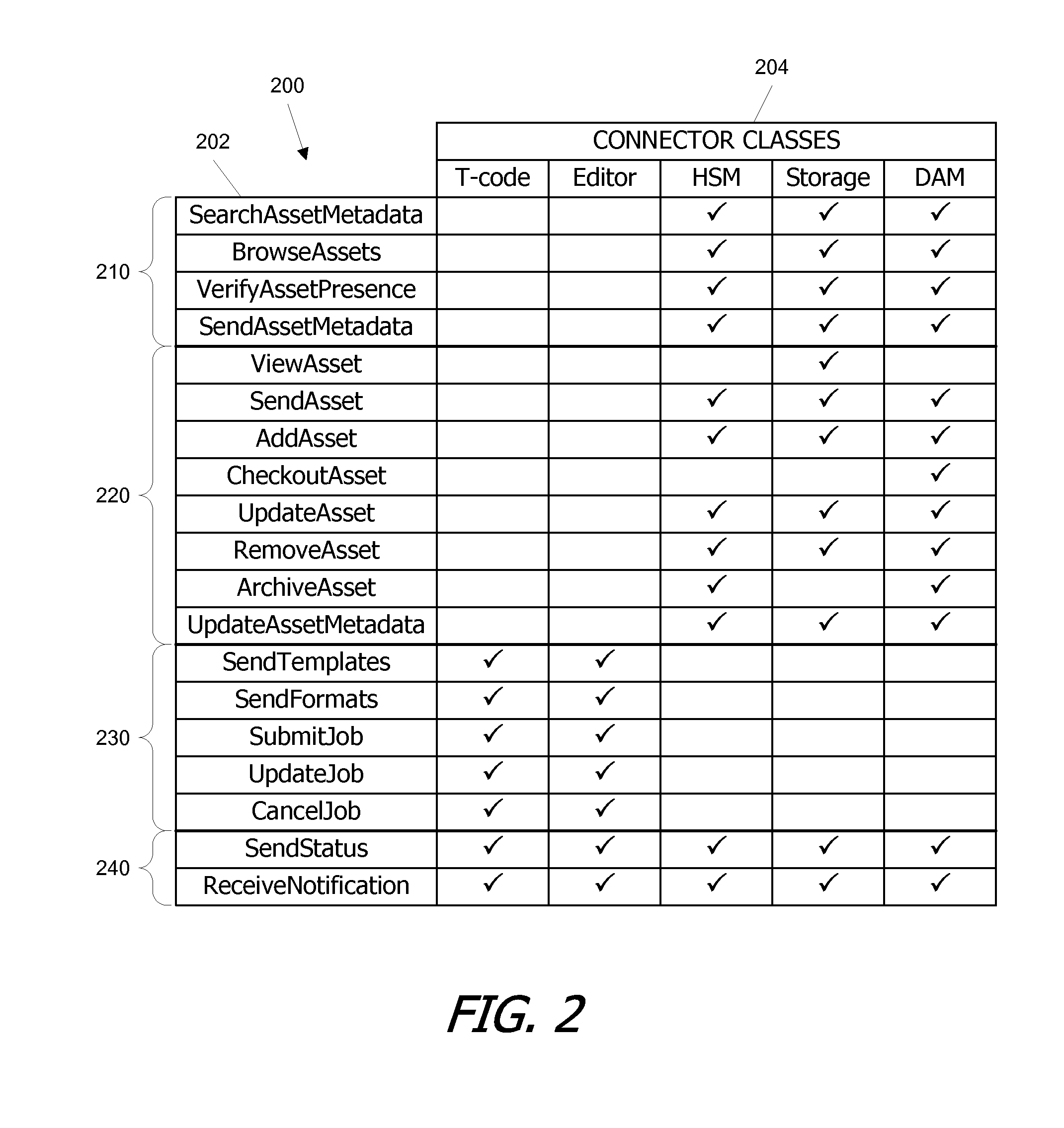
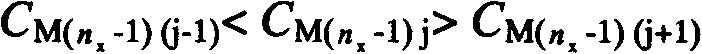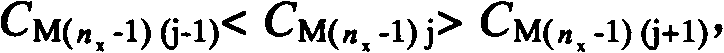Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
72 results about "Defined Procedure" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
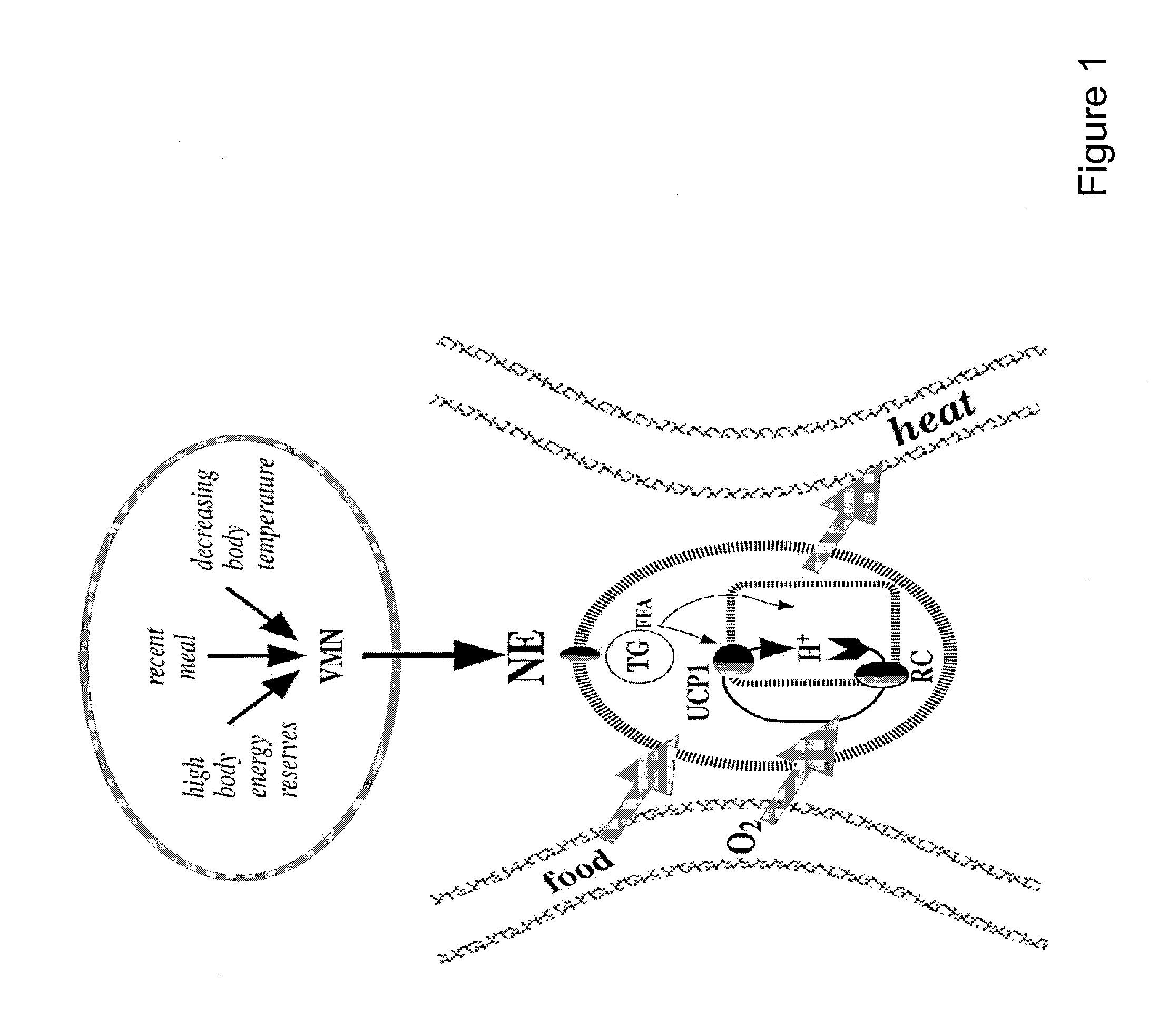
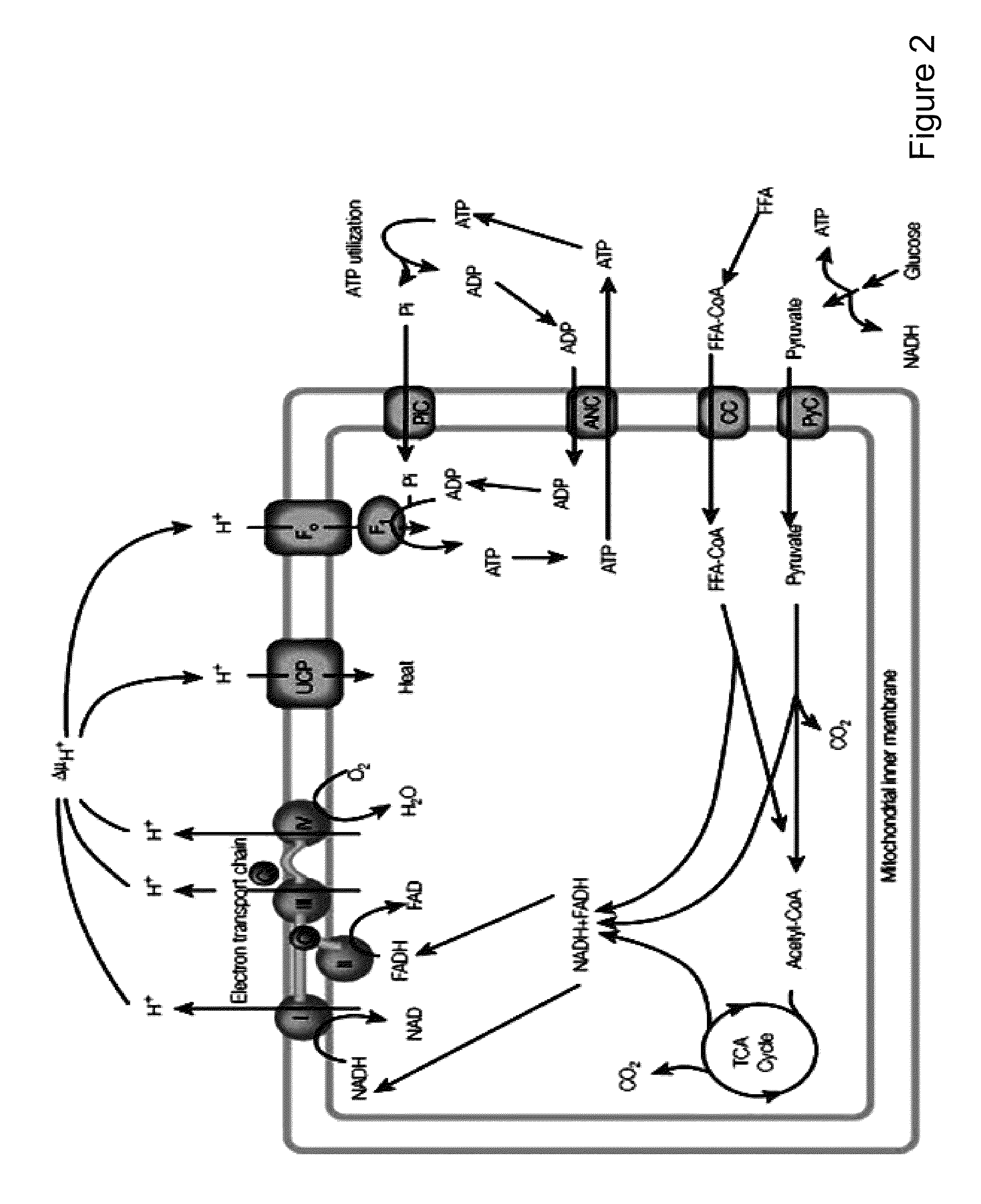
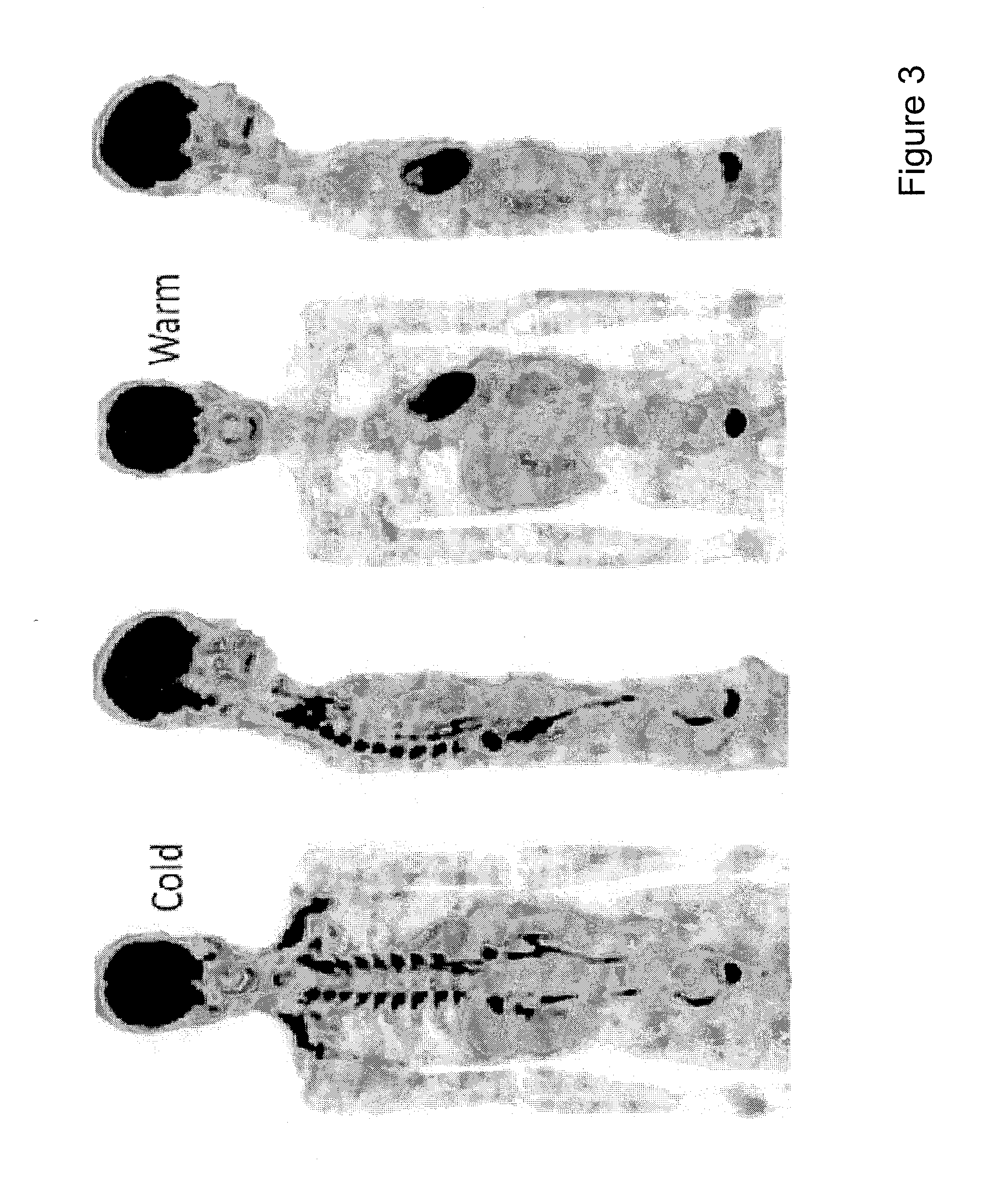
An activity defined at a global library level that is an action whose immediate and primary intention is the alteration of the physical condition of the study subject or experimental unit. EXAMPLE(S): Procedures may involve the disruption of some body surface (e.g. an incision in a surgical procedure). Conservative procedures such as reduction of a luxated joint, including physiotherapy such as chiropractic treatment, massage, balneotherapy, acupuncture, shiatsu.
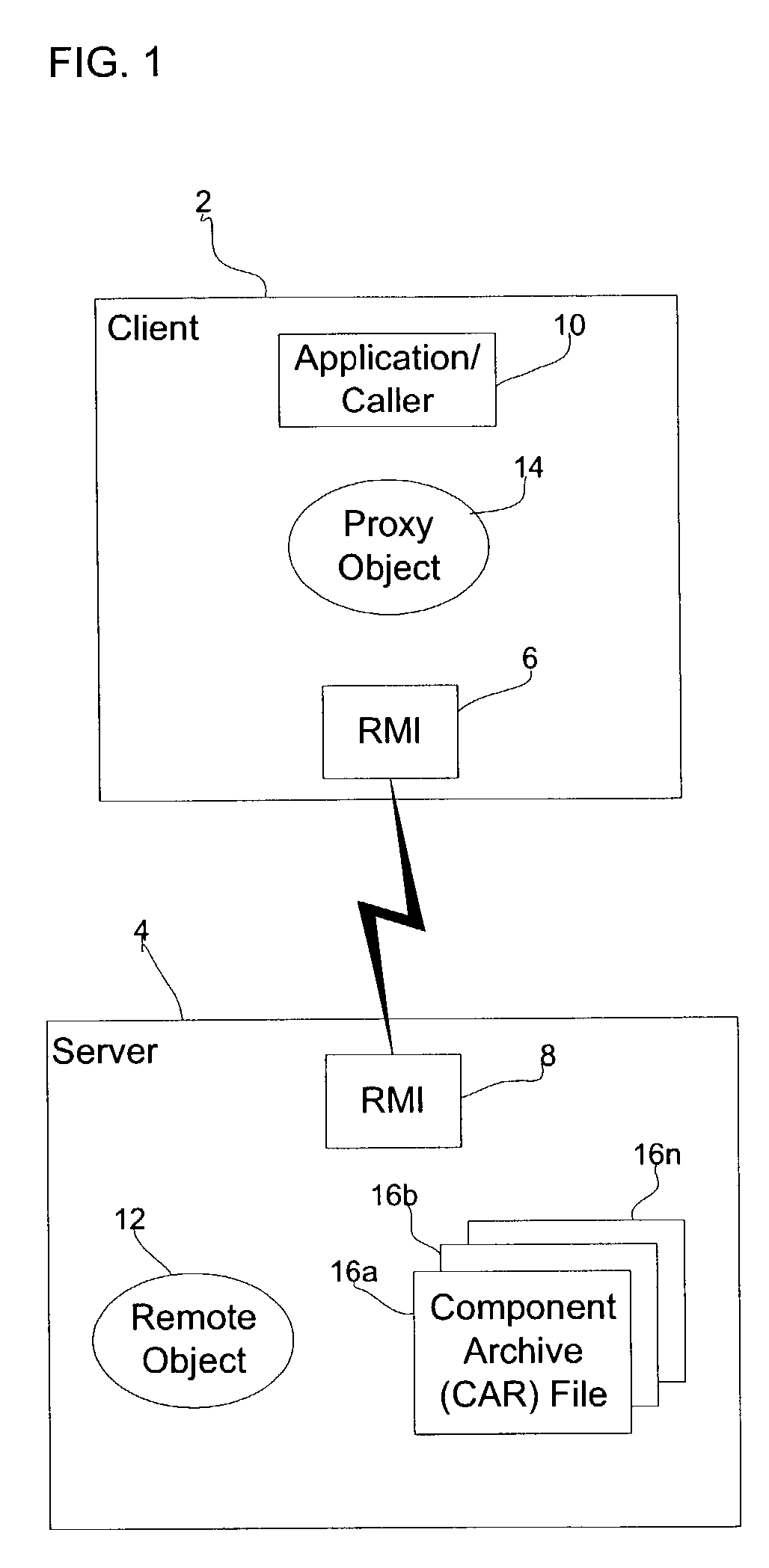
Methods of activating a melanocortin-4 receptor pathway in obese subjects
ActiveUS8476227B2Induce weight lossOrganic active ingredientsPeptide/protein ingredientsDefined ProcedureMC4 Receptor
Methods and therapeutics are provided for treating metabolic disorders by activation of melanocortin signaling pathways. Generally, the methods and therapeutics can induce activation of melanocortin receptor signaling to increase energy expenditure and induce weight loss. In one embodiment, a method for performing a diagnostic procedure can be chosen, energy expenditure then assess in light of the diagnostic procedure and a definitive procedure(s) can be selected