Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
890 results about "Source document" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
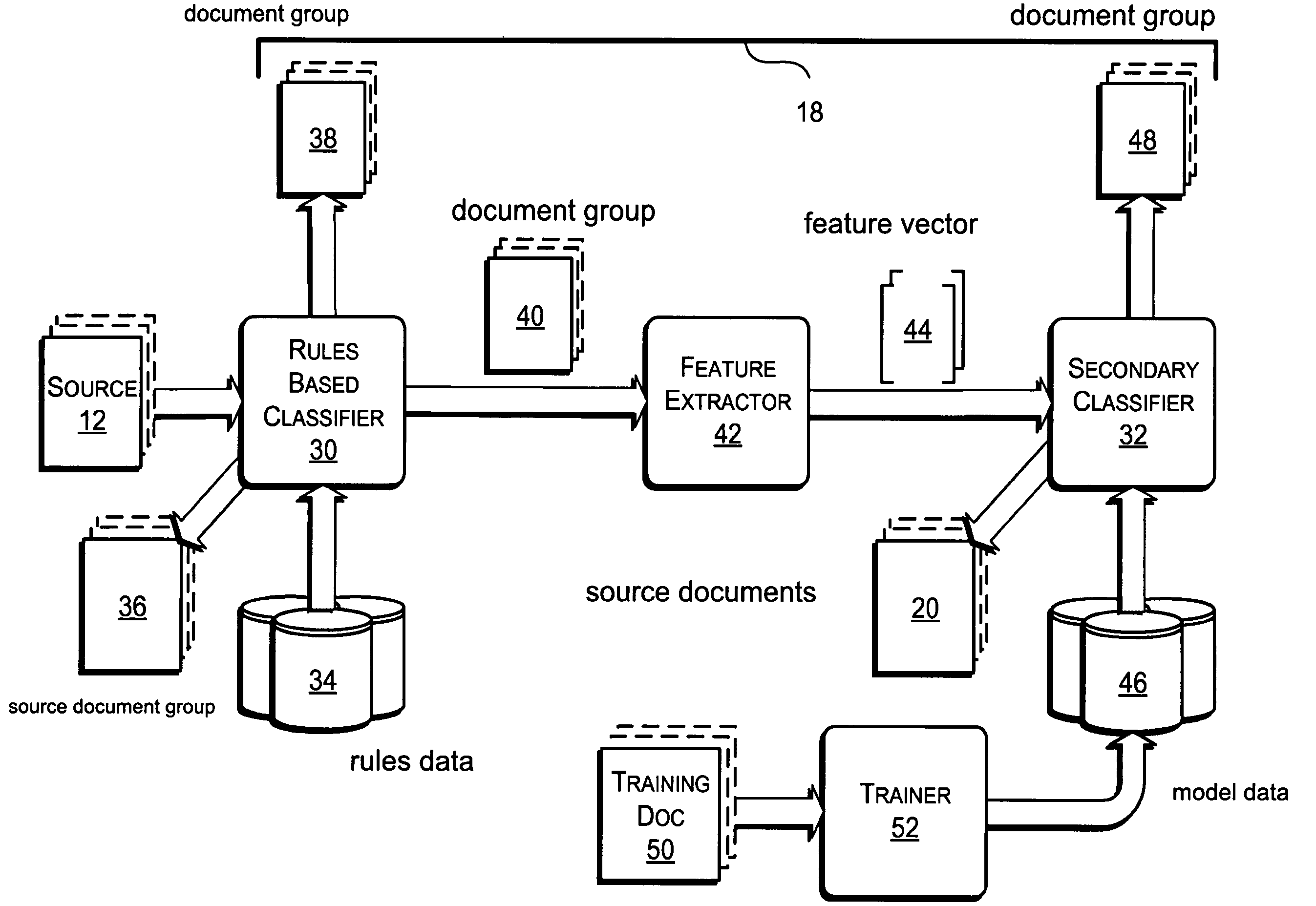
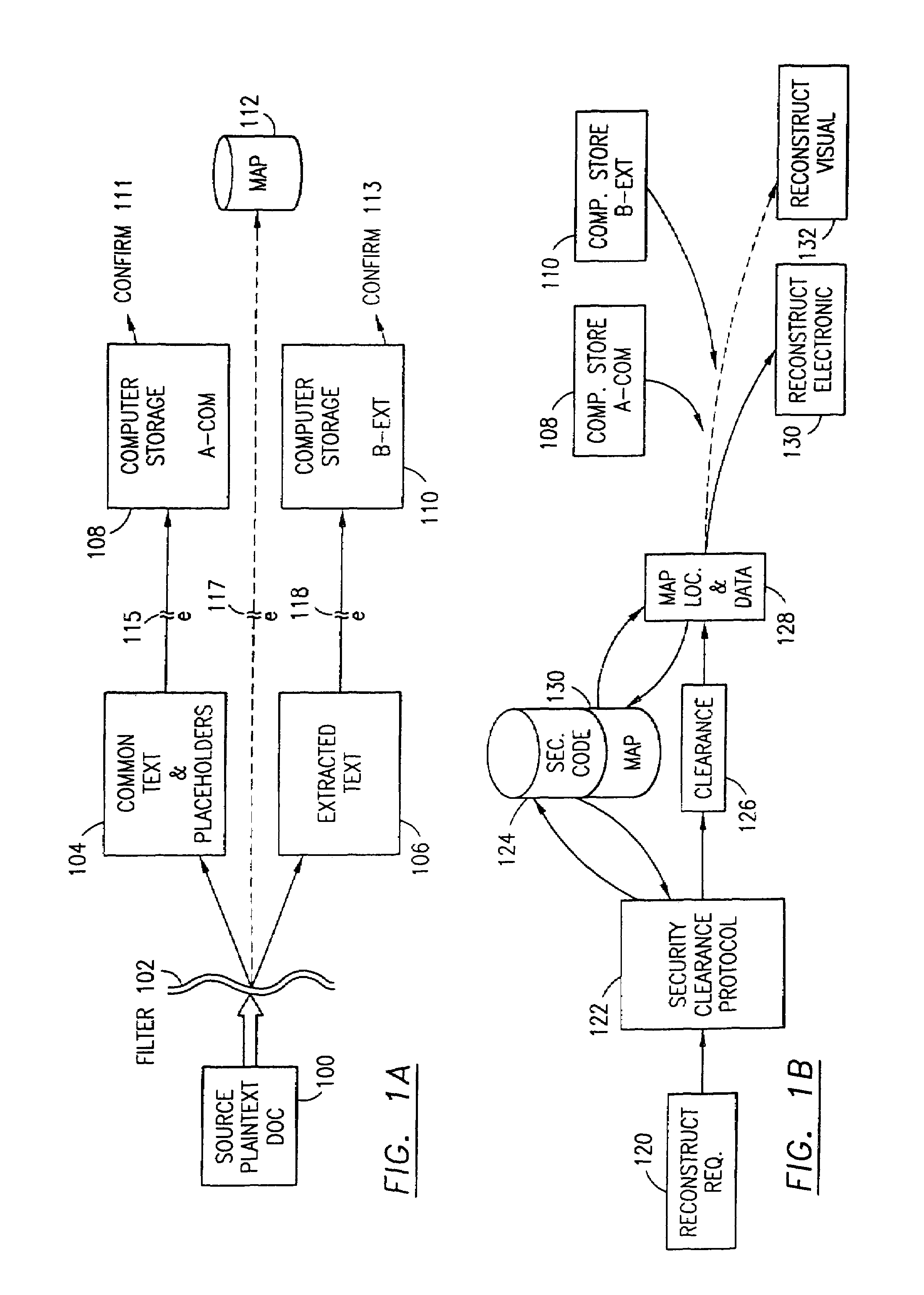
A source document is a document in which data collected for a clinical trial is first recorded. This data is usually later entered in the case report form. The International Conference on Harmonisation of Technical Requirements for Registration of Pharmaceuticals for Human Use (ICH-GCP) guidelines define source documents as "original documents, data, and records." Source documents contain source data, which is defined as "all information in original records and certified copies of original records of clinical findings, observations, or other activities in a clinical trial necessary for the reconstruction and evaluation of the trial."
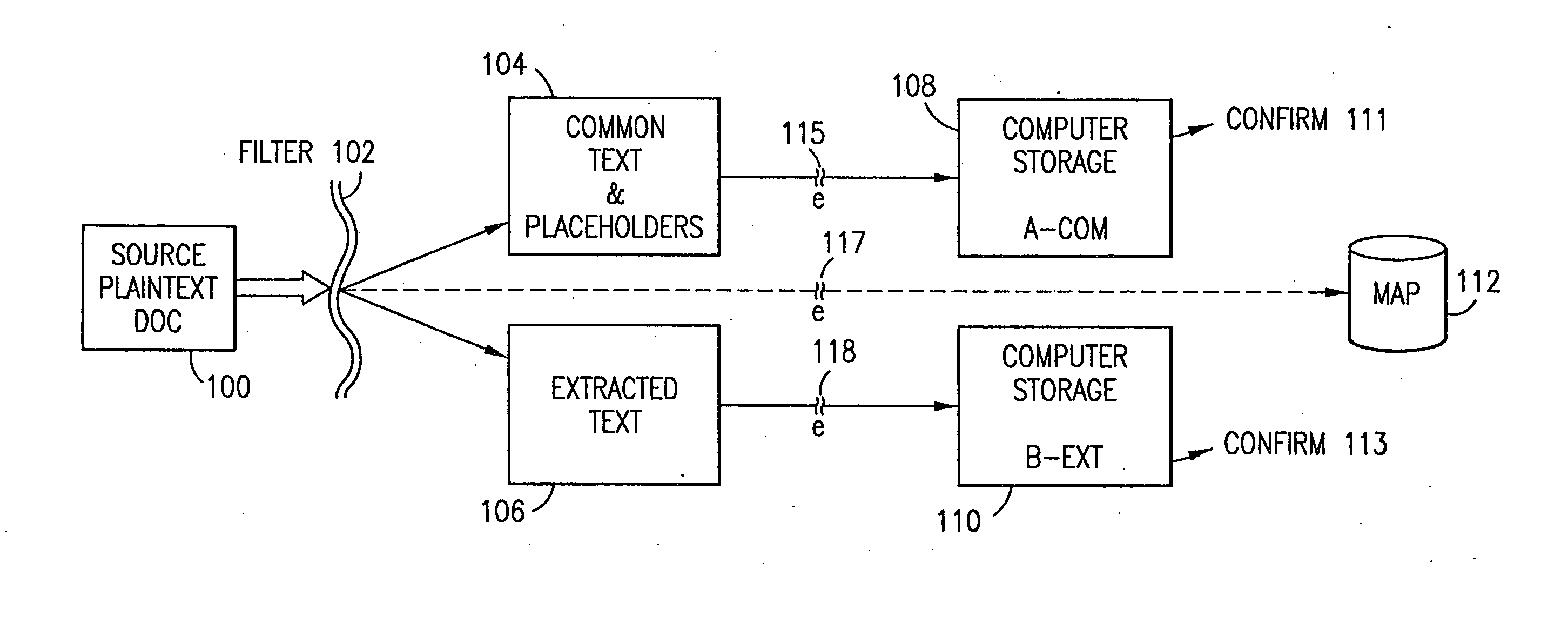
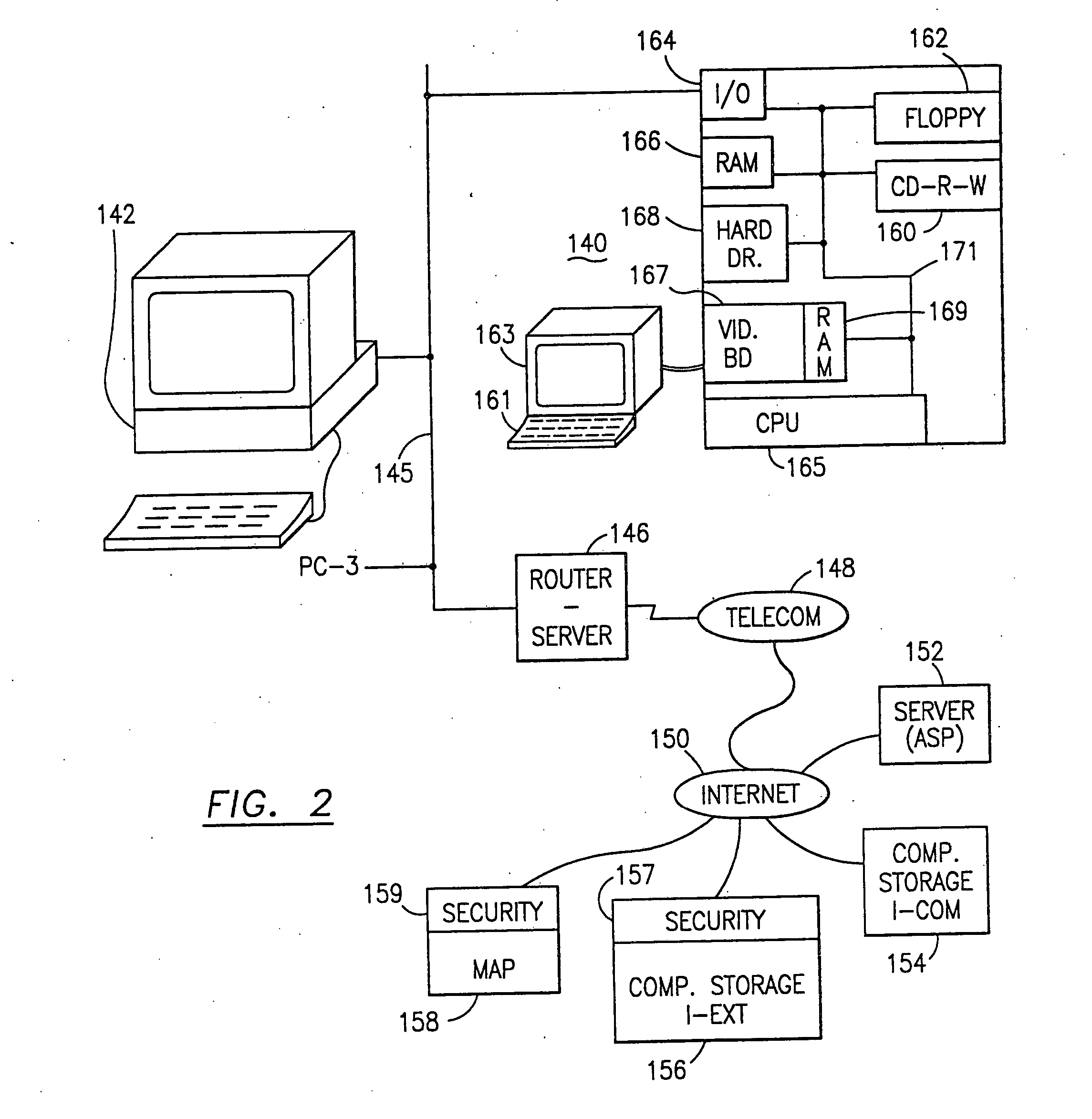
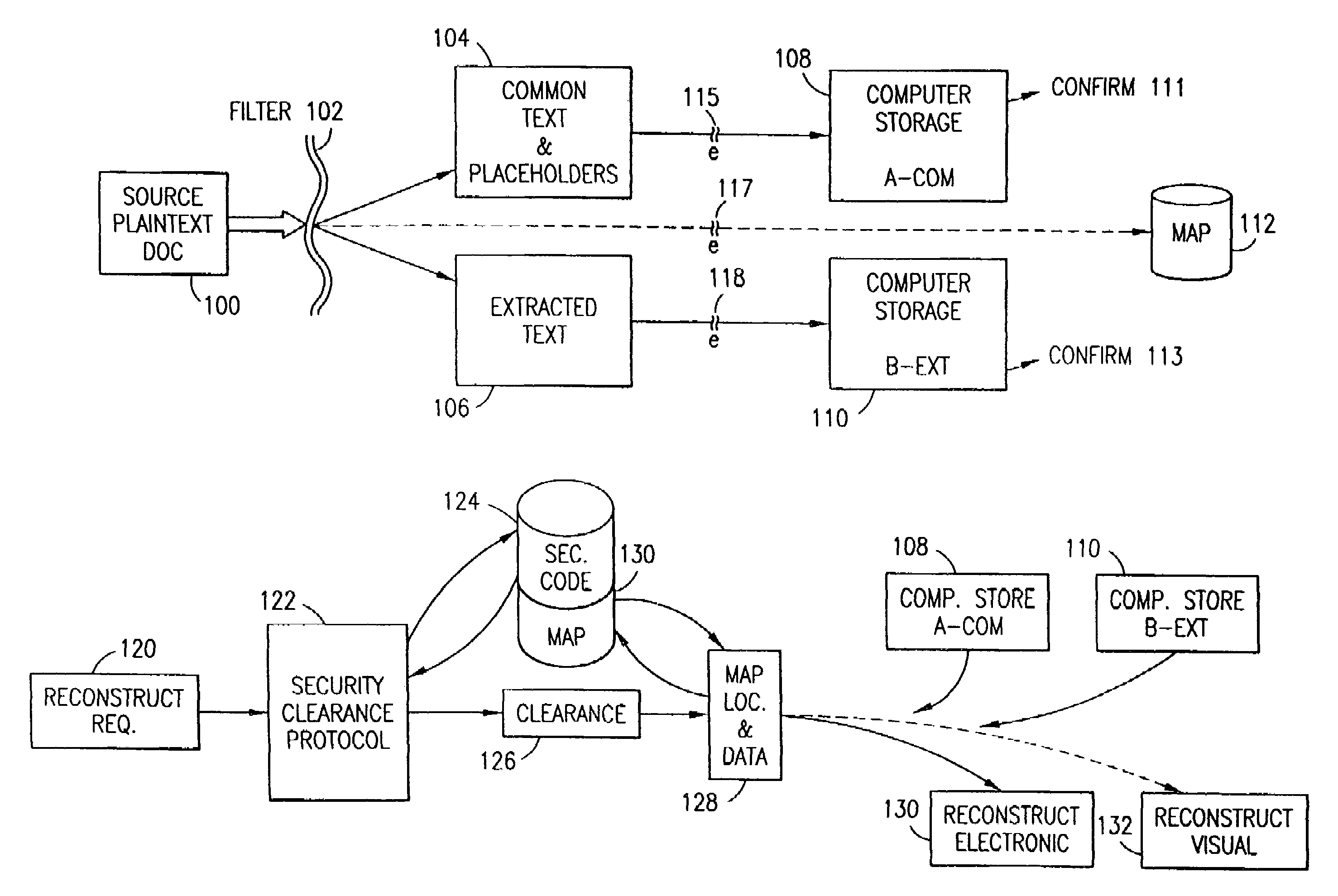
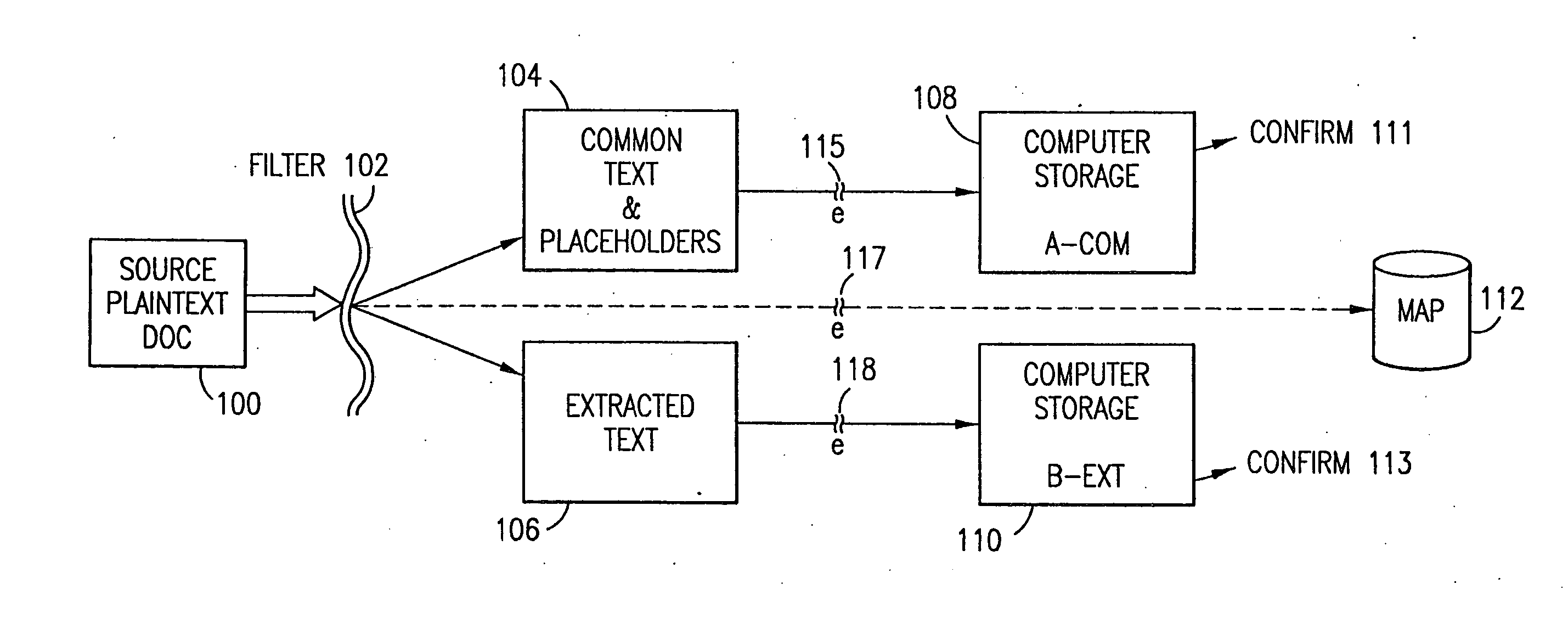
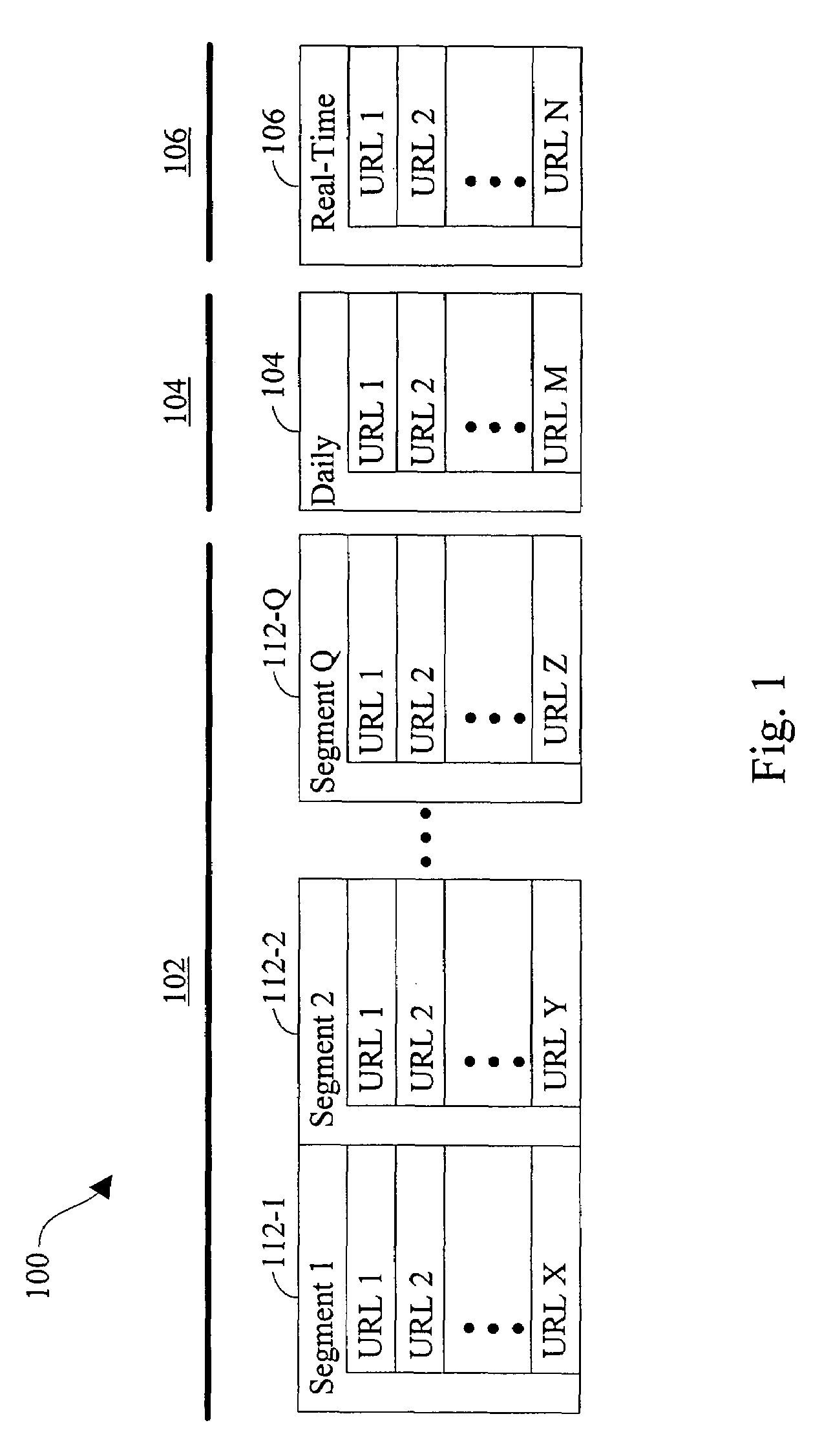
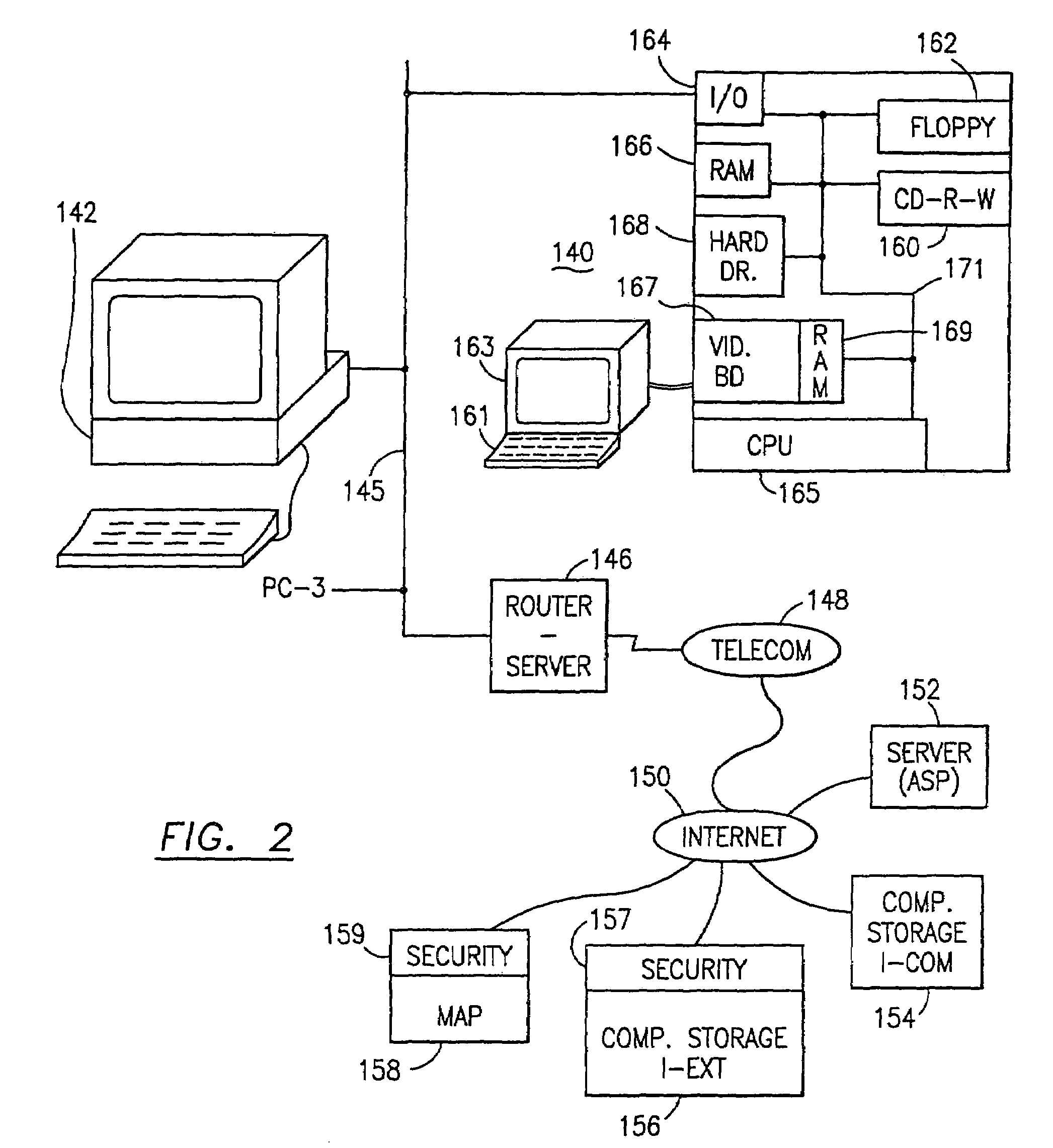
Data security system and method with editor
ActiveUS20050132070A1Ease overhead performanceHigh overhead performanceDigital data processing detailsTelephonic communicationFiltrationPaper document
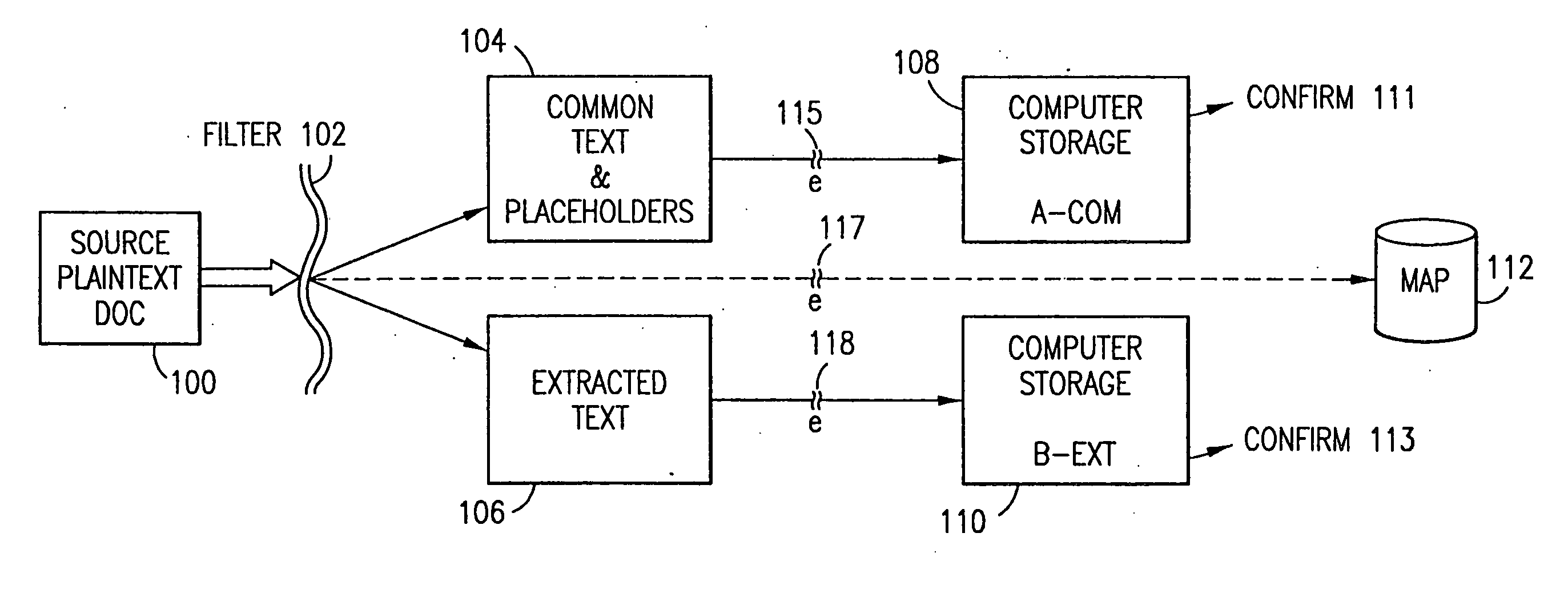
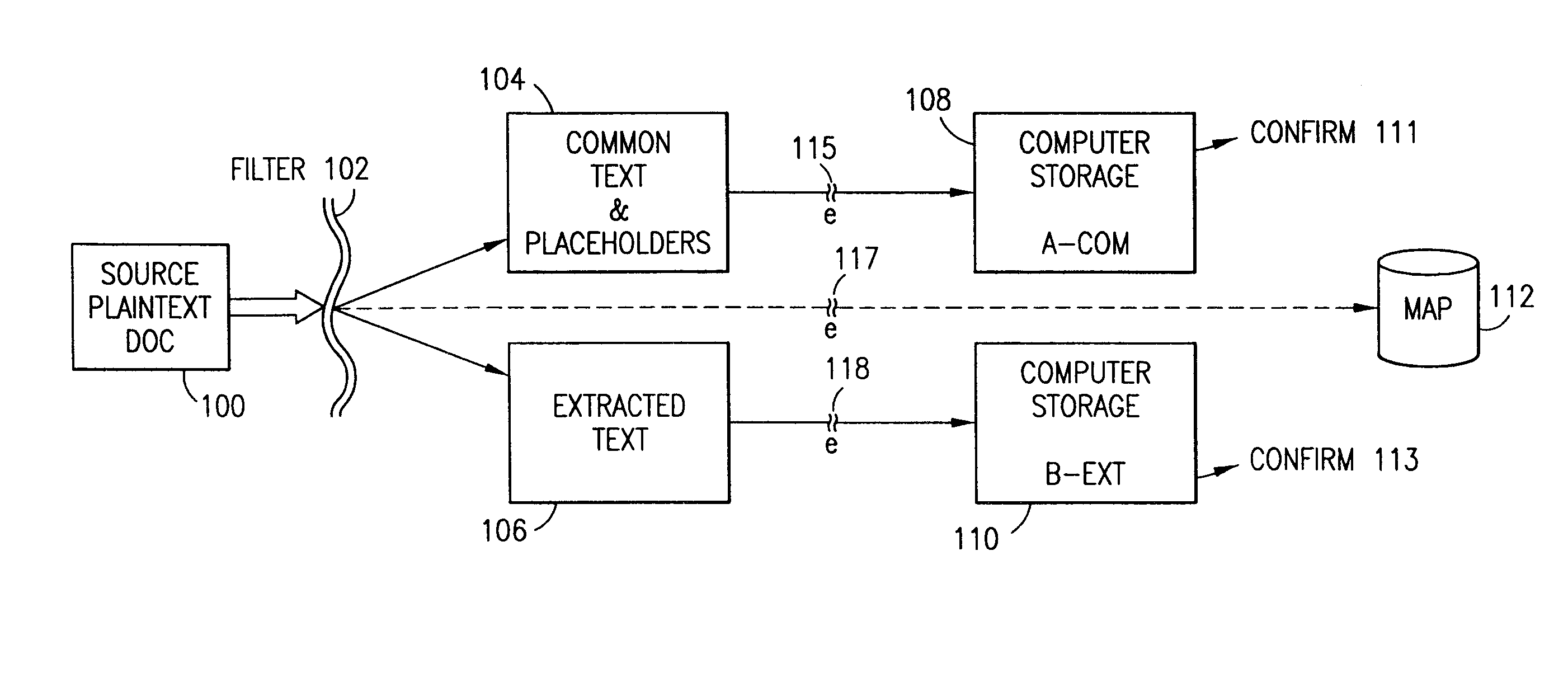
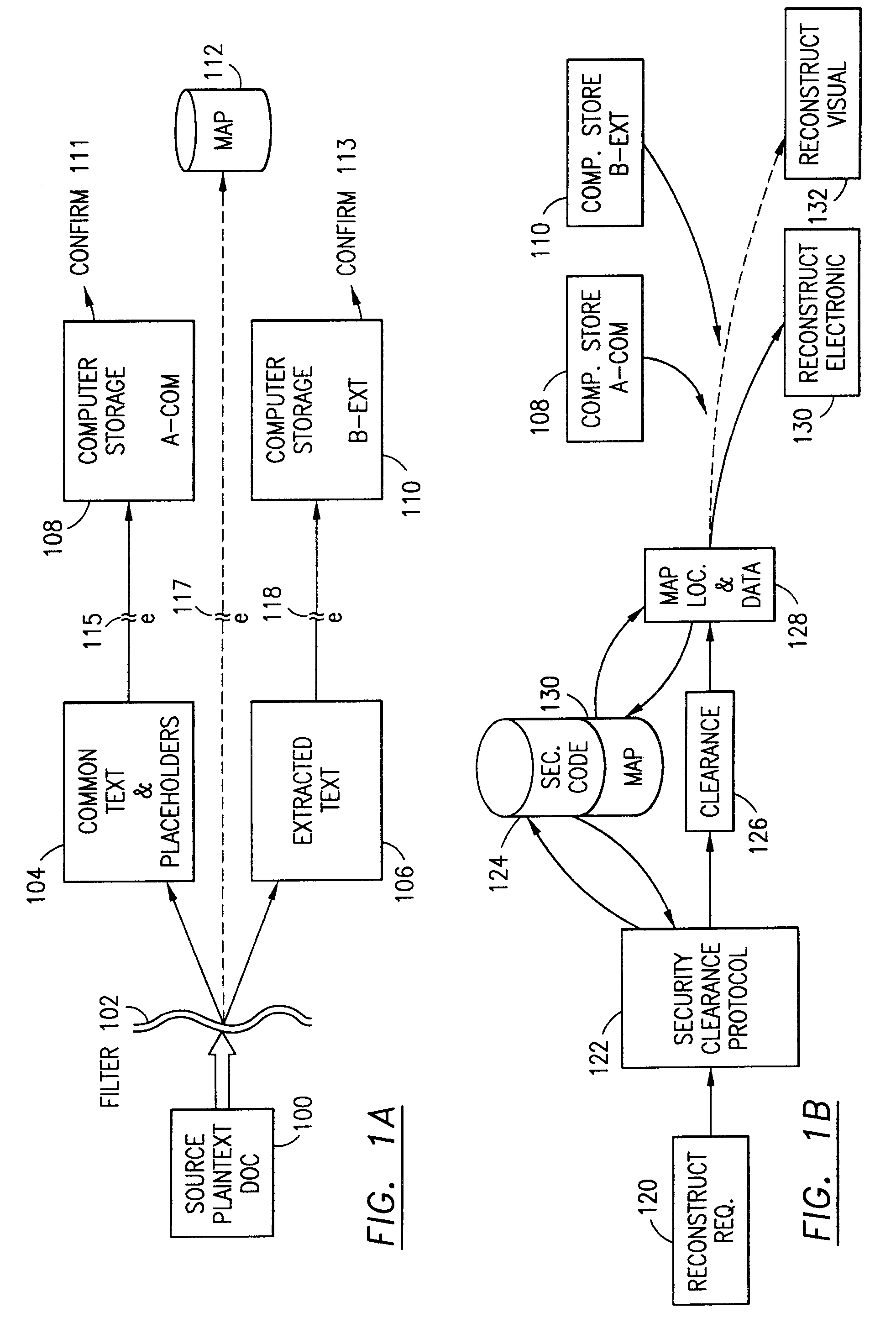
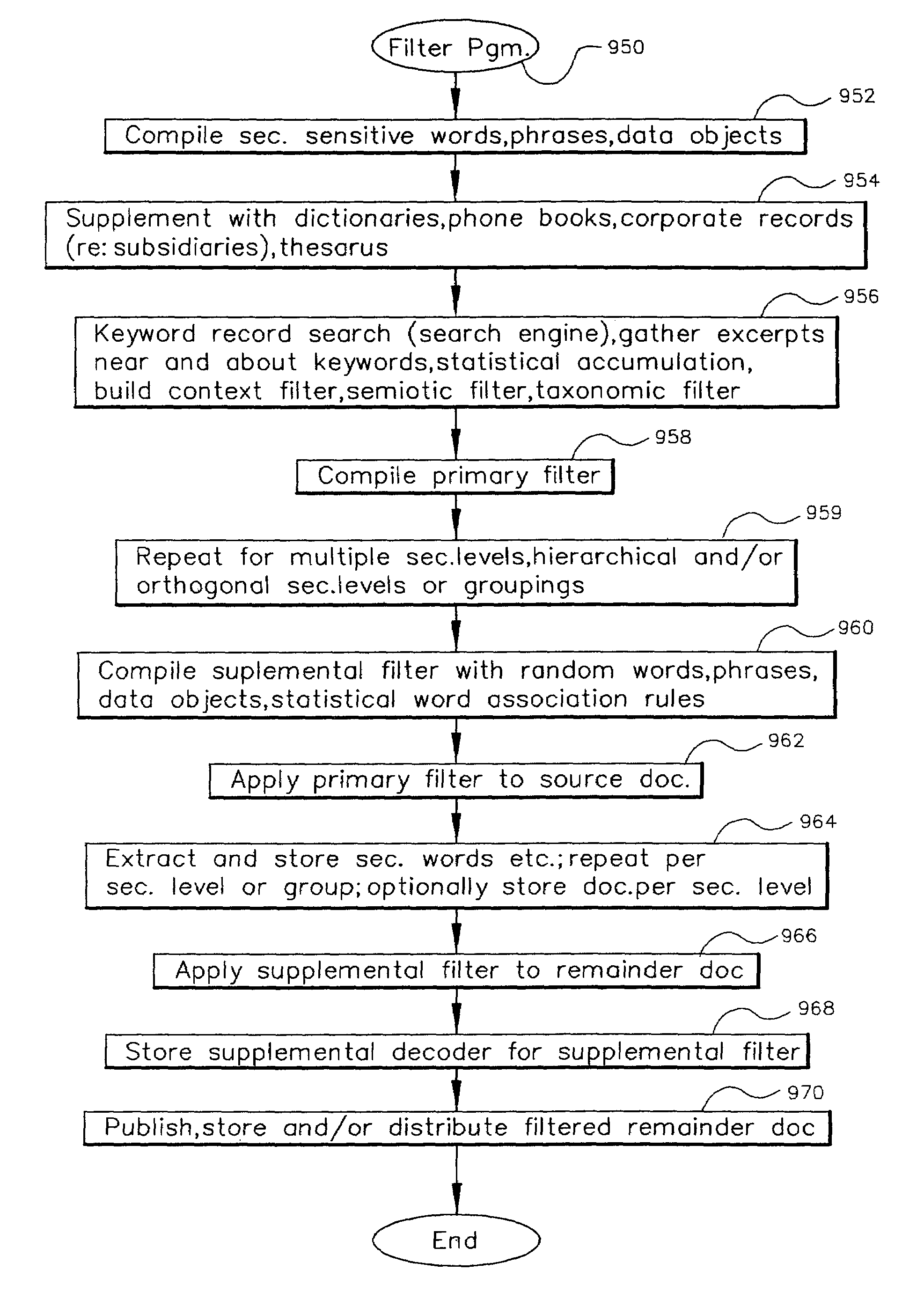
The method, program and system secures sensitive data / objects found in a data source document with an editor. The simple editor identifies and displays, in situ, the sensitive words / objects per each security level. Level tags are inserted and adjunctive words / objects are marked / displayed per the level's protocol. The precursor document is processed to extract sensitive and adjunctive words / objects. The stripped