Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
386 results about "Security guard" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
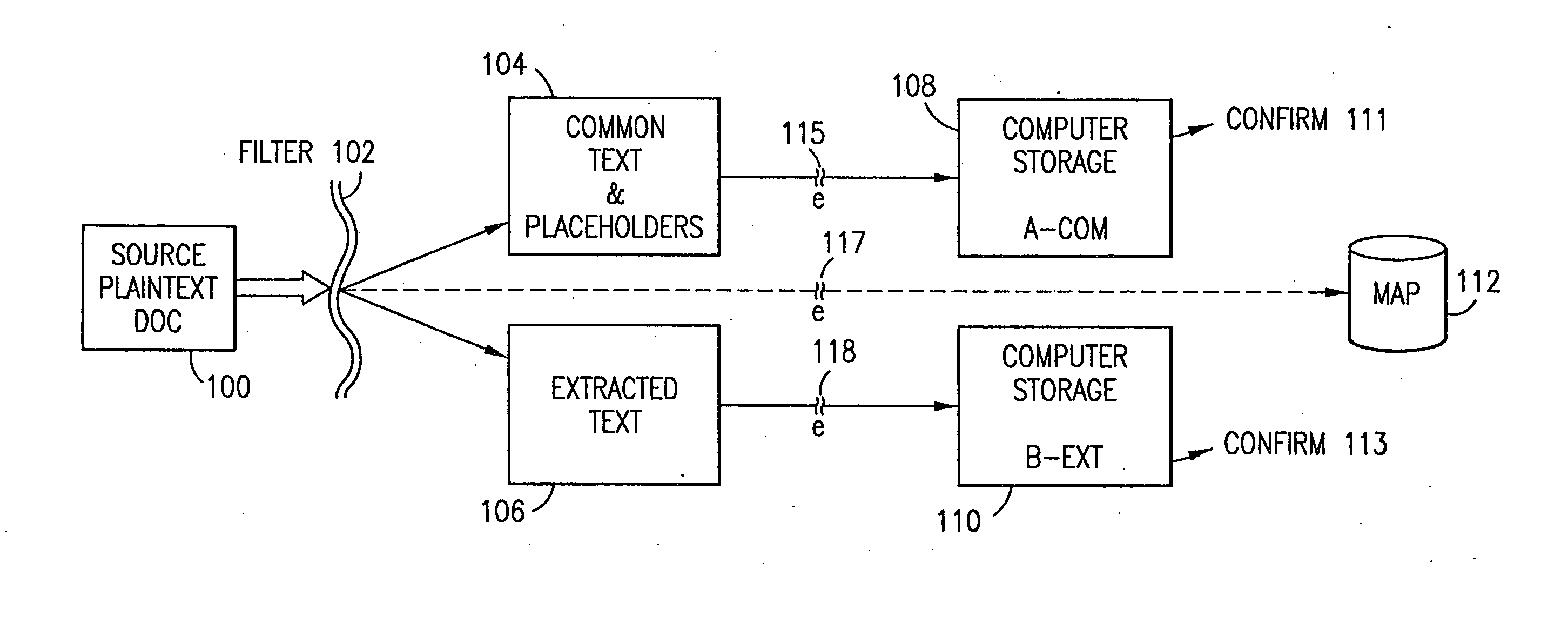
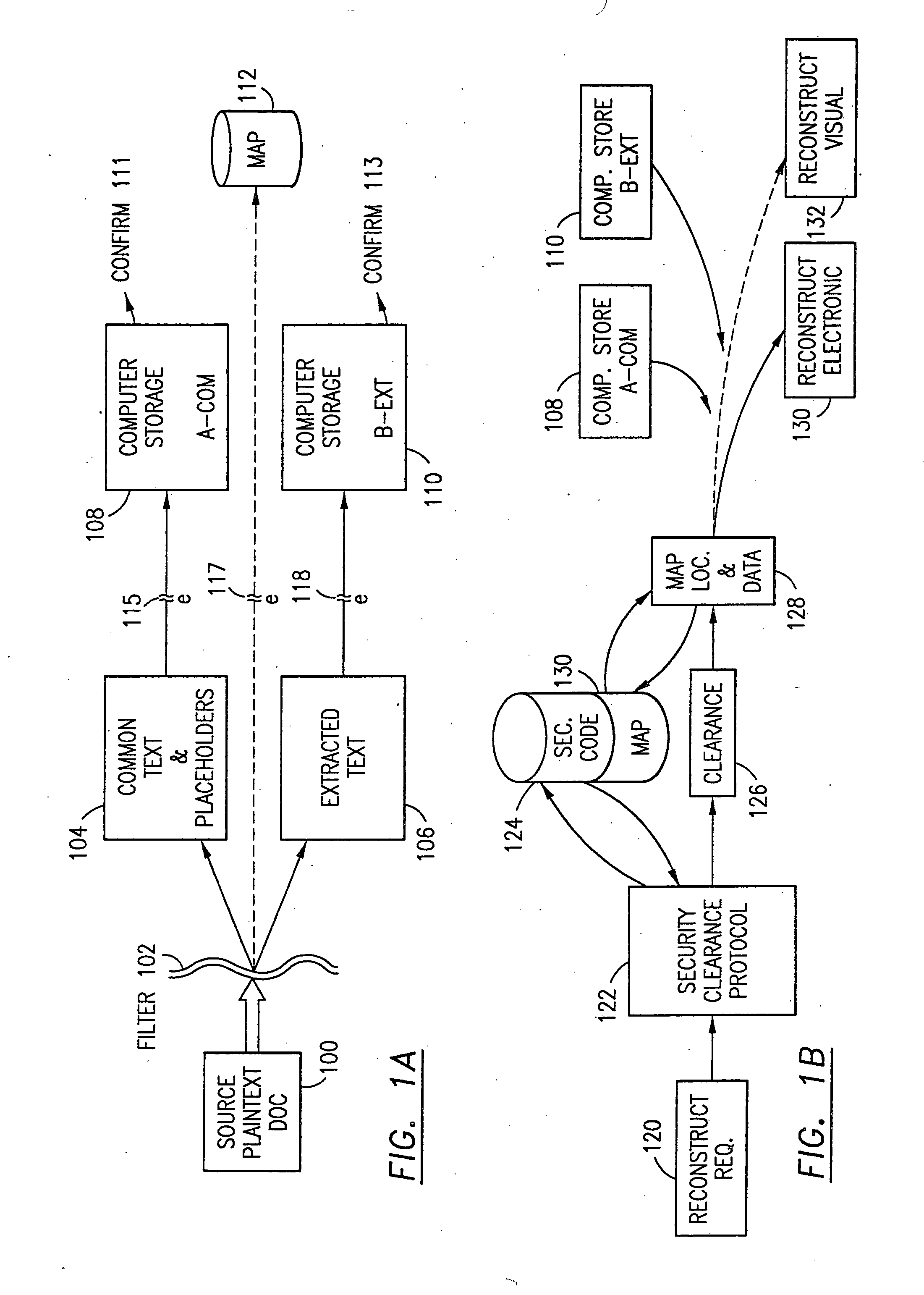
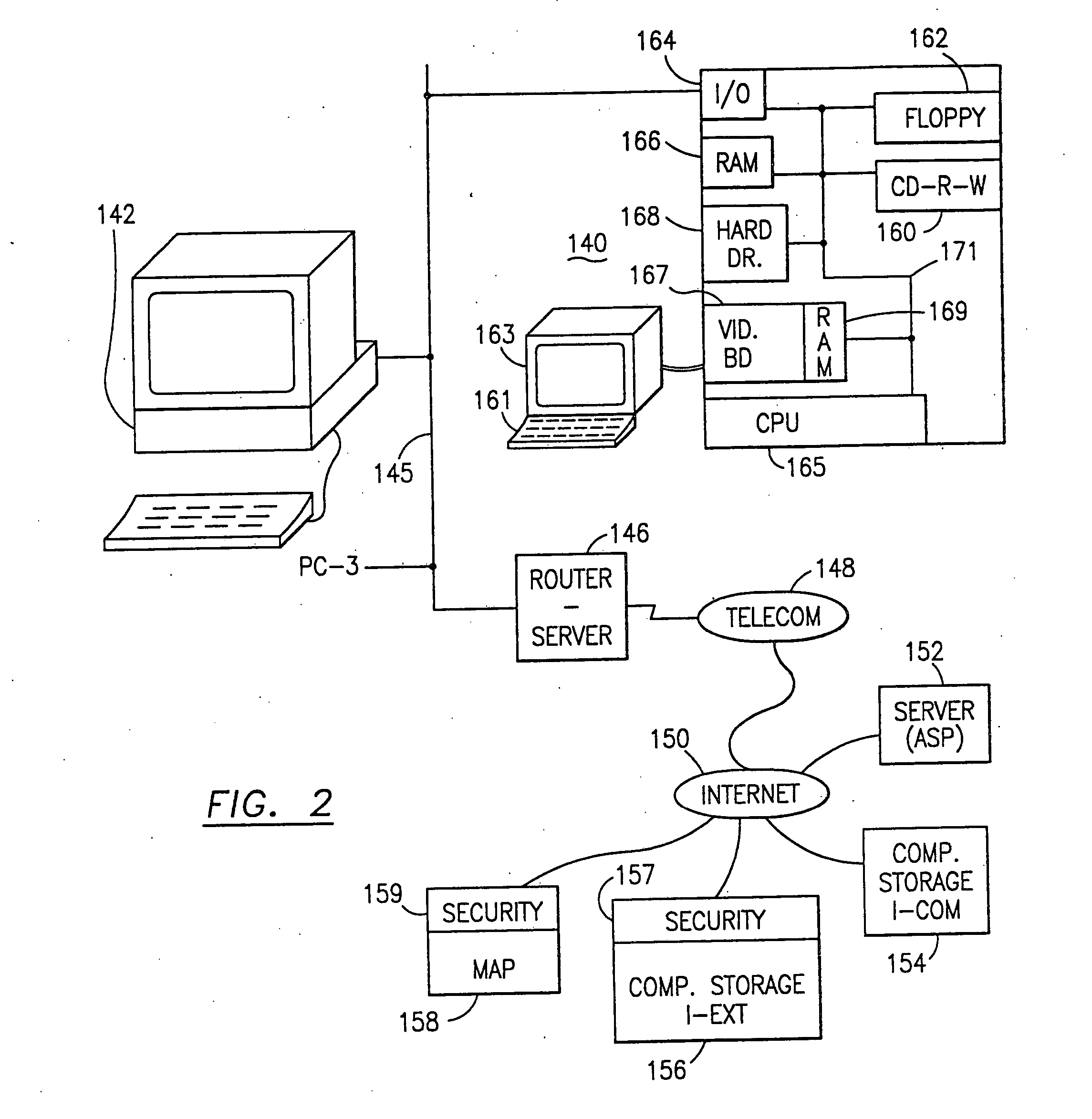
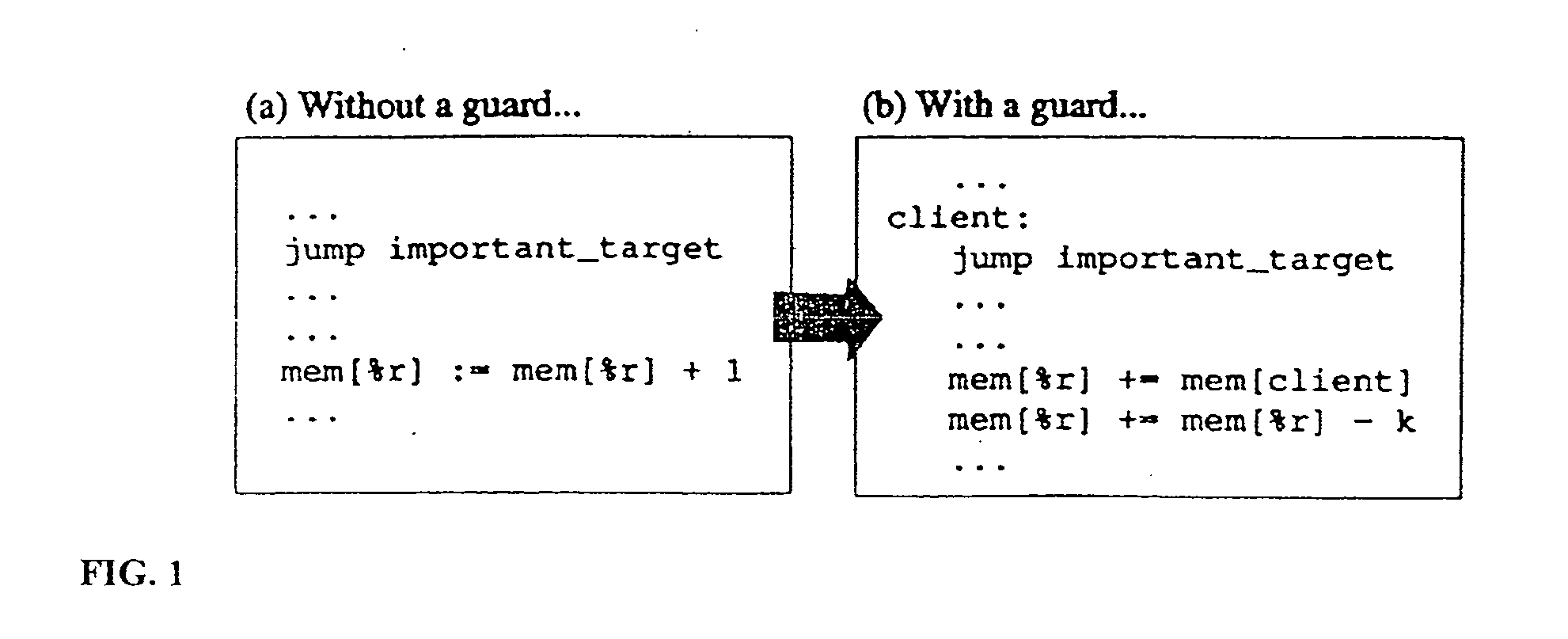
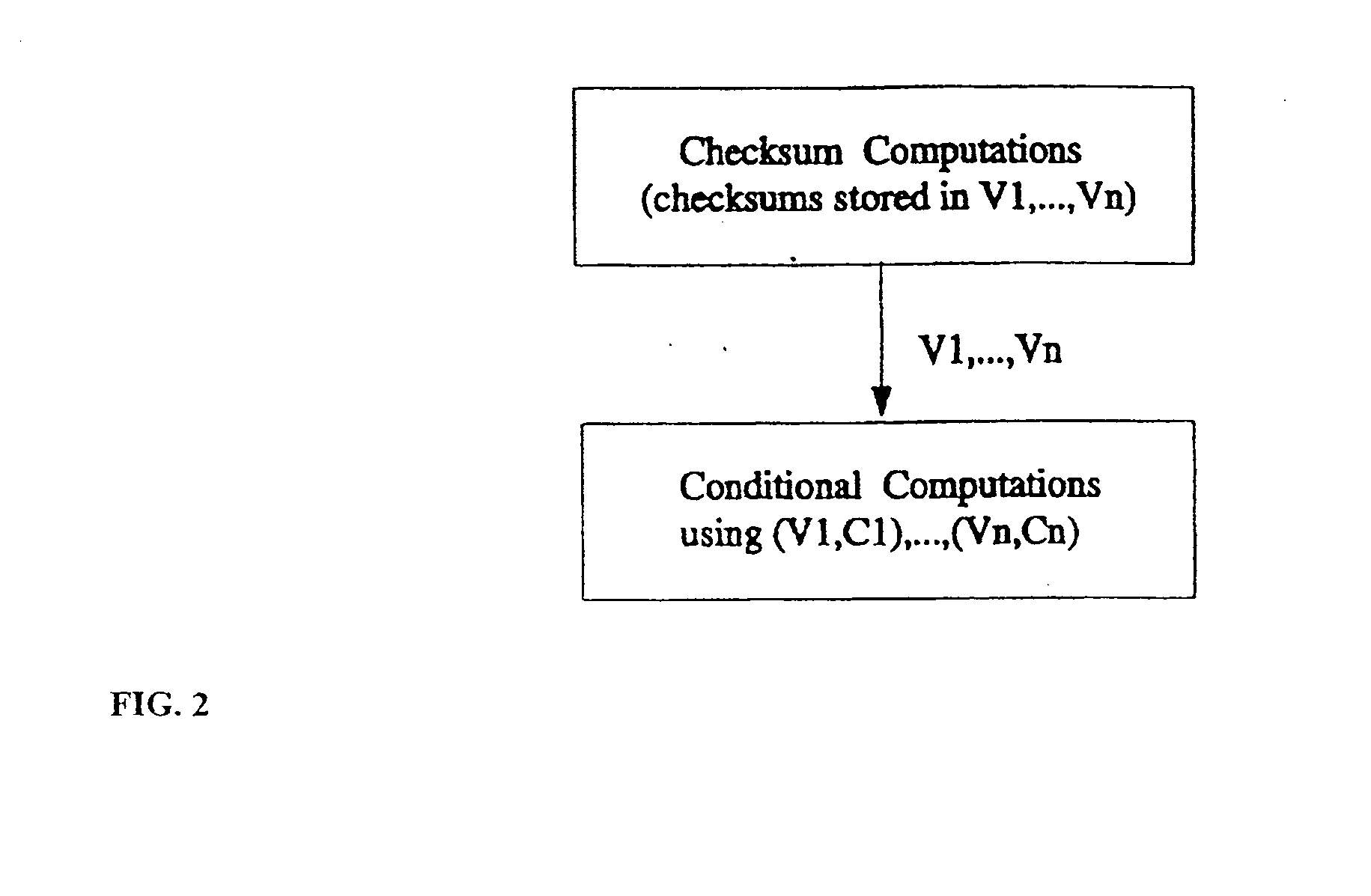
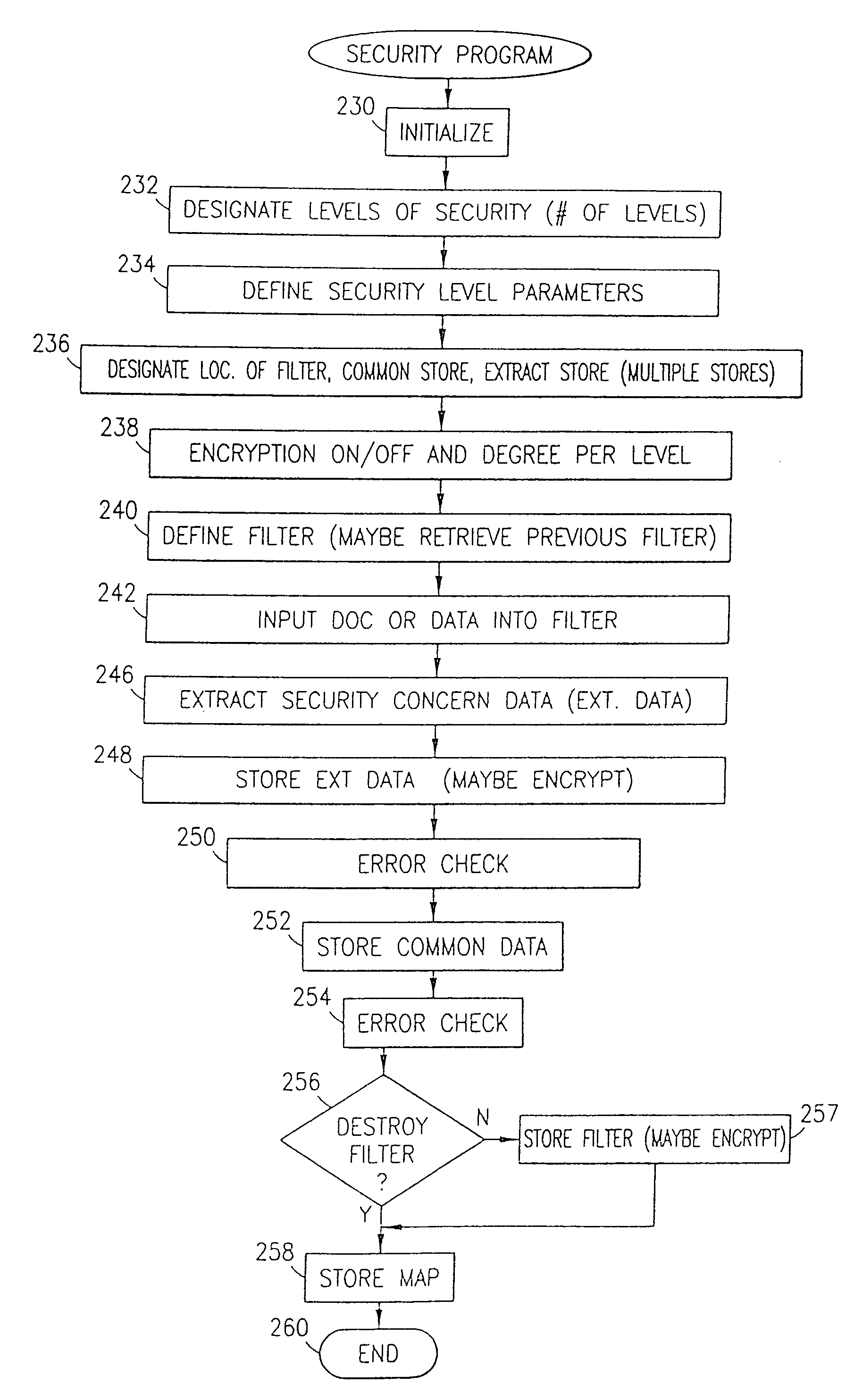
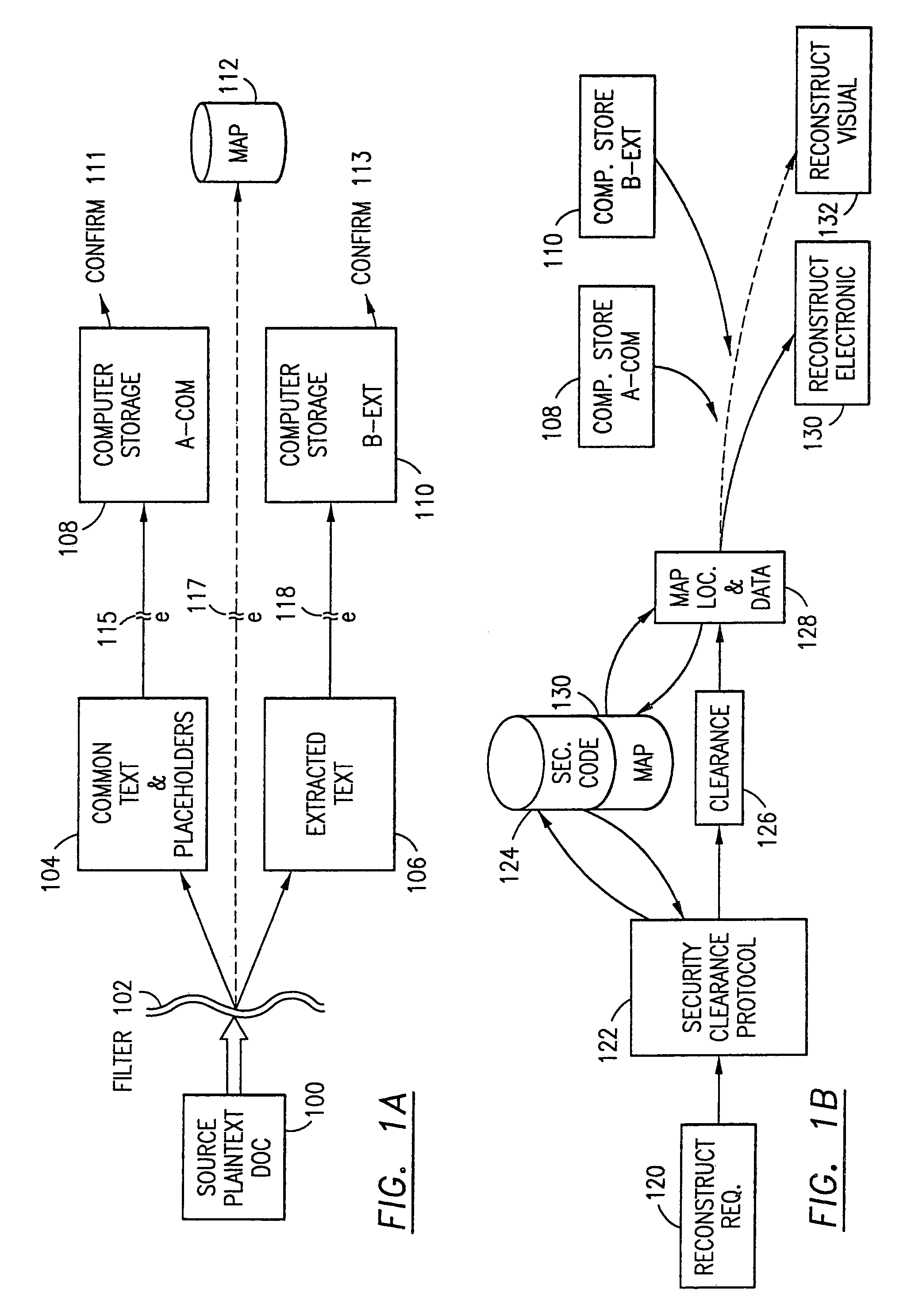
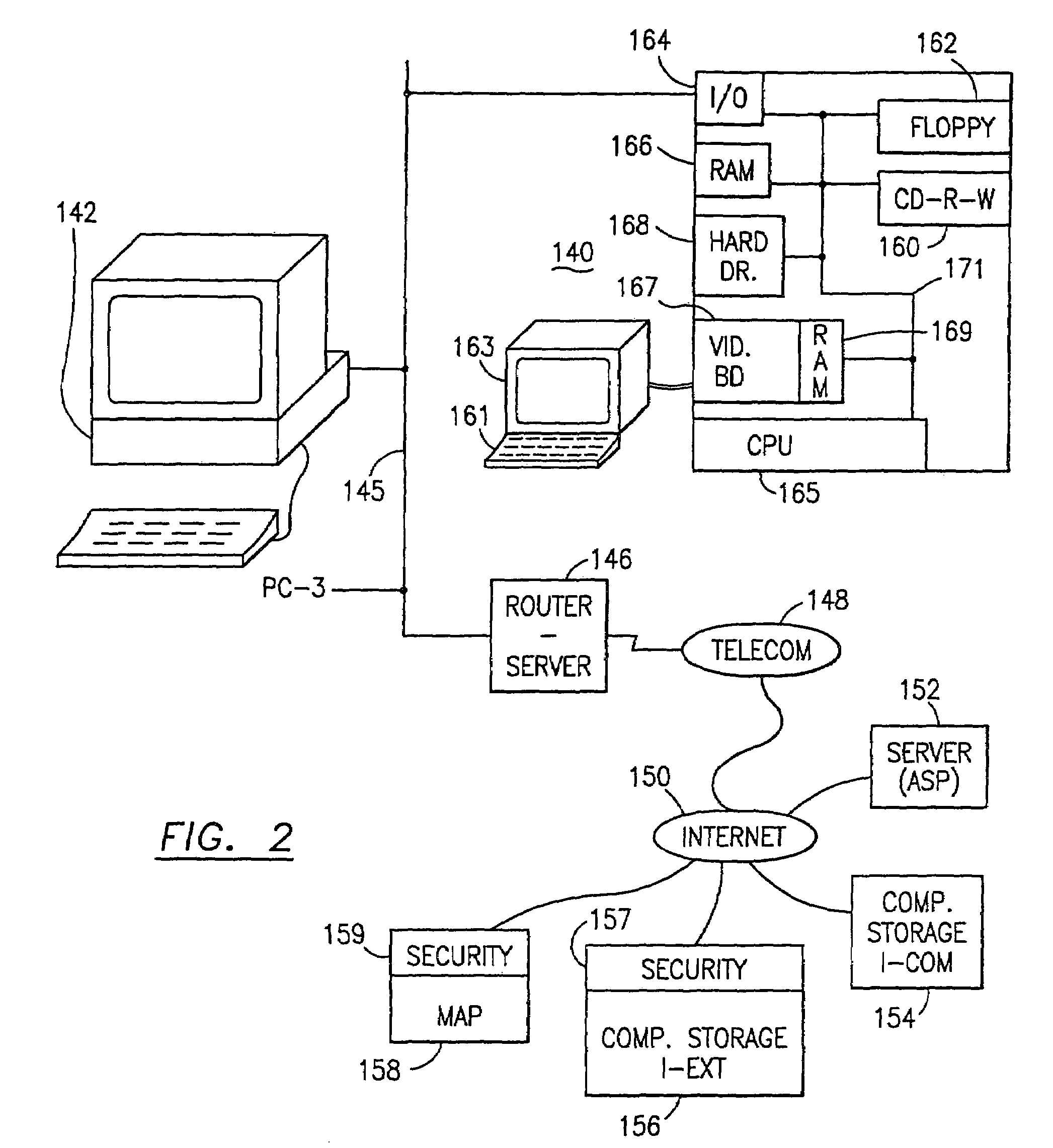
Data security system and method with multiple independent levels of security
InactiveUS20050138110A1Ease overhead performanceHigh overhead performancePeptide/protein ingredientsNGF/TNF-superfamilyInformation processingWorkstation
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC(or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
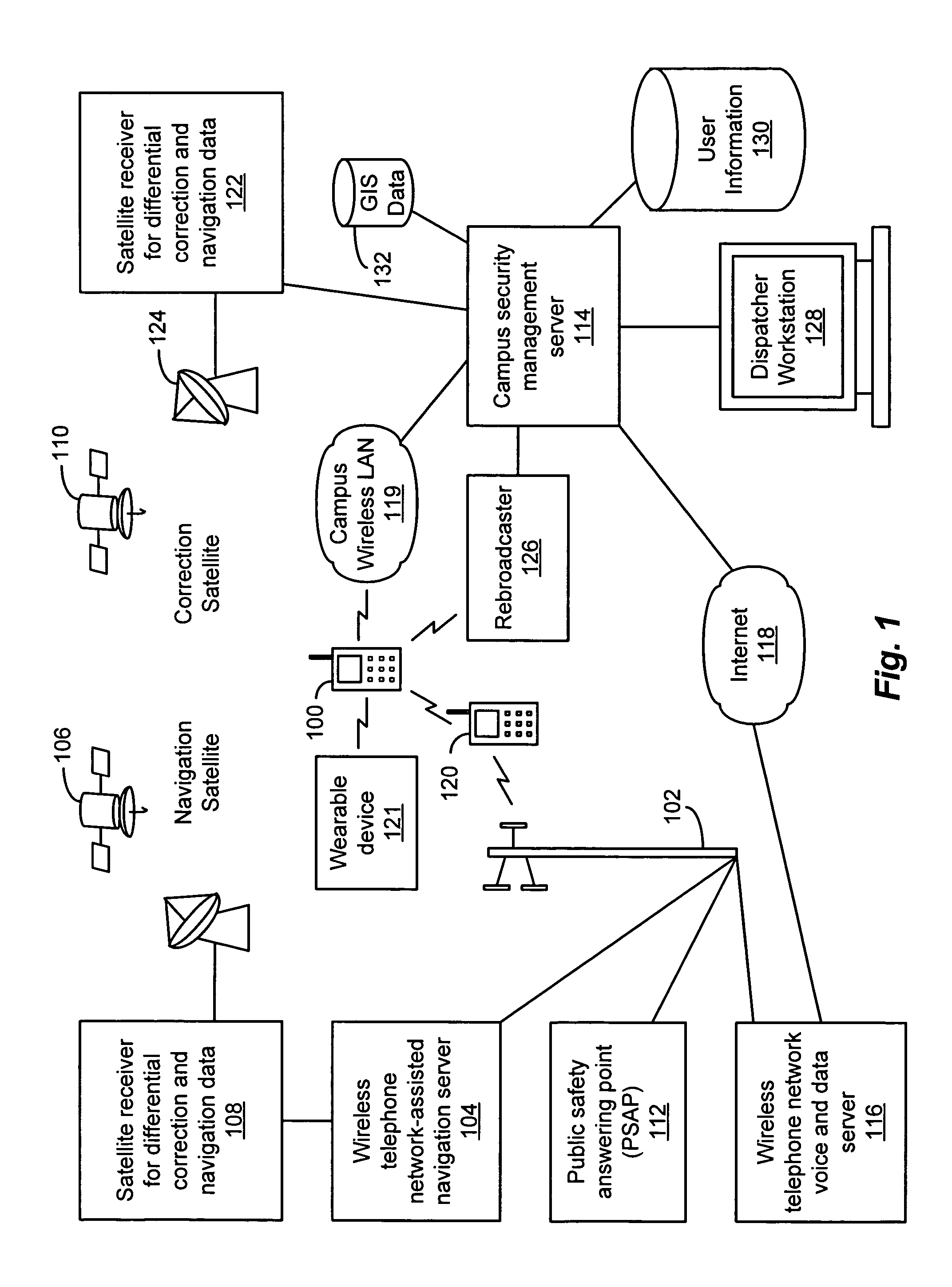
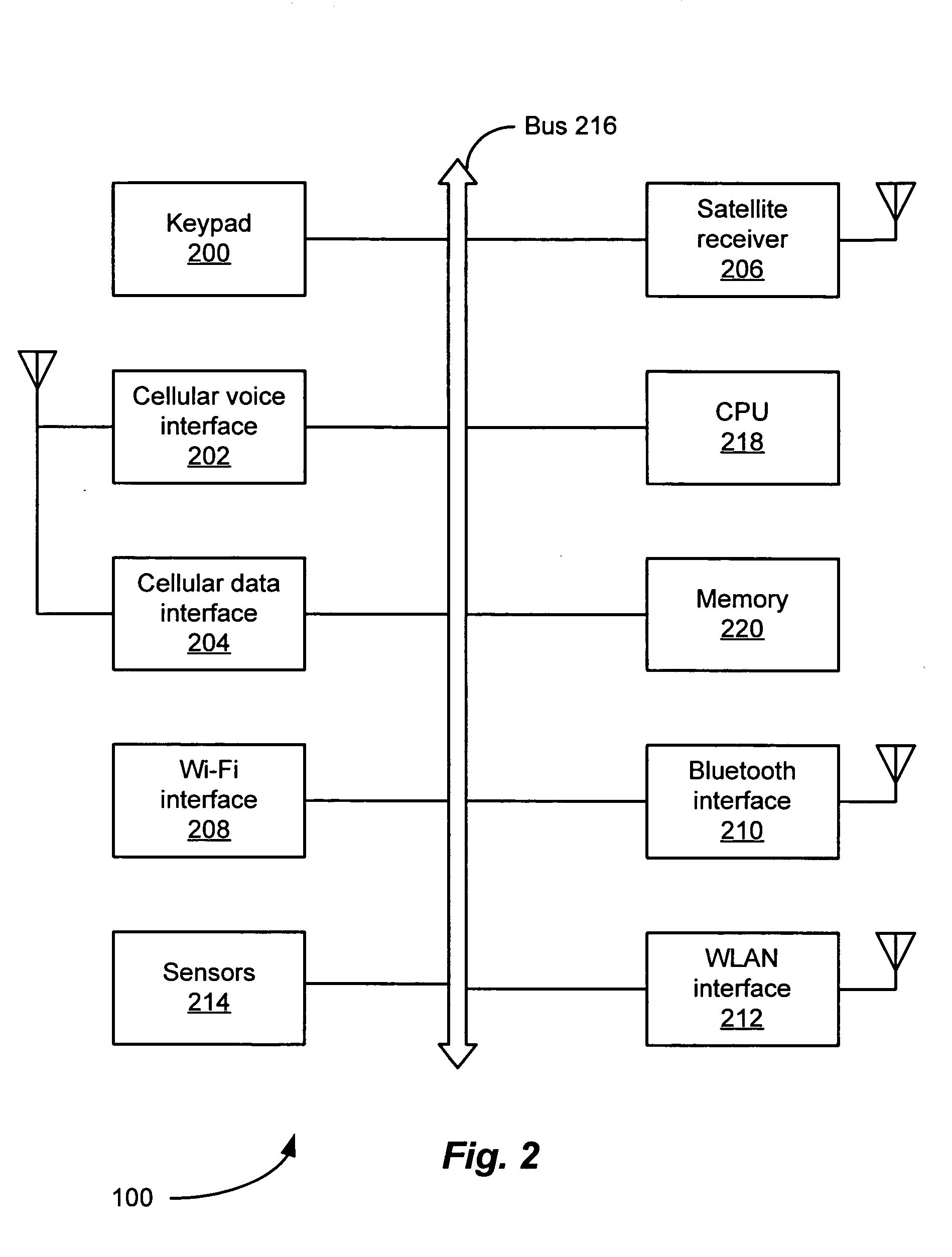
Wireless virtual campus escort system
InactiveUS20050075116A1Bioelectric signal measurementNavigational calculation instrumentsVirtual campusSecurity guard
Owner:AMERICAN TRAFFIC SOLUTIONS
System and method for security protection, inventory tracking and automated shopping cart checkout
The three major problems of retail / wholesale industry, i.e. Security, Inventory, Self CheckOut (SISCO) are achieved by “virtual salesperson” and provided by synergism techniques of 5W's (Weight, Who, What, Where and When). A system that includes combination of steps and / or means for uniquely identifying each and every product (UPC / USID indicium), at a vendor retail premises; steps and / or means for protecting the product / property (brain-like recognition); steps and / or means for detecting / registering a product at a vendor retail premises that has been taken from its storage or display location; steps and / or means for registering that the product has been put into a customer's shopping cart; steps and / or means for tracking customer's location with a unique ID tagging wireless device to a shopping cart; steps and / or means for automatically transacting a purchase of the product, steps and / or means for paying for the product at the vicinity of the products location with laptop / net computers at both ends of exit aisle and / or more computers at convenient places with attached scanner and card payment device; steps and / or means for notifying the customer to pay if the product has not been properly or timely paid for; any missed / unwanted items will be accounted for at reduced manned checkout stations, to received itemized purchases receipt and to sign signature, and steps and / or means for customer ID checking in and checking out by “security guard” wirelessly scans customer's receipt for inventory / security tracking.
Owner:RCL PRODS
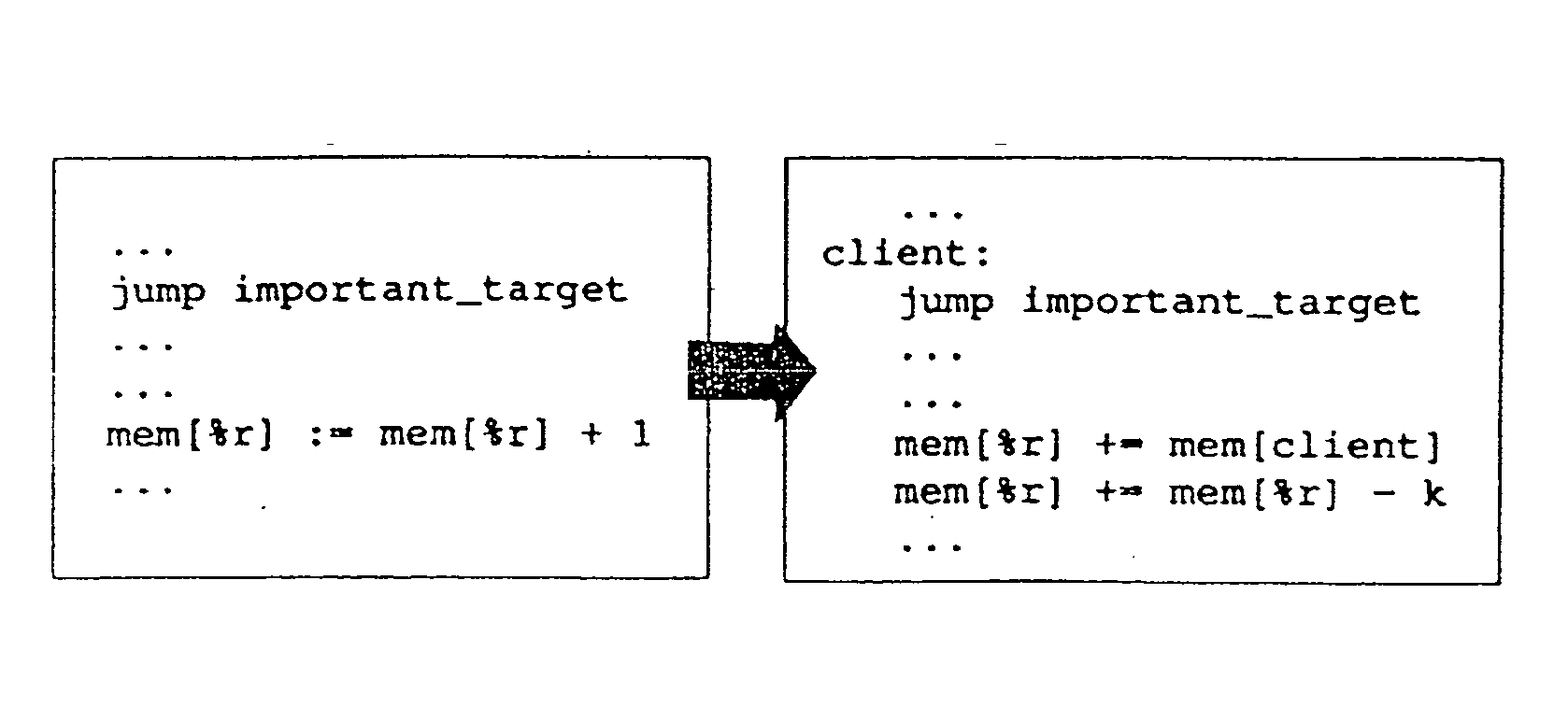
Method and system for tamperproofing software
InactiveUS20060031686A1User identity/authority verificationUnauthorized memory use protectionCoding blockObfuscation
Method of protecting host application code comprising a plurality of code blocks. The method includes steps of preprocessing the host application code; obfuscating the host application code; installing guards in the host application code to protect client blocks; randomly rearranging the code blocks of the host application code; linking the rearranged host application code with other resources to produce a binary executable image; and patching the binary executable image with data values to be used by the guard. The method can be used to install a plurality of guards to form a distributed network of guards that cooperatively protect the host application code and the other guards in the network. The installation of the guards can be performed automatically using a guard formation graph; and guard formation graph customization parameters. The obfuscation step can include control flow graph merging, cloning, and data-aliasing.
Owner:PURDUE RES FOUND INC
Data security system and method with multiple independent levels of security
InactiveUS7669051B2Peptide/protein ingredientsNGF/TNF-superfamilyInformation processingSecurity guard
