Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
9130 results about "Data memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
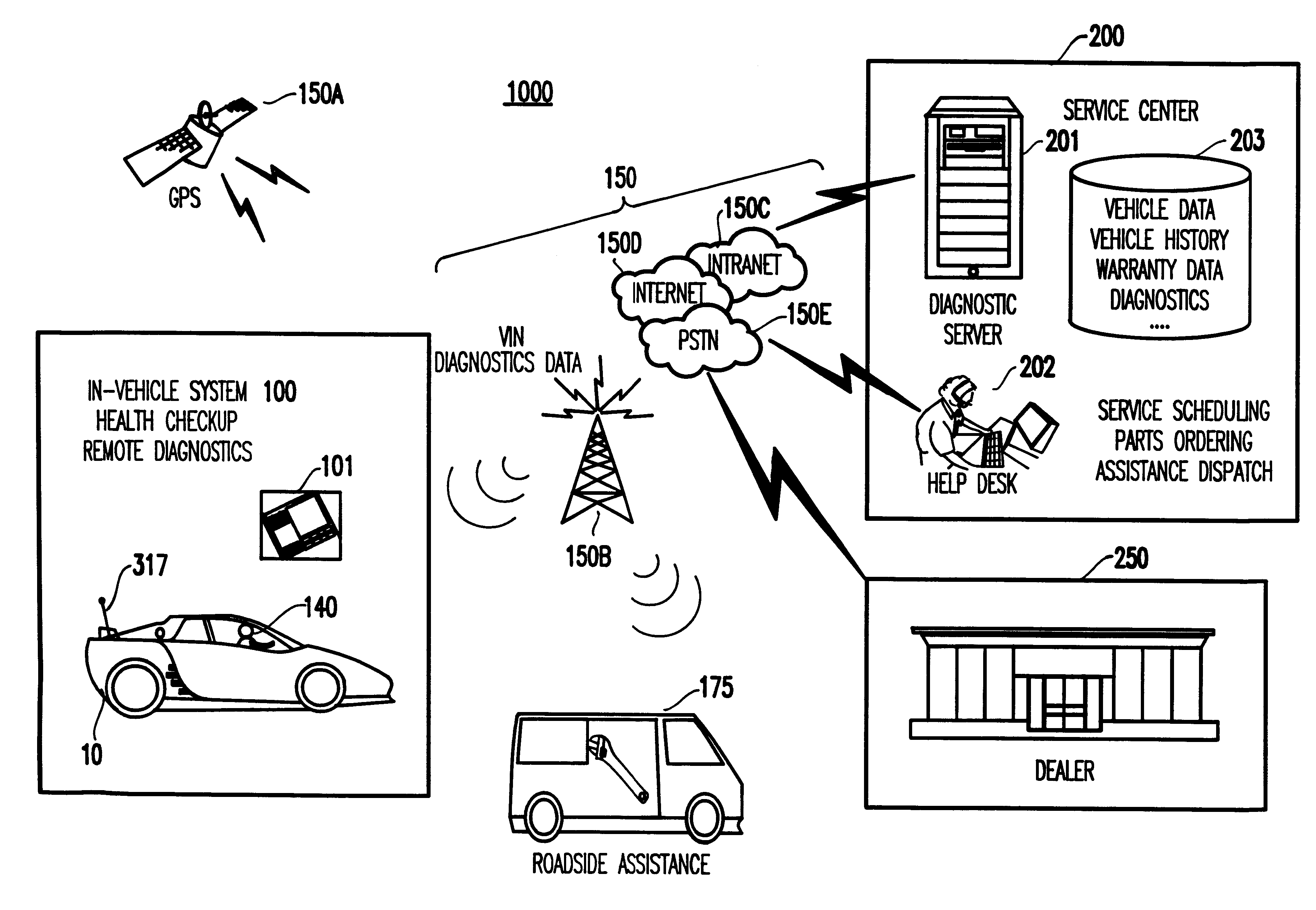
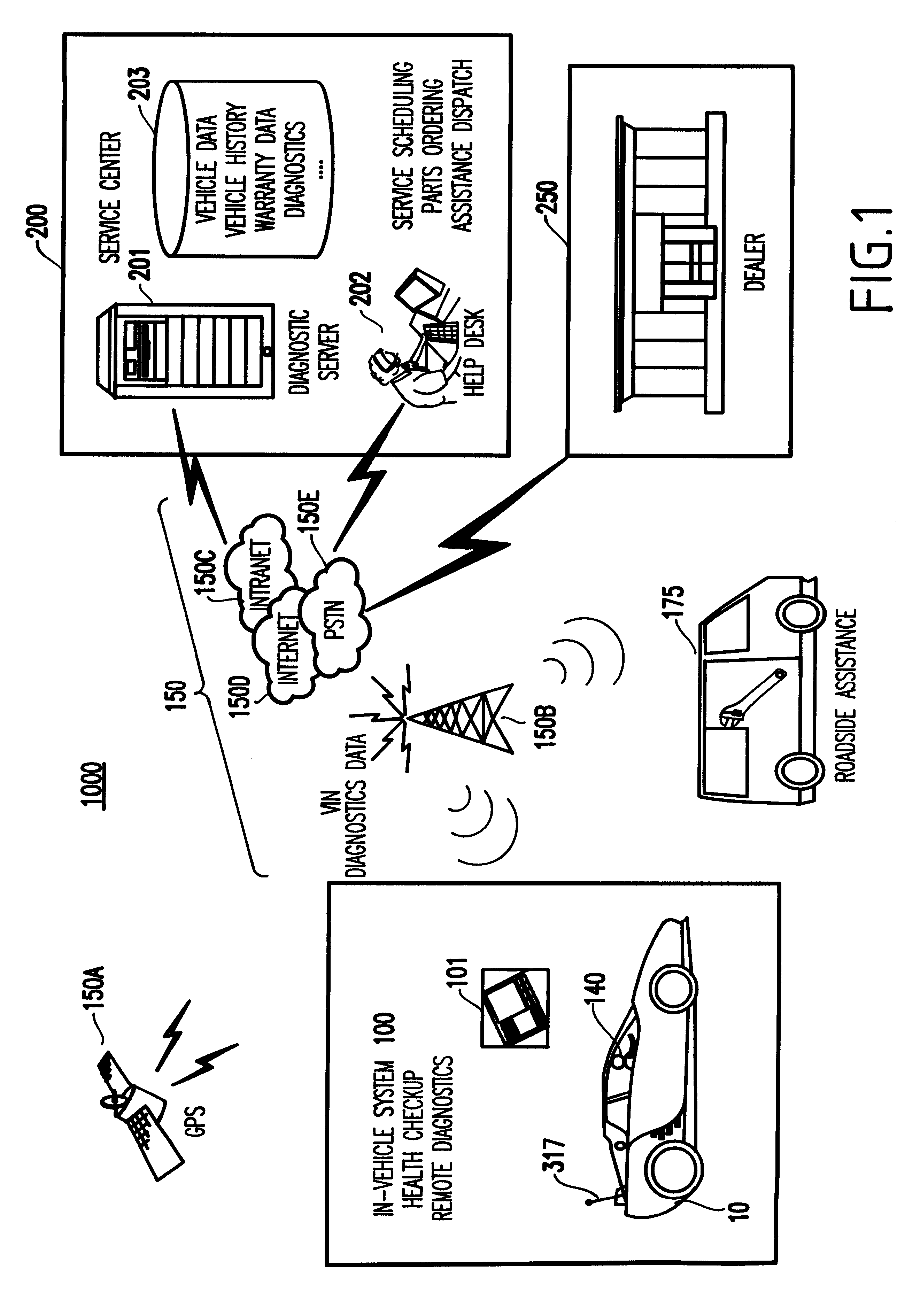
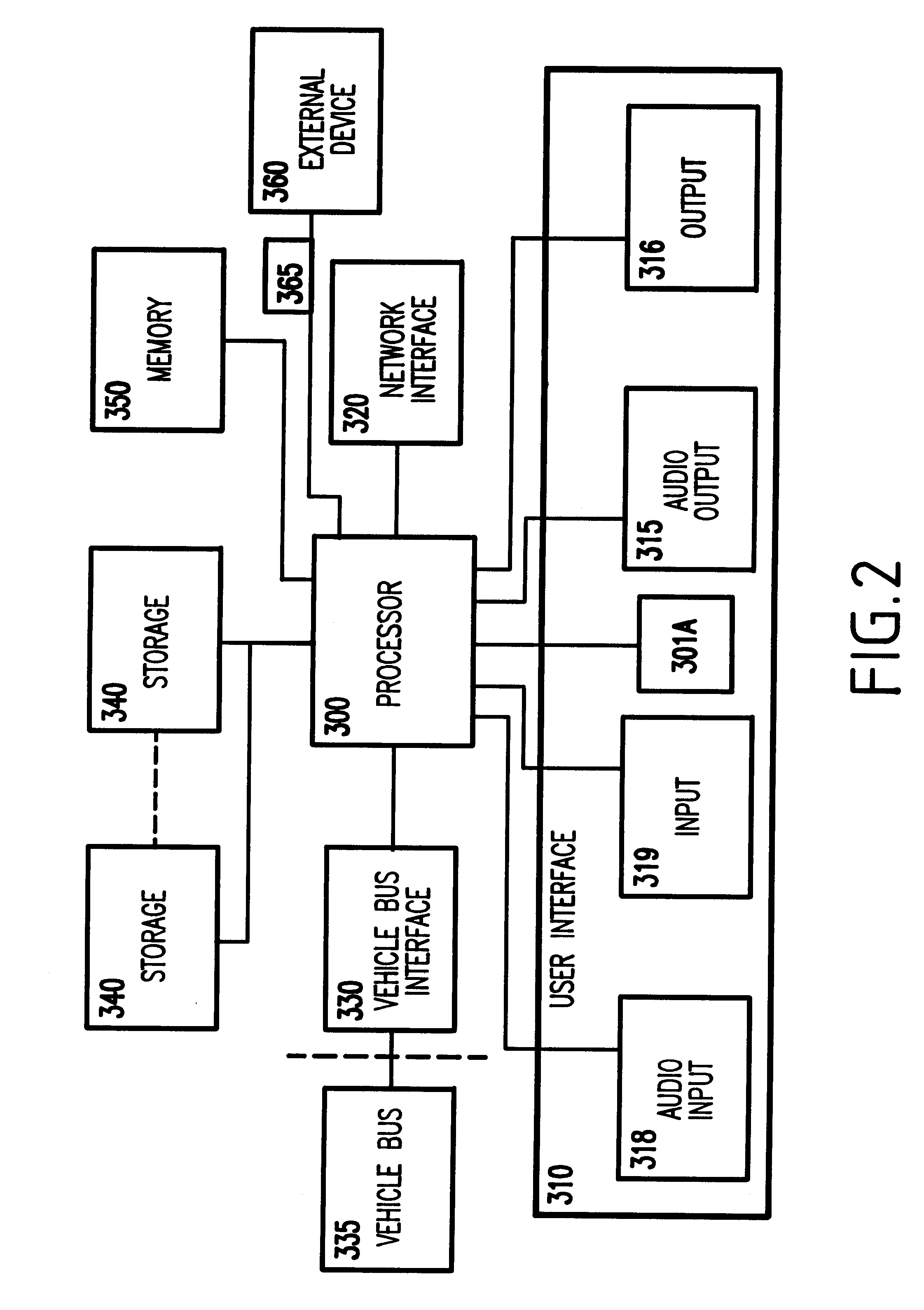
System and method for vehicle diagnostics and health monitoring
InactiveUS6330499B1Vehicle testingRegistering/indicating working of vehiclesSession managementCommunications system
A system and method for vehicle diagnostic and health monitoring includes a client computer device within the vehicle, coupled to the vehicle's monitoring systems, for data management, remote session management and user interaction, a communication system, coupled to the client computer device, for providing remote communication of data including data derived from internal monitoring systems of the vehicle, and a remote service center including a vehicle data store, a server computer, a diagnostic engine, and a communicator for communicating the results of analysis of vehicle information to the client computer device via the communication system.
Owner:CARRUM TECH LLC
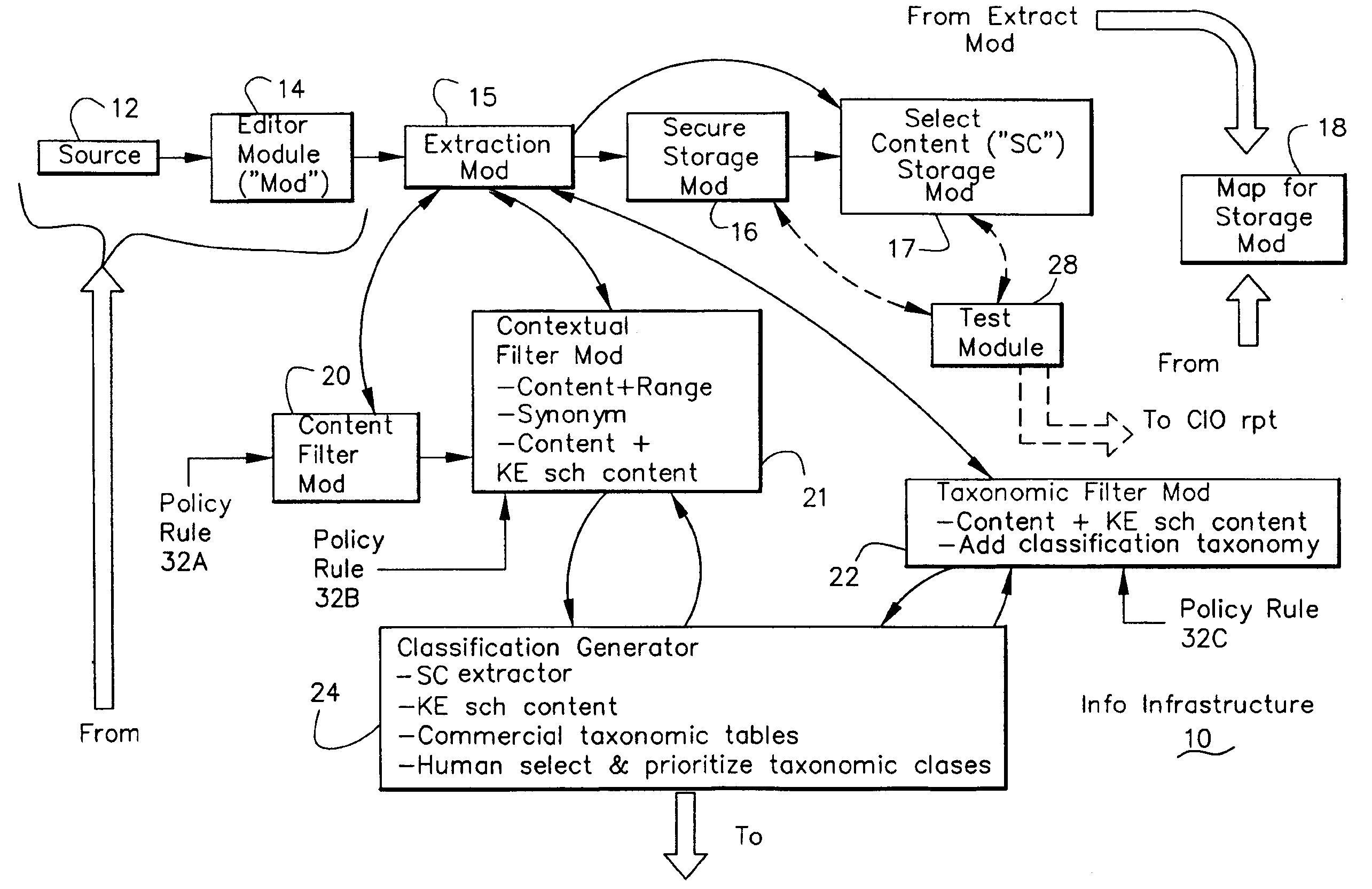
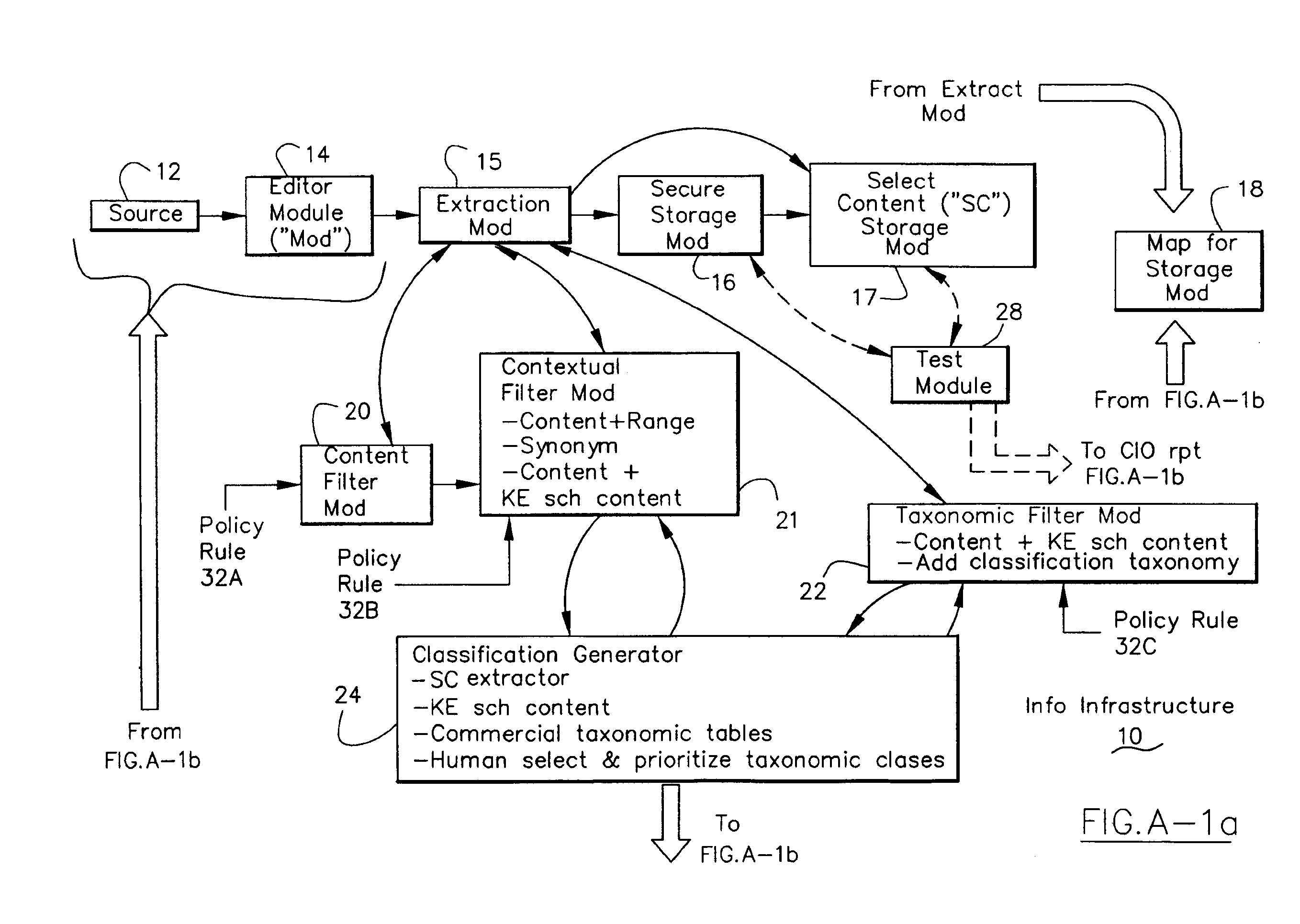
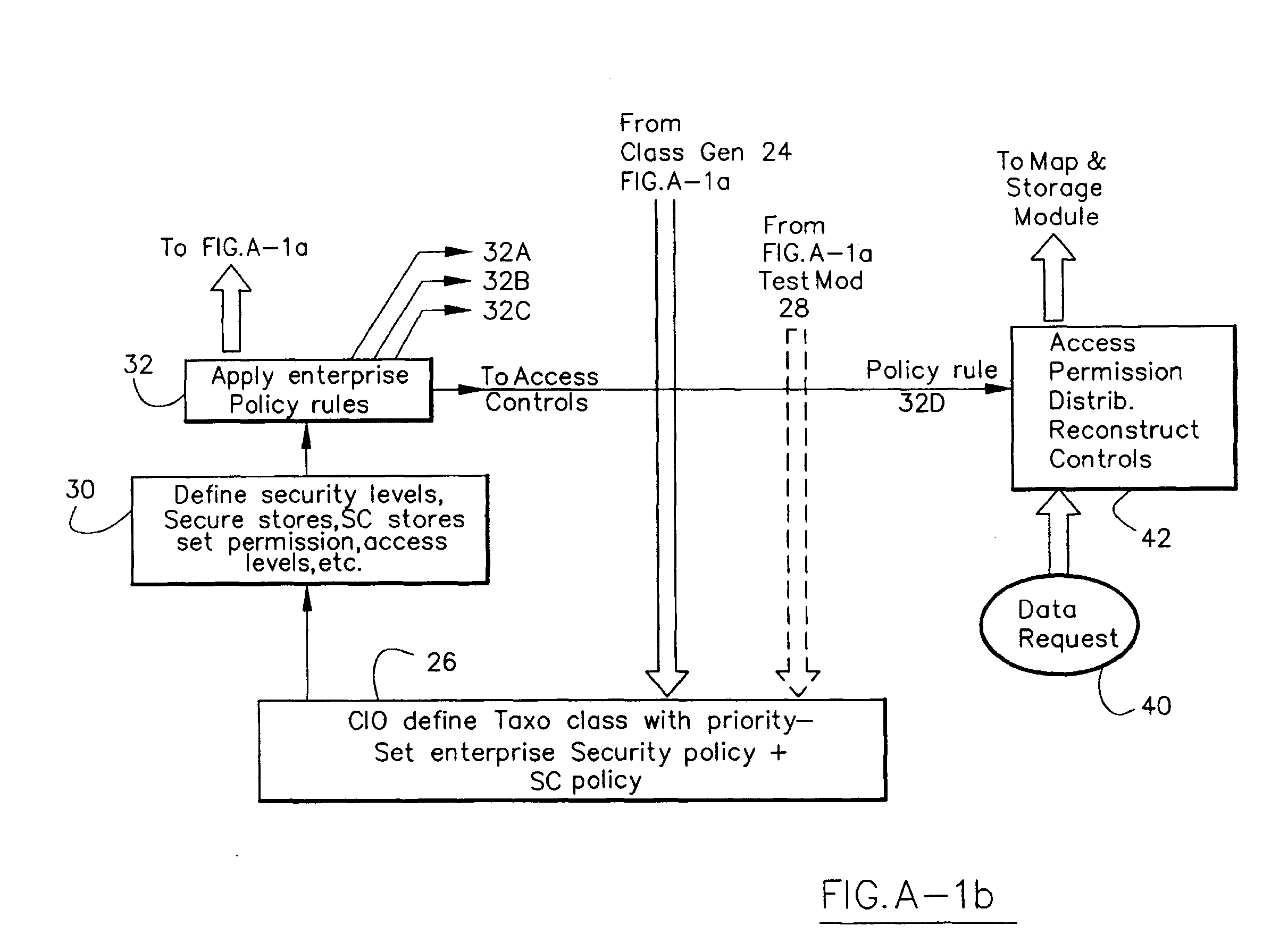
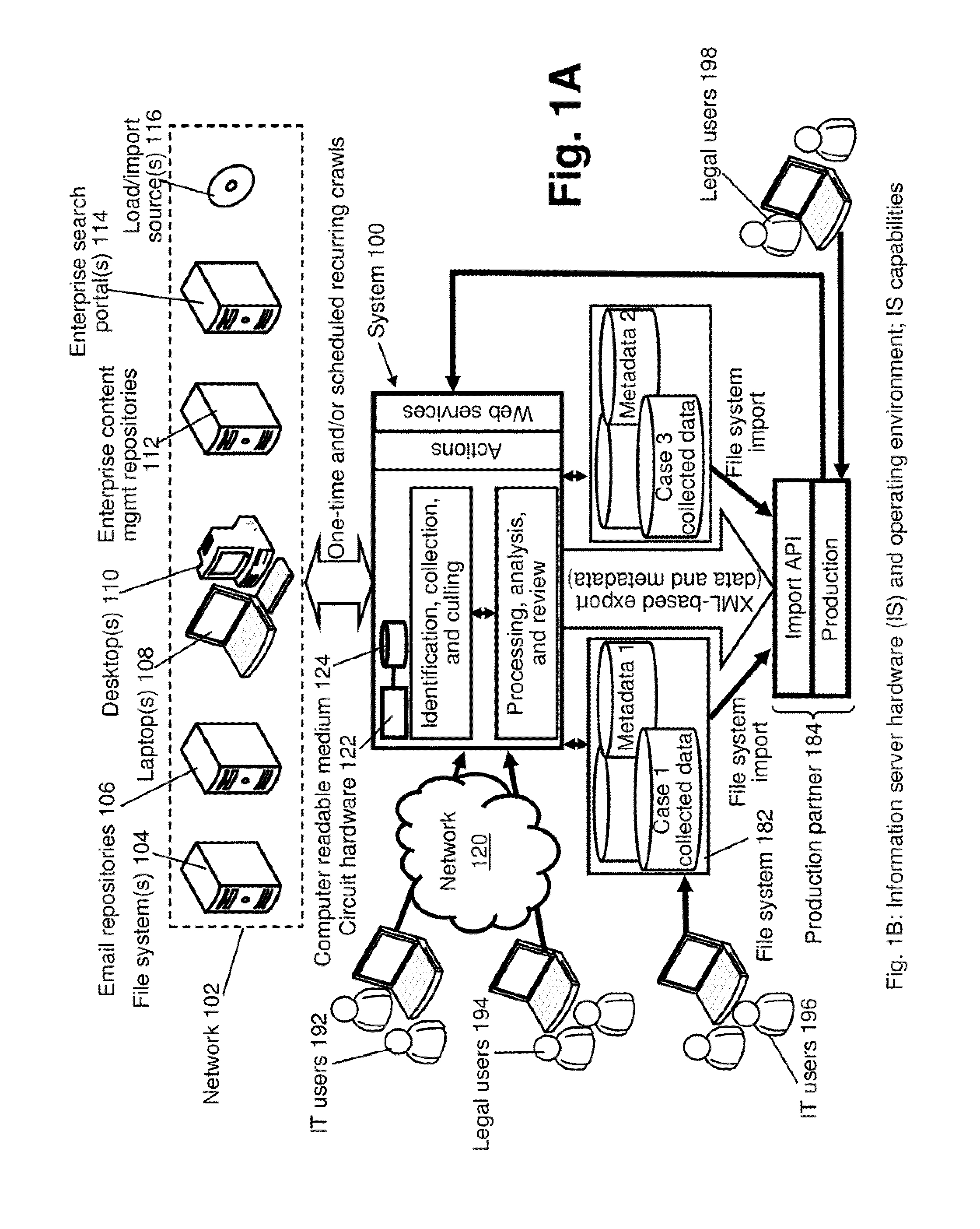
Information Infrastructure Management Tools with Extractor, Secure Storage, Content Analysis and Classification and Method Therefor
The present invention is a method of organizing and processing data in a distributed computing system. The invention is also implemented as a computer program on a computer medium and as a distributed computer system. Software modules can be configured as hardware. The method and system organizes select content which is important to an enterprise operating said distributed computing system. The select content is represented by one or more predetermined words, characters, images, data elements or data objects. The computing system has a plurality of select content data stores for respective ones of a plurality of enterprise designated categorical filters which include content-based filters, contextual filters and taxonomic classification filters, all operatively coupled over a communications network. A data input is processed through at least one activated categorical filter to obtain select content, and contextually associated select content and taxonomically associated select content as aggregated select content. The aggregated select content is stored in the corresponding select content data store. A data process from the group of data processes including a copy process, a data extract process, a data archive process, a data distribution process and a data destruction process is associated with the activated categorical filter and the method and system applies the associated data process to a further data input based upon a result of that further data being processed by the activated categorical filter utilizing the aggregated select content data.
