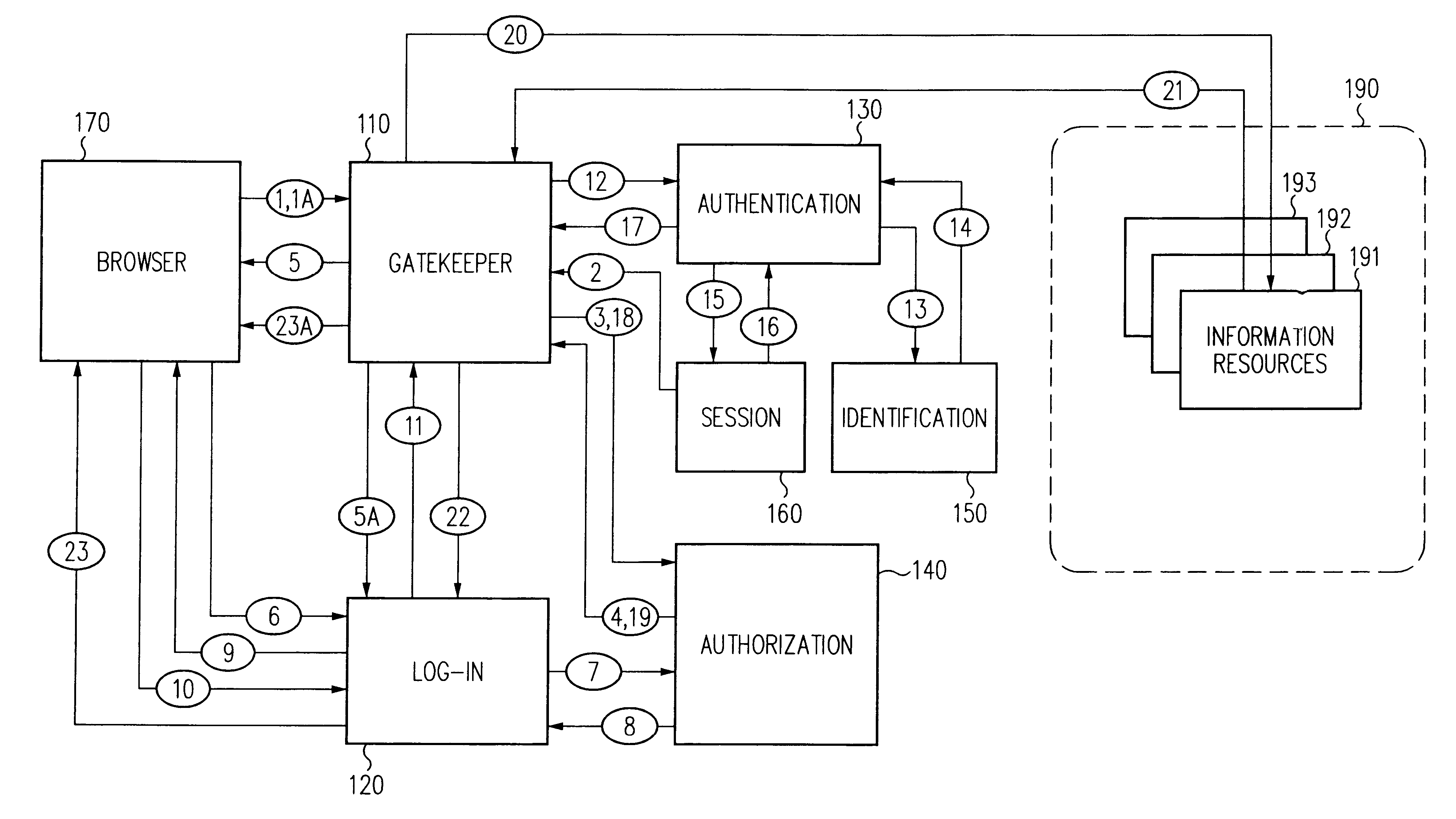
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient. The security architecture allows upgrade of credentials for a given session. This capability is particularly advantageous in the context of a single, enterprise-wide log-on. An entity (e.g., a user or an application) may initially log-on with a credential suitable for one or more resources in an initial resource set, but then require access to resource requiring authentication at higher trust level. In such case, the log-on service allows additional credentials to be provided to authenticate at the higher trust level. The log-on service allows upgrading and / or downgrading without loss of session continuity (i.e., without loss of identity mappings, authorizations, permissions, and environmental variables, etc.).
Owner:ORACLE INT CORP
System and method for an application provider framework
InactiveUS6904449B1Broaden applicationMultiple digital computer combinationsOffice automationService provisionElectronic form
Owner:ACCENTURE GLOBAL SERVICES LTD
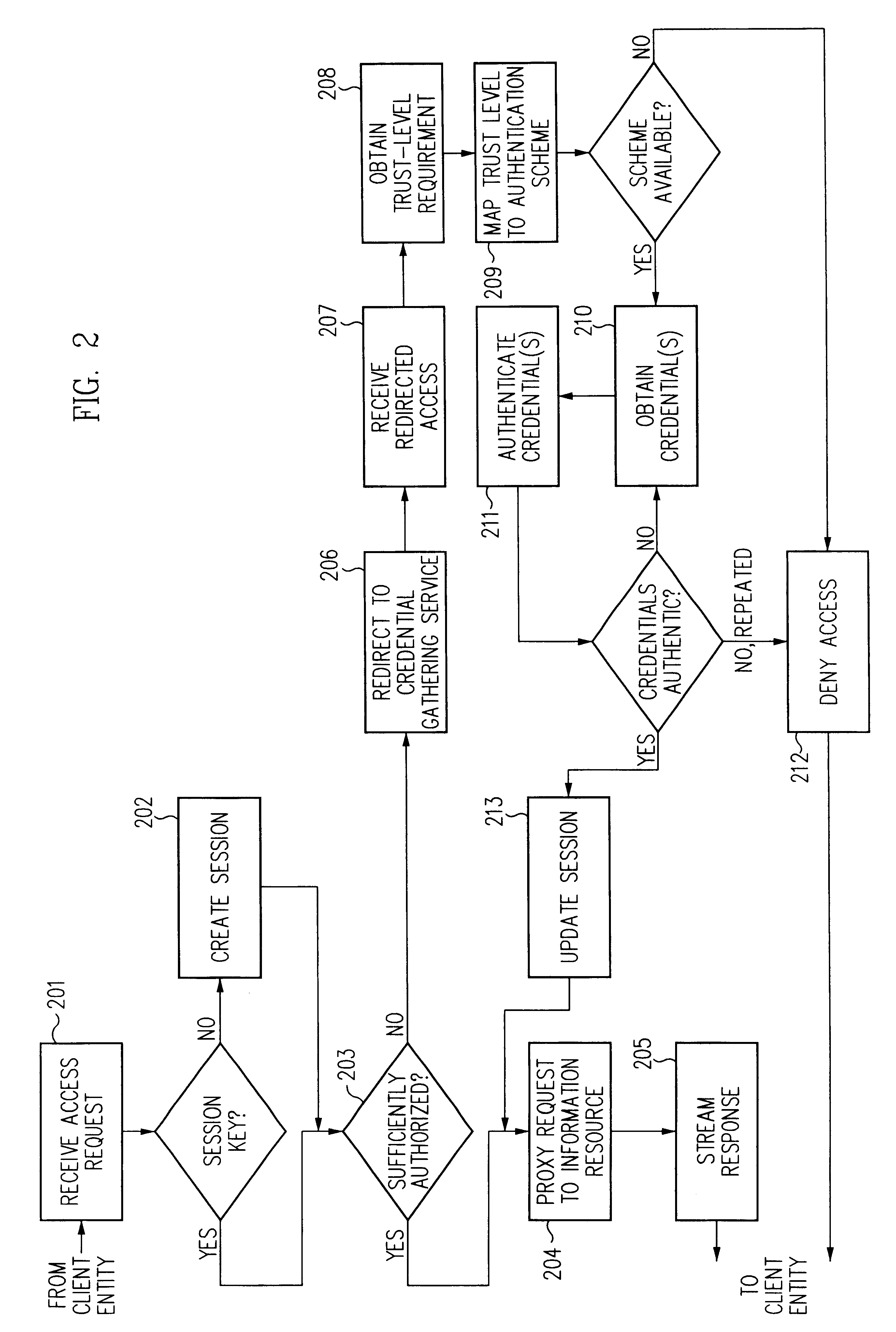
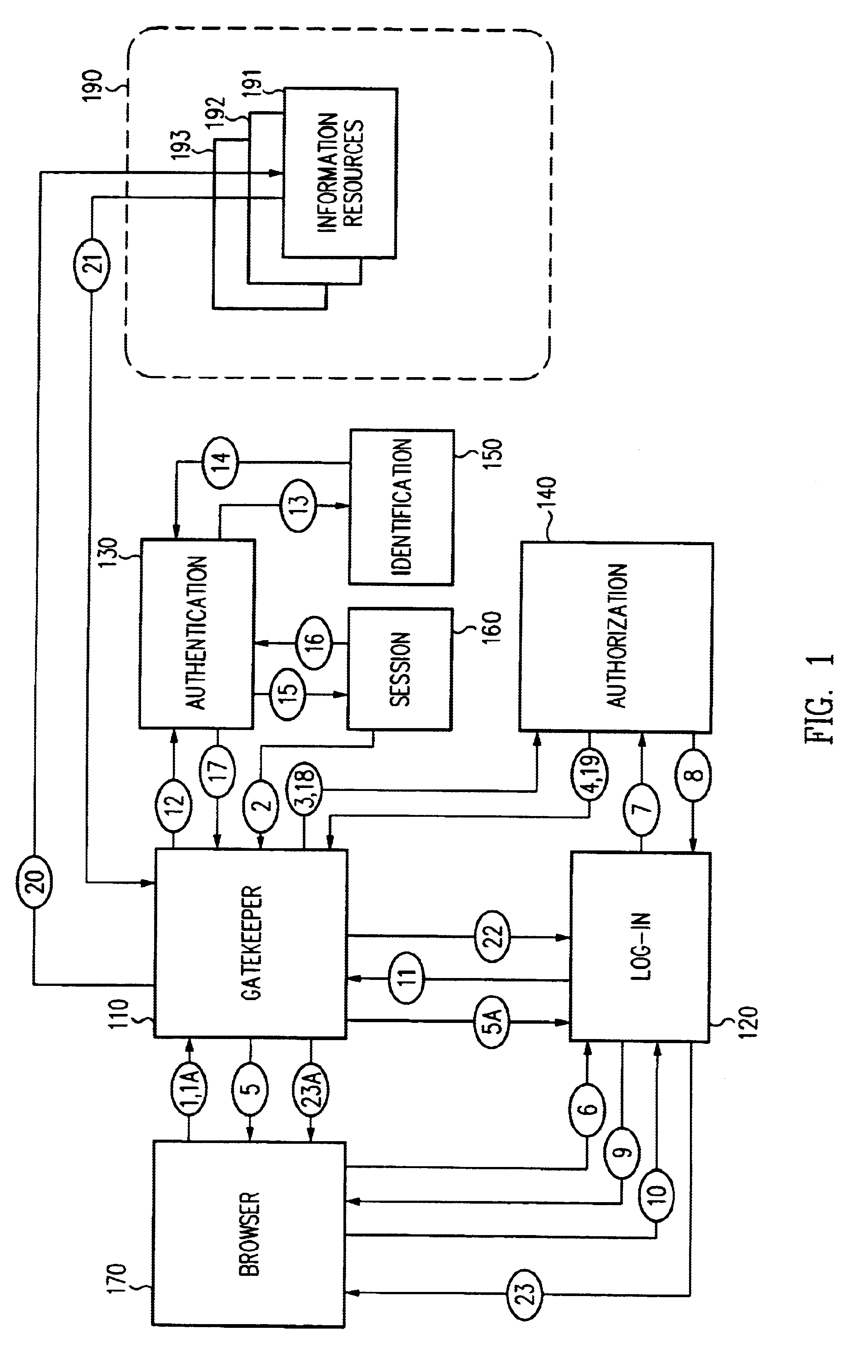
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
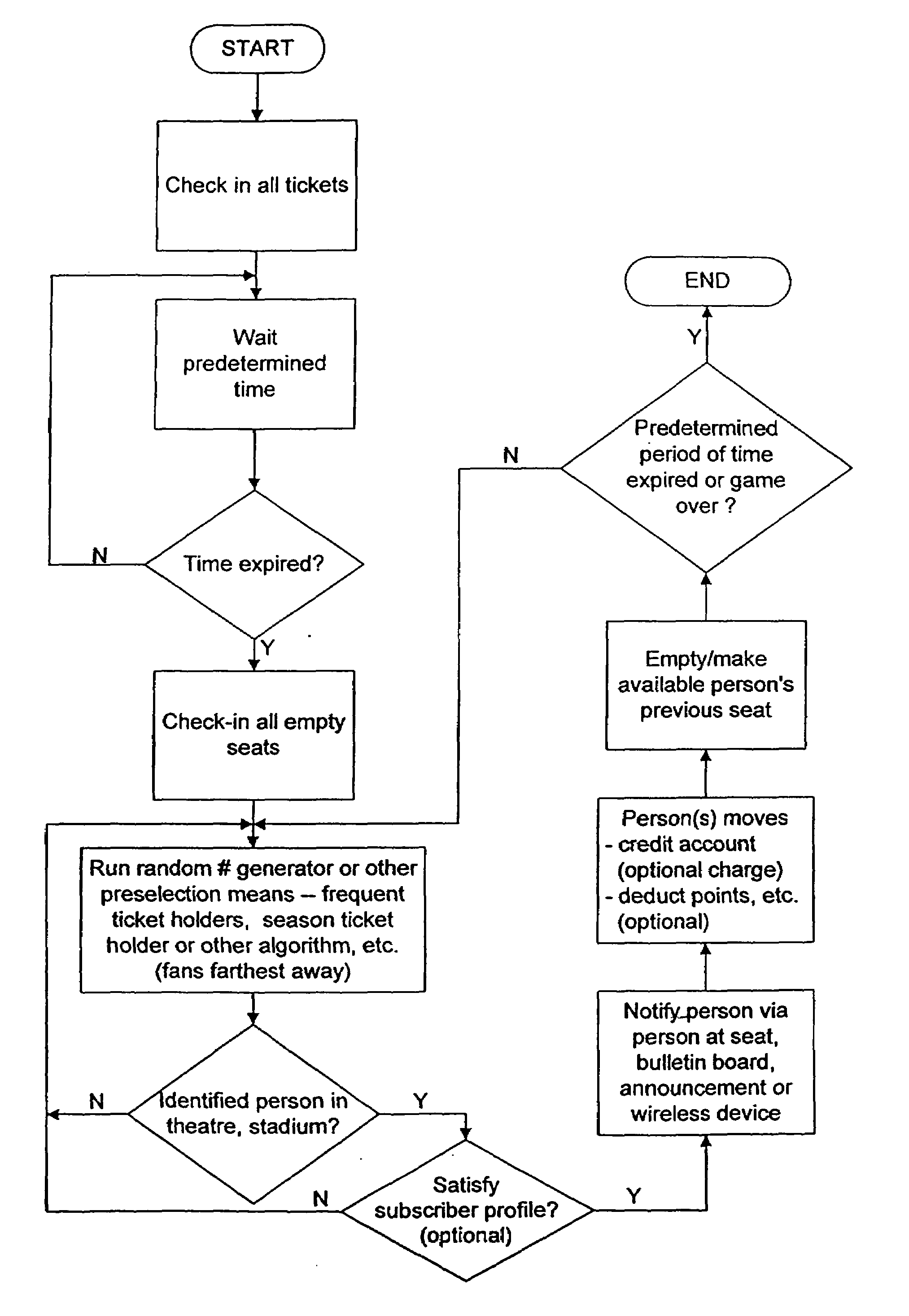
System and method for reallocating and/or upgrading and/or rewarding tickets, other event admittance means, goods and/or services
InactiveUS7031945B1To offer comfortIncrease the fun of activitiesMarket predictionsTicket-issuing apparatusPoint of saleUpgrade
Owner:EASTERN IX GRP +1
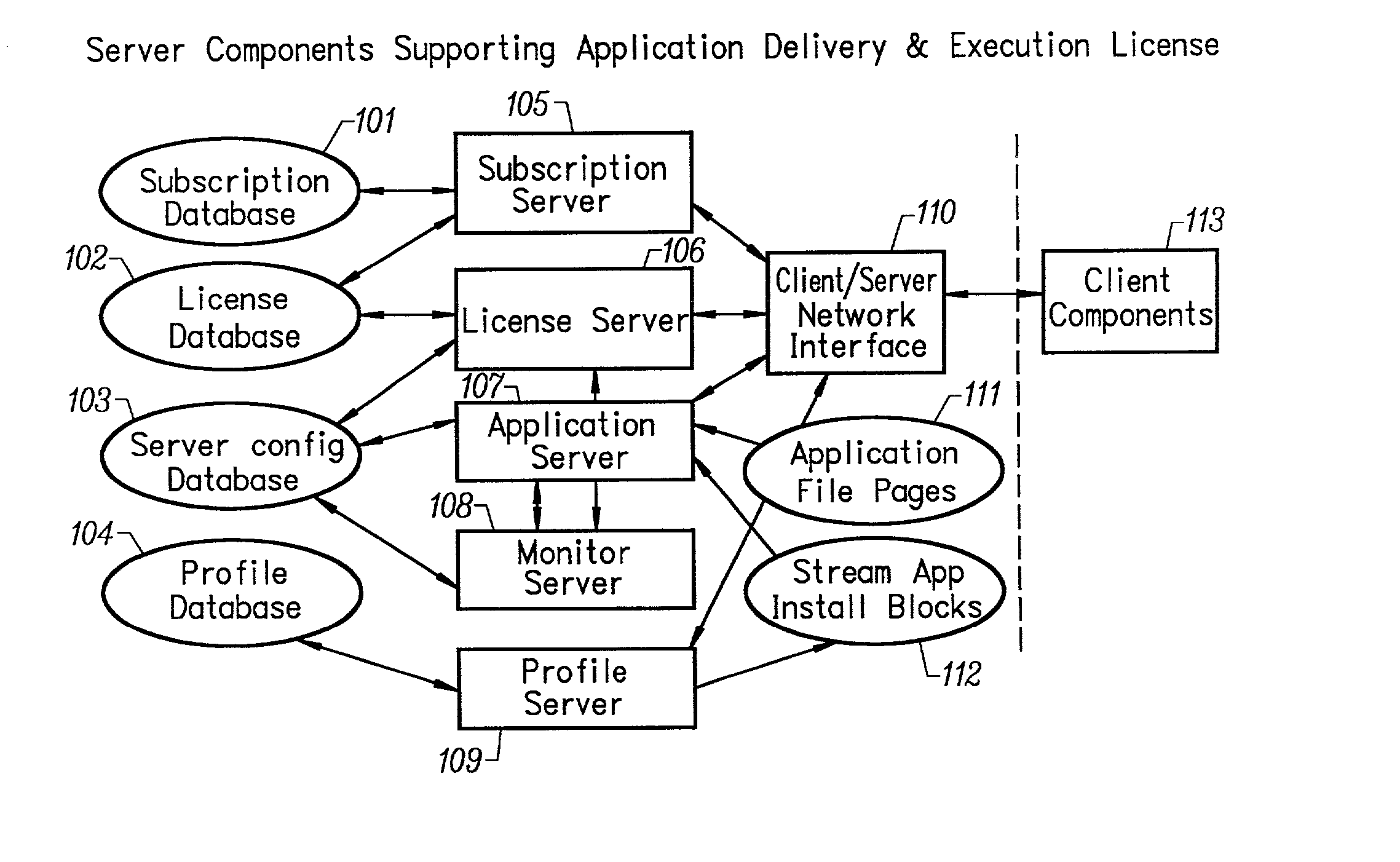
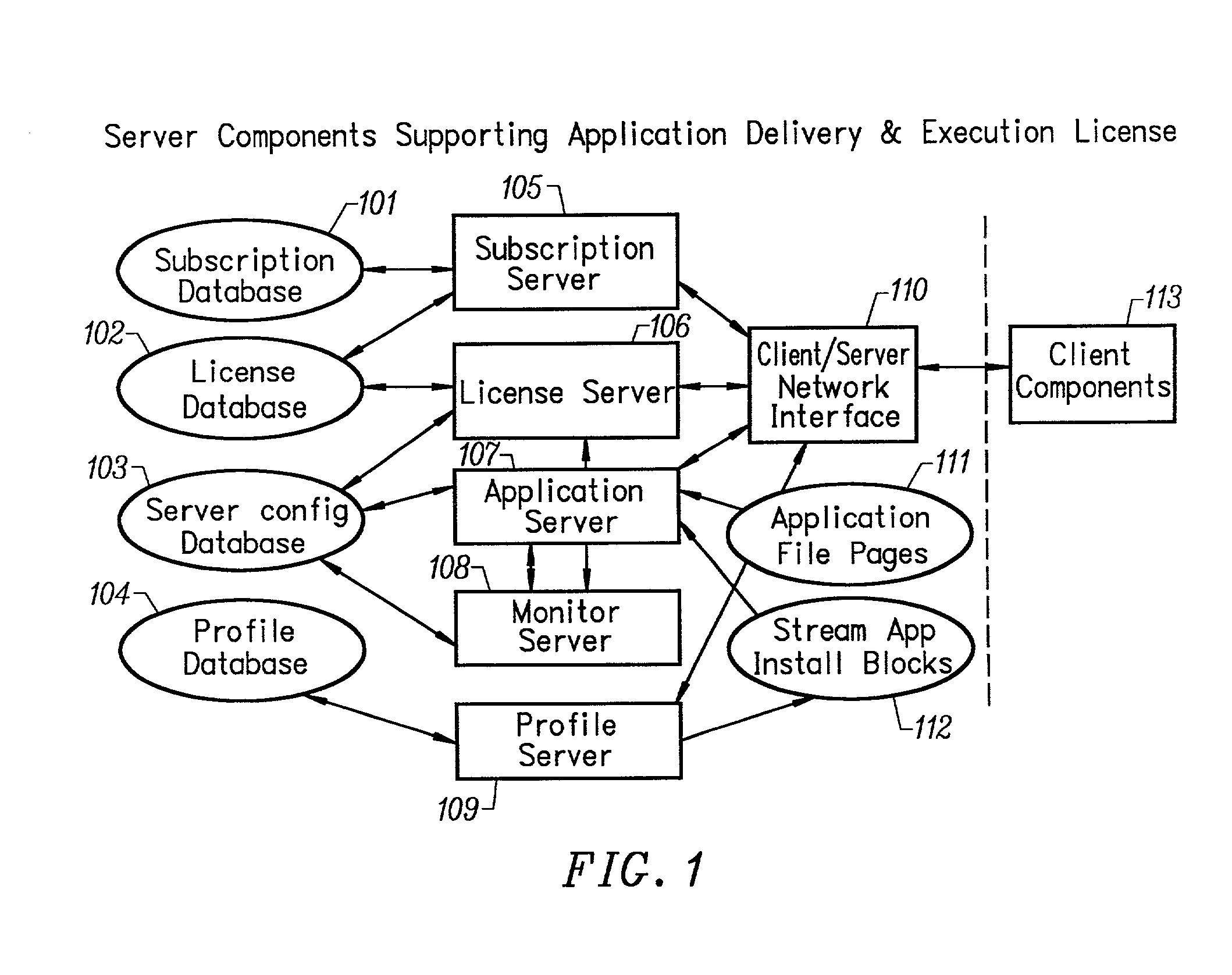
Conventionally coded application conversion system for streamed delivery and execution
InactiveUS20020083183A1Multiple digital computer combinationsProgram loading/initiatingData setMonitoring system
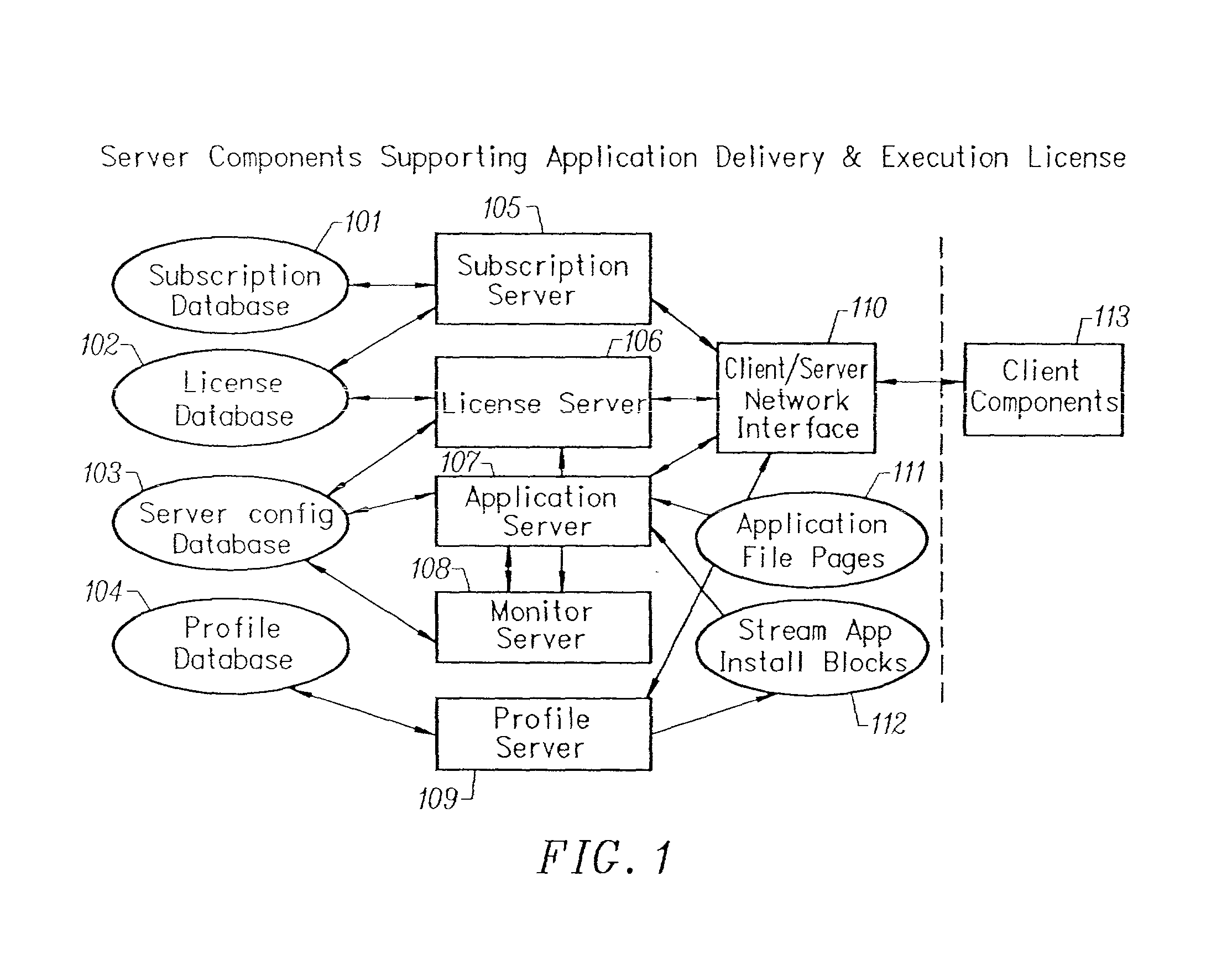
A conventionally coded application conversion system for streamed delivery and execution converts locally installable applications into a data set suitable for streaming over a network. The invention monitors two classes of information during an application installation on a local computer system. System registry modifications are monitored and the modification data are recorded when the installation program writes to the registry of the local computer system. File modification data are logged each time an installation program modifies a file on the system. This data is used to create an initialization data set which is the first set of data to be streamed from the server to the client and contains the information captured needed by the client to prepare the client machine for streaming a particular application. A runtime data set is also created that contains the rest of the data that is streamed to the client once the client machine is initialized for a particular application. A versioning table contains a list of root file numbers and version numbers which are used to track application patches and upgrades. The invention monitors a running application that is being configured for a particular working environment on the local computer system. The data acquired are used to duplicate the same configuration on multiple client machines.
