Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
232 results about "Procedure calls" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
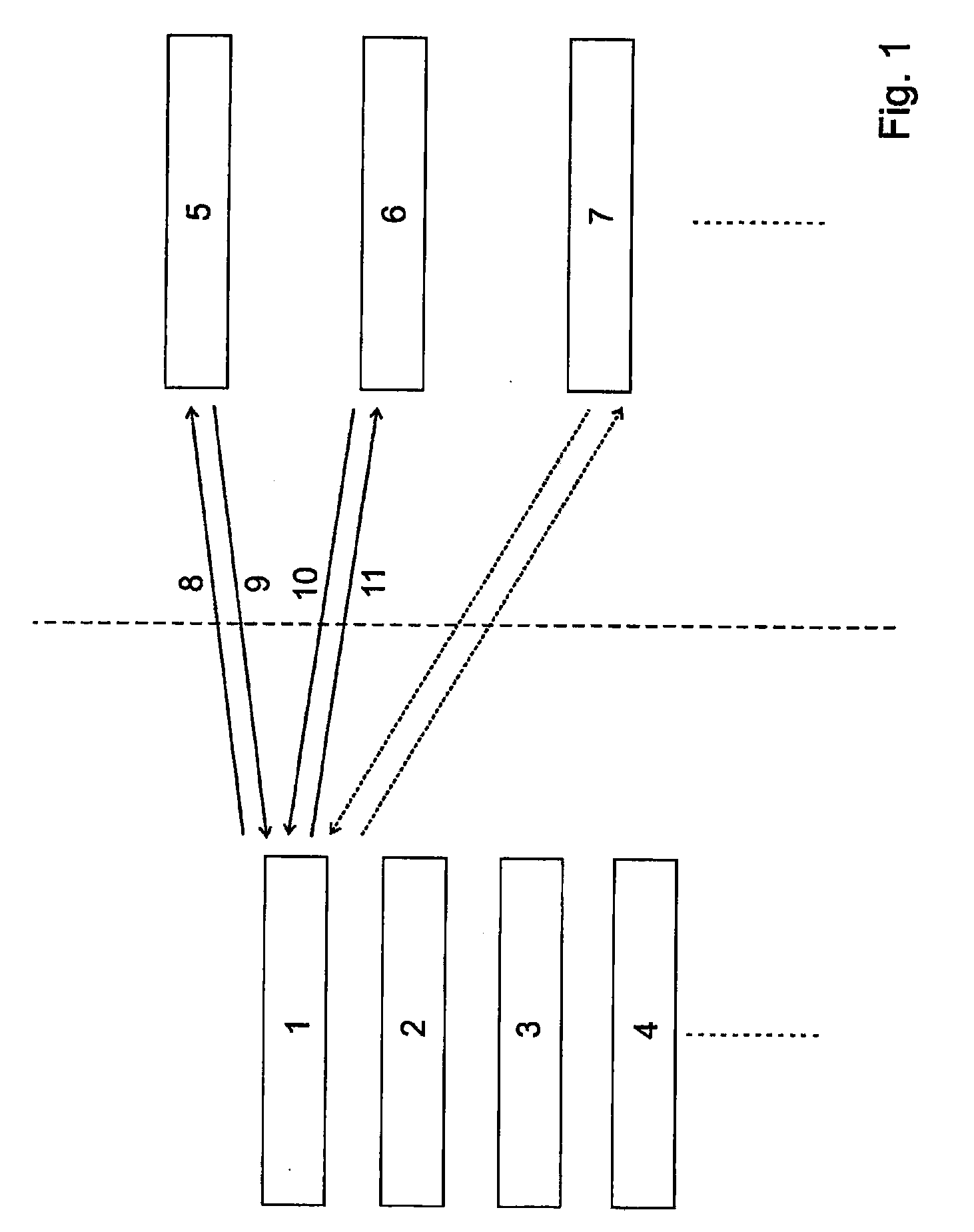
Procedure Calls. A procedure is an executable object stored on the data source. Generally, it is one or more SQL statements that have been precompiled. where procedure-name specifies the name of a procedure and parameter specifies a procedure parameter.
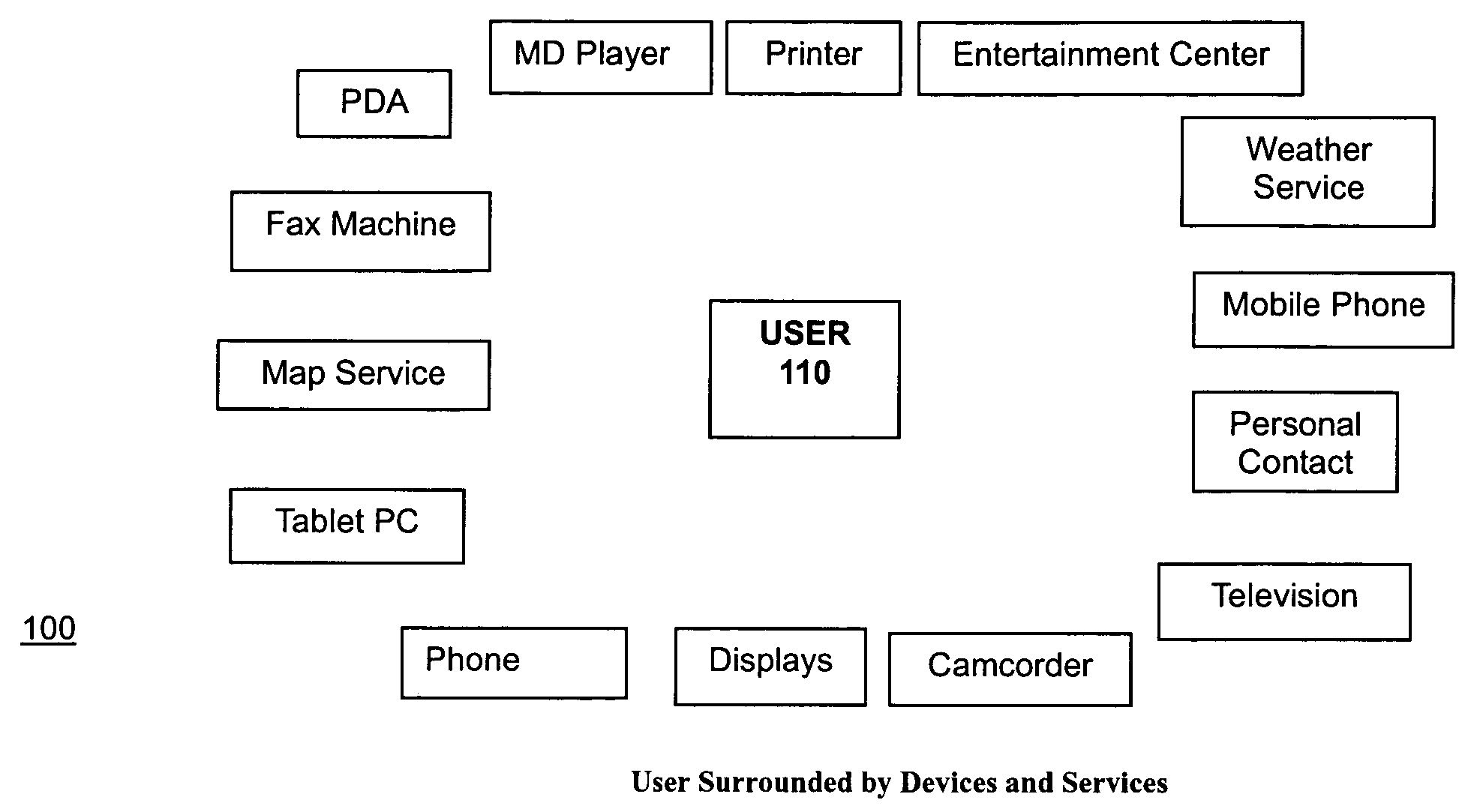
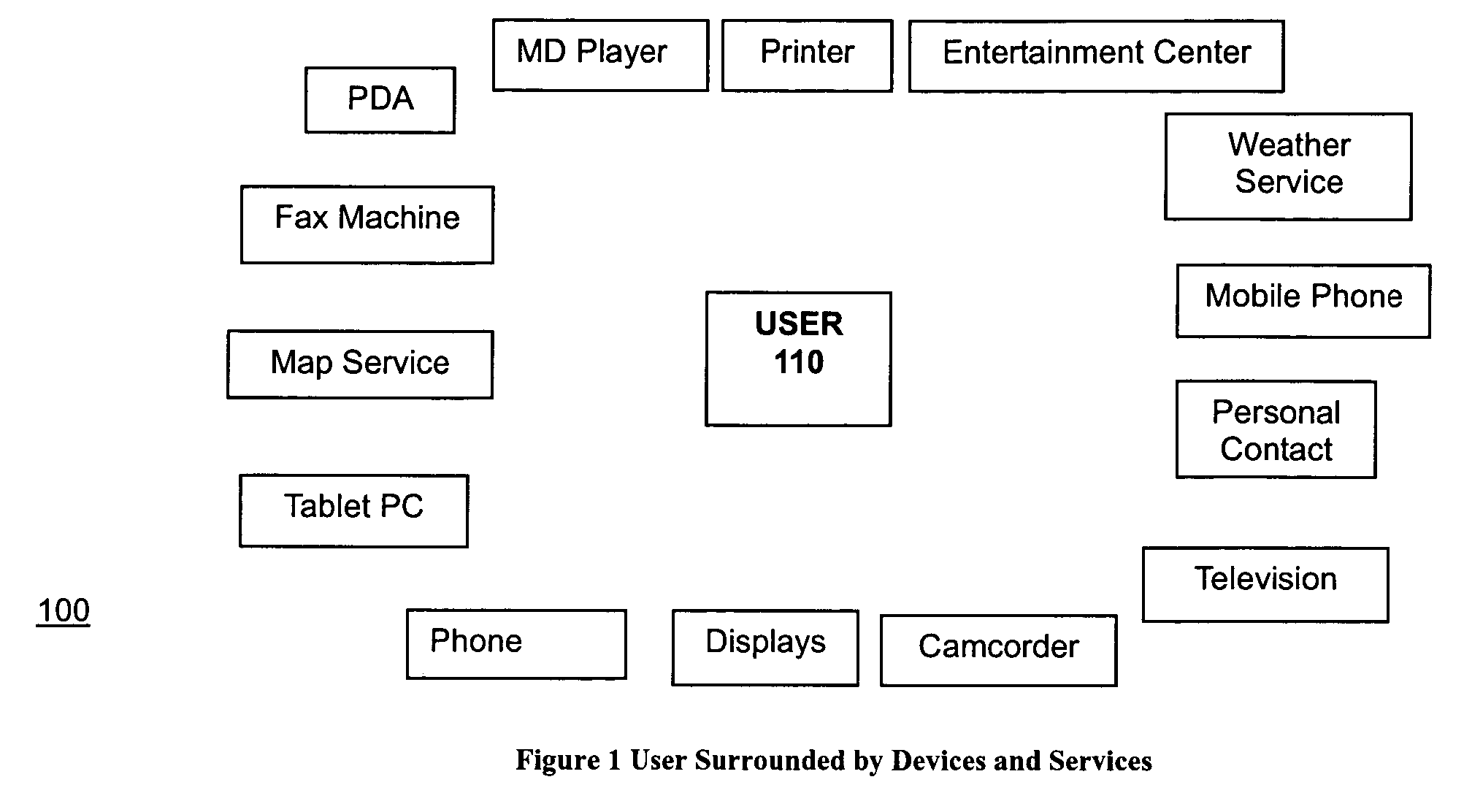
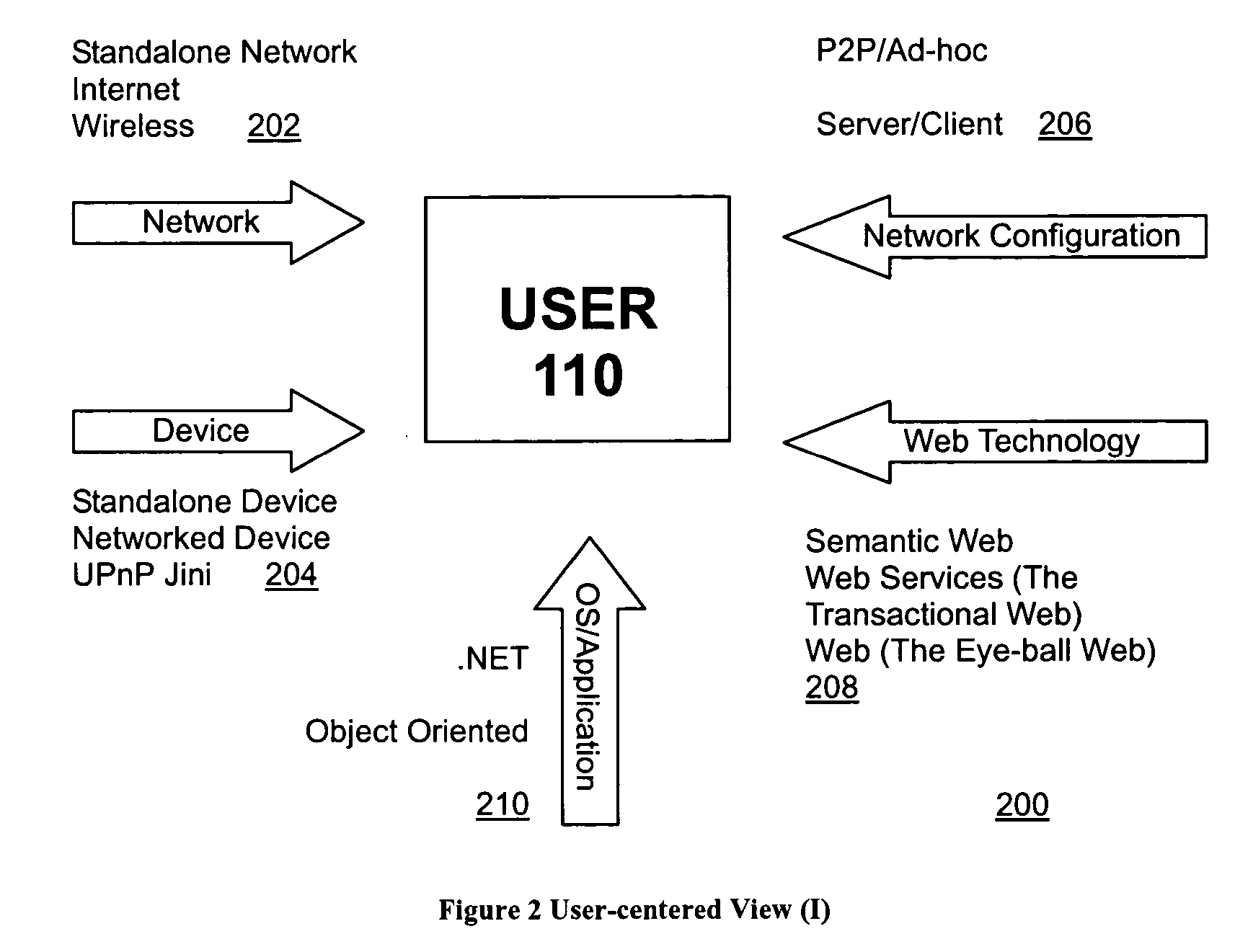
Task computing
InactiveUS20040230636A1General purpose stored program computerMultiprogramming arrangementsProcedure callsWeb service
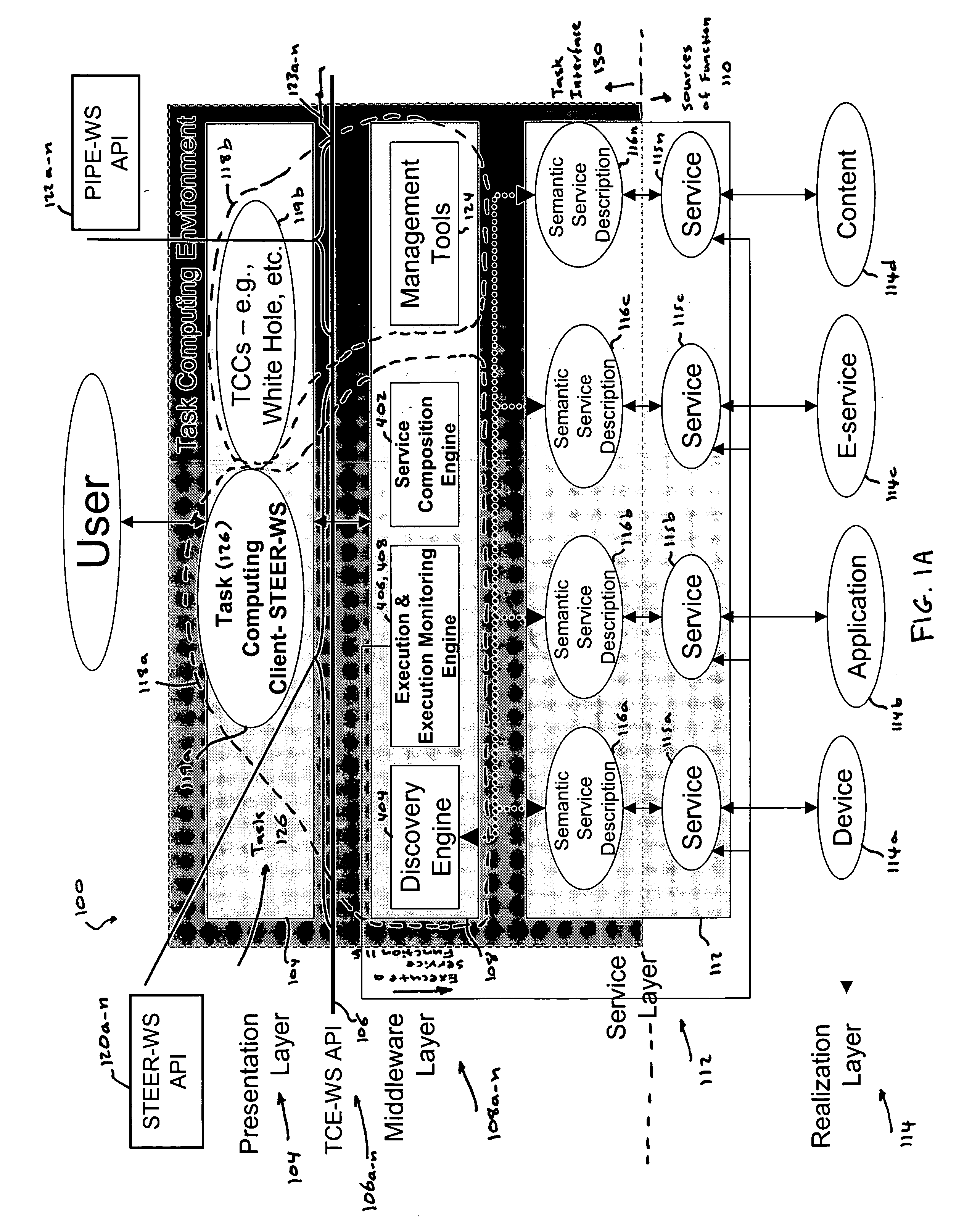
A computer-based system includes task computing enabling users to define tasks by combining available functionality and to execute such tasks. The computer-based system of includes available functionality which originates in devices, computing applications and electronic services available through local and remote procedure calls including Web Services, UPnP, CORBA, RMI, RPC, DCE, DCOM or comprises previously defined tasks. All available functionality is abstracted to the user as a service and each service is expressed in a service description language, and the services have a semantic description associated with them.
Owner:FUJITSU LTD
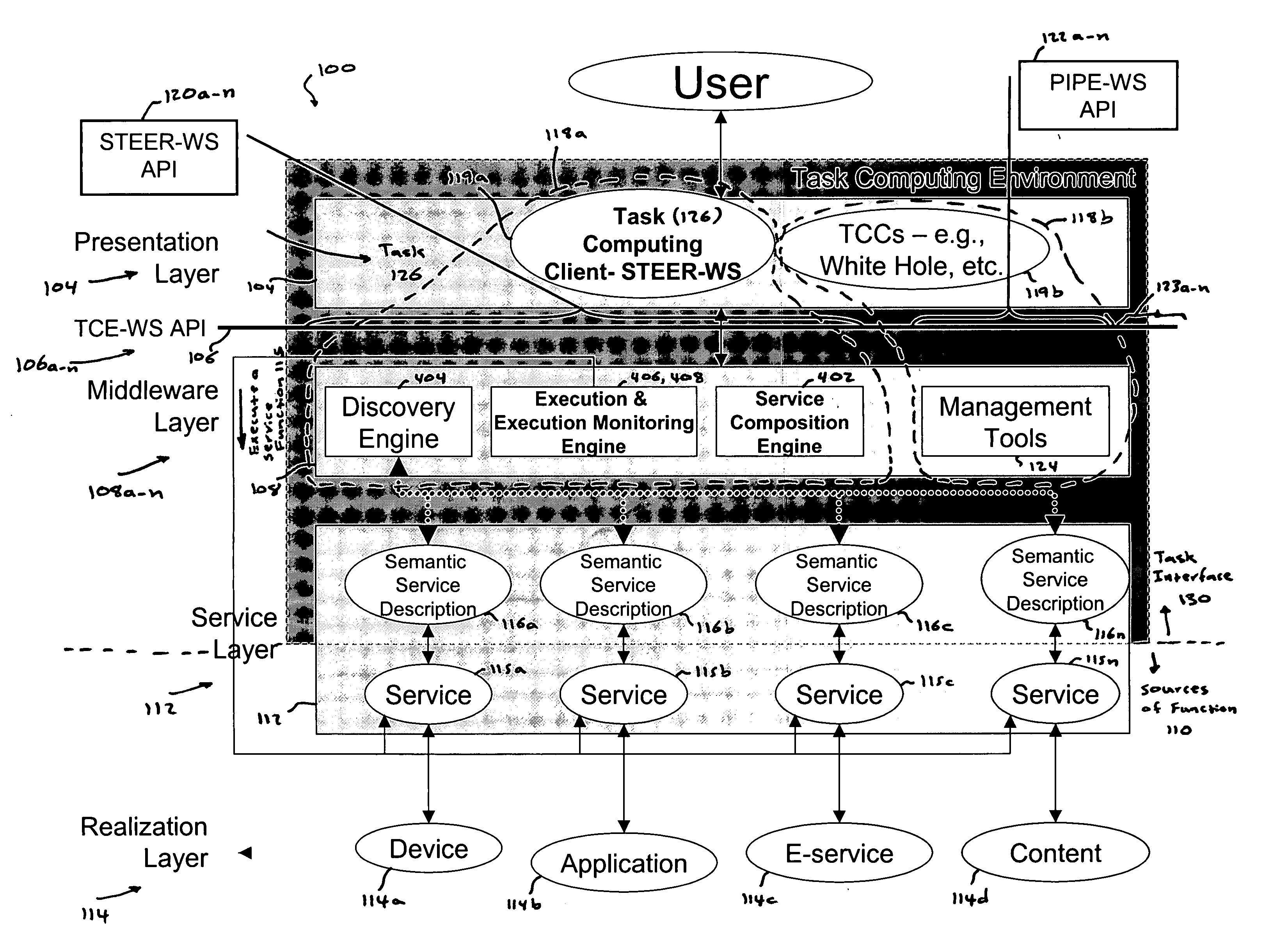
Task computing
InactiveUS20050246726A1Program control using stored programsConcurrent instruction executionLayer interfaceProcedure calls
Task Computing computer system by segmenting the system into a plurality of implementation tiers of a presentation layer, a remote procedure call programming interface (API), a middleware layer to which the presentation layer interfaces via the remote procedure call API to real-time, dynamically generate a computer implemented task interface at the presentation layer to a semantically described source of function as a service on a computer system, and a service layer and a function source realization layer providing the semantically described source of function as the service on the computer system to which the middleware layer interfaces. Real-time and dynamically composing an executable task that comprises one or more services using the generated task interface at the presentation layer to one or more services on the computer based upon the semantically described application-, device- and service-rich computer.