The method, program and information processing system secures data, and particularly security sensitive words, characters or data objects in the data, in a computer system with multiple independent levels of security (MILS). Each level of MILS has a computer sub-network with networked workstations. The MILS sub-networks are connected together via security guard computer(s) and each guard computer has separate memories for each level (TS, S, C, UC (or remainder)). The method extracts the security sensitive words / data (a granular action), from the source document for each MILS level, stores the extracted data in a corresponding extract store for each level and permits reconstruction / reassembly of the dispersed data via said extracted data at each said level of said multiple security levels and remainder data only in the presence of a predetermined security clearance commensurate with each MILS level.
Owner:DIGITAL DOORS
Thin client user interface for gaming systems
InactiveUS20060084502A1Easy accessApparatus for meter-controlled dispensingVideo gamesWeb browserDisplay device
An access system enables casino personnel to access casino information from a casino computer through a network accessible display device that contains a web browser. The access system comprises a thin client user interface server. Information provided to the casino computer can be requested from multiple files and provided in customized formats or from among numerous available formats at the request of the casino personnel. The request can be configured and responded to according to such diverse information requests as data / records specific to personnel (e.g., dealers, pit bosses, croupier, security guards, etc.), specific tables, specific games, specific classes of games, pits, wagering limits, shufflers, roulette wheels, and the like, and the requests can define bases of information such as performance, down time, volume, frequency, and individual round events (e.g., hands in cards or spins in roulette or tosses in craps), and the requests can be tailored on casino personnel input to specific time intervals or histories. Special software is not needed at the user side of the thin client user interface to access the database.
Owner:SHUFFLE MASTER
Plant-level comprehensive supervision platform
InactiveCN105187771ARealize centralized managementQuality improvementClosed circuit television systemsTransmissionVideo monitoringIntelligent lighting
The invention relates to a monitoring system and specifically relates to a plant-level comprehensive supervision platform. The plant-level comprehensive supervision platform comprises a front-end system, a transmission network and a master station system, wherein the front-end system is integrated with subsystems of video monitoring, environmental monitoring, security guard, fire alarm, one-card-through, entrance and exit control, maloperation prevention, gps positioning, intelligent lighting, intelligent control and the like in a thermal power plant; the transmission network functions as a bridge for connecting the front end and the platform; the master station system comprises a local monitoring center, a cloud computing system, an application platform and a whole network operation and maintenance platform. The comprehensive supervision platform is a large online monitoring system integrated with hardware, software and network; the platform software is taken as the core to realize centralized management on all zones; besides, centralized monitoring and uniformed management on the front-end system can be realized at a regulation and control center; in short, the plant-level comprehensive supervision platform escorts the smart grid.
Owner:SHANDONG CHUANGDE SOFTWARE TECH
Use of rfid tags and readers to automate real time alert signals in a security system
InactiveUS20060208857A1Safety arrangementElectric signal transmission systemsSecurity guardMobile device
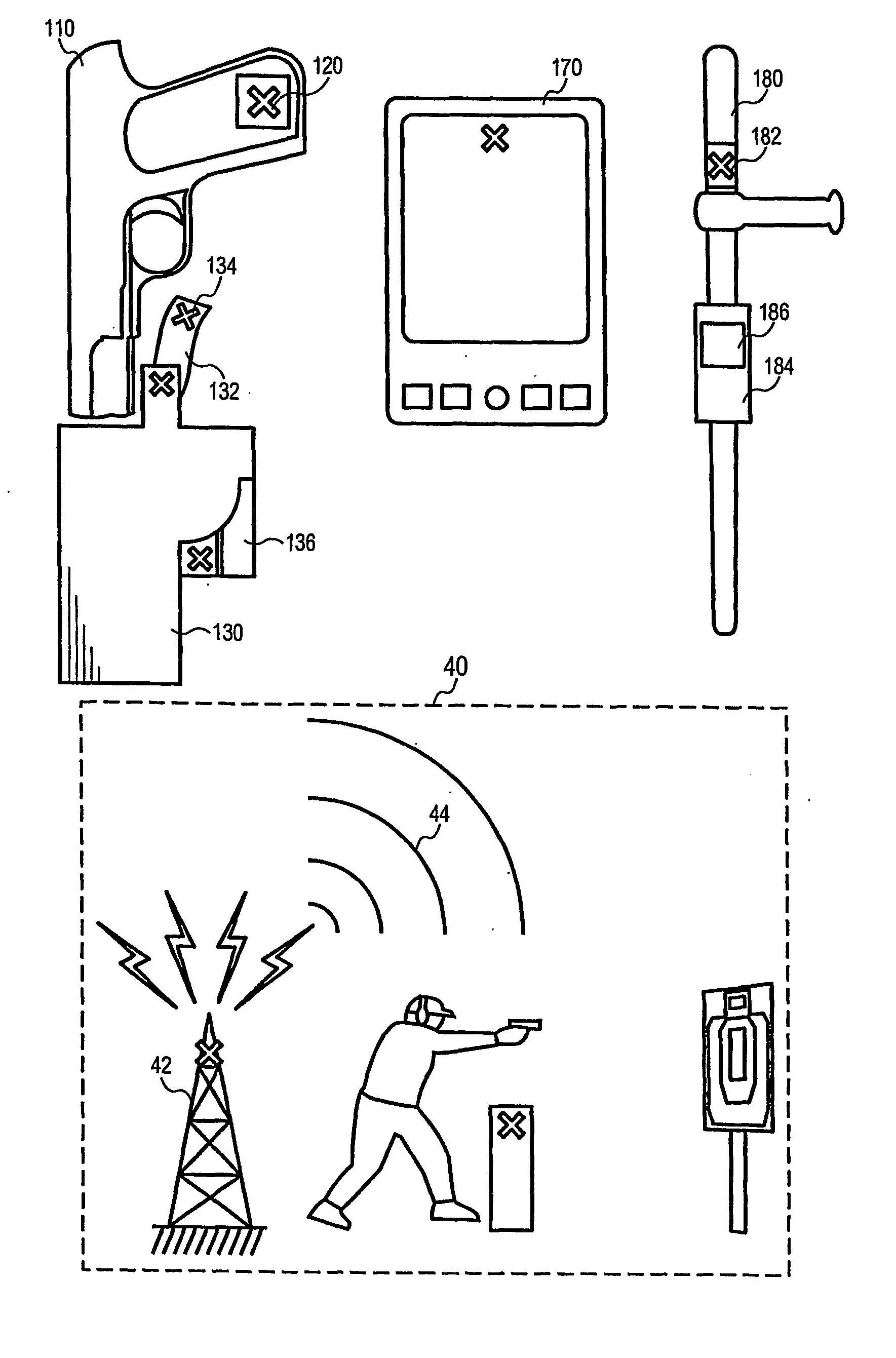
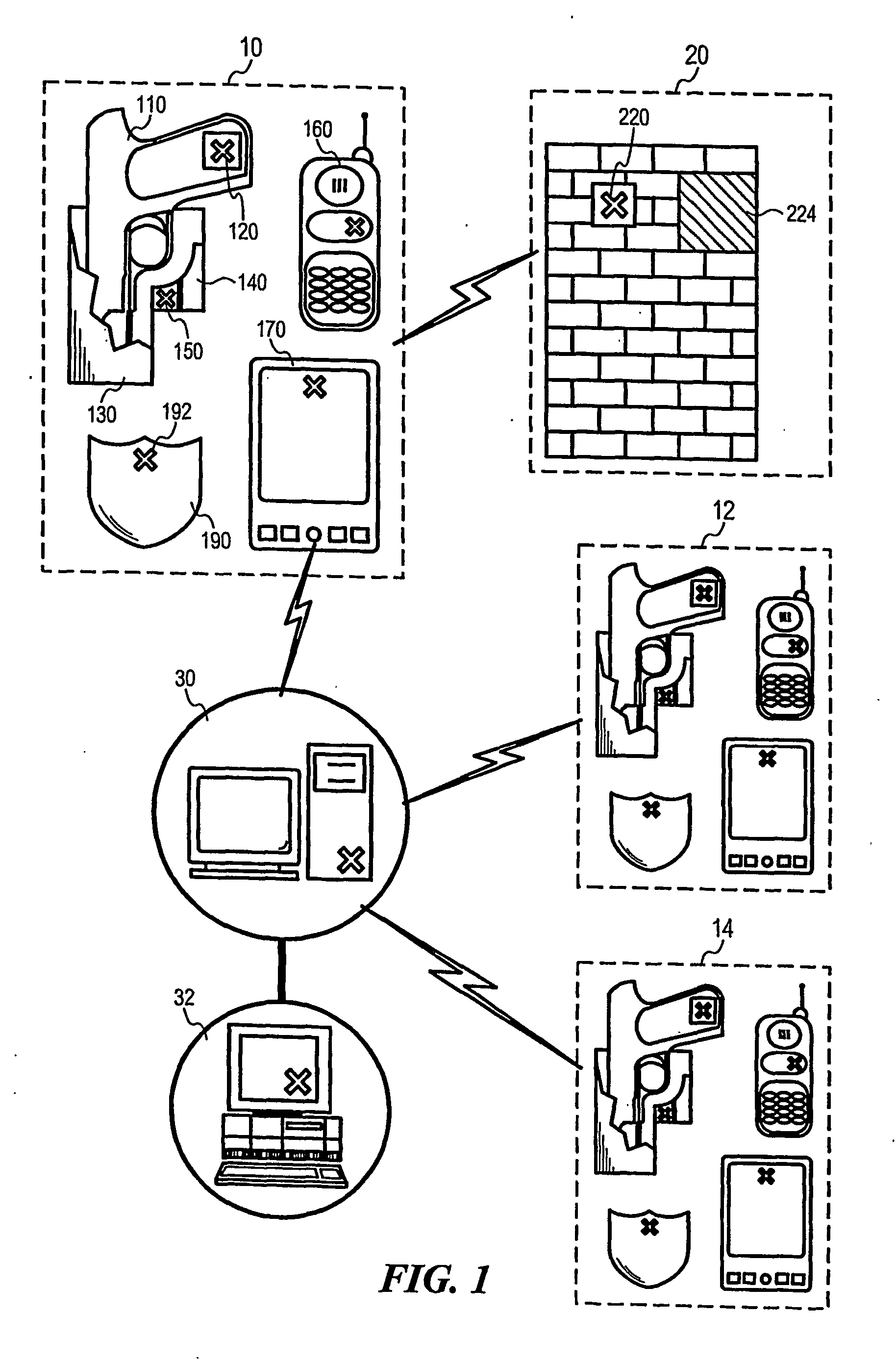
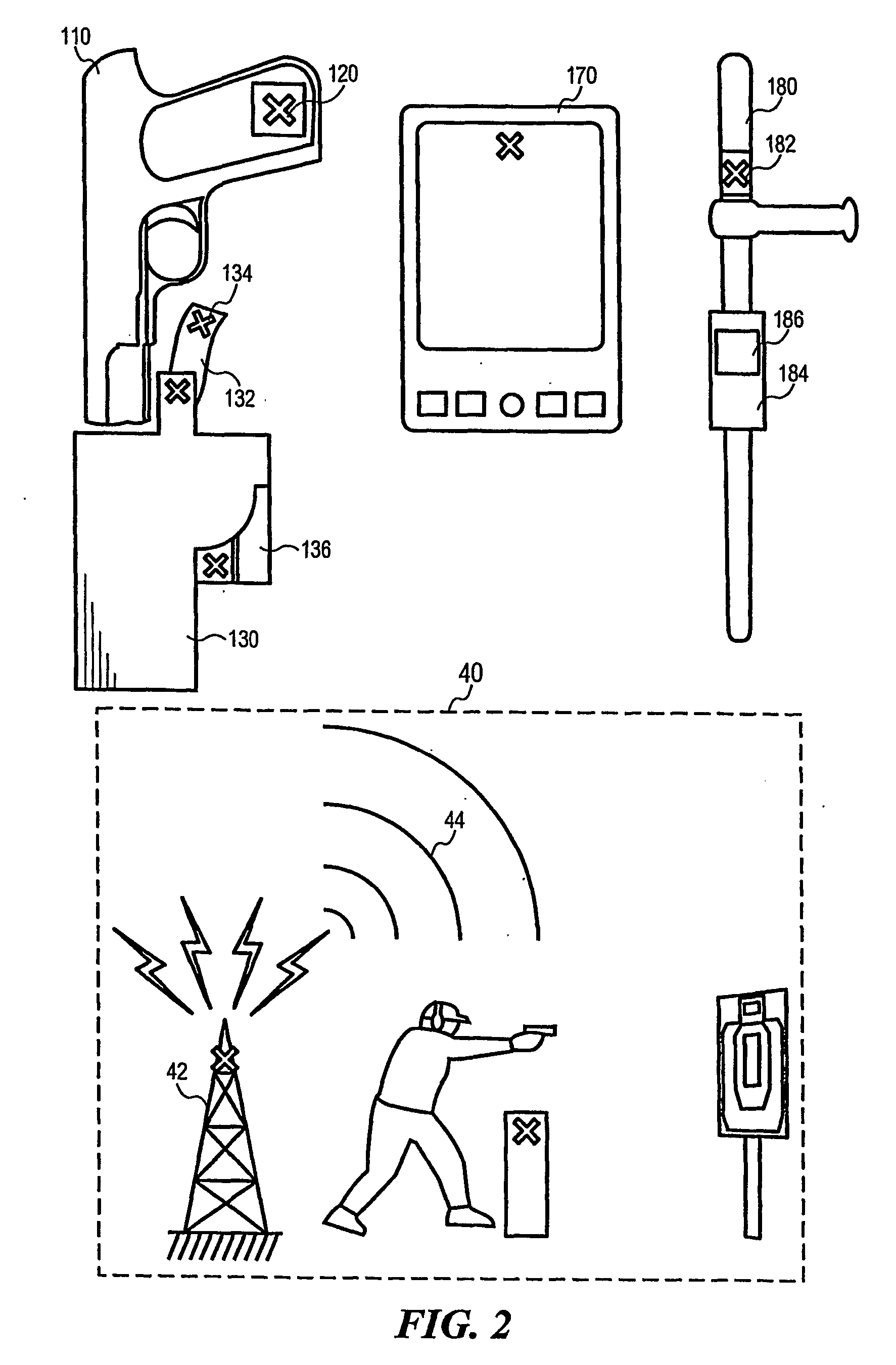
A security system for automatically transmitting alert signals when a security appliance such as a firearm (110) carried by a security officer is drawn from its holster (130), and the method of enabling such a function under the present invention is described. The present invention makes use of radio frequency identification tags (eg 120, 134) and readers (eg 136, 186) to trigger these automatic alerts. The present invention also uses s locator function associated with a mobile device to automatically direct aid to the officer in danger. The present invention also encompasses a method of conducting security guard patrols that monitors the progress of the security guard in real time as he logs each checkpoint of the tour, through the use of RFID tags and readers.