Owner:CREDIT MANAGERS OF CALIFORNIA
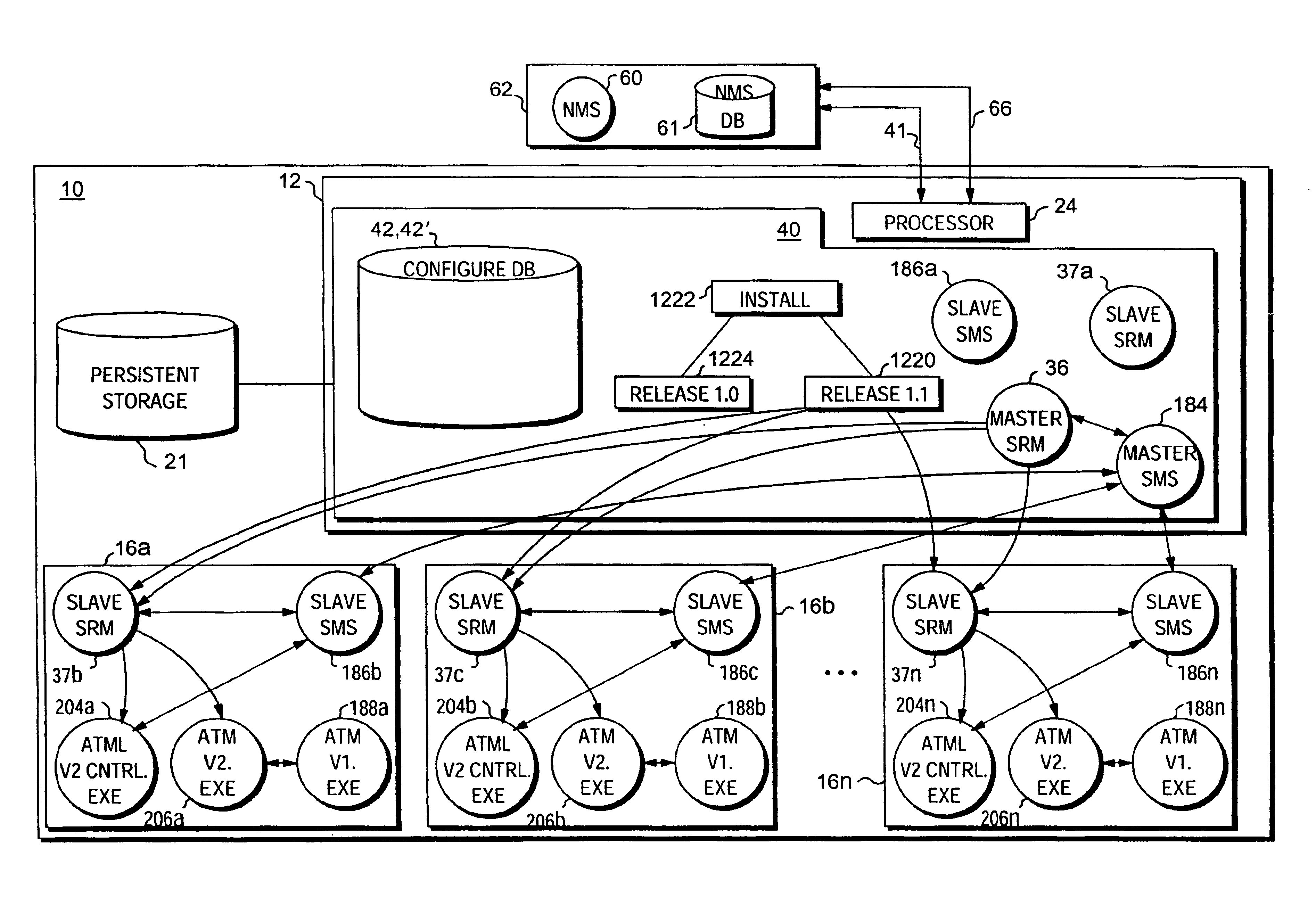
Signatures for facilitating hot upgrades of modular software components
InactiveUS6880086B2Facilitating hot upgradeAccurately determineSynchronisation information channelsMemory loss protectionComputer hardwareTelecommunications network
The present invention provides a method and apparatus for facilitating hot upgrades of software components within a telecommunications network device through the use of “signatures” generated by a signature generating program. After installation of a new software release within the network device, only those software components whose signatures do not match the signatures of corresponding and currently executing software components are upgraded. Signatures promote hot upgrades by identifying only those software components that need to be upgraded. Since signatures are automatically generated for each software component as part of putting together a new release a quick comparison of two signatures provides an accurate assurance that either the software component has changed or has not. Thus, signatures provide a quick, easy way to accurately determine the upgrade status of each software component.
Owner:CIENA
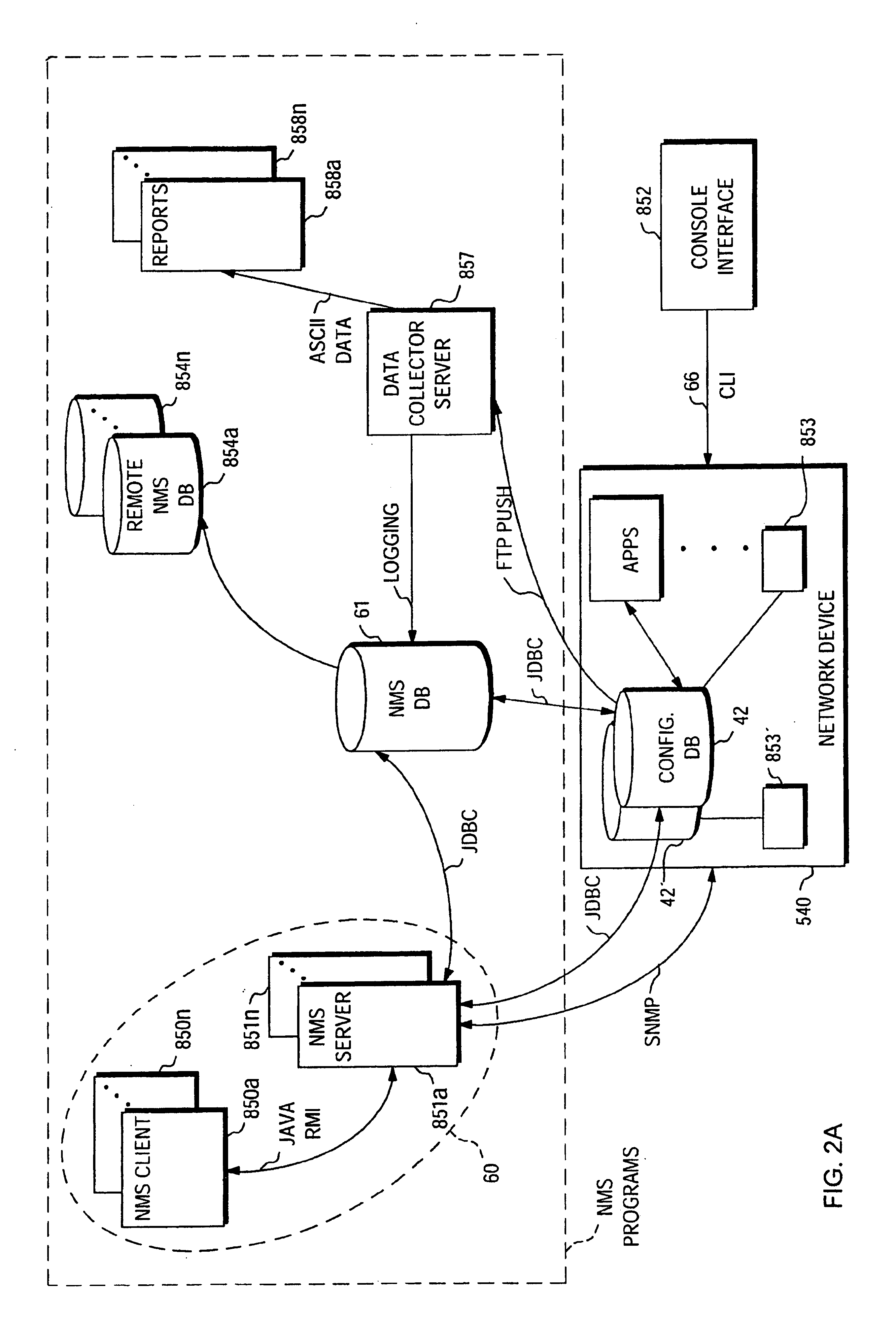
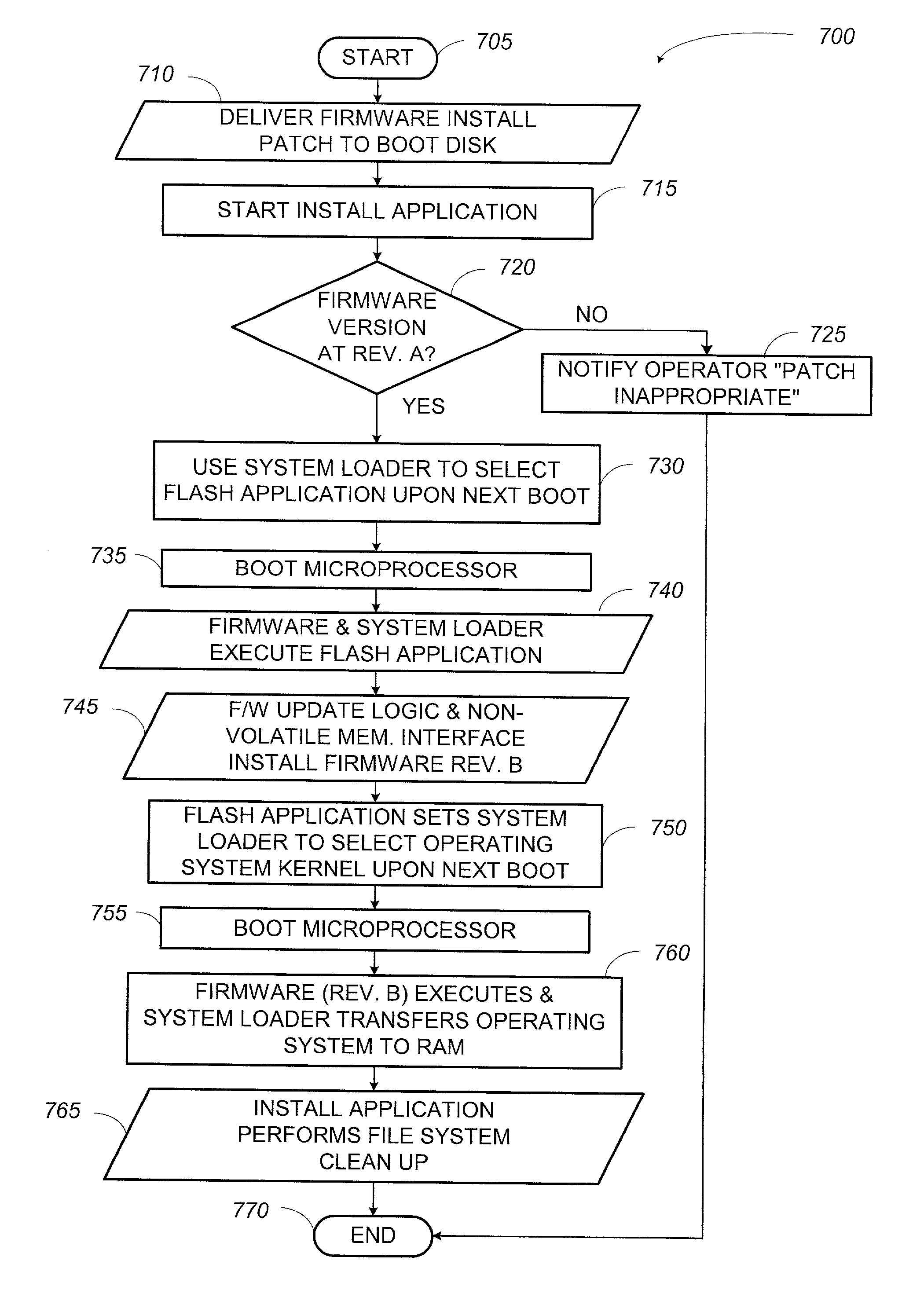
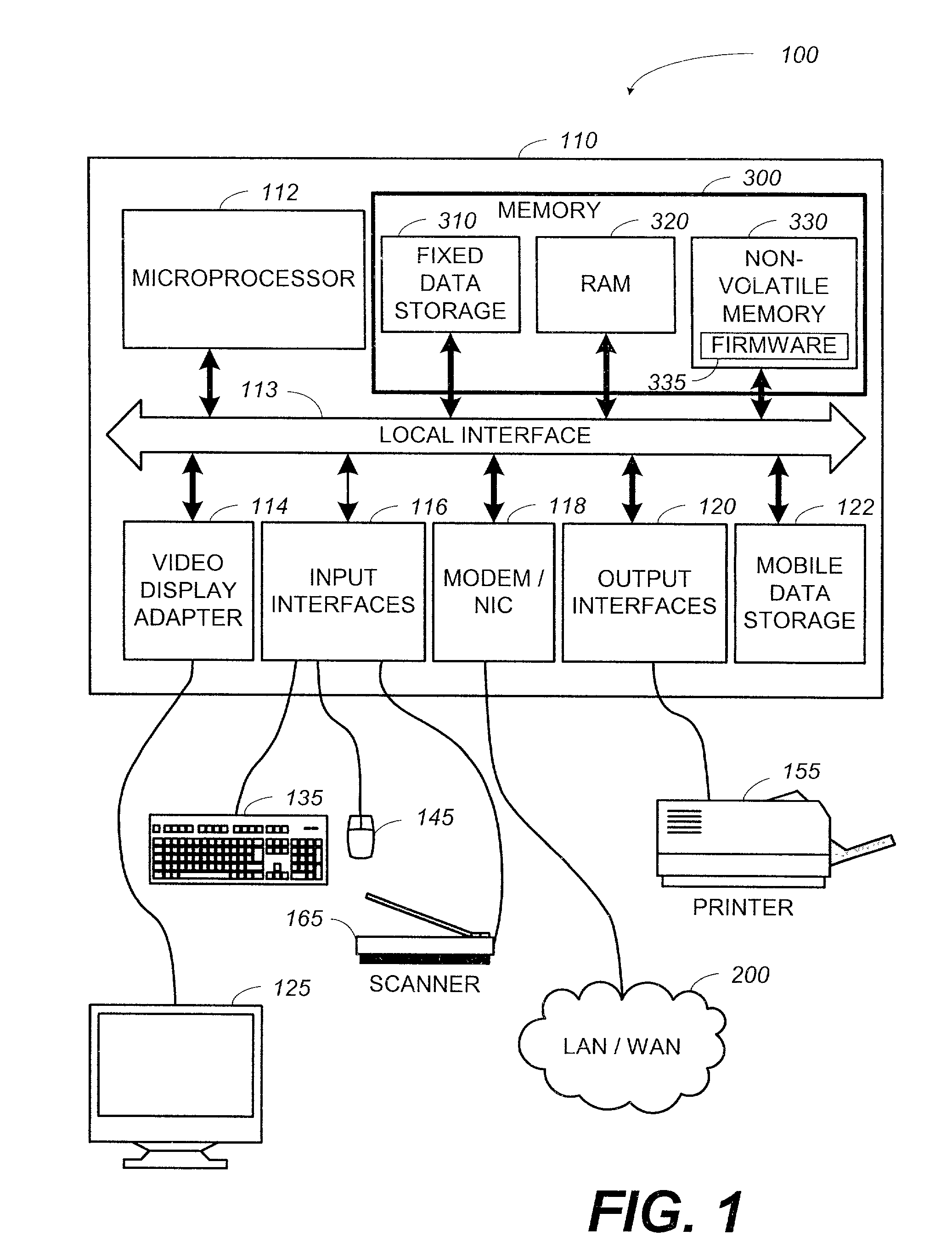
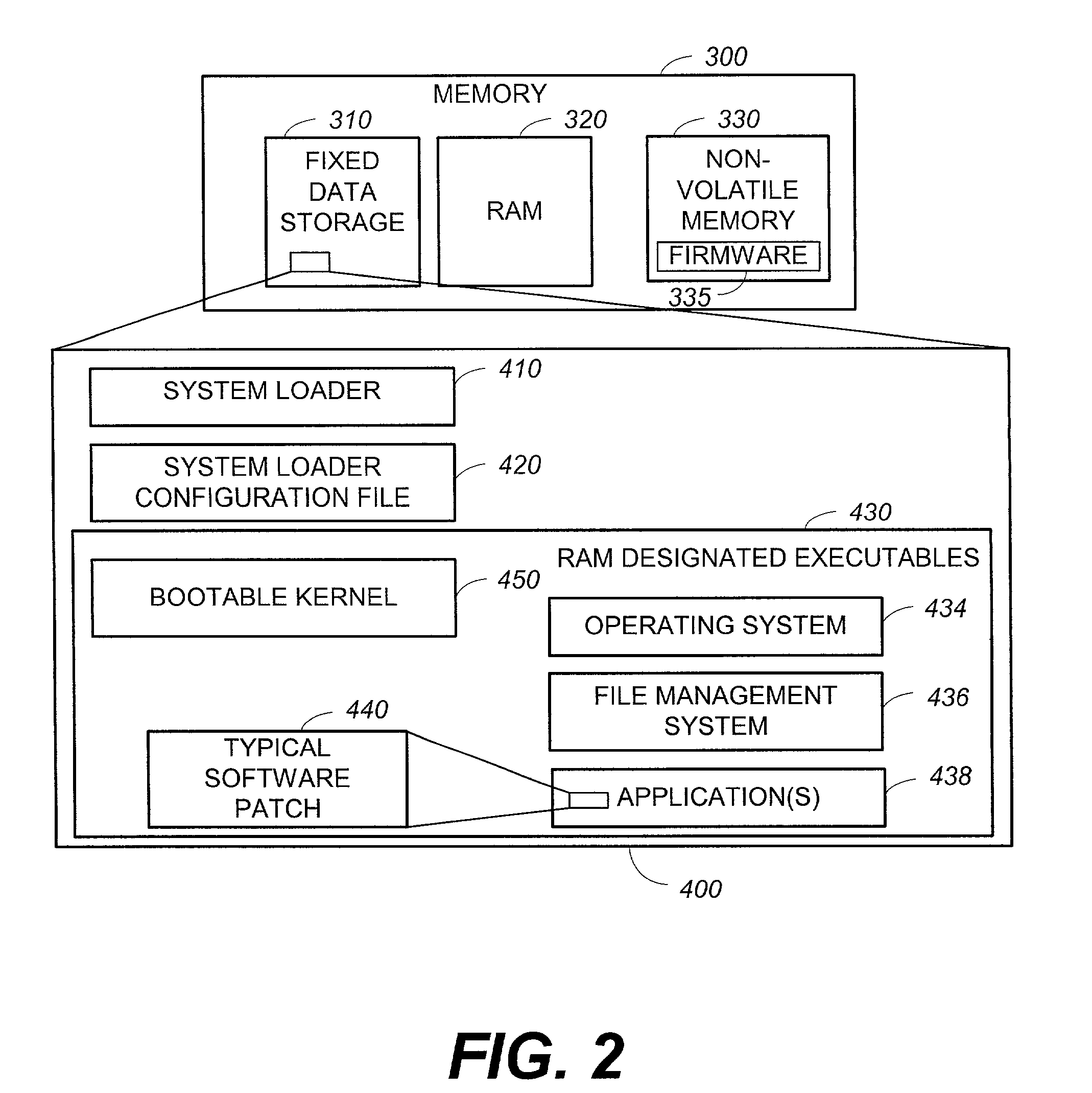
System and method for updating firmware
InactiveUS7055148B2Avoid manual interventionDigital computer detailsProgram loading/initiatingOperational systemFirmware version
A system and a method that uses a software application operable under a current firmware / operating system configuration to install a new firmware version without “compromising” the operating system are presented. The software application may configure a computer system to install a plurality of software fixes configured to enhance functionality under a new firmware / operating system environment after the firmware has been successfully upgraded. Such functionality enhancements may be associated with external peripherals, as well as, input / output circuit cards, processors, and the like. In addition, the software application may configure the computing device to “boot” under the new firmware / operating system environment upon subsequent system initializations. Furthermore, the software application permits the distribution of firmware upgrades via a network. The capability to install firmware remotely permits a system administrator to “push” the new firmware to a plurality of network coupled computing devices, thus avoiding manual intervention at each device.