Owner:FUJITSU LTD
XML remote procedure call (XML-RPC)
InactiveUS7028312B1Easy to implementLess complexMultiple digital computer combinationsSpecific program execution arrangementsProcedure callsXML-RPC
Owner:SOFTWARE AG USA
System and method for facilitating context-switching in a multi-context computer system
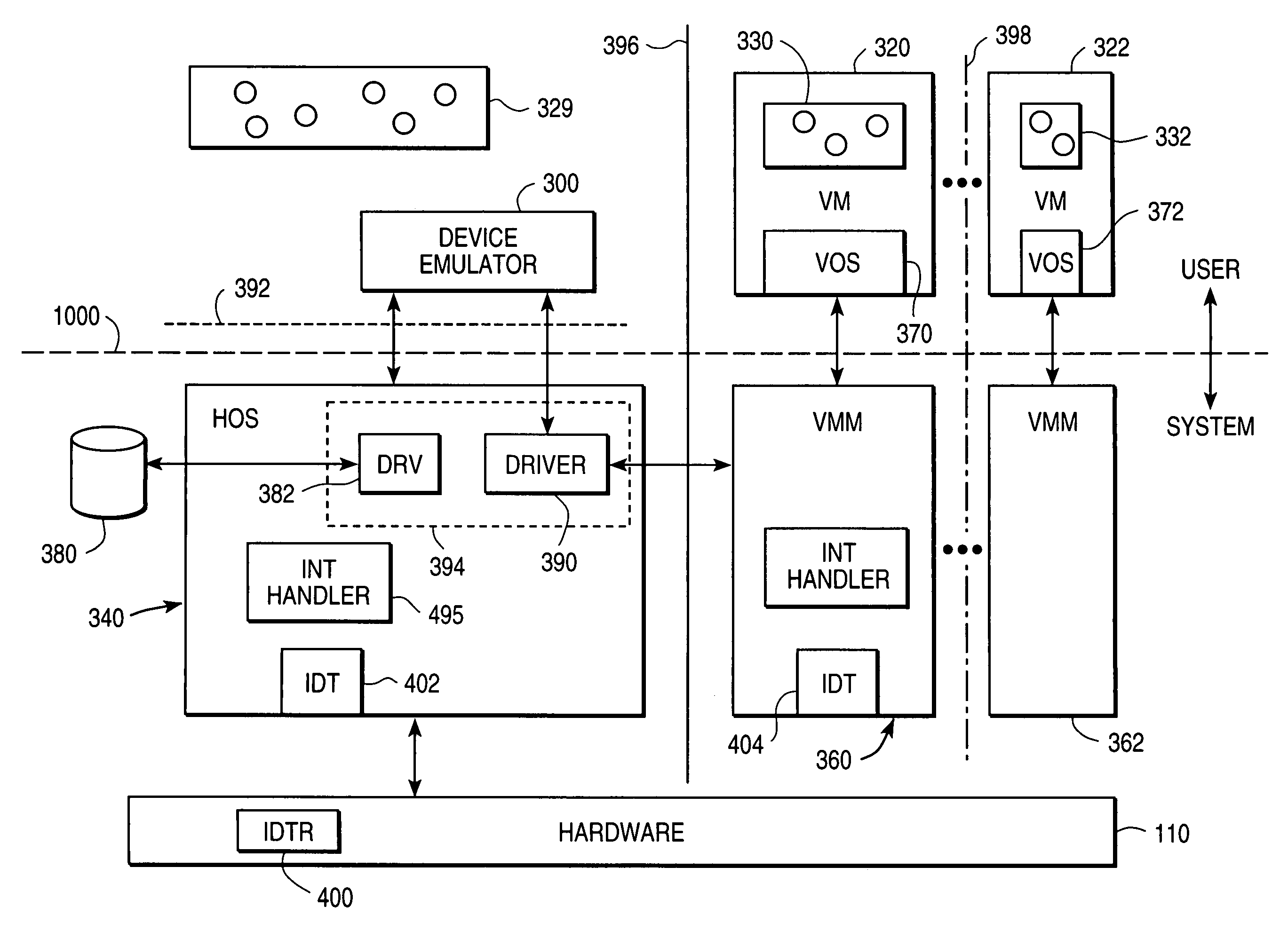
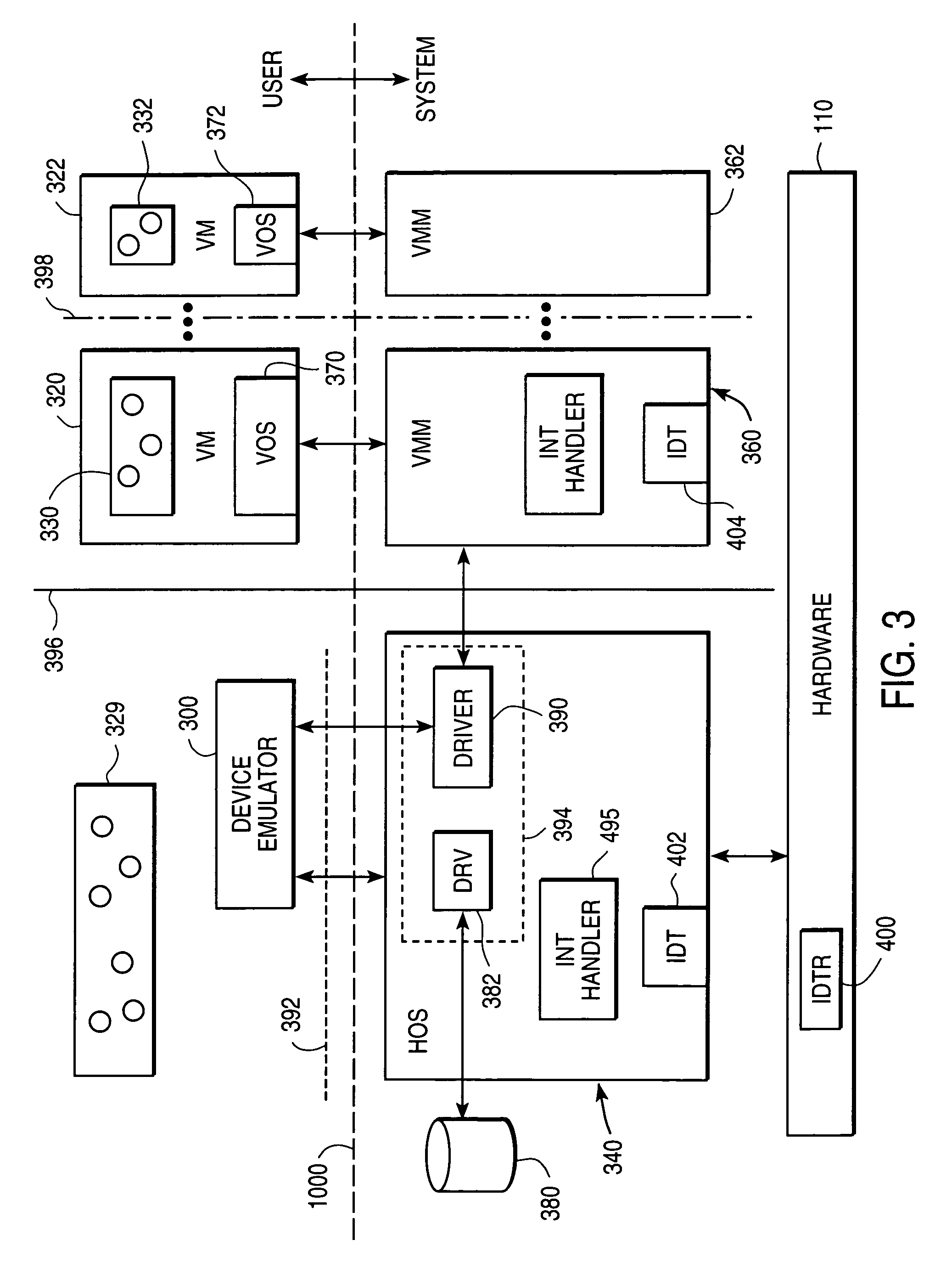
InactiveUS6944699B1Software simulation/interpretation/emulationMemory systemsOperational systemProcedure calls
A virtual machine monitor (VMM) is included in a computer system that has a protected host operating system (HOS). A virtual machine running at least one application via a virtual operating system is connected to the VMM. Both the HOS and the VMM have separate operating contexts and disjoint address spaces, but are both co-resident at system level. A driver that is downloadable into the HOS at system level forms a total context switch between the VMM and HOS contexts. A user-level emulator accepts commands from the VMM via the system-level driver and processes these commands as remote procedure calls. The emulator is able to issue host operating system calls and thereby access the physical system devices via the host operating system. The host operating system itself thus handles execution of certain VMM instructions, such as accessing physical devices.
Owner:VMWARE INC
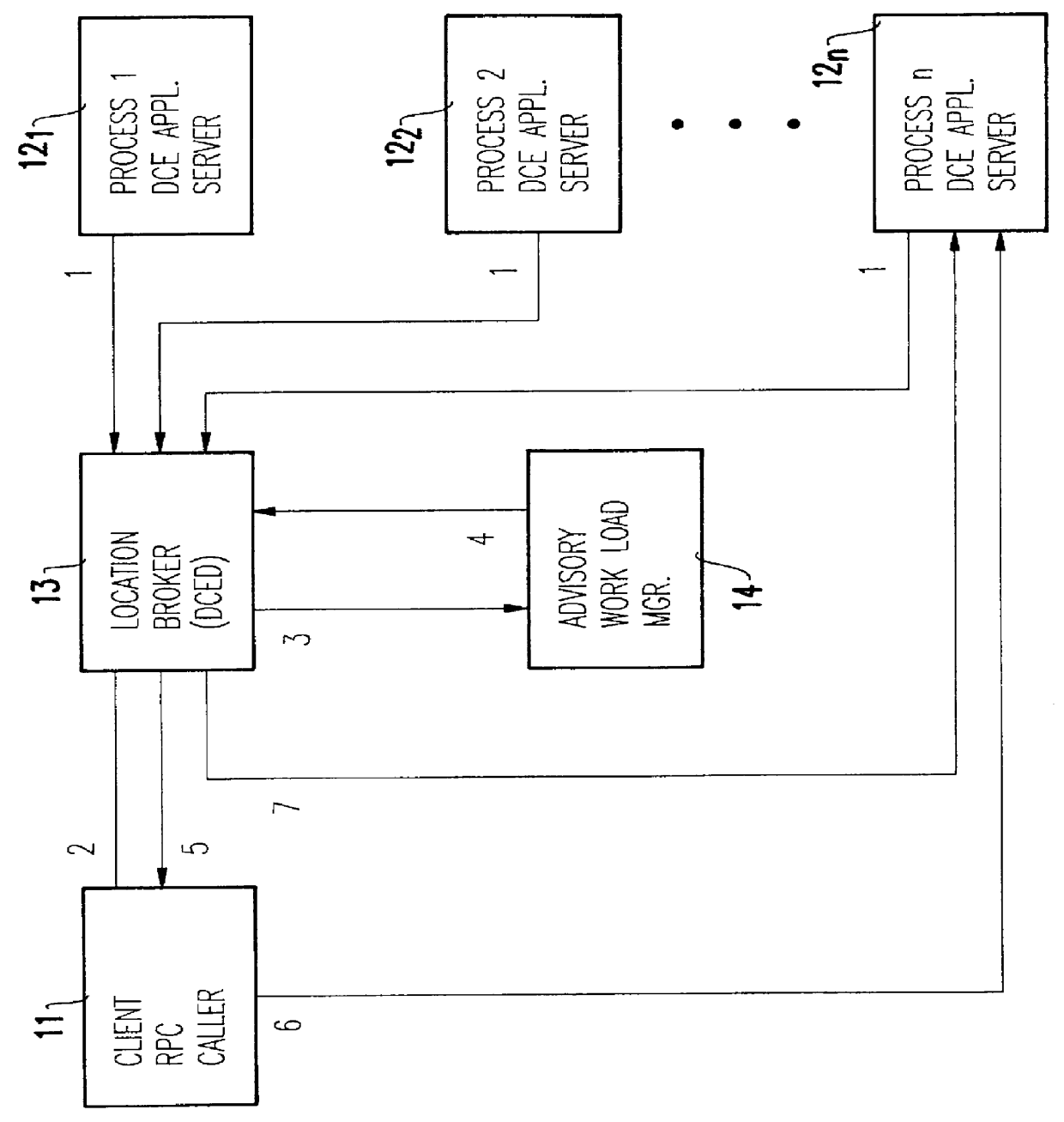
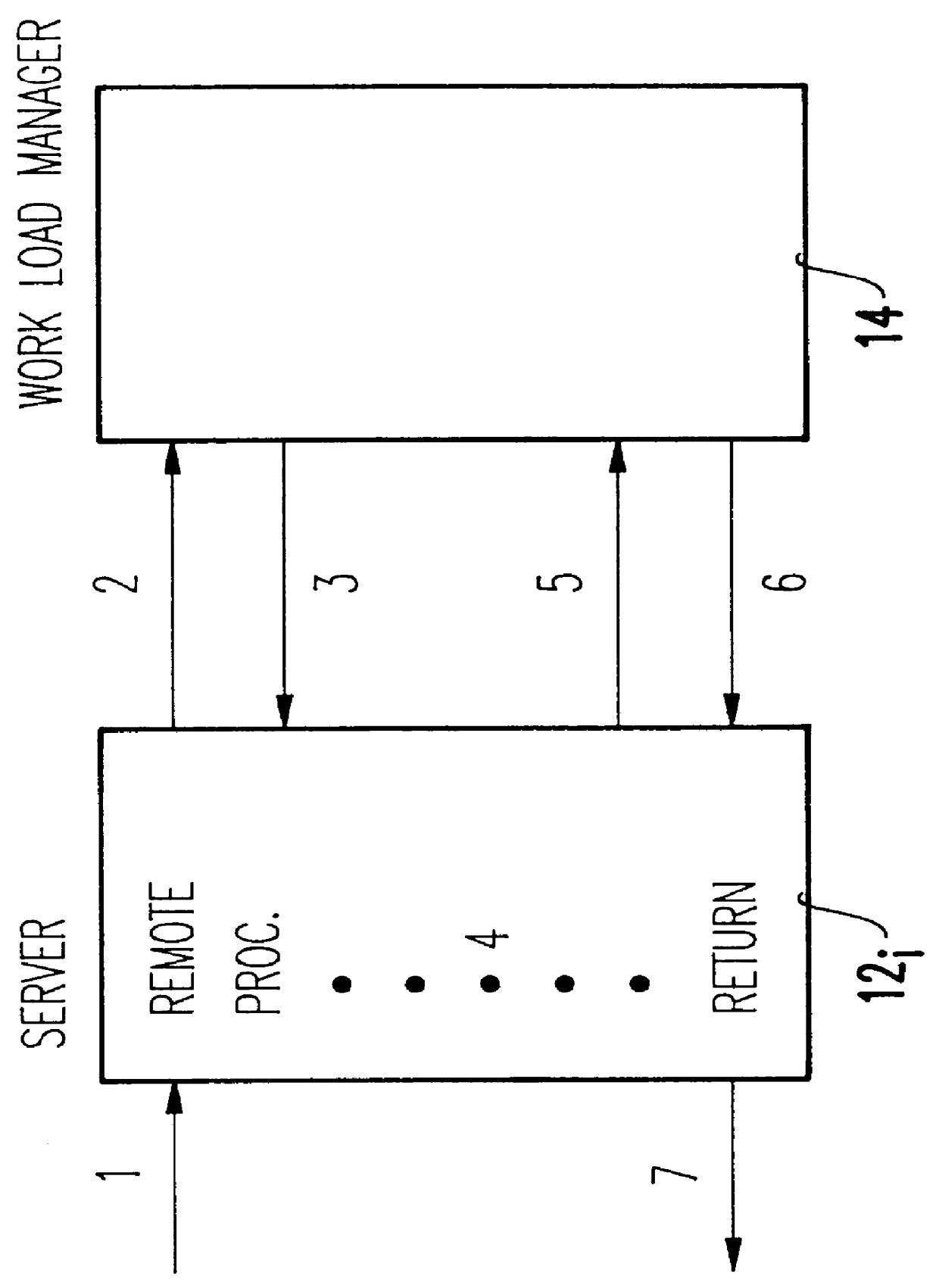
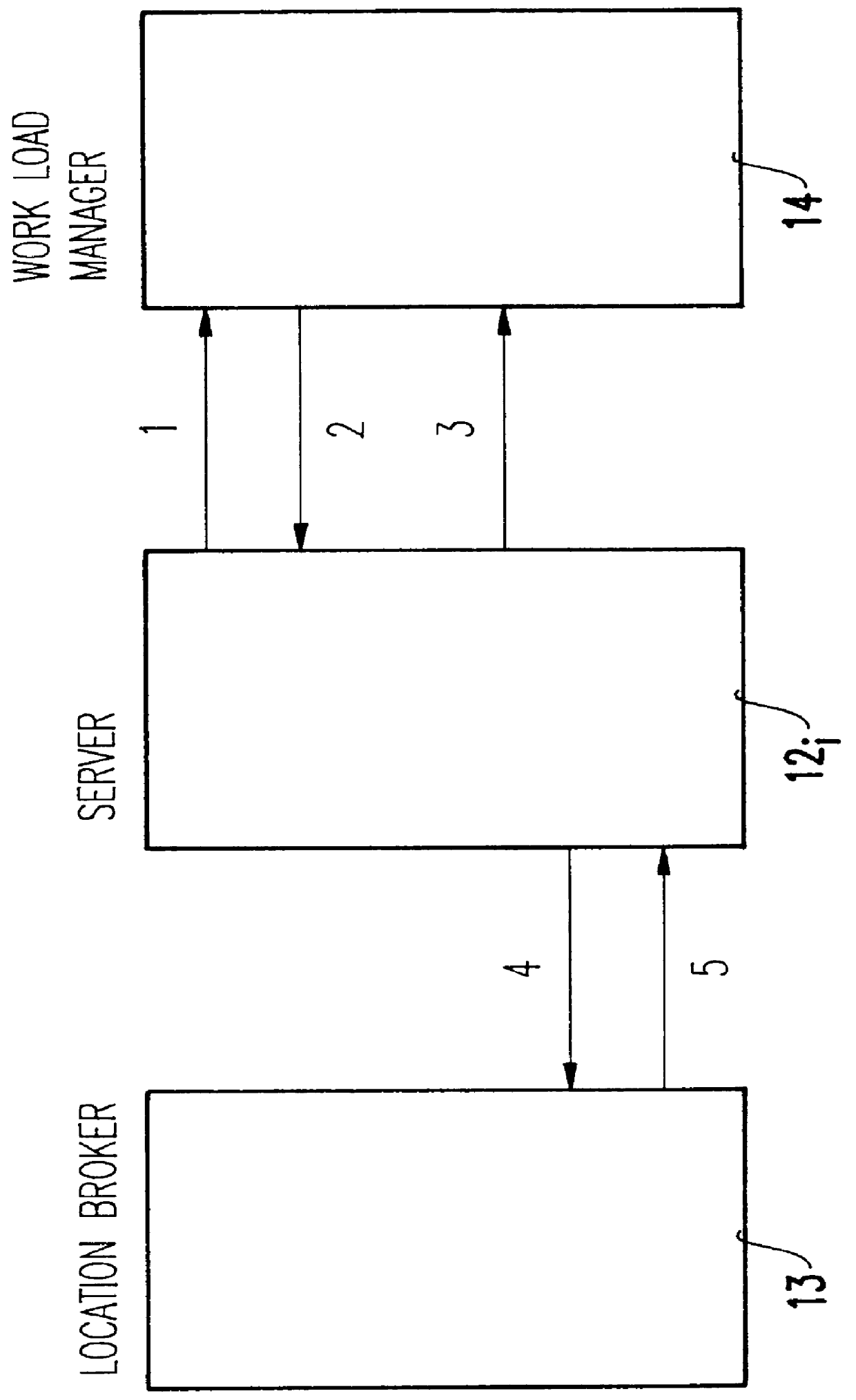
Integrating distributed computing environment remote procedure calls with an advisory work load manager
InactiveUS6067580AResource allocationMultiple digital computer combinationsAmbulatory systemDistributed Computing Environment
Distributed computing environment (DCE) remote procedure calls (RPCs) are integrated with an advisory work load manager (WLM) to provide a way to intelligently dispatch RPC requests among the available application server processes. The routing decisions are made dynamically (for each RPC) based on interactions between the location broker and an advisory work load manager. Furthermore, when the system contains multiple coupled processors (tightly coupled within a single frame, or loosely coupled within a computing complex, a local area network (LAN) configuration, a distributed computing environment (DCE) cell, etc.), the invention extends to balance the processing of RPC requests and the associated client sessions across the coupled systems. Once a session is assigned to a given process, the invention also supports performance monitoring and reporting, dynamic system resource allocation for the RPC requests, and potentially any other benefits that may be available through the specific work load manager (WLM).
Owner:IBM CORP
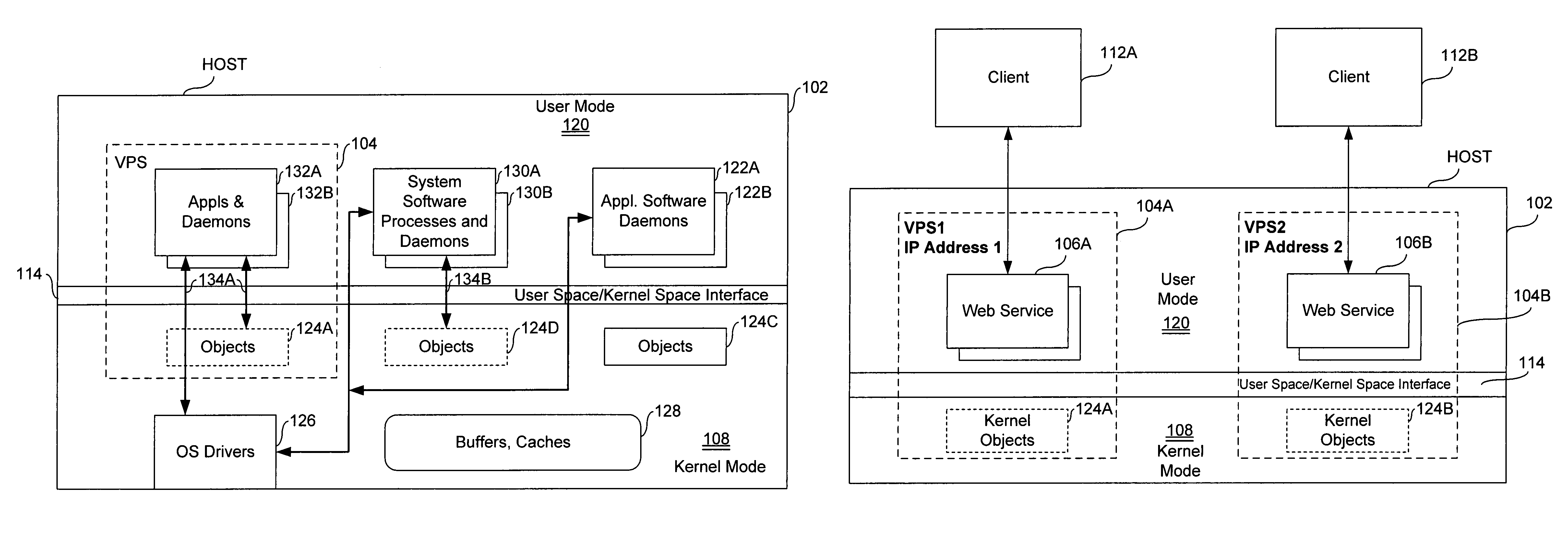
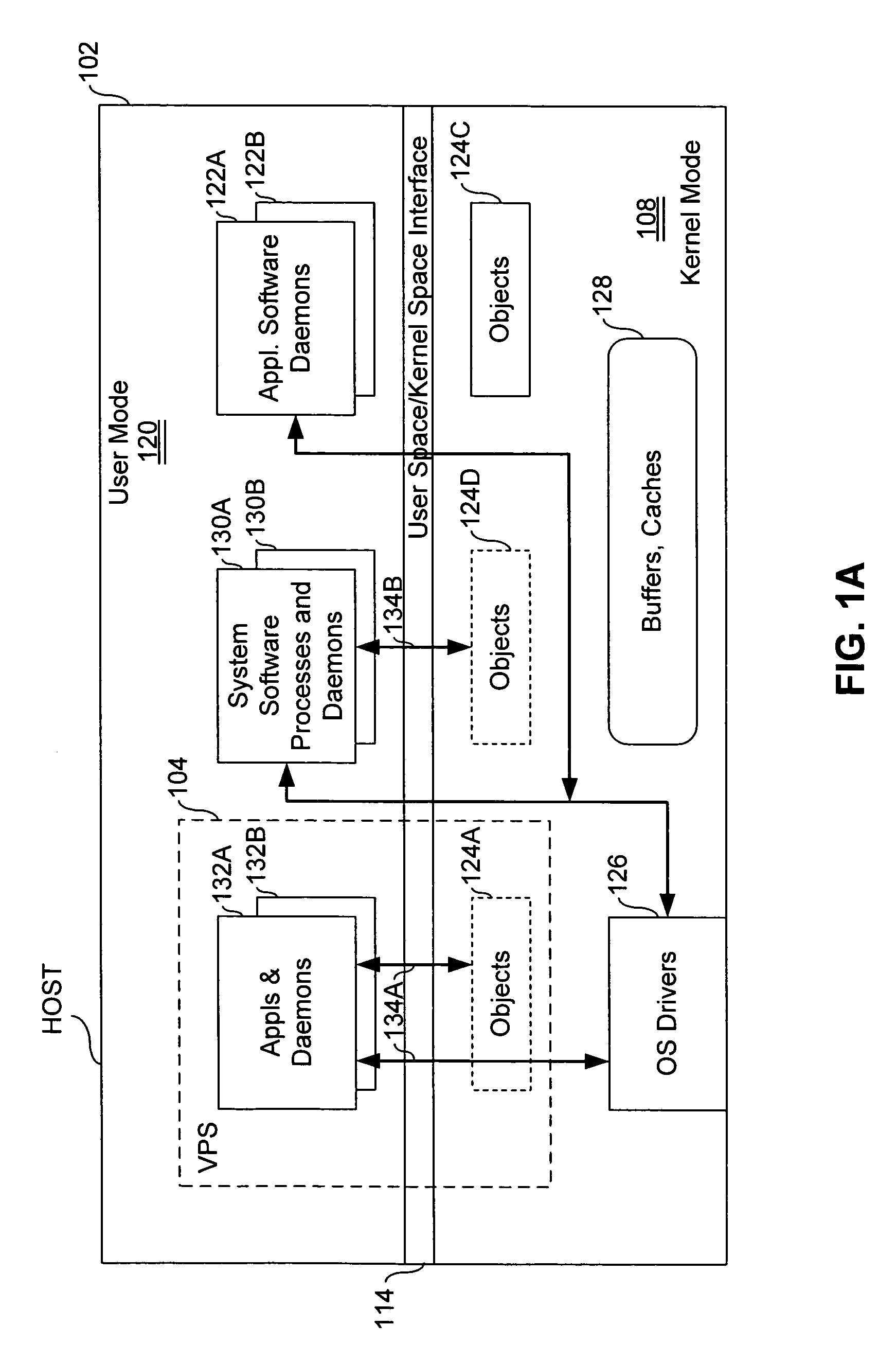
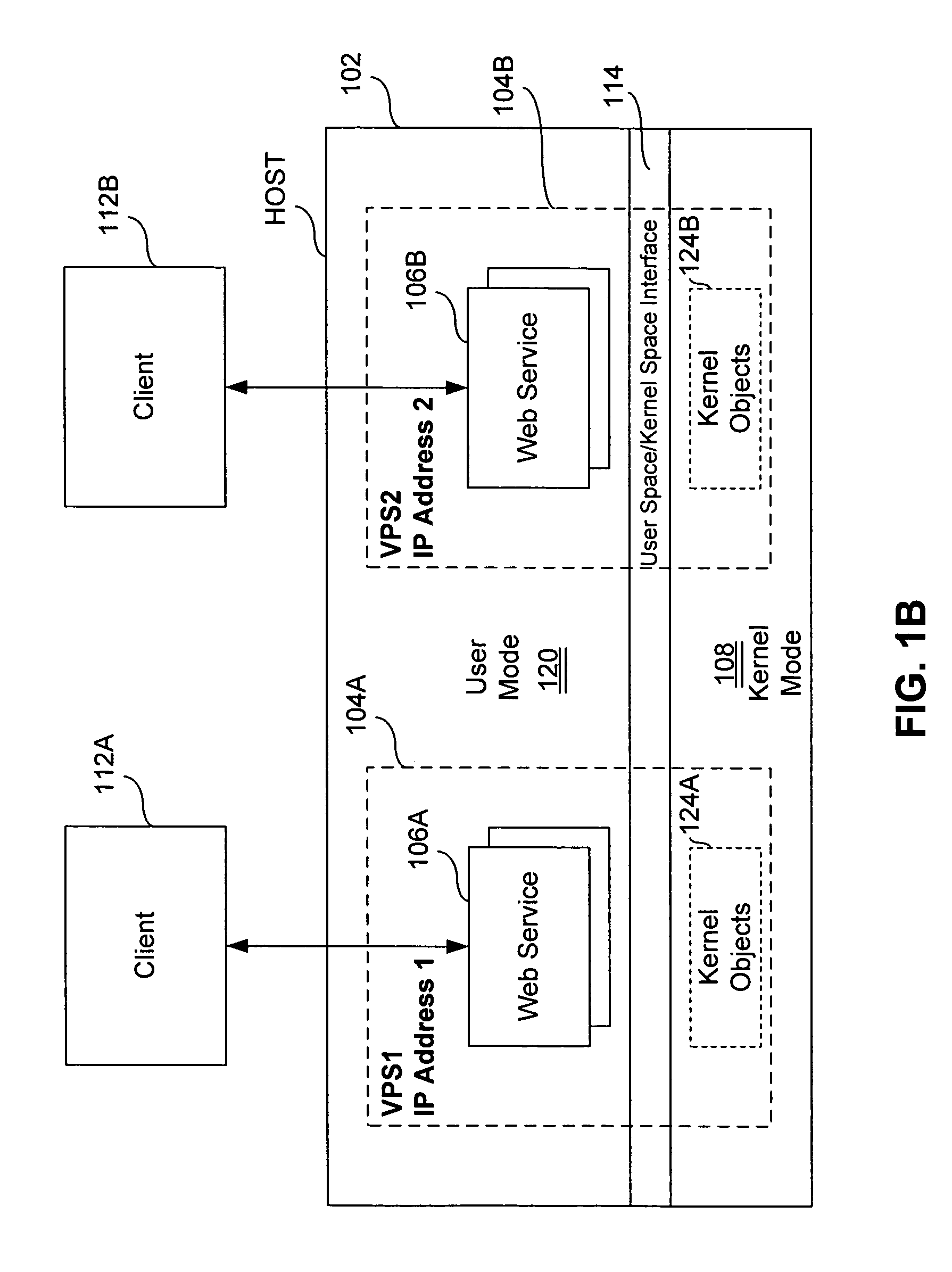
Virtual private server with enhanced security
ActiveUS7461144B1Improve securityData processing applicationsDigital computer detailsComputer resourcesOperational system
An end user computer includes a processor running an operating system. A plurality of virtual private servers (VPSs) are supported within the operating system. A plurality of applications are available to a user of the end user computer. The applications are launched within different VPSs. At least one of the VPSs has multiple applications launched within it. At least two of the applications are launched within different VPSs, and communicate with each other using secure communications means, such as firewalls, proxies, dedicated clipboards, named pipes, shared memory, dedicated inter-process communications, Local Procedure Calls / Remote Procedure Calls, API, network sockets, TCP / IP communications, network protocol communications and memory mapped files. The VPSs can be dynamically created and terminated. VPS control means are available to the user and include means for creation / termination of VPSs, a file system and registry backup, control information for backup / restore of data on a VPS level, placement of applications / processes rules for creation / support of corresponding VPSs, granulation of isolation for VPS / applications / processes, computer resource control, definition of permissible operations for inter-VPS communication, means for definition of permissible operations for inter-process communications.
