Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1983 results about "System call" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, a system call is the programmatic way in which a computer program requests a service from the kernel of the operating system it is executed on. This may include hardware-related services (for example, accessing a hard disk drive), creation and execution of new processes, and communication with integral kernel services such as process scheduling. System calls provide an essential interface between a process and the operating system.
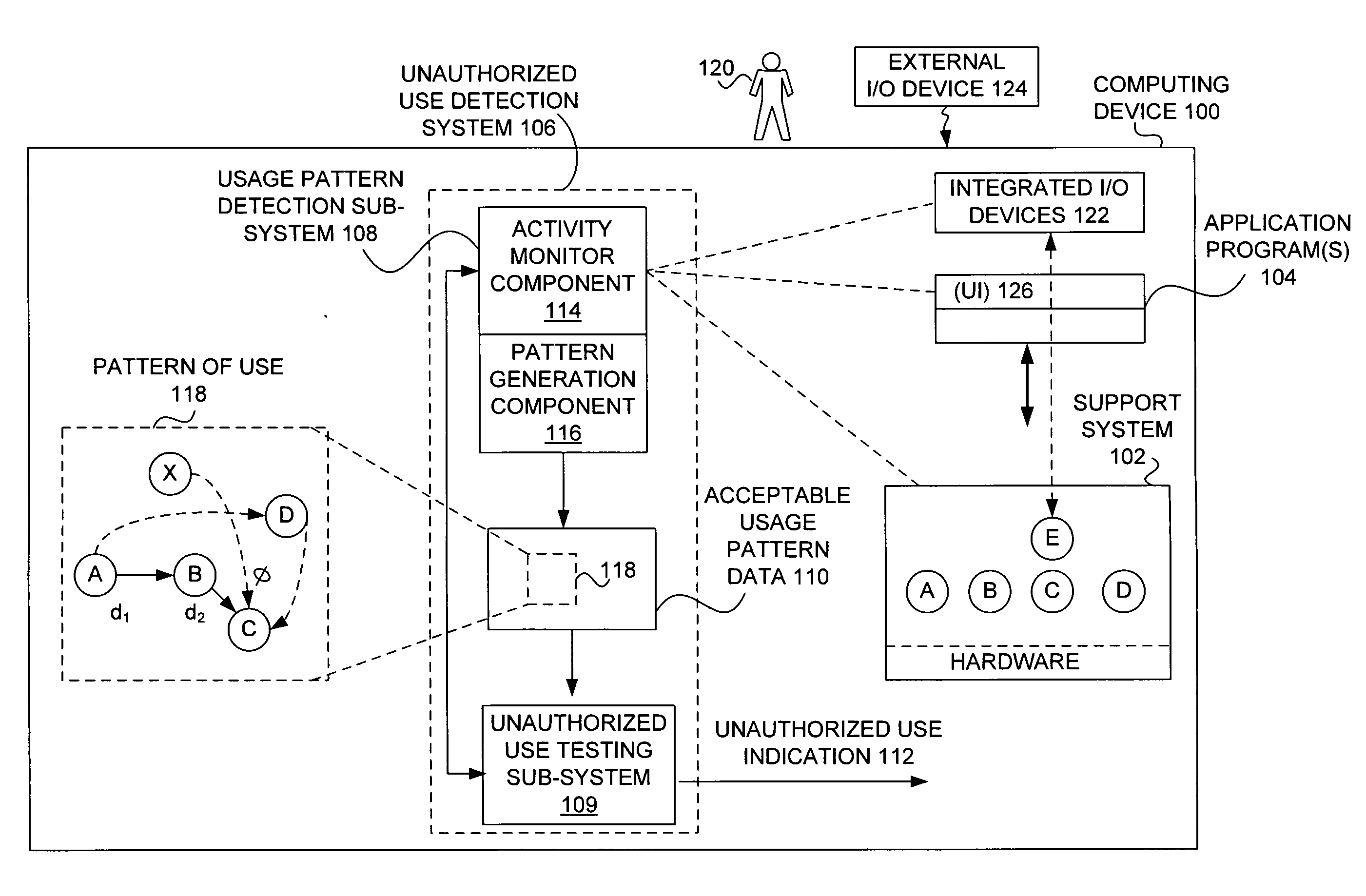
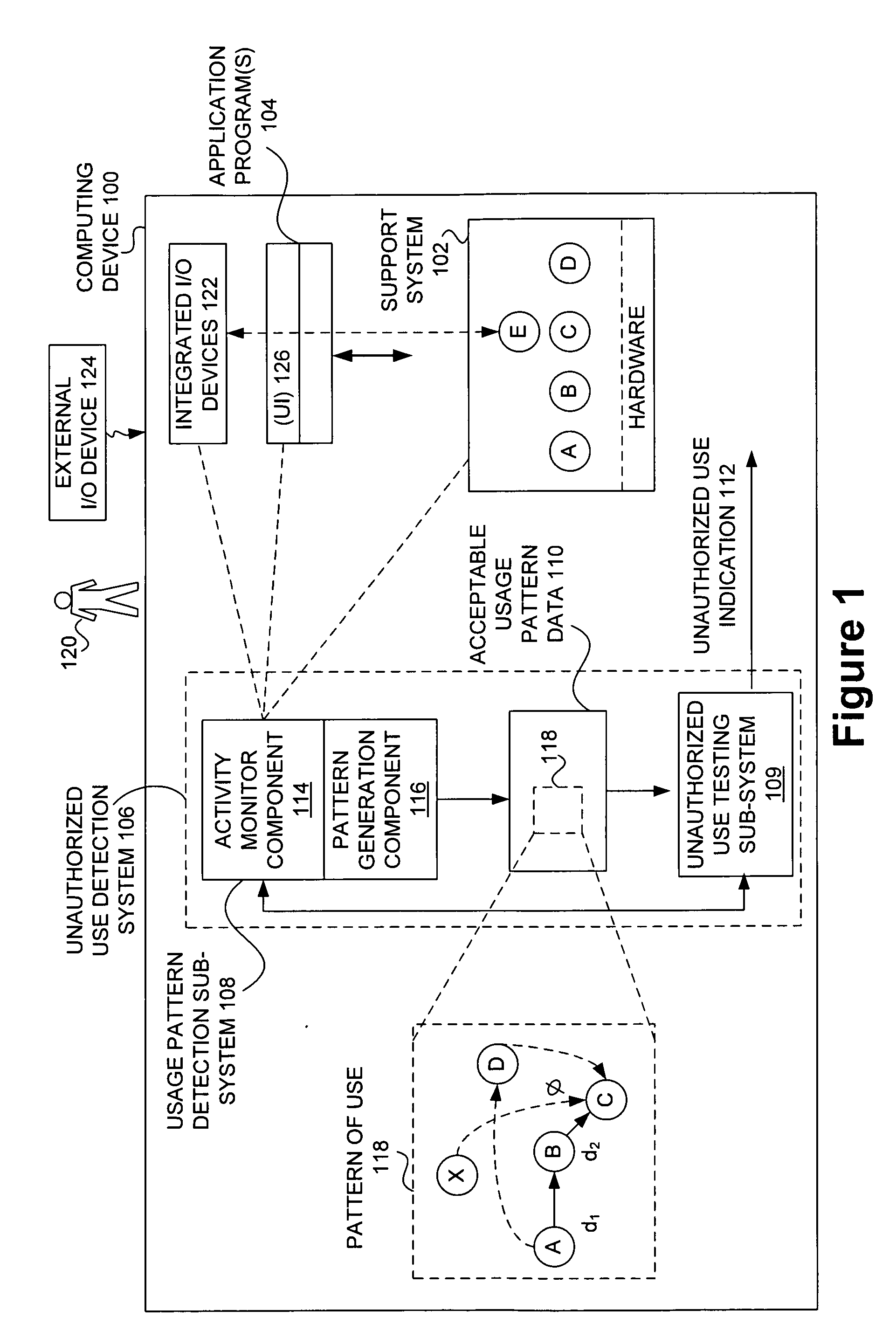
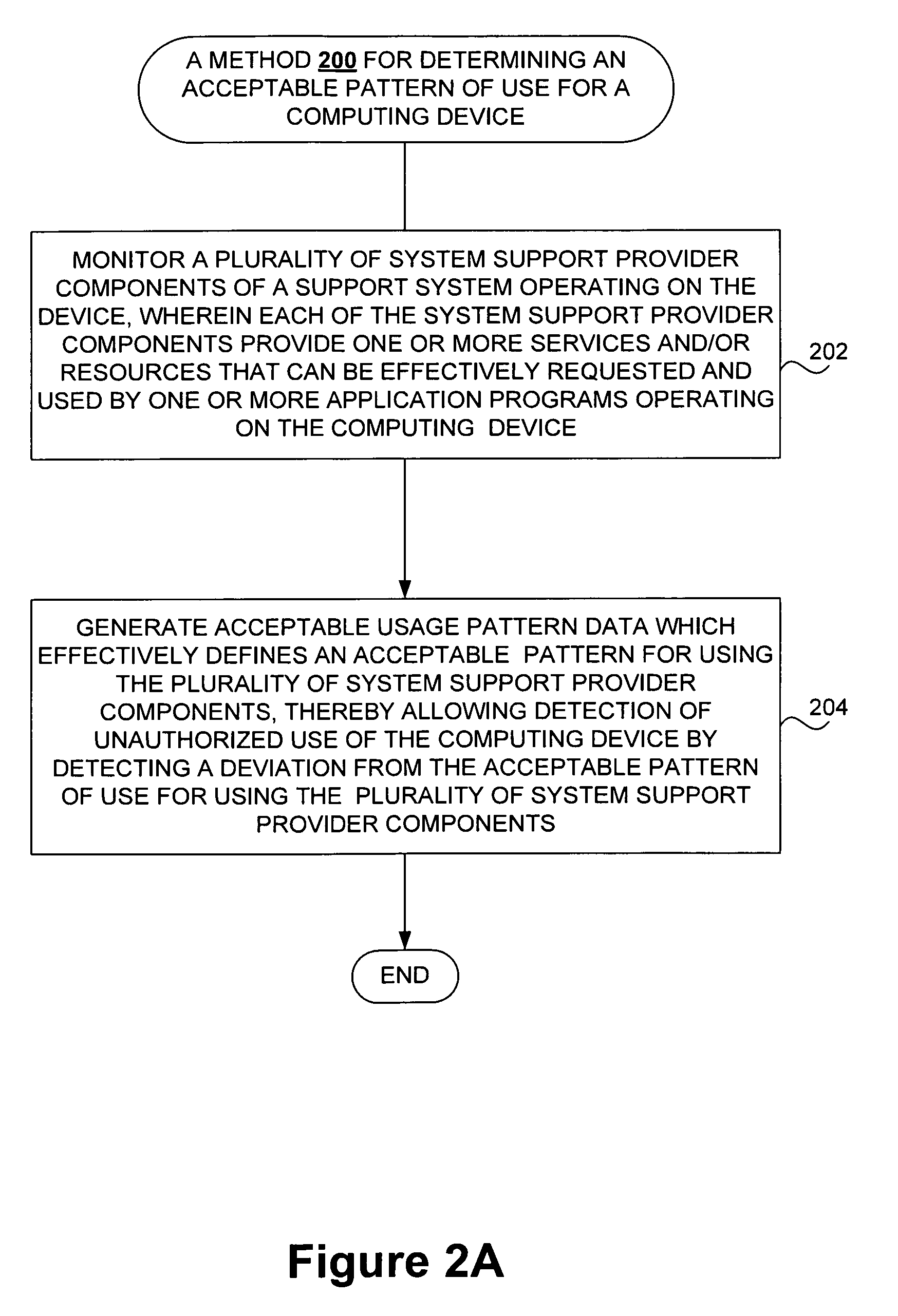
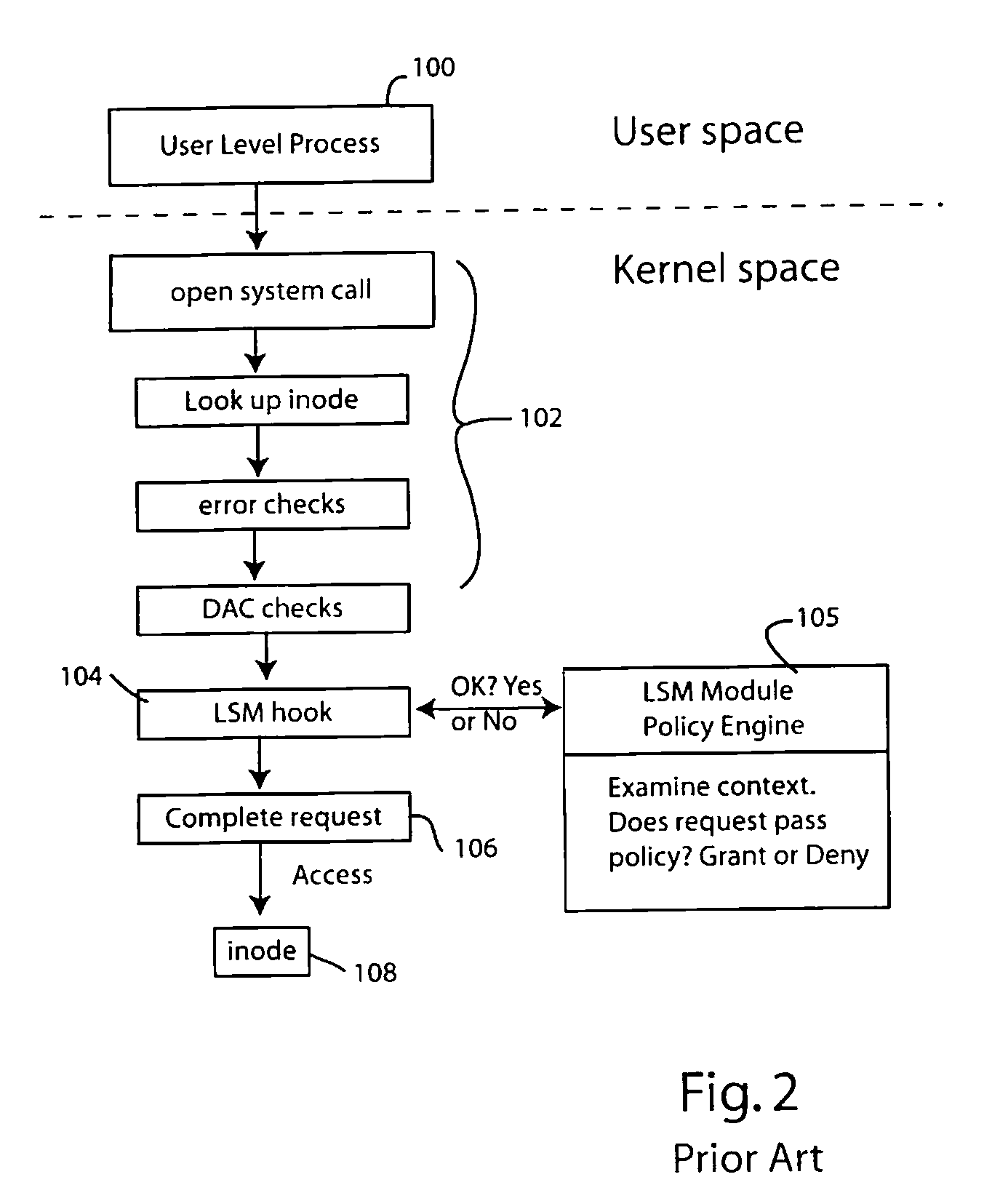
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS20090199296A1Efficiently definedMemory loss protectionError detection/correctionSupporting systemOperational system