Owner:HEWLETT PACKARD DEV CO LP
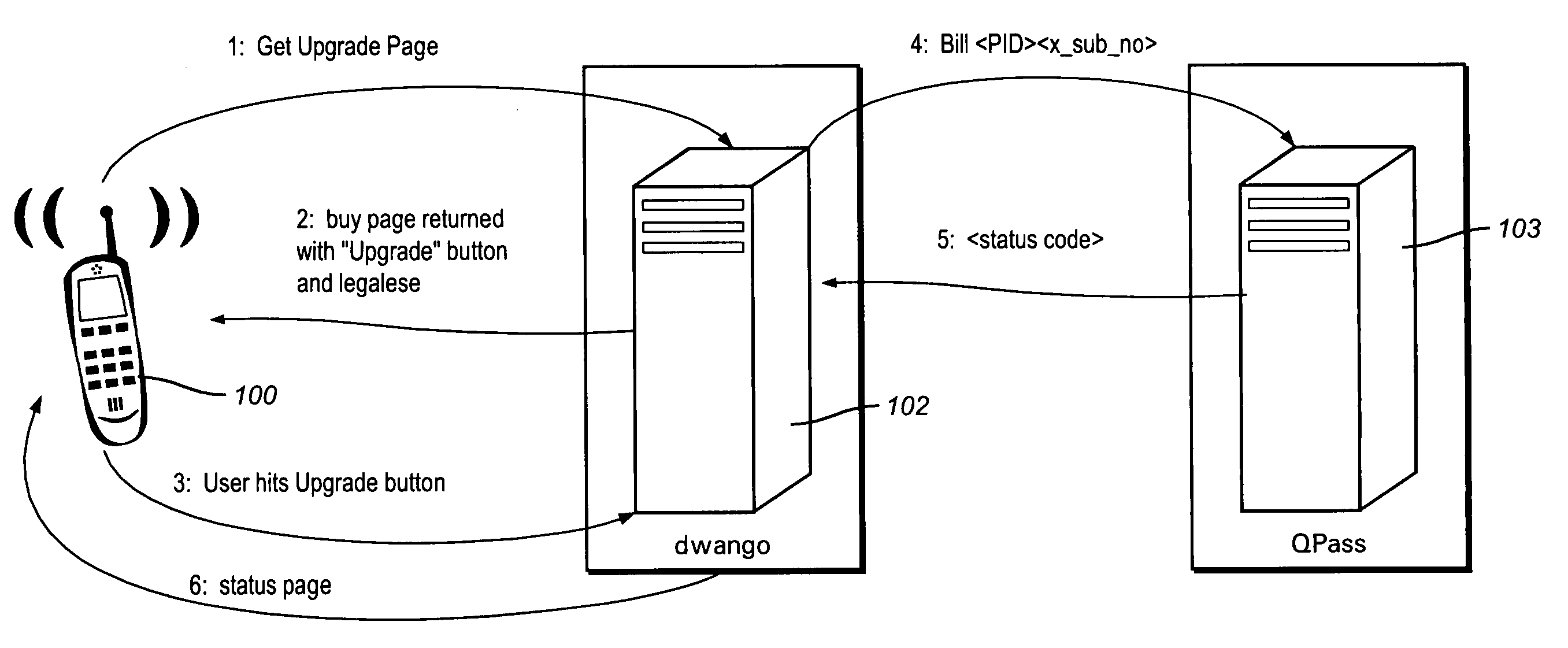
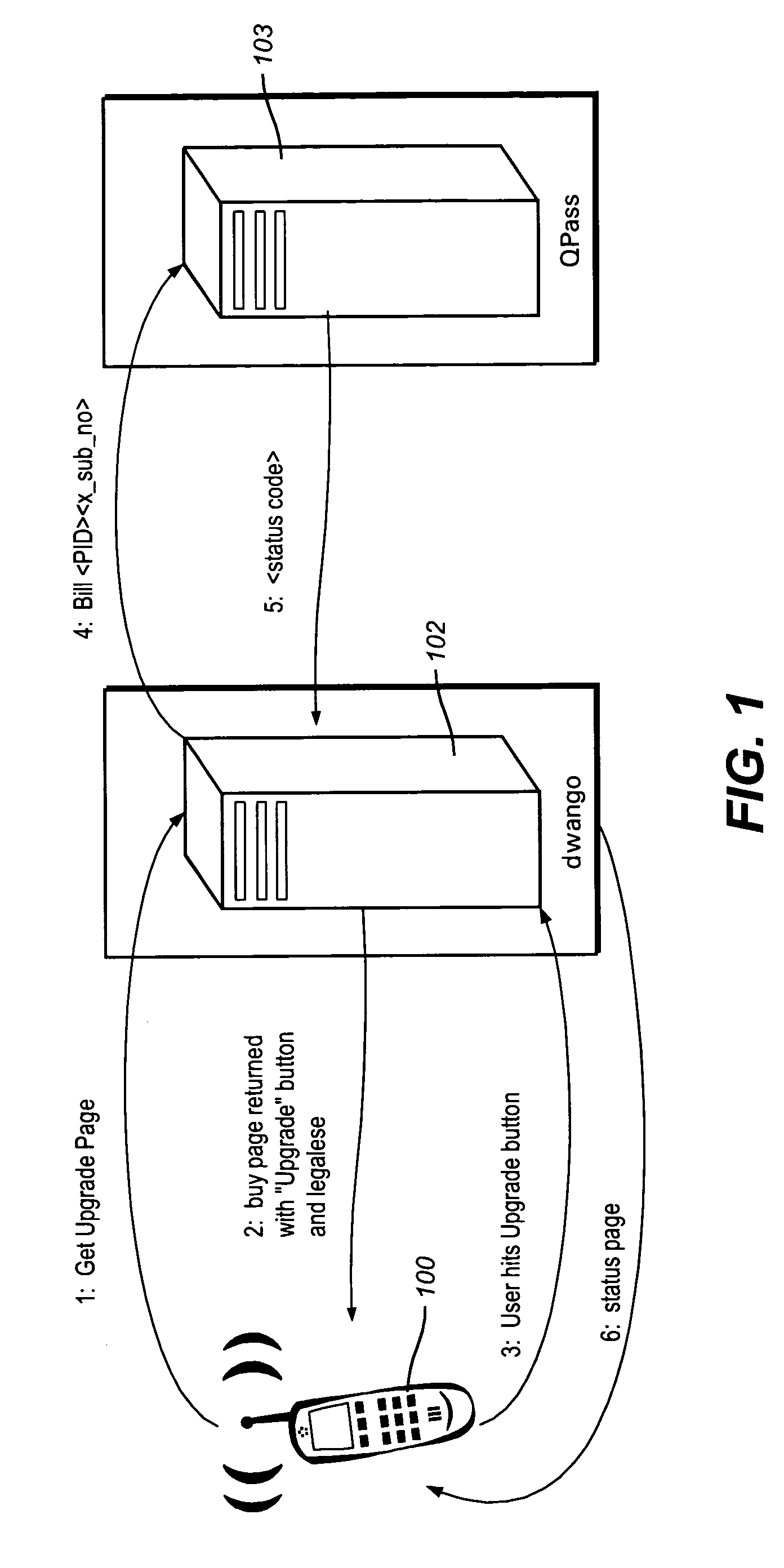
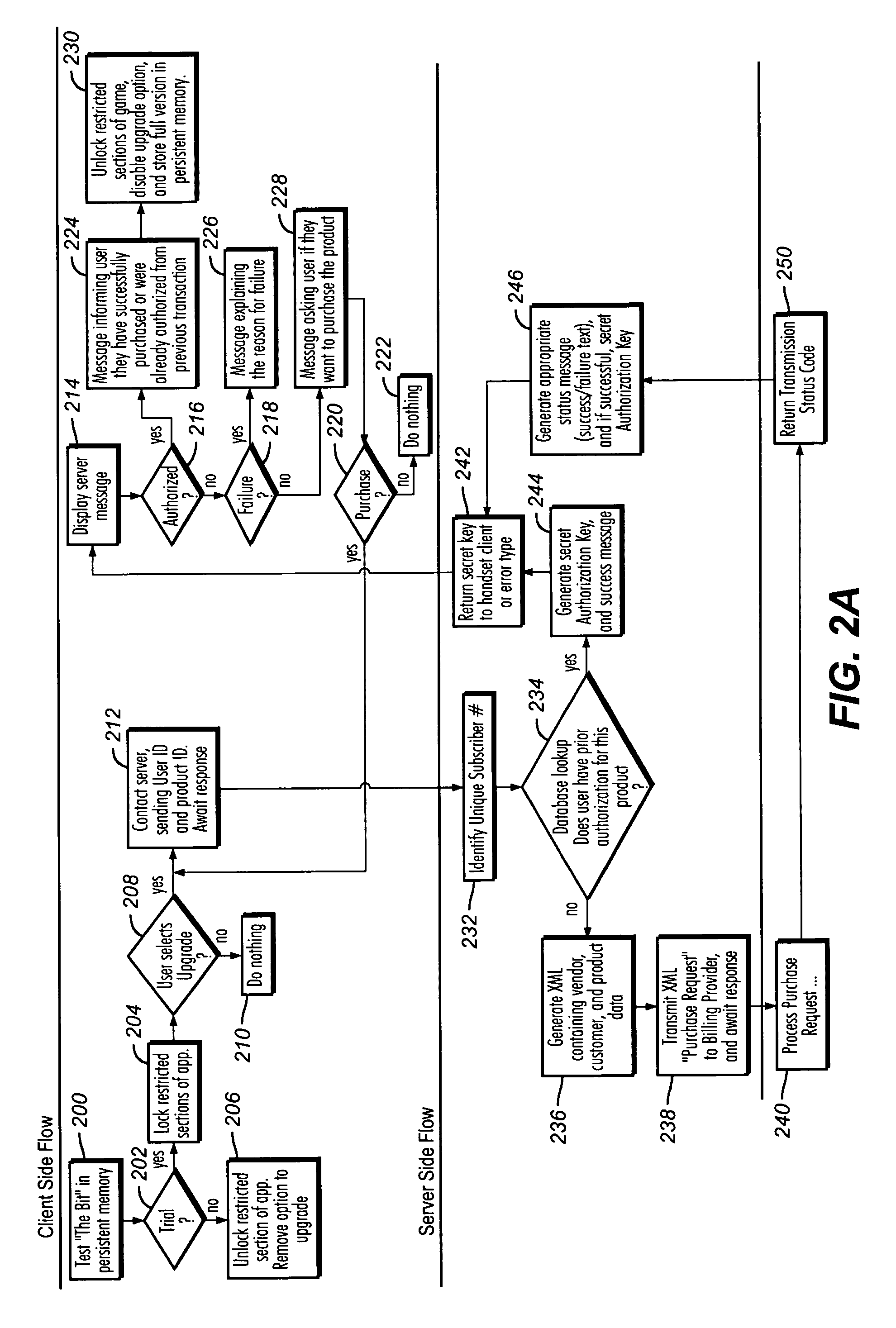
Method and apparatus for a one click upgrade for mobile applications
InactiveUS20050055309A1Reduces customer chumBroaden applicationFinancePayment architectureGame playRepertoire
The present invention enables a cell phone or PDA user to purchase a full version of an application with a single key stroke, without switching back and forth between the application and a browser. A one click upgrade is made available which is intuitive and quicker than prior methods known in the art. Trial versions in the present invention are full versions with most of the game disabled. Upgrades to the full version are enabled by setting a flag once the customer has paid for the upgrade. The customer is able to play one level or track for a game or to play the,game for limited period of time. Once the trial limit is reached, the content or game provider offers details on how to purchase the full version.
Owner:DIJJI
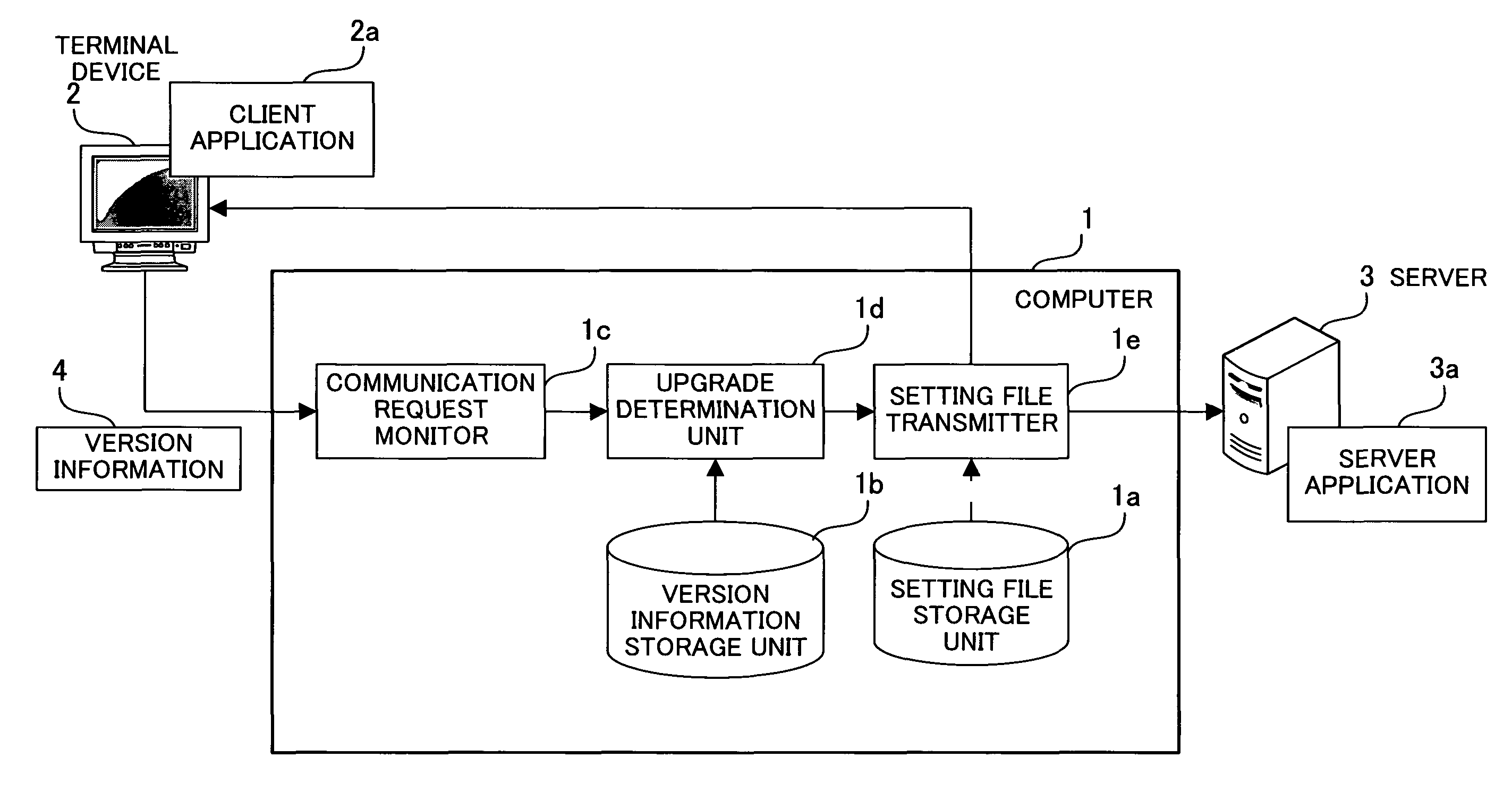
Computer-readable recording medium containing application management program, and method and apparatus for application management
InactiveUS8146074B2Program loading/initiatingMemory systemsApplication lifecycle managementProgram management
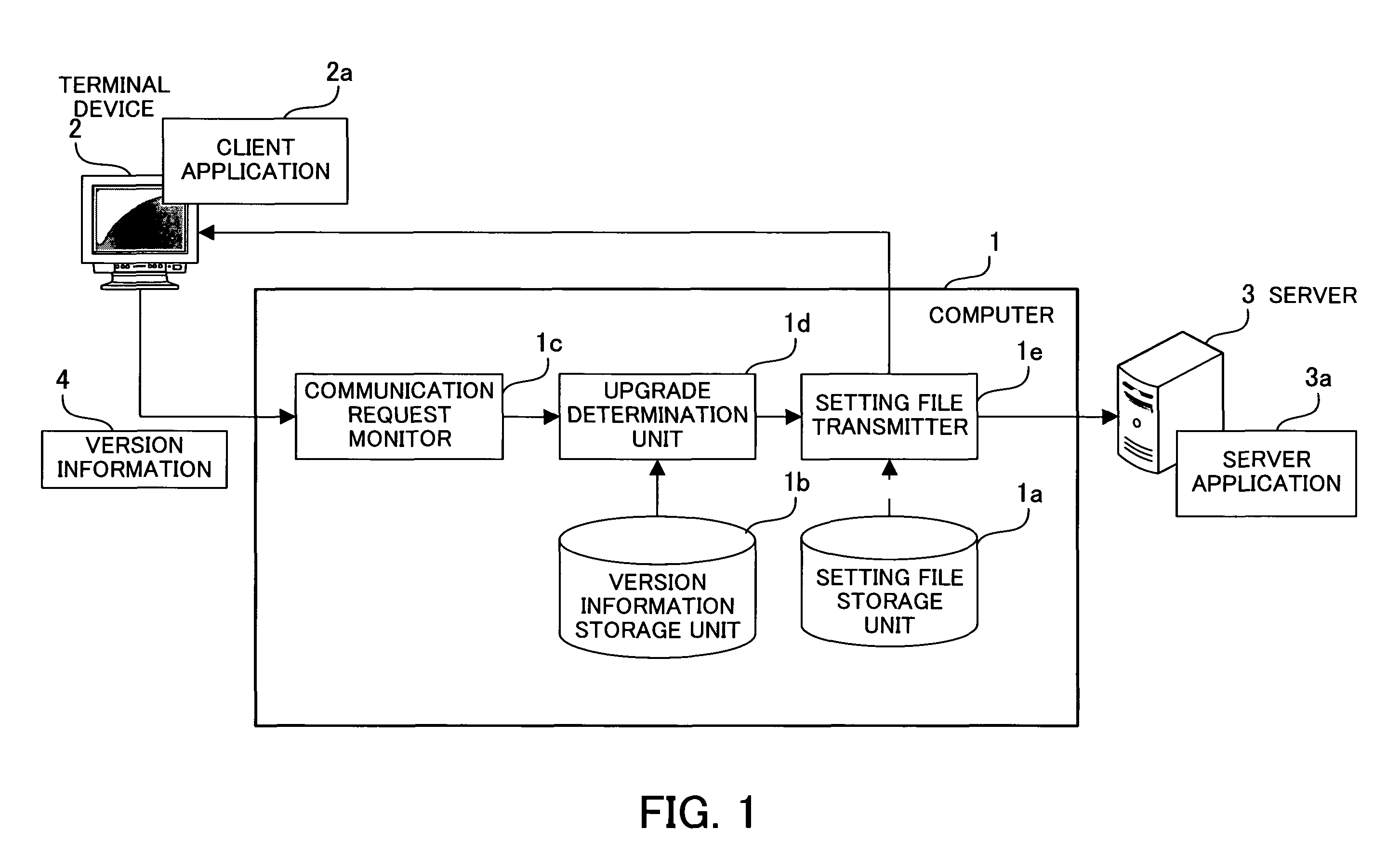
A computer-readable recording medium containing an application management program for automatically performing version management to surely manage versions of a client application that communicates with a server application. A communication request monitor acquires a communication request issued from a terminal device to a server, and extracts version information of a client application from the communication request. An upgrade determination unit determines whether the extracted version information shows the latest version, and determines that upgrade is necessary if the version is not the latest version. A setting file transmitter sends the communication request to the server if the upgrade determination unit does not determine that the upgrade is necessary. If the upgrade is necessary, on the contrary, the setting file transmitter discards the communication request and sends the client application setting file for the latest version to the terminal device sending the communication request.
Owner:FUJITSU LTD +1
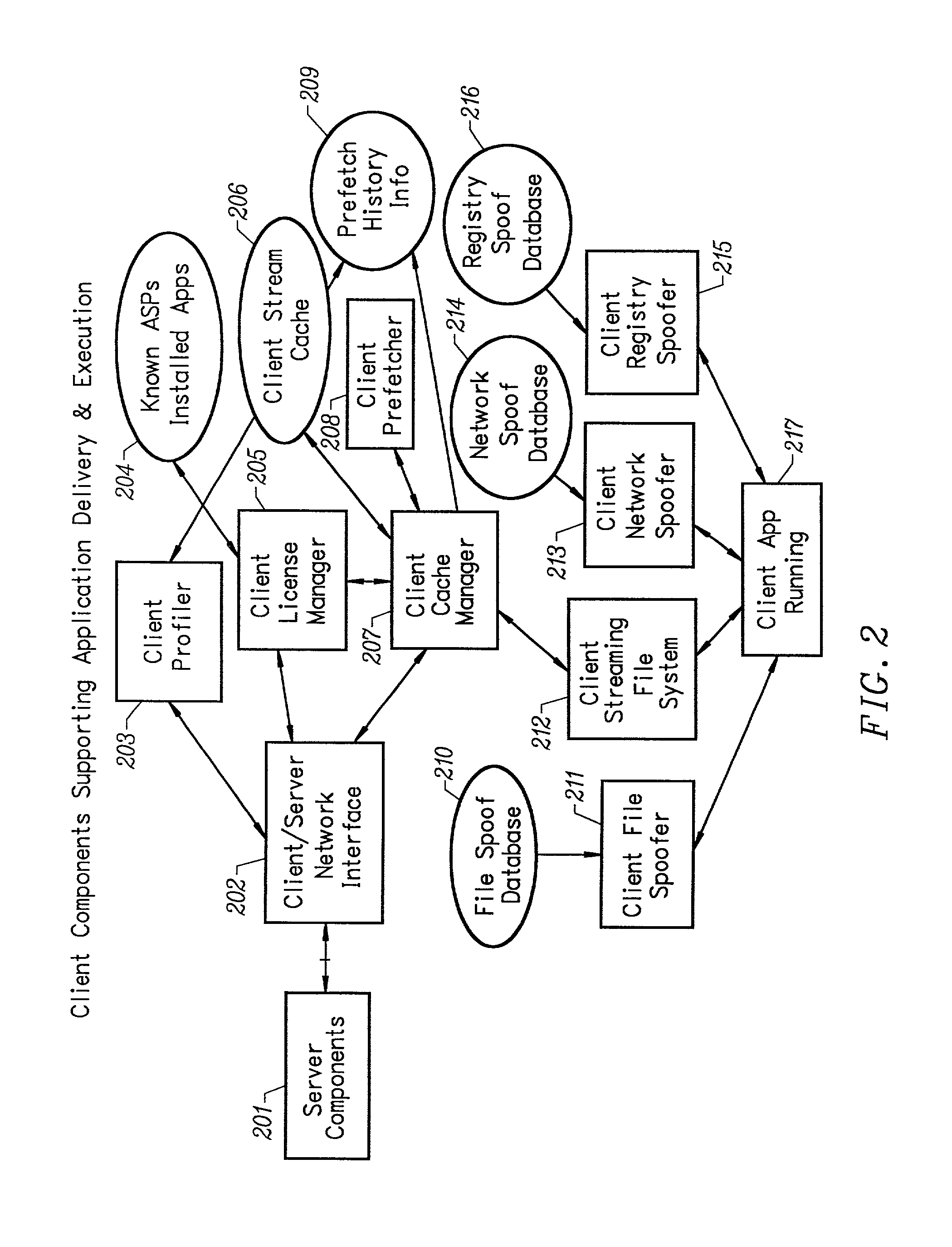
Client-side performance optimization system for streamed applications
InactiveUS20020091763A1Improve application performanceMultiple digital computer combinationsProgram loading/initiatingData fileApplication software
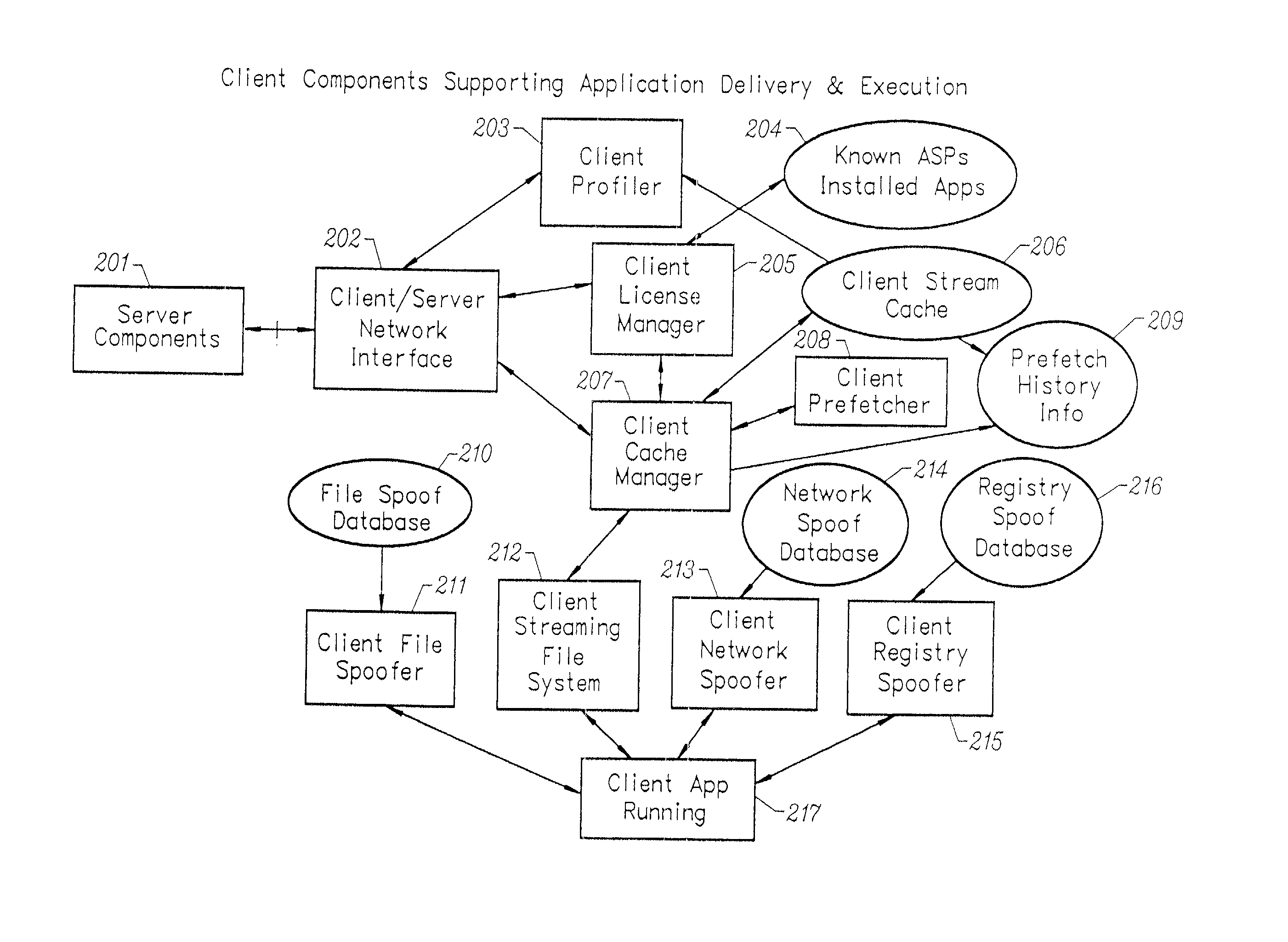
An client-side performance optimization system for streamed applications provides several approaches for fulfilling client-side application code and data file requests for streamed applications. A streaming file system or file driver is installed on the client system that receives and fulfills application code and data requests from a persistent cache or the streaming application server. The client or the server can initiate the prefetching of application code and data to improve interactive application performance. A client-to-client communication mechanism allows local application customization to travel from one client machine to another without involving server communication. Applications are patched or upgraded via a change in the root directory for that application. The client can be notified of application upgrades by the server which can be marked as mandatory, in which case the client will force the application to be upgraded. The server broadcasts an application program's code and data and any client that is interested in that particular application program stores the broadcasted code and data for later use.