Owner:VIRTUOZZO INT GMBH
System for sharing data objects among applications
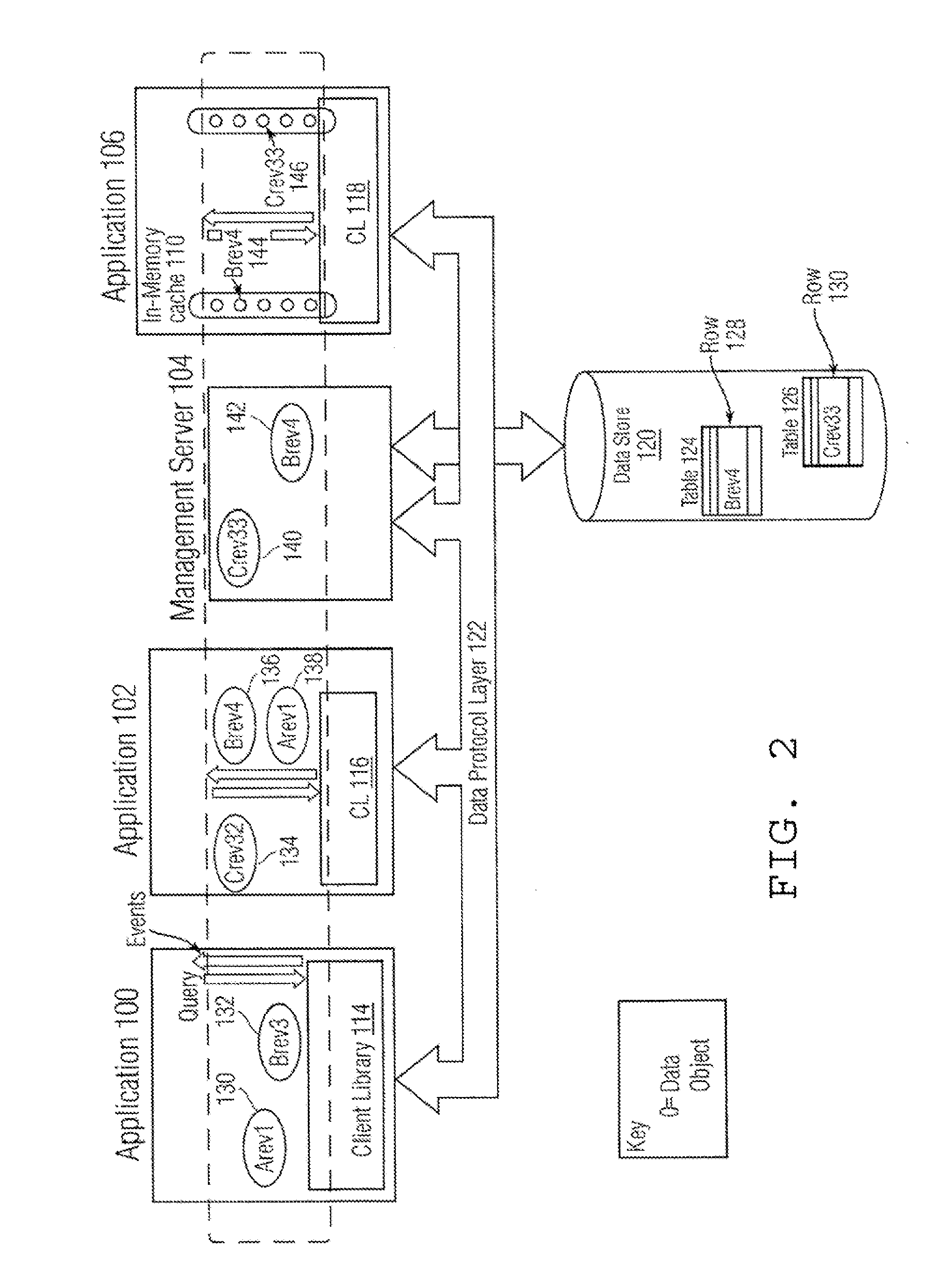
ActiveUS20090254601A1Multiple digital computer combinationsProgram controlProcedure callsClient-side
System and method for sharing data objects among applications. A portion of the data messages includes data objects. A client library is coupled to a requesting application. A client library requests data objects of a data-object set. Requests from the client library are received and parsed by a set of code (SOC) that performs tasks so as to retrieve any matching data objects and cause the return of such matching data objects to the client library. A registration module registers subscriptions from or on behalf of the applications and an event notification module compares a data object in an event message with the subscriptions and notifies the subscribed applications in response. The system can respond to requests in either a query or a procedure call format.
Owner:BROADWAY TECH
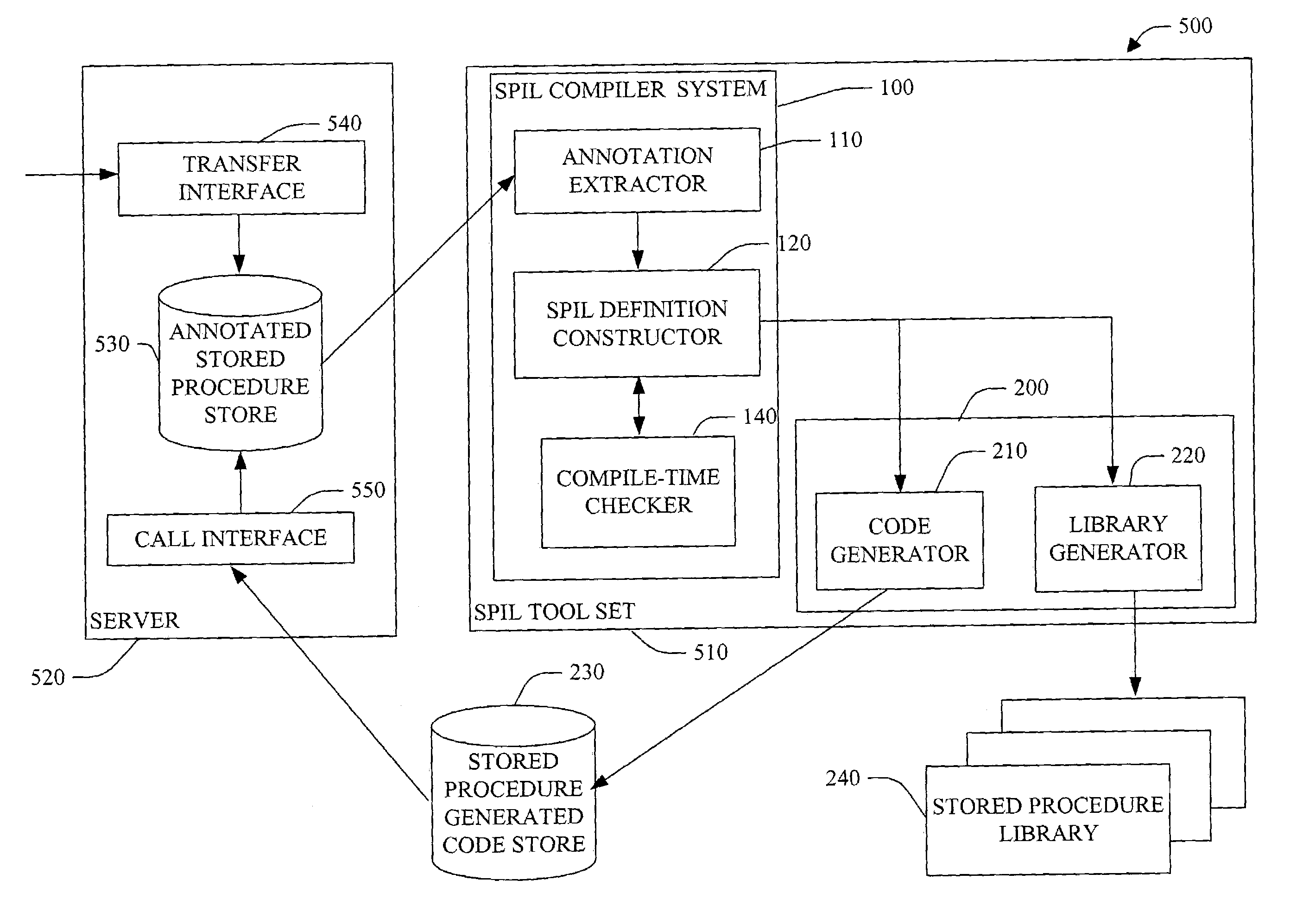
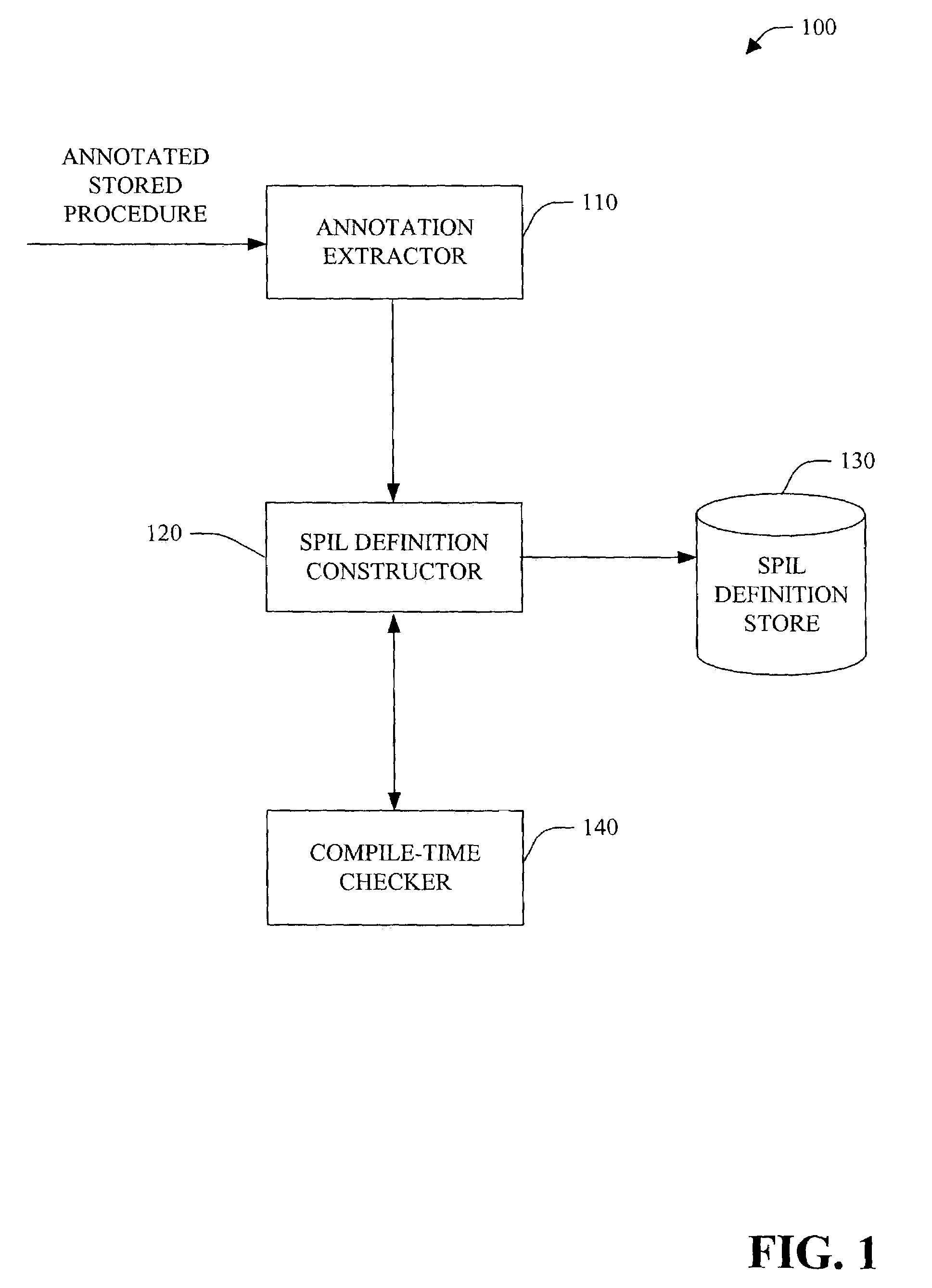
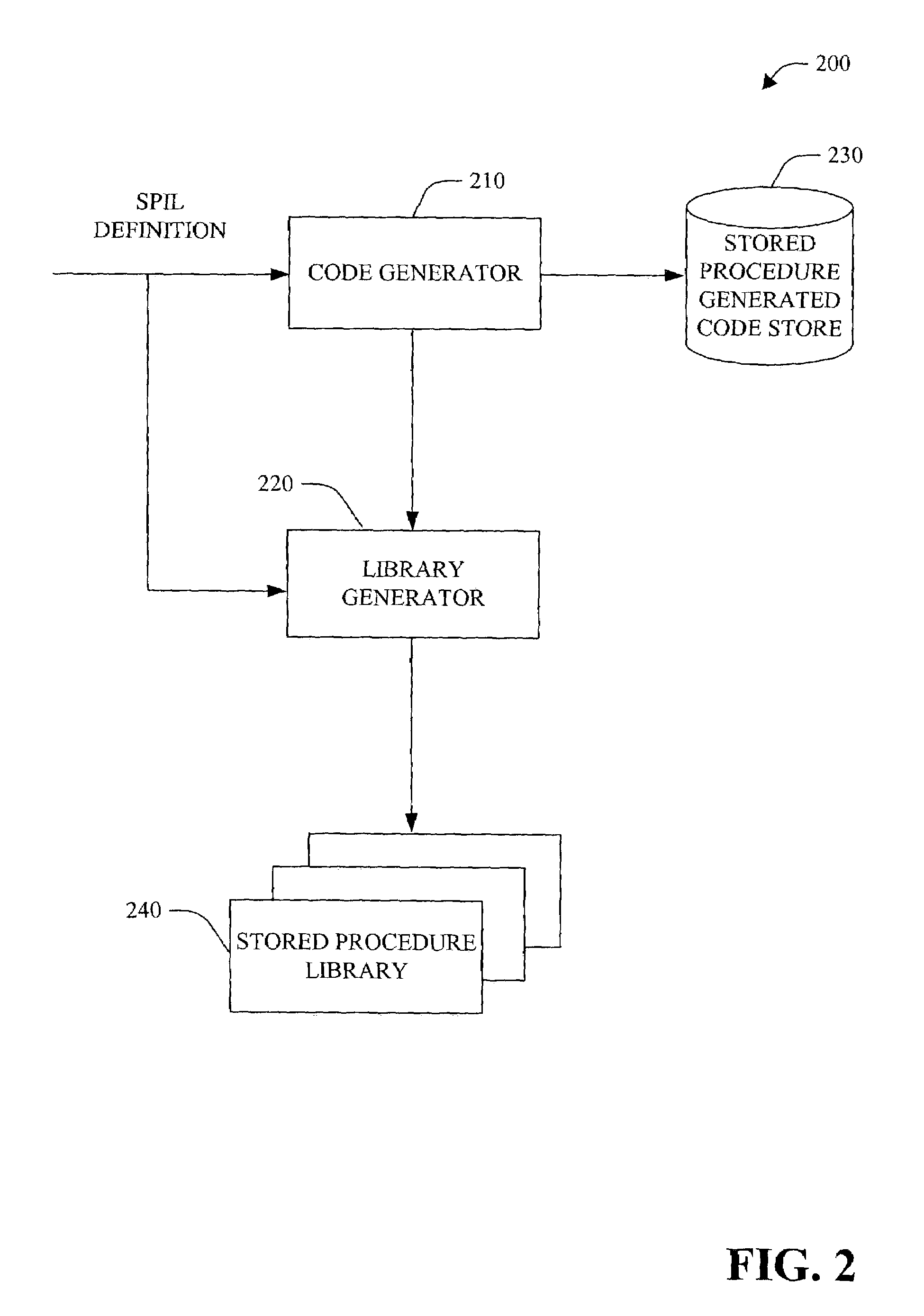
Stored procedure interface language and tools
InactiveUS7318215B1Reduce developmentReduce debuggingData processing applicationsDigital data processing detailsProcedure callsApplication software
The present invention relates to systems and methods to generate stored procedure calling code. The invention includes system and methods that utilize annotation(s) included in a stored procedure. The annotations comprise attributes that indicate the intent to have stored procedure calling code generated. After the annotated stored procedure becomes available, the code is compiled and, optionally, checked for errors, and an intermediate definition with metadata is created. The definition is a stored procedure interface language (SPIL) file. The SPIL definition is then utilized to generate high-level, stored procedure calling code, or class libraries. The high level code can then be employed within an application to invoke the stored procedure.
Owner:MICROSOFT TECH LICENSING LLC
Receive side scaling with cryptographically secure hashing
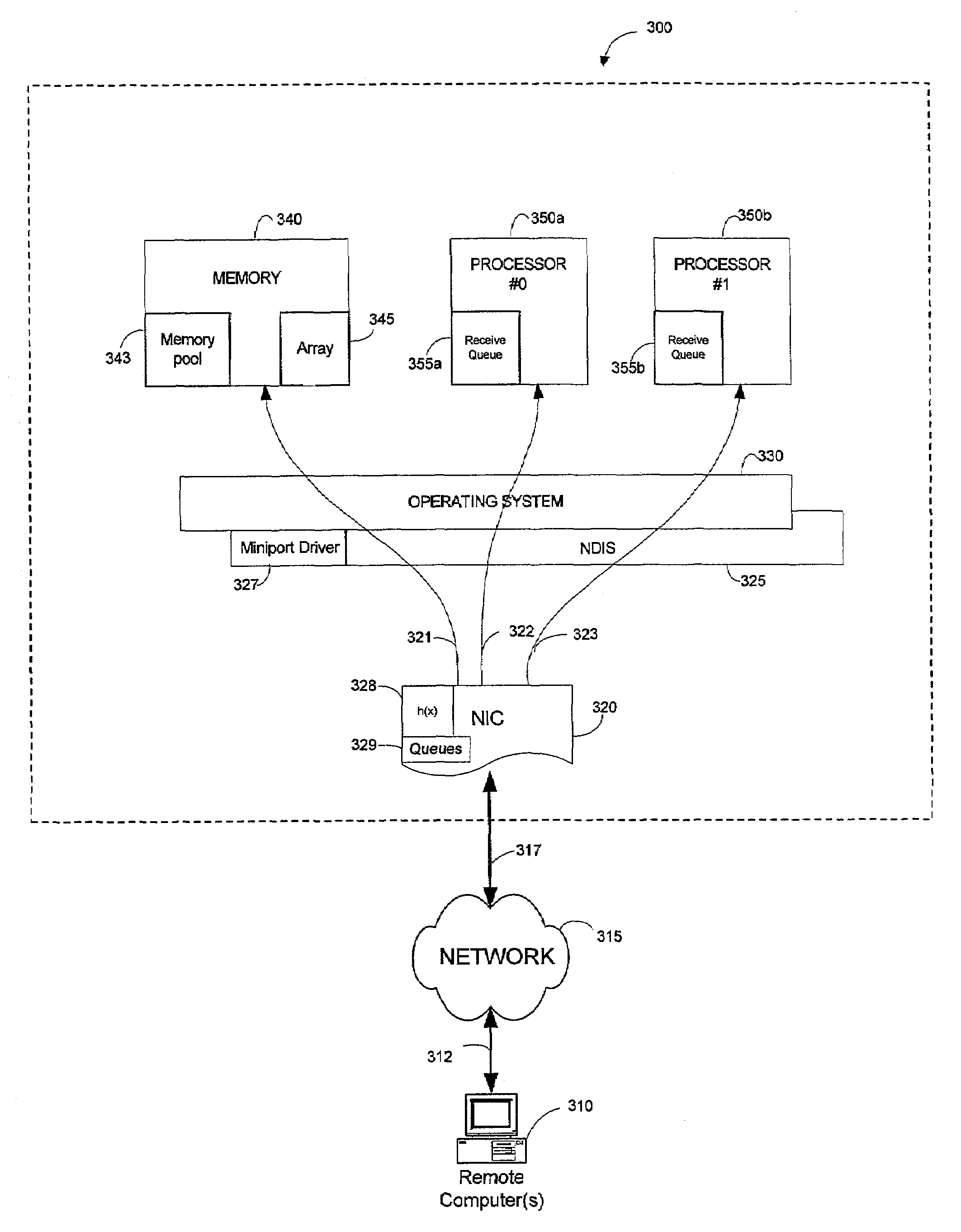
InactiveUS20060195698A1User identity/authority verificationUnauthorized memory use protectionData streamHash function
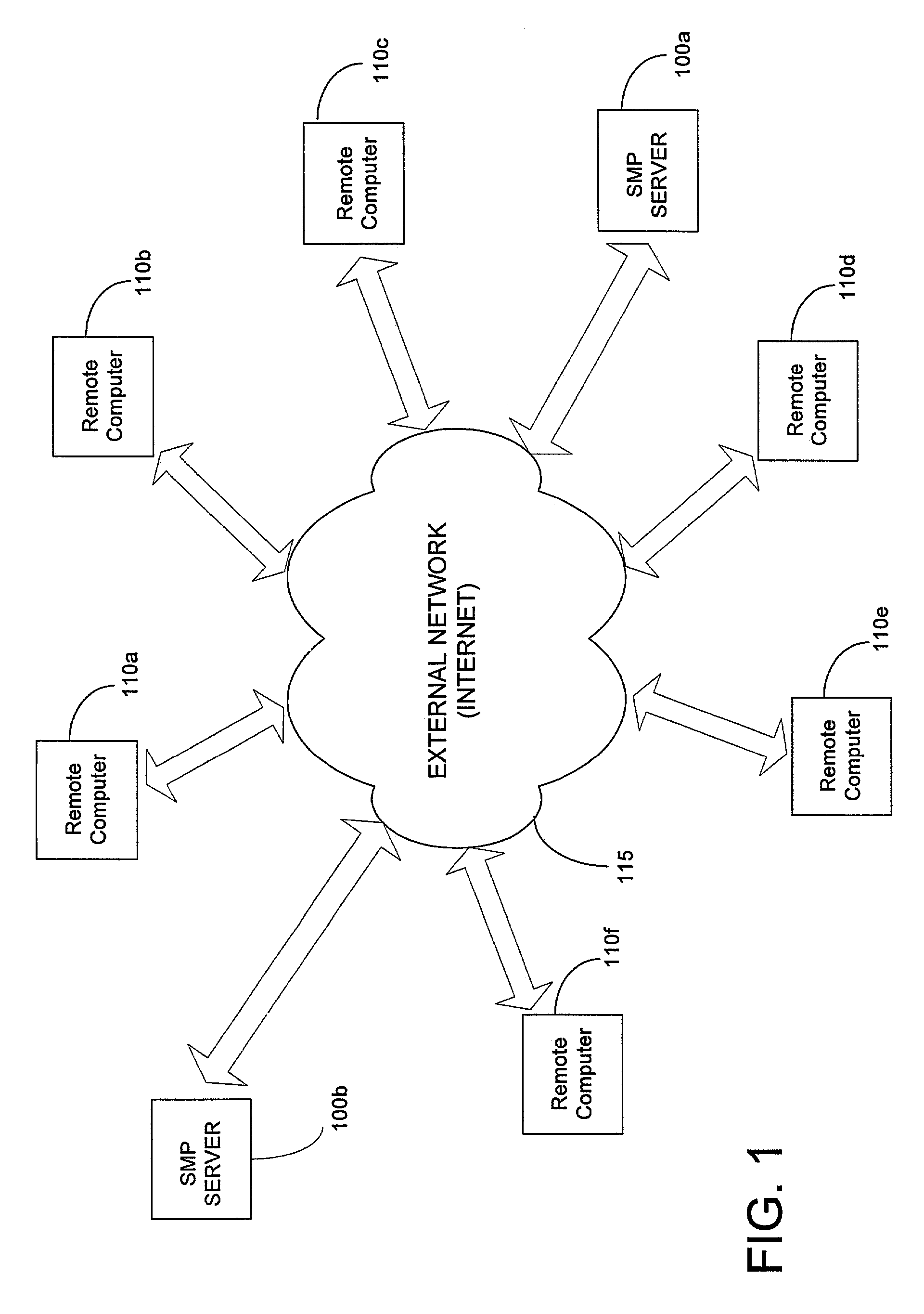
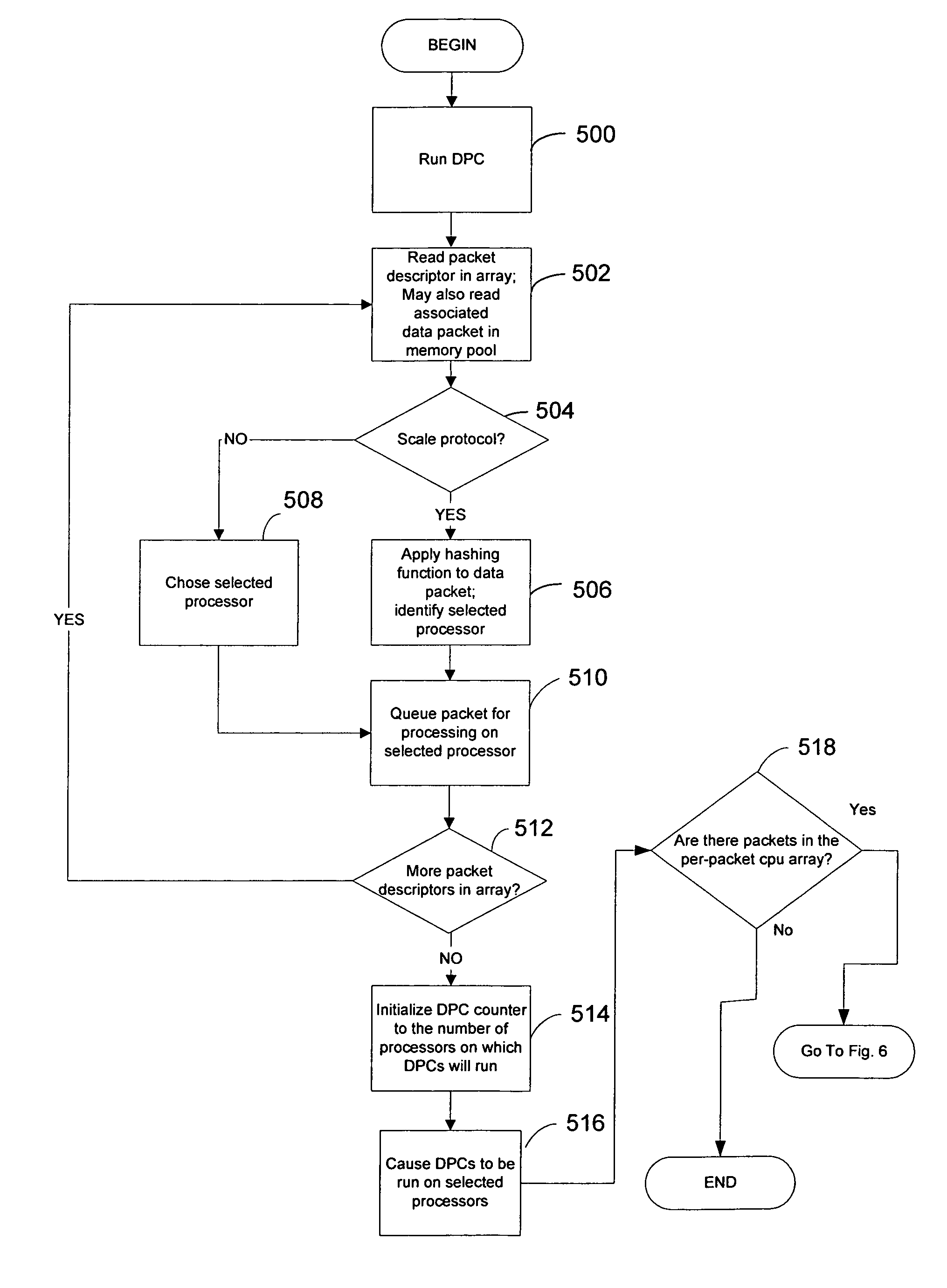
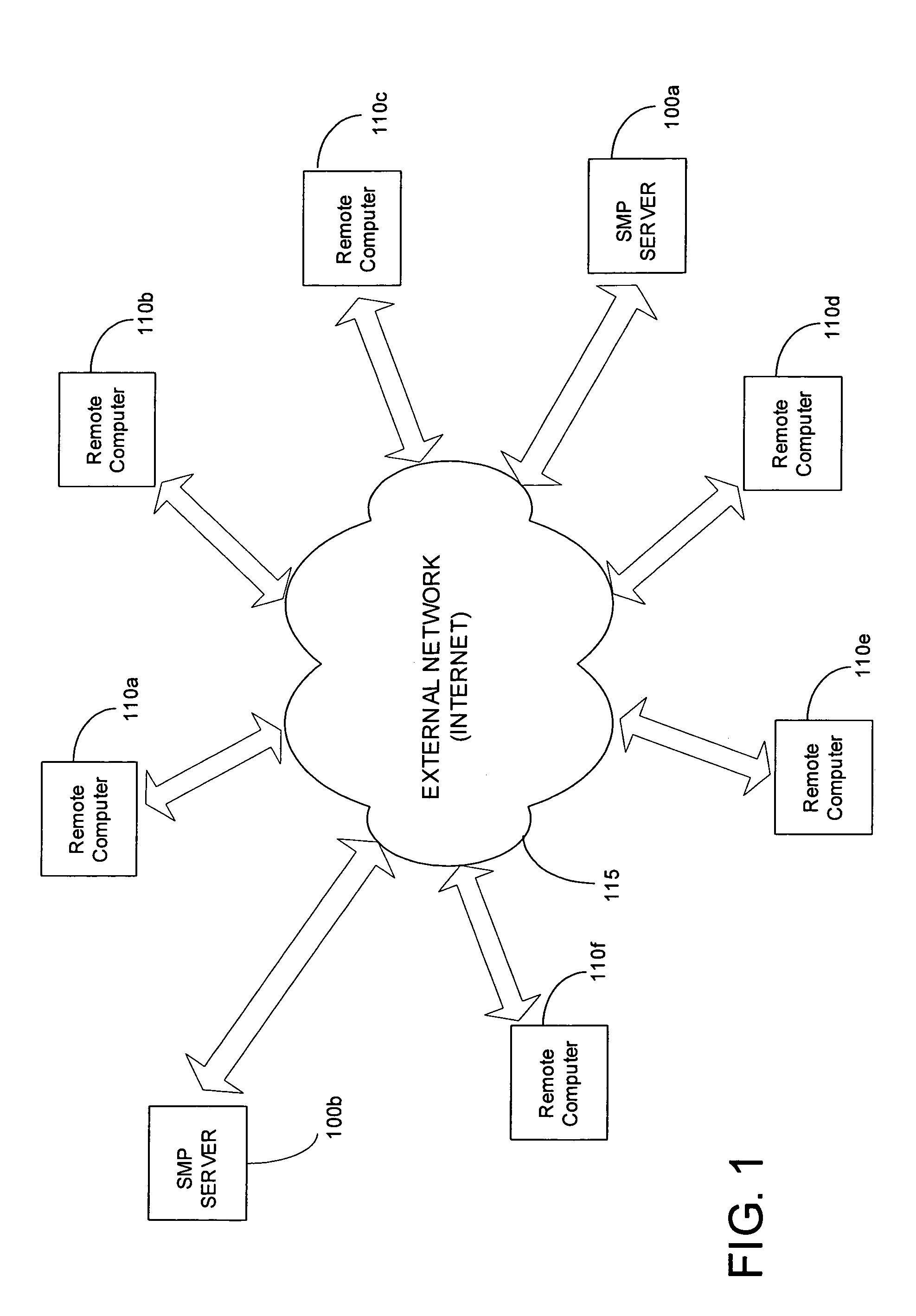
A new method and framework for scheduling receive-side processing of data streams received from a remote requesting client by a multiprocessor system computer is disclosed. The method receives data packets from the remote requesting client via a network and, for each data packet, applies a cryptographically secure hashing function to portions of the received data packet yielding a hash value. The method further applies the hash value to a processor selection policy to identify a processor in the multiprocessor system as a selected processor to perform receive-side processing of the data packet. The method queues the received data packet for processing by the selected processor and invokes a procedure call to initiate processing of the data packet.