dependent on the outcome of the energy assessment. In another embodiment, a diagnostic procedure can be chosen to activate melanocortin receptor pathways, energy expenditure can be assessed and a definitive procedure(s) can be chosen that selectively and optimally activate melanocortin receptor pathways.
Owner:ETHICON ENDO SURGERY INC +1
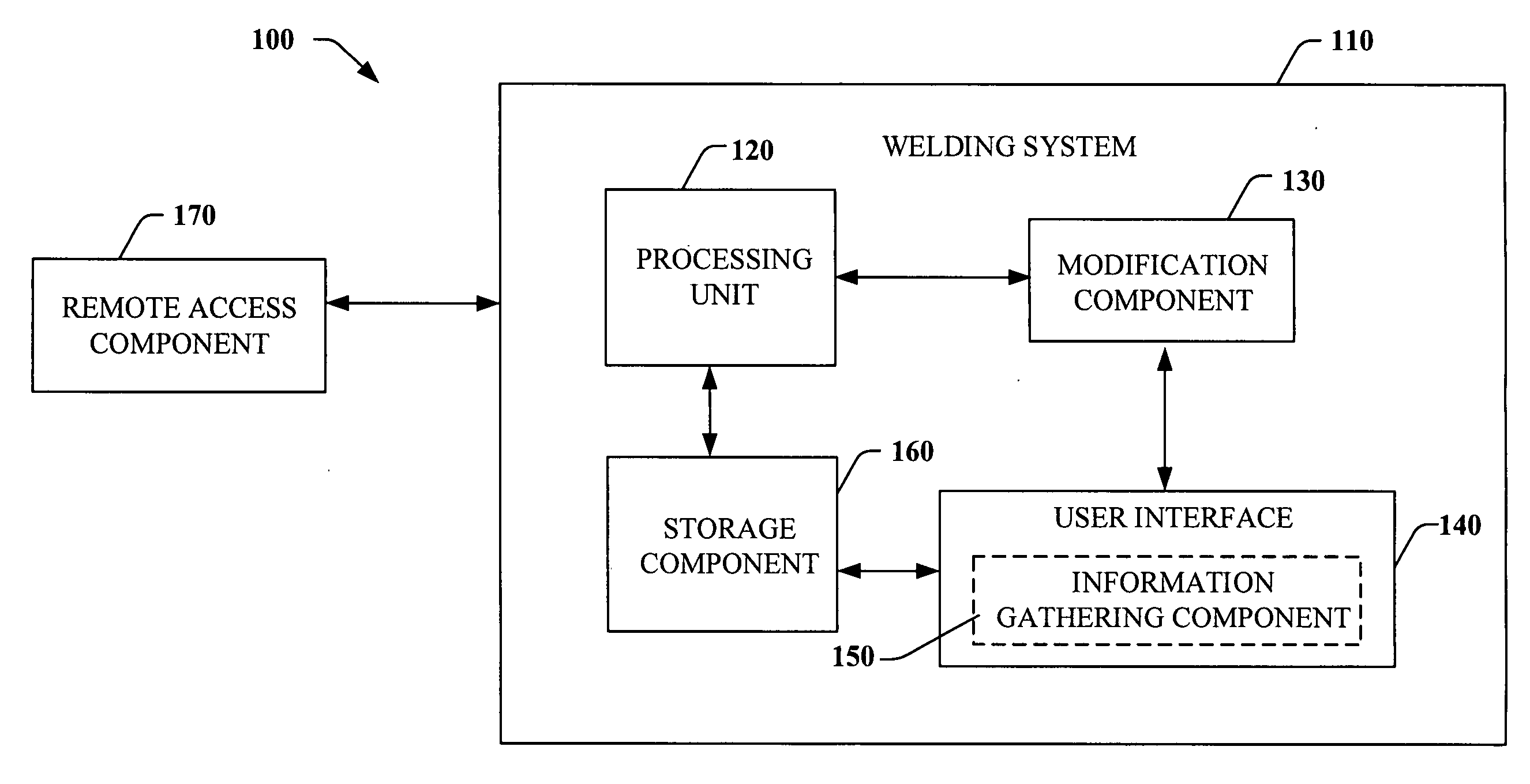
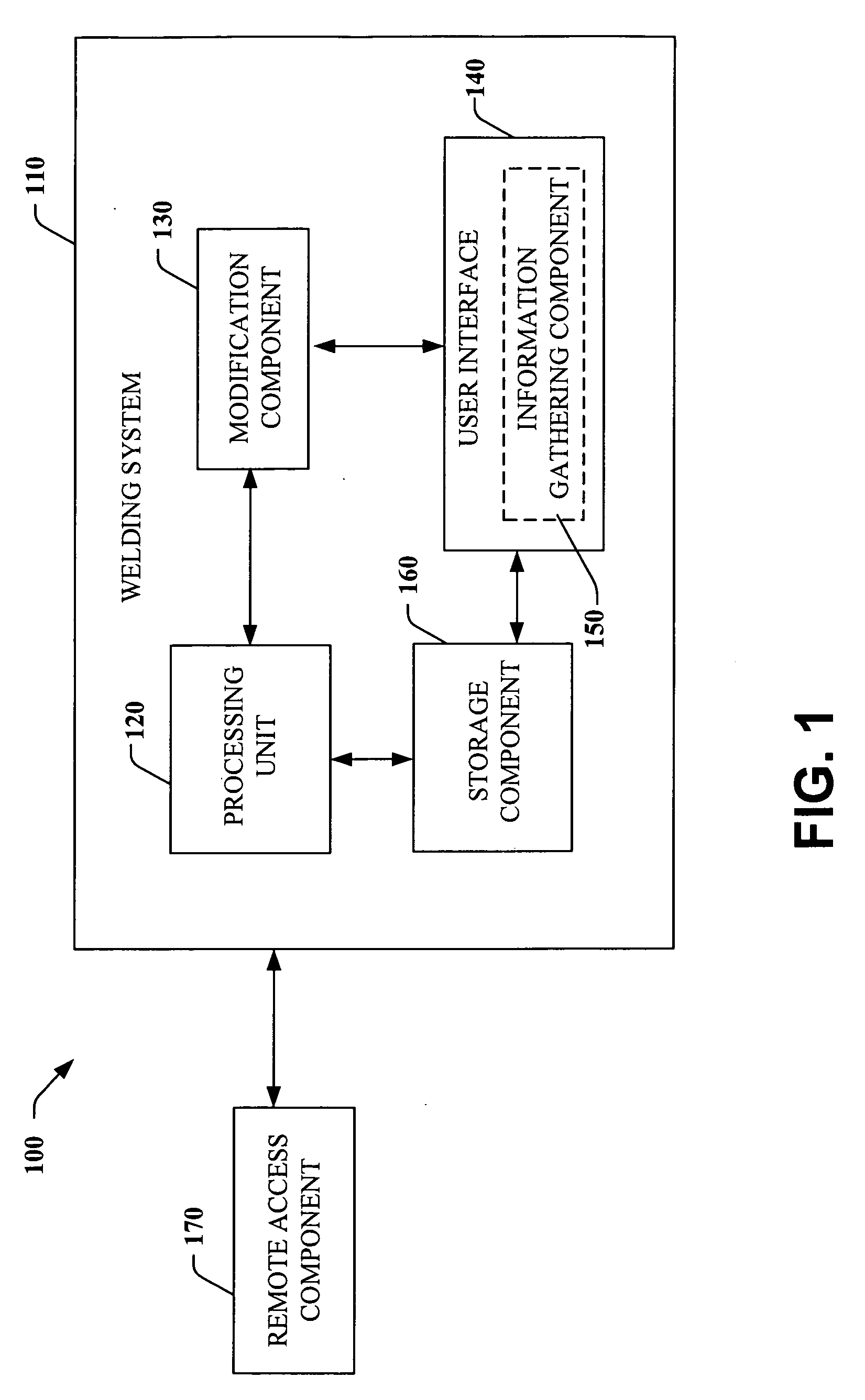
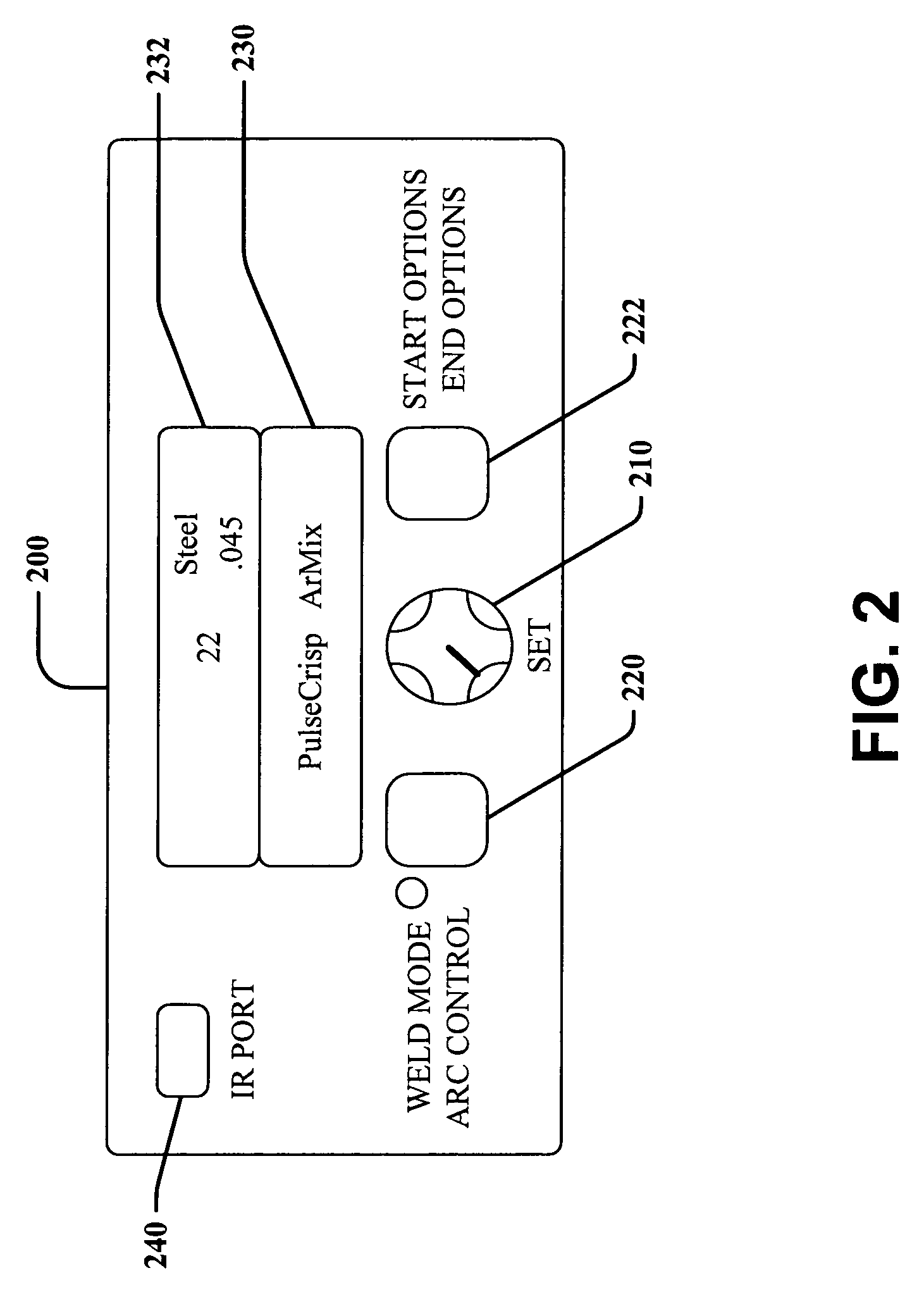
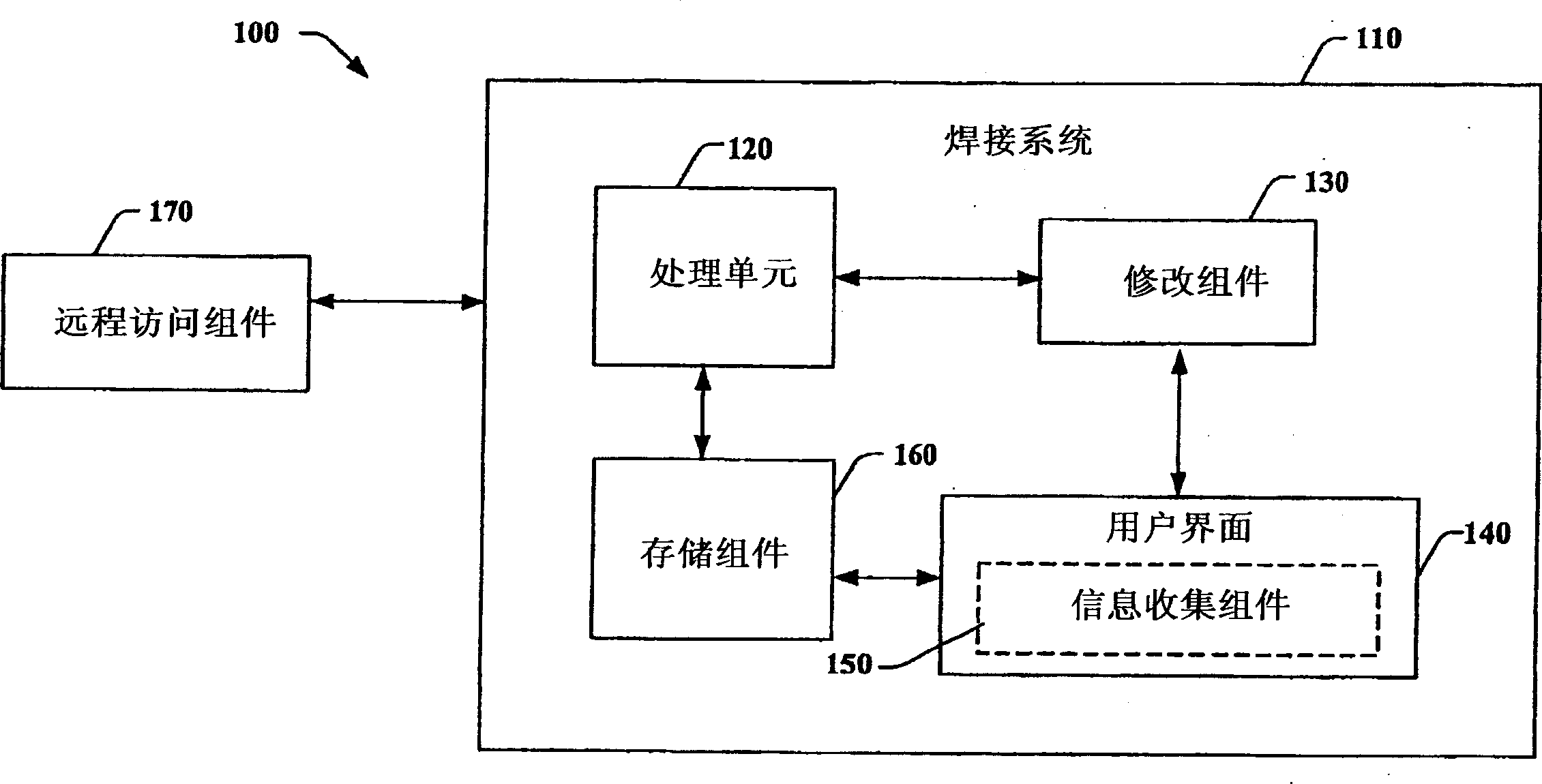
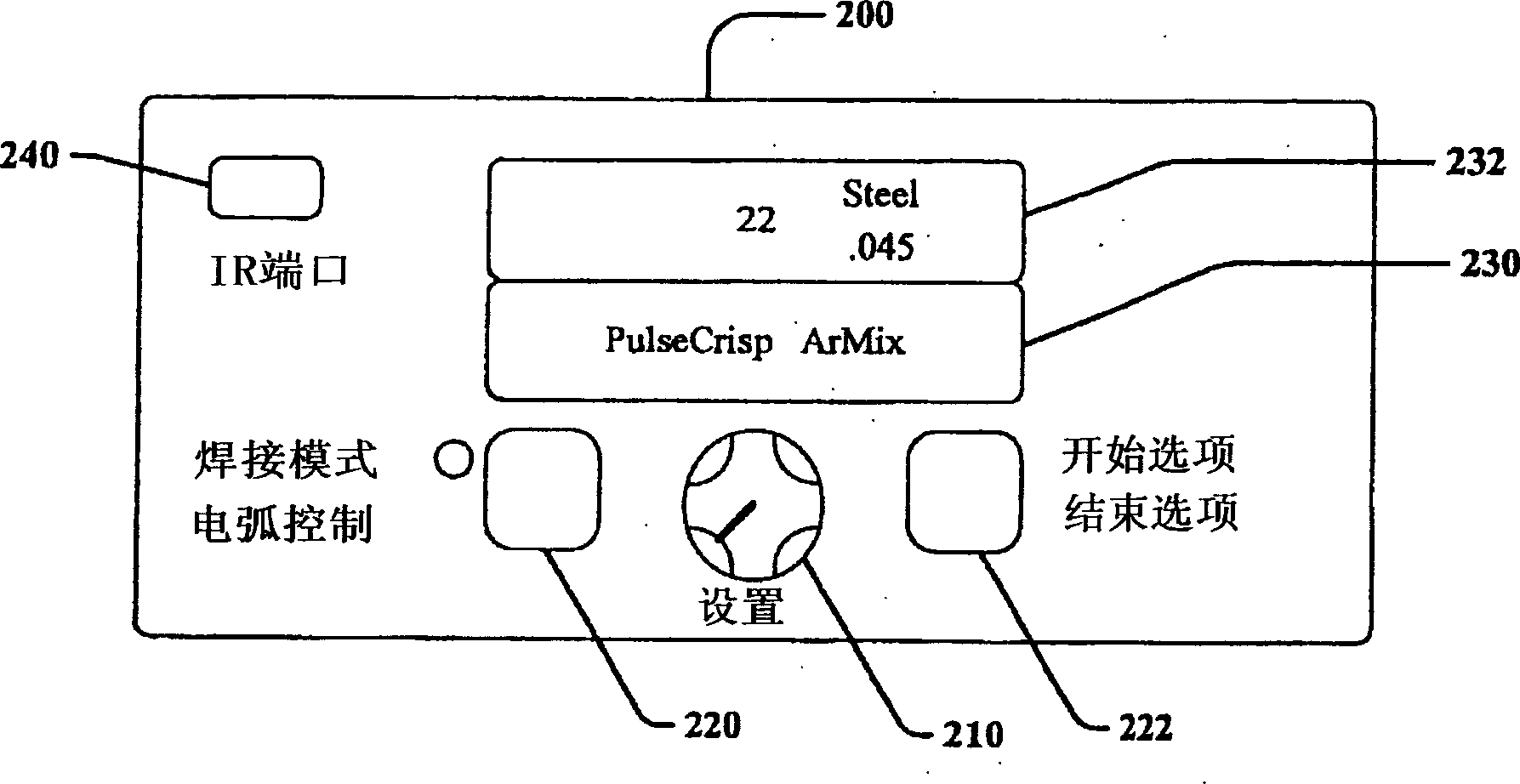
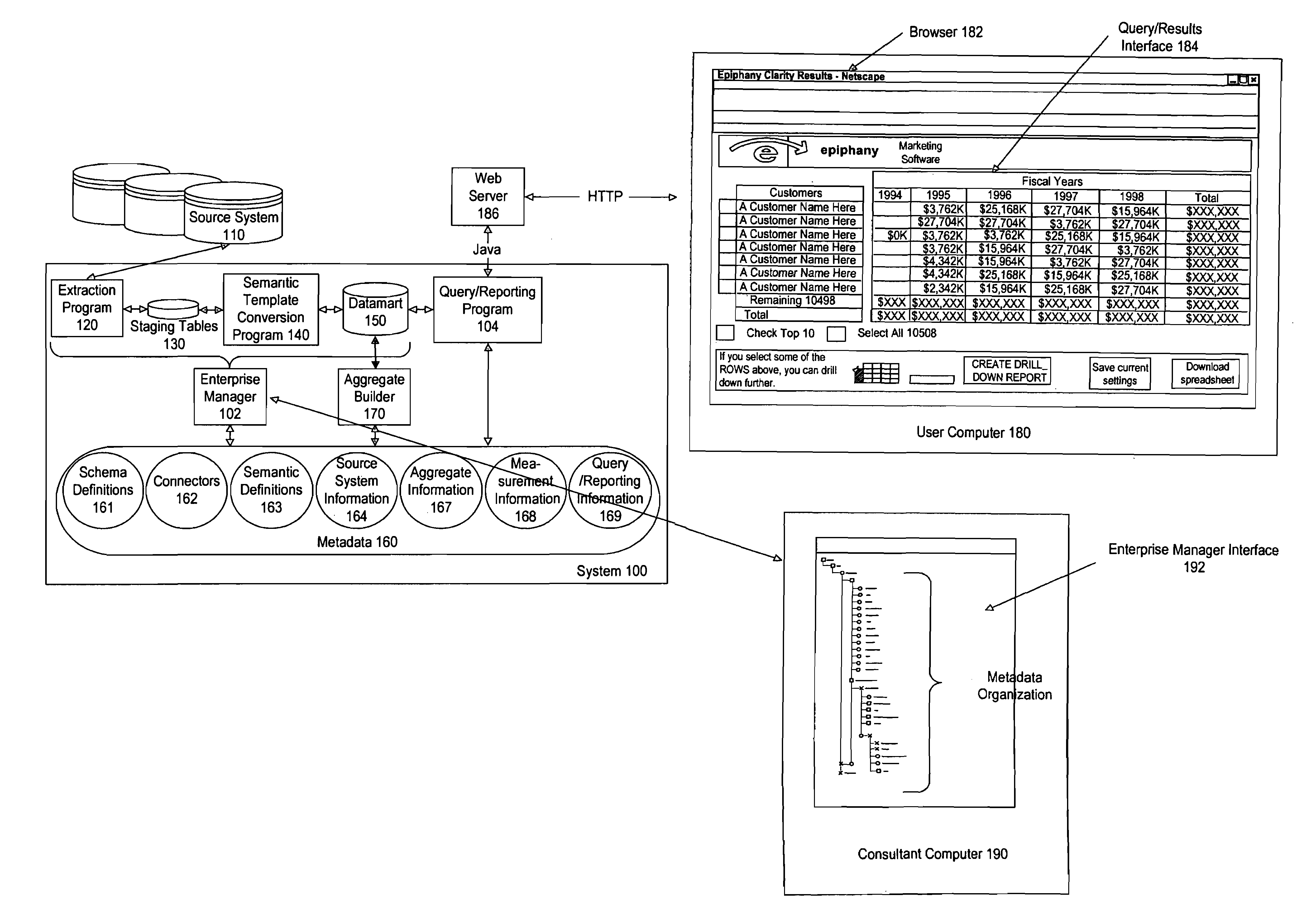
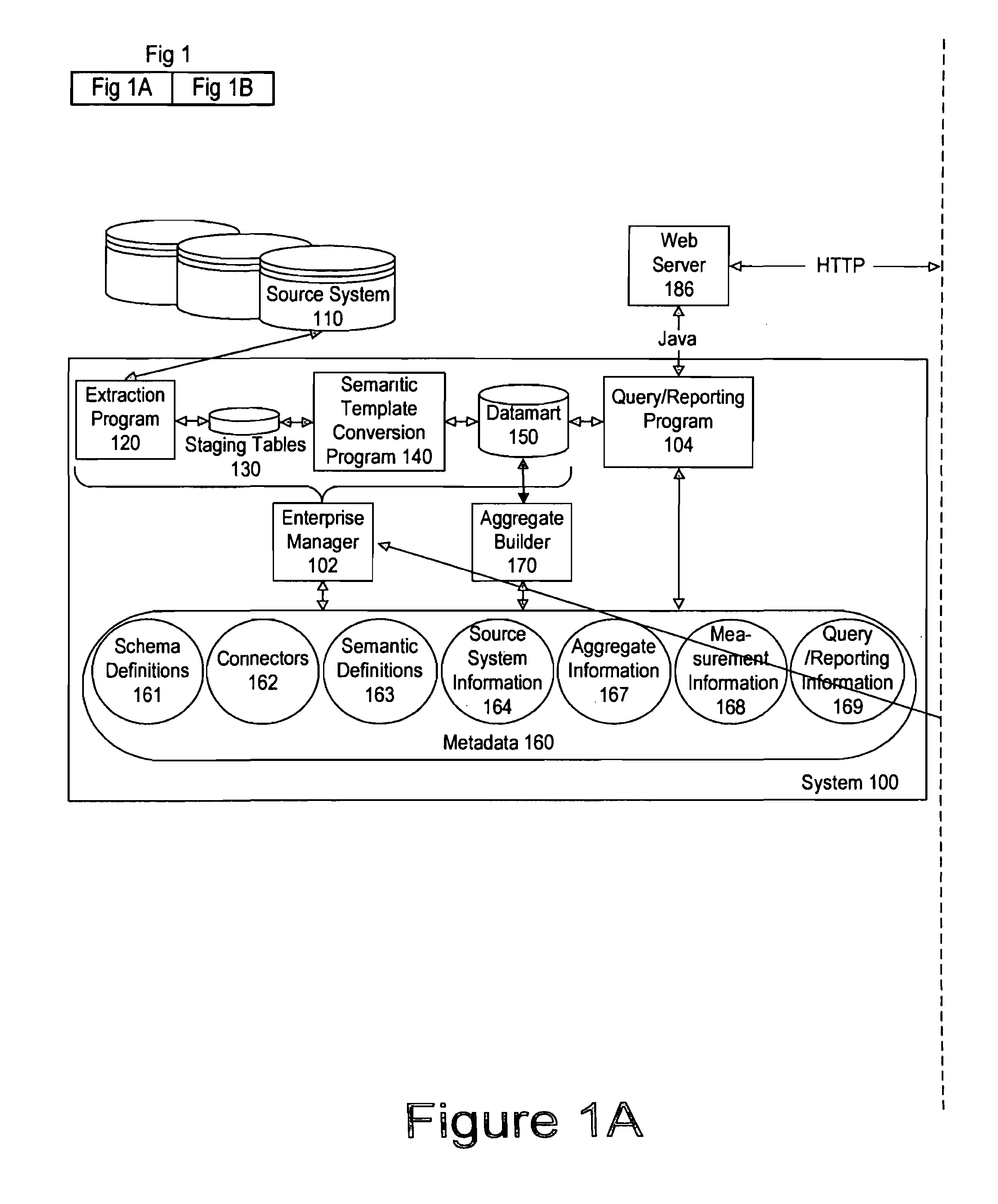
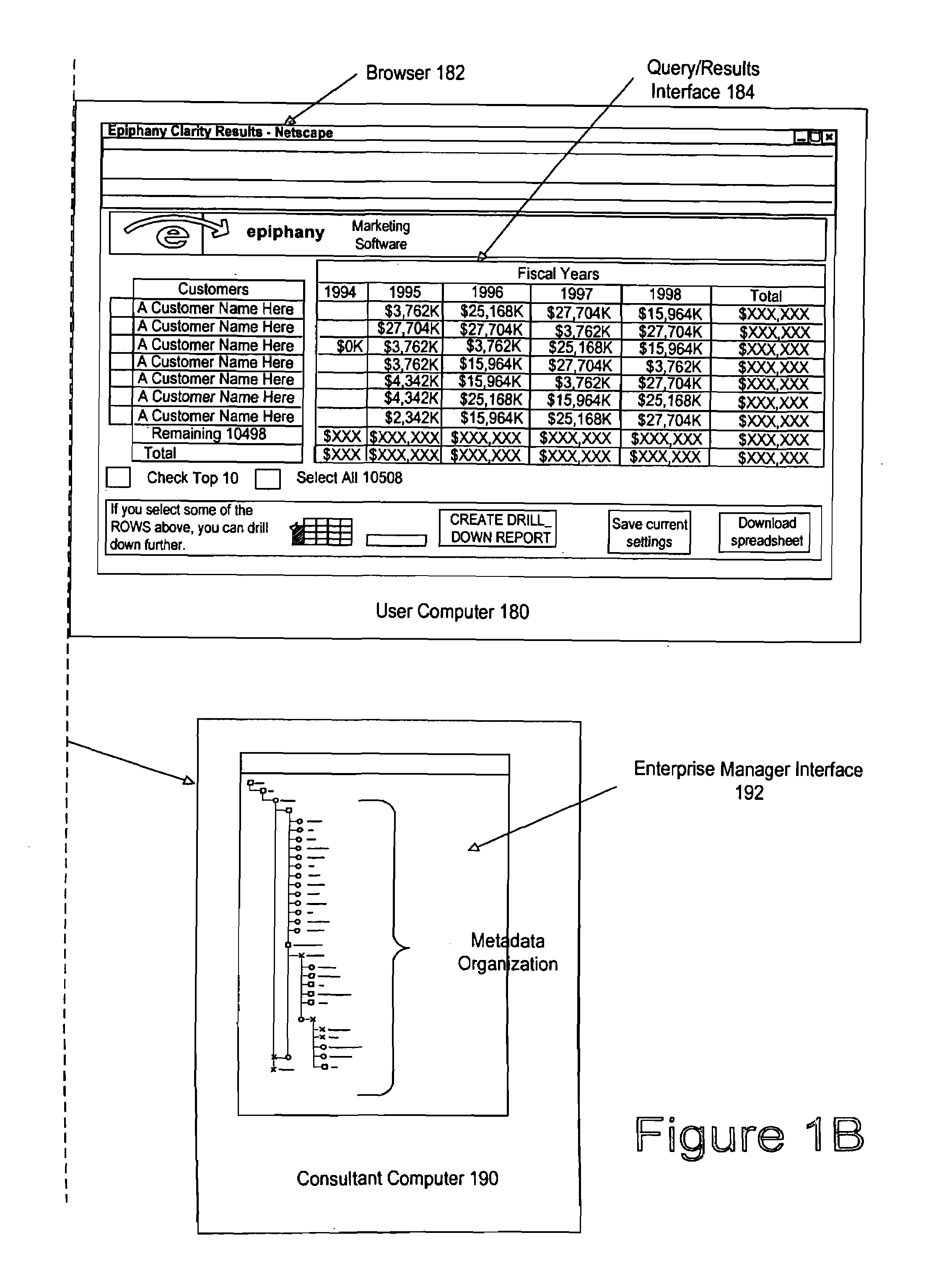
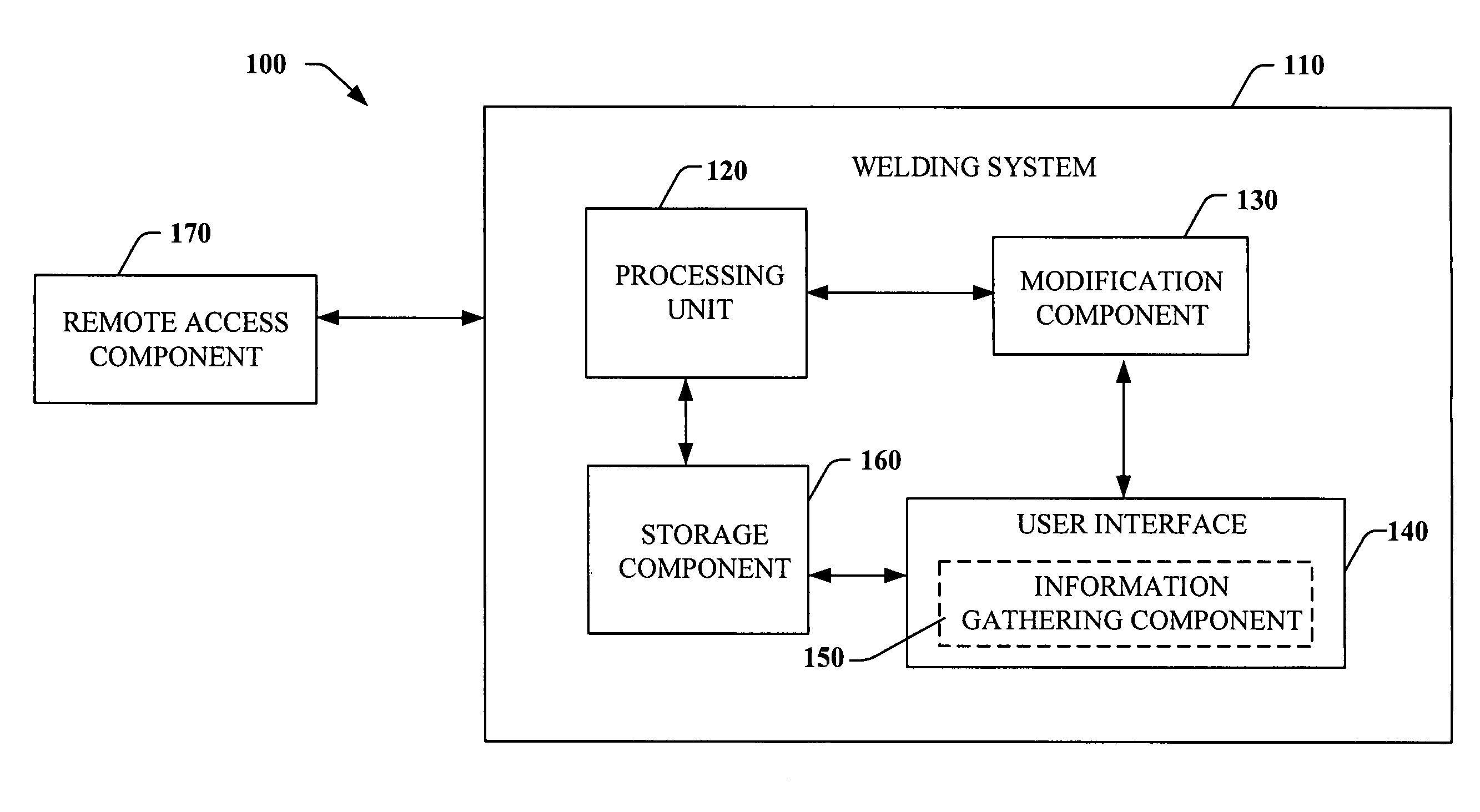
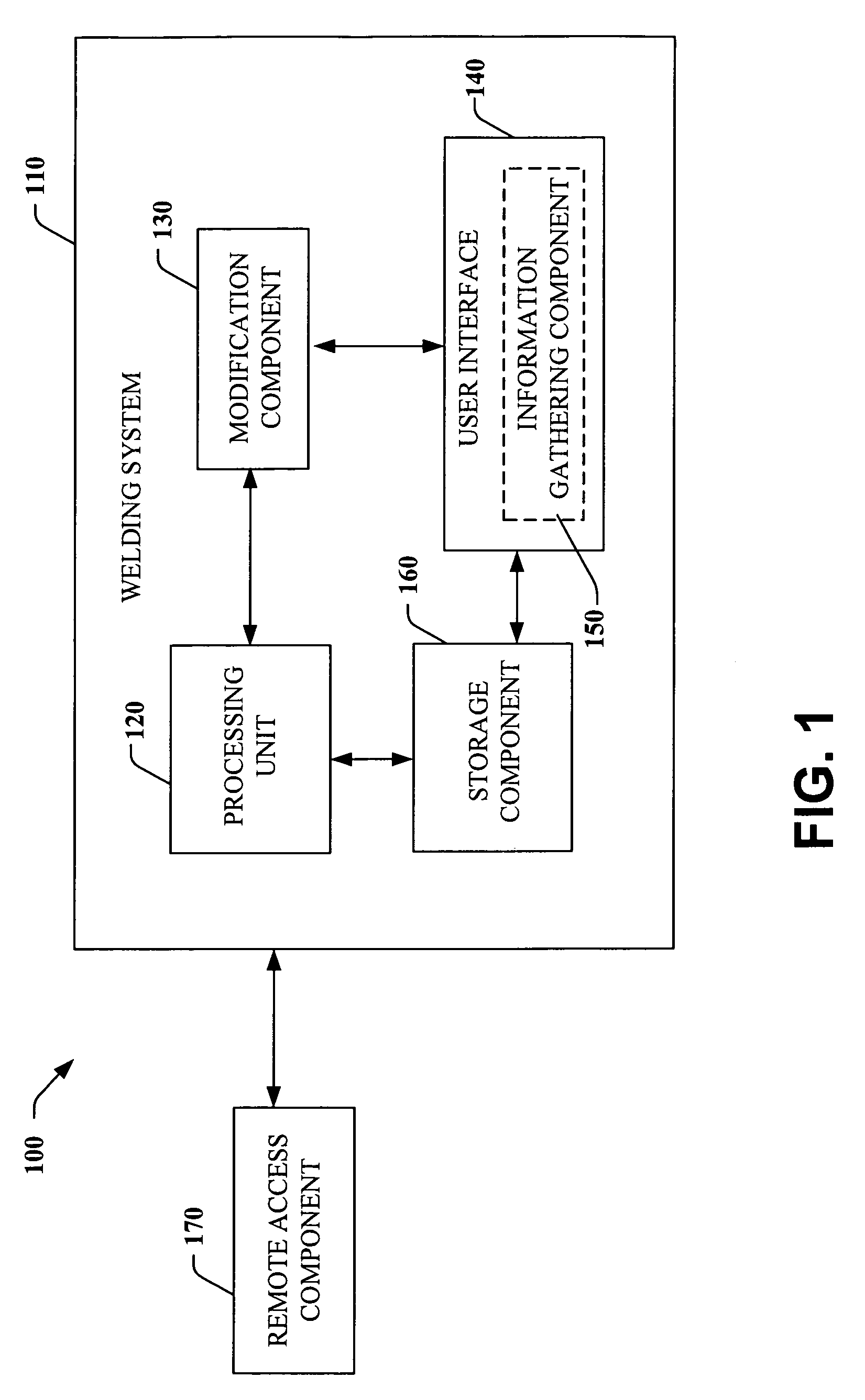
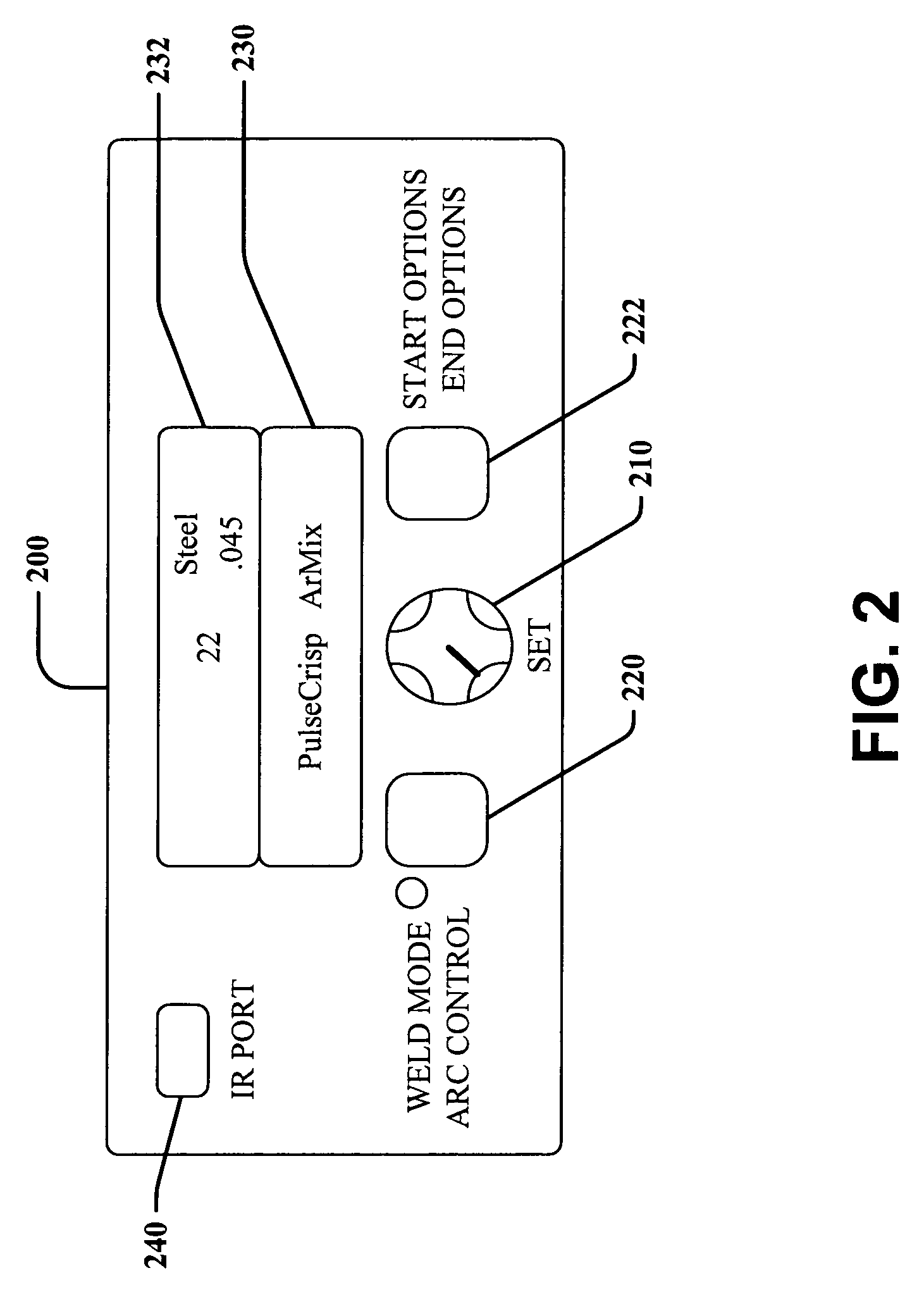
Comprehensive identification and designation of welding procedures
ActiveUS20060207980A1Easy selectionFacilitates namingElectric discharge heatingArc welding apparatusDefined ProcedureWaste management
System(s) and method(s) that facilitates comprehensive identification and designation of welding procedures. A configuration component facilitates configuring the welding system with respect to pre-defined procedures and / or parameters and facilitates naming of the configured welding system. A storage component that stores the configured welding system in a readily accessible memory location. A remote access component can facilitate remotely accessing the welding system, the configuration of the welding system alterable by way of the remote access component.