Owner:NUMECENT HLDG
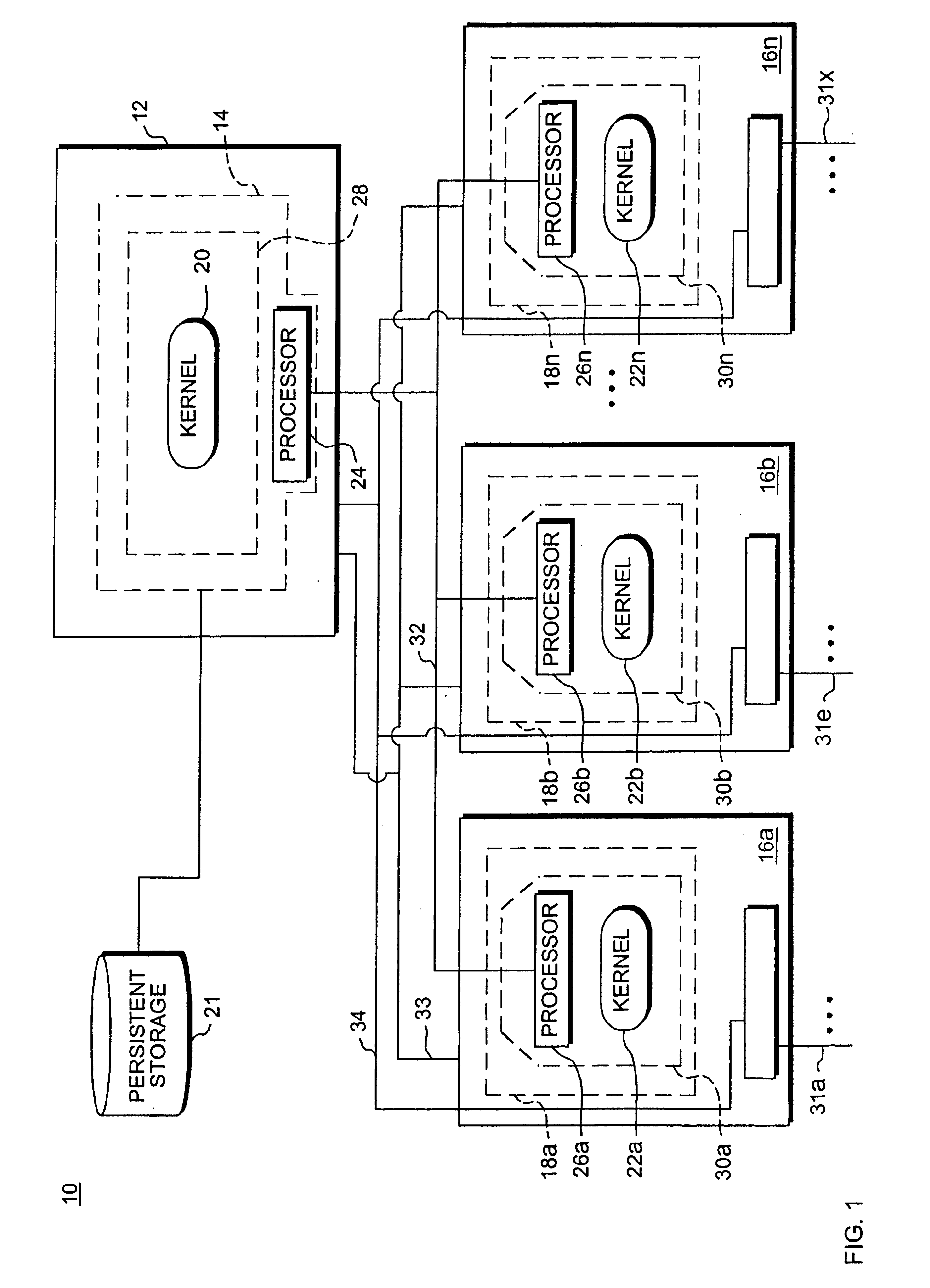
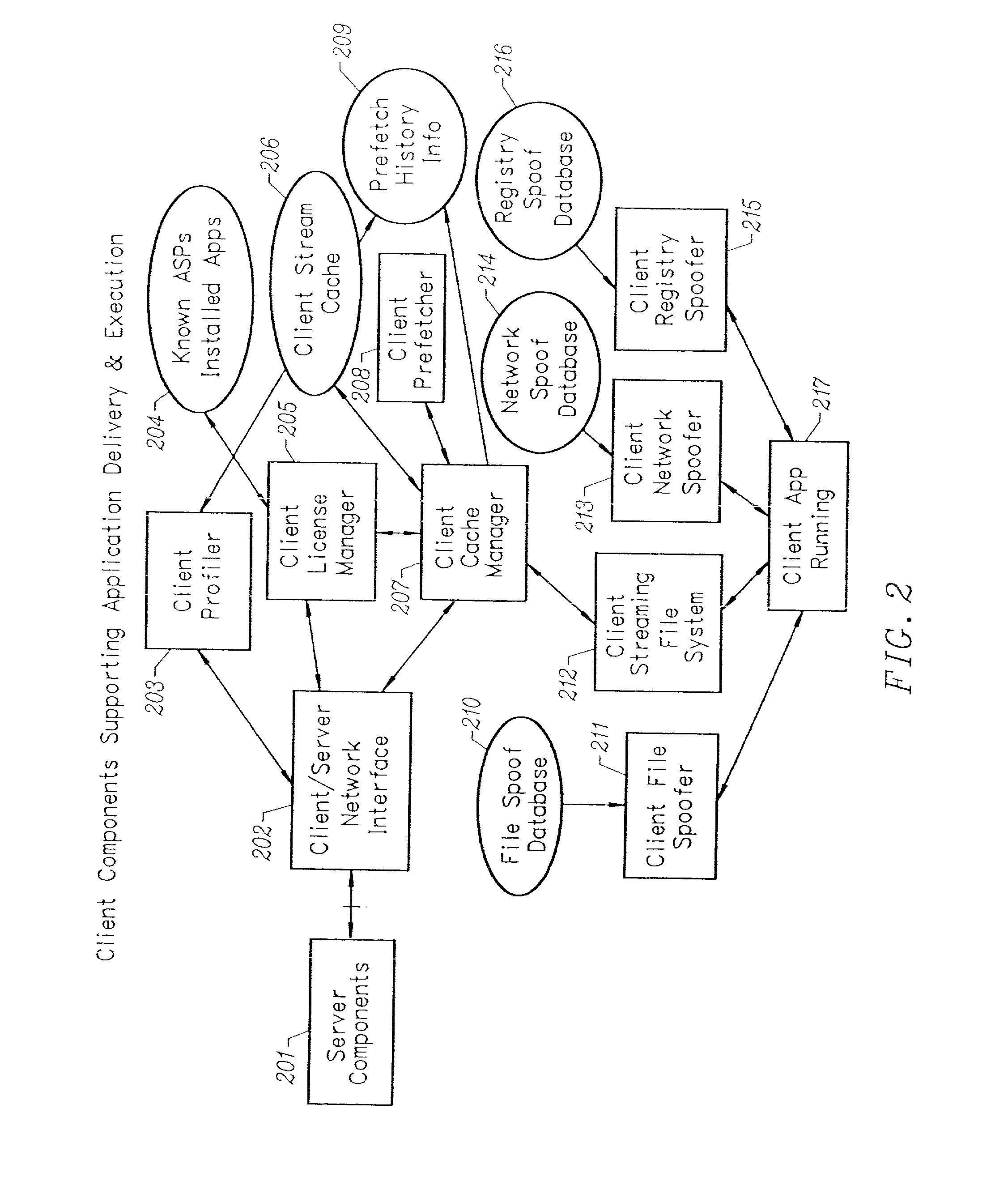
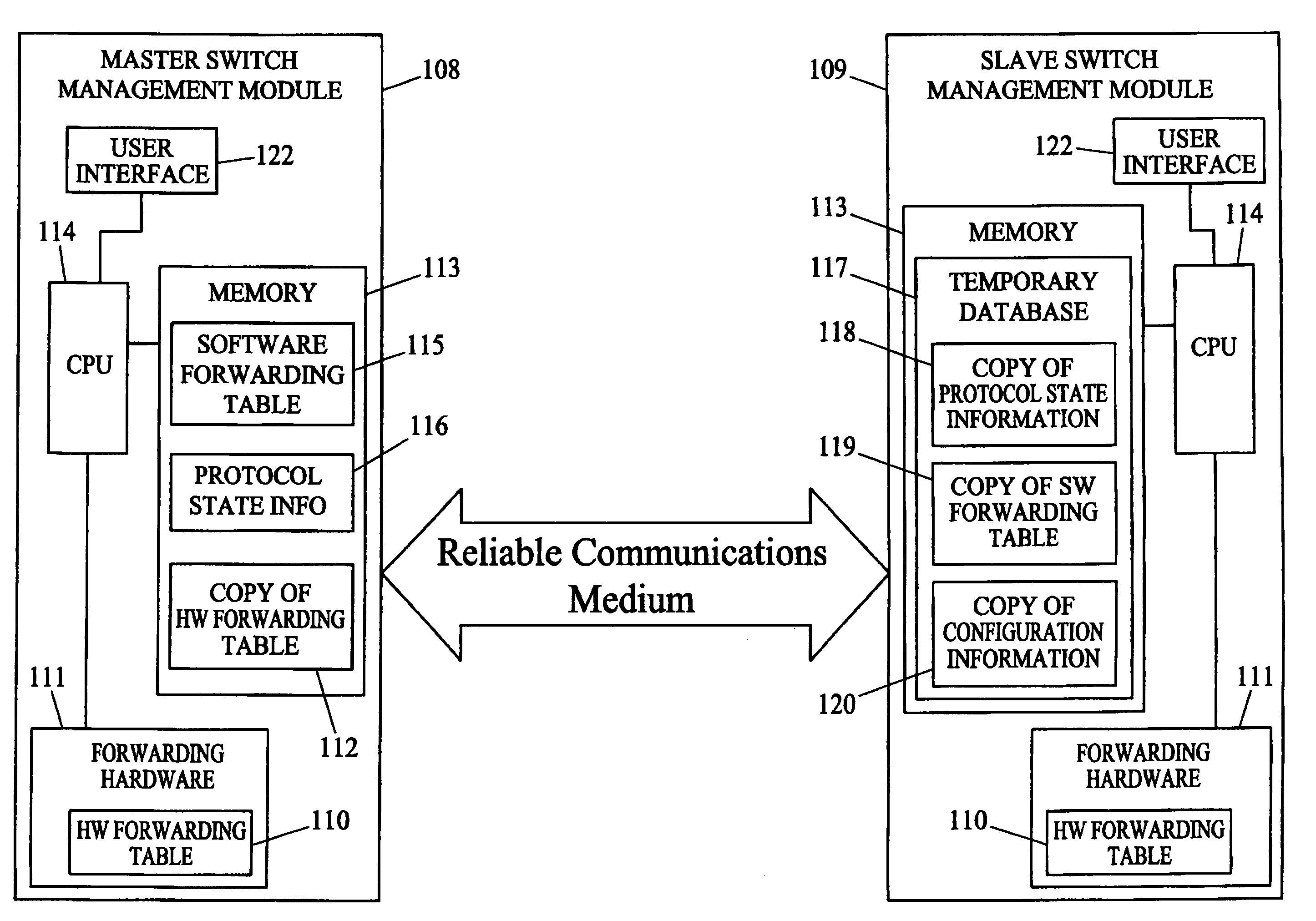
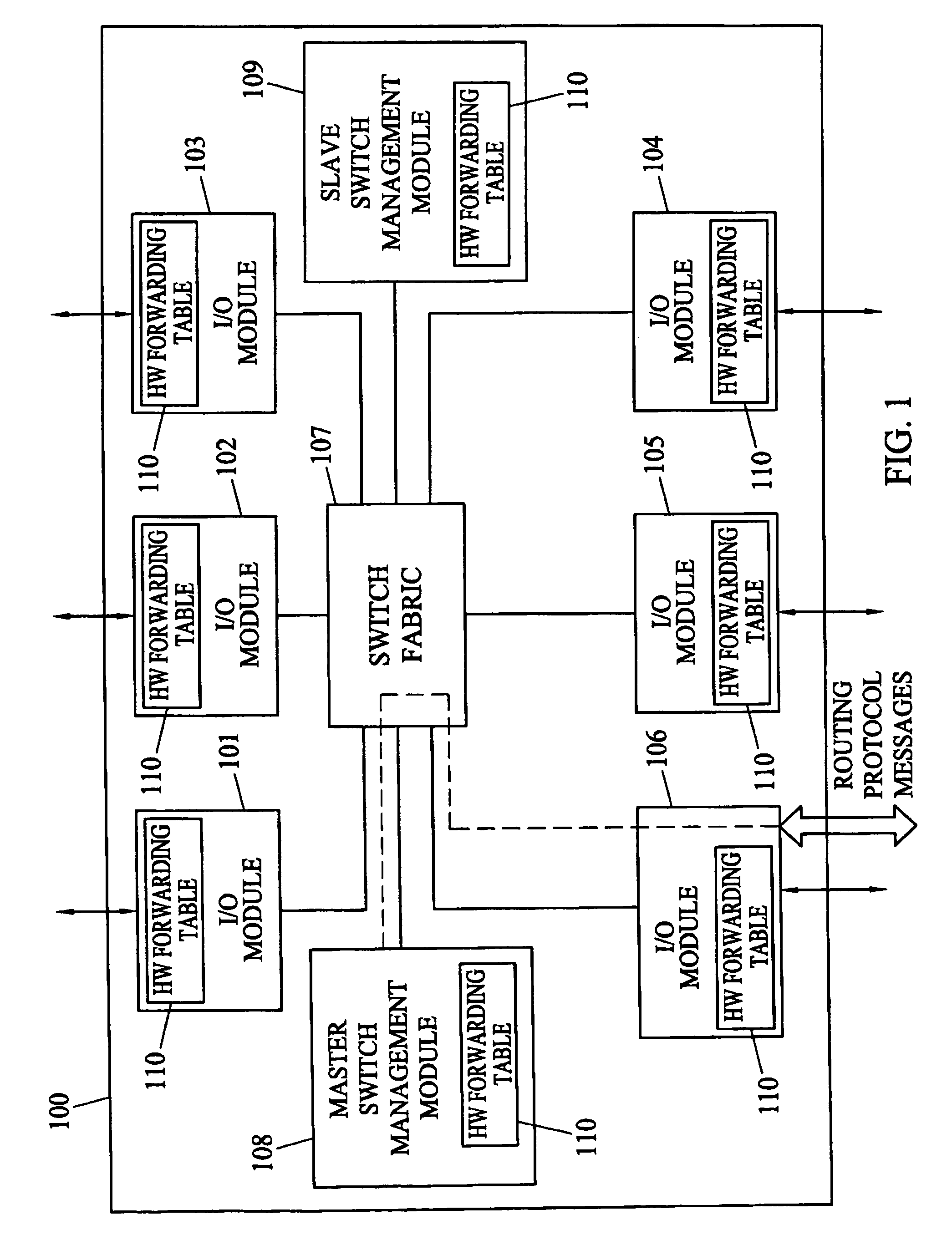
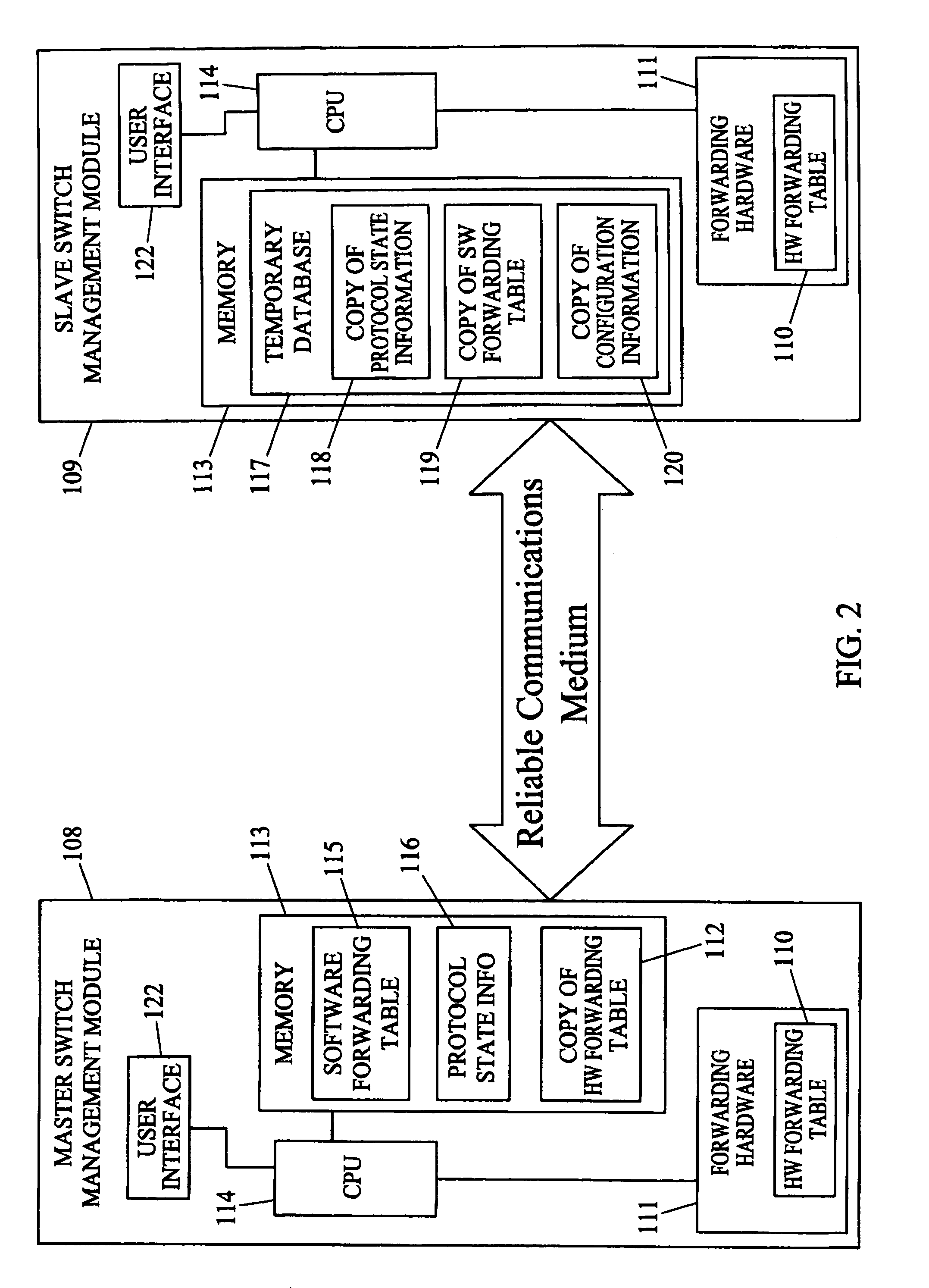
Methods and systems for hitless switch management module failover and upgrade
Methods and systems for hitless switch management module failover and upgrade are disclosed. According to one method, a master switch management module participates in network protocols and performs packet forwarding operations. The master switch management module distributes protocol state and packet forwarding information to the slave switch management module. The slave switch management module continuously monitors the operational state of the master switch management module. In response to detecting failure of the master switch management module or a forced failover initiated by the user interface on the master switch management module, the slave switch management module begins network protocol operation in the master mode in a state where the master switch management module last operated correctly.
Owner:EXTREME NETWORKS INC
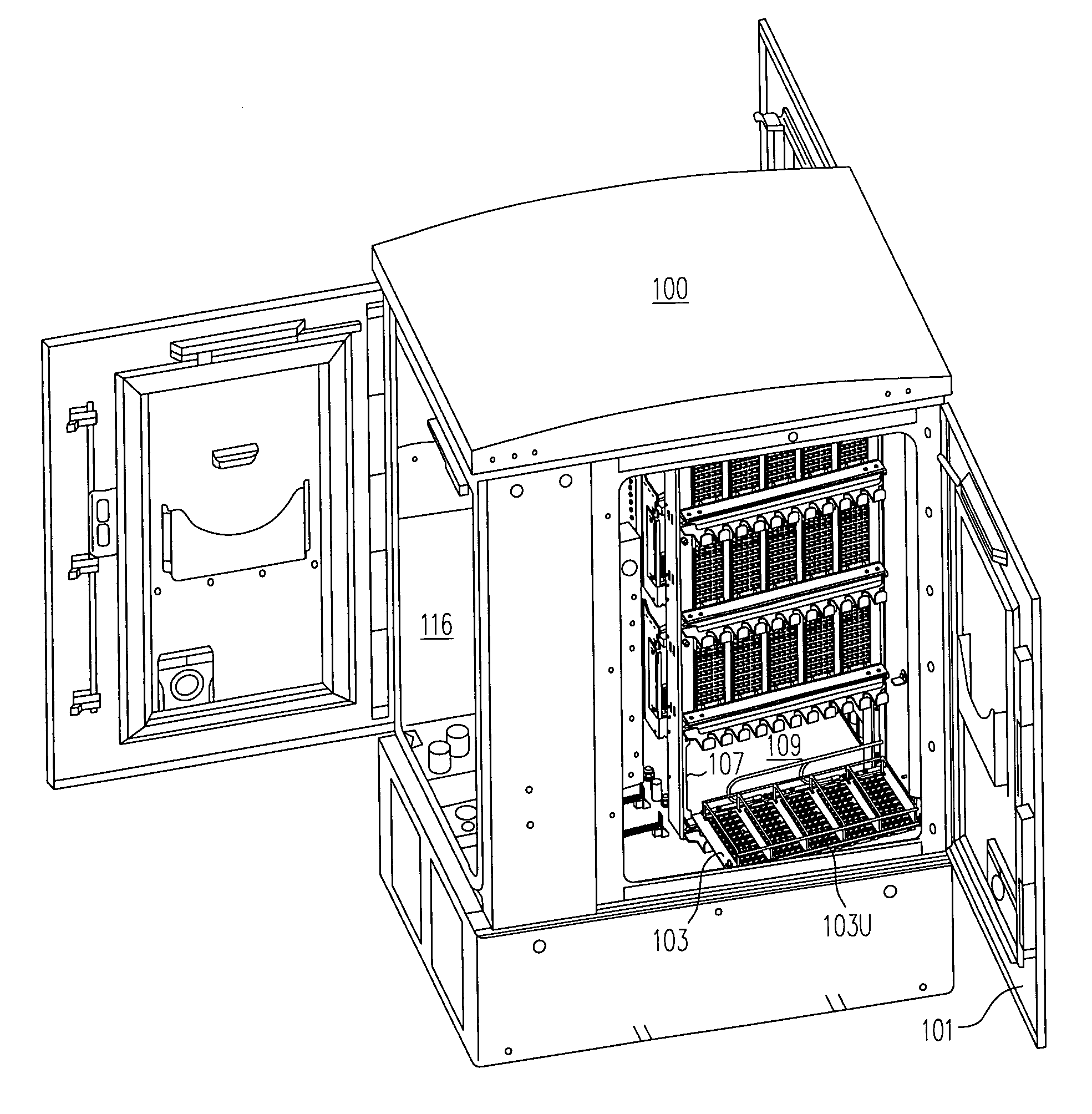
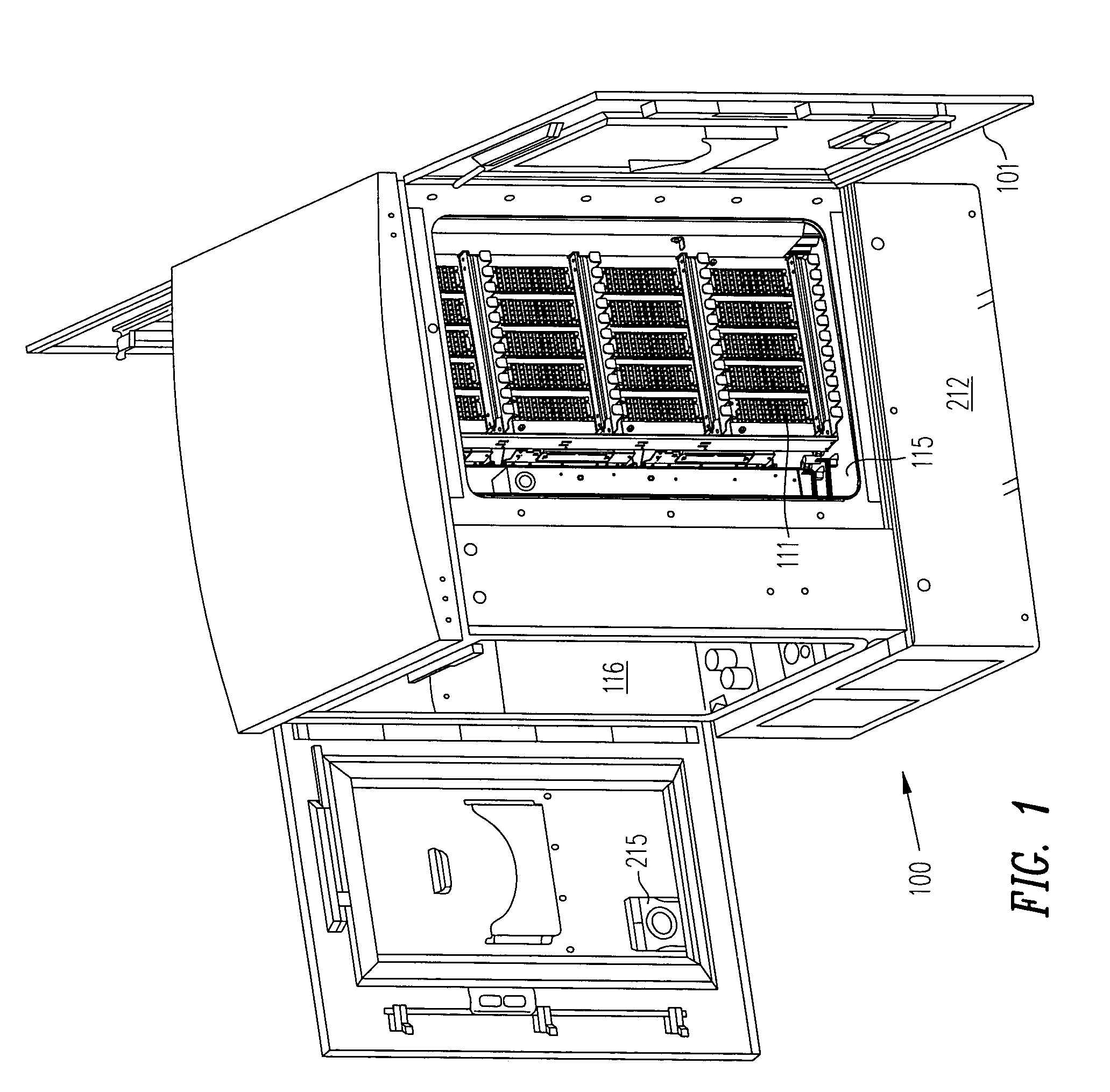
Space reuse during technology upgrade in a protection area of an outdoor enclosure
An outdoor enclosure for a remote terminal is designed so that a structure supporting protector modules (normally coupled between telephone lines and line cards to prevent damage from a surge in current or voltage) is easily reachable and removable. To upgrade from copper to fiber, the just-described hardware (also called “protect block”) is replaced with other hardware (also called “fiber fanout enclosure”) that supports adapters for receiving connectors of optical fibers. The protect block and the fiber fanout enclosure are designed to have approximately (or even exactly) the same footprint, so that they occupy at least some of the same space (before and after replacement). Reuse of the same space in this manner is advantageous over an outdoor enclosure designed to have additional space dedicated for adapters and fiber fanout enclosures to be added in future, because a more compact arrangement results from reuse of the same space.
Owner:WHITE OAK GLOBAL ADVISORS
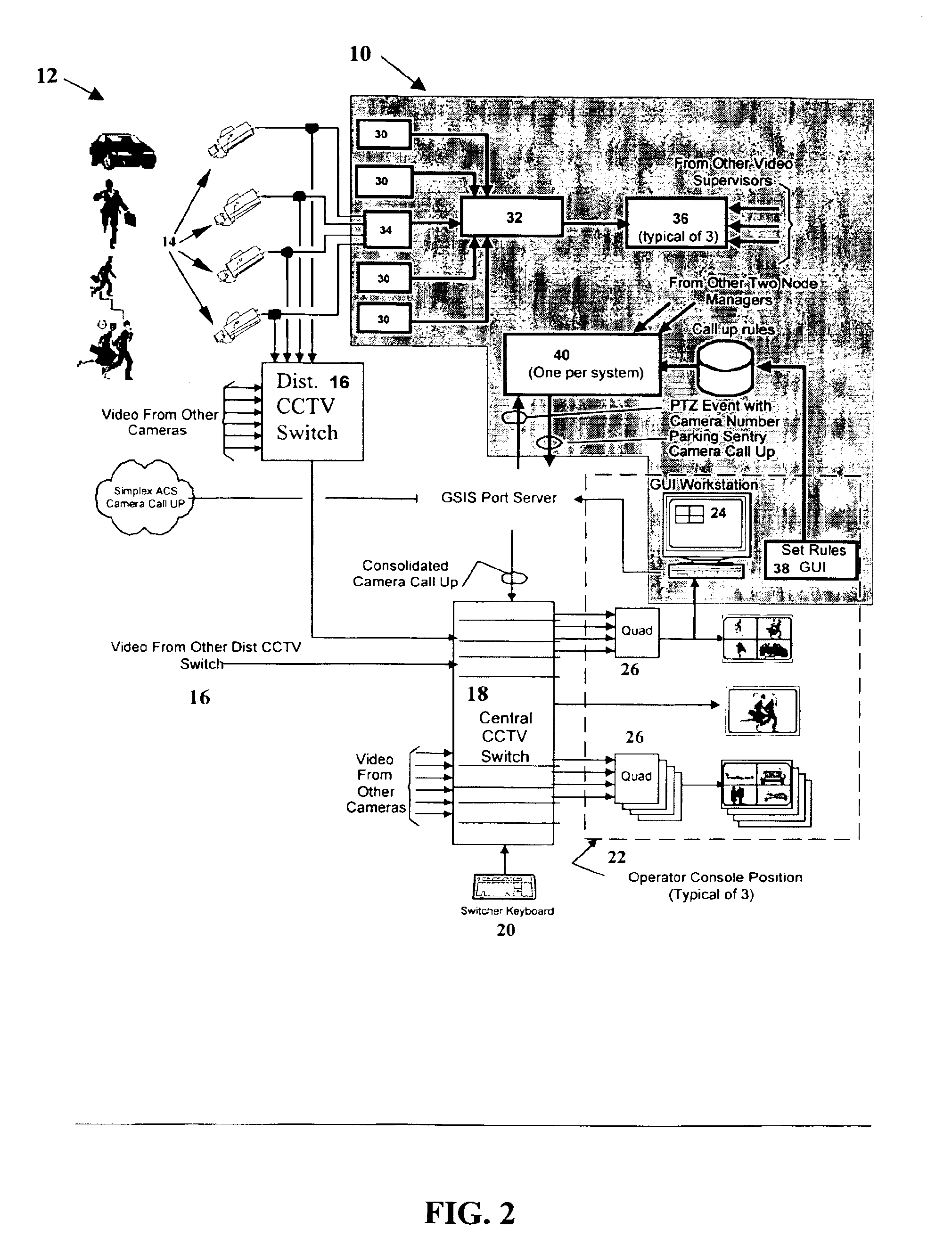
System for automated screening of security cameras
The present invention involves a system for automatically screening closed circuit television (CCTV) cameras for large and small scale security systems, as used for example in parking garages. The system includes six primary software elements, each of which performs a unique function within the operation of the security system to provide intelligent camera selection for operators, resulting in a marked decrease of operator fatigue in a CCTV system. Real-time image analysis of video data is performed wherein a single pass of a video frame produces a terrain map which contains parameters indicating the content of the video. Based on the parameters of the terrain map, the system is able to make decisions about which camera an operator should view based on the presence and activity of vehicles and pedestrians, furthermore, discriminating vehicle traffic from pedestrian traffic. The system is compatible with existing CCTV (closed circuit television) systems and is comprised of modular elements to facilitate integration and upgrades.