Owner:MICROSOFT TECH LICENSING LLC
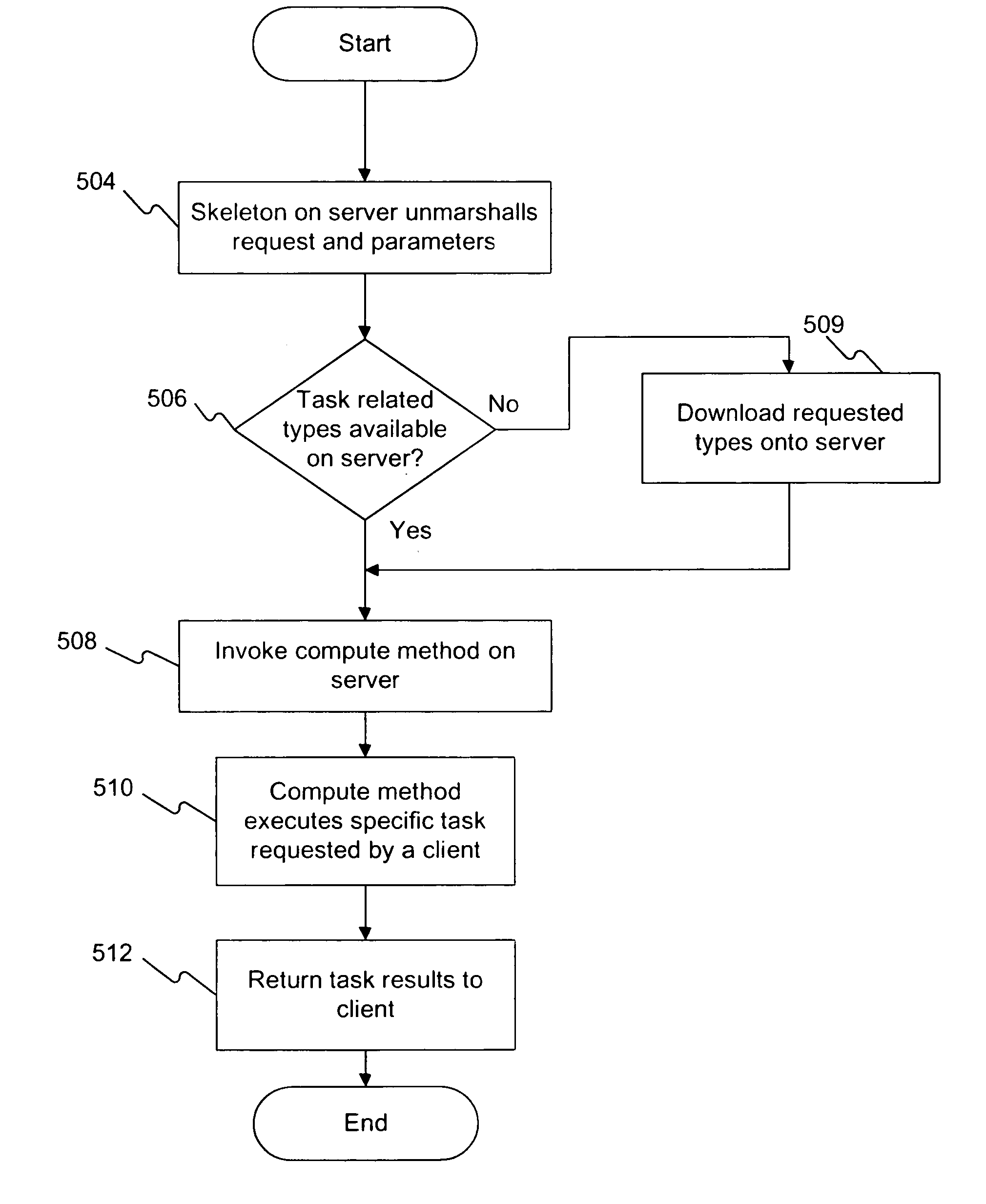
Method and apparatus for dynamic distributed computing over a network
A homogeneous execution environment operates within a heterogeneous client-server network. A client selects a server and transmits a procedure call with parameters. In response, a server dynamically and securely downloads code to a compute server; invokes a generic compute method; executes the code on the compute server; and returns the results to the calling client method, preserving the result on the compute server if requested. This technique is efficient in that it does not require multiple copies of code to be downloaded or compiled since server byte-codes can be executed on each of the different systems, therefore downloading or compiling multiple copies of code can be avoided. The code can be compiled once and downloaded as needed to the various servers as byte-codes and then executed.
Owner:SUN MICROSYSTEMS INC
Method and system for fast context based adaptive binary arithmetic coding
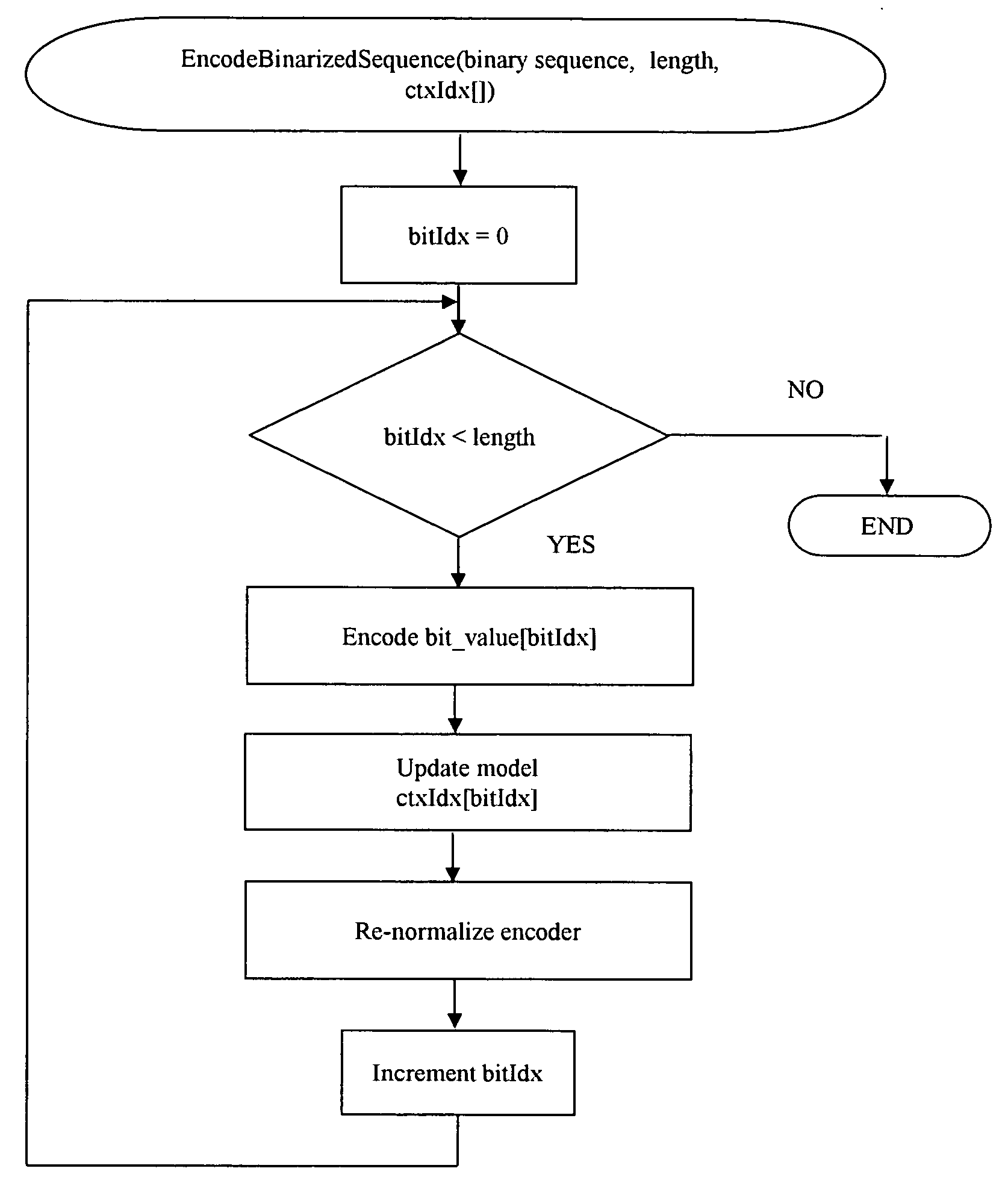
InactiveUS20070040711A1Increasing instruction level parallelismReduces function call overheadCode conversionCharacter and pattern recognitionProcedure callsContext-adaptive variable-length coding
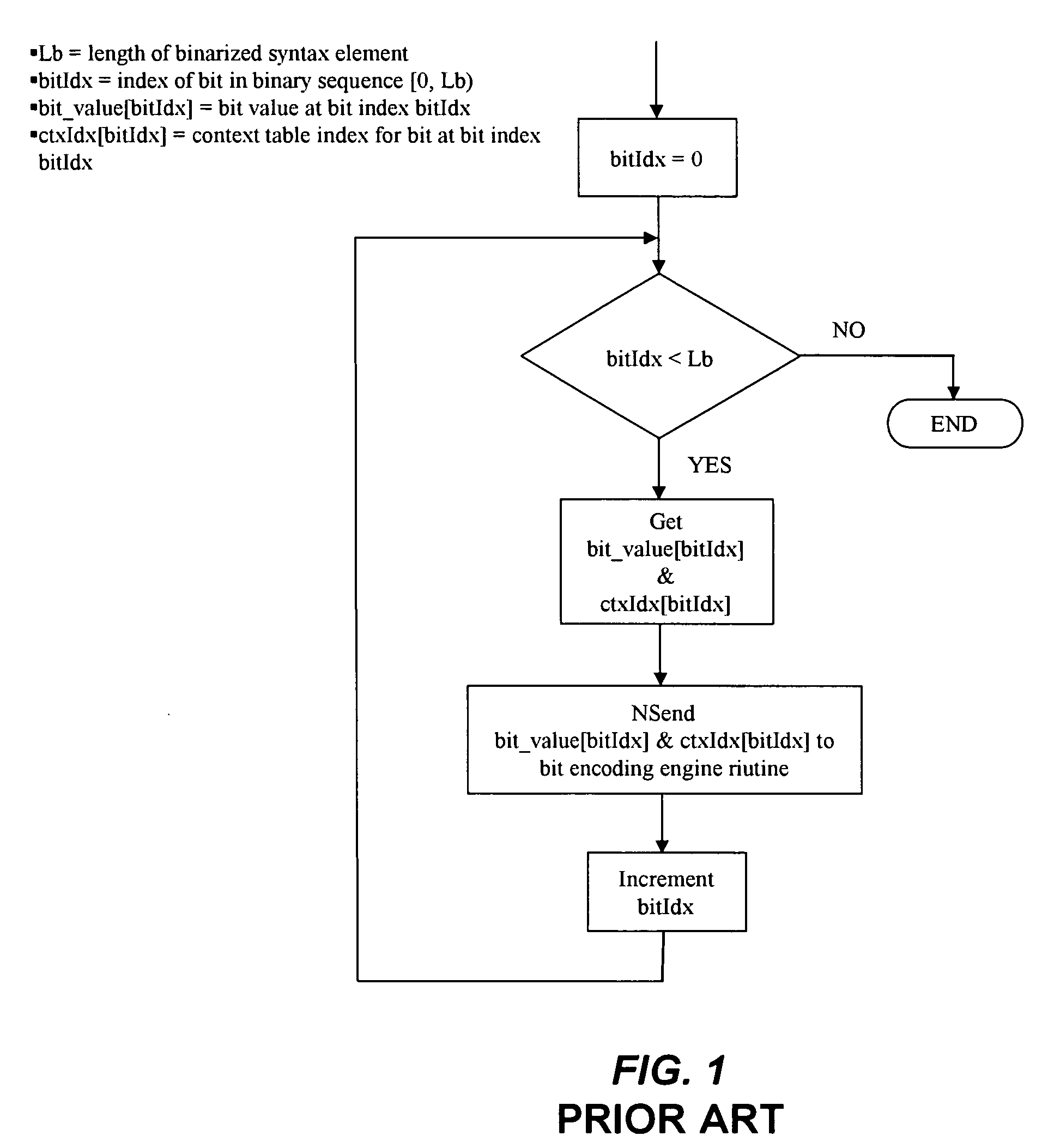
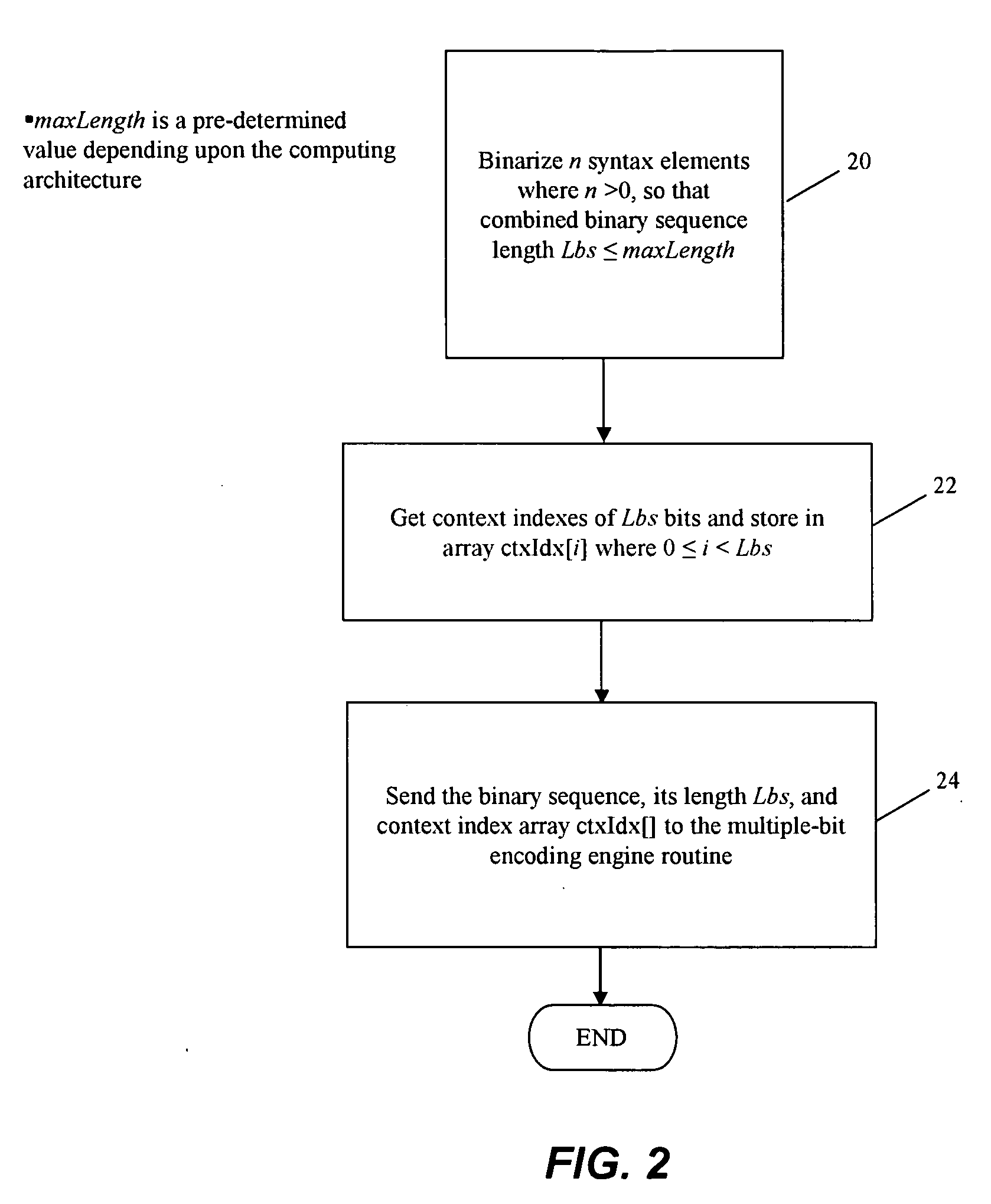
A method for efficient and fast implementation of context-based adaptive binary arithmetic encoding in H.264 / AVC video encoders is disclosed. The H.264 / AVC video standard supports two entropy coding mechanisms. These include Context Adaptive Binary Arithmetic Coding (CABAC) and Context Adaptive Variable Length Coding (CAVLC). The entropy coding efficiency of CABAC exceeds that of CAVLC by a clear margin. The method further provides techniques that make the implementation of CABAC on digital signal processors (DSPs) and other processing devices significantly faster. In one aspect, the method increases decoupling between the binarization process and the arithmetic encoding process from bit level to single or multiple syntax element(s) level. The binarized data is provided to the arithmetic encoding engine in bulk, thereby significantly reducing the overhead due to procedure calls. In another aspect, a CABAC arithmetic encoding engine format is provided which decreases data writing overhead and better exploits parallelism in the encoding process. This aspect is particularly advantageous to, for example, very long instruction word (VLIW) DSPs and media processors. In yet another aspect, the method discloses efficient CABAC binarization schemes for syntax elements.