Owner:LINCOLN GLOBAL INC
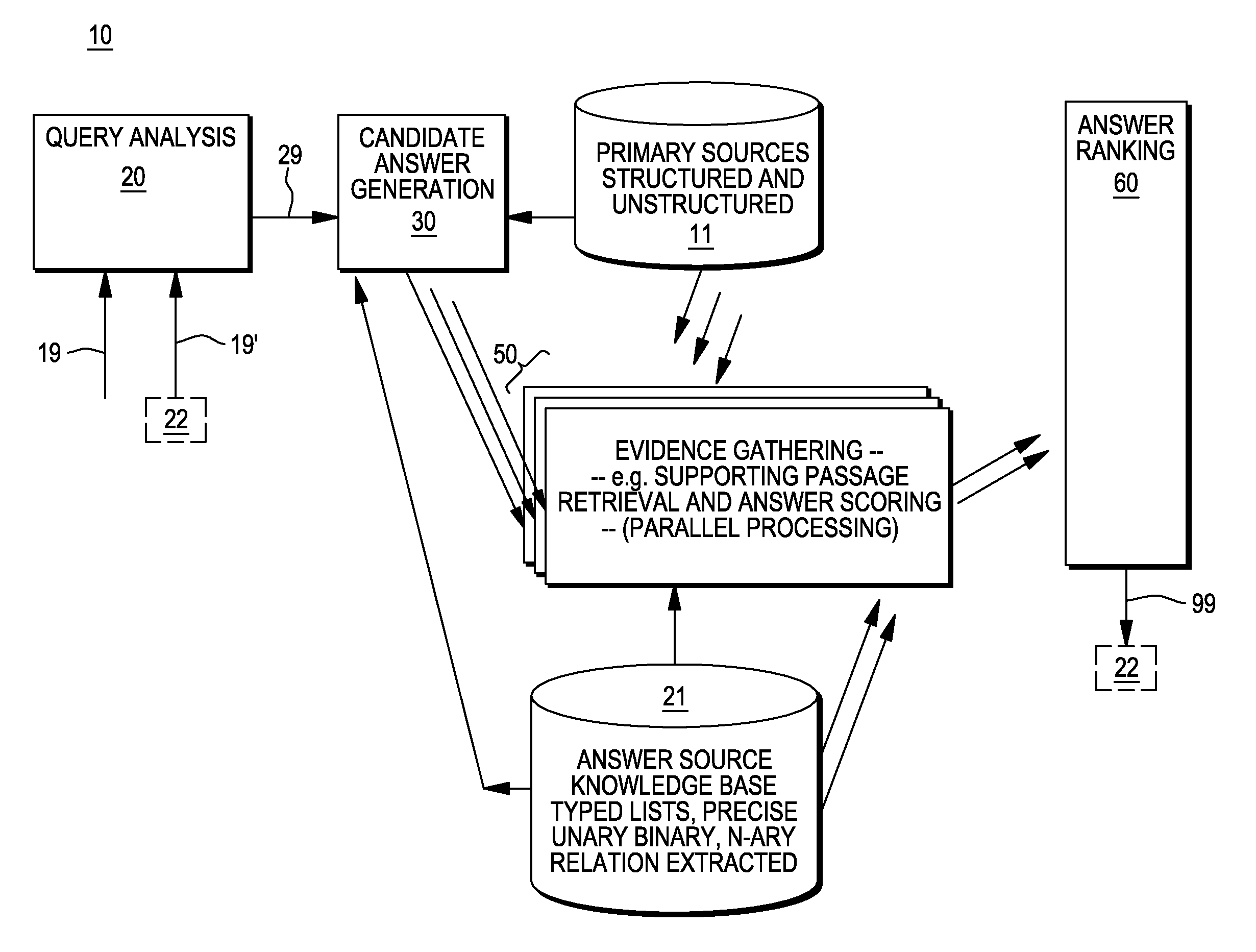
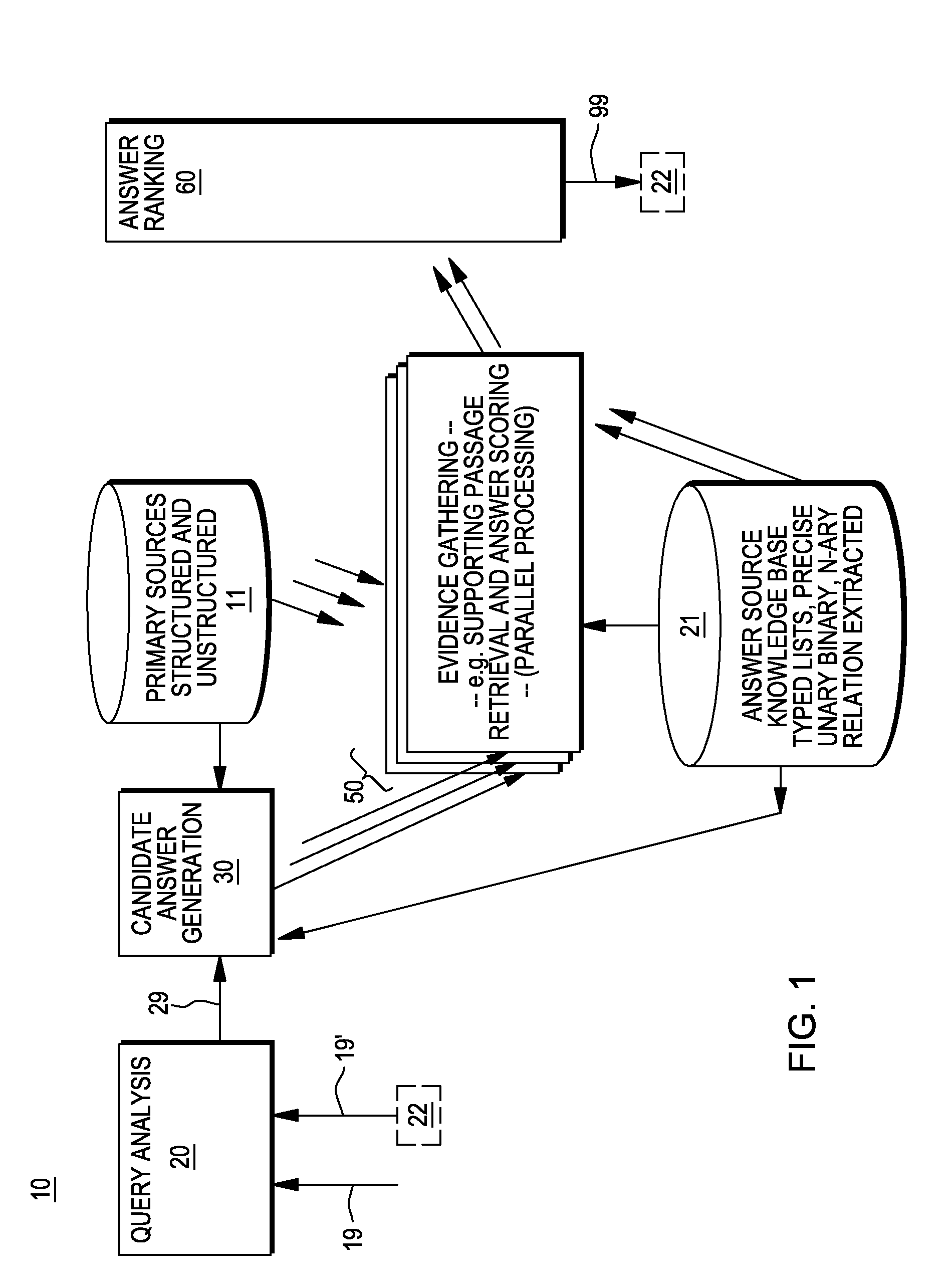
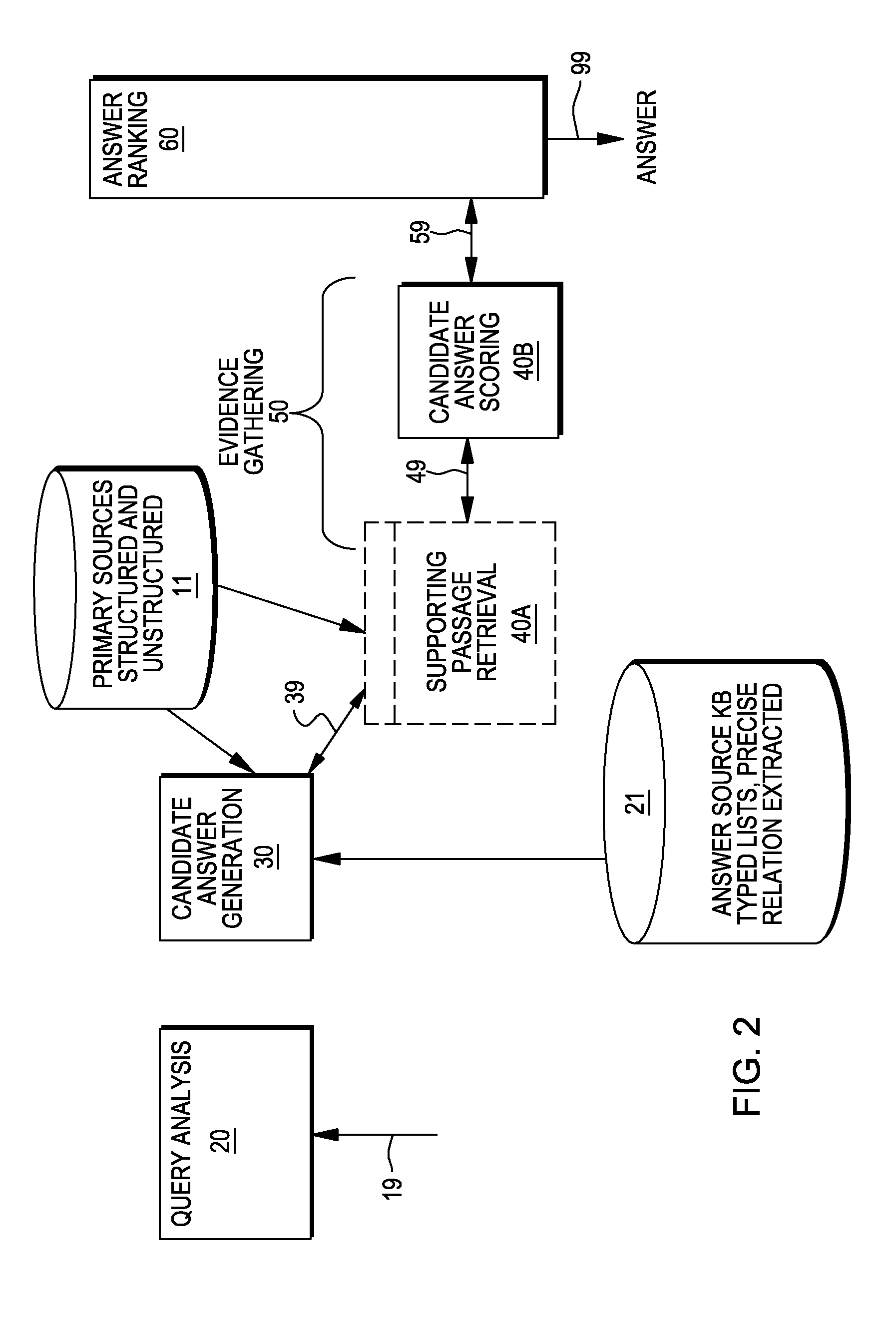
Providing answers to questions including assembling answers from multiple document segments
InactiveUS20120084293A1Digital data processing detailsComputer-assisted medical data acquisitionDefined ProcedureRanking
A method, system and computer program product for generating answers to questions. In one embodiment, the method comprises receiving an input query, identifying a plurality of candidate answers to the query; and for at least one of these candidate answers, identifying at least one proof of the answer. This proof includes a series of premises, and a multitude of documents are identified that include references to the premises. A set of these documents is selected that include references to all of the premises. This set of documents is used to generate one or more scores for the one of the candidate answers. A defined procedure is applied to the candidate answers to determine a ranking for the answers, and this includes using the one or more scores for the at least one of the candidate answers in the defined procedure to determine the ranking for this one candidate answer.
Owner:IBM CORP
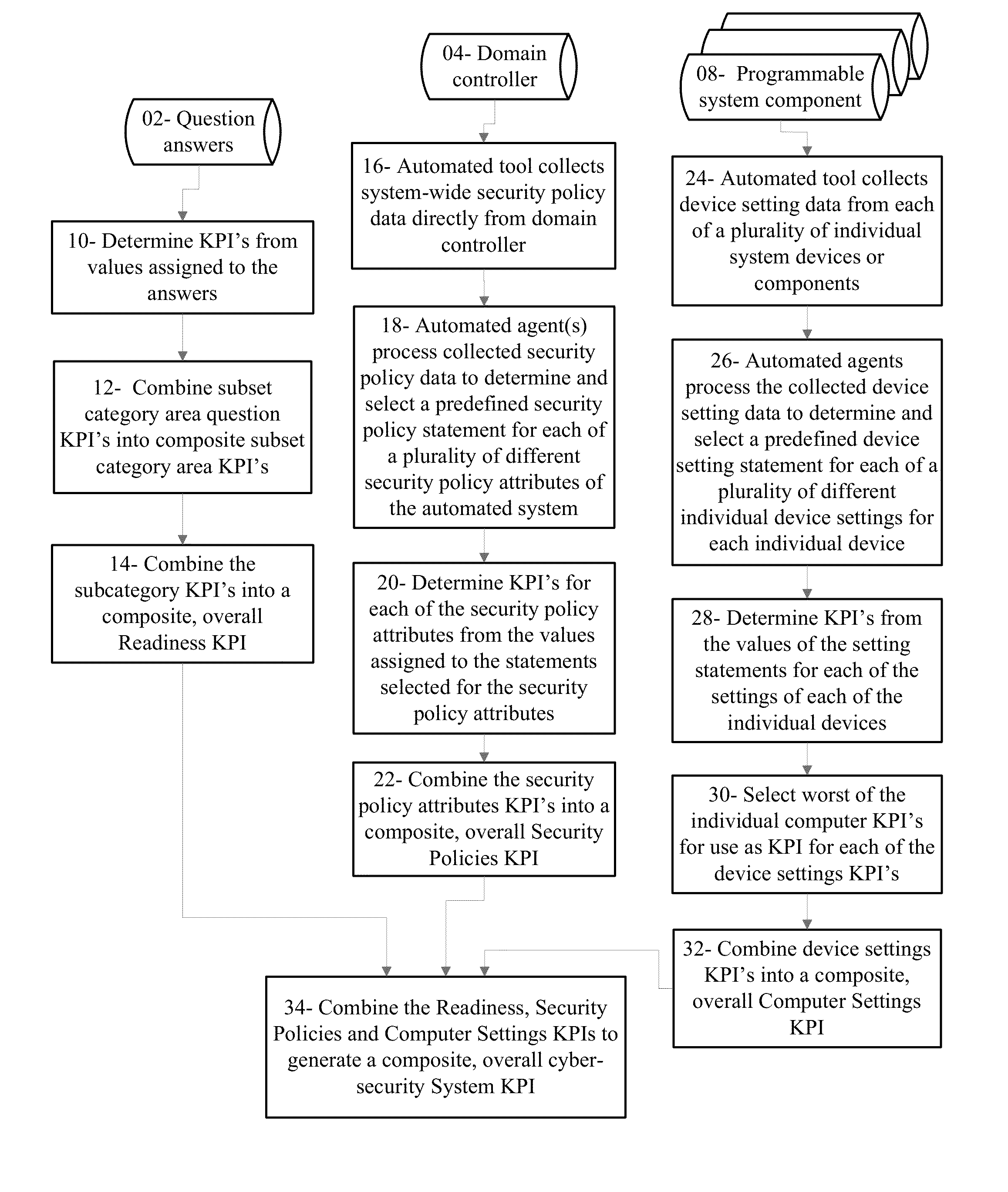
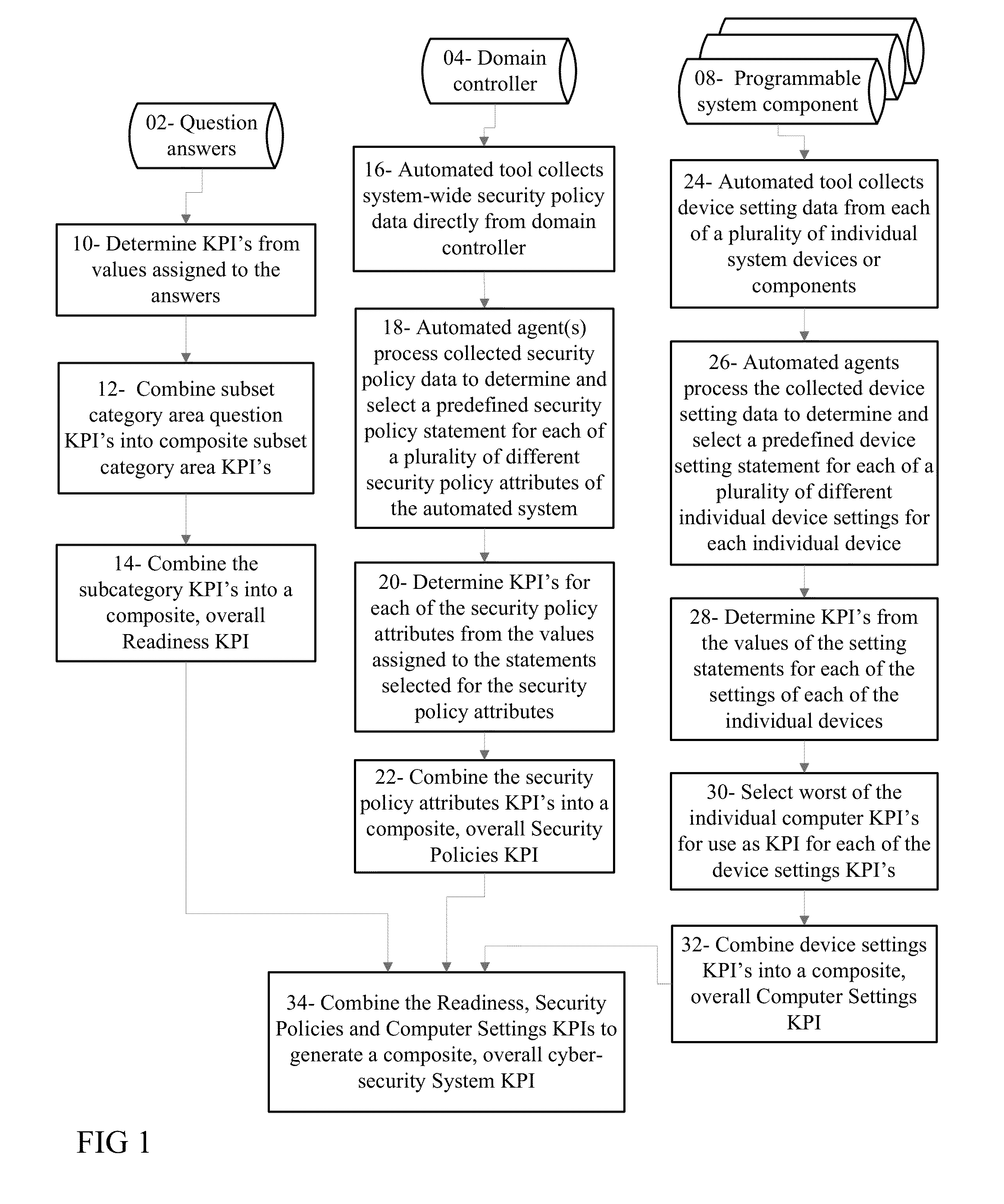
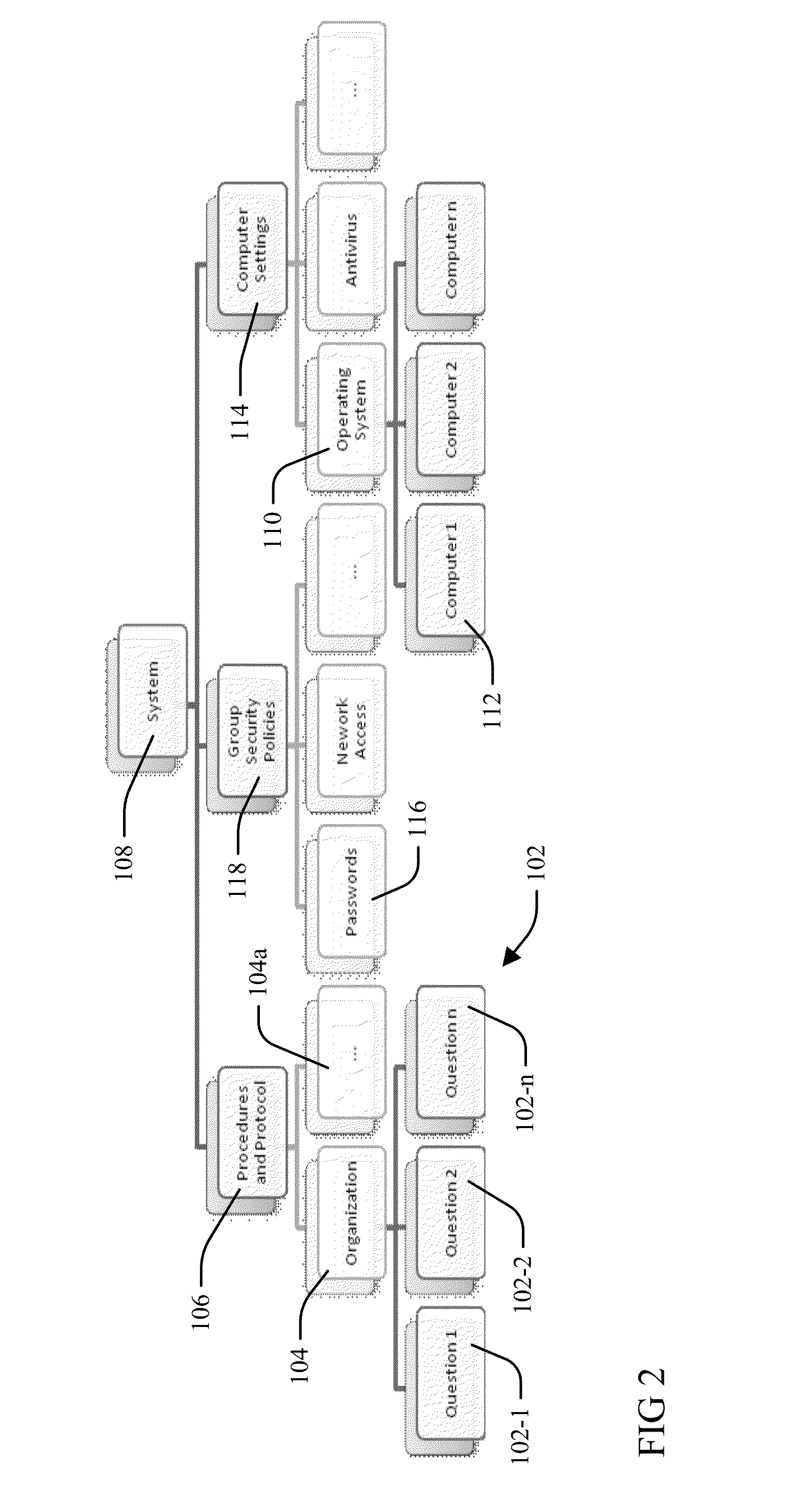
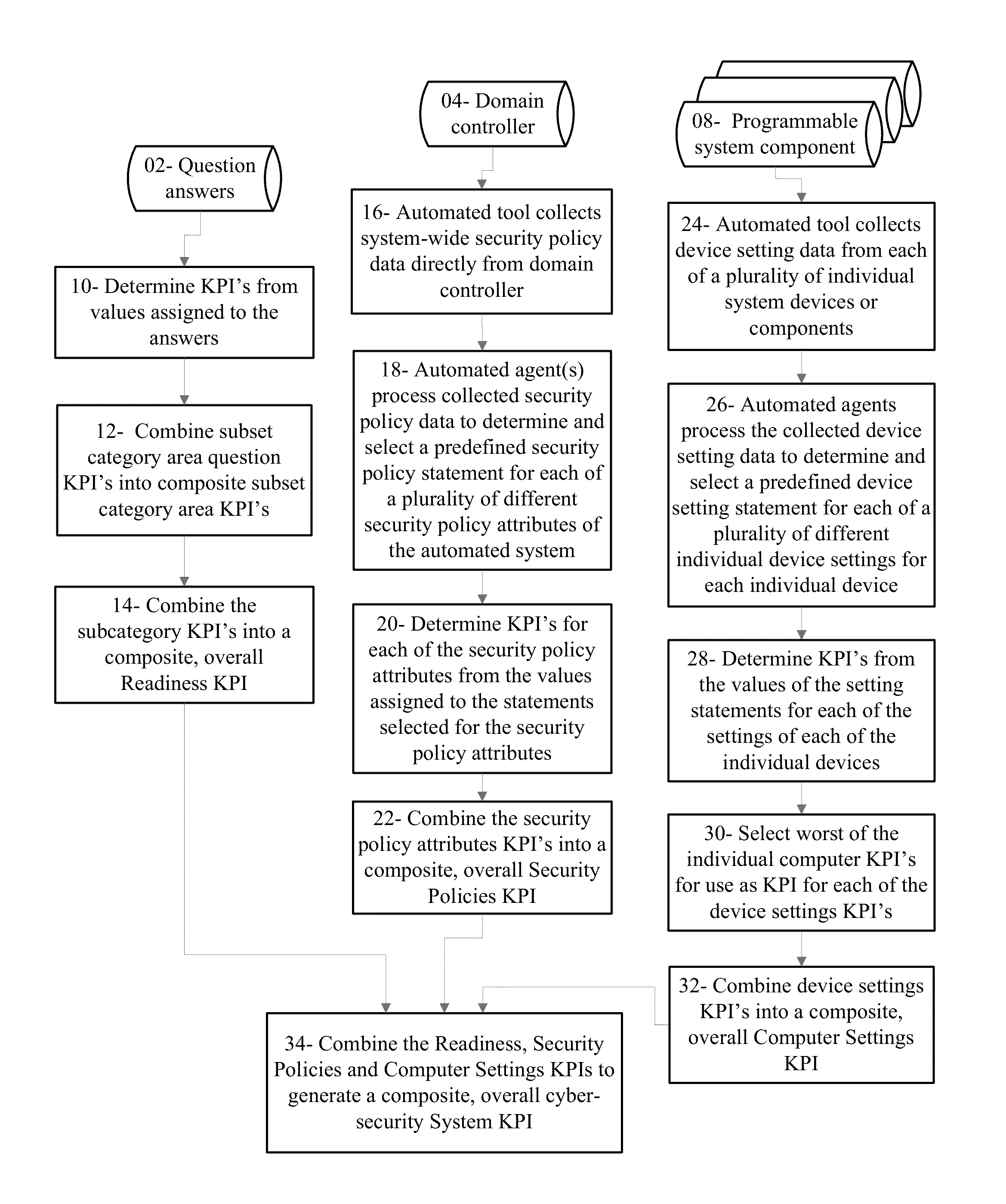
Cyber security analyzer
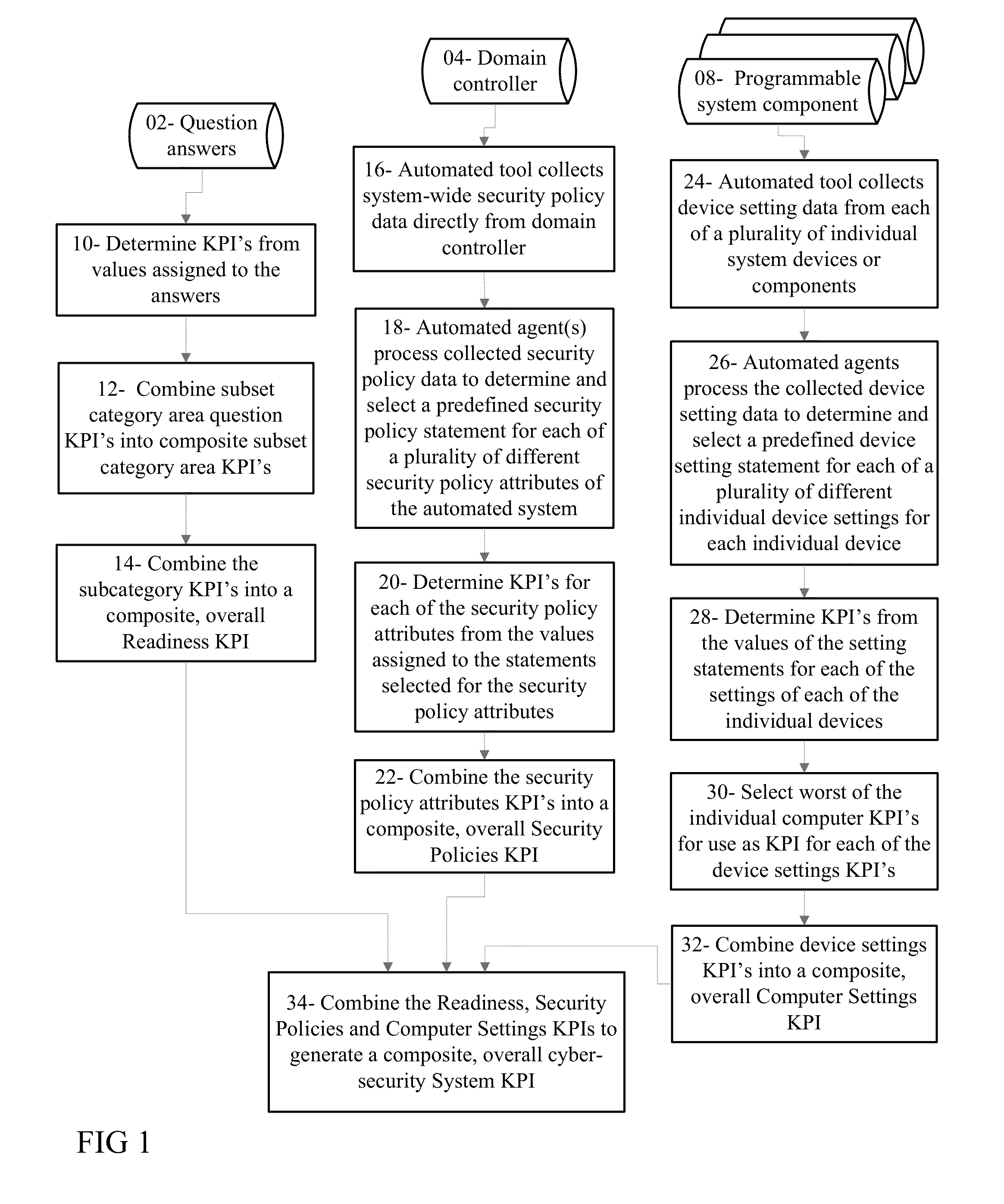
An overall cyber security risk diagram is generated from a hierarchy of determined KPI's by combining a Procedures and Protocol KPI determined from values assigned to answers to questions presented to organization personnel implementing a control systems, with a Group Security Policies KPI that is determined from system-wide policy information and settings of the automation system by an automated processing device tool, and a Computer Settings KPI determined from device setting data collected from individual system devices by the automated processing device tool and relevant to cyber security. The device setting data comprises service areas unique to each device that are not assessable by review of the domain data collected and used to determine the Group Security Policies KPI. Each level of the hierarchy of determined KPI's may be used to generate a representation of relative risk of a cyber-security attribute.