Owner:CHECKVIDEO
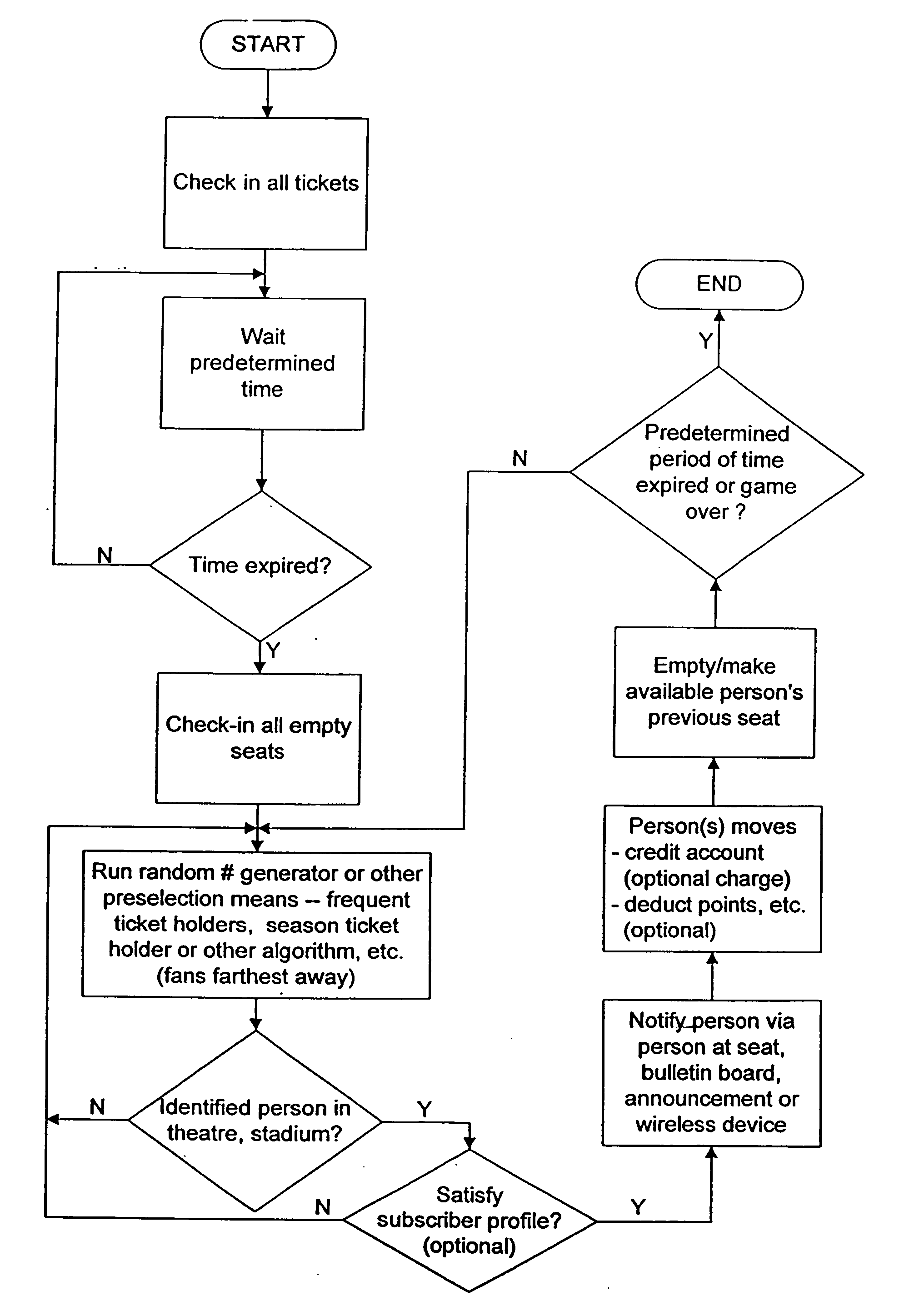
System and method for interactive messaging and/or allocating and/or upgrading and/or rewarding tickets, other event admittance means, goods and/or services
InactiveUS20060173781A1Bypassing any box officesEasy to buyMarket predictionsTicket-issuing apparatusPoint of saleData library
A method, system, server architecture and / or tangible medium upgrade and award admittance of events to an event customer, preferably via a data communication network. The method includes, for example, receiving a communication from the event customer, the communication including a request to obtain admittance to at least one event, the communication also including an identifier associated with the event customer, admitting the event customer at the point of sale system after verification of the request, and updating a database indicating that the request was processed. The method also includes determining first predetermined criteria associated with the event indicative of at least one other event customer not attending the event, releasing an allocation associated with the at least one other event customer, and notifying at least another of the event customers to perform the upgrade and / or reallocation.
Owner:MIND FUSION LLC
System and method for reallocating and/or upgrading and/or selling tickets, other even admittance means, goods and/or services
InactiveUS7162454B1To offer comfortIncrease the fun of activitiesTicket-issuing apparatusFinancePoint of saleAdmittance
A method, system, server architecture and / or tangible medium upgrade and award admittance of events to an event customer, preferably via a data communication network. The method includes, for example, receiving a communication from the event customer, the communication including a request to obtain admittance to at least one event, the communication also including an identifier associated with the event customer, admitting the event customer at the point of sale system after verification of the request, and updating a database indicating that the request was processed. The method also includes determining first predetermined criteria associated with the event indicative of at least one other event customer not attending the event, releasing an allocation associated with the at least one other event customer, and notifying at least another of the event customers to perform the upgrade and / or reallocation. Various optional embodiments are disclosed.
Owner:INTELLECTUAL VENTURES ASSETS 186 LLC
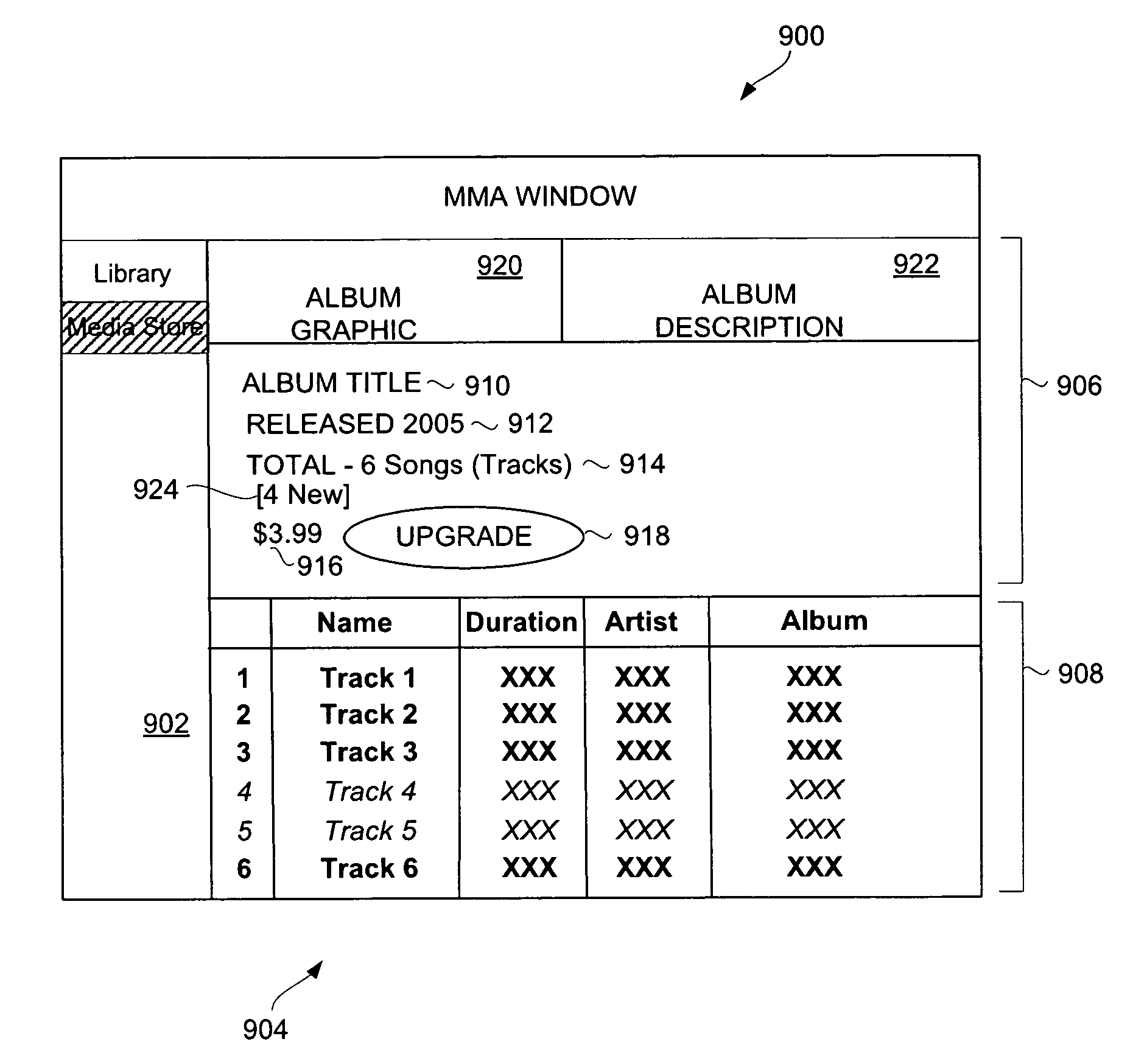
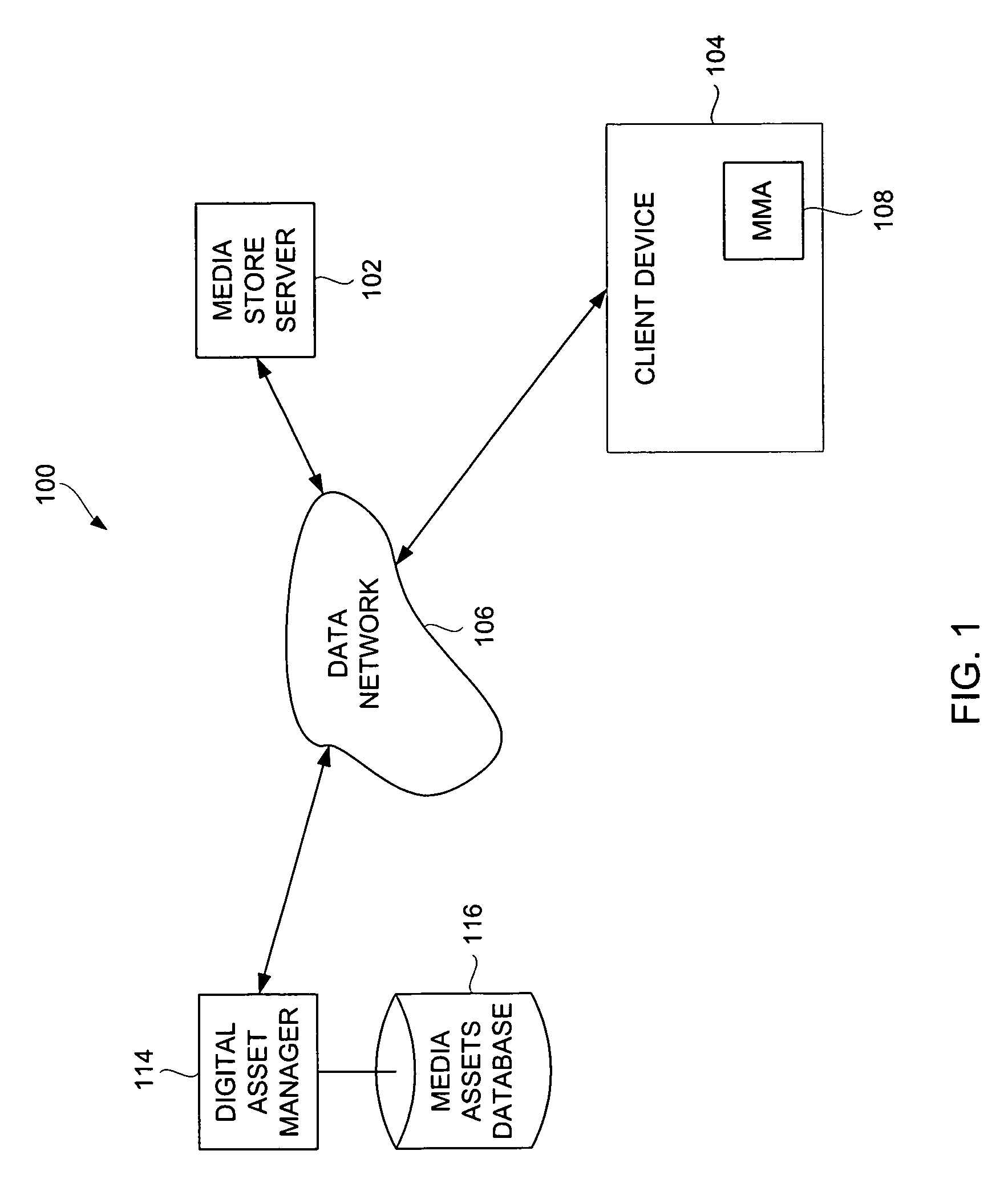
Method and system for upgrading a previously purchased media asset
ActiveUS8984442B2Facilitates presenting and requesting upgrade opportunityCommerceInput/output processes for data processingGraphicsGraphical user interface
Systems, graphical user interfaces and methods for upgrading from one or more digital media assets to a set of digital media assets over a network are described. A potential purchaser can be notified of available upgrade opportunities that are available for purchase. The potential purchaser can elect to pursue an upgrade opportunity so as to purchase a set of digital media assets. Upon upgrading to the set of digital media assets, the digital media assets within the set of digital media assets are made available to the purchaser. According to one aspect, a graphical user interface facilitates presenting and requesting upgrade opportunities. According to another aspect, equivalency rules and / or eligibility rules can be used to control which sets of digital media assets are available for upgrade by respective potential purchasers.
Owner:APPLE INC
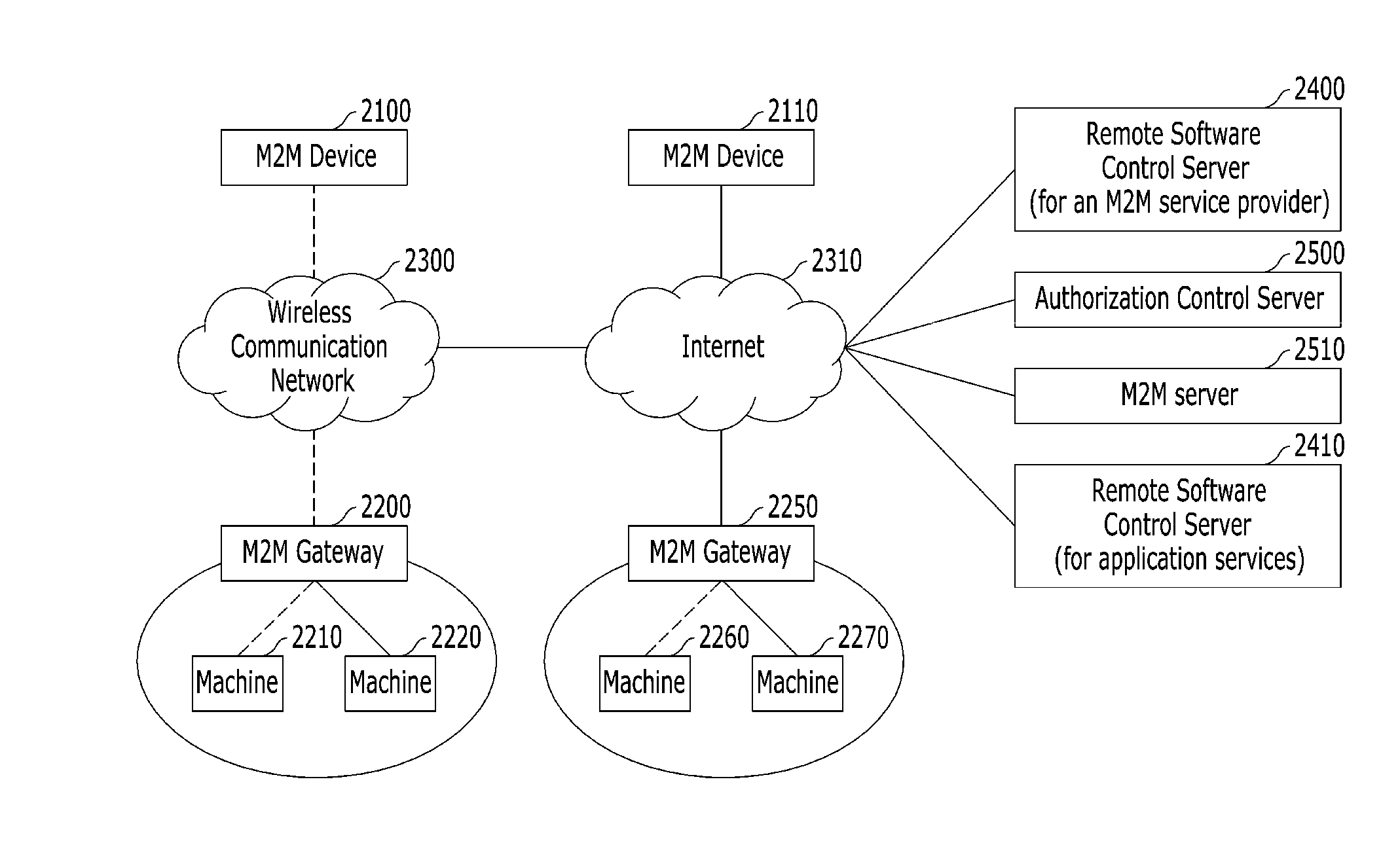
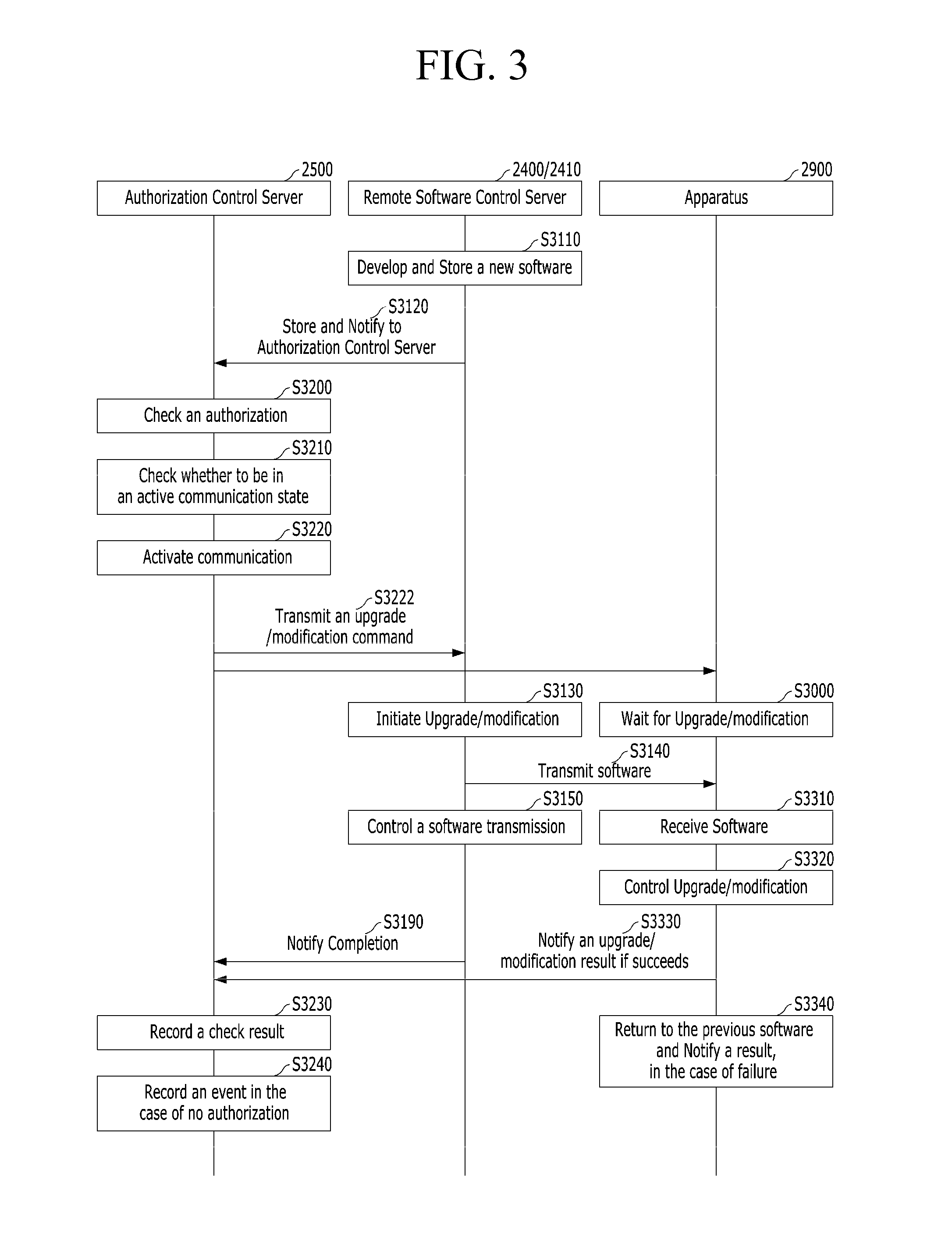
Separate upgrade/modification of remote software in machine to machine communication
InactiveUS20140007076A1Reduce work loadReducing wireless resource occupancyService provisioningProgram loading/initiatingUpgradeSoftware
The present disclosure is related to separately upgrading or modifying a remote software in a machine to machine (M2M) communication. Particularly, in the case of upgrading or modifying firmware of an M2M device or an M2M gateway, the present disclosure relates to separating an M2M service provider domain and a manufacturer domain, and independently upgrading or modifying each of the separated domains.
Owner:KT CORP
Virtual world electronic game
ActiveUS20080280684A1Heightened, more intense visual animationsVideo gamesSpecial data processing applicationsVisual presentationAnimation
An electronic game for playing on a portable handheld game unit and on-line includes a dynamic animated virtual character that can be customized and updated both visually and functionally through game play and that can translate from a two dimensional visual presentation on a game unit to a higher order visual presentation in an interactive multi-player virtual world on-line and back while retaining any customization or upgrades is provided. Different versions of the electronic game produce different virtual characters that can interact on-line or through wireless linkage between game units.