Owner:STREAMING NETWORKS PVT
Compilation of remote procedure calls between a timed HDL model on a reconfigurable hardware platform and an untimed model on a sequential computing platform
ActiveUS20050198606A1Guaranteed repeatabilityEasy to useElectrical testingSoftware simulation/interpretation/emulationTelecommunications linkProcedure calls
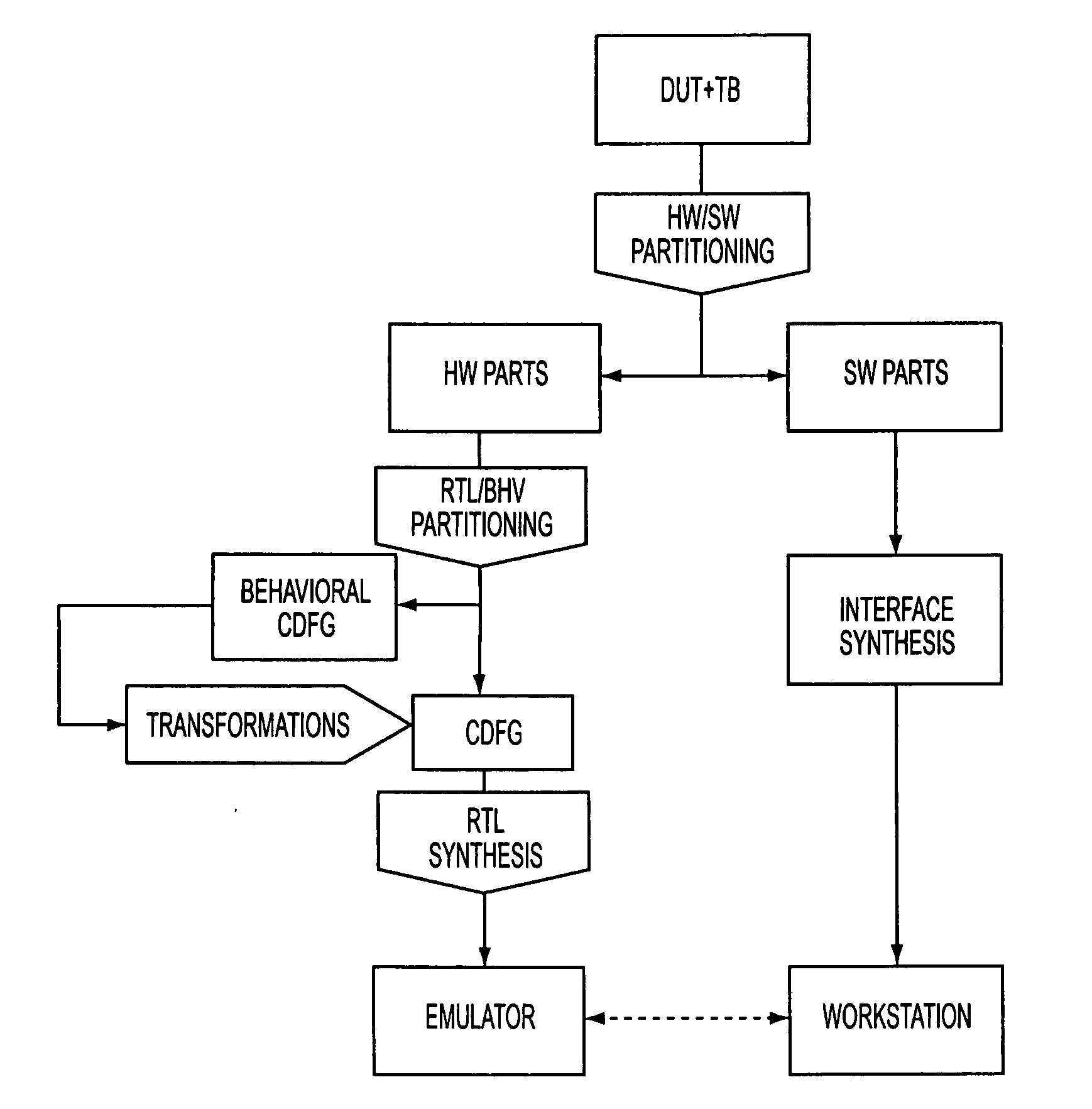
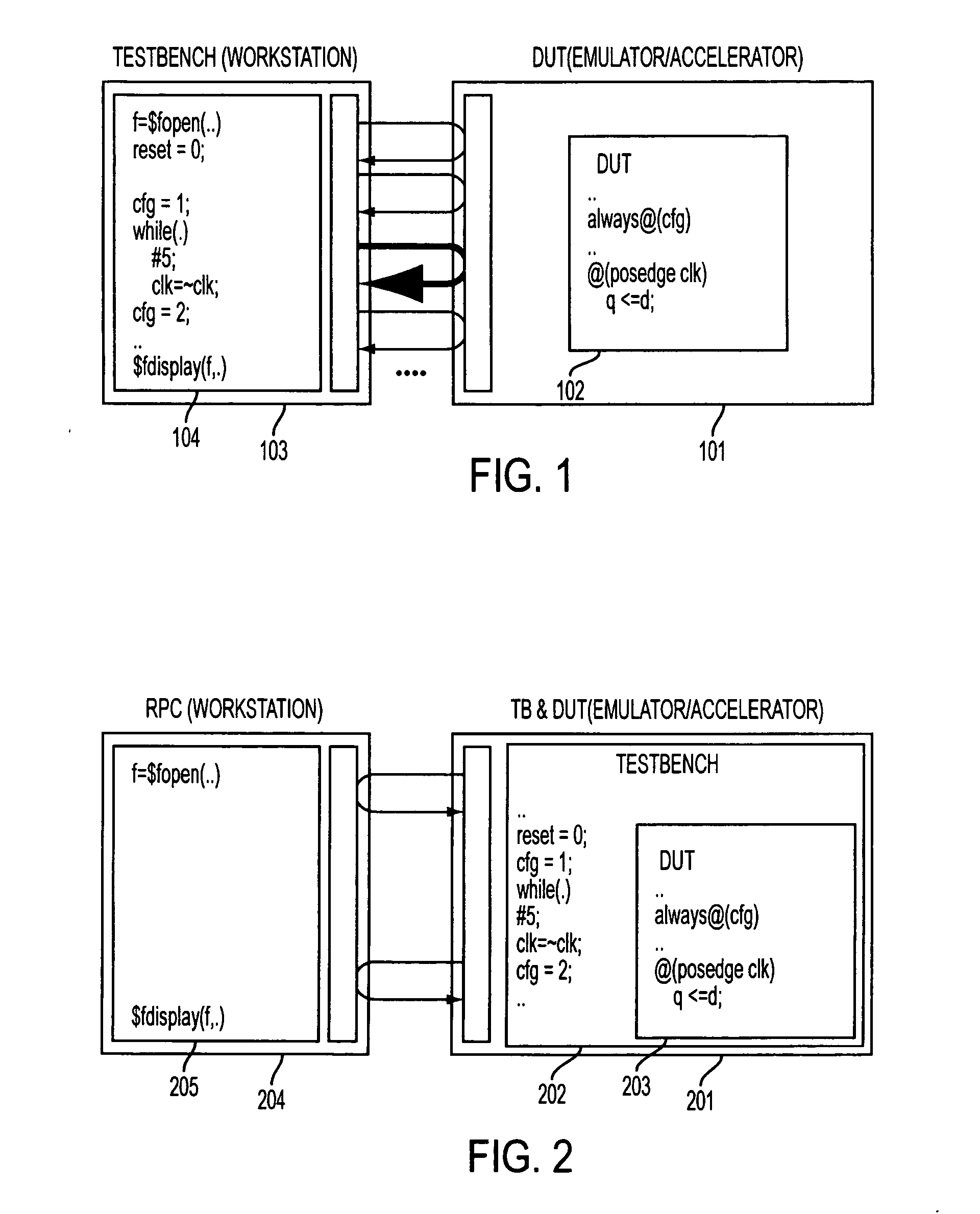
A system is described for managing interaction between an untimed HAL portion and a timed HDL portion of the testbench, wherein the timed portion is embodied on an emulator and the un-timed portion executes on a workstation. Repeatability of verification results may be achieved even though the HAL portion and the HDL portion run in parallel with each other. A communication interface is also described for synchronizing and passing data between multiple HDL threads on the emulator domain and simultaneously-running multiple HAL threads on the workstation domain. In addition, a remote procedural-call-based communication link, transparent to the user, is generated between the workstation and the emulator. A technique provides for repeatability for blocking and non-blocking procedure calls. FSMs and synchronization logic are automatically inferred to implement remote procedural calls. A subset of behavioral language is identified that combines the power of conventional modeling paradigms with RTL performance.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
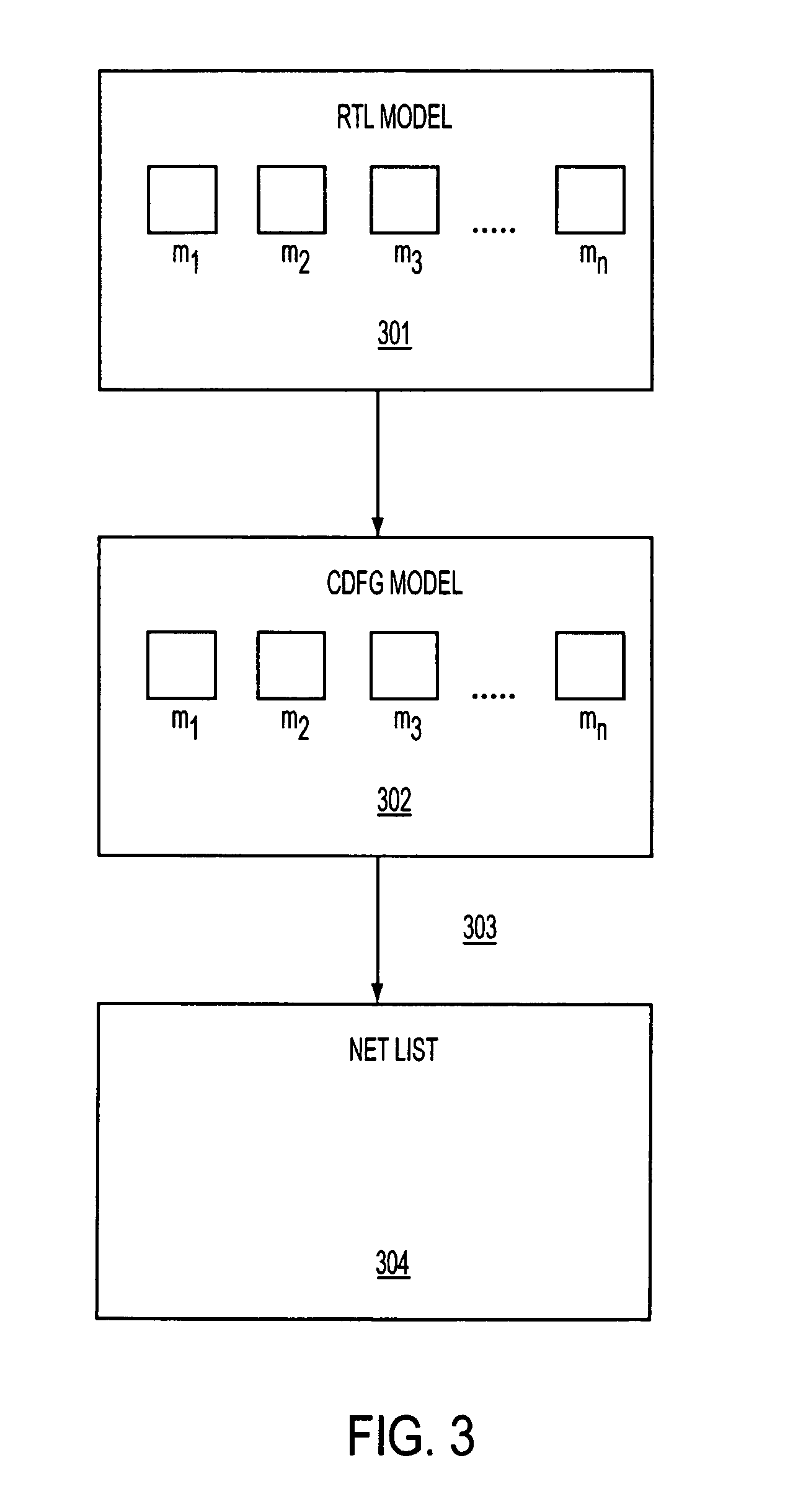
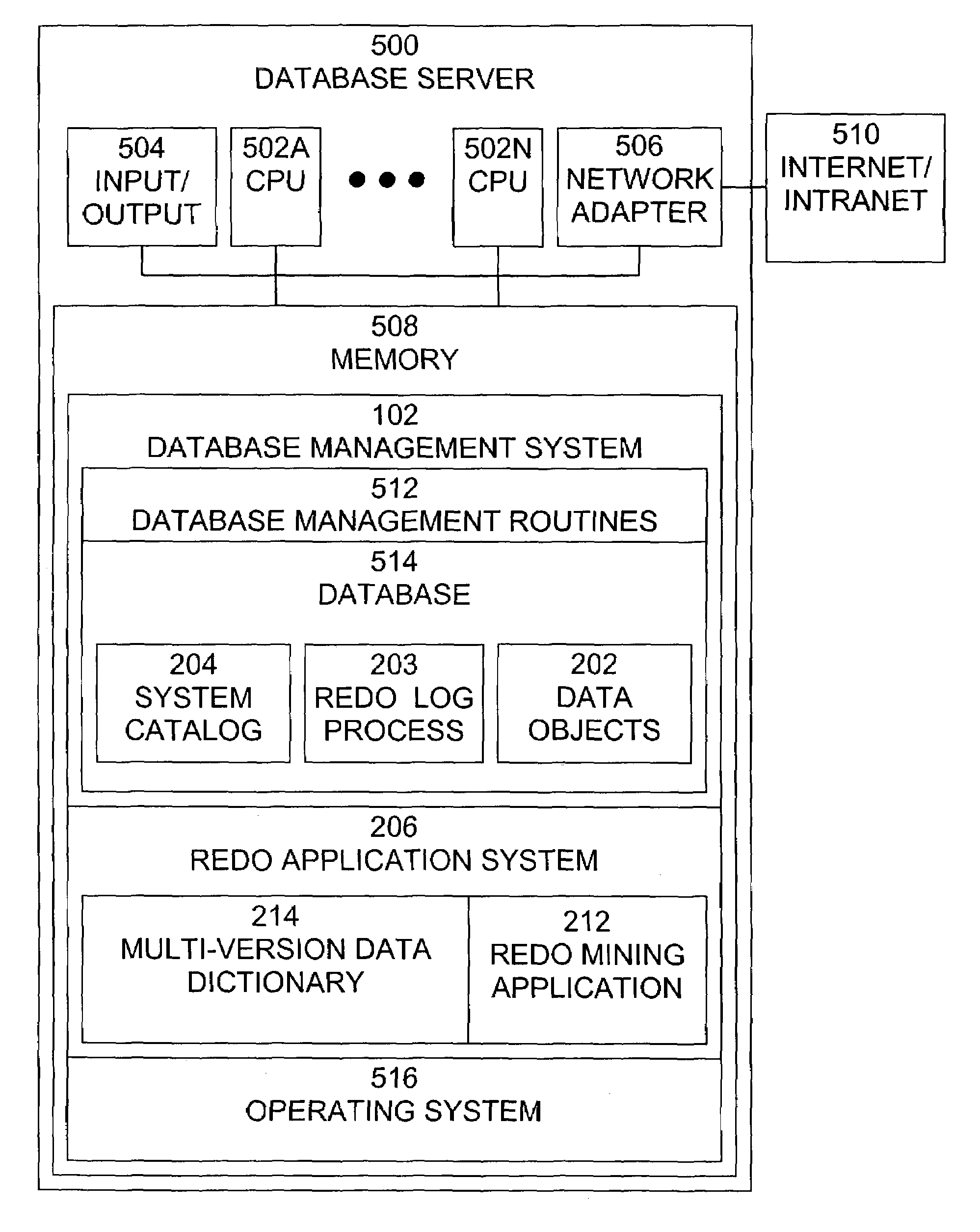
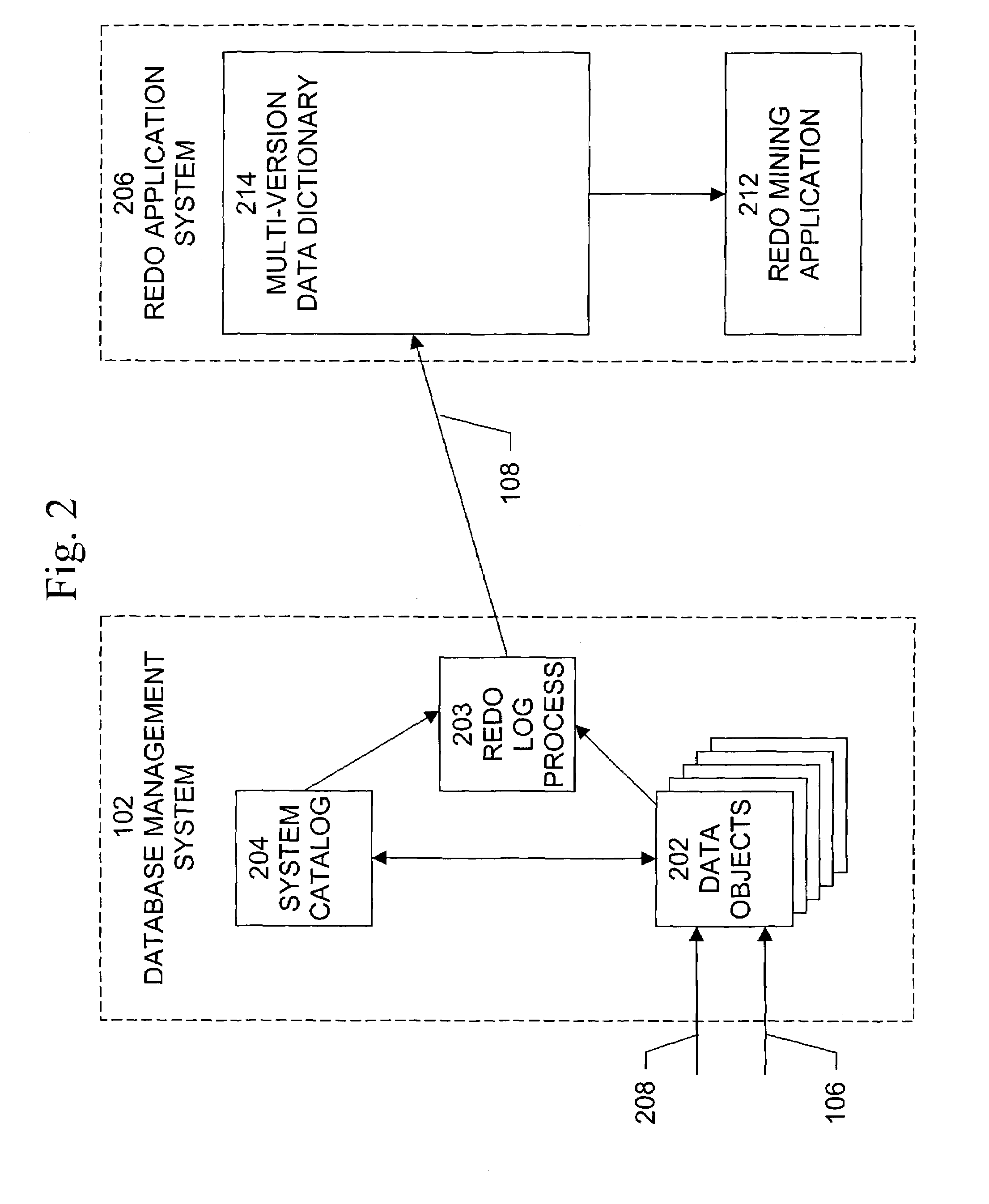
On-demand multi-version data dictionary to support distributed applications
ActiveUS7287034B2Increase productivityEfficient productionDigital data information retrievalData processing applicationsProcedure callsApplication software
Owner:ORACLE INT CORP
System and method for access control
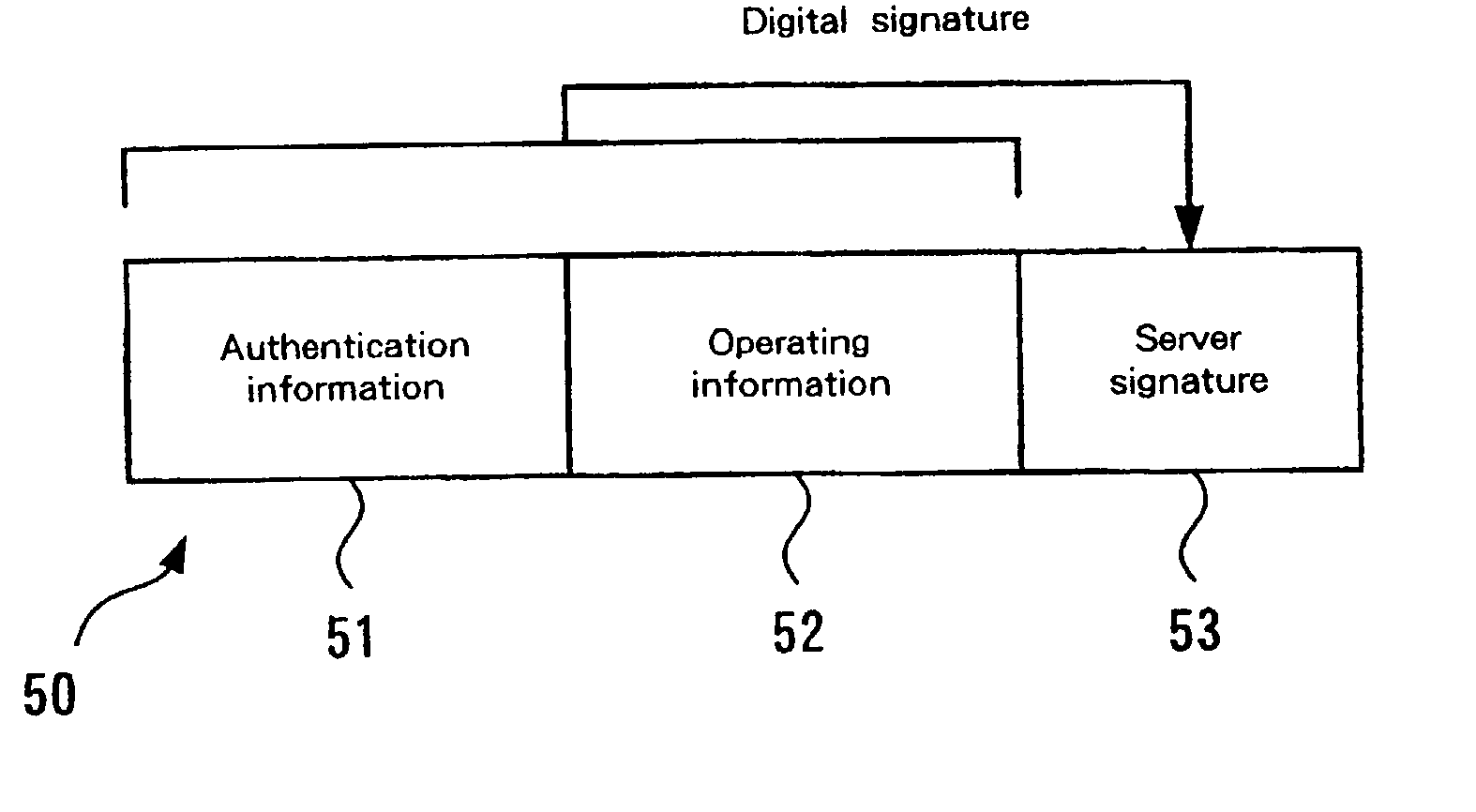
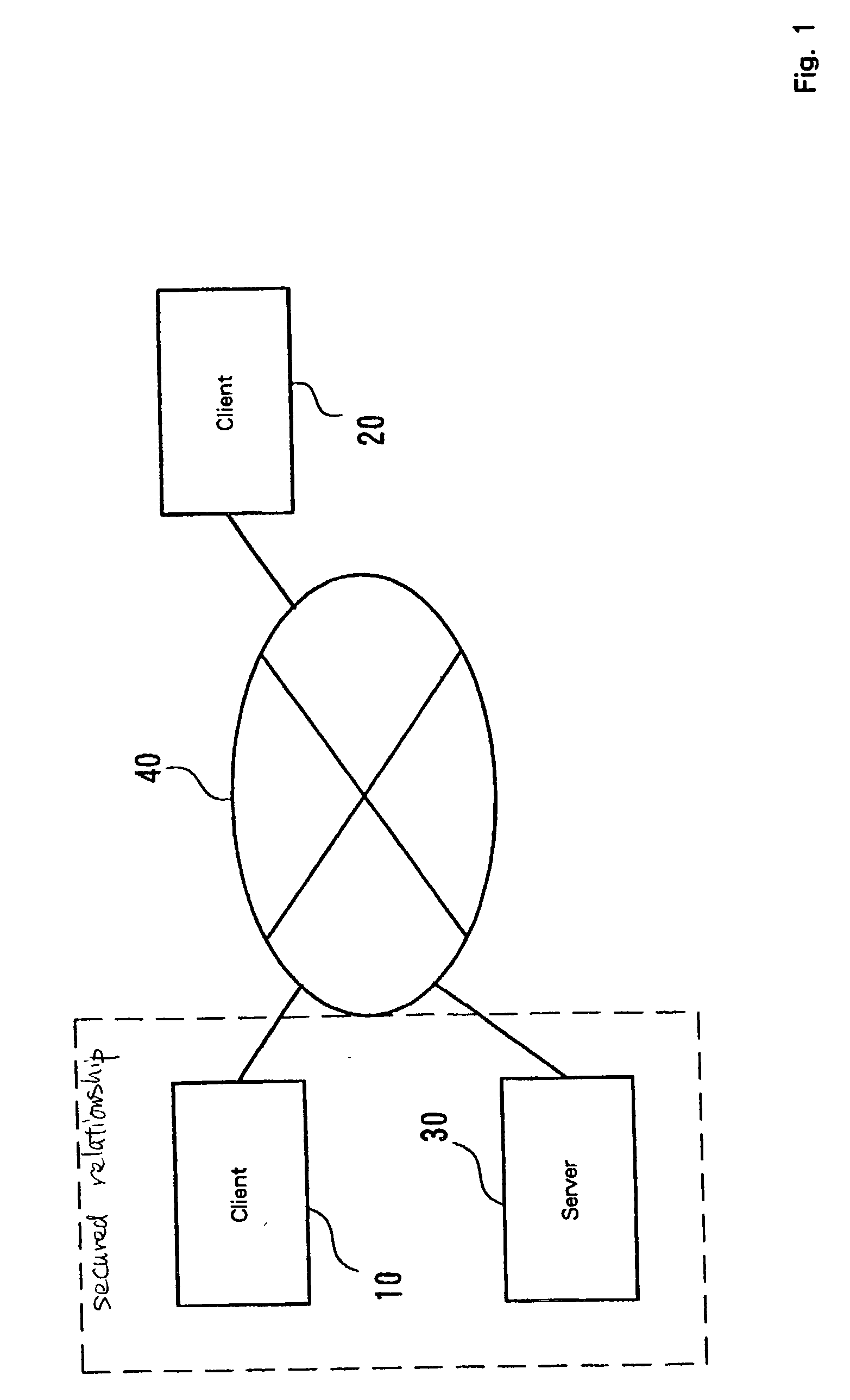
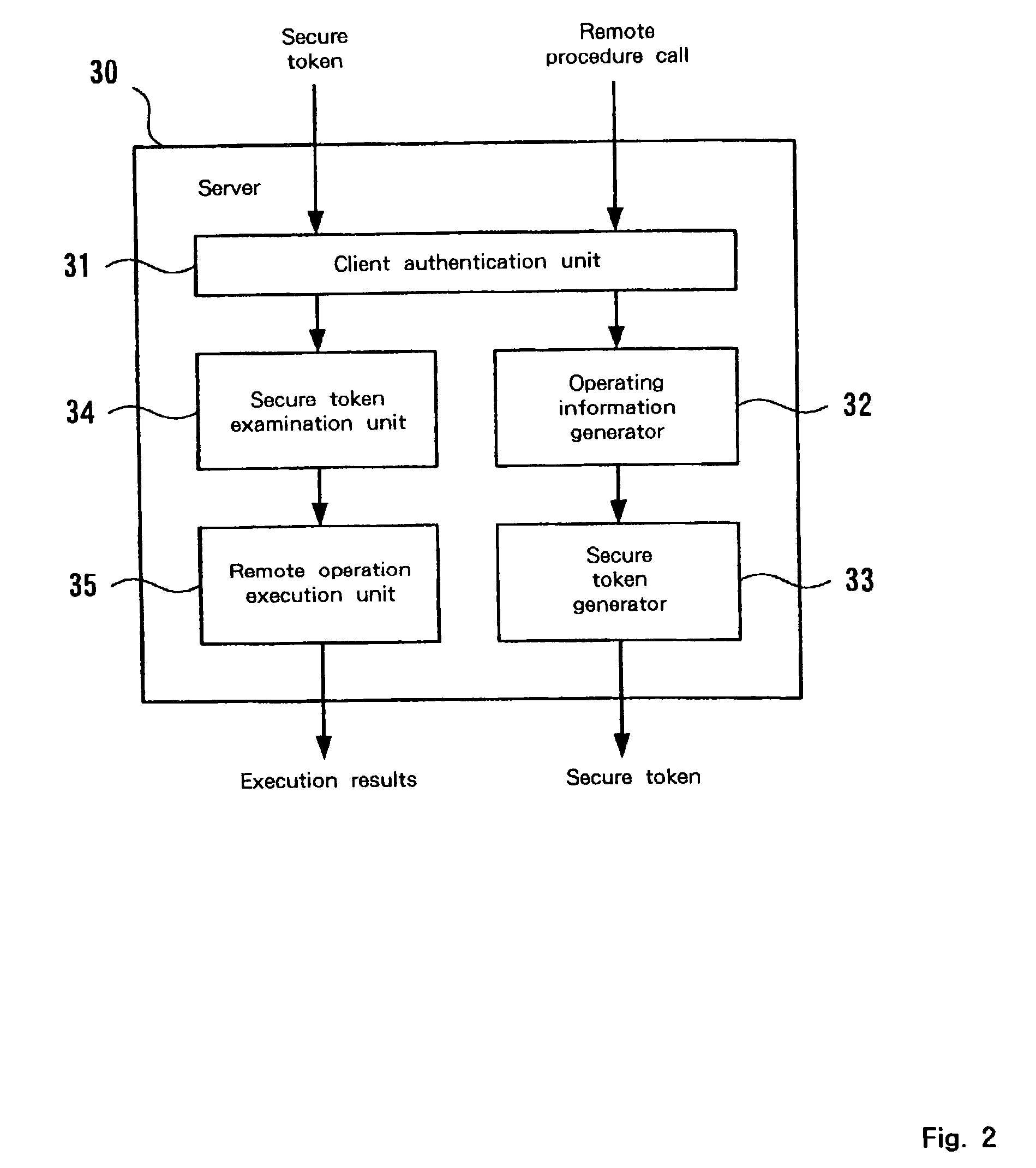
InactiveUS20030005333A1User identity/authority verificationUnauthorized memory use protectionData setAccess control matrix
A mechanism for access control based on remote procedure calls is established whereby server management costs for the processing associated with the authentication of client access rights and the provision of requested resources can be reduced by distributing these costs among clients. A first client, which has an access right to a server via a network, can issue a remote procedure call to the server. The first client can also communicate with a second client, which doesn't have an access right to the server. The first client requests the server to issue a token, which is a data set for permitting the second client a limited access to the server, and subsequently the token prepared by the server is transmitted to the second client. The second client originally has no access rights relative to the server. However, if the second client transmits a remote procedure call using the received token, limited access is granted. The server performs a process designated by the remote procedure call from the second client. The token includes operating information for designating an operation to be performed based on the remote procedure call, and identification information for identifying the second client.