Owner:DIGITAL DOORS
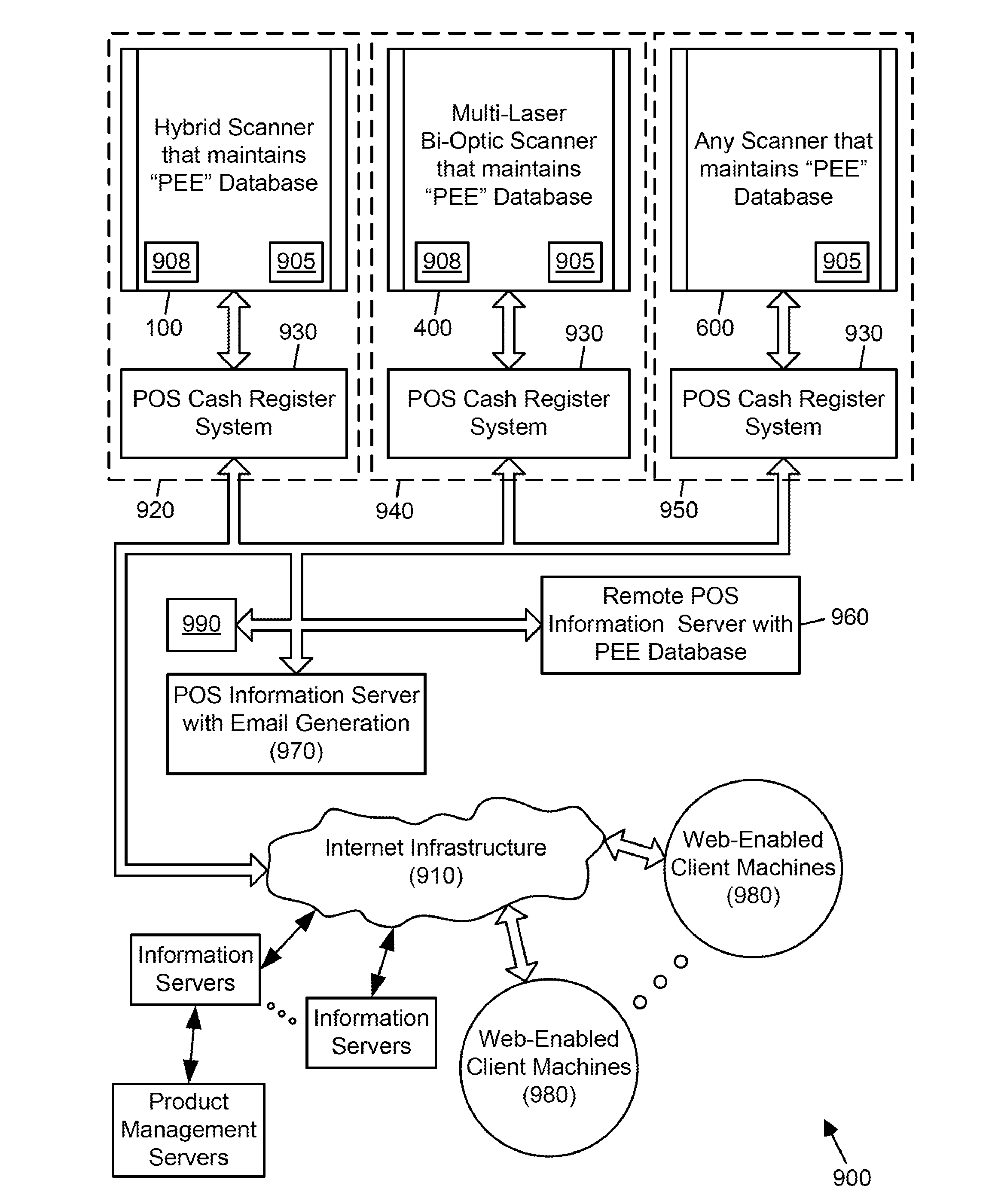
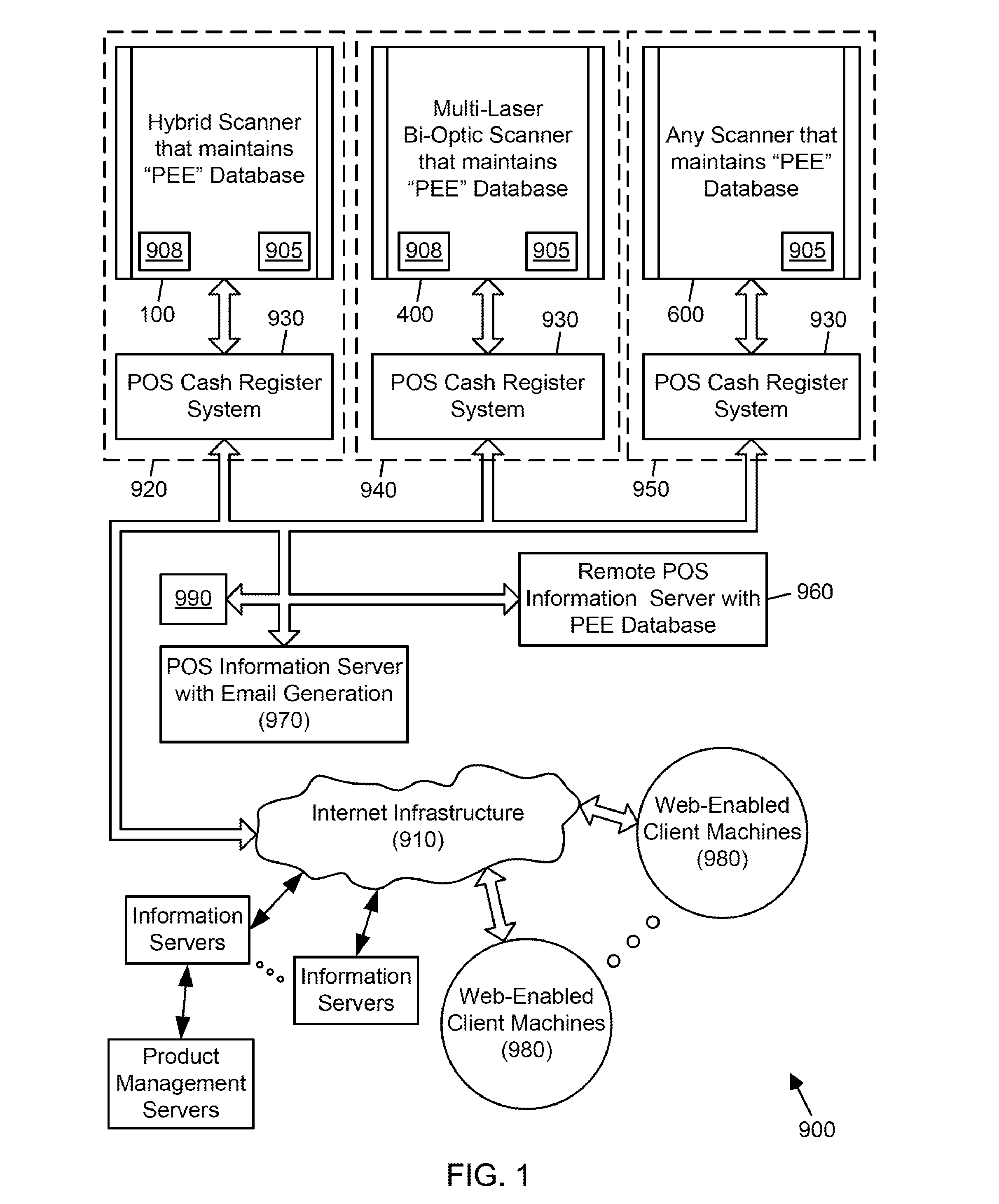
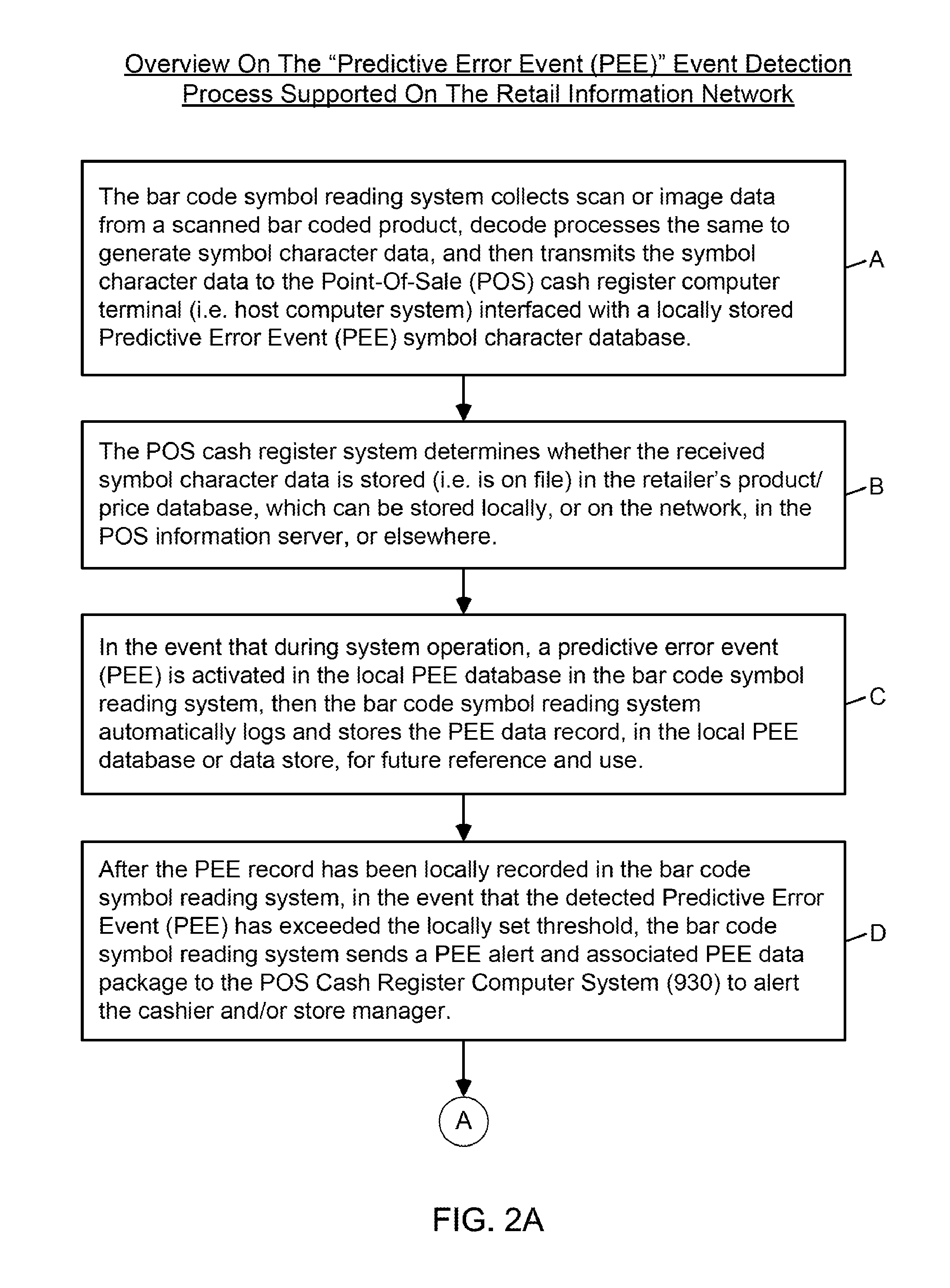
Symbol reading system having predictive diagnostics
ActiveUS9022288B2Improve the level ofEasy maintenanceTesting sensing arrangementsSensing by electromagnetic radiationInformation networksBarcode
A retail information network includes one or more POS scanning and checkout systems, each including (i) a bar code symbol reading subsystem, and (ii) a cash register computer subsystem interfaced with the bar code symbol reading subsystem and a network infrastructure, and each having access to product and price data maintained in a product / price database. The bar code symbol reading subsystem includes a local predictive error event (PEE) data store for logging and storing predictive error events (PEEs) detected within the bar code symbol reading system, wherein said PEEs are subsequently sent to POS information servers used to create predictive error alerts (PEAs) and corresponding instructions to maintain and / or repair certain aspects of the bar code symbol reading system.
Owner:METROLOGIC INSTR
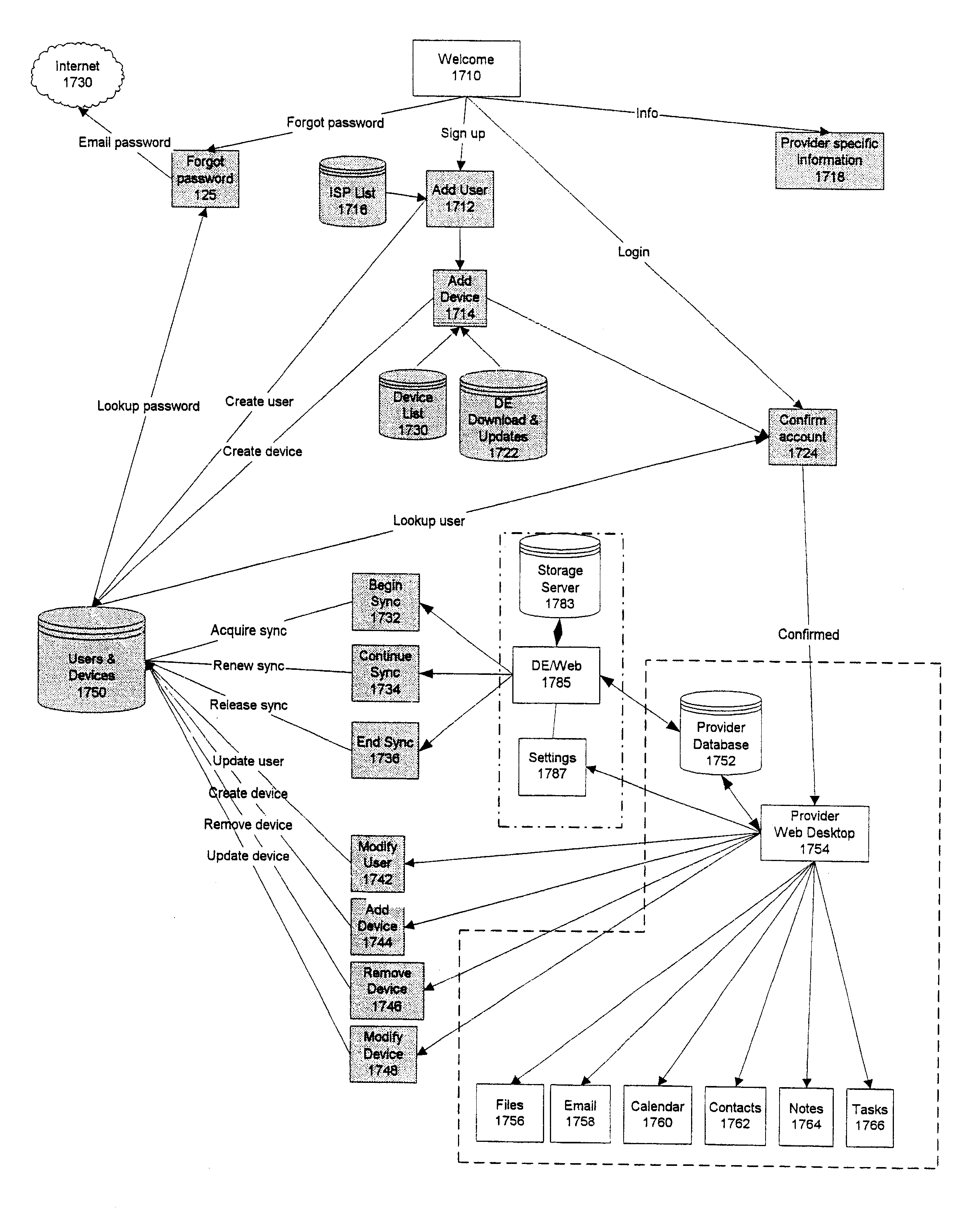
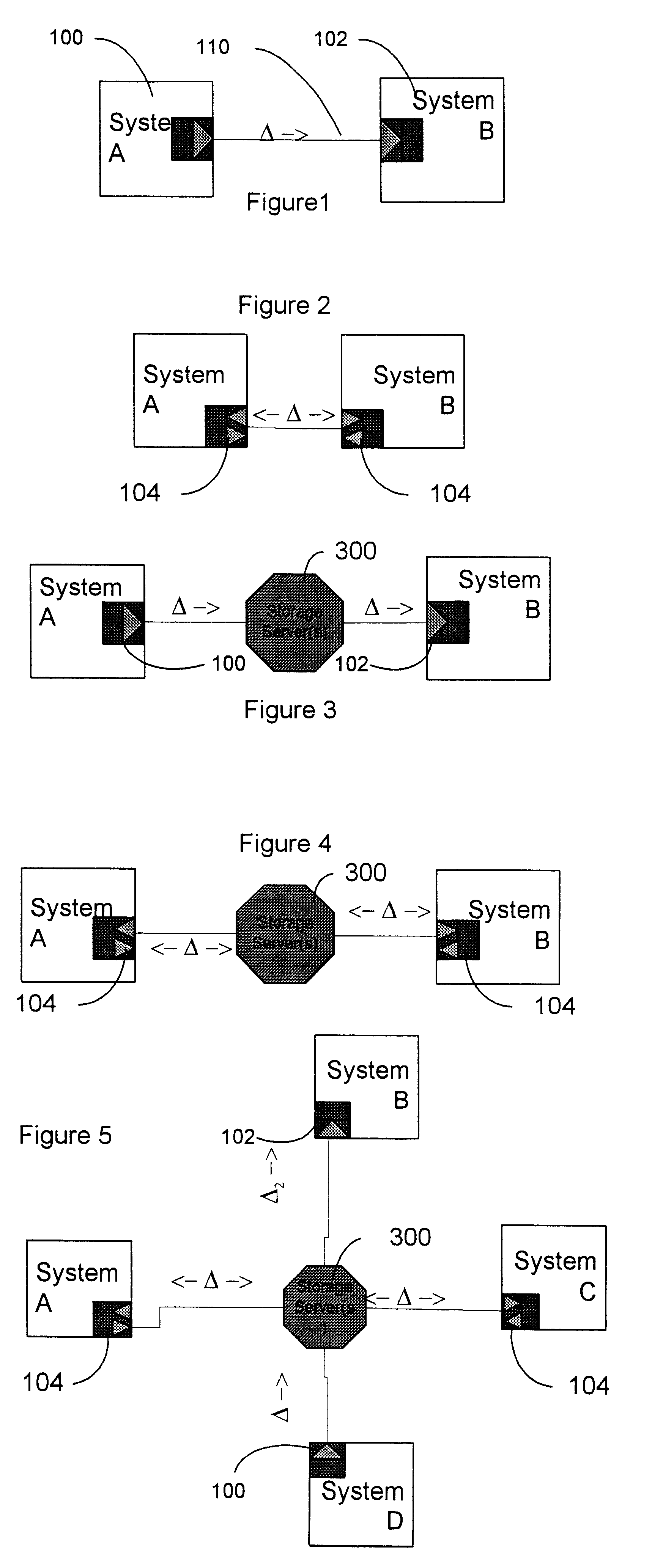
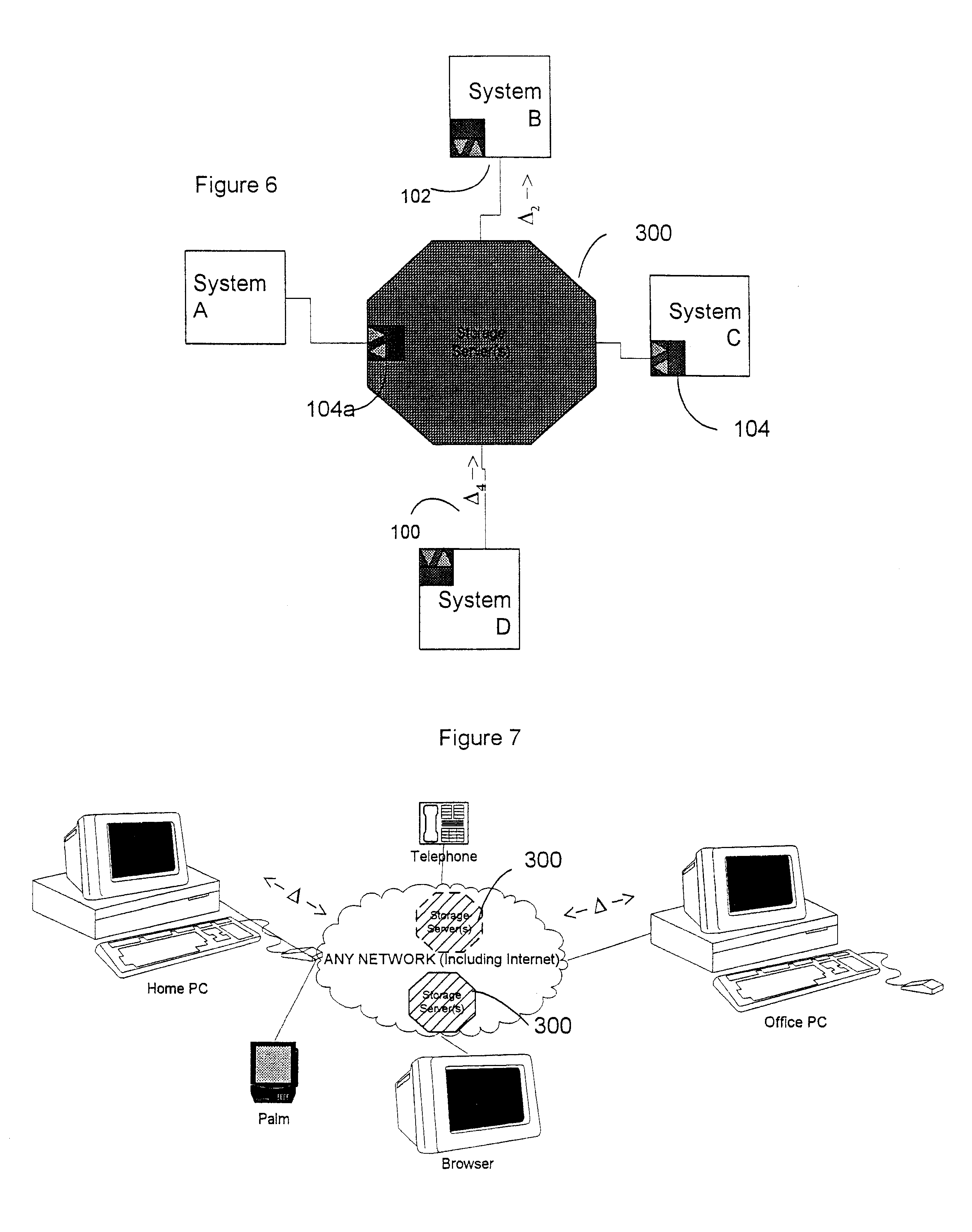
Data transfer and synchronization system
InactiveUS6671757B1Data processing applicationsUnauthorized memory use protectionThe InternetData memory
A system and method for synchronizing devices which can couple to the Internet, or any network. The system includes a first sync engine on the first system interfacing with data on the first system to provide difference information. A data store is coupled to the network and in communication with the first and second systems. A second sync engine is provided on the second system coupled to receive the difference information from the data store via the network, and interface with data on the second system to update said data on the second system with said difference information. Difference information is transmitted to the data store by the first sync engine and received from the data store from the second sync engine.
Owner:SYNCHRONOSS TECH
Rental/car-share vehicle access and management system and method
ActiveUS20130317693A1Reduce the time required for installationImprove reliabilityVehicle testingTicket-issuing apparatusMobile appsTablet computer
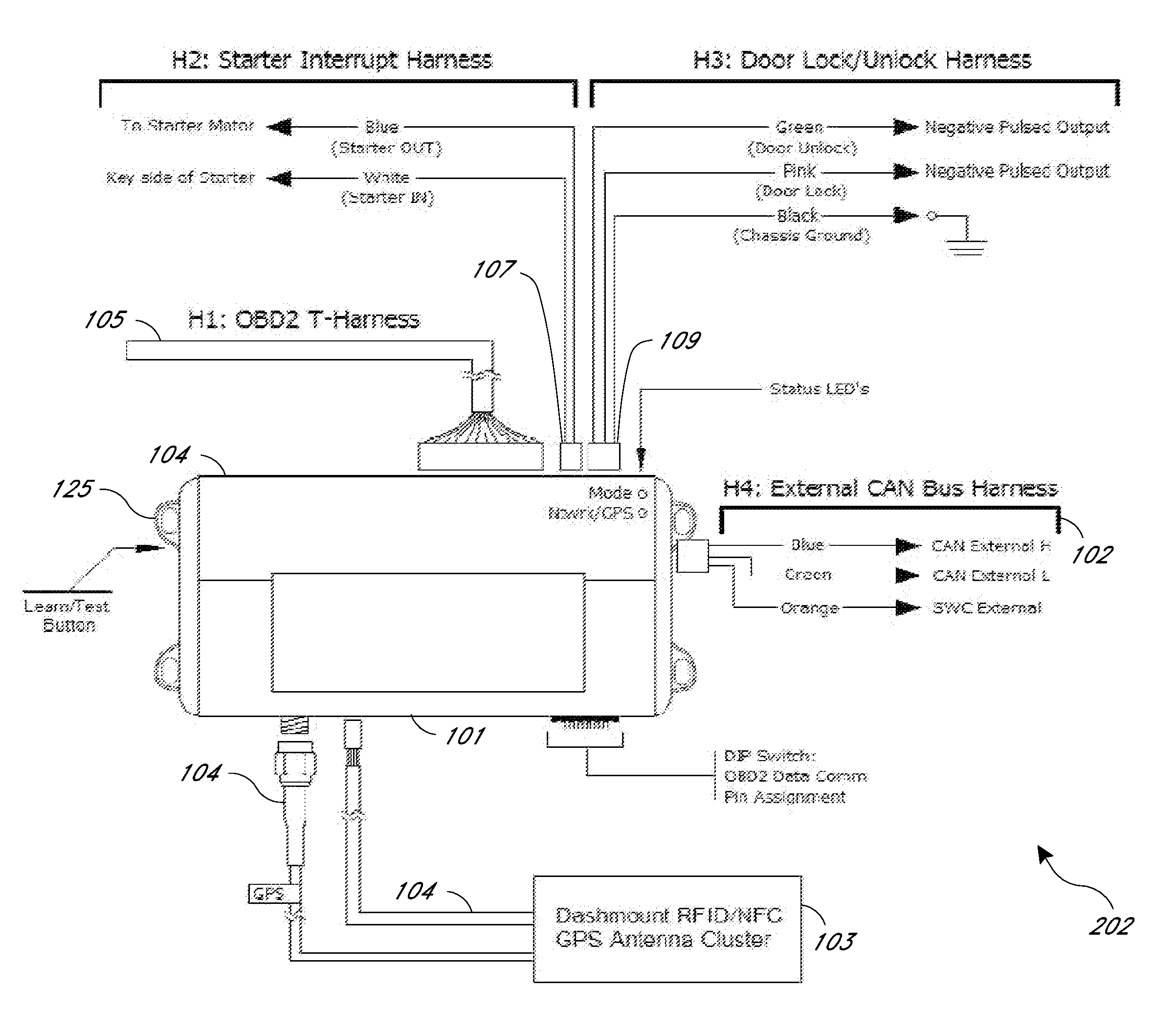
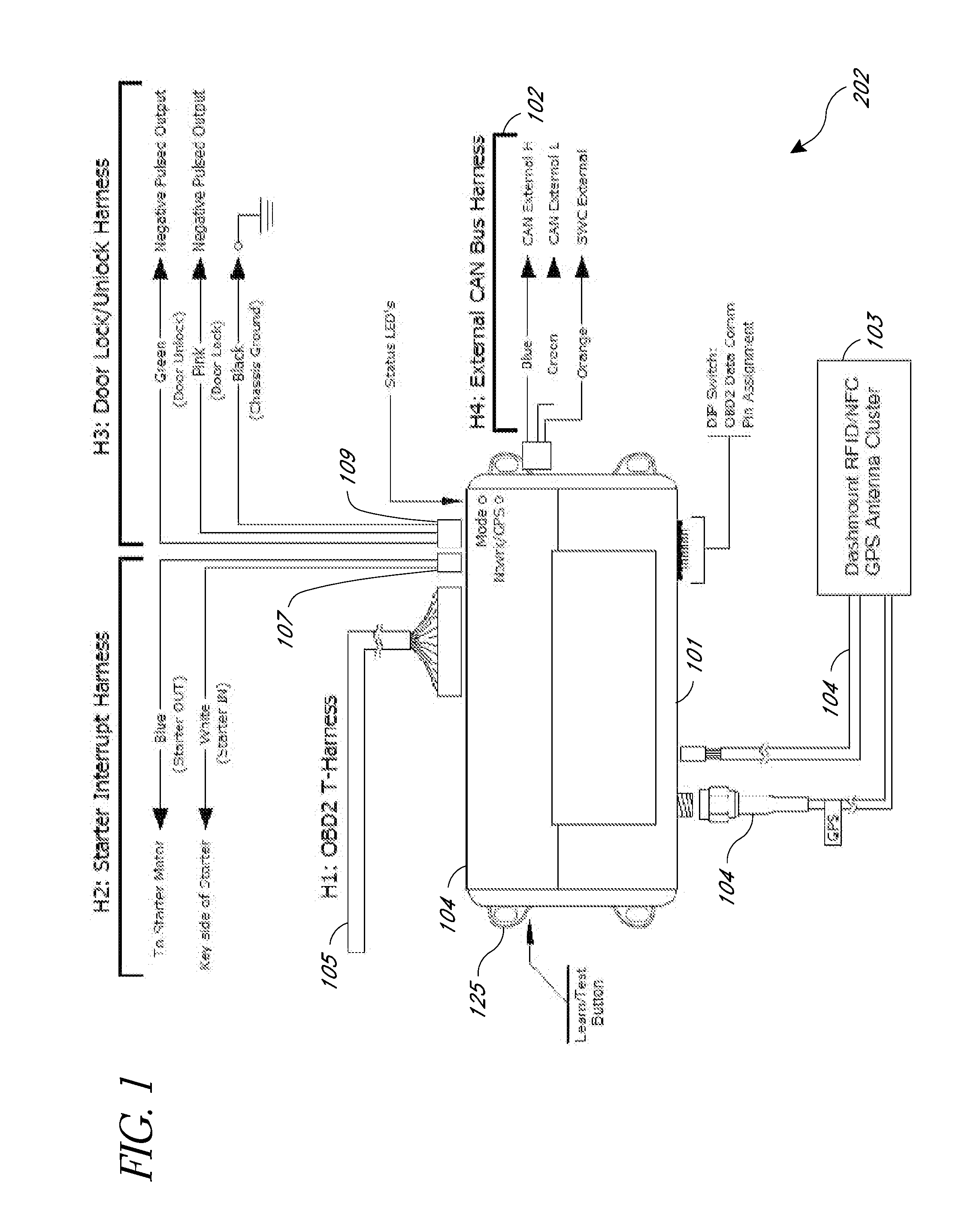
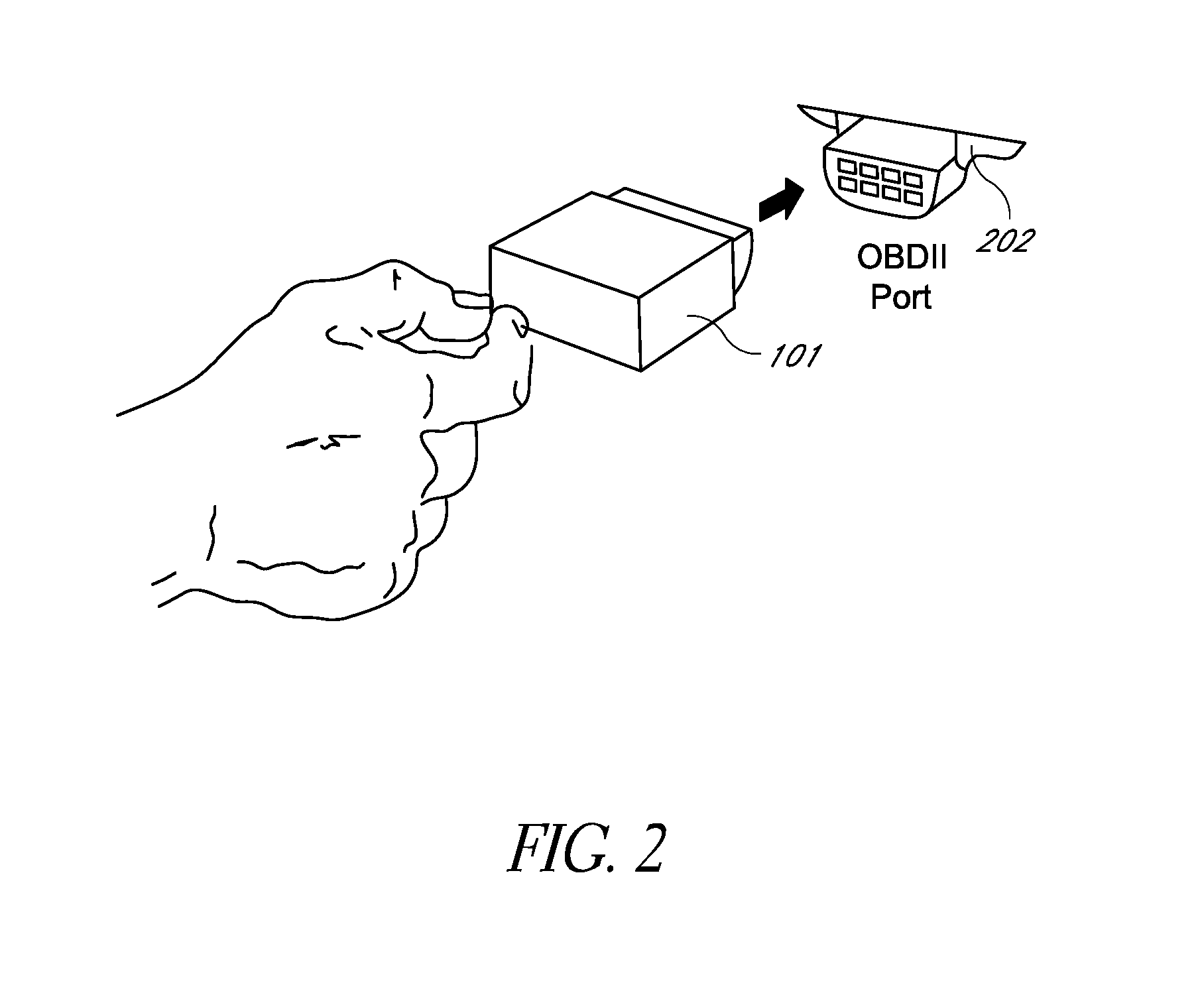
A rental / car-share (RCS) vehicle access and management system and method, in some embodiments, utilizes barcodes, QR codes (or NFC / RFID), GPS, and a mobile app coupled with a wireless network to enable customers to bypass the reservation desk and pickup and drop off reserved RCS vehicles using a mobile phone, tablet or laptop. The QR code, RFID, or NFC communication with the mobile application allows for identification of the vehicle by a mobile application, which, if authorized, can access the vehicle via a temporary access code issued by remote servers. The remote servers and / or mobile application communicates with a control module that plugs into the on-board diagnostics module of the rental / car-share (RCS) vehicle and includes a host processing unit with a processor, an accelerometer, data storage, a GPS with internal GPS antenna; a wireless modem with internal antenna, and CAN bus transceivers connected with the processor, and a USB programmable interface.