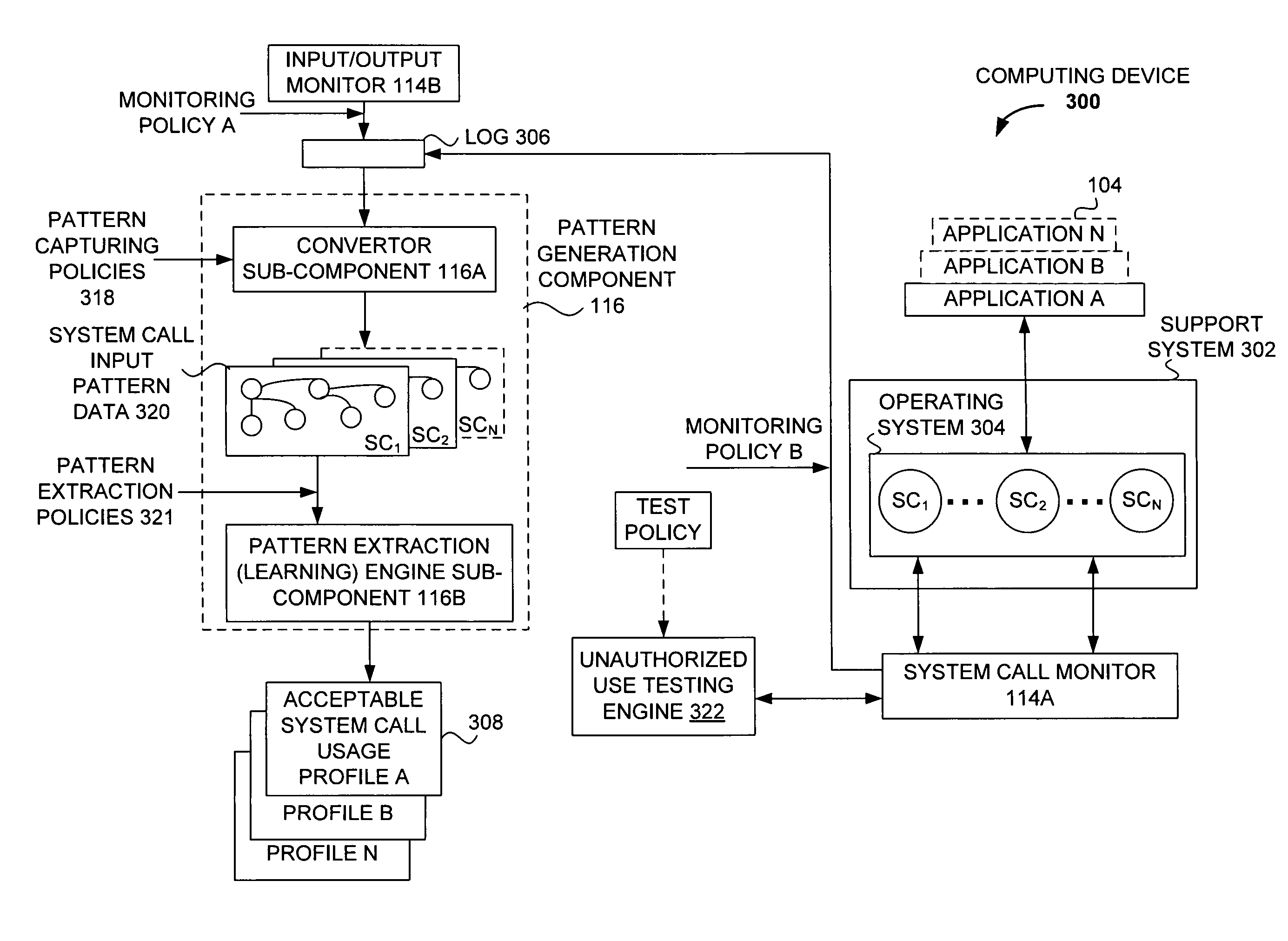
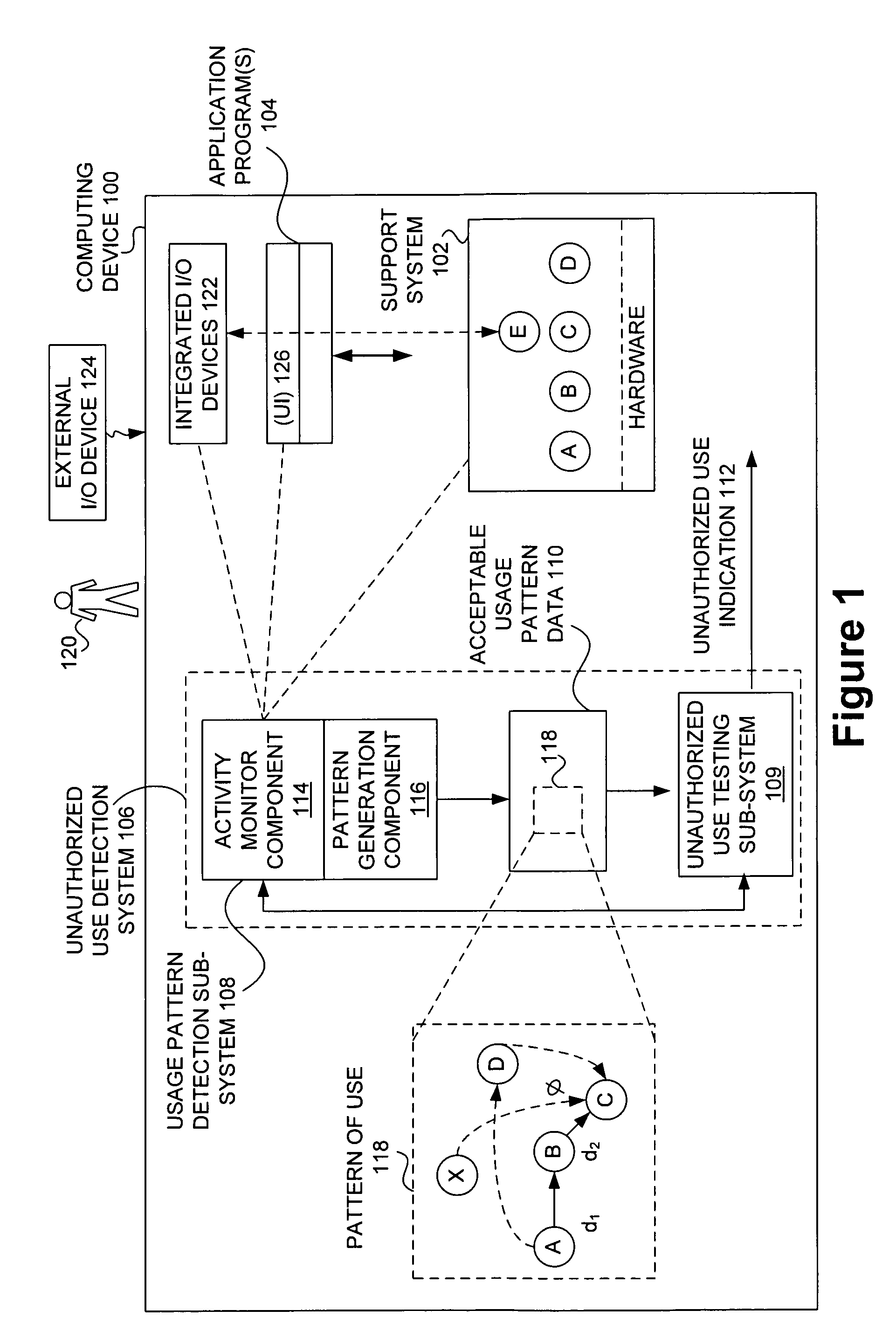
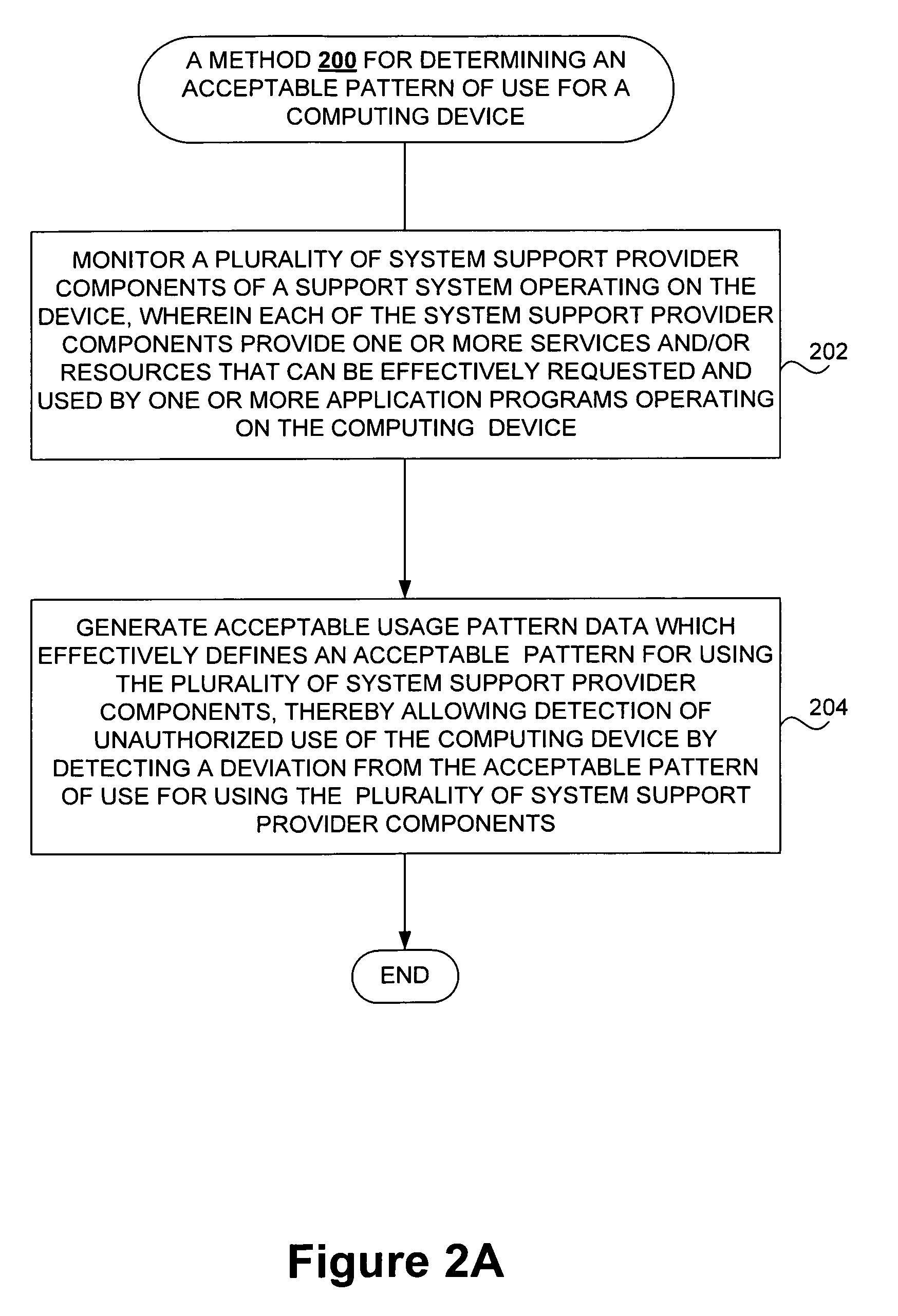
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
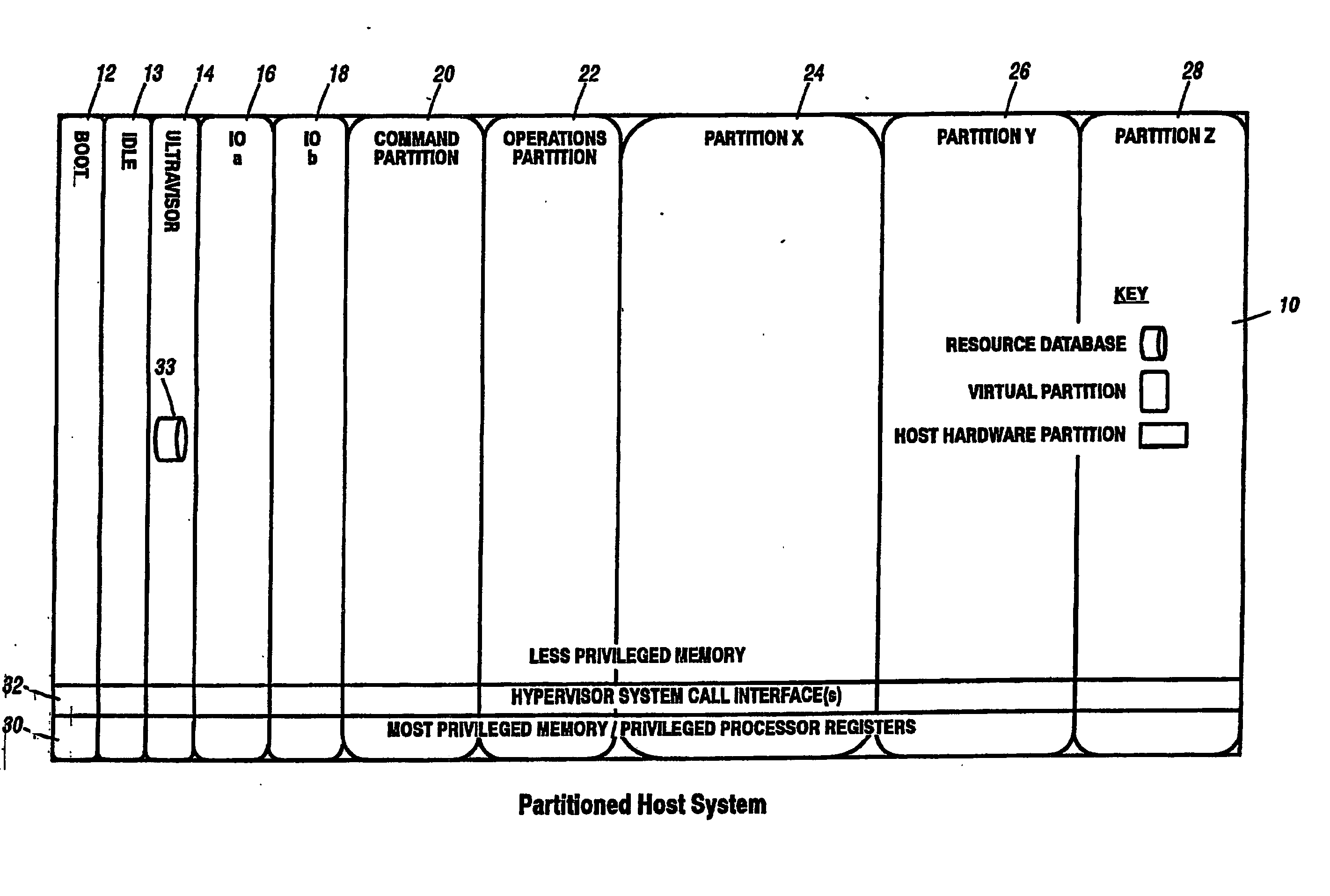
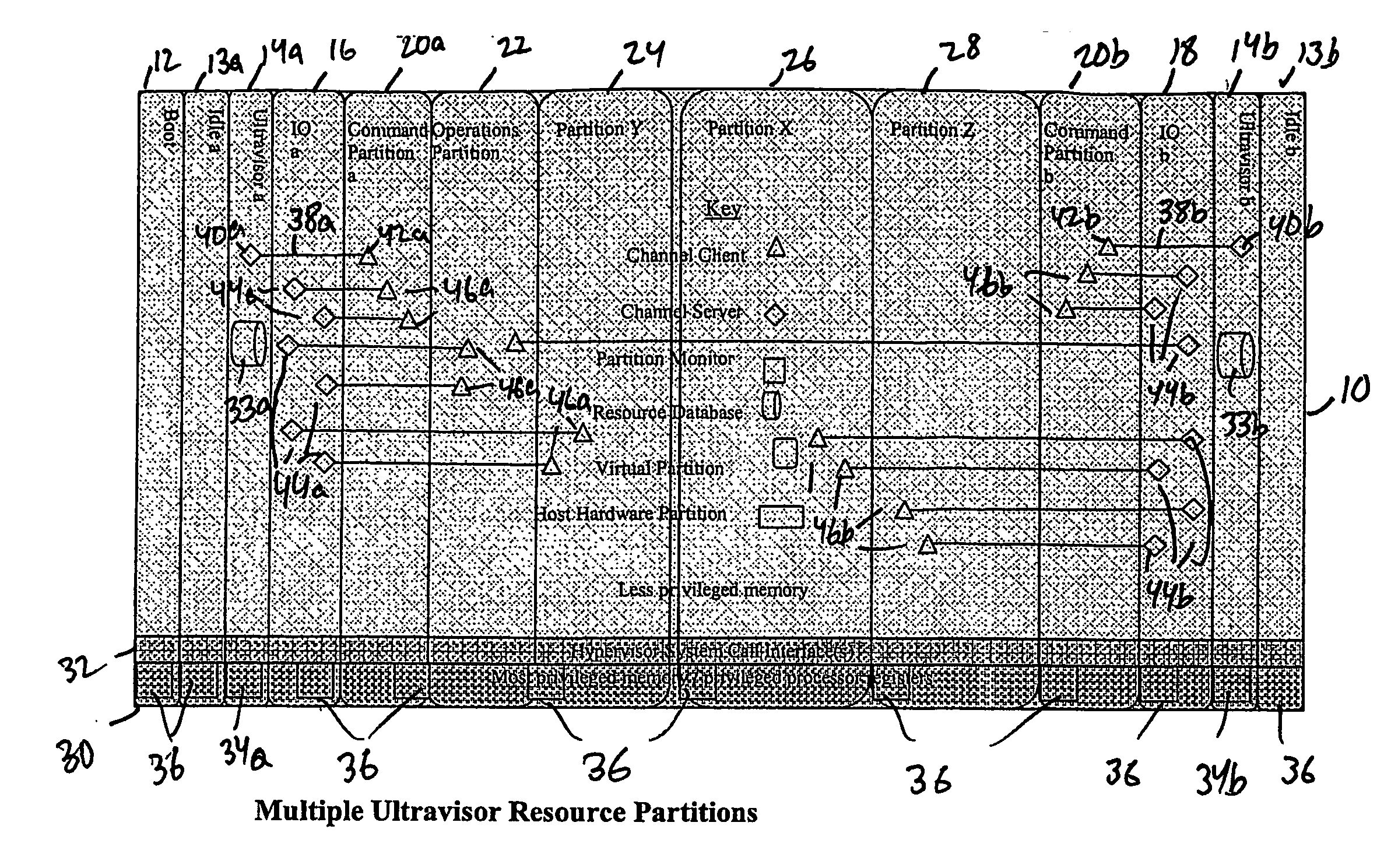
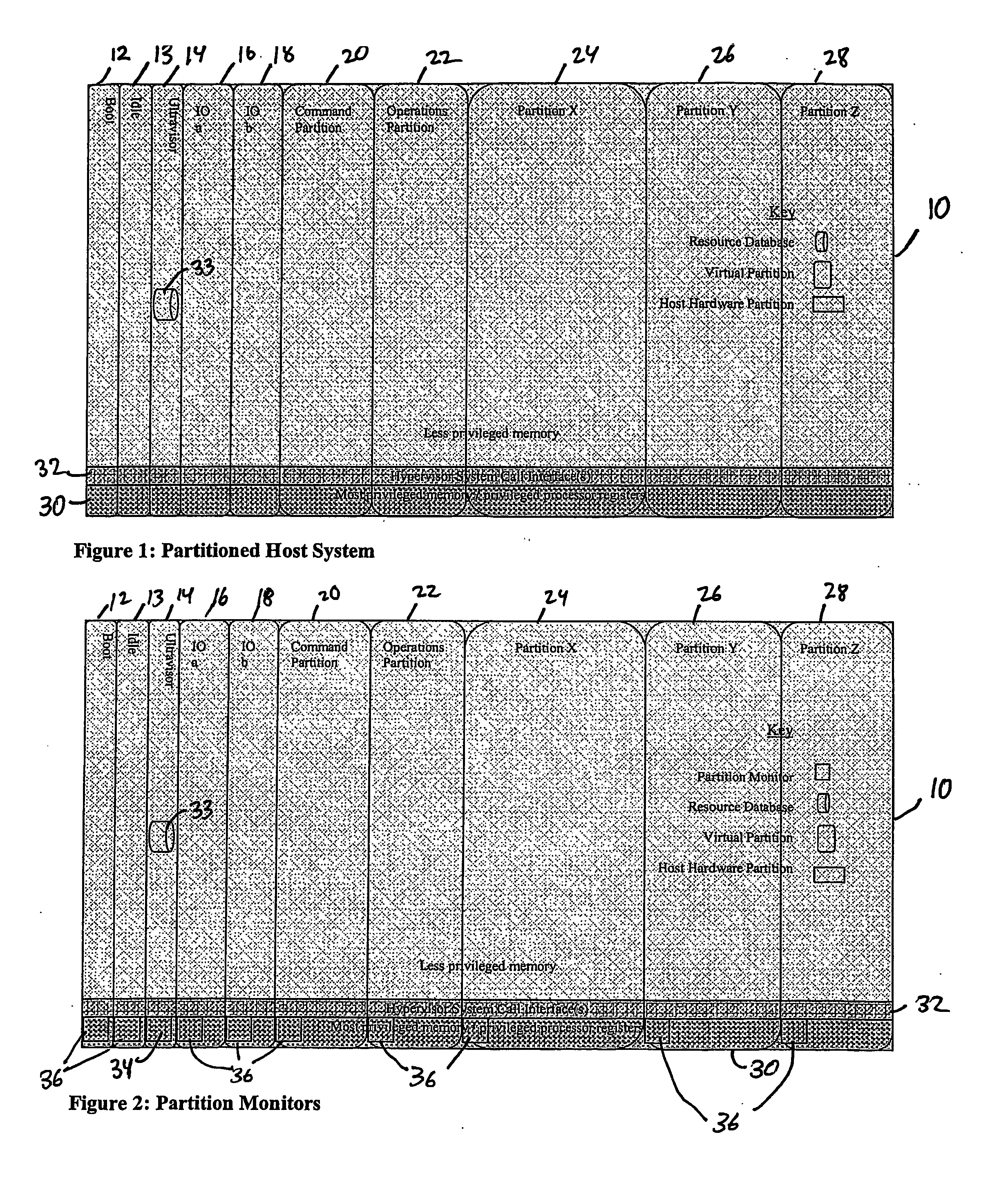
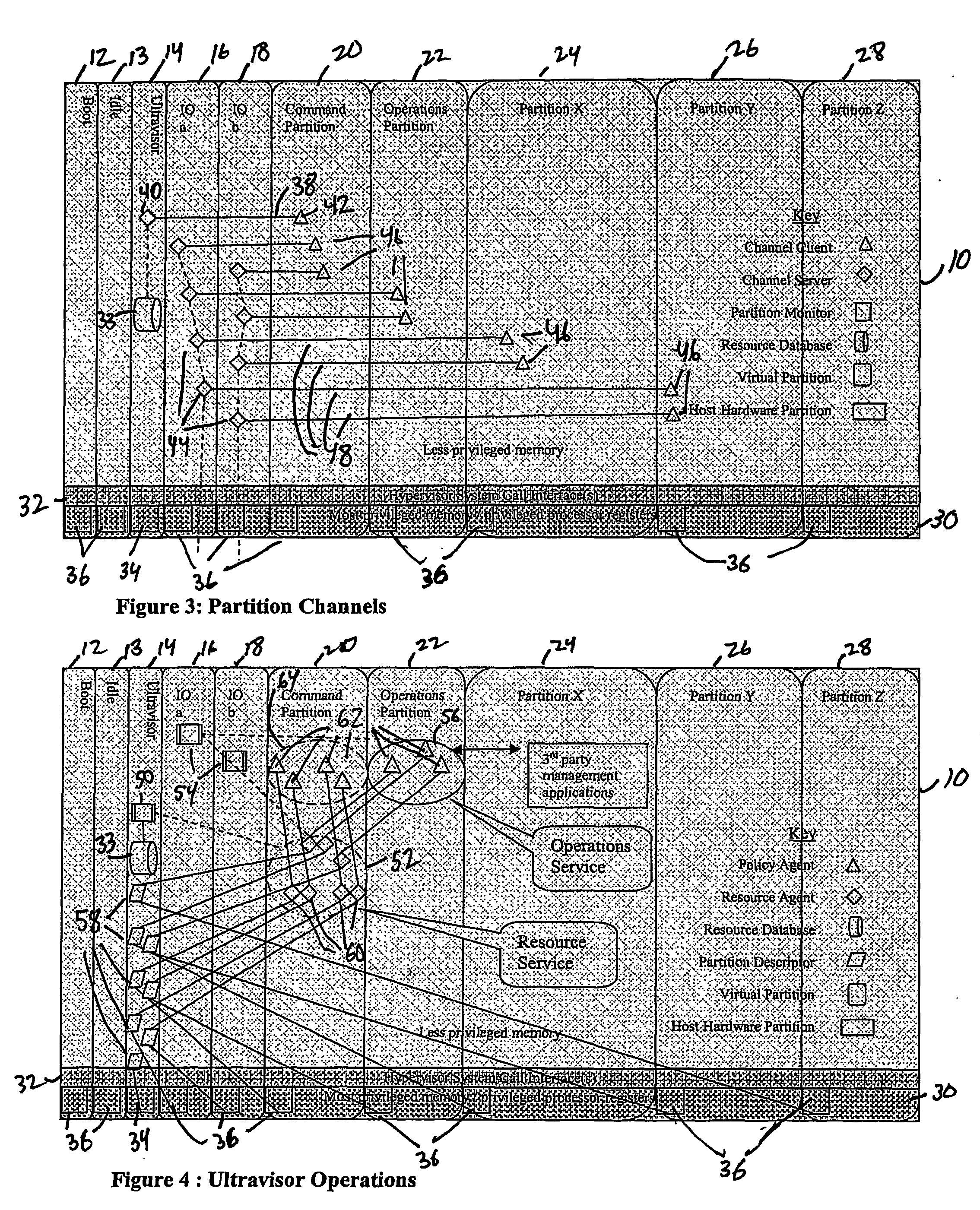
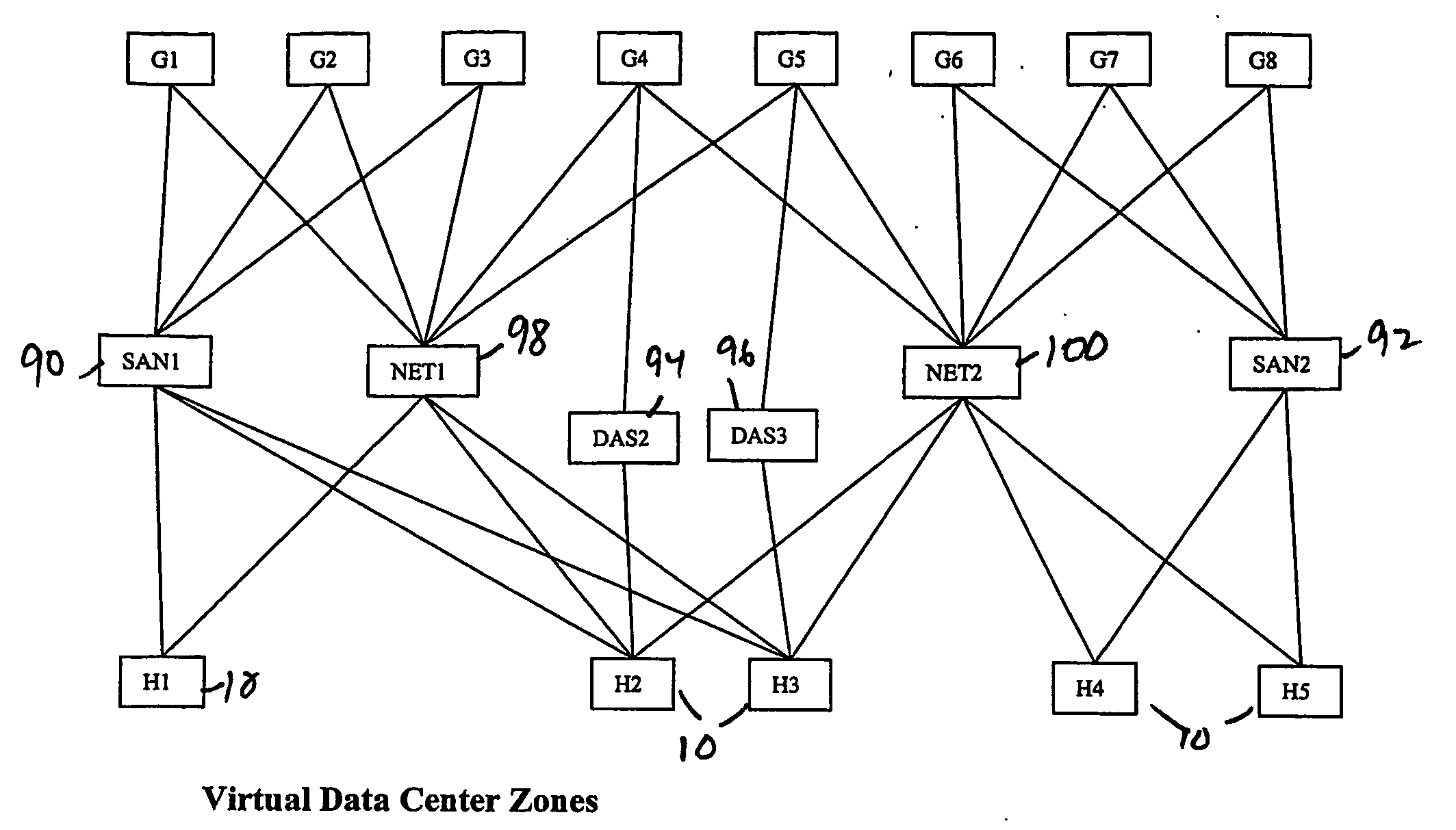
Virtual data center that allocates and manages system resources across multiple nodes
ActiveUS20070067435A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemData center
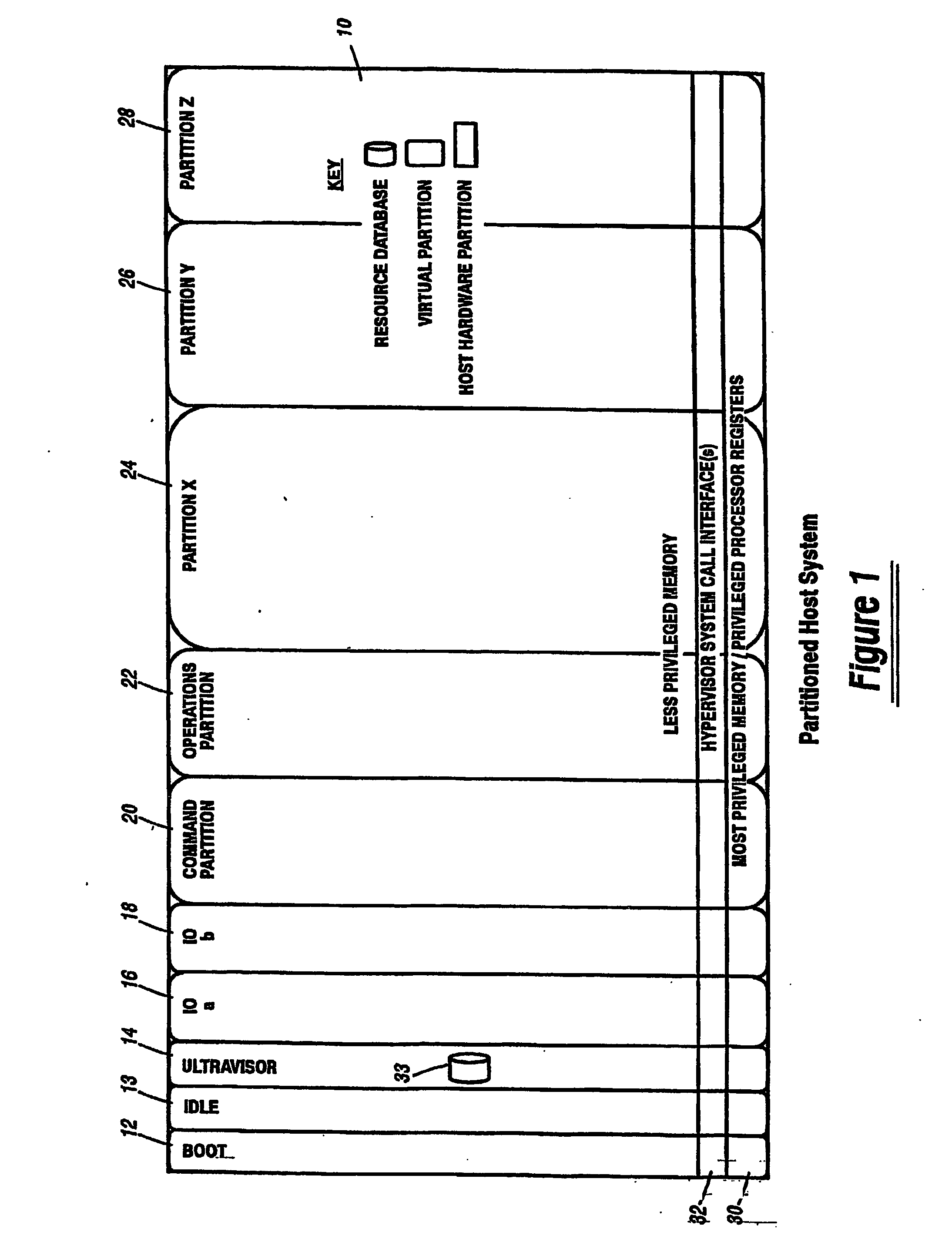
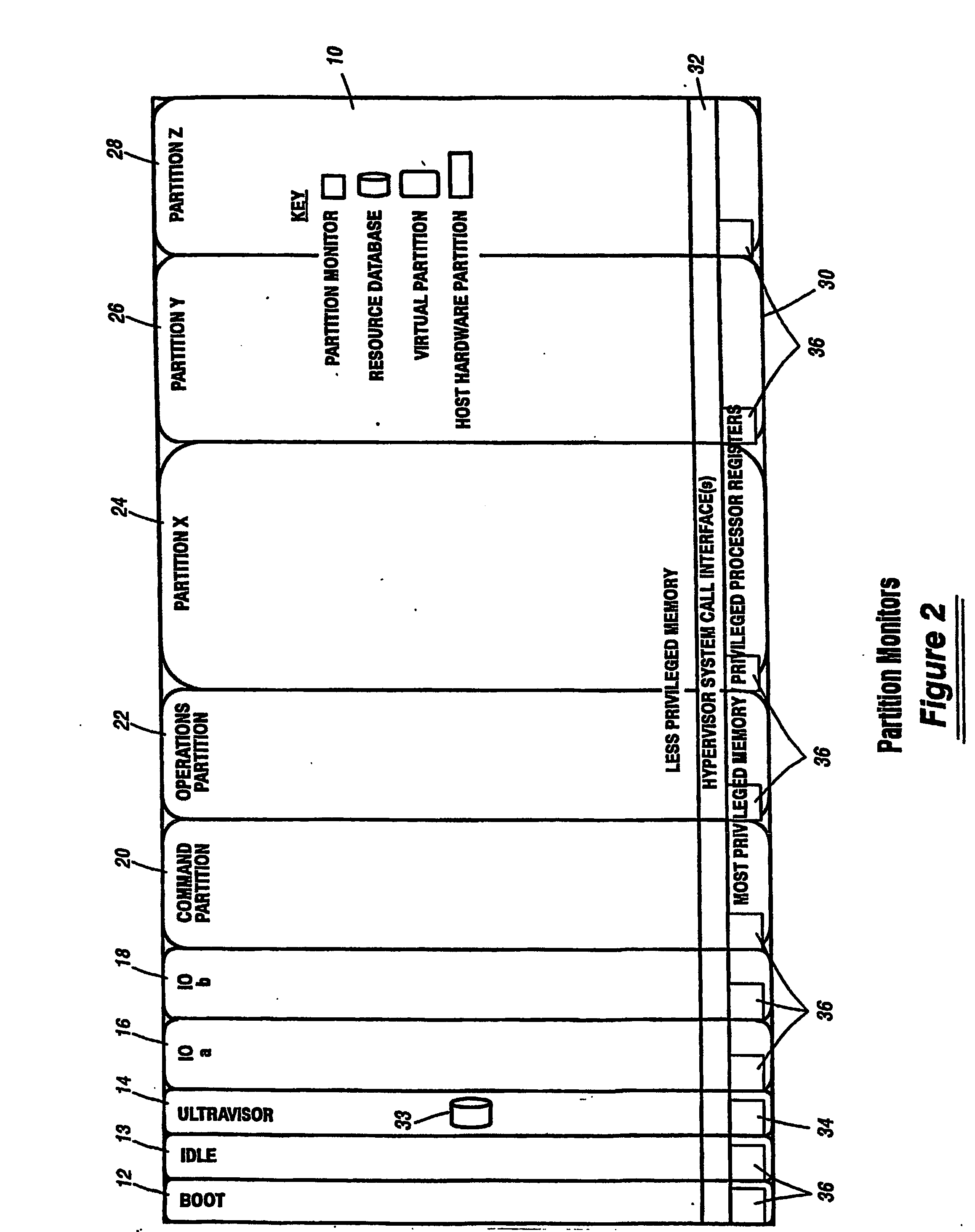
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps. System resources are separated into zones that are managed by a separate partition containing resource management policies that may be implemented across nodes to implement a virtual data center.