Owner:ABB (SCHWEIZ) AG
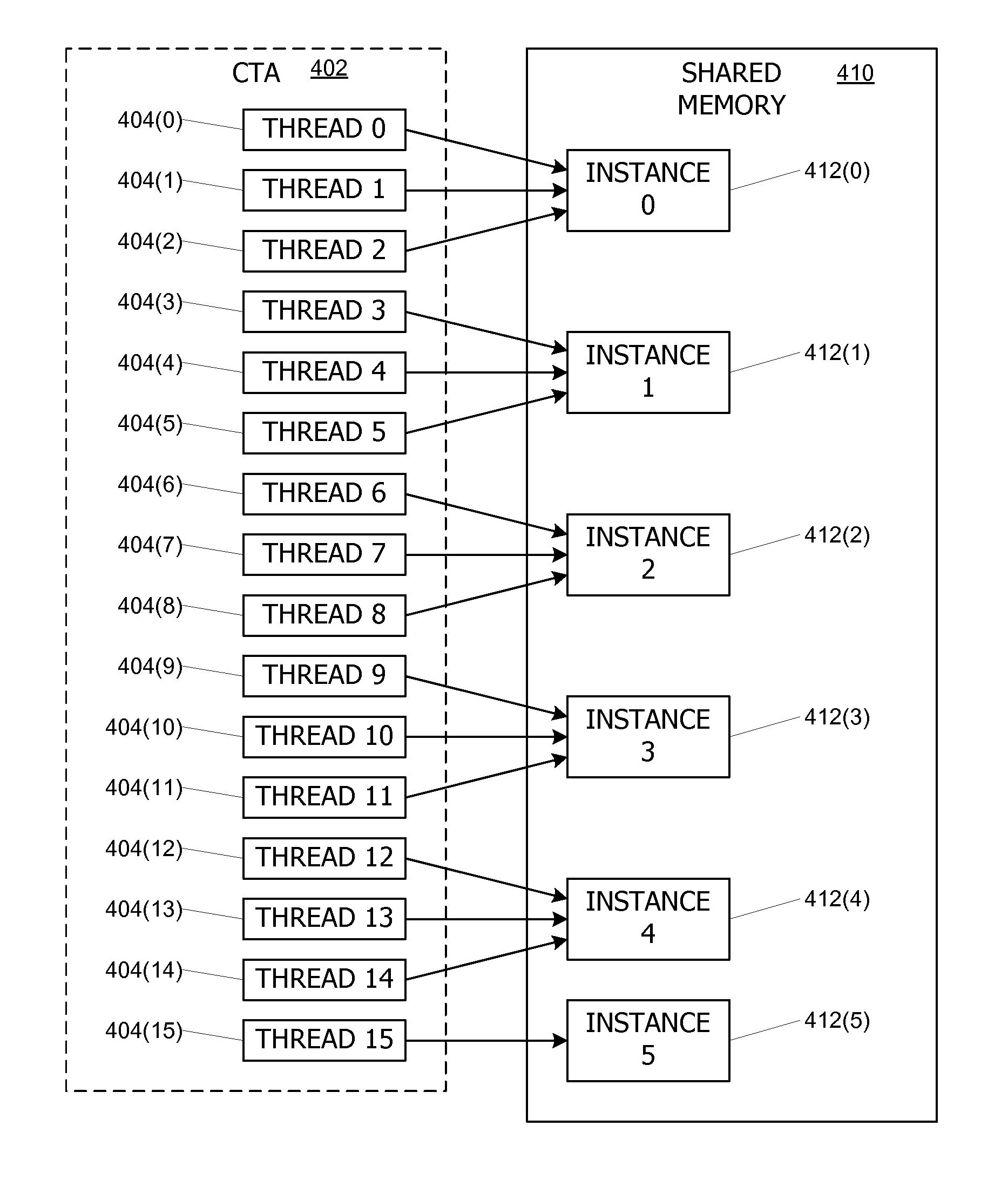
Controlling access to memory resources shared among parallel synchronizable threads
ActiveUS8108659B1Digital computer detailsSpecific program execution arrangementsDefined ProcedureUnique identifier
Thread synchronization techniques are used to control access to a memory resource (e.g., a counter) that is shared among multiple threads. Each thread has a unique identifier and threads are assigned to instances of the shared resource so that at least one instance is shared by two or more threads. Each thread assigned to a particular instance of the shared resource has a unique ordering index. A thread is allowed to access its assigned instance of the resource at a point in the program code determined by its ordering index. The threads are advantageously synchronized (explicitly or implicitly) so that no more than one thread attempts to access the same instance of the resource at a given time.
Owner:NVIDIA CORP
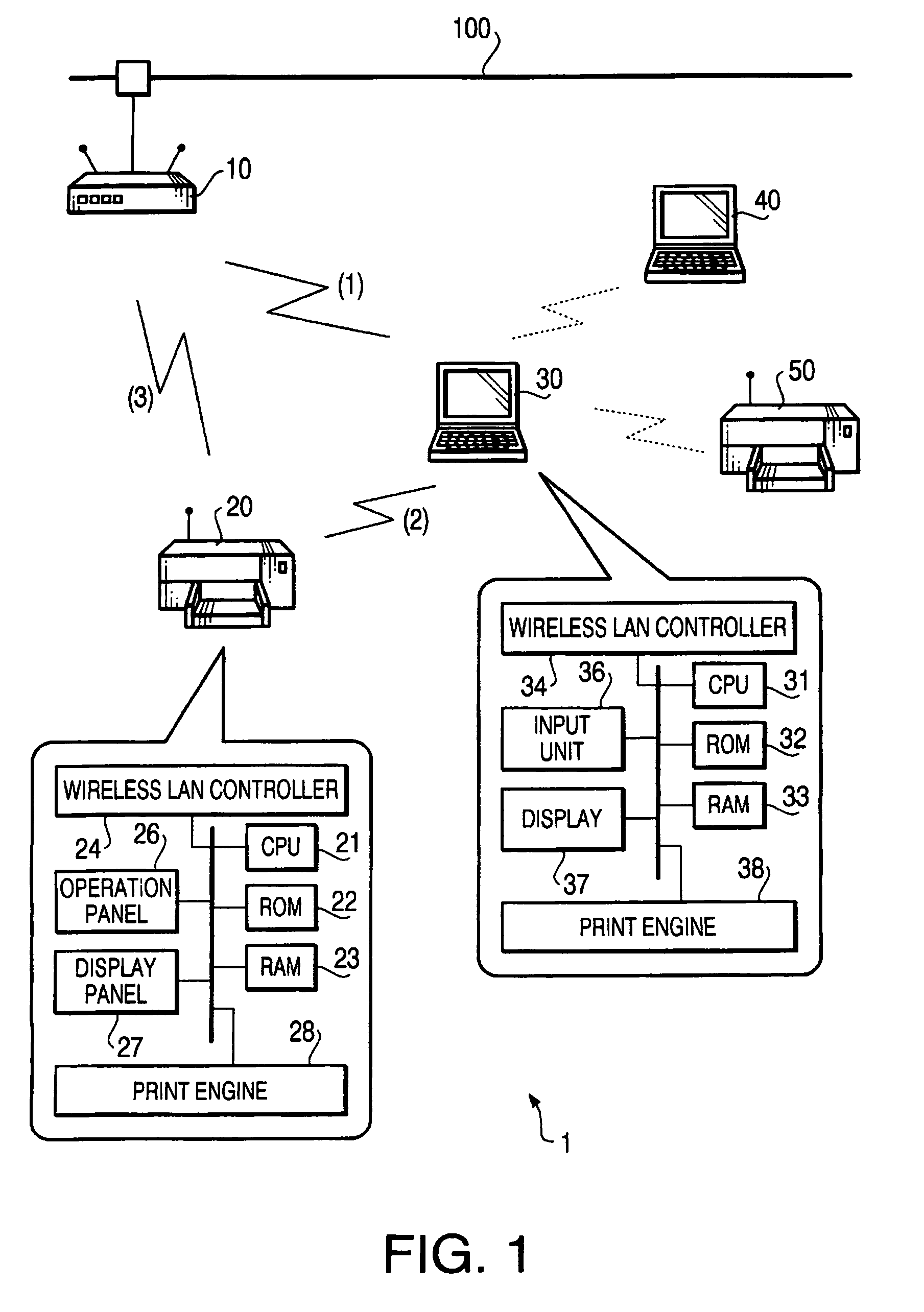
Wireless LAN setting system and communication terminal
ActiveUS7769837B2Deficiency in resolutionNetwork traffic/resource managementAssess restrictionDefined ProcedureComputer terminal
A computer program product for a wireless LAN system is configured such that connection settings necessary for a first communication terminal to connect with a wireless access point are made in accordance with an instruction from a second communication terminal, the second communication terminal being capable of performing data communication with the first communication terminal, the computer program product comprising computer readable instructions that cause a computer to function as the second communication terminal, the instructions defining procedures of determining, with performing data communication with the first communication terminal, whether the first communication terminal is capable of realizing a predetermined process regarding the connection settings by itself, and instructing the first communication terminal by sending the instruction for the connection settings to the first communication terminal in accordance with a result of determination made by the determining procedure.
Owner:BROTHER KOGYO KK
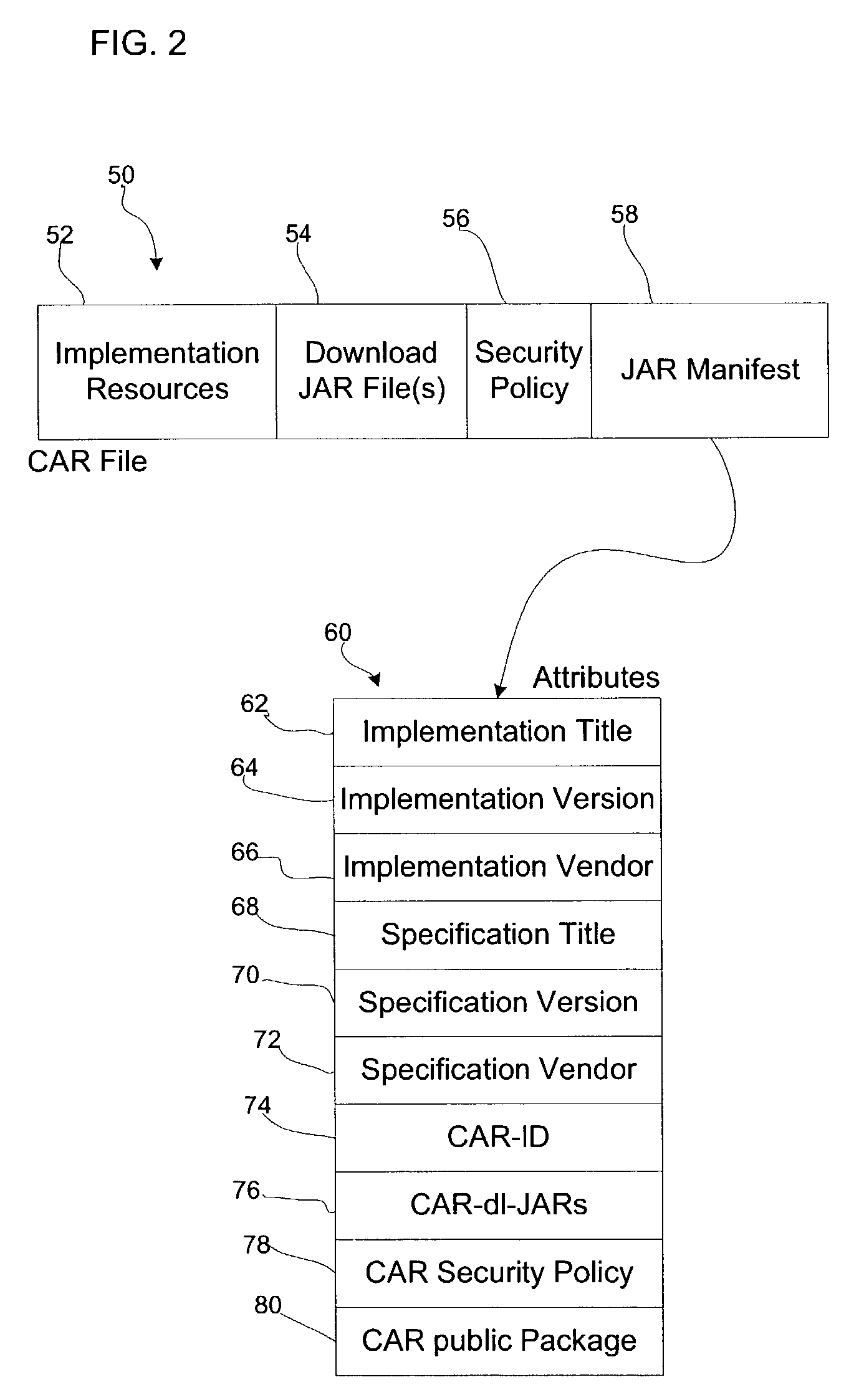
Method and system for creating a well-formed database using semantic definitions
InactiveUS7739224B1Digital data processing detailsMultiple digital computer combinationsDefined ProcedureOperational definition
A method of defining a well-formed database system by defining the organization of the data in the database, and by defining the operations for that data, is described. The definition can be used to automatically create and populate the well-formed database system. The well-formed database system conforms to rules of correctness and produces results that conform to the rules. The organization is defined by a data organization definition that specifies tables, their columns, and the relationships between tables. The operations define procedures that operate on the tables and the table columns. Importantly, the operations are defined along with the tables, columns, and relationships, so that the resulting system is well-formed.
Owner:COMDISCO
History-based call stack construction
InactiveUS20080209406A1Error detection/correctionSpecific program execution arrangementsCall stackDefined Procedure