Owner:ENTERPRISE HOLDINGS
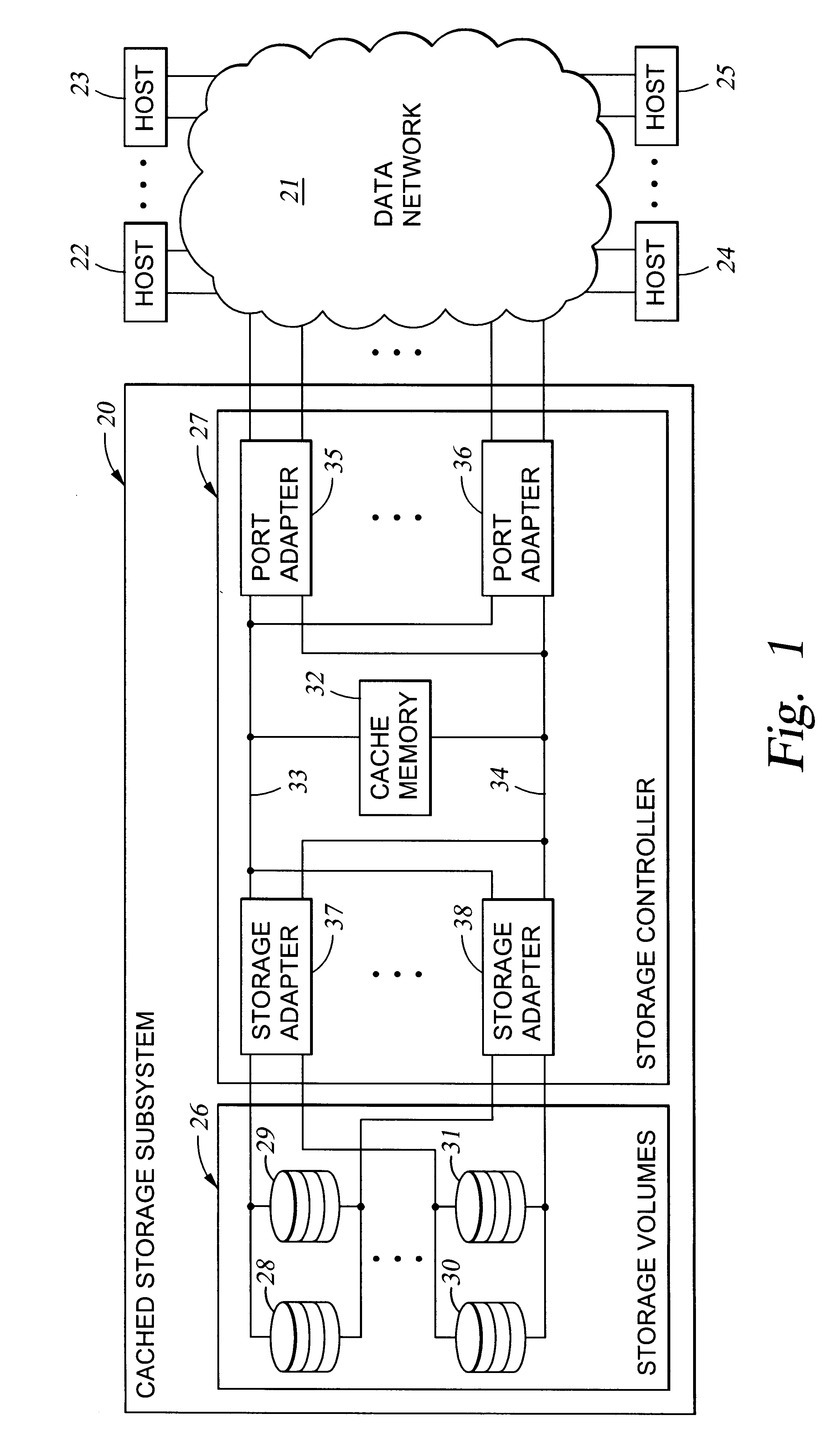
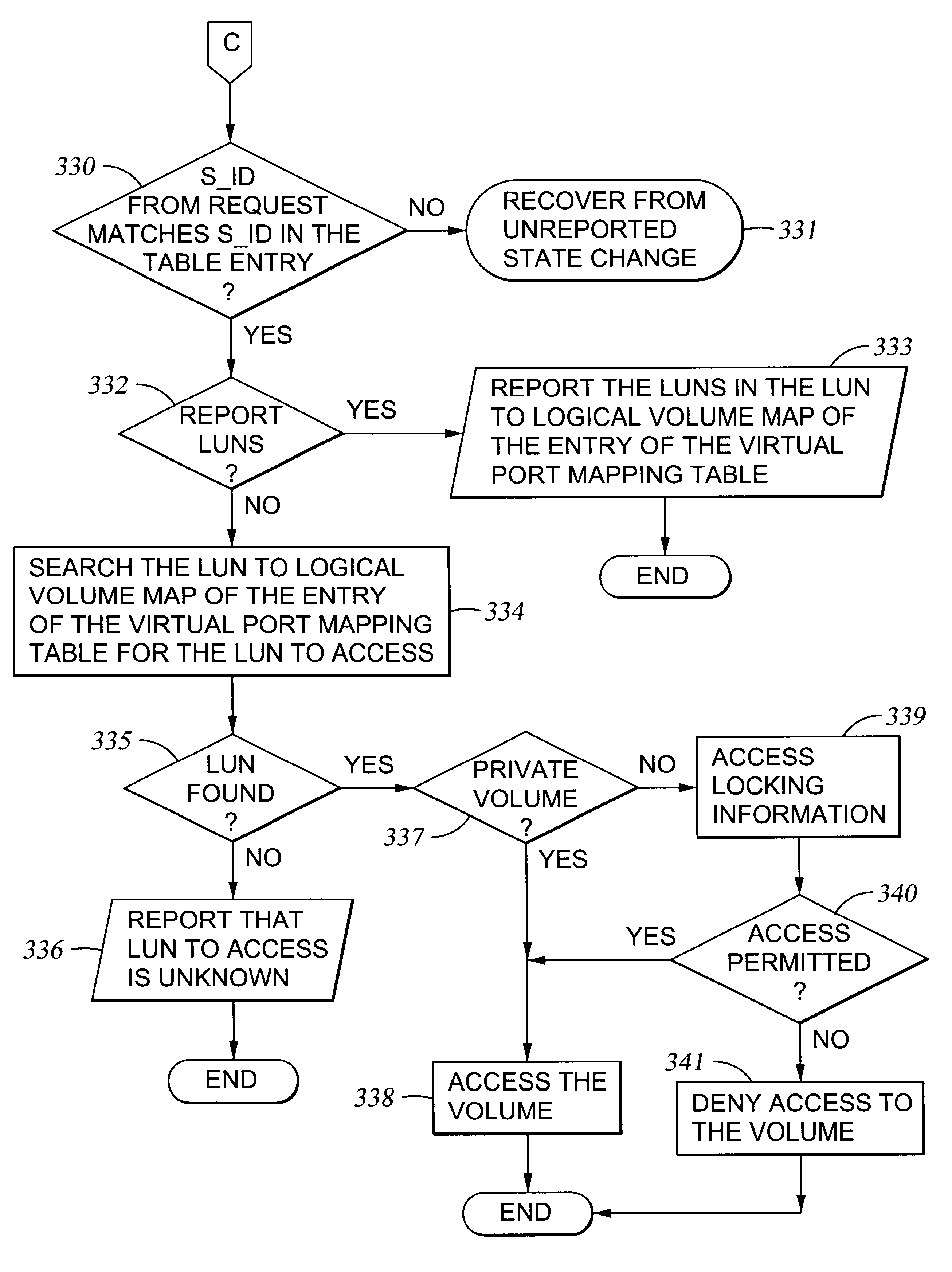
Storage mapping and partitioning among multiple host processors in the presence of login state changes and host controller replacement
InactiveUS6260120B1Input/output to record carriersData processing applicationsData portControl store
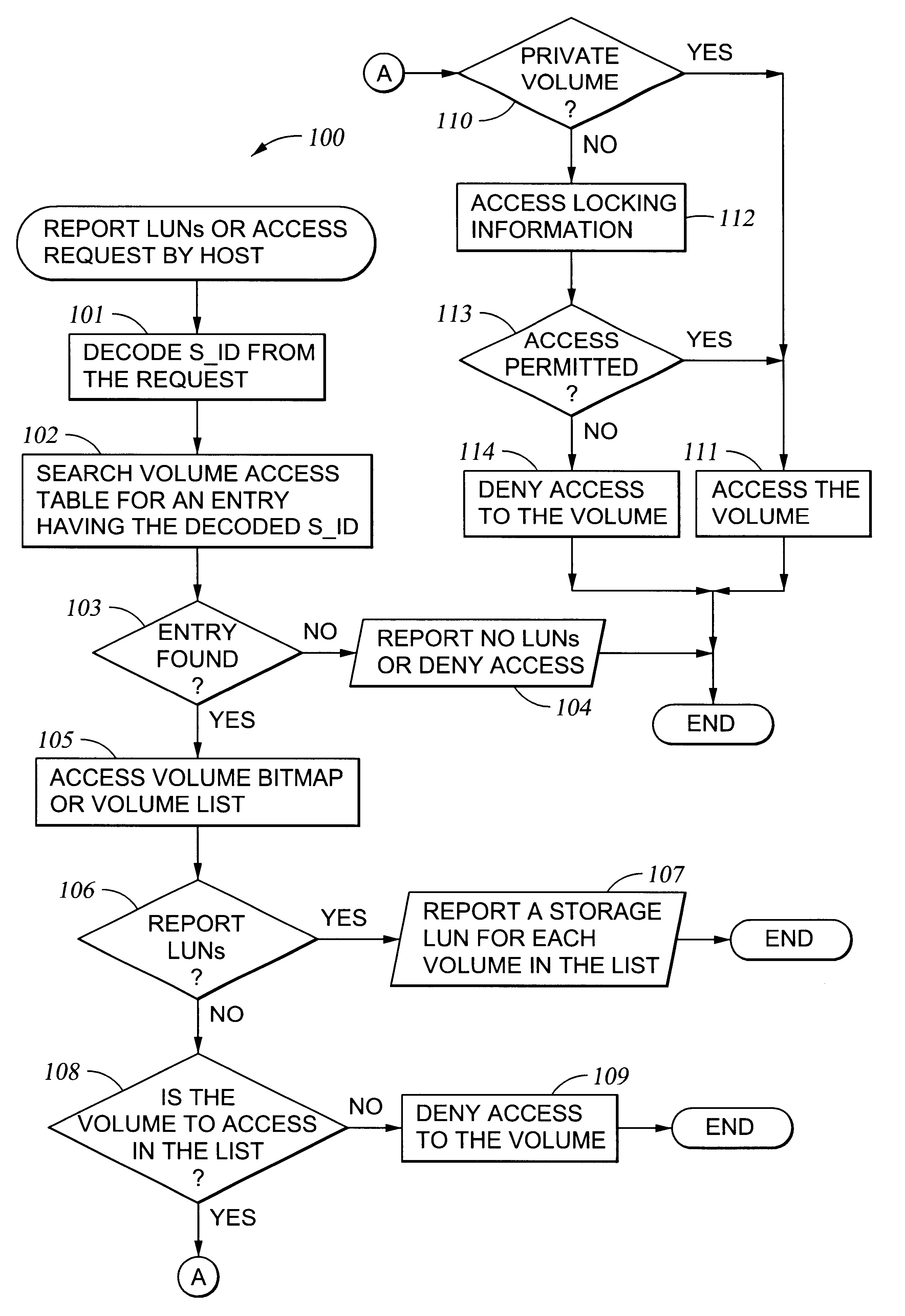
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
Business directory search engine
A system and method for efficiently searching directory listing information to obtain more relevant results is provided. In a computer system running a computing application, it is advantageous to provide search capabilities, in the form of a search engine, to operators to assist them in their effort of retrieving desired data. The search engine may cooperate with a data store having directory listing information to provide listings data to an operator. In an illustrative implementation, this search engine may be deployed on an Internet Web site that offers business listing information. The search system may comprise a user interface to enter search query information, a data store that houses a variety of directory listing information according to a predefined data taxonomy, and a means for displaying the search results. In operation, the search engine offers a variety of search options, such as, search by business name, by business categories levels, by geographic position of the user or the business, or a combination thereof. Depending on the search query entered, the search engine will perform either a bounded search (i.e. a search bounded to a specific geographic area), a proximity search (i.e. a search proximate to a computed centroid), or a combination of the two to find the most relevant directory listings. Using the inputted search qualifiers, the search engine polls the data store according to a predefined set of rules and instructions for the relevant directory listing information. These rules are directly related to the taxonomy of the data store.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for detecting glucose level data patterns
Systems and methods for detecting and reporting patterns in analyte concentration data are provided. According to some implementations, an implantable device for continuous measurement of an analyte concentration is disclosed. The implantable device includes a sensor configured to generate a signal indicative of a concentration of an analyte in a host, a memory configured to store data corresponding at least one of the generated signal and user information, a processor configured to receive data from at least one of the memory and the sensor, wherein the processor is configured to generate pattern data based on the received information, and an output module configured to output the generated pattern data. The pattern data can be based on detecting frequency and severity of analyte data in clinically risky ranges.
Owner:DEXCOM
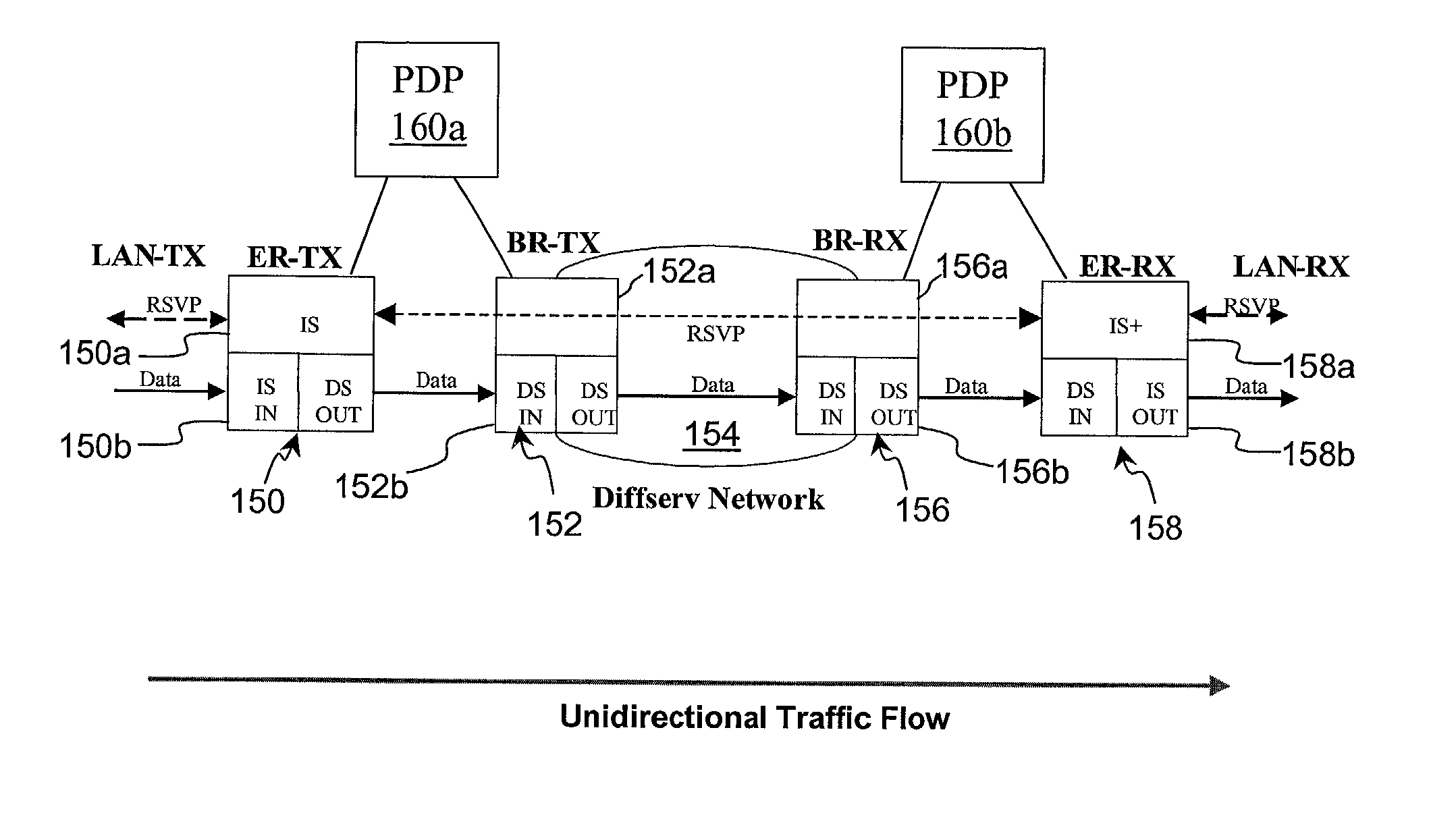
Policy-based synchronization of per-class resources between routers in a data network
ActiveUS20020194369A1Multiple digital computer combinationsProgram controlCommunication interfaceData stream
A data network may include an upstream router having one or more data handling queues, a downstream router, and a policy server. In one embodiment, the policy server includes processing resources, a communication interface in communication with the processing resources, and data storage that stores a configuration manager executable by the processing resources. The configuration manager configures data handling queues of the upstream router to provide a selected bandwidth to one or more of a plurality of service classes of data flows. In addition, the configuration manager transmits to the downstream router one or more virtual pool capacities, each corresponding to a bandwidth at the upstream router for one or more associated service classes among the plurality of service classes. In one embodiment, the configuration manager configures the data handling queues on the upstream router only in response to acknowledgment that one or more virtual pool capacities transmitted to the downstream router were successfully installed.
Owner:VERIZON PATENT & LICENSING INC
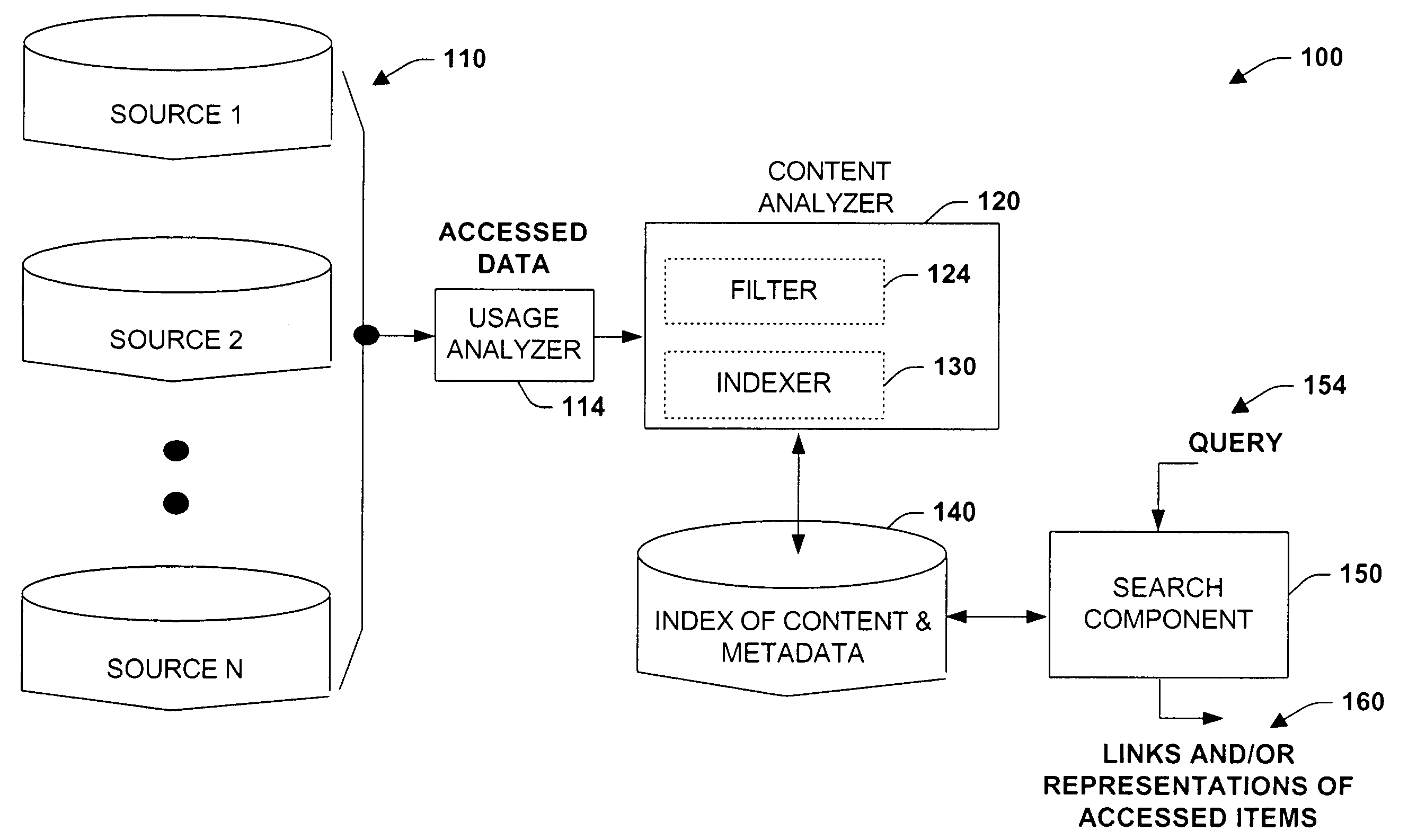
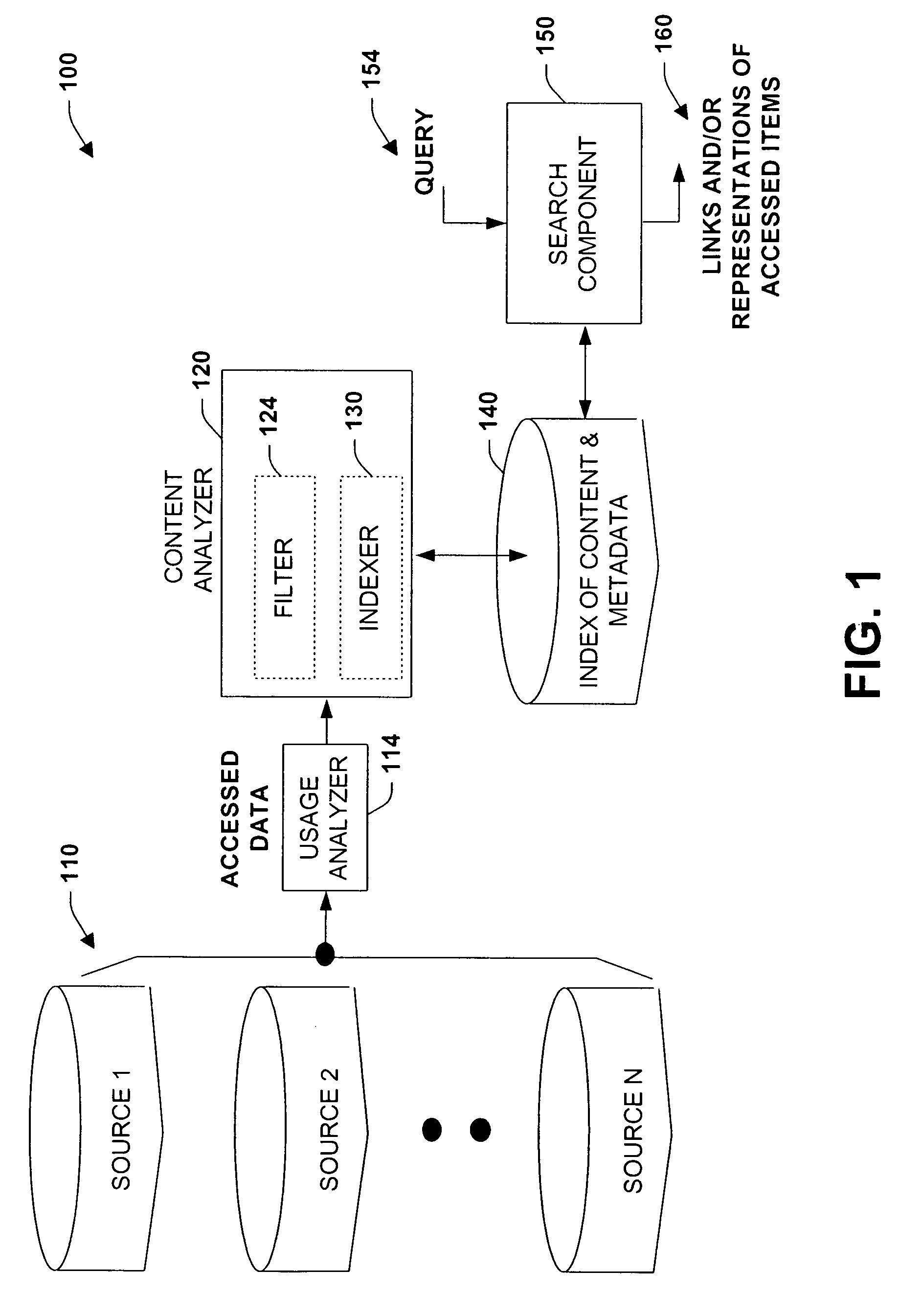
Method and system for usage analyzer that determines user accessed sources, indexes data subsets, and associated metadata, processing implicit queries based on potential interest to users
InactiveUS7162473B2Useful purposeFacilitate search for informationData processing applicationsText database indexingData accessContent analytics
The present invention relates to systems and methods providing content-access-based information retrieval. Information items from a plurality of disparate information sources that have been previously accessed or considered are automatically indexed in a data store, whereby a multifaceted user interface is provided to efficiently retrieve the items in a cognitively relevant manner. Various display output arrangements are possible for the retrieved information items including timeline visualizations and multidimensional grid visualizations. Input options include explicit, implicit, and standing queries for retrieving data along with explicit and implicit tagging of items for ease of recall and retrieval. In one aspect, an automated system is provided that facilitates concurrent searching across a plurality of information sources. A usage analyzer determines user accessed items and a content analyzer stores subsets of data corresponding to the items, wherein at least two of the items are associated with disparate information sources, respectively. An automated indexing component indexes the data subsets according to past data access patterns as determined by the usage analyzer. A search component responds to a search query, initiates a search across the indexed data, and outputs links to locations of a subset and / or provides sparse representations of the subset.
Owner:MICROSOFT TECH LICENSING LLC
Processor-cache system and method
ActiveUS9047193B2Shorten the counting processEfficient and uniform structureEnergy efficient ICTRegister arrangementsAddress generation unitProcessor register
A digital system is provided. The digital system includes an execution unit, a level-zero (L0) memory, and an address generation unit. The execution unit is coupled to a data memory containing data to be used in operations of the execution unit. The L0 memory is coupled between the execution unit and the data memory and configured to receive a part of the data in the data memory. The address generation unit is configured to generate address information for addressing the L0 memory. Further, the L0 memory provides at least two operands of a single instruction from the part of the data to the execution unit directly, without loading the at least two operands into one or more registers, using the address information from the address generation unit.
Owner:SHANGHAI XINHAO MICROELECTRONICS
Method and apparatus for cascading data through redundant data storage units
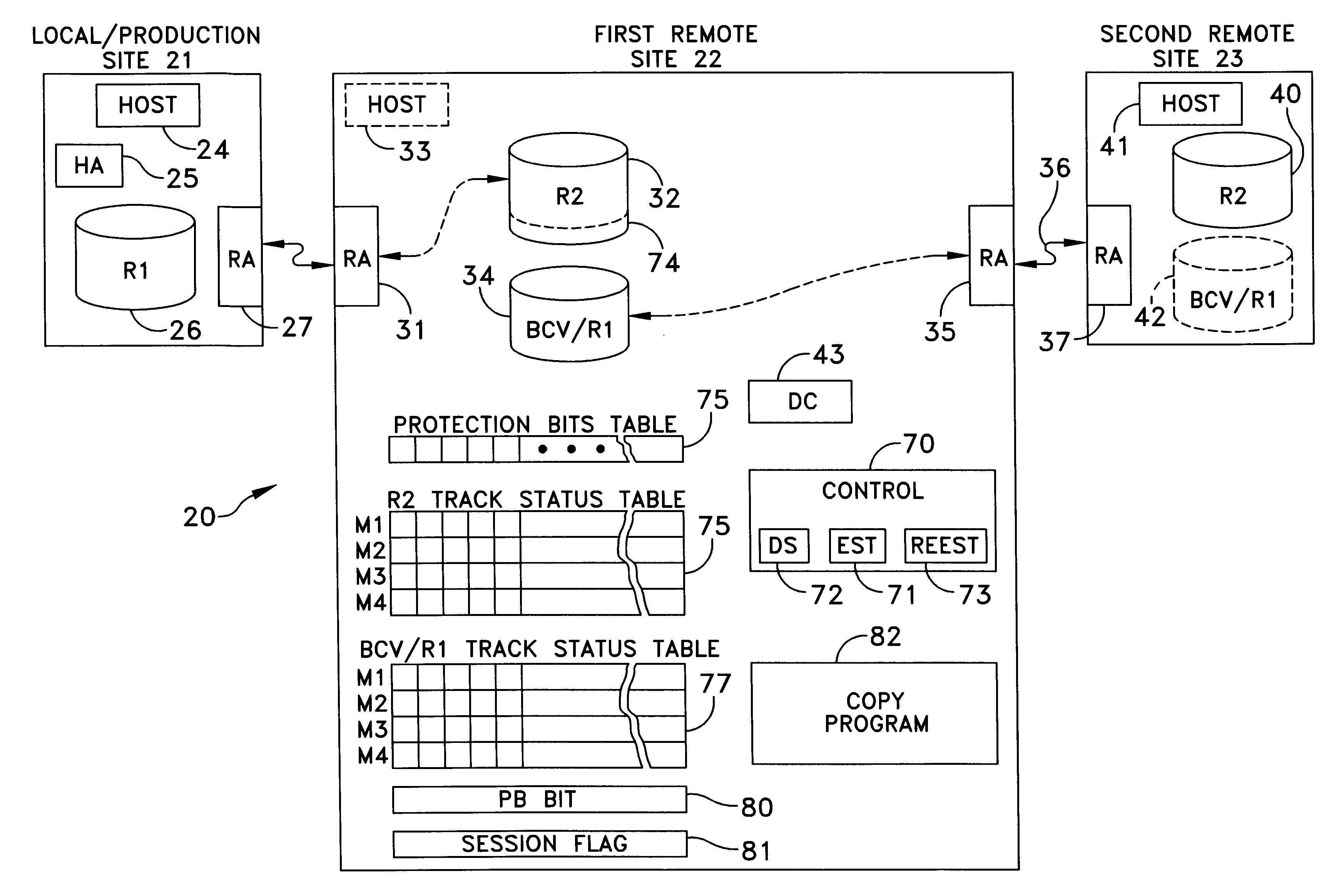
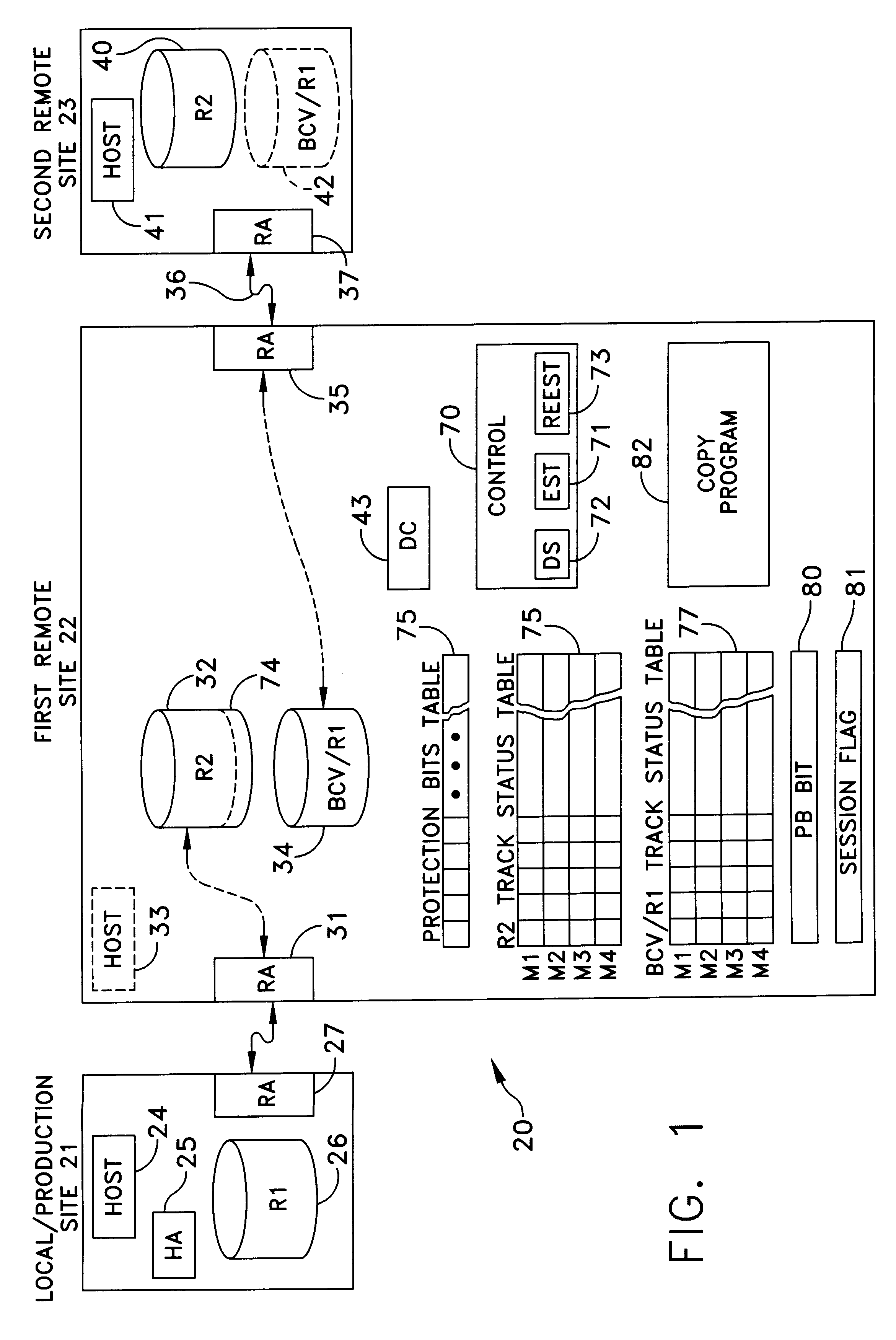
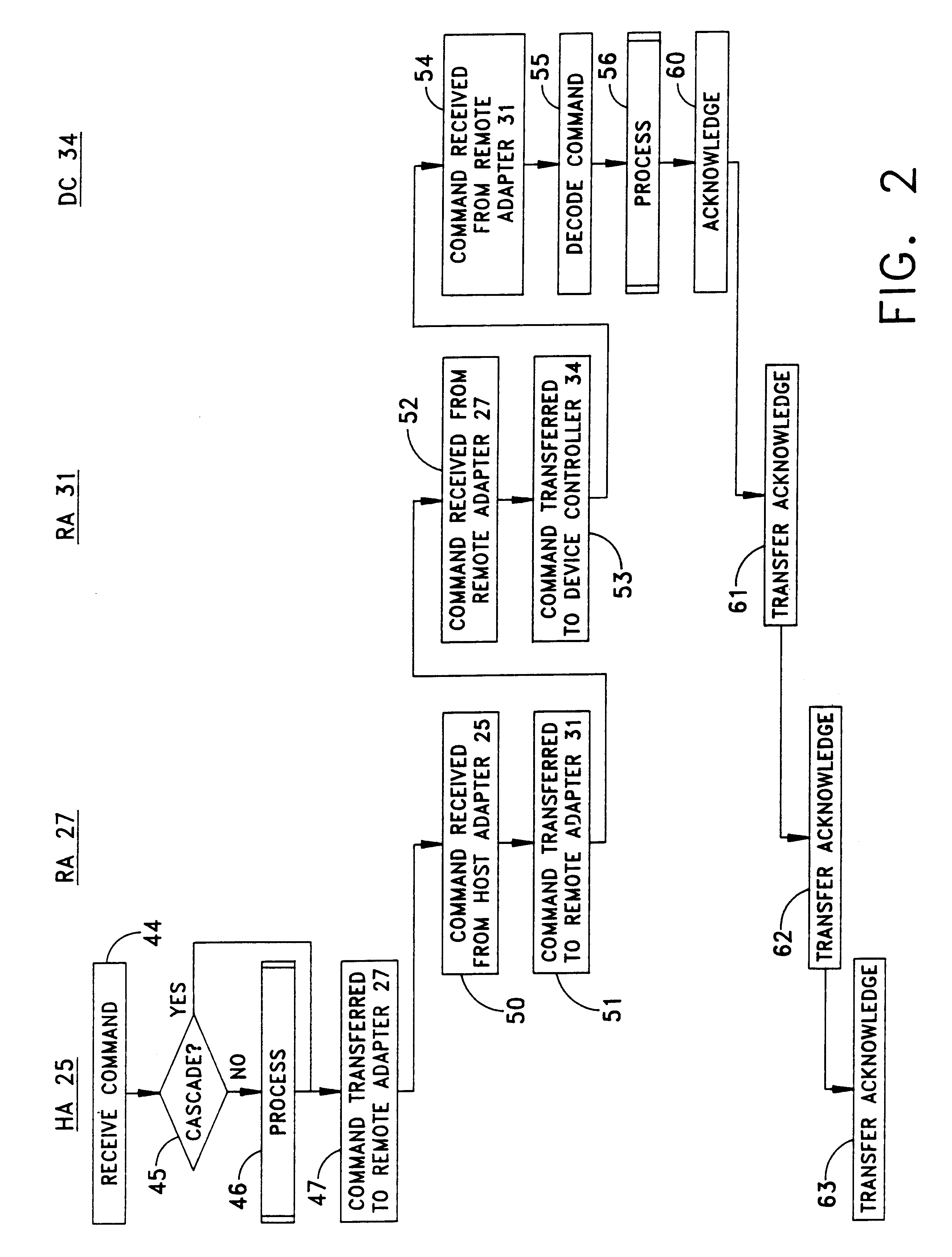
A data storage facility for transferring data from a data altering apparatus, such as a production data processing site to a remote data receiving site. The data storage facility includes a first data store for recording each change in the data generated by the data altering apparatus. A register set records each change on a track-by-track basis. A second data store has first and second operating modes. During a first operating mode the second data store becomes a mirror of the first data store. During a second operating mode the second data store ceases to act as a mirror and becomes a source for a transfer of data to the data receiving site. Only information that has been altered, i.e., specific tracks that have been altered, are transferred during successive operations in the second operating mode. Commands from the local production site initiate the transfers between the first and second operating modes.