Owner:MGA ENTERTAINMENT
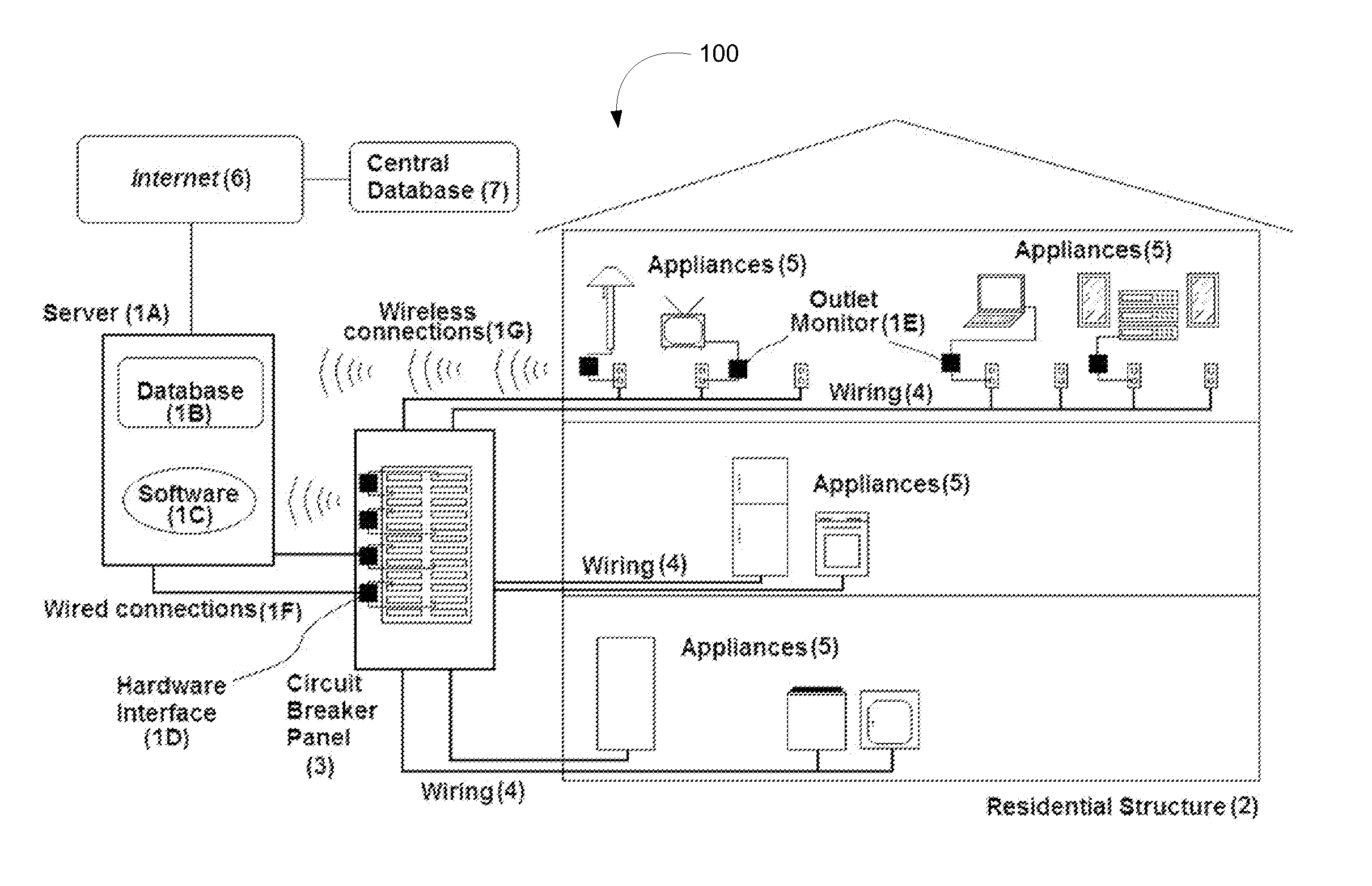
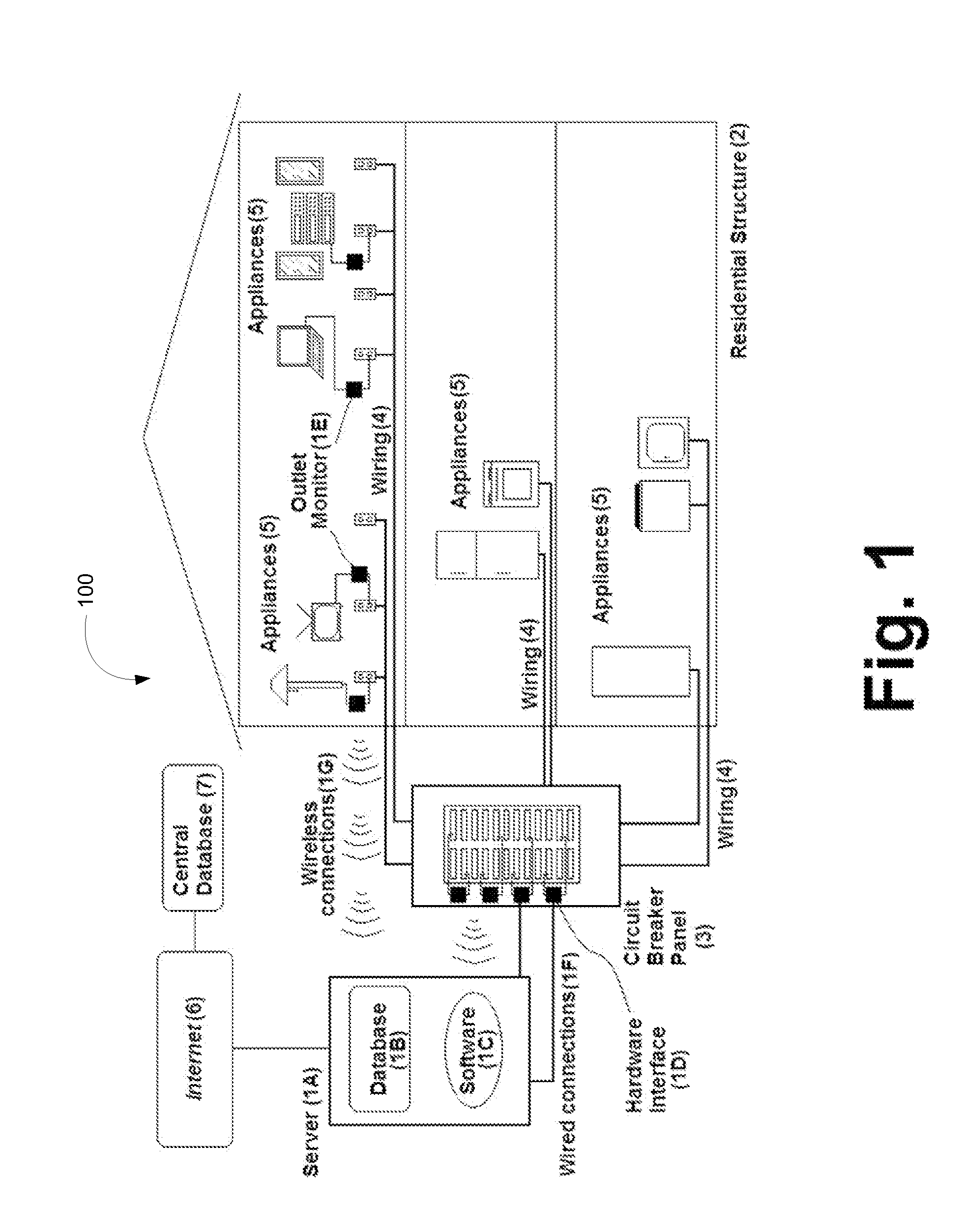
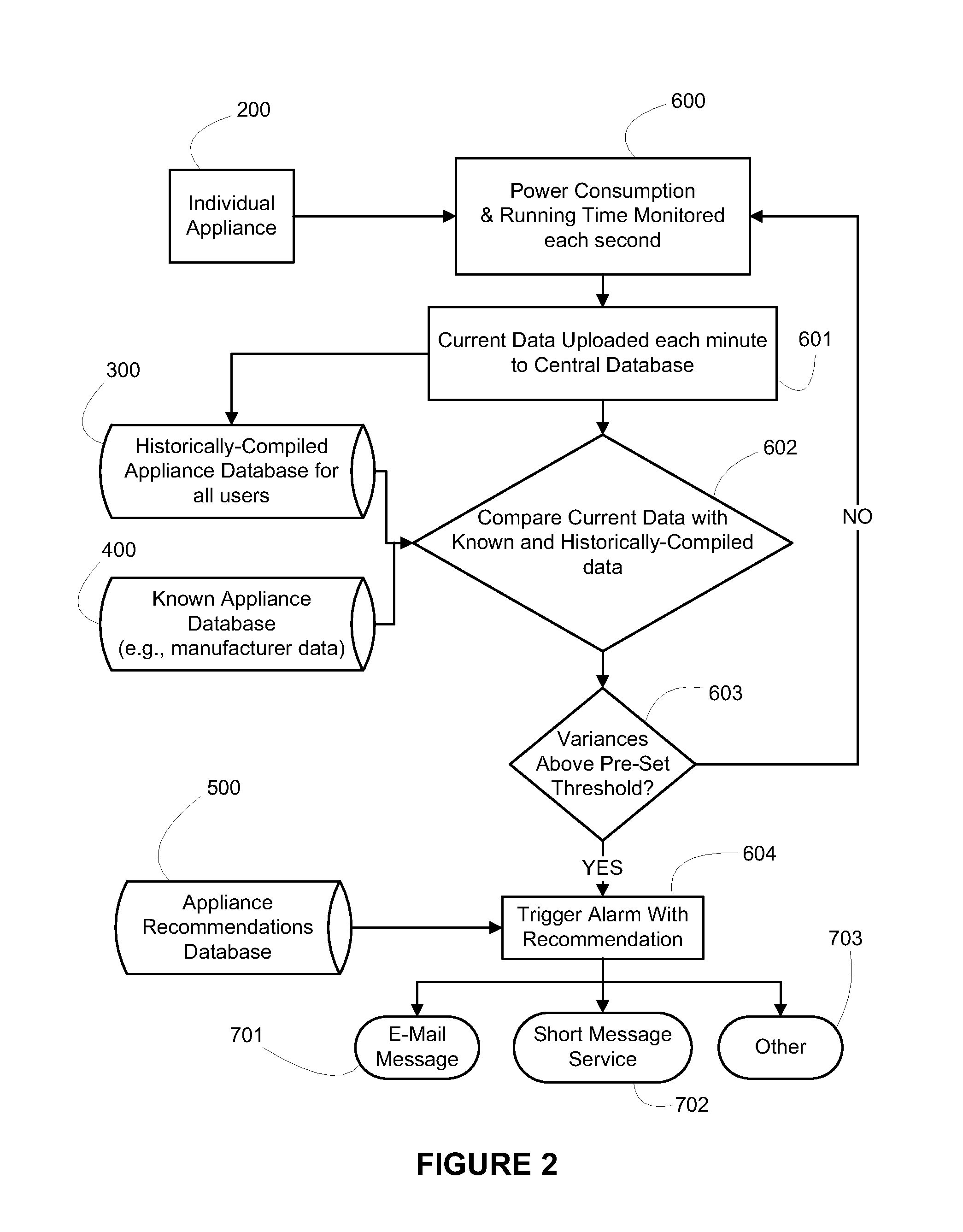
System and method to monitor and manage performance of appliances
ActiveUS20110040785A1Reduce energy consumptionSimple addressingDigital data processing detailsTesting/monitoring control systemsDecision takingComputer software
A system and method providing home and small business owners to monitor and manage one or more appliances. This enables a use to understand in detail their electrical consumption, to make informed decisions based on factual data about energy-saving upgrades to their current systems / appliances, and to provide Internet-based surveillance and control of systems for prevention of freezing, breakdown, or possible fire-related losses, including possible loss-of-life. The system and method includes through the use of Internet based computer software and databases, a hardware interface with electrical circuit panel(s) or fuse boxes in communication with the software and databases and optional wireless outlet monitoring units in communication with the software and databases. The databases being formed and created by the system and method for determining performance of appliances.
Owner:POWERHOUSE DYNAMICS
Intelligent automated data usage upgrade recommendation
A method of notifying a mobile station regarding data usage with a plan limit includes tracking an amount of data usage consumed by the mobile station. A first data usage limit and a first data usage time frame are determined from a user account. A comparison is made of the data usage to the first data usage limit and a present time to the first data usage time frame. From this comparison, a projected data usage amount is determined and whether the projected data usage exceeds the first data usage limit. If exceeded, the system analyzes a second data usage limit to determine if it is greater than the projected data usage amount. If greater, the server provides a message to the mobile station notifying the user of the projected overage and suggestions to change to a new plan offering the second data usage limit.
Owner:CELLCO PARTNERSHIP INC
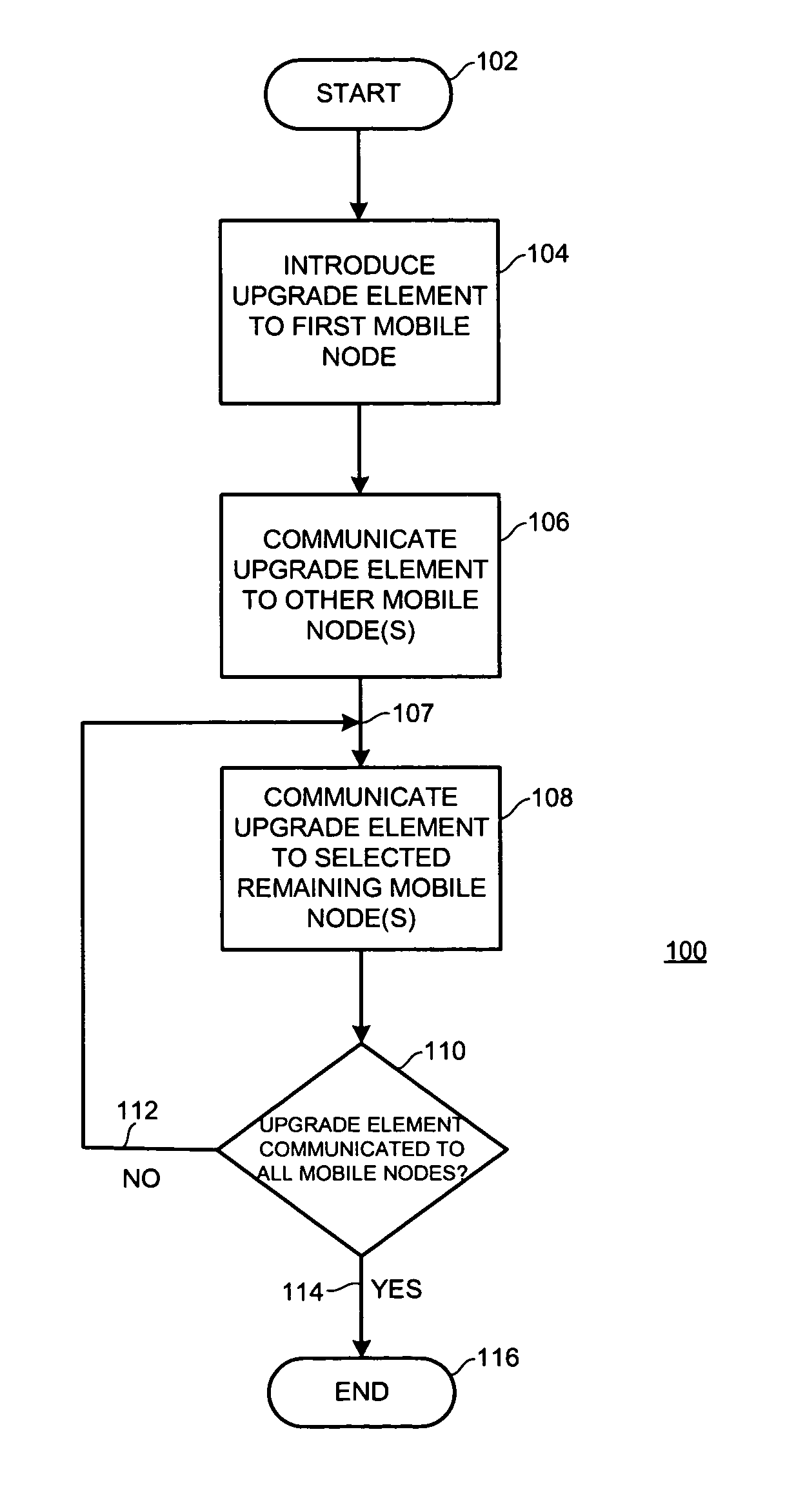
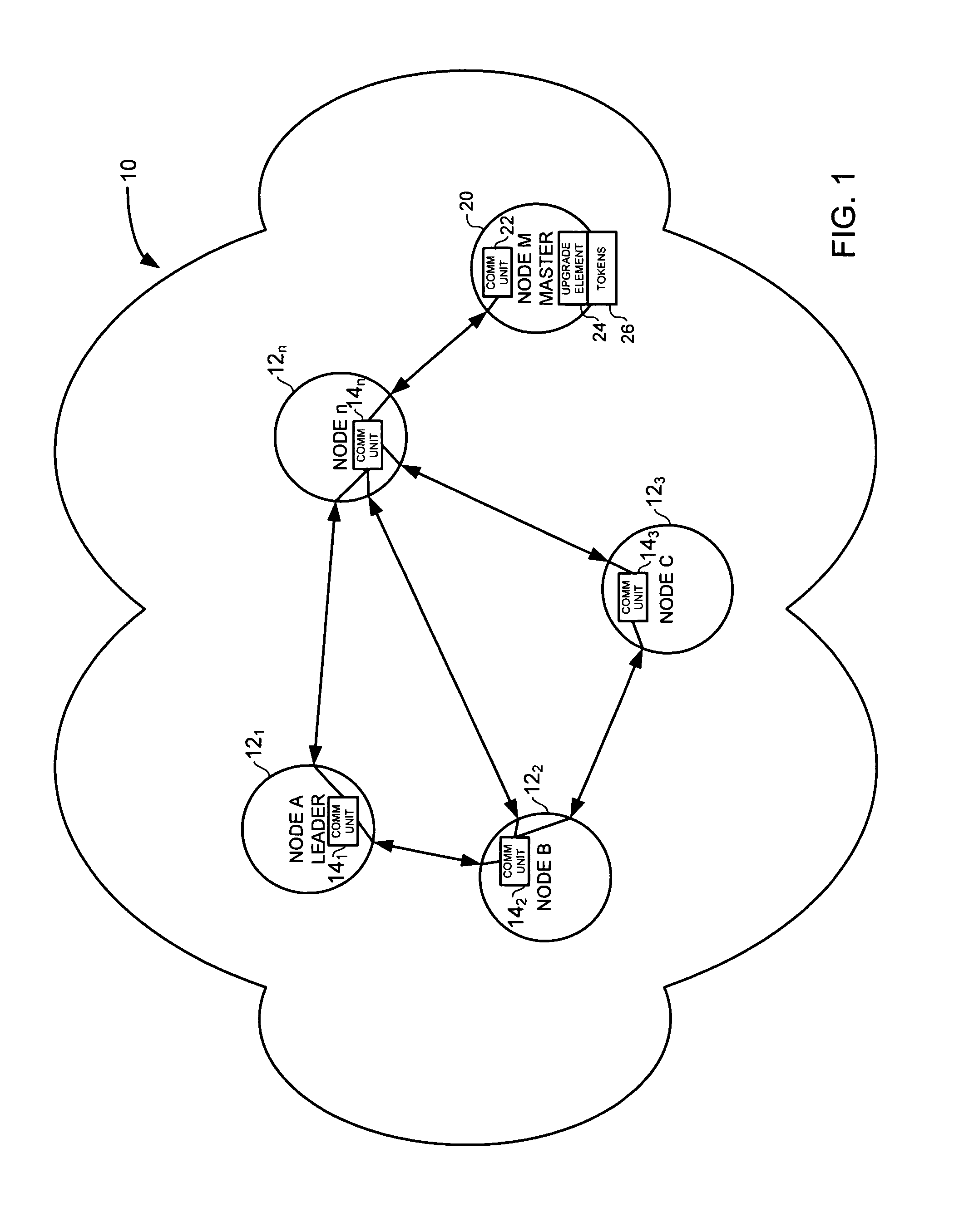
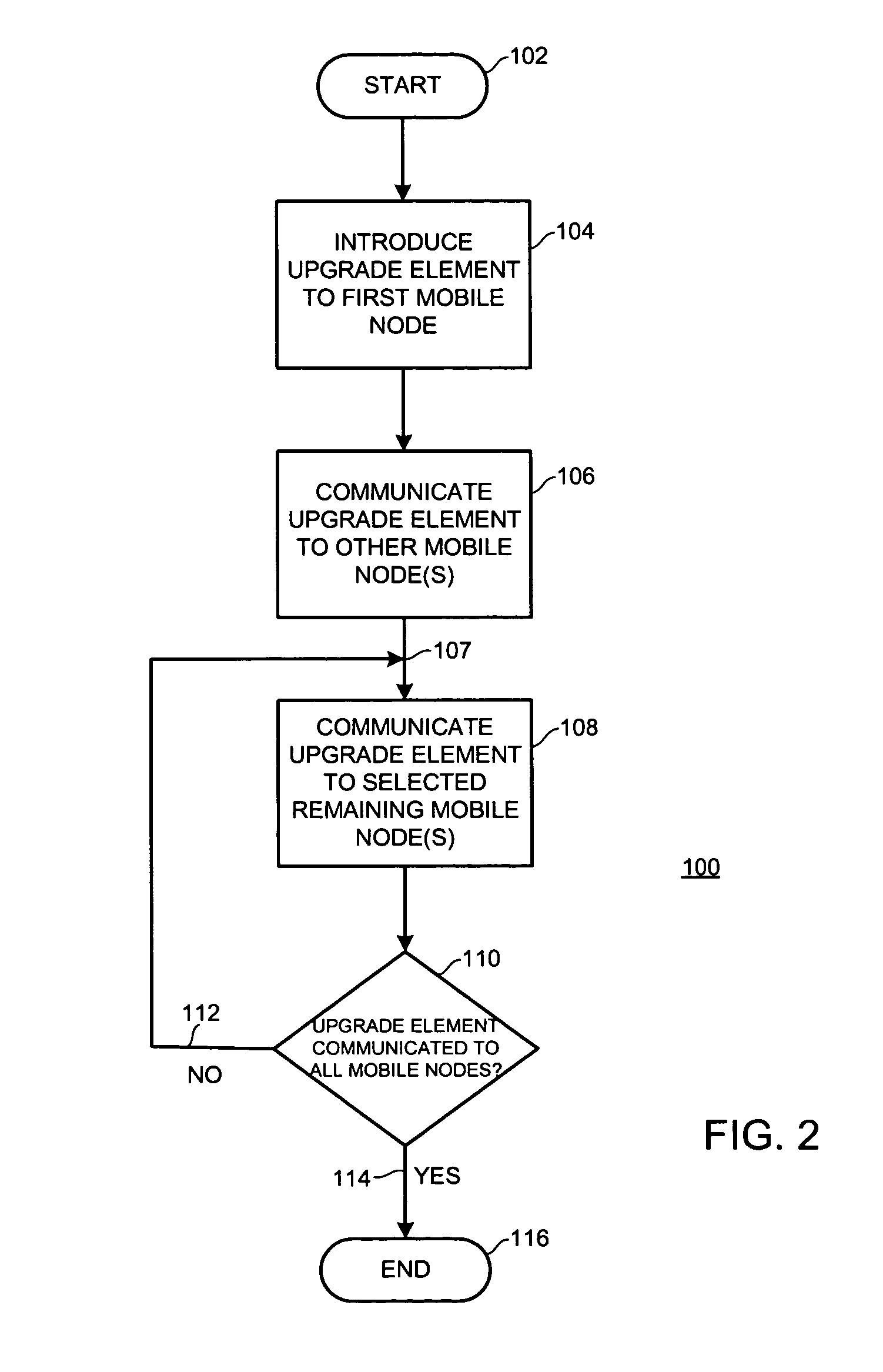
Method and system for distributing an upgrade among nodes in a network
Owner:ALCATEL LUCENT SAS
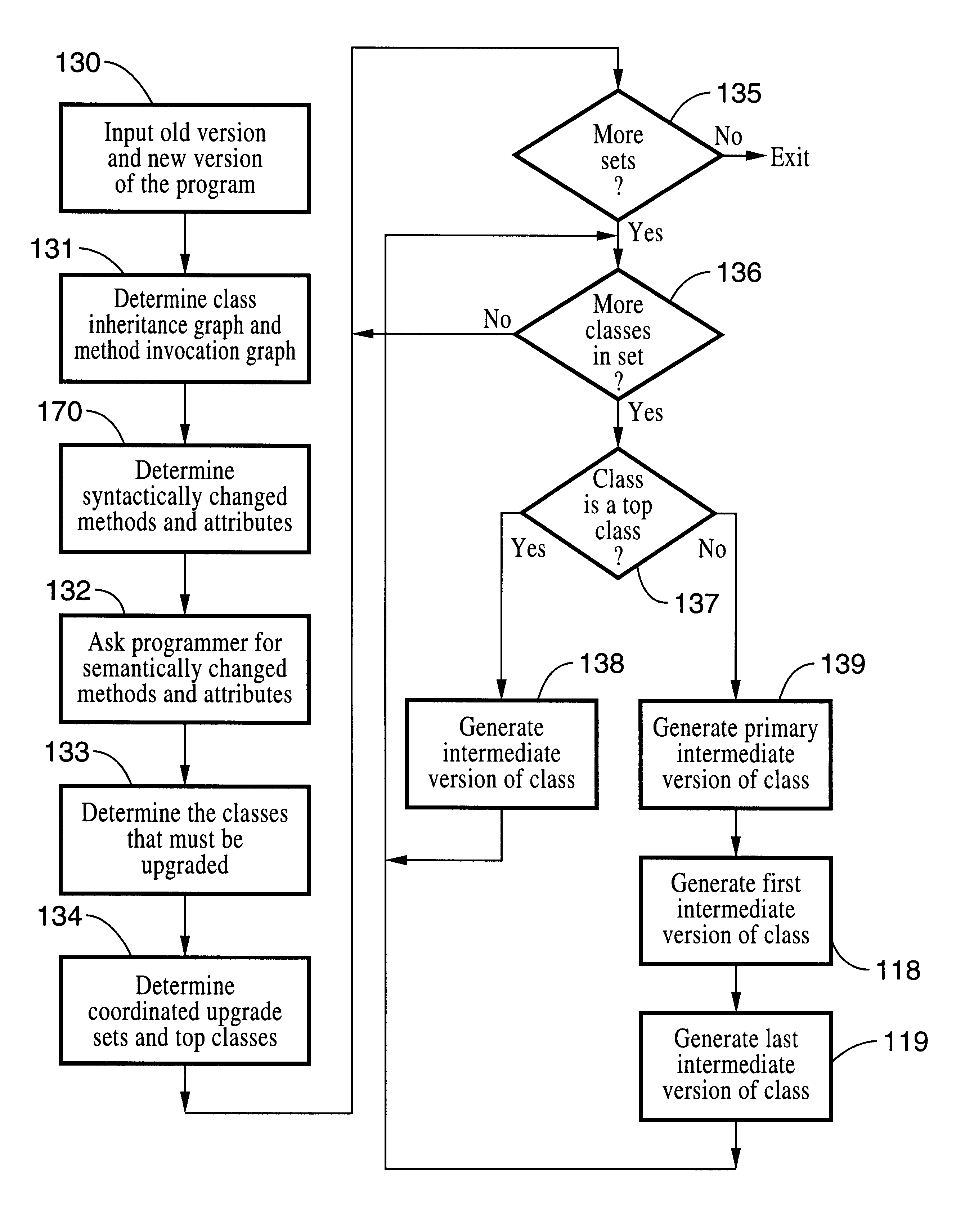
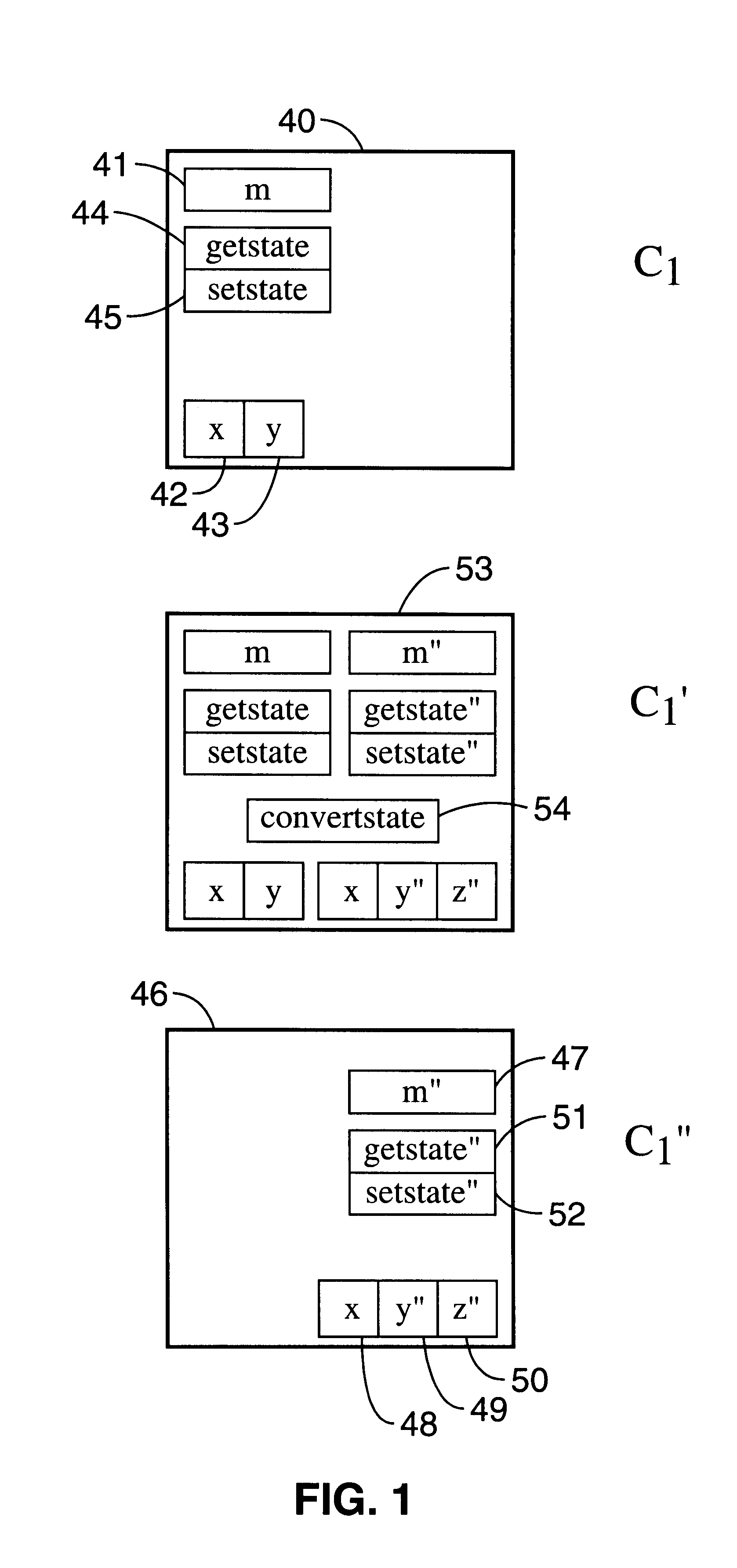
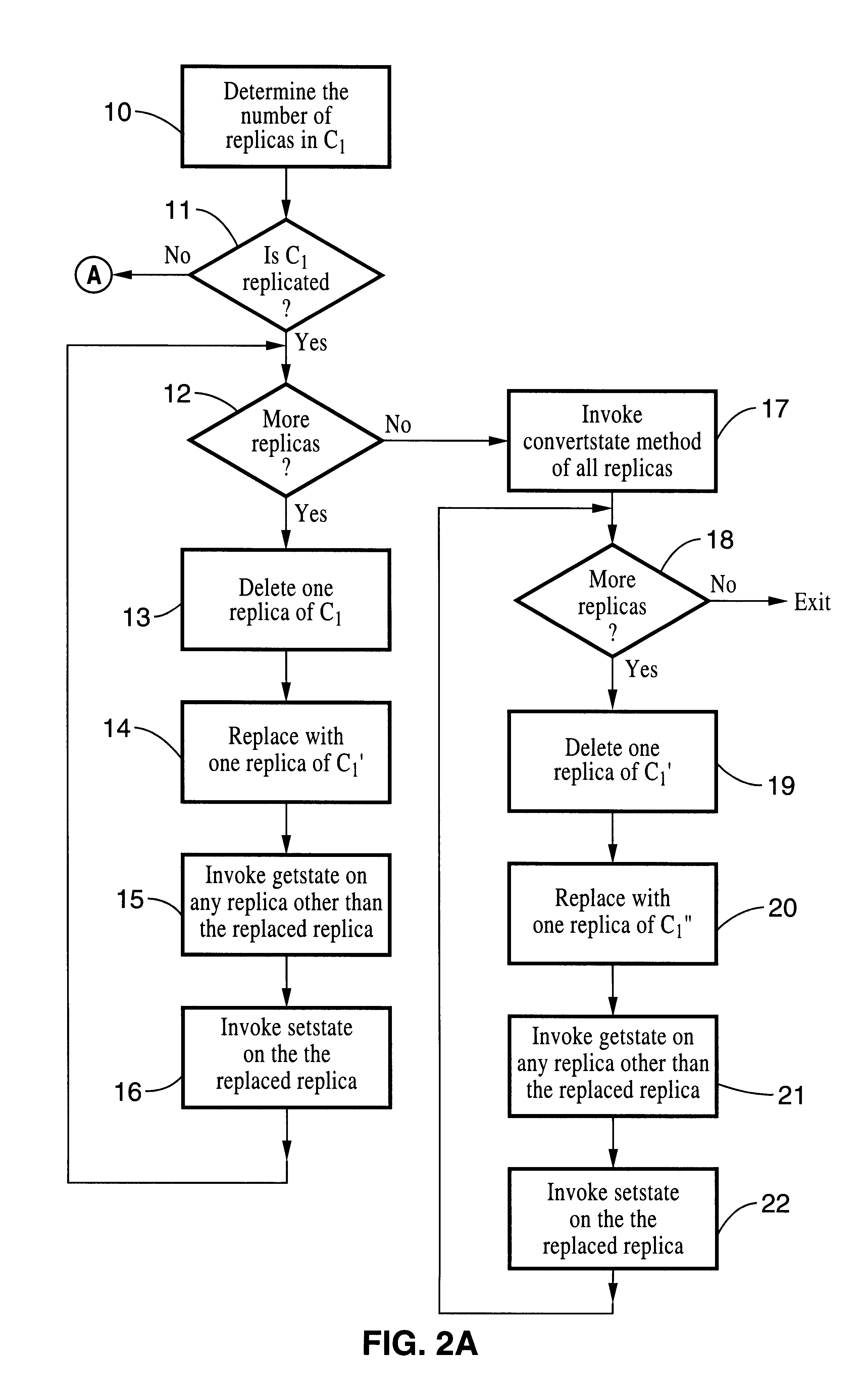
Live upgrade process for object-oriented programs
InactiveUS6360363B1Maintain consistencyData processing applicationsSoftware engineeringUpgradeThree-phase
A process that assists a computer programmer to perform an upgrade to a computer program while that program continues to operate and provide service. The upgrade process includes three phases: (1) the preparation by a computer programmer of a new computer program P'' that is to replace an existing computer program P, (2) an offline preparation of the upgrade from P to P'' with the assistance of the computer programmer, and (3) an online, fully automatic, live upgrade from P to P''.