data is either separately stored or partial versions of the secured document are stored per protocol. A comprehensive editor secures content data and meta data contained in a data document object model (DOM). The editor maps the source document root, branch and leaf components as binary files populated with content data and meta data. Security introns, earlier identified based upon the level's informational attributes, are excluded. Security exons are copied from the source content and meta data binary files into a security safe document (template). Filtration, extraction, dispersal and storage follow.
Owner:DIGITAL DOORS
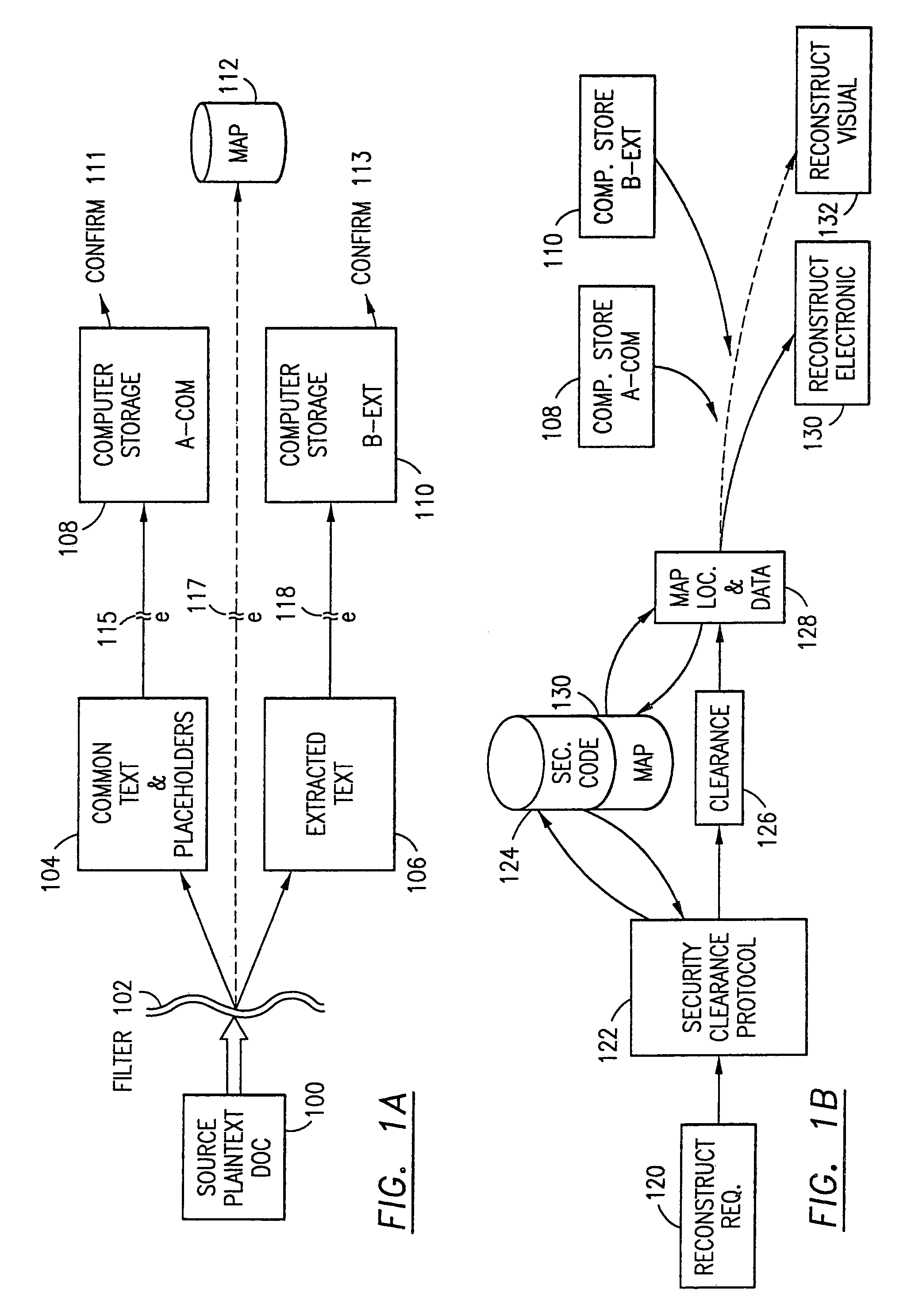
Data security system and method for separation of user communities
InactiveUS7140044B2Multiple keys/algorithms usageDigital data processing detailsInformation processingPlaintext
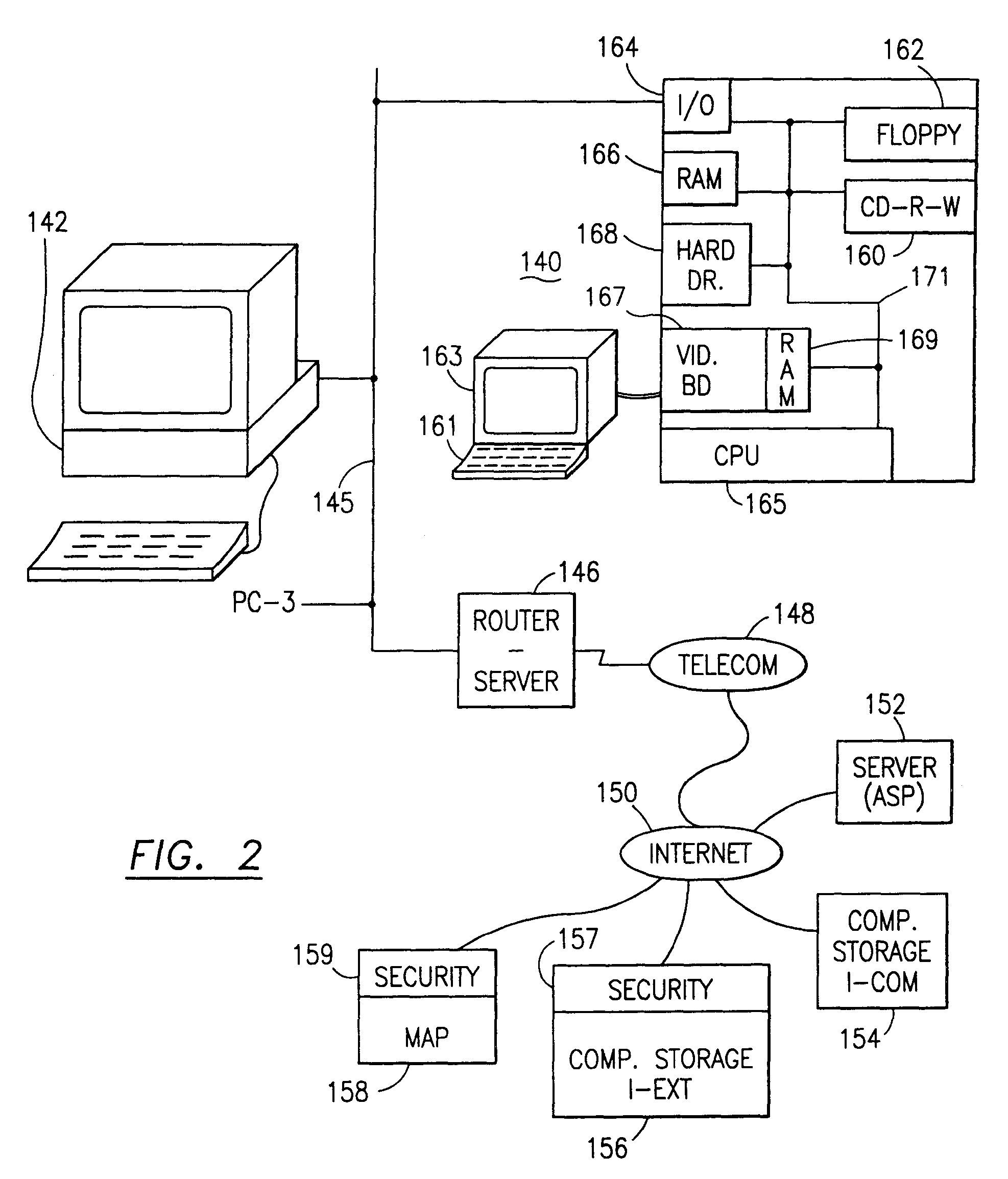
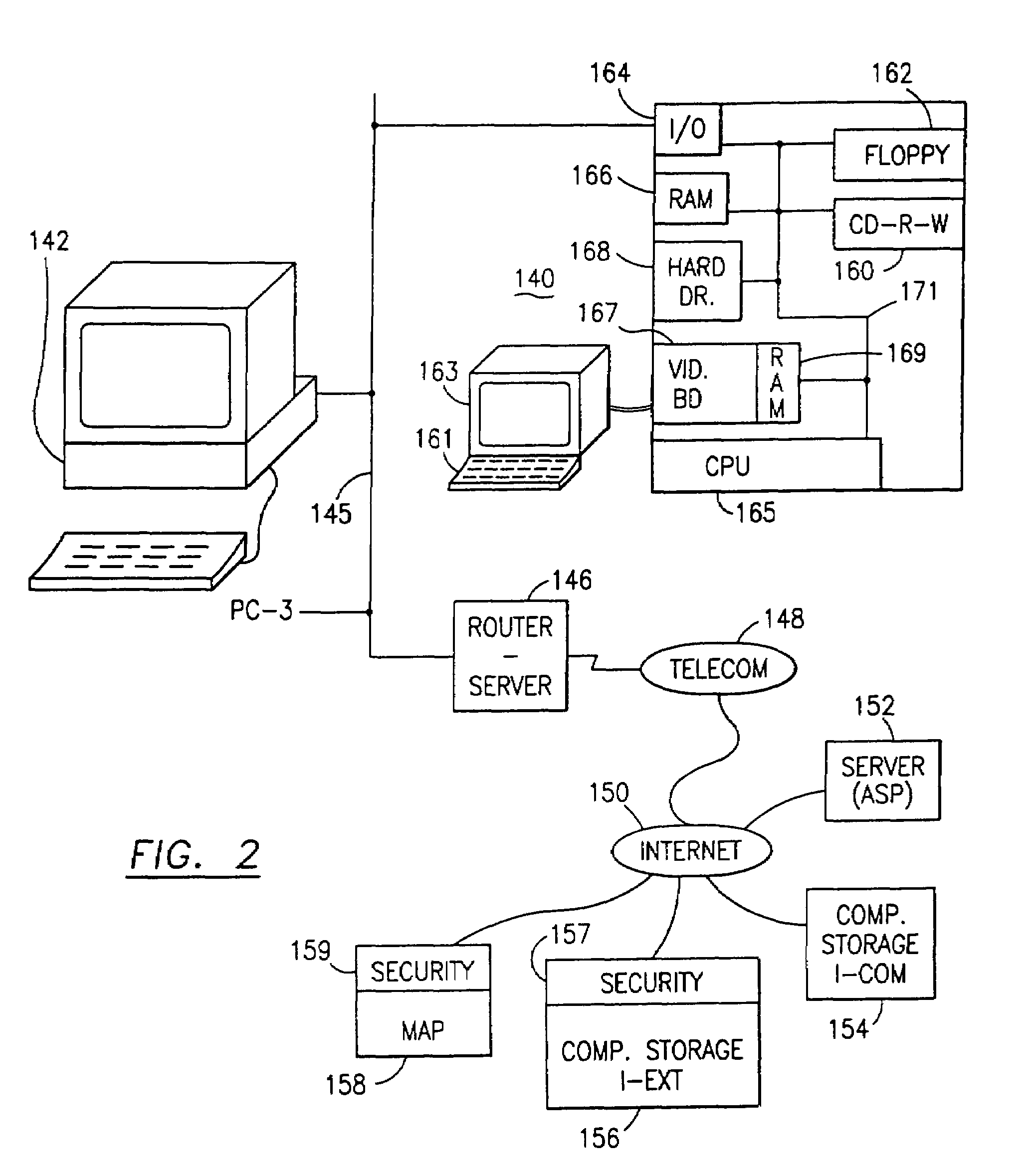
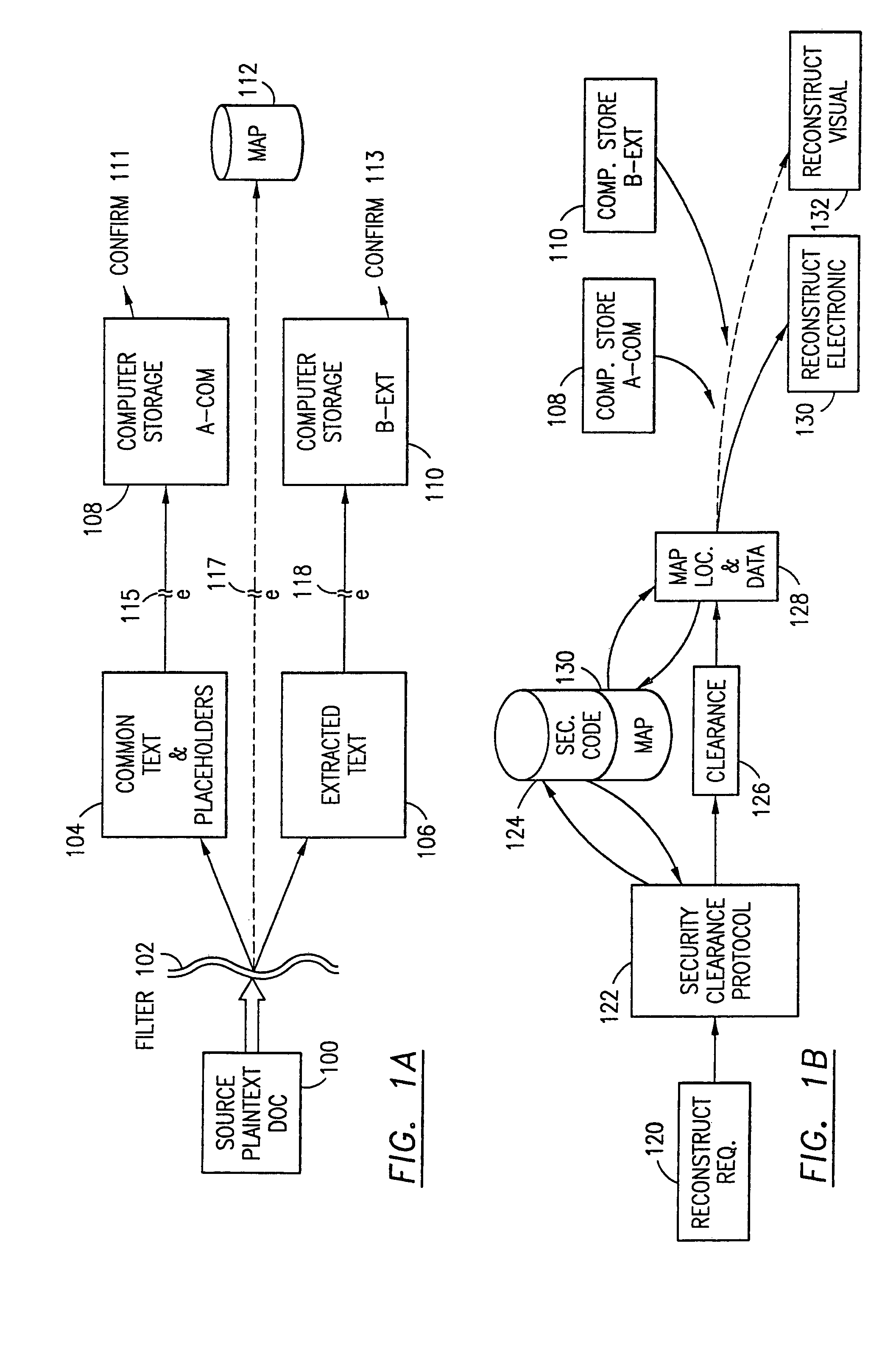
Data is secured in a computer network to transparently establish and manage a separation of user-based communities of interest based upon crypto-graphically separated, need to know, security levels. Data from a source document, data object or data stream is filtered to form subsets of extracted data and remainder data based upon security levels for the communities. Extracts are stored in assigned memories. Full or partial plaintext reconstruction is permitted only in the presence of assigned security clearance for the community of the inquiring party. Encryption, corresponding to security levels, establishes separation of secured data. The information processing system uses a data filter to extract security sensitive words, data objects, etc., a distributed storage system and a compiler is used to reconstruct plaintext based on security clearance. Multiple level encryption in one document is also available.
