Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3741 results about "Client machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
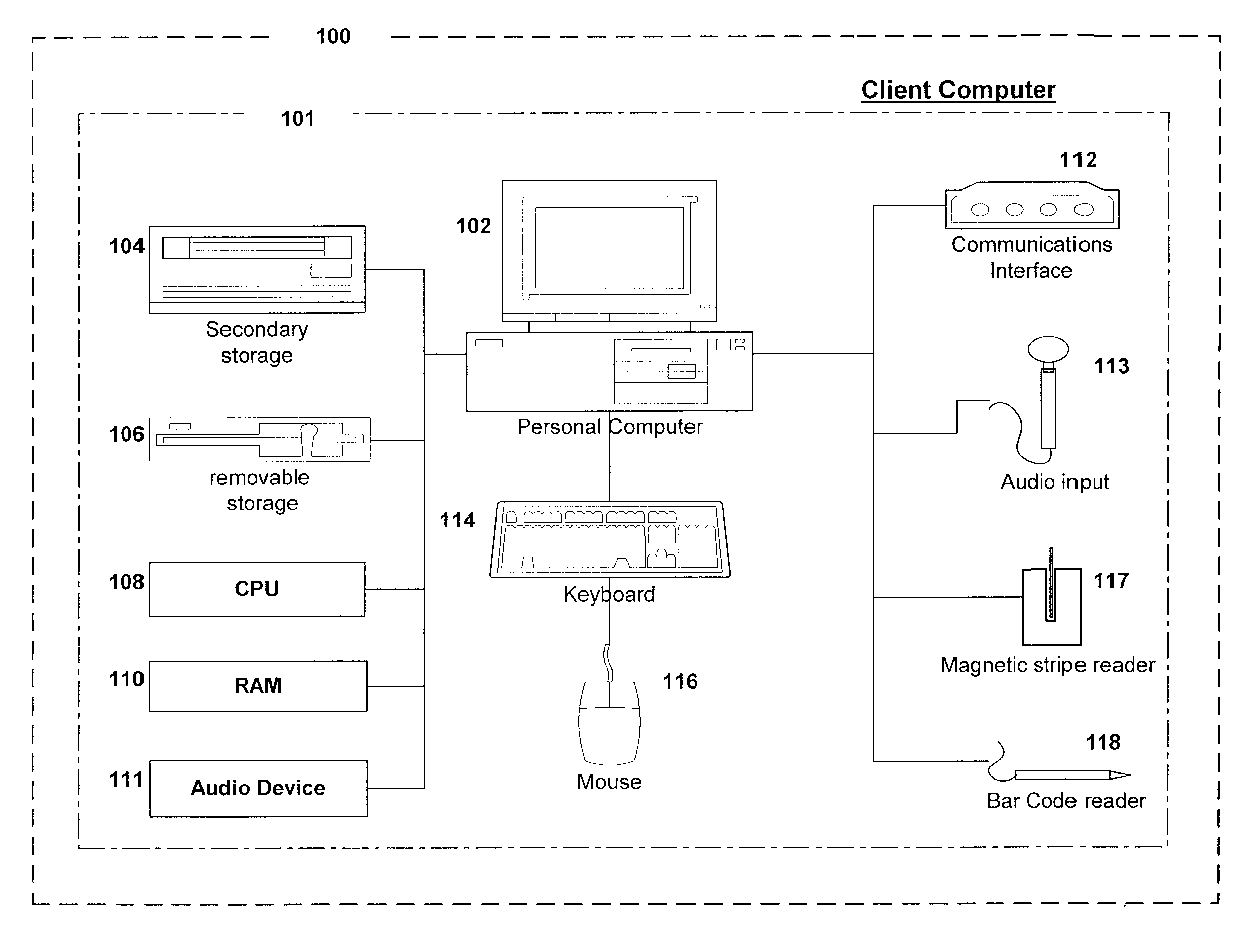
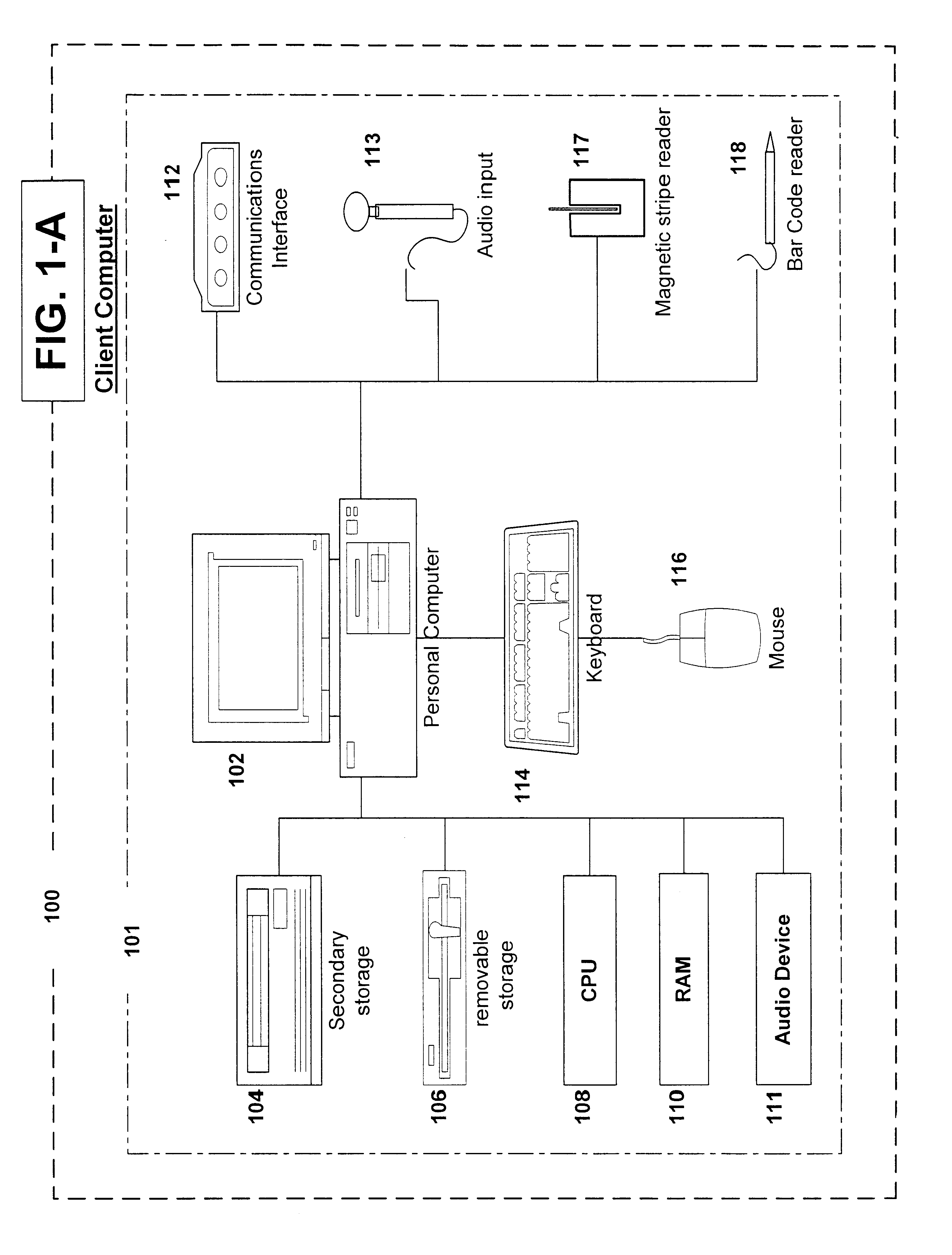
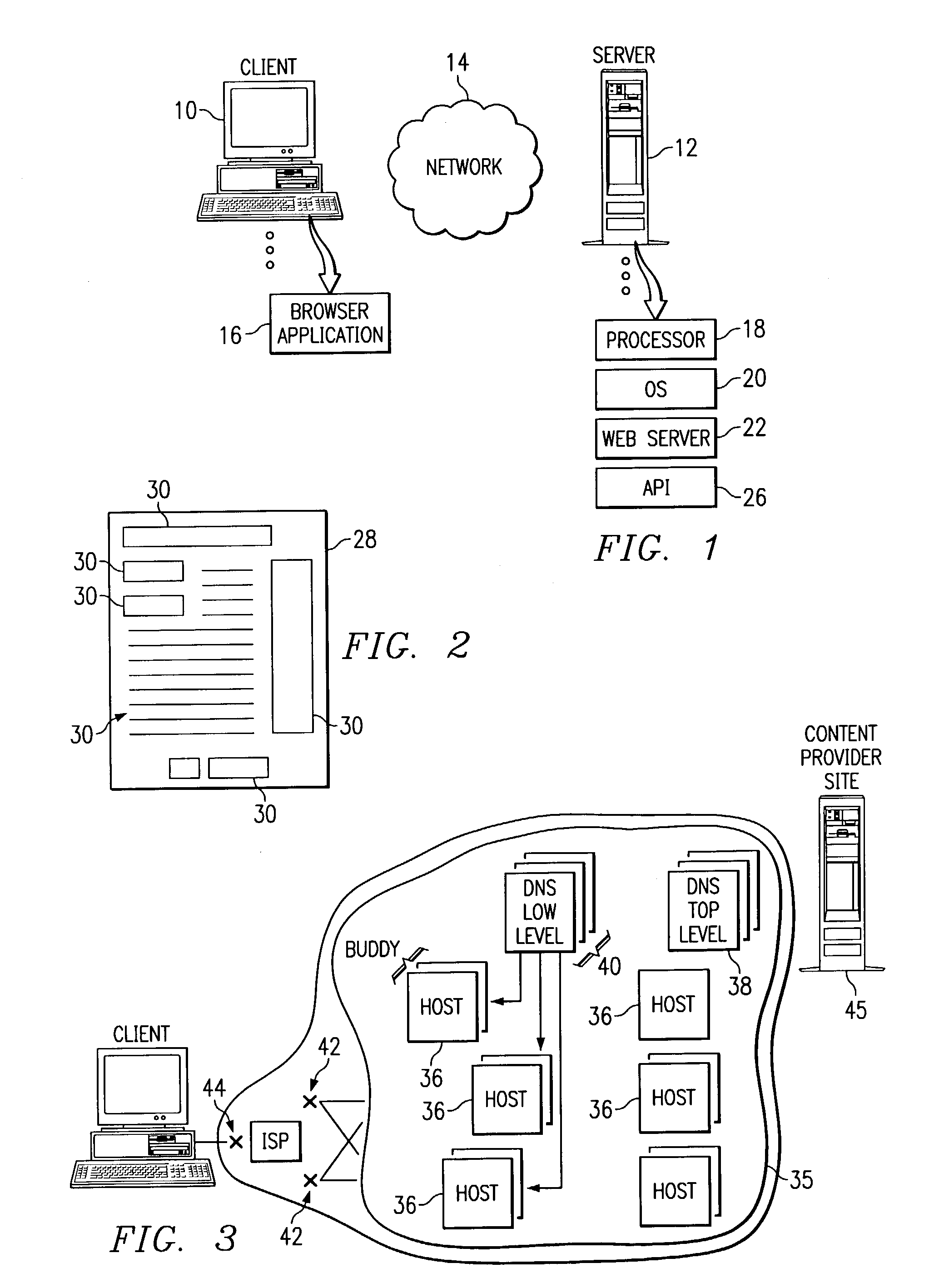
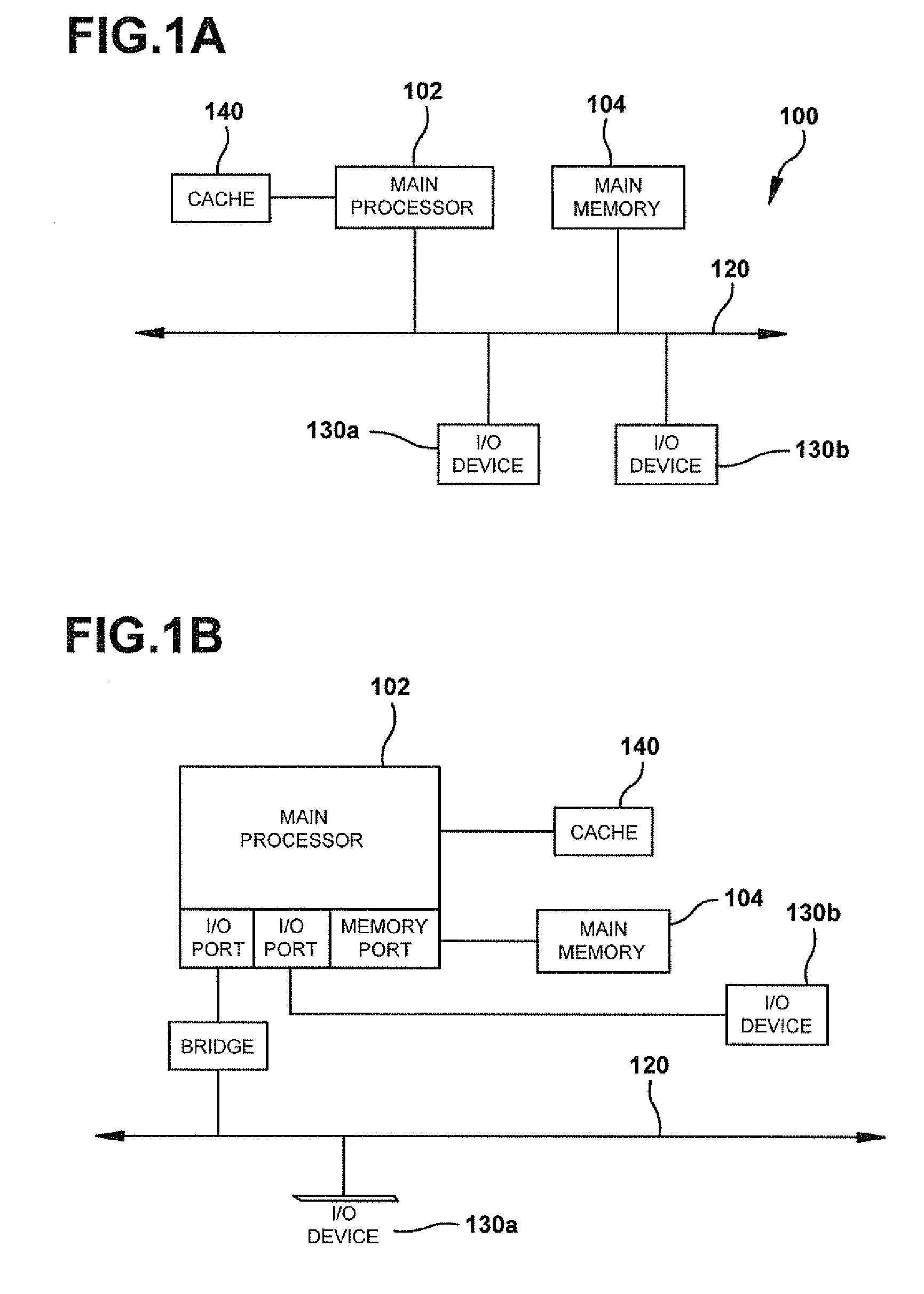
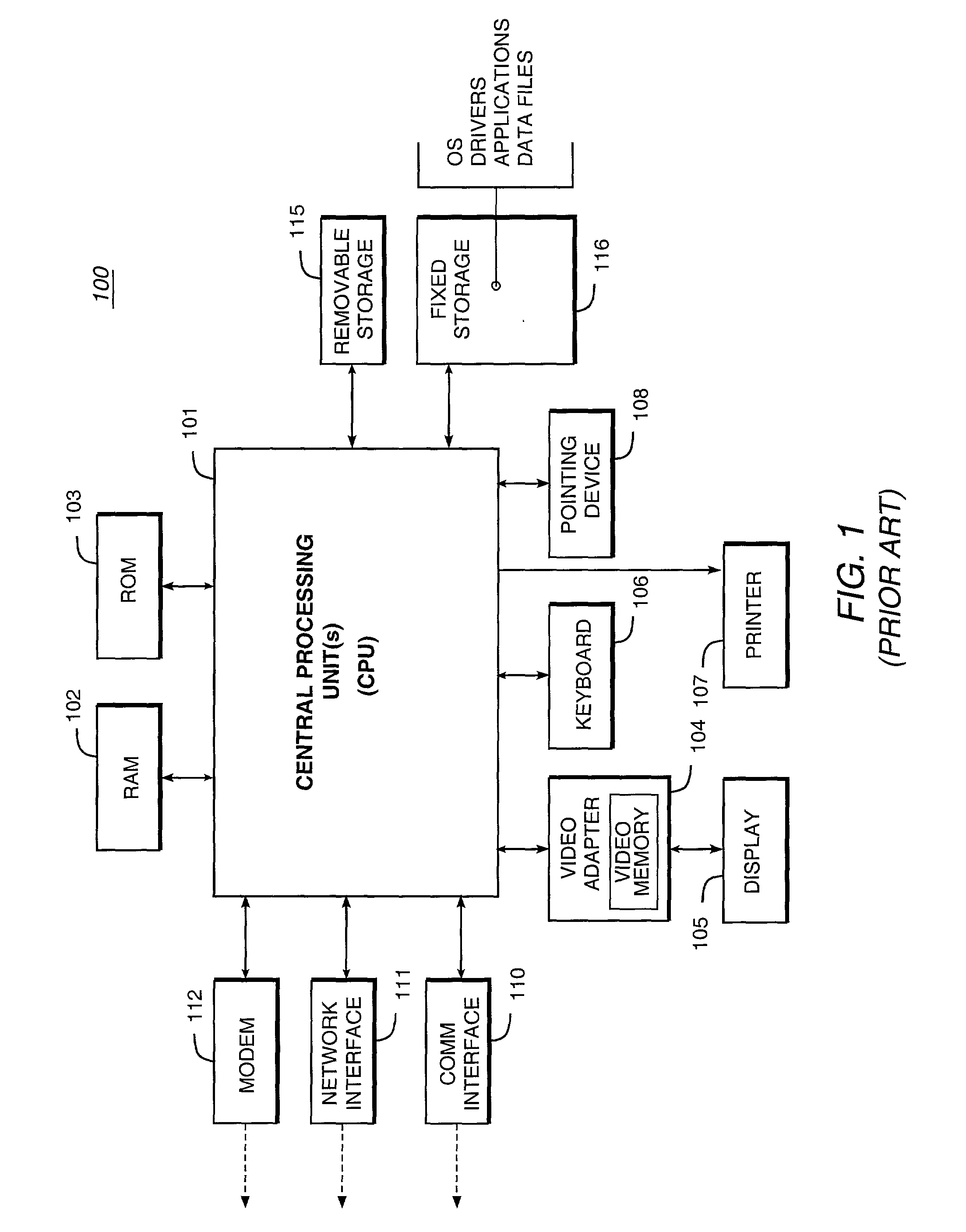
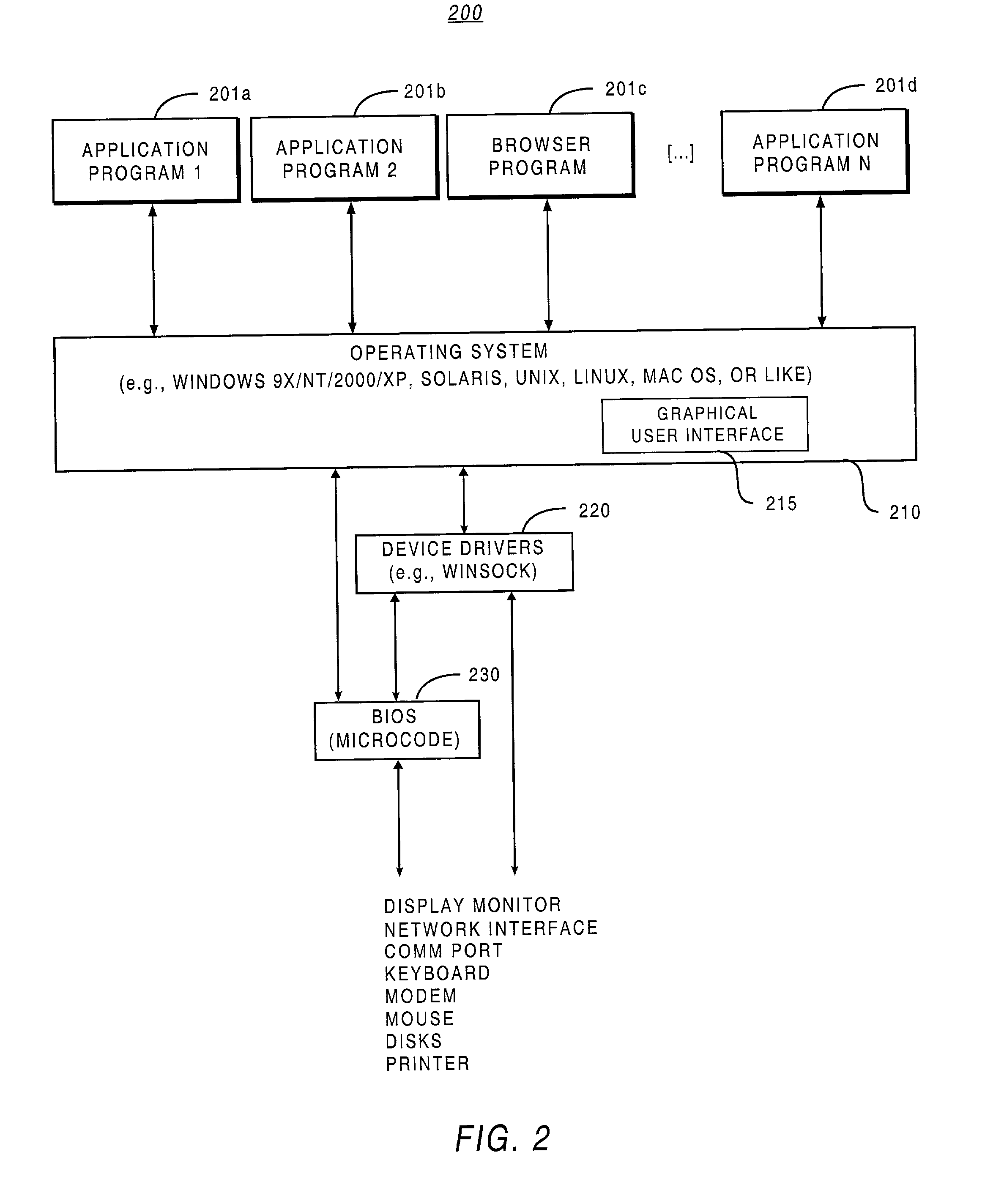
The term client machine refers to a user's computer that is connected to a network and accesses another computer, called a server, to request various kinds of resources, to save data or to run certain programs or perform certain functions.
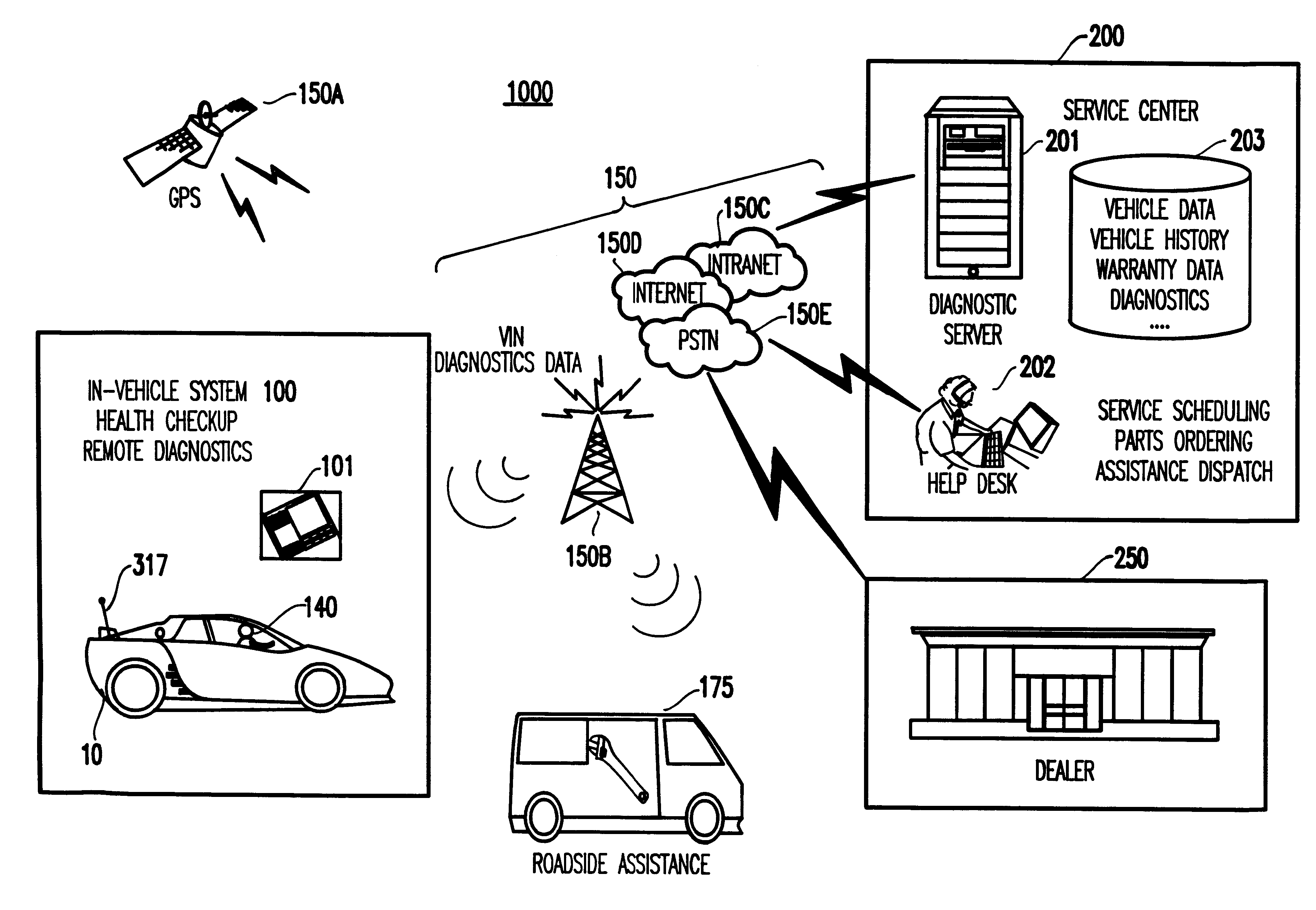
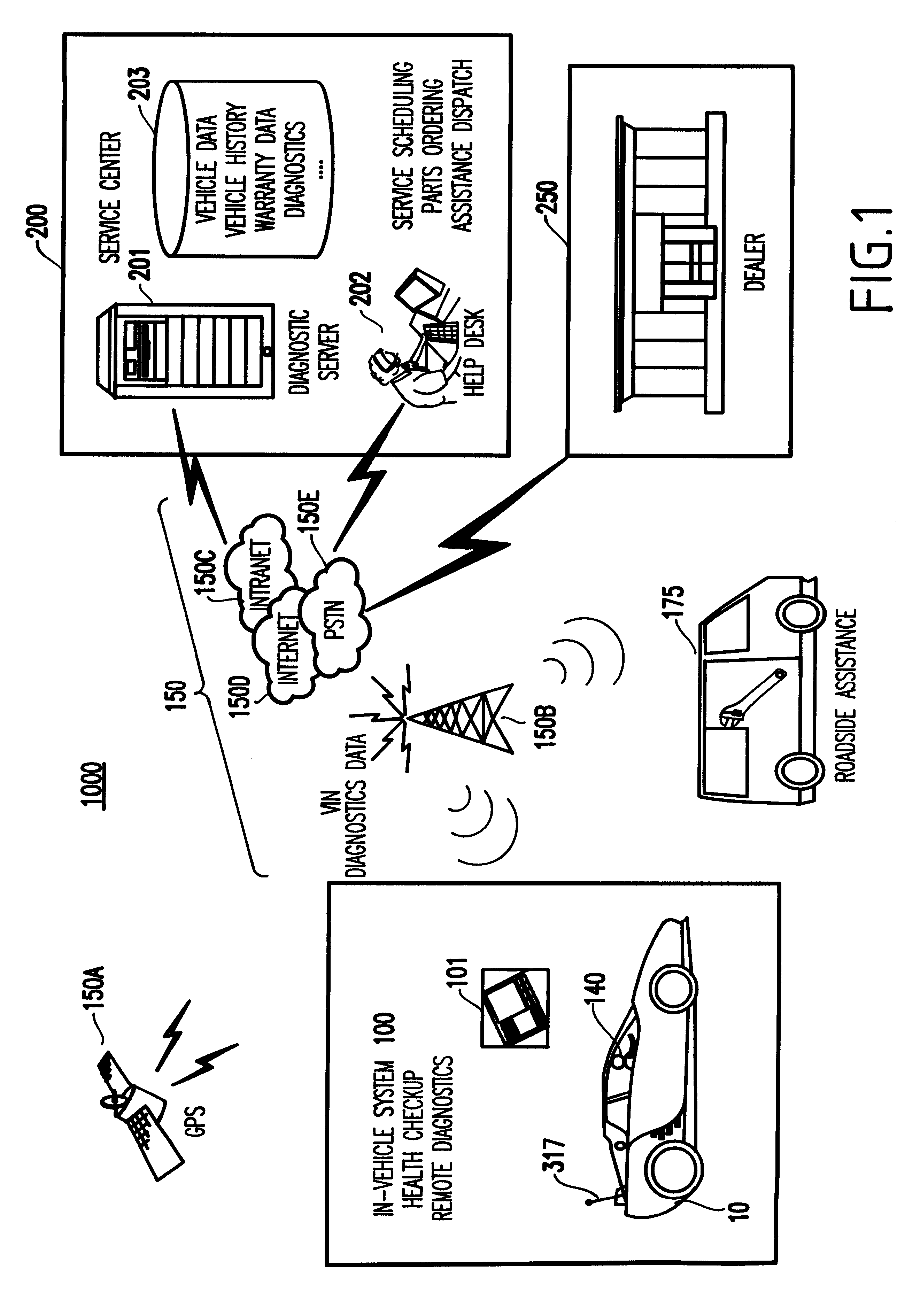
System and method for vehicle diagnostics and health monitoring
InactiveUS6330499B1Vehicle testingRegistering/indicating working of vehiclesSession managementCommunications system
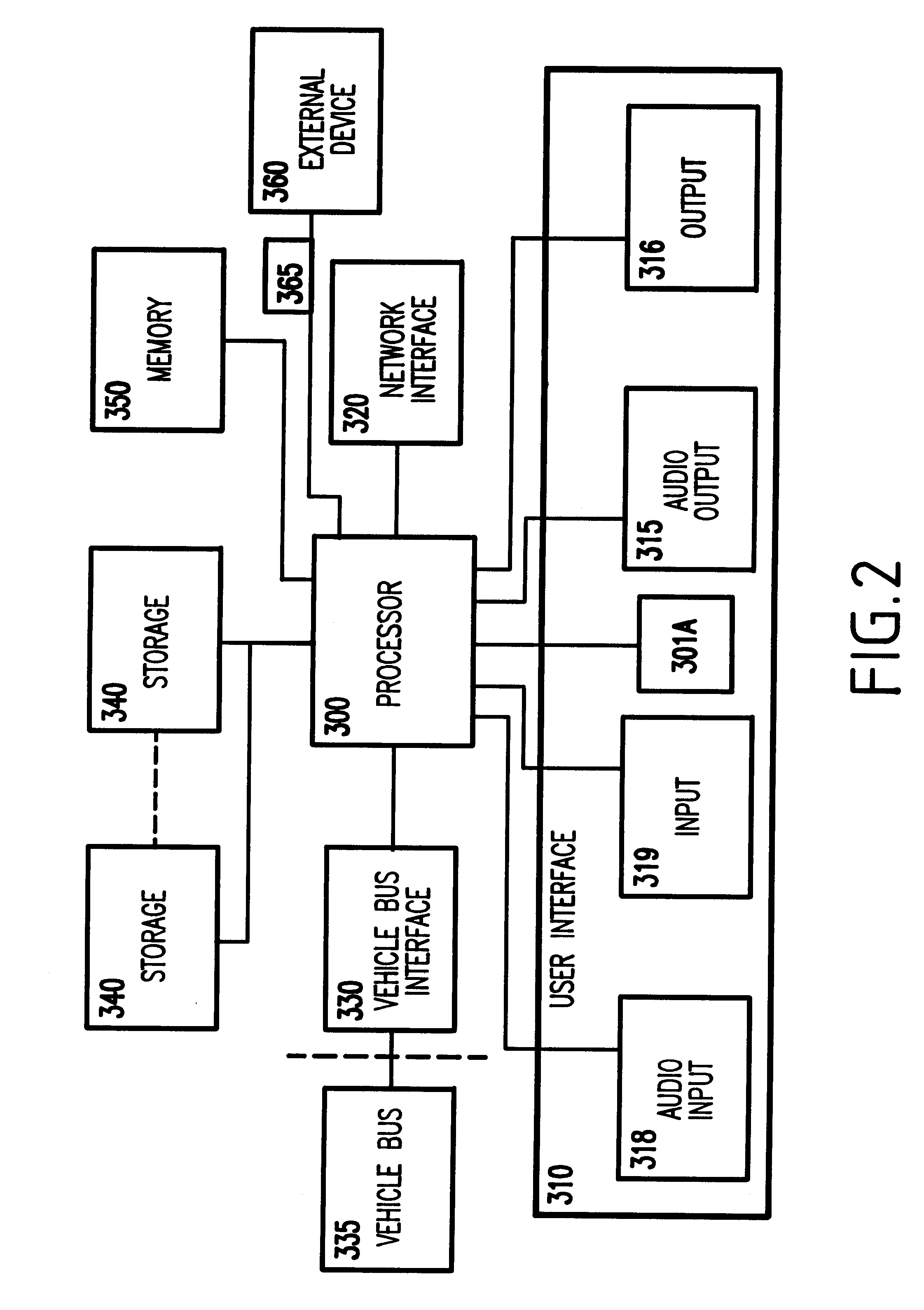
A system and method for vehicle diagnostic and health monitoring includes a client computer device within the vehicle, coupled to the vehicle's monitoring systems, for data management, remote session management and user interaction, a communication system, coupled to the client computer device, for providing remote communication of data including data derived from internal monitoring systems of the vehicle, and a remote service center including a vehicle data store, a server computer, a diagnostic engine, and a communicator for communicating the results of analysis of vehicle information to the client computer device via the communication system.