Owner:KENETICS INNOVATIONS PTE
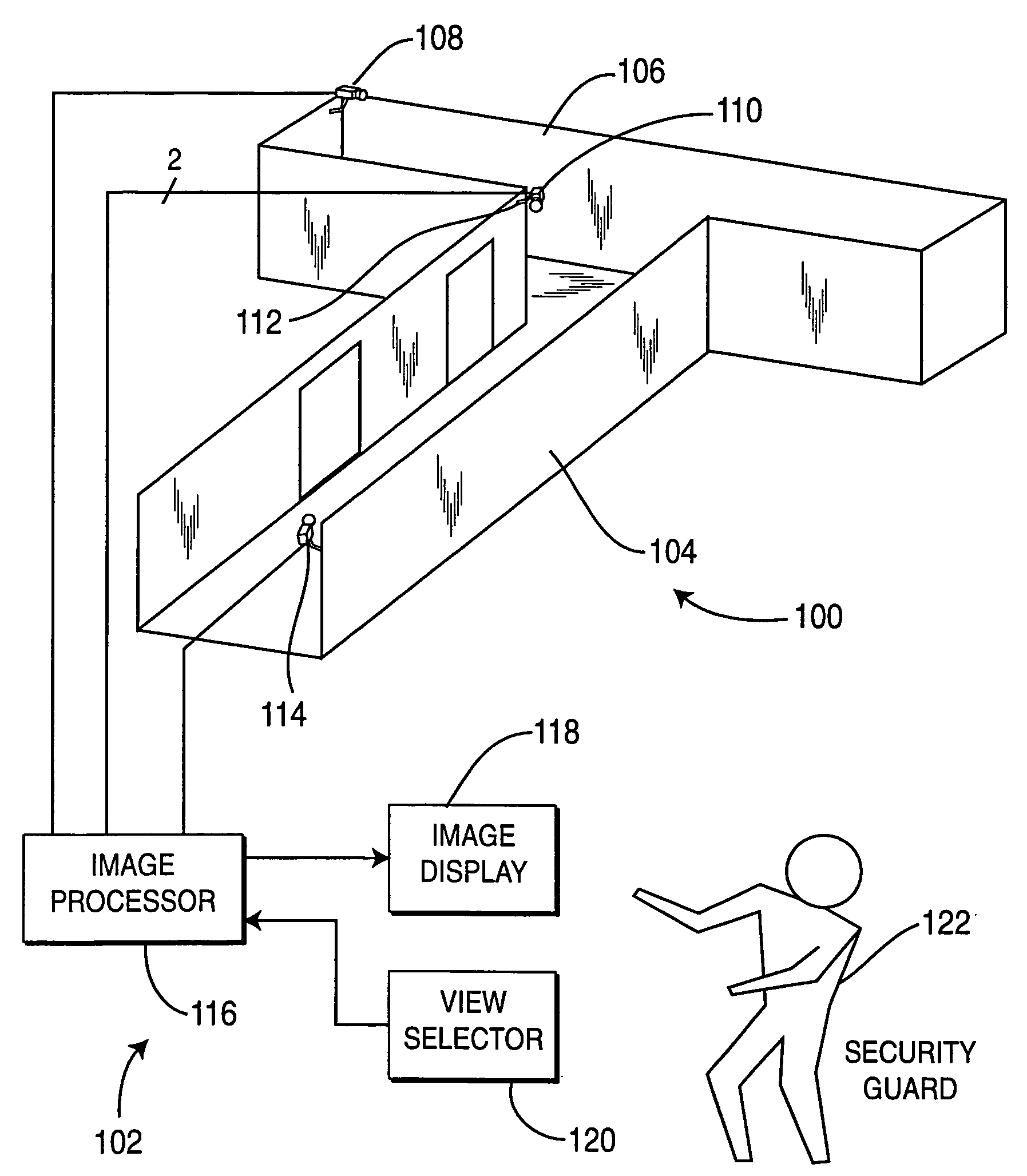
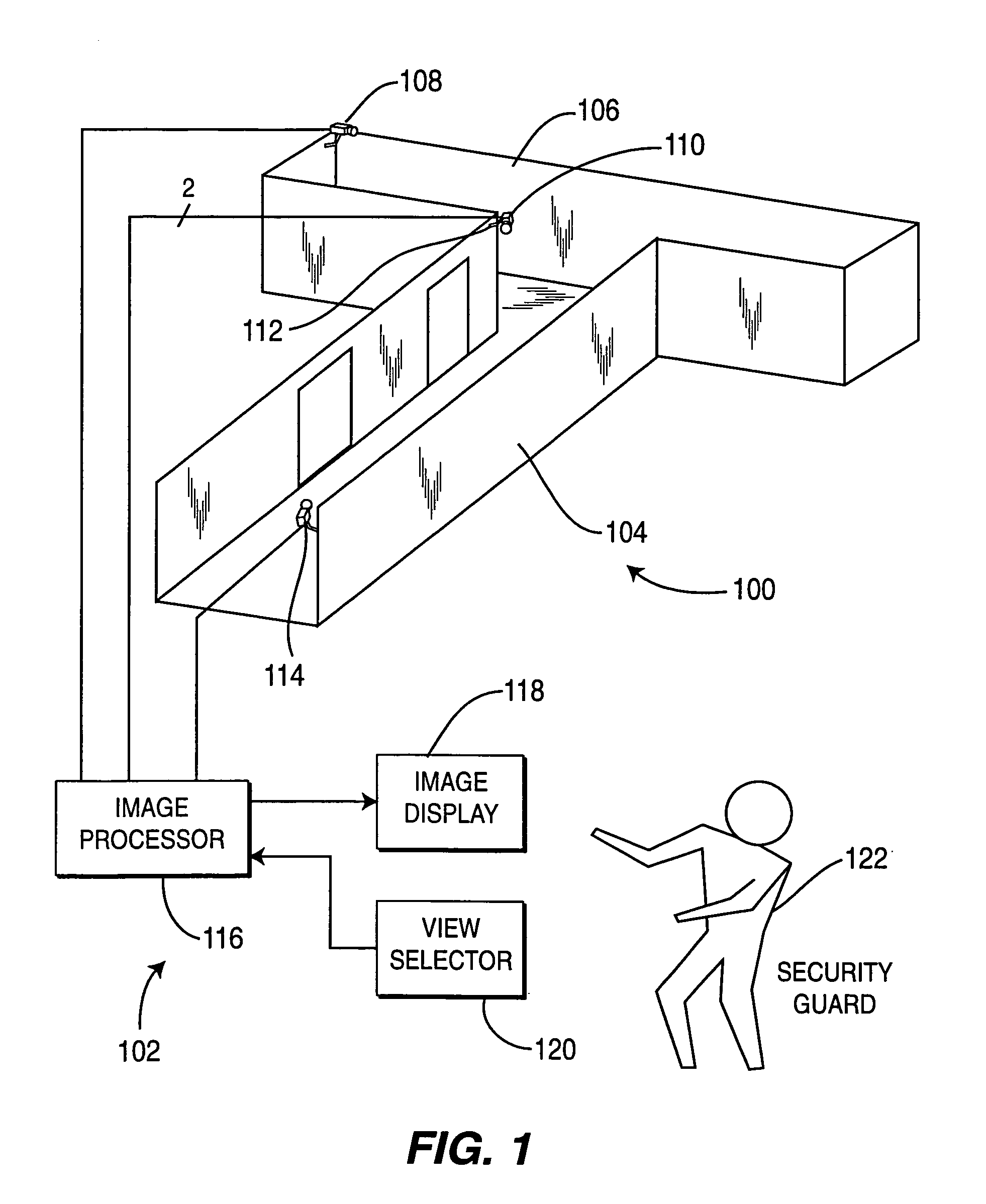
Method and apparatus for providing immersive surveillance
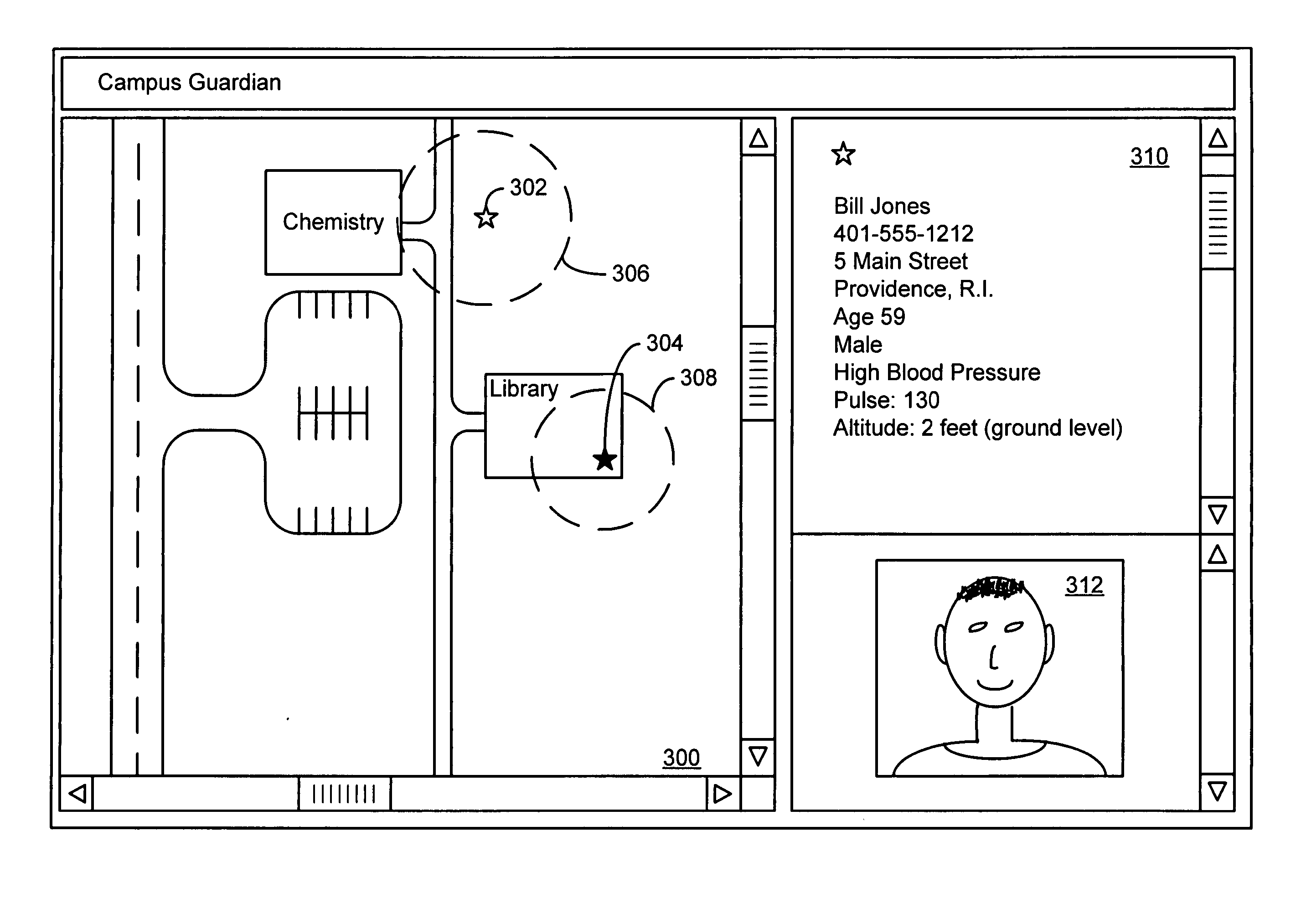
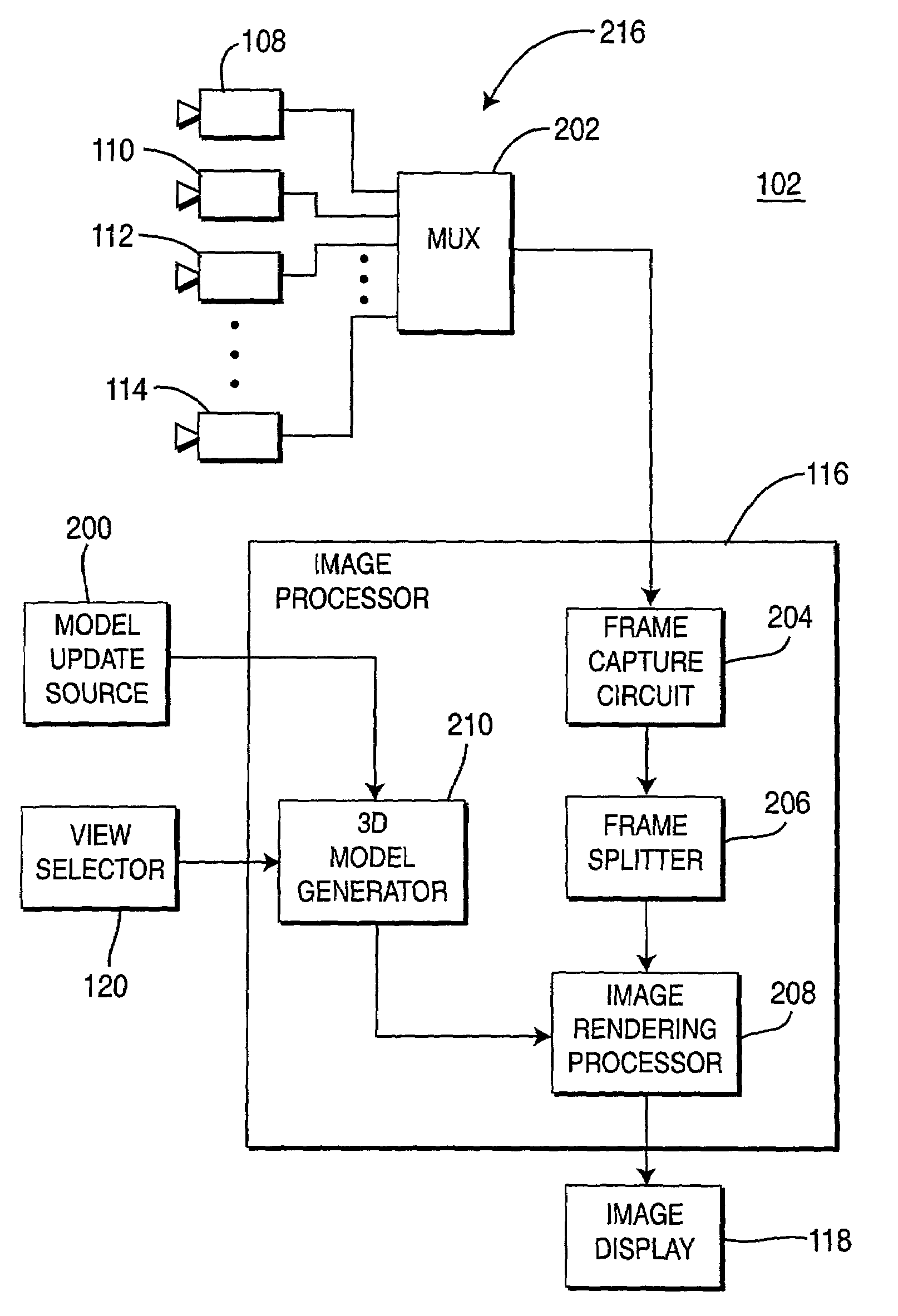
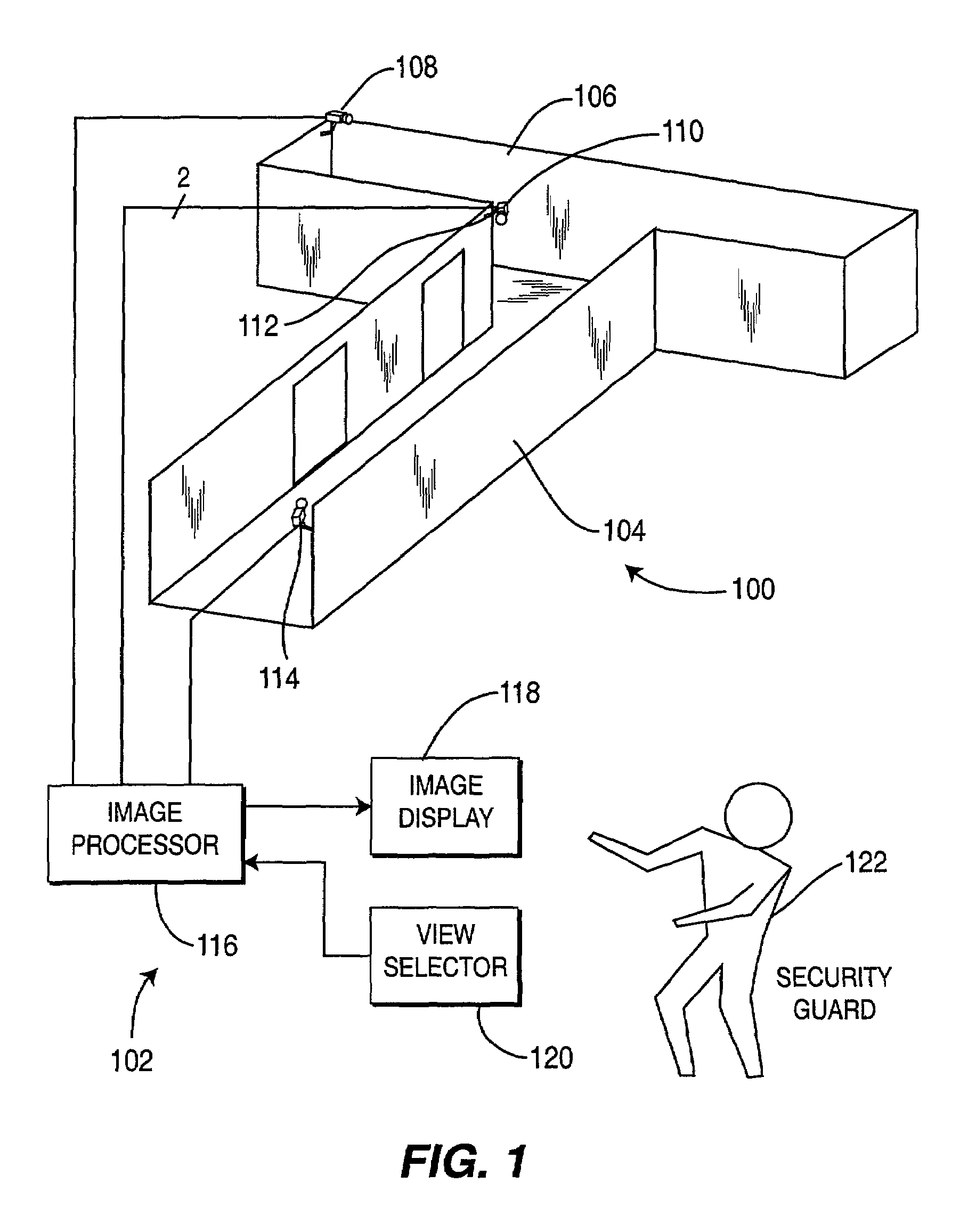
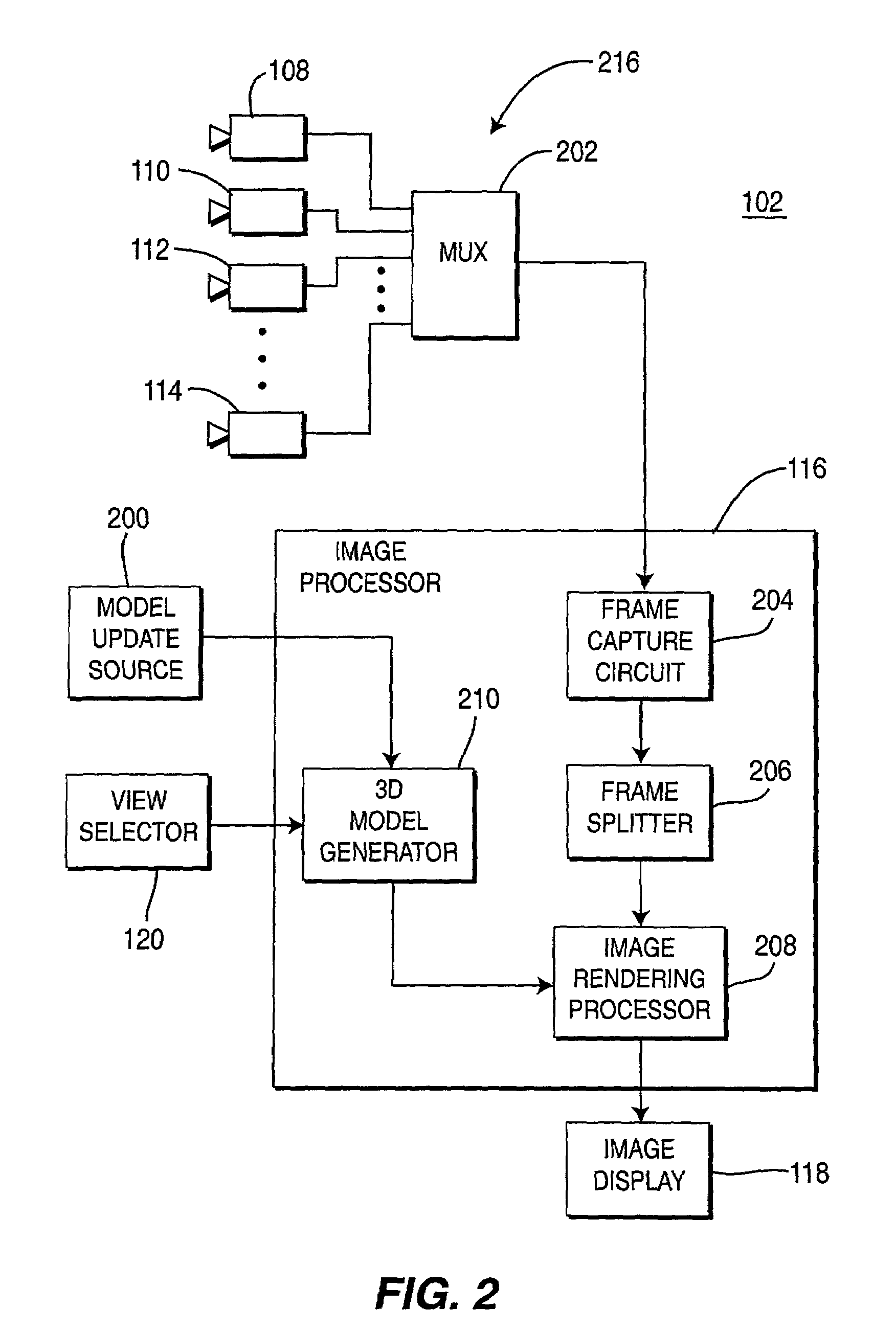
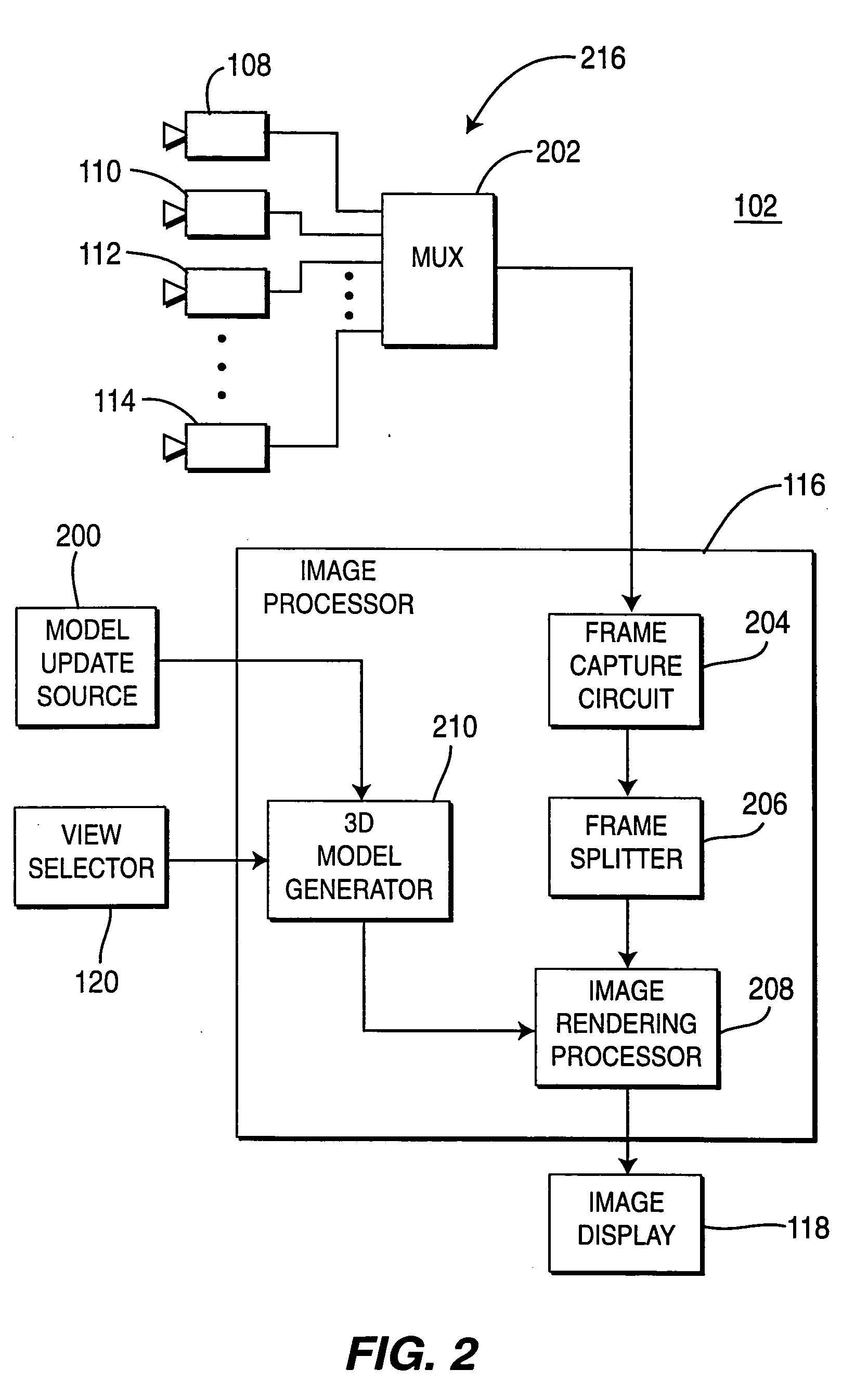
A method and apparatus for providing immersive surveillance wherein a remote security guard may monitor a scene using a variety of imagery sources that are rendered upon a model to provide a three-dimensional conceptual view of the scene. Using a view selector, the security guard may dynamically select a camera view to be displayed on his conceptual model, perform a walk through of the scene, identify moving objects and select the best view of those moving objects and so on.