Owner:DIGITAL DOORS
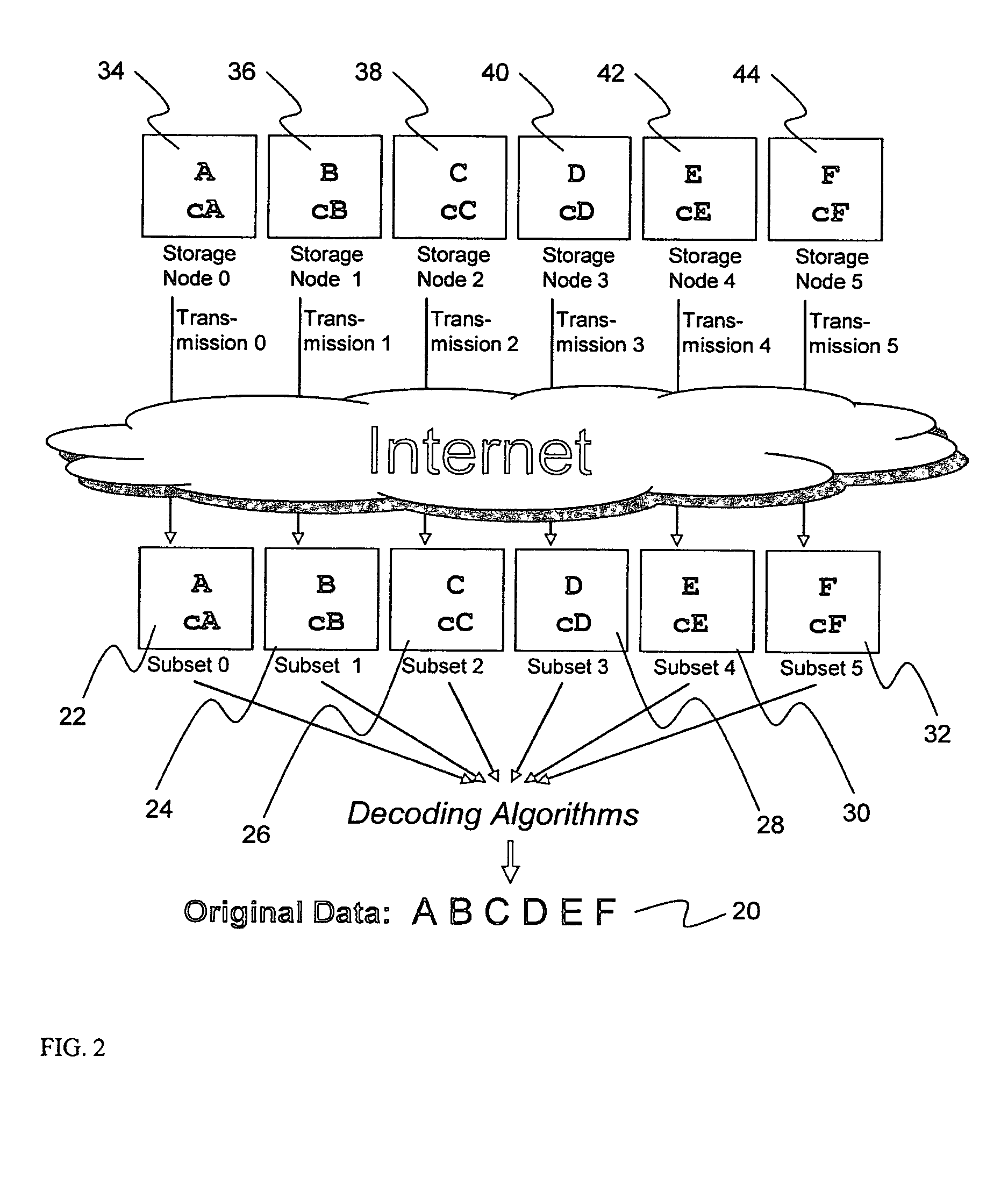
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
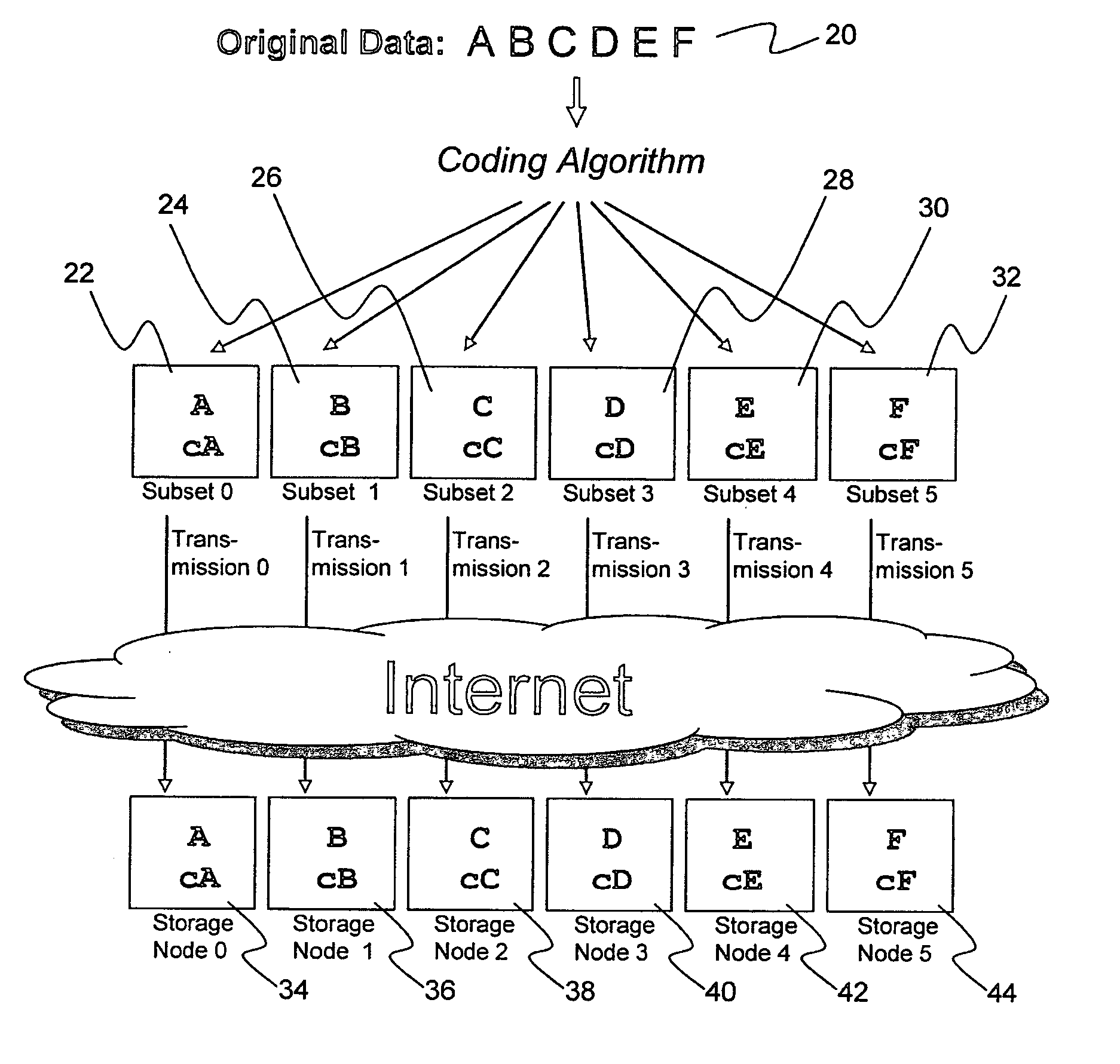
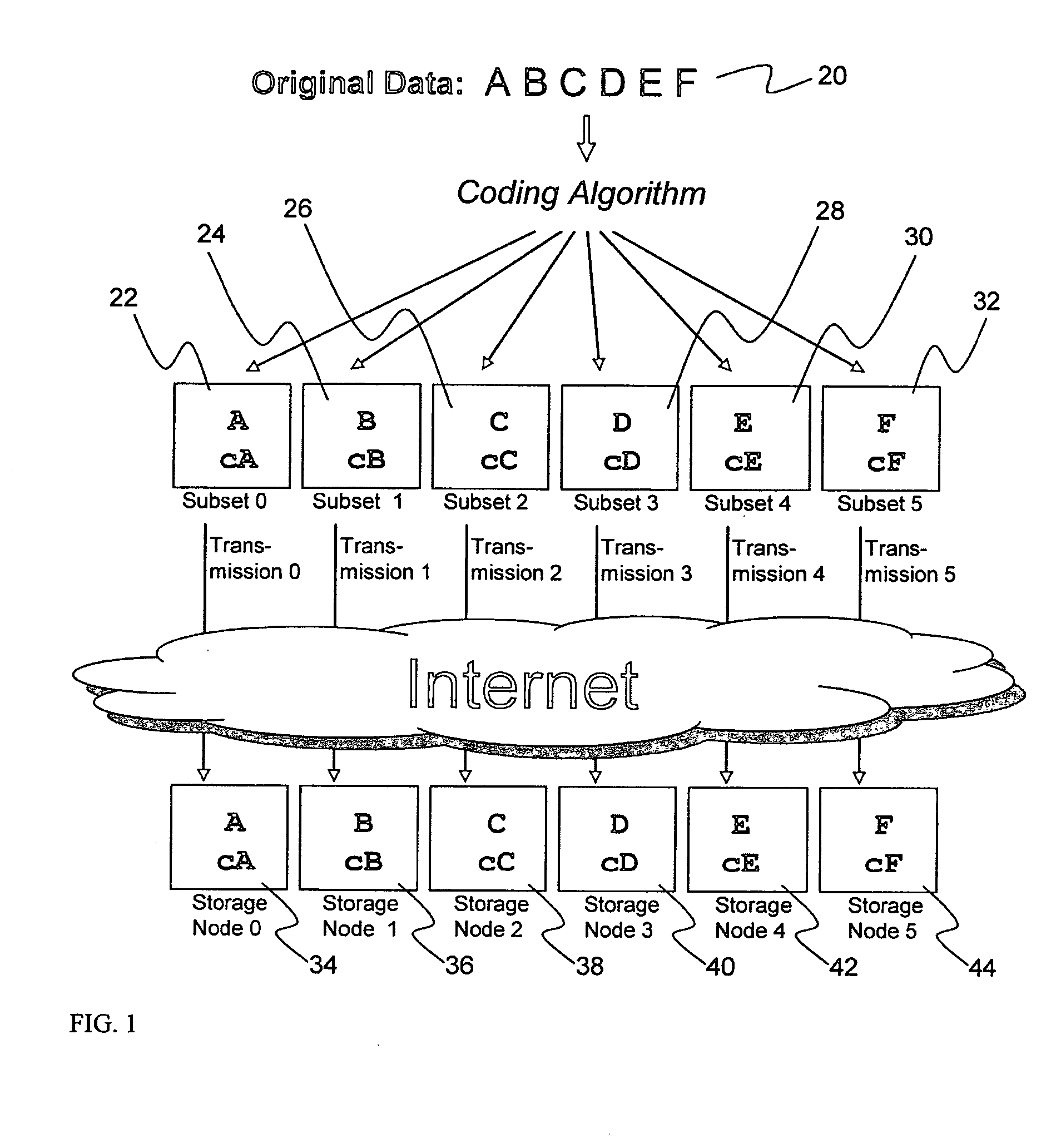
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
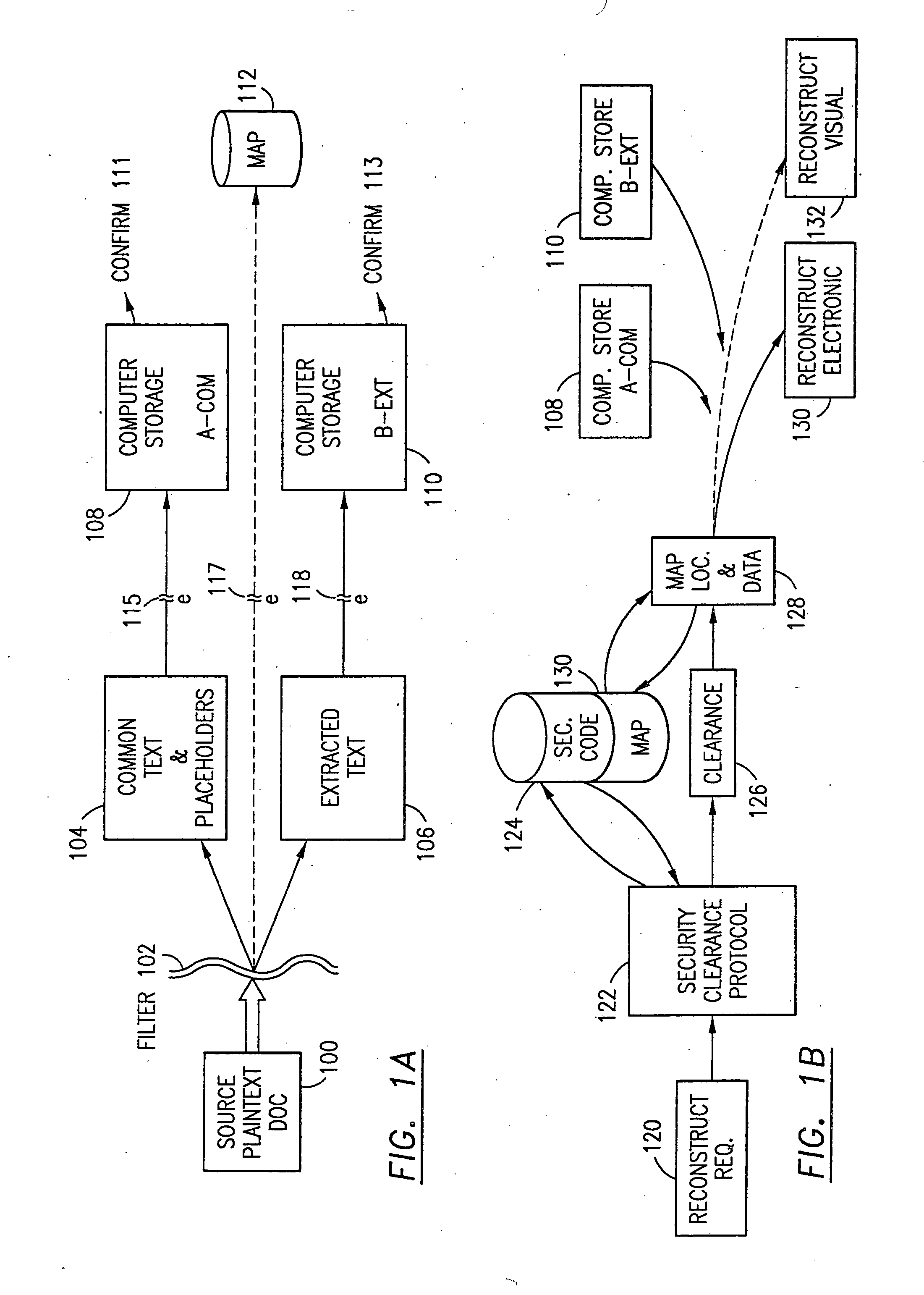
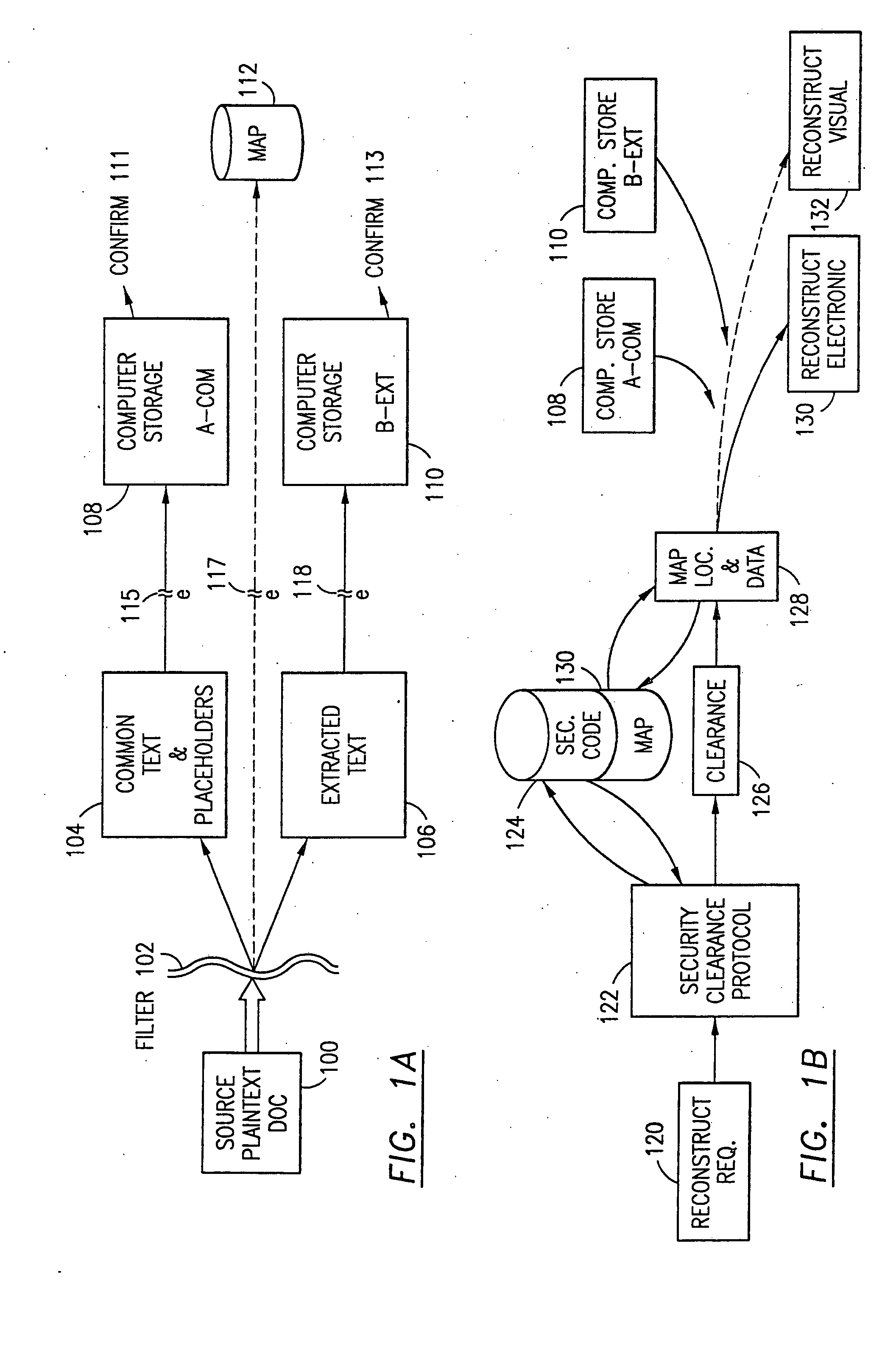
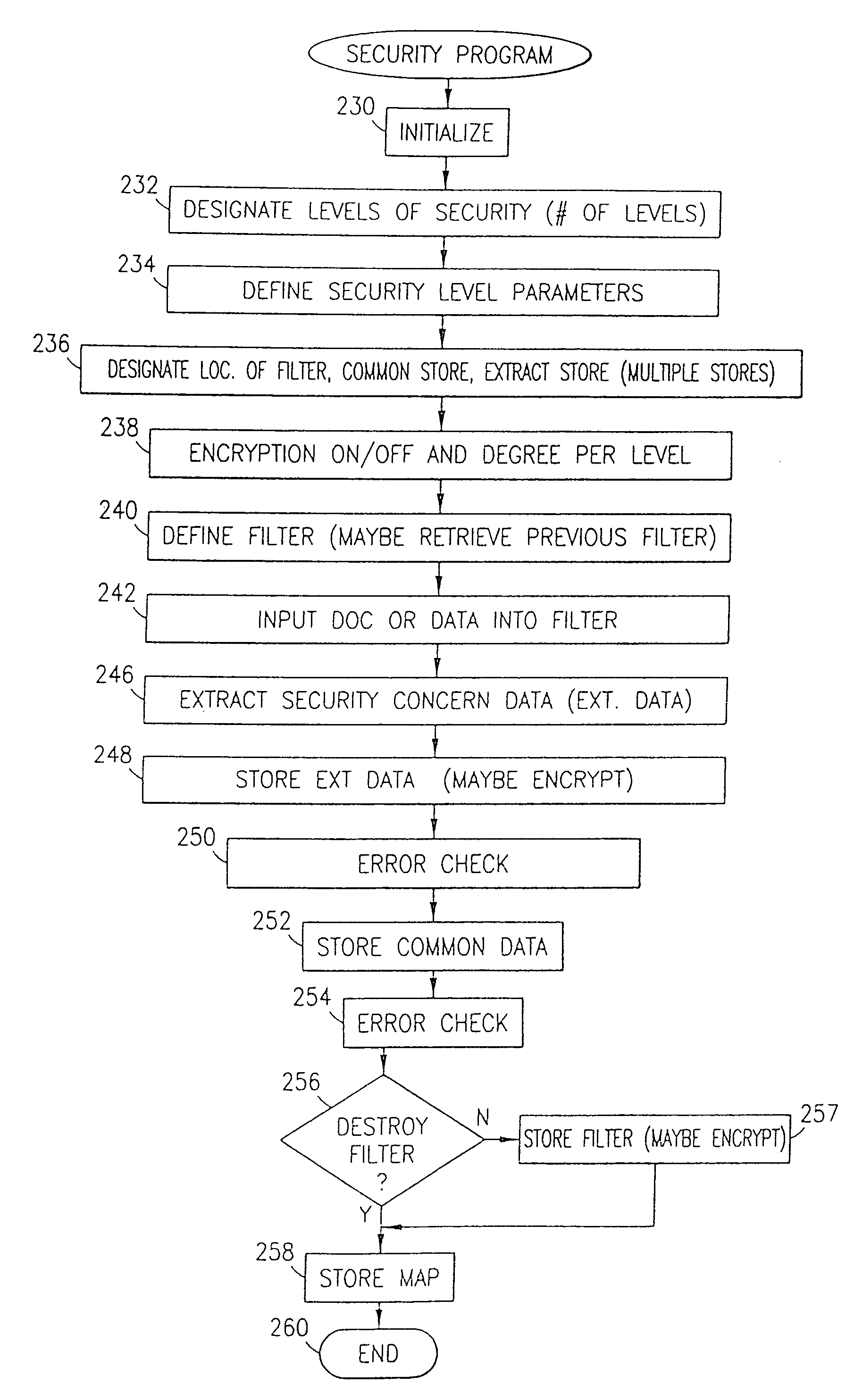
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
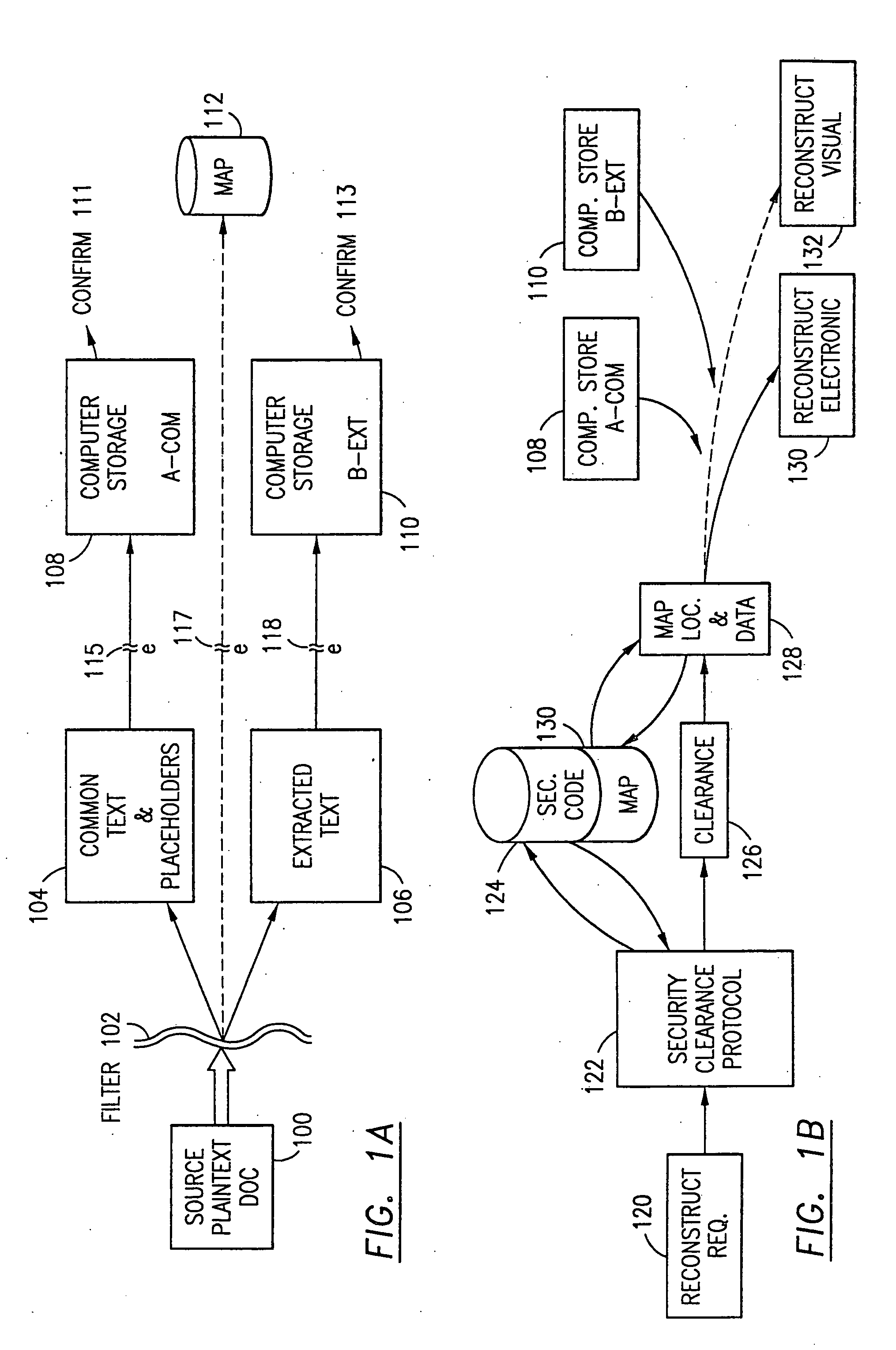
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
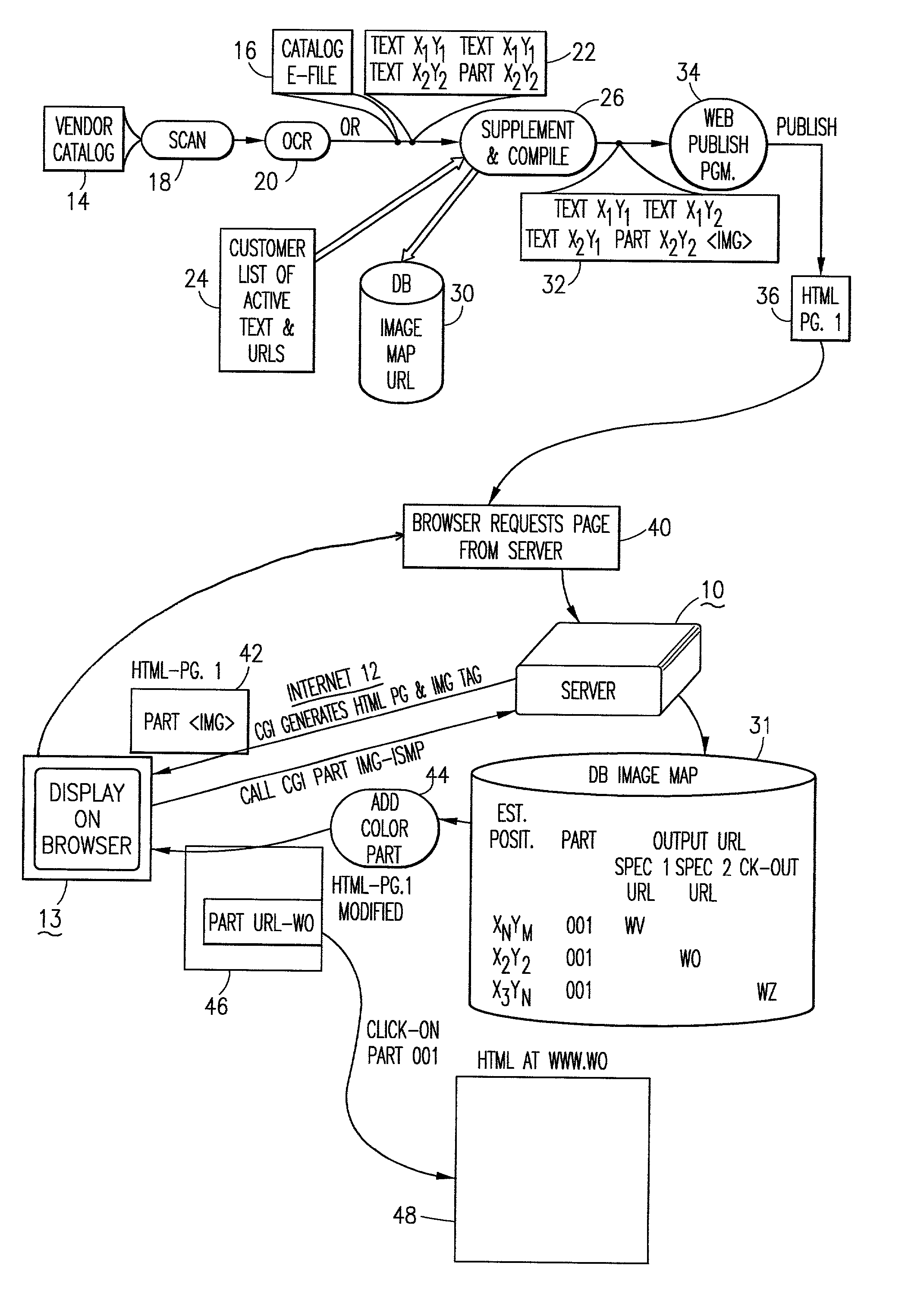
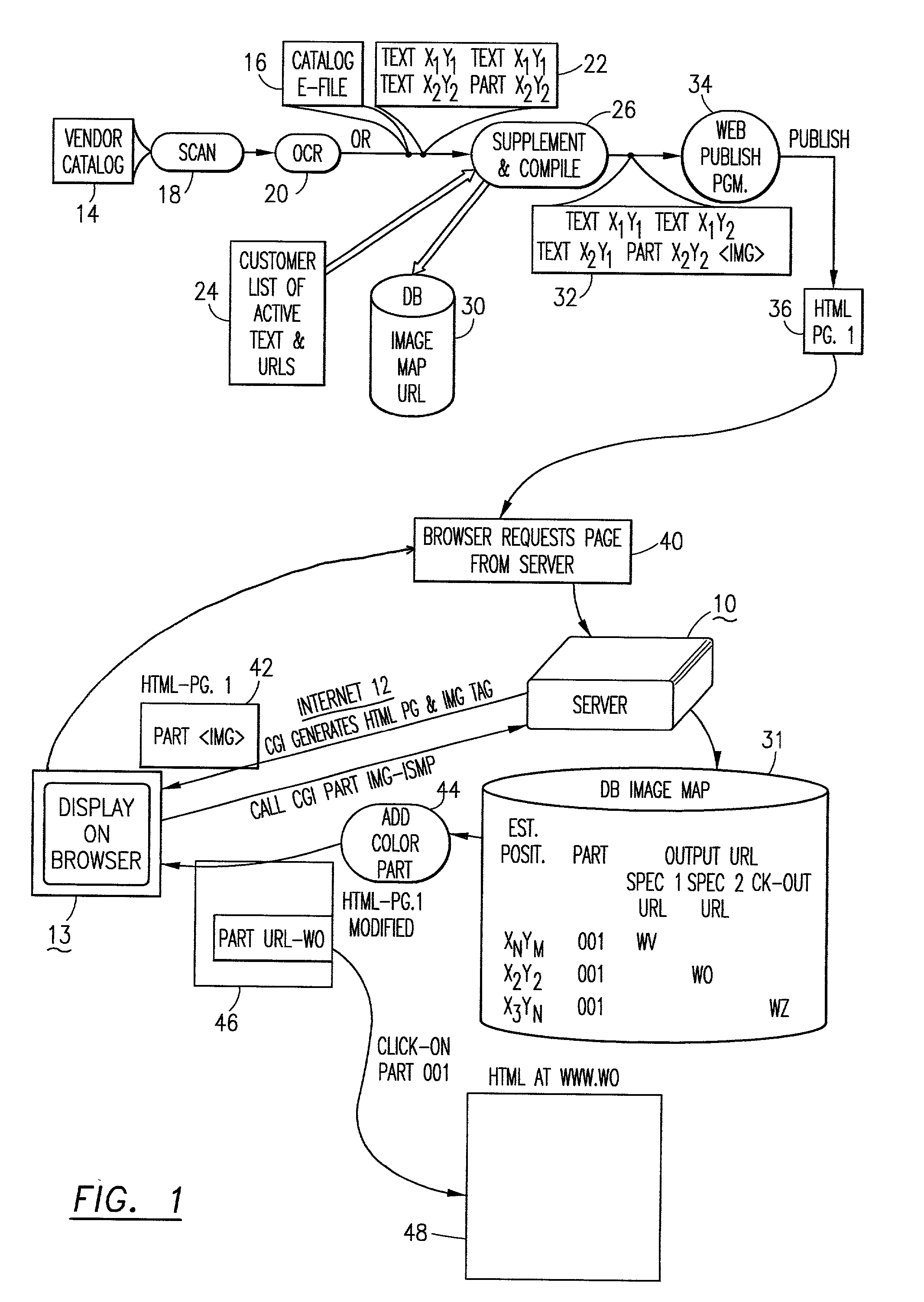
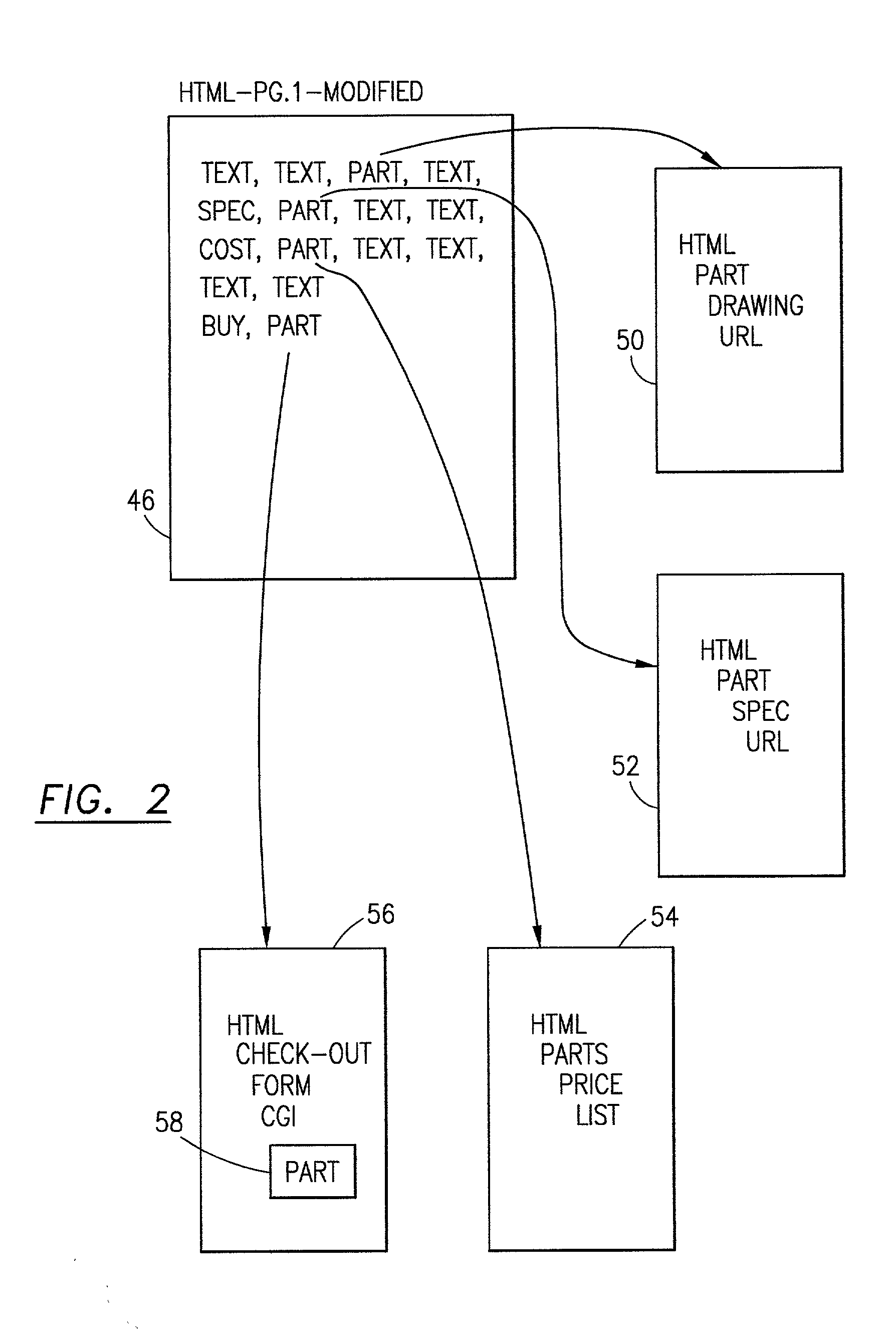
System and method for placing active tags in HTML document
InactiveUS20020069222A1Quick conversionNatural language data processingSpecial data processing applicationsInformation processingDocument preparation
The method and the information processing system dynamically creates an HTML document with at least one embedded hyperlink code therein. The HTML document is based upon a source document provided by a manufacturer or a supplier of services. Typically, the system and the method is operable in a client-server computer environment. A database is provided on the server computer system which database associates location data of a plurality of data strings in the source document with hyperlink addresses. The location data in the database maps at least one predetermined data string in the source document. An HTML document, based upon the source document, is published with an image tag on, in or near the predetermined data string. As an example, the string may be a "part number" or a string of words "SONY PLAYSTATION II.". The published HTML document has an image tag on, at or near the part number and a map attribute command which supplies or generates an HTML location data unique to the image tag location in the HTML document when the browser calls the server's common gateway interface (CGI). The image tag URL points to the database on the server. The server, via the database provides a corresponding hyperlink address, associated with the unique location data correlated to the HTML location data, to the browser on the client computer system. The method and the system then publishes and embeds in the original or initial HTML document at, on or near the predetermined data string or part number an active hyperlink tag (an embedded code) with the corresponding hyperlink address obtained from the database.