Owner:EMC IP HLDG CO LLC
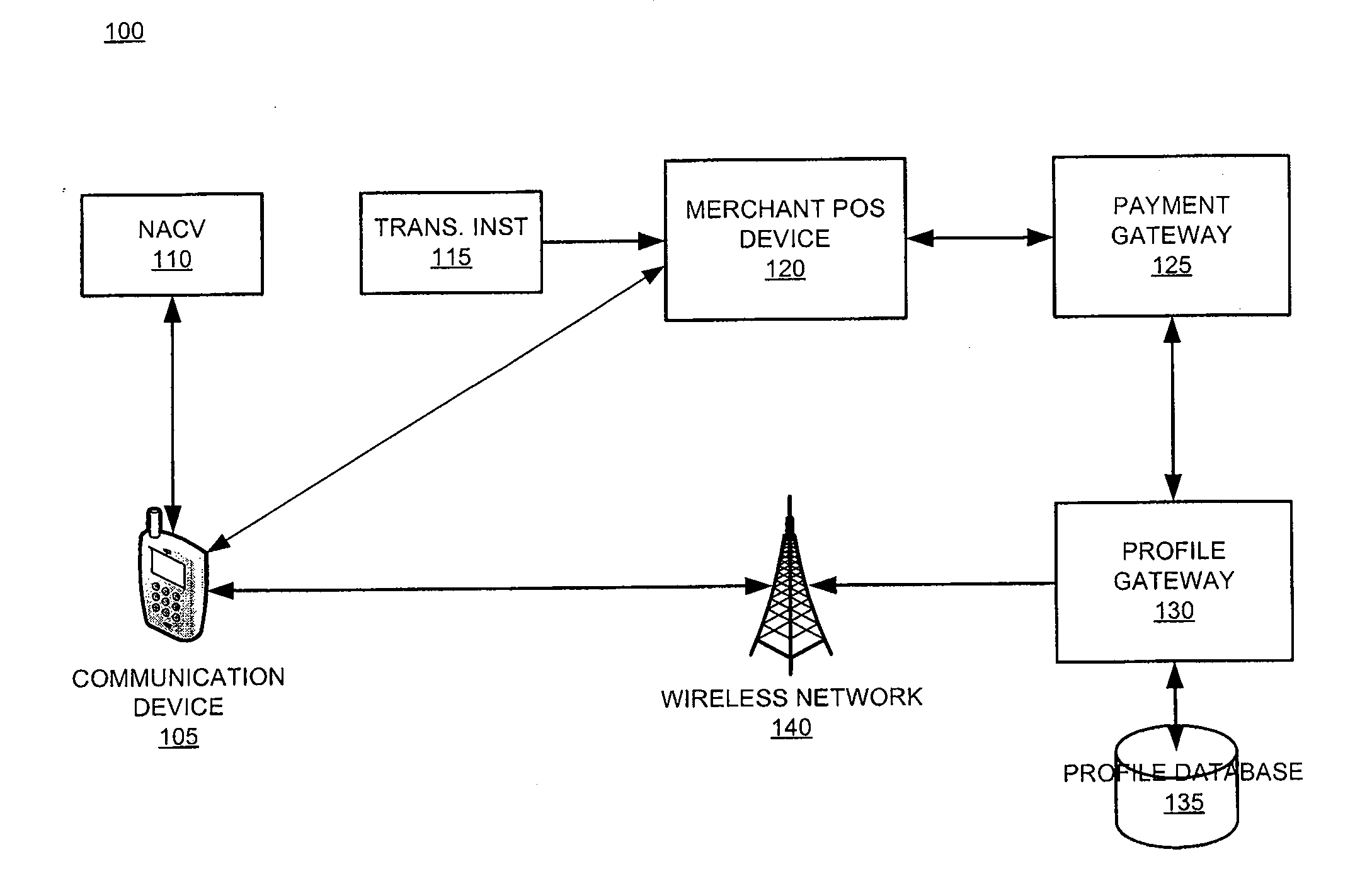
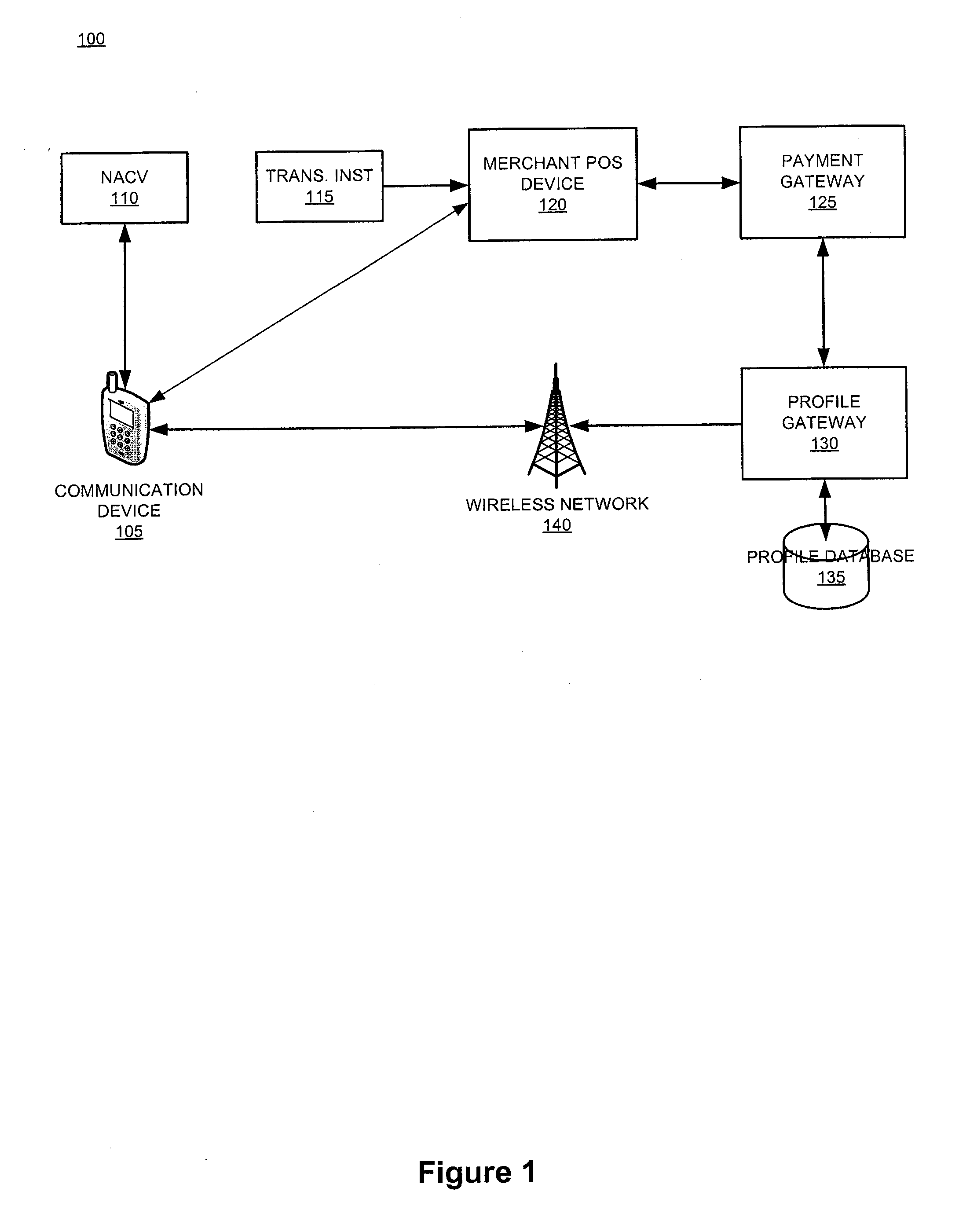
System and device for facilitating a transaction by consolidating sim, personal token, and associated applications for electronic wallet transactions
InactiveUS20120231844A1Increase dependenceFacilitating secure and convenient electronic transactionsPayment architectureSubstation equipmentPayment transactionSmart card
The invention relates generally to a smart card device that is configured to facilitate wireless network access and credential verification. Specifically, the device is configured to meet the physical and electrical specification for commercially available mobile devices utilizing a standard Subscriber Identity Module (SIM) for network access. The device combines the features of the SIM with Common Access Card or Personal Identity Verification card features to allow a network subscriber to invoke secure payment transactions over a carrier's network. The system includes data storage for maintaining a plurality of network and transaction instrument profiles and a profile gateway for receiving transaction information from a payment gateway, sending an authorization request to a user's mobile device, receiving a transaction authorization from the mobile device, and sending transaction information to a payment gateway to finalize the payment transaction.
Owner:APRIVA
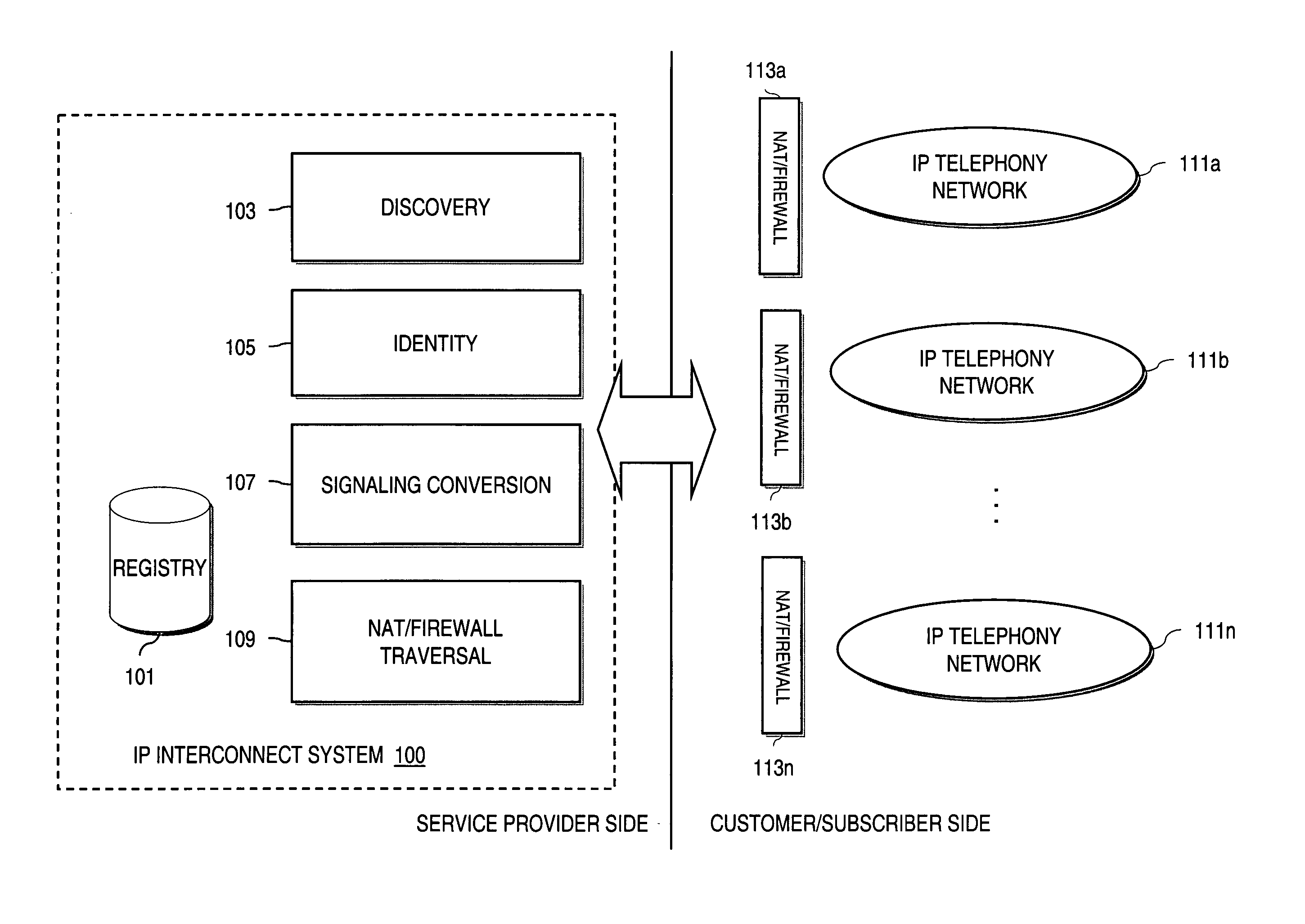
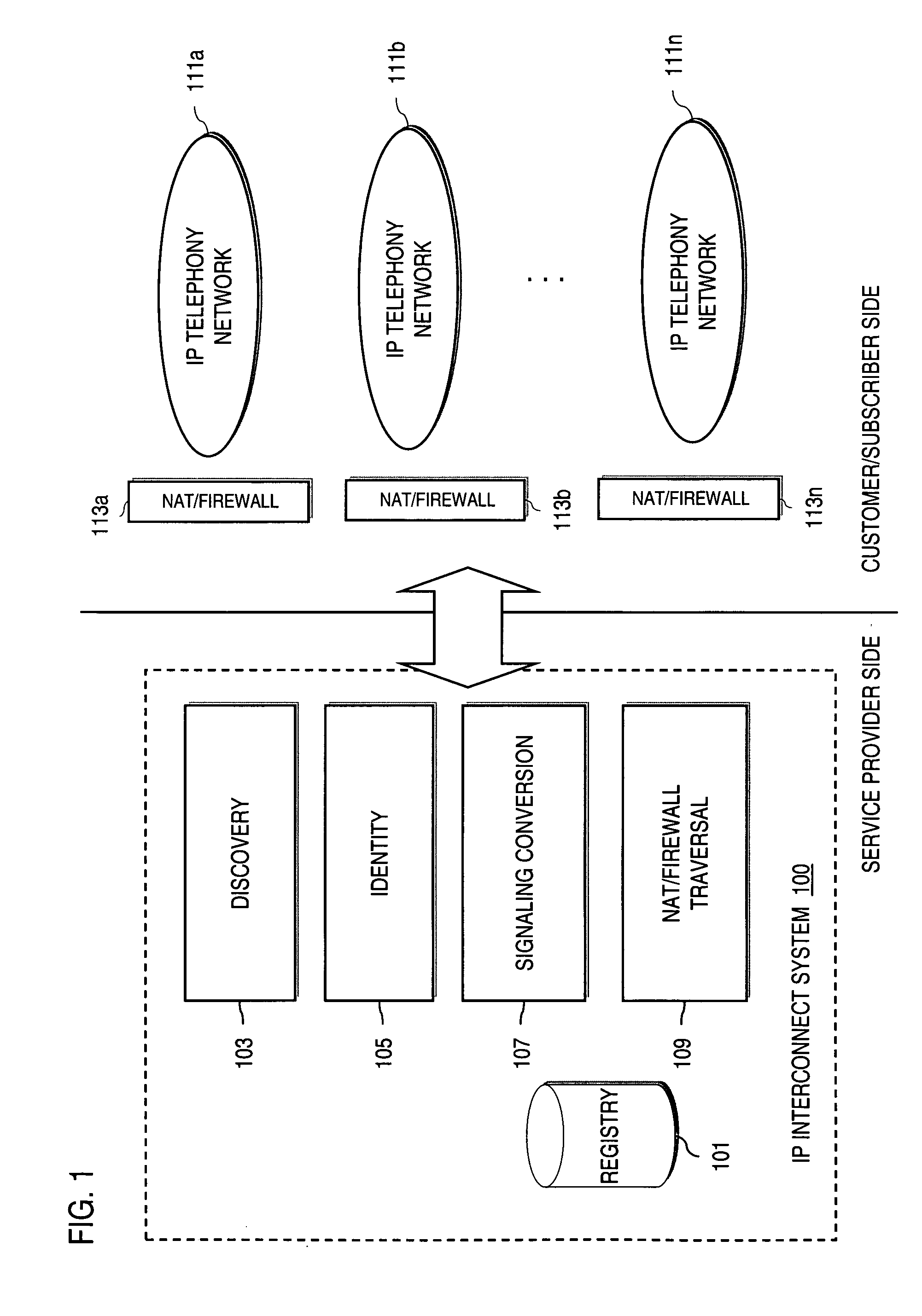
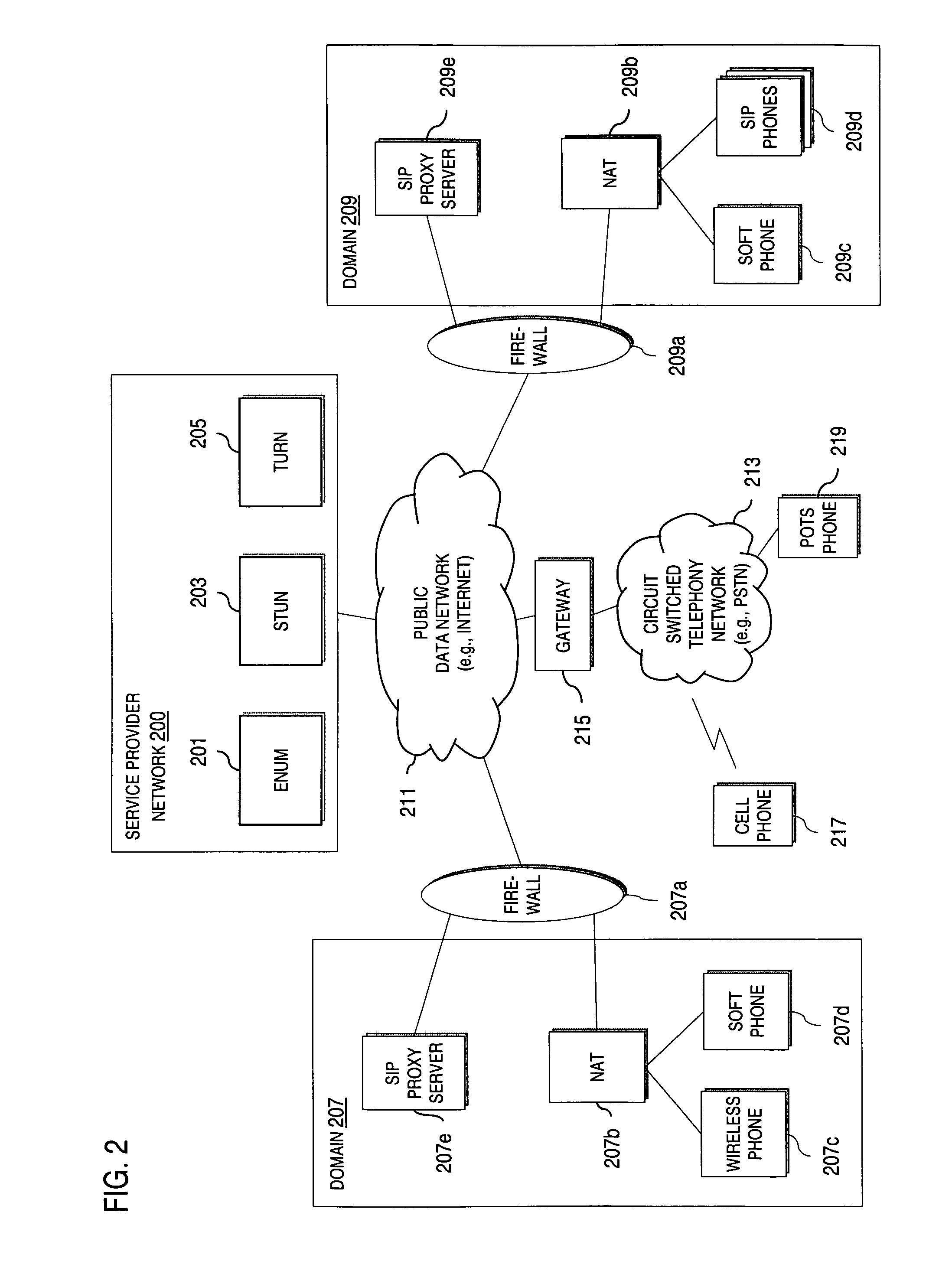
Method and system for providing voice over IP managed services utilizing a centralized data store
ActiveUS20070036143A1Interconnection arrangementsData switching by path configurationVoice over IPData memory
An approach provides interdomain traversal to support packetized voice transmissions. A centralized data store, maintained by a service provider, stores one or more user identifiers and an associated directory number. The centralized data store also stores routing information including one or more communication paths corresponding to the user identifier, wherein the routing information includes a data path or a circuit-switched path for establishing a call to the user. In response to a request for establishing the call to the directory number, the data store retrieves the routing information for use to establish the call.
Owner:VERIZON PATENT & LICENSING INC
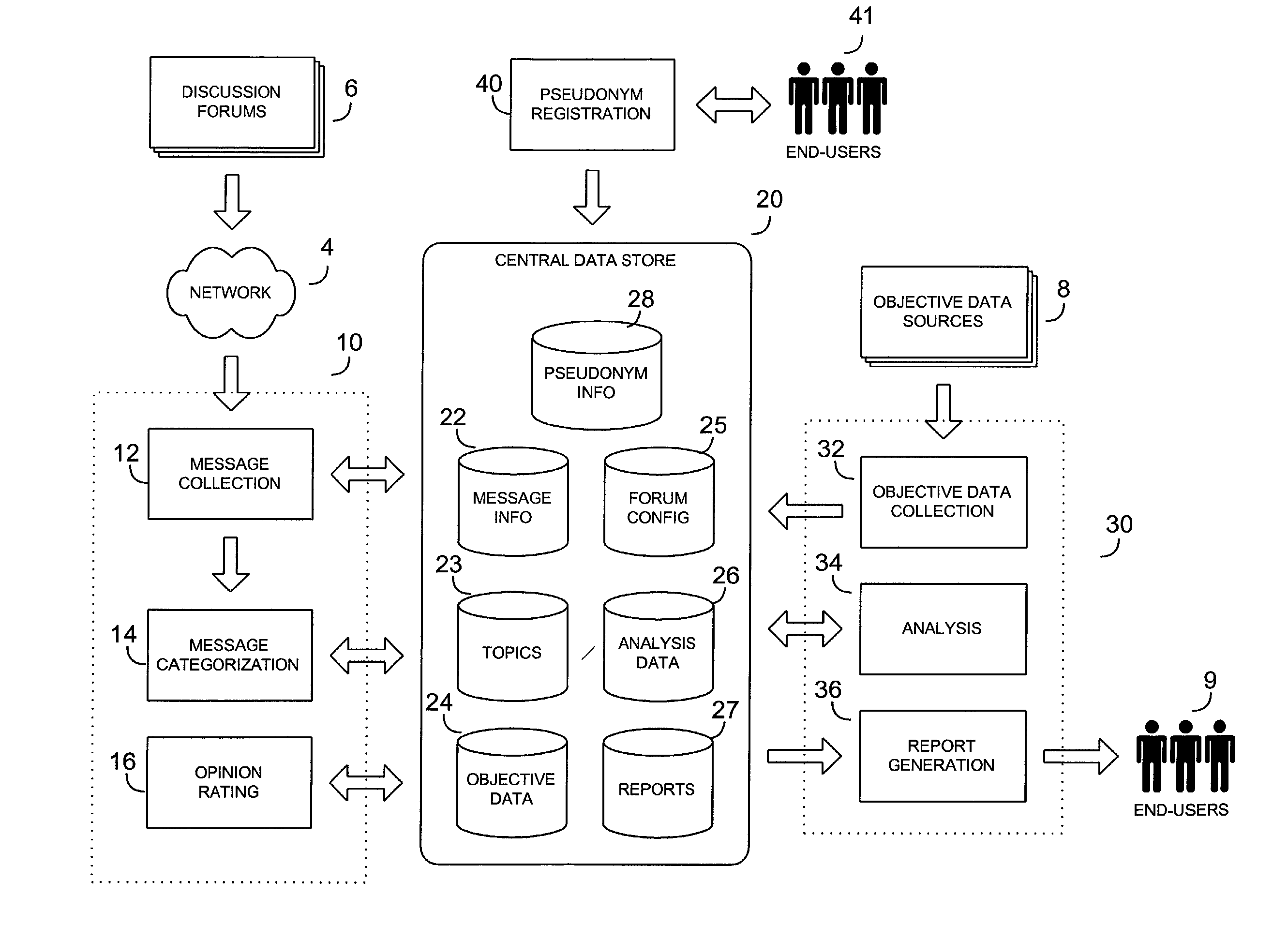
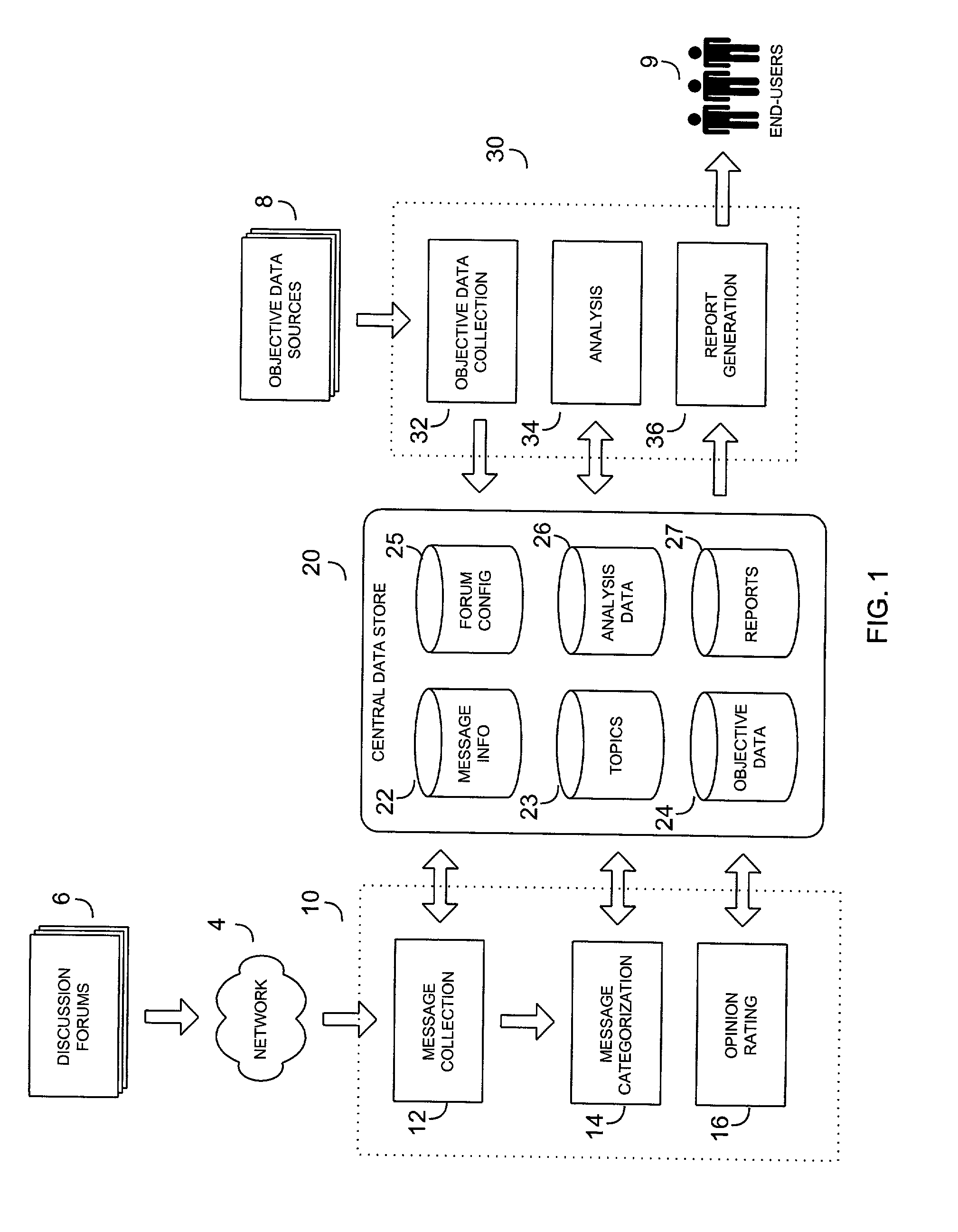
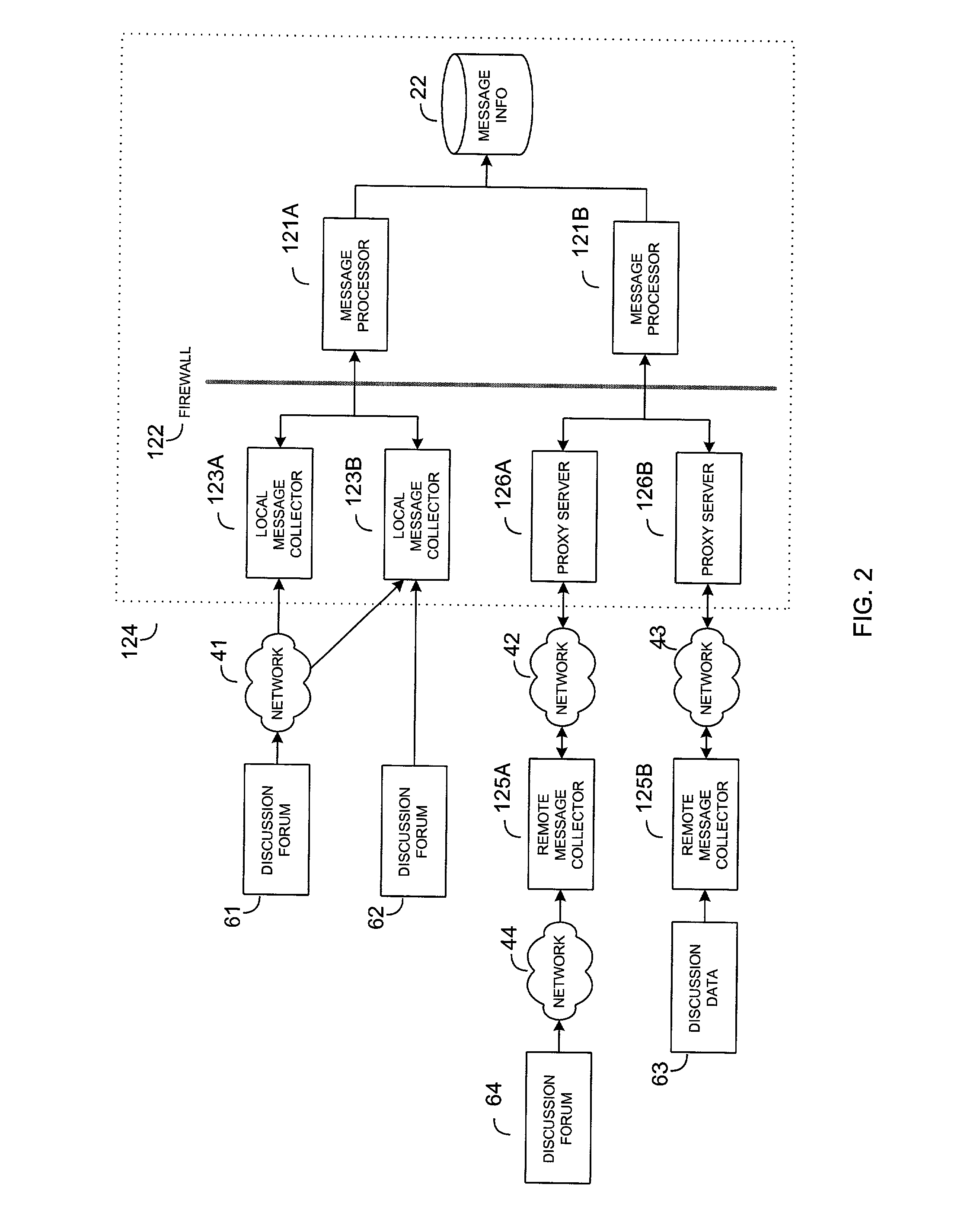
System and method for scoring electronic messages
A system and method for collecting and analyzing electronic discussion messages to categorize the message communications and the identify trends and patterns in pre-determined markets. The system comprises an electronic data discussion system wherein electronic messages are collected and analyzed according to characteristics and data inherent in the messages. The system further comprises a data store for storing the message information and results of any analyses performed. Objective data is collected by the system for use in analyzing the electronic discussion data against real-world events to facilitate trend analysis and event forecasting based on the volume, nature and content of messages posted to electronic discussion forums.