Owner:CARRUM TECH LLC
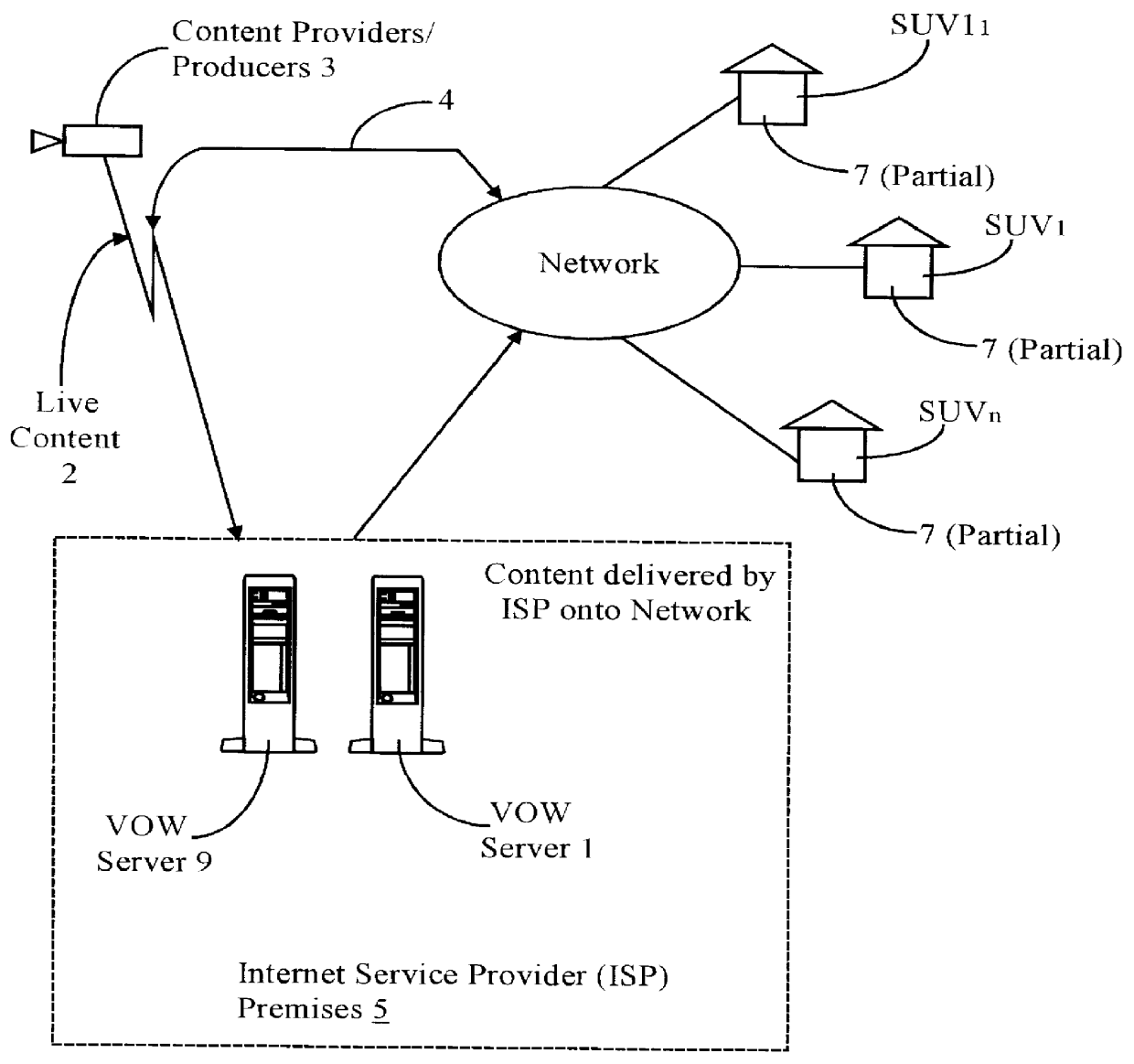
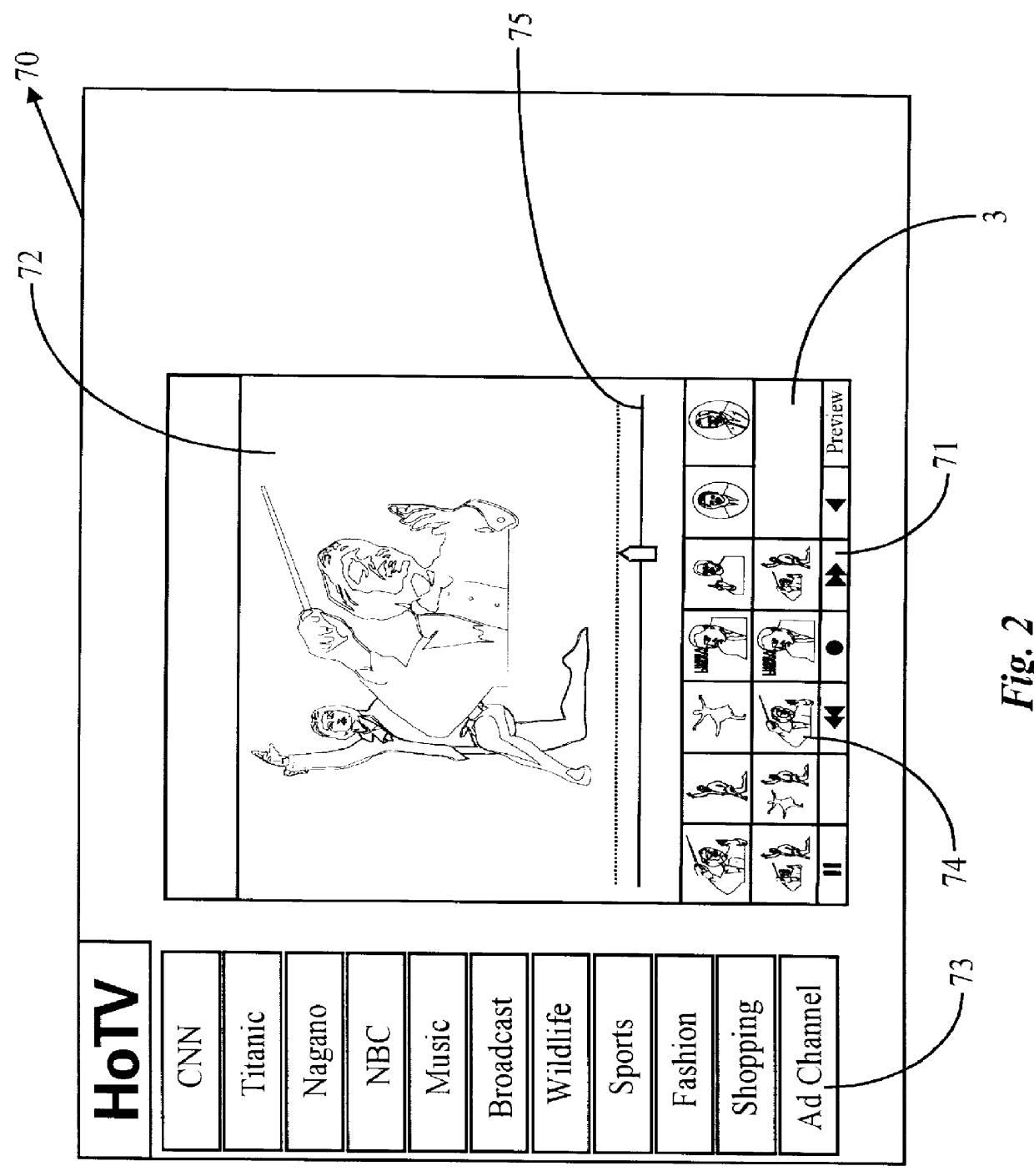
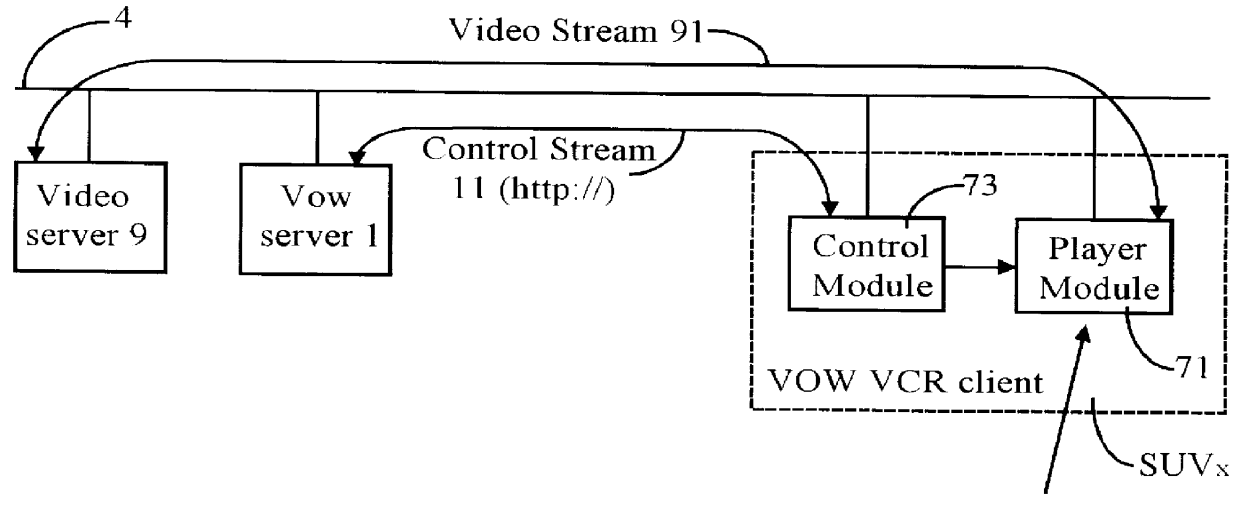
Real-time receipt, decompression and play of compressed streaming video/hypervideo; with thumbnail display of past scenes and with replay, hyperlinking and/or recording permissively intiated retrospectively
InactiveUS6154771AEfficient multicastingEasy to seeTelevision system detailsDigital data information retrievalFull customSoftware system
Streaming compressed digital hypervideo received upon a digital communications network is decoded (decompressed) and played in a client-computer-based "video on web VCR" software system. Scene changes, if not previously marked upstream, are automatically detected, and typically twenty-one past scenes are displayed as thumbnail images. Hyperlinks within the main video scene, and / or any thumbnail image, show as hotspots, with text annotations typically appearing upon a cursor "mouse over". All hyperlinks-as are provided and inserted by, inter alia, the upstream network service provider (the "ISP")-may be, and preferably are, full-custom dynamically-resolved to each subscriber / user / viewer ("SUV") upon volitional "click throughs" by the SUV, including retrospectively on past hypervideo scenes as appear within the thumbnail images. Hyperlinking permits (i) retrieving information and commercials, including streaming video / hypervideo, from any of local storage, a network (or Internet) service provider ("ISP"), a network content provider, and / or an advertiser network site, (ii) entering a contest of skill or a lottery of chance, (iii) gambling, (iv) buying (and less often, selling), (v) responding to a survey, and expressing an opinion, and / or (vi) sounding an alert.
Owner:TATA AMERICA INT
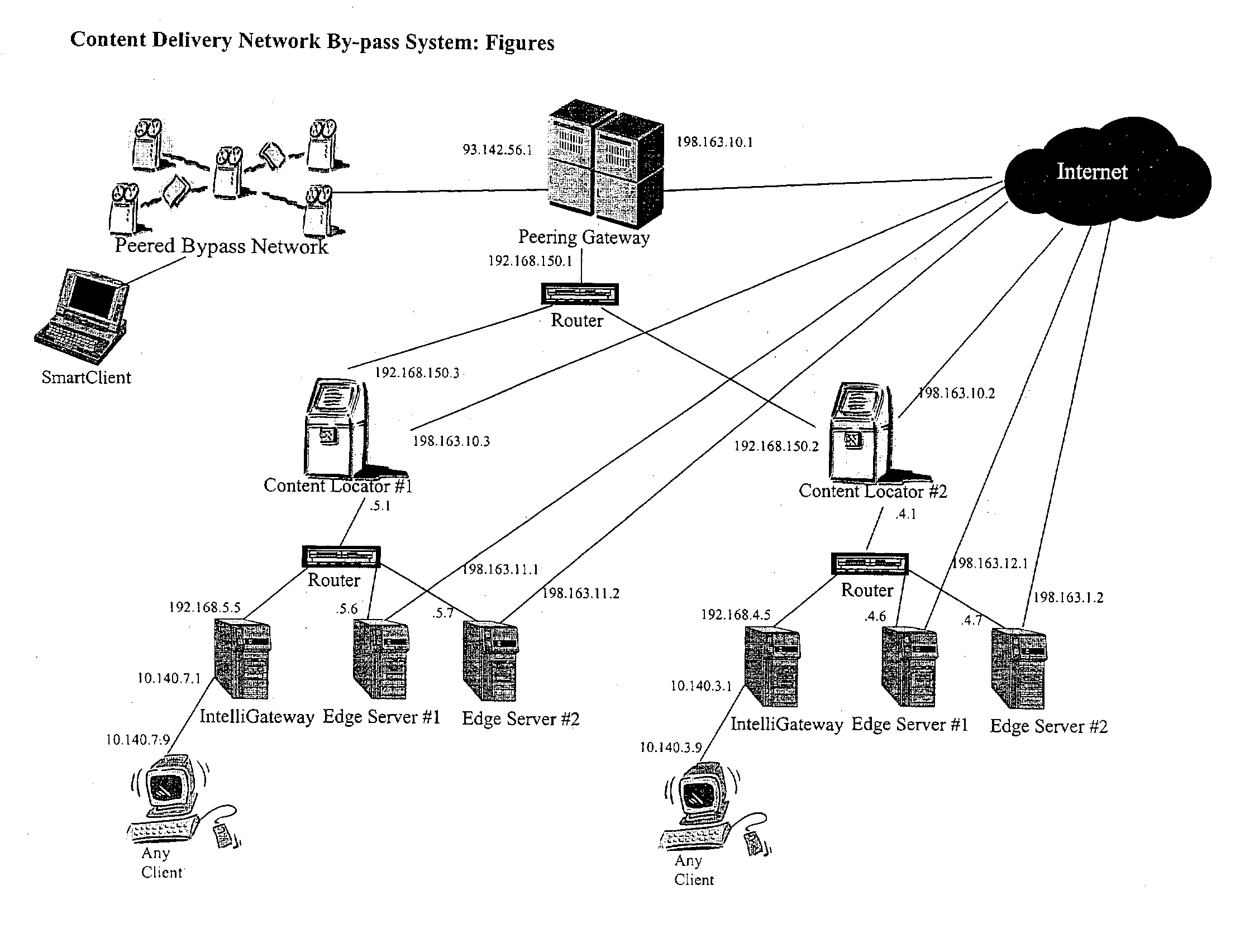
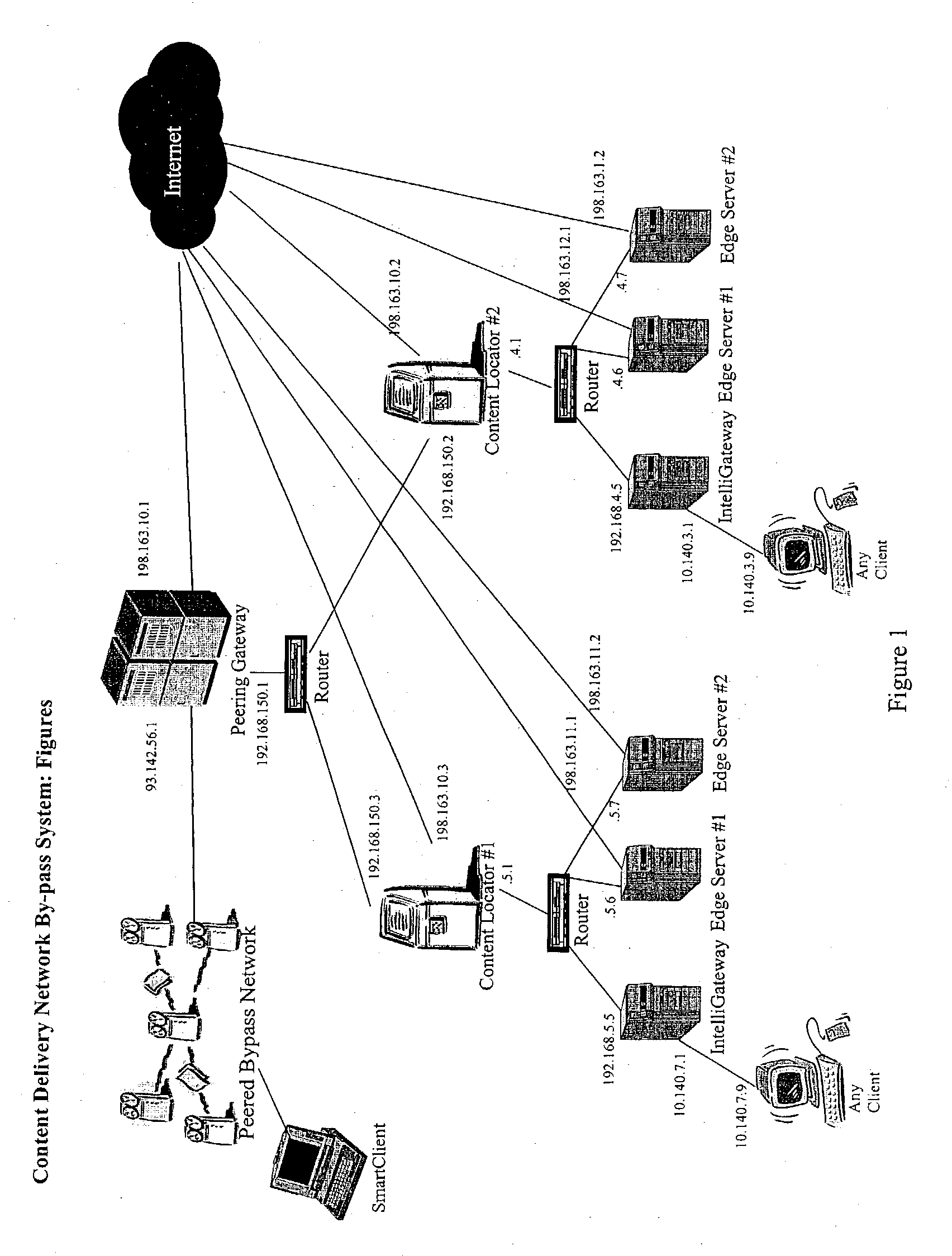
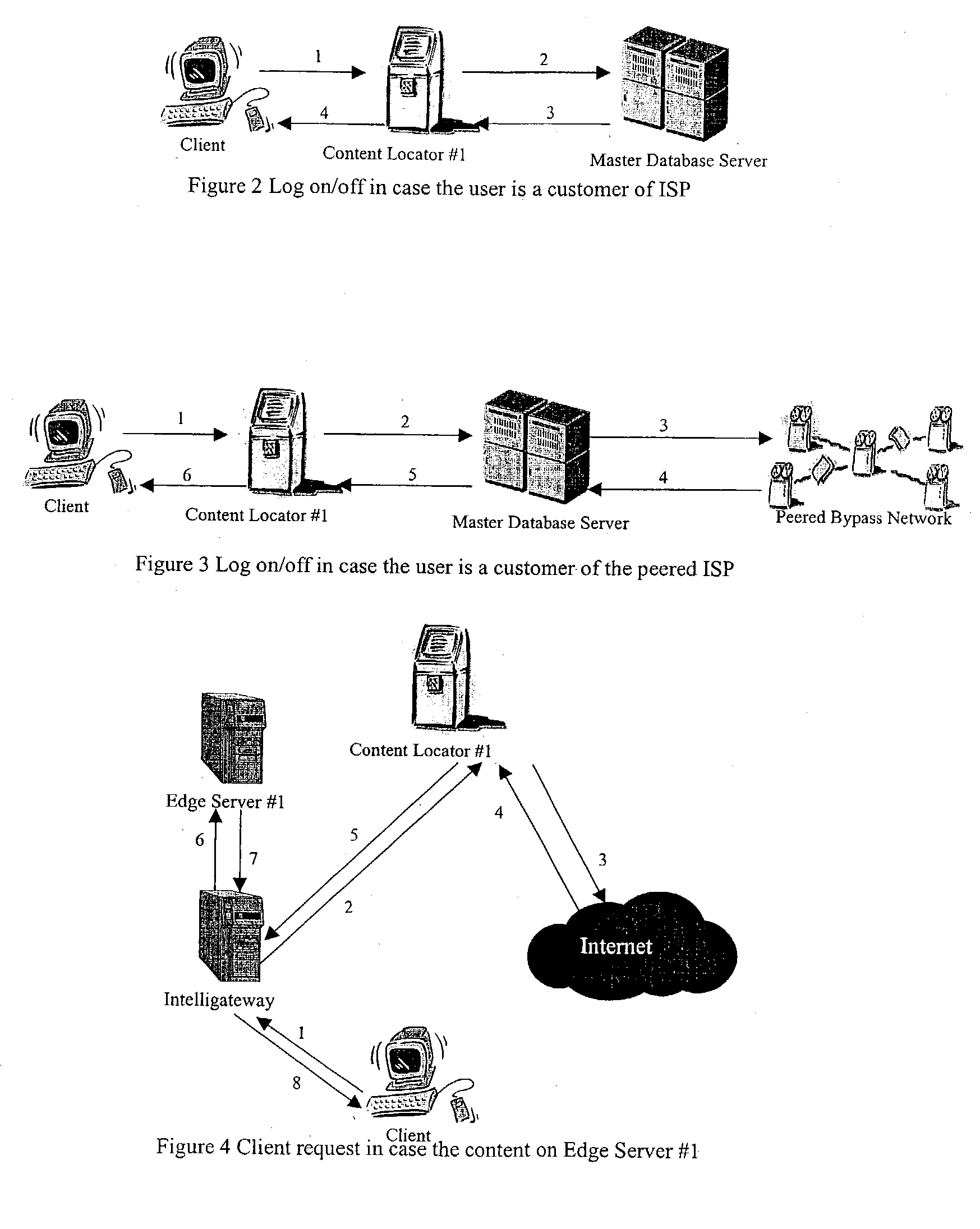
Content delivery network by-pass system
InactiveUS20030174648A1Increase capacityIncrease in sizeError preventionTransmission systemsWeb sitePeering
The bypass network is designed to provide fast access and high quality streaming media services anywhere anytime. There are five major components including Peering Gateway, Content Locator, Edge Server, Gateway and Client. The whole bypass network is divided into number of self-managed sub-networks, which are referred as local networks in this document. Each local network contains Edge Servers, gateways, and a Content Locator. The Edge Servers serve as cache storage and streaming servers for the local network. The gateways provide a connection point for the client computers. Each local network is managed by a Content Locator. The Content Locator handles all client requests by communicating with the Peering Gateway and actual web sites, and makes the content available on local Edge Servers. The Content Locator also balances the load on each Edge Server by monitoring the workload on them. One embodiment is designed for home users whose home machine does not move around frequently. A second embodiment is designed for business users who travel around very often where the laptops would self-configure as a client of the network.
Owner:TELECOMM RES LAB
Method of creating and editing a web site in a client-server environment using customizable web site templates
InactiveUS6026433AEasily and efficiently creatingEasily and efficiently and editingUnauthorized memory use protectionNatural language data processingWeb siteClient-side
A method for creating and editing a Web site in a client-server computer network using customizable templates is provided. To create a Web site, the present embodiment first stores a plurality of templates in a storage device coupled to the client-server computer network. When a client computer generates a request to create a new Web site, the server computer transmits a list of templates to the client for display. The templates contain a multitude of editable objects or elements. A template is then selected upon which the new Web site will be based on. The new site is then customized according to a user's preference by editing the objects or elements. The customized site is then published as a new Web site. To edit a Web site, a client computer generates a request to edit a Web site and passes the request on to the server computer. The server computer transmits the Web site to the client for display. The Web site contains a multitude of editable objects or elements. The elements of the Web site are then customized according to a user's preference. The Web site with the customized elements is then published as a Web site.
Owner:RED HAT
Methods and systems for interacting, via a hypermedium page, with a virtual machine executing in a terminal services session
ActiveUS20070171921A1Low costReduce difficultyDigital data information retrievalInterprogram communicationHyperlinkClient agent
A method for making a hypermedium page interactive, the hypermedium page displayed by a network browser, includes the step of selecting a hyperlink on the hypermedium page displayed on a client machine, the hyperlink identifying a desired computing resource. A hyperlink configuration file is retrieved, the hyperlink configuration file corresponding to the hyperlink and identifying a server machine. A client agent is started on the client machine. The client agent creates, via a terminal services session, a communication link to a virtual machine executing on the server identified by the hyperlink configuration file, the virtual machine executed by a hypervisor executing in the terminal services session provided by an operating system executing on the server. The client agent receives data from the virtual machine and displays, on the client machine, the received data without intervention by the network browser.