Owner:UNISYS CORP
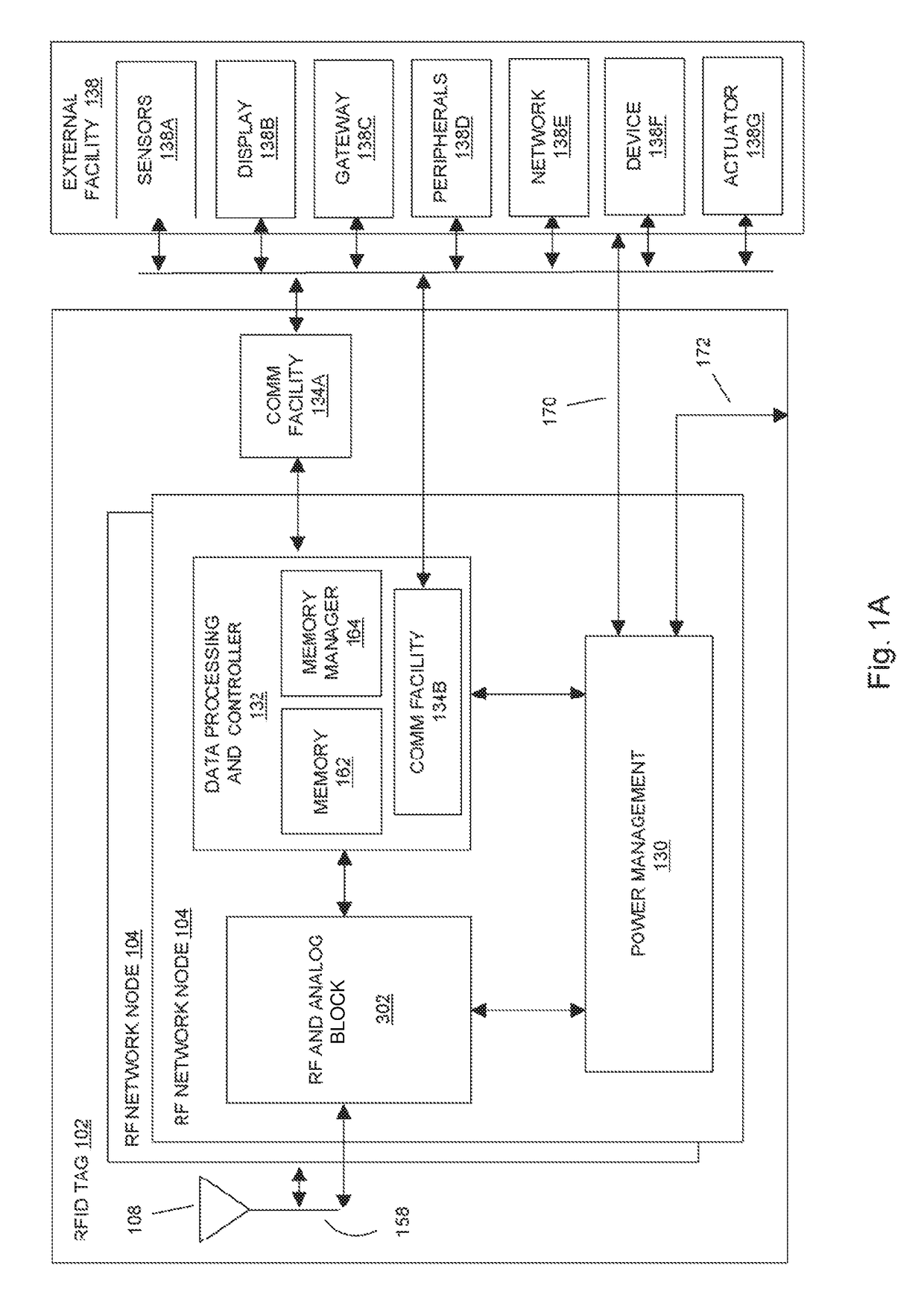
Operating systems for an RFID tag
ActiveUS9953193B2Enhanced radiationMemory record carrier reading problemsCo-operative working arrangementsComputer hardwareOperational system
Owner:TEGO INC
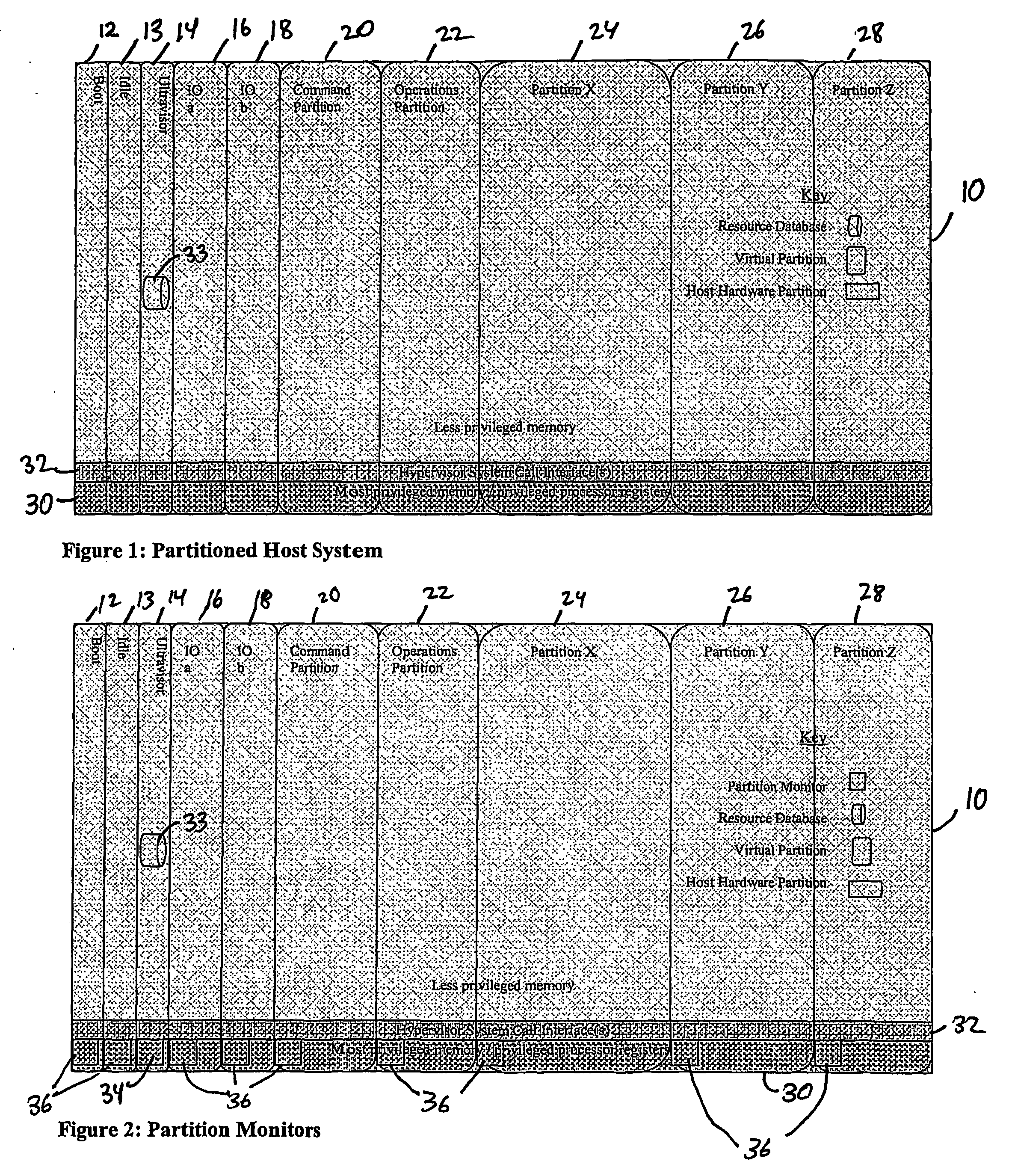
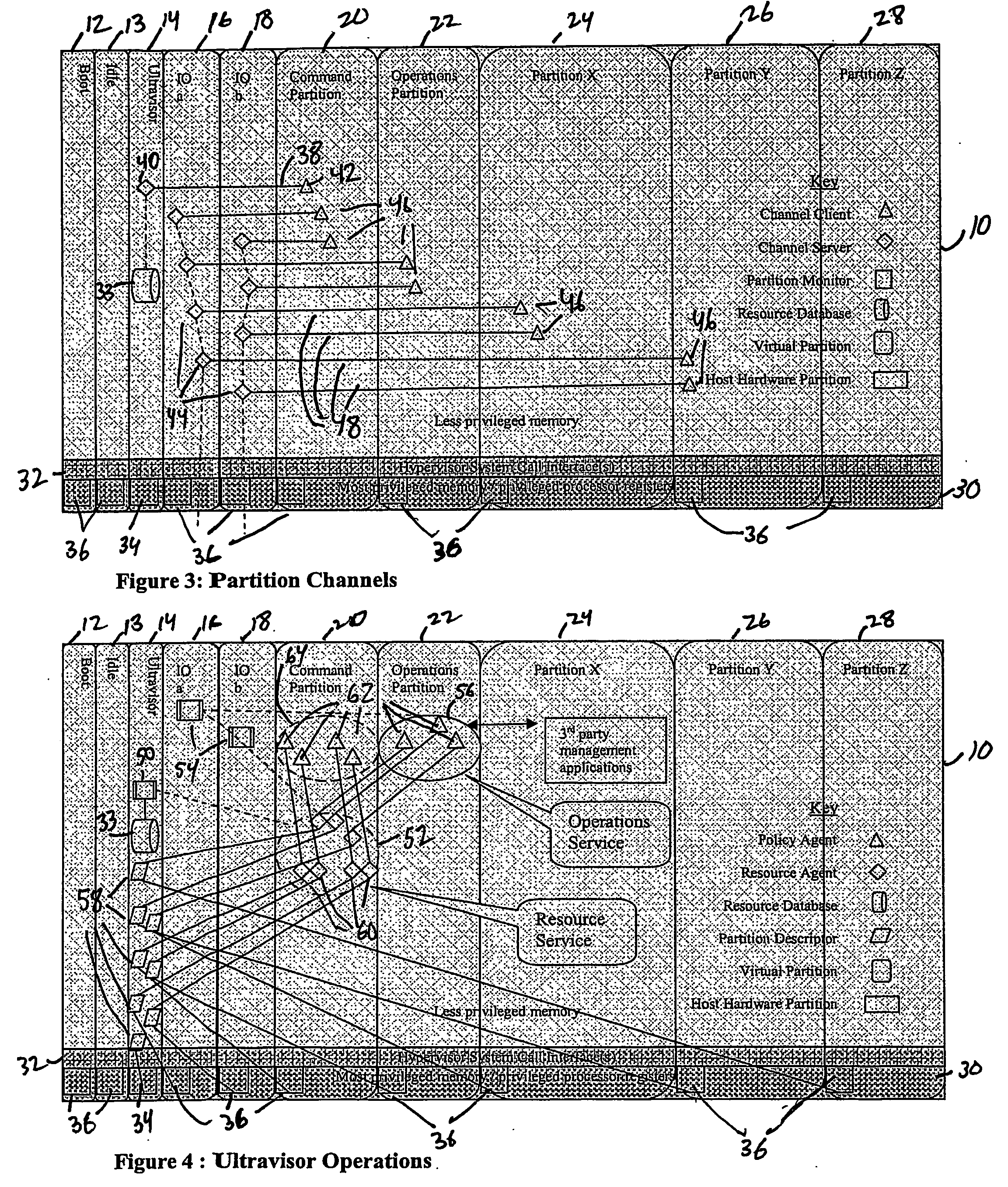
Computer system para-virtualization using a hypervisor that is implemented in a partition of the host system
ActiveUS20070028244A1Improve securityExcessive removalError detection/correctionMemory adressing/allocation/relocationOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
Para-virtualized computer system with I/0 server partitions that map physical host hardware for access by guest partitions
InactiveUS20070061441A1Improve efficiencyImprove securityError detection/correctionDigital computer detailsOperational systemSystem call
A virtualization infrastructure that allows multiple guest partitions to run within a host hardware partition. The host system is divided into distinct logical or virtual partitions and special infrastructure partitions are implemented to control resource management and to control physical I / O device drivers that are, in turn, used by operating systems in other distinct logical or virtual guest partitions. Host hardware resource management runs as a tracking application in a resource management “ultravisor” partition, while host resource management decisions are performed in a higher level command partition based on policies maintained in a separate operations partition. The conventional hypervisor is reduced to a context switching and containment element (monitor) for the respective partitions, while the system resource management functionality is implemented in the ultravisor partition. The ultravisor partition maintains the master in-memory database of the hardware resource allocations and serves a command channel to accept transactional requests for assignment of resources to partitions. It also provides individual read-only views of individual partitions to the associated partition monitors. Host hardware I / O management is implemented in special redundant I / O partitions. Operating systems in other logical or virtual partitions communicate with the I / O partitions via memory channels established by the ultravisor partition. The guest operating systems in the respective logical or virtual partitions are modified to access monitors that implement a system call interface through which the ultravisor, I / O, and any other special infrastructure partitions may initiate communications with each other and with the respective guest partitions. The guest operating systems are modified so that they do not attempt to use the “broken” instructions in the x86 system that complete virtualization systems must resolve by inserting traps.
Owner:UNISYS CORP
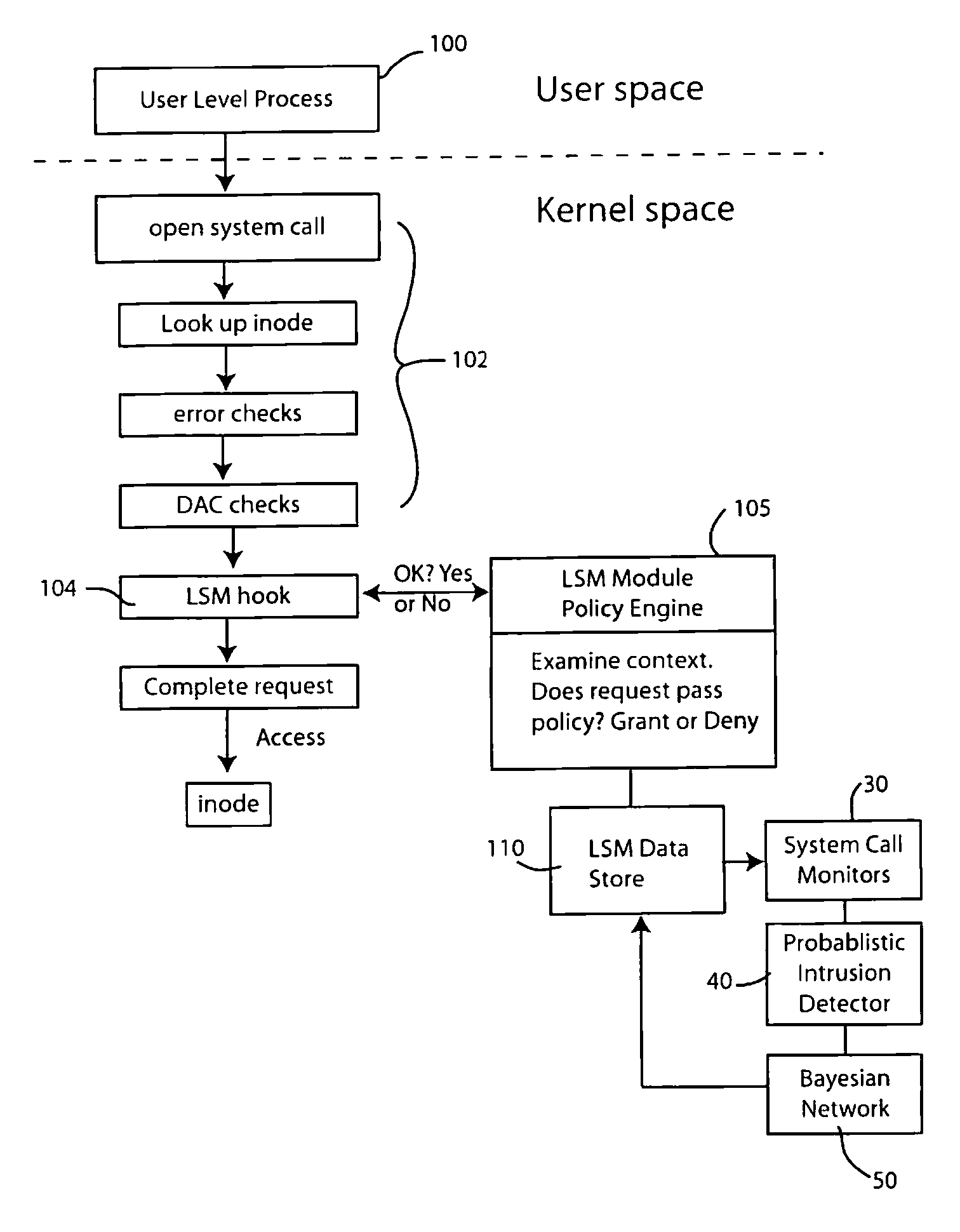
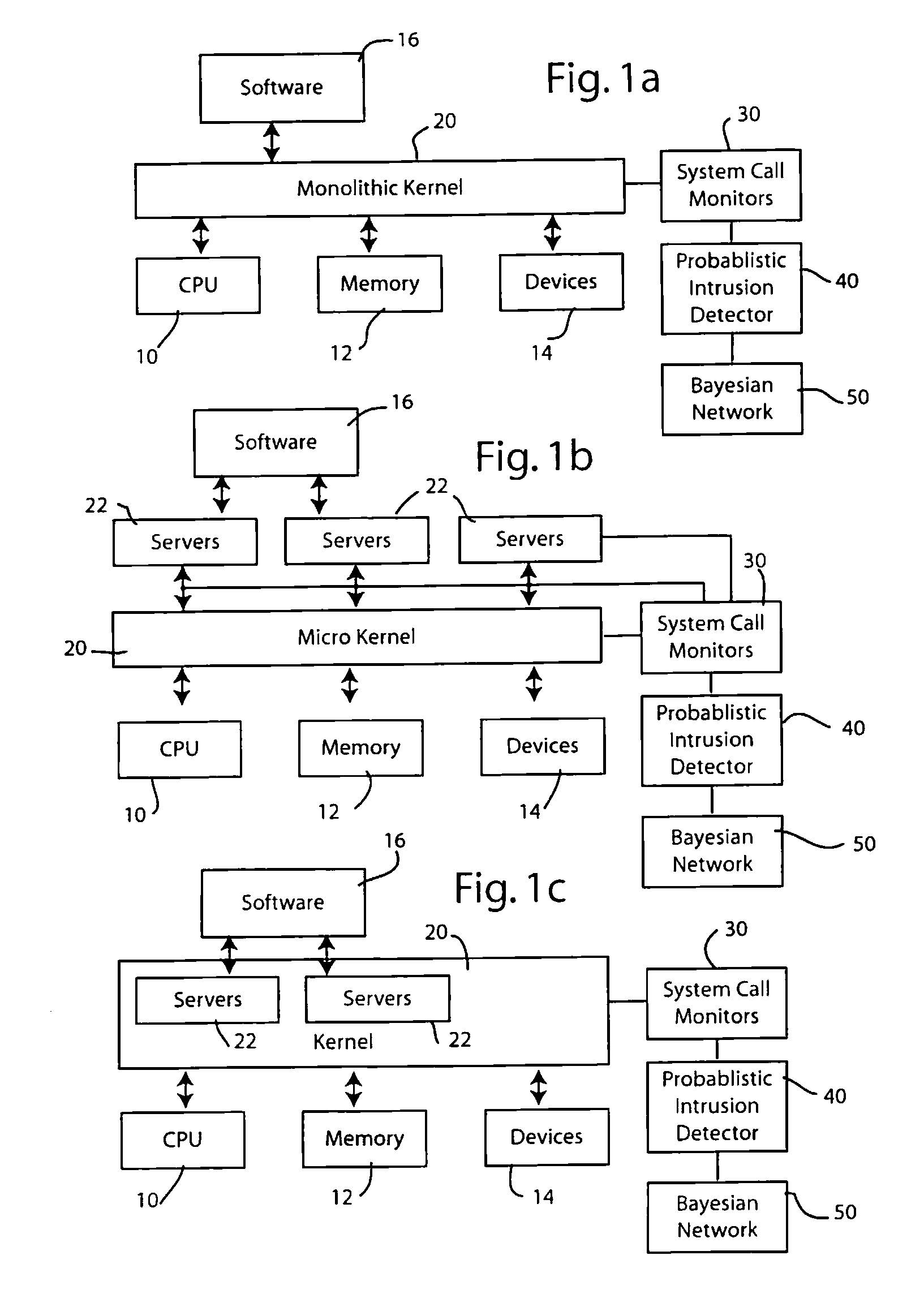
Intrusion detection using system call monitors on a bayesian network
InactiveUS20080201778A1Spread fastMemory loss protectionError detection/correctionSystem callBayesian network
Selected system calls are monitored to generate frequency data that is input to a probabilistic intrusion detection analyzer which generates a likelihood score indicative of whether the system calls being monitored were produced by a computer system whose security has been compromised. A first Bayesian network is trained on data from a compromised system and a second Bayesian network is trained on data from a normal system. The probabilistic intrusion detection analyzer considers likelihood data from both Bayesian networks to generate the intrusion detection measure.
Owner:PANASONIC CORP
Detecting unauthorized use of computing devices based on behavioral patterns
InactiveUS8595834B2Memory loss protectionError detection/correctionSupporting systemMonitoring system
Techniques for detecting unauthorized use (e.g., malicious attacks) of the computing systems (e.g., computing devices) are disclosed. Unauthorized use can be detected based on patterns of use (e.g., behavioral patterns of use typically associated with a human being) of the computing systems. Acceptable behavioral pattern data can be generated for a computing system by monitoring the use of a support system (e.g., an operating system, a virtual environment) operating on the computing system. For example, a plurality of system support provider components of a support system (e.g., system calls, device drivers) can be monitored in order to generate the acceptable behavioral pattern data in a form which effectively defines an acceptable pattern of use (usage pattern) for the monitored system support provider components, thereby allowing detection of unauthorized use of a computing system by detecting any deviation from the acceptable pattern of use of the monitored system support provider components.
Owner:SAMSUNG ELECTRONICS CO LTD
Detecting malicious software by analyzing patterns of system calls generated during emulation
InactiveUS6775780B1Follow exactlyEliminate detectionMemory loss protectionError detection/correctionOperational systemComputerized system
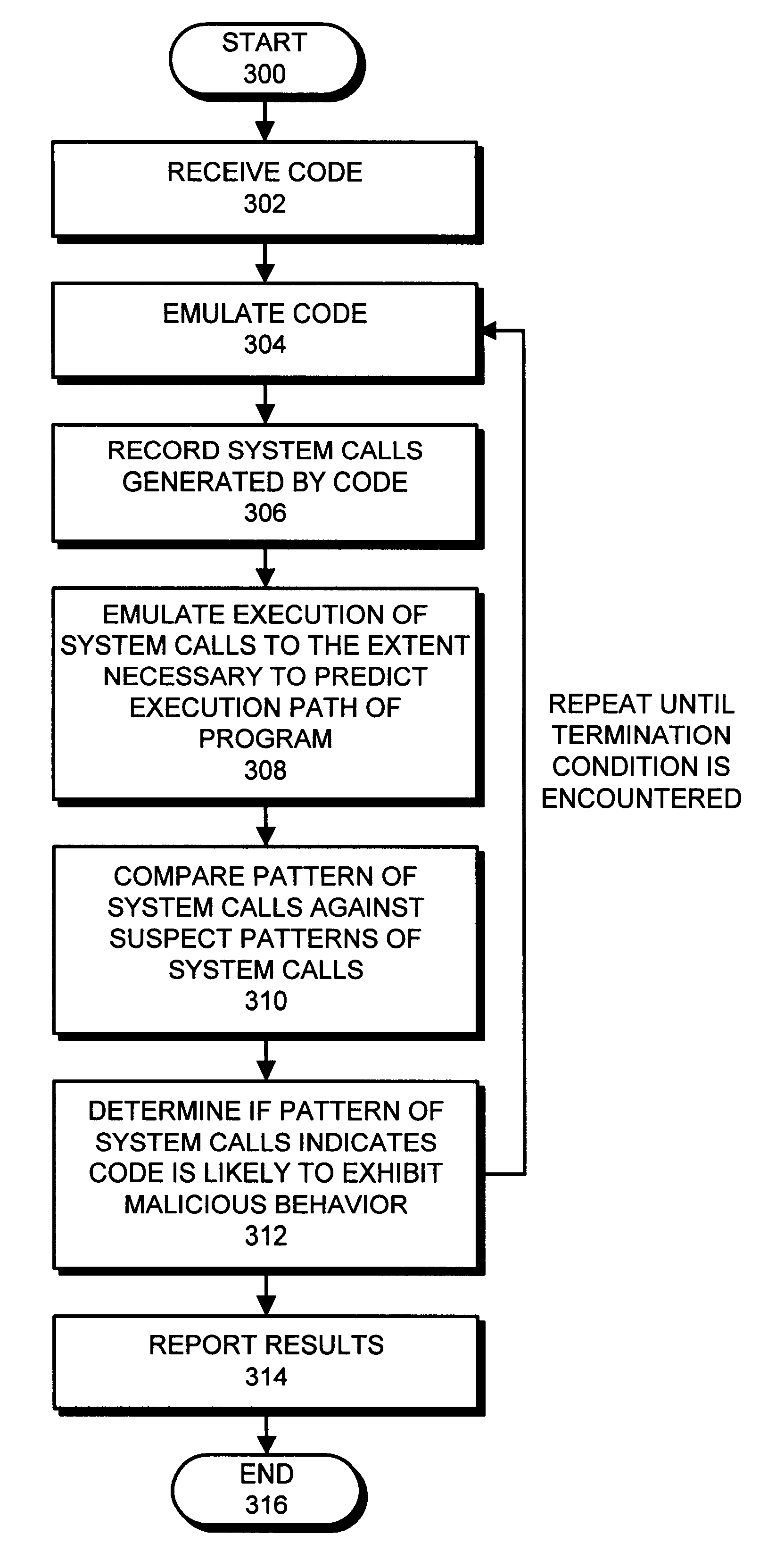
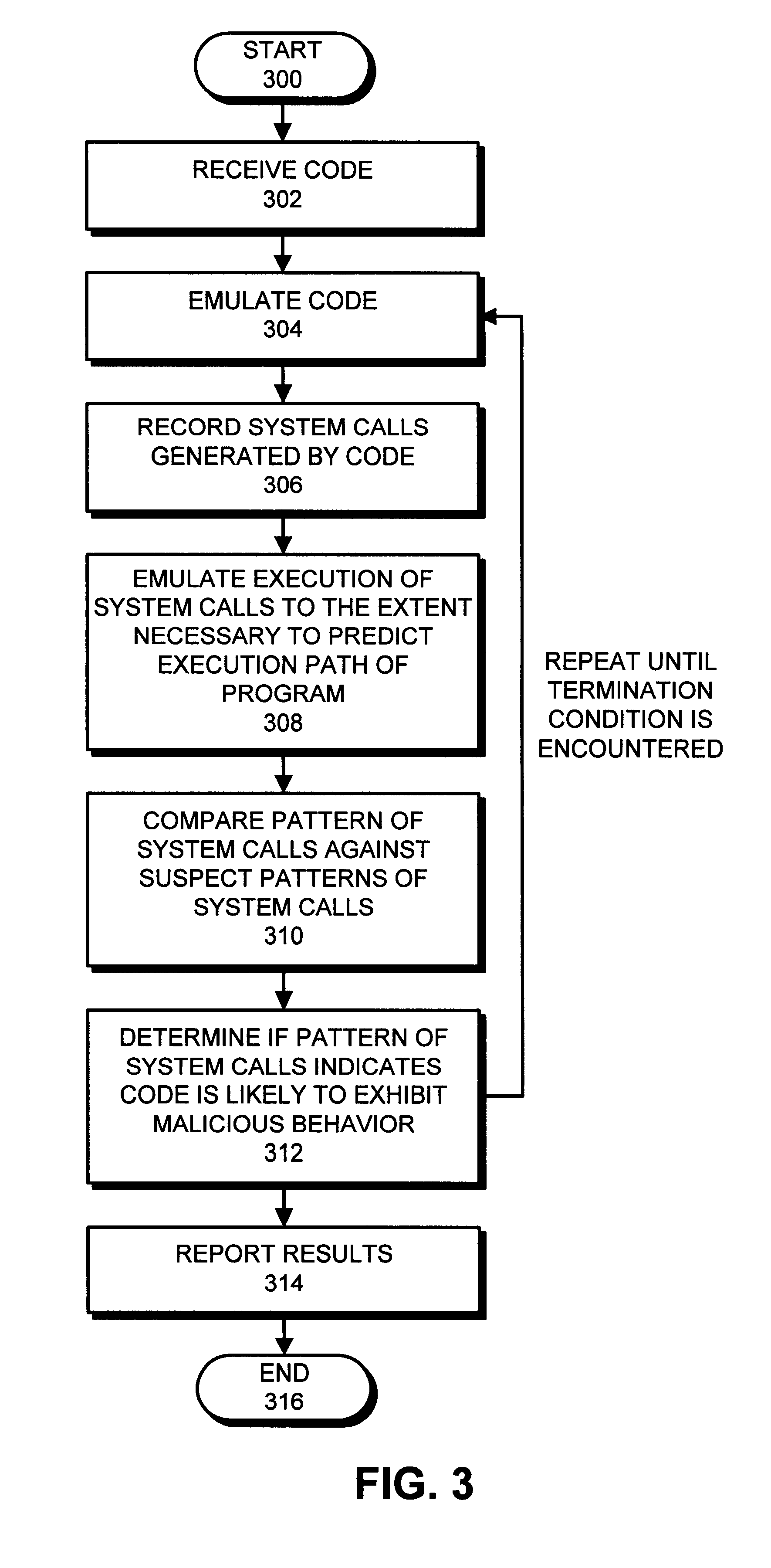
One embodiment of the present invention provides a system for determining whether software is likely to exhibit malicious behavior by analyzing patterns of system calls made during emulation of the software. The system operates by emulating the software within an insulated environment in a computer system so that the computer system is insulated from malicious actions of the software. During the emulation process, the system records a pattern of system calls directed to an operating system of the computer system. The system compares the pattern of system calls against a database containing suspect patterns of system calls. Based upon this comparison, the system determines whether the software is likely to exhibit malicious behavior. In one embodiment of the present invention, if the software is determined to be likely to exhibit malicious behavior, the system reports this fact to a user of the computer system. In one embodiment of the present invention, the process of comparing the pattern of system calls is performed on-the-fly as the emulation generates system calls.