Owner:BUZZMETRICS
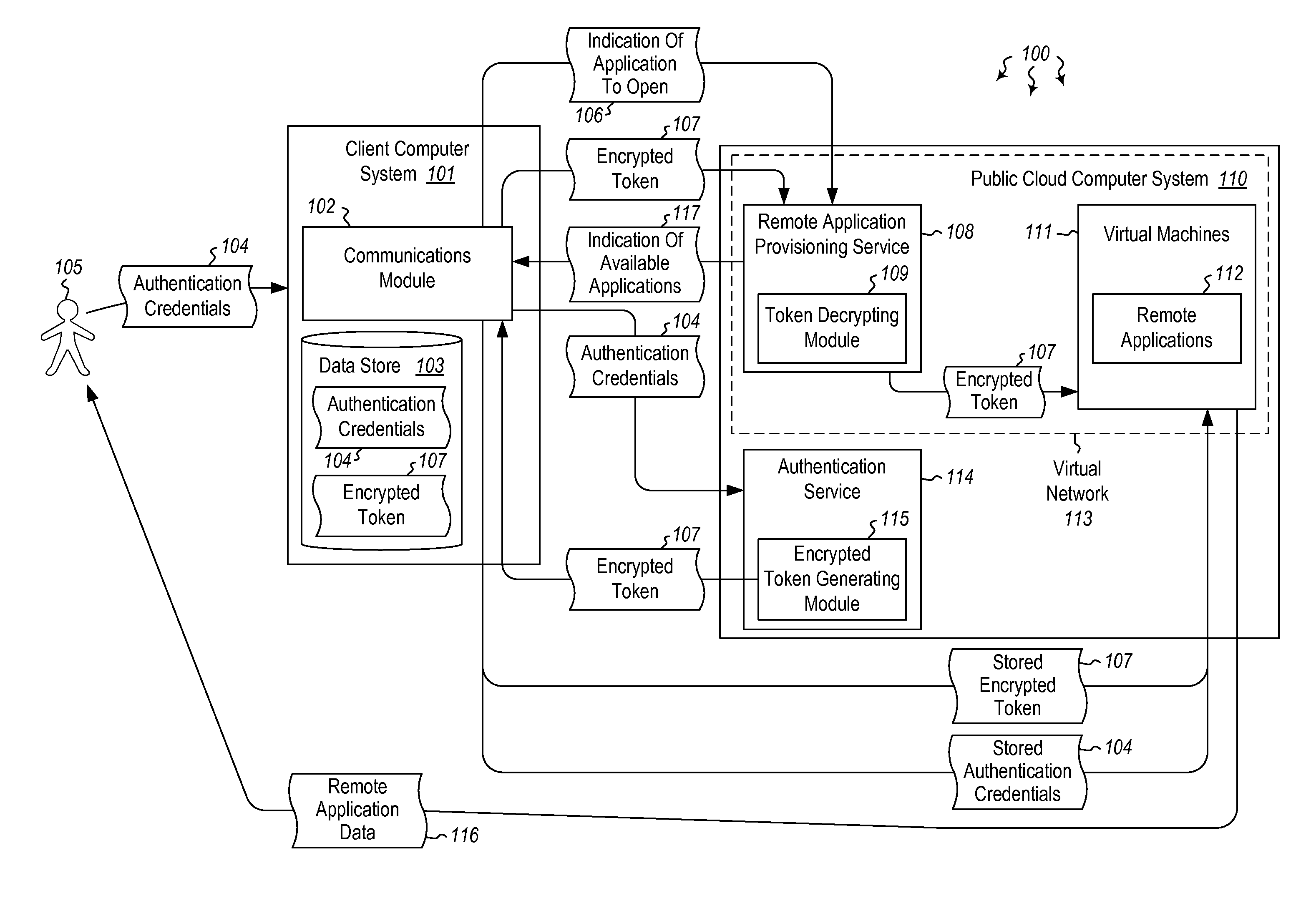
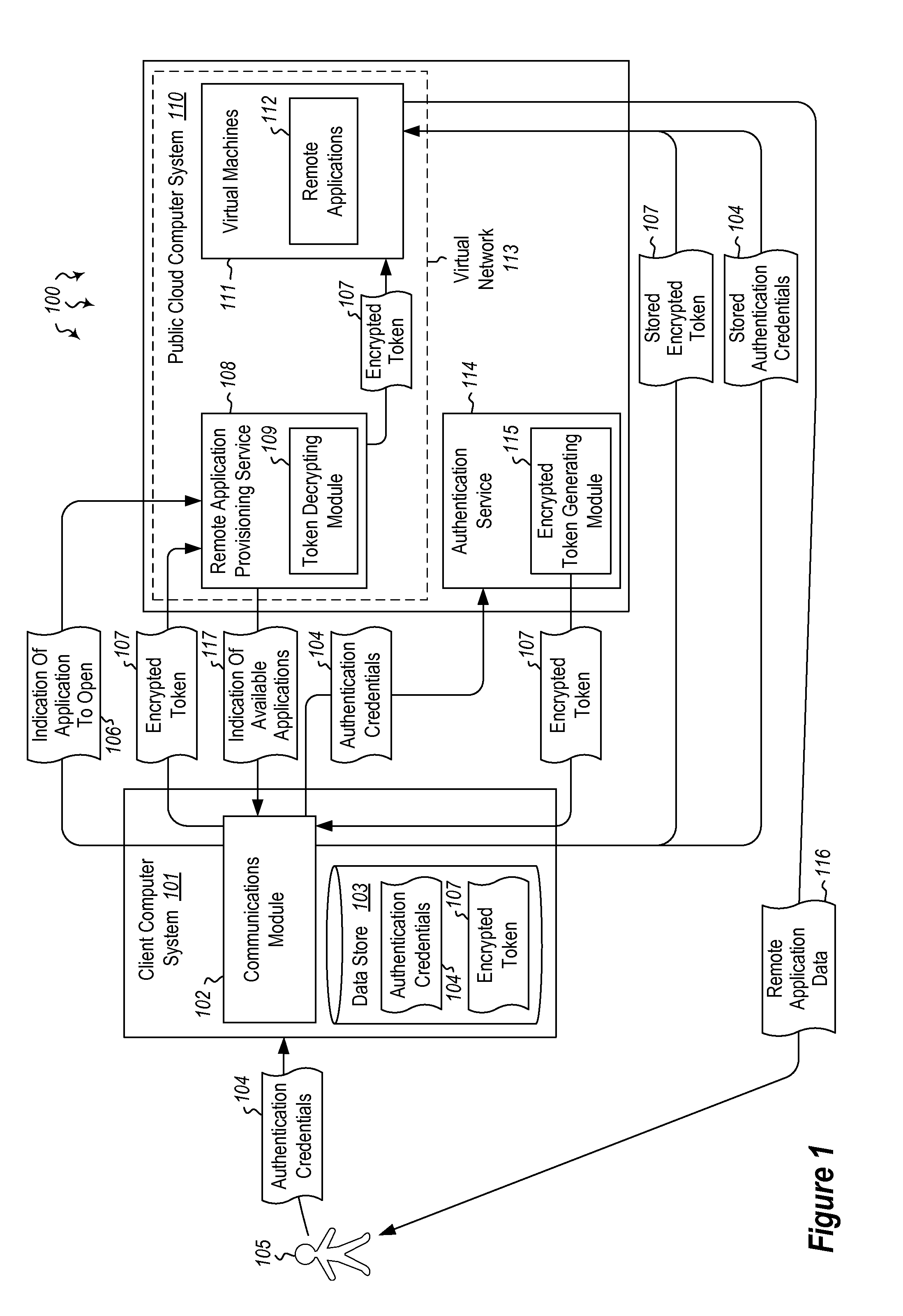
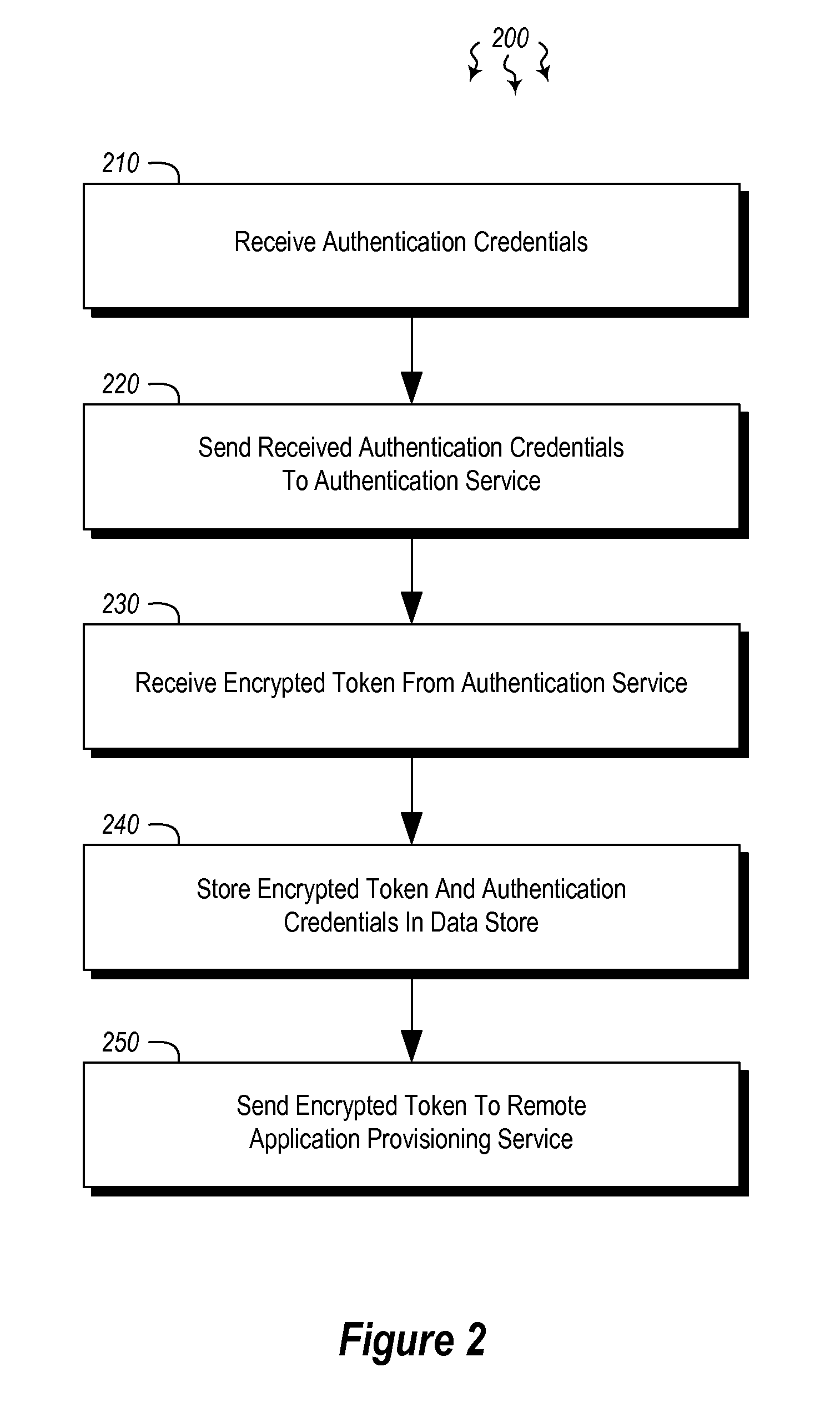
User authentication in a cloud environment
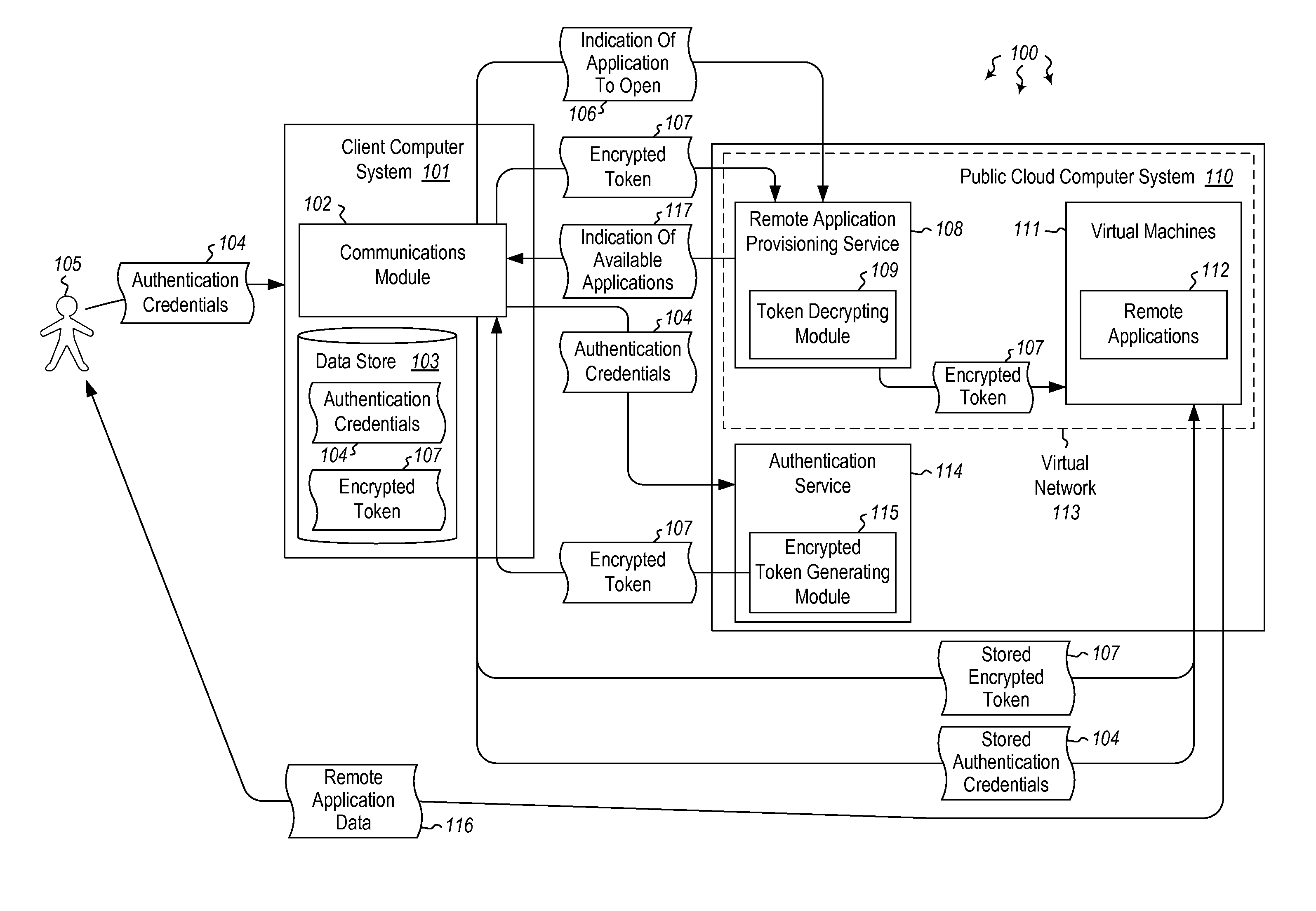
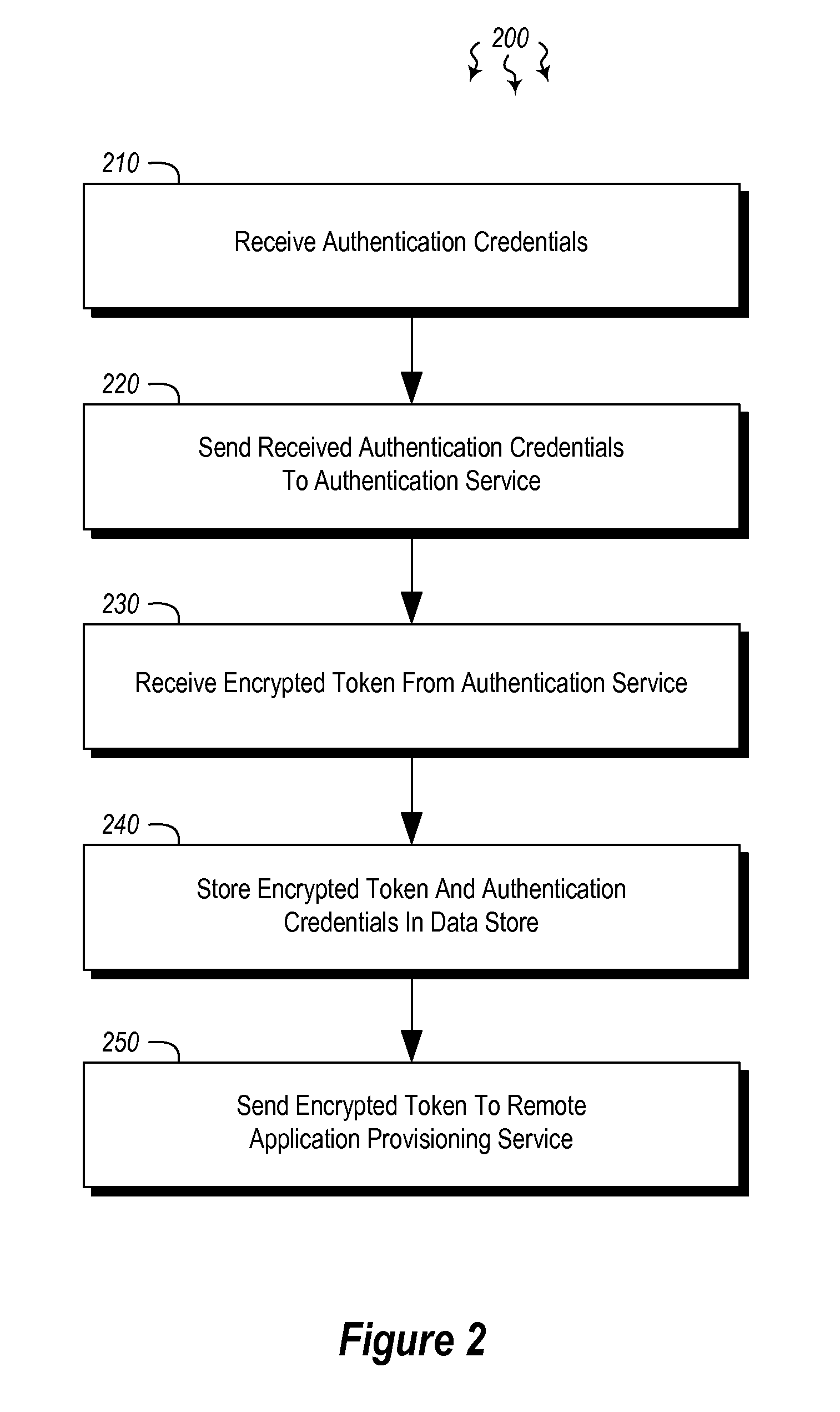
ActiveUS20140373126A1Well formedDigital data processing detailsComputer security arrangementsInternet Authentication ServiceData memory
Embodiments are directed to authenticating a user to a remote application provisioning service. In one scenario, a client computer system receives authentication credentials from a user at to authenticate the user to a remote application provisioning service that provides virtual machine-hosted remote applications. The client computer system sends the received authentication credentials to an authentication service, which is configured to generate an encrypted token based on the received authentication credentials. The client computer system then receives the generated encrypted token from the authentication service, stores the received encrypted token and the received authentication credentials in a data store, and sends the encrypted token to the remote application provisioning service. The encrypted token indicates to the remote application provisioning service that the user is a valid user.
Owner:MICROSOFT TECH LICENSING LLC
Storage server system including ranking of data source
InactiveUS6446141B1Improve performanceSimple equipmentInput/output to record carriersTransmissionCommunication interfaceOperational system
A storage server comprising: a processing unit, a bus system coupled with the processing unit, including a plurality of slots, slots in the plurality of slots including interfaces to respective data stores; a communication interface; and an operating system coupled with the processing unit the operating system including: logic controlling transfers among the plurality of slots over the bus system according to an internal format, logic for translating a storage transaction received over the communication interface into the internal format, and logic for configuring the plurality of slots according to a configuration data.
Owner:DELL PROD LP
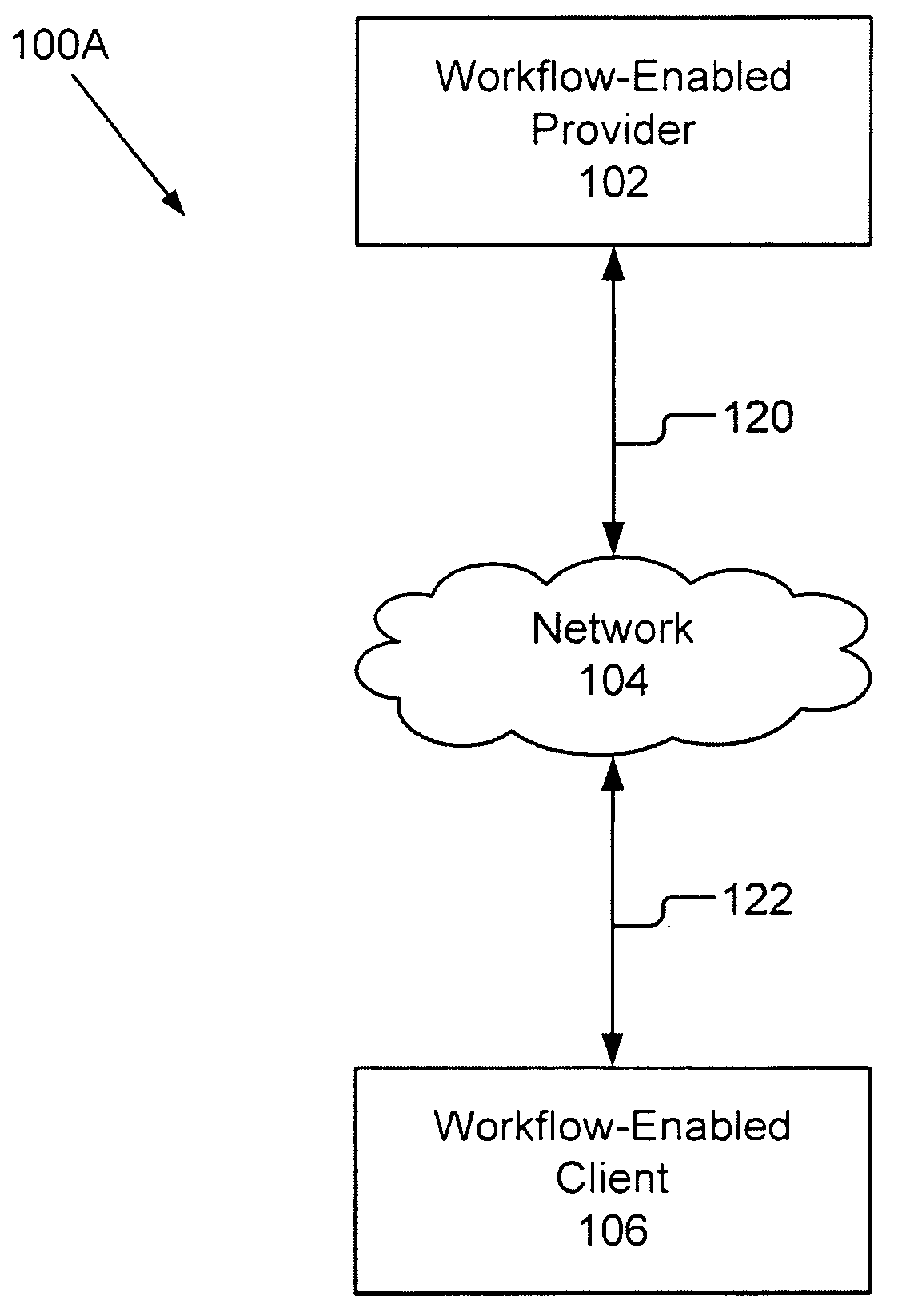
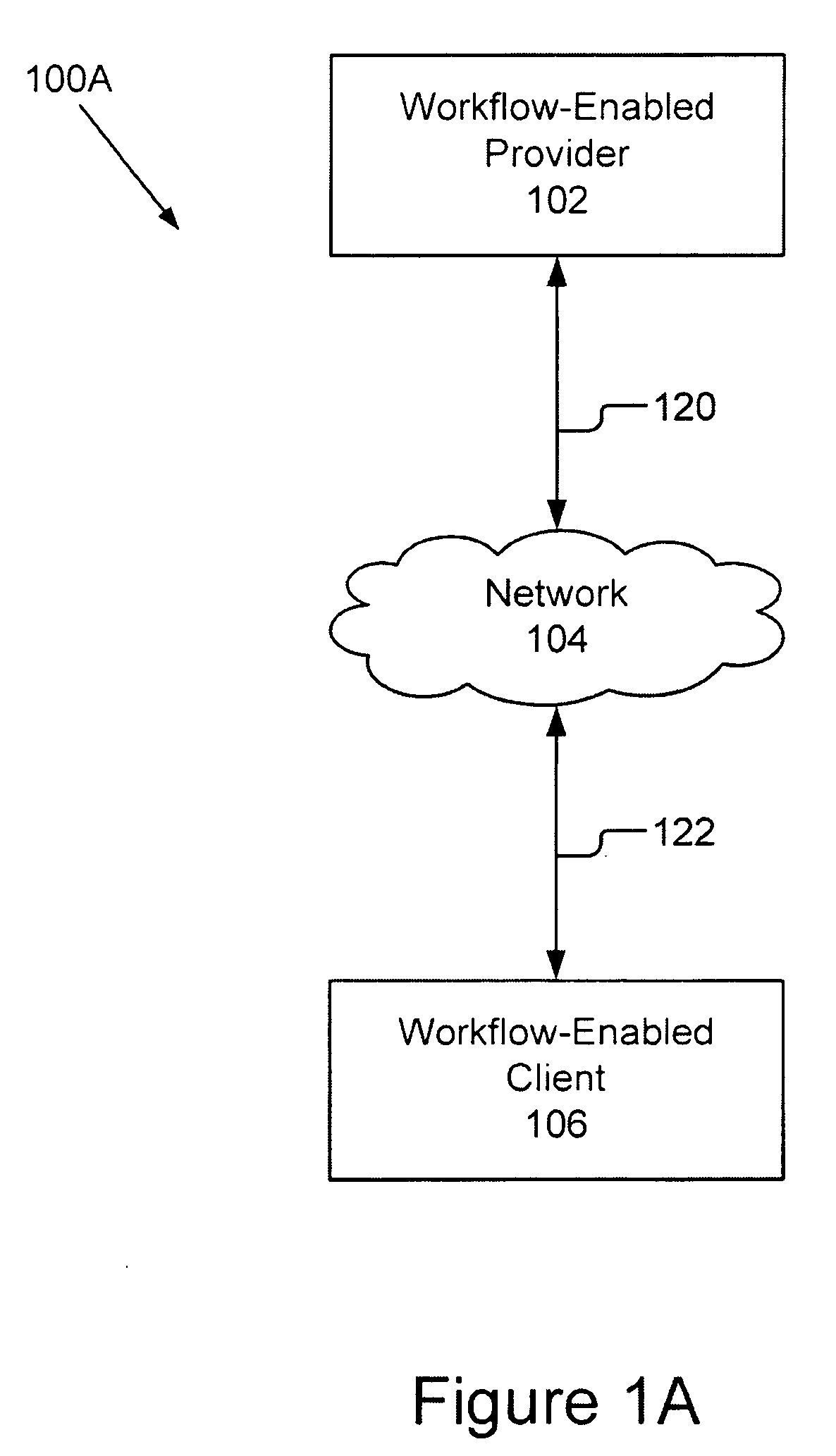
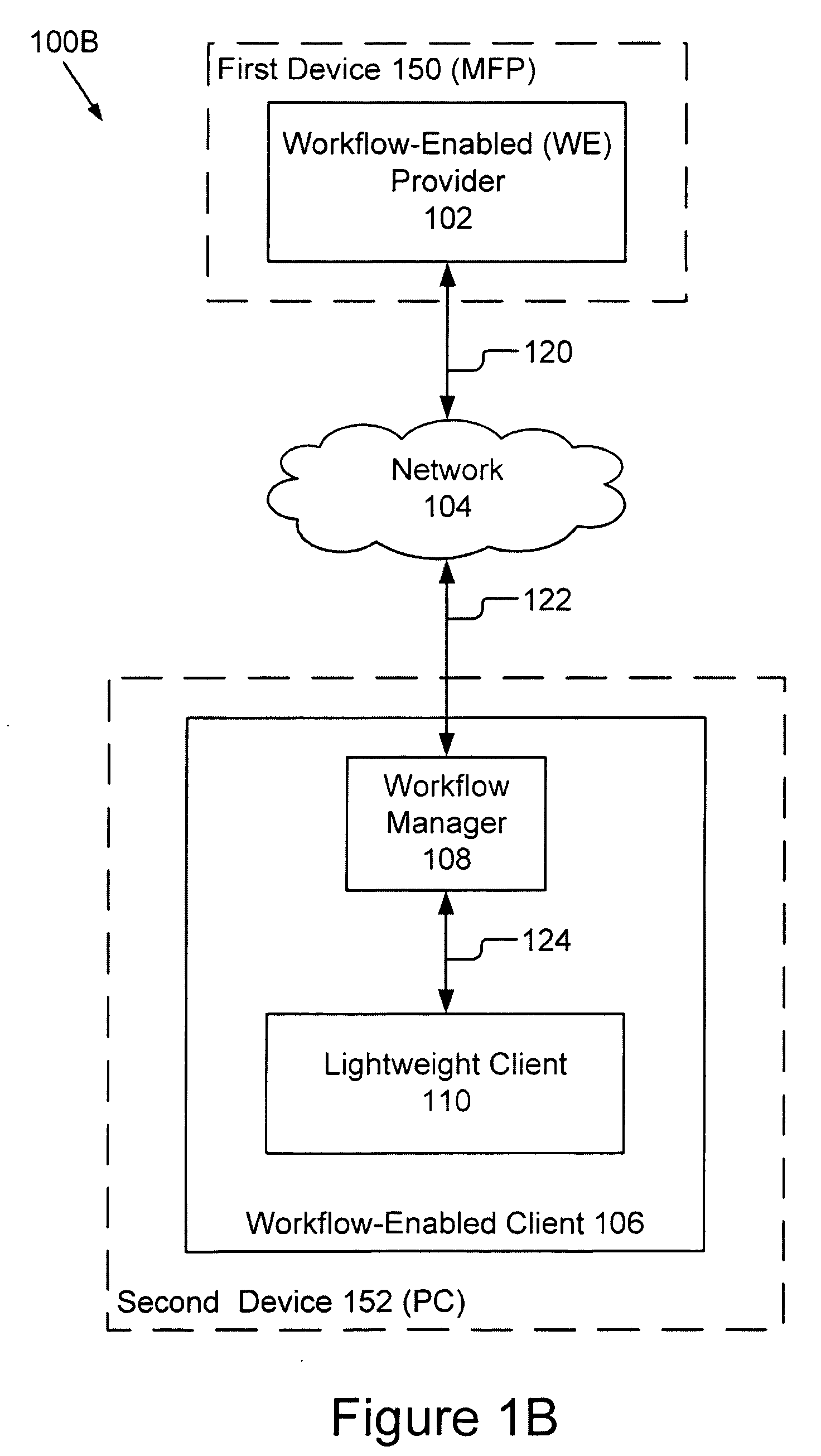
Workflow Manager For A Distributed System
ActiveUS20090077165A1Overcome deficienciesOperational securityMultiple digital computer combinationsDigital data authenticationData memoryBiological activation
A workflow manager handles the communication between a workflow-enabled provider and a workflow-enabled client. The workflow manager maintains a directory of clients, translates a transaction from a provider into multiple transactions suitable for the client, and handles security. In one embodiment, the workflow manager connects with the workflow-enabled client by registration and with the workflow-enabled provider by advertising and activation. Subsequent communications between the workflow manager and the workflow-enabled provider and the workflow-enabled client are with a request / response protocol. The workflow manager also comprises data storage for storing data for transmission to the workflow-enabled client or the workflow-enabled provider, and workflow storage for storing information related to registered clients. The present invention also includes a number of novel methods including a method for a method for registering a client and a method for activating a provider.