Owner:CITRIX SYST INC
Adaptive raid for an SSD environment
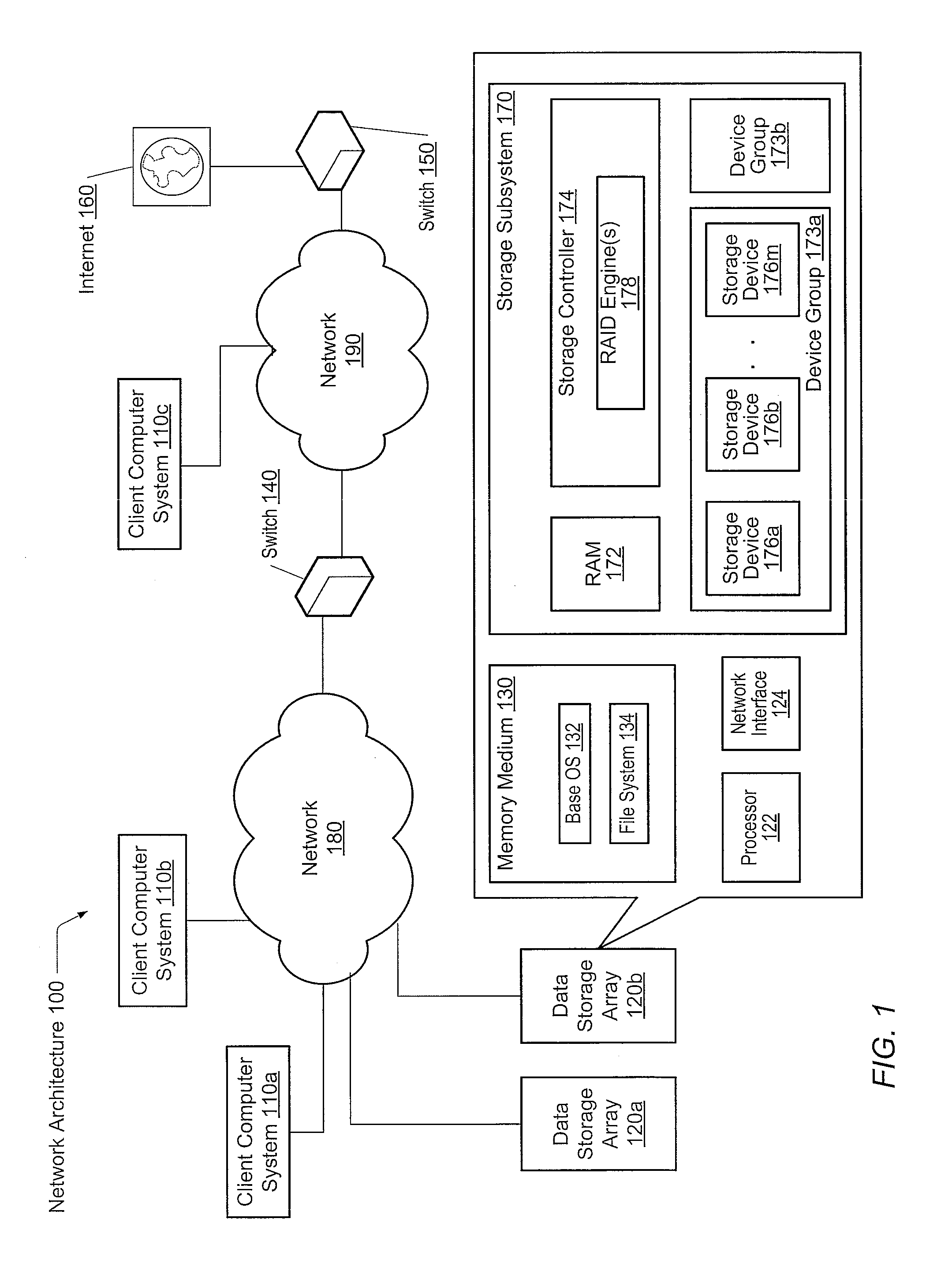
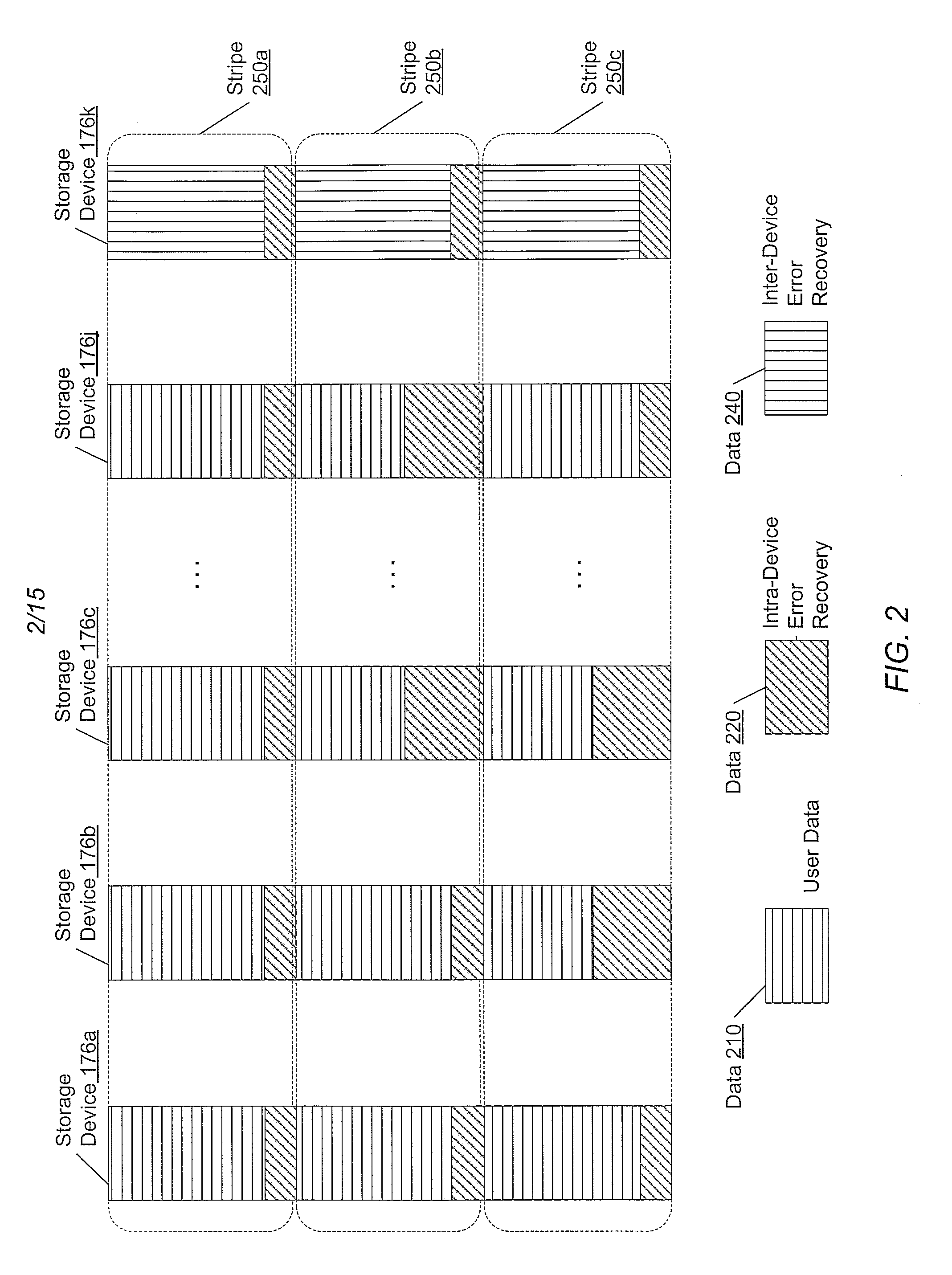
A system and method for adaptive RAID geometries. A computer system comprises client computers and data storage arrays coupled to one another via a network. A data storage array utilizes solid-state drives and Flash memory cells for data storage. A storage controller within a data storage array is configured to determine a first RAID layout for use in storing data, and write a first RAID stripe to the device group according to the first RAID layout. In response to detecting a first condition, the controller is configured to determine a second RAID layout which is different from the first RAID layout, and write a second RAID stripe to the device group according to the second layout, whereby the device group concurrently stores data according to both the first RAID layout and the second RAID layout.
Owner:PURE STORAGE
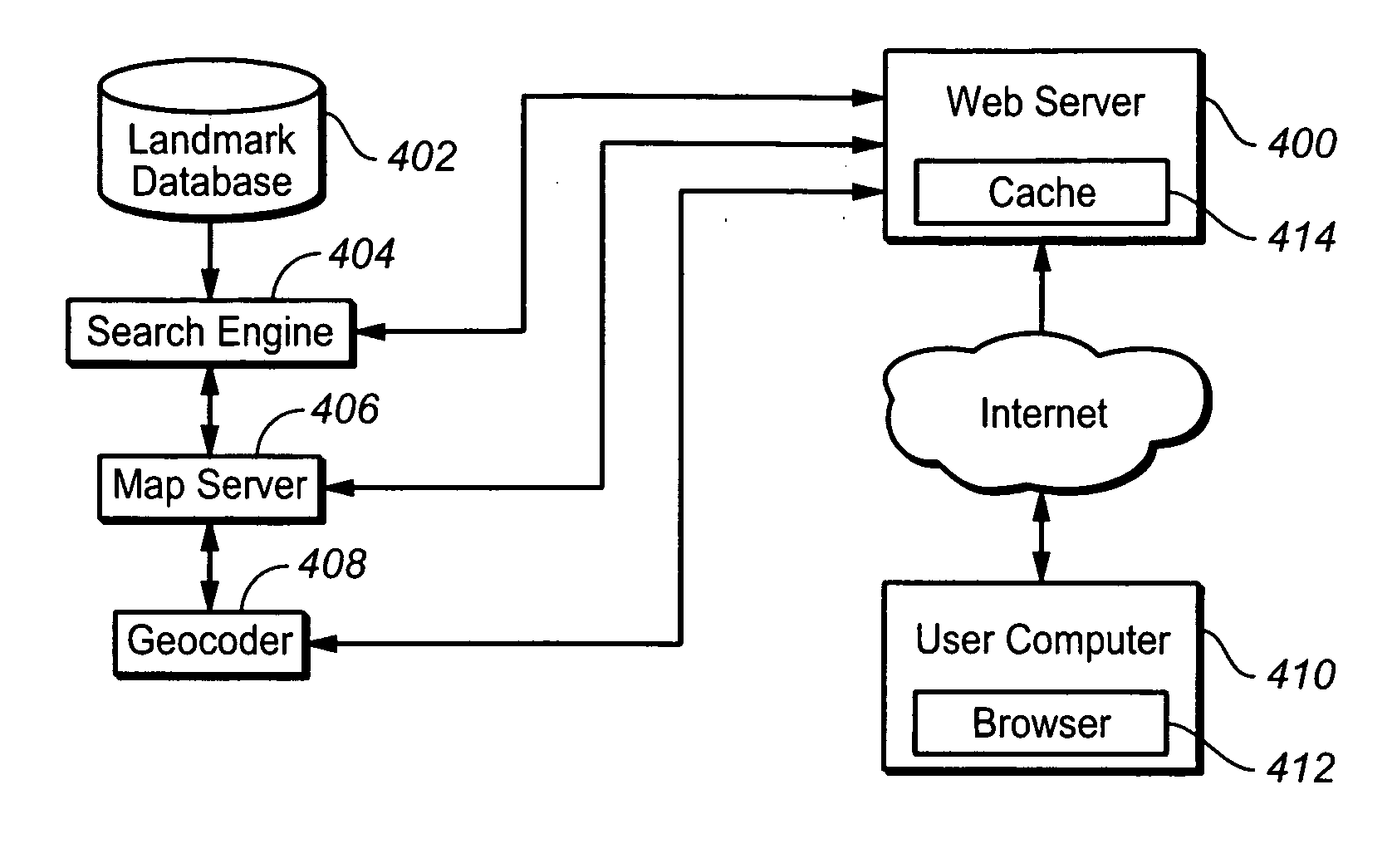
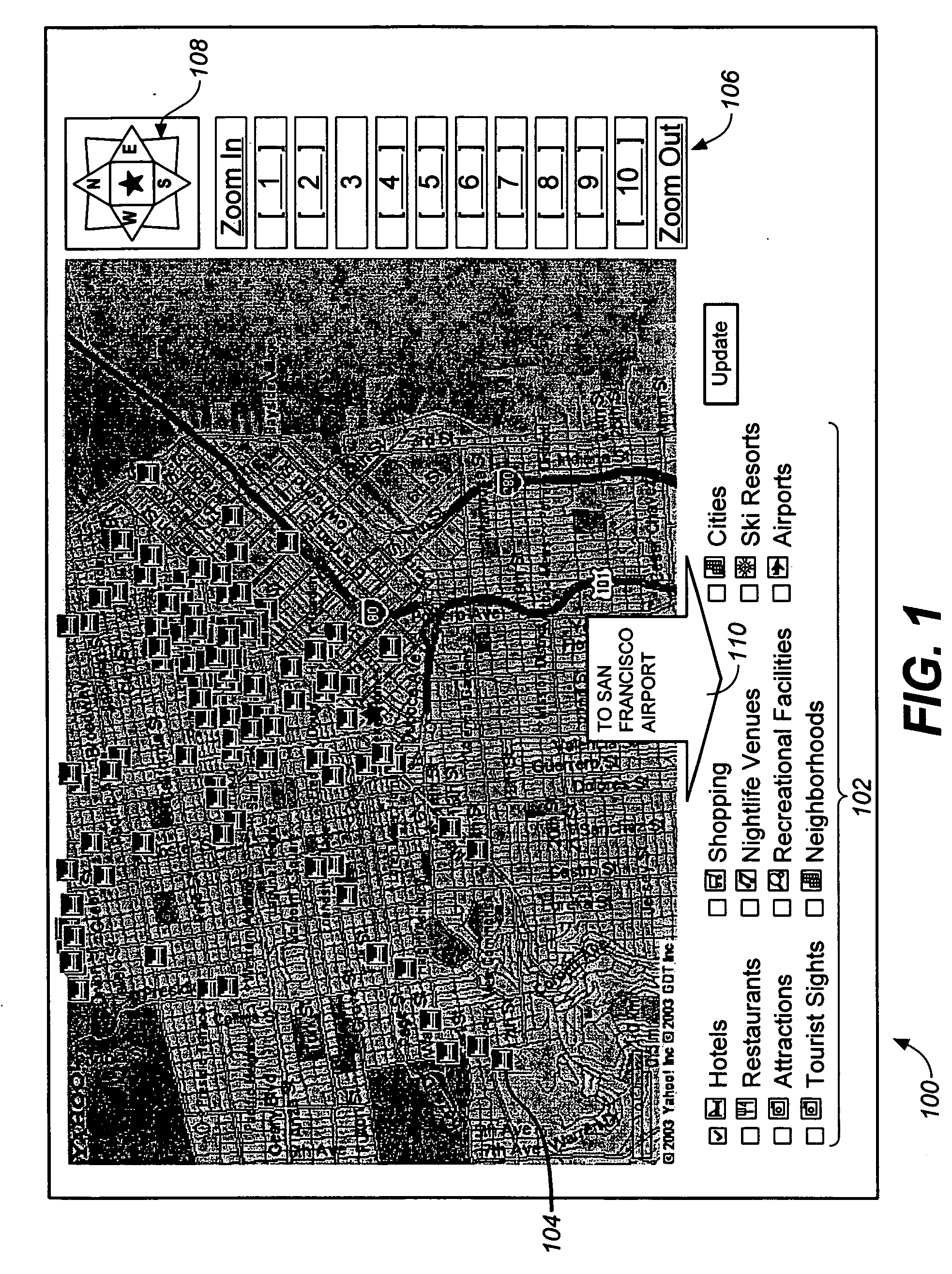
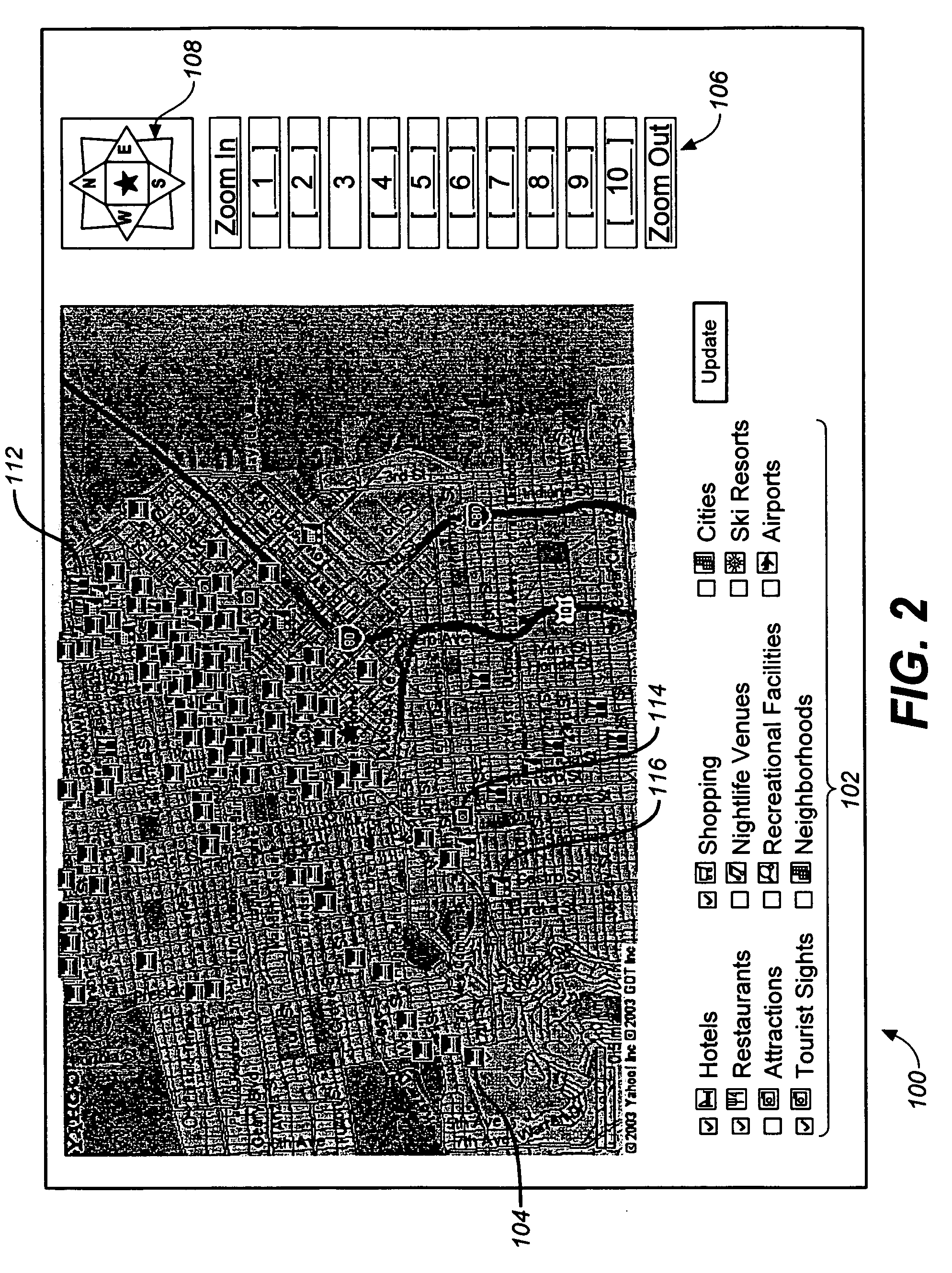
Mapping method and system
ActiveUS20060026170A1Geographical information databasesOther databases browsing/visualisationClient-sideDynamic data
A method comprises the steps of: transmitting a map request from a client computer to a server; receiving in the client computer data representing a map from a map server; receiving, in the client computer, dynamic, location-based data from a content provider separately from the data representing the map; generating within the client computer a rendering of the dynamic, location-based data overlaid on the map; and displaying the rendering on the client computer.
Owner:R2 SOLUTIONS
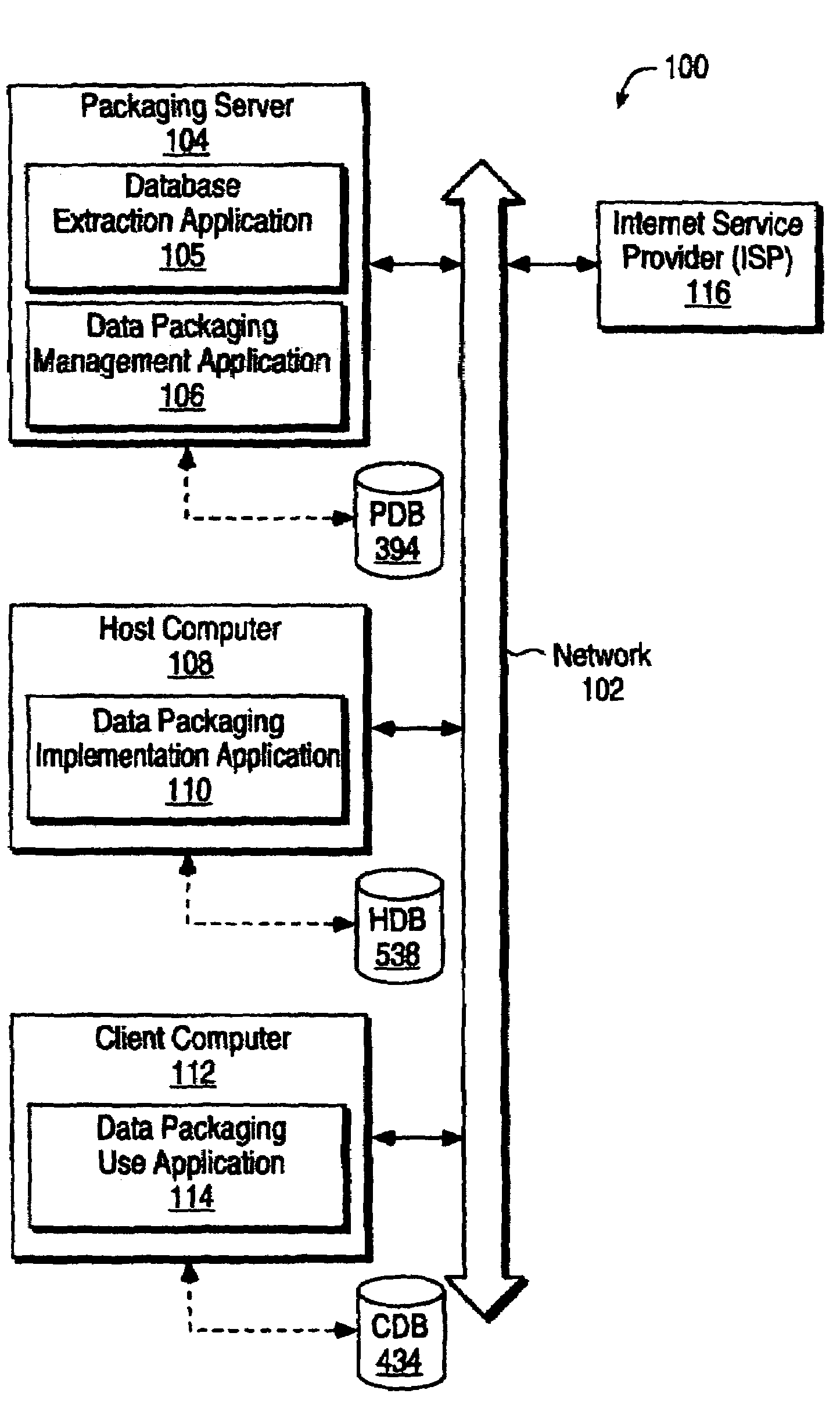
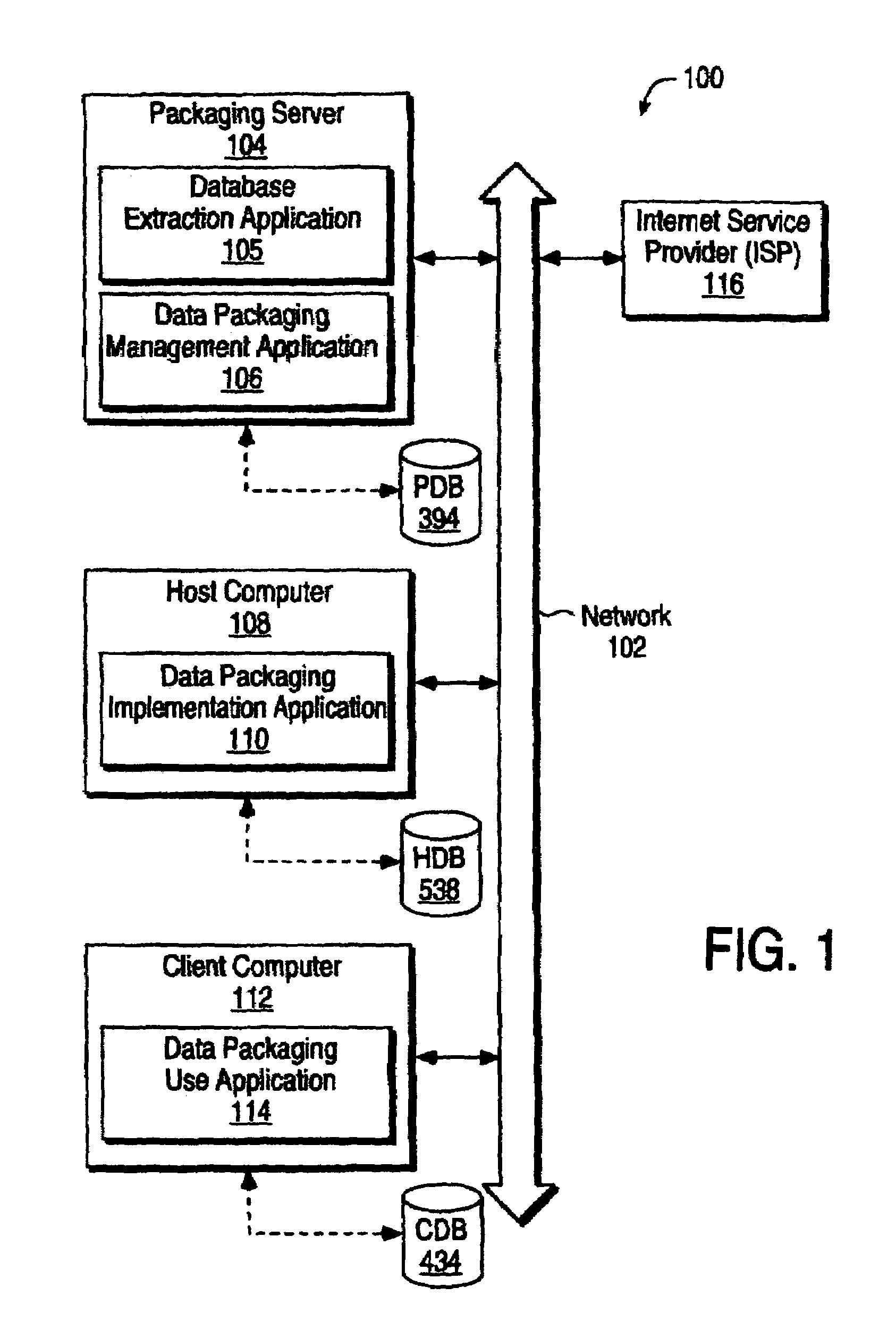
Method and apparatus for exchanging data in a platform independent manner
InactiveUS7010580B1Easy to packPromote exchangeData processing applicationsDigital data processing detailsClient-sideDocumentation
Provided is a system and method for easily packaging and exchanging complex information such as that contained in a database in the form of objects and attached documents. The invention may include a server configured to create a viewer package containing data and viewer code that allows a client computer to read data within the viewer package. The viewer code provides a client computer with the ability to perform functions that are as robust and as useful to common functions of a database for viewing, consuming and manipulating data. The data to be accessed may be formatted in one or more universal formats so that a user opening the viewer package can access the data, independent of the medium onto which it is received.