Owner:L 3 COMM CORP
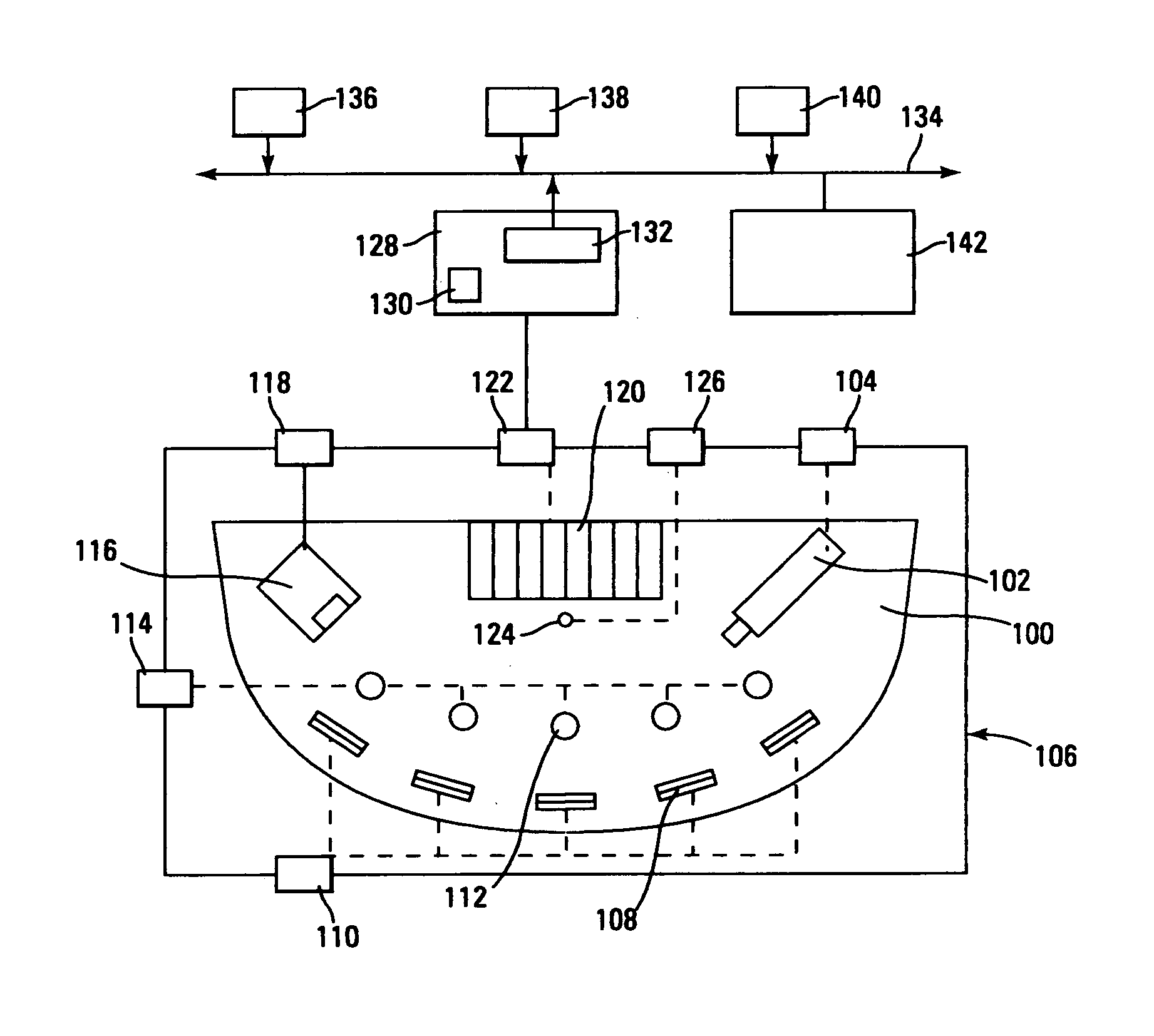
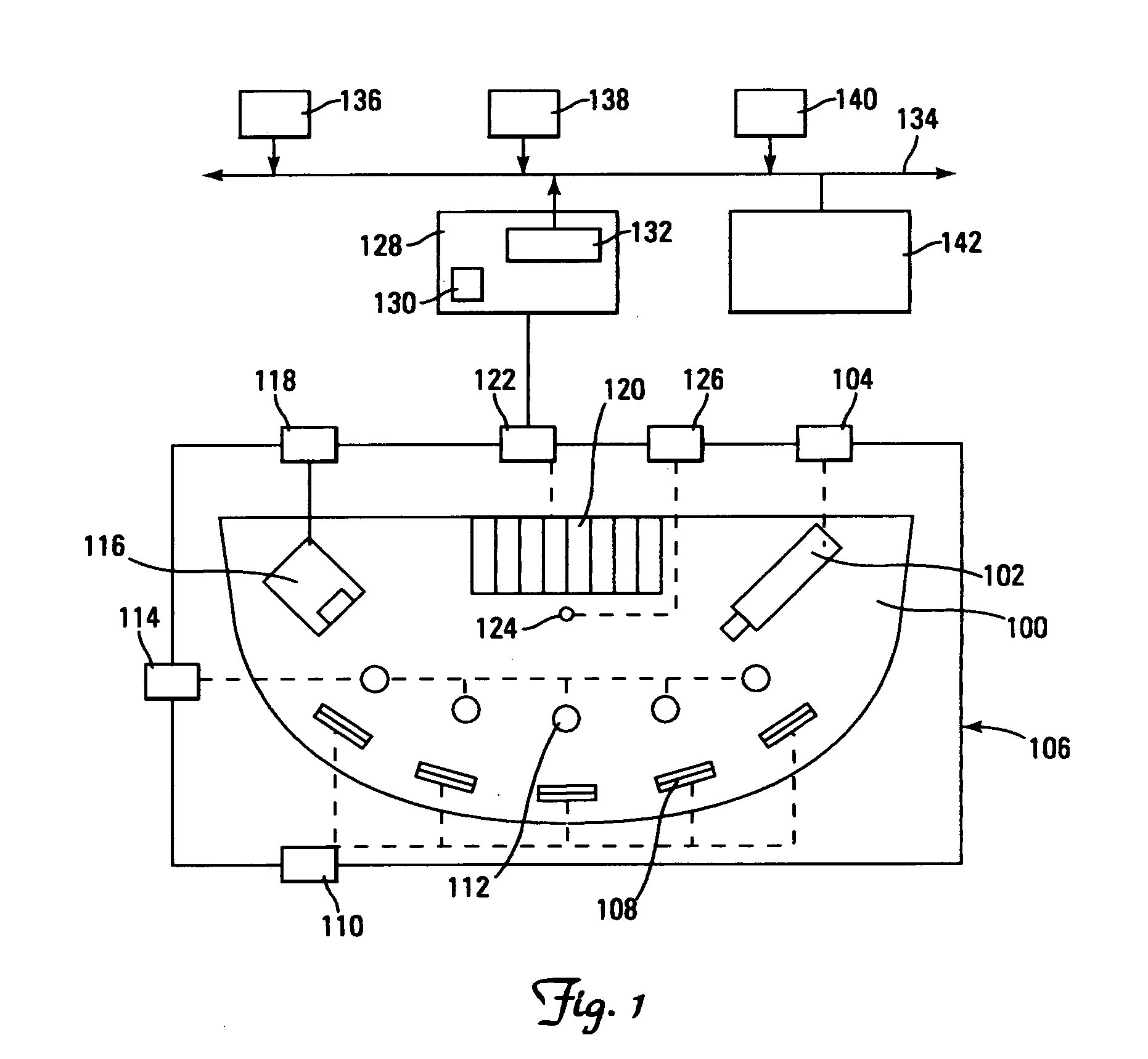
Human guard enhancing multiple site integrated security system
InactiveUS6894617B2Improve human performanceCathode-ray tube indicatorsBurglar alarmHand heldSystem configuration
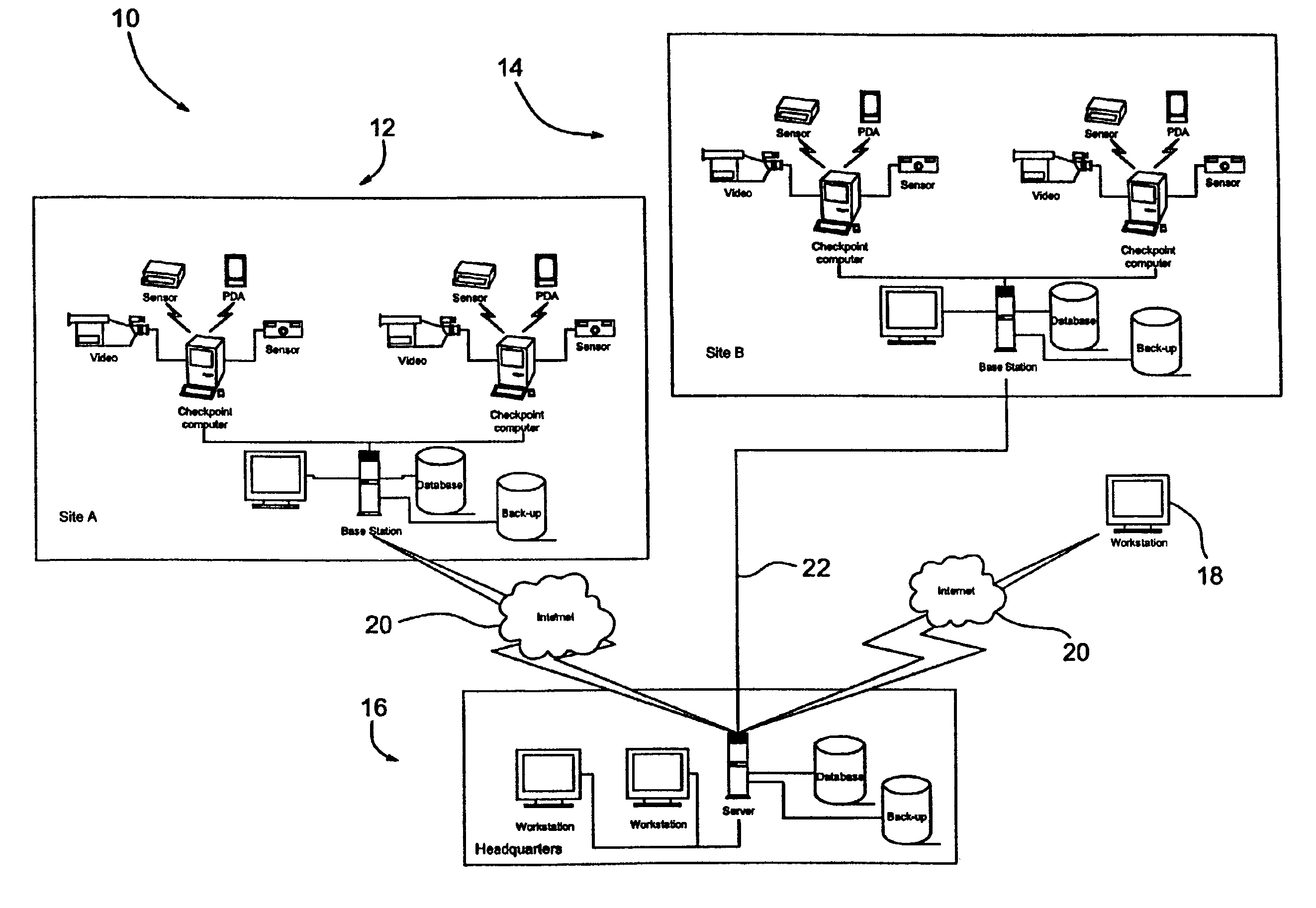
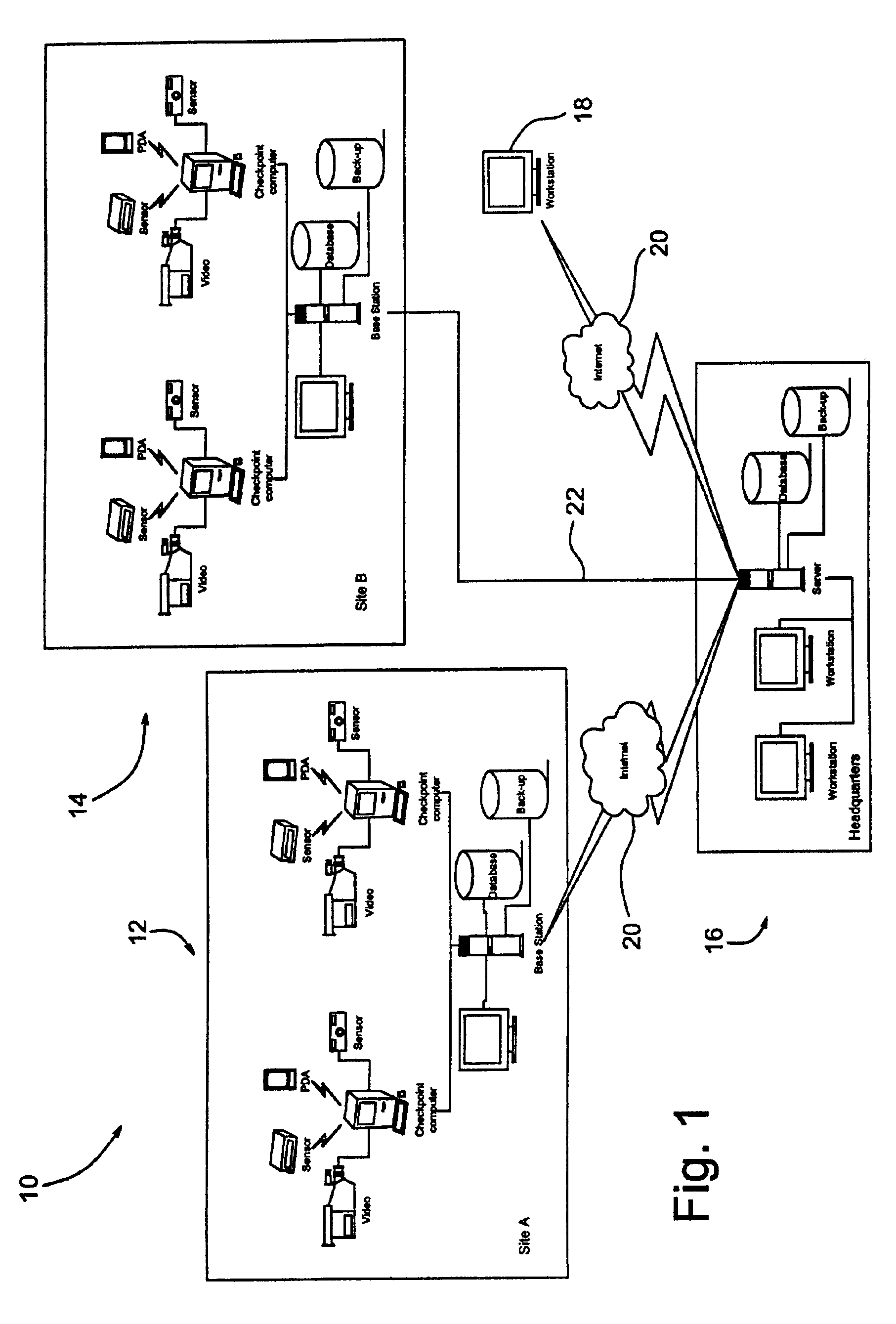
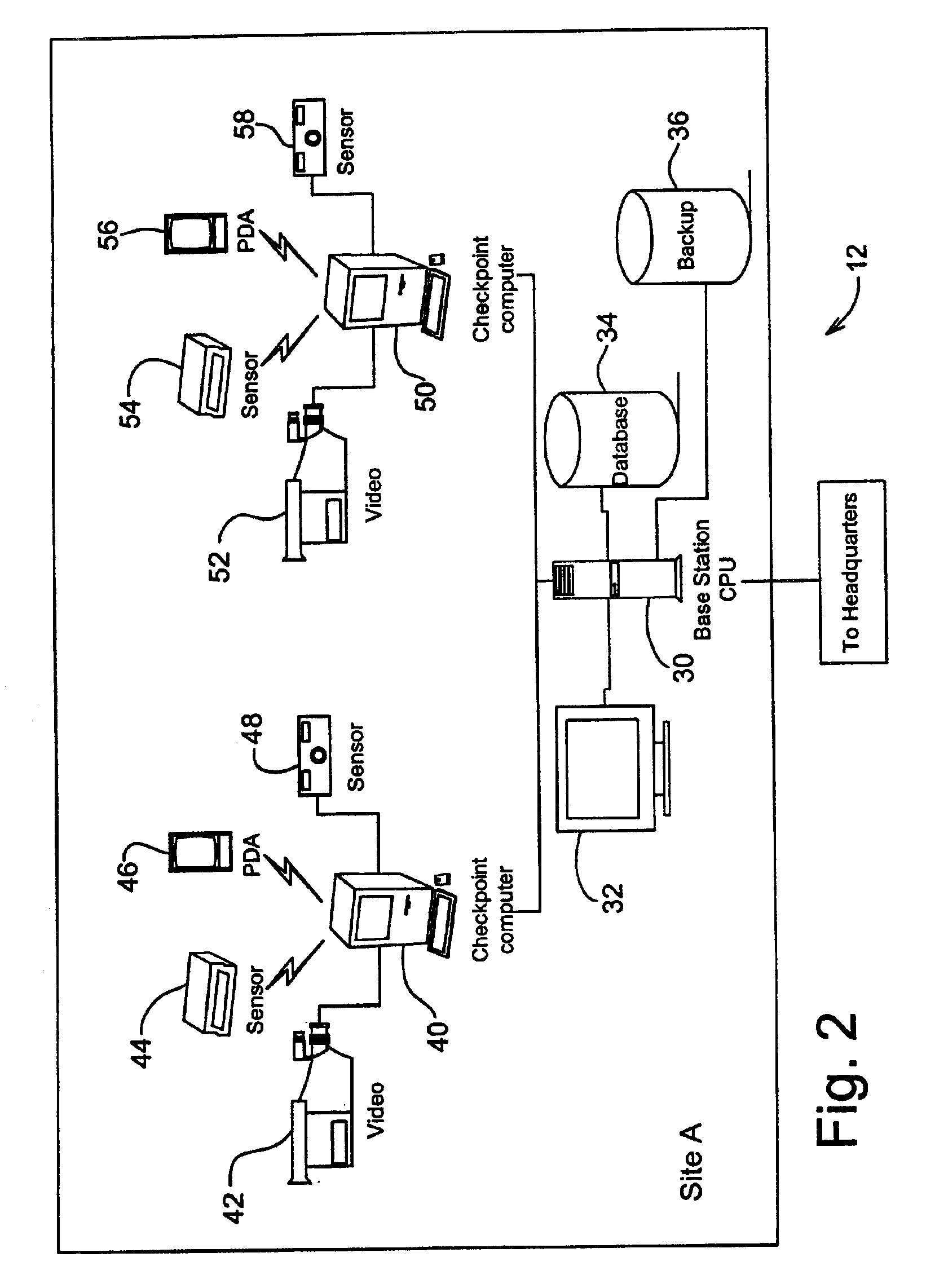
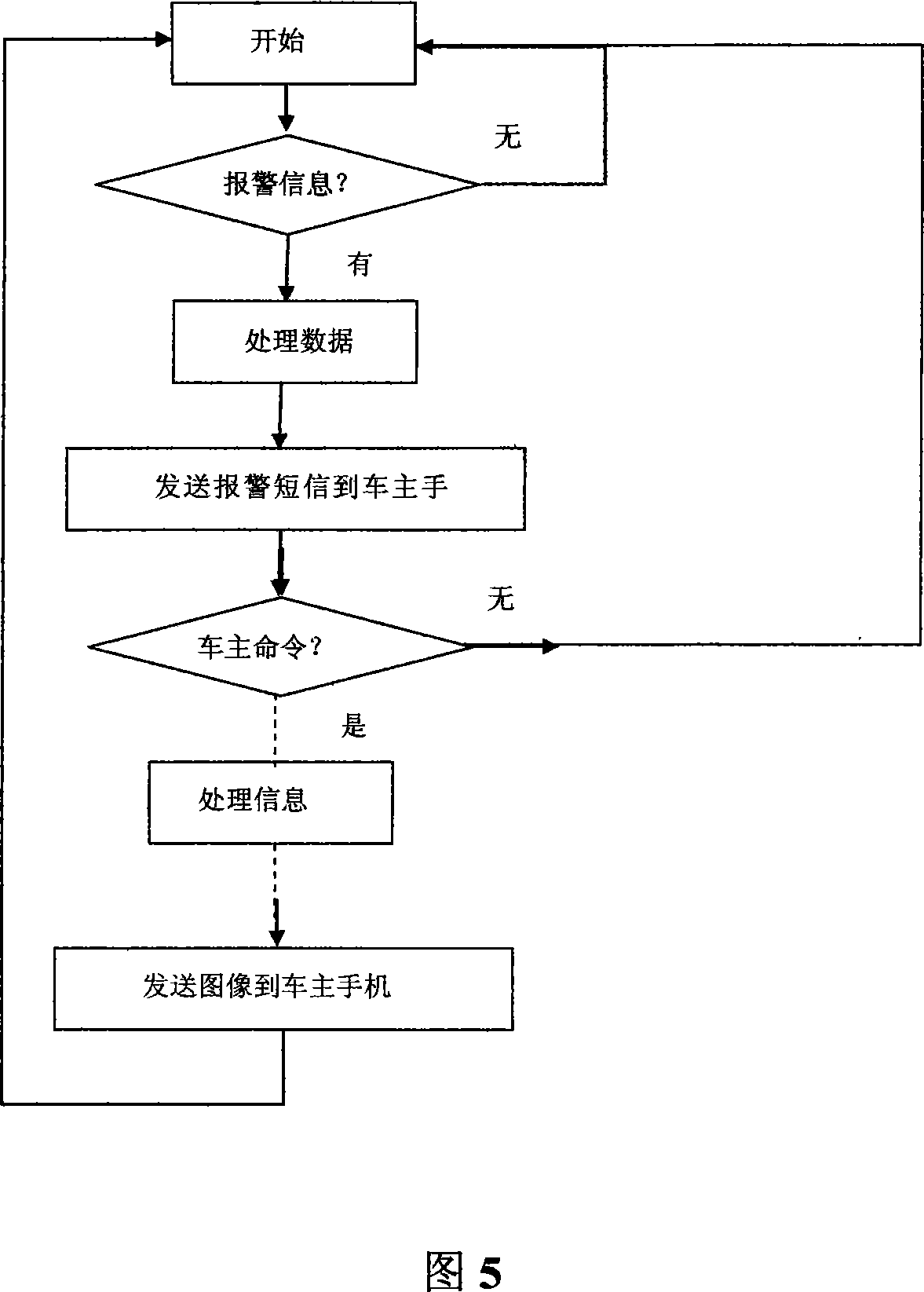
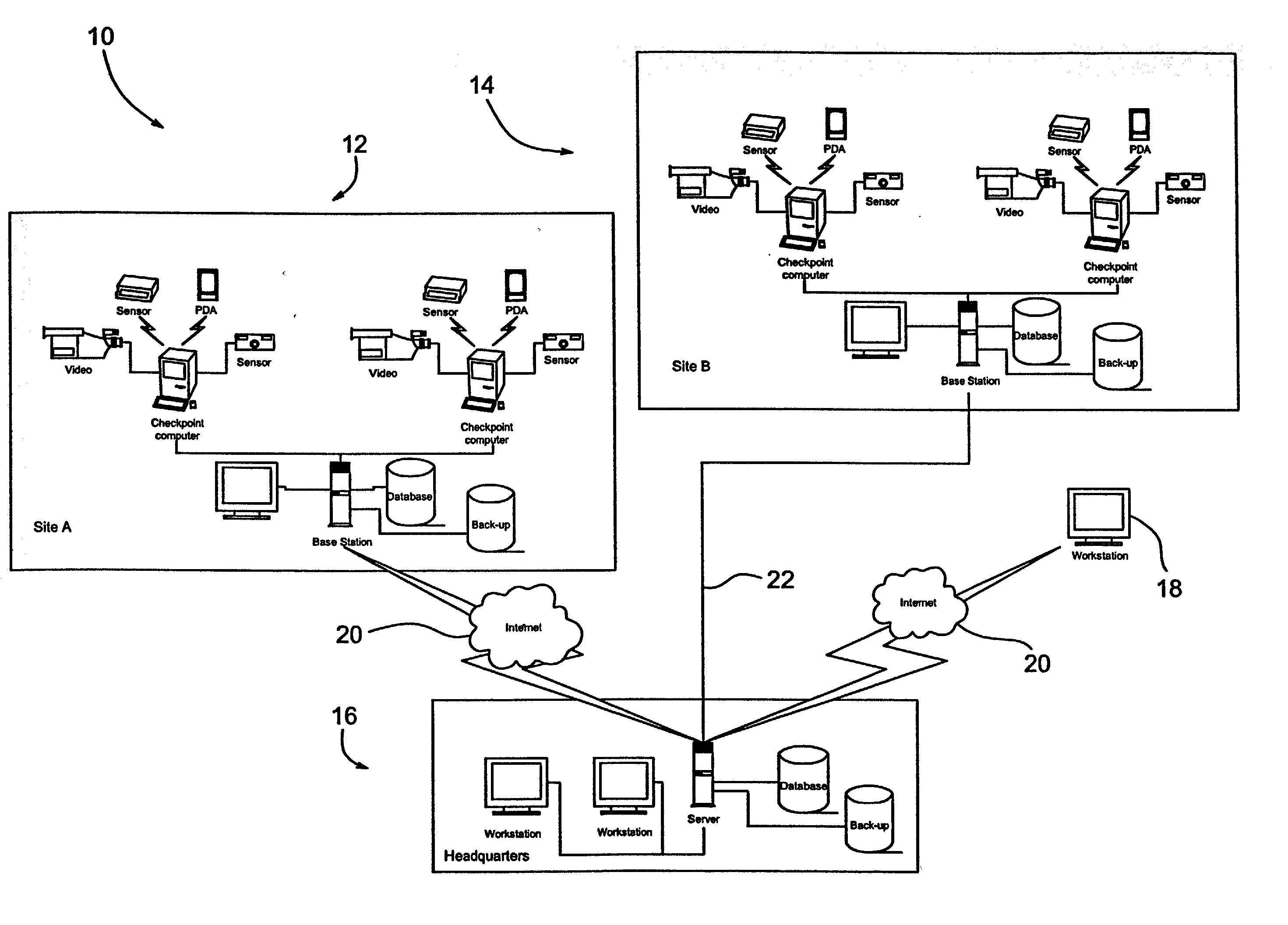
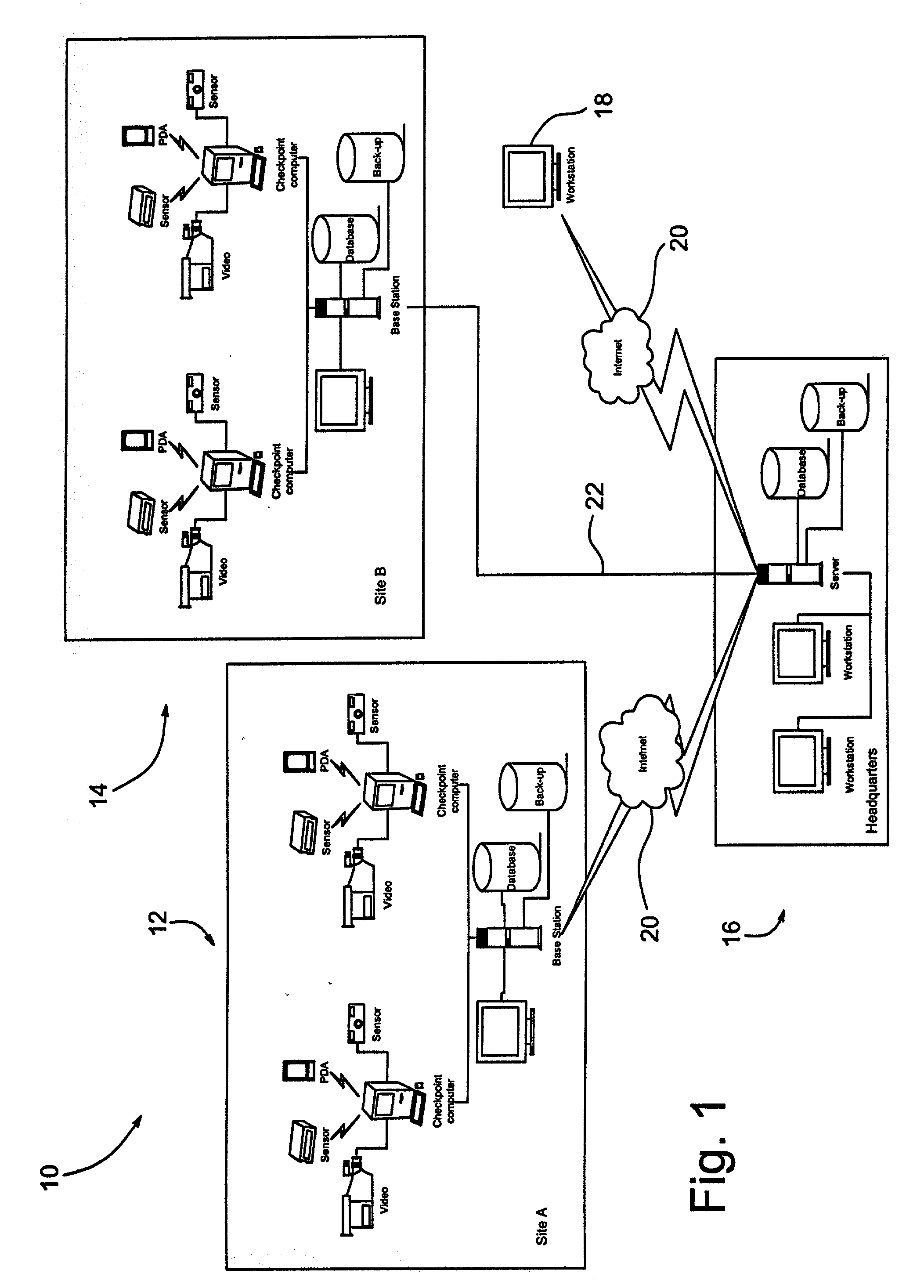
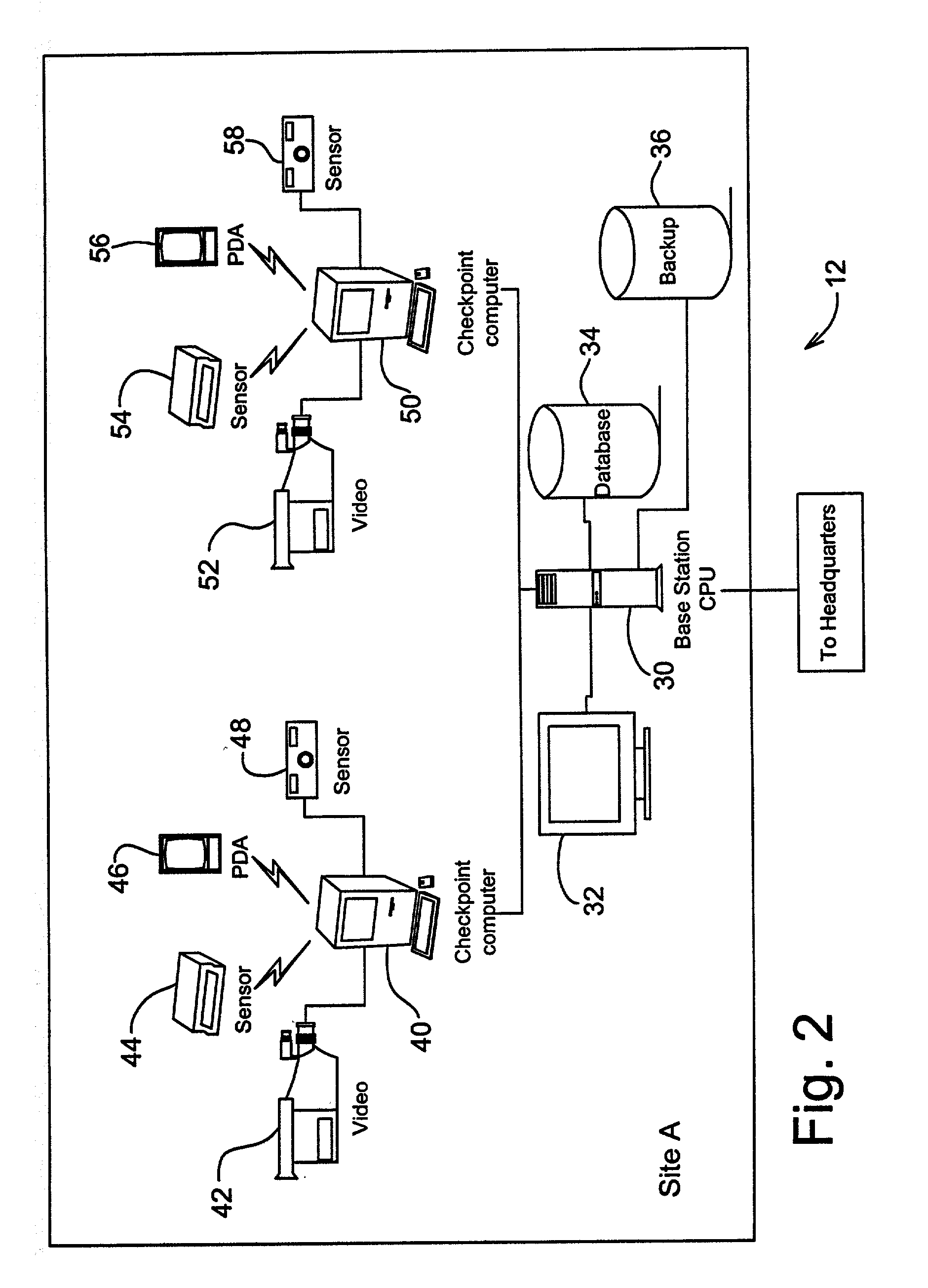
A guard enhancing multiple site, readily scalable security system combines human-based security personnel with a diverse array of fixed and movable electronic security enhancing components, and numerous modes of communications between said components, including hard wired and wireless applications. The security related components include event sensors, identification tracking for people and things, access control devices, security guard wearable computers and hand held computers as well as embedded data processing control and communications systems, with all sensors and sites capable of being monitored by a designated headquarters through checkpoint data processing components and base station components. The security system provides better trained security guards, who are more alert and responsive, and more closely supervised and easily scheduled, enhanced financial monitoring, more accurately paid and expensed security services, better archived and reported security related events, as