Owner:RICOH KK
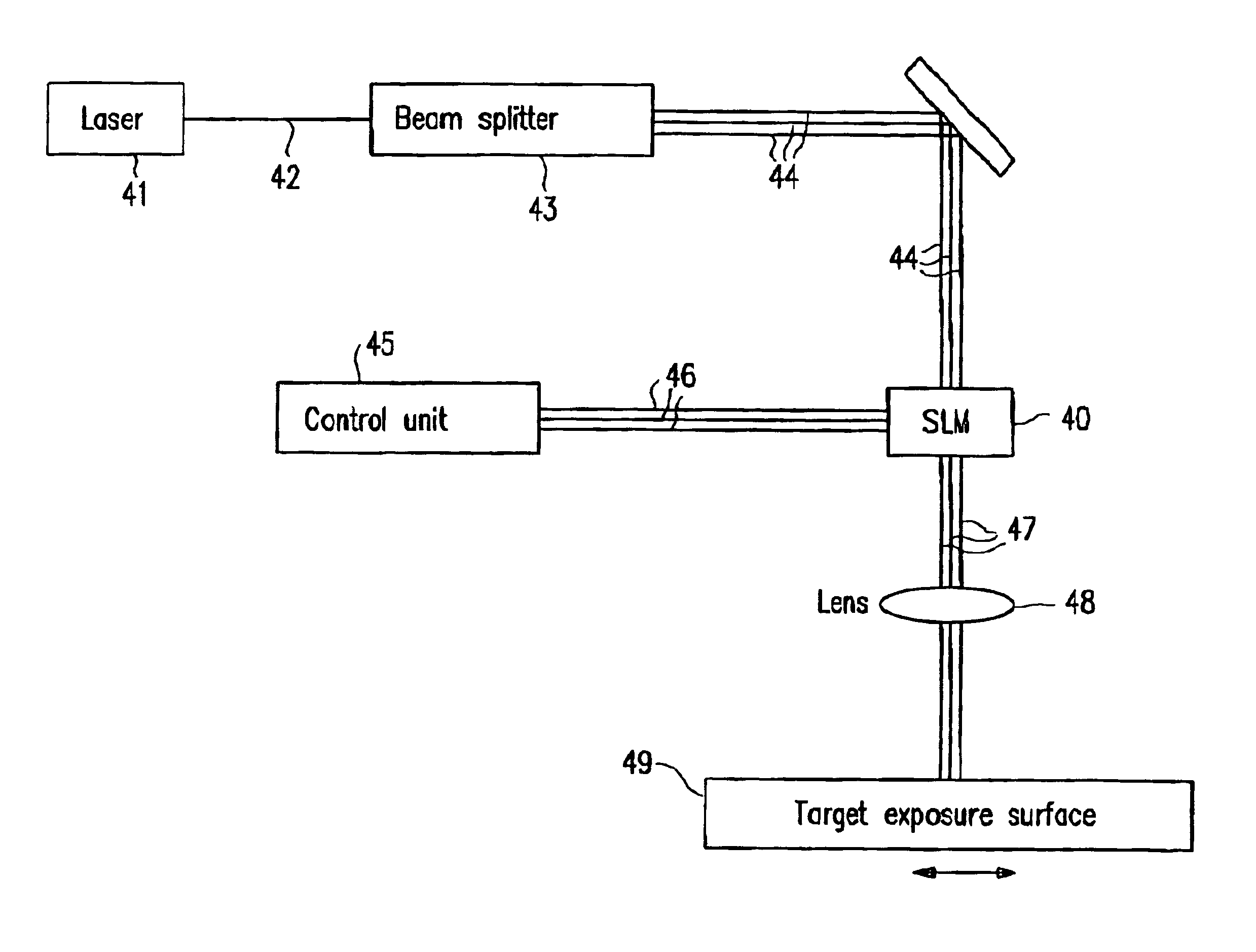
Lithography system
ActiveUS6958804B2Location somewhat remoteReduce transmission lossMirrorsElectric discharge tubesLithographic artistLight beam
A maskless lithography system for transferring a pattern onto the surface of a target. At least one beam generator for generating a plurality of beamlets. A plurality of modulators modulate the magnitude of a beamlet, and a control unit controls of the modulators. The control unit generates and delivers pattern data to the modulators for controlling the magnitude of each individual beamlet. The control unit includes at least one data storage for storing the pattern data, at least one readout unit for reading out the data from the data storage, at least one data converter for converting the data that is read out from the data storage into at least one modulated light beam, and at least one optical transmitter for transmitting the at least one modulated light beam to the modulation modulators.
Owner:ASML NETHERLANDS BV
User authentication in a cloud environment
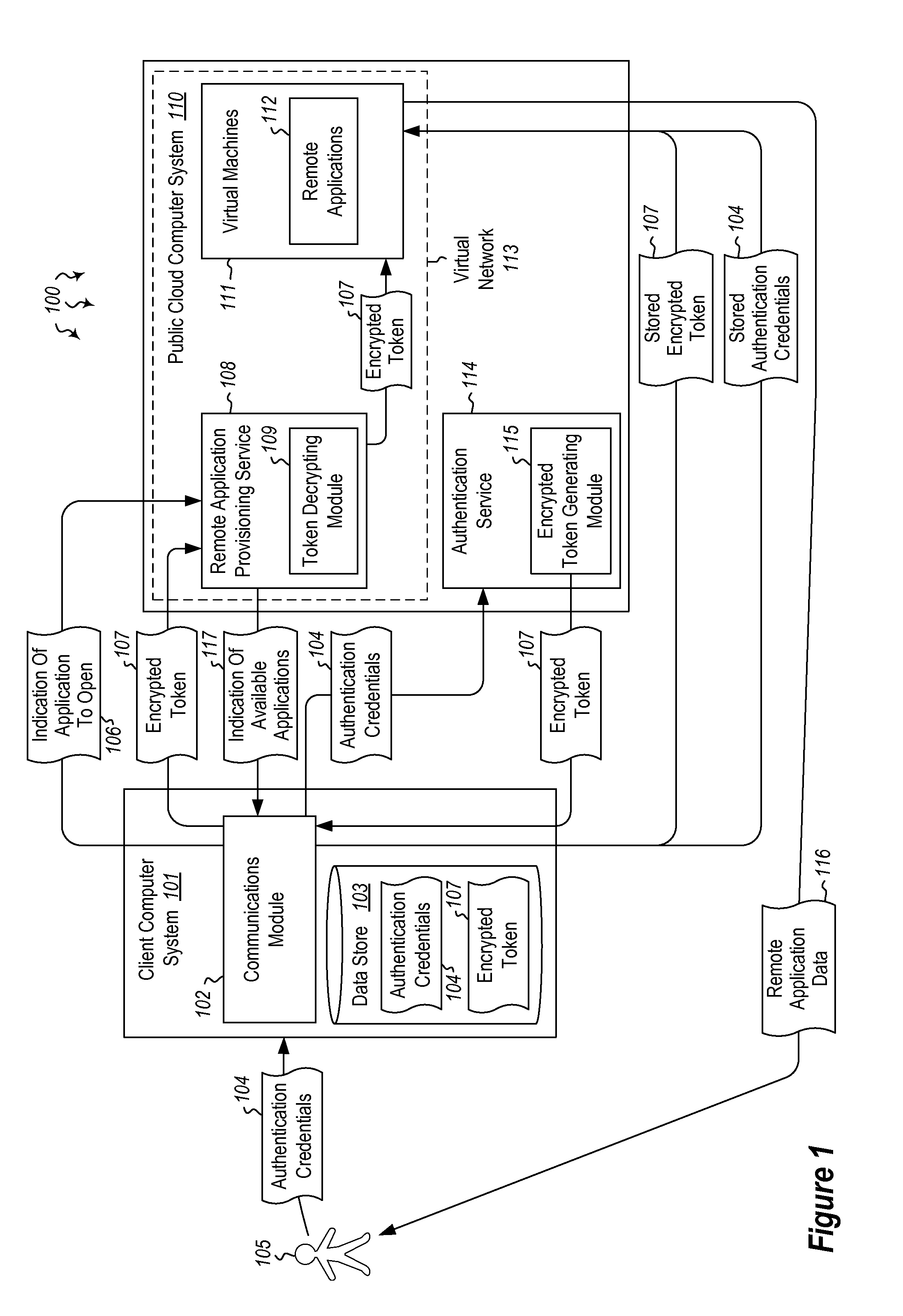
ActiveUS9124569B2Digital data processing detailsDigital data authenticationInternet Authentication ServiceData memory
Embodiments are directed to authenticating a user to a remote application provisioning service. In one scenario, a client computer system receives authentication credentials from a user at to authenticate the user to a remote application provisioning service that provides virtual machine-hosted remote applications. The client computer system sends the received authentication credentials to an authentication service, which is configured to generate an encrypted token based on the received authentication credentials. The client computer system then receives the generated encrypted token from the authentication service, stores the received encrypted token and the received authentication credentials in a data store, and sends the encrypted token to the remote application provisioning service. The encrypted token indicates to the remote application provisioning service that the user is a valid user.
Owner:MICROSOFT TECH LICENSING LLC
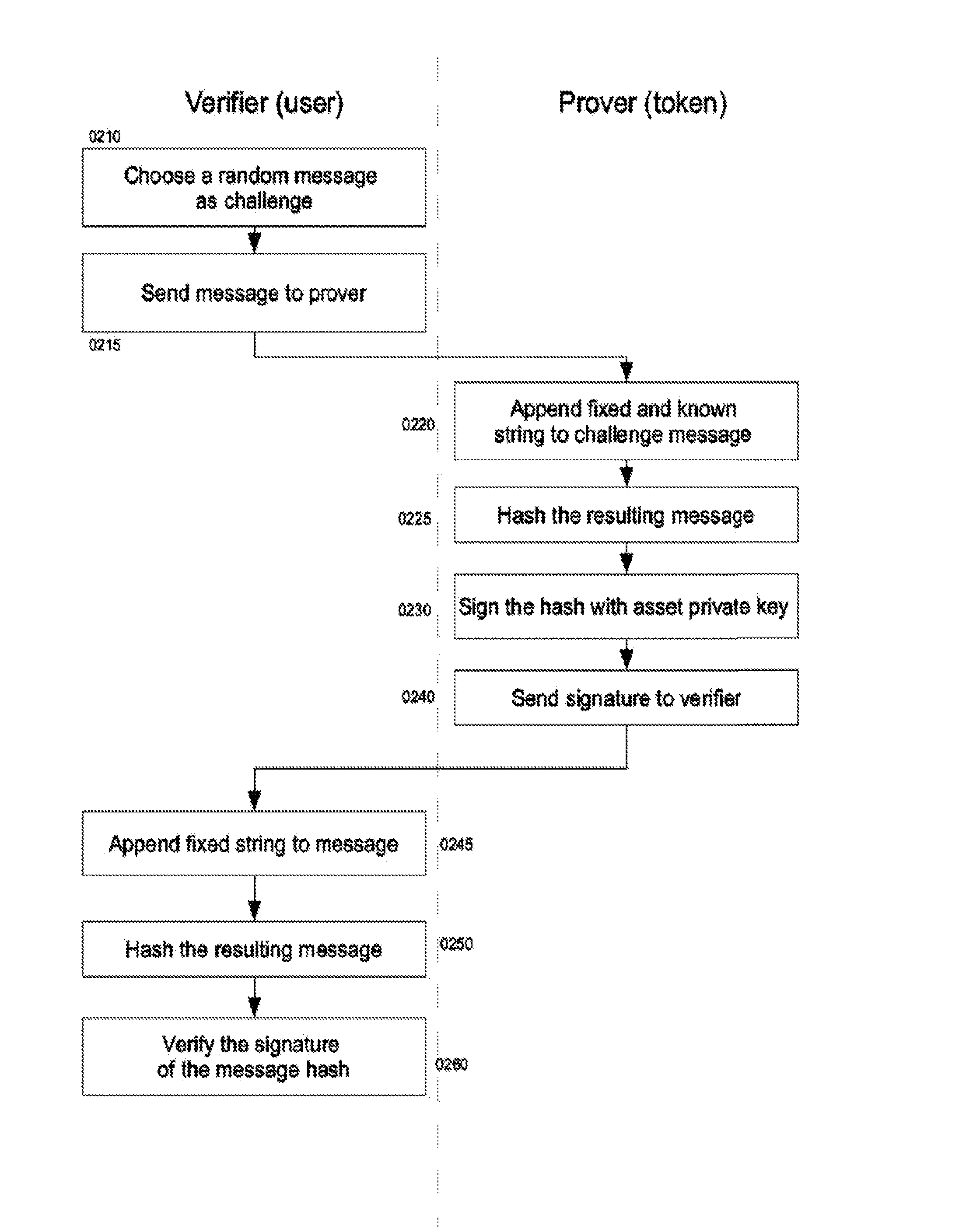
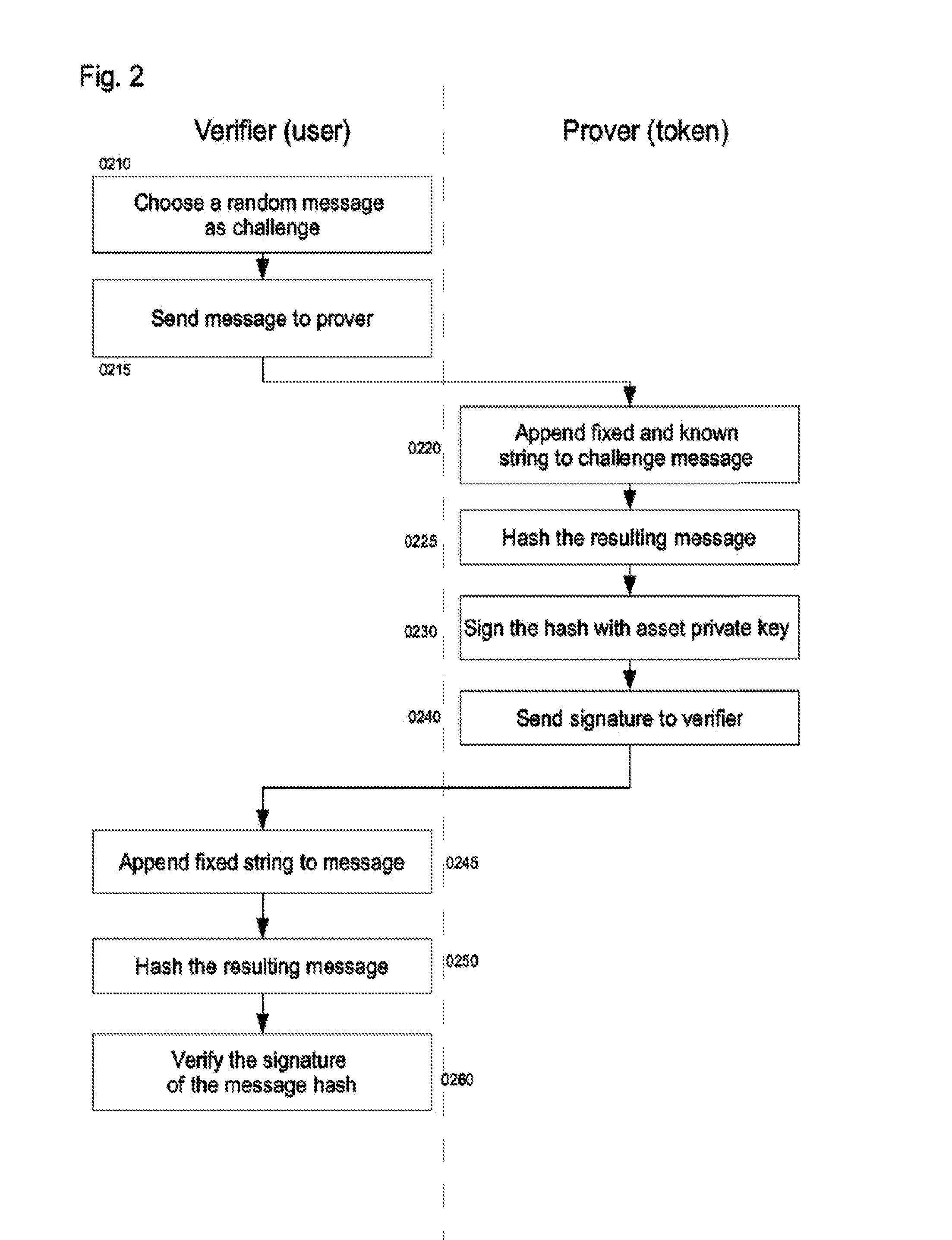
Secure Storing and Offline Transferring of Digitally Transferable Assets
InactiveUS20160085955A1Digital data processing detailsUnauthorized memory use protectionDigital signatureData memory
A handheld electronic device enables securely transferring control of a valuable asset associated with a code. The device includes a processor, non-transitory data storage, and a communication component configured to transmit data external to the device. A case houses the components, and is mechanically tamper evident. Software stores within the data storage at least one code, prevents transmission of any code through the communication component without authorization by the user, invalidates the association of a particular code with respect to a particular asset when the software carries out at least one of (i) authorizing transmission of the particular code, and (ii) authenticating a valid transaction using the particular code and authorizing transmission of the digital signature through the communication component.
Owner:DOOSRA
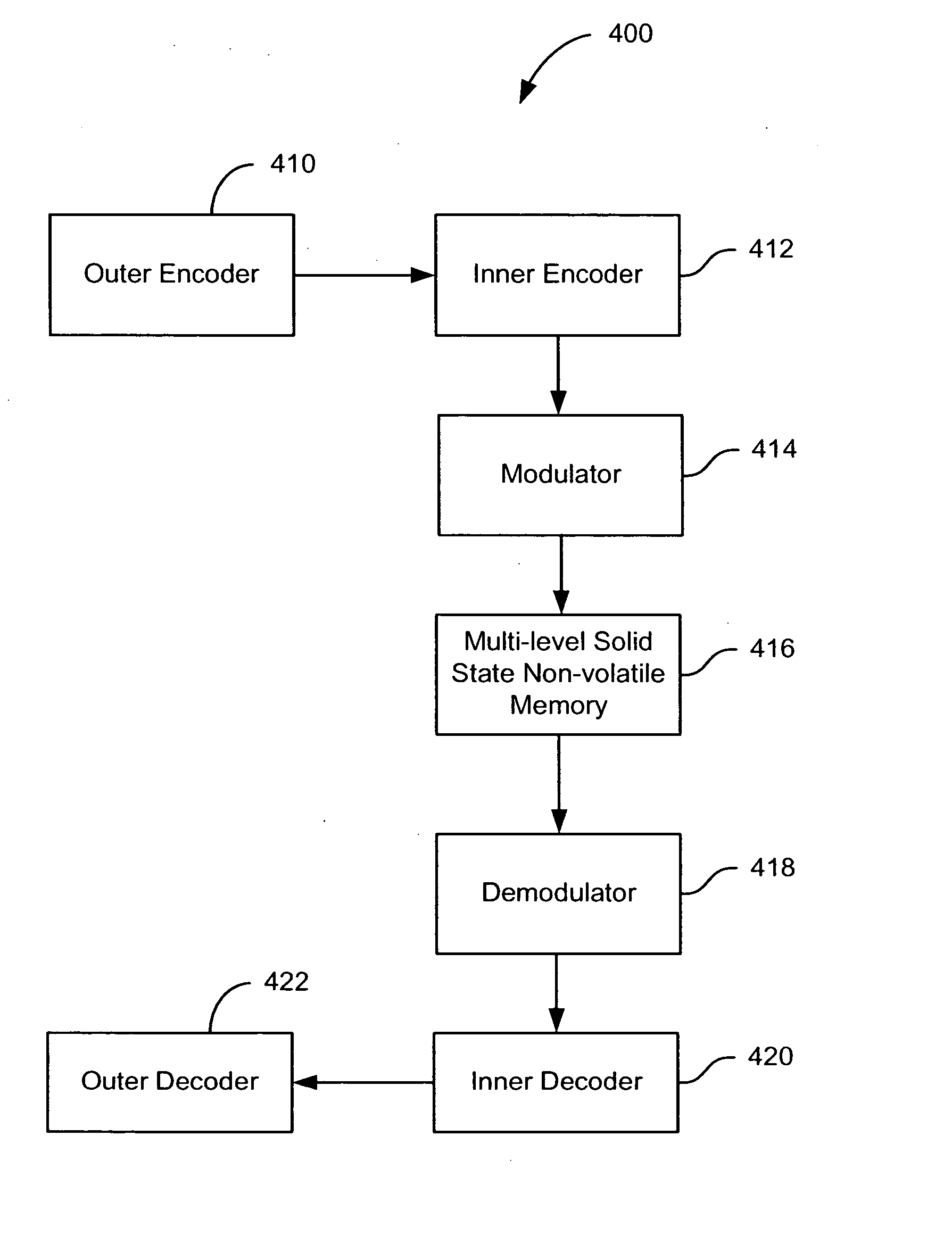
Method and system for error correction in flash memory
ActiveUS20070171730A1Improve storage densityImprove reliabilityMemory architecture accessing/allocationError detection/correctionA d converterData memory
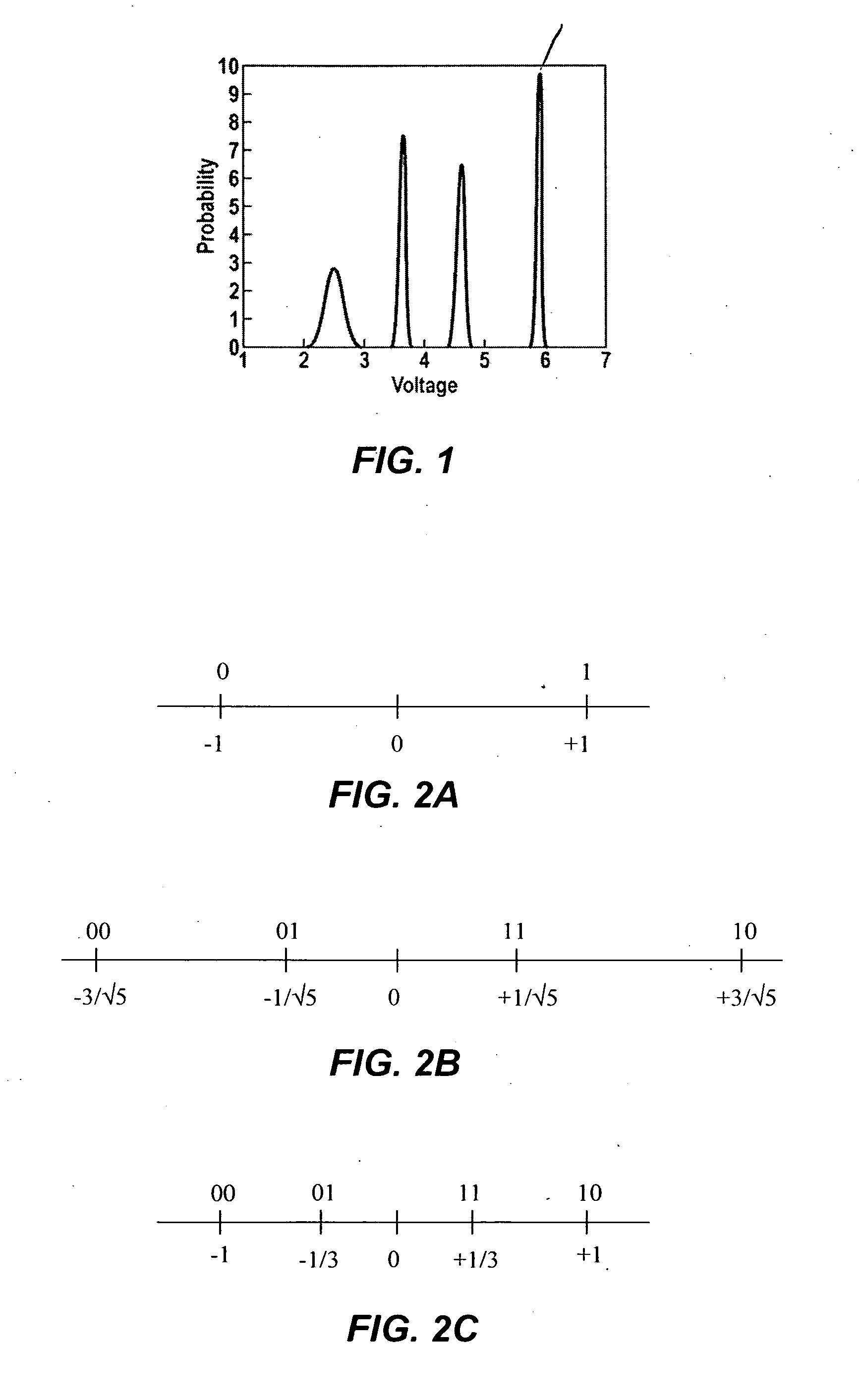
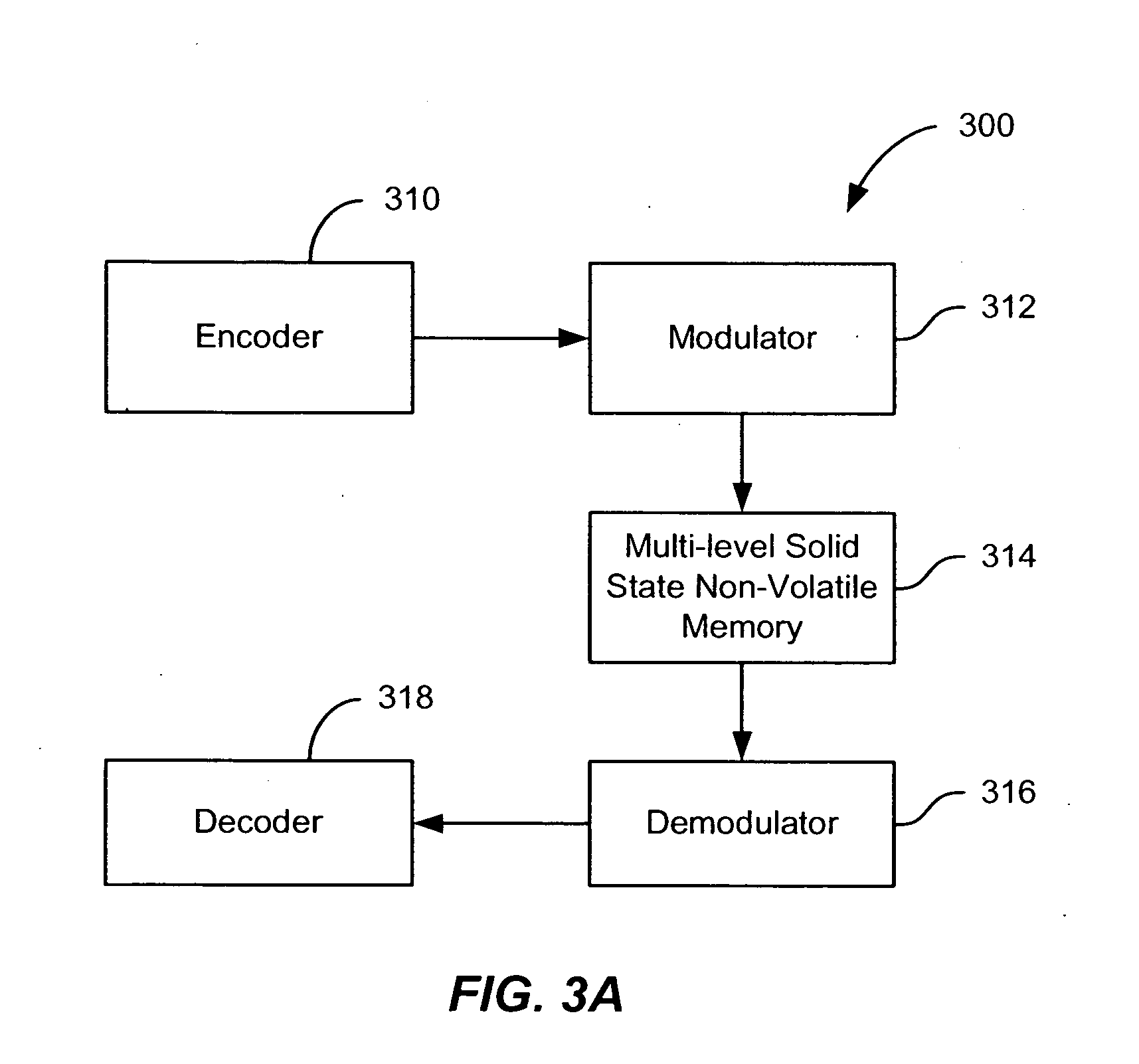
A solid state non-volatile memory unit. The memory unit includes a multi-level solid state non-volatile memory array adapted to store data characterized by a first number of digital levels. The memory unit also includes an analog-to-digital converter having an input and an output. The input of the analog-to-digital converter is adapted to receive data from the multi-level solid state non-volatile memory array. The output of the analog-to-digital converter is adapted to output a digital signal characterized by a second number of digital levels greater than the first number of digital levels.