Owner:AGILE SOFTWARE CORPORATION
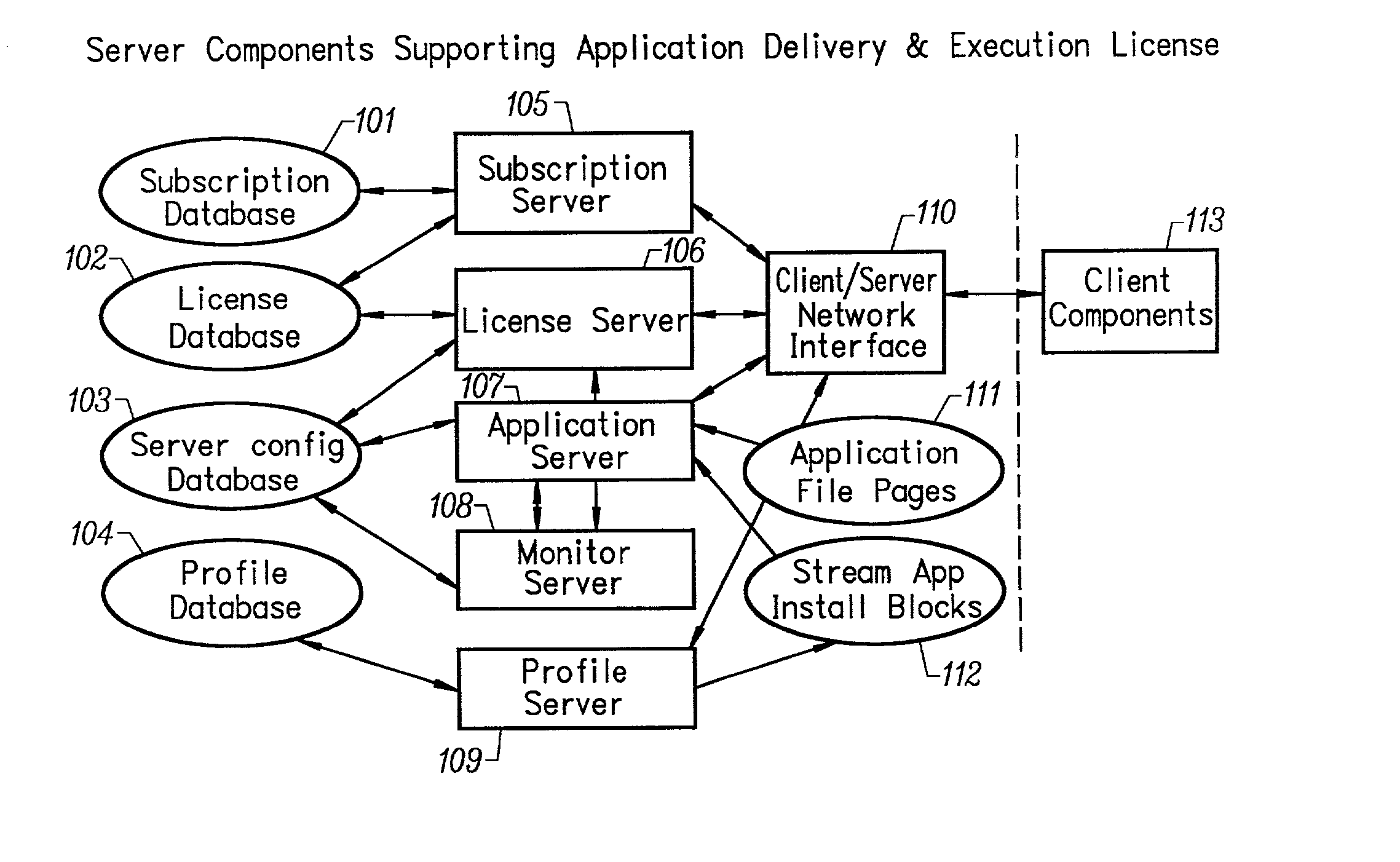
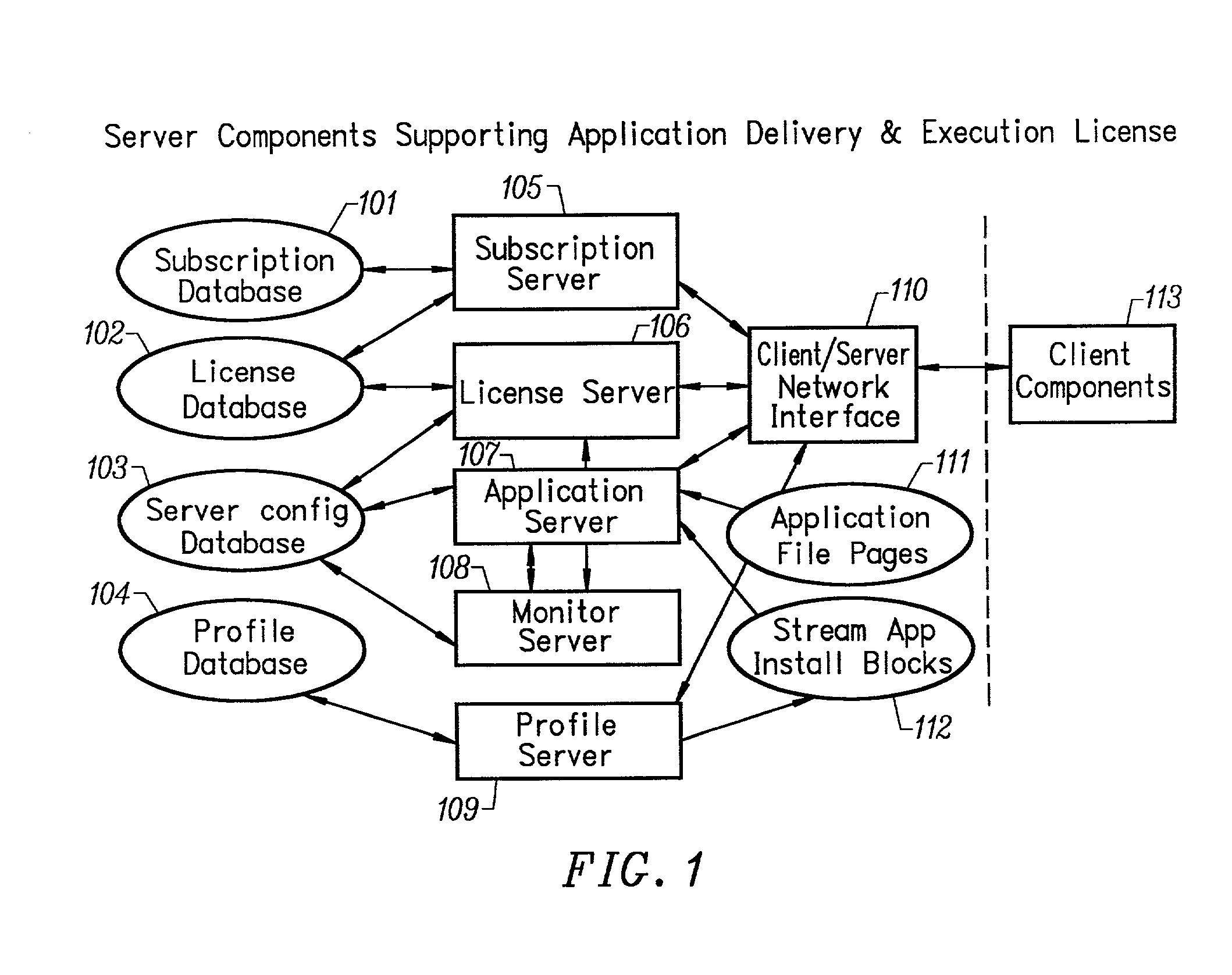
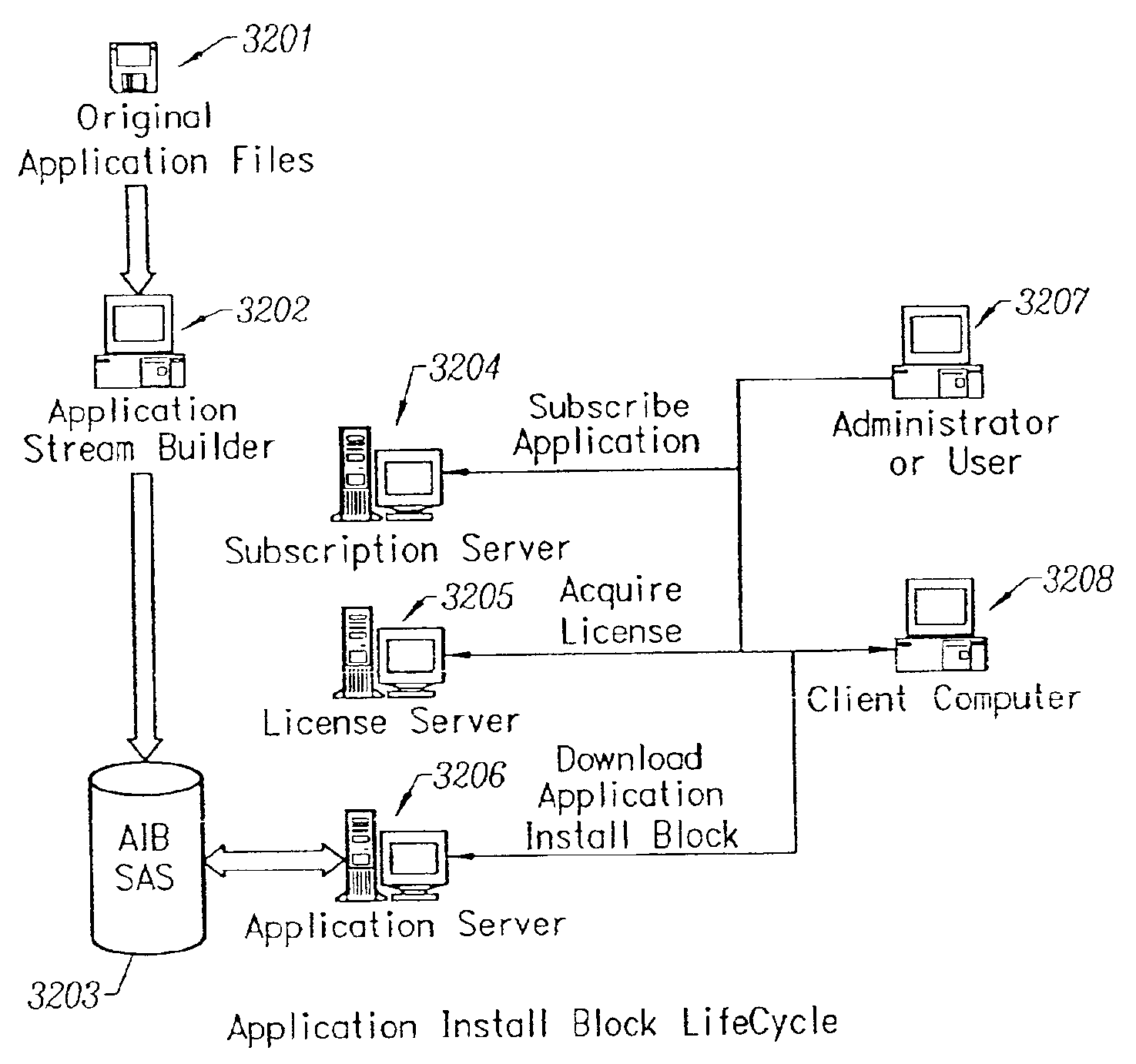
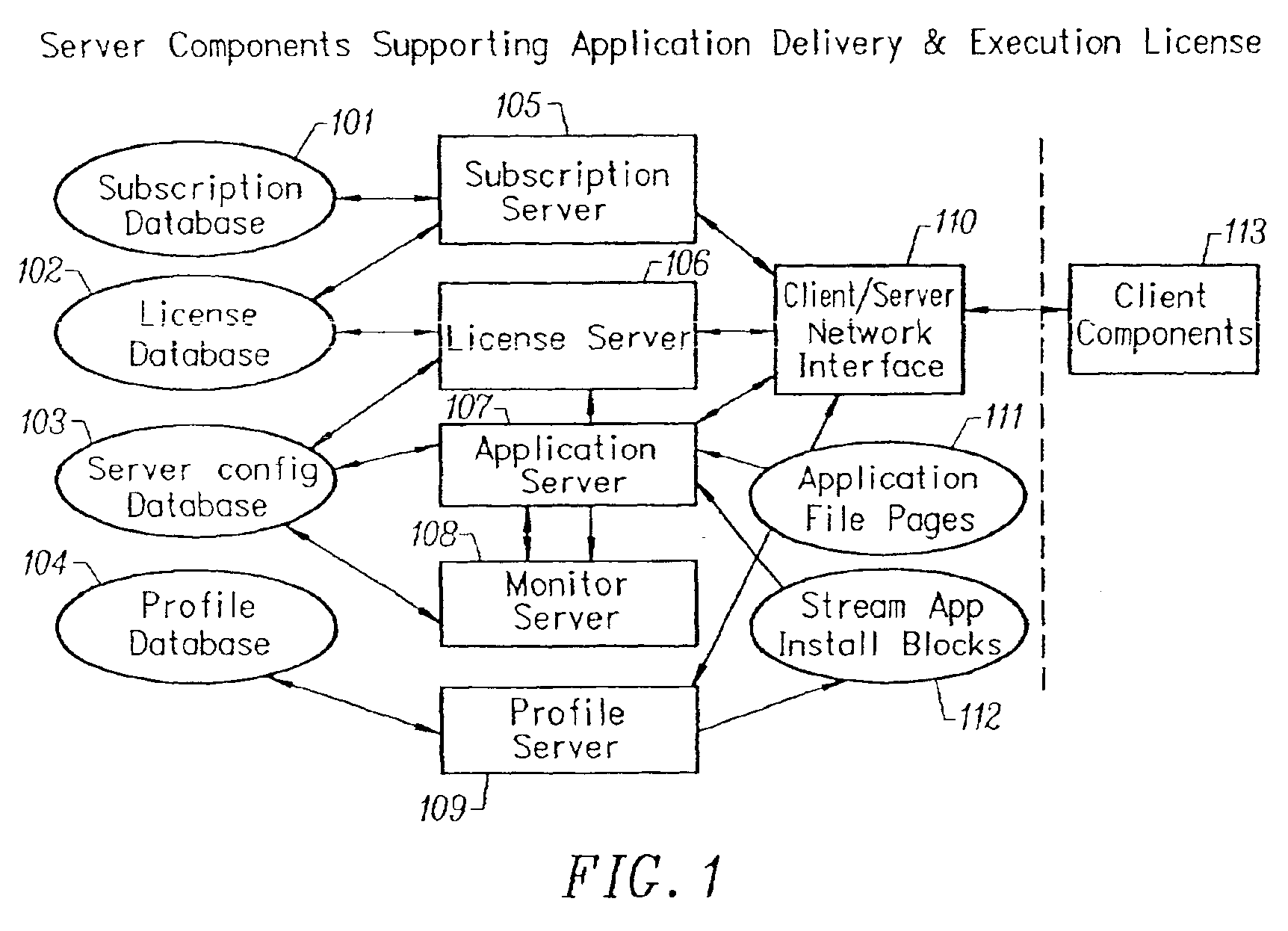
Conventionally coded application conversion system for streamed delivery and execution
InactiveUS20020083183A1Multiple digital computer combinationsProgram loading/initiatingData setMonitoring system
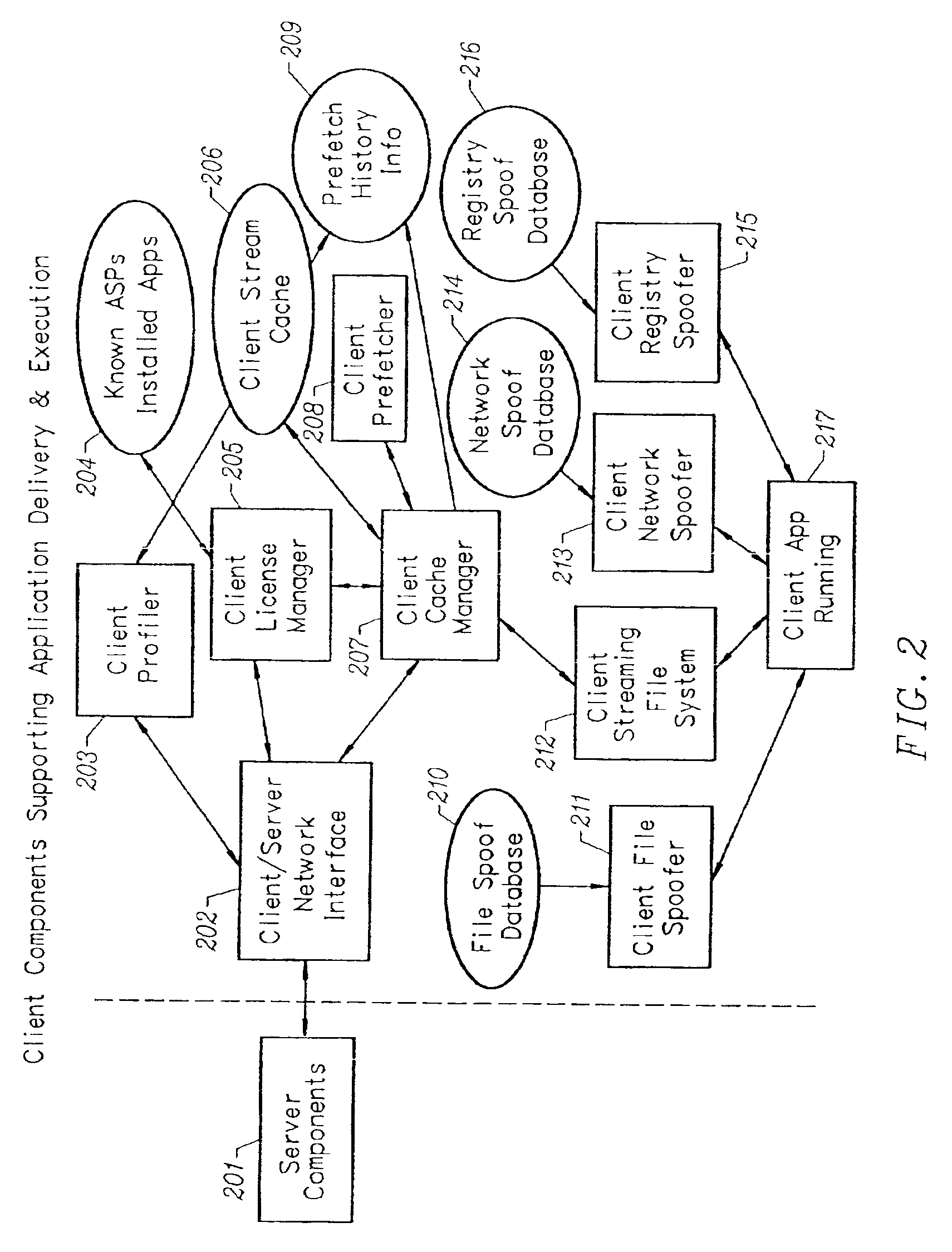
A conventionally coded application conversion system for streamed delivery and execution converts locally installable applications into a data set suitable for streaming over a network. The invention monitors two classes of information during an application installation on a local computer system. System registry modifications are monitored and the modification data are recorded when the installation program writes to the registry of the local computer system. File modification data are logged each time an installation program modifies a file on the system. This data is used to create an initialization data set which is the first set of data to be streamed from the server to the client and contains the information captured needed by the client to prepare the client machine for streaming a particular application. A runtime data set is also created that contains the rest of the data that is streamed to the client once the client machine is initialized for a particular application. A versioning table contains a list of root file numbers and version numbers which are used to track application patches and upgrades. The invention monitors a running application that is being configured for a particular working environment on the local computer system. The data acquired are used to duplicate the same configuration on multiple client machines.
Owner:CREDIT MANAGERS OF CALIFORNIA
Method and system for generating a document representation
ActiveUS20100228693A1Without structureHighly to changeDigital data information retrievalSemantic analysisPart of speechGrammatical relation
A method, system and computer program product for generating a document representation are disclosed. The system includes a server and a client computer, and the method involves: receiving into memory a resource containing at least one sentence of text; producing a tree comprising tree elements indicating parts-of-speech and grammatical relations between the tree elements; producing semantic structures each having three tree elements to represent a simple clause (subject-predicate-object); and storing a semantic network of semantic structures and connections therebetween. The semantic network may be created from a user provided root concept. Output representations include concept maps, facts listings, text summaries, tag clouds, indices; and an annotated text. The system interactively modifies semantic networks in response to user feedback, and produces personal semantic networks and document use histories.
Owner:IFWE
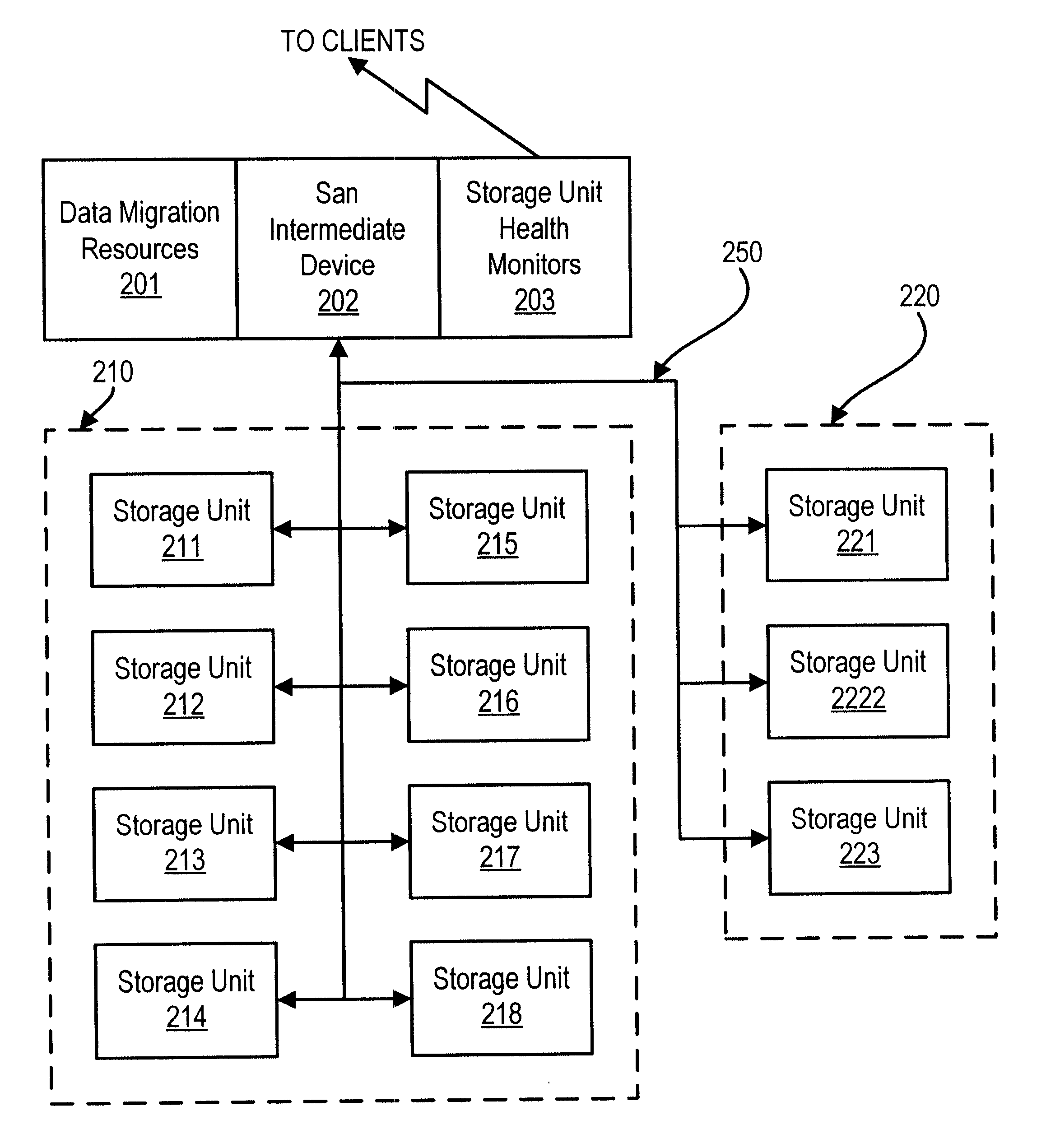
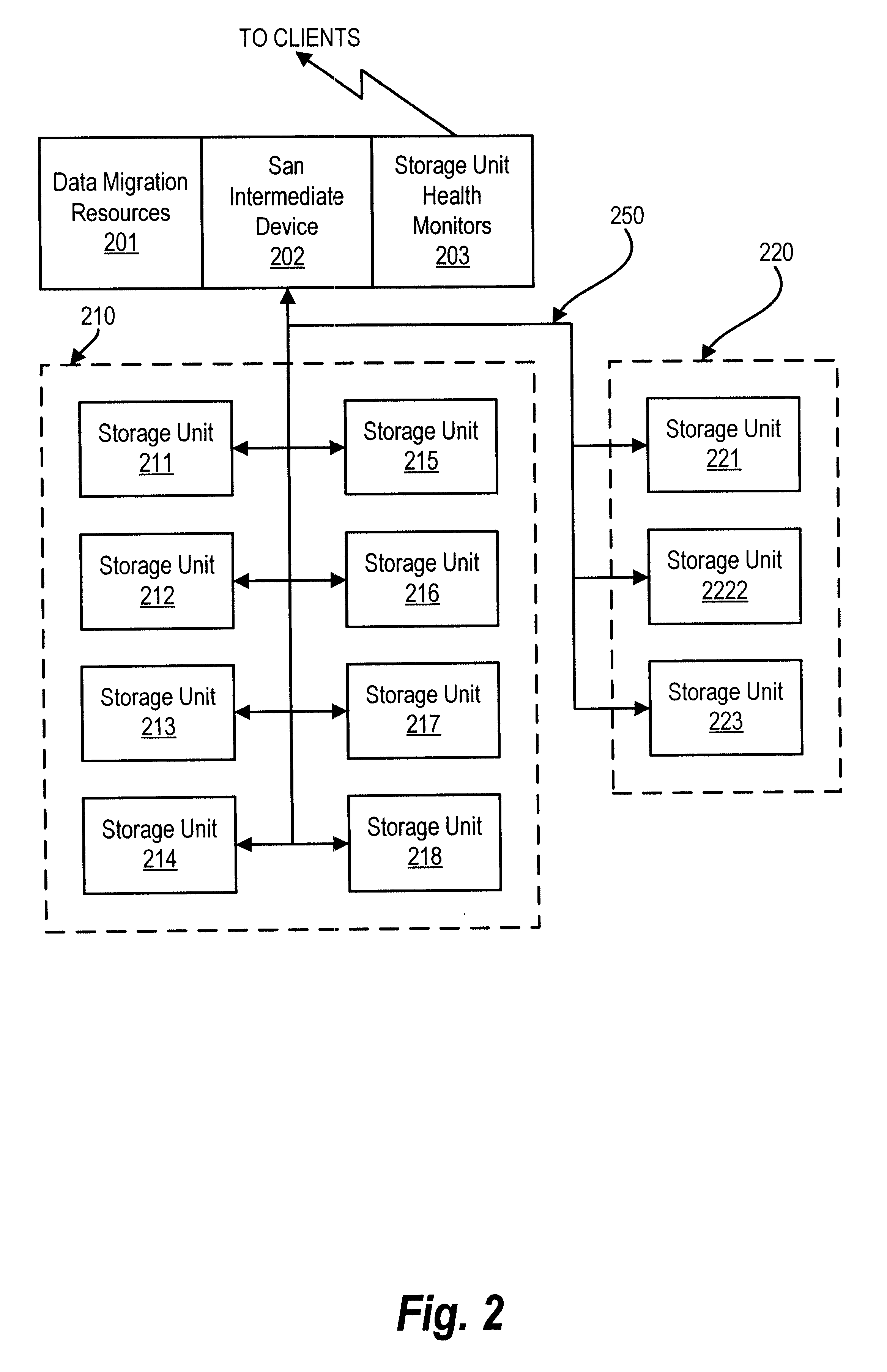
Method and apparatus for storage unit replacement in non-redundant array
InactiveUS6598174B1Lower performance requirementsMaintaining accessMemory loss protectionReliability/availability analysisRAIDData storing
A method and apparatus used in a storage network facilitates the protection of data in, and replacement of, storage devices about to fail before the failure happens. In a network that includes a set of storage devices organized as a non-redundant (for example RAID 0) array, a storage device about to fail in the non-redundant array can be replaced by another storage device, typically from a pool of spares. The method includes detecting a condition of a first particular storage device in the non-redundant array. Conditions which are detected according to various embodiments indicate that the first particular storage device is suffering events indicating that it is likely to fail, or otherwise suffering from reduced performance. The conditions are detected for example, by the receipt of a signal from the storage device itself, or by the monitoring of statistics concerning the performance of the storage device. The method further provides for selecting a particular spare storage device, which can be used in place of the first particular storage device. In response to detecting the condition, data stored in the first particular storage device is migrated to the second particular storage device, and the second particular storage takes the place of the first particular storage device in the non-redundant array. The first particular storage device can then be gracefully removed from the network without loss of service to the clients computers.
Owner:DELL PROD LP
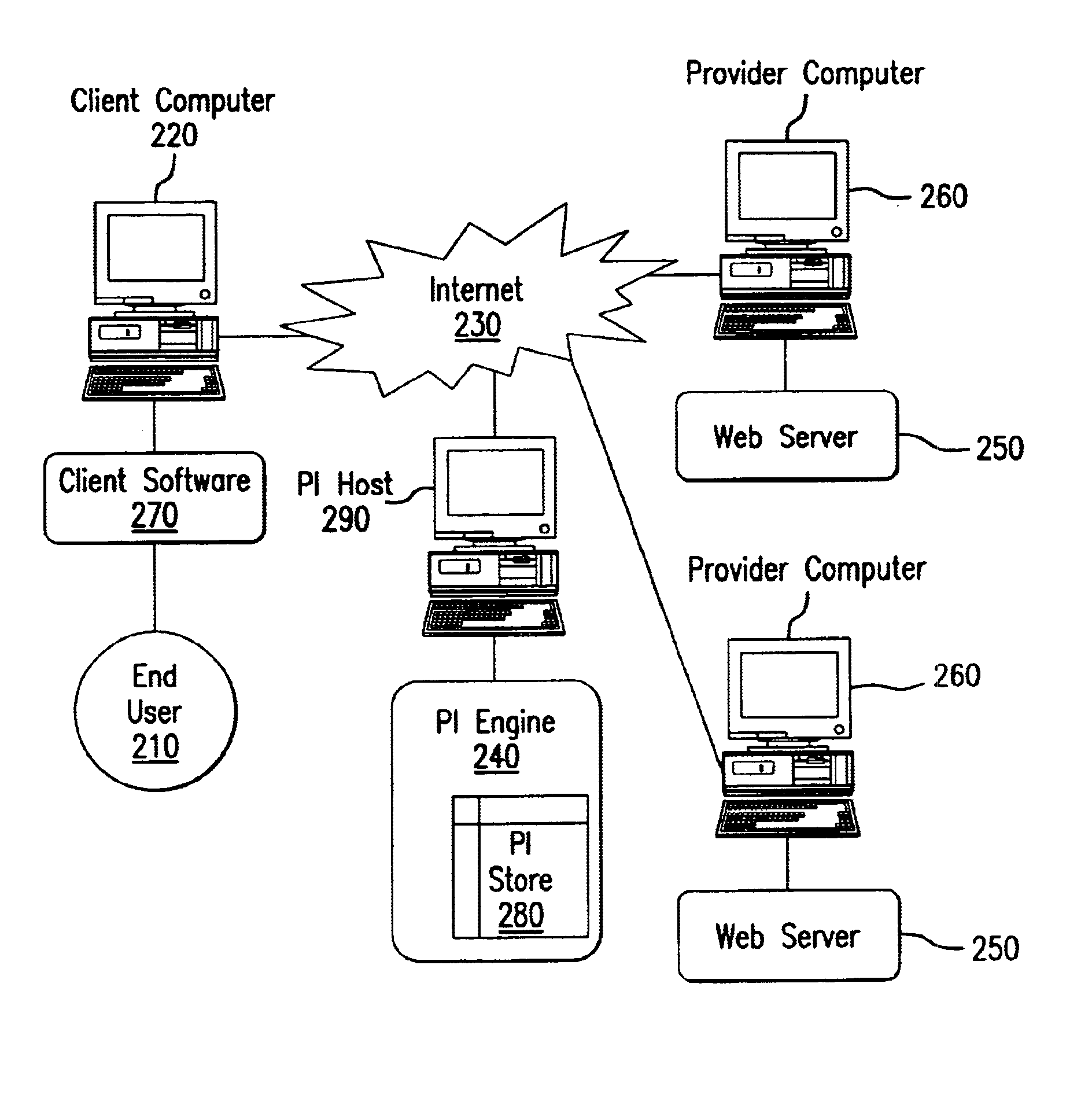
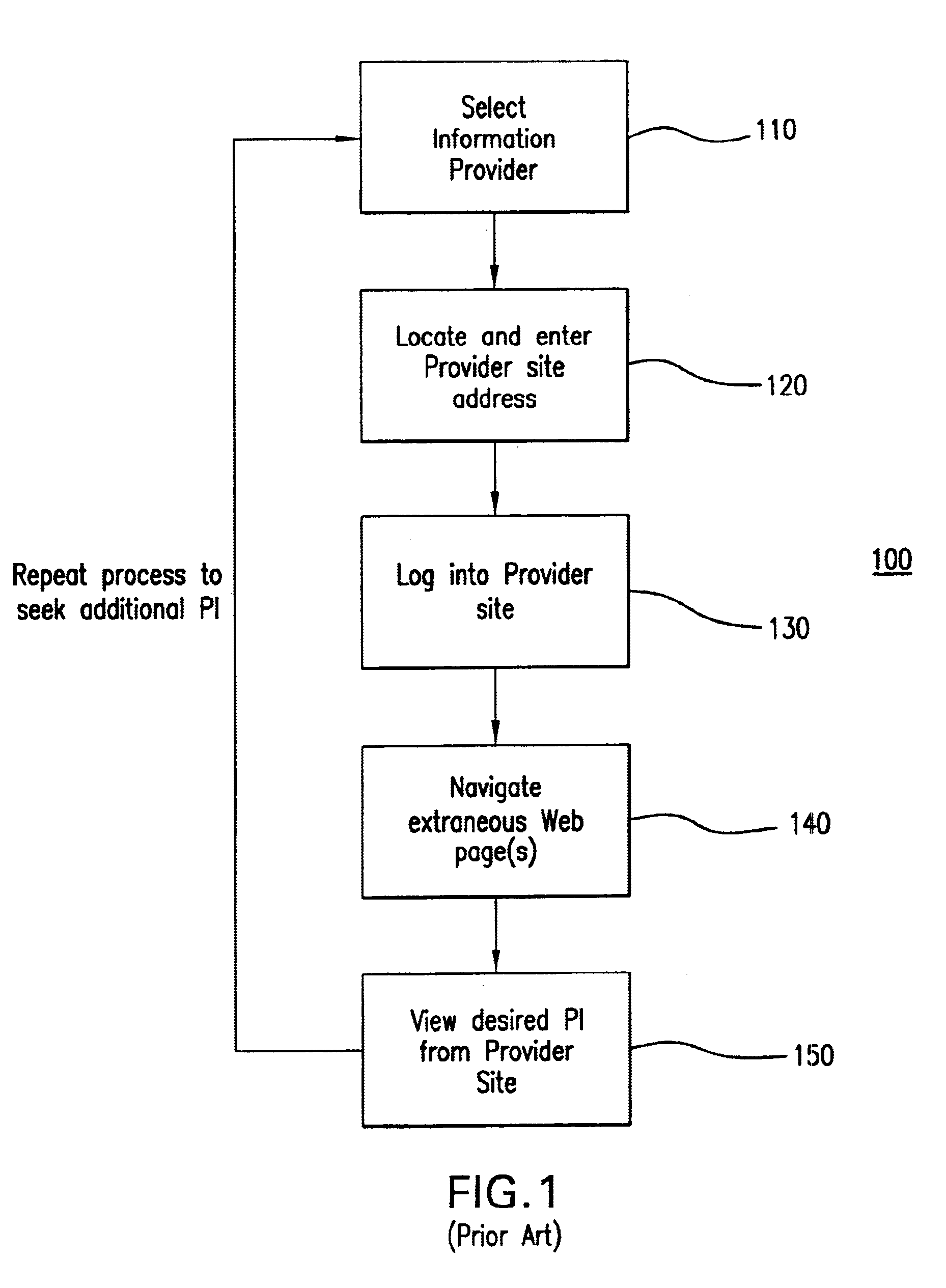
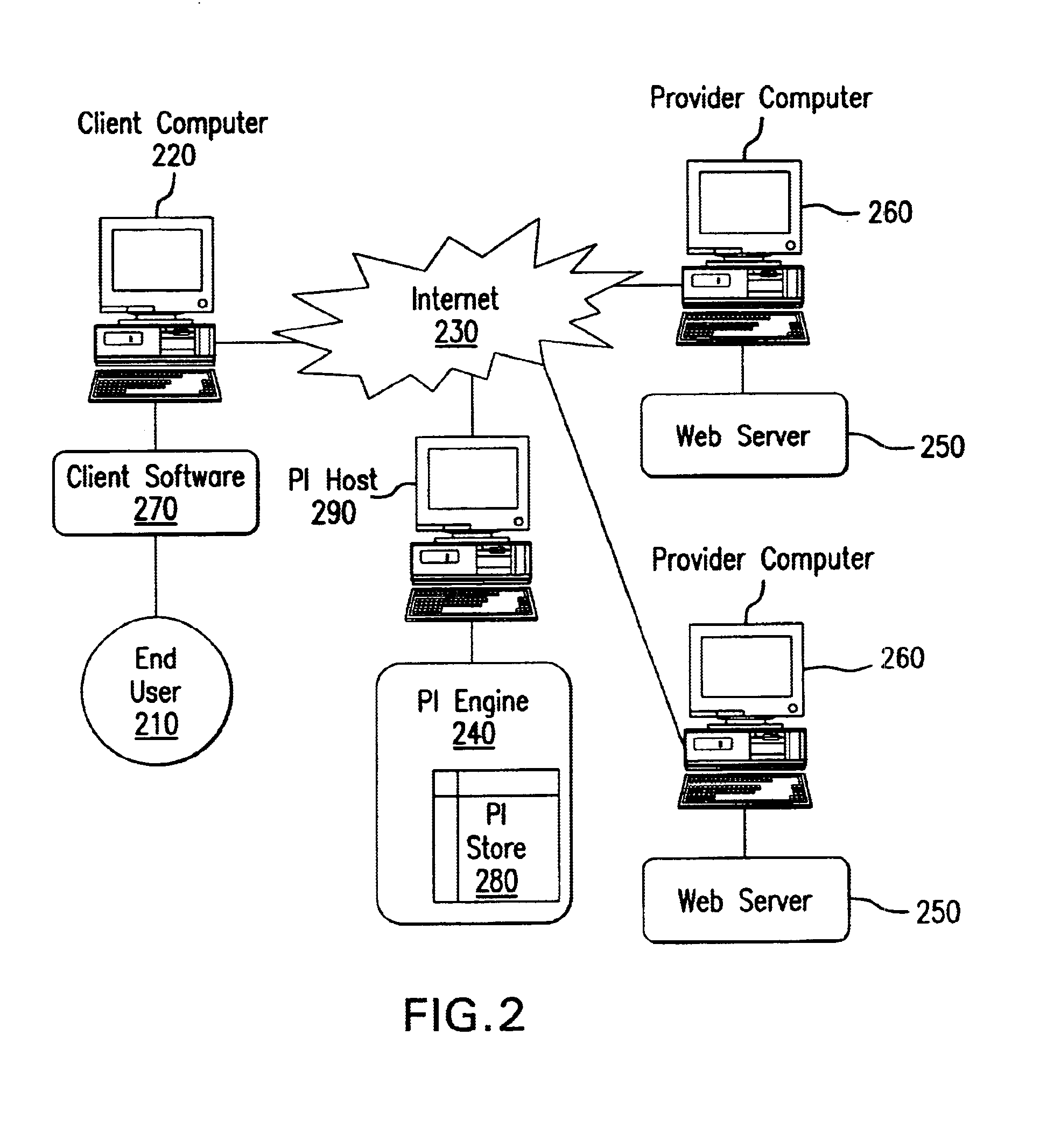
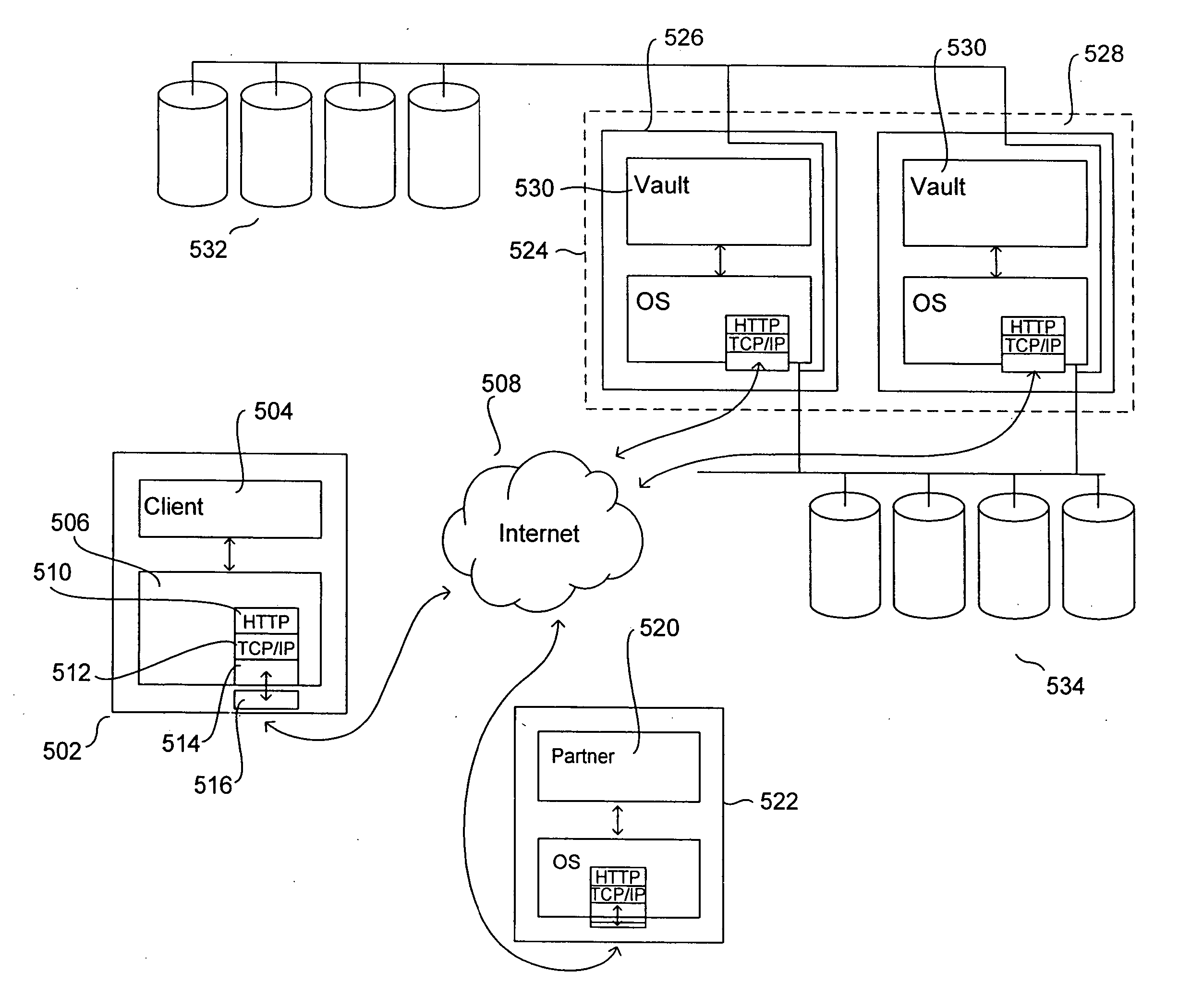
System and method for distributed storage and retrieval of personal information
A system for distributing, storing and retrieving information associated with an end user from one or more information providers between a host computer and a client computer associated with the end user according to the present invention includes a host computer with a processor. The processor aggregates information associated with the end user and transmits the information to the client computer associated with the end user. The processor receives requests concerning the aggregated information from a variety of sources. The processor also receives the previously transmitted aggregated information from the client computer. The processor proceeds to service the received request based on the aggregated information received from the client computer.