Owner:RED HAT
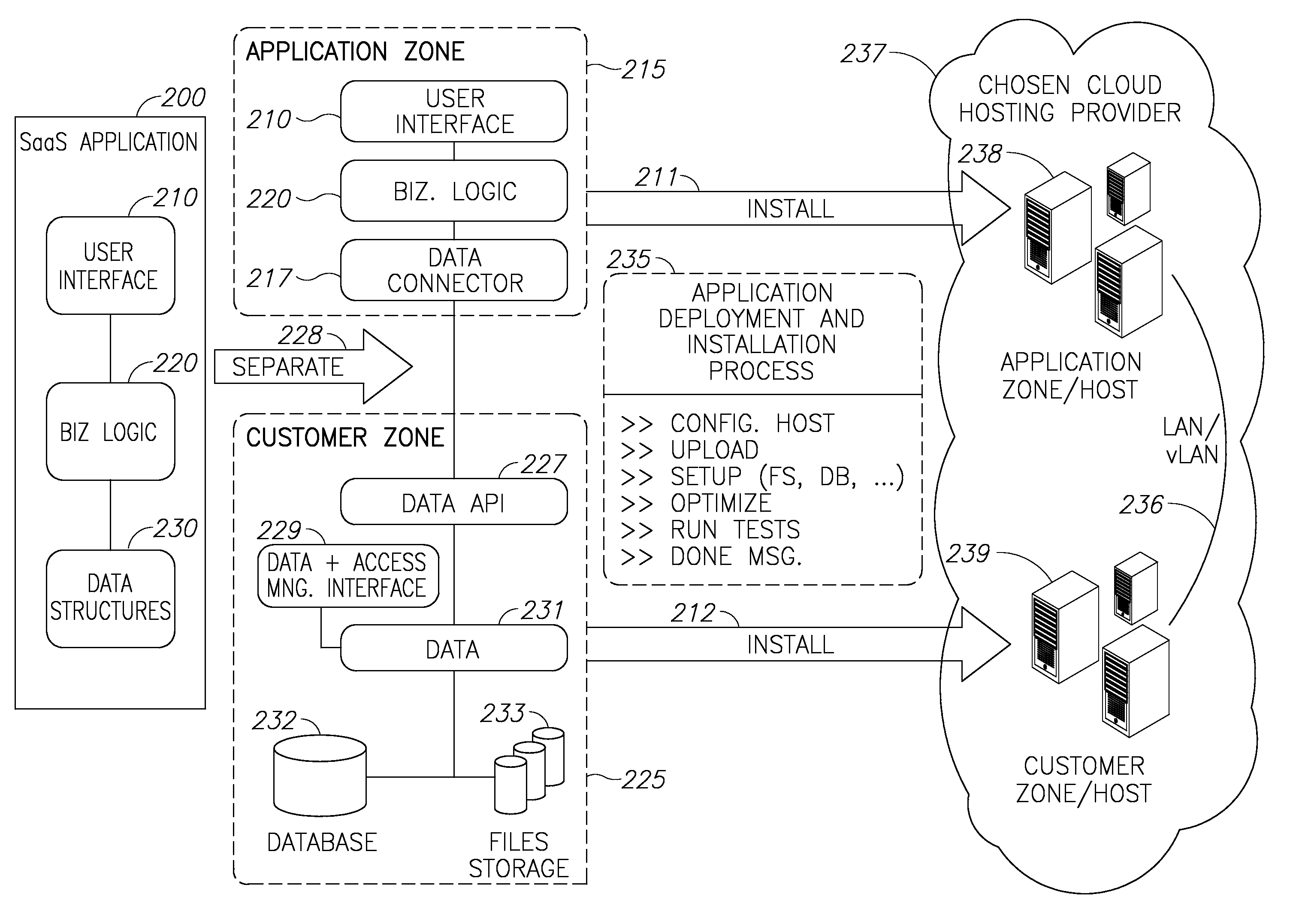
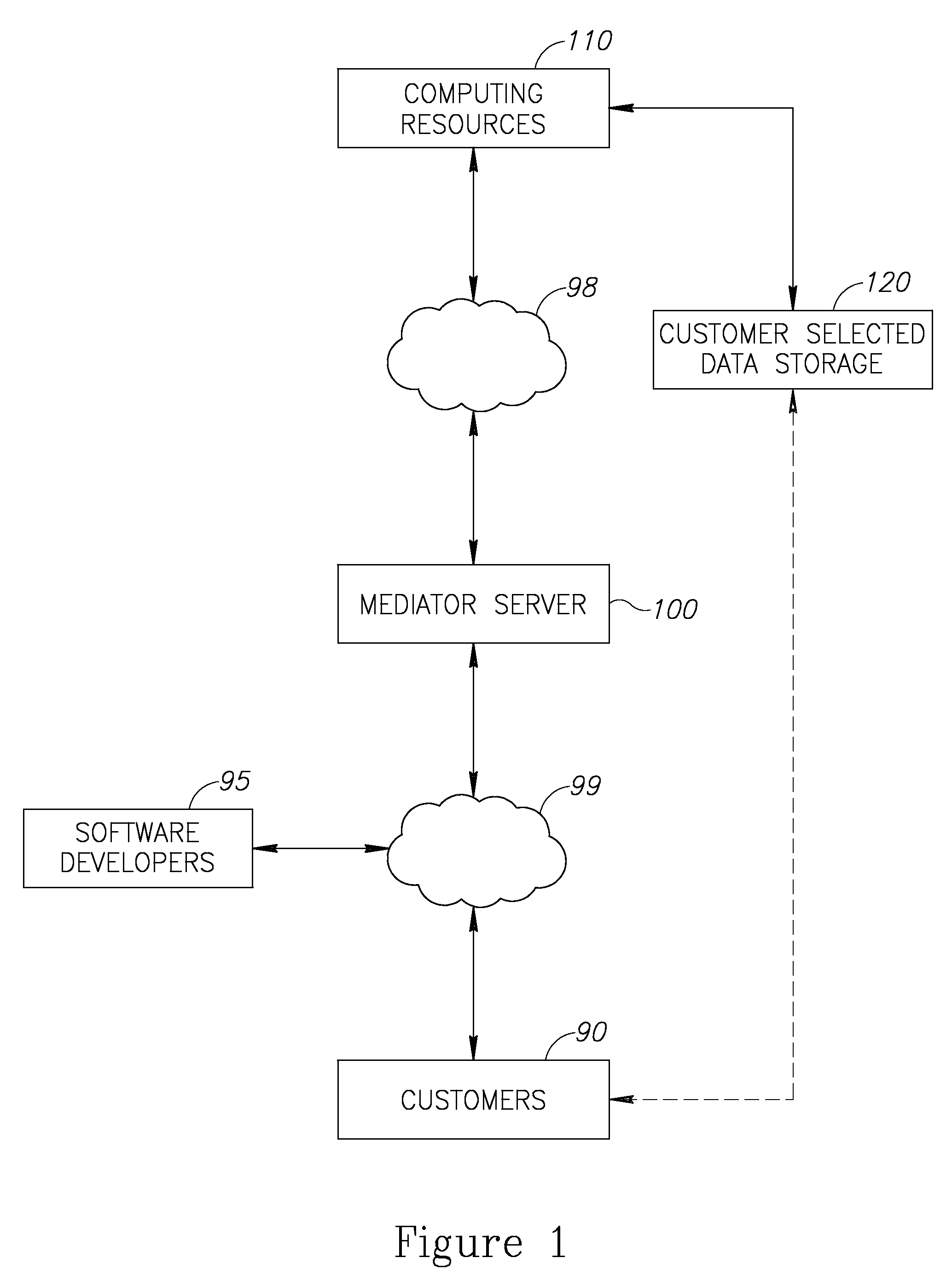
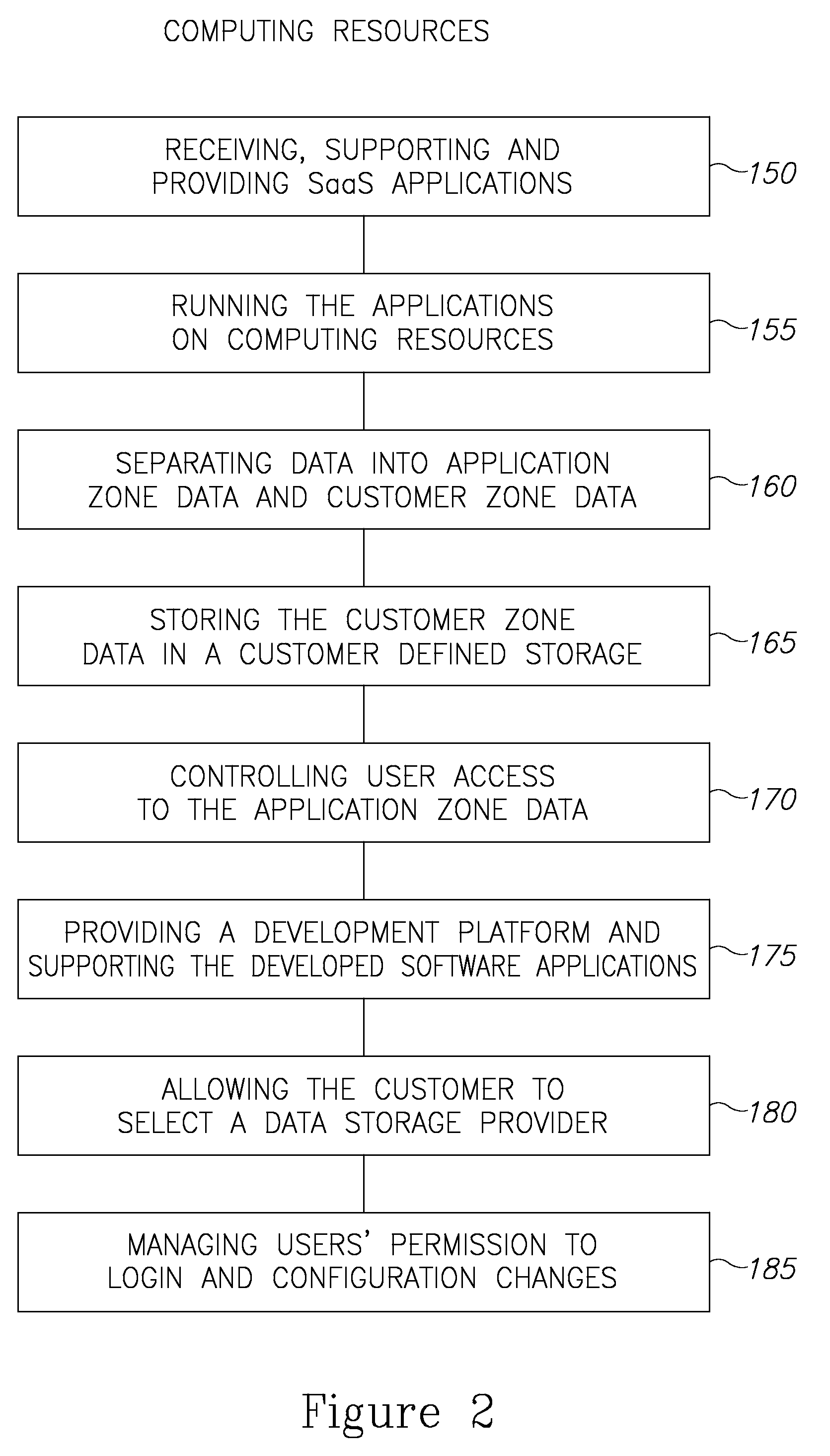
Cloud plarform for managing software as a service (SAAS) resources
InactiveUS20110126168A1Ensure availabilityEnsure data securityMultiple digital computer combinationsSpecific program execution arrangementsApplication softwareData availability
A cloud platform for managing Software as a Service (SaaS) resources is provided herein. The platform includes: a mediator server connected to computing resources, arranged to provide software developers a platform to develop SaaS applications, operable on the computing resources, wherein the SaaS applications and customer data are stored logically and physically independent of the computing resources, and data of SaaS application and the customer data are logically and physically separated. SaaS platform allows developers to provide software solutions via the mediator server directly to customers, and ensures data availability and data security. Access policy of users and developers to SaaS applications is centrally supervised and capable of integrating with other applications on the site of the customer. Upgrades to SaaS applications are performed in a predefined order of customers. Further, the SaaS platform facilitates selection and replacement of data storage provider.
Owner:CROWDSOURCE TECH
Fault diagnosis, repair and upgrades using the acoustic channel
InactiveUS20050028034A1Need be addressBroadcast information characterisationNon-redundant fault processingVocal tractEngineering
An acoustic channel is used for fault diagnosis, repair, and upgrades. Remote diagnosis uses self-test data encoded into sound waves. Repair data and upgrades are also encoded and transmitted as sound waves.
Owner:QUALCOMM INC
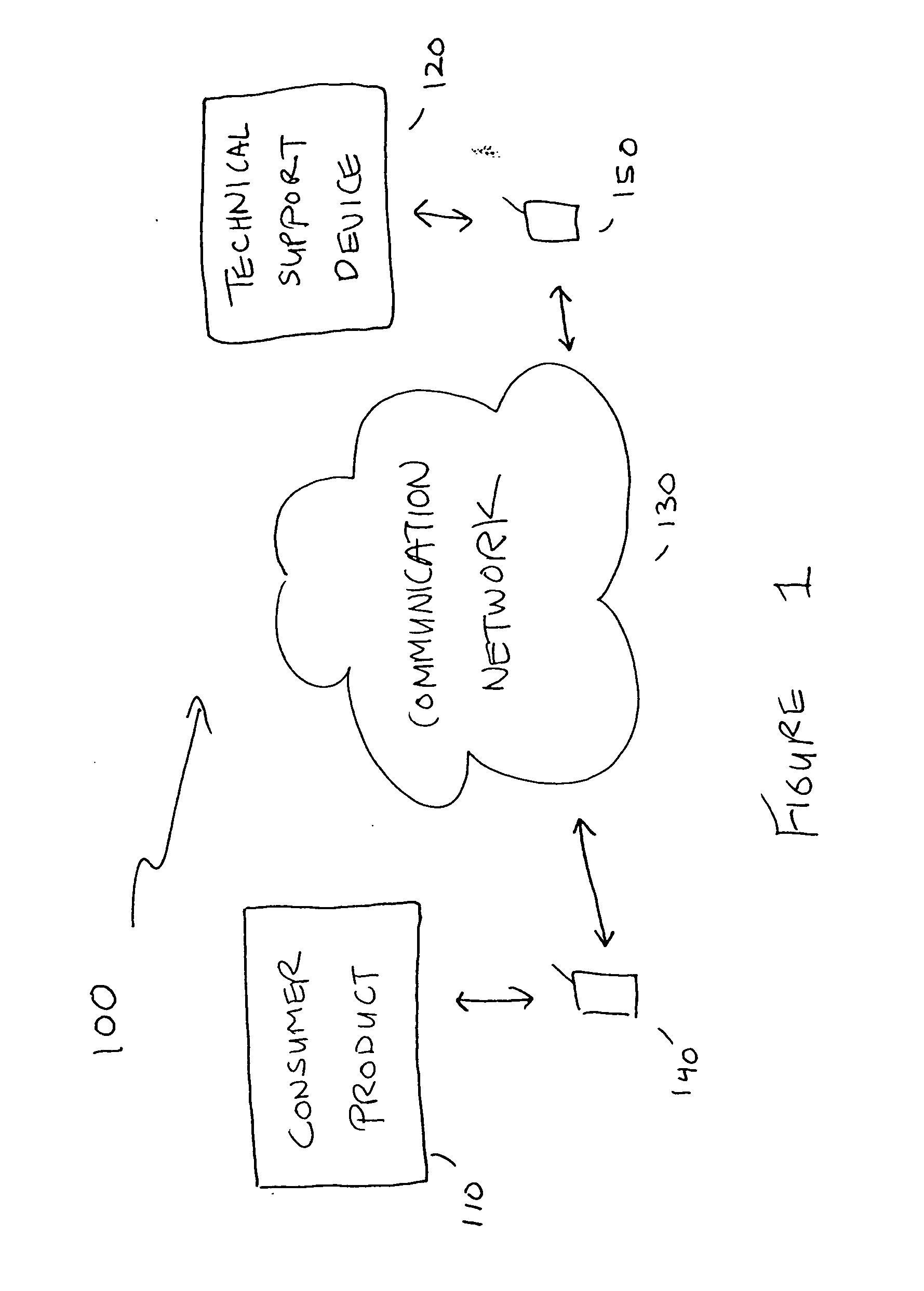
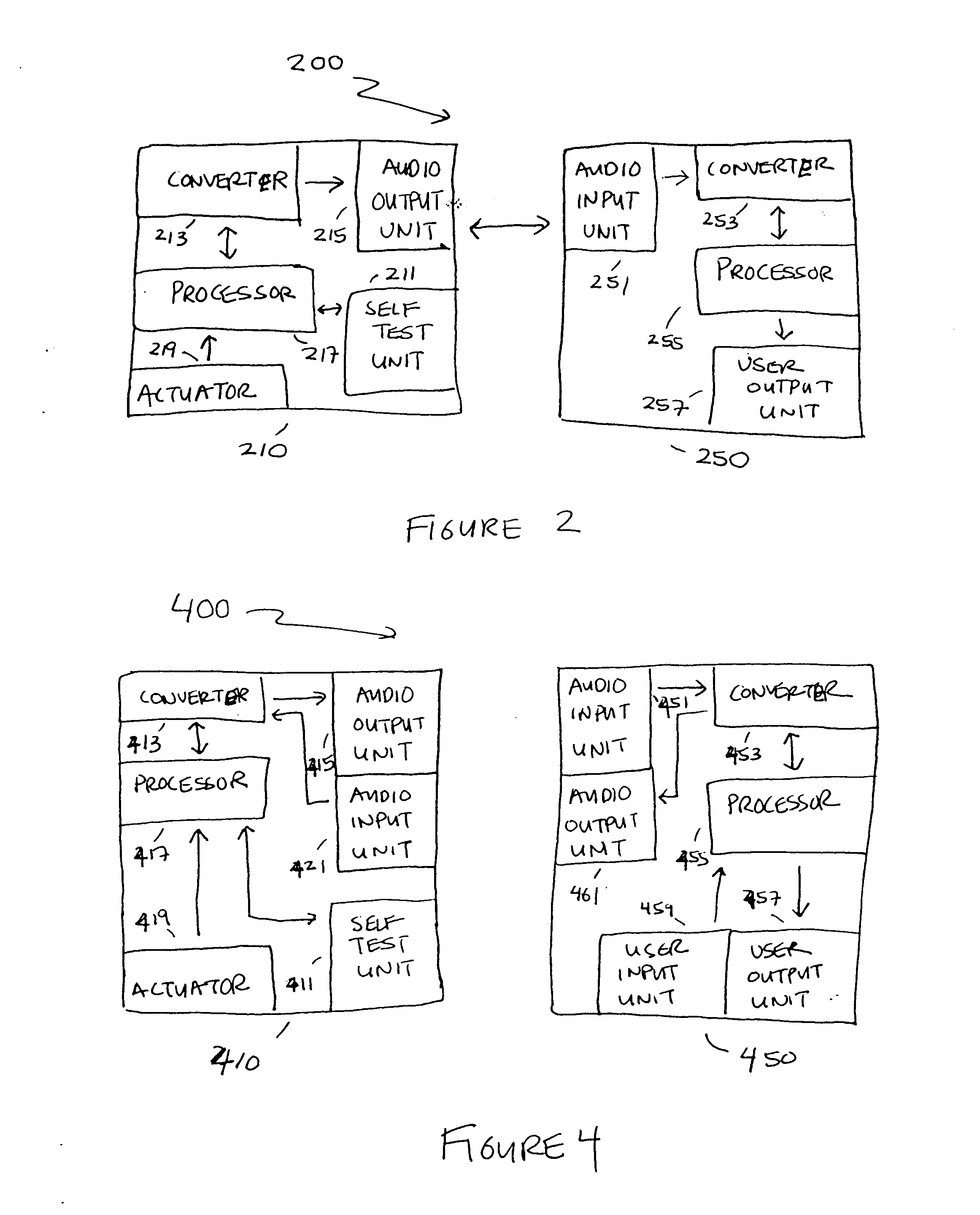
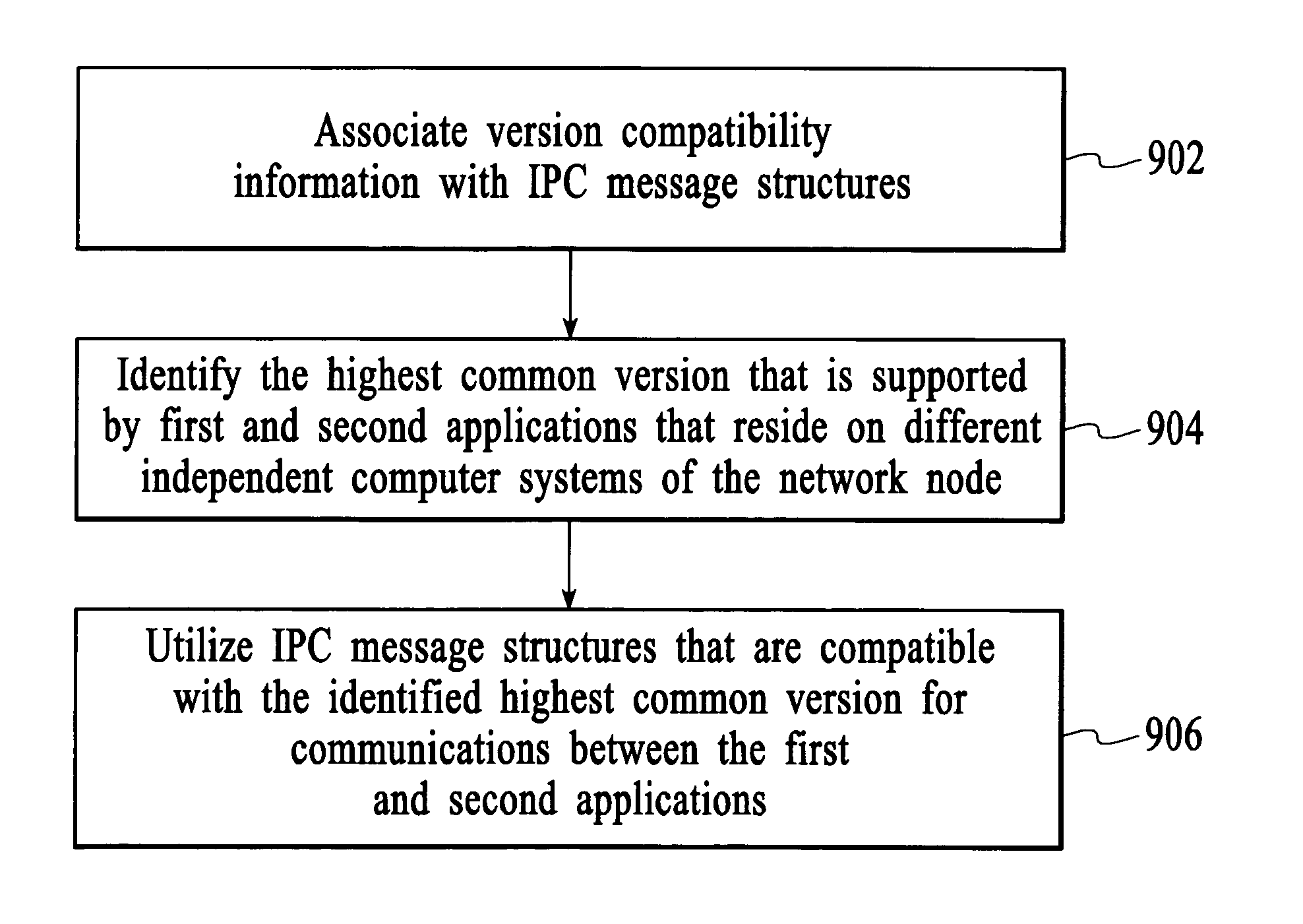
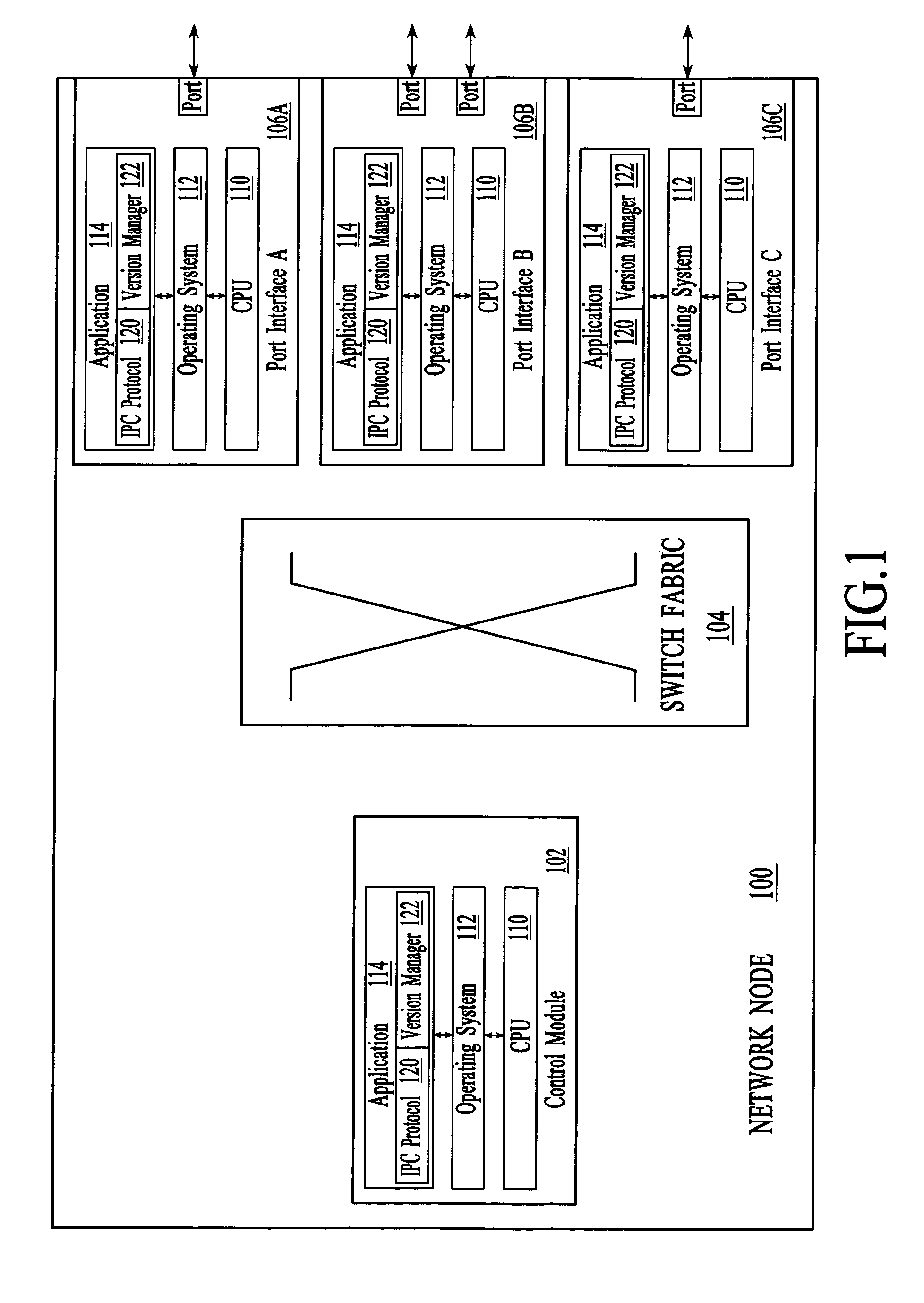
Implicit interprocess communications (IPC) versioning support
InactiveUS7653911B2Maintain compatibilityMultiprogramming arrangementsSpecific program execution arrangementsComputer compatibilityMessage structure
Owner:WSOU INVESTMENTS LLC
Configurable width buffered module having switch elements
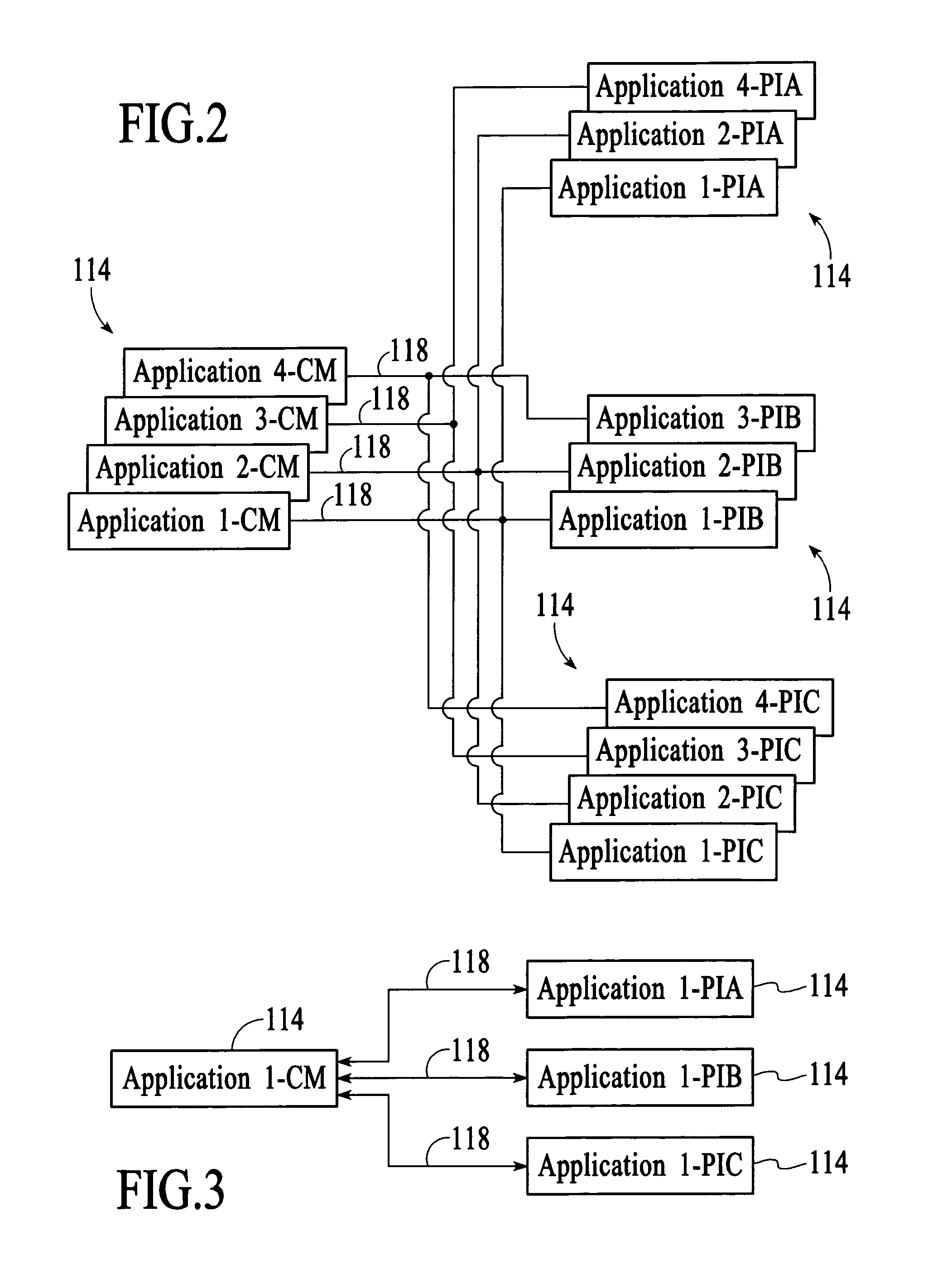
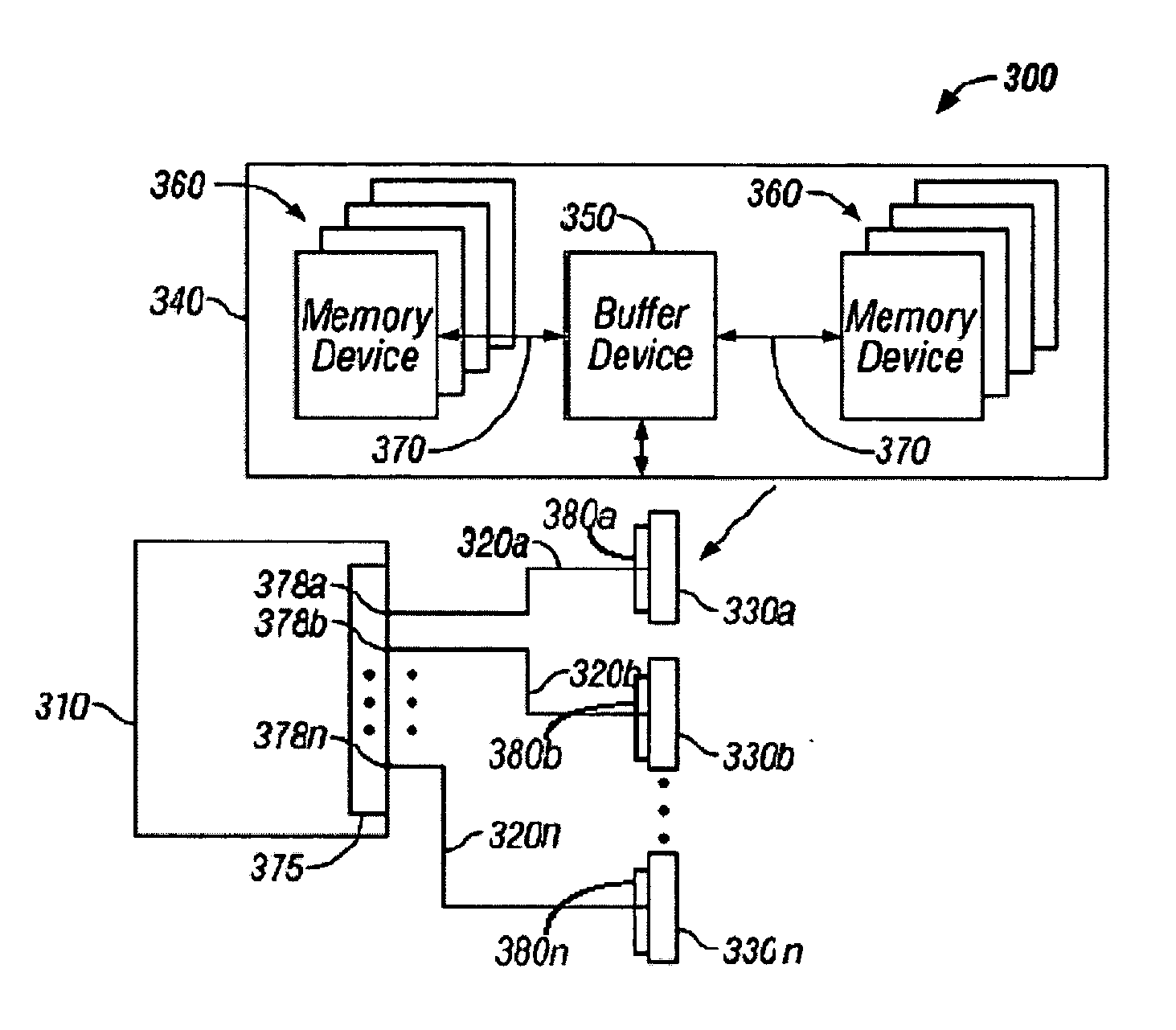
A memory system architecture / interconnect topology includes a configurable width buffered memory module having a configurable width buffer device with at least one switch element. A buffer device, such as a configurable width buffer device, is positioned between or with at least one integrated circuit memory device positioned on a substrate surface of a memory module, such as a DIMM. A switch element is positioned on or off a memory module and includes two transistors in embodiments of the invention. One or more switch elements are coupled to one or more channels to allow for upgrades of memory modules in a memory system. An asymmetrical switch topology allows for increasing the number of memory modules to more than two memory modules without adding switch elements serially on each channel. Switch elements allow for increasing the number of ranks of memory modules in a system, while also achieving many of the benefits associated with point-to-point topology.