Owner:WIZNET
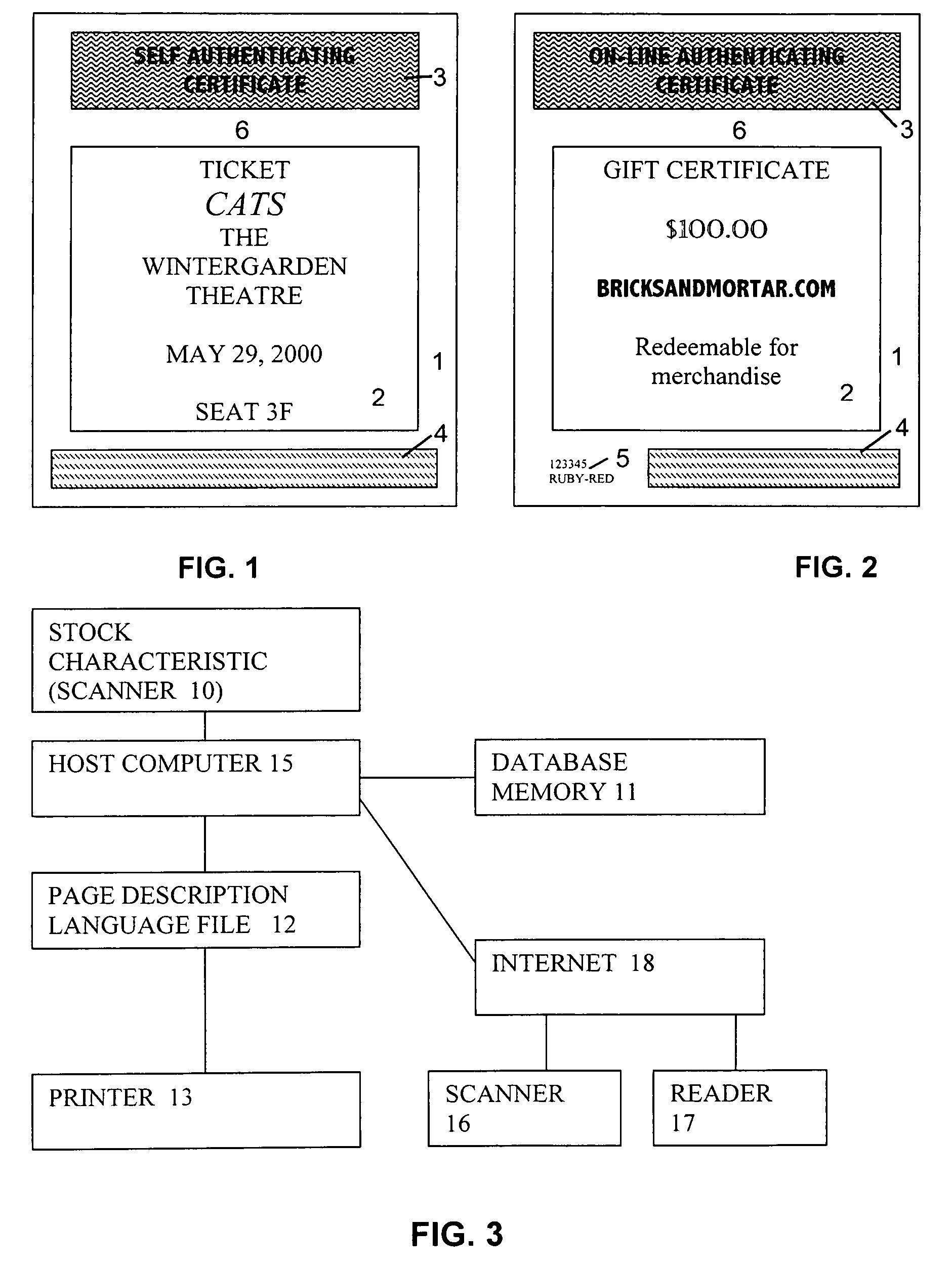
System and method for production and authentication of original documents
InactiveUS20050038756A1Improve shielding effectImprove accuracyOther printing matterUser identity/authority verificationDocument IdentifierPaper document
A system and method for authenticating documents and content thereof. A counterfeit resistant document recording medium is provided, having thereon a predefined unique document identifier and at least one security feature. The recording medium is thereafter imprinted with document content, which typically varies between documents. The document content is stored in a database, indexed by an associated document identifier. The document may then be authenticated by checking the security feature and comparing the stored document content with a perceived document content. The system provides a number of opportunities for commercial exploitation, including sales of identified recording media, recording of information in a database, on-line authentication transactions, differential accounting for document validations and counterfeit identifications, imprinting devices, authentication devices, and the like. The system prevents counterfeiting of valuable documents through casual means by providing both physical and logical security.
Owner:ESECUREDOCS
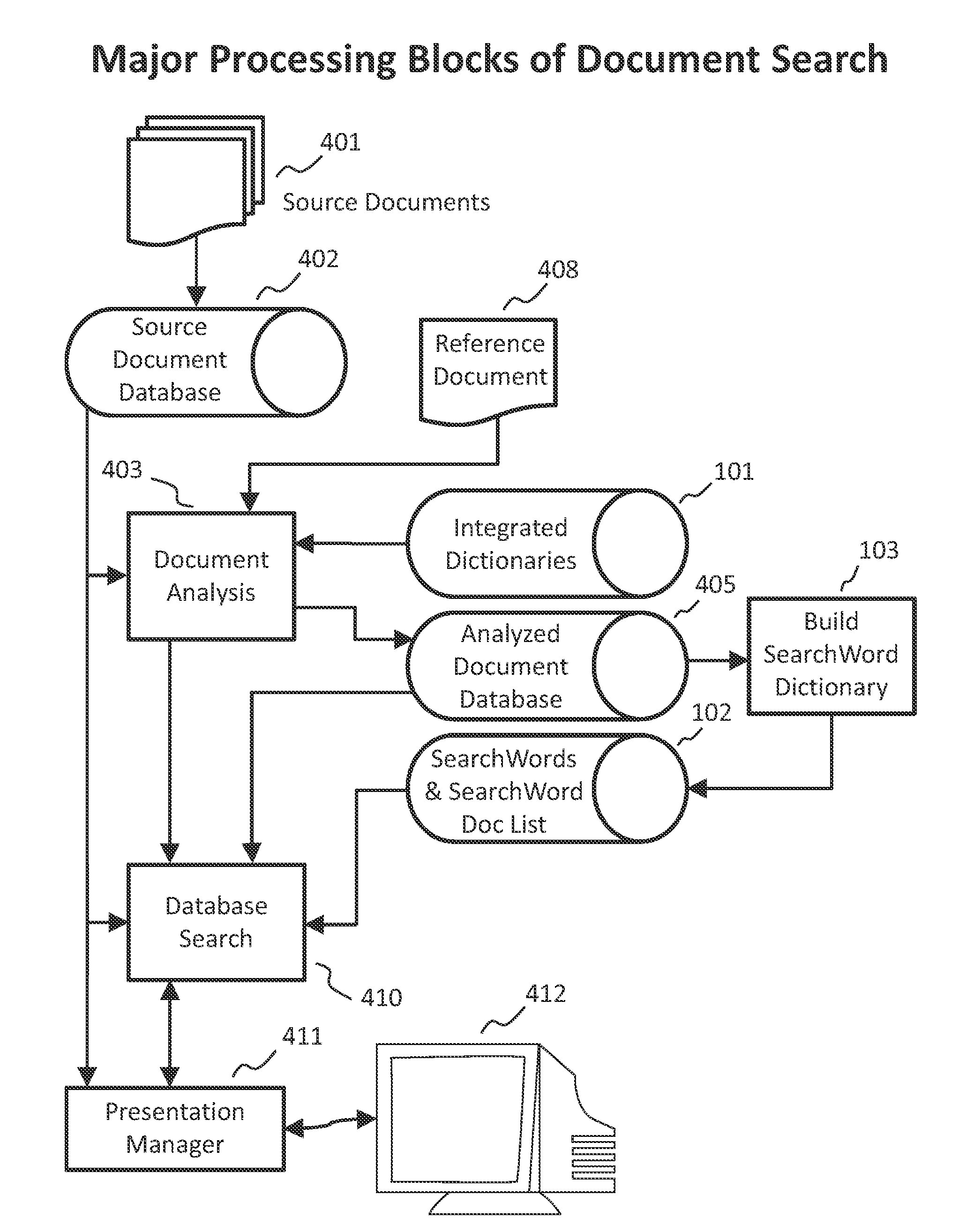
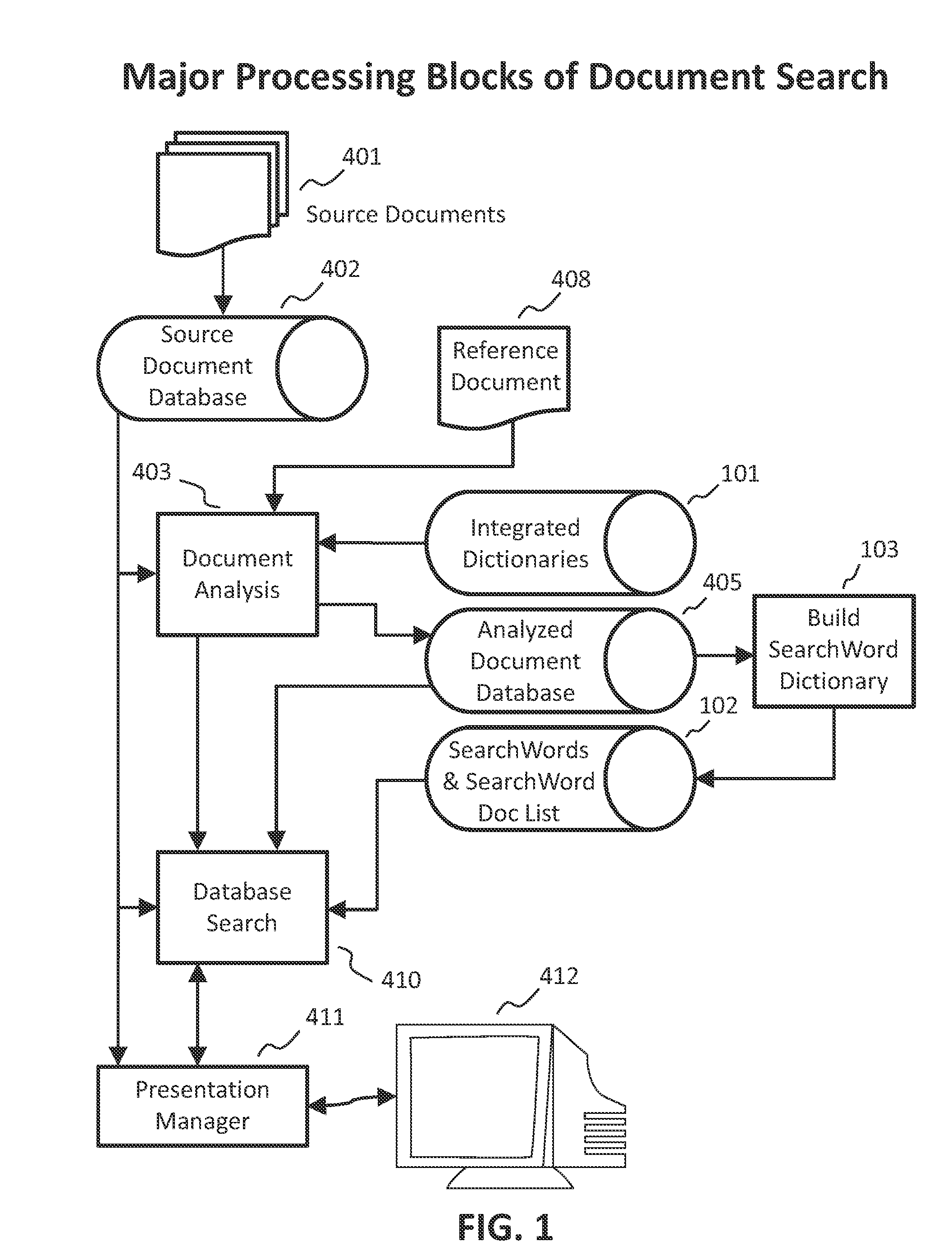
Method and system for document classification or search using discrete words
ActiveUS20120117082A1Quick matchImprove versatilityDigital data information retrievalDigital data processing detailsDocument preparationDocumentation
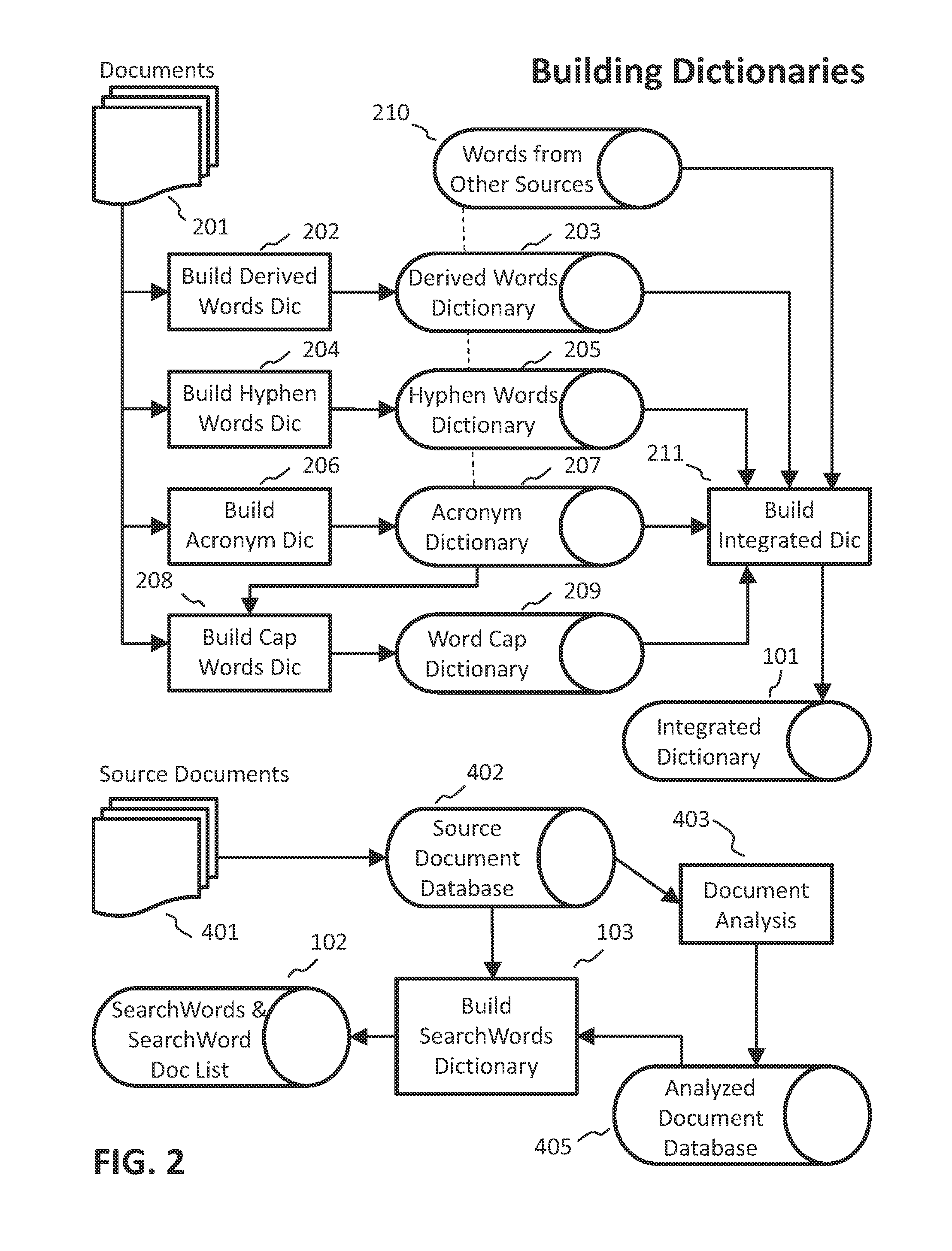
A method of operating a computerized document search system where information is matched against a database containing documents in response to user queries includes receiving a query identifying a source document that has information content related to the documents within the database. Important words within the source document are detected automatically, where at least one of the important words has been processed using at least two dictionary functions consisting of Derived Words, Acronym, Word Capitalization, and Hyphenation. An importance value is generated for important words in a processed document using a WordRatio and at least one of a selected set of values. A score is generated for a processed document based partly on the importance value of at least one important word in that document. A document list is created for identifying documents that are related to a source document.
Owner:NEXTGEN DATACOM
Enhanced transcoding of structured documents through use of annotation techniques
InactiveUS20030018668A1Digital data information retrievalDigital computer detailsDocumentation procedureTranscoding
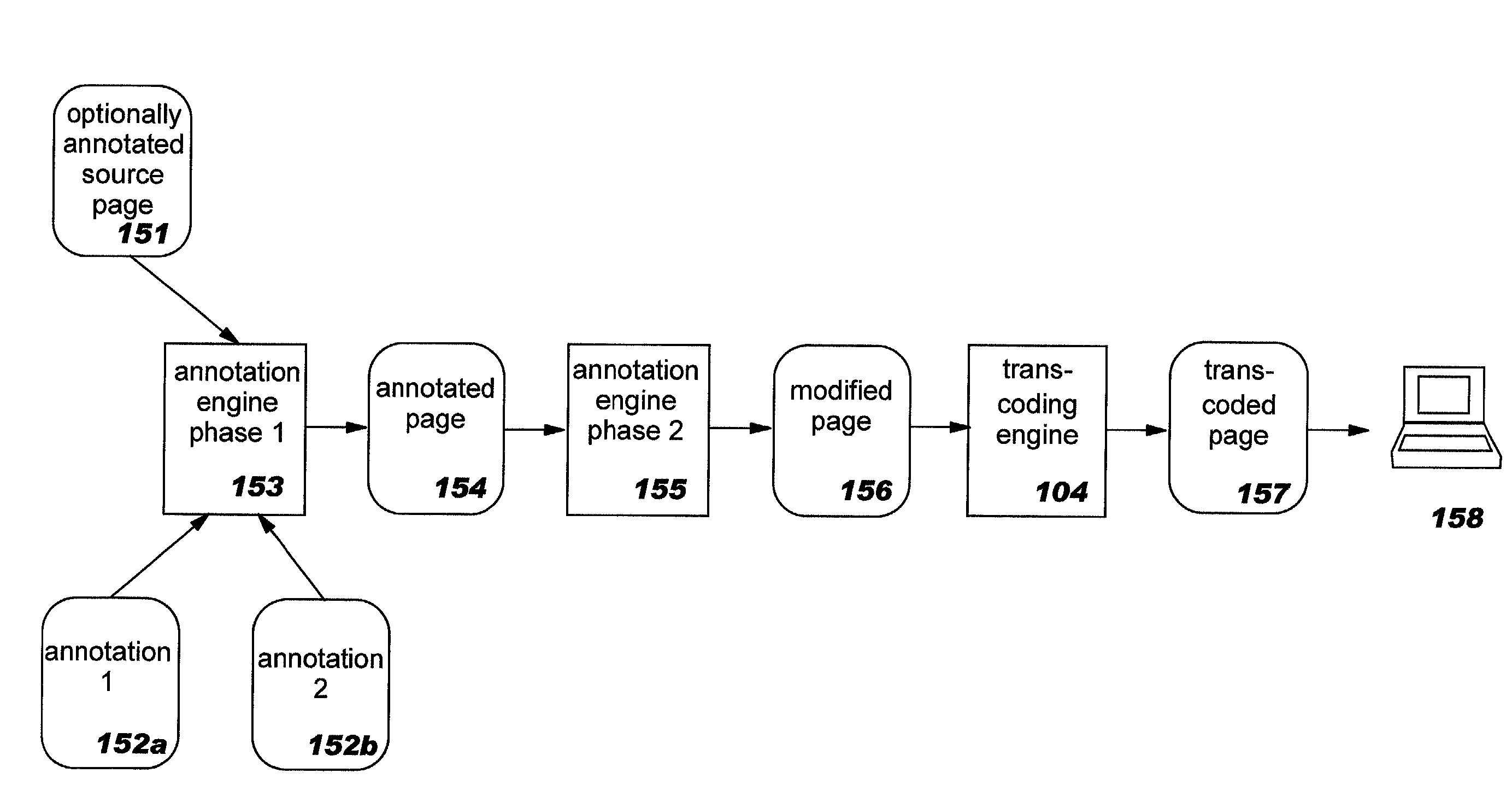
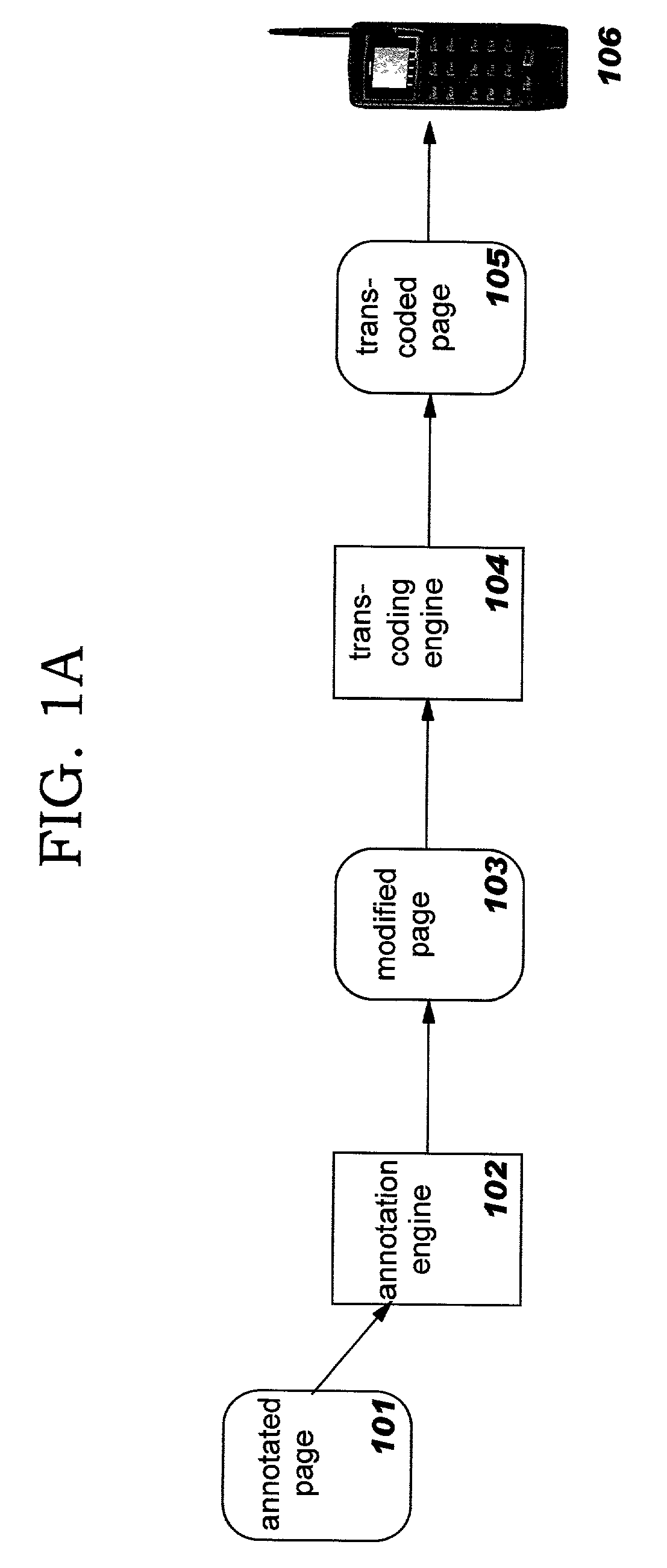
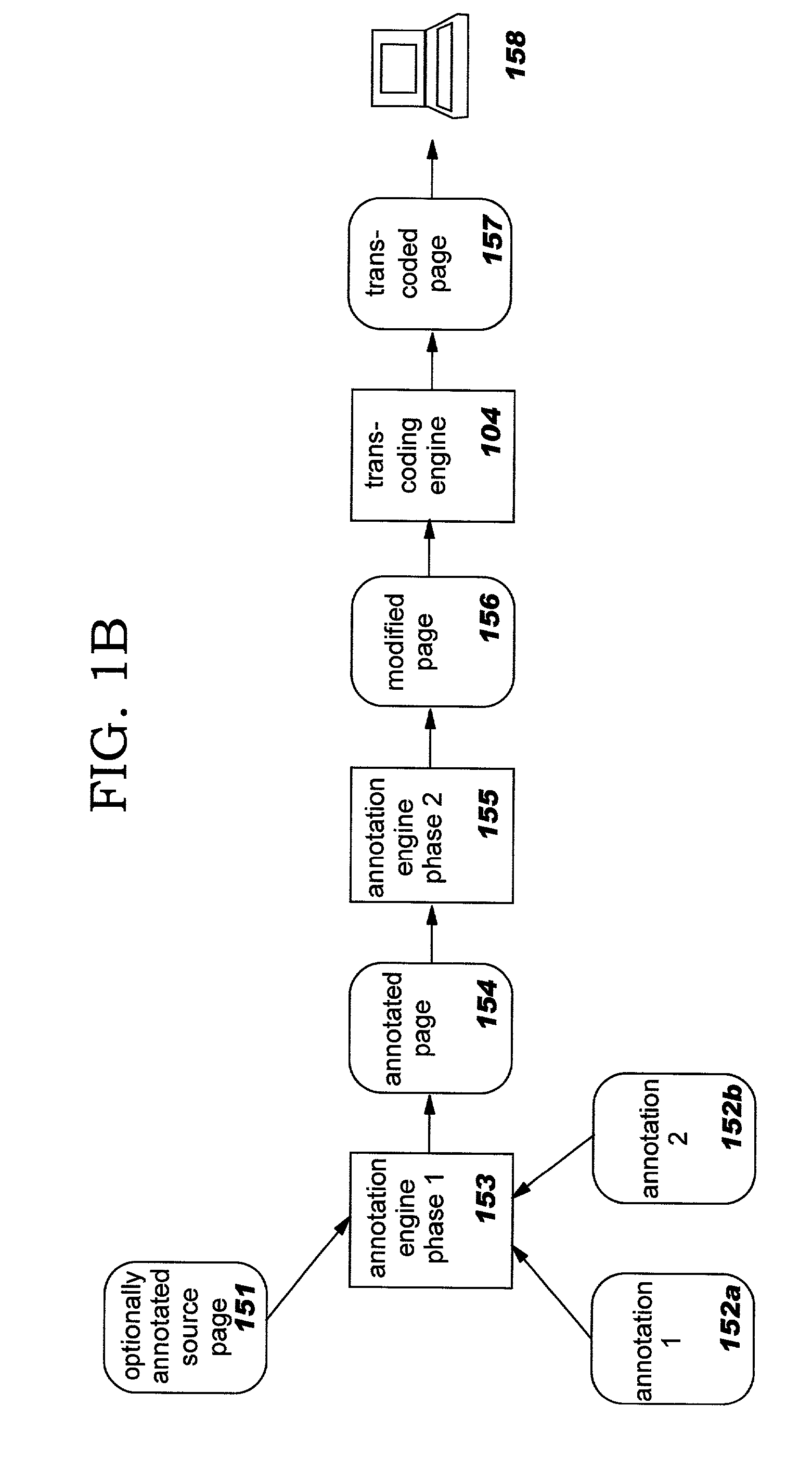
Methods, systems, and computer program products for improving the transcoding operations which are performed on structured documents (such as those encoded in the Hypertext Markup Language, or "HTML") through use of annotations. Source documents may be annotated according to one or more types of annotations. Representative types of annotations direct an annotation engine to perform selective clipping of document content, provide enhanced HTML form support, request node and / or attribute replacement or the insertion of HTML or other rendered markup syntax, and direct a transcoding engine to provide fine-grained transcoding preference support (such as controlling transcoding of tables on a per-row or per-column basis). The disclosed techniques may be used with statically-generated document content and with dynamically-generated content. Annotation is performed as a separate step preceding transcoding, and a modified document resulting from processing annotations may therefore be re-used for multiple different transcoding operations.