Owner:YODLEE COM INC
Business card and contact management system
InactiveUS6883000B1More cost-effectivelyMore accurateAdvertisementsOffice automationBusiness cardWeb browser
An Internet (or World-Wide-Web or other such public or private network) based business card and contact management system capable of conveying and managing advertising as well as traditional and other non-traditional business contact information. The invention is a system that: (1) accepts a Universal Contact Locator (UCL) as encoded on a business card in man and / or machine readable format and, when the Universal Contact Locator (UCL) is entered into a client program running on a client computer, (2) causes a web browser (or like program) and associated communications software to establish a communications session with a remote server computer which (3) accesses the stored contact and advertisement and news information of the card issuer associated with the Universal Contact Locator and (4) downloads the business contact and / or personal contact information and targeted advertisements and news items associated with the Universal Contact Locator to a client program running on a client computer which (5) loads the contact data into the Contact Management or Personal Information Management (PIM) system of the users choosing running on the users client computer and (6) stores the advertisements and news items downloaded from the server computer on the client computer's secondary storage device (i.e. hard disk) and (7) causes the advertisements and news items stored on the client computer's secondary storage device to be displayed to the user on a predetermined schedule in a portion of the client computer's output device (i.e. CRT or LCD panel).
Owner:MICROSOFT TECH LICENSING LLC
Method and system for providing content delivery to a set of participating content providers
InactiveUS7103645B2Low incomeLimited effectivenessData processing applicationsMultiple digital computer combinationsContent distributionNetwork architecture
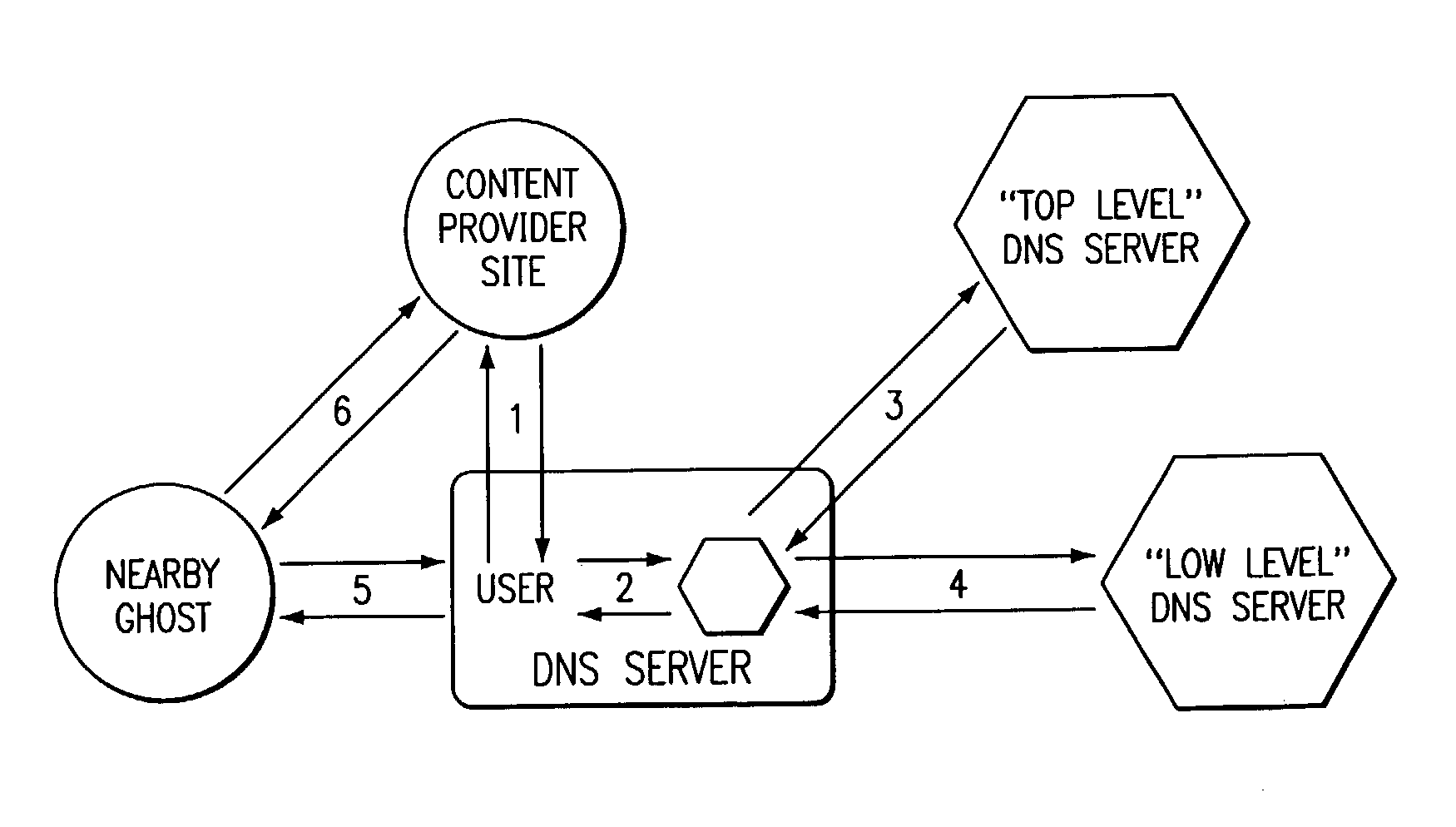
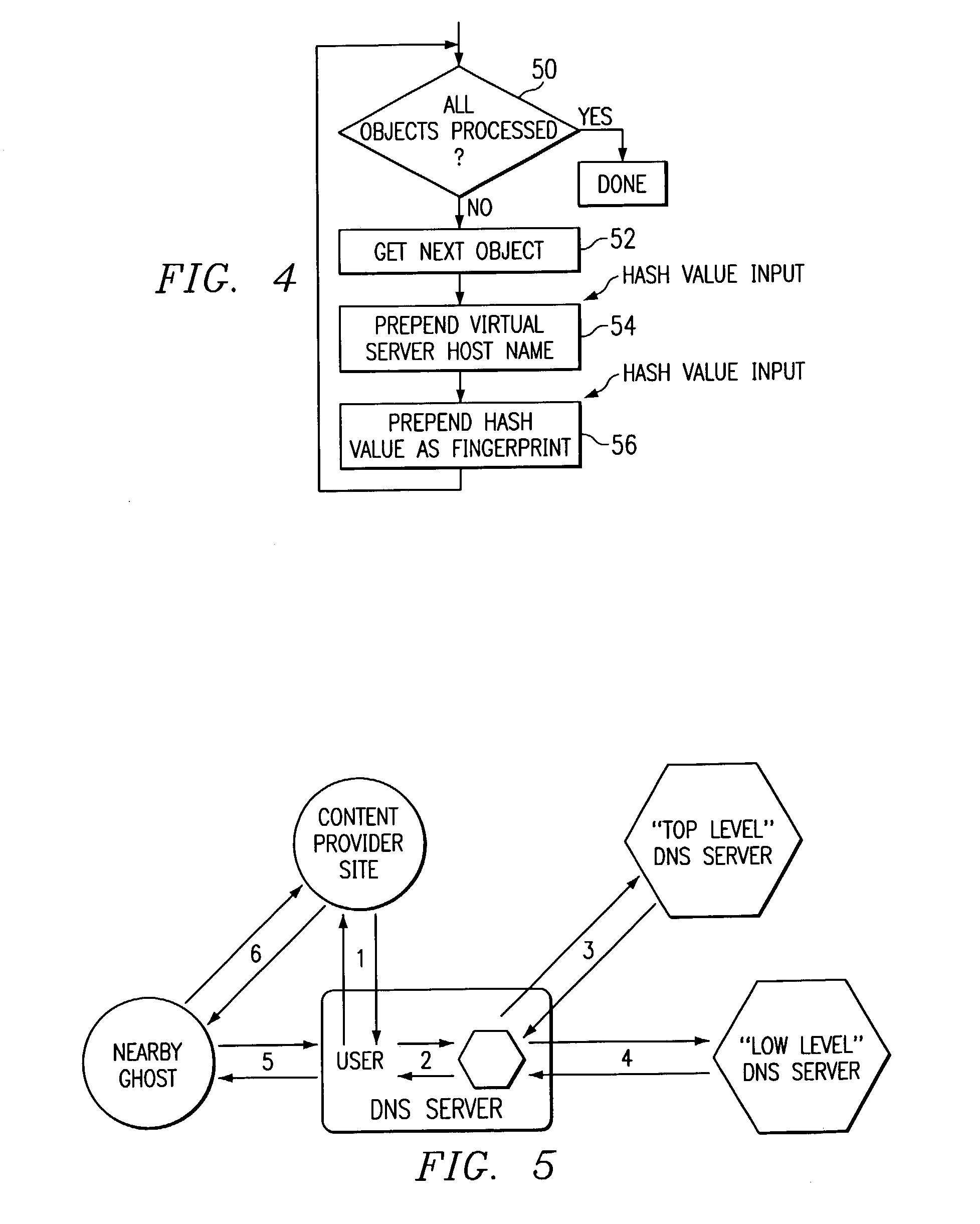
The present invention is a network architecture or framework that supports hosting and content distribution on a truly global scale. The inventive framework allows a Content Provider to replicate and serve its most popular content at an unlimited number of points throughout the world. The inventive framework comprises a set of servers operating in a distributed manner. The actual content to be served is preferably supported on a set of hosting servers (sometimes referred to as ghost servers). This content comprises HTML page objects that, conventionally, are served from a Content Provider site. In accordance with the invention, however, a base HTML document portion of a Web page is served from the Content Provider's site while one or more embedded objects for the page are served from the hosting servers, preferably, those hosting servers near the client machine. By serving the base HTML document from the Content Provider's site, the Content Provider maintains control over the content.
Owner:MASSACHUSETTS INST OF TECH
Methods and systems for providing authorized remote access to a computing environment provided by a virtual machine
ActiveUS20070179955A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
A method for providing authorized remote access to a computing environment provided by a virtual machine, includes the step of requesting, by a client machine, access to a resource. A collection agent gathers information about the client machine. A policy engine receives the gathered information. The policy engine makes an access control decision based on the received information. A computing environment already associated with the user is identified in response to the received information, the identified computing environment provided by a virtual machine. A broker server establishes, responsive to the access control decision, a connection between the client machine and the identified computing environment.
Owner:CITRIX SYST INC
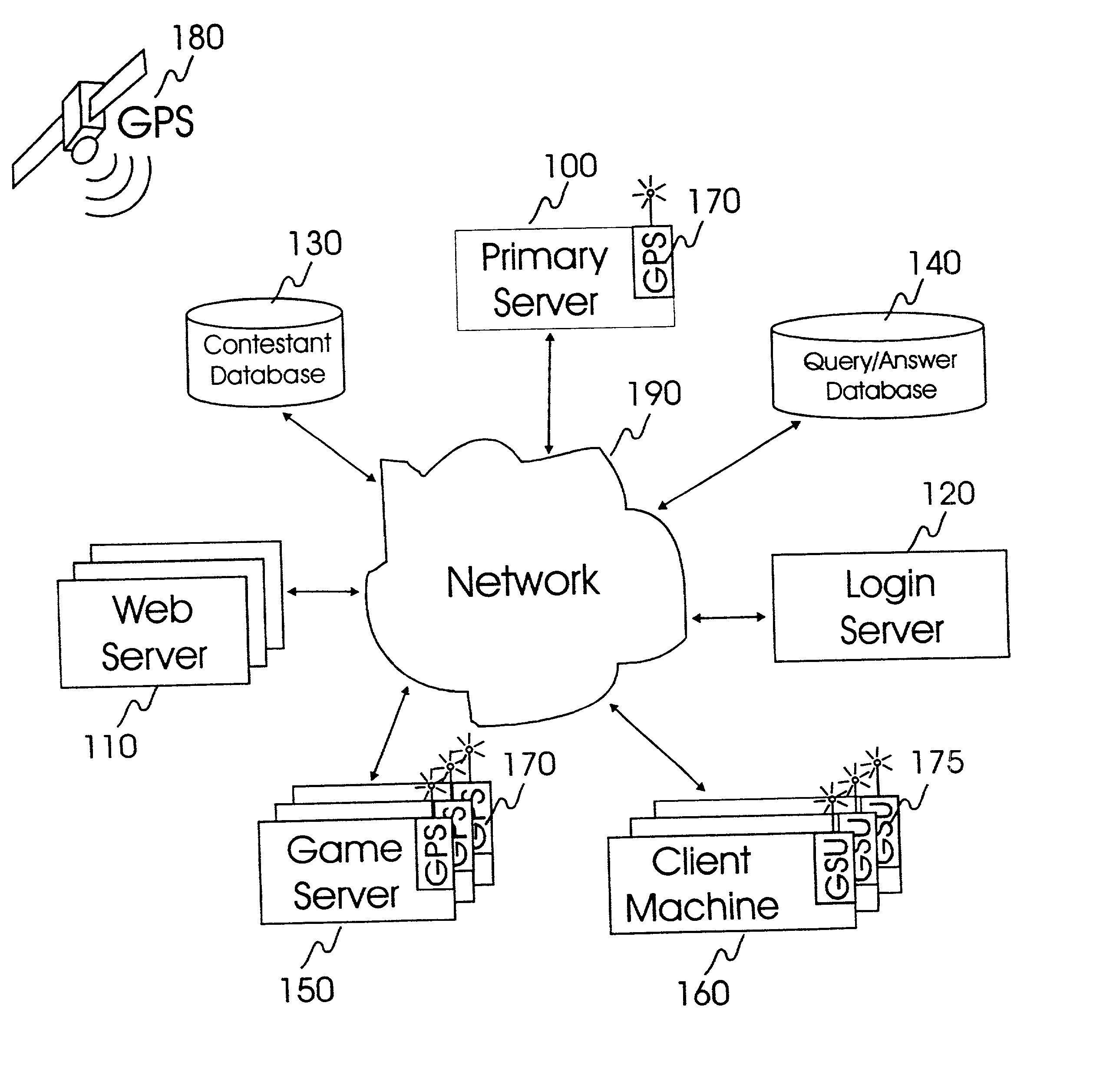
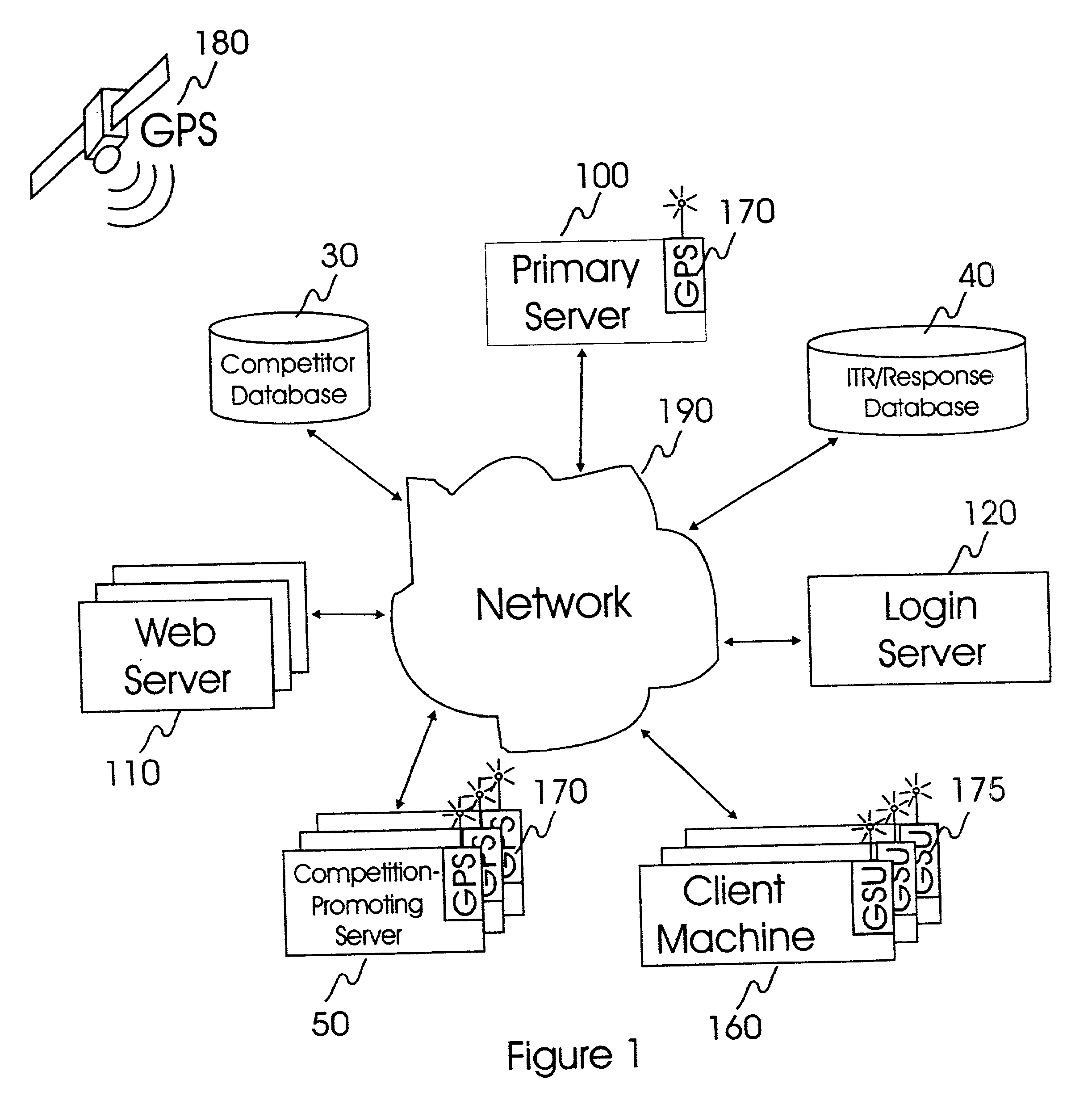
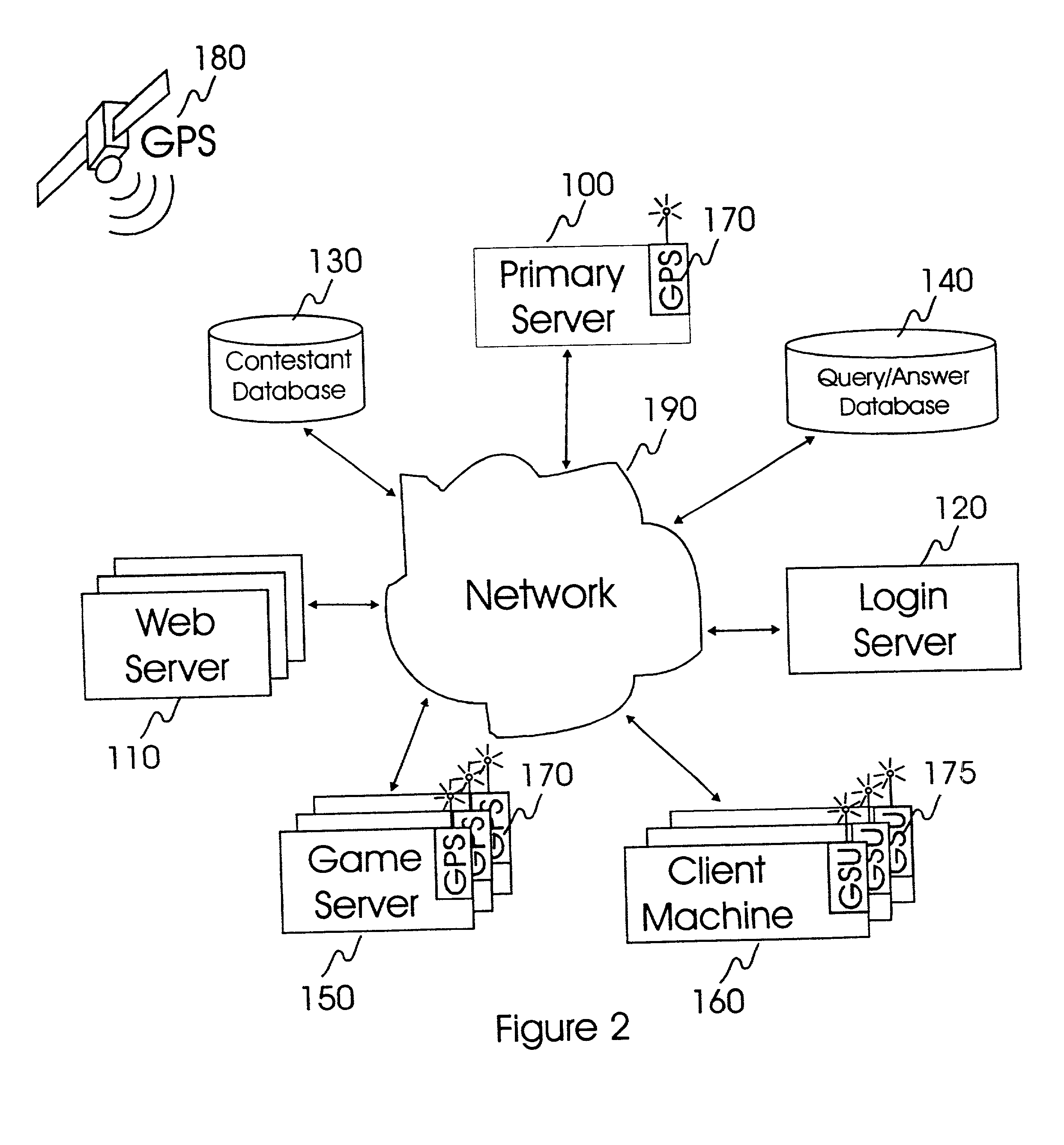
Internet-based system and method for fairly and securely enabling timed-constrained competition using globally time-sychronized client subsystems and information servers having microsecond client-event resolution
InactiveUS20020026321A1Avoiding shortcoming and drawbackBetterment of human societyBuying/selling/leasing transactionsVideo gamesTime responseTTEthernet
An improved system and method of fairly and securely enabling timed-constrained competitions over the Internet among millions of competitors while compensating for the variable network communication latencies experienced by client machines used by the competitors. The system employs globally time-synchronized Internet information servers and client machines in order to synchronize the initial display of each invitation to respond (e.g. stock price to buy or sell, query to answer, or problem to solve) on a client machine so each competitor can respond to the invitation at substantially the same time, regardless of his or her location on the planet, or the type of Internet-connection used by his or her client machine. Also, by using globally time-synchronized client machines, each competitor's response is securely time and space stamped at the client machine to ensure that competitor responses are resolved within microsecond accuracy.