In a computing system environment, methods and apparatus relate to constructing a call stack for a software program based upon a comprehensive recording of an execution history of the software program. Upon defining procedure calls and returns in the execution history, a call stack is constructed for the procedure calls having no corresponding returns, but without reading or otherwise examining allocated stack memory or registers, such as return addresses. In this manner, an accurate call stack can be constructed despite stack memory or registers being erased or corrupted or despite various compiler optimizations eliminating convenience or otherwise complicating the construction. Nuances for defining procedure calls and returns as well as stack pointer values for same are also contemplated. Still other embodiments relate to stand-alone computer program products (on computer-readable media or as a download, or other) or those working in conjunction with other programs.
Owner:RPX CORP
Comprehensive identification and designation of welding procedures
System(s) and method(s) that facilitates comprehensive identification and designation of welding procedures. A configuration component facilitates configuring the welding system with respect to pre-defined procedures and / or parameters and facilitates naming of the configured welding system. A storage component that stores the configured welding system in a readily accessible memory location. A remote access component can facilitate remotely accessing the welding system, the configuration of the welding system alterable by way of the remote access component.
Owner:LINCOLN GLOBAL INC
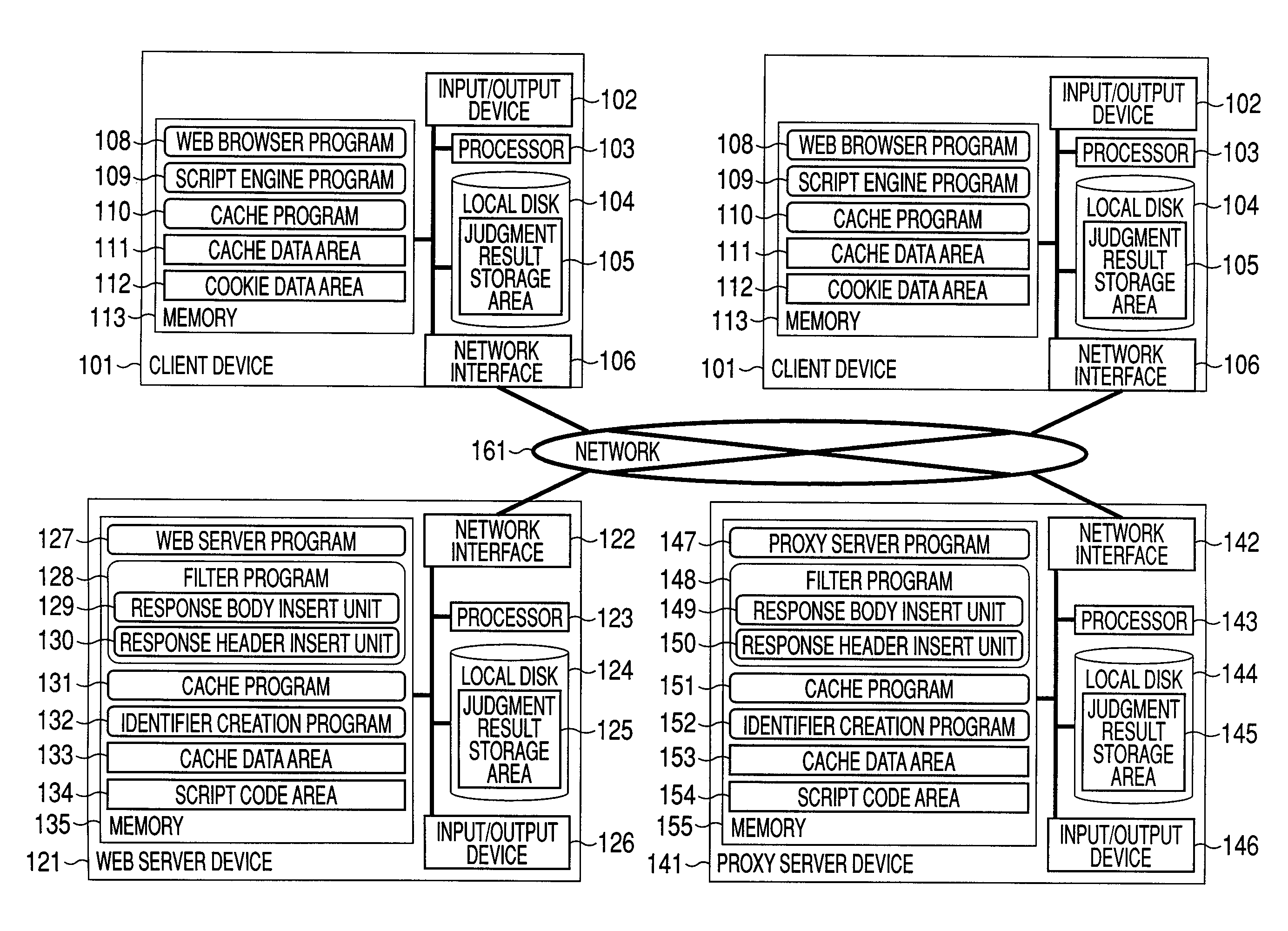
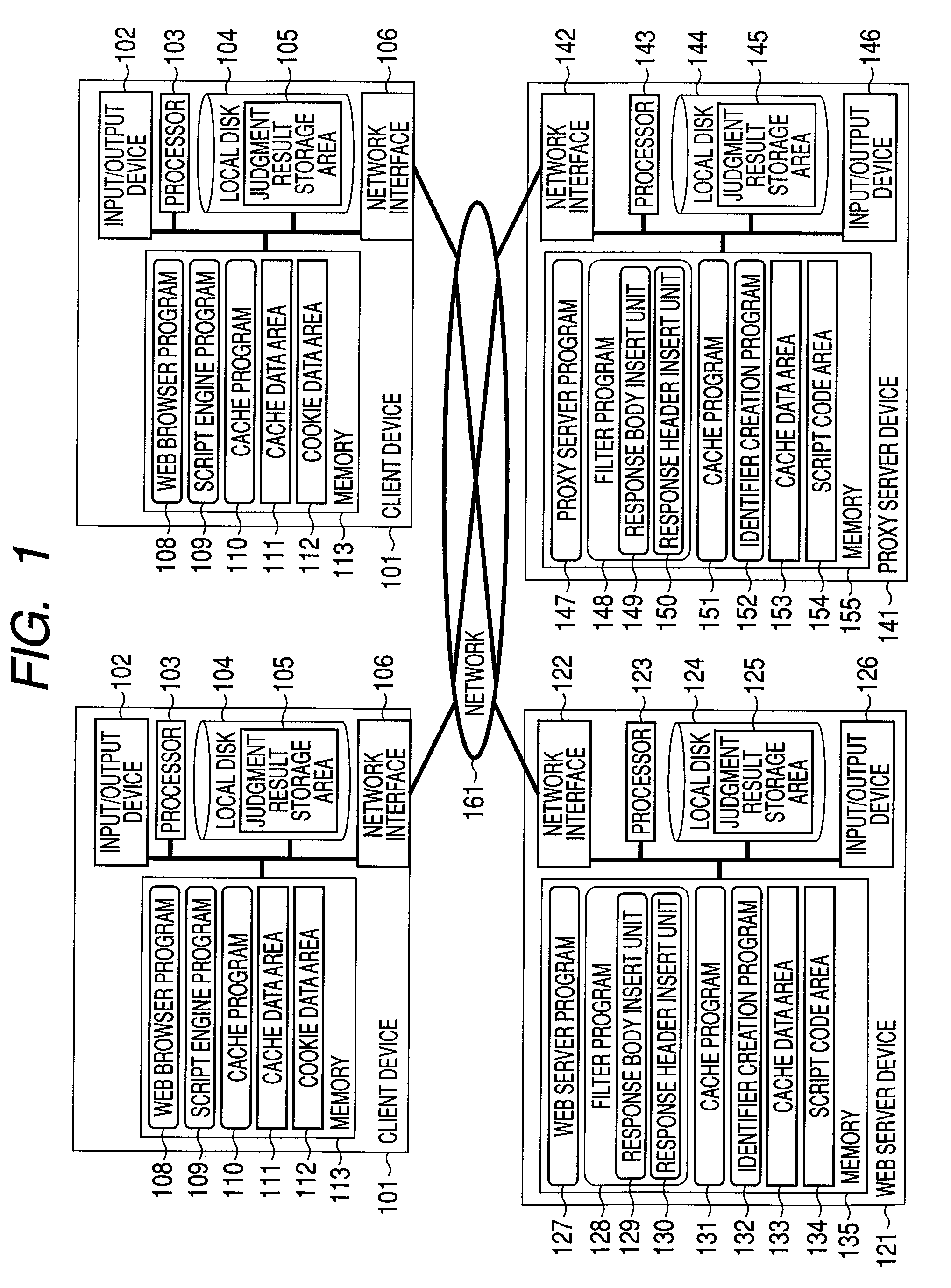
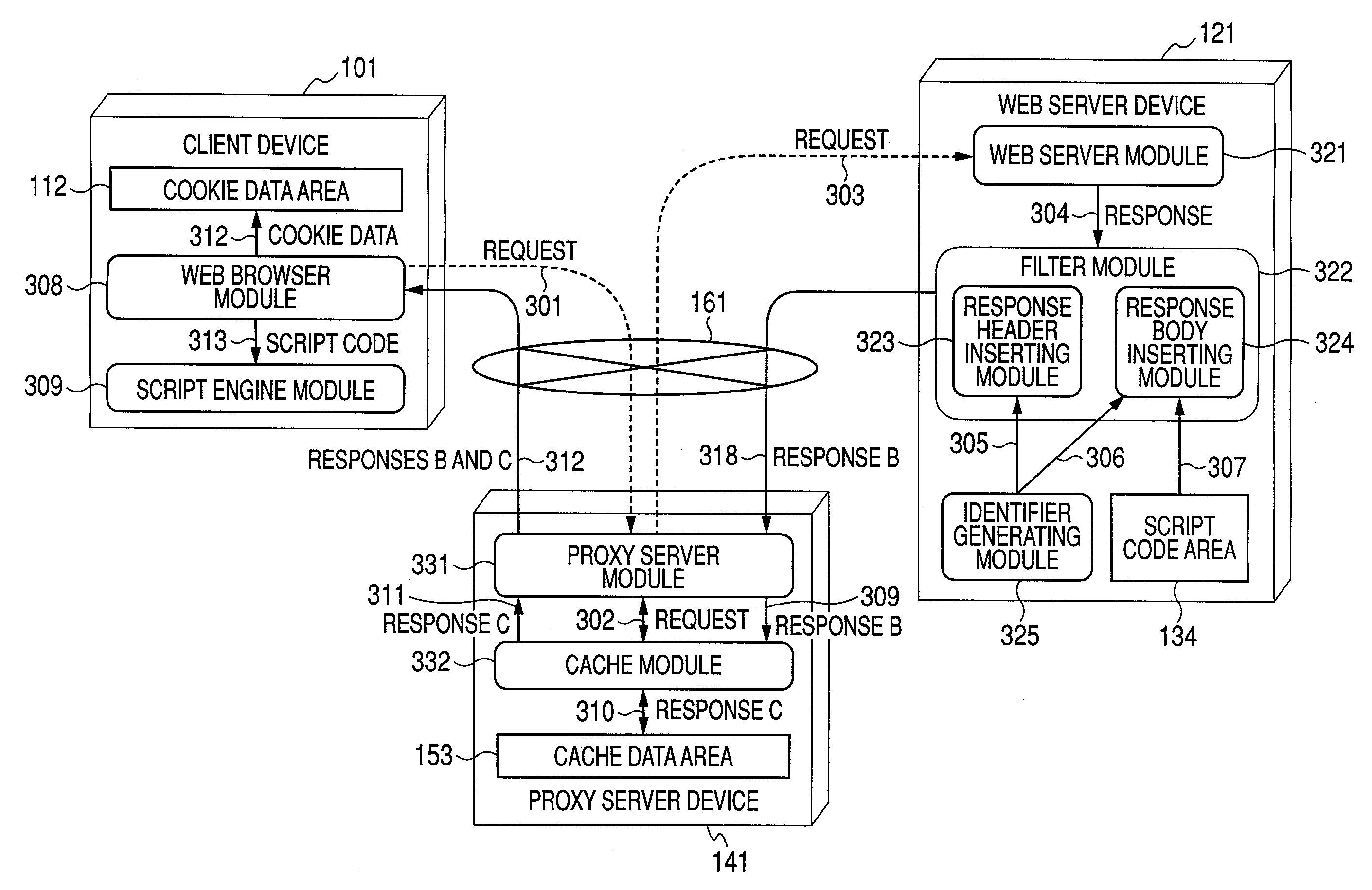
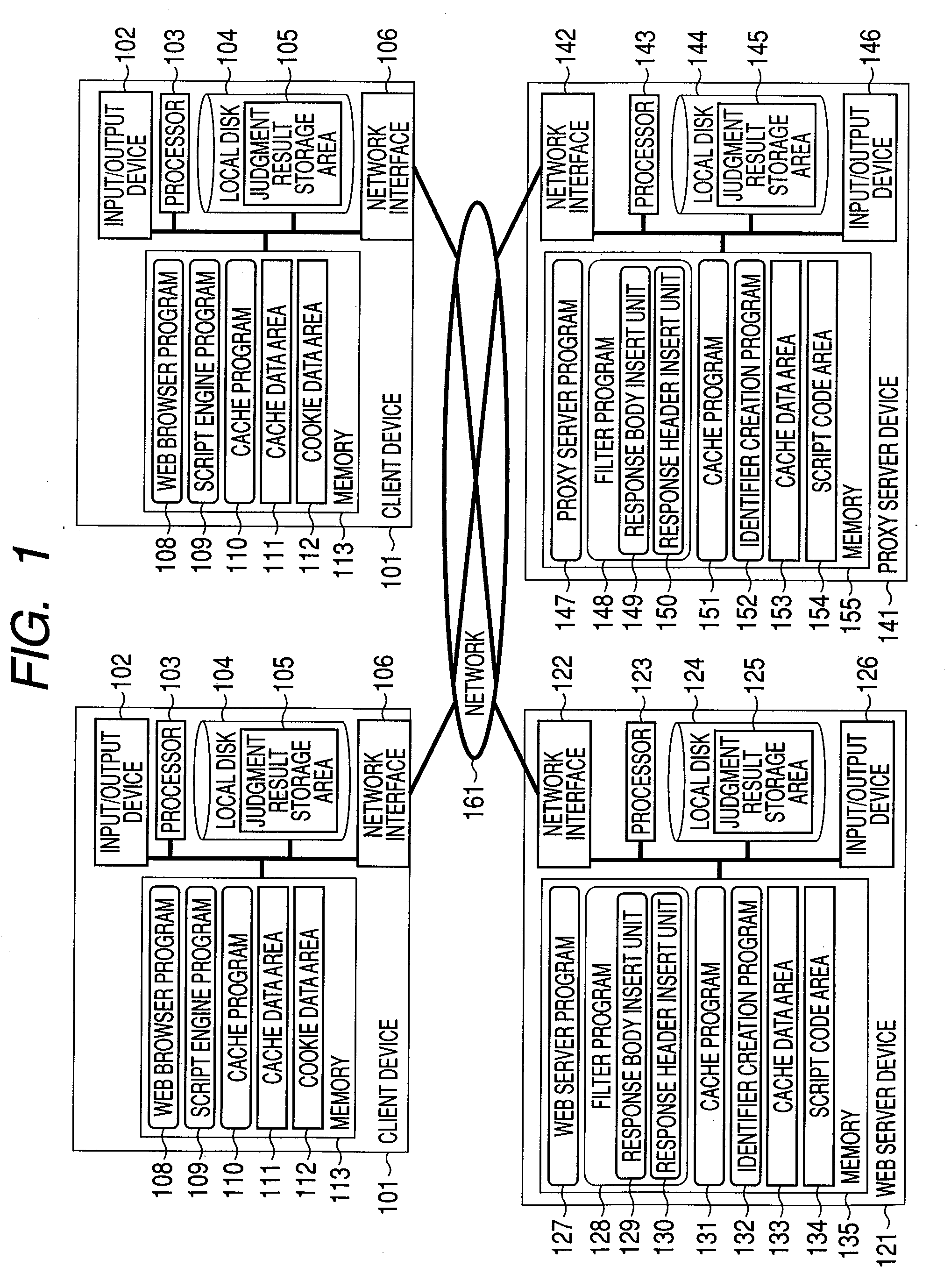
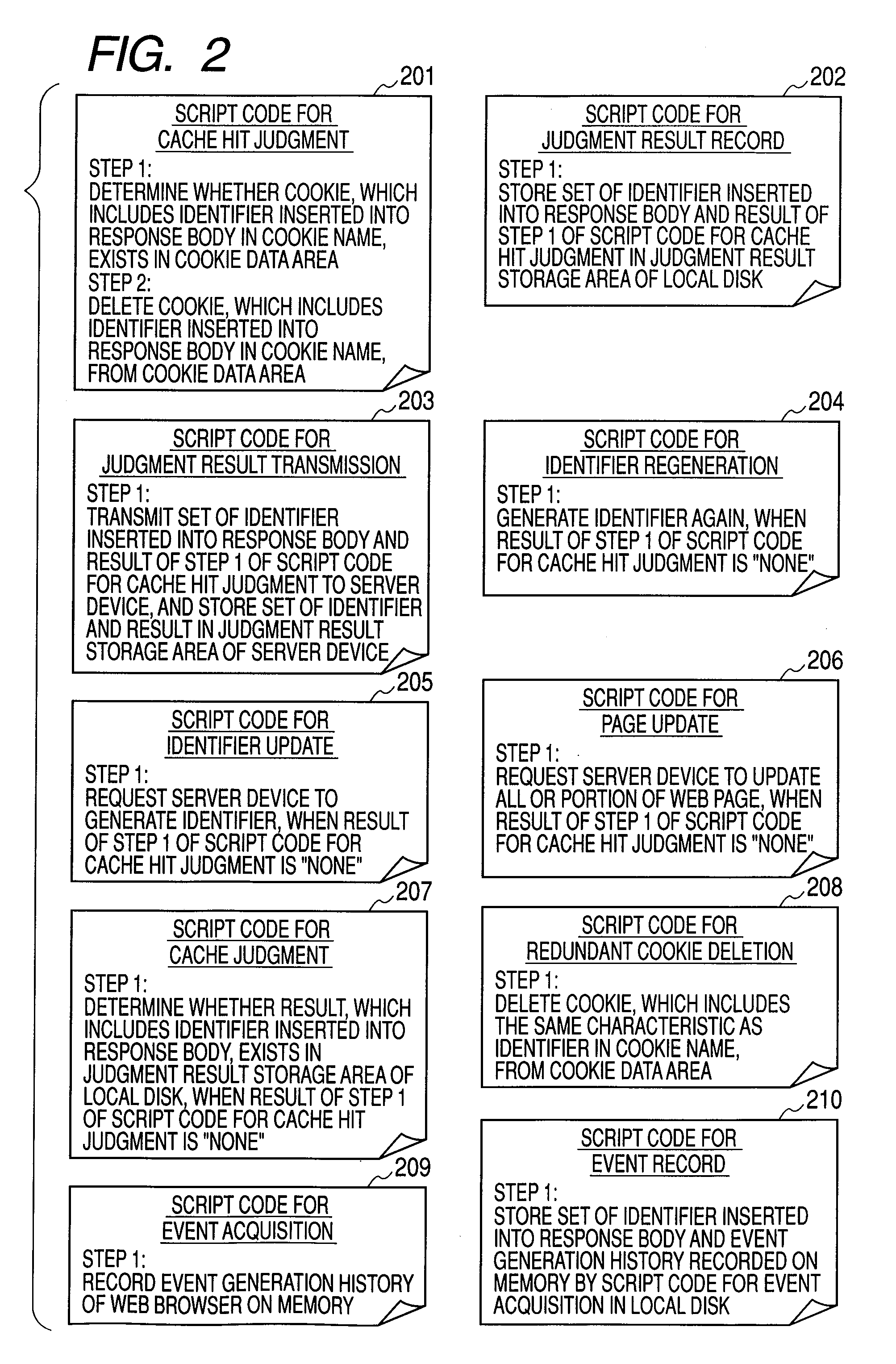
Application execution managing method, application execution server computer, and repeater
InactiveUS8150985B2Accurate operationMultiple digital computer combinationsTransmissionDefined ProcedureApplication software
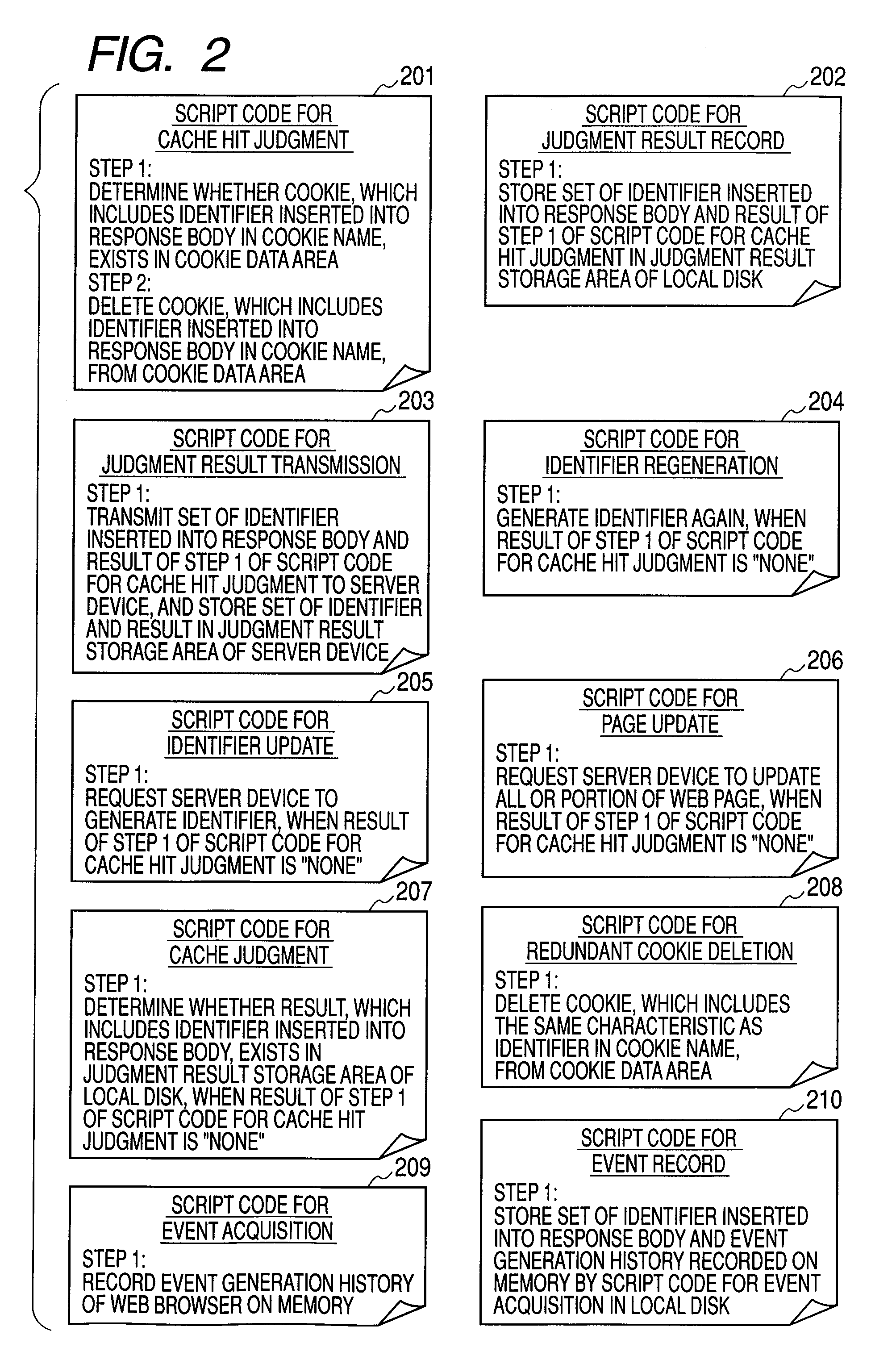
A cache hit determining method in a server client system, such as a web system, which can determine whether a response received by a client is a response generated by a server or a response returned from a cache in the server client system. In the cache hit determining method, when the server generates the response, the serve adds a program for a cache hit determination and data to the response and the client executes the program included in the response, thereby realizing a cache hit determination.
Owner:HITACHI LTD
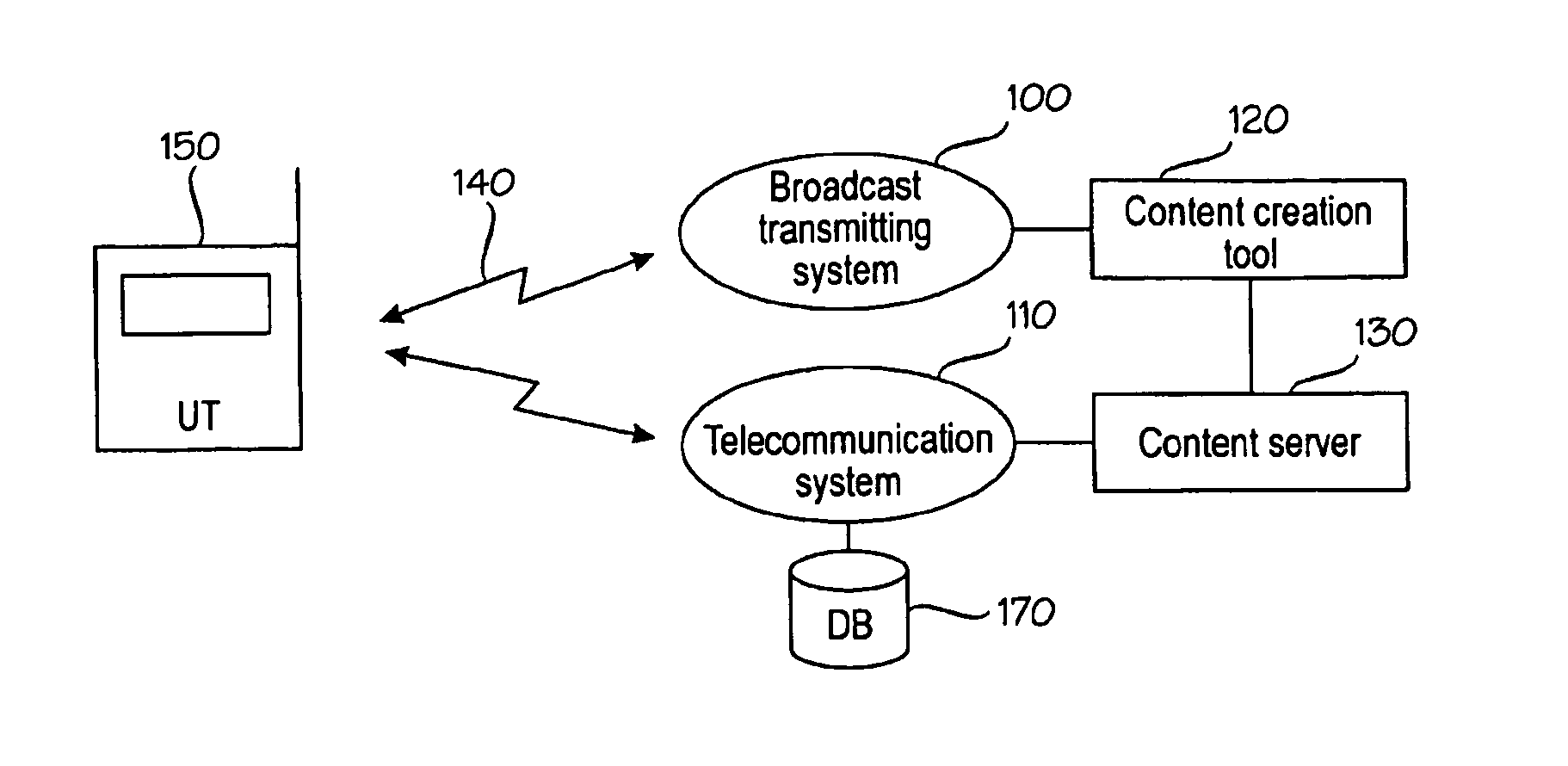
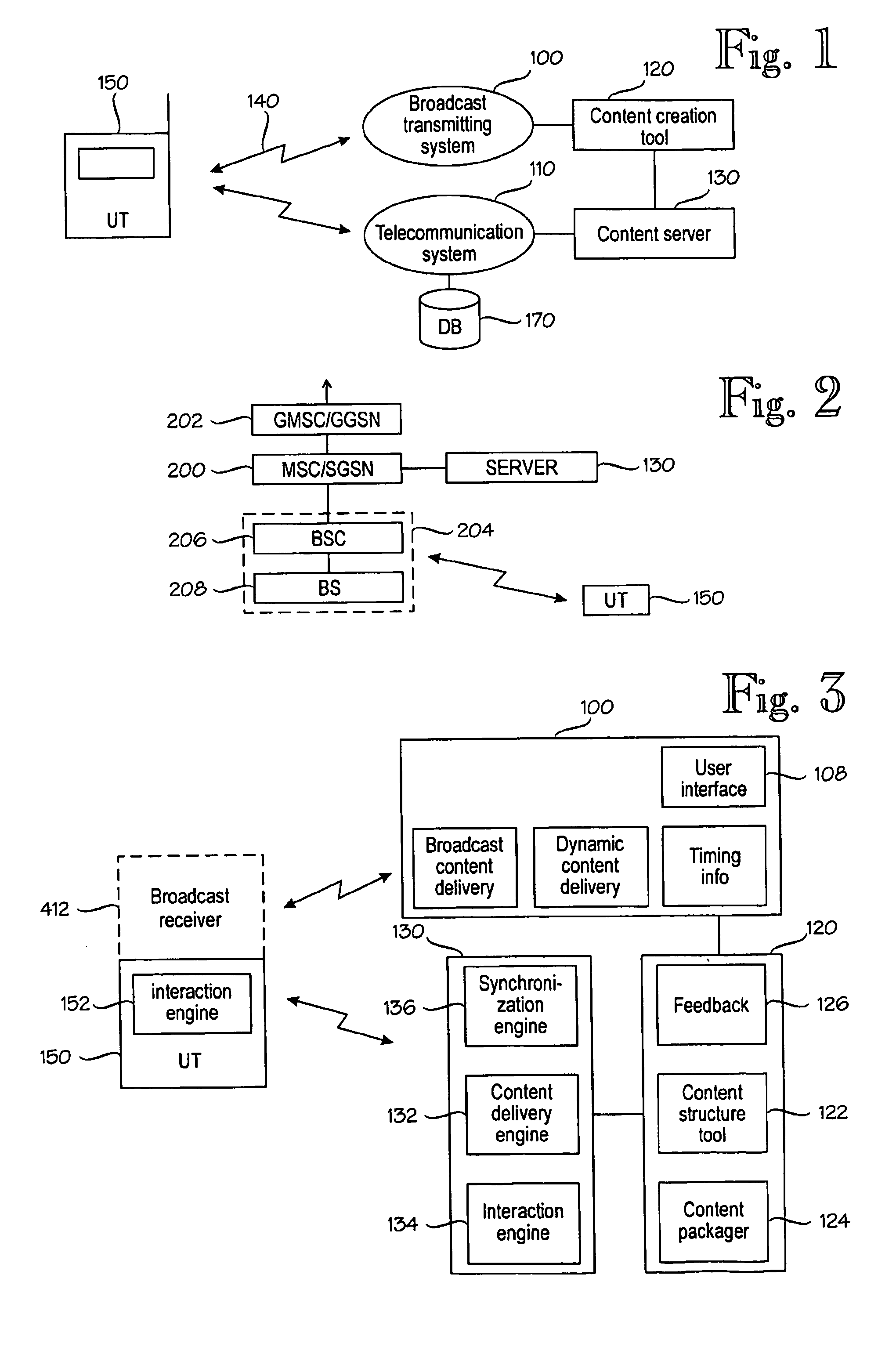
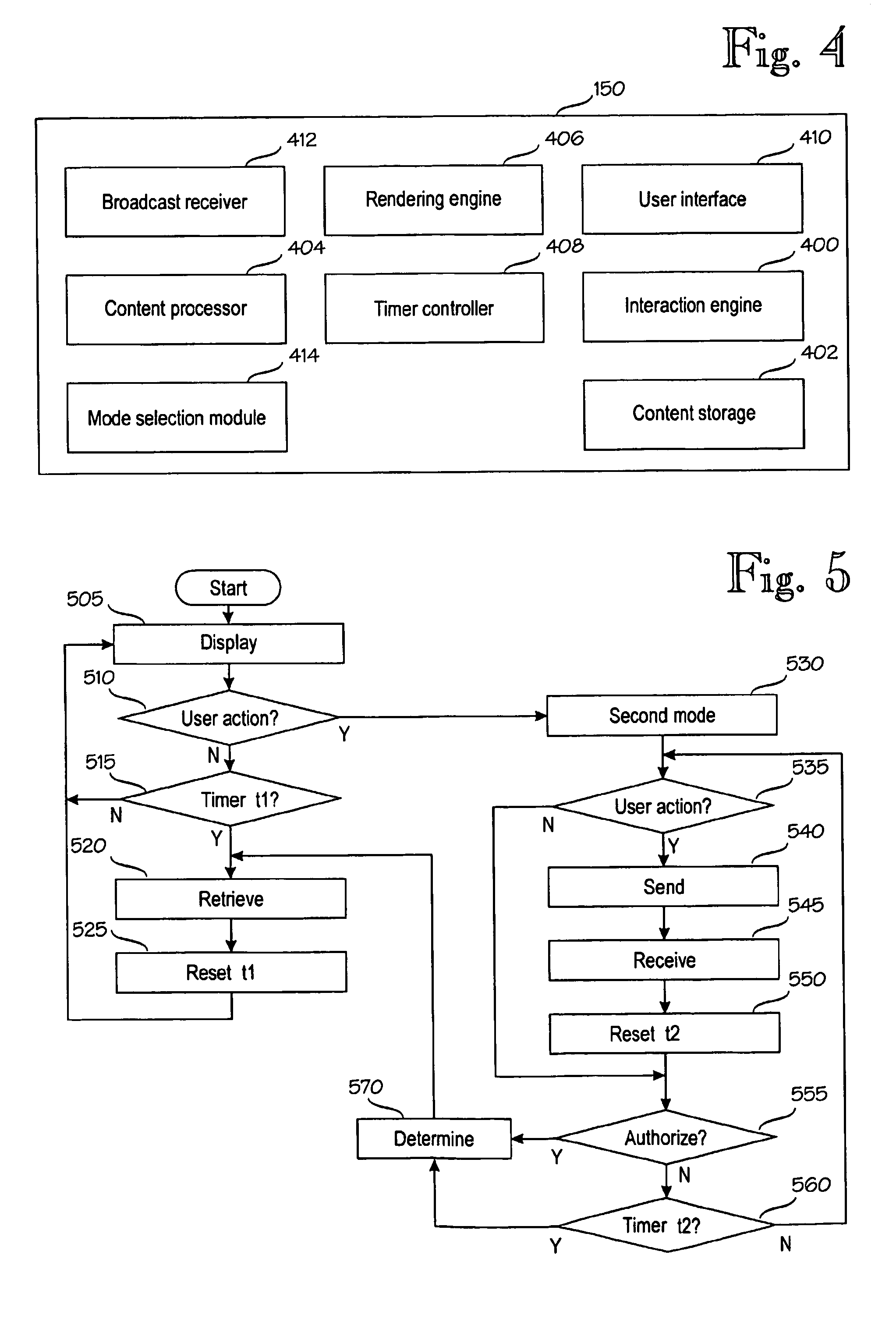
Method and system of displaying content associated with broadcast program
ActiveUS20060014490A1Broadcast transmission systemsBroadcast services for monitoring/identification/recognitionDefined ProcedureContent Time
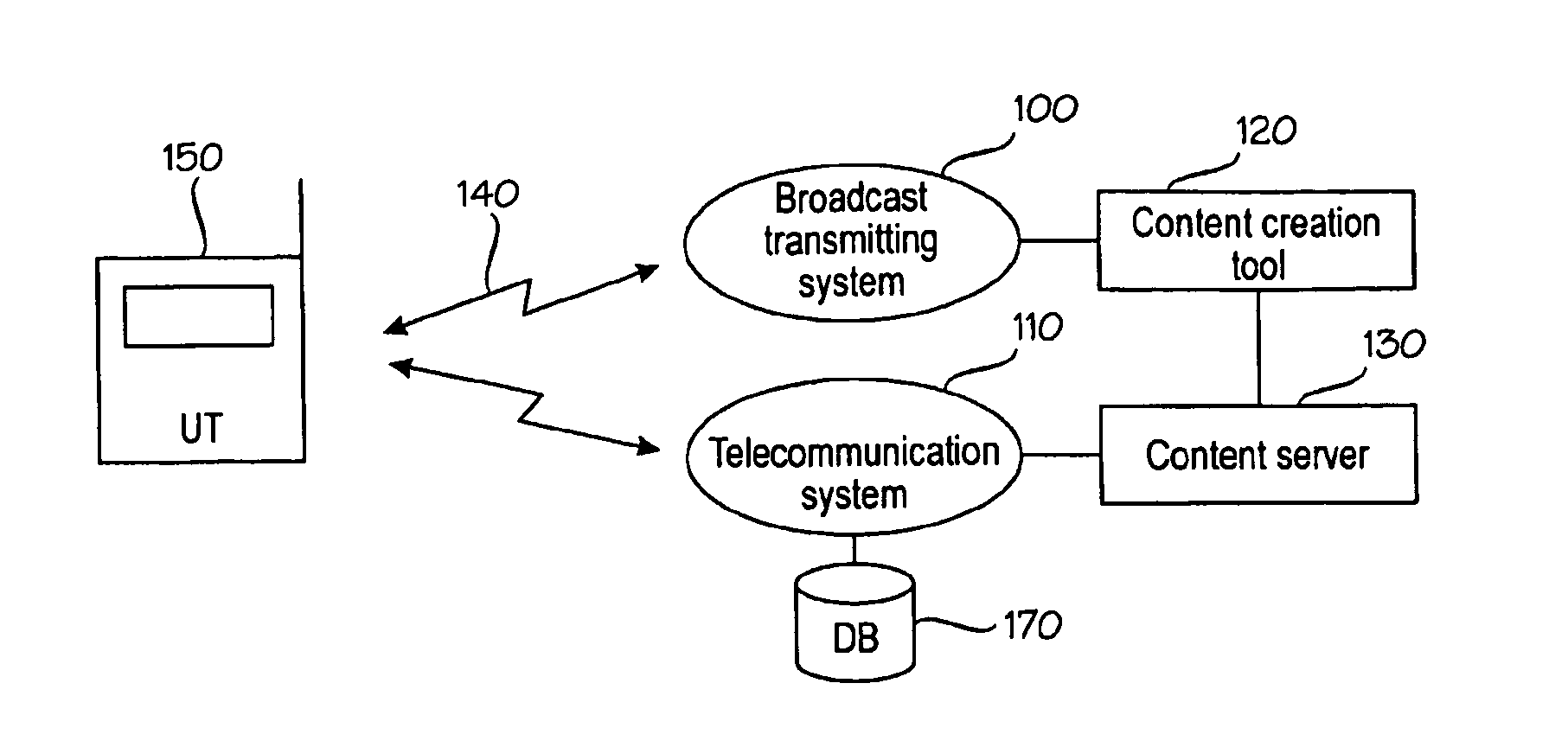
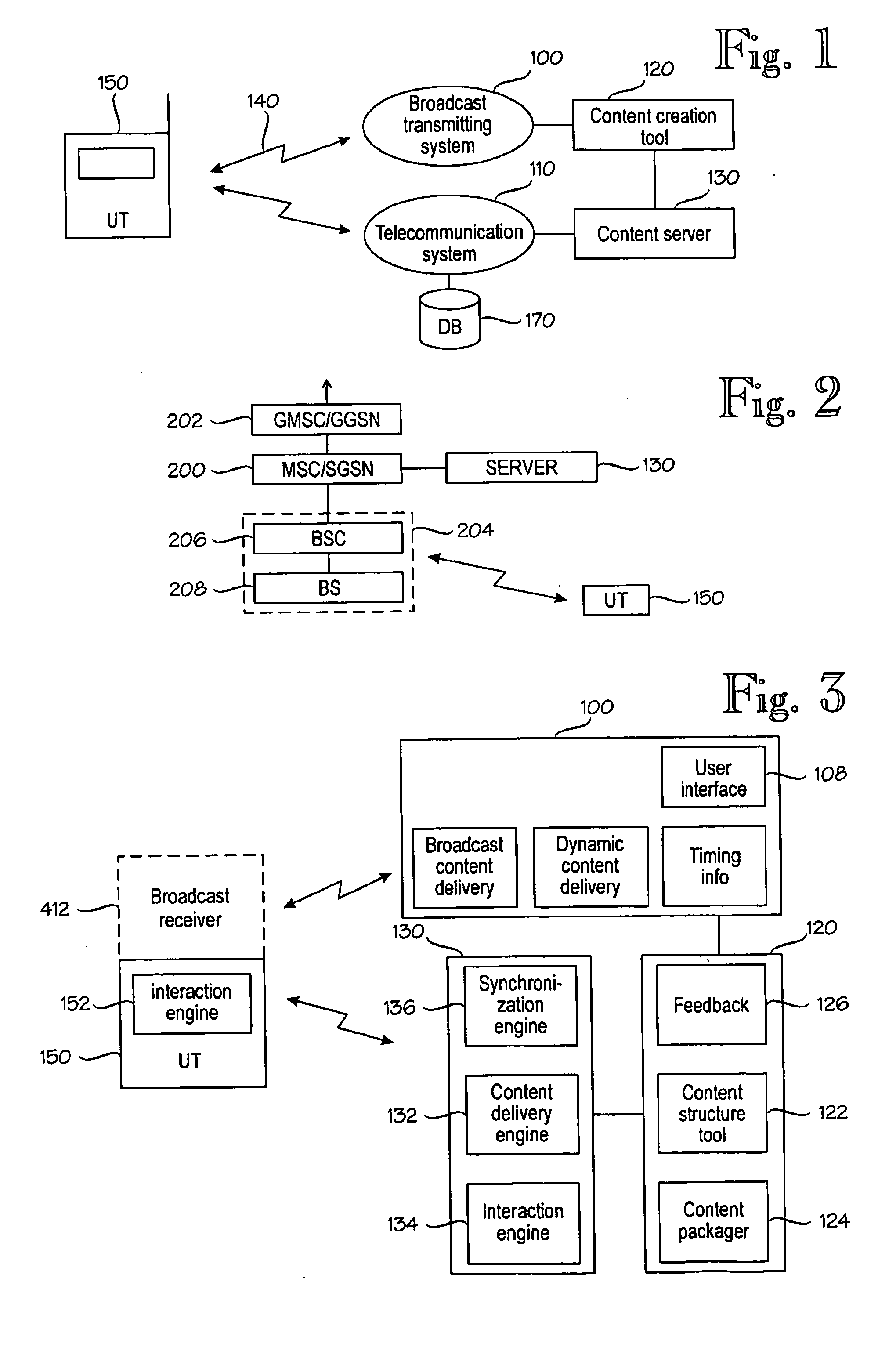
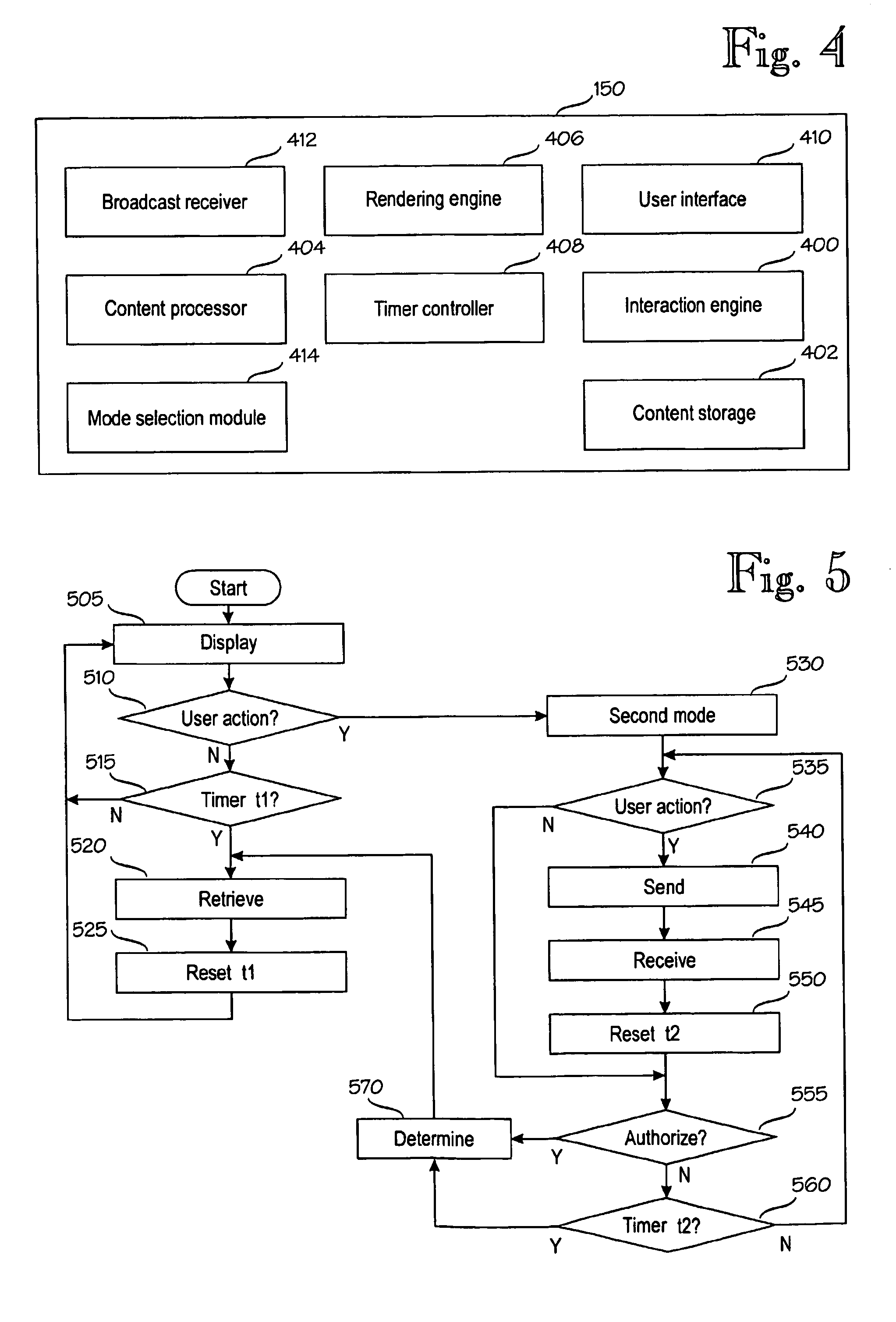
A media system comprising a broadcast system, a telecommunication system, a content processing system, and a user terminal. While a media stream is broadcast, a group of content items associated with the media stream are generated. The content items are presented in the user terminal in a first mode, wherein a presentation element corresponding to a content item is changed to another presentation element according to the timing information of the content item, or in a second mode wherein a presentation element is changed to another presentation element in response to a user action. Transition from the second mode is allowed only by authorization according to a pre-defined procedure. The interactive operations are thus controlled by the user and thus not overridden by content timed or pushed to the user terminal for display.