Owner:IBM CORP
Information classification paradigm
InactiveUS7529748B2Complex analysisData processing applicationsDigital data information retrievalDocument preparationLibrary science
Owner:MICROSOFT TECH LICENSING LLC
Formatting selected content of an electronic document based on analyzed formatting
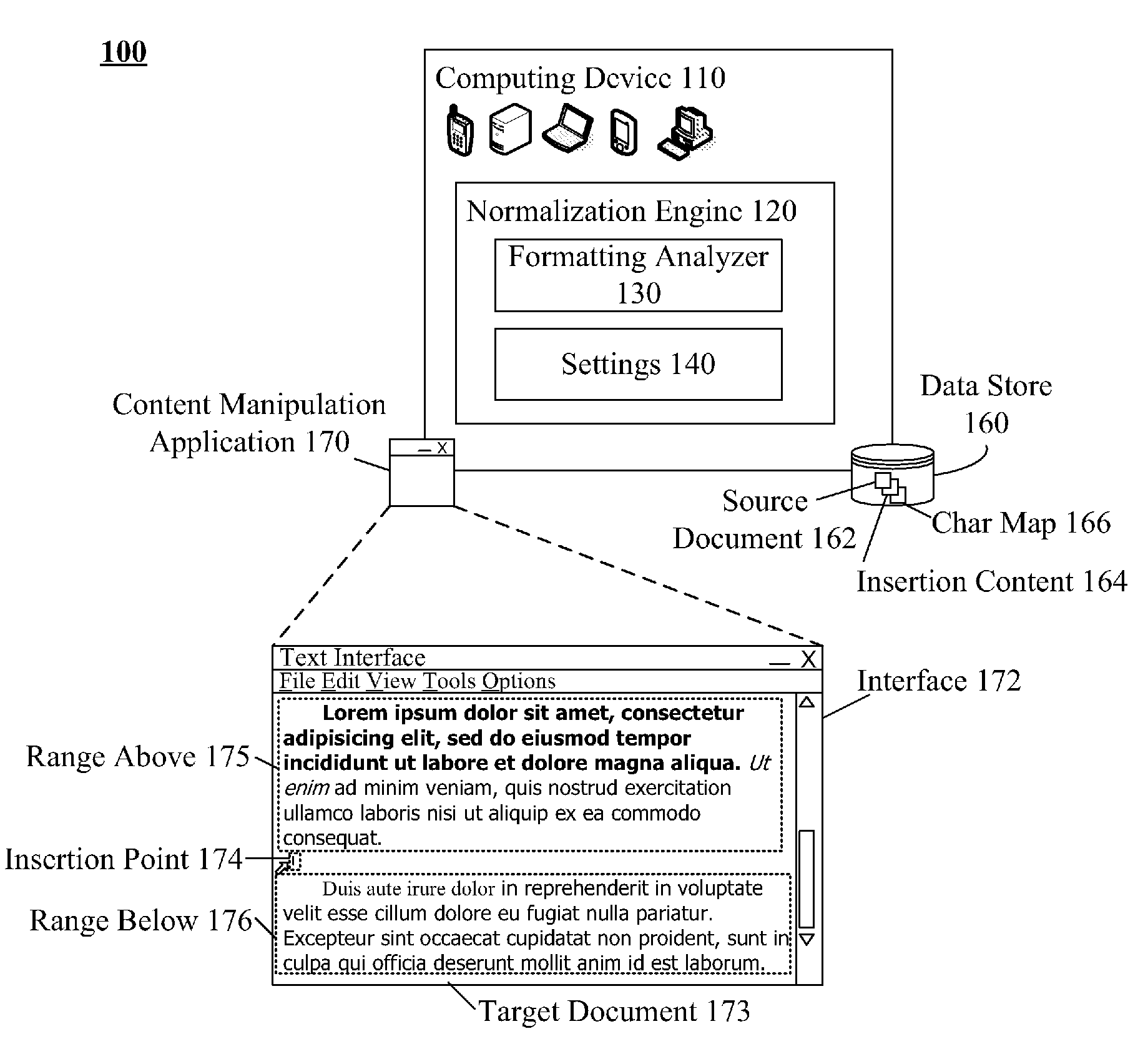
InactiveUS20090292987A1Natural language data processingProgram controlElectronic documentContent format
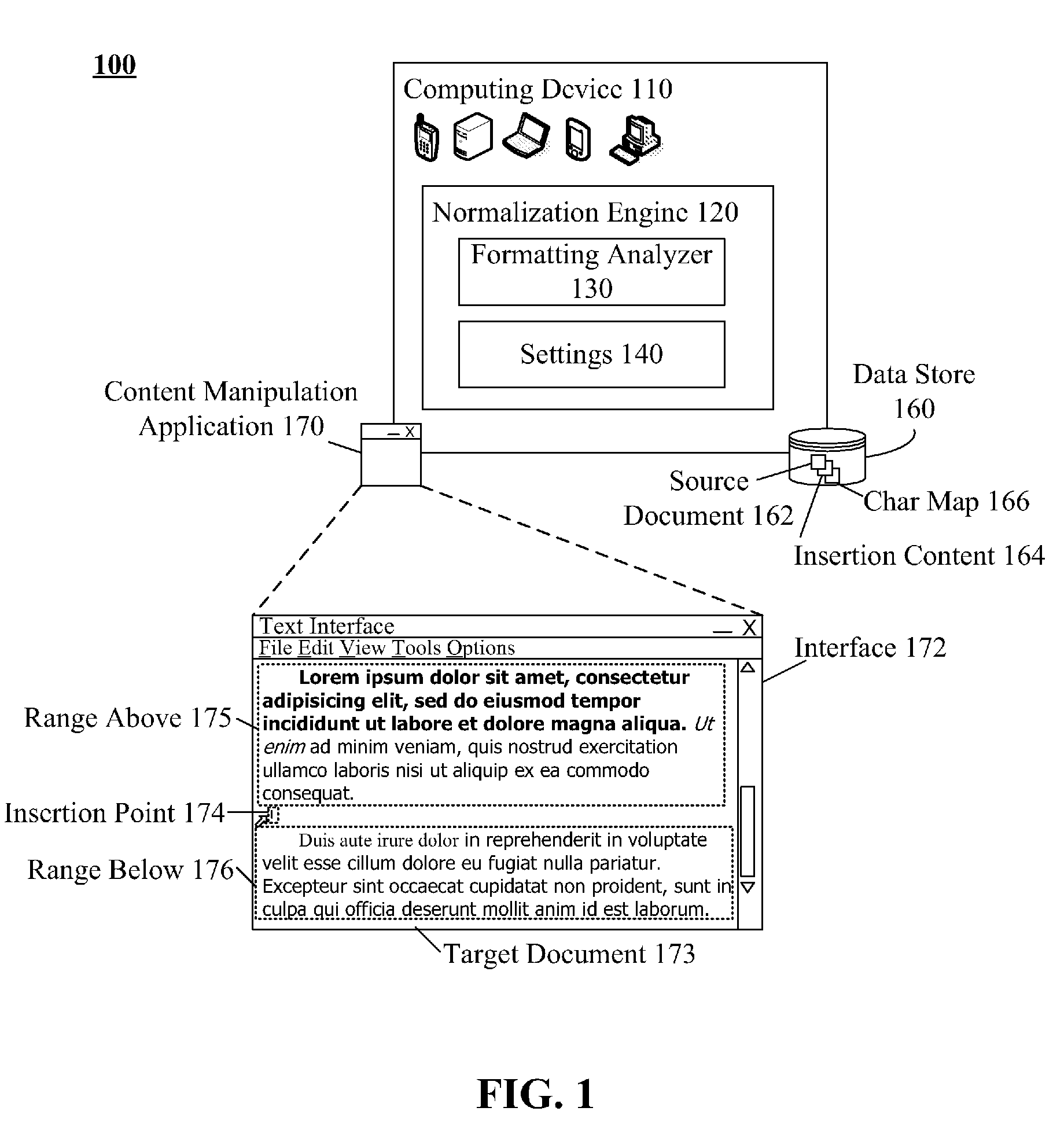
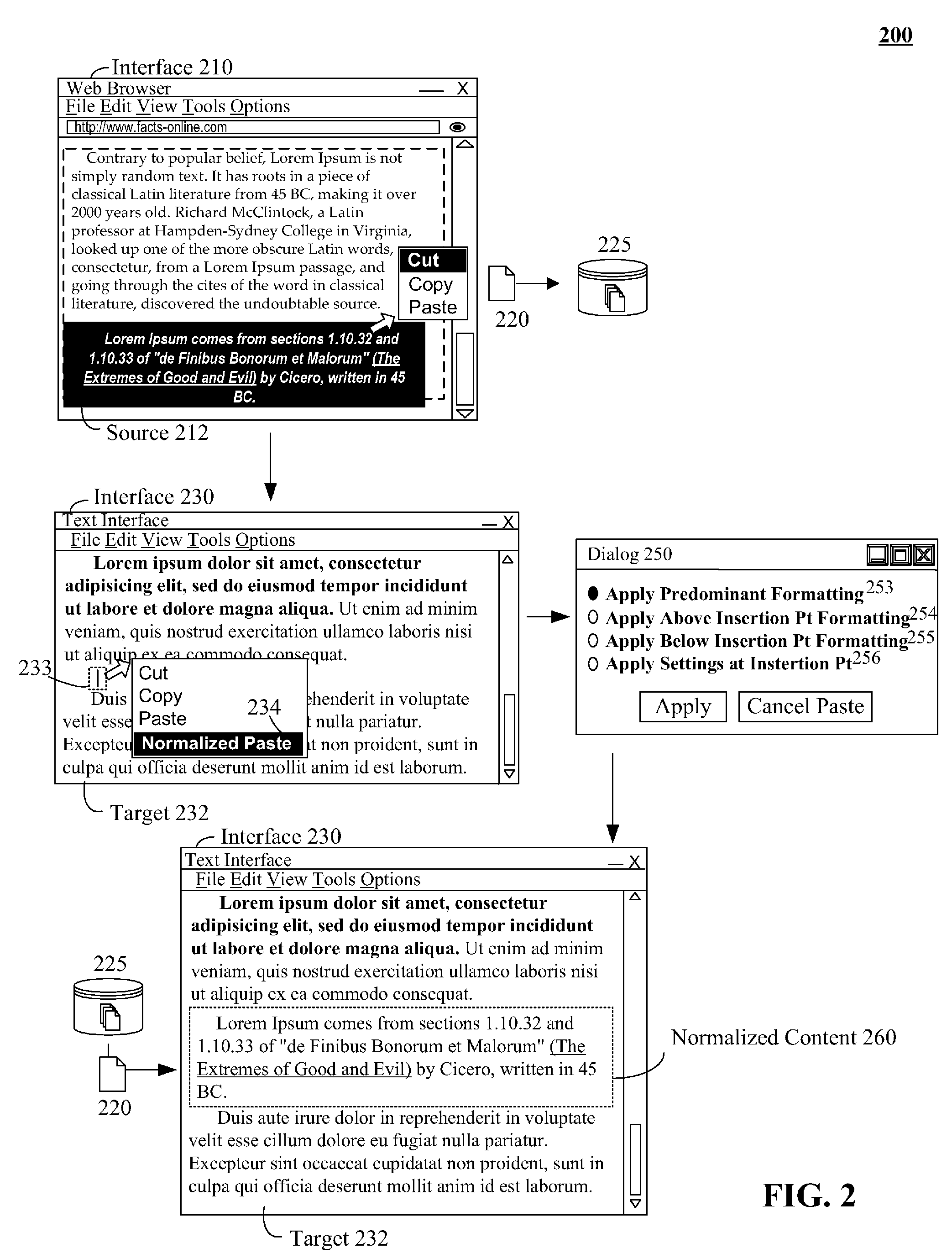
One aspect of the present invention can include a method, computer program product, system, and / or device for formatting content of an electronic document. In the aspect, pending content from a source document can be identified that is to be inserted into a target document. An insertion point in the target document can be identified. Format settings of pre-existing content of the target electronic document can be analyzed in a range about the insertion point. Predominant format settings for the pre-existing content in the range can be determined. The determined predominant format settings can be applied to the pending content to generate a version of the pending content formatted in accordance with the determined predominant format settings. The version pending content conforming to the predominant format of the target can then be added to the target document at the insertion point.
Owner:IBM CORP
Document processing system and method
InactiveUS20030093755A1Change structureData processing applicationsDigital computer detailsDatabaseSource document
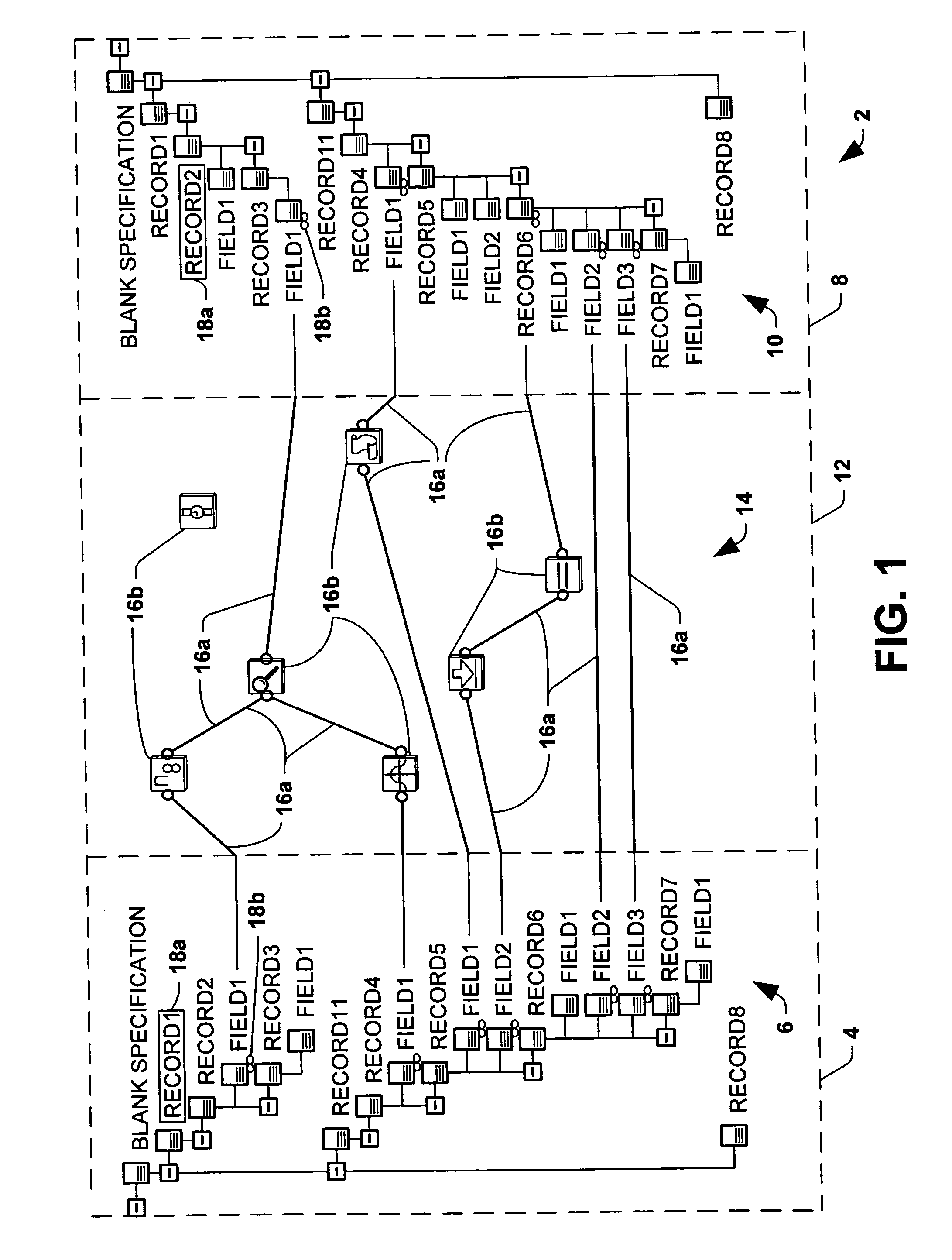
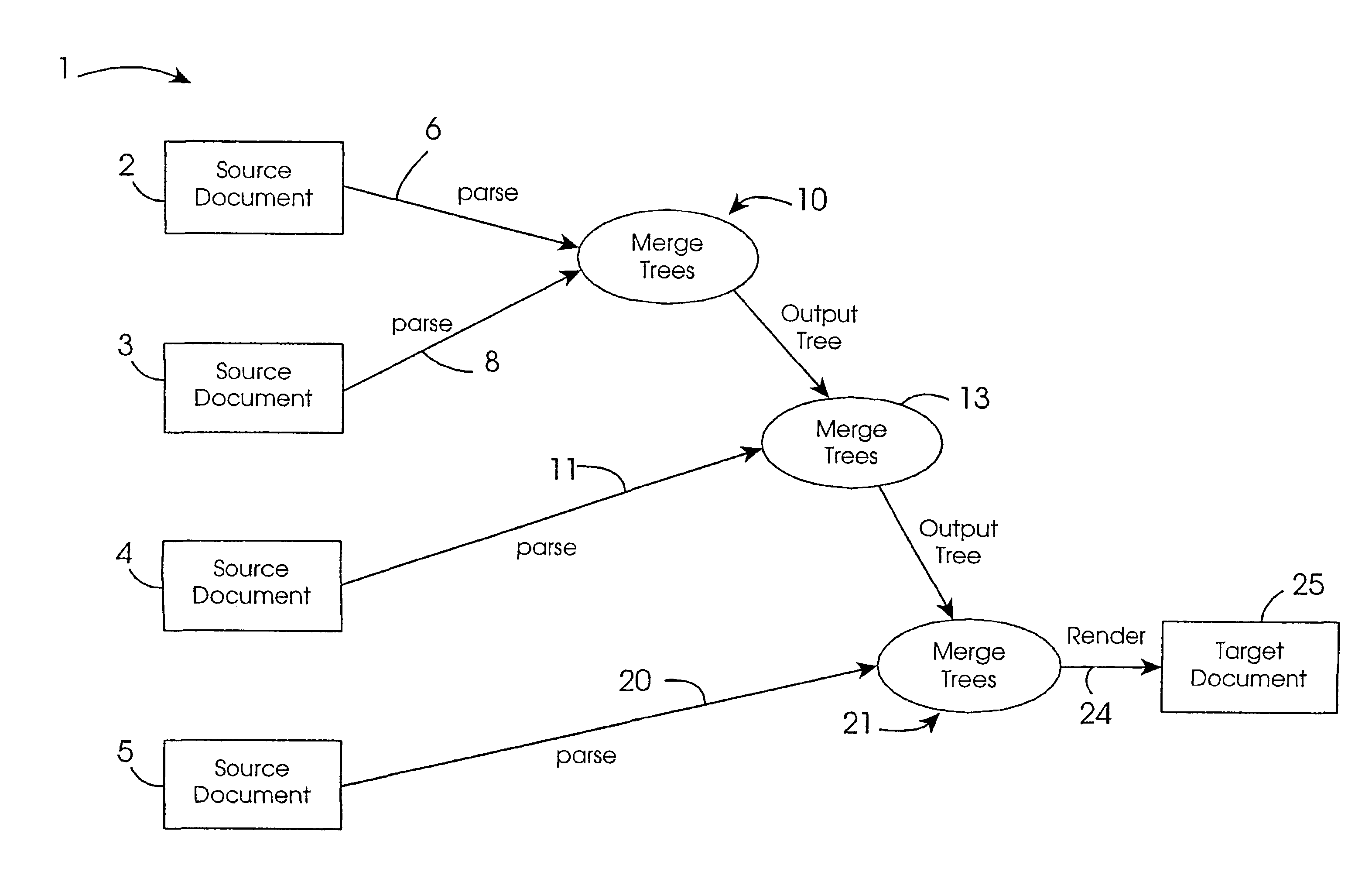
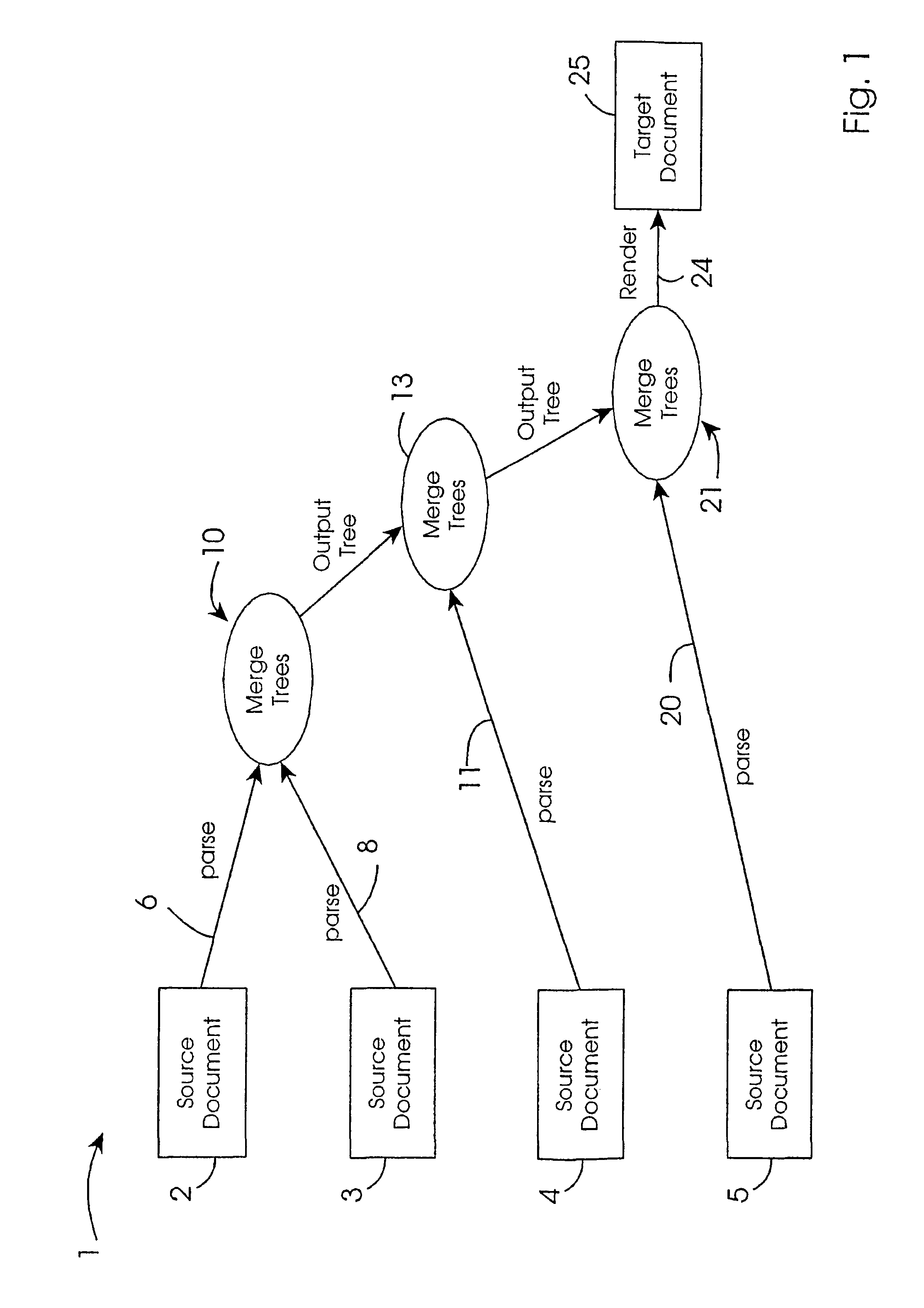
A target document (25) is generated by merging four source documents (2-5). There are three merge operations, an operation (10) for two source documents (2, 13), an operation (13) for an intermediate target document and a source document (4), and an operation (21) for a second intermediate target document and a final source document (5). In each merge operation one source document inherits from the other. An inheriting instruction is embedded within the inheriting document. Merging is performed by parsing a document (6, 8, 11, 20) into a hierarchical tree if it is not already in that form, and merging the trees. Matching nodes are identified and are combined or replaced according to a policy.