Owner:MARVELL ASIA PTE LTD
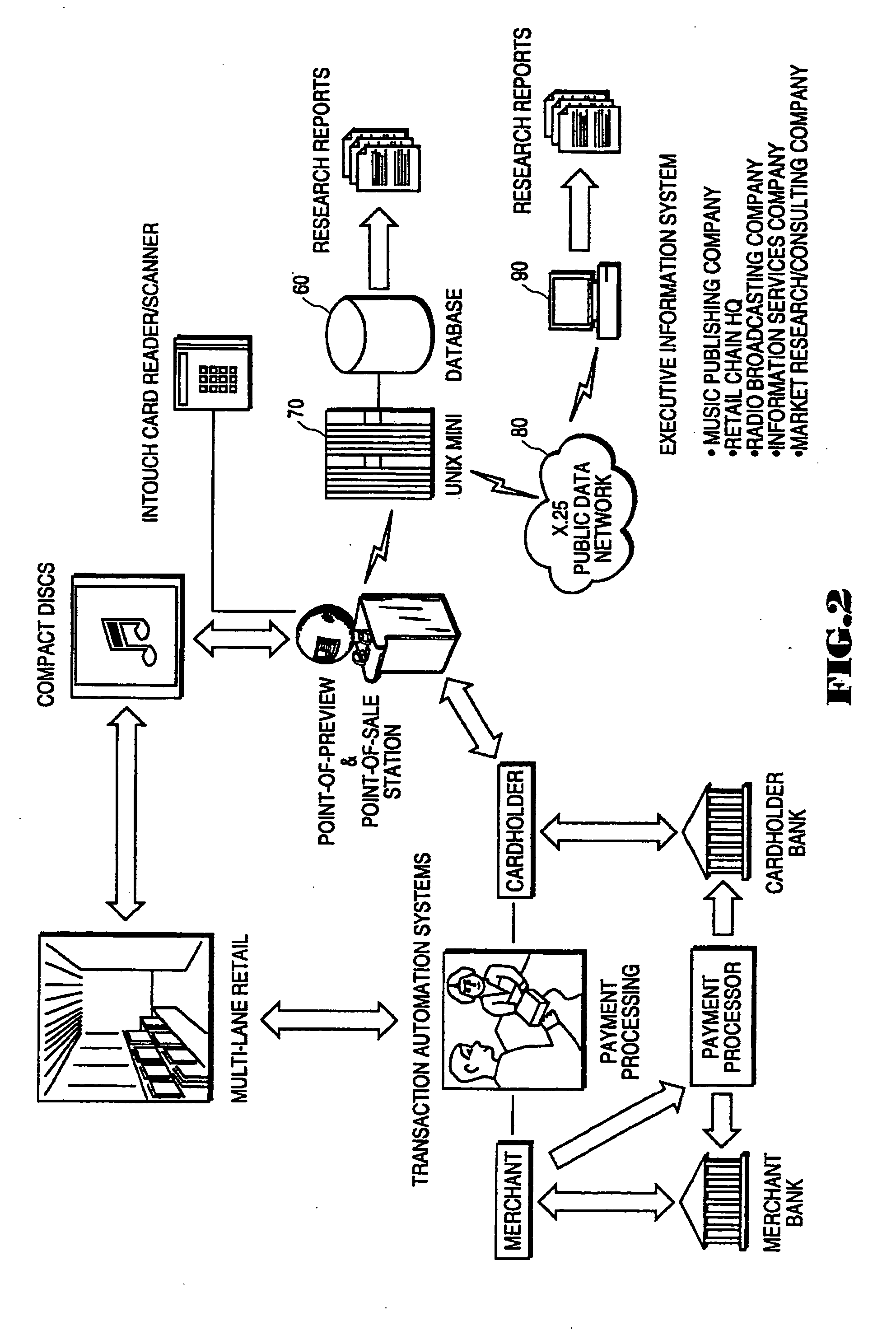
Network apparatus and method for preview of music products and compilation of market data
InactiveUS20050267819A1Electrophonic musical instrumentsDisc-shaped record carriersCompact discWeb site
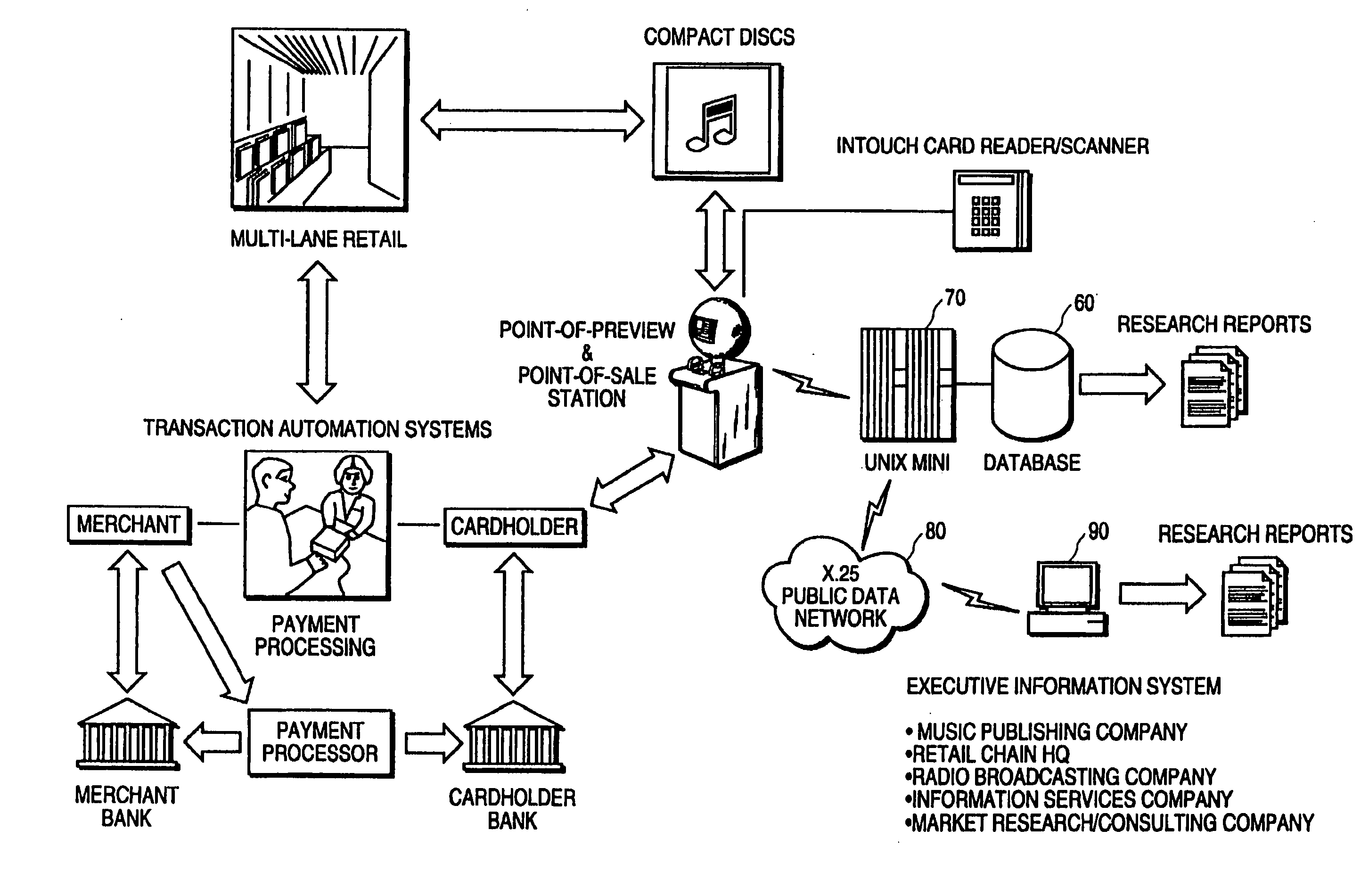
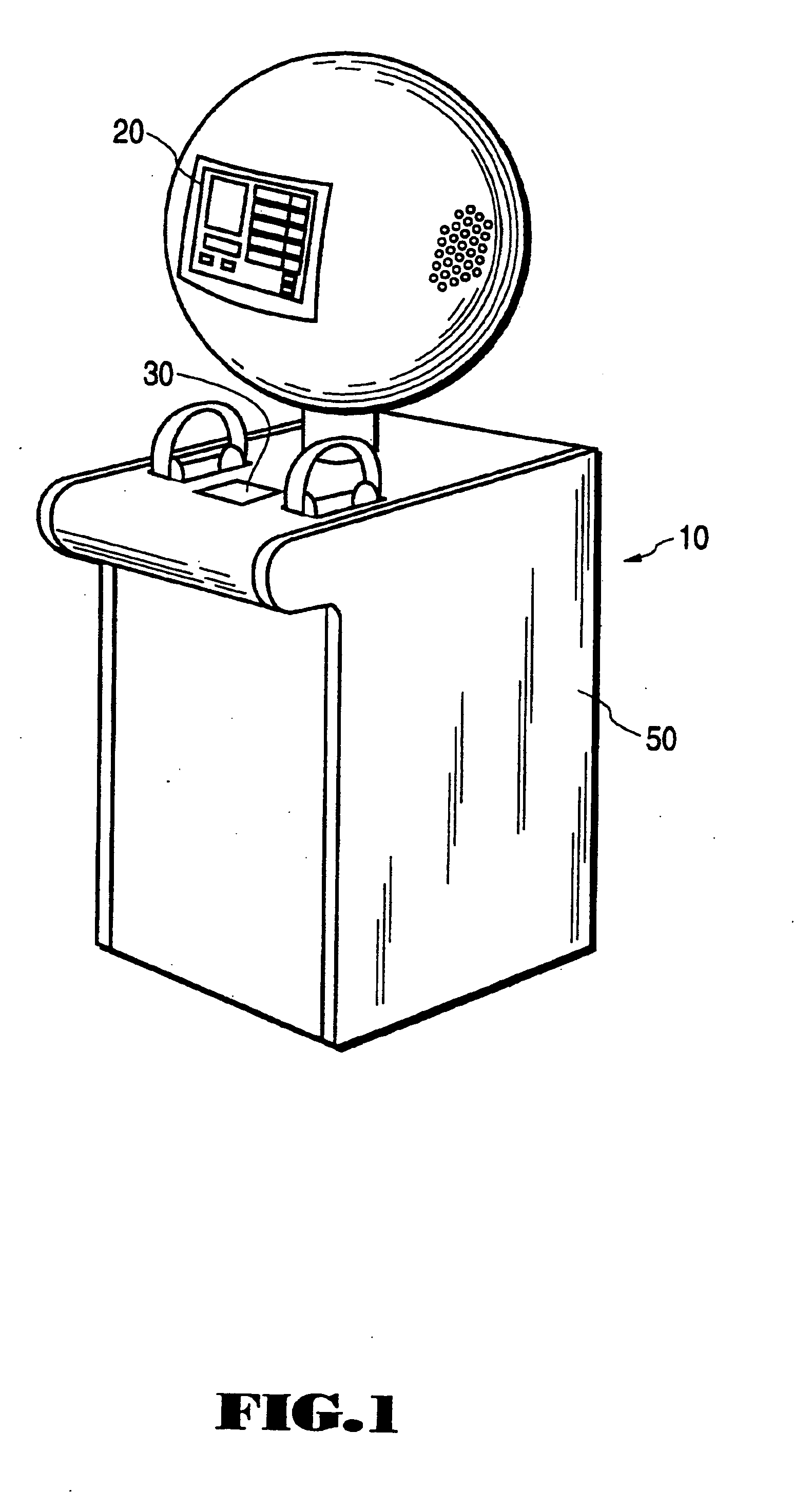
A system for on-line user-interactive multimedia based point-of-preview. The system provides for a network web site and accompanying software and hardware for allowing users to access the web site over a network such as the internet via a computer. The user is uniquely identified to the web site server through an identification name or number. The hardware associated with the web site includes storage of discrete increments of pre-selected portions of music products for user selection and preview. After user selection, a programmable data processor selects the particular pre-recorded music product from data storage and then transmits that chosen music product over the network to the user for preview. Subscriber selection and profile data (i.e. demographic information) can optionally be collected and stored to develop market research data. Since the system provides for multiple embodiments, the system contemplates previewing of audio programs such as music on compact discs, video programs such as movies and text from books and other written documents. Furthermore, it is contemplated that the network web site can be accessed from a publicly accessible kiosk, available, e.g. at a retail store location, or from a desk top computer.
Owner:KAPLAN JOSHUA D
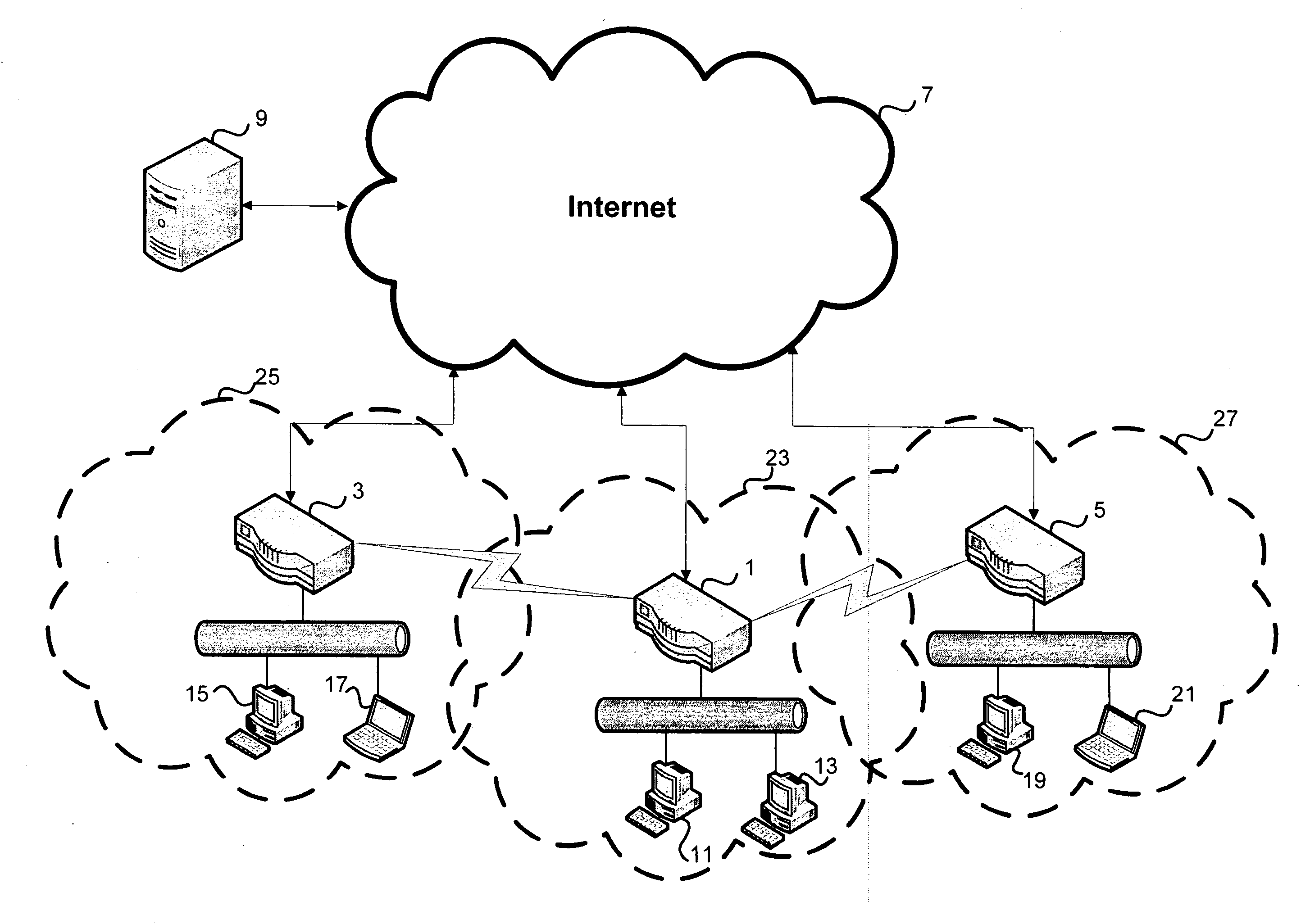
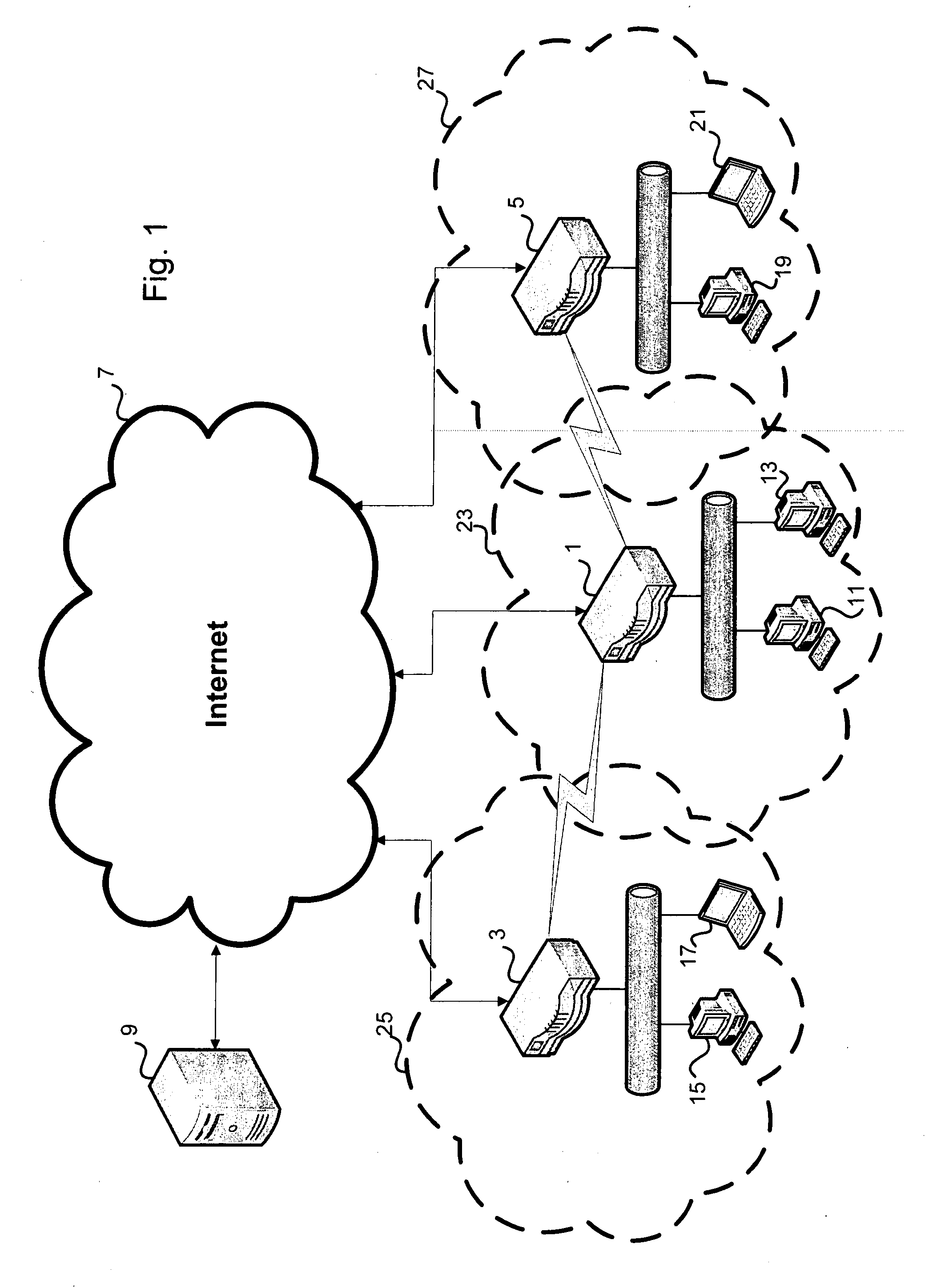
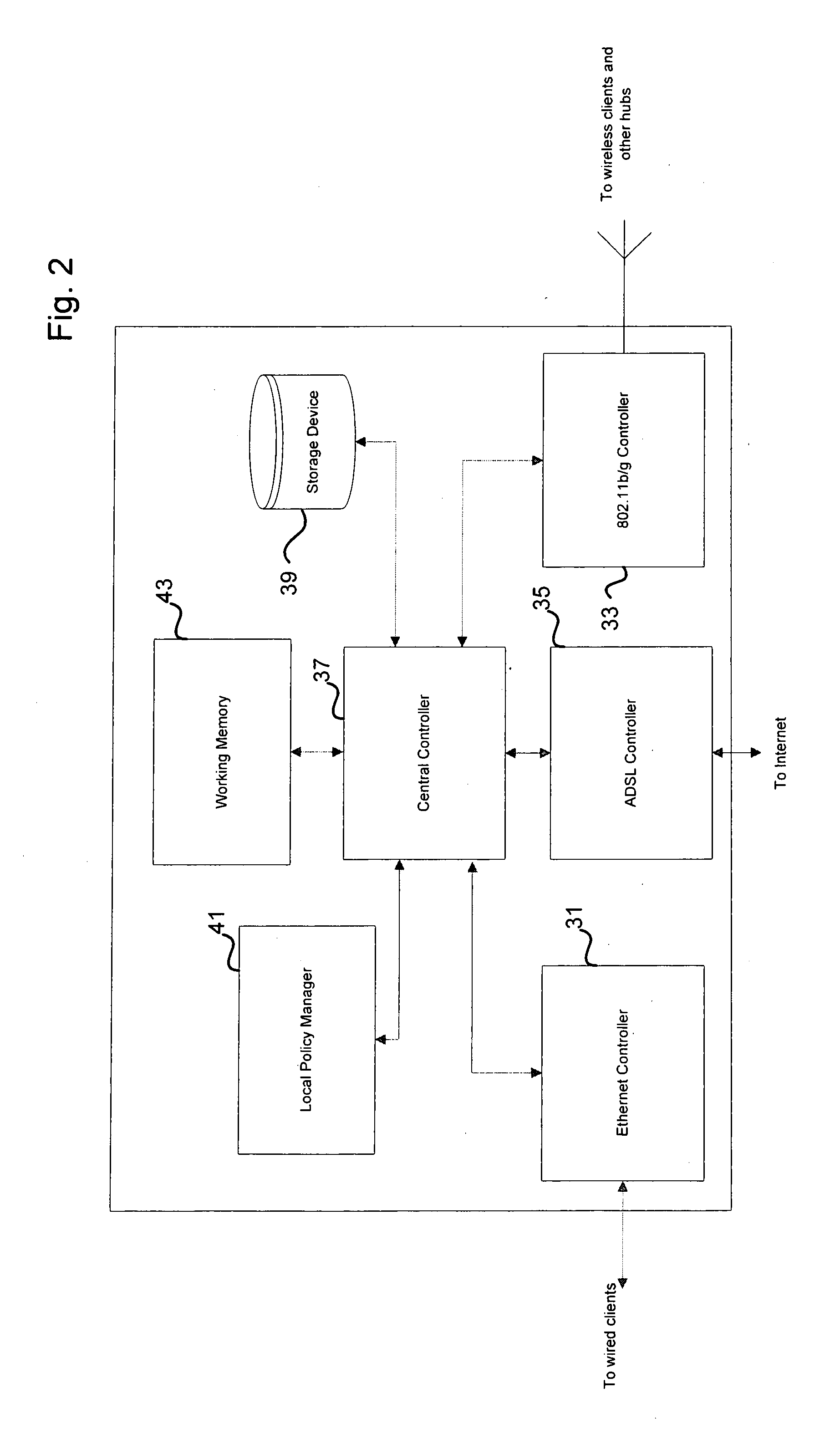
Content delivery
ActiveUS20100111059A1Pulse modulation television signal transmissionMultiple digital computer combinationsWireless routerThe Internet
Wireless routers having an ADSL or cable connection to content data available via the Internet, a wired connection for connecting local clients in a LAN and a wireless controller for connecting to other wireless routers and clients in a wireless local area networks (WLANs). The WLANs often intersect and therefore it is possible to communicate between wireless routers in order to exchange content data via the wireless LAN in addition to the ADSL or cable connection. Further, each wireless routers has a cache data store to cache content data requested by the user, or any other information sent to the wireless router from another wireless router. A central server can schedule transfer of content data between wireless routers by considering information packets stored on the server
Owner:BRITISH TELECOMM PLC
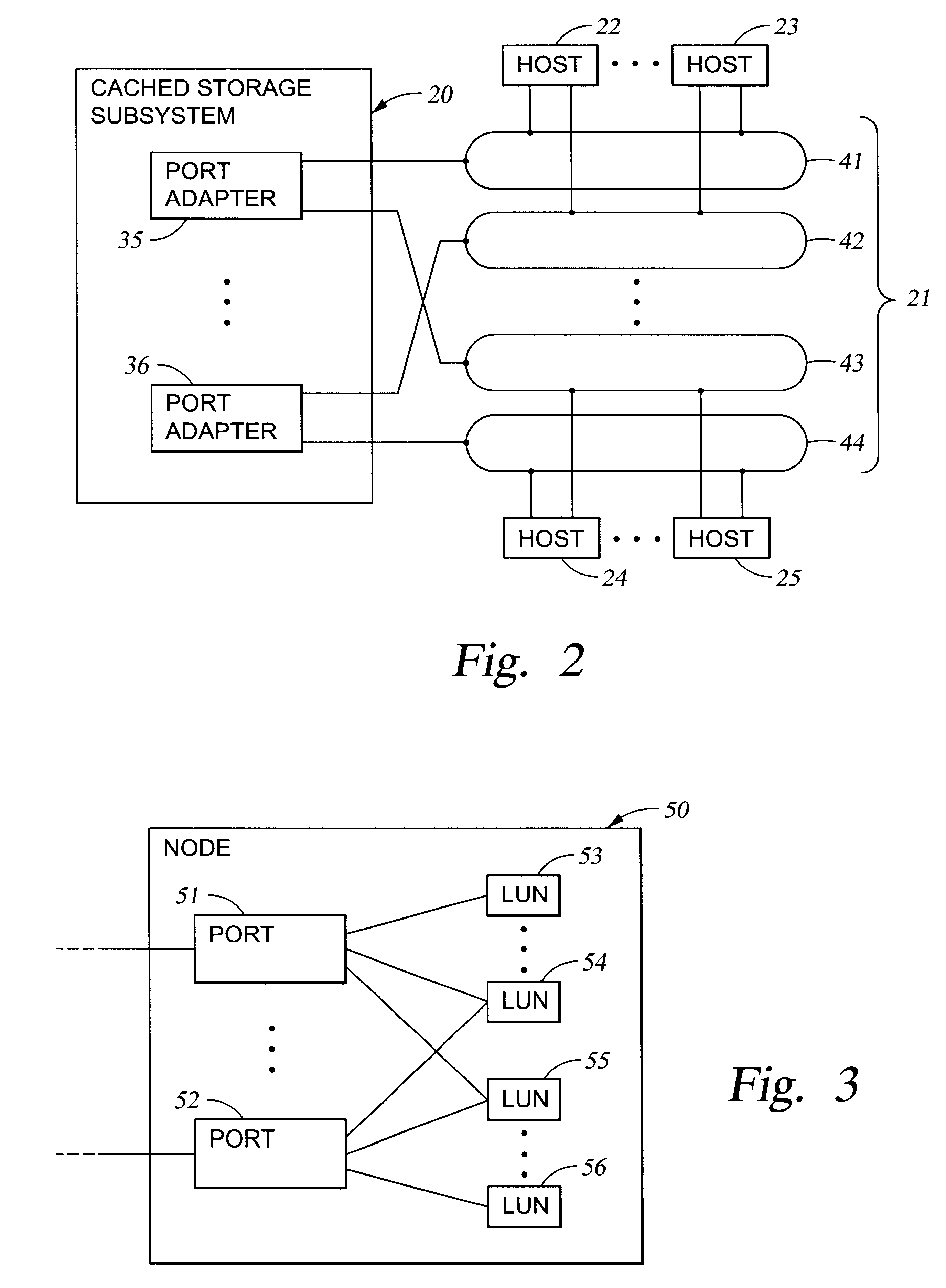
Storage mapping and partitioning among multiple host processors
InactiveUS6799255B1Input/output to record carriersData processing applicationsData portControl store
A storage controller for controling access to data storage has a memory and at least one data port for a data network including host processors. The memory is programmed to define a respective specification for each host processor of a respective subset of the data storage to which access by the host processor is restricted, and each specification is associated with a host identifier stored in the memory. When the storage controller receives a data access request from a host processor, it decodes a host identifier from the data access request, and searches the memory for a host identifier matching the host identifier decoded from the request. Upon finding a match, the respective specification of the respective subset for the host processor is accessed to determine whether or not storage specified by the storage access request is contained in the respective subset. If so, then storage access can continue, and otherwise, storage access is denied. Preferably the host identifier decoded from the request is a temporary address assigned by the network, and also stored in the memory in association with each respective specification is a relatively permanent identifier for the host processor.
Owner:EMC IP HLDG CO LLC
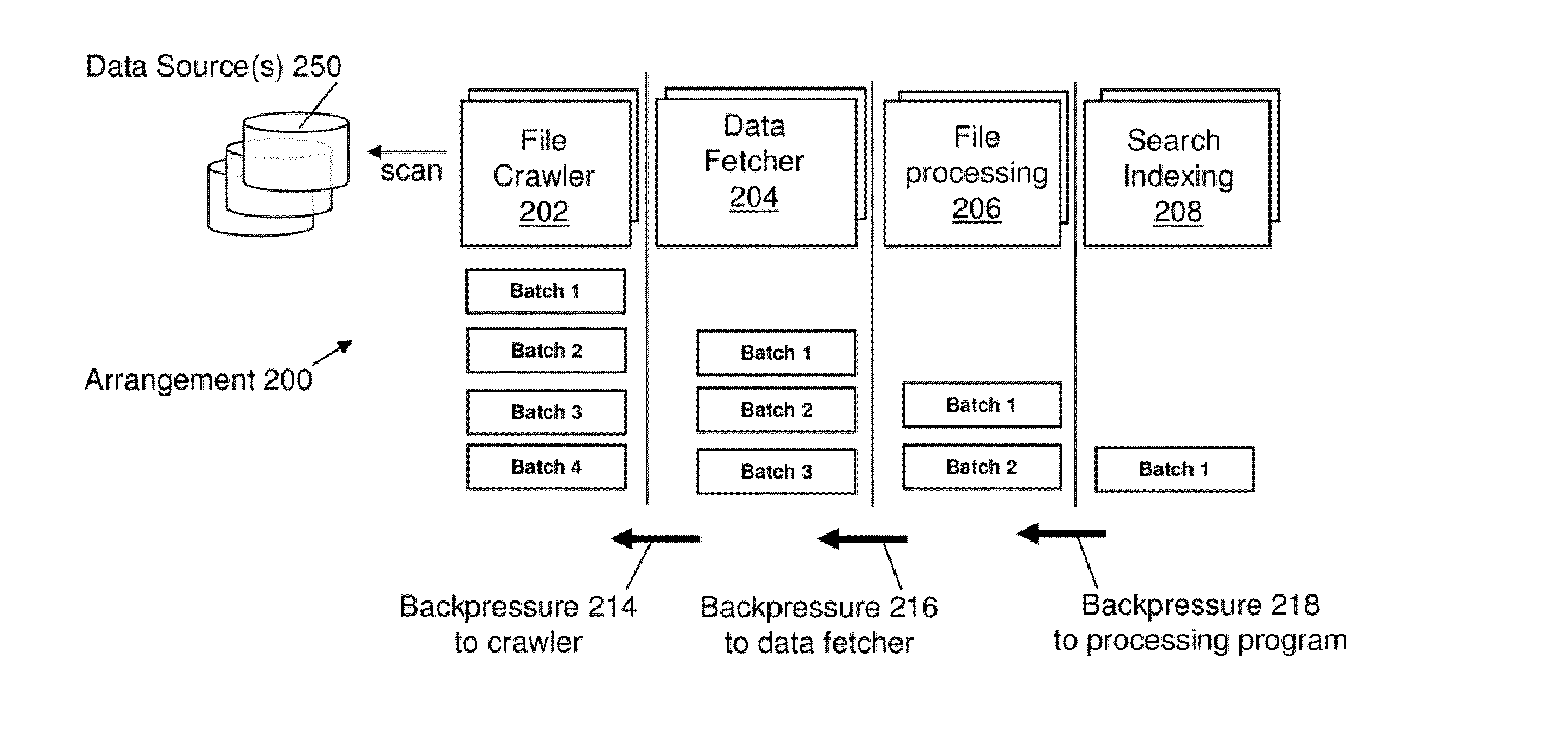
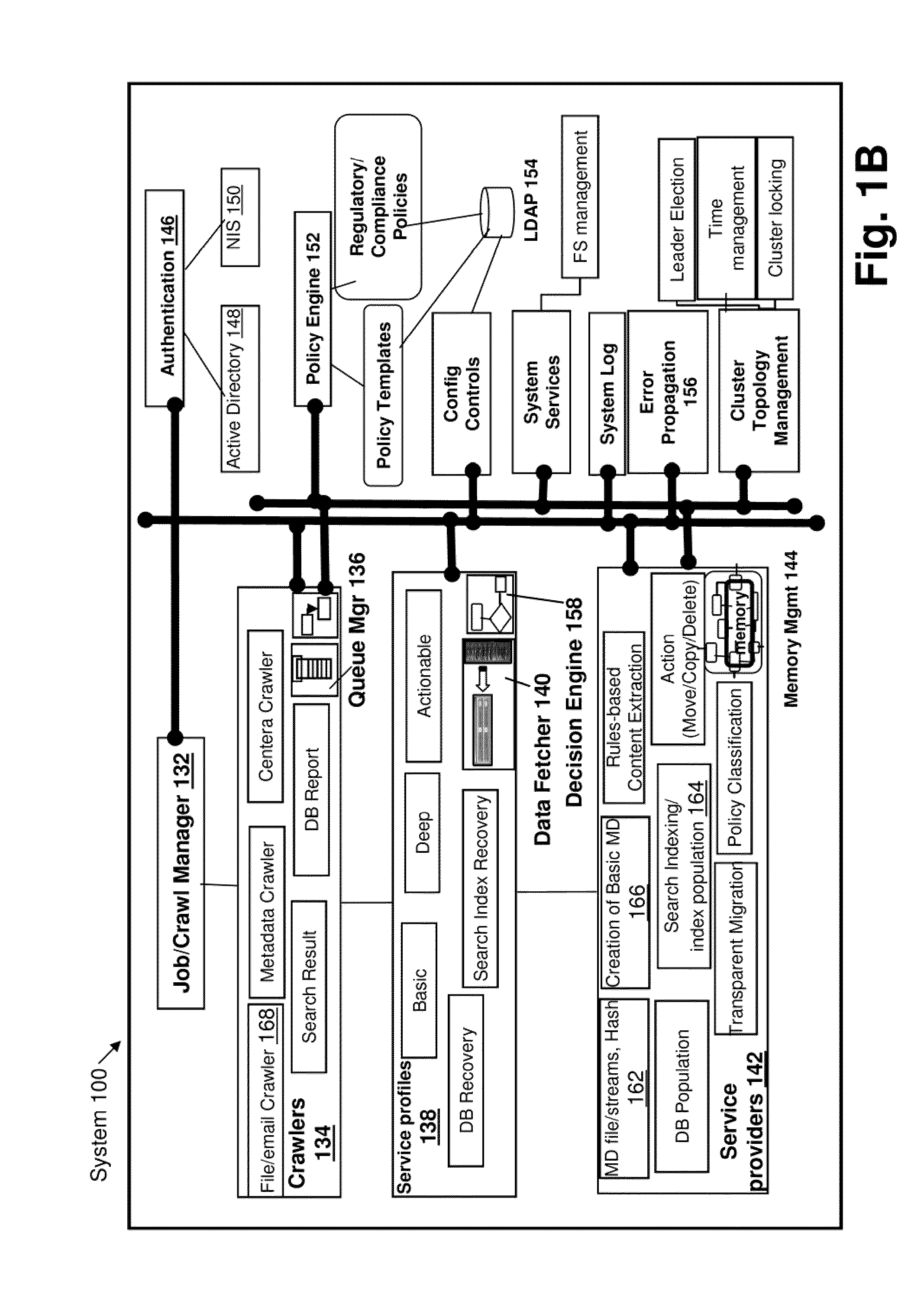
Systems and methods for facilitating data discovery
ActiveUS9135261B2Digital data information retrievalDigital data processing detailsData ingestionNetwork on
A system for facilitating data discovery on a network, wherein the network has one or more data storage devices. The system may include a crawler program configured to select at least a first set of files and a second set of files, each of the first set of files and the second set of files being stored in at least one of the one or more data storage devices. The system may also include a data fetcher program configured to obtain a copy of the first set of files, the data fetcher program being further configured to resist against obtaining a copy of the second set of files. The system may also include circuit hardware implementing one or more functions of one or more of the crawler program and the data fetcher program.