well as being better coordinated with public agencies, enhanced safety, and readily upgraded and integrated with existing and future technologies. The primary goal of the system configuration is to make human security guard tour tasks planned, controlled, monitored, recorded and paid in a highly efficient and effective manner.
Owner:RICHMAN TECH CORP
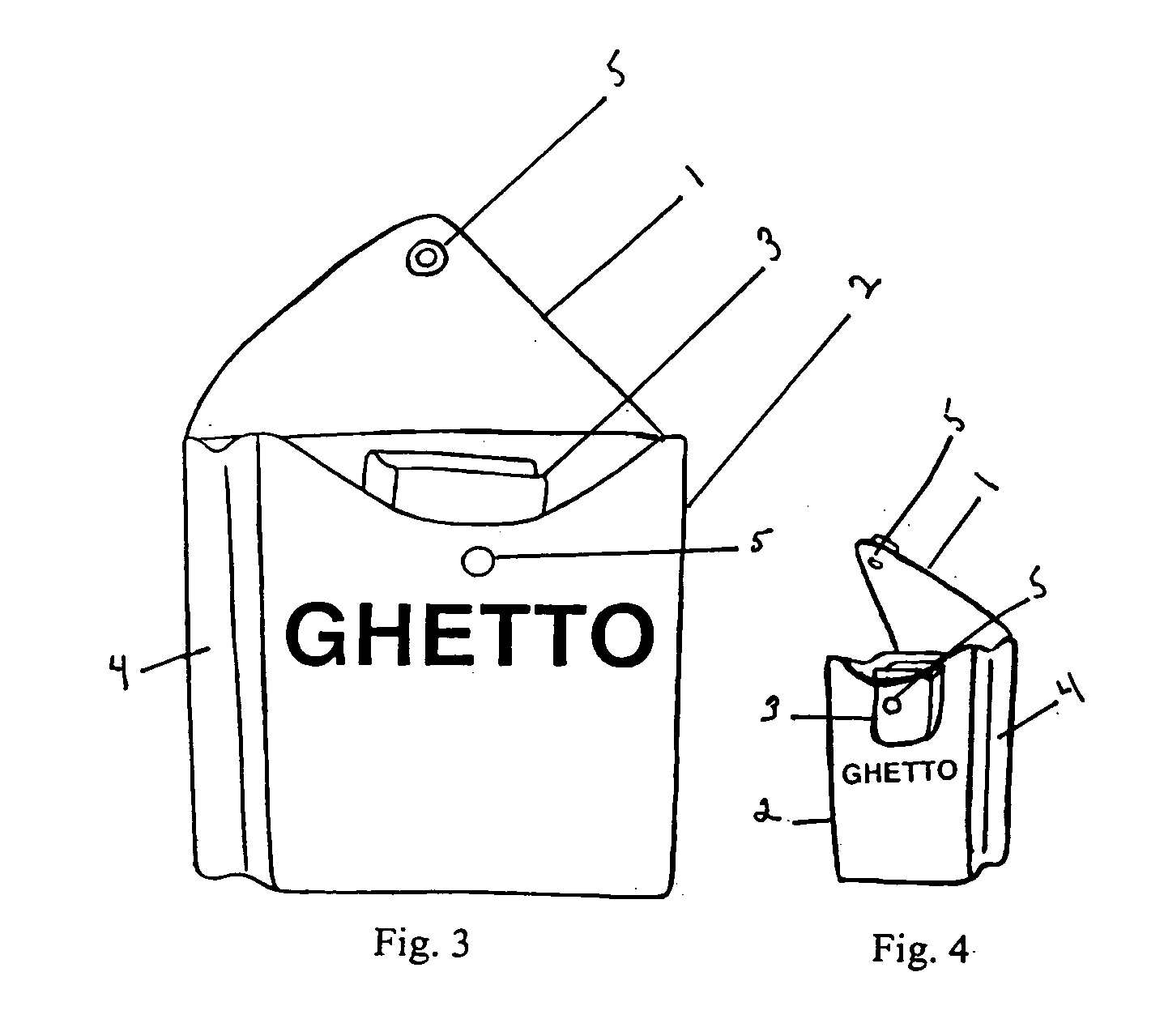
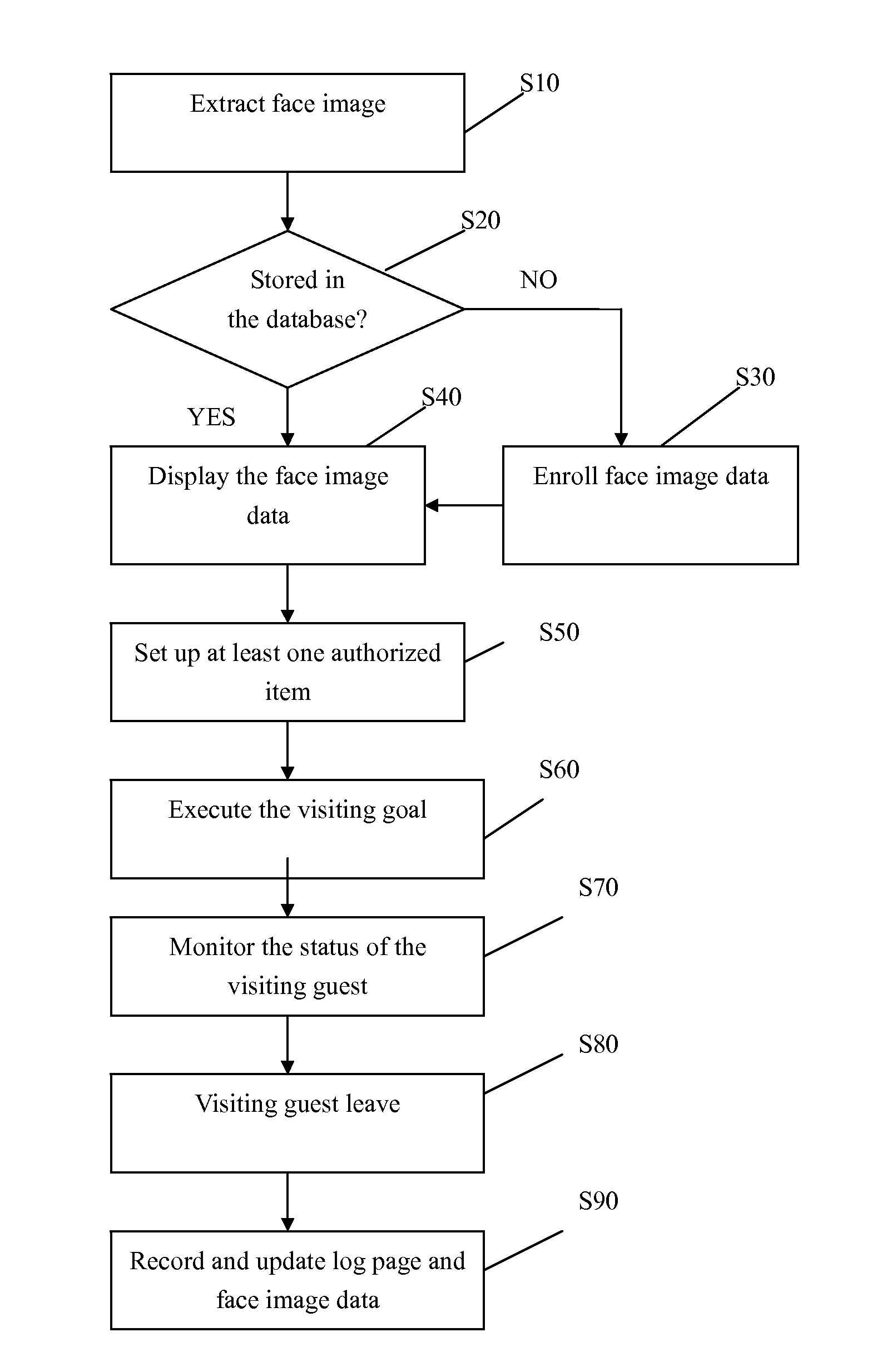
Method of managing visiting guests by face recognition
ActiveUS8750576B2Dramatically reducing their workloadCharacter and pattern recognitionDigital data authenticationPattern recognitionSecurity guard
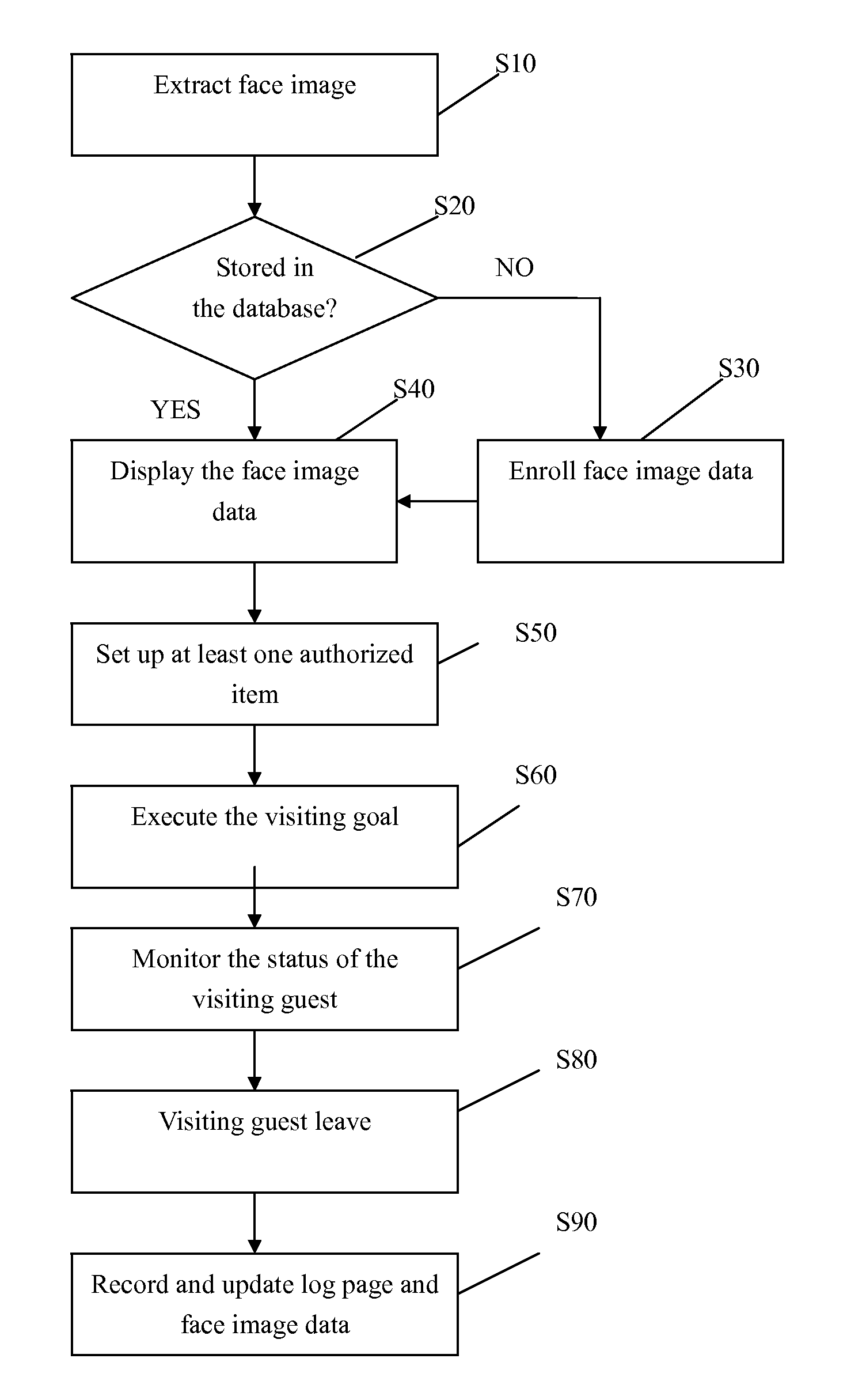
A method of managing visiting guests by face recognition includes: extract the face image of the visiting guest; determine if the face image of the guest is stored in the database; display the face image data comprising the face image, guest information and visiting information if the face image is stored or enroll the new face image data and then display the face image data just registered; set up at least one authorized item; execute the visiting goal confined by the authorized items; monitor the status of the visiting guest; wait until the guest leaves; and finally record and update log page and face image data of the visiting guest in the database. Therefore, the method can reduce security guard workload, assist security guards or automatically and solely execute the function of guard entrance without any careless mistakes, and update visiting guest information in real time.