Owner:MEC MANAGEMENT LLC
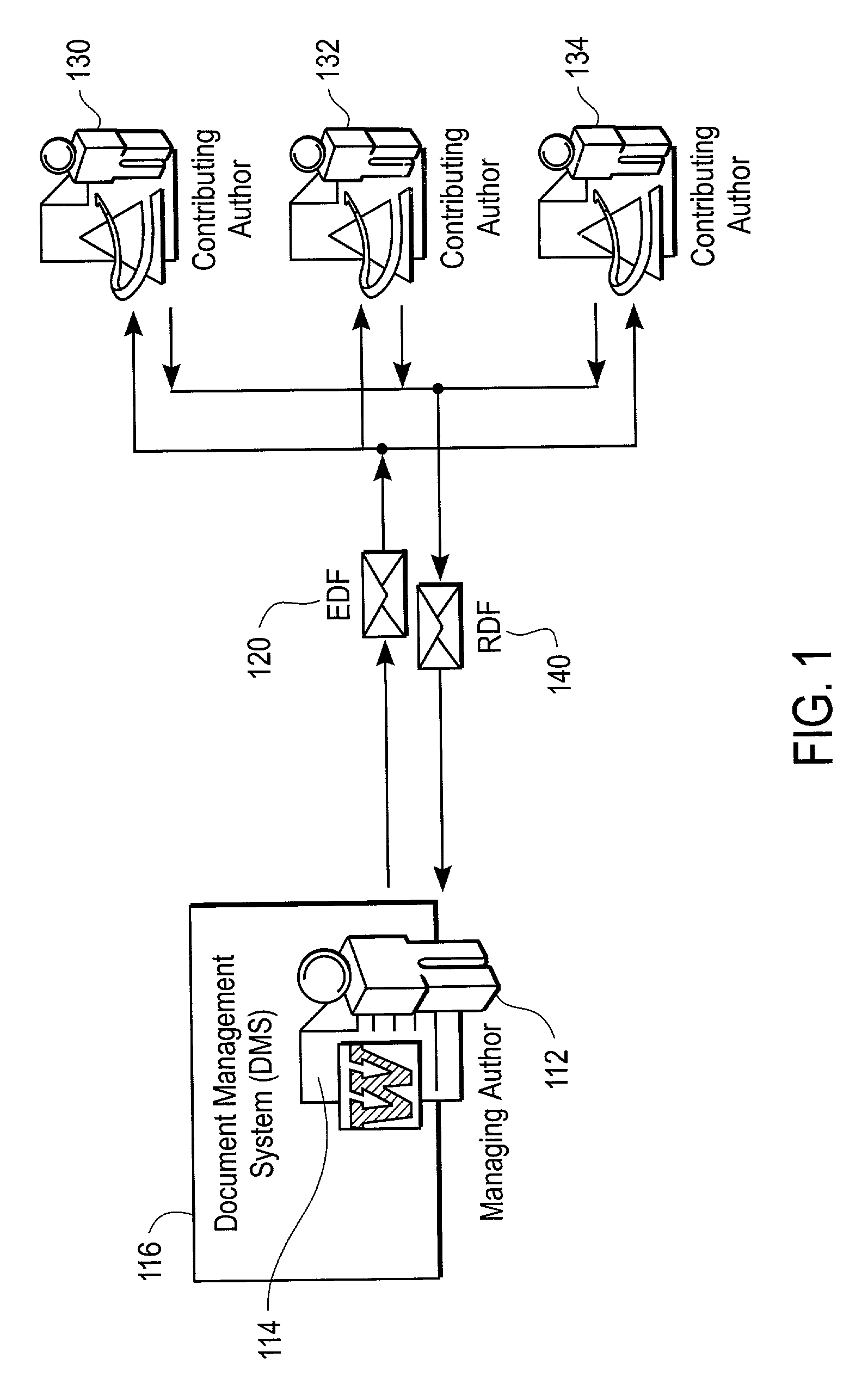
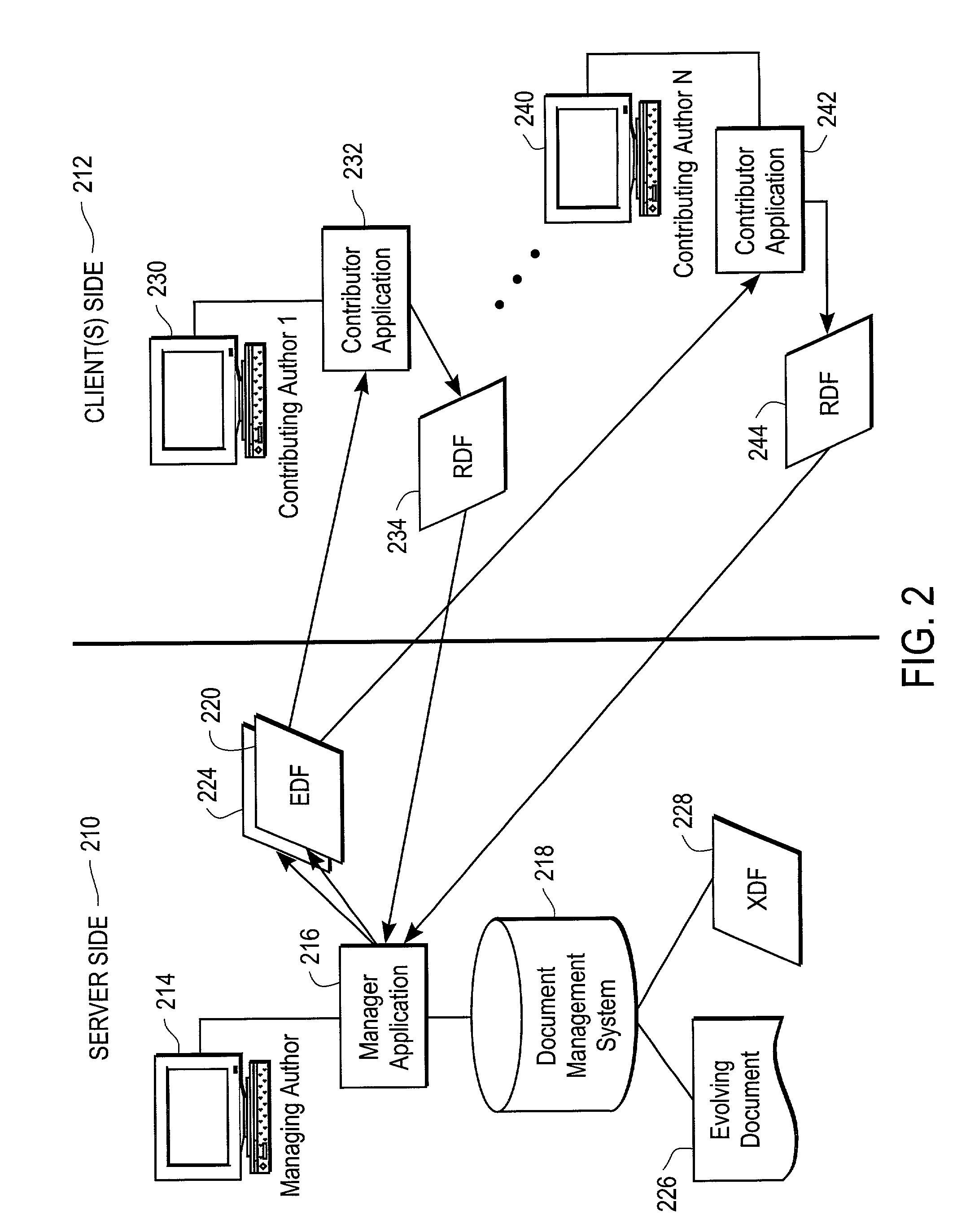
Method and system for document collaboration
InactiveUS7496841B2Office automationSpecial data processing applicationsGraphicsGraphical user interface
The present invention provides techniques, including a system and method, for document collaboration between a managing author using a document management system (DMS), and one or more contributing authors. In one embodiment the managing author selects an original document from the DMS. Next, a replica of the original document is made and securely sent by the managing author to the one or more contributing authors. A contributing author may make proposed changes and comments to the replica. The edited replica with the proposed changes is converted into a response that is sent back to the managing author. The proposed changes for the contributing author are determined using the response and displayed on a graphical user interface (GUI) for viewing by the managing author. The managing author accepts or rejects the proposed changes to the original document from the contributing author.
Owner:WORKSHARE TECH +1
Data security system and method associated with data mining
ActiveUS7322047B2Ease overhead performanceHigh overhead performancePeptide/protein ingredientsMultiple keys/algorithms usagePlaintextInternet privacy
The data security method, system and associated data mining enables multiple users, each having a respective security clearance level to access security sensitive words, data objects, characters or icons. The method extracts security sensitive words, data objects, characters or icons from plaintext or other source documents to obtain (a) subsets of extracted data and (b) remainder data. The extracted data is, in one embodiment, stored in a multilevel security system (MLS) which separates extract data of different security levels with MLS guards. Some or all of the original data is reconstructed via one or more of the subsets of extracted data and remainder data only in the presence of a predetermined security level. In this manner, an inquiring party, with the proper security clearance, can data mine the data in the MLS secured storage.
Owner:DIGITAL DOORS
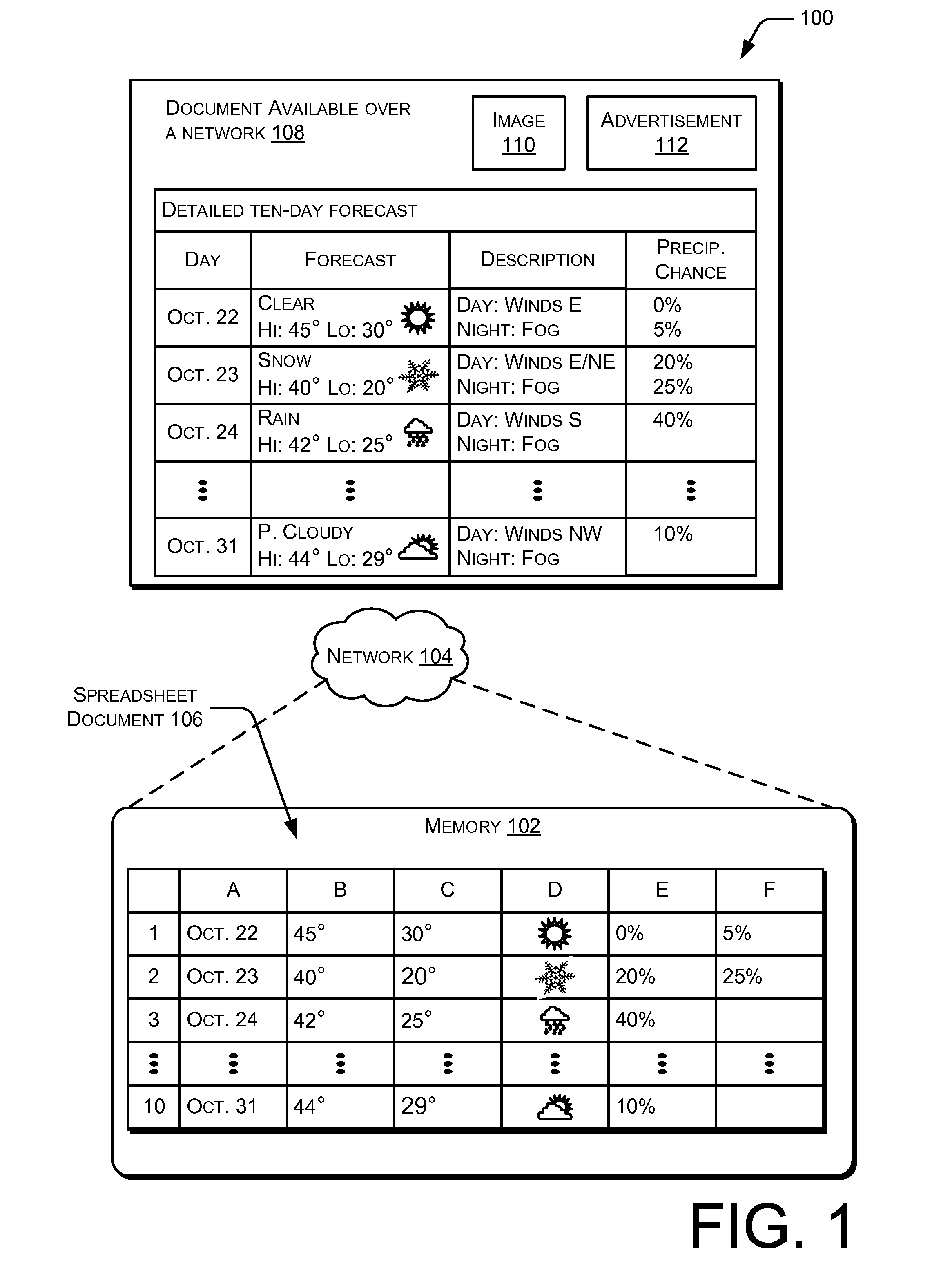
Interactive synchronization of web data and spreadsheets
Interactive synchronization of Web data and spreadsheets is usable to build data wrappers based on any type of data found in a document. Such data wrappers can be used to interact with source documents, crawl a network for additional data, map data from across domains, and / or synchronize data from dynamic Web documents.
Owner:MICROSOFT TECH LICENSING LLC
Data security system and method with adaptive filter
ActiveUS20050138109A1Ease overhead performanceHigh overhead performanceDigital data information retrievalDigital data processing detailsInformation processingAdaptive filter
The method, program and information processing system involves filtering and securing data (security sensitive words-characters-data objects) in a source document. The adaptive filter uses a compilation of additional data (typically networked) and identifies the sensitive words / objects in the compilation of additional data, retrieves contextual, semiotic and taxonomic words / objects from the additional data compilation that are related to the sensitive words / objects. A filter is compiled with the retrieved data and the filter is used to extract sensitive words / objects and the retrieved data (words / objects) from the source document to obtain extracted data and remainder data therefrom. Contextual words related to the security sensitive words / objects are obtained based upon statistical analysis of the additional data compilation. Semiotic words related to the security words are synonyms, antonyms, and pseudonyms, syntactics relative to the target words and retrieved words, and pragmatics relative to the sensitive words and retrieved words as reflected in the compilation of additional data.
Owner:DIGITAL DOORS
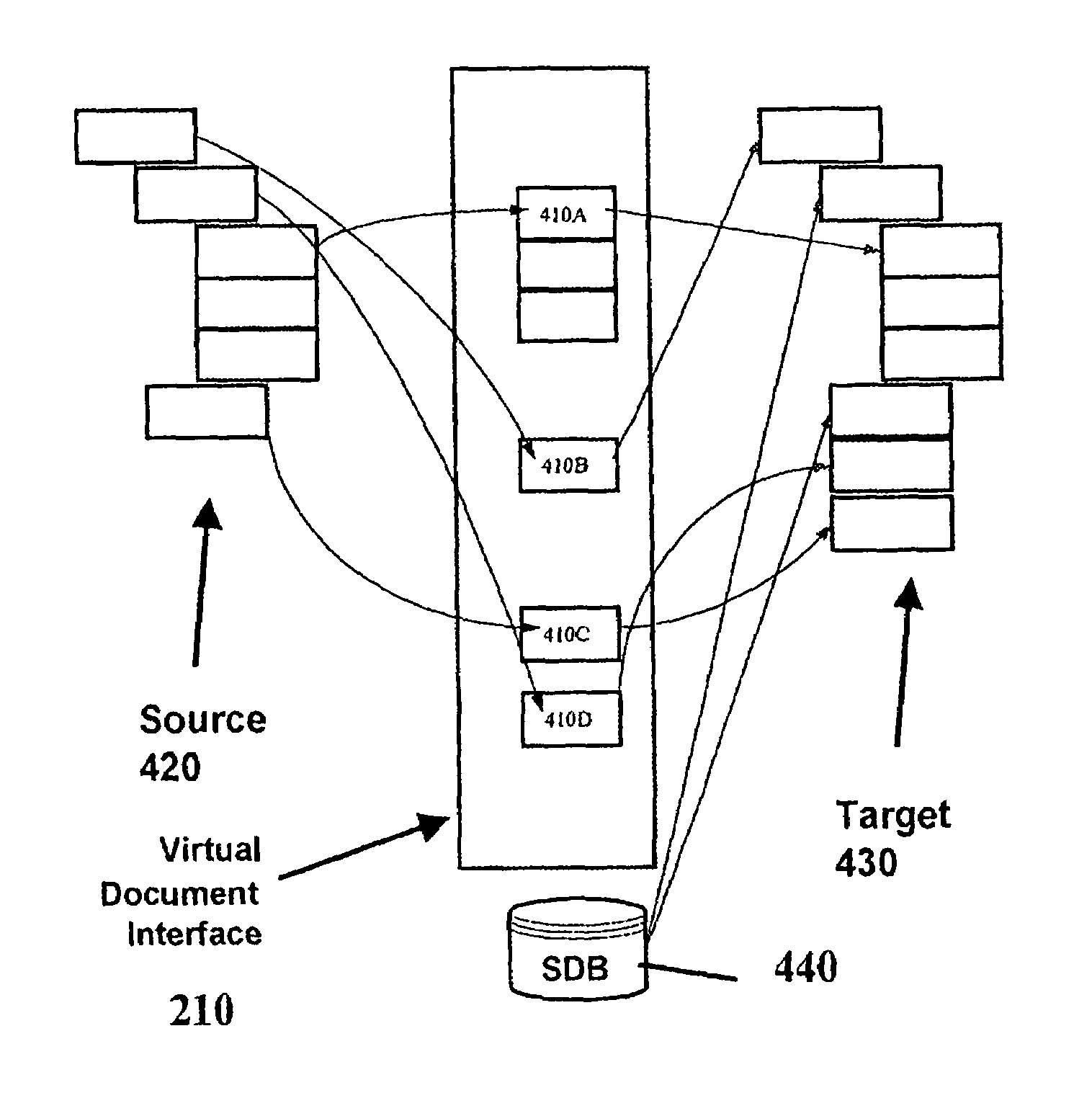
Mapping tool graphical user interface
InactiveUS20050015732A1Generate efficientlyEasy to useDigital data processing detailsInterprogram communicationGraphicsGraphical user interface
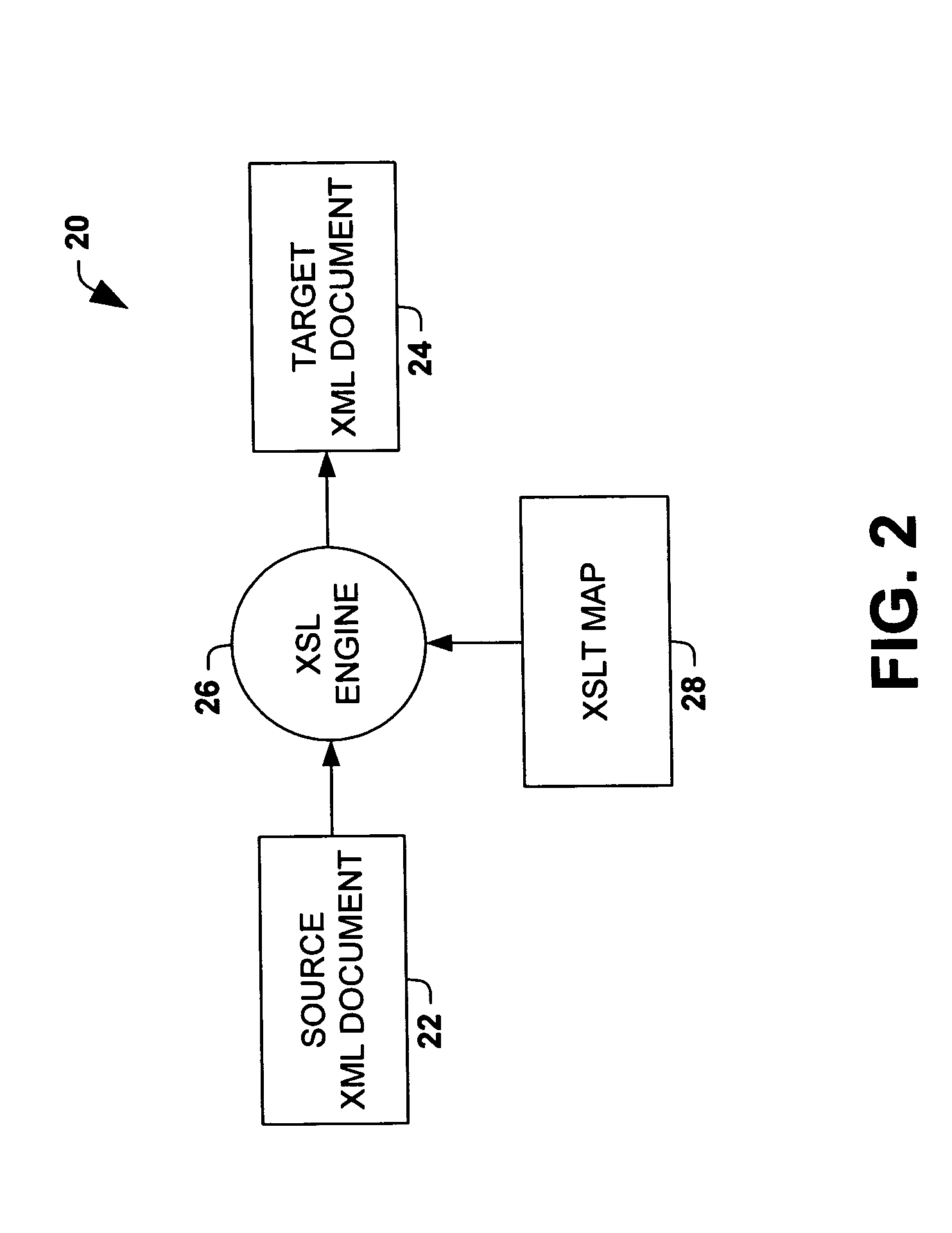
A graphical user interface and method for creating a mapping between a source object and a destination or target object are provided. The user interface includes a source screen region which displays a graphical representation of a source object, a target screen region which displays a graphical representation of a target object, and a mapping screen region which allows a user to create a mapping between the graphical representation of the source object and the graphical representation of the target object using graphical mapping indicia. The methodology includes displaying a graphical representation of a source object in a source screen region, displaying a graphical representation of a target object in a target screen region, creating a mapping between the graphical representation of the source object and the graphical representation of the target object in a mapping screen region using graphical mapping indicia, and displaying the mapping in the mapping screen region. The source and target objects may be schemas, spreadsheets, documents, databases, or other information sources, and the graphical mapping indicia may include link indicia and / or function objects linking nodes in the target object with nodes in the source object. The mapping may be compiled into code used by a runtime engine to translate source documents into target documents.
Owner:MICROSOFT TECH LICENSING LLC
Deep Model Statistics Method for Machine Translation
InactiveUS20090182549A1Improve accuracyNatural language translationSemantic analysisInput languageMachine translation
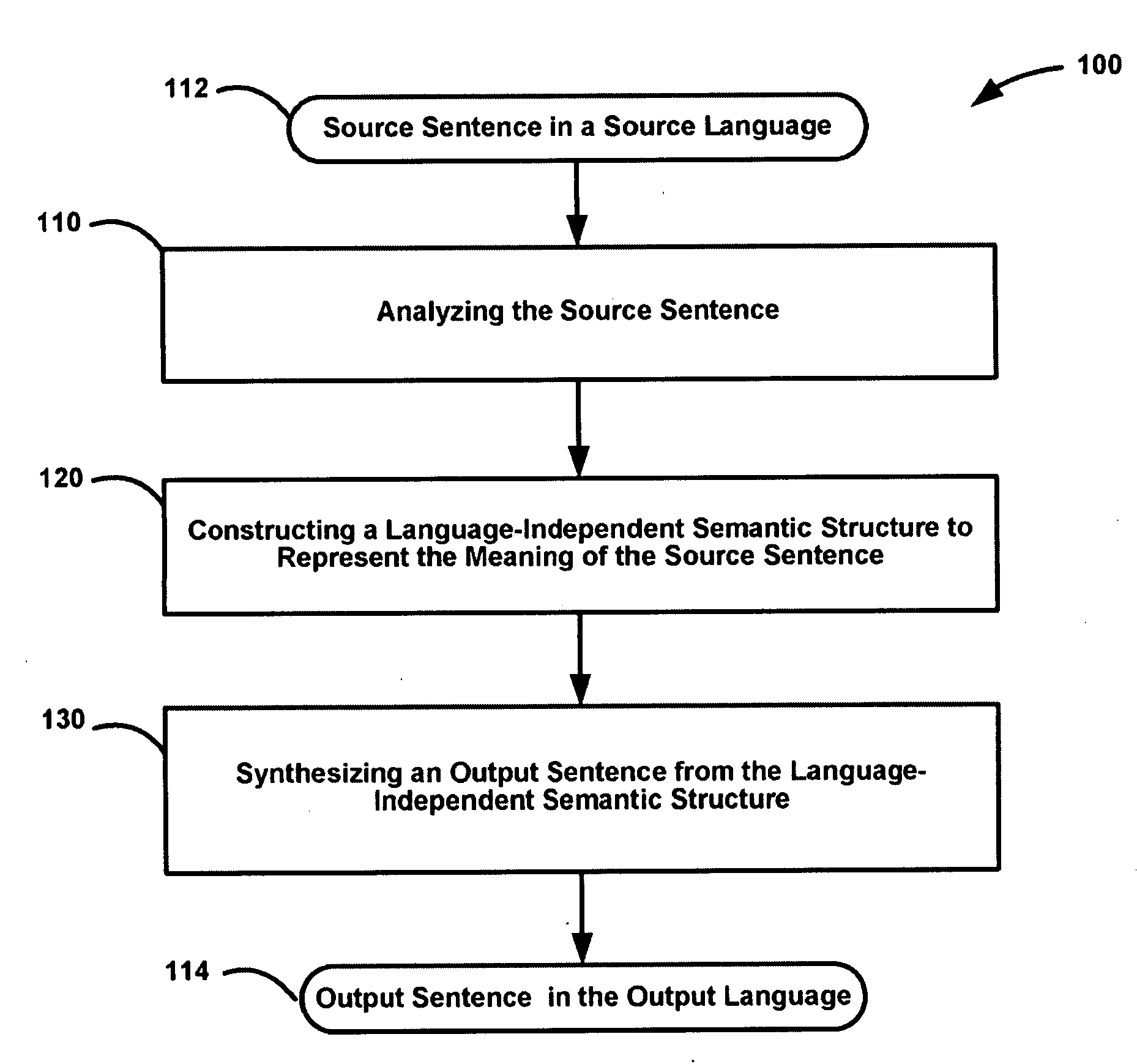
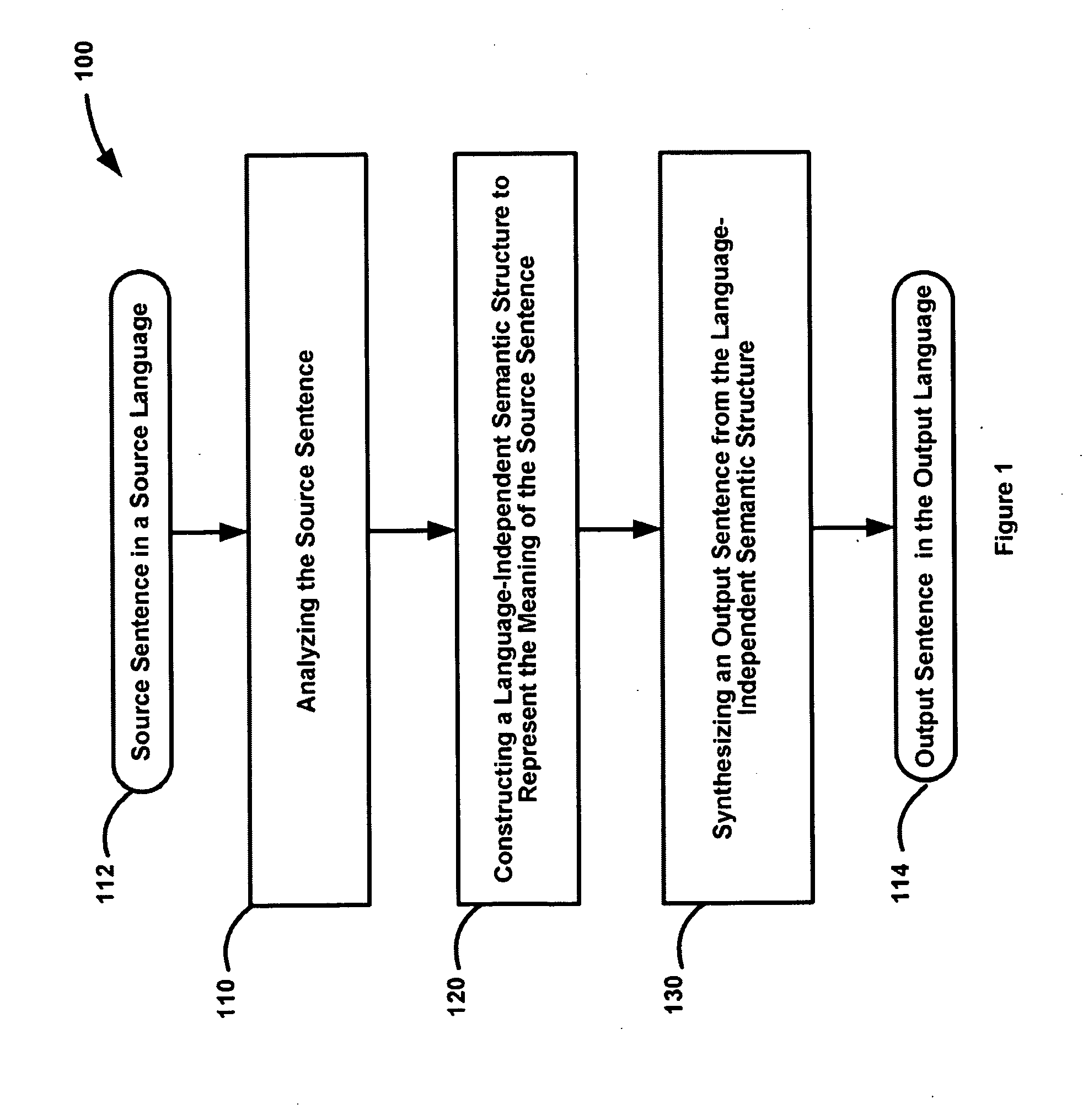
In one embodiment, the invention provides a method for machine translation of a source document in an input language to a target document in an output language, comprising generating translation options corresponding to at least portions of each sentence in the input language; and selecting a translation option for the sentence based on statistics associated with the translation options.
Owner:ABBYY PRODUCTION LLC
Electronic document processing system and method for merging source documents on a node-by-node basis to generate a target document
InactiveUS6772165B2More versatilityChange structureData processing applicationsNatural language data processingElectronic documentDocumentation
A target document (25) is generated by merging four source documents (2-5). There are three merge operations, an operation (10) for two source documents (2, 13), an operation (13) for an intermediate target document and a source document (4), and an operation (21) for a second intermediate target document and a final source document (5). In each merge operation one source document inherits from the other. An inheriting instruction is embedded within the inheriting document. Merging is performed by parsing a document (6, 8, 11, 20) into a hierarchical tree if it is not already in that form, and merging the trees. Matching nodes are identified and are combined or replaced according to a policy.