Owner:MCAFEE LLC
Hardware multithreading systems and methods
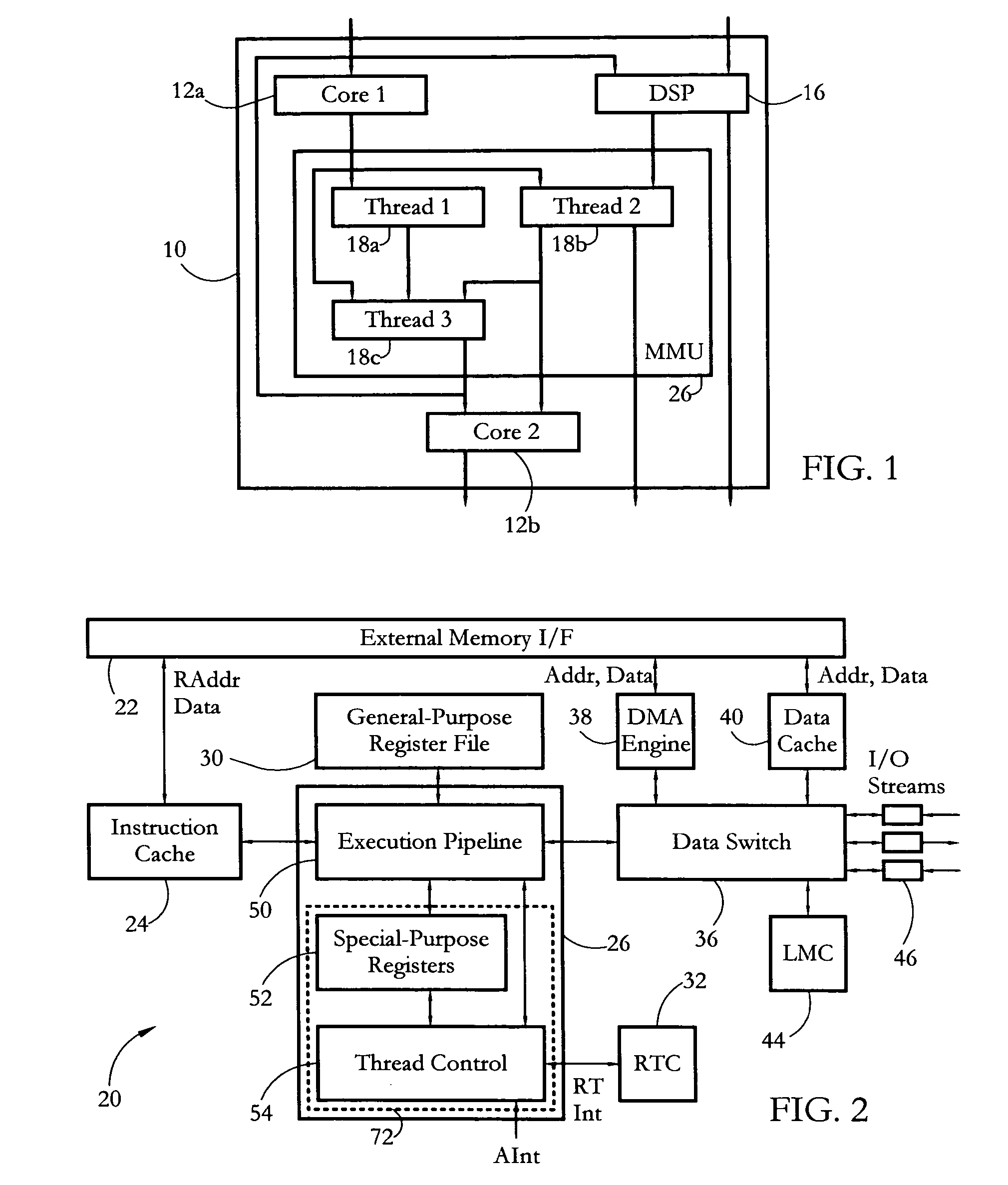
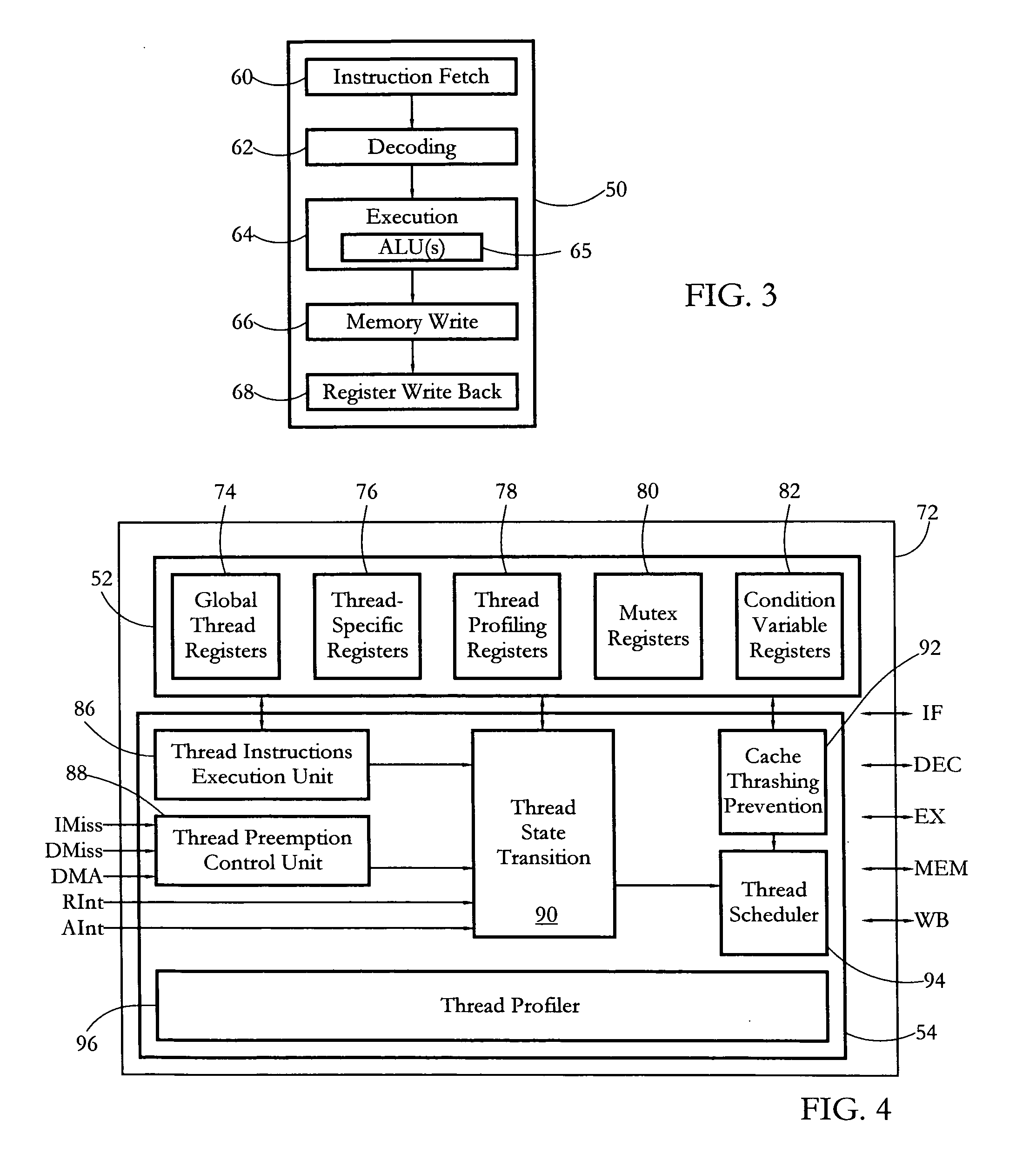
According to some embodiments, a multithreaded microcontroller includes a thread control unit comprising thread control hardware (logic) configured to perform a number of multithreading system calls essentially in real time, e.g. in one or a few clock cycles. System calls can include mutex lock, wait condition, and signal instructions. The thread controller includes a number of thread state, mutex, and condition variable registers used for executing the multithreading system calls. Threads can transition between several states including free, run, ready and wait. The wait state includes interrupt, condition, mutex, I-cache, and memory substates. A thread state transition controller controls thread states, while a thread instructions execution unit executes multithreading system calls and manages thread priorities to avoid priority inversion. A thread scheduler schedules threads according to their priorities. A hardware thread profiler including global, run and wait profiler registers is used to monitor thread performance to facilitate software development.
Owner:GEO SEMICONDUCTOR INC
System and method for facilitating context-switching in a multi-context computer system
InactiveUS6944699B1Software simulation/interpretation/emulationMemory systemsOperational systemProcedure calls
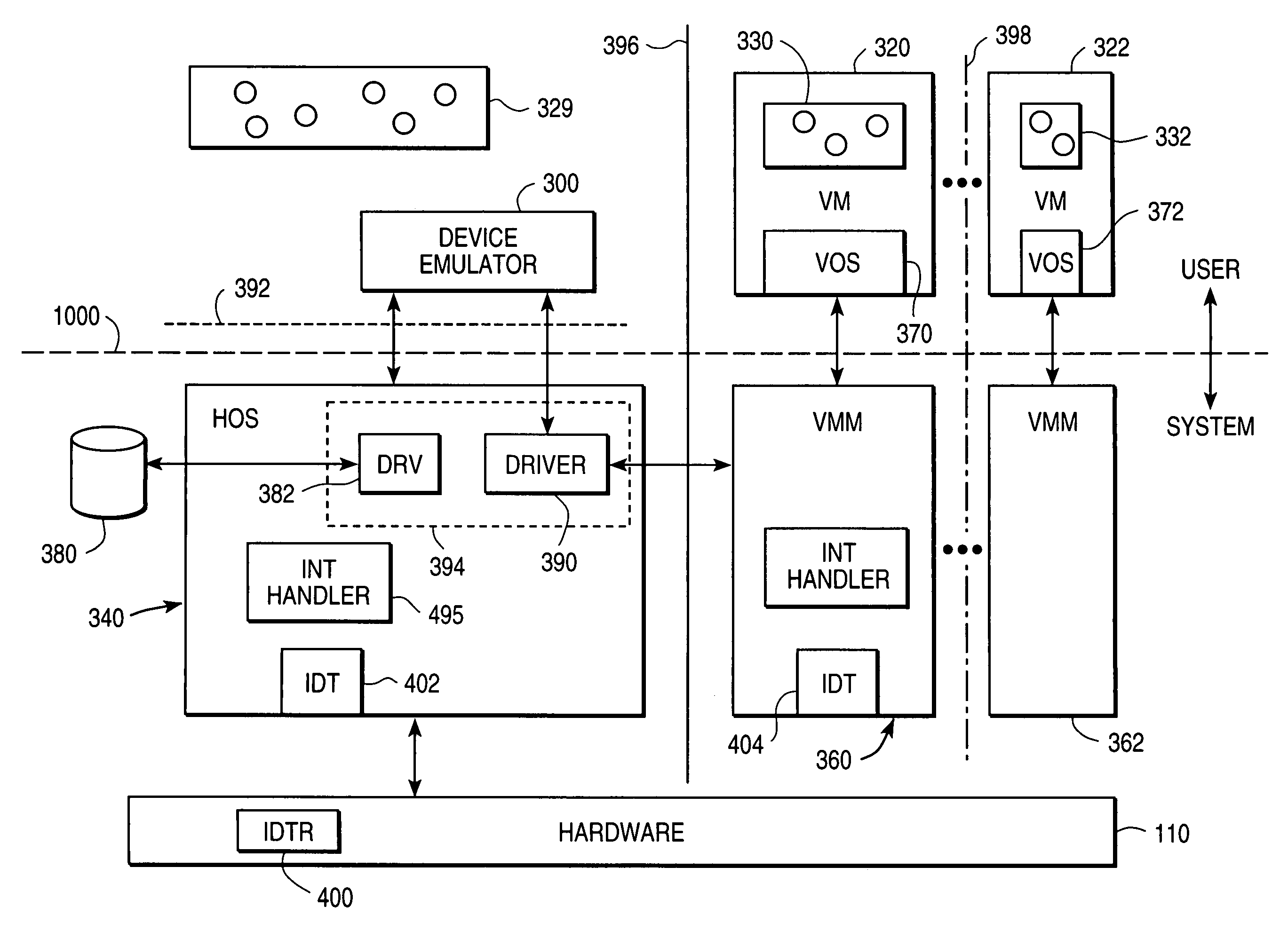
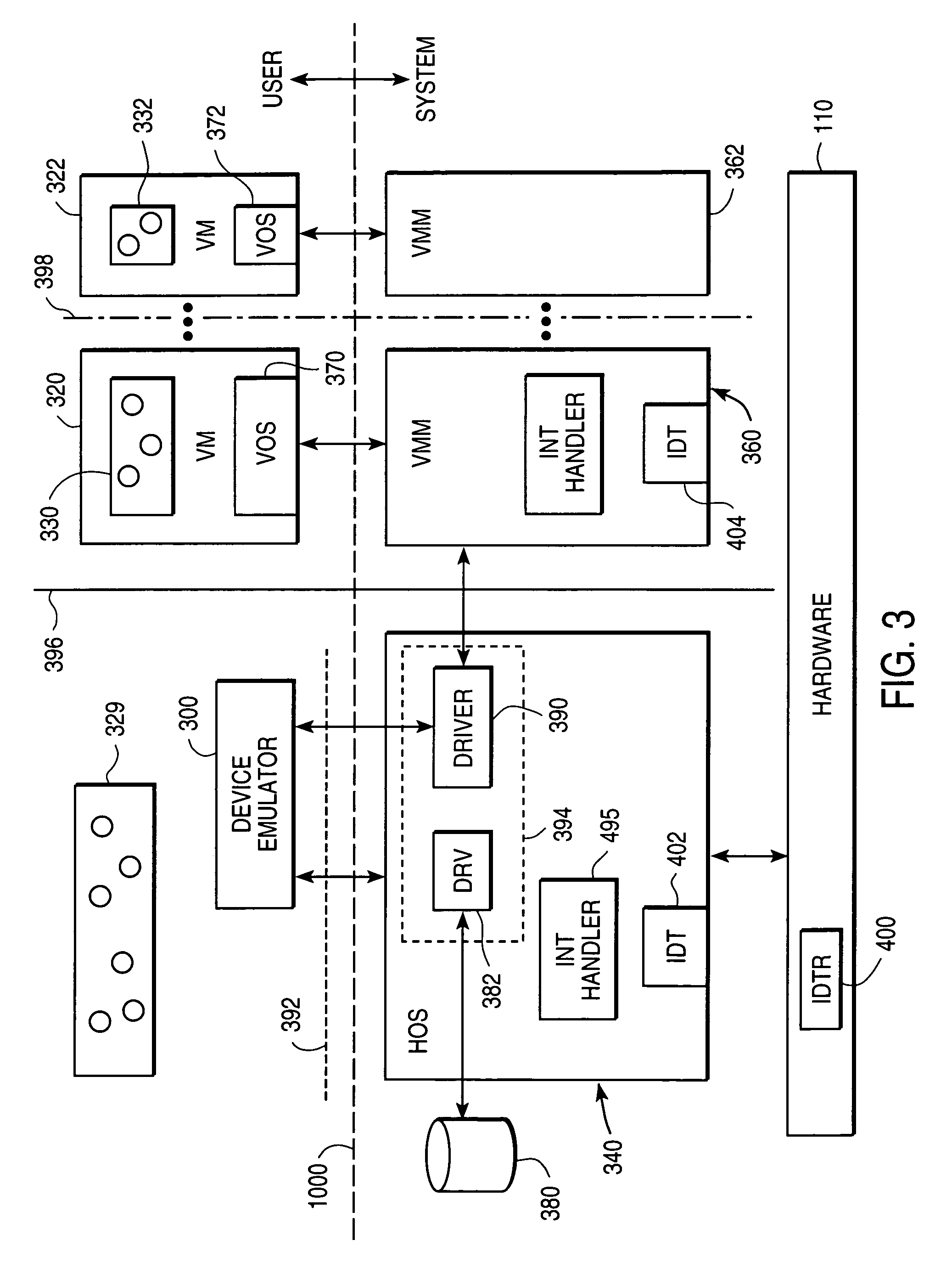
A virtual machine monitor (VMM) is included in a computer system that has a protected host operating system (HOS). A virtual machine running at least one application via a virtual operating system is connected to the VMM. Both the HOS and the VMM have separate operating contexts and disjoint address spaces, but are both co-resident at system level. A driver that is downloadable into the HOS at system level forms a total context switch between the VMM and HOS contexts. A user-level emulator accepts commands from the VMM via the system-level driver and processes these commands as remote procedure calls. The emulator is able to issue host operating system calls and thereby access the physical system devices via the host operating system. The host operating system itself thus handles execution of certain VMM instructions, such as accessing physical devices.
Owner:VMWARE INC
Virtual second line hybrid network communication system
InactiveUS6351464B1Reduce cost and inconvenienceReduce spreadInterconnection arrangementsSpecial service for subscribersMix networkIp address
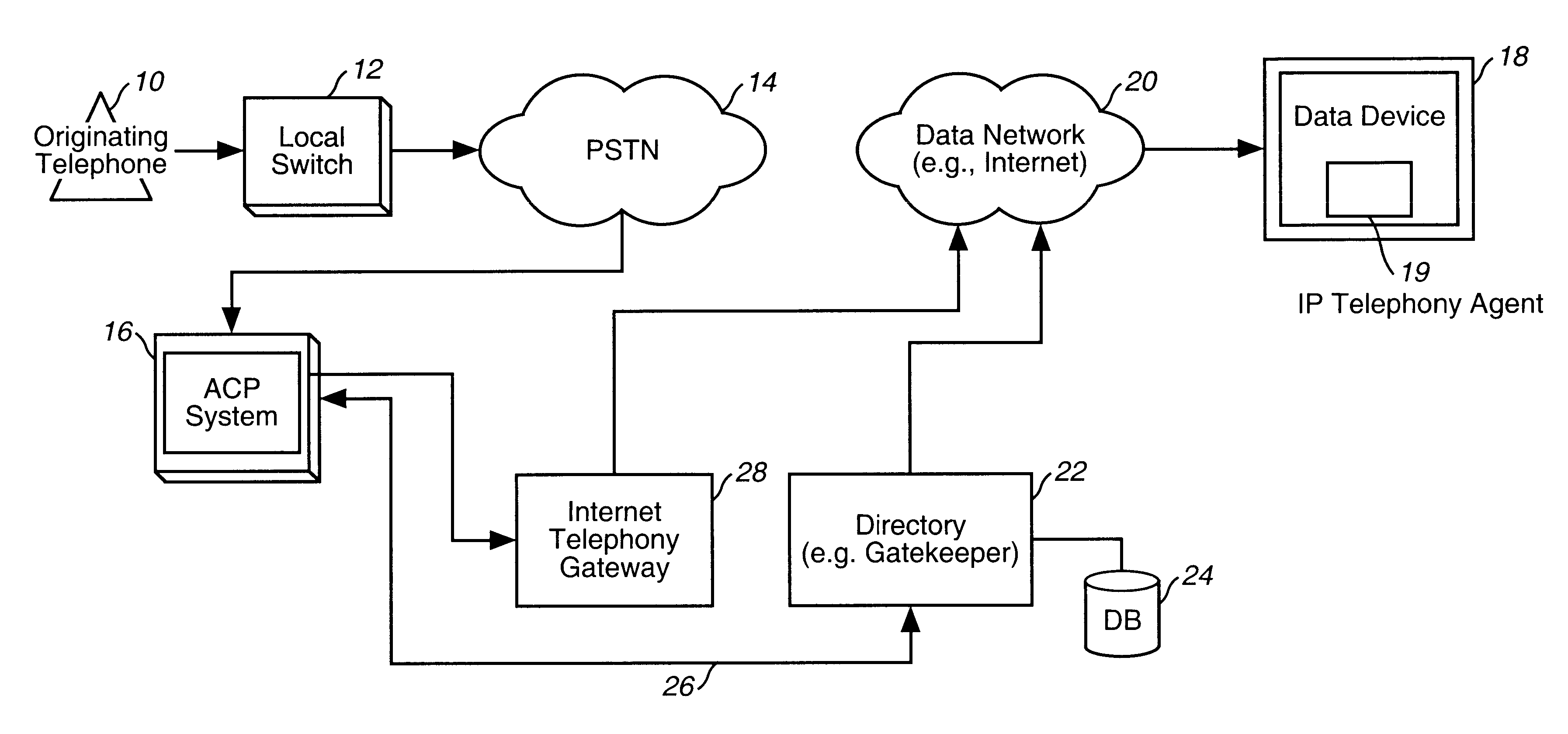
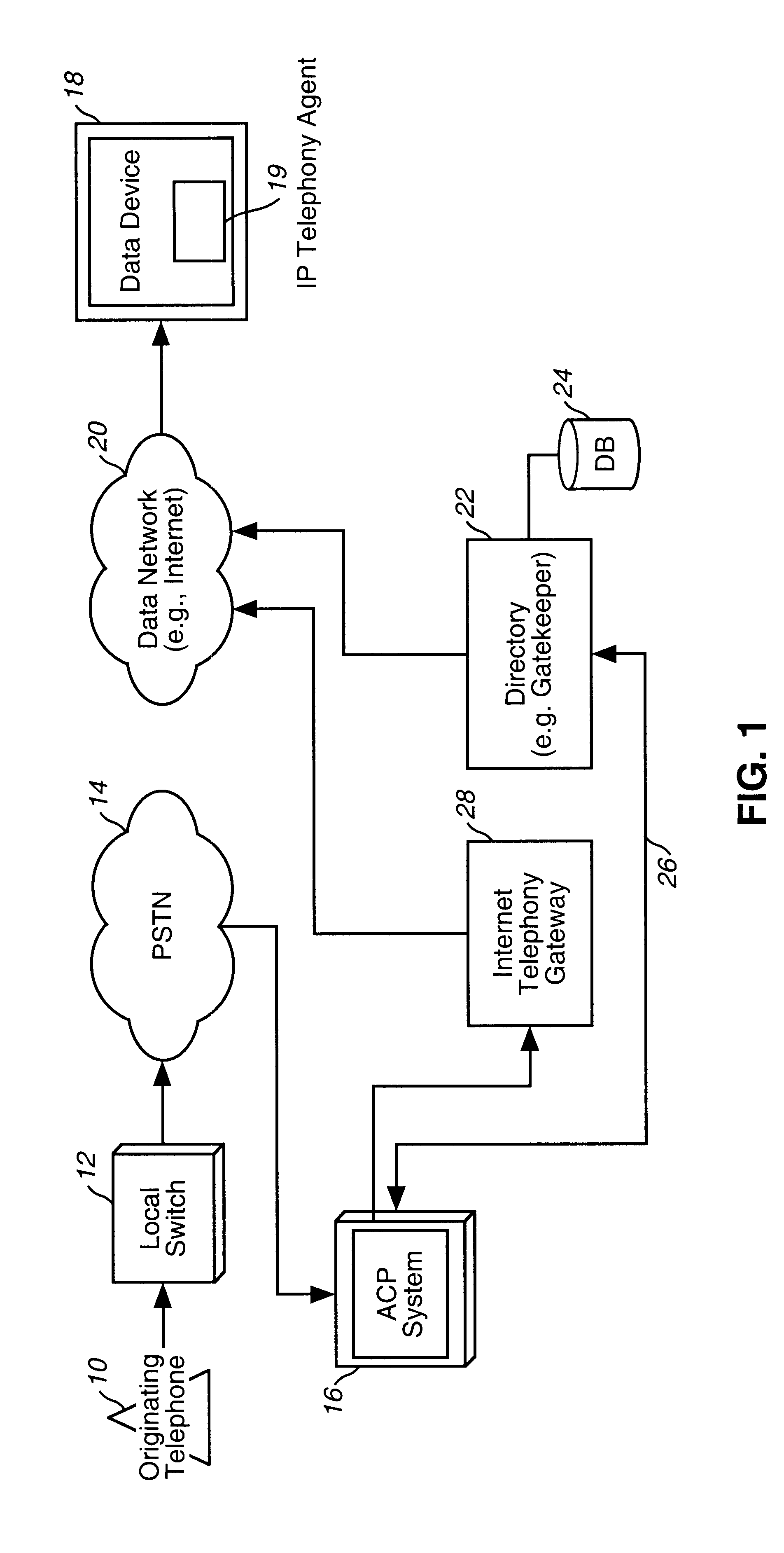
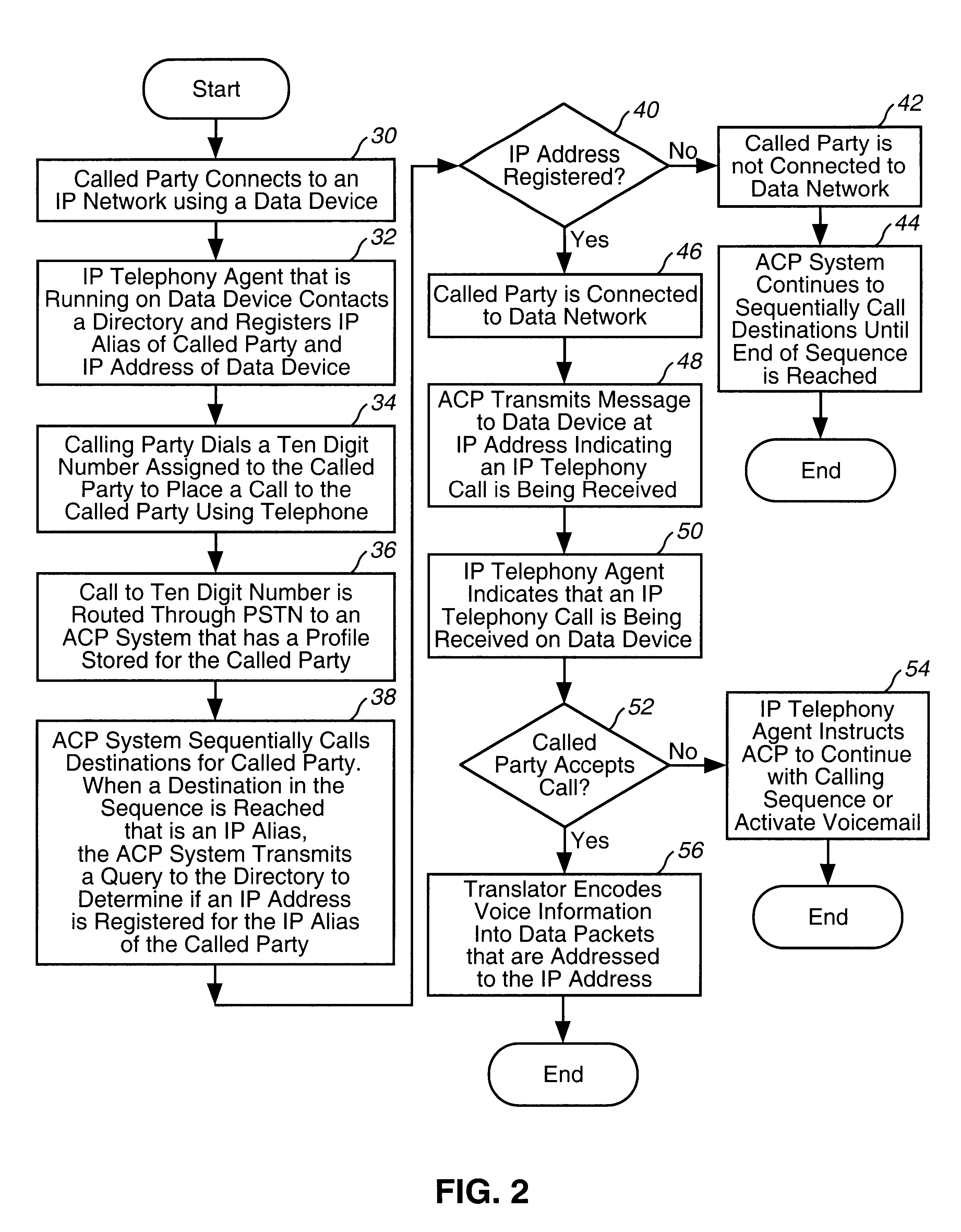
A system and method for routing a telephone call on a PSTN network to a data device. The present invention utilizes an automatic call processing system that has a one number location service. A called party provides a calling profile that is stored in the automatic call processing (ACP) system. When a call is placed to a telephone number that is assigned to the called party, the call is routed to the ACP system. The ACP system calls each of the numbers of the calling profile for that called party until that party is reached. At least one of the destinations in the calling profile is a logical address for a data network. The automatic call processing system recognizes the logical address and queries a directory to determine if an IP address has been registered in the directory for the logical address of the called party. If the called party is using a data device that is logged on the Internet, an IP telephony agent, such as an IP telephony client running on the data device, registers the IP address of the data device together with the logical address of the caller. If the ACP system determines if an IP address is registered with the directory, the ACP system will direct the call to an Internet telephony gateway. The Internet telephony gateway encodes and packetizes the voice information for transmission over the data network to the data device.