Owner:RPX CORP
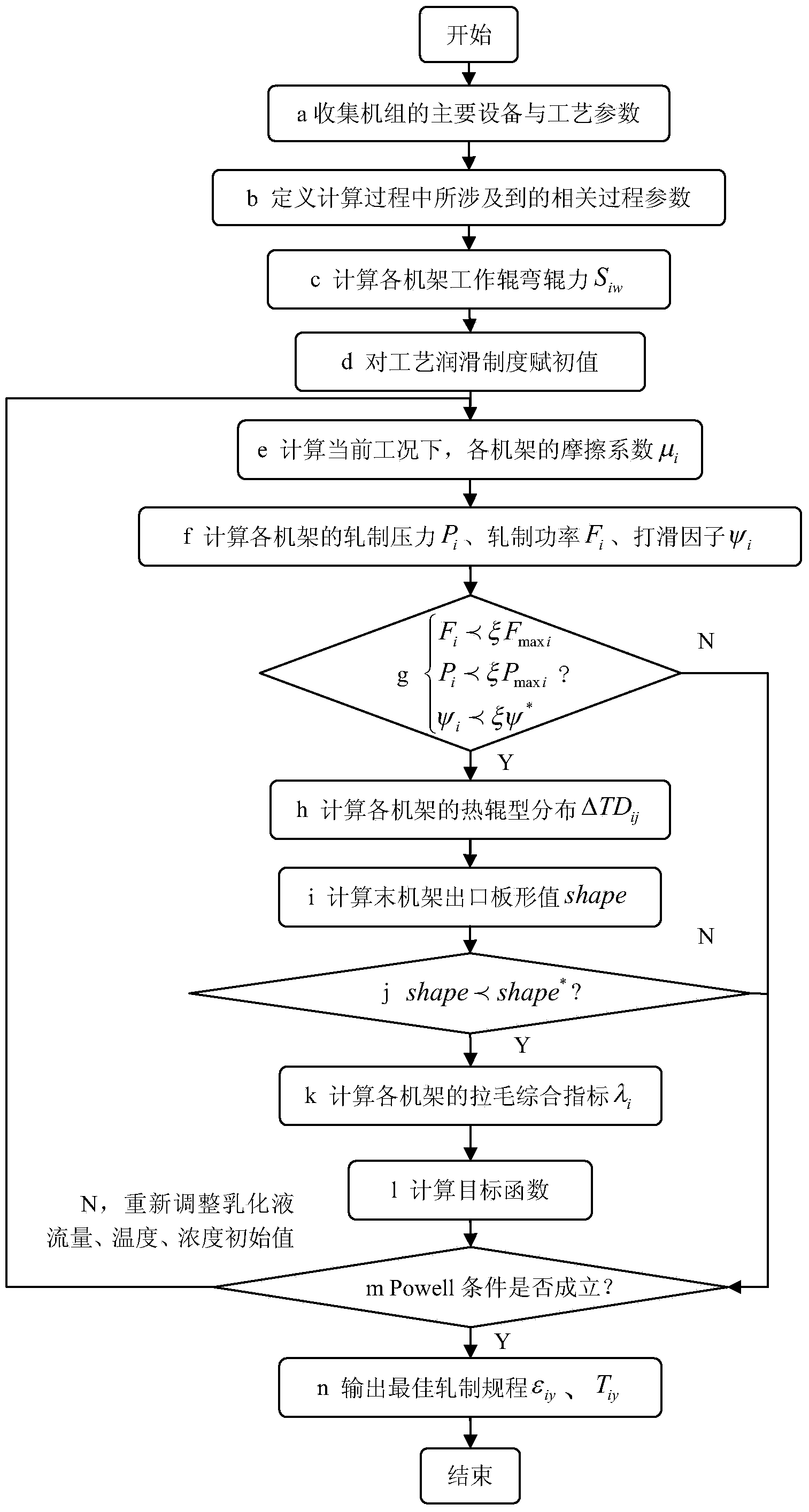
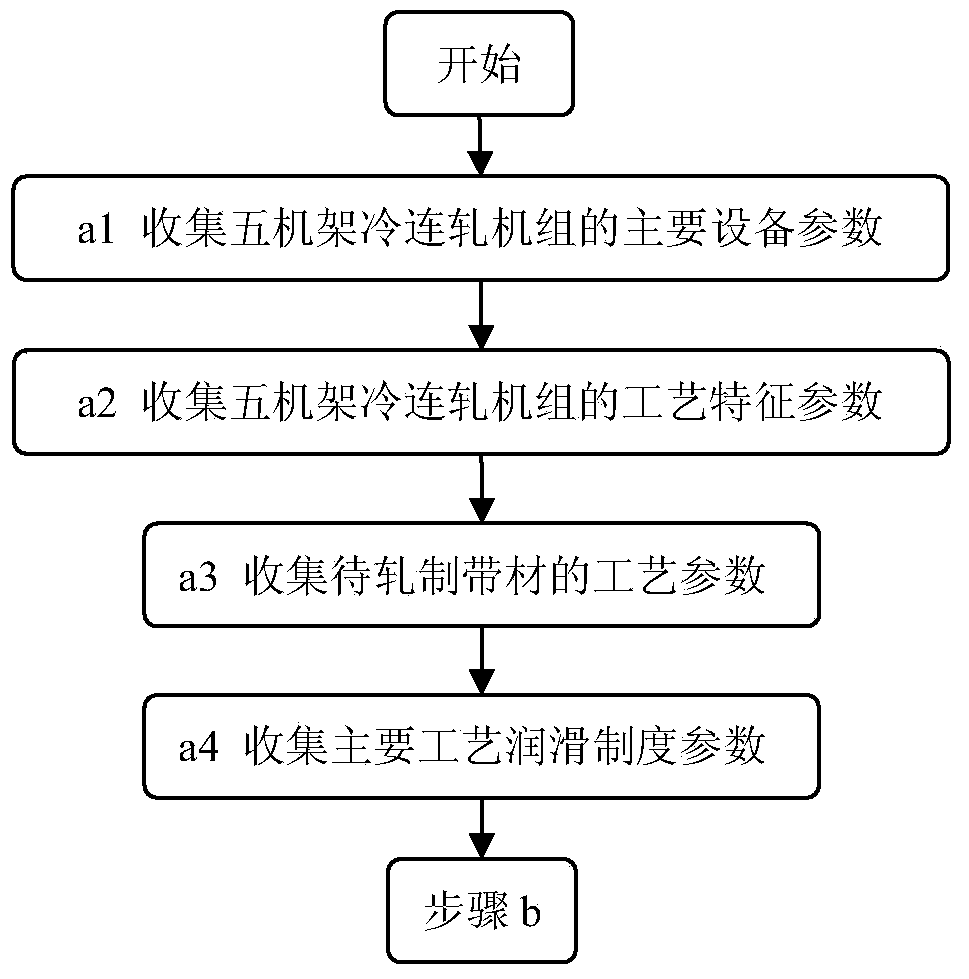
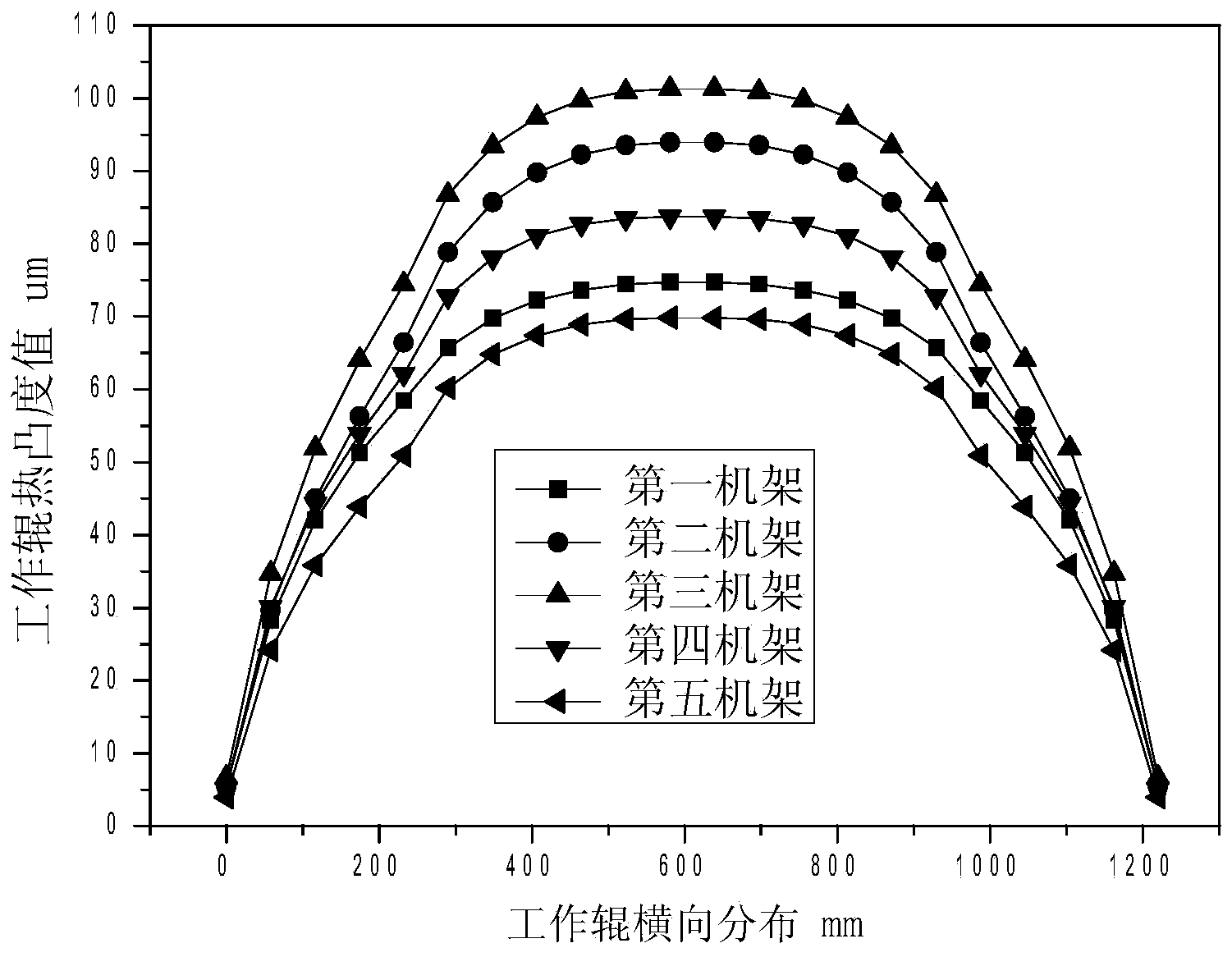
Optimization method of technological lubrication system taking galling prevention as objective for tandem cold mill
ActiveCN103611732AReduce picking defectsImprove surface qualityWork treatment devicesProfile control deviceDefined ProcedureEmulsion
Disclosed is an optimization method of a technological lubrication system taking galling prevention as an objective for a tandem cold mill. The method mainly comprises the following computer-executed steps: 1, collecting main equipment and technological parameters of a five-stand tandem cold mill; 2, defining procedure parameters related in the technological lubrication system optimization procedure; 3, giving initial values of emulsion flow, emulsion concentration and emulsion temperature of a first stand, a second stand, a third stand, a fourth stand and a fifth stand; 4, computing a friction coefficient mui of each stand in a current technological lubrication system and rolling schedule; 5, computing rolling pressure, rolling power and slip factors of each stand; 6, computing thermal crown distribution of a working roll of each stand; 7, computing an outlet flatness value of the tail stand; 8, computing a value of a comprehensive galling judgment index lambdai of each stand; 9, computing an optimization objective function in the current technological lubrication system; 10, completing optimal setting of the technological lubrication system, taking the galling prevention as the objective, of the tandem cold mill. By the method, galling defection occurrence probability of each stand is lowered, and outlet surface quality of strip steel is improved.
Owner:唐山市榕泽钢材加工有限公司
Cyber security analyzer
An overall cyber security risk diagram is generated from a hierarchy of determined KPI's by combining a Procedures and Protocol KPI determined from values assigned to answers to questions presented to organization personnel implementing a control systems, with a Group Security Policies KPI that is determined from system-wide policy information and settings of the automation system by an automated processing device tool, and a Computer Settings KPI determined from device setting data collected from individual system devices by the automated processing device tool and relevant to cyber security. The device setting data comprises service areas unique to each device that are not assessable by review of the domain data collected and used to determine the Group Security Policies KPI. Each level of the hierarchy of determined KPI's may be used to generate a representation of relative risk of a cyber-security attribute.
Owner:ABB (SCHWEIZ) AG
Method and system for monitoring additive manufacturing processes
ActiveUS9999924B2Additive manufacturing apparatusIncreasing energy efficiencyDefined ProcedureQuality assurance
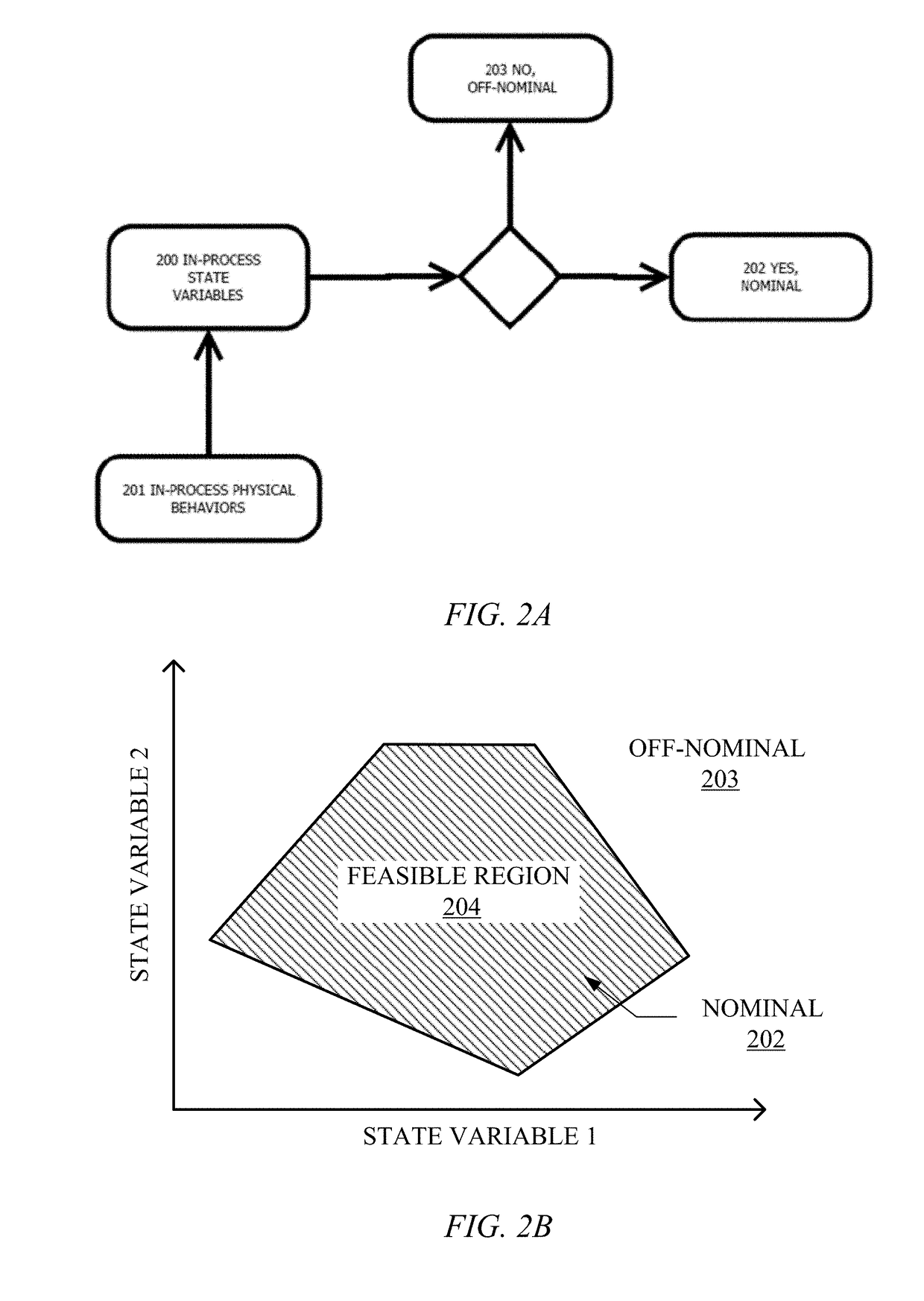
This invention teaches a quality assurance system for additive manufacturing. This invention teaches a multi-sensor, real-time quality system including sensors, affiliated hardware, and data processing algorithms that are Lagrangian-Eulerian with respect to the reference frames of its associated input measurements. The quality system for Additive Manufacturing is capable of measuring true in-process state variables associated with an additive manufacturing process, i.e. those in-process variables that define a feasible process space within which the process is deemed nominal. The in-process state variables can also be correlated to the part structure or microstructure and can then be useful in identifying particular locations within the part likely to include defects.
Owner:SIGMA LAB OF ARIZONA
Monitoring system
ActiveUS20120130701A1Convenient to accommodateSimple designProgramme controlSimulator controlSensor arrayProcedure requested
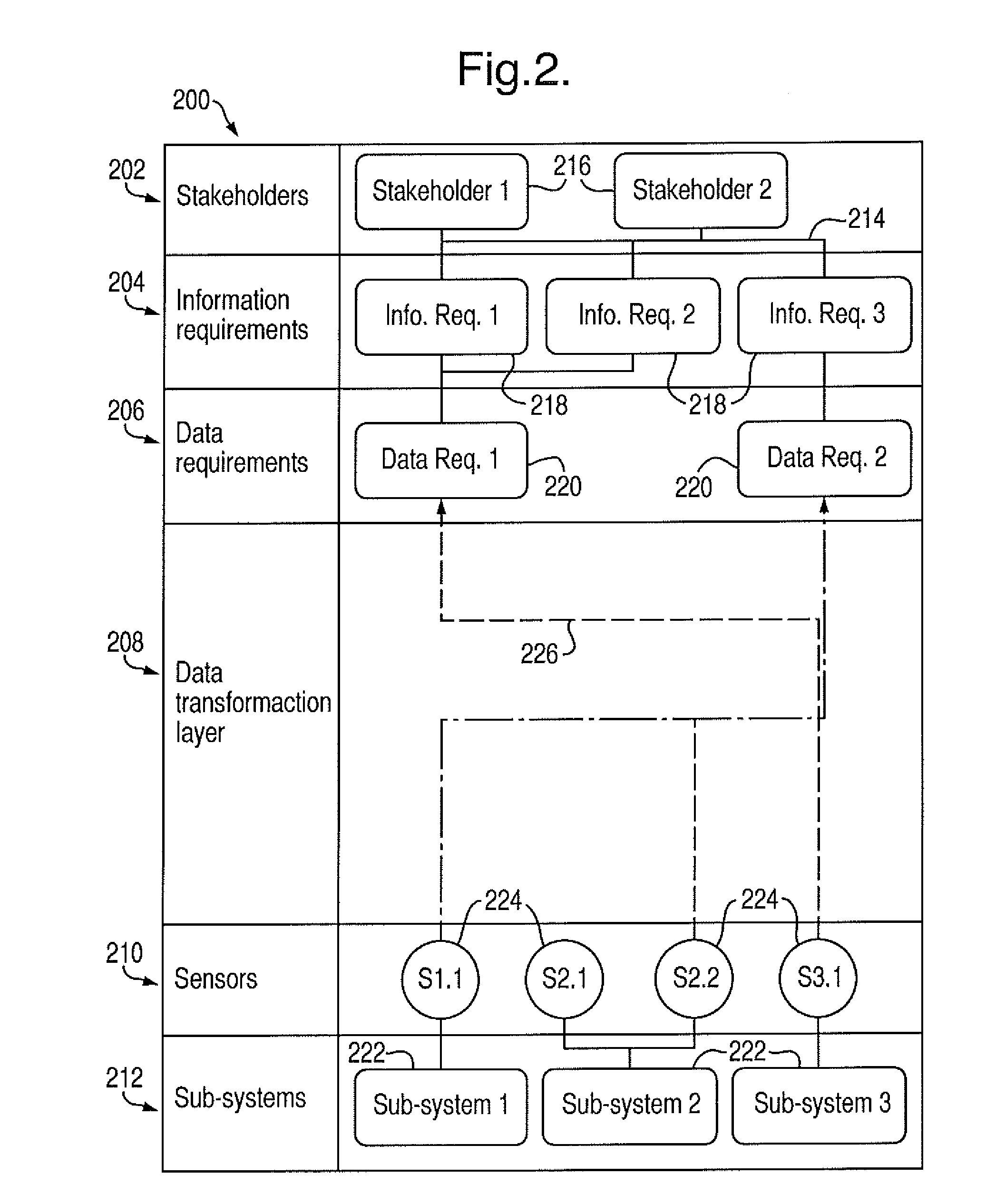
A method for designing a secondary sub-system for monitoring the condition of a platform is disclosed. The platform can include one or more primary sub-systems. The method can include identifying stakeholders of the platform, capturing information requirements of the stakeholders, determining data requirements corresponding to the information requirements, defining a sensor array comprising sensors suitable for providing output signals relating to condition characteristics of the one or more primary sub-systems, and defining procedures for converting the output signals from the sensor array to the data requirements, thereby to fulfil the information requirements of the stakeholders. The method can be implemented using a design tool having a graphical user interface with a hierarchical layer structure.