Owner:EMC IP HLDG CO LLC
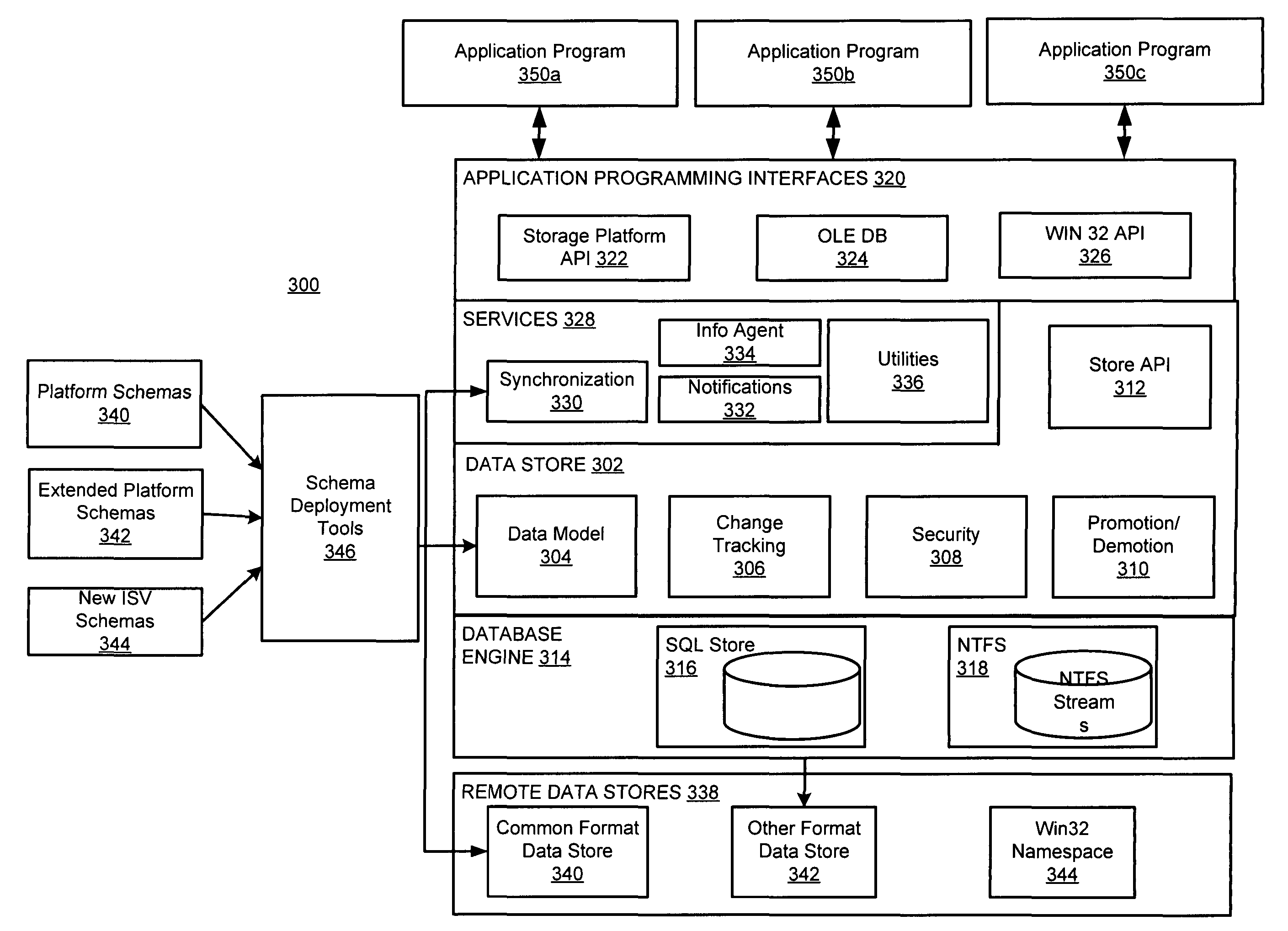
Storage platform for organizing, searching, and sharing data
ActiveUS20050050054A1Efficient application developmentFacilitate data sharingData processing applicationsDatabase management systemsFile systemApplication programming interface
Various embodiments of the present invention are directed to a storage platform comprising a database engine, a data store, an application programming interface. The data store is implemented on the database engine for storing data therein, and the data store implements a data model that supports the organization, searching, sharing, synchronization, and security of data stored in the data store. Specific types of data are described in schemas. The application programming interface enables application programs to access services and capabilities of the storage platform and to access the data described in the schemas. The storage platform supports interoperability with existing file systems, enables users and systems to synchronize data stored in different instances of the data store, and provides the ability for application programs to be notified about and to track changes made to the data in the data store.
Owner:MICROSOFT TECH LICENSING LLC
Methods and apparatus for monitoring local network traffic on local network segments and resolving detected security and network management problems occurring on those segments
InactiveUS20050060535A1Small sizeImprove search capabilitiesSecuring communicationElectric digital data processingData connectionData pack
A system for providing network security through manipulating data connections and connection attempts over a data-packet-network between at least two network nodes is provided. The system includes a system host machine, a first software application residing on the host machine for detecting and monitoring connection activity, a data store for storing connection related data, and a second software application for emulating one or more end nodes of the connections or connection attempts. In a preferred embodiment the system uses the detection software to detect one or more pre-defined states associated with a particular connection or connection attempt including states associated with data content transferred there over and performs at least one packet generation and insertion action triggered by the detected state or states, the packet or packets emulating one or more end nodes of the connection or connection attempt to cause preemption or resolution of the detected state or states.
Owner:PRAEMIO TECH
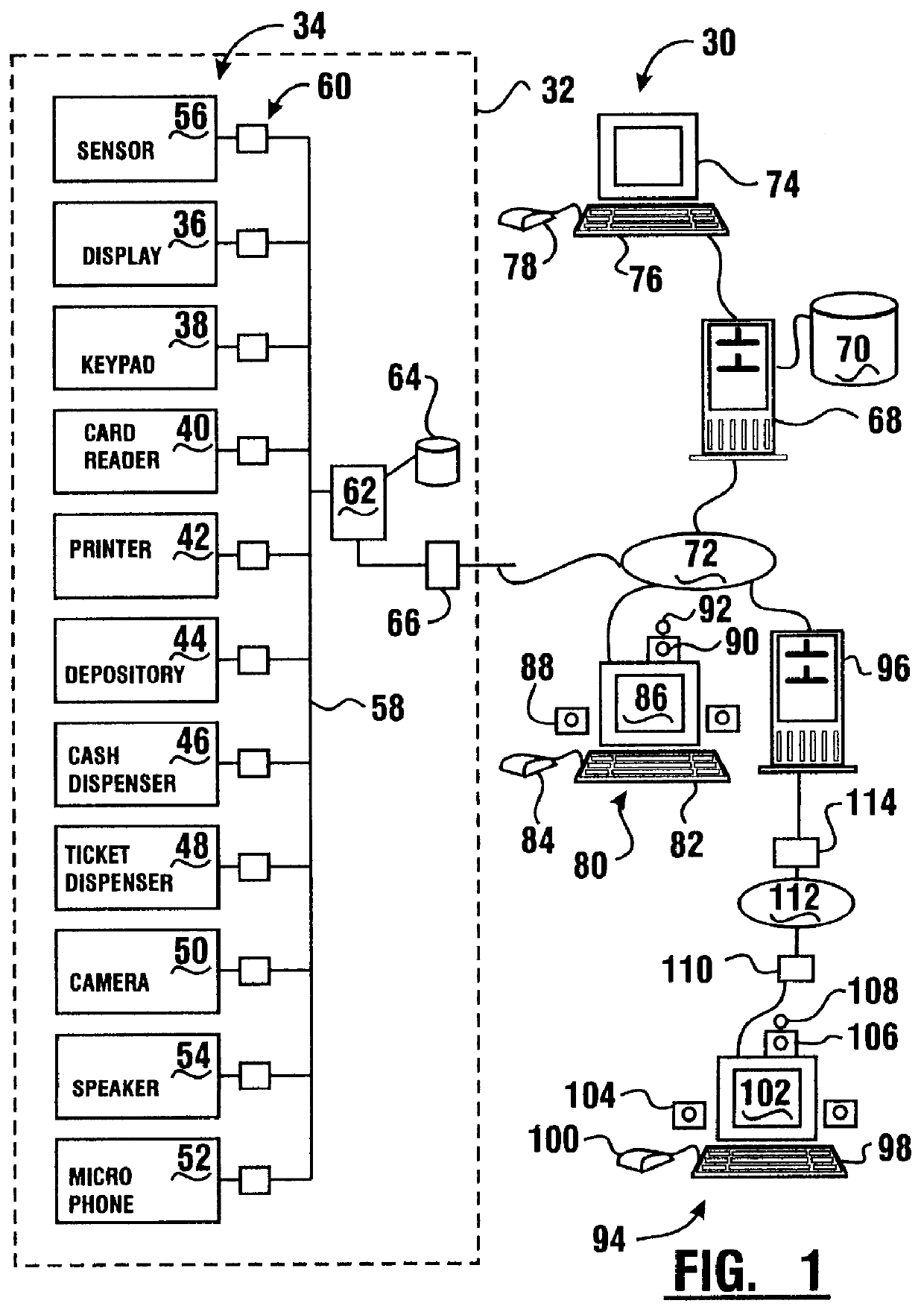
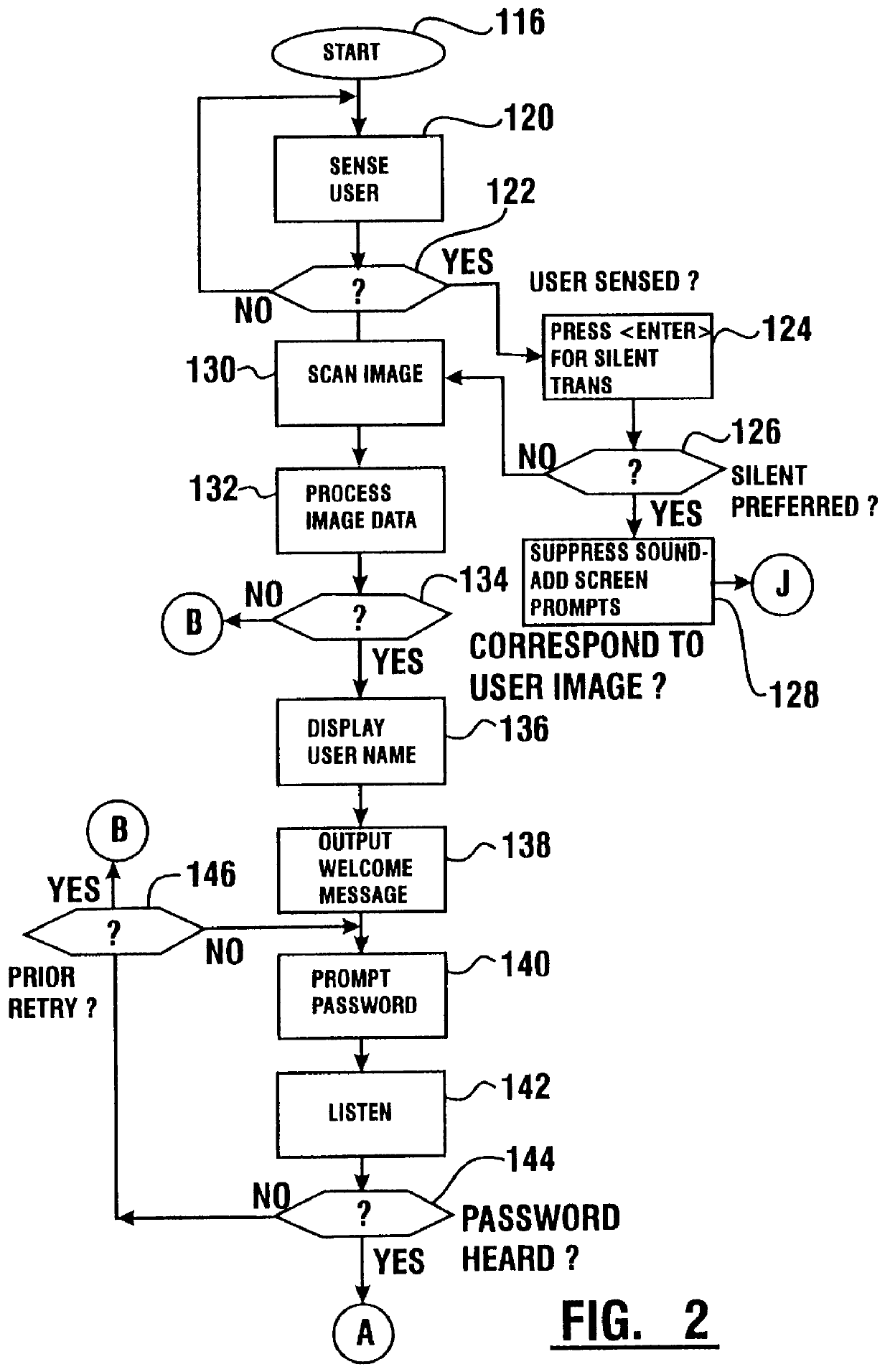
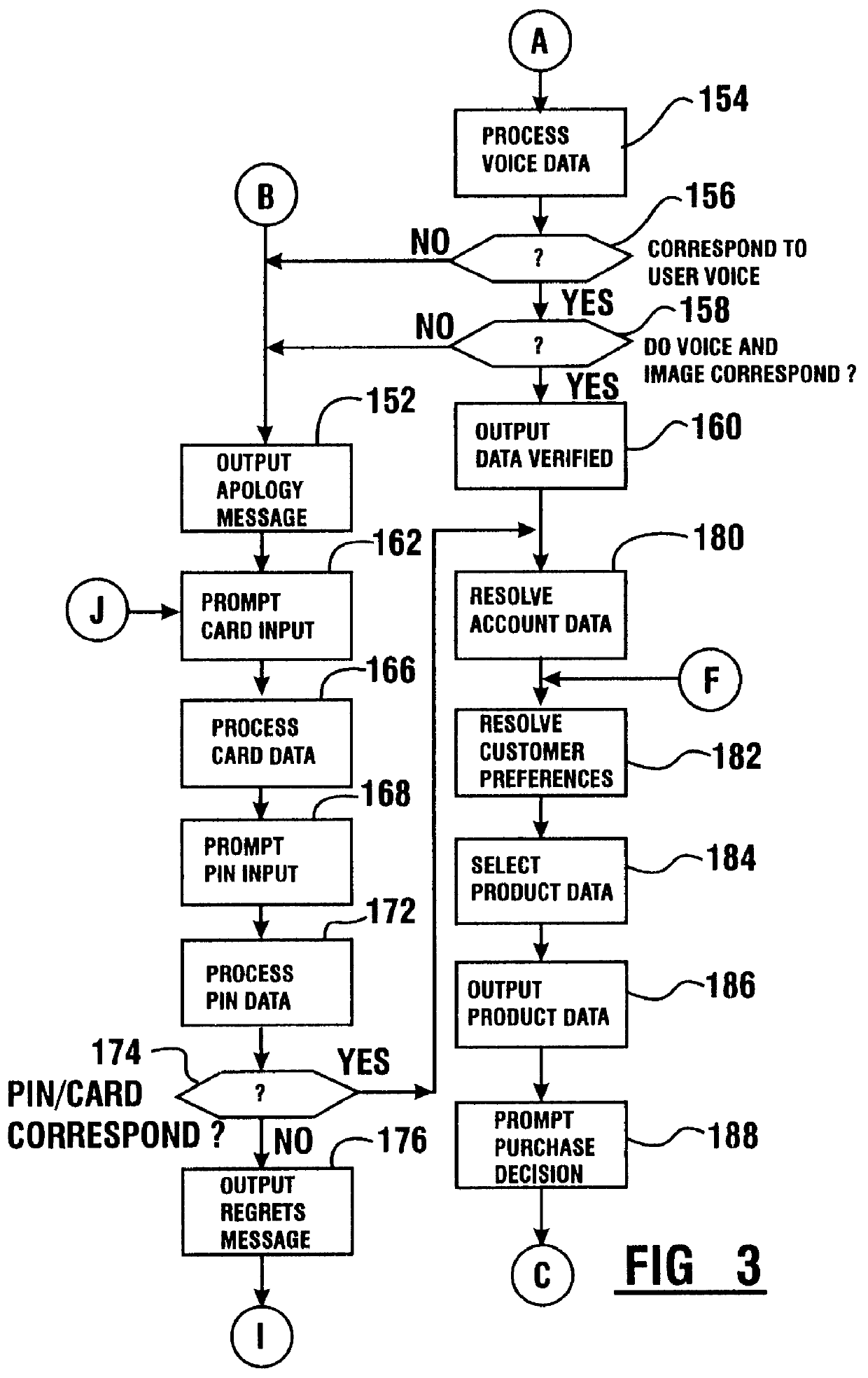
Transaction apparatus and method that identifies an authorized user by appearance and voice
A financial transaction apparatus (30) includes a financial transaction machine (32). The machine includes devices (34) including transaction function devices (42, 44, 46, 48) for carrying out operations associated with financial transactions. The terminal also includes an imaging device (50) and an audio input device (52), as well as a visual output device (36) and an audio output device (54). Terminal (32) is connected to a computer (68) which has an associated data store (70). The data store includes user data including image data and voice data corresponding to authorized users. The identity of a customer operating the machine is determined by resolving first identity data based on image signals from the imaging device which correspond to a user's appearance. Second identity data is resolved by the processor from voice signals from the audio input device corresponding to the user's voice. The computer enables operation of the transaction function devices if the level of correlation between the first and second identity data is sufficient to establish that the image and voice signals originate from a single authorized user.
Owner:DIEBOLD NIXDORF
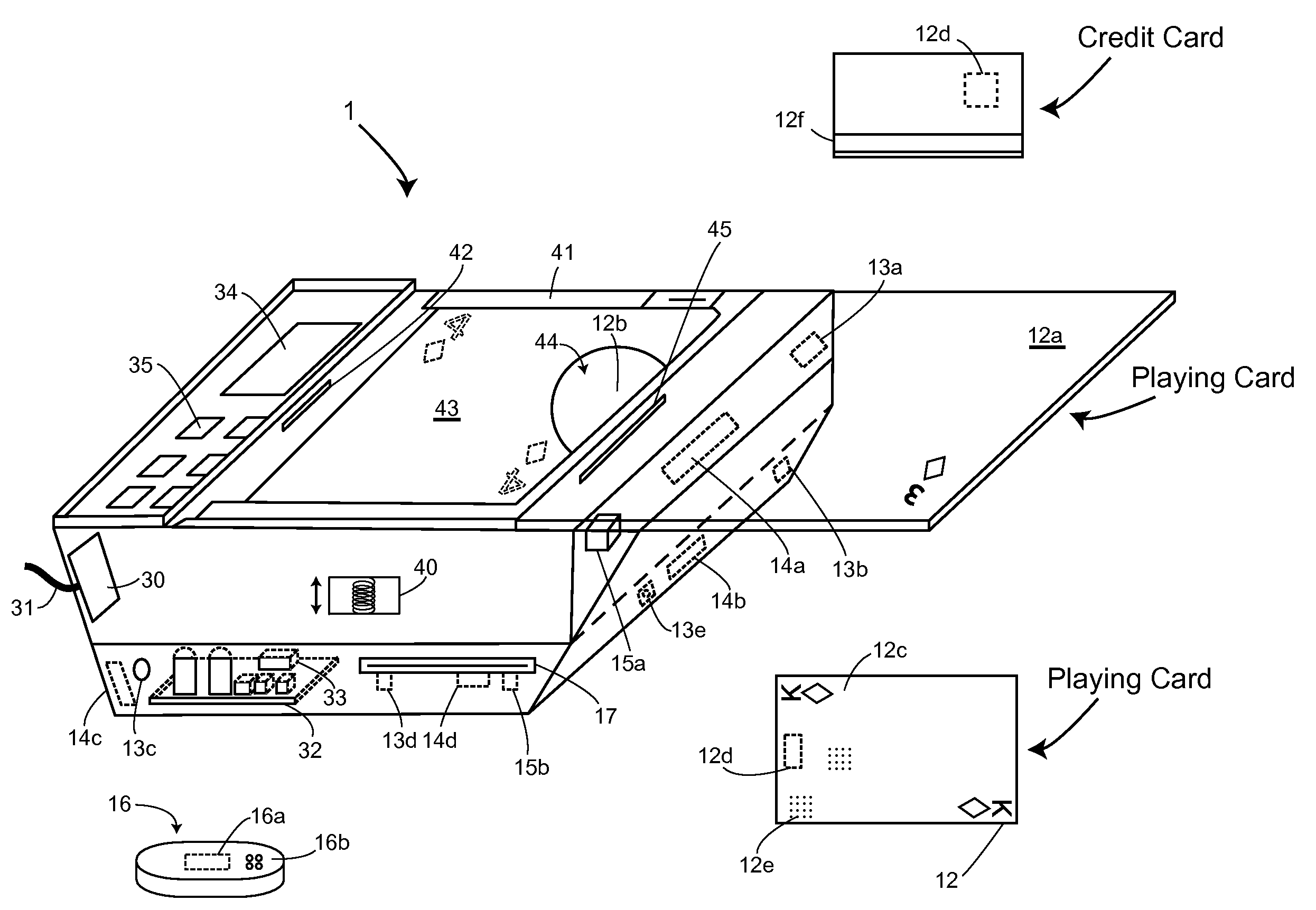
Table with sensors and smart card holder for automated gaming system and gaming cards
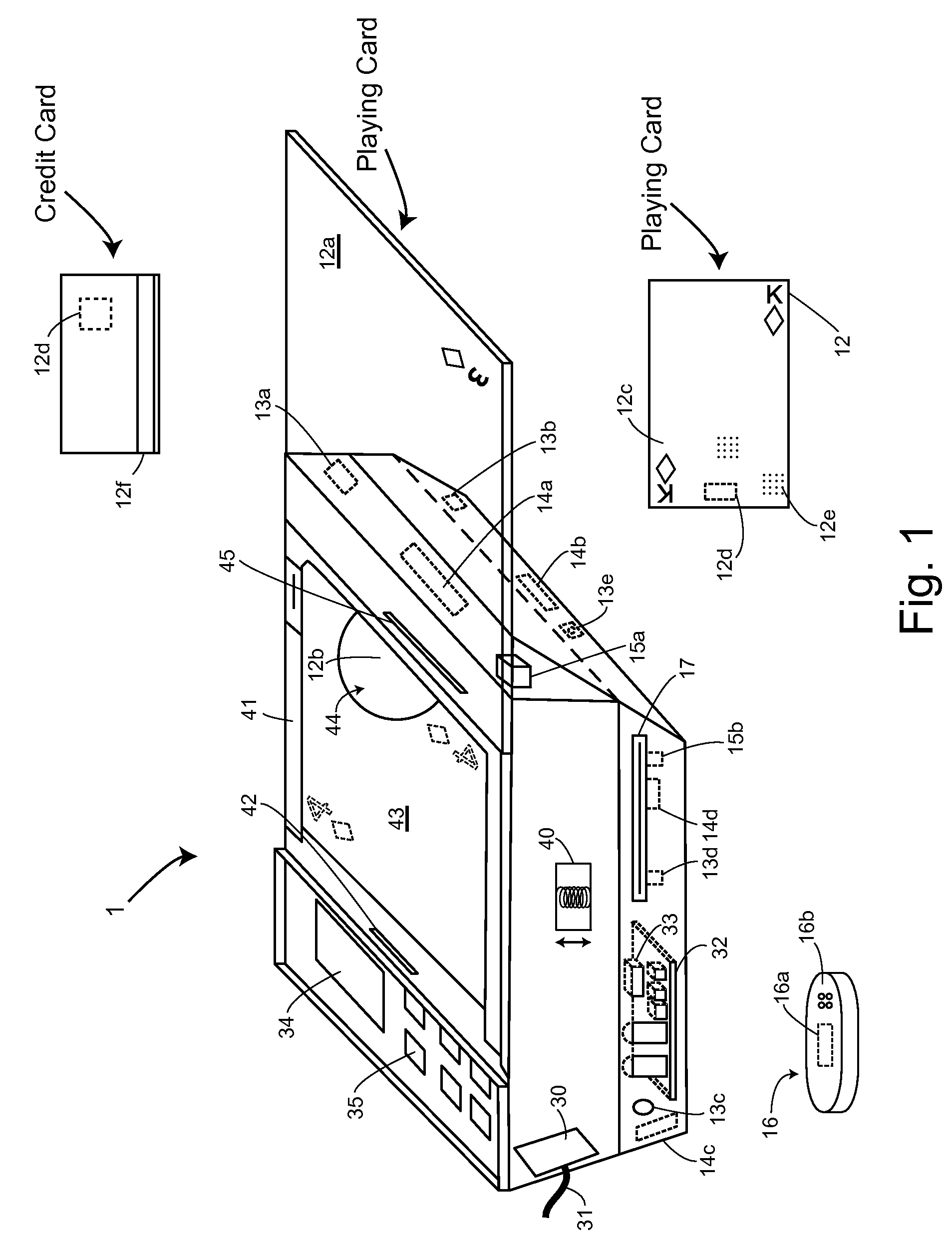
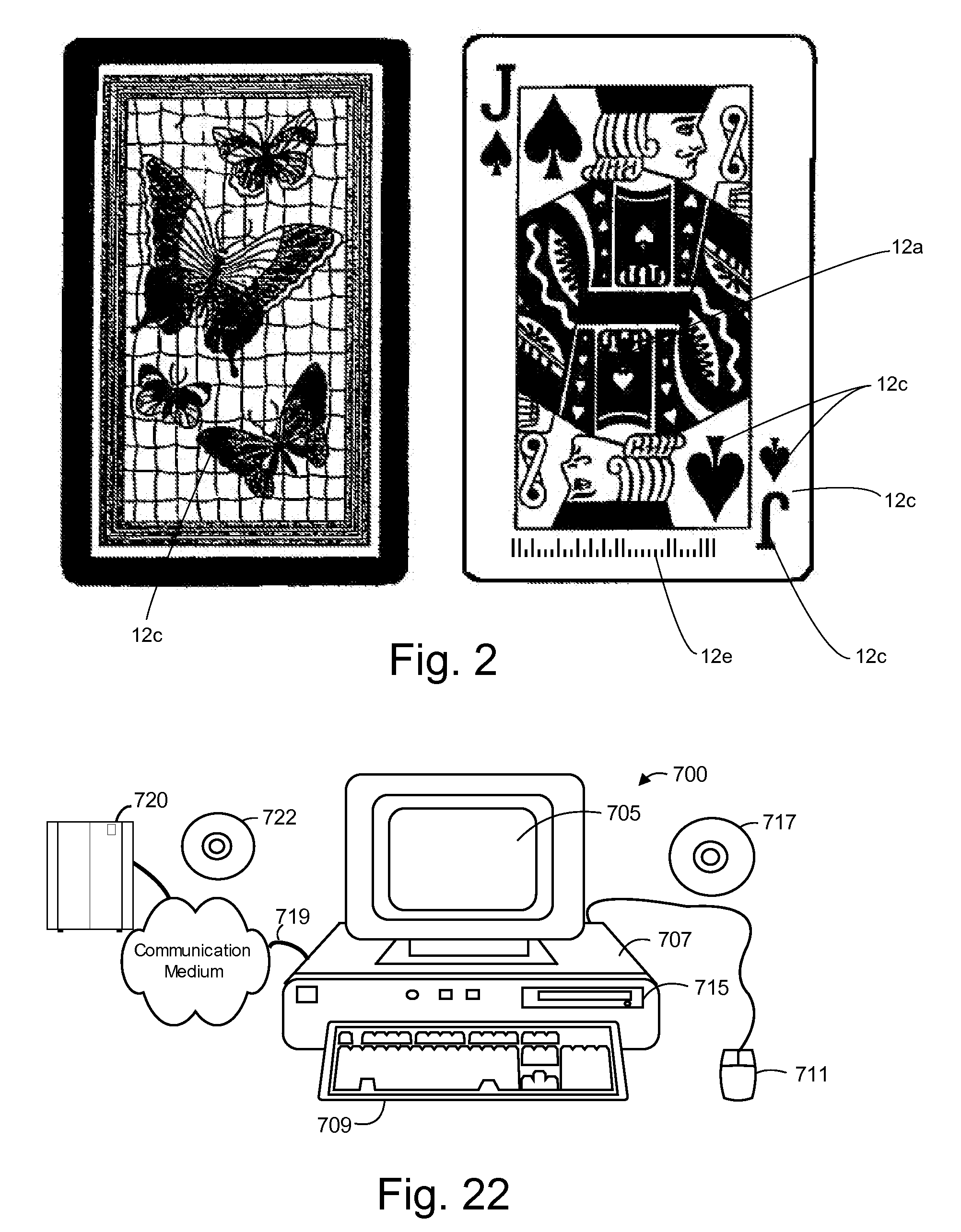
InactiveUS20090191933A1Low costMore secure and reliable gaming experienceCard gamesApparatus for meter-controlled dispensingHand heldSmart card
Methods and systems for intelligent tracking and / or play and / or management of card gaming use an intelligent card distribution or holding device with detectors for determining the value and unique identity of individual cards and for recording card play. Playing cards are equipped with a read / write data storage connected to a transponder and / or incorporated into electromagnetic writable particles or smart particles (smart dust). A system of the invention records various game play events on the playing cards themselves during game play and optionally also in a database on the system. In specific embodiments, the principal scanning and writing elements and electronic and optical interfaces are embodied into a hand-held card holder (HHCH). In specific embodiments, the system utilizes various types of sensors and / or indicators and / or and electronic circuits and software to scan, track, monitor, compute, and interface with electronic devices, to enable the automatic operation of Casino table games. The system can scan playing cards, scan gaming chips, indicate a players win / loss / draw, increase or decrease player betting positions, compute awards to players based on their playing activity, photograph individual players, and transmit player's images to casino security / surveillance departments and or other authorized casino personnel. The system may activate table displays that indicate each player's win / loss / draw of their bets, and / or dealers card count, indicate in the game of blackjack when a dealer has blackjack, or any other significant event that occurs such as indicating when a player has a winning / loss / draw on specific card combinations.
Owner:FRENCH JOHN B
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com