Owner:REVEO
Methods and systems for assigning access control levels in providing access to resources via virtual machines
ActiveUS20070180493A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideProxy server
Owner:CITRIX SYST INC
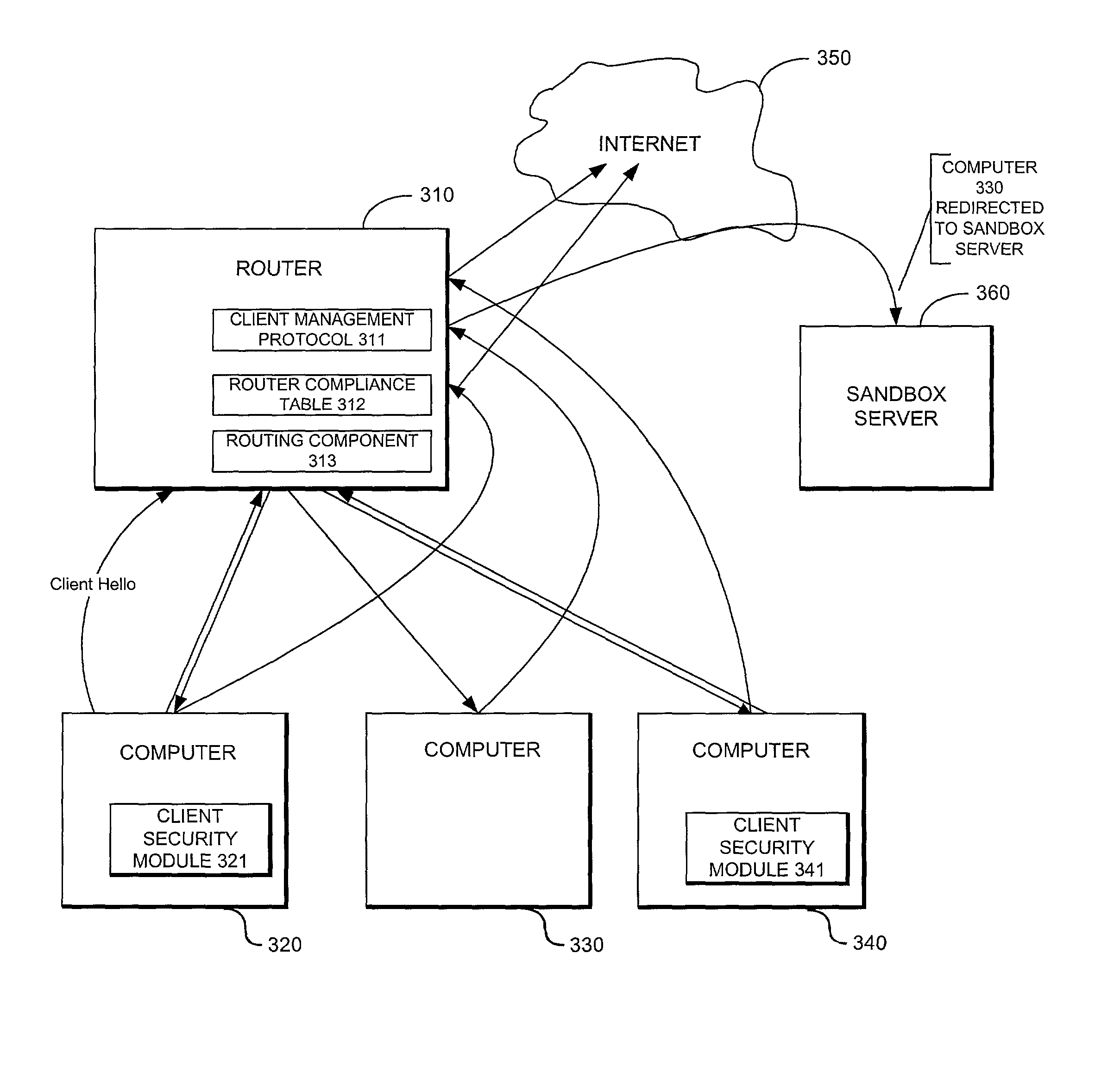
System providing internet access management with router-based policy enforcement
ActiveUS20030055962A1Multiple digital computer combinationsTransmissionInternet accessApplication software
A computing environment with methods for monitoring access to an open network such as the Internet, is described. The system includes one or more client computers, each operating applications (e.g., Netscape Navigator or Microsoft Internet Explorer) requiring access to an open network, such as a WAN or the Internet, and a router or other equipment that serves a routing function (e.g., a cable modem) for the client computers. A centralized security enforcement module on the router maintains access rules for the client computers and verifies the existence and proper operation of a client-based security module on each client computer. The router-side security module periodically sends out a router challenge via Internet broadcast to the local computers on the network. If the client-side security module is installed and properly operating, the client-side security module responds to the router challenge. The responses received by the router-side security module are maintained in a table. Each time the router receives a request from a client computer to connect to the Internet, the router-side security module reviews the table and analyzes whether or not the computer requesting a connection to the Internet properly responded to the most recent router challenge. If it determines that the computer has properly responded to the router challenge, then it permits the computer to connect to the Internet. If a computer has not properly responded or if a computer has not answered the router challenge, then the computer is not allowed to connect to the Internet as requested.
Owner:CHECK POINT SOFTWARE TECH INC
Method and system for data backup
ActiveUS20070100913A1Cost-effectiveAvoid accessMemory loss protectionError detection/correctionWeb serviceApplication software
Embodiments of the present invention are directed to Web-Services-based data backup and data-archiving applications that provide remote data backup and data archiving to private individuals, small businesses, and other organizations that need reliable, secure, geographically remote, and cost-effective data backup, data archiving, and backed-up and archived-data retrieval. In one embodiment of the present invention, a private or small-business client contracts with a service provider for data-backup and data-archiving services. The service provider, in turn, contracts with a remote data-storage facility to provide secure, reliable data backup and data archiving to the personal or small-business client. A client-side application is downloaded to the client computer and configured to allow the client to store locally encrypted data at the remote, data-storage facilities. Neither the service provider nor the data-storage facility can decrypt or otherwise access the information stored by the client. In addition, the encryption key or encryption keys used by the client to encrypt the data for remote storage are securely stored at the remote, data-storage facility for subsequent recovery by the client, should the client suffer damage or loss to a local computer system. However, the client encryption key is stored in a doubly encrypted fashion, preventing access to the client's encryption key by either the service provider or the data-storage facility. Certain embodiments of the present invention also provide local indexing for remotely stored, encrypted data and efficient storage of updates to already remotely stored data.
Owner:CARBONITE GMBH
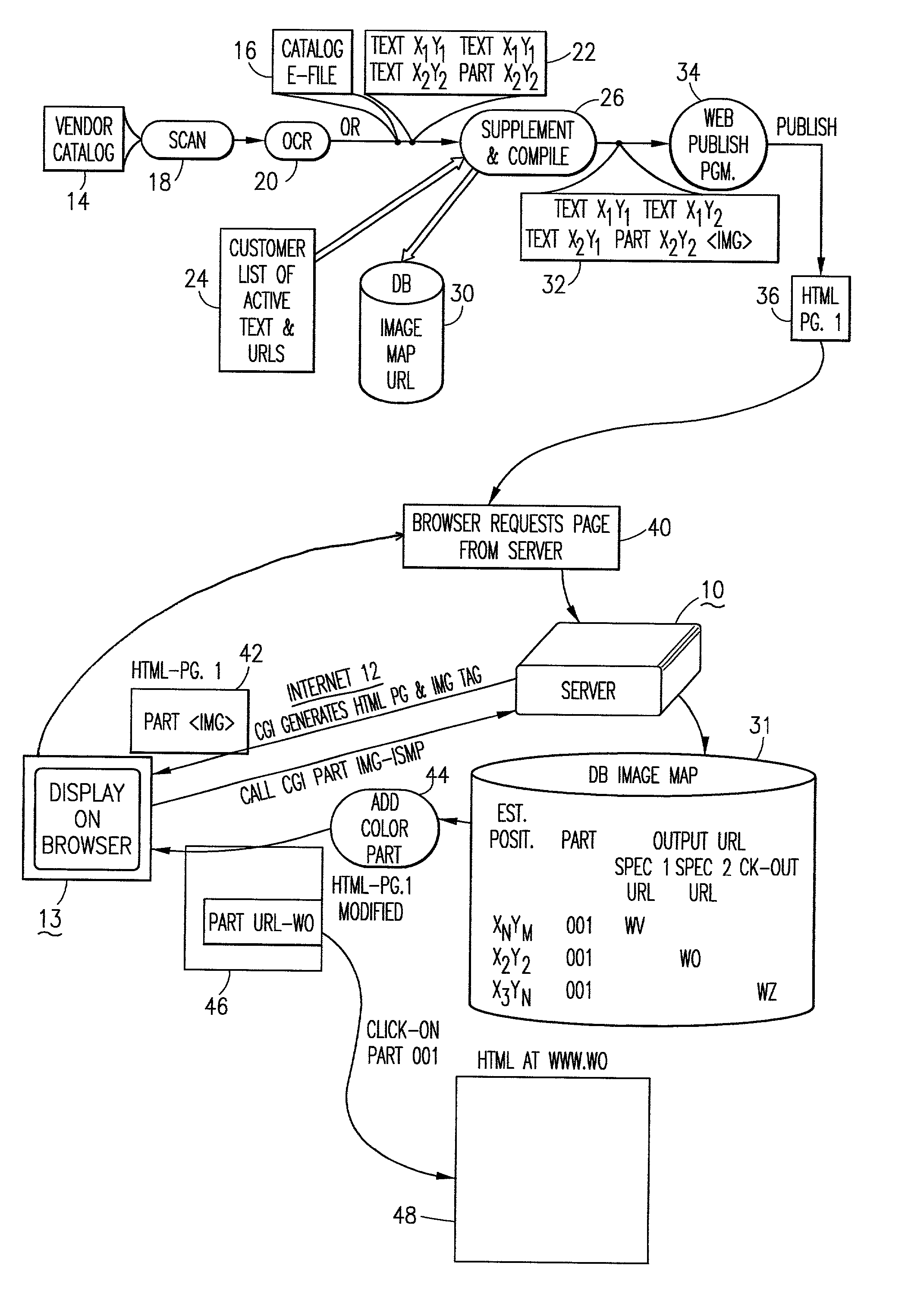
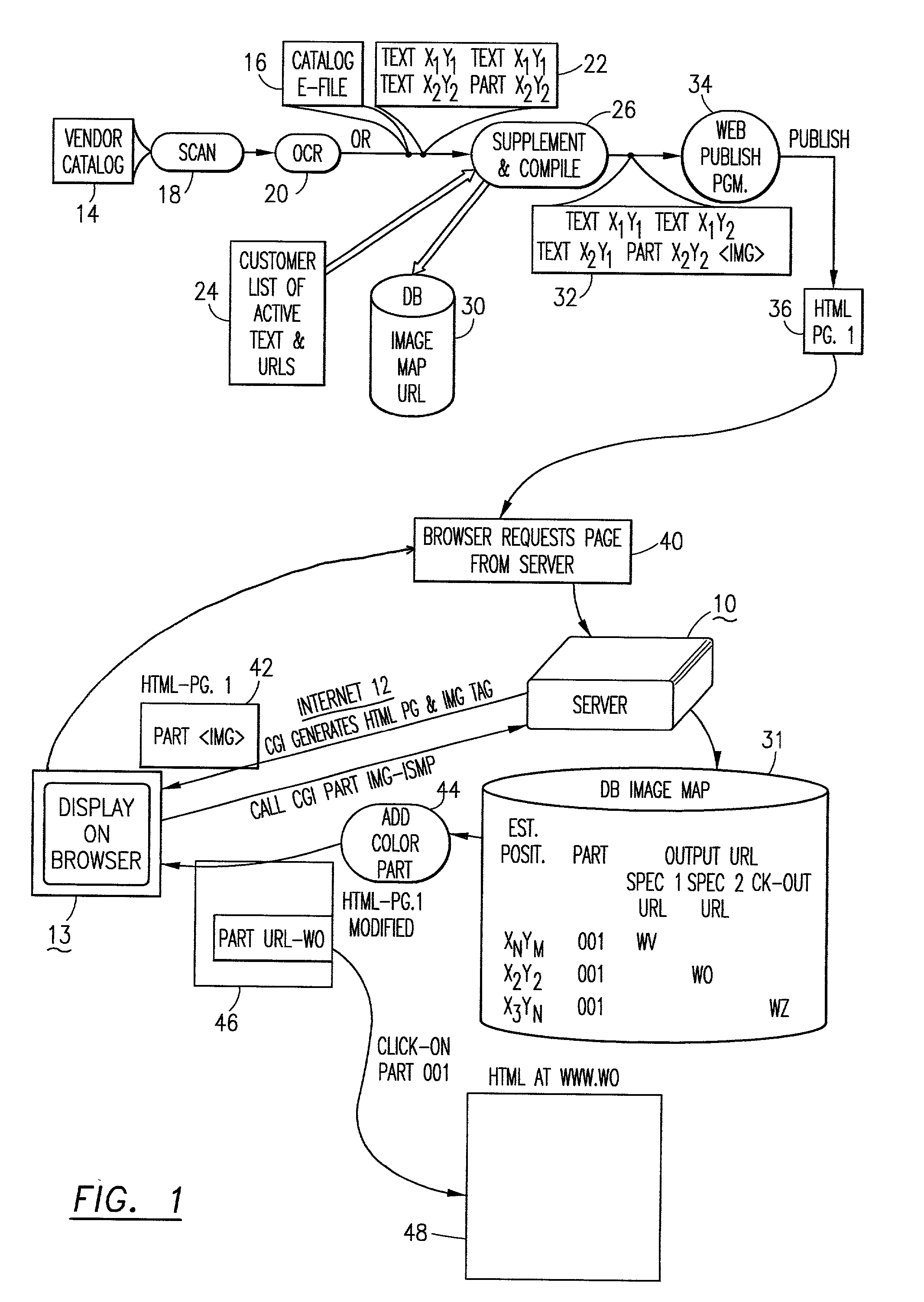
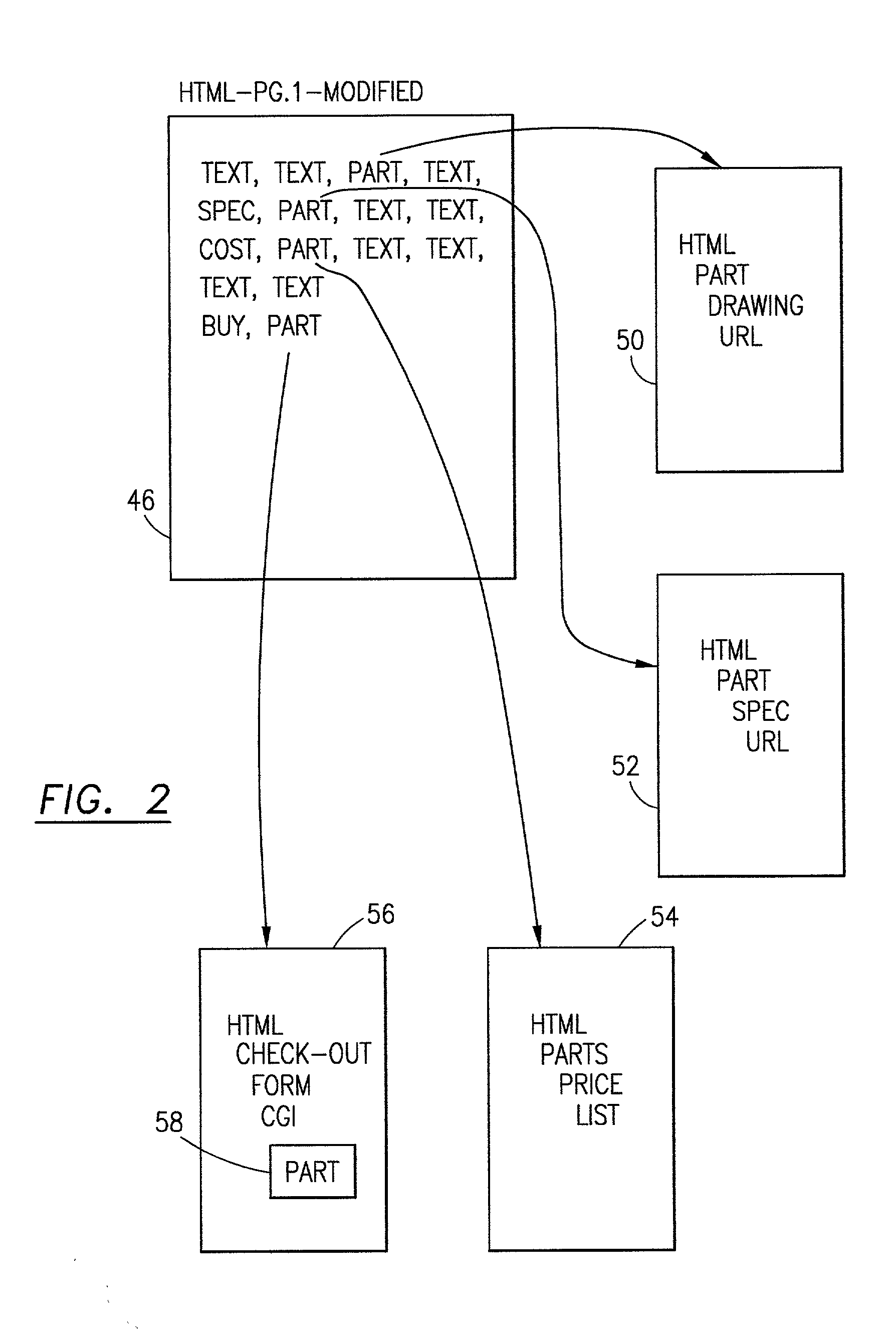
System and method for placing active tags in HTML document
InactiveUS20020069222A1Quick conversionNatural language data processingSpecial data processing applicationsInformation processingDocument preparation
The method and the information processing system dynamically creates an HTML document with at least one embedded hyperlink code therein. The HTML document is based upon a source document provided by a manufacturer or a supplier of services. Typically, the system and the method is operable in a client-server computer environment. A database is provided on the server computer system which database associates location data of a plurality of data strings in the source document with hyperlink addresses. The location data in the database maps at least one predetermined data string in the source document. An HTML document, based upon the source document, is published with an image tag on, in or near the predetermined data string. As an example, the string may be a "part number" or a string of words "SONY PLAYSTATION II.". The published HTML document has an image tag on, at or near the part number and a map attribute command which supplies or generates an HTML location data unique to the image tag location in the HTML document when the browser calls the server's common gateway interface (CGI). The image tag URL points to the database on the server. The server, via the database provides a corresponding hyperlink address, associated with the unique location data correlated to the HTML location data, to the browser on the client computer system. The method and the system then publishes and embeds in the original or initial HTML document at, on or near the predetermined data string or part number an active hyperlink tag (an embedded code) with the corresponding hyperlink address obtained from the database.
Owner:WIZNET
System and method for enabling application server request failover
InactiveUS6859834B1Resource allocationMultiple digital computer combinationsFailoverApplication server
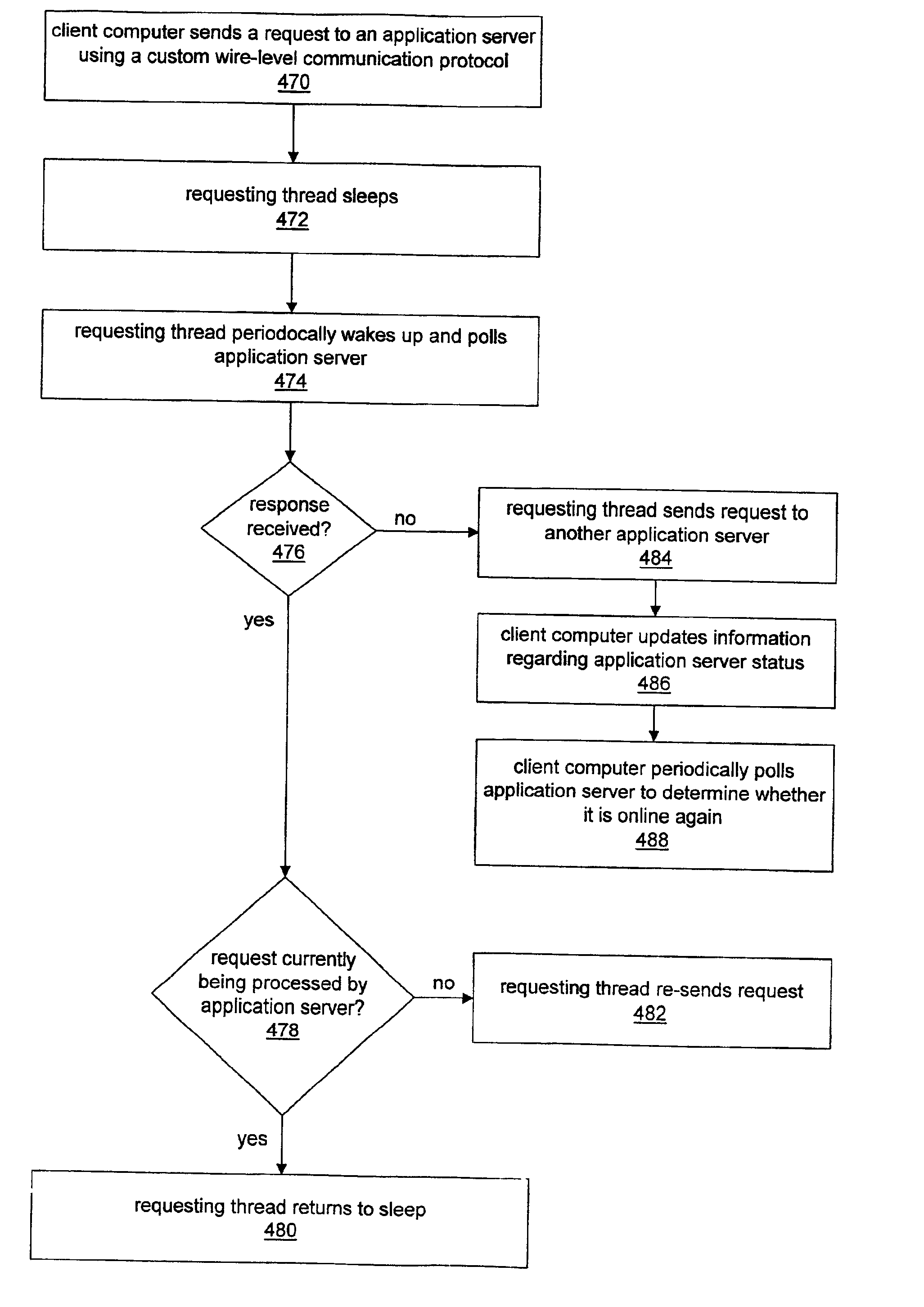
System and method for enabling application server request failover. For each application server request to be performed by a client computer, a requesting thread may be operable to utilize a custom wire-level communication protocol. Request failure detection mechanisms may be built into the custom wire-level communication protocol so that a requesting thread detects a failed request much sooner than if the thread utilized a standard communication protocol and relied on the client computer operating system for notification of failed requests. After sending a request to an application server, a requesting thread may be operable to “sleep” and then periodically wake up to poll the application server computer to determine whether the request has failed. If the requesting thread receives a response from the application server computer indicating that the request is not currently being processed, then the requesting thread may re-send the request. Receiving no response to the poll message may indicate that the application server computer is offline, e.g., due to a failure. The requesting thread may redirect the request to another application server computer if necessary.
Owner:ORACLE INT CORP
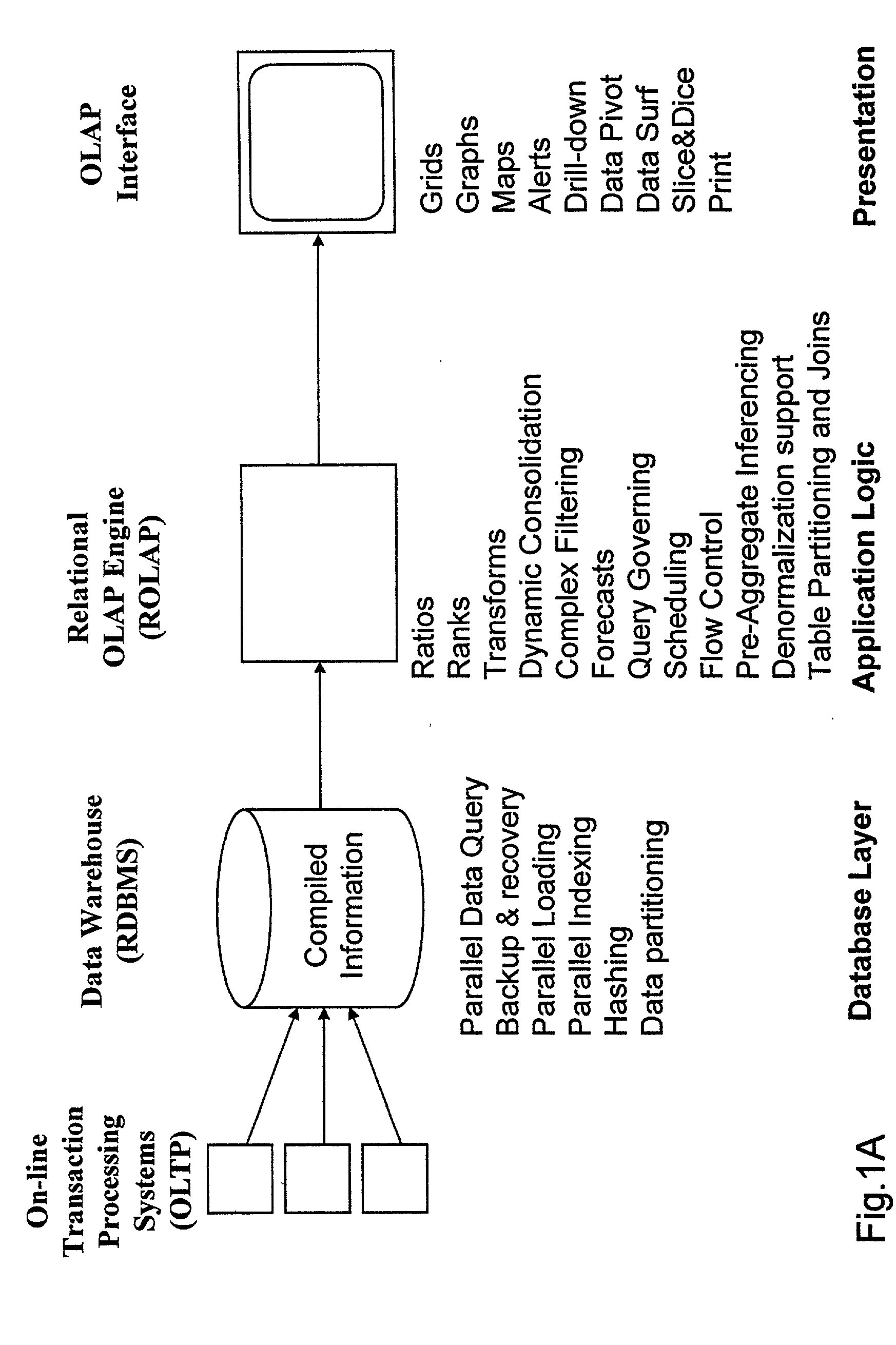
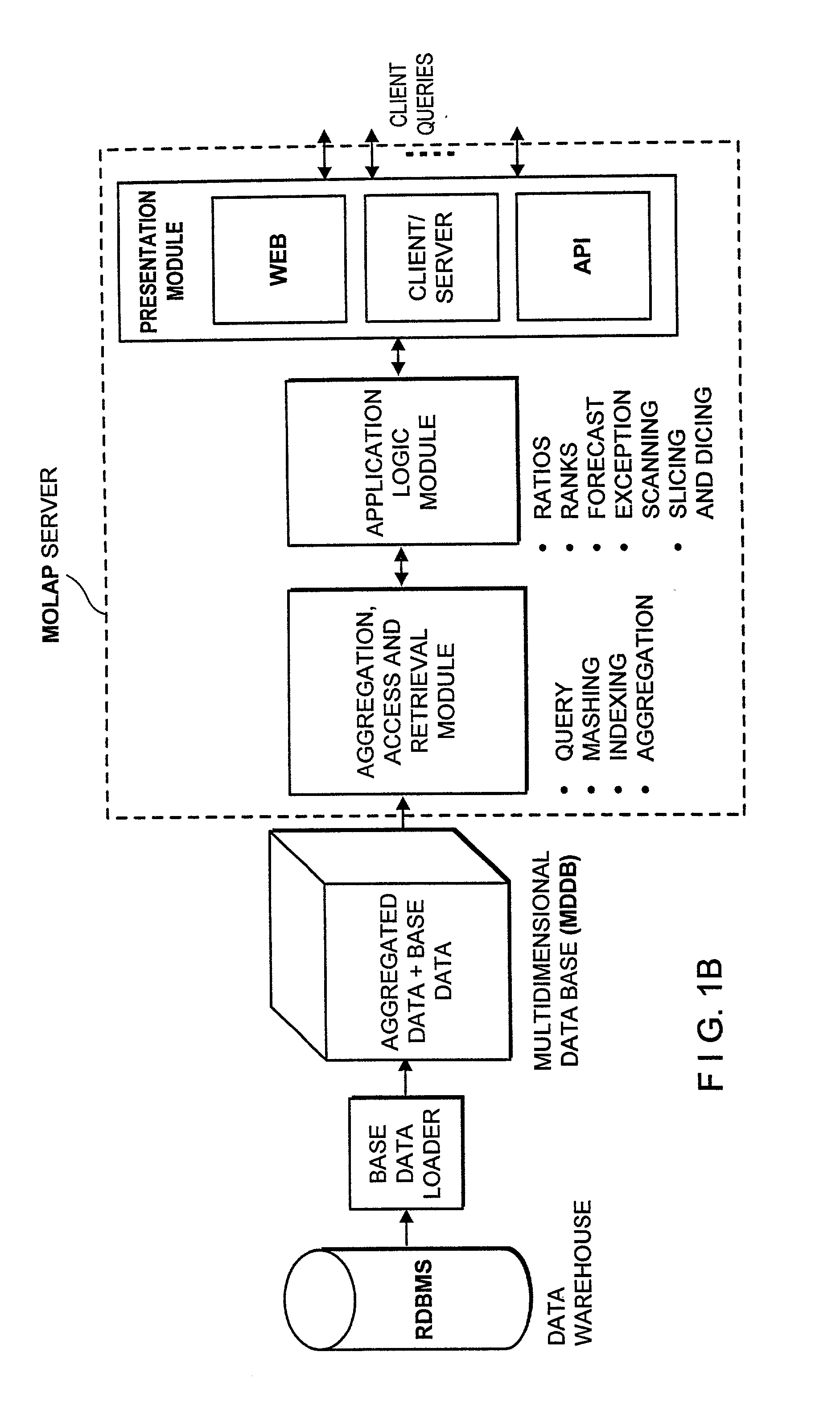
Data aggregation server for managing a multi-dimensional database and database management system having data aggregation server integrated therein
InactiveUS20020029207A1Reduce the burden onImprove system performanceData processing applicationsDigital data processing detailsData aggregatorThe Internet
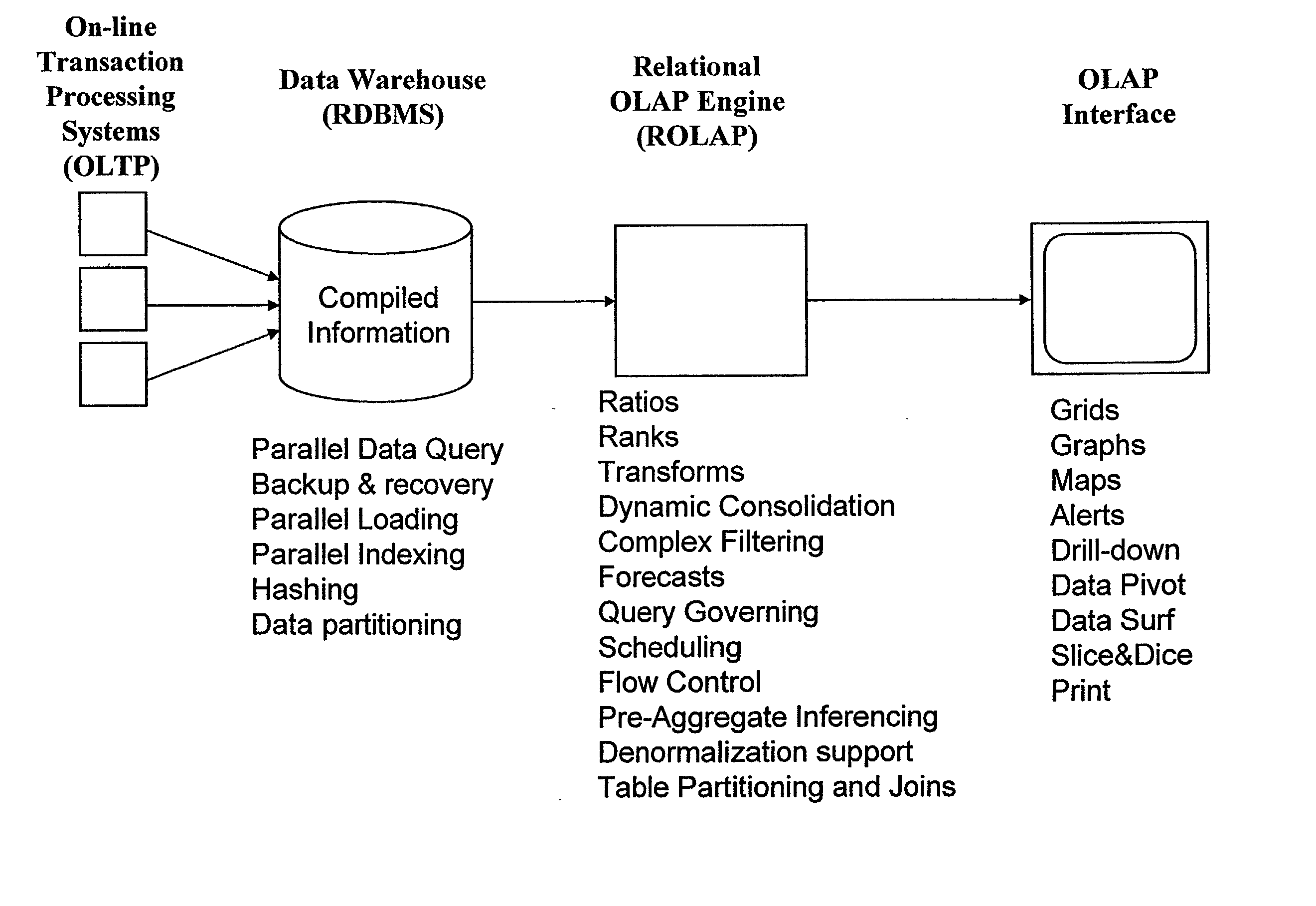
Improved method of and apparatus for aggregating data elements in multidimensional databases (MDDB). In one aspect of the present invention, the apparatus is realized in the form of a high-performance stand-alone (i.e. external) aggregation server which can be plugged-into conventional OLAP systems to achieve significant improments in system performance. In accordance with the principles of the present invention, the stand-alone aggregation server contains a scalable MDDB and a high-performance aggregation engine that are integrated into the modular architecture of the aggregation server. The stand-alone aggregation server of the present invention can uniformly distribute data elements among a plurality of processors, for balanced loading and processing, and therefore is highly scalable. The stand-alone aggregation server of the present invention can be used to realize (i) an improved MDDB for supporting on-line analytical processing (OLAP) operations, (ii) an improved Internet URL Directory for supporting on-line information searching operations by Web-enabled client machines, as well as (iii) diverse types of MDDB-based systems for supporting real-time control of processes in response to complex states of information reflected in the MDDB. In another aspect of the present invention, the apparatus is integrated within a database management system (DBMS). The improved DBMS can be used to realize achieving a significant increase in system performance (e.g. deceased access / search time), user flexibility and ease of use. The improved DBMS system of the present invention can be used to realize an improved Data Warehouse for supporting on-line analytical processing (OLAP) operations or to realize an improved informational database system, operational database system, or the like.