Owner:VERIZON PATENT & LICENSING INC
Snapshot restore of application chains and applications
InactiveUS6848106B1Data processing applicationsProgram initiation/switchingOperational systemSystem call
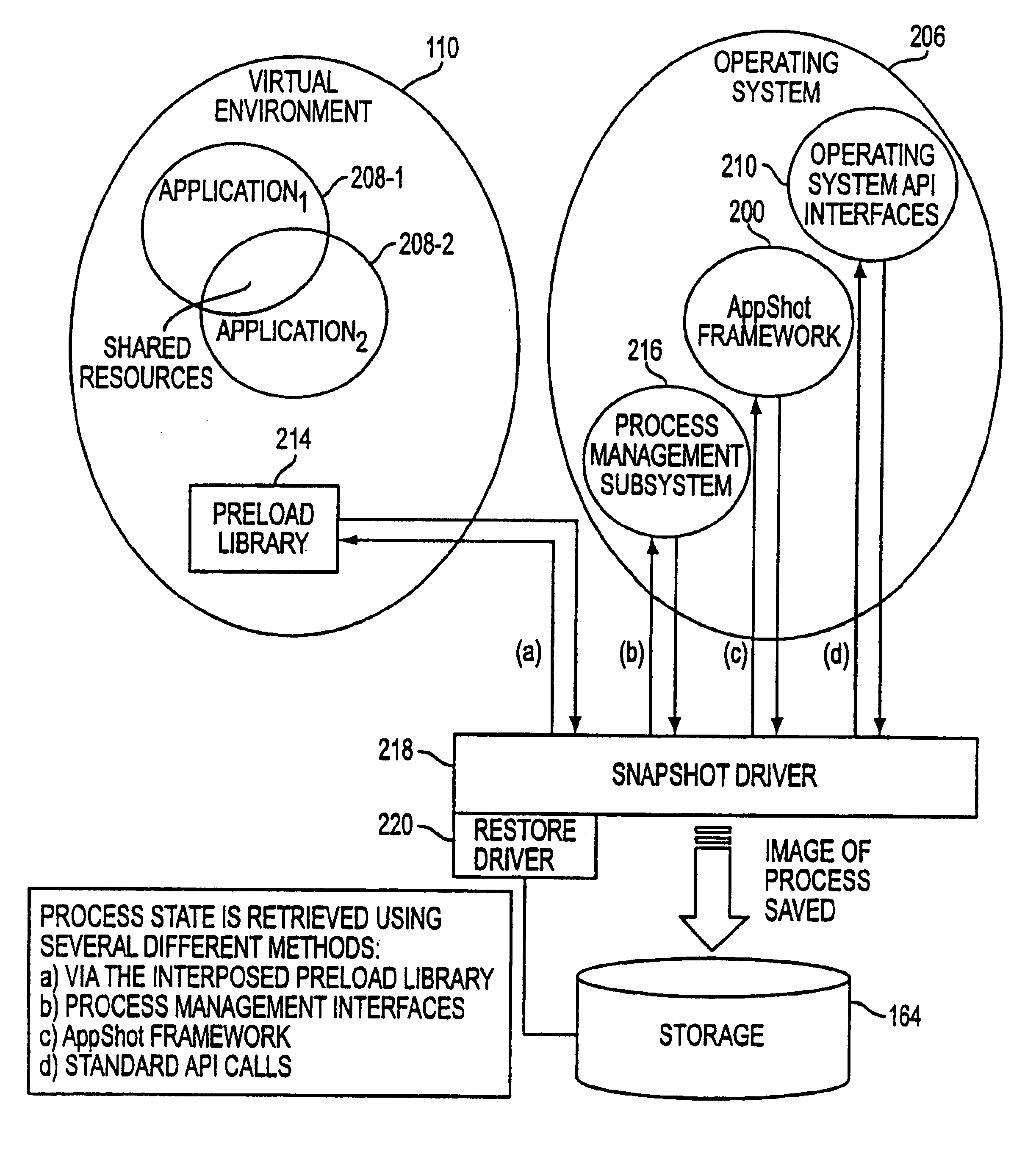
The present invention saves all process state, memory, and dependencies related to a software application to a snapshot image. Interprocess communication (IPC) mechanisms such as shared memory and semaphores must be preserved in the snapshot image as well. IPC mechanisms include any resource that is shared between two process or any communication mechanism or channel that allow two processes to communicate or interoperate is a form of IPC. Between snapshots, memory deltas are flushed to the snapshot image, so that only the modified-pages need be updated. Software modules are included to track usage of resources and their corresponding handles. At snapshot time, state is saved by querying the operating system kernel, the application snapshot / restore framework components, and the process management subsystem that allows applications to retrieve internal process-specific information not available through existing system calls. At restore time, the reverse sequence of steps for the snapshot procedure is followed and state is restored by making requests to the kernel, the application snapshot / restore framework, and the process management subsystem.
Owner:SYMANTEC OPERATING CORP
Method and apparatus for selecting an object within a user interface by performing a gesture
One embodiment of the present invention provides a system that facilitates invoking a command. During operation, the system suggests with a graphic element a gesture to use to invoke a command. The system then receives the gesture from a user at a device. Note that the gesture is received via an input mechanism, and also note that the gesture is a predetermined manipulation of the input mechanism. The system then determines a graphic element within the user interface that is associated with the gesture. Finally, upon determining the object associated with the gesture, the system invokes the command associated with the graphic element.
Owner:INTEL CORP
Smart gateway, smart home system and smart controlling method thereof
A smart controlling method applied to a smart home system for controlling a number of home appliances which may detect and act upon the approach of a user to the smart home. The smart home system learns the habits of a user from repeated inputs at repeated times by the same user to determine that a control command is a habit. When the user arrives at home or is discovered in proximity to the smart home, the smart home system calls a control command to control a relevant home appliance to execute certain operations. A smart gateway and a smart home system are also provided.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
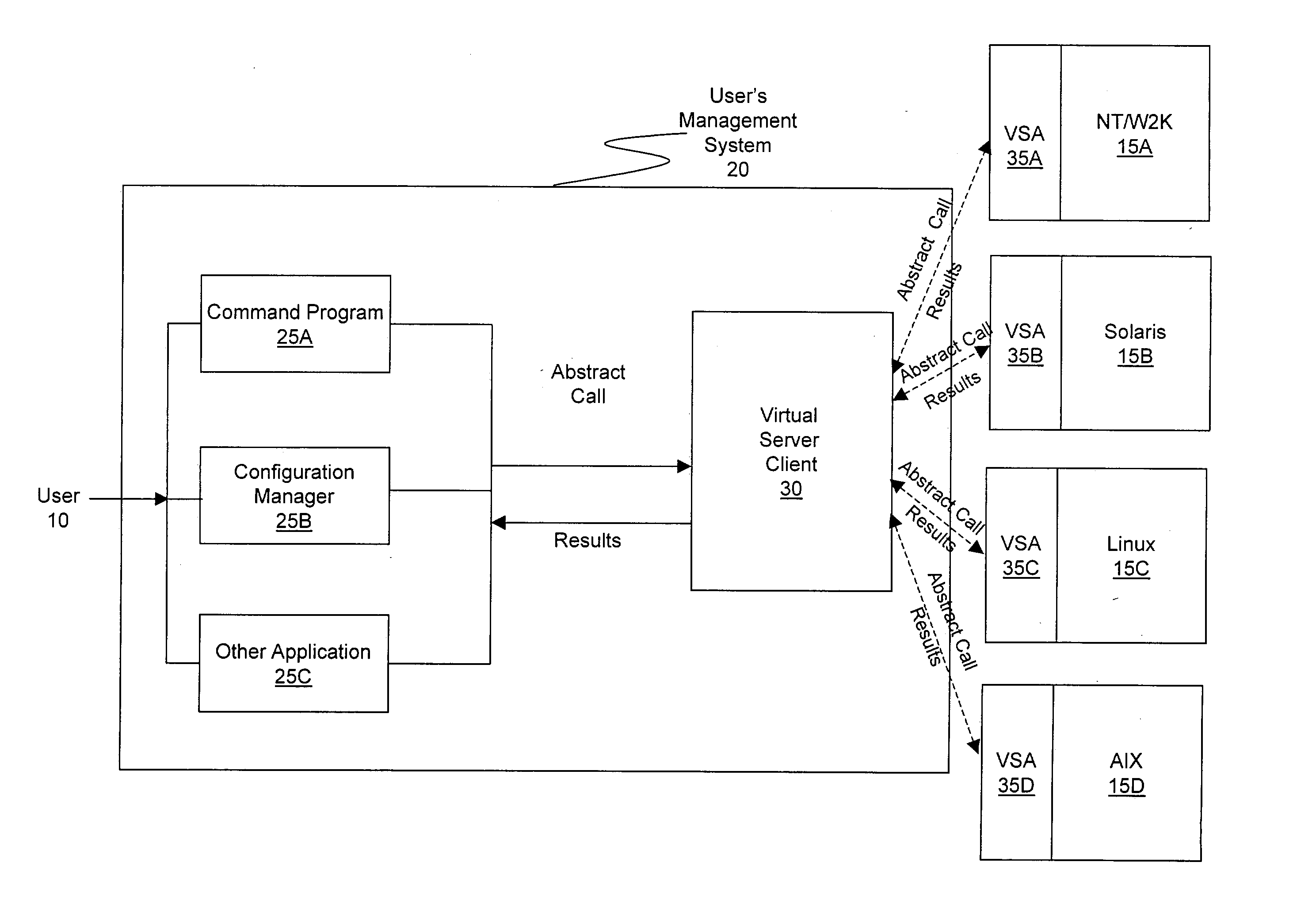
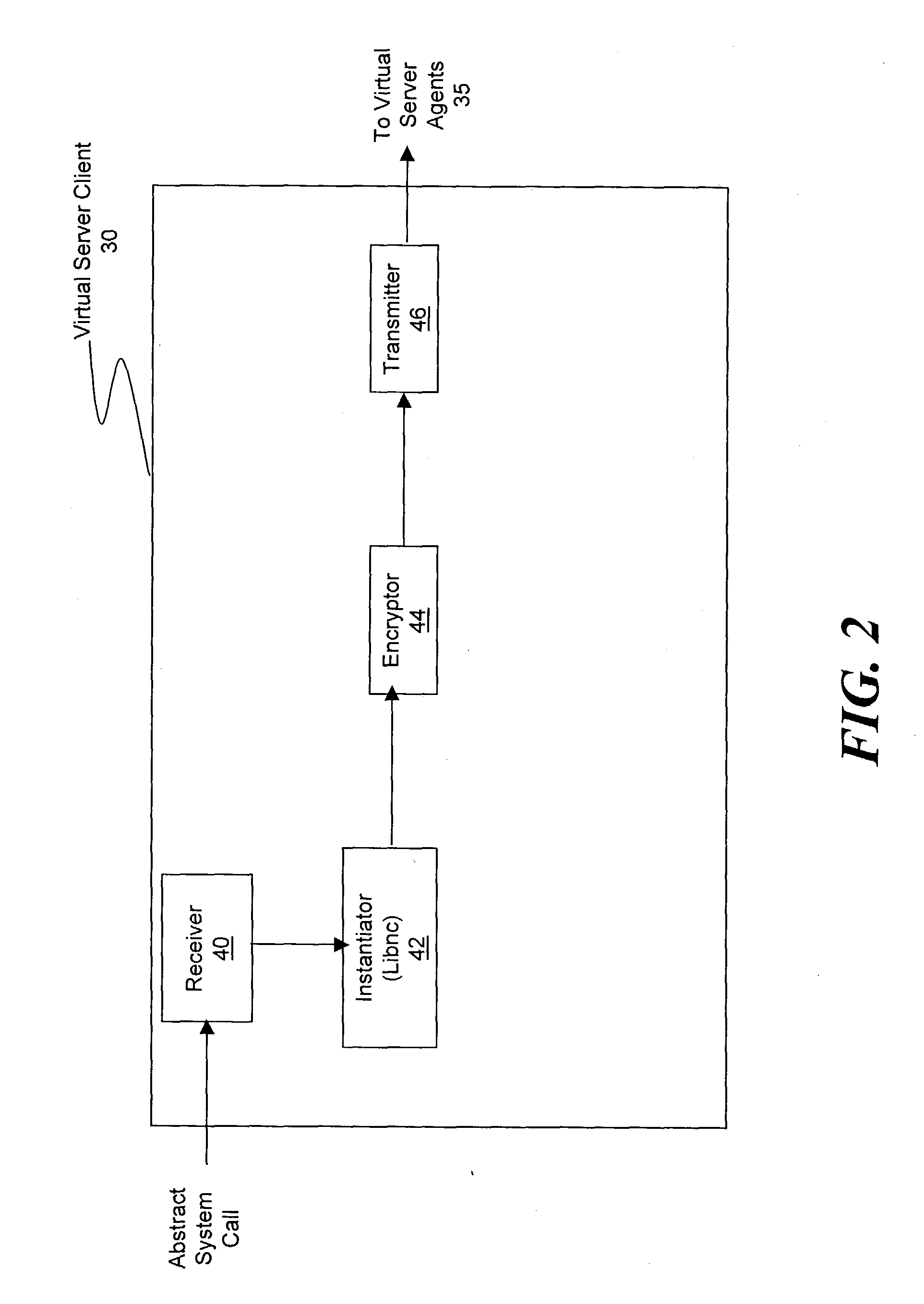
Method and system for simplifying distributed server management
ActiveUS20030233571A1Error detection/correctionInterprogram communicationOperational systemSystem call
A method and system for managing a large number of servers and their server components distributed throughout a heterogeneous computing environment is provided. In one embodiment, an authenticated user, such as a IT system administrator, can securely and simultaneously control and configure multiple servers, supporting different operating systems, through a "virtual server." A virtual server is an abstract model representing a collection of actual target servers. To represent multiple physical servers as one virtual server, abstract system calls that extend execution of operating-system-specific system calls to multiple servers, regardless of their supported operating systems, are used. A virtual server is implemented by a virtual server client and a collection of virtual server agents associated with a collection of actual servers.
Owner:BLADELOGIC
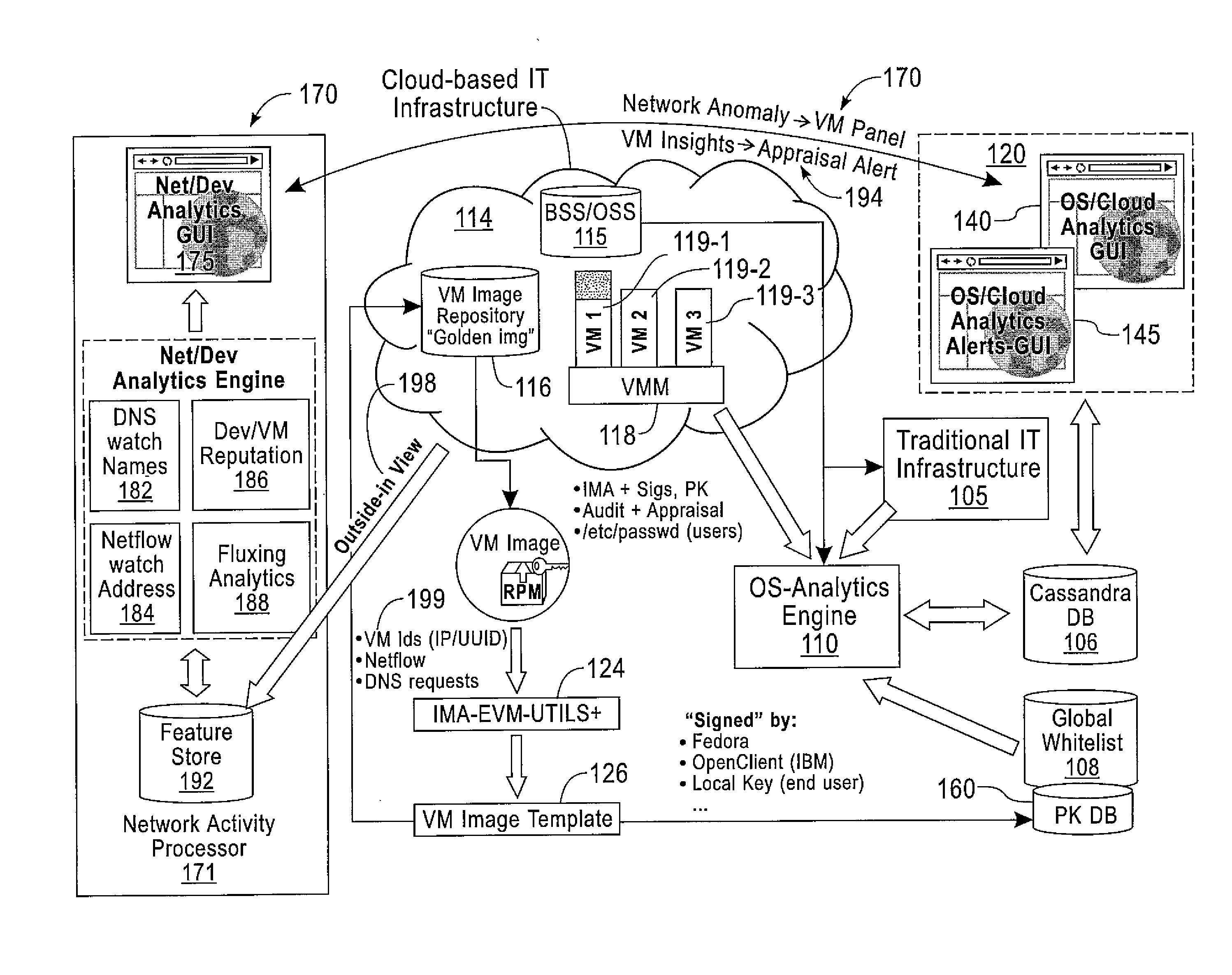
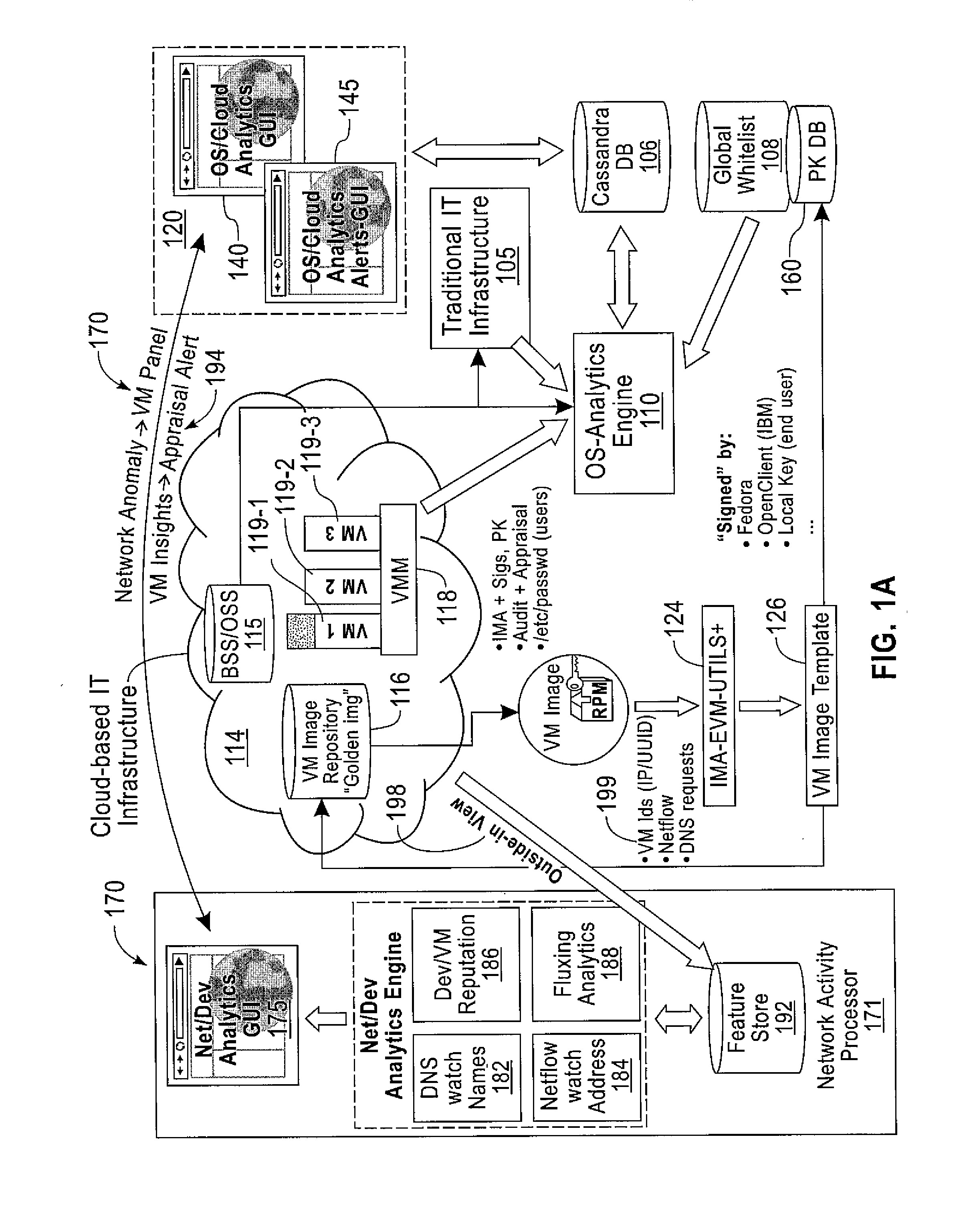
Computer Implemented Techniques for Detecting, Investigating and Remediating Security Violations to IT Infrastructure
A method includes collecting system calls and call parameters invoked by monitored applications for target computer systems. The system calls and call parameters are received from operating system kernels on the plurality of target computer systems. Sequences of systems calls and call parameters of the monitored applications are correlated among different target computer systems to deduce malicious activities. Remedial action(s) are performed in response to malicious activities being deduced as being malicious by the correlating. Another method includes determining that network activity at a specific time is deemed to be suspicious. Using IP addresses involved in the suspicious network activity, computer system(s) are determined that are sources of the suspicious network activity. Based on the specific time and the determined computer system(s), application(s) are determined that are executing on the determined computer system(s) that are causing the suspicious network activity. Remedial action(s) are performed for the determined computer system(s).