Owner:BAE SYSTEMS PLC
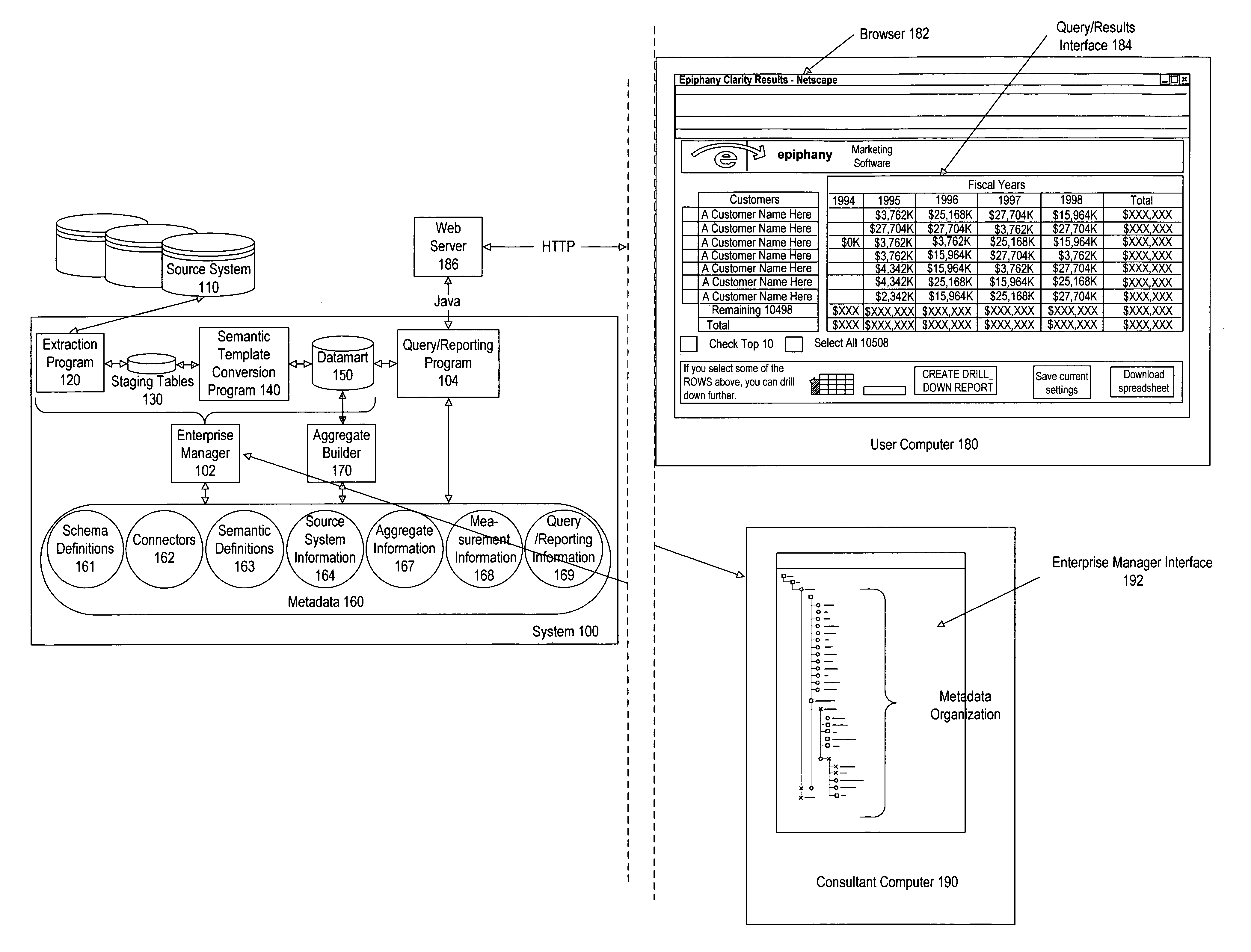
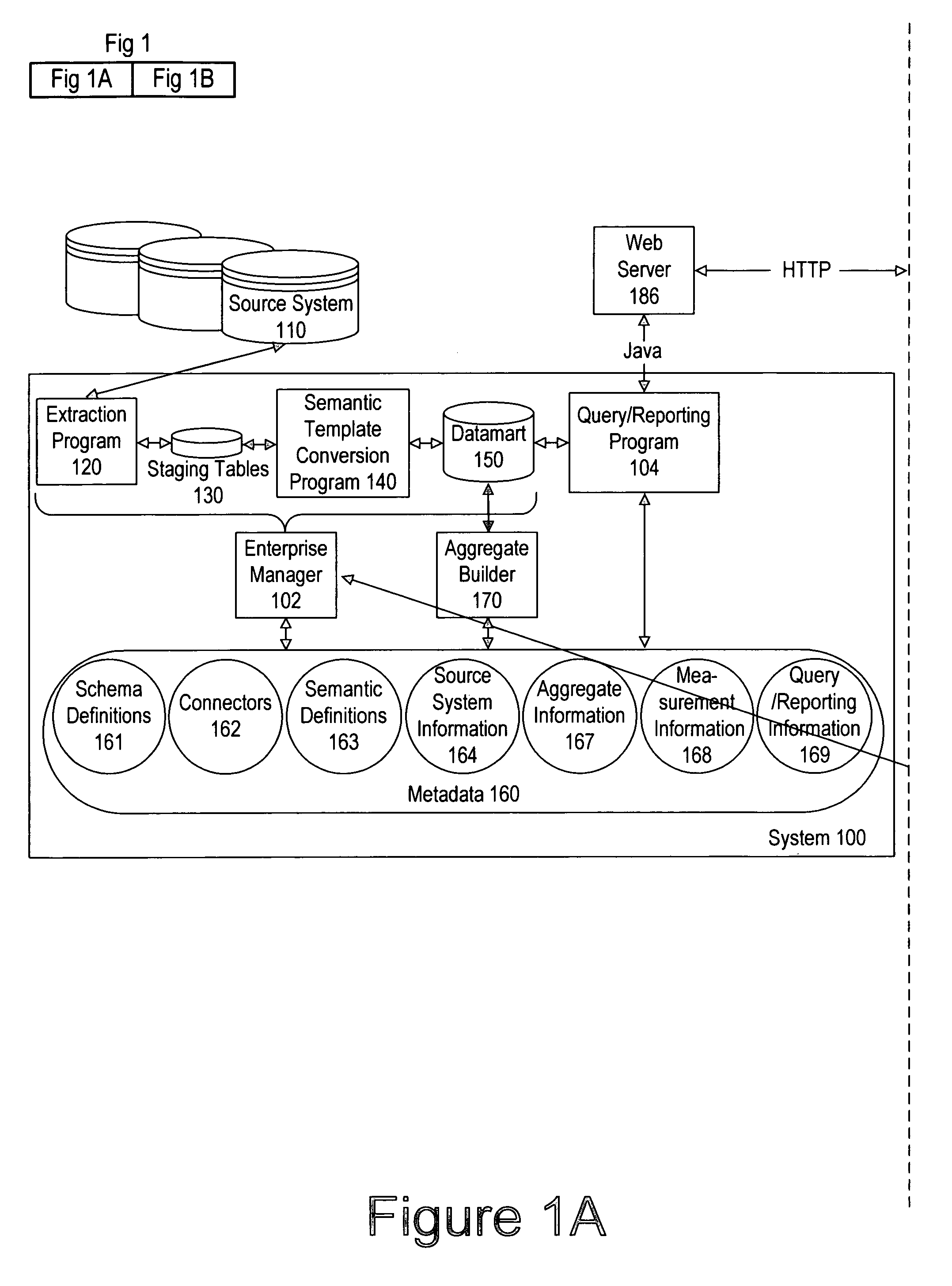
Method and apparatus for creating a well-formed database system using a computer
ActiveUS7461076B1Data processing applicationsDigital data processing detailsDefined ProcedureOperational definition
A method of defining a well-formed database system by defining the organization of the data in the database, and by defining the operations for that data, is described. The definition can be used to automatically create and populate the well-formed database system. The well-formed database system conforms to rules of correctness and produces results that conform to the rules. The organization is defined by a data organization definition that specifies tables, their columns, and the relationships between tables. The operations define procedures that operate on the tables and the table columns. Importantly, the operations are defined along with the tables, columns, and relationships, so that the resulting system is well-formed.
Owner:EPIPHANY INC
Comprehensive identification and designation of welding procedures
ActiveUS8115138B2Facilitates selection and namingOptimizationElectric discharge heatingArc welding apparatusDefined ProcedureWaste management
Owner:LINCOLN GLOBAL INC
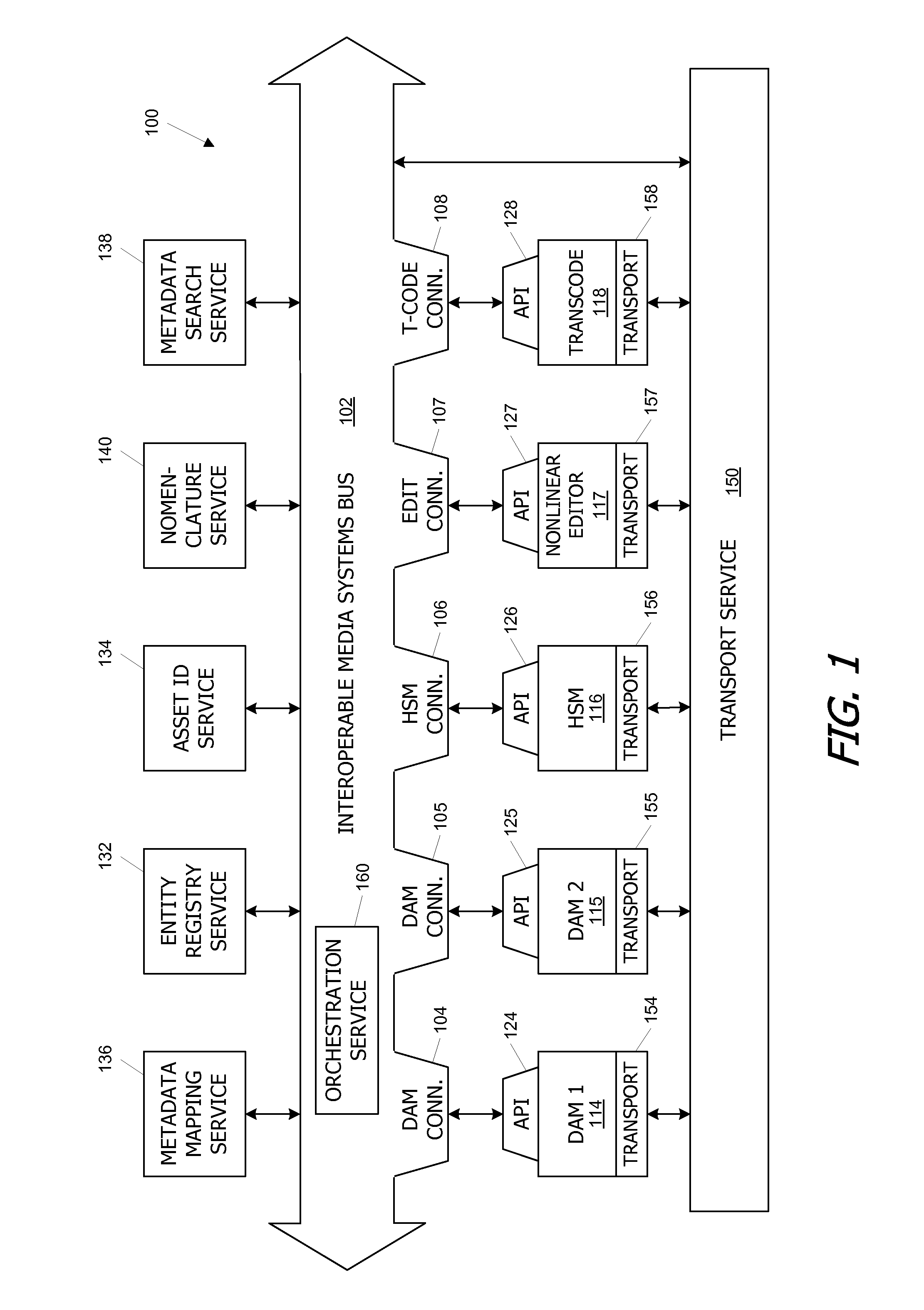
Systems and methods for interconnecting media services to an interface for transport of media assets
ActiveUS20100191656A1Multiple digital computer combinationsPayment architectureDefined ProcedureService provision
Systems and methods are provided to integrate disparate media services and applications across an organization. The media services are connected to an interoperable media services bus by creating a connector API for each service, thereby enabling the media services to exchange messages in a standardized format related to transactions to be performed involving media assets and / or metadata associated with media assets. Media assets are advantageously transported between different media systems using a transport interface that hides details of the transport operation from the sender and recipient media services. Each media service provides its own file transport parameters defining procedures for obtaining media assets therefrom and writing media assets thereto; the transport service determines particular protocols for each transport operation based on the information provided by the sender and recipient media services.
Owner:DISNEY ENTERPRISES INC
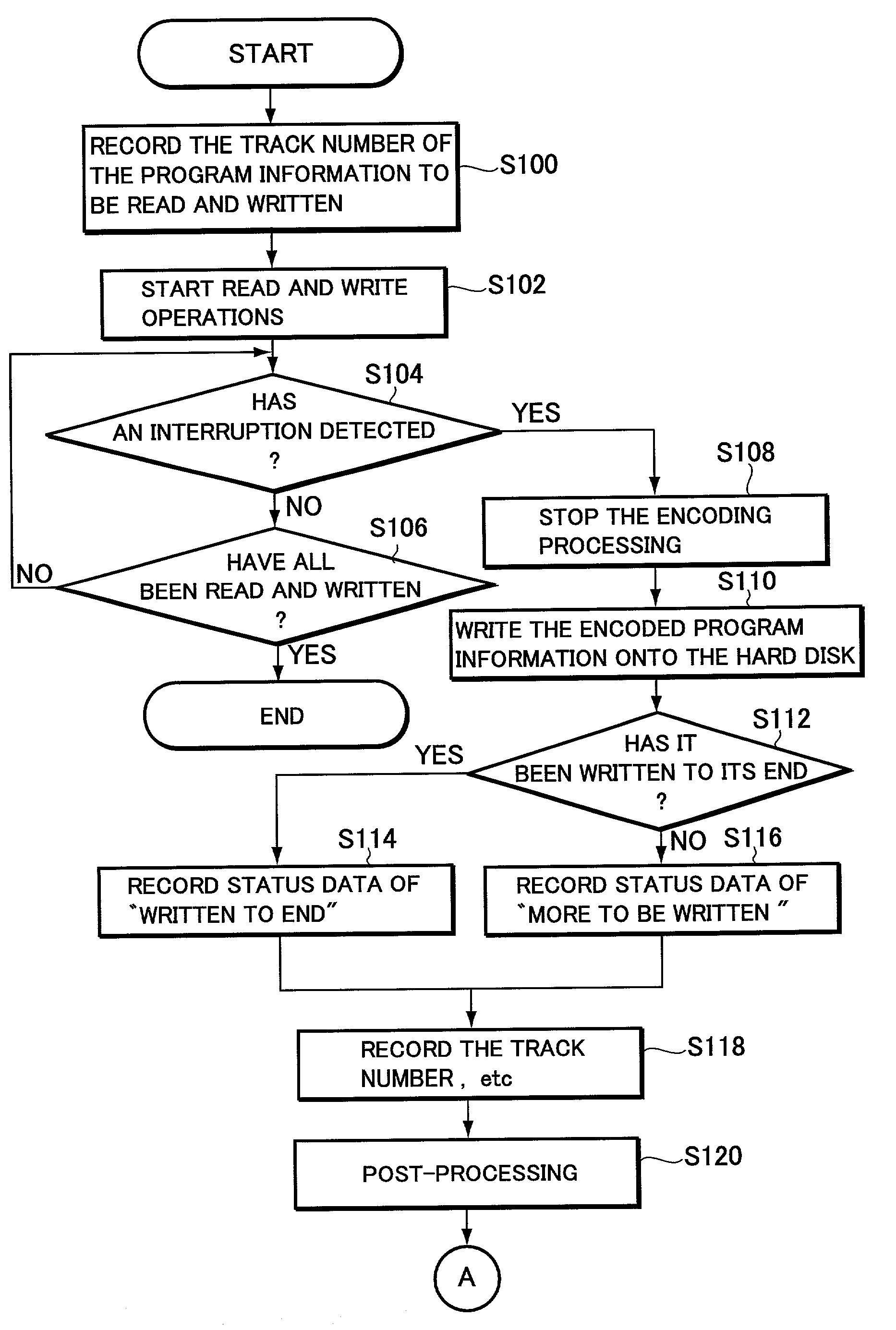
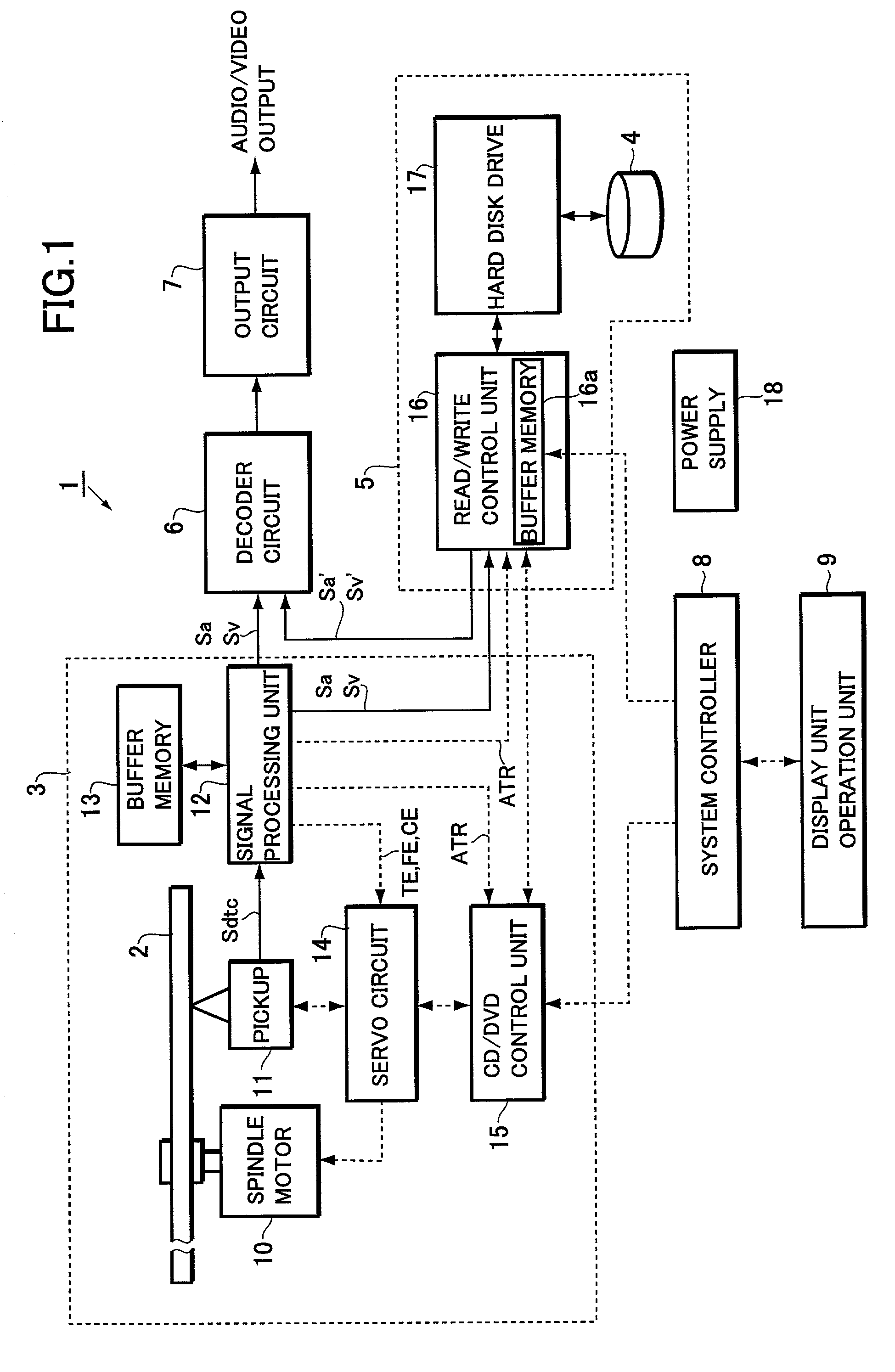
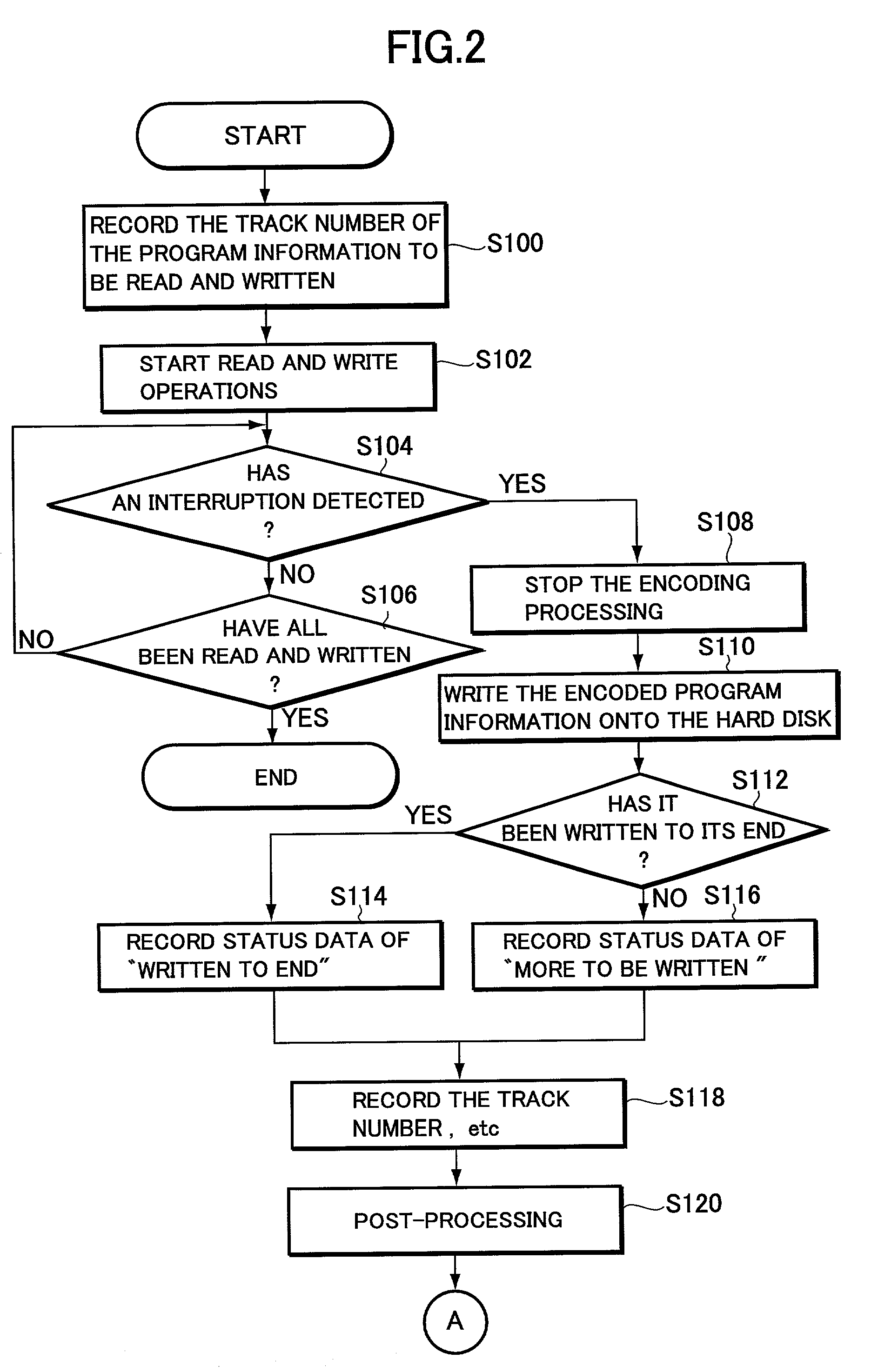
Apparatus and method for interruption of read and write operation and program storage medium for storing read and write procedure program
InactiveUS7266724B2Easy to operateFilamentary/web carriers operation controlInput/output to record carriersDefined ProcedureInformation storage
A method and an apparatus for performing high-quality read and write operations through a simple operation without being affected by an interruption even when the interruption has occurred in the course of a read / write operation between information storage media. When an interruption occurs in the course of reading program information stored on an optical disc to write the program information onto a hard disk, the write status of the program information which has encountered the interruption and the information for identifying the program information are stored on the hard disk. After the recovery from the interruption, read and write operations are restarted. Then, the program information capable of ensuring the continuity with the program information which has been properly written on the hard disk prior to the interruption is determined in accordance with the write status of the program information which has encountered the interruption and the information for identifying the program information. A read operation is performed from the program information thus determined and then a write operation to write the information on the hard disk.
Owner:PIONEER CORP
Anti-item for deletion of content in a distributed datastore
InactiveUS7774308B2Data processing applicationsDigital data information retrievalDefined ProcedureWaste collection
An apparatus and method efficiently delete a first items within a distributed datastore. In particular, an already well defined procedure for insertion of data is used for deletion. Deletion of a first item is effected through the insertion of a second item. The second item can contain a deletion key or be denoted by an appended flag or modified associated meta-data value. The first item can be deleted upon arrival of the second item or subsequent to arrival through an offline garbage collection process.
Owner:APPLIED INVENTION
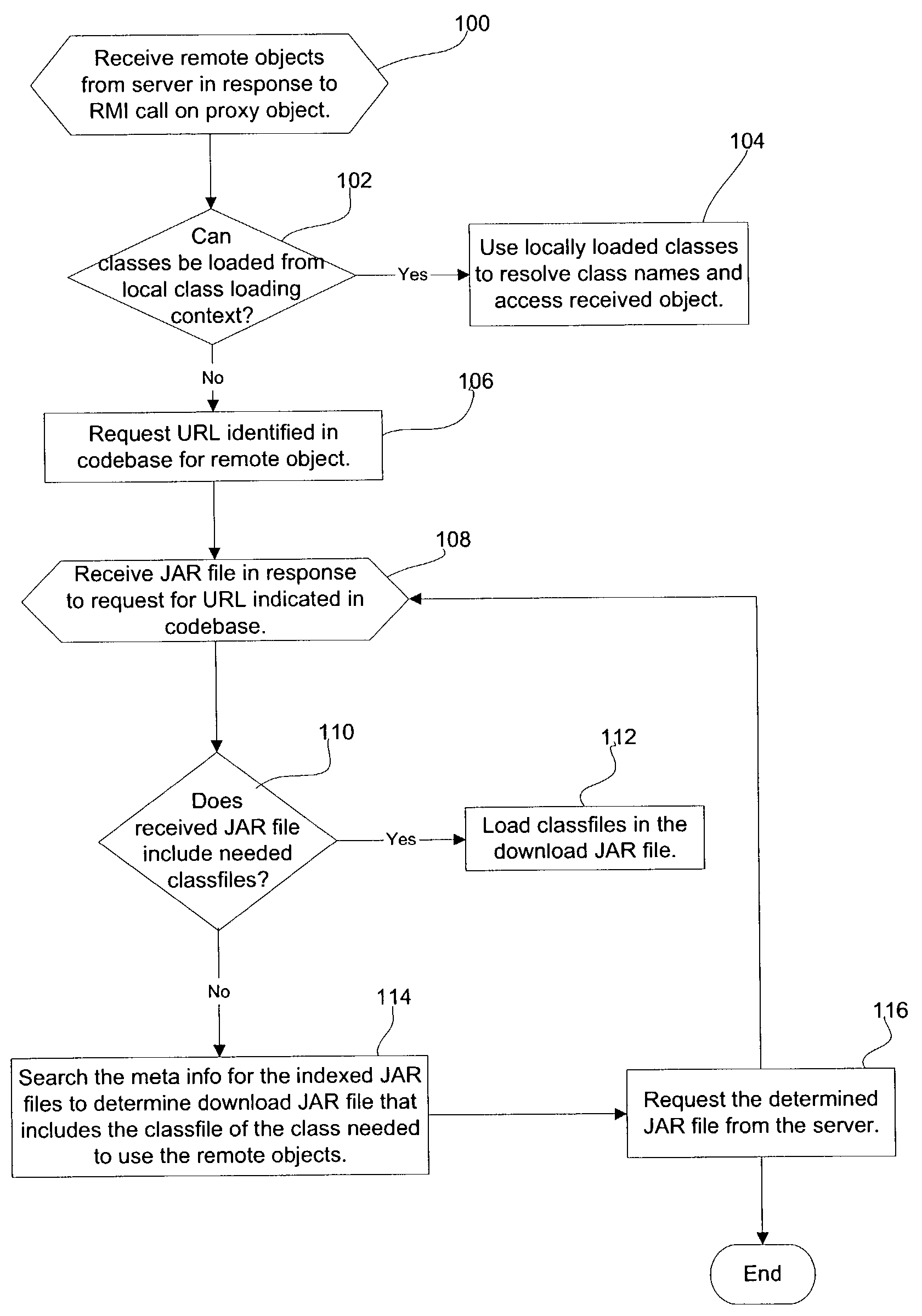
Method, system, and program for processing objects in a distributed computing environment
ActiveUS7234137B2Simple technologyProgram loading/initiatingMemory systemsDefined ProcedureDistributed Computing Environment
Provided are a method, system, and program for processing objects in a distributed computing environment. A determination is made of a program is needed to process a component. A file including the determined program is requested from a remote process. The requested file is received from the remote process, wherein the requested file includes a plurality of sections, each including different programs. At least one section includes programs that are intended only to be executed in a remote address space of the remote process and at least one other section includes programs that are intended to be downloaded from the remote process and execute in a client address space that is different than the remote address space. The programs are loaded from the section including the determined program to execute in the client address space to process the component.
Owner:ORACLE INT CORP
Method and system of displaying content associated with broadcast program
InactiveUS7551888B2Broadcast transmission systemsBroadcast services for monitoring/identification/recognitionDefined ProcedureContent Time
A media system comprising a broadcast system, a telecommunication system, a content processing system, and a user terminal. While a media stream is broadcast, a group of content items associated with the media stream are generated. The content items are presented in the user terminal in a first mode, wherein a presentation element corresponding to a content item is changed to another presentation element according to the timing information of the content item, or in a second mode wherein a presentation element is changed to another presentation element in response to a user action. Transition from the second mode is allowed only by authorization according to a pre-defined procedure. The interactive operations are thus controlled by the user and thus not overridden by content timed or pushed to the user terminal for display.
Owner:RPX CORP
Application execution managing method, application execution server computer, and repeater
InactiveUS20100063998A1Accurate operationMultiple digital computer combinationsTransmissionDefined ProcedureApplication software
A cache hit determining method in a server client system, such as a web system, which can determine whether a response received by a client is a response generated by a server or a response returned from a cache in the server client system. In the cache hit determining method, when the server generates the response, the serve adds a program for a cache hit determination and data to the response and the client executes the program included in the response, thereby realizing a cache hit determination.