Owner:MEC MANAGEMENT LLC
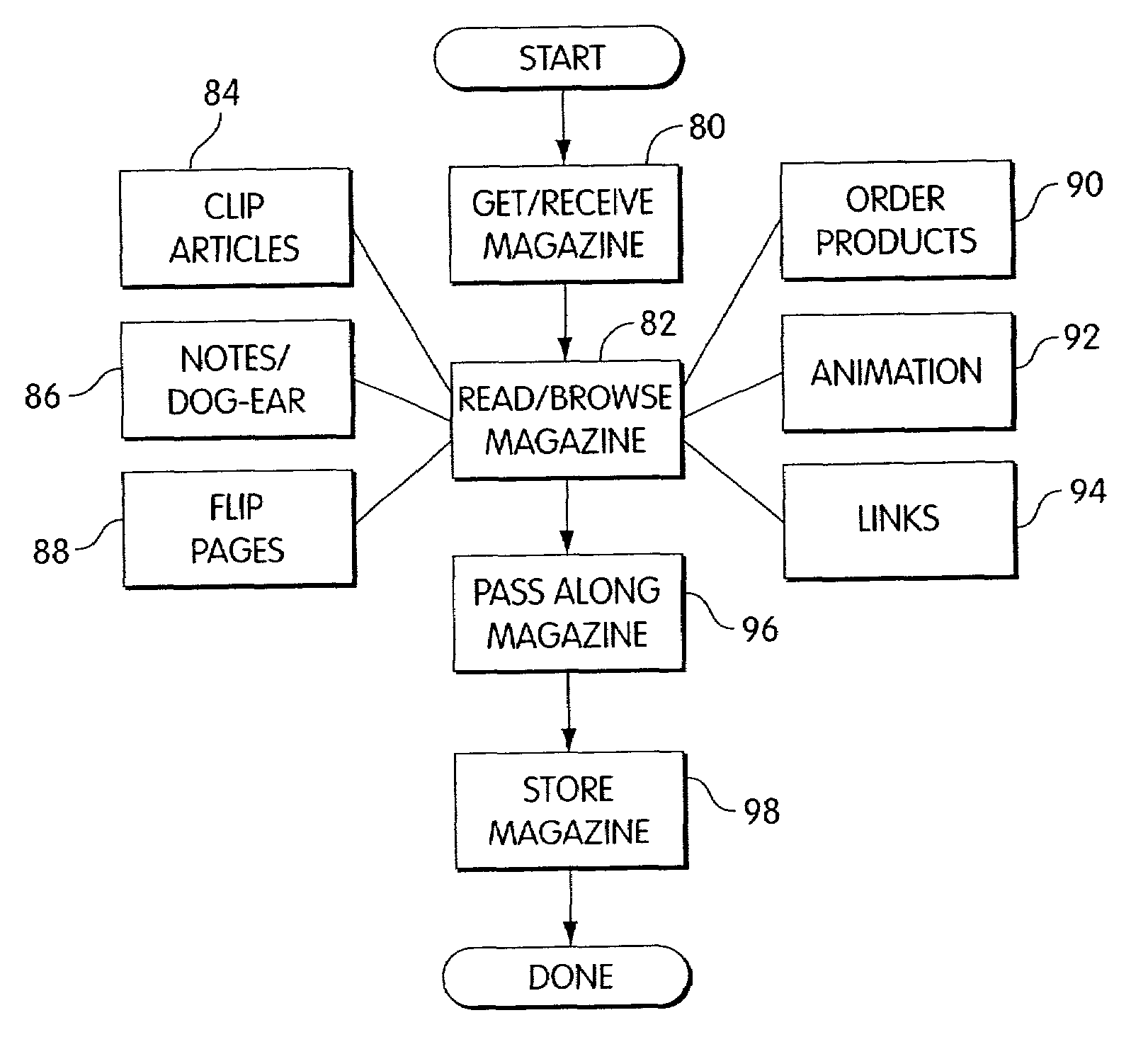
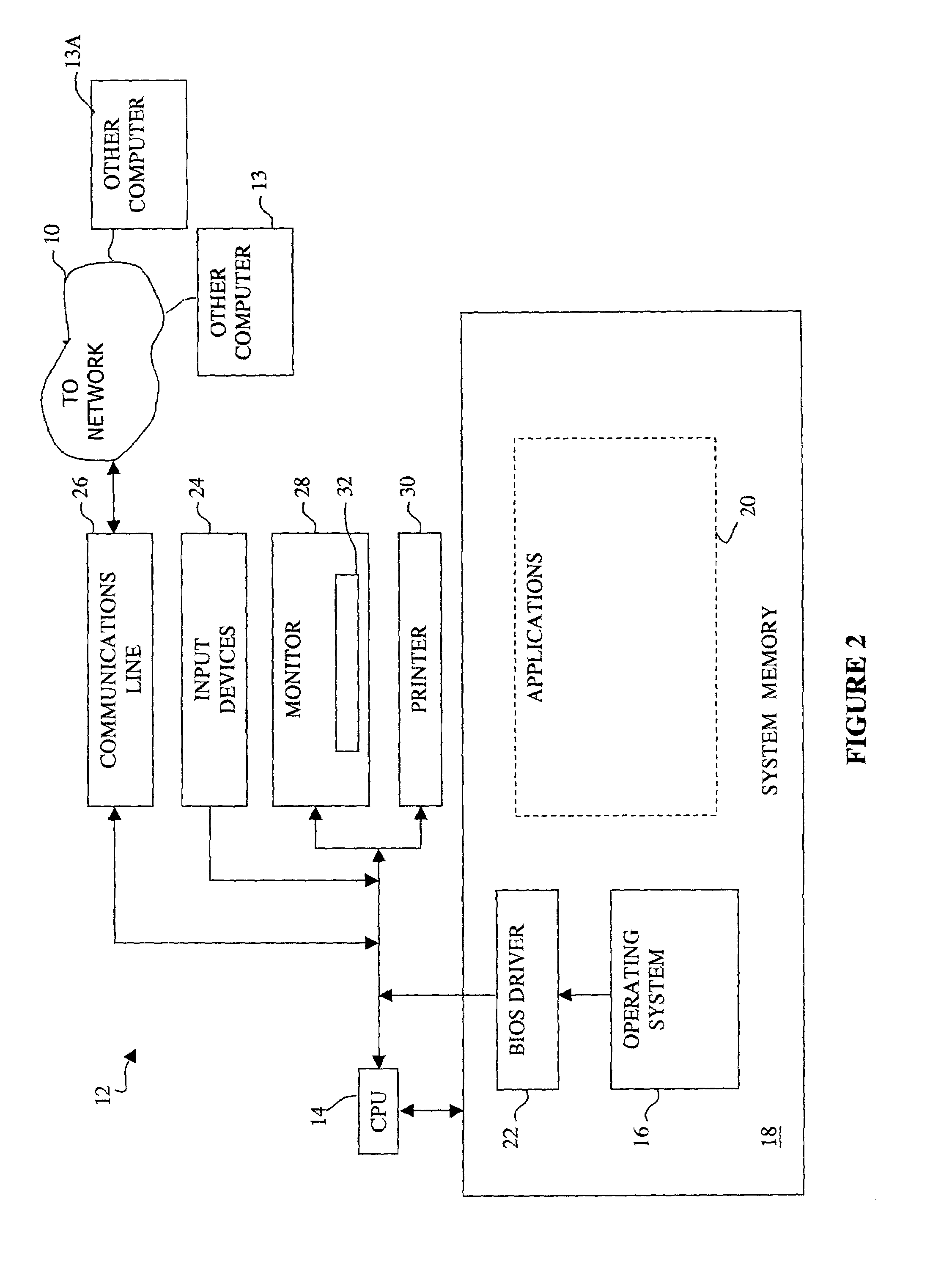
Systems and methods for distributing and viewing electronic documents
InactiveUS7290285B2Improve experienceEasy to placeDigital data processing detailsUser identity/authority verificationElectronic documentDistribution system
A system for distributing an electronic version of a printed document is disclosed. The system comprises a memory device storing at least one document file that is based at least in part on a source document, which is an electronic version of a printed document. The system further comprises a distribution system programmed for: responding to requests from a client for delivery of a document file; retrieving a file copy from the memory device; assigning at least one right to the file copy, the right defining at least one action capable of being performed on at least a portion of the file copy; encrypting the file copy with a key based at least in part on the identity of the client and on the at least one right; and providing the encrypted file copy, with the associated key, to the client.
Owner:ZINIO
Method and apparatus for annotating a line-based document
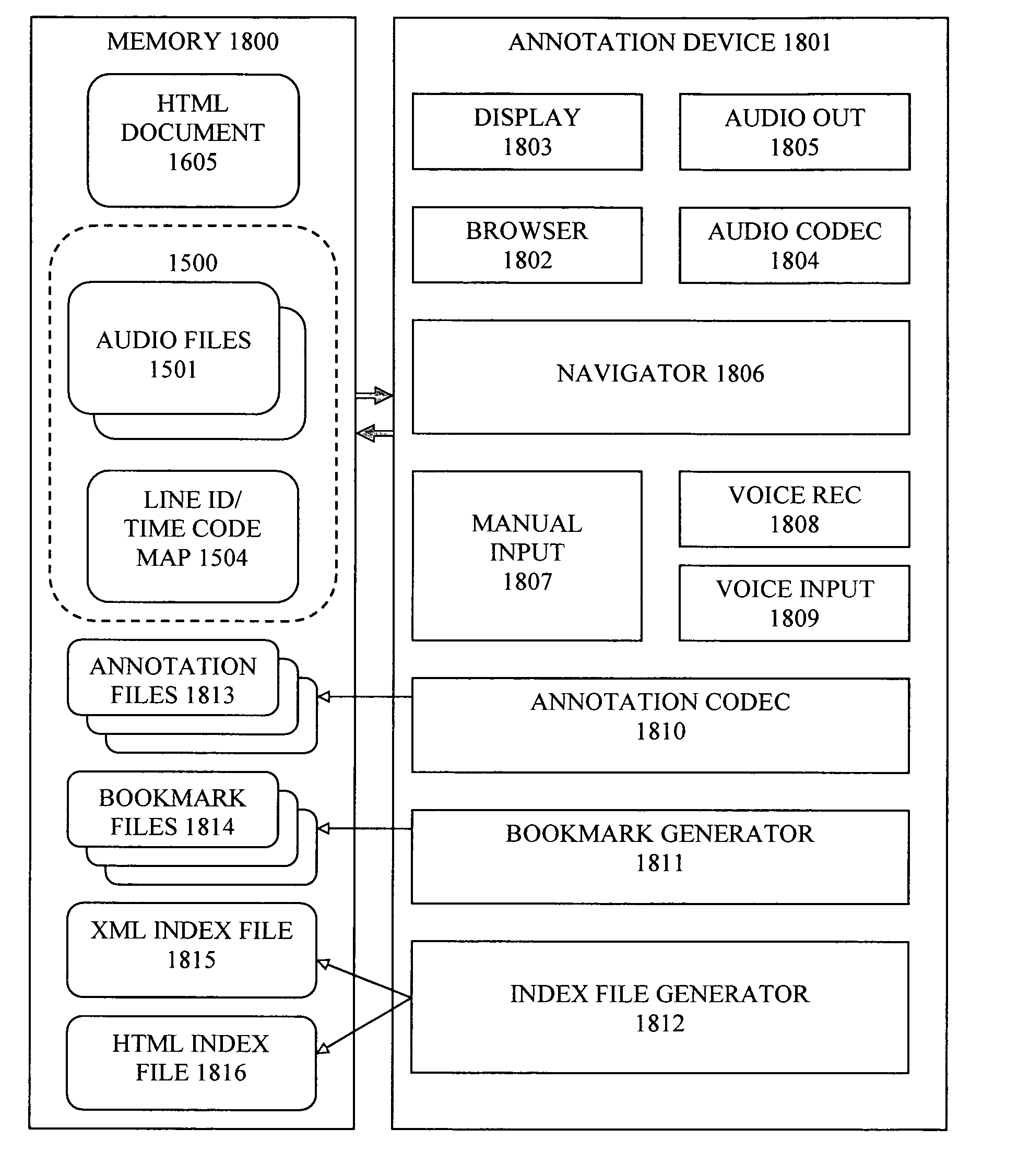
InactiveUS20060143559A1Way of increaseSimple methodNatural language data processingSpeech recognitionNumber timesText annotation
To facilitate the use of audio files for annotation purposes, an audio file format, which includes audio data for playback purposes, is augmented with a parallel data channel of line identifiers, or with a map associating time codes for the audio data with line numbers on the original document. The line number-time code information in the audio file is used to navigate within the audio file, and also to associate bookmark links and captured audio annotation files with line numbers of the original text document. An annotation device may provide an output document wherein links to audio and / or text annotation files are embedded at corresponding line numbers. Also, a navigation index may be generated, having links to annotation files and associated document line numbers, as well as bookmark links to selected document line numbers.
Owner:COPERNICUS INVESTMENTS
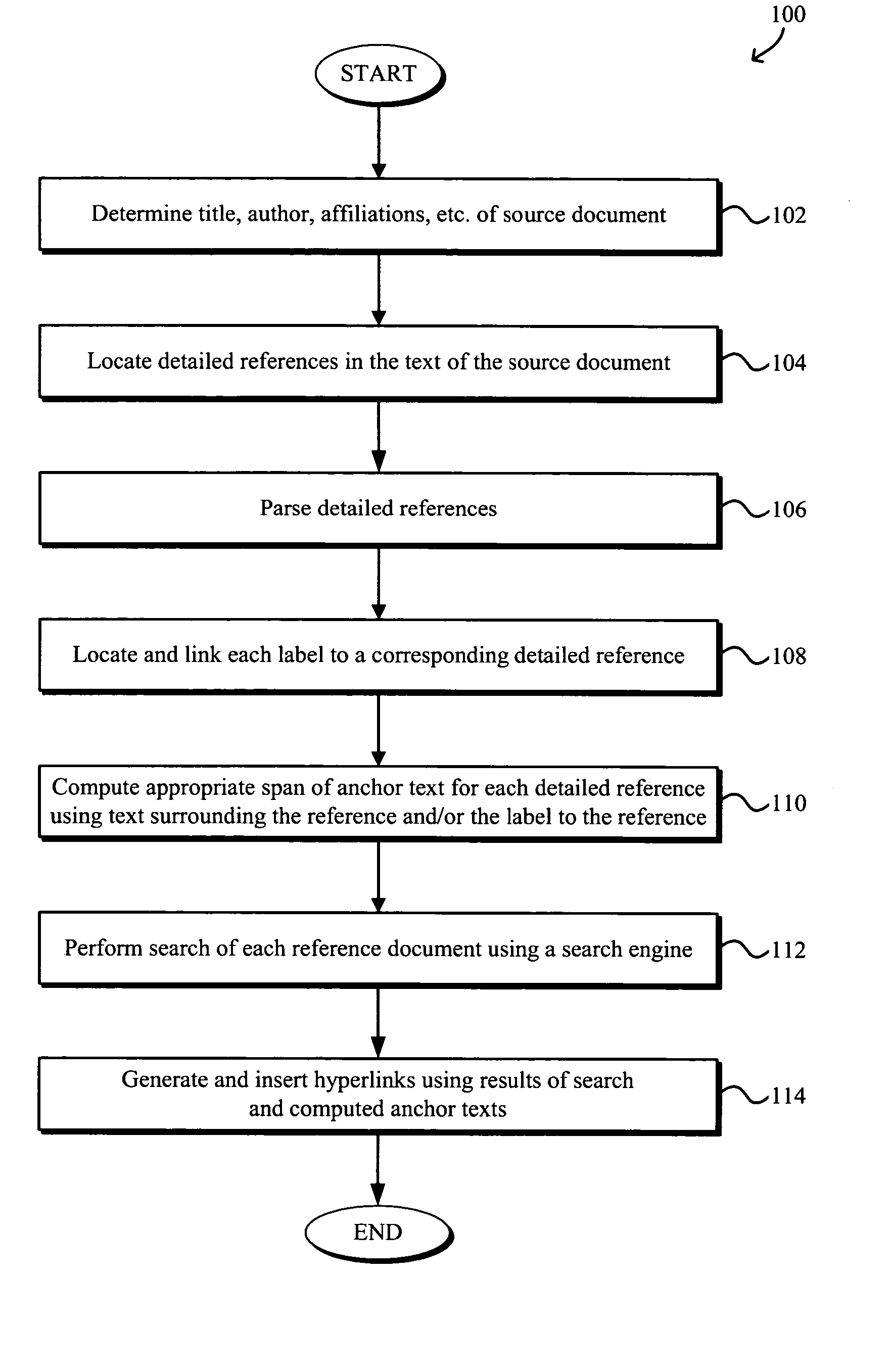
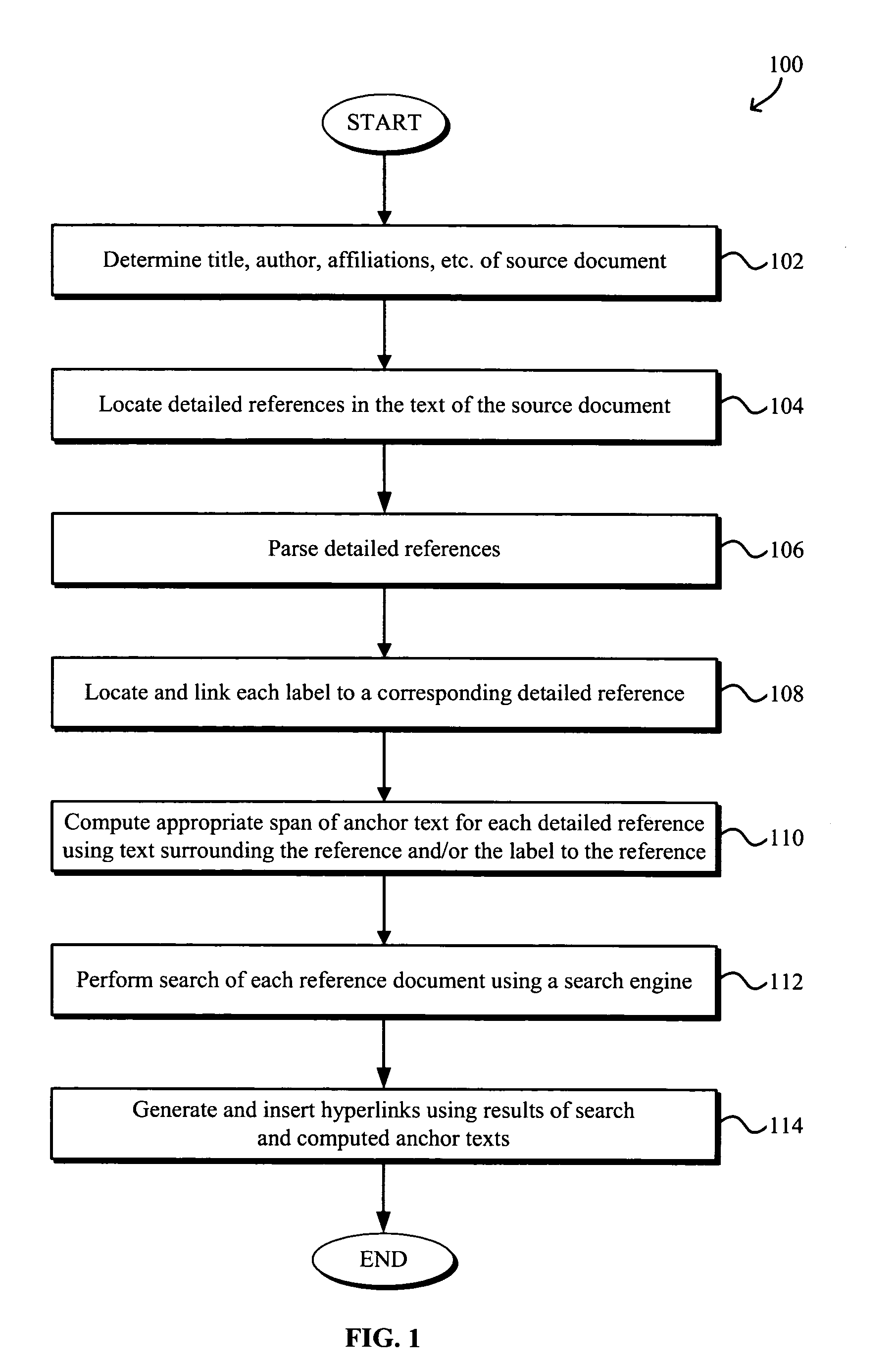
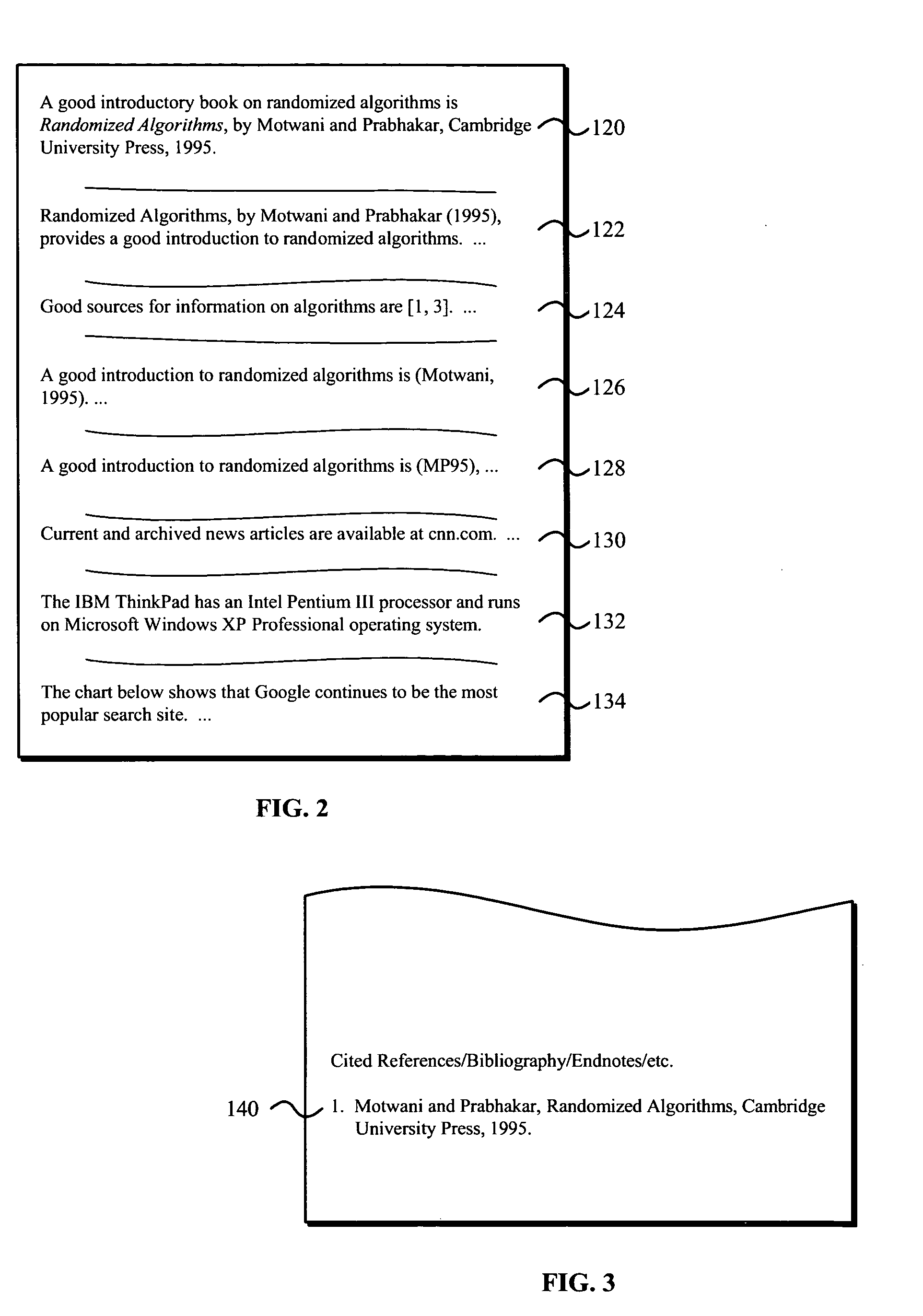
Generating hyperlinks and anchor text in HTML and non-HTML documents
InactiveUS20050149851A1Natural language data processingWebsite content managementHyperlinkDocument preparation
Systems and methods for generation of hyperlinks and anchor text from data such as reference text in HTML and in non-HTML documents are disclosed. The method generally includes locating a text reference in a source document, searching using a search engine for a target document relating to the text reference, computing anchor text from the text reference, generating a hyperlink to the target document, and associating the hyperlink with the computed anchor text. The locating and / or computing may be based on a respective statistical model of text formatting and / or lexical cues. The text reference may be parsed into pieces such that the searching, computing, generating, and associating are performed for each piece of text. The source document may be an HTML or non-HTML document. The text reference may be a reference to, for example, a paper, article, company, institution, product, search engine, image, object, and geographical location.
Owner:GOOGLE LLC
Data security system and method with adaptive filter
ActiveUS7546334B2Digital data information retrievalDigital data processing detailsInformation processingAdaptive filter
A method, program and information processing system filters and secures data (security sensitive words-characters-data objects) in a source document. The adaptive filter uses a compilation of additional data (typically networked) and identifies the sensitive words / objects in the compilation of additional data, and retrieves contextual, semiotic and taxonomic words / objects from the compilation related to the sensitive words / objects. The resulting compiled filter is used to extract sensitive words / objects and retrieved data (words / objects) from the source document to obtain extracted data and remainder data therefrom. Contextual words, related to the security sensitive words / objects, are based upon statistical analysis of the additional data compilation. Semiotic words related words are synonyms, antonyms, and pseudonyms, syntactics relative to the target words and retrieved words, and pragmatics relative to the sensitive words and retrieved words.
Owner:DIGITAL DOORS
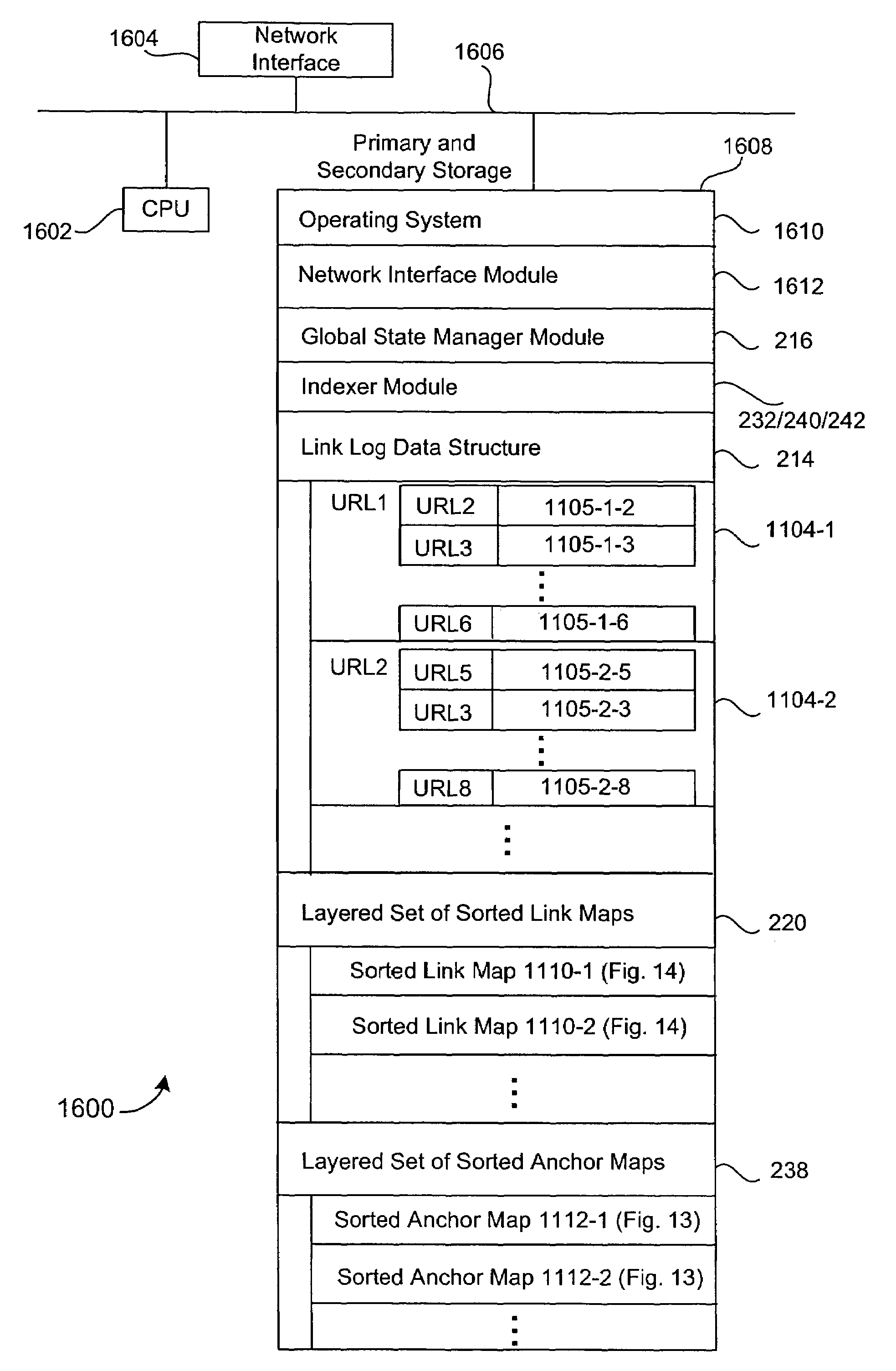
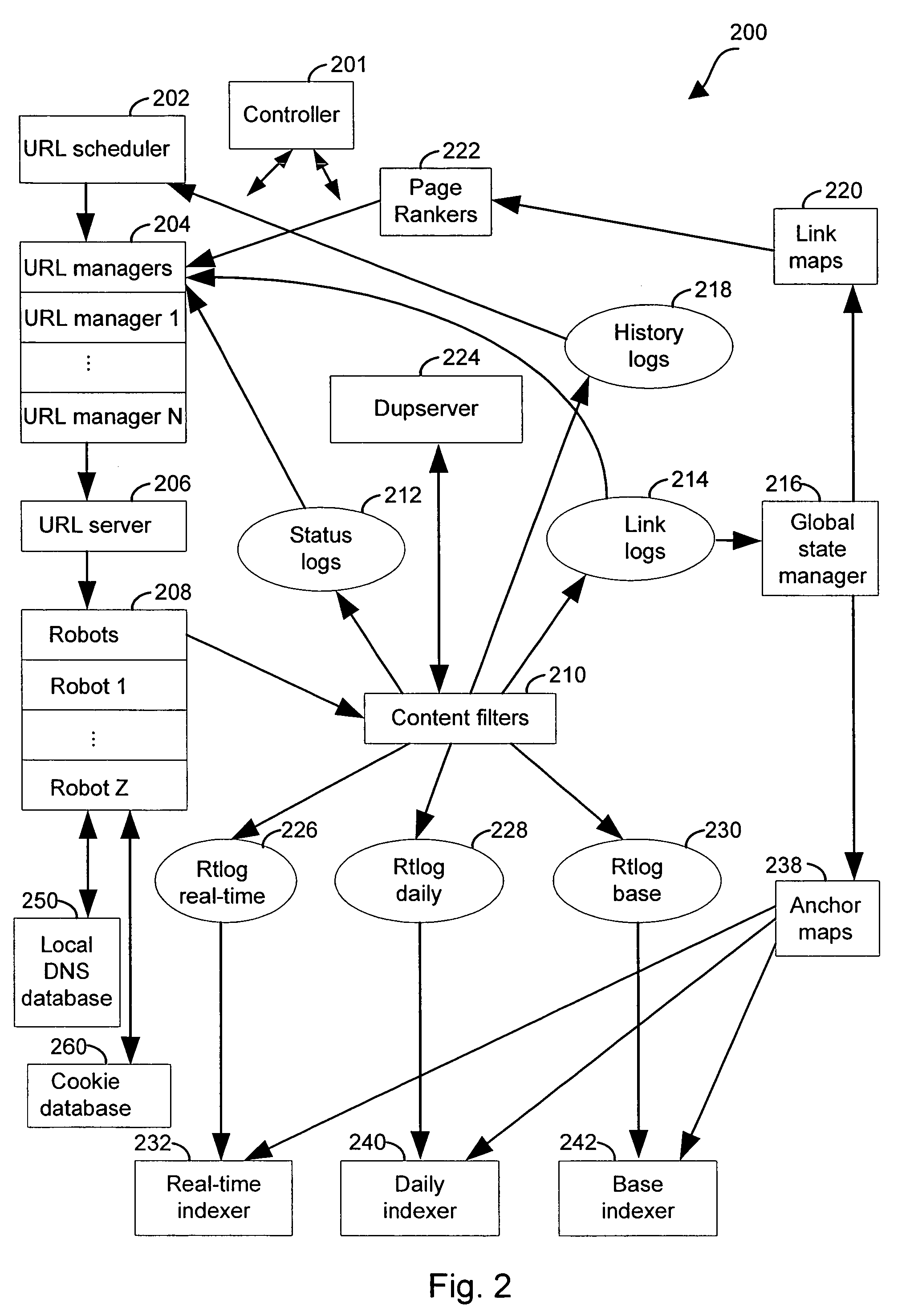
Anchor tag indexing in a web crawler system
ActiveUS7308643B1Facilitates indexing informationEffective and efficient text-based indexing systemWeb data indexingDigital computer detailsDocument IdentifierDocument preparation
Provided is a method and system for indexing documents in a collection of linked documents. A link log, including one or more pairings of source documents and target documents is accessed. A sorted anchor map, containing one or more target document to source document pairings, is generated. The pairings in the sorted anchor map are ordered based on target document identifiers.