Owner:IBM CORP
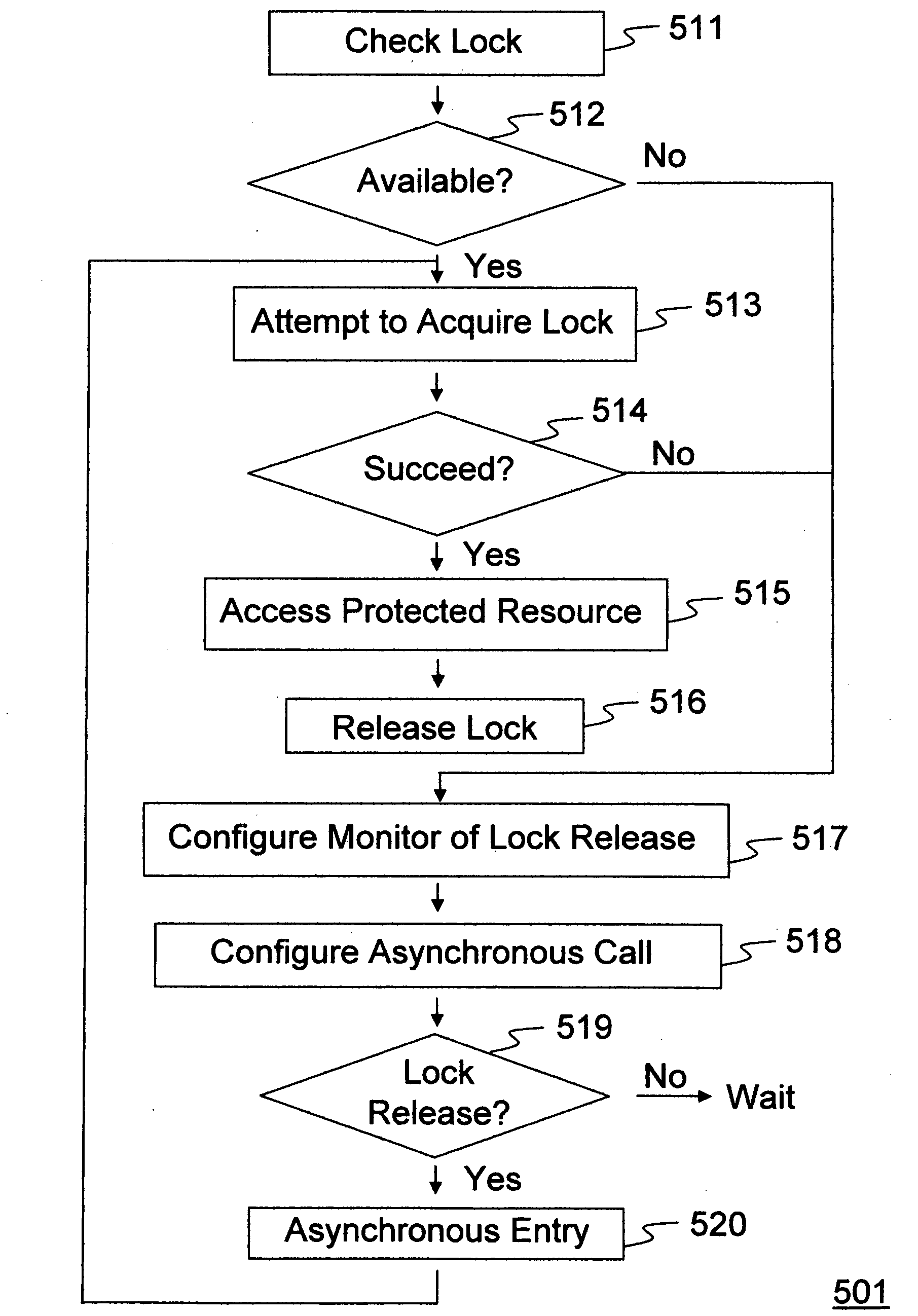
Method and system for enhanced thread synchronization and coordination
InactiveUS20070271450A1Digital computer detailsSpecific program execution arrangementsProcedure callsEmbedded system
Synchronization and communication between concurrent software threads is enhanced. An attempt may be made to acquire a lock associated with a resource. If the lock is not available and / or the attempt fails, a hardware monitor may be configured to detect release of the lock. An asynchronous procedure call responsive to detection of the lock release facilitates another attempt to acquire the lock. Alternatively, upon acquiring the lock a hardware monitor may be configured to detect any attempt to acquire the lock. Access to the protected resource may be maintained until an asynchronous procedure call responsive to the detection of such an attempt. Then state may be restored to a safe point for releasing the lock. Alternatively, processing of reader lock requests may be adapted to a turnstile processing when no writer holds or waits for the lock and then adapted to read-write lock processing whenever a writer requests the lock.
Owner:INTEL CORP
Remote application publication and communication system
InactiveUS7587459B2Web data indexingMultiple digital computer combinationsCommunications systemProcedure calls
The invention is a system and method for publishing distributed applications accessible over a distributed network without having publishing computer to accept remote procedure calls from clients, and also allow integration between such distributed applications. In one embodiment, the invention includes a remote application computer having a service agent, translation file, and published software application thereon. The service agent provides the ability to identify the remote application computer and communicate with the distributed network, the translation file provides parameters to the service agent for interpreting the data i / o format of the published application, and the published application monitors and reports on conditions of a building or structure's environmental, security, and occupancy status.
Owner:EUTECH CYBERNETICS PTE
Compiler system compiling method, and storage medium for storing compiling program
InactiveUS7073167B2Increase speedReducing necessary memory capacitySpecific program execution arrangementsMemory systemsCompilerProcedure calls
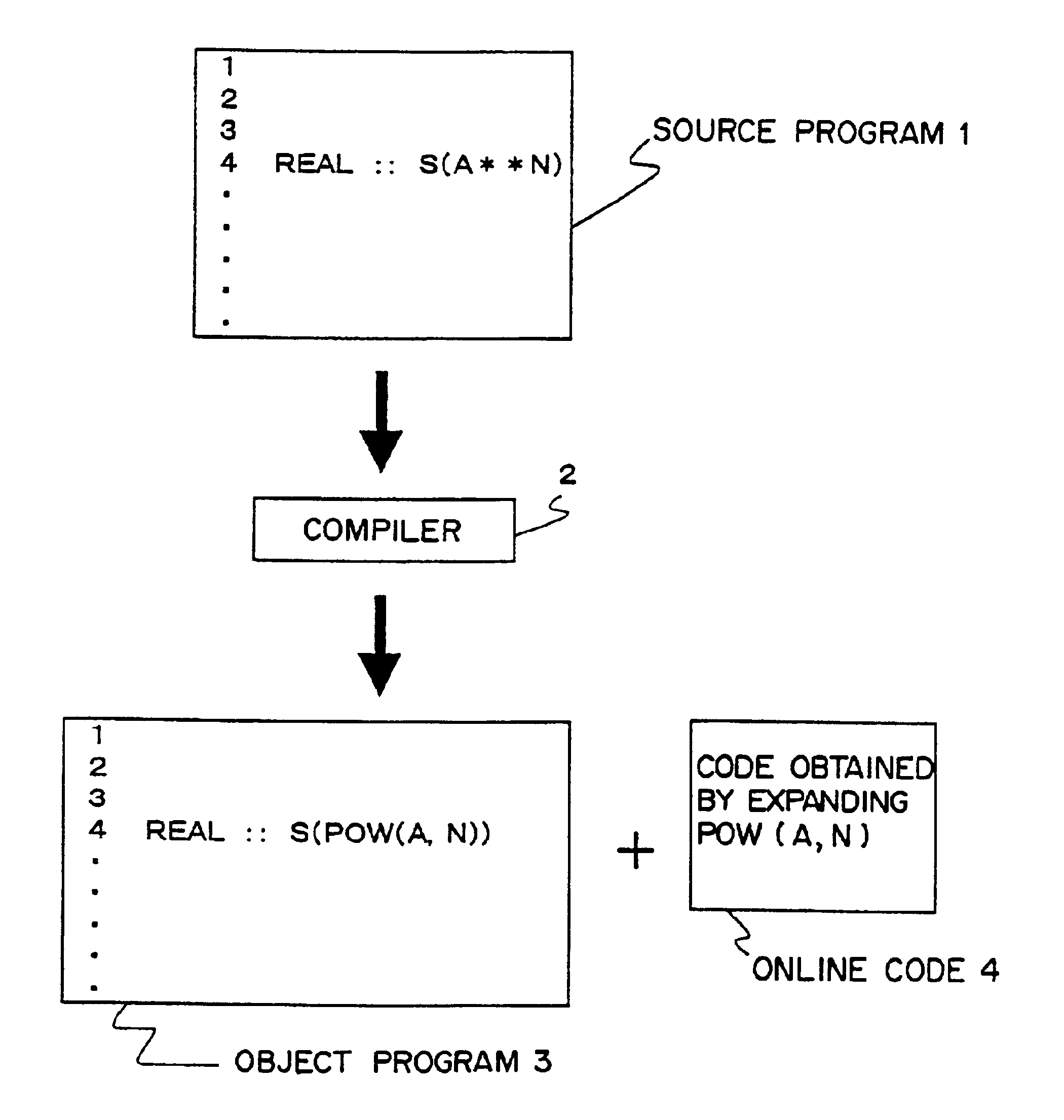
A compiler has a detection unit, a conversion unit, and a expansion unit. The detection unit detects a predetermined target from an input source program. The conversion unit converts the target detected by the detection unit into a procedure call. The expansion unit generates an online code describing a definition of a procedure to be called by the procedure call obtained by the detection unit. The compiler outputs a program in which the target detected by the detection unit is replaced with a procedure call, and an online code corresponding to the procedure call.
Owner:FUJITSU LTD
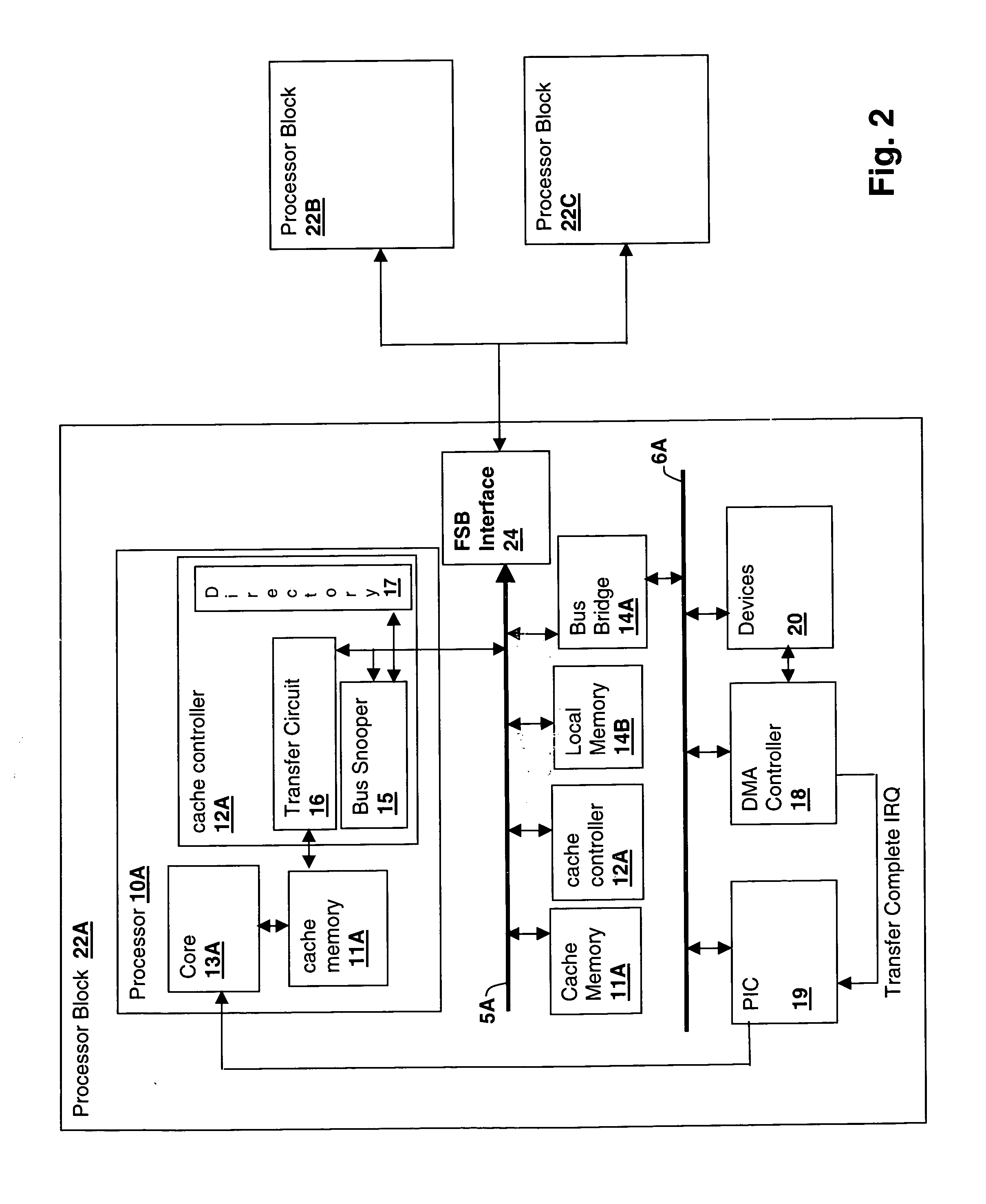
Method and system for managing cache injection in a multiprocessor system
A method and apparatus for managing cache injection in a multiprocessor system reduces processing time associated with direct memory access transfers in a symmetrical multiprocessor (SMP) or a non-uniform memory access (NUMA) multiprocessor environment. The method and apparatus either detect the target processor for DMA completion or direct processing of DMA completion to a particular processor, thereby enabling cache injection to a cache that is coupled with processor that executes the DMA completion routine processing the data injected into the cache. The target processor may be identified by determining the processor handling the interrupt that occurs on completion of the DMA transfer. Alternatively or in conjunction with target processor identification, an interrupt handler may queue a deferred procedure call to the target processor to process the transferred data. In NUMA multiprocessor systems, the completing processor / target memory is chosen for accessibility of the target memory to the processor and associated cache.
Owner:IBM CORP
Apparatus, system, and method for soap access to data source procedures
InactiveUS20080313660A1Eliminate requirementsInterprogram communicationTransmissionProcedure callsWeb service
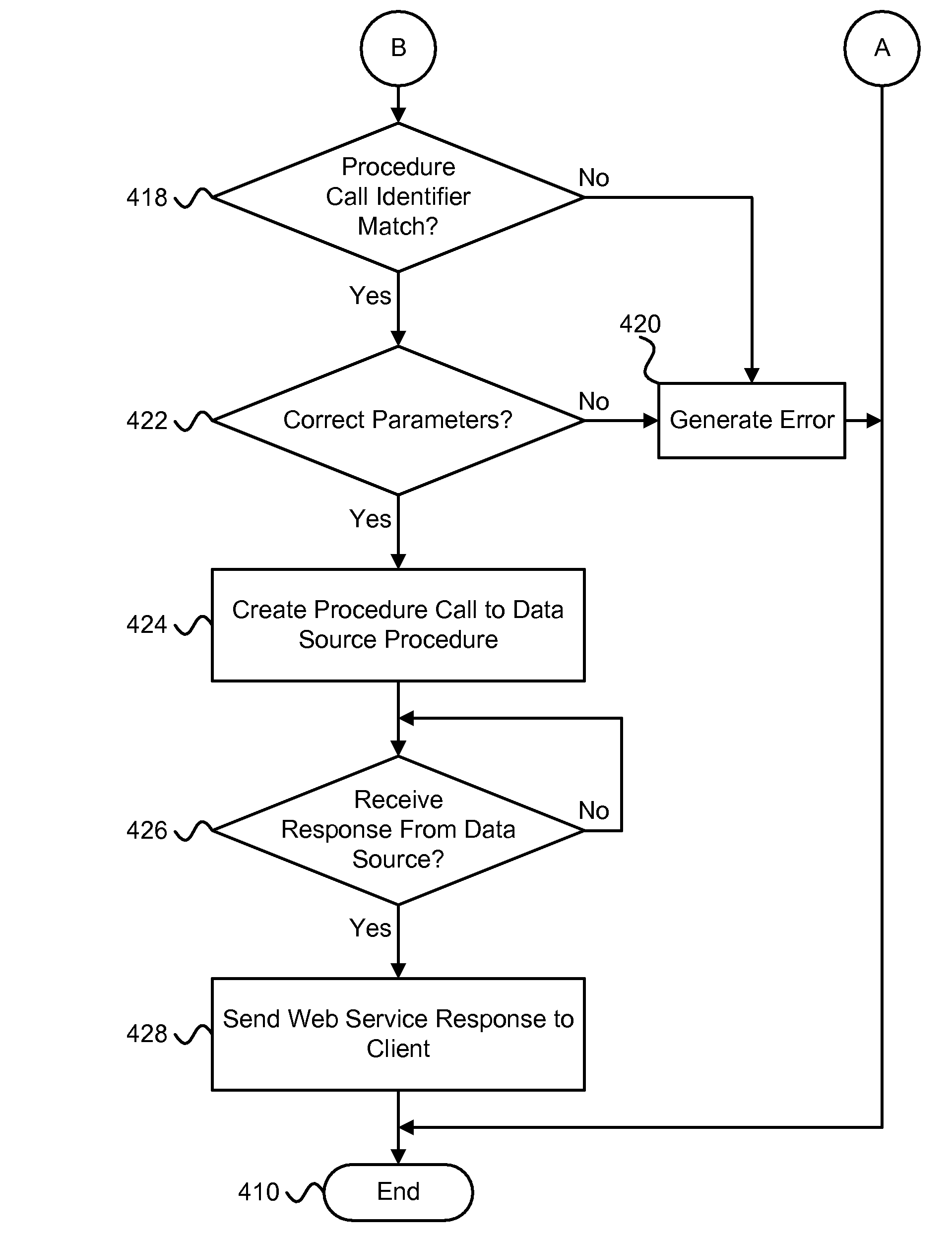
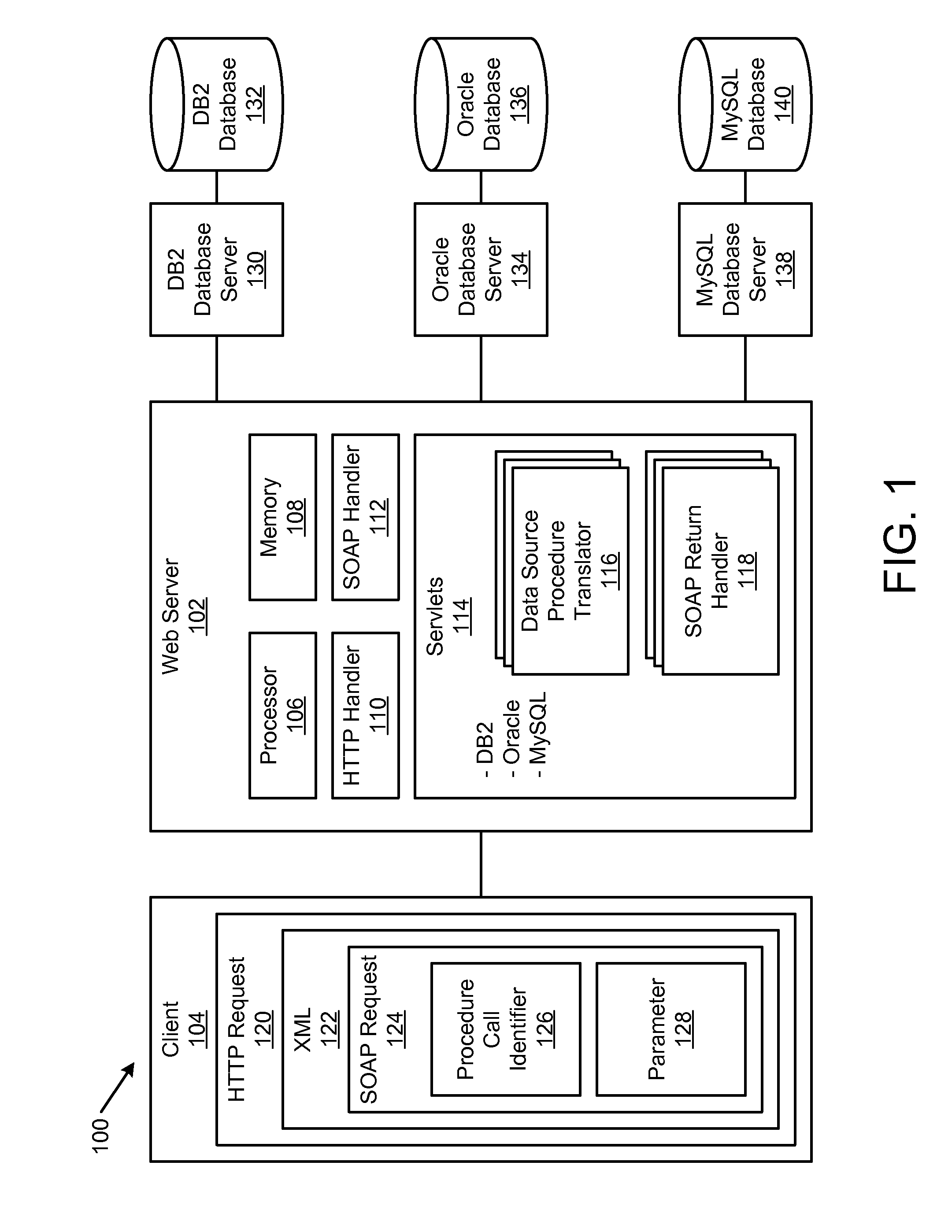
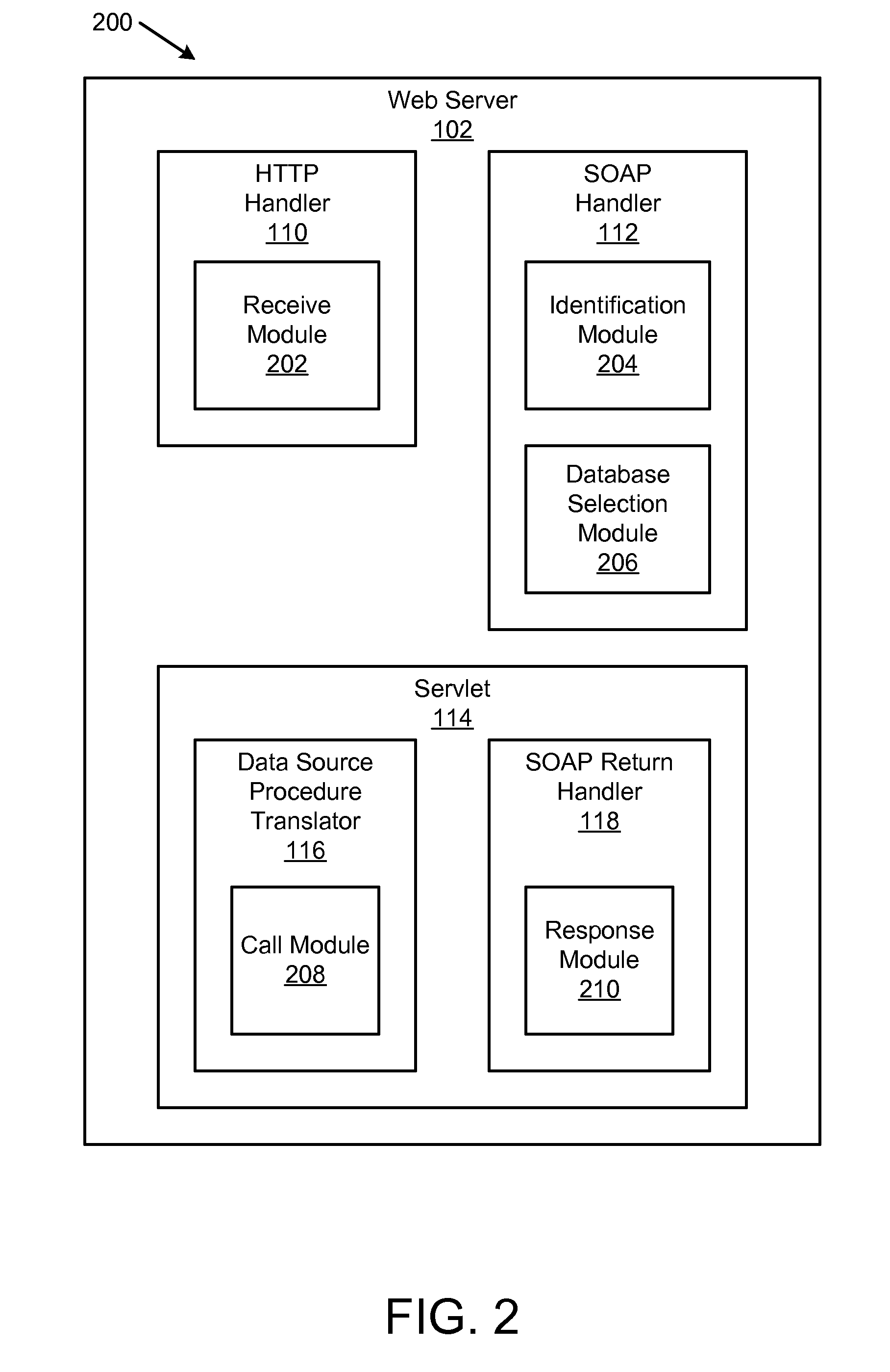
An apparatus, system, and method are disclosed for web service access to a remote data source procedure. The method includes receiving a web service request from a client and identifying the procedure call identifier within the web service request. The web service request includes a procedure call identifier and zero or more parameters. The method includes creating a procedure call to a data source procedure accessible through an Application Program Interface. The procedure call is created at least in part by ordering parameters of the procedure call based on an order of the zero or more parameters in the web service request. The parameters of the procedure call are ordered without using an explicit parameter mapping. The method includes sending a web service response to the client in response to receiving a response from the data source procedure. The web service response includes information responsive to the procedure call.