Owner:TAIWAN COLOR & IMAGING TECH CORP
Onboard system and control method with navigation and audio/video record and theft prevention function
InactiveCN101123866APrevent theftFacilitate qualitative handling of accidentsRegistering/indicating working of vehiclesTelephonic communicationKey pressingVideo record
The invention relates to the technical field of a vehicle navigation registering device. Specifically speaking, the invention is a vehicle system with the functions of navigation, audio / video registering and anti-theft; wherein, a MCU processor is respectively connected with an audio cell, a sensor cell, a LCD cell, a global positioning system, a communication module, a customer data interface, a key-press, an extended data memory cell, a data memory cell, a sensor interface of a sensor for vehicle and a communication interface of a video processing cell of a camera to realize data transmission and control, to make the system provide a navigation function and register the video and audio information and the sensor information inside the vehicle in a running process, to make the system ina security guard state by detecting the vibration in the sensor of the vehicle and the information of a acceleration transducer and to remind customers through a short message mode. Compared with theprior art, the invention combines the global positioning system with the audio and video processing technologies to resister the real situation of accidents intuitively as well as detect the sensor information, send alarm to cellphones to prevent vehicles from stealing.
Owner:刘西钉
Human guard enhancing multiple site integrated security system
InactiveUS20030206099A1Guards are greatly enhancedHighly effectiveCathode-ray tube indicatorsBurglar alarmHand heldSystem configuration
A guard enhancing multiple site, readily scalable security system combines human-based security personnel with a diverse array of fixed and movable electronic security enhancing components, and numerous modes of communications between said components, including hard wired and wireless applications. The security related components include event sensors, identification tracking for people and things, access control devices, security guard wearable computers and hand held computers as well as embedded data processing control and communications systems, with all sensors and sites capable of being monitored by a designated headquarters through checkpoint data processing components and base station components. The security system provides better trained security guards, who are more alert and responsive, and more closely supervised and easily scheduled, enhanced financial monitoring, more accurately paid and expensed security services, better archived and reported security related events, as well as being better coordinated with public agencies, enhanced safety, and readily upgraded and integrated with existing and future technologies. The primary goal of the system configuration is to make human security guard tour tasks planned, controlled, monitored, recorded and paid in a highly efficient and effective manner.
Owner:RICHMAN TECH CORP
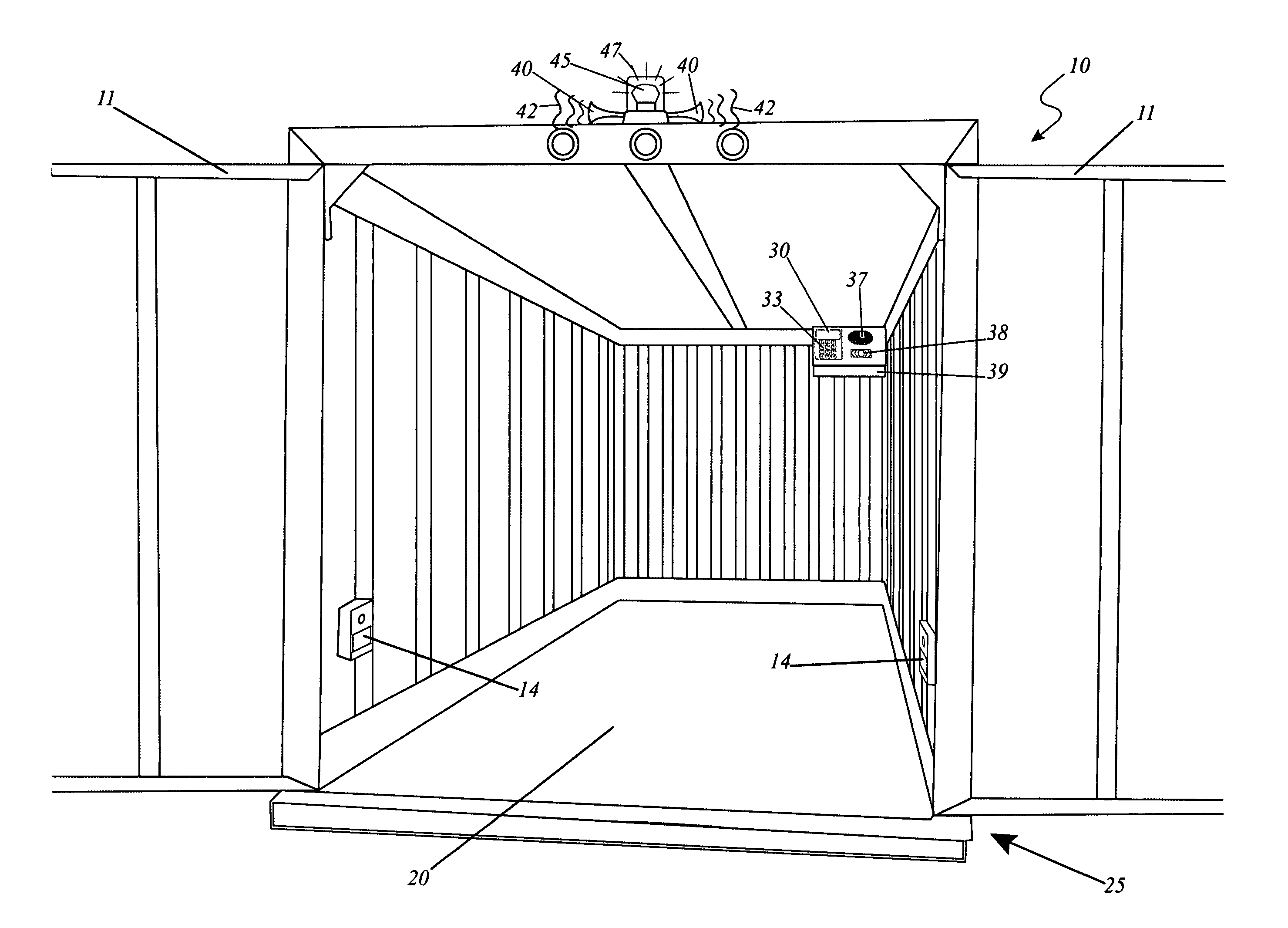
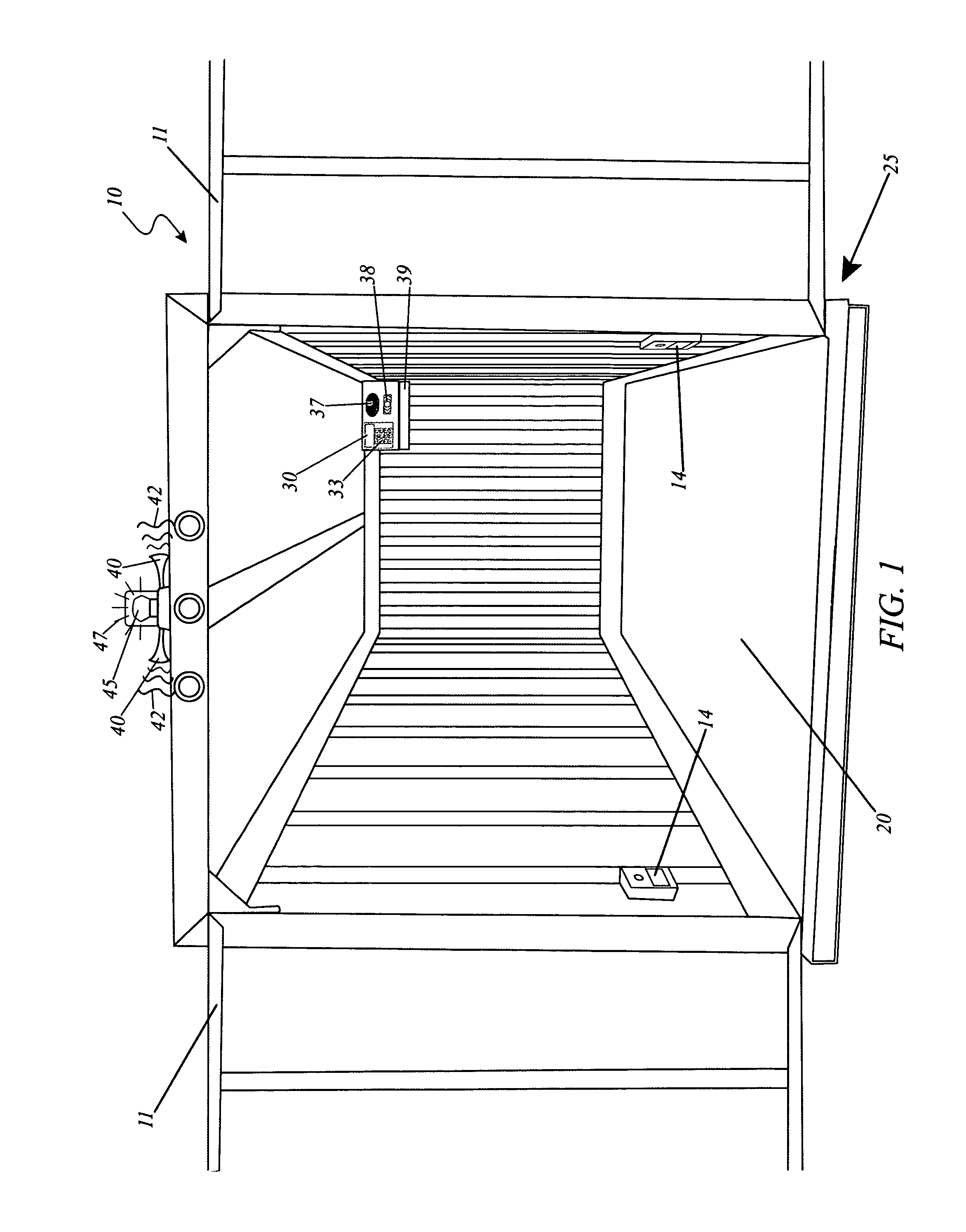
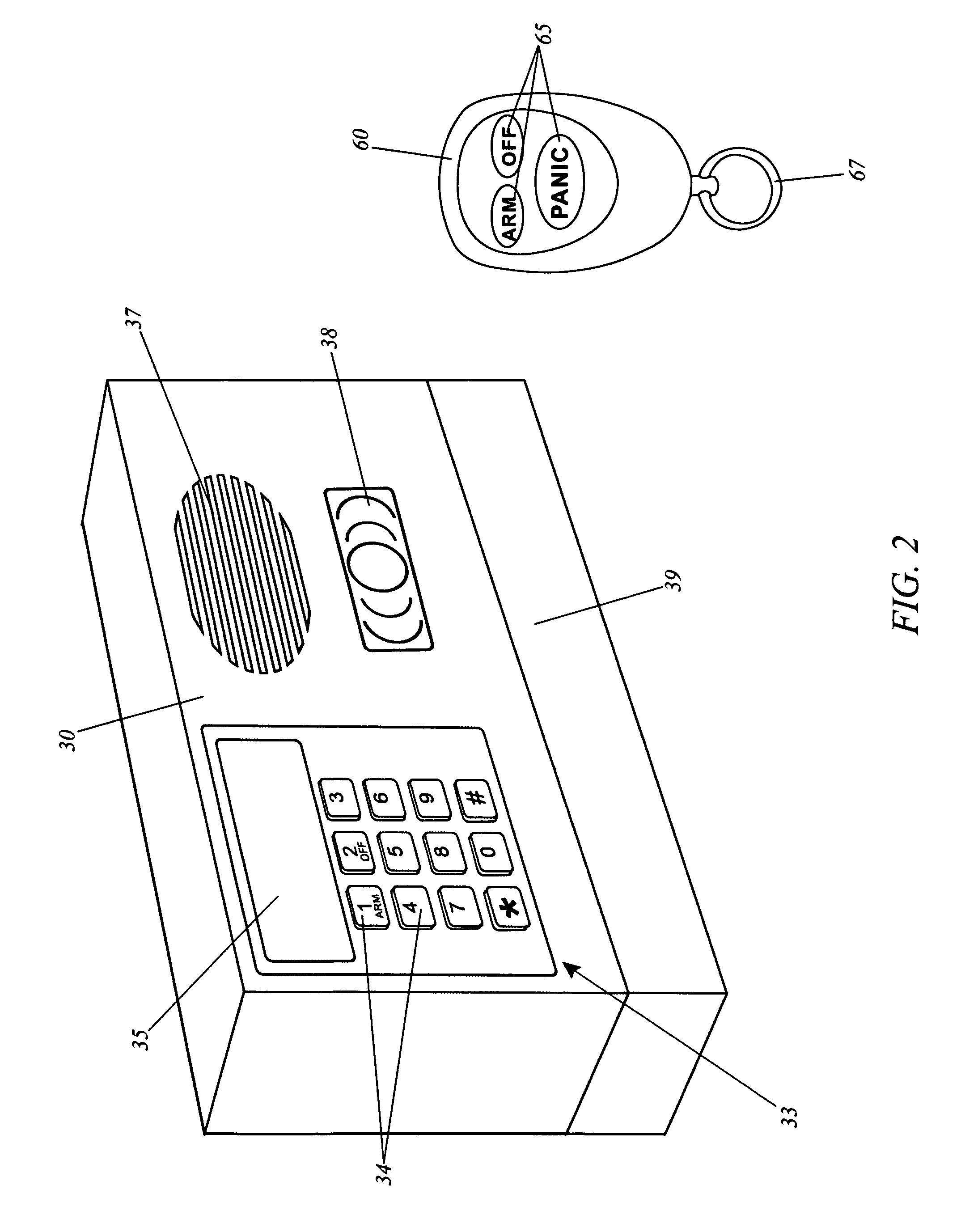
Alarm and tracking system for mobile units
A system for the detecting and alarming of unauthorized access to an enclosure is herein disclosed. Sensors mounted within the door and / or motion sensors provide a wireless signal to a centralized control panel that activates an alarm when armed. The alarm provides visual and aural indication of an intrusion within the enclosure and transmits a signal to a remote base unit via telemetry, and a Global Positioning System (GPS) may provide the location of the alarm to the base unit for subsequent dispatch of security personnel if the enclosure is in transport.
Owner:MORRIS DAVID E
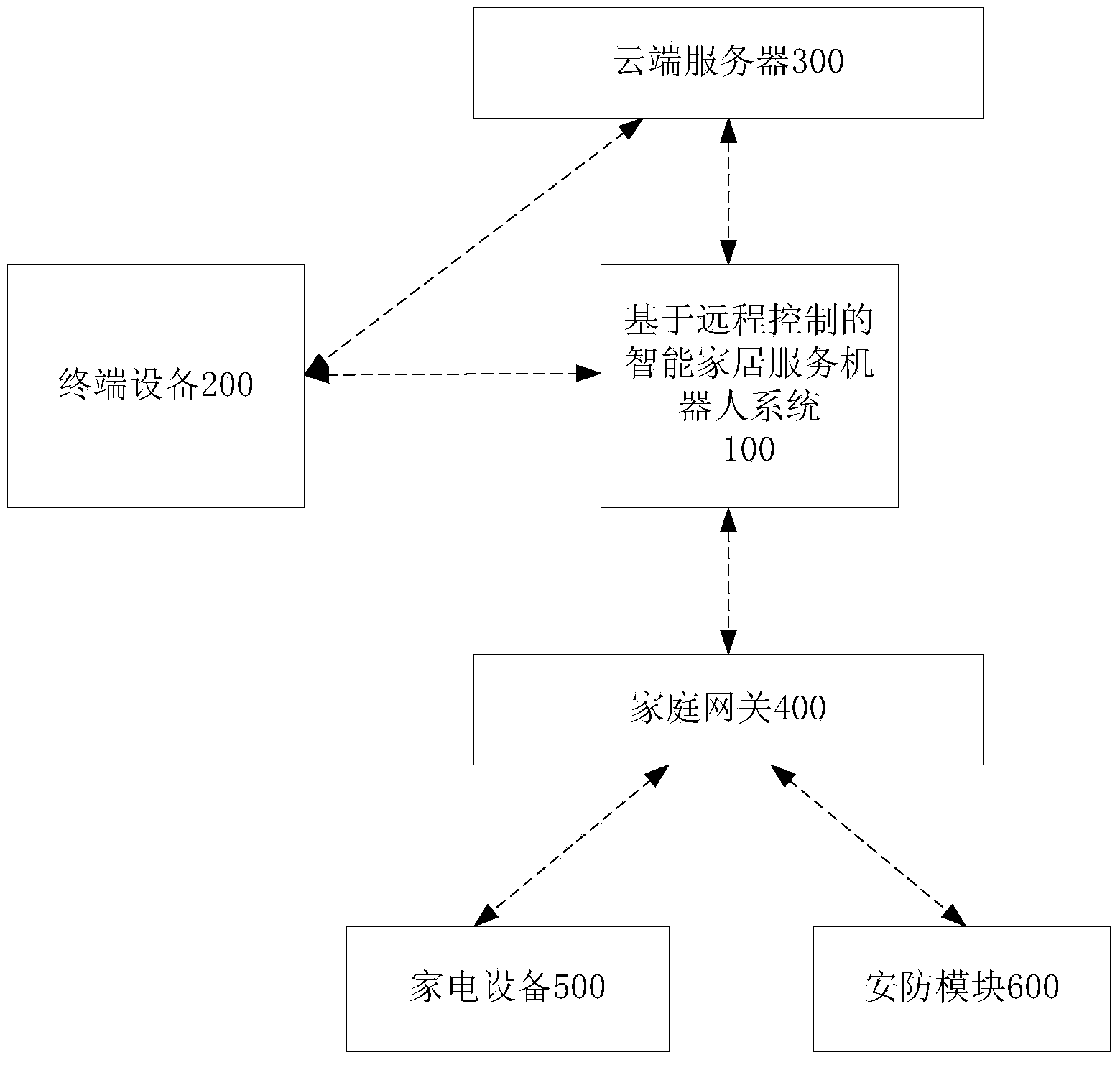
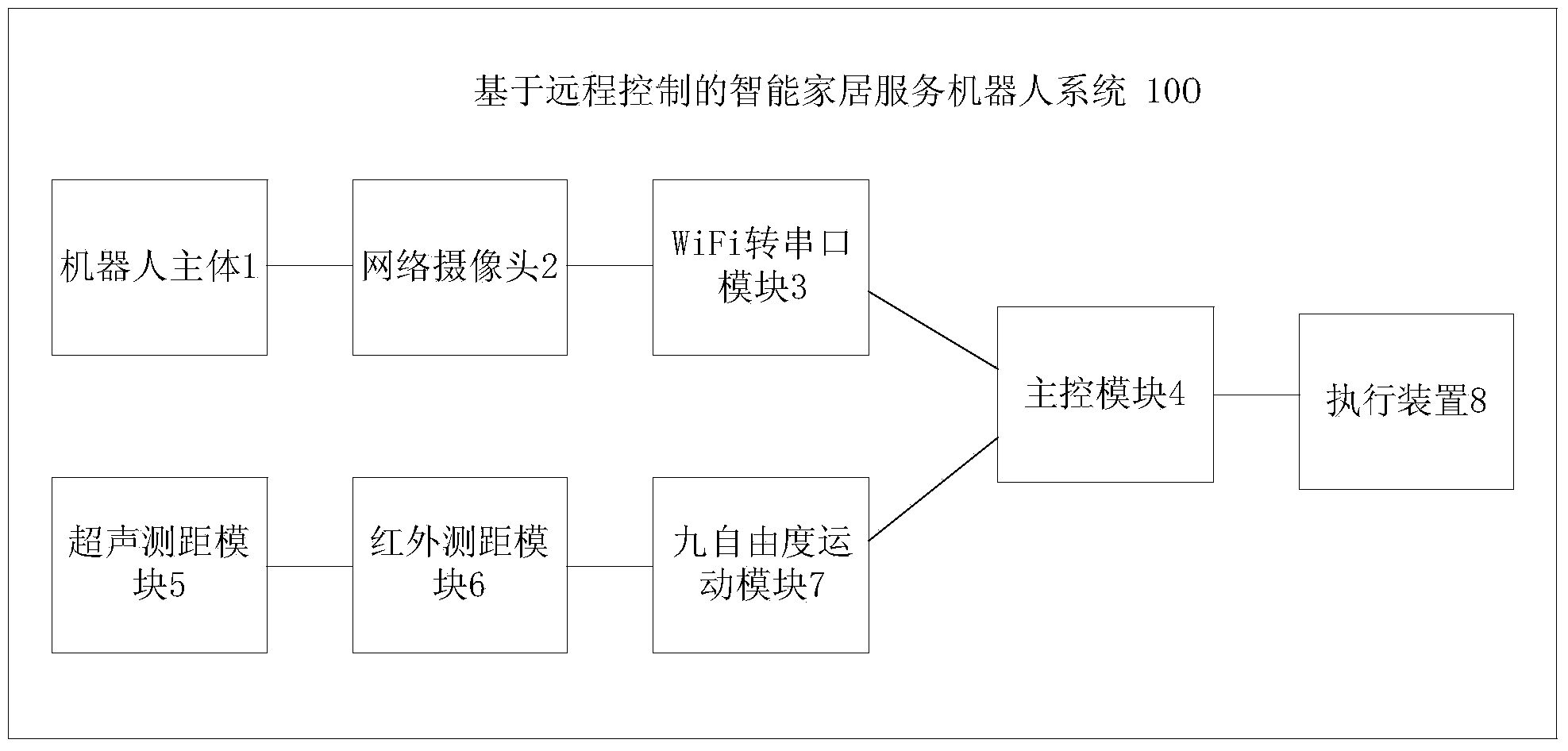
Remote control based smart home service robot system
ActiveCN104111655AImprove real-time performanceEasy to movePosition/course control in two dimensionsRemote controlDegrees of freedom
The invention provides a remote control based smart home service robot system. The remote control based smart home service robot system comprises a robot body, a network camera, a wireless fidelity (WiFi) to serial port module, a main control module, an ultrasonic distance measurement module, an infrared distance measurement, a nine-degree-of-freedom movement module and an execution device, wherein the network camera is used for shooting environmental information in front of the robot body, the WiFi to serial port module is used for converting a first instruction into a serial port instruction and sending the serial port instruction to the main control module, the ultrasonic distance measurement module is used for detecting distances between obstacles in multiple directions of the robot body and the robot body, the nine-degree-of-freedom movement module is used for detecting an angle of the front of the robot body, the main control module is used for sending a second instruction to the execution module, and the execution module executes corresponding actions according to the second instruction so as to perform automatic obstacle avoidance and control household appliances. The remote control based smart home service robot system is capable of adjusting and controlling indoor household appliances and the like and providing families with convenient functions of household appliances control, automatic obstacle avoidance, and security guards against theft.
Owner:安徽乐智机器人科技有限公司
Method and apparatus for providing immersive surveillance
A method and apparatus for providing immersive surveillance wherein a remote security guard may monitor a scene using a variety of imagery sources that are rendered upon a model to provide a three-dimensional conceptual view of the scene. Using a view selector, the security guard may dynamically select a camera view to be displayed on his conceptual model, perform a walk through of the scene, identify moving objects and select the best view of those moving objects and so on.
Owner:L 3 COMM CORP
Lens holding structure for wall-mounted surveillance camera
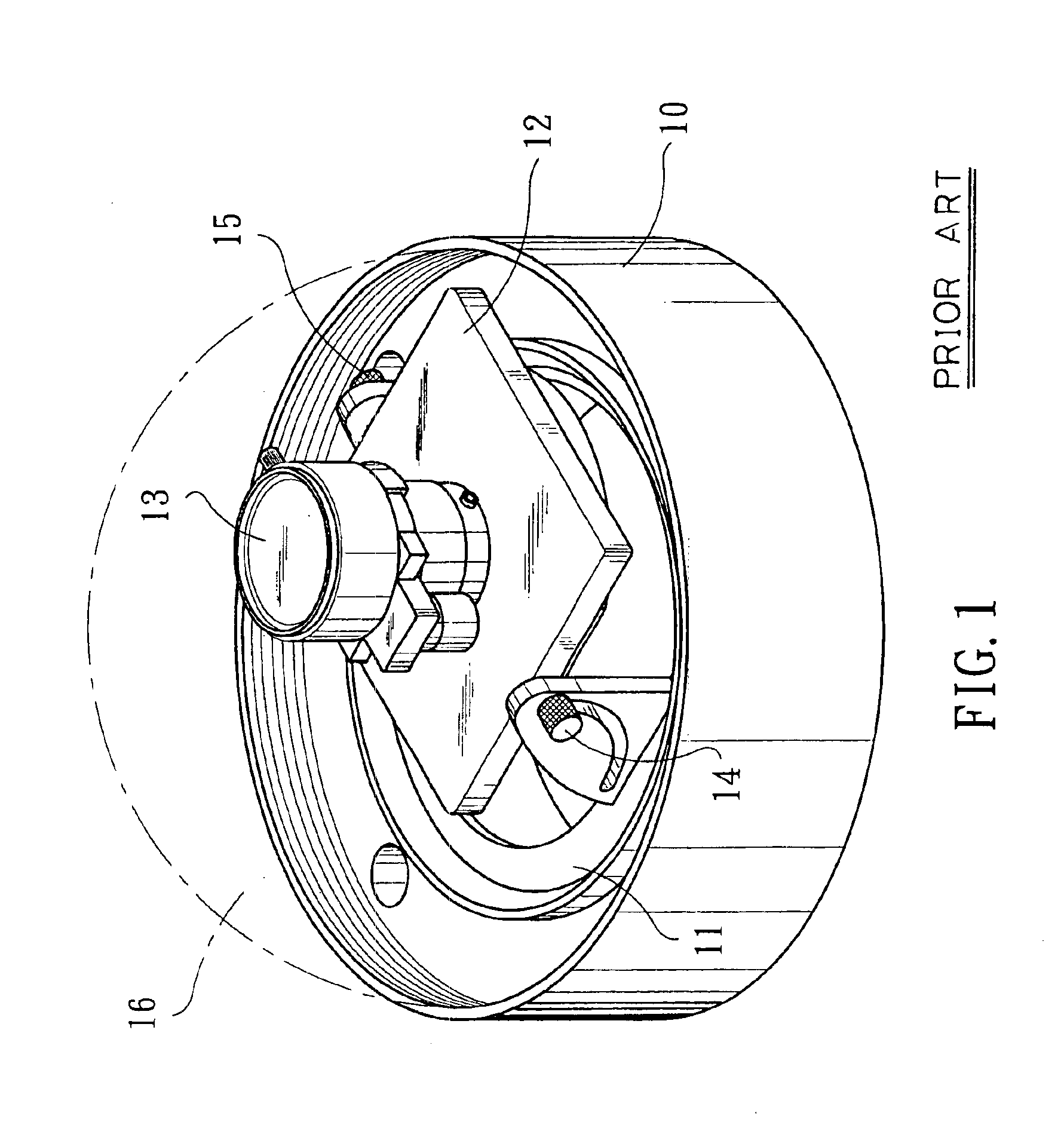
InactiveUS6860654B1Secure locationTelevision system detailsColor television detailsCamera lensSurveillance camera
A lens holding structure for wall-mounted surveillance camera is obtained via improving a basic structure of a conventional ceiling-mounted surveillance camera. The lens holding structure allows a lens of the wall-mounted surveillance camera to turn to any desired direction and be adjusted to any inclination, so that the surveillance camera may not only be directed toward any desired direction for surveillance, but also take an image free of deformation to facilitate effective surveillance by a security guard via a monitor connected to the camera.