Owner:RAMBUS INC
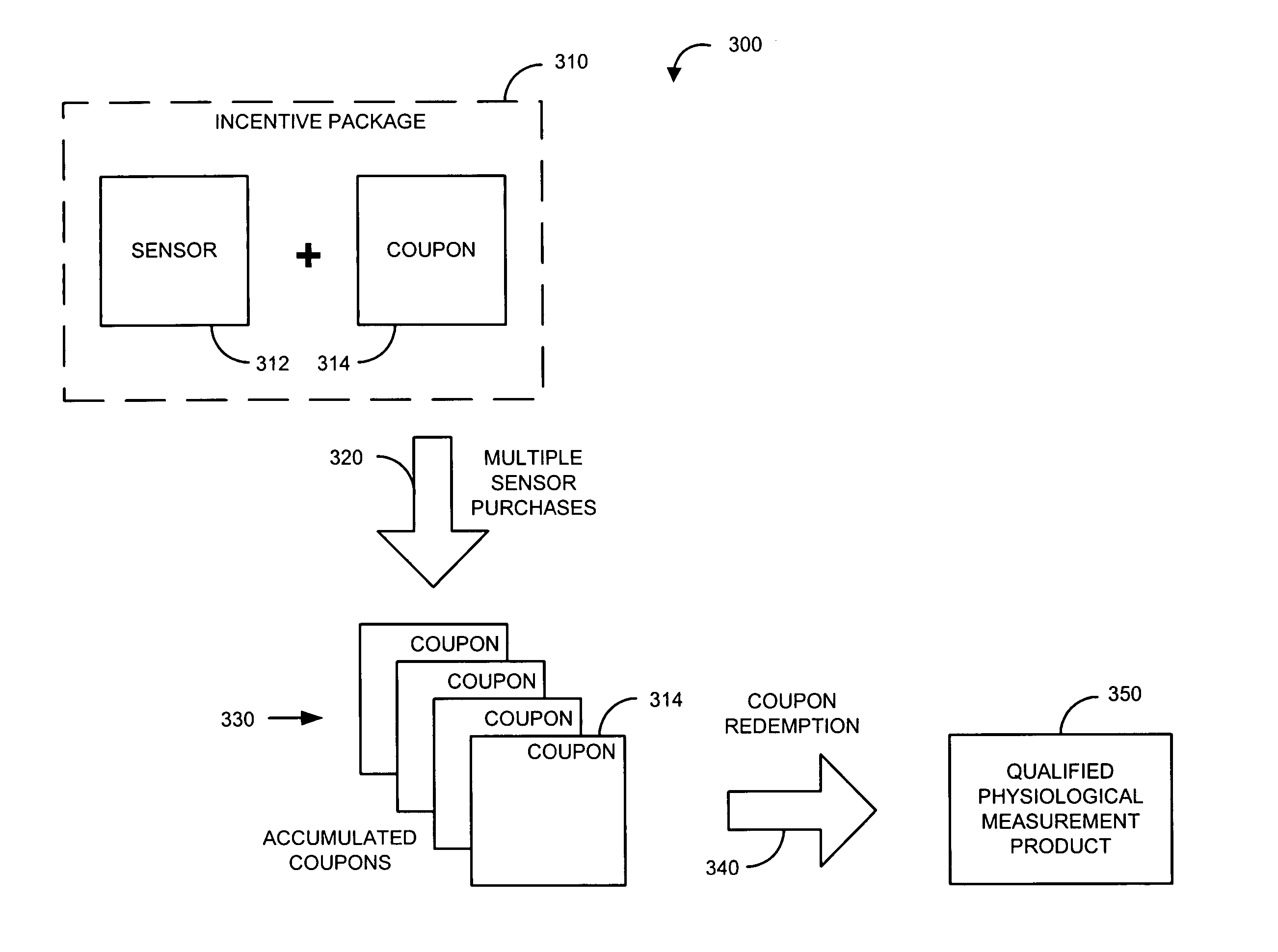
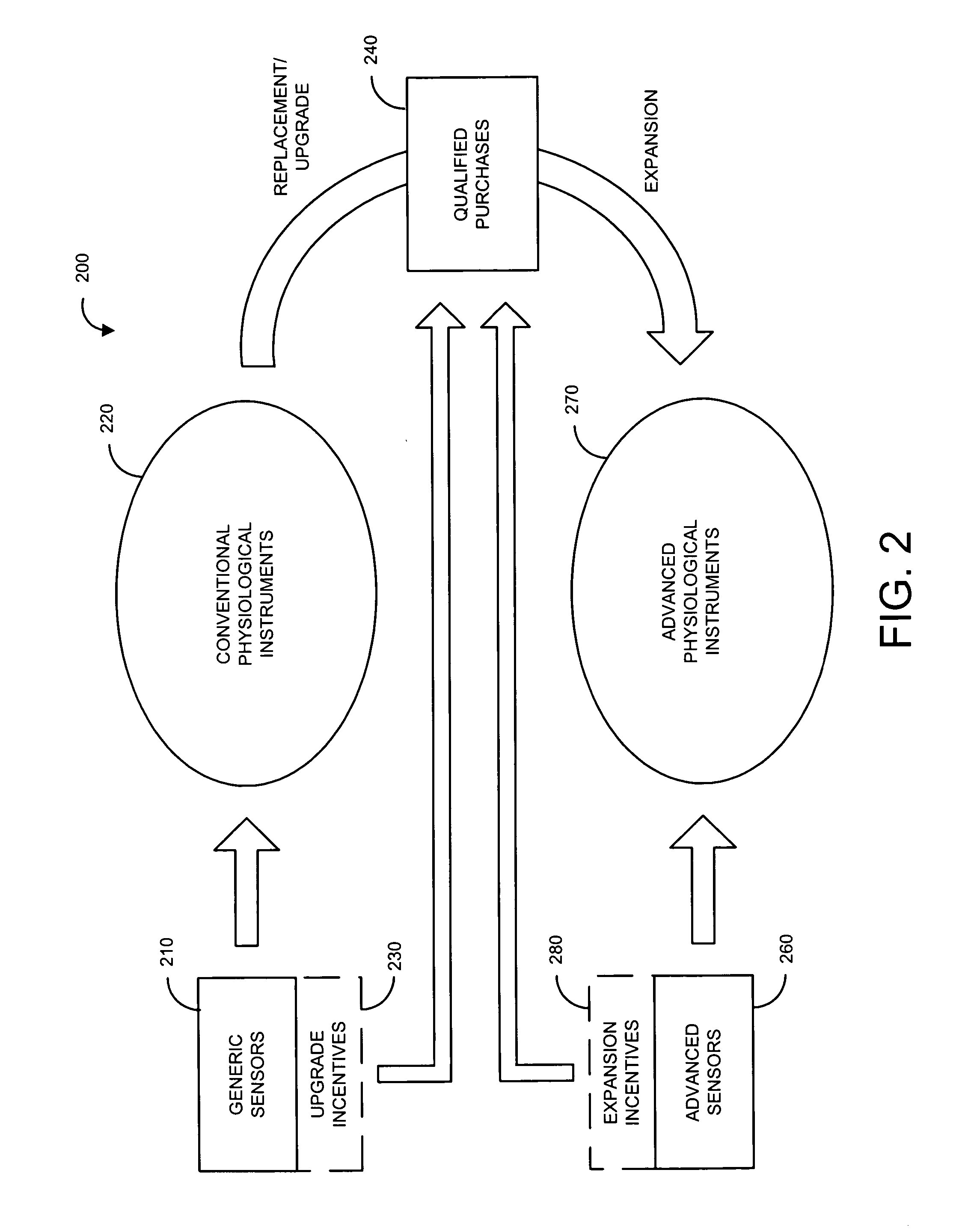
Sensor incentive method
InactiveUS20050055276A1Improve featuresImprove performanceDiscounts/incentivesSpecial data processing applicationsEngineeringMonetary value
A sensor incentive method provides a sensor adapted to function with an installed base of conventional physiological instruments. An incentive is associated with the sensor in connection with a sensor purchase. The incentive is applied to a qualified physiological instrument purchase so as to motivate or otherwise enable the upgrade or replacement of the installed base with advanced physiological instruments. The accumulation of multiple incentives may also apply to the purchase. In one embodiment, a coupon is associated with the sensor purchase, the coupon having a monetary value applicable to the purchase of advanced physiological instruments. The coupon is redeemed for the monetary value during the qualified purchase. Multiple coupons may be accumulated and redeemed for the monetary value times the number of coupons.
Owner:MASIMO CORP
Dynamic deployment of services in a computing network
InactiveUS20020178254A1Improve efficiencyMore efficient web hosting sitesResource allocationMultiple digital computer combinationsNetwork conditionsClient-side
Methods, systems, and computer program products for improving network operations by dynamically deploying services (such as web services or other network-accessible services) in a computing network. A process is defined whereby conditions such as usage metrics for incoming client requests (or other network conditions such as load balancing considerations) are monitored, and used to trigger dynamic deployment of web services to locations in the network in order to improve efficiency (e.g. by reducing response time to the client and / or reducing the burden on the back-end computing system resources). Service requests are dynamically routed to the destination where the service resides, in a manner which is transparent to the client. In an optional aspect, programmatic replication of system upgrades may be implemented by redeploying services using this same dynamic deployment approach, enabling the complexity of upgrading previously-deployed software to be reduced significantly. As another optional aspect, previously-deployed software may also be automatically and programmatically undeployed using disclosed techniques.
Owner:IBM CORP
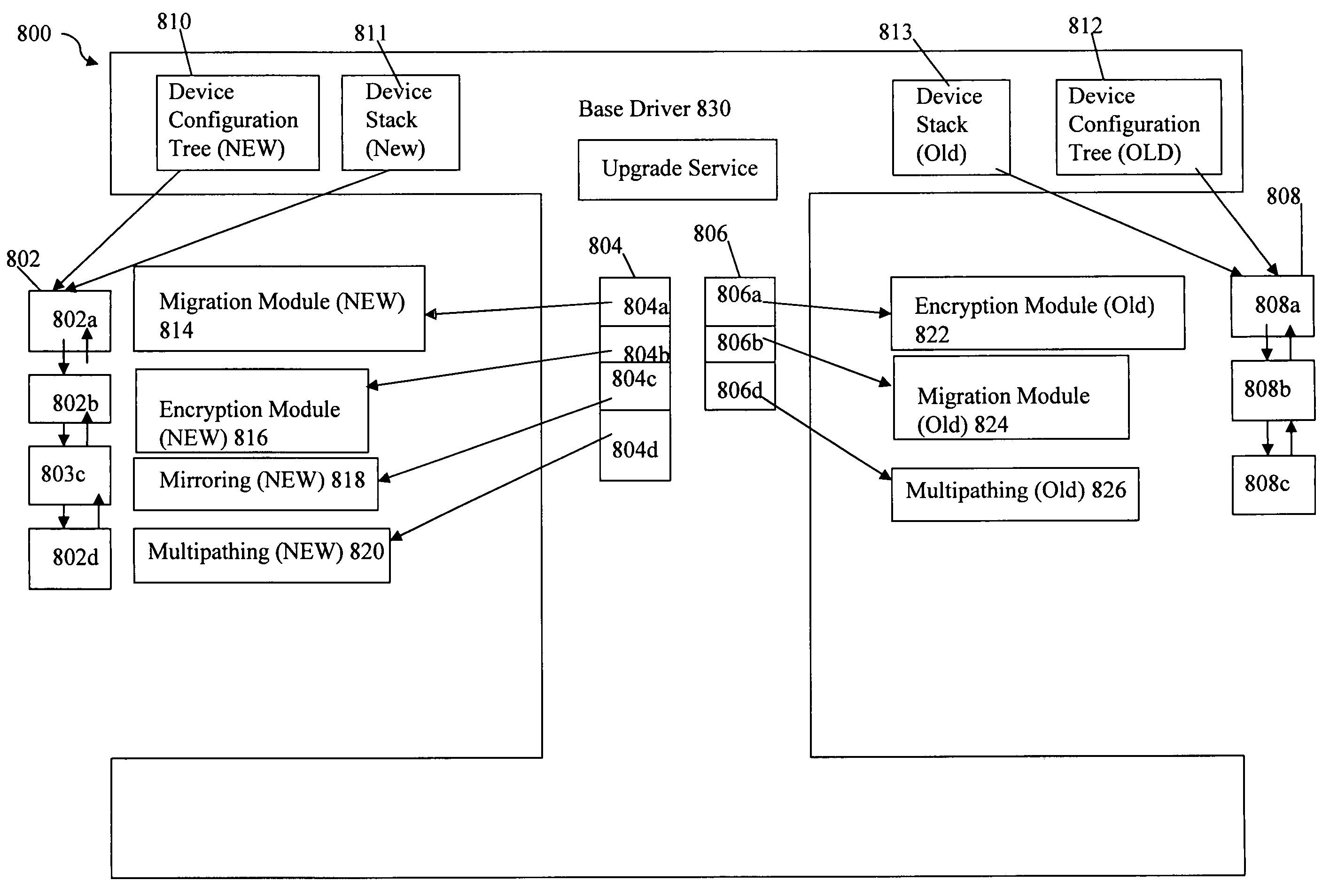
Techniques for non-disruptive upgrade
Described are techniques for upgrading a driver. A driver is installed which includes an upgrade facility, a base driver and a first set of one or more driver extension modules for processing input / output operations for one or more devices. Processing is performed to upgrade the driver using the upgrade facility. The processing includes loading one or more upgrade modules associated with a second version of said driver and performing cutover processing for each of the one or more devices.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com