Owner:IBM CORP
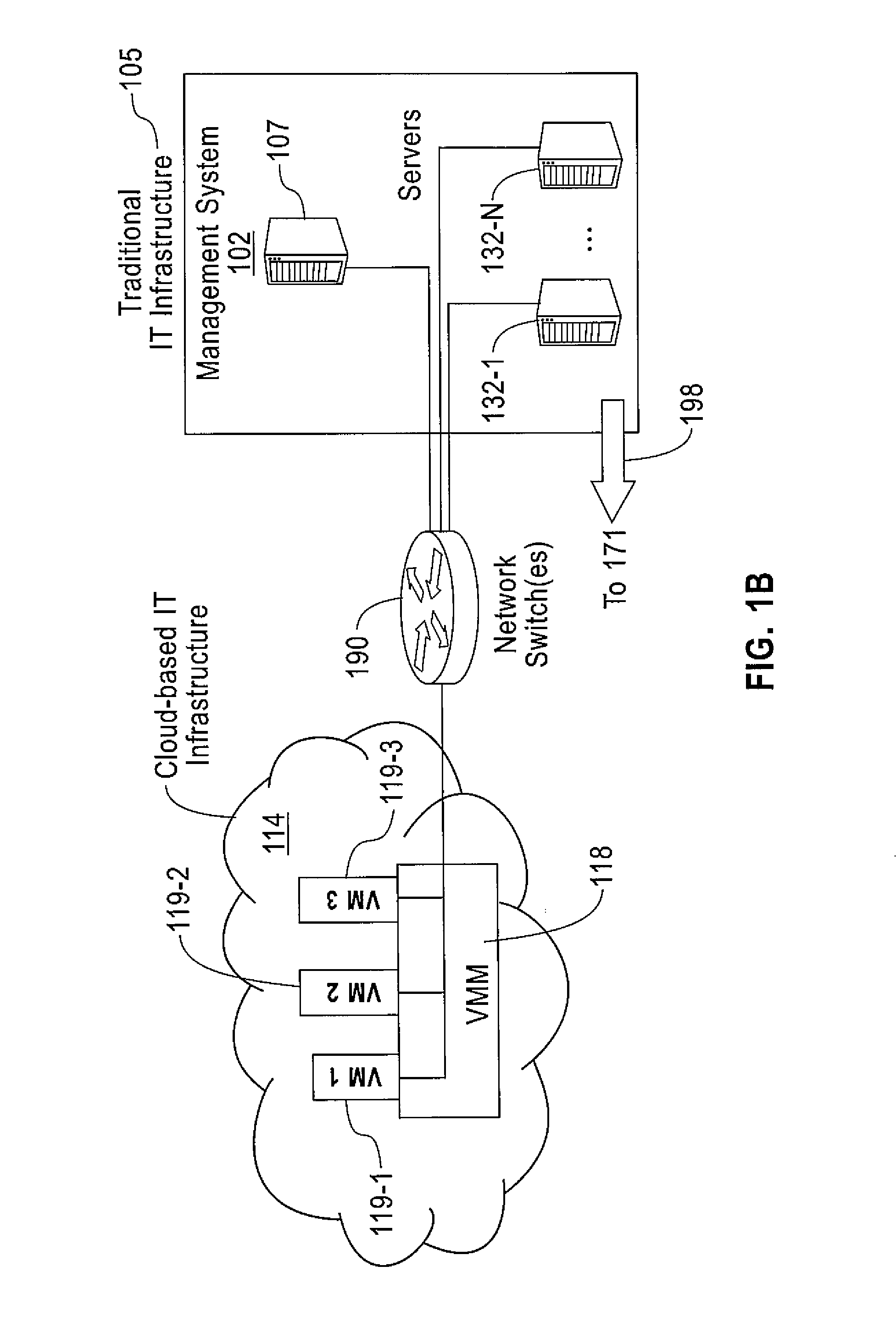
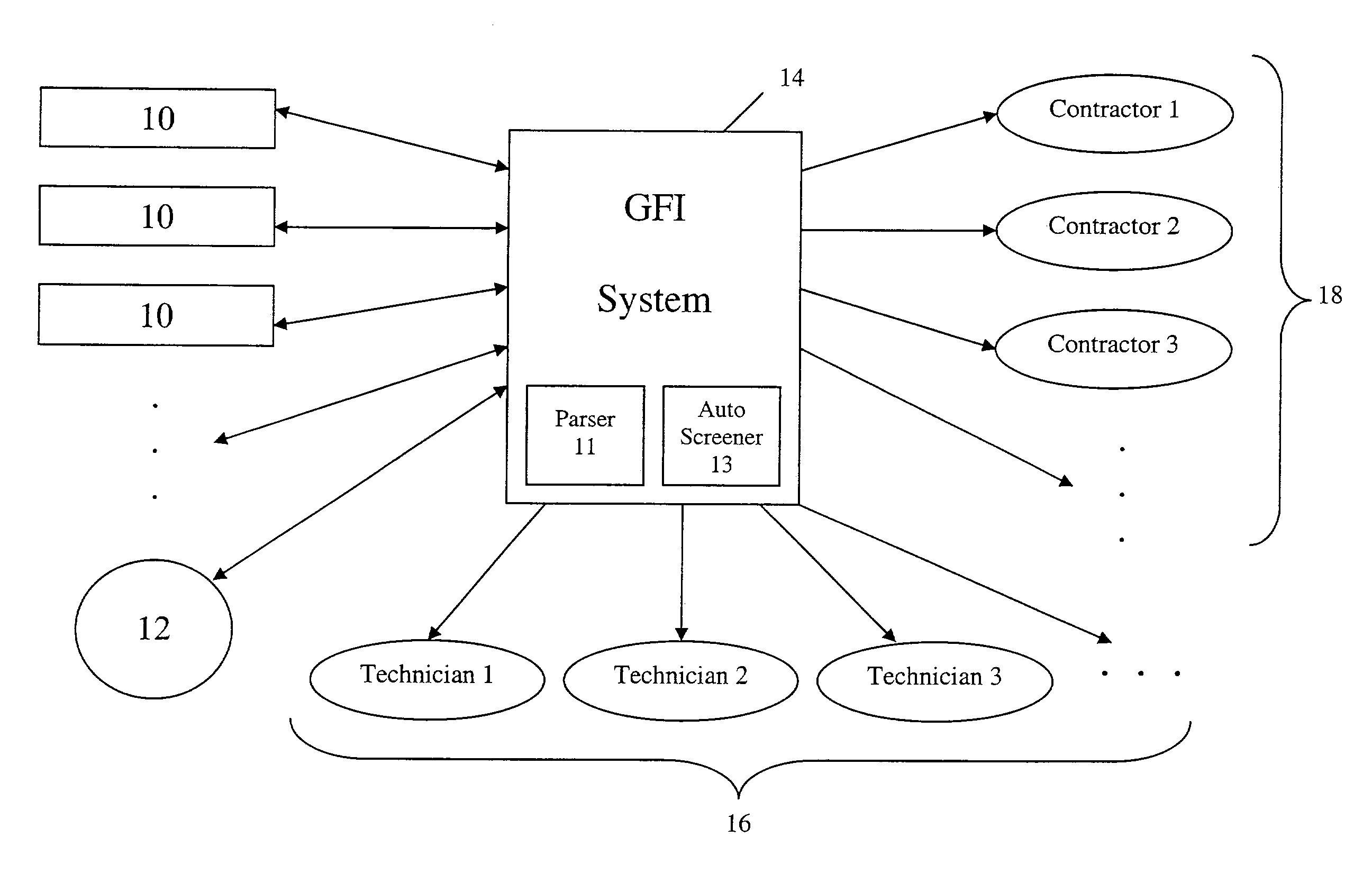
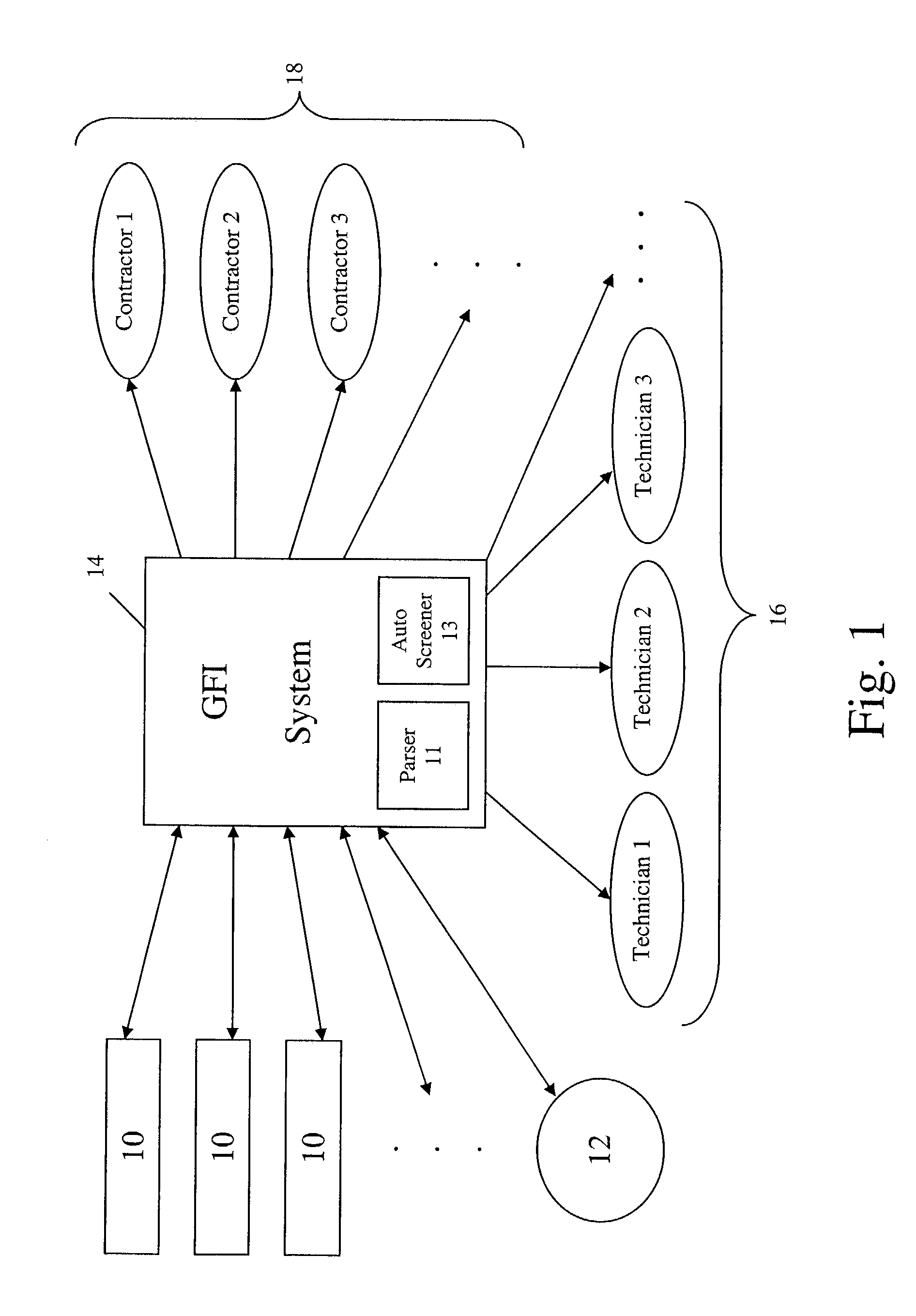
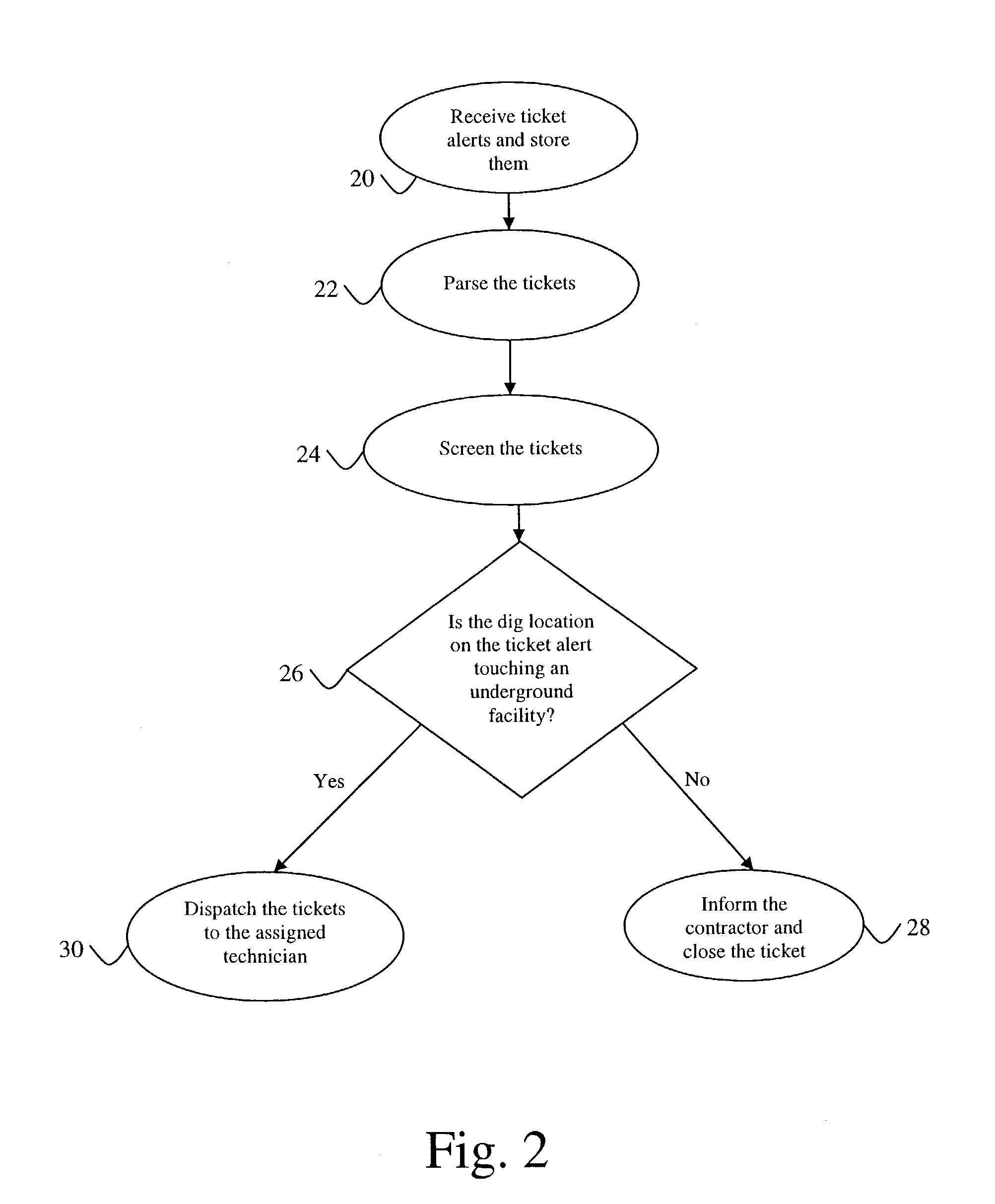
Method and apparatus for managing dig alerts in a network system
InactiveUS6958690B1Avoid damageElectric/magnetic detection for well-loggingFrequency-division multiplex detailsFiberSystem call
The present invention provides a most efficient, automated, fast and least expensive method and apparatus for processing the dig ticket alerts to prevent damage of underground facilities. All the functions required to process the ticket alerts are handled by one system called the geolink (geographical link to data) fiber integrity, i.e. GFI. The processing includes checking the ticket alerts for a dig location, automatically closing the ticket alerts if the dig location is not touching a cable buffer and forwarding the ticket alerts to the technician responsible for the ticket alert if the dig location is touching the cable buffer. The GFI system will receive and process thousands of dig ticket alerts on a daily basis without depending on any other system.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
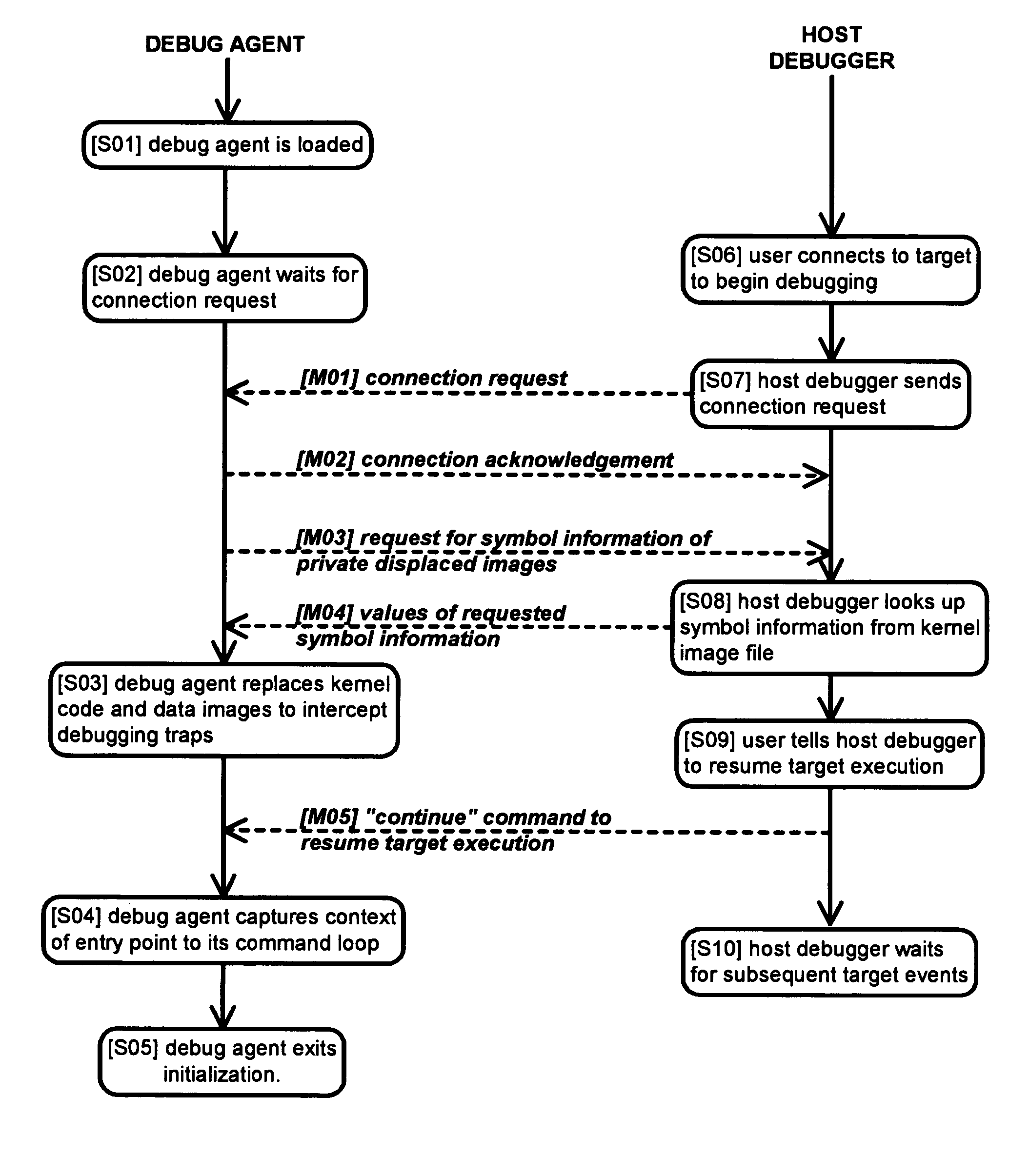
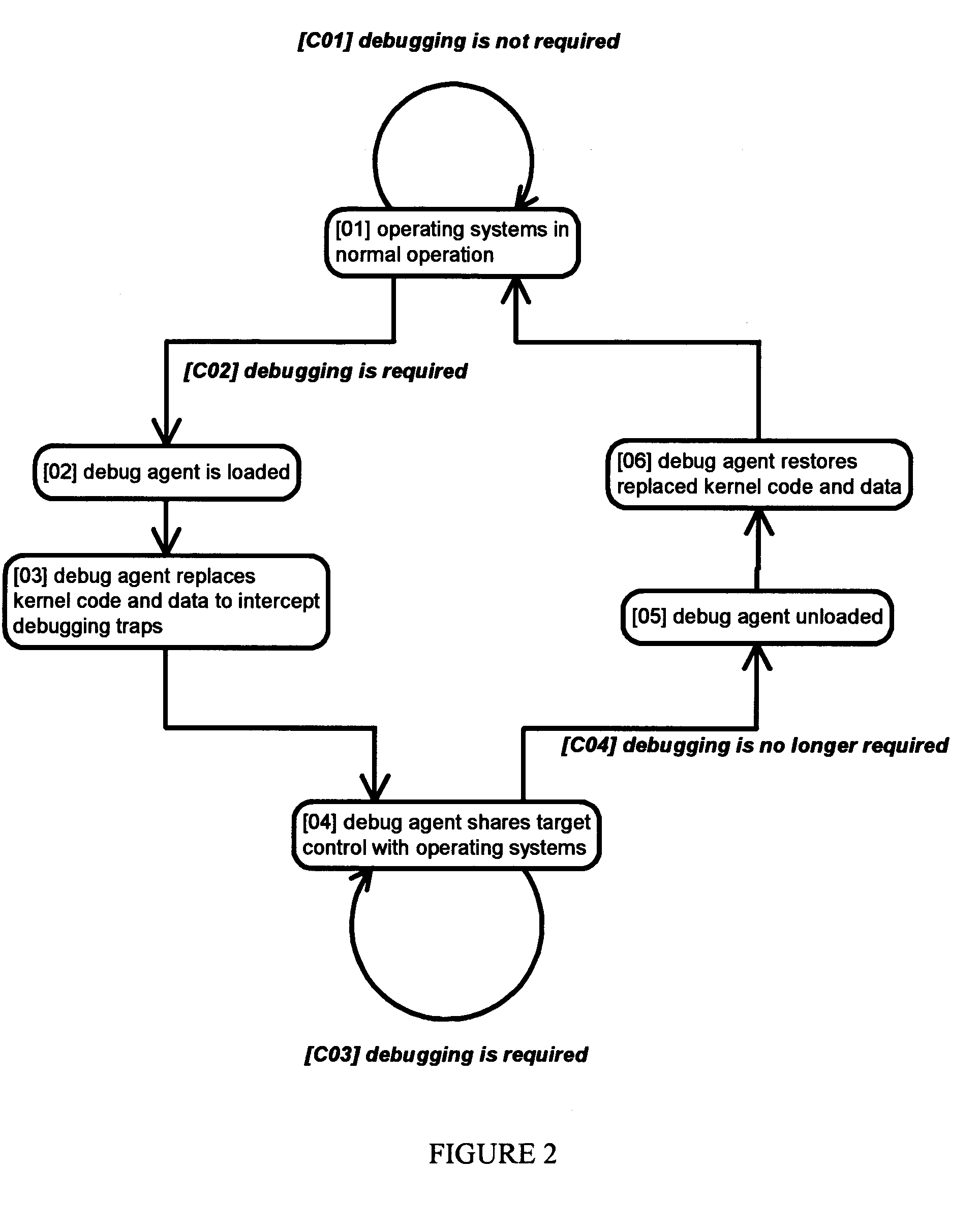
Method and apparatus for remote debugging of kernel and application software
InactiveUS20050216895A1Modified dynamicallyError detection/correctionSpecific program execution arrangementsOperational systemSystem call
A method and apparatus for debugging of OS kernel and applications software that does not require use of a hardware probe; can debug both user-mode programs and a significant body of the OS kernel code; allows the OS to continue servicing exceptions while debugging; leverages OS built-in device drivers for communicating devices to communicate with the host debugger; and can debug a production version of the OS kernel. When debugging is required, the running OS kernel dynamically loads a software-based debug agent on demand whereby such debug agent dynamically modifies the running production OS kernel code and data to intercept debugging traps and provide run-control. To provide debugging of loadable module, the debug agent implement techniques to intercept the OS module loading system call; set breakpoints in the loaded module initialization function; calculate the start address of the debugged module in memory; and asynchronously put the system under debug. By structuring command loop to execute in non-exception mode, and devising a process to transfer execution from the debug agent exception handler to the debug agent command loop and back, the debug agent can communicate with the host debugger using interrupt-driven input / output devices as well as allowing the system to service interrupts while under debug.
Owner:TRAN HIEU TRUNG
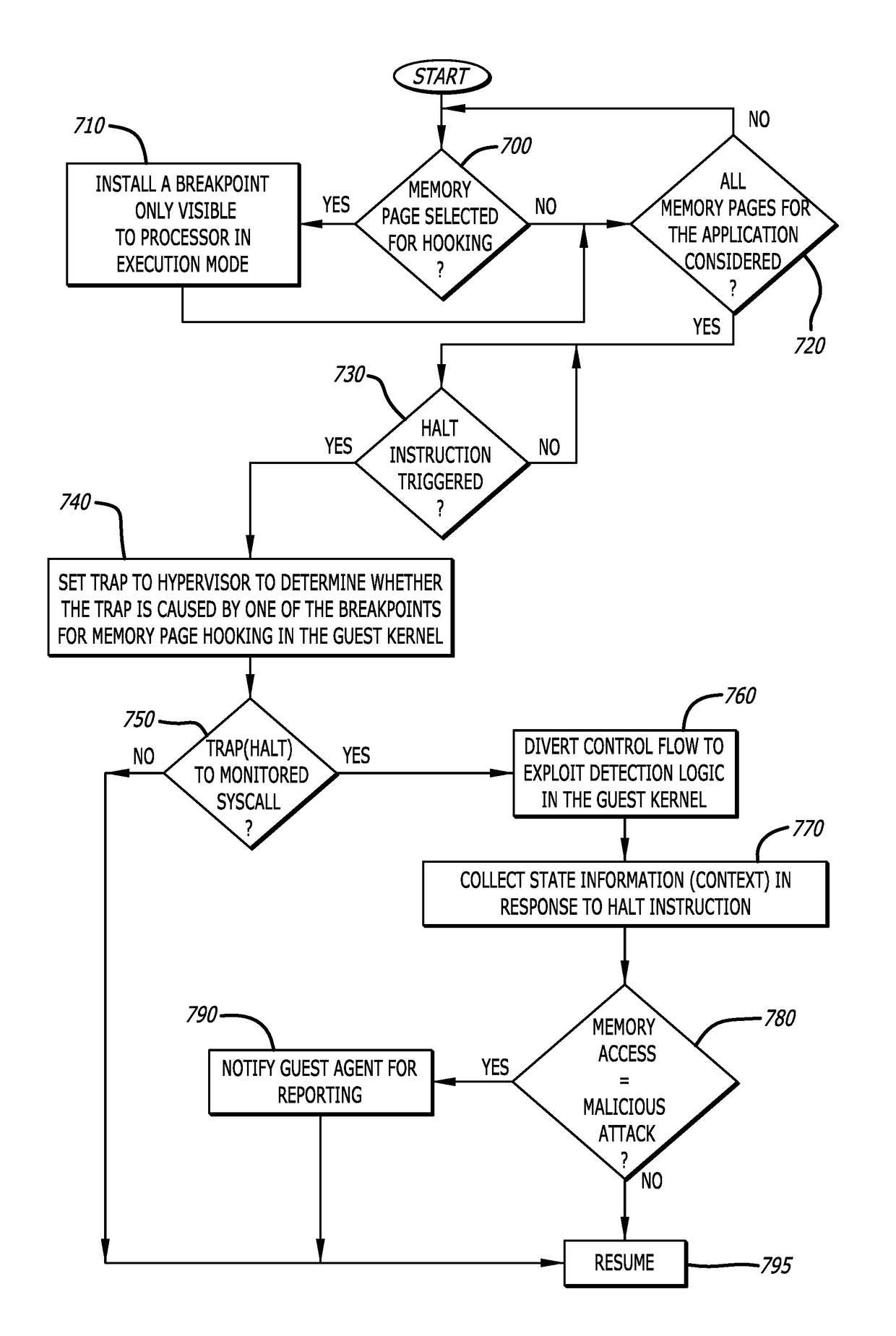
System and method of threat detection under hypervisor control
ActiveUS10033759B1Input/output to record carriersPlatform integrity maintainanceSystem callApplication software
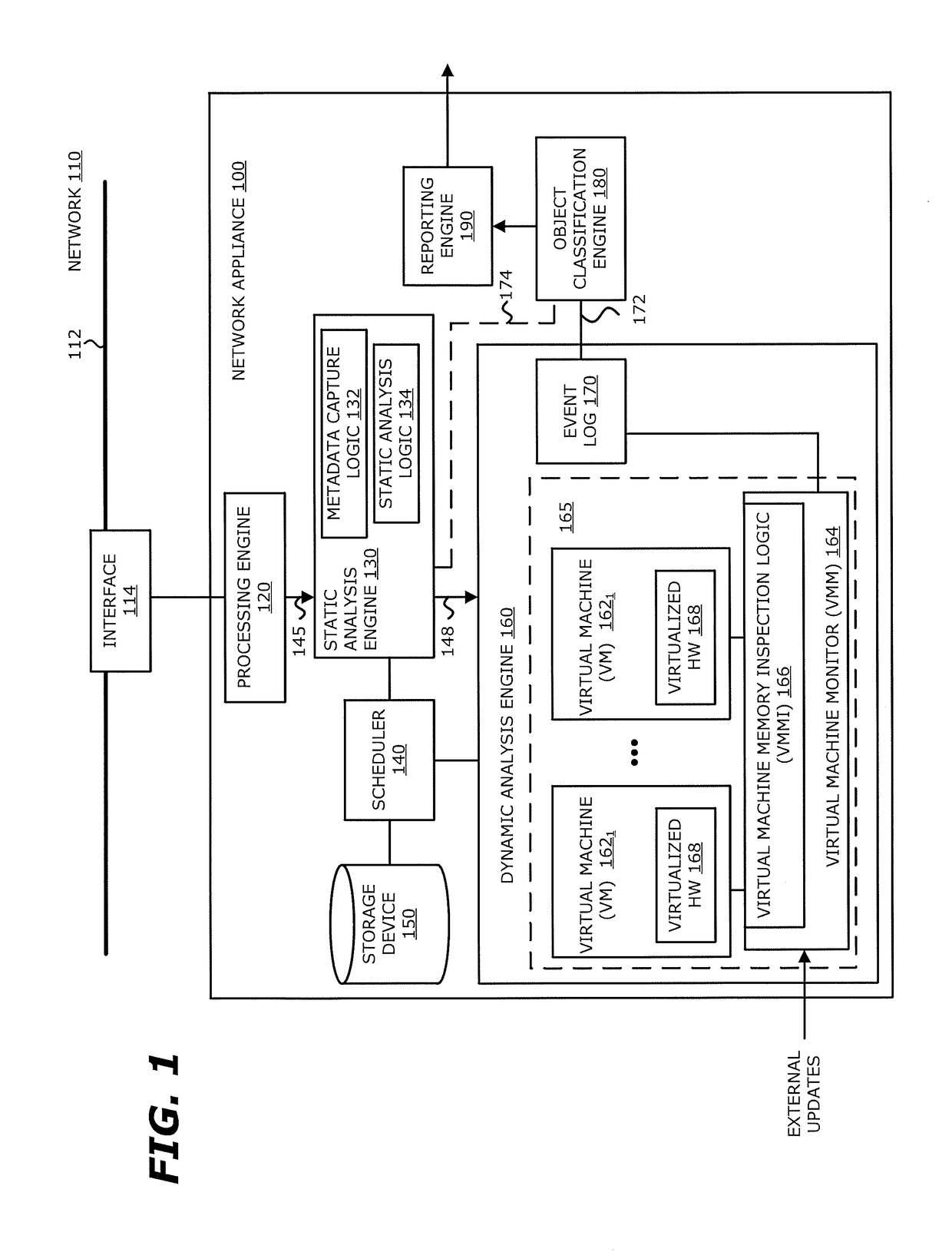
A computing device is described that comprises one or more hardware processors and a memory communicatively coupled to the one or more hardware processors. The memory comprises software that, when executed by the processors, operates as (i) a virtual machine and (ii) a hypervisor. The virtual machine includes a guest kernel that facilitates communications between a guest application being processed within the virtual machine and one or more virtual resources. The hypervisor configures a portion of the guest kernel to intercept a system call from the guest application and redirect information associated with the system call to the hypervisor. The hypervisor enables logic within the guest kernel to analyze information associated with the system call to determine whether the system call is associated with a malicious attack in response to the system call being initiated during a memory page execution cycle. Alternatively, the hypervisor operates to obfuscate interception of the system call in response to the system call being initiated during memory page read cycle.