Owner:A ONE OPTOELECTRONICS
A multi-function electronic guiding system
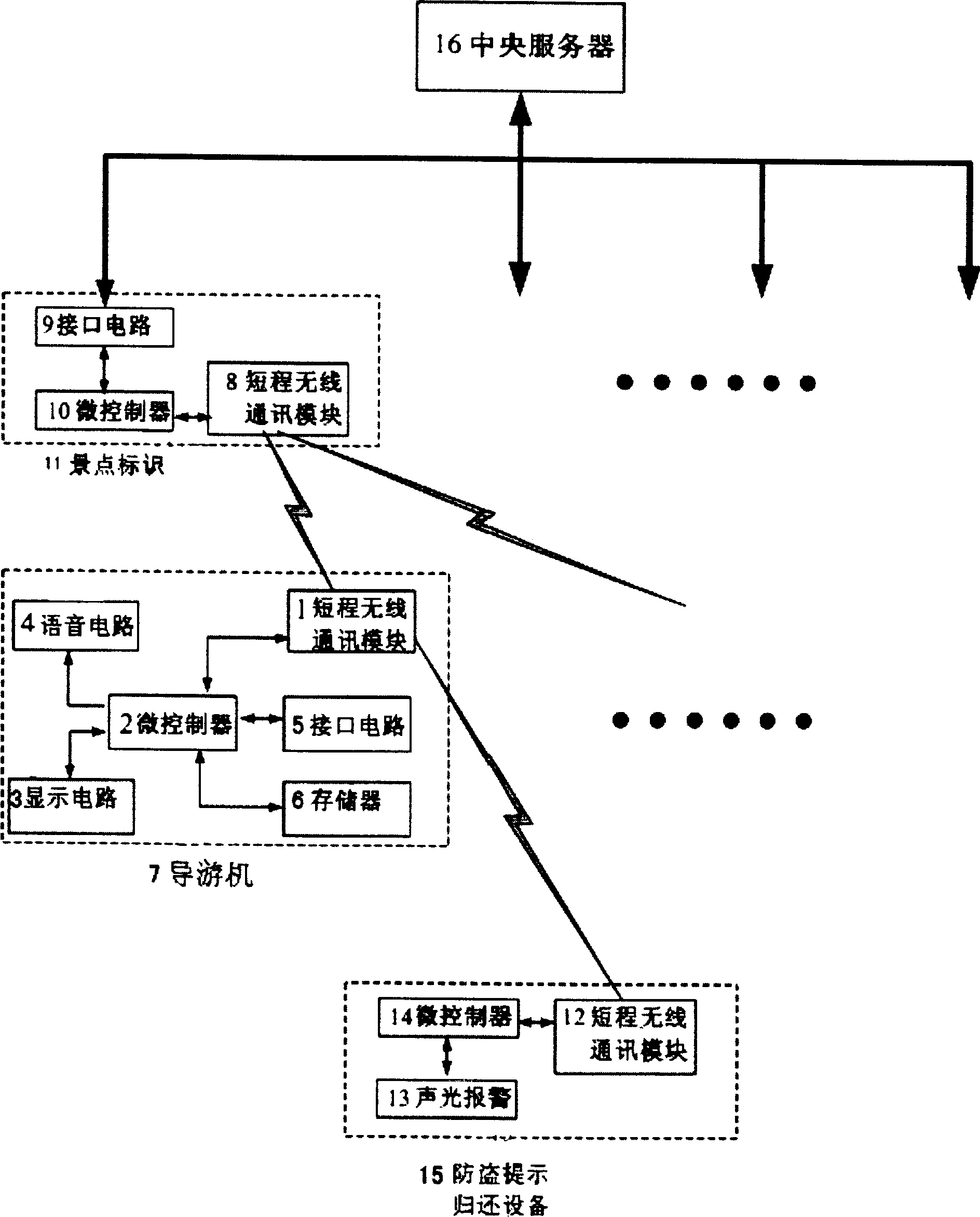
InactiveCN101145997AWork lessImprove efficiencyData switching by path configurationManagement efficiencySecurity guard
A multifunctional electronic guide system comprises a central computer server connected with a view spot receiving / transmitting device which is capable of receiving information transmitted by the view spot receiving / transmitting device. The view spot receiving / transmitting device is also connected, besides the central computer server, with a guide machine via a wireless communication mode; and the guide machine is connected with the view spot receiving / transmitting device by means of wireless communication and connected with an anti-theft prompt returning through wireless communication. The guide machine can identify different view spot transmitting / receiving devices and provide different interpretation information and road information to tourists. Additionally, the guide machine can also identify the anti-theft prompt returning device to remind the tourists to return and simultaneously remind security guard to supervise and prevent malicious theft. The central computer server can receive information transmitted from each view spot receiving / transmitting device, dynamically track and display the position of the guide machine through systemic software, and count the number of tourists and the residence time of the tourists, thereby significantly improving the management efficiency of view area.
Owner:上海真灼科技股份有限公司
Method for utilizing camera to automatically capture mine earthquakes and collapses of mine and timely record and alarm
InactiveCN103726879AQuickly grasp the historical traceabilityMining devicesClosed circuit television systemsVideo monitoringAlarm message
The invention discloses a method for utilizing a camera to automatically capture mine earthquakes and collapses of a mine and timely record and alarm. Through the video surveillance technology and the image analysis technology, collapses and mine earthquakes inside the mine can be automatically found and timely alarmed, and video signals can be stored. The method includes that a plurality of monitoring zones are set on a same monitoring screen, and pictures of the zones are intercepted circularly and compared with a screen of same zones of the previous frame; once differences are found, counting is performed in a massage center; when counting value reaches a preset threshold, alarm information is triggered, recording of monitoring content is started, and the alarm information is transmitted to a mobile client side through a wireless network for a security guard to monitor and process. By the application of the method, the security guard can timely discover dangerous signals inside the mine, check on-site situations in real time and check on-site images in a history record, and thus quick master of on-site situations and historical retrospection of events is facilitated.
Owner:辽宁晟通系统集成工程有限公司
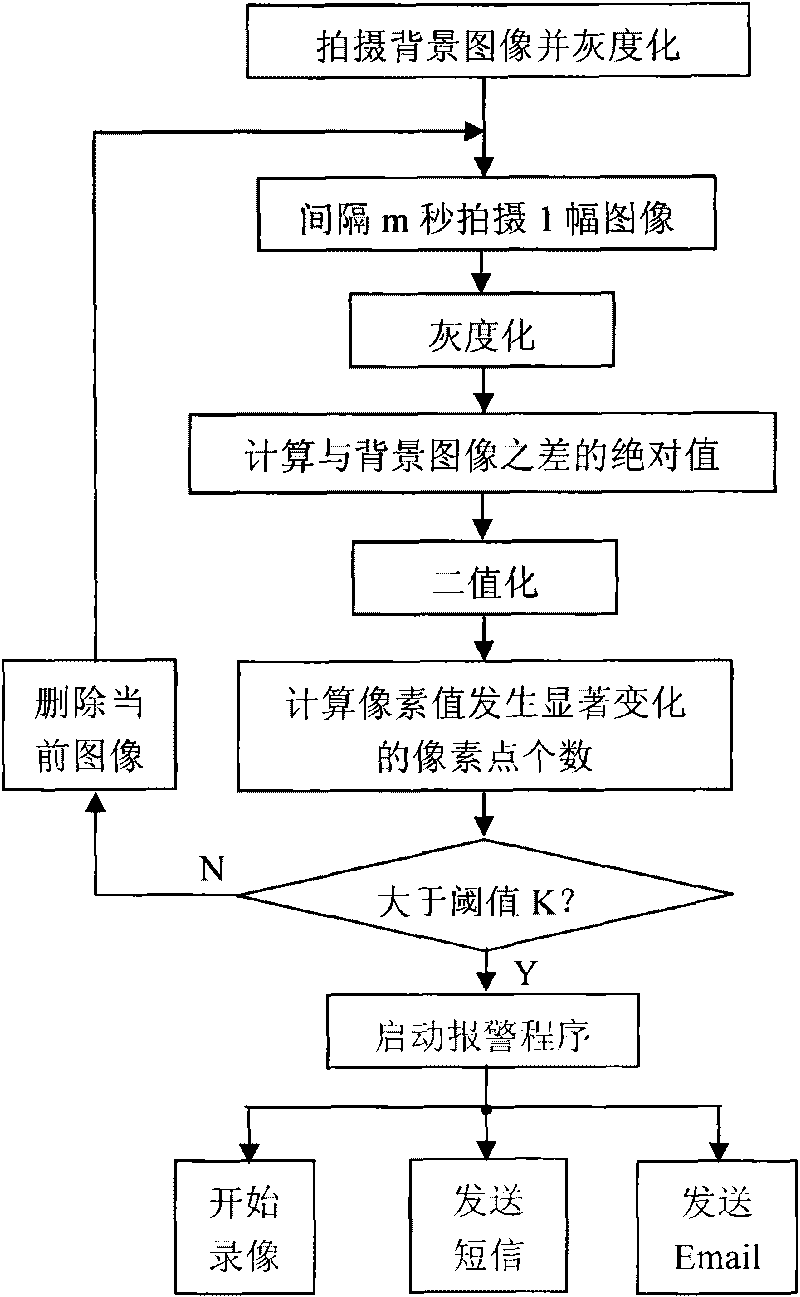
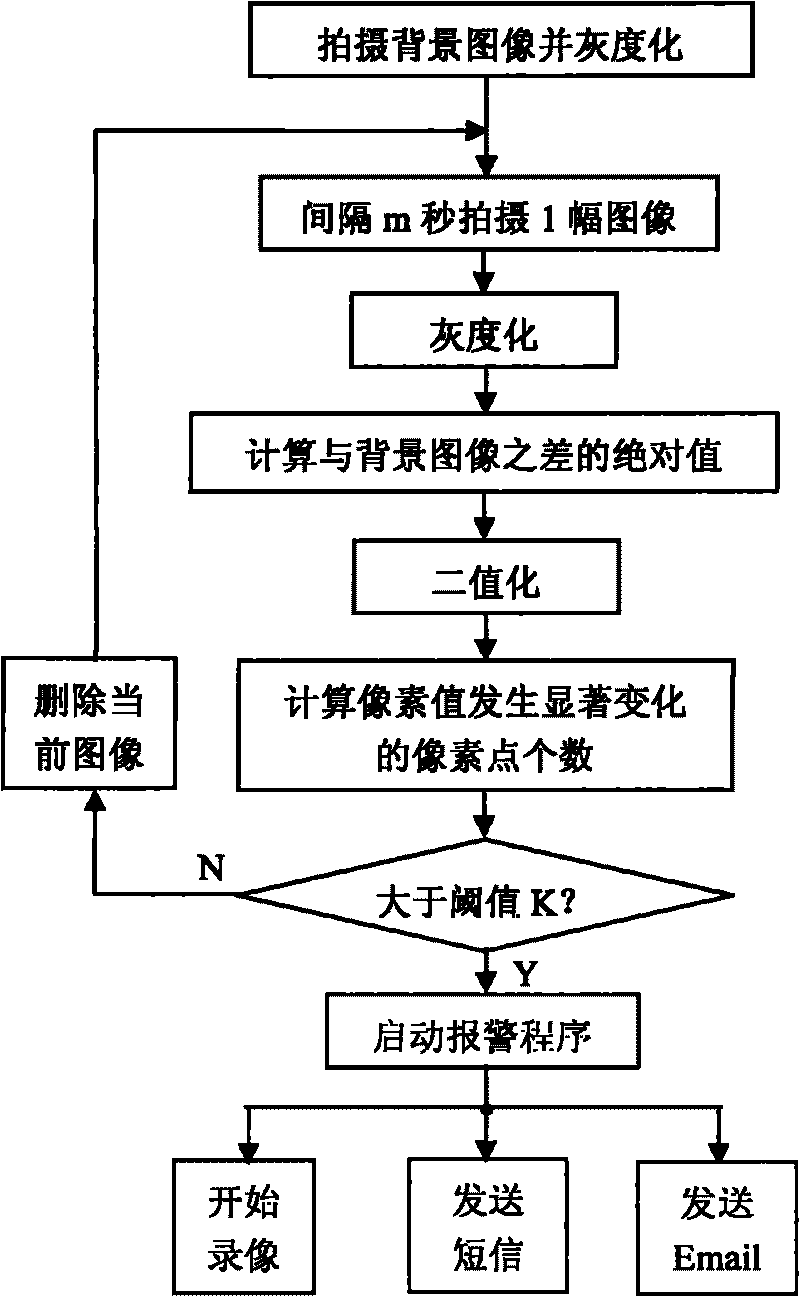
Difference method-based indoor video monitoring and alarming method
InactiveCN101720031ASave storage spaceSend quicklyTelevision system detailsColor television signals processingVideo monitoringSecurity guard
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Synthetic intelligent safety prevention system based on area safety
InactiveCN101303777AReach exchangeAchieve sharingCo-operative working arrangementsData switching by path configurationPersonalizationTime information
The invention discloses an integral intelligent security system based on the regional safety, which remotely controls and manages separate system by means of a TCP / IP network; not only video, access control, and alarm are included, but also the administration of the daily work of patrol, antitheft, and security guard personnel are brought into the system; the individualized target detecting technologies such as the RFID technology, the biometric identification technology, and the like, are additionally applied. The invention is a 'network system' of hierarchical network version and meets requirements for multi-level and multi-monitoring centers. The invention is highly practical , can provide real-time information to a user; meanwhile and provide a plurality of emergency solutions according to the collected real-time information. Therefore, the invention is applicable to overall regional safeguarding or security guard in some important places. The integral intelligent security system has very high compatibility and expansibility, can perform the regional networking from a point to a line and a point to a surface so as to ultimately form a multi-level safety guarding and emergency response system among regions.
Owner:INFORMATION RES INST OF SHANDONG ACAD OF SCI +1
Integrated intelligent community system based on internet of things
InactiveCN107659645ASolve the problem of over-reliance on offline personnelWide coverageHome automation networksVideo monitoringCommunity system
The invention discloses an integrated intelligent community system based on internet of things. The system comprises a real estate application layer, a data transmission layer and a service managementlayer; the data collection, the video monitoring, the automatic alarming and intelligent identification are integrated by taking the community as a unit and based on the internet of things technology; the networking control and processing are performed on the safety loophole information of the community, the resource utilization and the community service in a unified way; the referred fields comprise community security guard, electrical fire monitoring, fire-fighting equipment supervision, community energy management, service for life, service for the aged, the community entry-exit management, and intelligent parking; the coverage range is wide, the operation efficiency is high, a problem that the existing intelligent community system relies too heavily on the offline personnel, and the intelligent community management is really realized.
Owner:刘建国 +1
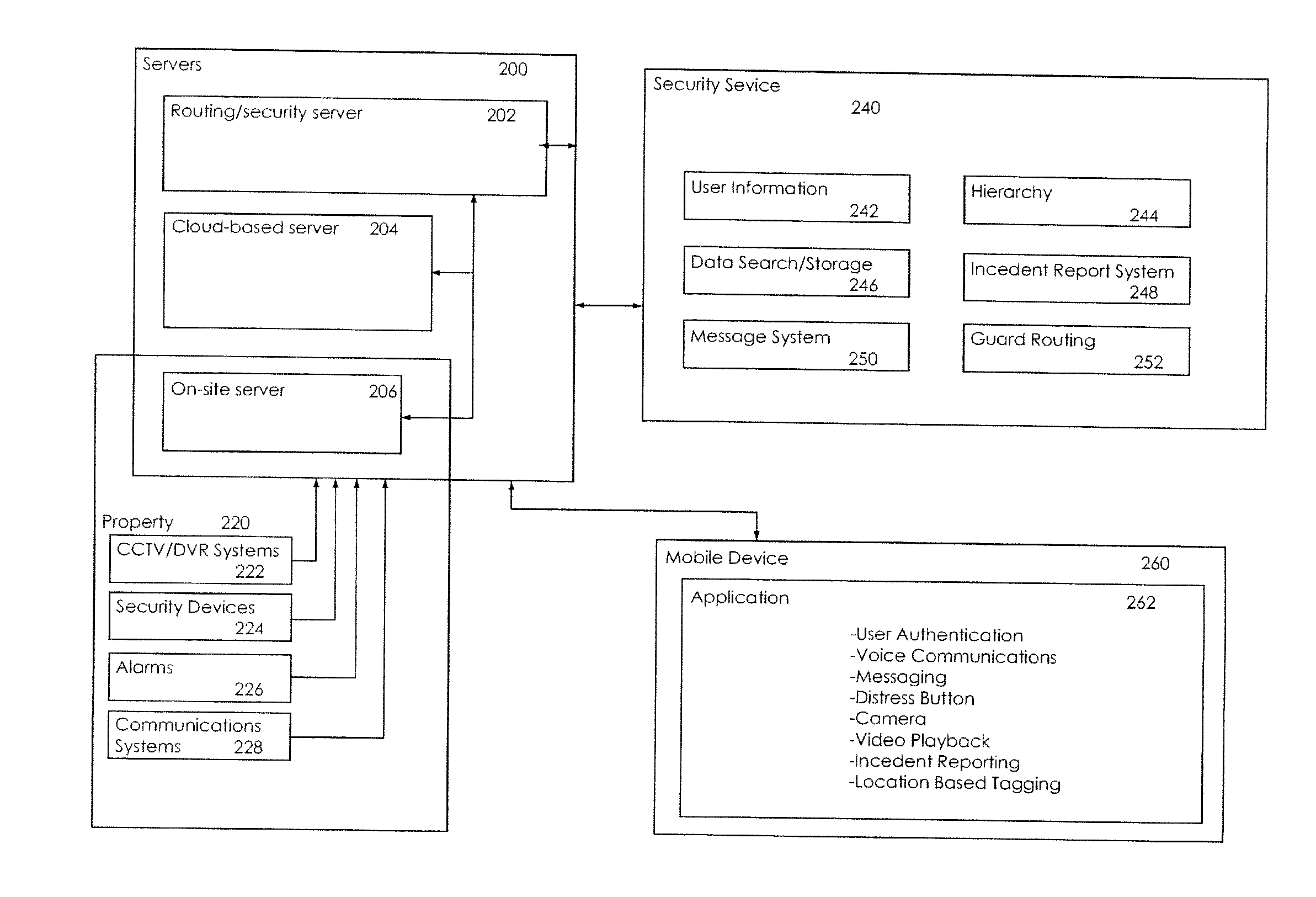
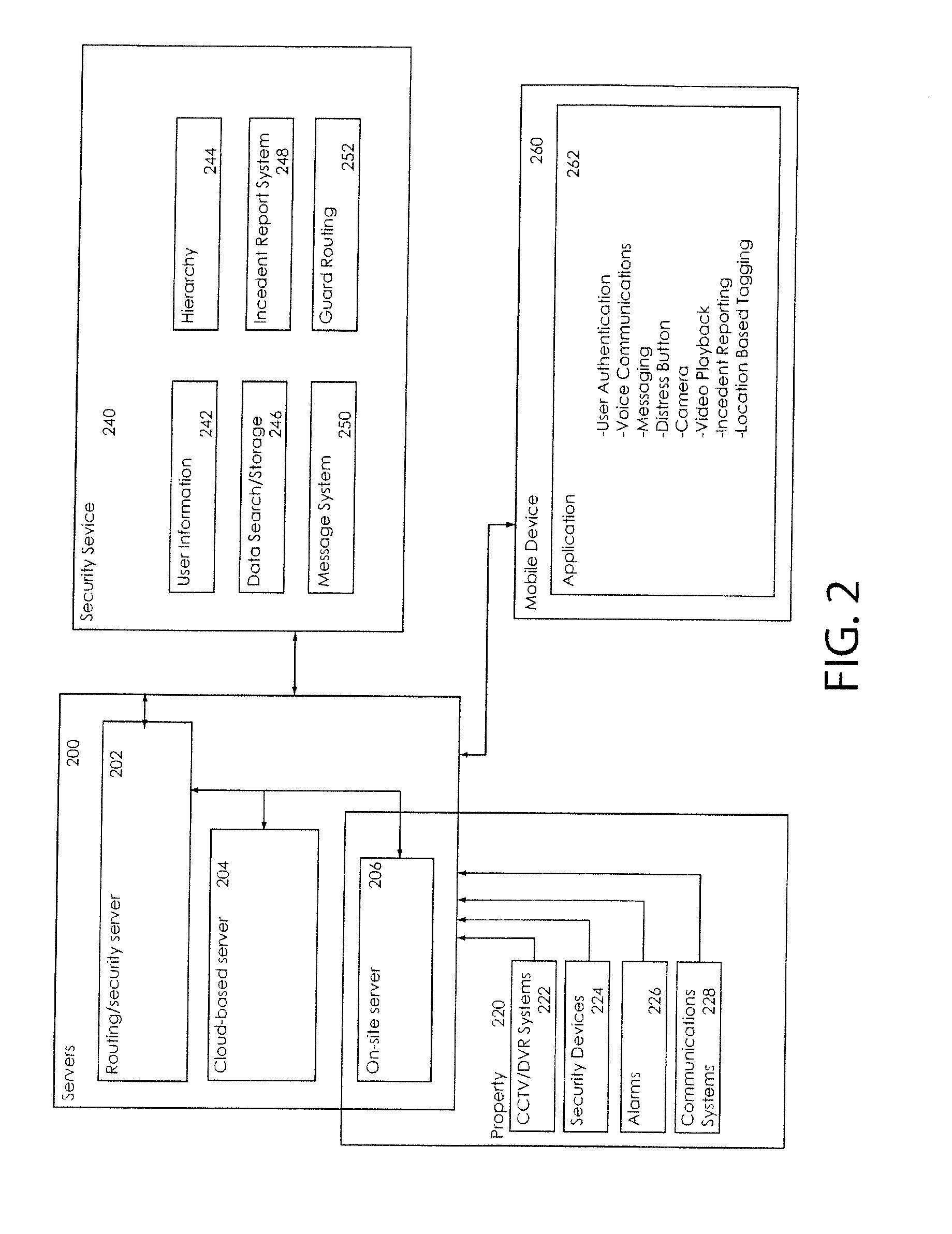
Systems, methods and devices that allow security and security guard functions to be performed using an integrated system and mobile devices
InactiveUS20150110459A1Good conditionEfficient use ofTelevision system detailsColor television detailsCamera phoneNetwork connection
This disclosure is directed at system which integrates many of the functions of existing security and security guard systems into a single integrated system, while adding new functions and increased functionality through the centralization of the systems. The present system uses a server based system to provide the backbone of a system which takes input and performs its functions through network connection through a web portal, to an application on mobile devices, to CCTV and / or DVR devices, and to any other network enabled device which is connected to the system. One major function of the system disclosed allows CCTV and / or DVR systems to be networked into the server system, allowing the server to store, document, and log the video and photos, along with any video and photos from any mobile devices, such as camera phones, which are networked into the system. Another feature, via an application on a mobile device, is intended to both perform a number of functions essential to guard duty, such as communication, surveillance, incident reporting, and patrol routing function, as well as to allow management to monitor guards by tracking their patrol routes and logging events and recordings. Additionally, the present invention allows a property's management, staff, residents and guests to view selected CCTV camera video and / or images on a mobile device.