Owner:IBM CORP
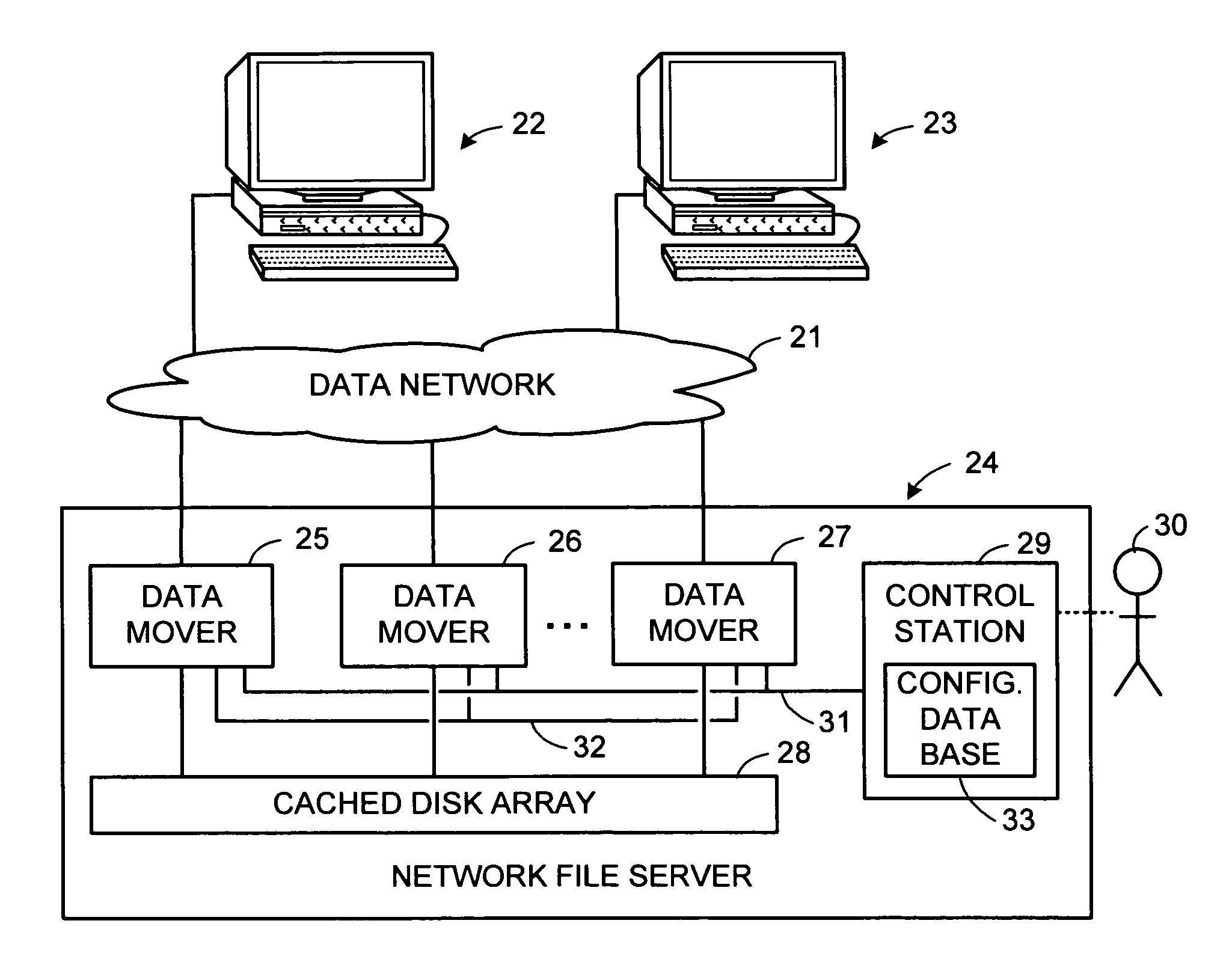
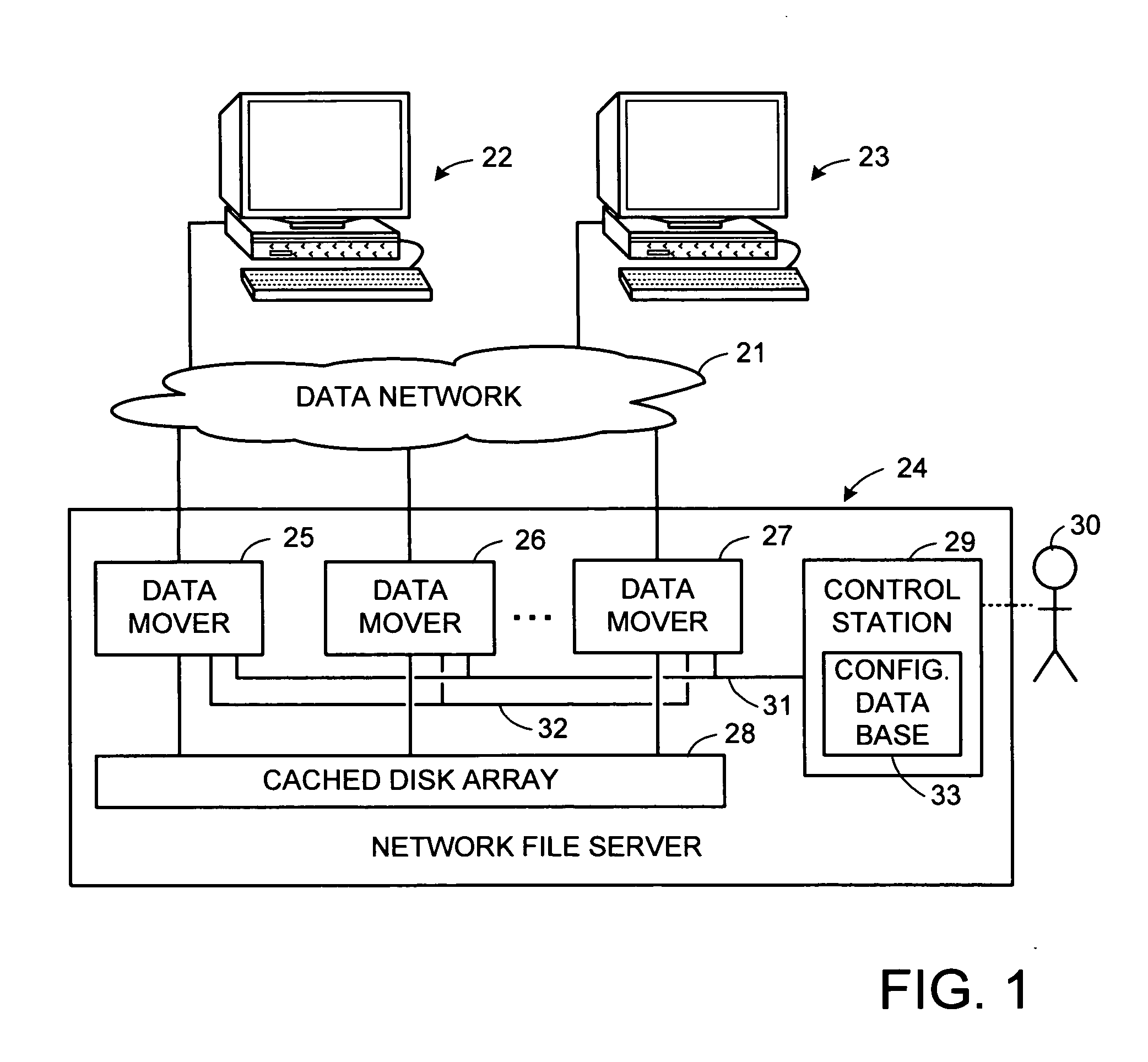
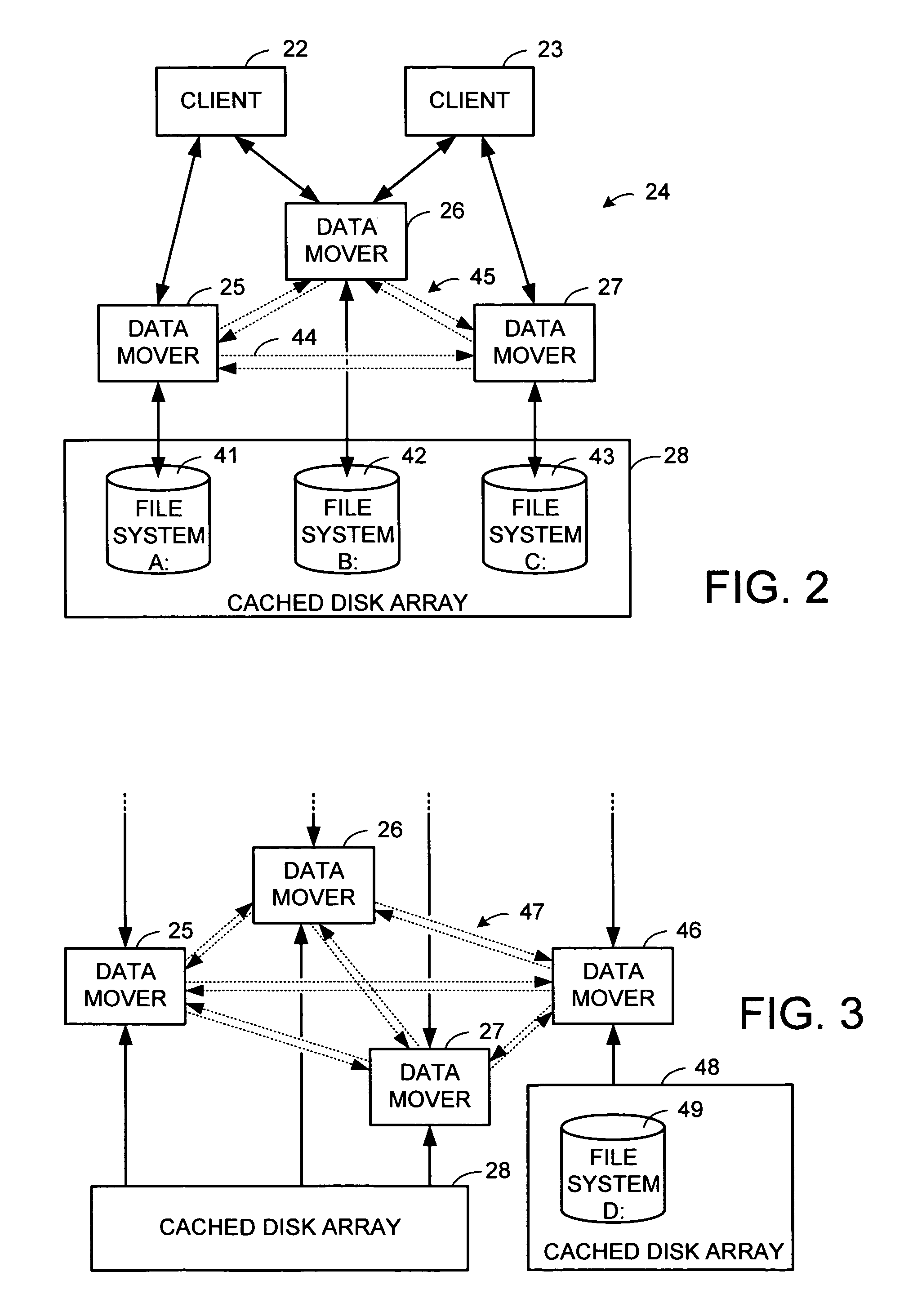
TCP forwarding of client requests of high-level file and storage access protocols in a network file server system
InactiveUS20060230148A1Reduce in quantityEasy to useDigital computer detailsTransmissionProcedure callsThe Internet
For each high-level protocol, a respective mesh of Transmission Control Protocol (TCP) connections is set up for a cluster of server computers for the forwarding of client requests. Each mesh has a respective pair of TCP connections in opposite directions between each pair of server computers in the cluster. The high-level protocols, for example, include the Network File System (NFS) protocol, and the Common Internet File System (CIFS) protocol. Each mesh can be shared among multiple clients because there is no need for maintenance of separate TCP connection state for each client. The server computers may use Remote Procedure Call (RPC) semantics for the forwarding of the client requests, and prior to the forwarding of a client request, a new unique transaction ID can substituted for an original transaction ID in the client request so that forwarded requests have unique transaction IDs.
Owner:EMC CORP
History-based call stack construction
InactiveUS20080209406A1Error detection/correctionSpecific program execution arrangementsCall stackDefined Procedure
In a computing system environment, methods and apparatus relate to constructing a call stack for a software program based upon a comprehensive recording of an execution history of the software program. Upon defining procedure calls and returns in the execution history, a call stack is constructed for the procedure calls having no corresponding returns, but without reading or otherwise examining allocated stack memory or registers, such as return addresses. In this manner, an accurate call stack can be constructed despite stack memory or registers being erased or corrupted or despite various compiler optimizations eliminating convenience or otherwise complicating the construction. Nuances for defining procedure calls and returns as well as stack pointer values for same are also contemplated. Still other embodiments relate to stand-alone computer program products (on computer-readable media or as a download, or other) or those working in conjunction with other programs.
Owner:RPX CORP
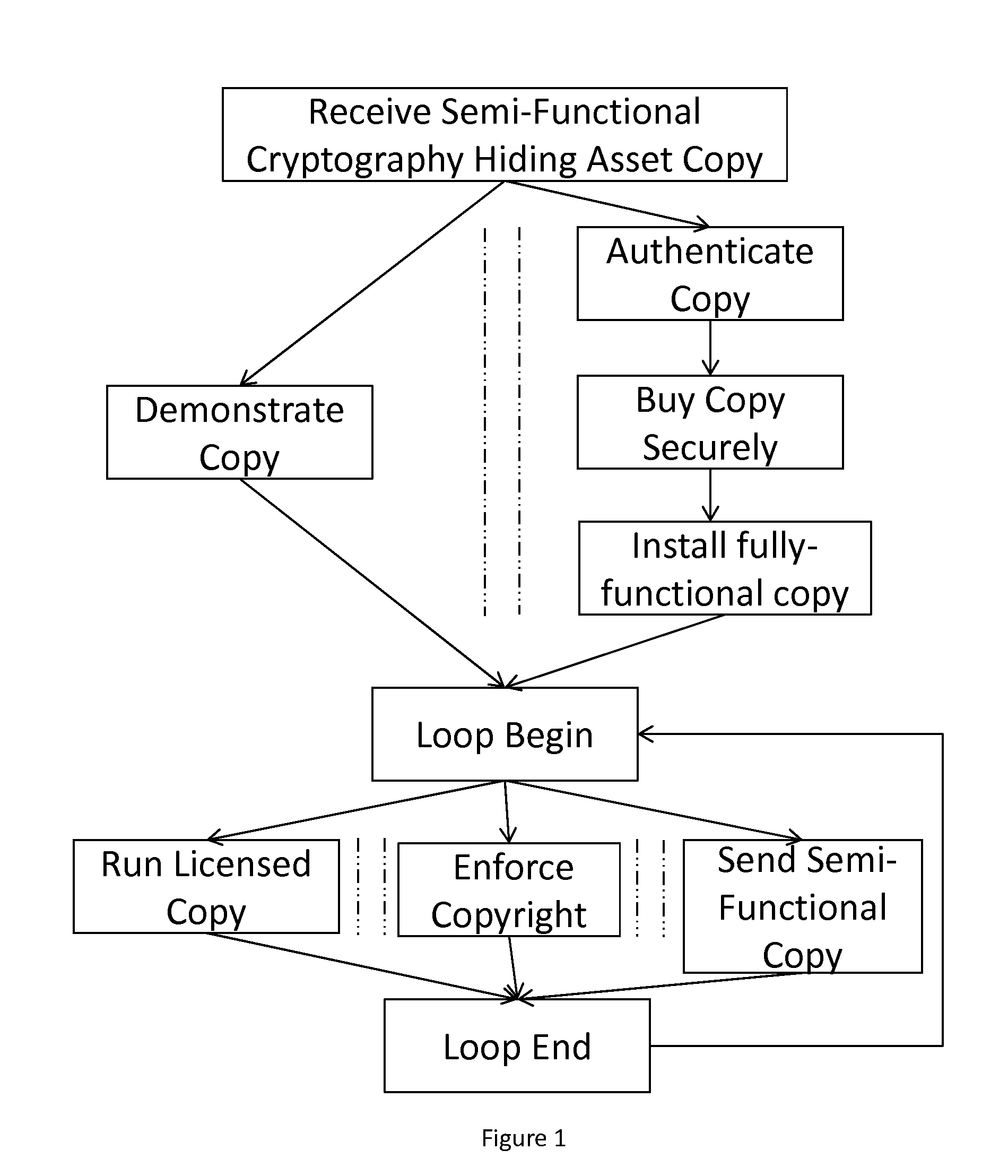
Potentate: A Cryptography-Obfuscating, Self-Policing, Pervasive Distribution System For Digital Content
InactiveUS20160364707A1Cryptography processingDigital data protectionSource transformationViral marketing
A system and method for self-policed, authenticated, offline / online, viral marketing and distribution of content such as software, text, and multimedia with effective copyright and license enforcement and secure selling. The system is based on key and cryptography hiding techniques, using source-to-source transformation for efficient, holistic steganography that systematically inflates and hides critical code by: computation interleaving; flattening procedure calls and obfuscating stack by de-stacking arguments; obfuscating memory management; and encoding scalars as pointers to managed structures that may be distributed and migrated all over the heap using garbage collection. Multimedia / text content may be partitioned and sold with expiry dates for protection and updates for long life. Authenticity of software installed on a machine may be monitored and ensured, supporting even authentic software deployment in an unknown environment. The system can be implemented with commonplace networking or browser software, commonplace hardware and content provision over a secure website (https standard).
Owner:VARMA PRADEEP
Remote procedure calling processing method, device and system, and electronic equipment
ActiveCN106161537AAvoid time-consuming traversalImprove performanceMultiprogramming arrangementsTransmissionRequest queueService process
The invention discloses a remote procedure calling processing method and device, a remote procedure calling method and device, a remote procedure calling processing system and electronic equipment, wherein the remote procedure calling processing method comprises the following steps of: receiving a service request corresponding to a specific service process sent by a calling process; storing the service request in a request queue to be processed of a service process; when the service request is processed, executing the service process according to the service request by an operating system so as to obtain a process result; and copying the process result in the storage space of the calling process from a kernel of the operating system. By means of the method provided in the invention, when remote process calling is realized, a practical I / O read-write request process cannot be blocked; the operating system does not need to traverse all user processes; data only needs to be copied in a user process for monitoring an event; and thus, the remote procedure calling performance can be improved.
Owner:ADVANCED NEW TECH CO LTD
Method and a system for the composition of services
InactiveUS20080288624A1Enhanced interactionNegative impactMultiple digital computer combinationsProgram controlService compositionDistributed Computing Environment
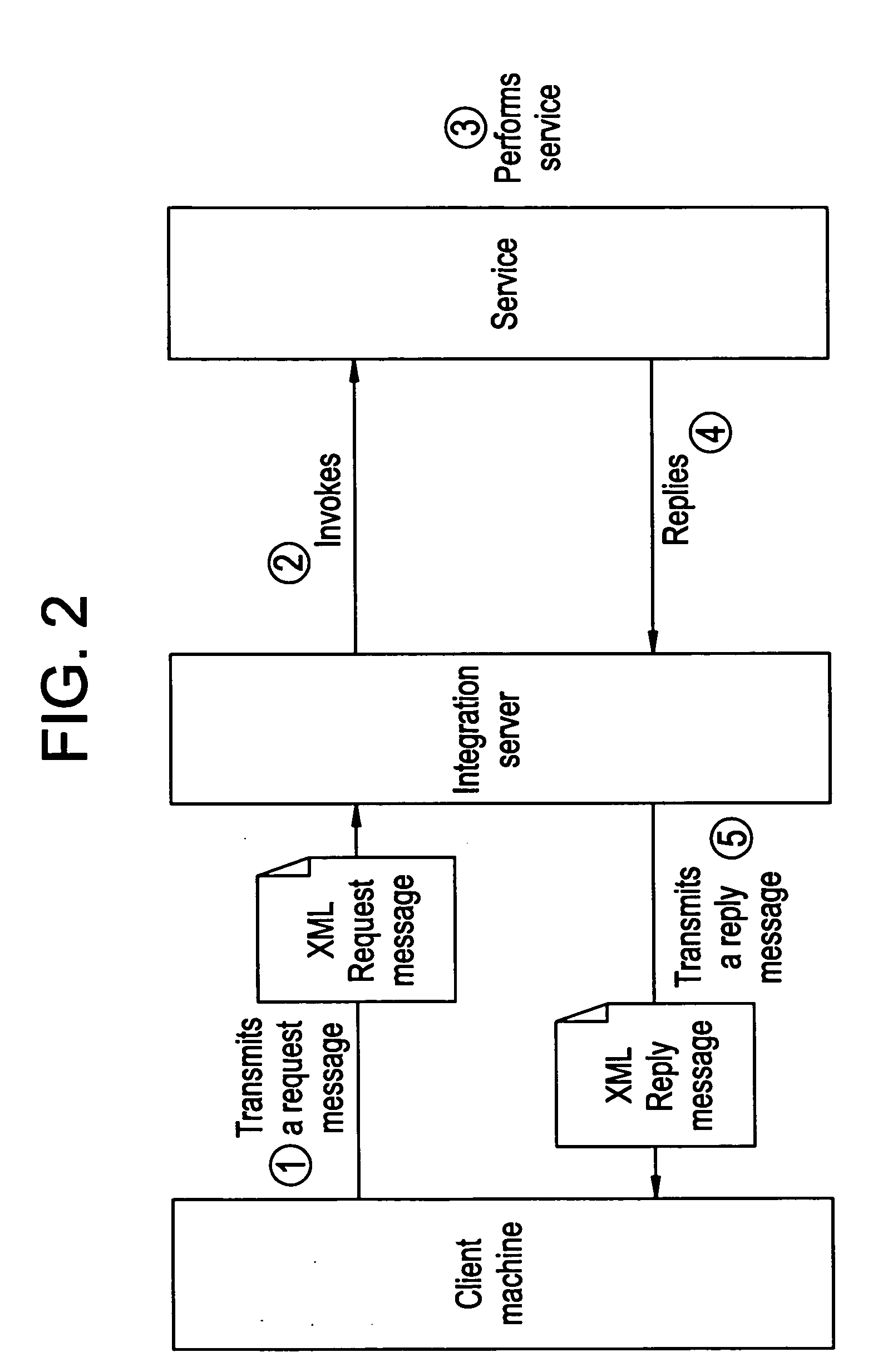
Method for multiphase service composition in a distributed computing environment comprising at least one client and at least one server, and involving at least one service, which defines a specific format for composition messages associated with multiphase remote procedure calls. This format is different from the one of regular server messages. Once such a composition message is received by the client, it recognizes this specific format and can automatically invoke at least one service on any server by sending a new request message including the arguments passed in this composition message.
Owner:ARMANGIL DOGA
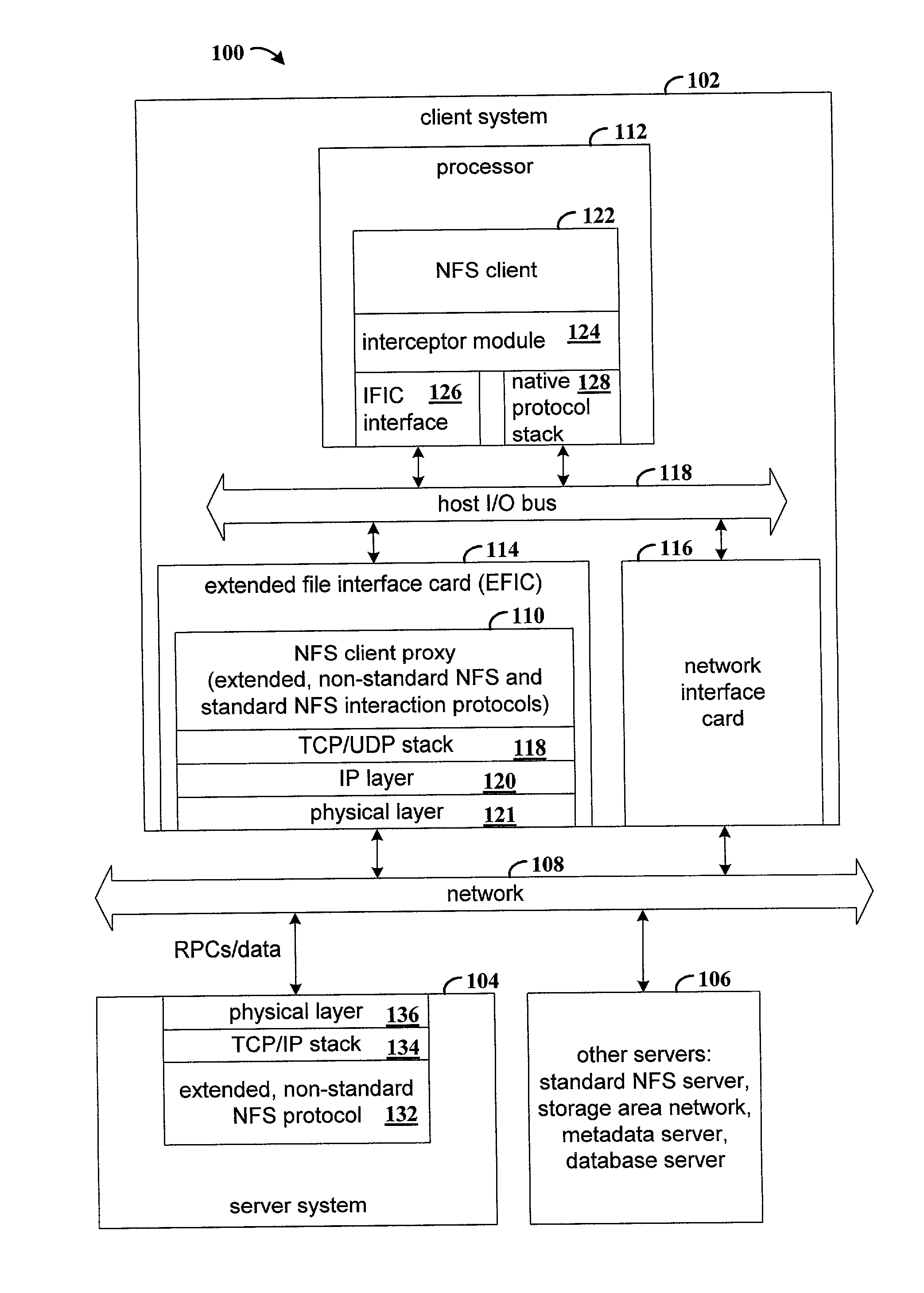
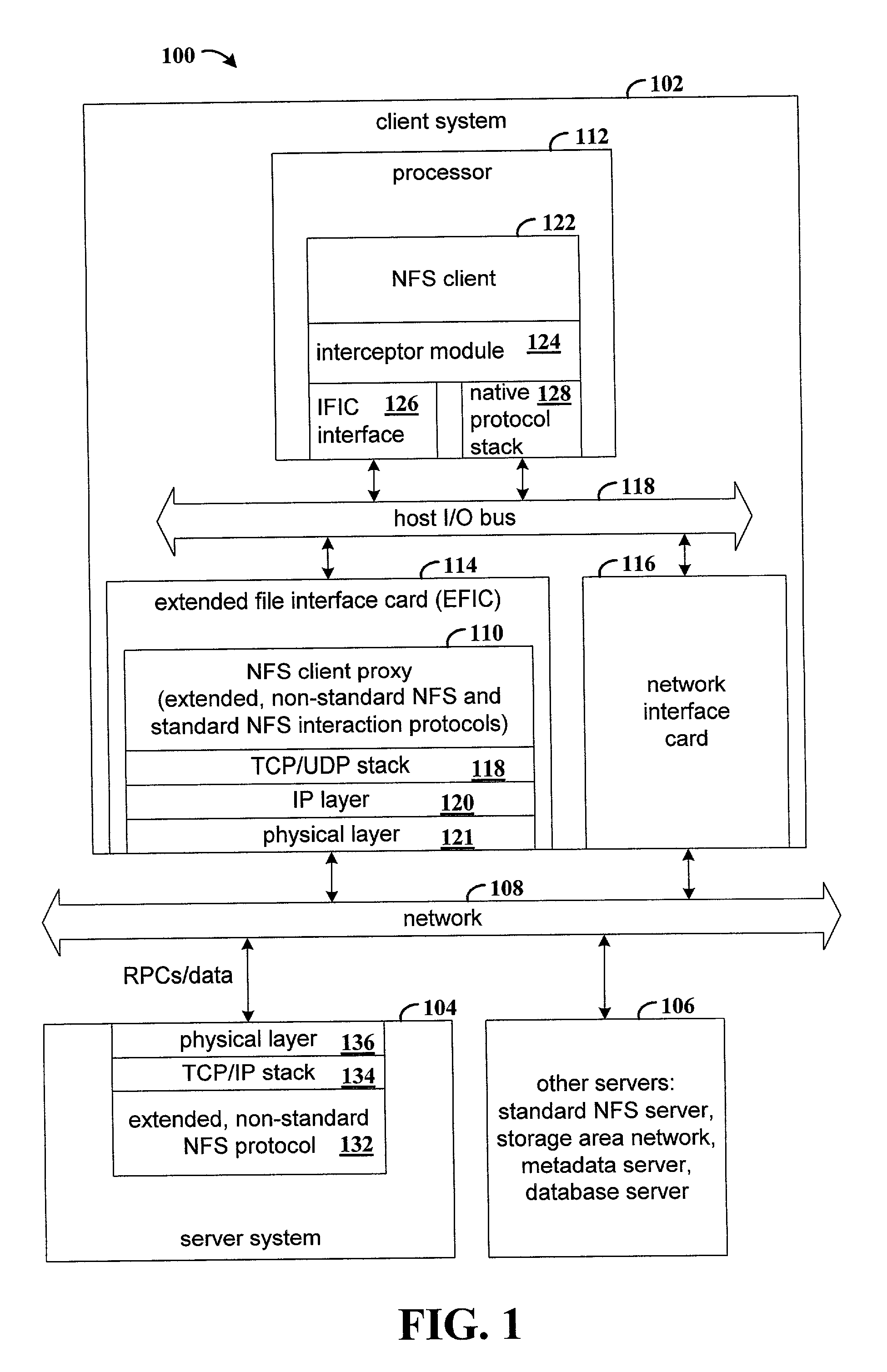
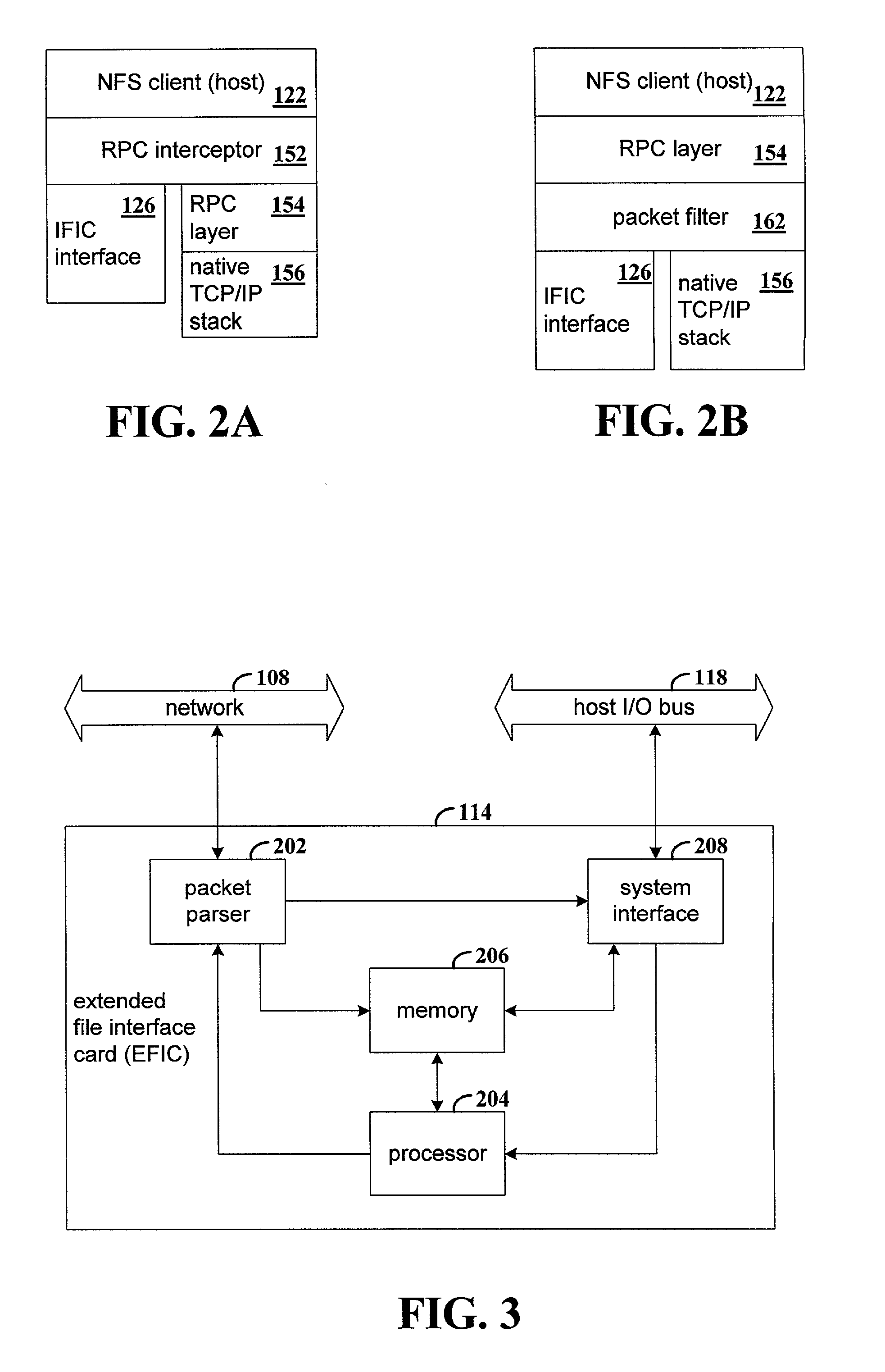
Extending a standard-based remote file access protocol and maintaining compatibility with a standard protocol stack
InactiveUS7171494B2Multiple digital computer combinationsSecuring communicationOperational systemProcedure calls
Apparatus and method for extending a standard-based remote file access protocol and maintaining compatibility with the standard protocol stack. Network file system (NFS) remote procedure calls (RPCs) that are submitted by an NFS client application are intercepted in a manner that is transparent to the client operating system. The intercepted NFS-RPCs are sent to a file interface card. The file interface card includes a processor that executes code that implements the standard NFS-RPC protocol, along with extensions to the standard NFS-RPC protocol. Non-NFS RPCs are sent to a conventional network interface card for processing.