Owner:GOOGLE LLC
Data security system and method with multiple independent levels of security
InactiveUS7669051B2Peptide/protein ingredientsNGF/TNF-superfamilyInformation processingSecurity guard
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC (or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
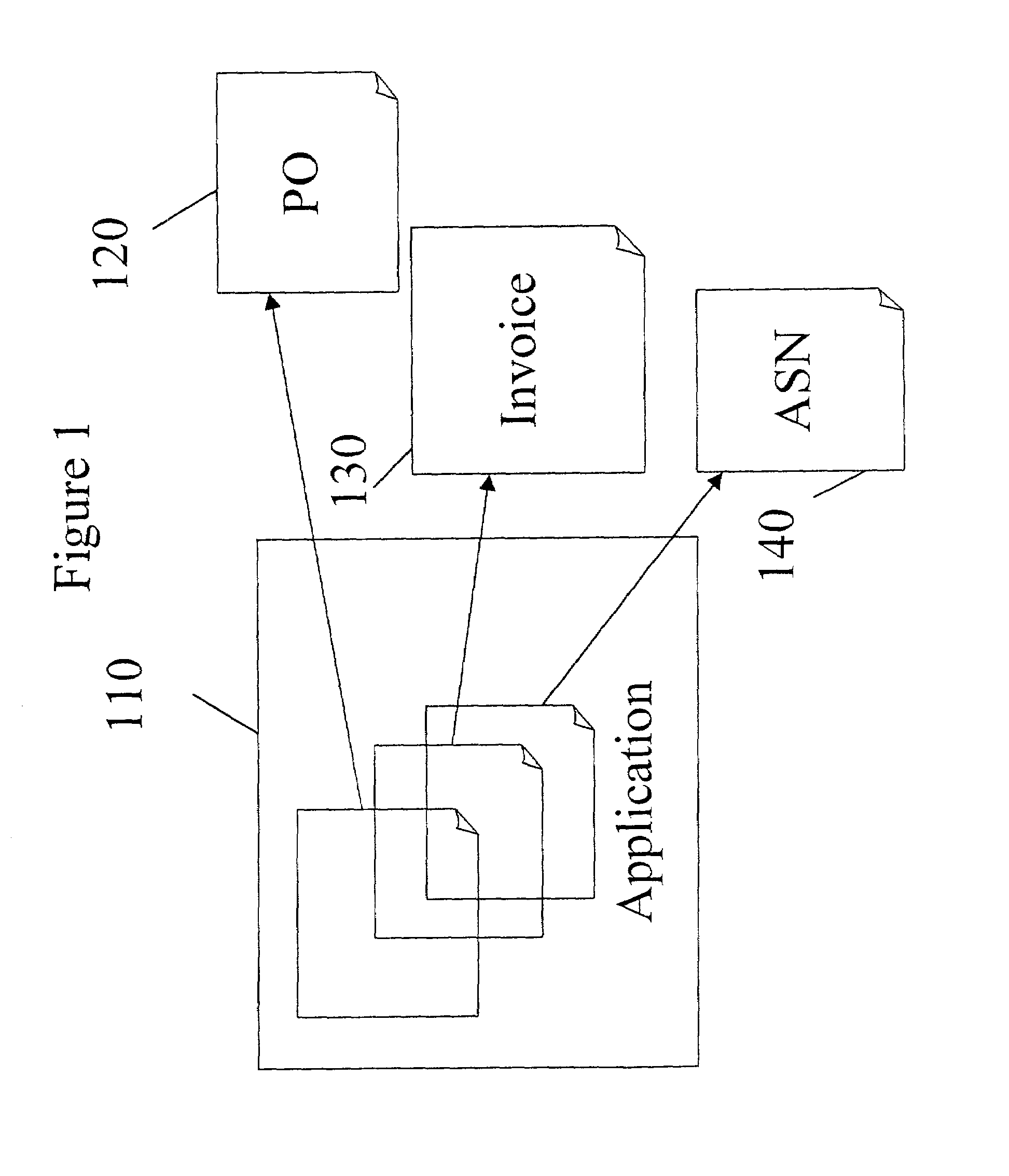
Document/message management
A computer implemented method, apparatus and software for automatically transforming data between Electronic Data Interchange (EDI) formats. For generating EDI documents or messages, a source data model with EDI related data is received. Data is transferred from metadata elements of the source data model to variables of a virtual document, based on a mapping that has been previously made. Data assigned to the variables of the virtual document are then transferred to metadata elements of a target data model. An EDI document or message corresponding to the target data model is automatically created as a result, which includes data from the source document or message.
Owner:FOOTHILL CAPITAL A CA +1
Expanding web documents by merging with linked documents
InactiveUS6016494AData processing applicationsDigital data processing detailsData processing systemDocument preparation
A method of accessing electronic information, by loading an original document onto a data processing system, selecting a link embedded in the original document (wherein the link is associated with a linked document), and creating a new document by merging the linked document with the original document. Other new documents can similarly be created by merging additional linked documents with the earlier new documents in response to the further selection of other links embedded in the new documents. The original document and one or more linked documents can thus be displayed as a single, unitary file, as well as being printed as a single document. The linked document can be merged with the original document in a variety of manners. The invention is particularly useful in accessing hypertext pages on the World Wide Web of the Internet.
Owner:IBM CORP
XML patterns language
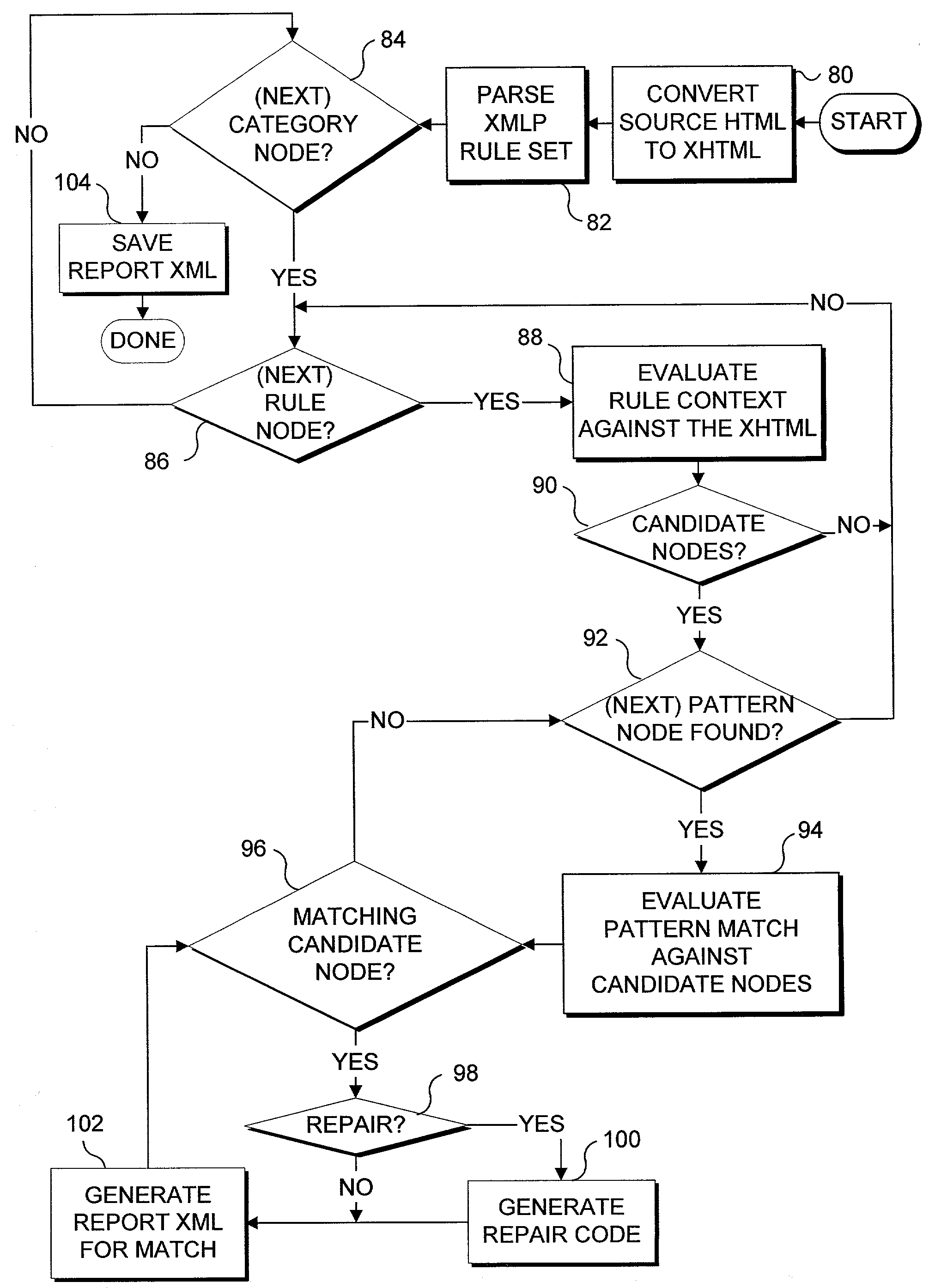
InactiveUS7240279B1Digital data processing detailsNatural language data processingGuidelinePattern matching
Evaluating a source document for compliance with a rule set that represents contextual guidelines to which the source document must conform. The rule set comprises a rule node that includes a context that is compared to the source document to identify candidate nodes for further evaluation. Each rule node also includes a descendant pattern node that includes a pattern matching expression representing at least one aspect of the contextual guidelines to which the source document must conform. Preferably a match between a candidate node and the pattern matching expression indicates a nonconformance to the contextual guideline(s), and a predefined action is initiated. Predefined actions include reporting the nonconformance, and automatically repairing the nonconformance through script code.
Owner:MICROSOFT TECH LICENSING LLC
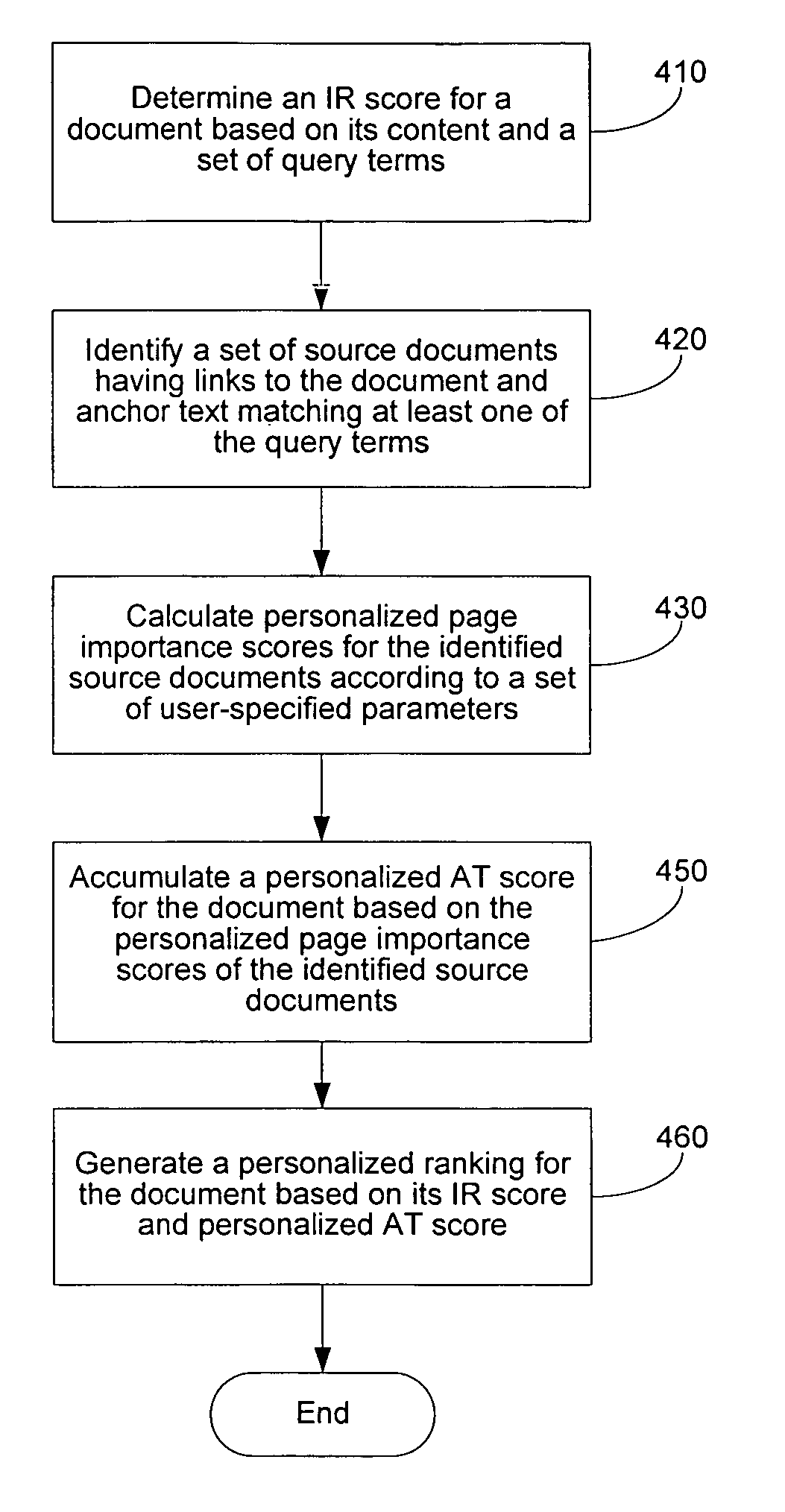
Personalizing anchor text scores in a search engine
A search engine identifies a list of documents from a set of documents in a database in response to a set of query terms. For each document in the list, the search engine determines an information retrieval score based on its content and the query terms, and also identifies a set of source documents that have links to the document and that also have anchor text satisfying a predefined requirement with respect to the query terms. The search engine calculates a personalized page importance score for each of the identified source documents according to a set of user-specific parameters and accumulates the personalized page importance scores to produce a personalized anchor text score for the document. The personalized anchor text score is then combined with the document's information retrieval score to generate a personalized ranking for the document. The documents are ordered according to their respective personalized rankings.
Owner:GOOGLE LLC
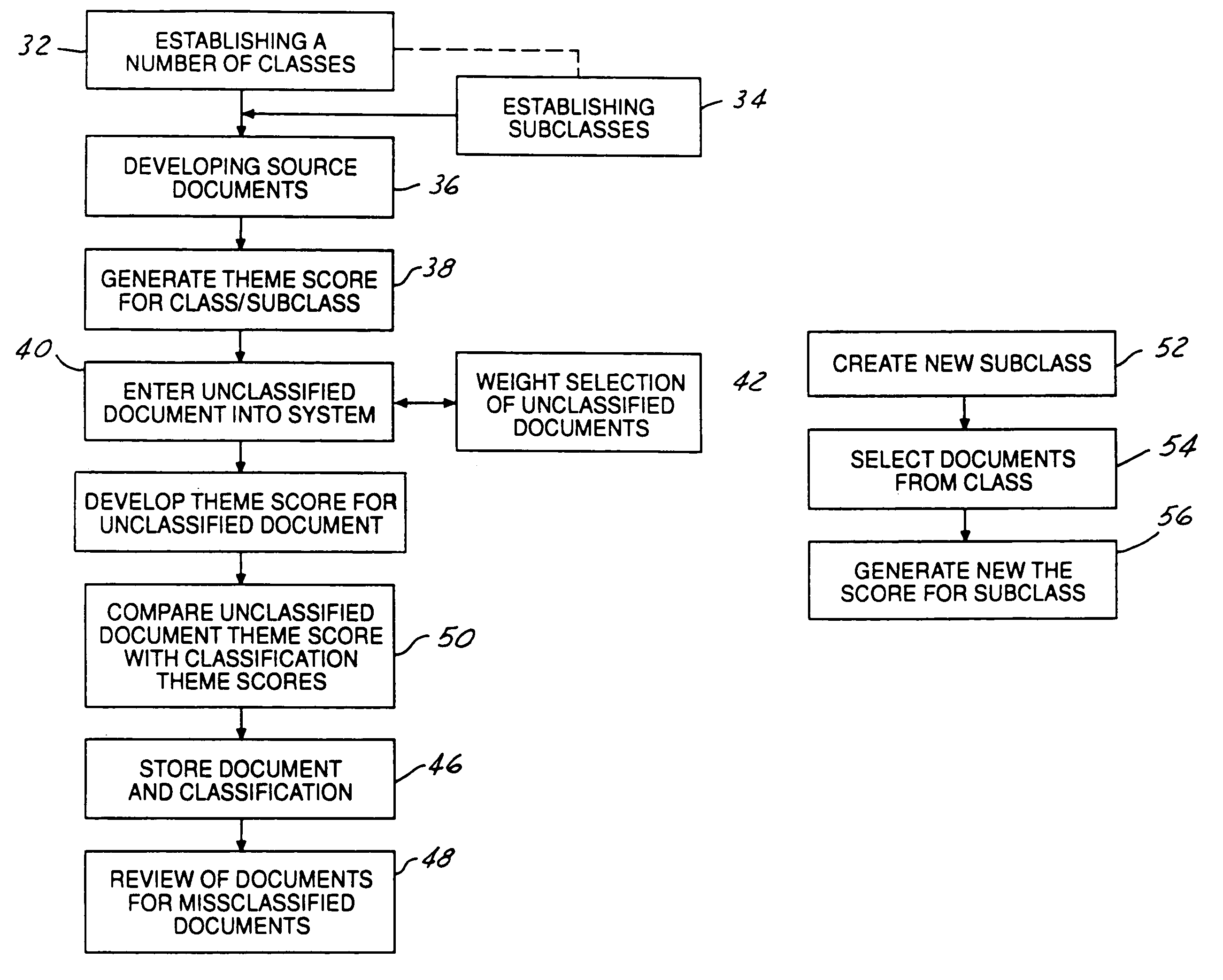
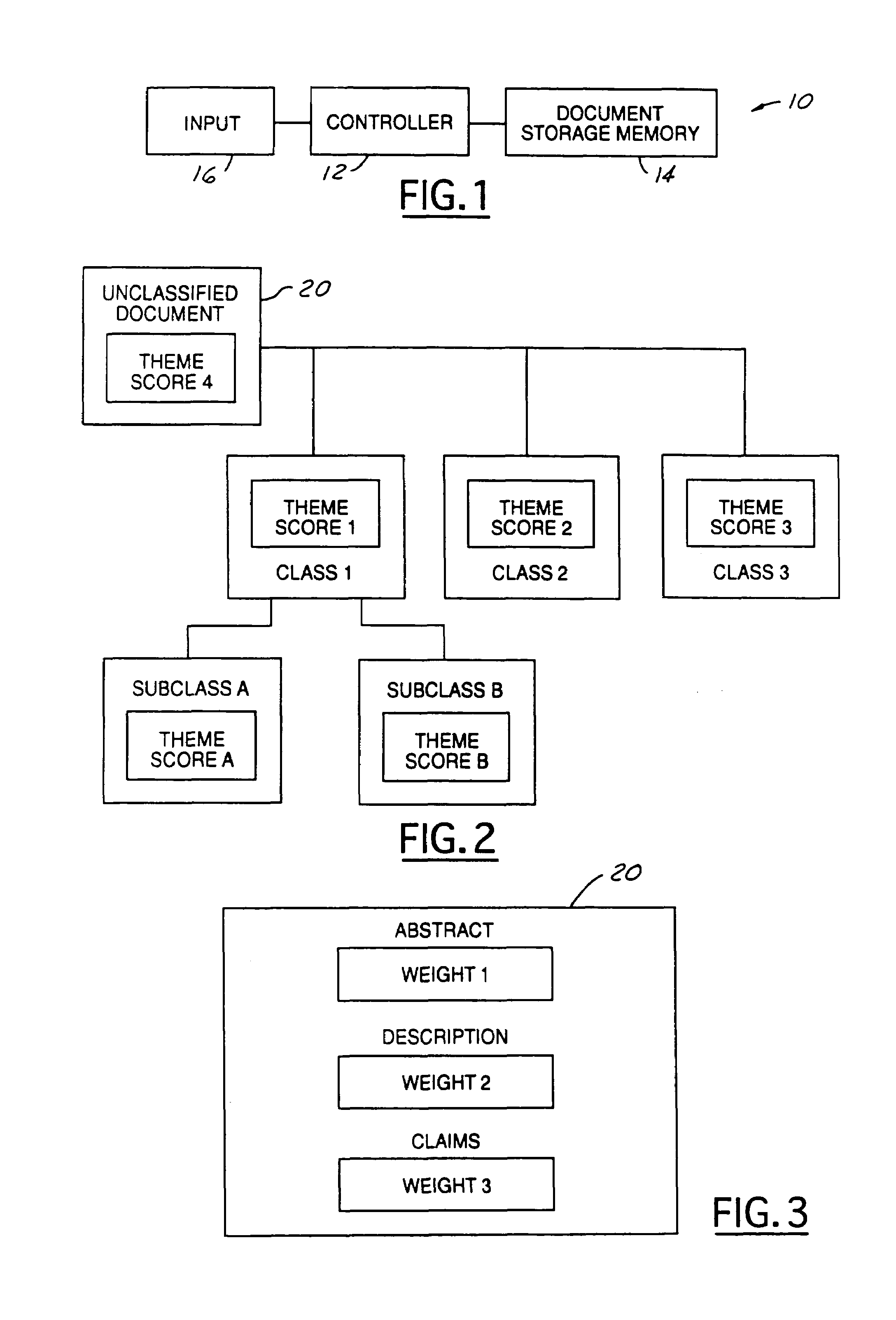
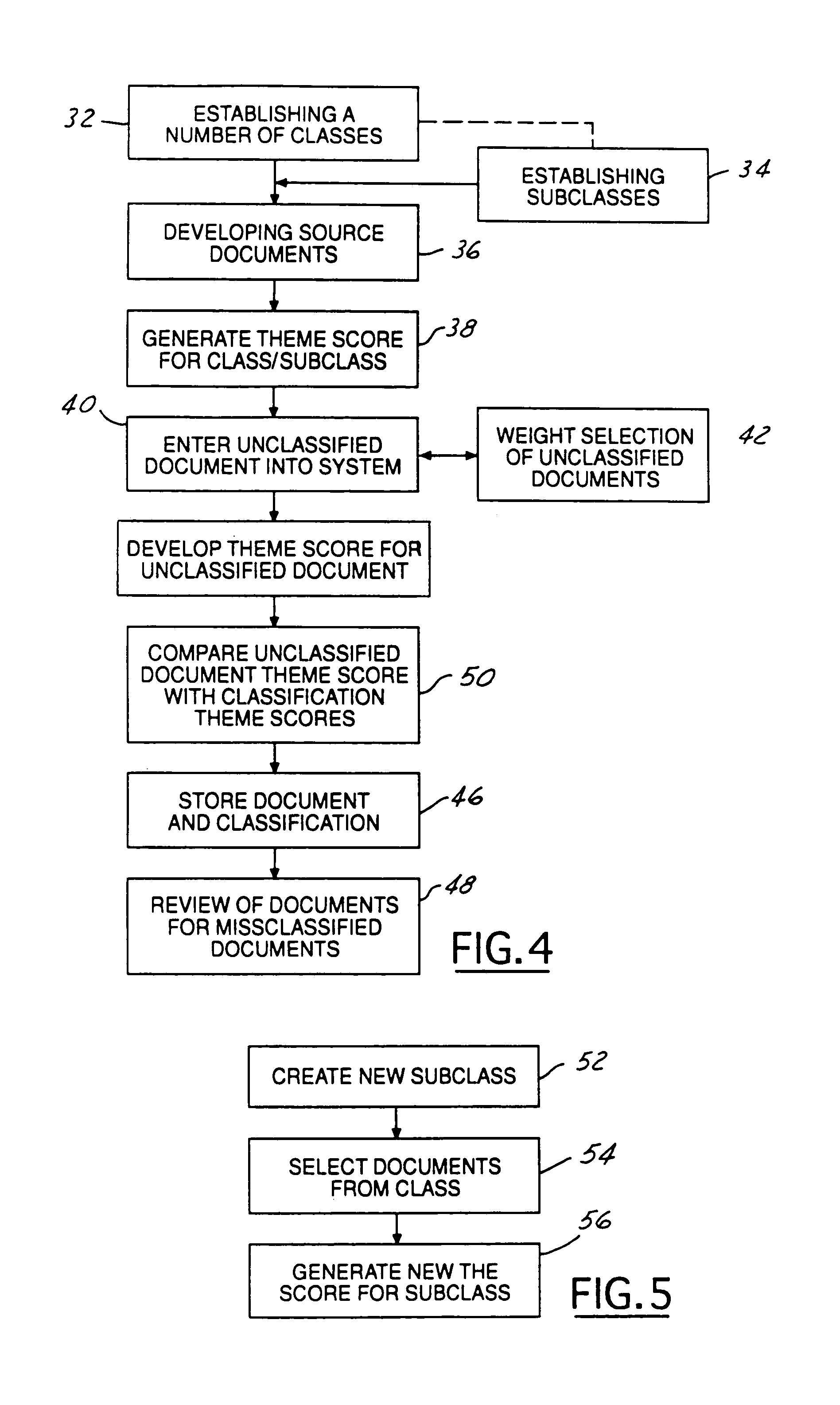
Theme-based system and method for classifying documents
InactiveUS7376635B1Data processing applicationsDigital data information retrievalDocumentationDocument classification
A classification system (10) having a controller (12), a document storage memory (14), and a document input (16) is used to classify documents (20). The controller (12) is programmed to generate a theme score from a plurality of source documents in a plurality of predefined source documents. A theme score is also generated for the unclassified document. The unclassified document theme score and the theme scores for the various classes are compared and the unclassified document is classified into the classification having the nearest theme score.
Owner:FORD GLOBAL TECH LLC
Web based data collaboration tool
A web based data collaboration tool includes a dynamic international collaborative environment in which system partners, including customers, technology partners and suppliers, can exchange information between one another in a truly collaborative environment. The web based data collaboration tool includes unique “fine grain” security at both the document and sub-document level. This allows one source document to be shared between the system partners, including partners from different companies and those located in different countries, based upon an individual document / sub-document security profile. Further, the web based data collaboration tool includes a secure “Sandbox” for peer-to-peer sharing of sensitive documents and electronically incorporates a business area export representative (BAER) approval process that includes the required retention of International Traffic in Arms Regulations (ITAR) documents making the web based data collaboration tool fully ITAR compliant.
Owner:UNITED TECH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com