Owner:YANICKLO TECH LIABILITY +1
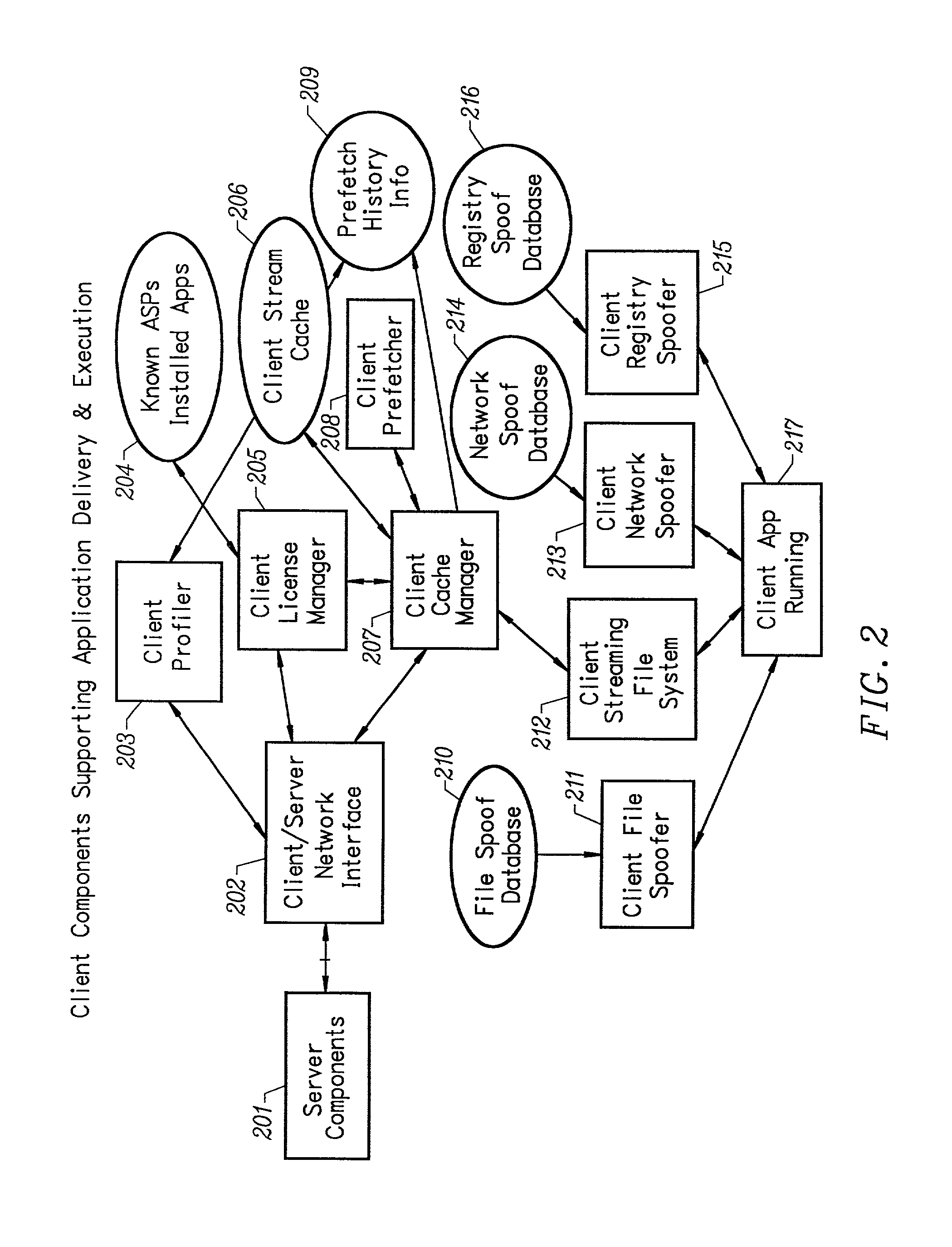
Client-side performance optimization system for streamed applications
InactiveUS6959320B2Efficiently stream and executeEasily integrates into client system 's operating systemMultiple digital computer combinationsProgram loading/initiatingApplication serverData file
An client-side performance optimization system for streamed applications provides several approaches for fulfilling client-side application code and data file requests for streamed applications. A streaming file system or file driver is installed on the client system that receives and fulfills application code and data requests from a persistent cache or the streaming application server. The client or the server can initiate the prefetching of application code and data to improve interactive application performance. A client-to-client communication mechanism allows local application customization to travel from one client machine to another without involving server communication. Applications are patched or upgraded via a change in the root directory for that application. The client can be notified of application upgrades by the server which can be marked as mandatory, in which case the client will force the application to be upgraded. The server broadcasts an application program's code and data and any client that is interested in that particular application program stores the broadcasted code and data for later use.
Owner:NUMECENT HLDG
Systems and Methods for Facilitating Distributed Authentication
ActiveUS20070107048A1Digital data processing detailsUser identity/authority verificationApplication serverClient-side
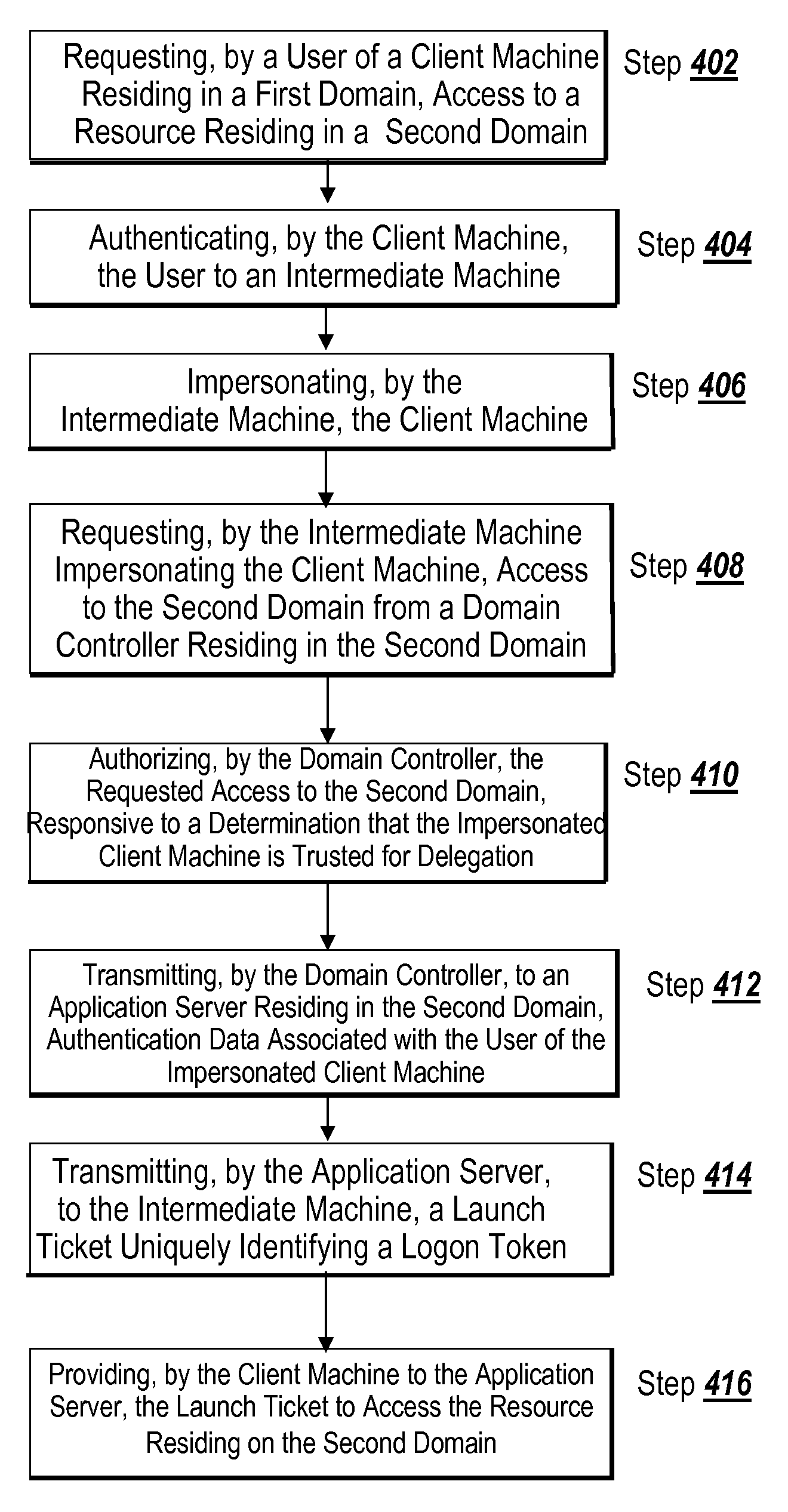
A method for facilitating distributed authentication includes the step of requesting, by a user of a client machine residing in a first domain, access to a resource residing in a second domain. The client machine authenticates the user to an intermediate machine. The intermediate machine impersonates the client machine. The intermediate machine impersonating the client machine requests access to the second domain from a domain controller residing in the second domain. The domain controller authorizes the requested access, responsive to a determination that the impersonated client machine is trusted for delegation. The domain controller transmits to an application server residing in the second domain, authentication data associated with the impersonated client machine. The application server transmits, to the intermediate machine, a launch ticket uniquely identifying a logon token. The client machine provides, to the application server, the launch ticket to access the resource residing in the second domain.
Owner:CITRIX SYST INC
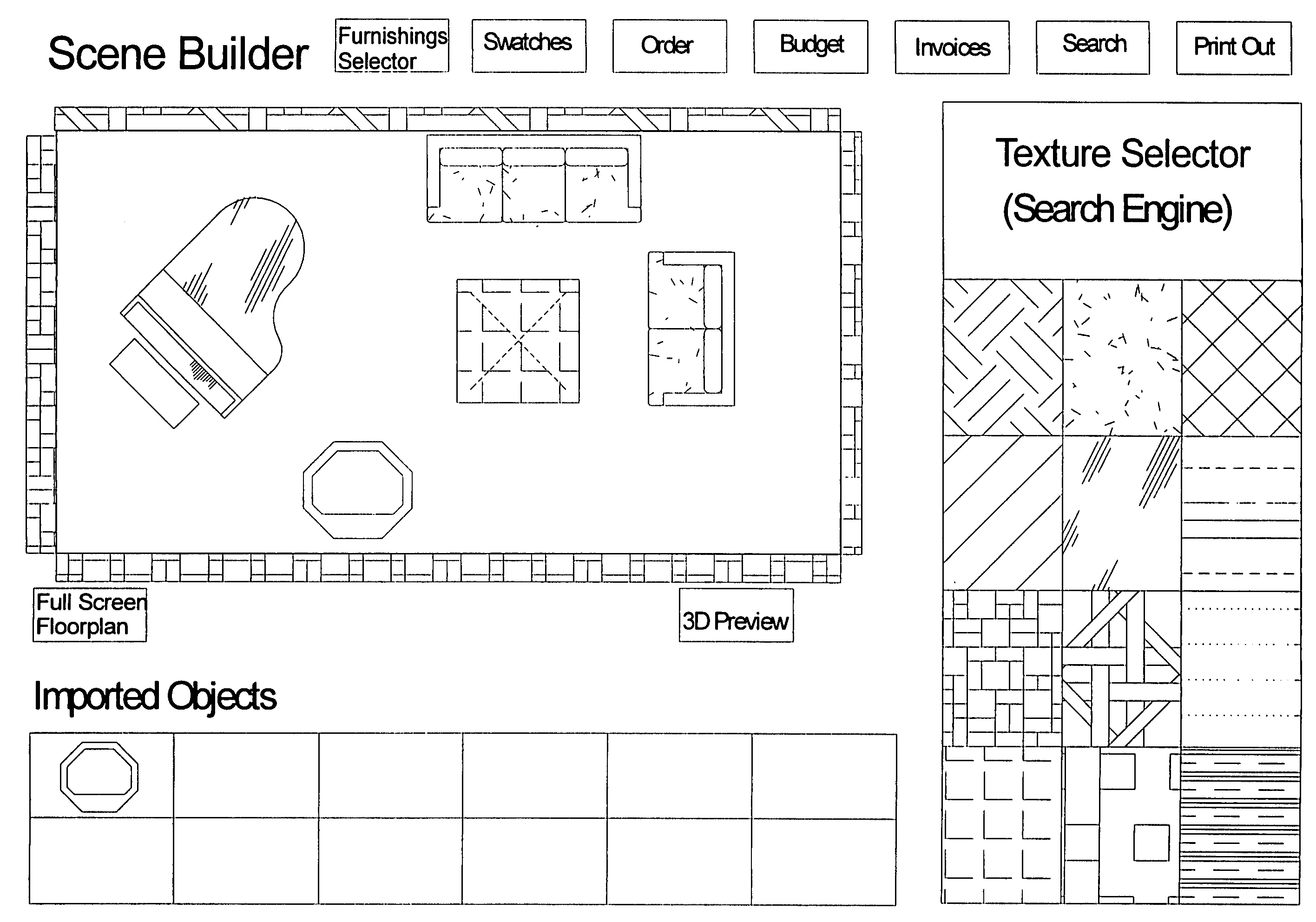
Network-linked interactive three-dimensional composition and display of saleable objects in situ in viewer-selected scenes for purposes of promotion and procurement
InactiveUS7062722B1Sufficiently accurateSufficiently appealingSpecial data processing applicationsMarketingFull custom3d image
A design professional such as an interior designer running a browser program at a client computer (i) optionally causes a digital image of a room, or a room model, or room images to be transmitted across the world wide web to a graphics server computer, and (ii) interactively selects furnishings from this server computer, so as to (iii) receive and display to his or her client a high-fidelity high-quality virtual-reality perspective-view image of furnishings displayed in, most commonly, an actual room of a client's home. Opticians may, for example, (i) upload one or more images of a client's head, and (ii) select eyeglass frames and components, to (iii) display to a prospective customer eyeglasses upon the customer's own head. The realistic images, optionally provided to bona fide design professionals for free, promote the sale to the client of goods which are normally obtained through the graphics service provider, profiting both the service provider and the design professional. Models of existing objects are built as necessary from object views. Full custom objects, including furniture and eyeglasses not yet built, are readily presented in realistic virtual image.Also, a method of interactive advertising permits a prospective customer of a product, such as a vehicle, to view a virtual image of the selected product located within a customer-selected virtual scene, such as the prospective customer's own home driveway. Imaging for all purposes is supported by comprehensive and complete 2D to 3D image translation with precise object placement, scaling, angular rotation, coloration, shading and lighting so as to deliver flattering perspective images that, by selective lighting, arguably look better than actual photographs of real world objects within the real world.
Owner:CARLIN BRUCE +3
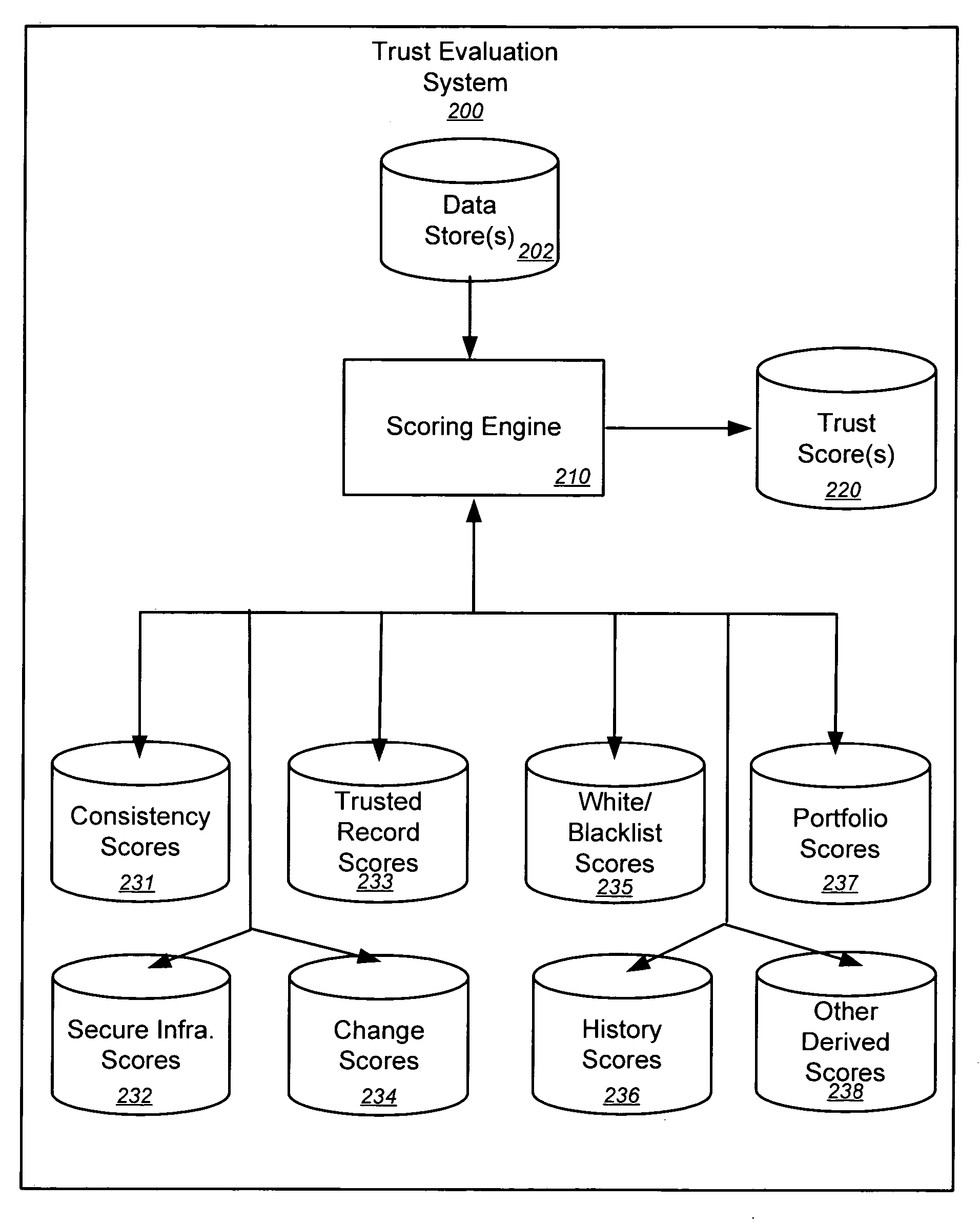
Implementing trust policies
InactiveUS20060212925A1Platform integrity maintainanceSpecial data processing applicationsInternet privacySality
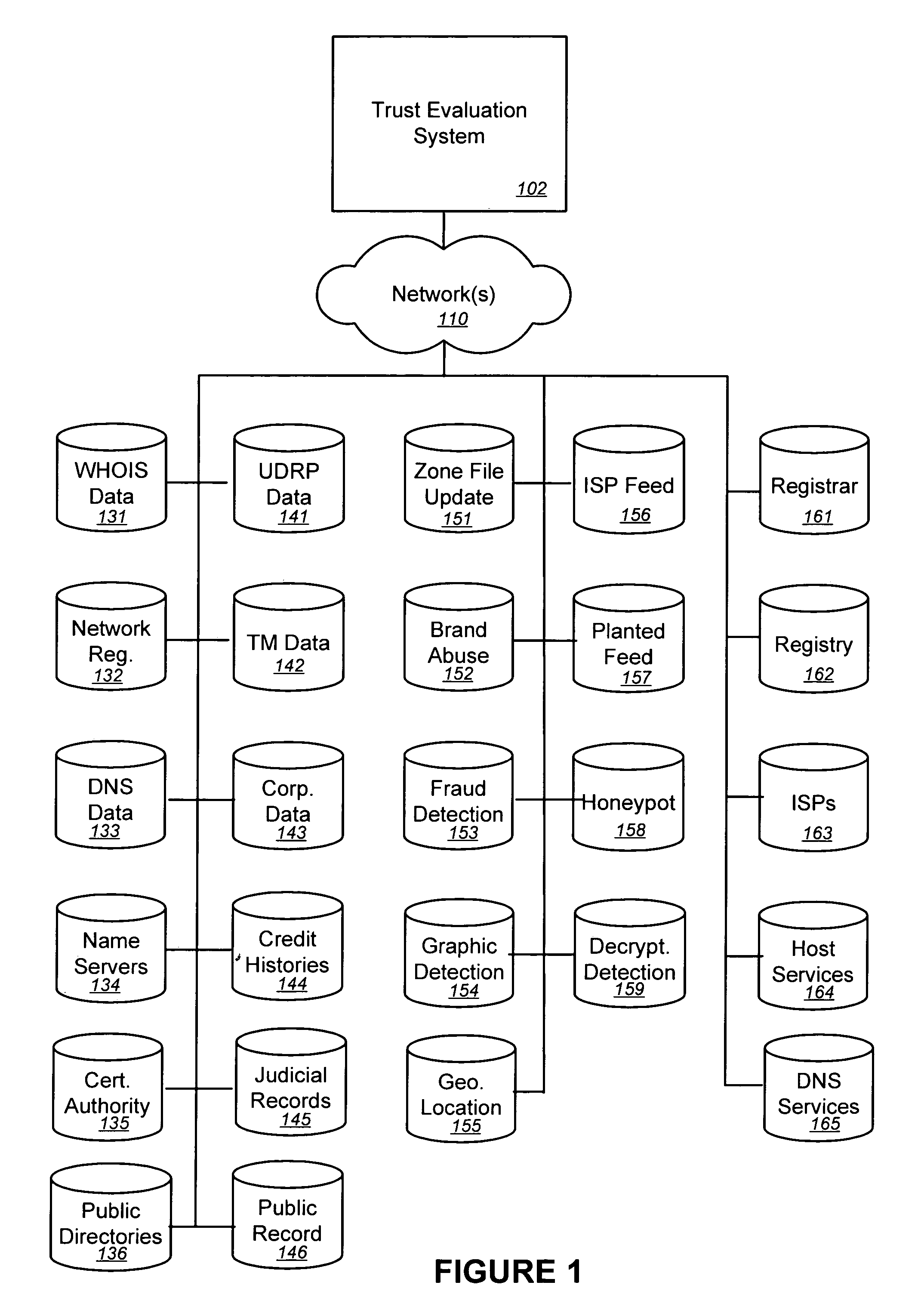
Embodiments of the present invention provide methods, systems, and software for implementing trust policies. Such policies may be implemented in a variety of ways, including at one or more border devices, client computers, etc. In accordance with various embodiments, a communication between a client computer (and / or application) and an online entity may be monitored and / or otherwise detected. The online entity may be identified, and / or one or more trust scores associated with the online entity may be obtained. Based on the trust scores, as well, perhaps as the nature of the communication, an action (such as allowing the communication, blocking the communication, quarantining the communication, warning a user, administrator, etc.) may be taken. In some cases, a trust policy may be consulted to determine what action should be taken with respect to a given communication.