Owner:HEWLETT PACKARD DEV CO LP
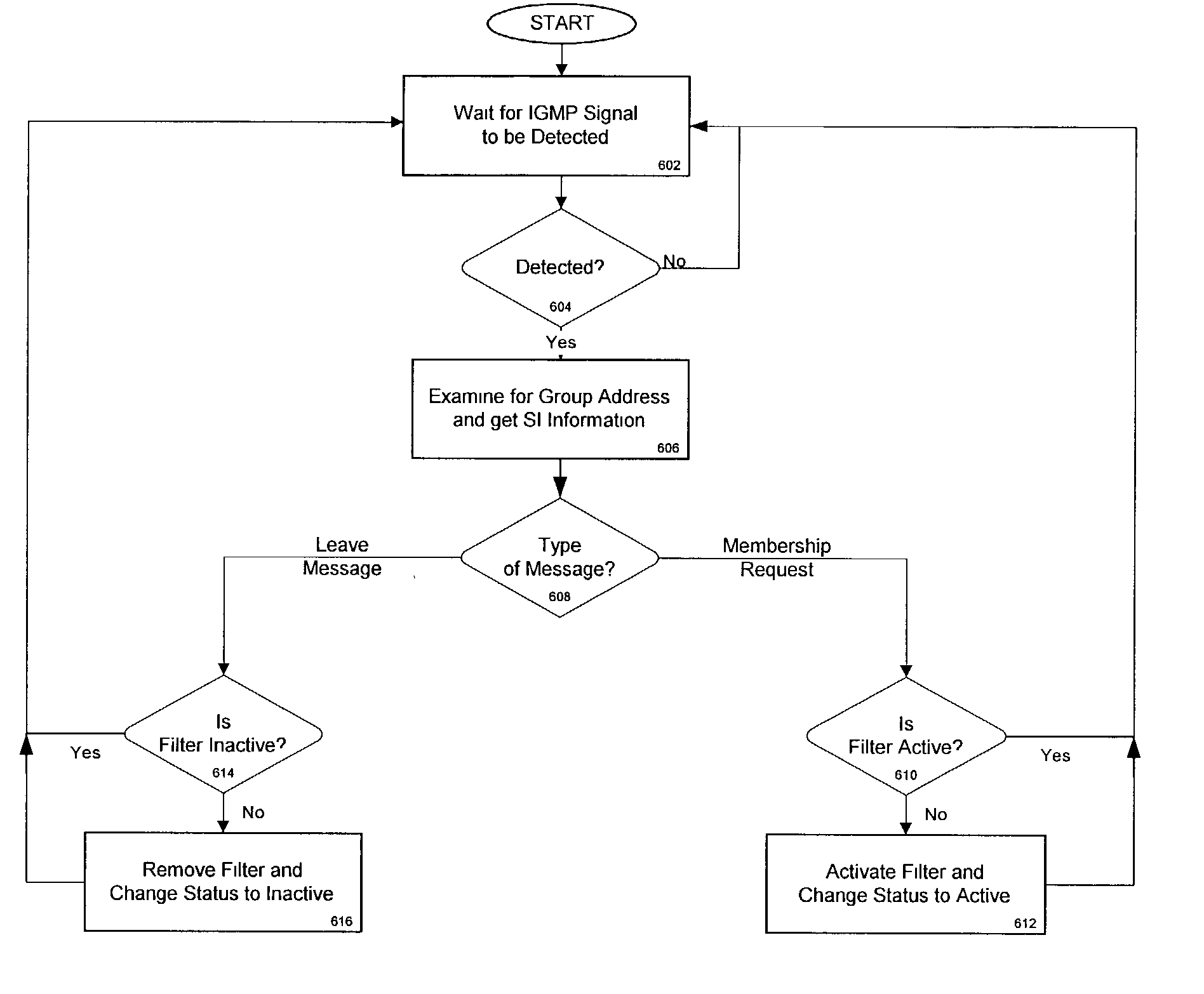
Event driven filter monitoring for IP multicast services
InactiveUS20050120378A1Special service provision for substationBroadcast transmission systemsProcedure callsIP multicast
Event driven methods for implementing or removing a filter used in receiving a multicast transmission are disclosed. An exemplary method for implementing a filter includes: detecting a message, such as an IPv6 MLD message, wherein the message comprises an address of a multicast group and a request to join the multicast group to receive a multicast transmission; in response to detecting the message, determining a filter parameter (e.g., a PID number and / or MAC address) needed to receive the multicast transmission; and implementing the filter parameter to receive the multicast transmission. Alternative methods wherein filter implementation or removal is based on the detection of direct procedure calls, such as a Setsockopt call, are also disclosed.
Owner:WSOU INVESTMENTS LLC
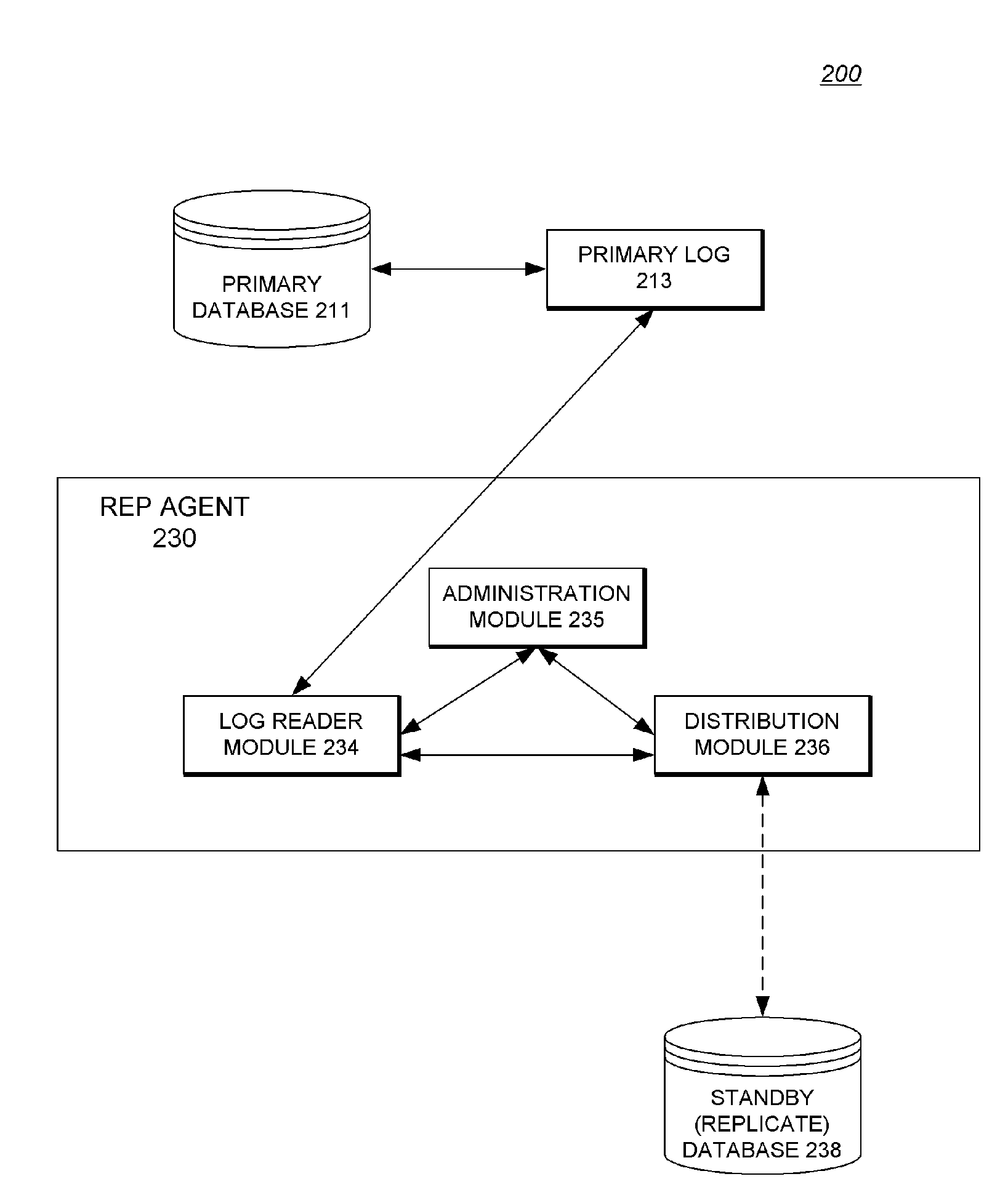
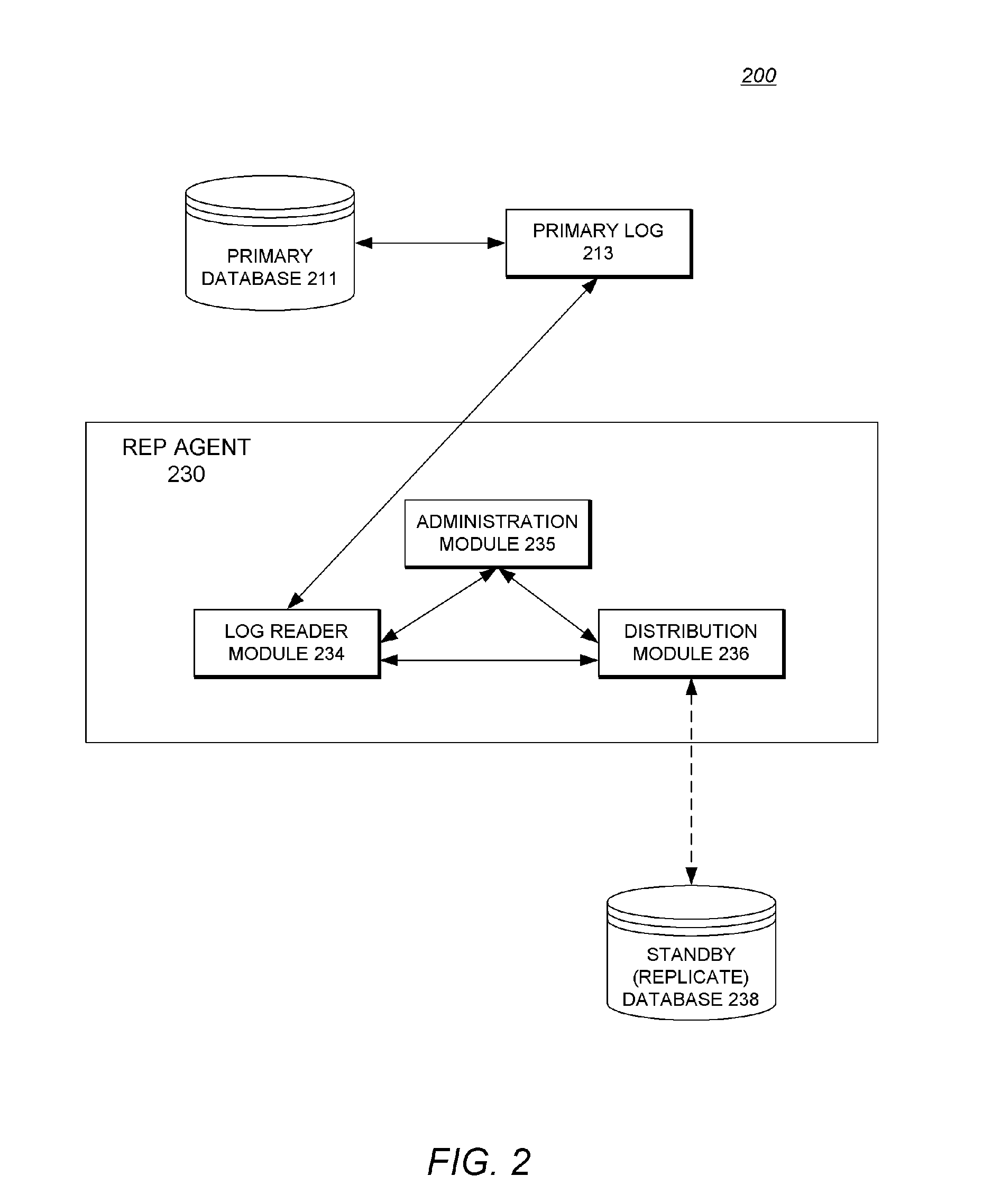
Replication System with Methodology for Replicating Stored Procedure Calls
ActiveUS20080034014A1Digital data processing detailsDatabase distribution/replicationProcedure callsData recording
A replication system with methodology for replicating stored procedure calls is described. In one embodiment, for example, in a database system without support for logging stored procedure invocations, a method of the present invention is described for replicating invocation of a stored procedure from a primary database to a replicate database, the method comprises steps of: inserting table data into the primary database for storing information sufficiently characterizing the procedure's invocation to allow its replication, the table data being logged to a log file; reading the log file, for determining changes to apply to the replicate database for replicating the procedure's invocation; and reconstructing the procedure's invocation at the replicate database based on the determined changes.
Owner:SYBASE INC
Symmetrical multiprocessing in multiprocessor systems
ActiveUS7219121B2Improve performanceProgram initiation/switchingResource allocationData streamProcedure calls
A new method and framework for scheduling receive-side processing of data streams received from a remote requesting client by a multiprocessor system computer is disclosed. The method receives data packets from the remote requesting client via a network and, for each data packet, applies a mapping algorithm to portions of the received data packet yielding a mapping value. The method further applies the map value to a processor selection policy to identify a processor in the multiprocessor system as a selected processor to perform receive-side processing of the data packet. The method queues the received data packet for processing by the selected processor and invokes a procedure call to initiate processing of the data packet.
Owner:MICROSOFT TECH LICENSING LLC
Receive side scaling with cryptographically secure hashing
InactiveUS7765405B2User identity/authority verificationUnauthorized memory use protectionData streamHash function
A new method and framework for scheduling receive-side processing of data streams received from a remote requesting client by a multiprocessor system computer is disclosed. The method receives data packets from the remote requesting client via a network and, for each data packet, applies a cryptographically secure hashing function to portions of the received data packet yielding a hash value. The method further applies the hash value to a processor selection policy to identify a processor in the multiprocessor system as a selected processor to perform receive-side processing of the data packet. The method queues the received data packet for processing by the selected processor and invokes a procedure call to initiate processing of the data packet.
Owner:MICROSOFT TECH LICENSING LLC
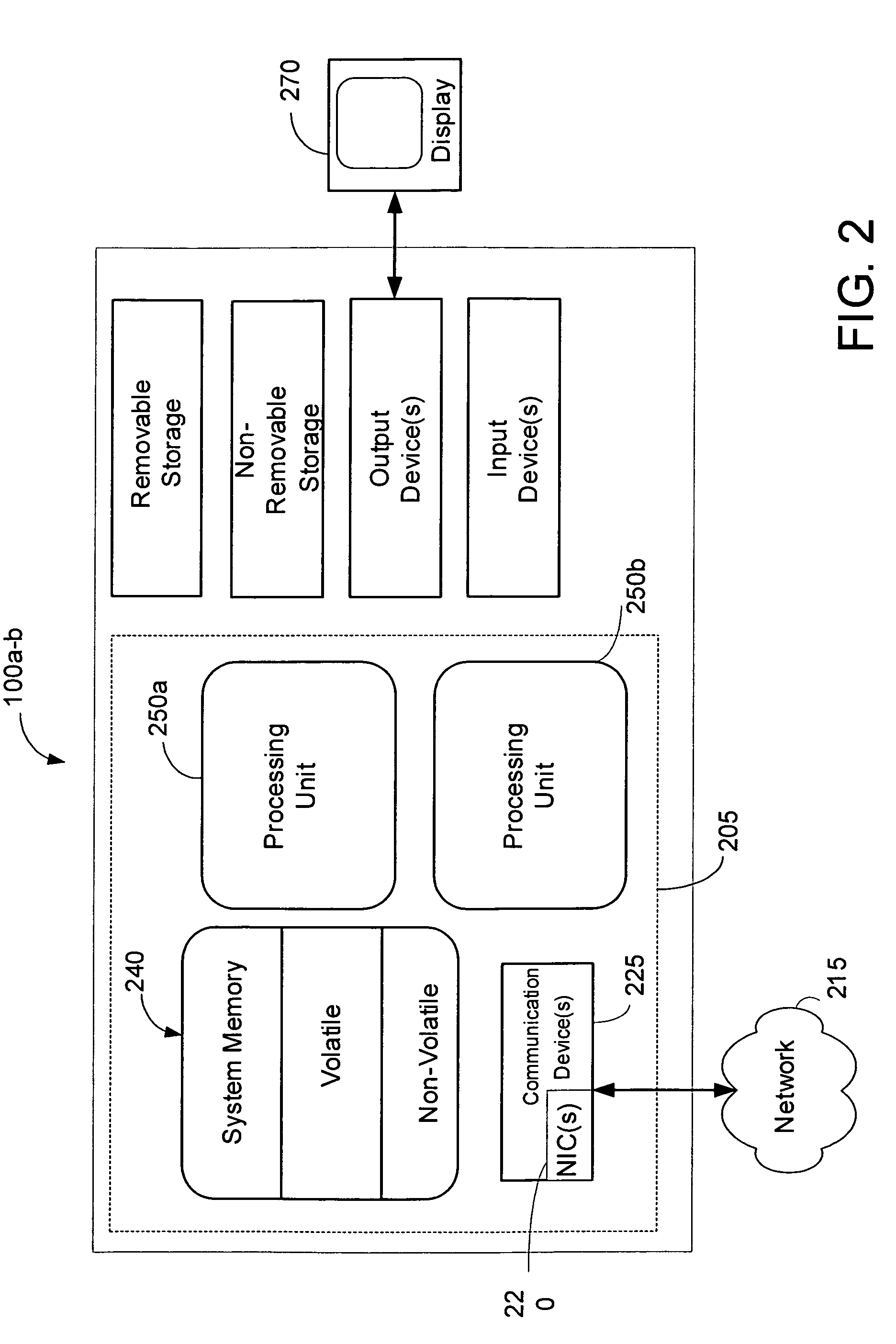
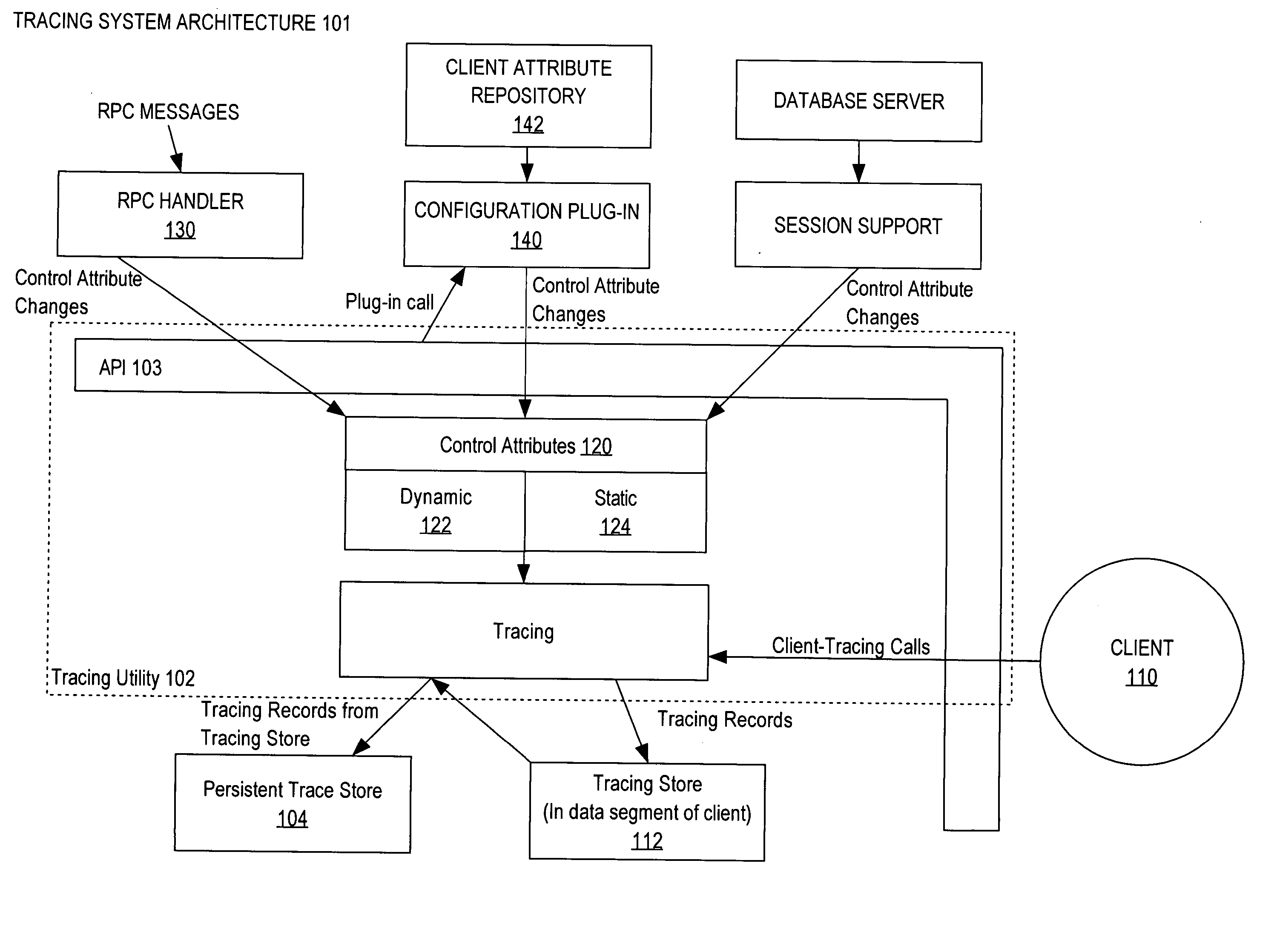
Lightweight highly available infrastructure to trace program execution
ActiveUS20070006165A1Error detection/correctionSpecific program execution arrangementsGranularityApplication programming interface
A portable tracing utility provides trace configuration, trace instrumentation and trace management functionality for single or multithreaded programs. Through various application programming interfaces (“APIs”) of the tracing utility, a client may control tracing behavior to setup in-memory data structures for storing trace records that record the program's history of execution or to alter the granularity of execution history being traced. The trace behavior can be modified during the life of a program by using the APIs, either dynamically when the program assumes certain states, or through remote procedure calls issued by, for example, an external interface. Programs are instrumented with these APIs to record the history of execution, which during execution of the program is stored in circular in-memory buffers.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com