Owner:FIREEYE SECURITY HLDG US LLC
Selective system call monitoring
ActiveUS9690606B1Platform integrity maintainanceSoftware simulation/interpretation/emulationVirtualizationSystem call
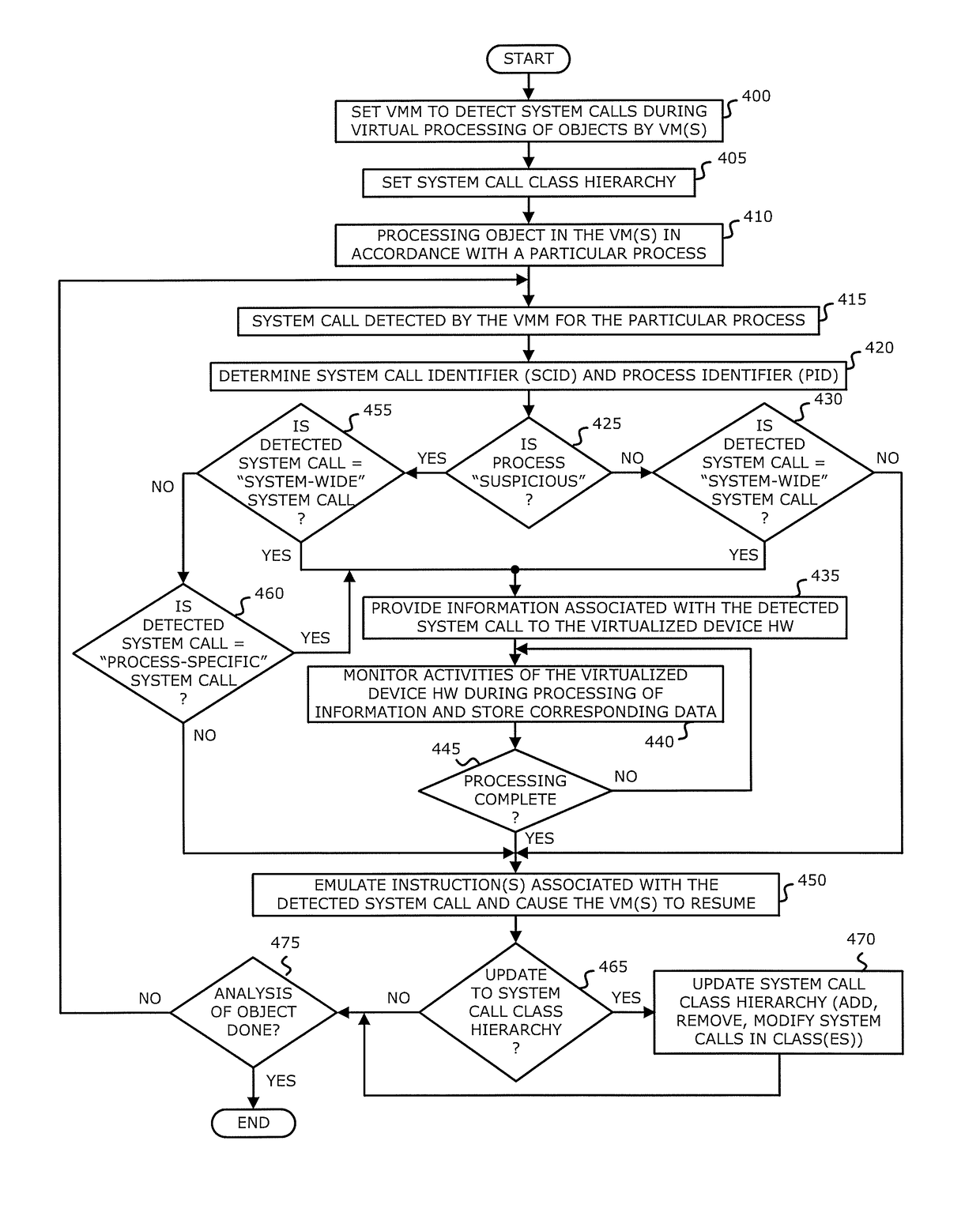
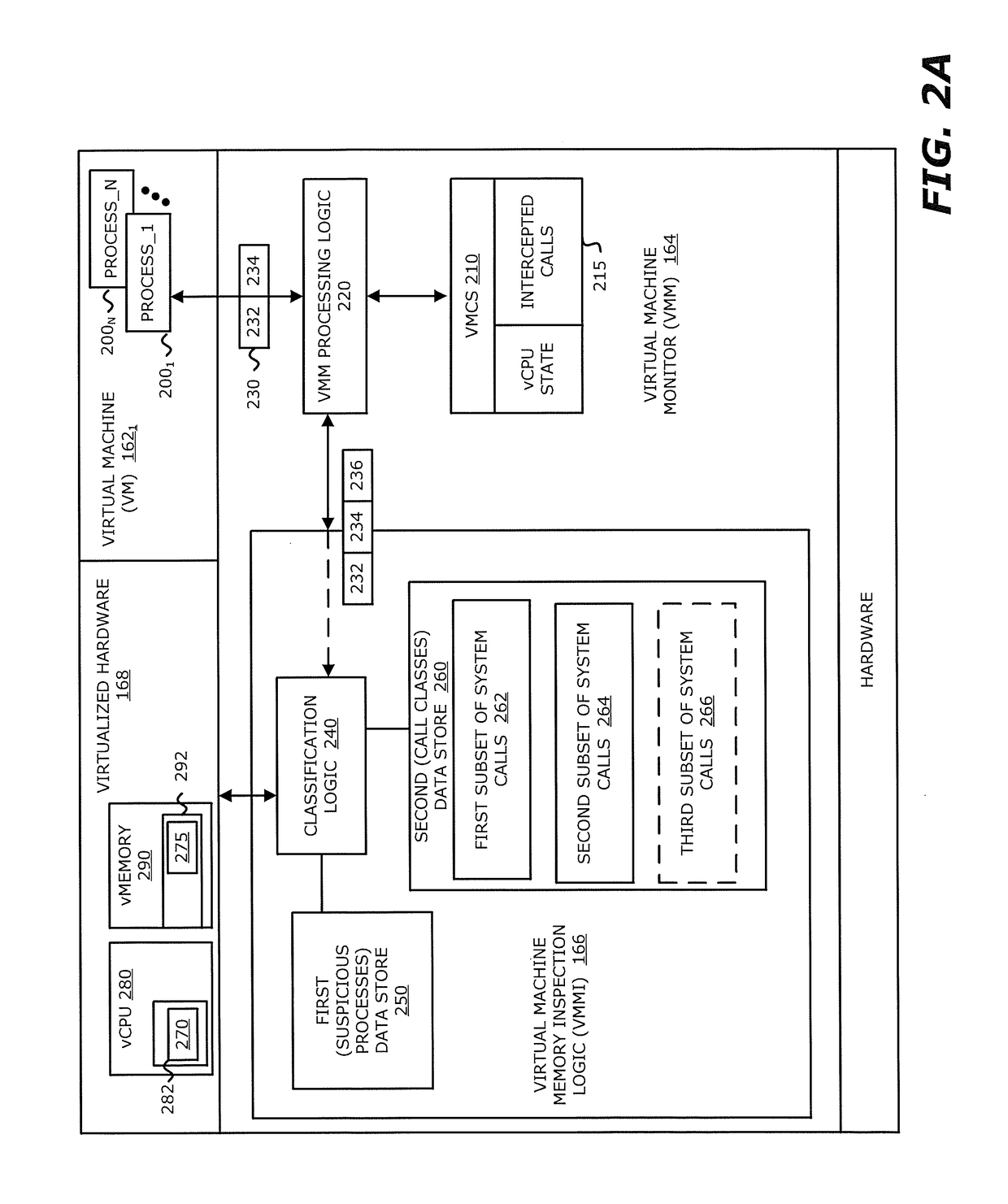
According to one embodiment of the invention, a computerized method is described for improved efficiency in malware detection. The method comprises detecting a system call initiated by a virtual machine and determining a class assigned to the detected system call. In response to determining that the system call is associated with a first class of system calls, providing information associated with the system call to virtualized device hardware. In contrast, in response to determining that the system call is associated with a second class of system calls, which is different from the first class of system calls, the virtual machine resumes virtual processing of an object without providing information to the virtualized device hardware.
Owner:FIREEYE SECURITY HLDG US LLC
System and method for providing communications to processes
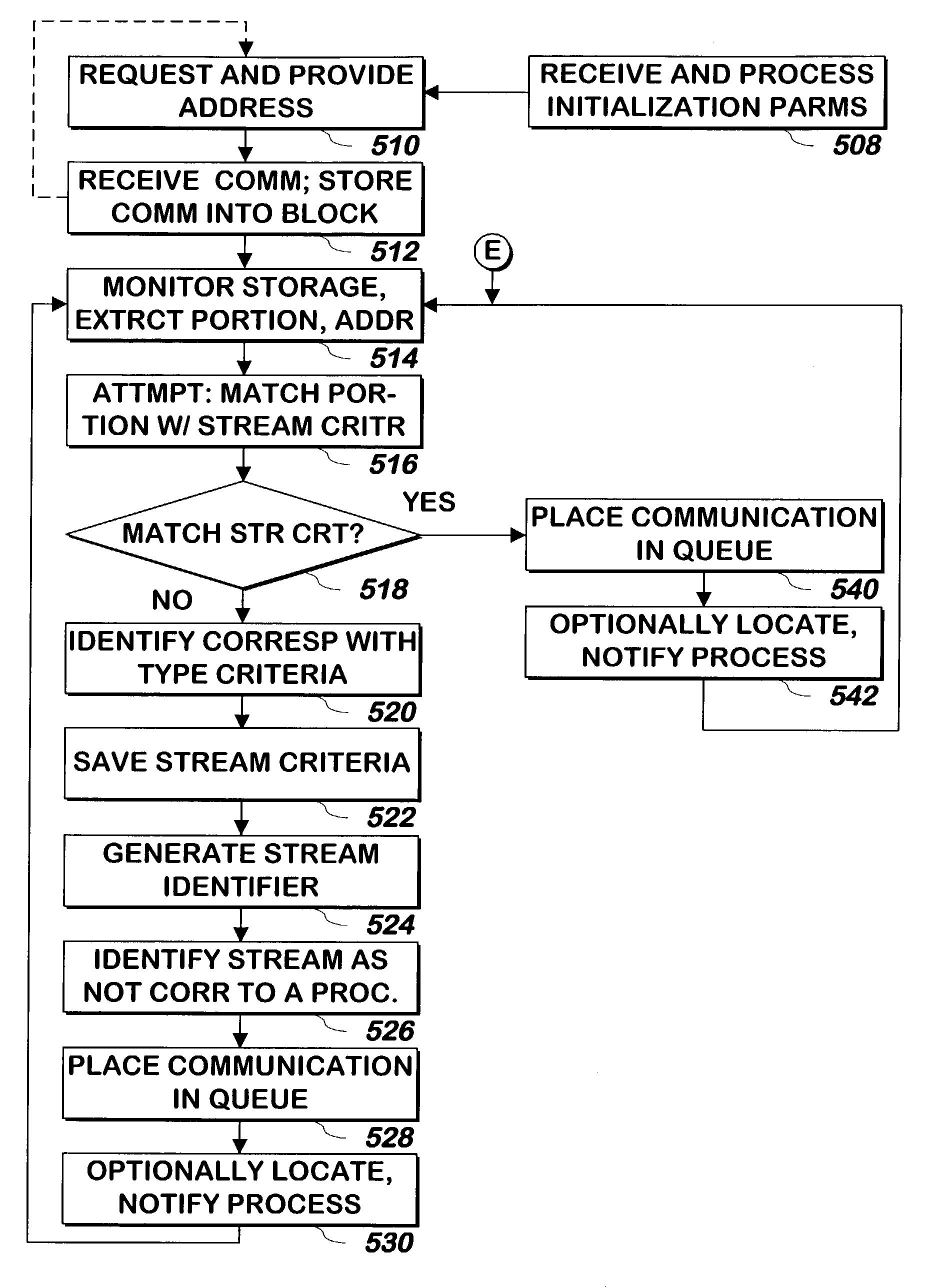
InactiveUS7240350B1Multiple digital computer combinationsSpecific program execution arrangementsOperational systemSystem call
A system and method provides communications to processes, handles transmissions of communications received from processes, and allows other manipulations of transmissions upon request by processes without an operating system call.
Owner:SLT LOGIC
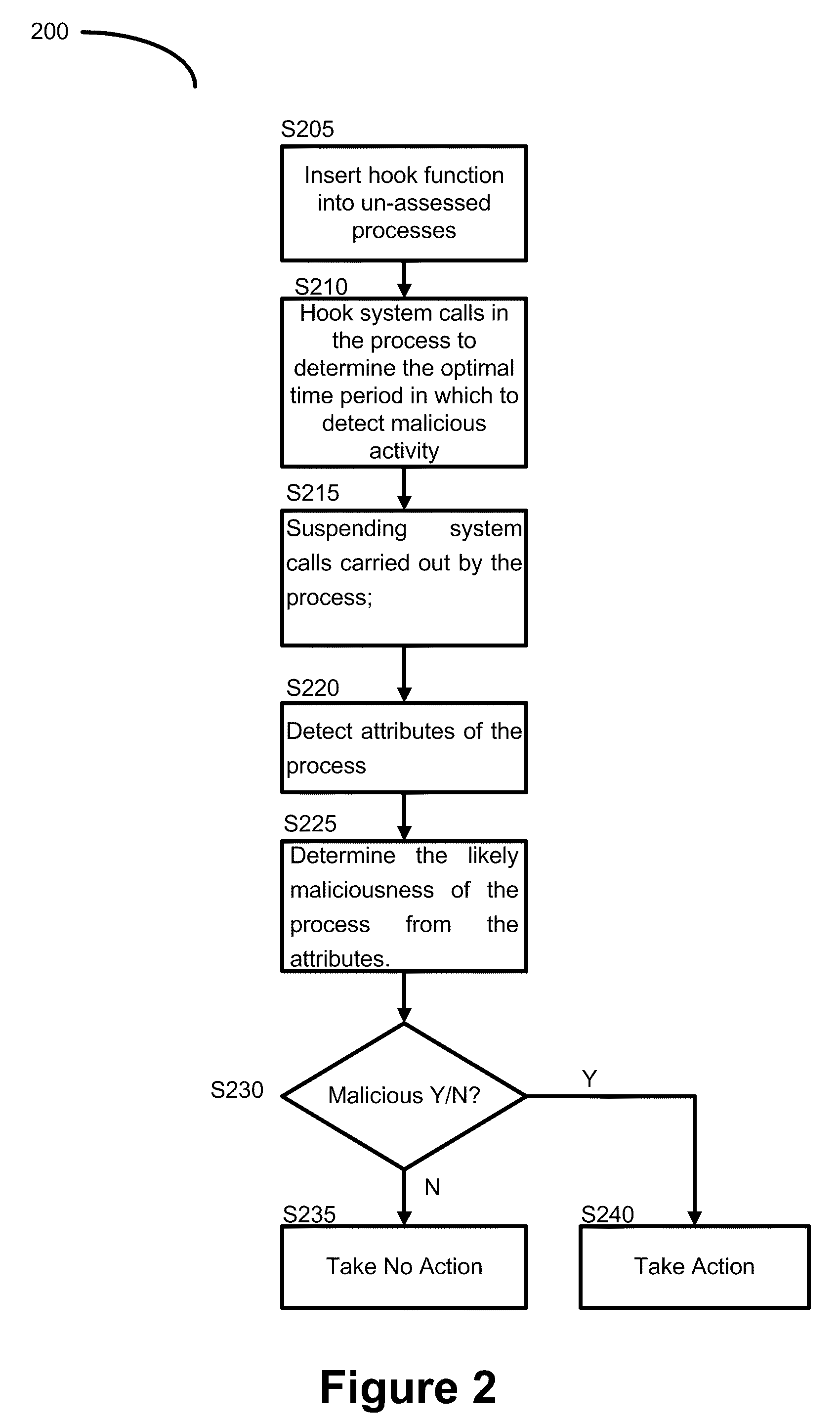
Method of detecting and blocking malicious activity
A method of detecting and blocking malicious activity of processes in computer memory during unpacking of a file after the code and data contained in the file are unpacked is described. The method includes inserting a hook function into one or more un-assessed processes running in the computer memory. A hook Is then placed on one or more system calls carried out by the one or more un-assessed processes; the one or more system calls determining an optimal time period in which to detect malicious activity in the un-assessed processes. During the optimal time period the one or more system calls carried out by the one or more un-assessed processes are suspended and attributes of the one or more un-assessed processes are detected and the likely maliciousness of the one or more un-assessed processes is determined from the attributes.
Owner:NORTONLIFELOCK INC
Detecting and preventing malcode execution
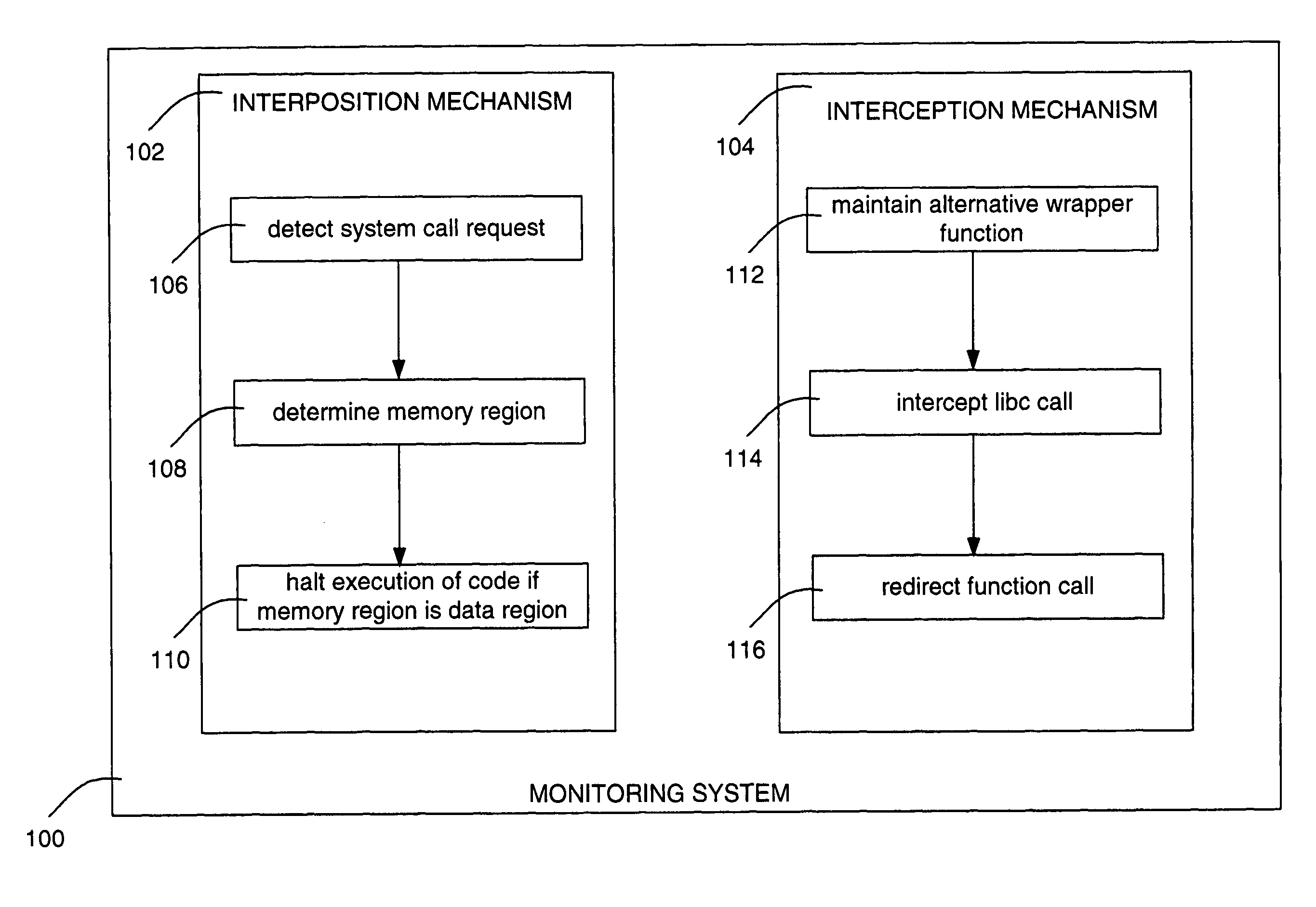
InactiveUS7971255B1Memory loss protectionUnauthorized memory use protectionSoftware engineeringTerm memory
A system for detecting and halting execution of malicious code includes a kernel-based system call interposition mechanism and a libc function interception mechanism. The kernel-based system call interposition mechanism detects a system call request from an application, determines a memory region from which the system call request emanates, and halts execution of the code responsible for the call request if the memory region from which the system call request emanates is a data memory region. The libc function interception mechanism maintains an alternative wrapper function for each of the relevant standard libc routines, intercepts a call from an application to one or more libc routines and redirects the call into the corresponding alternative wrapper function.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
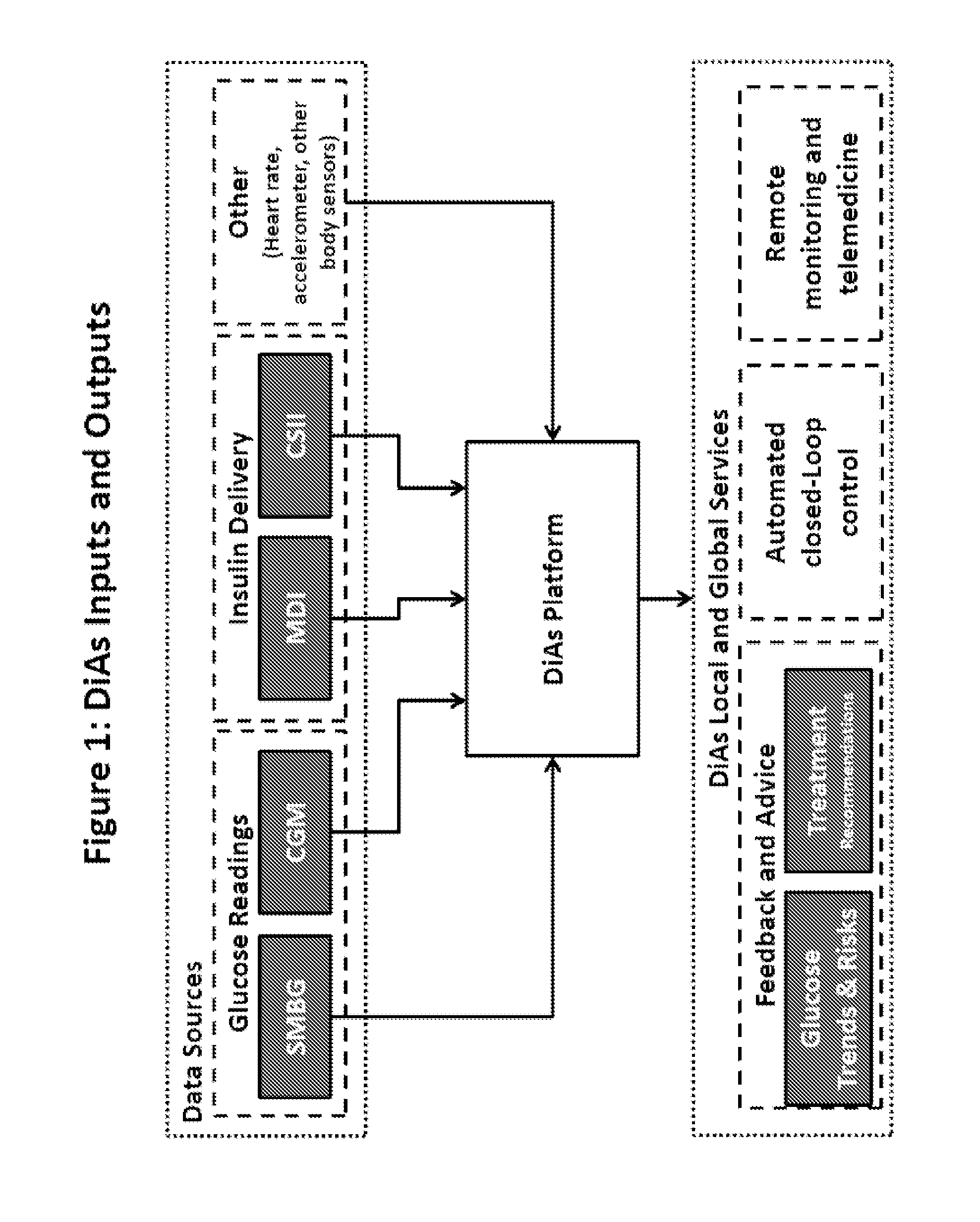
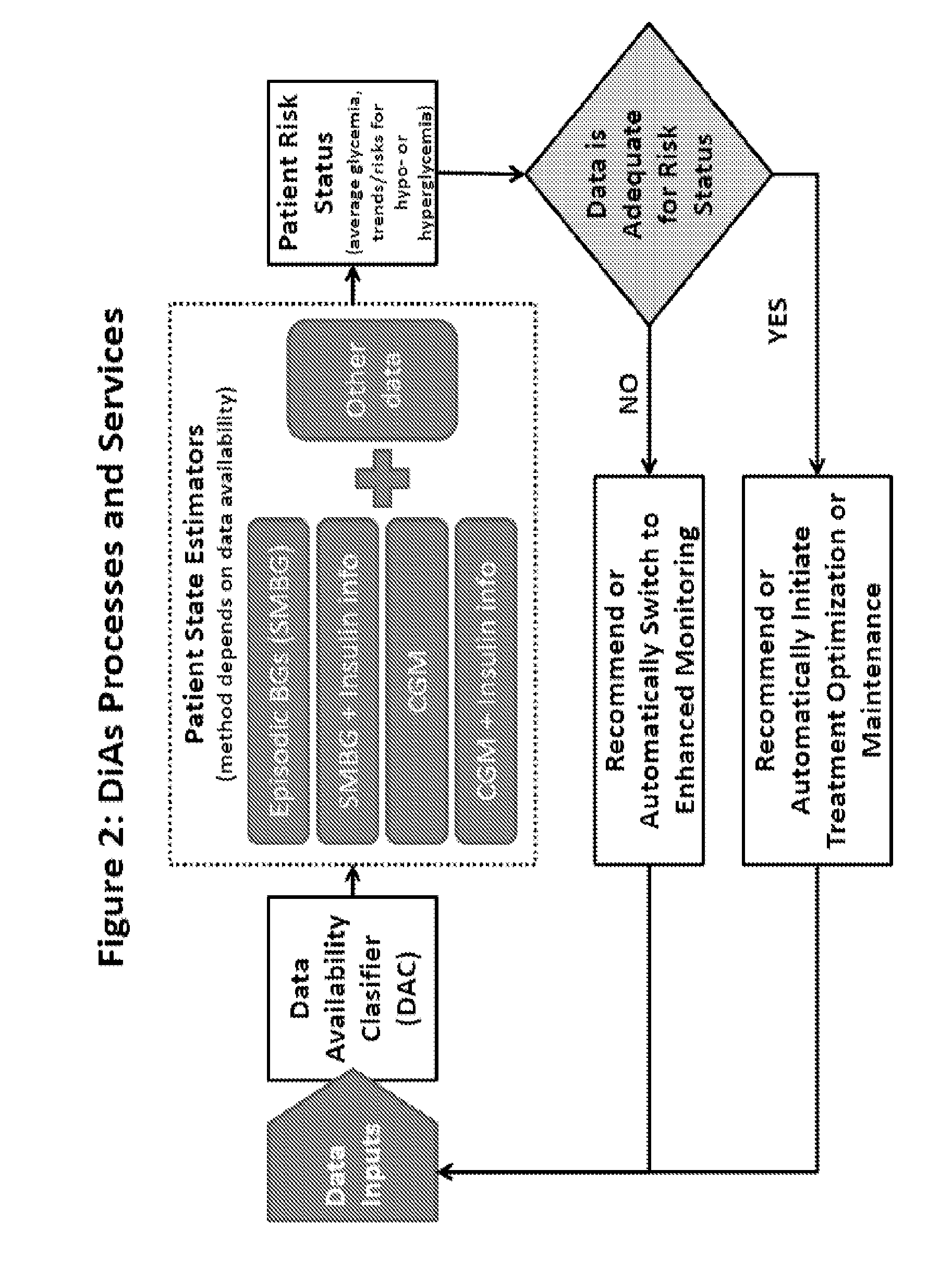
Unified Platform for Monitoring and Control of Blood Glucose Levels in Diabetic Patients
ActiveUS20150018633A1Easy to replaceGuaranteed uptimePeptide/protein ingredientsDrug and medicationsClosed loopSystem call
A flexible system capable of utilizing data from different monitoring techniques and capable of providing assistance to patients with diabetes at several scalable levels, ranging from advice about long-term trends and prognosis to real-time automated closed-loop control (artificial pancreas). These scalable monitoring and treatment strategies are delivered by a unified system called the Diabetes Assistant (DiAs) platform. The system provides a foundation for implementation of various monitoring, advisory, and automated diabetes treatment algorithms or methods. The DiAs recommendations are tailored to the specifics of an individual patient, and to the patient risk assessment at any given moment.