Owner:HITACHI LTD
Method for coordinating actions among a group of servers
InactiveUS7349974B2Multiple digital computer combinationsDigital data authenticationDefined ProcedureClient-side
Owner:INT BUSINESS MASCH CORP
Method for switching users between different subzones implemented within same station
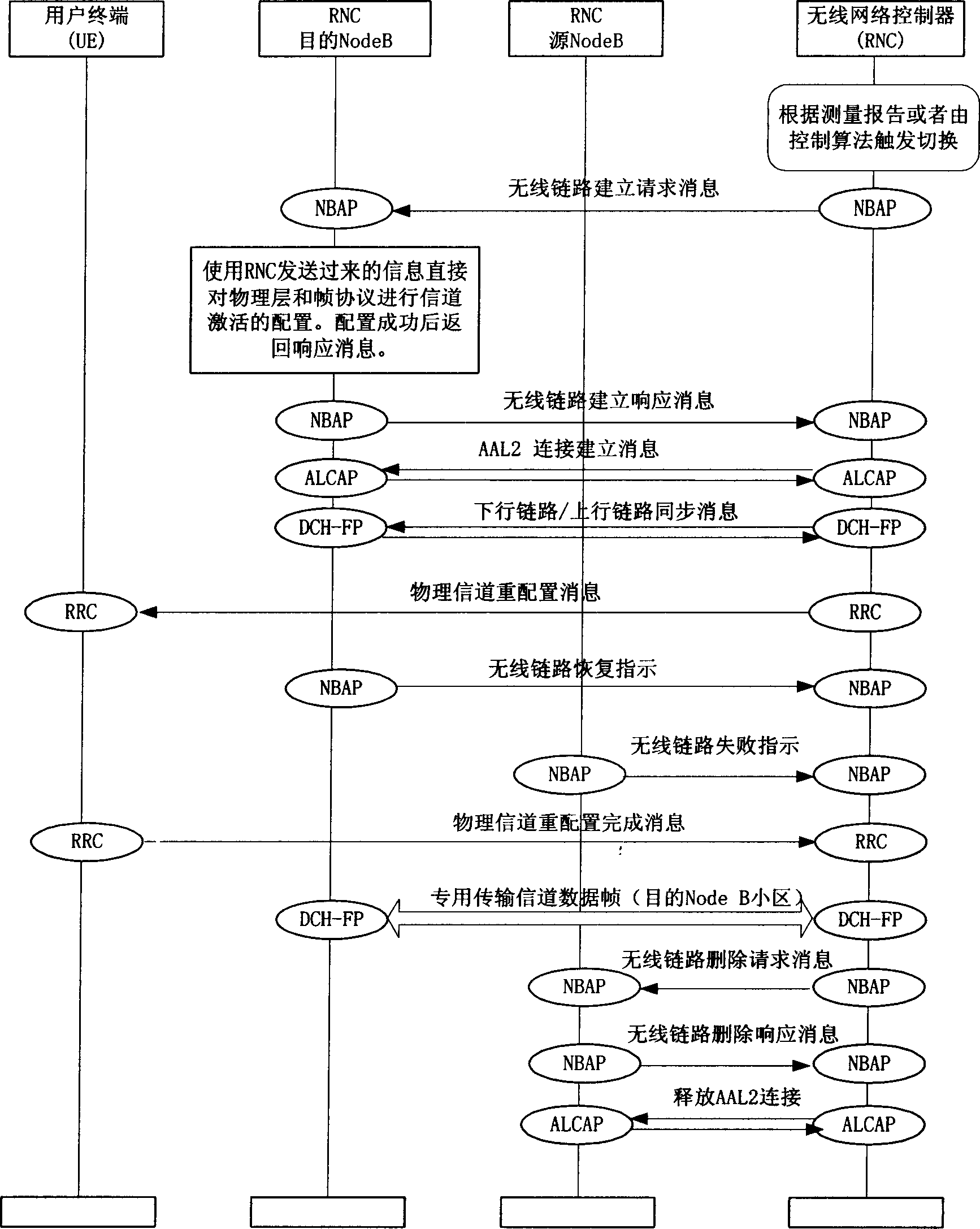
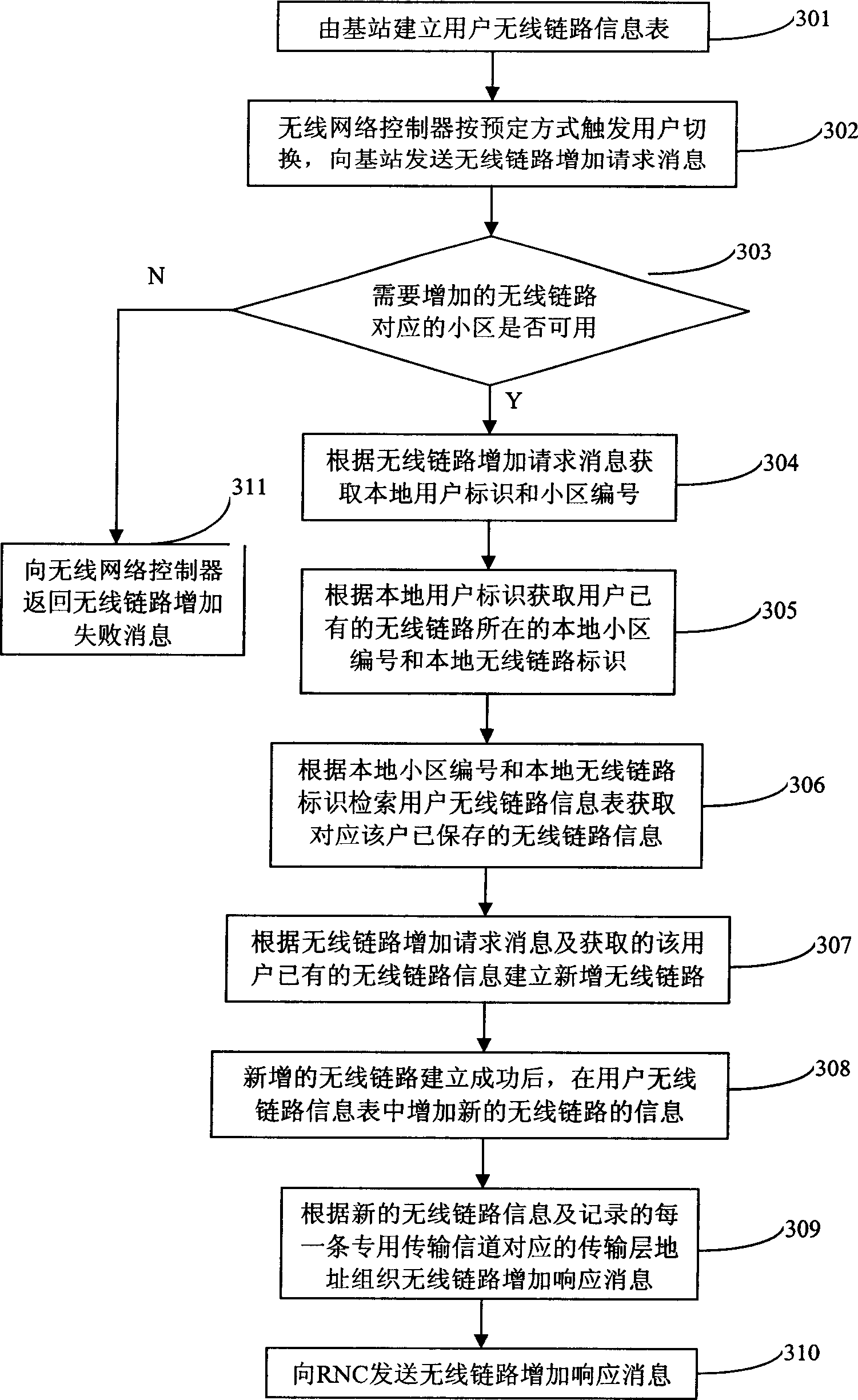
InactiveCN1662091AEasy to handleImprove switching efficiencyRadio/inductive link selection arrangementsWireless communicationDefined ProcedurePhysical layer
The method includes steps: according to prearranged mode, wireless network controller triggers user's switching, and sends request message for adding wireless link to base station; based on the said message, obtaining identifiers of local users and number of subzone corresponding to the said wireless link; based on the said request message, and information of wireless link of the user obtained, building new added wireless link; after the new added wireless link is built, a response message is sent to wireless network controller. The invention clearly defines procedure of adding or deleting wireless links, and treating mechanism in whole signaling switching flow in base station subsystem and physical layer at user end, as well as raises switching efficiency.
Owner:CHINA ACAD OF TELECOMM TECH
Anti-item for deletion of content in a distributed datastore
InactiveUS20060129517A1Data processing applicationsDigital data information retrievalDefined ProcedureDistributed data store
The invention provides an efficient apparatus and method for deleting items within a distributed datastore. In particular, the invention provides an apparatus and method of deletion that uses an already well defined procedure for insertion of data.
Owner:APPLIED INVENTION
Method for centralization of process sequence checking
ActiveUS20070168761A1Programme controlNon-redundant fault processingDefined ProcedureComputer science
Owner:GM GLOBAL TECH OPERATIONS LLC
Method for forecasting retention time of gas chromatography under temperature programming after shortening of chromatographic column
InactiveCN102507813AReduce intensityReduce experiment costComponent separationDefined ProcedureBenzene
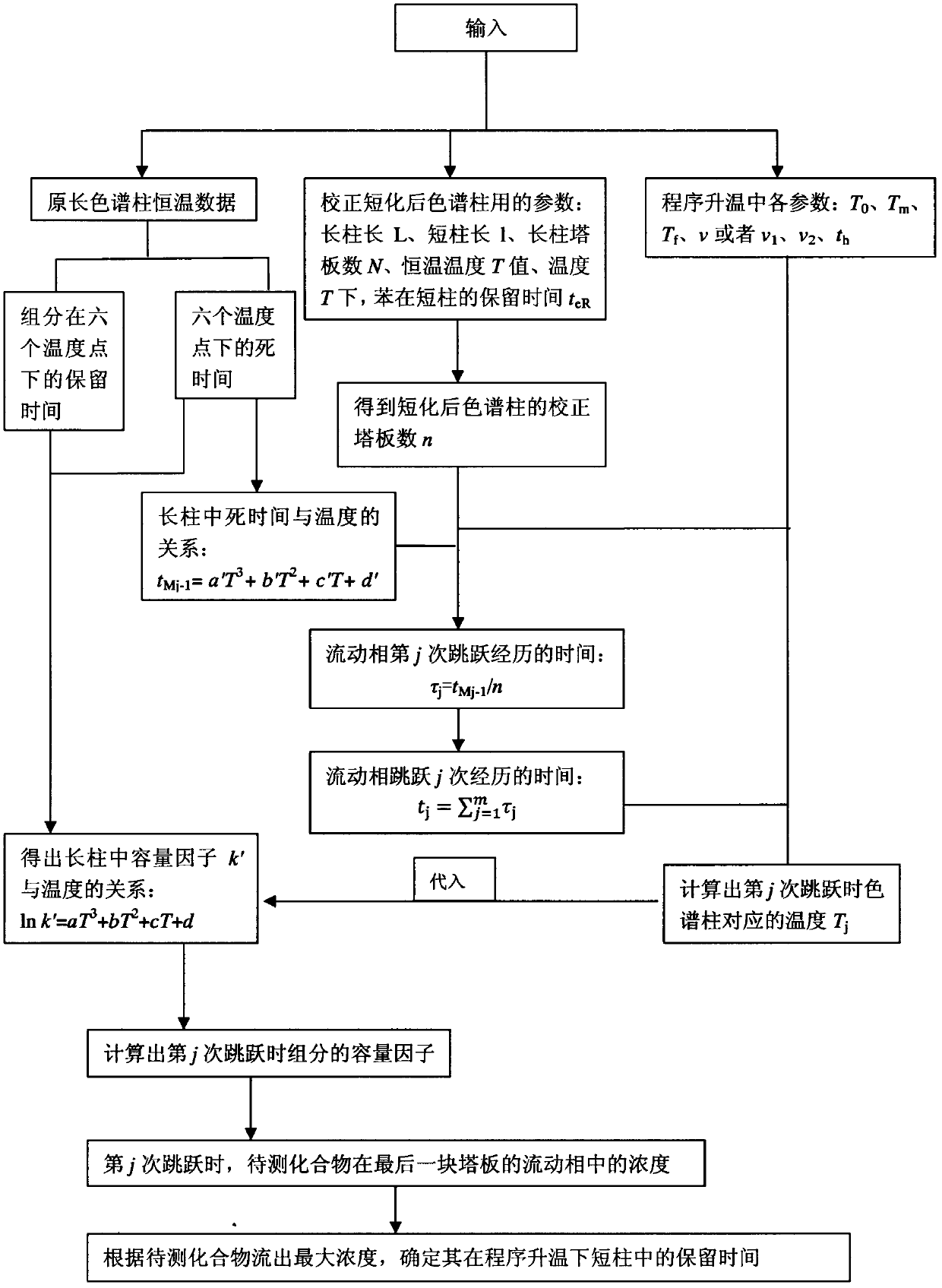
The invention discloses a method for forecasting retention time of gas chromatography under temperature programming after shortening of a chromatographic column. The method includes the steps: firstly, determining dead time and capacity factors corresponding to optional temperature points of an original chromatographic column and correcting the number of column plates of the shortened chromatographic column by using benzene as a standard substance; secondly, forecasting the retention time of components in the shortened chromatographic column under temperature programming; thirdly, measuring the retention time of the components in the shortened chromatographic column according to the determined temperature programming in the forecasting step; and fourthly, computing the relative deviation of the forecasted retention time of the components, and judging that forecasting precision meets requirements when the absolute value of the relative deviation is smaller than 2%. The method has the advantages that experimental cost is saved, the working intensity of analysis is reduced, practical ways are provided for selecting optimal separation conditions of the gas chromatography of the short column, the forecasting process is clear, and the method is applicable to wide-range popularization and application.
Owner:TIANJIN UNIV
Method for processing mounting system based on active addressing and position memory
InactiveCN1394714AAvoid the influence of machining accuracySolve the clamping problemAssembly machinesNumerical controlDefined ProcedureEngineering
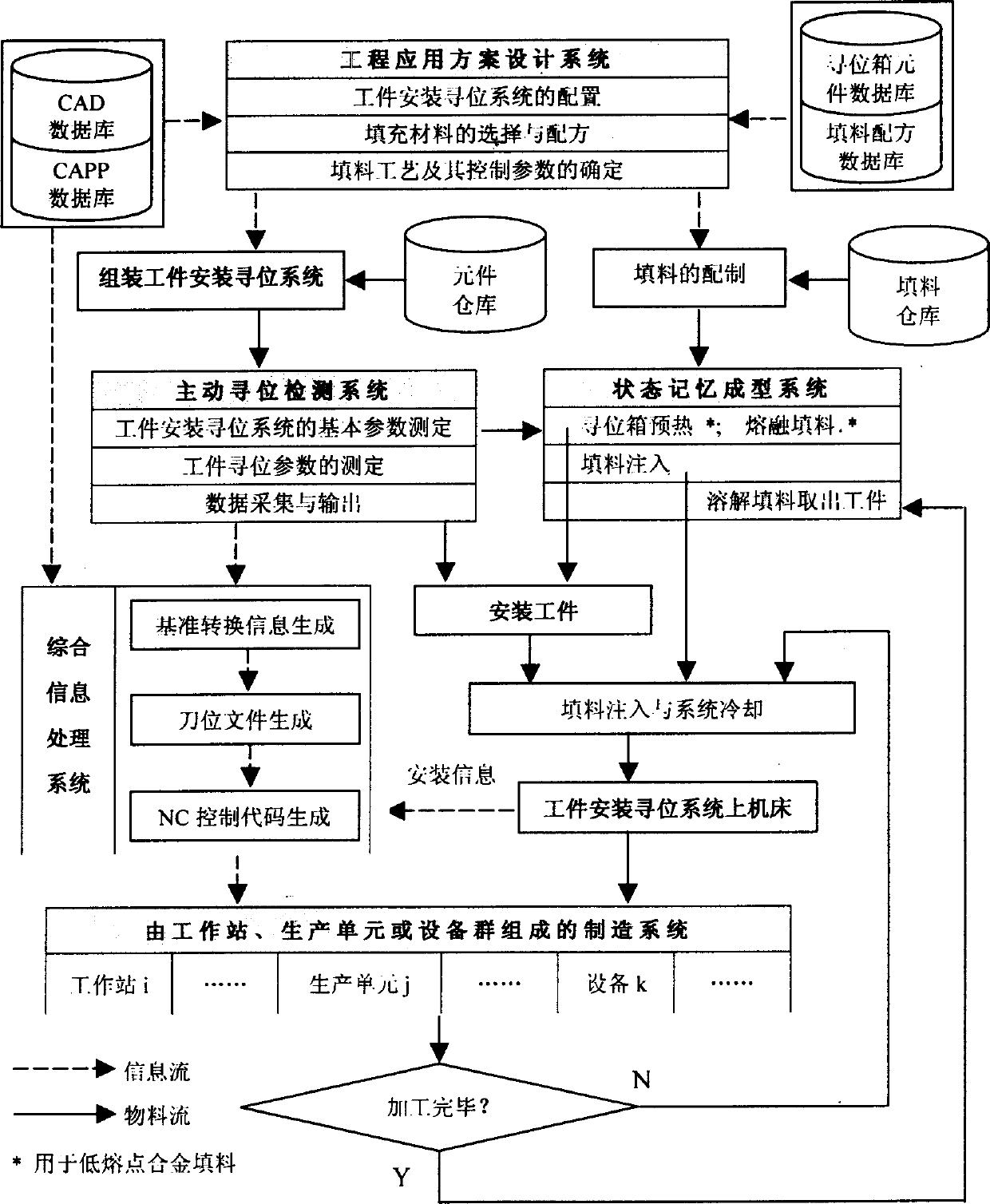
The machining method based on active location and position memory mounting system is mainly characterized by that said method includes the following steps: adopting standard location box to blank to be machined and make the blank face with arbitrary shape; adopting filler state of restore memory position so as to make the original mounting position of workpiece in the arbitrarily-changed procedure conversion do not produce change; based on the original mounting reference of workpiece and coordinate conversion method calculating procedure coordinate parameter and making digital control machining program. The workpiece blank is placed into location box, accurately positioned by using location element and fastening element, the filler is injected and the original mounting position of the workpiece can be defined, then can be machined according to the defined procedure.
Owner:DONGHUA UNIV
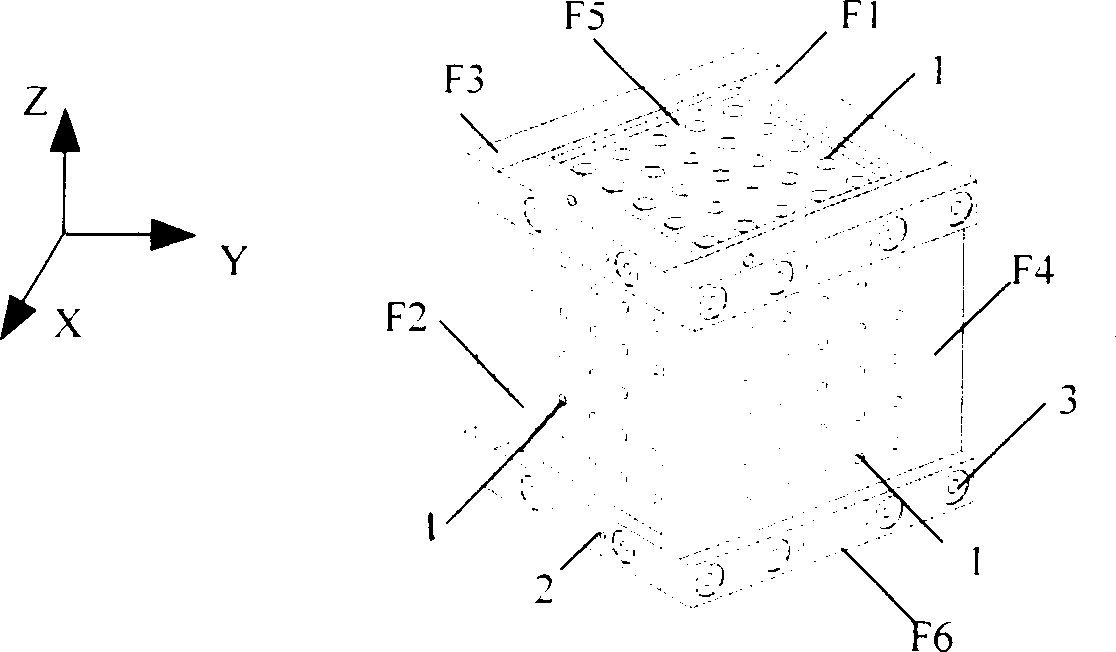
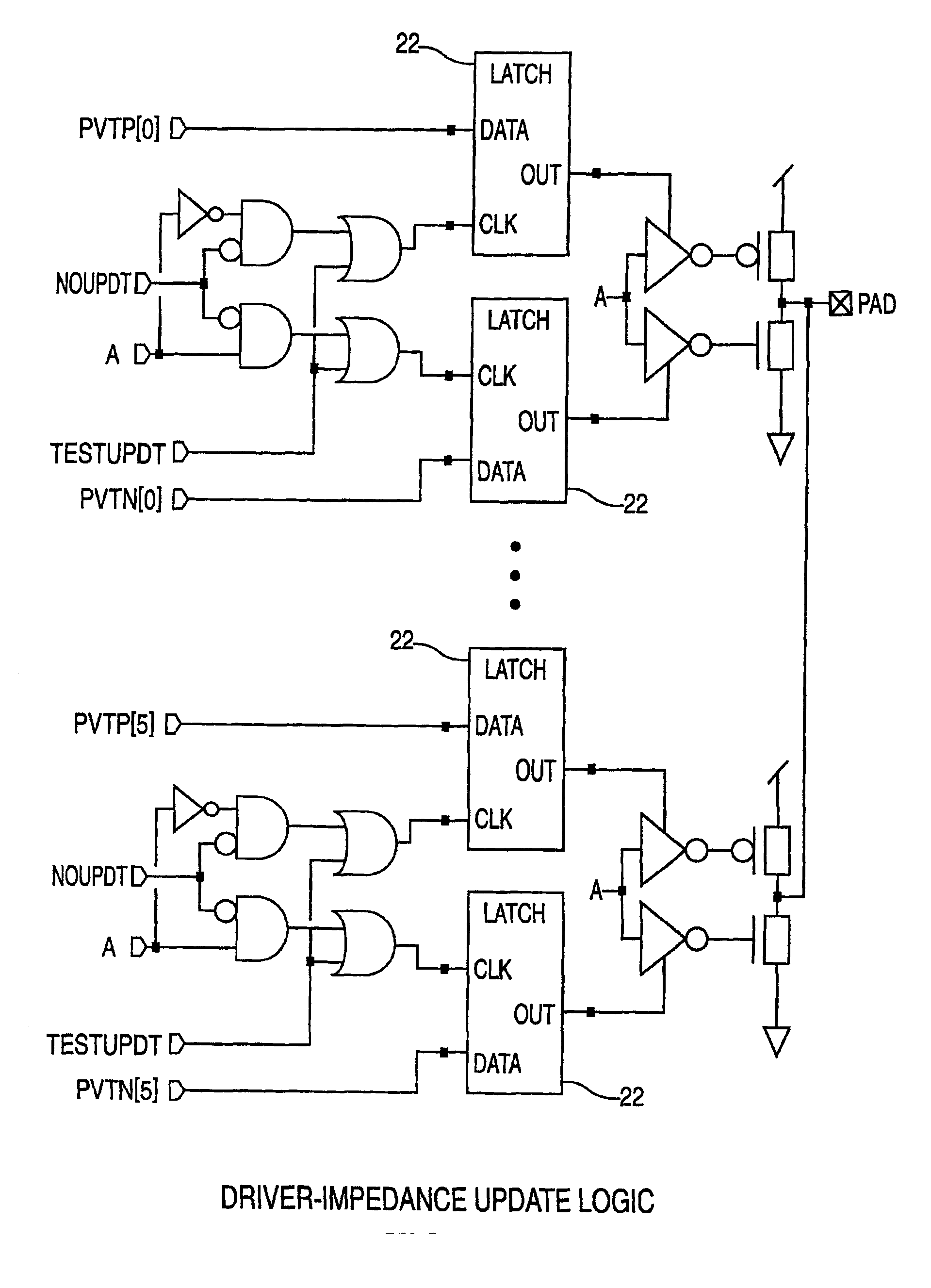
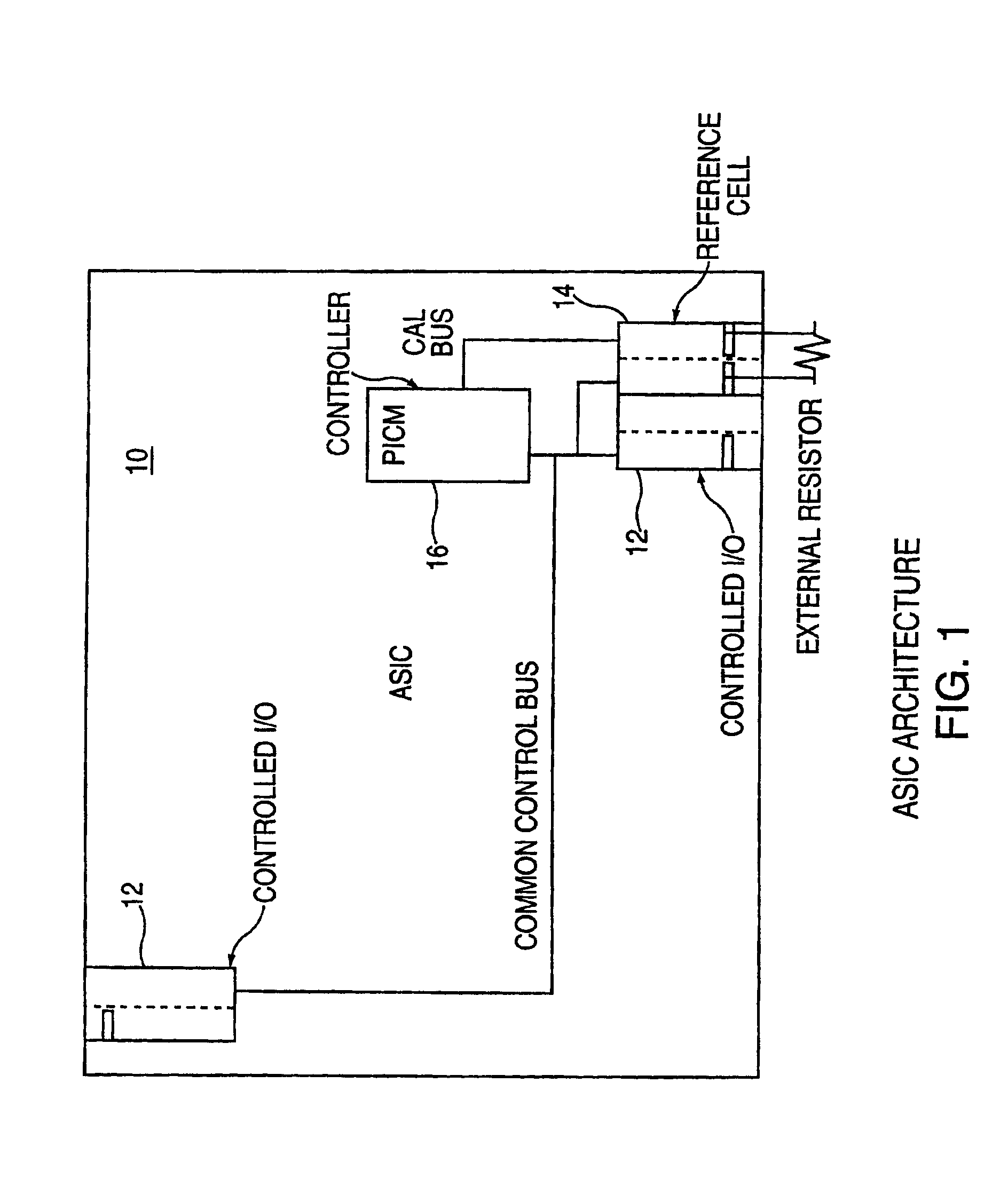
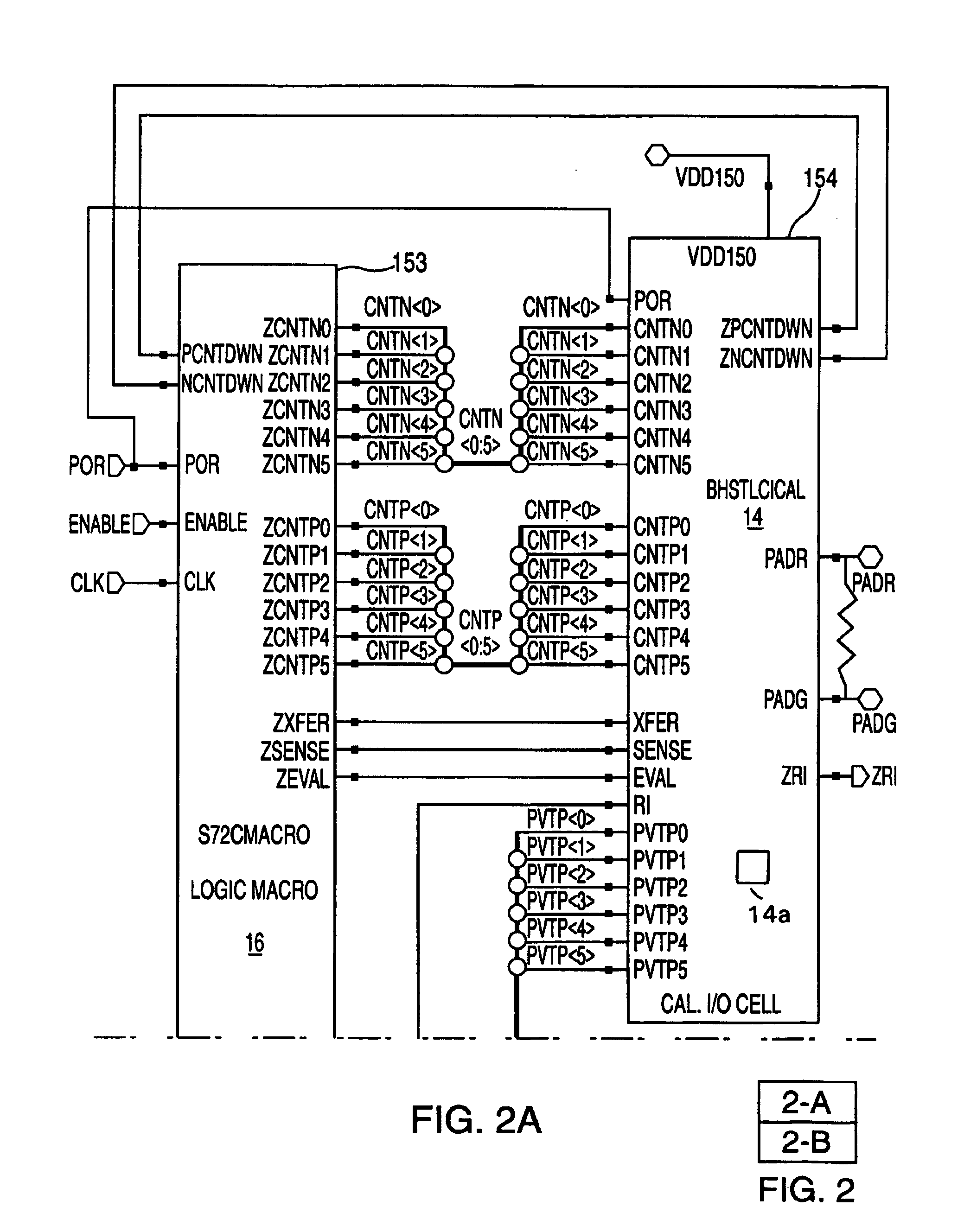
ASIC architecture for active-compensation of a programmable impedance I/O
InactiveUS6922074B2Meet the requirementsInput/output impedence modificationReliability increasing modificationsDefined ProcedureVoltage reference
A method of, and a circuit for, impedance control. The method comprises the steps of providing an input / output cell having a controllable input / output impedance, providing a reference cell including a node having a variable voltage, and comparing the voltage of the node to a reference voltage. The voltage of the node is adjusted during a defined period and according to a defined procedure, and during that defined period, a digital signal is generated. That digital signal is transmitted to the input / output cell to adjust the input / output impedance. Preferably, the circuit is embodied as a digital controller designed as a synthesized core or macro. The advantage of this implementation is that it never has to be redesigned in future technologies. The digital controller may be carried over to future technologies in the form of VHDL code, which is pure logic and independent of technology.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com