Owner:GOMOBILE SECURITY SOLUTIONS
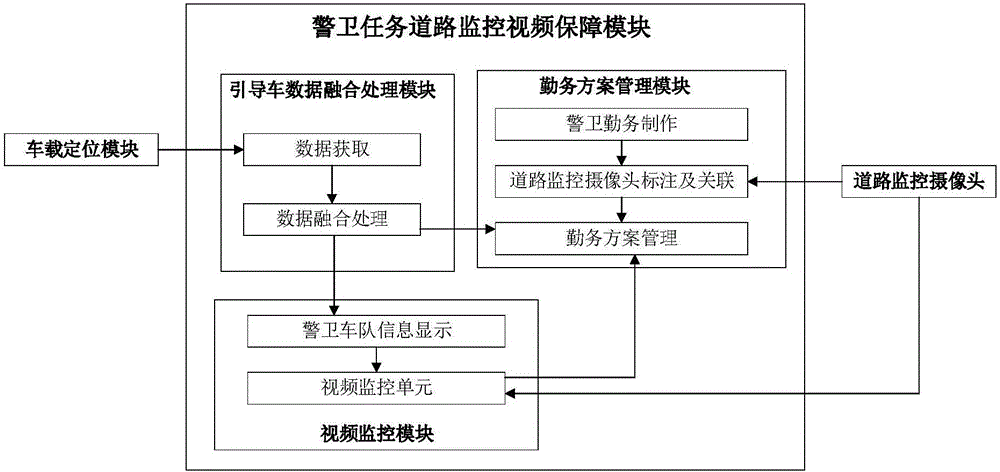
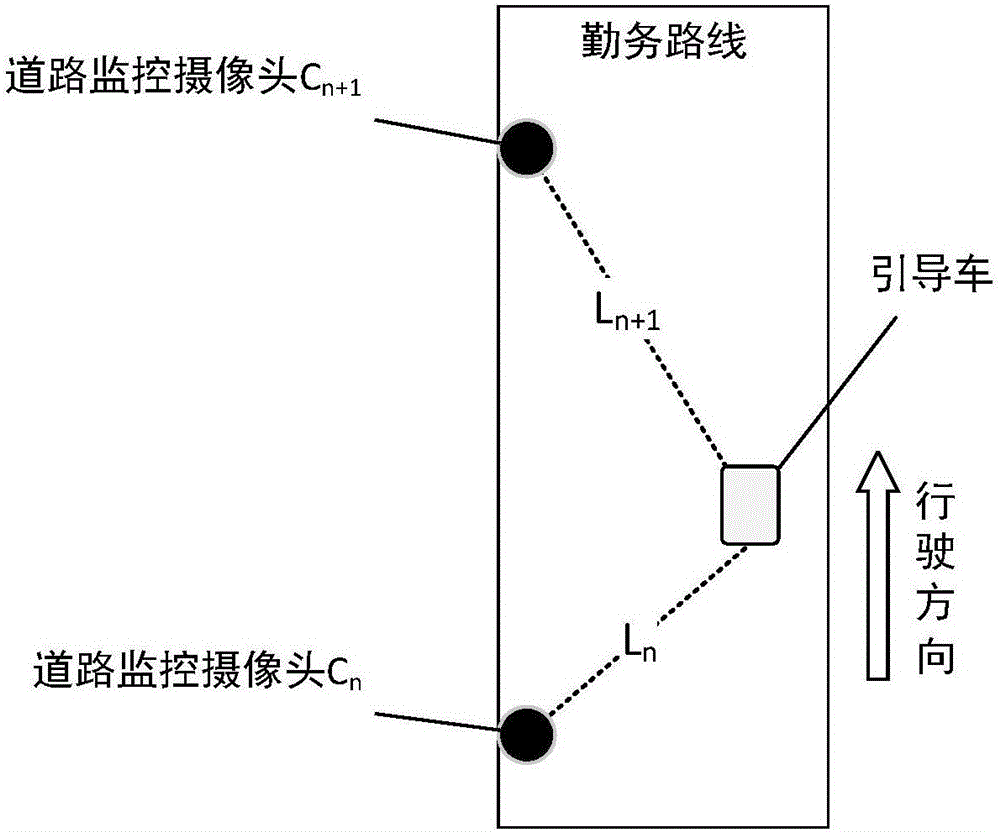
Method and system for switching road monitoring video along with position of guiding vehicle in security task
ActiveCN105847755AImprove the level of security intelligenceImprove the level of intelligenceTelevision system detailsColor television detailsSecurity guardWorkload
The invention discloses a method and system for switching a road monitoring video along with the position of a guiding vehicle in a security task, which comprise a method for automatically switching a road monitoring video along with the position of a guiding vehicle in real time in a security task and a security service road monitoring video guarantee system. The road monitoring video is one of indispensable guarantee elements for guaranteeing various large-scale security guard tasks in real time. According to the scheme provided by the invention, in actual security task execution process, position information of the guiding vehicle is obtained in real time, a video image is automatically switched along with the position of the guiding vehicle through a data processing technology, security object fleet information can be dynamically displayed on the monitoring video, a conventional tedious mode of manually switching the road monitoring video by support personnel, the workload of the support personnel is mitigated, and the visualization and intelligent level of security task support is improved.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
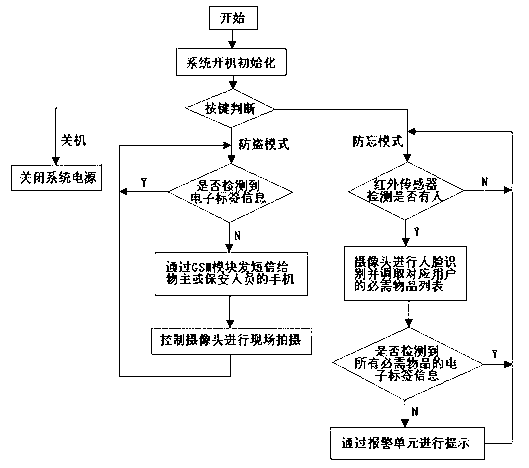
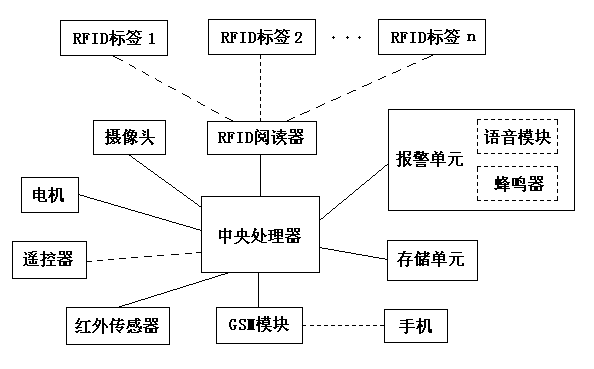
Electronic management system based on RFID
The invention relates to an electronic management system based on RFID. The electronic management system based on the RFID comprises two modes of an anti-forgetting mode and an anti-theft mode. According to the anti-forgetting mode, electronic tags are adhered to essential articles which need to be carried when a person goes out at ordinary times, a reader connected with a central processor is placed at the doorway, the articles are carried completely if signals of the electronic tags of all the essential articles are detected, and the central processor controls a voice module to issue out voice prompt corresponding to the essential articles which are not carried if the essential articles are not completely carried. According to the anti-theft mode, electronic tags are adhered to valuable articles, the valuable articles are placed in a detectable range of the reader, when a person moves the articles to a range where the reader can not detect the articles, the central processor controls a GSM module to send alarm information to a cell phone of an owner or cell phones of security personnel, and meanwhile the central processor controls a plurality of cameras to carry out shooting on spot to facilitate evidence preservation. The electronic management system based on the RFID can achieve anti-forgetting and anti-theft functions and is applied to places of homes, offices and the like, and a using method is simple and easy to understand.
Owner:FUZHOU UNIV
Virtual entry assistant using automated greeter
ActiveUS8040216B2Allow accessElectric signal transmission systemsMultiple keys/algorithms usageMedia serverReceptionists
A virtual security guard or receptionist automatically allows entry to an area by determining a user's identity and comparing that to an access list. If the user is authorized, then the user is allowed entry to the area. The receptionist can be implemented by either a sign, or by using a virtual receptionist to shows a picture selected from a media server that has many different pictures. Computer intelligence can be used to allow the receptionist to carry out almost any operation that is carried out by a real receptionist.
Owner:PATENTIAL HLDG INC
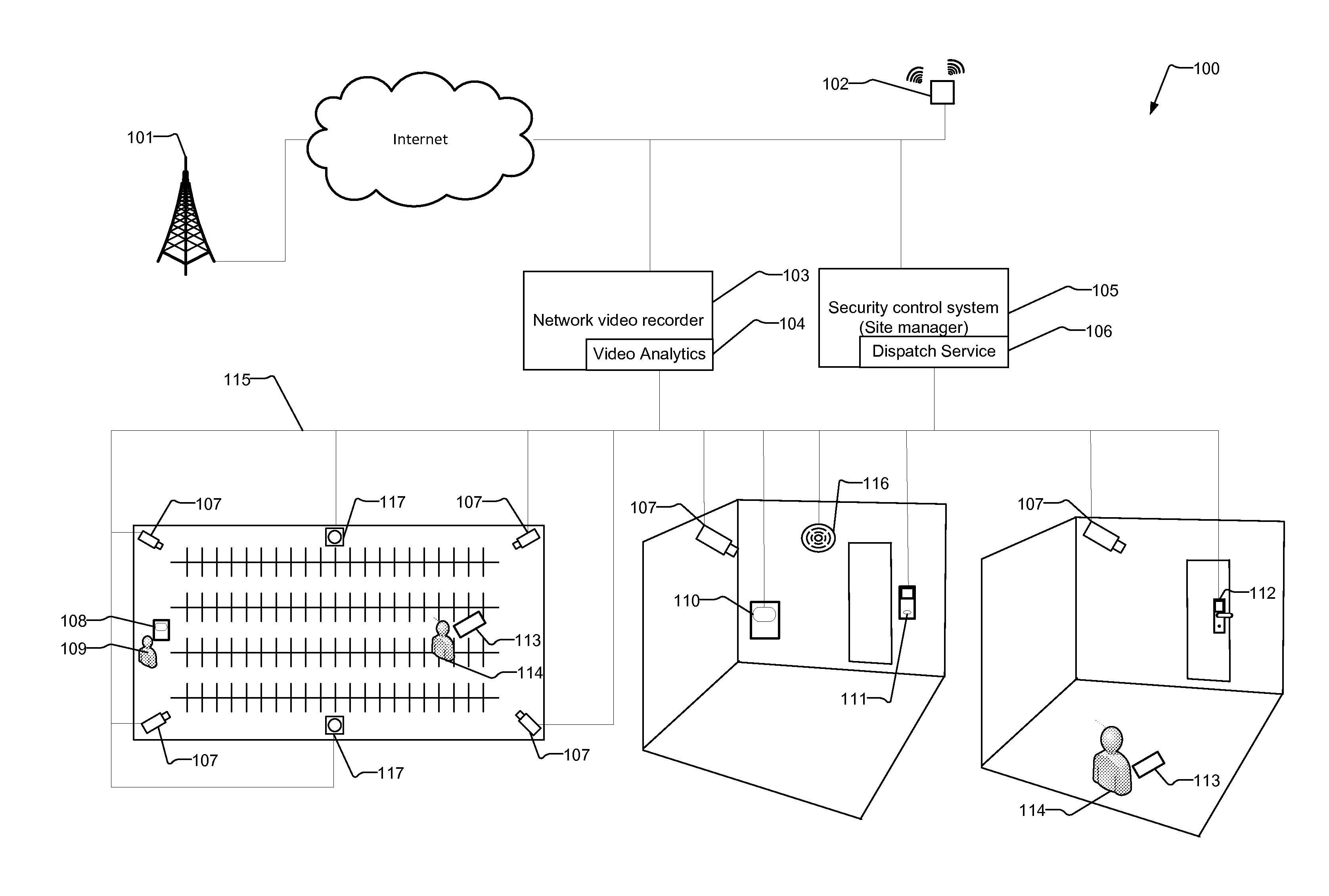
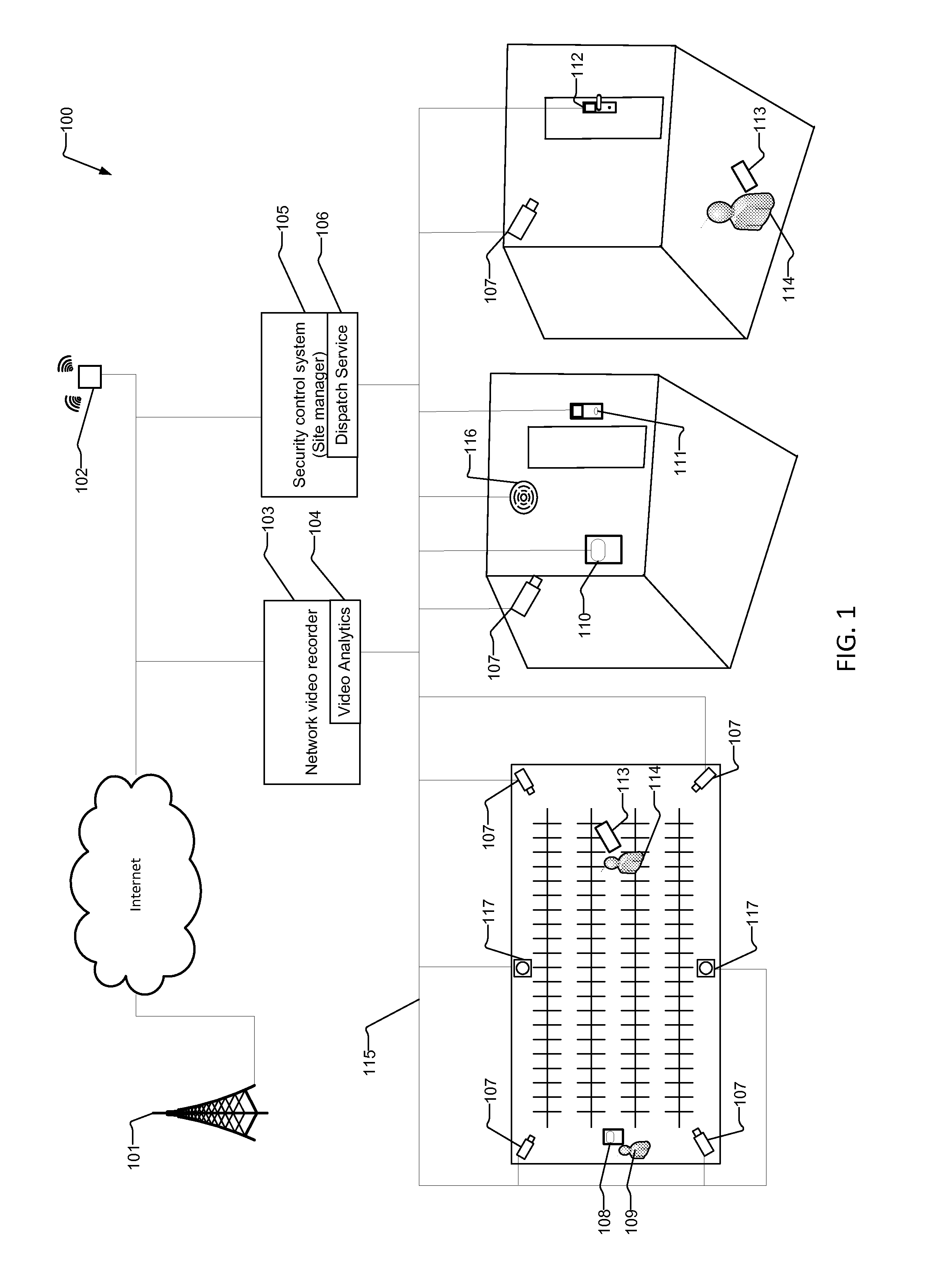
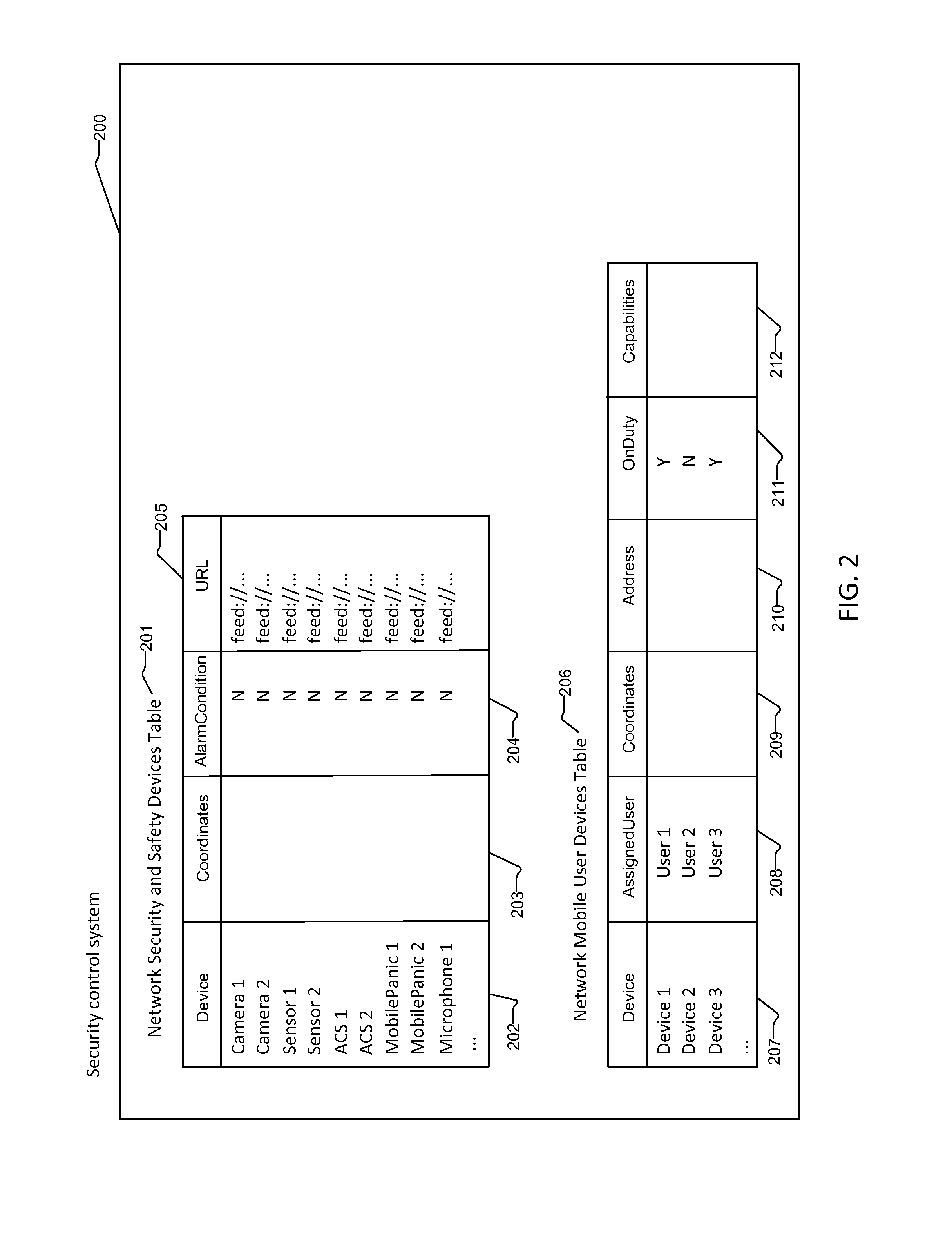
System and Method for Video/Audio and Event Dispatch Using Positioning System
ActiveUS20150049190A1Without wasting timeReduce bandwidth utilizationColor television detailsClosed circuit television systemsVideo transmissionSystem call
A system and method for operating a network security system implementing security cameras, motion sensors, access control systems, security door locks, and mobile panic button devices within a monitored area. Security cameras transmit video to a network video recorder and the video is analyzed by a video analytics system to determine if a security event is occurring. If a security event occurs, a security control system calls a dispatch service, which transmits a notification to only those security guards who are within a given area of the event.
Owner:JOHNSON CONTROLS TYCO IP HLDG LLP
Dual hip cell phone and CD player pocket
The nature of this invention is a pocket for a cell phone / s or portable CD player that fits snug against the hip, has a secure closure and is quickly accessible. Loss or breakage of the delicate plastic clip that hold the cell phones in place will not occur. Millions of people walk around with their CD player in their hand, which is uncomfortable, inconvenient and dangerous. The pocket allows a music device to be carried and used without implementing the hands when listening to music. The earplug connection is at a perfect relaxed distance from the user's ear / s. This invention will become a standard for everyone in the world who uses cell phones and portable CD players and wants the convenience of a pocket positioned on the hip more easily accessible to the hands, eyes and ears. No pockets currently exist like this type located on the hip area of clothing. The two cell phone pockets (one on each hip) for those who need two cell phones or one pocket can be used for a small digital music player when not using both pockets for cell phones.This shows how versatile the pocket can be. The two cell phone pockets can be made for use on the same side of the pants (one cell pocket at the hip and one cell pocket just above the knee), which allows users quick access while sitting down on a bus, car, plane or train. If someone is sitting next to you, you can switch your cell from your hip are to the pocket just above the knee and make access more comfortable for you and you will not disturb the person next to you. The front cell pocket can be manufactured to set on the front thigh area as a top cell phone pocket. The pocket has dual functions and can also be used as a pager pocket. It can be manufactured on both sides of right and left top thigh area.The walkie-talkie pocket is the larger version of the cell phone pocket and is to be used by maintenance workers, police and security guards with larger radios and a taller antenna. No pocket exists to accommodate that size electronic and would also be located on the hip and there would no longer be a need for a belt or clip on the radio.The cell phone and CD player pocket is unisex on slacks, jeans and pants. Also, it will be on dresses, skirts, jackets and coats located on the hip and on the top front chest area on coats, shirts and blouses.
Owner:JOHNSON GREGORY WALKER
Method of managing visiting guests by face recognition
ActiveUS20130279767A1Updating of informationDramatically reducing their workloadCharacter and pattern recognitionDigital data authenticationPattern recognitionWorkload
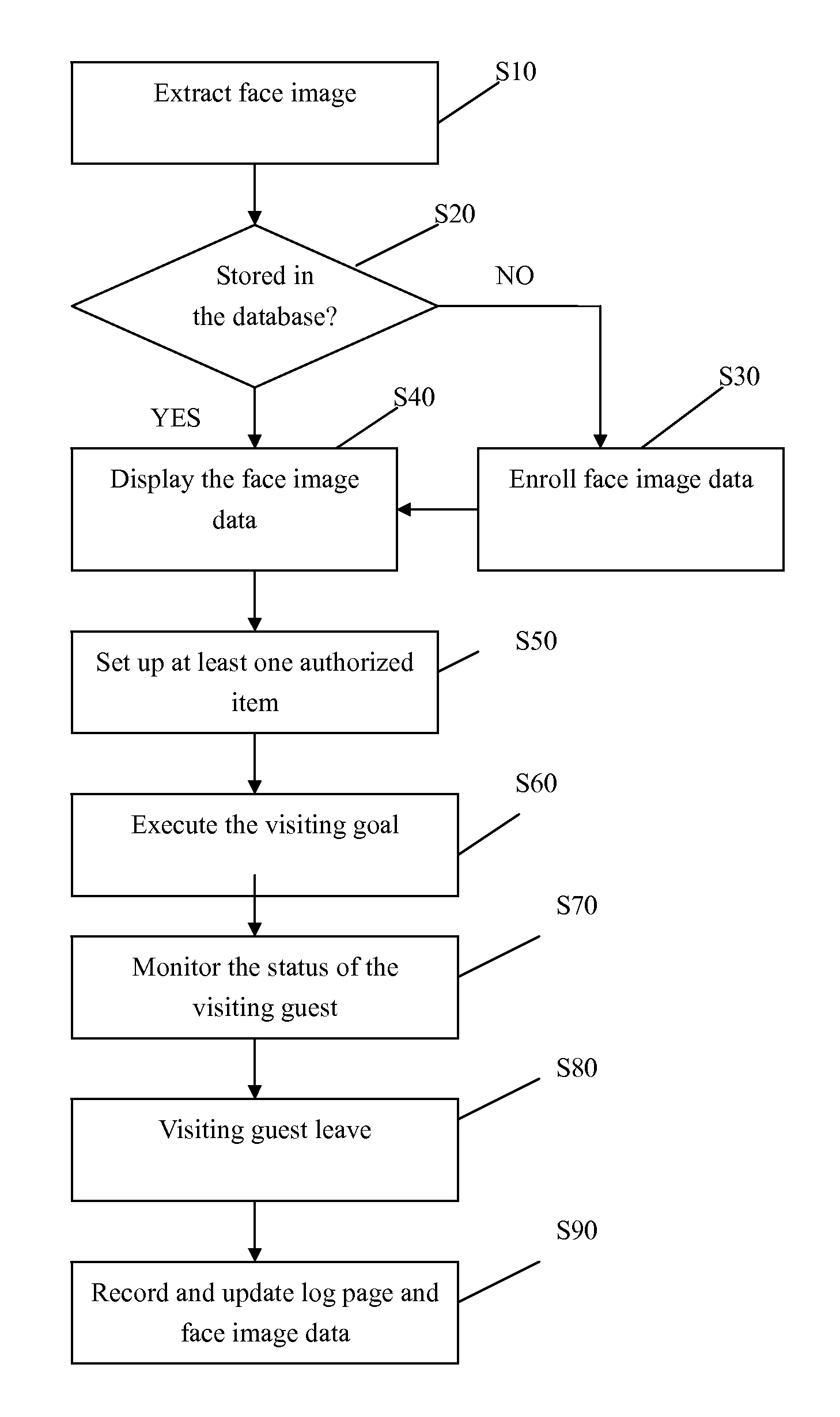
A method of managing visiting guests by face recognition includes: extract the face image of the visiting guest; determine if the face image of the guest is stored in the database; display the face image data comprising the face image, guest information and visiting information if the face image is stored or enroll the new face image data and then display the face image data just registered; set up at least one authorized item; execute the visiting goal confined by the authorized items; monitor the status of the visiting guest; wait until the guest leaves; and finally record and update log page and face image data of the visiting guest in the database. Therefore, the method can reduce security guard workload, assist security guards or automatically and solely execute the function of guard entrance without any careless mistakes, and update visiting guest information in real time.
Owner:TAIWAN COLOR & IMAGING TECH CORP
Family safety guard and emergency call intelligentized automatic control system
InactiveCN101290704APrevent door-to-door "stepping on the spot" behaviorRealize offline queryTelephonic communicationAlarmsVideo monitoringIntelligent Network
The invention discloses an intelligent automatic control system with household security guard and emergency alarm, which takes a household security maintenance intelligent controller as a core to connect other household intelligent security defense devices to construct the intelligent automatic control system with household security guard and emergency alarm. The system comprises the household security maintenance intelligent controller having an input end connected with an outgoing defense setting and canceling switch, a wired security defense detector, a wired disaster defense detector, a sleeping defense setting and canceling switch and a portable wireless emergency alarm, and an output end connected with an intelligent network video monitor and a remote control execution device; meanwhile, the household security maintenance intelligent controller is also in two-way communication with a unit / outdoor talk back device and a talk back type emergency alarm, thereby realizing the effect of preventing the invasion with an overall 'emulation' mode, and meeting comprehensive requirements of a modern family to a security guarding product in aspects such as remote alarm, voice talk back, video monitoring, convenient operation and humanized running.
Owner:陈达理 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com