Owner:MARKMONITOR
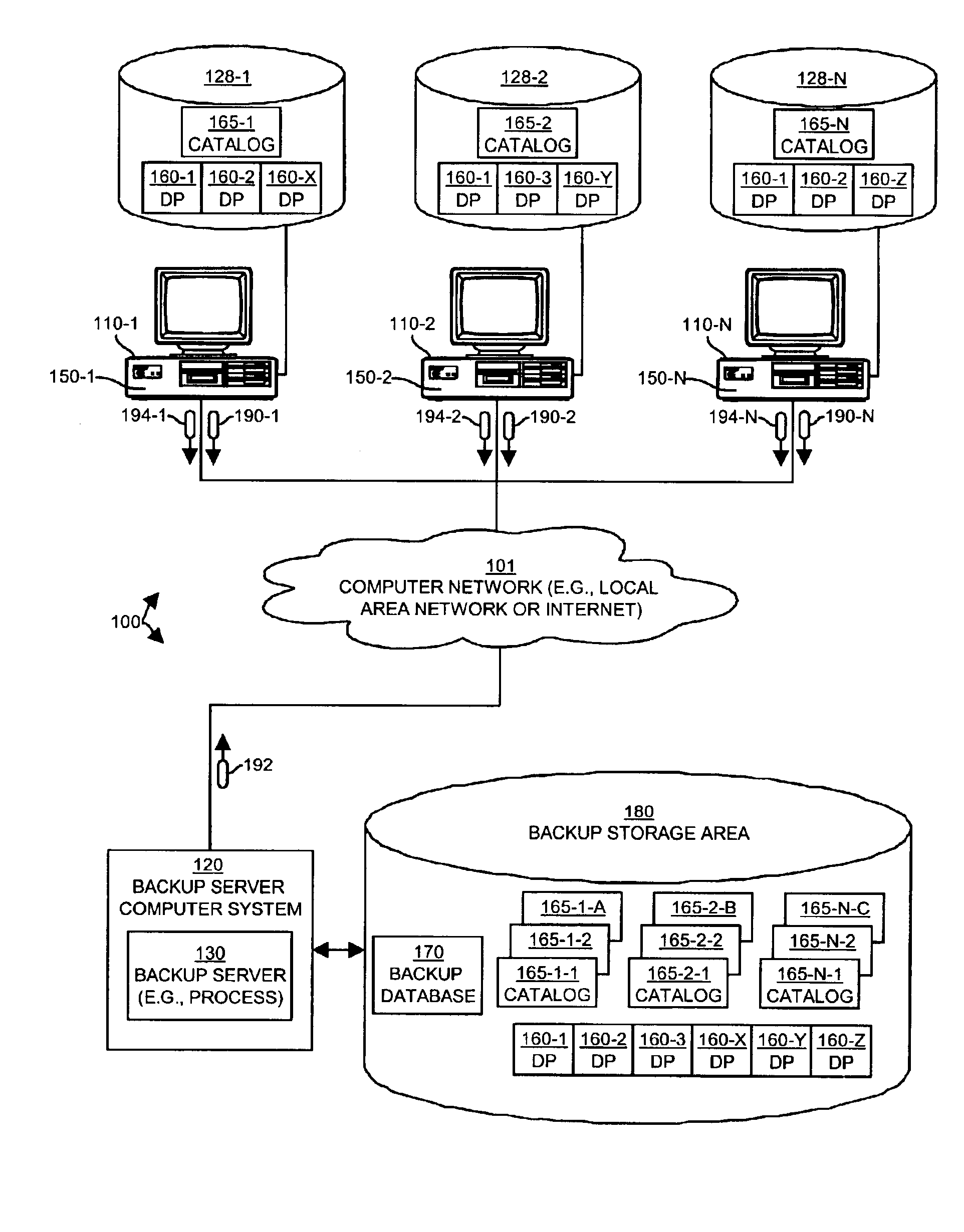
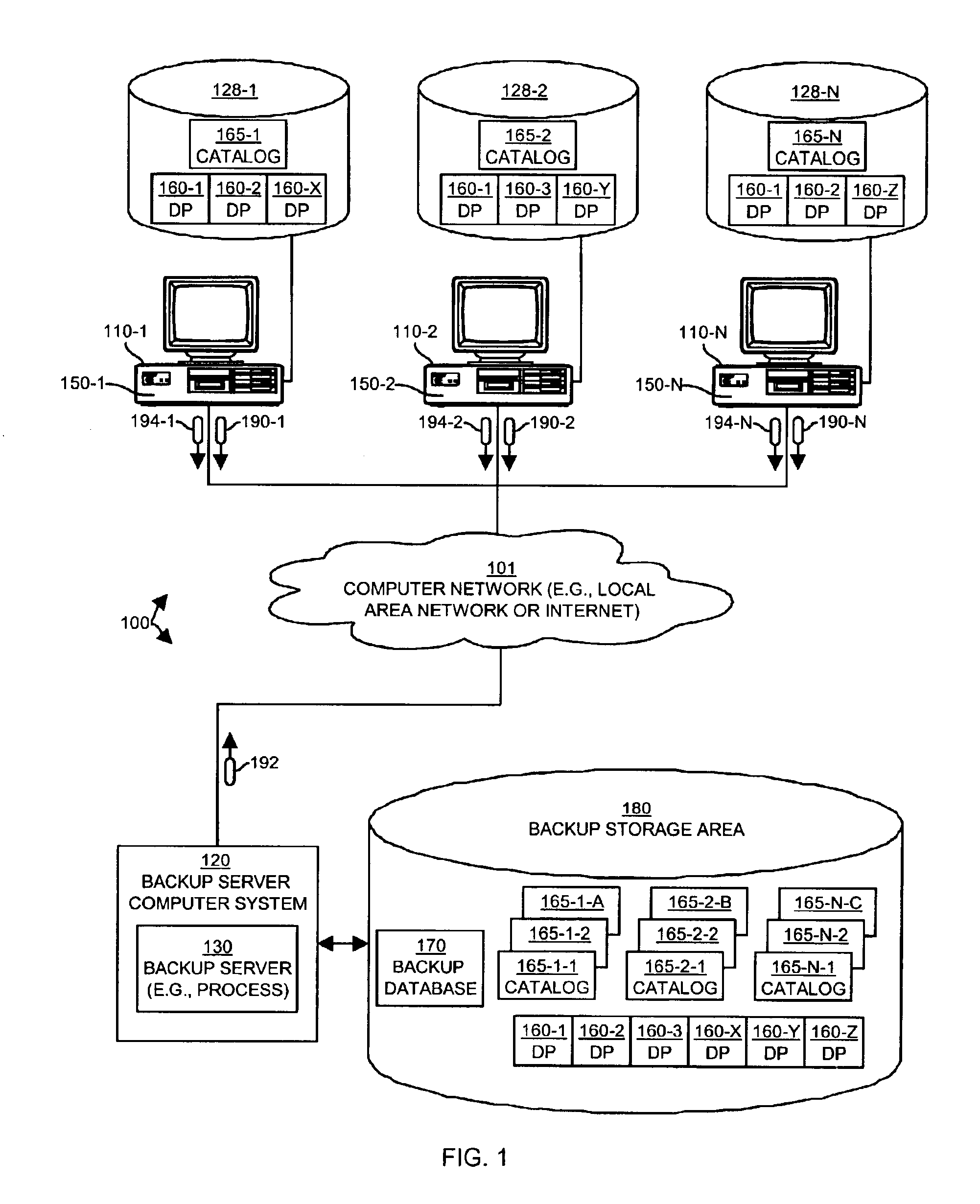
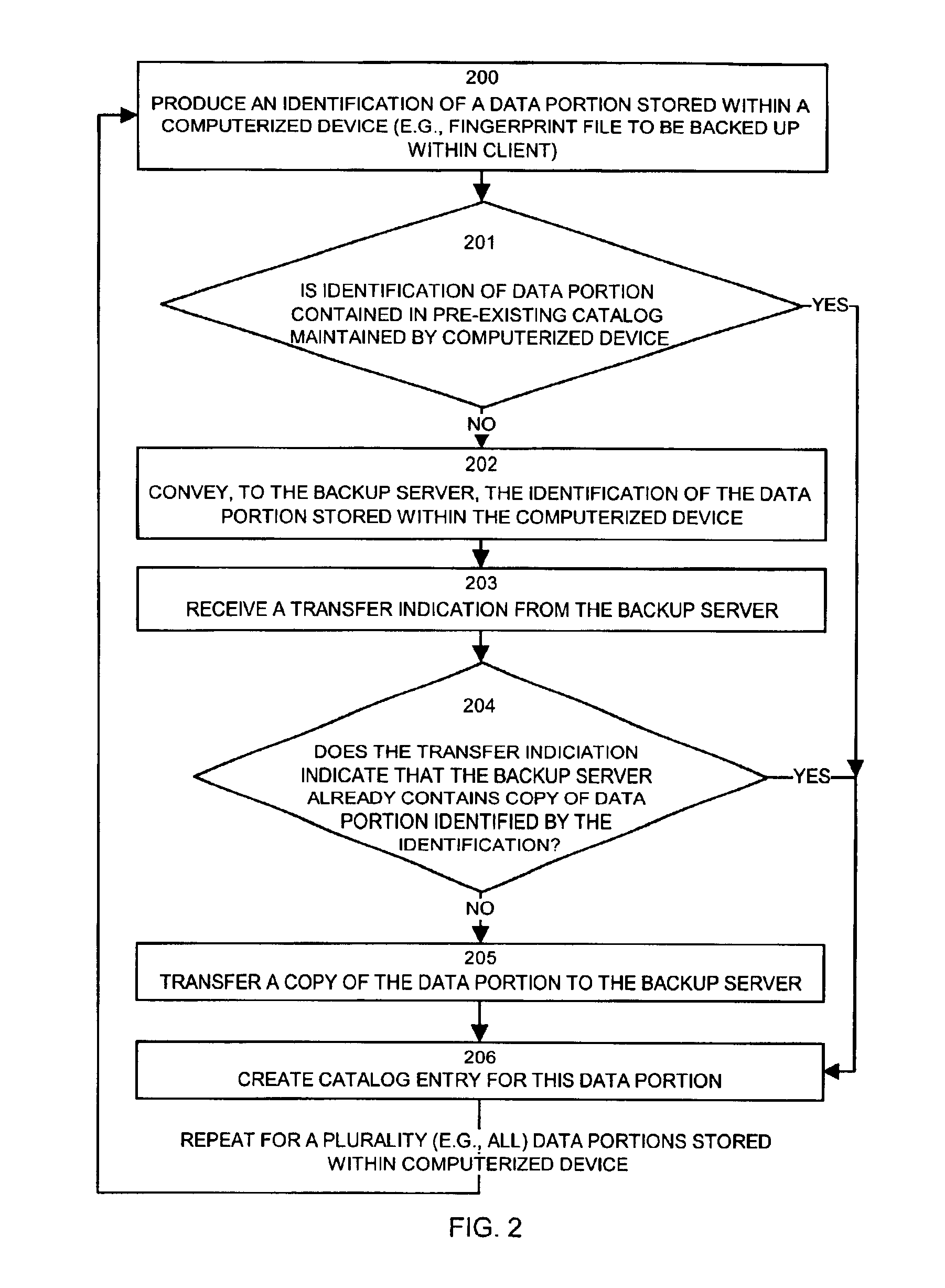
Methods and apparatus for backing up and restoring data portions stored in client computer systems
InactiveUS6865655B1NeedEliminate needData processing applicationsMemory systemsCommunication interfaceClient-side
Mechanisms and techniques operate in a computerized device to perform backup and restore operations on data portions such that if a backup server already has a copy of the content of a data portion, no client computer systems need to transfer a copy of the data portion to the backup server, even if the data portion in those clients has a different name, location, or other attributes. A backup client produces an identification of a data portion stored within a first computerized device to be backed up. The backup client conveys, to a backup server, the identification of the data portion stored within the computerized device and receives, over the communications interface, a transfer indication from the backup server. The backup client determines if the transfer indication indicates that the backup server already contains a copy of the data portion identified by the identification, and if not, the backup client transfers a copy of the data portion from the local storage device to the backup server over the communications interface.
Owner:ORACLE INT CORP
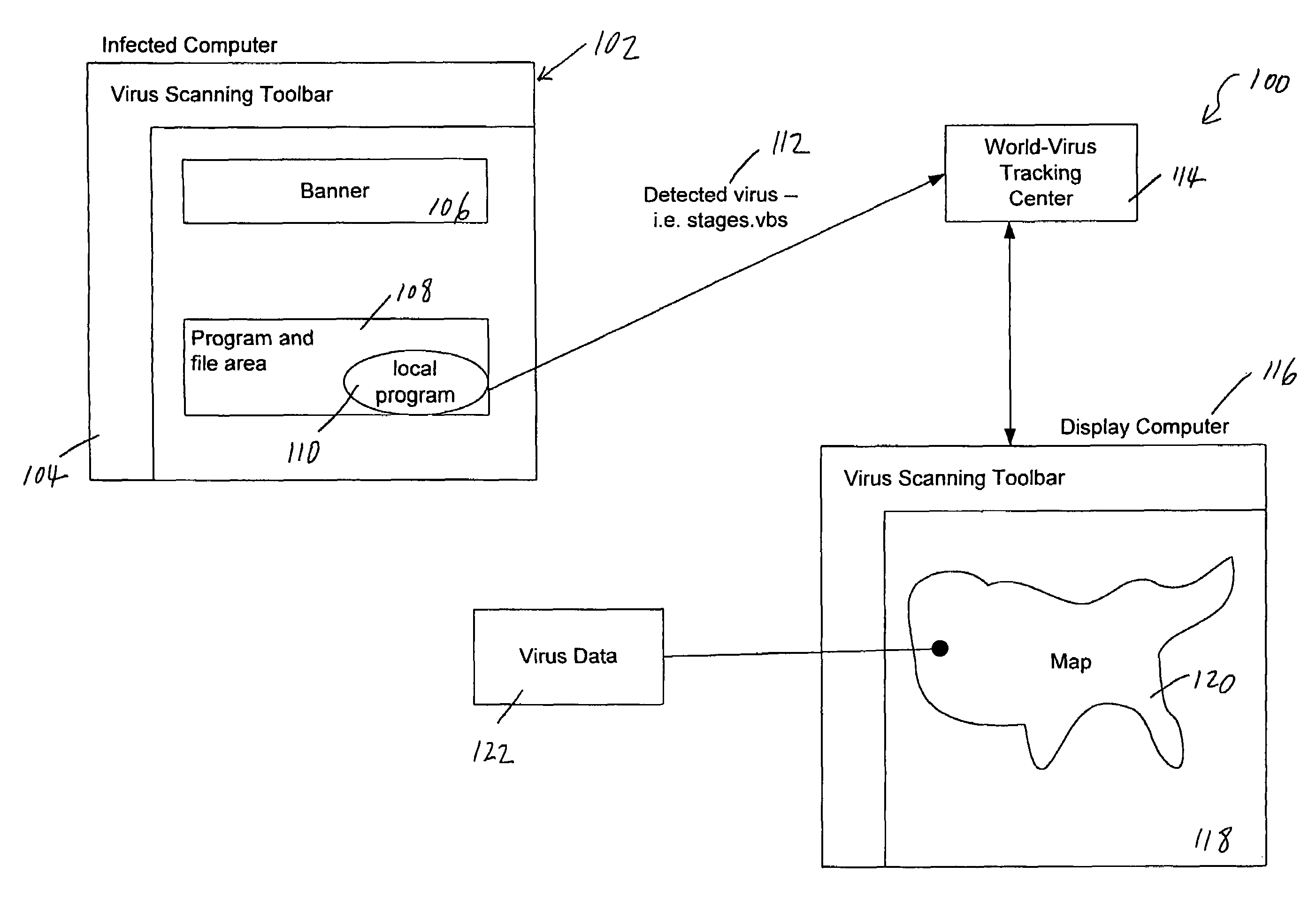
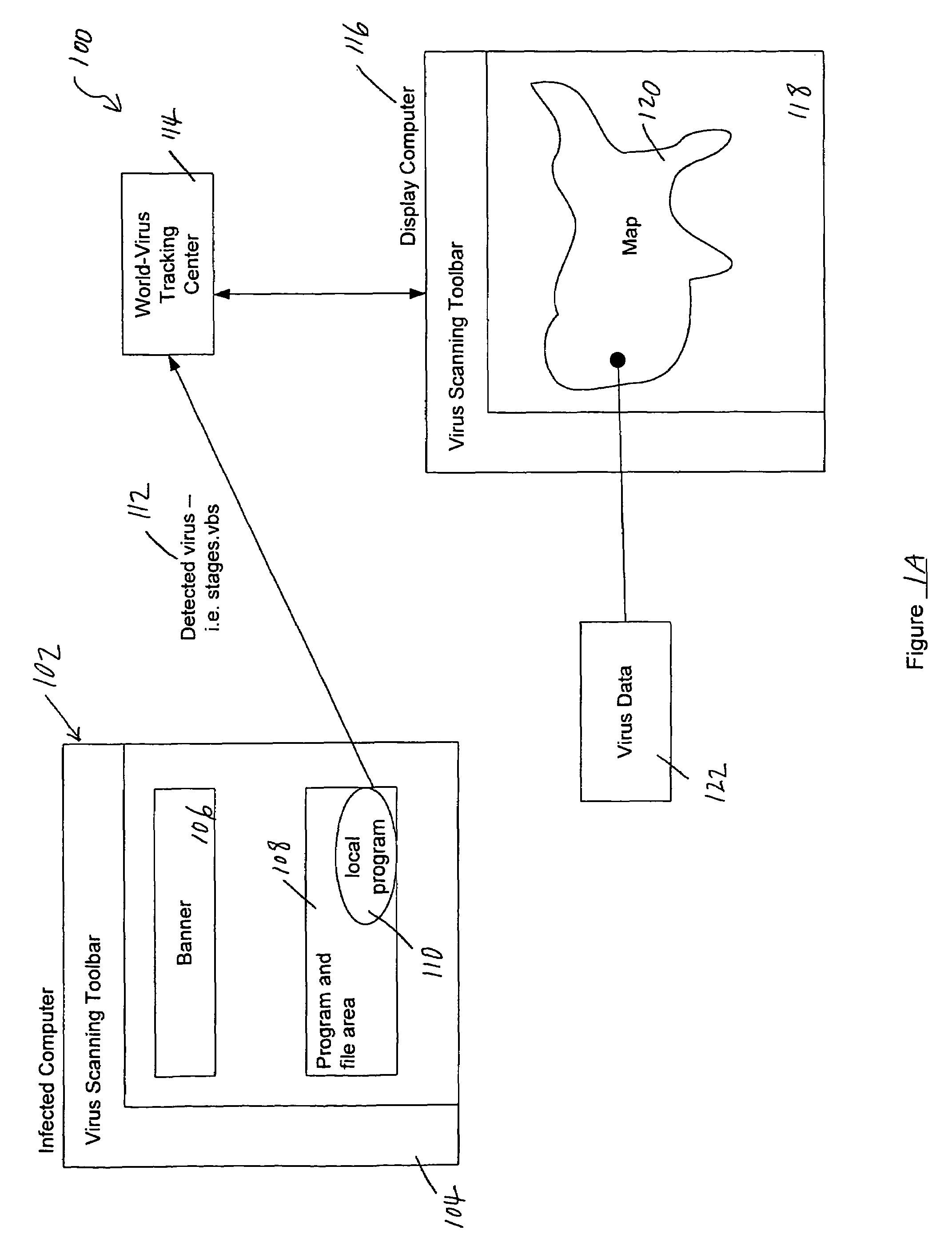
Tracking and reporting of computer virus information
An apparatus and method for providing real-time tracking of virus information as reported from various computers on a distributed computer network. Each client computer on the distributed network contacts an anti-virus scanning site. The site provides a small program or applet that resides in temporary memory of the client computer. The client-user invokes the scan with supplied pattern updates for detecting recent viruses. When the scan has been completed, the user is prompted to supply a country of origin. The name of the virus, its frequency of occurrence, and the country are forwarded as a virus scan log to a virus tracking server, which receives the virus information and thereafter stores it in a database server, which is used to further calculate virus trace display information. A tracking user contacts the virus tracking server and receives map information, which traces the virus activity. The maps show, according to user preference, the names of the viruses encountered in each country, and their frequencies of occurrence.
Owner:TREND MICRO INC
Methods and systems for selecting a method for execution, by a virtual machine, of an application program
ActiveUS20070180450A1Low costReduce difficultyDigital data information retrievalDigital data processing detailsClient-sideClient machine
A method for selecting a method of execution for an application includes the step of receiving credentials. A plurality of applications available to a client machine is enumerated responsive to the received credentials. A request to execute an enumerated application is received. One of a predetermined number of methods for executing the requested application is selected responsive to a policy, the predetermined number of methods including a method for executing the requested application in a computing environment provided by a virtual machine.
Owner:CITRIX SYST INC
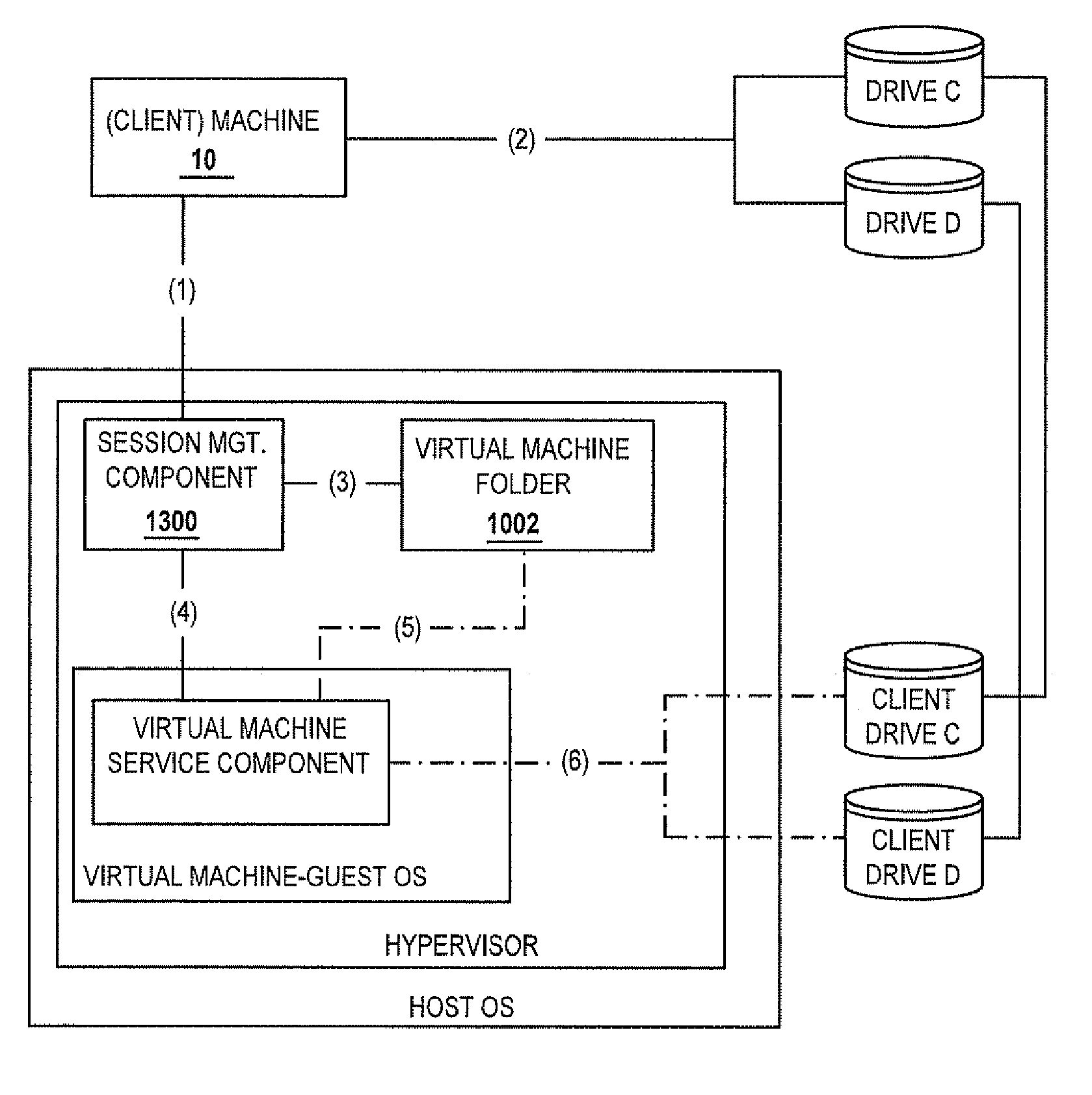
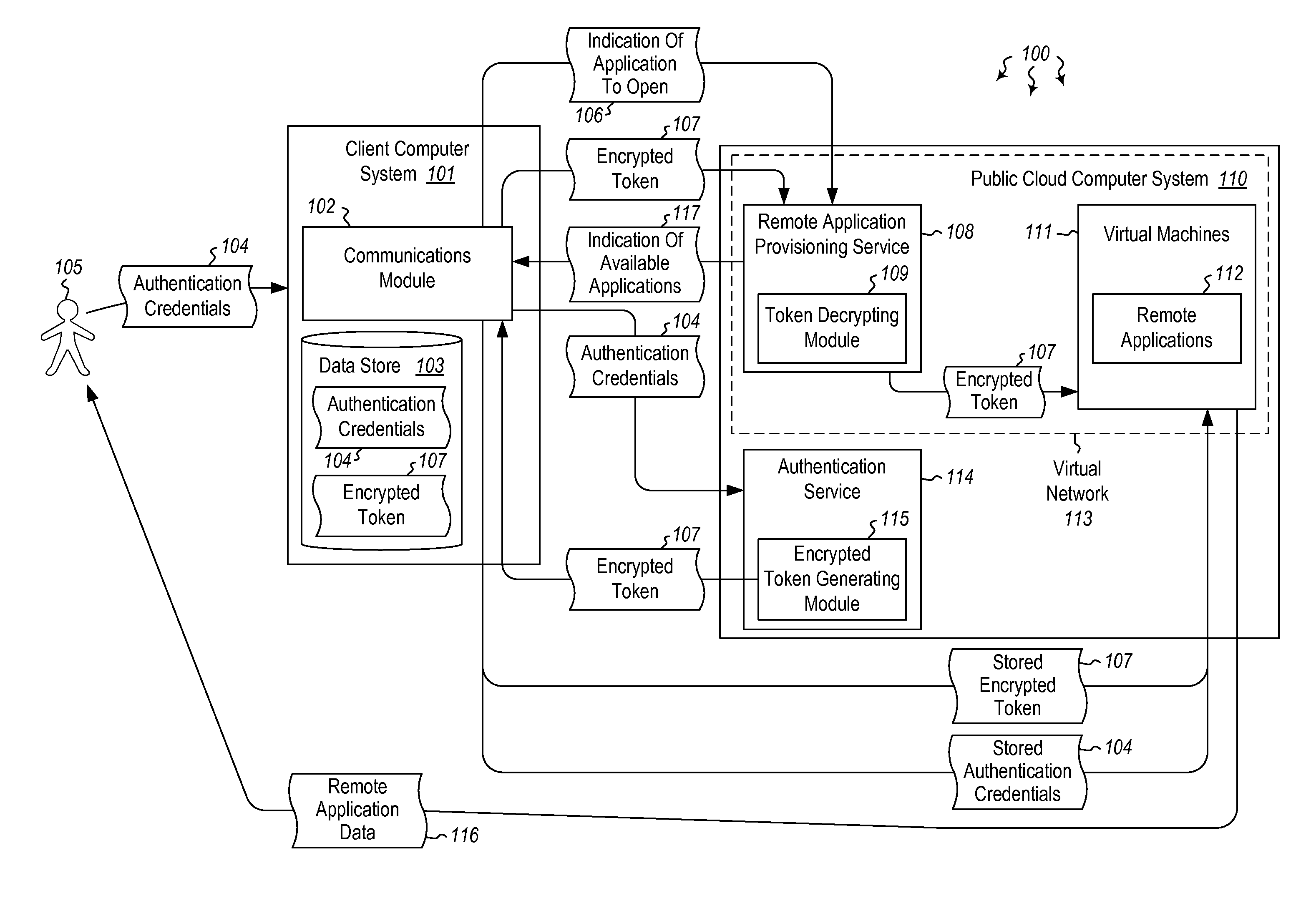
User authentication in a cloud environment
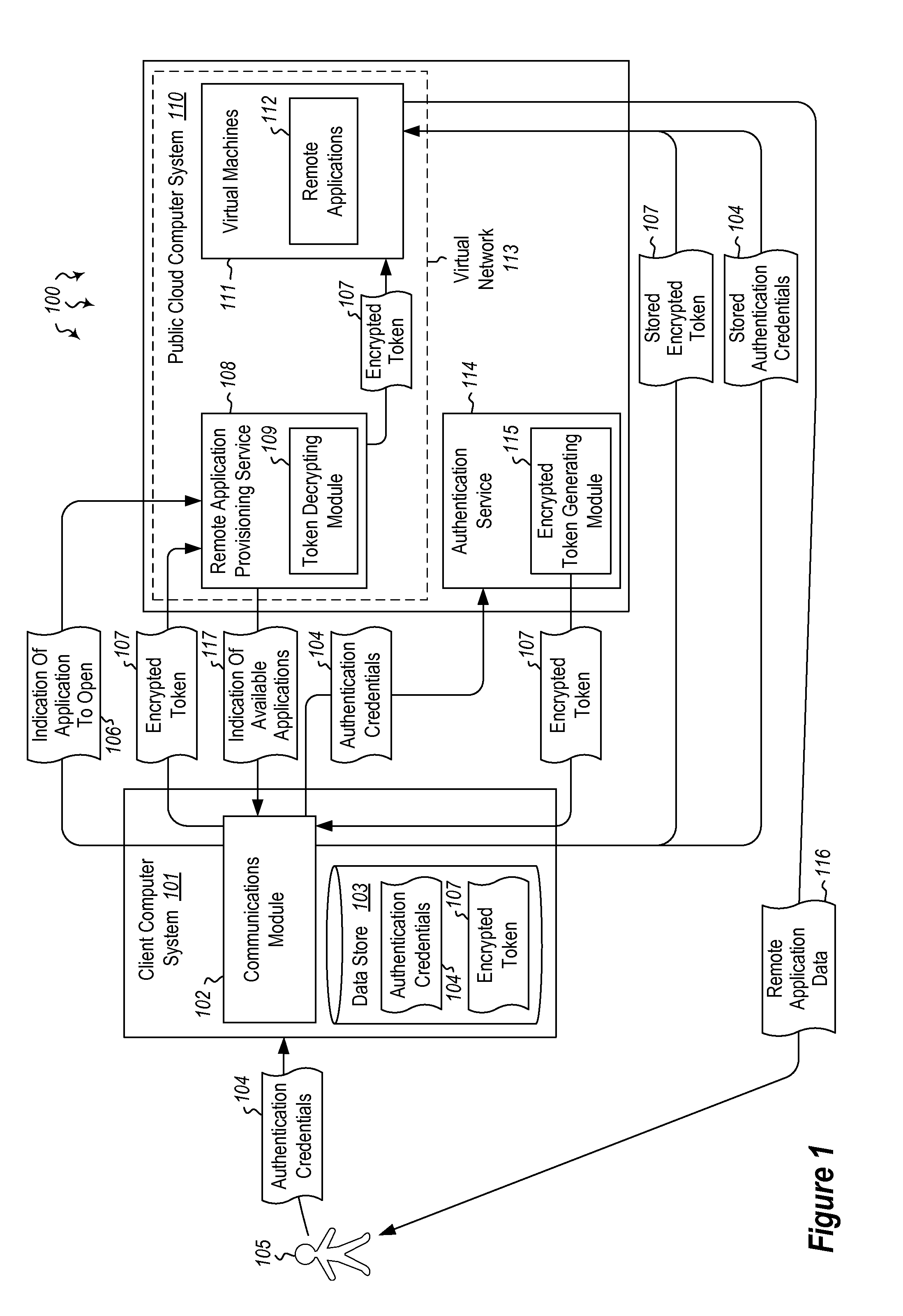
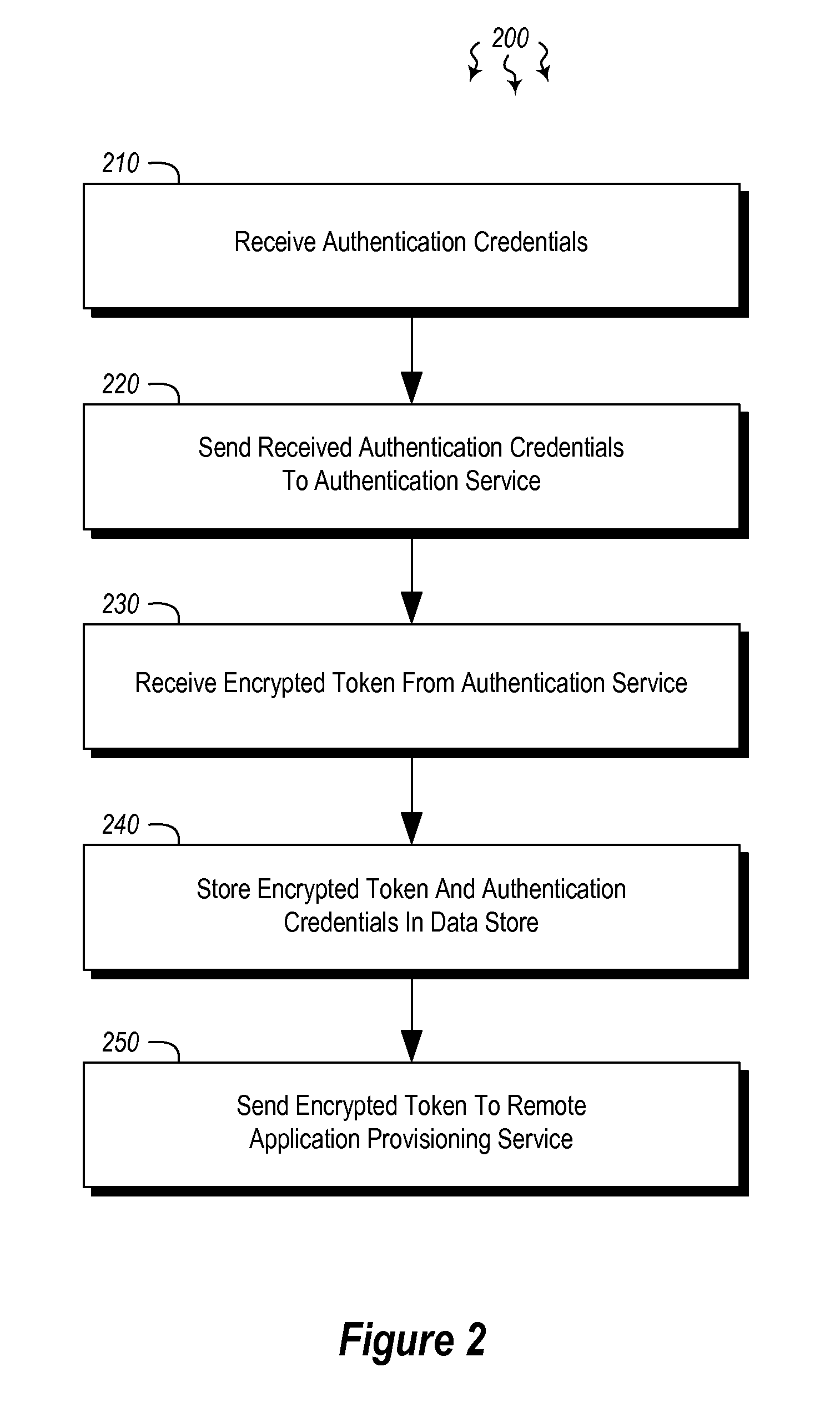
ActiveUS20140373126A1Well formedDigital data processing detailsComputer security arrangementsInternet Authentication ServiceData memory
Embodiments are directed to authenticating a user to a remote application provisioning service. In one scenario, a client computer system receives authentication credentials from a user at to authenticate the user to a remote application provisioning service that provides virtual machine-hosted remote applications. The client computer system sends the received authentication credentials to an authentication service, which is configured to generate an encrypted token based on the received authentication credentials. The client computer system then receives the generated encrypted token from the authentication service, stores the received encrypted token and the received authentication credentials in a data store, and sends the encrypted token to the remote application provisioning service. The encrypted token indicates to the remote application provisioning service that the user is a valid user.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com