Owner:UNIV OF VIRGINIA ALUMNI PATENTS FOUND
Creating secure process objects
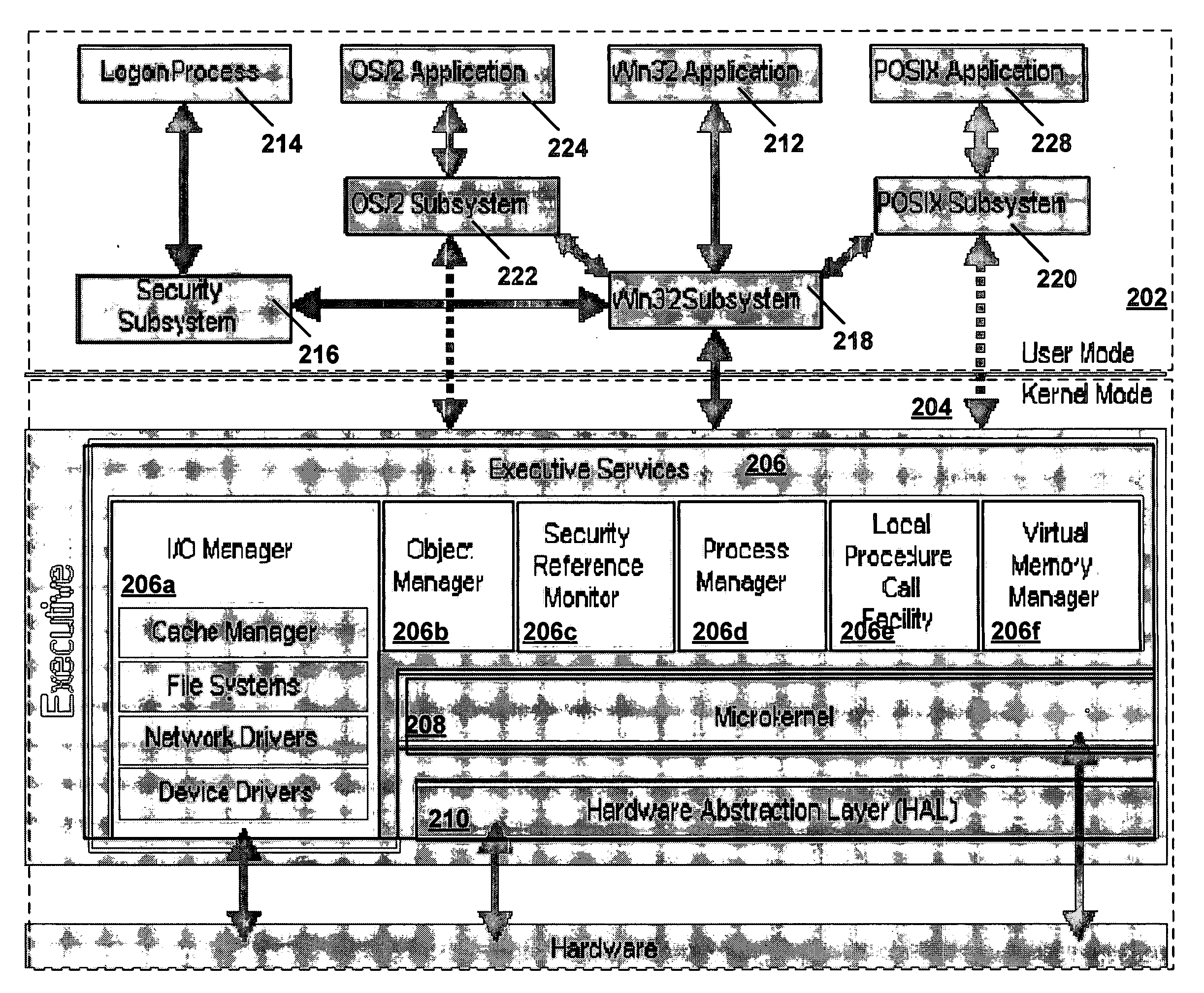
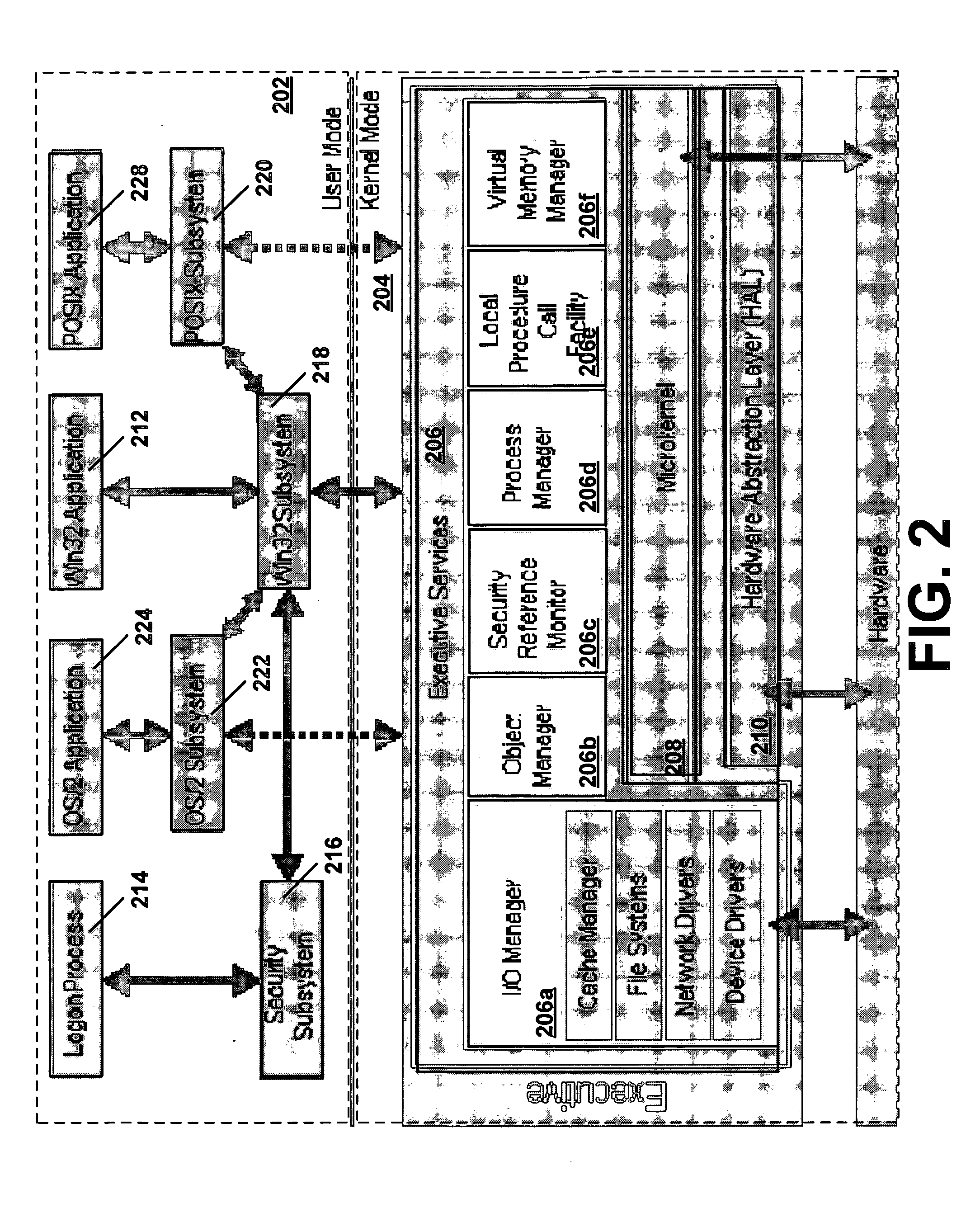
InactiveUS20060259487A1Precise processingReduce in quantityDigital data processing detailsAnalogue secracy/subscription systemsVirtual memoryInit
A secure process may be created which does not allow code to be injected into it, does not allow modification of its memory or inspection of its memory. The resources protected in a secure process include all the internal state and threads running in the secure process. Once a secure process is created, the secure process is protected from access by non-secure processes. Process creation occurs atomically in kernel mode. Creating the infrastructure of a process in kernel mode enables security features to be applied that are difficult or impossible to apply in user mode. By moving setup actions previously occurring in user mode (such as creating the initial thread, allocating the stack, initialization of the parameter block, environment block and context record) into kernel mode, the need of the caller for full access rights to the created process is removed. Instead, enough state is passed from the caller to the kernel with the first system call so that the kernel is able to perform the actions previously performed using a number of calls back and forth between caller and kernel. When the kernel returns the handle to the set-up process, some of the access rights accompanying the handle are not returned. Specifically, those access rights that enable the caller to inject threads, read / write virtual memory, and interrogate or modify state of the threads of the process are not returned to the caller.
Owner:MICROSOFT TECH LICENSING LLC
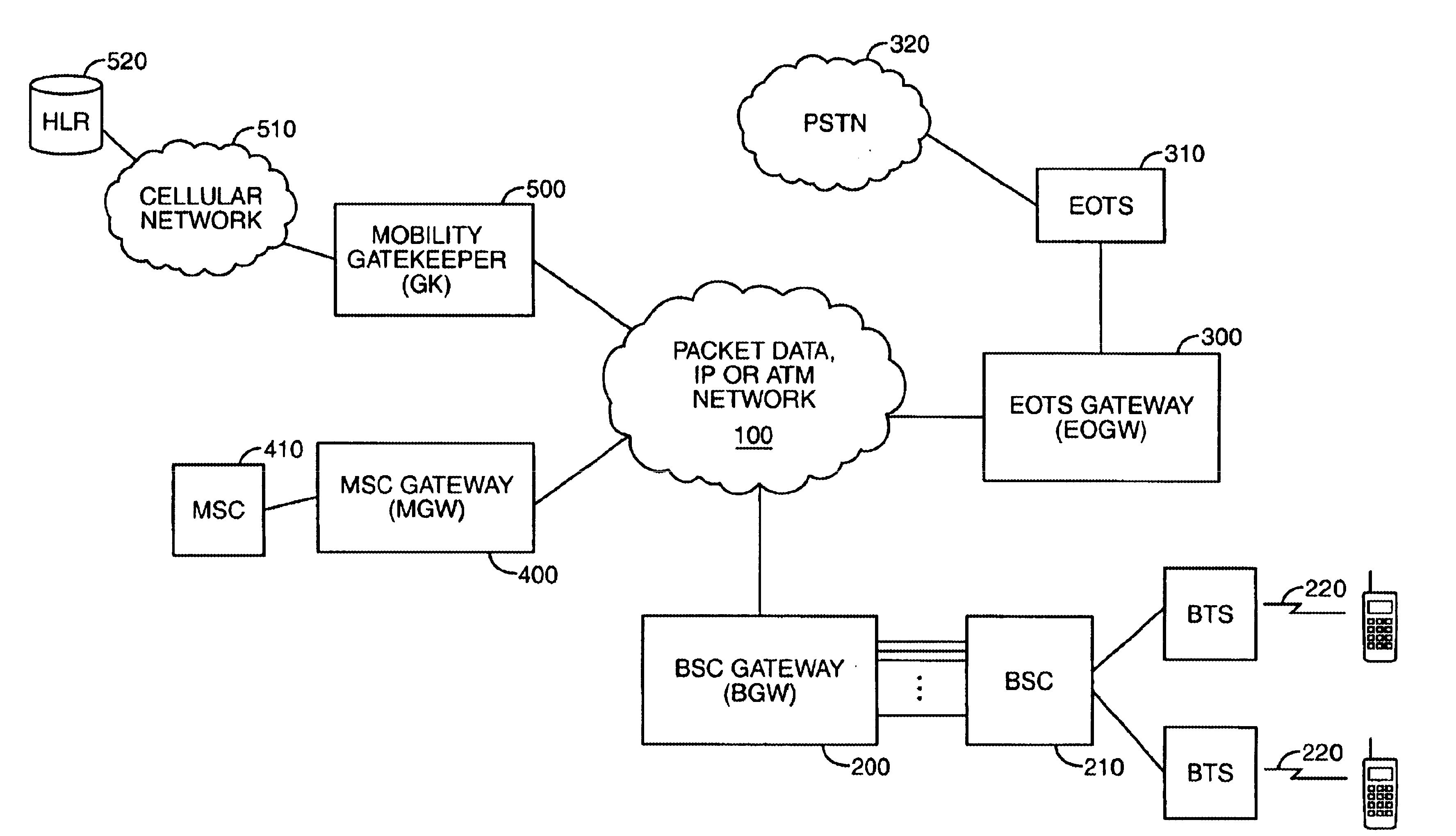
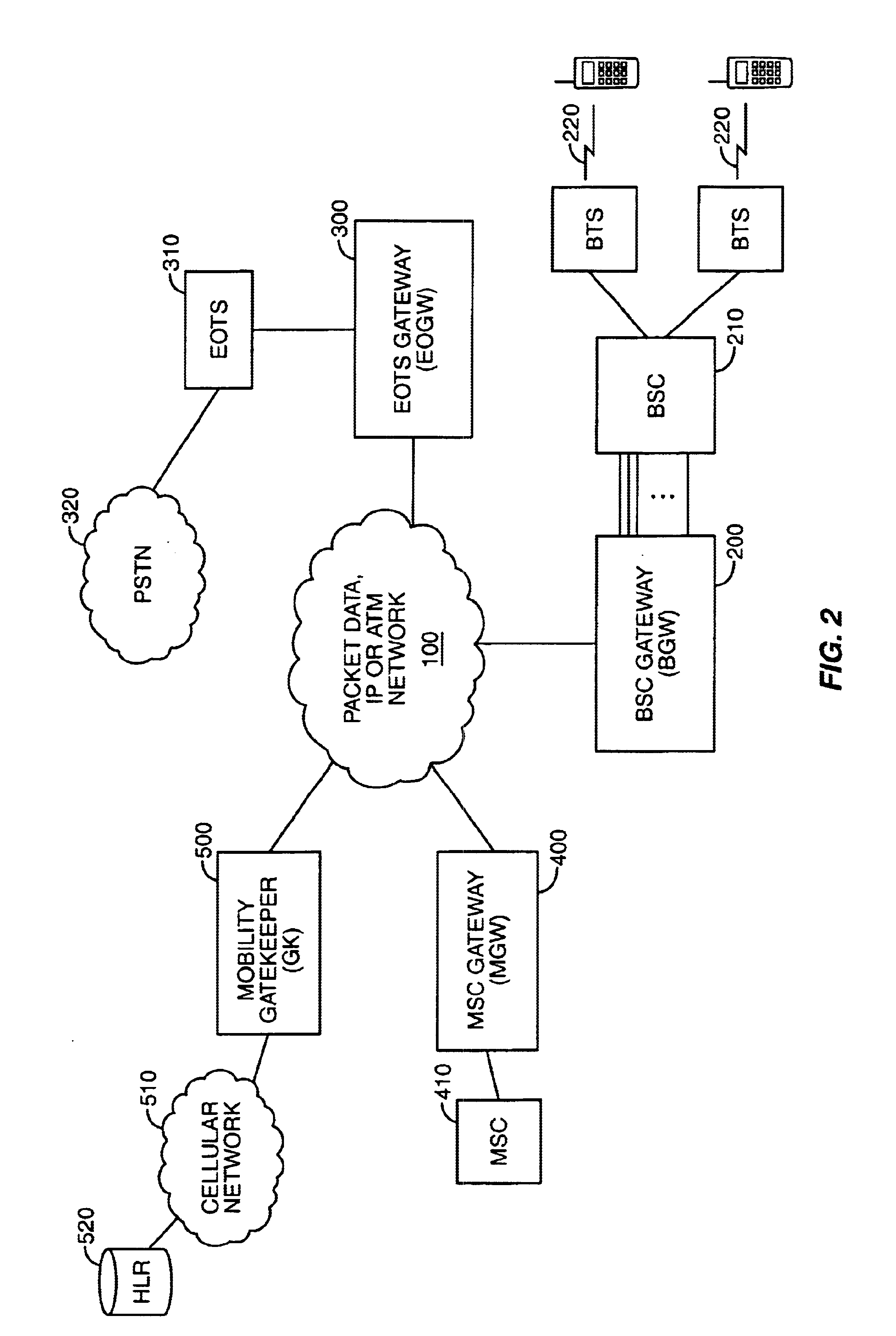
System, method, and computer program product for connectivity of wireless base station to PSTN via an IP data network
InactiveUS6888803B1Special service provision for substationMultiplex system selection arrangementsCable telephonySystem call
A system for providing wireline telephone services to wireless subscribers utilizing a packet data network 100. The system includes a base station controller (BSC) 210 a base station controller gateway (BGW) 200 for providing client based services to mobile subscribers and providing protocol mapping between a mobile protocol and a packet data network protocol. The system further comprises a mobility gatekeeper (GK) 500 for managing network mobility services for each wireless call including the establishment of a call control path and a speech path between said base station controller and a serving end office telephone point. The system also comprises a end office gateway (EOGW) 300 for providing protocol conversion between the packet data network protocol and the end office point data protocol such that a wireless subscriber has access to all wireline services provided by the end office point. A mobile switching center (MSC) 410 and mobile switching center gateway (MGW) 400 are included to facilitate inter-system call handoffs into an existing circuit-switched wireless telephony network.
Owner:BLACKBERRY LTD
Dynamic RDF groups
InactiveUS20030093597A1Input/output to record carriersData processing applicationsRemote systemComputerized system
Described are techniques used in dynamically modifying RDF groups. A system call is issued by a host computer system to execute a remote system call on a first data storage system to create, remove, or modify an RDF group between the first data storage system and another data storage-system-that is remotely connected to the first data storage system in an RDF switched environment. As part of executing the remote system call, data is pushed from the first to the second data storage systems without having an established link between the data storage systems. Each data storage system performs processing to make the necessary modifications in all directors in accordance with the dynamic RDF group. A status indicating success or failure of the remote system call is returned to the host computer system.
Owner:EMC IP HLDG CO LLC
Method and apparatus for improving performance in a network with high delay times
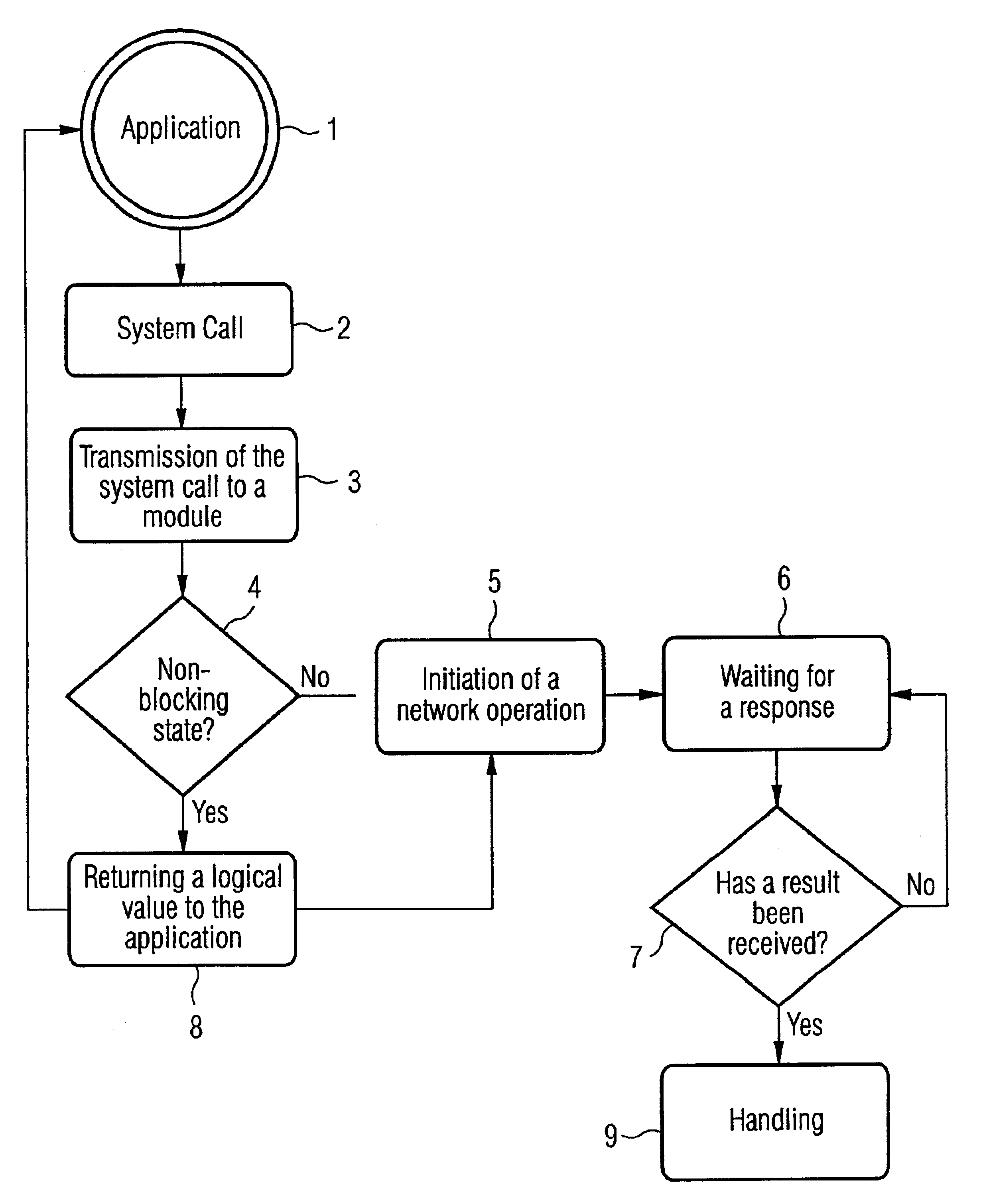
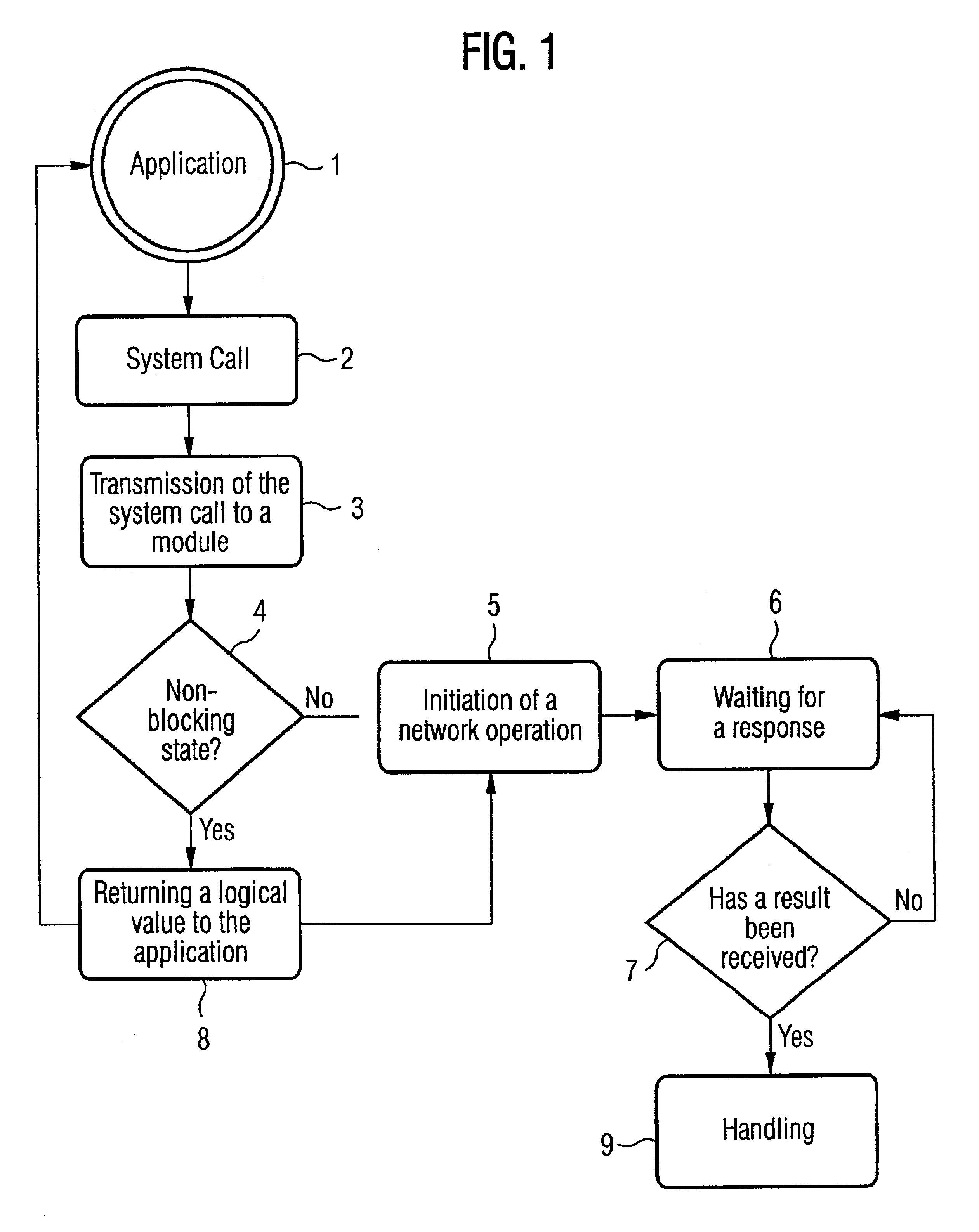
InactiveUS6820269B2Improve performanceAddressing slow performanceMultiprogramming arrangementsData switching networksDelayed timeComputer module
Method and a device are disclosed for a fast performance of network operations via a network with high delay times by means of a module for processing system calls of an application layer and for initiating network operations of a network layer. In the module a differentiation between a blocking and non-blocking implementation mode is made. A non-blocking execution mode means that the considered system call returns a logical value as a result to the application, which signals whether the system call was successfully executed. In this case it is provided by the method and device to directly send a logical value to the application when a non-blocking system call is called, without having waited for the actual result of the operation executed in the communicating partner instance and corresponding to the system call. The handling of the results of the actually executed operations takes place at a later time. With this modification, the network operations, which are derived from the system calls, are executed faster, as the actual result is not waited for at each call, which also implies the reduction of the number of required RTTs (Round Trip Time).
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for simulating computer network attacks
ActiveUS20090007270A1Memory loss protectionError detection/correctionOperational systemNetwork agent
The present invention provides a system and method for providing computer network attack simulation. The method includes the steps of: receiving a network configuration and setup description; simulating the network configuration based on the received network configuration; receiving at least one confirmed vulnerability of at least one computer, machine, or network device in the simulated network; receiving a method for compromising the confirmed vulnerability of the at least one computer, machine, or network device; and virtually installing a network agent on the at least one computer, machine, or network device, wherein the network agent allows a penetration tester to execute arbitrary operating system calls on the at least one computer, machine, or network device.
Owner:FORTRA LLC
Multipath multihop remote data facility
InactiveUS20010050915A1Error detection/correctionTime-division multiplexRemote systemData operations
A computer system may include one or more hosts and a plurality of data storage devices for providing multihop system calls. The data storage devices are interconnected and also connected to the one or more hosts. Each data storage device classifies a data operation as a system call, a remote system call, or a multihop system call. Also described is a multipath multihop system call in which one or more communication paths may be selected using predetermined and / or dynamic communication path selection techniques. The number of communication paths determined may be in accordance with parameters that are included in a multipath multihop system call, tunable system parameters, or a combination of the foregoing.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com